Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
854 results about "Integrity check" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Detect. The Integrity Check can identify missing objects which are referred by other objects in the configuration like missing custom fields, groups, users in workflows, groups in project roles. Integrity Check detects several types of errors in the whole Jira configuration:
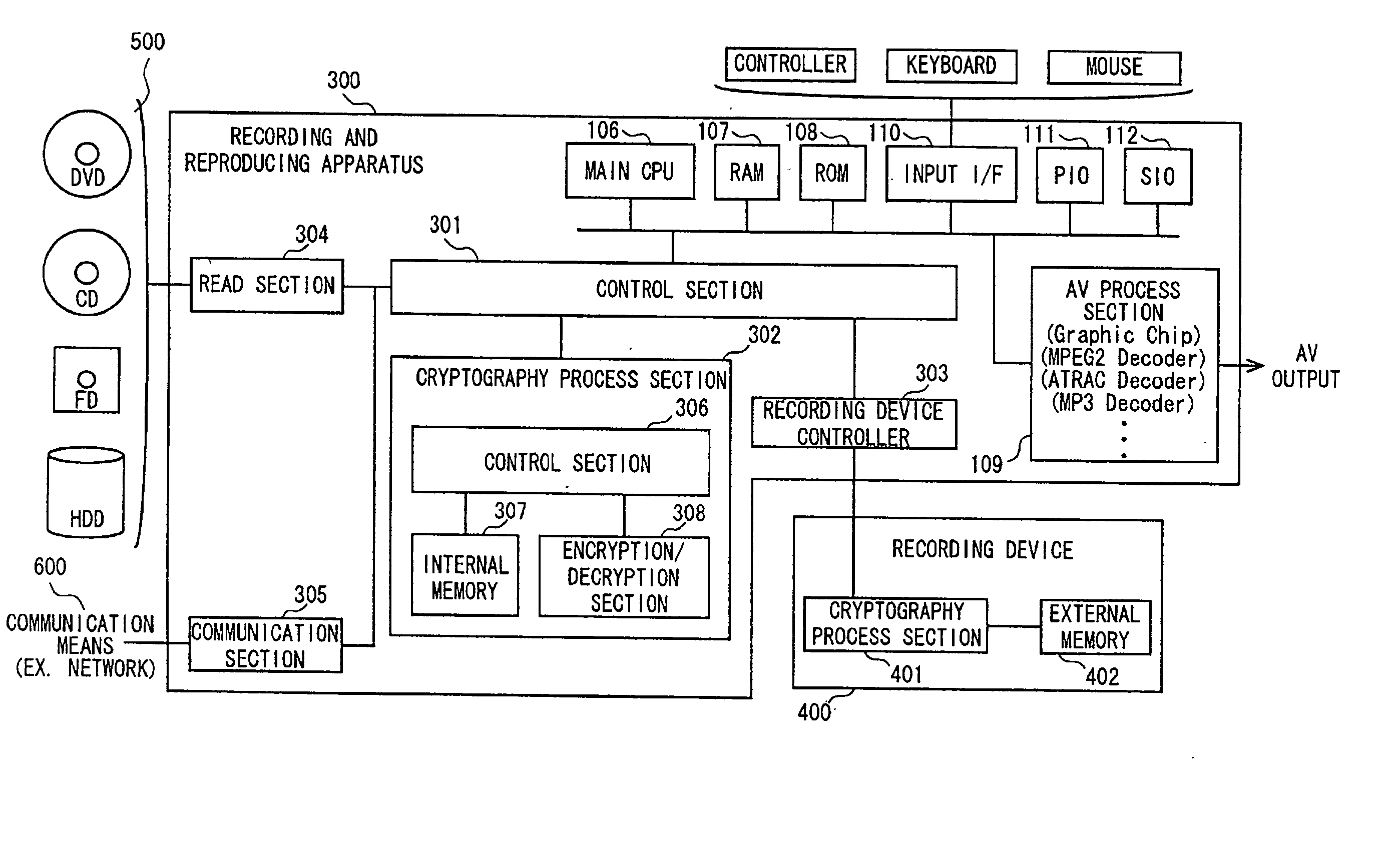
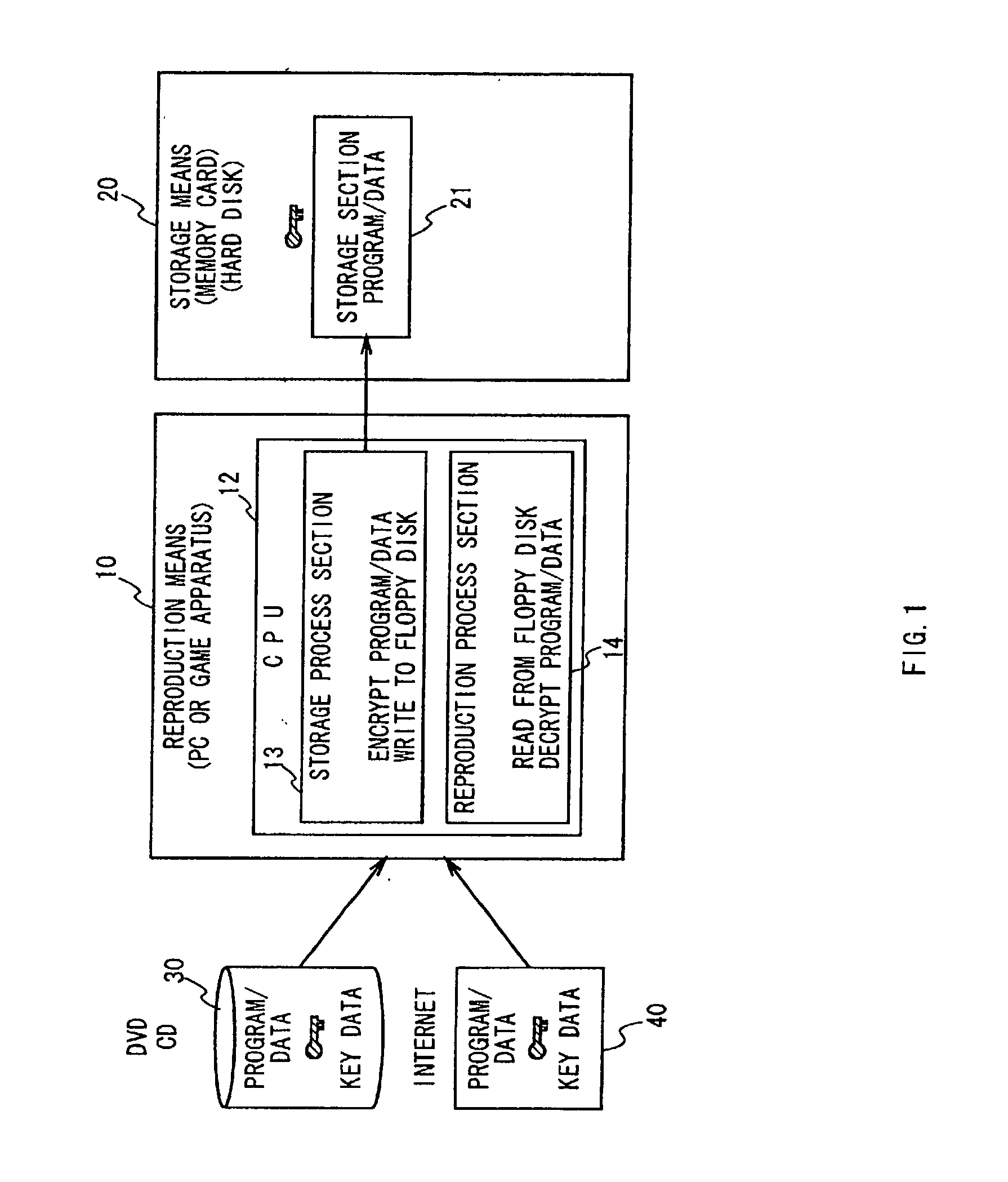
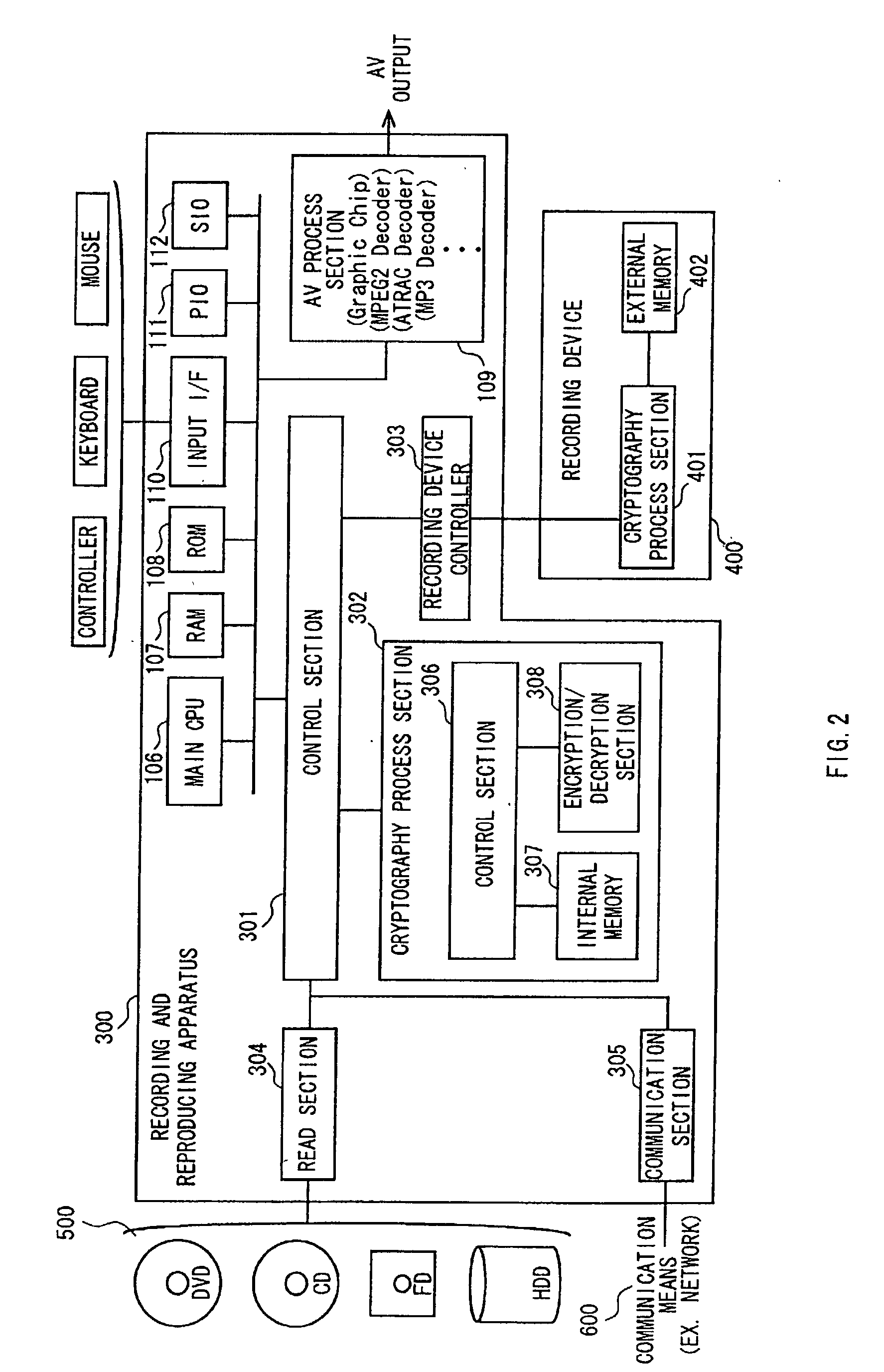
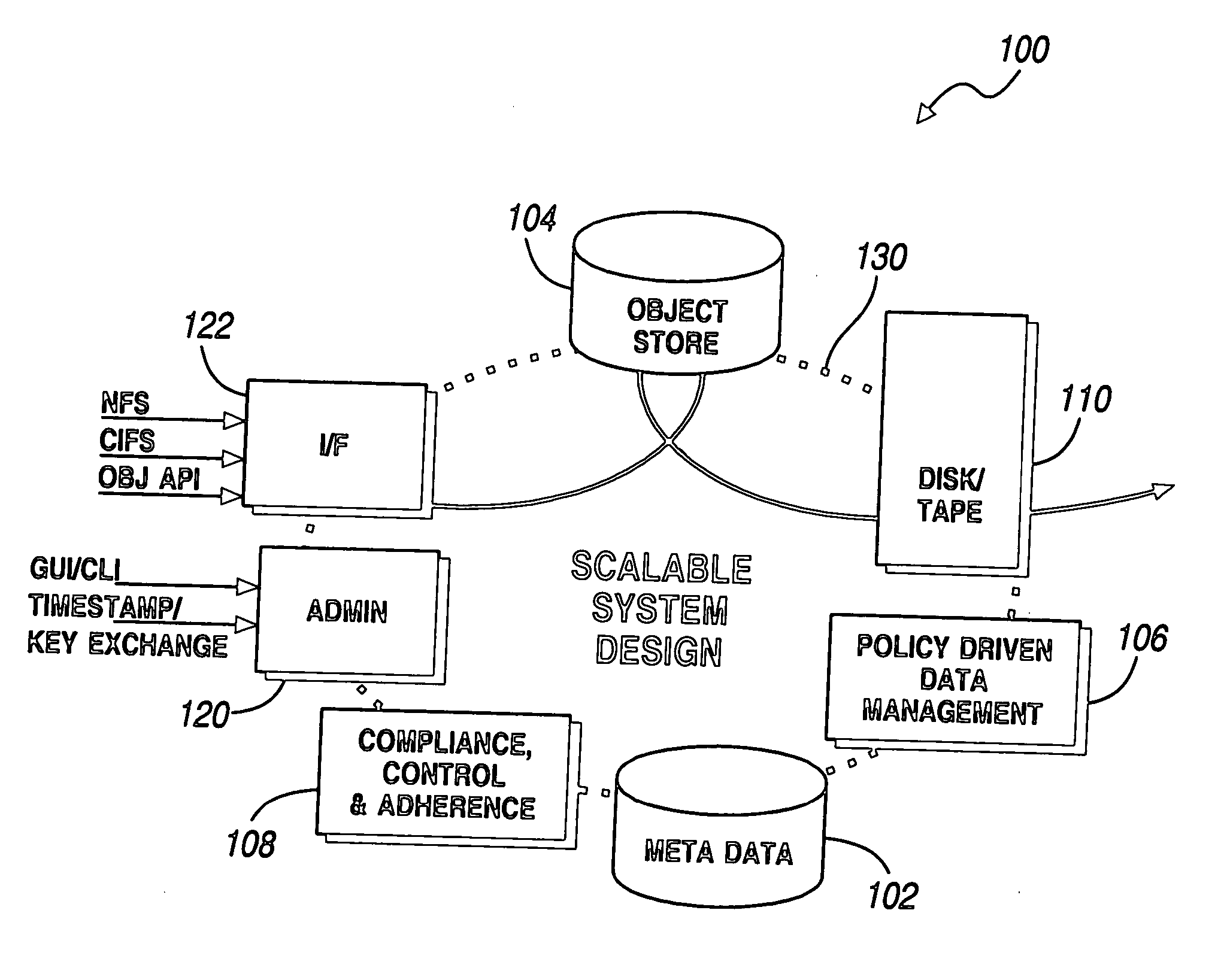
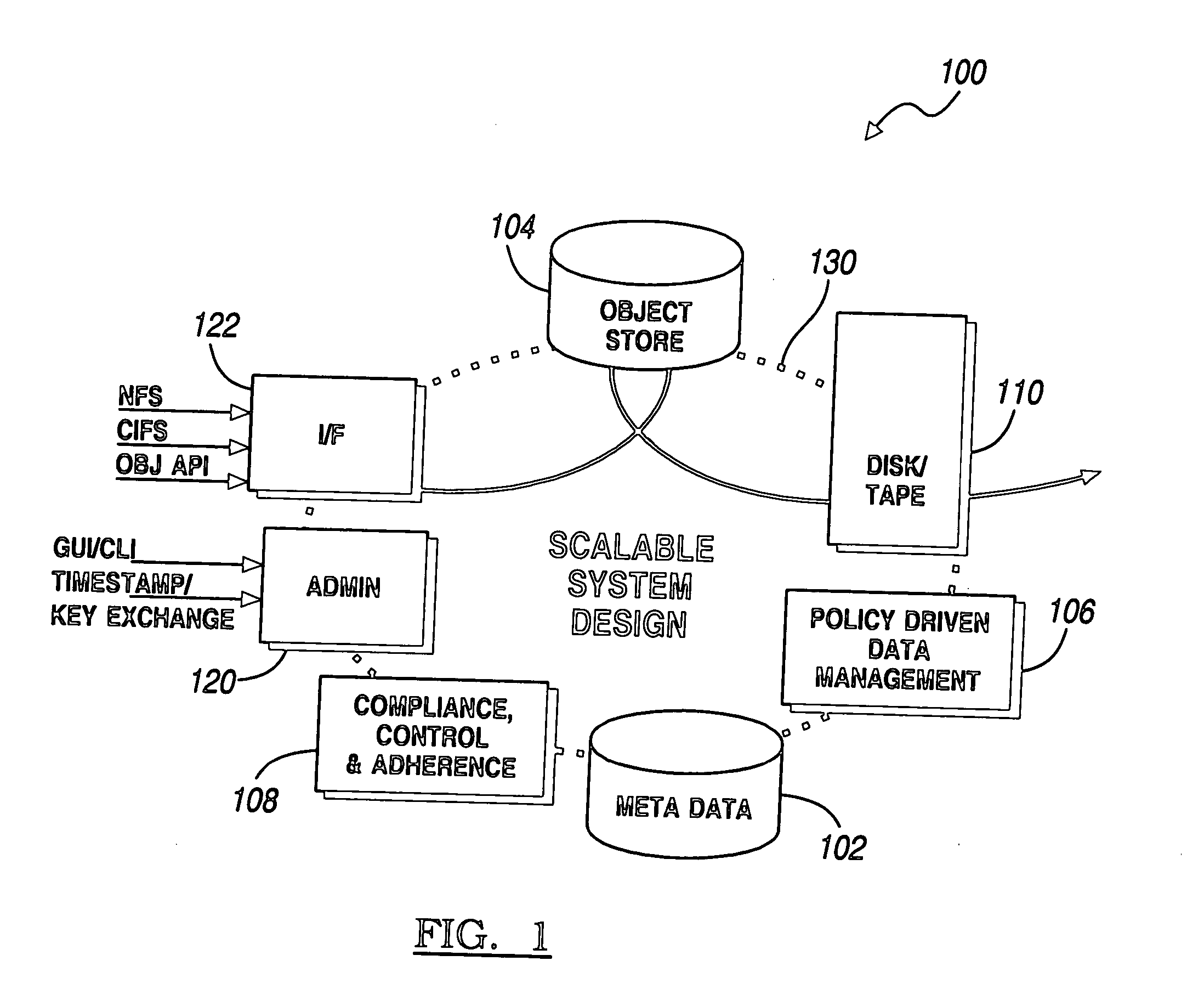
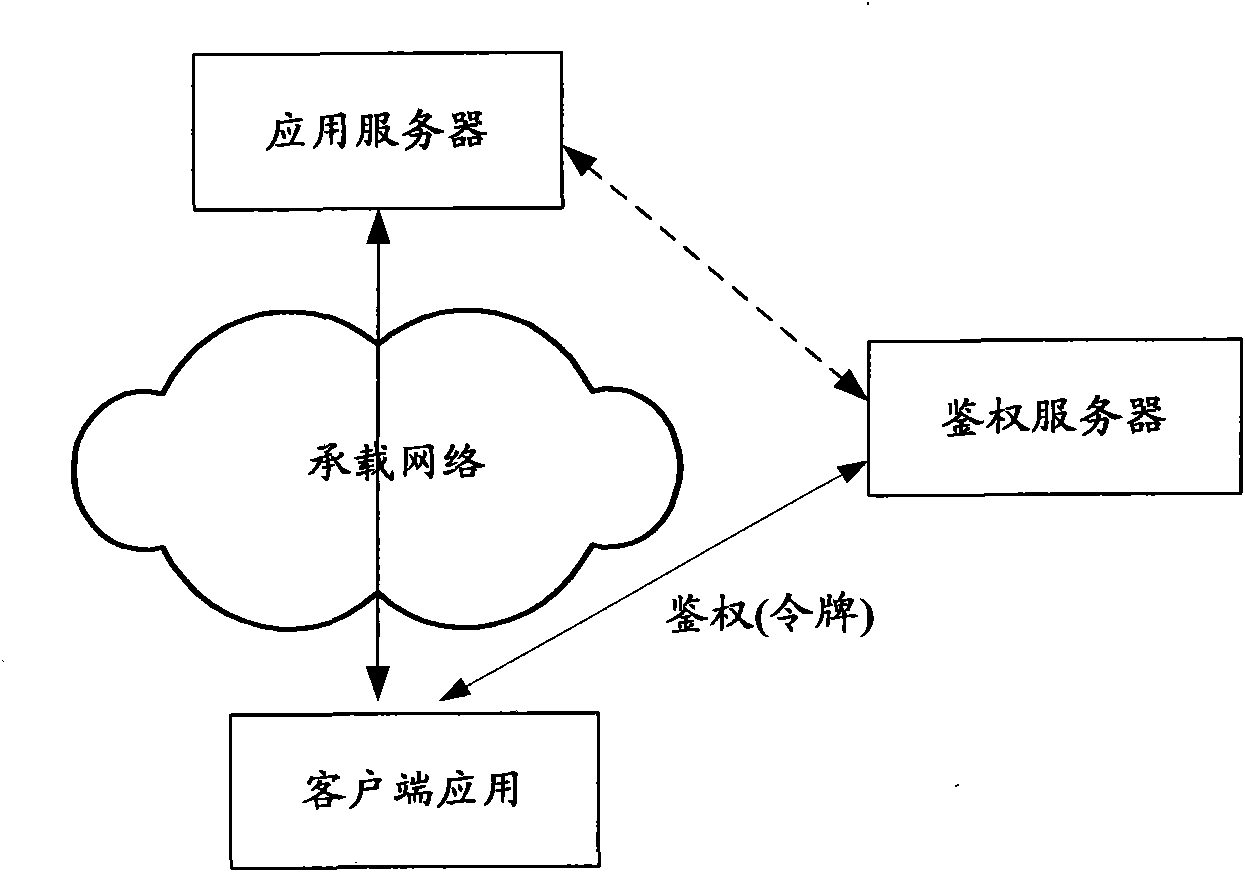
Data authentication system
InactiveUS20020169971A1Efficient verificationPossibility of leakageTelevision system detailsMultiple keys/algorithms usageKey storageMaster key
A data processing apparatus a data processing method efficiently ascertain that data are valid, prevent encryption processing key data from leaking, eliminate illegal use of contents data, restrict contents utilization, apply a different plurality of data formats to contents and efficiently execute reproduction processing of compressed data. The verification process of partial data is executed by collating the integrity partial data as check values for a combination of partial data of a content, and the verification process of the entirety of the combination of partial data is executed by collating partial-integrity-check-value-verifying integrity check values that verify the combination of the partial integrity check values. Master keys to generate individual keys necessary for a process of such as data encryption are stored in the storage section and keys are generated as required. An illegal device list is stored in the header information of a content and referred to when data is used. Keys specific to a data processing apparatus and common keys are stored and the keys are selectively used according to the content use restriction. Plural content blocks are coupled, and at least a part of the content blocks is applied to an encryption process by an encryption key Kcon, then encryption key data that is the encryption key Kcon encrypted by an encryption key Kdis is stored in the header section. A content data is made of compression data and an expansion processing program or a combination of types of compression programs and the reproducing apparatus can determine an expansion program applicable to a compressed content.
Owner:SONY CORP
Inspection of playing cards
A playing card integrity checker utilises a blue light source to illuminate the playing face of each card to use template matching to identify the value and suit of each card based on stored templates from cards of the same card manufacturer. This information and the number of cards counted is matched against the cards needed for a predetermined game. The absence of required cards or the presence of superfluous cards is reported. Cards that have their faces reversed or appear marked are also reported.
Owner:DOLPHIN ADVANCED TECH
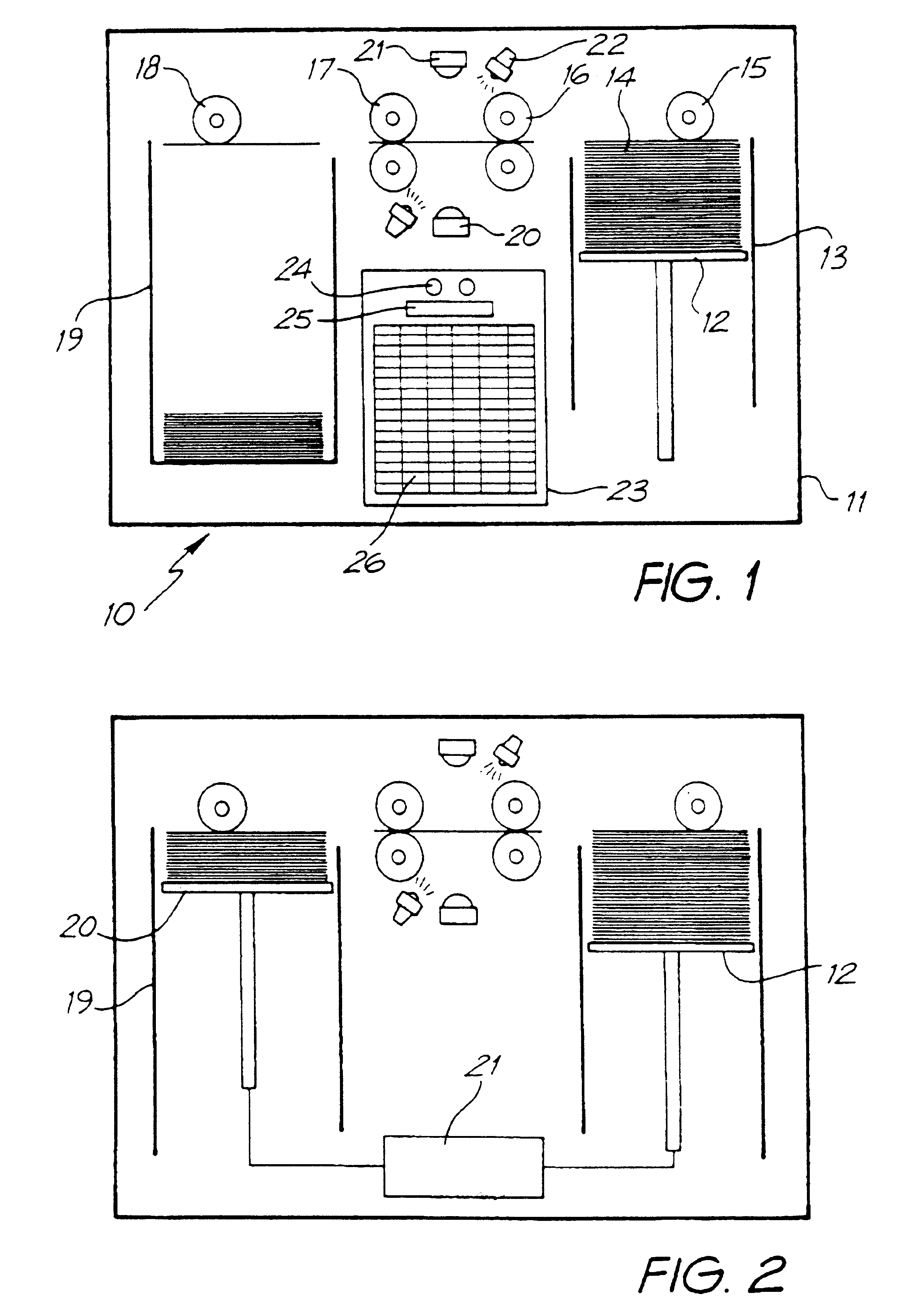
Clustered hierarchical file services
ActiveUS20050195660A1Make up for deficienciesData processing applicationsDigital data information retrievalCommand-line interfaceGraphics
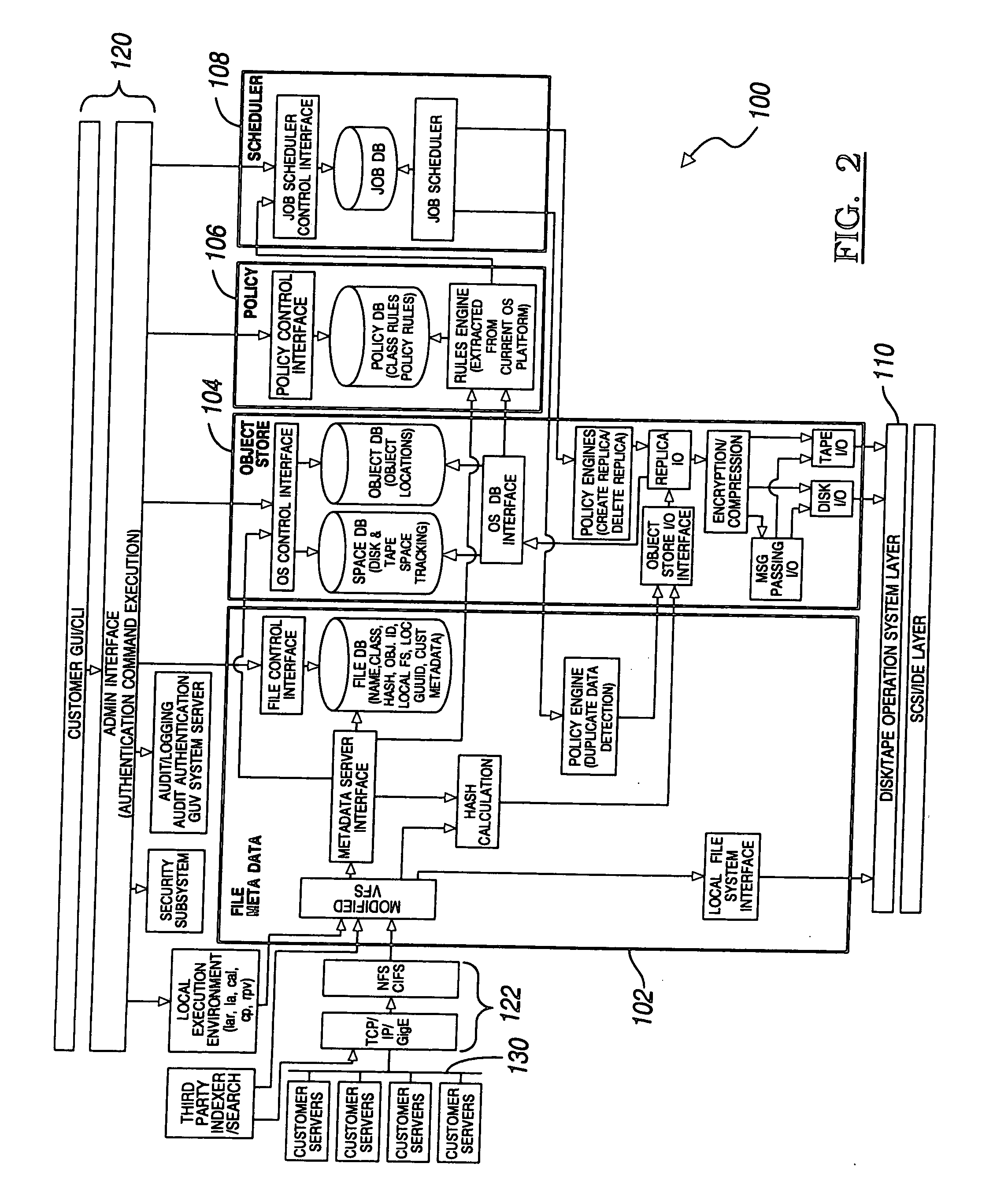
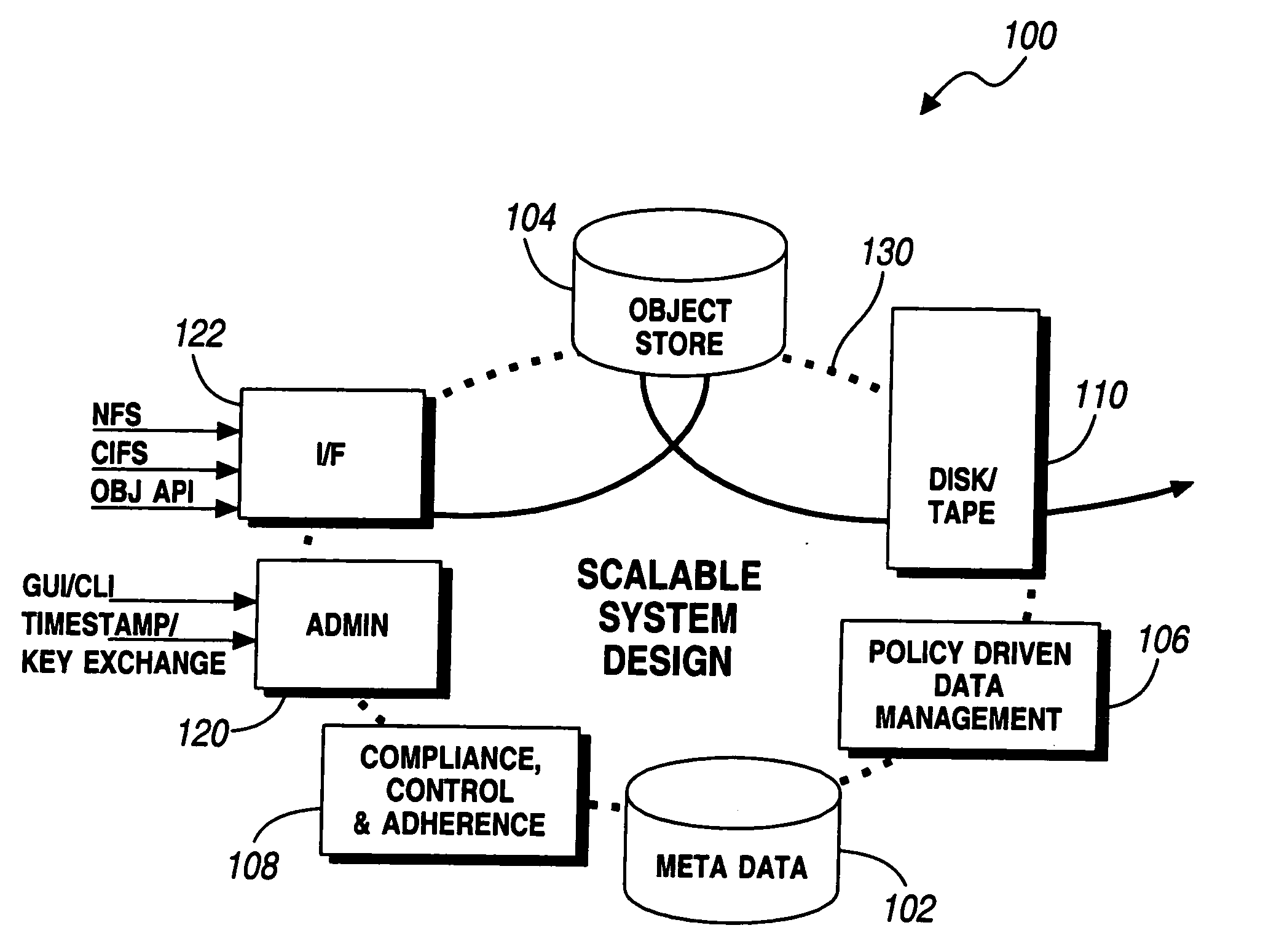
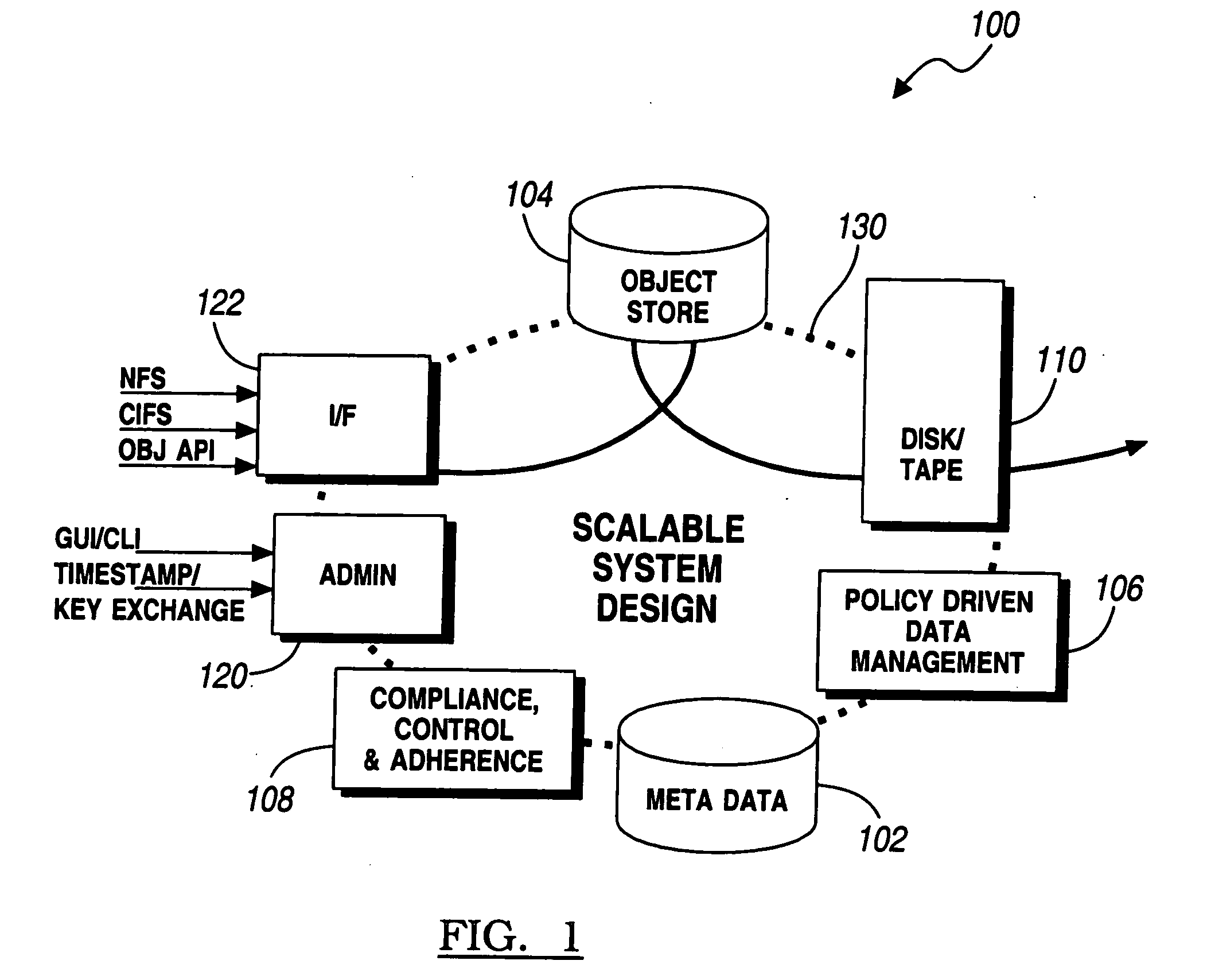
A system for object-based archival data storage includes an object-based storage subsystem having respective data storage devices, at least one file presentation interface that interfaces to client platforms, an administration interface having graphical user interface (GUI) and a command line interface (CLI), a meta data subsystem for storing meta data about files, and includes a virtual file subsystem having a virtual file server (VFS), a policy subsystem, and a scalable interconnect to couple the object-based storage subsystem, the at least one file presentation interface, the administration interface, the meta data subsystem, and the policy subsystem, wherein the policy subsystem provides system rules predetermined by a user for at least one of hash based integrity checking, read-only / write-ability / erase-ability control, and duplicate data treatment corresponding to files and file objects.
