Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
196 results about "Program security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
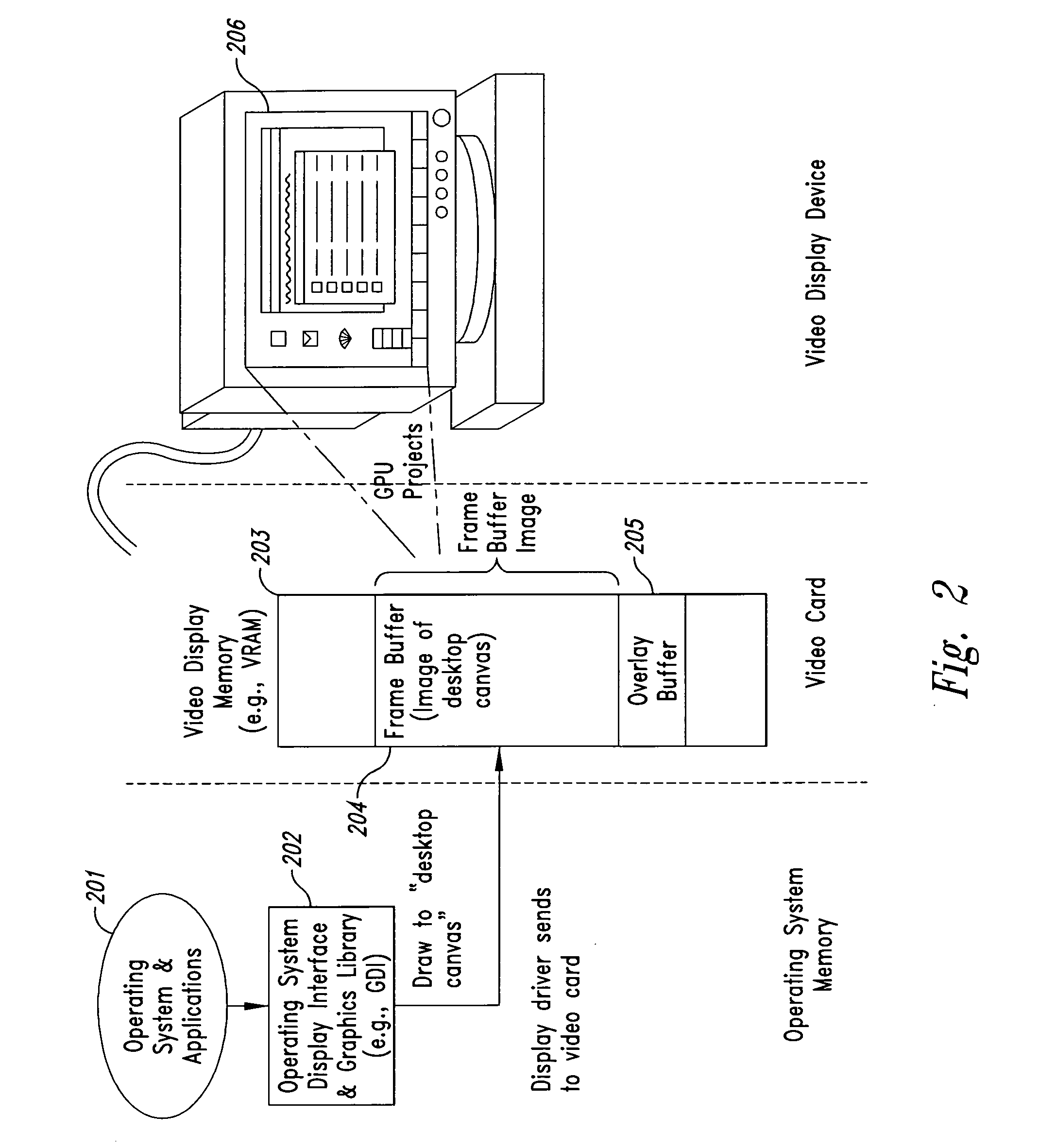
A security program is a documented set of your company's information security policies, procedures, guidelines, and standards. Your security program should provide a roadmap for effective security management practices and controls.
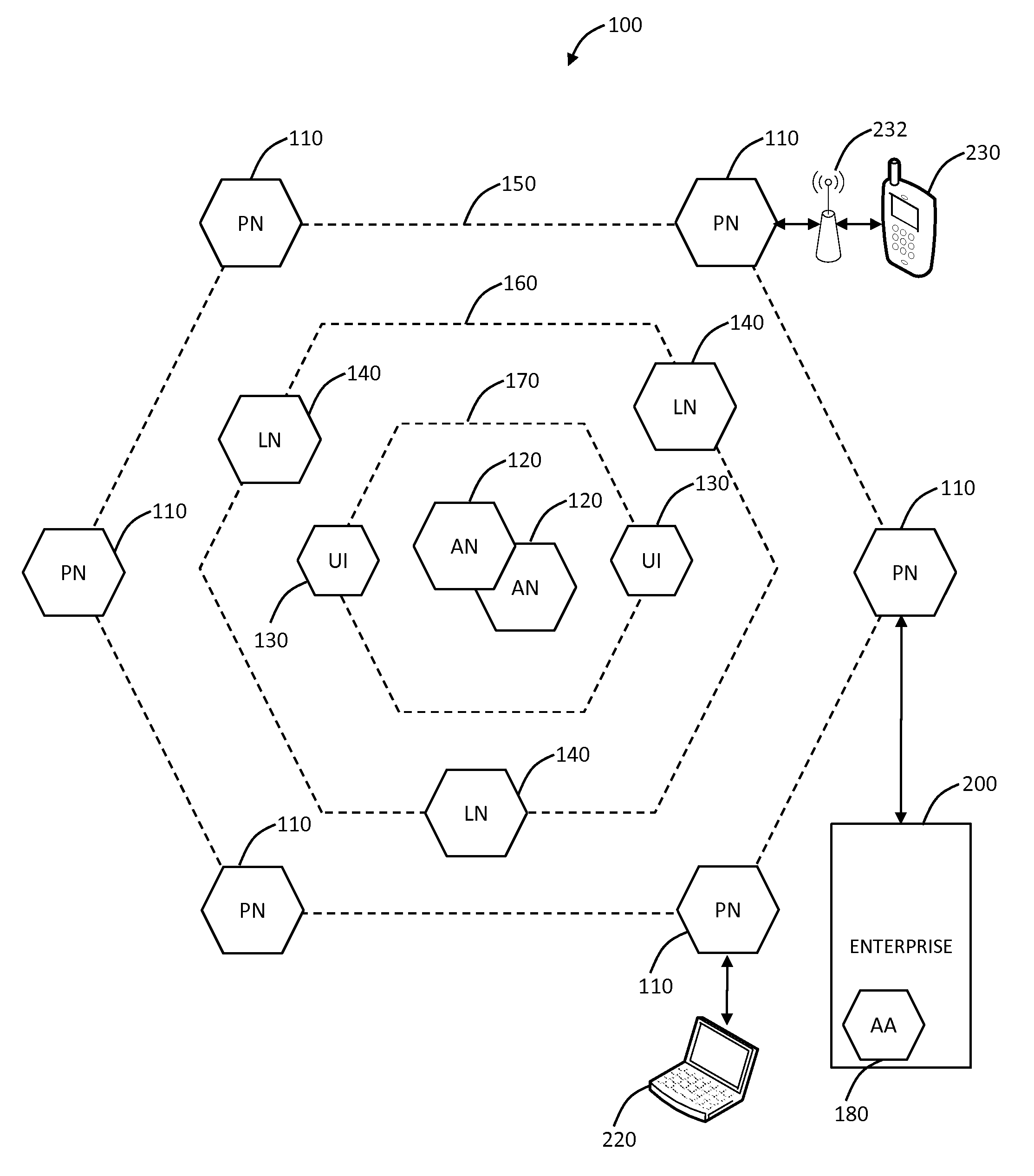
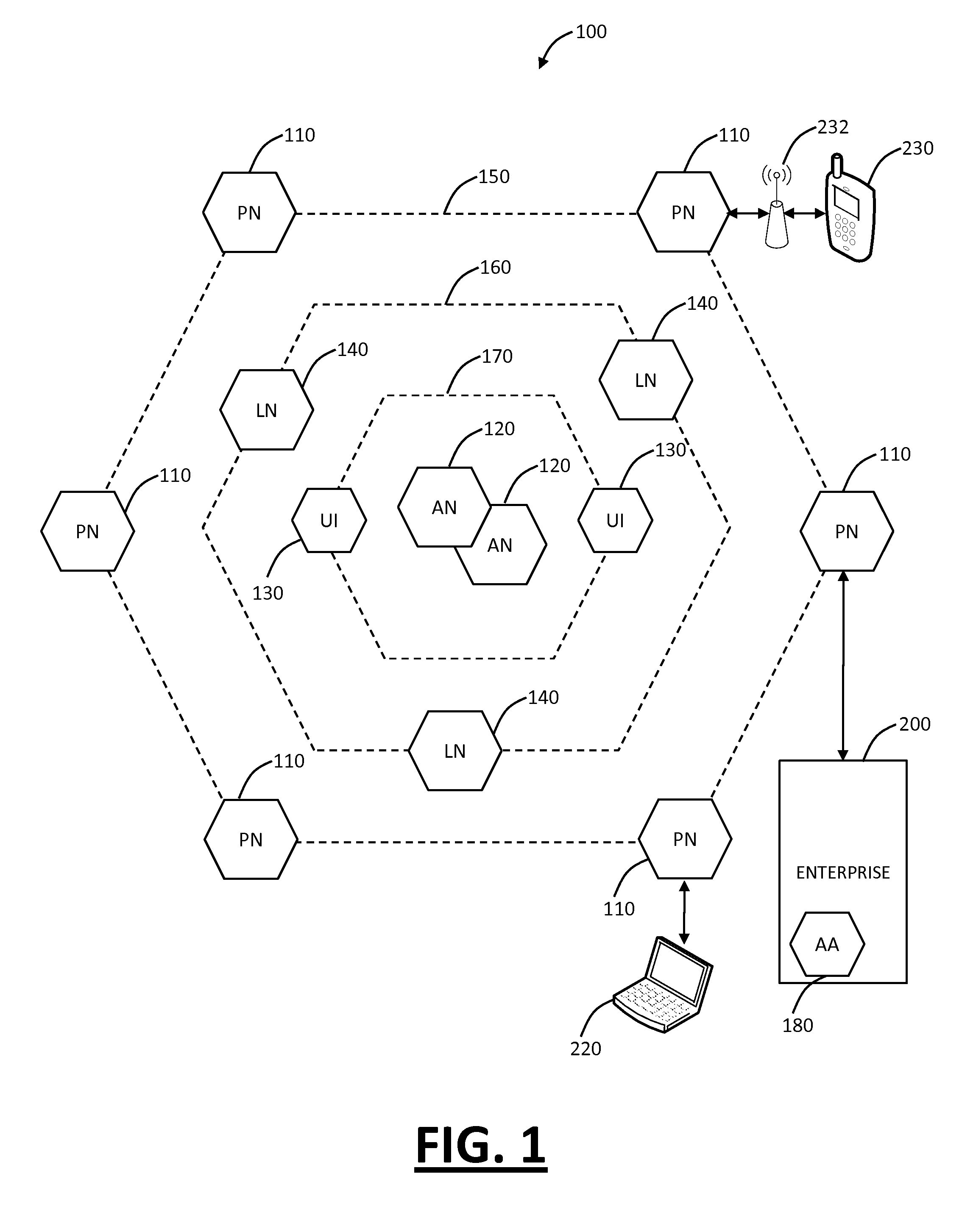
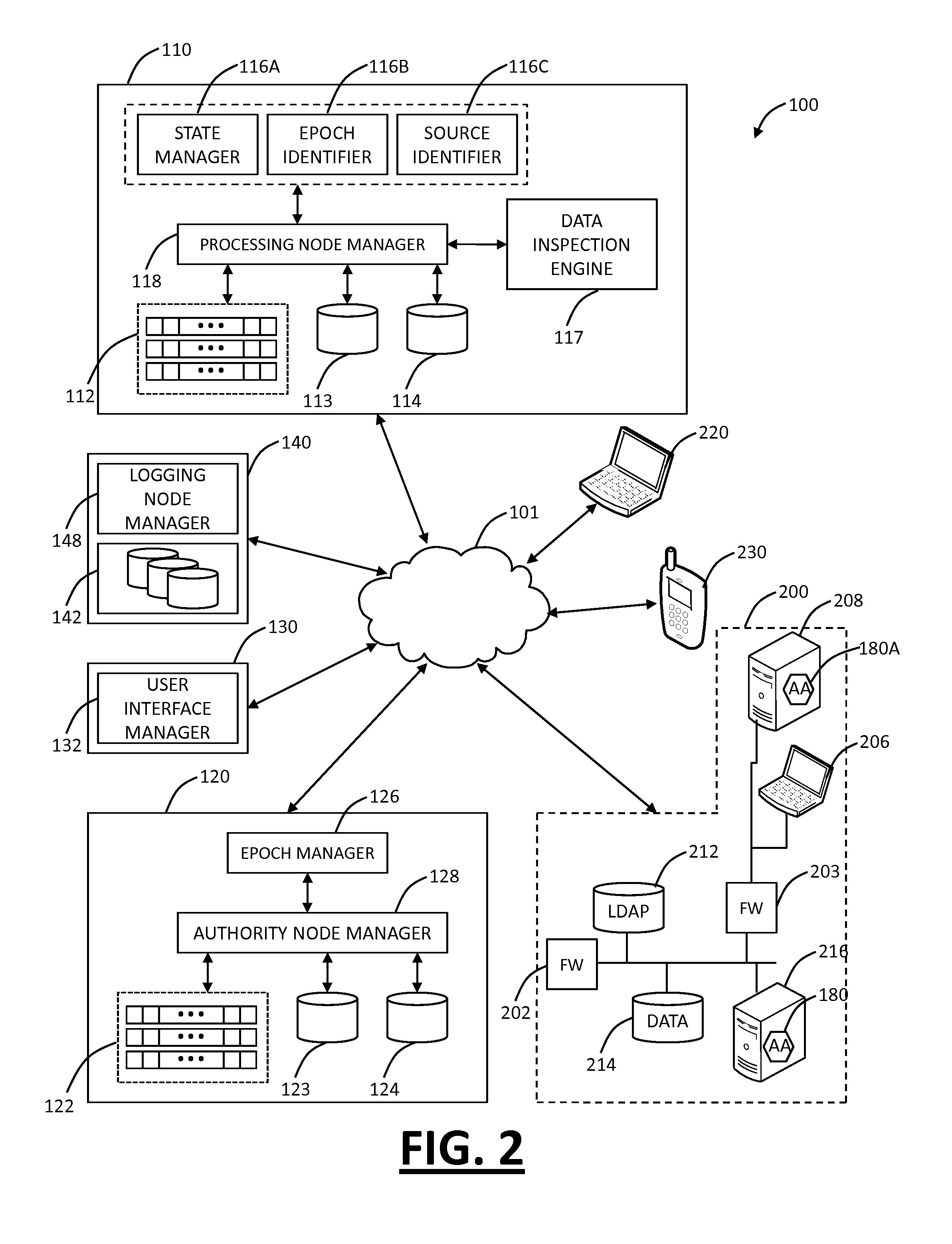
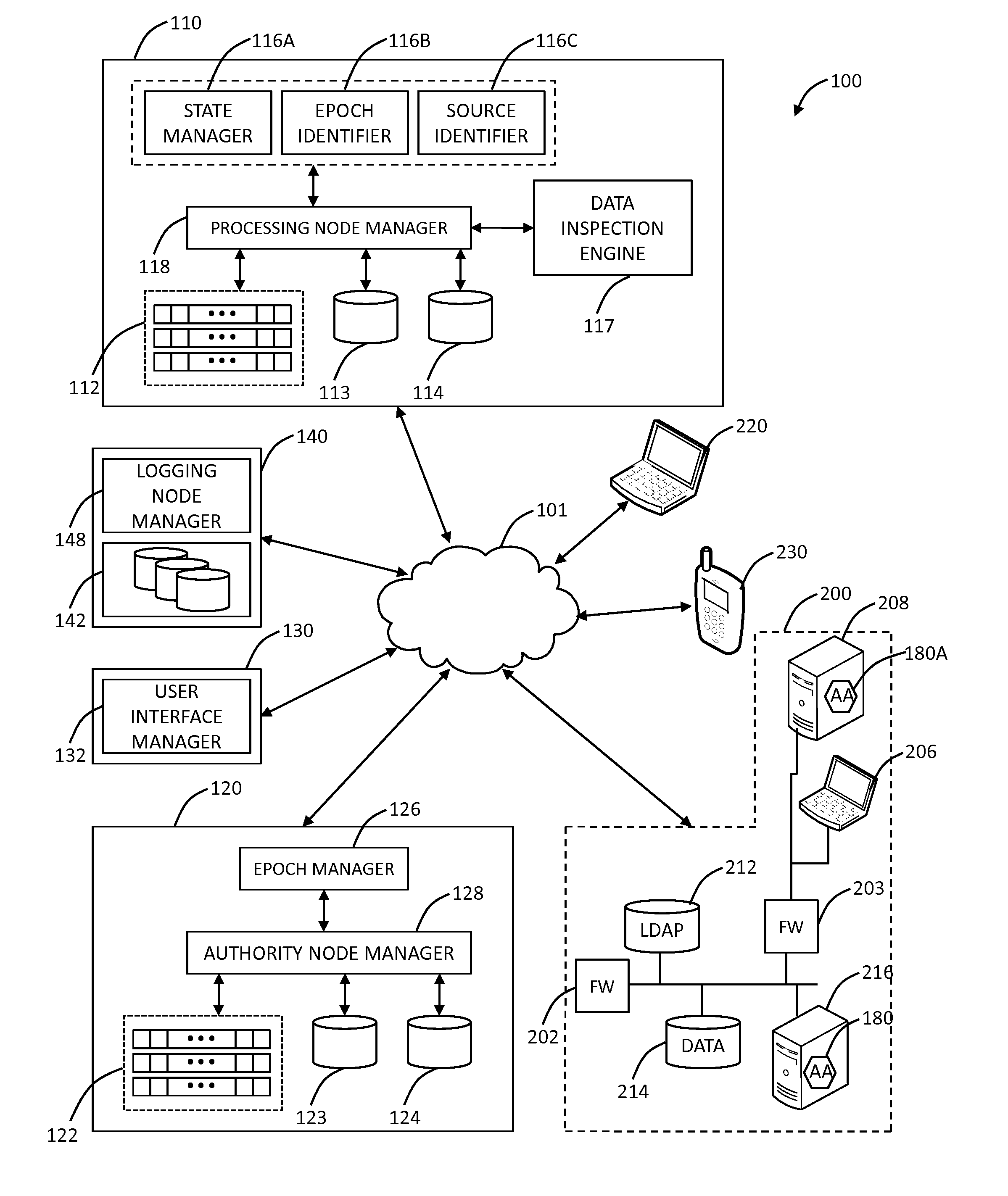
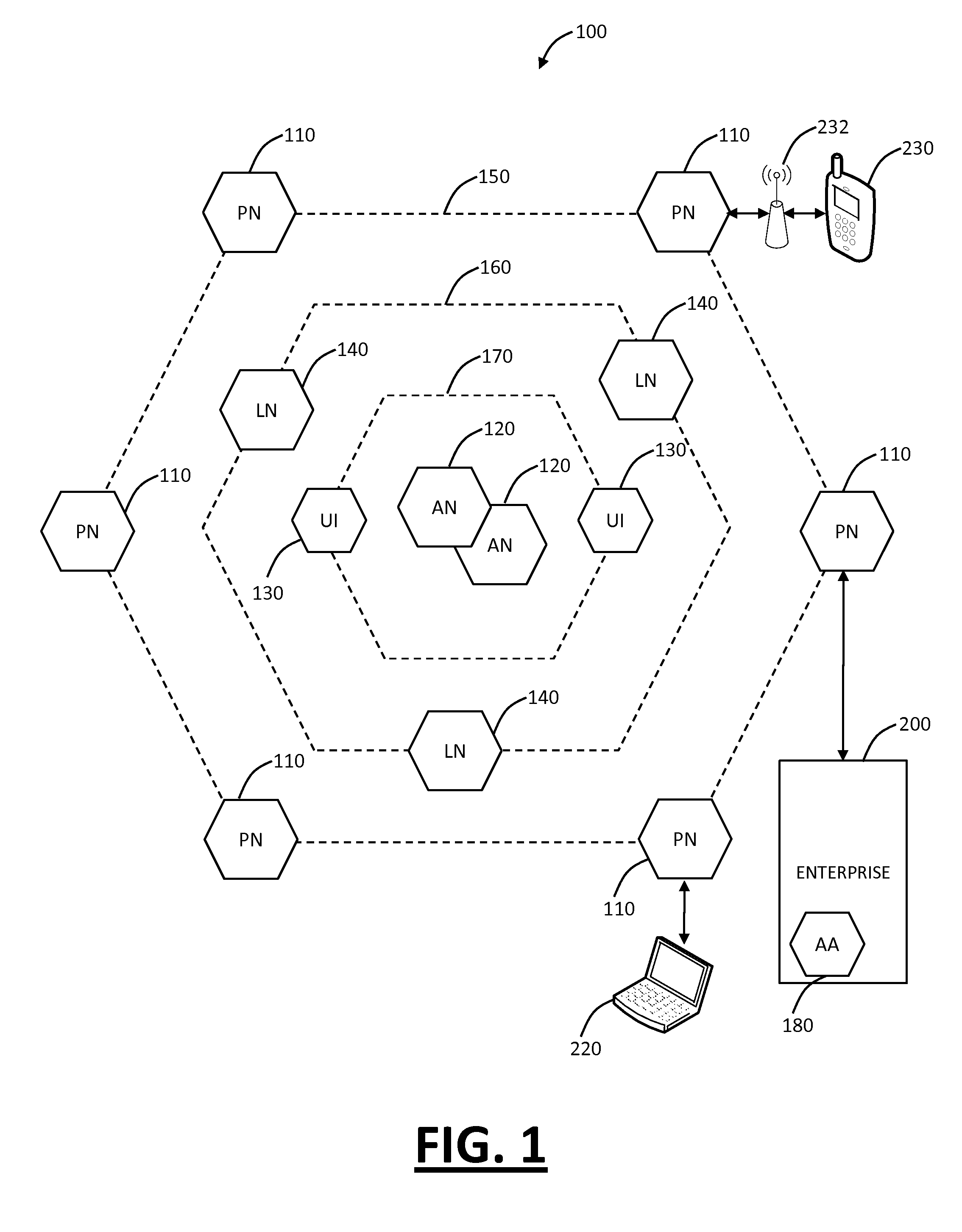
Systems and methods for mobile application security classification and enforcement
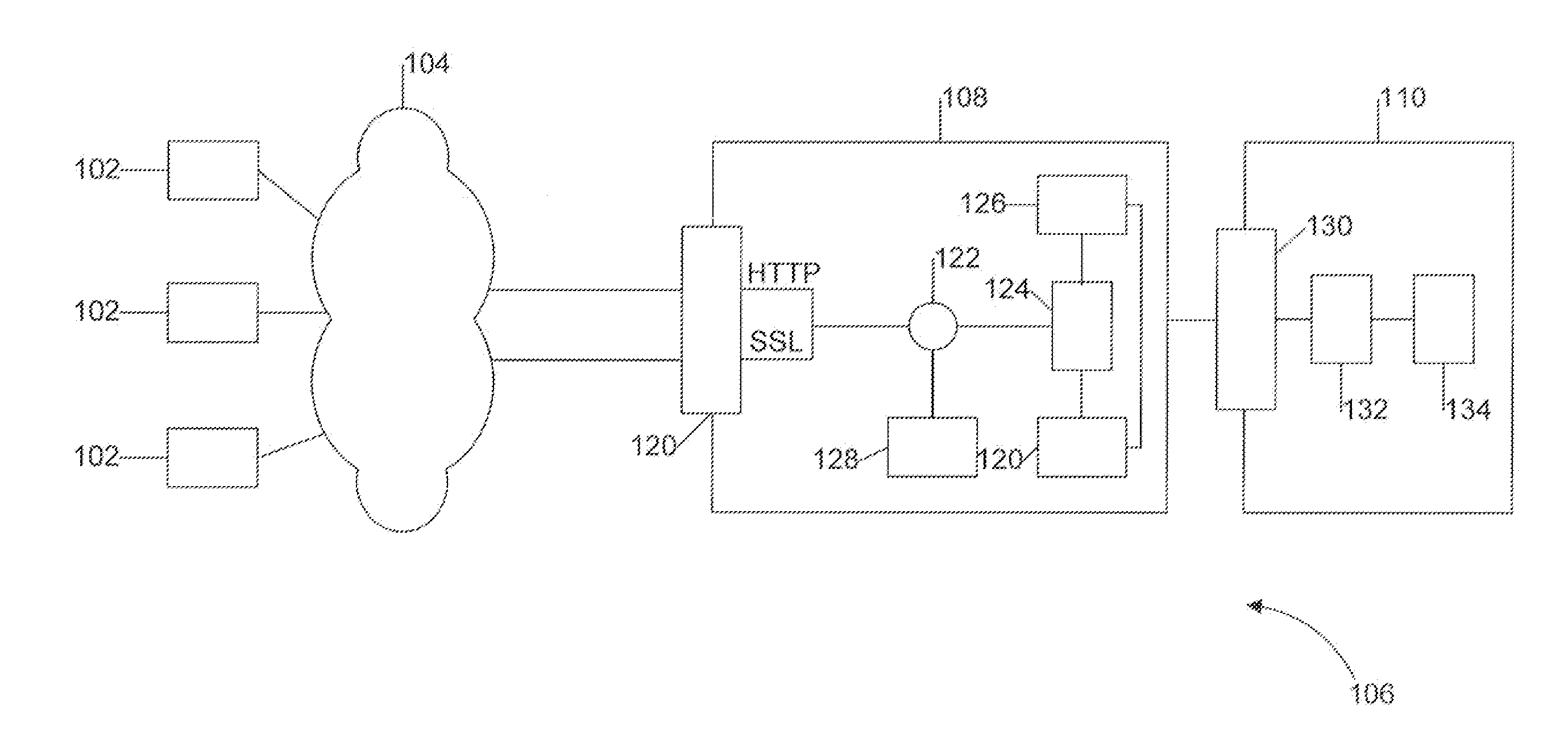
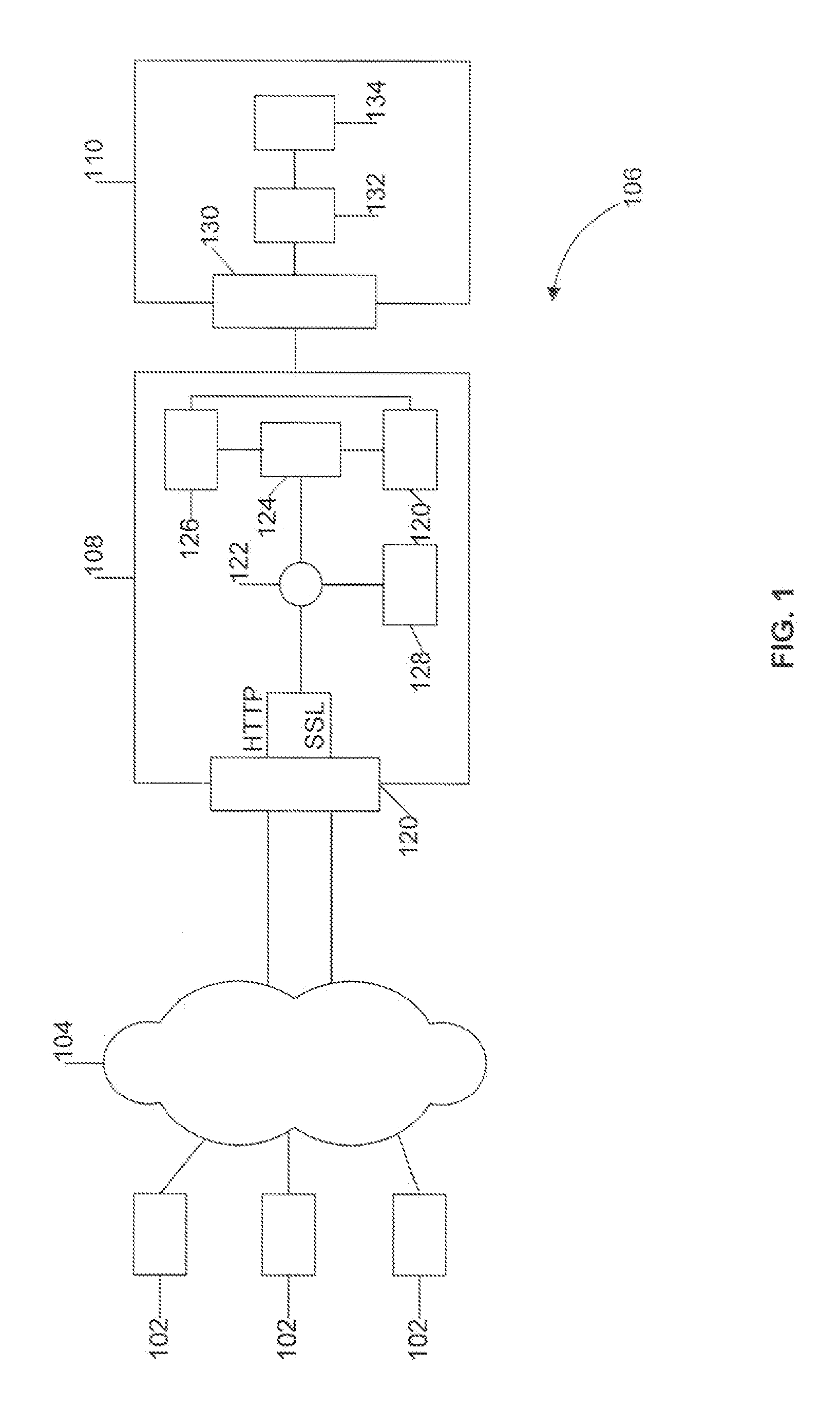
ActiveUS20110167474A1Avoid forwardingMemory loss protectionError detection/correctionUser deviceThe Internet
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
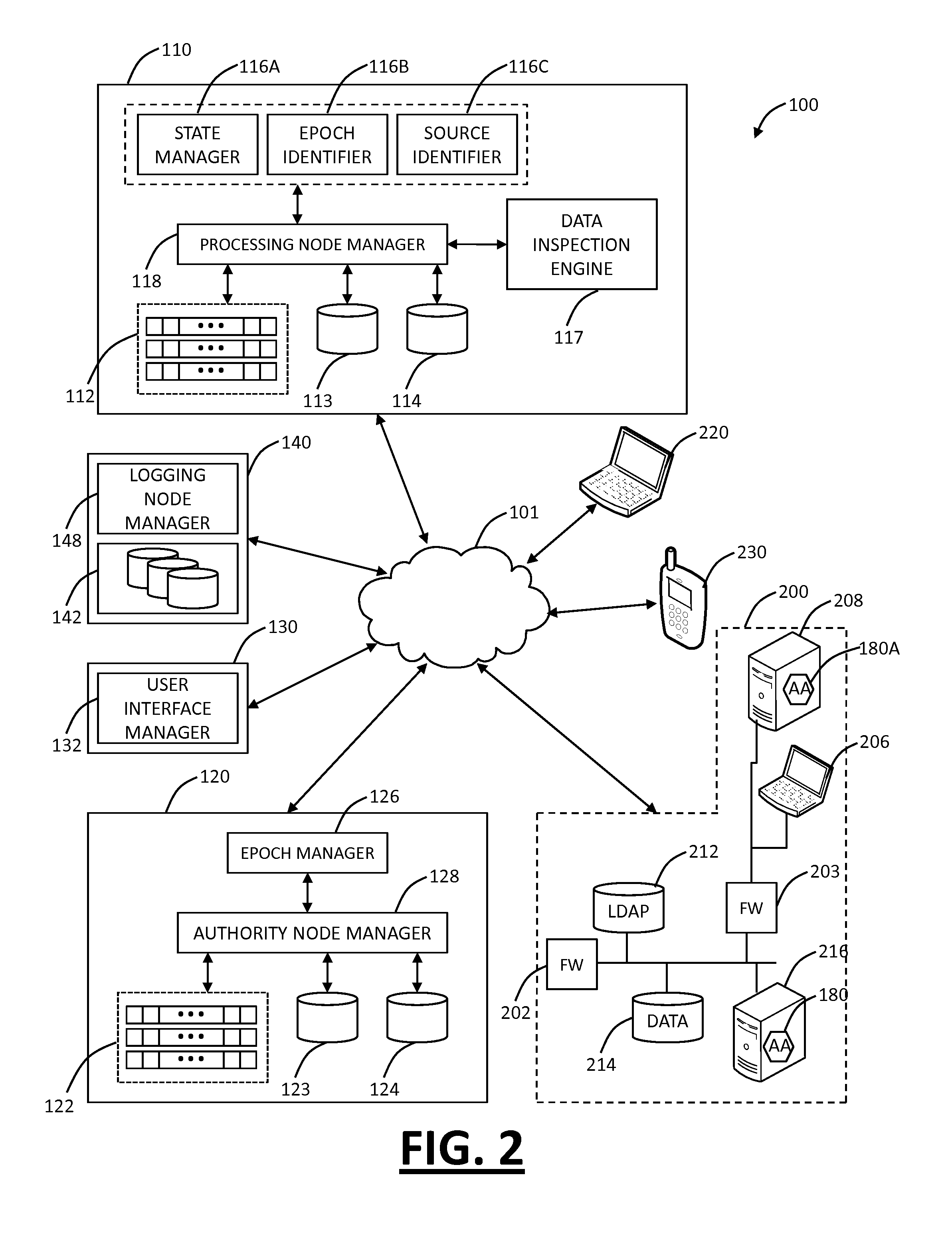
Systems and methods for mobile application security classification and enforcement
The present disclosure provides systems and methods for mobile application security classification and enforcement. In particular, the present invention includes a method, a mobile device, and a distributed security system (e.g., a “cloud”) that is utilized to enforce security on mobile devices communicatively coupled to external networks (i.e., the Internet). Advantageously, the present invention is platform independent allowing it to operate with any current or emerging mobile device. Specifically, preventing malicious applications from running on an end user's mobile device is challenging with potentially millions of applications and billions of user devices; the only effective way to enforce application security is through the network that applications use to communicate.
