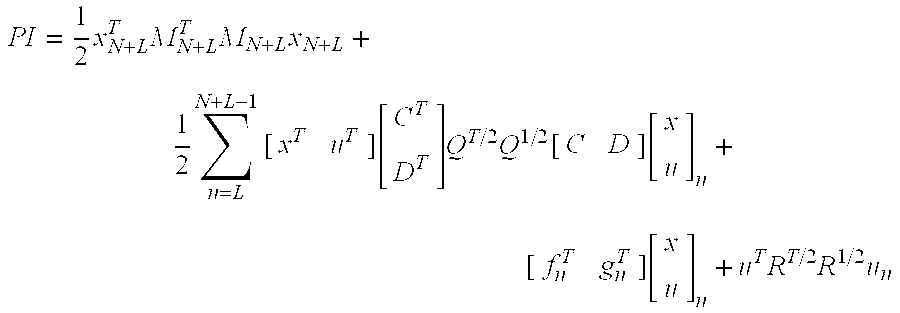Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1073 results about "Physical system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In physics, a physical system is a portion of the physical universe chosen for analysis. Everything outside the system is known as the environment. The environment is ignored except for its effects on the system.
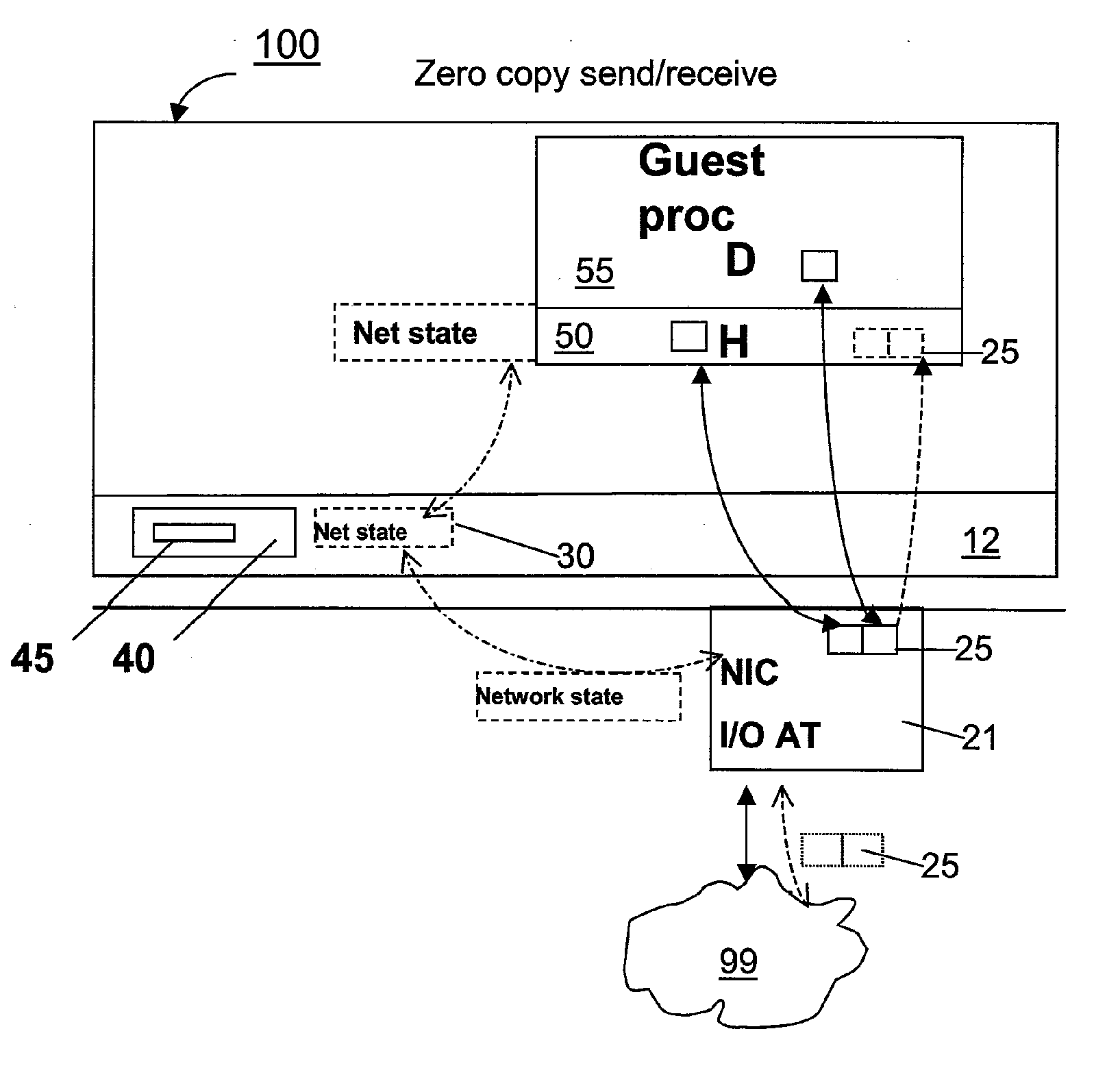
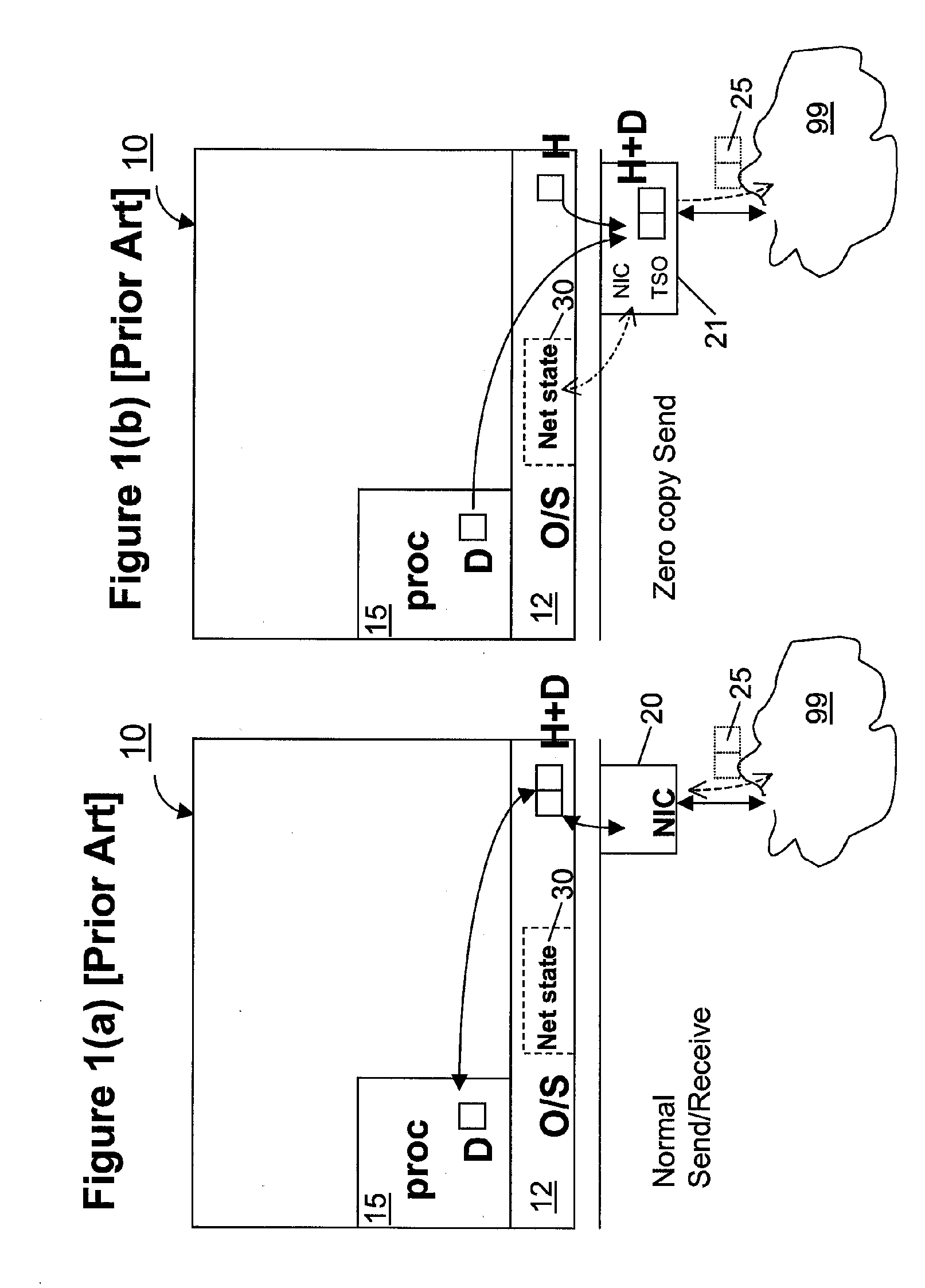
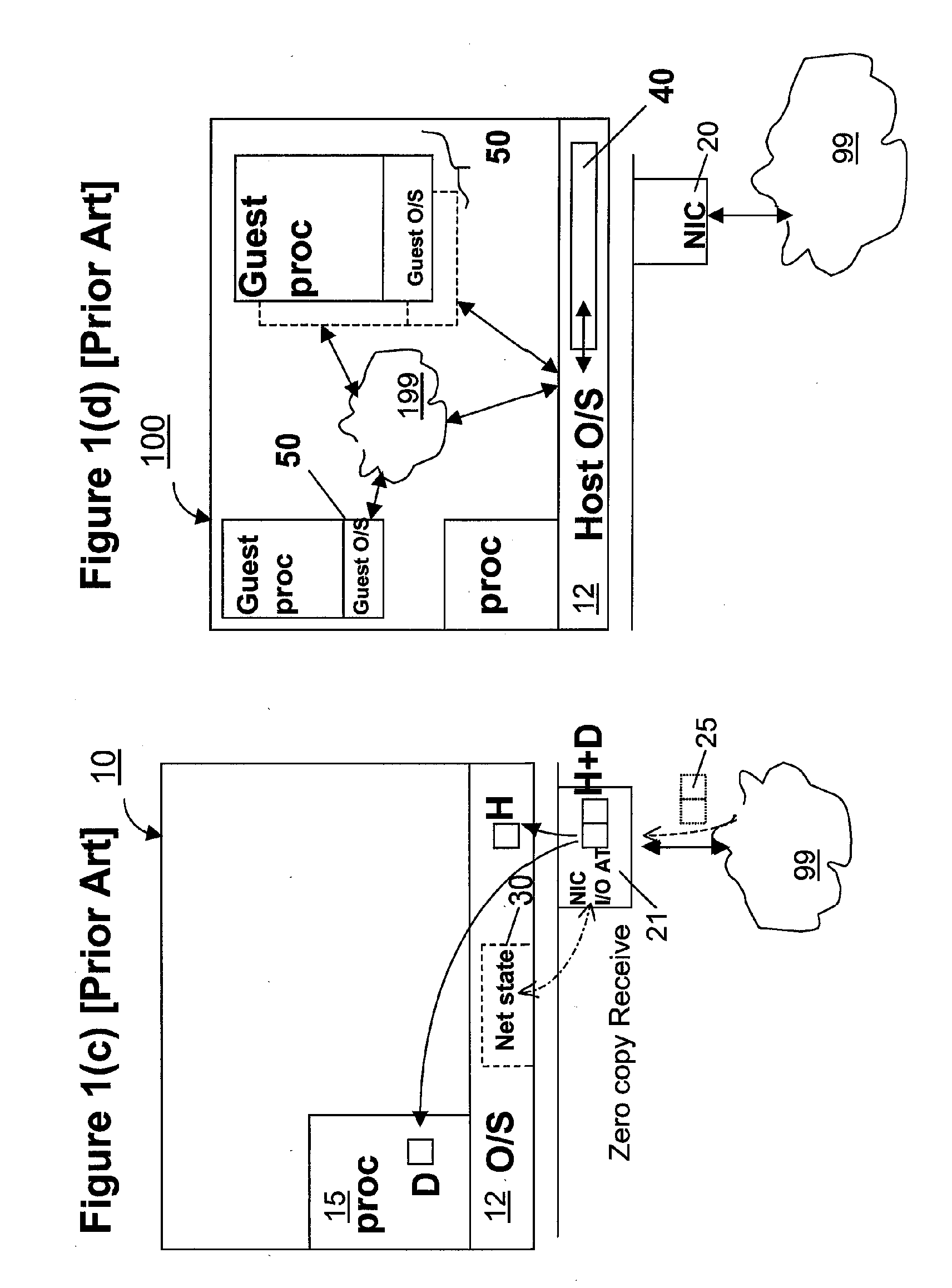
Zero-copy network I/O for virtual hosts
ActiveUS20070061492A1Eliminate the problemSolve excessive overheadDigital computer detailsTransmissionData packVirtualization
Techniques for virtualized computer system environments running one or more virtual machines that obviate the extra host operating system (O / S) copying steps required for sending and receiving packets of data over a network connection, thus eliminating major performance problems in virtualized environment. Such techniques include methods for emulating network I / O hardware device acceleration-assist technology providing zero-copy I / O sending and receiving optimizations. Implementation of these techniques require a host O / S to perform actions including, but not limited to: checking of the address translations (ensuring availability and data residency in physical memory), checking whether the destination of a network packet is local (to another virtual machine within the computing system), or across an external network; and, if local, checking whether either the sending destination VM, receiving VM process, or both, supports emulated hardware accelerated-assist on the same physical system. This optimization, in particular, provides a further optimization in that the packet data checksumming operations may be omitted when sending packets between virtual machines in the same physical system.
Owner:RED HAT
A System and Method for Modelling System Behaviour
ActiveUS20170147722A1Reduce the impactReduce impactMedical simulationDesign optimisation/simulationCollective modelModel system
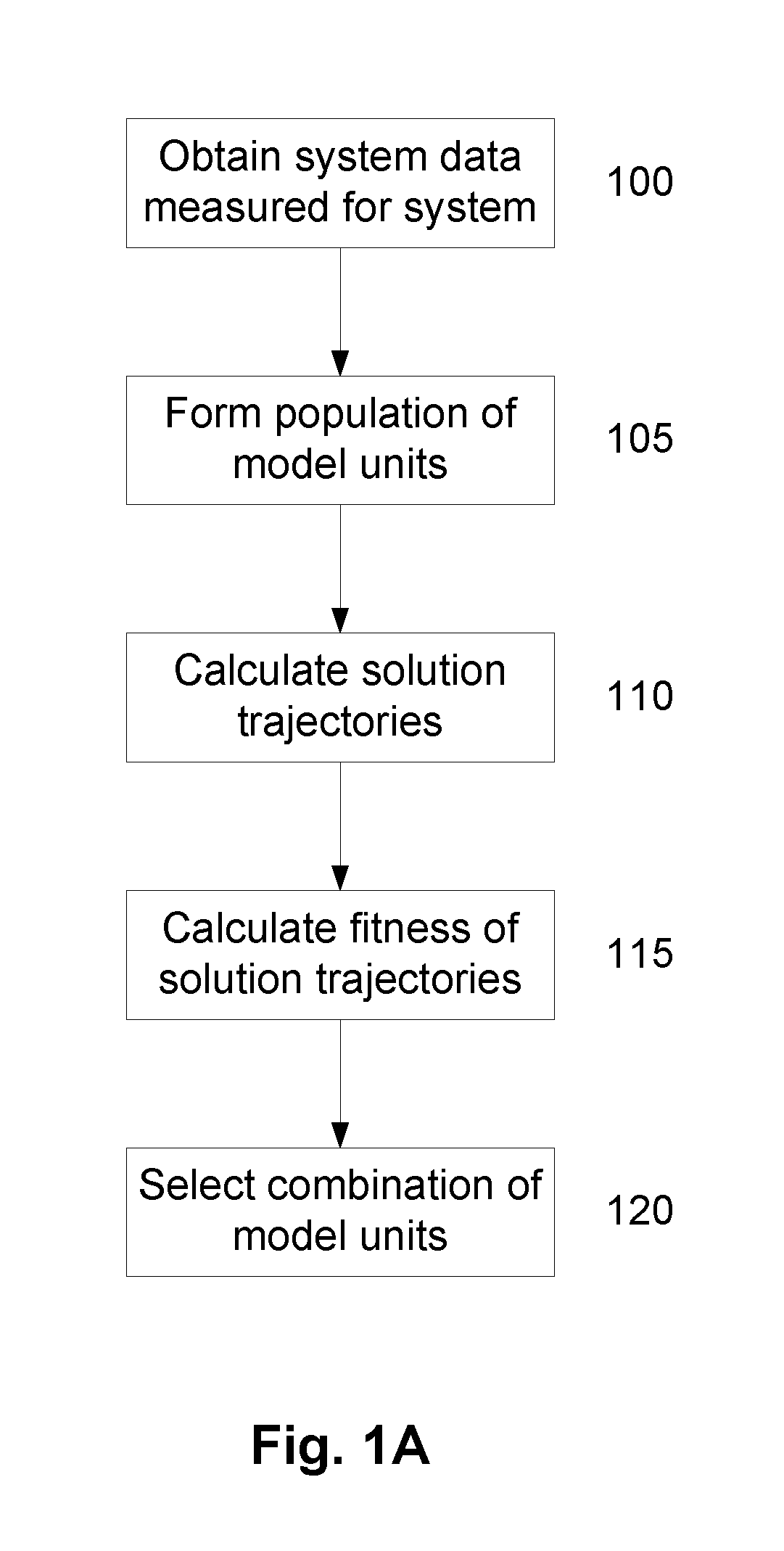
A method of modelling system behaviour of a physical system, the method including, in one or more electronic processing devices obtaining quantified system data measured for the physical system, the quantified system data being at least partially indicative of the system behaviour for at least a time period, forming at least one population of model units, each model unit including model parameters and at least part of a model, the model parameters being at least partially based on the quantified system data, each model including one or more mathematical equations for modelling system behaviour, for each model unit calculating at least one solution trajectory for at least part of the at least one time period; determining a fitness value based at least in part on the at least one solution trajectory; and, selecting a combination of model units using the fitness values of each model unit, the combination of model units representing a collective model that models the system behaviour.
Owner:EVOLVING MACHINE INTELLIGENCE
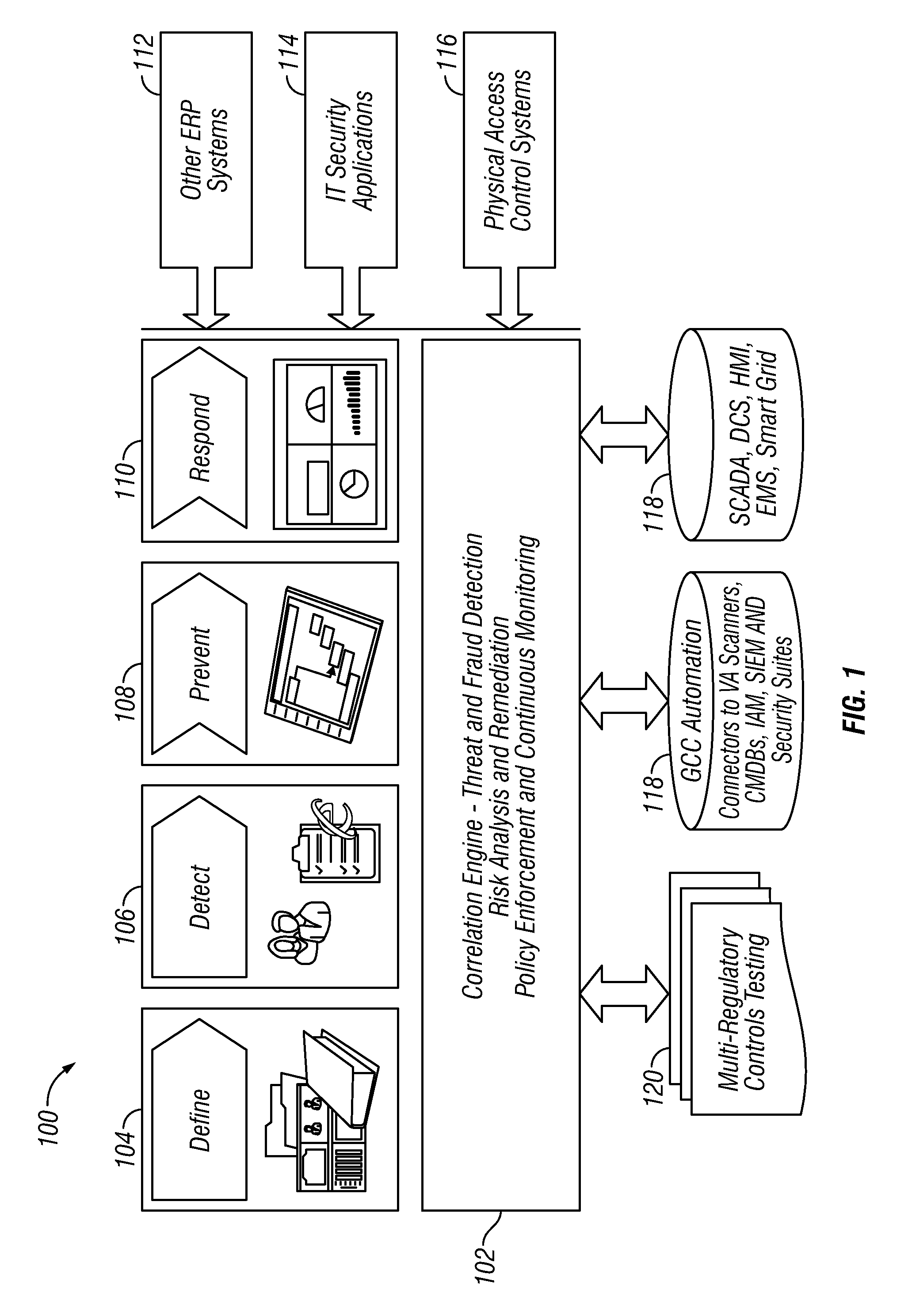
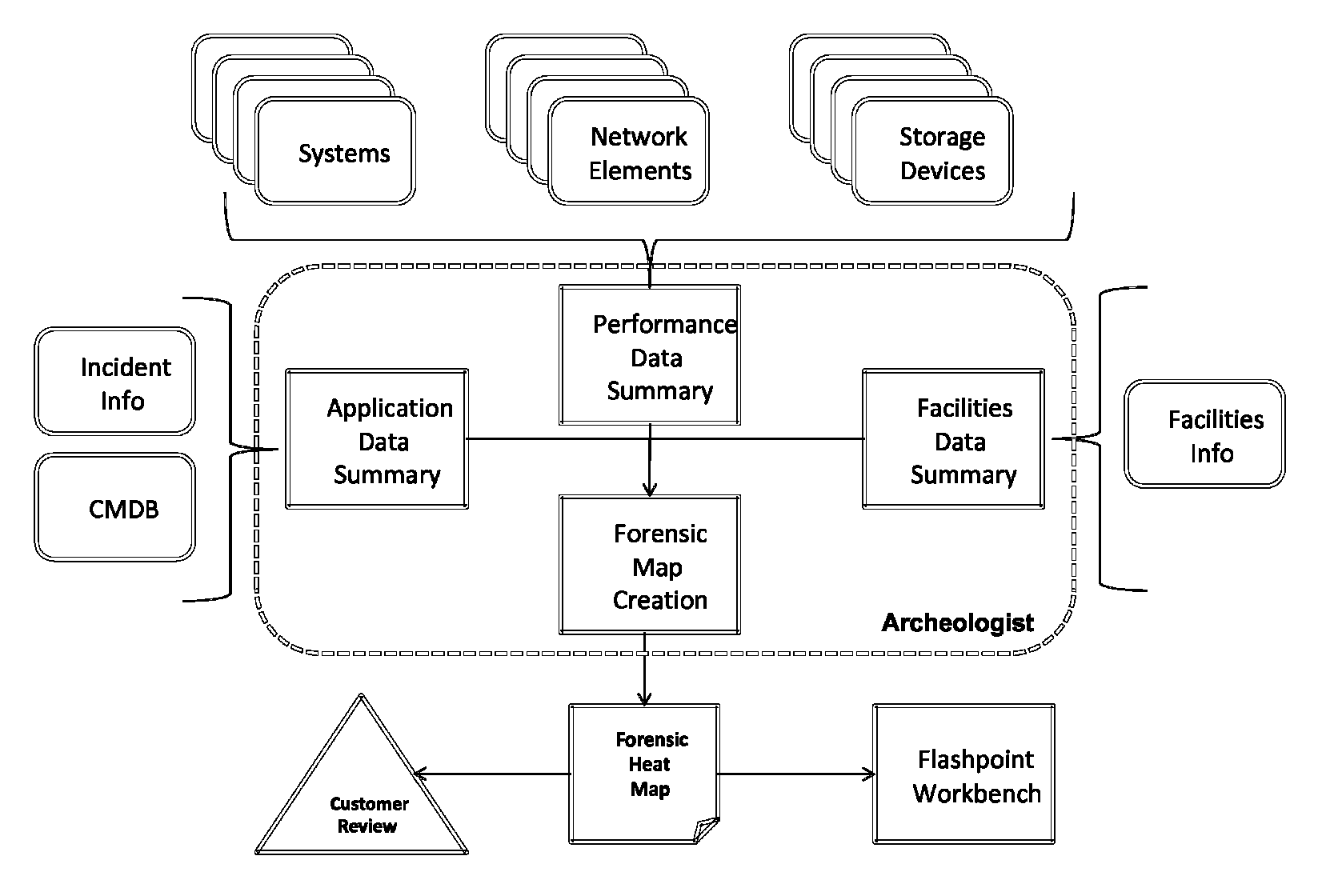
Integrated forensics platform for analyzing it resources consumed to derive operational and architectural recommendations
ActiveUS20110145657A1Easy to analyzeHardware monitoringResourcesStructure of Management InformationPhysical system
A method for facilitating forensic analysis of operational data for an IT infrastructure includes deriving performance data from a plurality of physical systems, network elements and storage devices in an IT infrastructure via a toolset comprising a plurality of IT monitoring and metrics tools, importing the performance data into an integrated forensics platform, aggregating the imported data, and analyzing the aggregated data to determine resources consumed. Each tool is communicatively interfaced with one or more of the physical systems, network elements and storage devices.
