Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
275 results about "Security enhancement" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Security enhancements of digital watermarks for multi-media content
InactiveUS20060239501A1Reliable methodLow costUser identity/authority verificationSpeech analysisTheoretical computer scienceSecurity enhancement
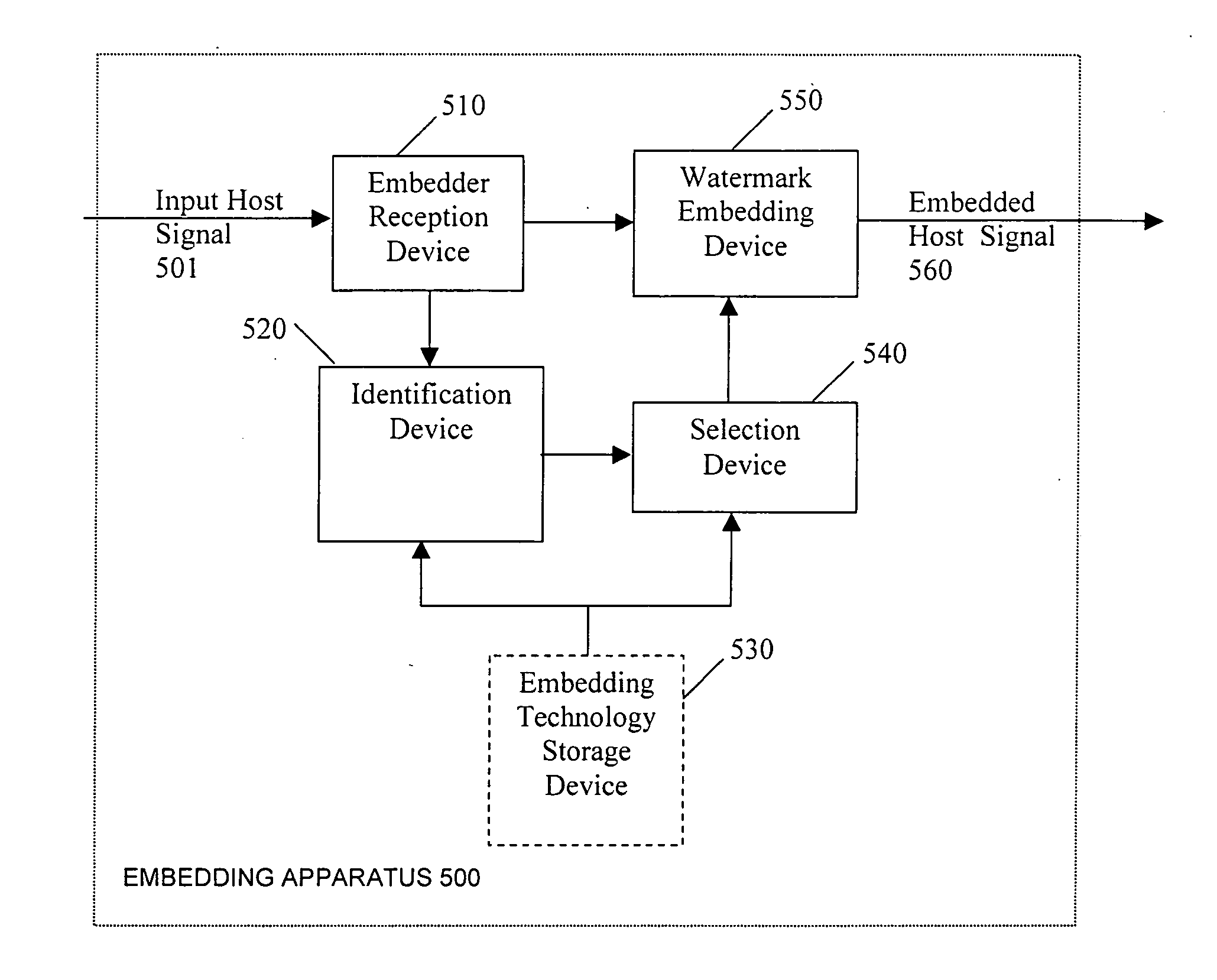
Methods and apparatus for embedding digital watermarks into a digital host content are provided. A digital host content is received, e.g., at a receiver or other device incorporating a receiver. One or more watermark embedding technologies is selected. Multiple embedding opportunities are identified within the host content. A subset of the identified embedding opportunities is selected. A multiplicity of digital watermarks are then embedded into the host content in accordance with the selected subset of embedding opportunities utilizing the one or more selected watermark embedding technologies. The selecting of the subset of embedding opportunities may be adapted to provide a desired tradeoff between levels of robustness, security, and transparency of the watermark. A plurality of watermarking embedding technologies may be selected and used in the embedding step.
Owner:VERANCE
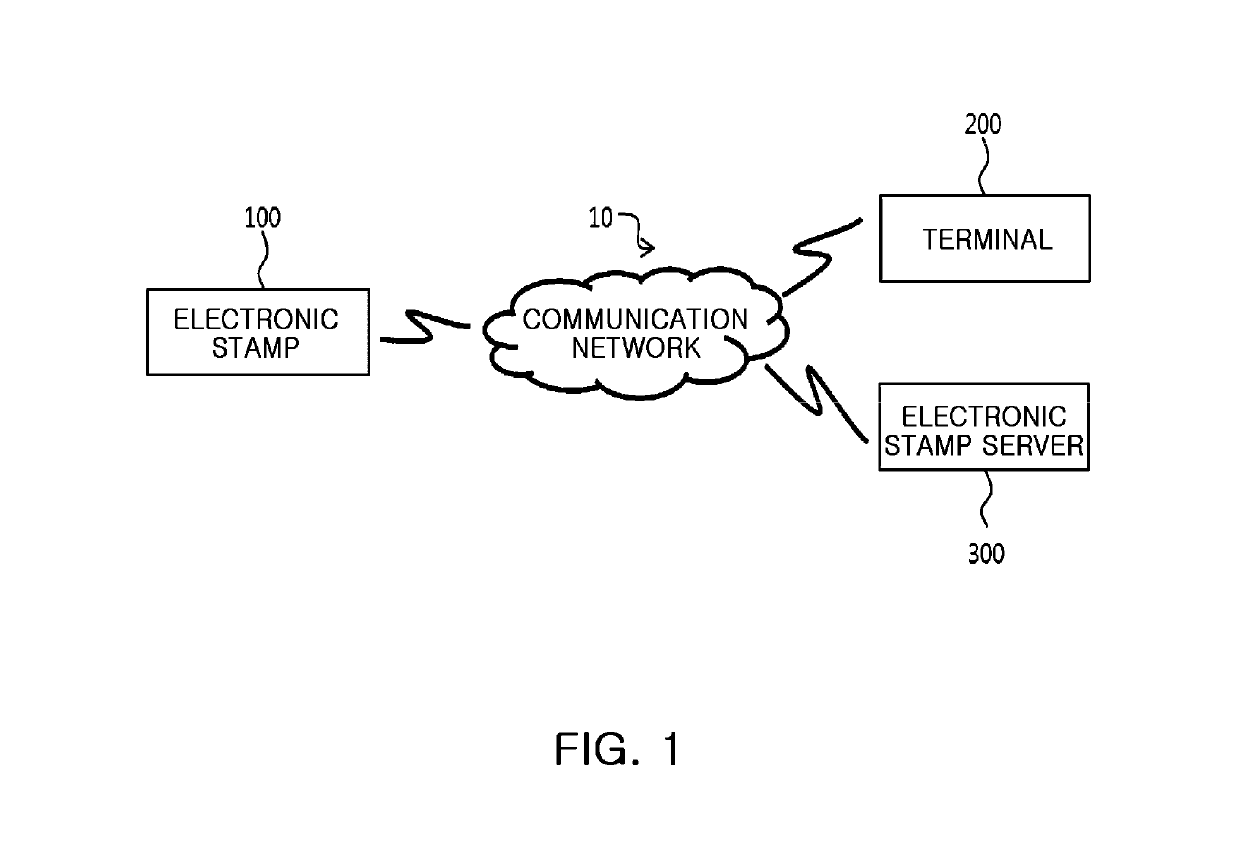
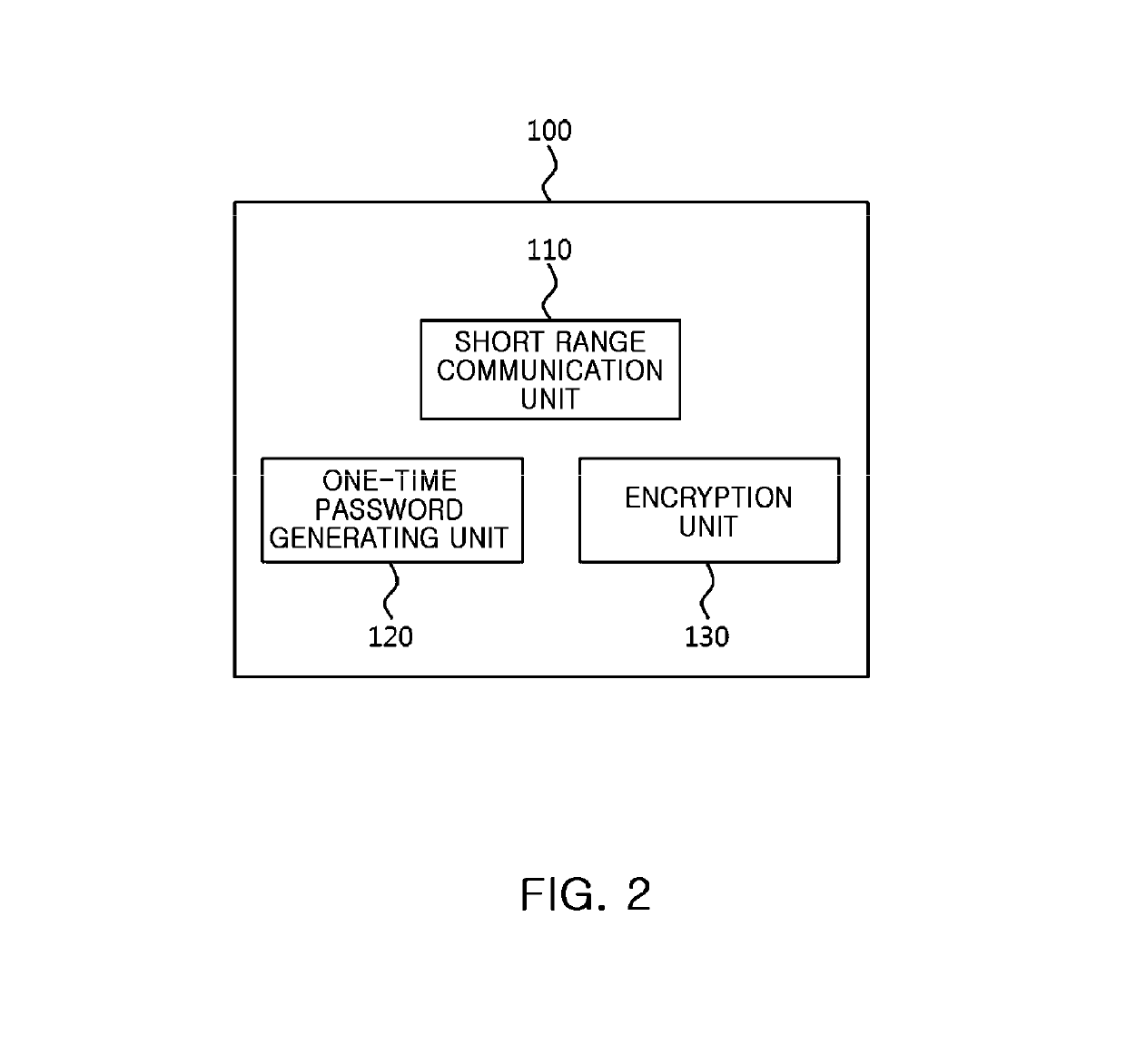
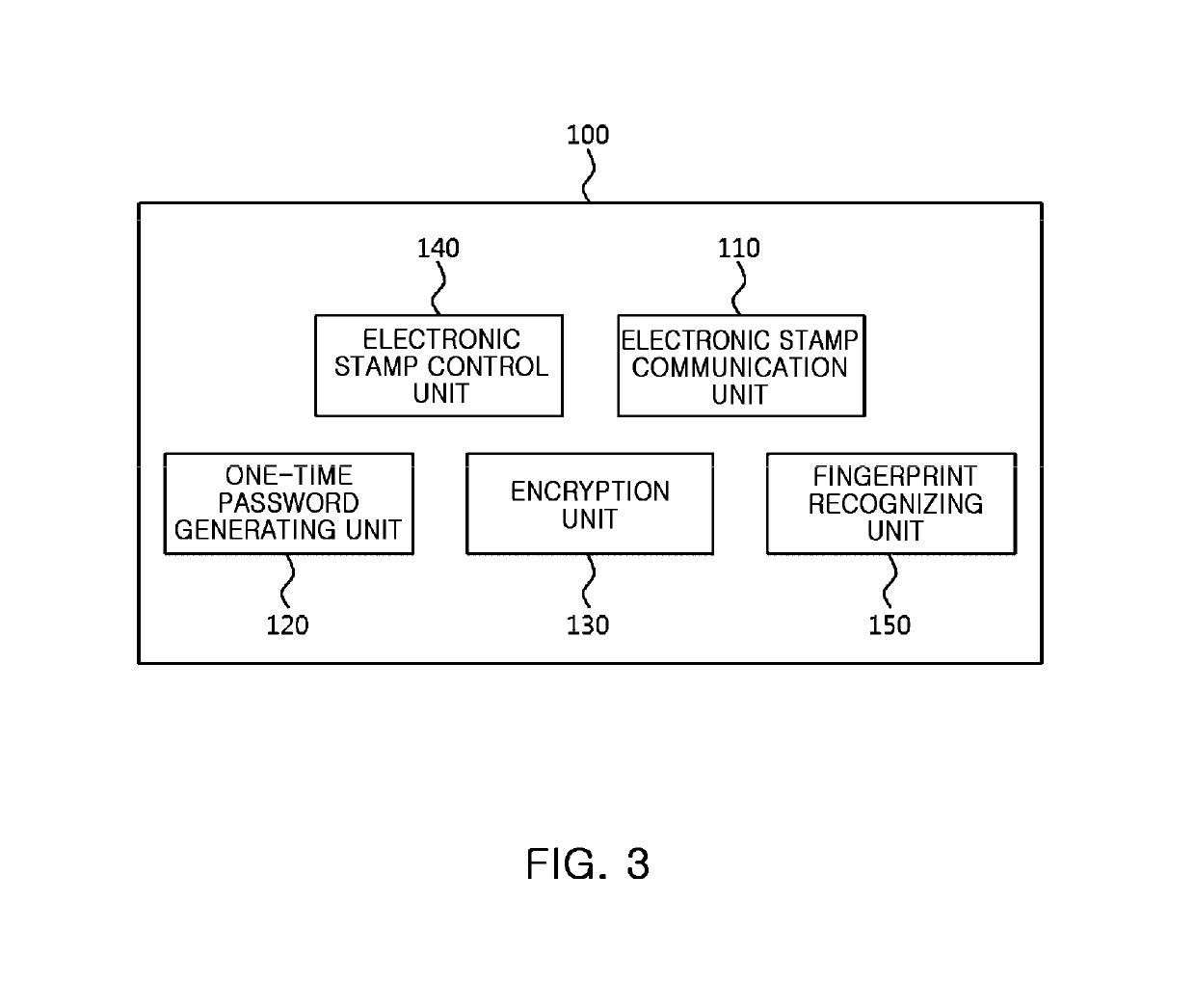
Electronic stamp system for security intensification, control method thereof, and non-transitory computer readable storage medium having computer program recorded thereon
ActiveUS10361857B2Key distribution for secure communicationDiscounts/incentivesComputer hardwareOne-time password
Provided are an electronic stamp system for security intensification, a control method thereof, and a non-transitory computer readable storage medium having a computer program recorded thereon. According to the invention, it is possible to generate an encrypted value based on a membership ID related to a user of a terminal provided from the terminal and an one-time password such as an OTP generated in the electronic stamp and provide the generated encrypted value to the terminal in the electronic stamp, provide the membership ID, electronic stamp information, and the encrypted value to an electronic stamp server from the terminal, and obtain a decryption key based on the electronic stamp ID extracted from the electronic stamp information and then decrypts the encrypted value based on the obtained decryption key, and verify authenticity of the electronic stamp by comparing the decrypted value and the membership ID in the electronic stamp server.
Owner:SK PLANET CO LTD
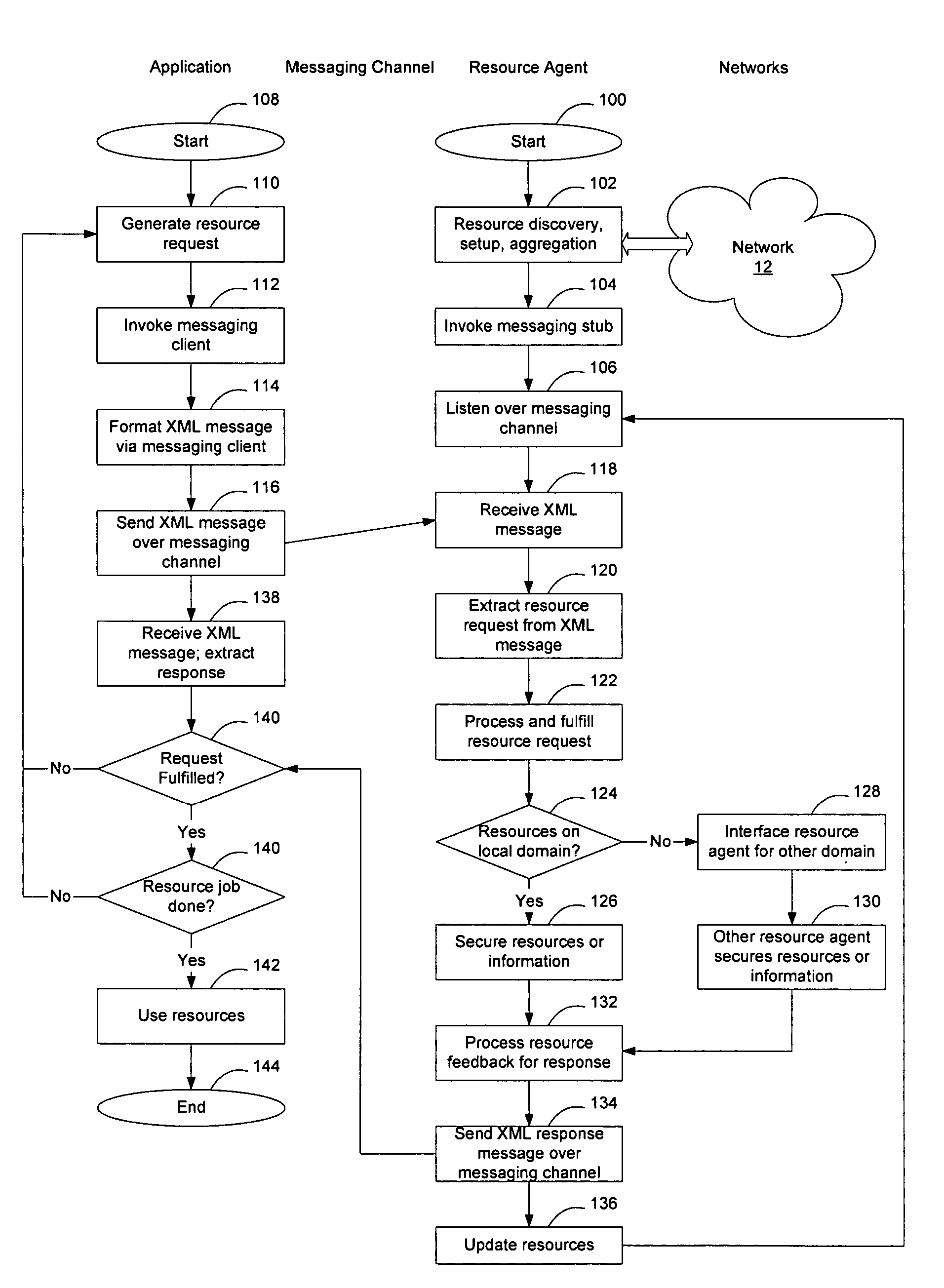
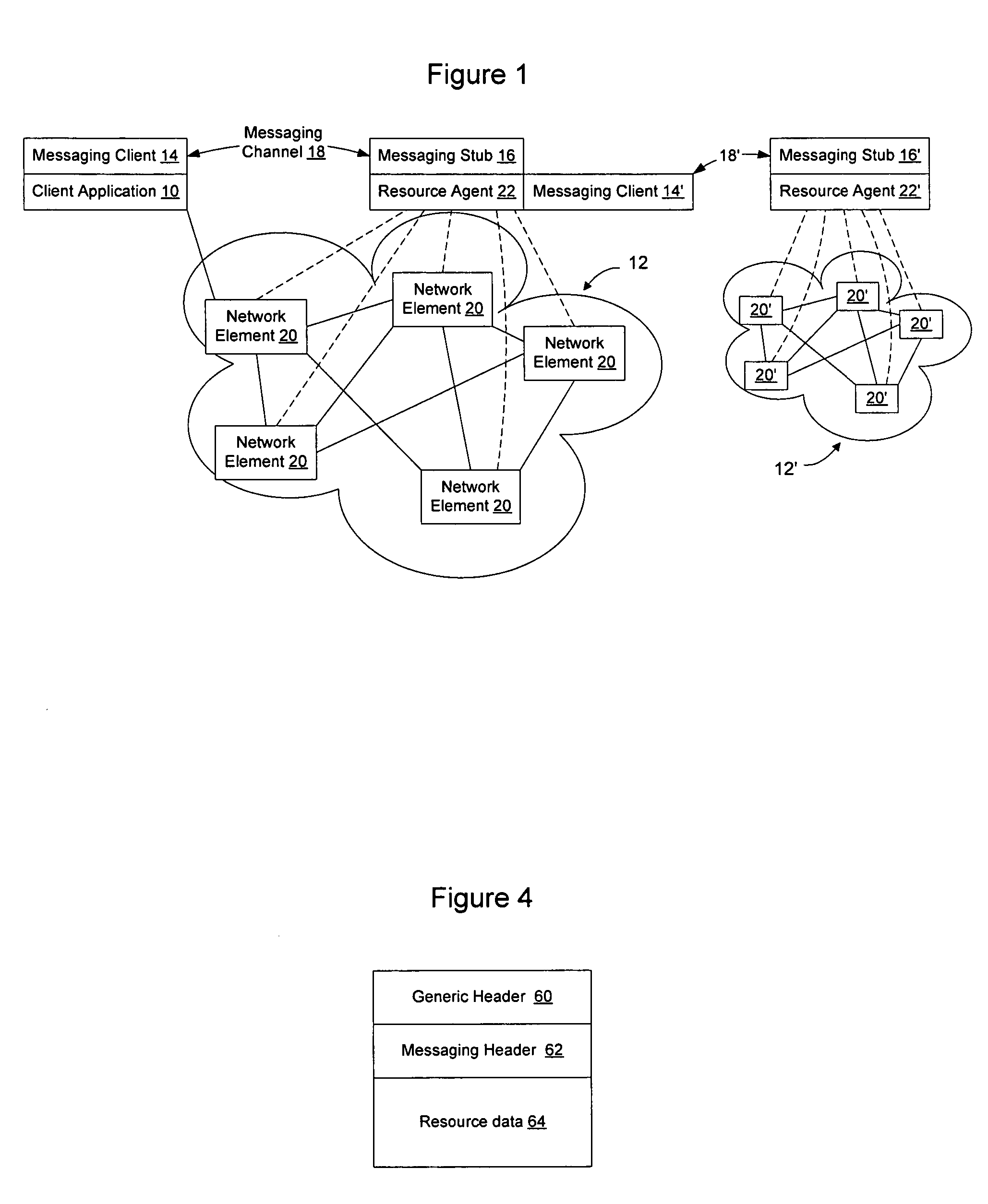
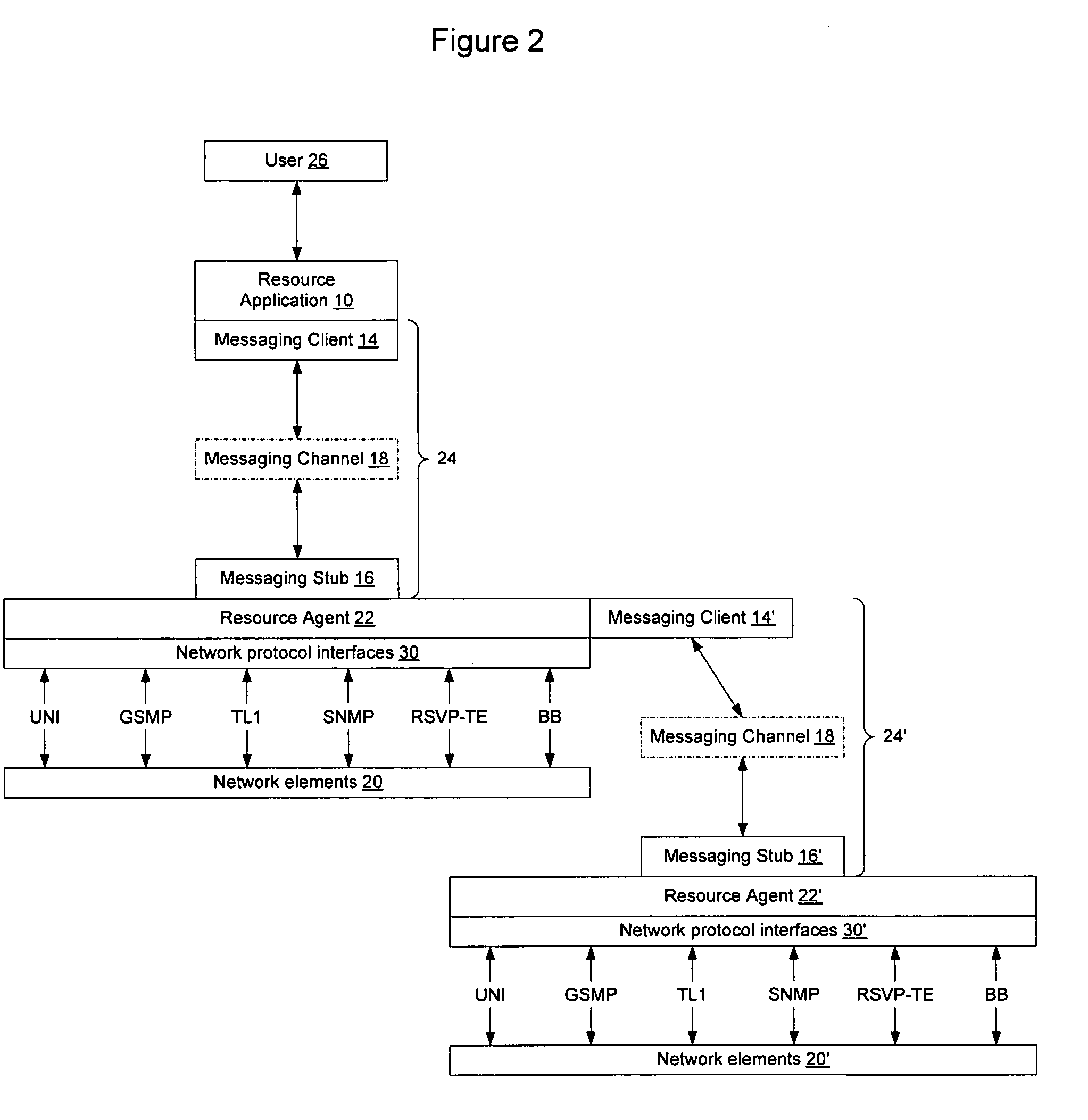
Extensible resource messaging between user applications and network elements in a communication network
InactiveUS20060075042A1Easily use new network resourceAvoid resourcesMultiple digital computer combinationsTransmissionXML schemaMessage passing
Extensible resource messaging in a communication network is provided through creation of a flexible, extensible, and secure messaging environment. A client-server architecture may be implemented in which user applications employ messaging clients to send resource requests for network information, allocation and other operations and receive resource responses, and in which network elements, through resource agents, may use messaging servers to accept resource requests and return resource responses. Resource agents in different network domains may interact through the messaging environment and work together to fulfill resource requests. An XML-based messaging mechanism may be built with a defined message format that can provide flexible message contexts. Network resource semantics may be specified using XML schemas so that network resources are expressed as resource-specific XML elements and network updates can be implemented by updating the XML resource schemas. Secure enhancements may be realized by secure transport, message verification and other means.
