Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
760 results about "Pointing systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Point system. n. 1. A system of evaluating academic achievement based on grade points. 2. Any of various printing or writing systems for the blind, such as Braille, that use an alphabet of raised symbols or dots that correspond to letters.
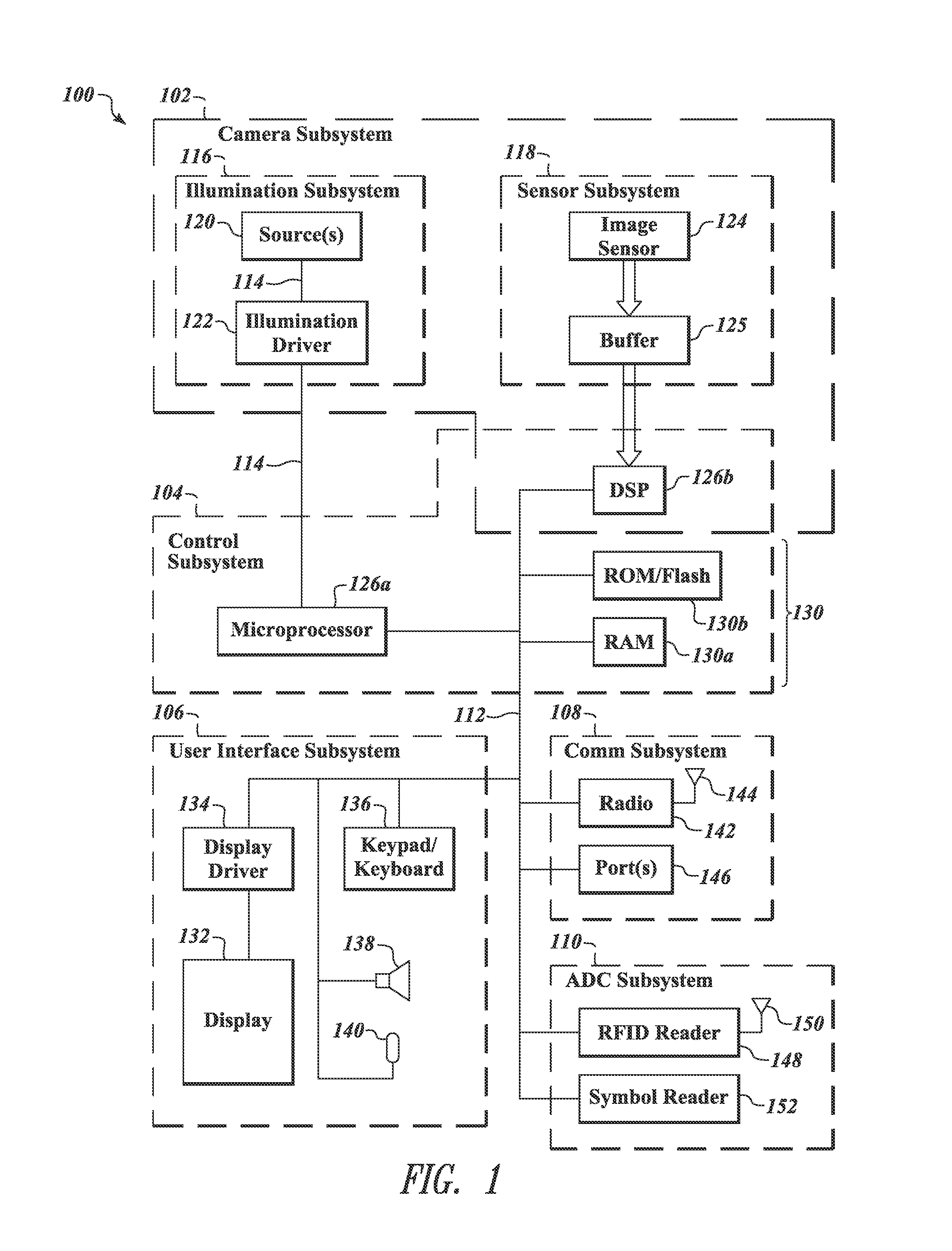
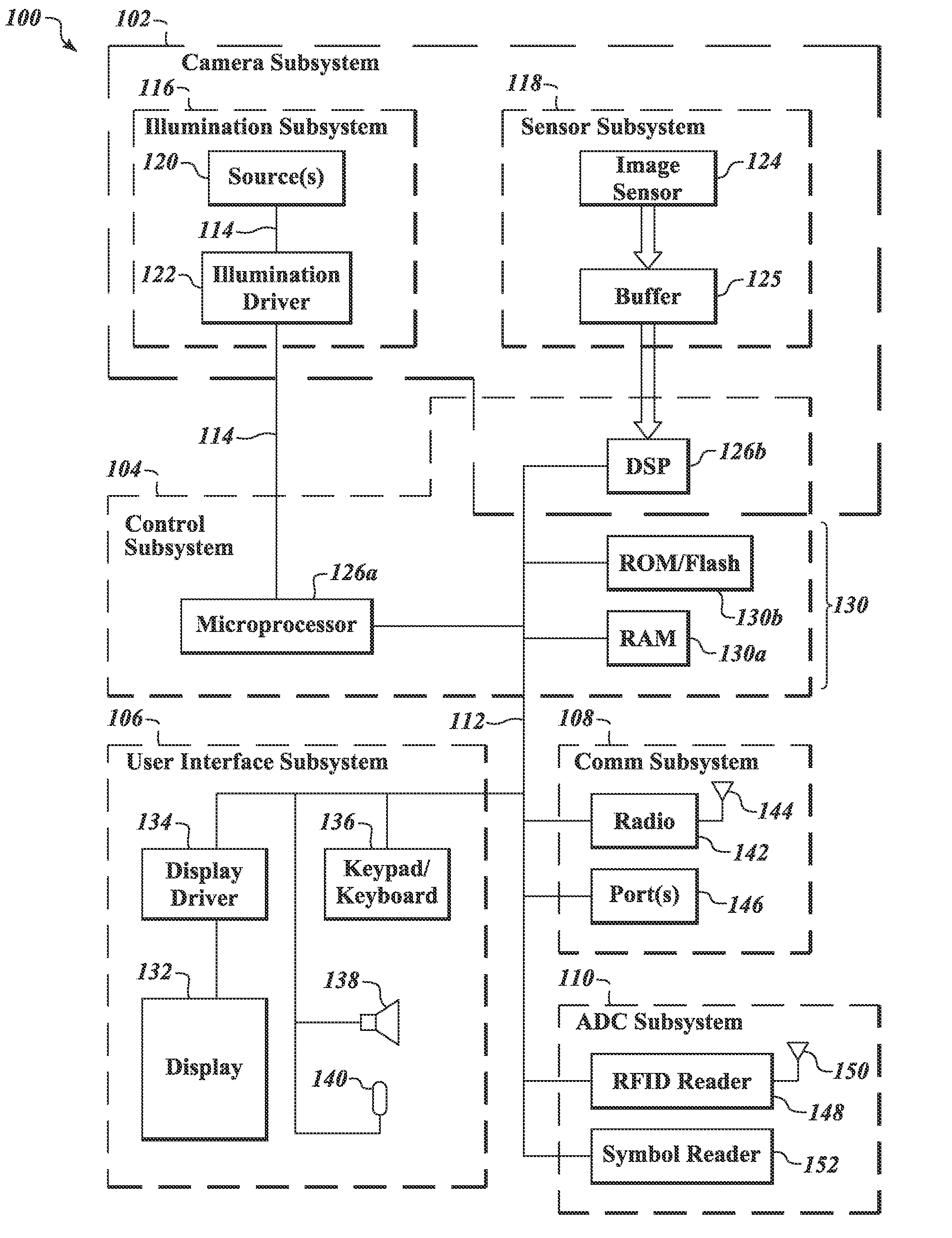
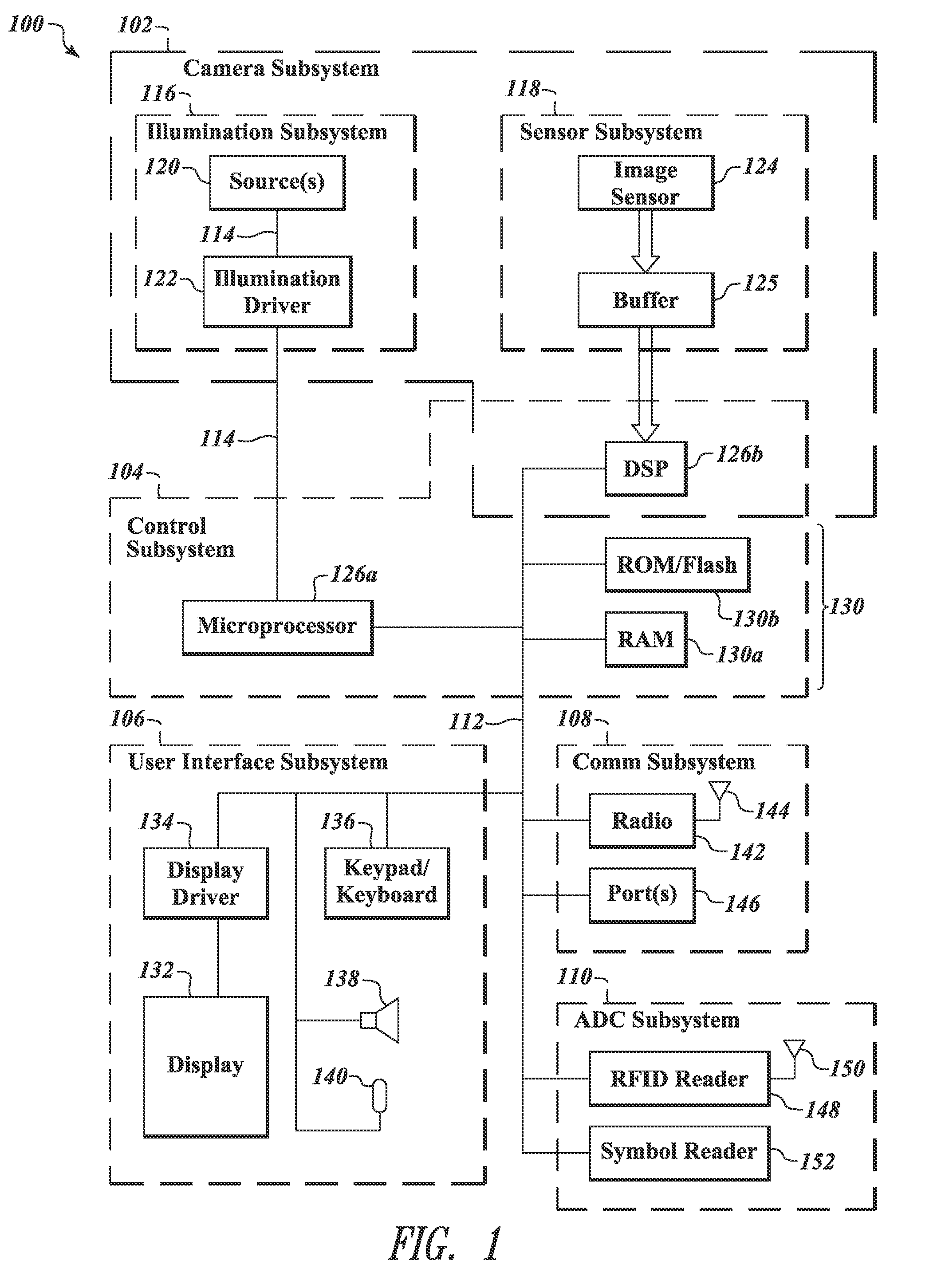
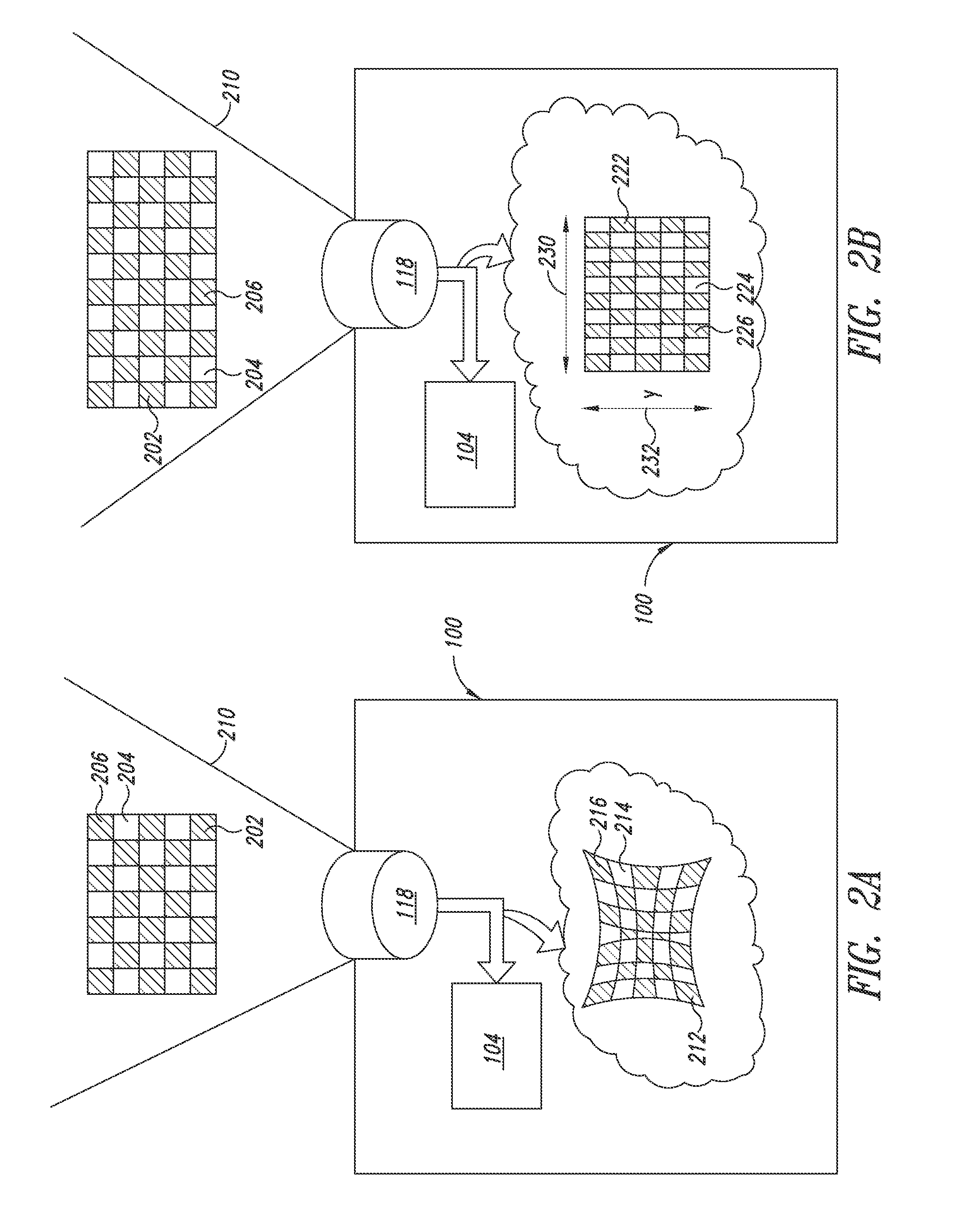
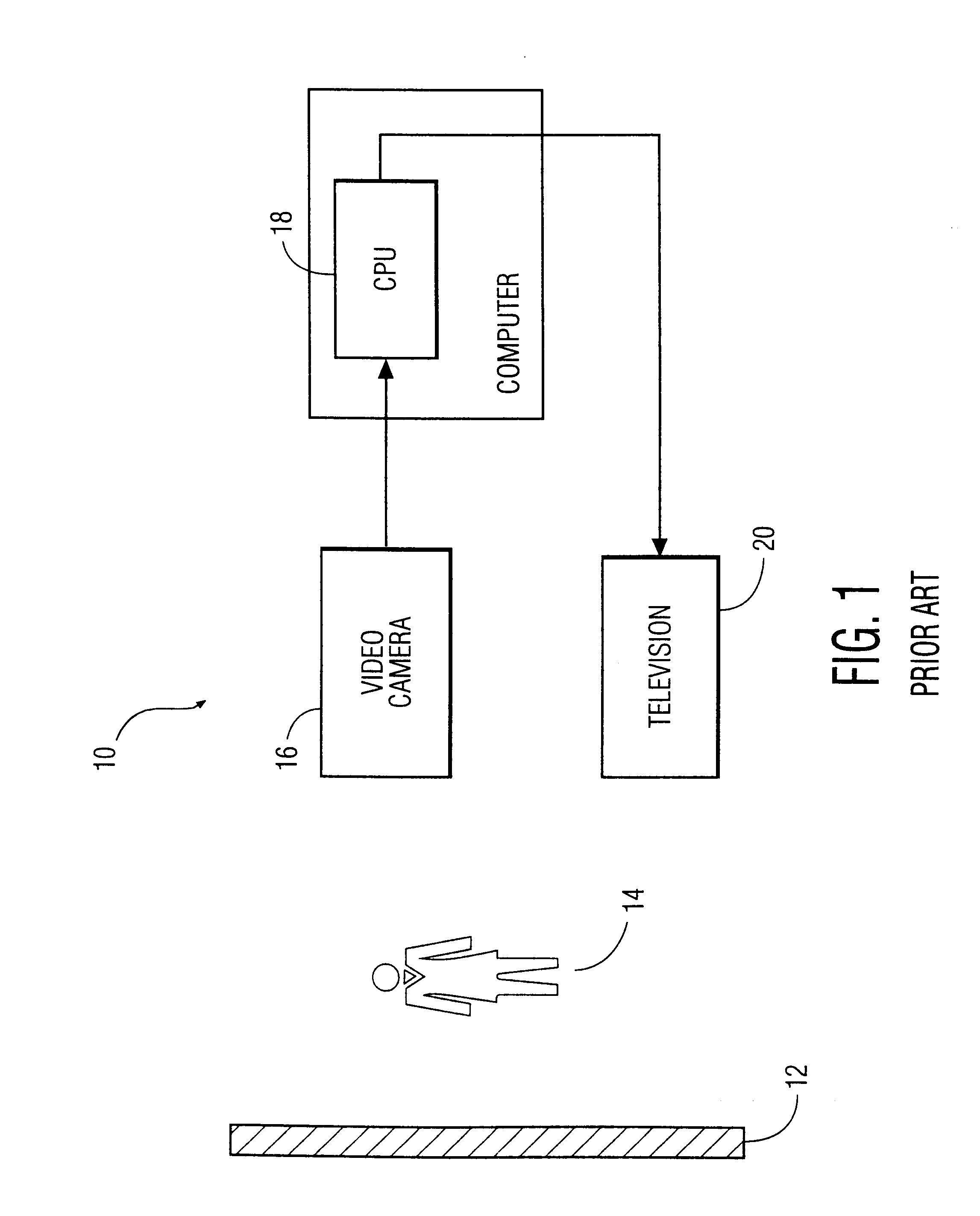
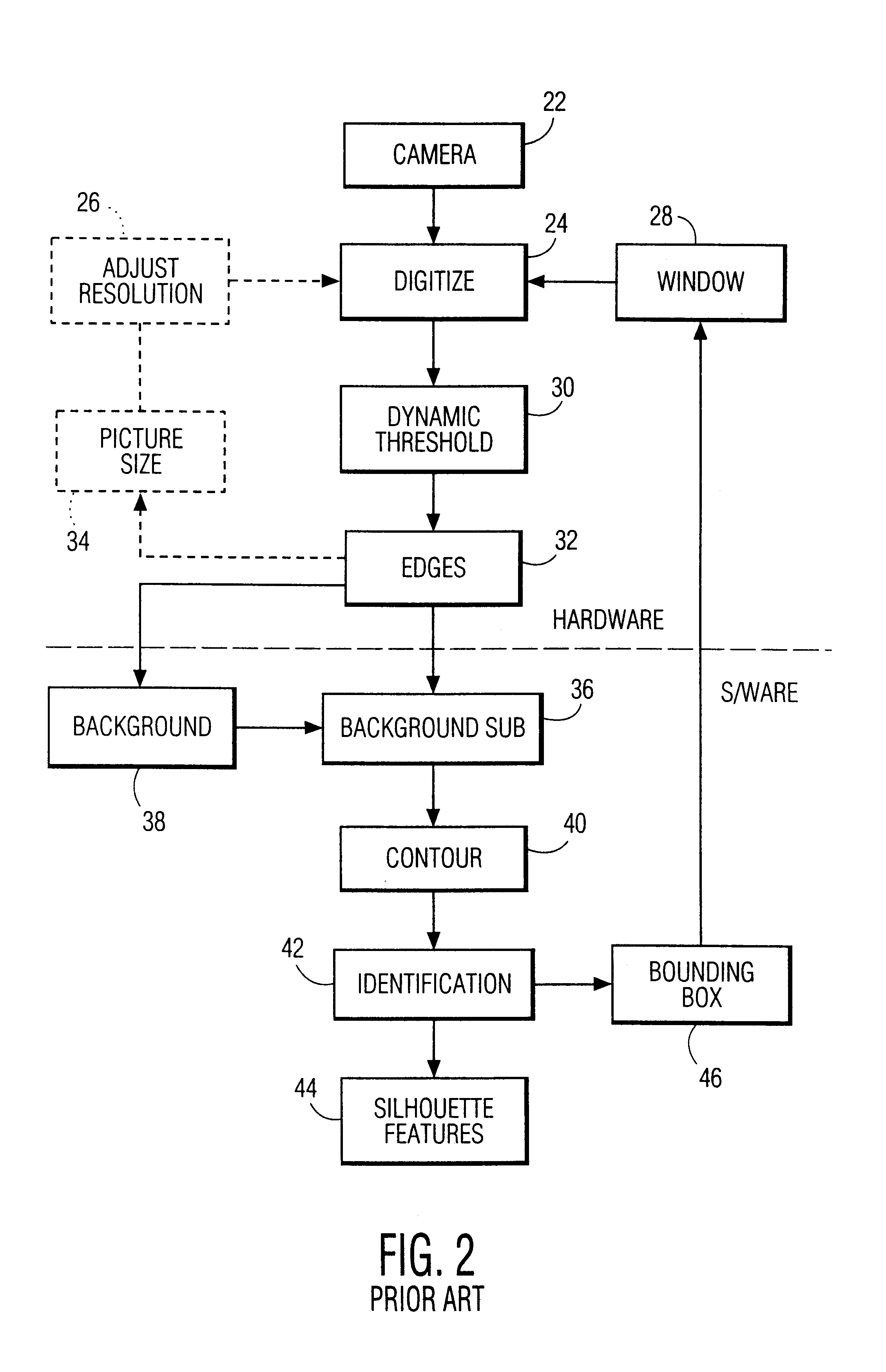
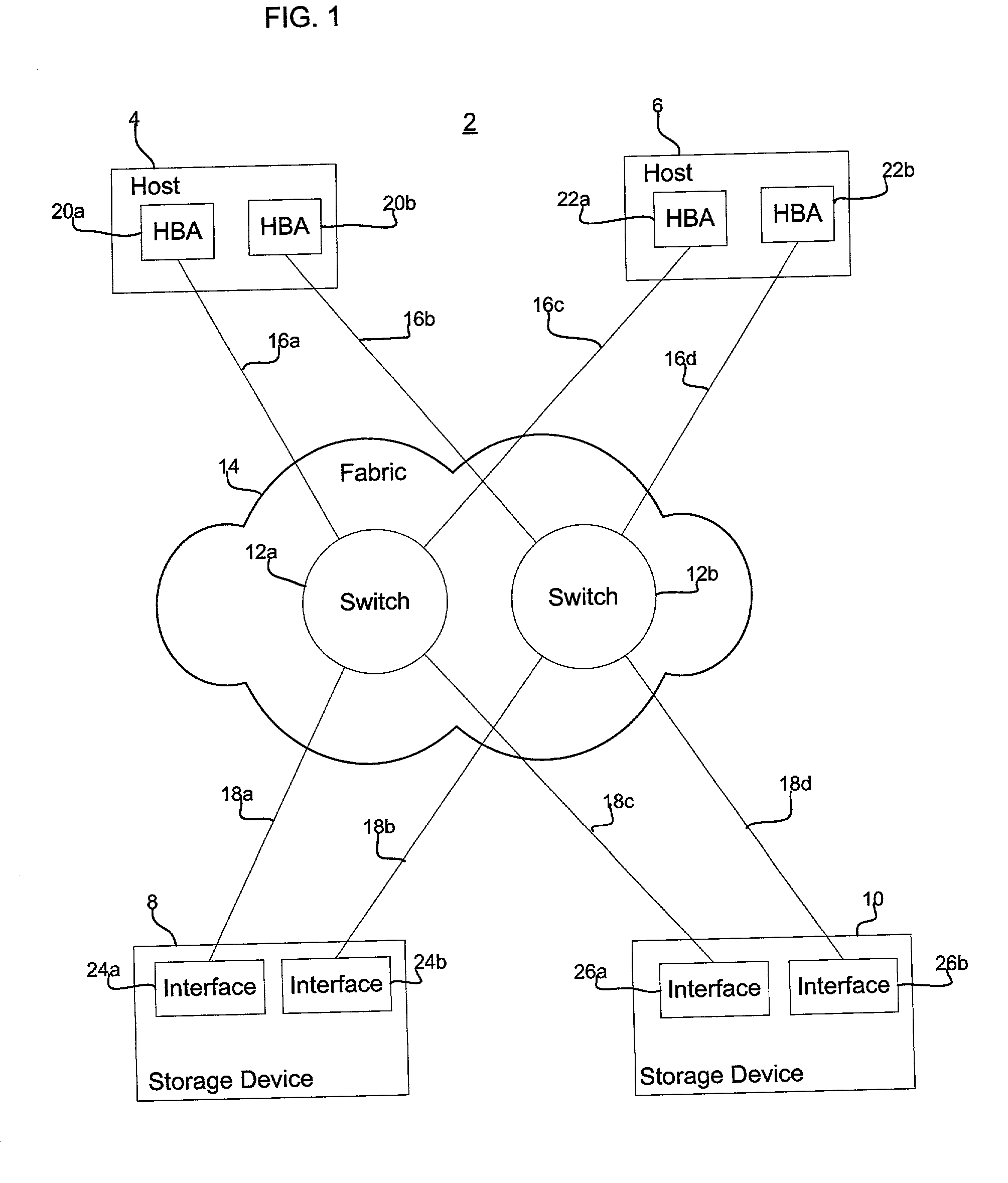
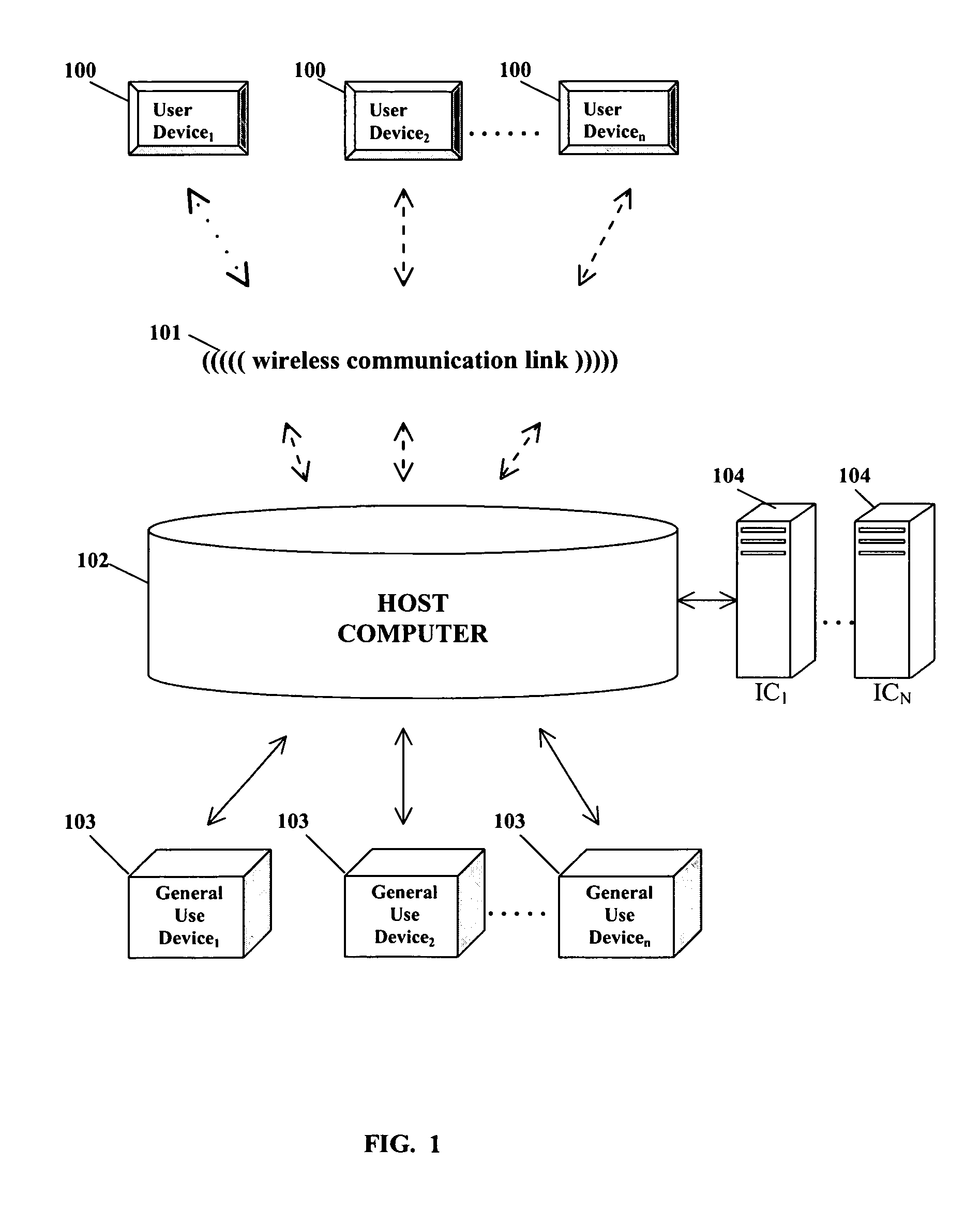
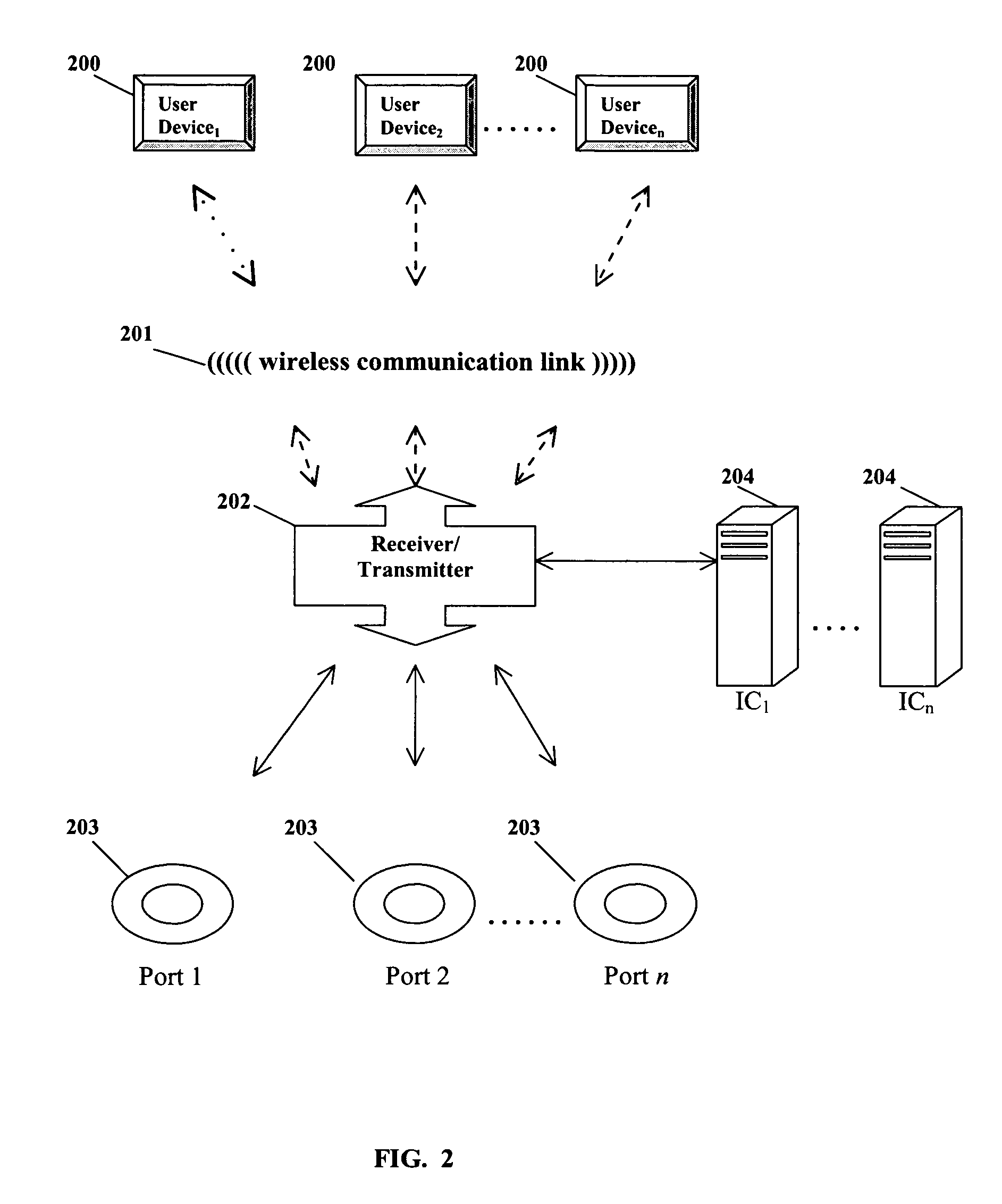
System and method for permitting three-dimensional navigation through a virtual reality environment using camera-based gesture inputs
InactiveUS6181343B1Input/output for user-computer interactionCosmonautic condition simulationsDisplay deviceThree dimensional graphics
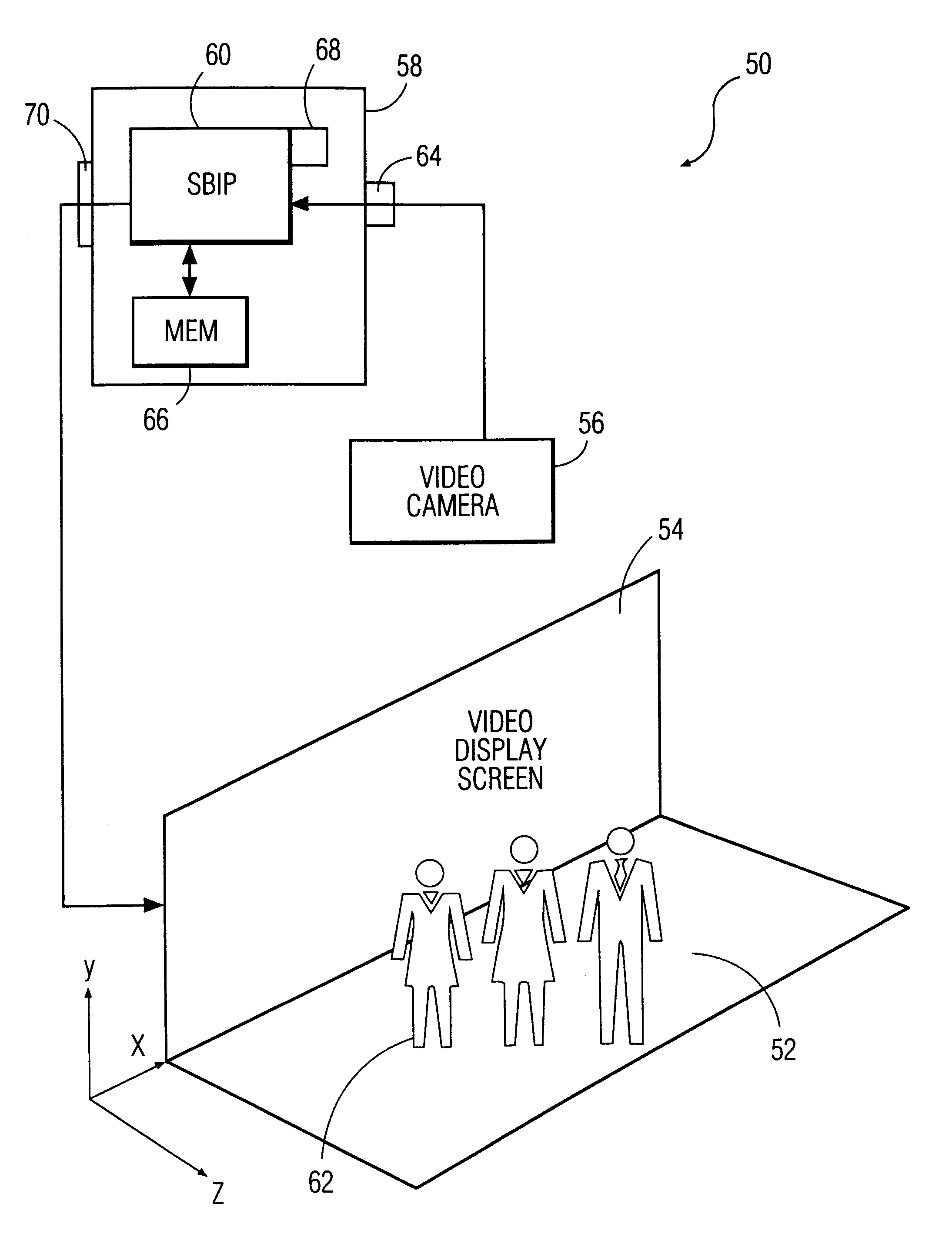
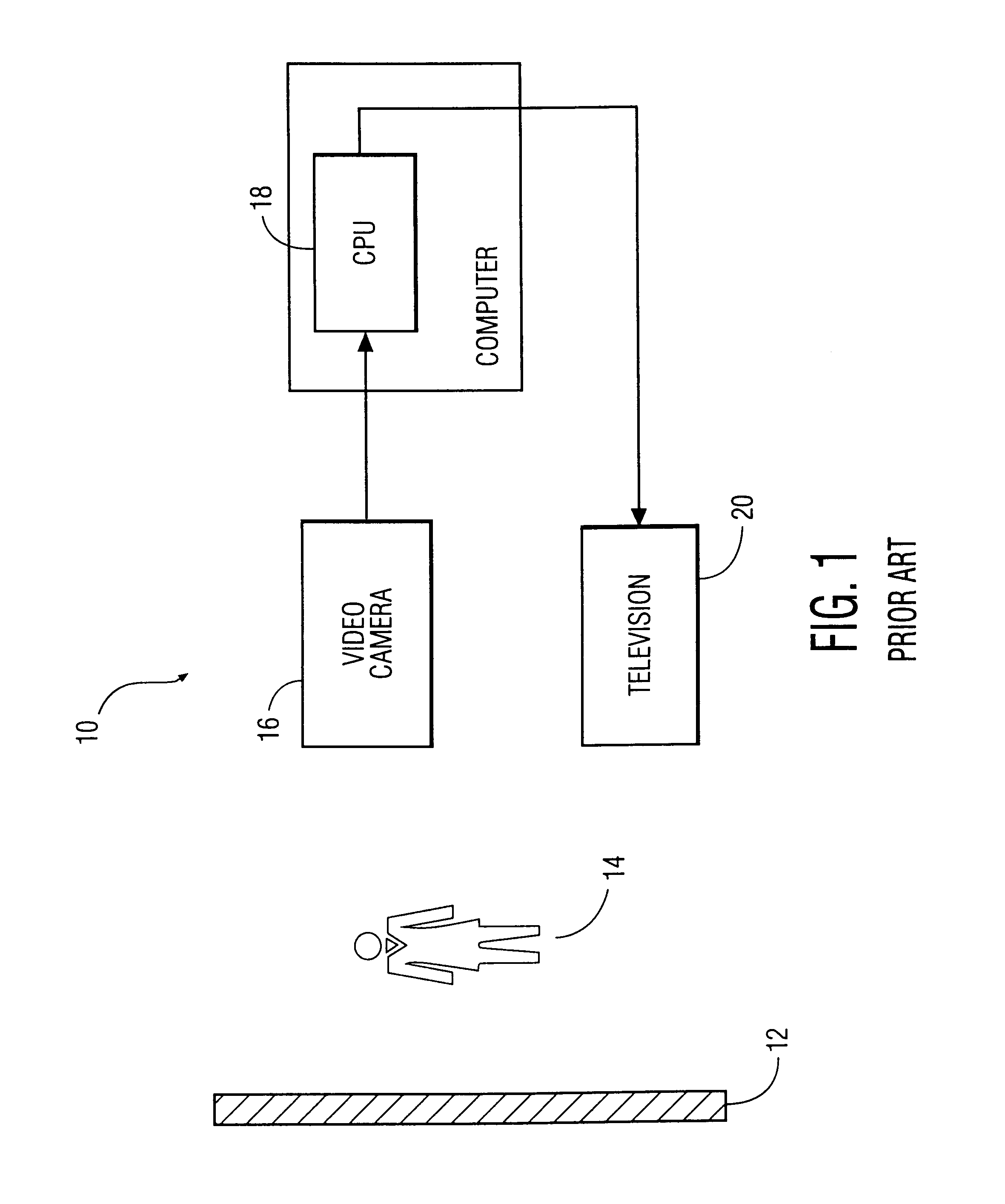
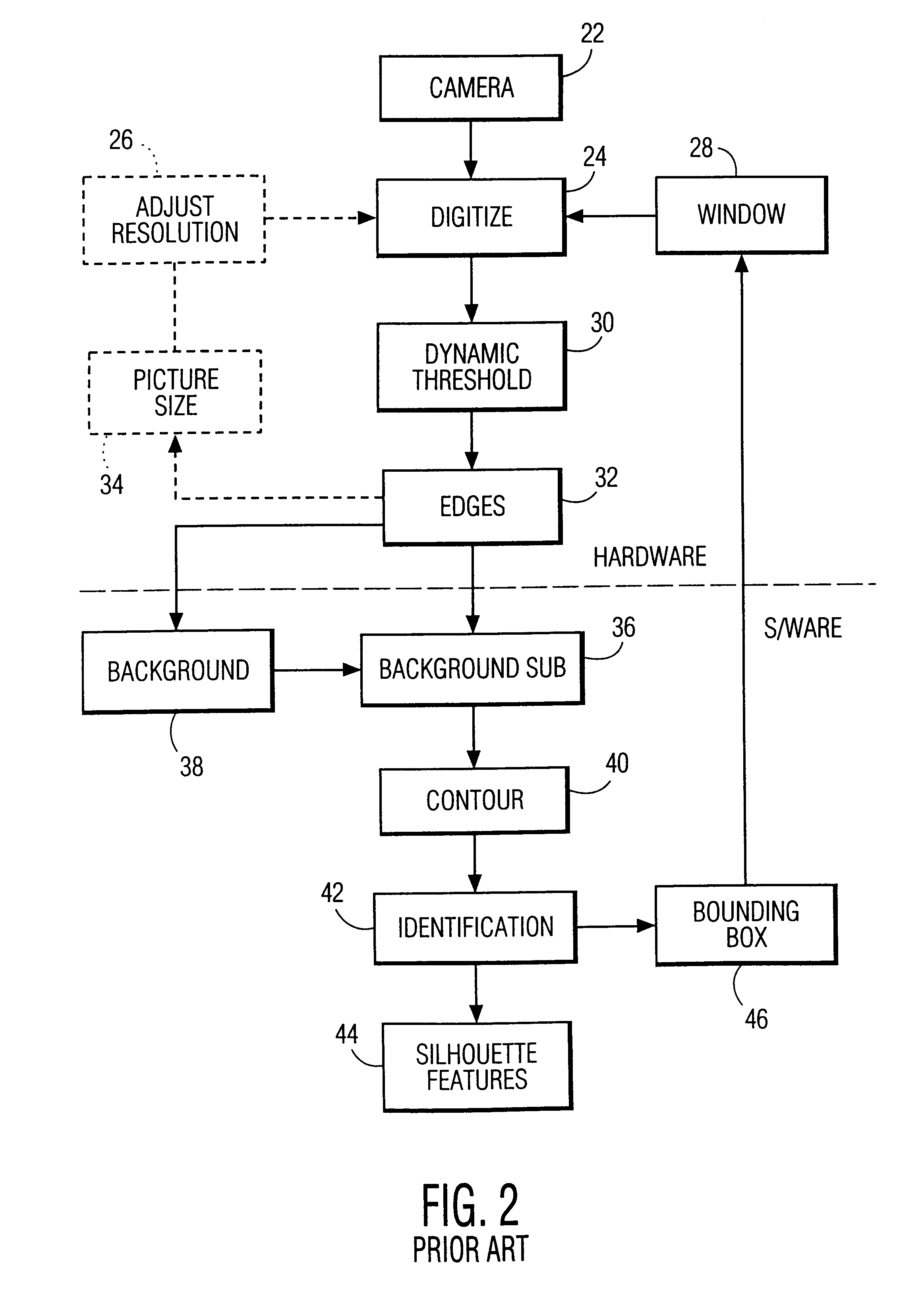
A system and method for permitting three-dimensional navigation through a virtual reality environment using camera-based gesture inputs of a system user. The system comprises a computer-readable memory, a video camera for generating video signals indicative of the gestures of the system user and an interaction area surrounding the system user, and a video image display. The video image display is positioned in front of the system user. The system further comprises a microprocessor for processing the video signals, in accordance with a program stored in the computer-readable memory, to determine the three-dimensional positions of the body and principle body parts of the system user. The microprocessor constructs three-dimensional images of the system user and interaction area on the video image display based upon the three-dimensional positions of the body and principle body parts of the system user. The video image display shows three-dimensional graphical objects within the virtual reality environment, and movement by the system user permits apparent movement of the three-dimensional objects displayed on the video image display so that the system user appears to move throughout the virtual reality environment.
Owner:PHILIPS ELECTRONICS NORTH AMERICA
Volume dimensioning system calibration systems and methods