Owner:ZSCALER INC
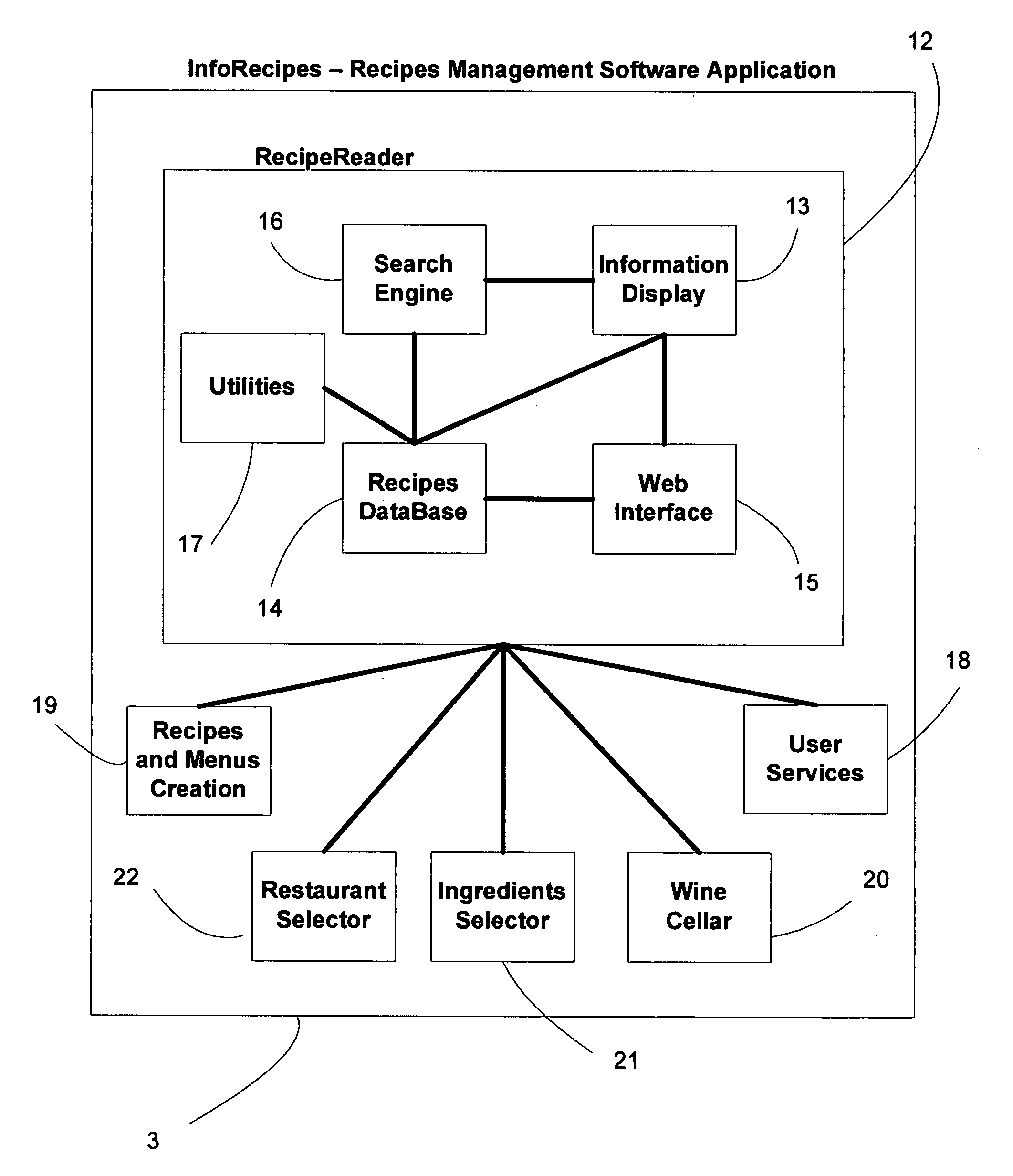
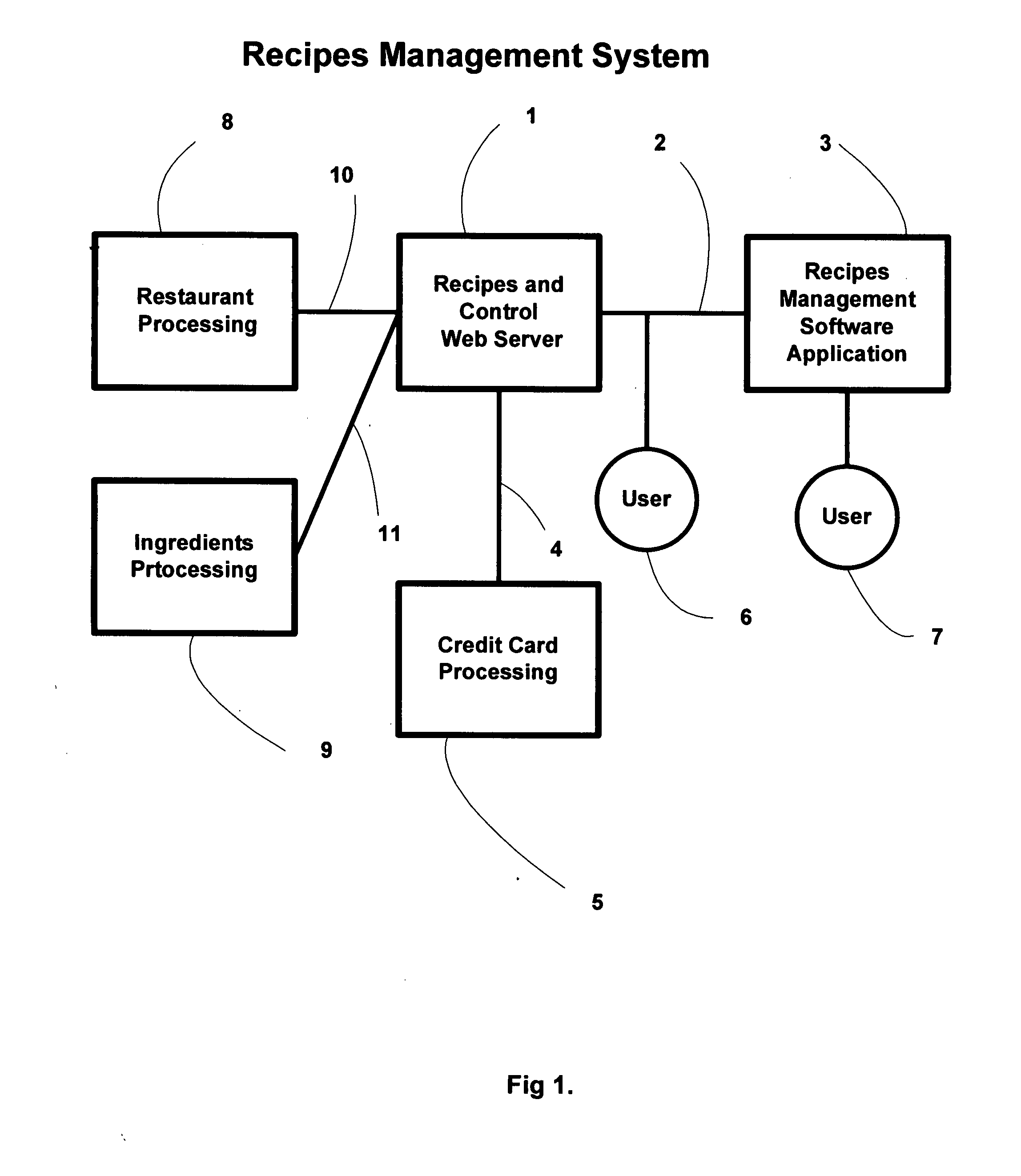
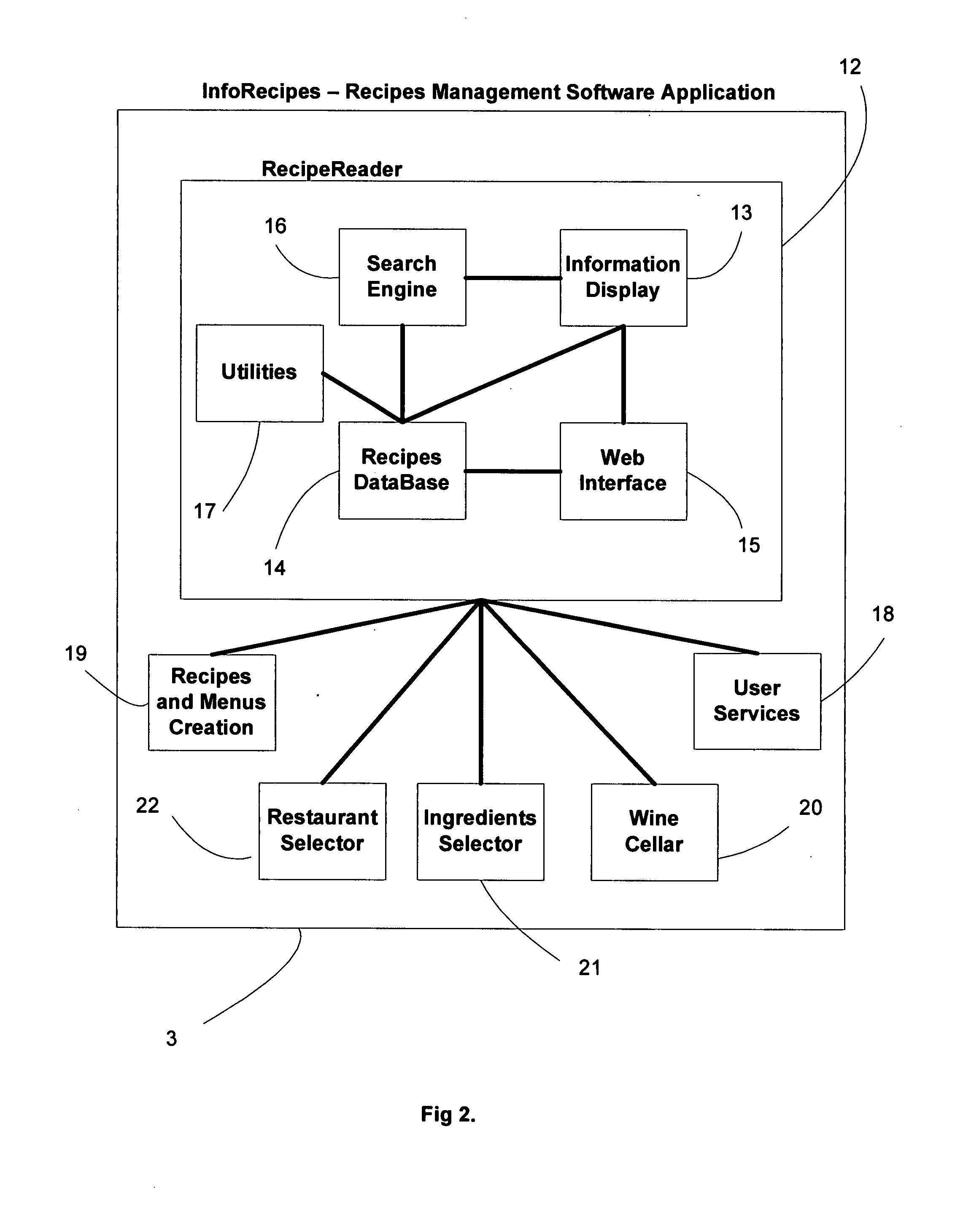
Recipes management system
InactiveUS20090157752A1Buying/selling/leasing transactionsSpecial data processing applicationsProgram managementWeb service
The present invention is generally related to a system for managing recipes using a web server and an off-line software application. A user using the software application will be able to create, display, print, modify, and search recipes and menus. The web server will be a recipe store where a user can buy and download individual recipes and electronic cookbooks into the software application secure database storage. The software application has a web interface to communicate with the recipe store, allowing the user to have an extended set of facilities like posting his / her own recipes for sale, requesting restaurant and food store services for a given recipe or menu, requesting the restoration of their recipe database, and receiving suggested drinking dates for their current wine inventory. The software application comes in two versions: the read-only and the all-inclusive version. With the read-only version a user will not be able to create or modify a recipe or use any of the extended facilities. The read-only version will be free to download from the recipe store.
Owner:GONZALEZ CARLOS
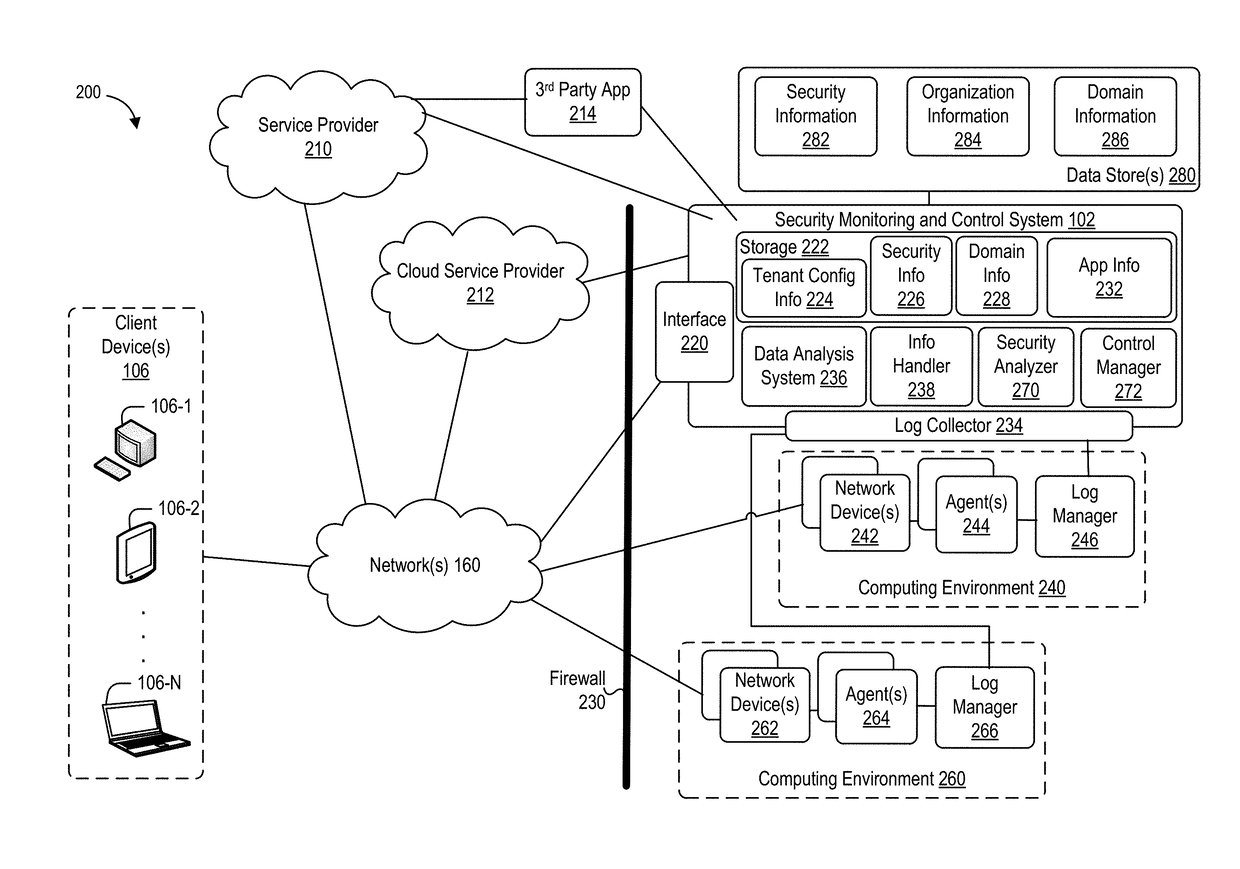
Techniques for discovering and managing security of applications
ActiveUS20170251013A1Minimizing security threatMinimizing riskTransmissionSafety management systemsData source
Techniques for discovery and management of applications in a computing environment of an organization are disclosed. A security management system discovers use of applications within a computing environment to manage access to applications for minimizing security threats and risks in a computing environment of the organization. The security management system can obtain network data about network traffic to identify unique applications. The security management system can perform analysis and correlation, including use of one or more data sources, to determine information about an application. The system can compute a measure of security for an application (“an application risk score”) and a user (“a user risk score”). The score may be analyzed to determine a threat of security posed by the application based on use of the application. The security system can perform one or more instructions to configure access permitted by an application, whether access is denied or restricted.
Owner:ORACLE INT CORP
System and method of securing networks against applications threats
InactiveUS20080047009A1Easy to deployMinimal impactMemory loss protectionError detection/correctionWeb applicationInternet privacy
A system and method for protection of Web based applications are described. A Web application security system is included within a computer network to monitor traffic received from a wide area network, such as the Internet, and determine if there is a threat to the Web application. The Web application security system monitors web traffic in a non-inline configuration and identifies any anomalous traffic against a profile that identifies acceptable behavior of a user of the application. Any anomalous traffic is analyzed and appropriate protective action is taken to secure the Web application against an attack.
Owner:TRUSTWAVE HOLDINGS
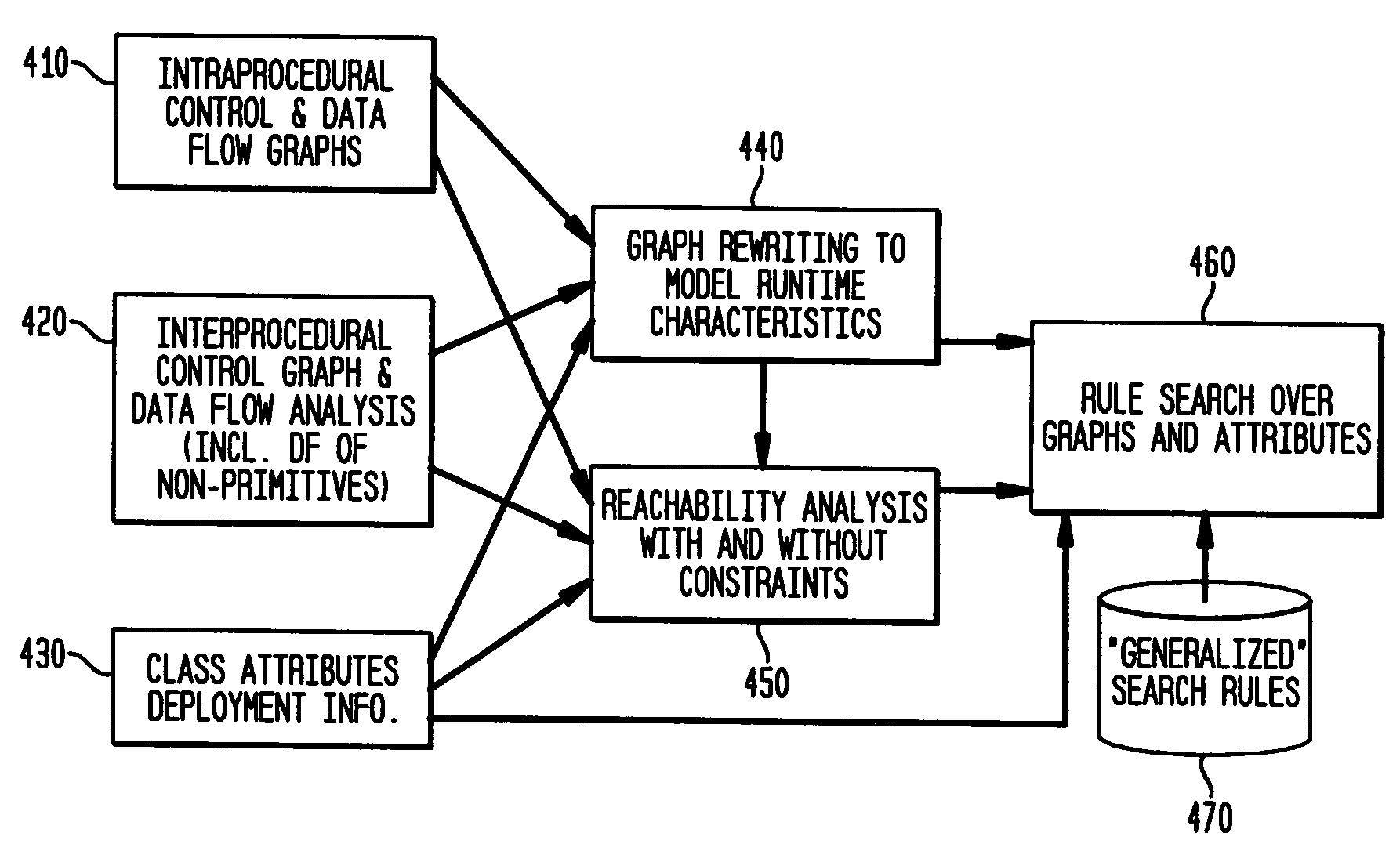
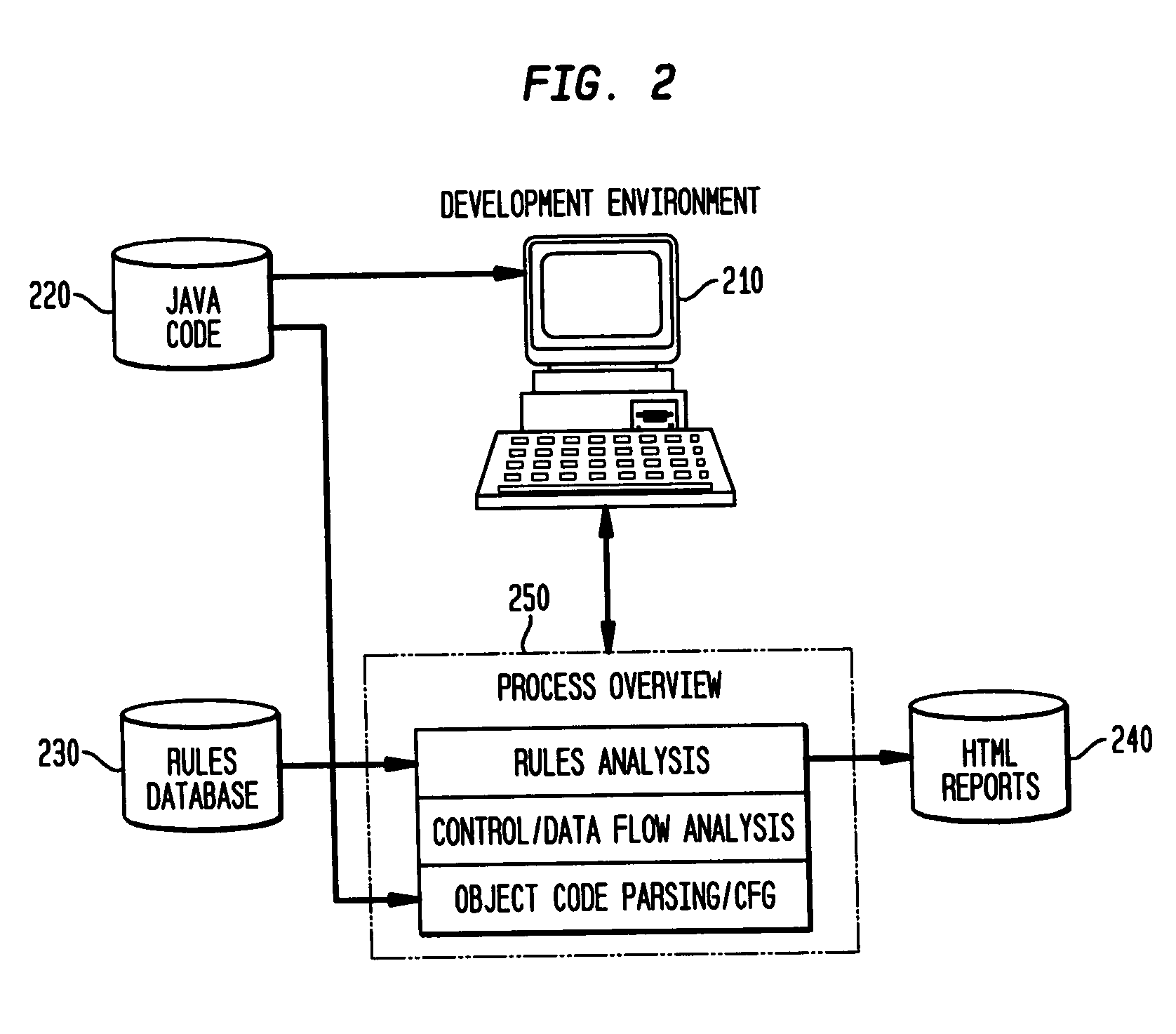
Static analysis based error reduction for software applications
InactiveUS20050015752A1Easy to liftSimple technologyError detection/correctionSpecific program execution arrangementsError reductionMaintainability
A system and method for providing “static analysis” of programs to aid in improving runtime performance, stability, security and privacy characteristics of deployed application code. The method includes performing a set of analyses that sifts through the program code and identifies programming security and / or privacy model coding errors. In particular the invention focuses on identifying coding errors that cause loss of correctness, performance degradation, security, privacy and maintainability vulnerabilities. A deep analysis of the program is performed using detailed control and data flow analyses. These deeper analyses provide a much better perspective of the overall application behavior. This deep analysis is in contrast to shallow analyses in current industry tools, which inspect or model a single or a few classes at a time.