Owner:NORTEL NETWORKS LTD
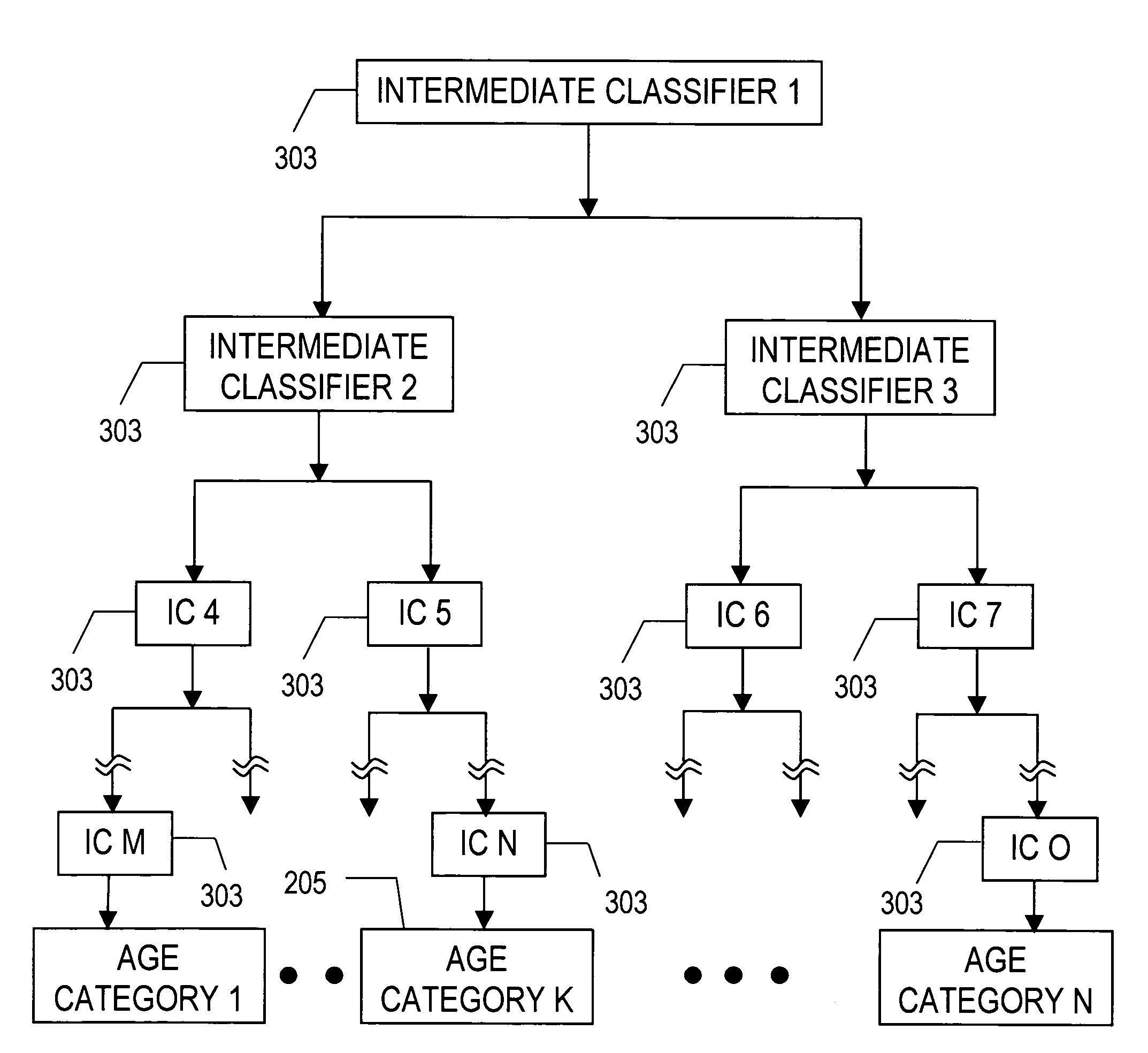
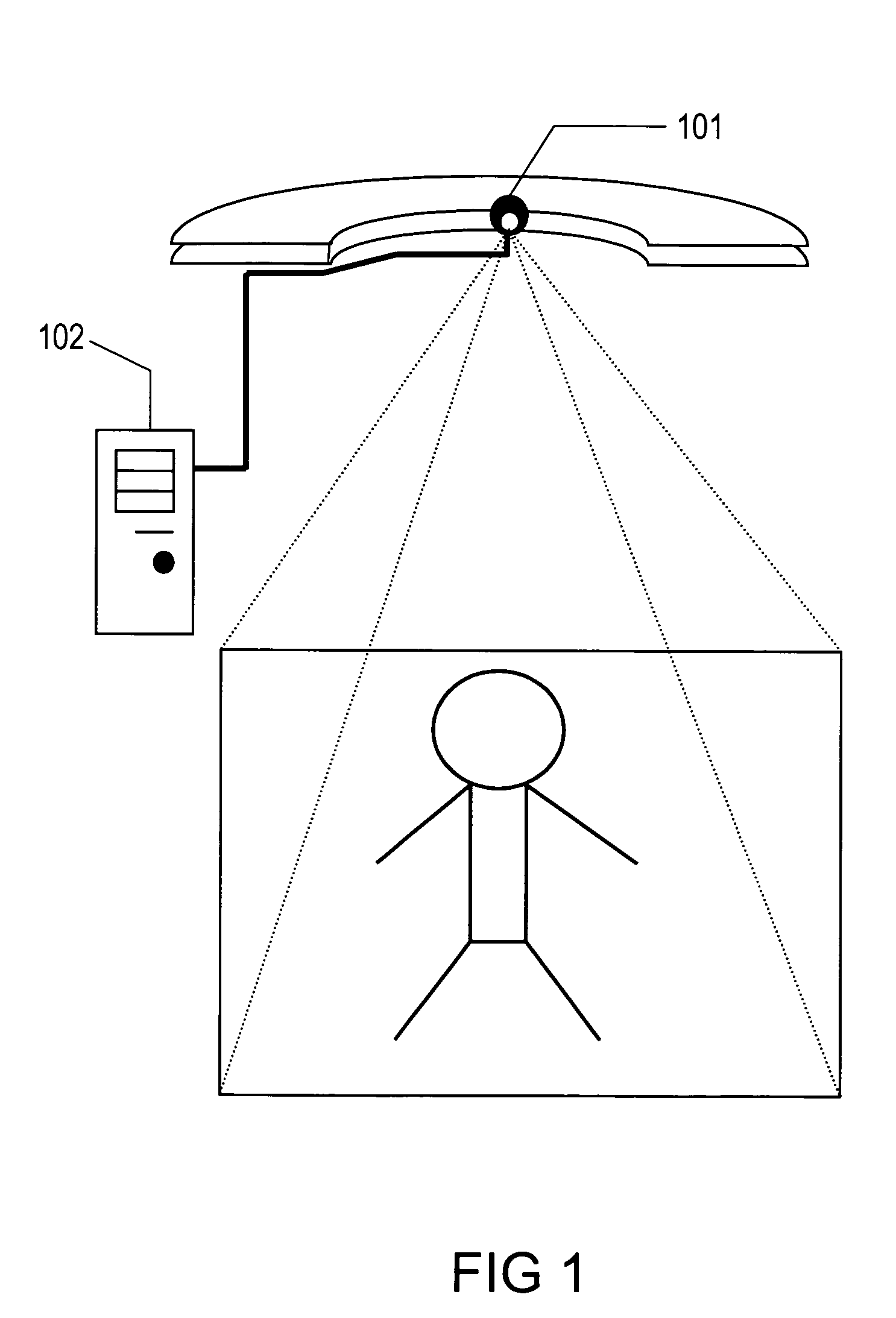
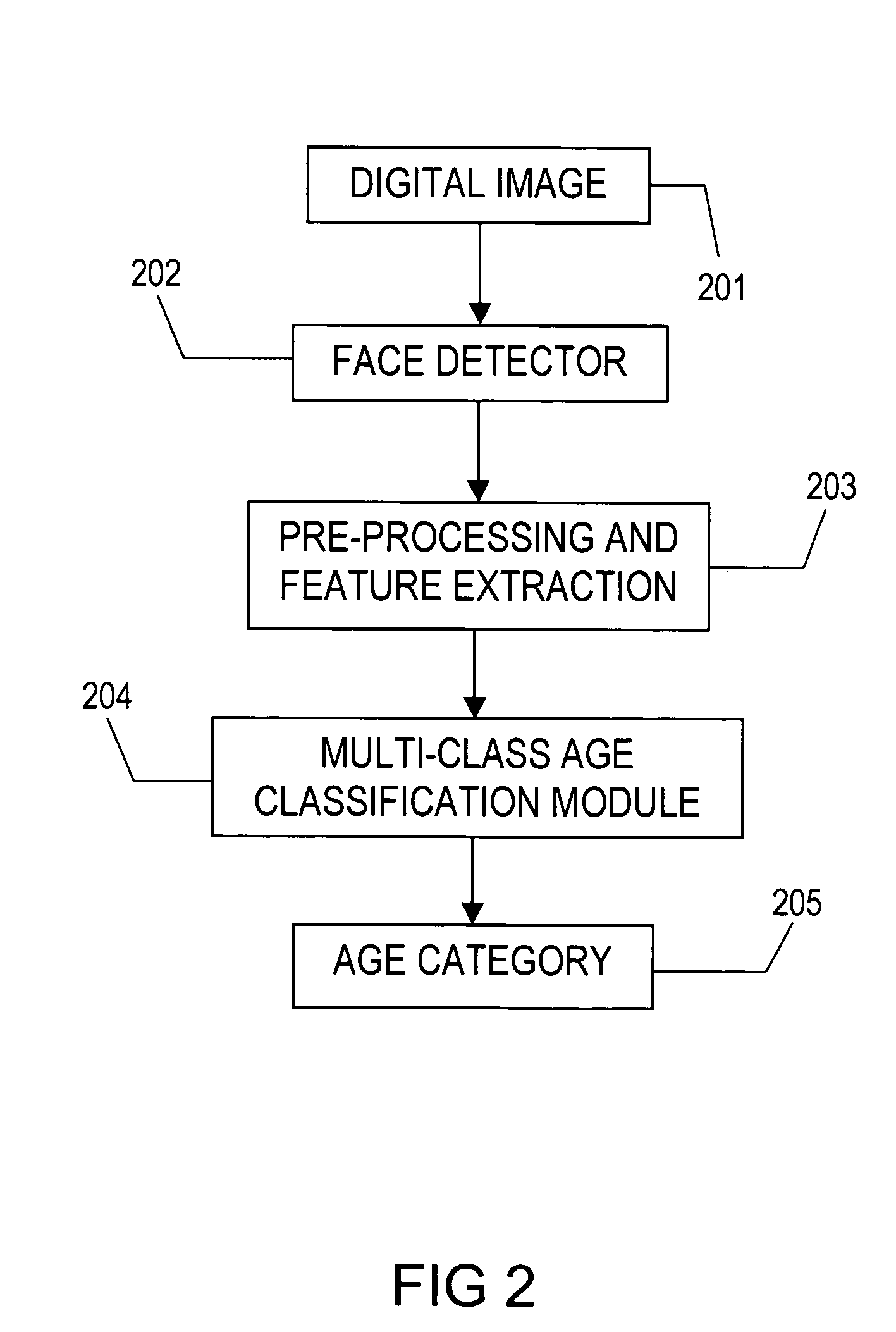
Classification of humans into multiple age categories from digital images
The present invention includes a method and system for automatically extracting the multi-class age category information of a person from digital images. The system detects the face of the person(s) in an image, extracts features from the face(s), and then classifies into one of the multiple age categories. Using appearance information from the entire face gives better results as compared to currently known techniques. Moreover, the described technique can be used to extract age category information in more robust manner than currently known methods, in environments with a high degree of variability in illumination, pose and presence of occlusion. Besides use as an automated data collection system wherein given the necessary facial information as the data, the age category of the person is determined automatically, the method could also be used for targeting certain age-groups in advertisements, surveillance, human computer interaction, security enhancements and immersive computer games.
Owner:VIDEOMINING CORP
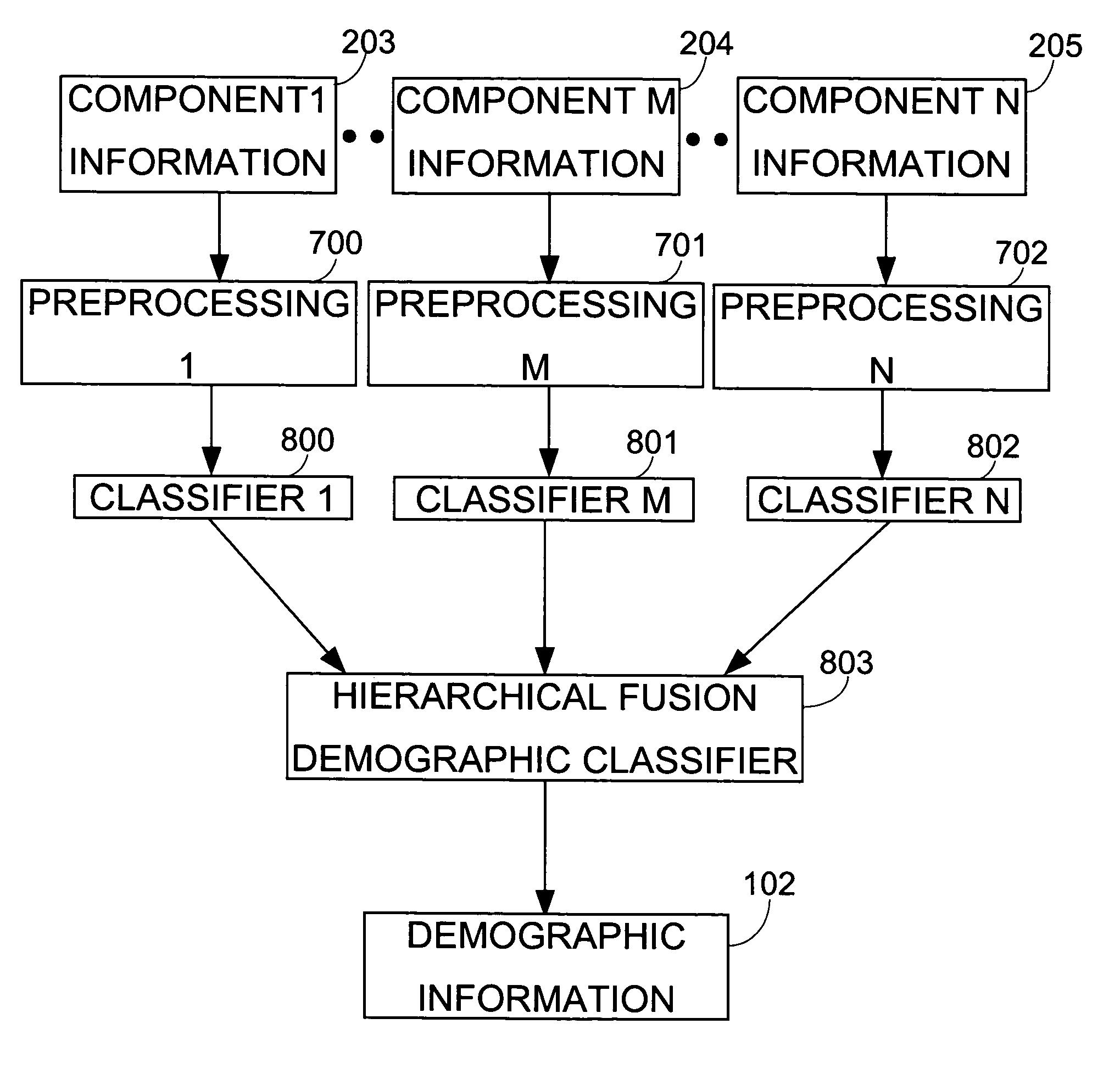
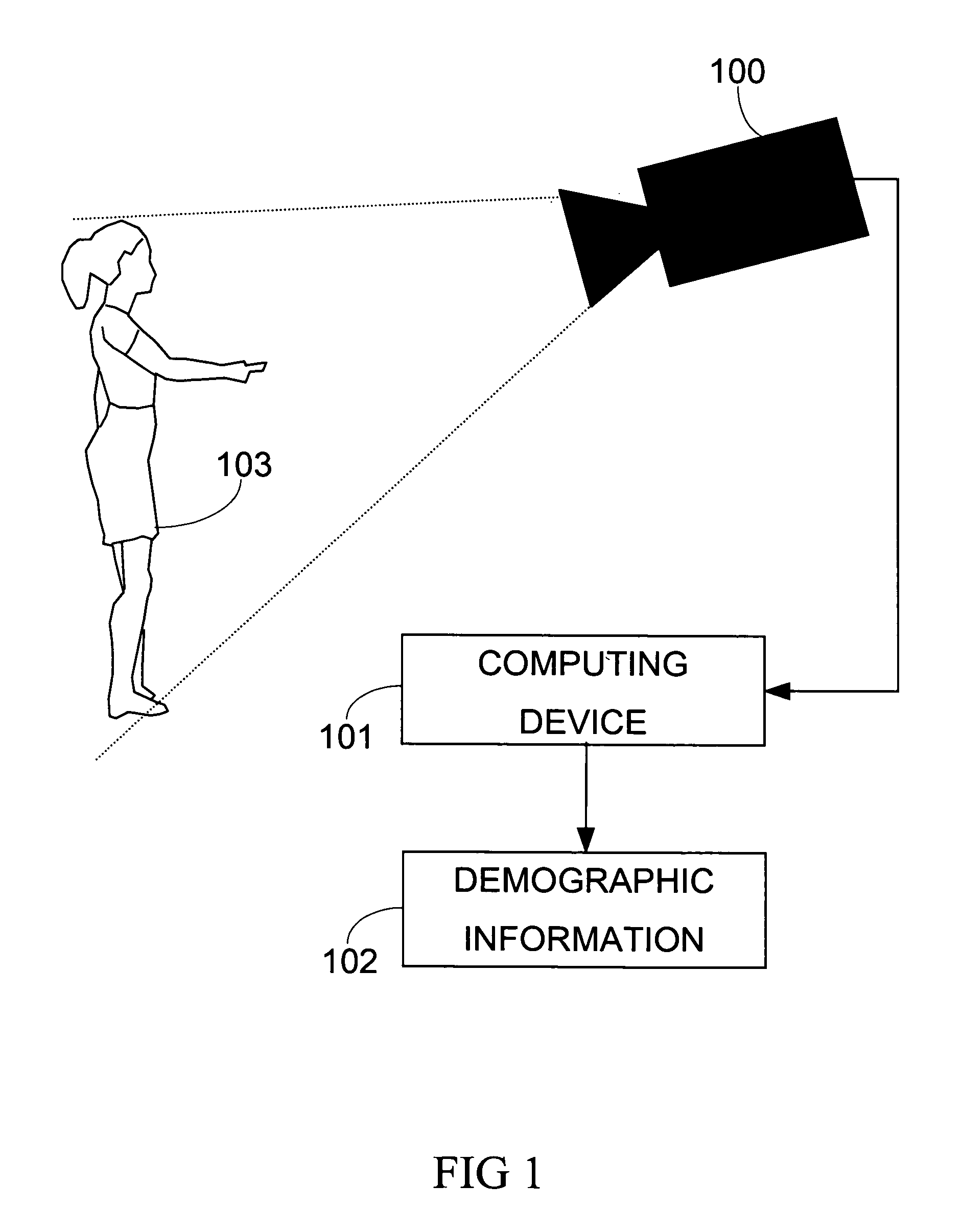
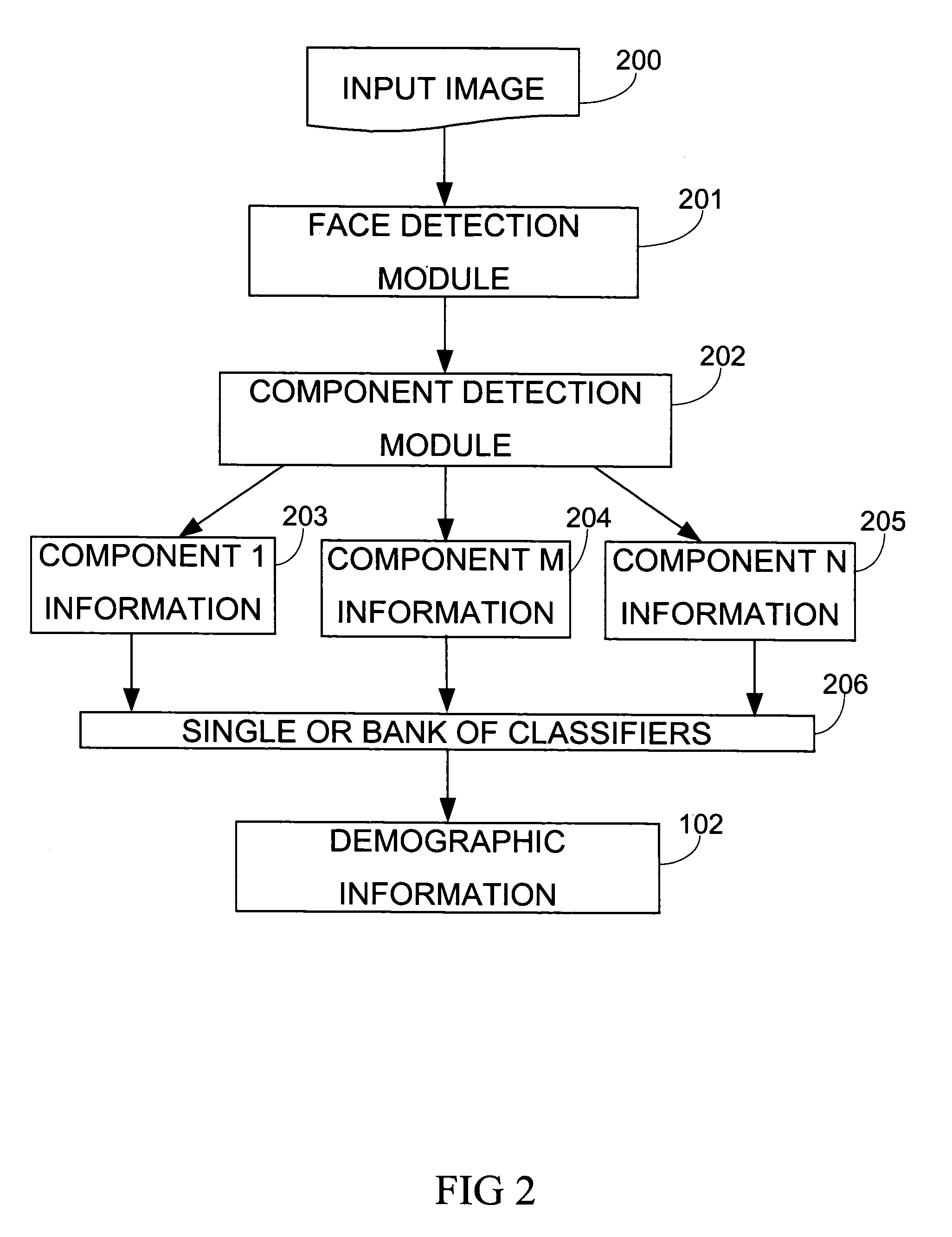
Demographic classification using image components
The present invention includes a system and method for automatically extracting the demographic information from images. The system detects the face in an image, locates different components, extracts component features, and then classifies the components to identify the age, gender, or ethnicity of the person(s) in the image. Using components for demographic classification gives better results as compared to currently known techniques. Moreover, the described system and technique can be used to extract demographic information in more robust manner than currently known methods, in environments where high degree of variability in size, shape, color, texture, pose, and occlusion exists. This invention also performs classifier fusion using Data Level fusion and Multi-level classification for fusing results of various component demographic classifiers. Besides use as an automated data collection system wherein given the necessary facial information as the data, the demographic category of the person is determined automatically, the system could also be used for targeting of the advertisements, surveillance, human computer interaction, security enhancements, immersive computer games and improving user interfaces based on demographic information.