ActiveUS20140049635A1Small sizeFacilitate ongoing and operationally transparent and calibrationColor television detailsClosed circuit television systemsGuidelineTechnical standard
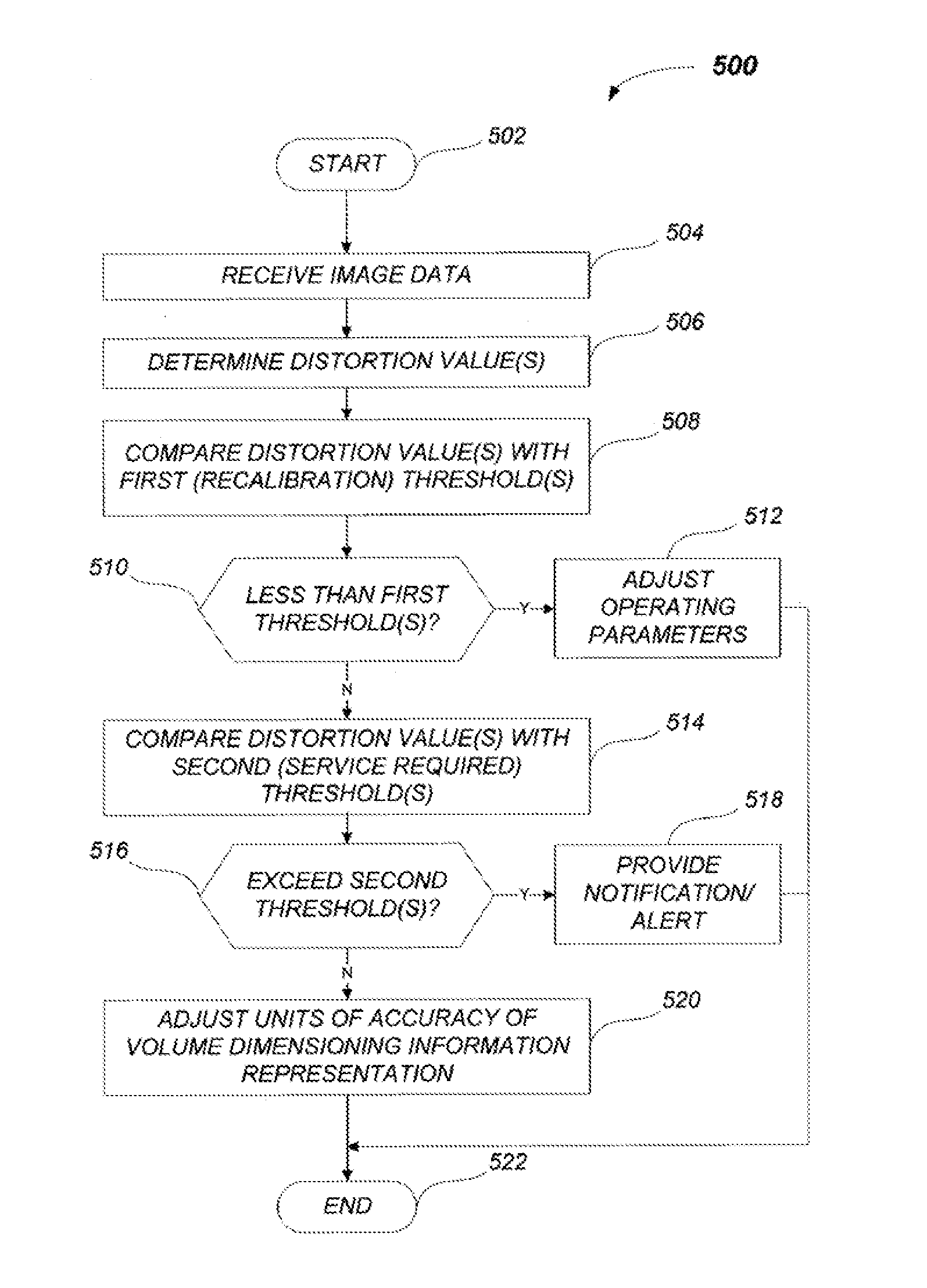
Various corporate, industry, and regulatory guidelines, best practices and standards are used in establishing acceptable levels of accuracy for volume dimensioning systems used in commerce. A volume dimensioning system can determine at least one distortion value that is indicative of an amount of distortion present in the system and responsive to the amount of distortion, autonomously alter or adjust the units of accuracy of information reported by the system. Such alteration or adjustment of units of accuracy may be performed based on an assessment of the distortion relative to a number of distortion thresholds. Responsive to the assessment, the volume dimensioning system can adjust a unit of accuracy in a representation of volume dimensioning related information.
Owner:INTERMEC IP
Volume dimensioning system calibration systems and methods
InactiveUS20150009338A1Facilitate ongoing and operationally transparent and calibrationTelevision systemsTesting/calibration for volume measurementGuidelineTechnical standard
Owner:INTERMEC IP CORP
System and method for constructing three-dimensional images using camera-based gesture inputs
InactiveUS6195104B1Input/output for user-computer interactionTelevision system detailsBody areaDisplay device
A system and method for constructing three-dimensional images using camera-based gesture inputs of a system user. The system comprises a computer-readable memory, a video camera for generating video signals indicative of the gestures of the system user and an interaction area surrounding the system user, and a video image display. The video image display is positioned in front of the system users. The system further comprises a microprocessor for processing the video signals, in accordance with a program stored in the computer-readable memory, to determine the three-dimensional positions of the body and principle body parts of the system user. The microprocessor constructs three-dimensional images of the system user and interaction area on the video image display based upon the three-dimensional positions of the body and principle body parts of the system user. The video image display shows three-dimensional graphical objects superimposed to appear as if they occupy the interaction area, and movement by the system user causes apparent movement of the superimposed, three-dimensional objects displayed on the video image display.