Owner:EMC IP HLDG CO LLC
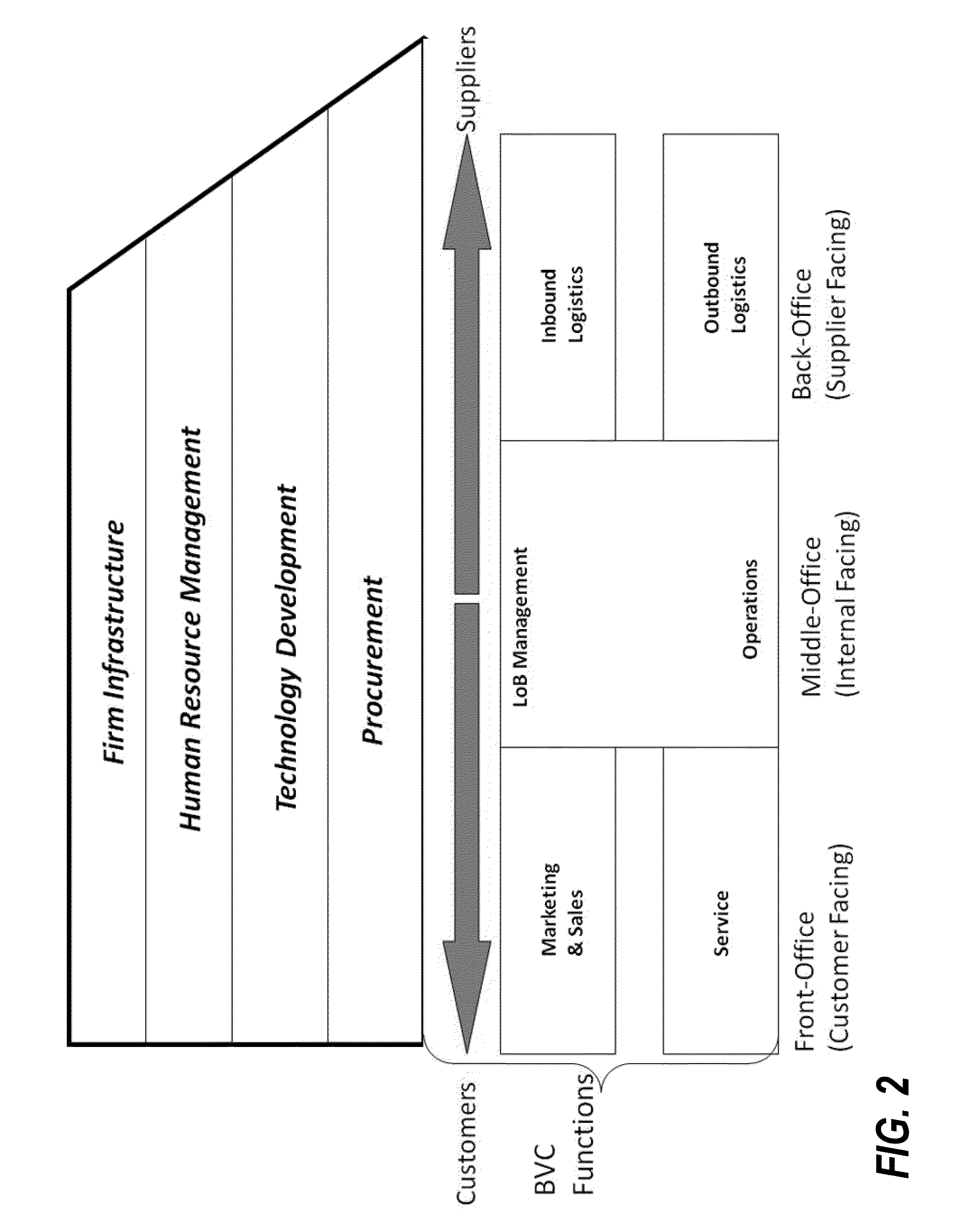
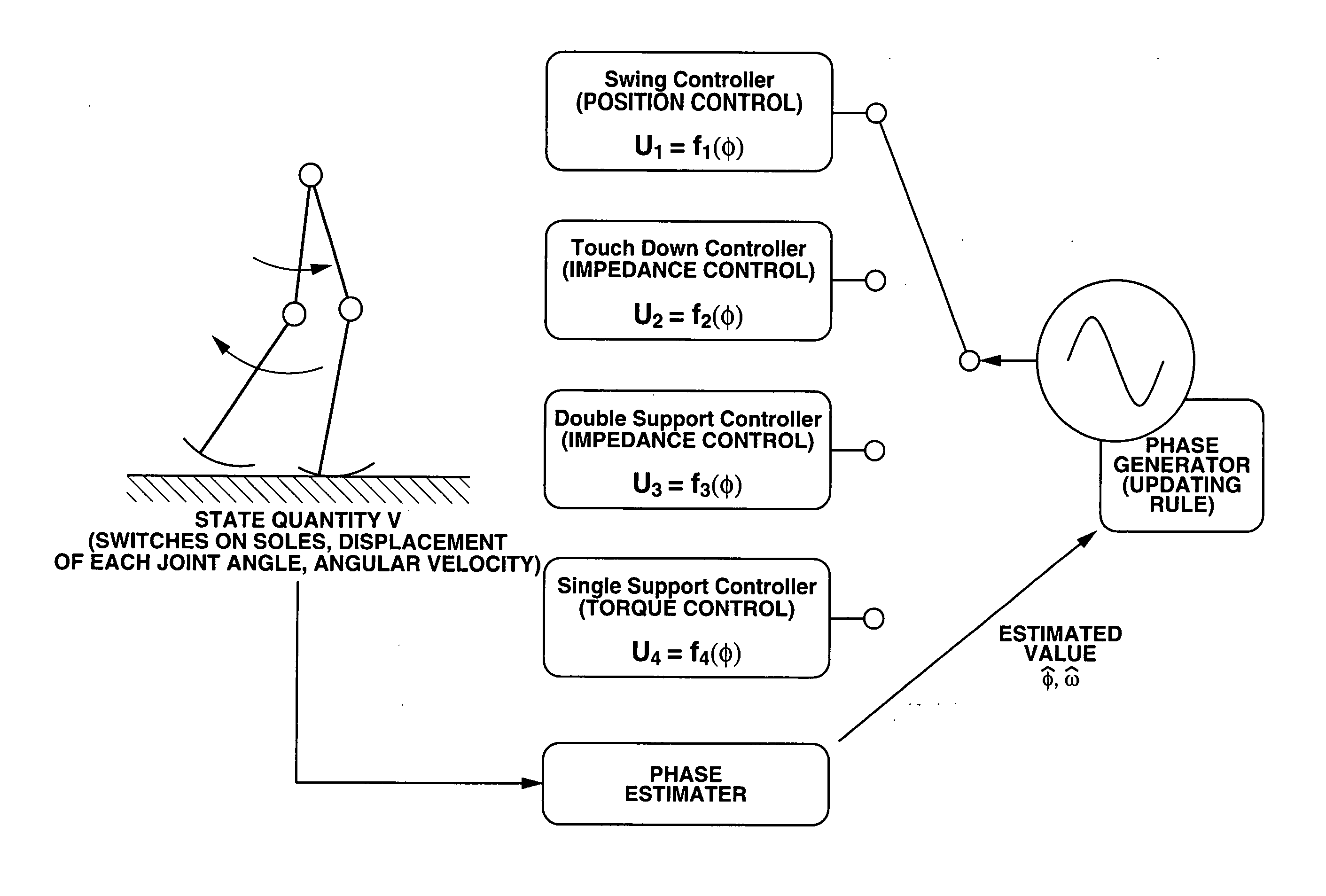
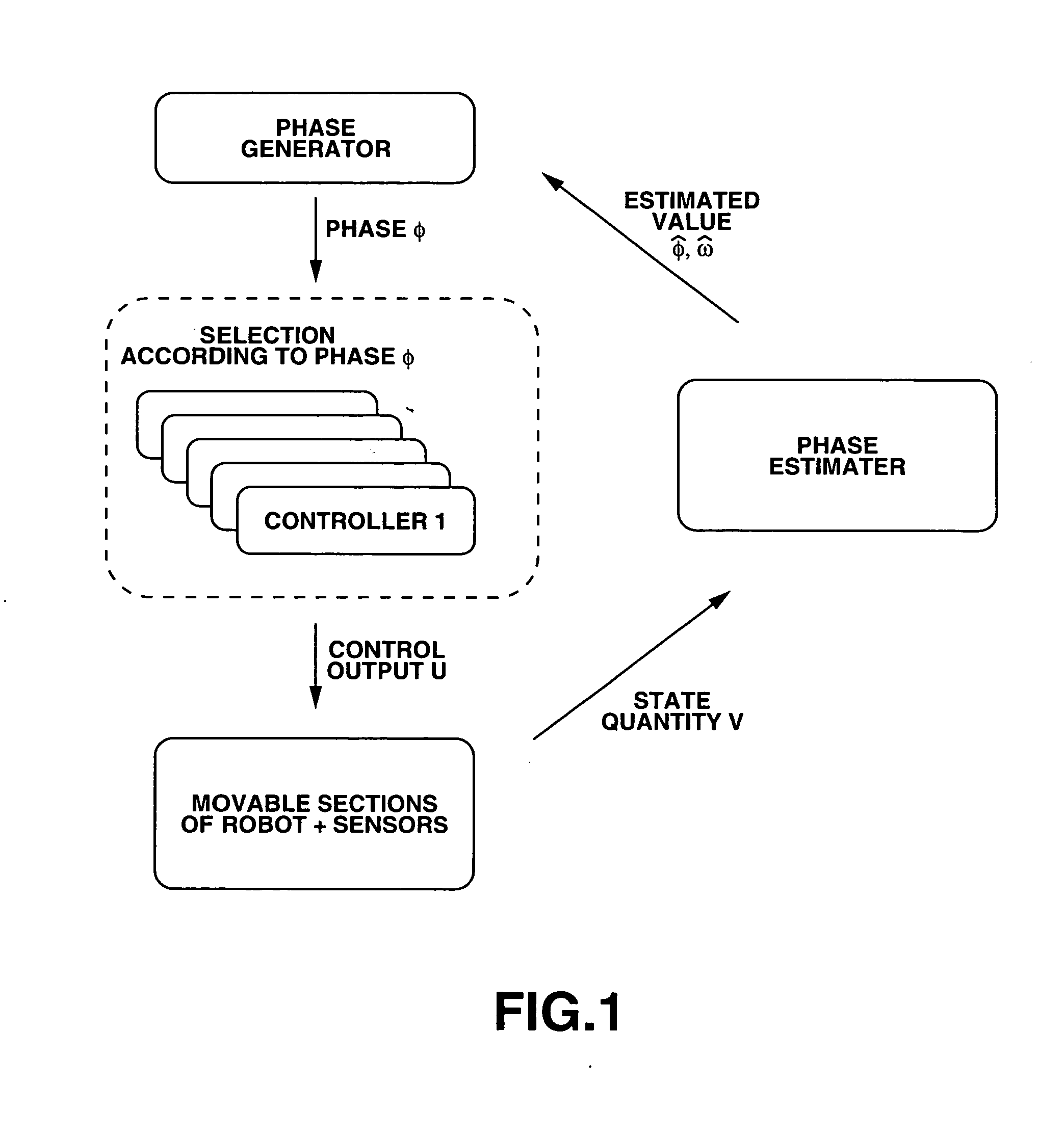
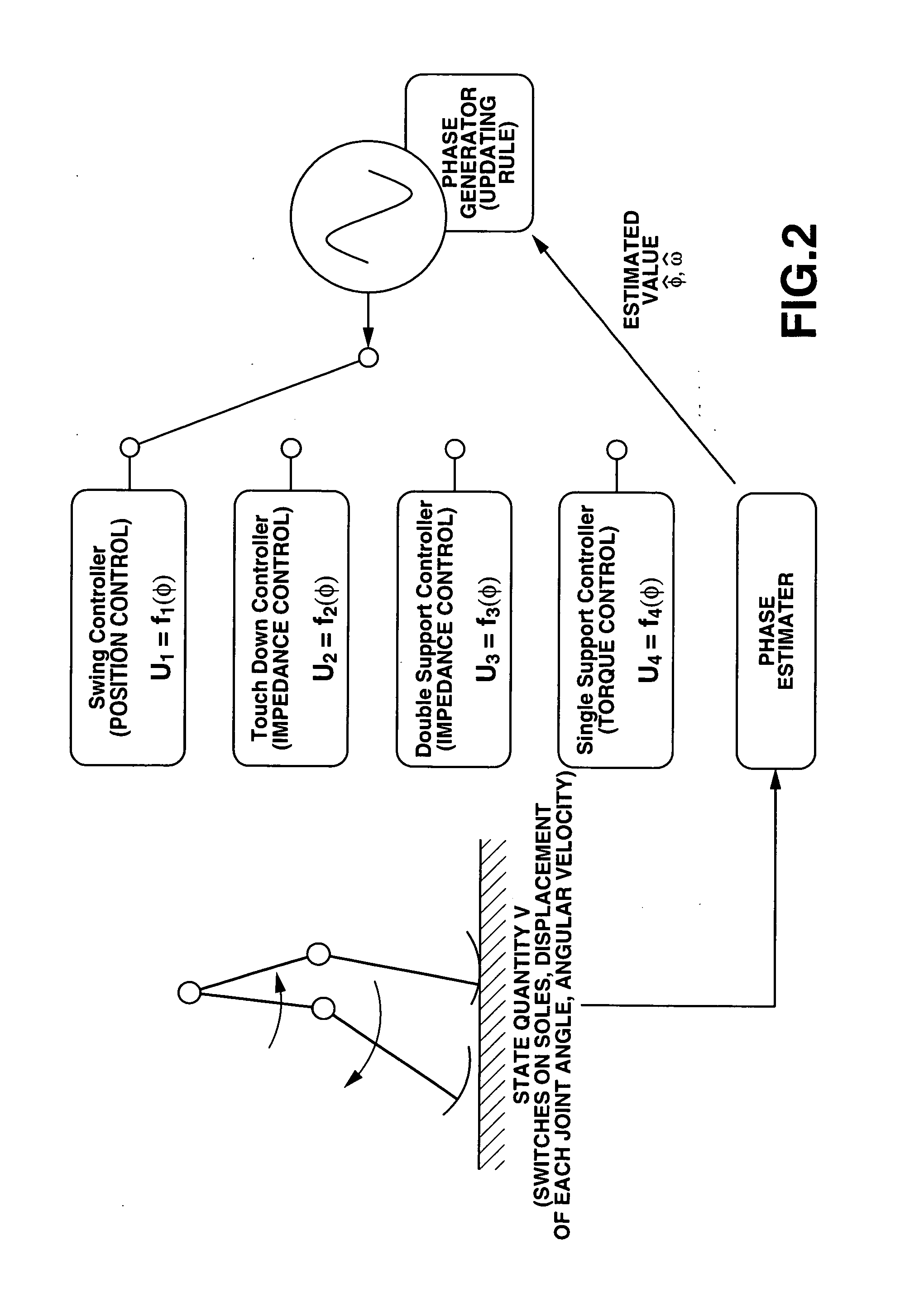
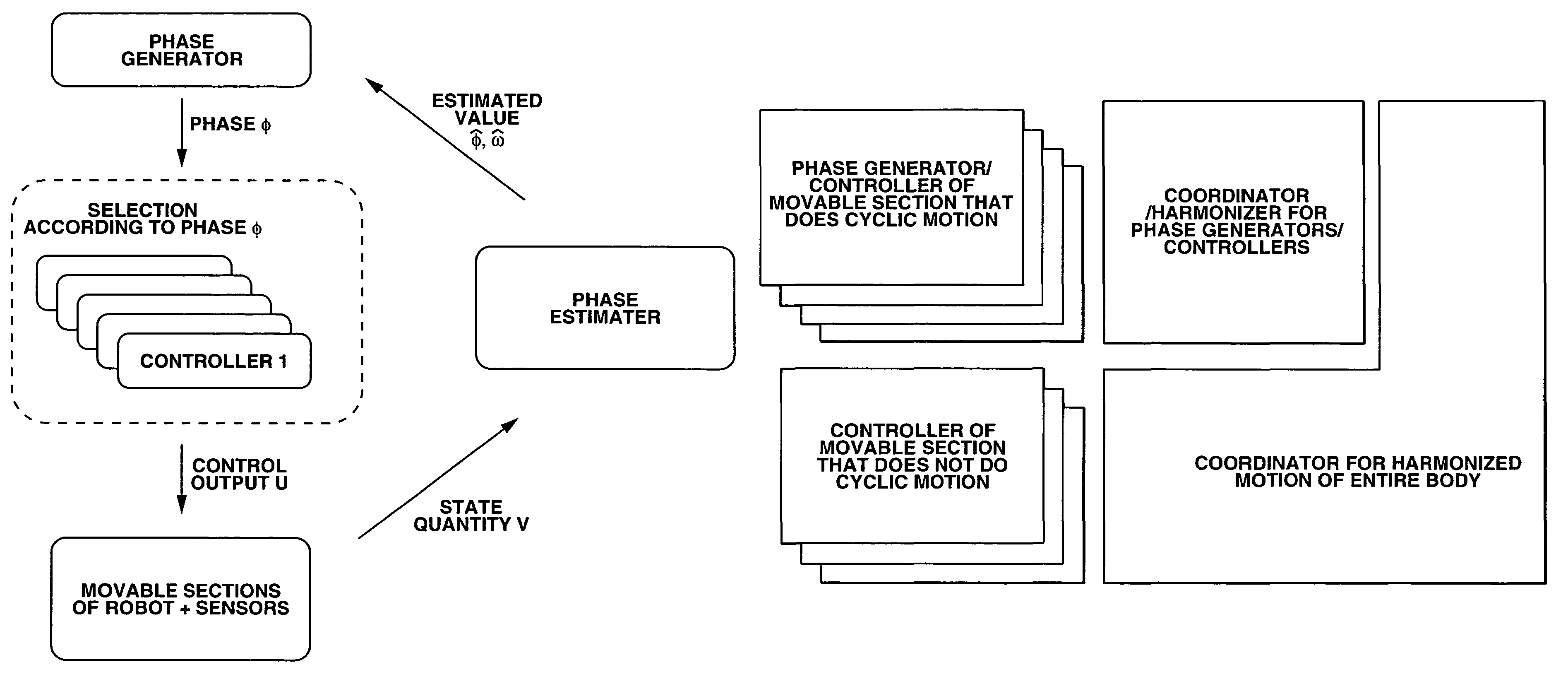
Robot and attitude control method of robot
ActiveUS20050113973A1Maintain stabilityStable controlProgramme-controlled manipulatorDigital dataRobotic systemsAttitude control
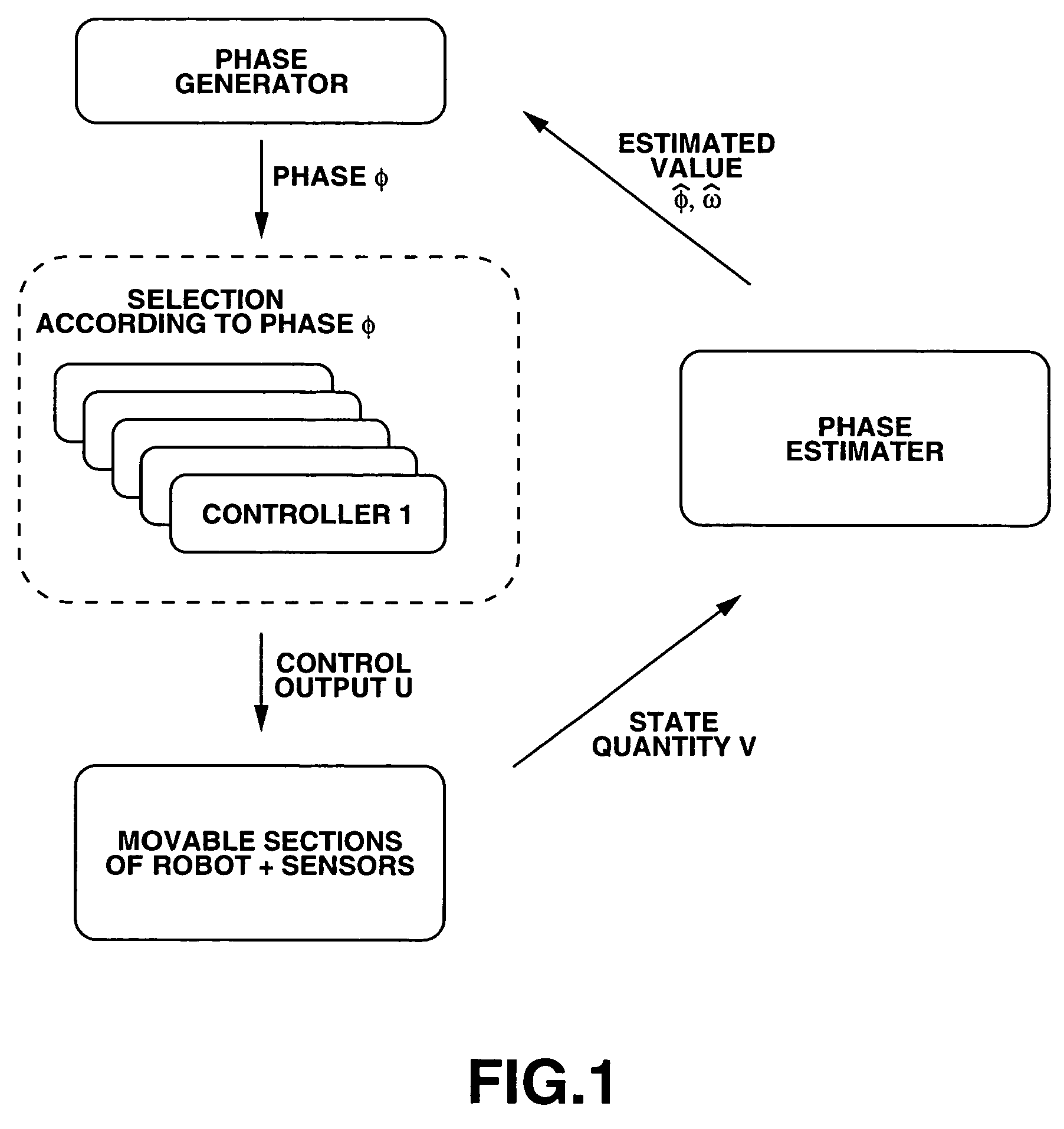
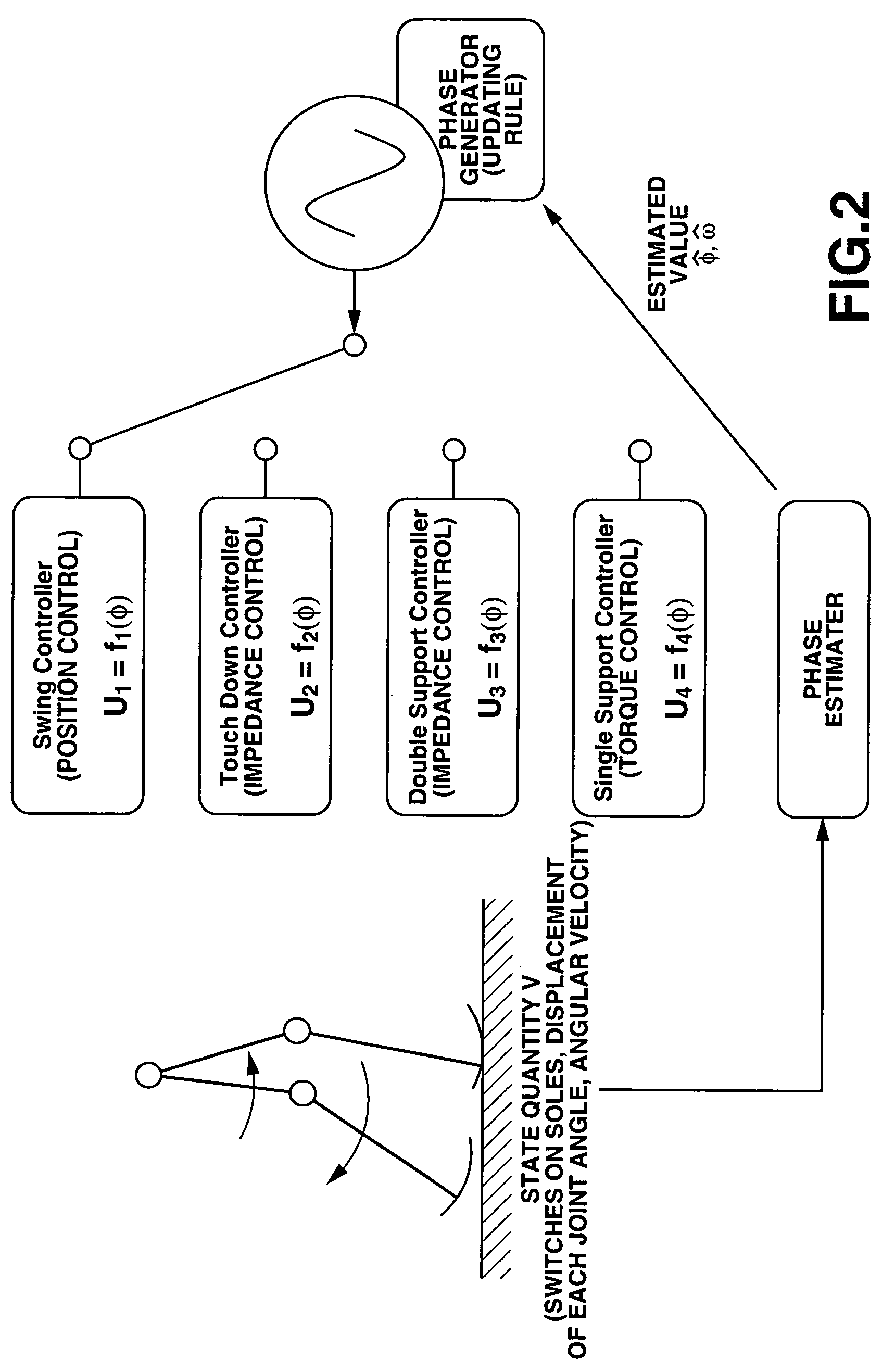
The motion of the movable sections of the robot is taken for a periodic motion so that the attitude of the robot can be stably controlled in a broad sense of the word by regulating the transfer of the movable sections. More specifically, one or more than one phase generators are used for the robot system and one of the plurality of controllers is selected depending on the generated phase. Then, the controller controls the drive of the movable sections according to continuous phase information. Additionally, the actual phase is estimated from the physical system and the frequency and the phase of the phase generator are regulated by using the estimated value, while the physical phase and the phase generator of the robot system are subjected to mutual entrainment so that consequently, it is possible to control the motion of the robot by effectively using the dynamics of the robot.
Owner:SONY CORP +1
Fault diagnostics and prognostics based on distance fault classifiers
InactiveUS7188482B2Easy to interpret, calibrate and implementMaximize distanceAir-treating devicesSpace heating and ventilationOnline algorithmAir filter
The present invention is directed to a mathematical approach to detect faults by reconciling known data driven techniques with a physical understanding of the HVAC system and providing a direct linkage between model parameters and physical system quantities to arrive at classification rules that are easy to interpret, calibrate and implement. The fault modes of interest are low system refrigerant charge and air filter plugging. System data from standard sensors is analyzed under no-fault and full-fault conditions. The data is screened to uncover patterns though which the faults of interest manifest in sensor data and the patterns are analyzed and combined with available physical system information to develop an underlying principle that links failures to measured sensor responses. These principles are then translated into online algorithms for failure detection.
Owner:CARRIER CORP
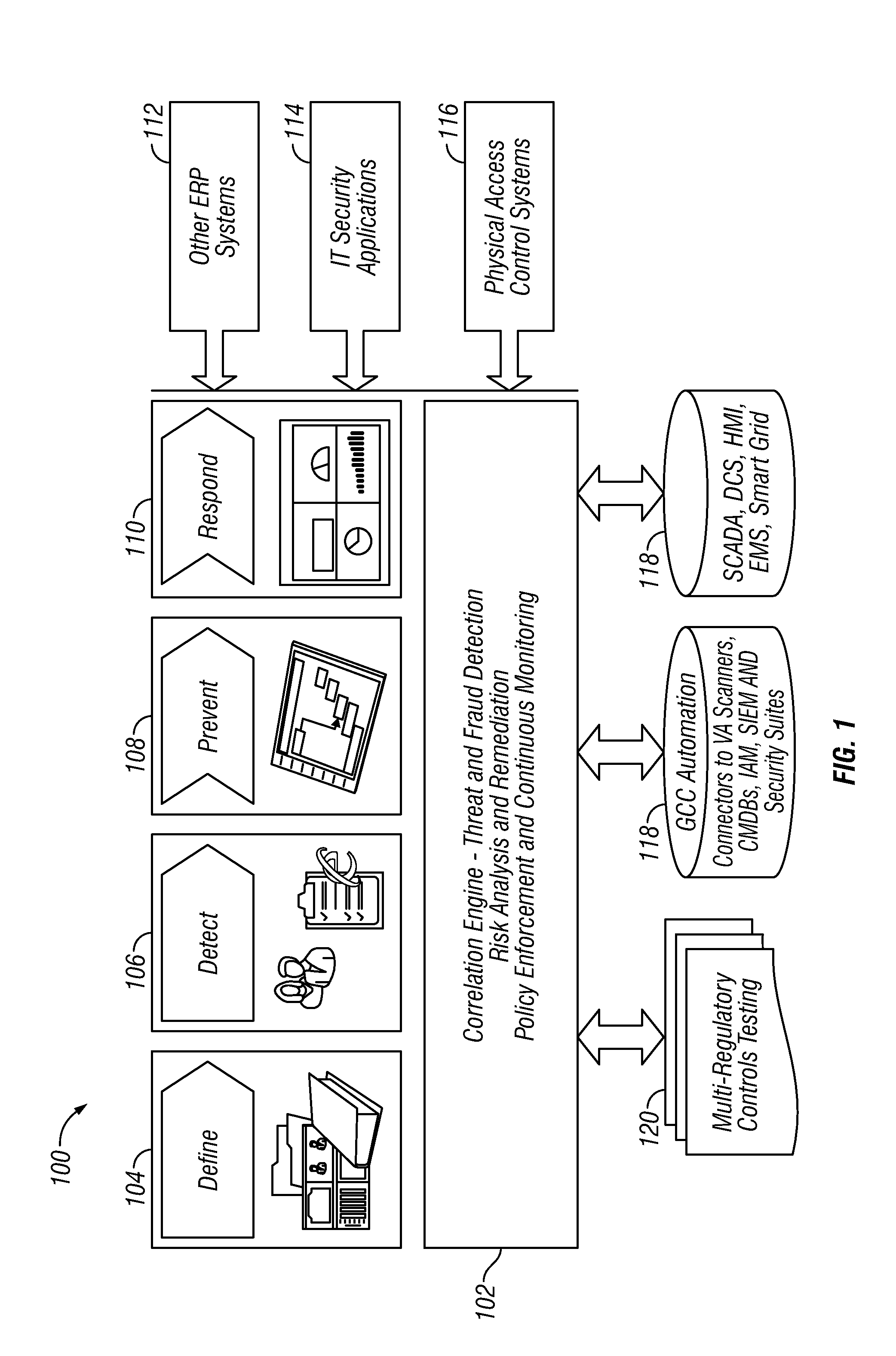
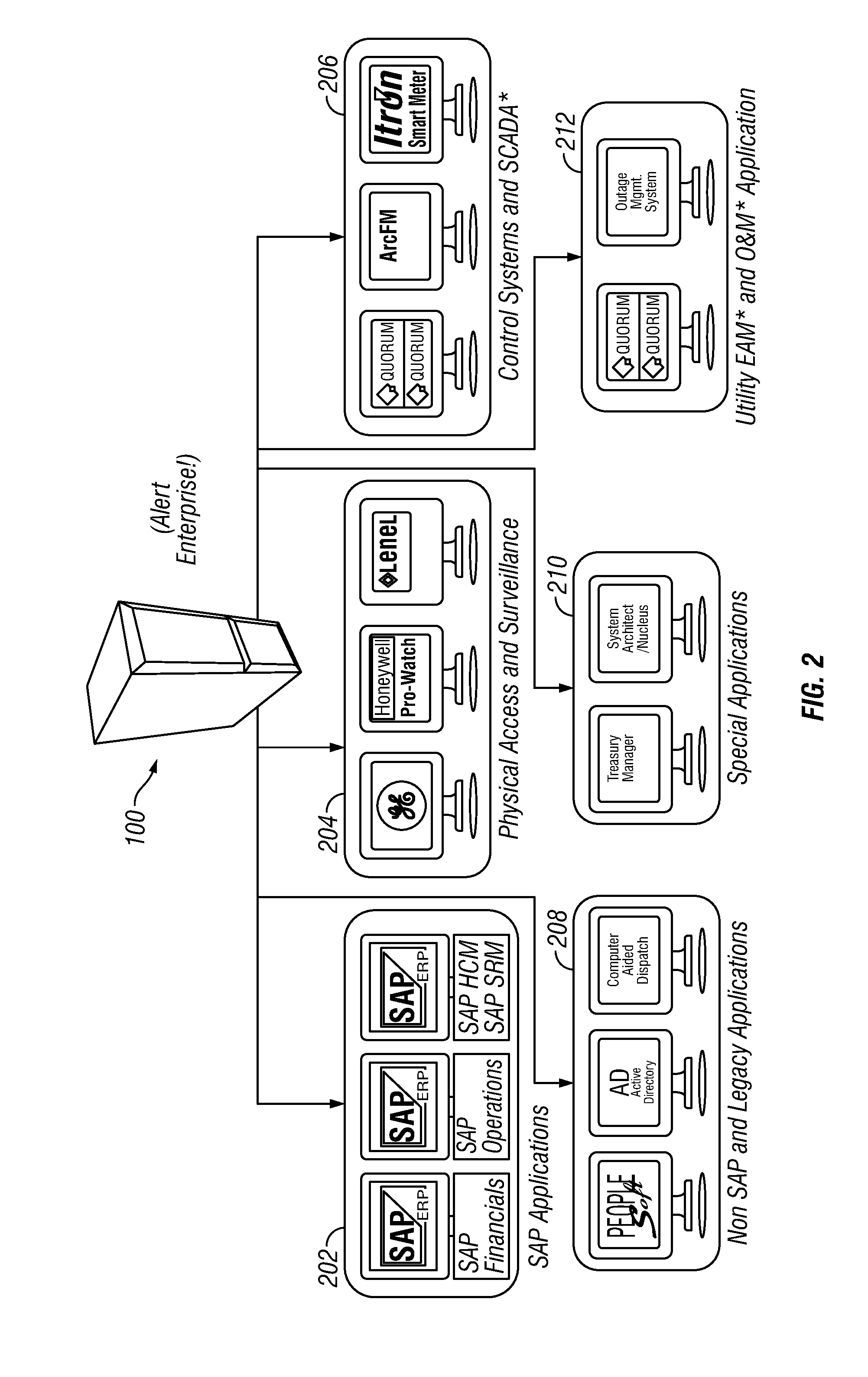
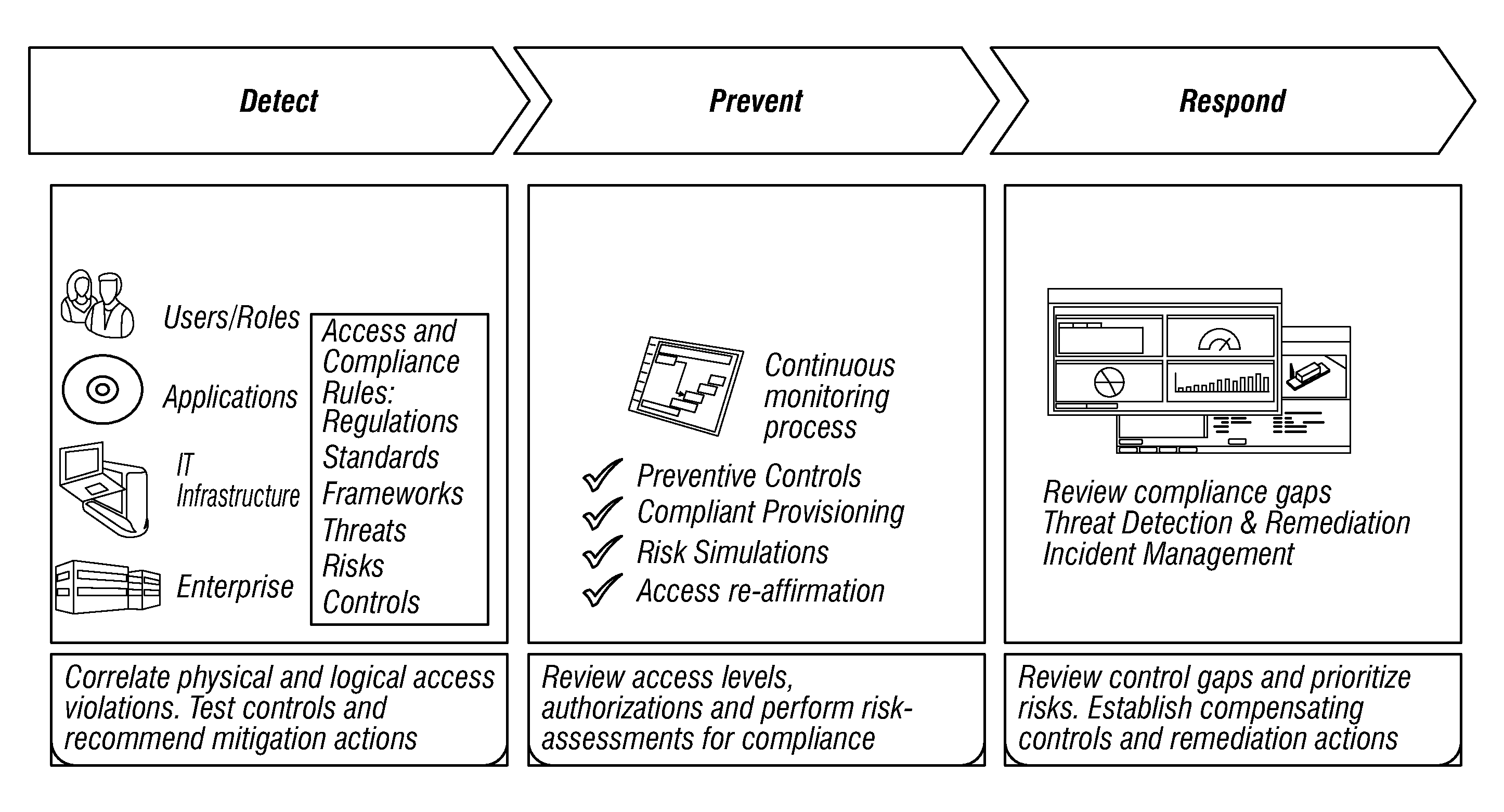
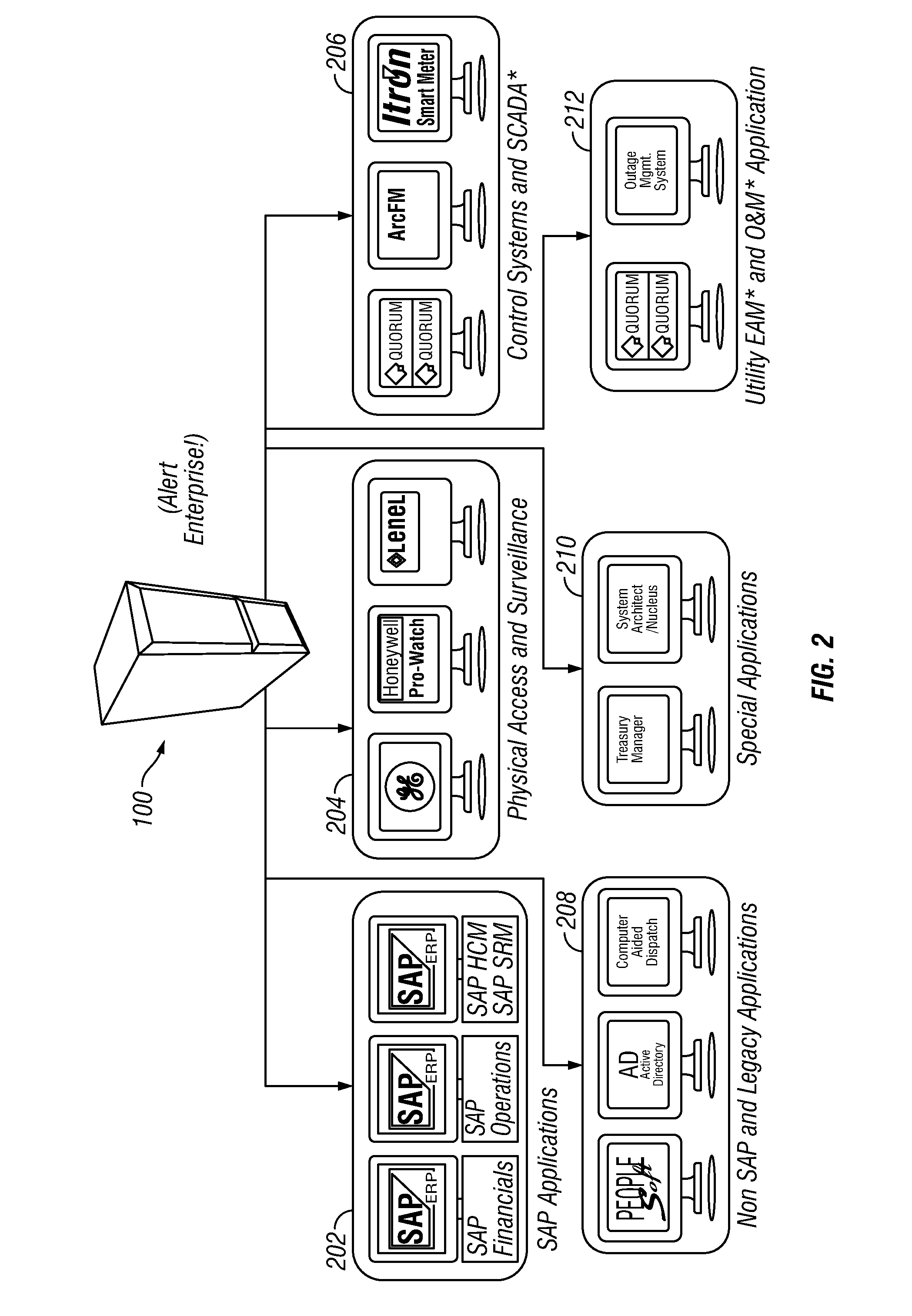
Situational intelligence
ActiveUS20120224057A1Color television detailsClosed circuit television systemsDashboardRemedial action
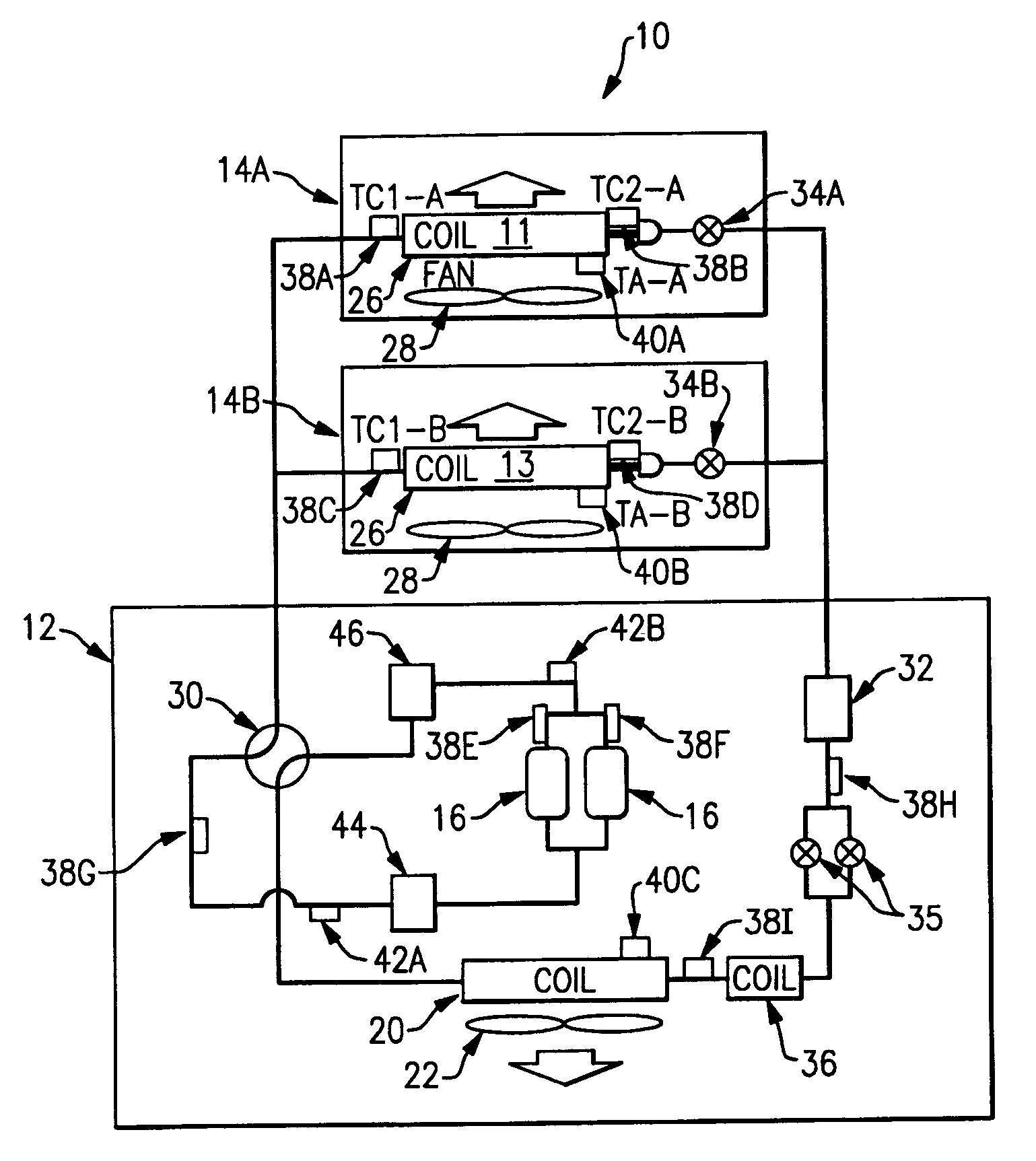
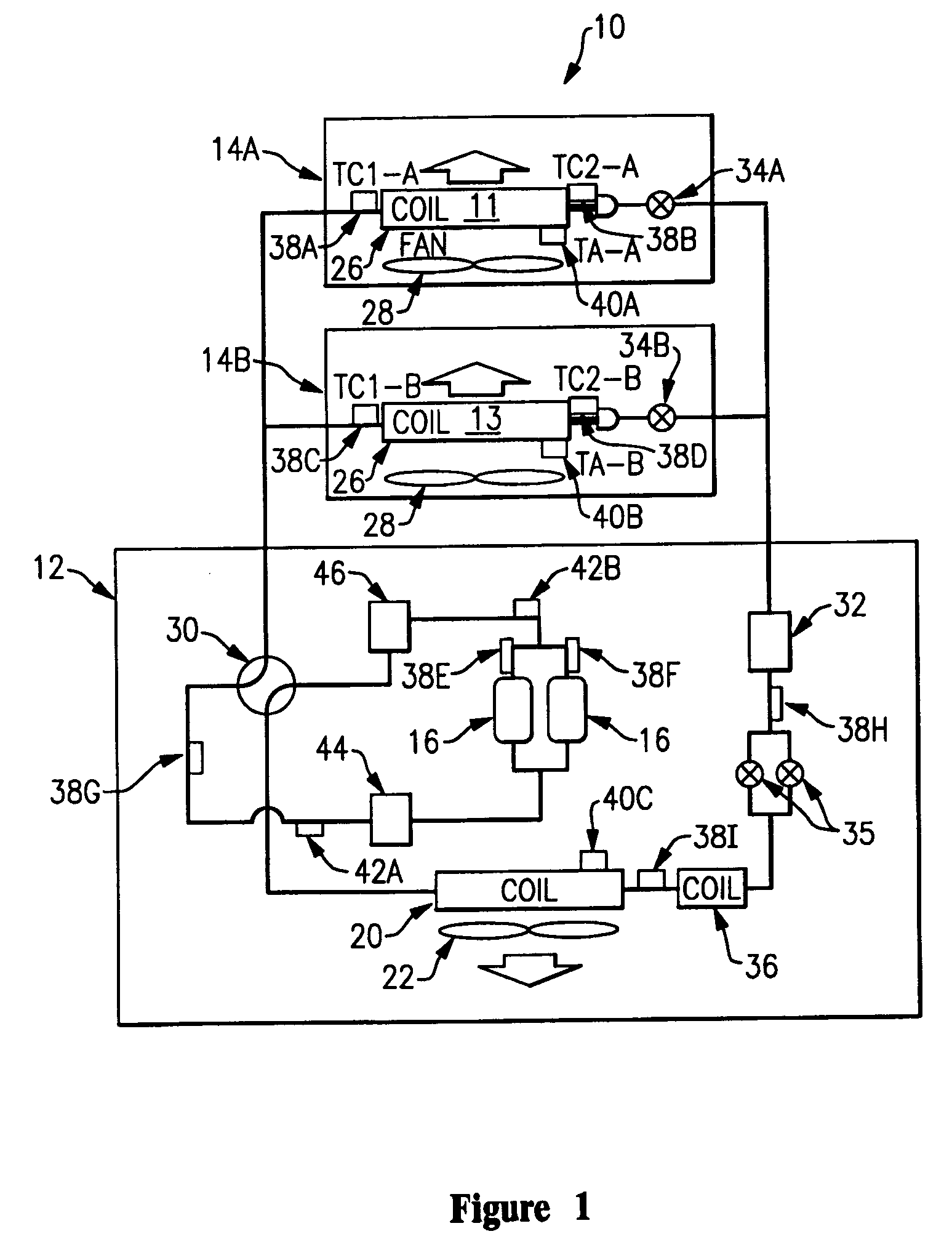
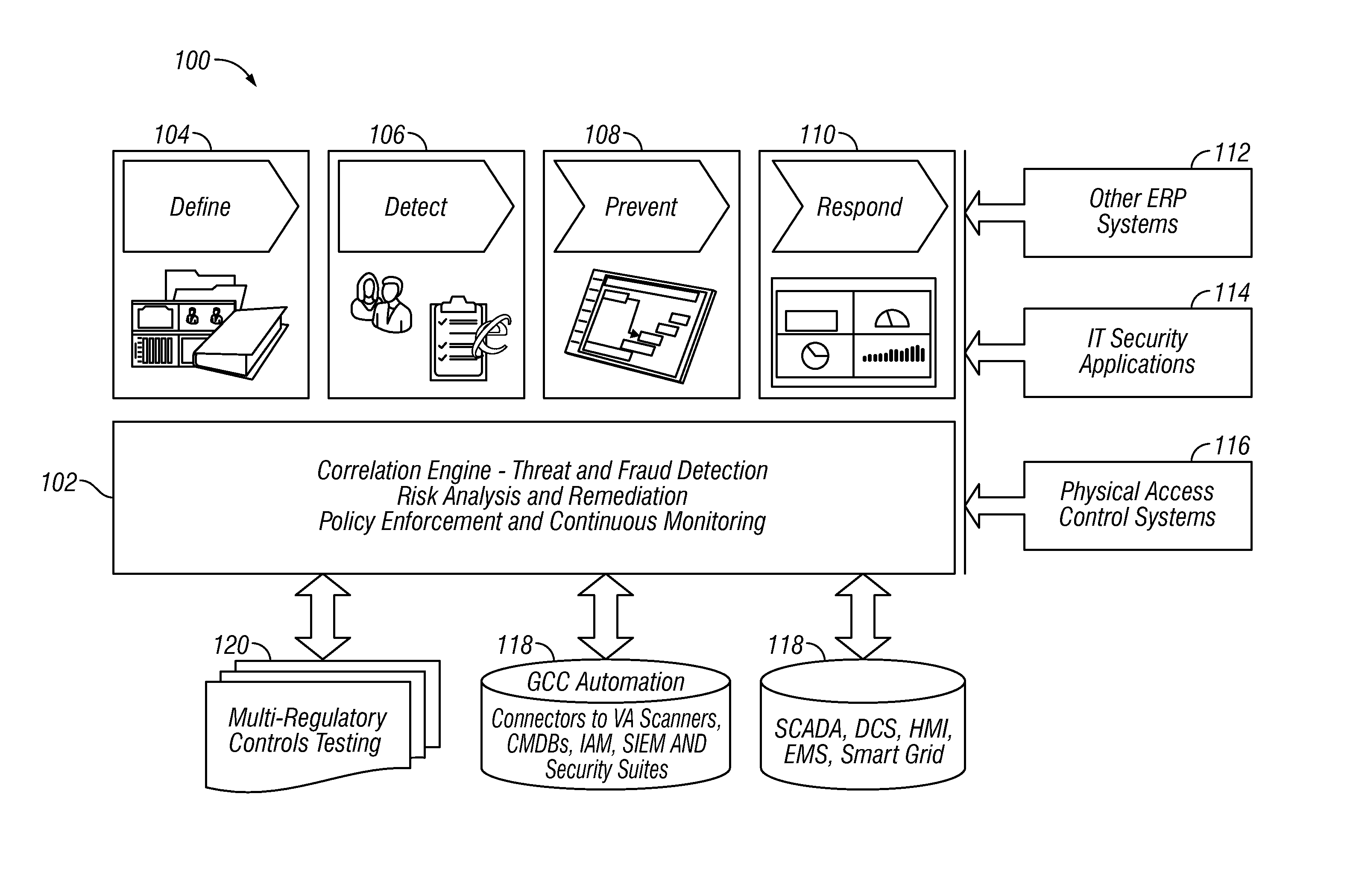
A method and apparatus is provided that includes techniques for providing complete solutions for role-based, rules-driven access enforcement, the techniques including situational awareness and video surveillance. An embodiment addresses blended risk assessment and security across logical systems, IT applications, databases, and physical systems from a single analytic dashboard, with auto-remediation capabilities. Further, an embodiment provides capability and functionality for co-relating seemingly innocent events and activities to detect real threats and risks, while providing powerful alerting and automated remedial action strategies for decisive action.