Owner:ORACLE INT CORP
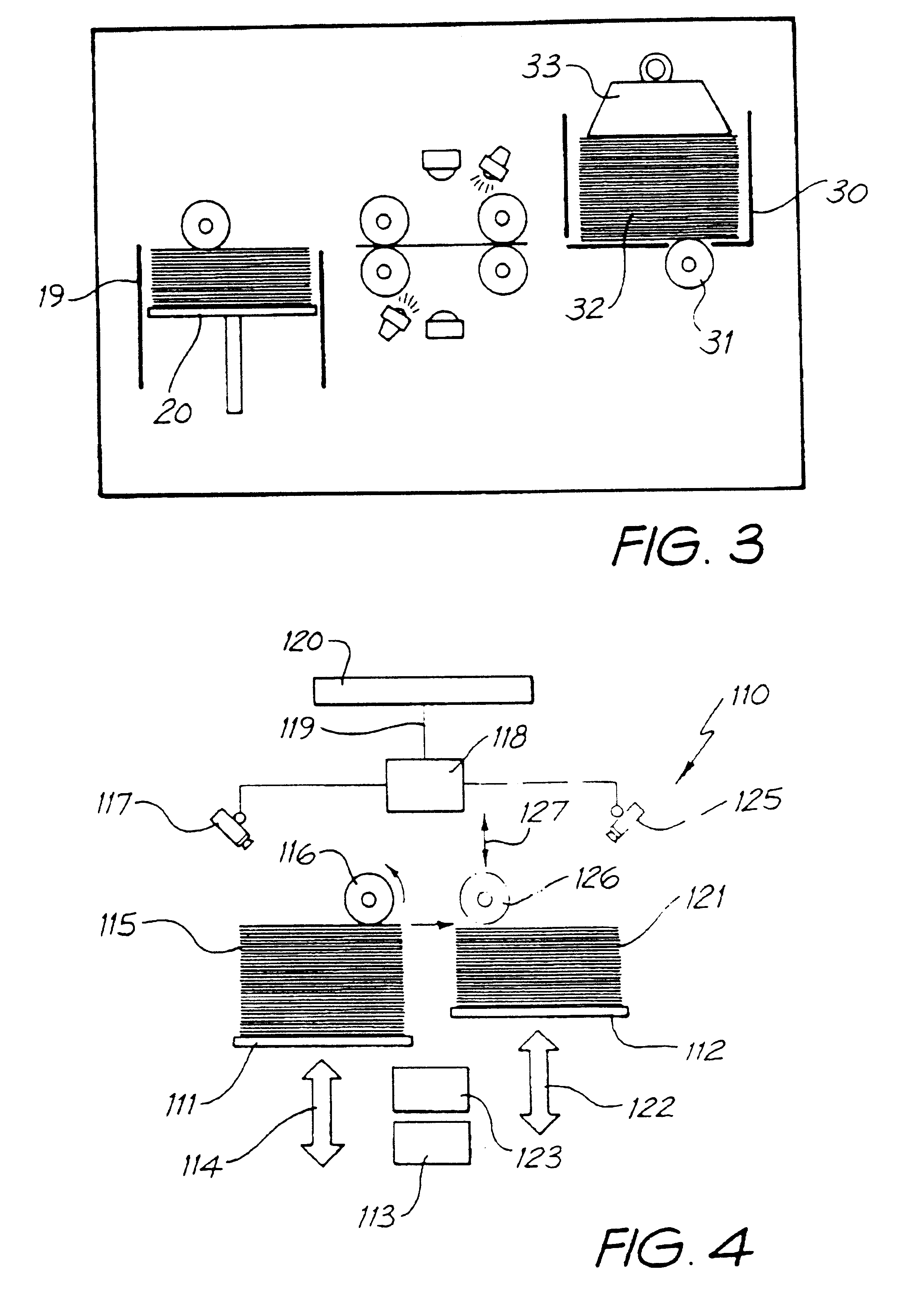
Clustered hierarchical file services
ActiveUS20050226059A1Input/output to record carriersData processing applicationsCommand-line interfaceGraphics
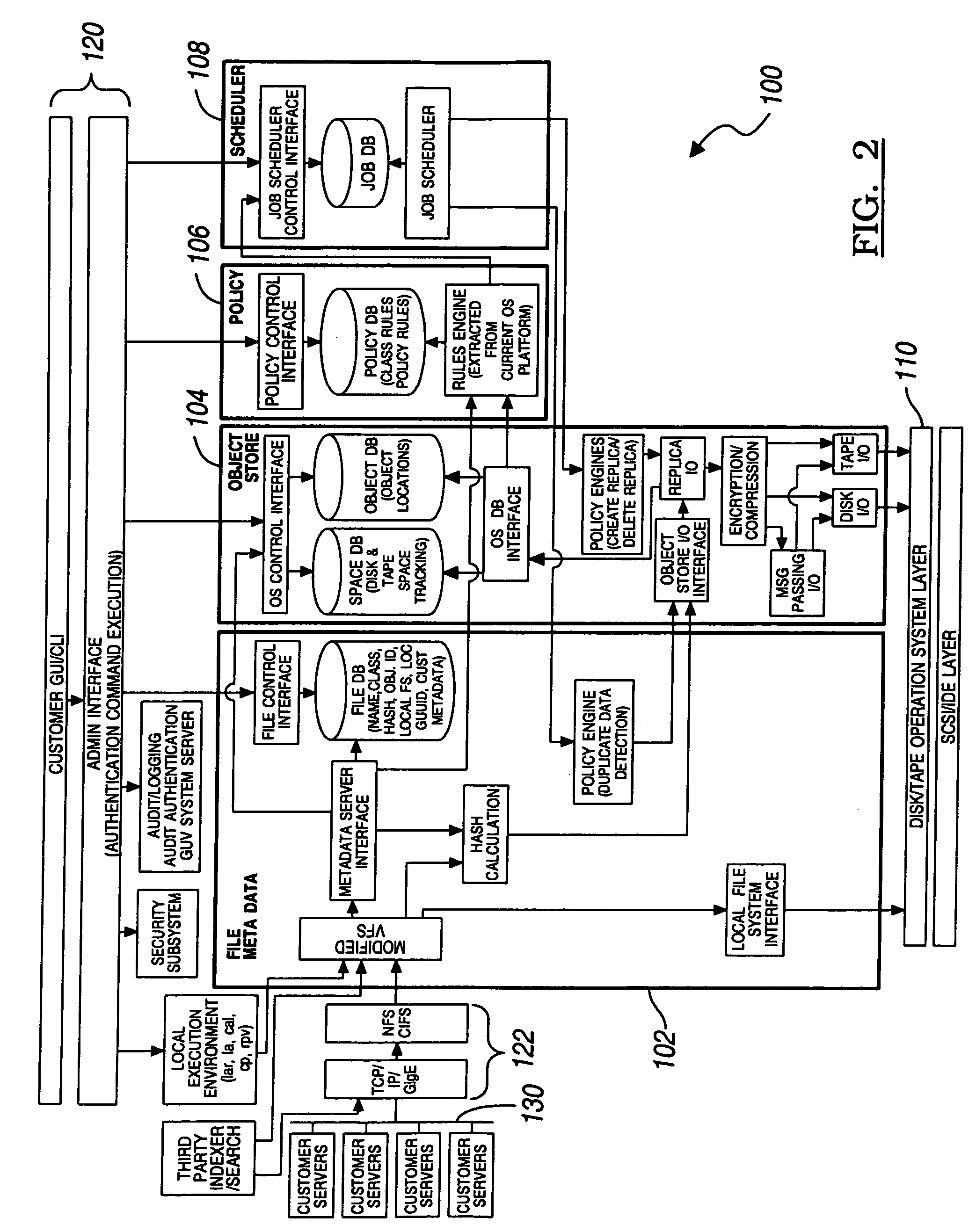
A system for object-based archival data storage includes an object-based storage subsystem having respective data storage devices, at least one file presentation interface that interfaces to client platforms, an administration interface having graphical user interface (GUI) and a command line interface (CLI), a meta data subsystem for storing meta data about files, and includes a virtual file subsystem having a virtual file server (VFS), a policy subsystem, and a scalable interconnect to couple the object-based storage subsystem, the at least one file presentation interface, the administration interface, the meta data subsystem, and the policy subsystem, wherein the policy subsystem provides system rules predetermined by a user for at least one of hash based integrity checking, read-only / write-ability / erase-ability control, and duplicate data treatment corresponding to files and file objects.
Owner:STORAGE TECHNOLOGY CORPORATION
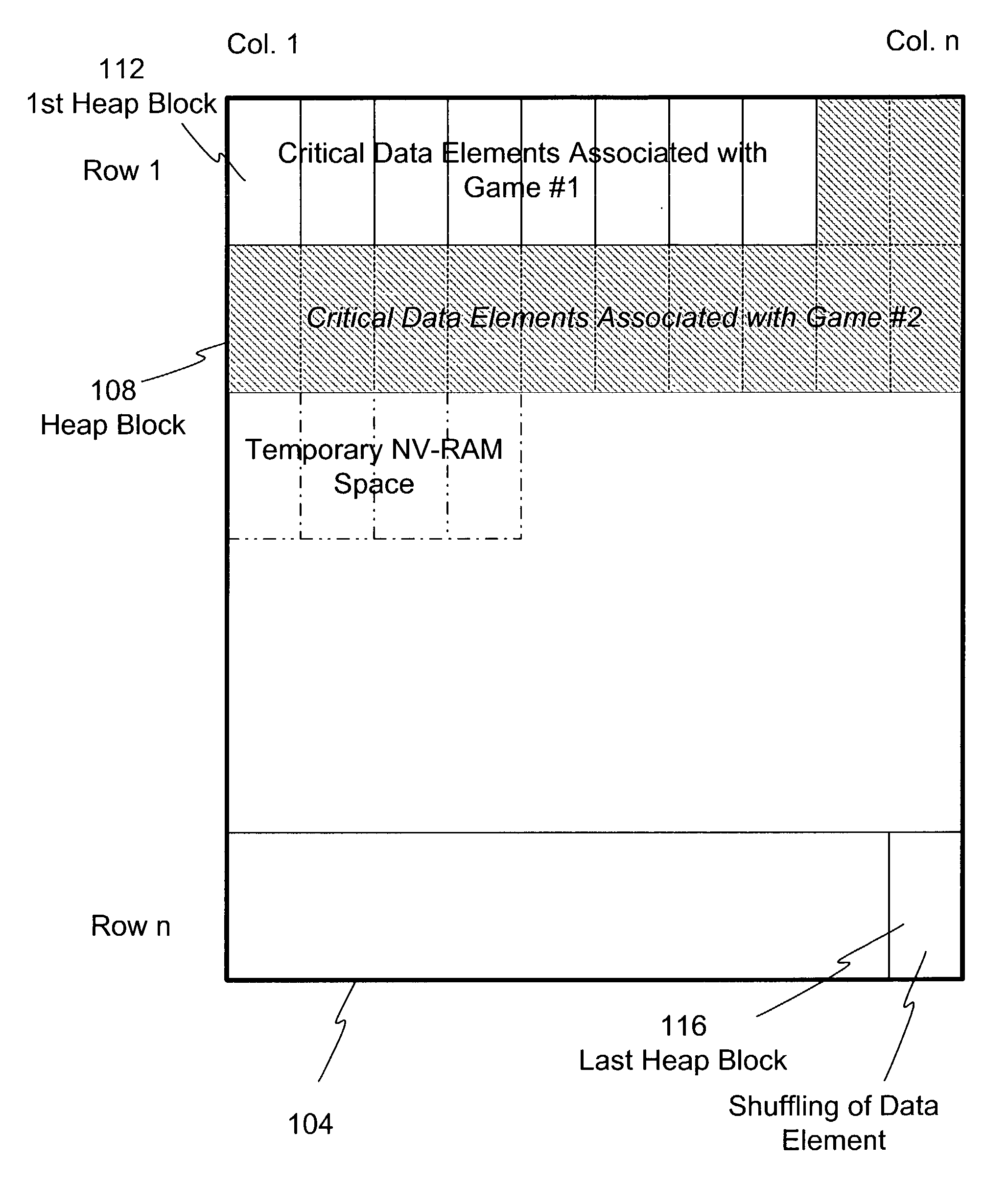
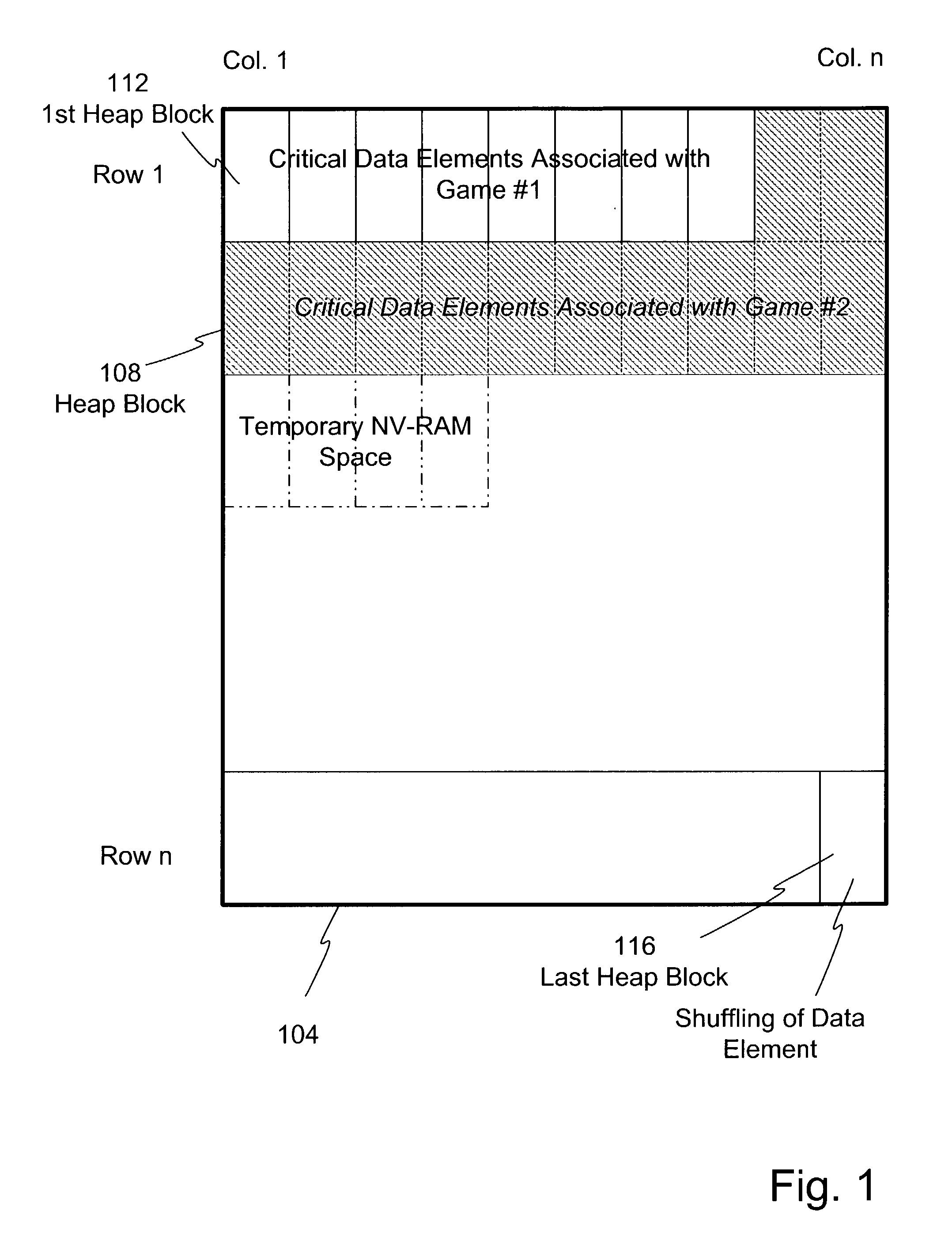
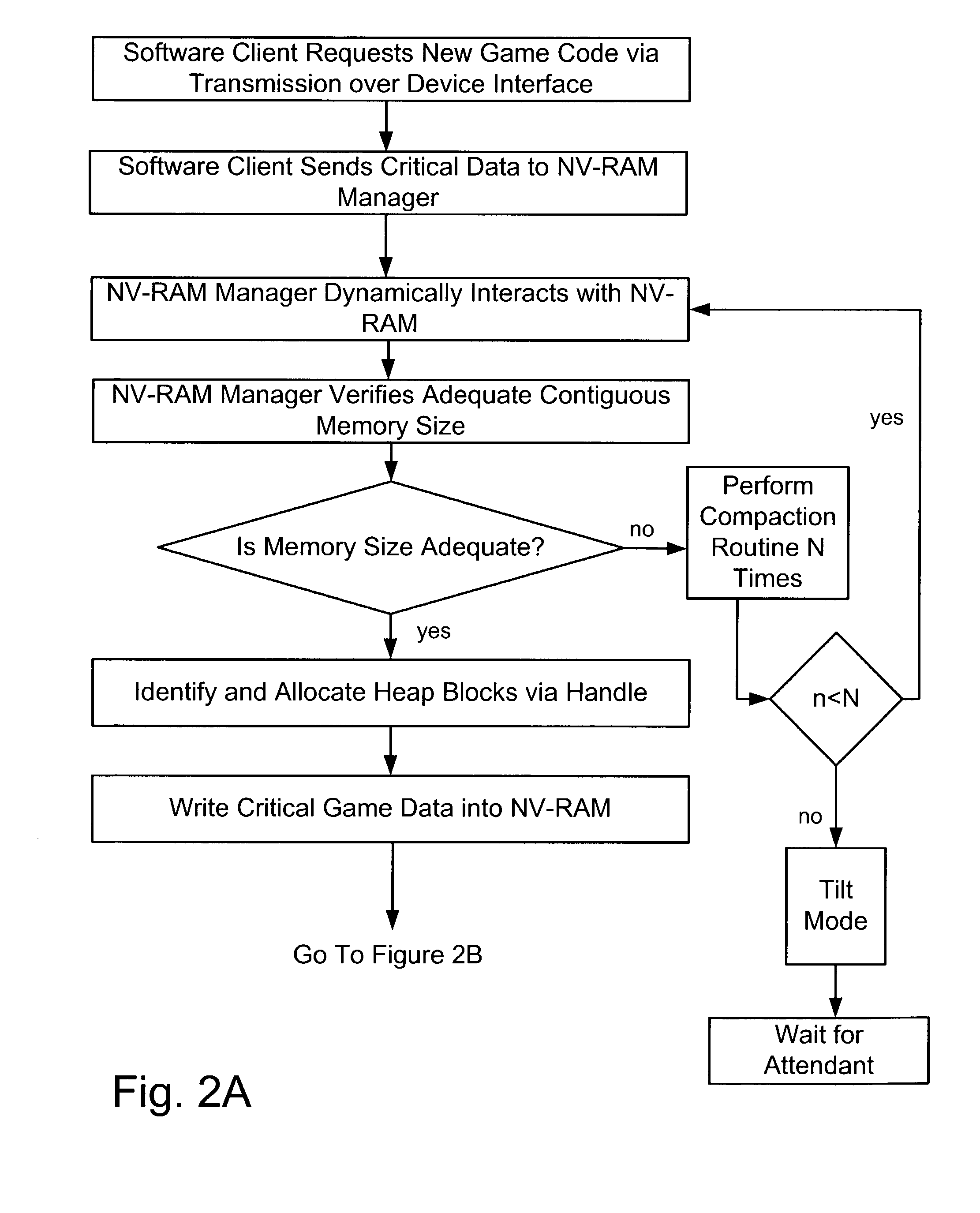
Dynamic NV-RAM
InactiveUS7111141B2Maximize useMemory architecture accessing/allocationMemory adressing/allocation/relocationParallel computingDynamic storage
A method and apparatus of dynamically storing critical data of a gaming machine by allocating and deallocating memory space in a gaming machine is disclosed. One or more embodiments describe downloading or removing a new game to a gaming machine such that all existing critical data in NV-RAM memory is left intact. In one embodiment, the invention discloses a method and apparatus for dynamically allocating and deallocating memory space to accommodate either permanent or temporary storage in an NV-RAM. A method and apparatus is provided to monitor available memory space and dynamically resize the memory in NV-RAM. In one embodiment, a method is disclosed for performing an integrity check of the NV-RAM and determining whether a critical data error has occurred. In one or more embodiments, methods of compacting and shifting contents of an NV-RAM are described to consolidate available memory space or to prevent unauthorized access of NV-RAM memory.