Owner:PHILIPS ELECTRONICS NORTH AMERICA
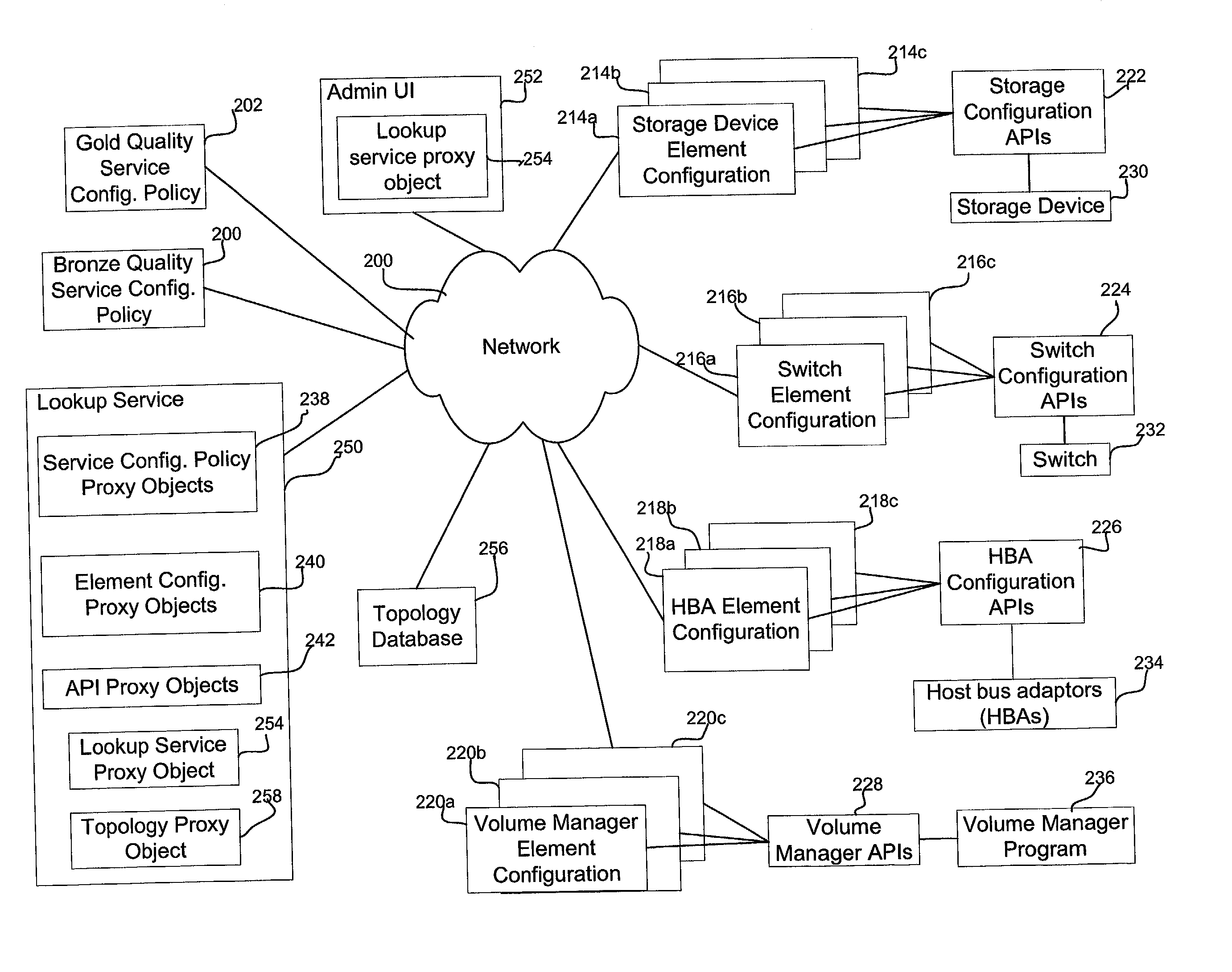
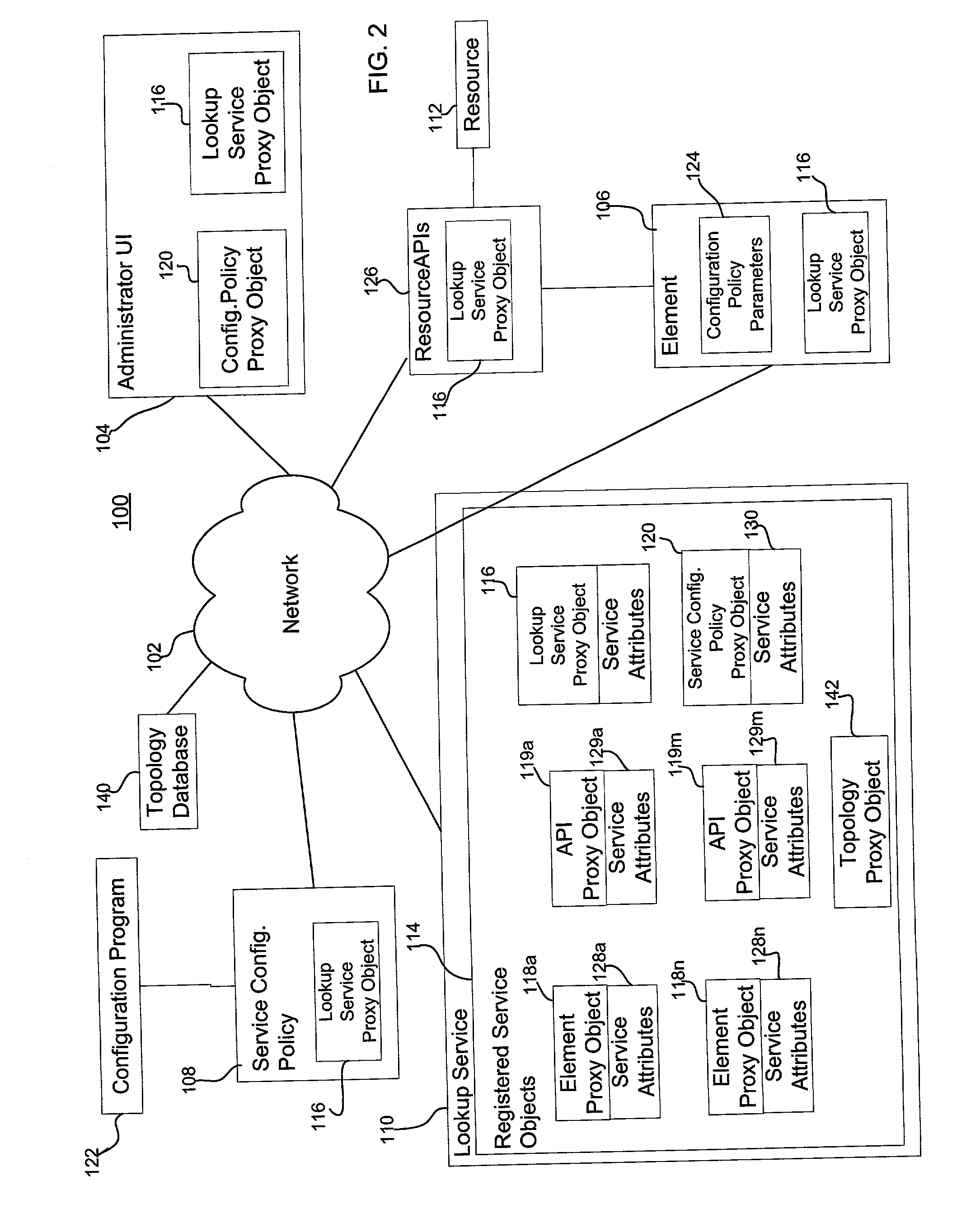
Method, system, and program for determining a modification of a system resource configuration
InactiveUS20030135609A1Resource allocationMultiple digital computer combinationsManagement systemReal-time computing
Provided are a method, system, and program for managing multiple resources in a system at a service level, including at least one host, network, and a storage space comprised of at least one storage system that each host is capable of accessing over the network. A plurality of service level parameters are measured and monitored indicating a state of the resources in the system. A determination is made of values for the service level parameters and whether the service level parameter values satisfy predetermined service level thresholds. Indication is made as to whether the service level parameter values satisfy the predetermined service thresholds. A determination is made of a modification to one or more resource deployments or configurations if the value for the service level parameter for the resource does not satisfy the predetermined service level thresholds.
Owner:SUN MICROSYSTEMS INC
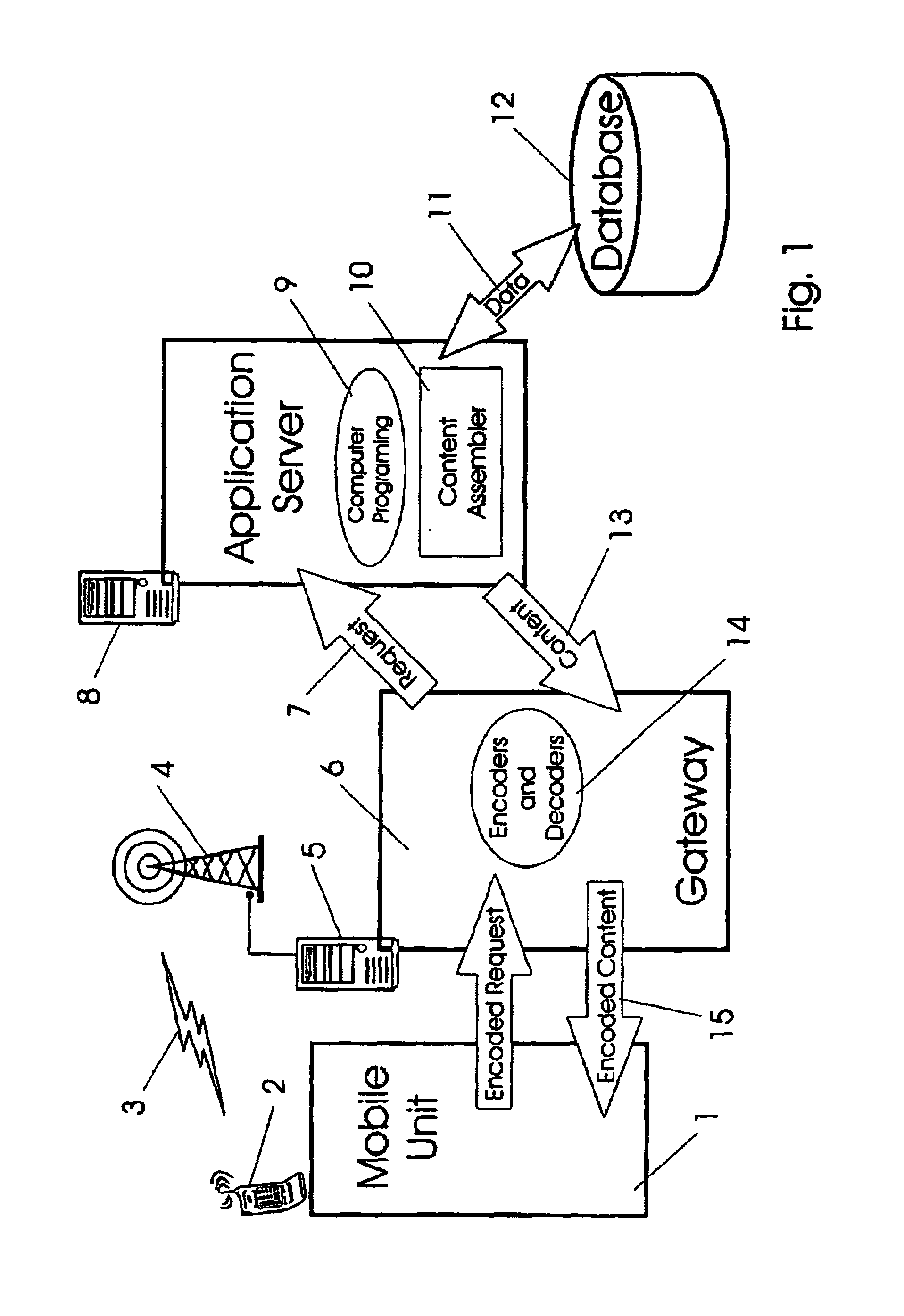
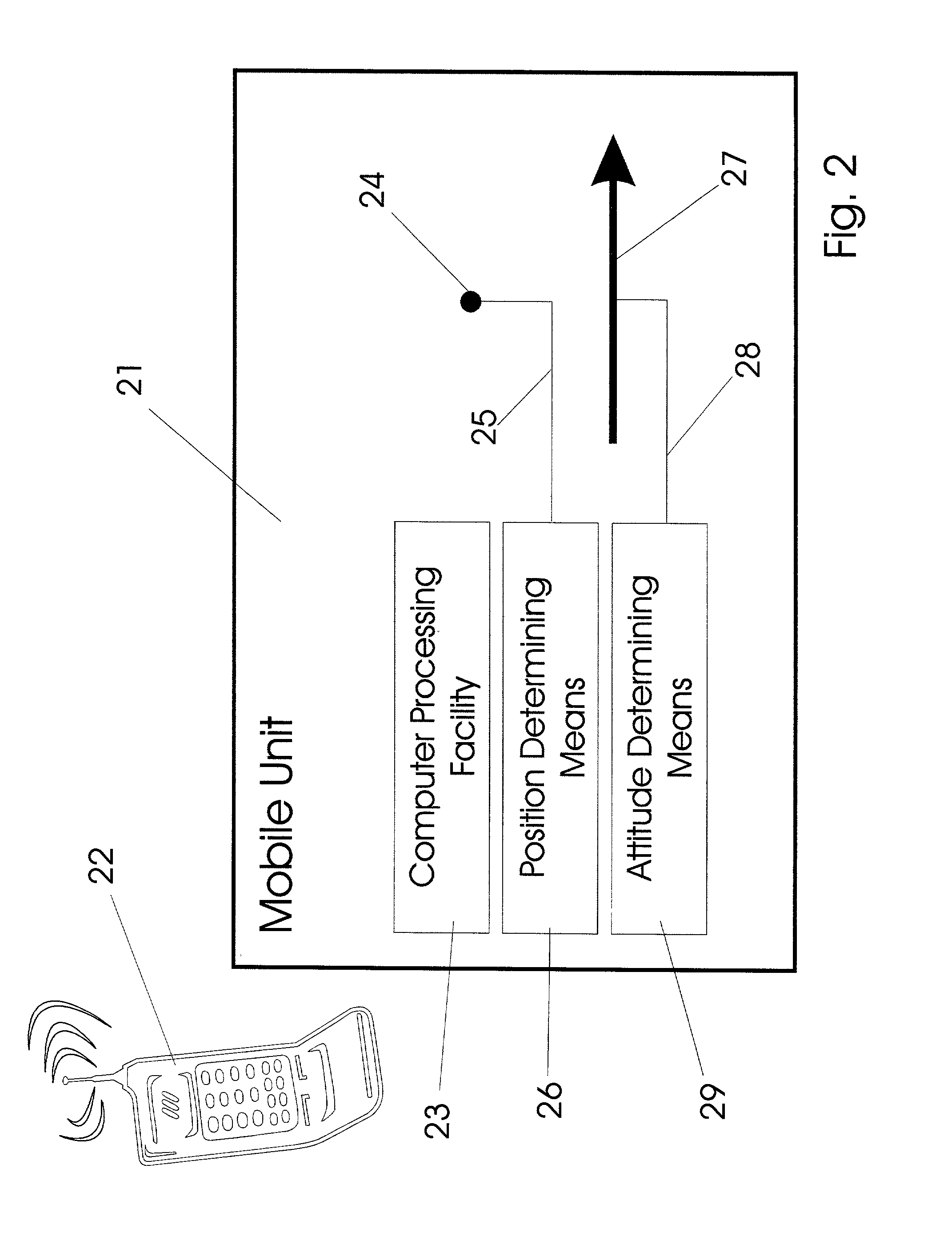
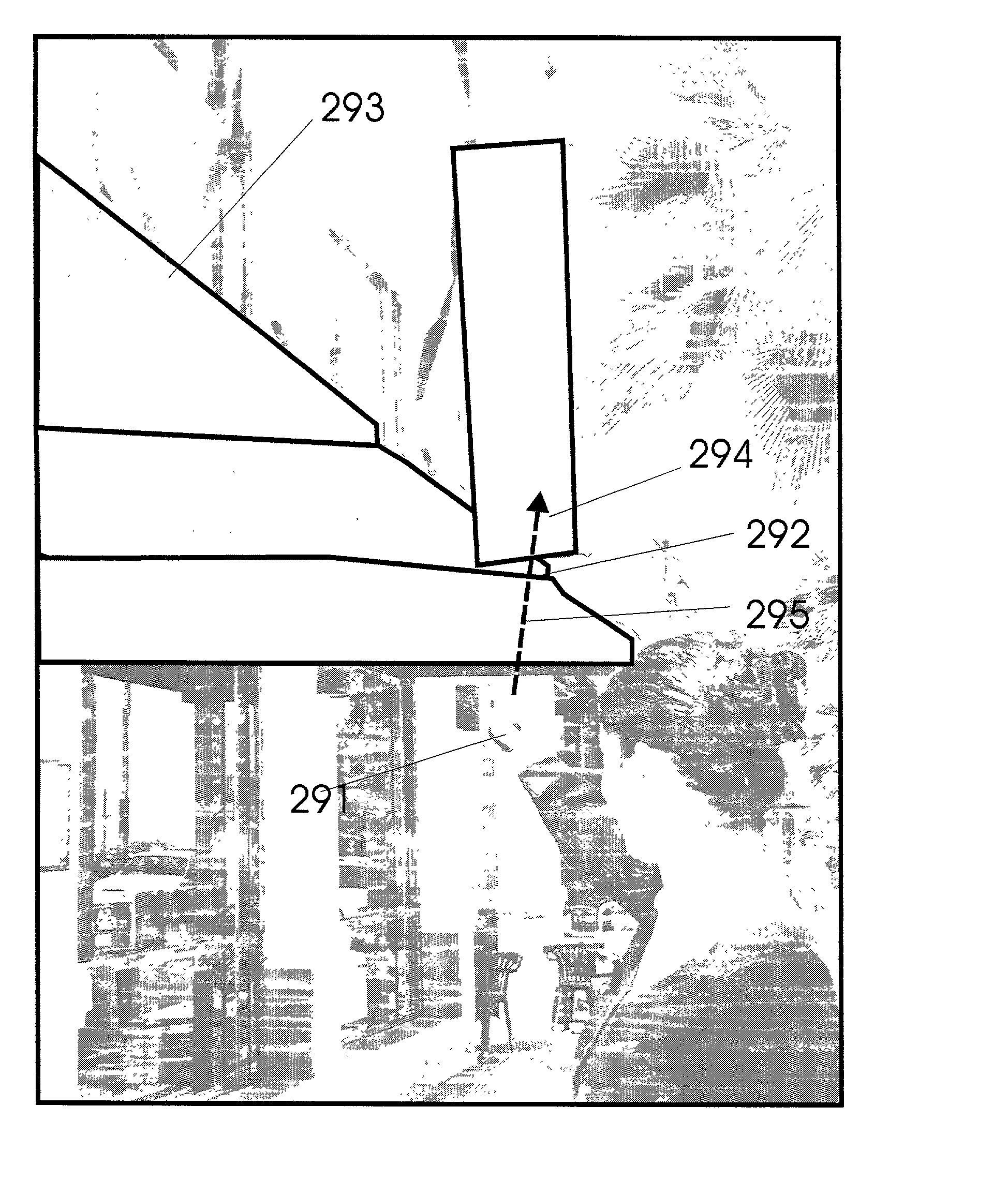
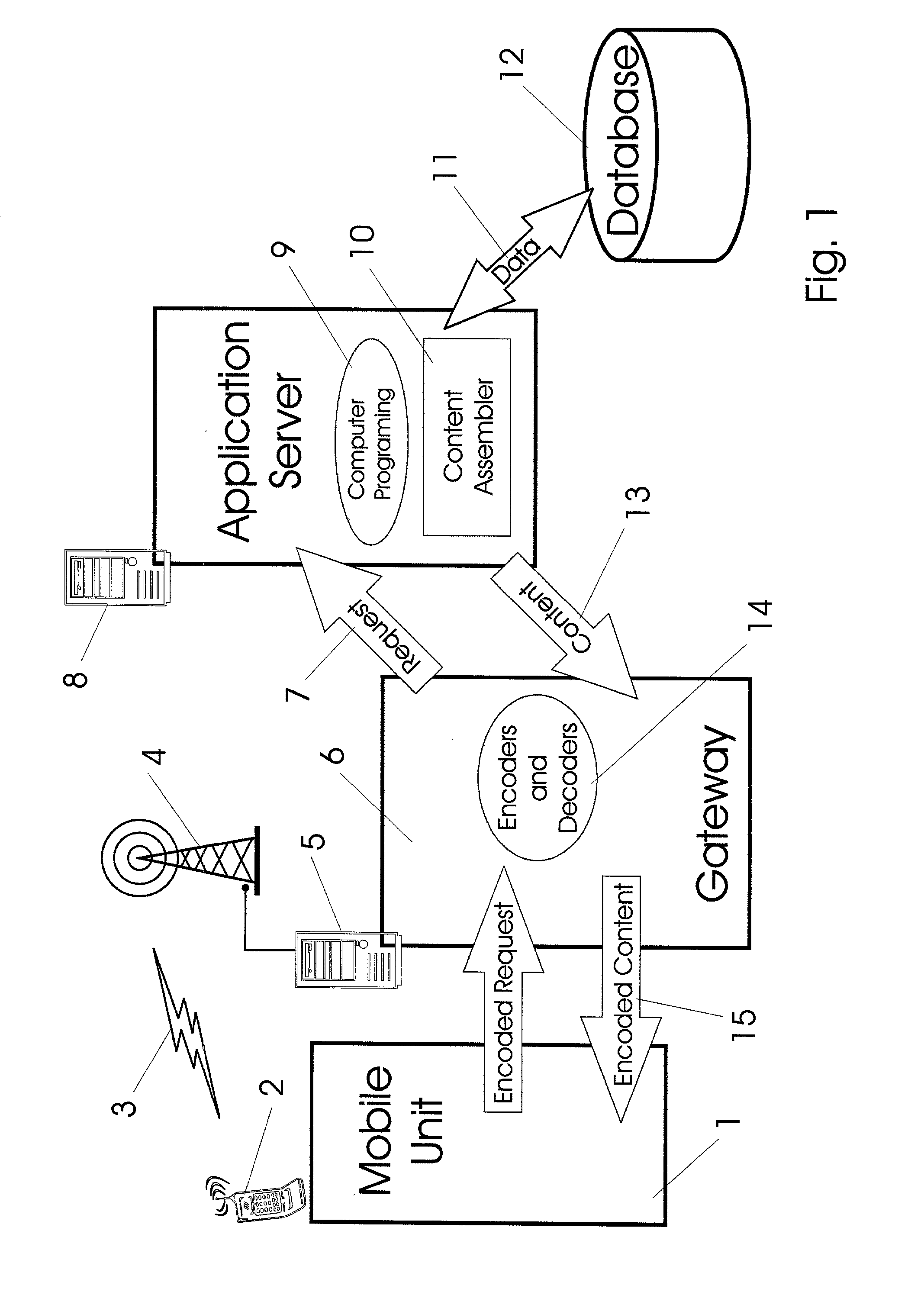
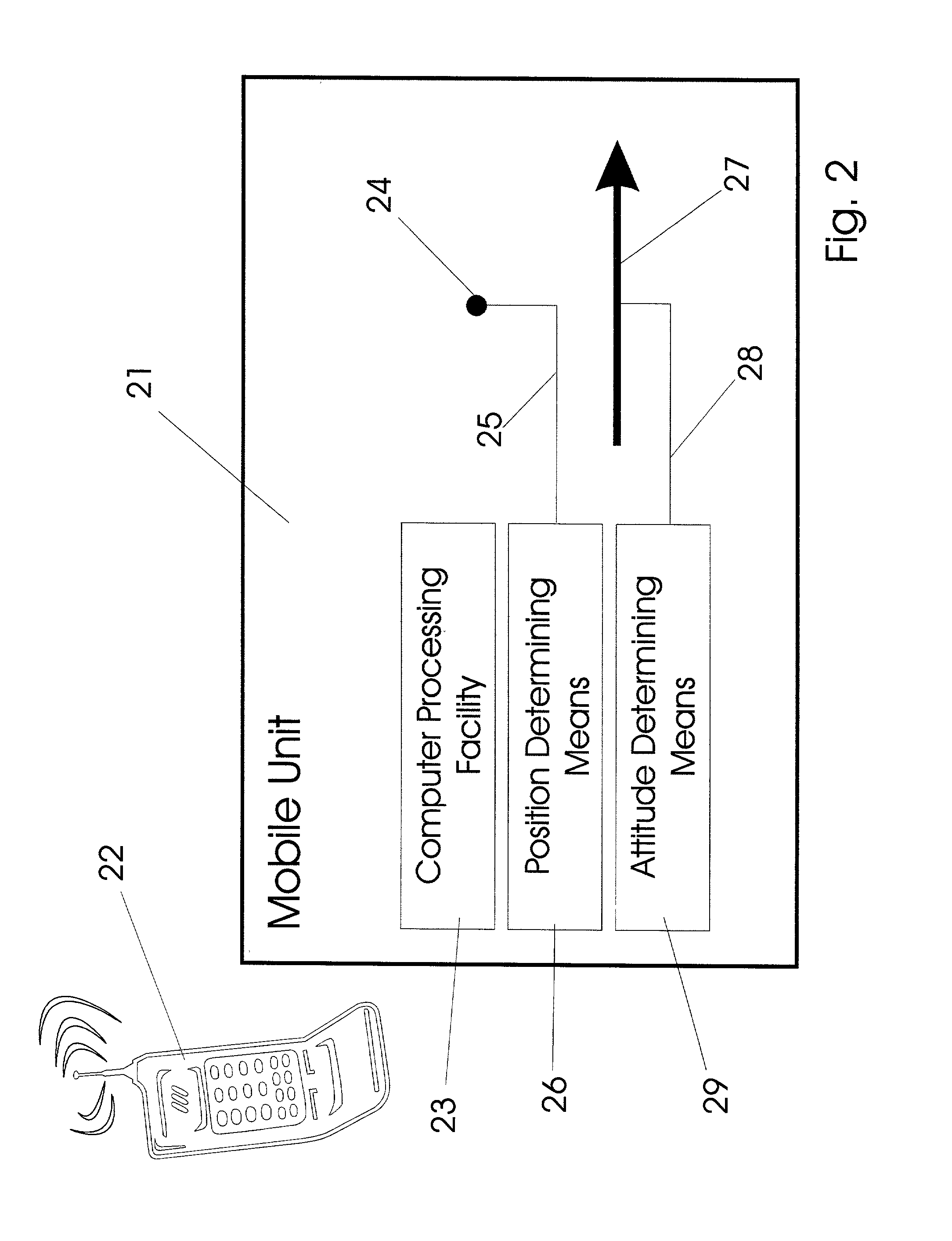
Pointing systems for addressing objects
InactiveUS7031875B2Navigational calculation instrumentsDigital data processing detailsHand heldHand held devices
Systems are arranged to provide a user information which relates to objects of interest. A user may point a hand held device toward an object to address it. The device determines which objects are being addressed by making position and attitude measurements and further a reference and search of a database containing preprogrammed information relating to objects. Information relating to objects determined as objects presently being addressed is thereafter presented at a user interface. Devices of these systems include a point reference, a direction reference, a position determining support, attitude determining support, a computer processor and database, and a user interface. Methods of systems include the steps of addressing an object, determining position and attitude, searching a database, and presenting information to a user.
Owner:GEOVECTOR
Pointing systems for addressing objects
InactiveUS20020140745A1Quickly availableNavigational calculation instrumentsDigital data processing detailsHand heldHand held devices
Systems are arranged to provide a user information which relates to objects of interest. A user may point a hand held device toward an object to address it. The device determines which objects are being addressed by making position and attitude measurements and further a reference and search of a database containing preprogrammed information relating to objects. Information relating to objects determined as objects presently being addressed is thereafter presented at a user interface. Devices of these systems include a point reference, a direction reference, a position determining support, attitude determining support, a computer processor and database, and a user interface. Methods of systems include the steps of addressing an object, determining position and attitude, searching a database, and presenting information to a user.
