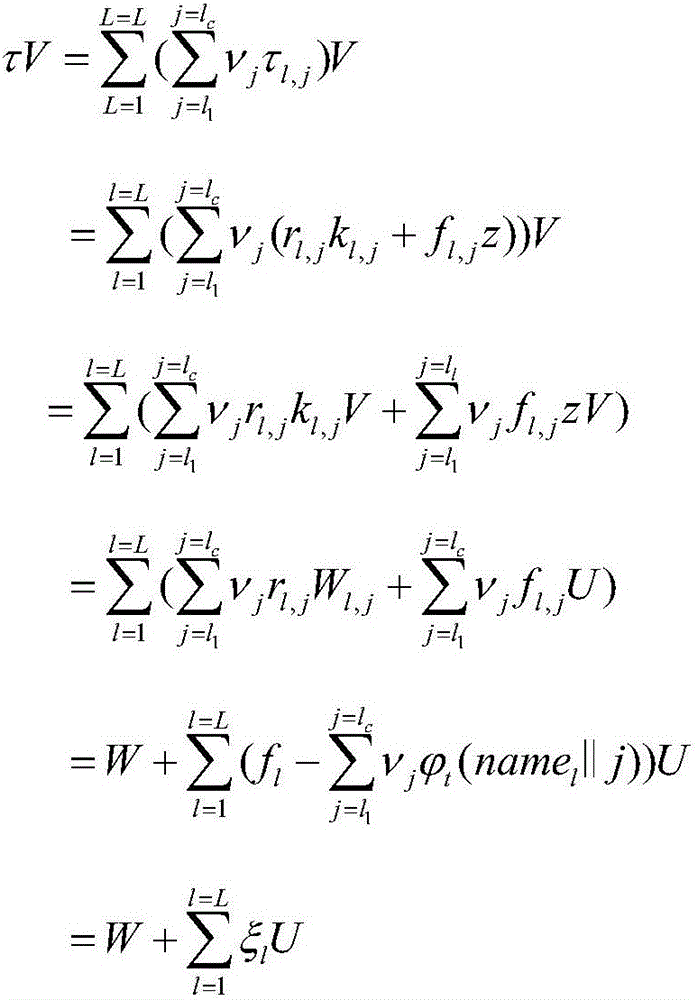Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
243results about How to "Verify integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
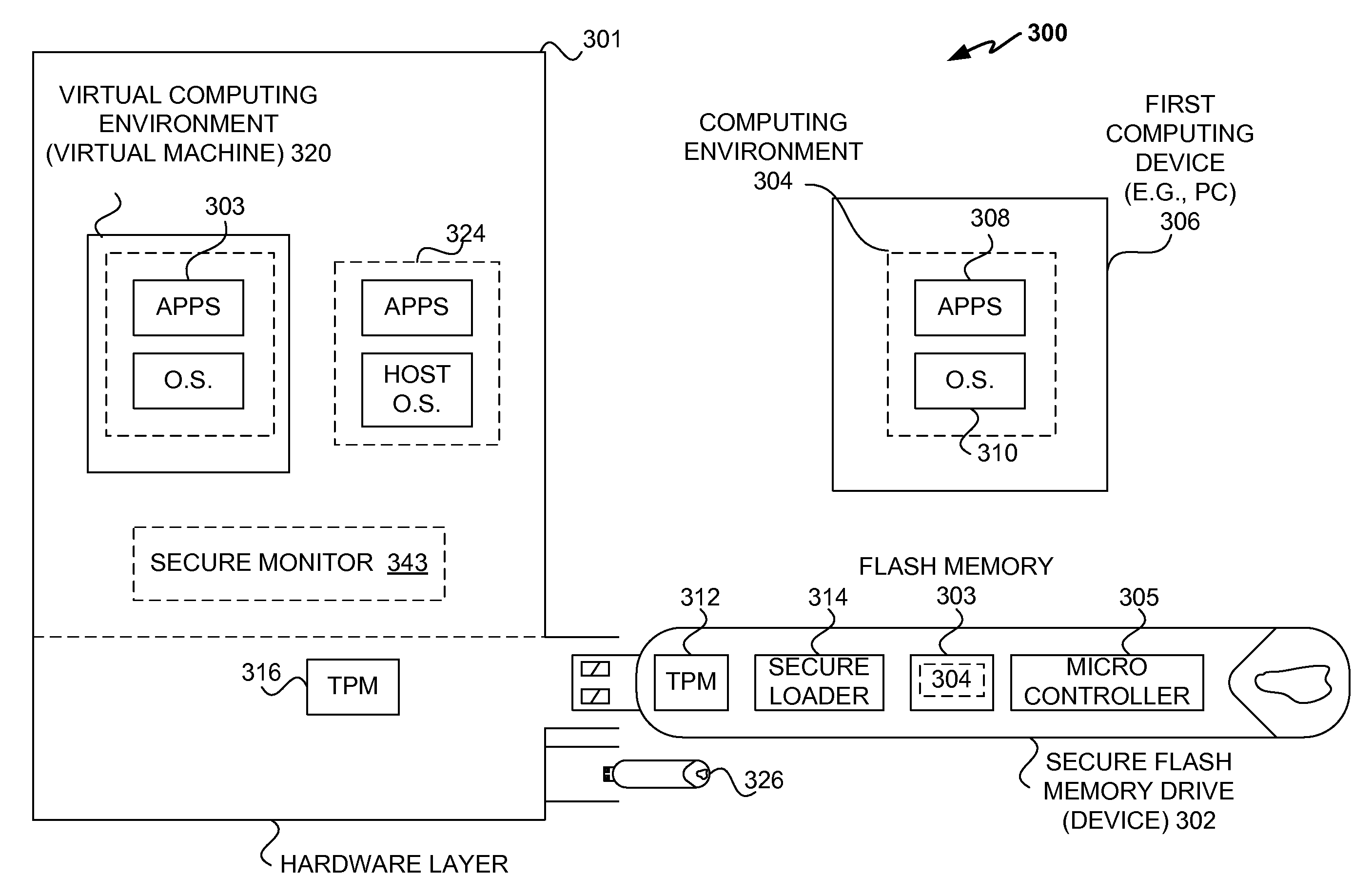
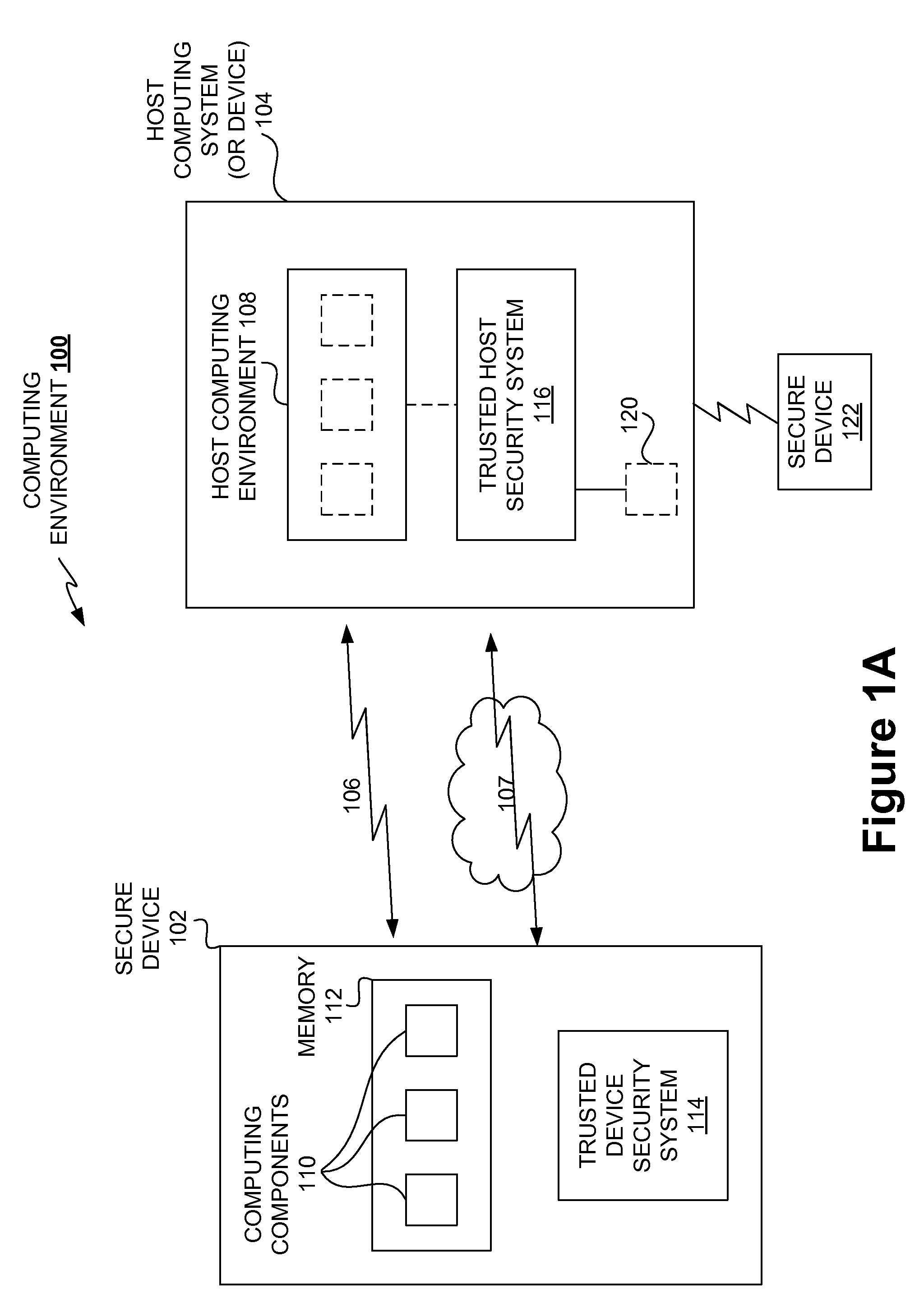
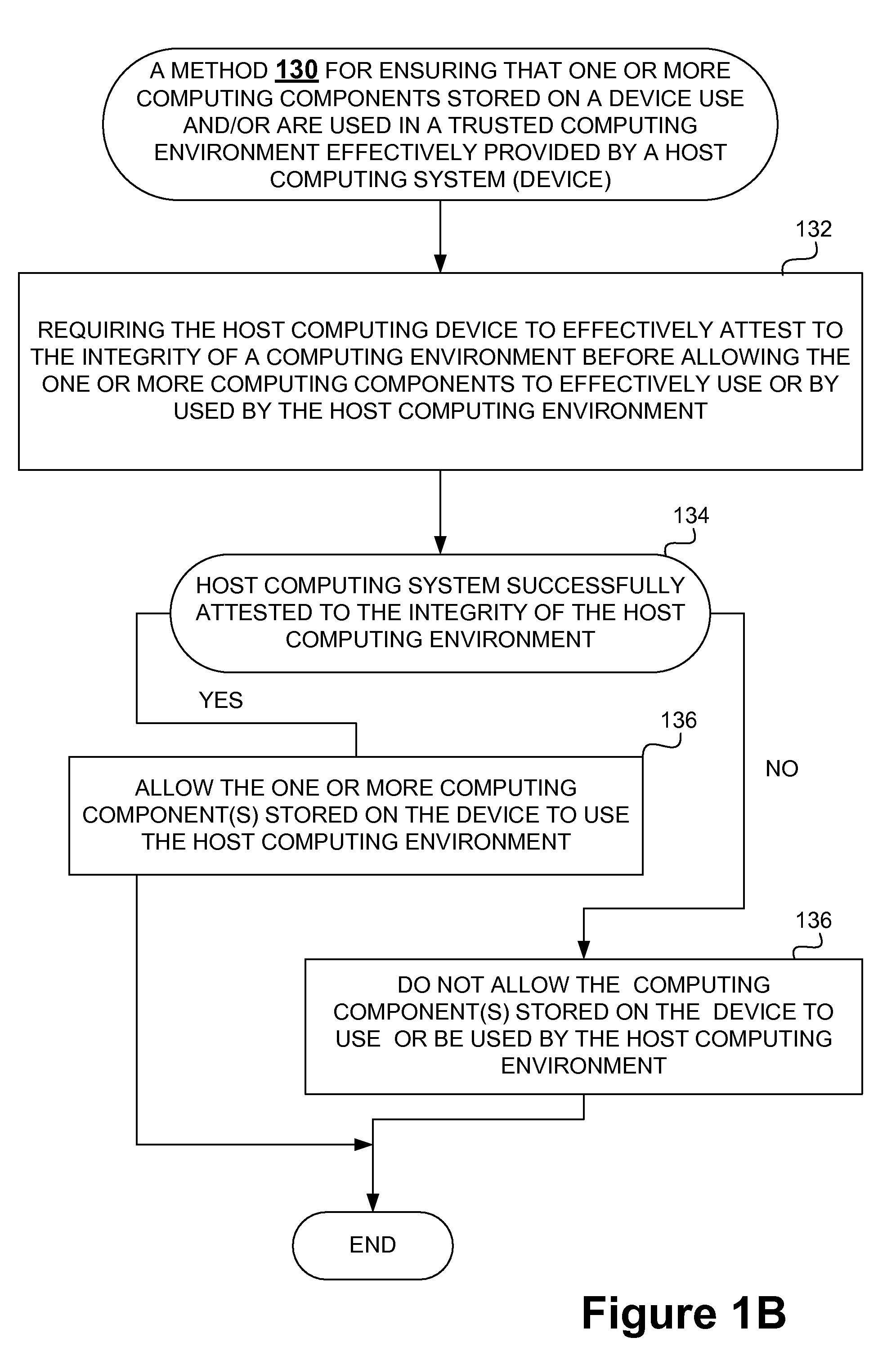
Securing stored content for trusted hosts and safe computing environments
InactiveUS20090049510A1Safe computing environmentEasy to usePublic key for secure communicationDigital data processing detailsHosting environmentComputer science
Techniques for protecting content to ensure its use in a trusted environment are disclosed. The stored content is protected against harmful and / or defective host (or hosted) environments. A trusted security component provided for a device can verify the internal integrity of the stored content and the host before it allows the content to come in contact with the host. As a counter part, a trusted security component provided for the host can verify and attest to the integrity of the host and / or specific host computing environment that can be provided for the content stored in the device. The trusted security component provided for a device effectively verify the host integrity based on the information attested to by the trusted security component provided for the host. If the trusted security component trusts the host, it allows the trusted host to provide a trusted host computing environment trusted to be safe for the content stored in the device. A trusted host can effectively provide a safe virtual environment that allows a content representing a copy (or image) of an original computing environment to operate on the host computing system to give a similar appearance as the original computing environment.
Owner:SAMSUNG ELECTRONICS CO LTD
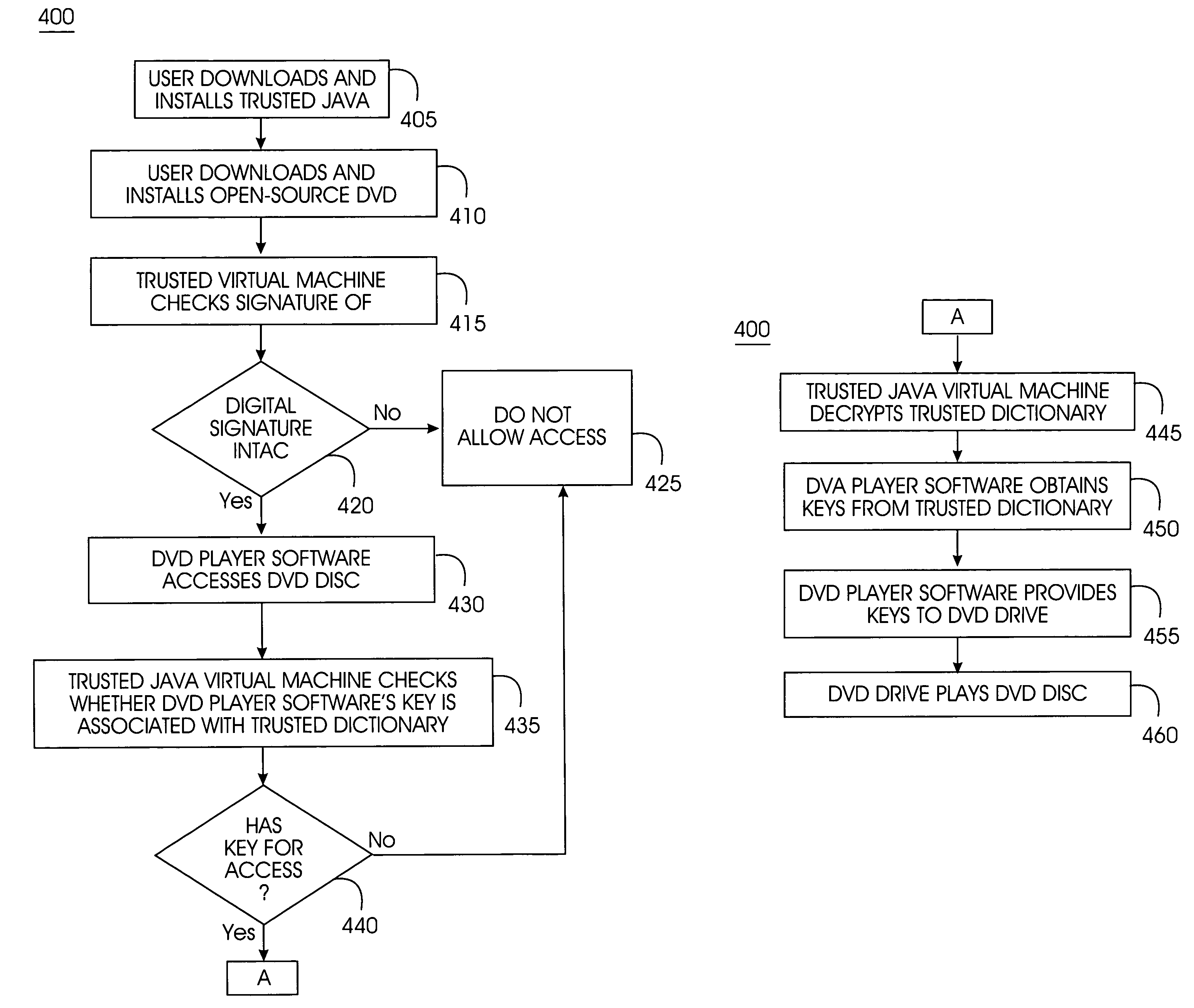
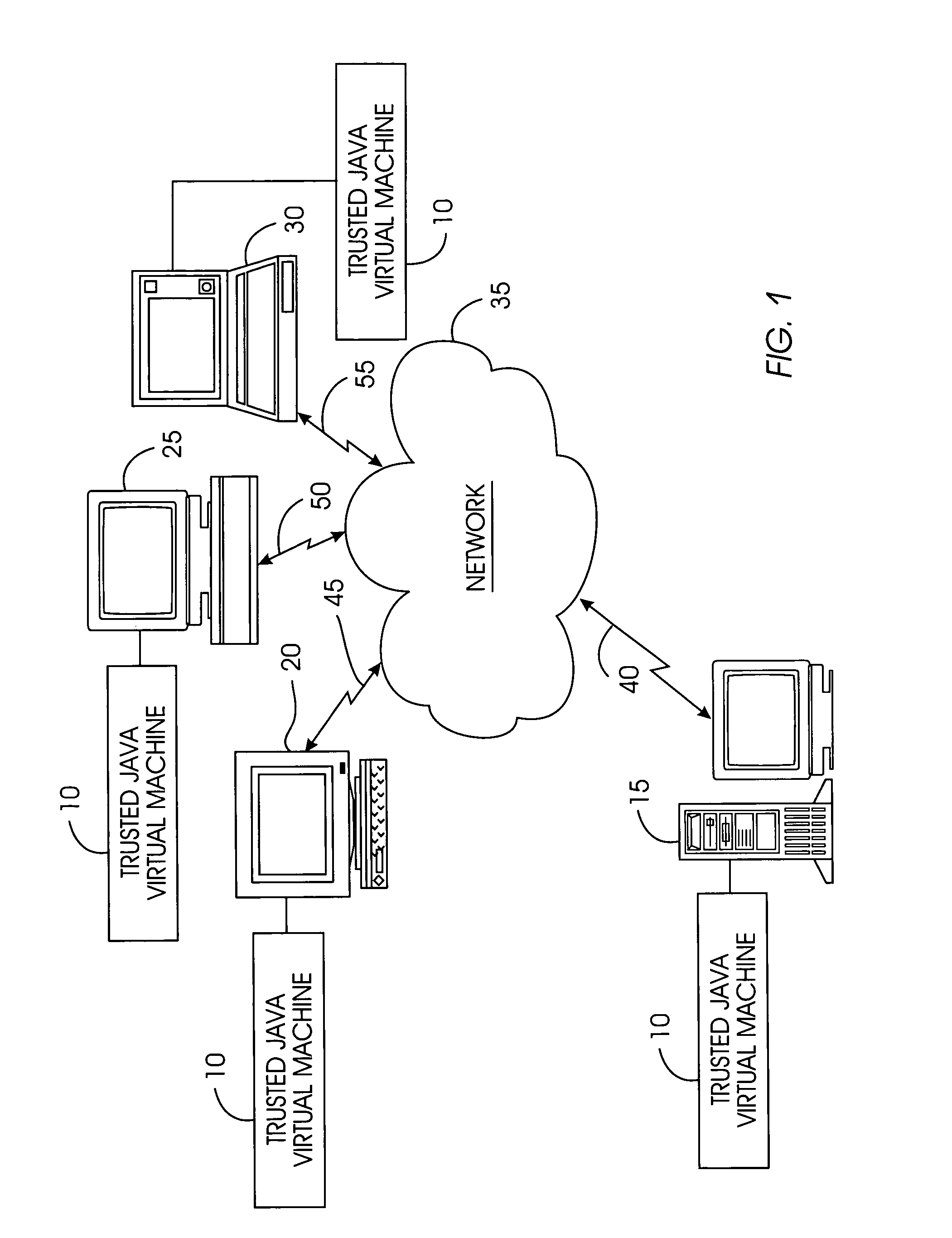
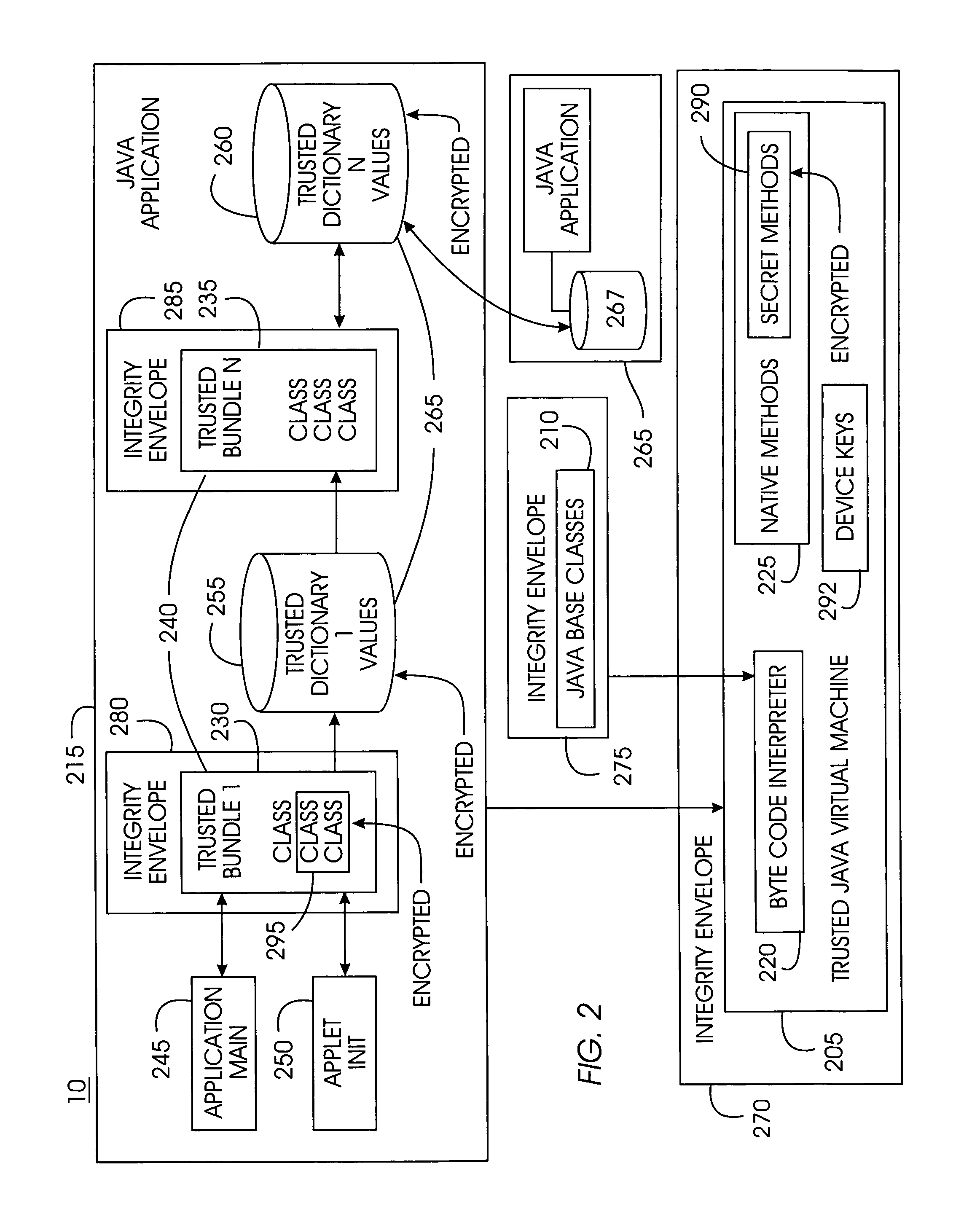
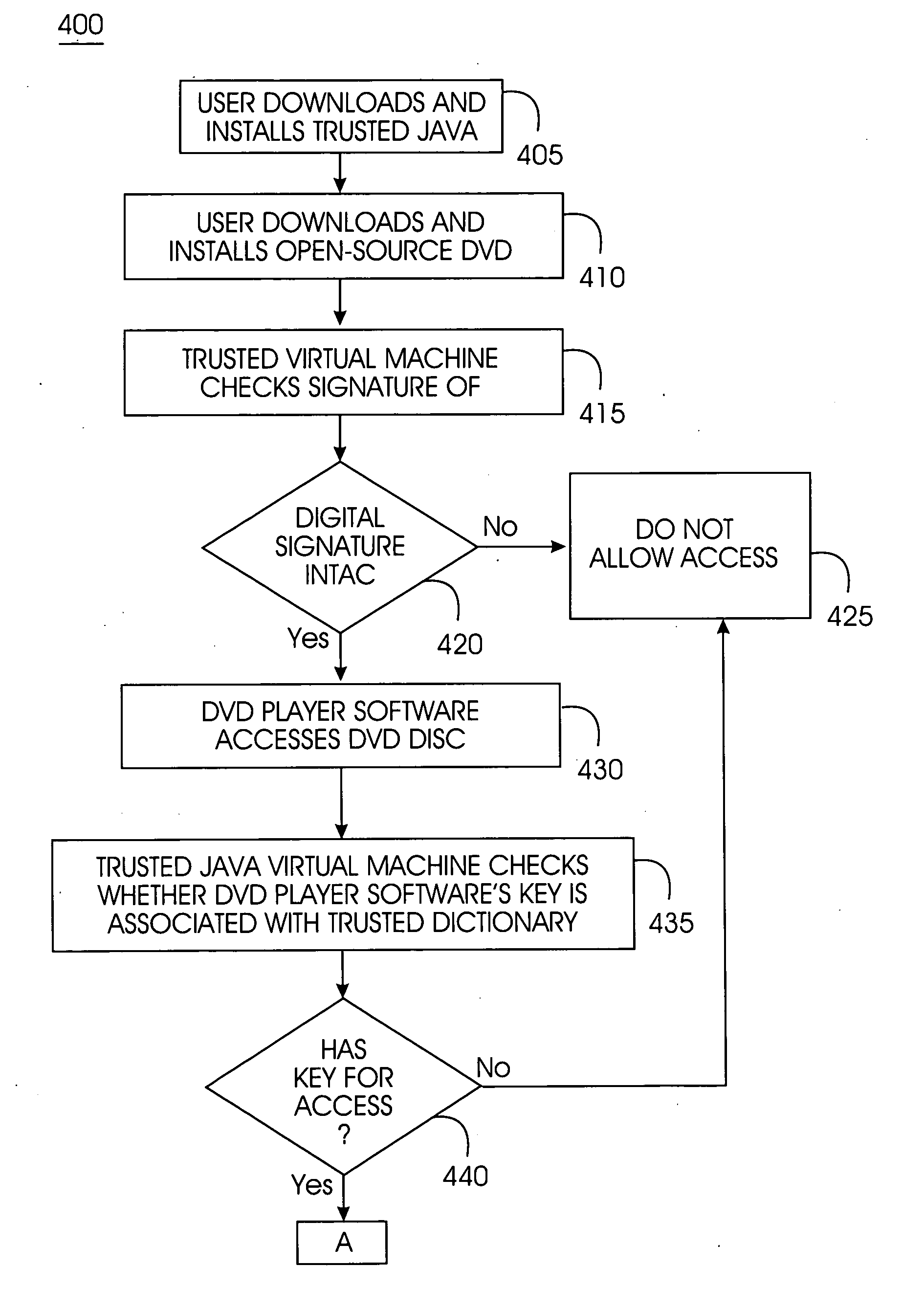
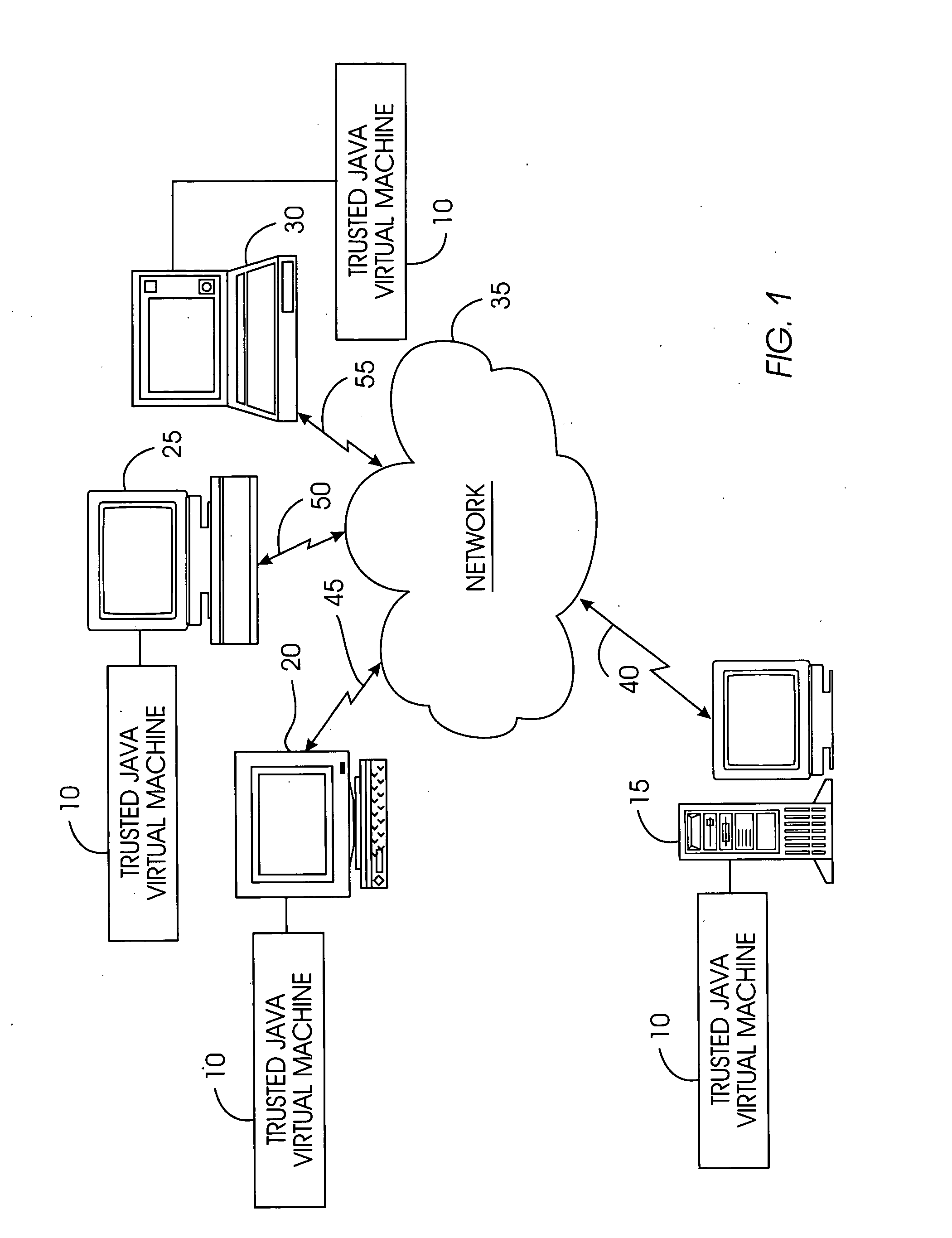
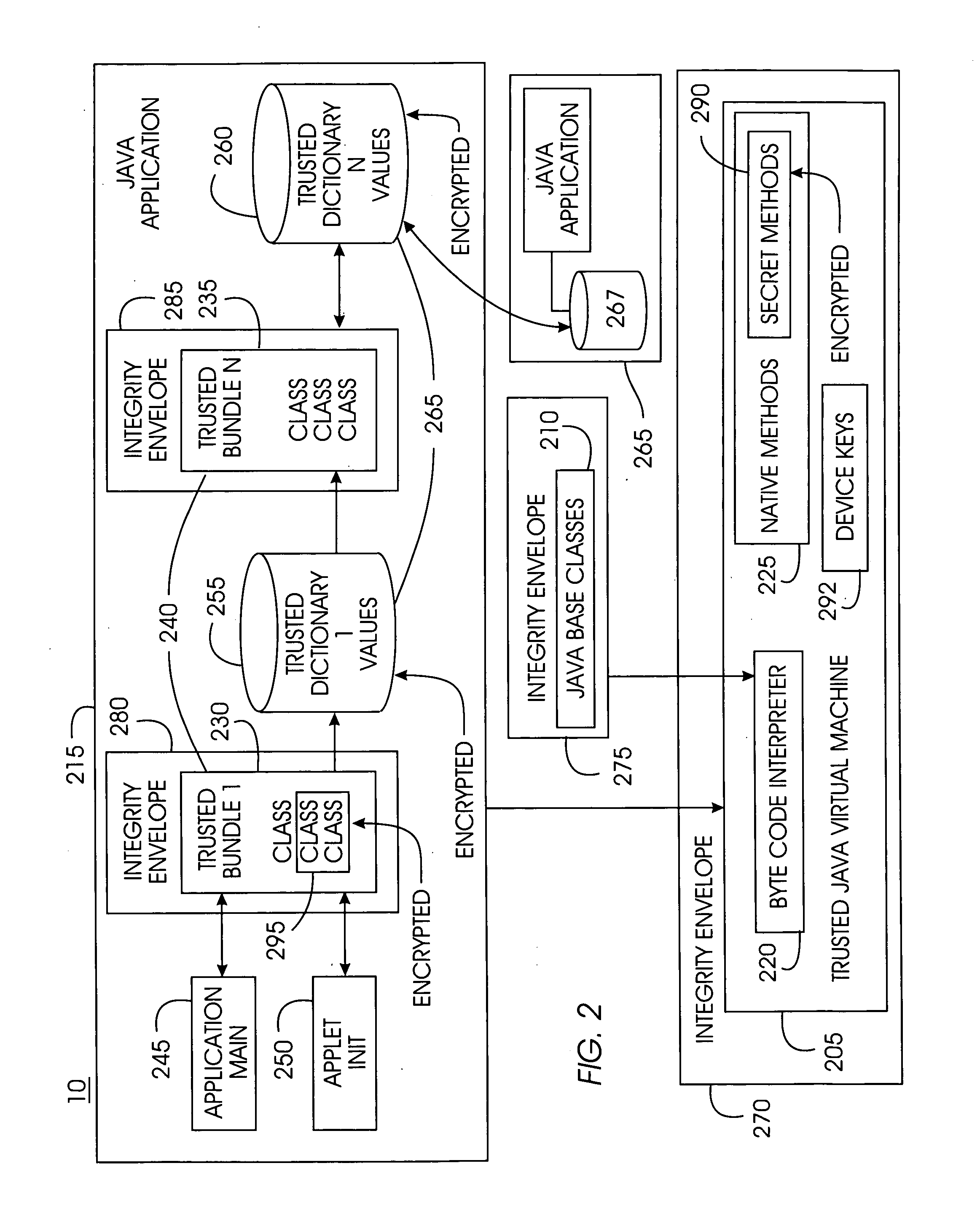
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS7516331B2Slow processEnsure integrityProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:INT BUSINESS MASCH CORP
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS20050114683A1Easy to processSatisfies needProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:IBM CORP
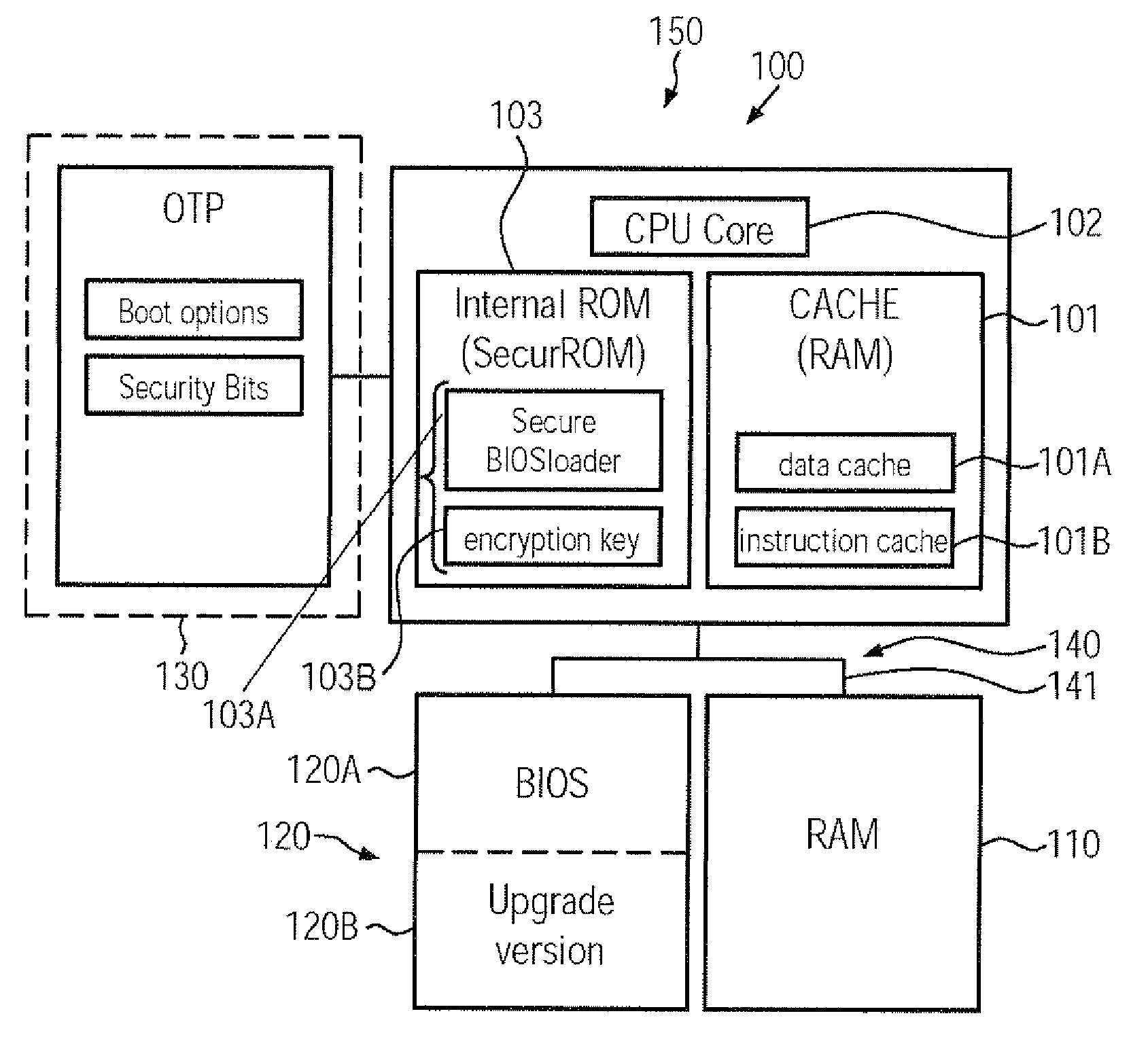
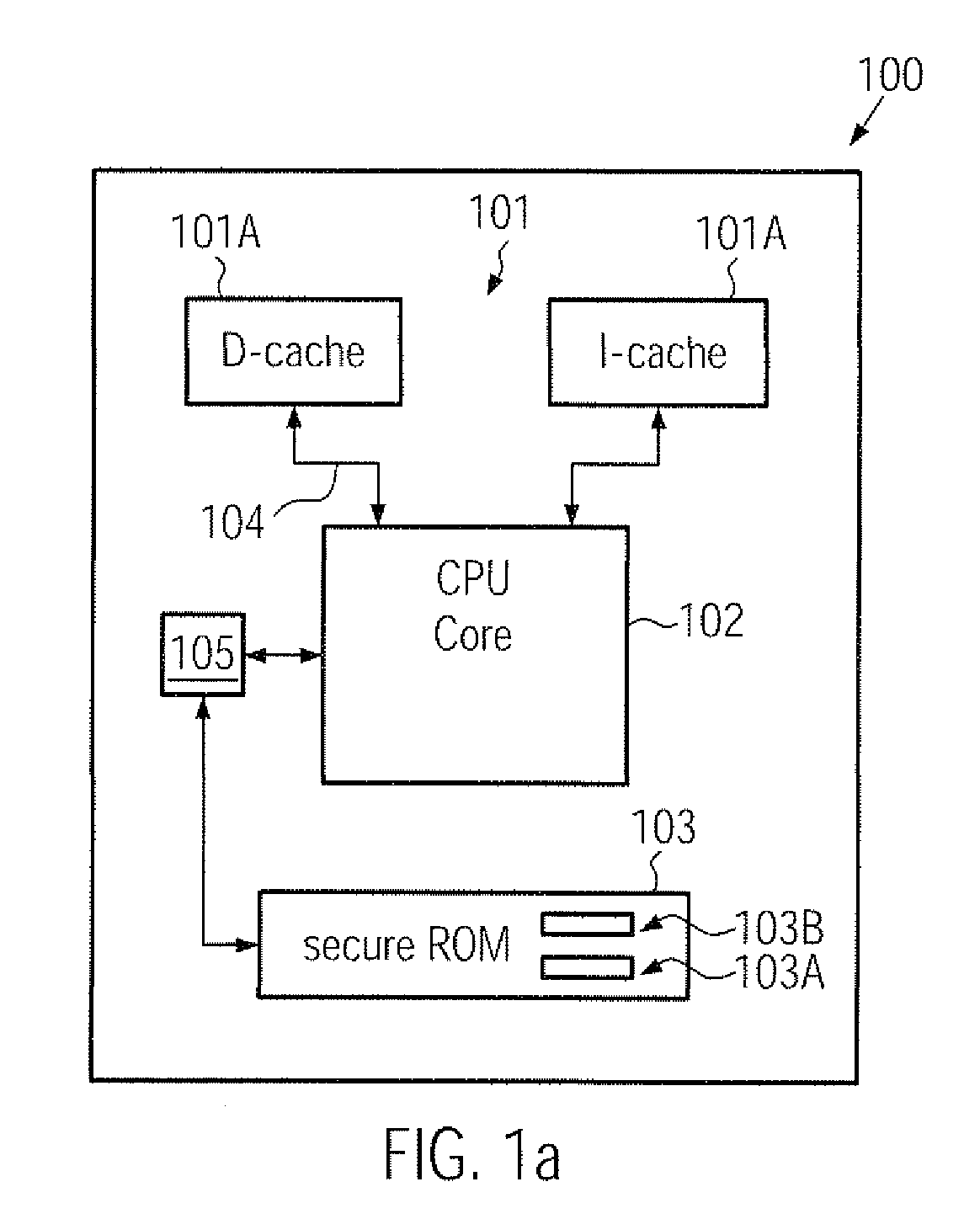
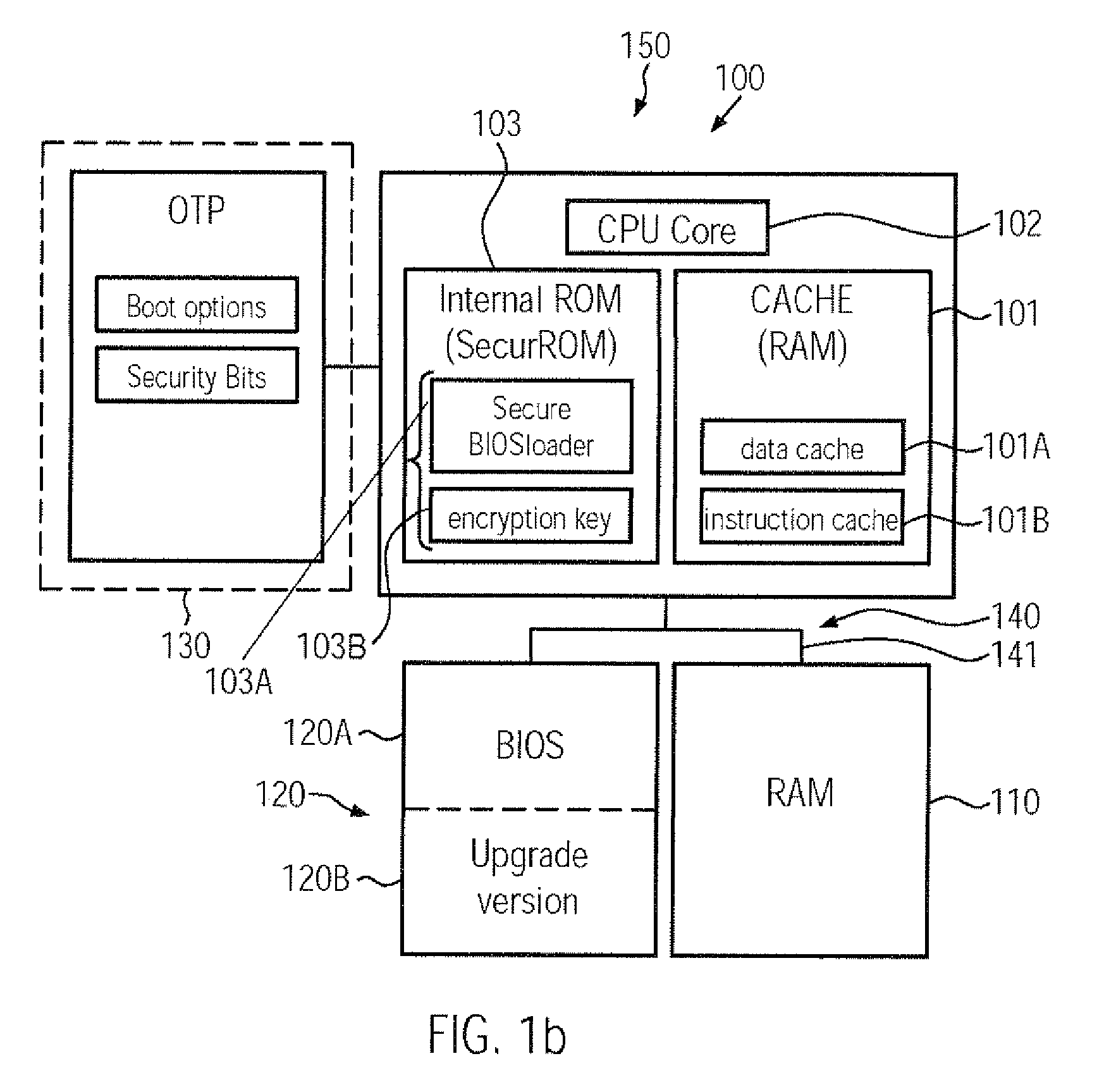
Computer system comprising a secure boot mechanism on the basis of symmetric key encryption