Owner:IBM CORP
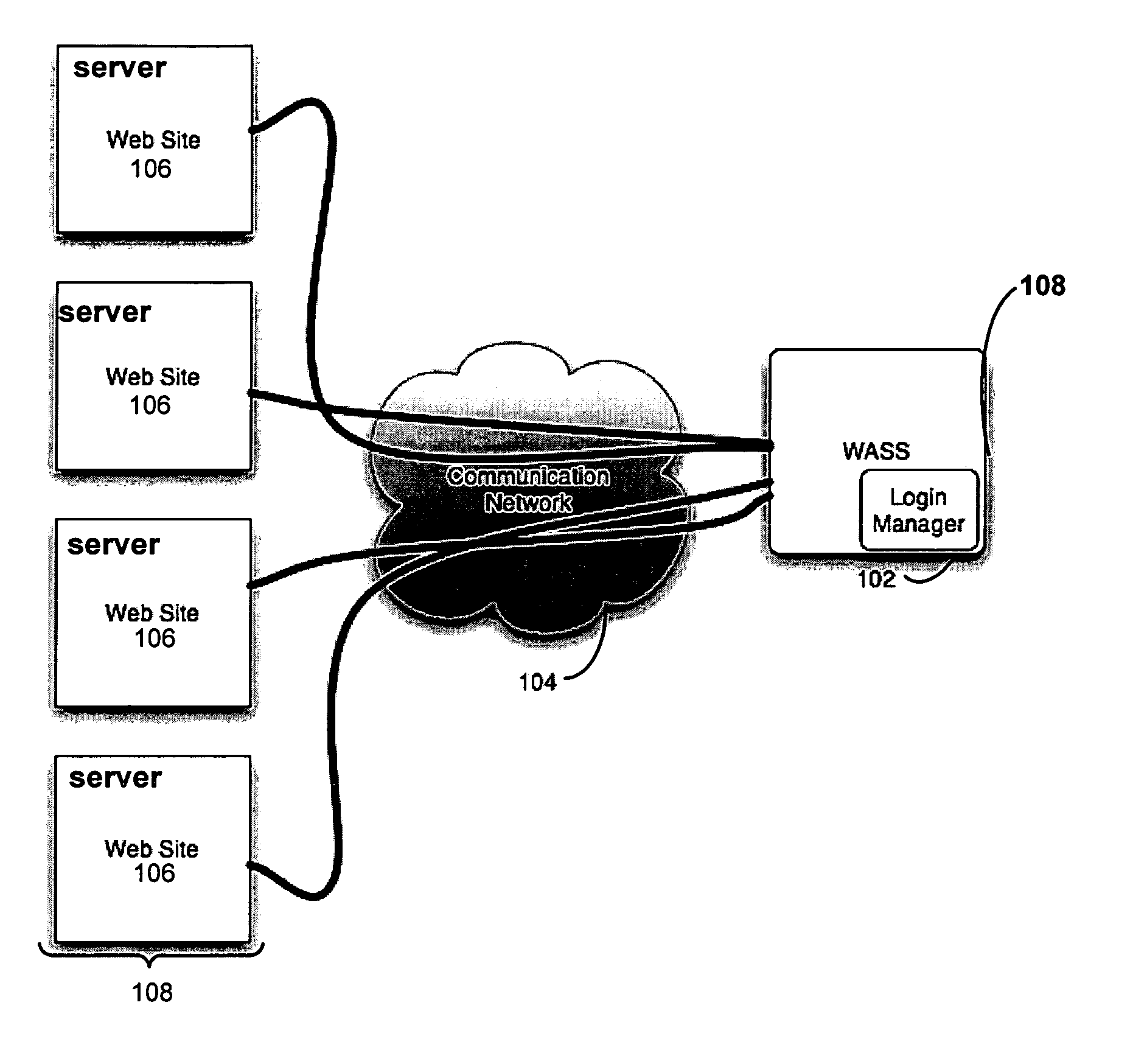
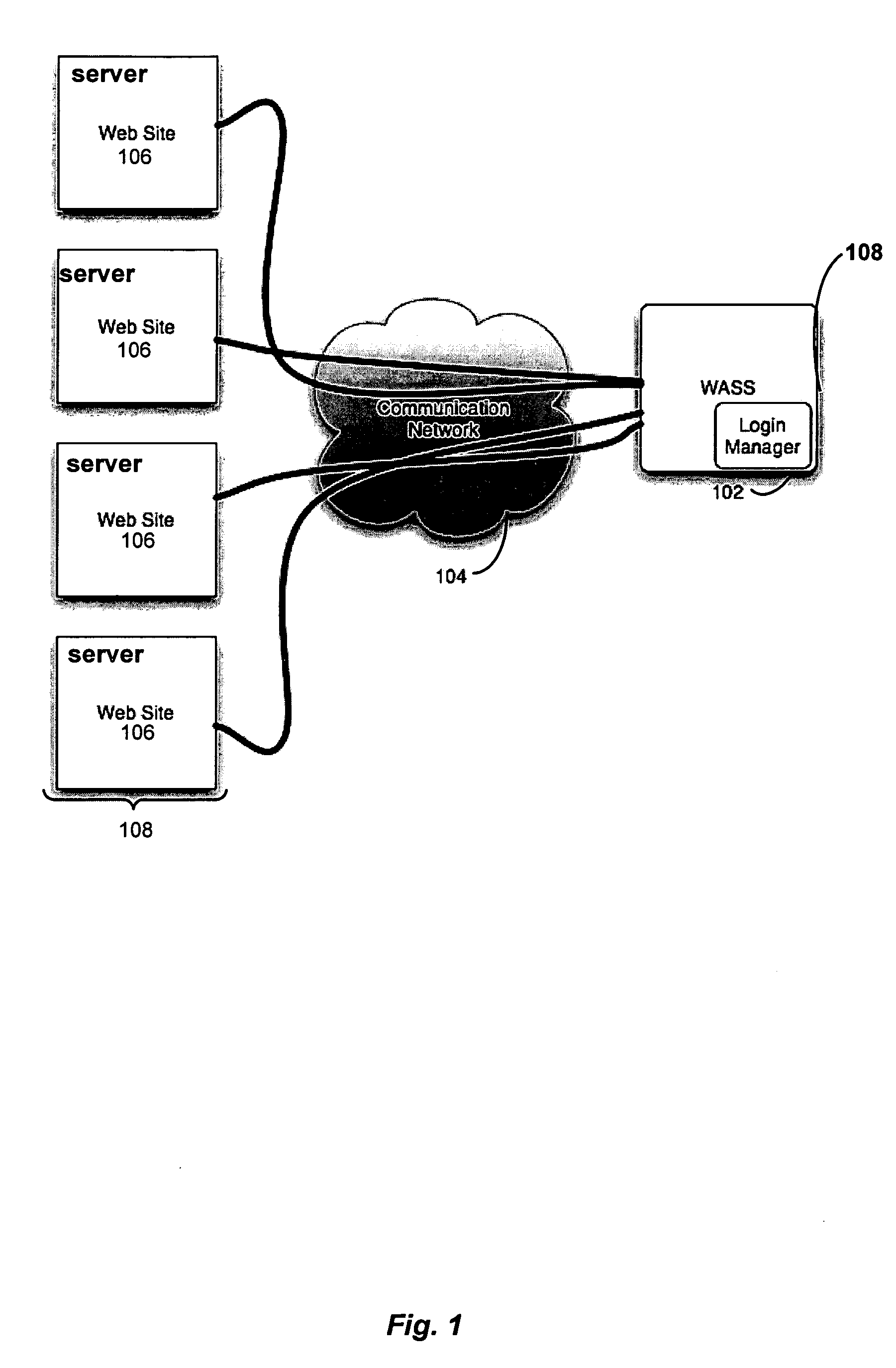
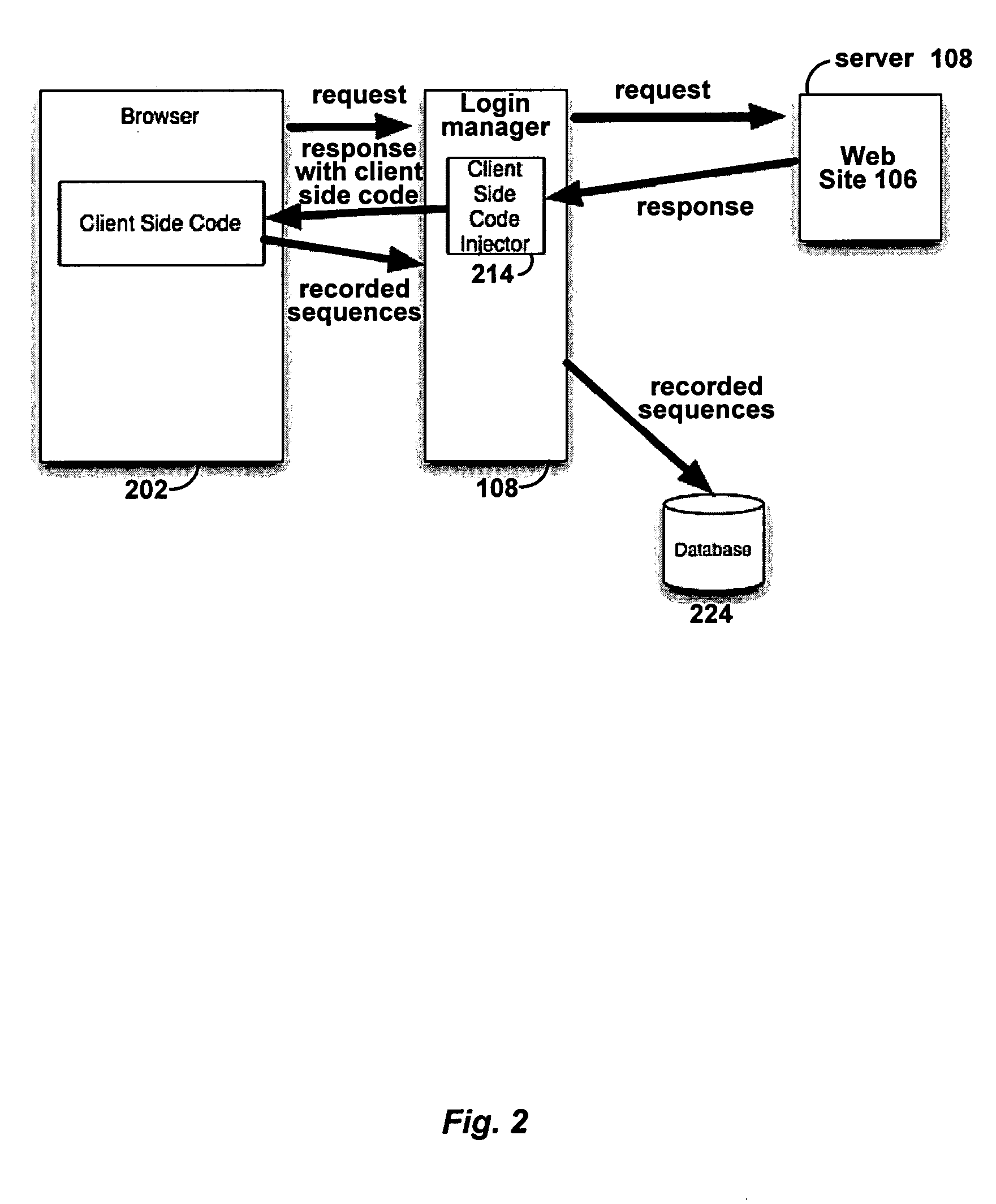
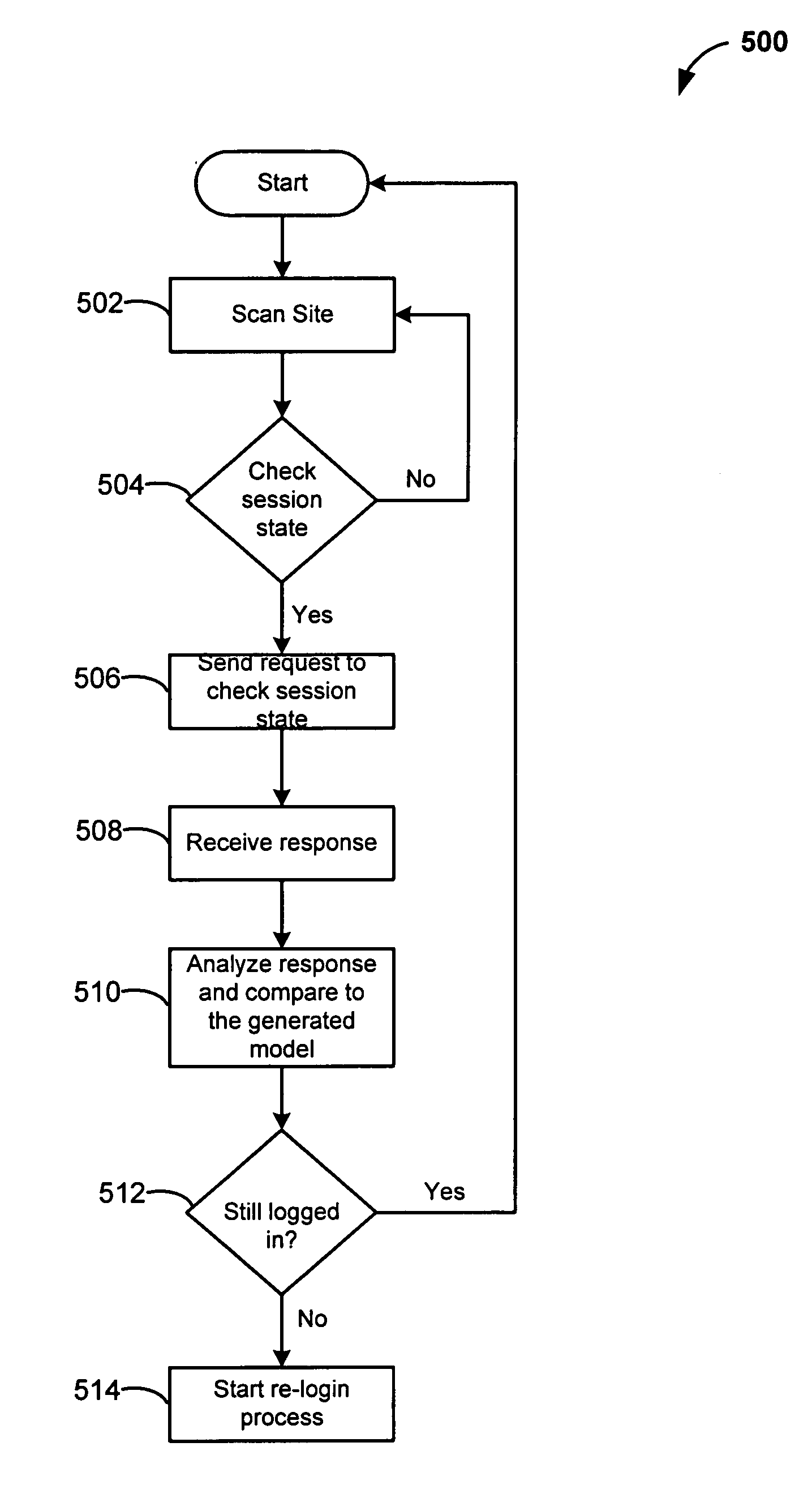
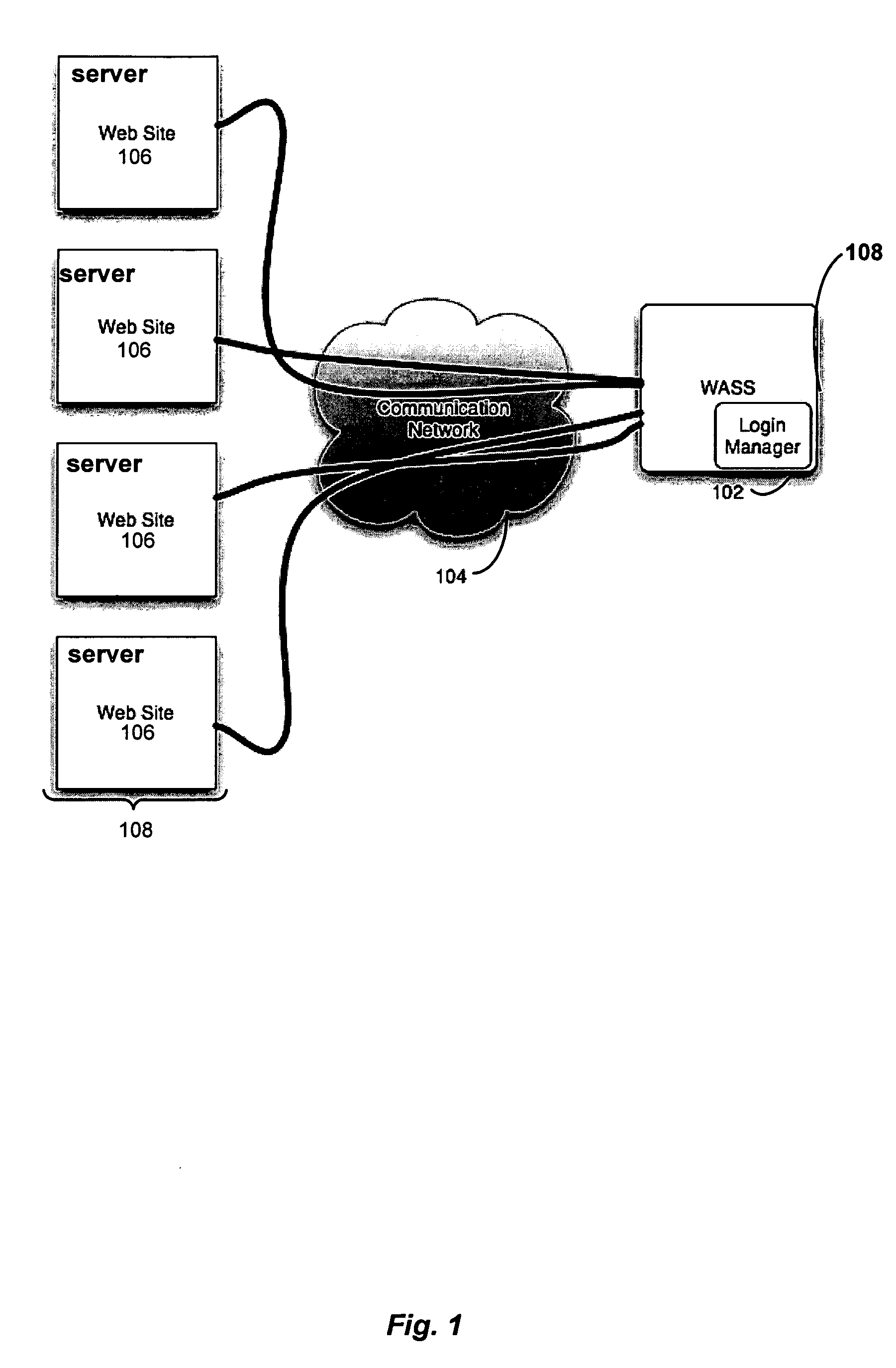
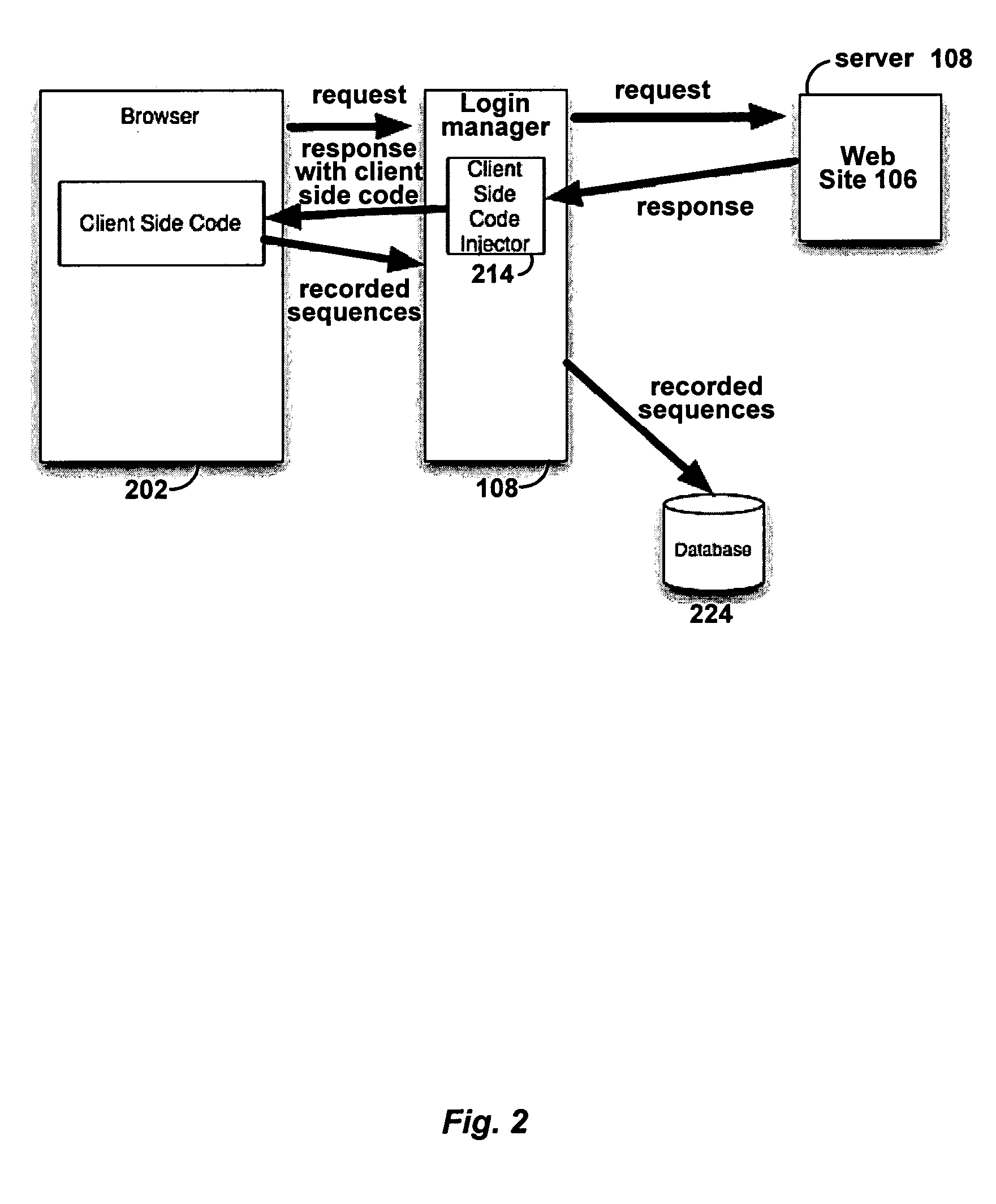
Automated login session extender for use in security analysis systems
ActiveUS20060048214A1Digital data processing detailsUser identity/authority verificationWeb siteProgram security
A web application security scanner (WASS) includes a login manager configured to perform an automated login to a web site. The automated login may be performed when the login manager detects that a login session has ended. The login manager is configured to determine credentials for the web site to allow the WASS to access the web site. The WASS may then use the credentials to continue scanning the web site. Thus, previously unscannable web pages may be accessed in the web site because of the automated login process.
Owner:SYNOPSYS INC
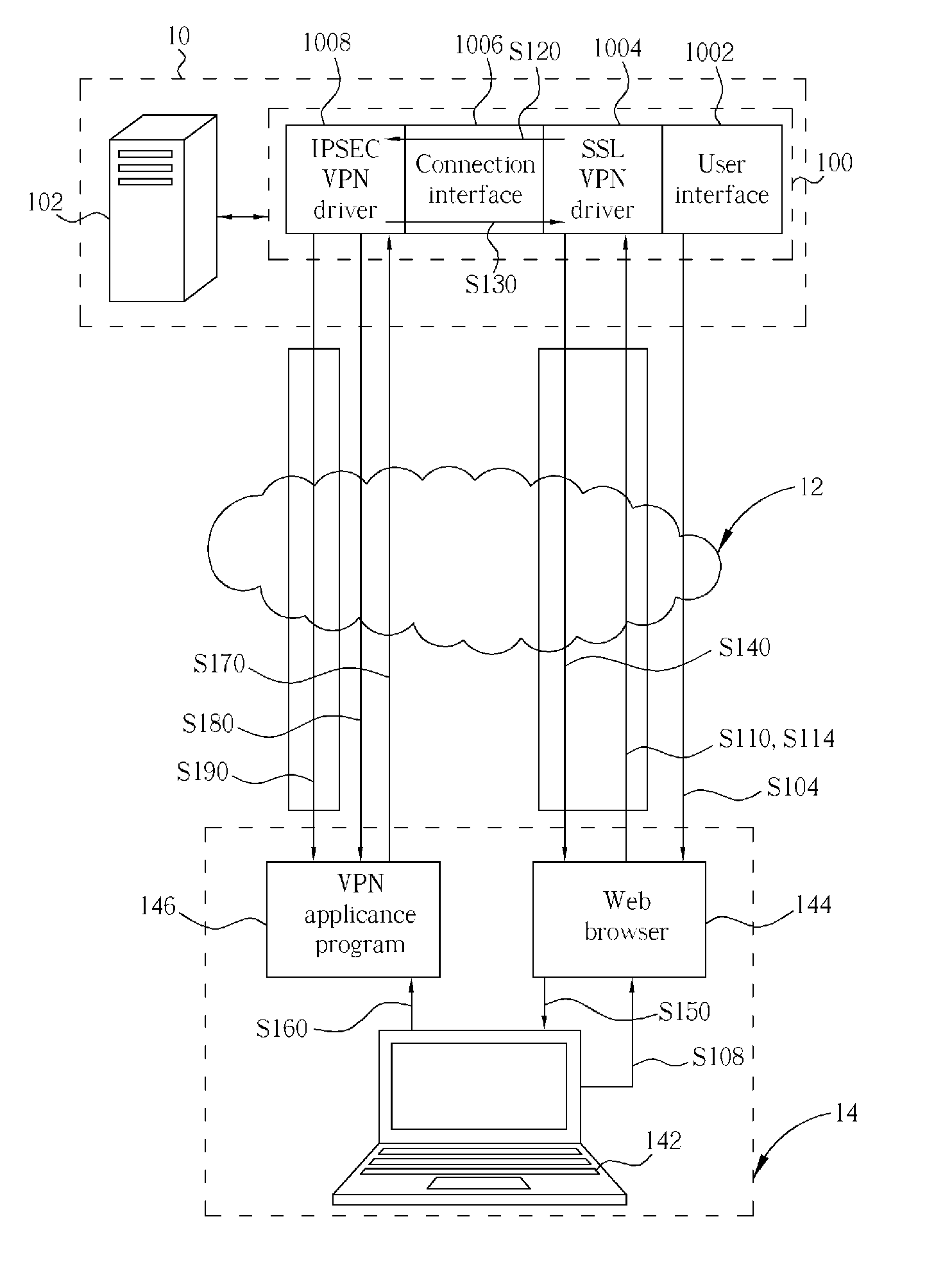
Security gateway utilizing SSL protocol protection and related method
InactiveUS20060005008A1Improve securitySecure transmissionSecuring communicationNetworked systemIPsec
A security gateway, for use in a network system for linking at least a client end and a server end, includes a user interface, a SSL VPN driver, a connection interface and an IPSEC VPN driver. The security gateway supports IPSEC and SSL protocols. Before establishing an IPSEC VPN between a client end and a server end, the security gateway will perform ID authentication for the user of the client end with a widely-used SSL protocol, so as to establish a SSL VPN between a server end and a client end. When the ID of the client end is authorized, a configuration file comprising the SA is generated and then safely sent to the client end through the SSL VPN tunnel. After the client end receives and executes the configuration file having the SA, an IPSEC VPN tunnel between the server end and the client end is established.
Owner:ICP ELECTRONICS
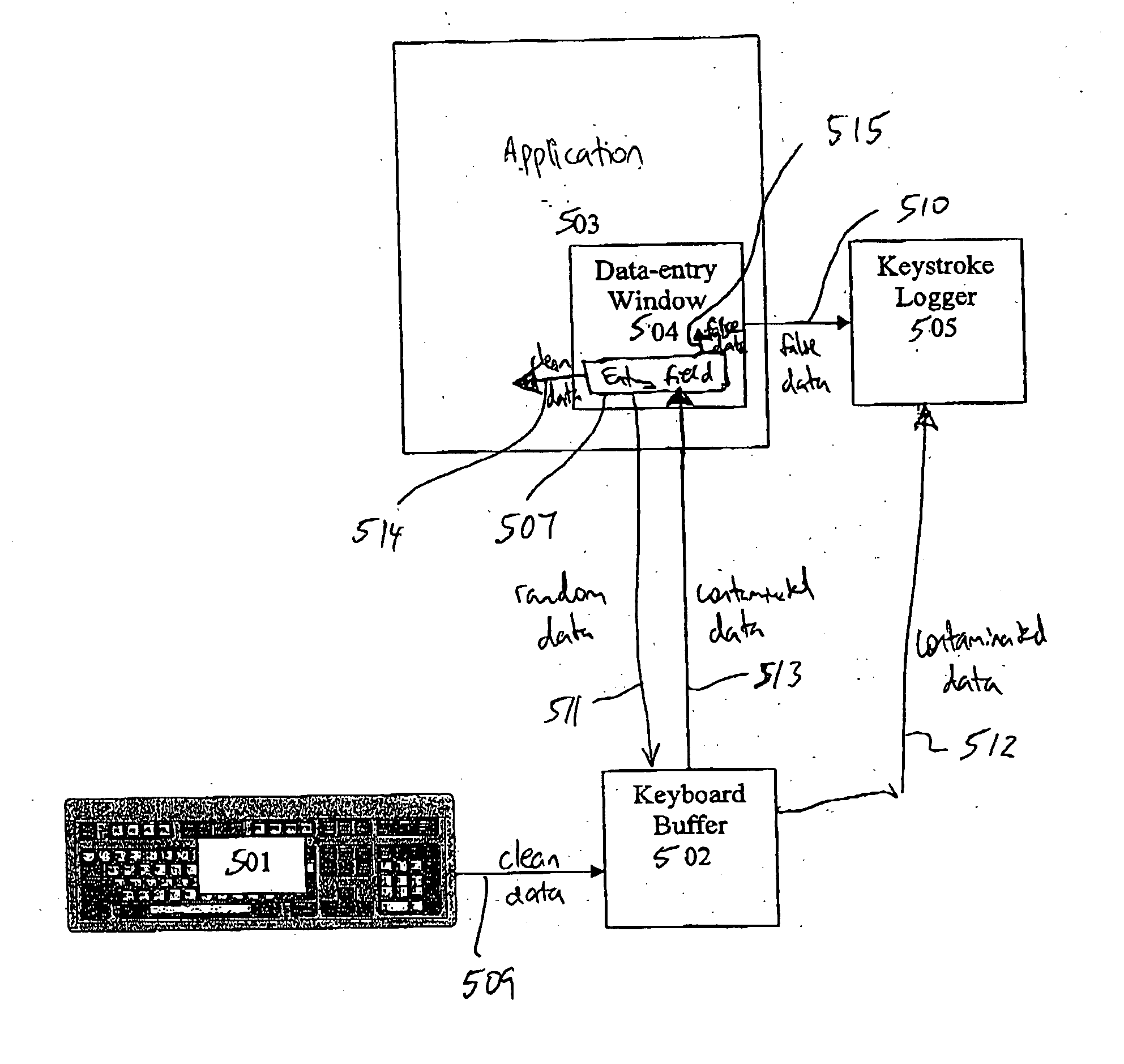
System for preventing keystroke logging software from accessing or identifying keystrokes
ActiveUS20060101128A1Invade privacySecurity threatMemory loss protectionDigital data processing detailsOperational systemUser input
A computer program is adapted for securing user entry data against keyboard login attempts. The program masks user input data, either insulating the data from vulnerable parts of the operating system or application, or contaminating user data that is supplied to those vulnerable parts of the operating system or application. The program securely stores data, either intercepted prior to reaching the vulnerable parts of the operating system or extracted from the contaminated data, and securely provides the data directly to a verified application.
Owner:SENTRYBAY
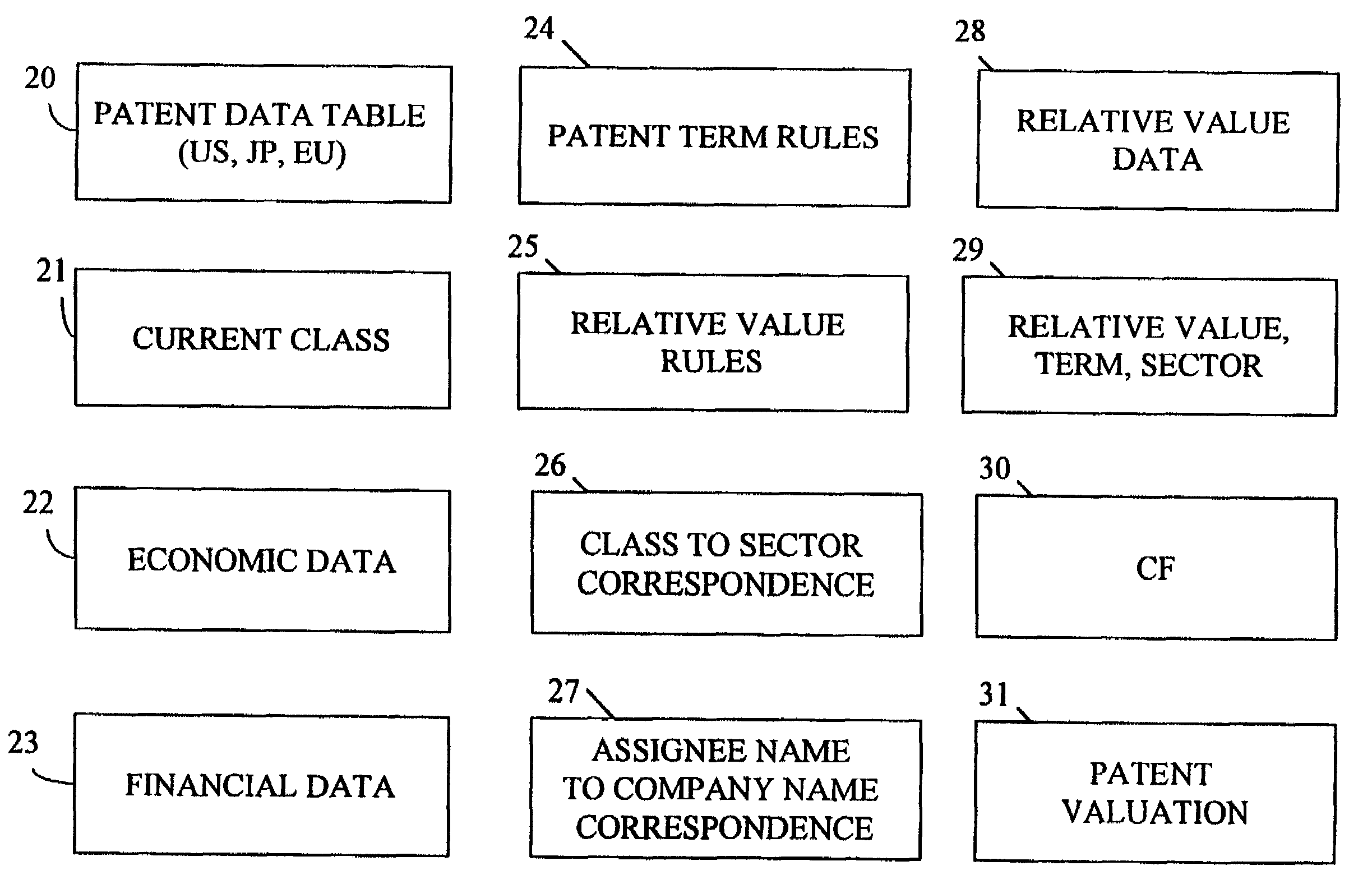
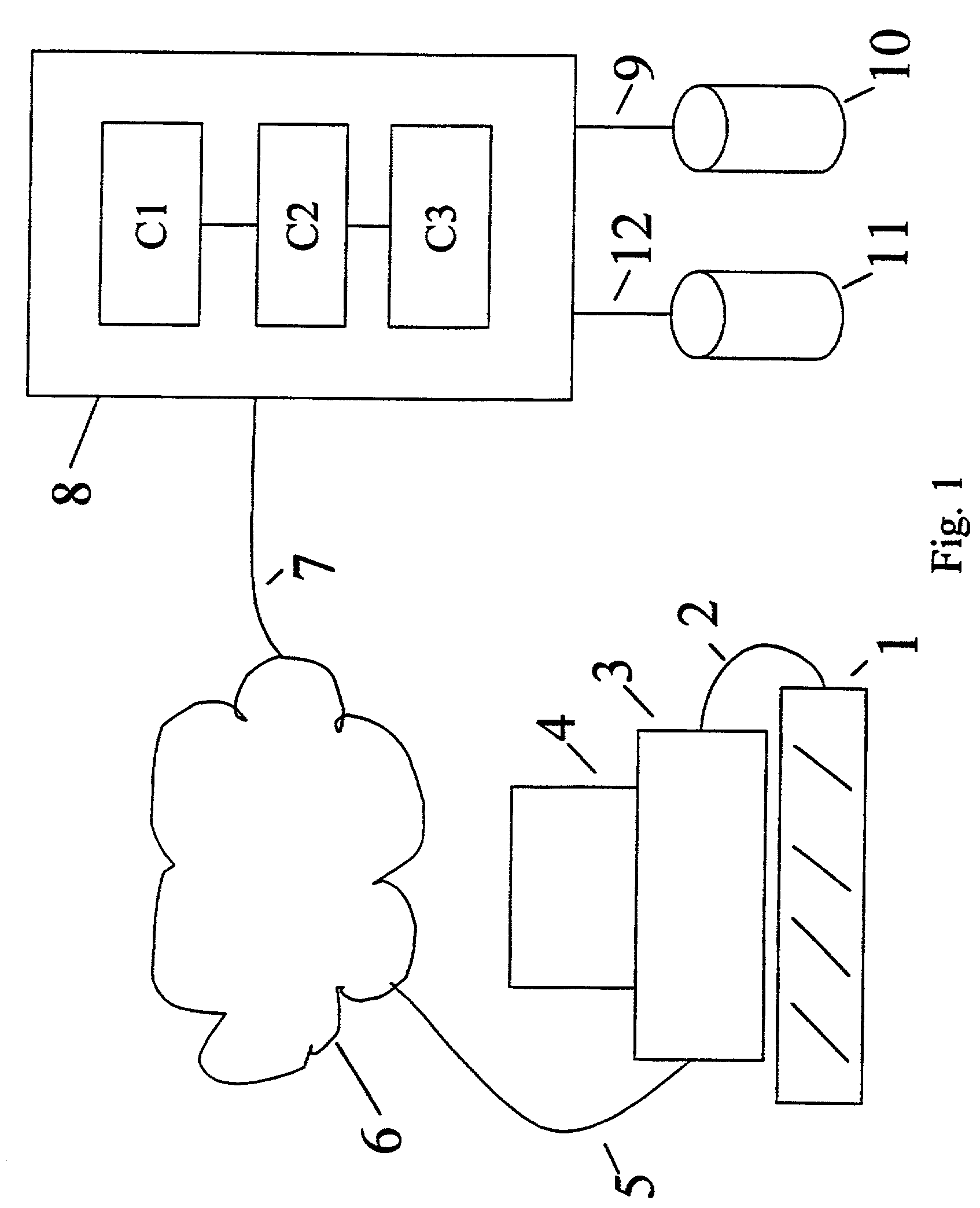
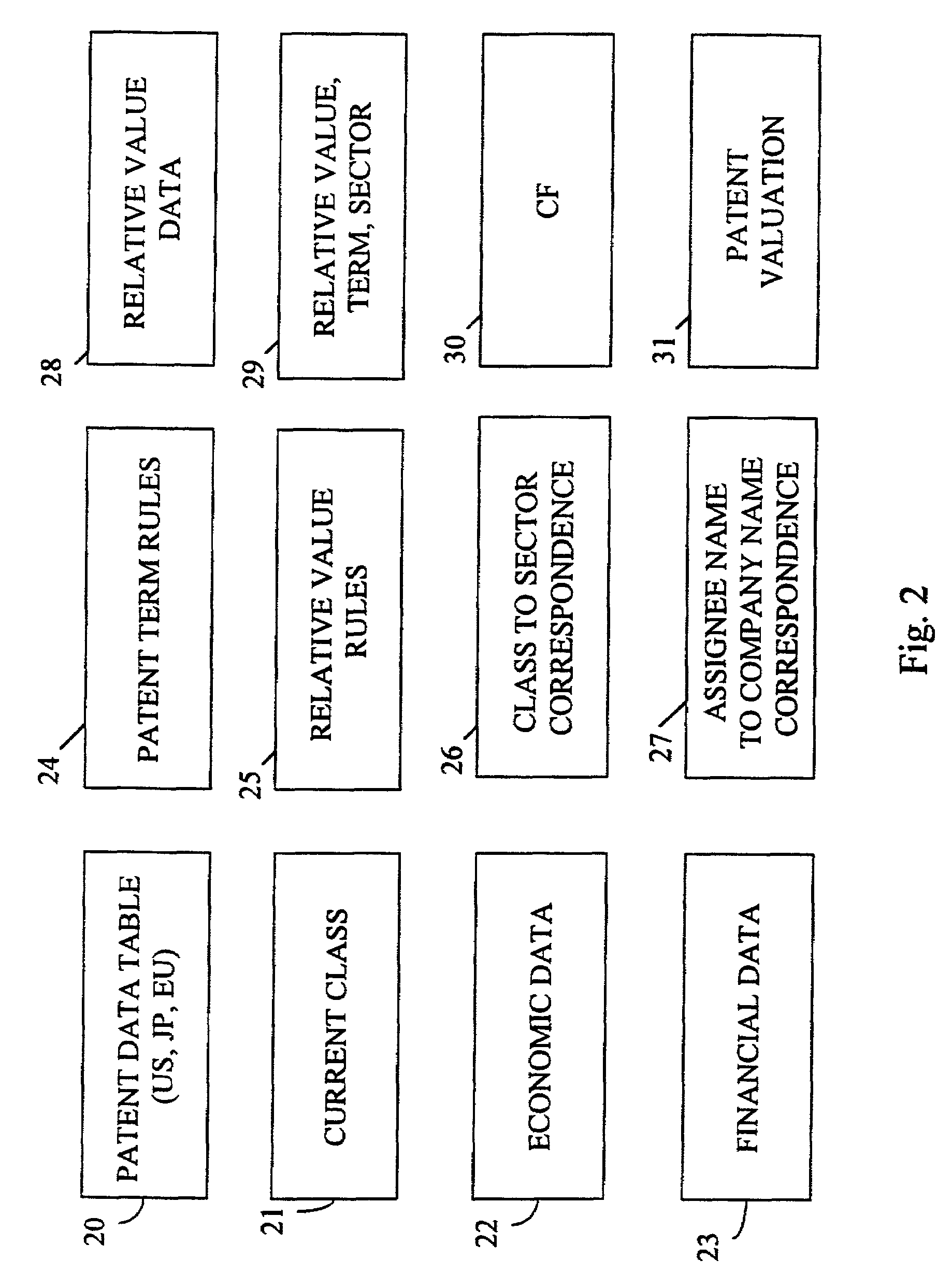
System and method for valuing patents
InactiveUS7676375B1Effective valueImprove accuracyFinanceProduct appraisalPaymentComputerized system
A computer system implementing a macro economic model based upon macroeconomic data and relative value characteristics data of patents that determines nominal values for (1) goods and services and (2) profits generated by sales that are covered by the rights of a patent, implements an income value theory to value the patent based upon the predicted values of profits or goods and services covered by the patent, determines patent terms from patent filing, publication, and issue dates, determines patent assignees from patent data, and uses the value of a company's patents, the patent issuance data and term date data, to determine trends versus time in: the number of a company's enforceable patents; the number of a company's patents obtained; the nominal value of net earnings and of goods and services sold that are covered by the company's patents; the nominal value of the sum of the company's patents, and provides comparisons of those trends between companies, regions, and economic sectors, providing the results of the analysis to users of the computer system. The computer system employs a user database enabling a novel electronic accounting model enabling payment by affiliates, programmed securities trading, and accrediting of investors.