Owner:GEOVECTOR
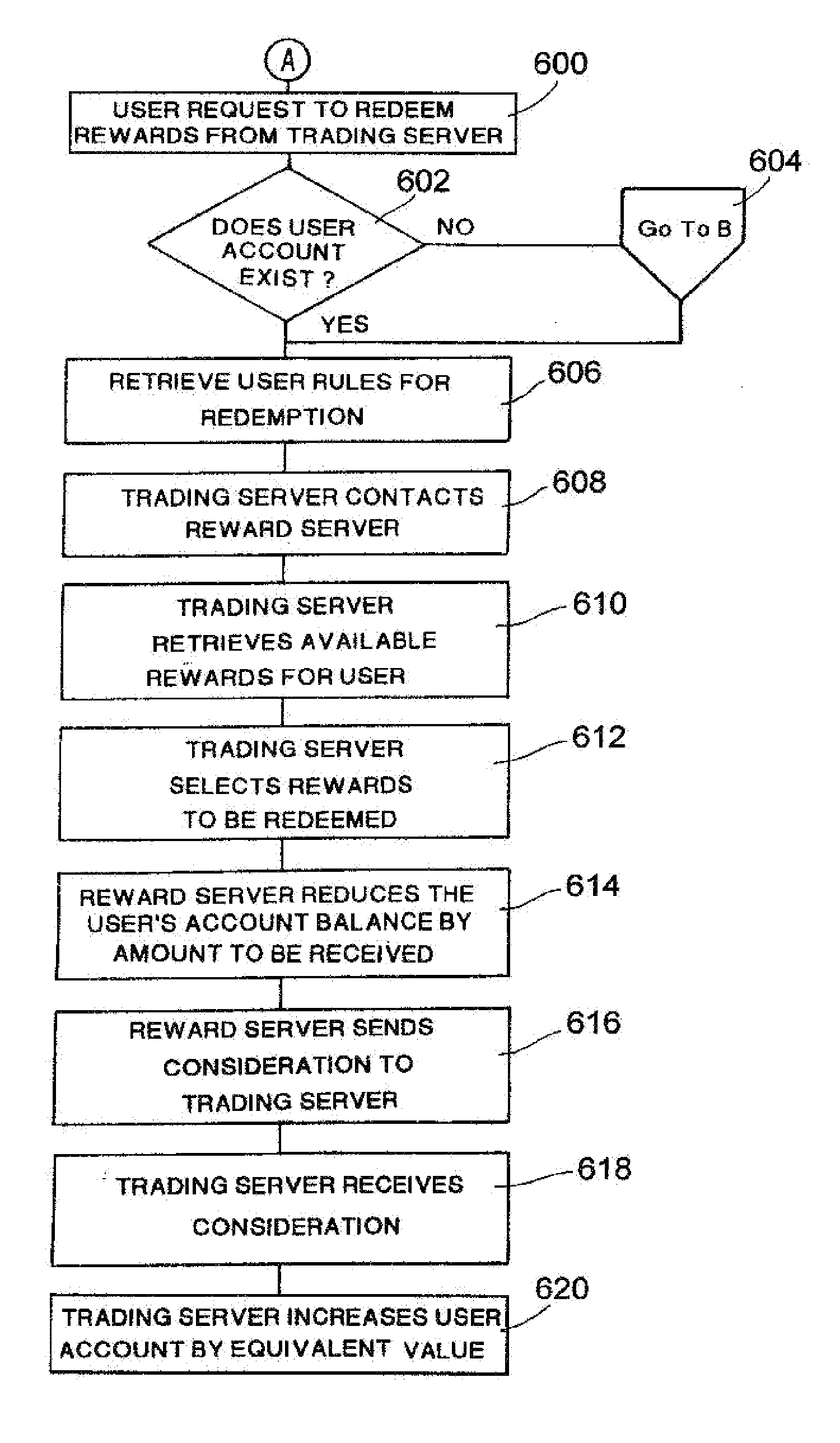
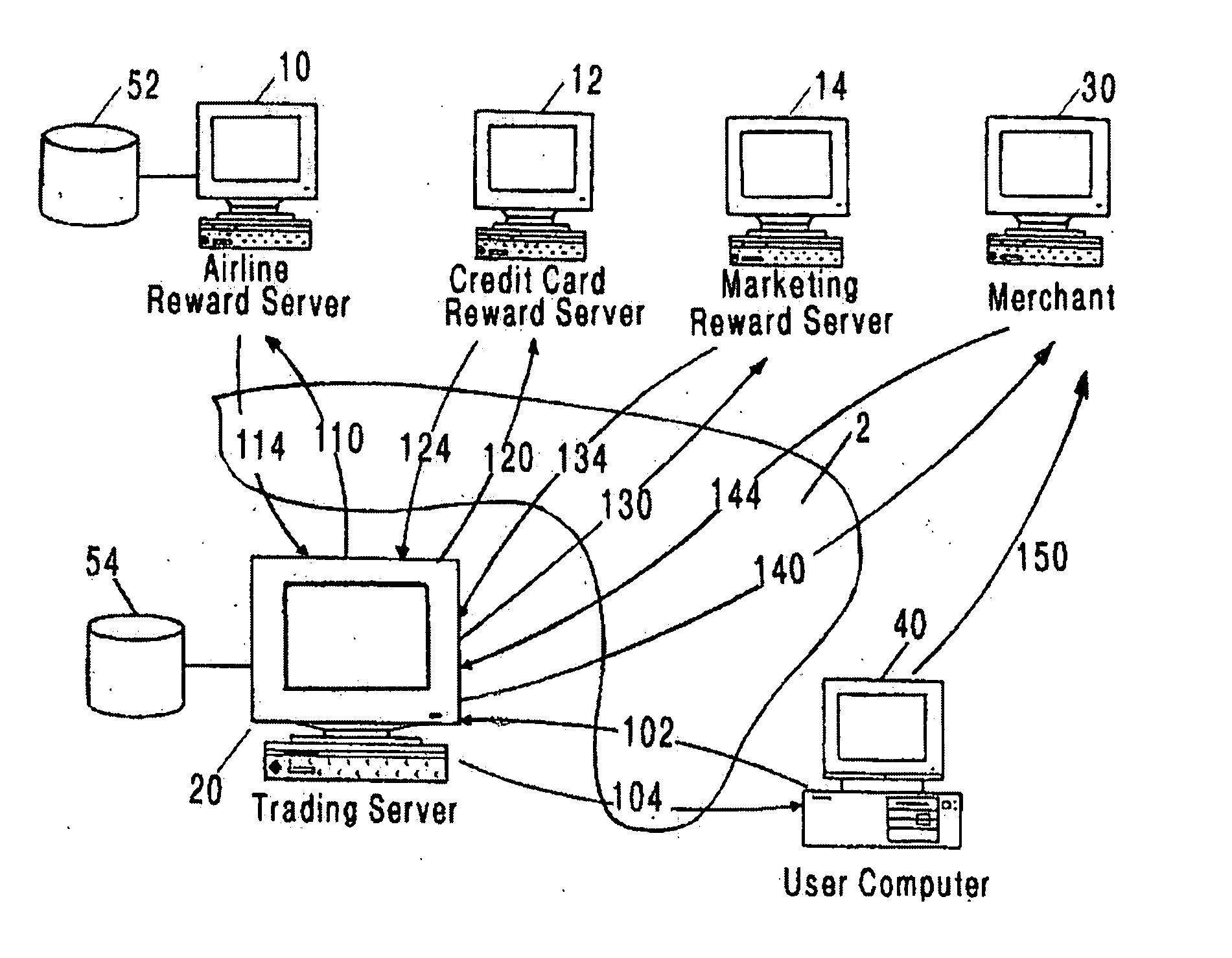
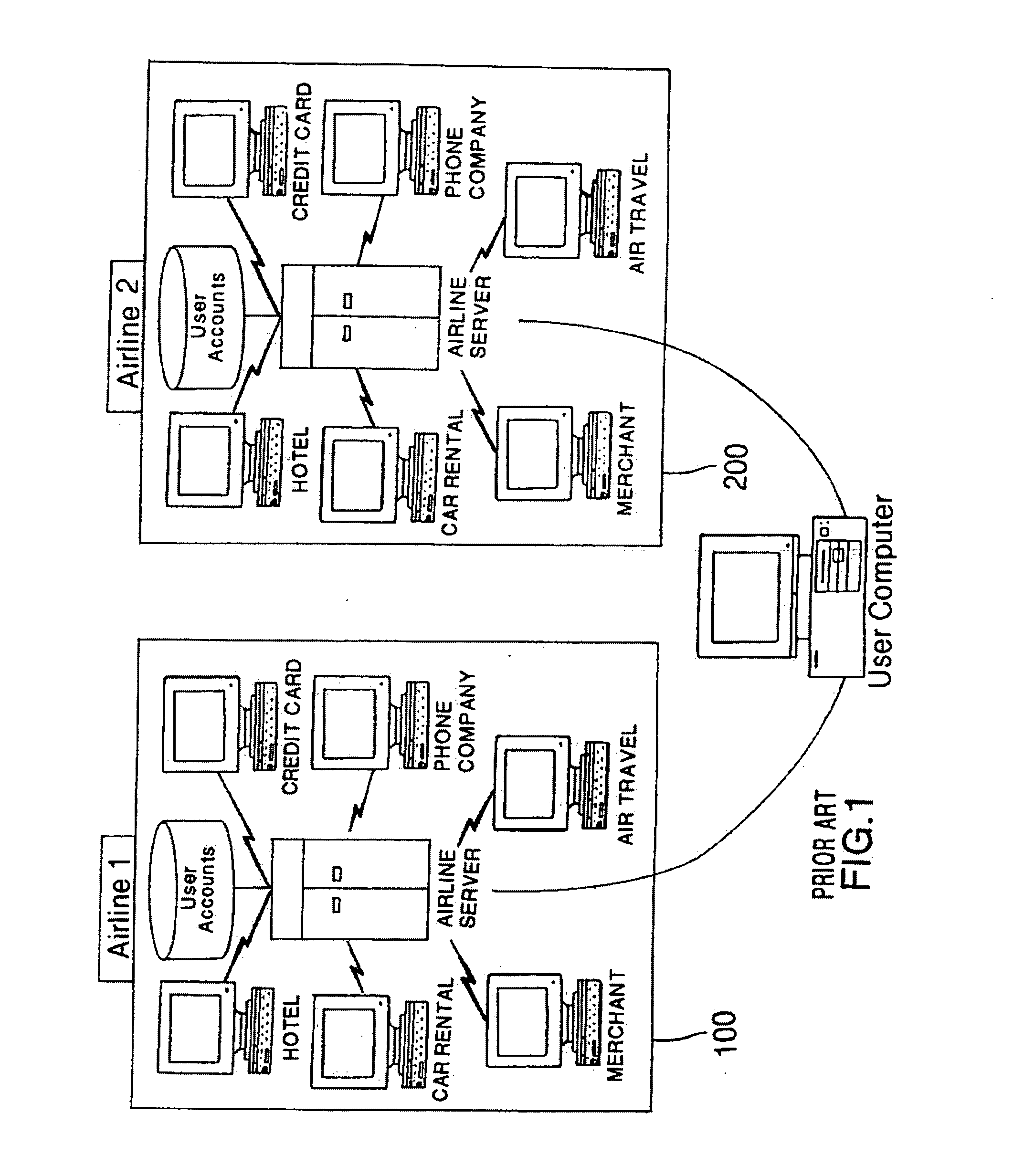
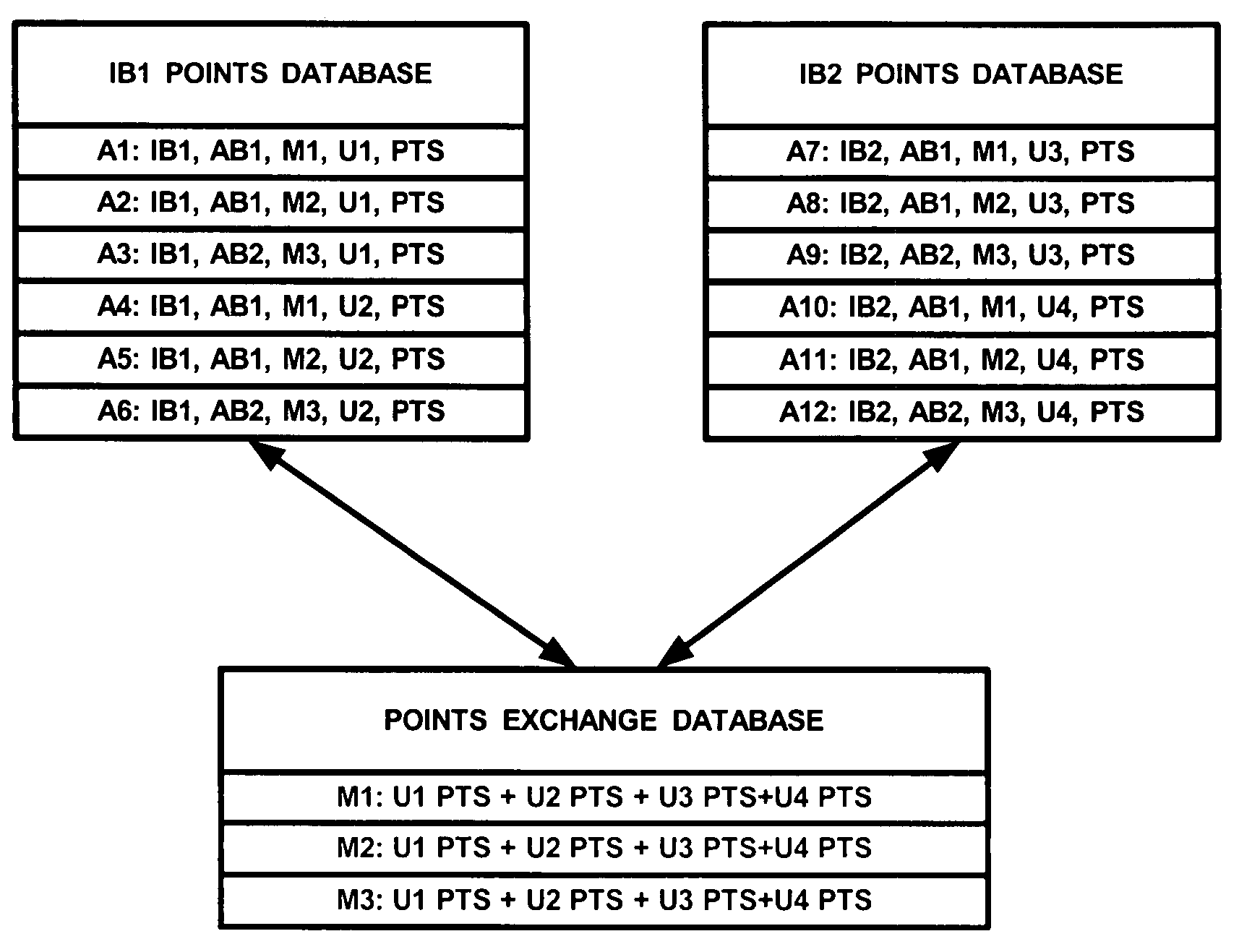
Method and system for issuing, aggregating and redeeming merchant loyalty points with an acquiring bank
InactiveUS20050021401A1High cost of administrationHigh cost of setupPayment architectureMarketingCredit cardComputer science
A loyalty reward point system that utilizes the pre-existing infrastructure of network such as a credit card network. A user makes a purchase at a merchant using a token such as a credit card. As part of the purchase transaction, the user is awarded reward points from the merchant based on the purchase, which are stored in an account associated with the merchant and the user by the acquiring bank. The reward account is maintained on the acquiring bank server on behalf of the merchant and the user, and the number of reward points in the user's account for that merchant is increased accordingly. The user may redeem the reward points earned from the transaction with the merchant at a later time, or may redeem the points with another merchant in the same marketing cluster, or may aggregate those reward points with those of other merchants into a reward point exchange account, and then redeem the aggregated reward points for goods or services from any approved merchant on the network, depending on the configuration of the system.
Owner:SIGNATURE SYST
Method and system for issuing, aggregating and redeeming merchant reward points with a credit card network
A loyalty reward point system that utilizes the pre-existing infrastructure of network such as a credit card network. A user makes a purchase at a merchant using a token such as a credit card. As part of the purchase transaction, the user is awarded reward points from the merchant based on the purchase, which are stored in an account associated with the merchant and the user by a member bank of the credit card network, which may be an issuing bank or an acquiring bank. The reward account is maintained on the member bank server on behalf of the merchant and the user, and the number of reward points in the user's account for that merchant is increased accordingly. The user may redeem the reward points earned from the transaction with the merchant at a later time, or may redeem the points with another merchant in the same marketing cluster, or may aggregate those reward points with those of other merchants into a reward point exchange account, and then redeem the aggregated reward points for goods or services from any approved merchant on the network, depending on the configuration of the system.
Owner:SIGNATURE SYST
Method and system for issuing, aggregating and redeeming merchant loyalty points with an issuing bank
InactiveUS20050149394A1High cost of administrationHigh cost of setupSpecial data processing applicationsMarketingIssuing bankCredit card
A loyalty reward point system that utilizes the pre-existing infrastructure of network such as a credit card network. A user makes a purchase at a merchant using a token such as a credit card. As part of the purchase transaction, the user is awarded reward points from the merchant based on the purchase, which are stored in an account associated with the merchant and the user by the issuing bank. The reward account is maintained on the issuing bank server on behalf of the merchant and the user, and the number of reward points in the user's account for that merchant is increased accordingly. The user may redeem the reward points earned from the transaction with the merchant at a later time, or may redeem the points with another merchant in the same marketing cluster, or may aggregate those reward points with those of other merchants into a reward point exchange account, and then redeem the aggregated reward points for goods or services from any approved merchant on the network, depending on the configuration of the system.
Owner:SIGNATURE SYST
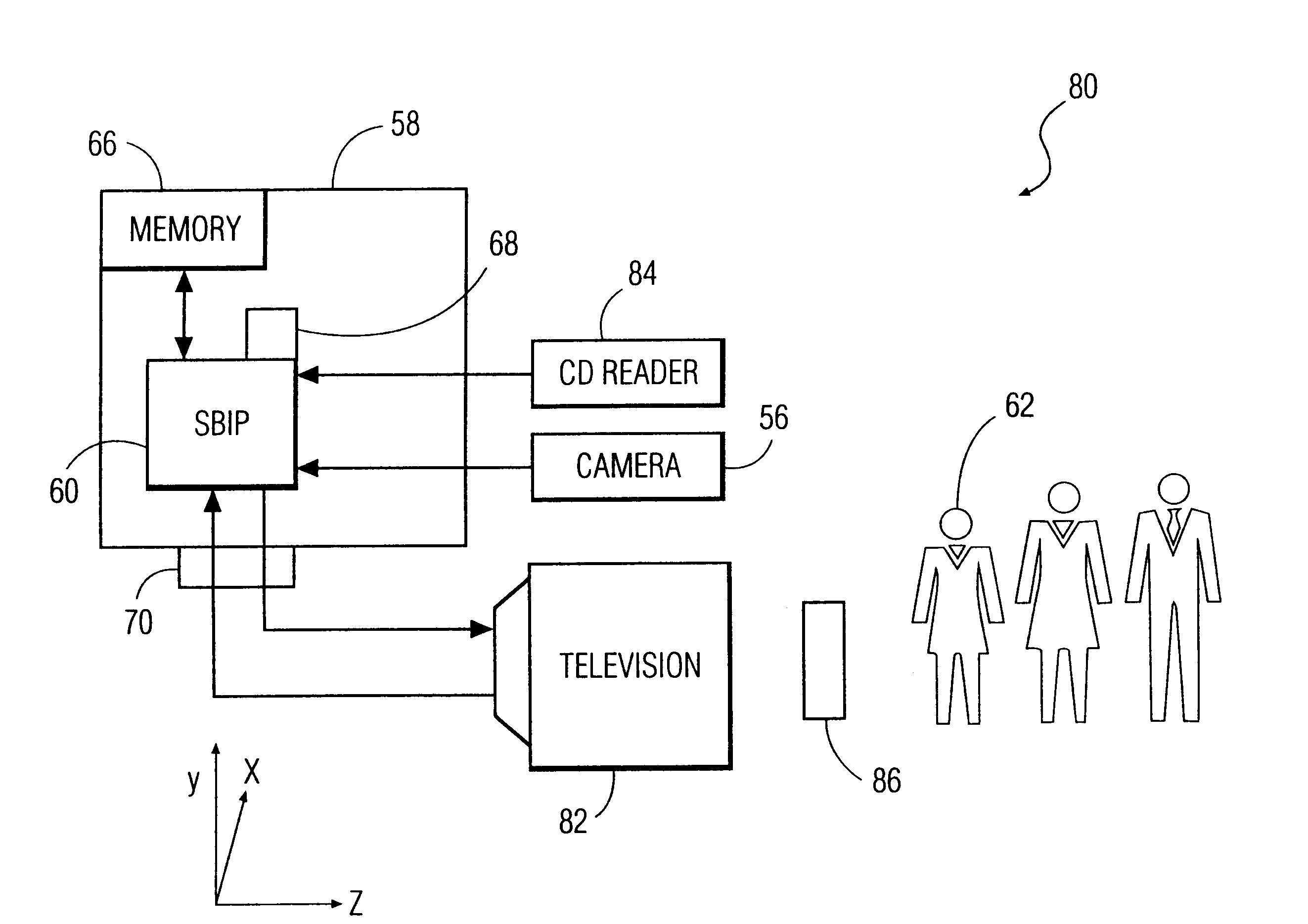
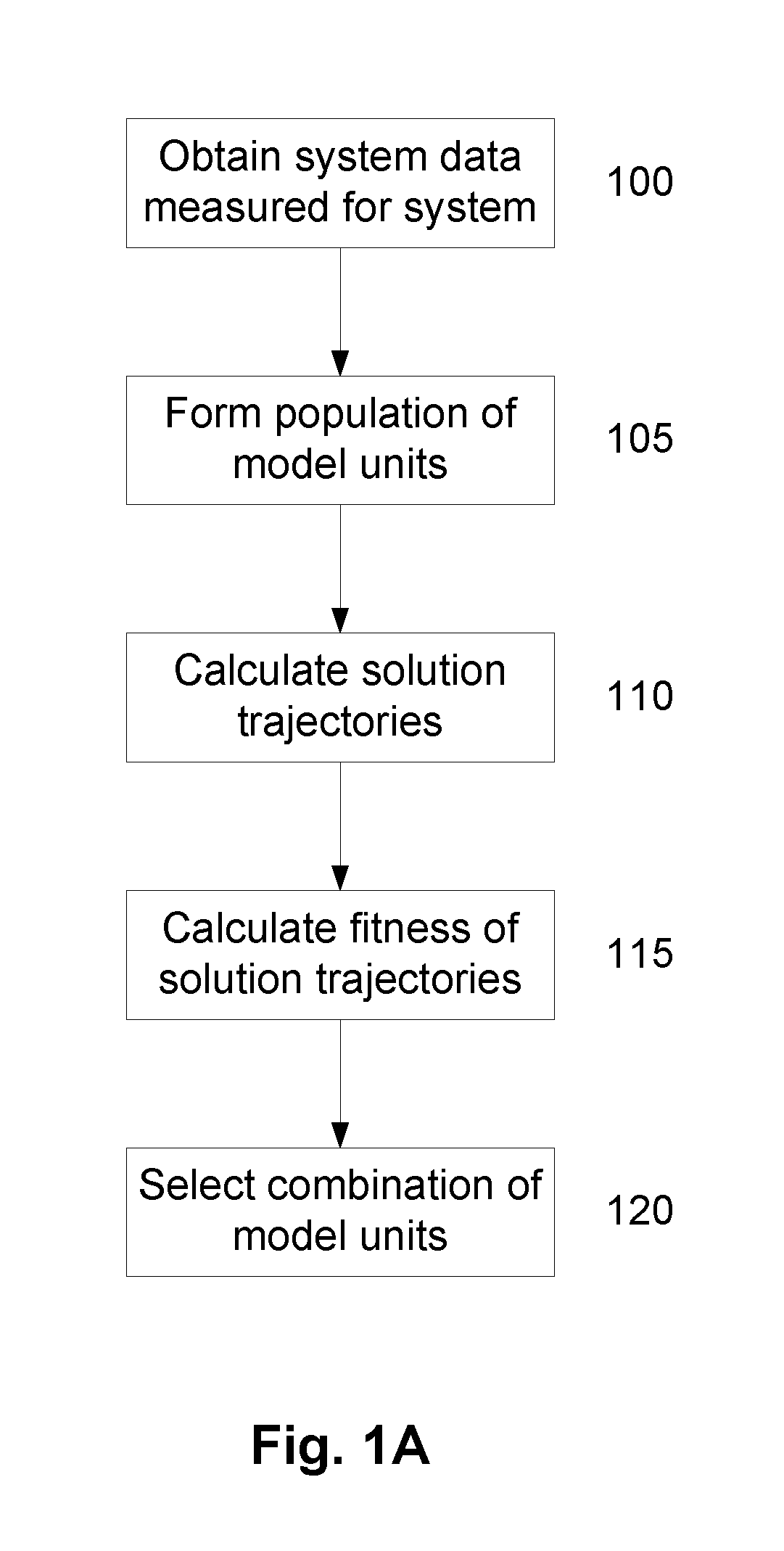
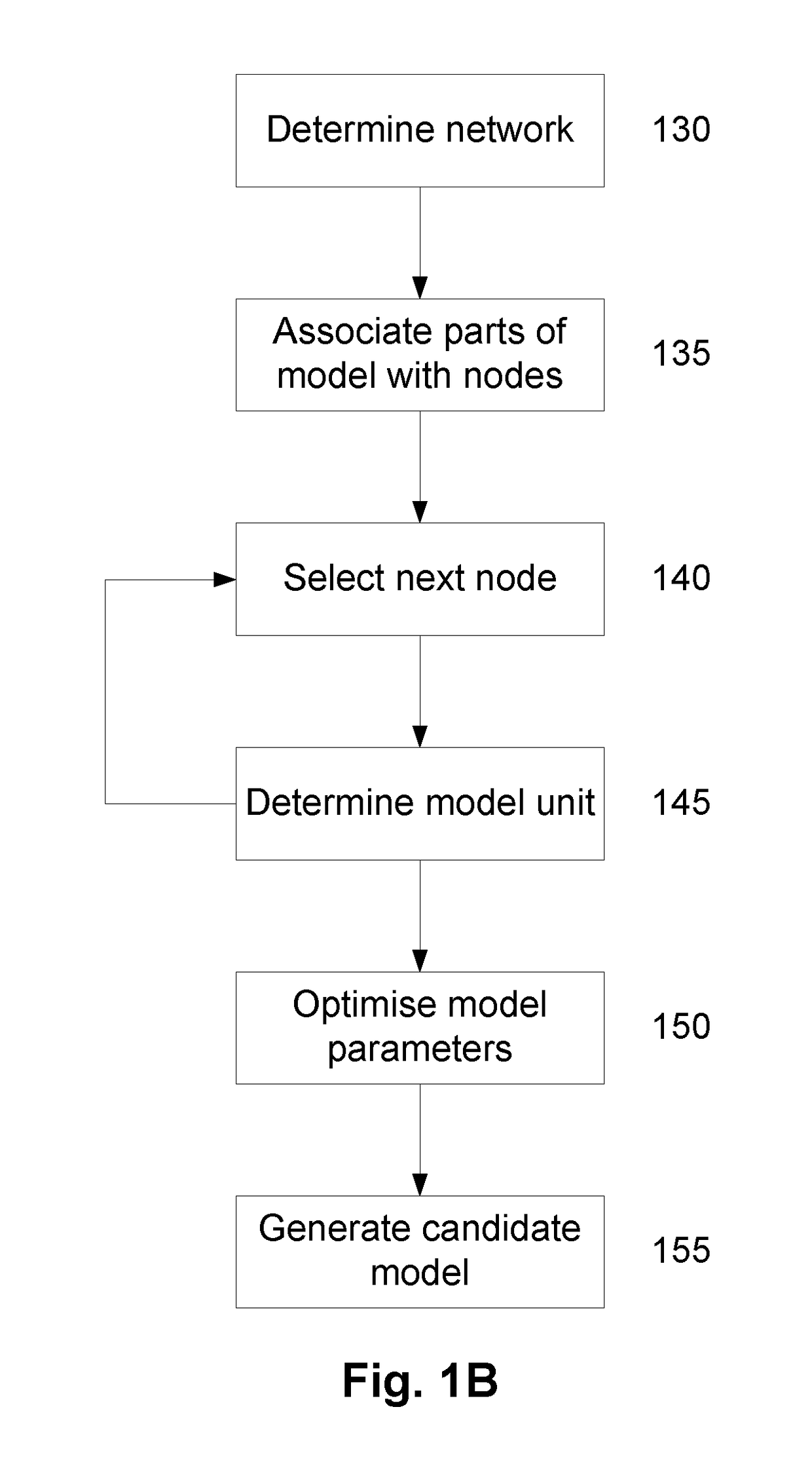
A System and Method for Modelling System Behaviour
ActiveUS20170147722A1Reduce the impactReduce impactMedical simulationDesign optimisation/simulationCollective modelModel system
A method of modelling system behaviour of a physical system, the method including, in one or more electronic processing devices obtaining quantified system data measured for the physical system, the quantified system data being at least partially indicative of the system behaviour for at least a time period, forming at least one population of model units, each model unit including model parameters and at least part of a model, the model parameters being at least partially based on the quantified system data, each model including one or more mathematical equations for modelling system behaviour, for each model unit calculating at least one solution trajectory for at least part of the at least one time period; determining a fitness value based at least in part on the at least one solution trajectory; and, selecting a combination of model units using the fitness values of each model unit, the combination of model units representing a collective model that models the system behaviour.