ActiveUS20090276617A1Improve integrityHigh protection levelUser identity/authority verificationDigital computer detailsCryptographic key generationComputerized system
A CPU, a computer system and a secure boot mechanism are provided in which a symmetric encryption key may be incorporated into a non-volatile memory area of the CPU core, thereby substantially avoiding any tampering of the encryption key by external sources. Moreover, pre-boot information may be internally stored in the CPU and may be retrieved upon a reset or power-on event in order to verify a signed boot information on the basis of the internal symmetric encryption key. Furthermore, the BIOS information may be efficiently updated by generating a signature using the internal encryption key.
Owner:MEDIATEK INC
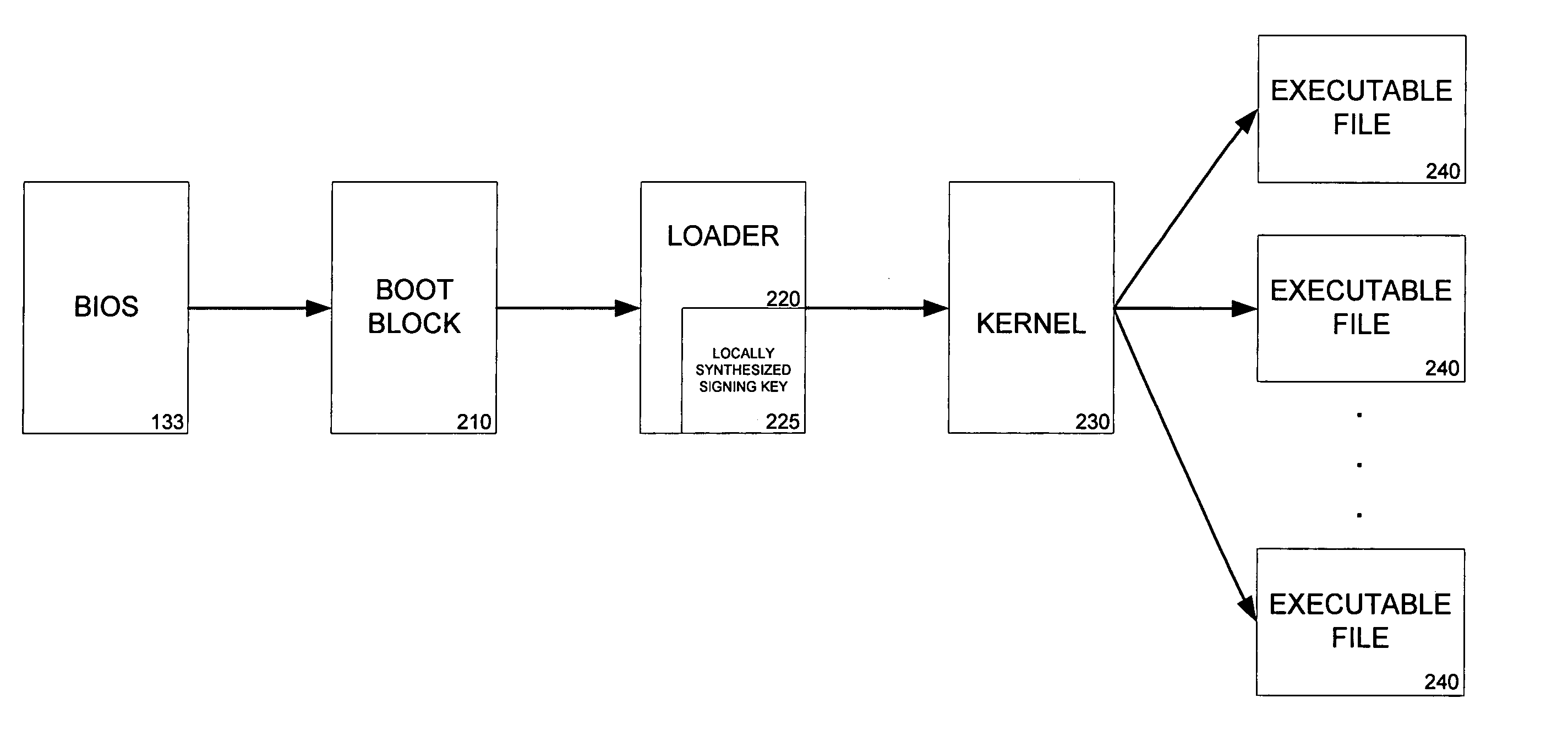
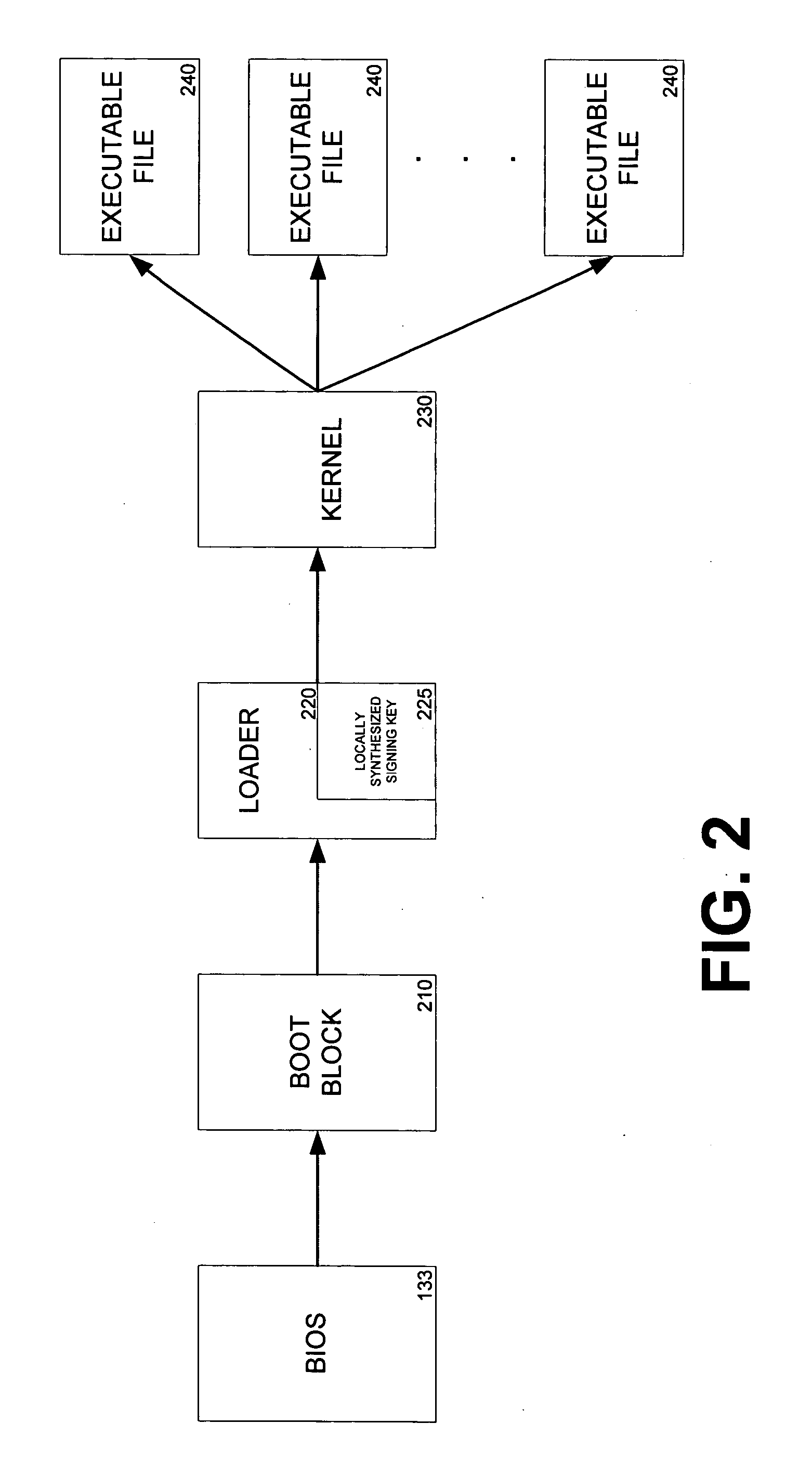
Secure boot
InactiveUS20060236122A1Verify integrityProgram control using stored programsUnauthorized memory use protectionOperational systemExecution control
Systems and methods for performing integrity verifications for computer programs to run on computing systems are provided. An integrity check is completed before passing execution control to the next level of an operating system or before allowing a program to run. The integrity check involves the use of a locally stored key to determine if a program has been modified or tampered with prior to execution. If the check shows that the program has not been altered, the program will execute and, during the boot process, allow execution control to be transferred to the next level. If, however, the check confirms that the program has been modified, the computing system does not allow the program to run.
Owner:MICROSOFT TECH LICENSING LLC
Methods and apparatus for facilitating a secure session between a processor and an external device
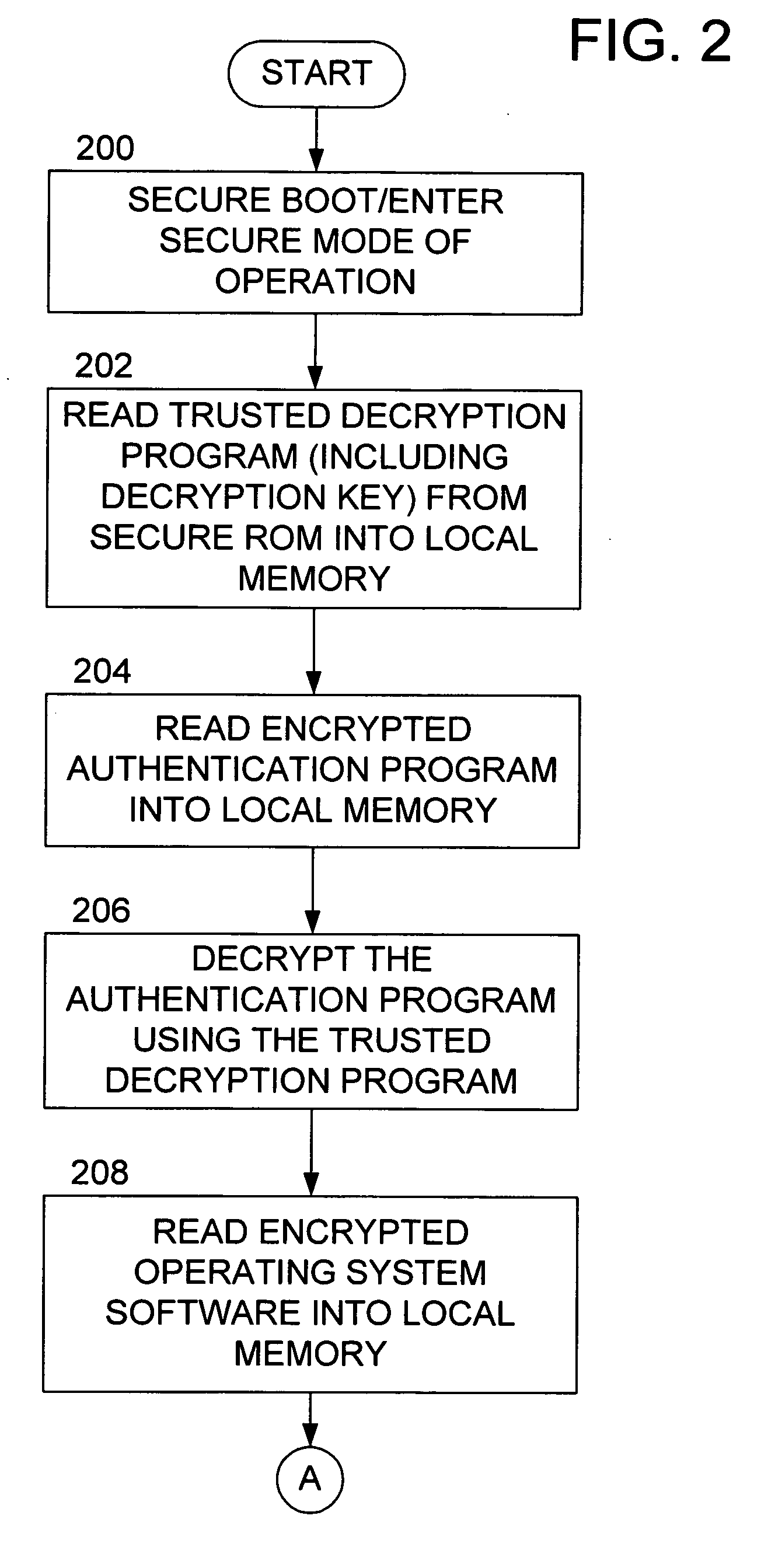
InactiveUS20060179324A1Verify integrityUnauthorized memory use protectionHardware monitoringOperational systemCourse of action
Methods and apparatus provide for verifying operating system software integrity prior to being executed by a processor, the processor including an associated local memory and capable of operative connection to a main memory such that data may be read from the main memory for use in the local memory; storing a status flag indicating whether the operating system software integrity is or is not satisfactory; and ensuring that the status flag indicates that the operating system software integrity is satisfactory before permitting the processor to continue in a course of action.
