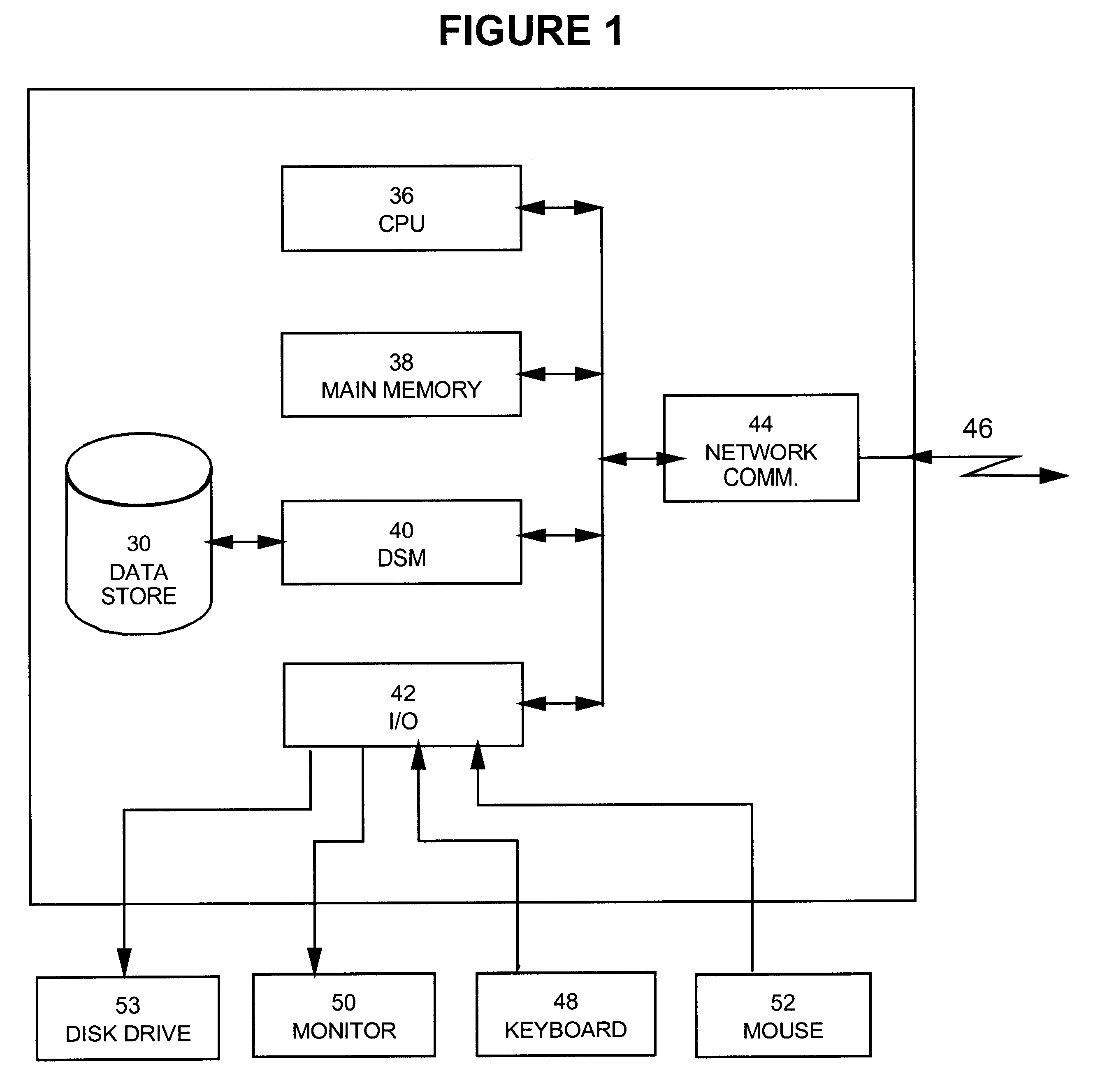
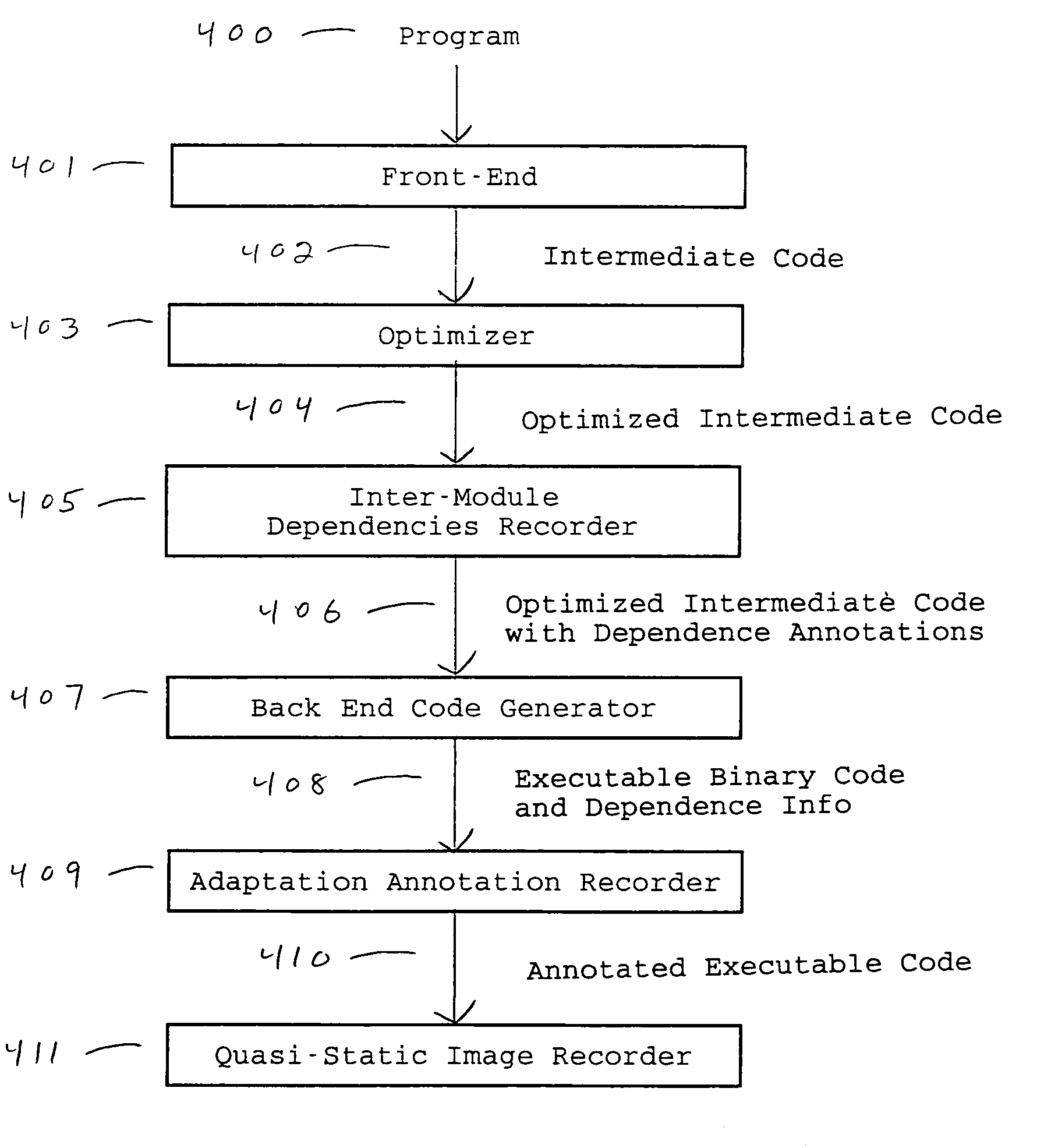
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
603 results about "Java virtual machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
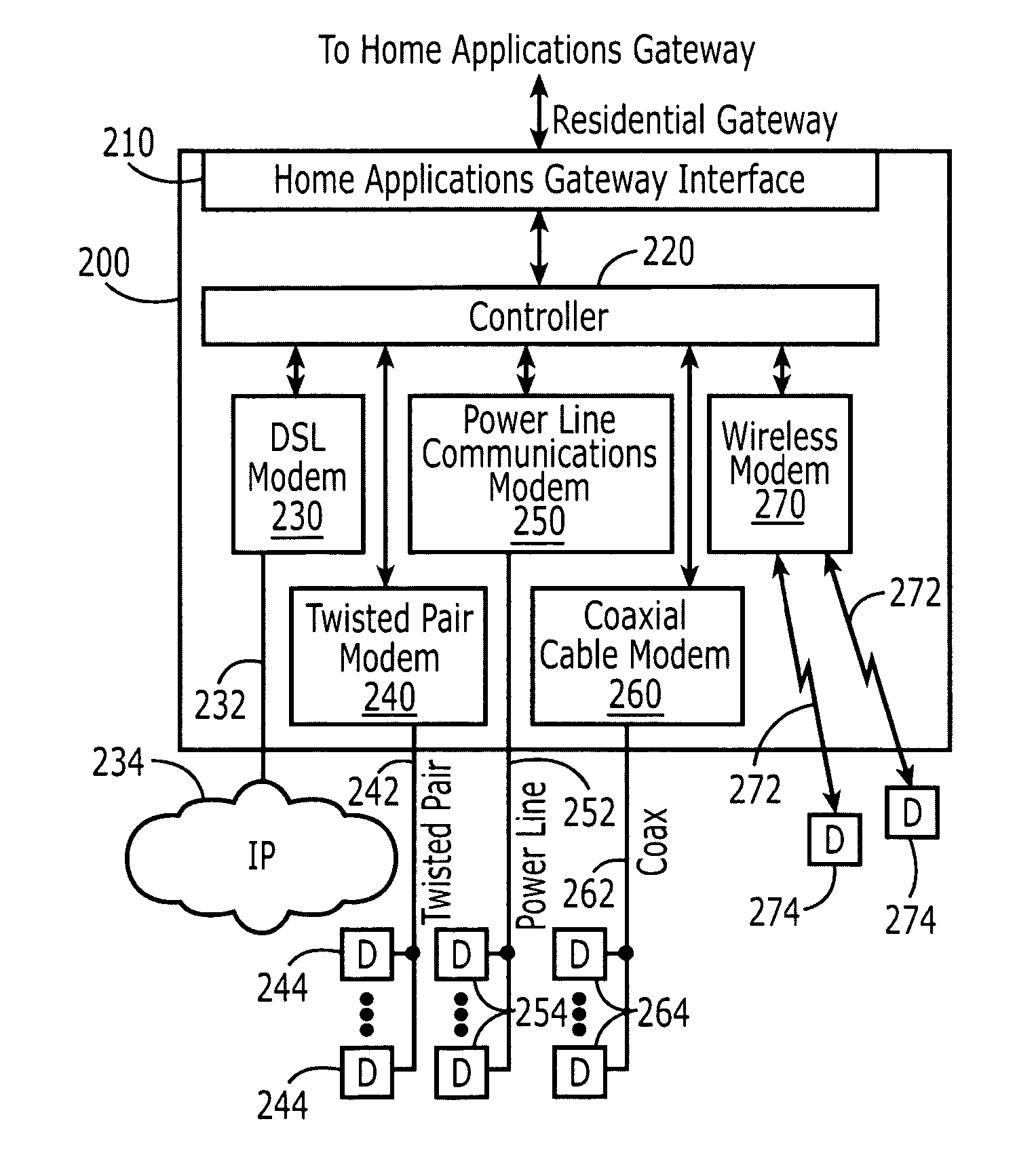
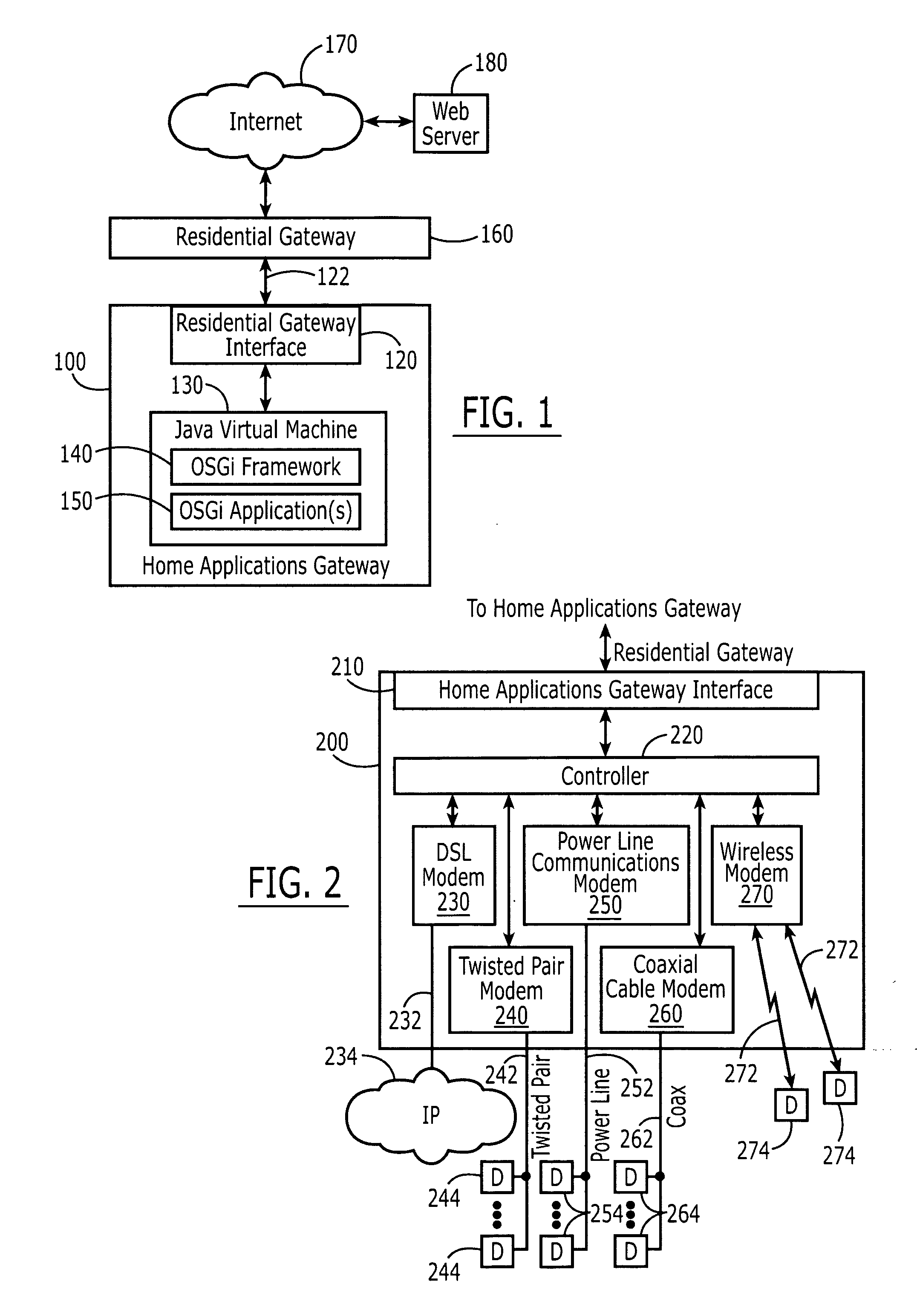
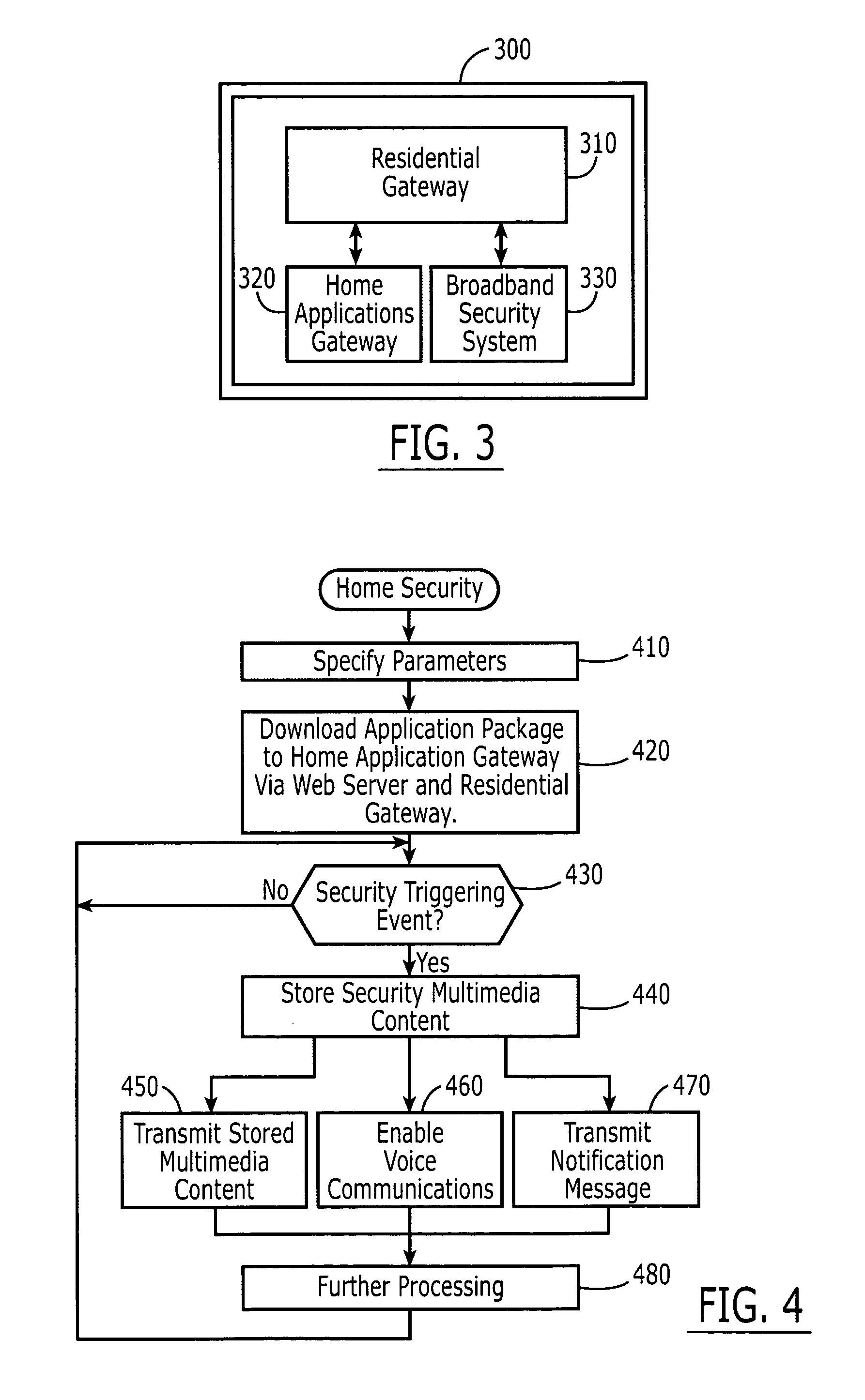
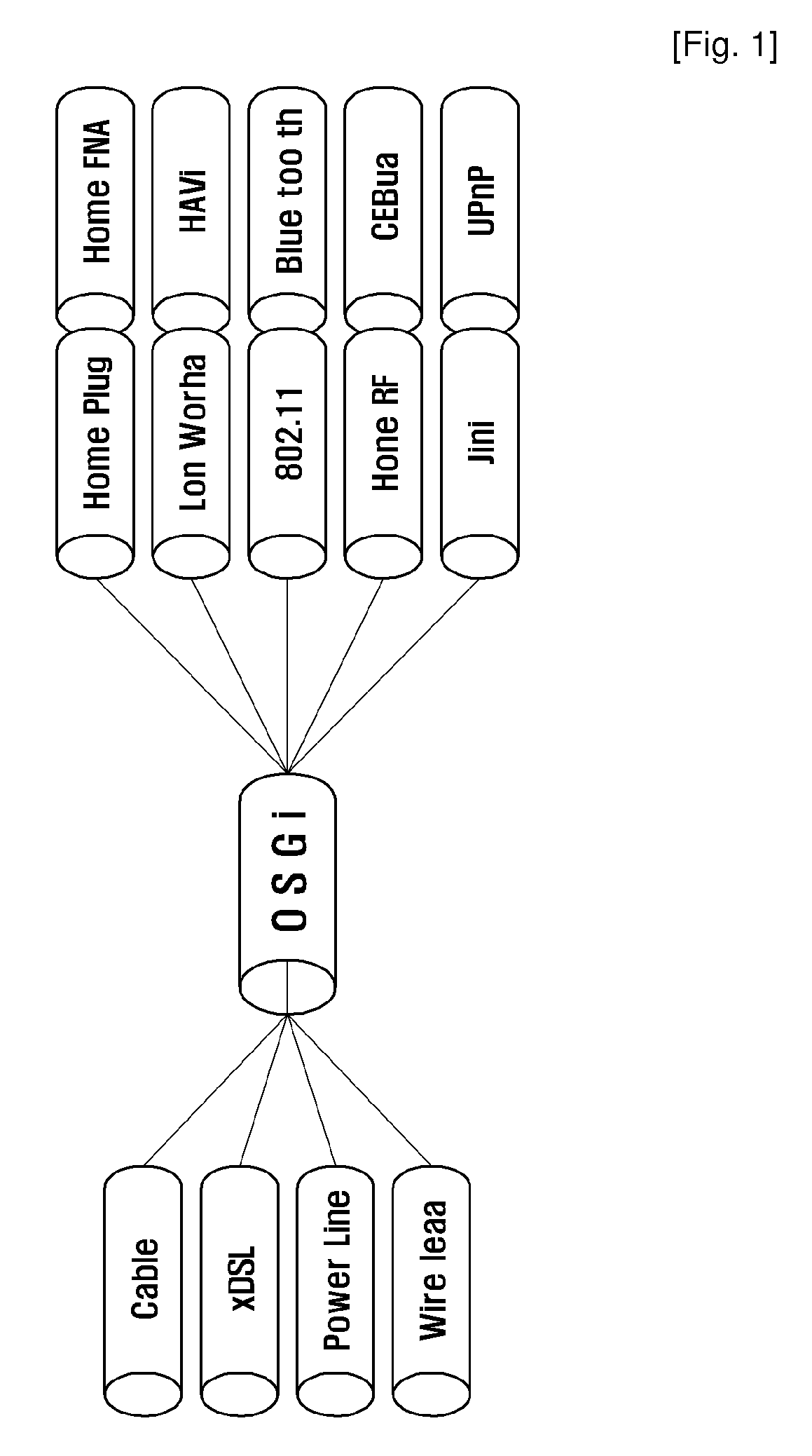
Broadband home applications gateway/residential gateway systems, methods and computer program products
A home applications gateway includes a residential gateway interface that is configured to connect to a residential gateway, and a Java Virtual Machine (JVM) that includes an Open Services Gateway initiative (OSGi) framework configured to execute OSGi Java applications that are downloaded and life cycle managed from a Web server through the residential gateway interface. The OSGi Java applications can include a video monitoring application that is configured to provide in-home and out-of-home access to Internet Protocol (IP)-based home video cameras and video files captured by the IP-based home video cameras, at a Web page. The OSGi Java applications can further include a lighting control application that is configured to control activation and deactivation of home lighting from the Web page. The OSGi Java applications can also include a home monitoring and control application that is configured to monitor home sensors and take action upon their activation.
Owner:BELLSOUTH INTPROP COR
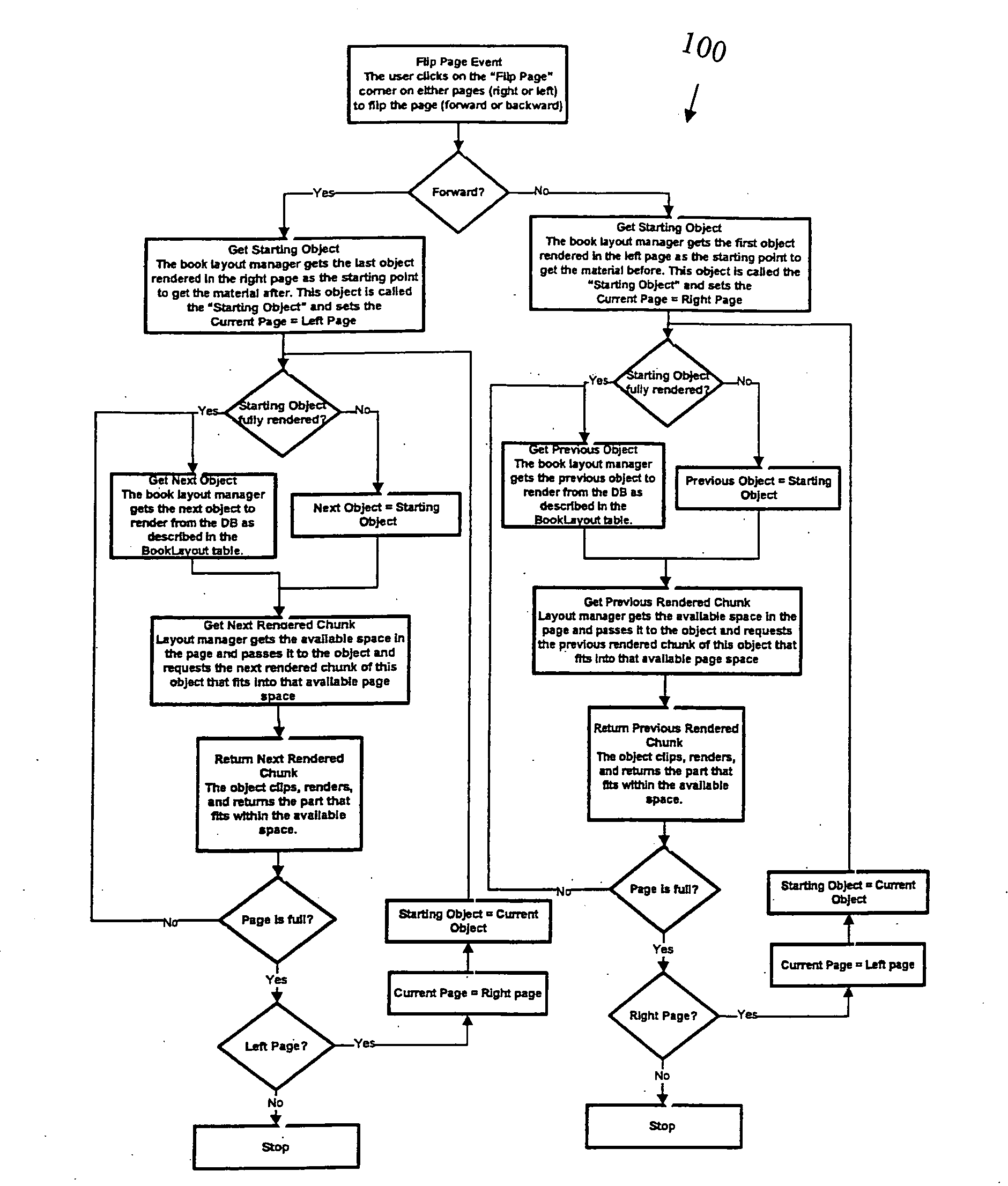
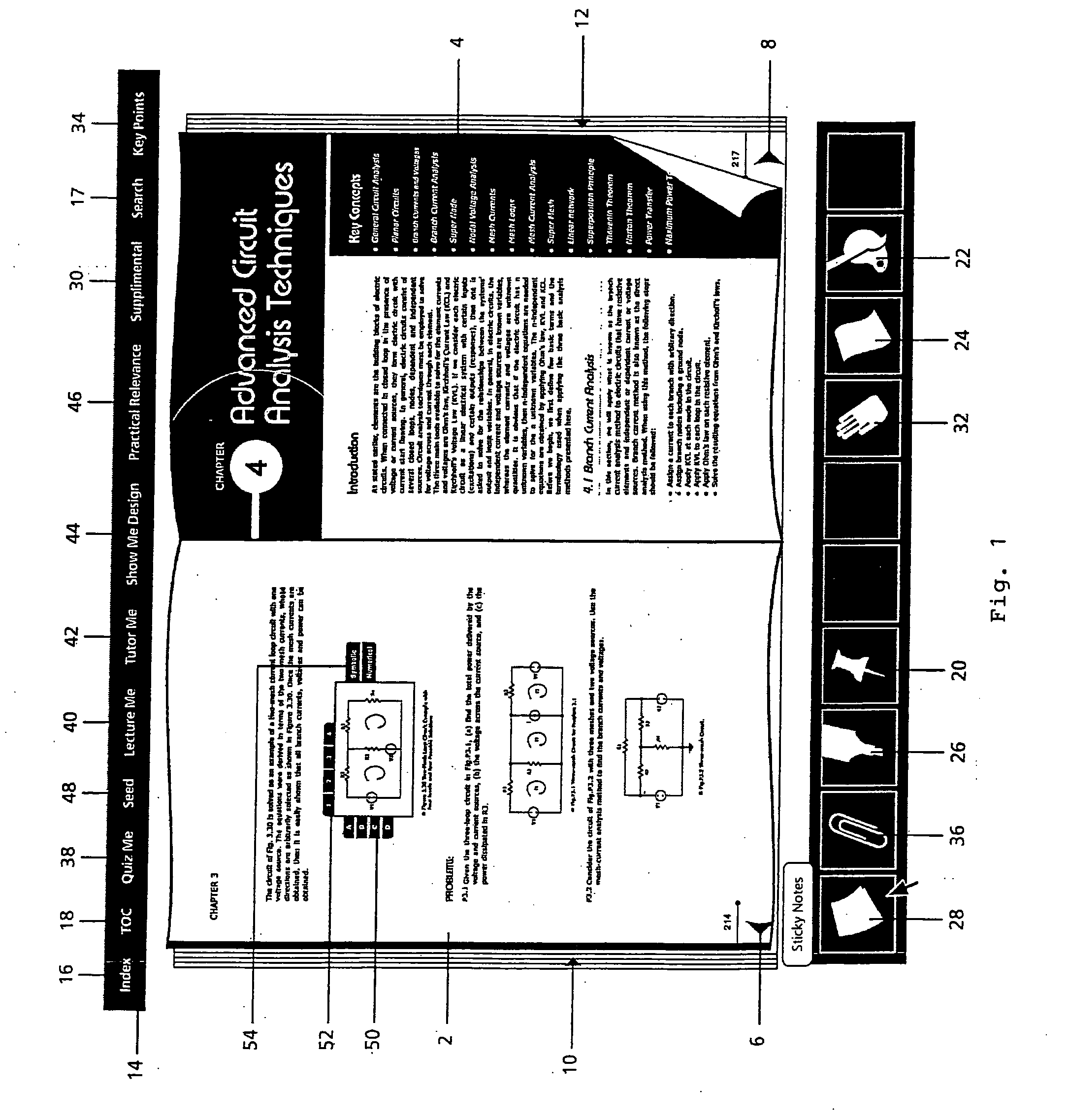
Interactive Electronic Book Operating Systems And Methods
ActiveUS20080222552A1High interactive representationRich book effectDigital data processing detailsDigital computer detailsOperational systemRandom seed
Interactive electronic book operating systems and methods for displaying and allowing customization of content of scientific, engineering and other technical and professional digital books. The systems and methods allow for a single screen for displaying digital books covering scientific and technical topics having a classical look and feel on operating platforms(such as portable laptops, desktops, and small handheld displays) that are capable of running the Java Virtual Machine. The display screen can include icon toolbars about the screen and / or directly on the screen to manipulate the pages and content of the digital book. The icons can allow for forward and backward page turning, generating of dynamic indexing and tables of contents, bookmarking, color themes, floating pages, highlighting, adding sticky notes, hiding selected content on the pages, quizzing the reader, lecturing the reader, tutoring the reader, showing the reader additional designs and practical relevance, and allowing the instructor to generate uniform seed numbers for problems and designs and / or allowing the instructor to generate random seed values for problems and designs.