Owner:INNOVATIONQ
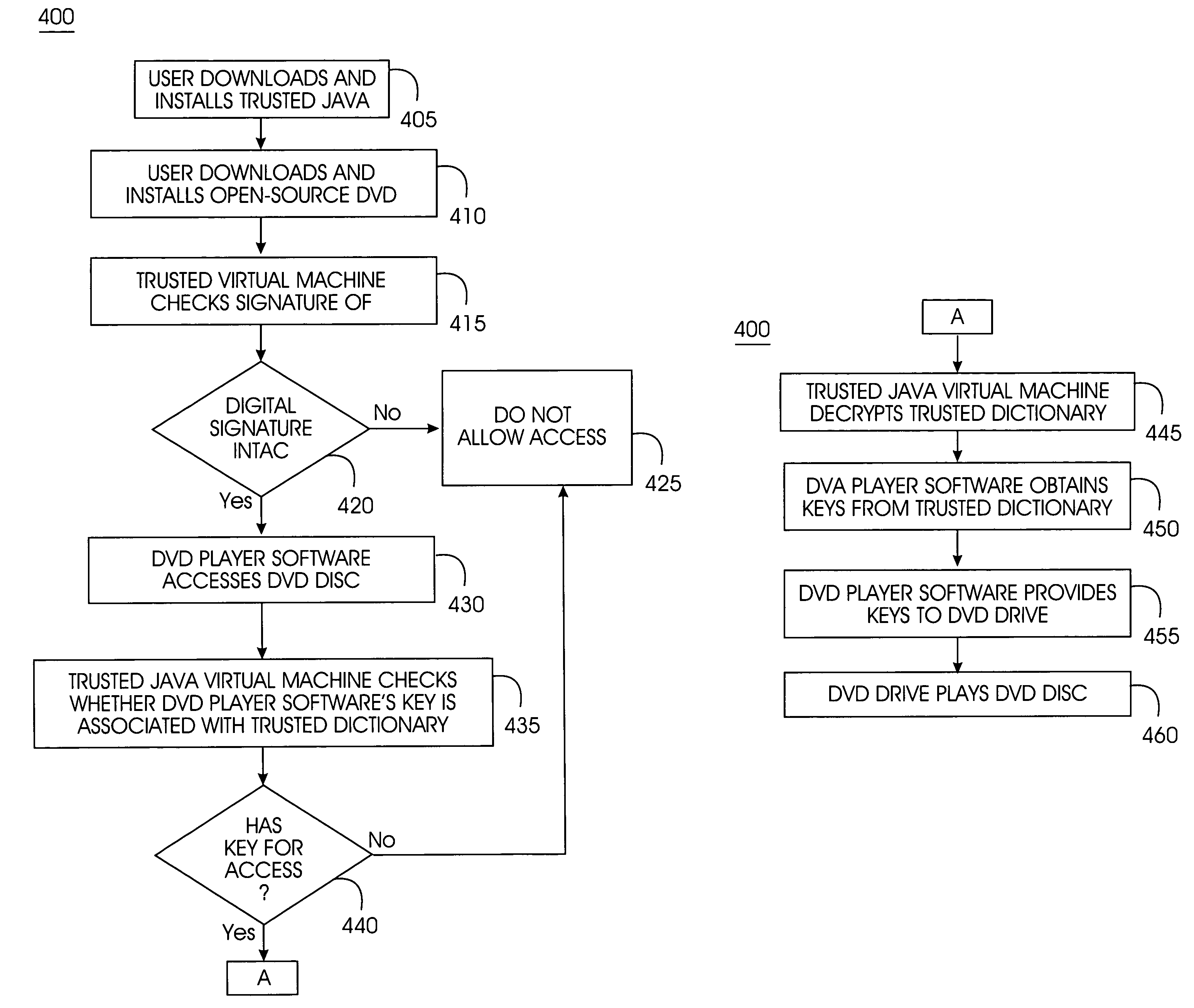
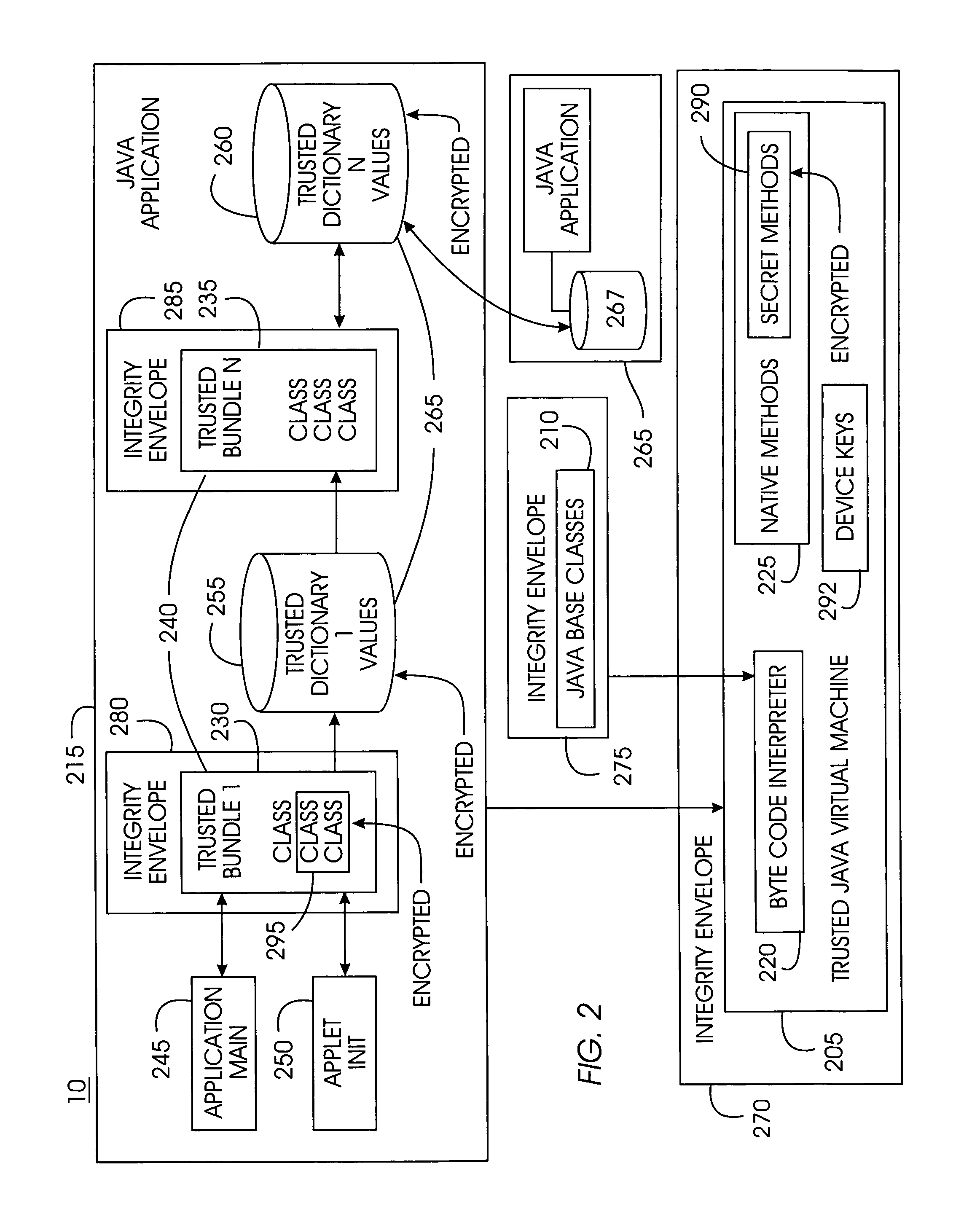
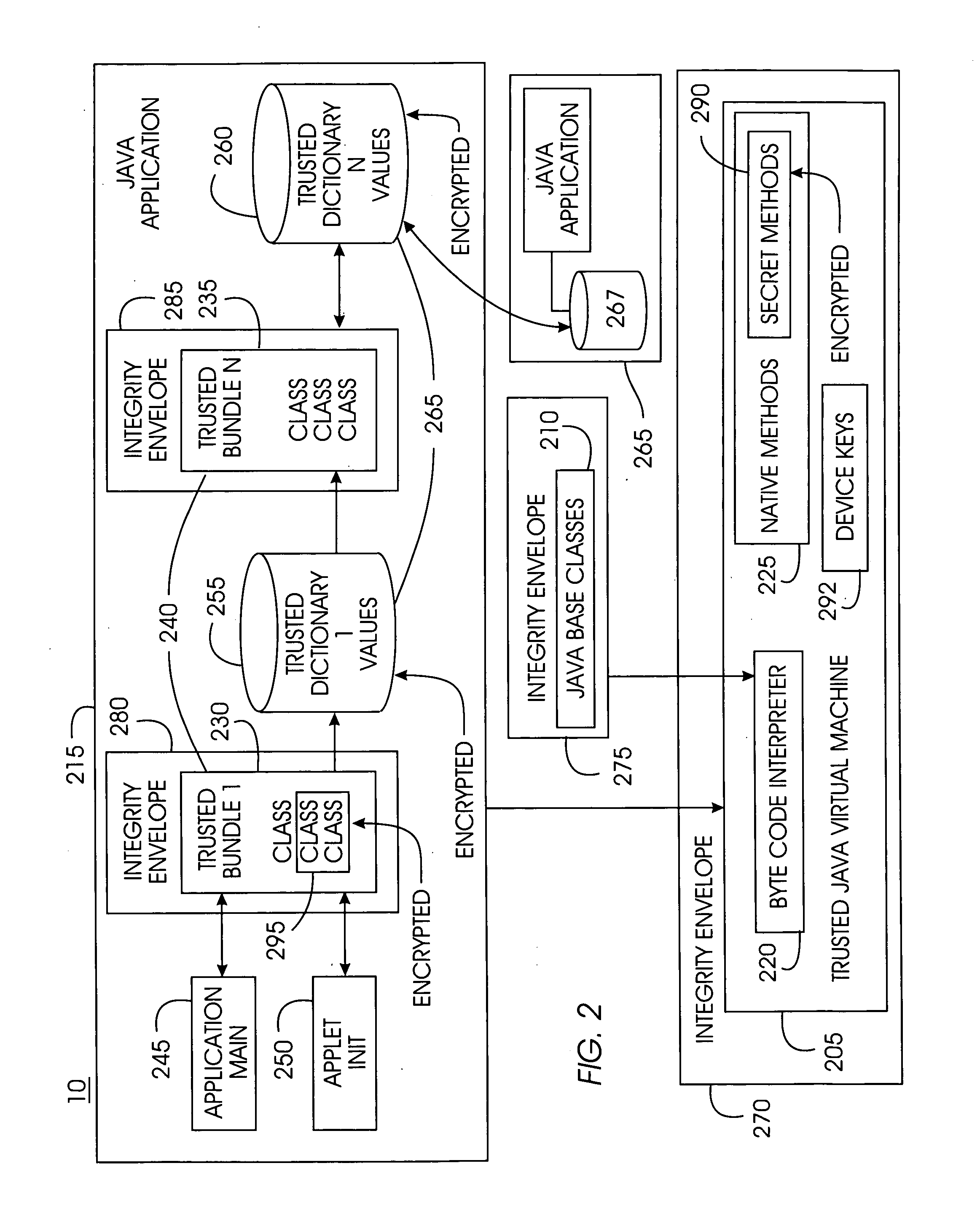
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS7516331B2Slow processEnsure integrityProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:INT BUSINESS MASCH CORP
Tamper-resistant trusted java virtual machine and method of using the same
InactiveUS20050114683A1Easy to processSatisfies needProgram control using stored programsUser identity/authority verificationOpen sourceProgram security
A trusted Java virtual machine provides a method for supporting tamper-resistant applications, ensuring the integrity of an application and its secrets such as keys. The trusted Java virtual machine verifies the integrity of the Java application, prevents debugging of the Java application, and allows the Java application to securely store and retrieve secrets. The trusted Java virtual machine environment comprises a TrustedDictionary, a TrustedBundle, an optional encryption method for encrypting and decrypting byte codes, and an underlying trusted Java virtual machine. The encrypted TrustedDictionary protects data while the TrustedBundle protects programming code, allowing applications to store secret data and secure counters. The application designer can restrict TrustedBundle access to only those interfaces that the application designer explicitly exports. The open source code may optionally be encrypted. Secrets required by the open source programming code of the application are encrypted in TrustedDictionary.
Owner:IBM CORP
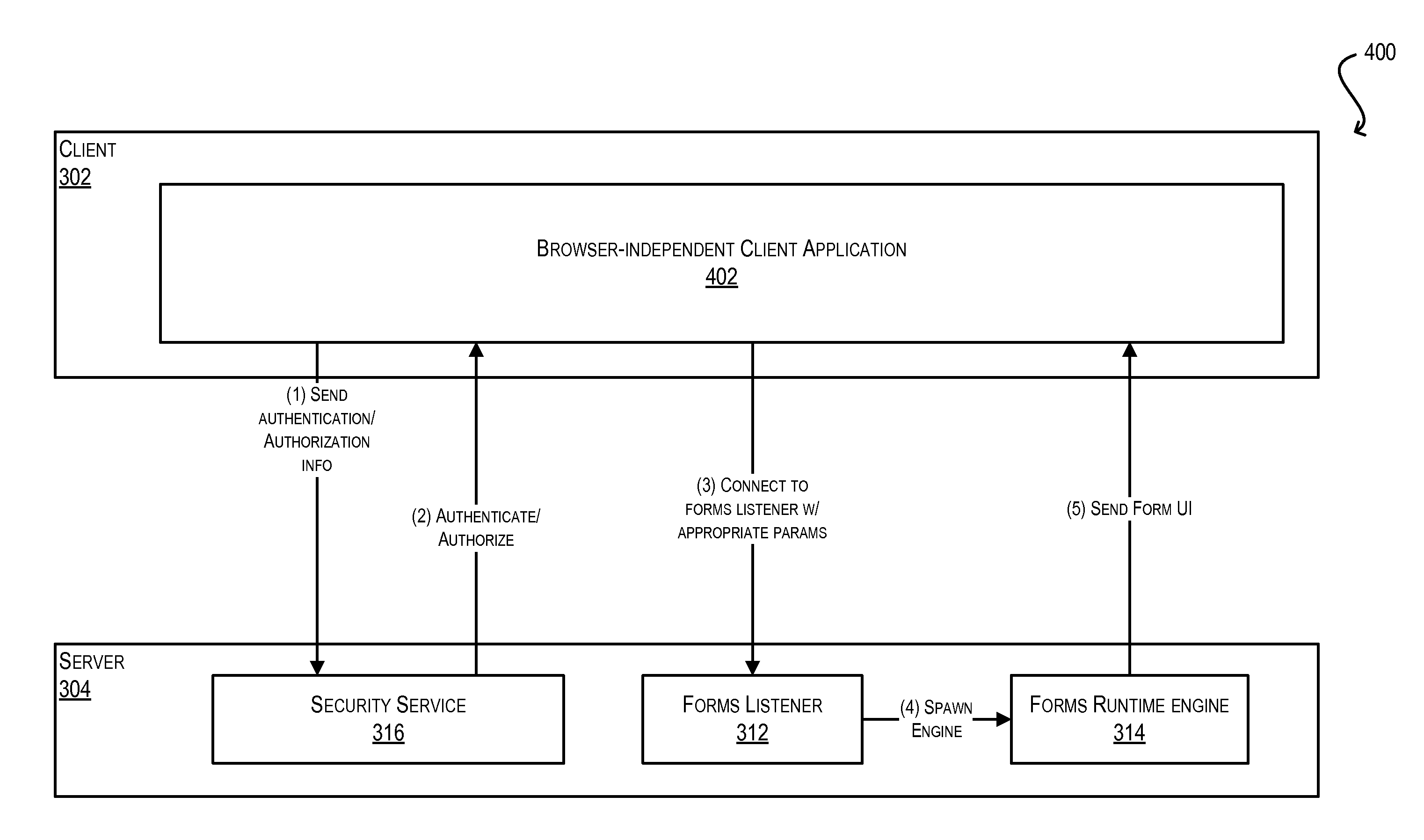
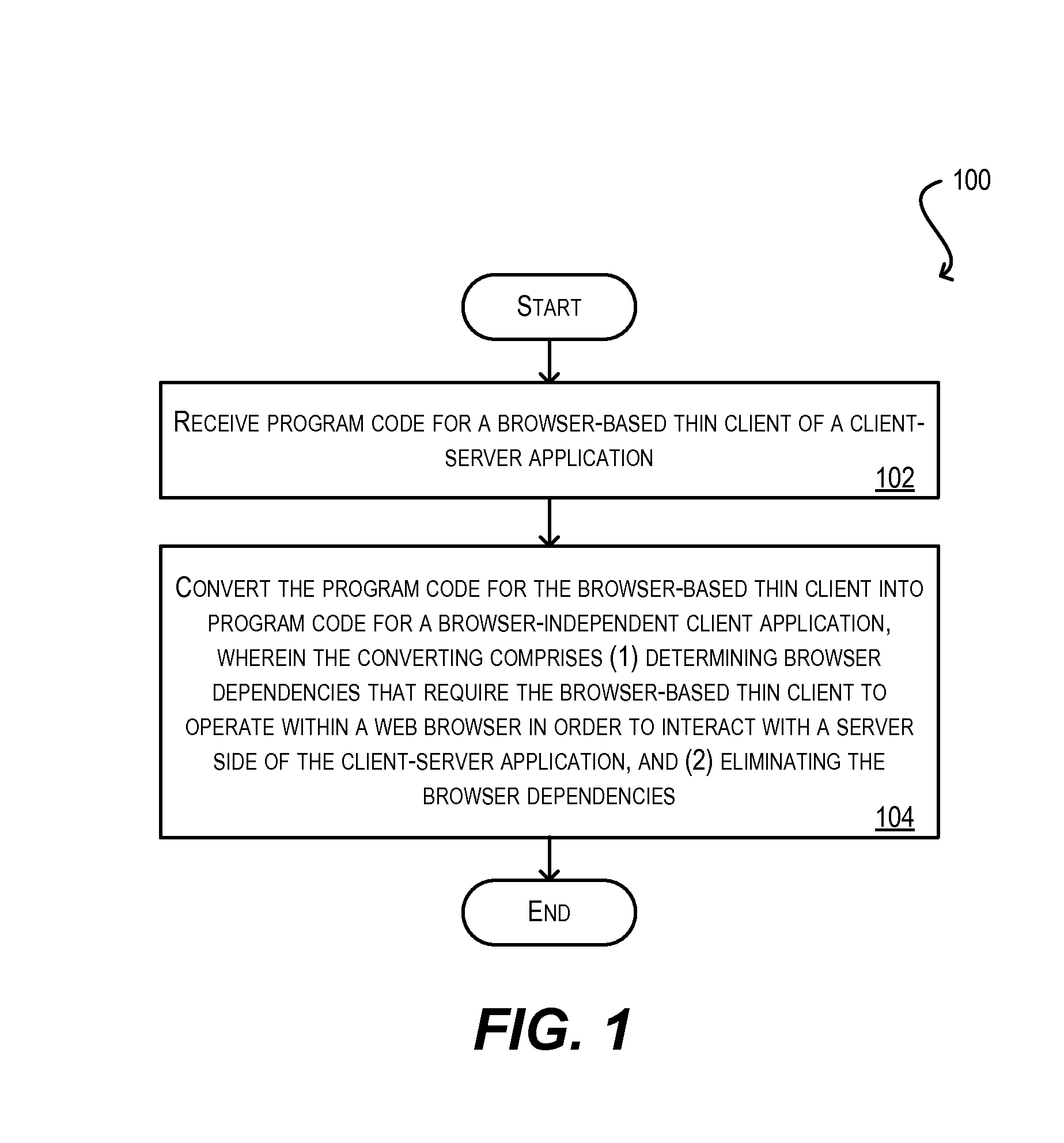
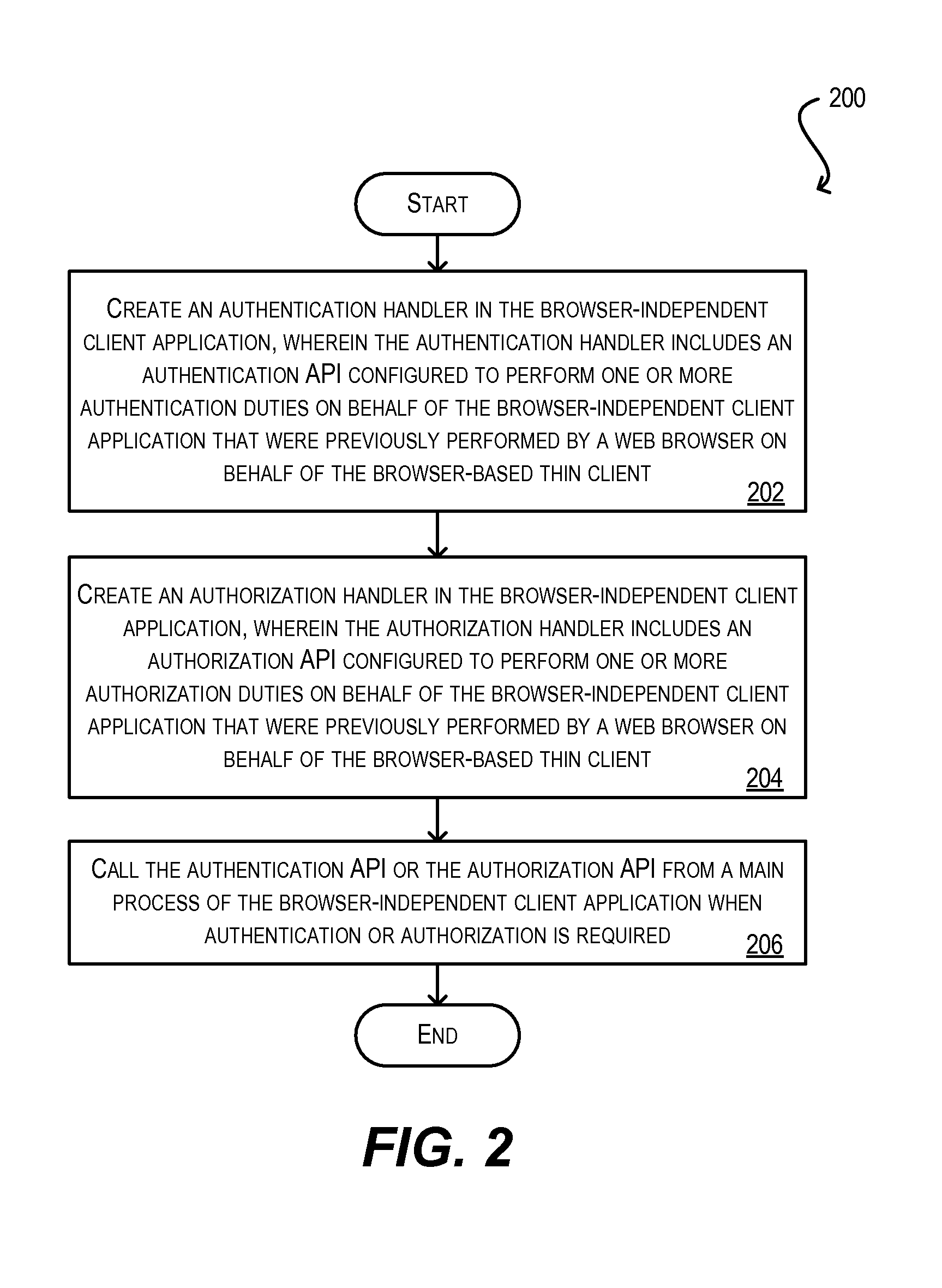
System and method for integration of browser-based thin client applications within desktop rich client architecture
ActiveUS20100057836A1Easy to reuseEliminating the one or more browser dependenciesSoftware maintainance/managementMultiple digital computer combinationsProgramming languageWeb browser
Techniques for facilitating the reuse of a browser-based thin client of a client-server application in a browser-independent context. These techniques may be used, for instance, to integrate the functionality of a browser-based thin client in a desktop-based, rich client infrastructure. In one set of embodiments, these techniques include determining one or more browser dependencies that require the thin client to operate within a web browser. For example, the thin client may depend on a web browser to handle application security, the loading / caching of client-side files, the receipt / passing of application parameters, and the like. These browser dependencies are then eliminated. As a result, the thin client can be subsequently reused without the presence of a web browser. In one set of embodiments, this process is performed by a conversion utility that automatically converts program code for the browser-based thin client into program code for a browser-independent client application.