Owner:VIDEOMINING CORP
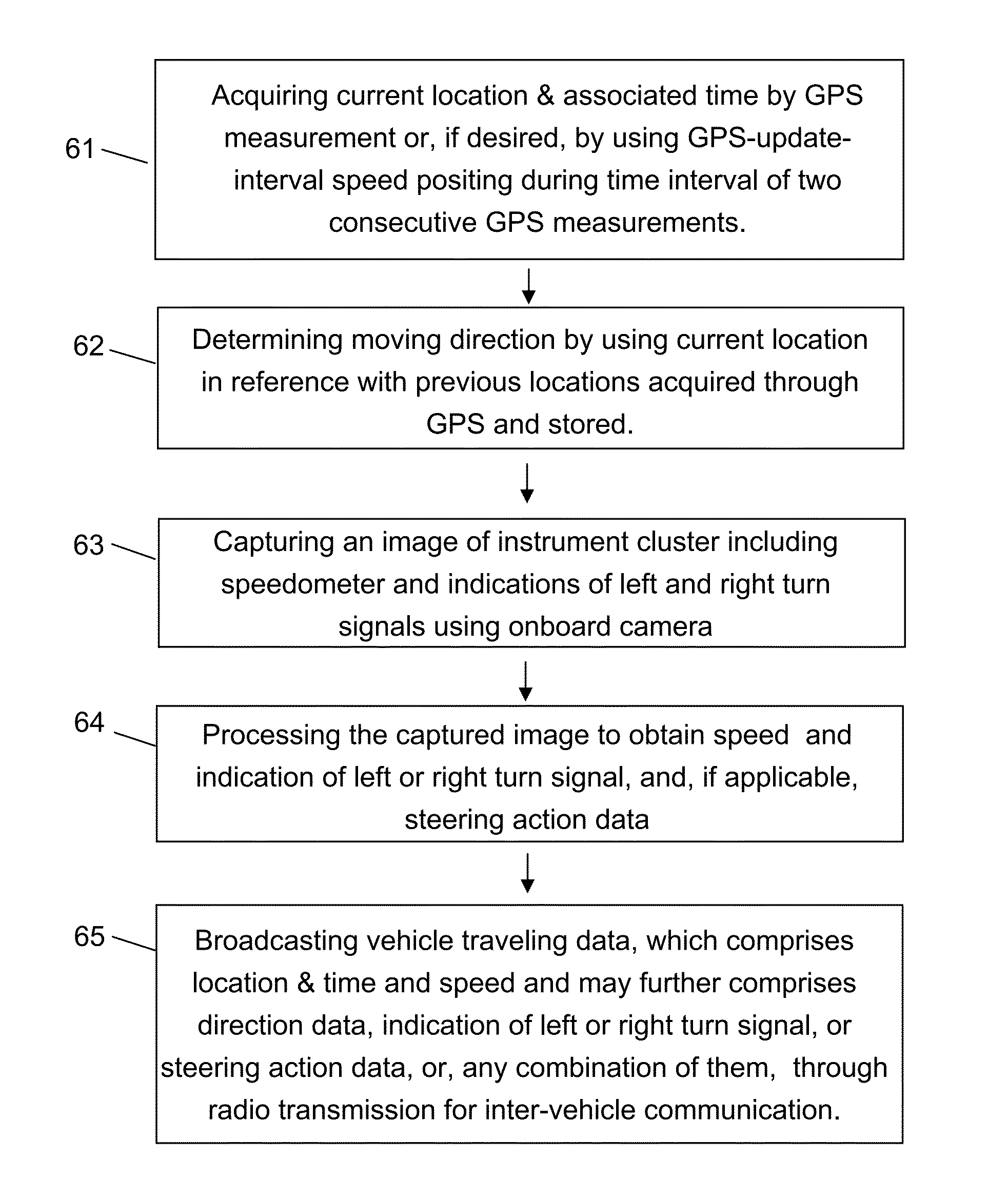
Methods for road safety enhancement using mobile communication device
InactiveUS20130082874A1Sufficiently accurateQuick responseRegistering/indicating working of vehiclesDetection of traffic movementKinematic couplingSimulation
Methods for road safety enhancement use mobile communication device (MCD) onboard vehicle to share traveling data through inter-vehicle communication broadcasting, perform road hazard warning, enhance road navigation, and provide autonomous road assistance. The methods have a variety of vehicle status data, such as moving data, steering data, or indicator data, obtained through GPS or image capturing and recognition of instrument cluster of vehicle. The image capturing and recognition allows to get speed data from indication of speedometer, indication of left or right turn signal, steering action data corresponding to steering wheel rotation, and light-on indication of system status indicators. To facilitate that, the MCD may be placed in front of steering wheel, and, if applicable, also in coupling with movement of steering wheel. The MCD may perform relative positioning map-matching lane correlation and GPS-update-interval speed positioning to improve data quality regarding vehicle moving status.
Owner:ZHANG WEI
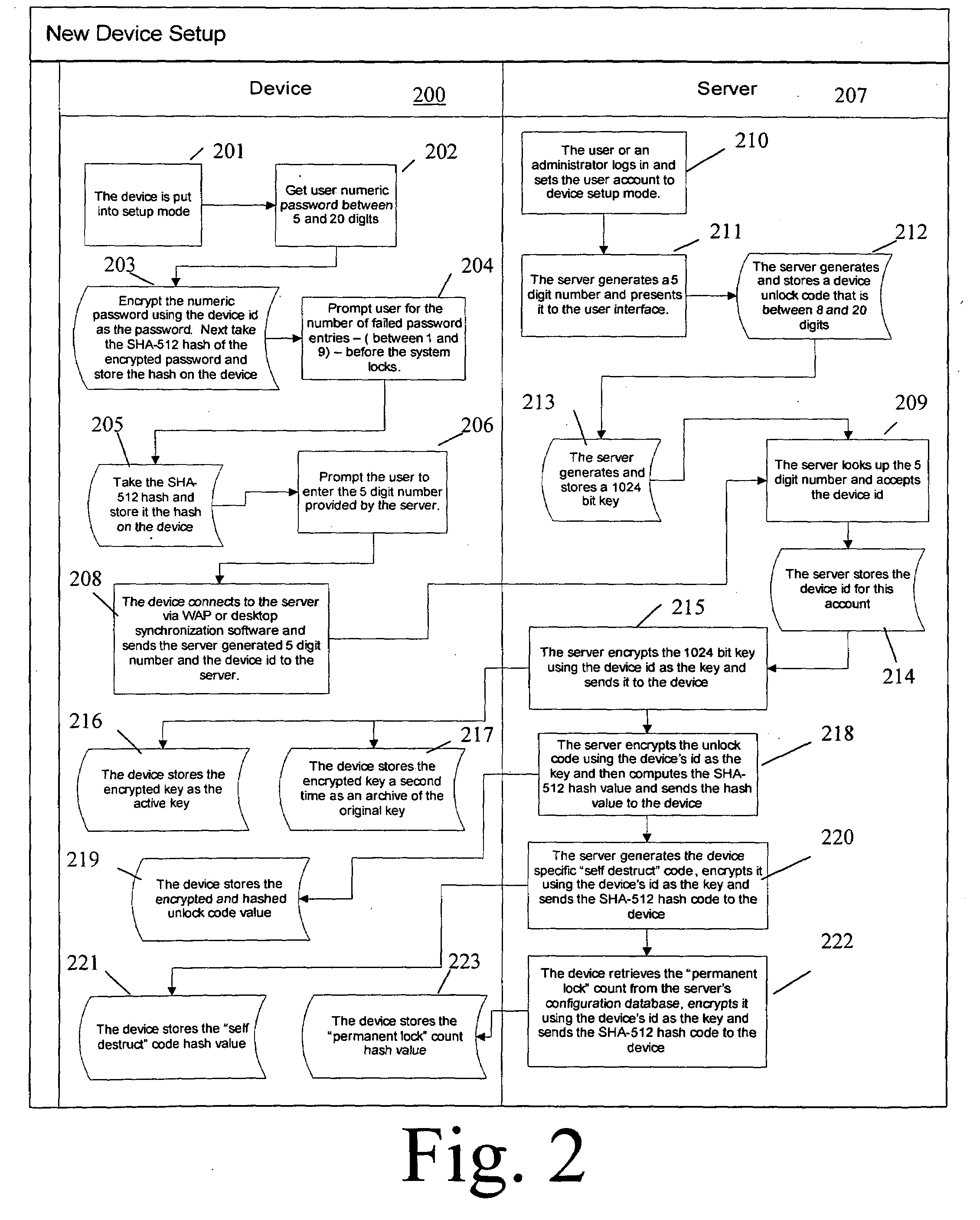
Tamper-resistant authentication techniques for identification documents
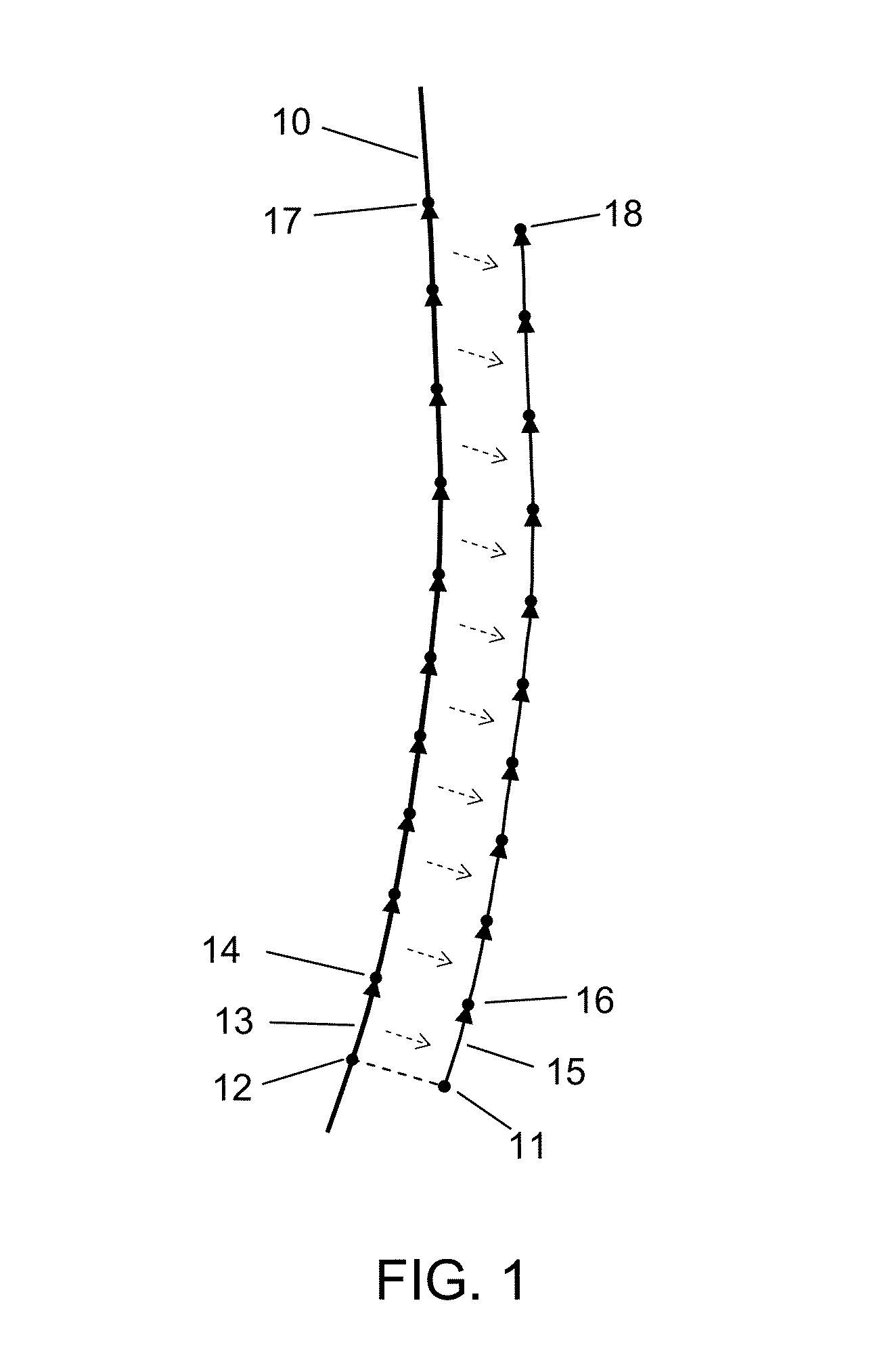
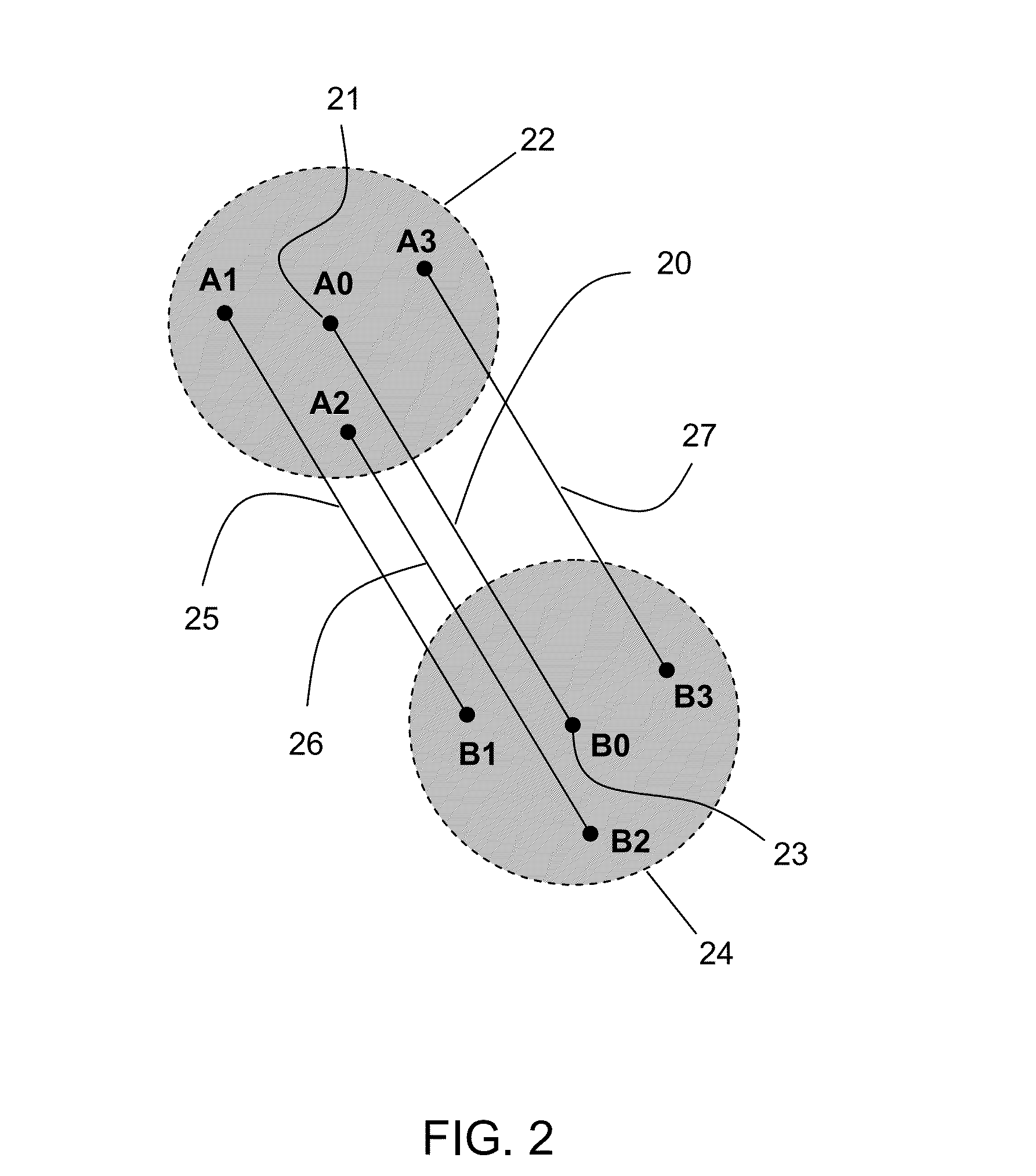
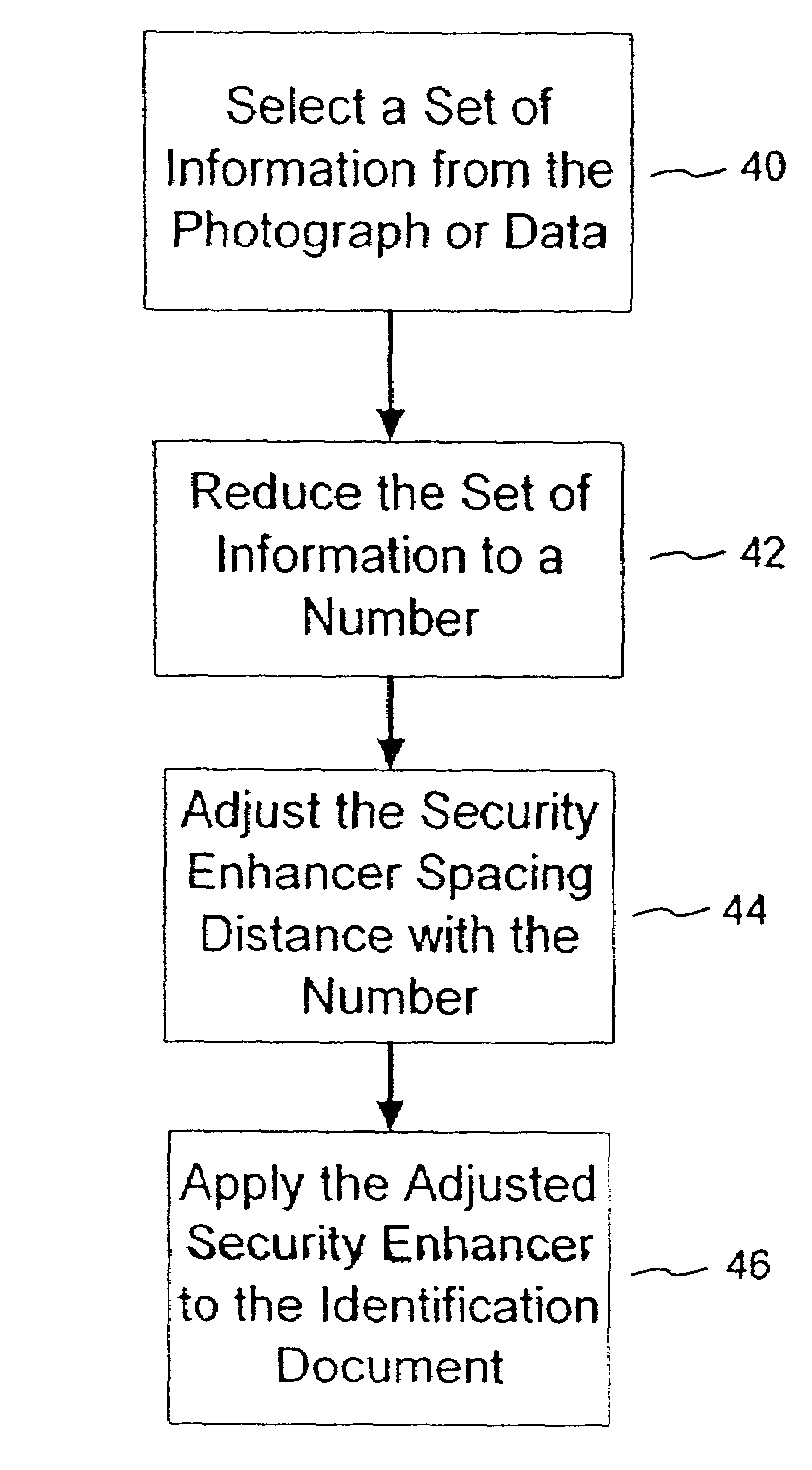
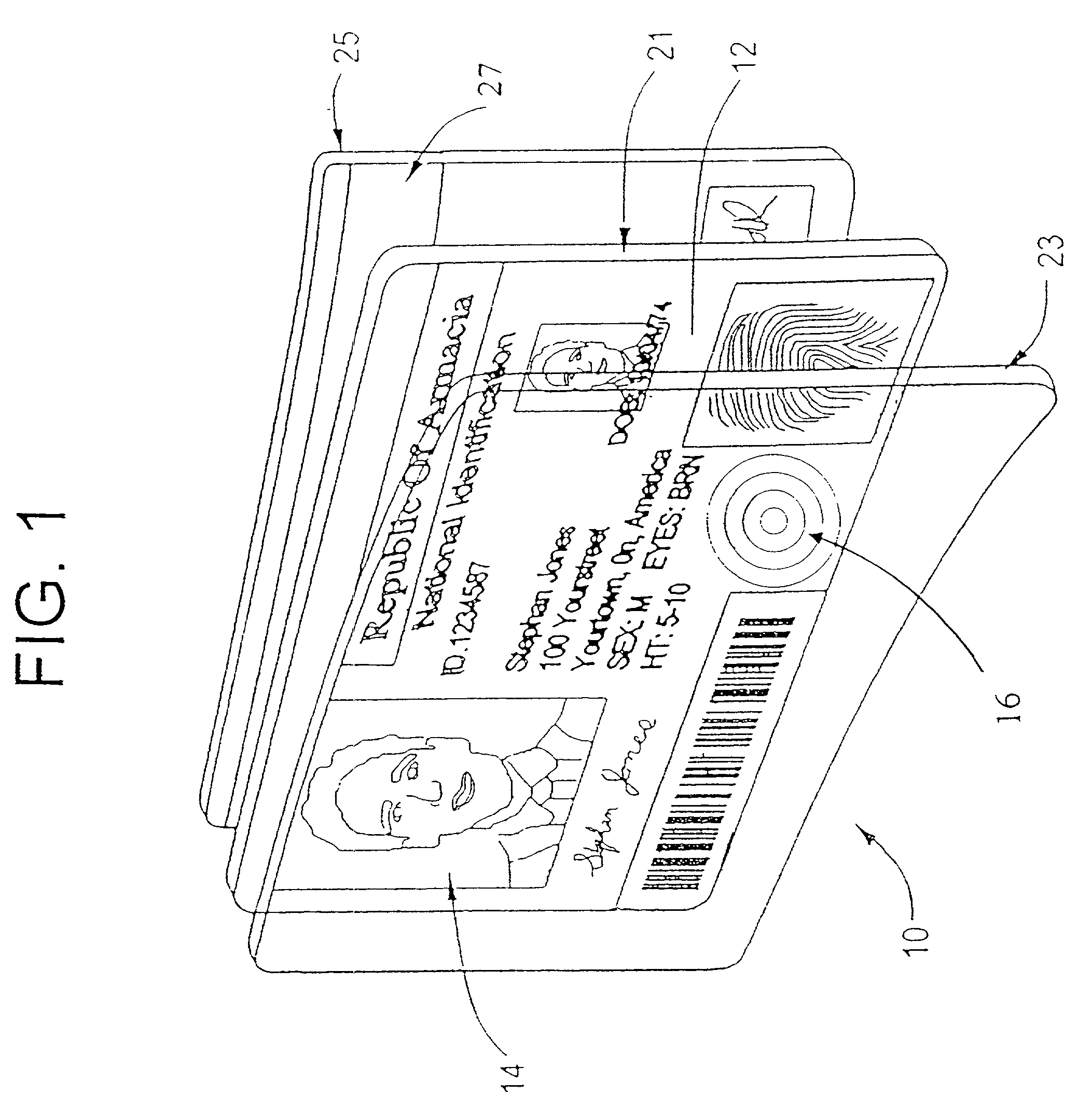
The present invention provides techniques that are helpful in resolving the authentication of an identification document or banknote. The document or banknote includes a security enhancer. The enhancer can be a graphic or artwork design, or can be realized with line art. In the case of an identification document, the spatial characteristics of the security enhancer are preferably altered in accordance with information contained in the identification document. For example, if the ID document includes a photograph, a hashing algorithm will reduce the photograph to a number. The number is used to set a repeated spacing distance of elements in the security enhancer. The repeated spacing yields an identifiable frequency response that is related to the identification document photograph.