Owner:SONY COMPUTER ENTERTAINMENT INC
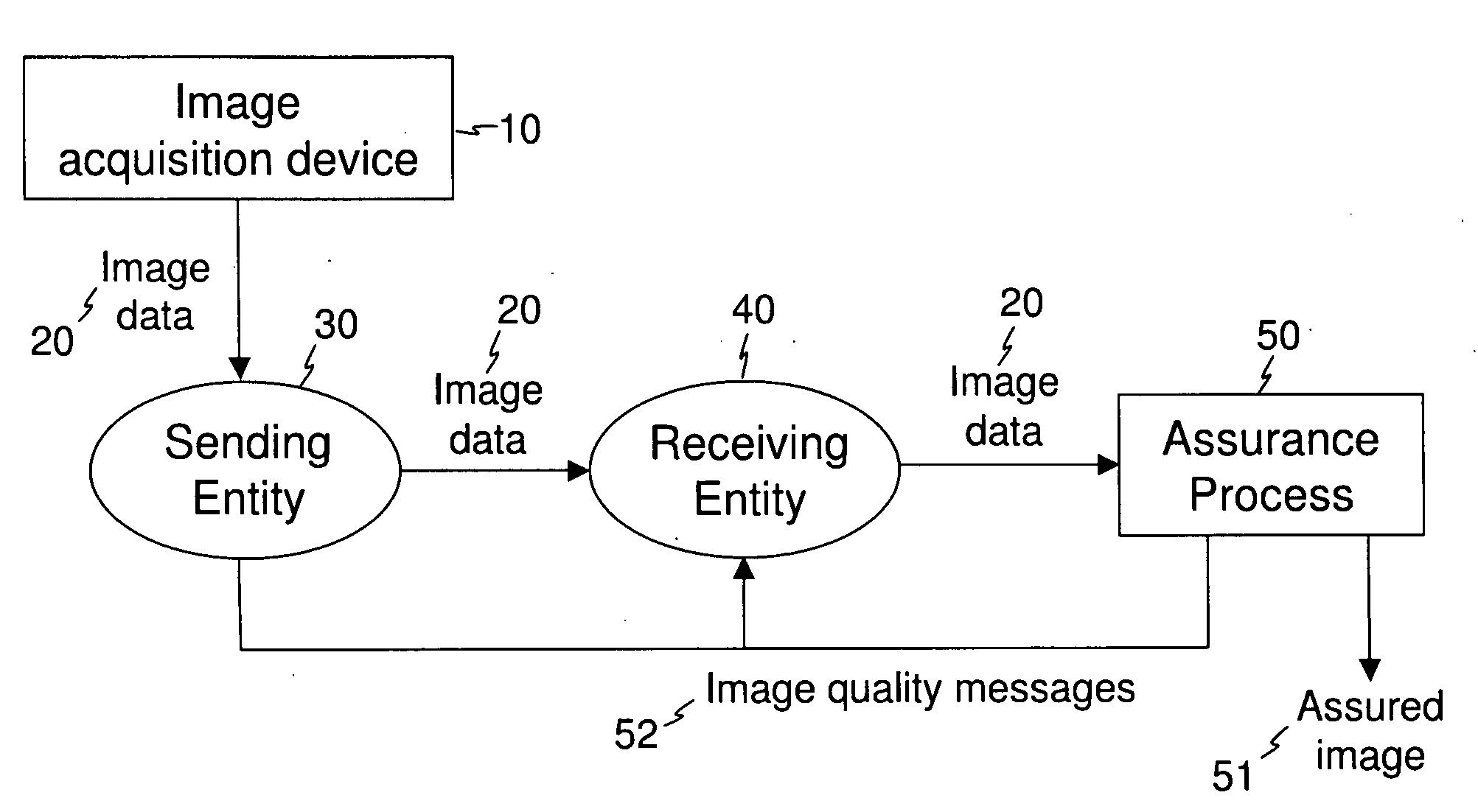
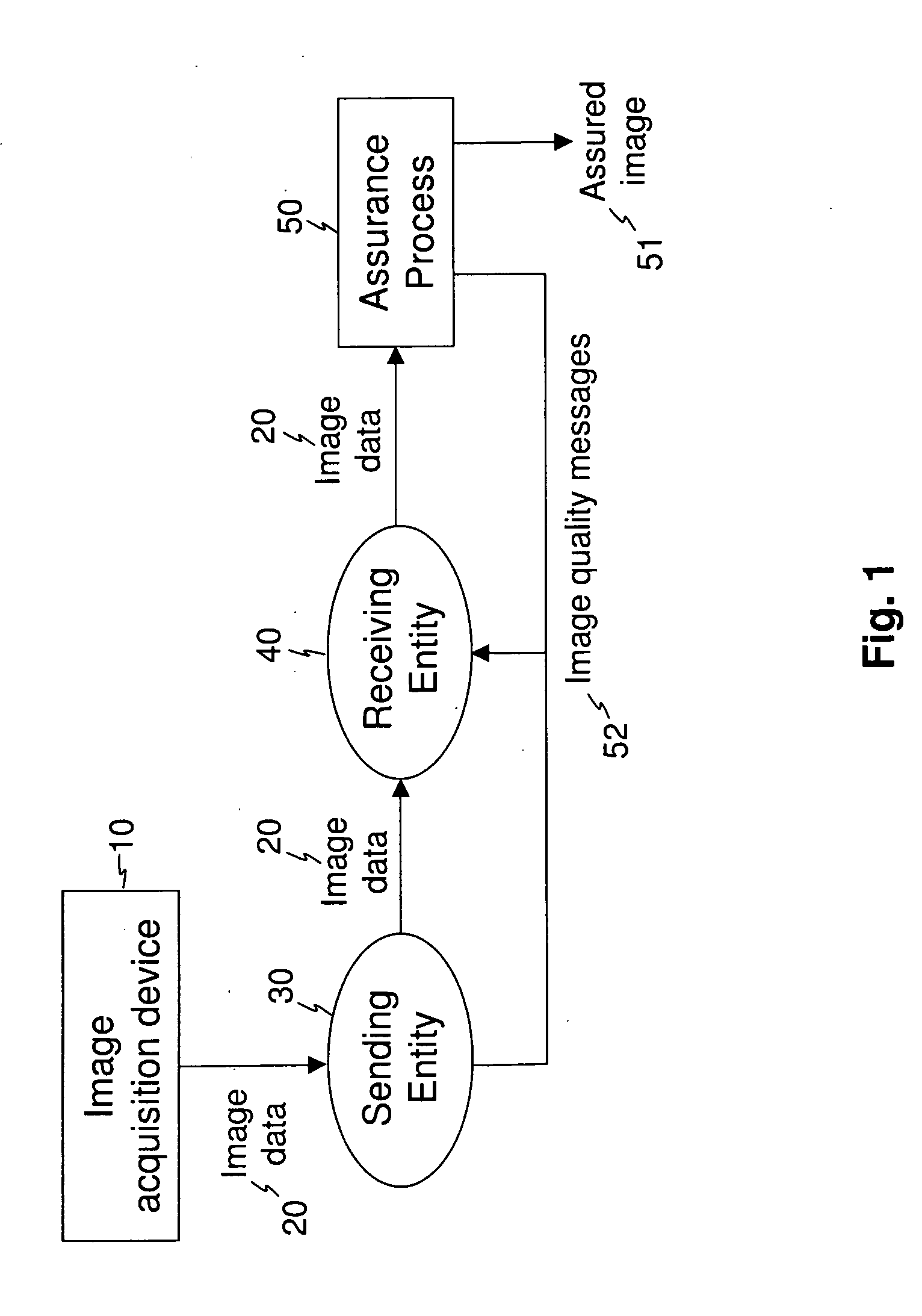
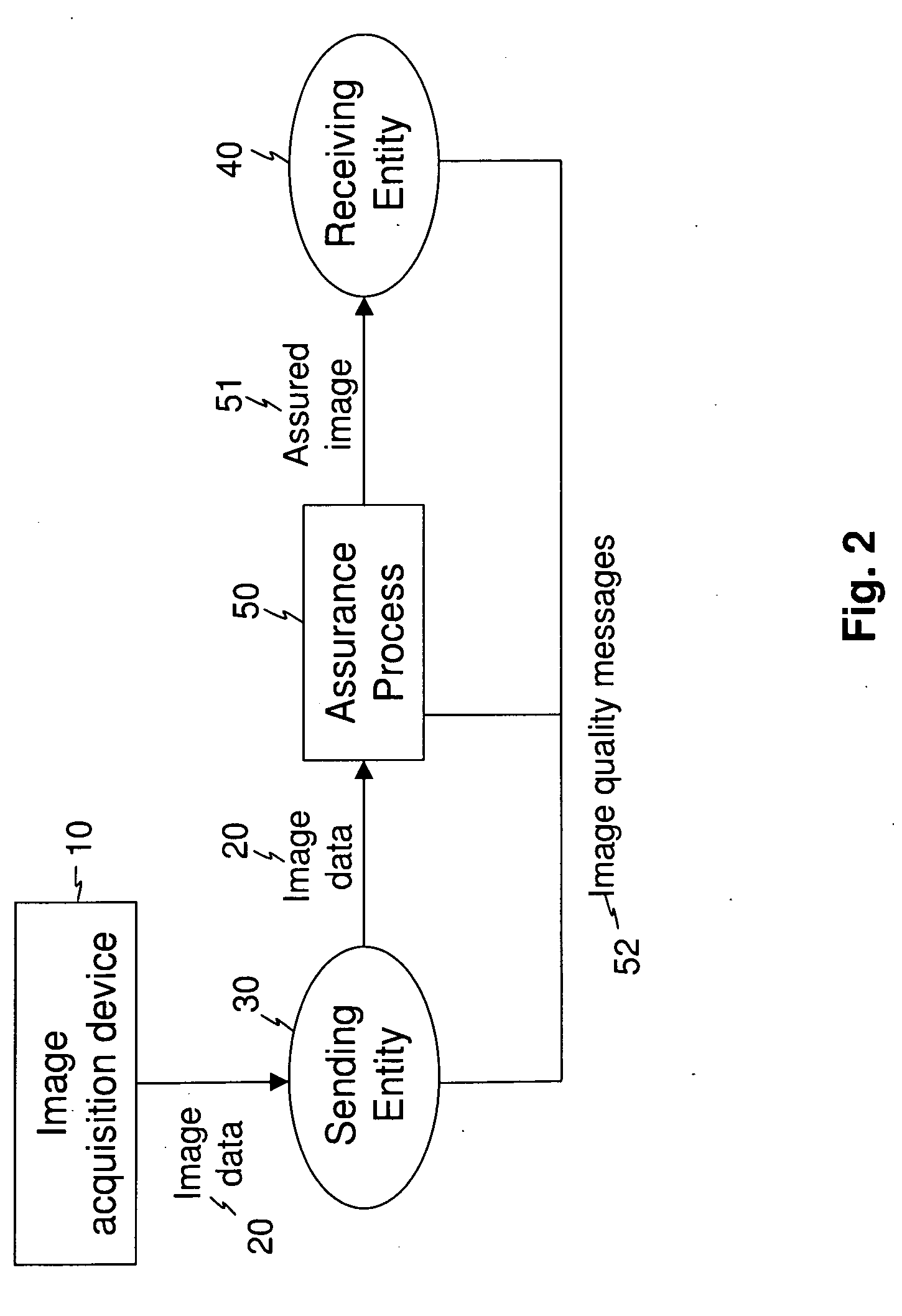
Image transfer with secure quality assessment
InactiveUS20090147988A1Verify integrityAss qualityCharacter and pattern recognitionPictoral communicationImage transferImaging quality
A method for producing an assured image from image data that is transferred from a first entity to a second entity acquires image data, transfers the acquired image data from the first entity to the second entity, forms secure assurance data according to image quality measurements obtained from the acquired image data, and forms an assured image that includes the acquired image data and the secure assurance data. At least one image quality message is generated that indicates the transfer of the acquired image data from the first entity to the second entity and is representative of the image quality measurements. The at least one image quality message is presented to at least one of the first entity and the second entity.
Owner:CERTIFI MEDIA
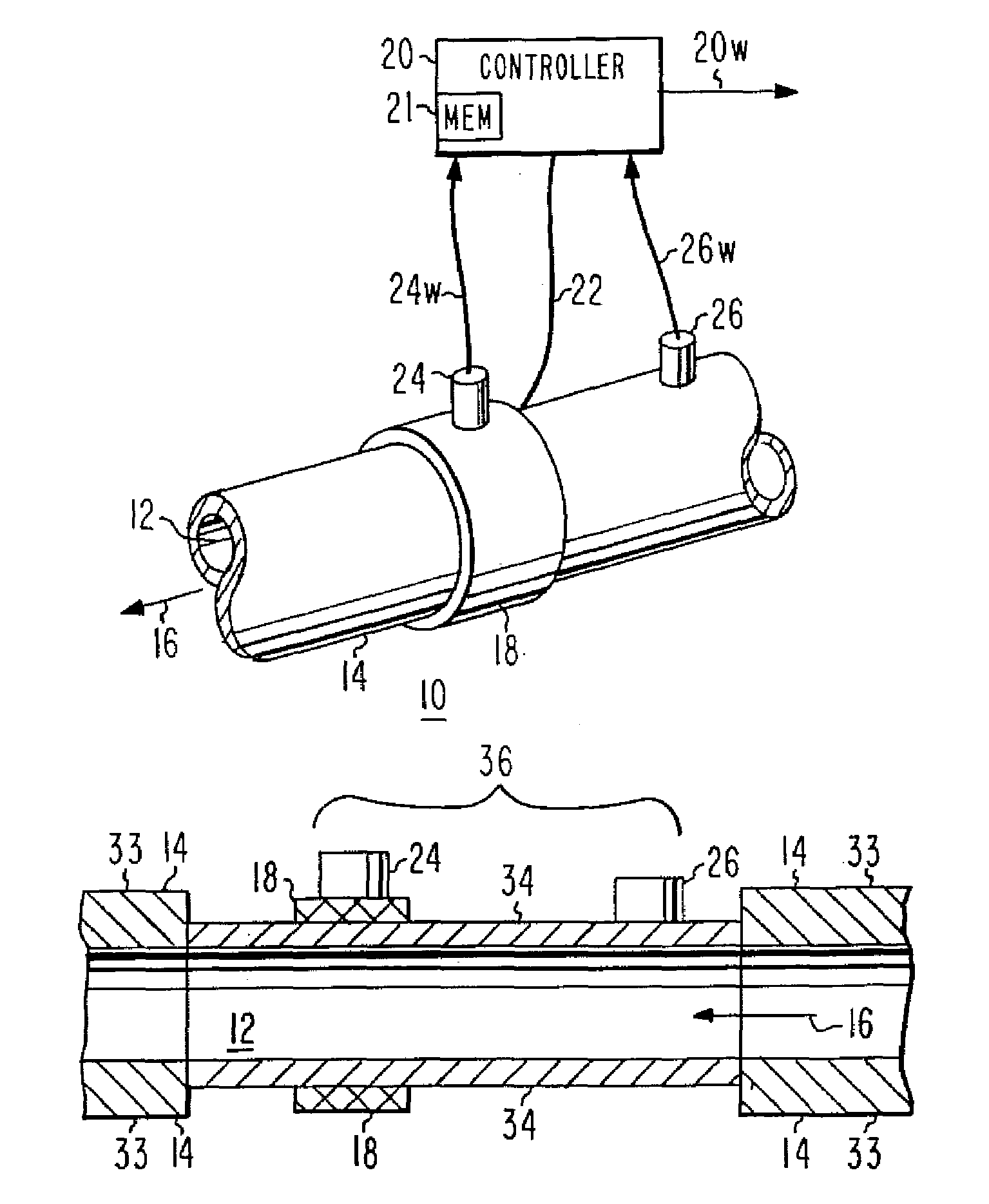
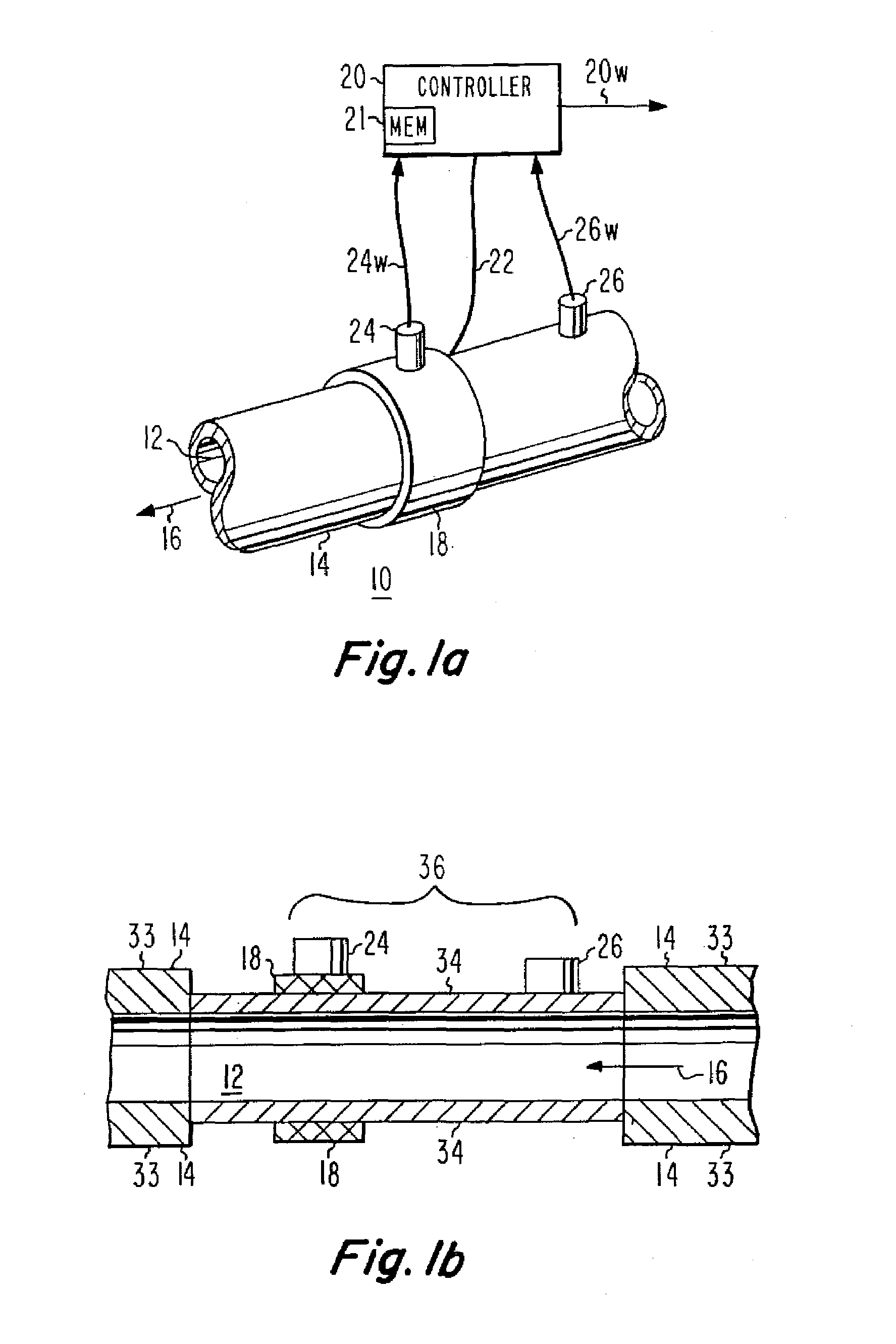
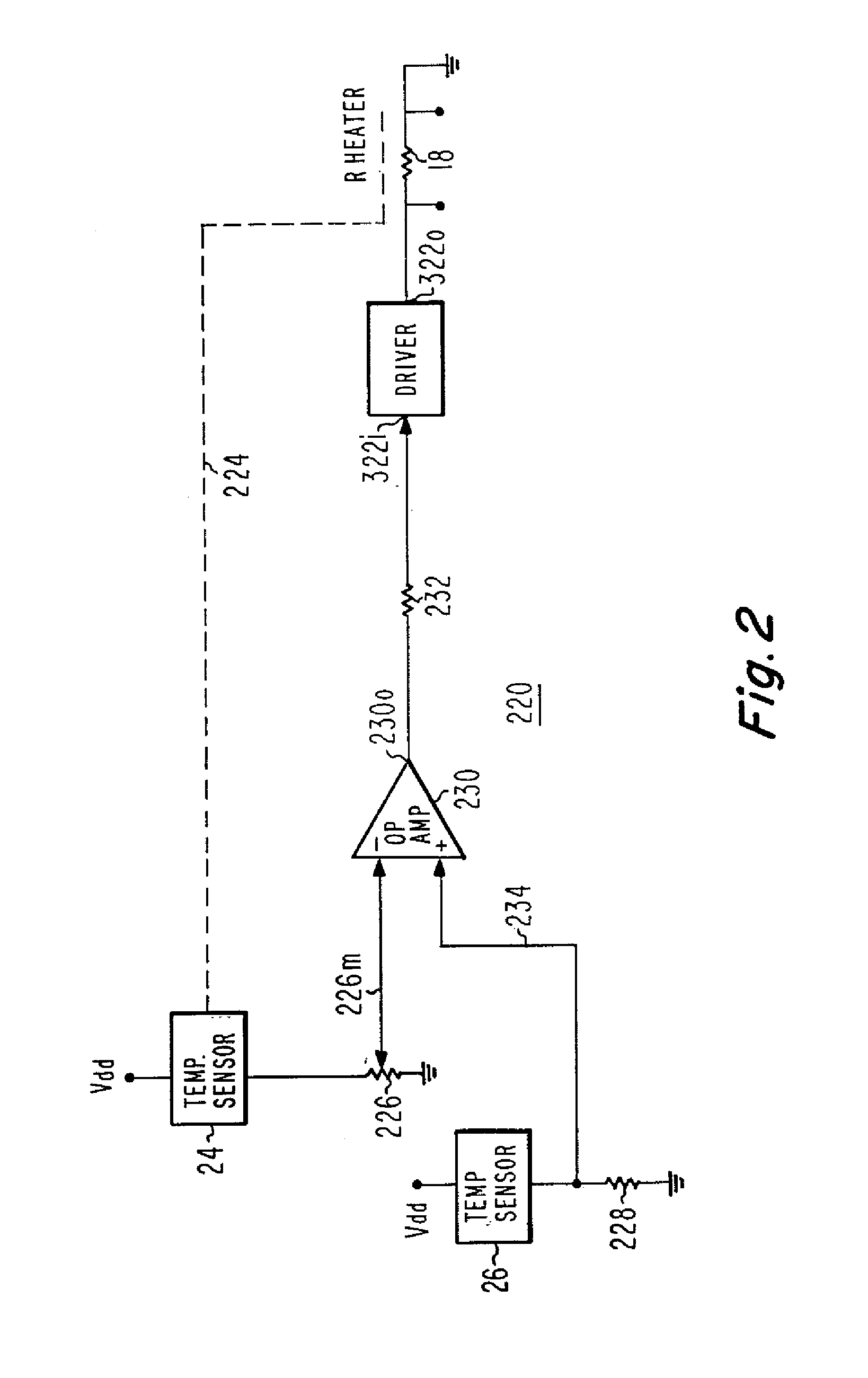
Constant-temperature-difference flow sensor, and integrated flow, temperature, and pressure sensor
InactiveUS7624632B1Verify integrityVolume/mass flow by thermal effectsFluid-tightness measurementFlow transducerElectric force
An integrated sensor for automated systems includes a flow sensor, a temperature sensor, a pressure sensor, and a network interface. In a particular embodiment of the invention, the flow sensor includes a temperature sensor (26) which determines the temperature of the fluid flowing in a flow path (12). A heater (18) is coupled to the flow path, and is energized by a controller (20) with sufficient electrical power to raise the temperature of the heater above the measured fluid temperature by a fixed temperature difference. In order to aid in determining the temperature difference, a sensor (24) may be associated with the heater (18). The amount of power required to maintain the temperature difference is a measure of the flow velocity. The volumetric flow rate is the product of the flow velocity multiplied by the area of the flow sensor. The mass flow rate is the product of the volumetric flow rate multiplied by the mass density of the fluid. In a particular embodiment, the pressure sensor is ratiometric.
Owner:GENERAL ELECTRIC CO +1
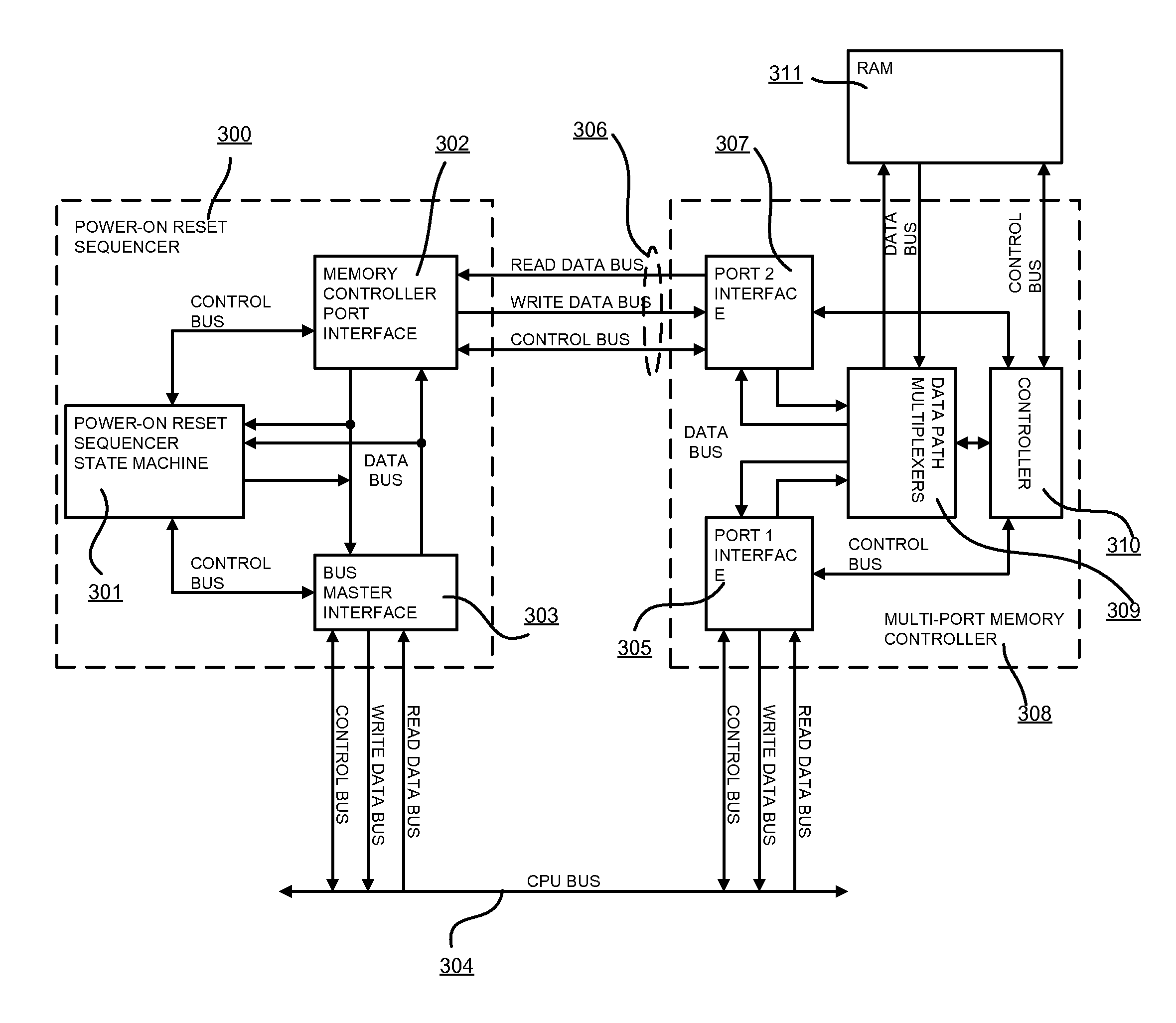
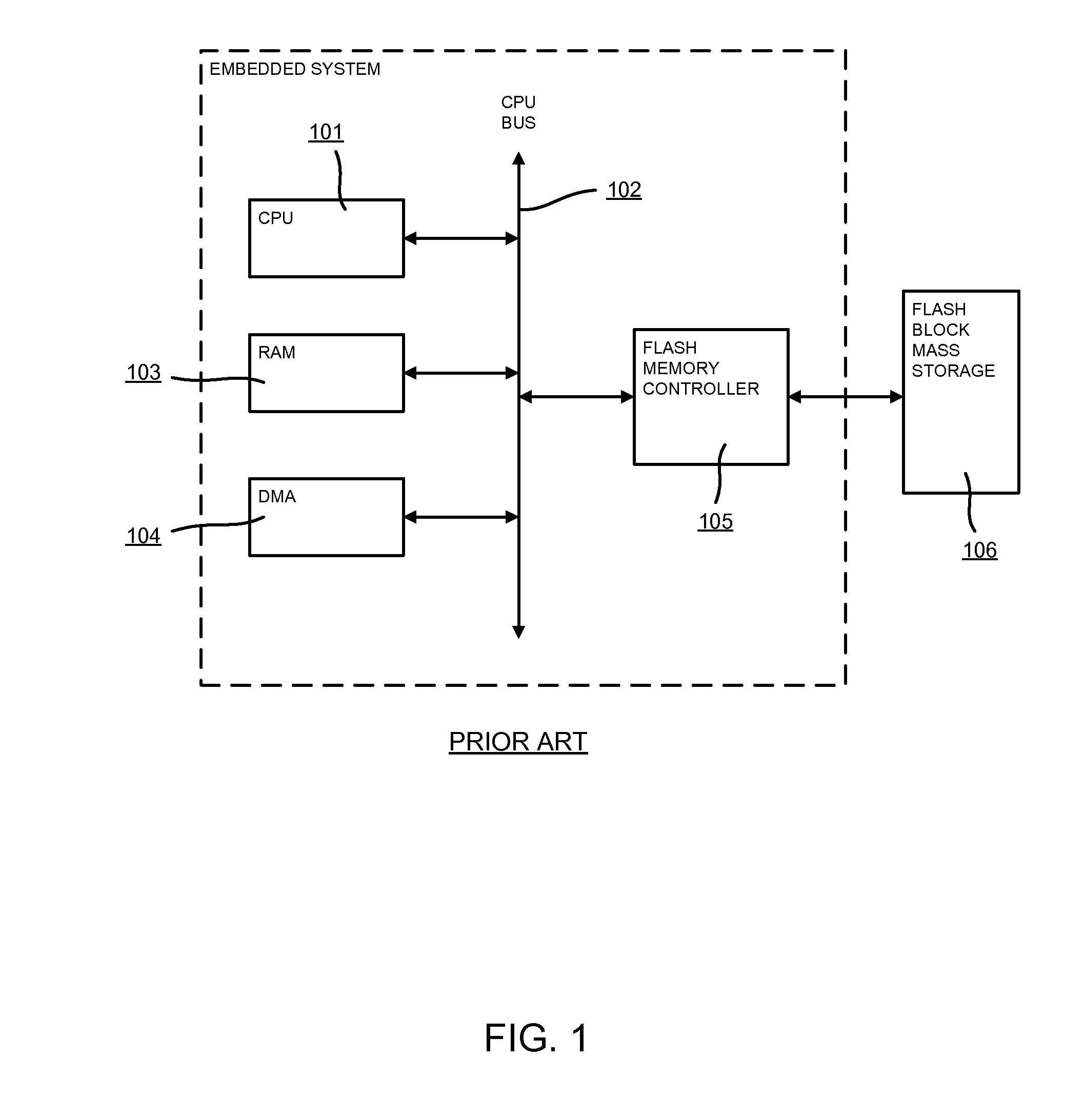
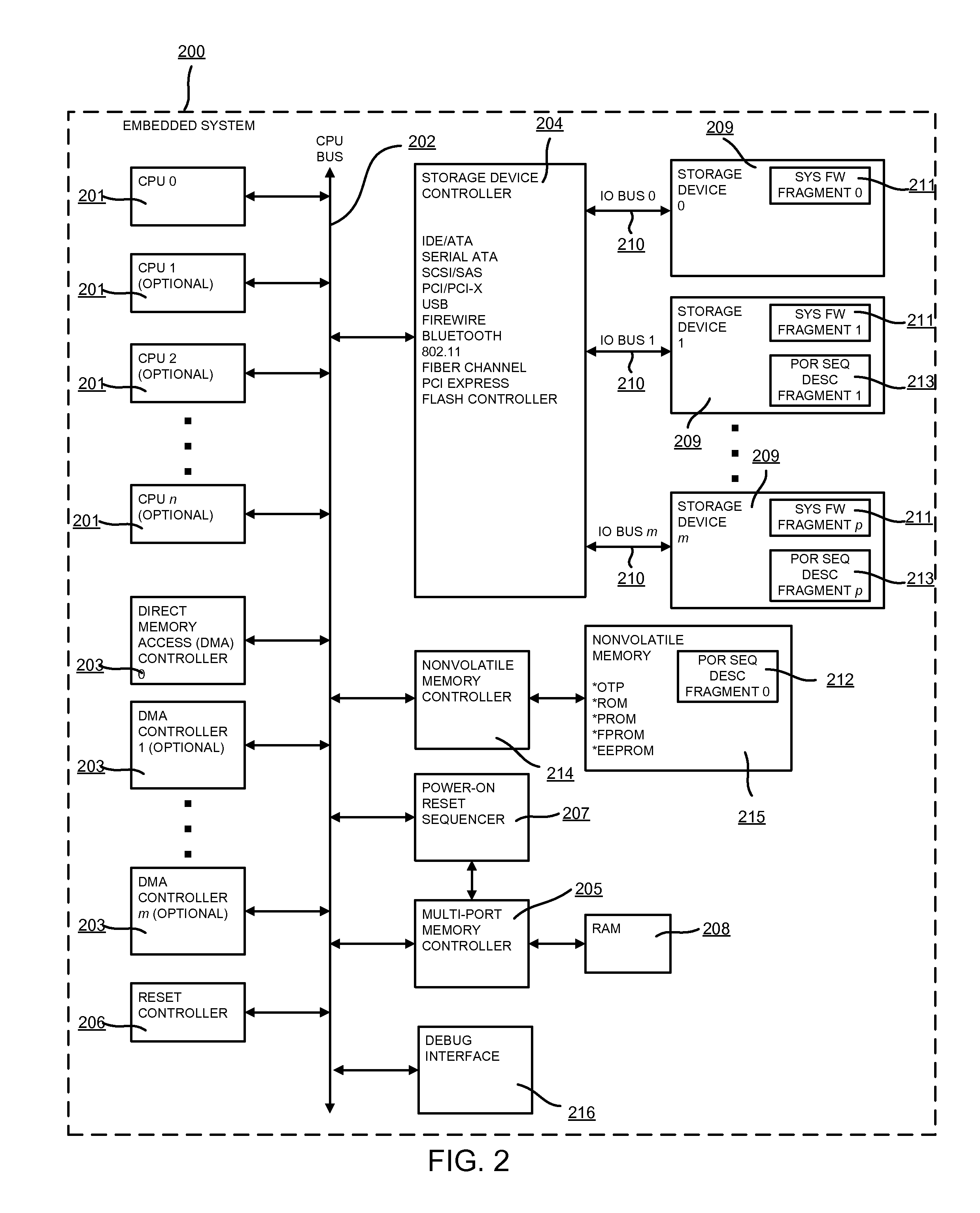
Embedded system boot from a storage device
ActiveUS20140331034A1Small sizeMinimal amountDigital computer detailsData resettingPower-on resetElectricity
A mechanism of booting up a system directly from a storage device and a means of initializing an embedded system prior to activating a CPU is presented. The said system is comprised of one or more CPUs, a reset controller, a storage device controller, one or more direct memory access controllers, a RAM and its controller, a ROM and its controller, a debug interface and a power-on reset (POR) sequencer. The POR sequencer controls the overall boot process of the embedded system. Said sequencer uses descriptors (POR Sequencer descriptors) which are used to update the configuration registers of the system and to enable CPU-independent data transfers with the use of DMA controllers.Using a minimal amount of non-volatile memory for booting up a system brings down costs associated with increased silicon real estate area and power consumption. Capability of pre-initializing the system even before a CPU is brought out of reset provides flexibility and system robustness. Through the use of the Power-On Reset Sequencer module, integrity of program code and user data used in the boot up process can be verified thus providing a resilient boot up sequence.