Owner:EVOLVING MACHINE INTELLIGENCE
Method and system for issuing, aggregating and redeeming points based on merchant transactions
A loyalty or reward point system that utilizes the pre-existing infrastructure of a typical credit card network. In one embodiment, a user makes a purchase at a merchant of a product using a credit card. The merchant contacts the acquiring bank (which may be any type of financial institution but is referred to generically herein as a bank) with which it has contracted for credit card network services, and as known in the art, will get an approval or decline message after the acquiring bank contacts the issuing bank of the credit card used by the purchaser. Assuming that the purchase transaction is approved, the user is awarded loyalty points from the merchant based on the amount of the purchase (e.g. 100 points for a $100 purchase). A central server resides on the credit card network and tracks the transaction between the merchant, the acquiring bank, and the issuing bank. A reward account is maintained on the central server on behalf of the merchant and the user, and the number of reward points in the user's account for that merchant is increased accordingly. In an alternative embodiment, the user's reward points are logged in an account maintained by the acquiring bank on behalf of the merchant (with which it has a contractual relationship) and the user. The user may redeem the reward points earned from the transaction with the merchant at a later time, or may redeem the points with another merchant on the credit card network, or may aggregate those reward points with those of other merchants into a central exchange account, and then redeem the aggregated points for goods or services from any approved merchant on the network, depending on the configuration of the system.
Owner:SIGNATURE SYST
Multi-touch surface providing detection and tracking of multiple touch points
InactiveUS20100073318A1Less expensiveInput/output processes for data processingPoint systemCapacitance transducer
System and method for touch sensitive surface provide detection and tracking of multiple touch points on the surface by using two independent arrays of orthogonal linear capacitive sensors.
Owner:PANASONIC CORP
REC credit distribution system and method
InactiveUS20080086411A1Easy to recycleImprove participationSustainable waste treatmentAcutation objectsReward systemDistribution system
A method for promoting recycling from a fund established with revenue generated from the sale of environmental and / or power generation attributes by an entity producing renewable energy. The method comprises providing a point system by which a recycling consumer is credited for recycled materials collected. Further, the method provides for a reward system for redemption of points accumulated by the recycling consumer, the reward system including redeemable fund certificates drawn against the fund. The method further includes collecting recyclable materials from the recycling consumer and crediting an account in the name of the recycling consumer based on the quantity and / or quality of the recyclable material collected. Then the method provides for awarding fund certificates to the recycling consumer upon the accumulation of a sufficient point level.
Owner:CASELLA WASTE SYSTEMS
Systems and methods for adaptive medical decision support
The current invention is directed to a system for adaptive medical decision support. The invented system provides a system that allows users to efficiently enter, access, and analyze medical information, without disrupting patient-doctor interactions or medical facility course of business; which assists in all stages of medical assessment and treatment; and which is tailored to the particular medical practice or specialty and taking into account the developing habits, preferences, performance, and individual patient histories, of an individual user. The invention provides a learning capacity configured to learn previously presented data and decisions and predict data or decisions based on data that it receives from the user, thereby adapting its operations to the developing habits, preferences, performance, and individual patient histories of an individual user. The system may also provide a “virtual specialist” feature, whereby the system can be instructed to produce the probable actions or recommendations of particular medical specialists.
Owner:RECARE
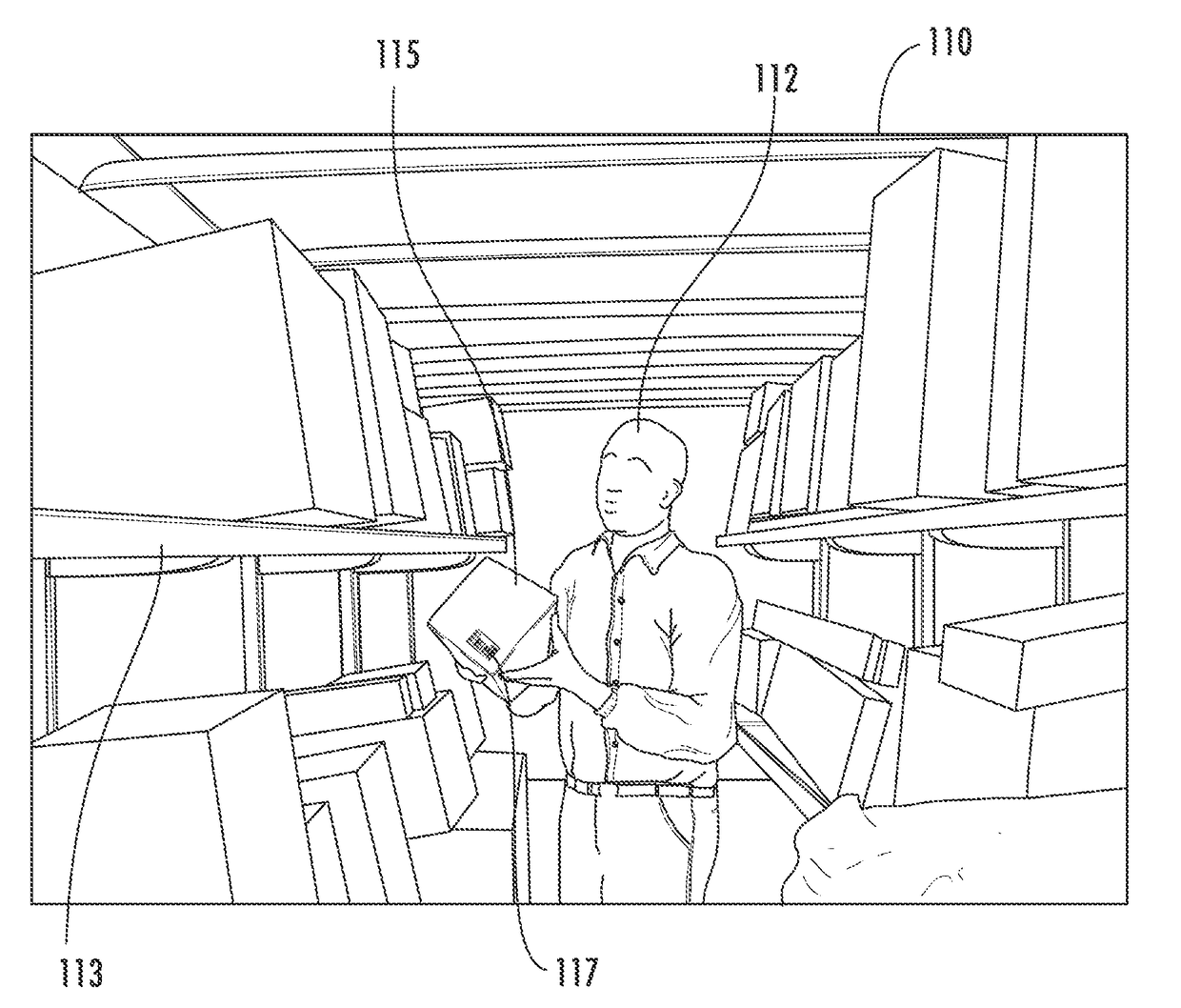
In-vehicle package location identification at load and delivery times
A shelving and package locating system for delivery vehicles includes one or more shelves for storing packages within a delivery vehicle during delivery. Each package is associated with both a geographic delivery address and an assigned location on a particular shelf within the delivery vehicle. A GPS unit determines the location of the delivery vehicle during delivery, and a computer provides the shelf location of a particular package when that package's delivery-location information substantially corresponds to vehicle location information. Several embodiments exist for registering the location of the package in the vehicle at load time, such as scanned location indicia, light sensors on shelves, pressure sensors on shelves, pressure sensors on the floor of the vehicle, and light spot. Several embodiments exist for locating the package in the vehicle at delivery time, such as a pick-to-light system that employs variable length lighting and a light pointer system that generates a light spot.
Owner:HAND HELD PRODS
Offline-online incentive points system and method
InactiveUS7424617B2User identity/authority verificationBuying/selling/leasing transactionsProgram planningEngineering
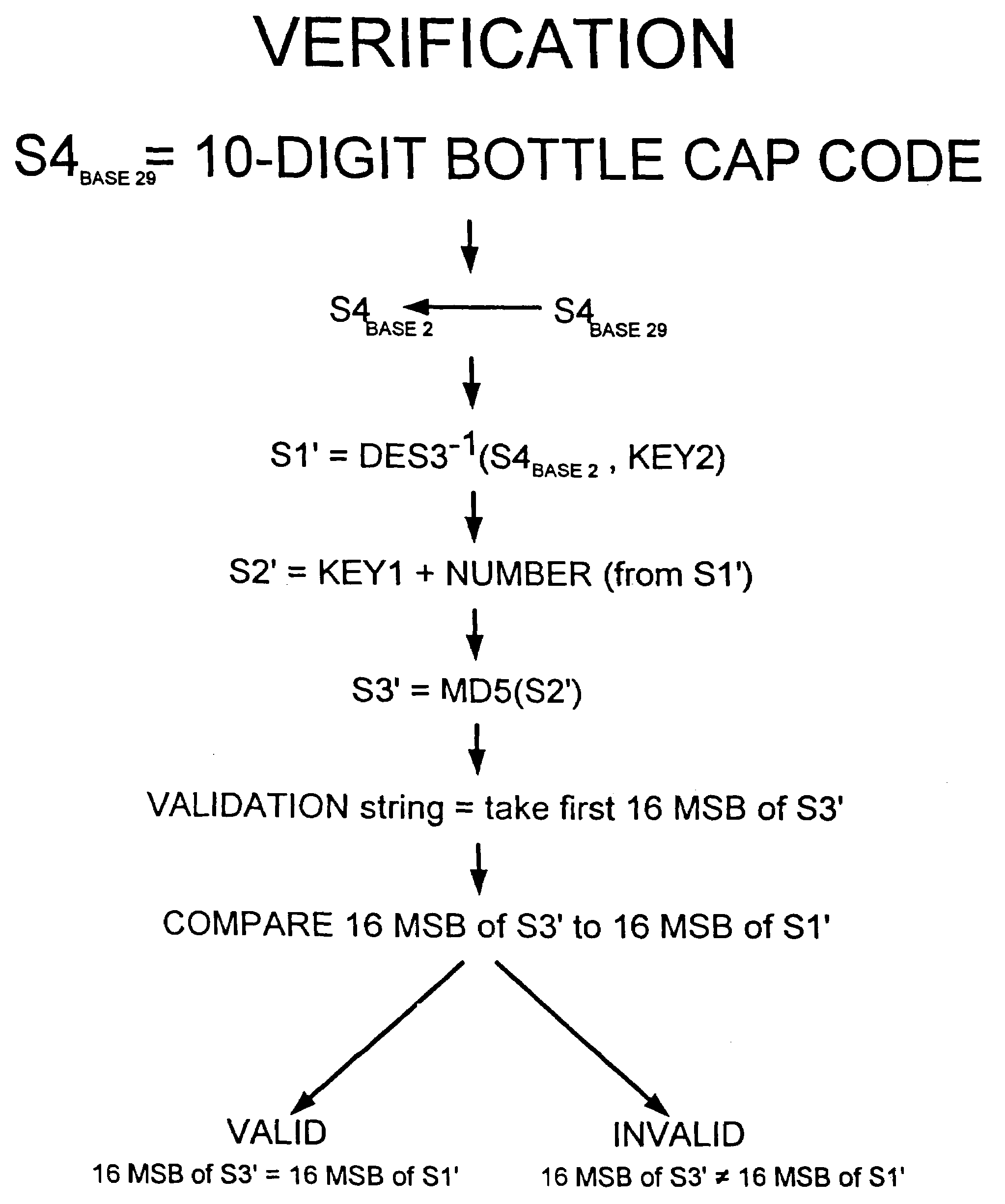
An electronic points system that allows consumers to redeem online those points that were earned offline is described. In one implementation, the offline-online points system is applied to a soft drink bottle caps program. A soft drink company is sponsoring a promotions program where certain bottle caps are worth so many points. A consumer buys a soft drink bottle at a local store. The lucky consumer discovers that he is the beneficiary of a winning bottle cap, and in particular, a bottle cap that is worth N points. Instead of redeeming this winning bottle cap in the traditional way, the consumer logs onto the soft drink company's website and registers his bottle cap code. Thereafter, after registration, the consumer can redeem these points for any merchandise that is available for purchase with these points at any participating company's online store.
Owner:R2 SOLUTIONS
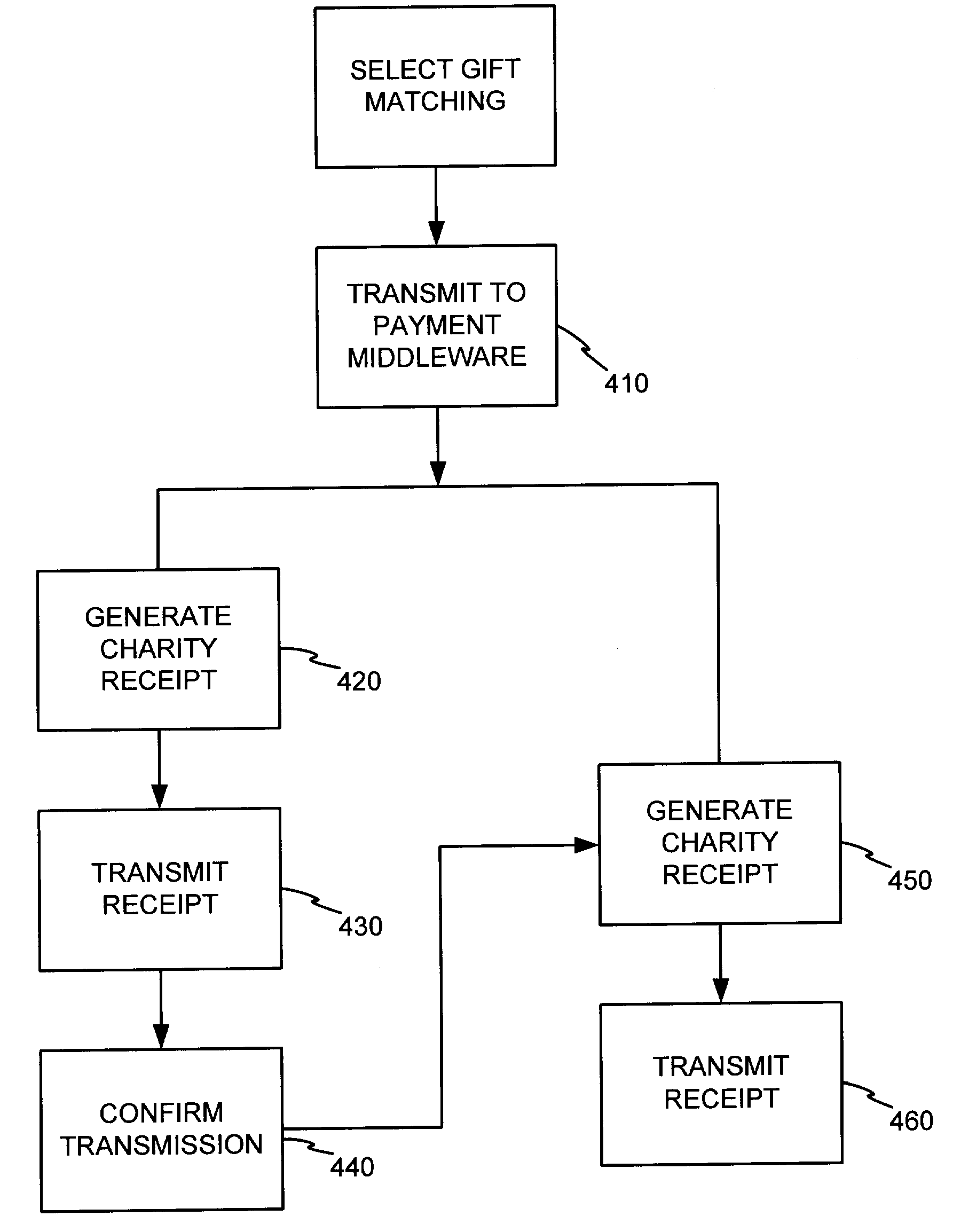
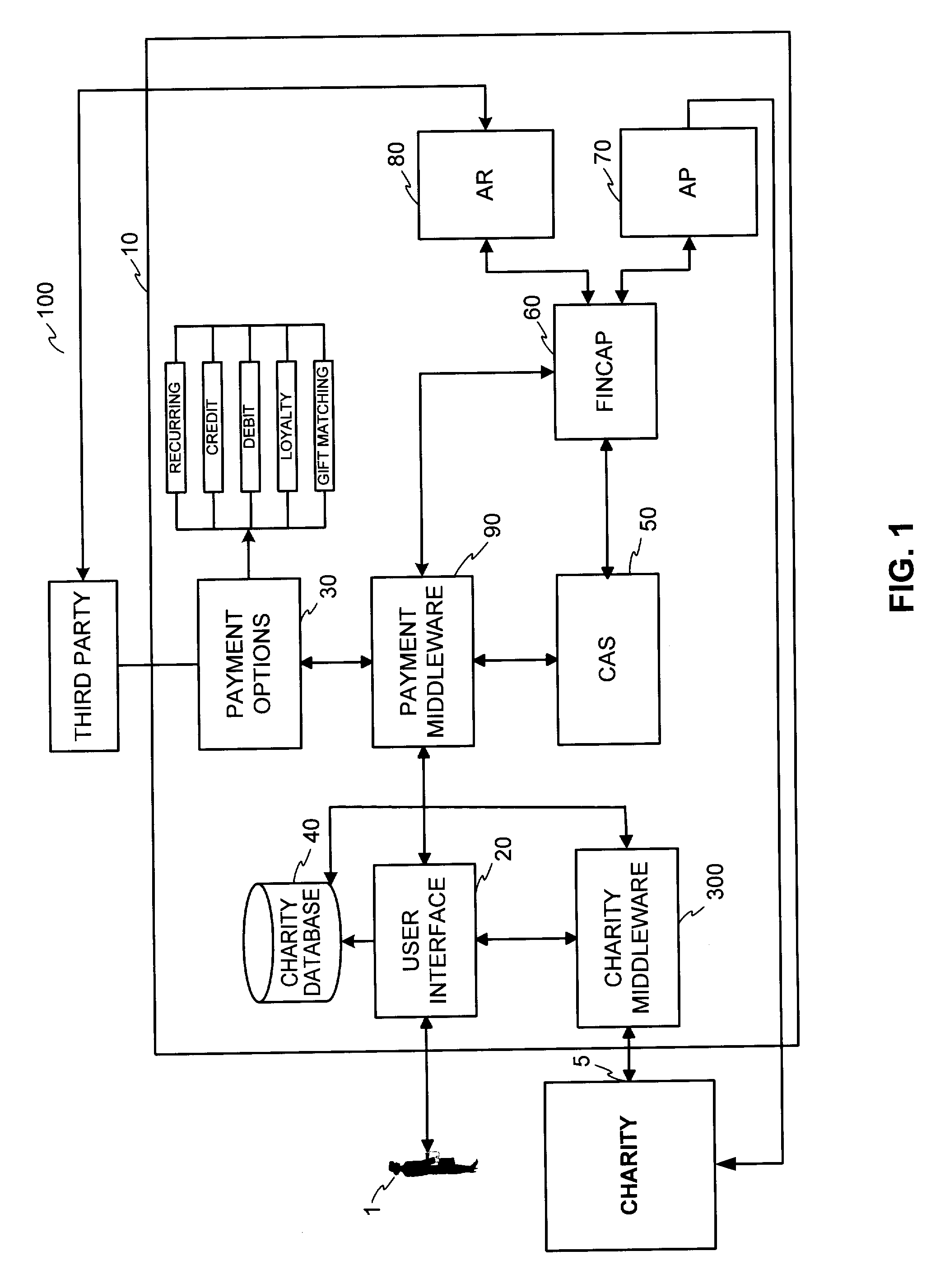
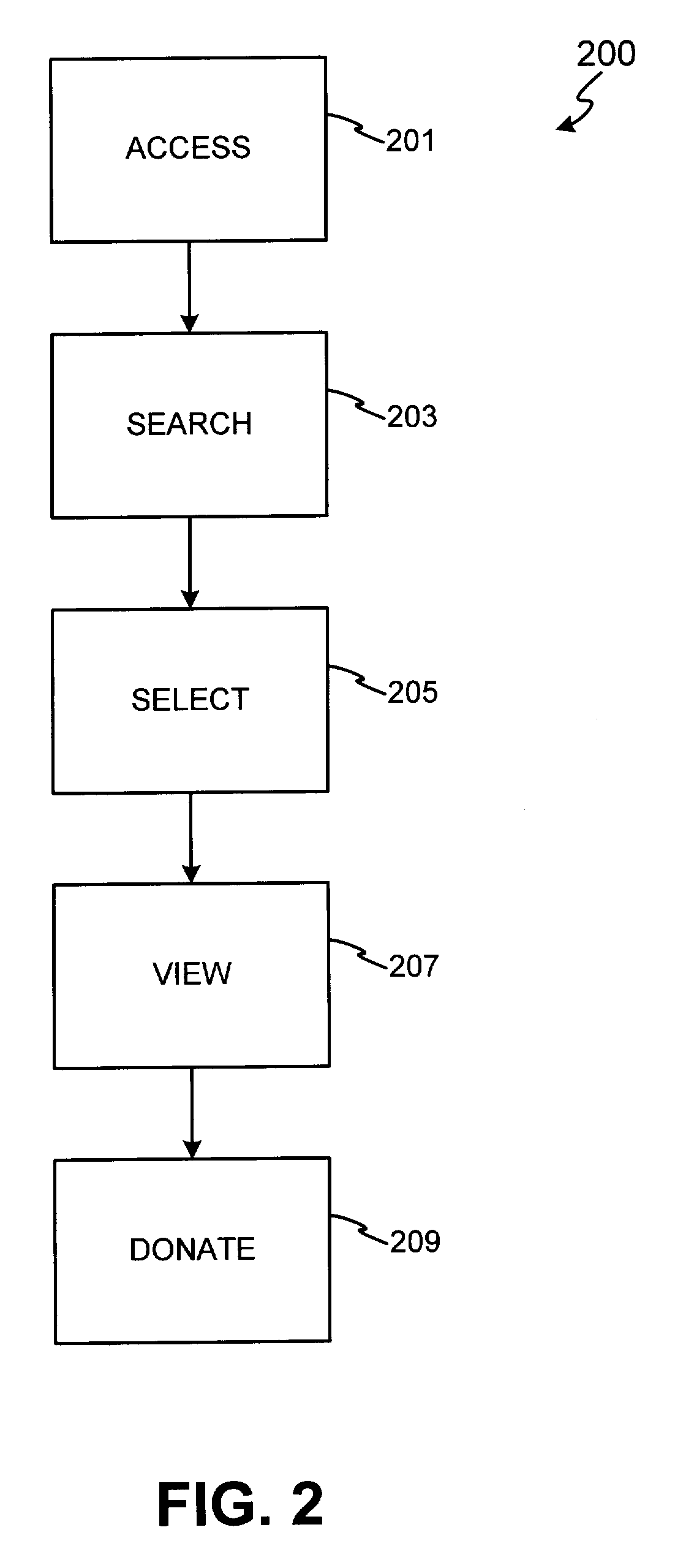
Donation system and method
InactiveUS20050021353A1Facilitate employee gift matchingComplete banking machinesFundraising managementPaymentEngineering
The present invention includes an automatic bill payment enrollment system for recurring donations, which allows donors to automatically charge charitable donations on a recurring basis to a financial account. In one embodiment, the invention uses a donation portal having various webpages to allow a donor to donate to all U.S. 501(c)(3) organizations. In an alternative embodiment, a donor may donate to any other desired organizations. The system may also incorporate a filter for restricting monies being sent to terrorist organizations. The invention also includes a loyalty point system, wherein loyalty points may be donated to a charity. In another exemplary embodiment, the invention also facilitates employee gift matching.