Owner:ALERT ENTERPRISE
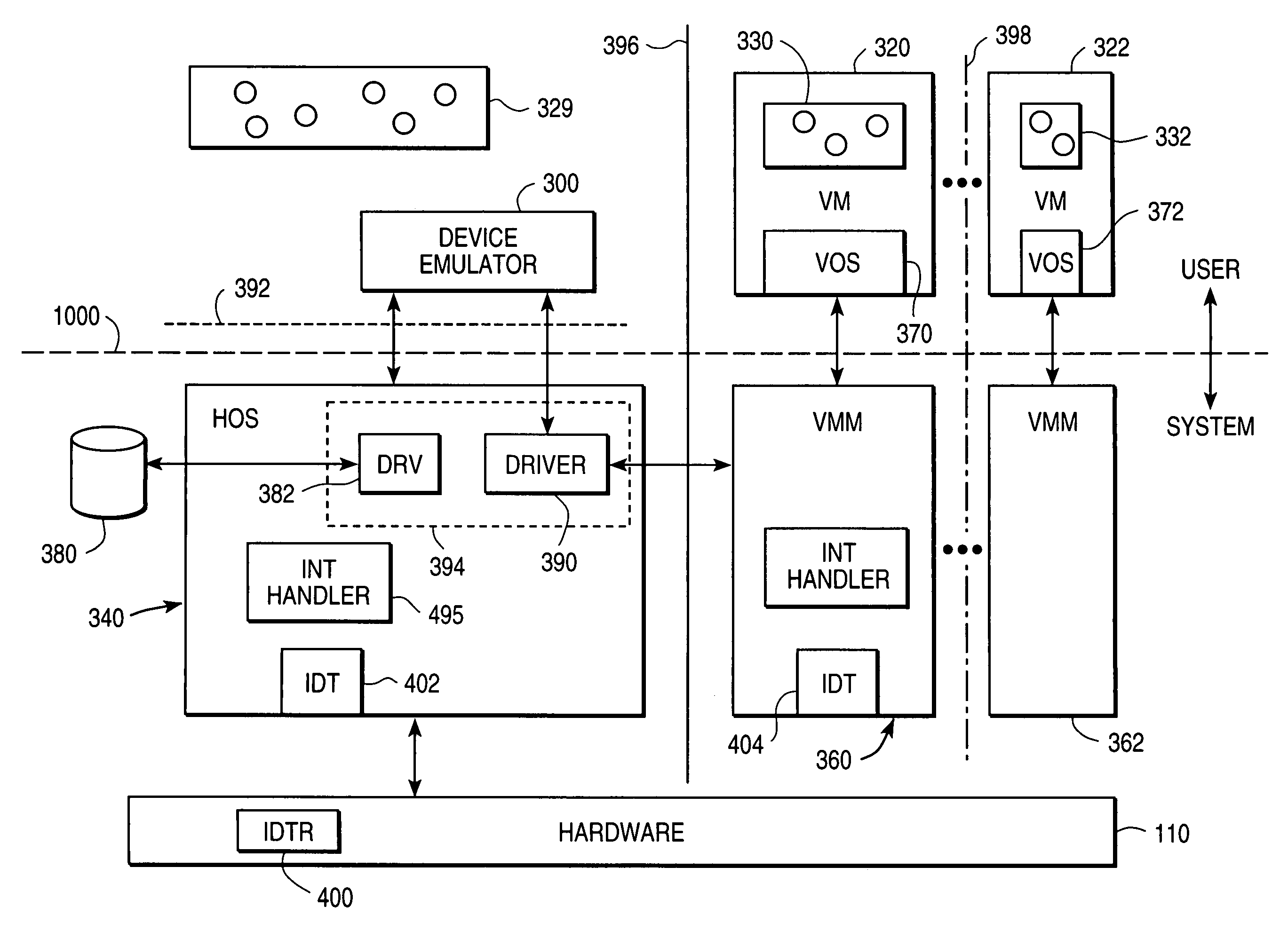
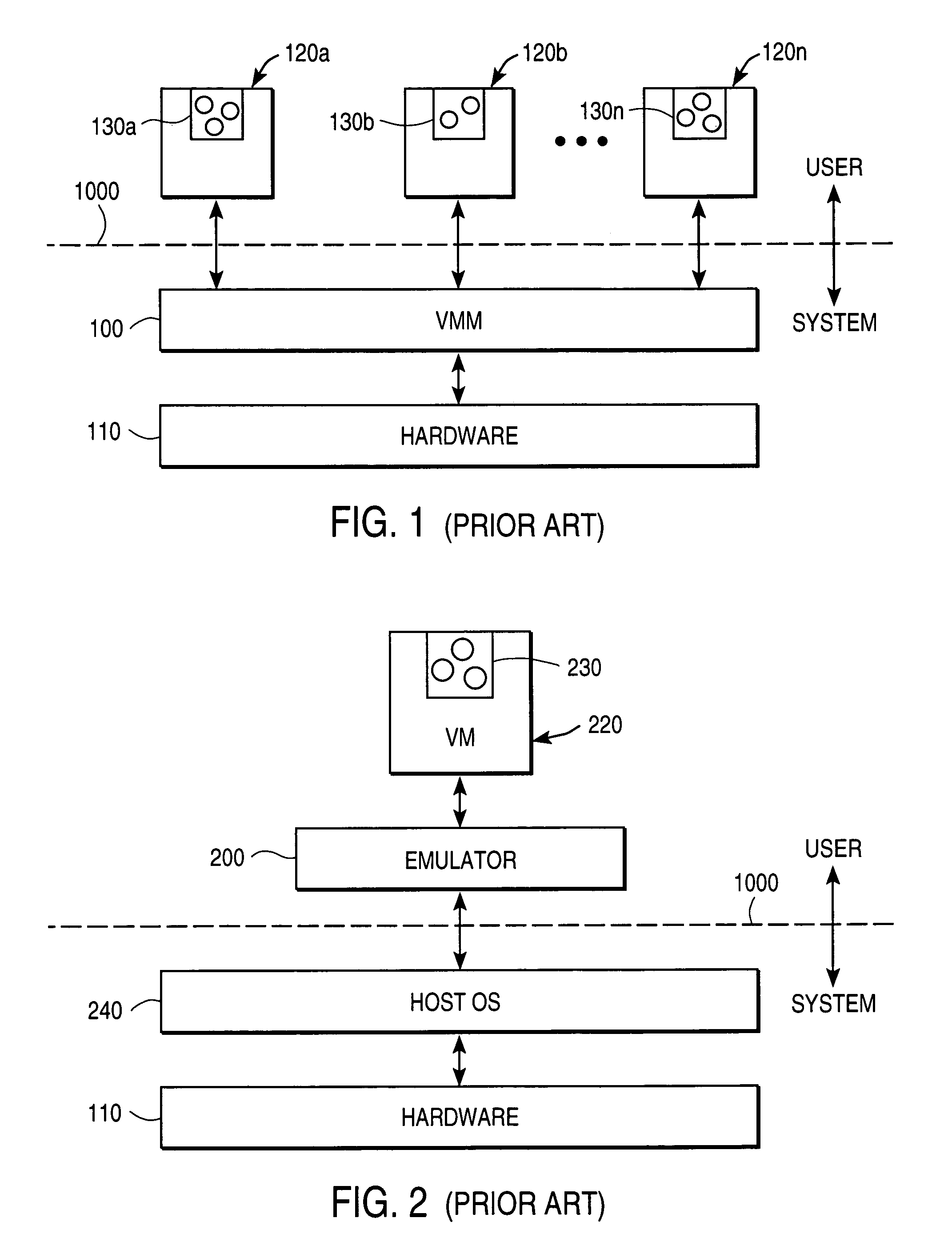
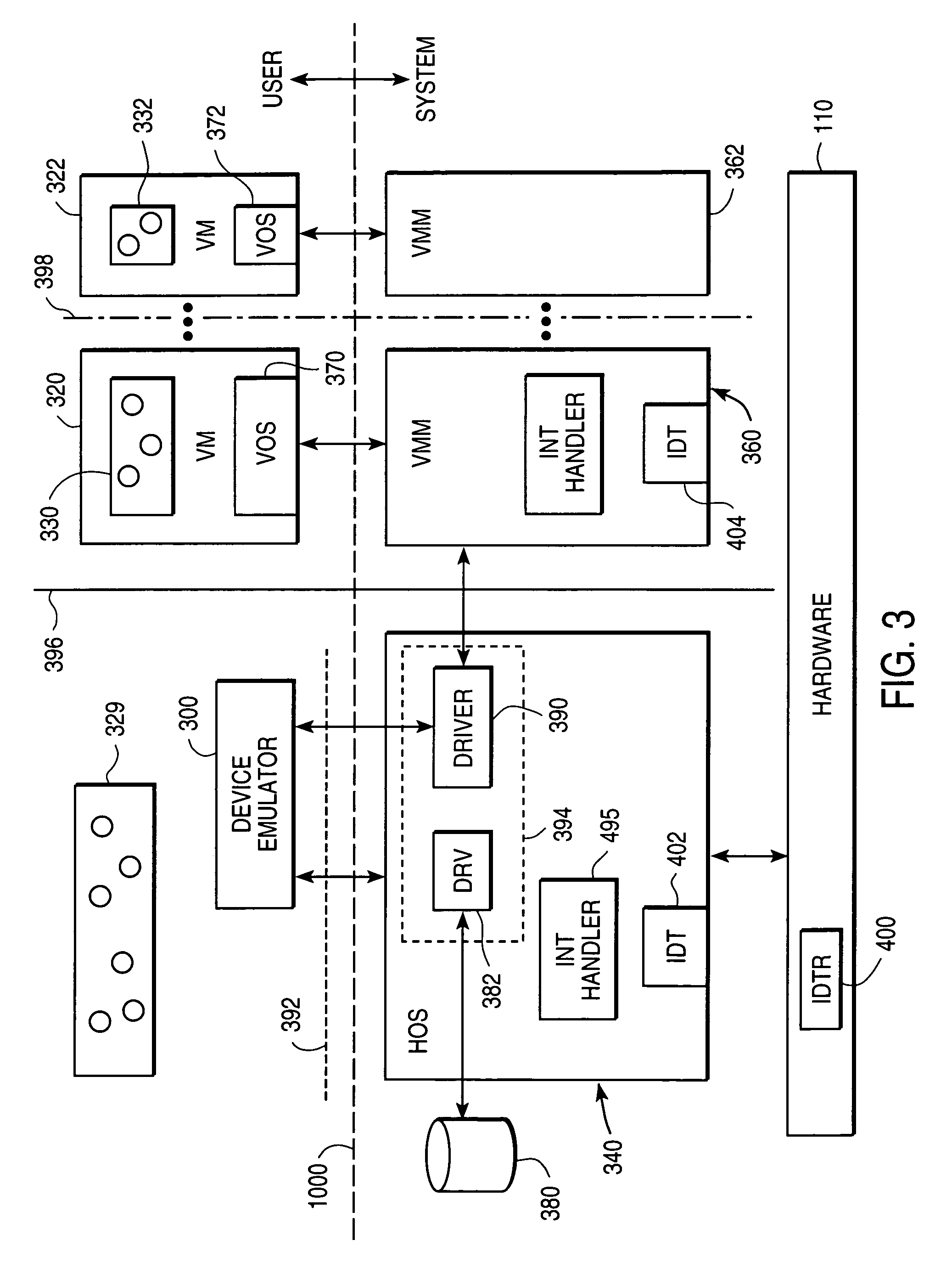
System and method for facilitating context-switching in a multi-context computer system
InactiveUS6944699B1Software simulation/interpretation/emulationMemory systemsOperational systemProcedure calls
A virtual machine monitor (VMM) is included in a computer system that has a protected host operating system (HOS). A virtual machine running at least one application via a virtual operating system is connected to the VMM. Both the HOS and the VMM have separate operating contexts and disjoint address spaces, but are both co-resident at system level. A driver that is downloadable into the HOS at system level forms a total context switch between the VMM and HOS contexts. A user-level emulator accepts commands from the VMM via the system-level driver and processes these commands as remote procedure calls. The emulator is able to issue host operating system calls and thereby access the physical system devices via the host operating system. The host operating system itself thus handles execution of certain VMM instructions, such as accessing physical devices.
Owner:VMWARE INC
Policy/rule engine, multi-compliance framework and risk remediation
Owner:ALERT ENTERPRISE
Integrated forensics platform for analyzing IT resources consumed to derive operational and architectural recommendations
ActiveUS8880682B2Easy to analyzeHardware monitoringMultiple digital computer combinationsStructure of Management InformationPhysical system
A method for facilitating forensic analysis of operational data for an IT infrastructure includes deriving performance data from a plurality of physical systems, network elements and storage devices in an IT infrastructure via a toolset comprising a plurality of IT monitoring and metrics tools, importing the performance data into an integrated forensics platform, aggregating the imported data, and analyzing the aggregated data to determine resources consumed. Each tool is communicatively interfaced with one or more of the physical systems, network elements and storage devices.
Owner:EMC IP HLDG CO LLC
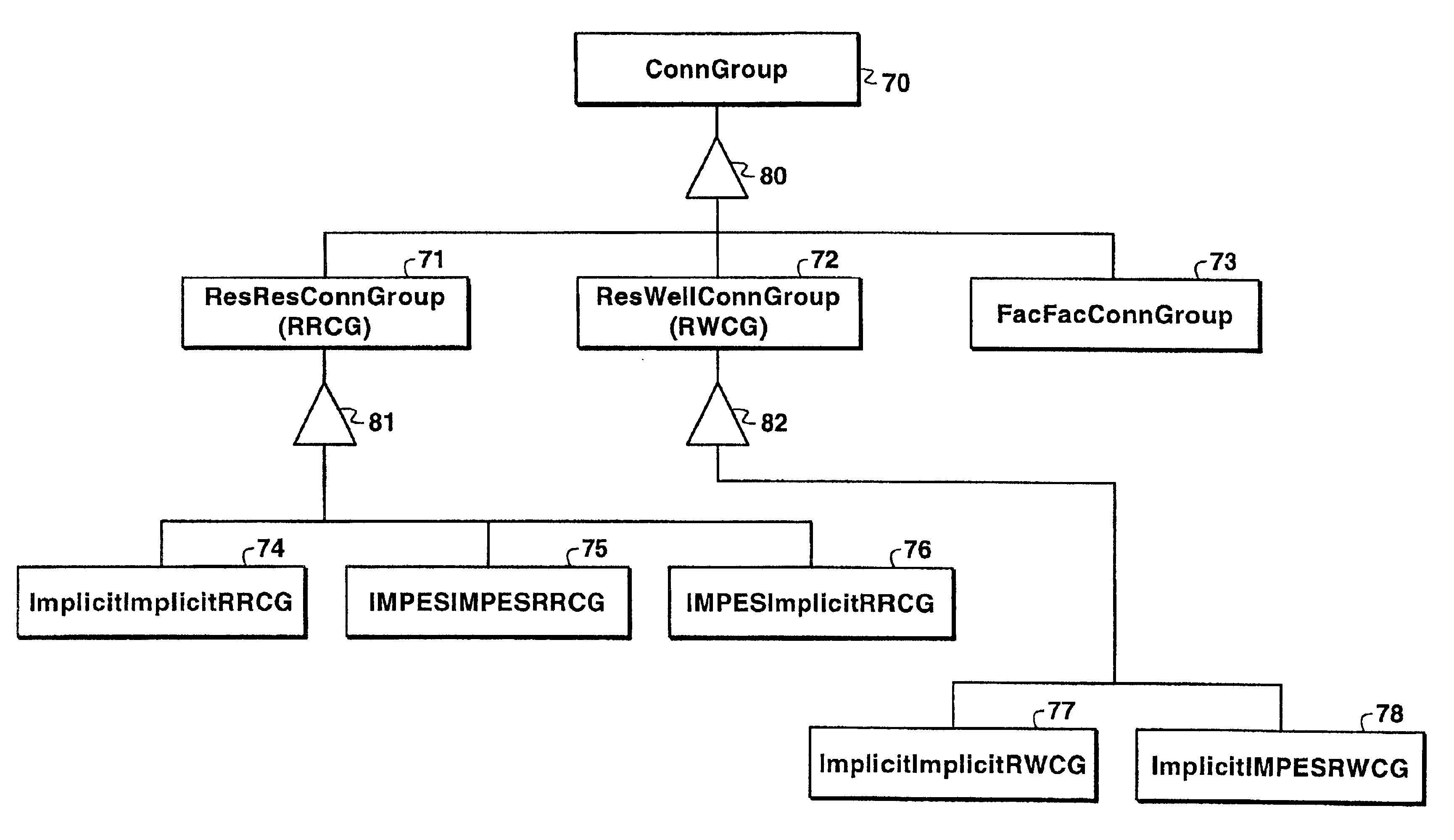
Method and program for simulating a physical system using object-oriented programming
InactiveUS6928399B1Electric/magnetic detection for well-loggingFluid removalPhysical systemComputer science
The invention relates to an object-oriented method for simulating a property of at least one fluid in a fluid-containing physical system in which the physical system is represented by a multiplicity of volumetric cells and a multiplicity of connections between cells. The method uses cell-group objects and connection-group objects in the simulation. The invention can optionally comprise additional objects such as an object containing the entire model of the simulation and another object containing a portion of the entire model.