Owner:IGT
Computer system with backup function and method therefor
ActiveUS20110173378A1Avoid lostIncrease chanceMemory loss protectionMemory adressing/allocation/relocationMass storageDevice failure
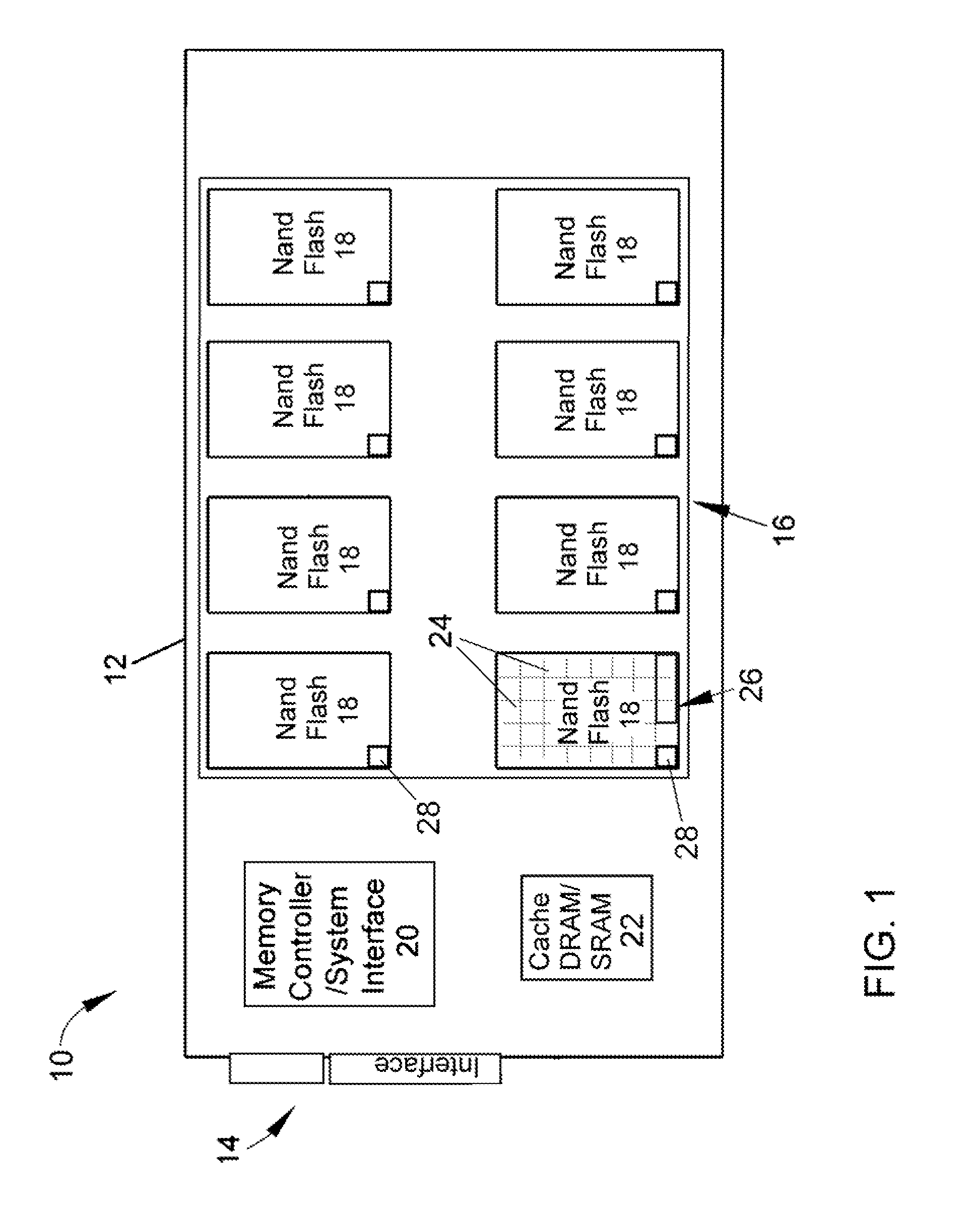
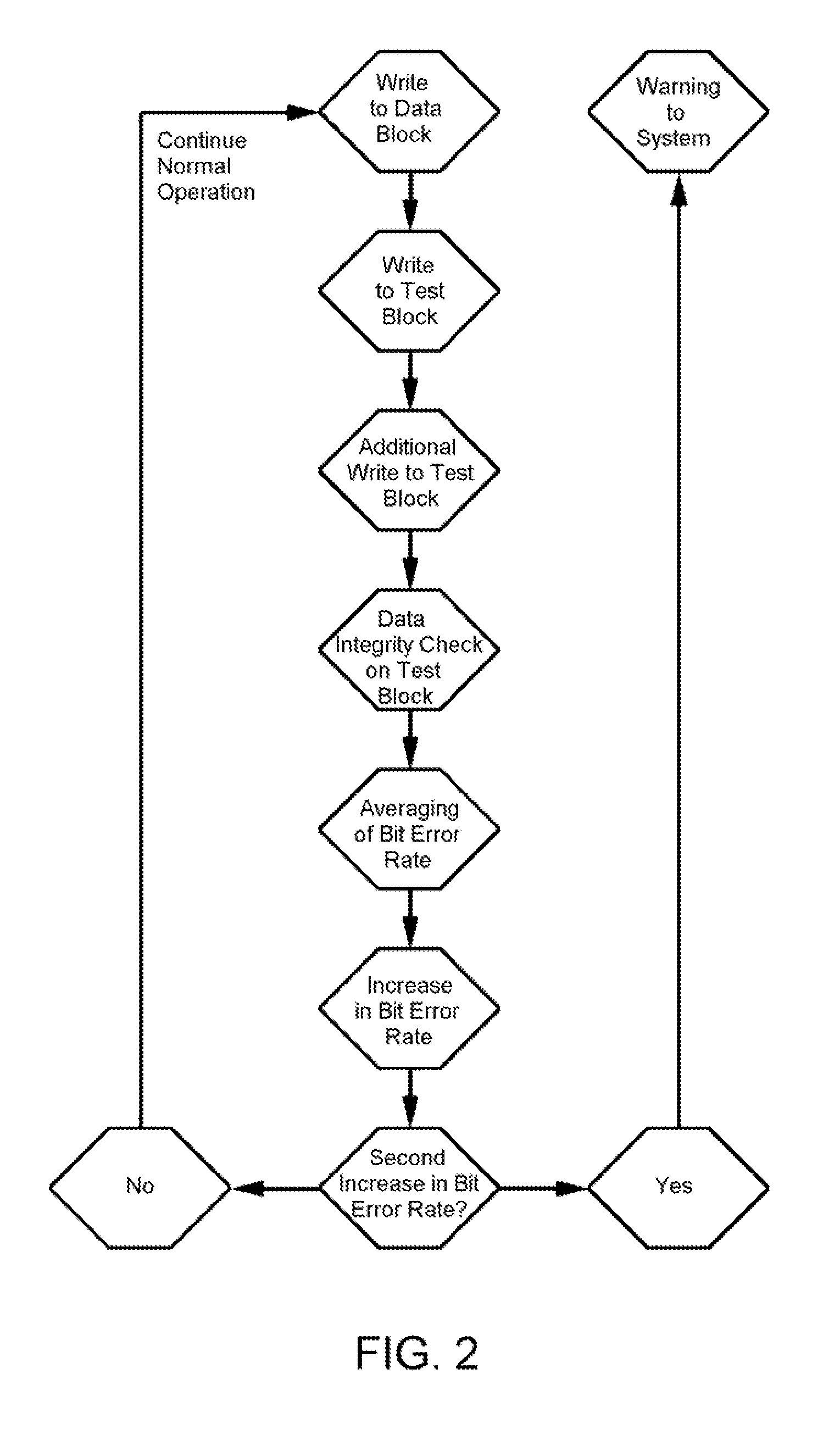
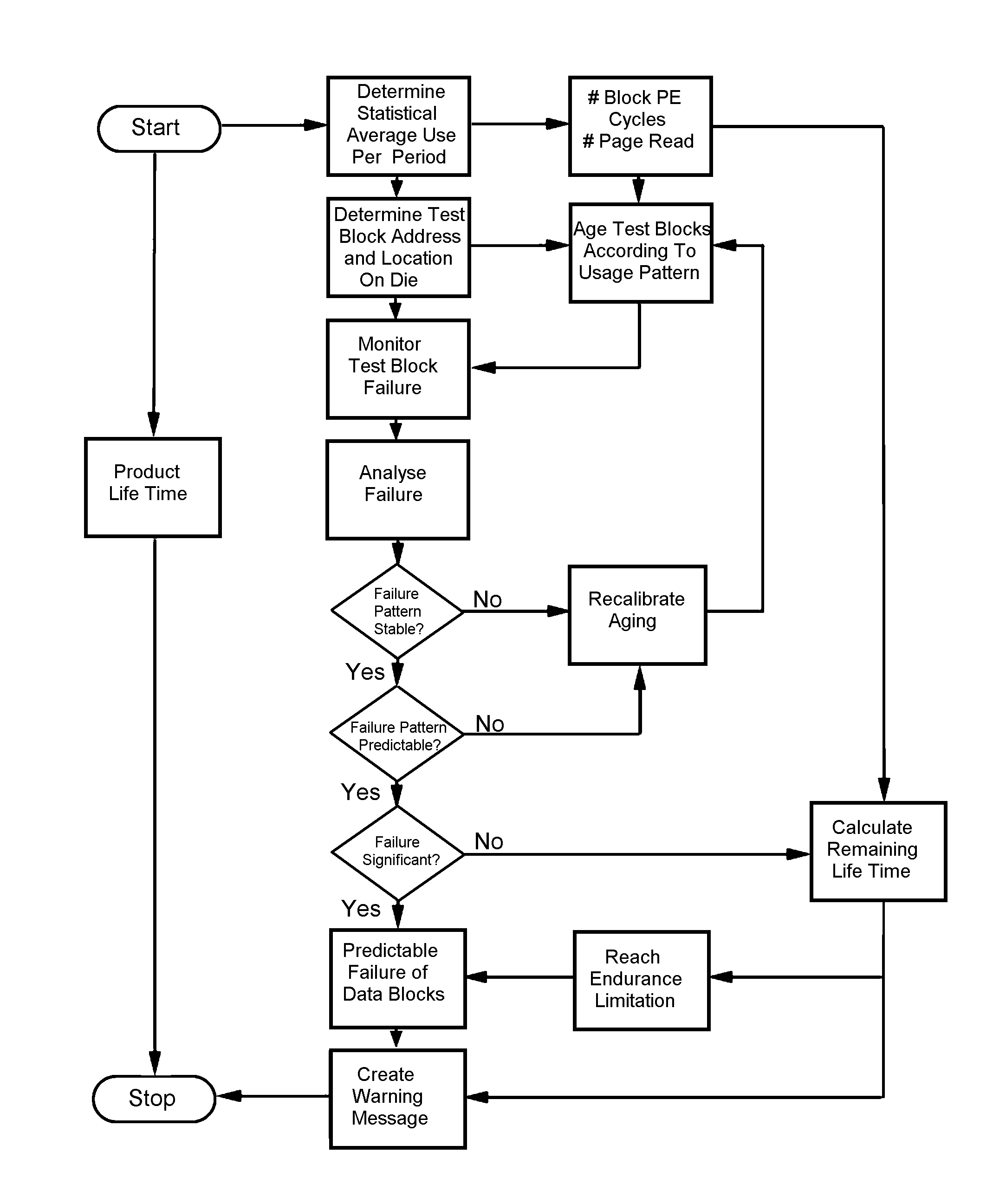
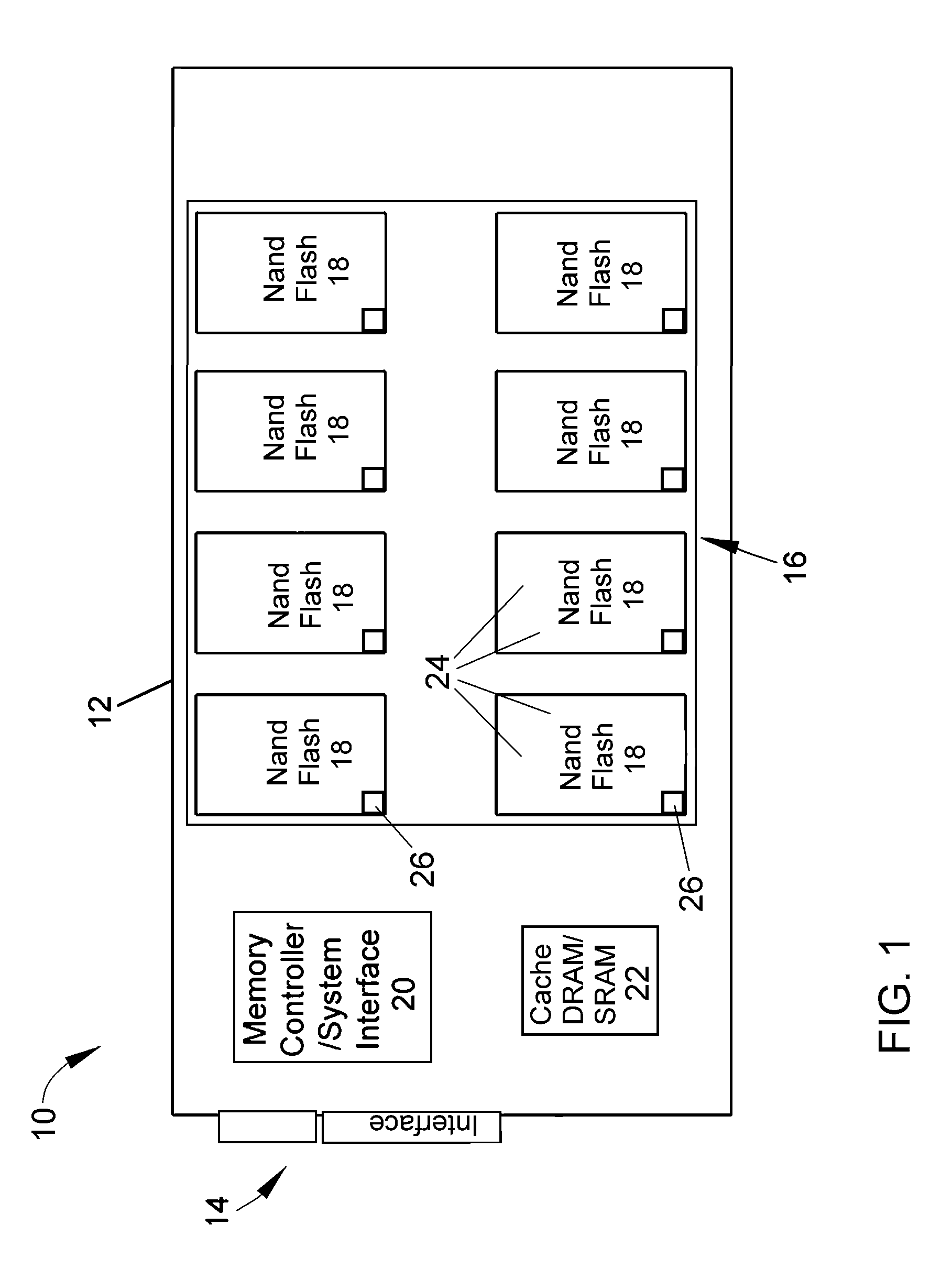
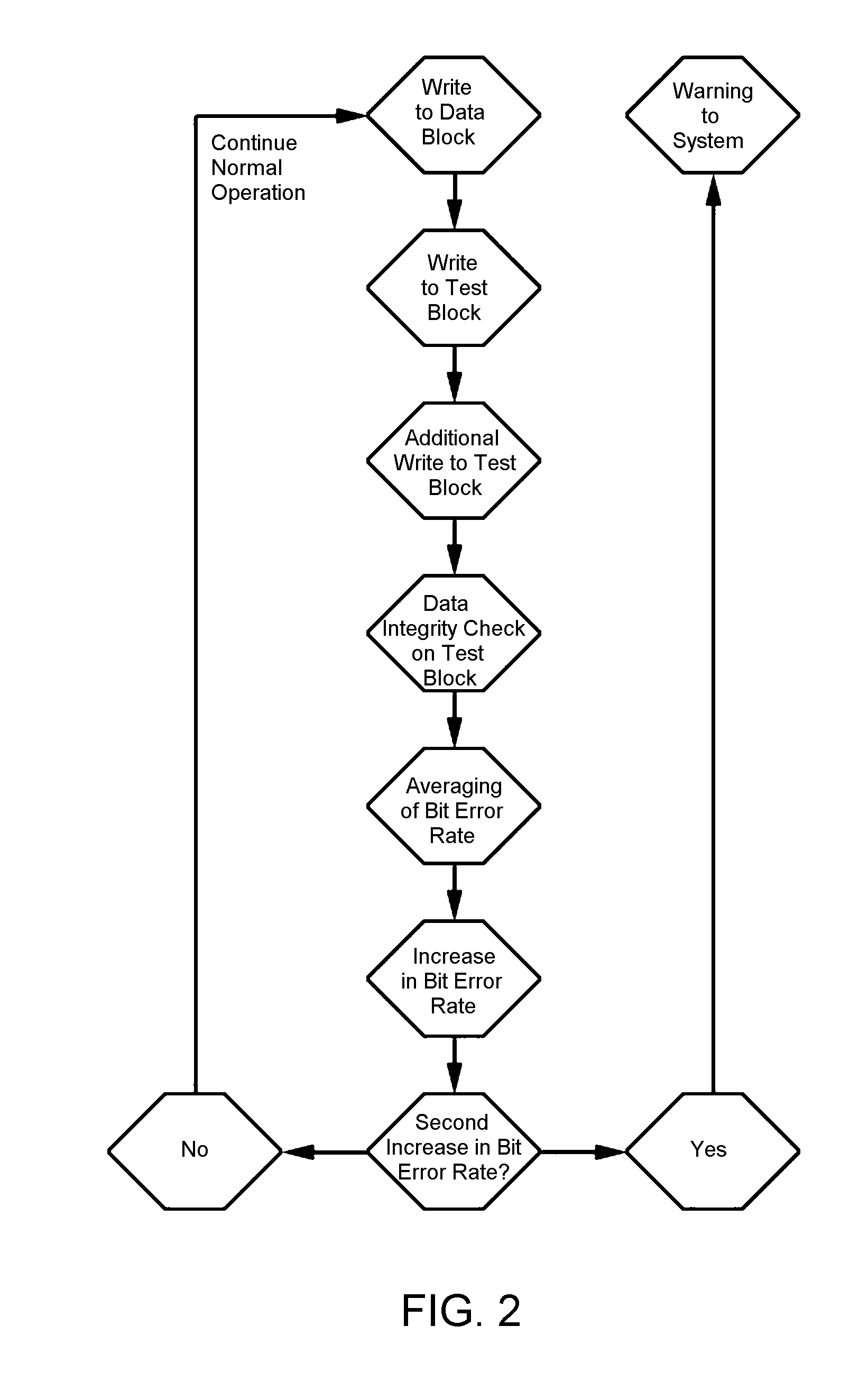
A solid-state mass storage device and method of anticipating a failure of the mass storage device resulting from a memory device of the mass storage device reaching a write endurance limit. A procedure is then initiated to back up data to a second mass storage device prior to failure. The method includes assigning at least a first memory block of the memory device as a wear indicator, using other memory blocks of the memory device as data blocks for data storage, performing program / erase (P / E) cycles and wear leveling on the data blocks, subjecting the wear indicator to more P / E cycles than the data blocks, performing integrity checks and monitoring the bit error rate of the wear indicator, and taking corrective action if the bit error rate increases, including the initiation of the backup procedure and generating a request to replace the device.
Owner:KIOXIA CORP
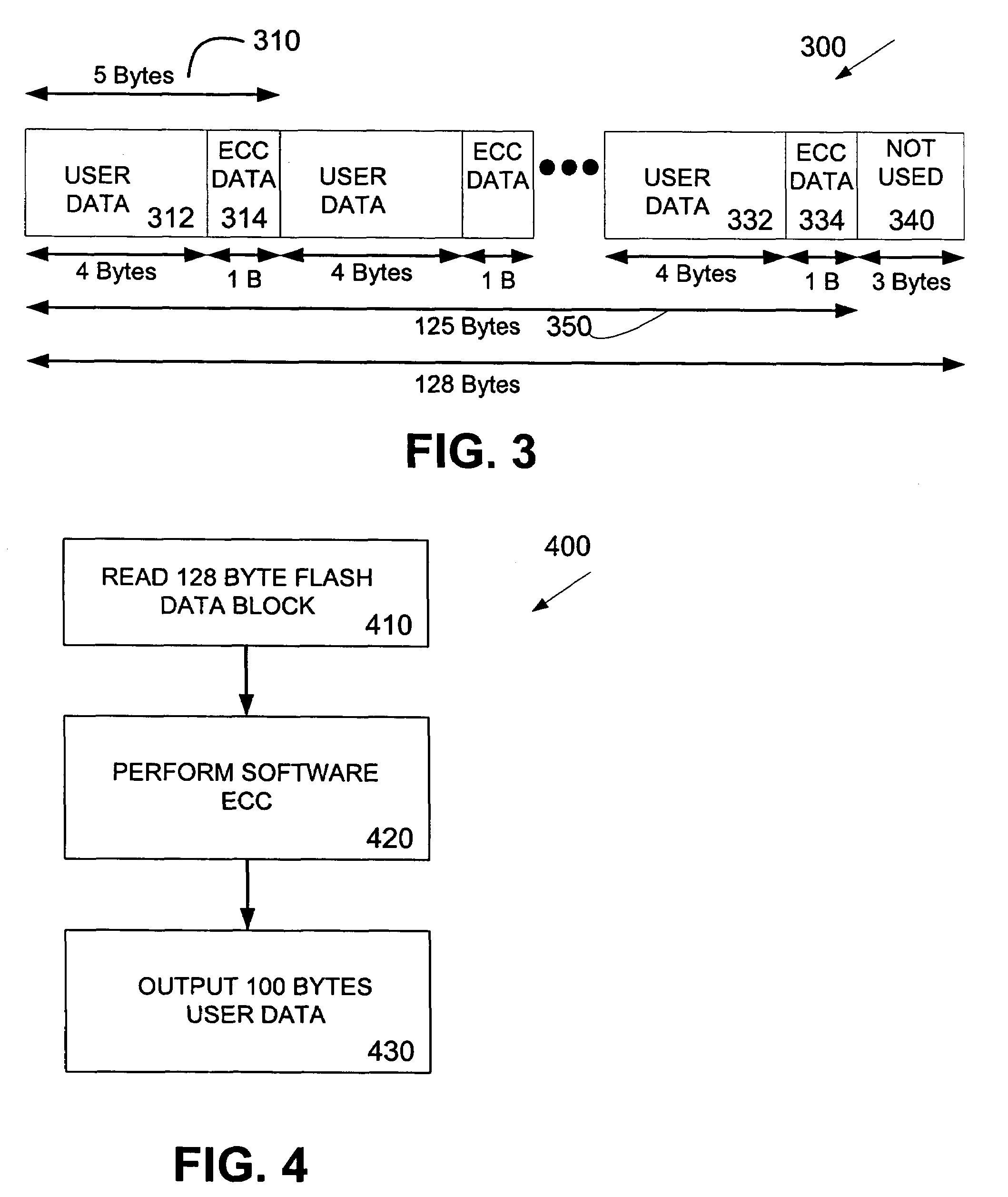
System and method for efficient uncorrectable error detection in flash memory
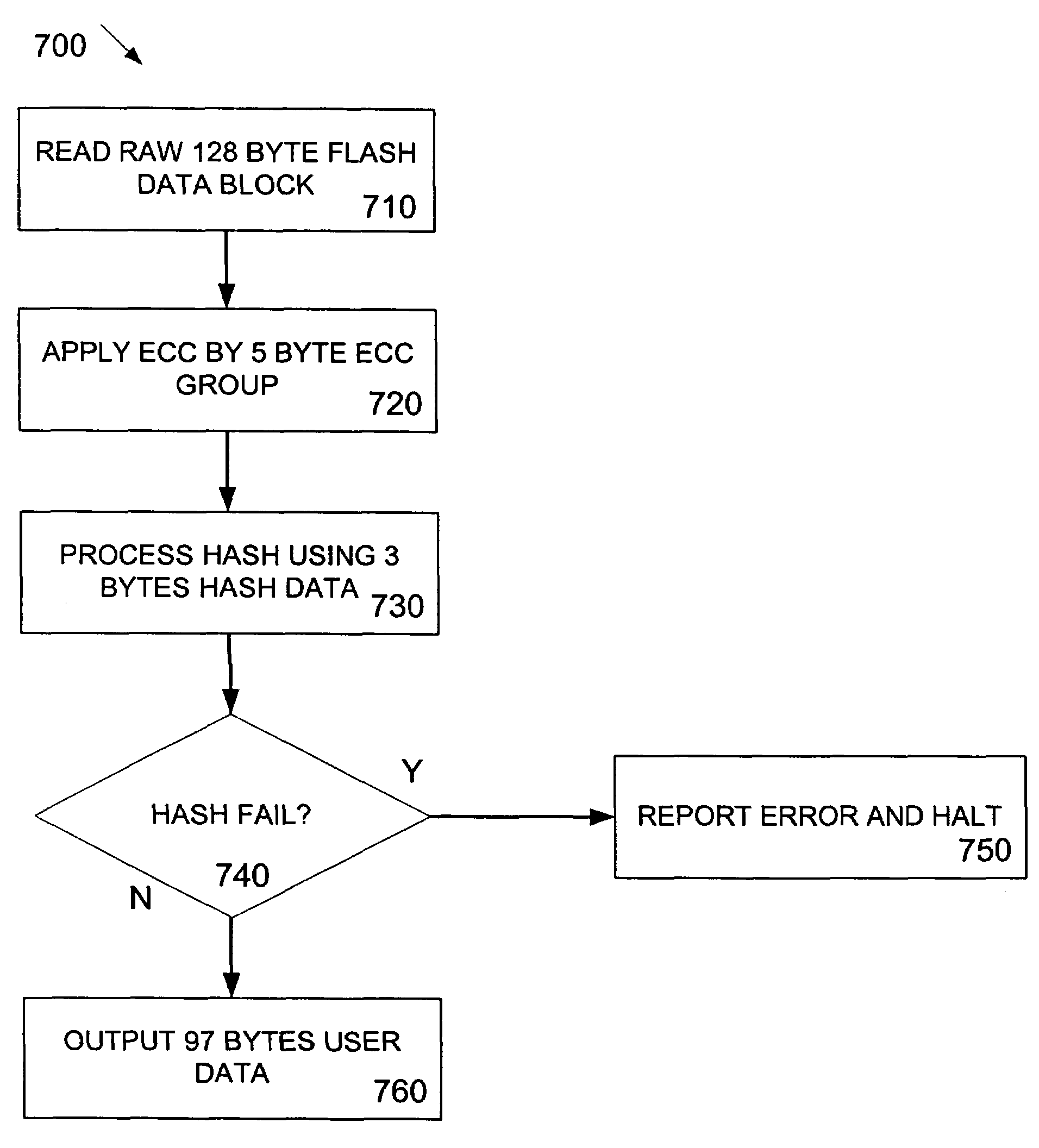
InactiveUS7707481B2Efficient uncorrectable error detectionEfficient and robust detectionError detection/correctionCode conversionMicrocontrollerHash function
A system and method for efficient uncorrectable error detection in flash memory is described. A microcontroller including a non-volatile flash memory utilizes an Error Correction Code (ECC) having a certain error detection and correction bit strength. The user data is first processed by a hash function and hash data is stored with the user data. Then, the user data and hash data are processed by the ECC system. In detection, the hash ensures that a relatively low bit-strength ECC system did not incorrectly manipulate the user data. Such a hash integrity check provides an efficient, robust detection of incorrectly corrected user data resulting from errors beyond the correction but strength of the ECC system utilized.
Owner:PITNEY BOWES INC
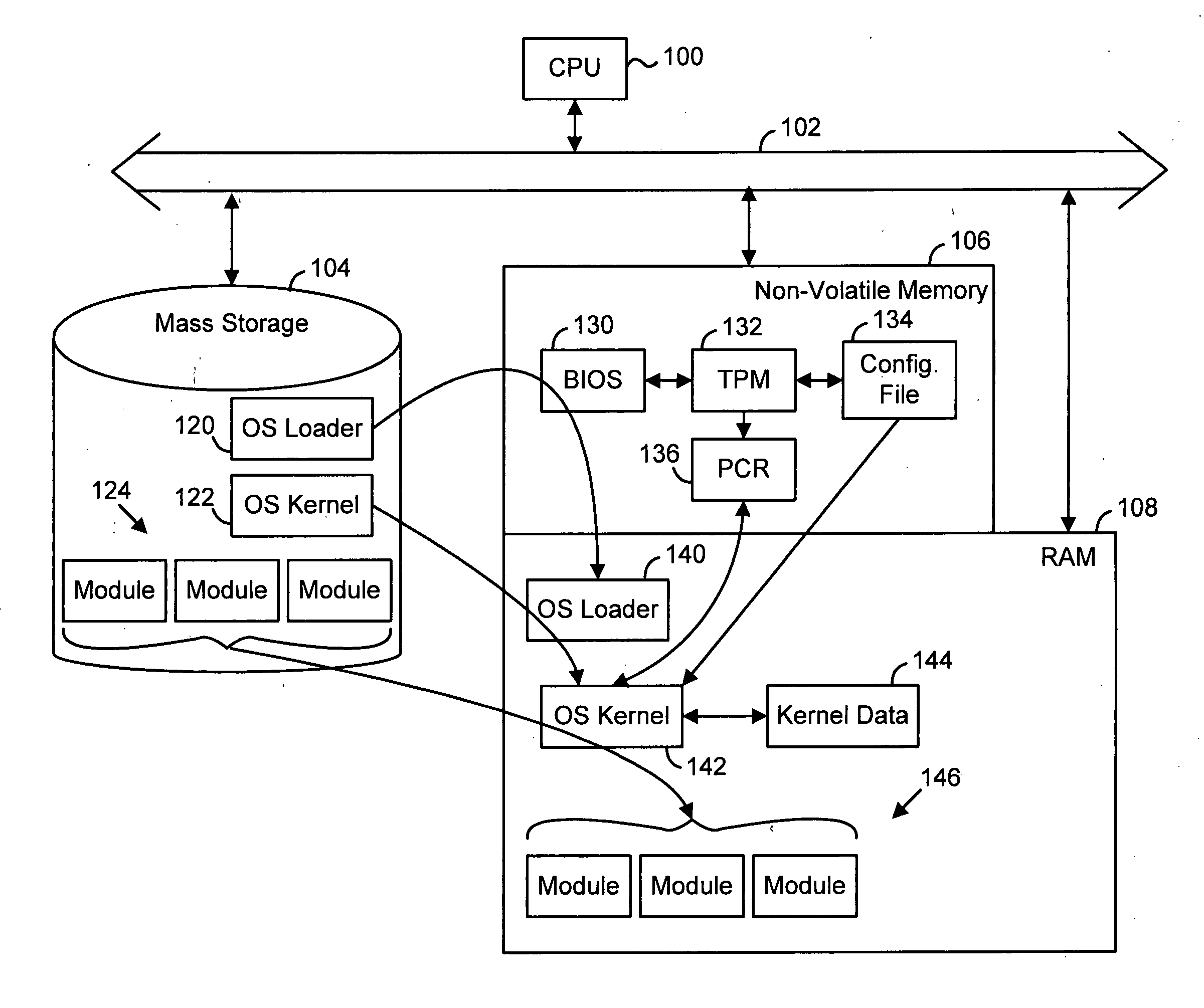
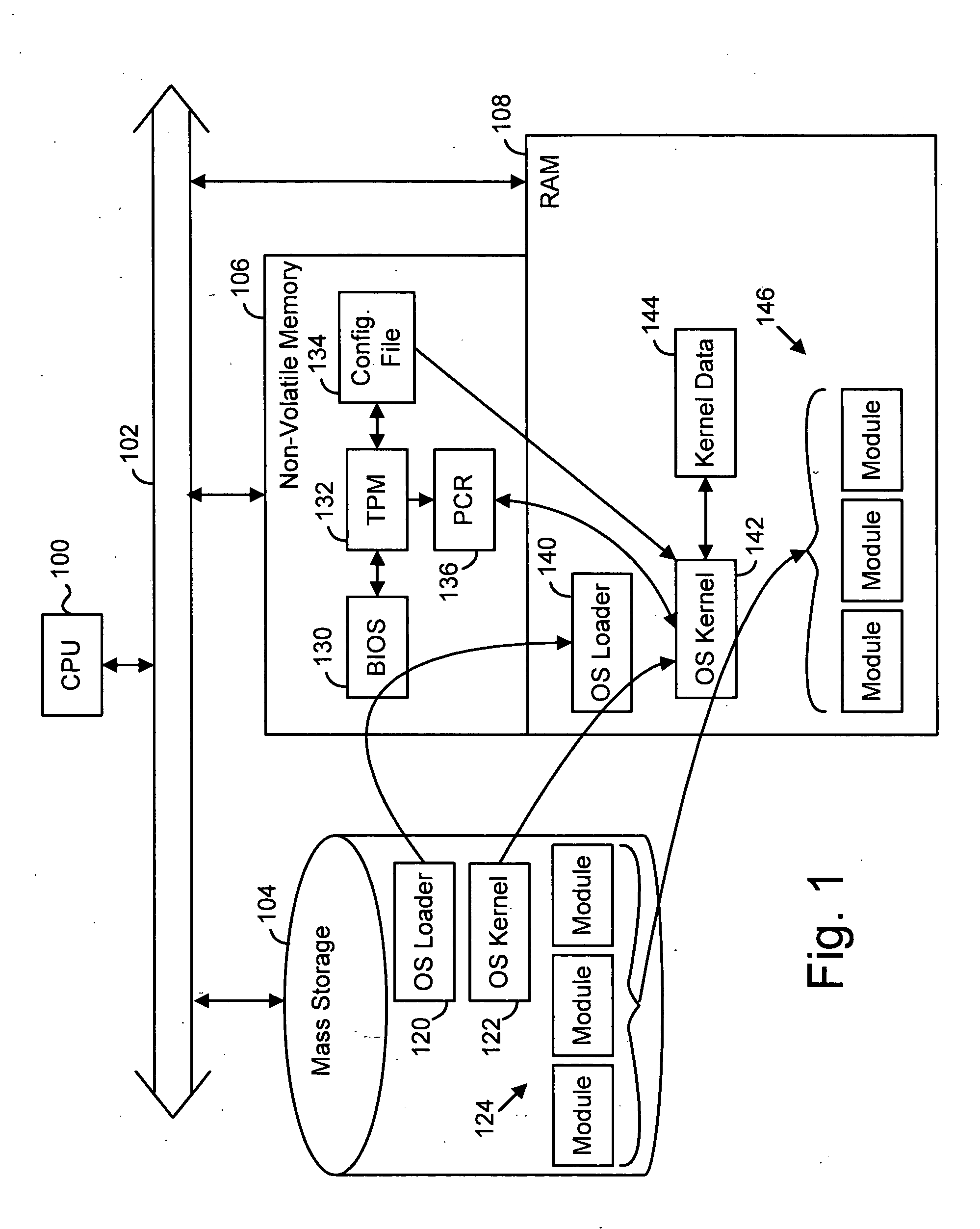
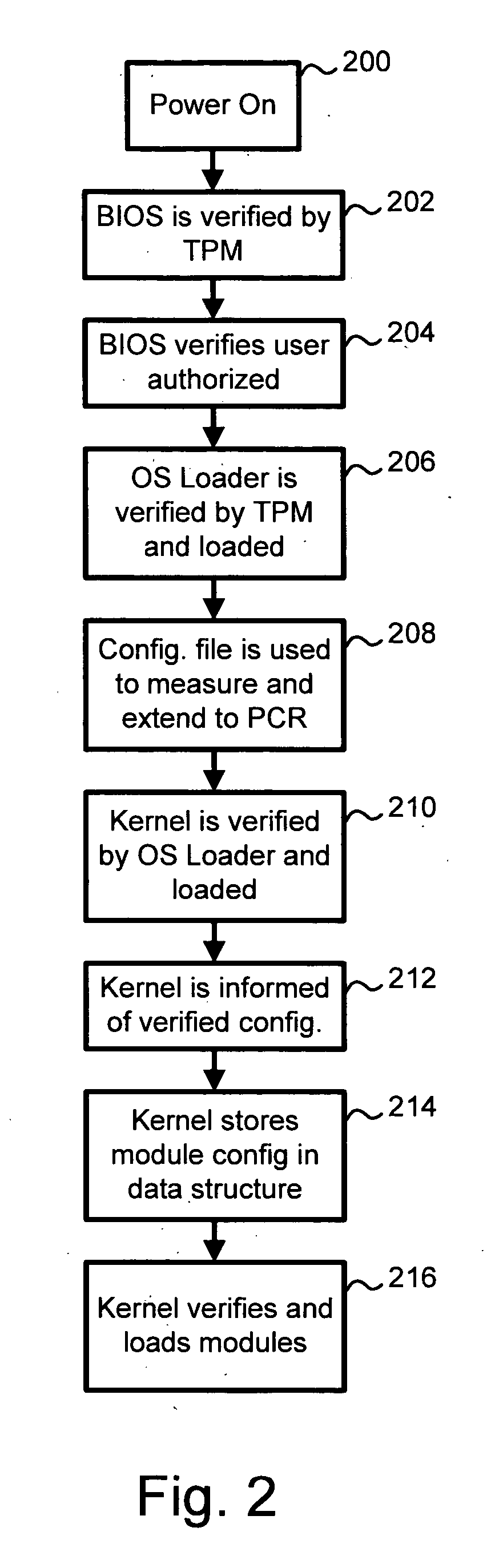
Establishing a trusted platform in a digital processing system
InactiveUS20060015717A1User identity/authority verificationUnauthorized memory use protectionDigital signal processingOperational system
A trusted platform in a digital processing system is maintained even when modules, or other processes or data, are loaded after a boot sequence. A configuration file is used to include measurements (e.g., hash values, signatures, etc.) of modules to be loaded. After secure boot-up the operating system kernel uses the configuration file to check module integrity prior to loading and executing. If a module does not verify against the configuration file data then the system can prevent further operation, restrict certain operations, indicate the non-trusted nature of the system or take other actions. In one embodiment, if a module does not pass the integrity check then the failed measurement is extended into a specific Platform Configuration Register (PCR) within a Trusted Platform Manager (TPM) process. Subsequently, client applications can determine if the platform is trustable based on the return of the PCR value. A local application (application running in the same platform) can “seal” secrets to a trusted platform. The operation of the application relies on the secrets, which can only be revealed in a trusted platform.