Owner:UNIV OF CENT FLORIDA RES FOUND INC
Using a virtual machine instance as the basic unit of user execution in a server environment
InactiveUS20050132368A1Data processing applicationsMultiple digital computer combinationsOperational systemExecution unit
Techniques are provided for instantiating separate Java virtual machines for each session established by a server. Because each session has its own virtual machine, the Java programs executed by the server for each user connected to the server are insulated from the Java programs executed by the server for all other users connected to the server. The separate VM instances can be created and run, for example, in separate units of execution that are managed by the operating system of the platform on which the server is executing. For example, the separate VM instances may be executed either as separate processes, or using separate system threads. Because the units of execution used to run the separate VM instances are provided by the operating system, the operating system is able to ensure that the appropriate degree of insulation exists between the VM instances.
Owner:ORACLE INT CORP
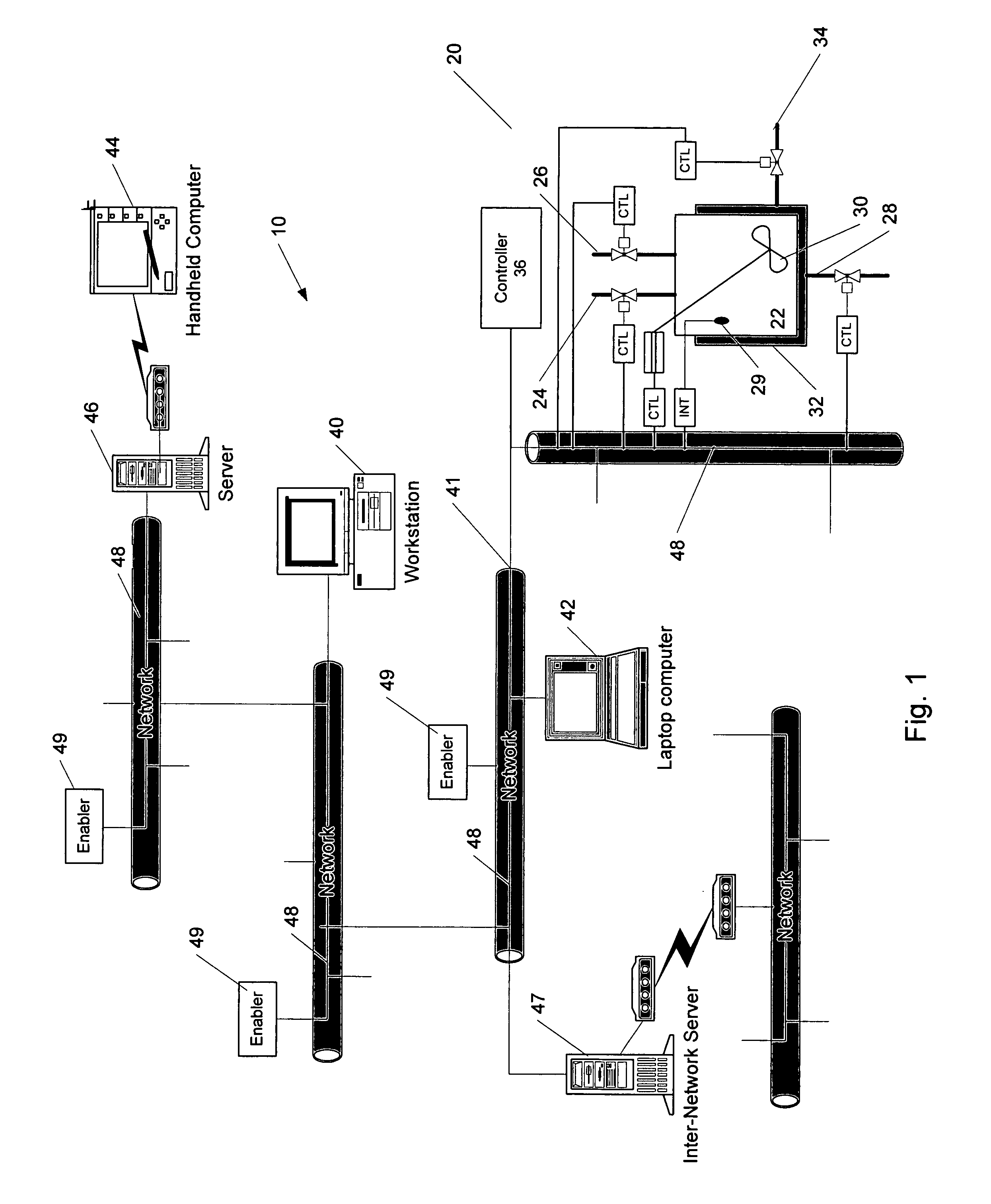
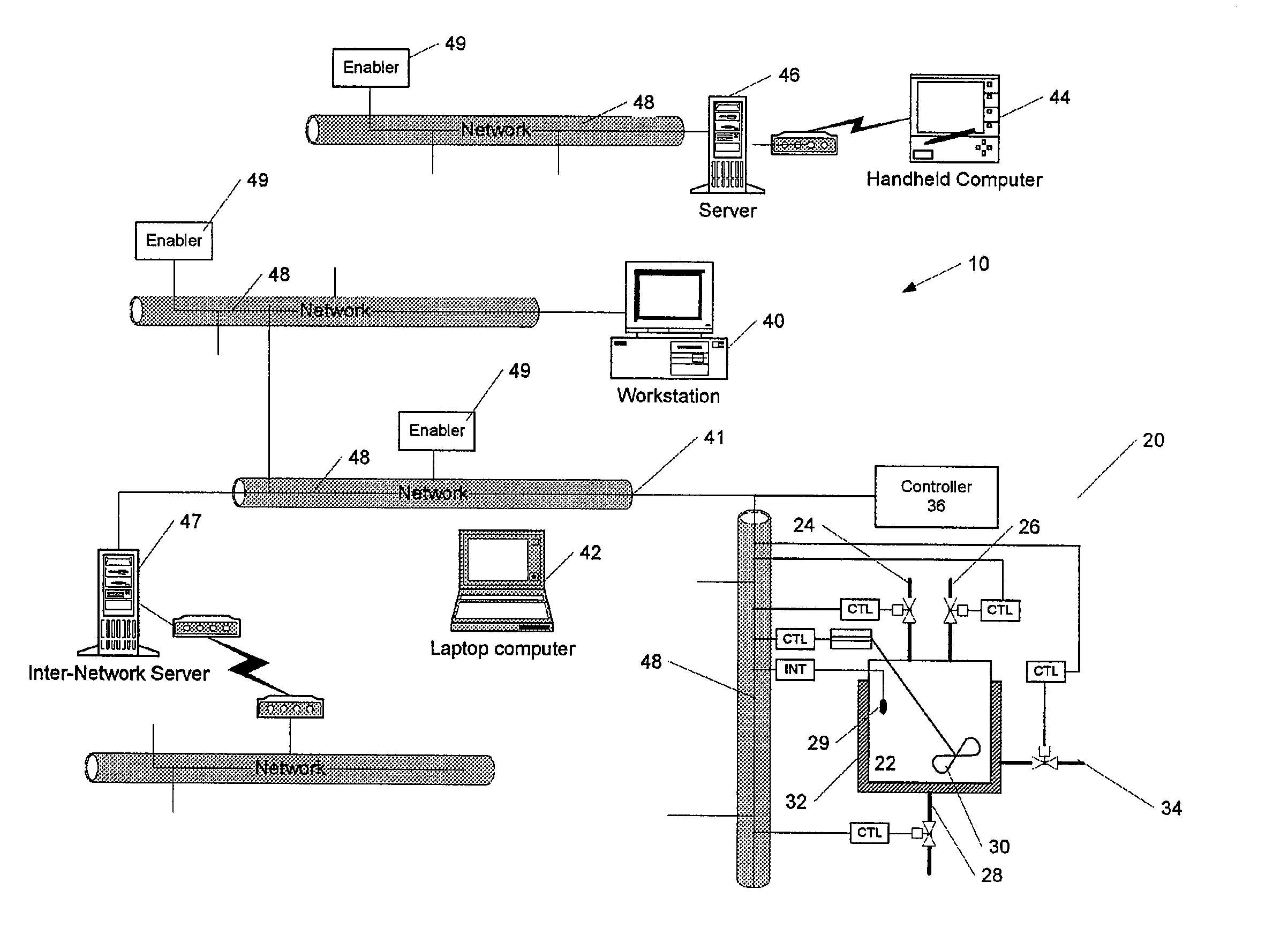
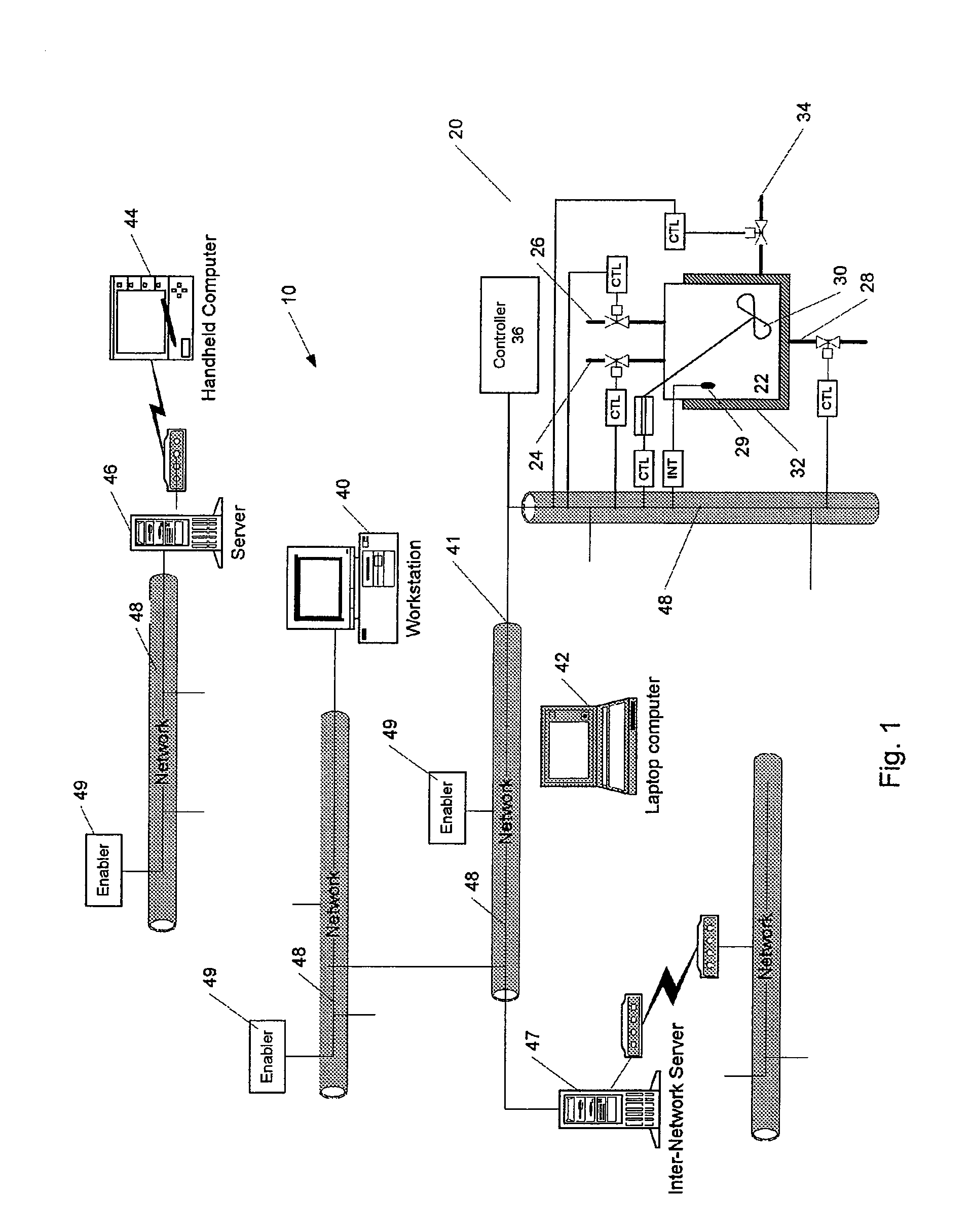
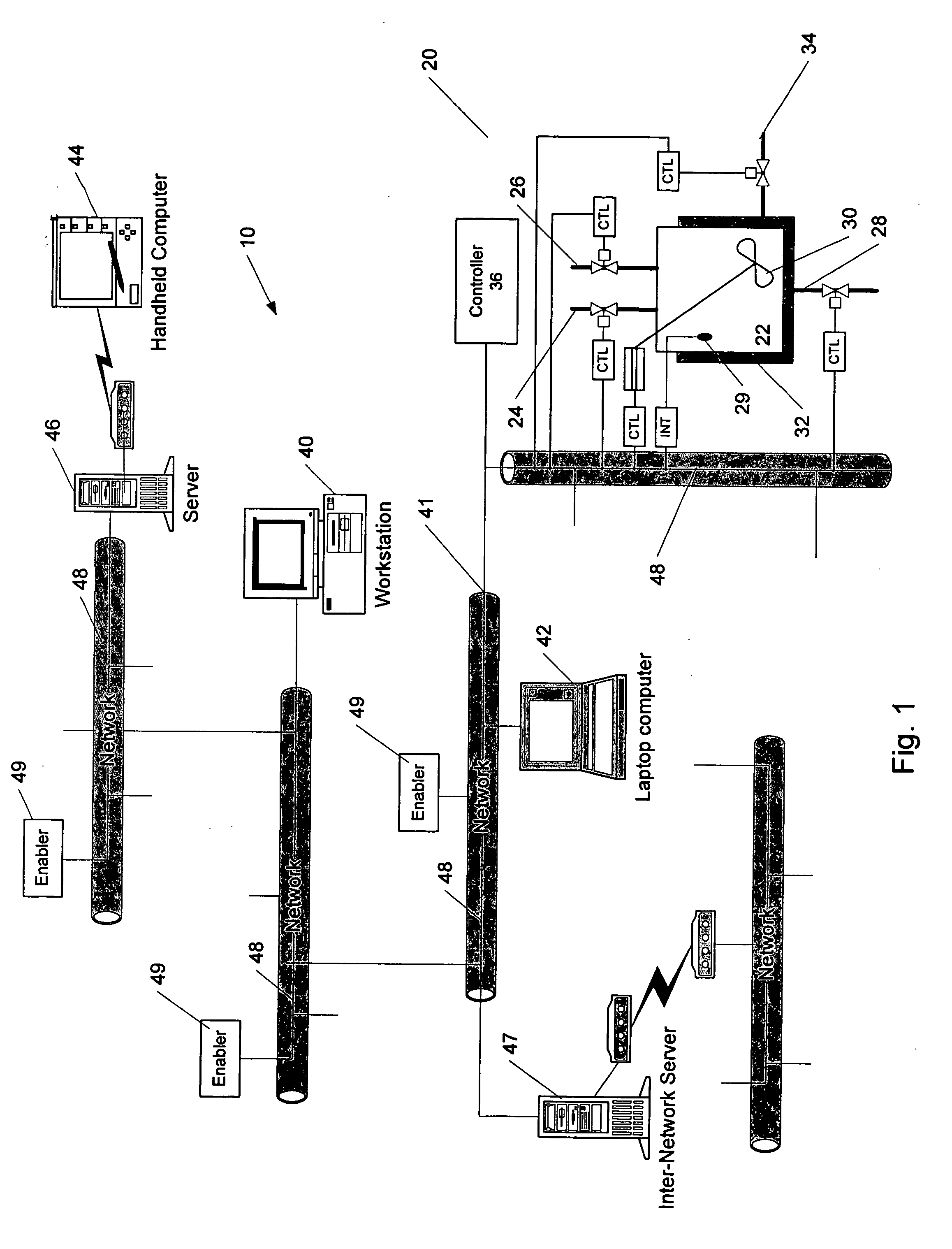
Methods and apparatus for control using control devices that provide a virtual machine environment and that communicate via an IP network
The invention provides improved methods and apparatus for control using field and control devices that provide a virtual machine environment and that communicate via an IP network. By way of non-limiting example, such field device can be an “intelligent” transmitter or actuator that includes a low power processor, along with a random access memory, a read-only memory, FlashRAM, and a sensor interface. The processor can execute a real-time operating system, as well as a Java virtual machine (JVM). Java byte code executes in the JVM to configure the field device to perform typical process control functions, e.g., for proportional integral derivative (PID) control and signal conditioning. Control networks can include a plurality of such field and control devices interconnected by an IP network, such as an Ethernet.
Owner:SCHNEIDER ELECTRIC SYST USA INC
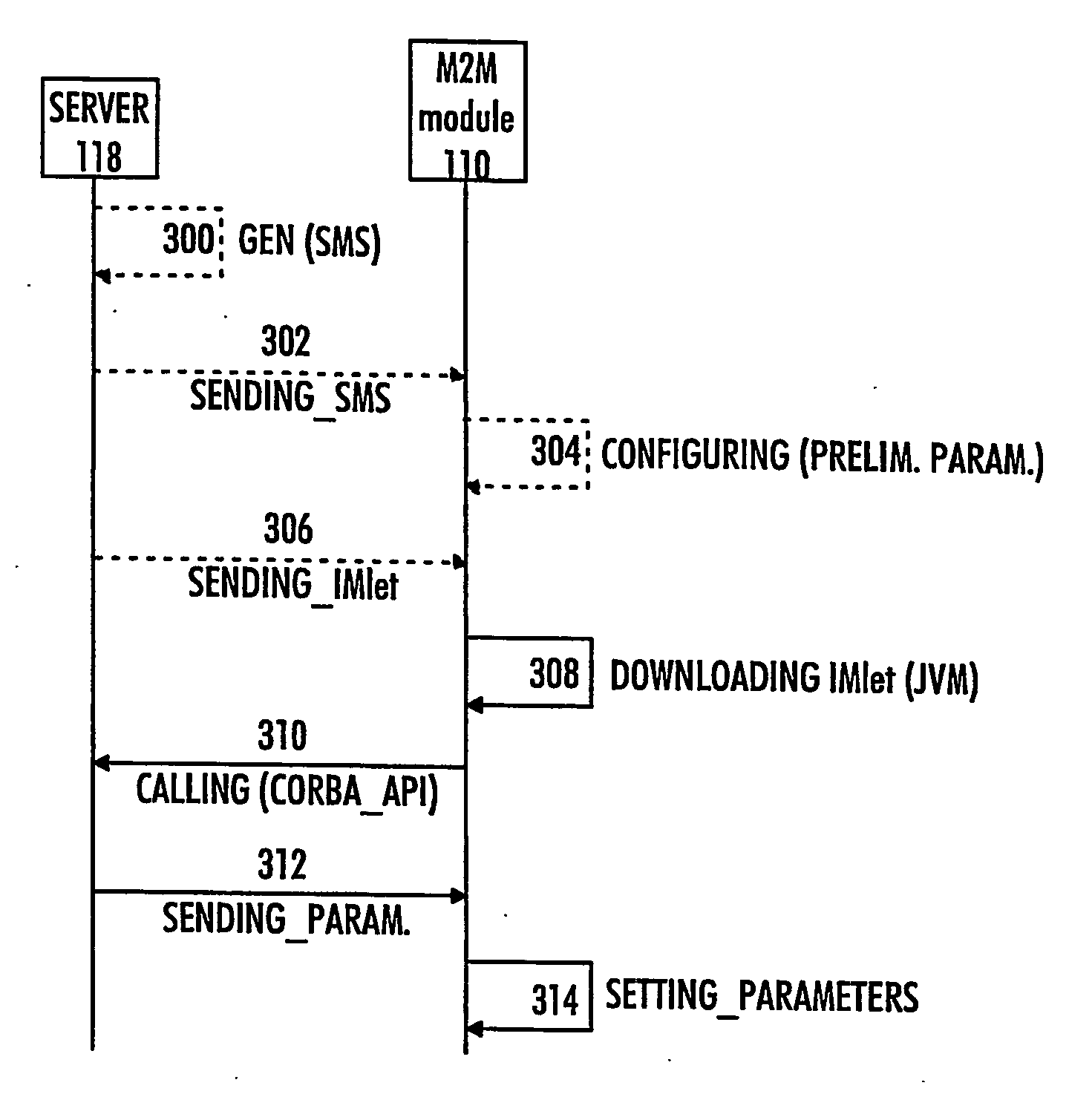
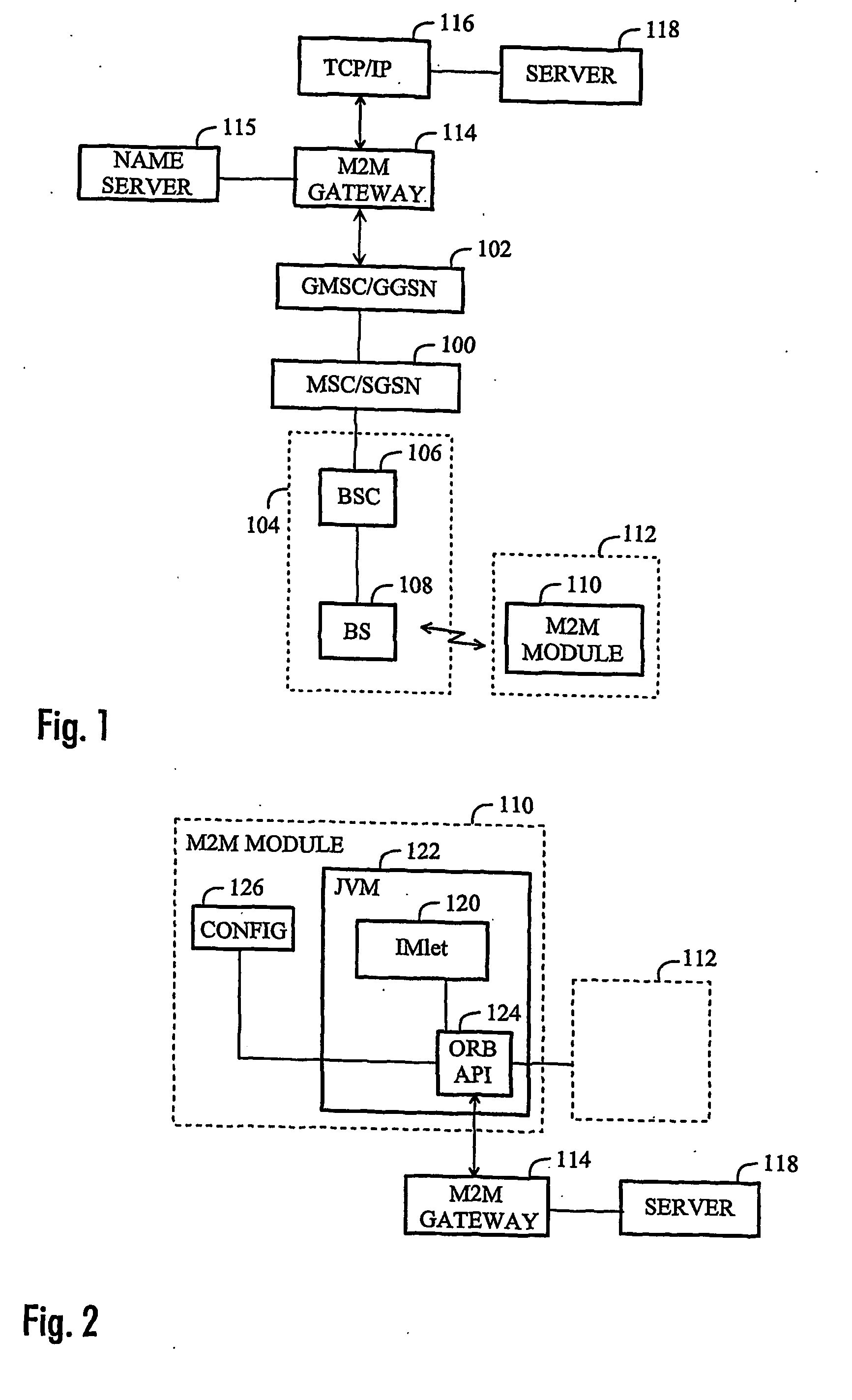
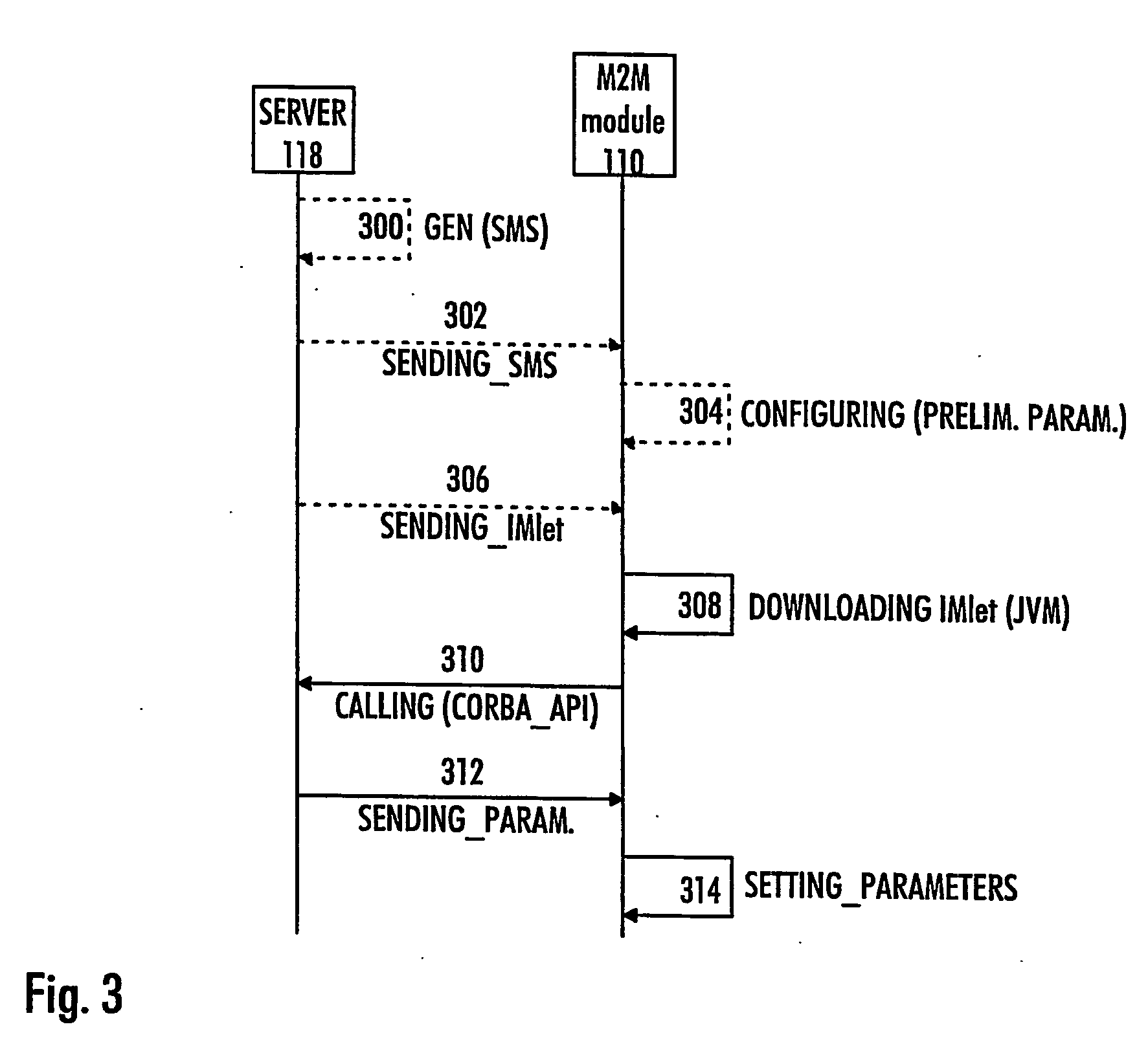
Method of configuring parameters of machine-to-machine module and machine-to-machine module
InactiveUS20070169107A1Services signallingProgram loading/initiatingApplication programming interfaceJava virtual machine
The invention relates to an M2M (machine-to-machine) module and to a method of configuring parameters of an M2M module, the method comprising establishing a connection between the M2M module and a server. The method comprises: downloading, to the M2M module, an application having an application programming interface (API) for configuring the M2M module, the application being configured to run on a Java virtual machine (JVM); communicating with the server by the application for receiving configuration parameters; and setting the parameters of the M2M module by the application based on the received configuration parameters.