Owner:EXXONMOBIL UPSTREAM RES CO
System and method for monitoring water content or other dielectric influences in a medium
Owner:BATTELLE ENERGY ALLIANCE LLC +1
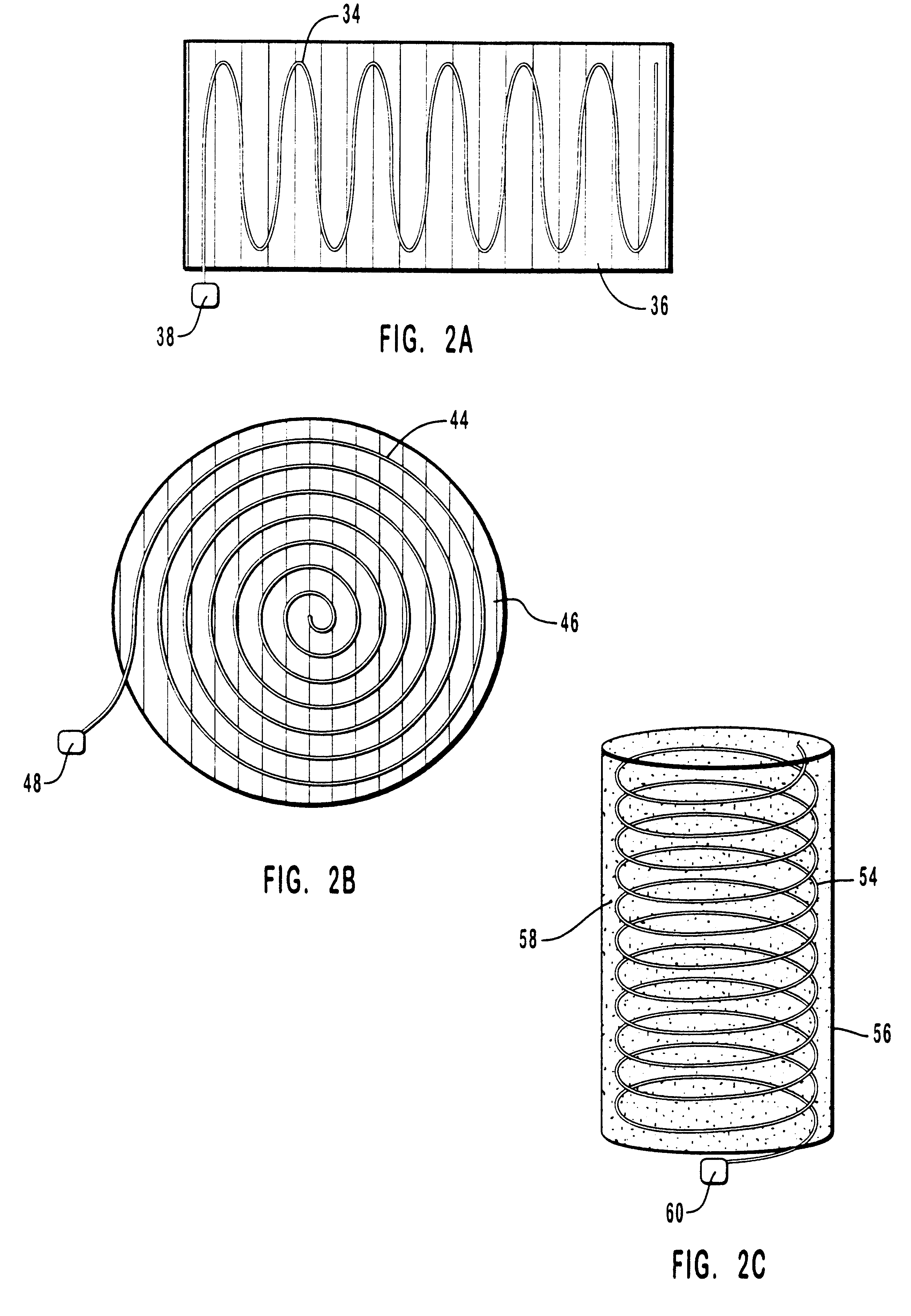
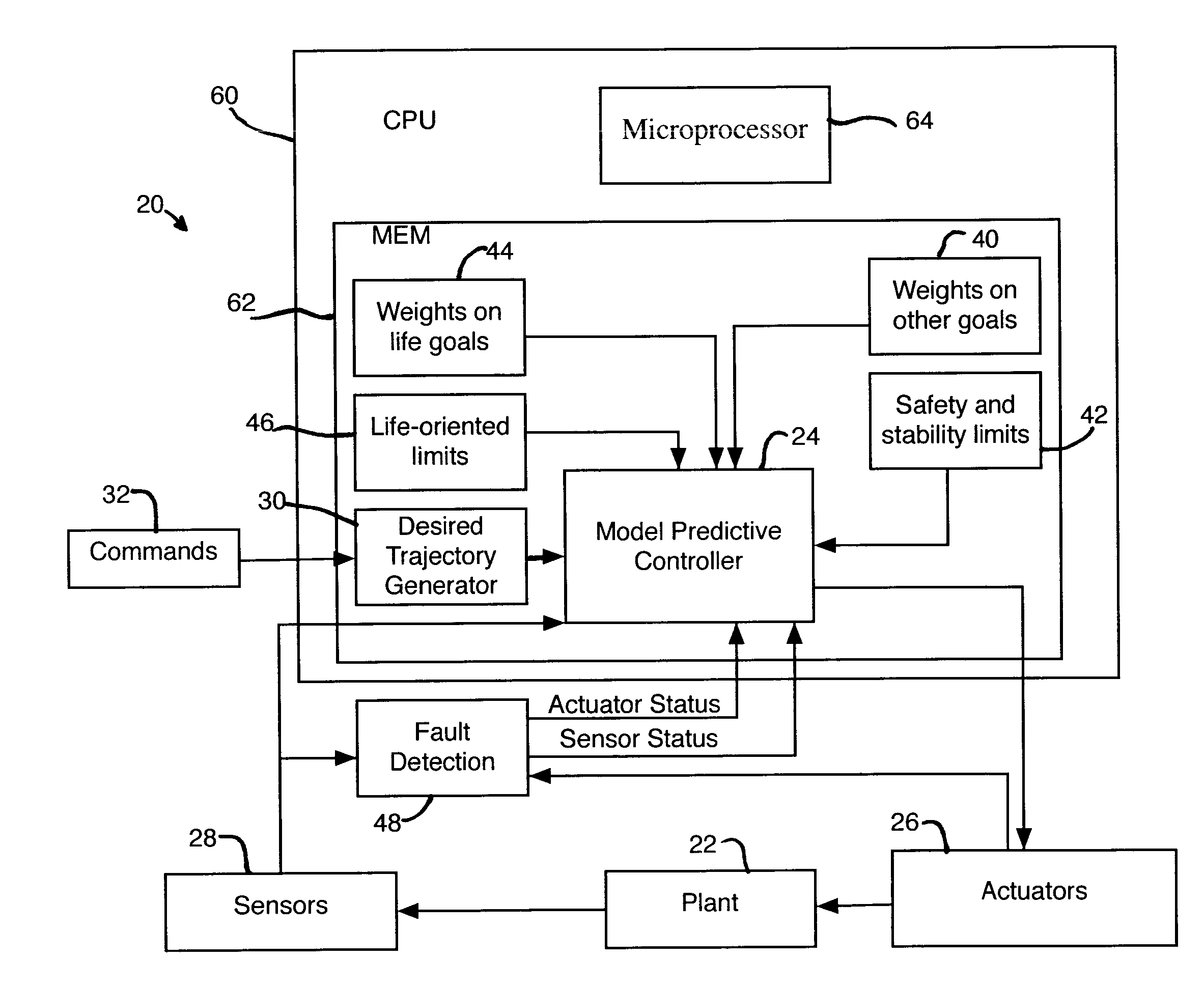
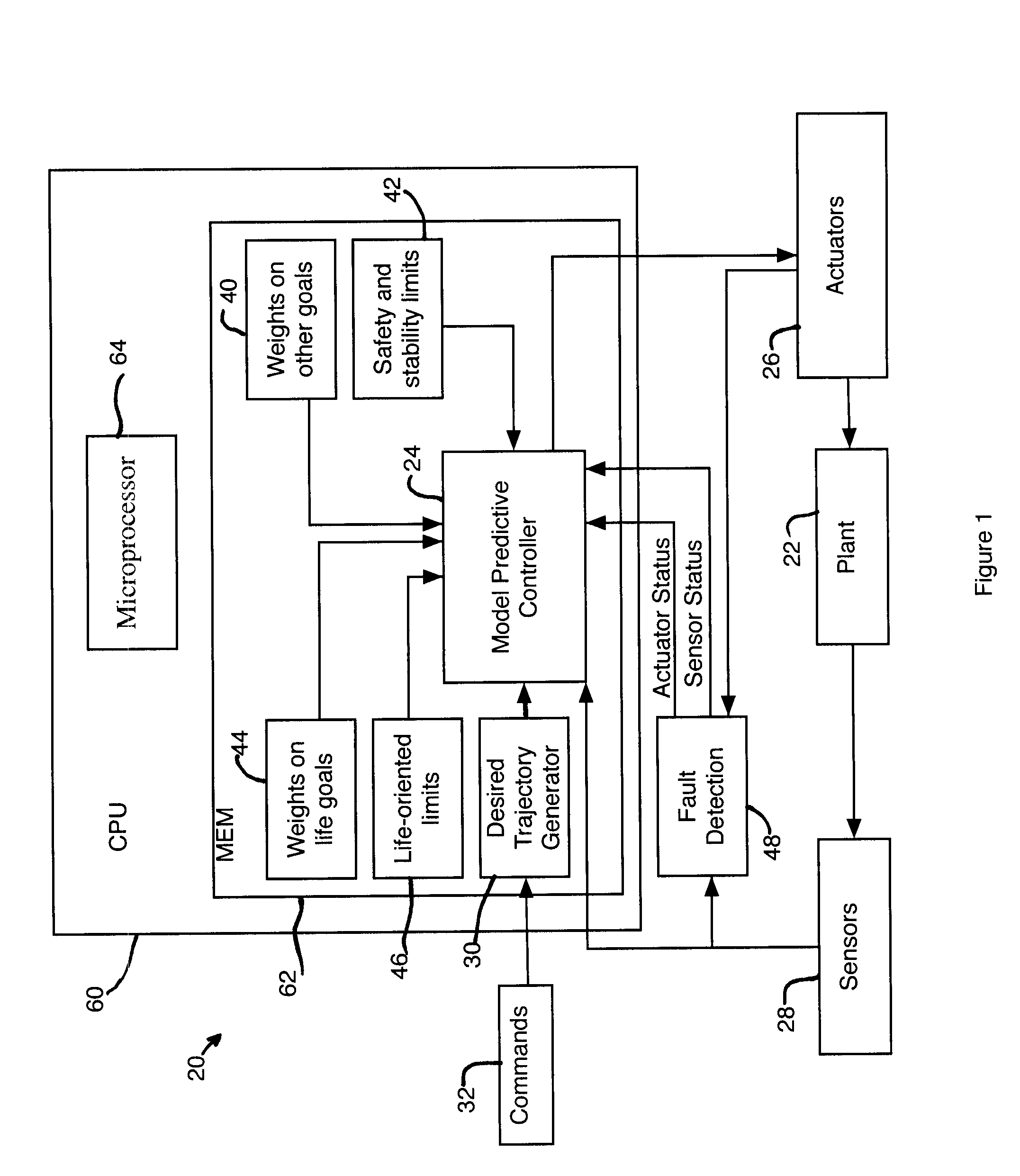
Model predictive controller with life extending control
ActiveUS7203554B2Reduce in quantityProlong lifeElectric testing/monitoringSpecial data processing applicationsControl systemPredictive controller
An MPC Control system provides a life extending control that includes life-extending goals in the performance index of the MPC controller and limits in the inequality equations. The MPC controller performs the normal functions of a control system for a physical system, but does so in a manner that extends the life or time-to-next maintenance or reduces the number of parts that need to be replaced. If the life extending functions do not degrade other control functions, they can be always enabled, making the system less expensive to maintain. If the life extending functions degrade some other control functions, they can be adjusted in-the-field or on-the-fly to stretch the time-until-maintenance until it is more convenient, but with some impact on performance.
Owner:RTX CORP
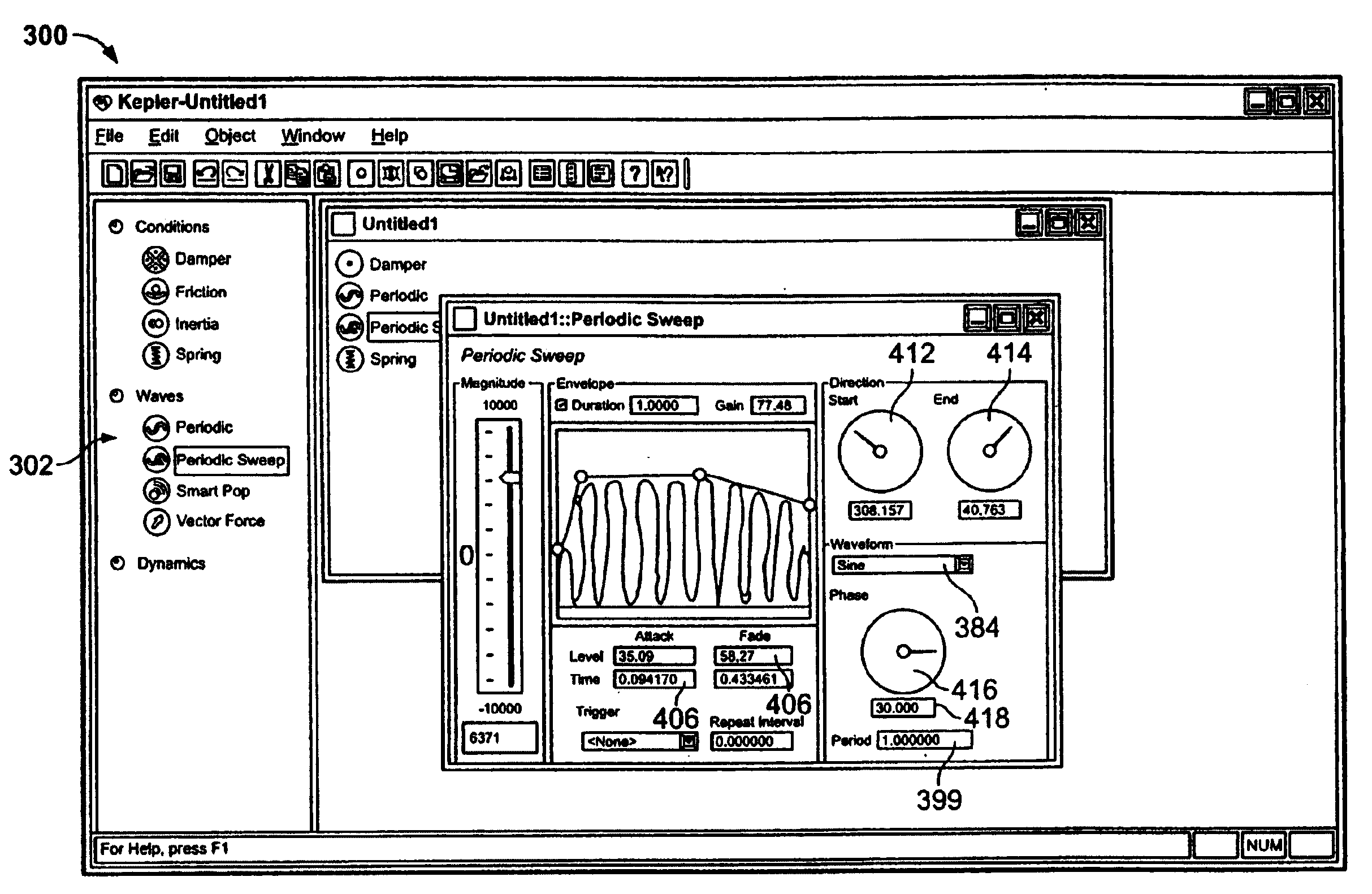
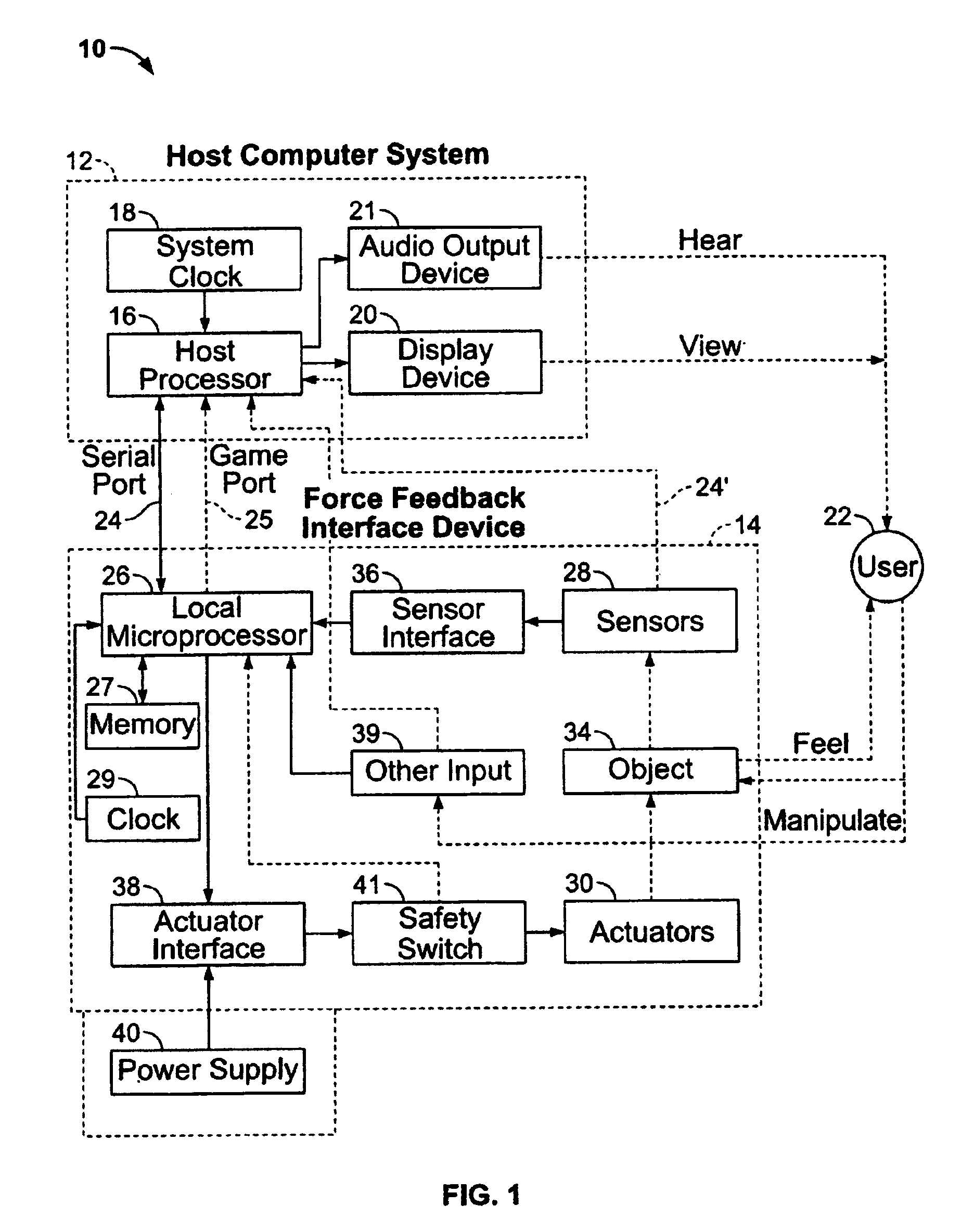
Method and apparatus for providing dynamic force sensations for force feedback computer applications
InactiveUS7039866B1Simple and intuitive designPromoting further understandingInput/output for user-computer interactionManual control with multiple controlled membersGraphicsJoystick
A method and apparatus for providing dynamic force sensations for use with a force feedback interface device. A force feedback interface device is connected to a host computer that implements a graphical environment. The host sends commands and command parameters to the interface device to initiate and characterize dynamic force sensations output on a user manipulatable object, such as a joystick. The interface device can include a local microprocessor for implementing force sensations by controlling actuators and reading sensors according to the host commands. A dynamic force routine can control the dynamic force sensations by implementing a simulated physical system including a simulated mass capable of motion independent of the user object. The physical system provides forces on the user object influenced by motion of both the user object and the simulated mass.
Owner:IMMERSION CORPORATION
Robot and attitude control method of robot
ActiveUS7657345B2Stable controlProgramme-controlled manipulatorDigital dataRobotic systemsAttitude control
The motion of the movable sections of the robot is taken for a periodic motion so that the attitude of the robot can be stably controlled in a broad sense of the word by regulating the transfer of the movable sections. More specifically, one or more than one phase generators are used for the robot system and one of the plurality of controllers is selected depending on the generated phase. Then, the controller controls the drive of the movable sections according to continuous phase information. Additionally, the actual phase is estimated from the physical system and the frequency and the phase of the phase generator are regulated by using the estimated value, while the physical phase and the phase generator of the robot system are subjected to mutual entrainment so that consequently, it is possible to control the motion of the robot by effectively using the dynamics of the robot.
Owner:SONY CORP +1
Intelligent production system and method based on edge calculation and digital twinning
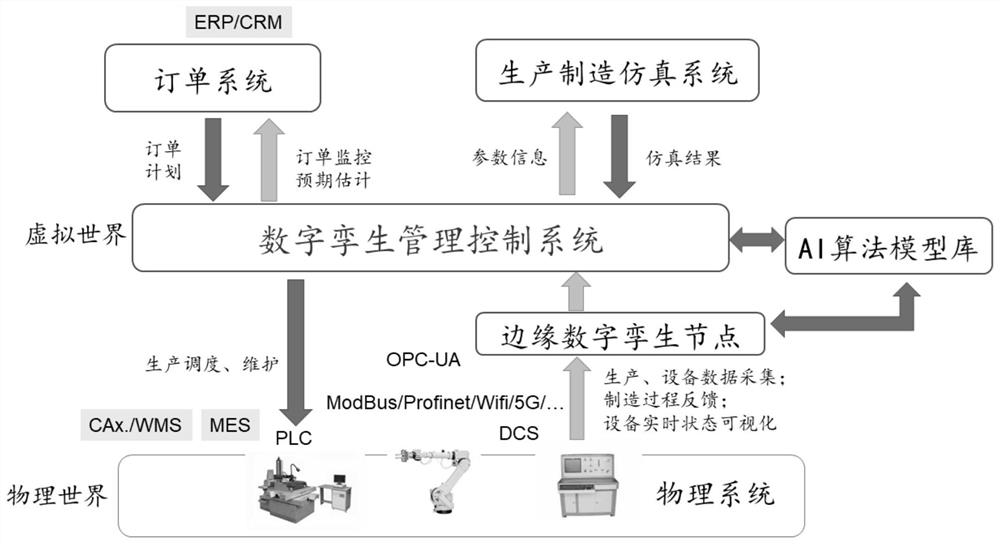
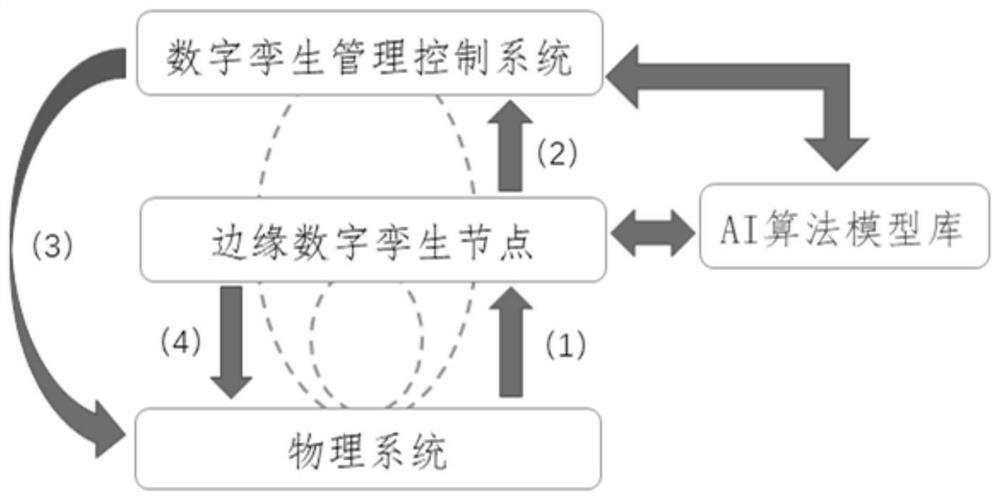
ActiveCN111857065ARealize nearby processingImplement extractionTechnology managementTotal factory controlPhysical systemReliability engineering
Owner:BEIJING UNIV OF POSTS & TELECOMM
System for establishing a cryptographic key depending on a physical system
ActiveUS20120072737A1Reduction of informationReduce decreaseKey distribution for secure communicationDigital data processing detailsComputer hardwareCryptographic nonce
In systems for establishing a cryptographic key depending on a physical uncloneable function (PUF) it may be a problem that internal information correlated with the cryptographic key is leaked to the outside of the system via a side-channel. To mitigate this problem a cryptographic system for reproducibly establishing a cryptographic key is presented. The system comprises a physical system comprising a physical, at least partially random, configuration of components from which an initial bit-string is derived. An error corrector corrects deviations occurring in the initial bit-string. Through the use of randomization the error corrector operates on a randomized data. Information leaking through a side channel is thereby reduced. After error correction a cryptographic key may be derived from the initial bit-string.