Owner:DIGIMARC CORP (FORMERLY DMRC CORP) +1
Bio-Cryptograhpy : Secure cryptographic protocols with bipartite biotokens
ActiveUS20090271634A1Improve securityEasy to solveUser identity/authority verificationDigital data authenticationBiotechnologyCryptographic protocol
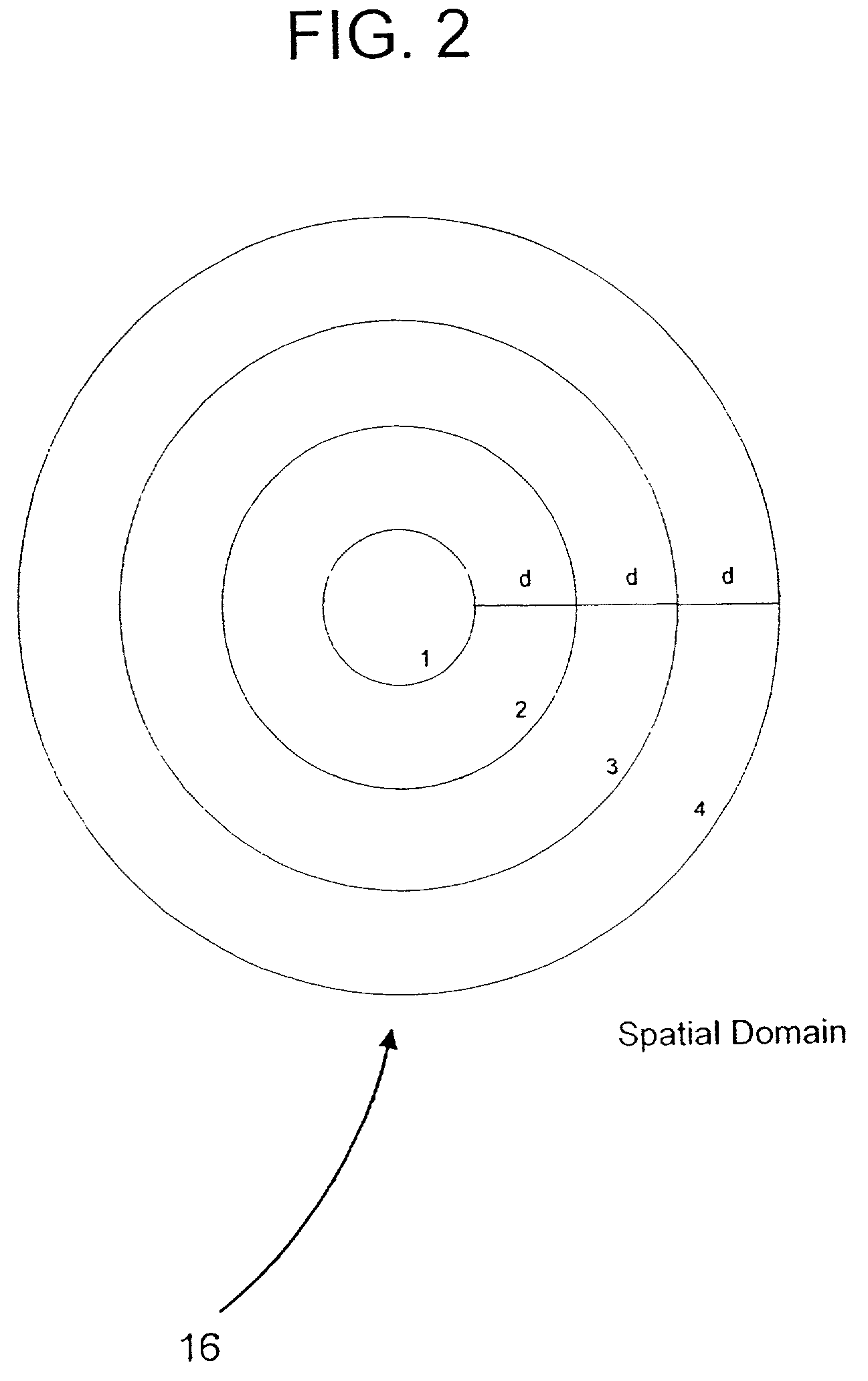
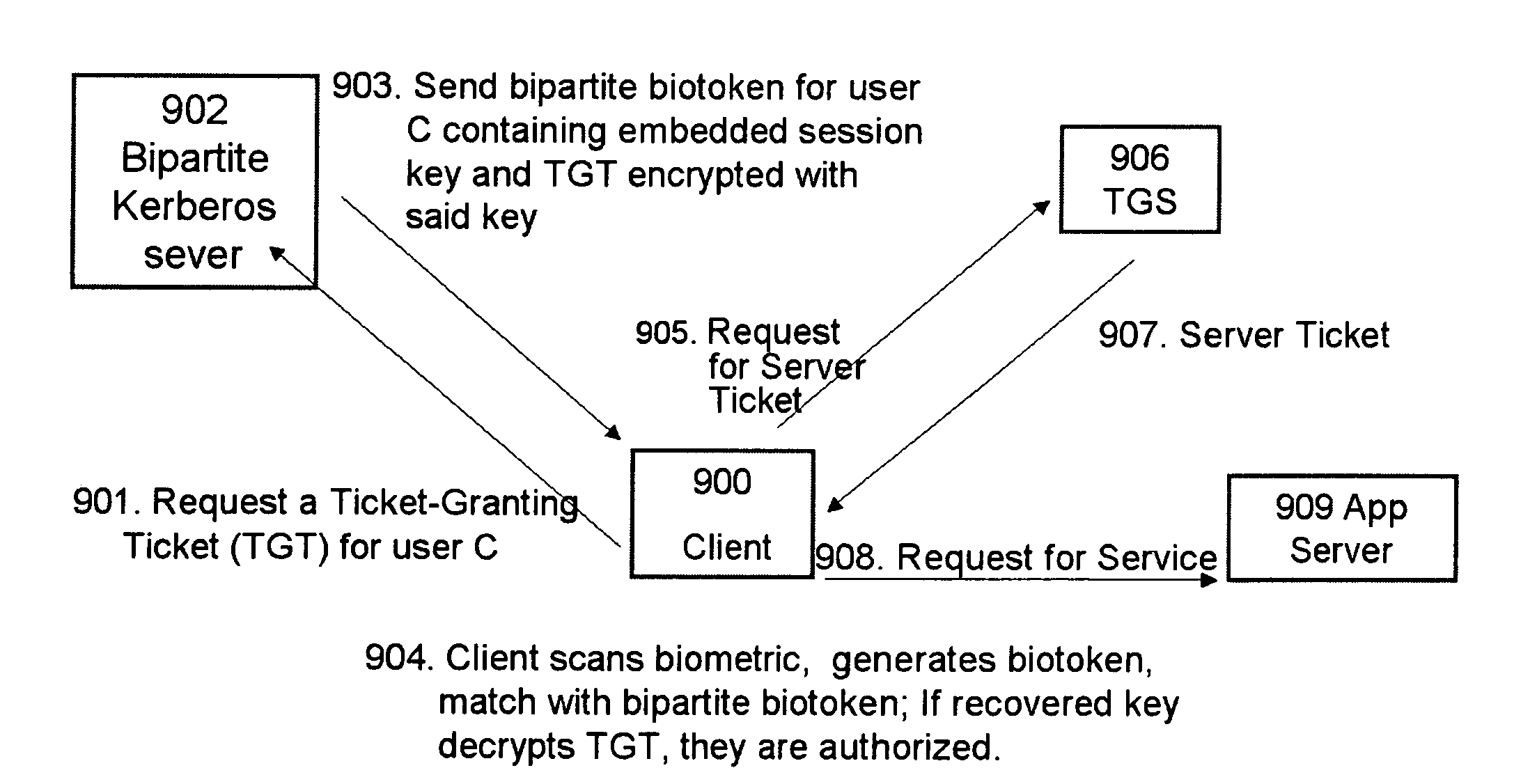
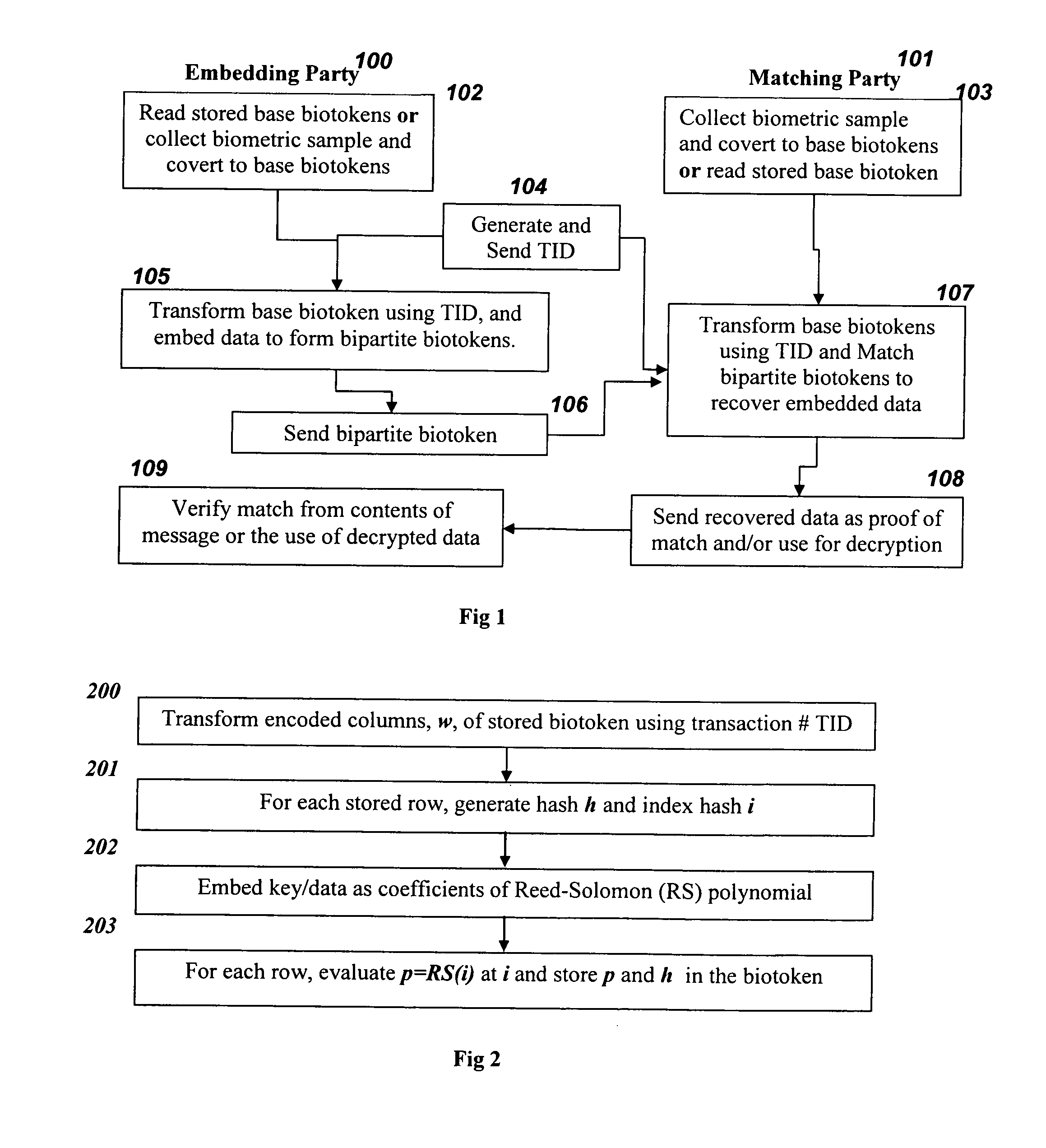
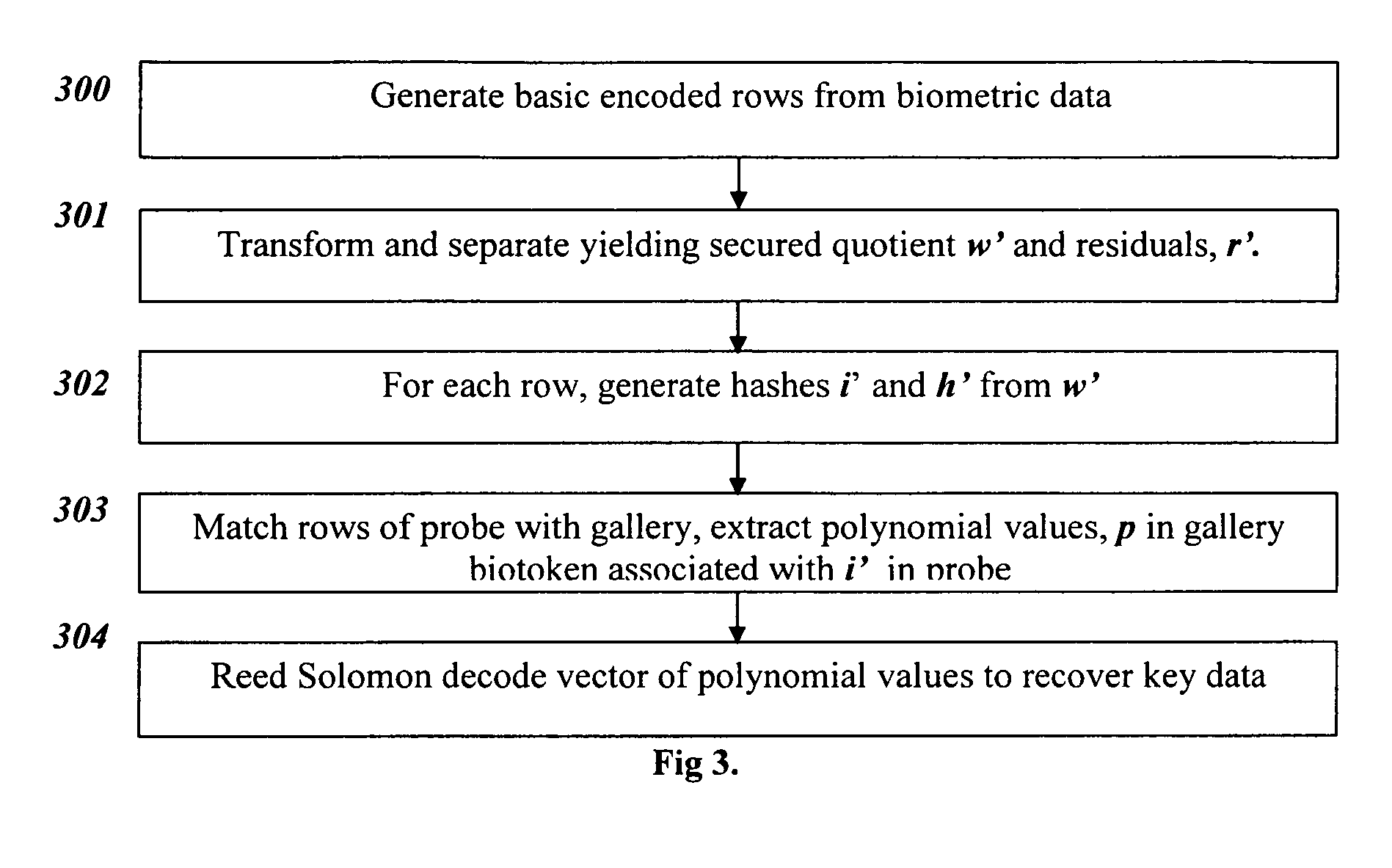
Techniques, systems and methods are described relating to combining biometric and cryptographic techniques to support securely embedding data within a token and subsequent biometrically-enabled recovery of said data. Various transformation approaches are described that provide a secure means for transforming a stored or live, secure biometric-based identity token, embedding data into such tokens and biometric-based matching to both verify the user's identity and recover the embedded data. Security enhancements to a range of existing protocols are described using the techniques. Systems using novel protocols based on these techniques are described
Owner:UNIV OF COLORADO THE REGENTS OF +1
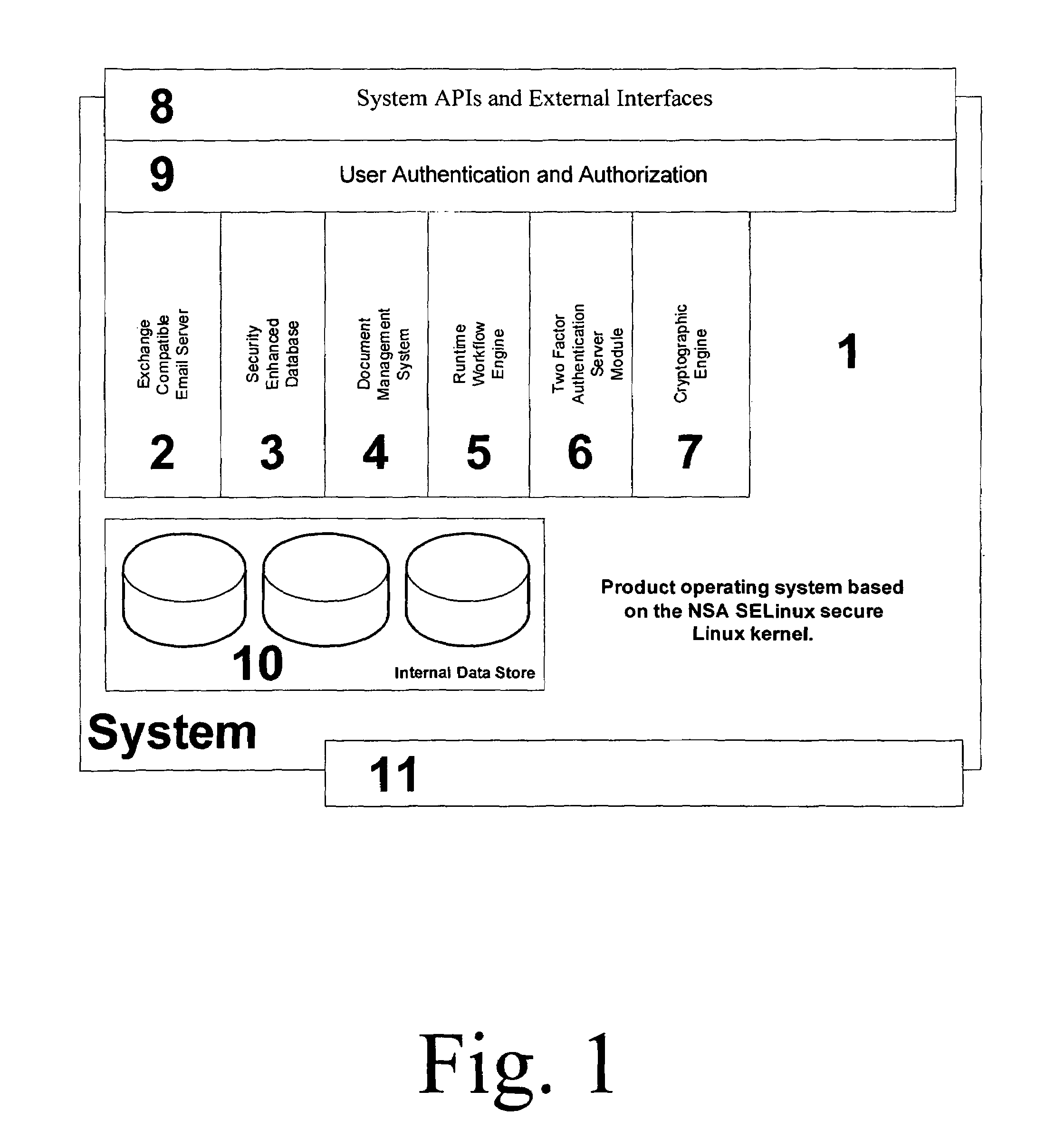
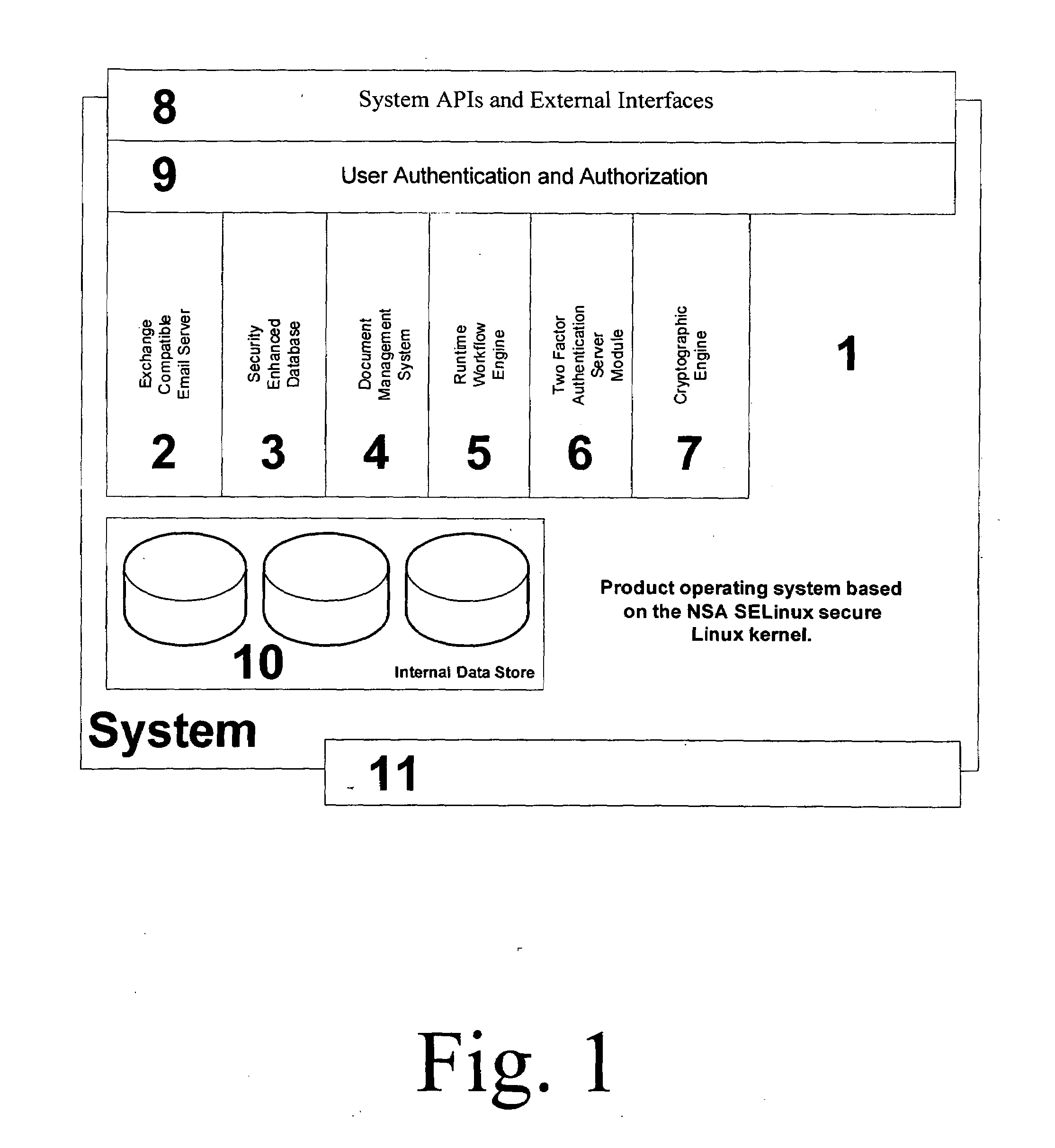
Security Enhanced Data Platform
InactiveUS8161527B2Improve securityConvenient access controlDigital data processing detailsUnauthorized memory use protectionUser PrivilegeInternet privacy
The security enhanced data platform is comprised of two primary subsystems and a host of supporting subsystems. The first primary subsystem is a document management system. A set of client side tools provides the user a way to specify classifications and compartments for selected areas of a document, and a way to save the document in the format required by the system in order to allow the system to enforce the rules and privileges dictated to the system. The second subsystem is a security enhanced database management system. In documents the system allows different user privilege requirements on the document as a whole as well as on pages, paragraphs, sentences, words, and / or letters of a word. A history of document changes is maintained to provide an audit trail after the fact of who did what changes, where those changes were made and when those changes were made.