Owner:BITMICRO LLC
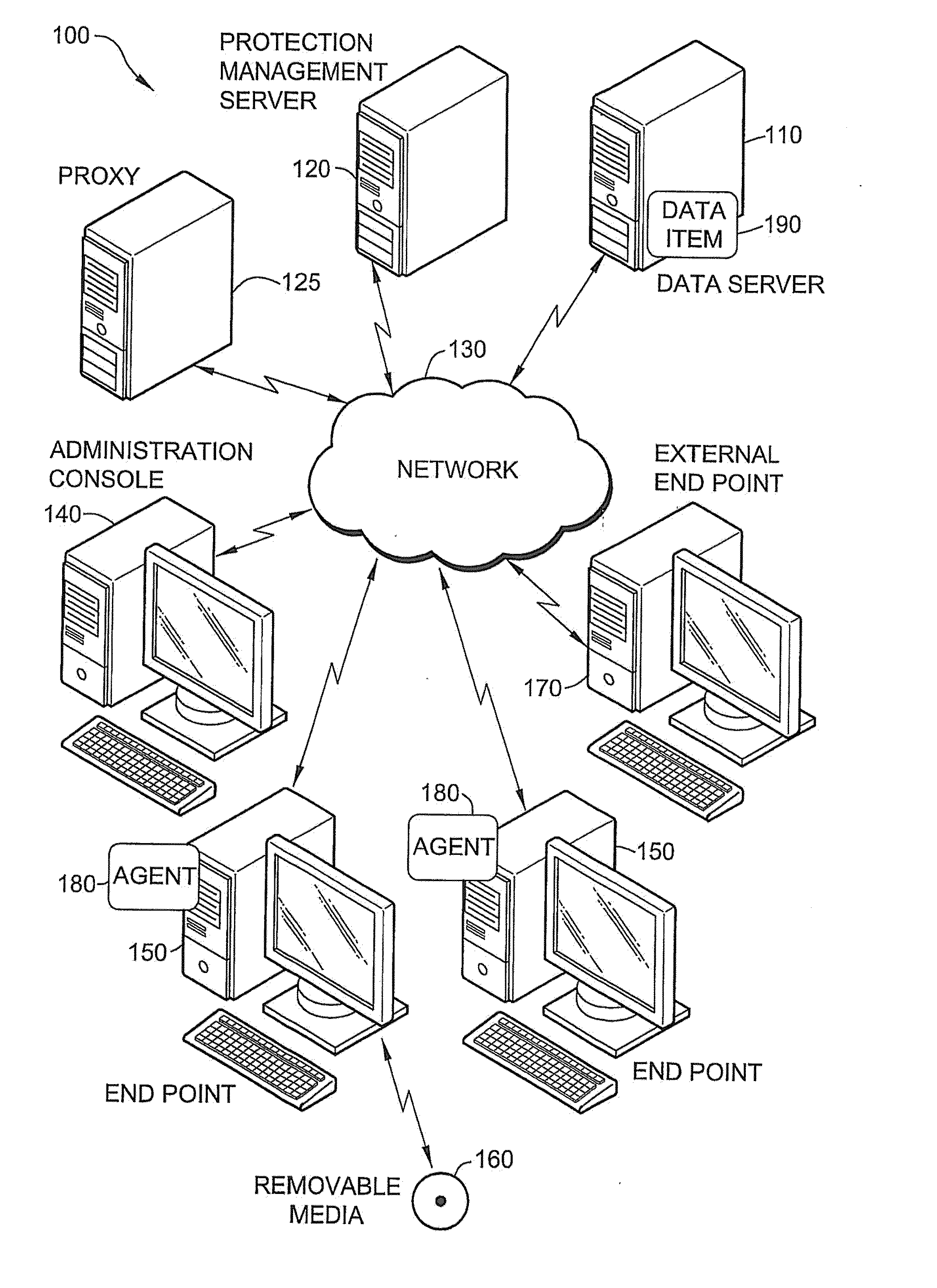
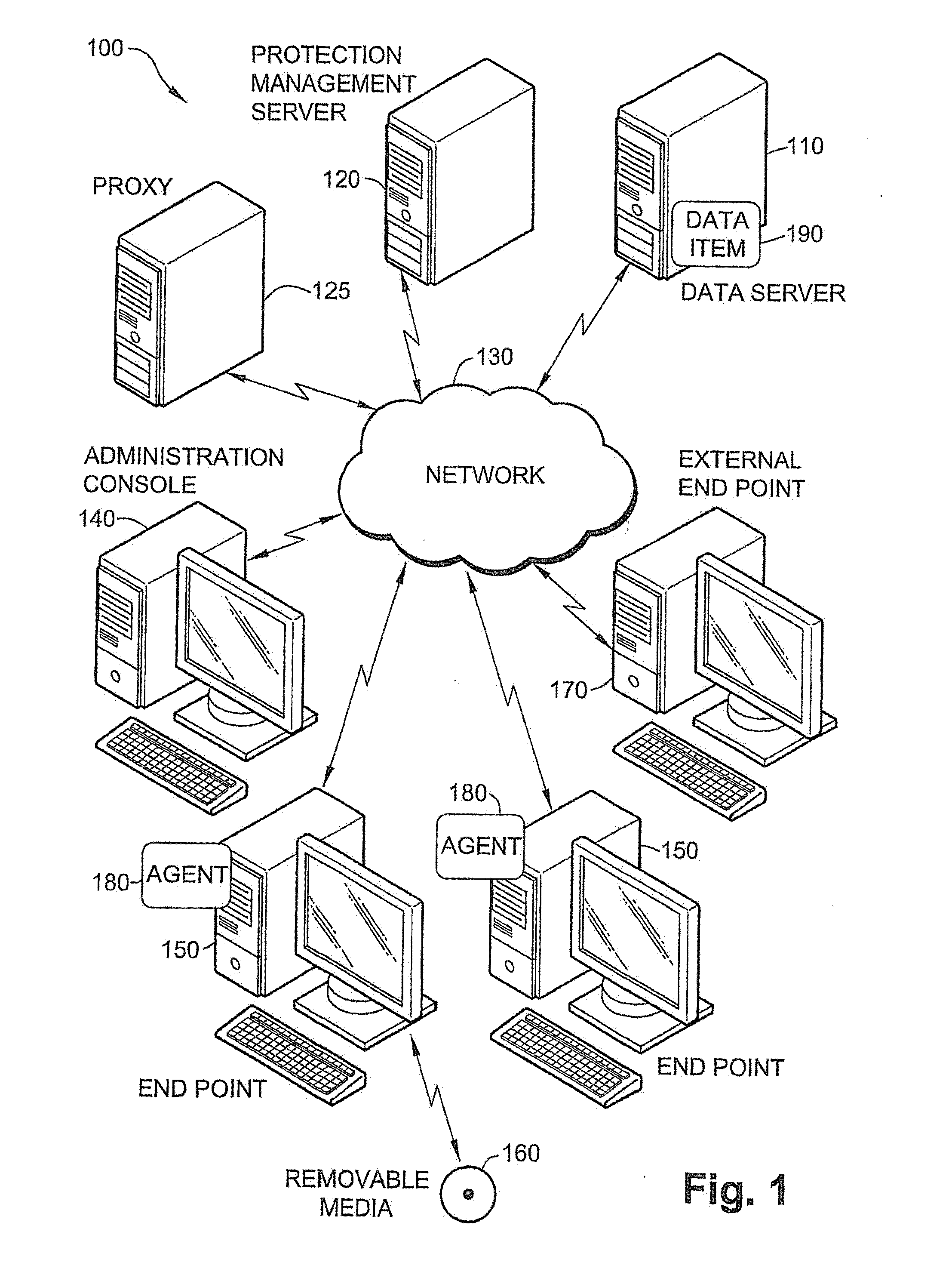
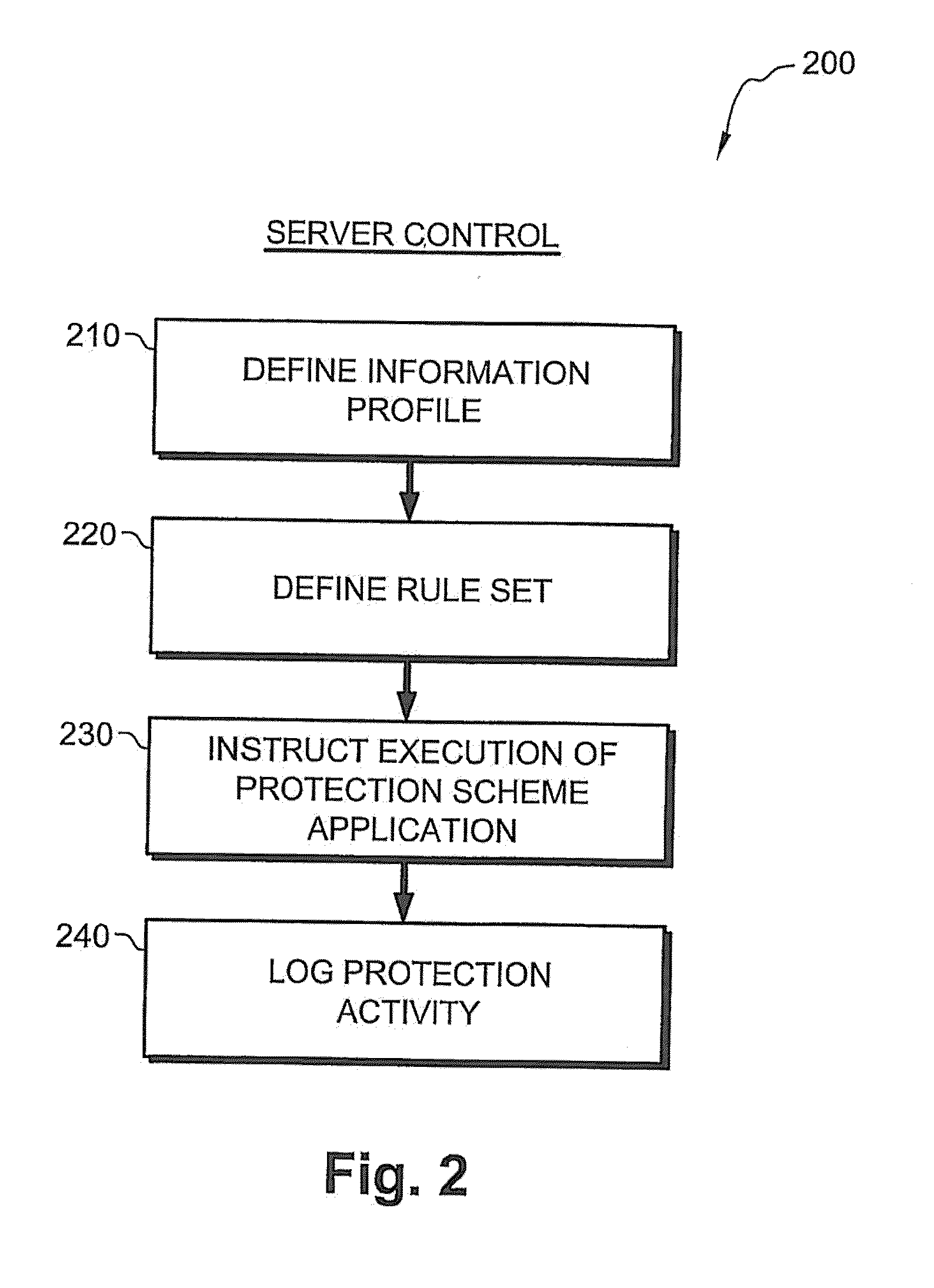
System and method for automatic data protection in a computer network
ActiveUS20100146600A1Prevents unauthorized duplicationVerify integrityDigital data processing detailsUser identity/authority verificationInternet privacy
A method of protecting data items in an organizational computer network, including, defining multiple information profiles for classifying the data item, defining rules for protecting the data item belonging to a specific information profile, classifying the data item according to the defined information profiles, applying a protection method to the data item responsive to the classification and the defined rules, automatically updating the classification of the data item responsive to a change in the content or location of the data item; and automatically transforming the applied protection method, throughout the lifecycle of the data item, responsive to a change in classification or location of the data item, according to the defined rules.
Owner:MICROSOFT TECH LICENSING LLC
Voting system and method for secure voting with increased voter confidence
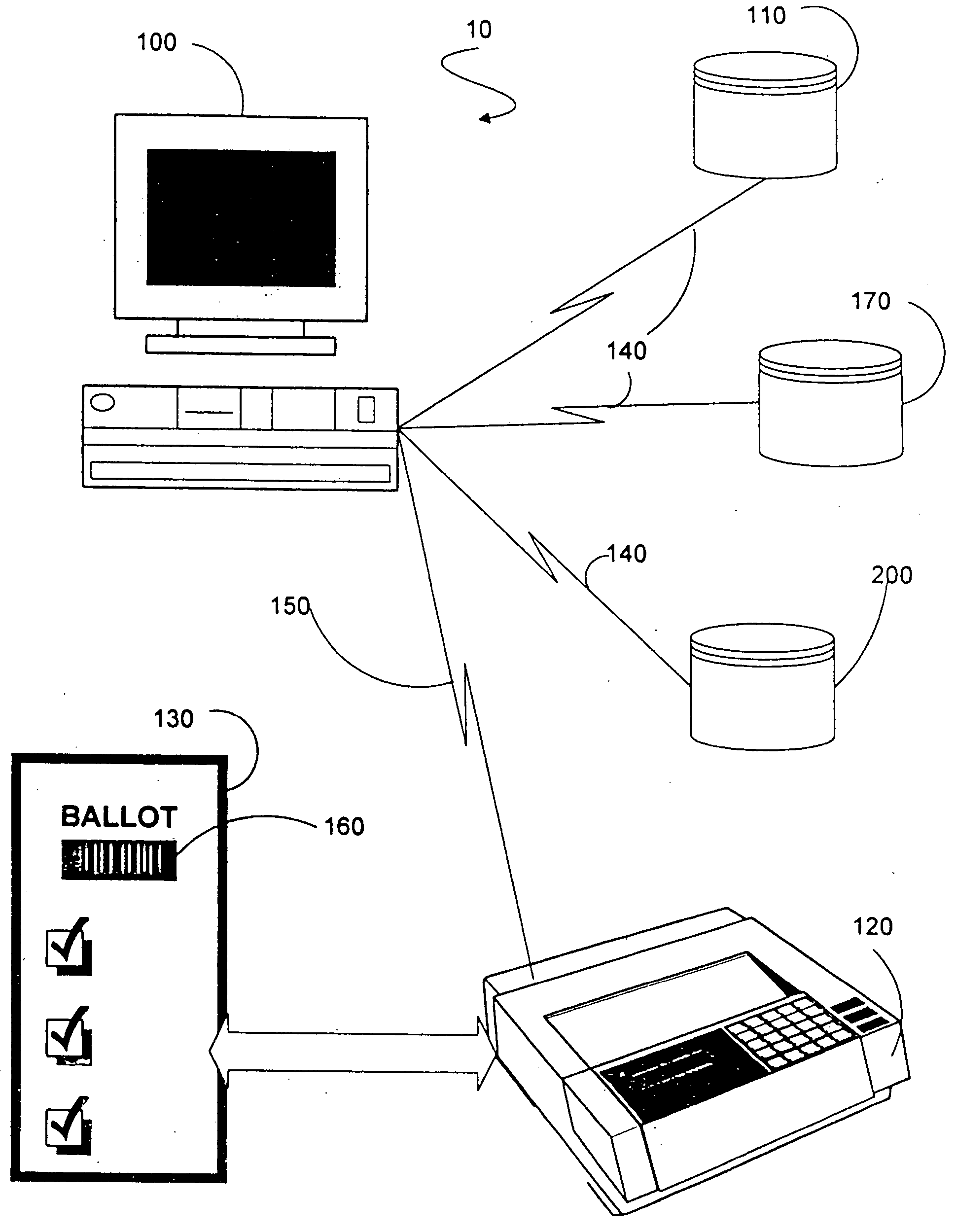
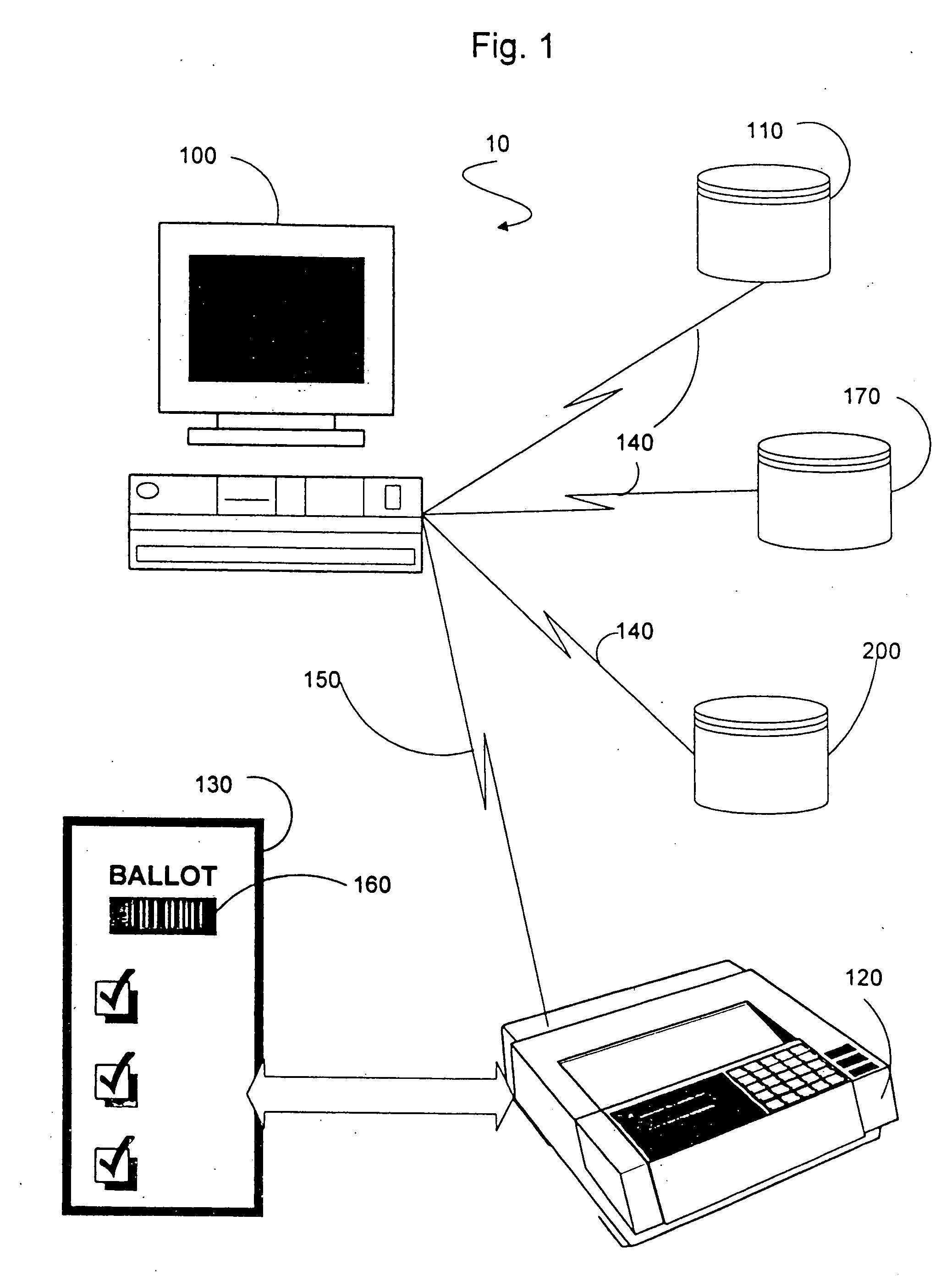
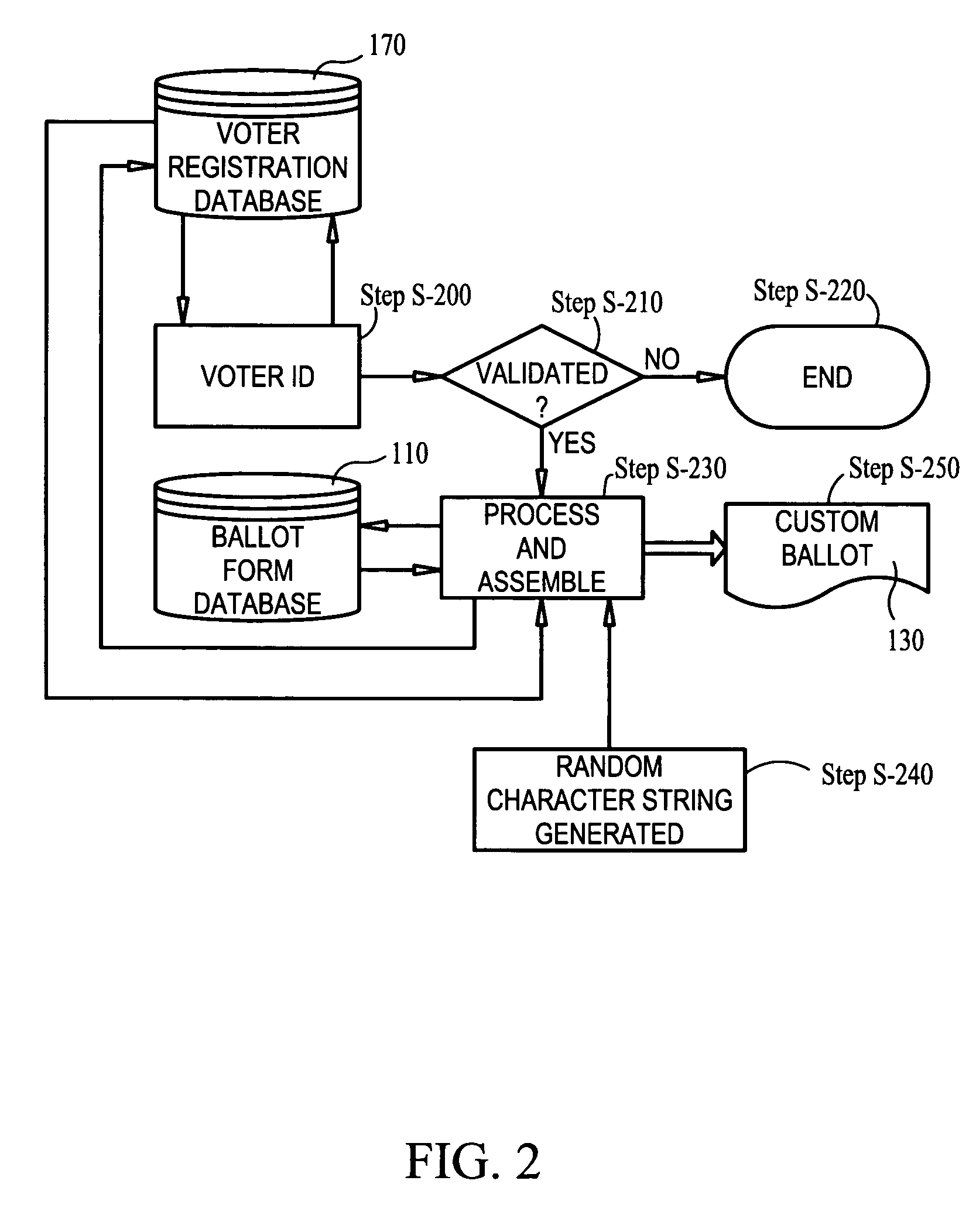
InactiveUS20050211778A1Verify integrityAccurate countVoting apparatusDigital data processing detailsSystem errorDatabase
An information gathering system and method that utilizes a computer to authenticate, poll and store user responses to a customized questionnaire. The questionnaire can be a ballot. The computer utilizes various databases to authenticate and generate the customized questionnaire. The computer records user responses securely and anonymously. User and / or system errors are eliminated before finalizing the response database. An identification number is assigned to each user which allows the user to verify the integrity of the user's response by accessing a response database. The user is provided access to a tabulation database to allow the user to verify the user's voting choices and the voting choices of other voters.