Owner:INTRINSIC ID
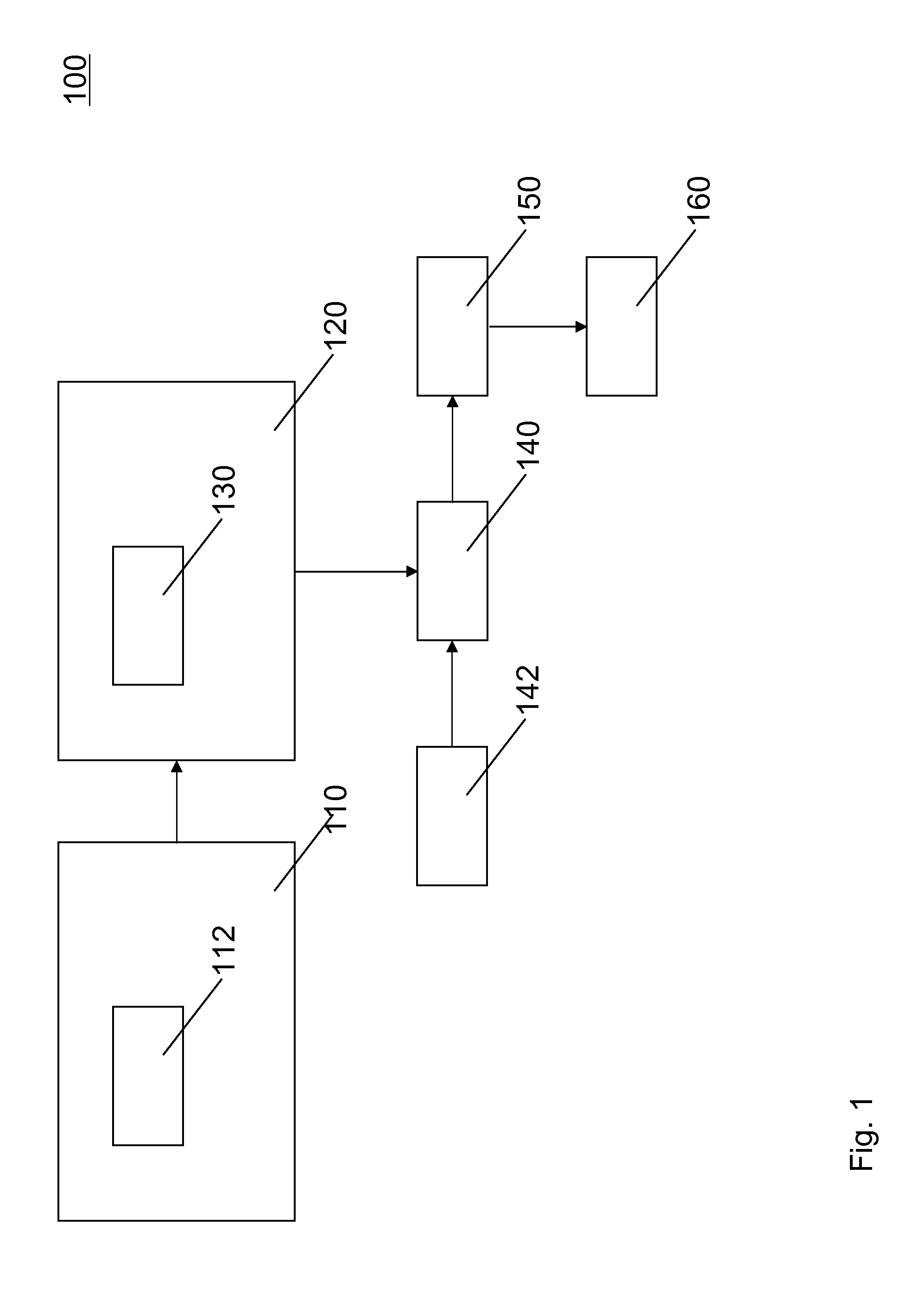
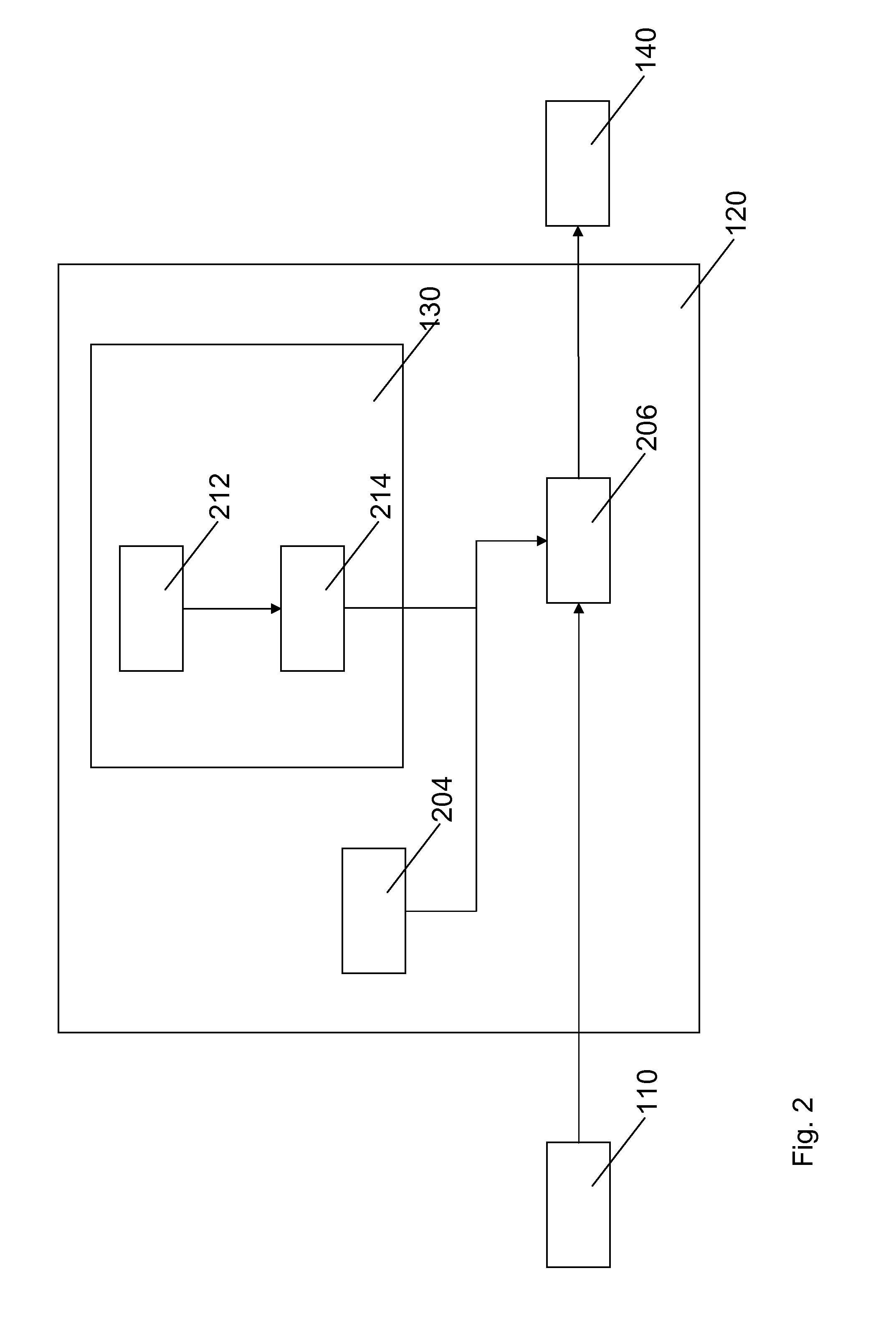
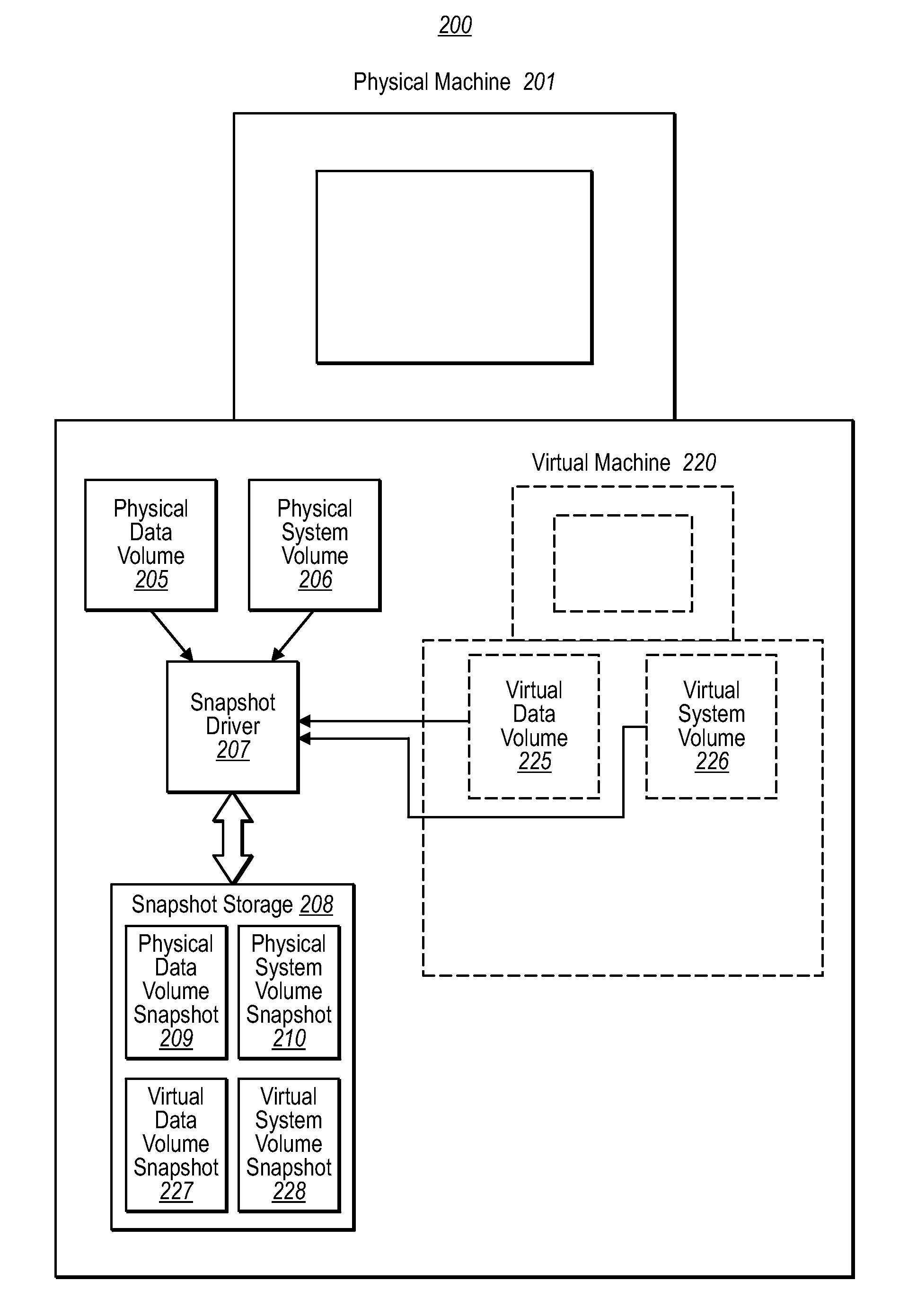
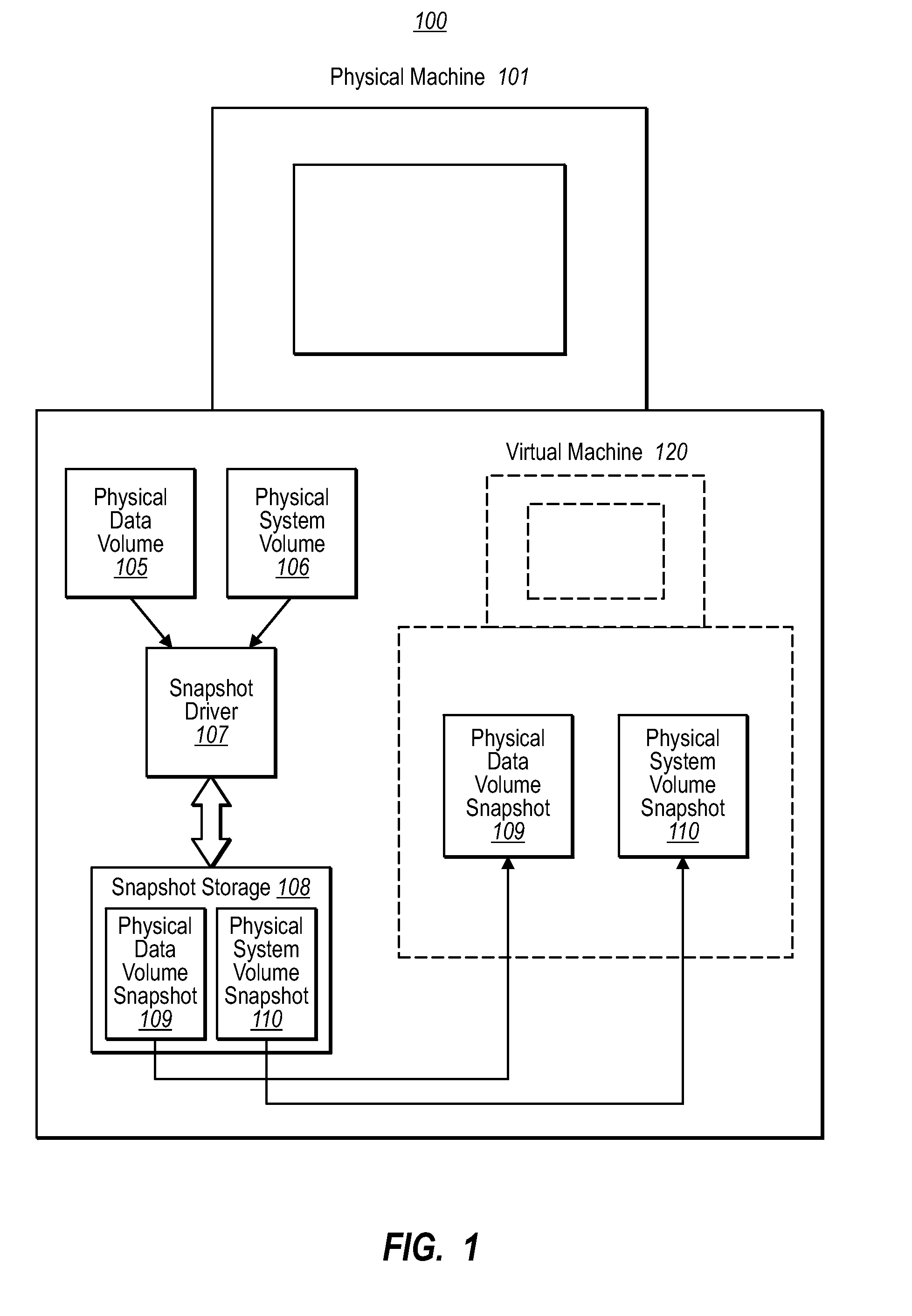
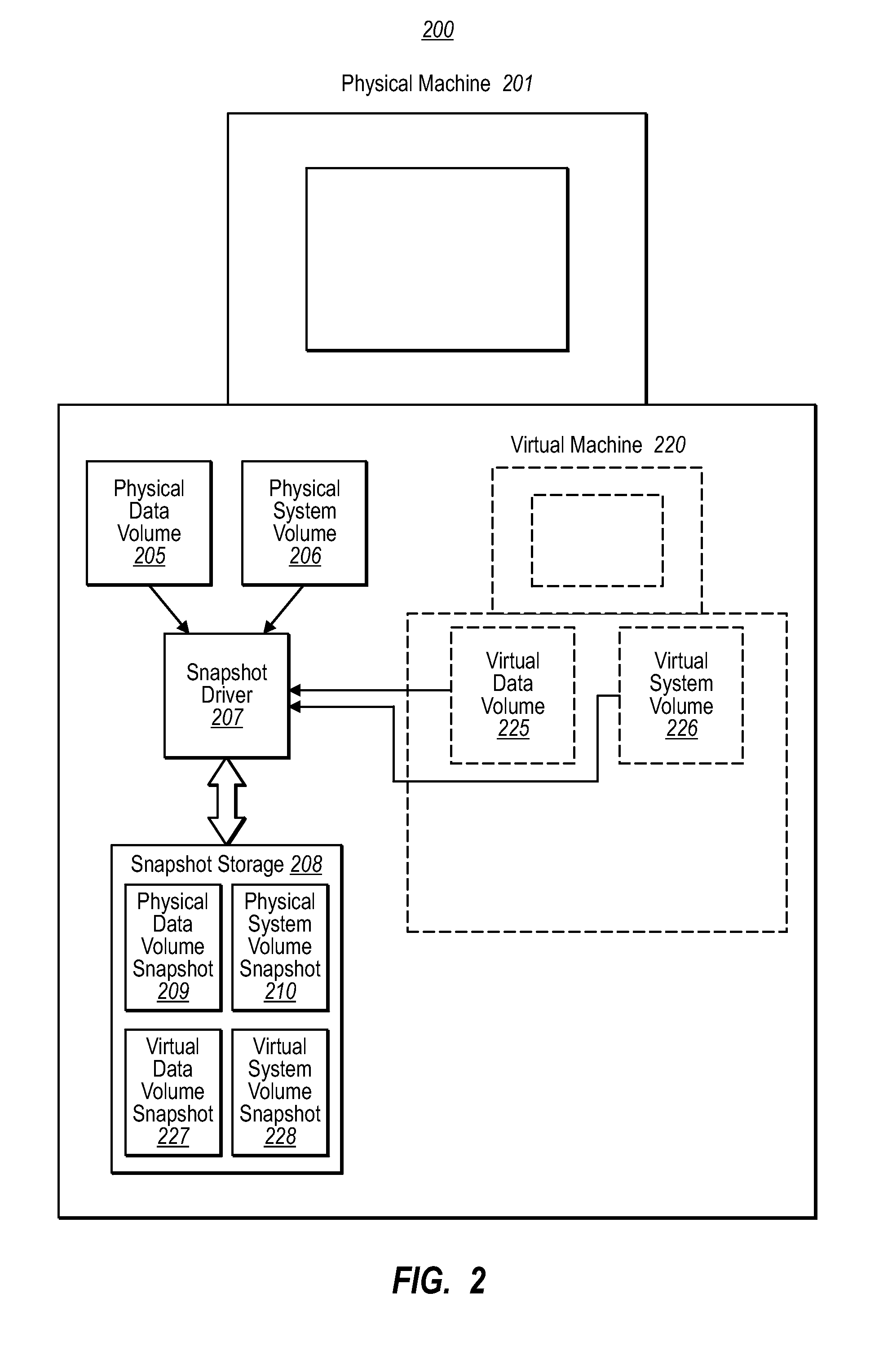
Running a virtual machine directly from a physical machine using snapshots
ActiveUS20080133208A1Well formedDigital computer detailsNon-redundant fault processingPhysical systemVirtual machine
Embodiments of the present invention are directed to the running of a virtual machine directly from a physical machine using snapshots of the physical machine. In one example, a computer system performs a method for running a virtual machine directly from a physical machine using snapshots of the physical machine. A snapshot component takes a snapshot of the physical system volume while the physical system volume is in an operational state. The virtual machine initializes using the physical system volume snapshot thereby allowing the physical system volume snapshot to be a virtual system volume snapshot representing an initial state of a virtual system volume. The physical system volume snapshot includes instances of all the files within the physical system volume at the time the snapshot was taken.
Owner:CA TECH INC
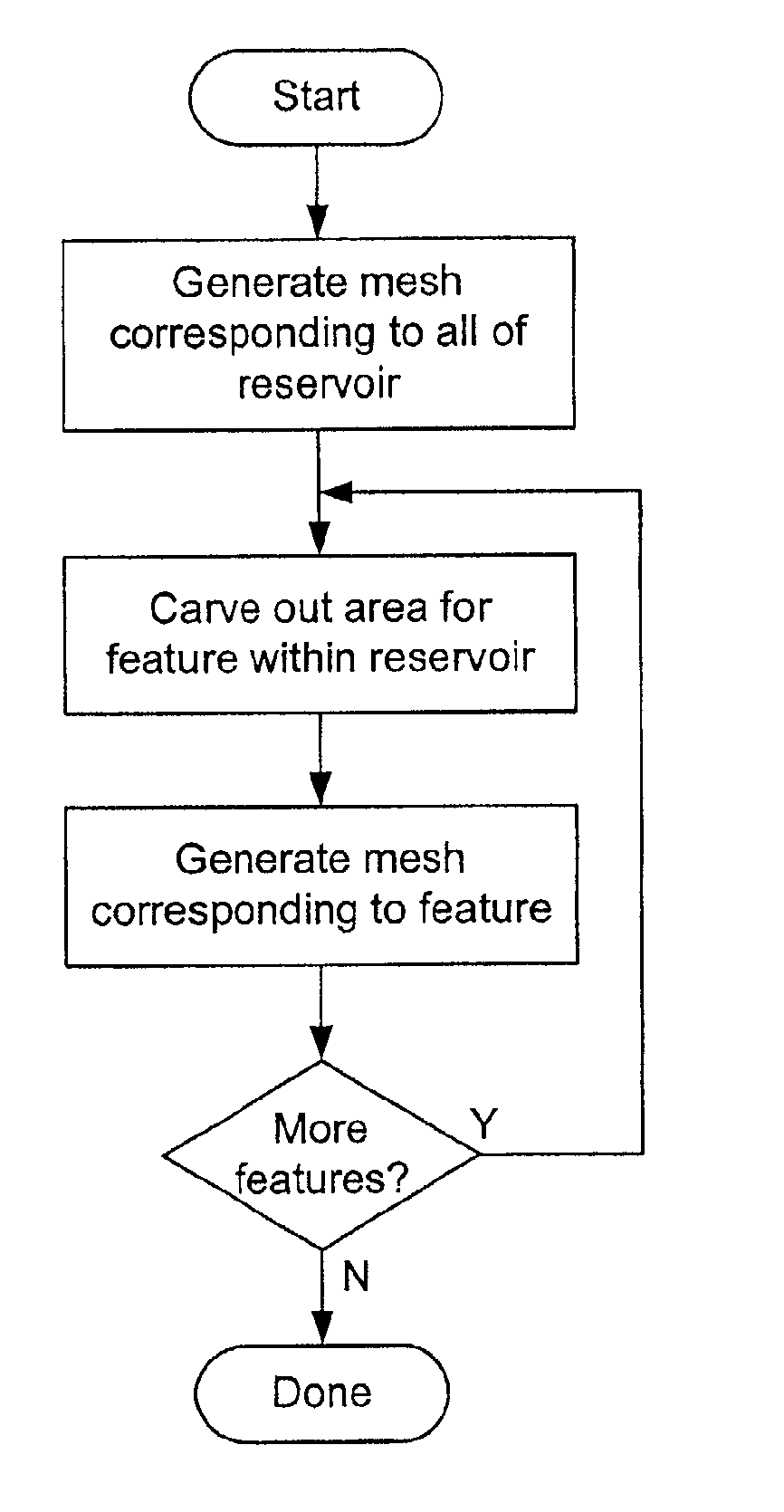
Feature modeling in a finite element model
ActiveUS6941255B2Accurate representationSmall amount of calculationGeometric CADComputation using non-contact making devicesFinite element techniqueElement model
A method for simulating a physical system using finite element techniques, wherein two or more distinct models corresponding to distinct regions within the modeled system are solved, each with a corresponding evaluator. Nodes which lie on the boundaries between the models may have different values corresponding to the different models. When a particular model is solved, the evaluator for that model is used to obtain the appropriate values for each of these common nodes. In one embodiment, a first model is defined, then a region corresponding to a particular feature within the system is carved out of it. A finite element model corresponding to the feature is then inserted into the region. The finite elements may be adapted to share nodes on the boundaries between them.
Owner:LANDMARK GRAPHICS
Wireless Encrypted Control of Physical Access Systems
InactiveUS20110291798A1Safety issue is lessenedImprove securityElectric signal transmission systemsTicket-issuing apparatusComputer hardwareDigital signature
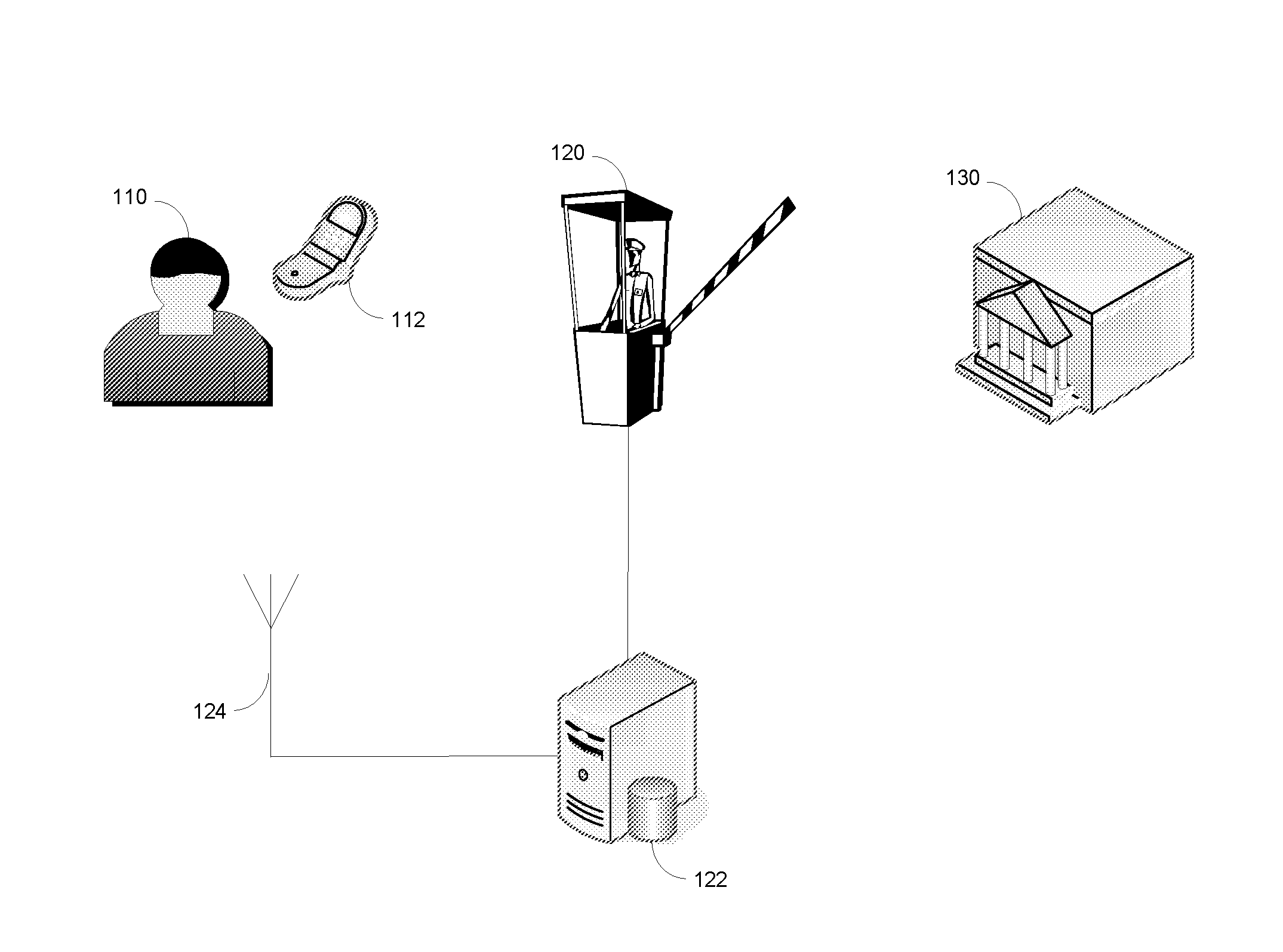
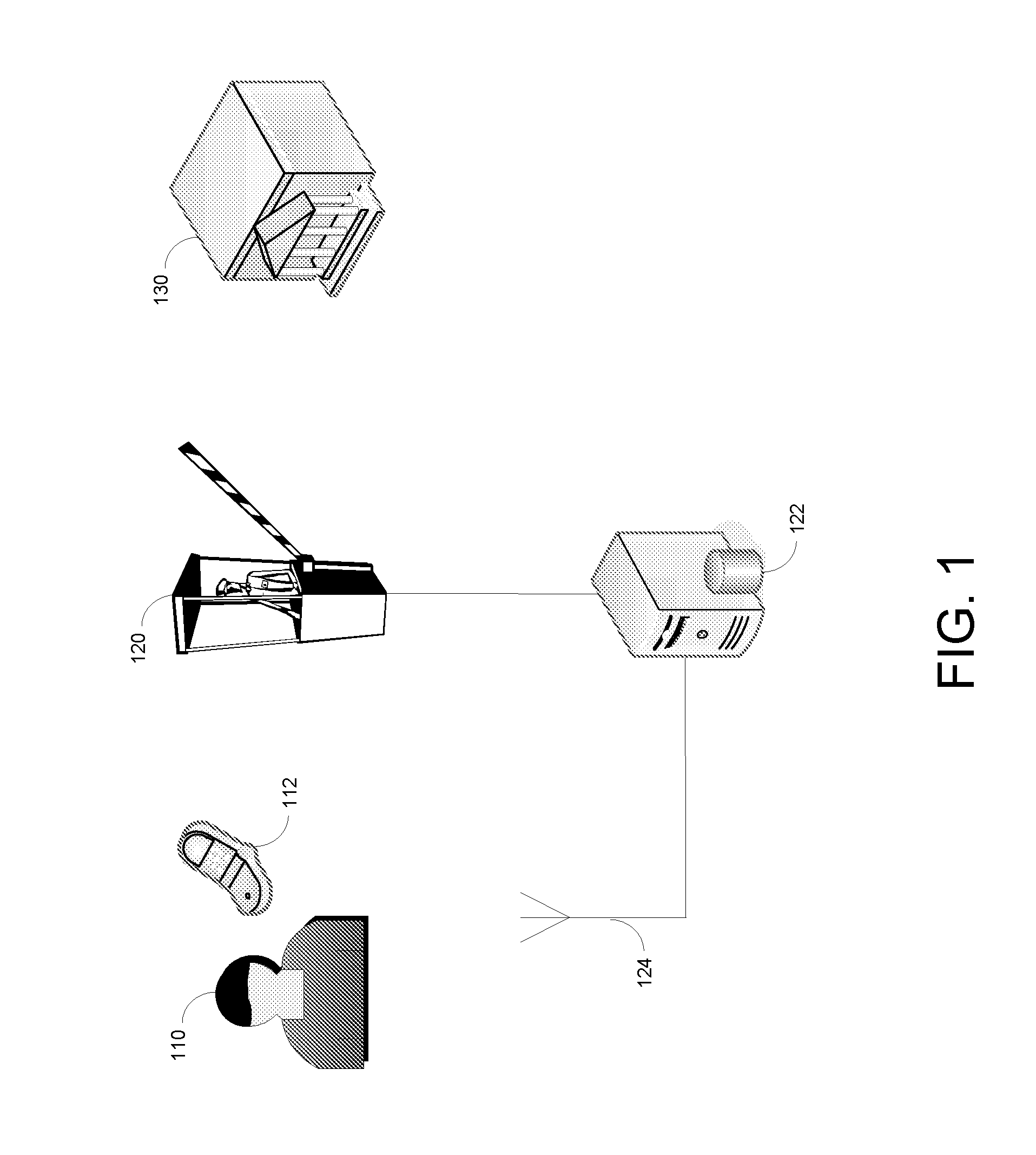
Physical access systems and methods securely grant physical access to restricted areas in high-volume applications. An electronic device, such as a smartphone, stores a digitally signed physical access rights file. An individual uses this rights file to gain access to a restricted area only after self-authenticating to the device. A physical access control system receives the rights file, validates it, and determines whether to permit passage through a physical barrier. The determination may be made by a physical barrier system, or by a remote access control headend. An access control gateway, which may be an access control headend, may either unlock the physical barrier system when the electronic device is near the physical barrier, or it may transmit an authorization code to the electronic device and the physical barrier system, whereby passage is only permitted if the barrier system subsequently receives the authorization code from the electronic device using near field communications.
Owner:SURIDX
Totally integrated intelligent dynamic systems display
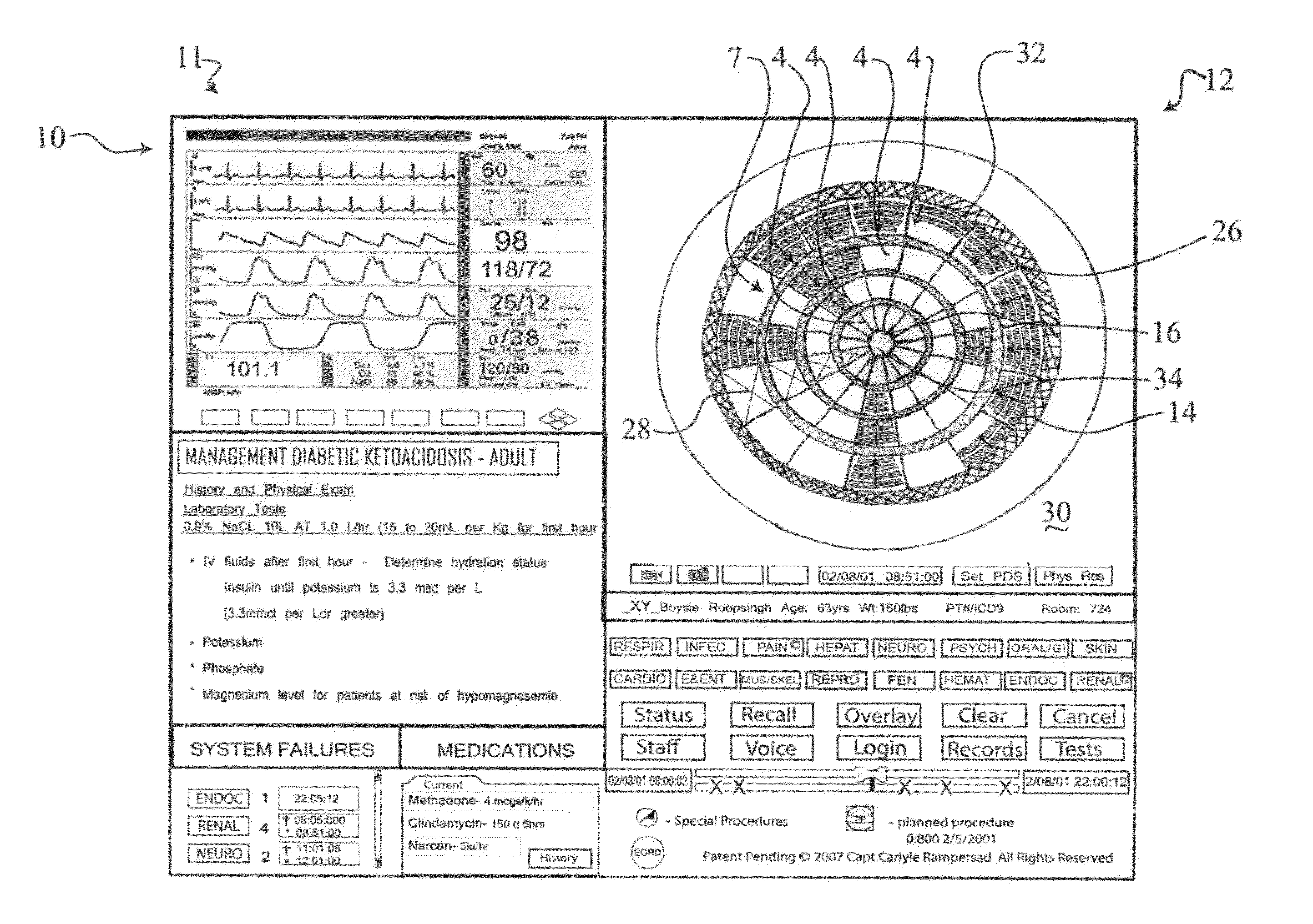
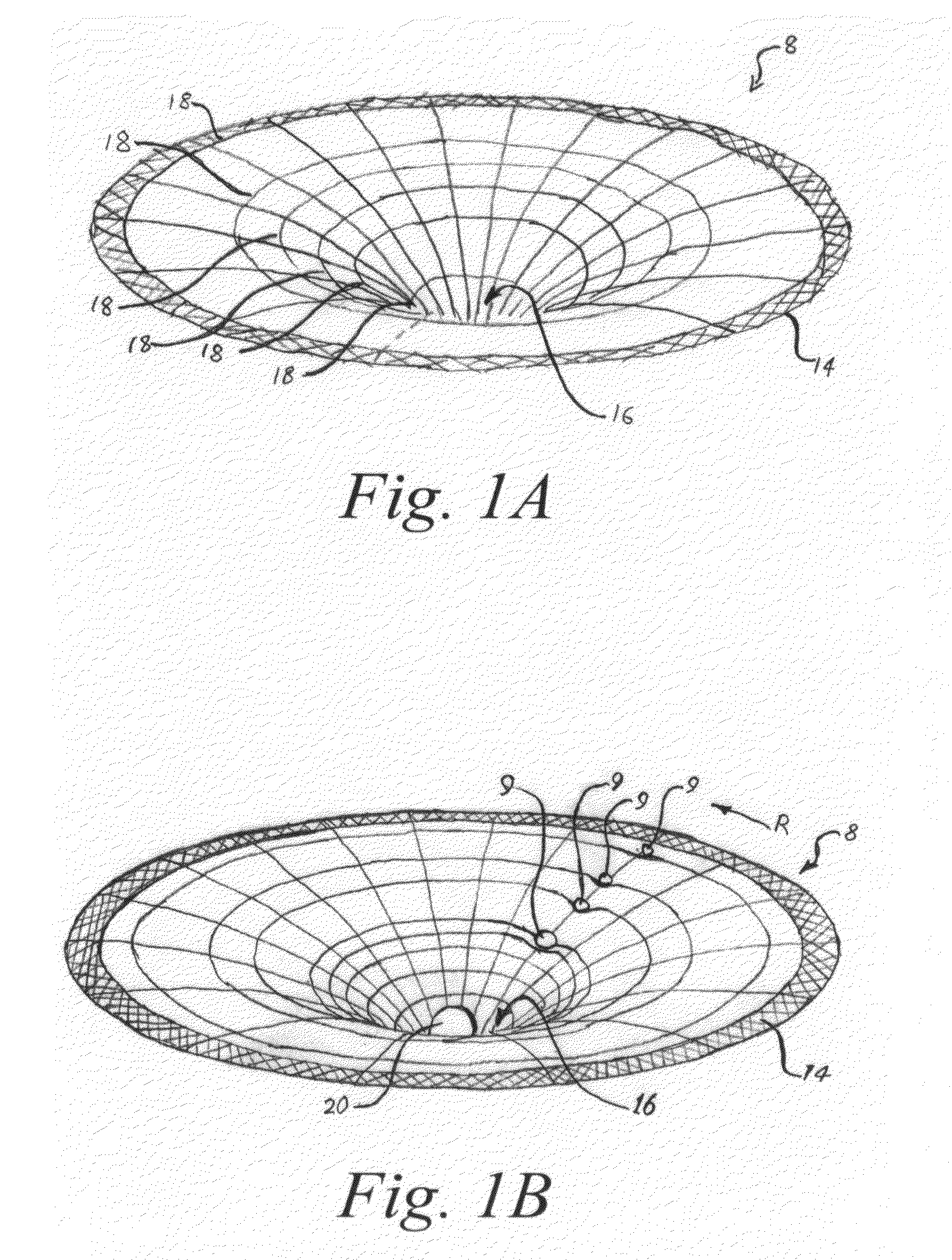
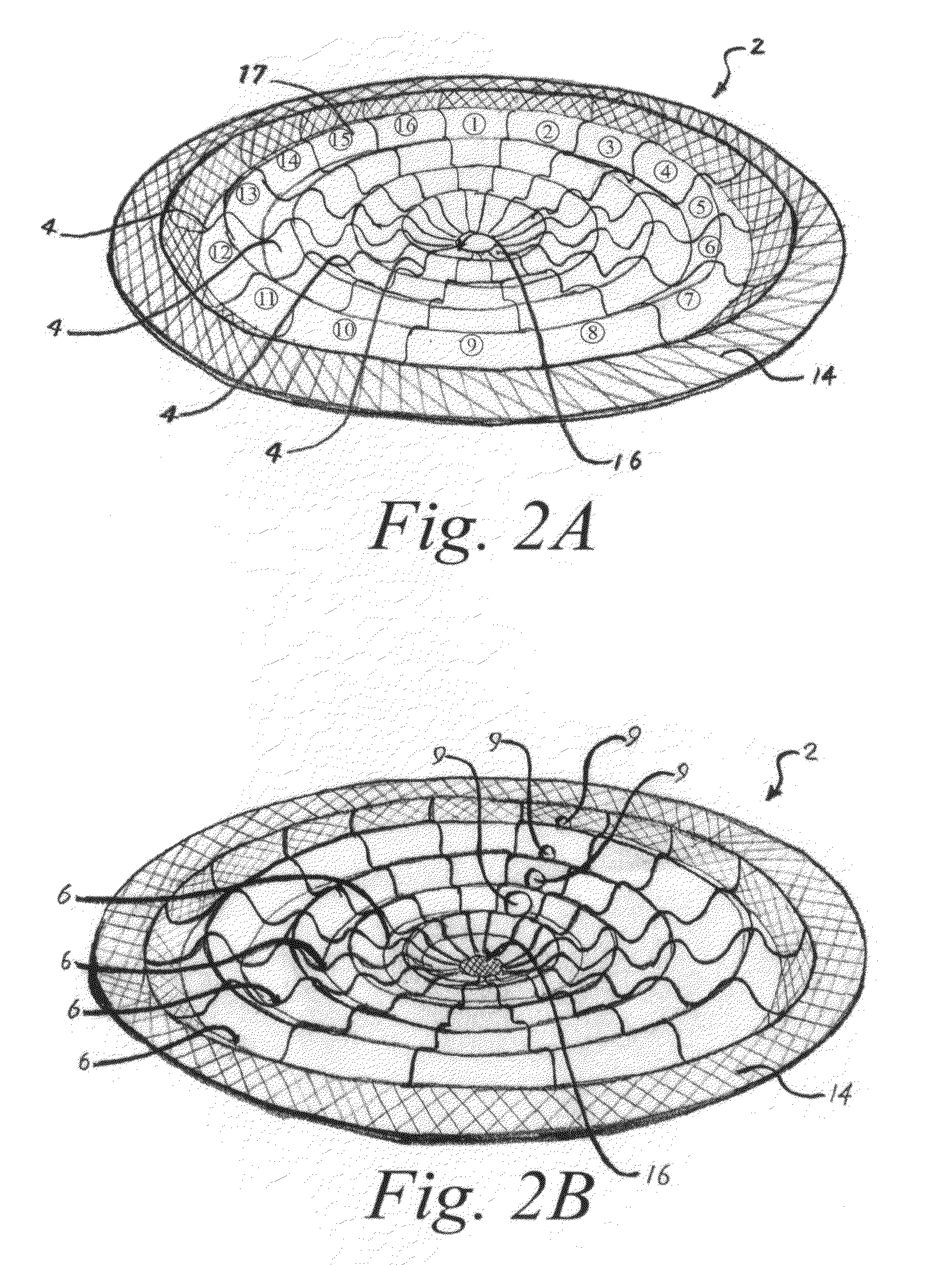
An apparatus for graphically displaying analytical data, comprising a generic model to graphically represent a complex set of physical characteristics potentially leading to catastrophic failure of a physical system. A central region represents failure of the physical system; a series of concentric ridges represents level of function. Wedge shaped regions upon the ridges represent predetermined subsystems of the physical system. An icon is displayed with changes in the icon proportional to time, and any one or more of color, position, shape, and rotation of the icon representing prescribed analysis of the physical characteristics. Mappings correlate predetermined characteristics of the system with failure of the physical system, levels of functioning represented by the ridges, subsystems represented by the wedge shaped regions, and / or analysis of the physical characteristics represented in the icon. A sensor interface receives measurements, and a graphics generator prepares a presentation of the model.