Owner:CURREN EDWARD
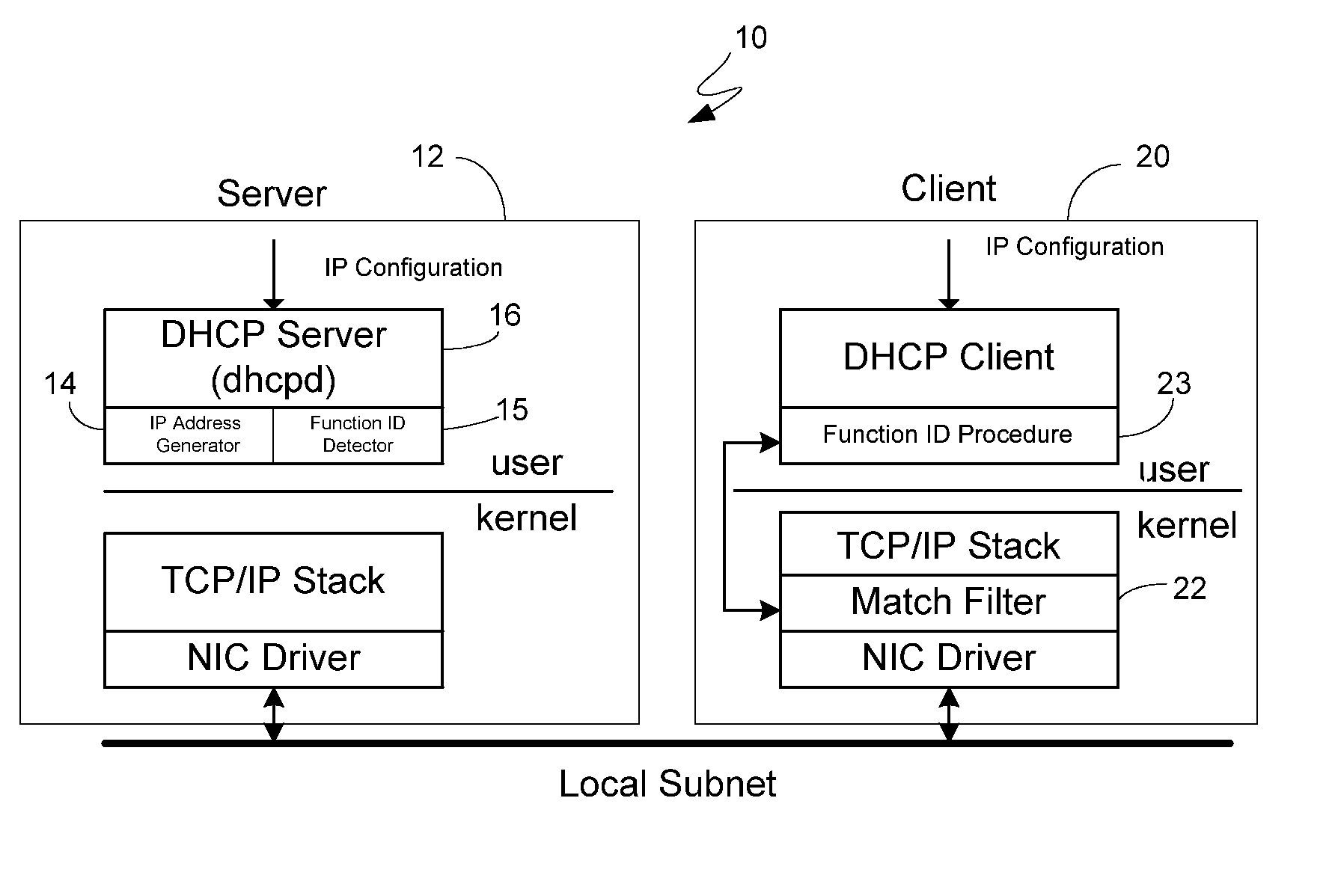
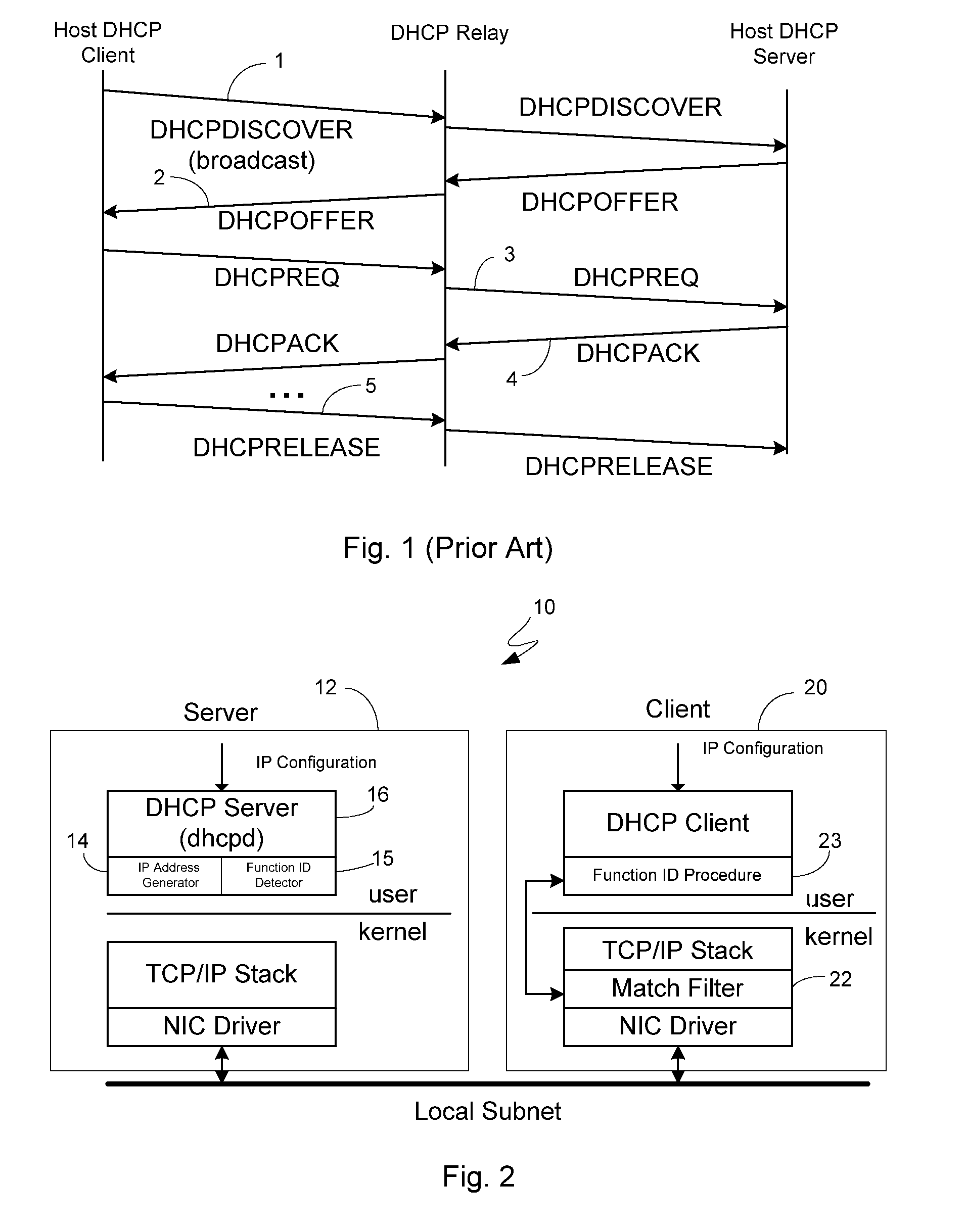
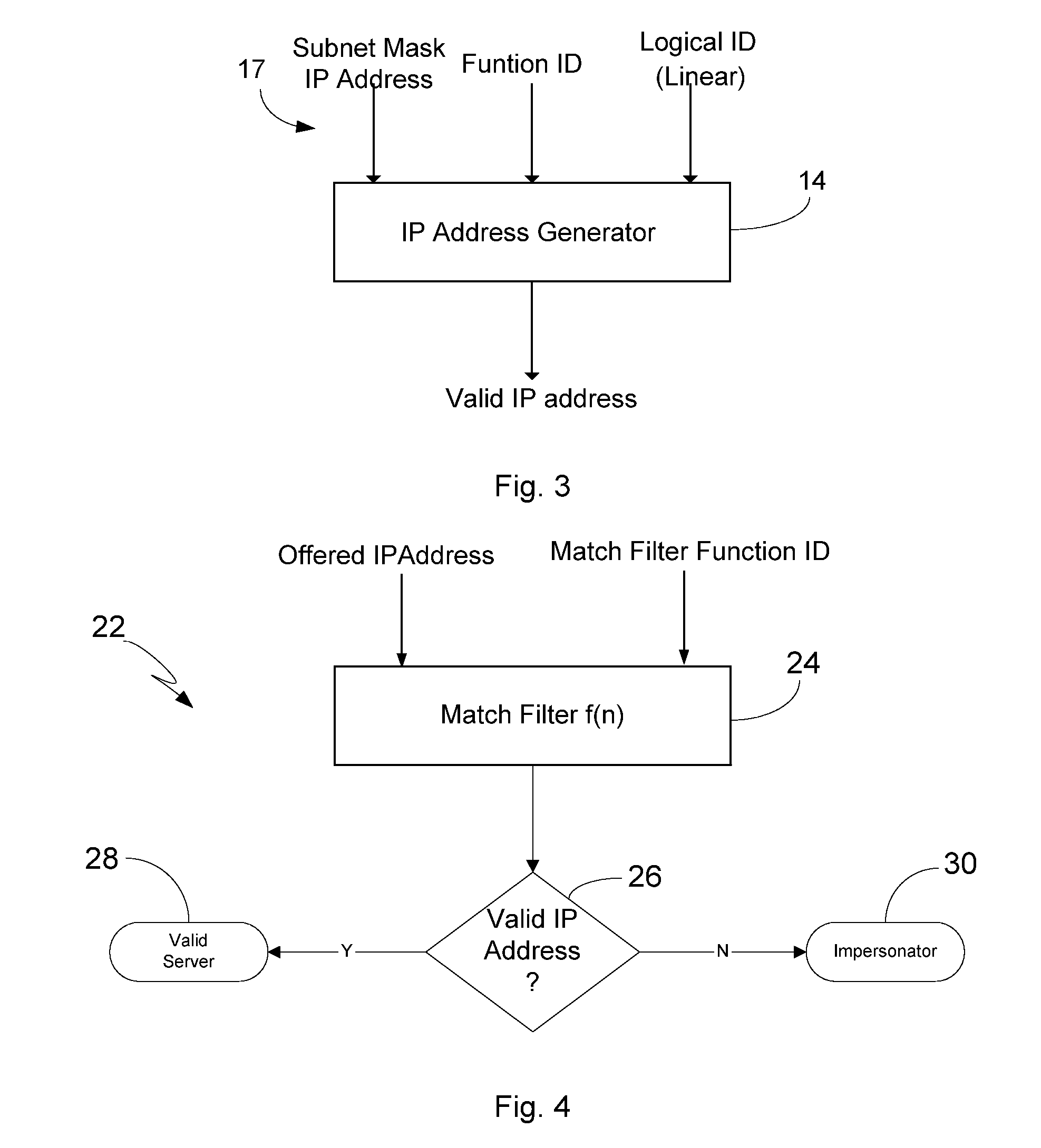
Security Enhanced Methods And System For IP Address Allocation
InactiveUS20060195610A1Easy to understandMultiple digital computer combinationsTransmissionAddress generatorSpamming
The present invention relates to methods and a system for enhancing DHCP to promote a more secure IP address allocation model. The invention advantageously accomplishes this through the utilization of an address generator which is compatible with the existing DHCP protocol, and which incorporates an algorithm for use in producing a selected IP address as one of a sub-set of allocable addresses that are non-sequentially distributed within an address pool. As such, the invention offers robust security and allows for the rapid detection of unauthorized activity such as network intrusion, worms, virus propagation, network scanners, and SPAM.
Owner:SYTEX
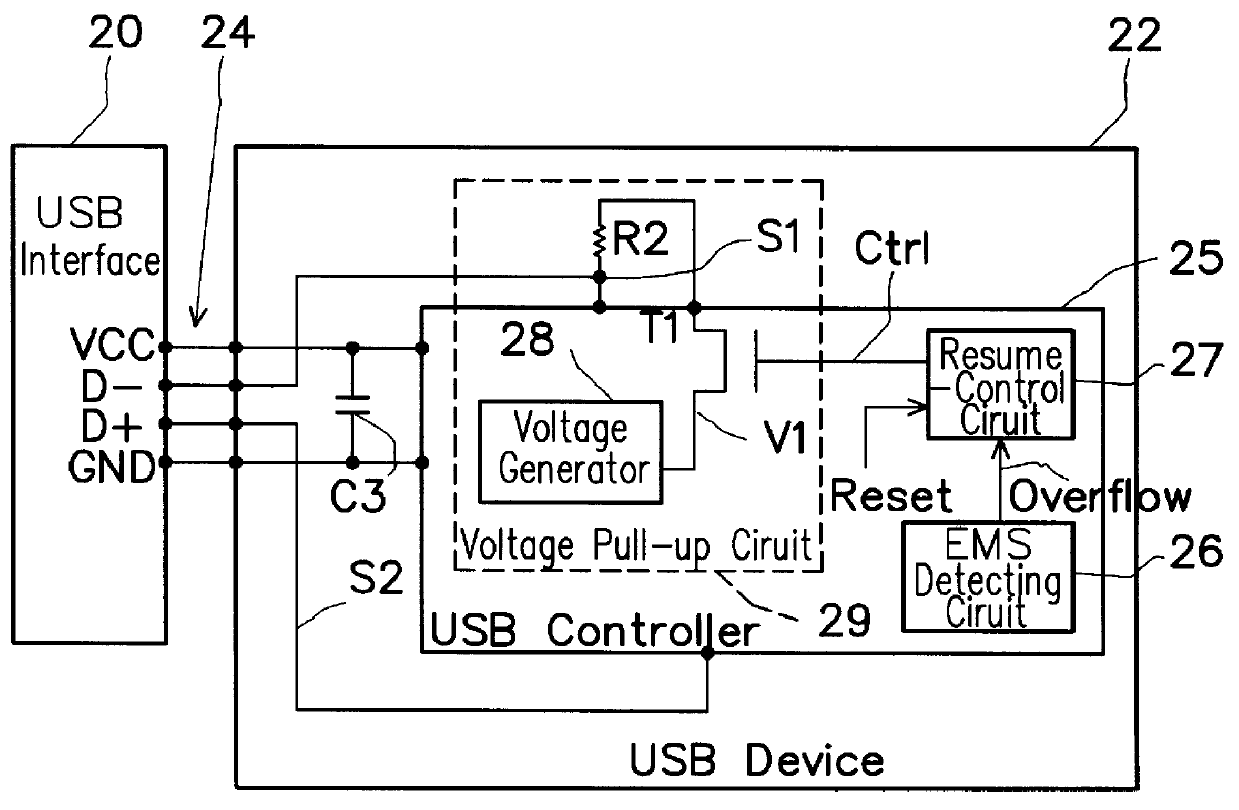
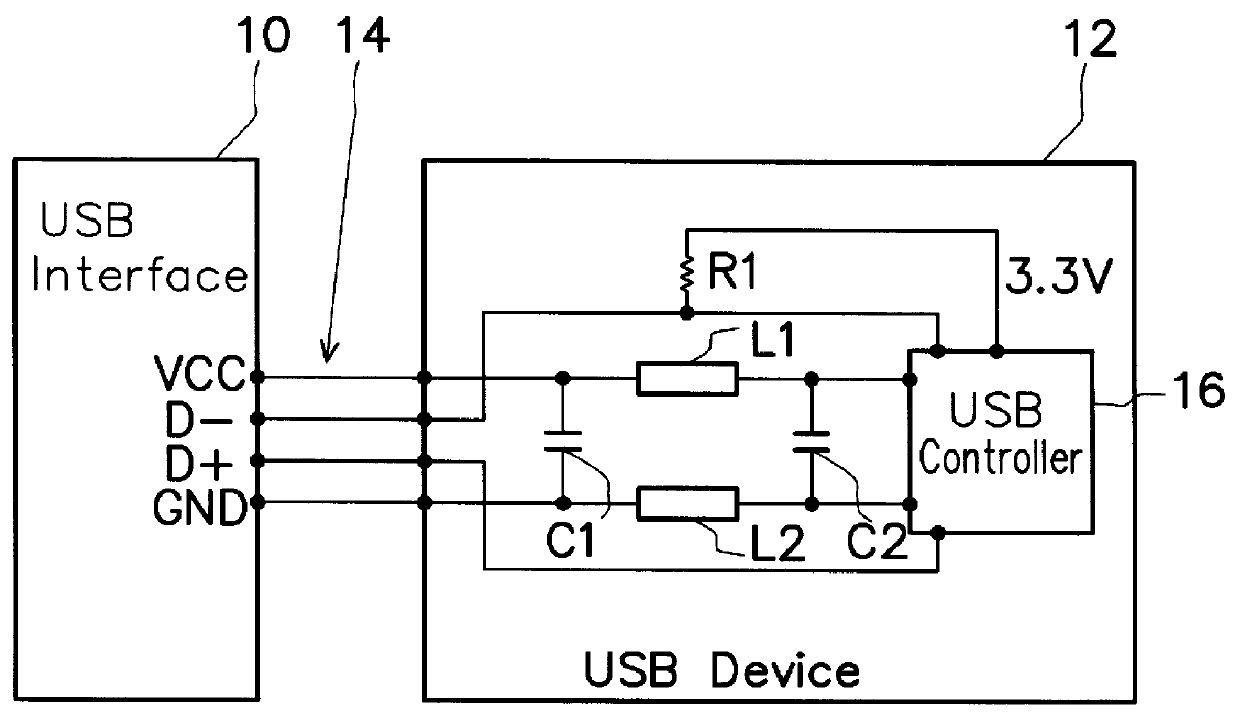
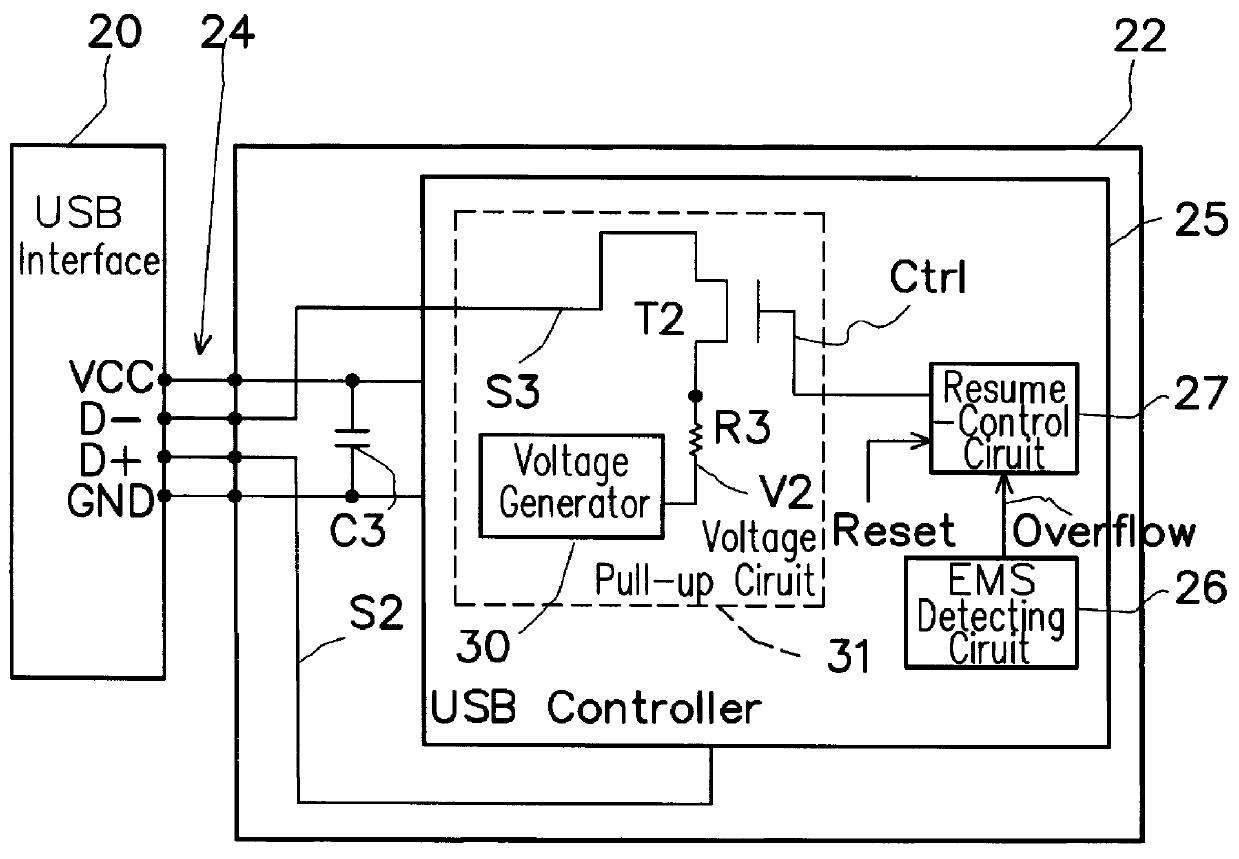
Electromagnetic safety enhancement circuit for universal serial bus systems
InactiveUS6101076ACircuit-breaking switches for excess currentsEmergency protective arrangement detailsControl signalElectromagnetic interference
An electromagnetic safety (EMS) enhancement circuit is provided for a USB (Universal Serial Bus) system, which can simulate an unplugging and replugging action so as to ensure continuous operation of the USB device after being disconnected from the USB interface due to electromagnetic interferences. The EMS enhancement circuit utilizes an EMS detection unit to detect the EMS condition of the data communication between the USB device and the USB interface; if abnormal, the EMS detection unit will output an overflow signal to a resume-control unit. The resume-control unit can output a pull-up control signal to a voltage pull-up circuit so as to control the voltage pull-up circuit in such a manner that, when the USB device is disconnected from the USB interface, the voltage pull-up circuit is first inhibited from outputting a voltage signal to one data line of the USB interface to thereby simulate an unplugging action and, after a preset time, be enabled again to output the voltage signal to thereby simulate a replugging action. The simulated unplugging and replugging action can then automatically reconnect the USB device to the USB interface for continuous operation of the USB device.