Owner:SONY ELECTRONICS INC +1
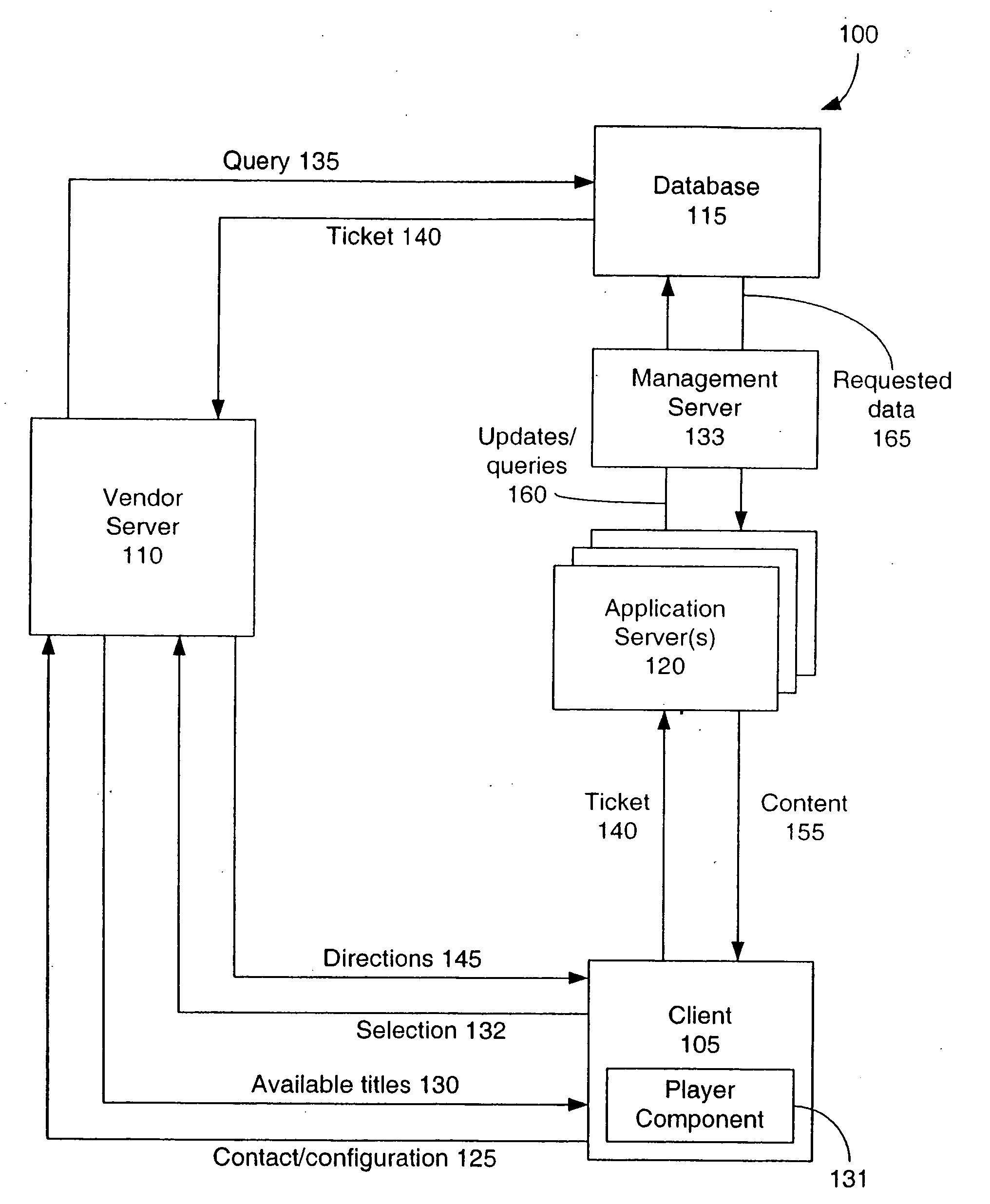
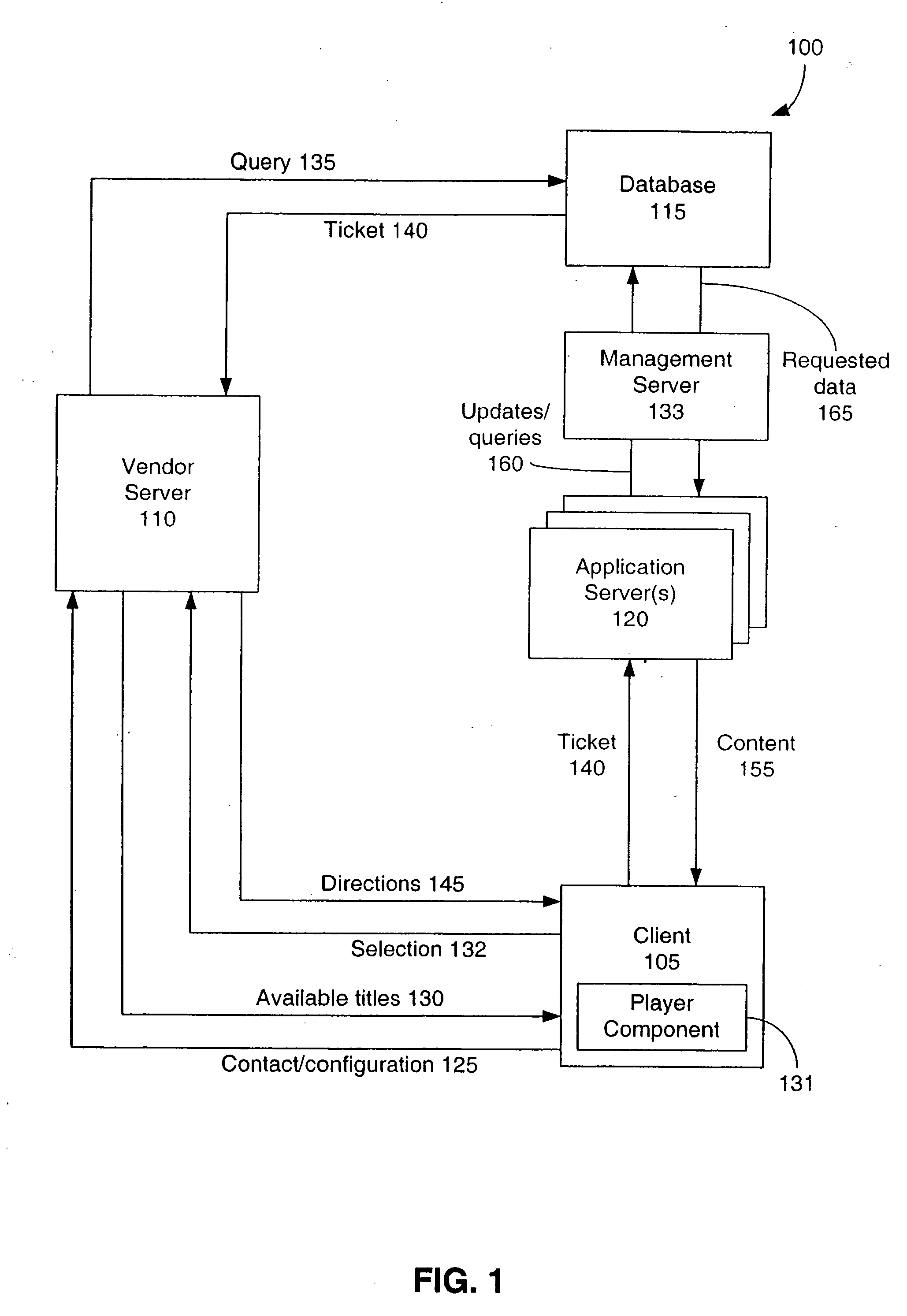
Secure digital content licensing system and method
InactiveUS7155415B2Office automationProgram/content distribution protectionWeb siteTelecommunications link
Owner:BLOCKBUSTER LLC
Online Protection Of Information And Resources
InactiveUS20110321139A1Avoid interceptionAvoid manipulationDigital data processing detailsMultiple digital computer combinationsThird partyApplication software
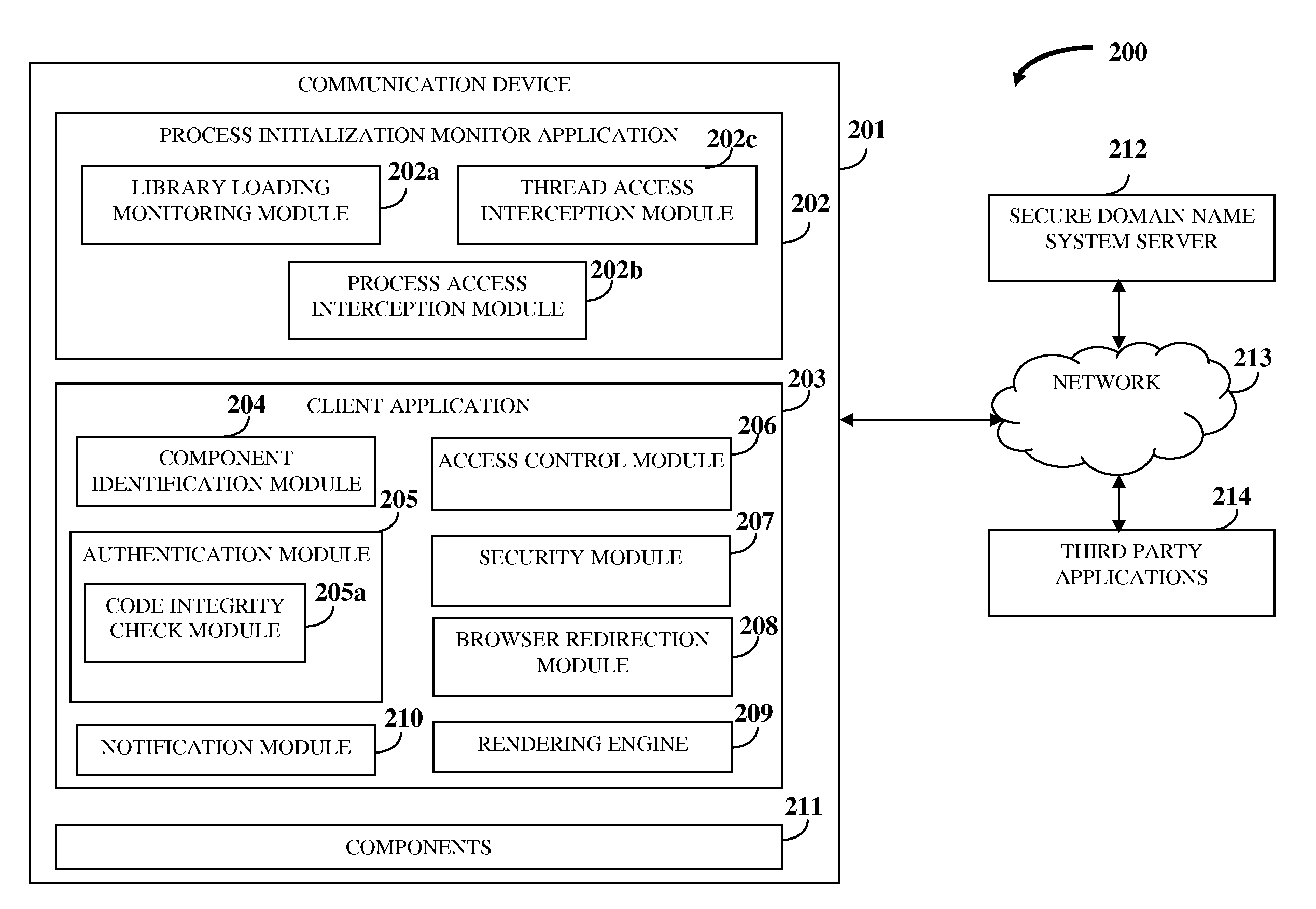
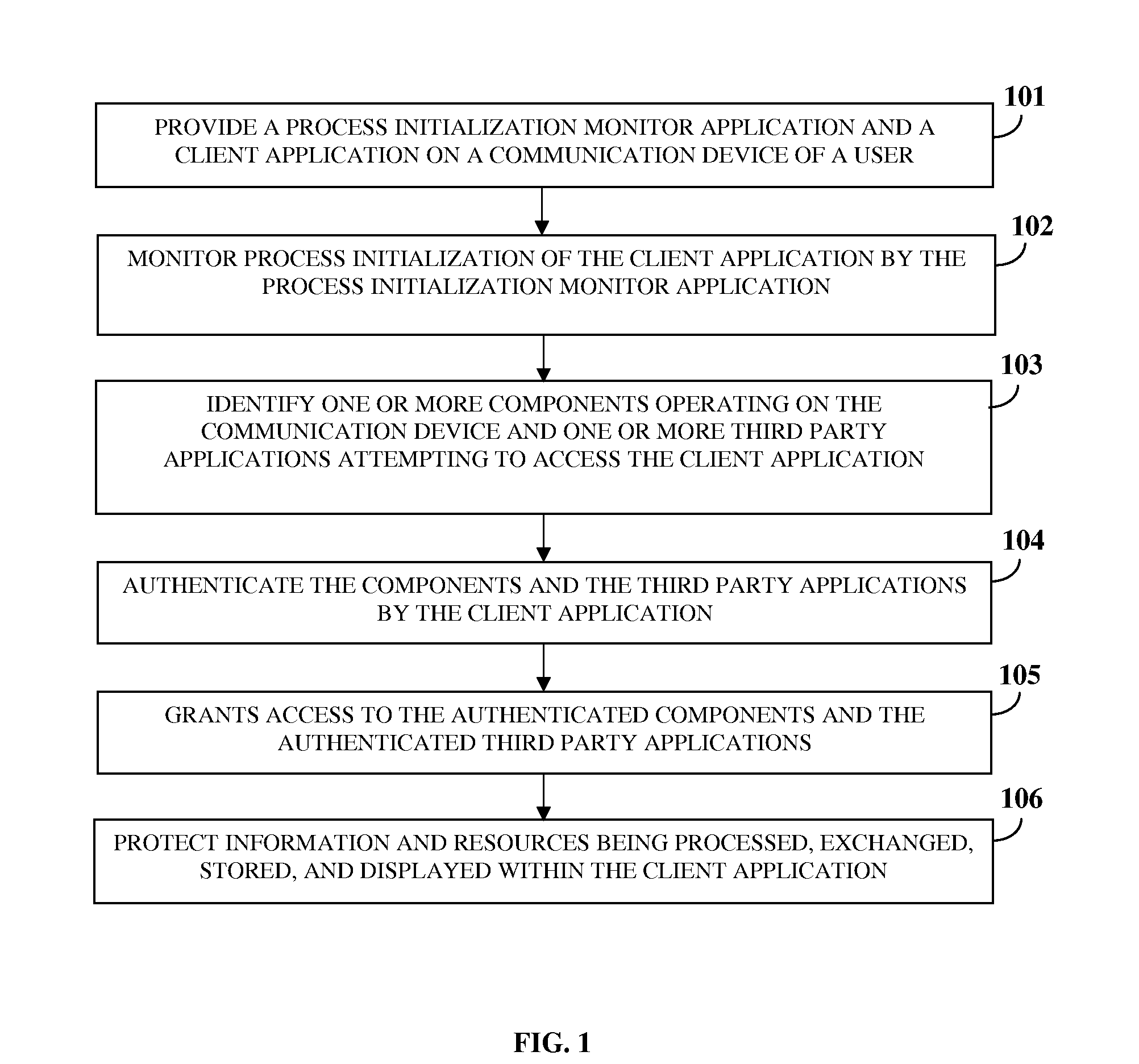
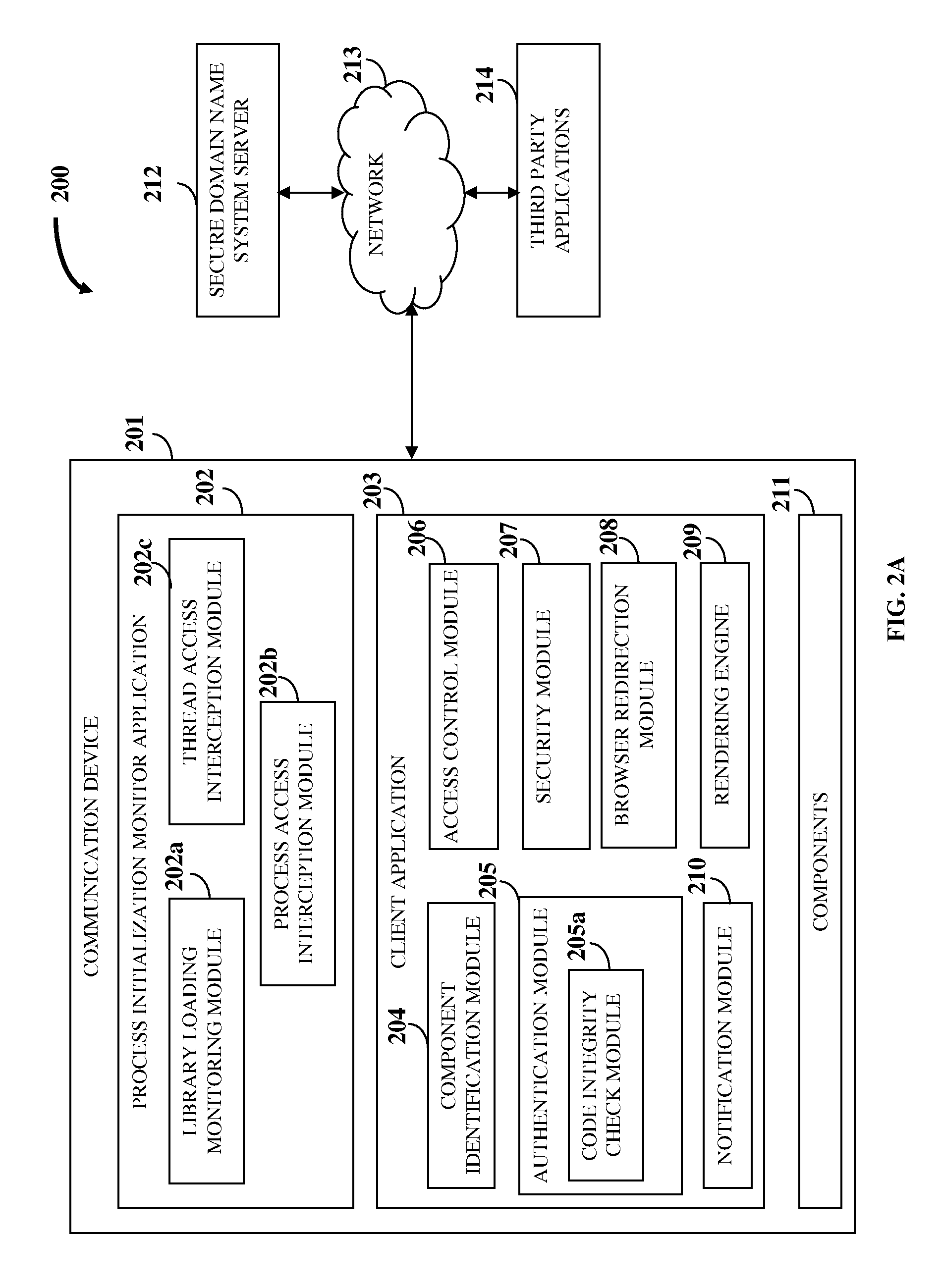
A computer implemented method and system for protecting information and resources in an online environment is provided. A process initialization monitor application monitors process initialization of a client application provided on a user's communication device. The client application identifies and authenticates one or more components operating on the communication device and one or more third party applications attempting to access the client application. The client application performs the authentication by performing a code integrity check integrated in the client application independent of the communication device, and grants access to the authenticated components and the authenticated third party applications. The client application protects information being processed, exchanged, stored, and displayed within the client application. The client application masks input information, encrypts a communication channel that transfers the input information, blocks attempts to monitor, intercept and manipulate information by unauthorized entities, and prevents access of certificates, resources, etc., by unauthorized entities.
Owner:K7 COMPUTING PRIVATE
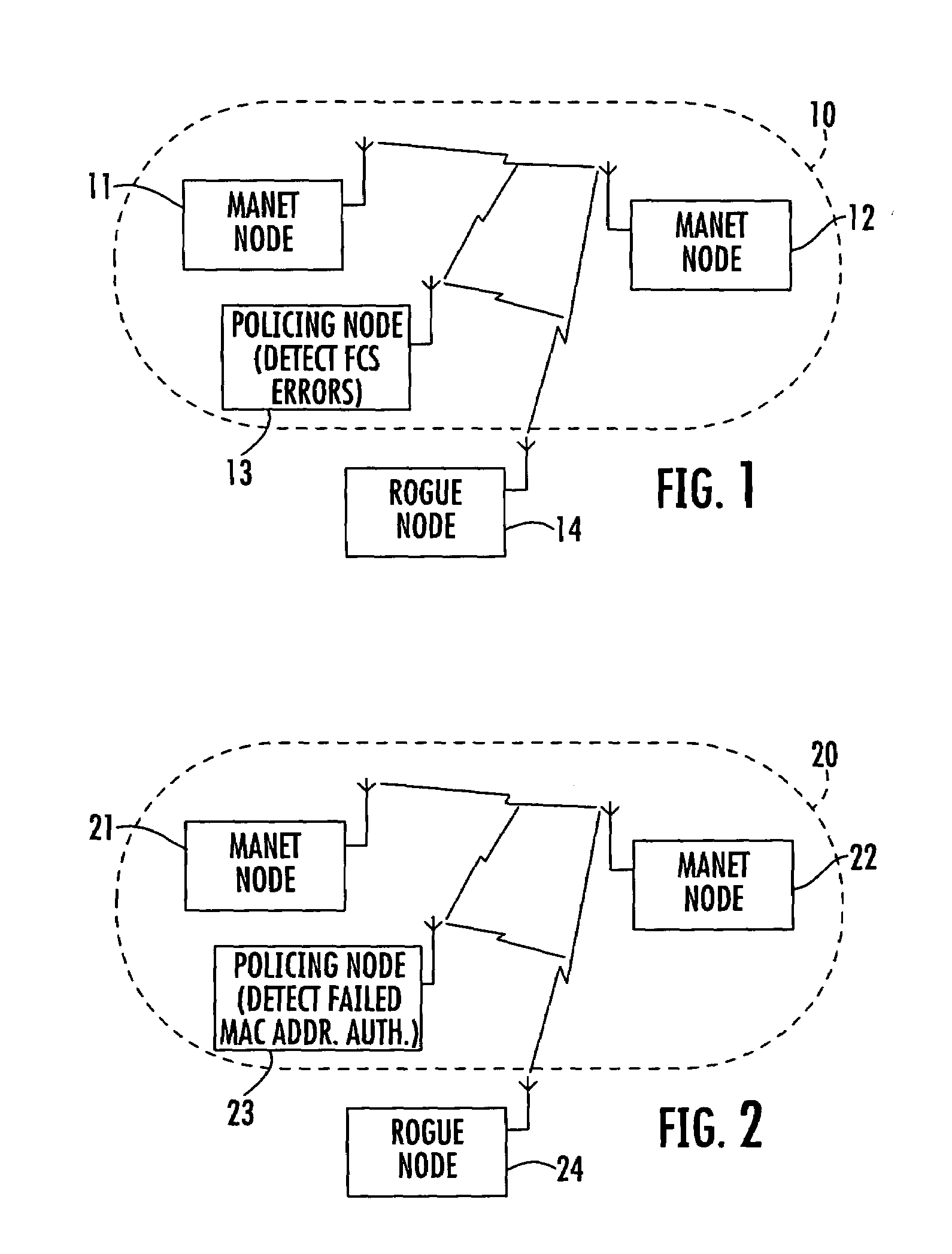
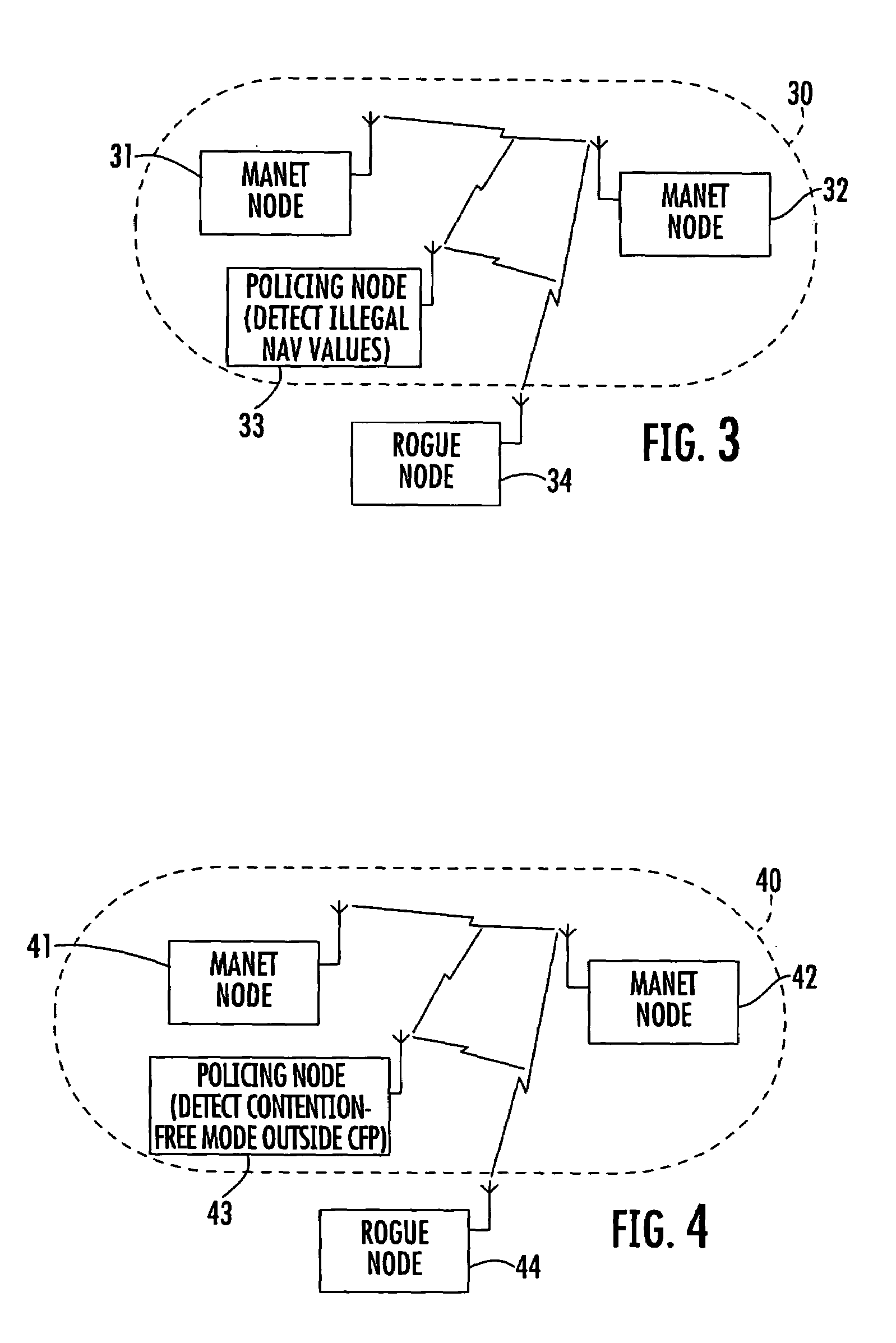
Mobile ad-hoc network with intrusion detection features and related methods
Owner:STINGRAY IP SOLUTIONS LLC
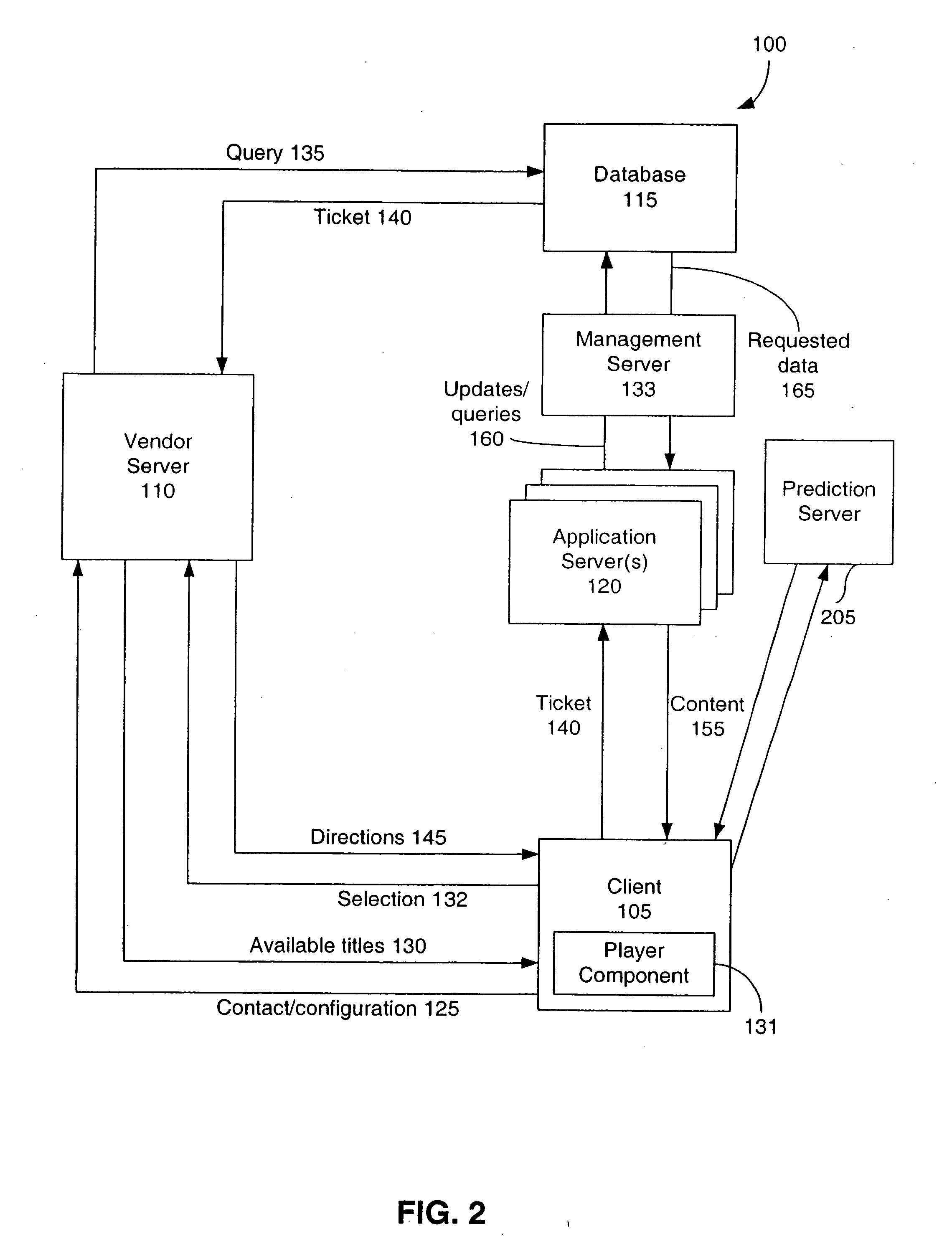
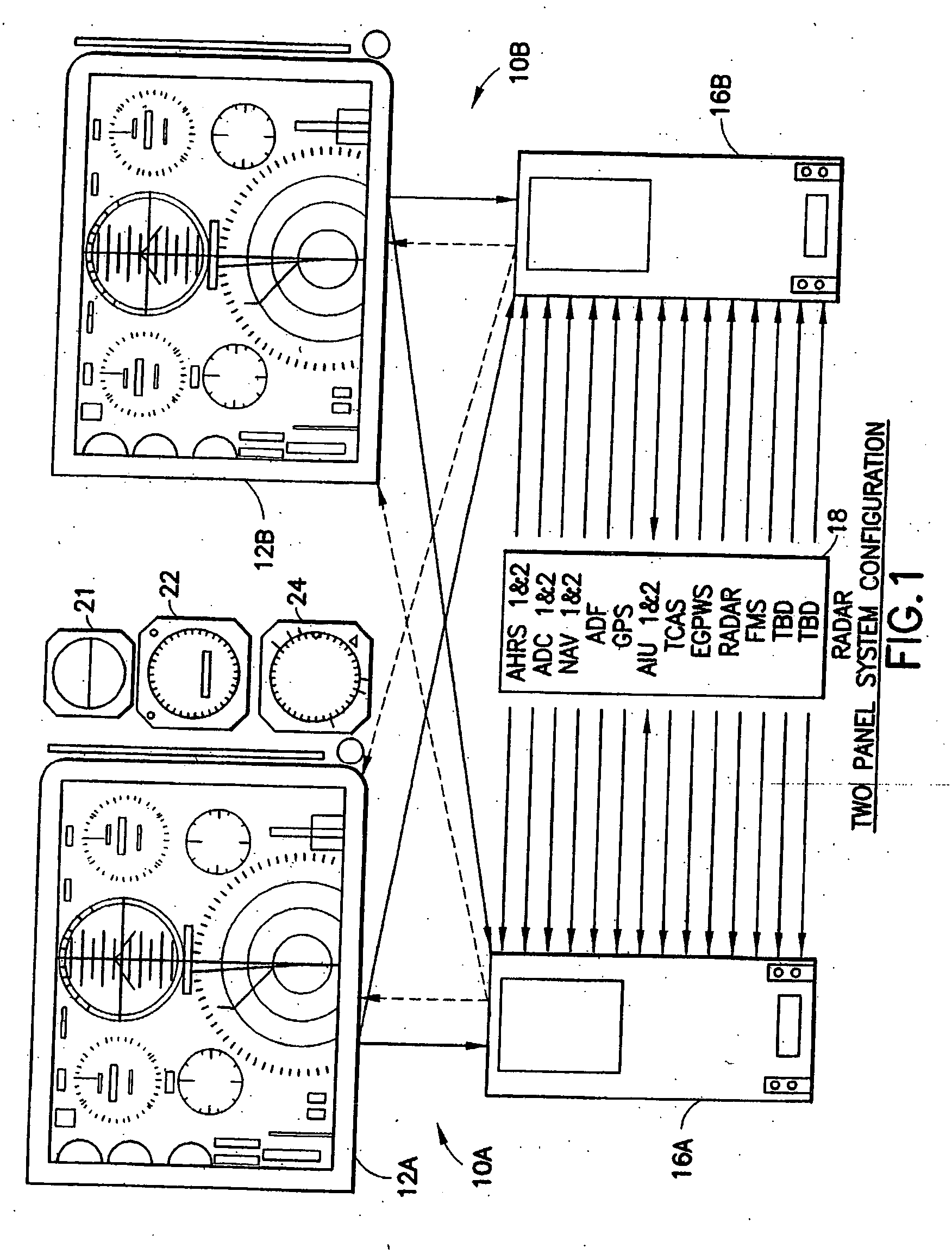
Aircraft flat panel display system with improved information availability
ActiveUS20070046680A1Low fidelitySimplified representationData processing applicationsAircraft displaysData availabilityFlat panel display
Owner:INNOVATIVE SOLUTIONS & SUPPORT
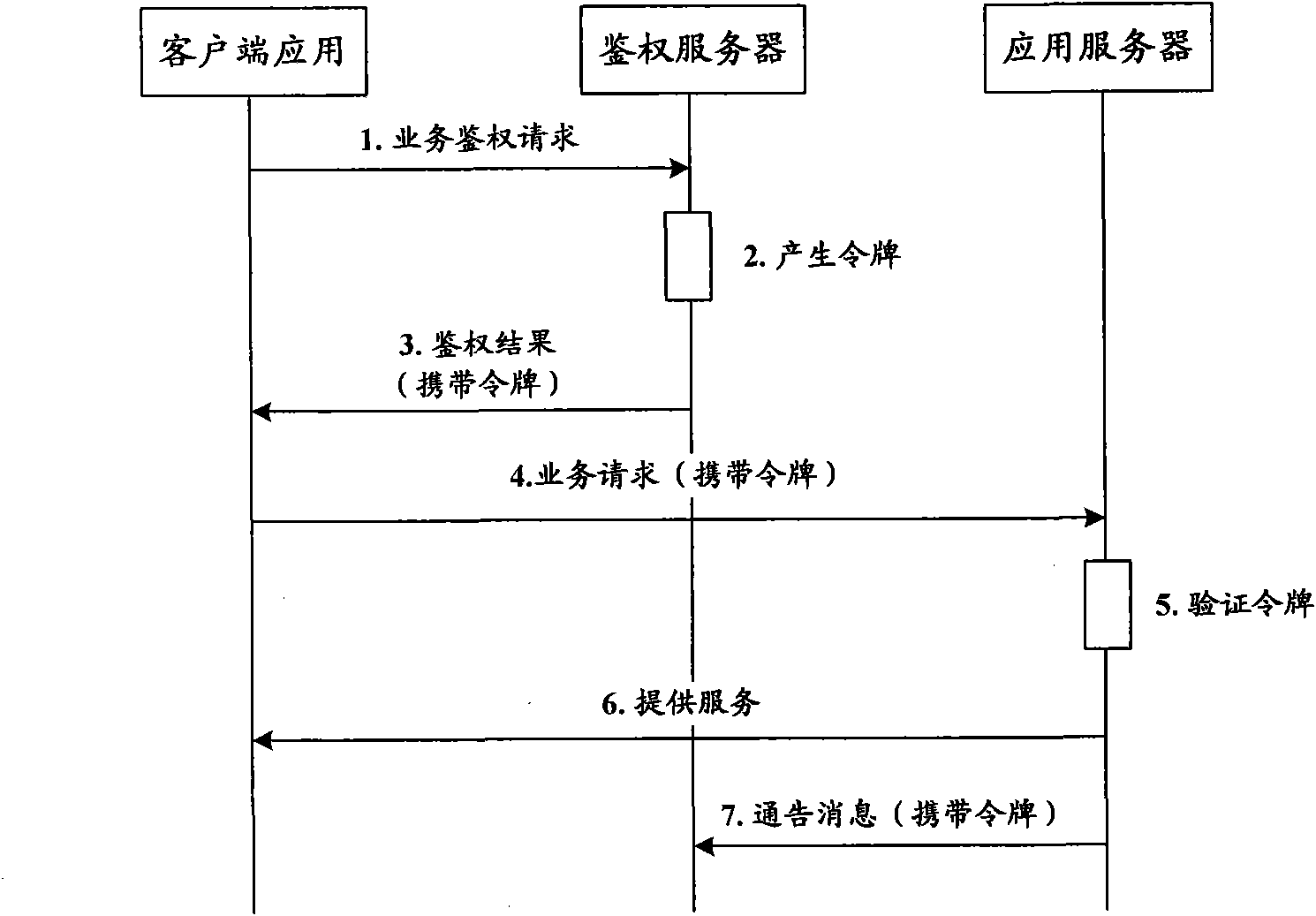
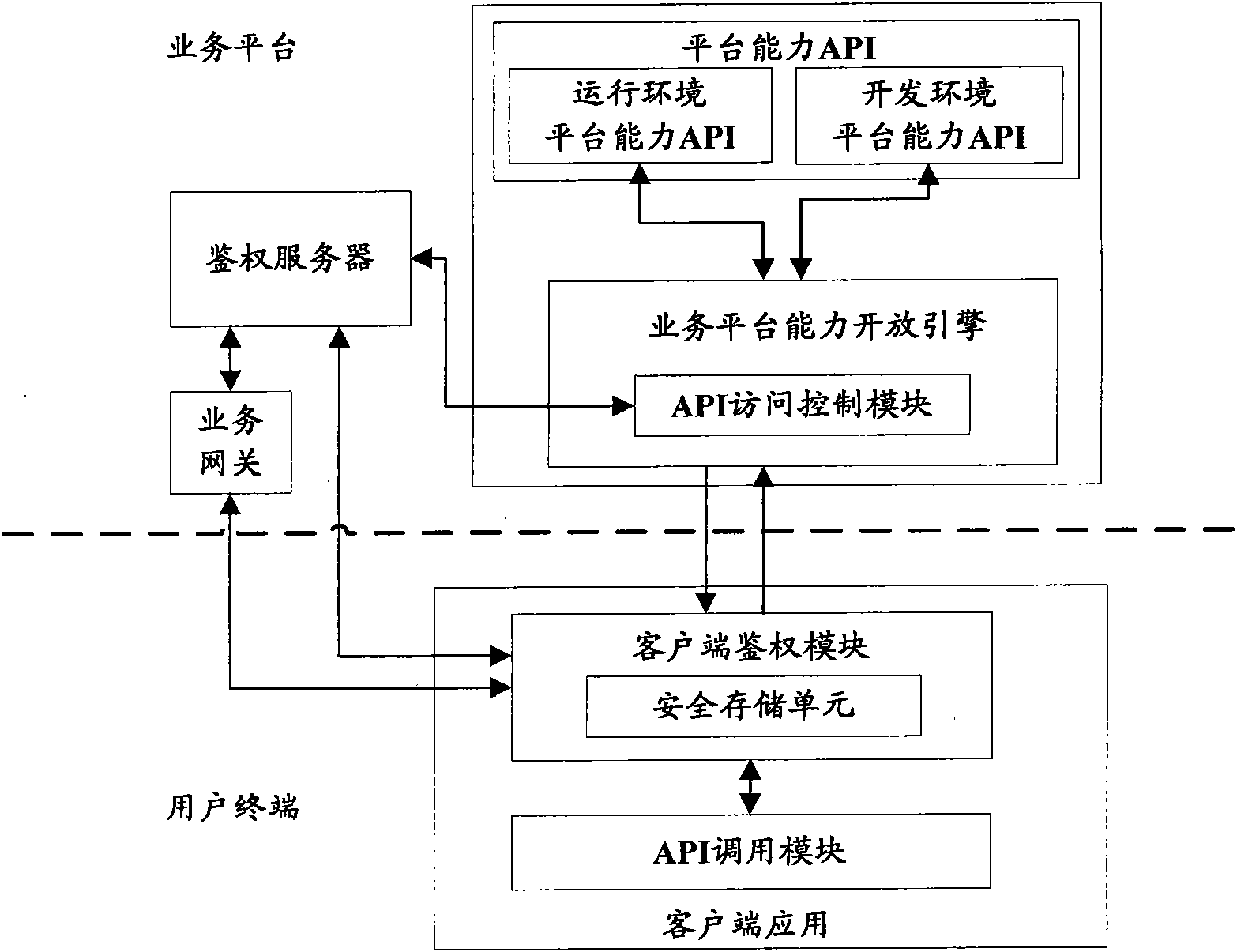
Method, device and system of authentication and service calling
ActiveCN102378170ARealization of legality authentication and authenticationAddressing Security VulnerabilitiesTransmissionSecurity arrangementApplication programming interfaceAuthentication server
The invention discloses a method, device and system of authentication and service calling, used for realizing legality authentication of an authentication server in a service platform to a client side application and promoting the safety reliability of a calling mechanism of a platform capacity API (Application Programming Interface). The authentication server realizes the safe distribution of a clientKey by displacing a test authentication module in the client side application to a client side authentication module preset with an MAC (Media Access Control) fingerprint and the clientKey. When the client side application satisfies a trigger condition, the client side authentication module firstly passes an integrity check based on an MAC fingerprint mechanism and applies for registration to the authentication server based on an MAC1 generated by the shared clientKey and obtains a random authentication factor. When the client side application needs to call the platform capacity API, a dynamic token is generated based on the authentication factor to be carried in a service request. After the dynamic token authentication passes, the platform capacity API is allowed to be called.