Owner:OJARALI SYST LLP
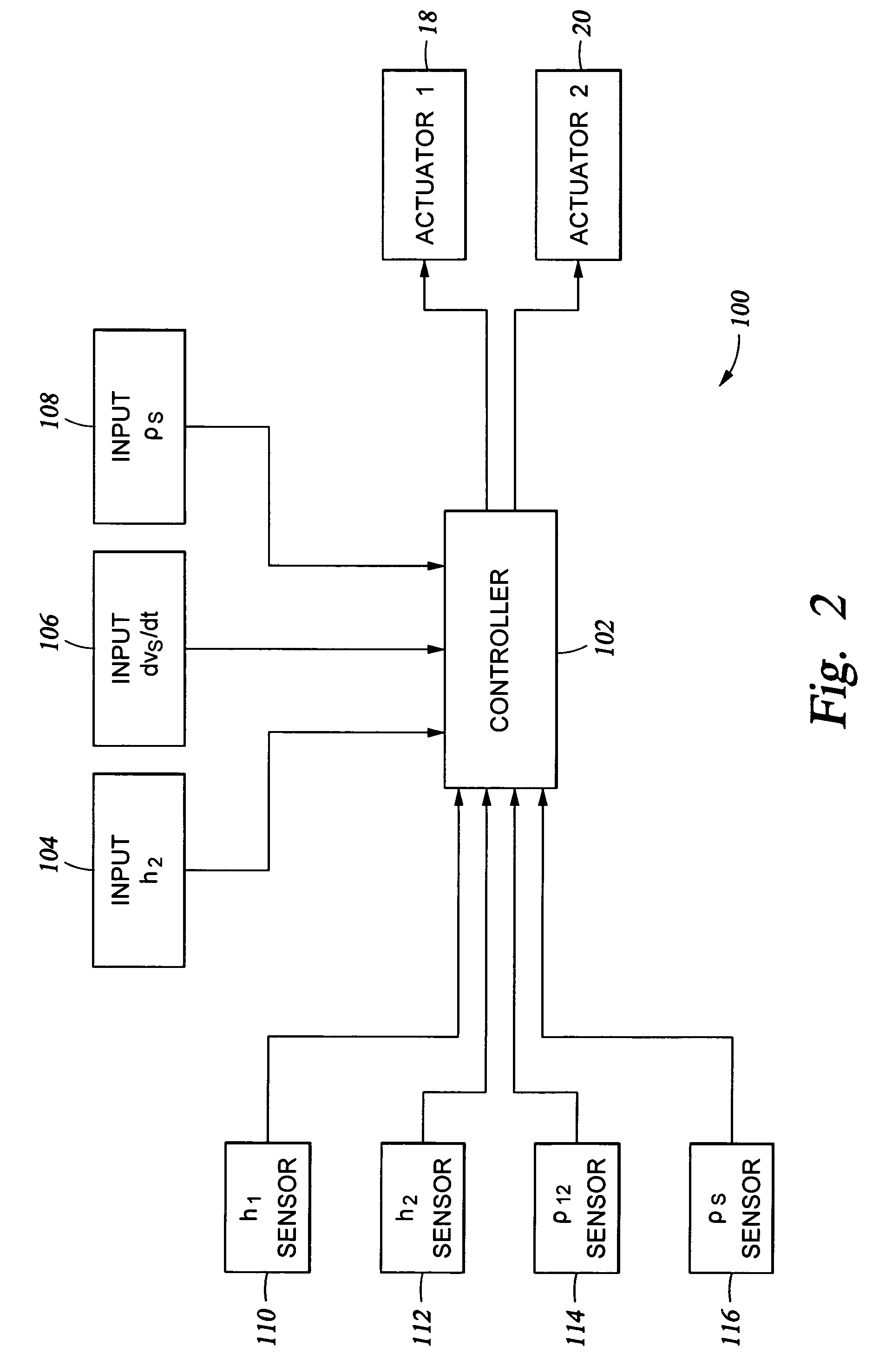
Control system design for a mixing system with multiple inputs
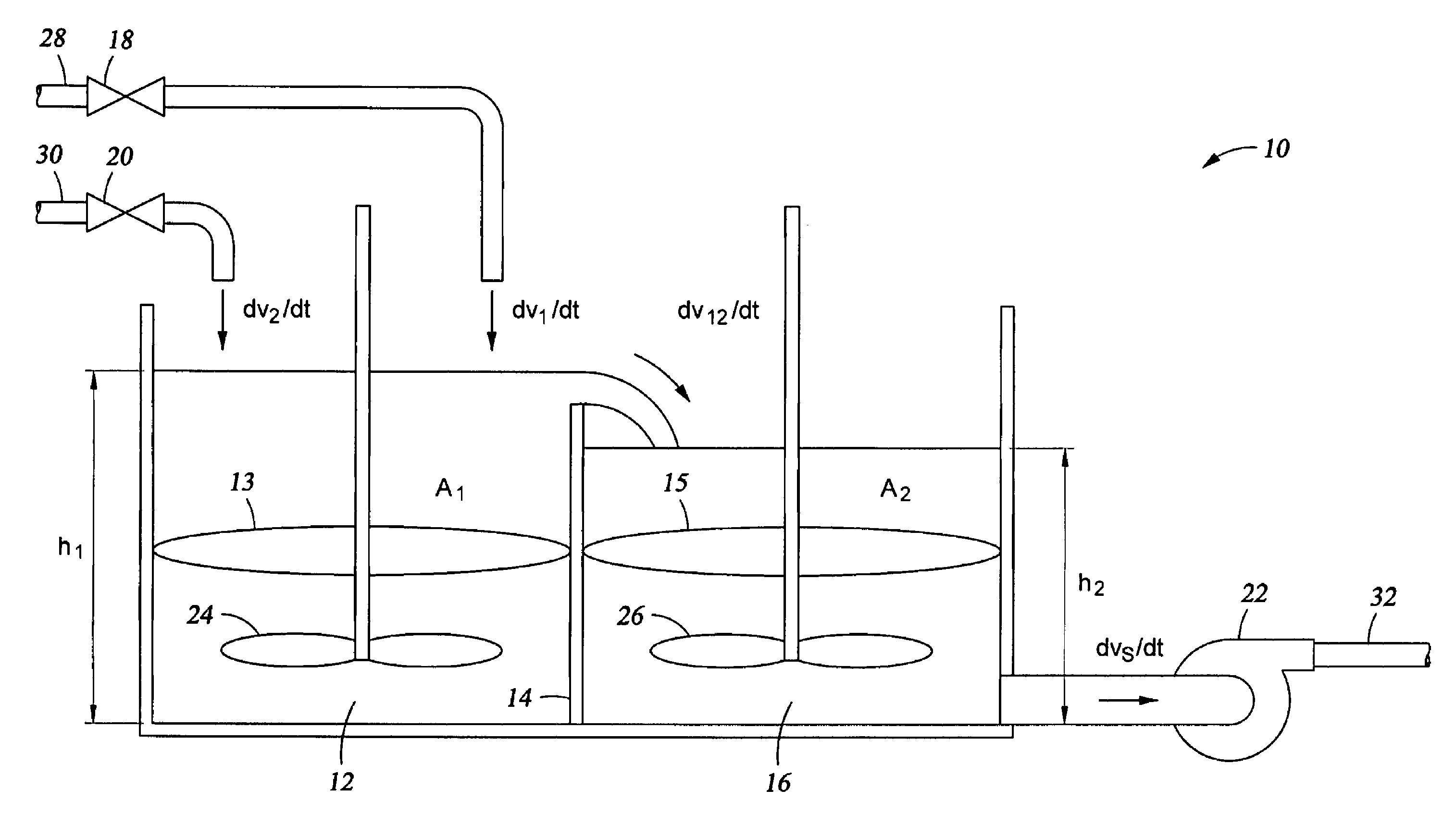
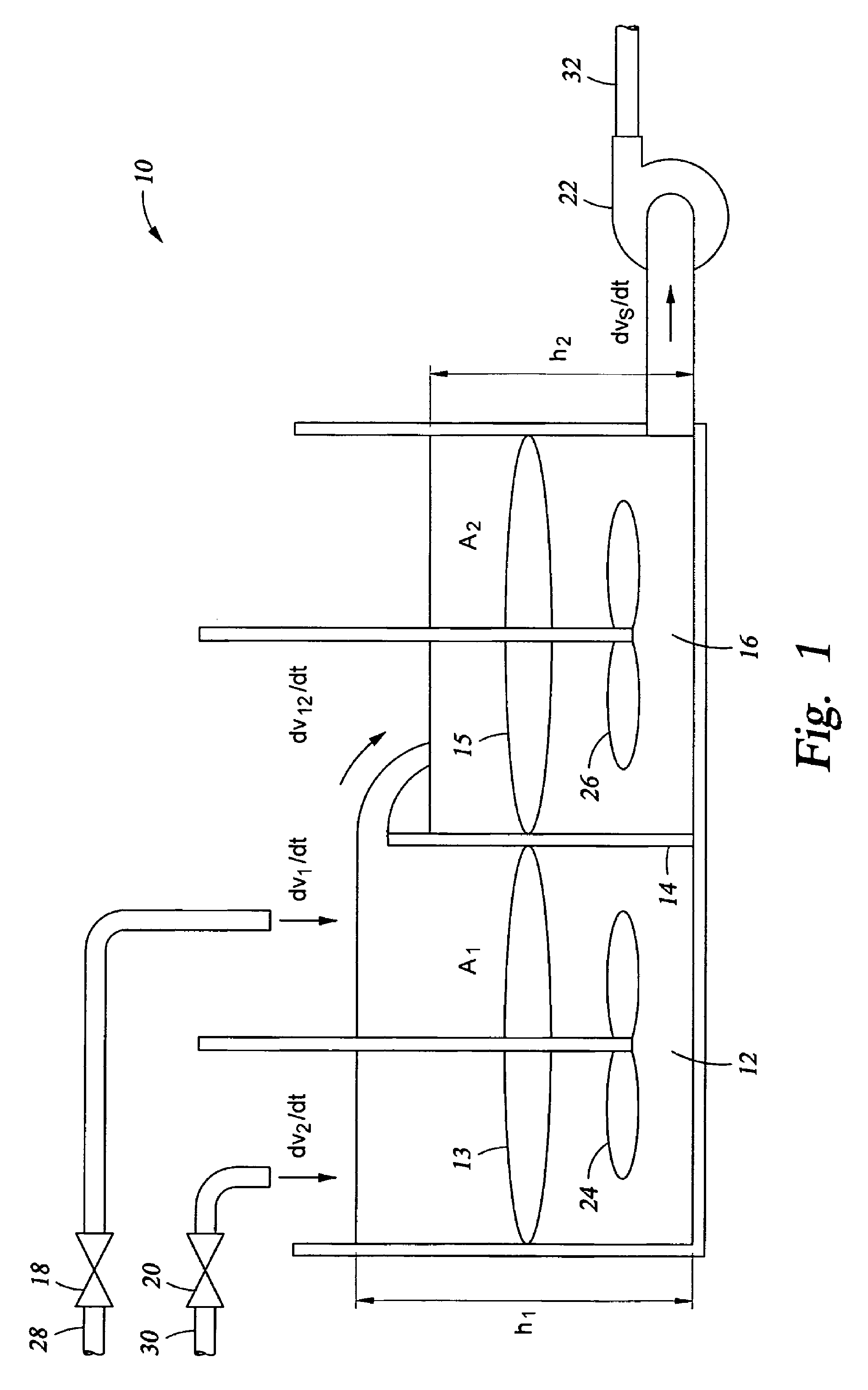
ActiveUS7494263B2Controlling ratio of multiple fluid flowsMixing operation control apparatusHybrid systemControl system design
A control system for mixing at least two materials in a physical system having two or more tanks comprises at least two actuators, each actuator being operable to introduce a material into a first tank to form a first mixture, the first mixture flowing into a second tank to form a second mixture and a controller operable, based on a commanded input, to control the at least two actuators to obtain a density of either the first mixture or the second mixture and a volume flow rate of the second mixture out of the second tank, wherein the density is controlled independently from the volume flow rate.
Owner:HALLIBURTON ENERGY SERVICES INC
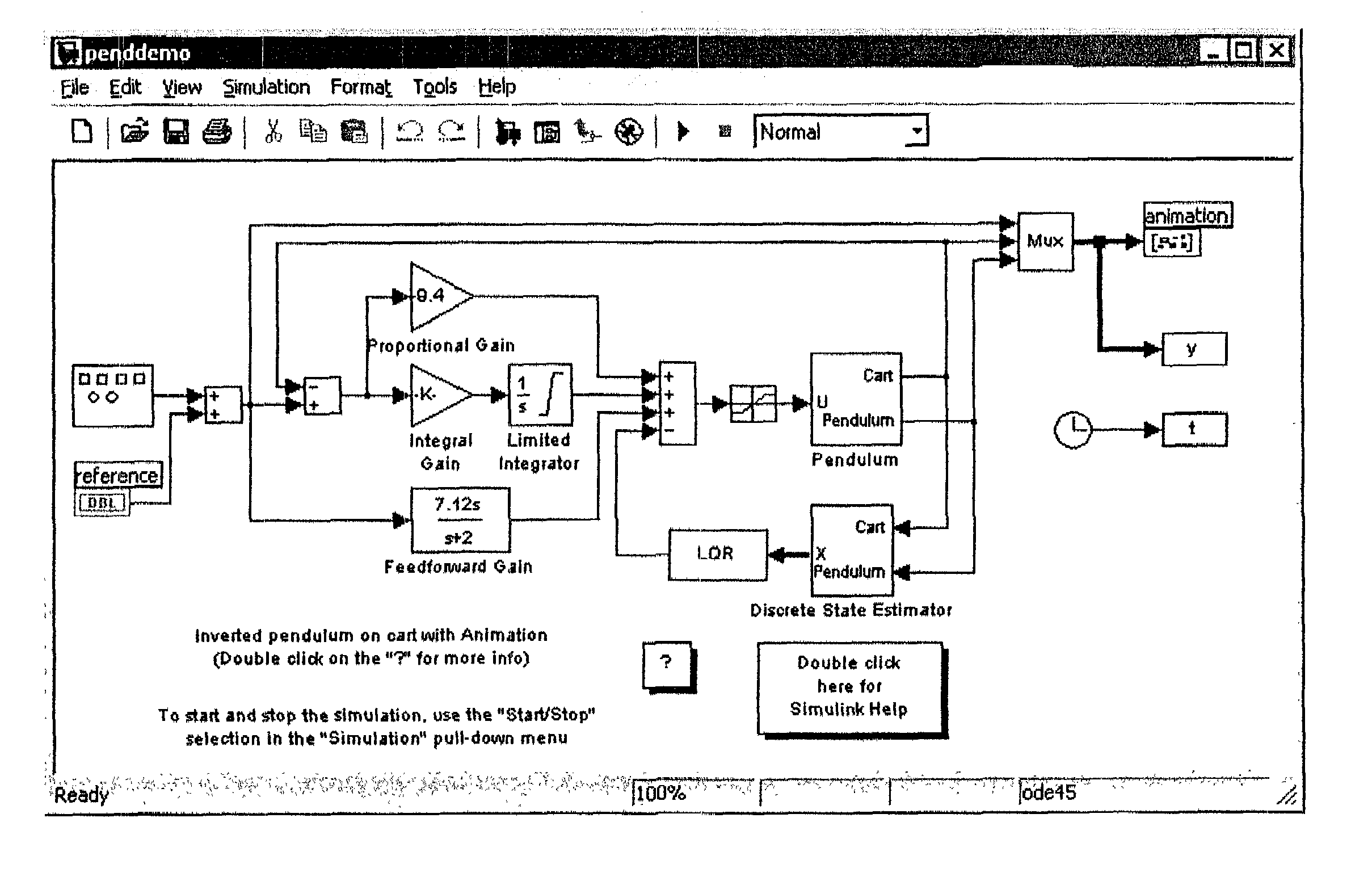
System and method for performing rapid control prototyping using a plurality of graphical programs that share a single graphical user interface
InactiveUS7076740B2Quick and easy testingSpeed up the development processData processing applicationsCathode-ray tube indicatorsGraphicsGraphical user interface
A system and method for performing rapid control prototyping using a plurality of graphical programs that share a single graphical user interface. A first graphical program may be created that models a product being designed. The first graphical program may be deployed on a target device for execution. A second graphical program that performs a measurement function may be created. The target device may be coupled to a physical system. The first graphical program may be executed on the target device to simulate operation of the product. The second graphical program may be executed to measure characteristics of the operation of the physical system and / or characteristics of the operation of the product. A single graphical user interface comprising a first one or more graphical user interface elements for the first graphical program and a second one or more graphical user interface elements for the second graphical program may be displayed.
Owner:NATIONAL INSTRUMENTS
Automated method of generalized building automation from atomic physical models and control loops thereof
ActiveUS10845771B2Improve efficiencyImprove performanceProgramme controlComputer controlControl cellPhysical model
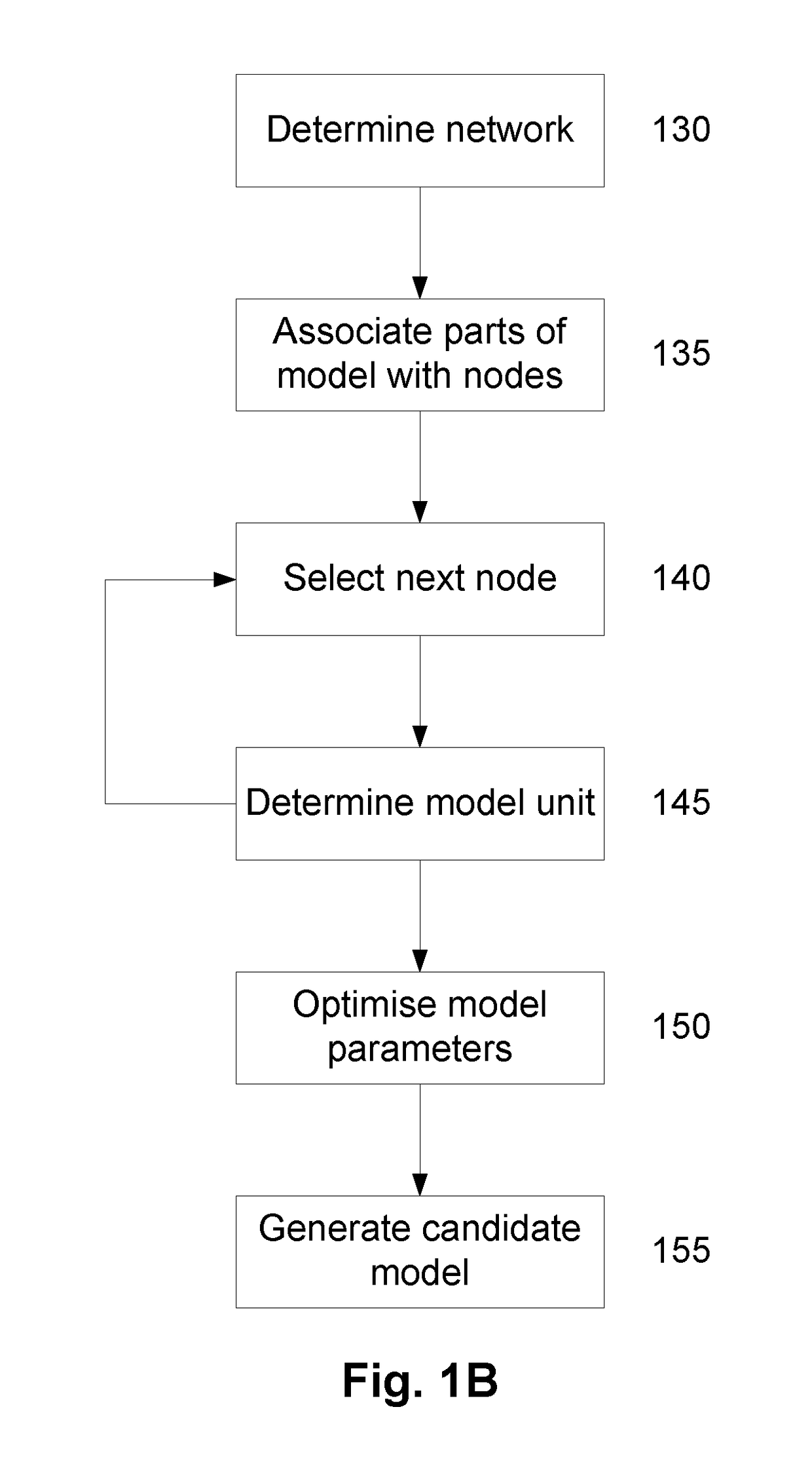
Disclosed is a system and method for classifying units of control and concomitant model units from a larger physical system model. The system enables model-based simulation of decoupled system units for improved simulation efficiency. Further, the system allows for automated reasoning about the classification of said units, producing both machine-interpretable and human-readable, natural language descriptions of the decisions and reasons for said decisions made during the classification process, for use in heuristics and user feedback.