Owner:ORACLE INT CORP
System and method for lost data destruction of electronic data stored on portable electronic devices
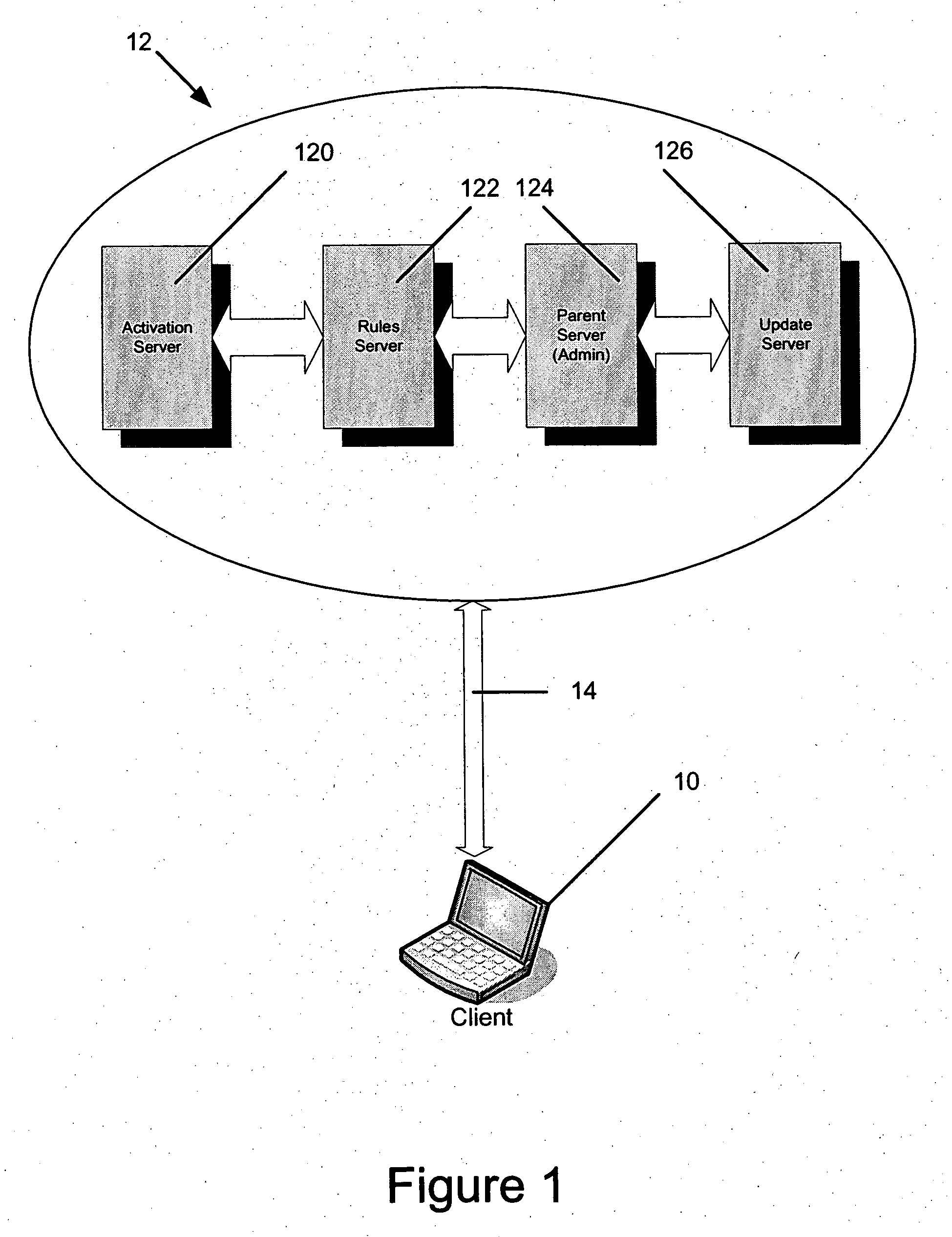
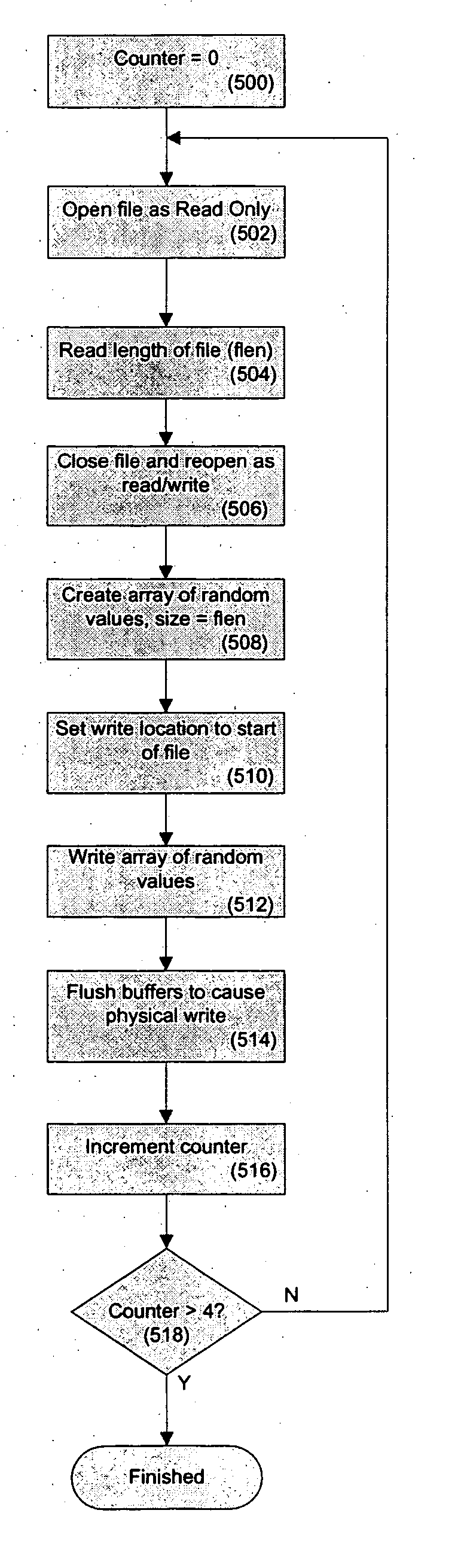
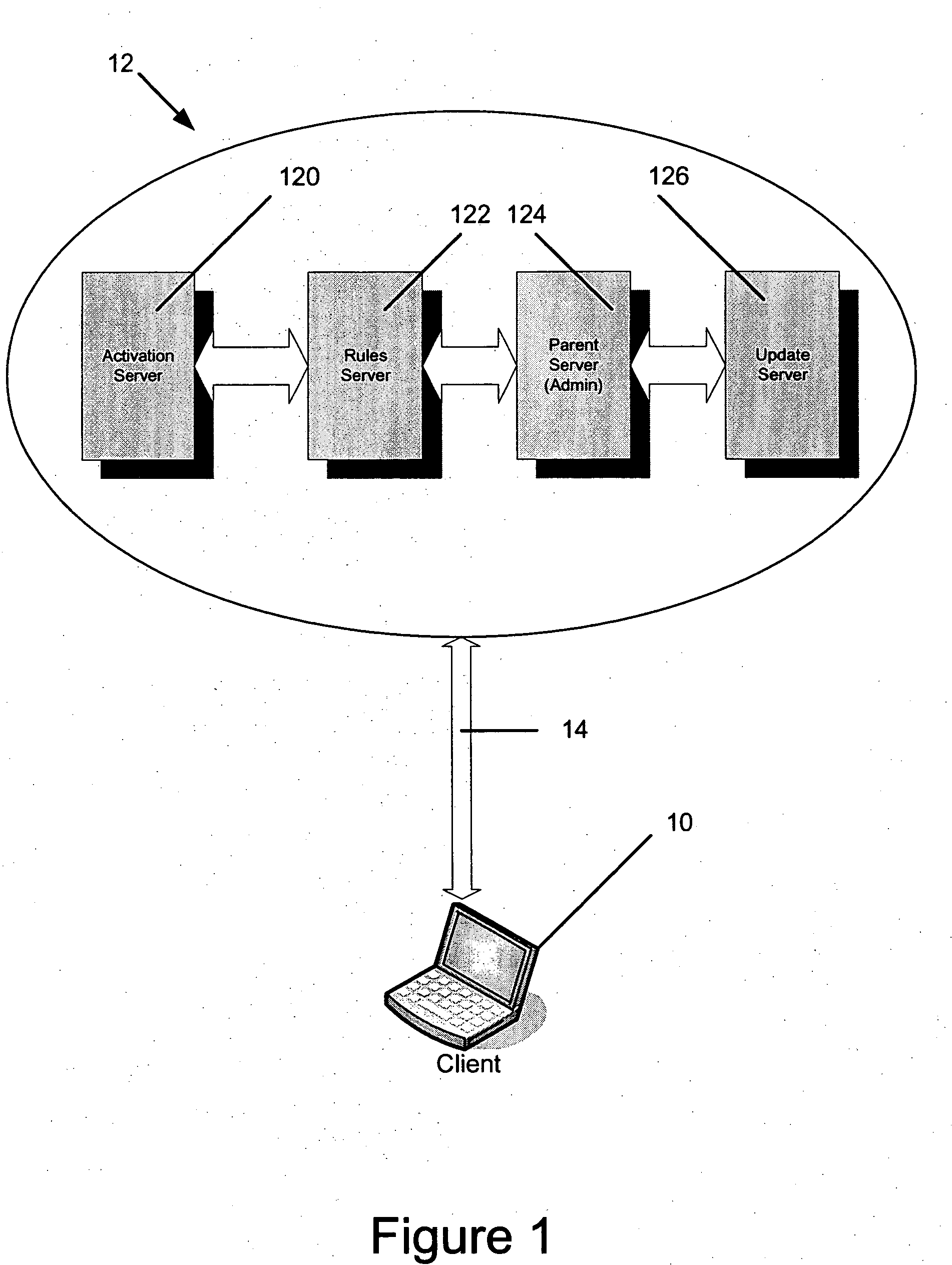
ActiveUS20060021007A1Reduces and eliminates riskReduce dataDigital data processing detailsUser identity/authority verificationBiological activationData loss
A data security system and method protects stored data from unauthorized access. According to one aspect of the invention, a client computing device communicates periodically with a server. If communications is note established between the client and the server for a selected activation interval and a subsequent grace period, the data is determined to be lost, and programmed security rules are automatically executed. Rules relating to encryption, as well as other security procedures, can be defined and entered by an administrator with access to the server, and then disseminated to each of a plurality of clients that access the server.
Owner:BEACHHEAD SOLUTIONS
System and method for lost data destruction of electronic data stored on a portable electronic device which communicates with servers that are inside of and outside of a firewall
ActiveUS20060021006A1Reduces and eliminates riskReduce riskDigital data processing detailsUser identity/authority verificationBiological activationData loss
A data security system and method protects stored data from unauthorized access. According to one aspect of the invention, a client computing device communicates periodically with a server. If communications is note established between the client and the server for a selected activation interval and a subsequent grace period, the data is determined to be lost, and programmed security rules are automatically executed. The server with which the client computer device communicates includes one server located inside the firewall of a particular organization, or a mirror server located outside the firewall, and thereby allow for the re-setting of the activation interval when the client is properly outside of the firewall through communication with the mirror server, as well as the to provide command an control over a lost or stolen client by pushing updated rules if communication is subsequently attempted with the mirror server.
Owner:BEACHHEAD SOLUTIONS
Automated login session extender for use in security analysis systems
ActiveUS7467402B2Random number generatorsUser identity/authority verificationWeb siteProgram security
A web application security scanner (WASS) includes a login manager configured to perform an automated login to a web site. The automated login may be performed when the login manager detects that a login session has ended. The login manager is configured to determine credentials for the web site to allow the WASS to access the web site. The WASS may then use the credentials to continue scanning the web site. Thus, previously unscannable web pages may be accessed in the web site because of the automated login process.
Owner:SYNOPSYS INC
Wireless communication terminal, method for protecting data in wireless communication terminal, program for having wireless communication terminal protect data, and recording medium storing the program
InactiveUS20090158400A1Digital data processing detailsAssess restrictionTelecommunicationsComputer terminal
Security of a file or an application program saved in a wireless communication terminal is maintained. A process performed by the wireless communication terminal includes the steps of: detecting an access point for wireless LAN (Local Area Network) based on a signal sent from a wireless communication I / F; obtaining an SSID (and a MAC address) of the detected access point; referring to access management data stored in a hard disk based on the obtained SSID; and restricting access to the file or the program based on the access management data.
Owner:FUNAI ELECTRIC CO LTD
Program authentication on environment
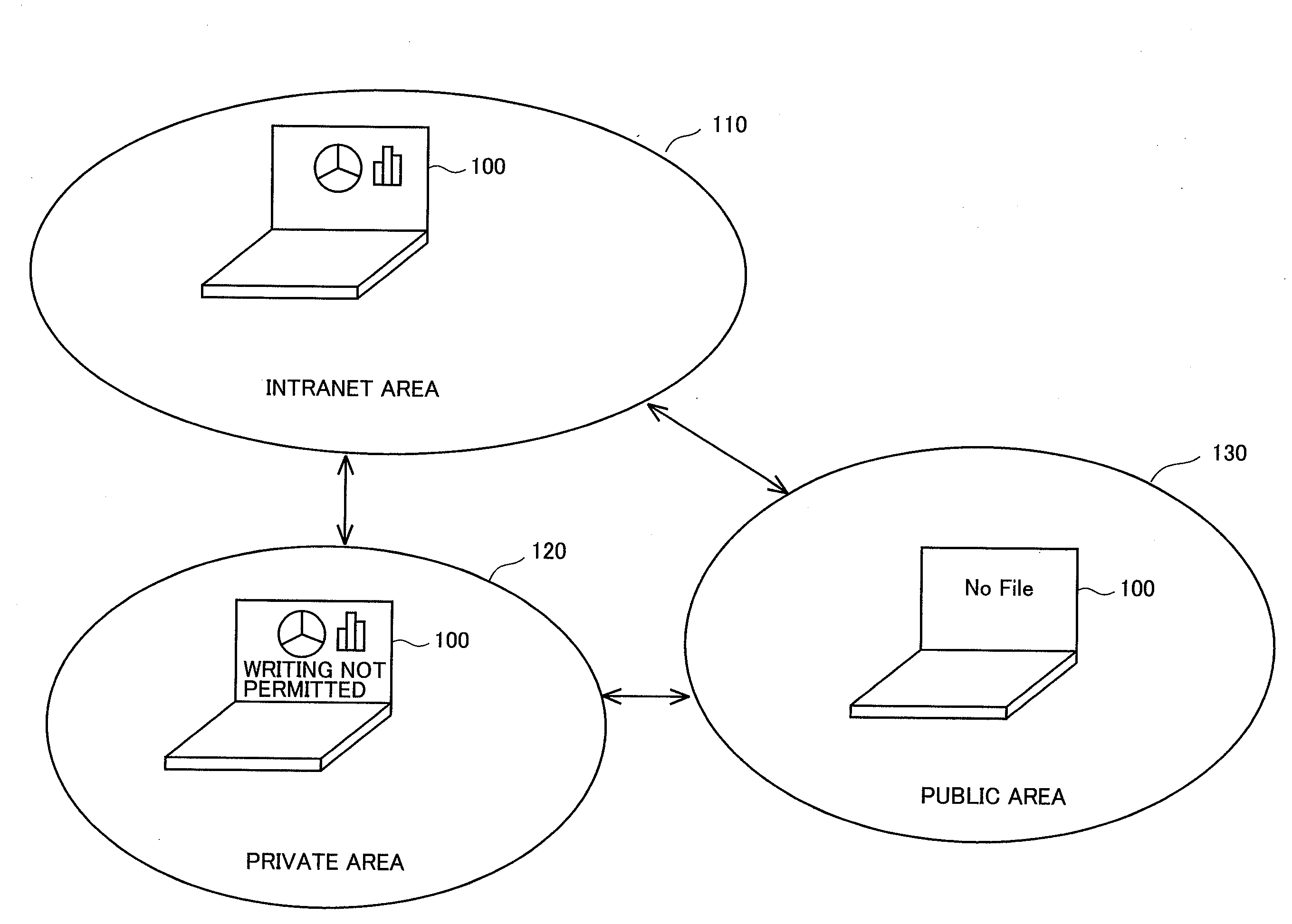
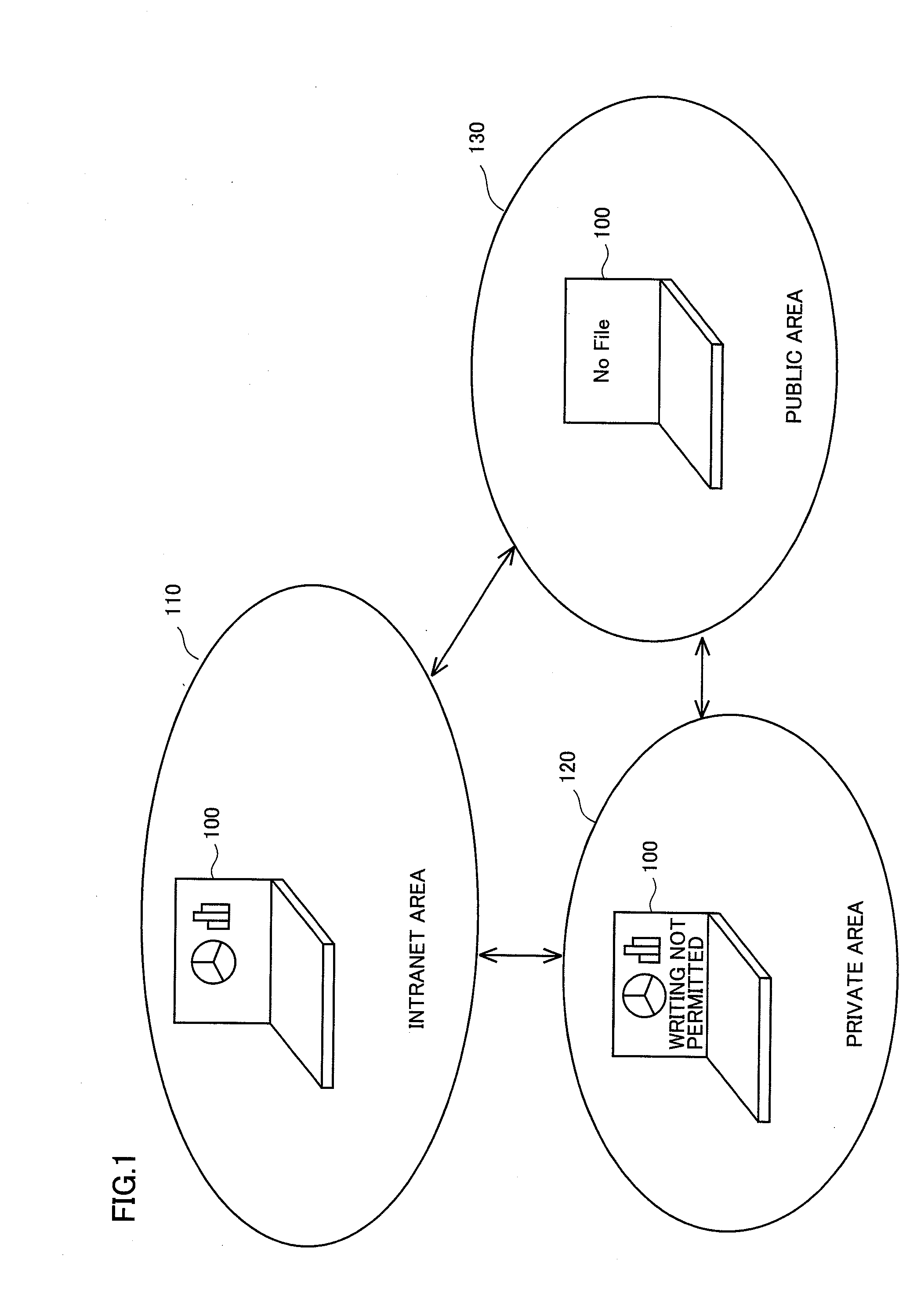
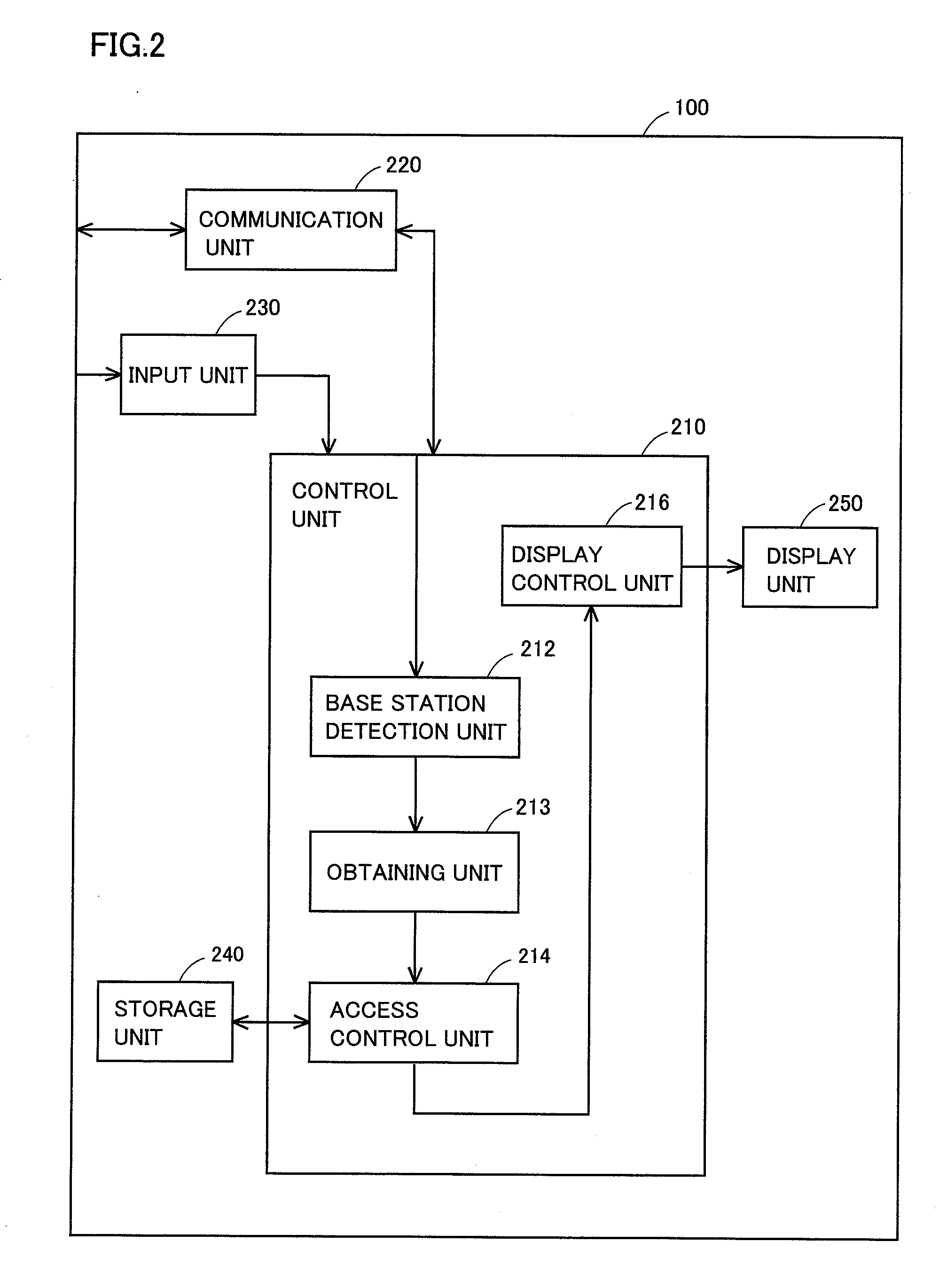
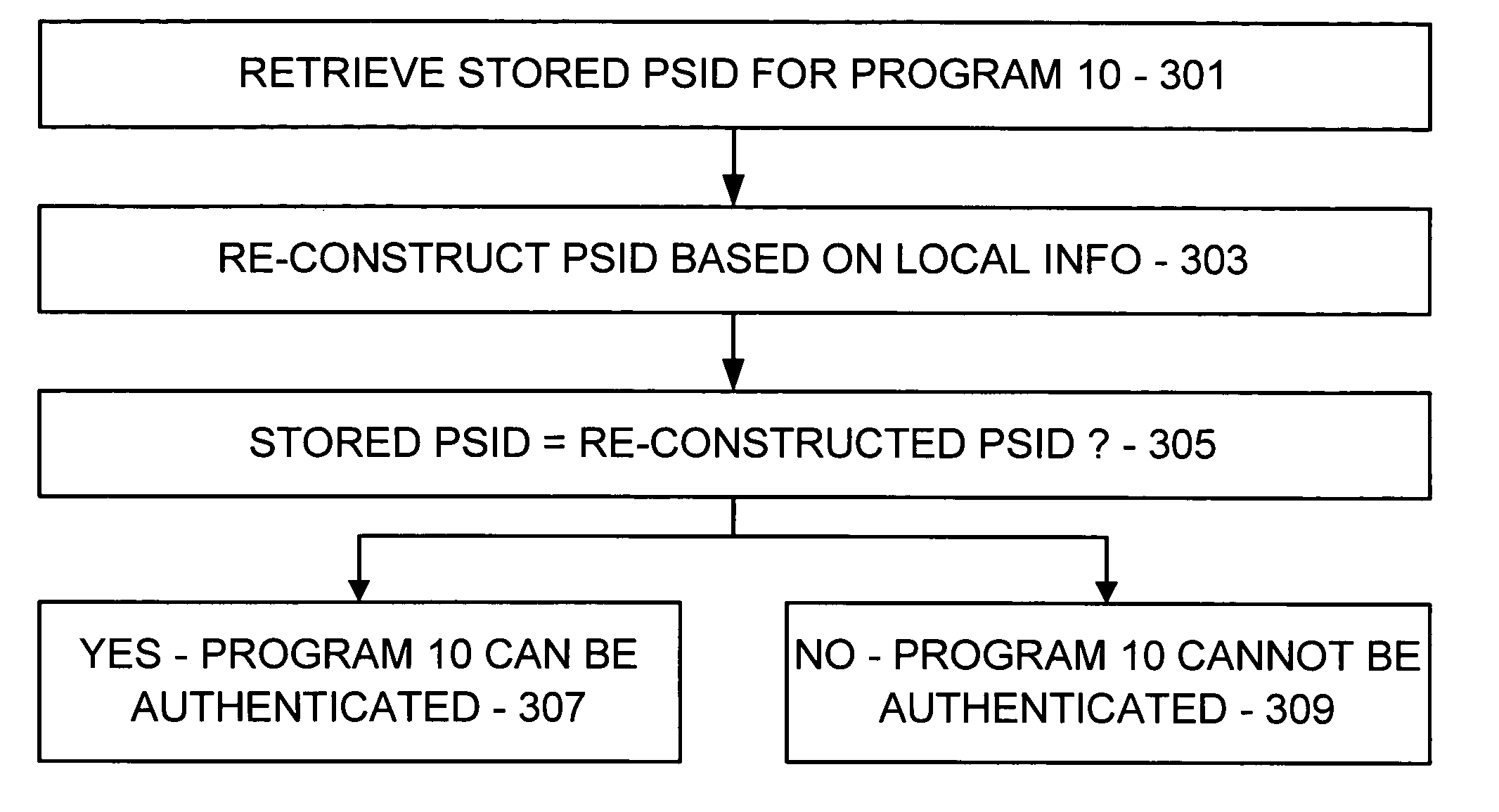
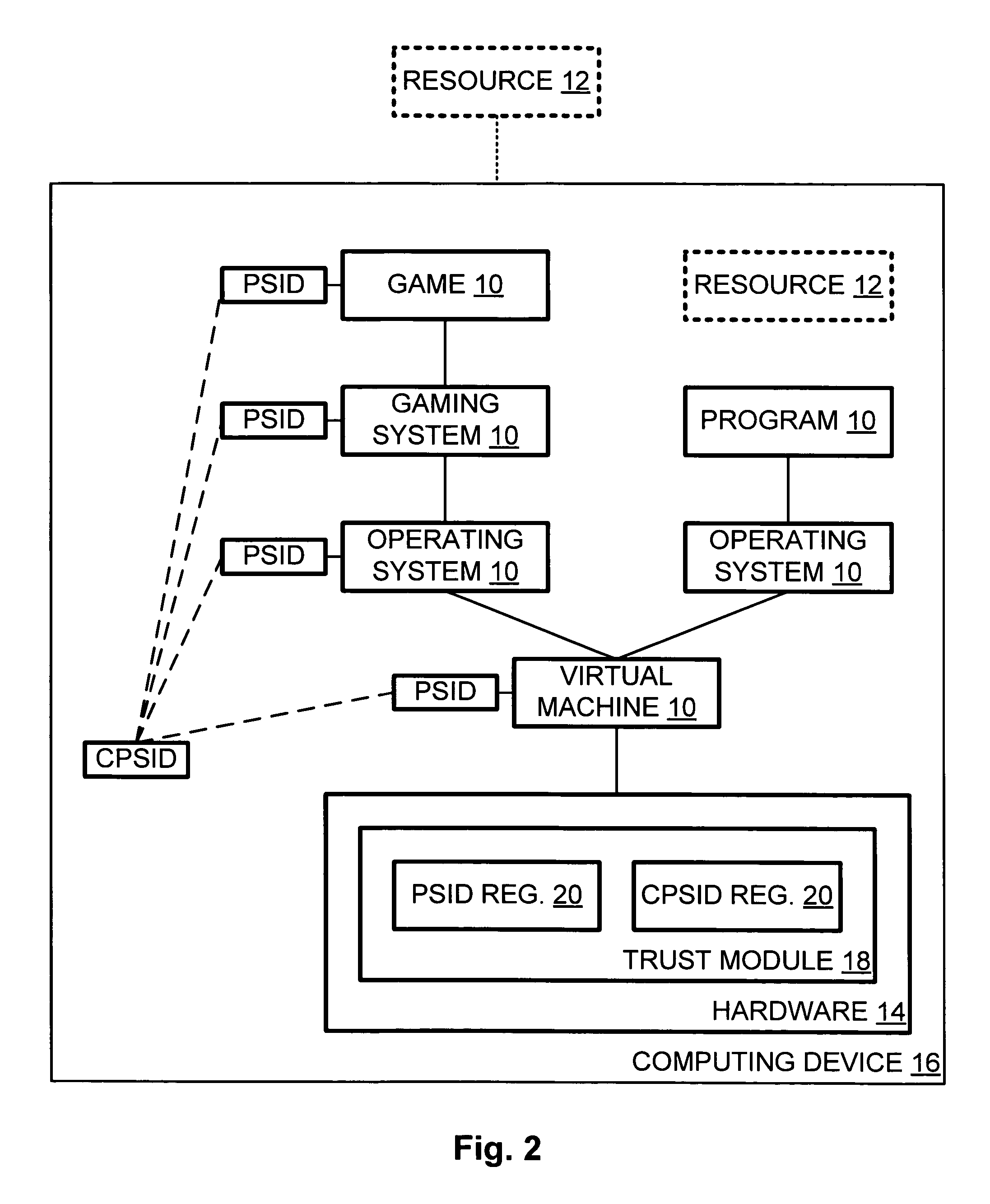
To authenticate a program on a computing device to a resource local to or remote from the computing device, a stored program security identifier (PSID) corresponding to the program is retrieved, where the stored PSID includes information taking into account the program itself, the execution setting of the program, and any inputs and initializations that are provided to the program. The PSID is re-constructed based on the same information as obtained from local sources, and the stored and reconstructed PSIDs are compared to determine whether a match exists. If so, it may be concluded that the program operates in a trusted manner according to an approved set of conditions.
Owner:MICROSOFT TECH LICENSING LLC
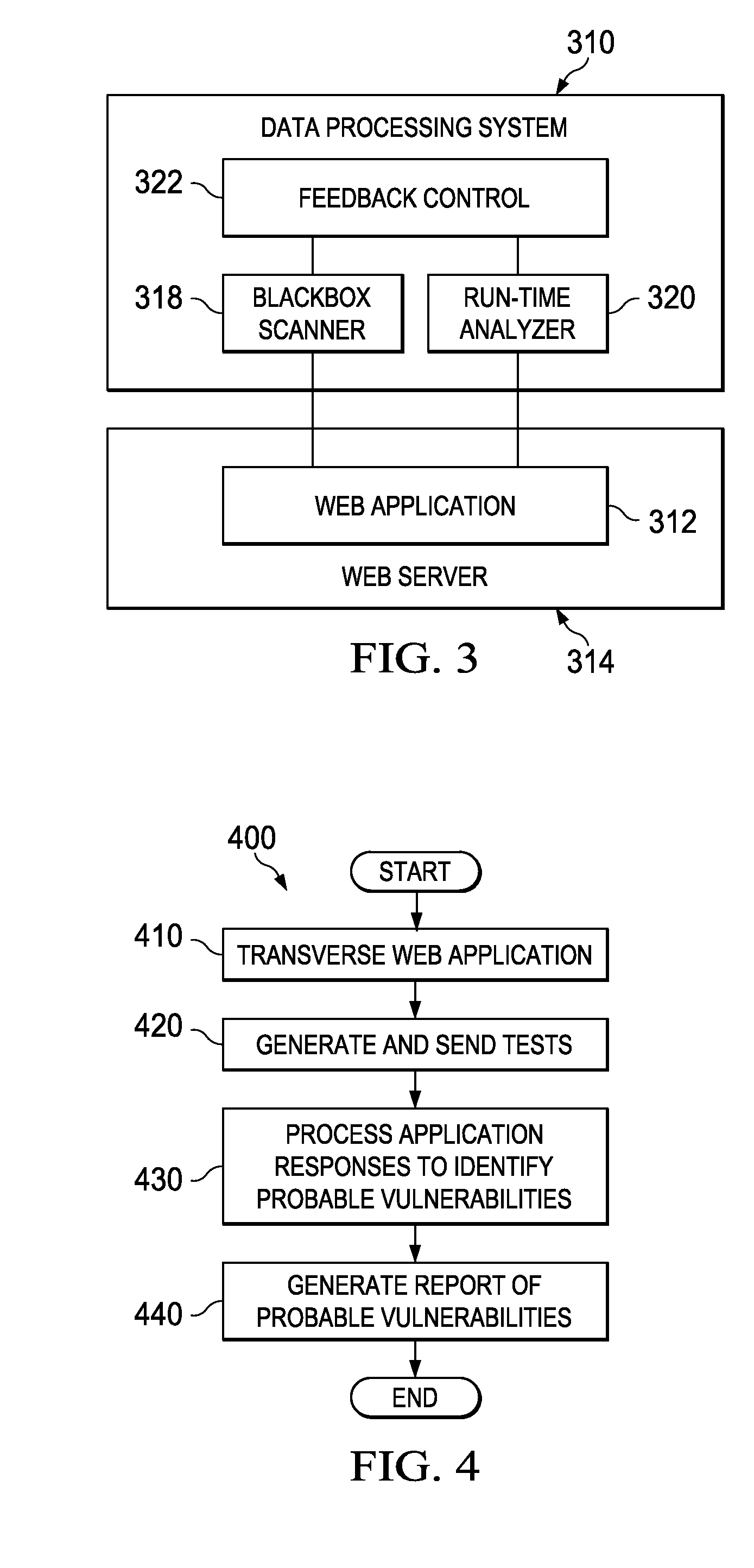
Measuring Coverage of Application Inputs for Advanced Web Application Security Testing
ActiveUS20100169974A1Memory loss protectionError detection/correctionData processing systemWeb application
A computer implemented method, a data processing system, and a computer usable recordable-type medium having a computer usable program code monitor a black box web application security scan. A black box scan of a web application is initiated. The black box scan sends a test is sent to a plurality of web application inputs of the web application. A runtime analysis is performed on the black box scan of the web application. Based on the run time analysis of the black box scan, the black box scan is modified.