Owner:CHINA MOBILE COMM CO LTD
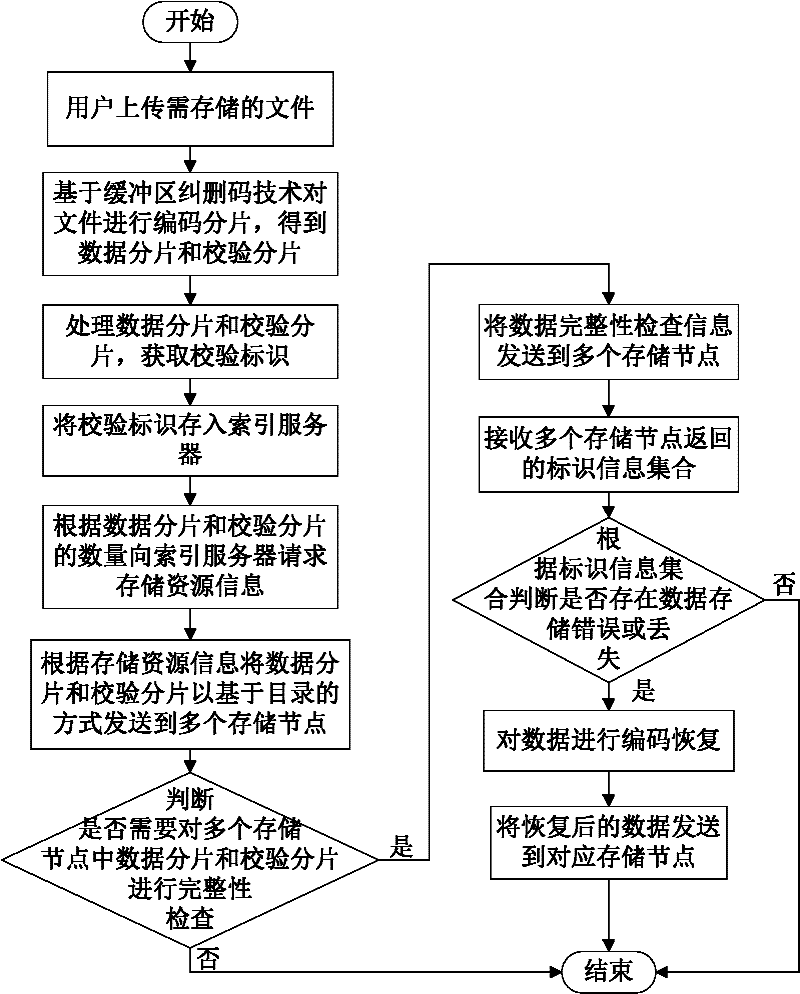
Data storage method of cloud storage system
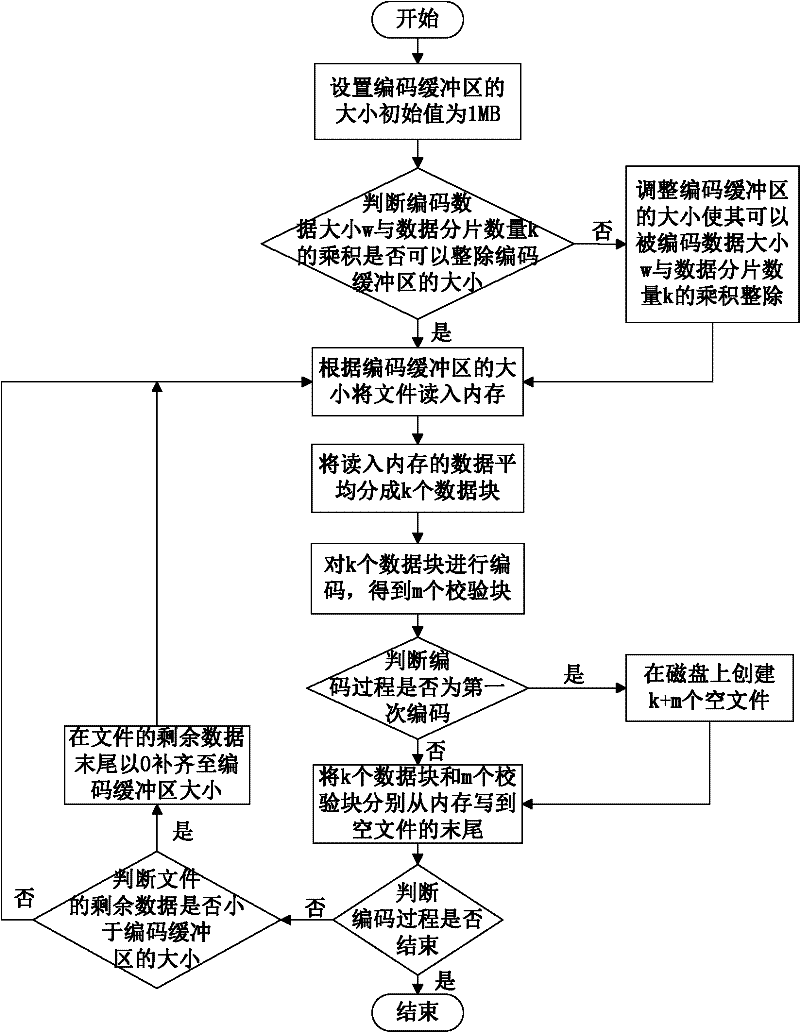
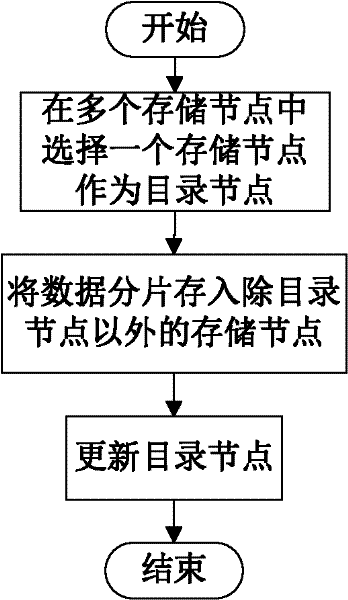
InactiveCN102546755ADoes not affect recoveryImprove data availabilityTransmissionSpecial data processing applicationsComputer hardwareData integrity
The invention discloses a data storage method of a cloud storage system, which comprises the steps of: carrying out coding fragmentation on a file on the basis of a buffer zone erasure code technology to obtain data fragments and check fragments; processing the data fragments and the check fragments to obtain a check identification; storing the check identification in an index server; requesting storage resource information to the index server according to the quantity of the data fragments and the check fragments; sending the data fragments and the check fragments to a plurality of storage nodes according to the storage resource information; judging whether needing to carry out integrity check on the data fragments and the check fragments in the storage nodes; if needing to carry out integrity check on the data fragments and the check fragments in the storage nodes, sending the data integrity check information to the storage nodes, receiving an identification information set returned by the storage nodes, and judging whether data storage errors or data losses exist according to the identification information set, if yes, coding for recovering the data, and sending the recovered data to the corresponding storage nodes.
Owner:HUAZHONG UNIV OF SCI & TECH
Integrity check in a communication system
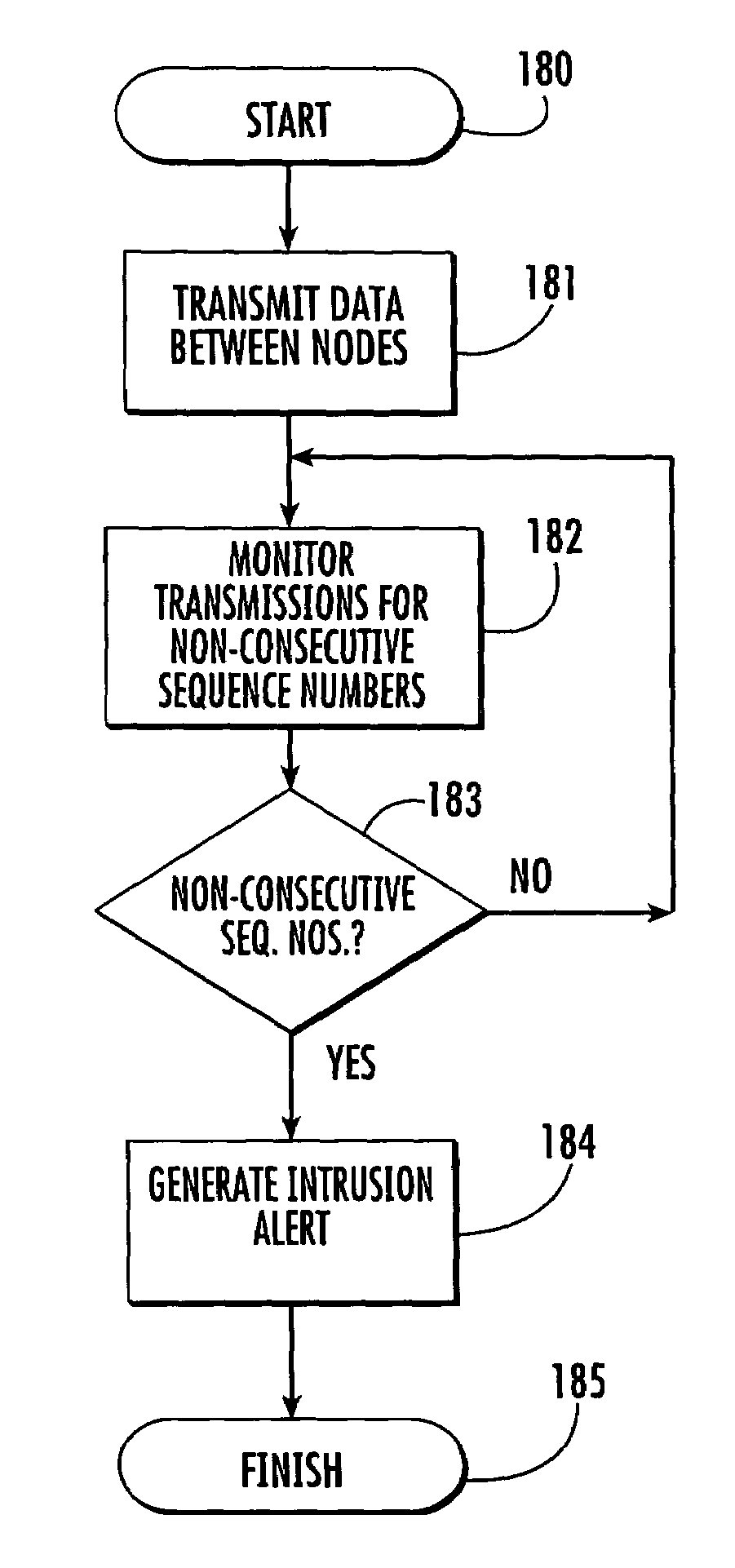
InactiveUS20020044552A1Improve user securityPrevent replay attacksError preventionTransmission systemsComputer hardwareCommunications system
A method of communication between a first node and a second node for a system where a plurality of different channels is provided between said first and second node. The method comprises the step of calculating an integrity output. The integrity output is calculated from a plurality of values, some of said values being the same for said different channels. At least one of said values is arranged to comprise information relating to the identity of said channel, each channel having a different identity. After the integrity output has been calculated, Information relating to the integrity output is transmitted from one of said nodes to the other.
Owner:NOKIA TECHNOLOGLES OY
Symmetric key authenticated encryption schemes
InactiveUS6963976B1Low costSame level of securityData processing applicationsEncryption apparatus with shift registers/memoriesComputer hardwareCiphertext
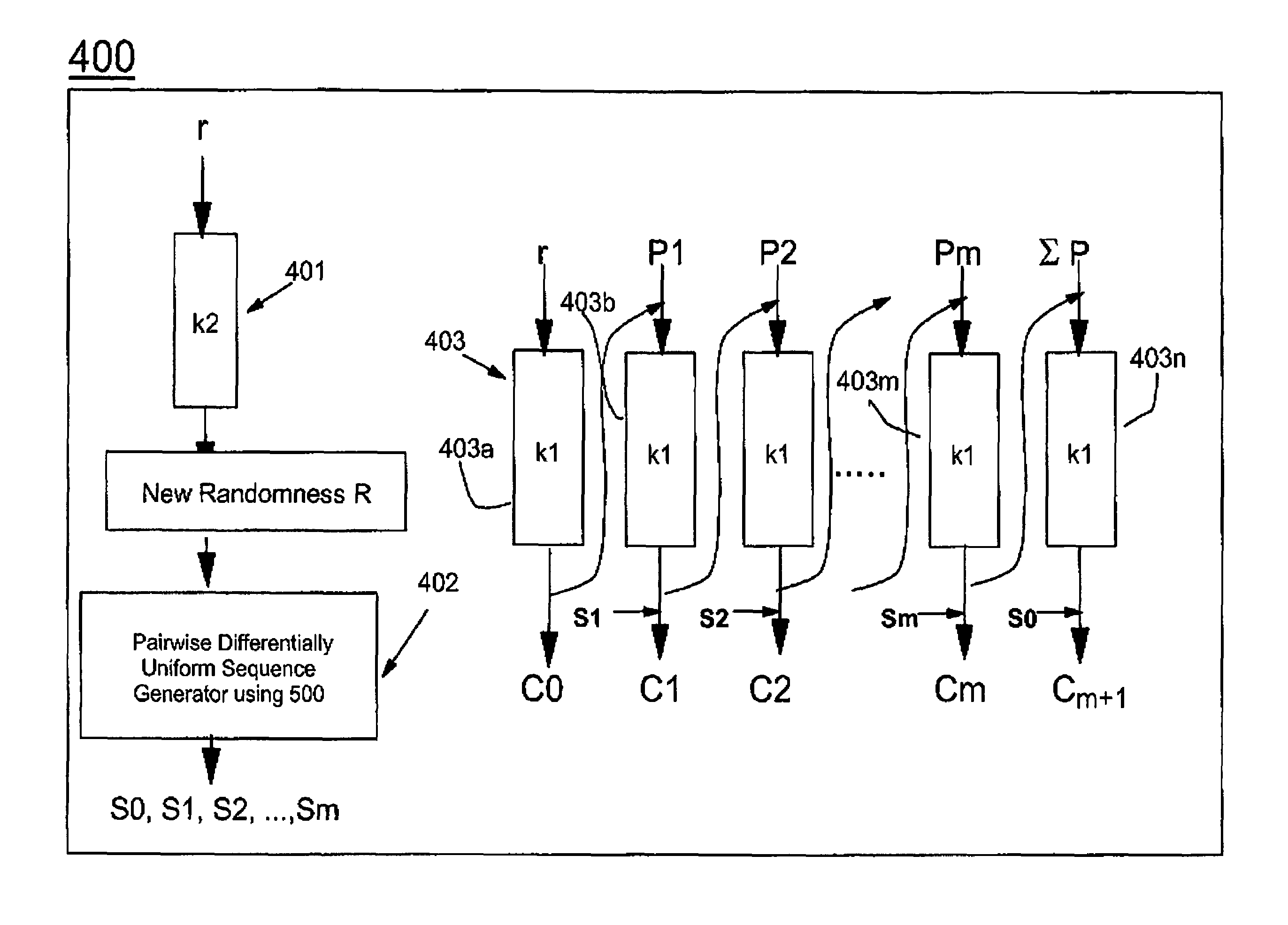
The present invention provides encryption schemes and apparatus which securely generate a cipher-text which in itself contains checks for assuring message integrity. It also provides compatible decryption schemes confirming message integrity. The encryption scheme generates a cipher-text with message integrity in a single pass with little additional computational cost, while retaining at least the same level of security as schemes based on a MAC. One embodiment encrypts a plain-text message by dividing the plain-text message into a multitude of plain-text blocks and encrypting the plain-text blocks to form a multitude of cipher-text blocks. A single pass technique is used in this process to embed a message integrity check in the cipher-text block. A message integrity check is embedded in the cipher-text blocks by embedding a set of pseudo random numbers, which may be dependent, but are pair-wise differentially uniform. We also describe an embodiment which is highly parallelizable.
Owner:IBM CORP +1
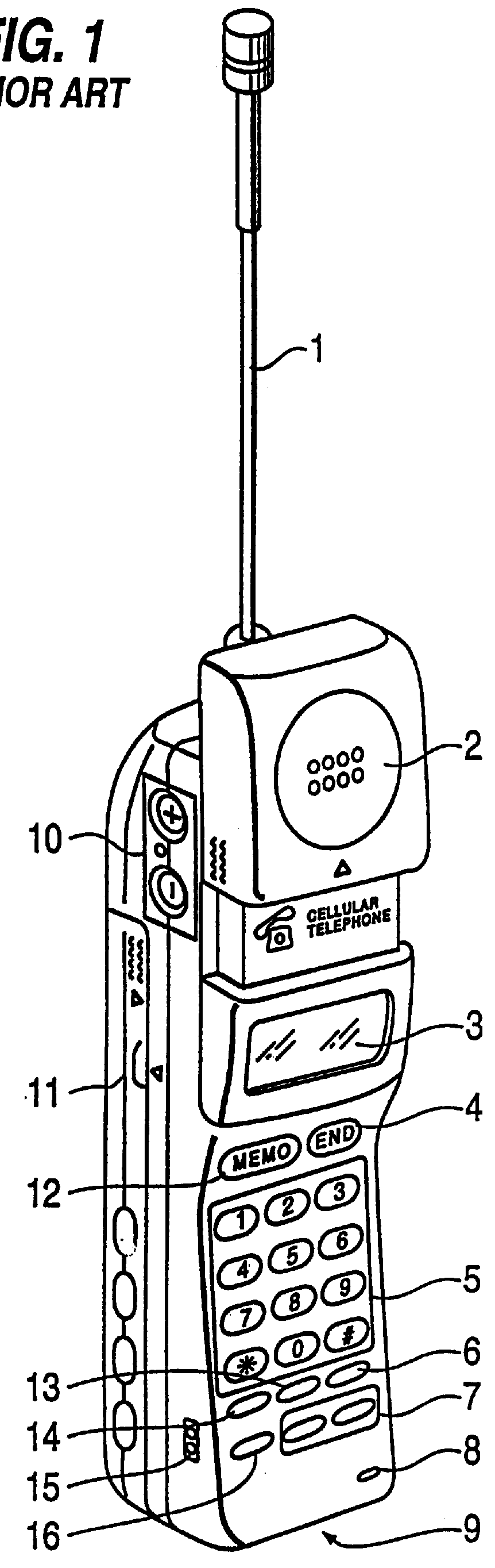
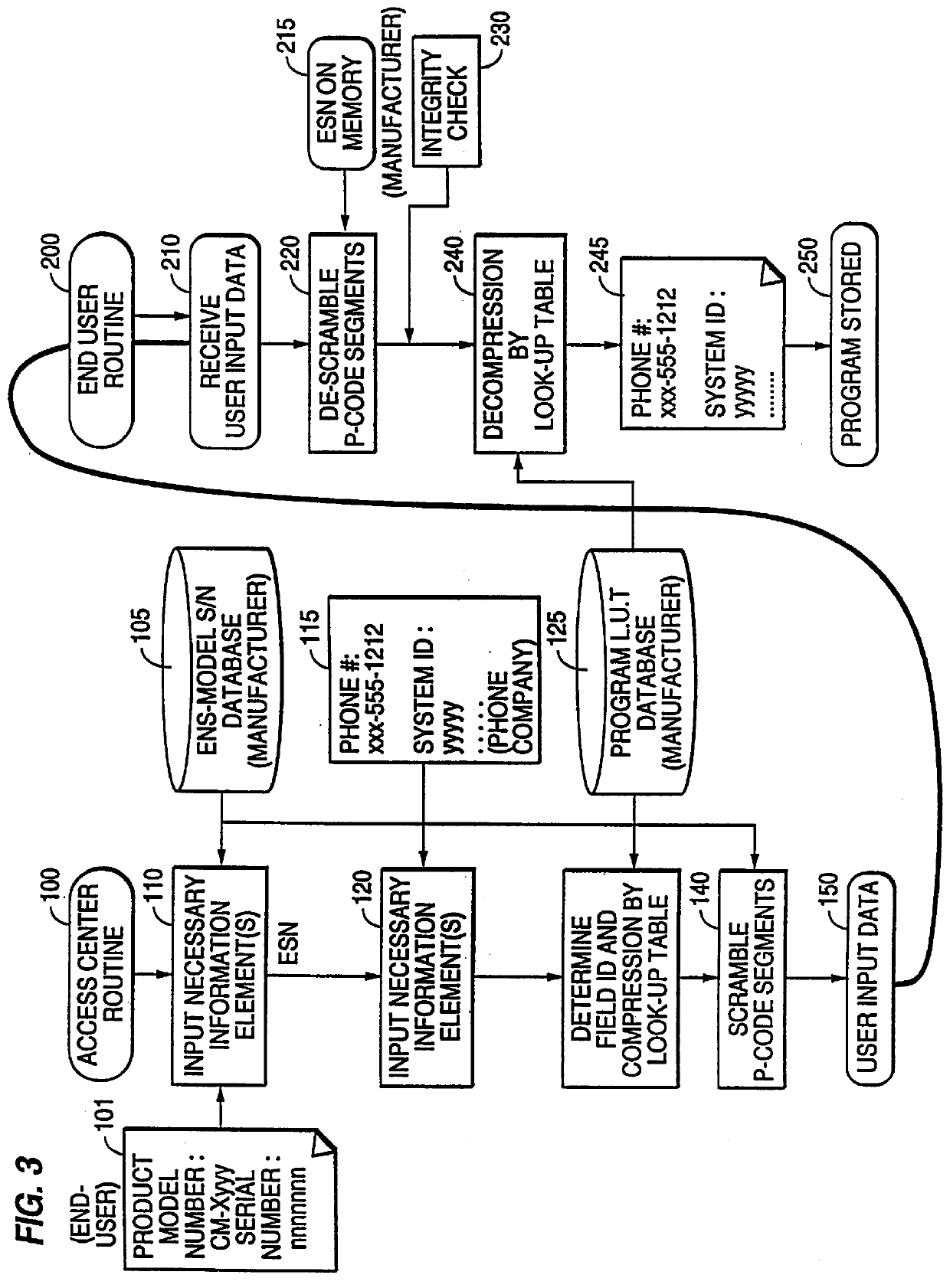
Programmable cellular telephone and system
InactiveUS6018656ARadio/inductive link selection arrangementsAutomatic exchangesCode moduleUser input
A module (P-code module) provides parameter information to a Number Assignment Module (NAM) in a cellular phone unit by processing a simple programming code (P-code) entered by the user through a telephone keypad. The P-code employs a flexible length telephone keypad coding that can be translated into programmable parameters of cellular phone products. Field identification numbers and look-up tables are used to shorten the P-code length for more frequently used information. To activate a cellular phone, the user provides product and serial number information to a dial-up access center which then generates a scrambled P-code for entry by the user. The P-code module within the processor unit of the cellular phone likewise descrambles, decompresses, and performs an integrity check on the sequence of digits being entered by the user. Activation information is then provided by the access center to the manufacturer of the cellular phones in order to plan future production, target marketing and track dealer inventory.