Owner:PASSIVELOGIC INC
Method used in the control of a physical system affected by threats
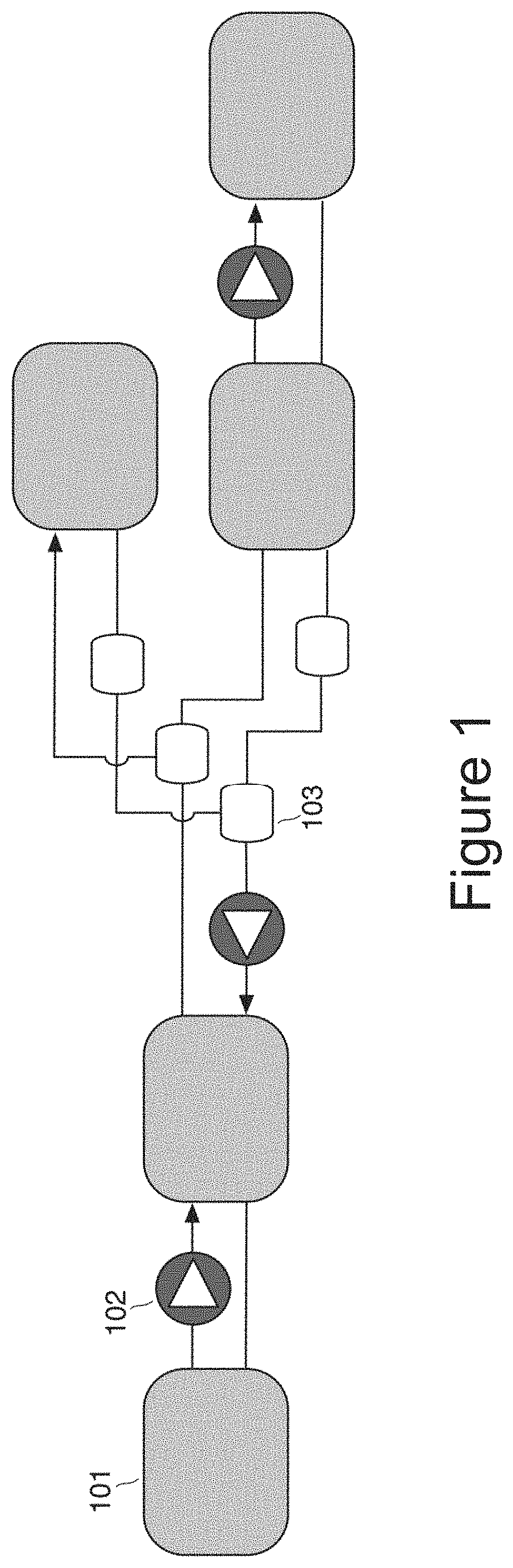
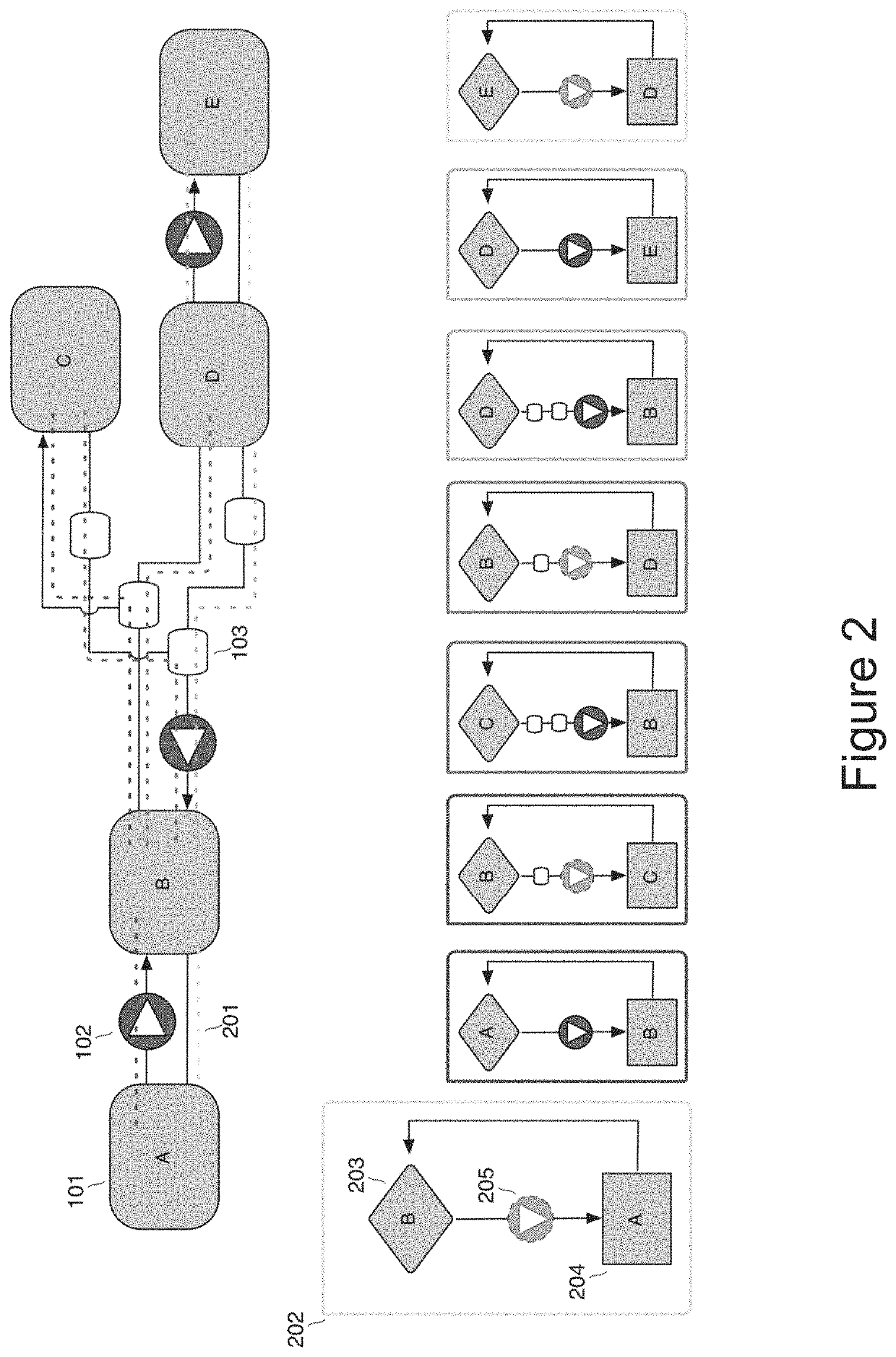
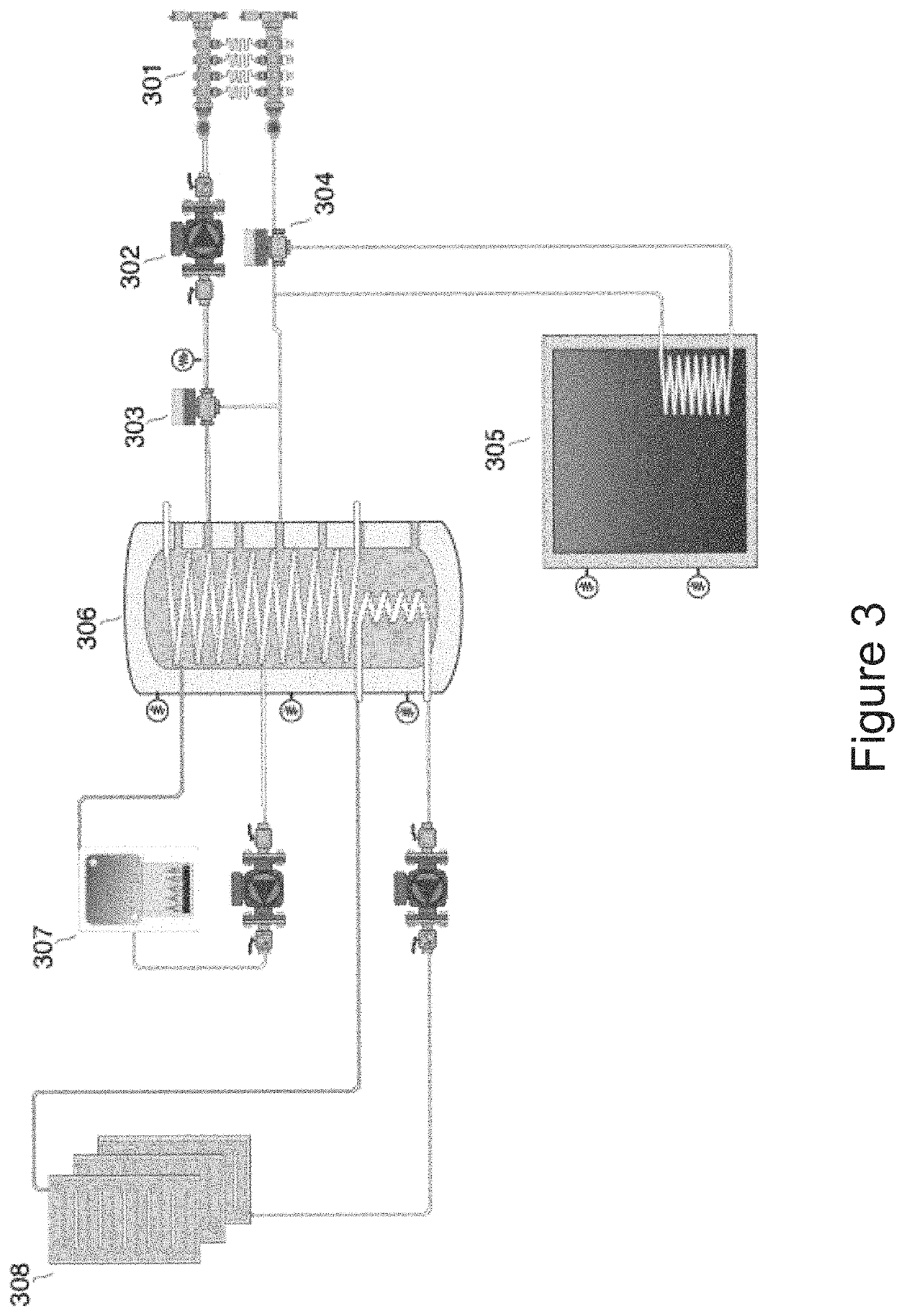
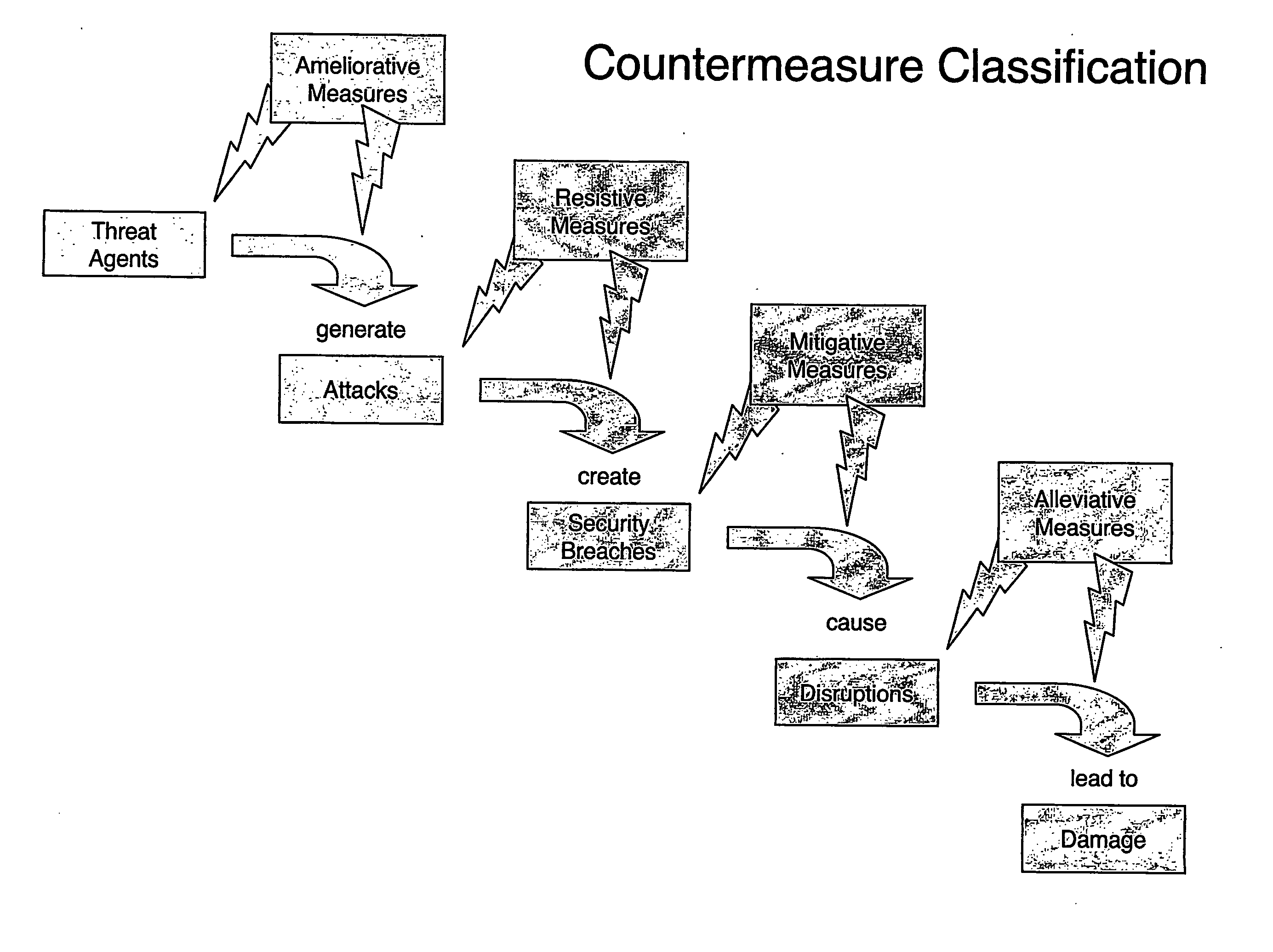
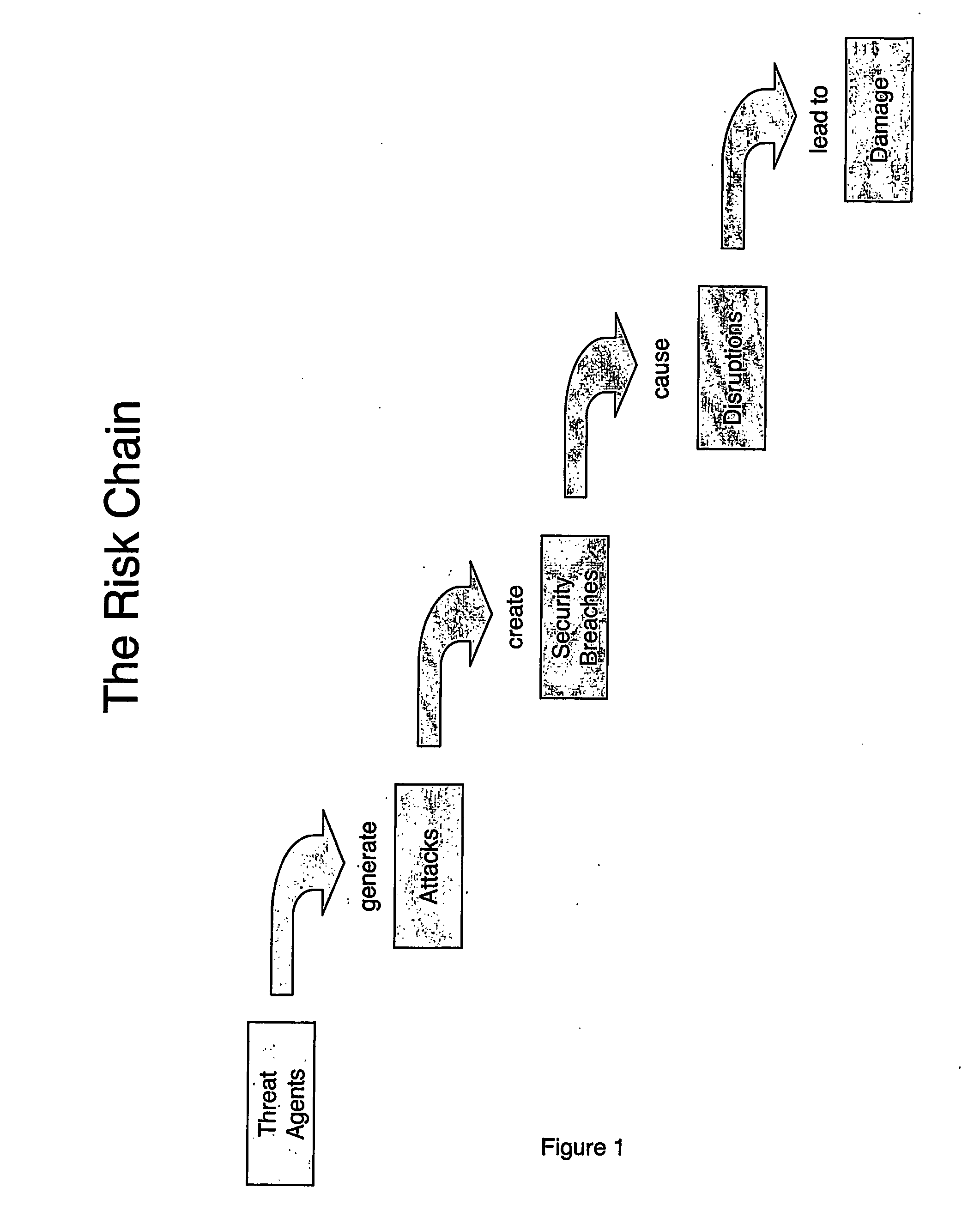
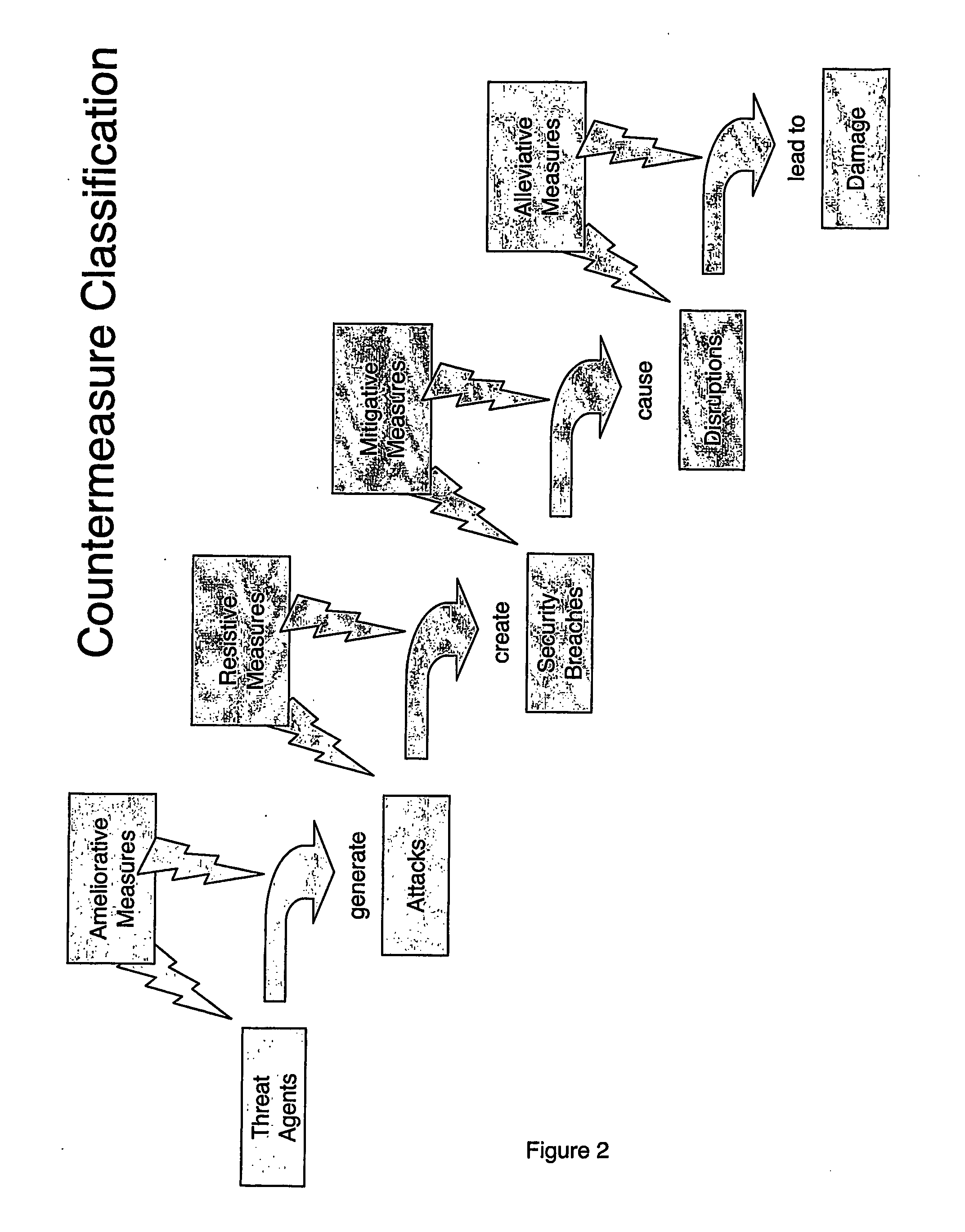
InactiveUS20070113281A1Improve algorithm accuracyImprove accuracyFinanceMemory loss protectionCountermeasurePhysical system
The method involves (a) modelling how an entity generates another entity to form a risk chain, the risk chain being a series of two or more entities that each model a discrete part of how a threat leads to damage to the system, each entity being described as a population of elements distributed in a parameter or parameters; and (b) controlling the physical system by using results of the modelling. Implementations provide a method for calculating the likelihood and characteristics of security breaches as a function of the measured security threats and the countermeasures deployed.
Owner:LEACH JOHN
Method, system and program storage device for simulating fluid flow in a physical system using a dynamic composition based extensible object-oriented architecture
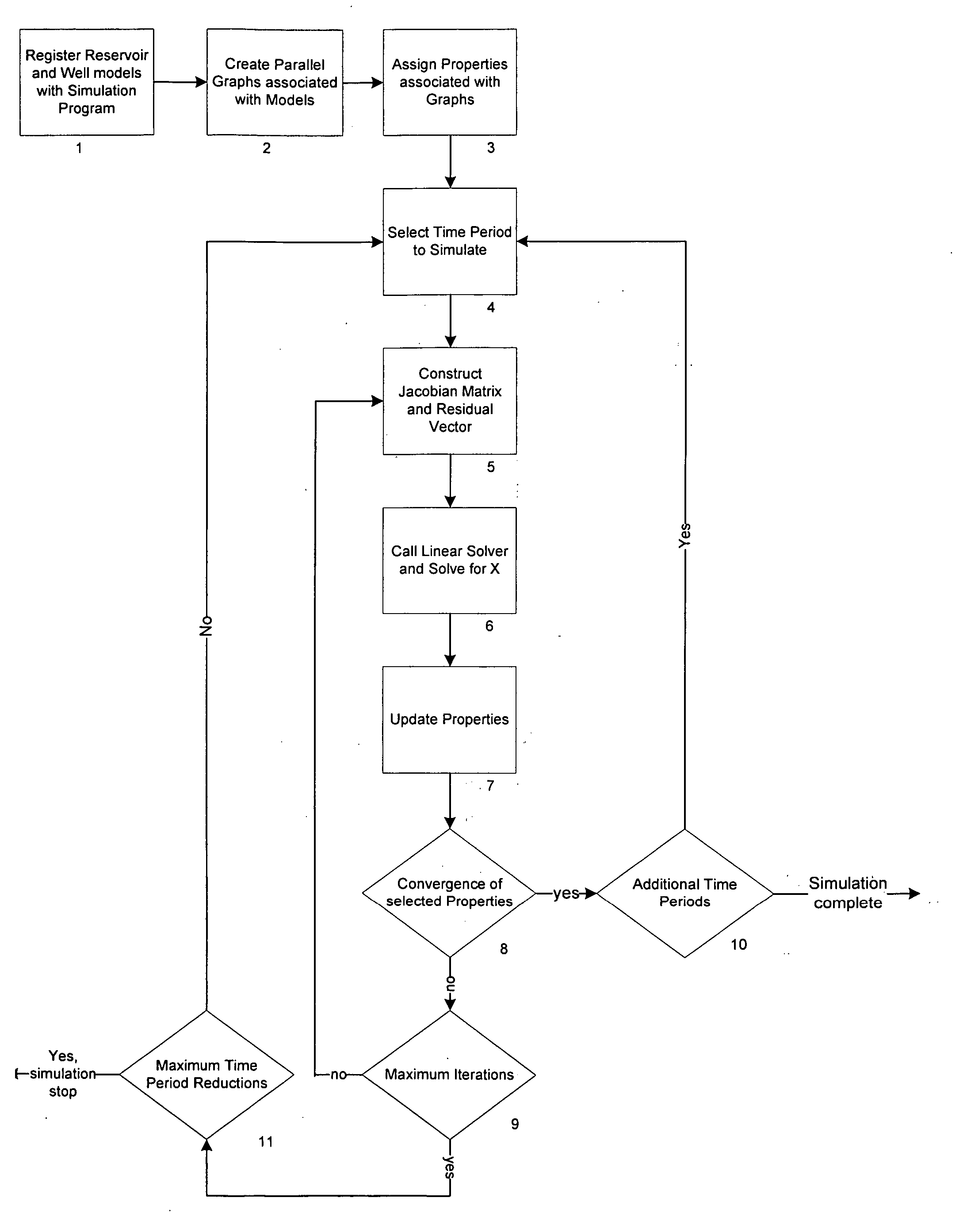
ActiveUS20060282243A1Minimizing combinatorial expansionMinimizing expansionDesign optimisation/simulationSpecial data processing applicationsComputational sciencePhysical system
The present invention provides a method, a system and a program storage device containing instructions for simulating the flow of fluid in a physical system using a composition-based extensible object-oriented program. A computer program includes: (i) a framework subsystem providing a graph package, a compute package and a property package; (ii) an engine subsystem including engine subsystem packages for performing numerical simulation, the engine subsystem packages including a linear solver package and a non-linear solver package; and (iii) a set of model components providing physical and numerical modeling behaviors utilized by the engine subsystem, the model components including at least one of a reservoir model, a well model, an aquifer model, a fluid model and a SCAL model. The framework subsystem, the engine subsystem and the model components work with one other to simulate the flow of fluid. Preferably, a partition package is used to create a partition of subsets of node and edge indices which can be used optimize computations by the program.
Owner:SCHLUMBERGER TECH CORP +1
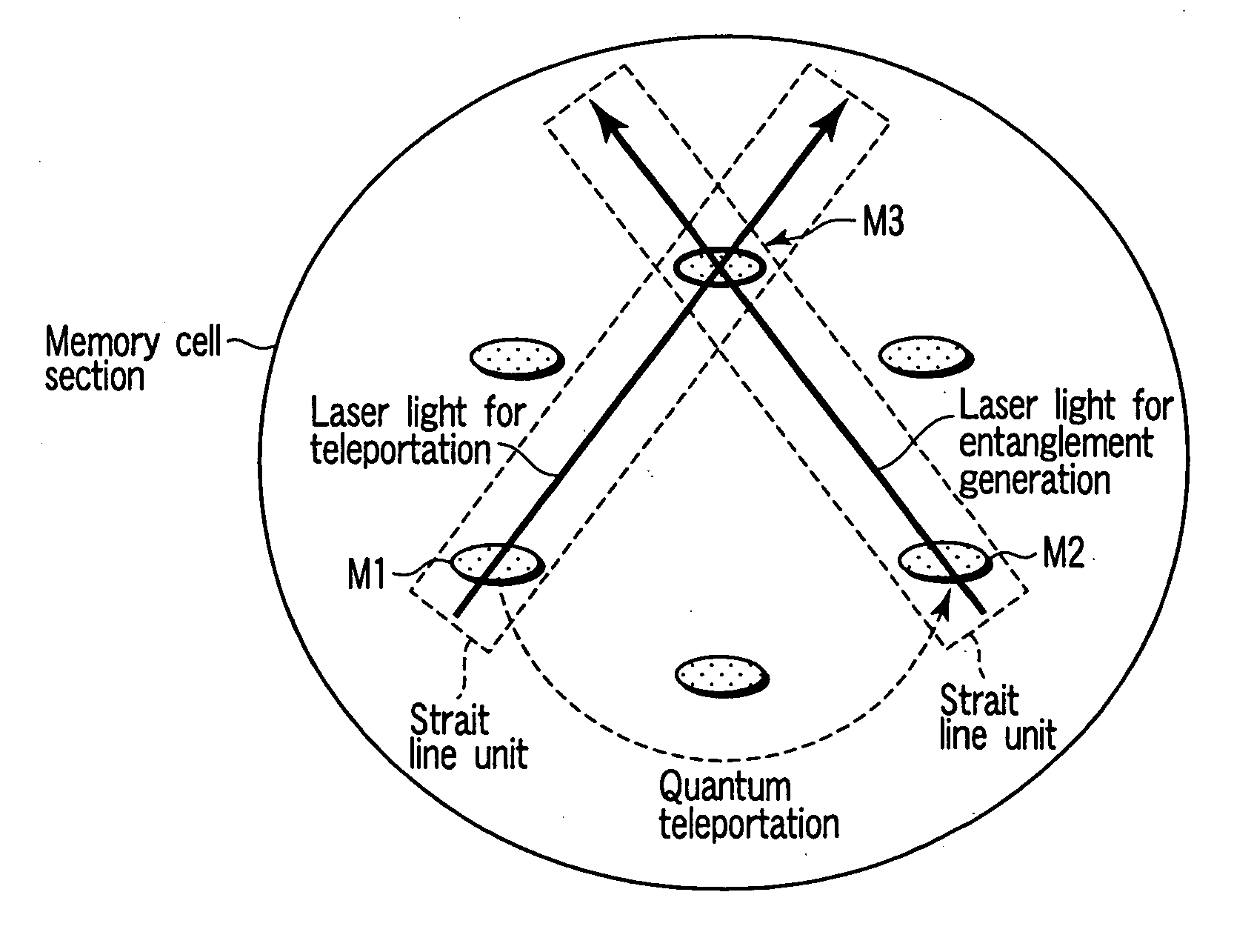
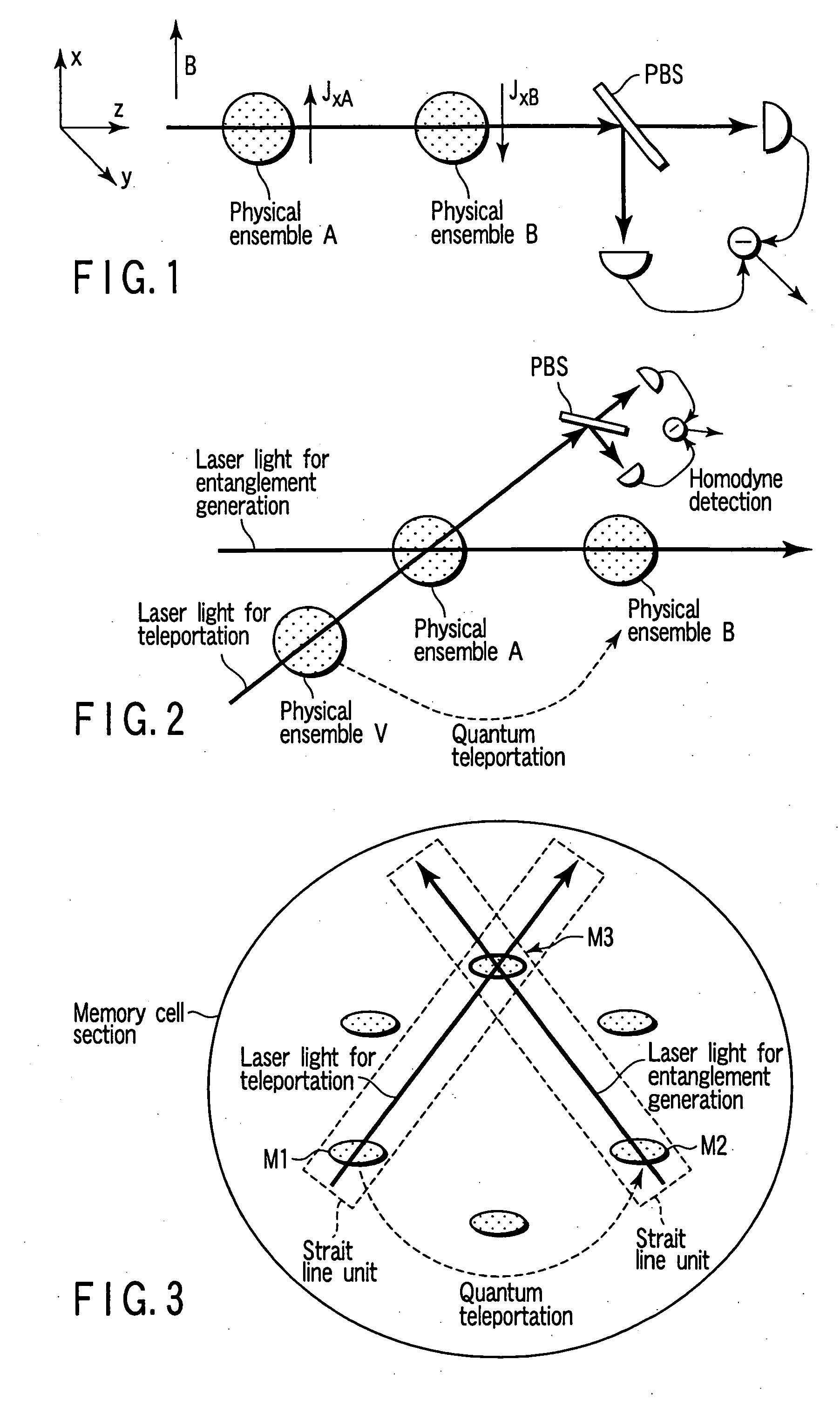
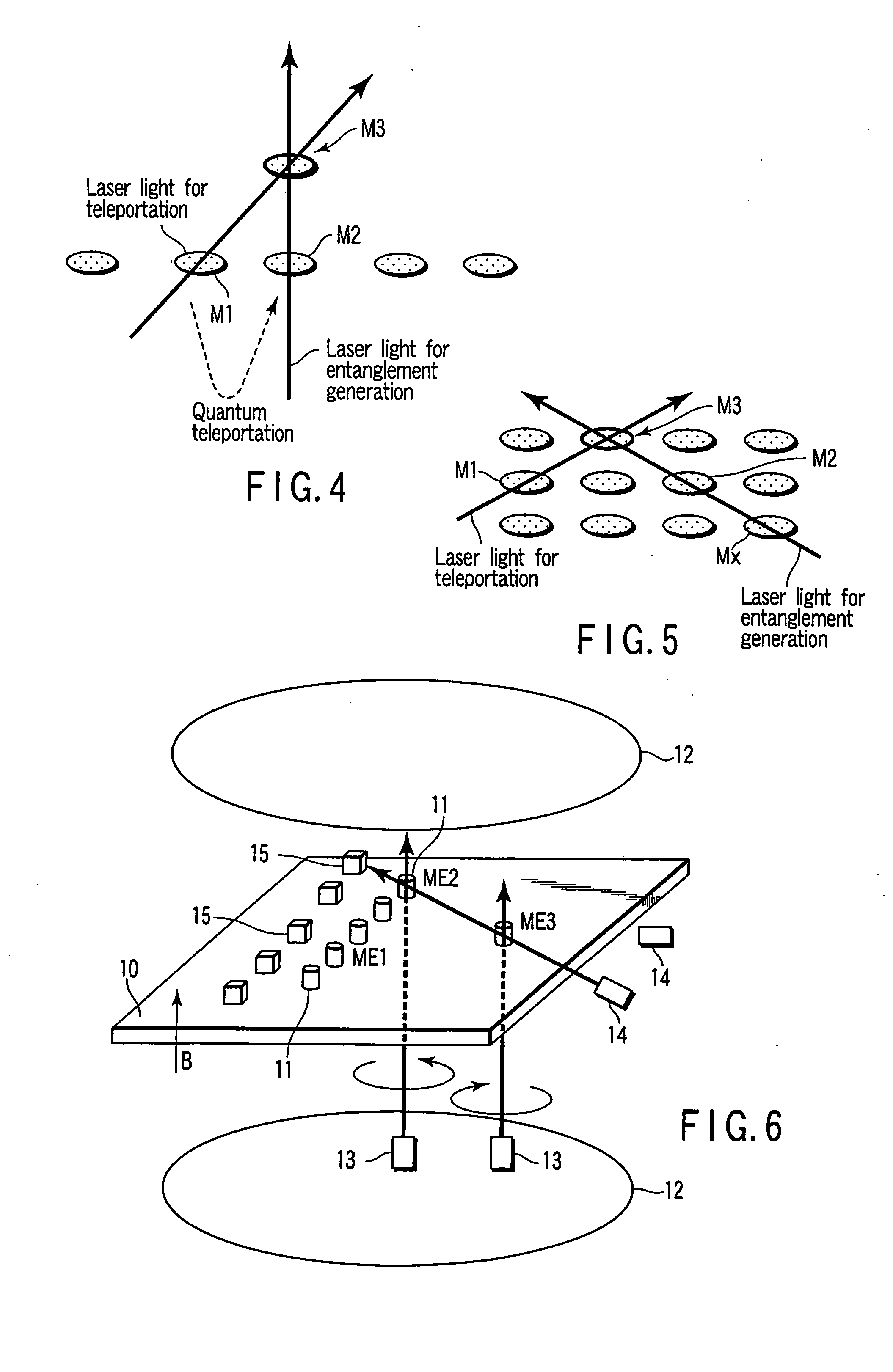
Quantum memory and information processing method using the same
InactiveUS20050190637A1Avoid interferenceQuantum computersNanoinformaticsInformation processingPhysical system
A quantum memory includes memory cells each comprising a physical system ensemble, quantum information of the physical system ensemble being expressed by a quantum state of whole amount of the total angular momentum of the physical systems, and the memory cells including two storage memory cells storing the quantum state and a transfer memory cell transferring the quantum state, only two of the memory cells being present on a straight line. The quantum memory also includes a magnet applying a magnetic field to the two storage memory cells and the transfer memory cell, a first light source irradiating the two storage memory cells and the transfer memory cell with right-handed or left-handed polarized light, a second light source simultaneously irradiating one of the two storage memory cells and the transfer memory cell with a laser beam, and a detector detecting a polarization state of the laser beam.