Owner:BIDDULPH DAVID L
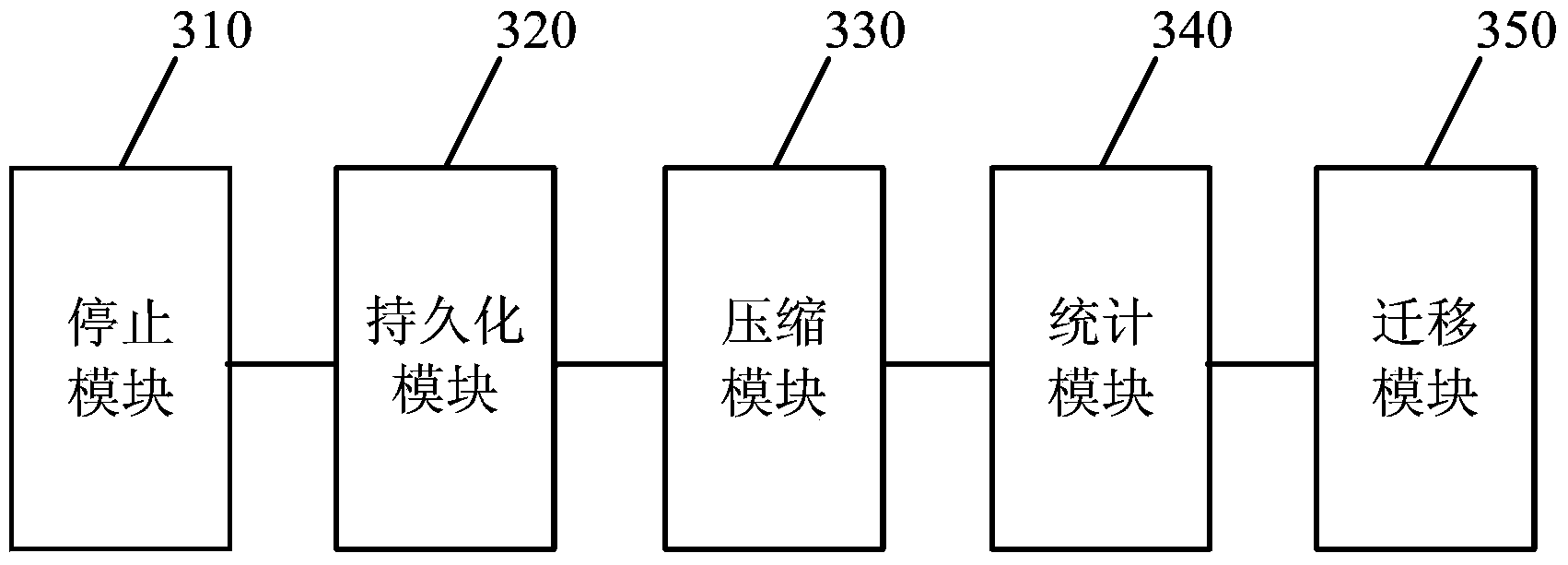
Cross-cluster data migration method and system
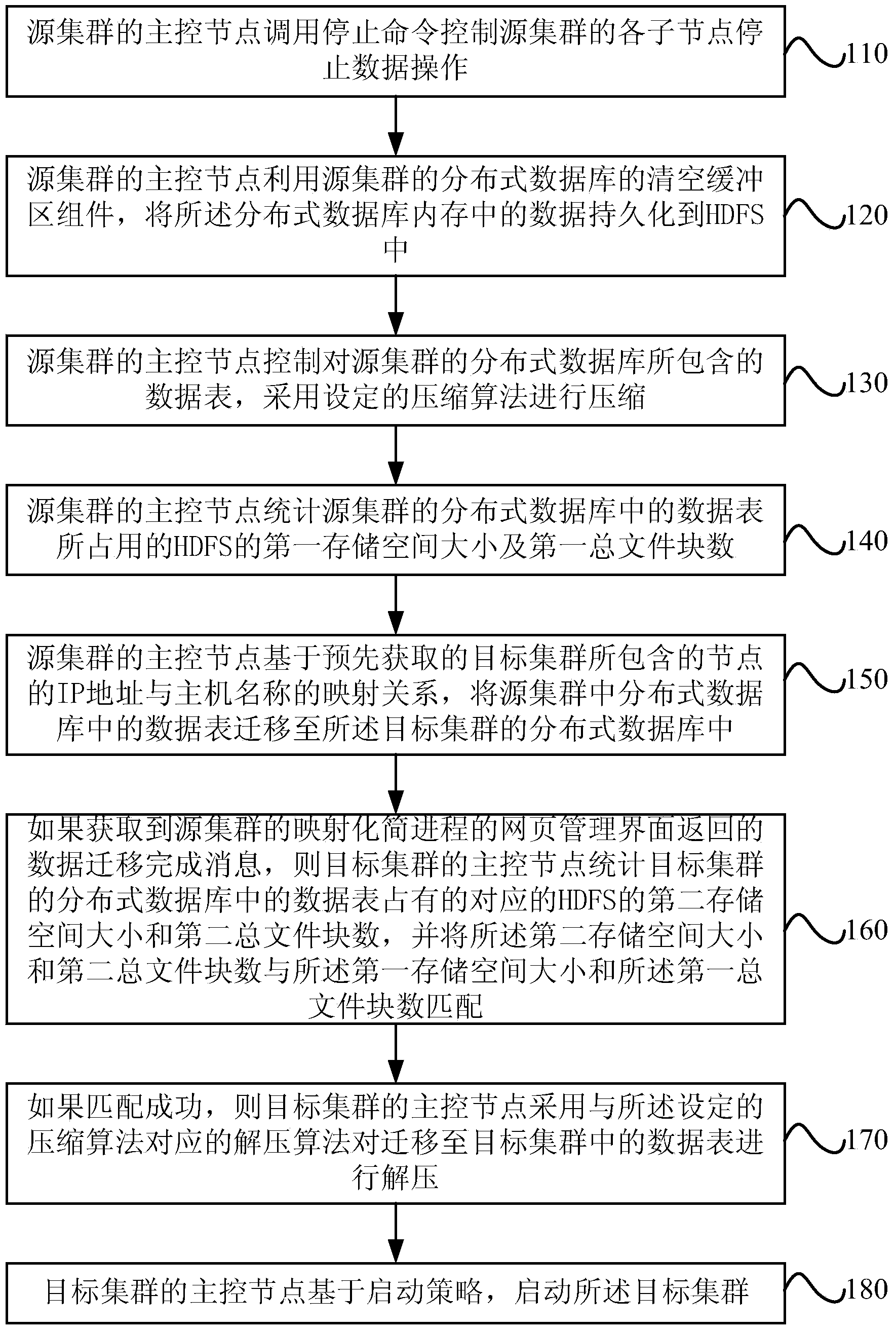
ActiveCN104239493AAchieve persistenceReduce transfer volumeDatabase distribution/replicationSpecial data processing applicationsClustered dataData operations
An embodiment of the invention provides a cross-cluster migration method and system. According to the cross-cluster migration method and system, persistence of data inside a distributed database of a source cluster before migration can be achieved due to data operation interruption through all child nodes of the source cluster and persistence of memory data of the distributed database of the source cluster; the data transmission amount can be reduced due to compression of data tables in the distributed database of the source cluster, the compressed data tables in the distributed database of the source cluster are migrated to a target cluster, and the migration efficiency is improved; then occupied storage space and total file blocks of the data tables in the distributed database of the source cluster before migration are matched with occupied space and total file blocks of the data tables of the target cluster, after migration and accordingly the migration integrity can be verified according to a matching result.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
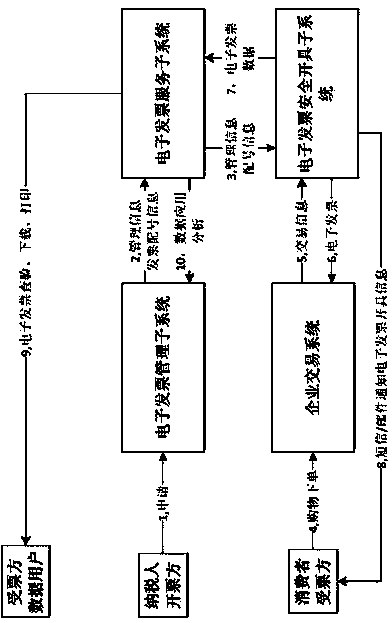
Electronic invoice security management service system based on cloud computing and cryptography
InactiveCN103870983AReduce application couplingIsolate dependenciesDigital data protectionBilling/invoicingInformatizationInvoice
The invention relates to the technical field of electronic invoice service management, in particular to an electronic invoice security management service system based on cloud computing and cryptography. The electronic invoice security management service system based on the cloud computing and the cryptography adopts technologies of the cloud computing, big data, anti-fake encryption, internet and mobile internet to ensure the correct generation, reliable storage, safety and uniqueness of electronic invoices, and provides convenient query authentication and other electronic invoice data services. The system can ensure the correct generation, reliable storage, query authentication, safety and uniqueness of electronic invoice information, realizes paperless, electronic, networked and automatic management of invoices, reduces the invoice cost and improves the informatization management level.
Owner:INSPUR QILU SOFTWARE IND
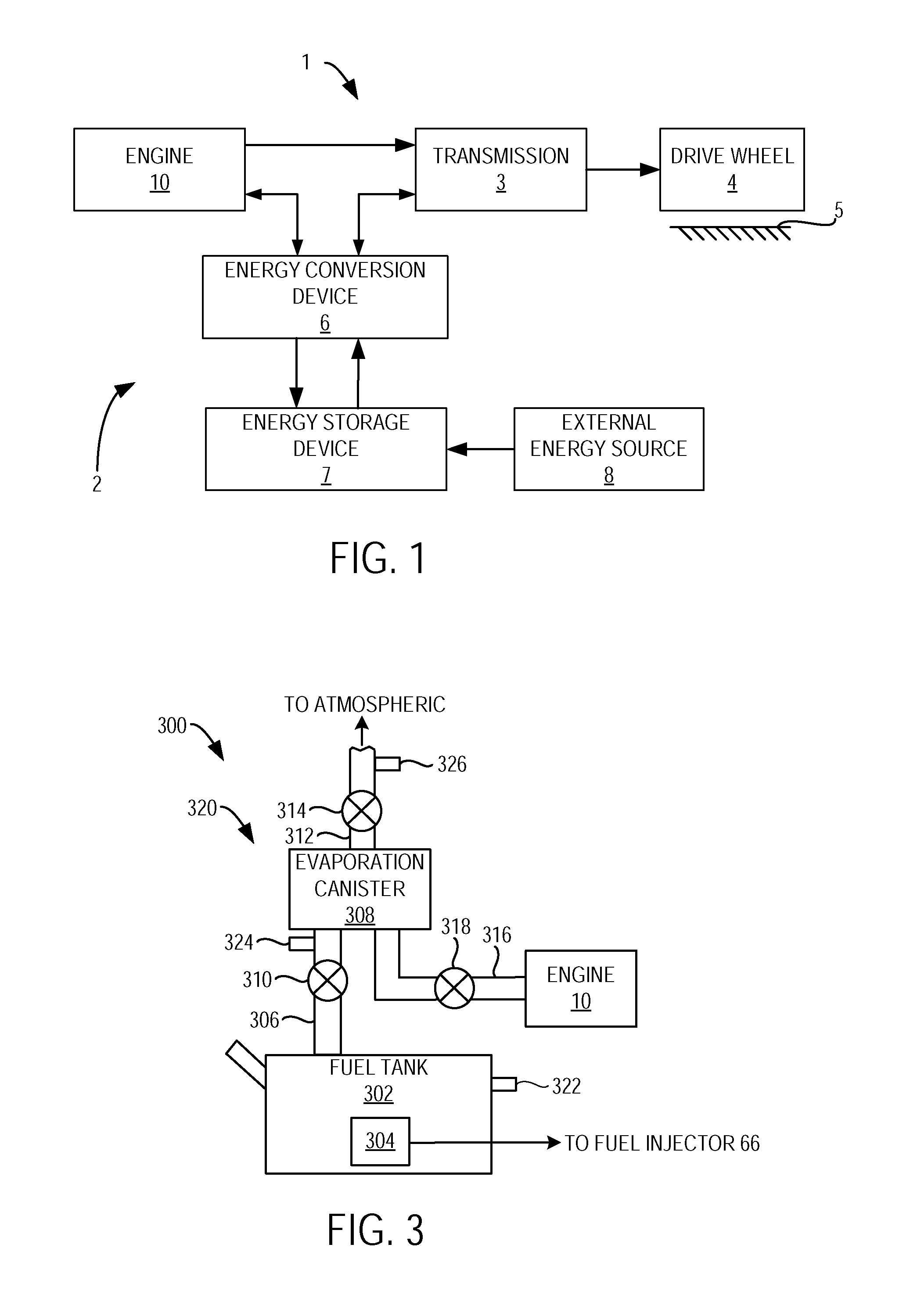
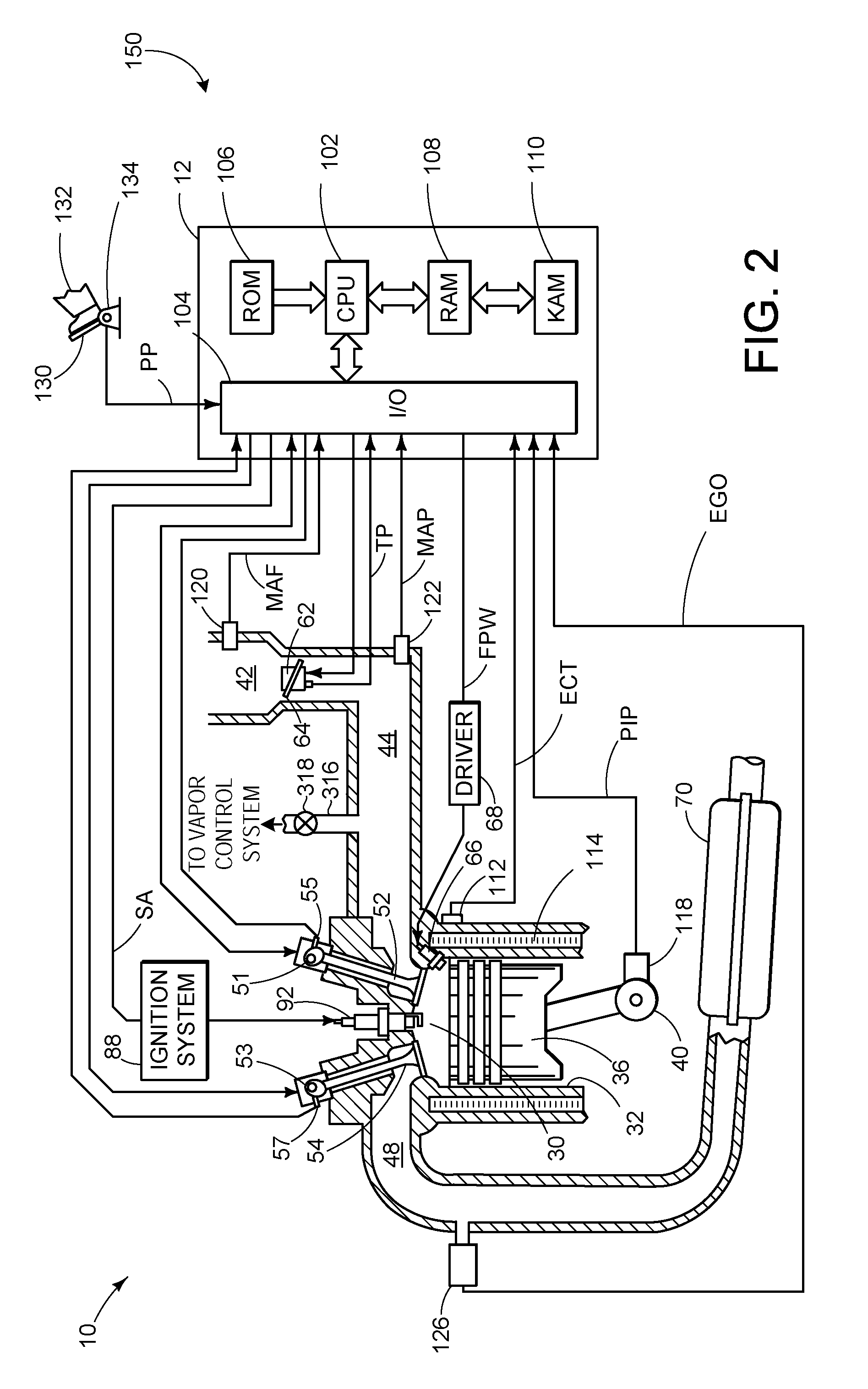
Diagnostic strategy for a fuel vapor control system
InactiveUS20110079201A1Reduce vapor releasedLow operating efficiencyNon-fuel substance addition to fuelMachines/enginesVerification systemPressure response
A method for operating a fuel vapor control system included in a vehicle having an internal combustion engine is provided. The method may include storing positive pressure or negative pressure in an isolated fuel tank, transferring at least a portion of the positive pressure or the negative pressure to an evaporation canister region, and determining degradation of the evaporation canister based on a pressure response of the evaporation canister region while the evaporation canister region is isolated from the fuel tank. In this way, it is possible to utilize pressure that may be passively generated in one portion of the system, even during shut-down engine operation, to verify the integrity of another portion of the system.
Owner:FORD GLOBAL TECH LLC
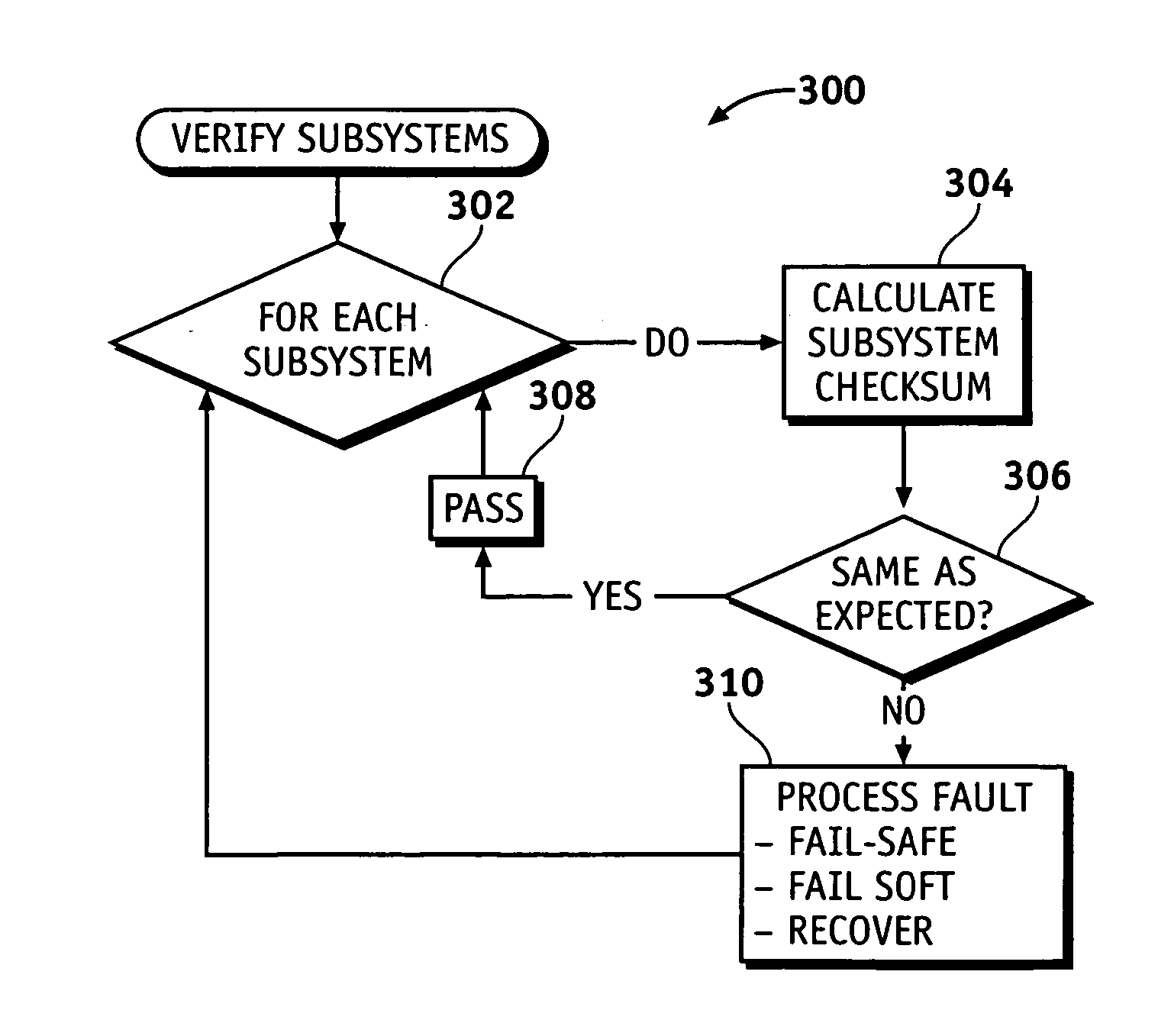
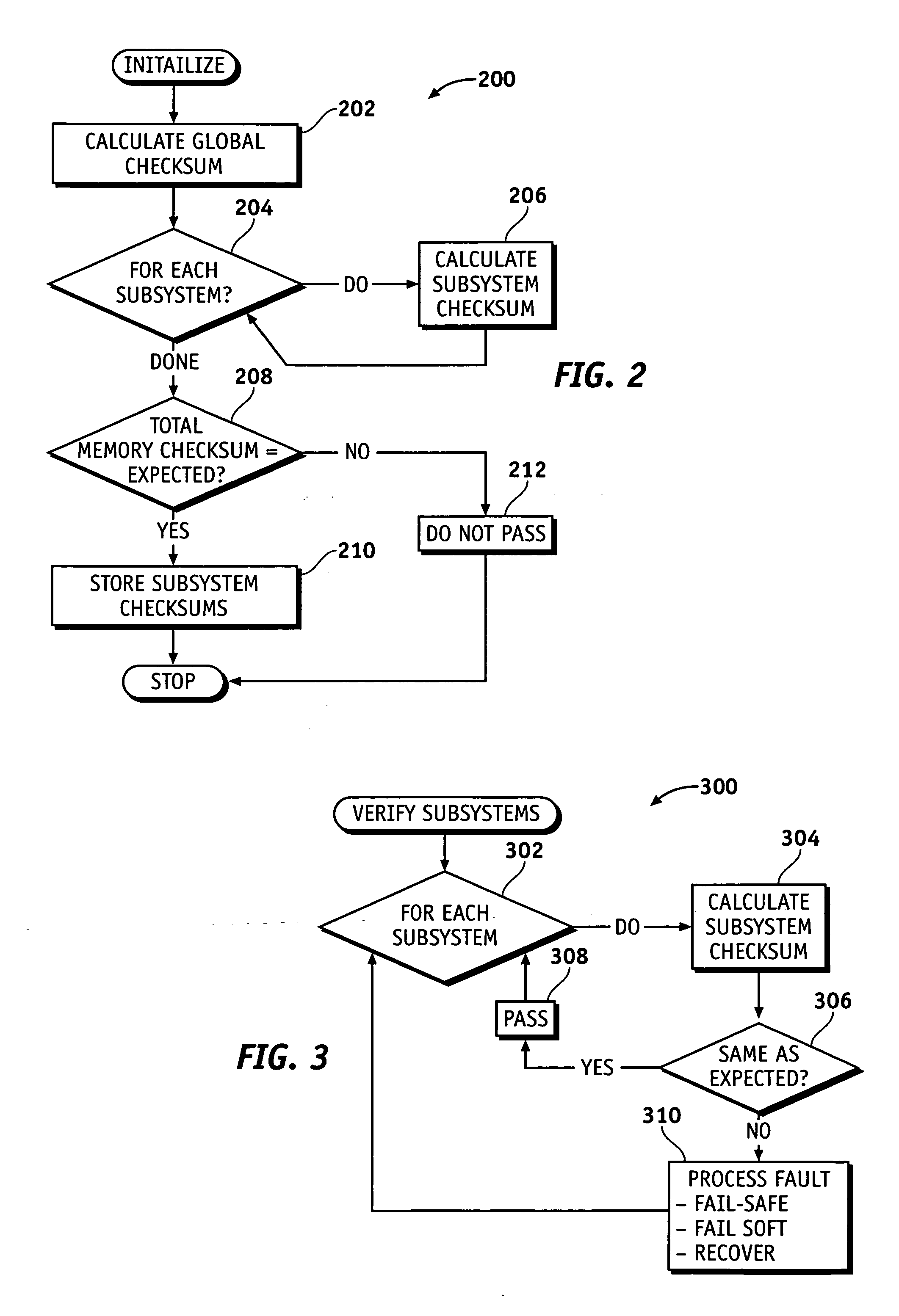
Method and system for performing function-specific memory checks within a vehicle-based control system
InactiveUS20070101236A1Verify integrityDigital data processing detailsError detection/correctionSpatial correlationControl system
Integrity of data stored in a memory space associated with a vehicle-based control system (such as a traction enhancement system) is verified through the use of sub-module checksums. A checksum for one or more subsystem modules is initially calculated based upon a checksum routine and the values of data residing in the portions of the memory space associated with the subsystem of interest. A global checksum is also initially calculated based upon data associated with the entire memory space. If the global checksum matches an expected value, the subsystem checksum(s) are stored as expected subsystem checksums. During subsequent operation, a second subsystem checksum is calculated and compared against the expected checksum value for the subsystem to verify the integrity of data residing within the memory space associated with the subsystem.
Owner:GM GLOBAL TECH OPERATIONS LLC
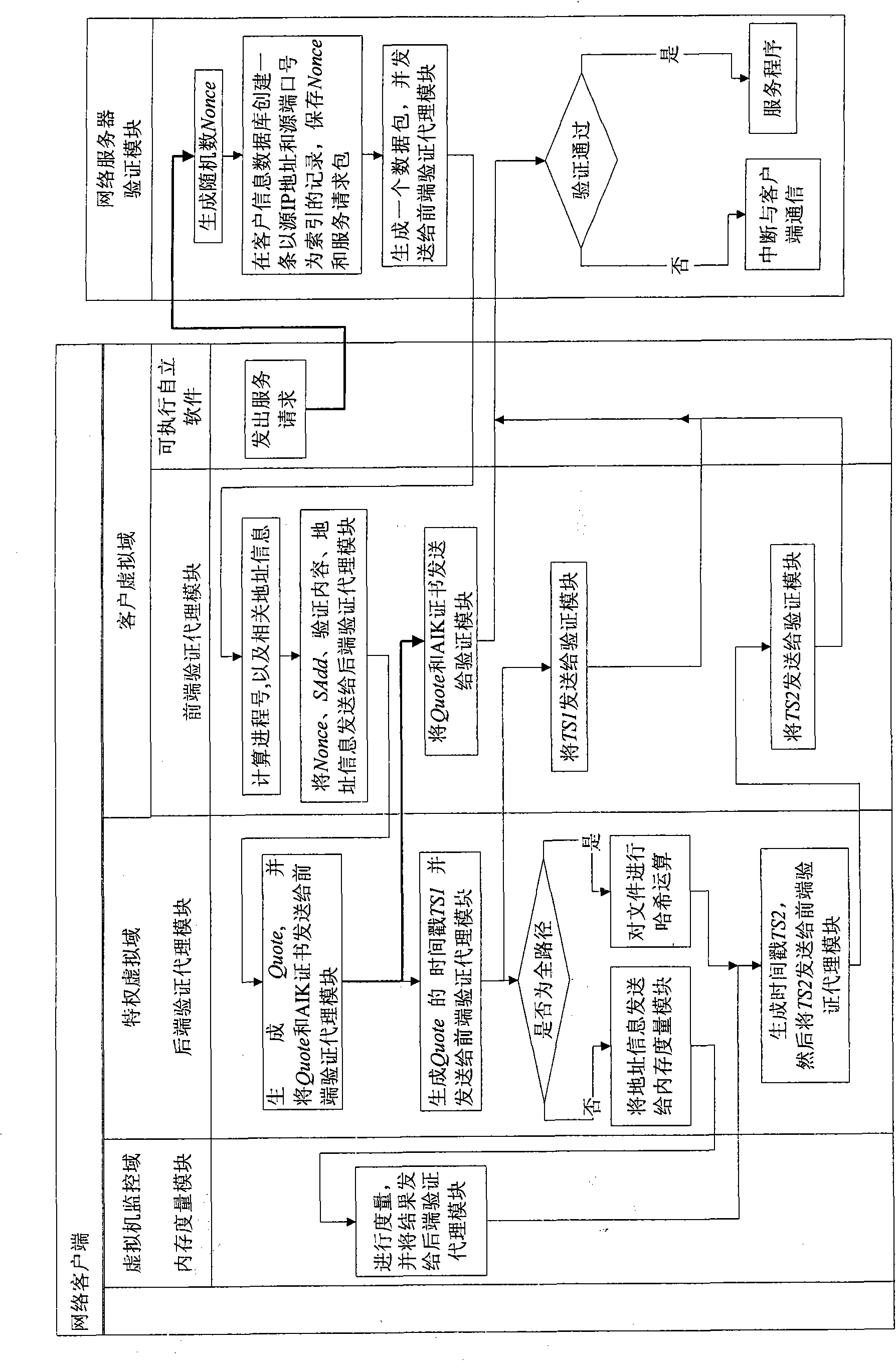
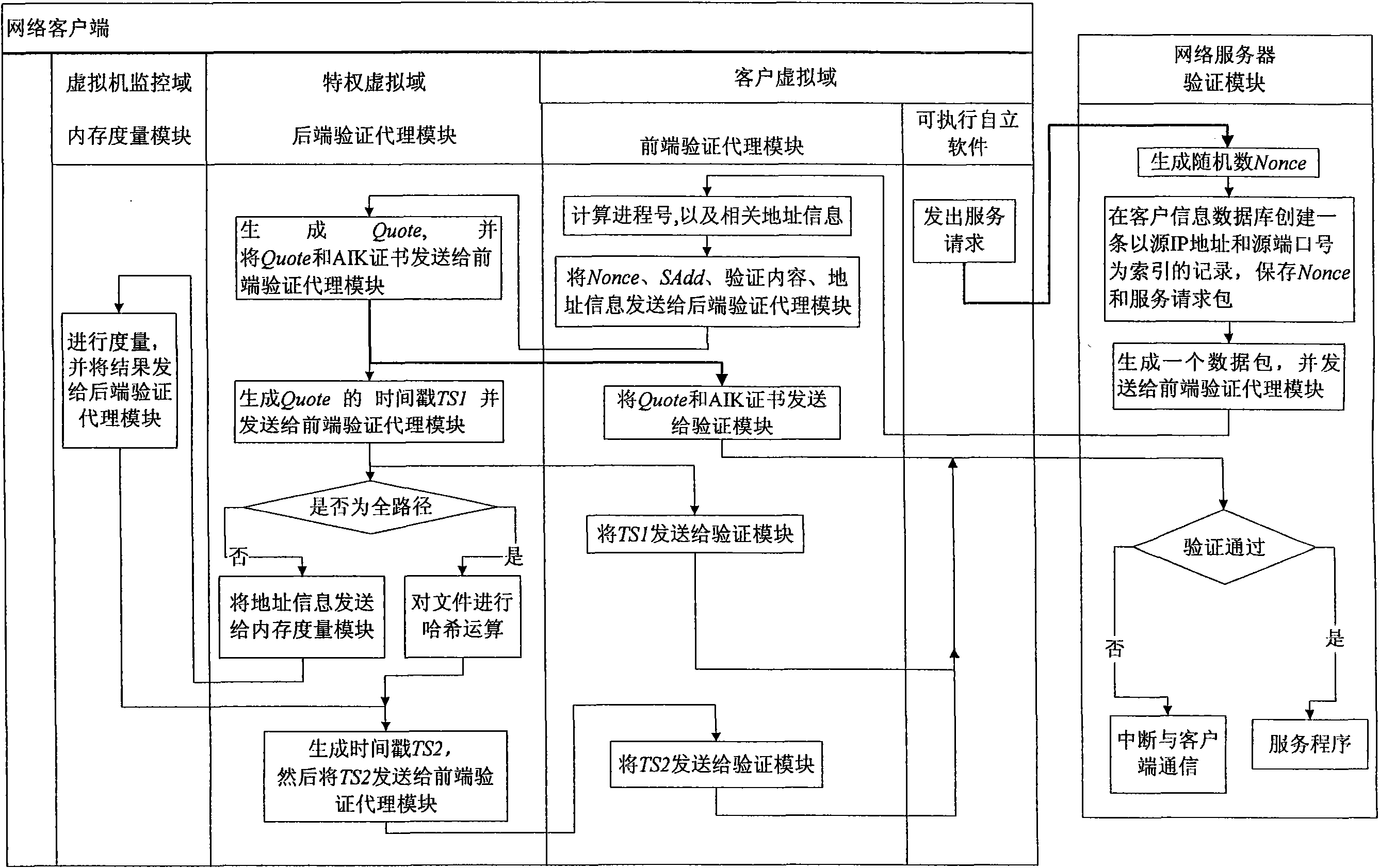
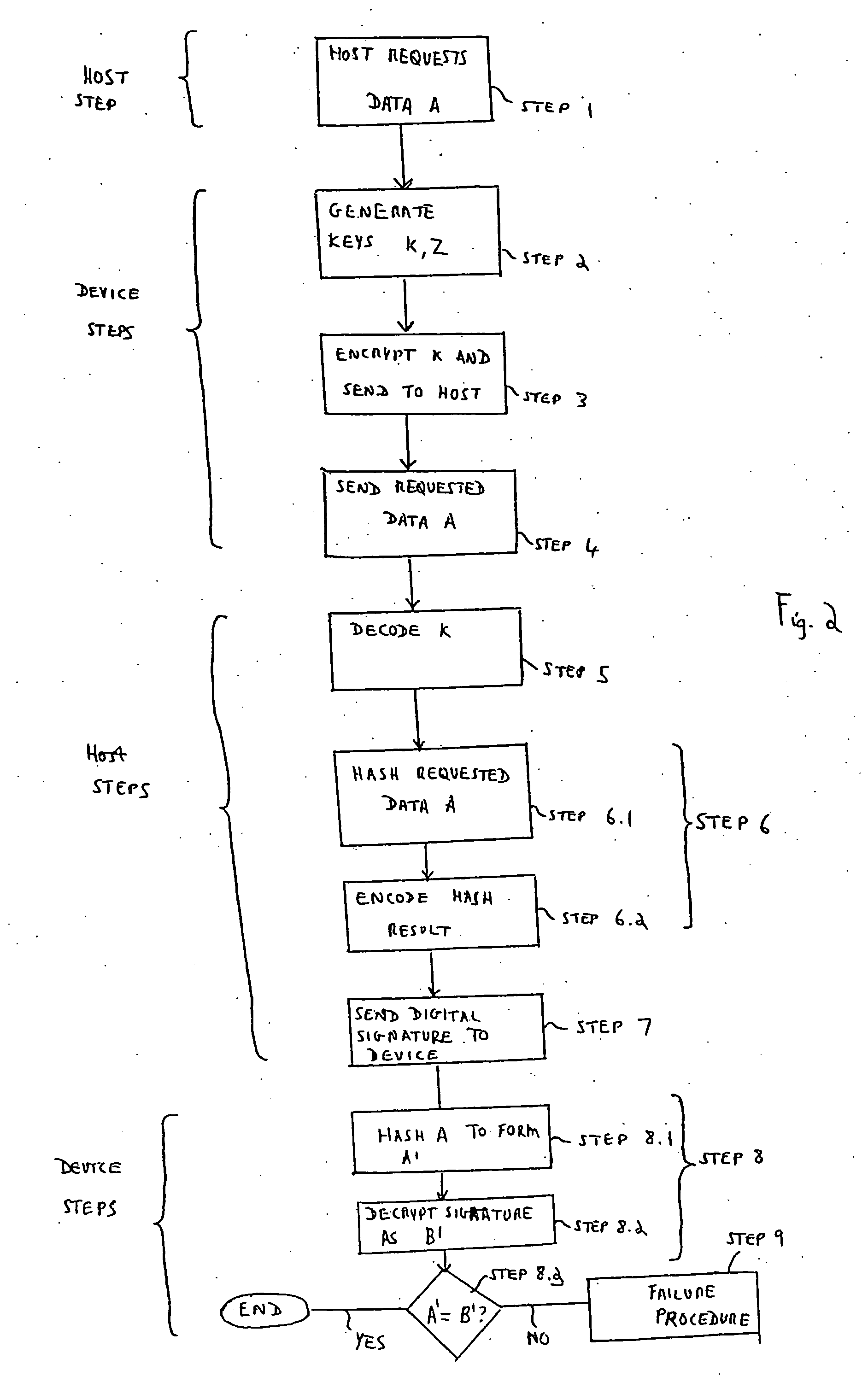
Method for remote dynamic verification on integrality of client software
The invention provides a method for remote dynamic verification on integrality of client software. In the method, a TCG (Trusted Computing Group) remote verification method, an Xen virtual machine security isolation property and a Trusted Platform Module (TPM) timestamp function are adopted to realize remote dynamic verification of a network server on self-contained executables of a network client untrusted client virtual domain. The network client is configured with a security chip TPM (Trusted Platform Module) and an Xen virtual machine system is also installed. A remote dynamic verification framework adopted by the method comprises three parts of an integrality measuring mechanism, a reporting mechanism and a verification mechanism, wherein the integrality measuring mechanism is completed by a back-end verification agent module installed in a network client privileged virtual domain and a memory measuring module installed in a network client virtual machine monitor; the reporting mechanism is completed by a front-end verification agent module installed in the network client virtual domain; and the verification mechanism is completed by a verification module installed d in the network server.