Owner:IRONWORKS PATENTS LLC
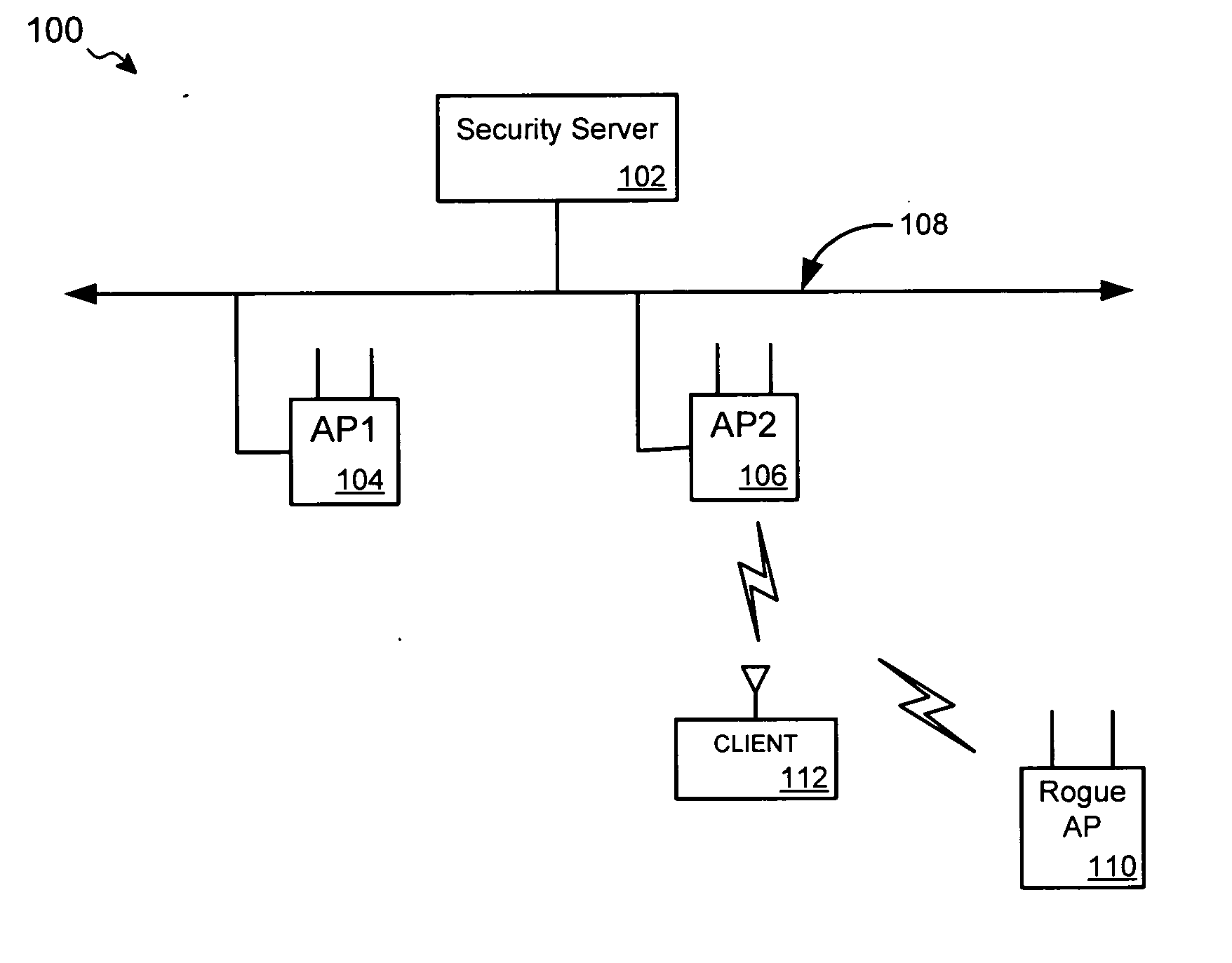
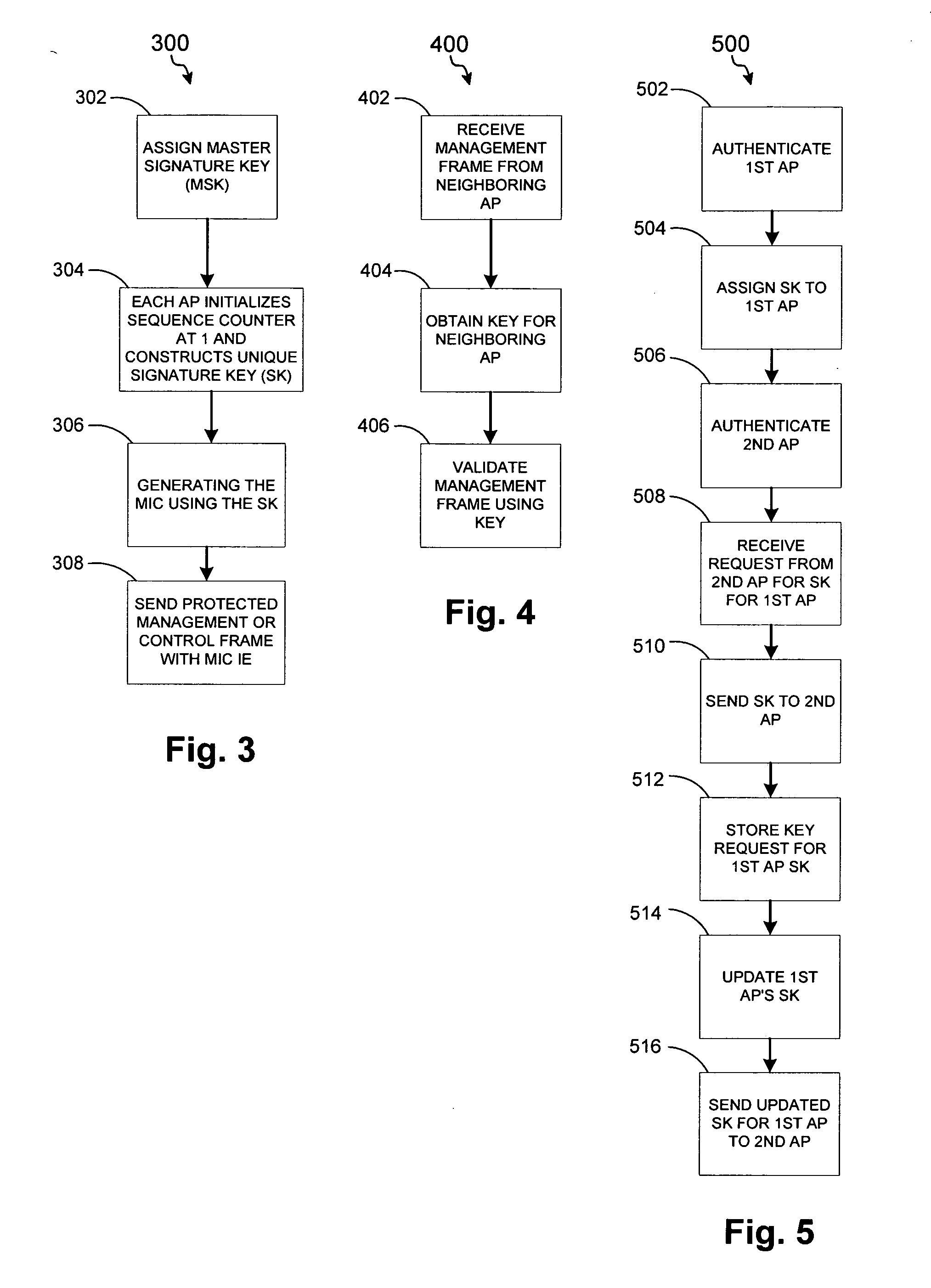
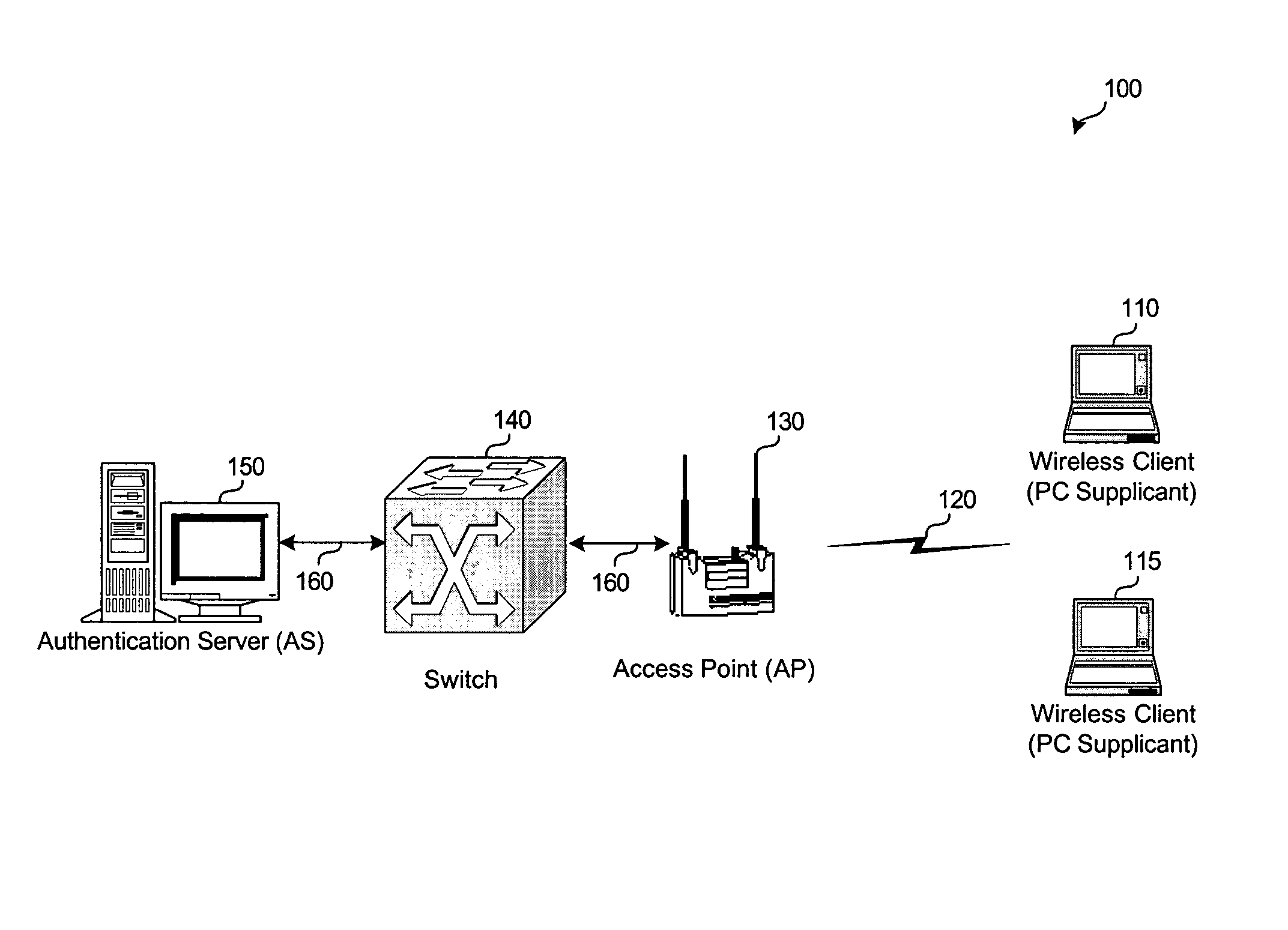
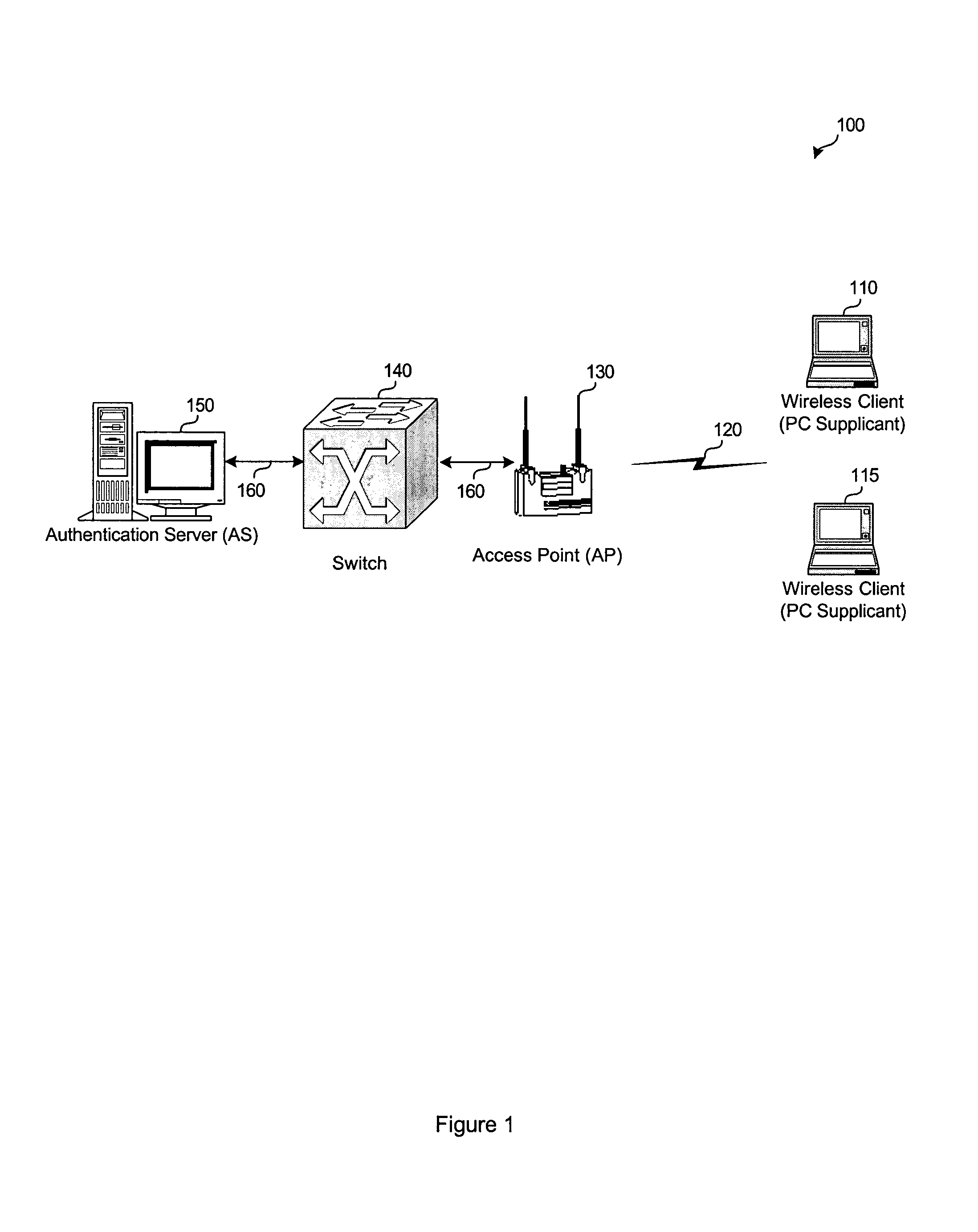
Network infrastructure validation of network management frames
ActiveUS20050141498A1Network topologiesData switching by path configurationNetwork managementMessage integrity
A detection-based defense to a wireless network. Elements of the infrastructure, e.g., access points or scanning-only access points, detect intruders by detecting spoofed frames, such as from rogue access points. Access points include a signature, such as a message integrity check, with their management frames in a manner that enables neighboring access points to be able to validate the management frames, and to detect spoofed frames. When a neighboring access point receives a management frame, obtains a key for the access point sending the frame, and validates the management frame using the key.
Owner:CISCO TECH INC
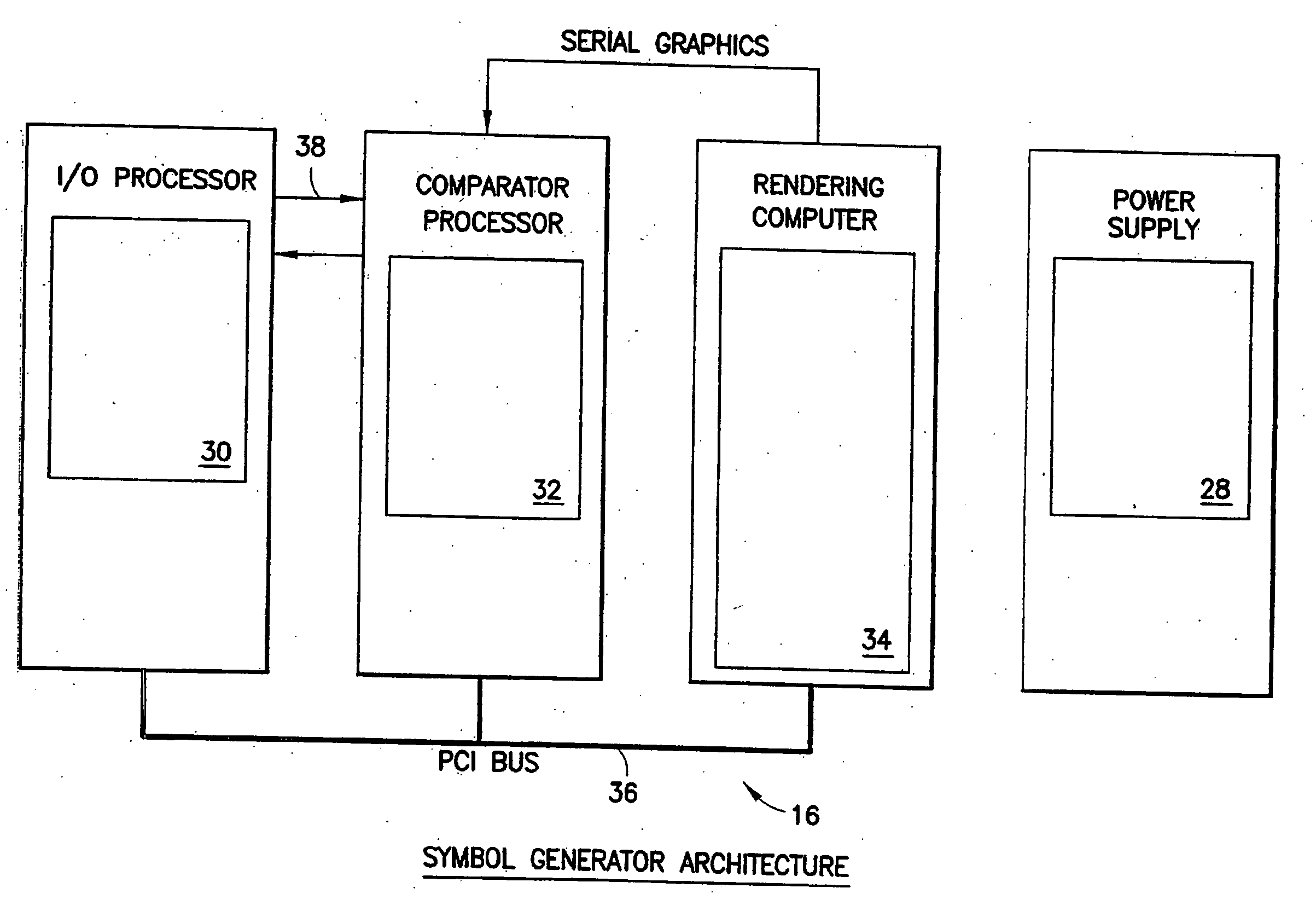
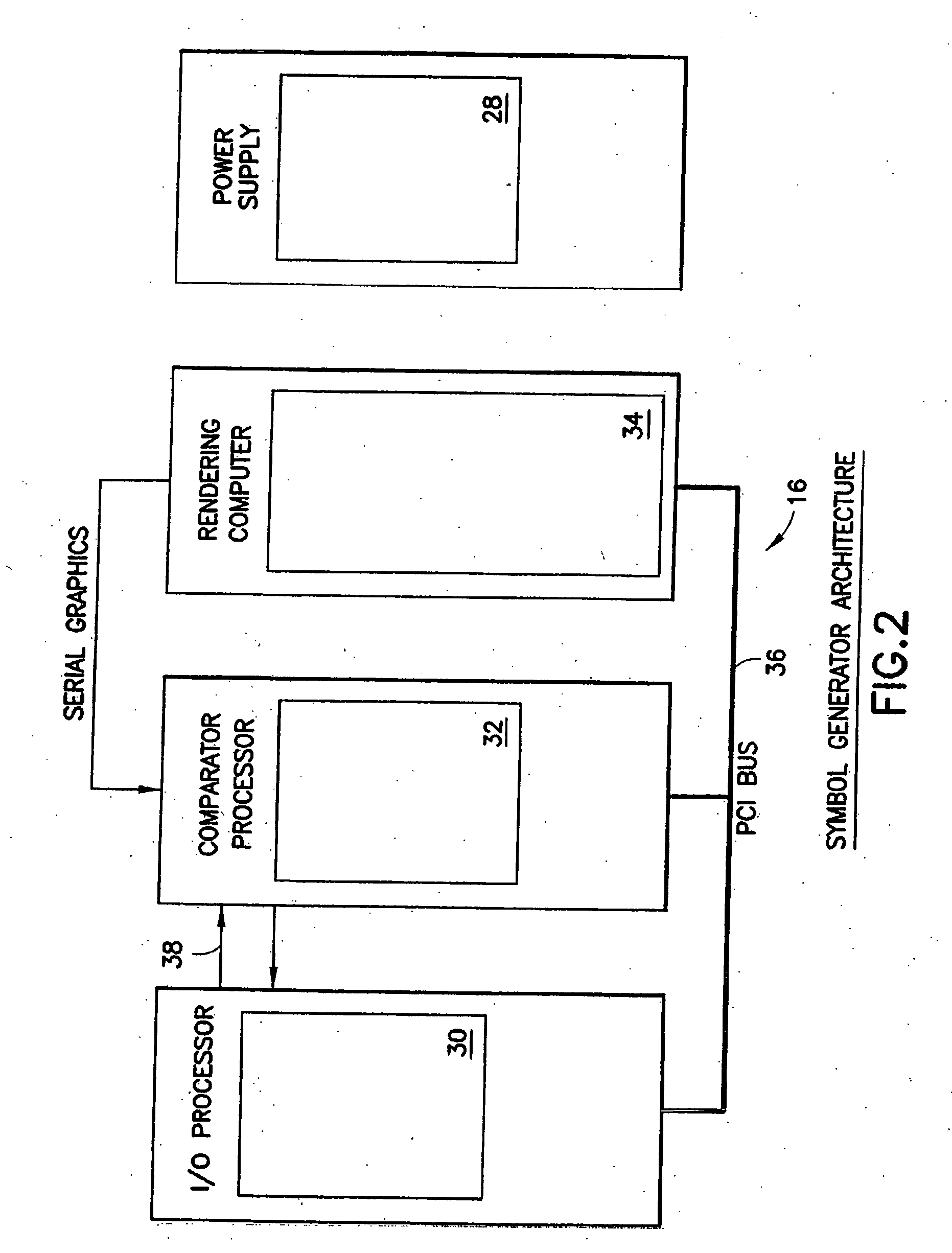
Dependable microcontroller, method for designing a dependable microcontroller and computer program product therefor
ActiveUS7472051B2Improve reliabilityEfficient use ofAnalogue computers for electric apparatusHardware monitoringMicrocontrollerFault tolerance
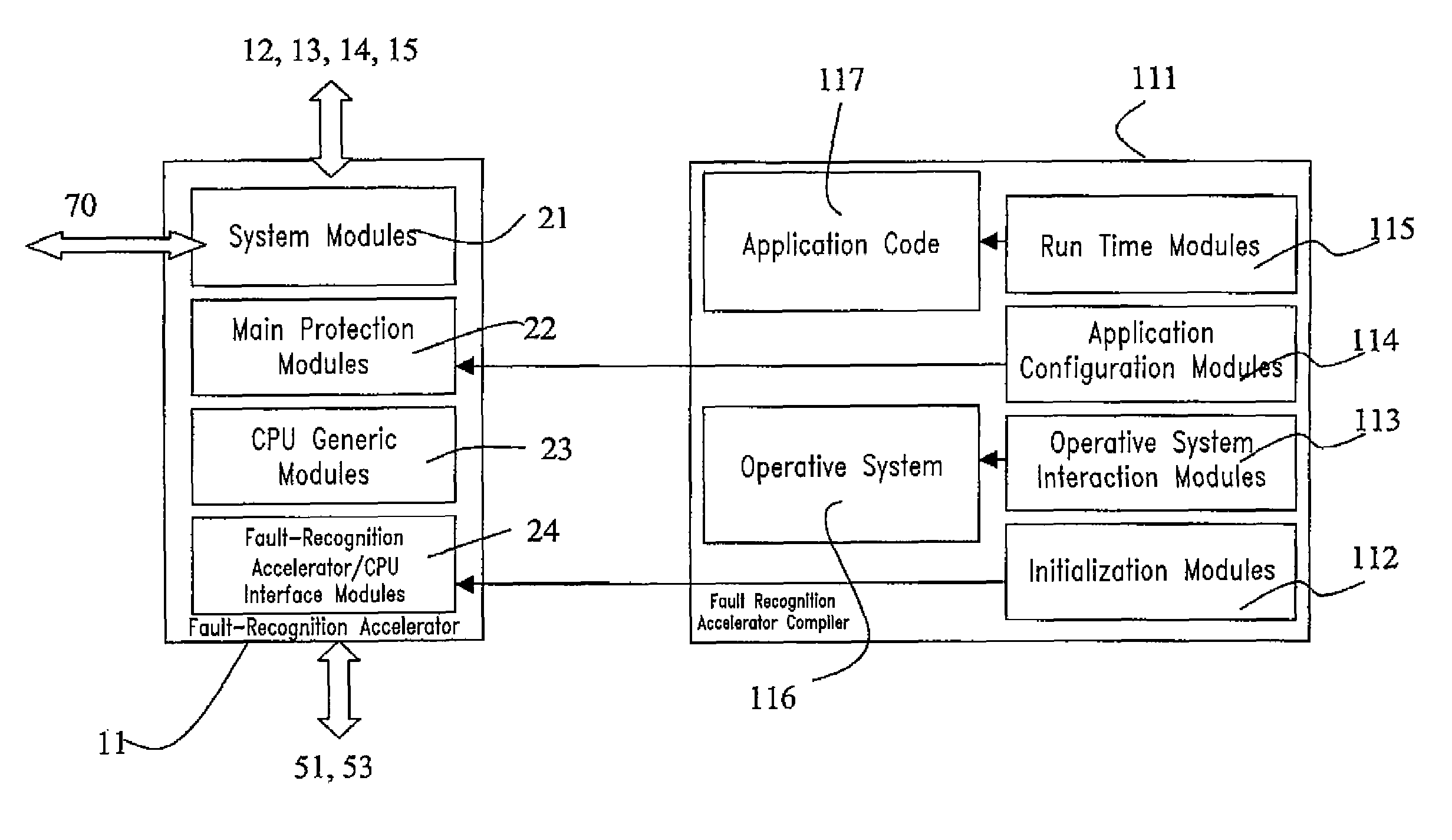
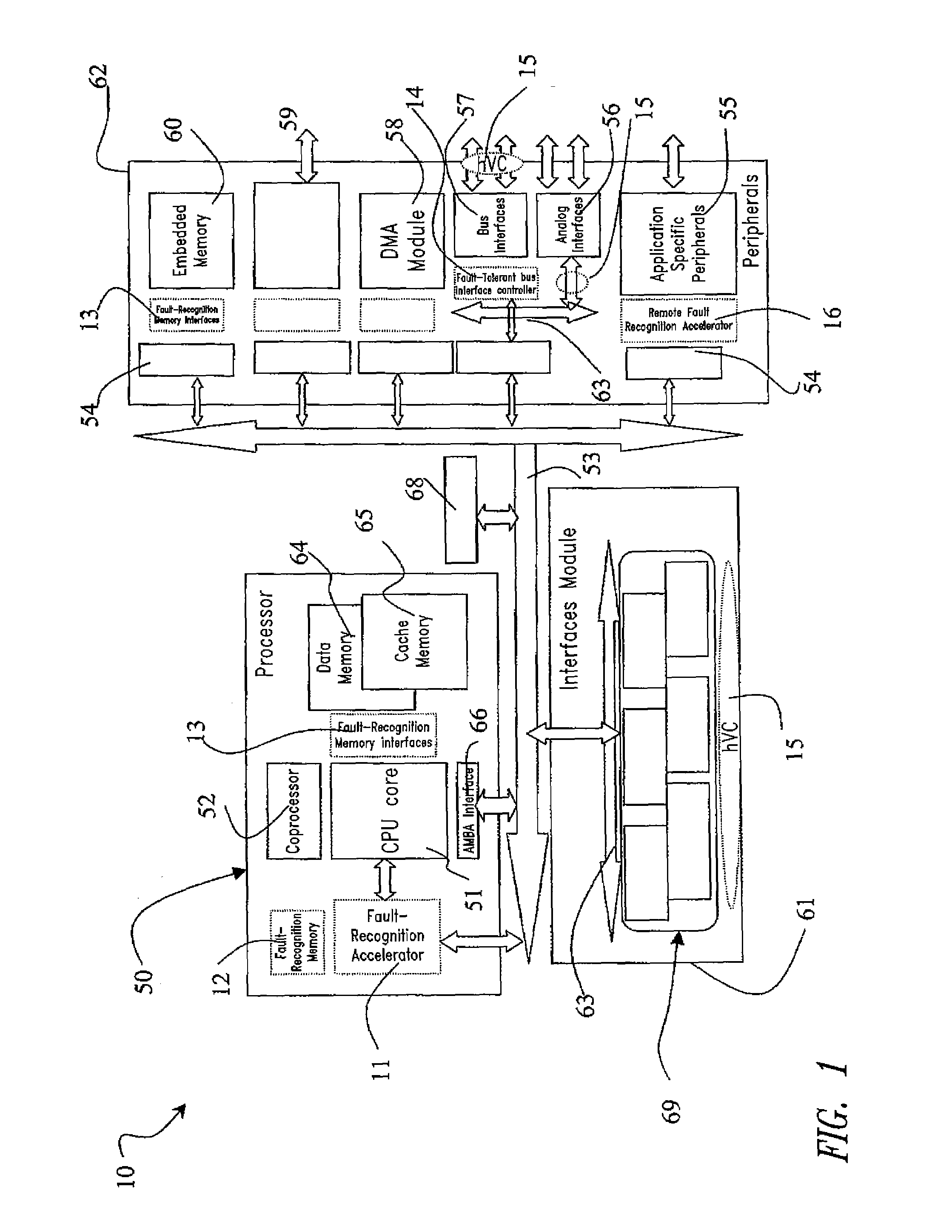
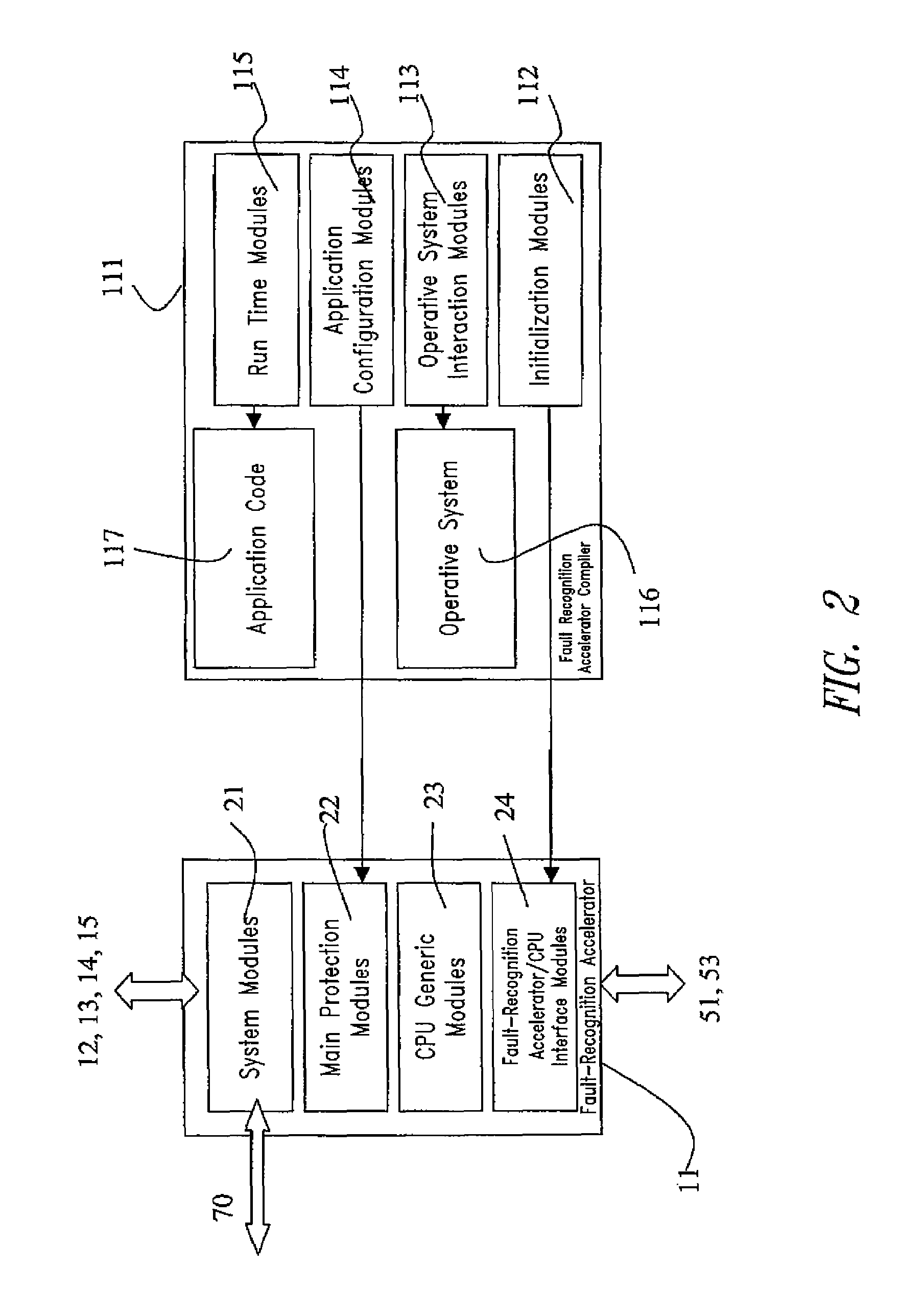
A microcontroller comprising a central processing unit and a further fault processing unit suitable for performing validation of operations of said central processing unit. The further fault processing unit is external and different with respect to said central processing unit and said further fault processing unit comprises at least a module for performing validation of operations of said central processing unit and one or more modules suitable for performing validation of operations of other functional parts of said microcontroller. Validation of operations of said central processing unit is performed by using one or more of the following fault tolerance techniques: data shadowing; code&flow signature; data processing legality check; addressing legality check; ALU concurrent integrity checking; concurrent mode / interrupt check. The proposed microcontroller is particularly suitable for application in System On Chip (SoC) and was developed by paying specific attention to the possible use in automotive System On Chip. The invention also includes a method for designing and verify such fault-robust system on chip, and a fault-injection technique based on e-language.