Owner:NOKIA CORP
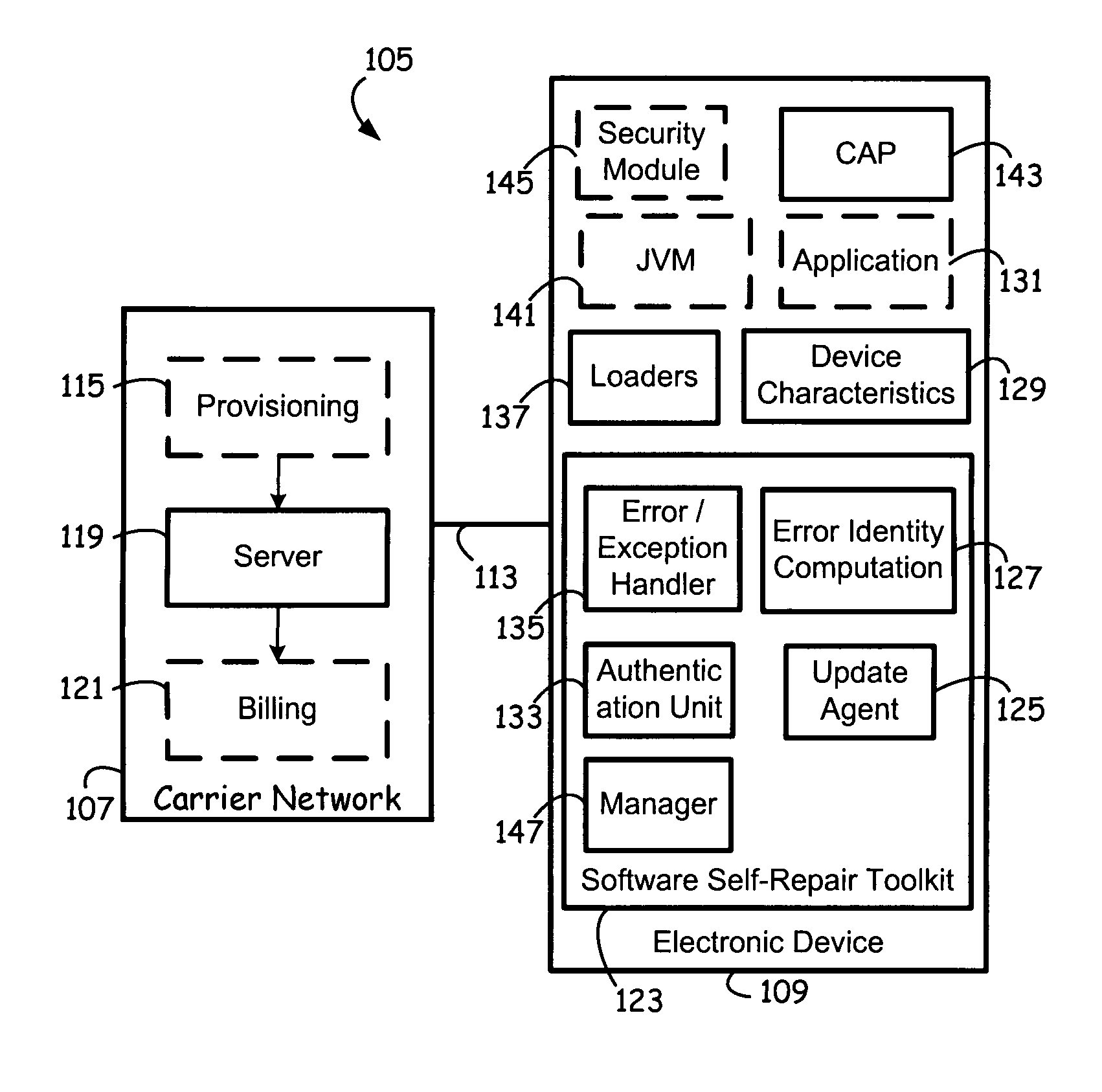
Software self-repair toolkit for electronic devices
ActiveUS20060190773A1Error detection/correctionProgram loading/initiatingSoftware bugJava virtual machine
A device and method supporting the identification and correction of firmware and / or software errors is described. Upon the occurrence of a firmware / software error or exception, an embodiment in accordance with the present invention may gather parameters for identifying the error or exception, and the execution environment in which the error occurred, and may communicate the parameters or an identifier to a server, to retrieve update information for correcting the firmware / software error or exception. The execution environment may be single or multi-threaded, and may be a java virtual machine. The device may restart / reboot during the update process, and may log an error if update information is not available to correct the error or exception. The device may communicate the error log information to the server via the communication network. The communication network may be a wireless network.
Owner:QUALCOMM INC
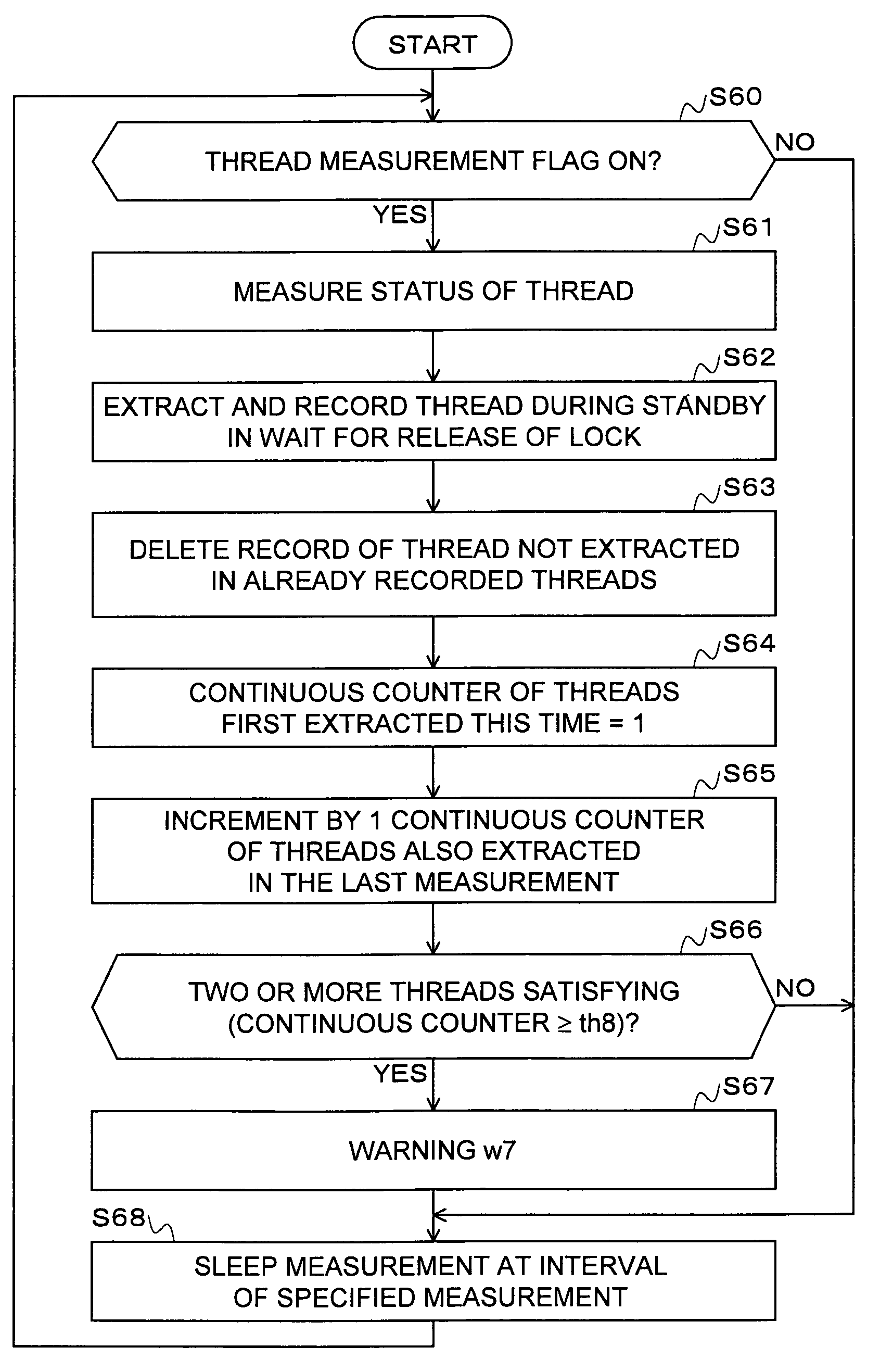
Method for predicting and avoiding danger in execution environment
InactiveUS7516292B2Reduce loadShort timeData processing applicationsMemory adressing/allocation/relocationApplication serverParallel computing
Measurement / analysis unit in a Java virtual machine has the function of measuring data when an event of garbage collection occurs, and the function of periodically measuring data. The measurement / analysis unit analyzes the measured data and predicts a danger of a memory shortage, and predicts a danger using an algorithm depending on the type of garbage collection used by the Java virtual machine. An application server is notified of a warning of the predicted danger of a memory shortage by an analysis result notification means by an inter-process communication, or the like. The measurement / analysis unit calculates a memory capacity required to avoid the predicted danger of a memory shortage, and the calculated memory capacity is transmitted to the application server by the analysis result notification means by an inter-process communication, or the like in the same way as the warning.
Owner:FUJITSU LTD
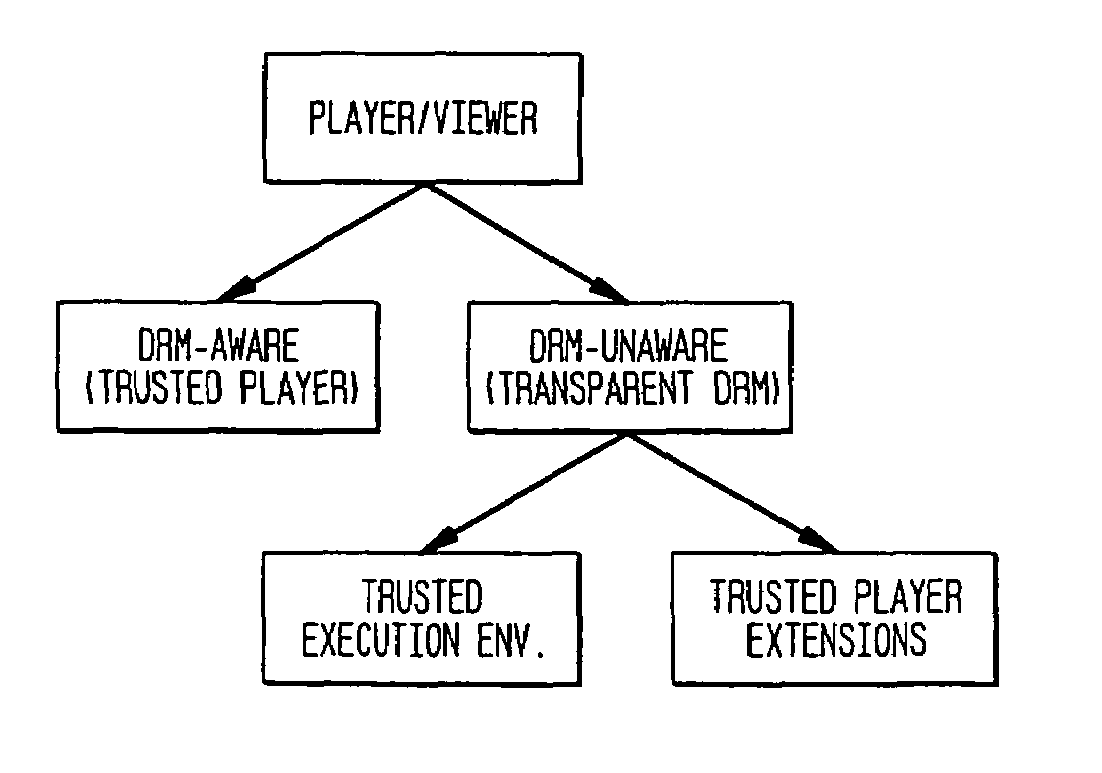
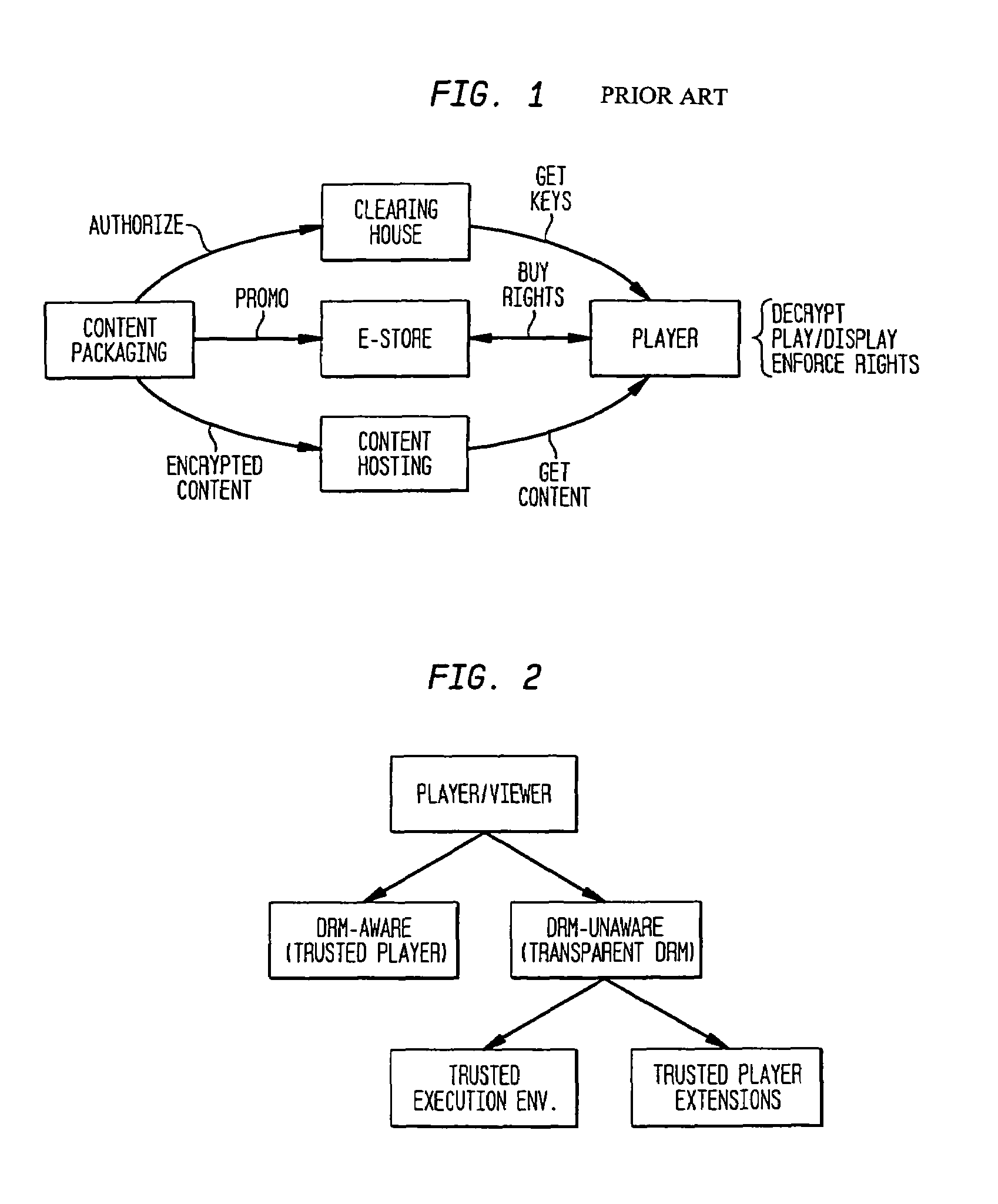
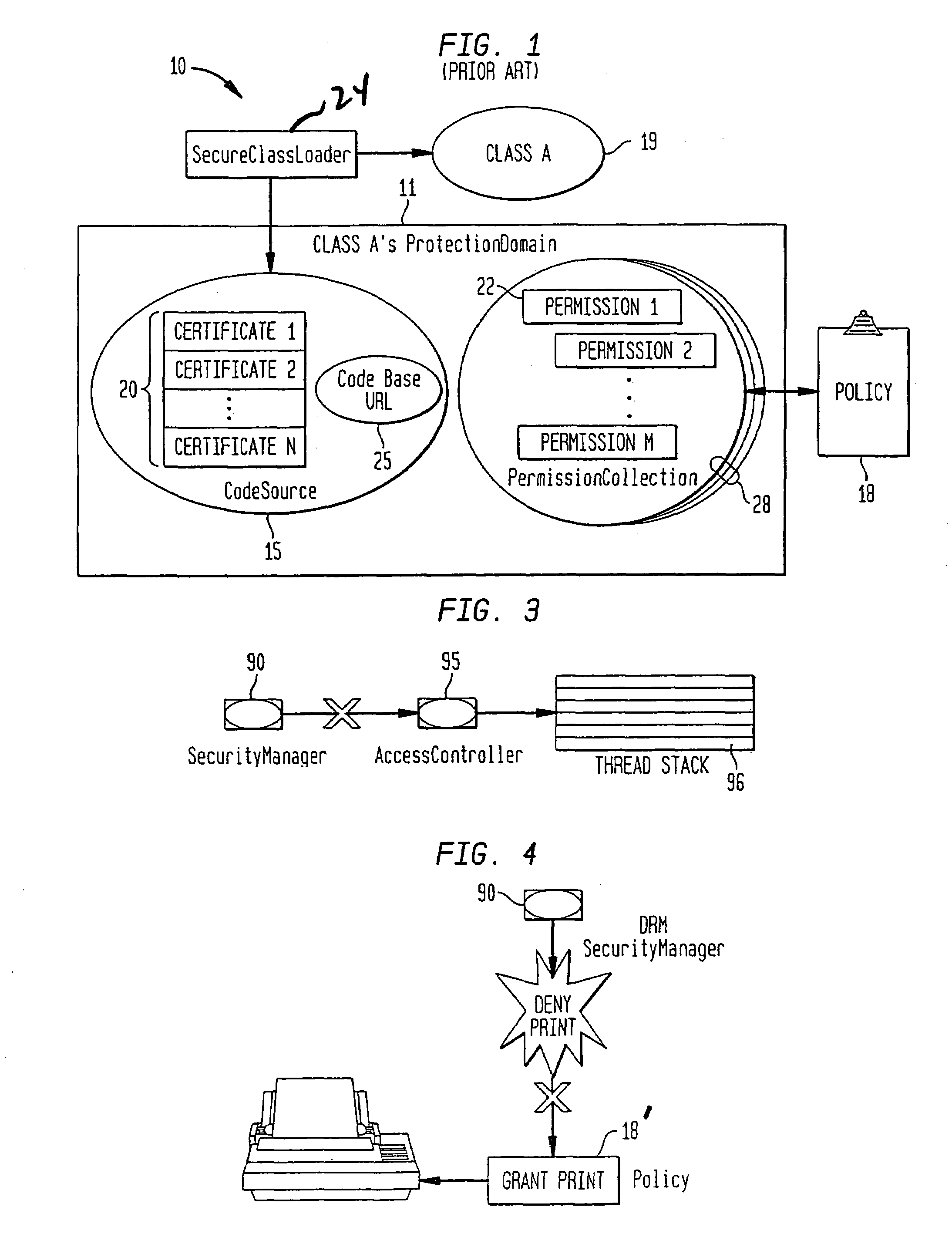
Transparent digital rights management for extendible content viewers
InactiveUS7171558B1Facilitate communicationDigital data processing detailsUser identity/authority verificationWeb browserDigital rights management system
A digital rights management system for controlling the distribution of digital content to player applications. The system comprises a verification system, a trusted content handler, and a user interface control. The verification system is provided to validate the integrity of the player applications; and the trusted content handler is used to decrypt content and to transmit the decrypted content to the player applications, and to enforce usage rights associated with the content. The user interface control module is provided to ensure that users of the player applications are not exposed to actions that violate the usage rights. The preferred embodiment of the present invention provides a system that enables existing content viewers, such as Web browsers, document viewers, and Java Virtual Machines running content-viewing applications, with digital rights management capabilities, in a manner that is transparent to the viewer. Extending content viewers with such capabilities enables and facilitates the free exchange of digital content over open networks, such as the Internet, while protecting the rights of content owners, authors, and distributors. This protection is achieved by controlling access to the content and constraining it according to the rights and privileges granted to the user during the content acquisition phase.
Owner:IBM CORP
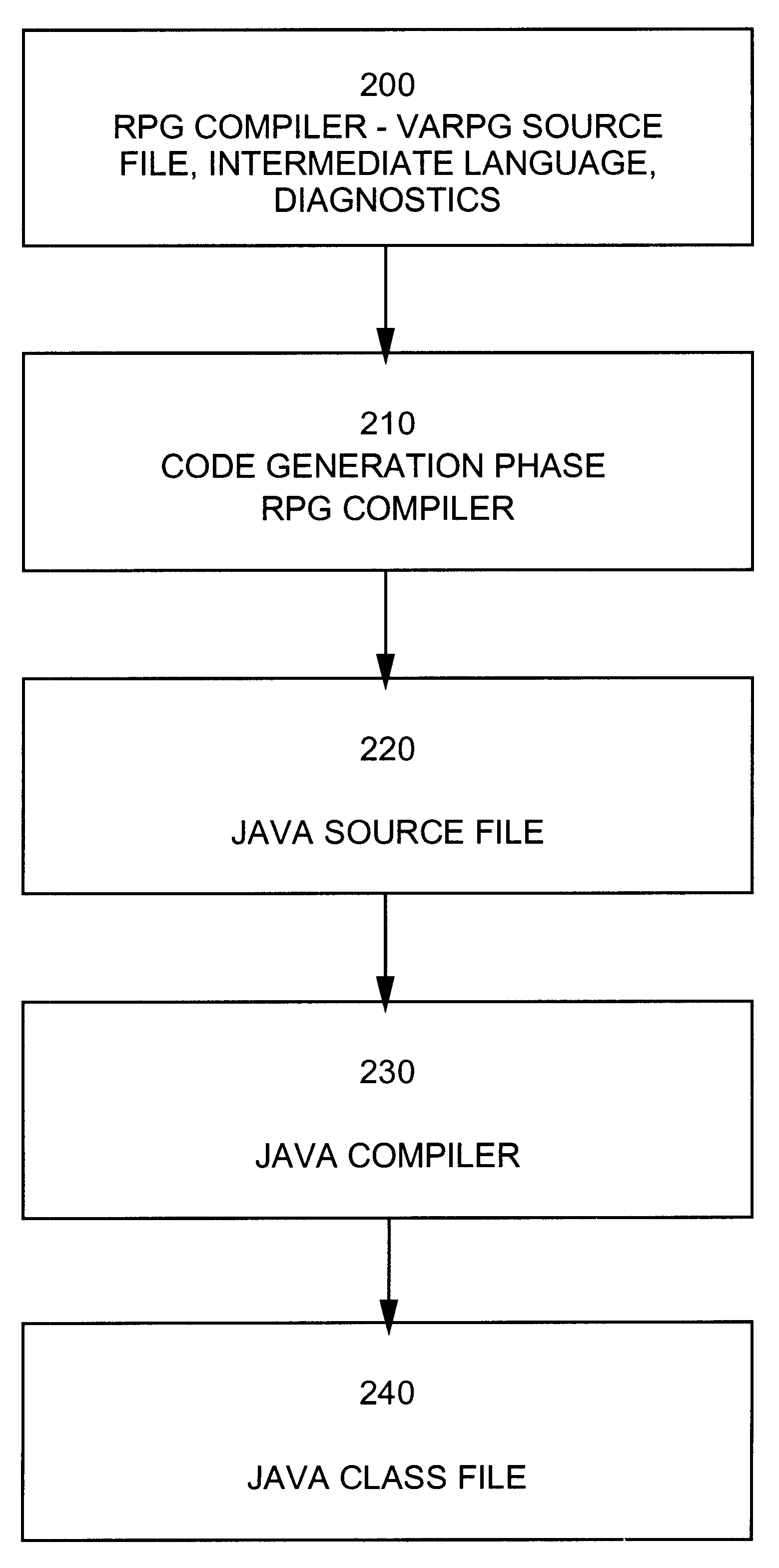
Report program language source code translation to object-oriented language source code which emulates report program language behavior
InactiveUS6467079B1Specific program execution arrangementsMemory systemsThe InternetApplication software
A computer-implemented method in which report program language is converted to object-oriented source code, such as Java, using the report program language compiler. The object-oriented source code emulates the behaviour of the report program language, such as VARPG. Applications written in RPG are converted to Java and therefore can run on every platform for which a Java virtual machine exists. RPG programmers now have the ability to write internet applications. Java applications and applets can be written in RPG and existing RPG applications can be converted to Java applets.