Owner:BEIJING JIAOTONG UNIV
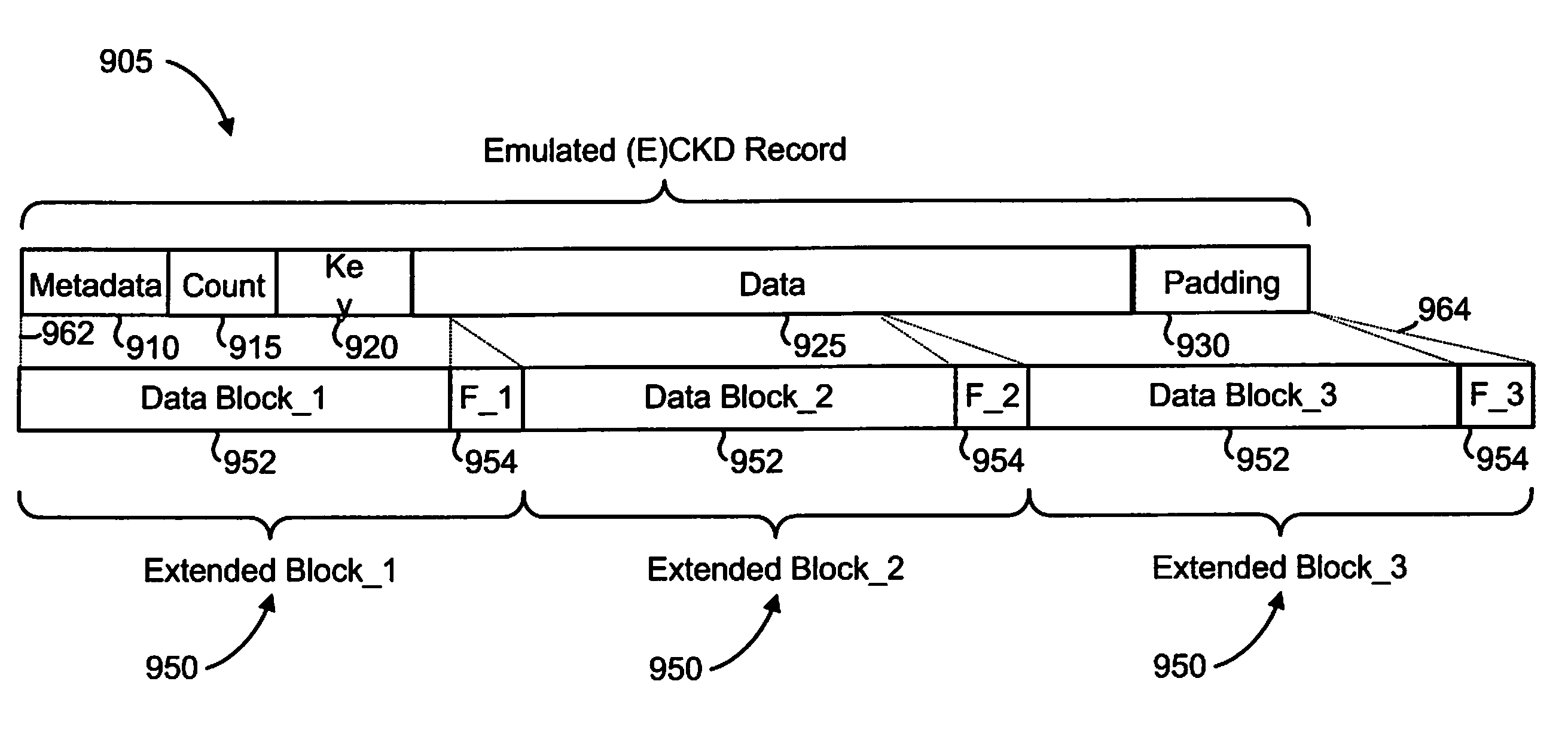
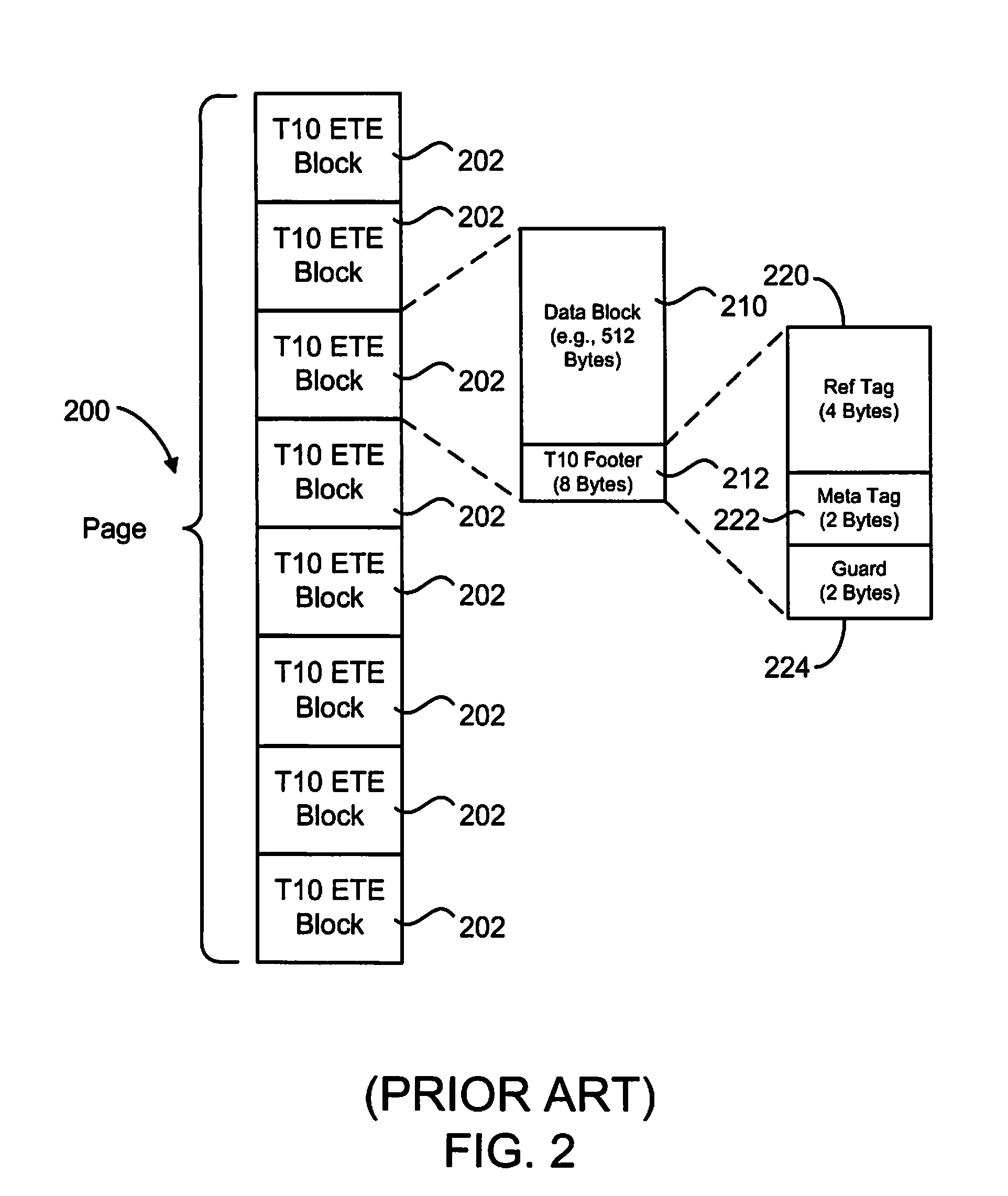
Data Protection Method for Variable Length Records by Utilizing High Performance Block Storage Metadata
ActiveUS20090259924A1Ensure protectionVerify integrityCode conversionRecord information storageVariable-length codeChecksum
An enhanced mechanism for providing data protection for variable length records utilizes high performance block storage metadata. In an embodiment, an emulated record that emulates a variable length record, such as a Count-Key-Data (CKD) record or an Extended-Count-Key-Data (ECKD) record, is generated by a Host Bus Adapter (HBA) of a mainframe system. The emulated record comprises a sequence of extended fixed-length blocks, each of which includes a data block and a footer. A confluence of the footers defines a high performance block storage metadata unit associated with the emulated record and includes a checksum that covers all data blocks and all footers of the entire emulated record. In one embodiment, the checksum is checked during transit of the emulated record between a HBA and a storage subsystem (e.g., by the HBA when the emulated record is received from the storage subsystem, and / or by a switch in the data transfer path), during a hardening step when writing the emulated record to a disk, and / or during a verification step when reading the emulated record from the disk.
Owner:IBM CORP
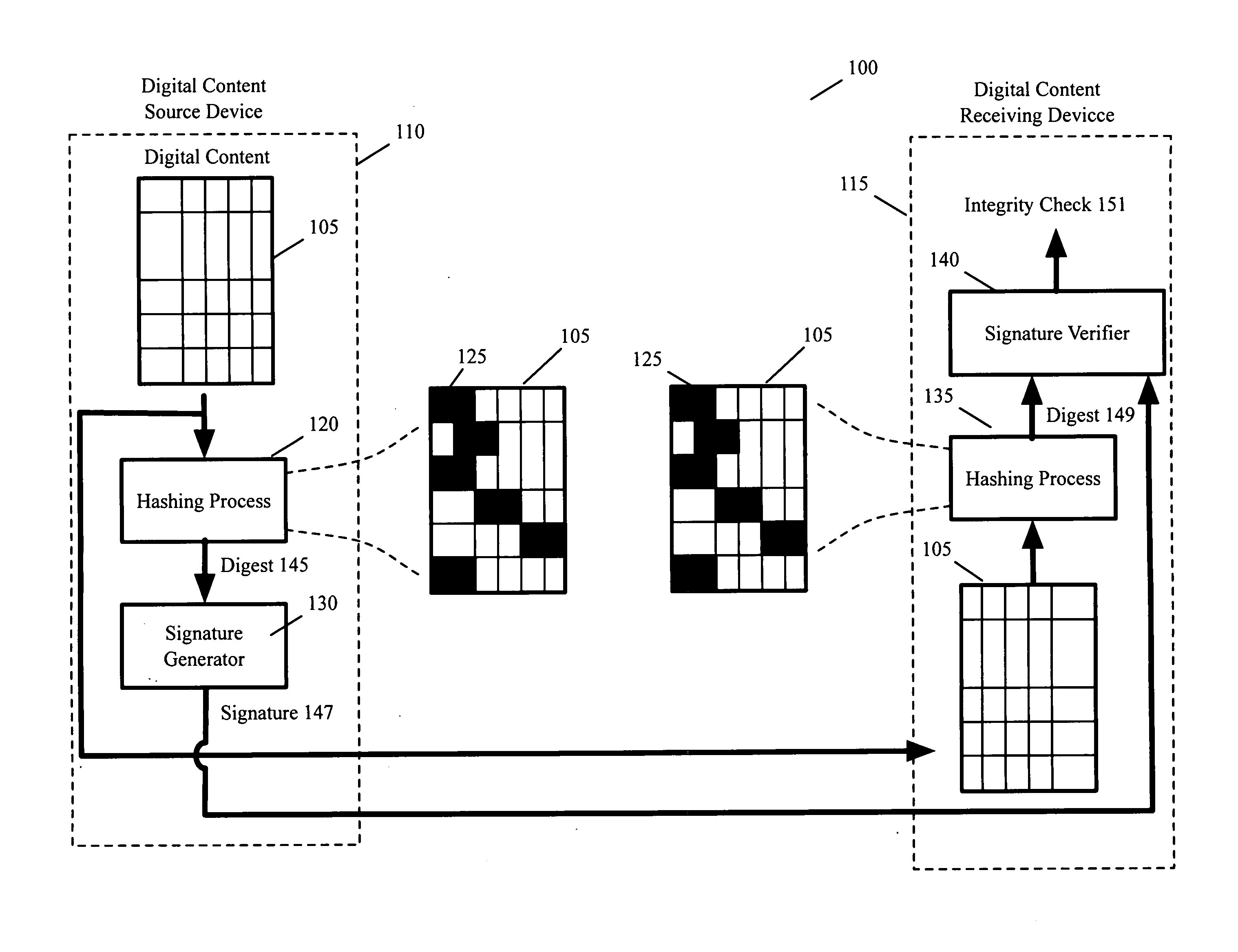
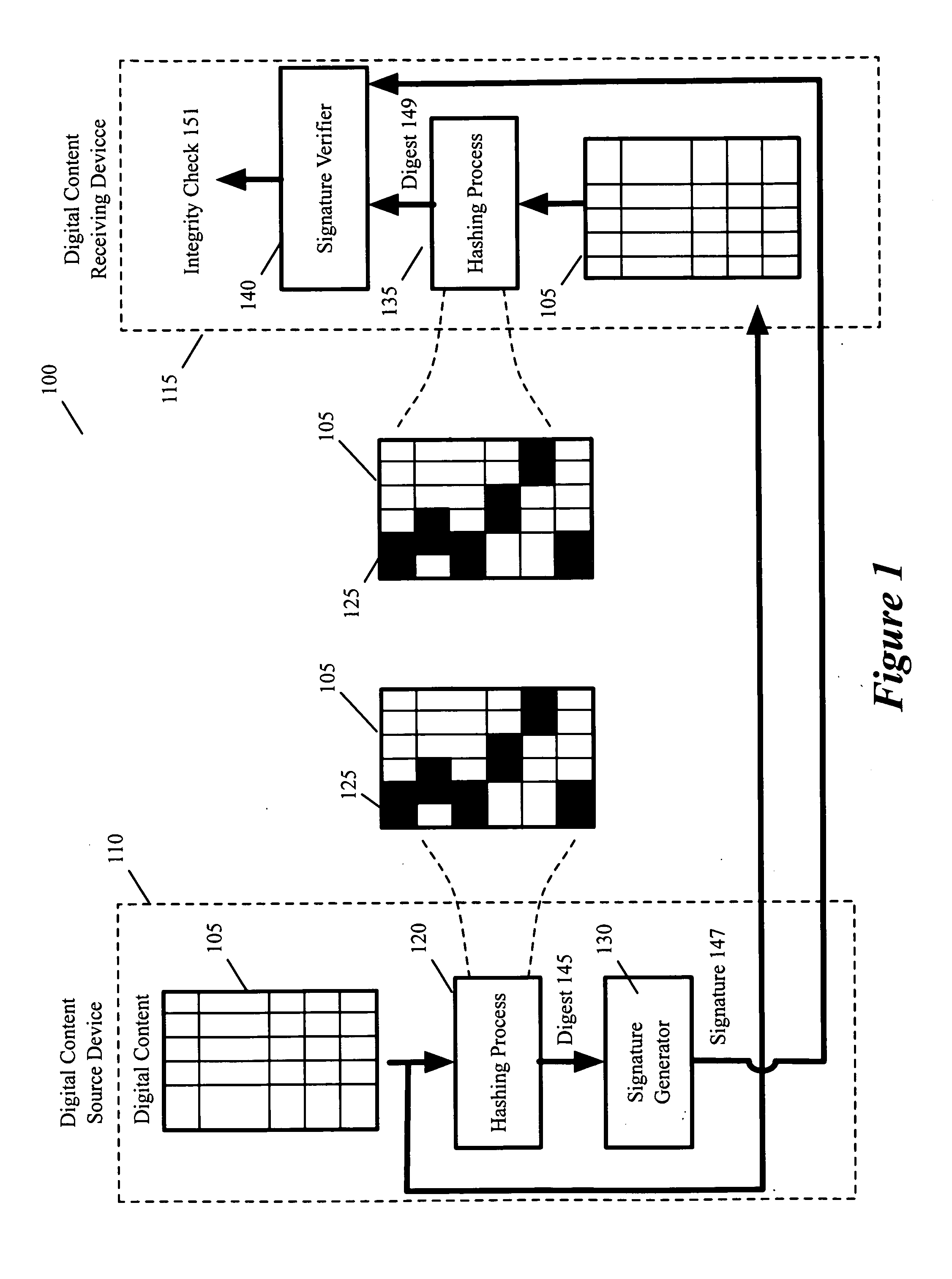
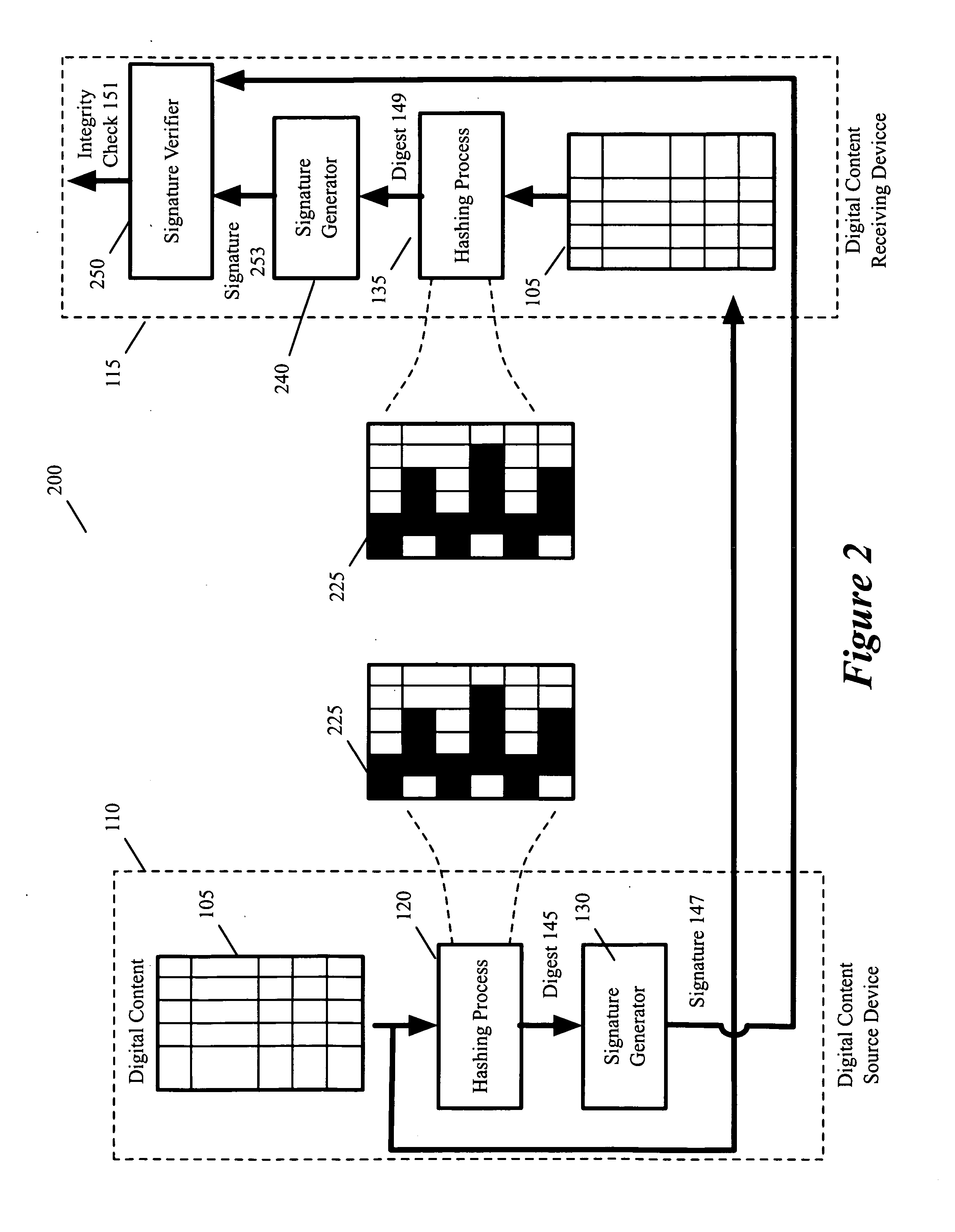
Optimized integrity verification procedures
ActiveUS20070220261A1Verify integrityDigital data processing detailsUser identity/authority verificationHash functionDigital content
Some embodiments of the invention provide a method of verifying the integrity of digital content. At a source of the digital content, the method generates a signature for the digital content by applying a hashing function to a particular portion of the digital content, where the particular portion is less than the entire digital content. The method supplies the signature and the digital content to a device. At the device, the method applies the hashing function to the particular portion of the digital content in order to verify the supplied signature, and thereby verifies the integrity of the supplied digital content.
Owner:APPLE INC
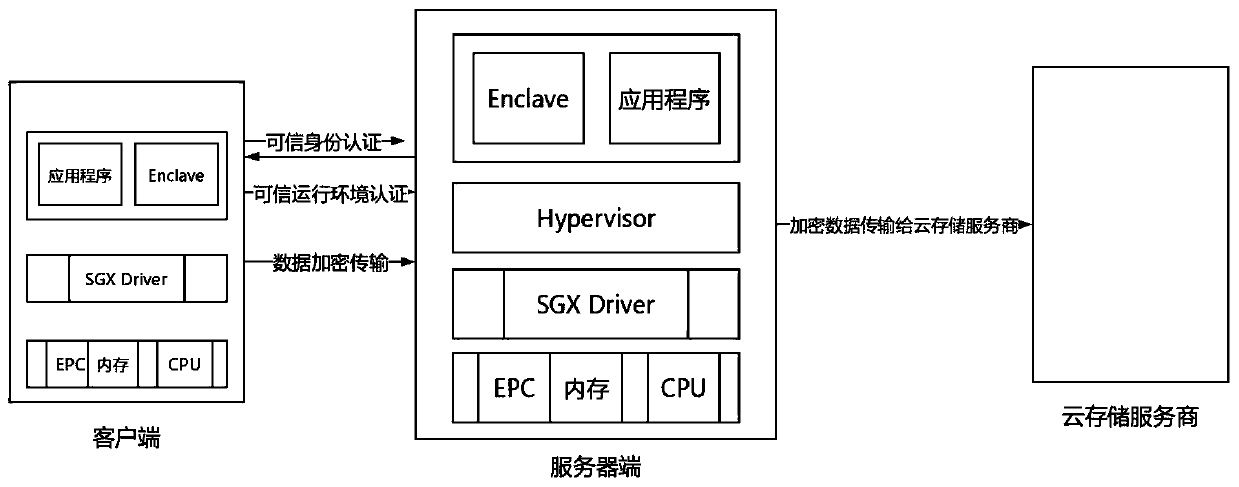
Secure cloud storage method based on SGX
The invention belongs to the technical field of trusted cloud computing, and particularly relates to a secure cloud storage method based on SGX. The method is suitable for a client / server architecturesystem based on SGX, and comprises the following steps: a trusted identity authentication step: a client performs bidirectional authentication of a trusted identity with a server through a trusted identity authentication module of the server, and establishes a session with the server after the trusted identity authentication is completed; a credible operation environment authentication step: after the client passes the credible identity authentication, the client verifies the legality of the operation environment of the server to the server through a credible operation environment authentication module of the server; a credible execution step: the client transmits the data to an endclave of the server through a credible channel, and the endclave encrypts the data; and a cloud storage step: the server side sends the encrypted data to a cloud storage service provider. According to the method, the problems of trusted authentication and key packaging of the client and the server are solved.
Owner:NORTHEASTERN UNIV
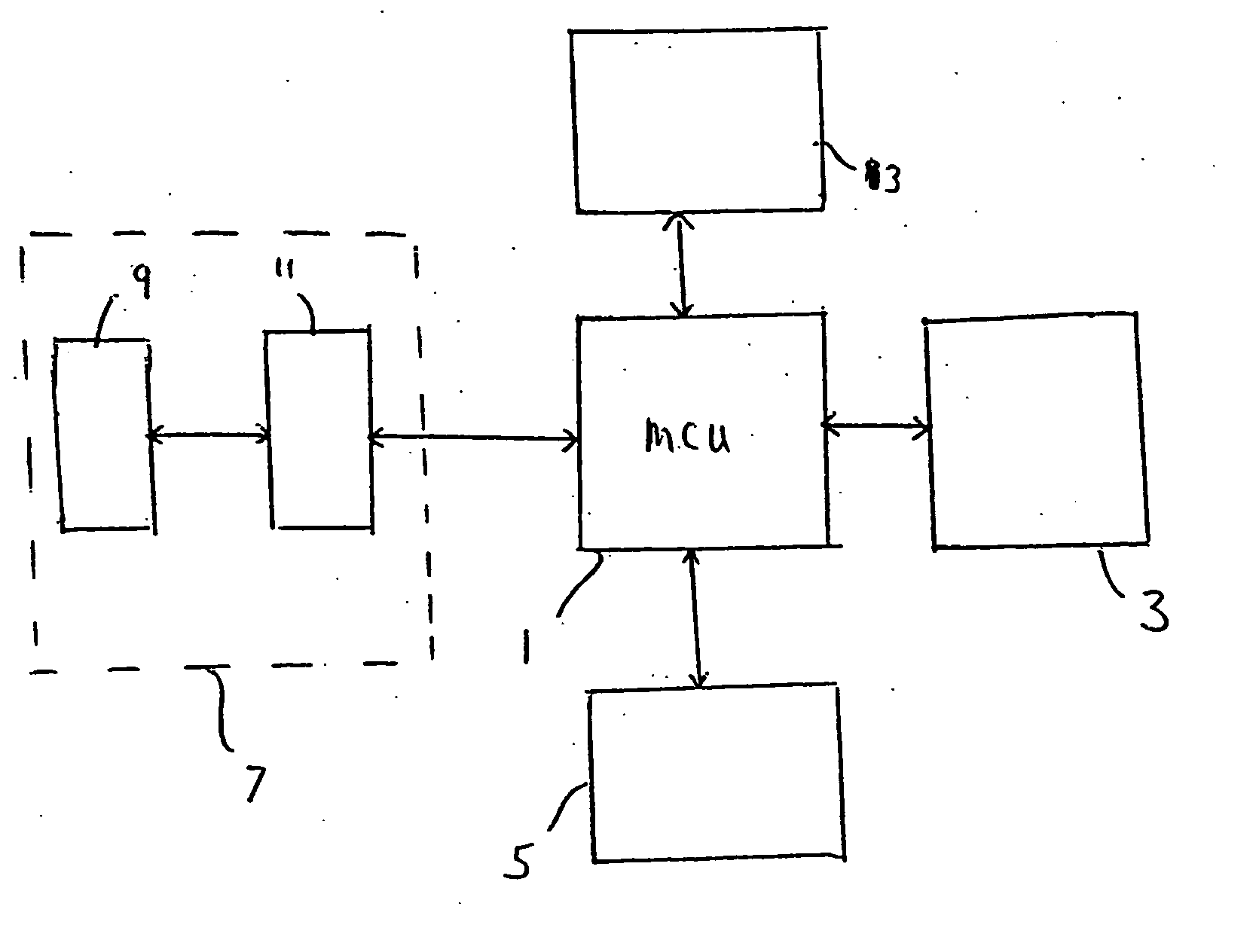
Portable storage device with encryption system
ActiveUS20060105748A1Verify integrityKey distribution for secure communicationUnauthorised/fraudulent call preventionNon-volatile memoryIntegrated circuit
A portable data storage device has a non-volatile memory 3 for storing user data, an interface section 7 for receiving and transmitting data to a host, and a master control unit 1 for transferring data to and from the non-volatile memory 3. The portable data storage device further includes an integrated circuit 13 for generating a public / private key pair. The portable data storage device is arranged to transmit at least one of the keys out of the device. In different embodiments, the host can verify that the data it receives is correct, and the device can verify that the host has received the correct data.