Owner:LIBERTY PEAK VENTURES LLC
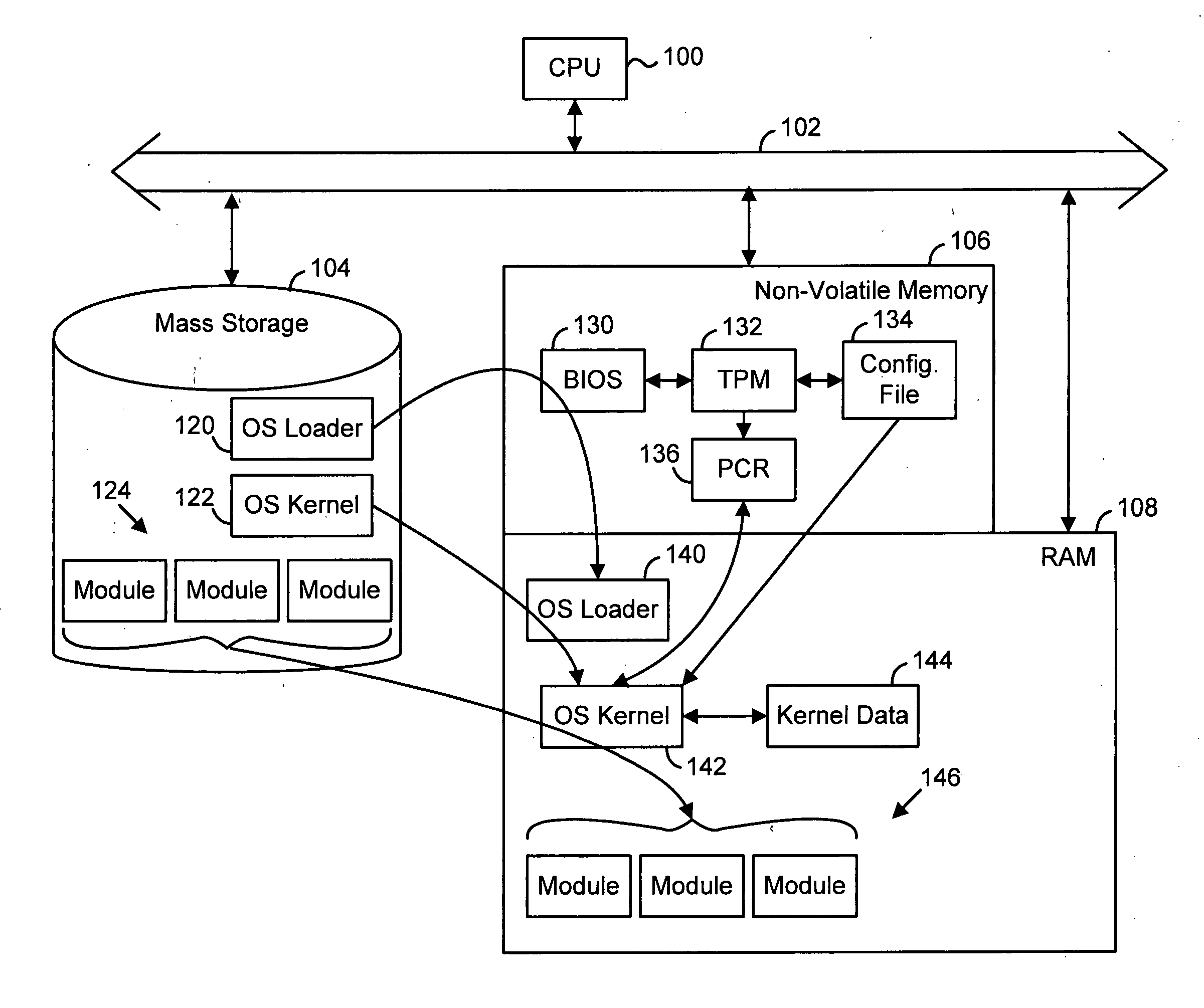
Establishing a trusted platform in a digital processing system
InactiveUS20060015717A1User identity/authority verificationUnauthorized memory use protectionDigital signal processingOperational system
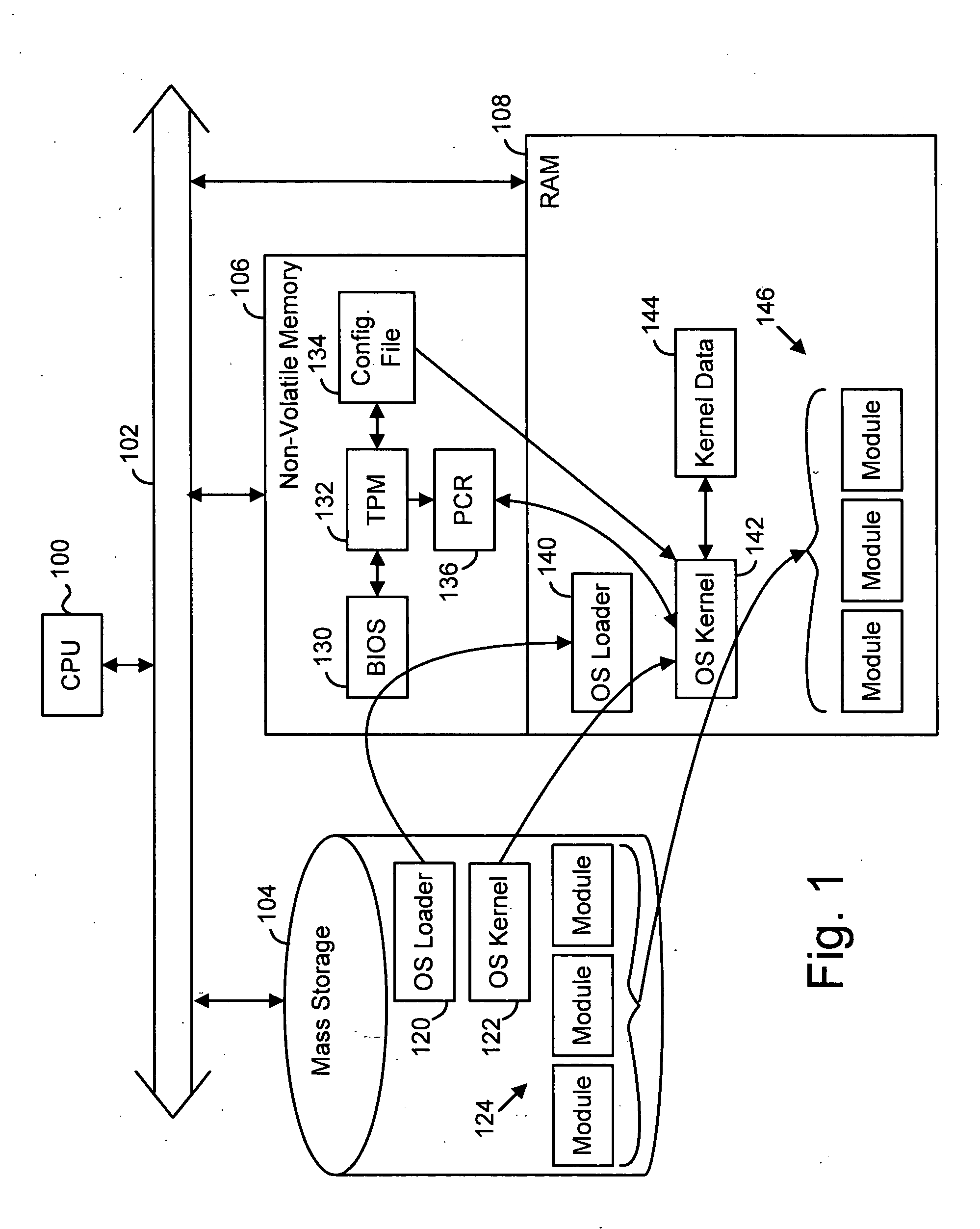
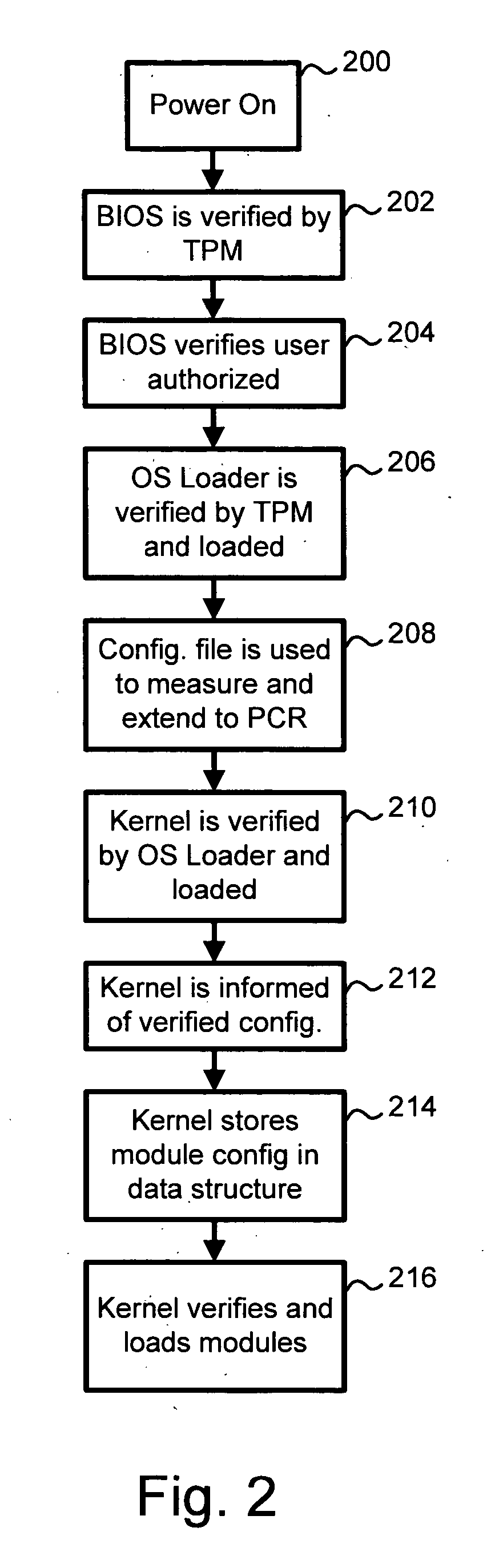
A trusted platform in a digital processing system is maintained even when modules, or other processes or data, are loaded after a boot sequence. A configuration file is used to include measurements (e.g., hash values, signatures, etc.) of modules to be loaded. After secure boot-up the operating system kernel uses the configuration file to check module integrity prior to loading and executing. If a module does not verify against the configuration file data then the system can prevent further operation, restrict certain operations, indicate the non-trusted nature of the system or take other actions. In one embodiment, if a module does not pass the integrity check then the failed measurement is extended into a specific Platform Configuration Register (PCR) within a Trusted Platform Manager (TPM) process. Subsequently, client applications can determine if the platform is trustable based on the return of the PCR value. A local application (application running in the same platform) can “seal” secrets to a trusted platform. The operation of the application relies on the secrets, which can only be revealed in a trusted platform.
Owner:SONY ELECTRONICS INC +1
Loyalty points system and method with supplemental authorizations
The invention facilitates pooling, gifting or transferring of geographic area loyalty points between accounts. The invention also facilitates a transfer of geographic area loyalty points from a consumer account associated with a sponsoring company to a consumer account associated with a host company. The invention may also facilitate gifting of loyalty points to charitable organizations on a recurring basis, wherein the gifting may transfer any portion of geographic based points to various charities. The system may also convert the geographic area loyalty points to a monetary value, thereby allowing the points to be donated to a charity such that the donation appears to be a monetary value donation to the charity.
Owner:LIBERTY PEAK VENTURES LLC +1
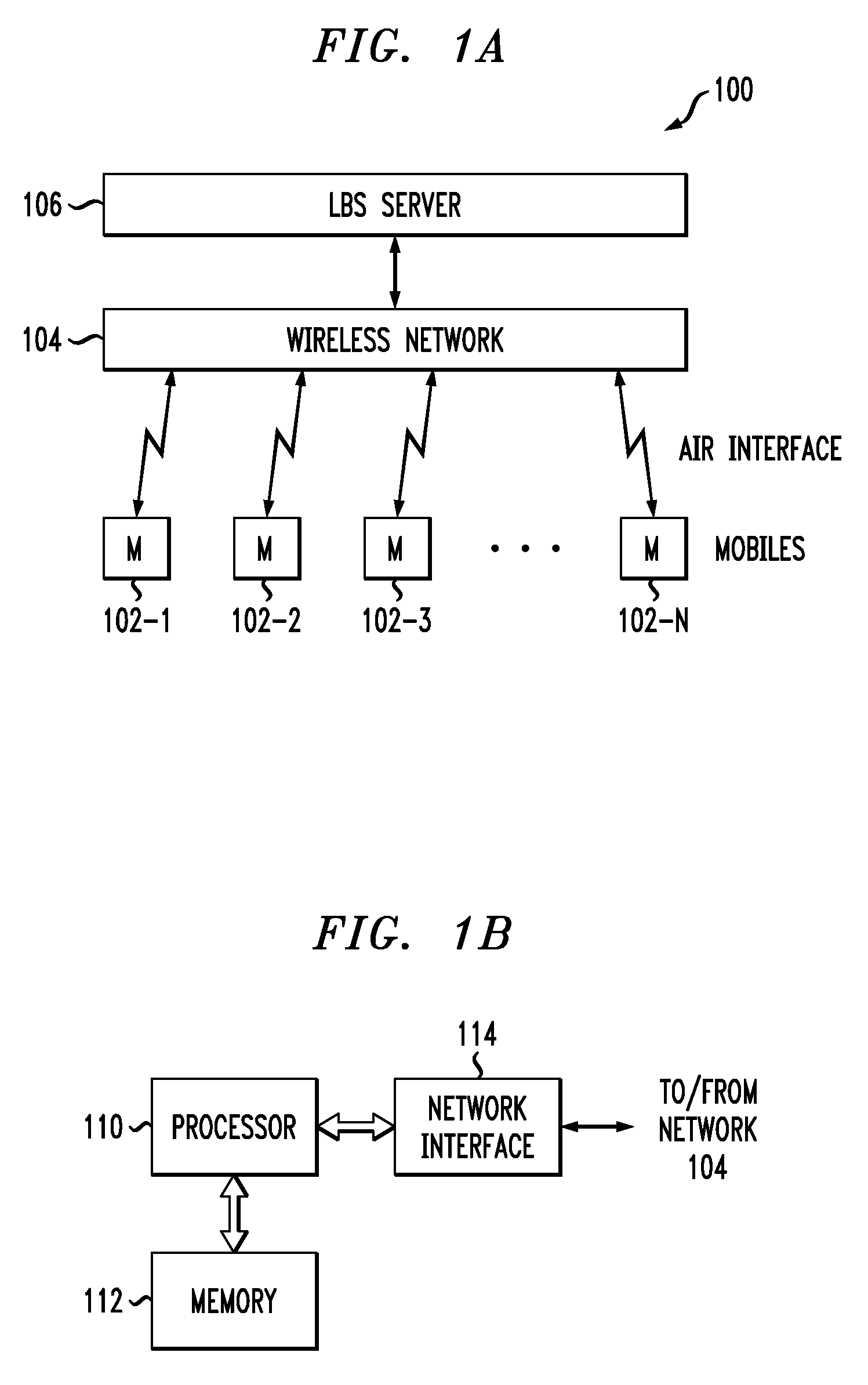
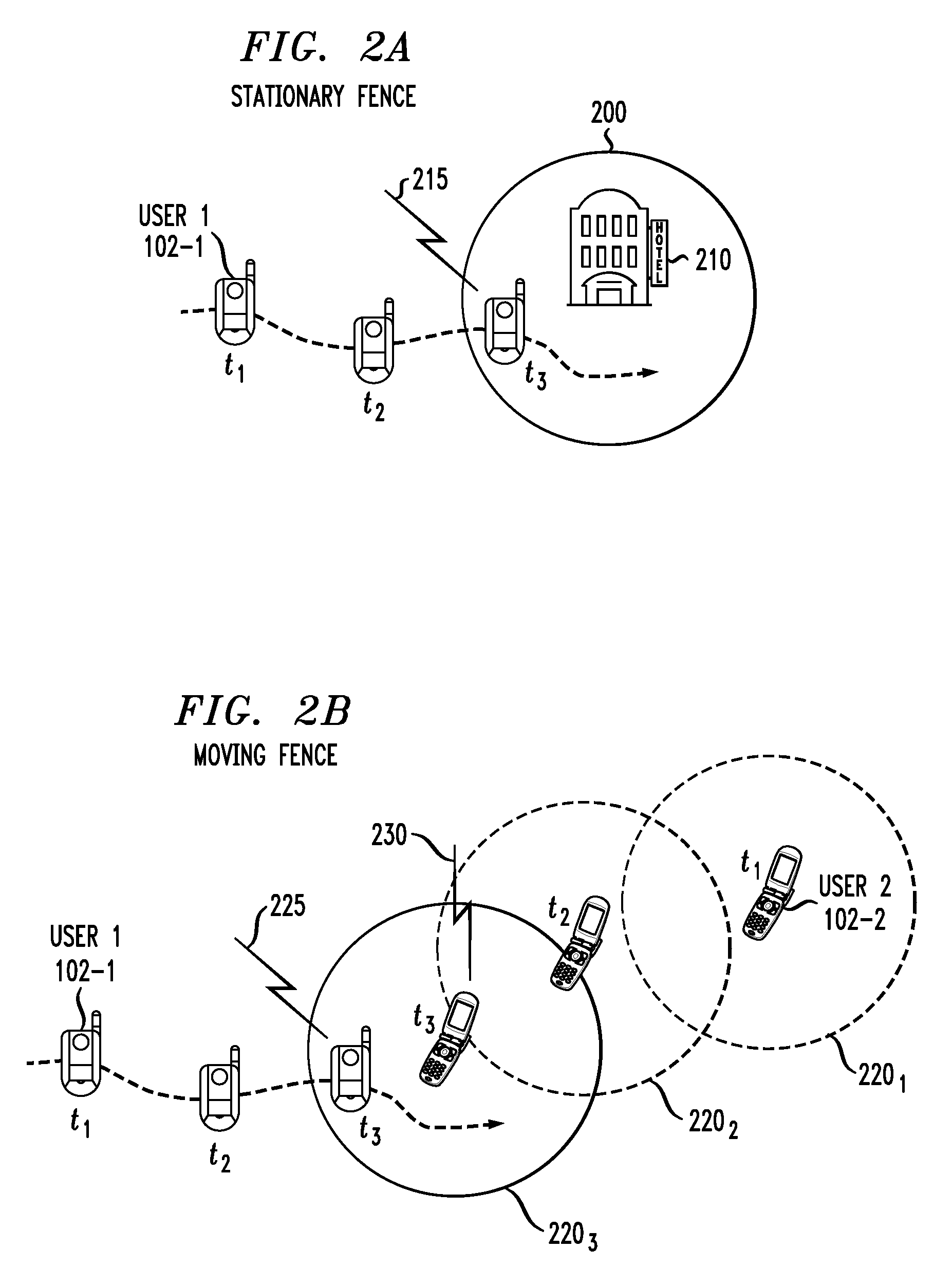
Location-Based Services Using Geofences Generated from Learned Patterns of Movement
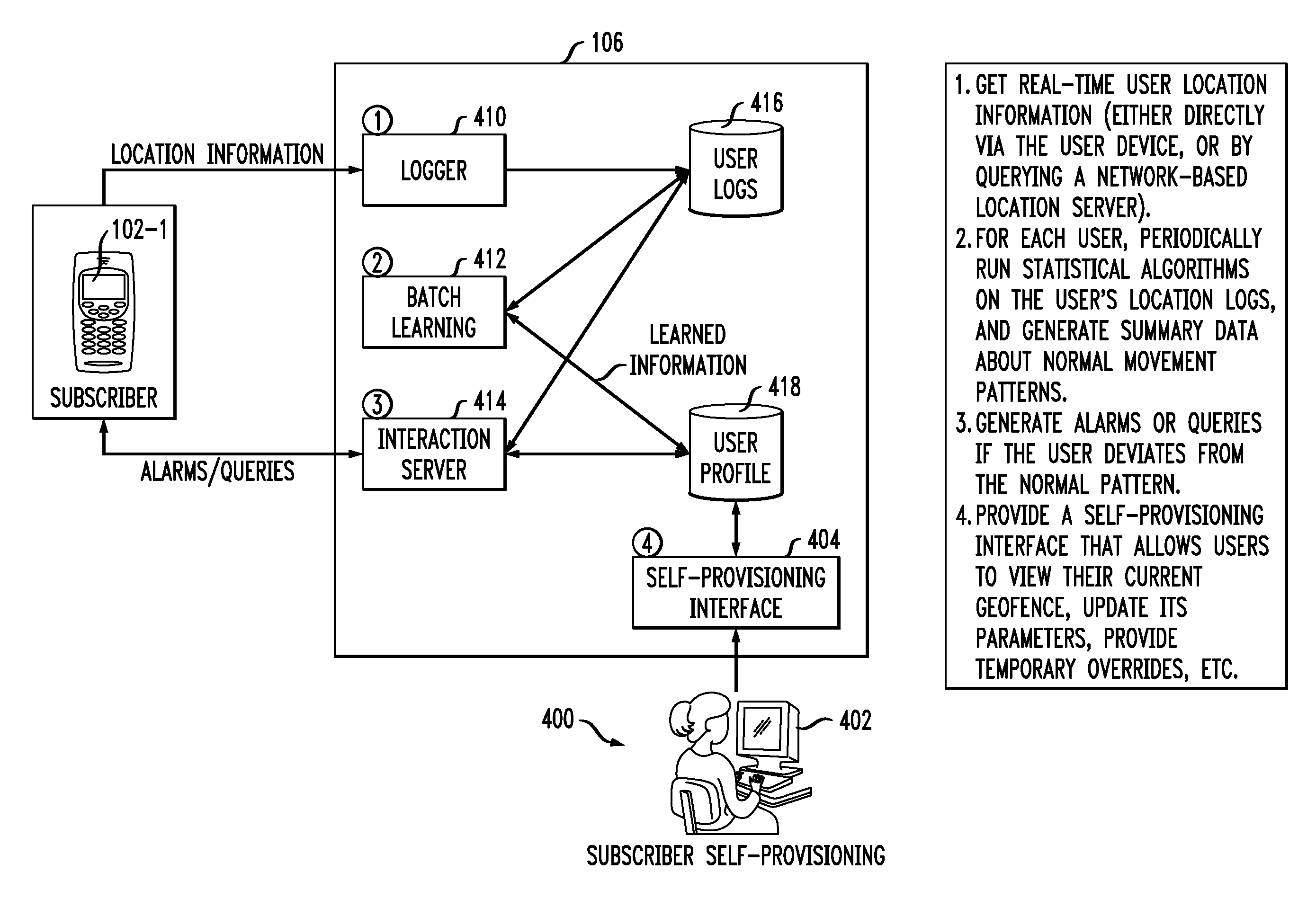
InactiveUS20100203901A1High resolutionReduce in quantityLocation information based serviceNetwork data managementCommunications systemUser device
Location-based services are provided in a communication system comprising a wireless network. In one aspect, information indicative of location of a given mobile user device of the system is periodically collected. The collected location information is processed in a server or other processing device of the system to determine at least one normal pattern of movement of the mobile user device from at least a first location to a second location. An alert is generated if subsequent movement of the mobile user device from the first location to the second location exhibits a significant deviation from the normal pattern of movement. The normal pattern of movement may be used to generate a multidimensional geofence that includes, in addition to a geographic area dimension, at least one additional dimension such as, for example, a speed of movement dimension, a direction of movement dimension, a stop duration dimension, or a related device proximity dimension.