Owner:NOVATEK MICROELECTRONICS CORP
Open flow table security enhancement method and device
ActiveCN103095701AEasy to carry outProtect against zero-day attacksTransmissionVirtualizationPrivate network
The invention discloses an open flow table security enhancement method which can enable a security control function to be separated from a security executive function. The method includes the steps of obtaining security application corresponding to each security service, extracting security strategies, security protocols and feature libraries corresponding to the various security services from the security application, analyzing the security strategies of the security services to generate a security flow table, and creating a matching rule in the security flow table, and carrying out access control to messages and inspection for a state firewall, a security virtual private network (VPN) and deep messages according to the matching rule in the security flow table. The invention simultaneously discloses an open flow table security enhancement device. The open flow table security enhancement method and the open flow table security enhancement device can enable the security execution and the security application to be independently evolved and upgraded, and bring convenience to development of new security services, and can intensively carry out security management, resist zero-day attack, and relieve distributed denial of service attack according to the security strategies, and also support a virtualization multi-tenant security mode.
Owner:ZTE CORP
Method and apparatus for supporting broadcast efficiency and security enhancements
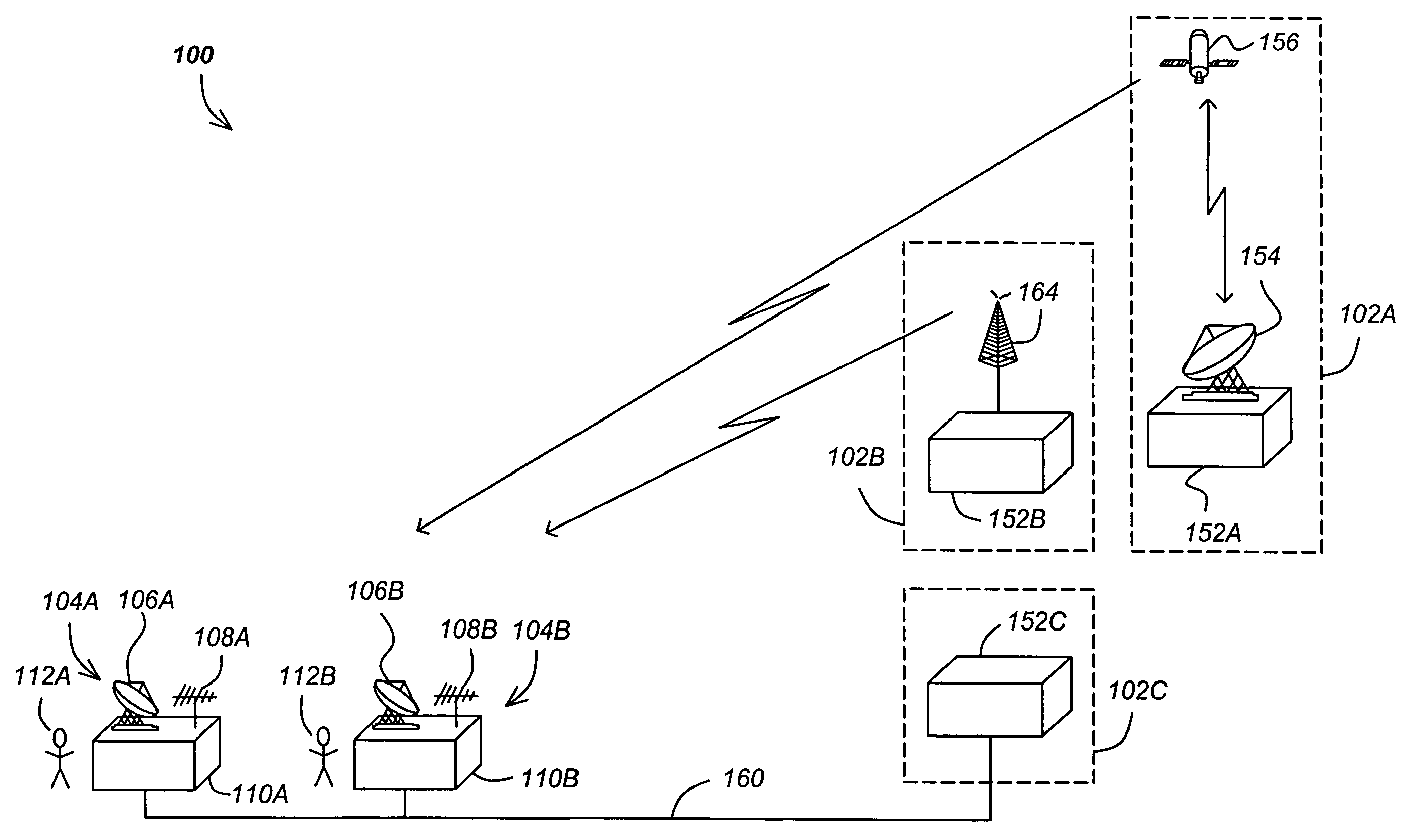
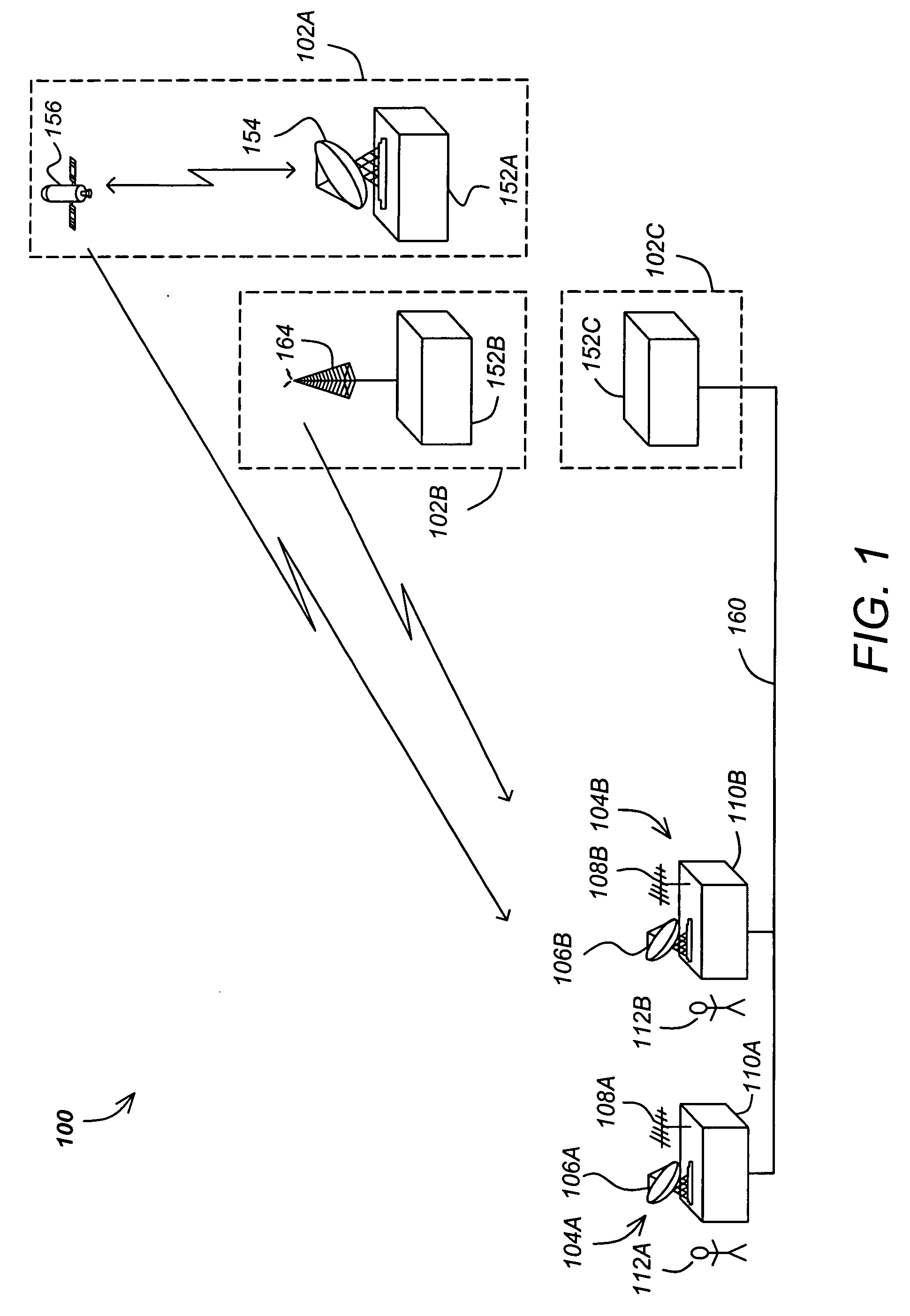
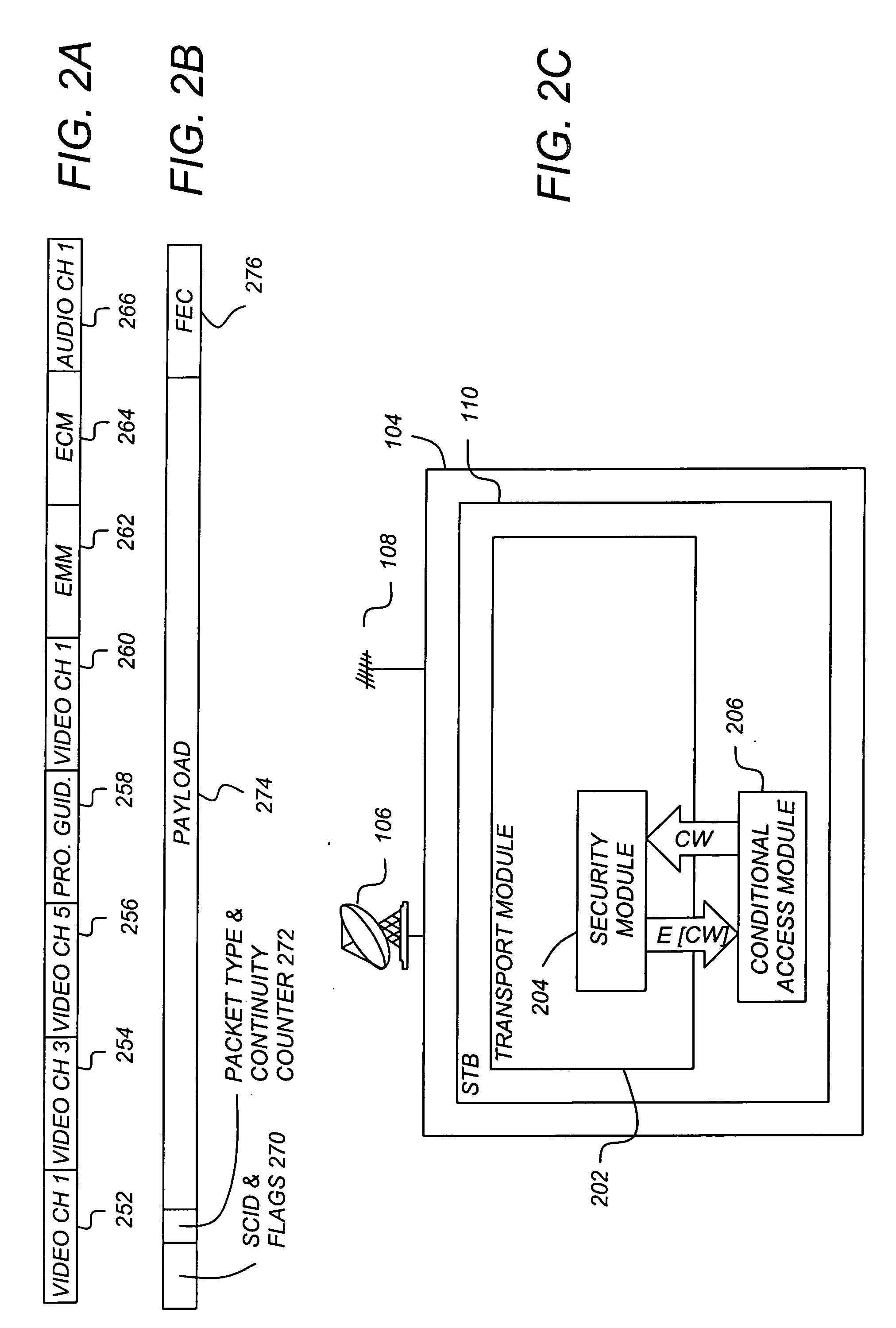
InactiveUS20070286422A1Reduce bandwidth requirementsIncreasing throughputTelevision systemsSelective content distributionTelecommunicationsConditional access
A method and apparatus for providing conditional access to media programs is described. An exemplary method comprising the steps of transmitting media information encrypted according to a control word (CW) to a receiver station, transmitting entitlement management information (EMI) to the receiver station, the EMI comprising a service bitmap, and transmitting entitlement control information (ECI) to the receiver station, the entitlement control information including the control word (CW) encrypted according to a key (K) and an index to an element of the service bitmap, wherein the control word (CW) is decrypted by the receiver stations according to a value of the indexed element of the service bitmap.
Owner:RAMBUS INC
Security Enhanced Data Platform
InactiveUS20100189251A1Improve securityConvenient access controlDigital data processing detailsUser identity/authority verificationUser PrivilegeDocumentation procedure
The security enhanced data platform is comprised of two primary subsystems and a host of supporting subsystems. The first primary subsystem is a document management system. A set of client side tools provides the user a way to specify classifications and compartments for selected areas of a document, and a way to save the document in the format required by the system in order to allow the system to enforce the rules and privileges dictated to the system. The second subsystem is a security enhanced database management system. In documents the system allows different user privilege requirements on the document as a whole as well as on pages, paragraphs, sentences, words, and / or letters of a word. A history of document changes is maintained to provide an audit trail after the fact of who did what changes, where those changes were made and when those changes were made.
Owner:CURREN EDWARD
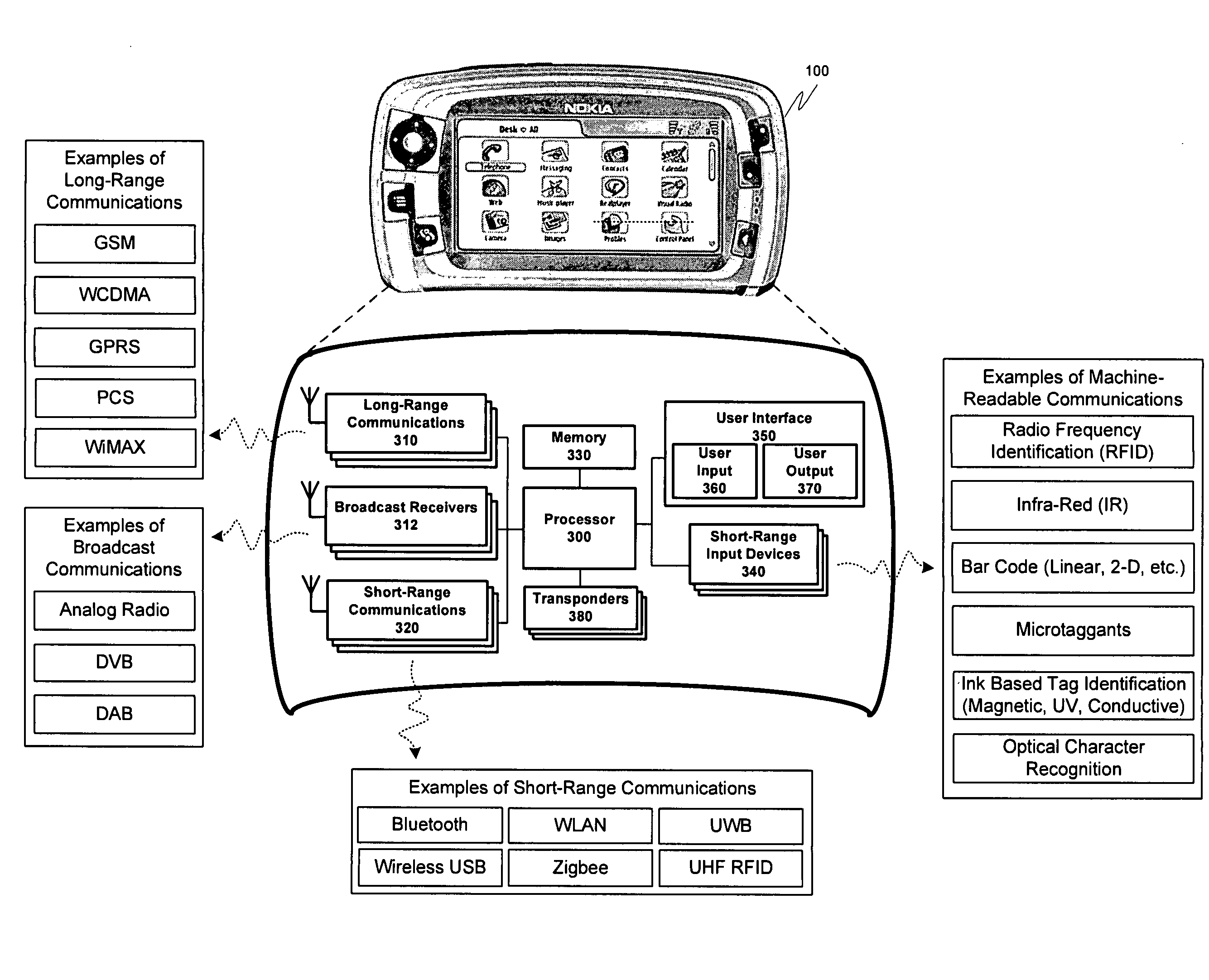
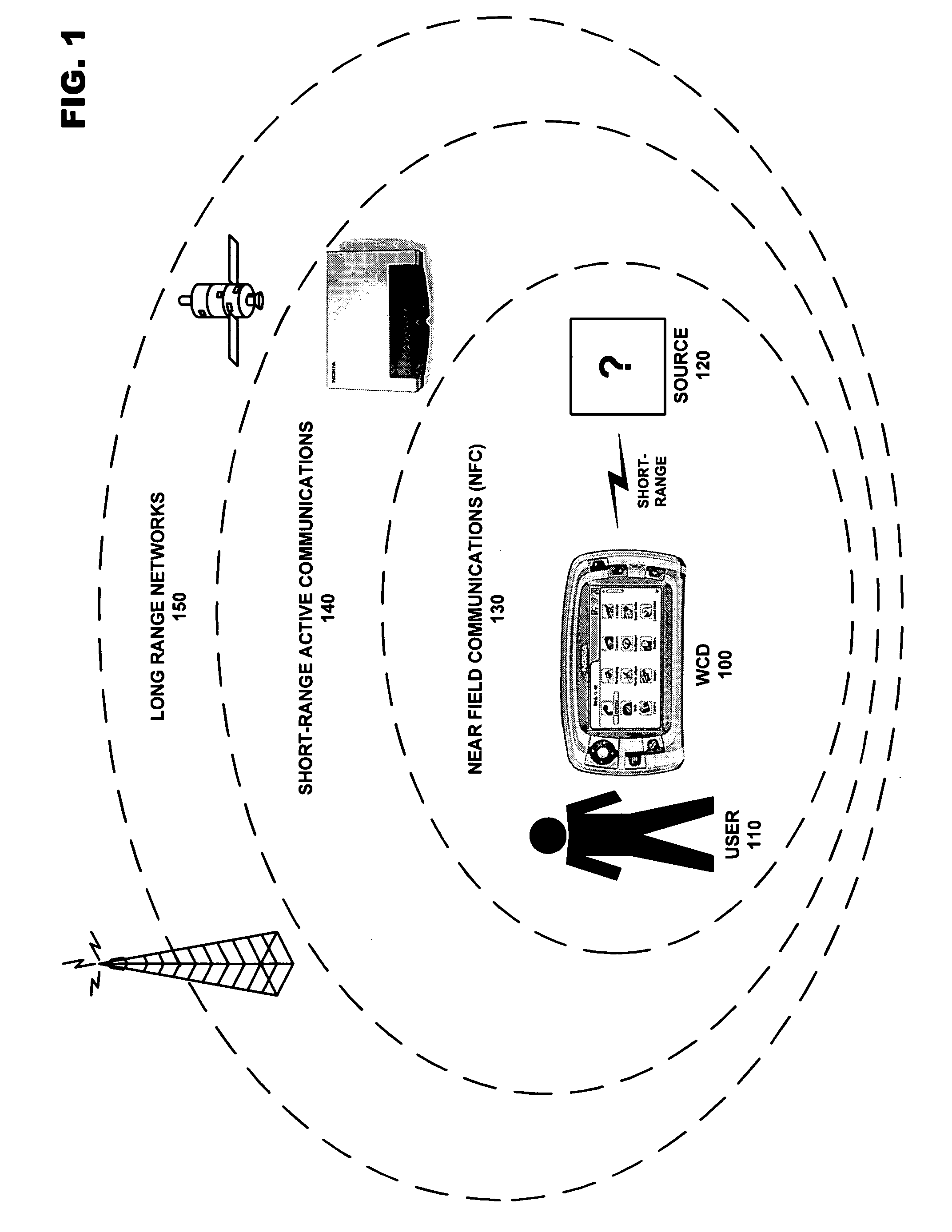
Address privacy in short-range wireless communication
ActiveUS20070293197A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunicationsCommunications media
A security enhancing system for creating temporary identification information used to mask actual identification in a wireless communication device. The temporary identification information conforms to a standard usable by at least one wireless communication medium, and may be used by other devices in communicating with the wireless communication device, however, only other devices possessing secret address component information may determine the actual identity of the masked wireless communication device. The temporary identification information may further be recompiled when a threshold condition is satisfied.
