Method and system for maintaining secure data input and output
a data input and data security technology, applied in the field of methods and systems for maintaining the security of data, can solve problems such as invalid data when accessed, and achieve the effect of enhancing the security of data during input, prohibiting and/or faking attempts by illegitimate processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
case 4
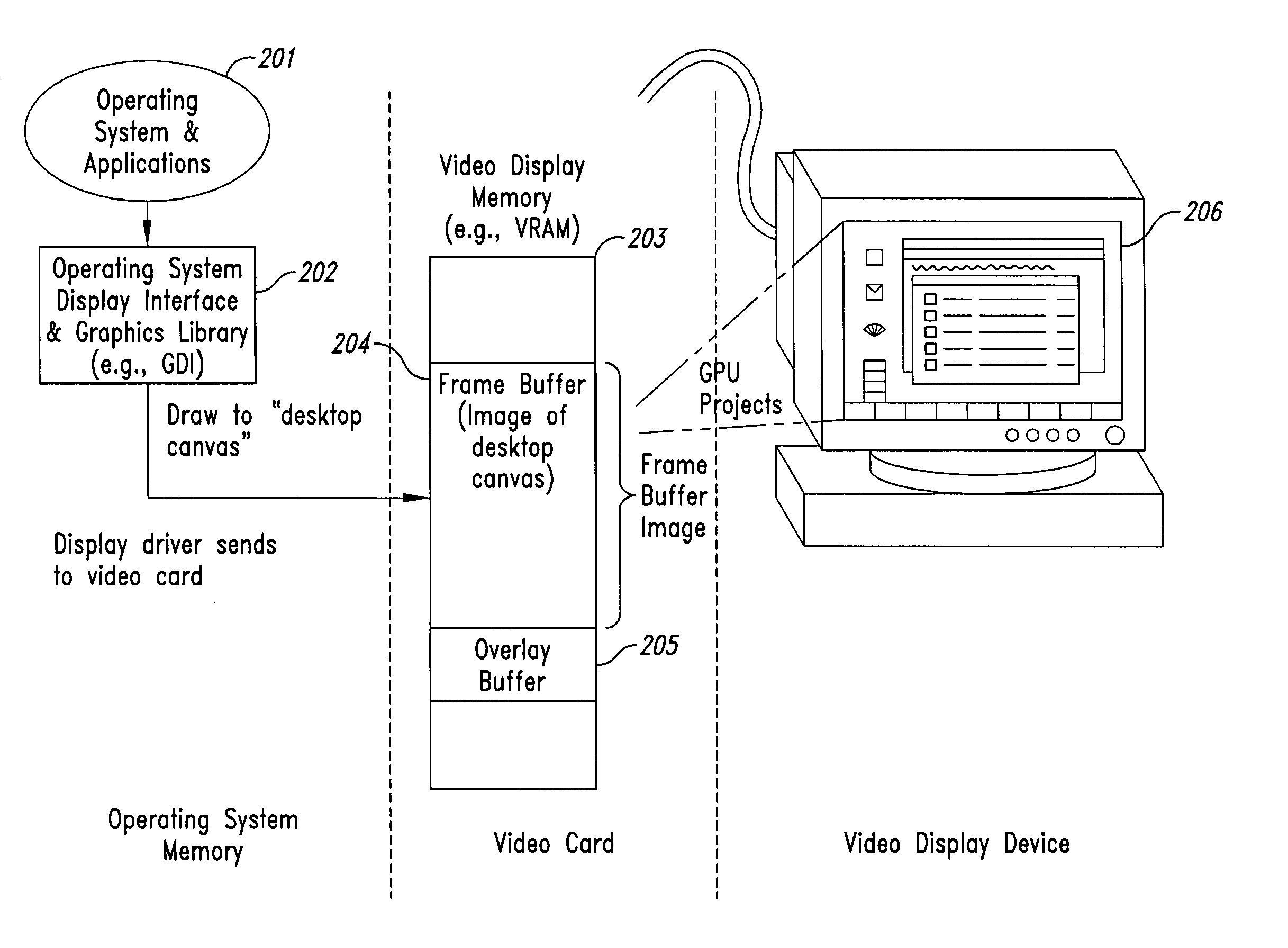
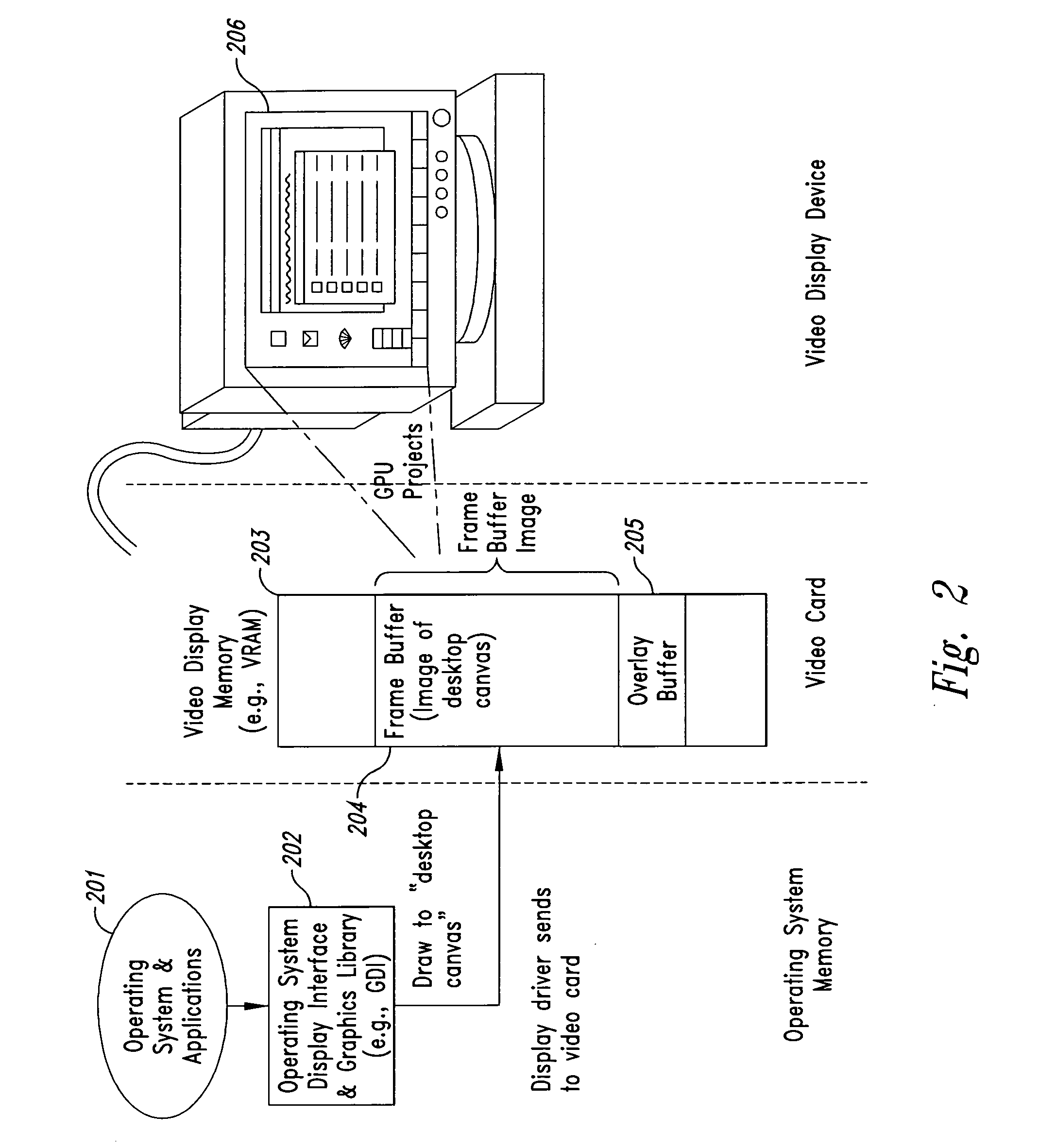
[0059] In Case 4, valid data is only stored in a more secure form (such as stored as encrypted or masked data) in secure data buffer (SDB) 805. This same encrypted or masked data (since it is “obfuscated” data) is used as the invalid data to be copied in to the secure portion of the FB when obfuscated data is to replace the valid data in the frame buffer. A mask or key is stored in mask buffer (MB) 804 to be used by the SEDD to decrypt or de-mask the secure data stored in SDB 805. Thus, the SEDD, at an appropriate time prior to the time when the contents of the secure portion 802 needs to be valid for projection, creates valid data to copy in from the SDB 805 by applying (decrypting or de-masking) a key or mask from the MB 804 to the secure data stored in the SDB 805, and copies out the result (valid data) to the secure portion of the FB 802. Similarly, after the valid data stored in the secure portion 802 has been scanned and copied out for projection (or thereabouts), the SEDD cop...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com