Owner:IBM CORP
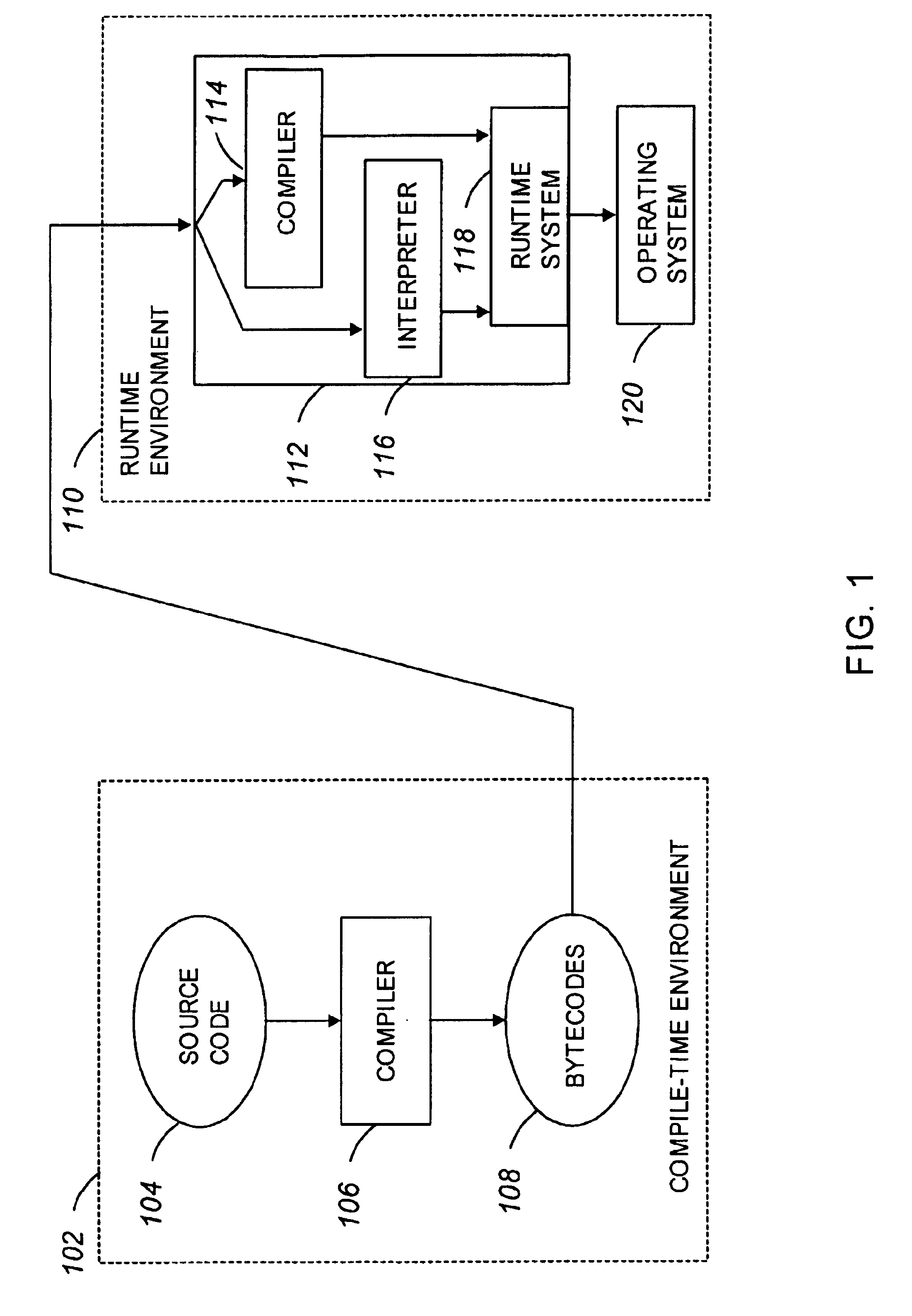
Method for compiling program components in a mixed static and dynamic environment
InactiveUS6973646B1Simple methodReduce the amount requiredUser identity/authority verificationProgram controlProgramming languageDynamic compilation
This invention describes a method and several variants for compiling programs or components of programs in a mixed static and dynamic environment, so as to reduce the amount of time and memory spent in run-time compilation, or to exercise greater control over testing of the executable code for the program, or both. The invention involves generating persistent code images prior to program execution based on static compilation or dynamic compilation from a previous run, and then, adapting those images during program execution. We describe a method for generating auxiliary information in addition to the executable code that is recorded in the persistent code image. Further, we describe a method for checking the validity of those code images, adapting those images to the new execution context, and generating new executable code to respond to dynamic events, during program execution. Our method allows global interprocedural optimizations to be performed on the program, even if the programming language supports, or requires, dynamic binding. Variants of the method show how one or several of the features of the method may be performed. The invention is particularly useful in the context of implementing Java Virtual Machines, although it can also be used in implementing other programming languages.
Owner:IBM CORP
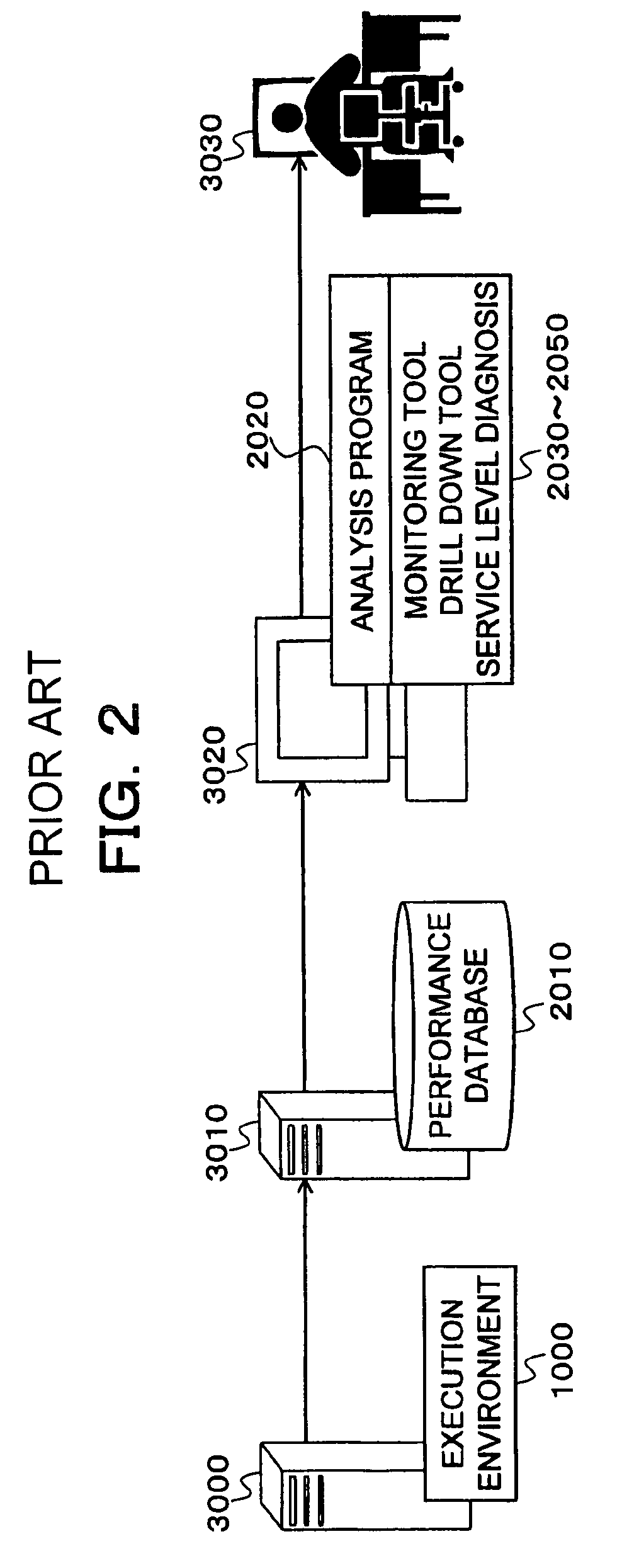
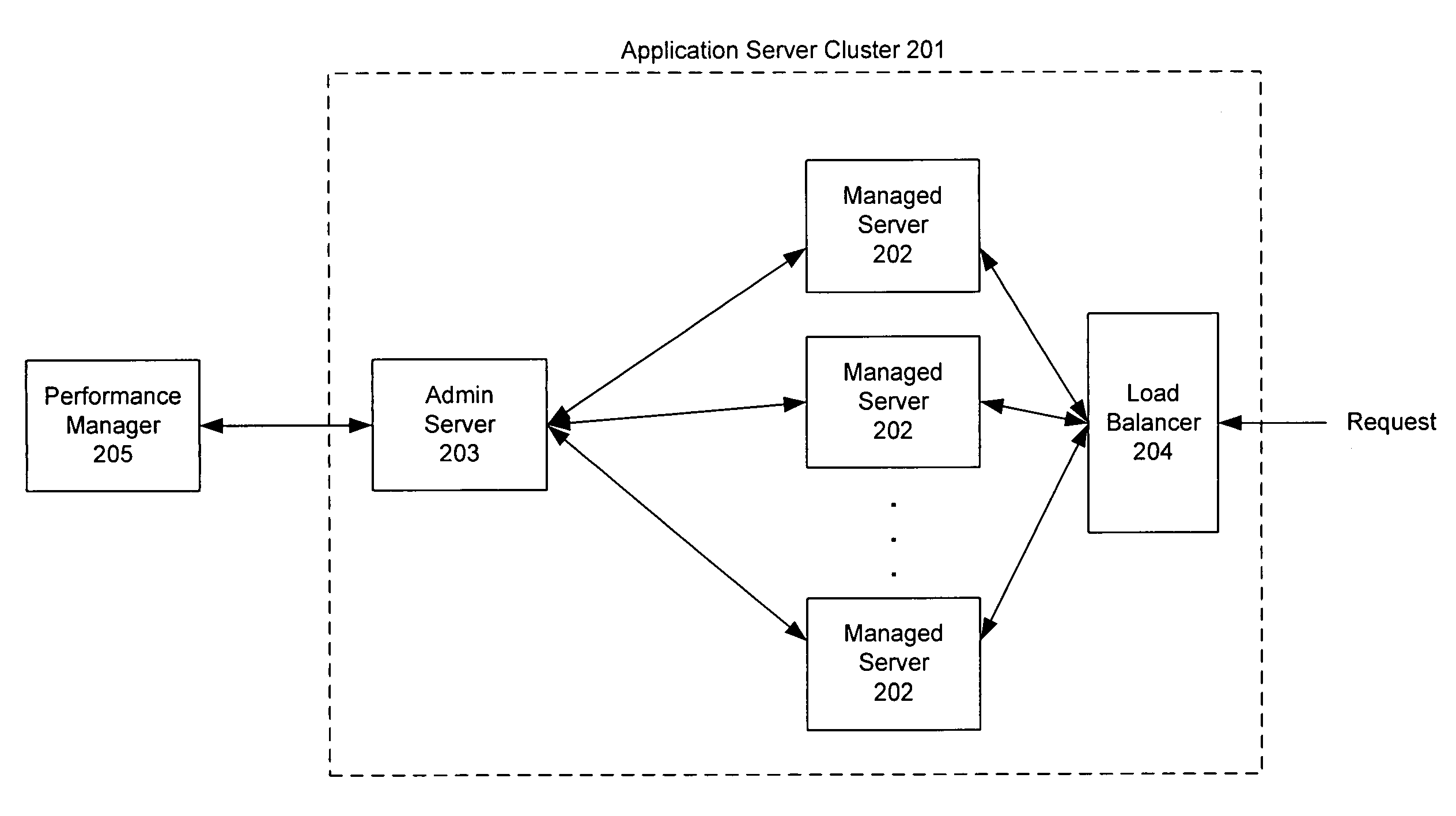
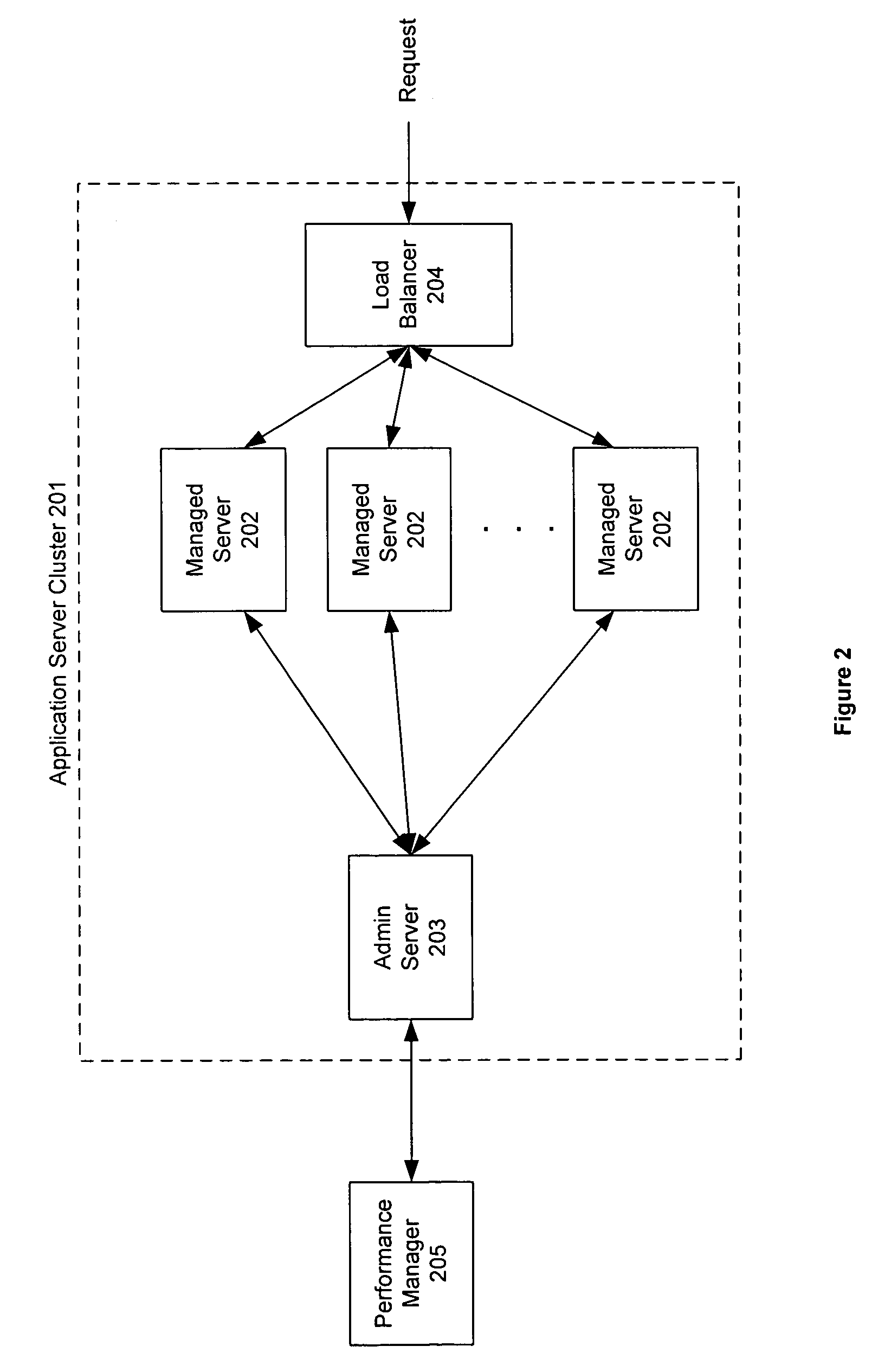
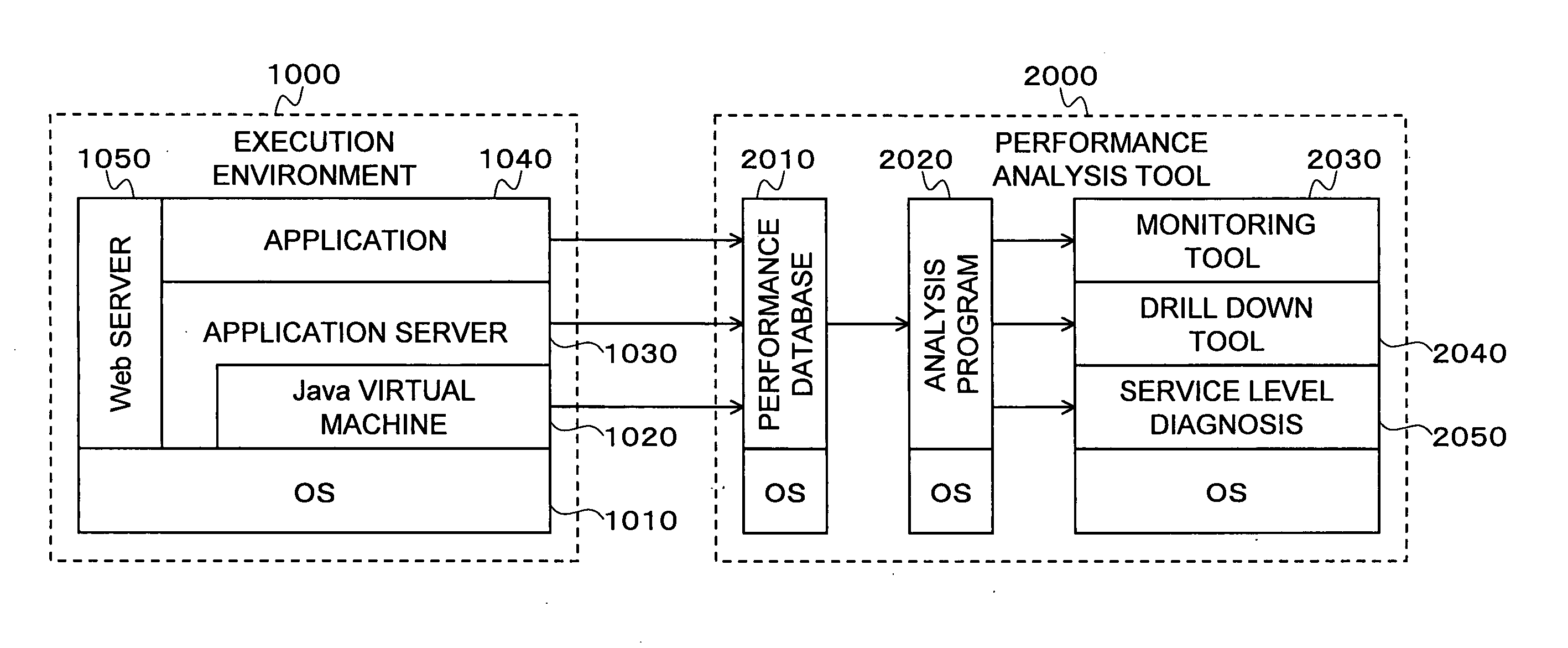
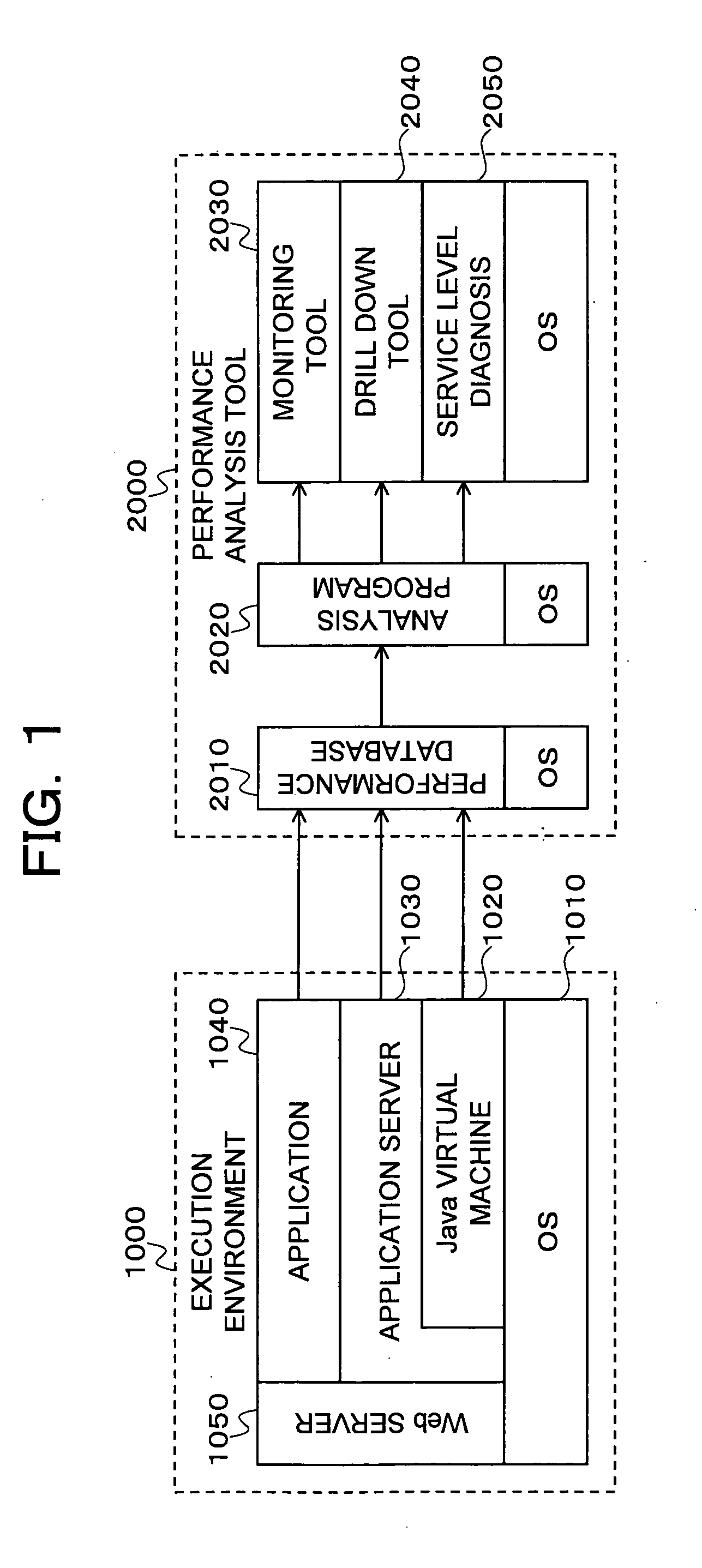
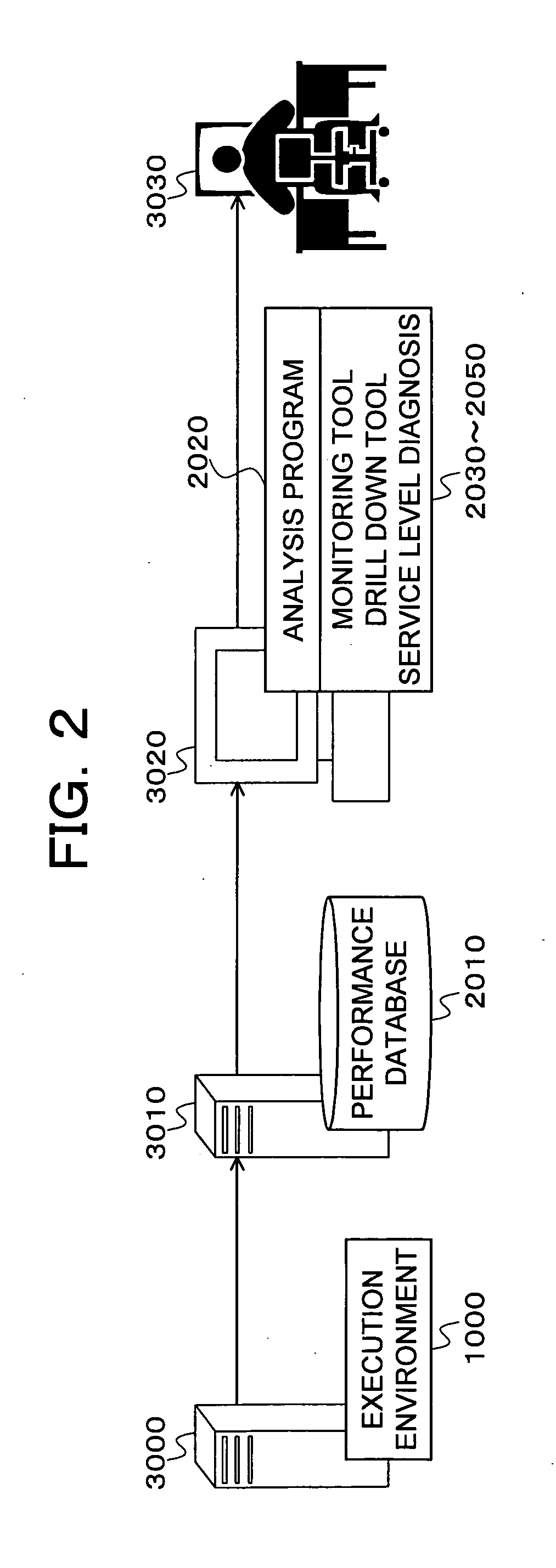
Monitoring and performance management of component-based applications
ActiveUS7627671B1Error detection/correctionDigital computer detailsManagement toolApplication software
Invention manages underlying application objects that support implemented business functions. A performance manager accesses and interprets application metadata and execution environment metadata, using a hierarchical entity to model complex relationships between application abstractions, components and resources. The performance manager encodes common behavioral and architecture information in models resulting from analysis of component architecture standards, vendor application servers, development tools and administration tools. The performance manager conducts inter-component dependency and control flow analysis, for example by generating control flow graphs from application metadata and performing byte code analysis without access to application source code. The performance manager collects metrics from standardized and vendor-specific sources, instruments interpreters (such as the Java Virtual Machine), and collects and utilizes resource metrics, code performance metrics, configuration parameters, and transaction, failure and lifecycle events.