Owner:TAHOE RES LTD
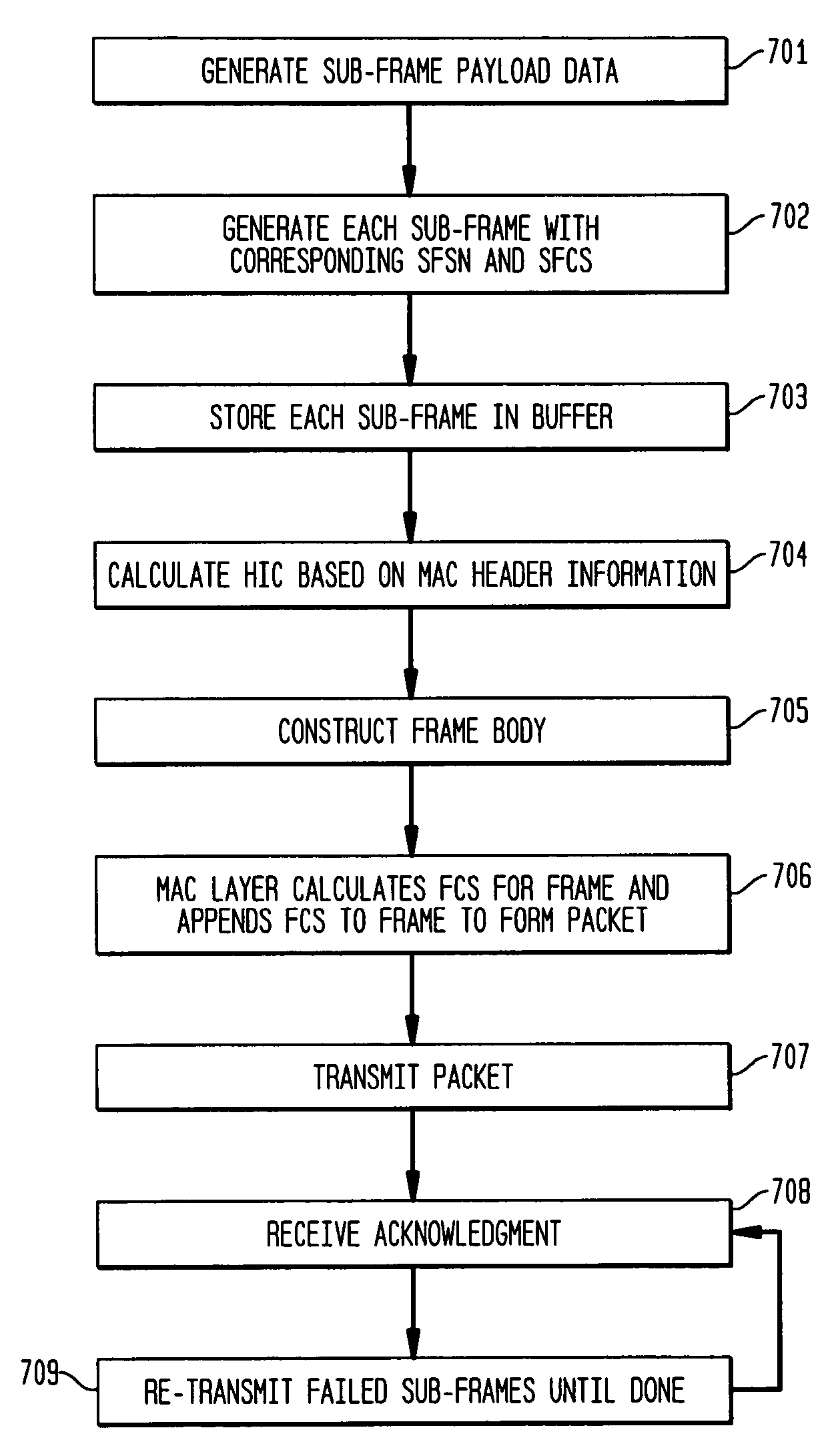
Packet sub-frame structure for selective acknowledgment
ActiveUS20050157715A1Error prevention/detection by using return channelNetwork topologiesWireless lanIntegrity check
A wireless local area network includes transmission of data packets between endpoints in which packet frames are divided into sub-frames. On reception of a frame, the integrity of each individual sub-frame is checked. Sub-frames that pass the integrity check are acknowledged and retransmission is requested only for sub-frames that failed the integrity check. Consequently, only the affected sub-frames require retransmission instead of the whole frame.
Owner:AVAGO TECH INT SALES PTE LTD
System executing a fast boot wake-up
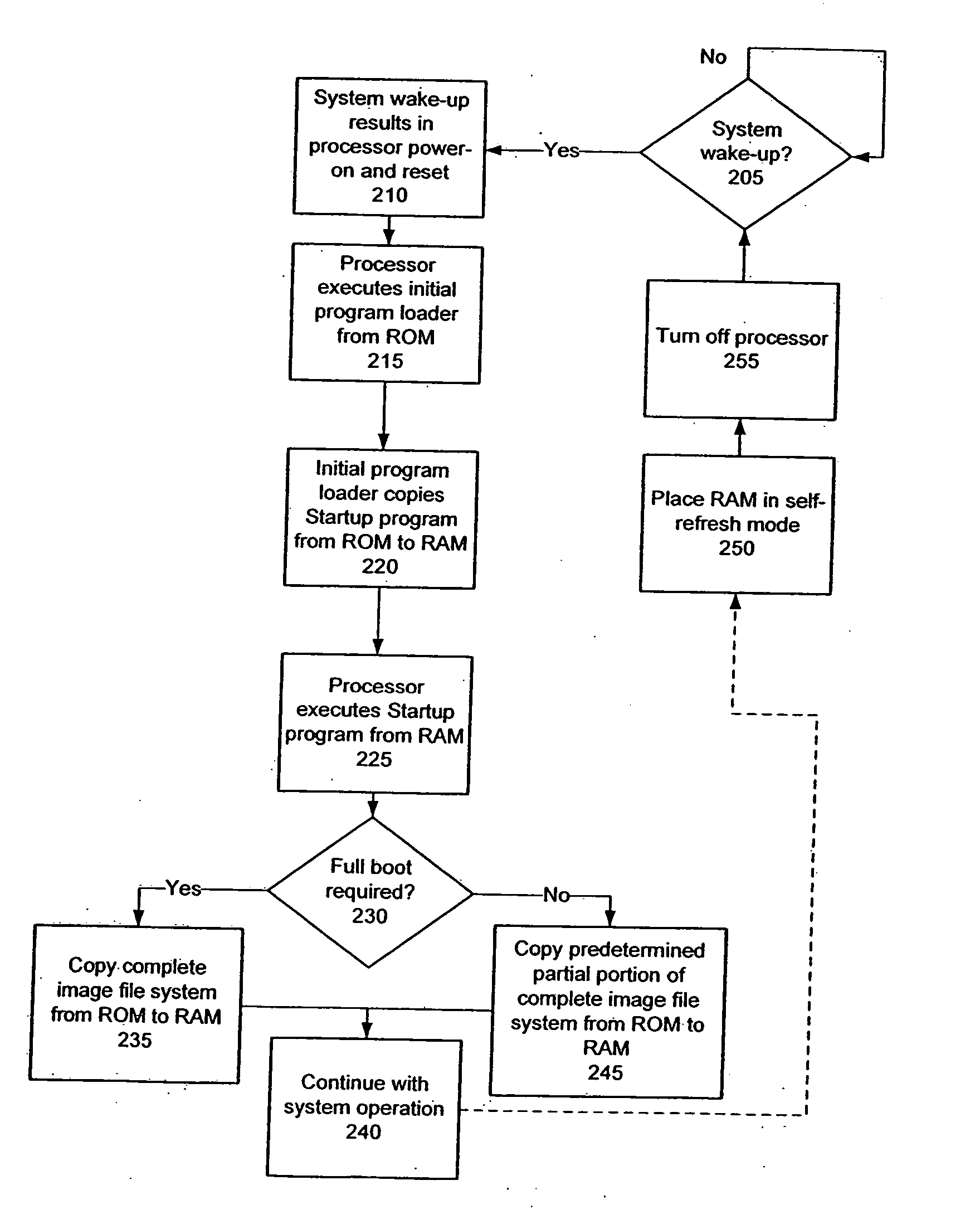
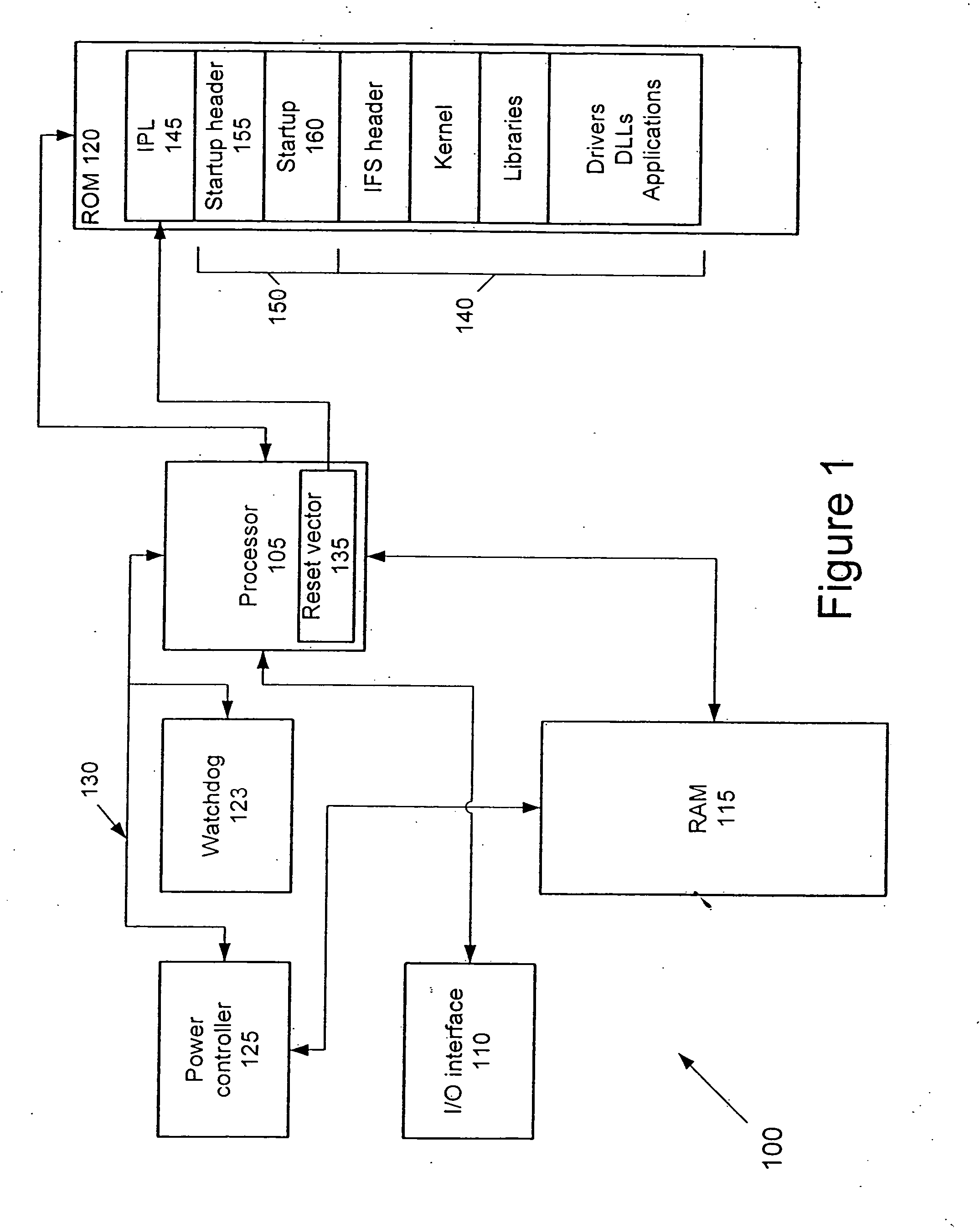
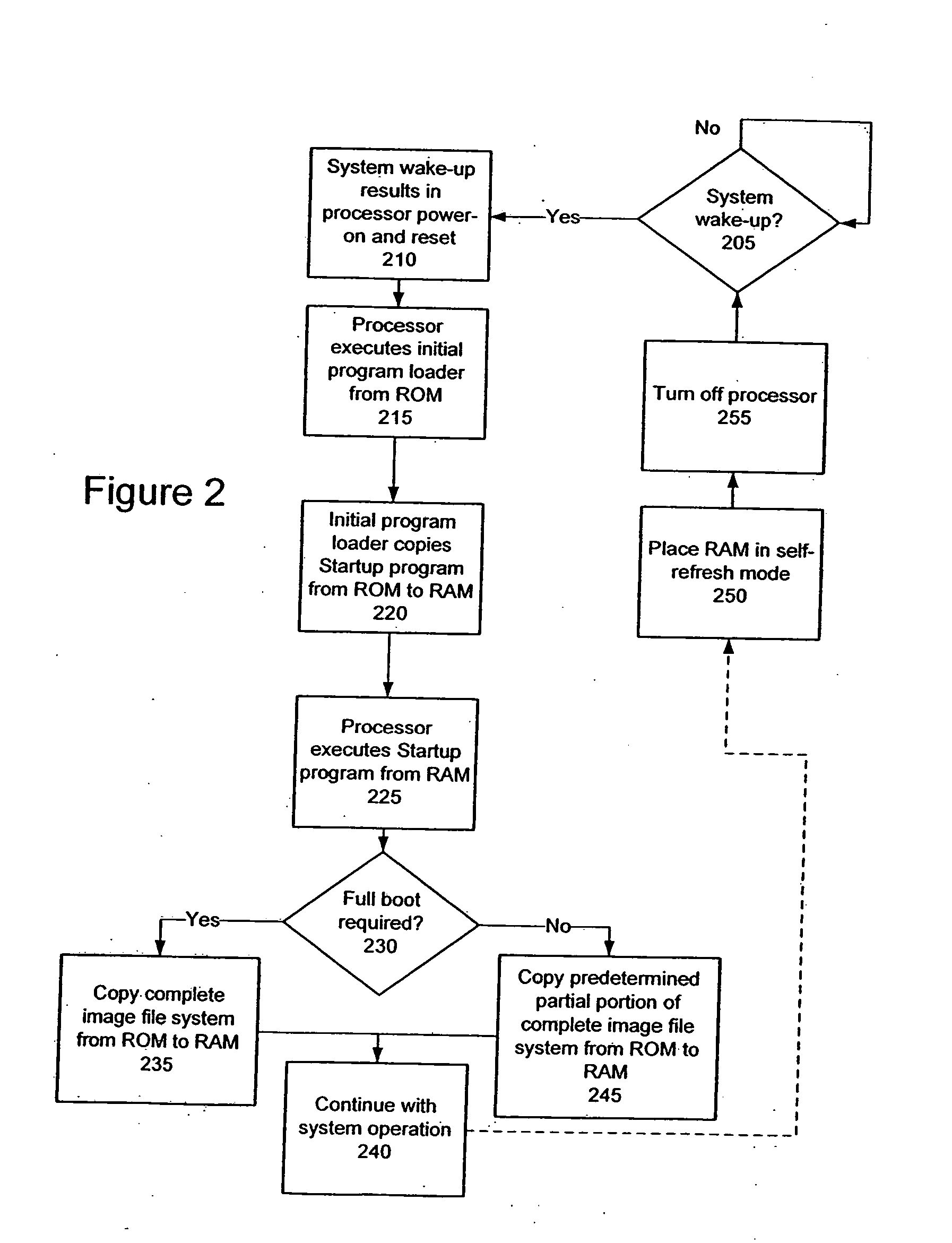
ActiveUS20070260867A1Error detection/correctionVolume/mass flow measurementPower modeOperational system
A processing system is set forth that includes a processor, read only memory storing an operating system image file accessible by the processor, and random access memory that is also accessible by the processor. The processing system also includes a boot program that is executable by the processor to initialize the processing system in response, for example, to a power-on event, reset event, or a wake-up event. A power-on event occurs when power is initially provided to the processing system while a wake-up event occurs when the processing system is to exit a low-power mode of operation. A reset event occurs when, for example, a fault is detected that causes the system to restart. The boot program selectively performs a full boot copy of the operating system image file from the read only memory to the random access memory or a fast boot copy of only predetermined portions of the operating system image file from the read only memory to the random access memory. For example, the boot program may execute the full boot copy operation in response to the power-on event and the fast boot copy operation in response to the wake-up event and / or reset event. Further, the boot program may limit execution of the fast boot copy operation to those instances in which the random access memory passes an integrity check of the contents of one or more areas containing selected portions of the operating system copied from the read only memory during a prior full boot copy operation.
Owner:MALIKIE INNOVATIONS LTD
Integrity check in a communication system
InactiveUS7009940B2Improve user securityPrevent replay attacksError preventionFrequency-division multiplex detailsComputer hardwareCommunications system
A method of communication between a first node and a second node for a system where a plurality of different channels is provided between said first and second node. The method comprises the step of calculating an integrity output. The integrity output is calculated from a plurality of values, some of said values being the same for said different channels. At least one of said values is arranged to comprise information relating to the identity of said channel, each channel having a different identity. After the integrity output has been calculated, Information relating to the integrity output is transmitted from one of said nodes to the other.
Owner:NOKIA TECHNOLOGLES OY
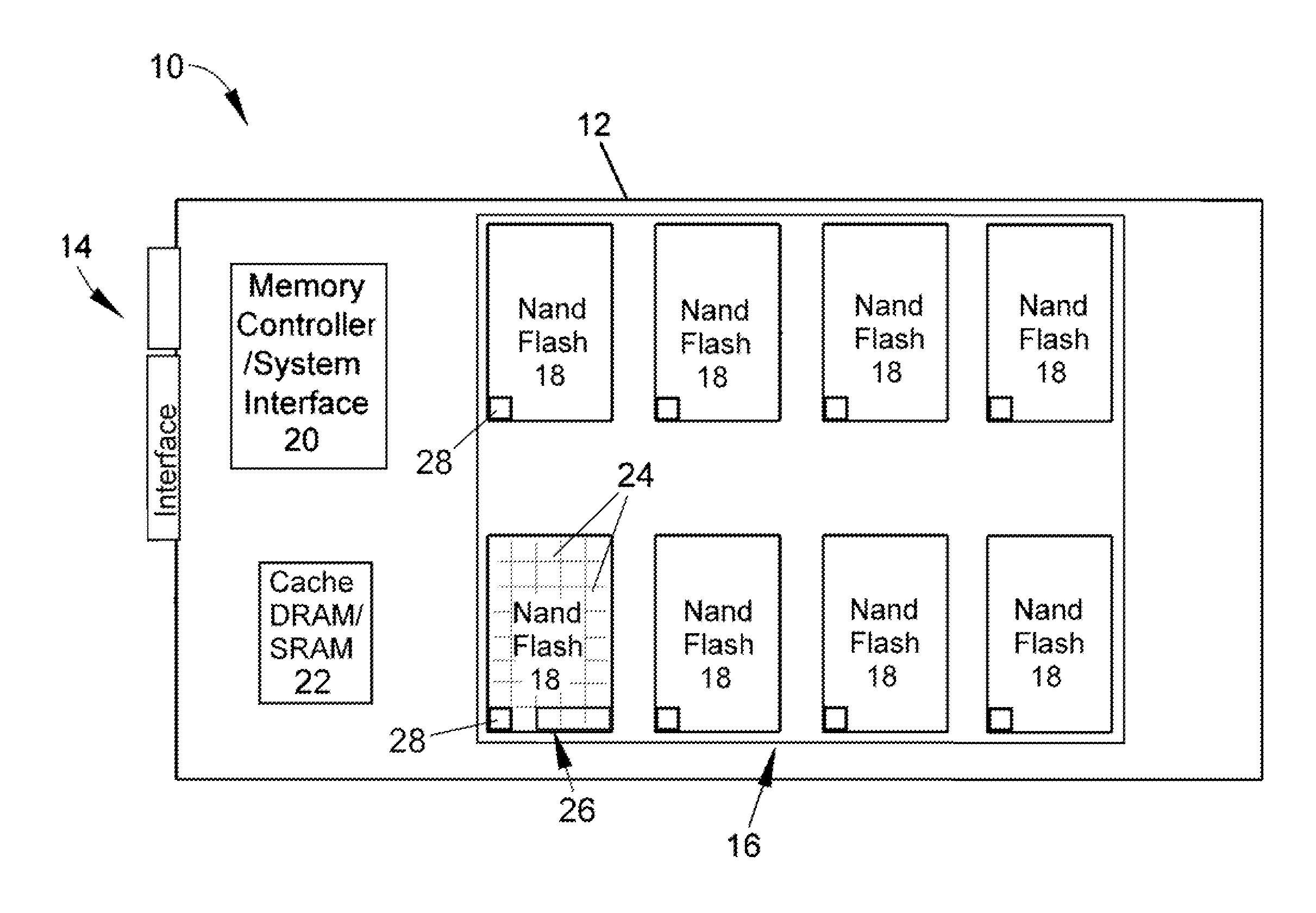
Solid-state mass storage device and method for failure anticipation
ActiveUS20110173484A1Accurately predict the fatigue threshold of a solid-state drive (SSD)Increase chanceFault responseStatic storageMass storageData memory
A solid-state mass storage device and method of operating the storage device to anticipate the failure of at least one memory device thereof before a write endurance limitation is reached. The method includes assigning at least a first memory block of the memory device as a wear indicator that is excluded from use as data storage, using pages of at least a set of memory blocks of the memory device for data storage, writing data to and erasing data from each memory block of the set in program / erase (P / E) cycles, performing wear leveling on the set of memory blocks, subjecting the wear indicator to more P / E cycles than the set of memory blocks, performing integrity checks of the wear indicator and monitoring its bit error rate, and taking corrective action if the bit error rate increases.
Owner:KIOXIA CORP
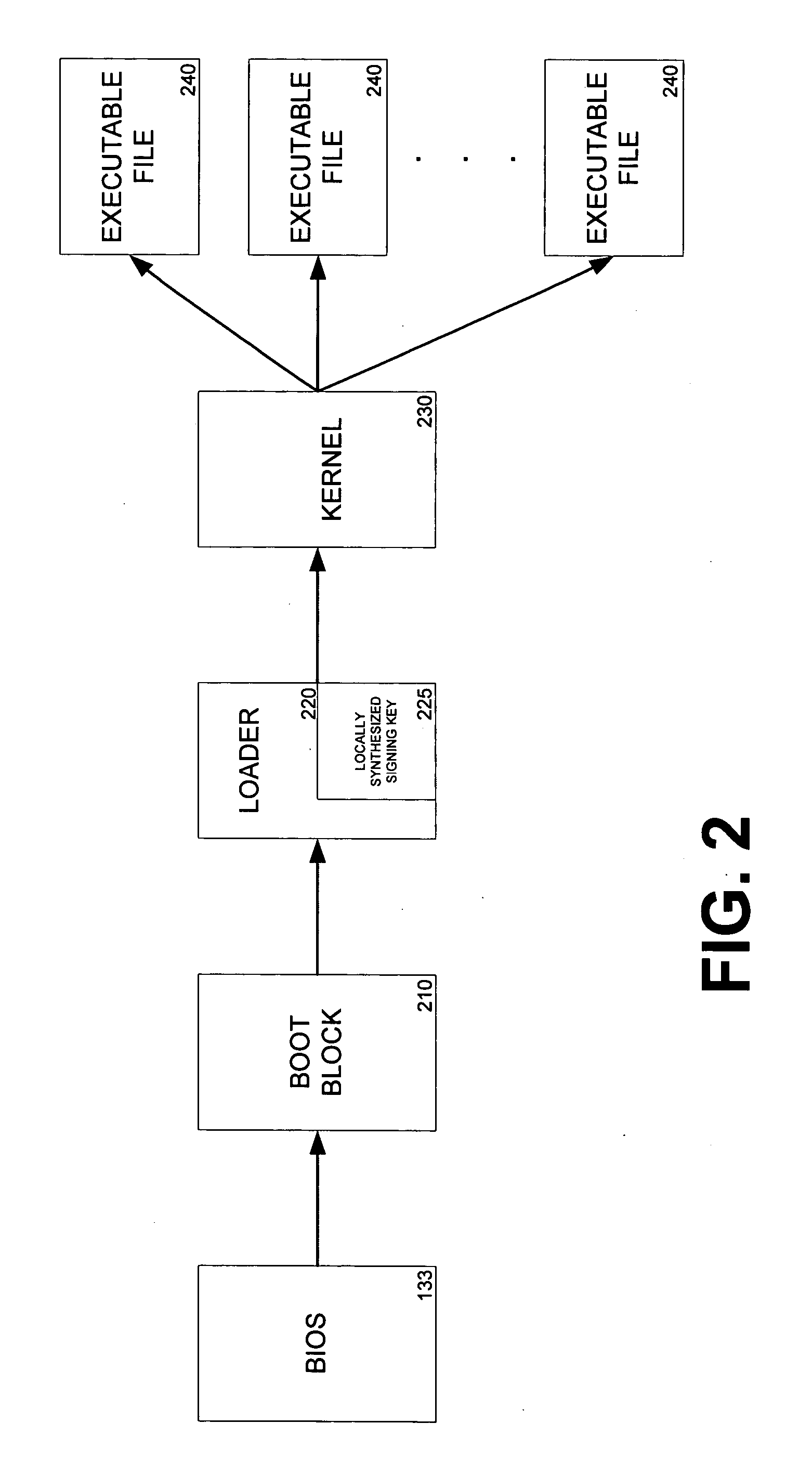
Secure boot
InactiveUS20060236122A1Verify integrityProgram control using stored programsUnauthorized memory use protectionOperational systemExecution control
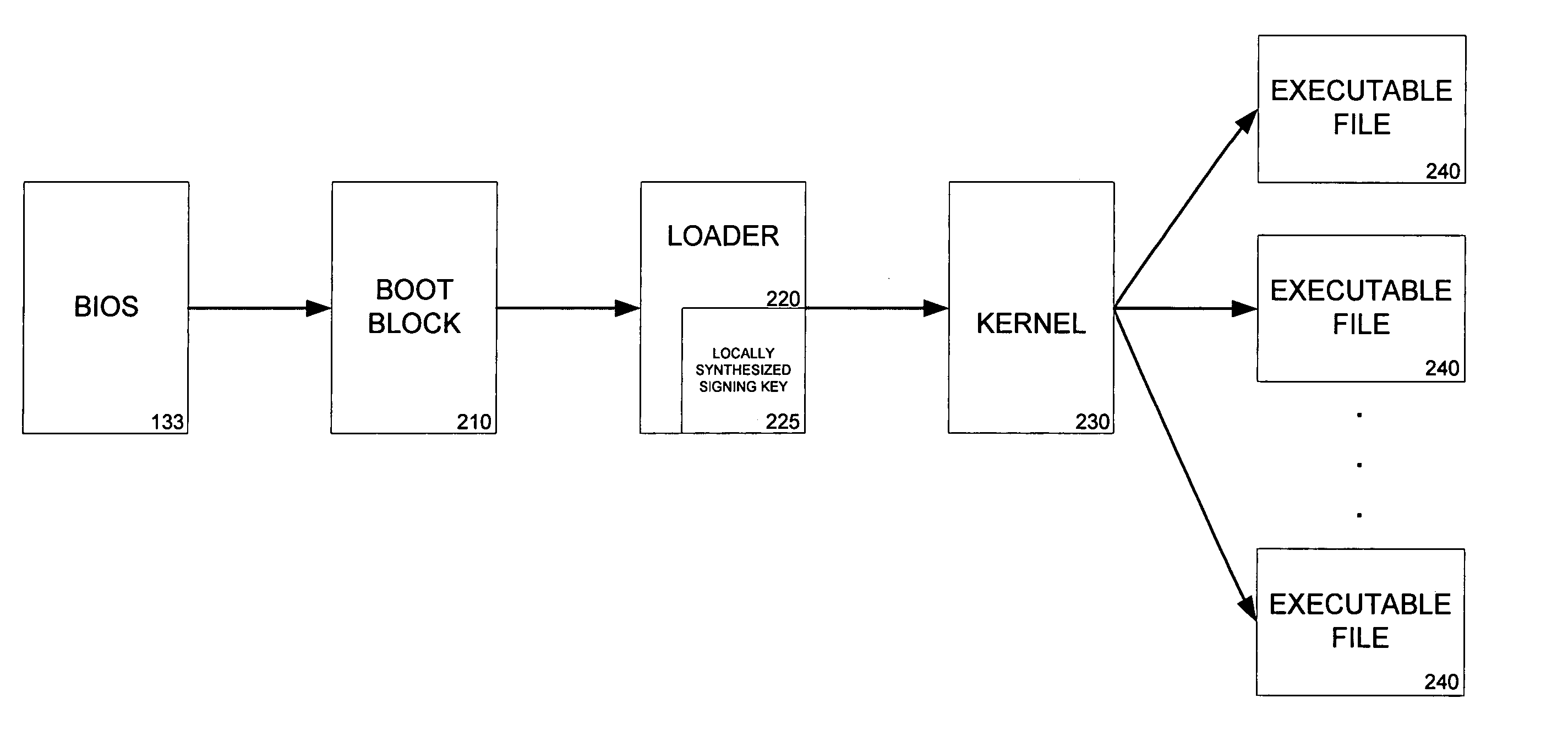
Systems and methods for performing integrity verifications for computer programs to run on computing systems are provided. An integrity check is completed before passing execution control to the next level of an operating system or before allowing a program to run. The integrity check involves the use of a locally stored key to determine if a program has been modified or tampered with prior to execution. If the check shows that the program has not been altered, the program will execute and, during the boot process, allow execution control to be transferred to the next level. If, however, the check confirms that the program has been modified, the computing system does not allow the program to run.
Owner:MICROSOFT TECH LICENSING LLC
System and method for protecting network management frames
InactiveUS20050086465A1Convenient verificationNetwork topologiesData switching by path configurationMessage integrityNetwork communication
System architecture and corresponding method for securing the transmission of management frame packets on a network (e.g. IEEE 802.11) is provided. Once a trust relationship is created between a transmitter and a receiver on the network such that the transmitter is authorized to communicate over the network, a key and corresponding message integrity check may be generated in order to sign management frame communications via the network. The message integrity check and a replay protection value may be transmitted with the management frame packet. Upon receipt, the message integrity check and replay protection value are authenticated to verify permitted transmission of the management frame packet.