Owner:KK TOSHIBA
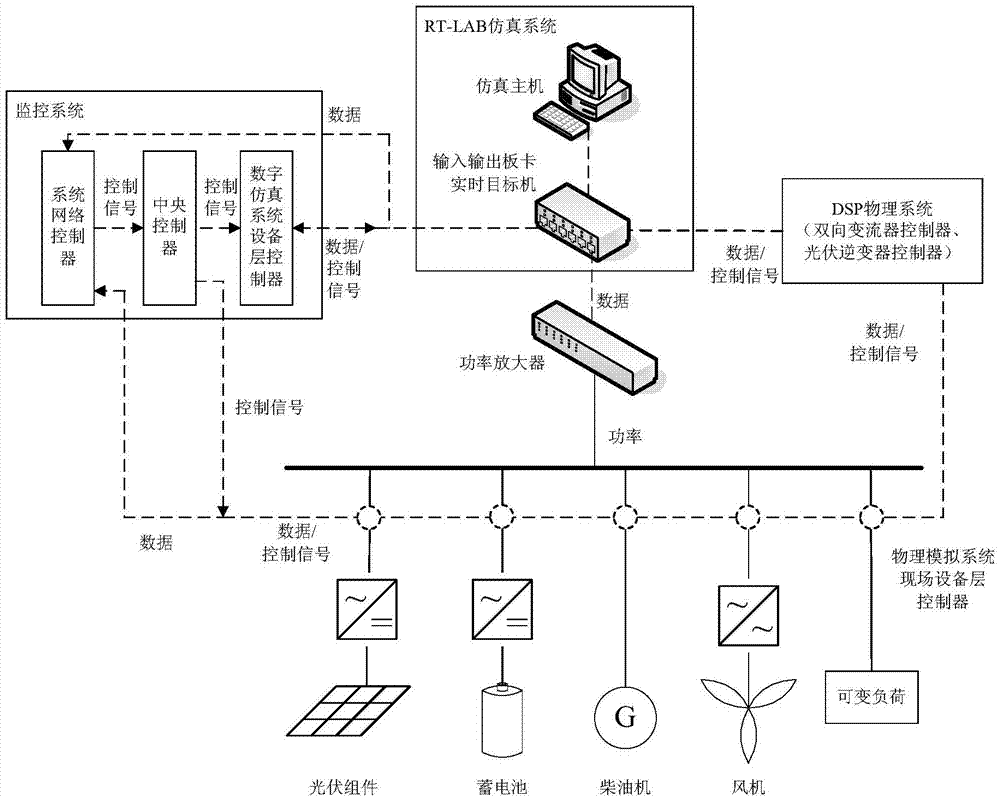
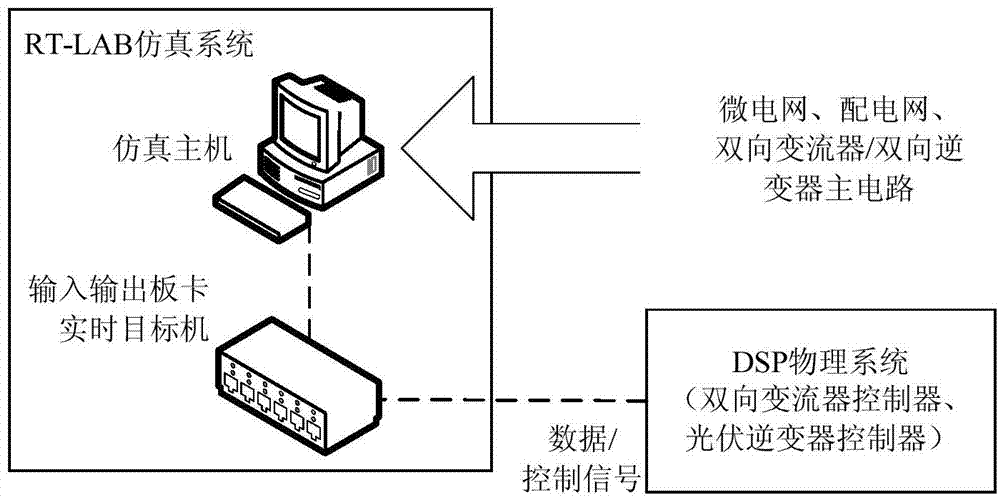
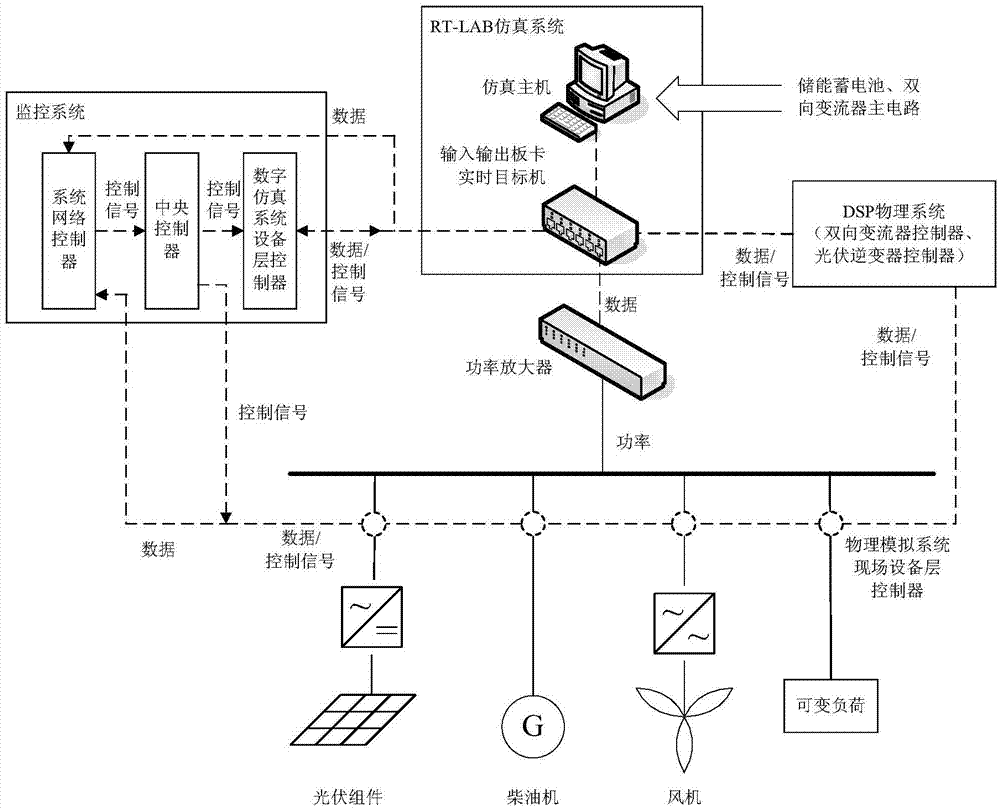
RT-LAB based microgrid simulation testing system
ActiveCN104330980AExpandable and flexibleAdapt to development needsSimulator controlElectric testing/monitoringMicrogridElectric power system
The invention discloses an RT-LAB based microgrid simulation testing system. The system comprises an RT-LAB simulation system, a DSP physical system, a power amplifier, a microgrid physical simulation system and a microgrid monitoring system; the RT-LAB simulation system is used for building microgrid and distribution network simulation models and providing a real-time simulation environment; the DSP physical system is used for producing a control signal to a converter circuit built in the simulation system; the power amplifier is used for connecting the RT-LAB simulation system and the microgrid physical simulation system; the microgrid physical imitating system is used for forming a digital physical microgrid with the RT-LAB simulation system and accepting the monitoring and dispatching control of the monitoring system; the microgrid monitoring system is used for monitoring the DSP physical system, a microgrid digital simulating model and the physical simulation system. According to the system, the microgrid and distribution network simulating models are built on the RT-LAB, the microgrid physical simulation system is provided, so as to truly simulate the running states of a power system and the microgrid; the system has the advantages of real-time simulating, online parameter adjusting, and being rich in interfaces, rich in testing type, flexible to switch the testing mode, simple to operate, safe and reliable, efficient and economical.
Owner:GUANGZHOU INST OF ENERGY CONVERSION - CHINESE ACAD OF SCI
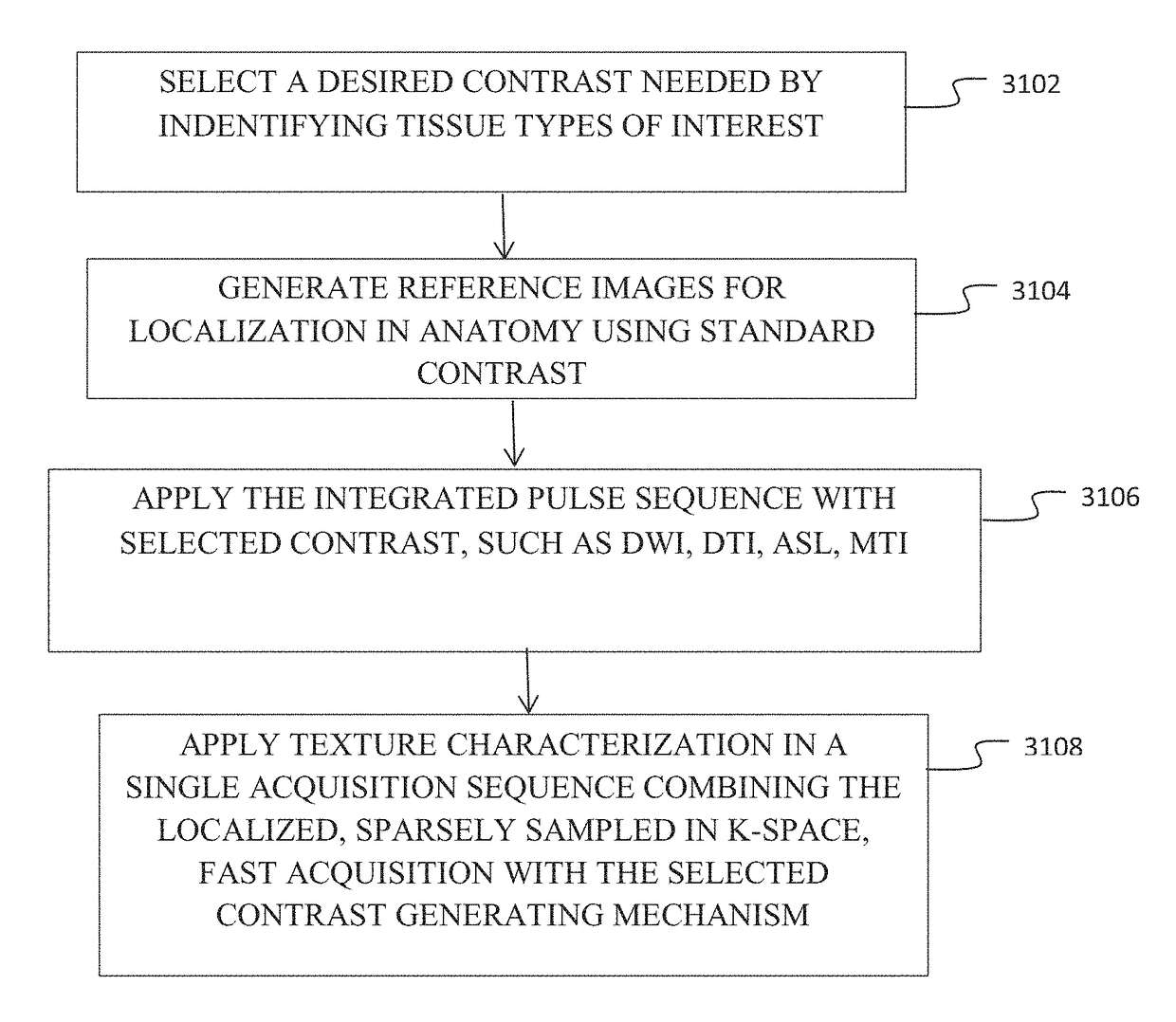
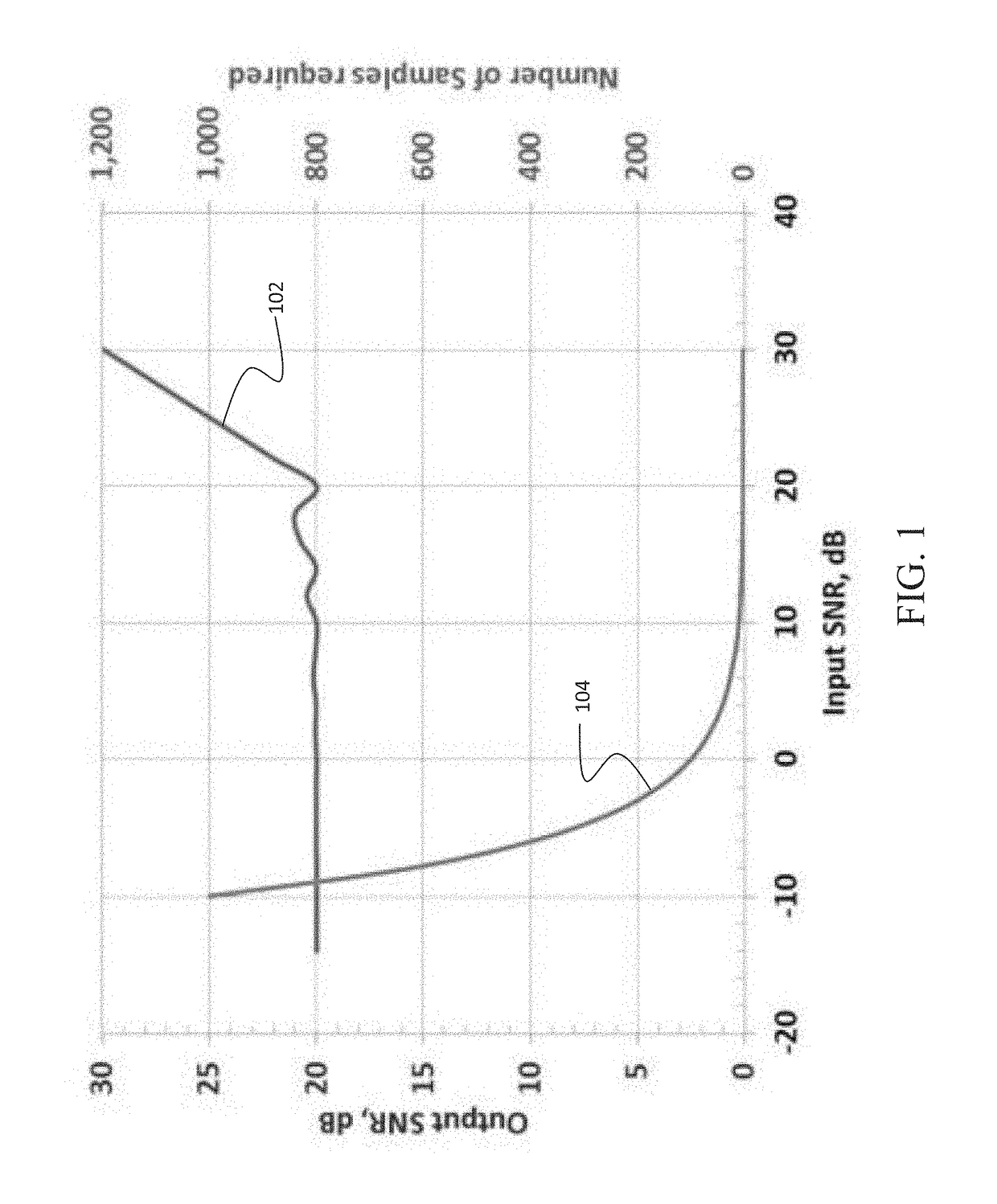
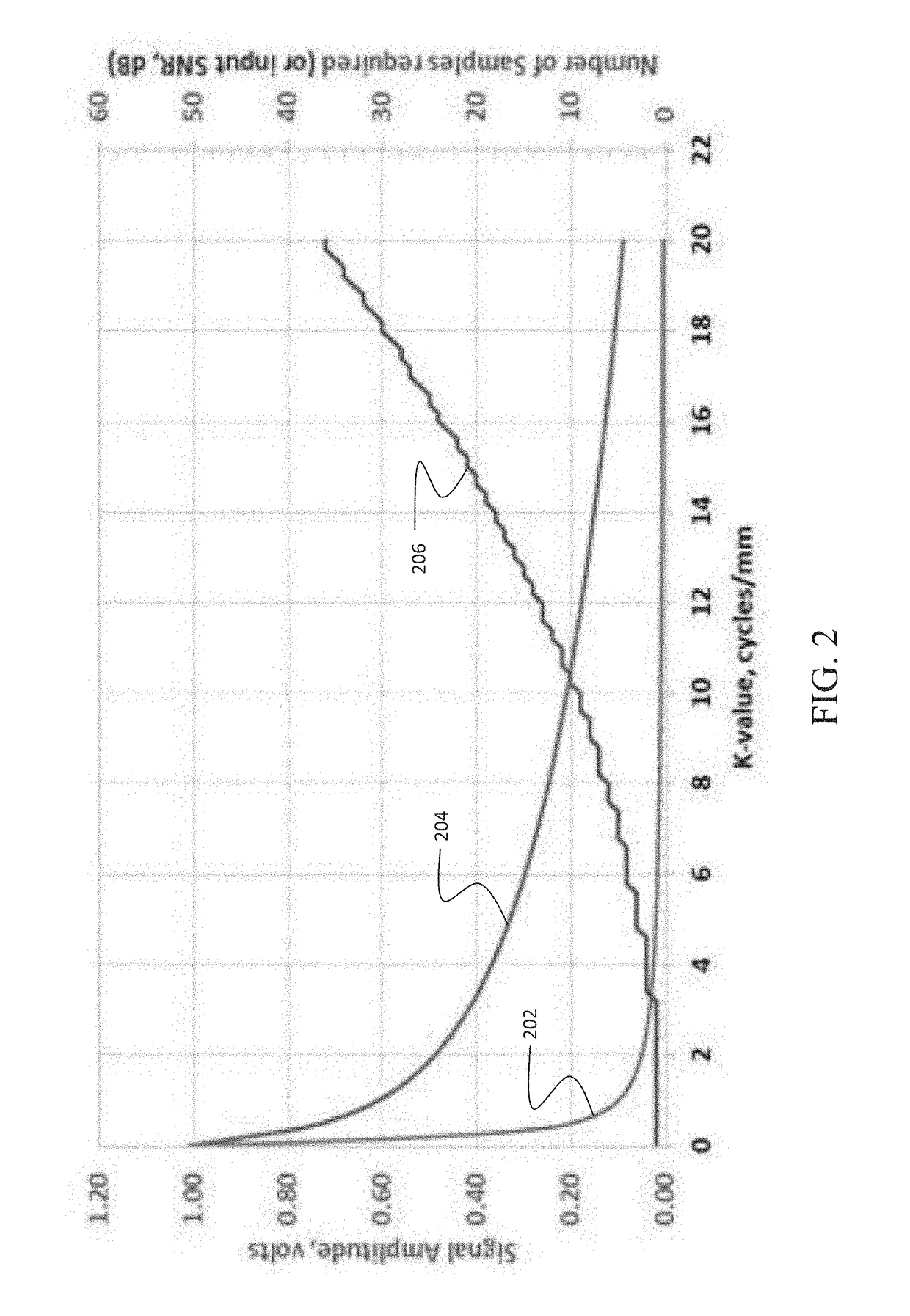
Selective sampling for assessing structural spatial frequencies with specific contrast mechanisms
The disclosed embodiments provide a method for acquiring MR data at resolutions down to tens of microns for application in in vivo diagnosis and monitoring of pathology for which changes in fine tissue textures can be used as markers of disease onset and progression. Bone diseases, tumors, neurologic diseases, and diseases involving fibrotic growth and / or destruction are all target pathologies. Further the technique can be used in any biologic or physical system for which very high-resolution characterization of fine scale morphology is needed. The method provides rapid acquisition of signal at selected values in k-space, with multiple successive acquisitions at individual k-values taken on a time scale on the order of microseconds, within a defined tissue volume, and subsequent combination of the multiple measurements in such a way as to maximize SNR. The reduced acquisition volume, and acquisition of only signal values at select places in k-space, along selected directions, enables much higher in vivo resolution than is obtainable with current MRI techniques.
Owner:BIOPROTONICS
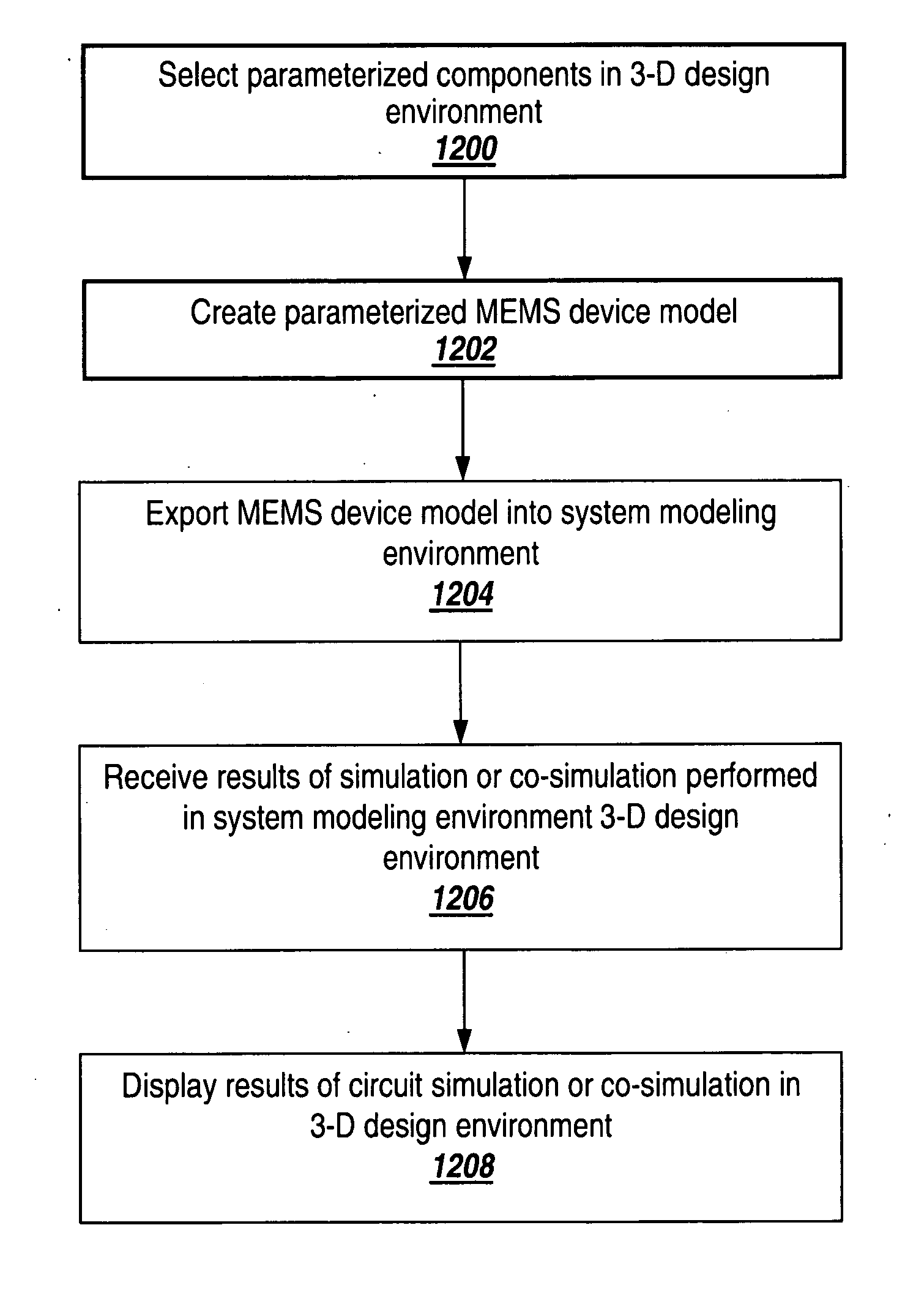
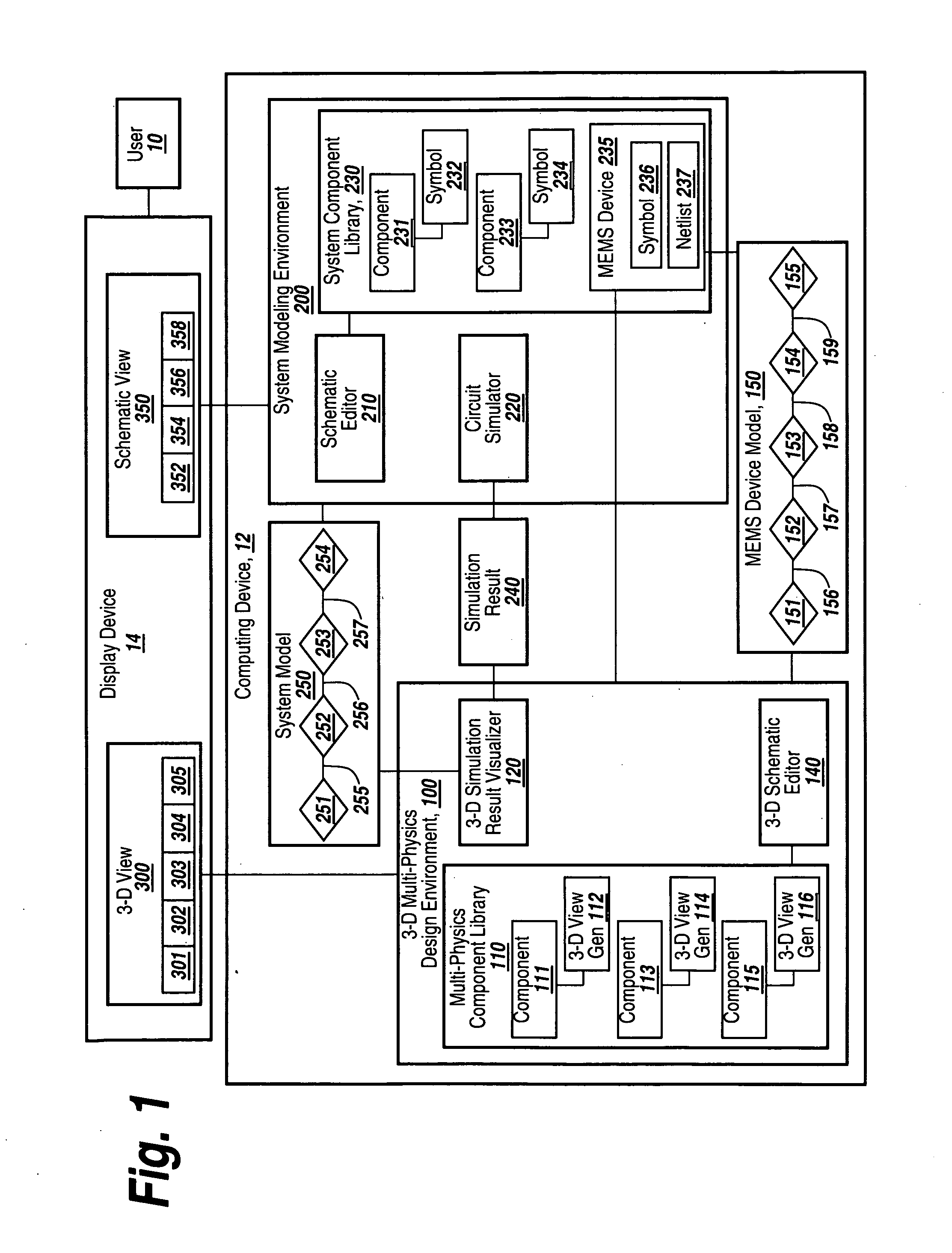
System and method for three-dimensional schematic capture and result visualization of multi-physics system models
A 3-D multi-physics design environment (“3-D design environment”) for designing and simulating multi-physics devices such as MEMS devices is discussed. The 3-D design environment is programmatically integrated with a system modeling environment that is suitable for system-level design and simulation of analog-signal ICs, mixed-signal ICs and multi-physics systems. A parameterized MEMS device model is created in a 3-D graphical view in the 3-D design environment using parameterized model components that are each associated with an underlying behavioral model. After the MEMS device model is completed, it may be exported to a system modeling environment without subjecting the model to preliminary finite element meshing.
Owner:COVENTOR
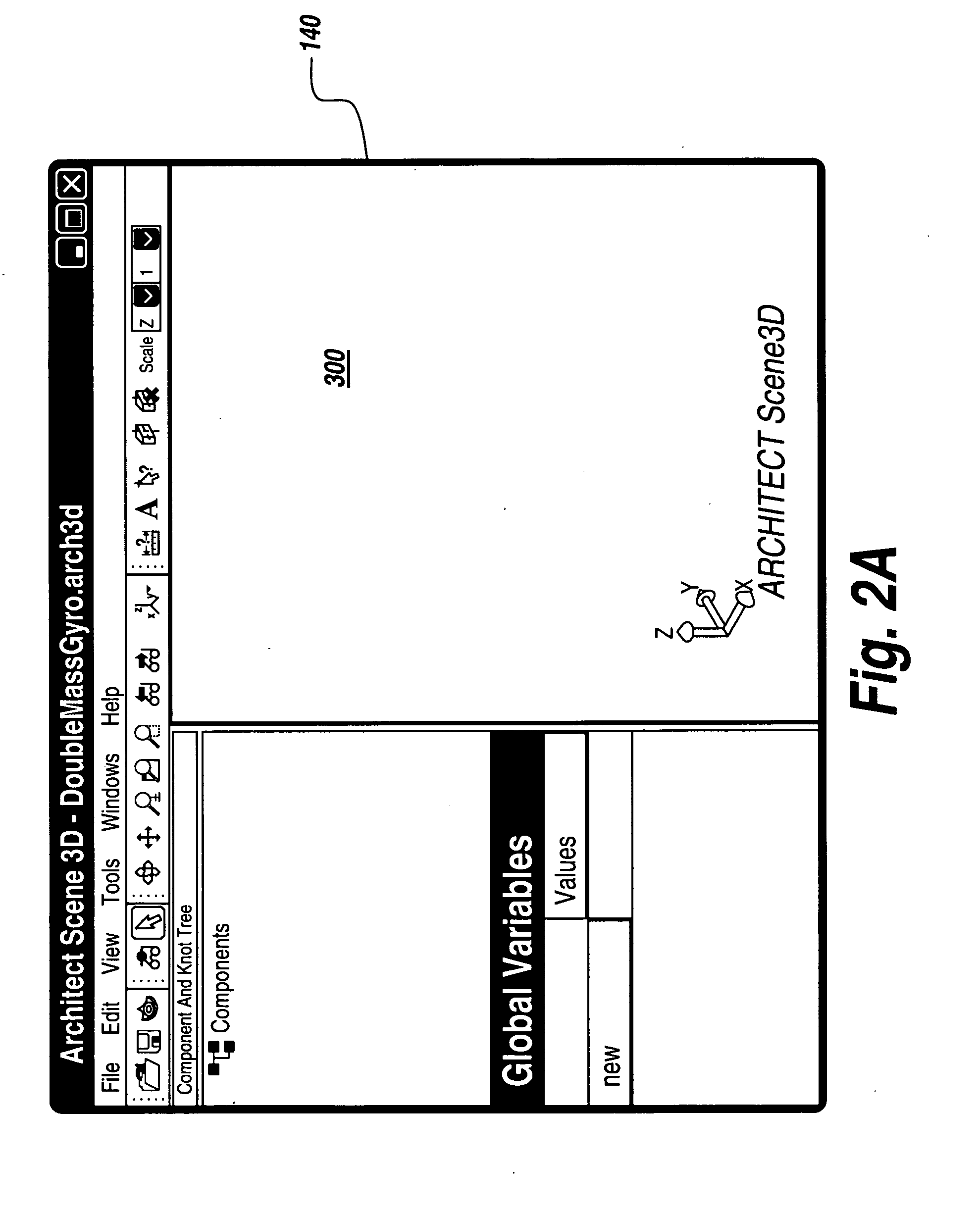
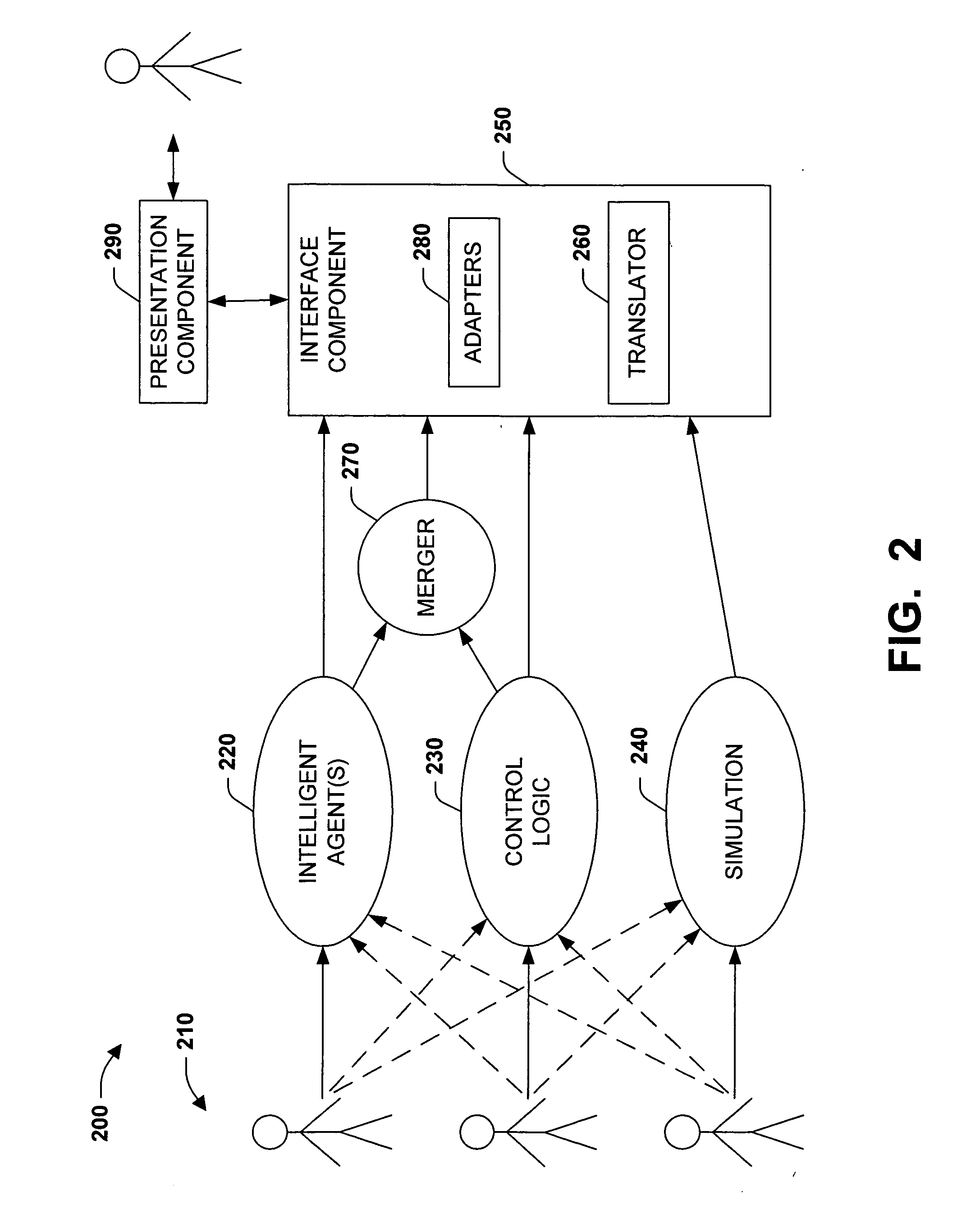
Agent simulation development environment
ActiveUS20060167667A1Simple designImprove performanceProgramme controlSampled-variable control systemsSynchronous controlPhysical system
The subject invention relates to integrating agents, control logic, and simulations in order to simulate and validate a control strategy for a physical system. The systems and methods integrate agents and control logic with simulations, and utilize the integrated agents, control logic, and simulations to generate a proxy. The proxy can be employed to couple one or more controllers executing the agents and control logic with the simulations. Visualization is utilized to visualize the simulation, including the agents and the control logic. In addition, the systems and methods utilize a synchronization algorithm to synchronize the execution times of the controllers and the simulations. The foregoing mitigates validation through building and testing physical system and / or test beds. Upon validating control strategies, associated agents and logic can be loaded in one or more industrial controllers controlling the physical system, and the simulation can be utilized to represent the physical system.
Owner:ROCKWELL AUTOMATION TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com