Owner:NOKIA TECHNOLOGLES OY
Dynamic enterprise security control based on user risk factors
Aspects dynamically set enterprise-level security rules by assessing risk factors associated with a user. Risk values representing likelihoods of loss of enterprise secure data are determined for different attributes of a user, and added together to generate a user risk factor. If the risk factor does not meet one or more off-site access threshold value(s), additional security enhancements applicable to the user and not enabled within currently applied security are iteratively selected and used to revise the security settings, and the risk factor is revised by a risk abrogation value of each of the selected security enhancements, until either the revised risk factor meets the off-site access threshold value(s) (wherein access is granted to the secure data from the off-site location pursuant to the revised security settings), or until no additional applicable security enhancements are available (wherein user access to the secure data from the off-site location is denied).
Owner:KYNDRYL INC
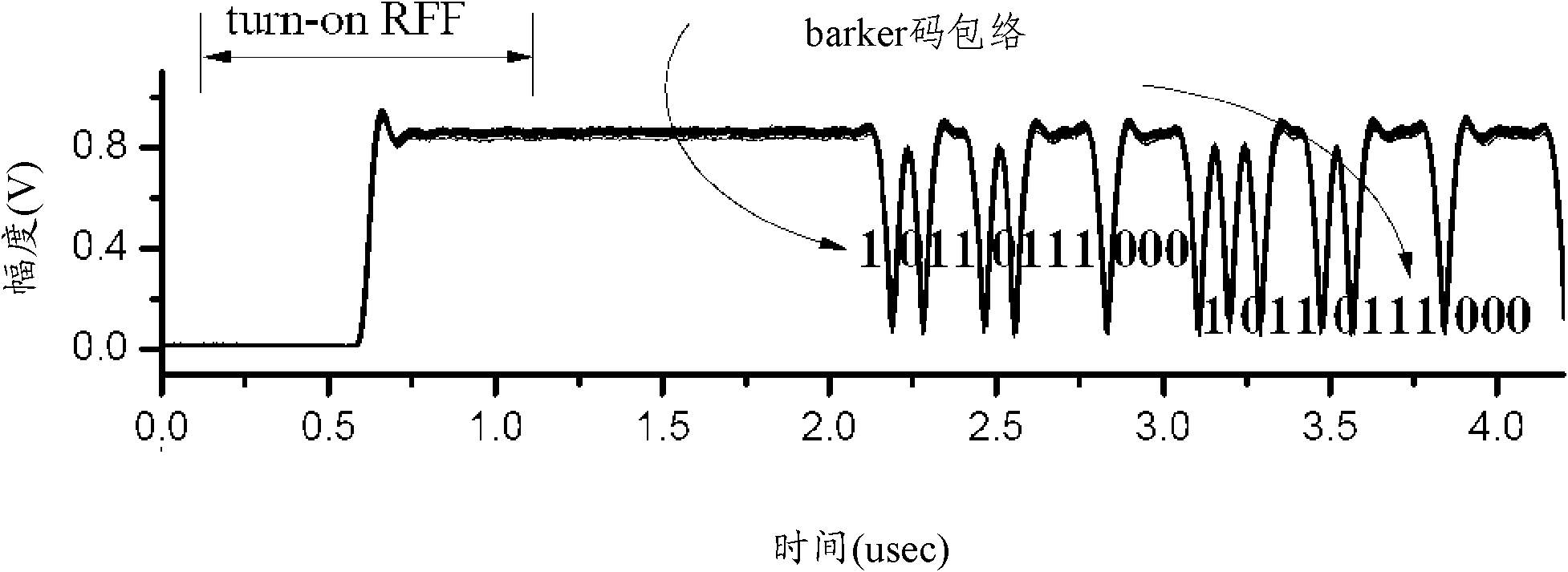
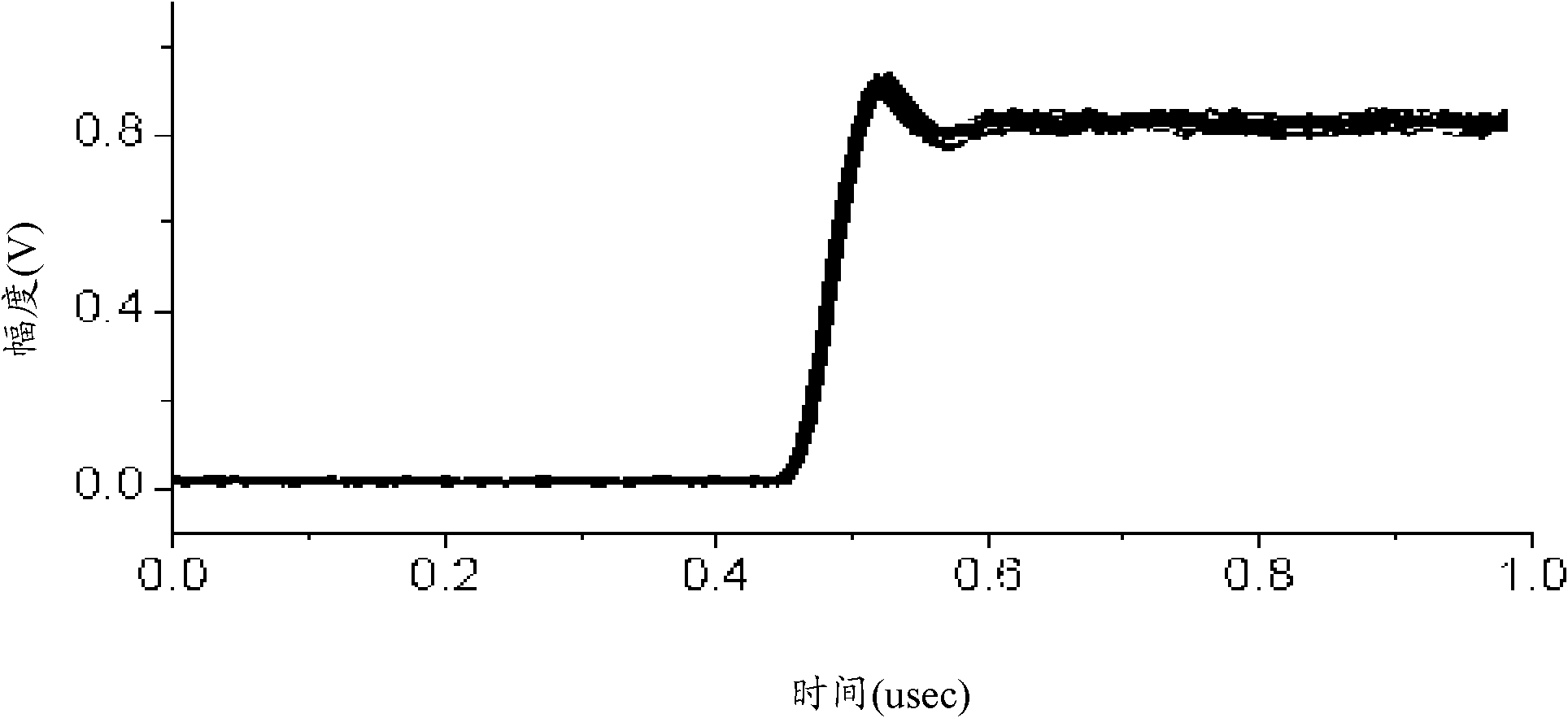
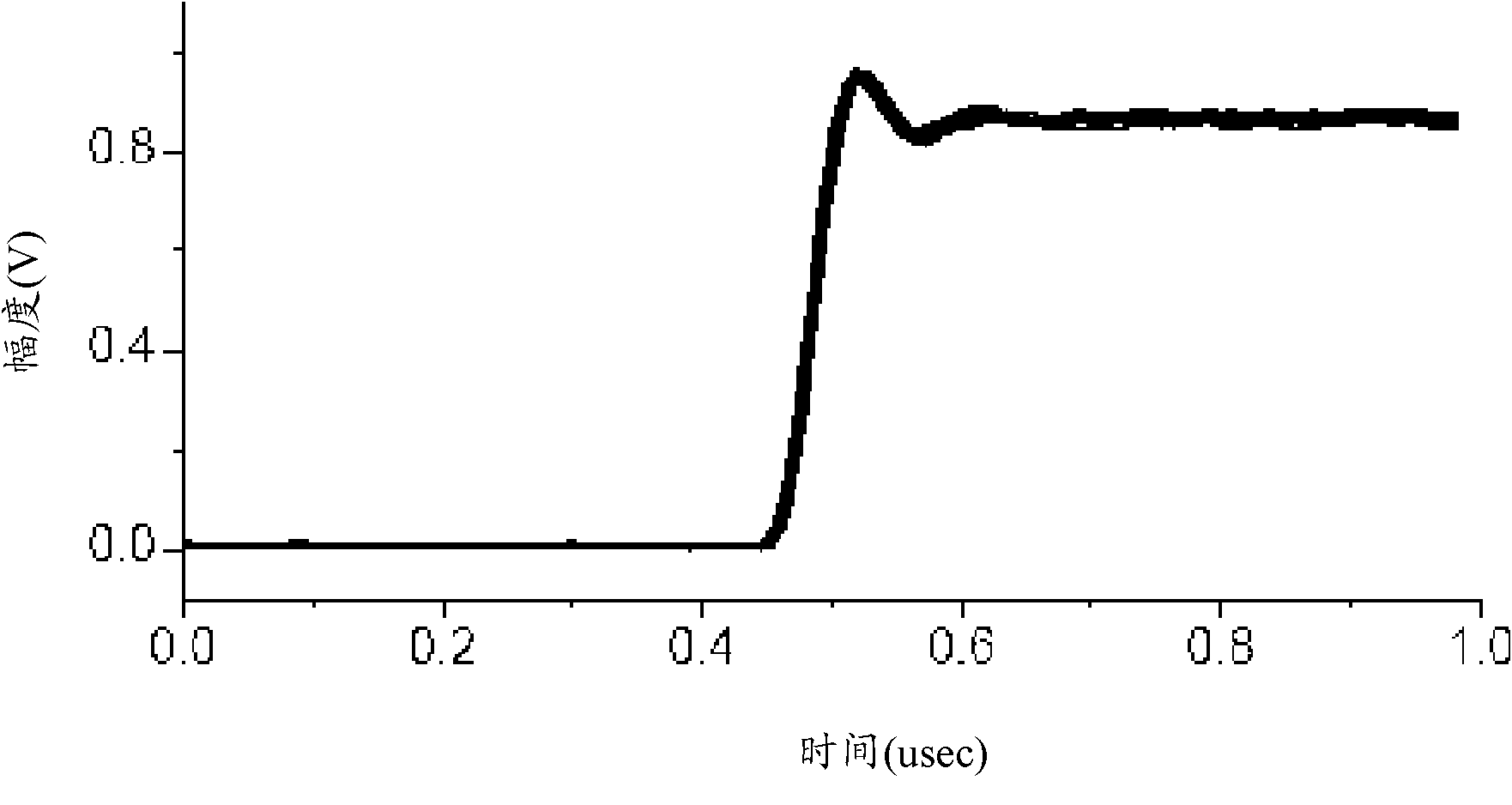
Identification method of wireless transmitter based on RF fingerprints (RFF)
ActiveCN102693411AGood divisibilityImplement security enhancementsCharacter and pattern recognitionSensing record carriersFeature extractionPhysical layer
The invention discloses an identification method of a wireless transmitter based on RF fingerprints (RFF). The method comprises the following steps: receiving a wireless signal transmitted by the wireless transmitter, wherein the wireless signal is a preamble sequence transmitted by the wireless transmitter while power is increased gradually; detecting reference time of the wireless signal; according to the detected reference time, carrying out preamble signal interception on the wireless signal; converting the intercepted preamble signal into the RFF; carrying out feature extraction on the converted RFF and carrying out identification on the wireless transmitter. According to the identification method of the wireless transmitter based on the RFF, through using advantages that RFF separability is good and a required sampling rate is low, ramp-up RFF can be used for multiple RFF identification of wireless equipment based on the preamble so that purposes of increasing wireless network physical layer safety and so on can be realized, wherein the advantages are possessed by the ramp-up RFF (radio frequency fingerprints RFF) which is obtained through converting the preamble signal transmitted during the power is obliquely ascended.
Owner:NANTONG UNIVERSITY
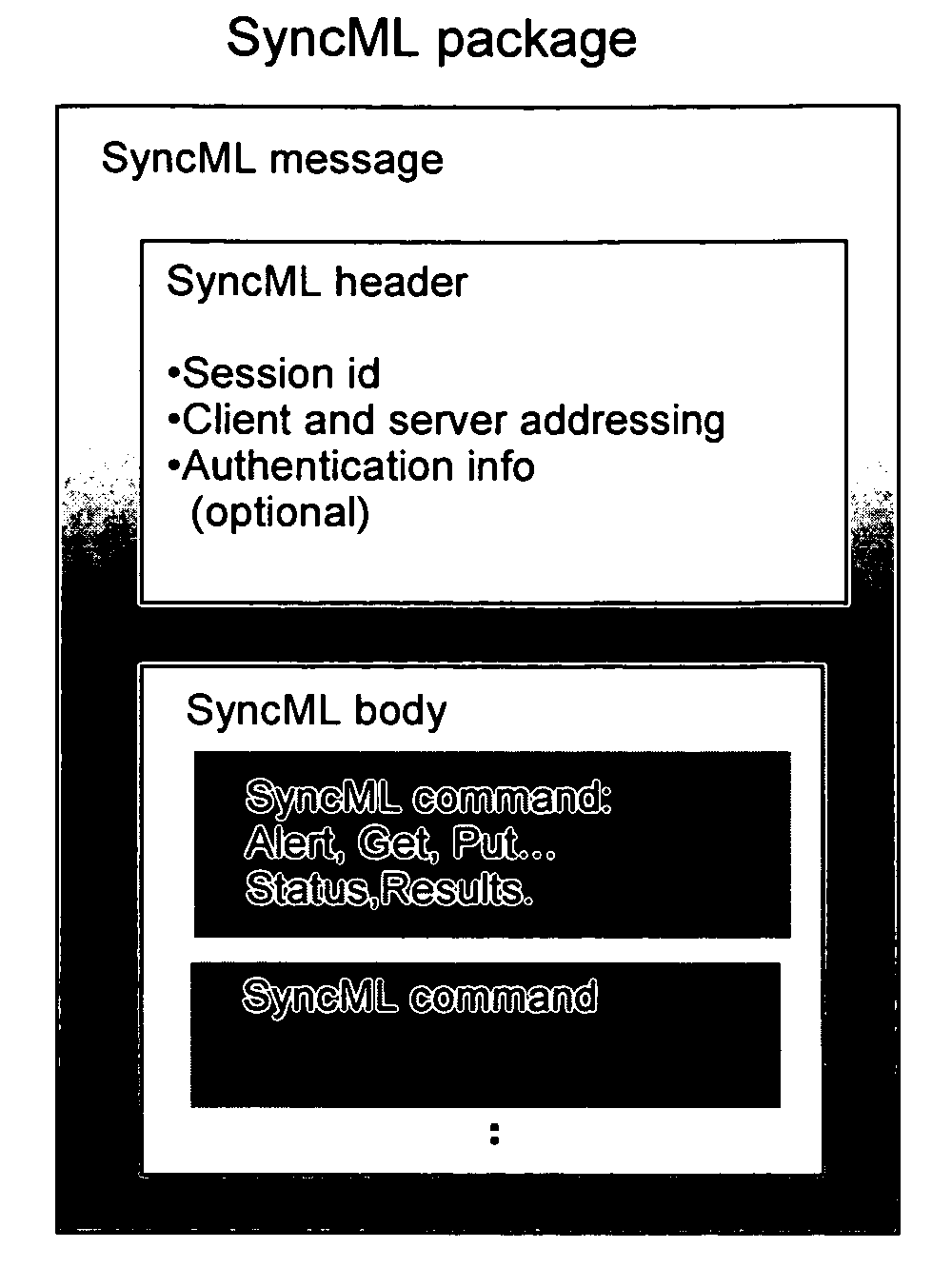
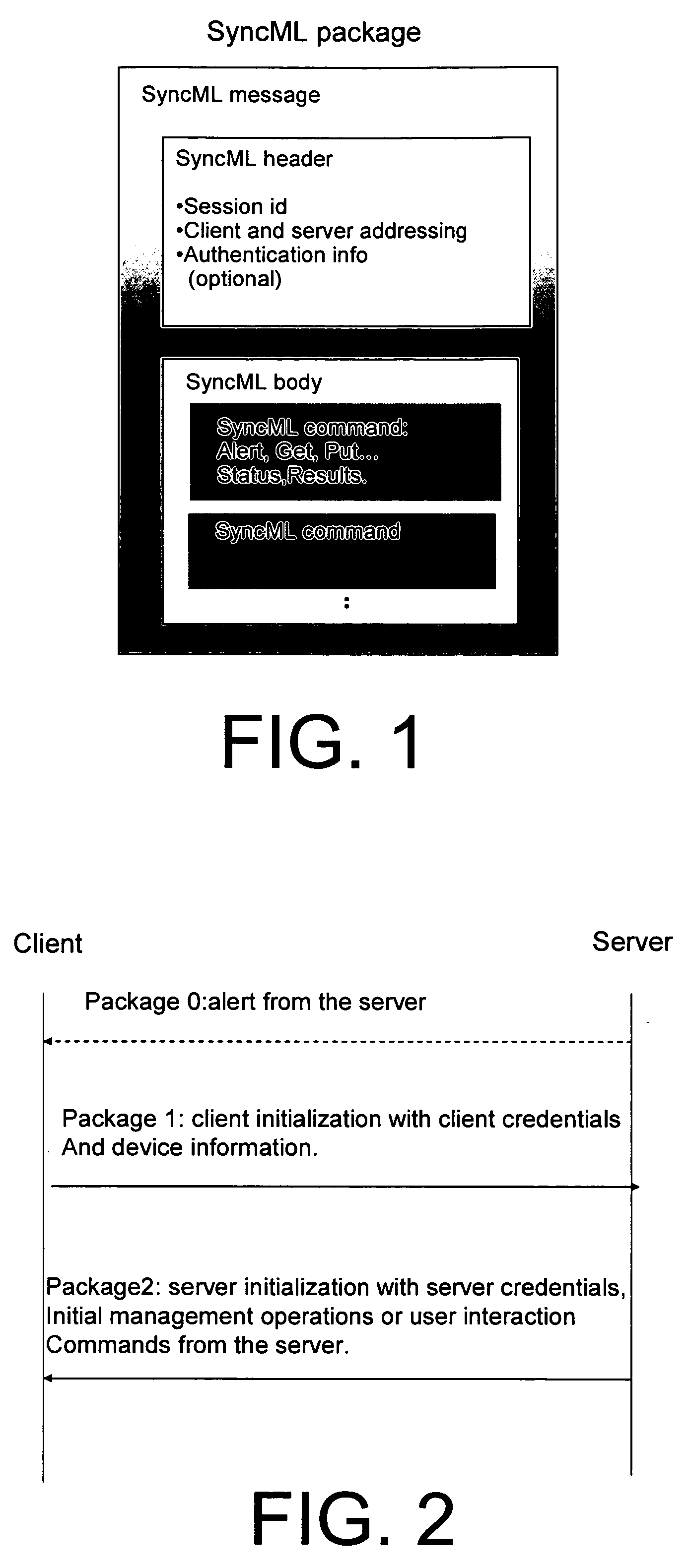
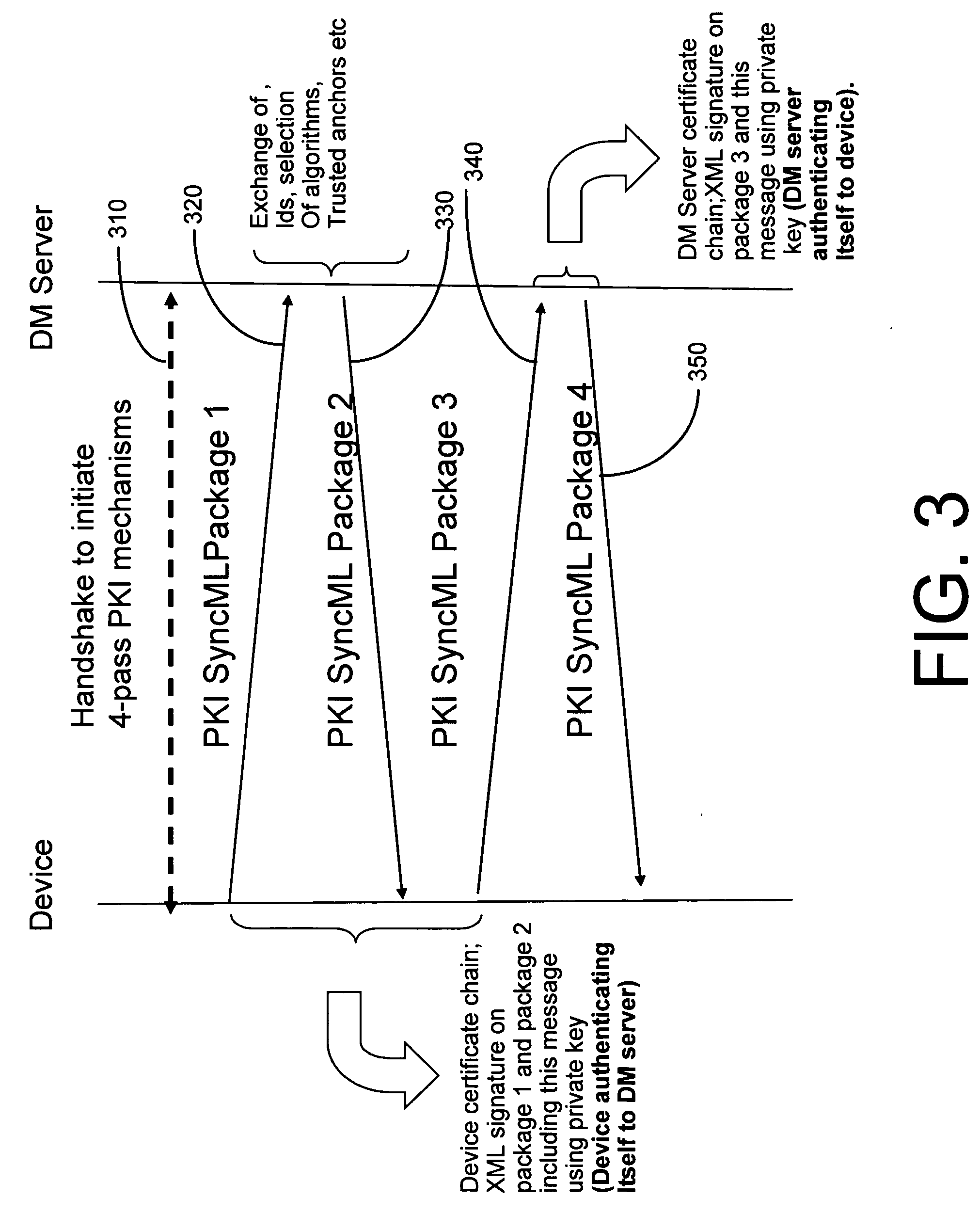
System and method for integrating PKI and XML-based security mechanisms in SyncML
Additions of extensions to SyncML protocol to incorporate PKI-based and XML-based security mechanisms. The present invention involves the partial incorporation of the PKI based mechanisms present in the Rights Object Acquisition Protocol (ROAP) suite of OMA DRMv2 model into the SyncML protocol, resulting in security enhancements for SyncML.