Owner:ALCATEL-LUCENT USA INC
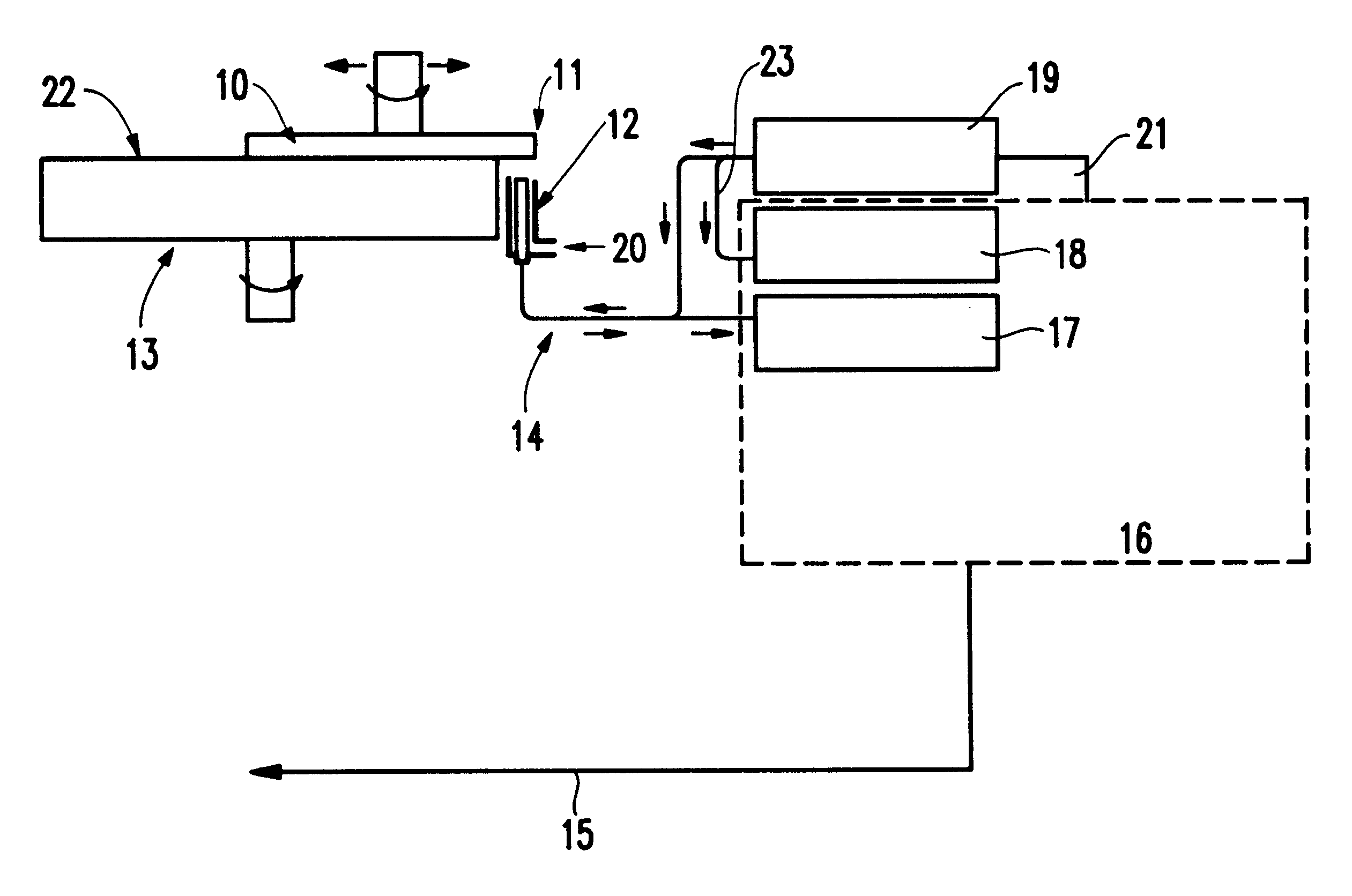
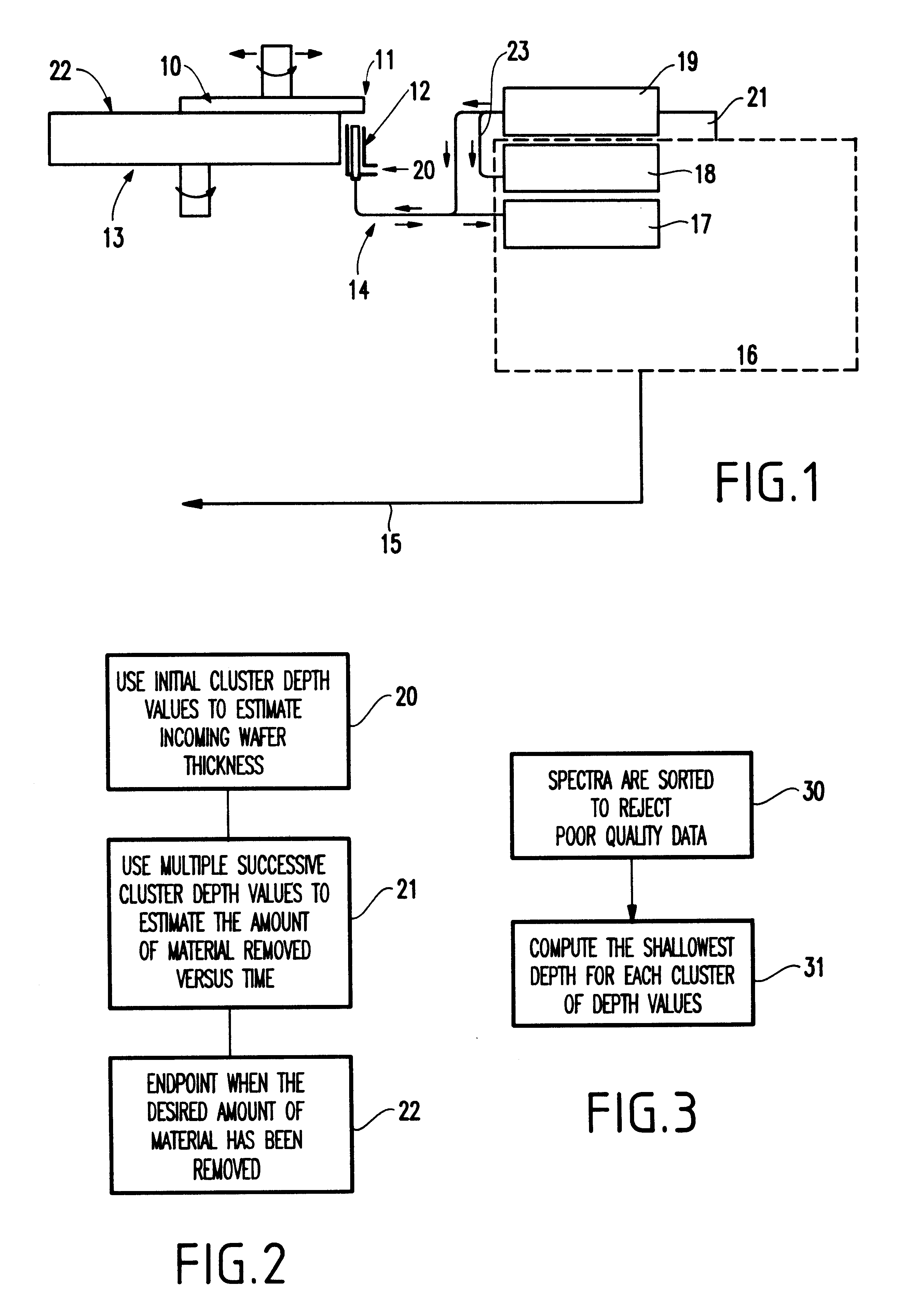
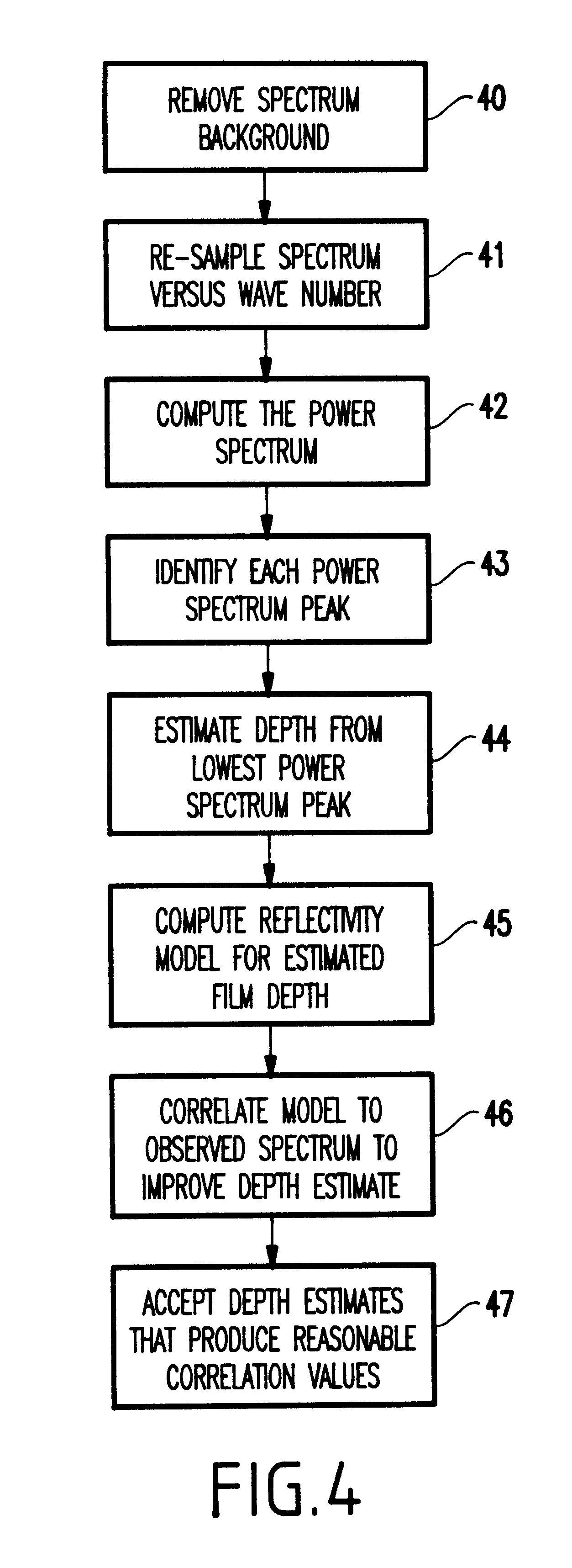
Chemical mechanical polishing in-situ end point system
InactiveUS6334807B1Improve accuracyMaterial removalEdge grinding machinesSemiconductor/solid-state device manufacturingCompound (substance)Point system
A structure and method for polishing a device include oscillating a carrier over an abrasive surface (the carrier bringing a polished surface of the device into contact with the abrasive surface, the oscillating allowing a portion of the polished surface to periodically oscillate off the abrasive surface), optically determining a reflective measure of a plurality of locations of the polished surface as the portion of the device oscillates off the abrasive surface and calculating depths of the locations of the polished surface based of the reflective measure.
Owner:GLOBALFOUNDRIES INC
Method and system for issuing, aggregating and redeeming merchant rewards with an issuing bank
A loyalty reward point system that utilizes the pre-existing infrastructure of network such as a credit card network. A user makes a purchase at a merchant using a token such as a credit card. As part of the purchase transaction, the user is awarded reward points from the merchant based on the purchase, which are stored in an account associated with the merchant and the user by the issuing bank. The reward account is maintained on the issuing bank server on behalf of the merchant and the user, and the number of reward points in the user's account for that merchant is increased accordingly. The user may redeem the reward points earned from the transaction with the merchant at a later time, or may redeem the points with another merchant in the same marketing cluster, or may aggregate those reward points with those of other merchants into a reward point exchange account, and then redeem the aggregated reward points for goods or services from any approved merchant on the network, depending on the configuration of the system.
Owner:SIGNATURE SYST
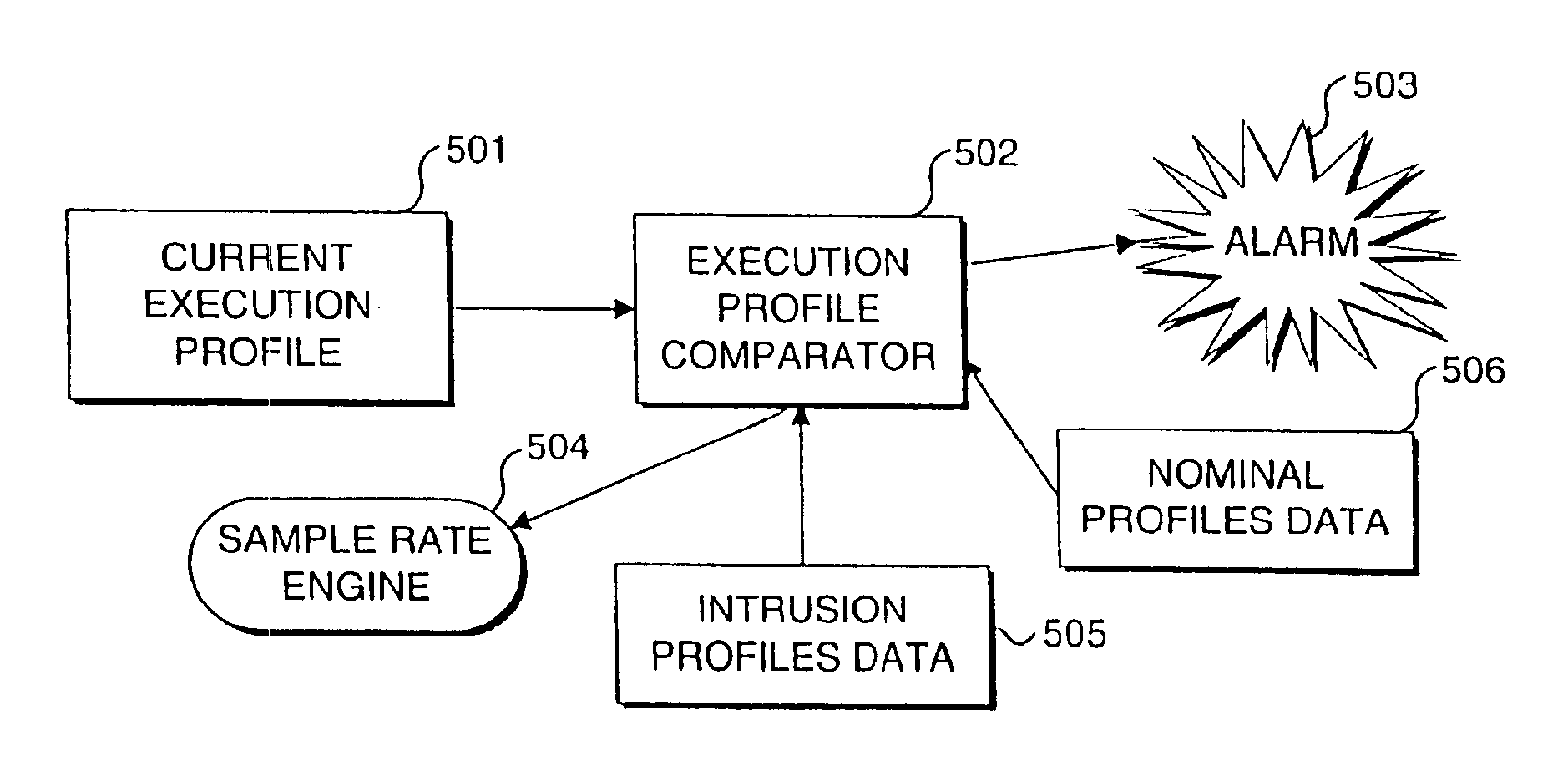
Method of and system for detecting an anomalous operation of a computer system
InactiveUS6963983B2Memory loss protectionDigital data processing detailsSoftware systemTheoretical computer science
A real-time approach for detecting aberrant modes of system behavior induced by abnormal and unauthorized system activities that are indicative of an intrusive, undesired access of the system. This detection methodology is based on behavioral information obtained from a suitably instrumented computer program as it is executing. The theoretical foundation for the present invention is founded on a study of the internal behavior of the software system. As a software system is executing, it expresses a set of its many functionalities as sequential events. Each of these functionalities has a characteristic set of modules that is executed to implement the functionality. These module sets execute with clearly defined and measurable execution profiles, which change as the executed functionalities change. Over time, the normal behavior of the system will be defined by the boundary of the profiles. An attempt to violate the security of the system will result in behavior that is outside the normal activity of the system and thus result in a perturbation of the system in a manner outside the scope of the normal profiles. Such violations are detected by an analysis and comparison of the profiles generated from an instrumented software system against a set of known intrusion profiles and a varying criterion level of potential new intrusion events.
Owner:STRATACLOUD
Mechanism for delivering messages to competing consumers in a point-to-point system
InactiveUS7525964B2Avoids distributed transactionQuality improvementData switching by path configurationMessage deliveryData transmission
A method, system, and computer program for delivering messages and data to competing consumers. One aspect of the invention includes a message delivery system including a destination messaging engine, one or more receiver messaging engines, and a message pool. The destination messaging engine is configured to distribute data from one or more producers. The receiver messaging engines are configured to request data from the destination messaging engine and transmit the data to one or more consumers. The message pool is configured to store data from the producers, with the destination messaging engine arbitrating data in the message pool among the receiver messaging engines.
Owner:ACTIVISION PUBLISHING
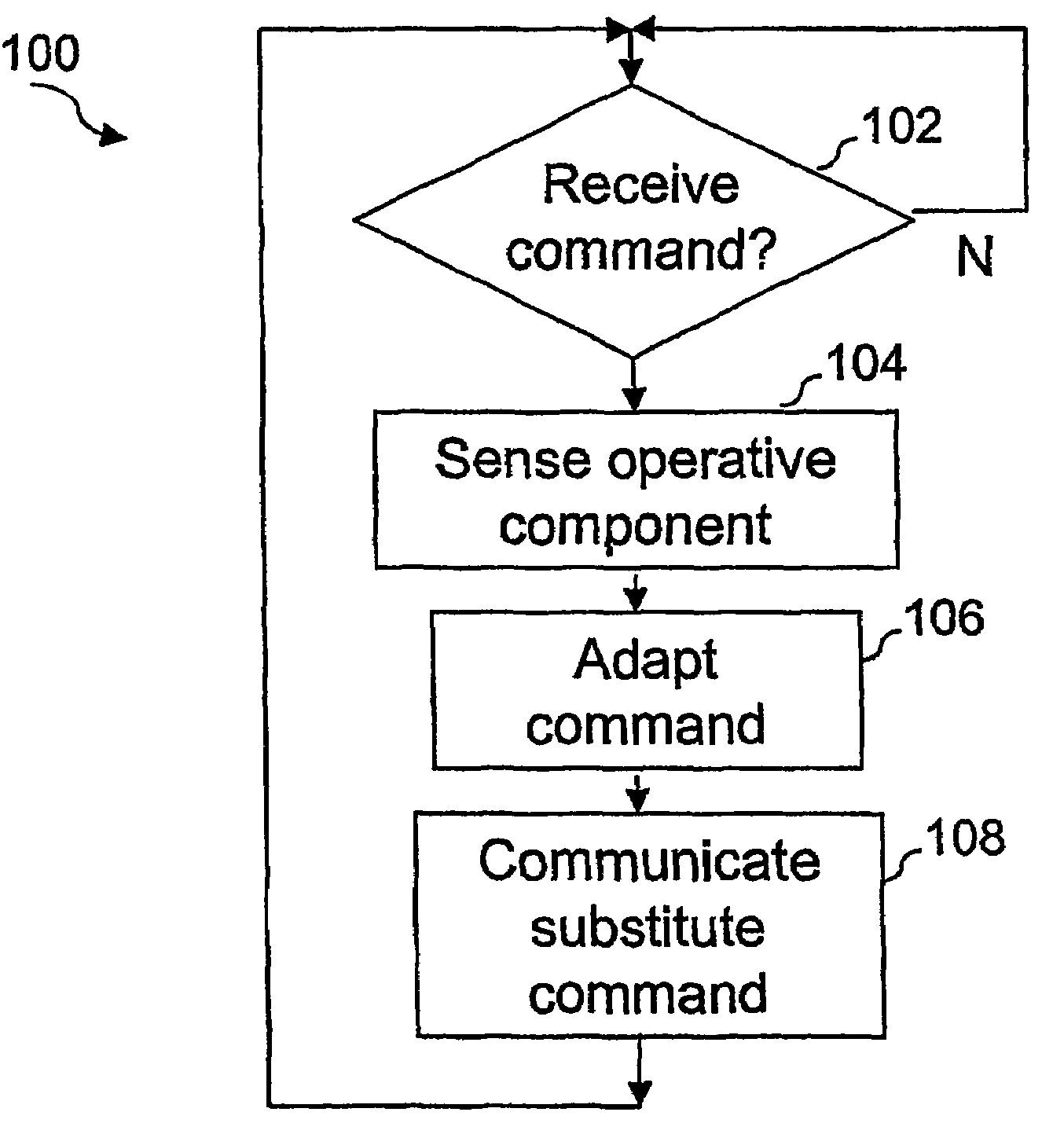
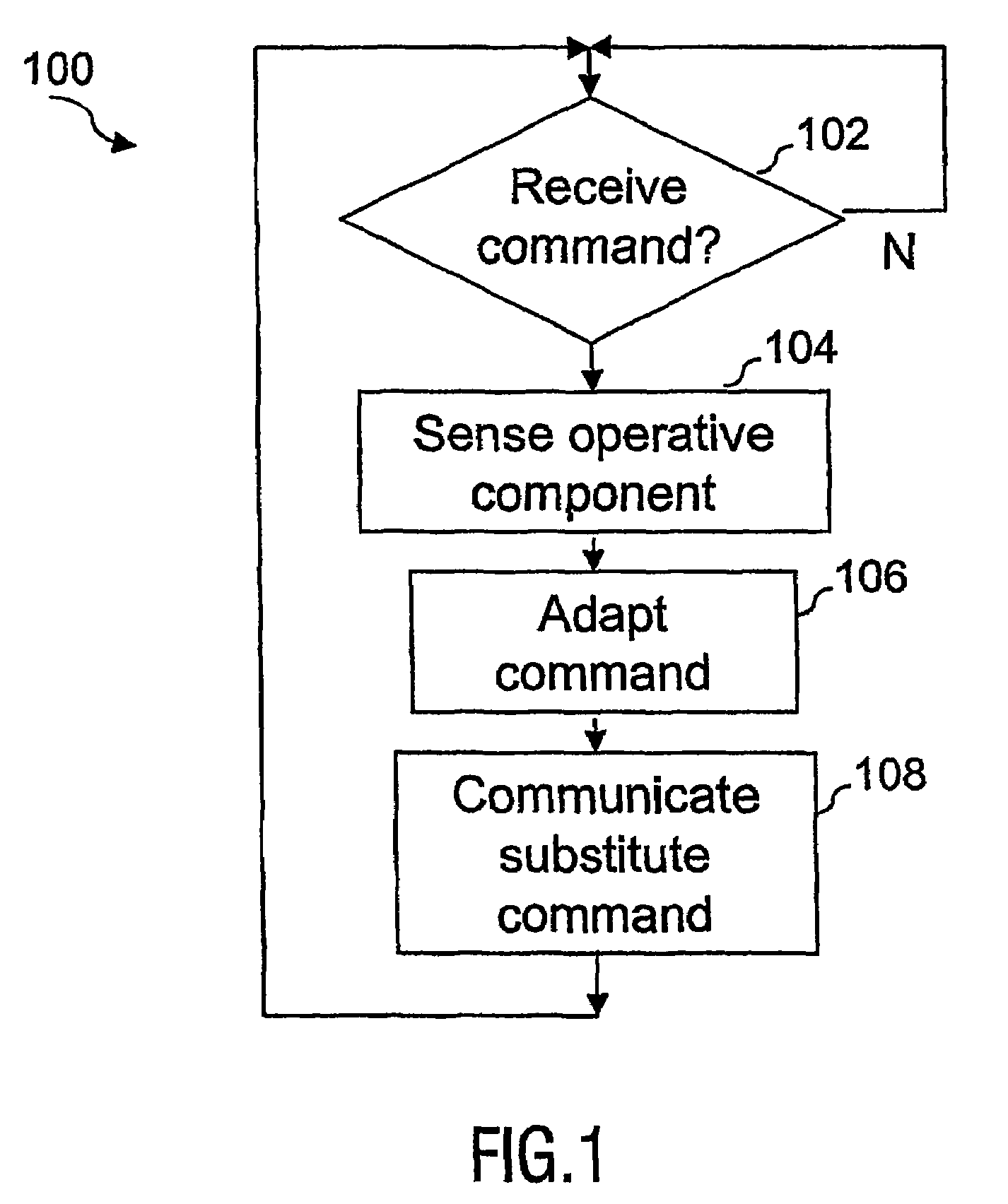
Controlling a home electronics system
InactiveUS7135985B2Remove the burdenTelevision system detailsElectric signal transmission systemsElectronic systemsEmbedded system
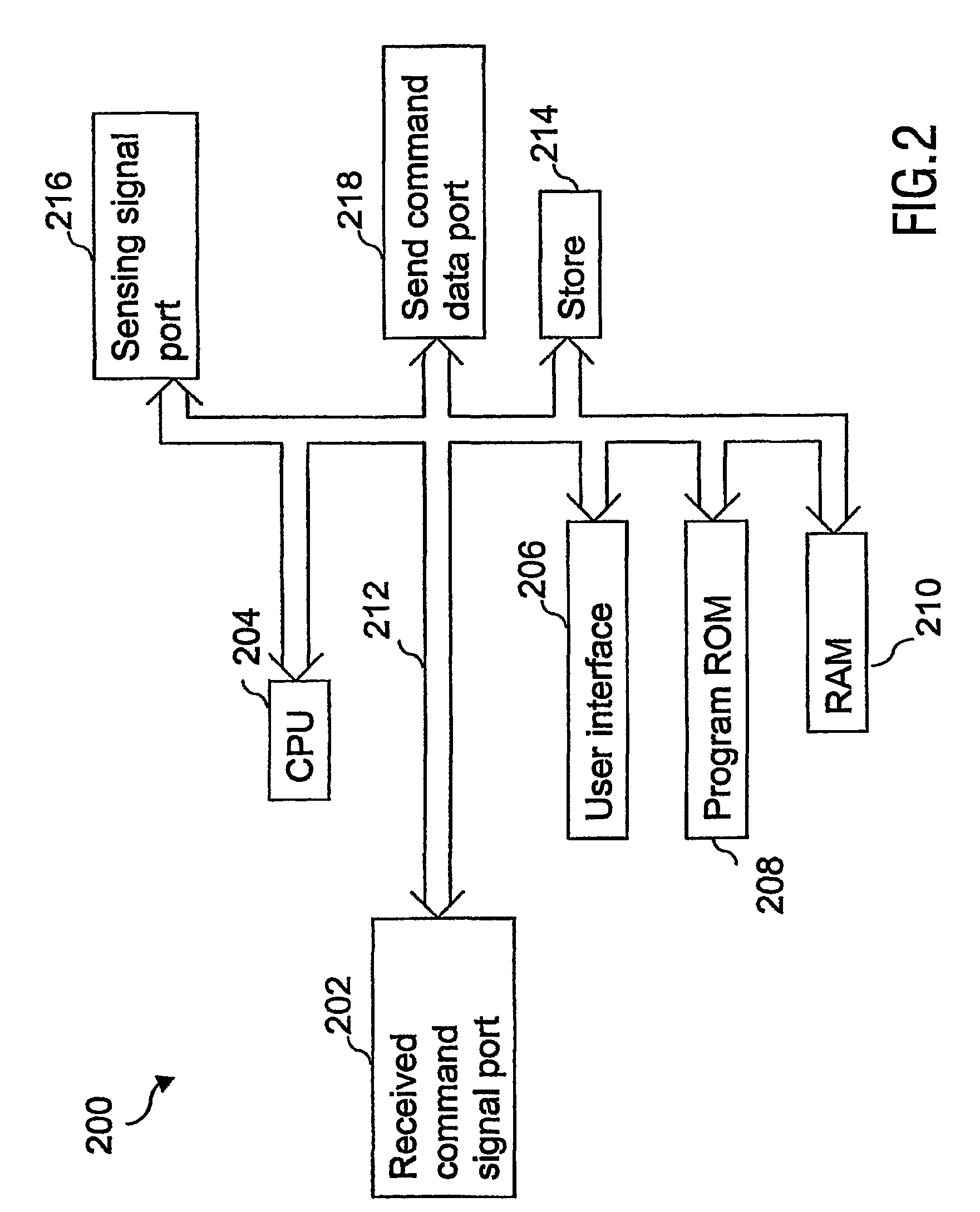
In an apparatus (200) arranged to control a home electronics system, the apparatus being managed independently of a user, the apparatus includes a data processing unit (CPU (204), Program ROM (208) and RAM (210)), a first communications port (202) operable to receive a command, a second communications port (216) operable to receive a signal indicating an operative component in the system, and a third communications port (218) operable to output a substitute command to a component in the system. On receiving a command, the data processing unit may produce at least one substitute command in dependence on the operative component, this substitute command then being communicated to a component in the system.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Dsl System Estimation
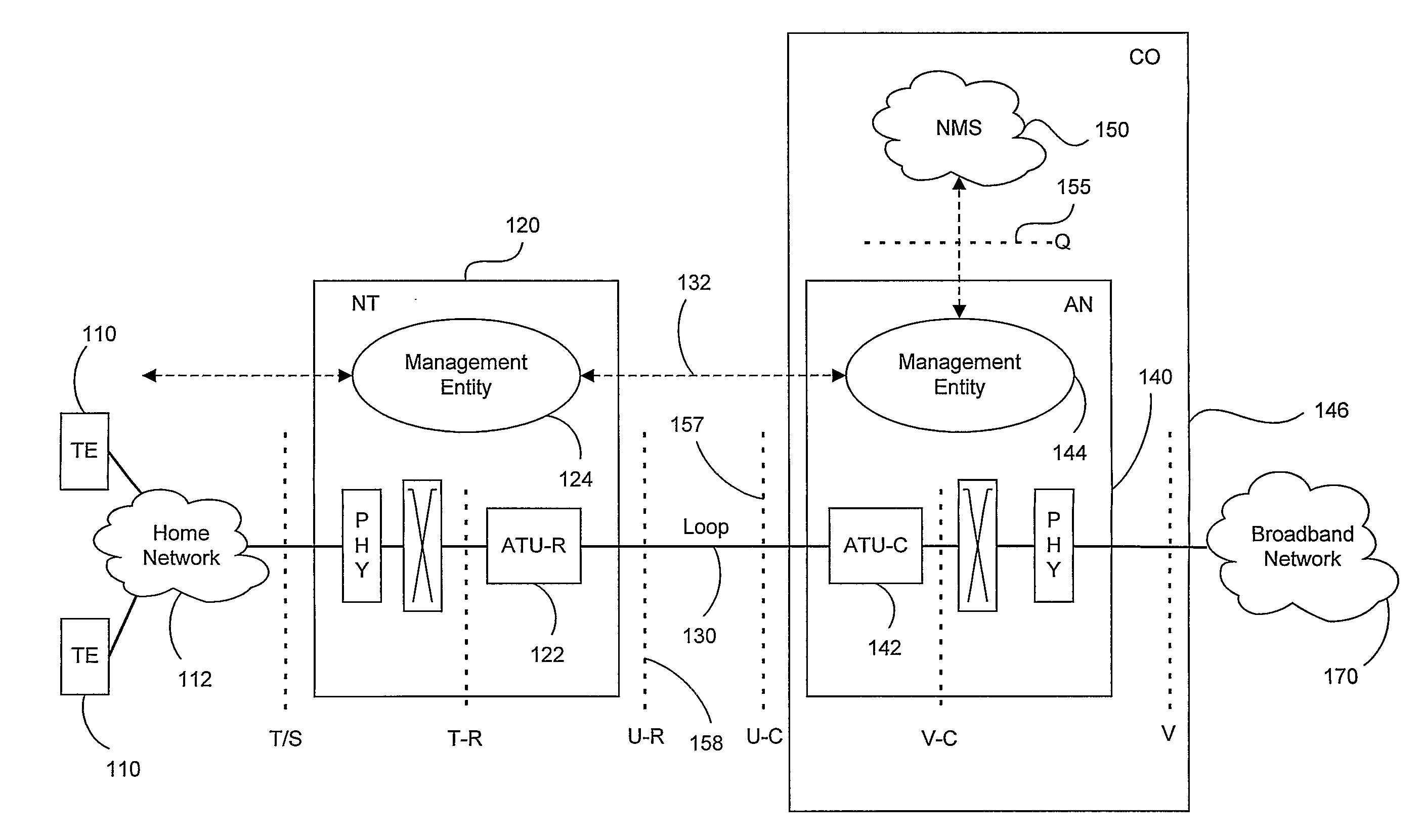
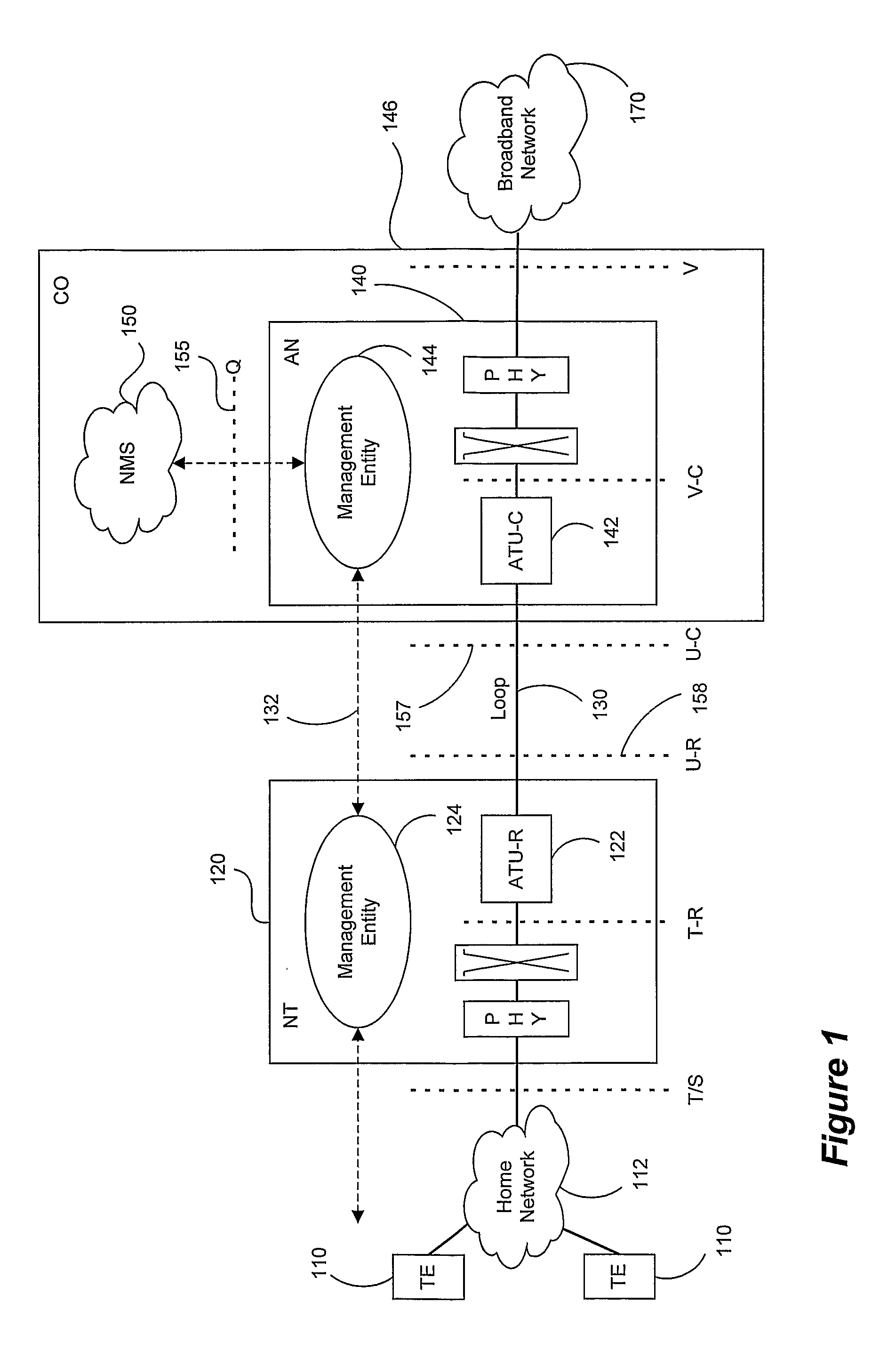
InactiveUS20080205501A1Shorten the lengthEasy to useError preventionFrequency-division multiplex detailsCommunications systemElement management system
Estimates of a communication system configuration, such as a DSL system, are based on operational data collected from a network element management system, protocol and users. The operational data collected from the system can include performance-characterizing operational data that typically is available in the OSL system via element-management-system protocols. Generated estimates and / or approximations can be used in evaluating system performance and directly or indirectly dictating / requiring changes or recommending improvements in operation by transmitters and / or other parts of the indication system. Data and / or other information may be collected using internal means or using system elements and components via e-mail and / or other extra means. The likelihood of the models accuracy can be based on various data, information and / or indicators of system performance, such as observed normal operational data, test data and / or prompted operational data that shows operating performance based on stimulation signals.