Owner:TREK 2000 INT
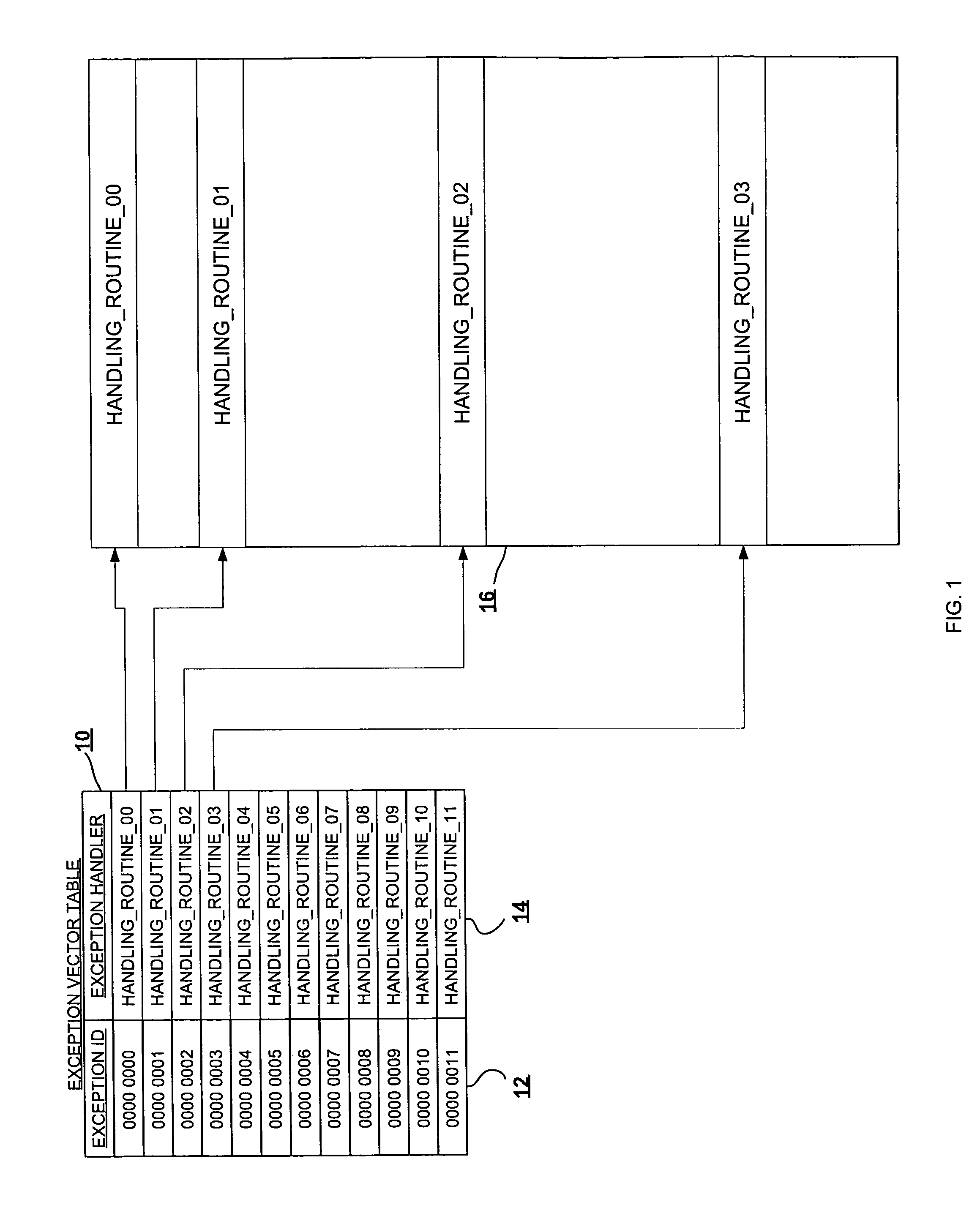
Method and system for protecting against the execution of unauthorized software
ActiveUS8239686B1Verify integrityUnauthorized memory use protectionHardware monitoringComputer hardwareClient-side
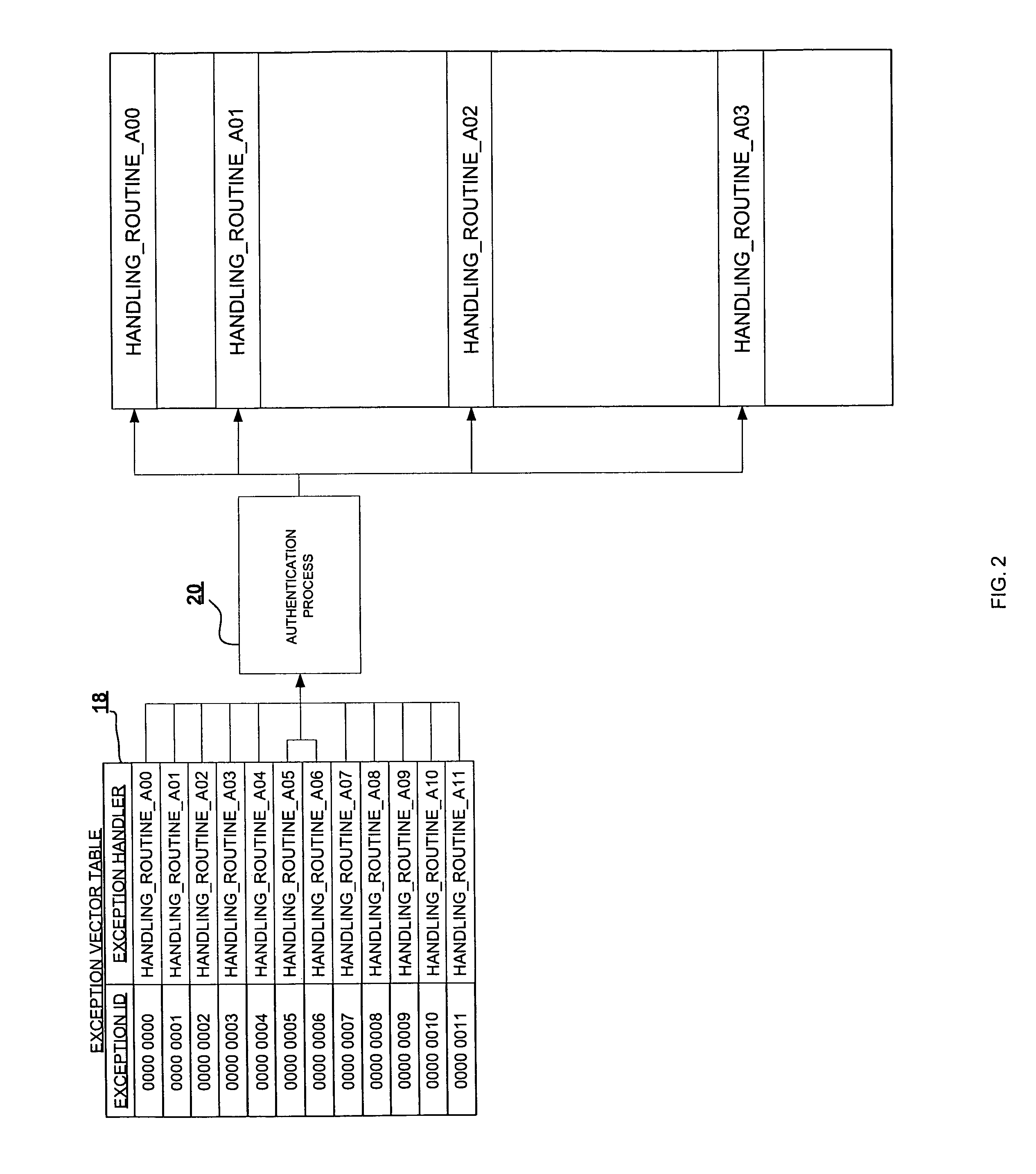
In accordance with an embodiment of the present invention, a client device is protected against the execution of unauthorized software. The client includes a code authentication process that verifies the integrity of executable code, by generating and comparing a first hash value of the executable code with a known hash value of the original code. Furthermore, during boot-up, the client initializes a CPU exception vector table with one or more vector table entries. One or more, or all, of the vector table entries direct the CPU to execute the code authentication process prior to executing an event handler when an exception event occurs. Consequently, the code authentication process is virtually guaranteed to execute, thereby protecting against the execution of unauthorized code.
Owner:NBCUNIVERSAL
Behavior-based software trusted measurement system and method
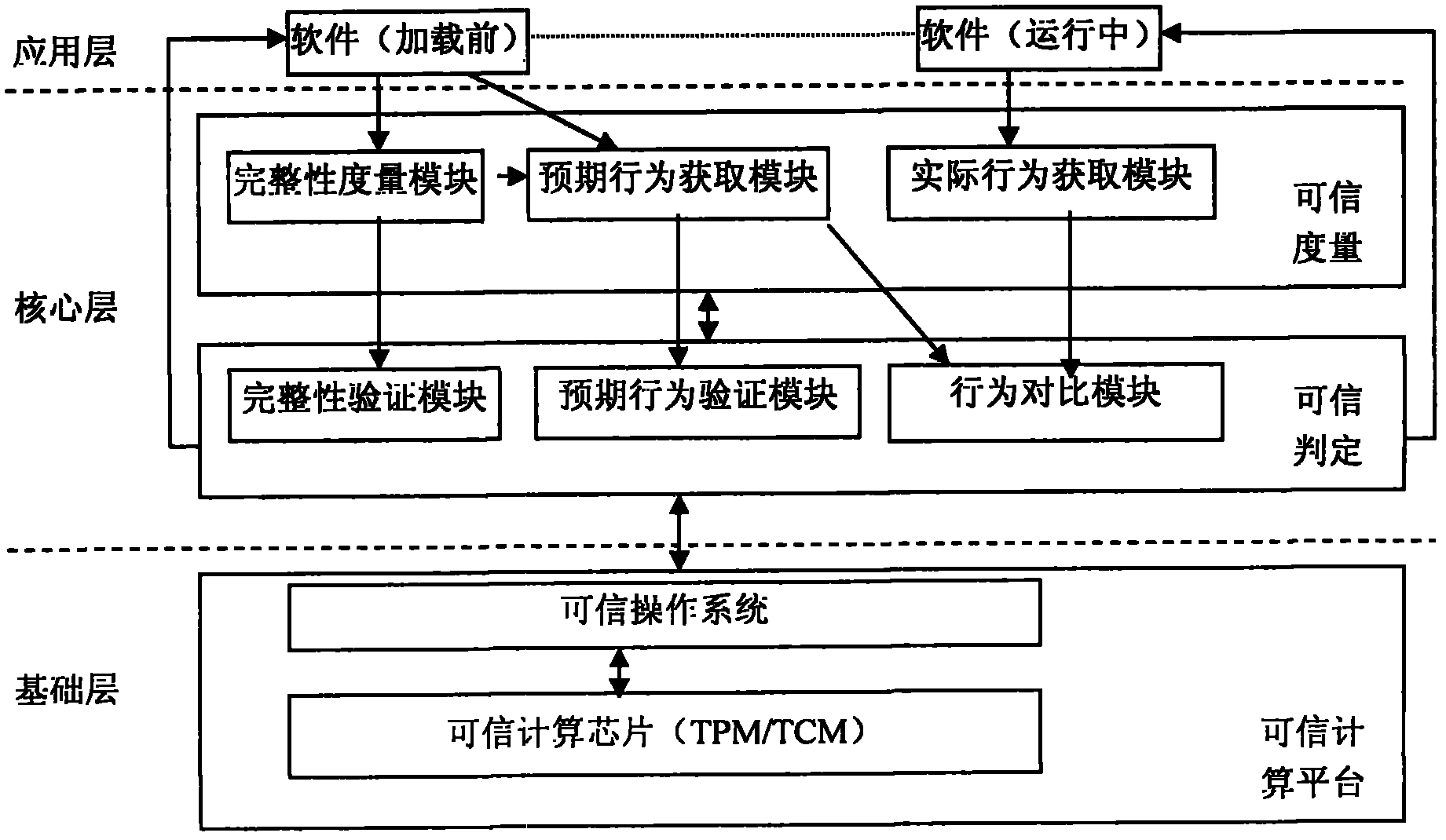
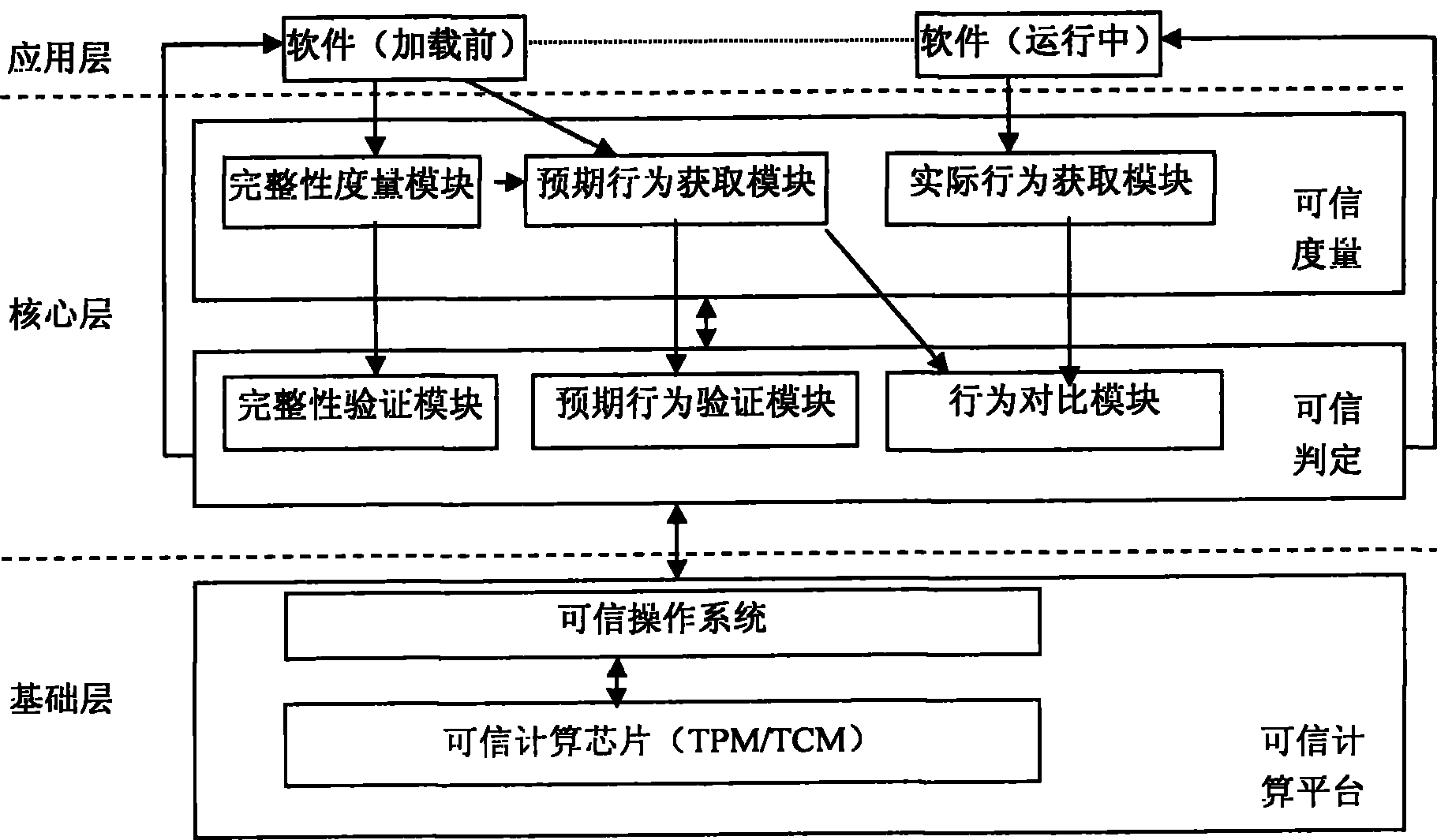
InactiveCN102073816AImplement dynamic metricsVerify integrityPlatform integrity maintainanceSoftware trustworthinessSoftware
The invention discloses a behavior-based software trusted measurement system and a behavior-based software trusted measurement method. The system consists of a basic layer, a core layer and a user layer, wherein the trusted measurement of the software is realized by comparing an expected behavior of the software which is extracted in advance before the software is installed with a behavior in actual running of the software. The method solves the problem of trusted measurement when the software runs so as to ensure that 'an expected behavior achieves an expected target'.
Owner:BEIHANG UNIV
Method and apparatus for verifiably migrating WORM data
ActiveUS20060126468A1Verify integrityFilamentary/web record carriersUser identity/authority verificationFile systemWrite once read many
A file system in a storage system allows a user to designate data as write-once read-many (WORM) data. The WORM data are stored in a first set of storage media of the storage system. Signature data are generated from the WORM data. Using the signature data, the integrity of the WORM data can be verified.
Owner:NETWORK APPLIANCE INC
Method and apparatus for remotely verifying memory integrity of a device
ActiveUS20070150857A1Verify integrityElectronic circuit testingError detection/correctionComputer hardwareTerm memory
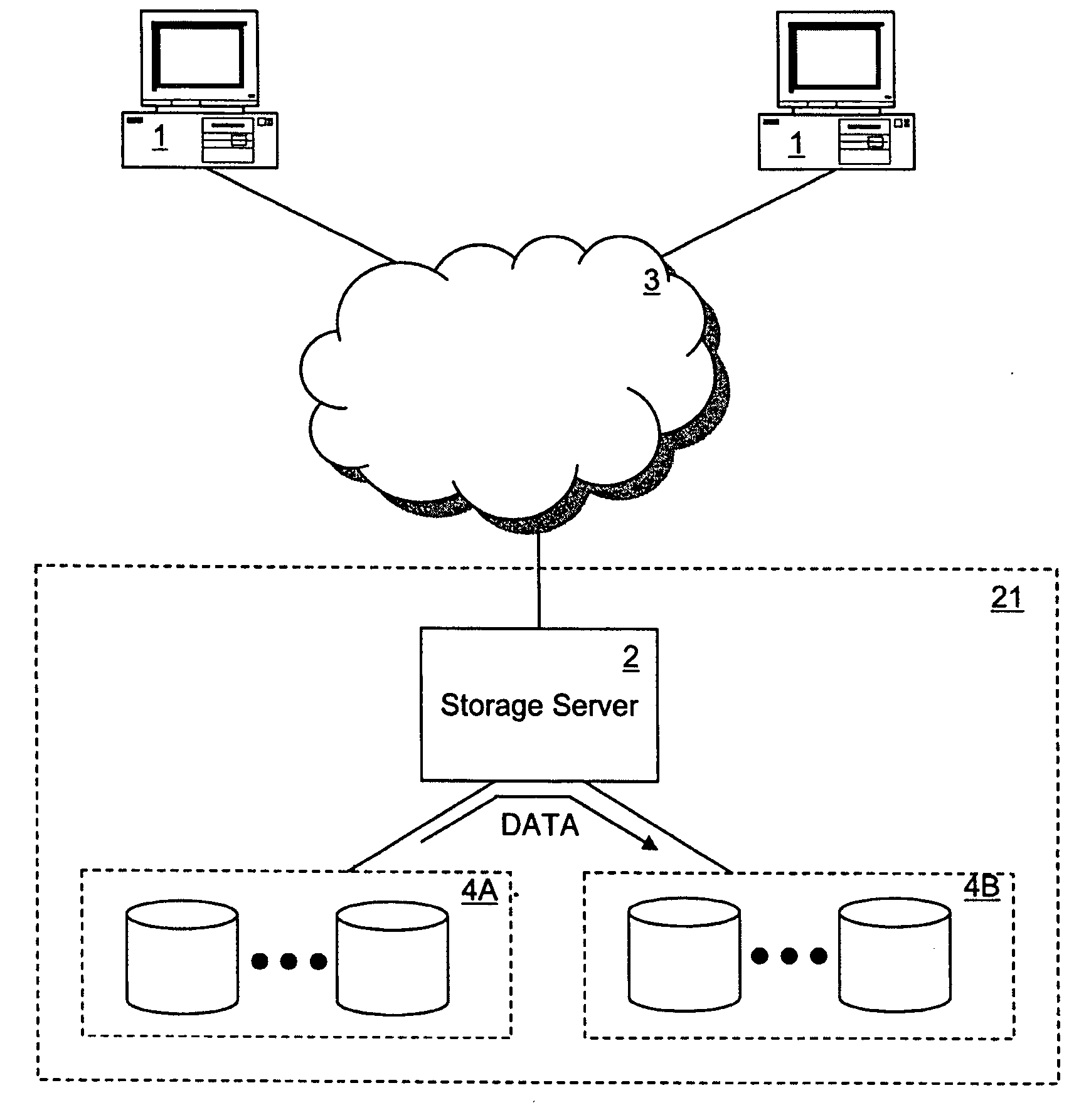
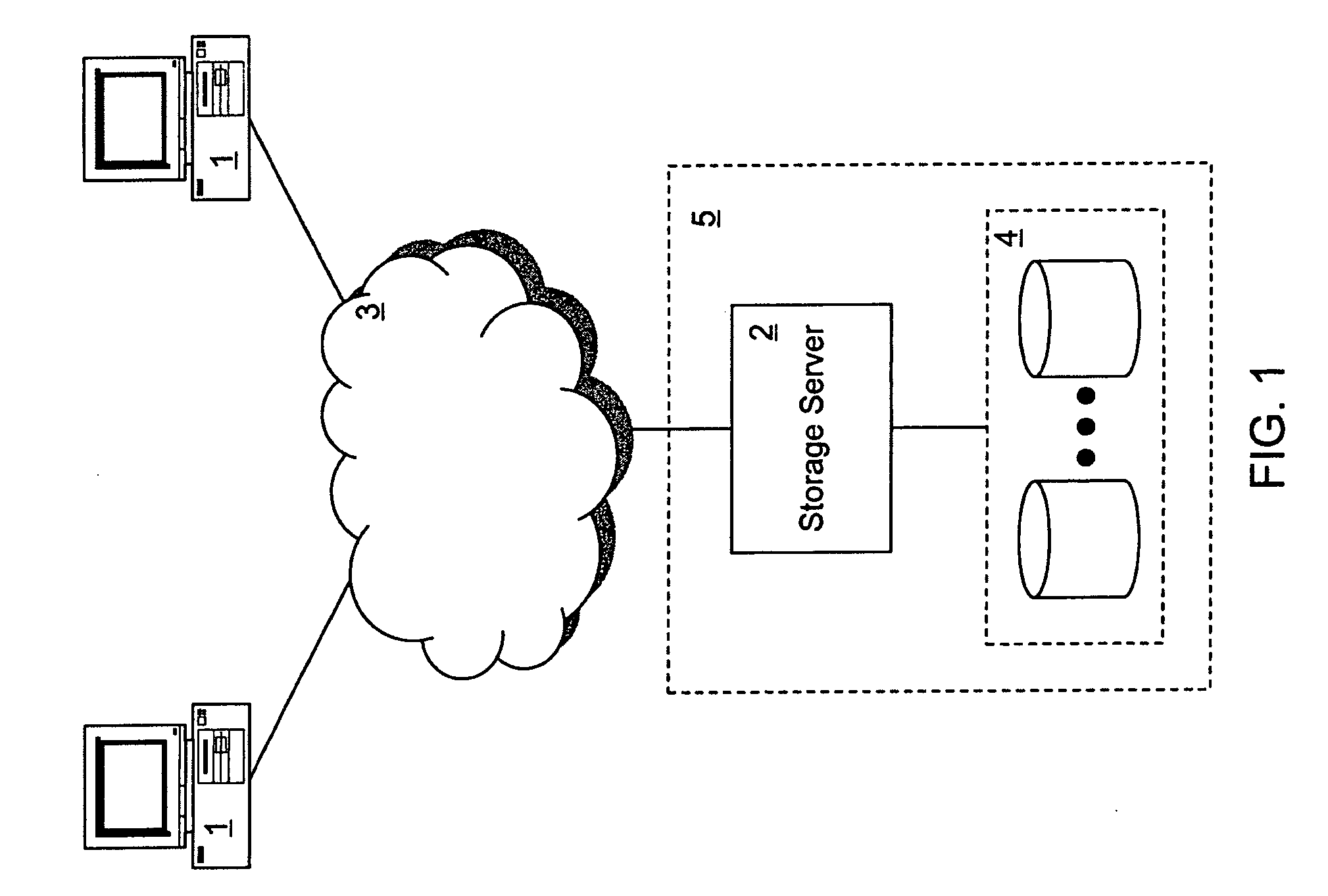
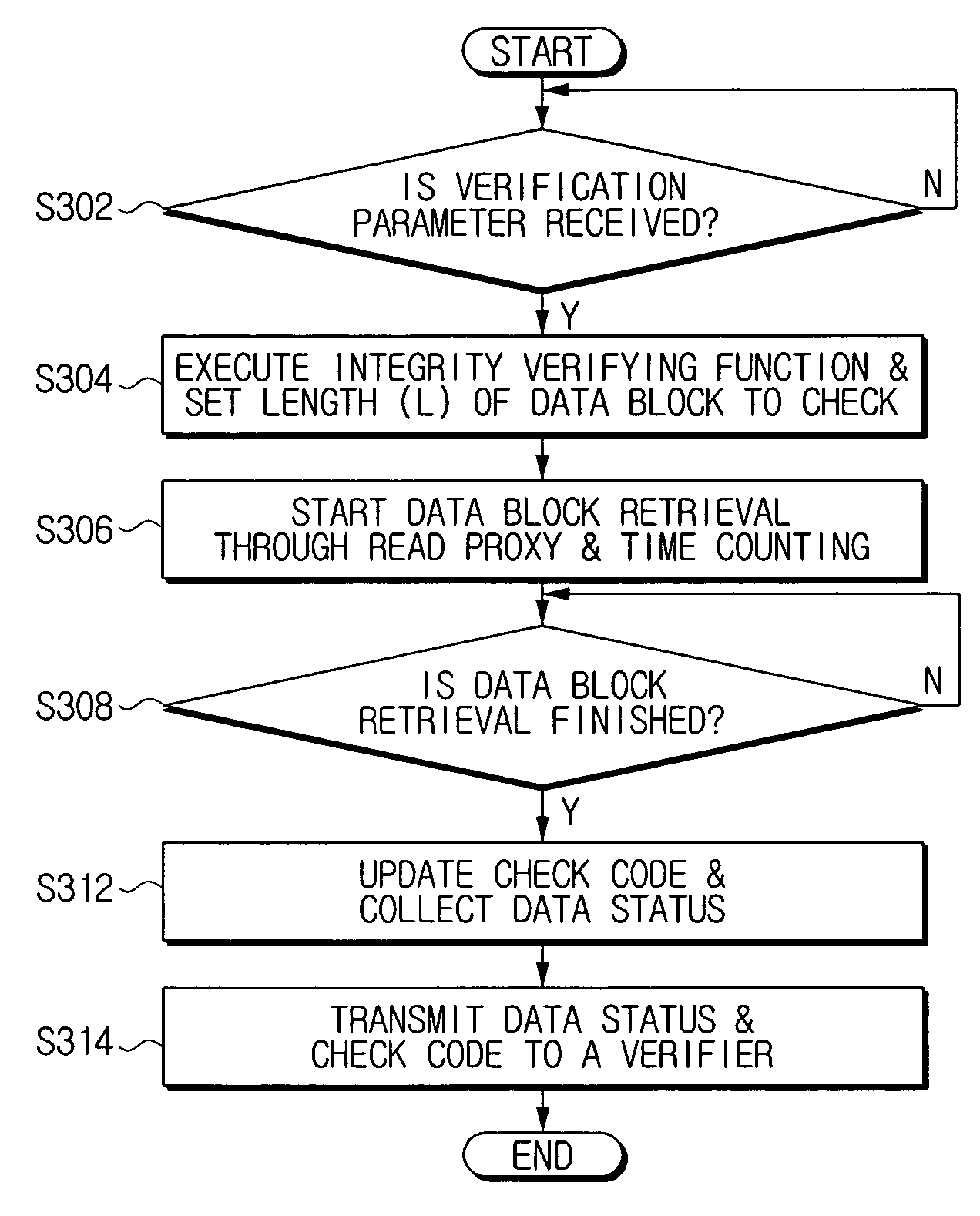
A device and method for verifying the integrity of a memory in a remote device are provided. An exemplary memory integrity verification method compares, based on a verification parameter received from a verifier, the time for retrieving data block of a memory of a remote device with a maximum threshold time allowed to read the memory, and transmits to the verifier a remote verification code and a data status according to the result of comparison so that the verifier can verify the integrity of the memory. Instead of relying on the verifier, the remote device provides data status information for integrity verification by using the memory retrieval time. As a result, accurate integrity verification is provided, and no independent hardware is required to verify integrity.