Owner:CISCO TECH INC
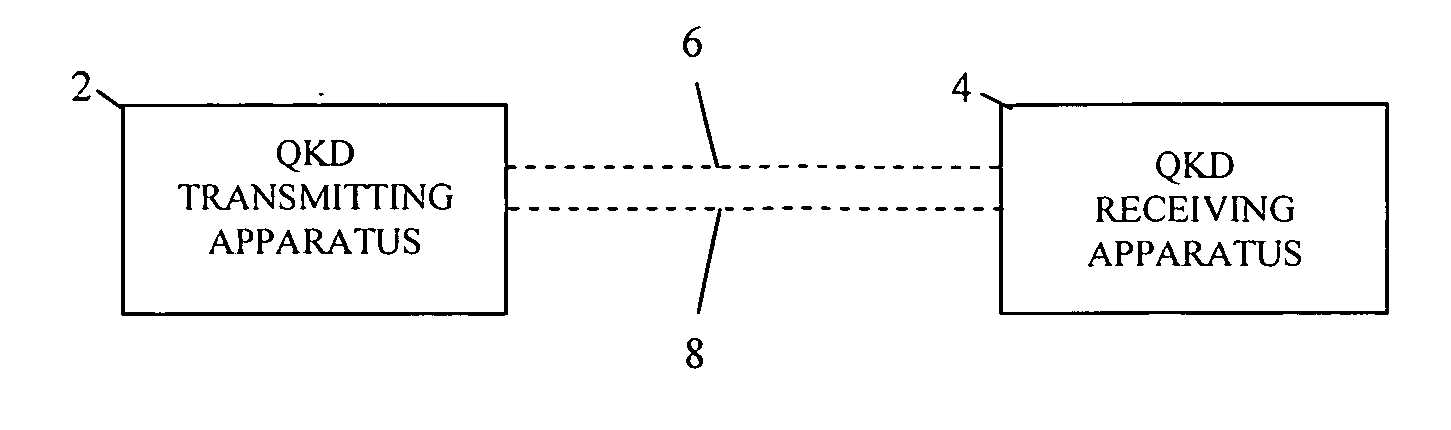
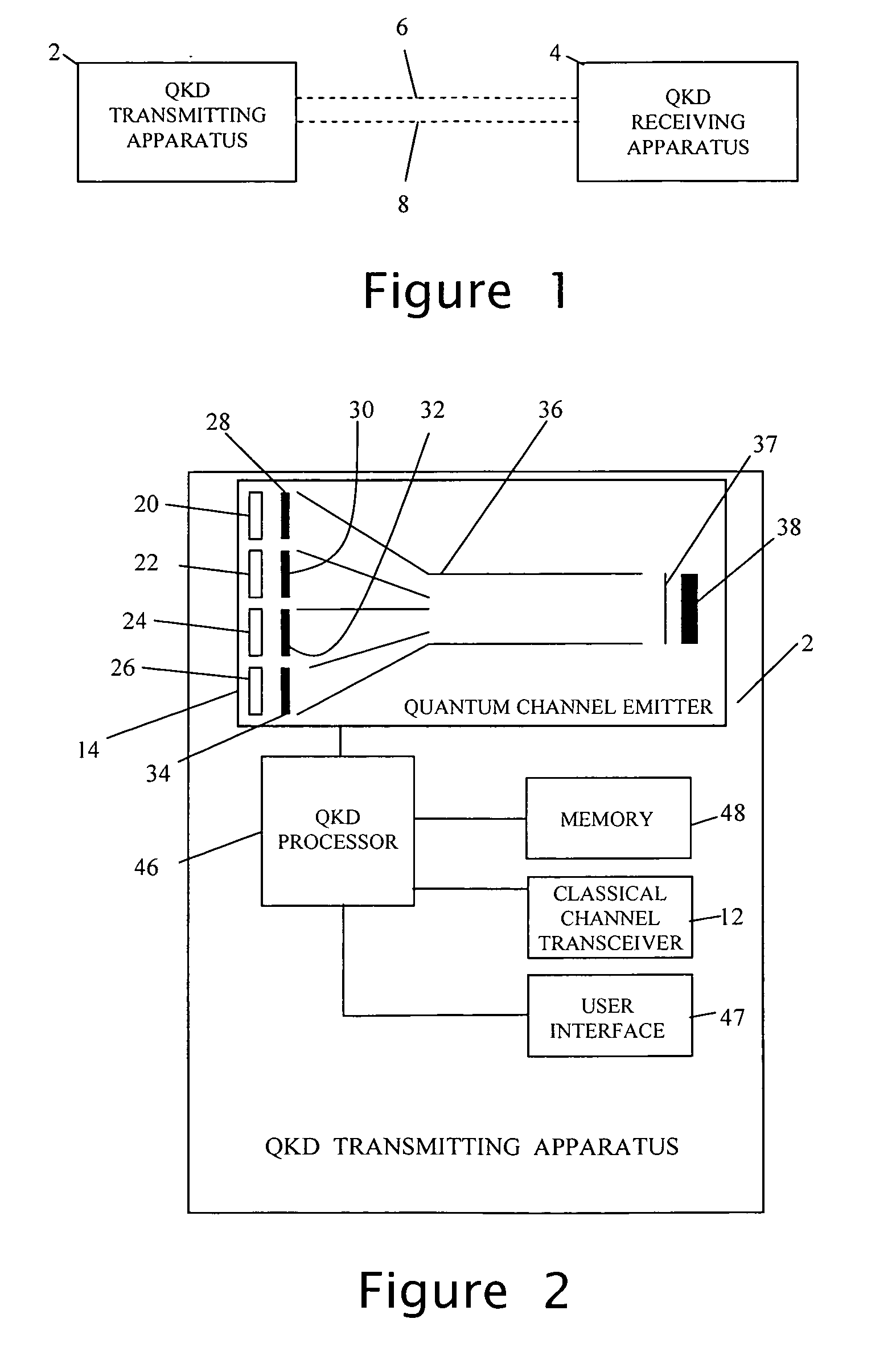
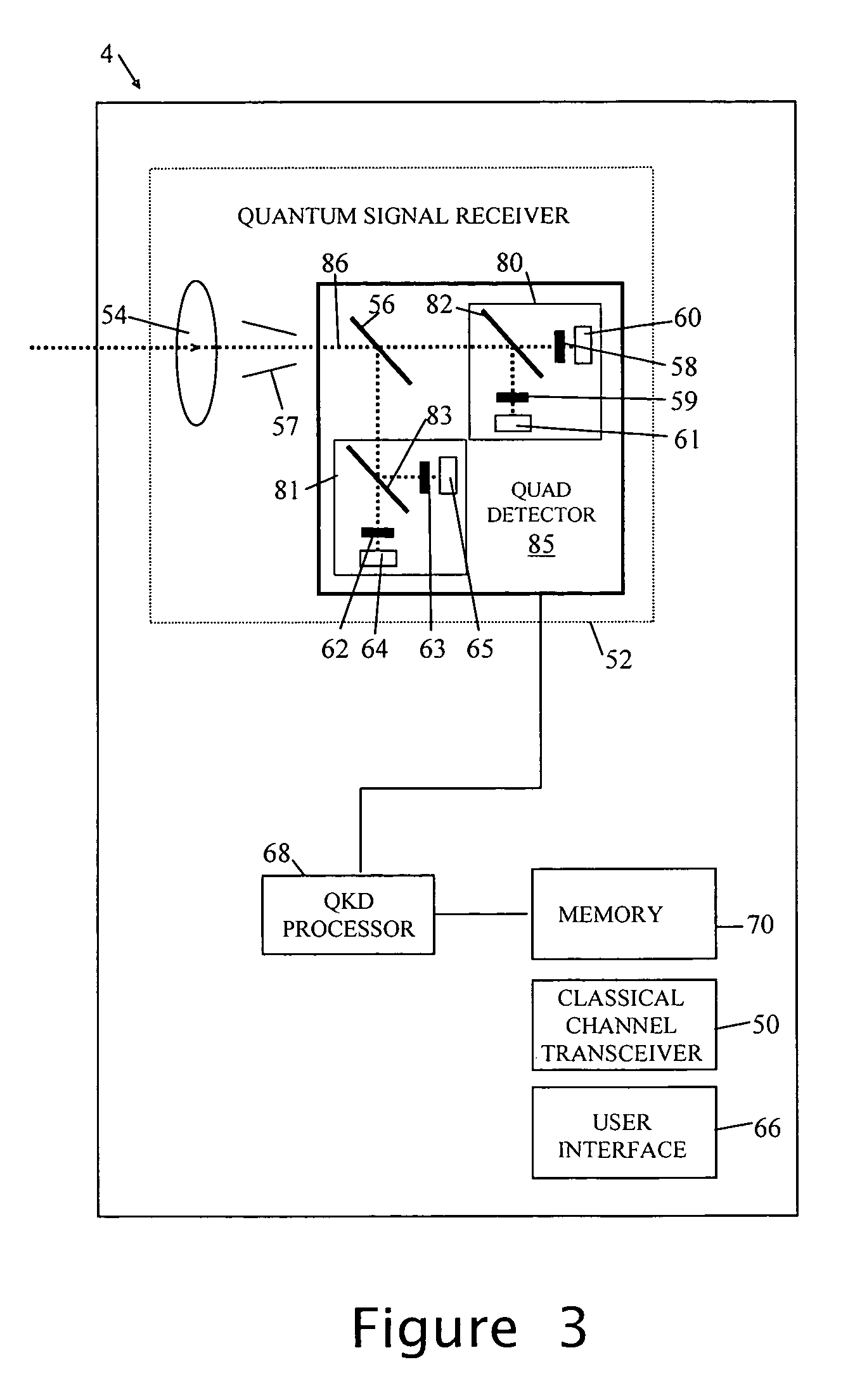
Quantum key distribution method and apparatus
InactiveUS20070014415A1Key distribution for secure communicationDigital data processing detailsData setComputer science
A quantum key distribution (QKD) method involves the sending of random data from a QKD transmitter to a QKD receiver over a quantum signal channel, and the QKD transmitter and receiver respectively processing the data transmitted and received over the quantum signal channel in order to seek to derive a common random data set. This processing is effected with the aid of messages exchanged between QKD transmitter and receiver over an insecure classical communication channel. The processing concludes with a check, effected by an exchange of authenticated messages over the classical communication channel, that the QKD transmitter and receiver have derived the same random data set. At least some of the other messages exchanged during processing are exchanged without authentication and integrity checking. A QKD transmitter and QKD receiver are also disclosed.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
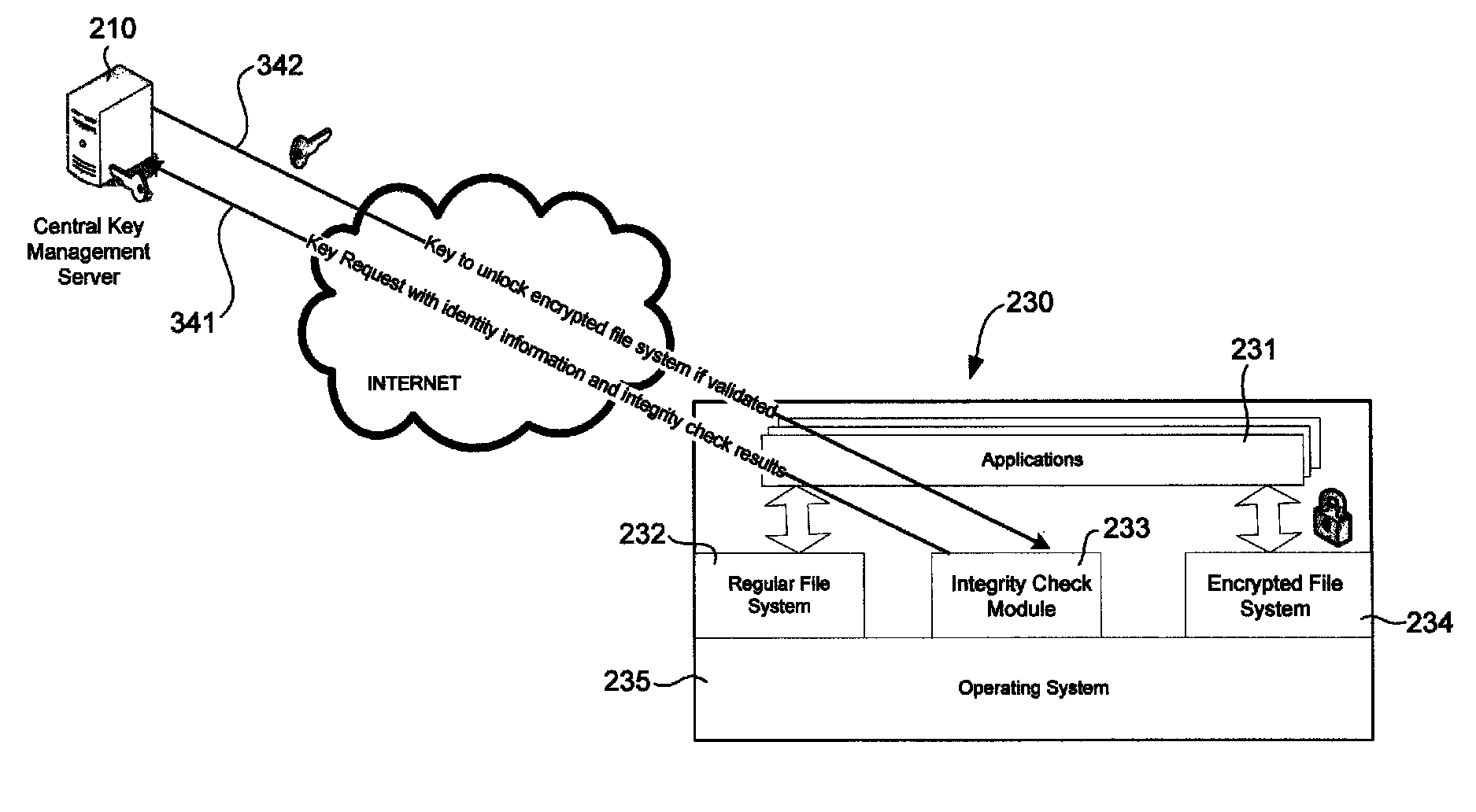
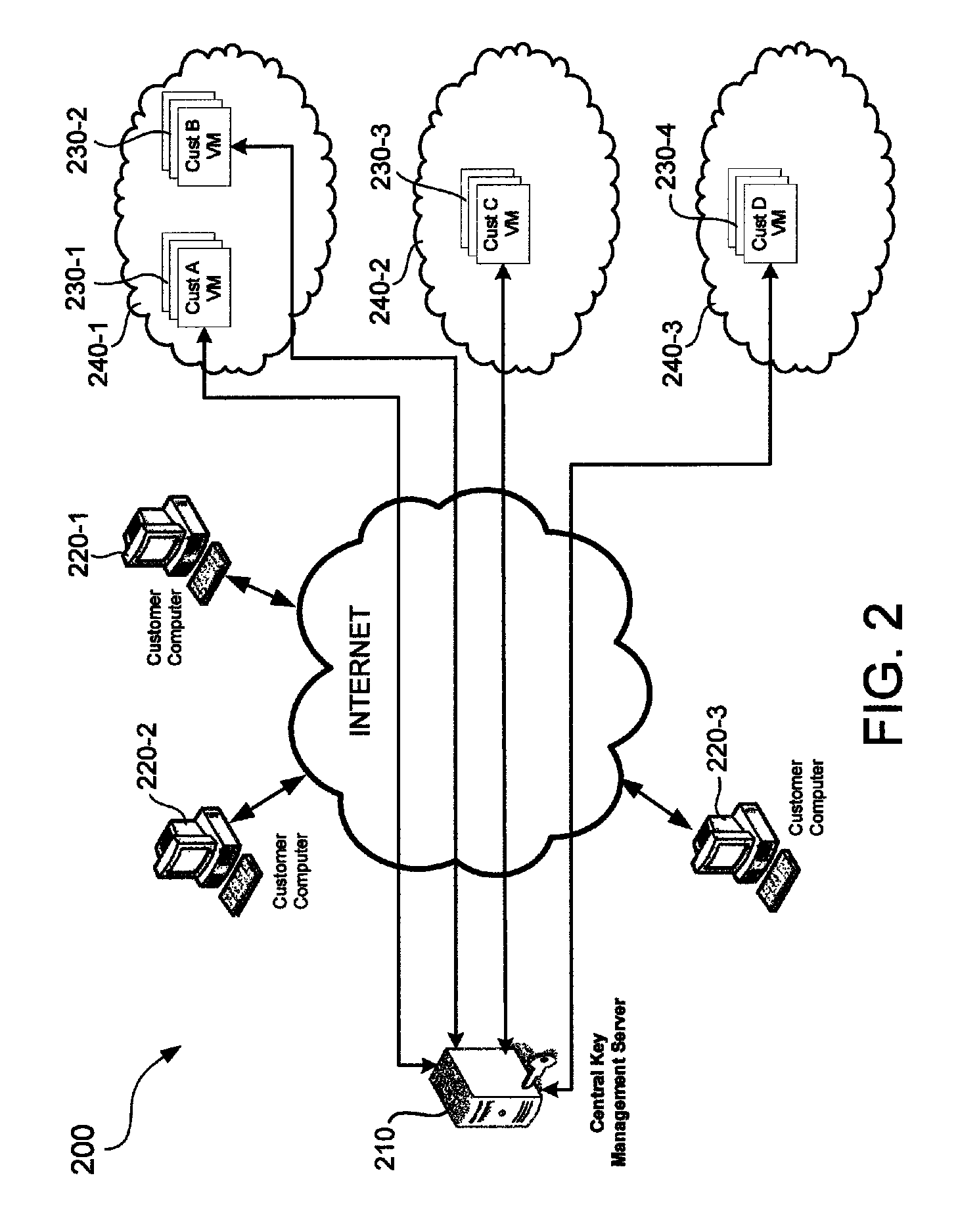
Protection of customer data in cloud virtual machines using a central management server
ActiveUS8826013B1Complete banking machinesKey distribution for secure communicationEncrypted file systemCentral management
A cloud computing environment includes a key management server and a cloud computer system running several virtual machines. A virtual machine hosted by the cloud computer system includes an integrity check module for checking the integrity of the virtual machine and getting identity information of the virtual machine. The integrity check module sends a key request to a key management server, which provides key service to different cloud computer systems. The key management server validates the request and, if the request is valid, provides the key to the virtual machine. The key is used to unlock an encrypted file system in the virtual machine.
Owner:TREND MICRO INC
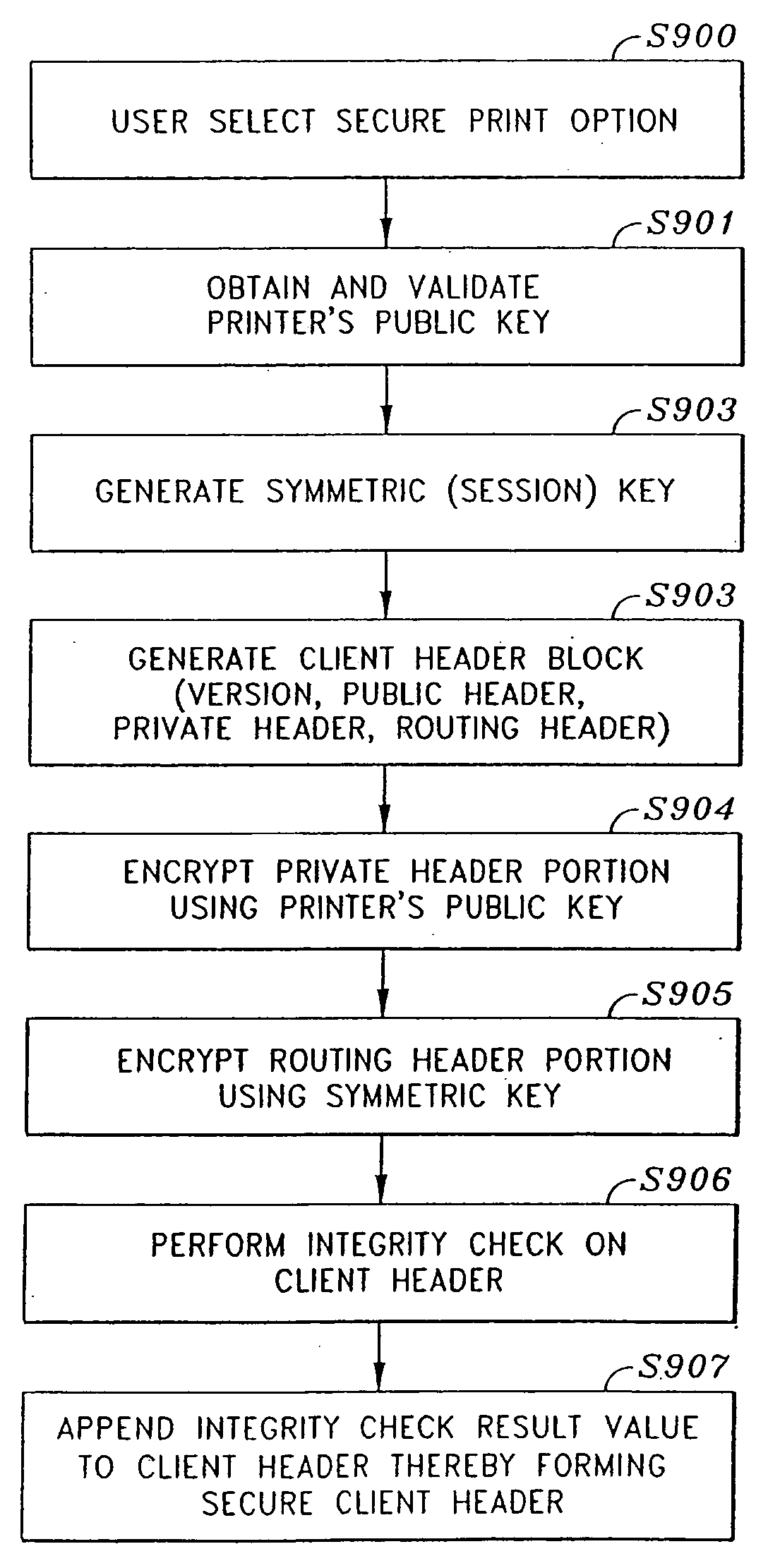
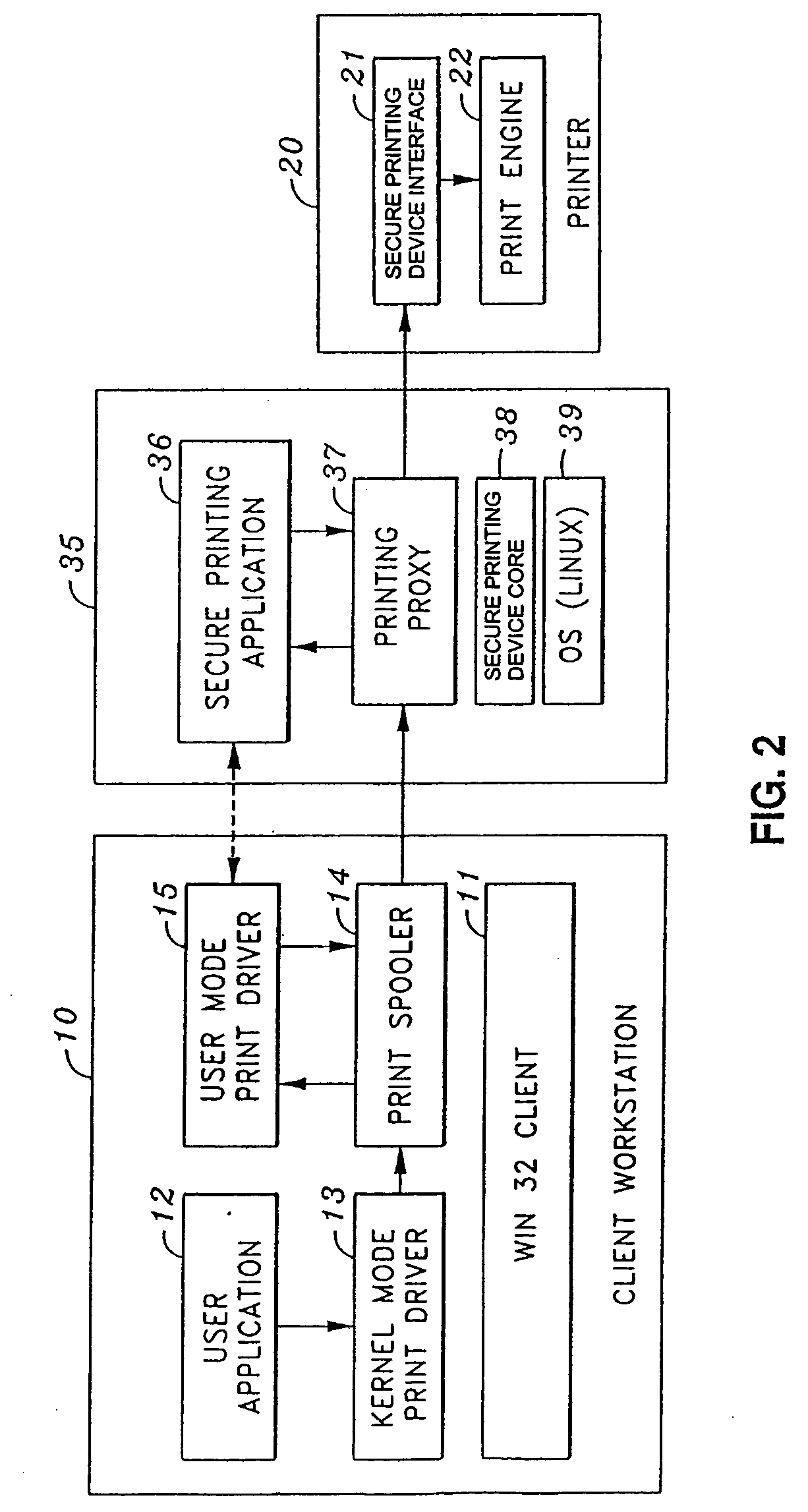
Secure file format
A file format for a secure file for use with a block cipher or a stream cipher, the secure file having a secure client header and a data block appended to the secure client header. The client header has a client information block comprised of a public information block, a private information block and an initialization vector. At least a portion of the private information block is encrypted, and a client information block integrity check value is appended to the client information block, the client information block integrity check value being obtained by performing an integrity check on the client information block. The data block is preferably encrypted and is comprised of a plurality of encrypted data blocks each appended with its own respective integrity check result value. Each of the plurality of data blocks and their respective integrity check result values are obtained by dividing the encrypted data block into n encrypted data blocks, performing an integrity check on a first one of the n encrypted data blocks and the client information integrity check result value appended to the client information block, so as to obtain a first encrypted data block integrity check result value, appending the first encrypted data block integrity check result value to the first encrypted data block, and repeatedly performing, for each of the subsequent n encrypted data blocks, an integrity check on the subsequent encrypted data block and an integrity check result value appended to a previous one of the n encrypted data blocks, so as to obtain an integrity check result value for the subsequent encrypted data block, and appending the subsequent integrity check result value to the subsequent encrypted data block.
Owner:CANON KK
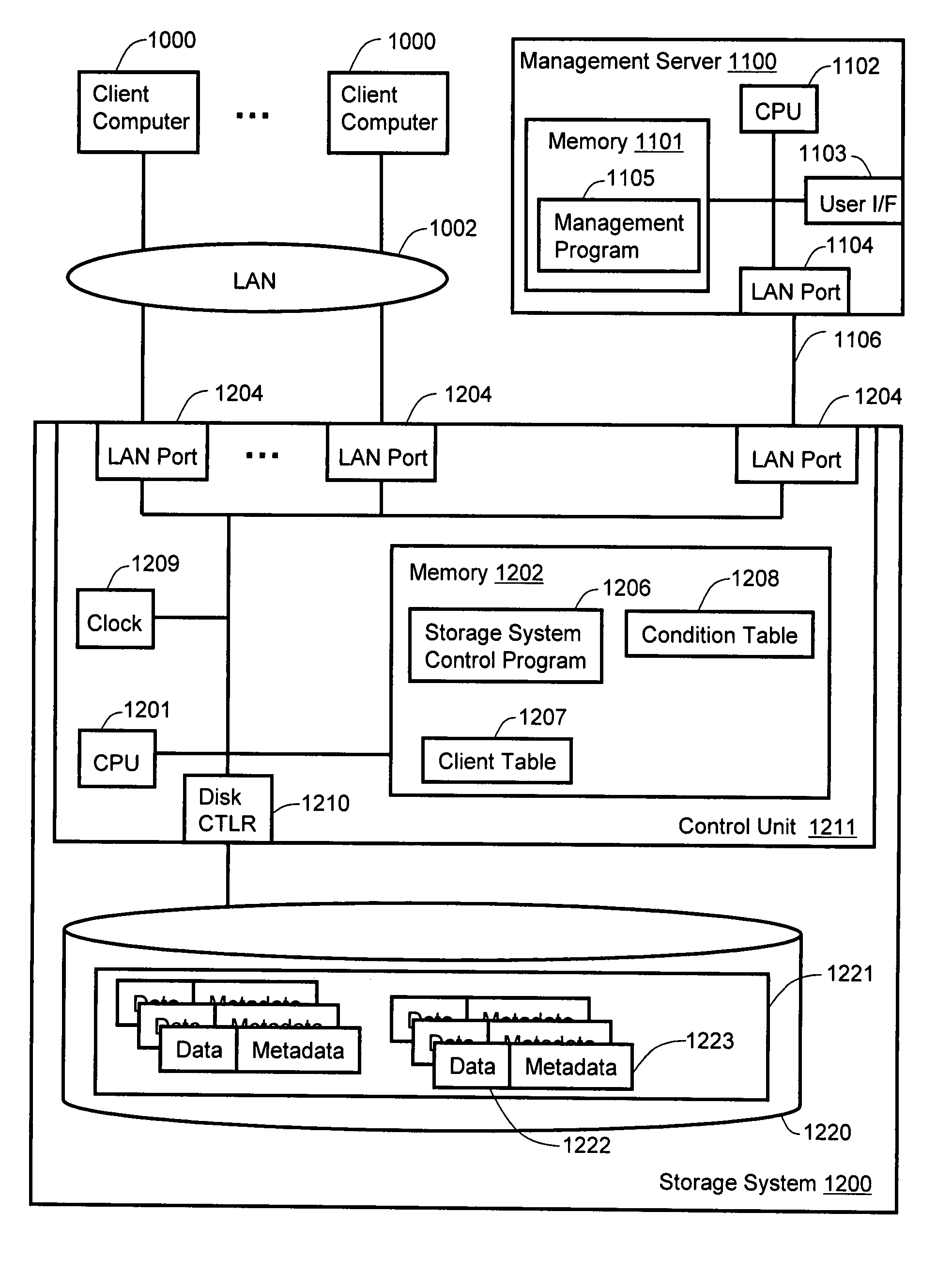
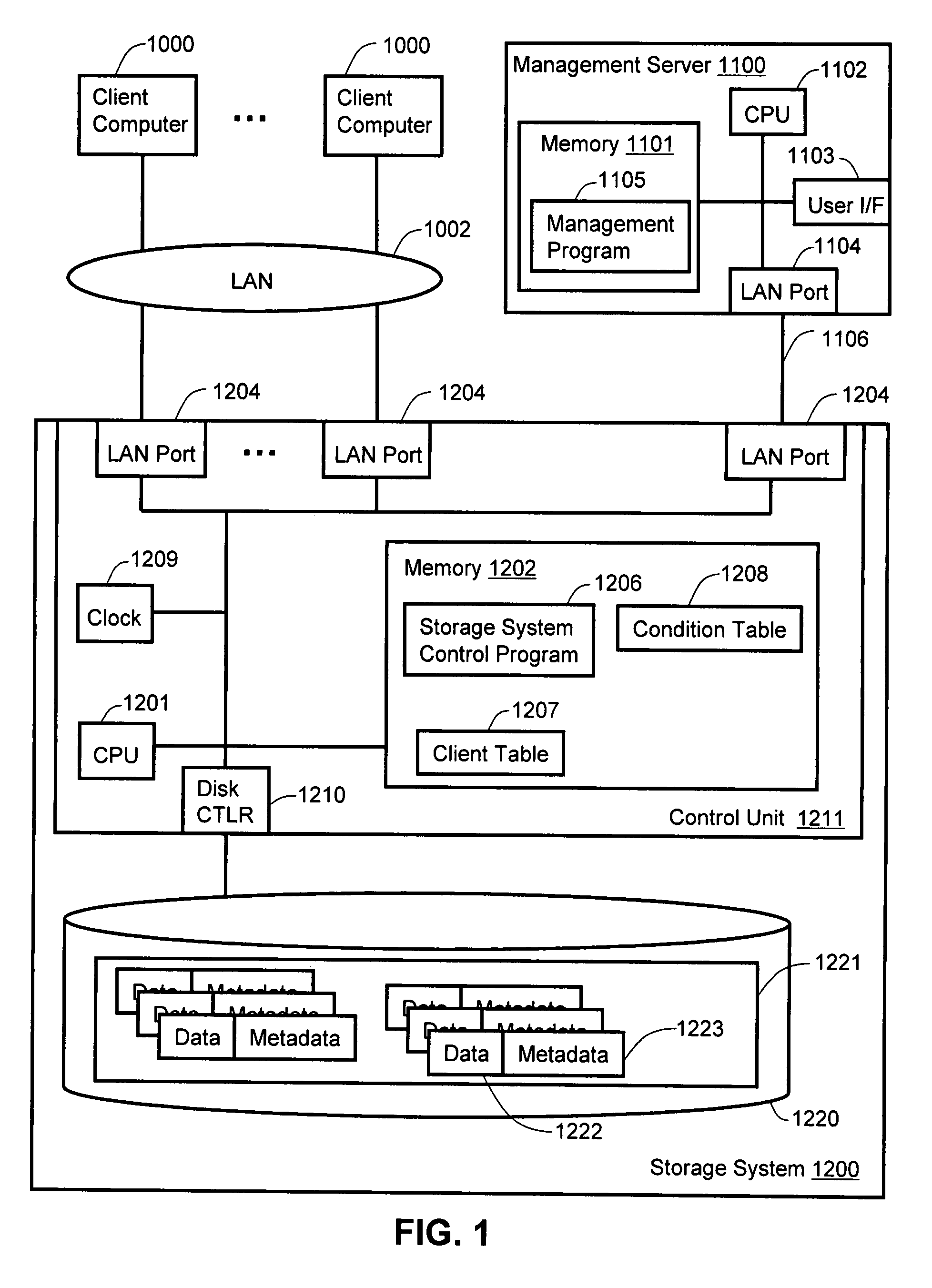
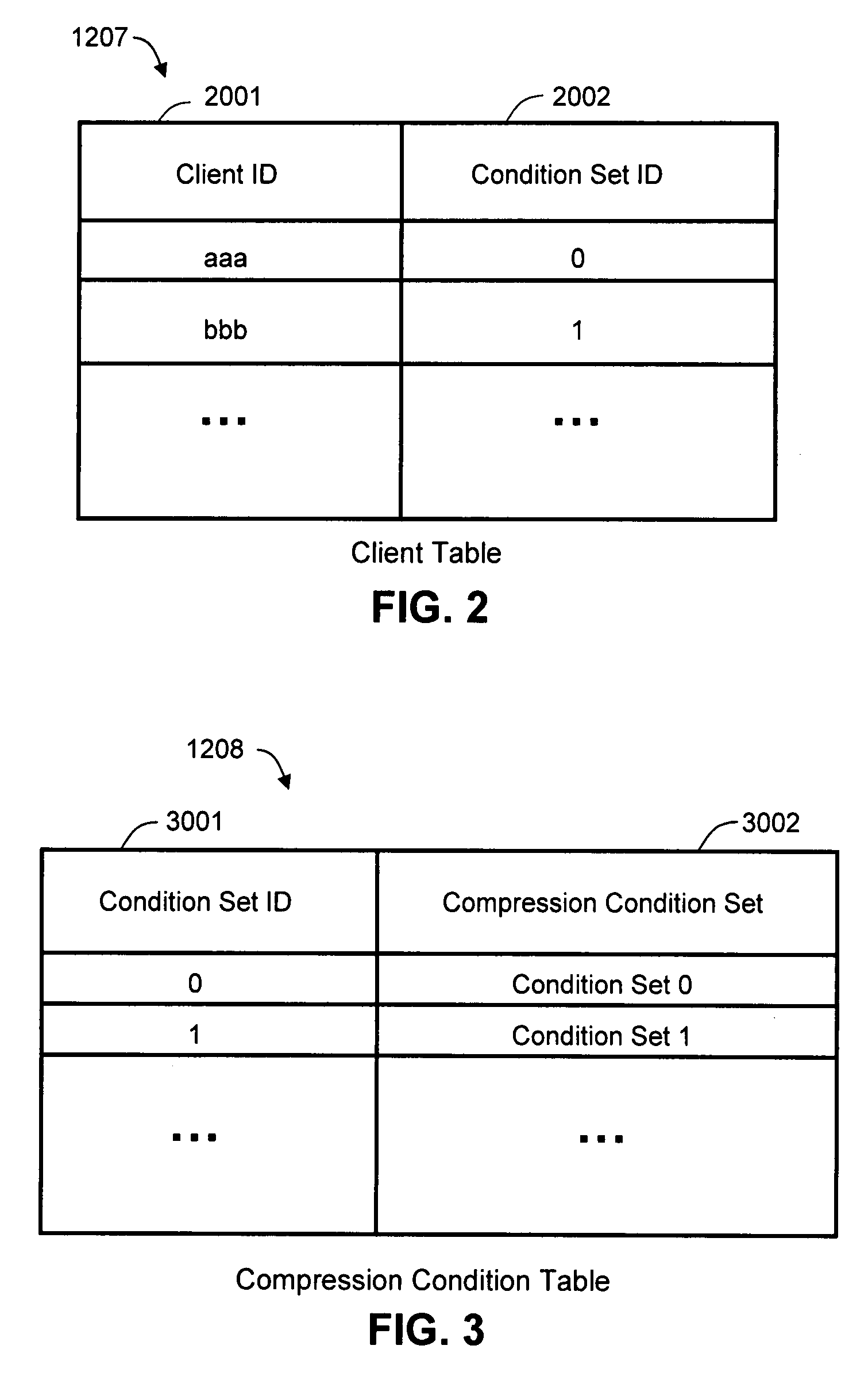
Method and apparatus for managing data compression and integrity in a computer storage system
A storage system stores discrete data units and corresponding metadata. The storage system receives data for storage, calculates a first hash value for the data, and identifies a set of compression conditions that correspond to a client ID associated with the data. When the compression conditions indicate that the data should be compressed, the data is compressed to create compressed data. Following compression of the data, the storage system calculates a second hash value for the compressed data, and stores the second hash value in the metadata, while also retaining the first hash value in the metadata. The storage system stores the compressed data, and deletes the uncompressed version of the data. An integrity check of the data stored in the storage system can be carried out periodically using the first or second hash values contained in metadata for each discrete data unit.
Owner:HITACHI LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com