Owner:ASSIA SPE LLC CO THE CORP TRUST CO
Scheduling delivery of products via the internet
InactiveUS7139721B2Accurate pictureMarket predictionsBuying/selling/leasing transactionsComputerized systemThe Internet
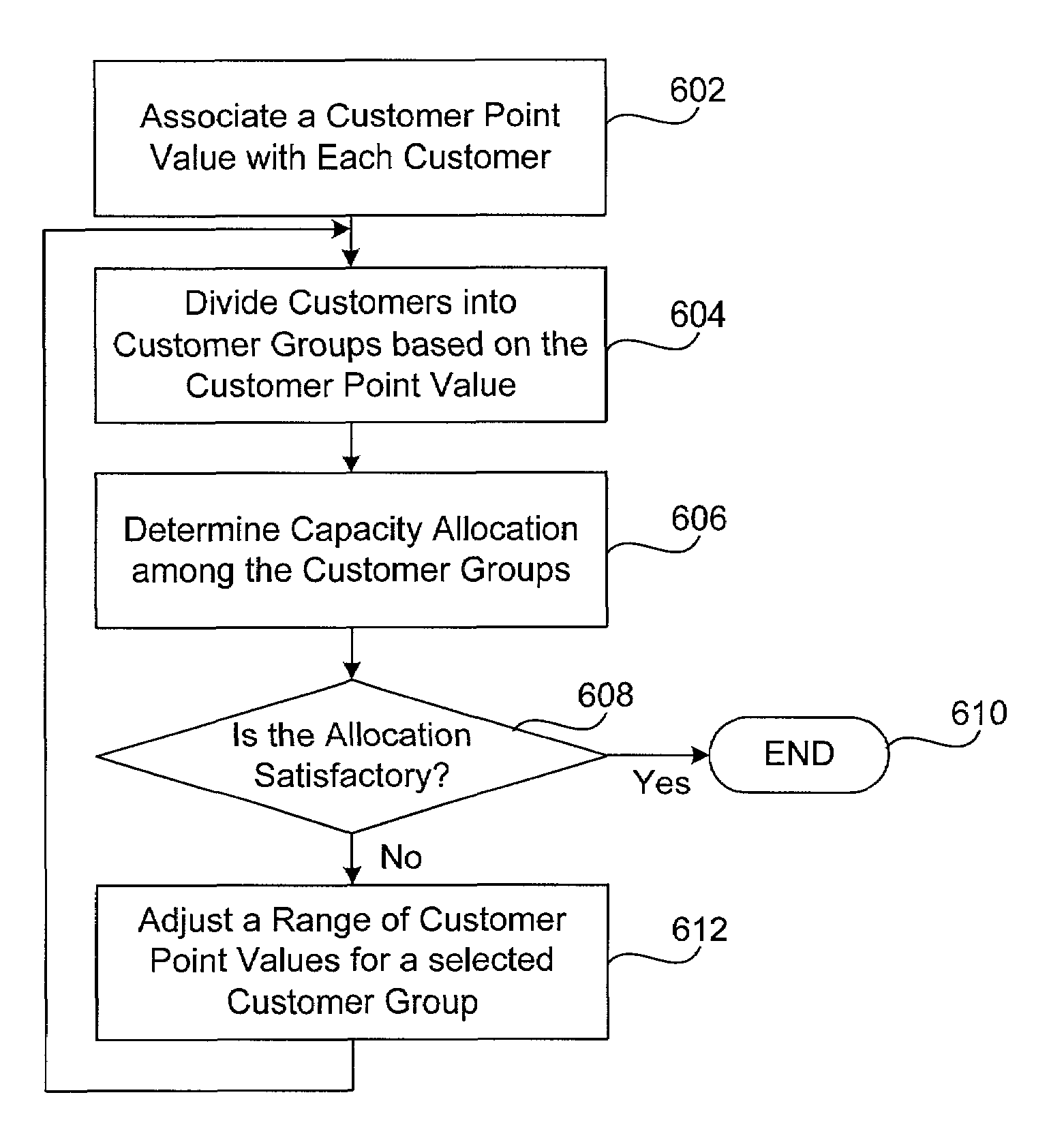
Methods and apparatus for scheduling delivery of an order via a wide area network. A computer system associates a customer point value with each customer according to a customer point system. The customer point values is determined with reference to customer order data. The computer system then divides the customers into customer groups, each of which has a range of customer point values. The system determines an actual capacity allocation distribution among the customer groups based on the customer order data. The system adjusts the range of customer point values for customer groups to cause the actual capacity allocation distribution to converge to a target capacity allocation distribution.
Owner:JUNE RAY
Systems and methods for mitigating interference between access points
InactiveUS20110032849A1Easy to useDense reuseTime-division multiplexRadio transmissionEngineeringPoint system
Systems and methods which implement cooperative techniques at wireless network access points to provide interference mitigation are shown. Embodiments utilize cooperative antenna beam adaptation techniques wherein antenna beam selection, selective antenna beam transmission power, and / or antenna beam null selection is implemented based upon the communication environment created by a plurality of access points. Additionally or alternatively, embodiments utilize cooperative antenna beam isolation techniques wherein narrow channel filters are implemented with respect to antenna beam signals and / or shielding is provided between various antenna beams based upon the communication environment created by a plurality of access points. Embodiments additionally or alternatively utilize cooperative antenna beam coordination techniques wherein transmission and / or reception of signals is coordinated, the use of antenna beams is coordinated, and / or interference cancellation is implemented based upon the communication environment created by a plurality of access points.
Owner:FIMAX TECH
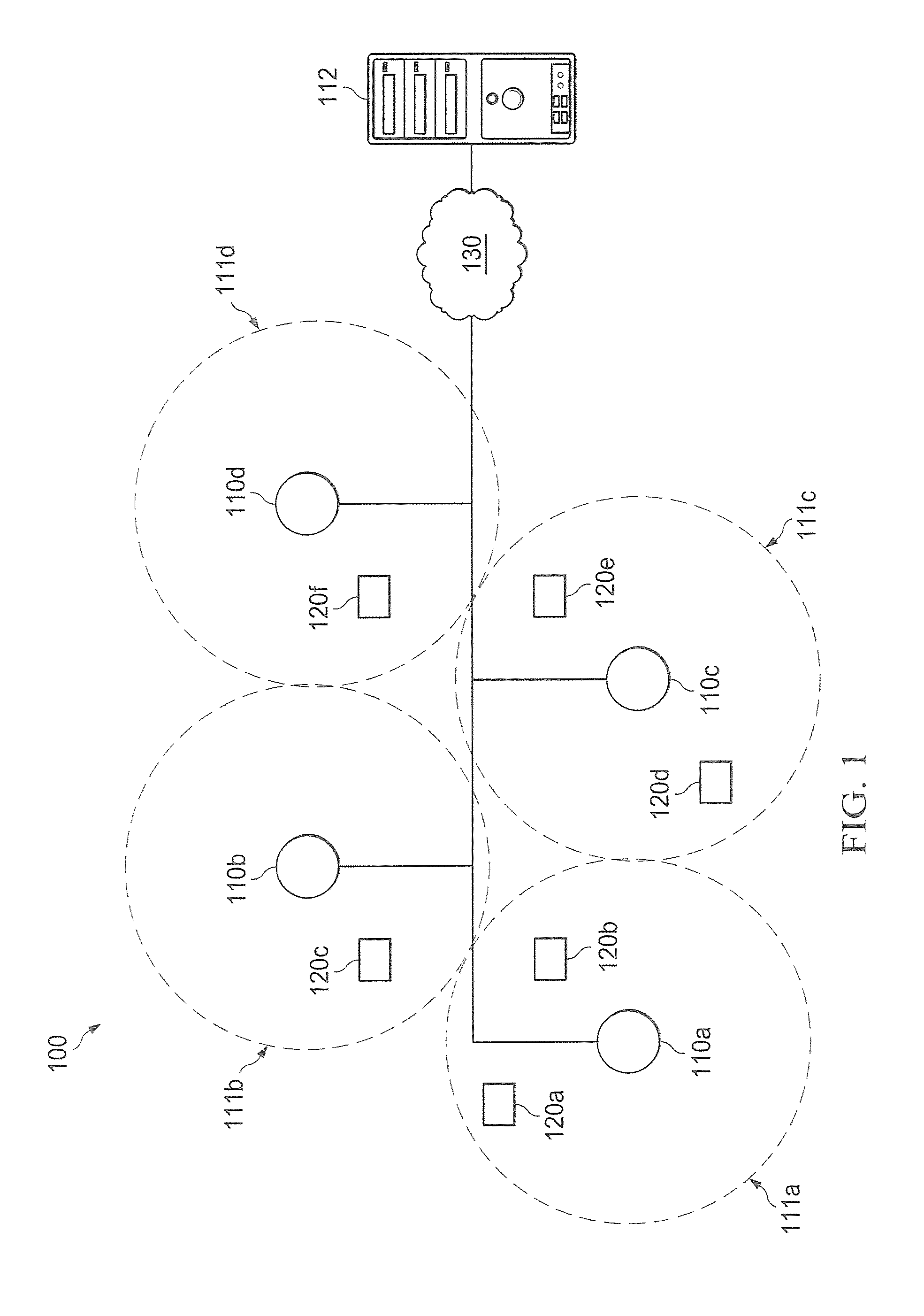
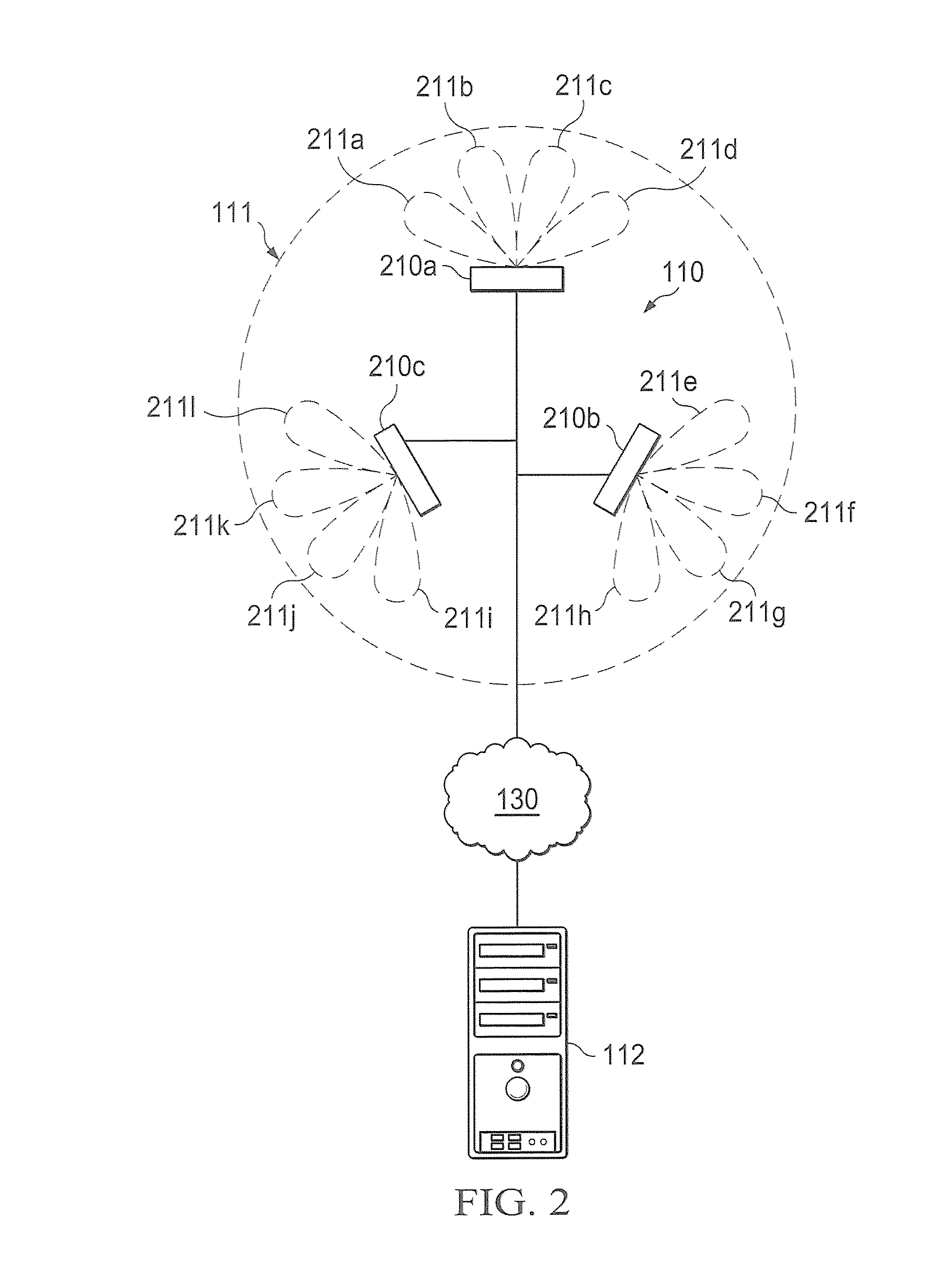
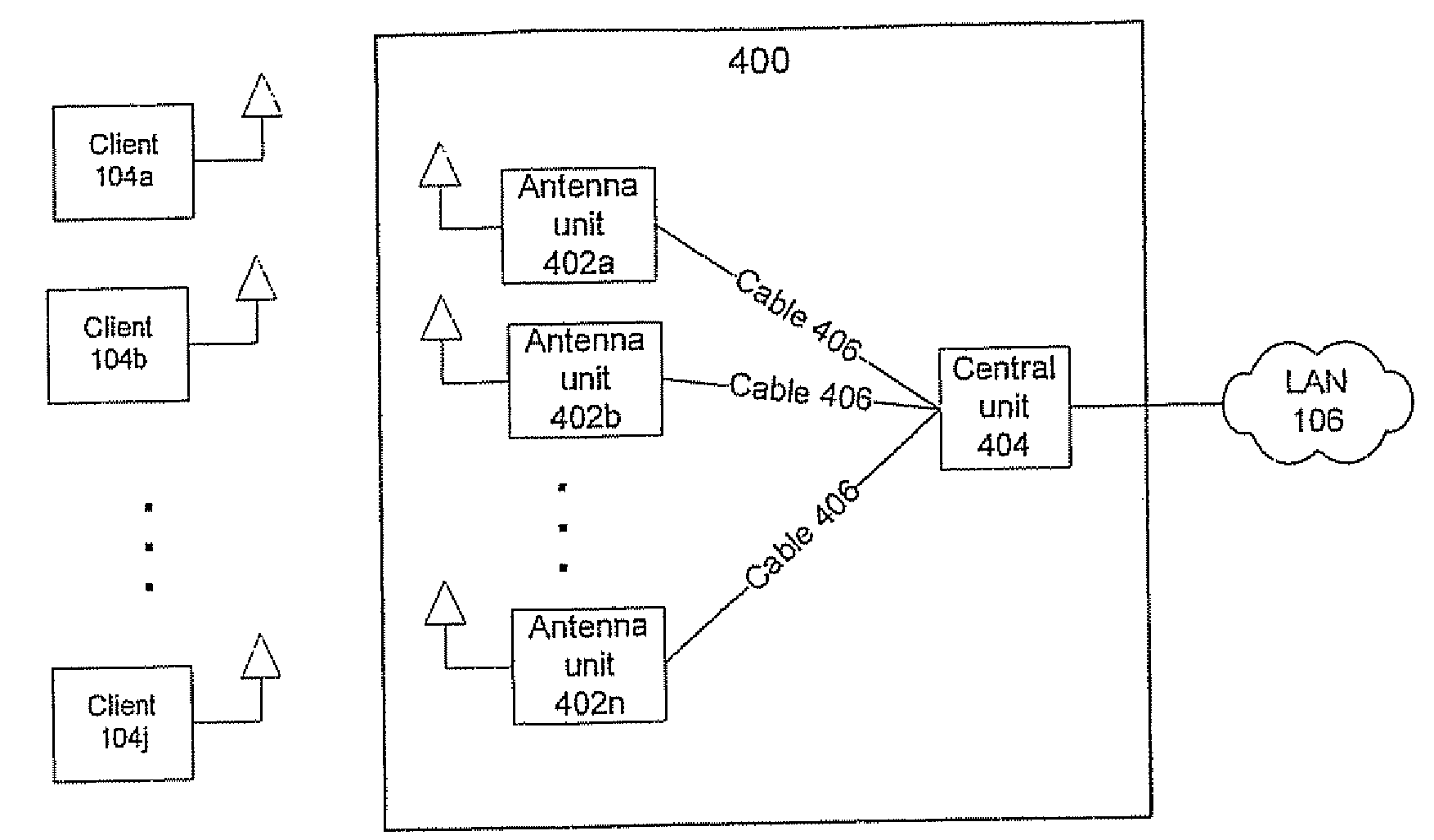
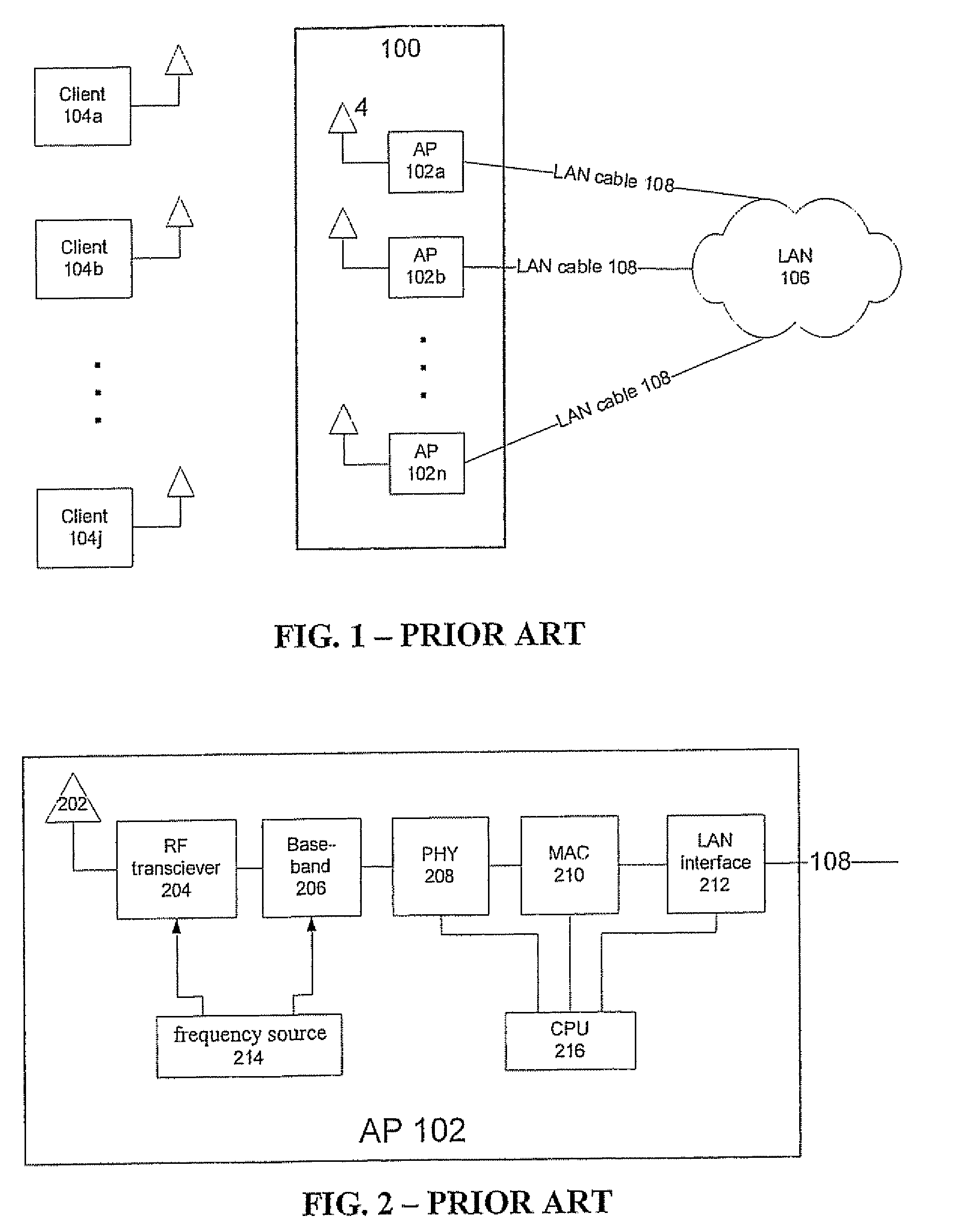
Distributed Antenna Wlan Access-Point System and Method
InactiveUS20080267142A1Easy to implementAddress limitationsData switching by path configurationRadio/inductive link selection arrangementsRadio frequencyPoint system
A wireless local area network (WLAN) access point (AP) system comprises a first plurality of distributed remote antenna units operative to transmit and receive RF signals and a central WLAN beam-forming unit connected to each distributed remote antenna unit and operative to provide communication between the antenna units and a second plurality of wireless clients. The WLAN AP system can be used for simultaneous communications with the wireless clients over the same radio frequency (RF) channel while avoiding mutual interferences.
Owner:STELLARIS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com