Owner:IBM CORP
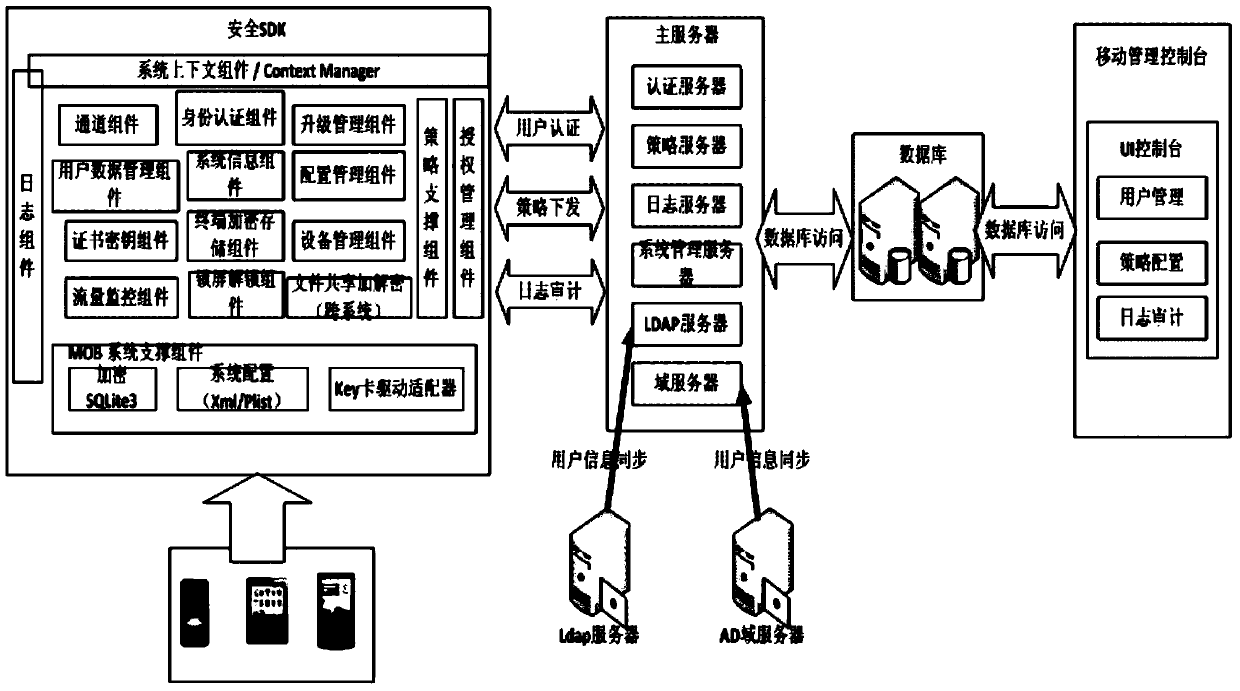
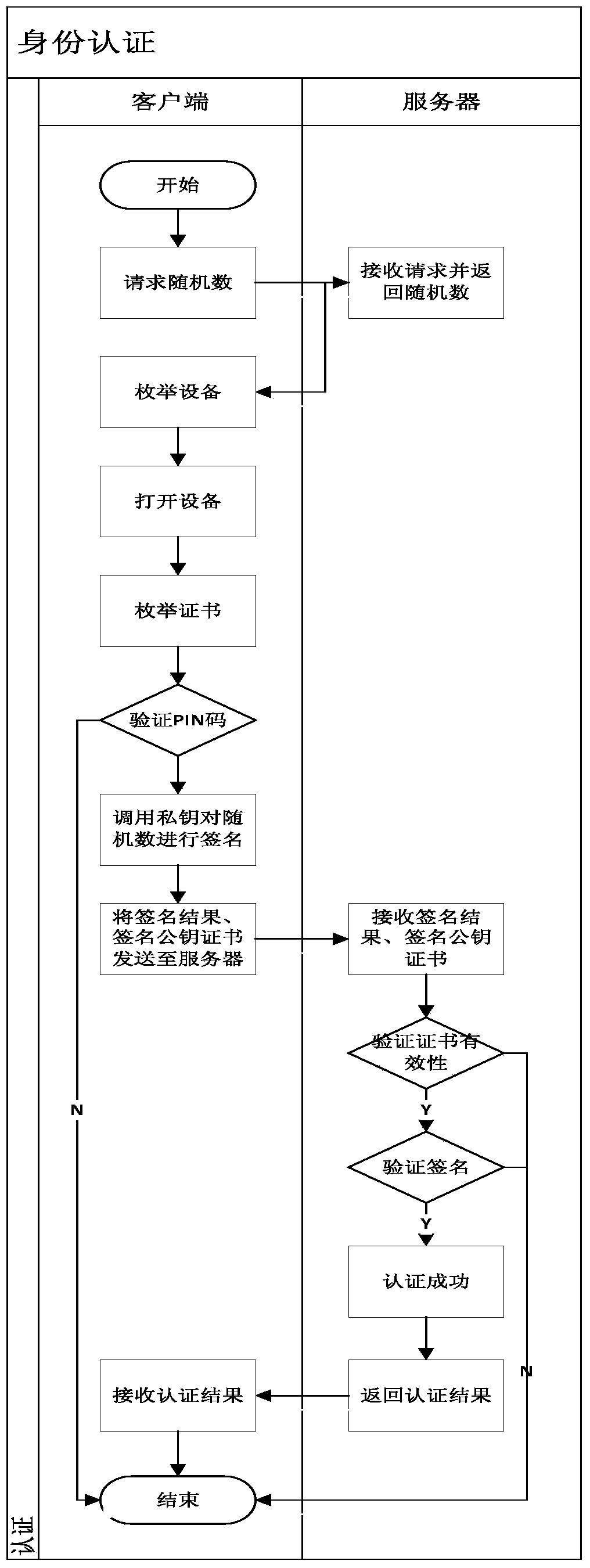
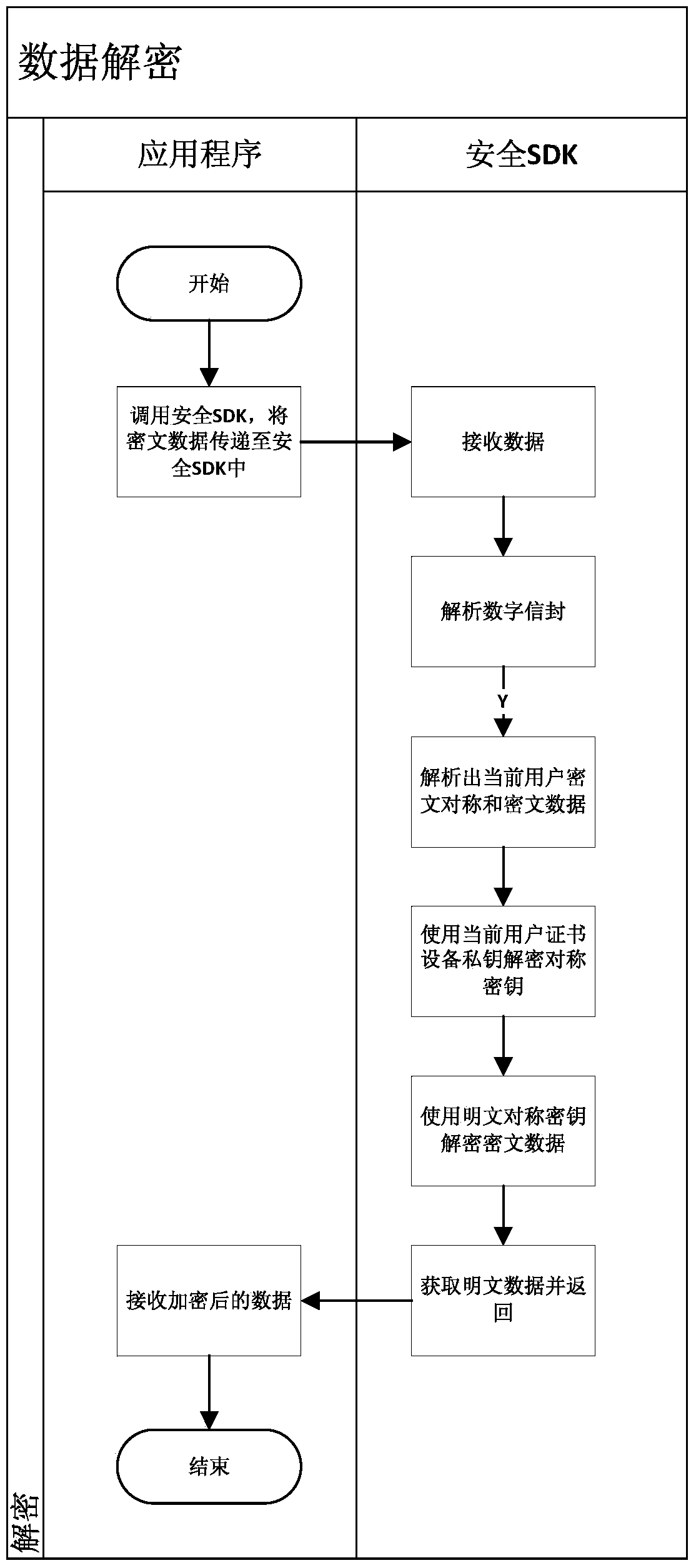
Development method and system based on mobile terminal application program security application
ActiveCN103812871AAvoid security issuesAvoid authenticationPublic key for secure communicationUser identity/authority verificationData informationCiphertext
The invention discloses a development method and system based on mobile terminal application program security application. The system comprises a sending terminal, a safe software development kit (SDK), a server and a receiving terminal. The method includes that the sending terminal requests a random number from the server, after the requested random number is received, a private key of the sending terminal is called to perform signing on the random number, and a signing result and a signing public key certificate are sent to the server; after the success of identity authentication, the safe SDK is called, received data information is encrypted through symmetric keys, the symmetric keys are encrypted by a public key of the receiving terminal, and encrypted symmetric keys and data information are sent to the receiving terminal; the receiving terminal calls the safe SDK to decrypt encrypted data. By means of the development method and system based on mobile terminal application program security application, related problems such as identity authentication, data breach and equipment controlling of data information safety are avoided.
Owner:北京明朝万达科技股份有限公司
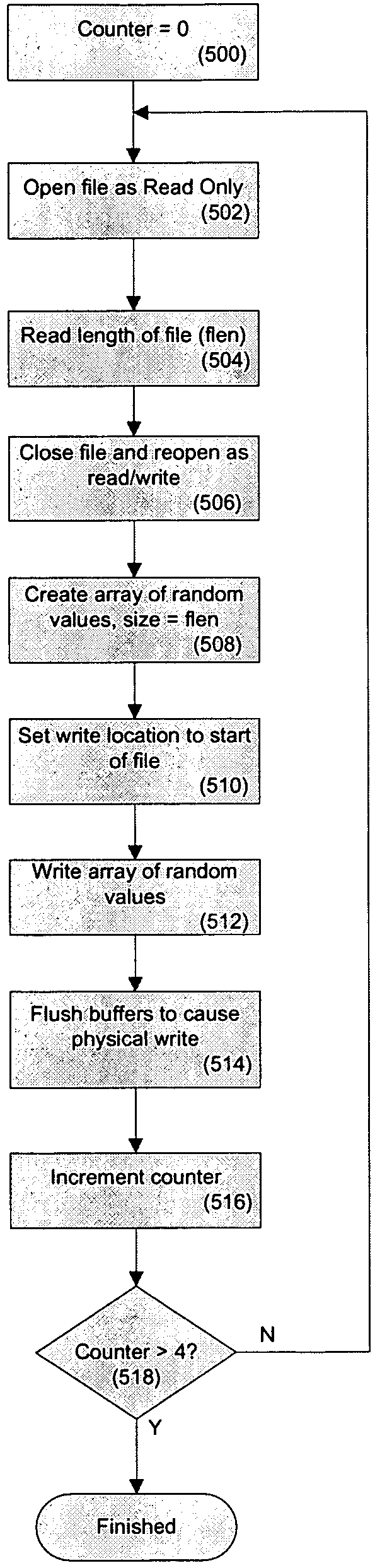
System and method for lost data destruction of electronic data stored on a portable electronic device using a security interval
ActiveUS20060021005A1Reduces and eliminates riskReduce riskDigital data processing detailsUser identity/authority verificationProgram securityBiological activation
A data security system and method protects stored data from unauthorized access. According to one aspect of the invention, a client computing device communicates periodically with a server. If communications is not established between the client and the server for a selected activation interval and a subsequent grace period, the data is determined to be lost, and programmed security rules are automatically executed.
Owner:BEACHHEAD SOLUTIONS
Method and system for operating and installing software
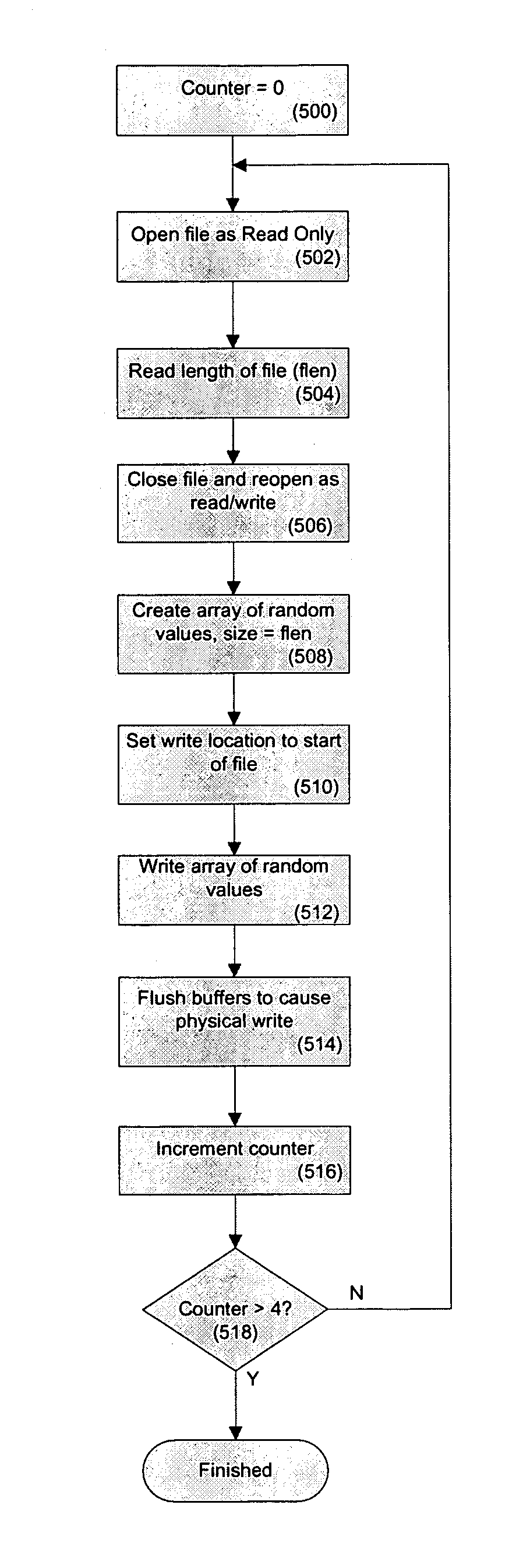
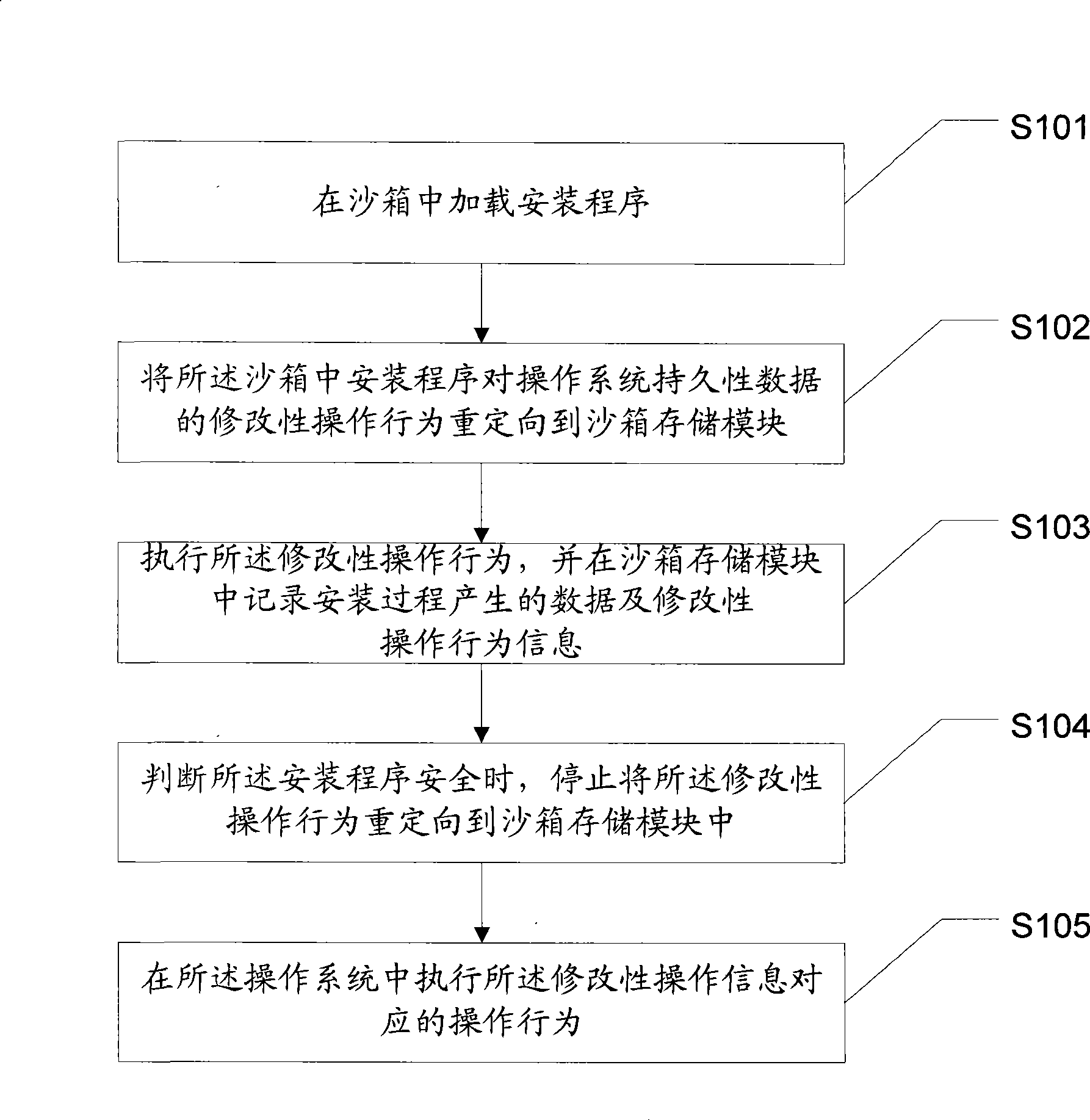
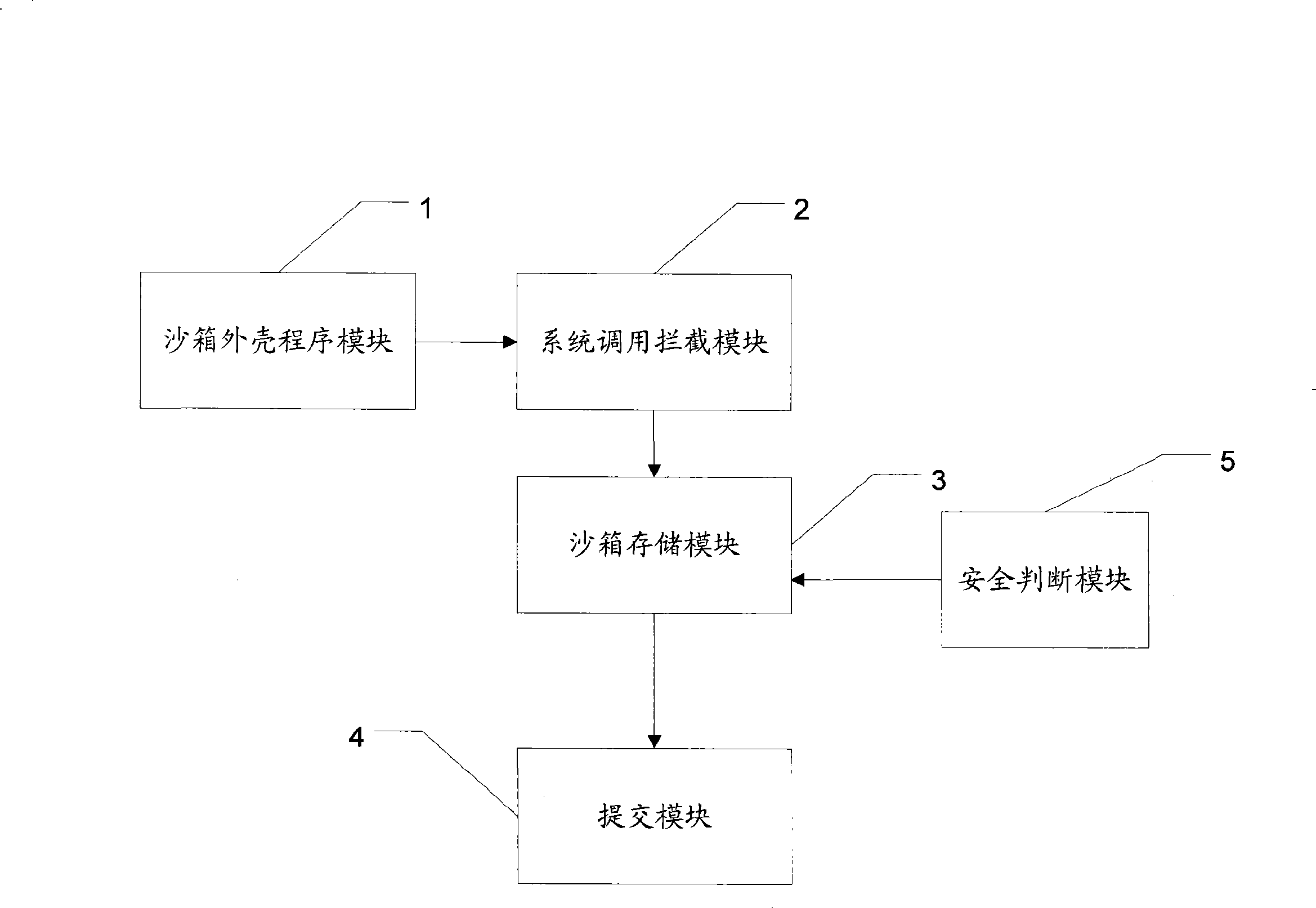
ActiveCN101425016AThe effect of safe and direct installationAvoid Malicious ModificationsPlatform integrity maintainanceProgram loading/initiatingOperational systemProgram security
The invention discloses a method and a system for running installed software. The method comprises the following steps: an install program is loaded in a sandbox; a changing operation action of the installed program to the persistent data of an operating system is reorientated to a sandbox storage module; the changing operation action is executed, corresponding changing operation action information and data generated during the installation are recorded in the sandbox storage module; when the install program is judged to be safe, the operation of reorientated the changing operation action to the sandbox storage module is stopped; and a corresponding operation action of the changing operation information is executed in the operating system. The technical proposal of the invention achieves the effect of actually installing the operating system after the install program is united to the operating system, and improves the practicability of the install program while ensuring the safety of the install process.
Owner:GUANGZHOU HUADUO NETWORK TECH
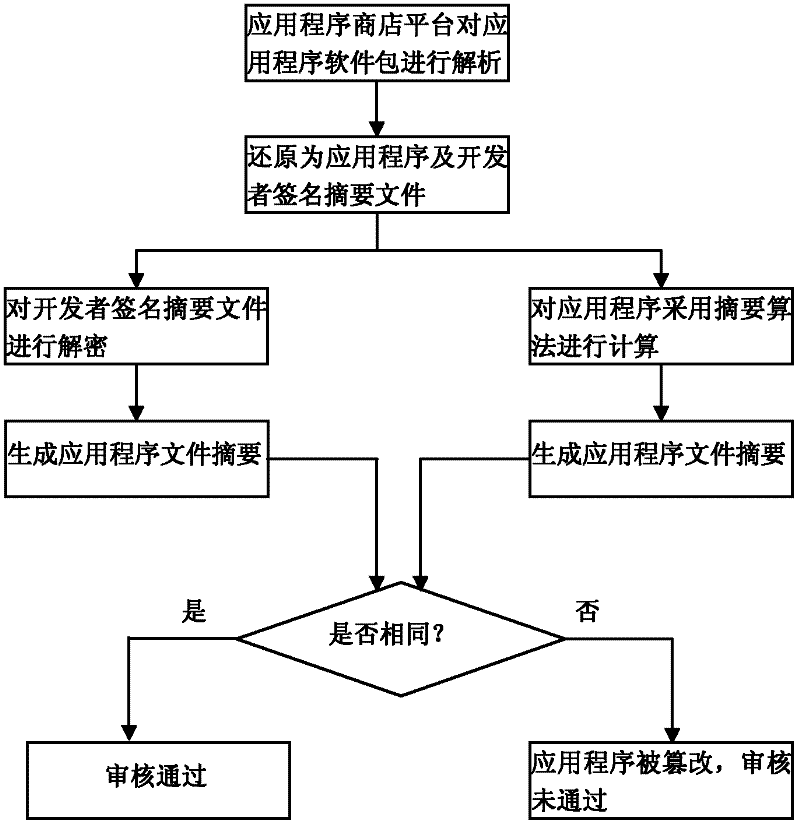
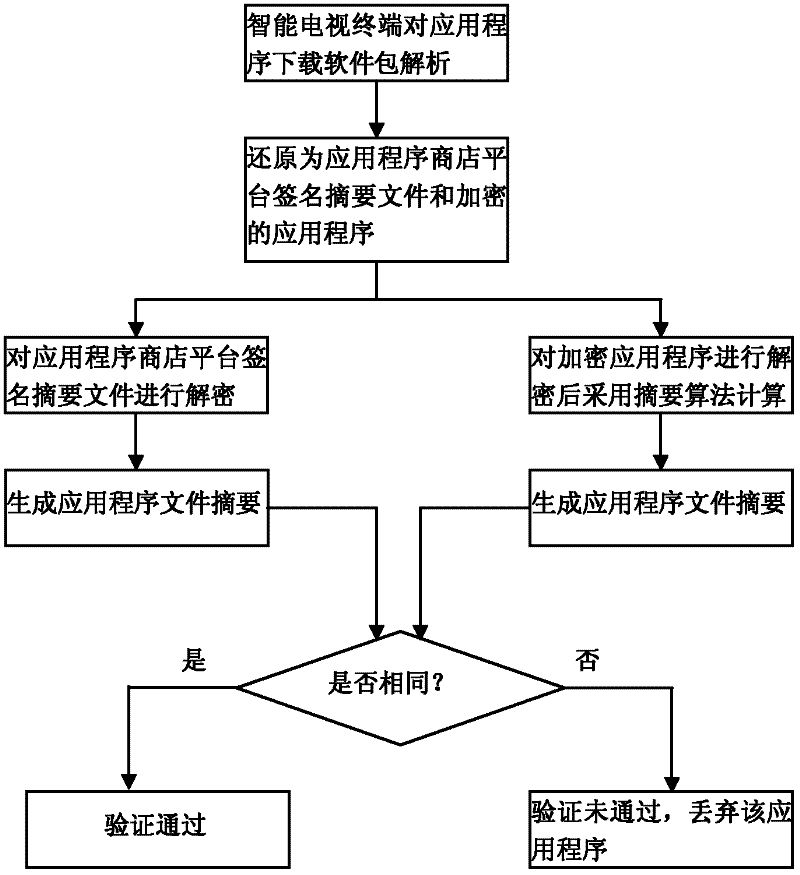
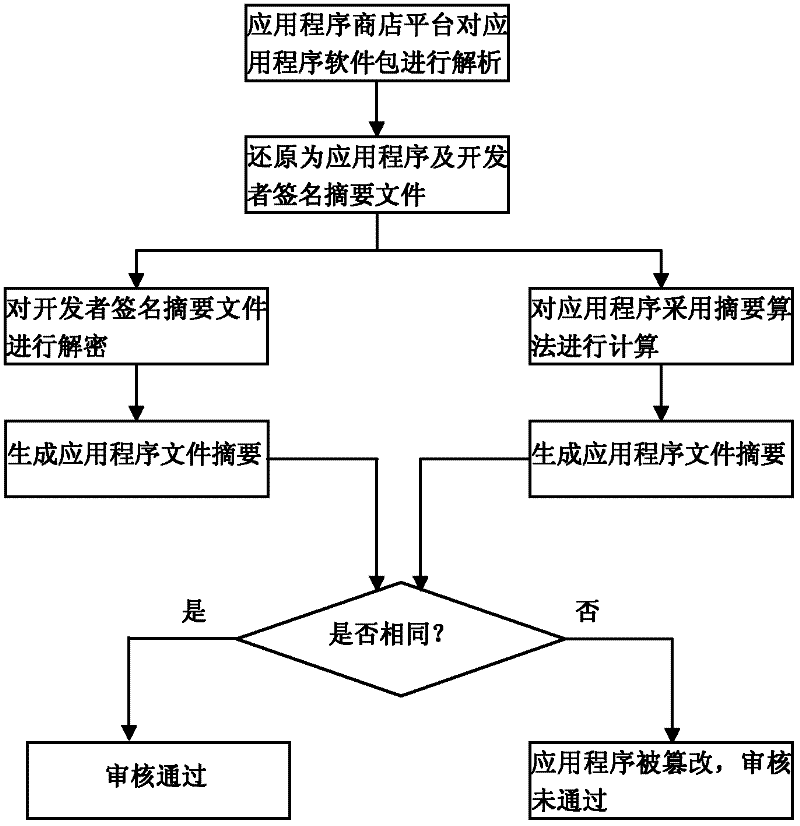
Security control method of intelligent television application program
ActiveCN102546604AGuaranteed legalityEnsure safetyUser identity/authority verificationSelective content distributionNetwork connectionApp store
The invention relates to software security control technology and discloses a security control method of intelligent television application programs, wherein the security of application software is monitored from a plurality of levels, thereby ensuring the security of application software downloaded and installed in an intelligent television terminal. The key points of the technical scheme are summarized as that an application program developer signs for the first time when packing and uploading the application program to an application program store platform; signature of the second time is performed after the application program store platform verifies the application program; the intelligent television terminal hands over a public key of the intelligent television terminal to the platform through a network connection platform, the software is encrypted using the public key at the platform and transmitted to the intelligent television terminal, the intelligent television terminal performs security verification to the application program, and the application program is installed after the verification is accepted. Legitimacy and security of application of the application program is ensured with such method, and such method is applicable for security control of the application software.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