Owner:ORACLE INT CORP
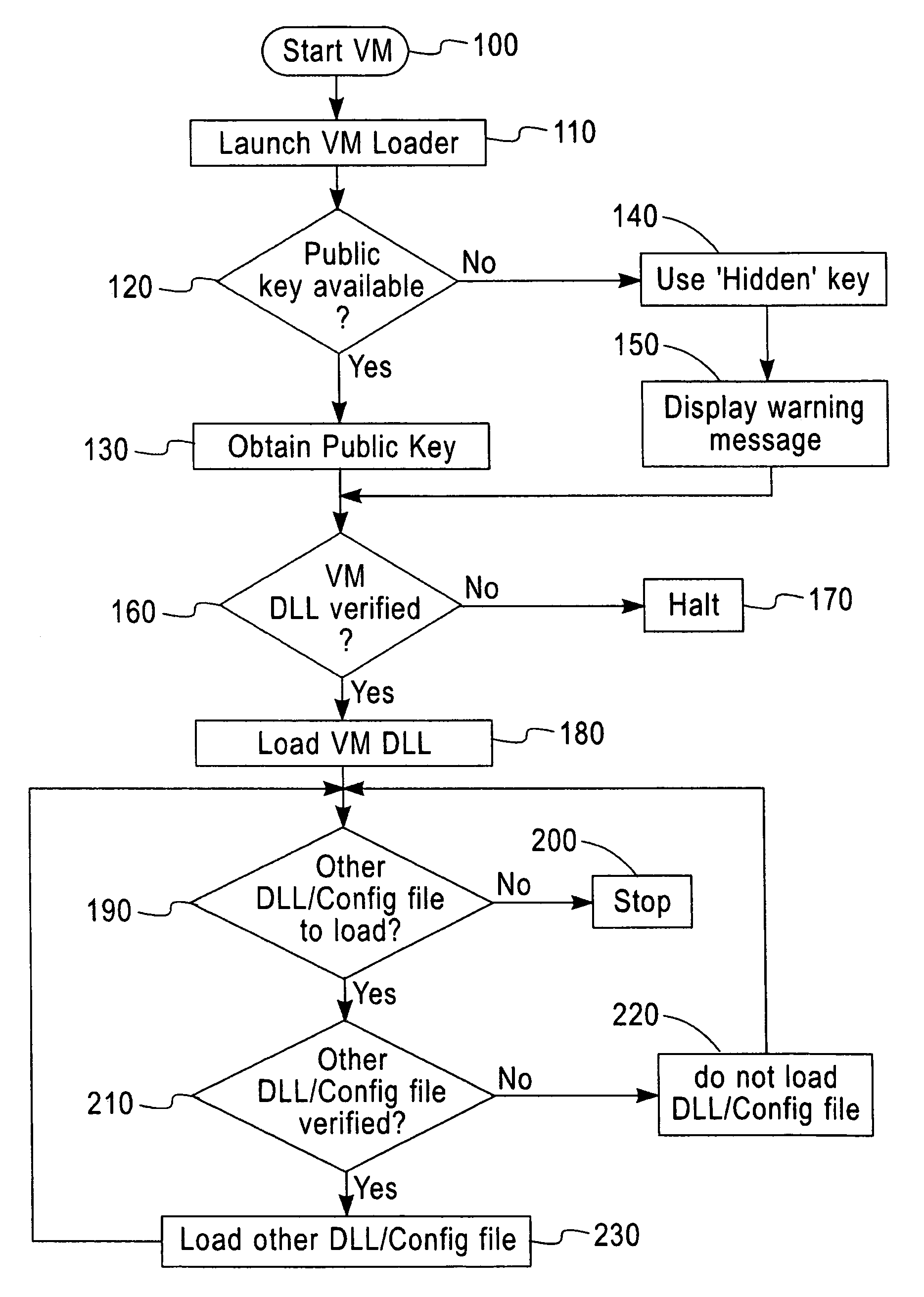
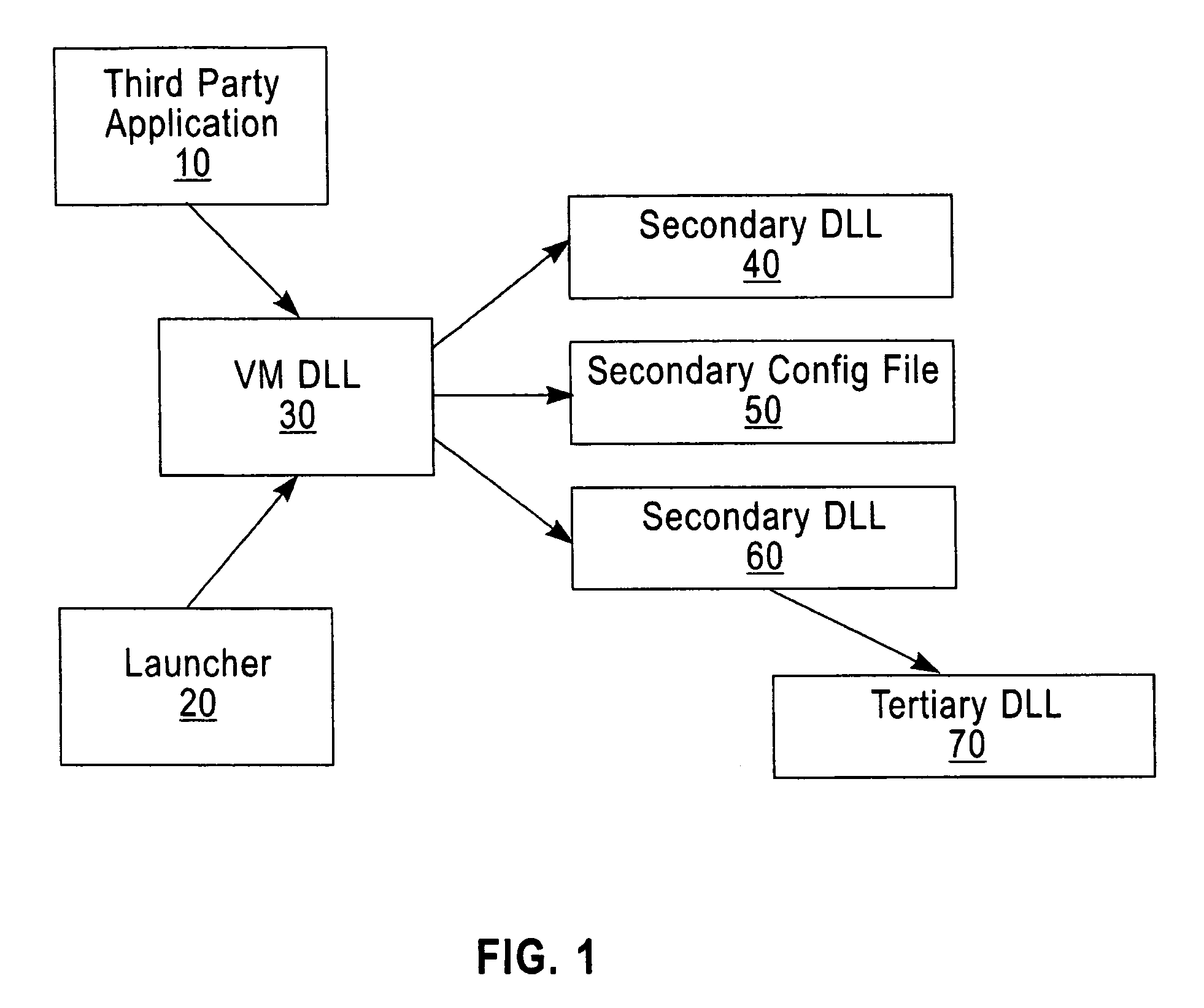
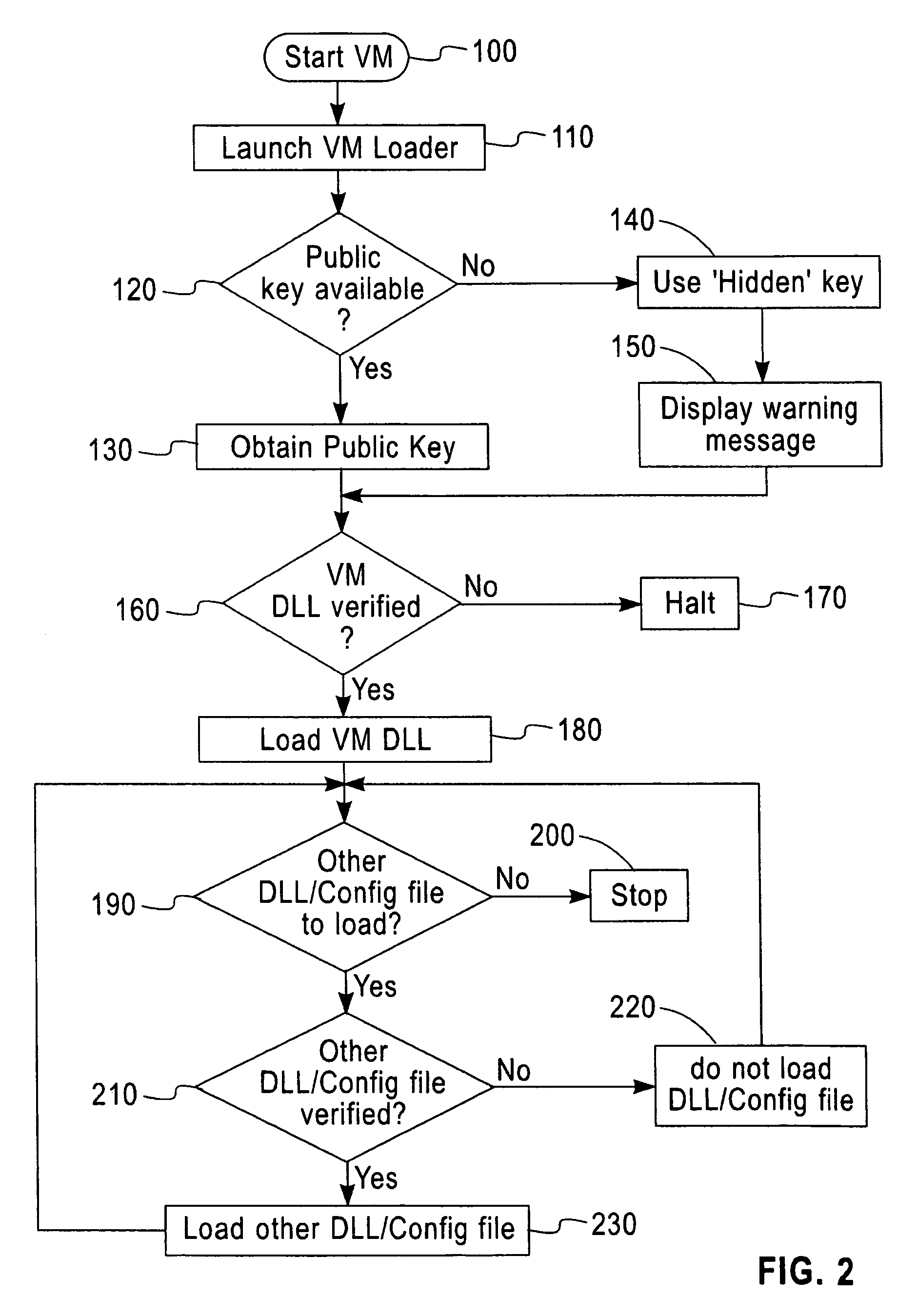
Software verification system, method and computer program element
InactiveUS7496757B2Improve securityGreat confidenceUser identity/authority verificationUnauthorized memory use protectionDigital signatureApplication software
A software security system is arranged to verify the authenticity of each element of a Java Virtual Machine installation. A digital signature is attached to each file of the JVM installation. A loader (20) verifies the digital signature of the JVM DLL (30). The JVM DLL 30 then verifies the digital signature of each other DLL and configuration file to be loaded (40, 50, 60, 70), and only loads those files which have successfully verified digital signatures. In this way the security of the JVM is enhanced, a user has greater confidence that the Java applications will function correctly, and the detection of incorrect or damaged JVM installations is improved.
Owner:TREND MICRO INC
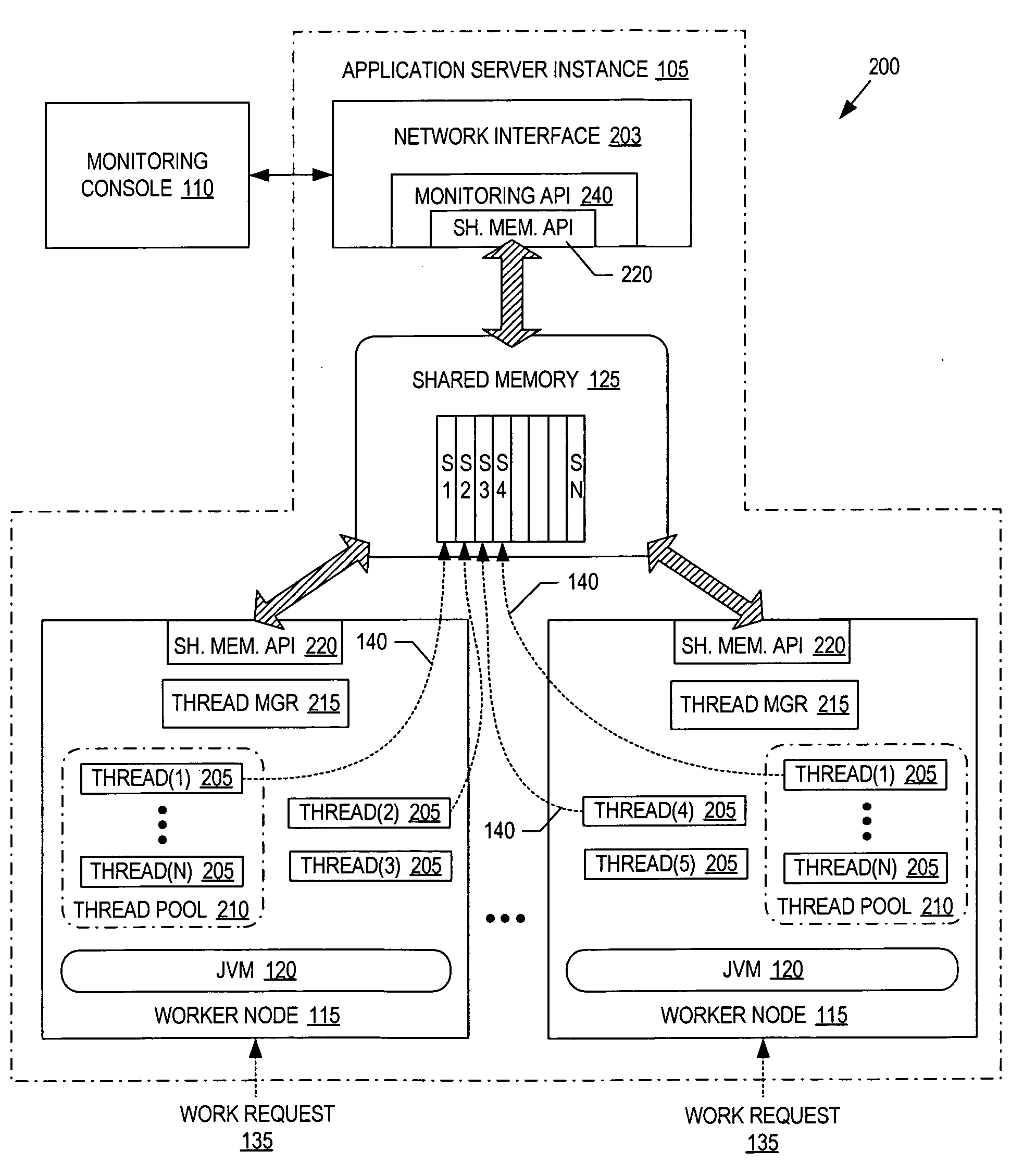
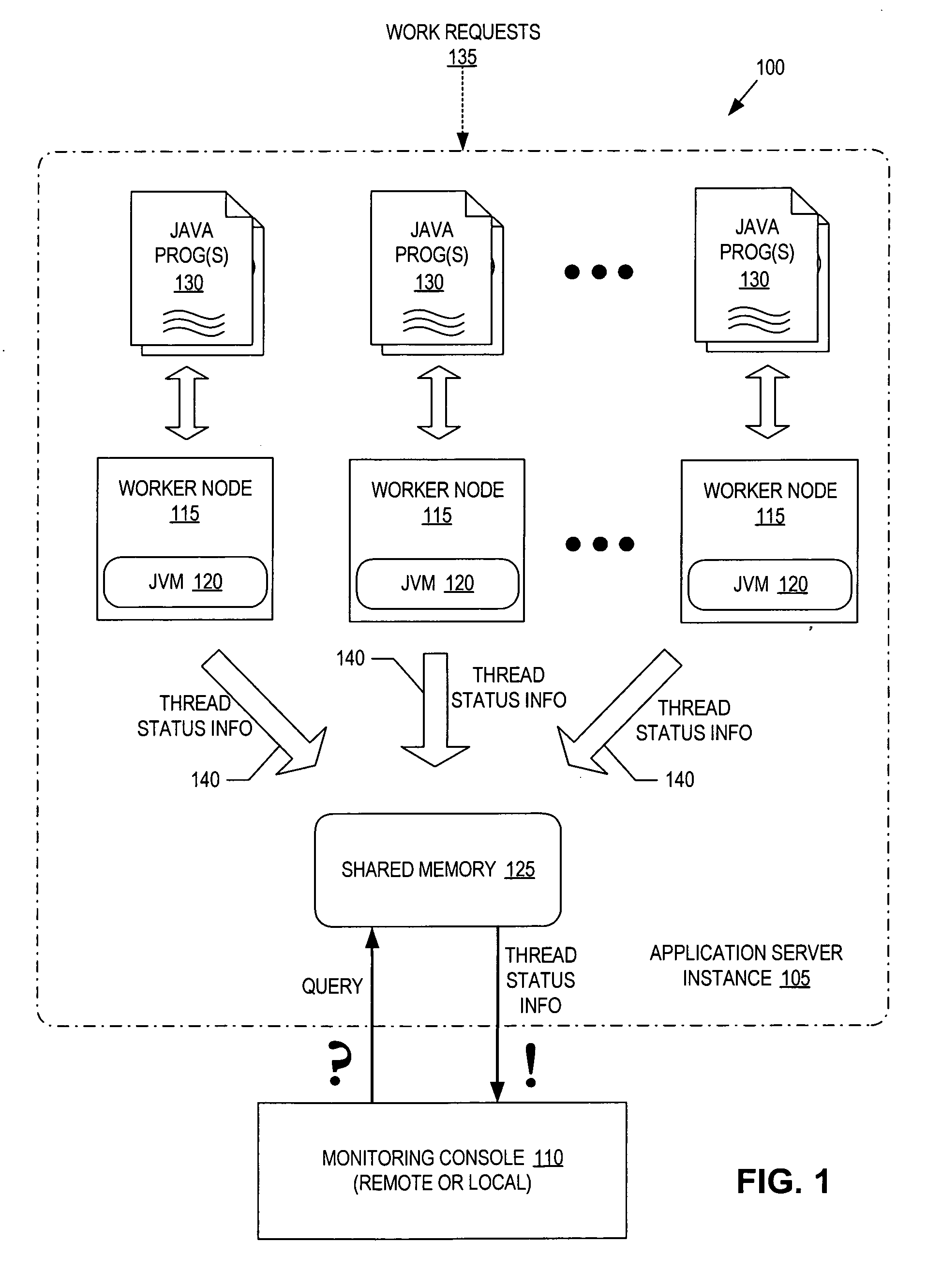
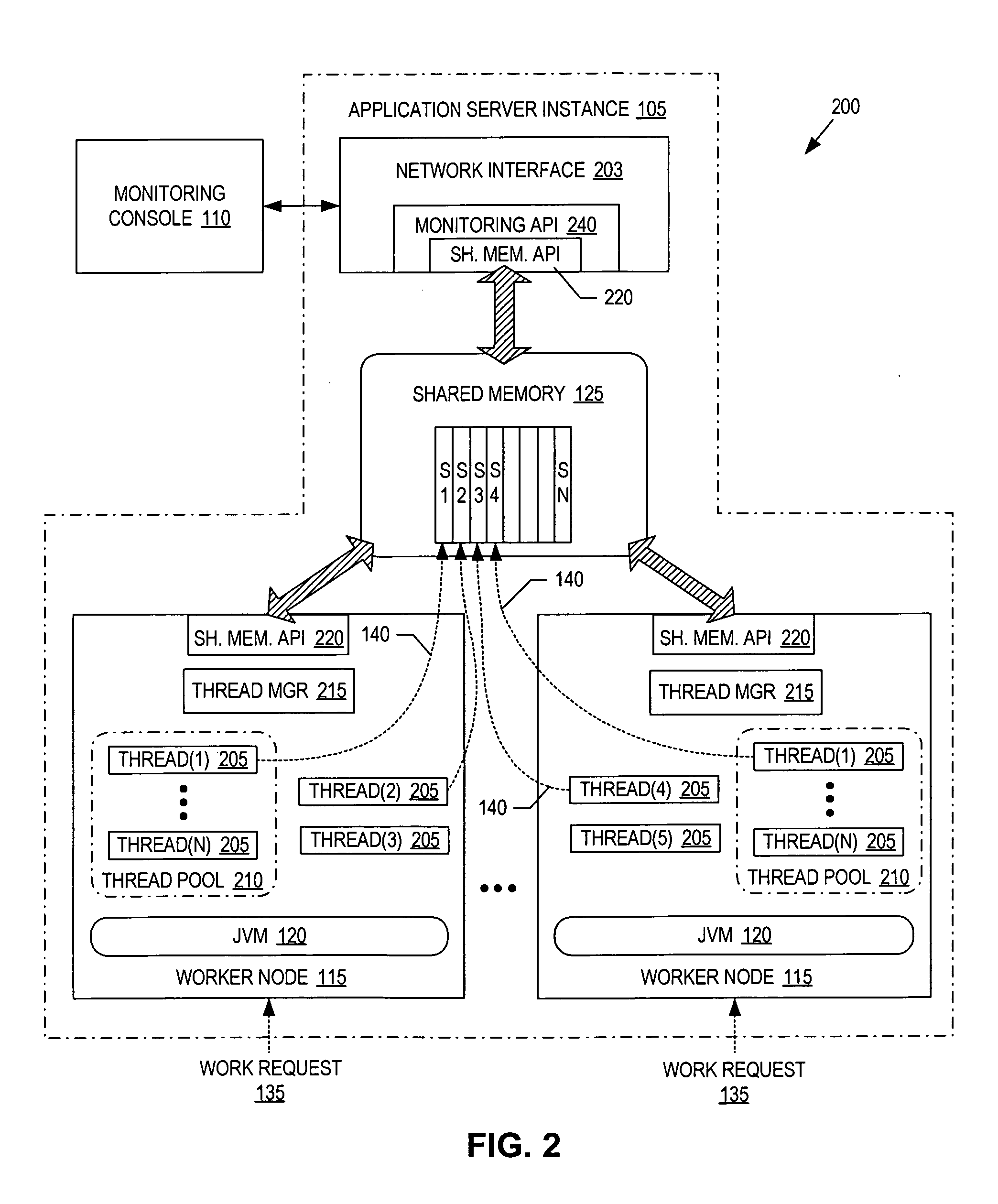
Thread monitoring using shared memory
ActiveUS20060143608A1Error detection/correctionMultiprogramming arrangementsTerm memoryComputer science
A system and method to monitor worker threads within a Java virtual machine. At least one program is executed on the Java virtual machine to perform a task. A worker thread of the Java virtual machine is assigned to perform the task. Status information for the worker thread is generated and reported into memory external to the Java virtual machine to enable monitoring of the worker thread from external to the Java virtual machine.
Owner:SAP AG
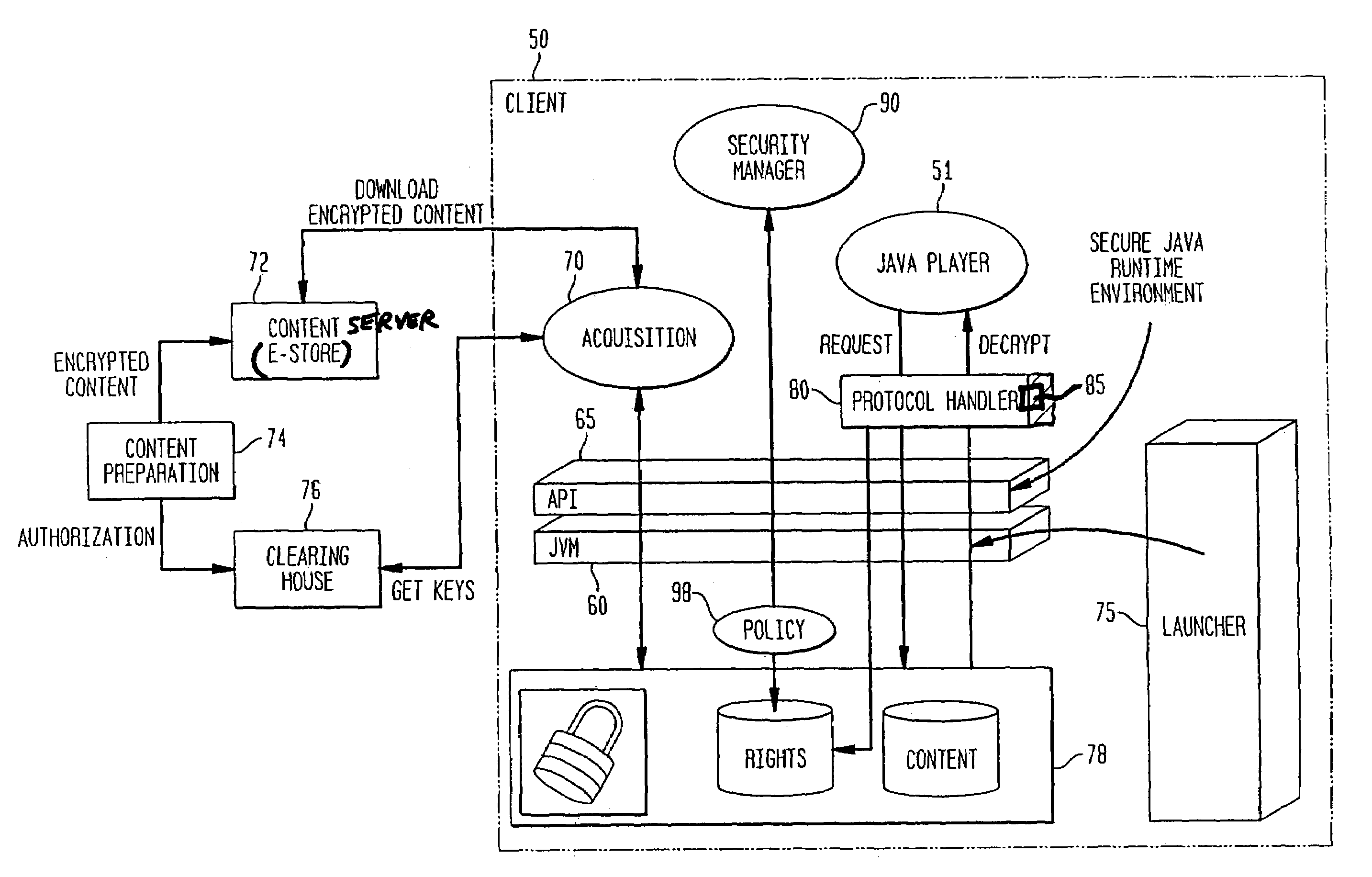
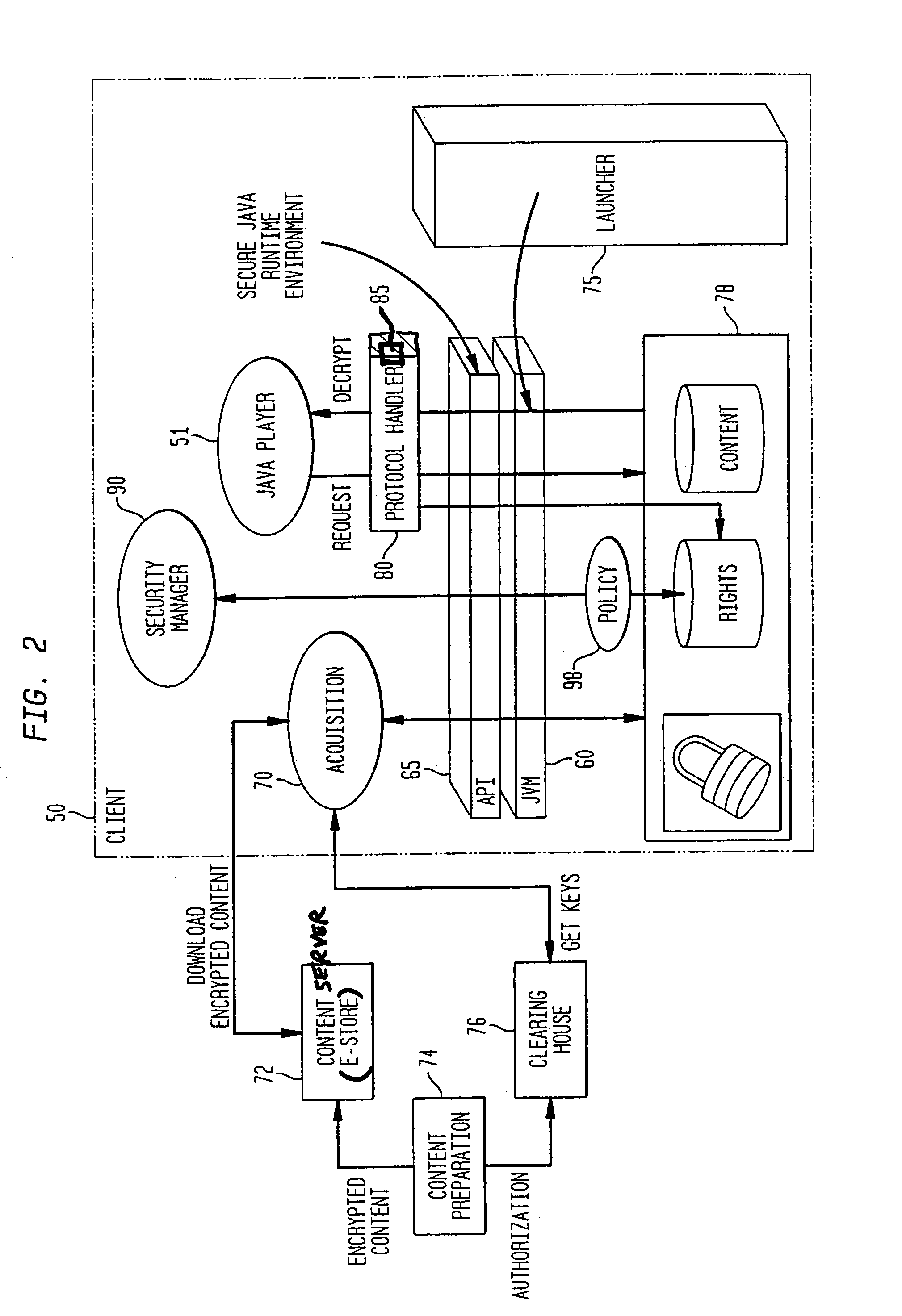
System and method for supporting digital rights management in an enhanced Java™ 2 runtime environment
InactiveUS7308717B2Provide protectionDigital data processing detailsAnalogue secracy/subscription systemsDigital rights management systemSoftware engineering
A digital rights management (DRM) system and methodology for a Java client implementing a Java Runtime Environment (JRE). The JRE comprises a Java Virtual Machine (JVM) and Java runtime libraries components and is capable of executing a player application for presenting content that can be presented through a Java program (e.g., a Java application, applet, servlet, bean, etc.) and downloaded from a content server to the client. The DRM system includes an acquisition component for receiving downloaded protected contents; and a dynamic rights management layer located between the JRE and player application for receiving requests to view or play downloaded protected contents from the player, and, in response to each request, determining the rights associated with protected content and enabling viewing or playing of the protected contents via the player application if permitted according to the rights. By providing a Ad DRM-enabled Java runtime, which does not affect the way non-DRM-related programs work, DRM content providers will not require the installation of customized players. By securing the runtime, every Java™ player automatically and transparently becomes a DRM-enabled player.