Owner:SAMSUNG ELECTRONICS CO LTD
Statistical analysis method for secret key leakage resisting encrypted data aggregation in smart power grid
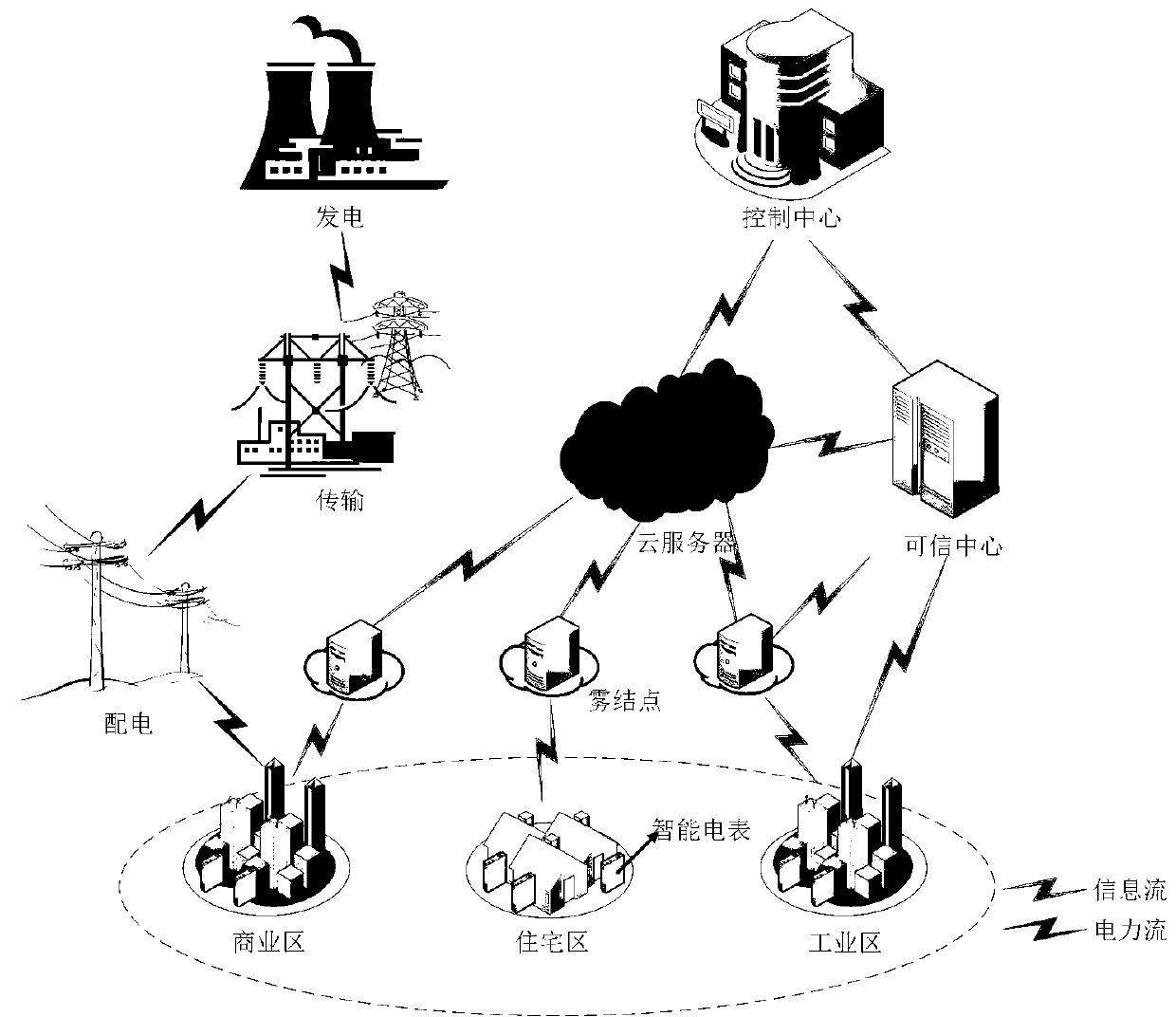
ActiveCN111294366AAchieve privacyAchieve protectionData processing applicationsMultiple keys/algorithms usageStatistical analysisCiphertext
The invention discloses a statistical analysis method for secret key leakage resisting encrypted data aggregation in a smart power grid. Each user area is responsible for one fog node; the fog node serves as a data aggregation gateway and a data repeater; user electric energy consumption data sent by an intelligent electric meter in a user area is aggregated for the first time by a fog node to obtain a fog-level aggregation ciphertext, the fog-level aggregation ciphertext is signed, and then the fog-level aggregation ciphertext and signature information are sent to a cloud server to be stored;the cloud server stores the aggregated ciphertext data and the signature information of different user areas in a database; data query, statistics and analysis services are provided for a control center of the intelligent power grid system; the cloud server can provide enough information for the control center on the premise of not destroying the privacy of any single user, so that the control center can calculate the sum, average value and variance of power consumption data of all users in a specified user area by utilizing the information.
Owner:SOUTHWEST PETROLEUM UNIV
Data encryption method, device, data decryption method and device
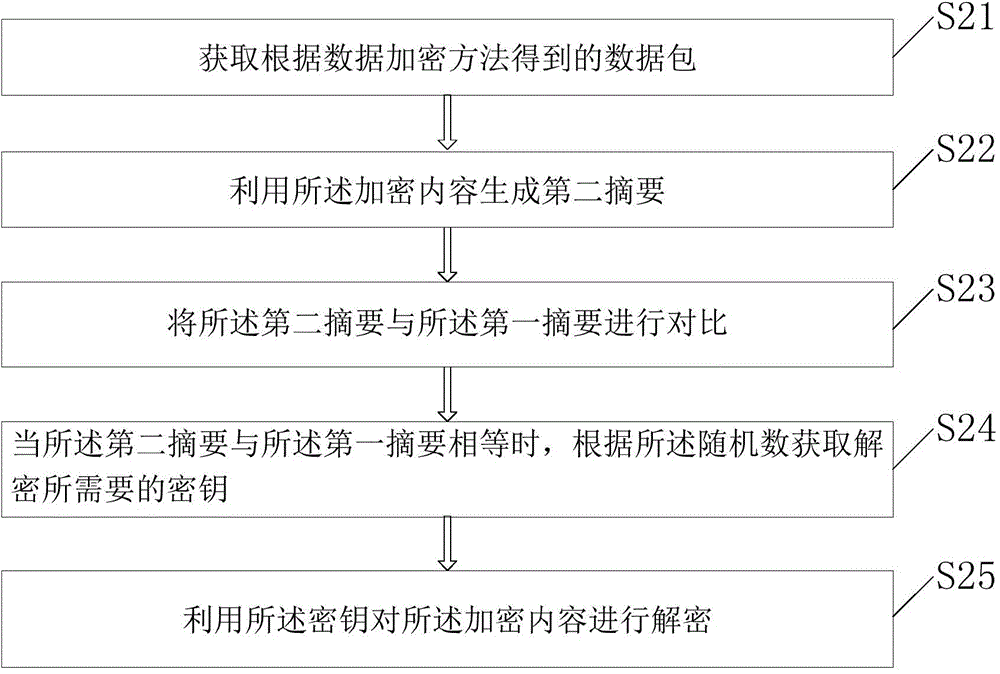
InactiveCN105763331AImprove securityVerify integrityUser identity/authority verificationData contentComputer hardware
The invention provides a data encryption method, a data encryption device, a data decryption method and a data decryption device. The data encryption method includes the following steps that: a random number is obtained; a key required by encryption is obtained according to the random number; the key is utilized to encrypt content to be encrypted; and a first abstract is generated by using the encrypted content. With the data encryption method provided by the embodiments of the invention adopted, the corresponding key obtained according to the obtained random number can be selected to encrypt the data content, and an encryption mode can be more flexible with low cost; and information such as the abstract can be added into the data, and therefore, the integrity of the encrypted content can be verified, and therefore, the safety of the encrypted data can be improved.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
Trusted safety network system
InactiveCN107493271AImprove safety and reliabilityVerify integrityKey distribution for secure communicationUser identity/authority verificationNetworked systemAuthentication server
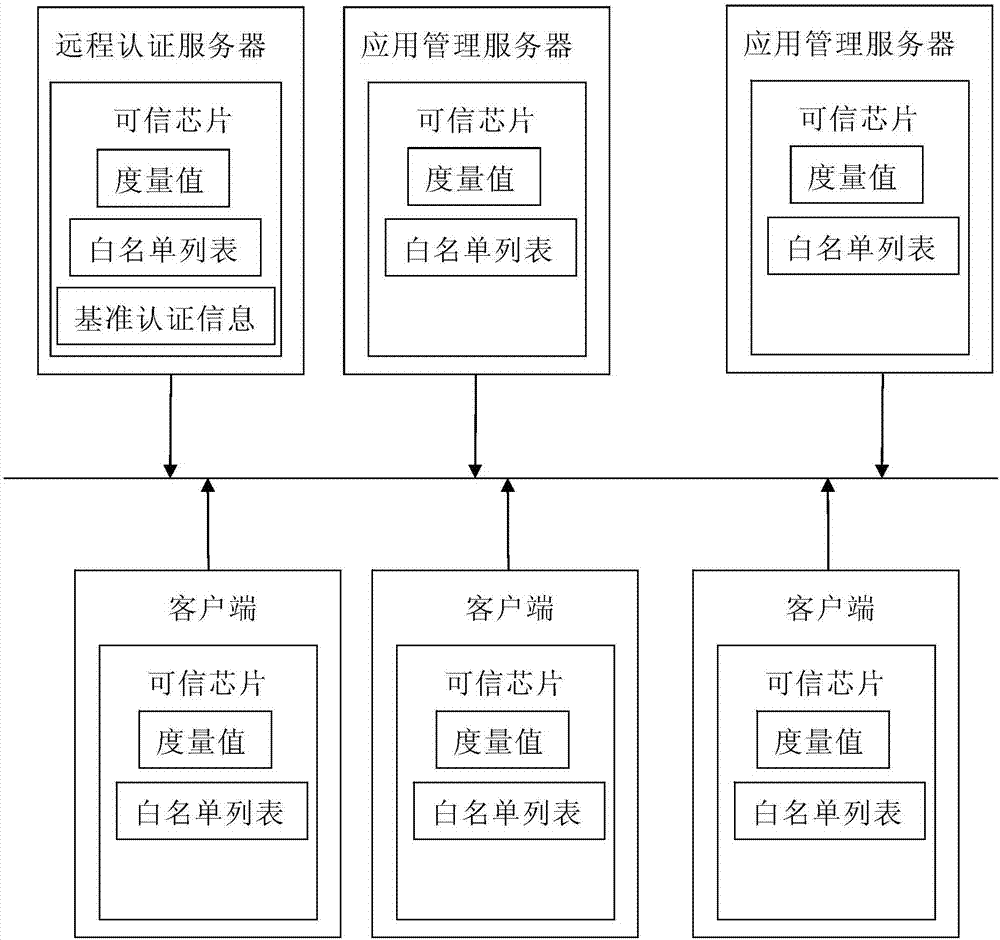
The invention discloses a trusted safety network system which is implemented on the basis of a client-server architecture, wherein each network node is a trusted host provided with a trusted chip, and each network node carries out a trusted starting process on the basis of the trusted chip; a white list is stored in the trusted chip of each network chip, the white list comprises application software allowed to be executed and a measured value of a key code of the application software, and when the application software is operated, the integrity of the application software is verified by the white list; a remote authentication server is configured, and datum authentication information for carrying out identity authentication and integrity verification is stored in a trusted chip of the remote authentication server; and an application management server is configured and used for carrying out deployment and management of application on each network node. The invention constructs the trusted safety network system implemented on the basis of the trusted chip, and safety reliability of the network system can be improved.
Owner:DATANG GAOHONG XINAN ZHEJIANG INFORMATION TECH CO LTD
Verification of transactional integrity
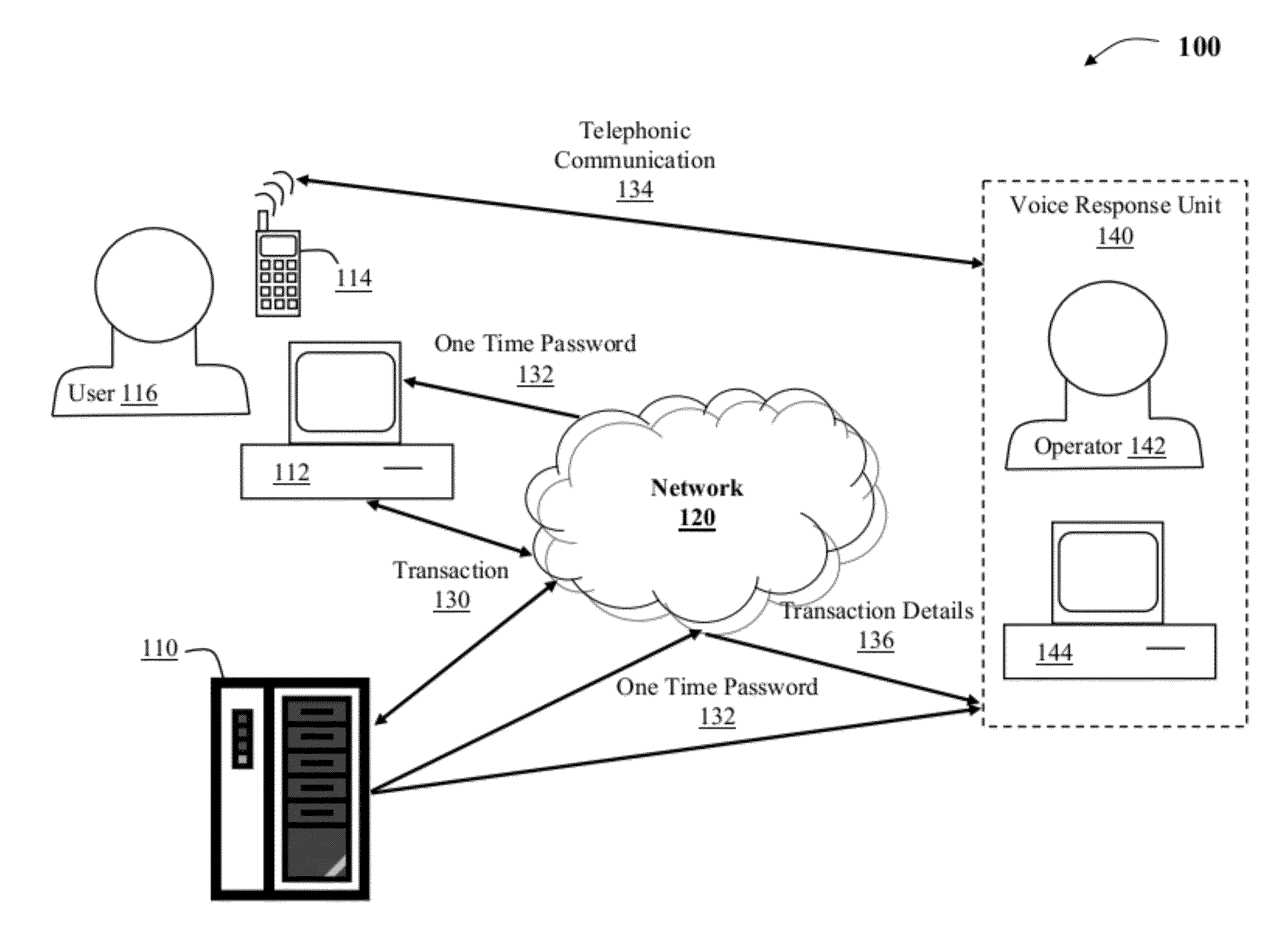
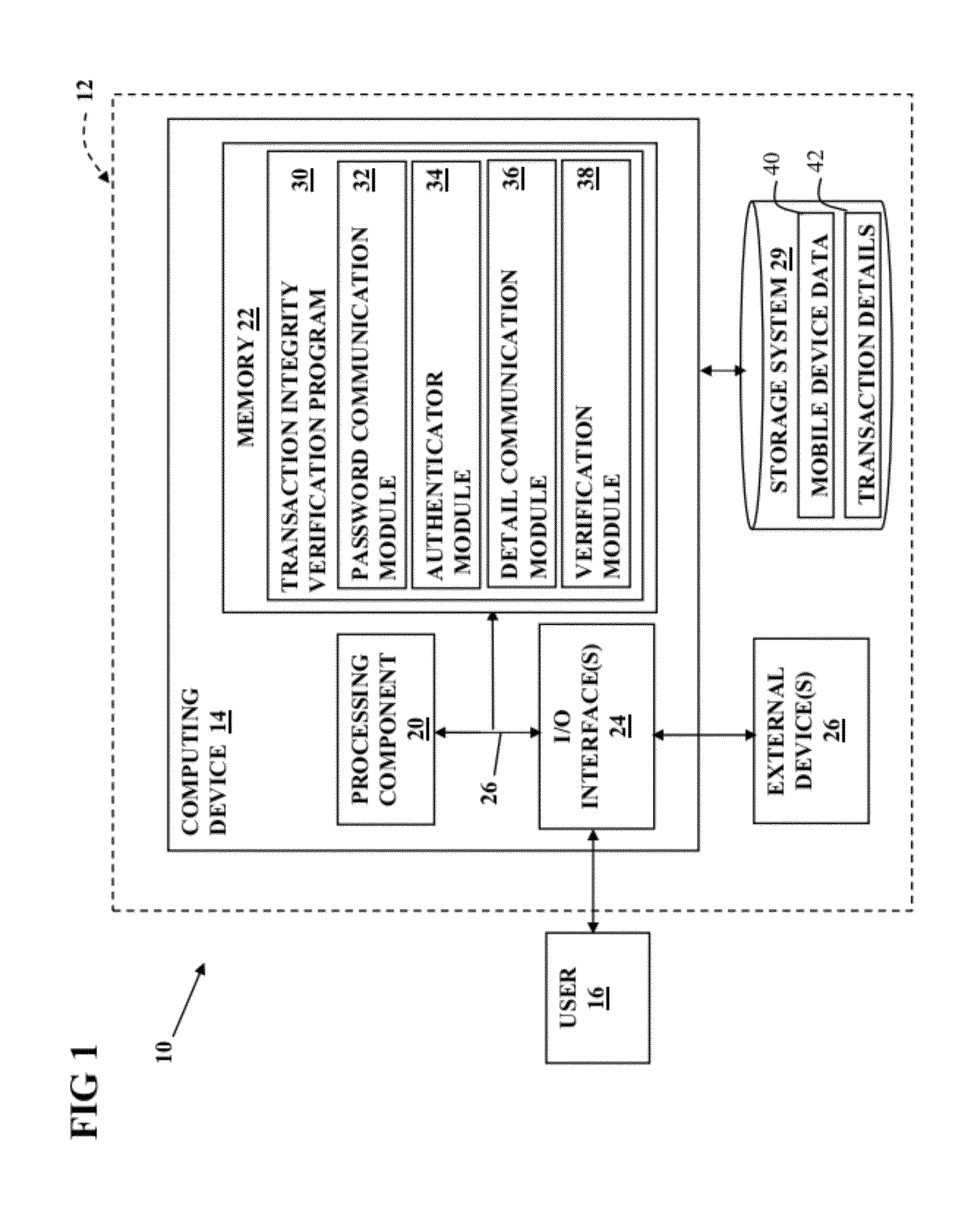
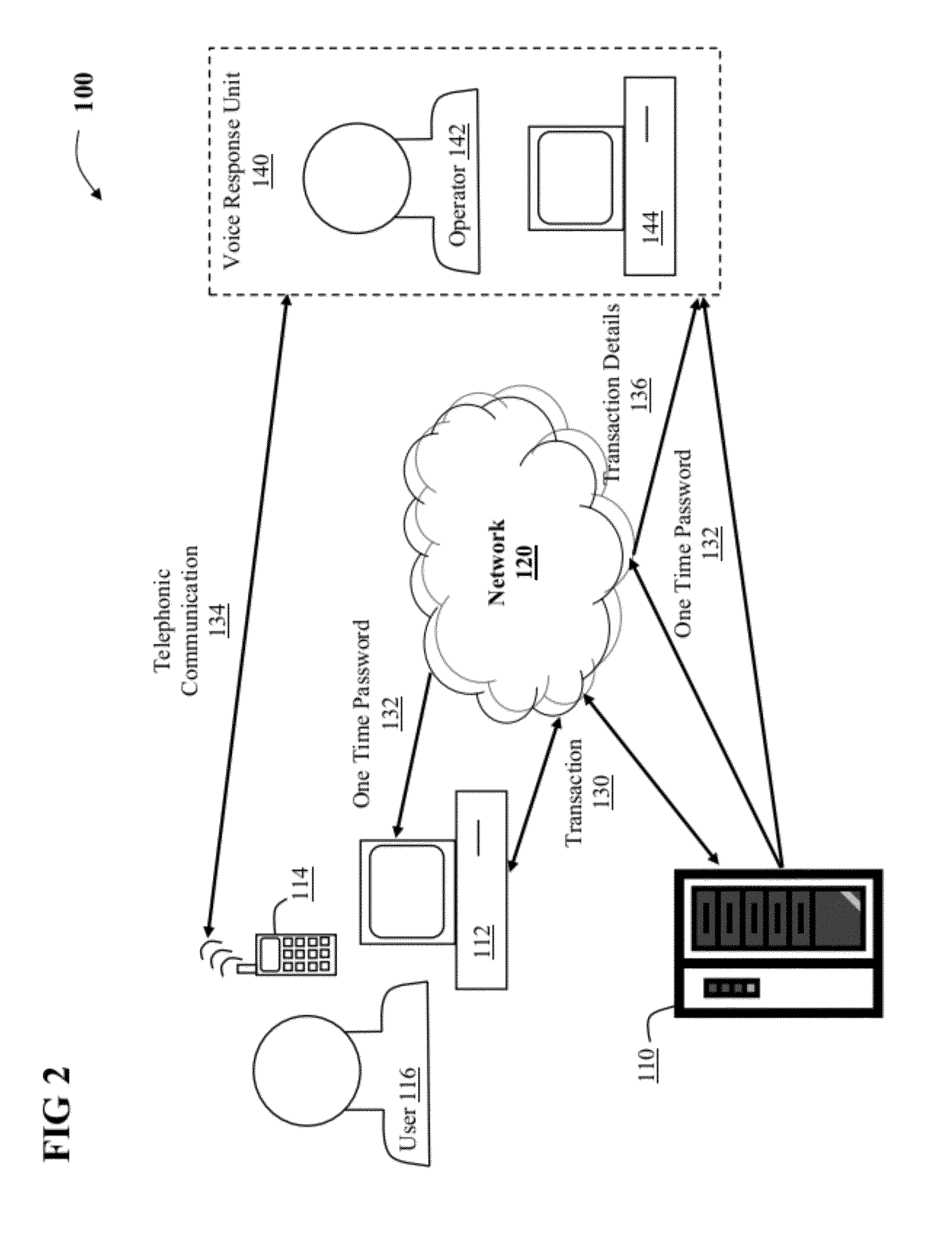
InactiveUS20120264405A1Facilitate communicationVerify integritySpecial service for subscribersComputer security arrangementsMobile telephonyTelephone equipment
Aspects of the present invention provide a solution for verifying the integrity of a transaction. In response to receipt of a confirmed electronic transaction from a user, a one time password is forwarded to the user. The user then initiates a telephonic communication with a verifier on the user's wireless device and provides the one time password to the verifier. The verifier authenticates the mobile telephonic device based on the device's caller identification number and determines whether the one time password provided by the user matches the one forwarded to the user. After the user is authenticated, the verifier communicates the details of the transaction that were received and the user confirms whether the details match those originally entered.
Owner:IBM CORP
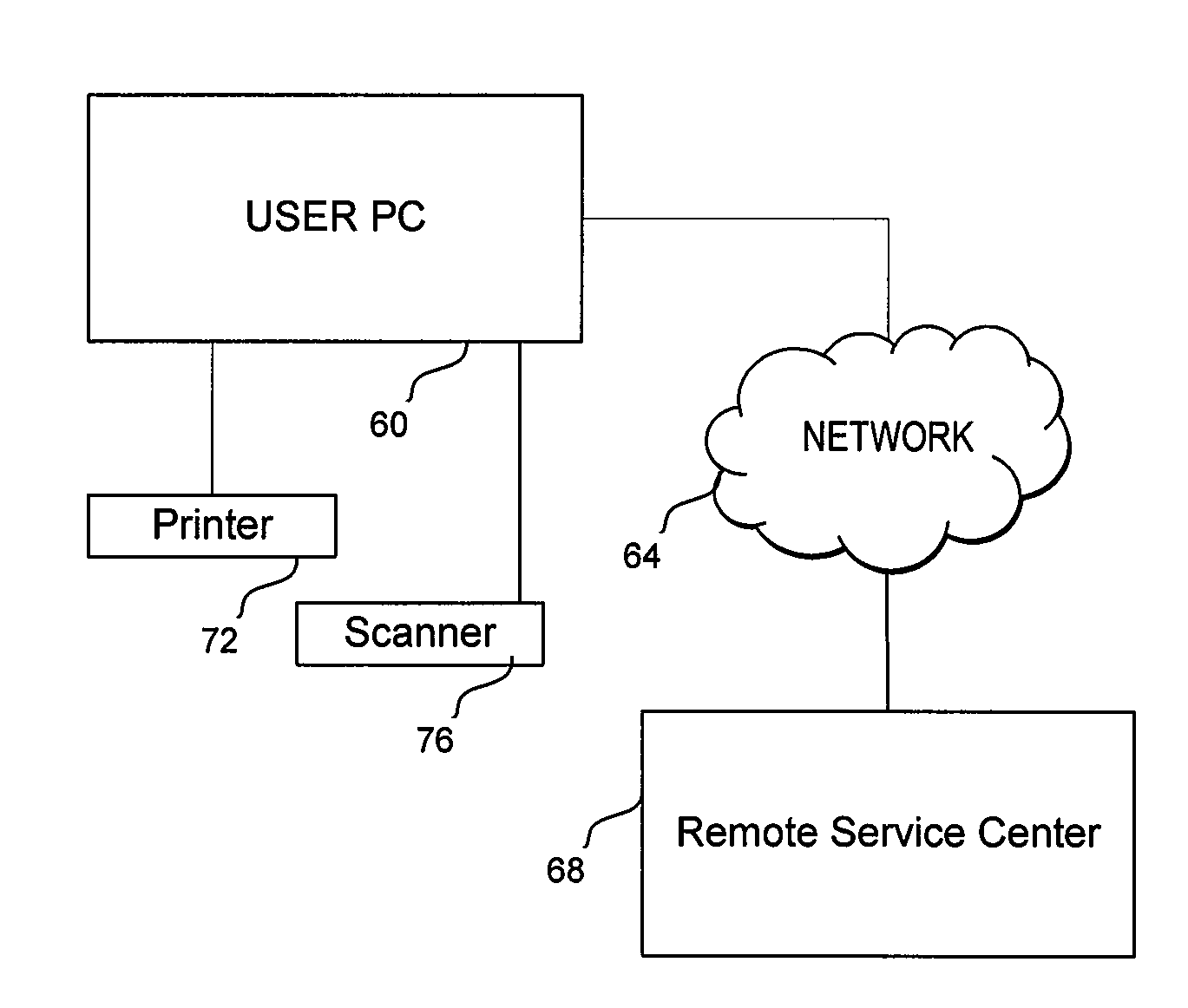
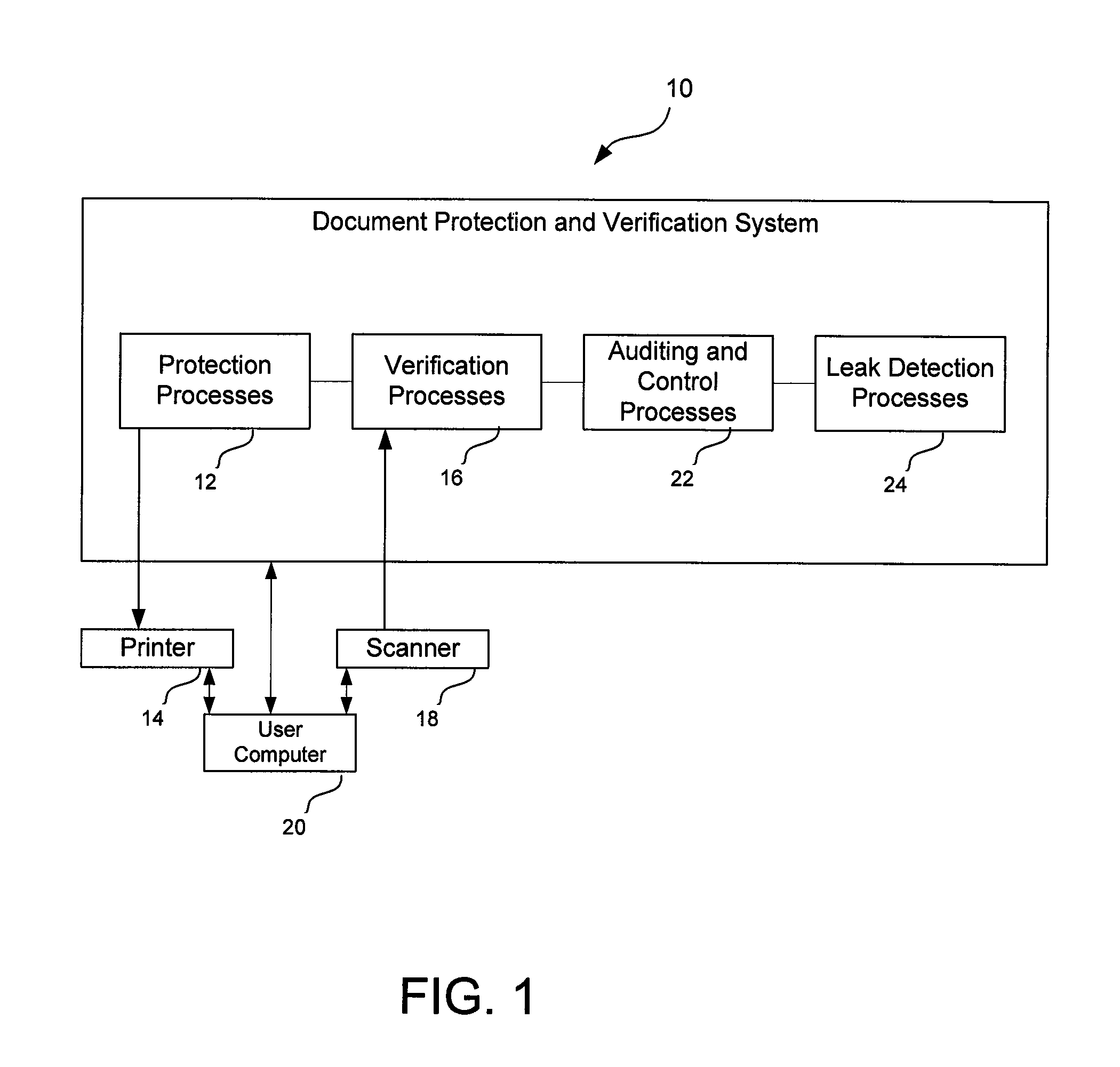
Systems and processes of protection and automatic verification of paper documents against falsification, adulteration and leakage
ActiveUS20100111301A1Improve protectionDecentralized controlDigital data protectionVisual presentationPaper documentSecurity function
Protection of documents printed in paper is provided by processes for detection, immediately and clearly, of different types of falsification, adulteration, inclusion and omission. A network accessible system is capable of detecting several fraud aspects. A “Remote Expertise Center” or a remote service data center accessible from and to any location in which there is a connection to the network, such as through the Internet provides customized protection and automatic verification of document pages. Documents pages are generated by the Remote Expertise Center and transmitted to remote printers, bypassing user operational system, using a specific driver of each printer, avoiding any access to protected document before effective printing. Documents include multiple types of security features, such that in the event that any of them is surpassed, the document will remain protected by the other types of security protection. Security features may include, among others, background images, computer readable code containing the printed content, identification information readable only with a predetermined optical filter, a copy alert that changes appearance when the printed document is copied, and personalized items to identify individuals responsible for non authorized document disclosure or leakage.
Owner:WANDERLEY LUIZ ALBERTO
Batch self-auditing method for cloud storage data
InactiveCN105978695AGuaranteed confidentialityVerify integrityUser identity/authority verificationCloud userCiphertext
The invention belongs to the technical field of information security, and in particular relates to a batch self-auditing method for cloud storage data. The method of the present invention mainly includes: generating a public-private key pair based on an elliptic curve digital signature algorithm, a public-private key pair of a lightweight signature algorithm, and a lightweight symmetric encryption algorithm: calculating digital signatures of multiple data files, data files Tags and ciphertexts of data files are sent to the cloud server; cloud users generate audit challenge information and send it to the cloud server; the cloud server returns the aggregated audit proof response information to the cloud user; cloud users For the response information, use the digital signature algorithm based on the elliptic curve and the symmetric encryption algorithm to verify the legitimacy of the aggregated audit proof response. The beneficial effect of the present invention is that it solves the problem of batch integrity verification of cloud storage data, enabling users to effectively verify the integrity of multiple data files at the same time.
Owner:SOUTHWEST PETROLEUM UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com