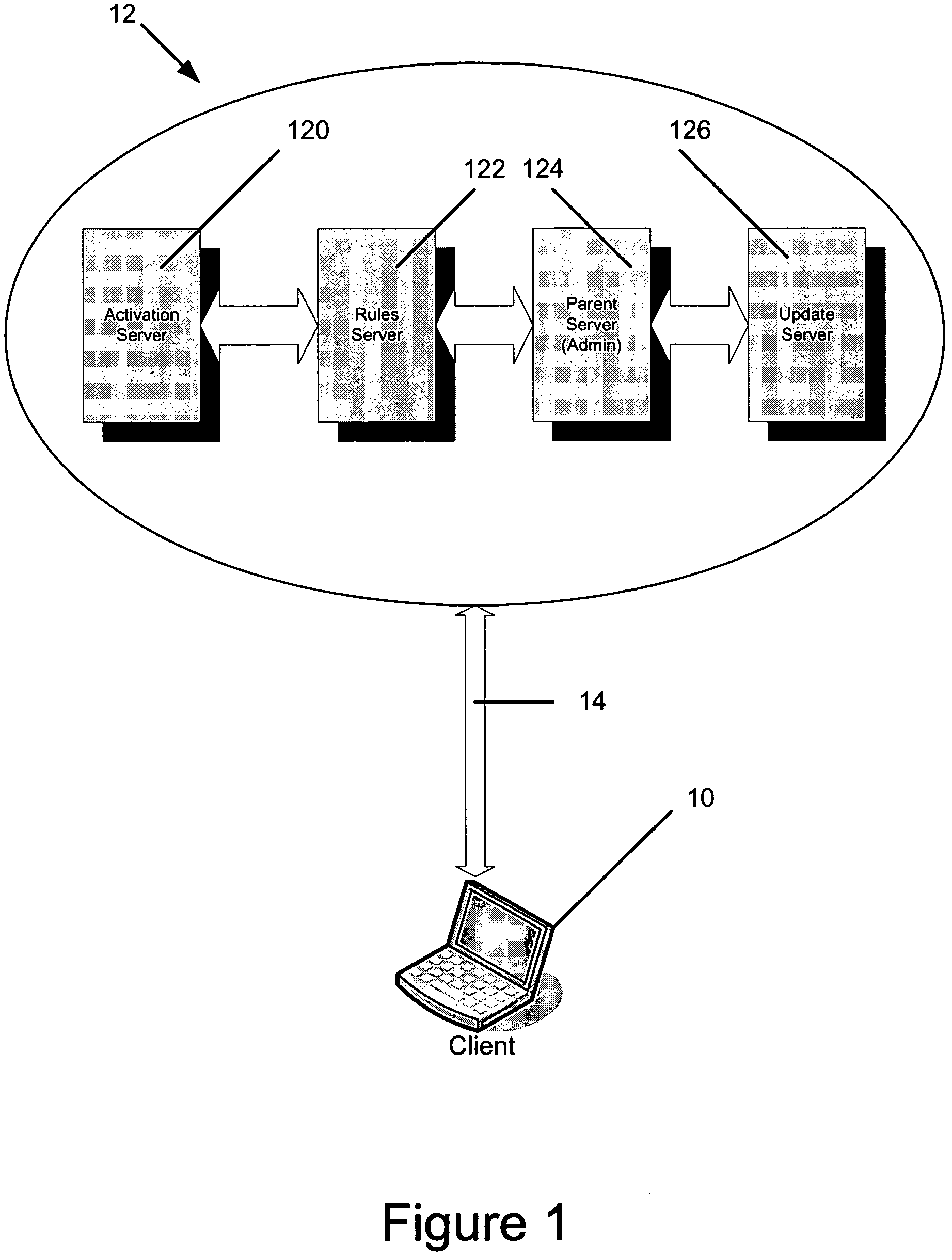
Method and apparatus for programming electronic security token
InactiveUS20070132548A1Alleviates and overcomesImprove security levelElectric signal transmission systemsCredit registering devices actuationProgram securityData storing
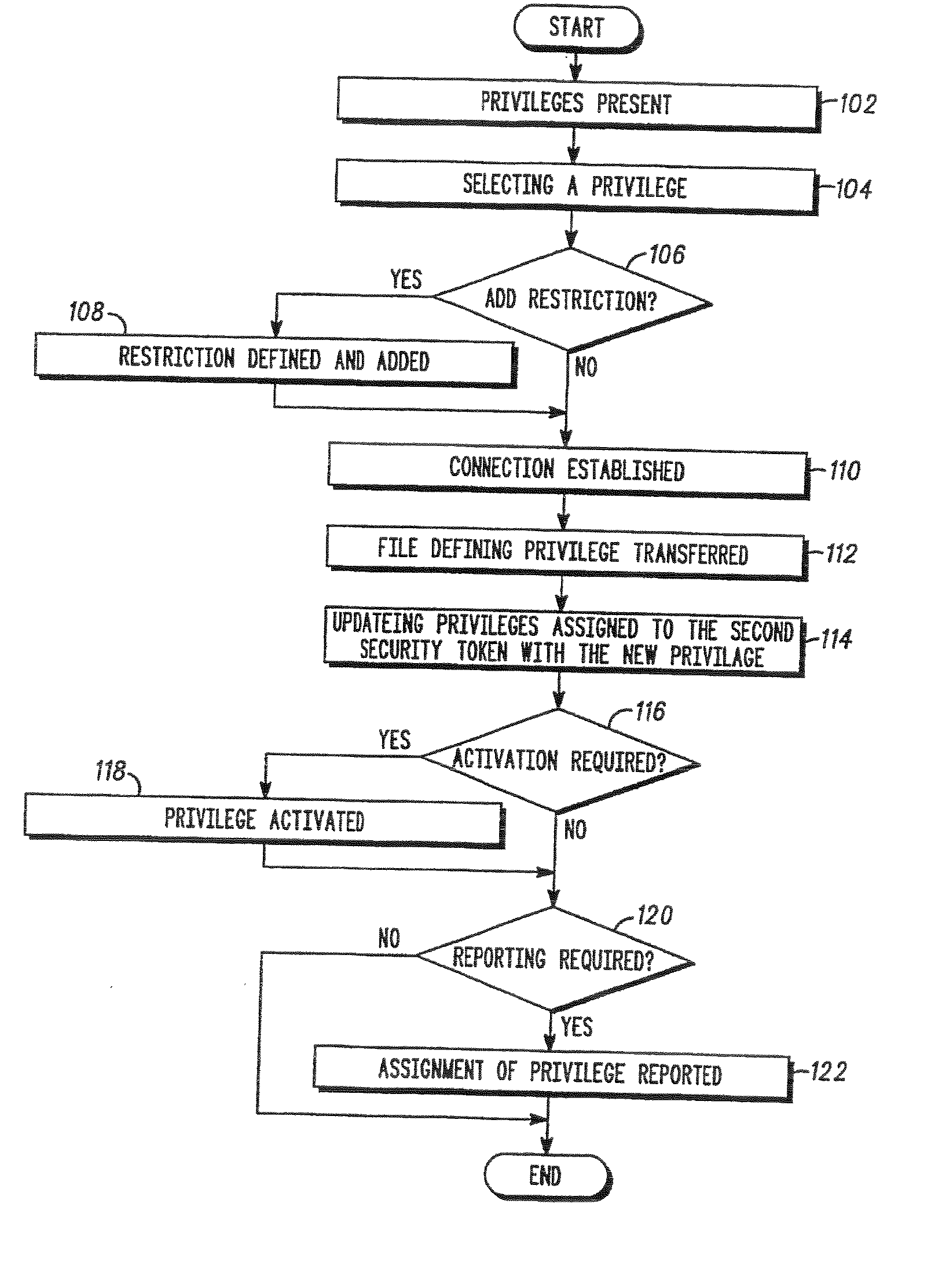
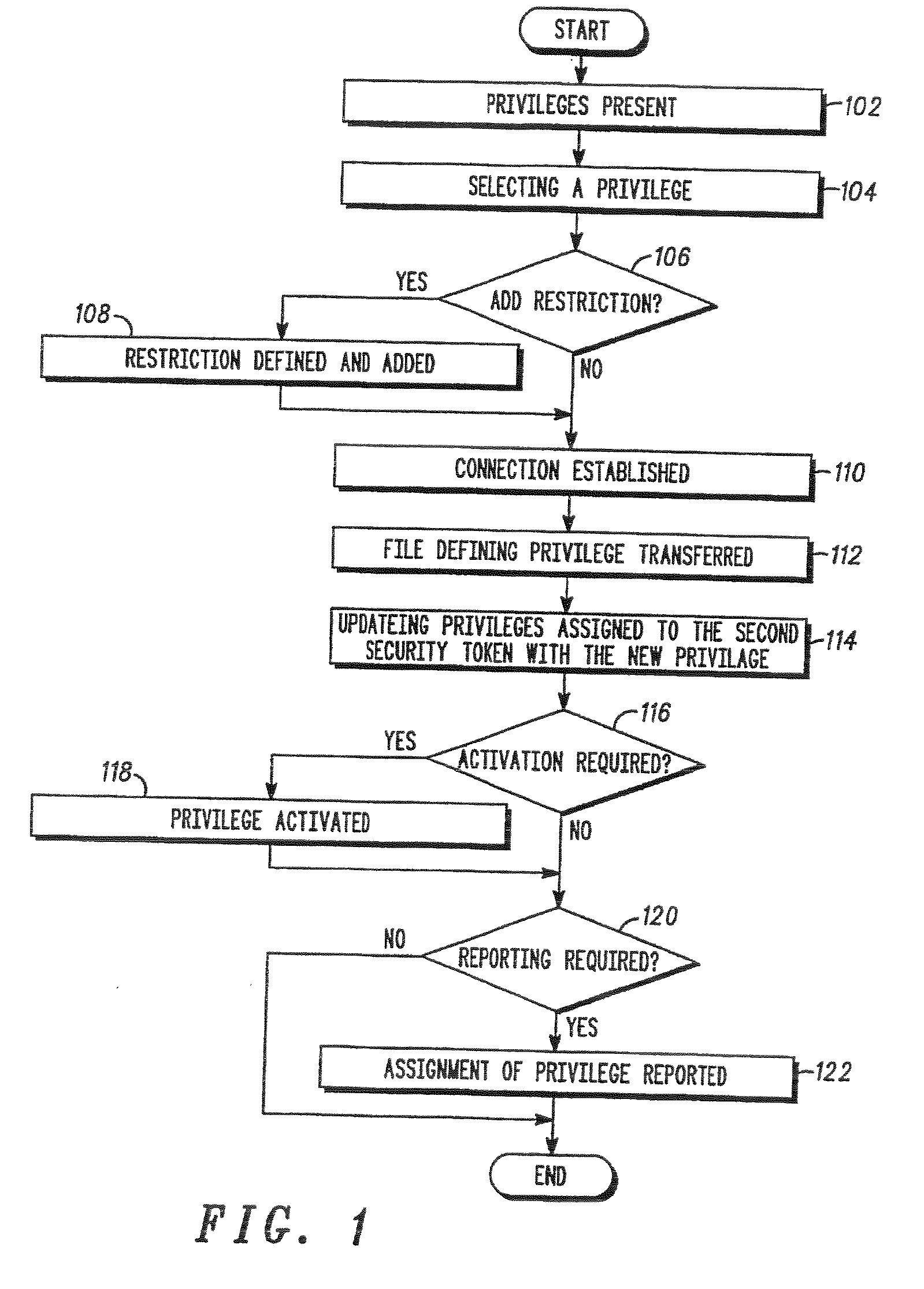
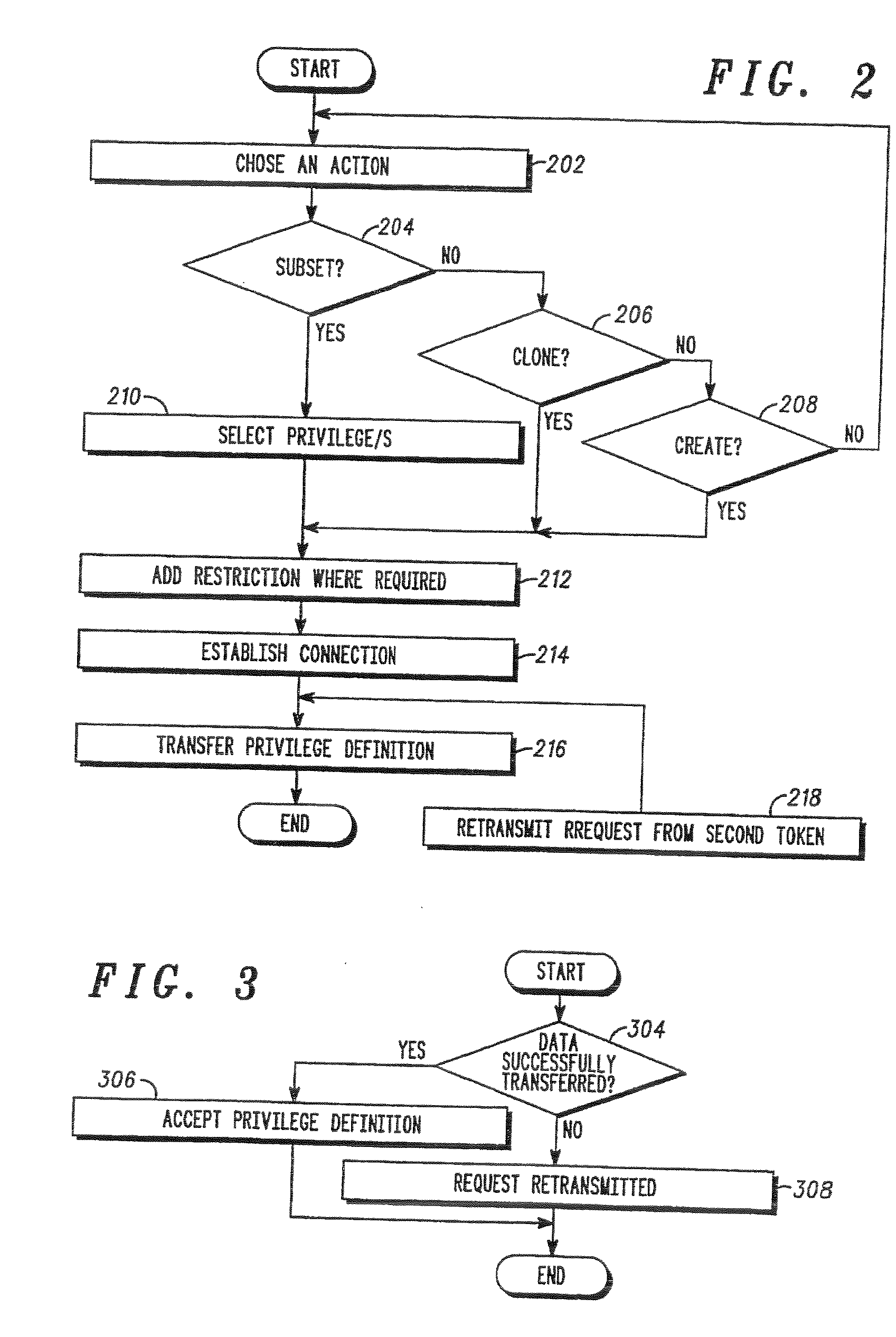
A method of programming a second security token using data stored on a first security token, wherein a privilege to be assigned to the second security token is selected by a user of the first security token. The user selects from privileges derived from a first set of privileges assigned the first security token. A file containing a definition of the privilege to be assigned to the second security token is transferred from an apparatus for programming security tokens to the second security token.
Owner:MOTOROLA INC
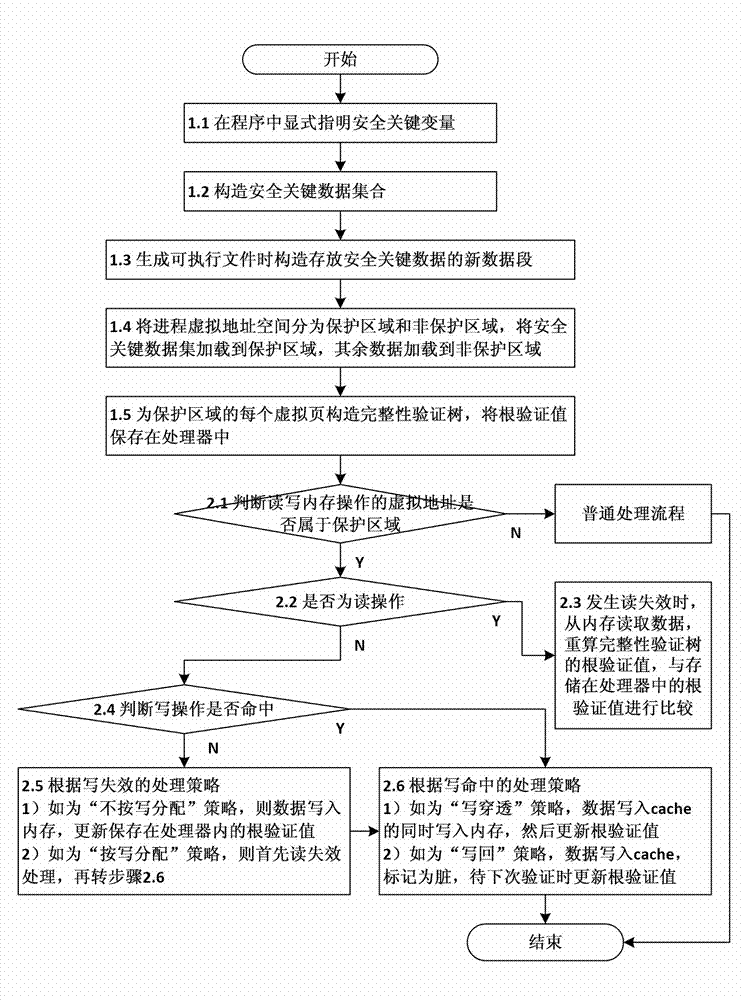
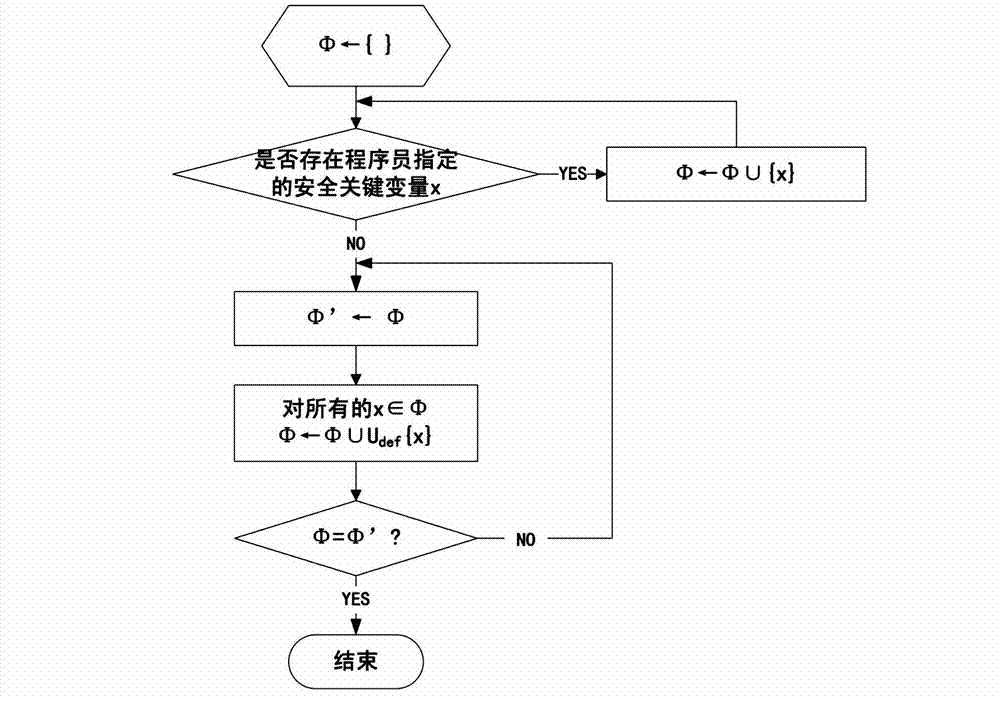
Method and device for verifying integrity of security critical data of program in process of running
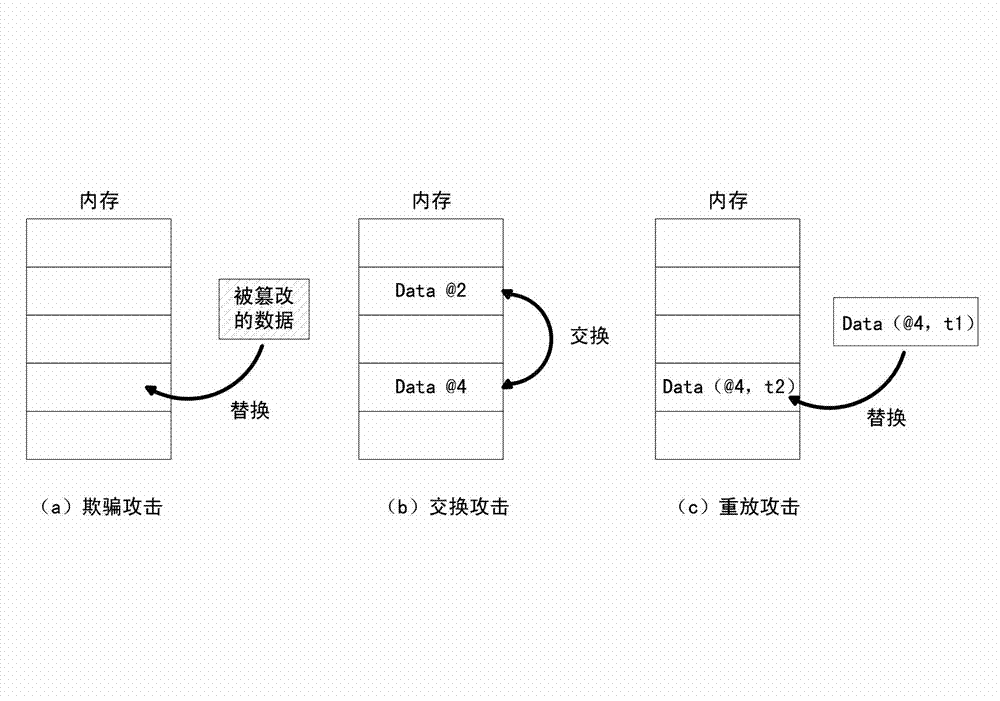
ActiveCN102930185AAvoid attackIntegrity verification implementationProgram/content distribution protectionData setData integrity
The invention discloses a method and a device for verifying the integrity of security critical data of a program in the process of running. The method comprises the following steps: 1) indicating a security critical variable in the program, generating a security critical data set in the process of compiling, dividing a virtual address space of the program into a protected area and a non-protected area in the process of loading the program, loading the security critical data set to the protected area, and constructing an integrity verification tree for a virtual page of the protected area of the program; and 2) in the process of writing program data into a memory, updating a root verification value; and in the process of reading program data from the memory, generating a new root verification value, comparing the new root verification value with the original root verification value, if the two are equal, determining that the security critical data set is not tampered, otherwise, determining that the security critical data set is tampered. The device comprises a data integrity verification circuit, a root verification value storage module and a comparator. The method and the device disclosed by the invention have the advantages of high safety performance, strong attack prevention performance, small calculated amount, and less occupied storage space.
Owner:NAT UNIV OF DEFENSE TECH
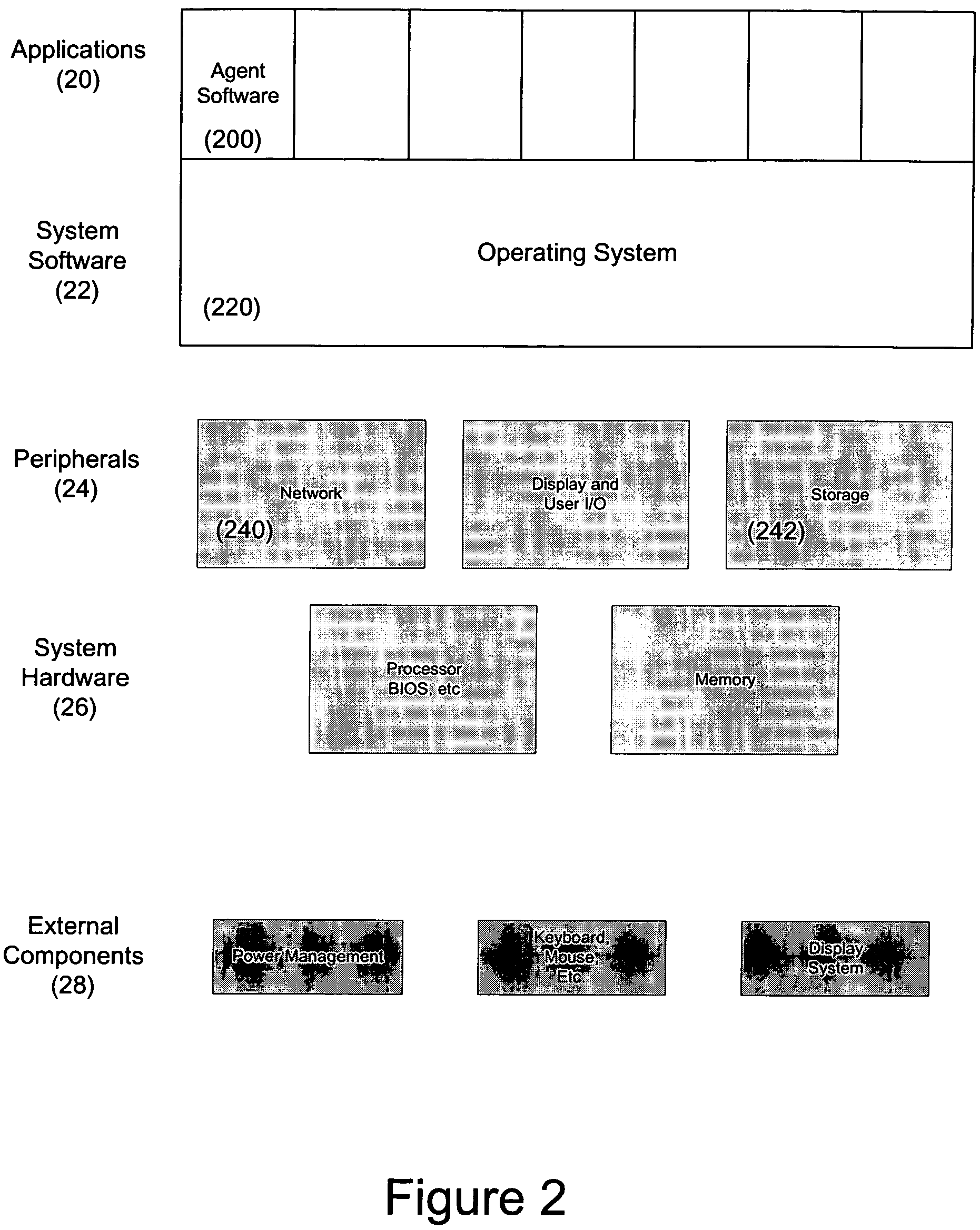
Method and system for maintaining secure data input and output
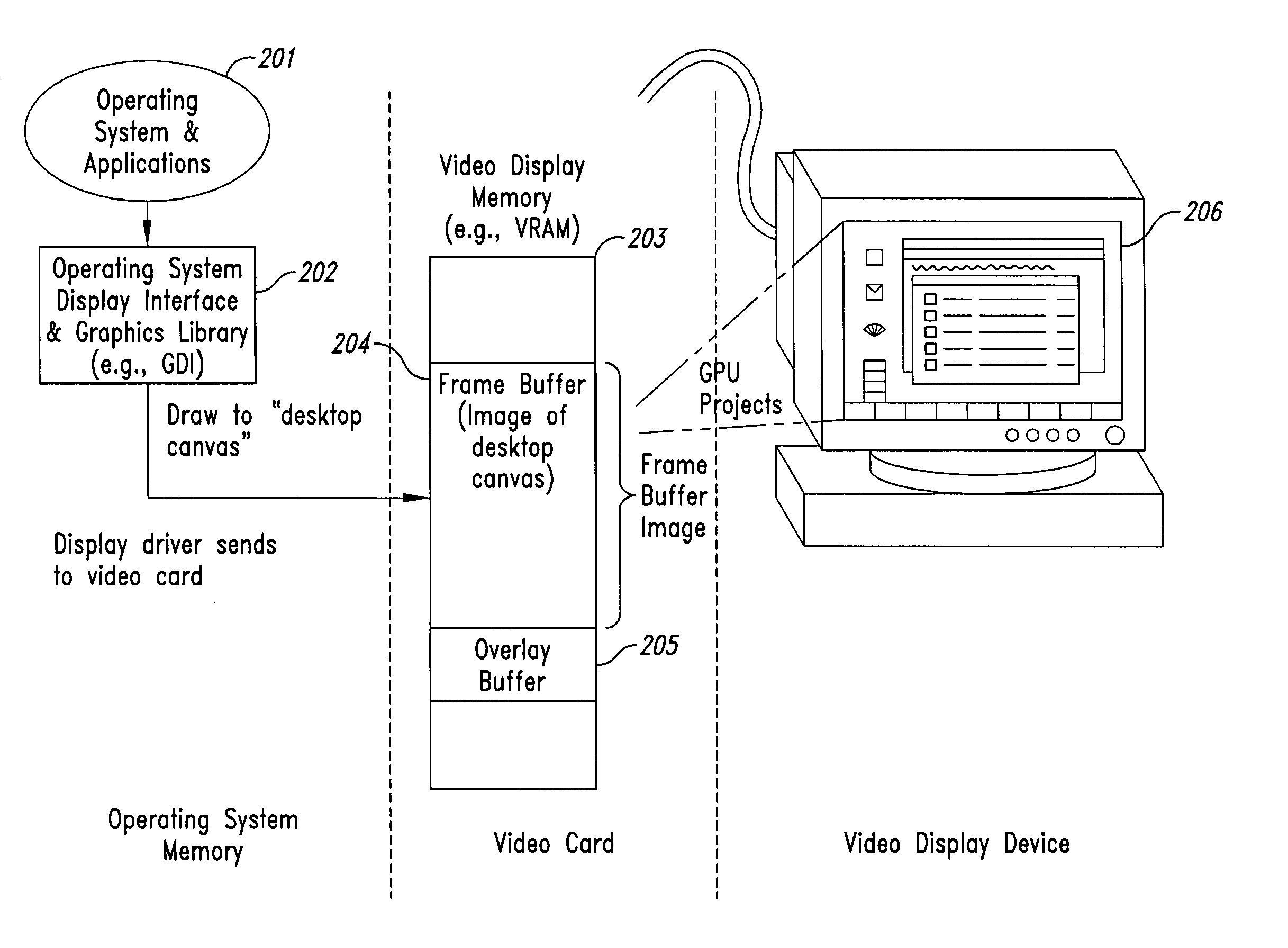
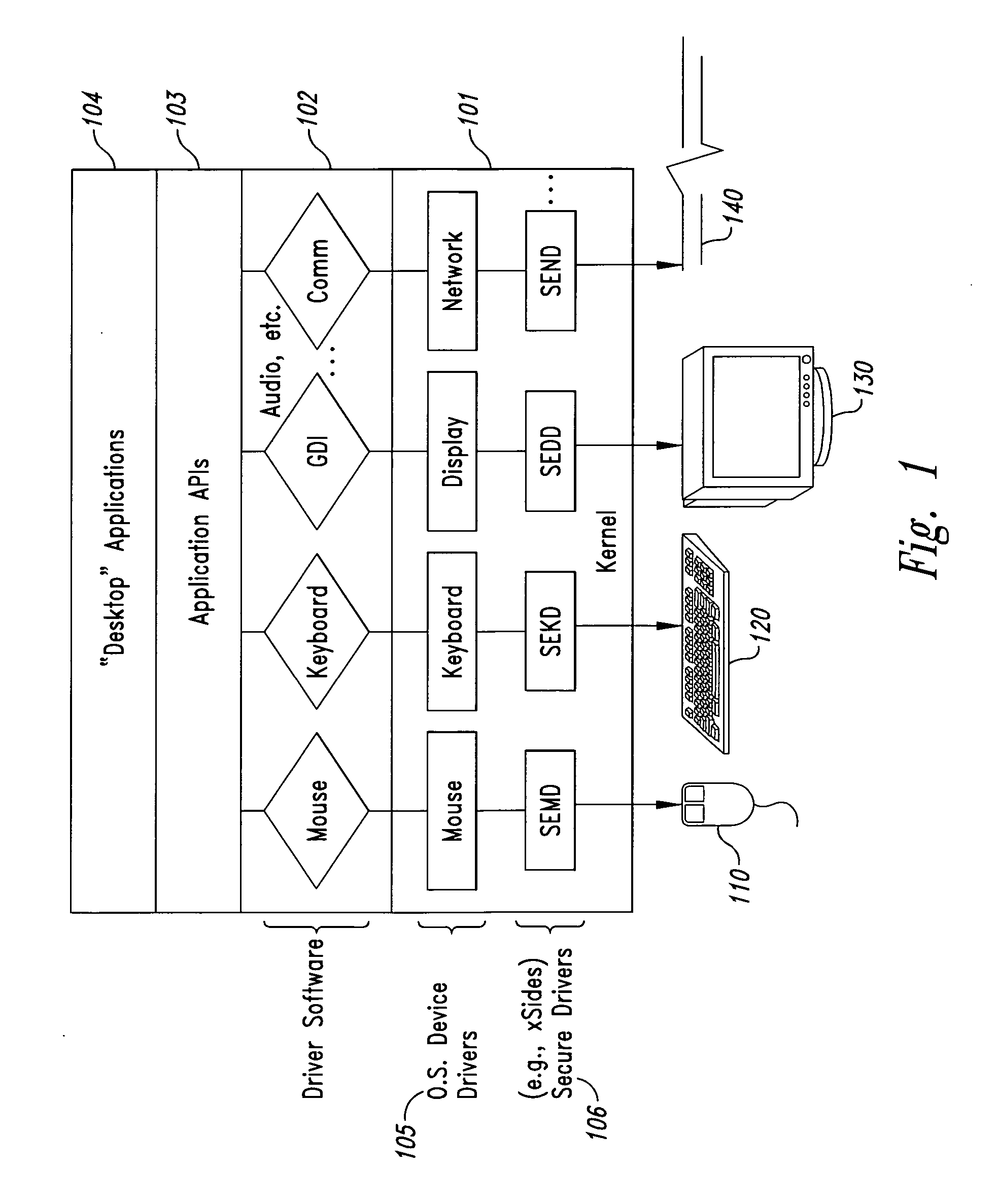
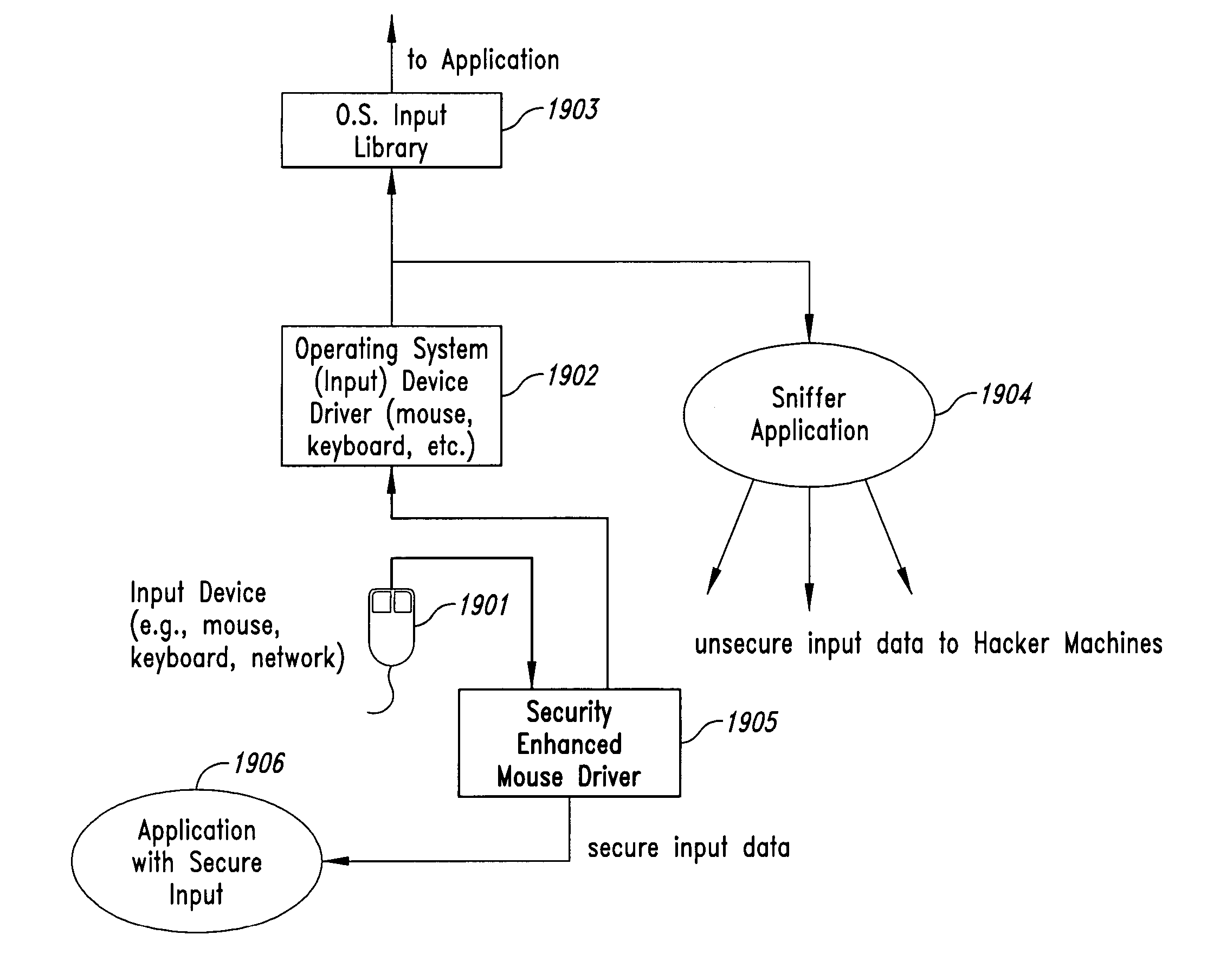
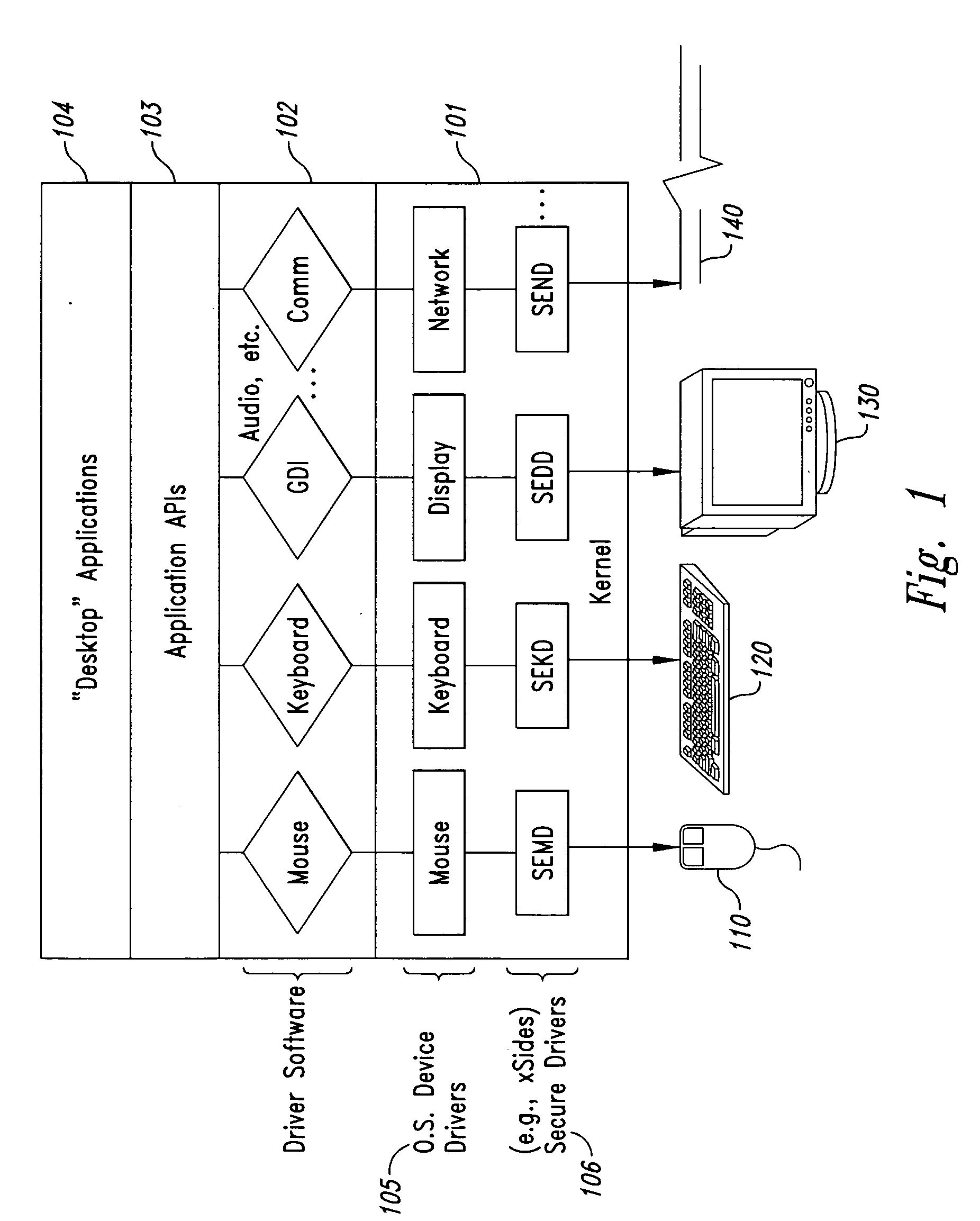
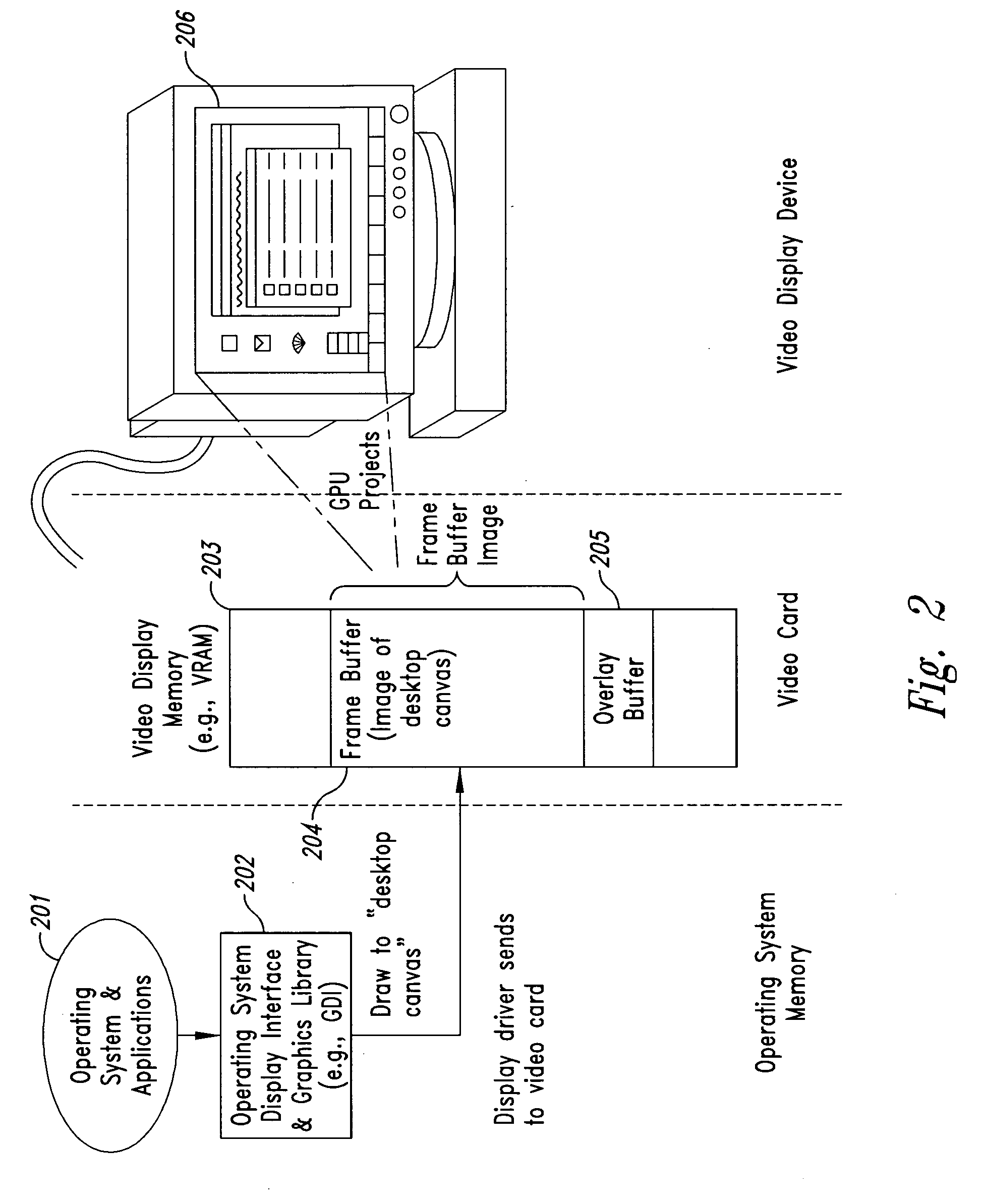
InactiveUS20050102266A1Improve data securityProhibit and frustrate attemptData processing applicationsDigital data processing detailsObfuscationProgram security
Methods and systems for enhancing the security of data during input and output on a client computer system are provided to prevent attempts by unauthorized code to access, intercept, and / or modify data. Example embodiments provide a plurality of obfuscation techniques and security enhanced drivers that use these obfuscation techniques to prohibit unauthorized viewing / receiving of valid data. When the drivers are used together with the various obfuscation techniques, the security enhanced drivers provide mechanisms for “scheduling” the content of the storage areas used to store the data so that valid data is not available to unauthorized recipients. When unauthorized recipients attempt to access the “data,” they perceive or receive obfuscated data. The obfuscation techniques described include “copy-in,”“replace and restore,” and “in-place replacement” de-obfuscation / re-obfuscation techniques. In one embodiment, a security enhanced display driver, a security enhanced mouse driver, a security enhanced keyboard driver, and a security enhanced audio driver are provided. To complement the security enhancements, the methods and systems also provide for a watchdog mechanism to ensure that the driver is functioning as it should be and various user interface techniques for denoting security on a display device.