Owner:IBM CORP
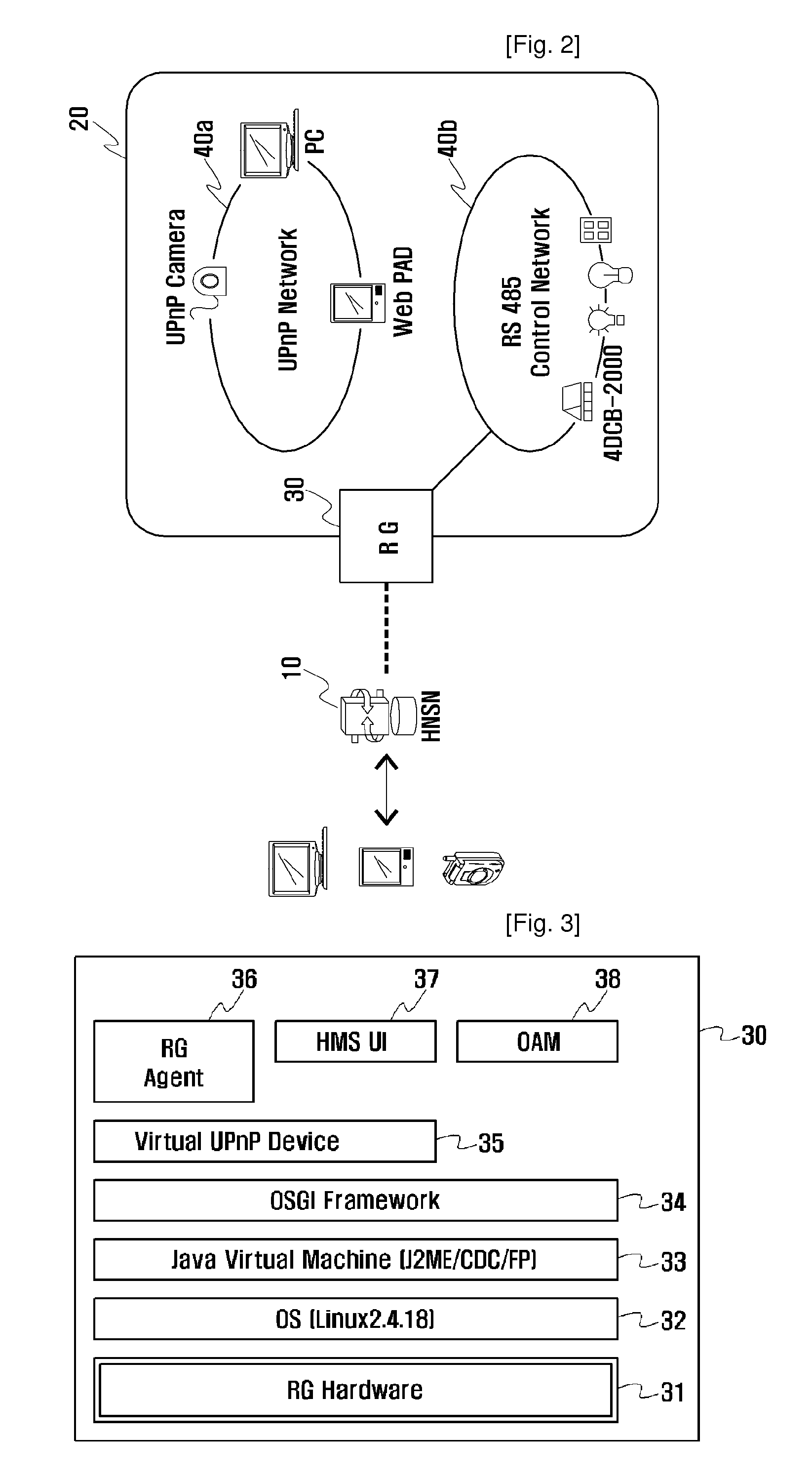
Residential Gateway System for Home Network Service
InactiveUS20080205419A1Detailed informationGood serviceNetwork connectionsHome automation networksOperational systemService gateway
Disclosed herein is a Residential Gateway (RG) system for home network service. The RG system receives various supplementary services through a Home Network Serving Node (HNSN) that provides home network service. The system includes an Open Service Gateway initiative (OSGi) framework, an RG agent, a virtual Universal Plug and Play (UPnP) device, and a Java virtual machine. The RG agent is installed on the OSGi framework and implemented in bundle form. The UPnP device is registered on the OSGi framework by the RG agent. The Java virtual machine is ported by the RG agent to hardware on which an operating system is installed.
Owner:SK TELECOM CO LTD
System and method for providing customer personalized and modifiable subscriber services
InactiveUS6411697B1Special service for subscribersSoftware simulation/interpretation/emulationPersonalizationService provision
A telephone system provides subscribers with access to a service provider's platform logic and data implemented in any runtime environment. In one embodiment, the service logic is embodied in Java applets and Java beans in a JAVA virtual machine for subscriber personalizing and modifying the service logic. The provider provides the subscriber a tool kit or access to a support server for writing service logic modifications as JAVA beans. The service logic modification is achieved in a process in which the service requirements and objectives are set. The service specifications are designed, implemented, tested, and rolled out. Initial service provisioning and support is provided a subscriber, service modification by the subscriber is made to subscriber data provisioning and subscriber service logic provisions. A modified service logic is locally tested by the subscriber, followed by remote testing of the modification on the service provider's premises. The service provider provisions and then supports the modified service logic.
Owner:IBM CORP
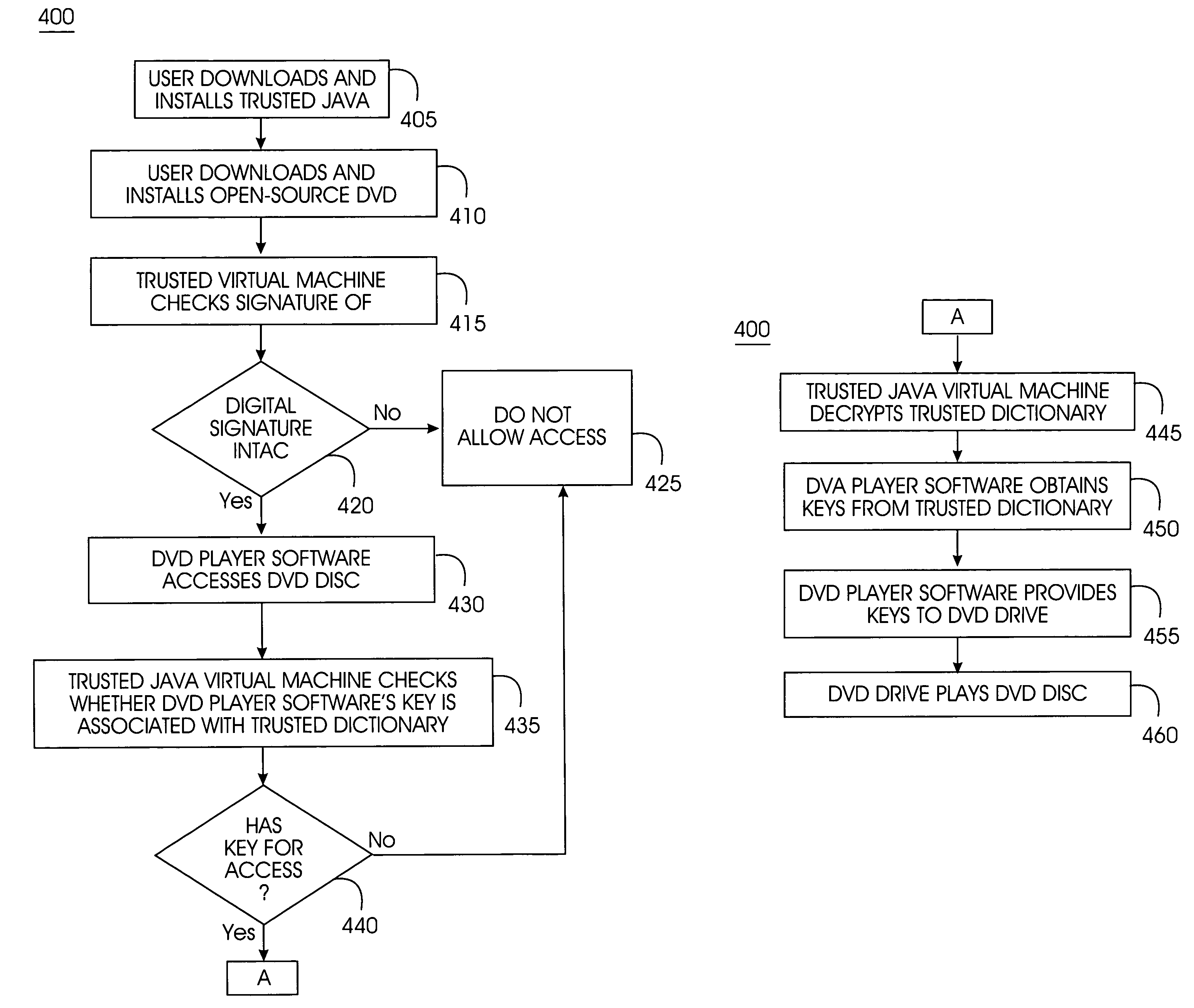
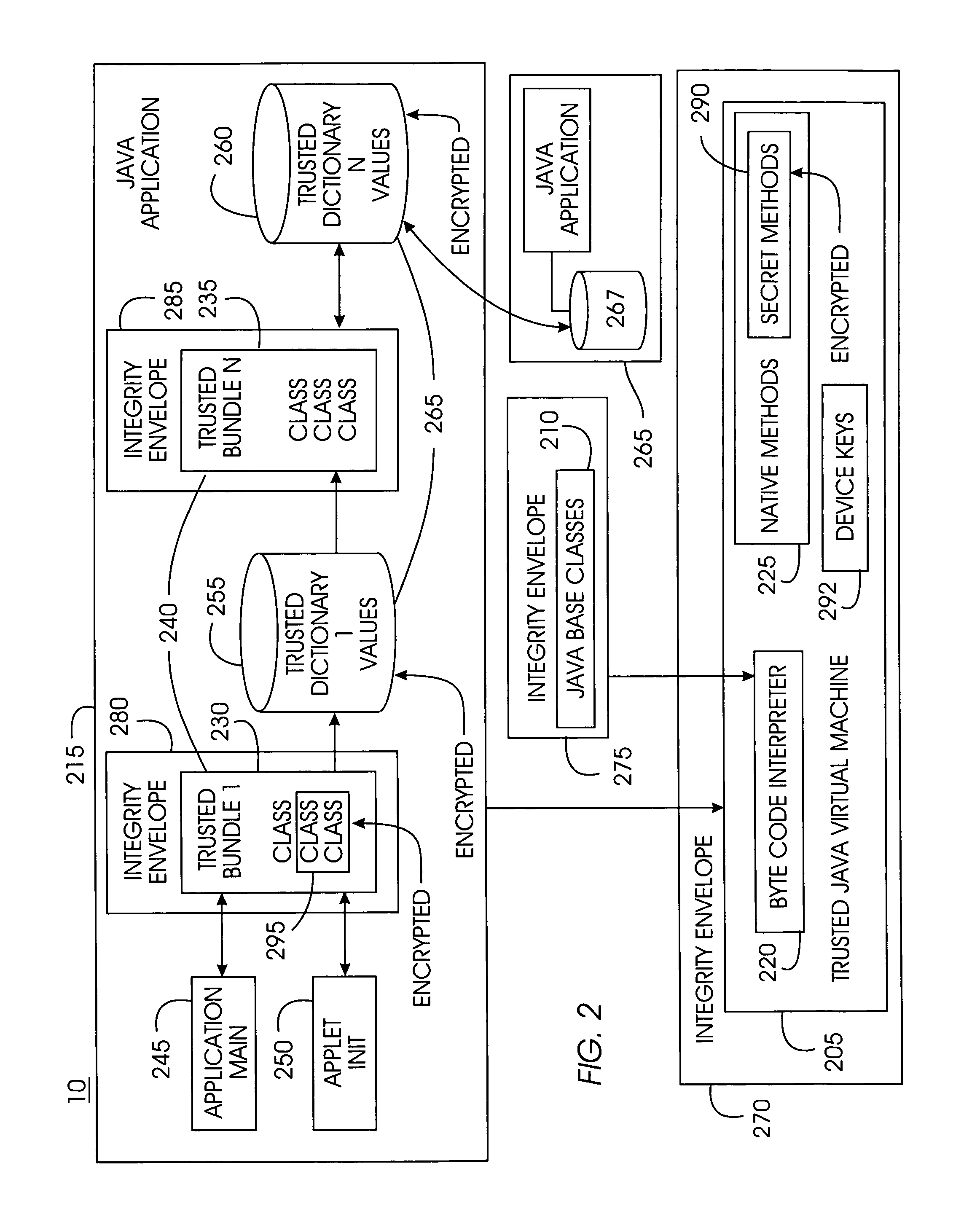
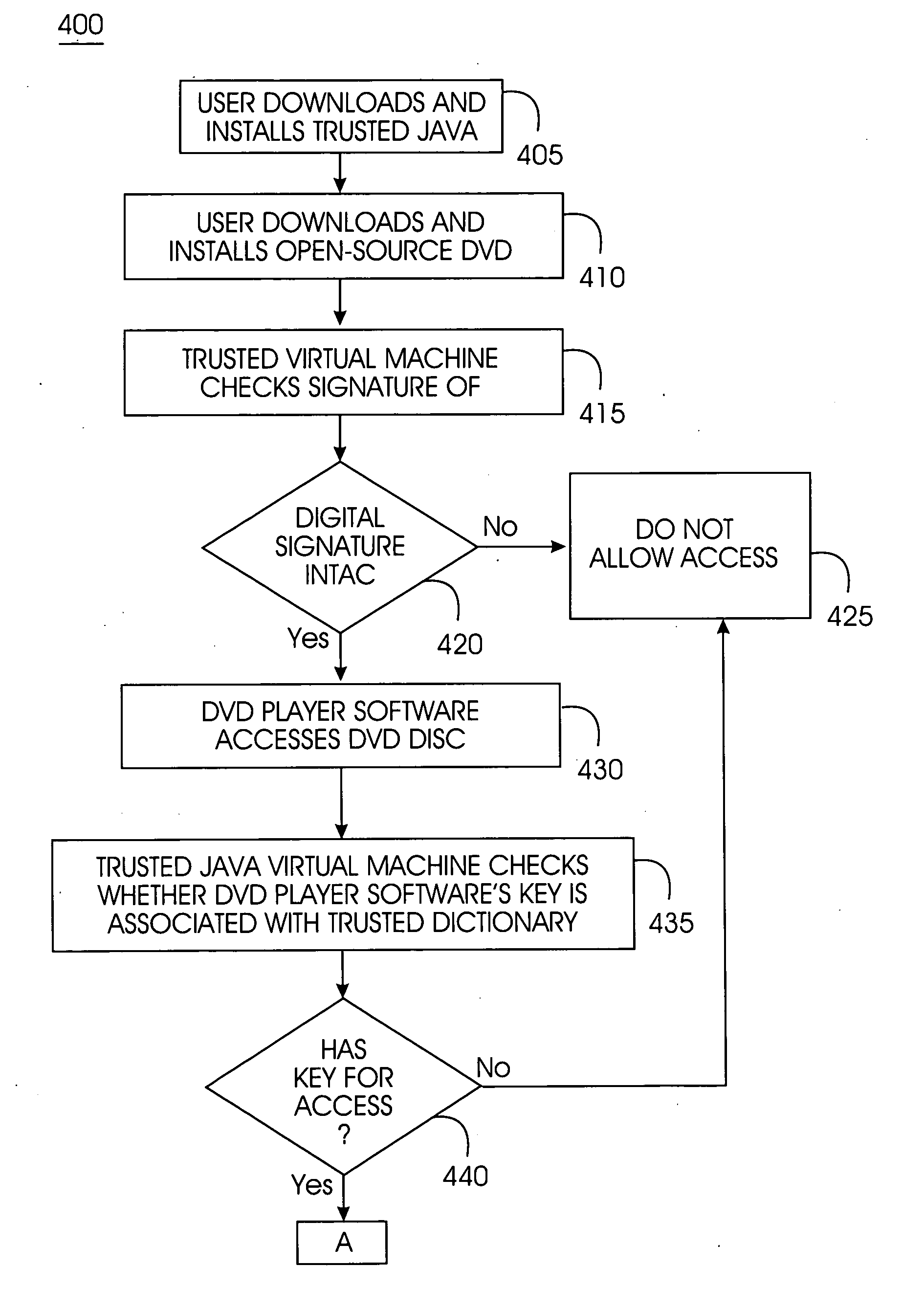
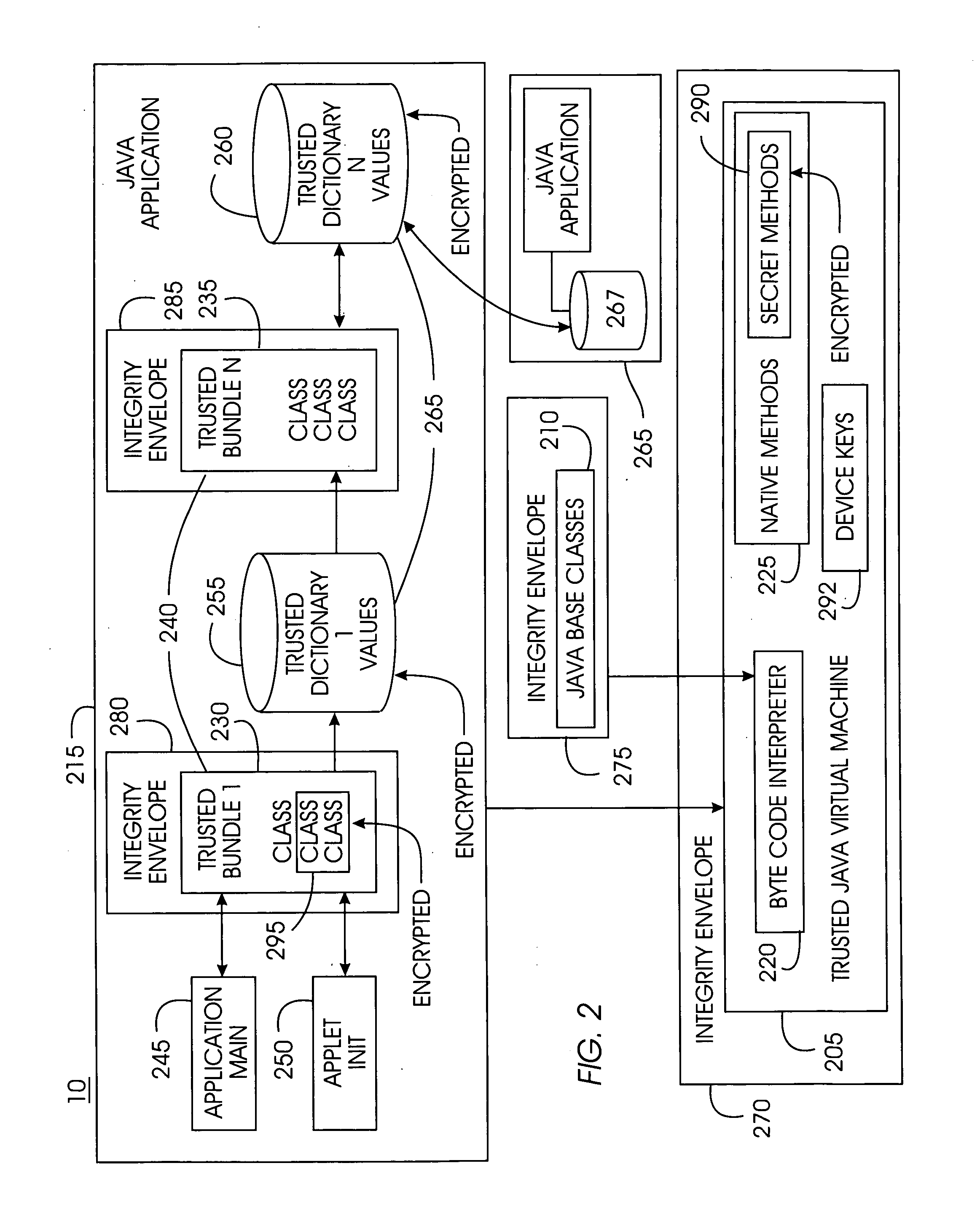
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS7516331B2Slow processEnsure integrityProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:INT BUSINESS MASCH CORP
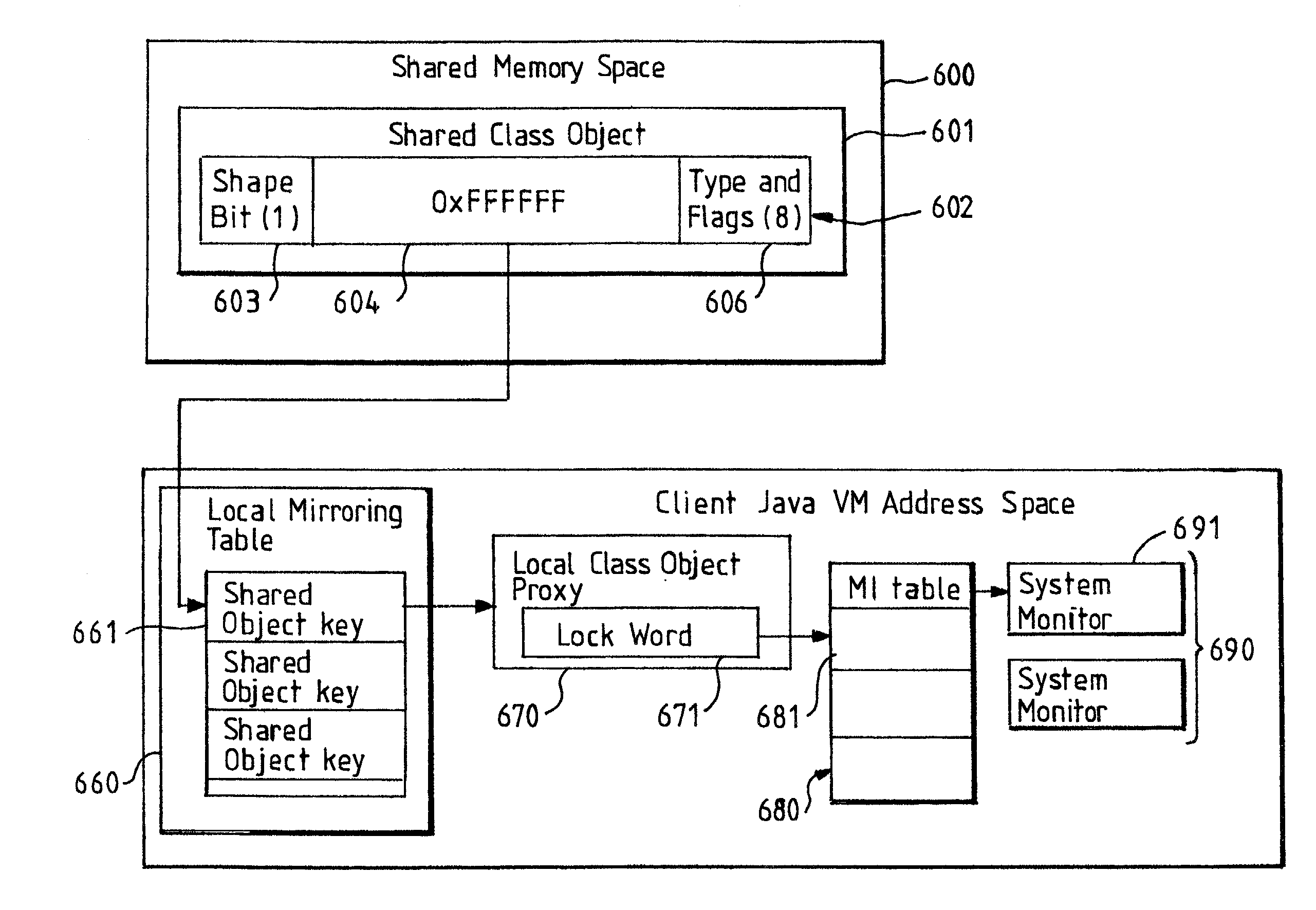
Object locking in a shared VM environment
InactiveUS7035870B2Avoiding scalability problemMaintain consistencyData processing applicationsProgram synchronisationShared objectJava virtual machine
A system is provided which comprises multiple Java virtual machines (VMs). Each VM is capable of running a plurality of threads. The system includes at least one object which is shared between the VMs so that it is accessible from two or more VMs, and at least one non-shared object which is accessible only from a single VM. In order to perform a lock operation on a shared object, it is first detecting that an object is a shared object. In a preferred embodiment, this is accomplished by locating a predefined value in a particular lock data word in the object. In response to the detection, a monitor is used to control local access to the shared object for the thread that is requesting the object. The monitor is on the same VM as the requesting thread. In addition, a data structure, which may be a proxy object, is updated in order to associate the monitor with the shared object.
Owner:IBM CORP
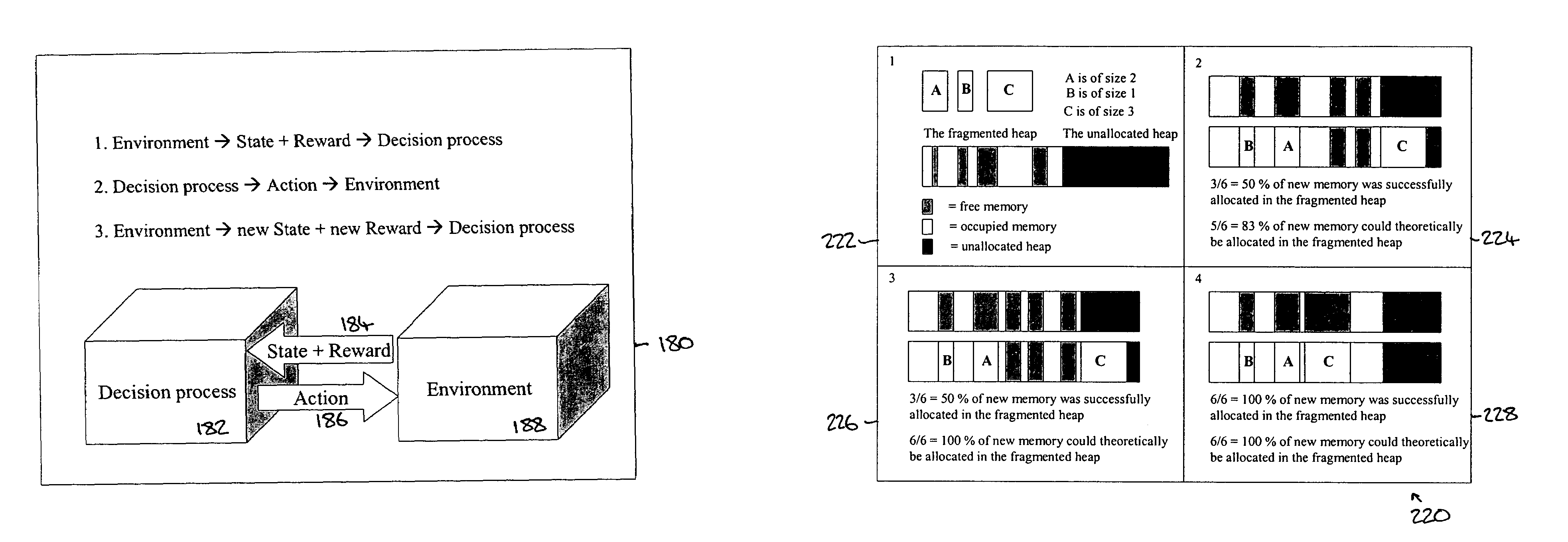
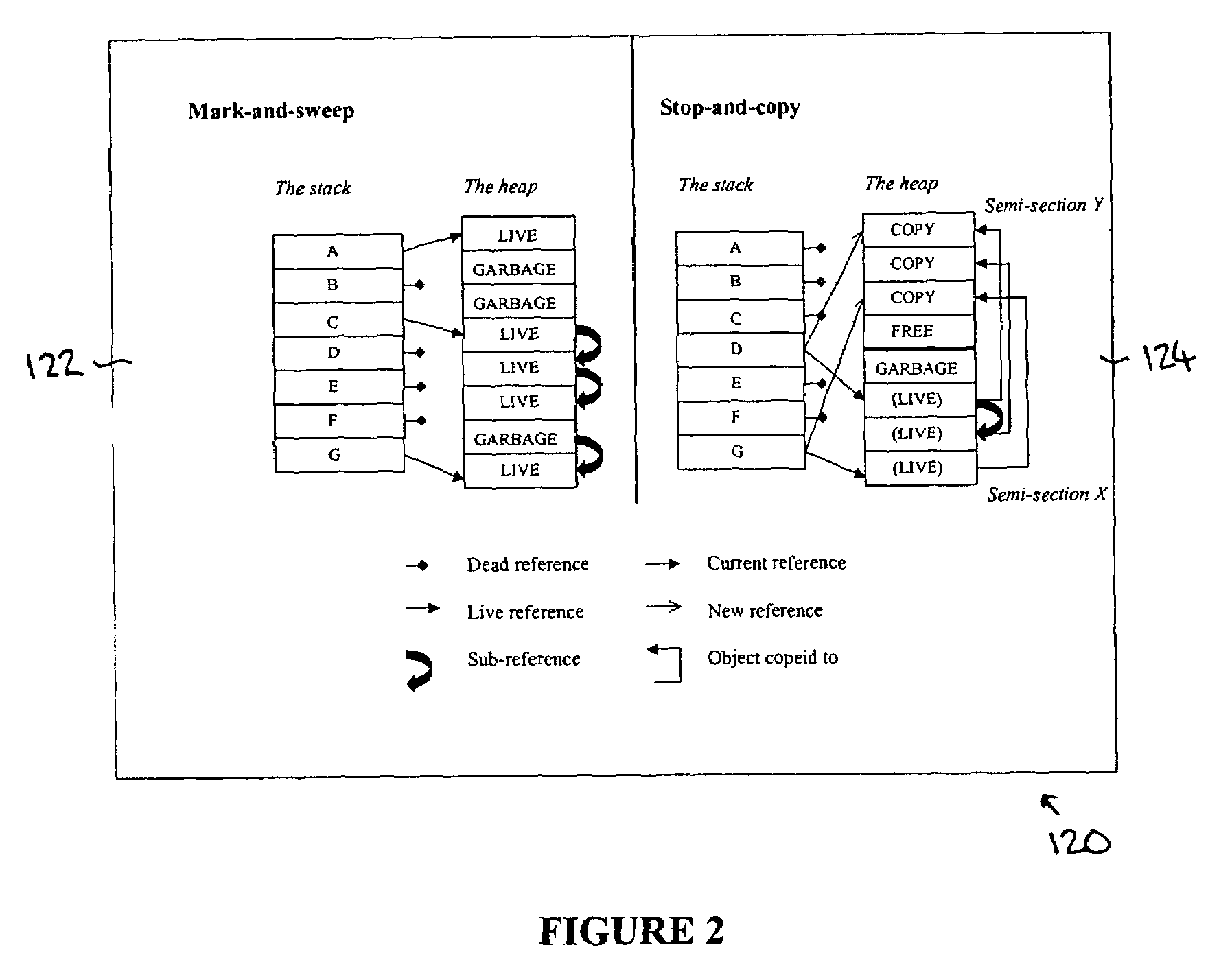
System and method for garbage collection in a computer system, which uses reinforcement learning to adjust the allocation of memory space, calculate a reward, and use the reward to determine further actions to be taken on the memory space
ActiveUS7174354B2Easy to collect and processSimple designData processing applicationsMemory adressing/allocation/relocationWaste collectionComputerized system
A system and method for use with a virtual machine, including an adaptive, automated memory management process that takes decisions regarding which garbage collector technique should be used, based on information extracted from the currently active applications. Reinforcement learning is used to decide under which circumstances to invoke the garbage collecting processing. The learning task is specified by rewards and penalties that indirectly tell the RLS agent what it is supposed to do instead of telling it how to accomplish the task. The decision is based on information about the memory allocation behavior of currently running applications. Embodiments of the system can be applied to the task of intelligent memory management in virtual machines, such as the Java Virtual Machine (JVM).
Owner:ORACLE INT CORP
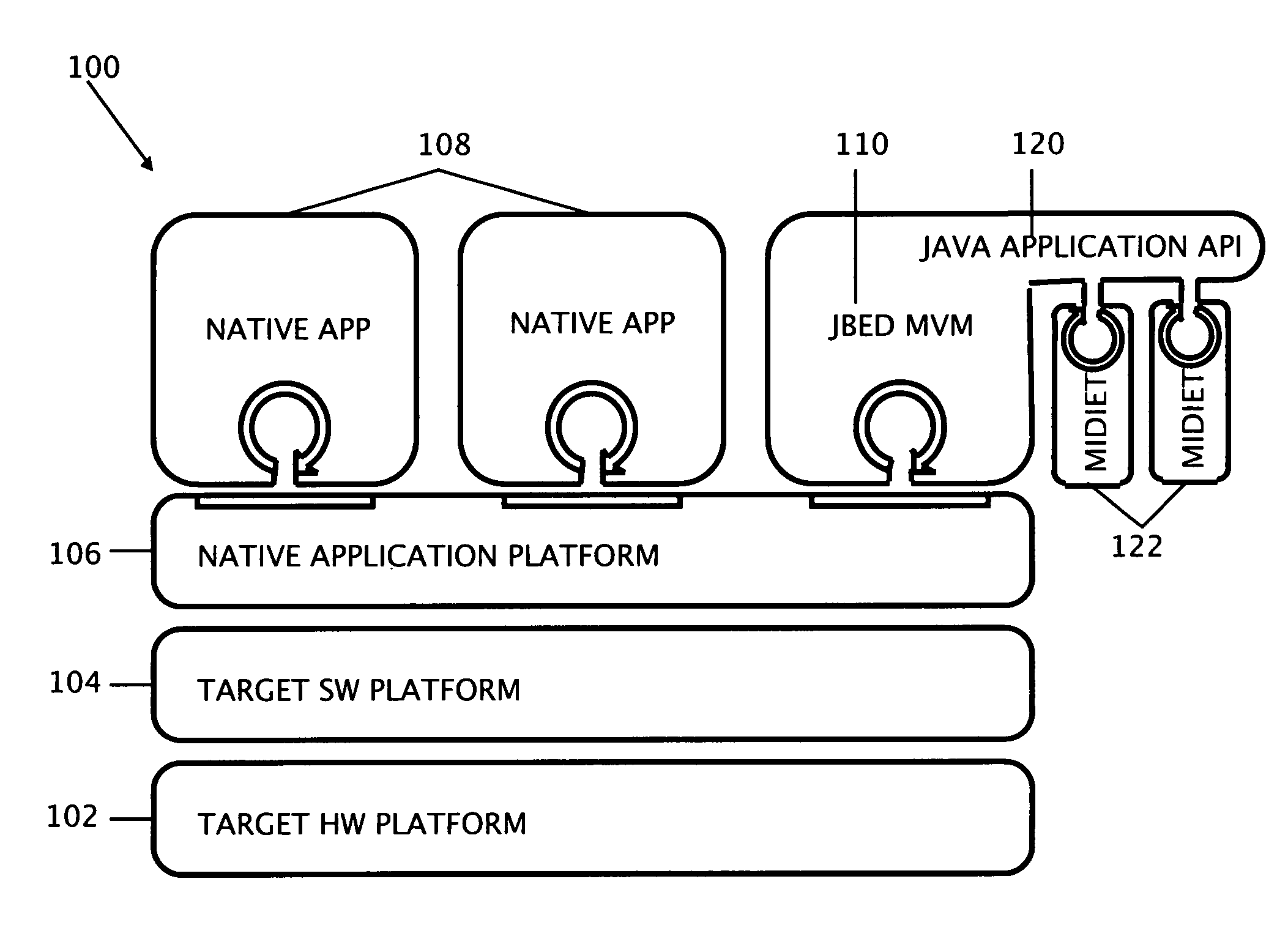
Unified mobile platform
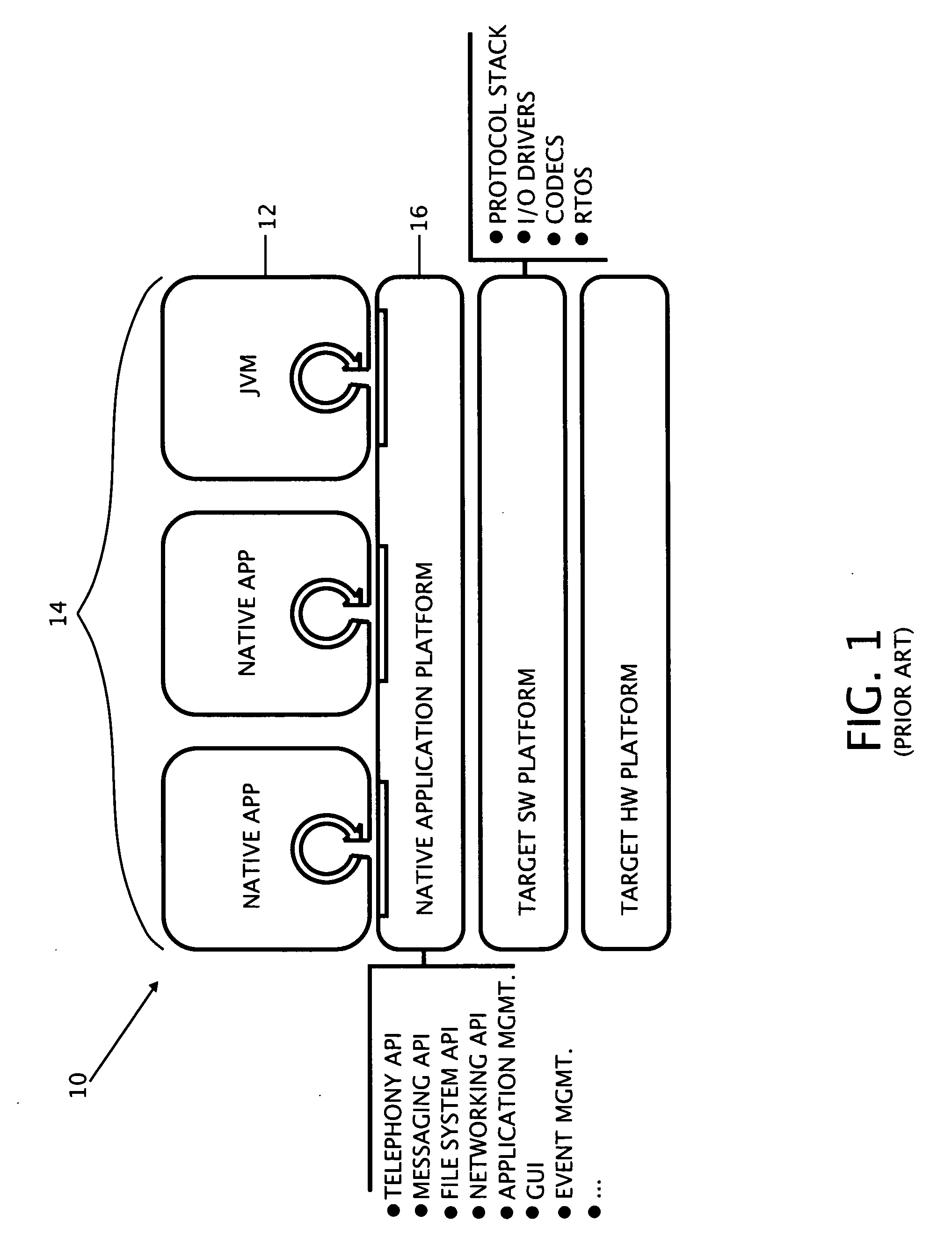
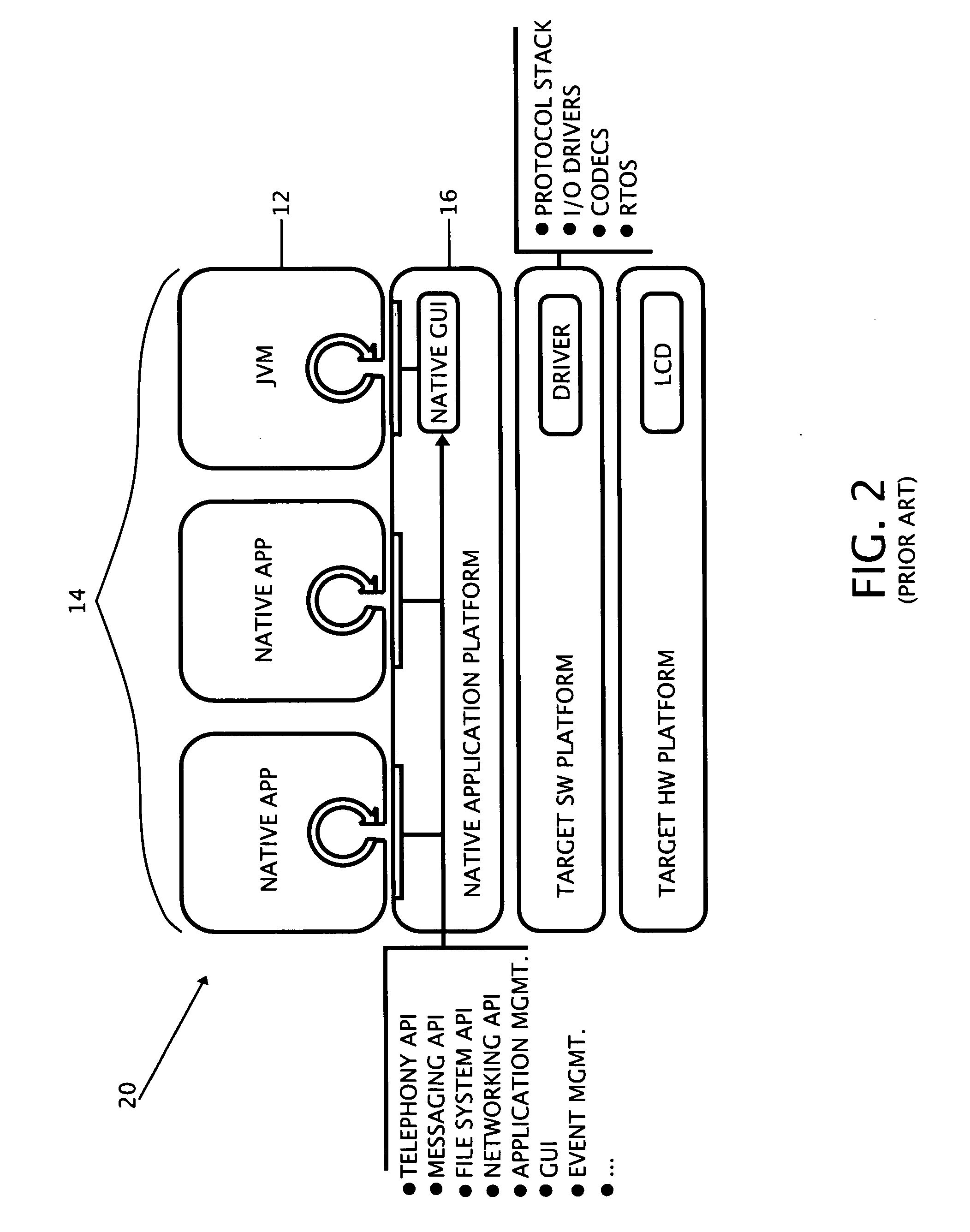
InactiveUS20070168953A1Avoid applicationSpecific program execution arrangementsMemory systemsApplication softwareMobile device
The present invention teaches a variety of systems, platforms, applications, and methods, and relates to mobile platforms, embedded native applications, Java virtual machines, user interfaces, and the like. The present invention discloses a mobile platform which unifies the worlds of the Java virtual machine and native applications to provide a unified and consistent environment for multitasking both Java and native applications within a mobile device.
Owner:MYRIAD GROUP
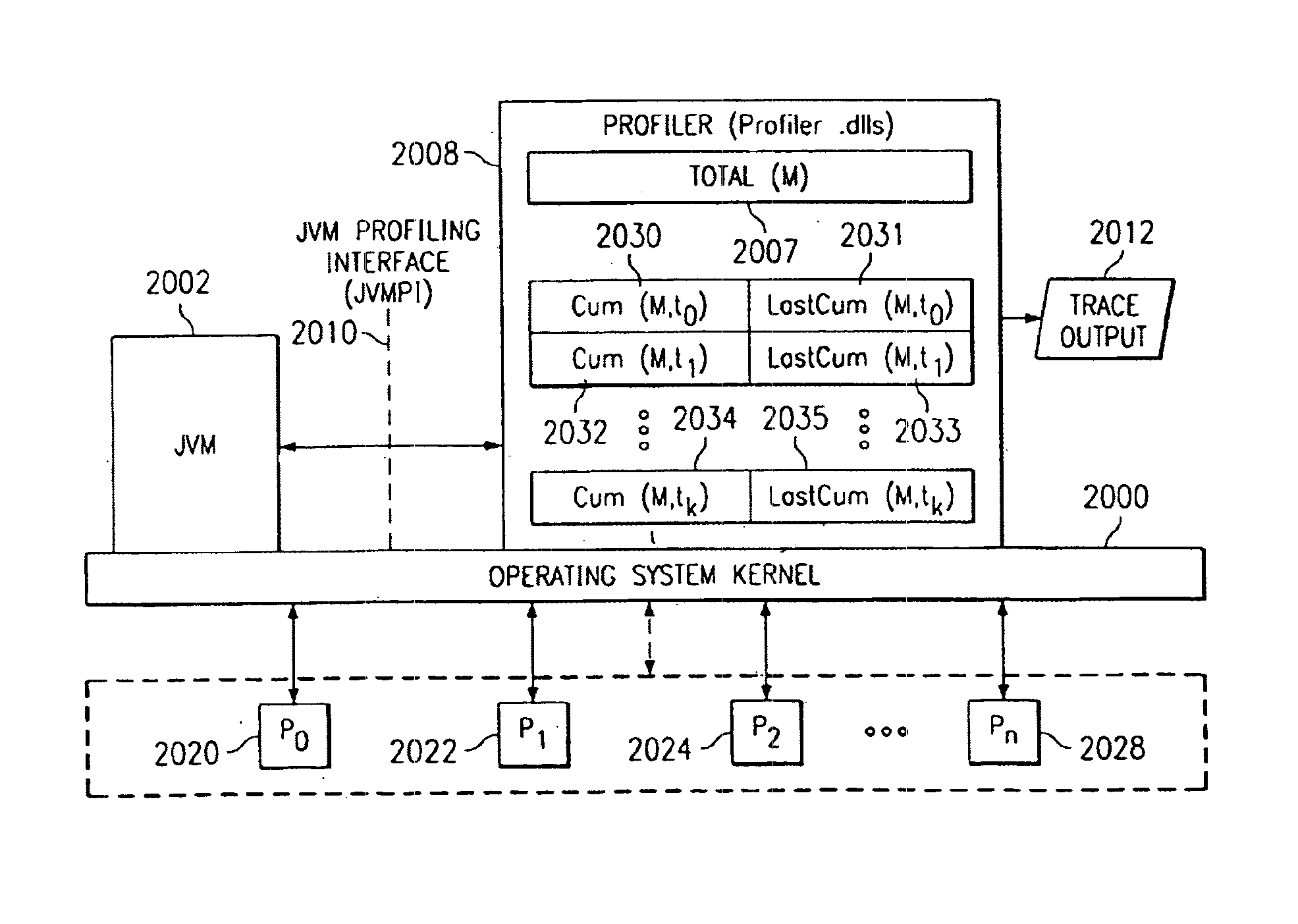
Method and system for apportioning changes in metric variables in an symmetric multiprocessor (SMP) environment
A method and system for monitoring performance of a program using global metric variables to provide the support in an symmetric multiprocessor (SMP) system. A Java virtual machine (Jvm) either calls the profiler whenever bytes are allocated or provides an interface to allow the profiler to determine the value of the change in the metric for the current thread. The profiler then applies the changes to a metric for the current thread. Alternatively, per processor data areas are maintained for storing per processor metric values. Whenever a thread switch occurs or there is a request for the metric on a specified thread, an operating system kernel updates the thread level metric values with changes in the values per processor metrics.
Owner:IBM CORP
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS20050114683A1Easy to processSatisfies needProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:IBM CORP
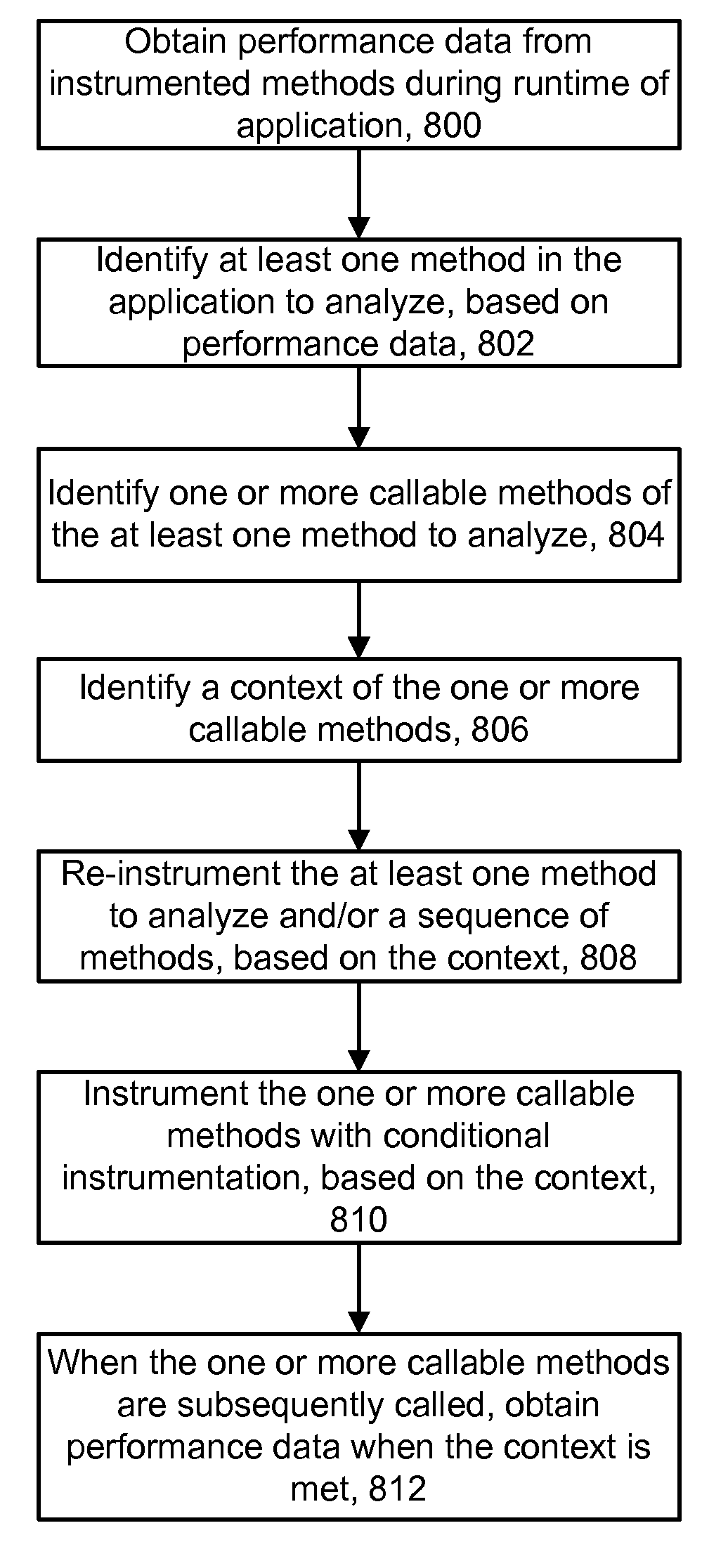
Conditional dynamic instrumentation of software in a specified transaction context
ActiveUS20110283263A1Error detection/correctionSoftware maintainance/managementDynamic instrumentationTransaction data
Techniques for analyzing software in which un-instrumented components can be discovered and conditionally instrumented during a runtime of the software. Initially, software such as an application can be configured with a baseline set of instrumented components such as methods. As the application runs, performance data gathered from the instrumentation may indicate that the performance of some methods is below expectations. To analyze this, any methods which are callable from a method at issue are discovered, such as by inspecting the byte code of loaded classes in a JAVA Virtual Machine (JVM). To limit and focus the diagnosis, the instrumentation which is added to the discovered components can be conditional, so that the instrumentation is executed only in a specified context. The context can involve, e.g., a specified sequence of components in which a discovered component is called, and / or transaction data in which a discovered component is called.
Owner:CA TECH INC
Methods and apparatus for control using control devices that provide a virtual machine environment and that communicate via an IP network
InactiveUS20080040477A1Reduce complexityReduce confusionMultiple digital computer combinationsResourcesOperational systemActuator
Owner:SCHNEIDER ELECTRIC SYST USA INC
Method for multi-tasking multiple Java virtual machines in a secure environment
InactiveUS7178049B2Operational securitySpecific access rightsError detection/correctionOperational systemReal-time operating system
The present invention allows construction of a secure, real-time operating system from a portable language such as Java that appears to be a Java virtual machine from a top perspective but provides a secure operating system from a bottom perspective. This allows portable languages, such as Java, to be used for secure embedded multiprocessor environments.