Owner:XSIDES
System and method for lost data destruction of electronic data stored on a portable electronic device using a security interval
ActiveUS7421589B2Reduces and eliminates riskReduce riskDigital data processing detailsUnauthorized memory use protectionProgram securityBiological activation
Owner:BEACHHEAD SOLUTIONS
Altered Token Sandboxing
ActiveUS20100057774A1Digital data processing detailsUnauthorized memory use protectionProgram securityApplication software
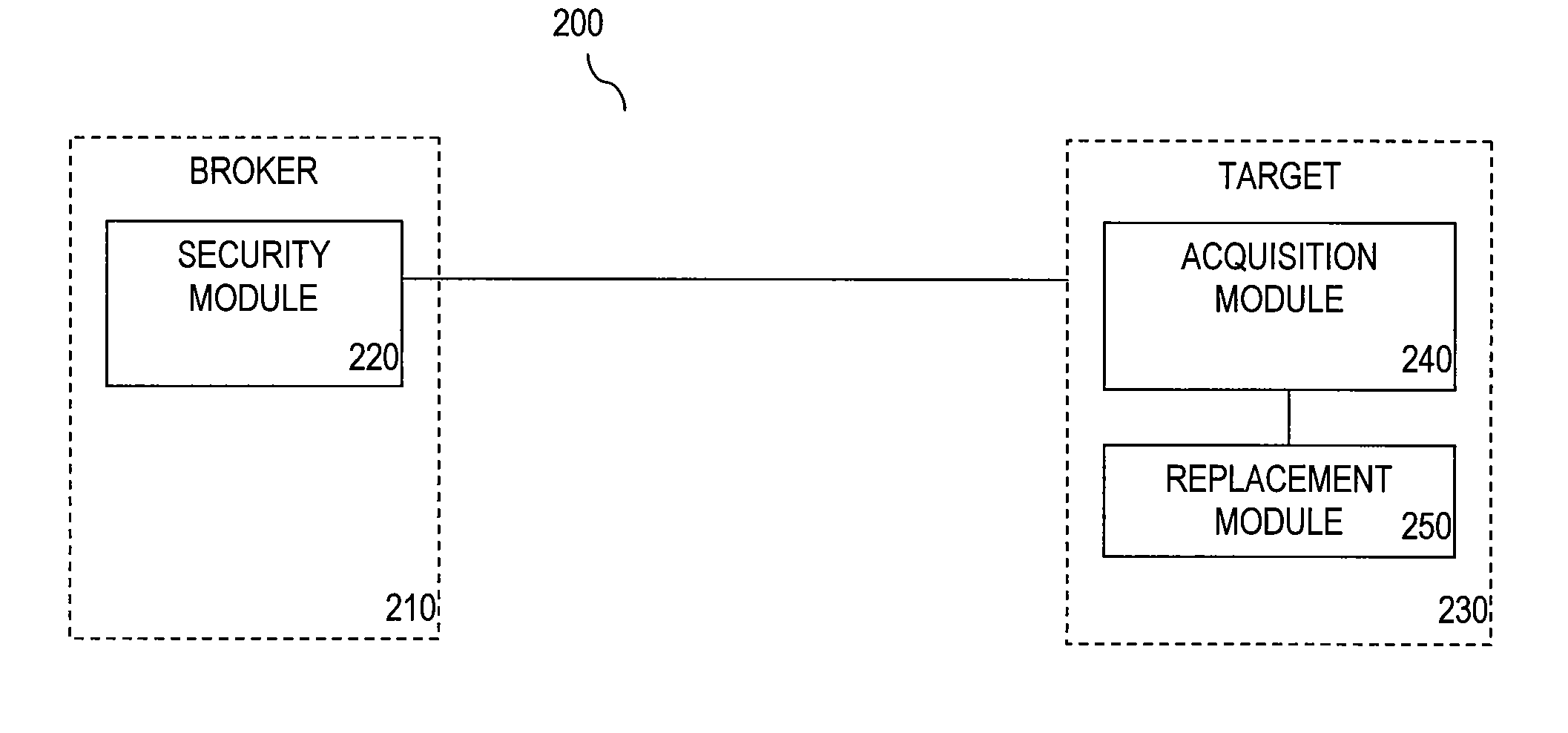
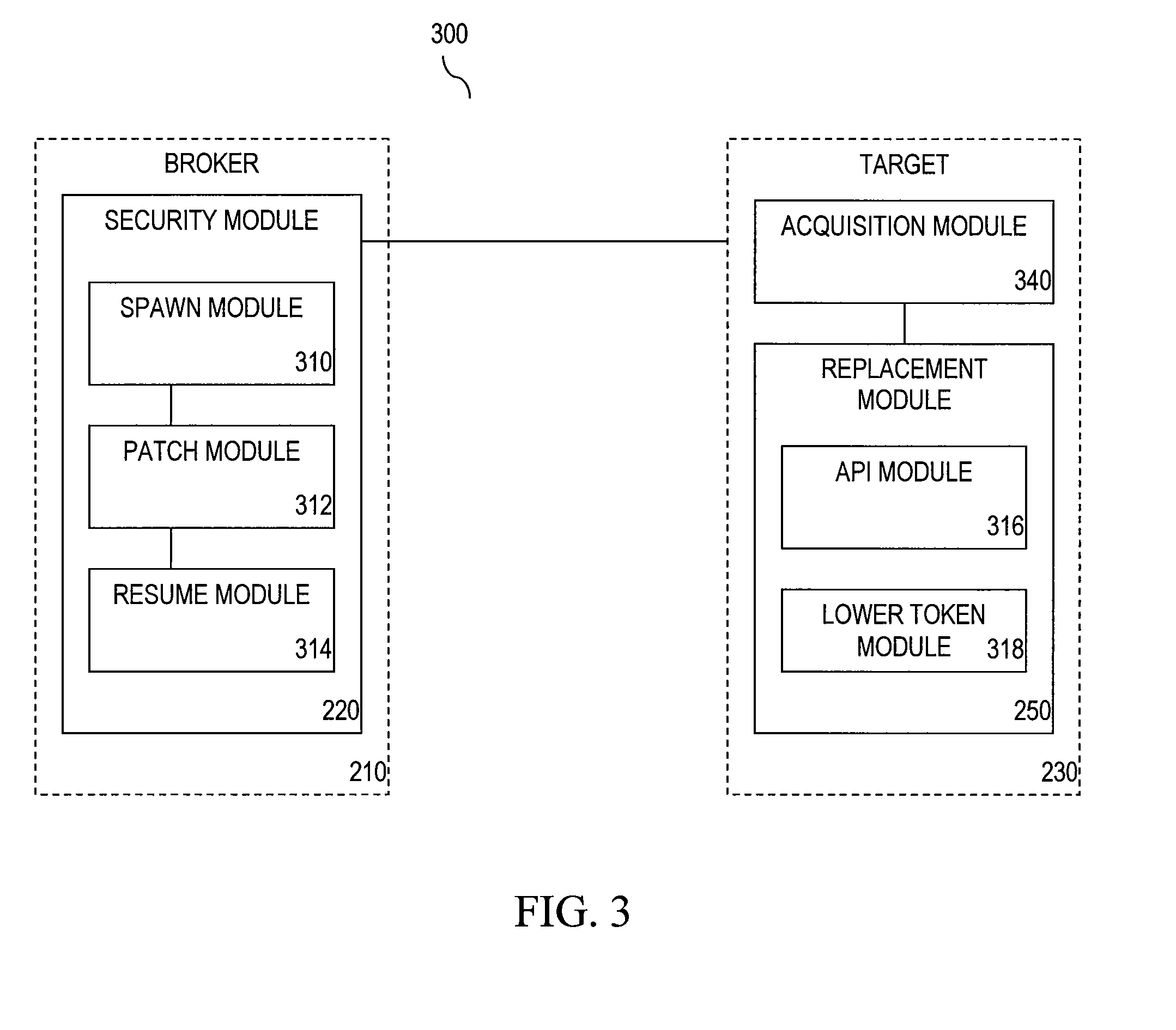
Embodiments of the present invention relate generally to application security. In an embodiment, a method for altered token sandboxing includes creating a process based on a naked token and suspending the process. The method further includes obtaining an impersonation token and resuming the process with the impersonation token. The method further includes acquiring resources needed for the process with the impersonation token. The method also includes replacing the impersonation token with the naked token. In a further embodiment, the method further includes executing the suspended process with the naked token and the acquired resources. In another embodiment, a system for user-mode, altered token sandboxing includes a security module, an acquisition module and a replacement module. In a further embodiment, the system may include an execution module. In another embodiment, the system may include a request module.
Owner:GOOGLE LLC
Method and system for maintaining secure data input and output
InactiveUS20050086666A1Improve data securityProhibit and frustrate attemptData processing applicationsDigital data processing detailsObfuscationProgram security
Methods and systems for enhancing the security of data during input and output on a client computer system are provided to prevent attempts by unauthorized code to access, intercept, and / or modify data. Example embodiments provide a plurality of obfuscation techniques and security enhanced drivers that use these obfuscation techniques to prohibit unauthorized viewing / receiving of valid data. When the drivers are used together with the various obfuscation techniques, the security enhanced drivers provide mechanisms for “scheduling” the content of the storage areas used to store the data so that valid data is not available to unauthorized recipients. When unauthorized recipients attempt to access the “data,” they perceive or receive obfuscated data. The obfuscation techniques described include “copy-in,”“replace and restore,” and “in-place replacement” de-obfuscation / re-obfuscation techniques. In one embodiment, a security enhanced display driver, a security enhanced mouse driver, a security enhanced keyboard driver, and a security enhanced audio driver are provided. To complement the security enhancements, the methods and systems also provide for a watchdog mechanism to ensure that the driver is functioning as it should be and various user interface techniques for denoting security on a display device.
Owner:XSIDES
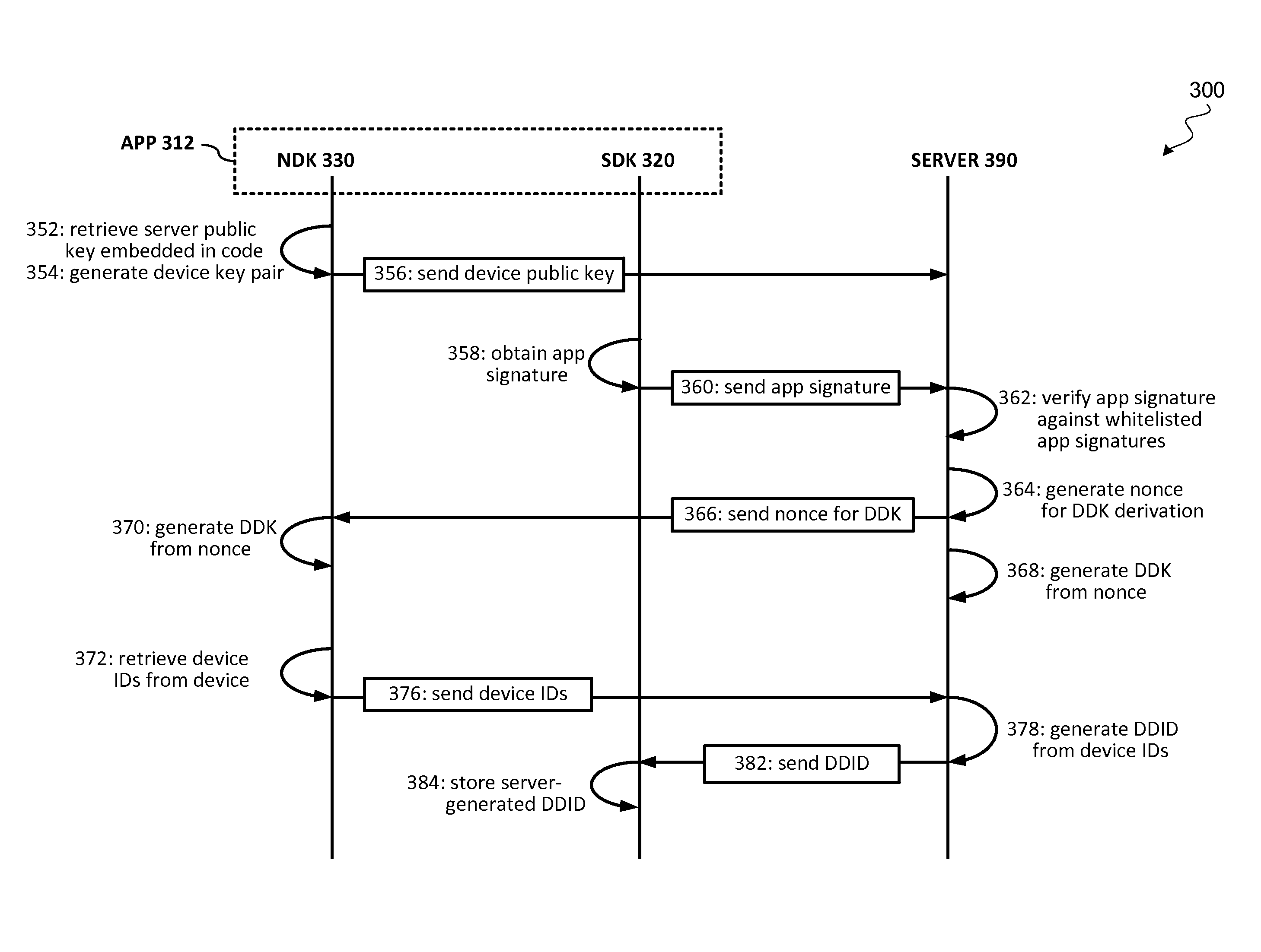
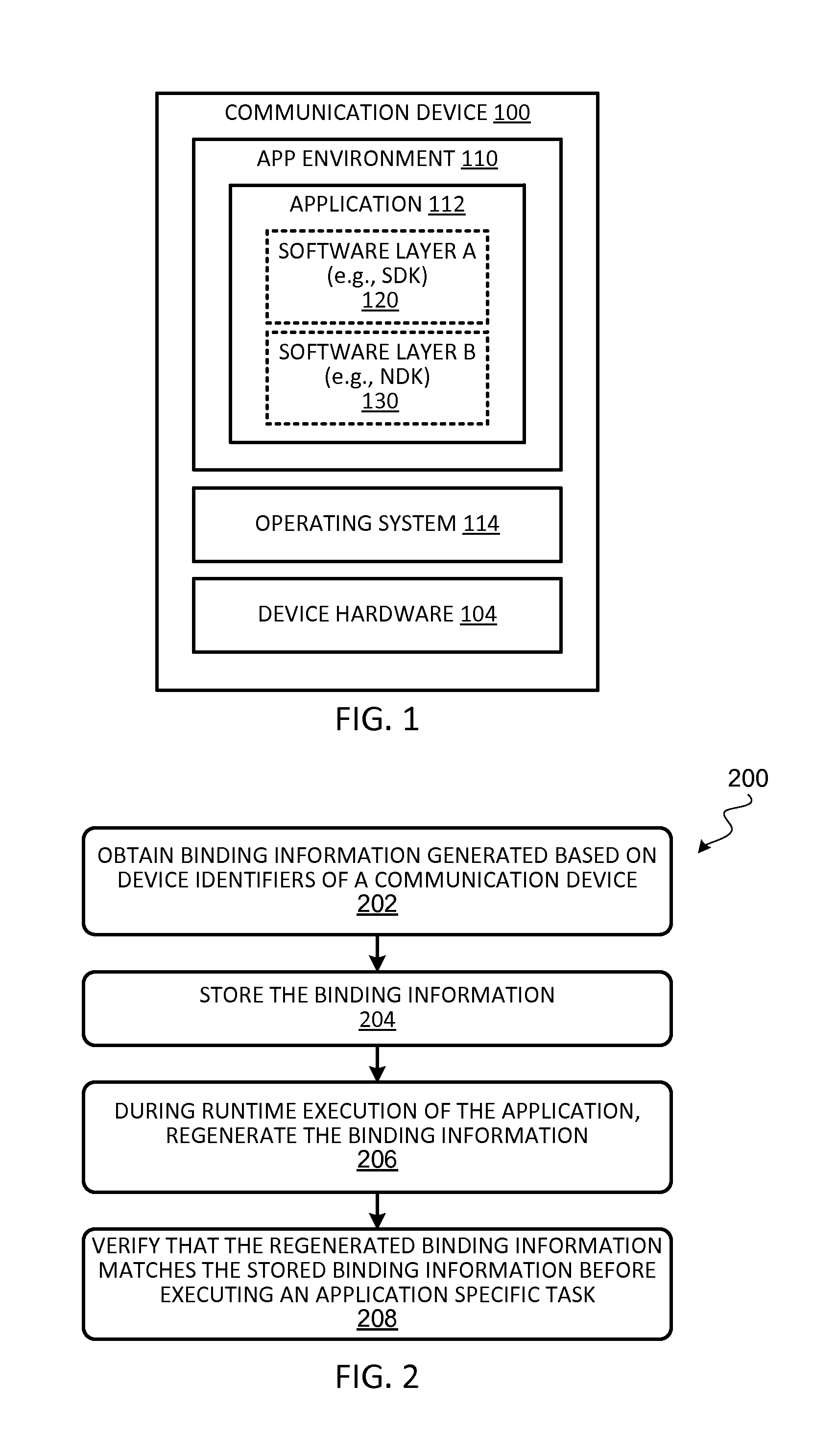
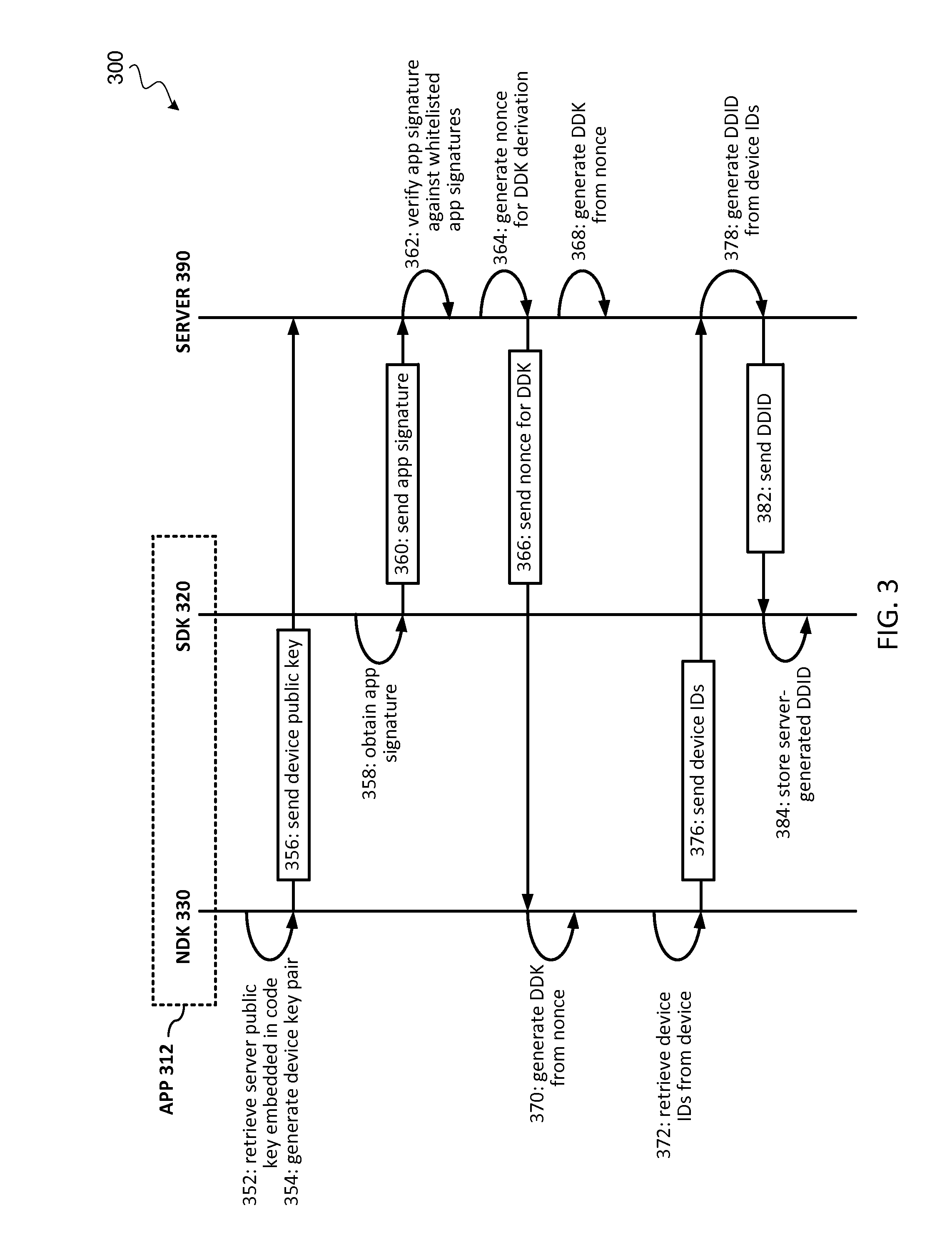
Secure binding of software application to communication device
ActiveUS20170063975A1Preventing executionProgram initiation/switchingInternal/peripheral component protectionProgram securityApplication specific
Techniques for securely binding a software application to a communication device may include sending a set of device identifiers associated with the computing device to a server, receiving a server-generated dynamic device identifier that is generated based on the set of device identifiers; and storing the server-generated dynamic device identifier during initialization of the application. During runtime execution of the application, the application may receive a request to execute an application specific task. In response to receiving the request, the application may generate a runtime dynamic device identifier, determine whether the runtime dynamic device identifier matches the server-generated dynamic device identifier, execute the application specific task when the runtime dynamic device identifier matches the server-generated dynamic device identifier; and prevent the application specific task from being executed when the runtime dynamic device identifier does not match the server-generated dynamic device identifier.
Owner:VISA INT SERVICE ASSOC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com