Owner:MICROPAIRING TECH LLC
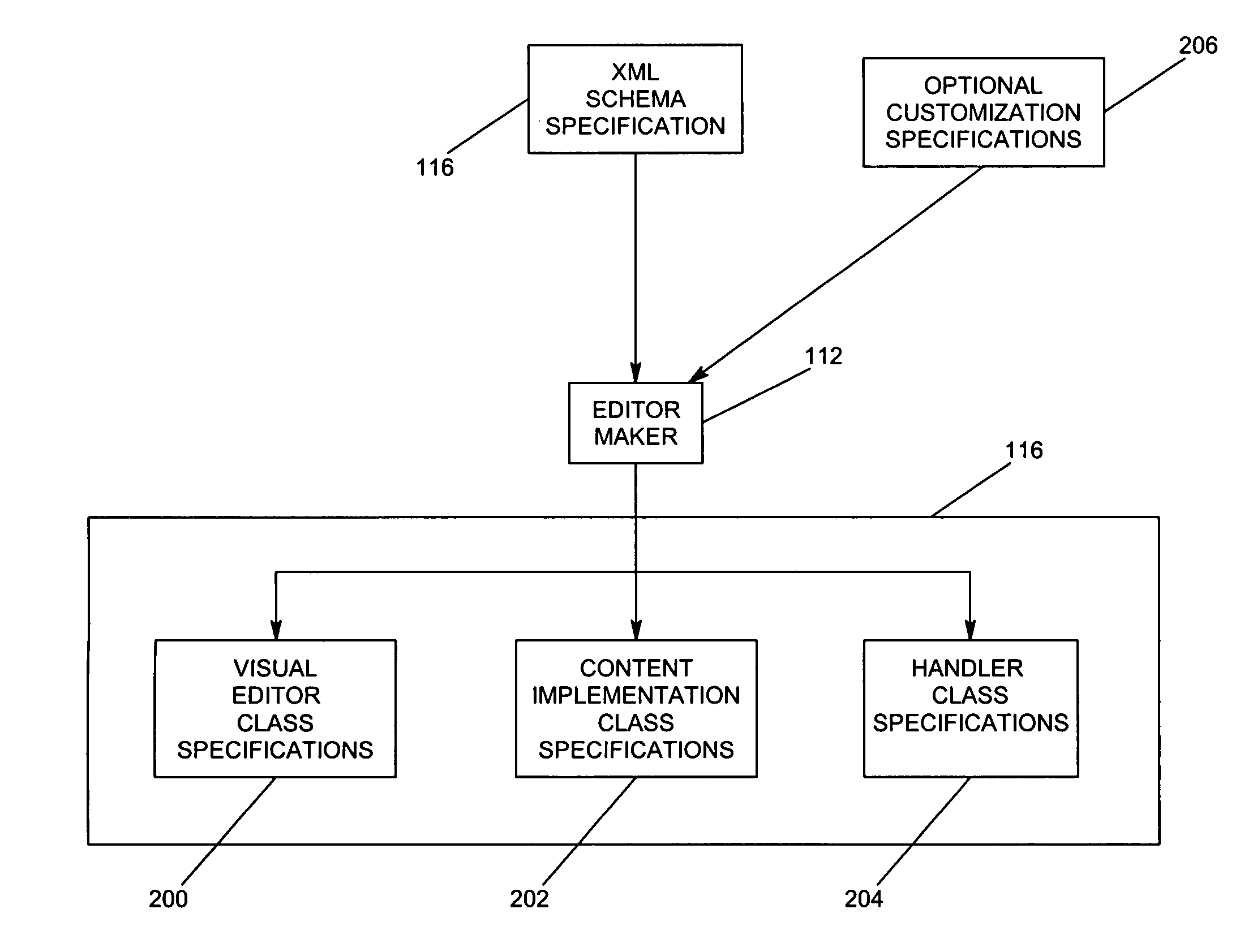
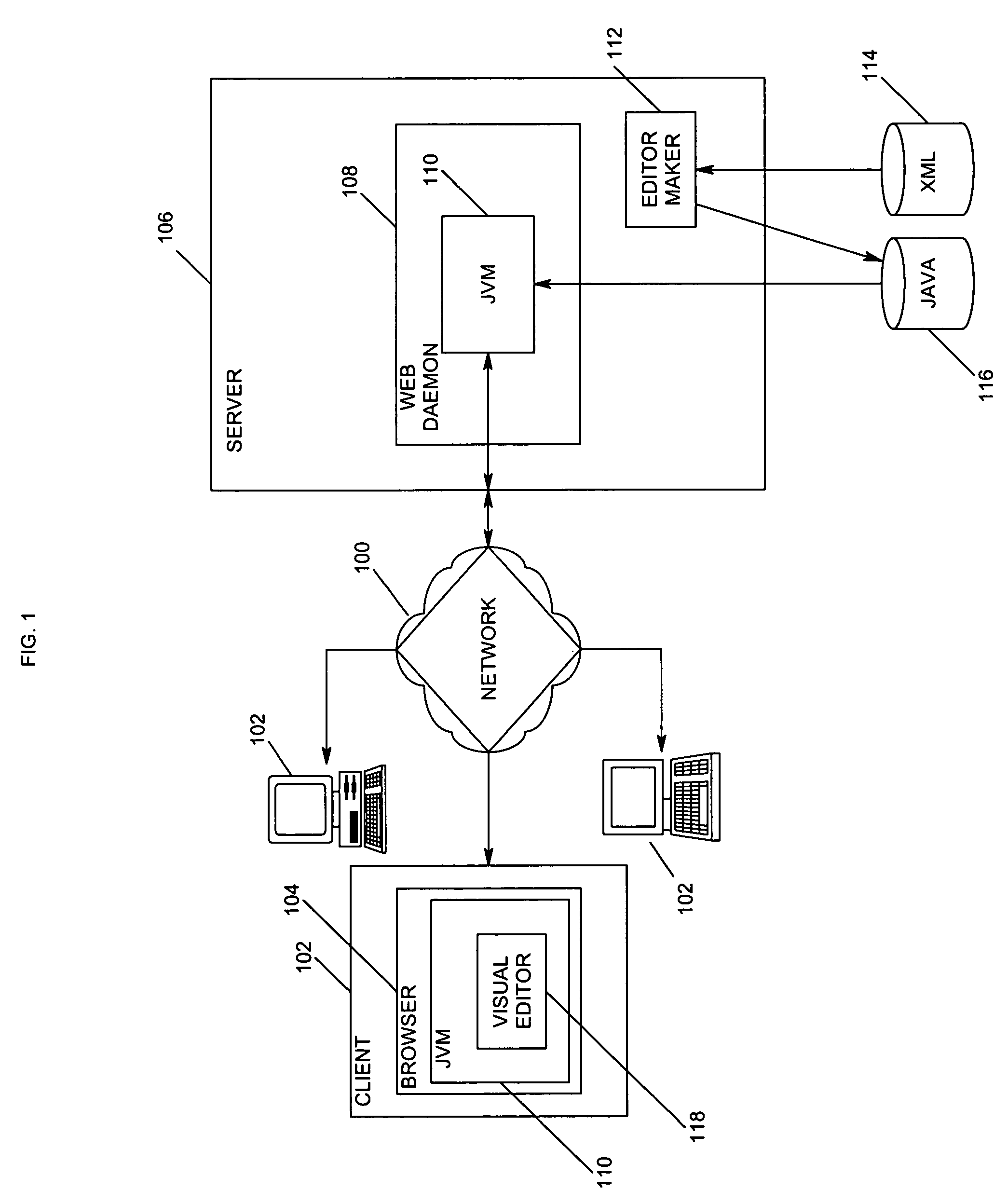
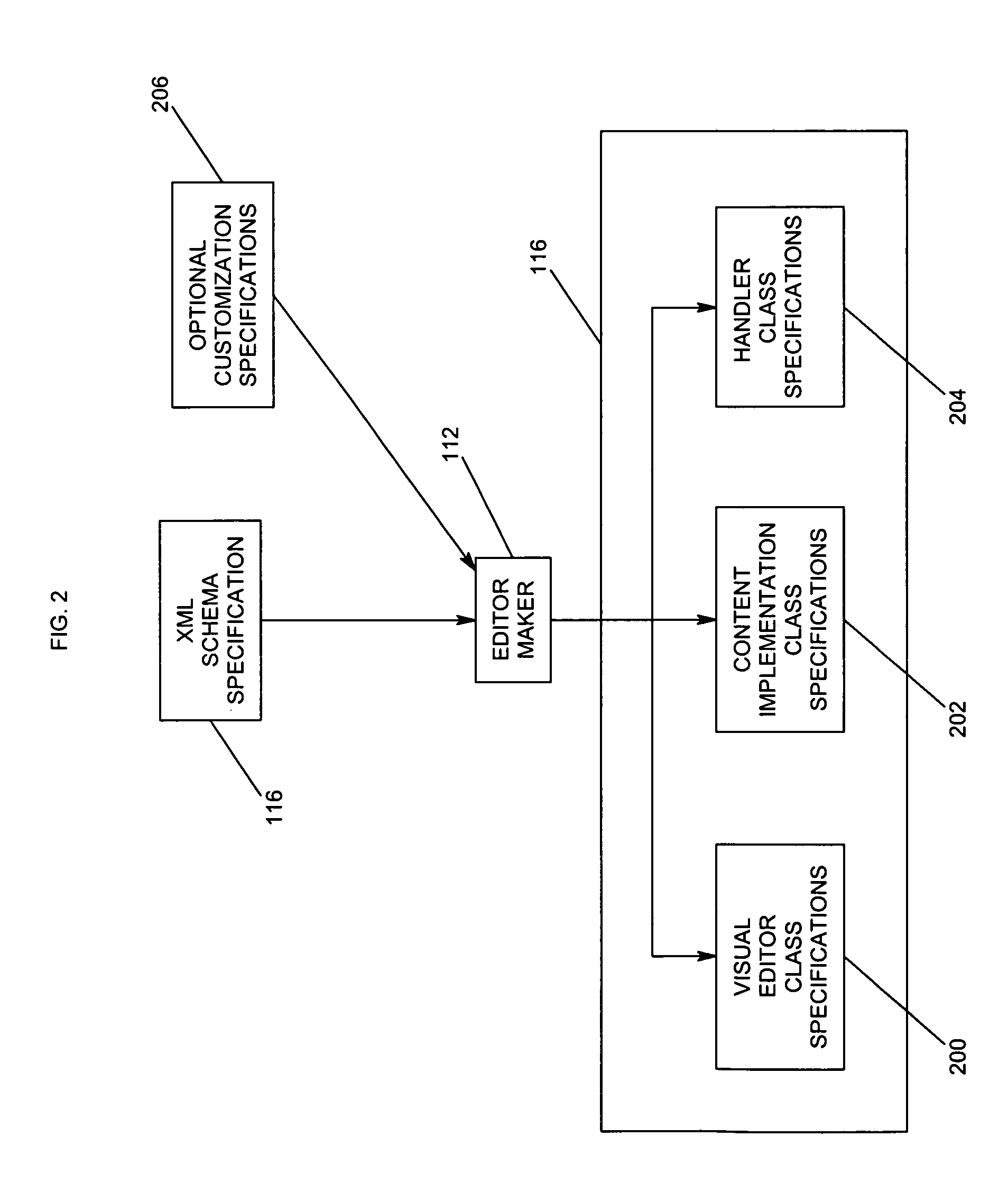
Generating visual editors from schema descriptions
InactiveUS7039859B1Data processing applicationsDigital computer detailsXML schemaDocumentation procedure
A visual editor is automatically generated from an eXtensible Markup Language (XML) schema and then used to edit the data contained in corresponding XML documents. The entities within an XML schema are mapped to components of the visual editor, such as forms, widgets, etc., that are generated as class specifications. These class specifications can be customized through the use of a customization specification file, as desired. The class specifications are then instantiated as objects in a Java Virtual Machine to perform the functions of the visual editor.
Owner:IBM CORP
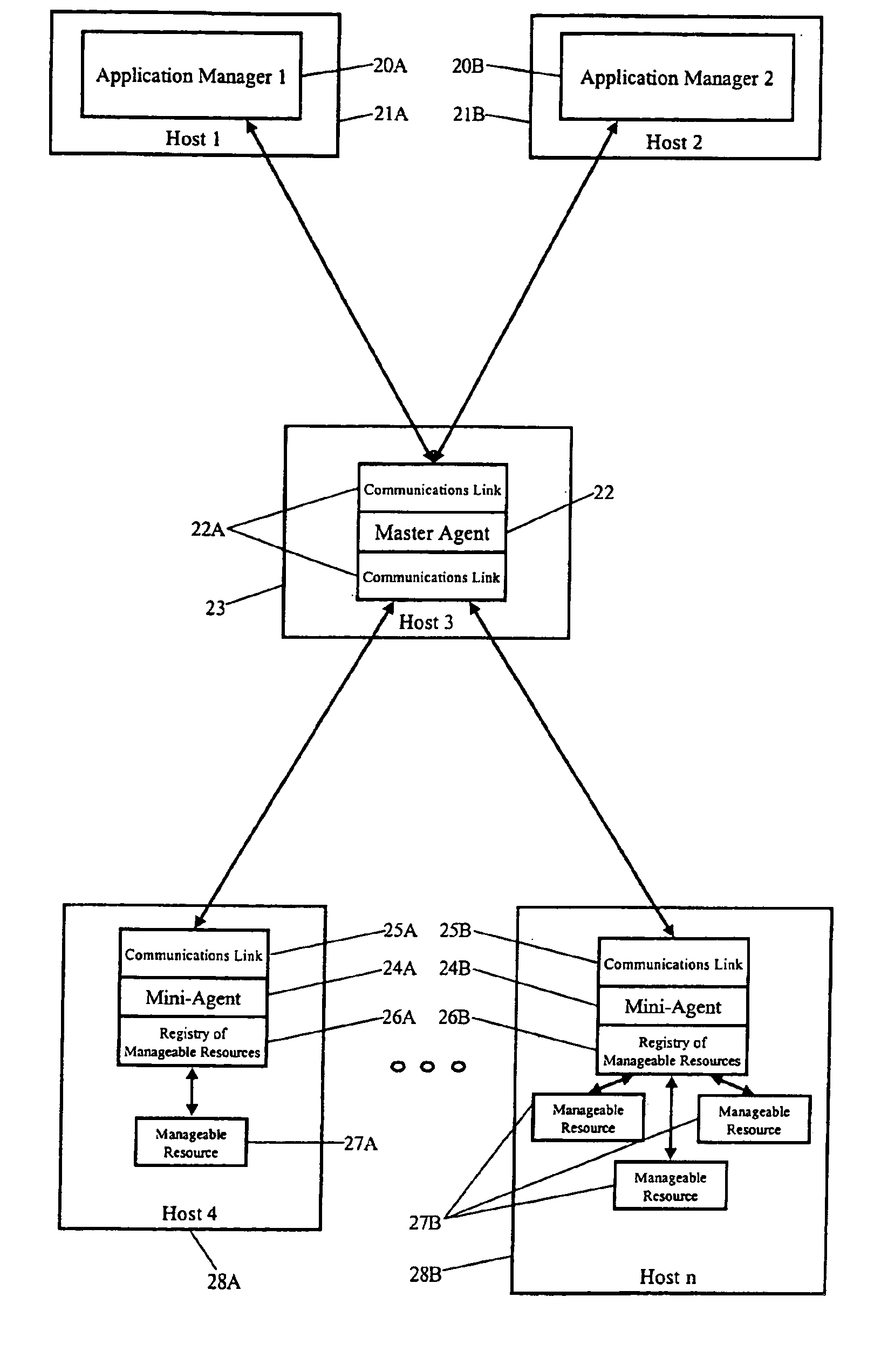
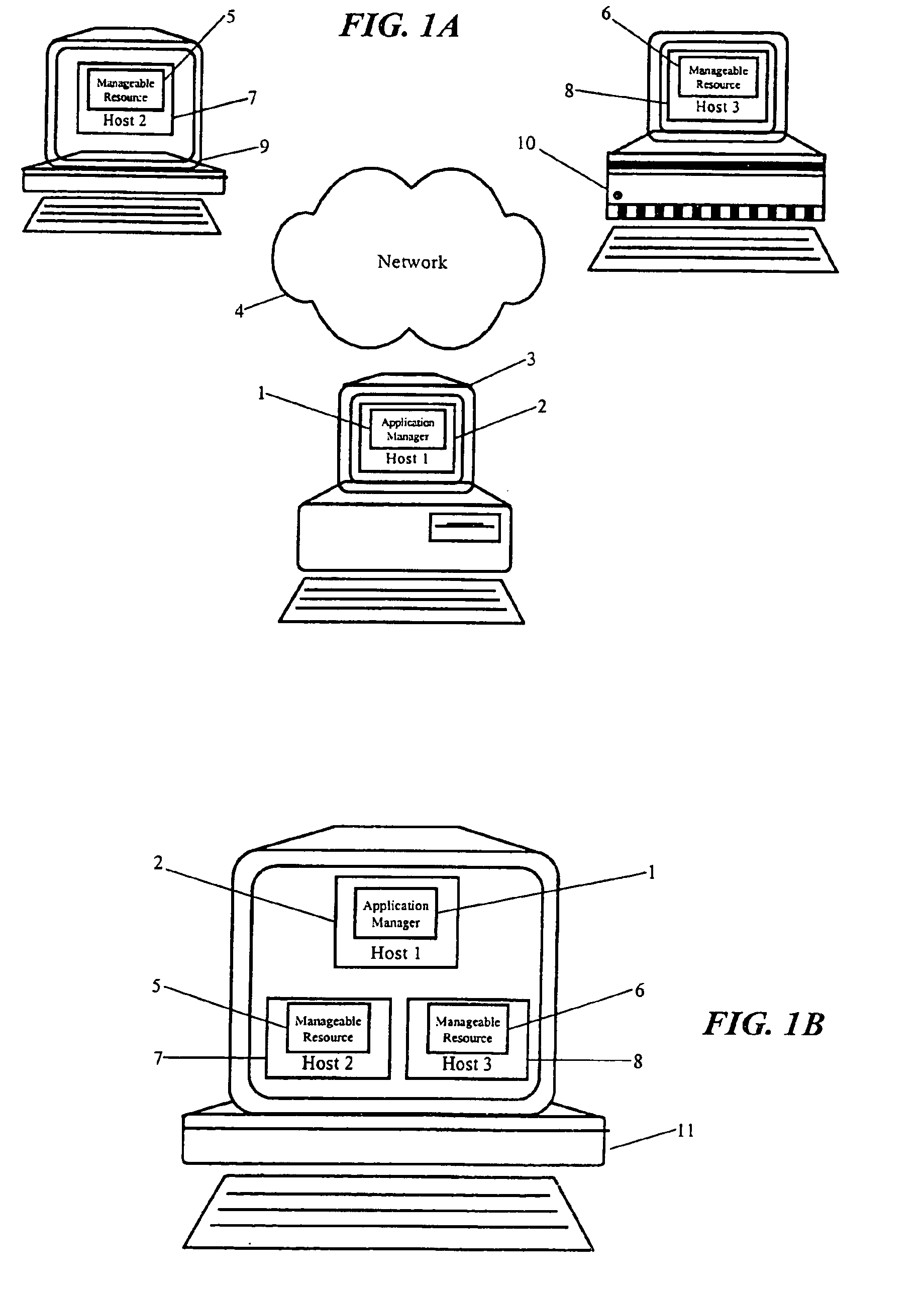
System uses application manager and master agent to communicate with mini-agents for remotely managing application resources distributed across multiple Java virtual machines
InactiveUS6874020B1Multiprogramming arrangementsMultiple digital computer combinationsCommunication interfaceProgram management
A method of remotely managing an application distributed across multiple application hosts can include, in a master agent, receiving from an application manager in a second application host a management command for performing a management operation directed to a manageable resource in a remote application host; communicating the management command to a mini-agent in the remote application host; and, in the mini-agent, performing the management operation on the manageable resource by accessing an exposed member of the manageable resource according to the management operation. The step of communicating the management command to the mini-agent can include accessing the mini-agent through a JMX communications connector. The step of accessing the mini-agent can include invoking methods of the mini-agent through an RMI communications interface. Additionally, the step of performing the management operation can include accessing a method of the manageable resource through a management interface to the manageable resource. Notably, the management interface can be an MBean registered in an MBean server in the mini-agent. Accordingly, the step of accessing the method through the interface can include accessing the method exposed by the MBean through the MBean server according to the management operation.
Owner:IBM CORP
Methods and apparatus for control using control devices that provide a virtual machine environment and that communicate via an IP network
Owner:INVENSYS SYST INC
Method for predicting and avoiding danger in execution environment
InactiveUS20050240641A1Reduce loadShort timeData processing applicationsMemory adressing/allocation/relocationApplication serverOut of memory
Measurement / analysis unit in a Java virtual machine has the function of measuring data when an event of garbage collection occurs, and the function of periodically measuring data. The measurement / analysis unit analyzes the measured data and predicts a danger of a memory shortage, and predicts a danger using an algorithm depending on the type of garbage collection used by the Java virtual machine. An application server is notified of a warning of the predicted danger of a memory shortage by an analysis result notification means by an inter-process communication, or the like. The measurement / analysis unit calculates a memory capacity required to avoid the predicted danger of a memory shortage, and the calculated memory capacity is transmitted to the application server by the analysis result notification means by an inter-process communication, or the like in the same way as the warning.
Owner:FUJITSU LTD
Creating multiple sets of data by spawning a secondary virtual machine
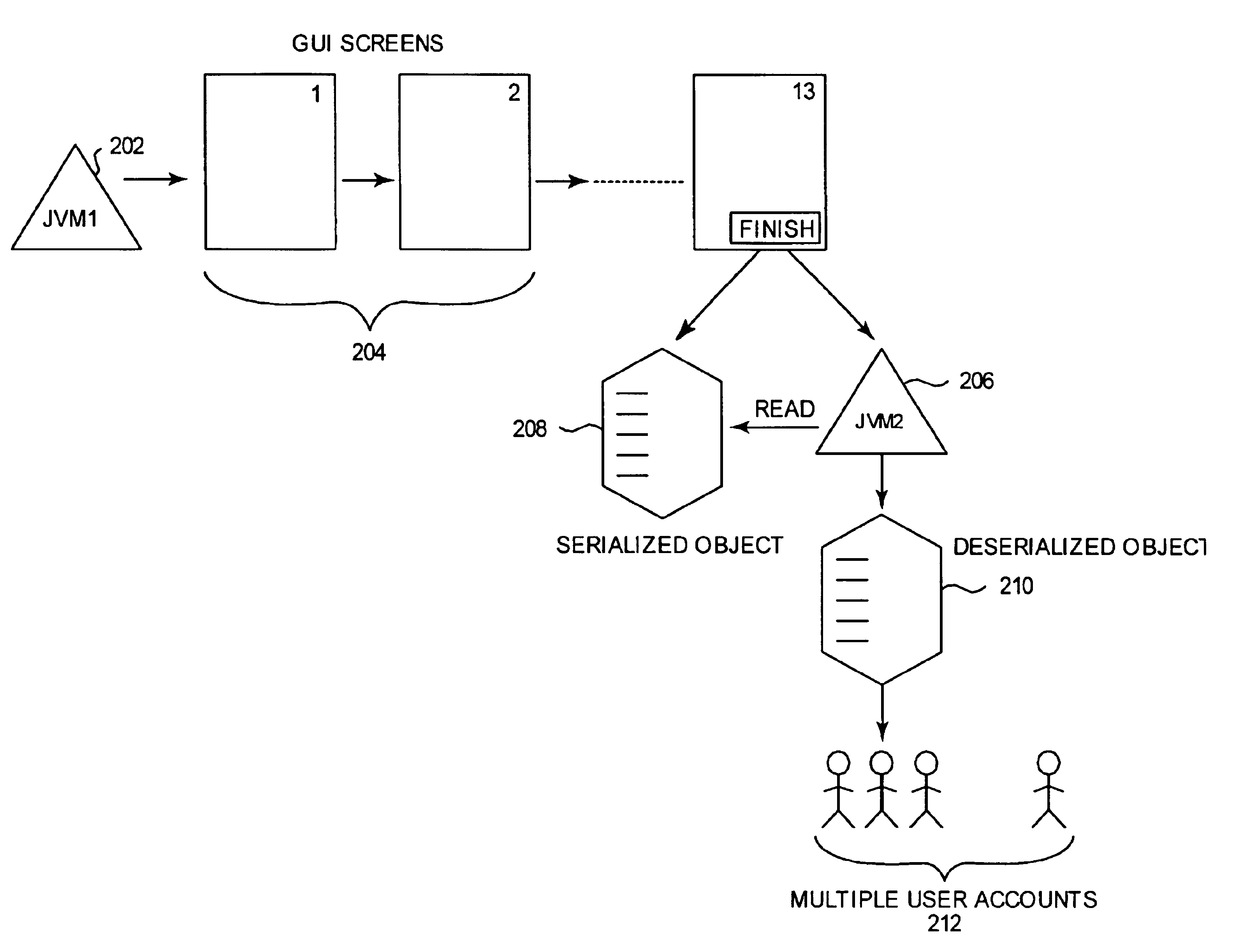
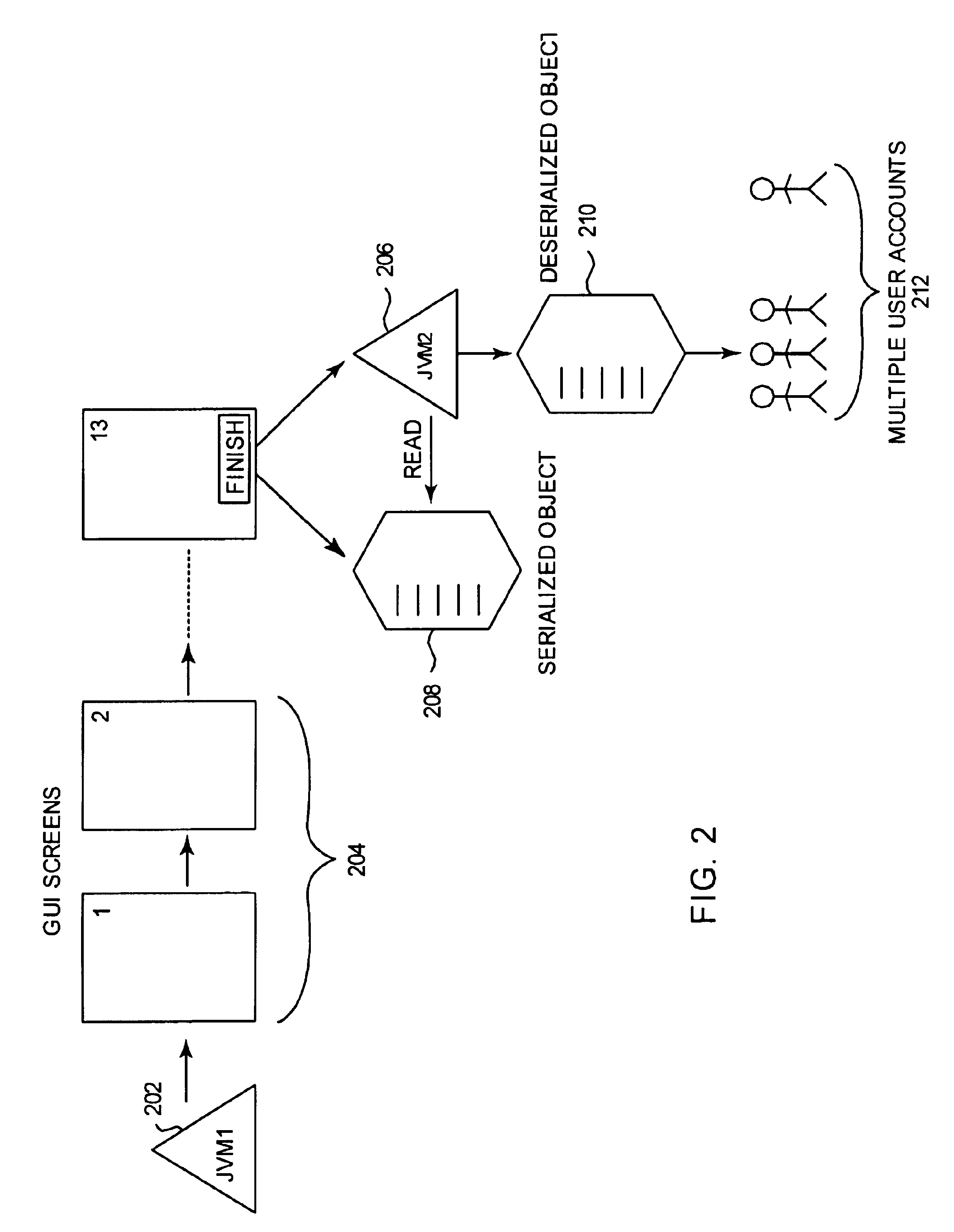
InactiveUS6850953B1Data processing applicationsDigital data processing detailsData setComputerized system
Methods, systems, and computer-readable media are disclosed for having a primary process spawn a secondary process to create multiple data sets, thereby allowing the primary process to continue performing other tasks or to terminate. The primary and secondary processes can be virtual machines, such as Java Virtual Machines running in a computer system. The primary process gathers the raw data used to create the multiple data sets and stores the data in a serialized object. The primary process also runs a script to spawn a secondary process which accepts the serialized object as input. The serialized object is then deserialized and the raw data is operated on by the secondary process without any interference from the primary process. The primary process, responsible for maintaining a GUI for the user, can perform other tasks or terminate without effecting the secondary process. Thus, a user of the primary process is free to continue using the GUI and perform other tasks while the multiple data sets are created by the secondary process in the background.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com