Owner:NOKIA CORP
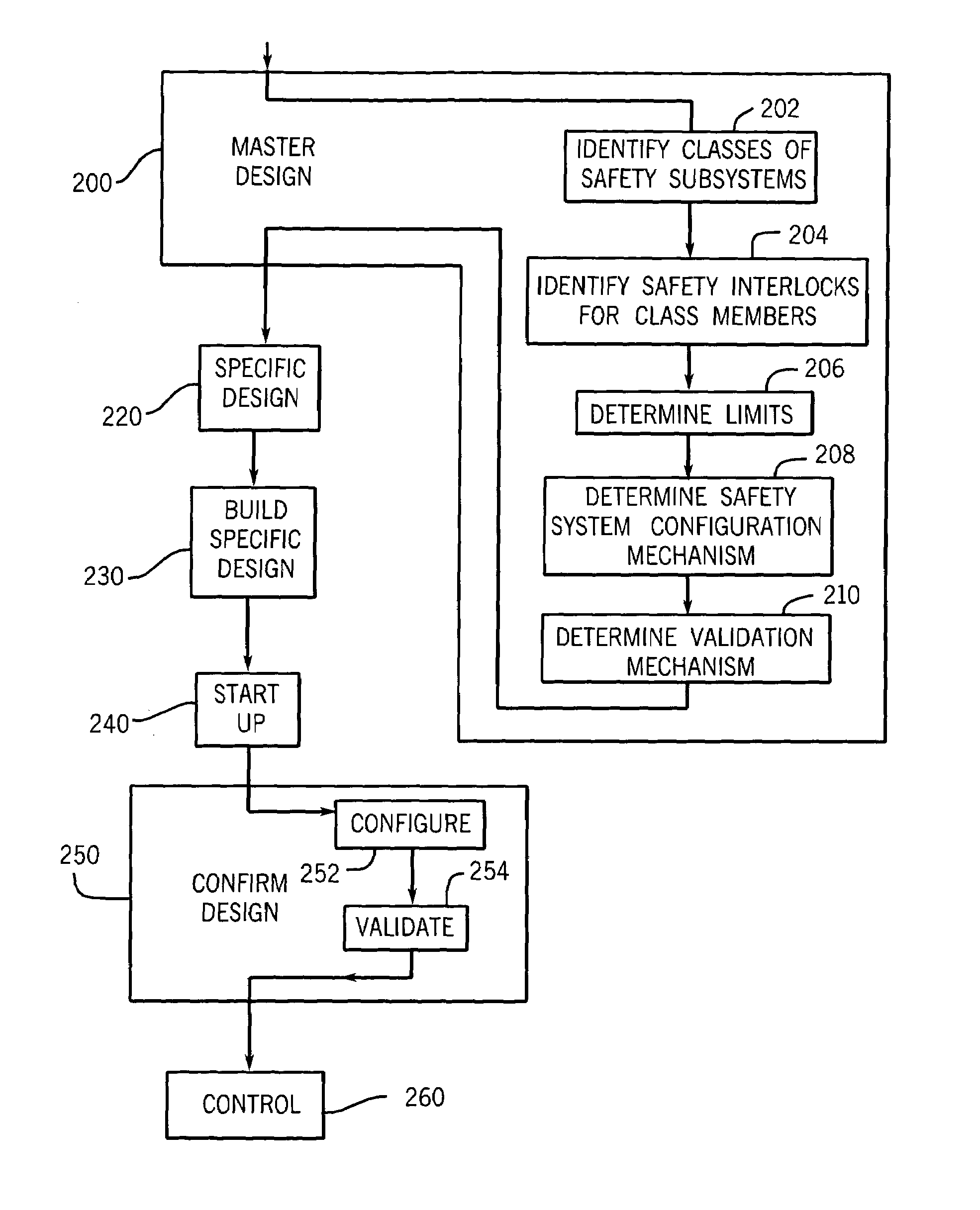
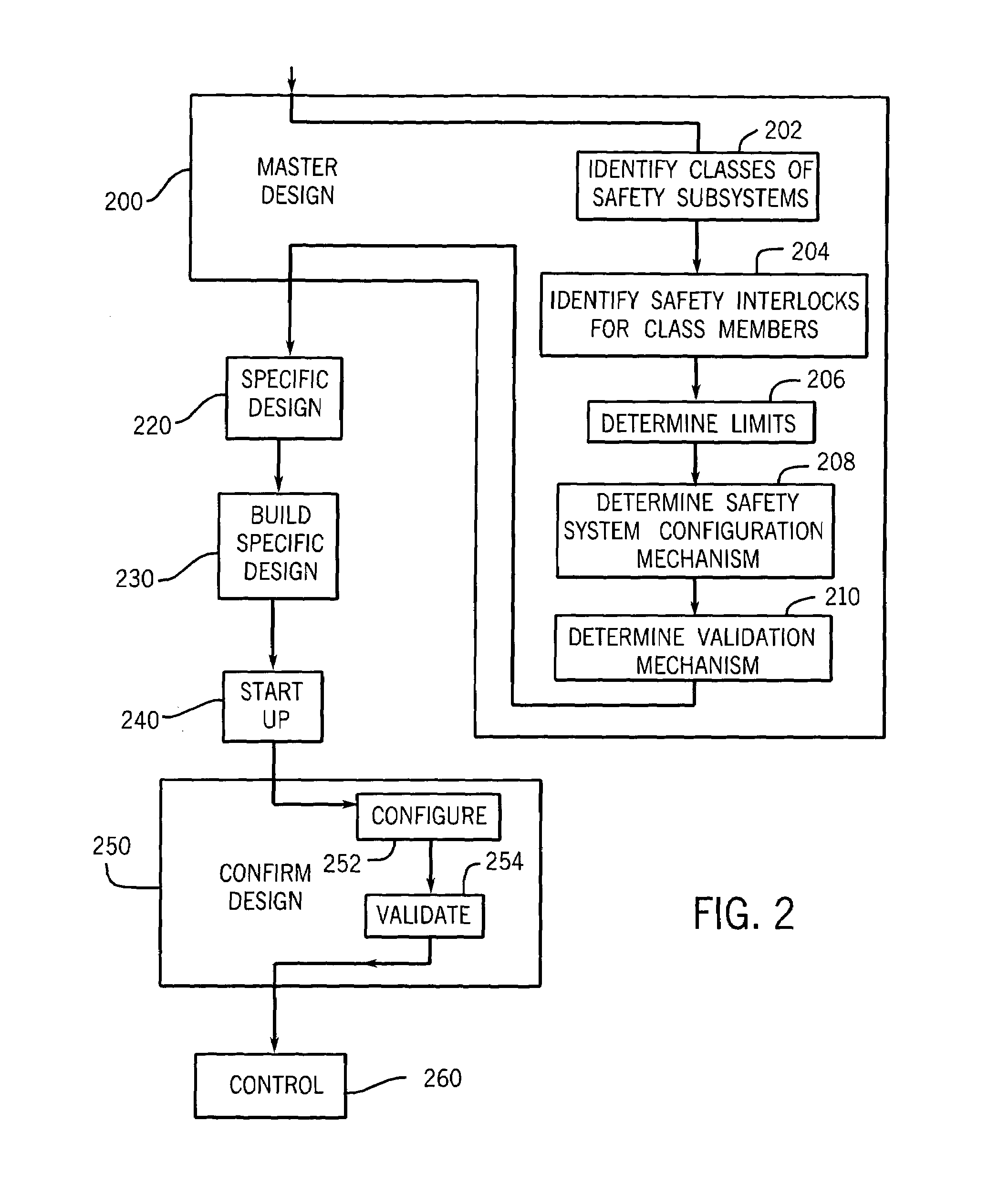
Configurable safety system for implementation on industrial system and method of implementing same
A configurable control system for operating an industrial system in a reliable, safety-enhanced manner, and method of implementing such a system in any of a variety of particular industrial systems of a given class, are disclosed. The method includes storing, onto a controller of a particular industrial system, a master program capable of being used to operate a generalized industrial system having a maximum number of safety subsystems of a given type, where the particular industrial system falls within a class defined by the generalized system. The method also includes receiving a configuration input indicative of an absence / presence of a safety subsystem of the first type; validating the input; automatically configuring the master program to arrive at a configured program capable of operating the particular industrial system; and activating the controller for operation according to the configured program, which can include activating visualization or annunciation mechanisms representing the configured system.
Owner:ROCKWELL AUTOMATION TECH
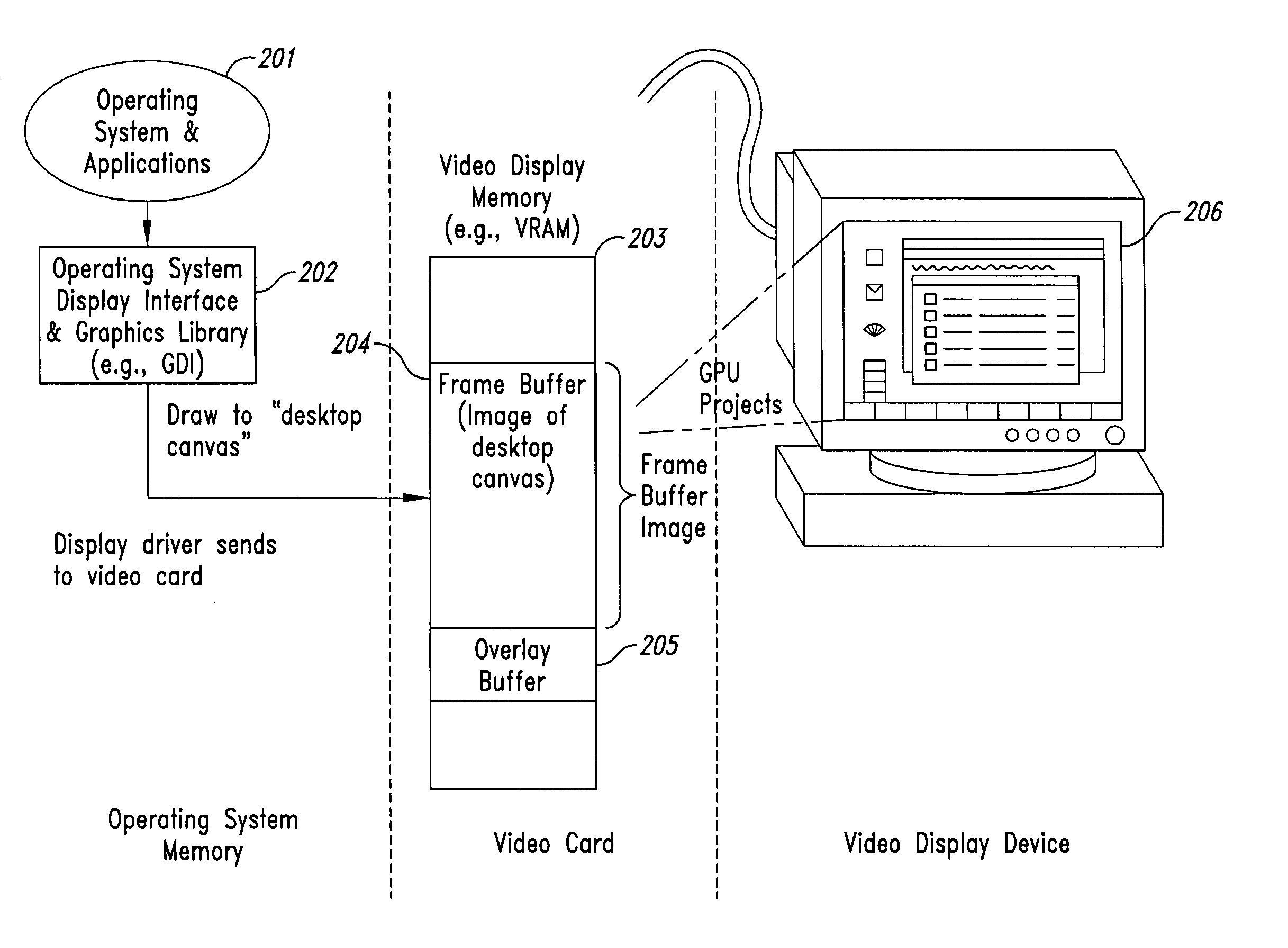
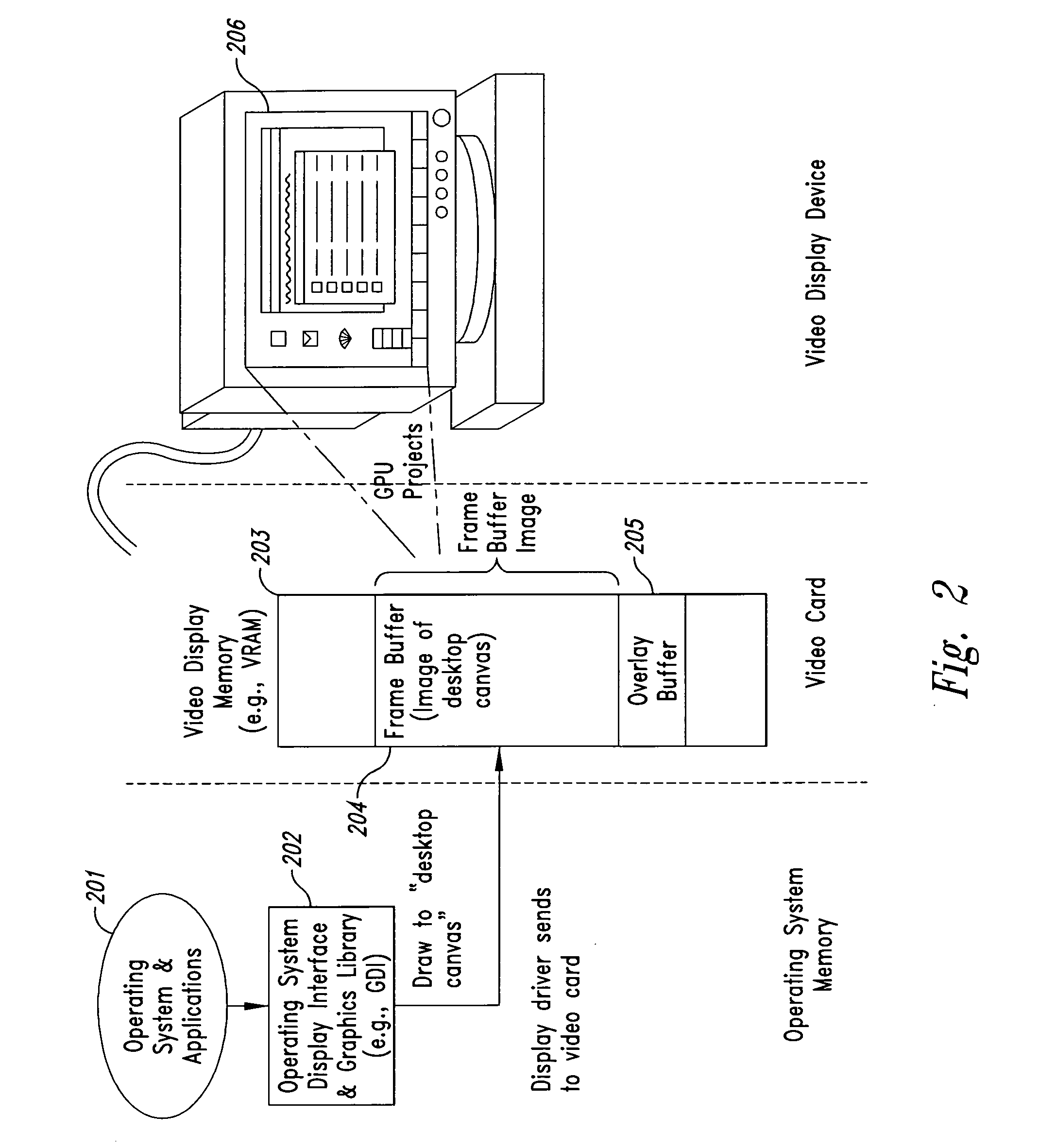
Method and system for maintaining secure data input and output
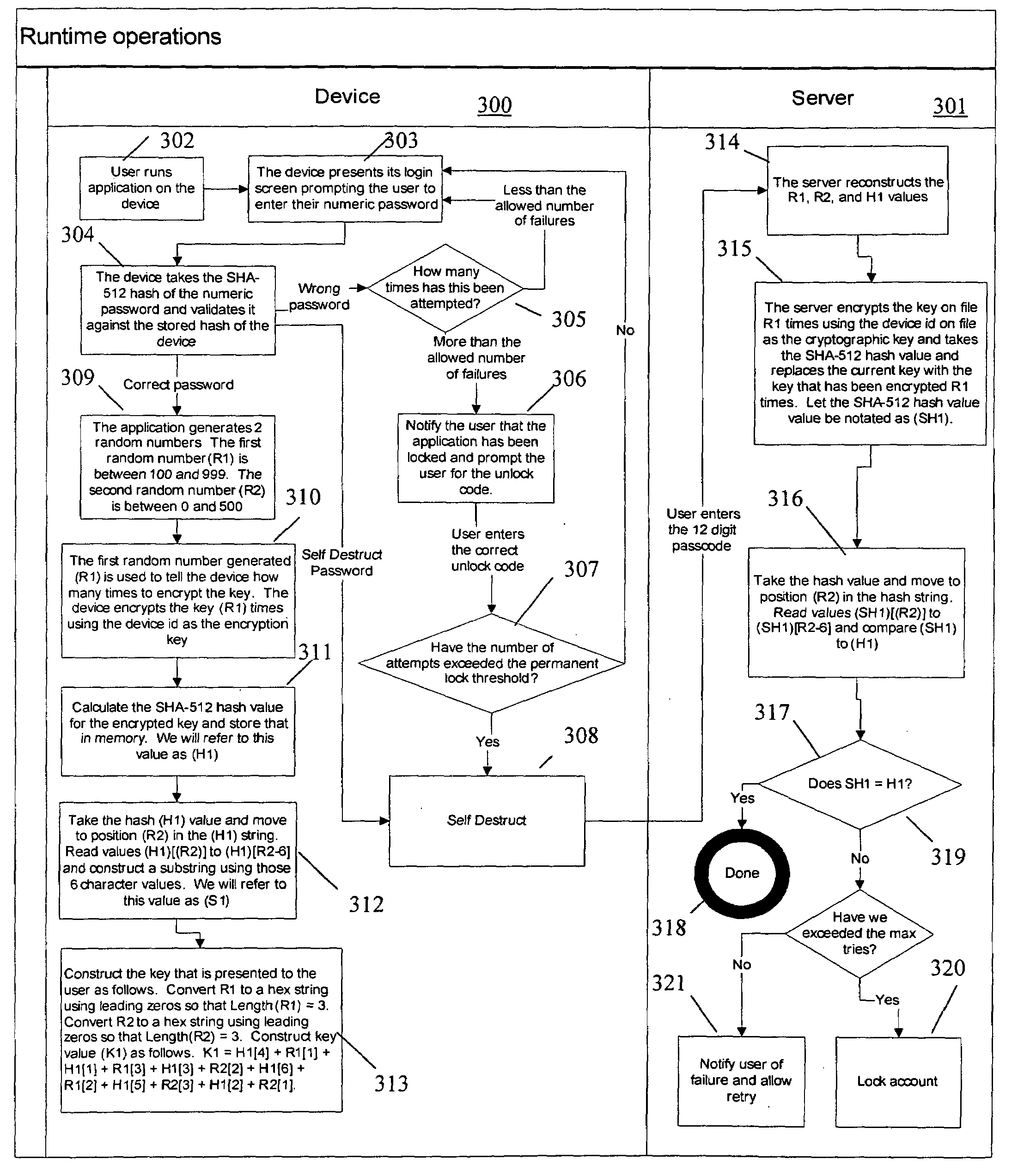
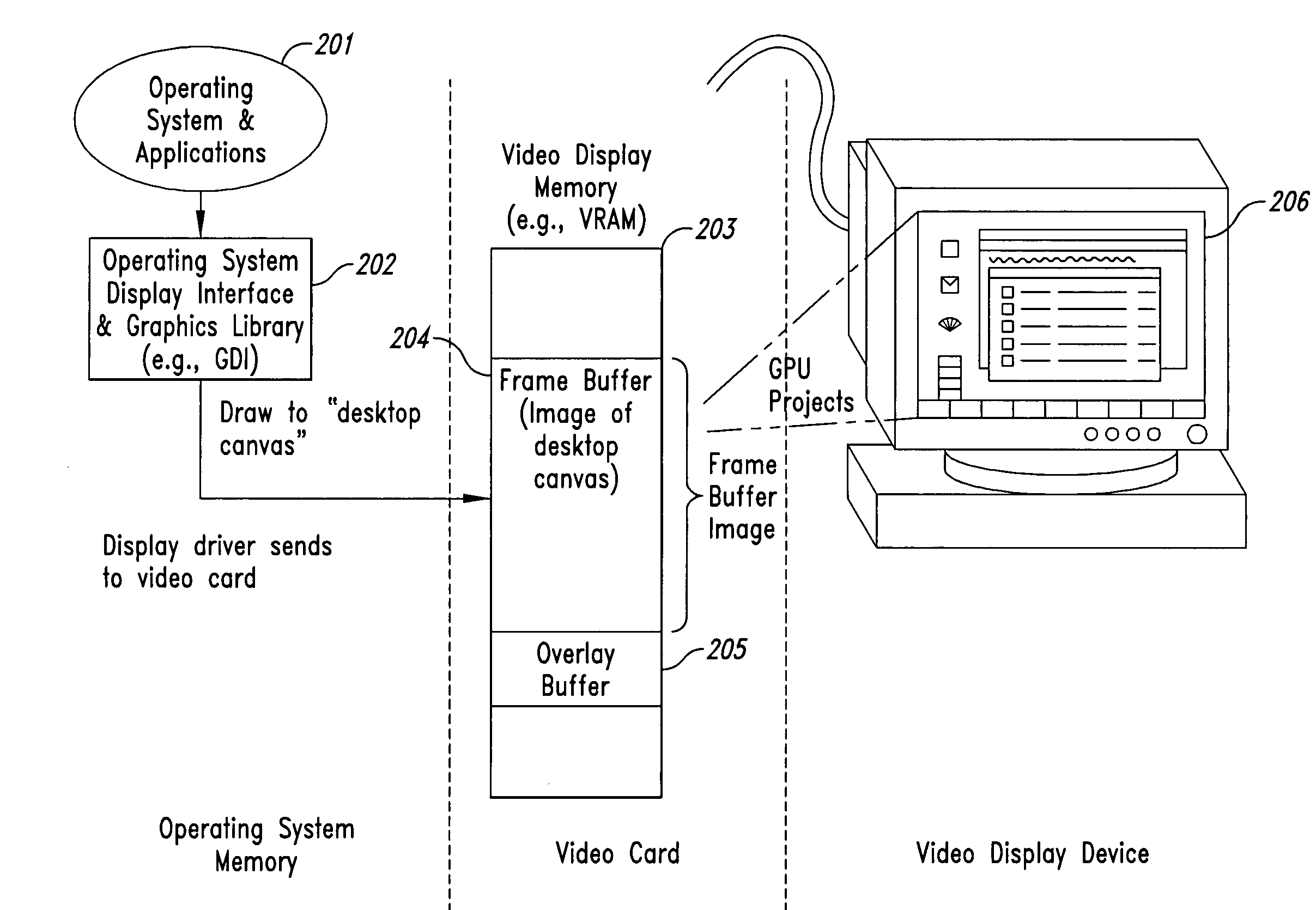
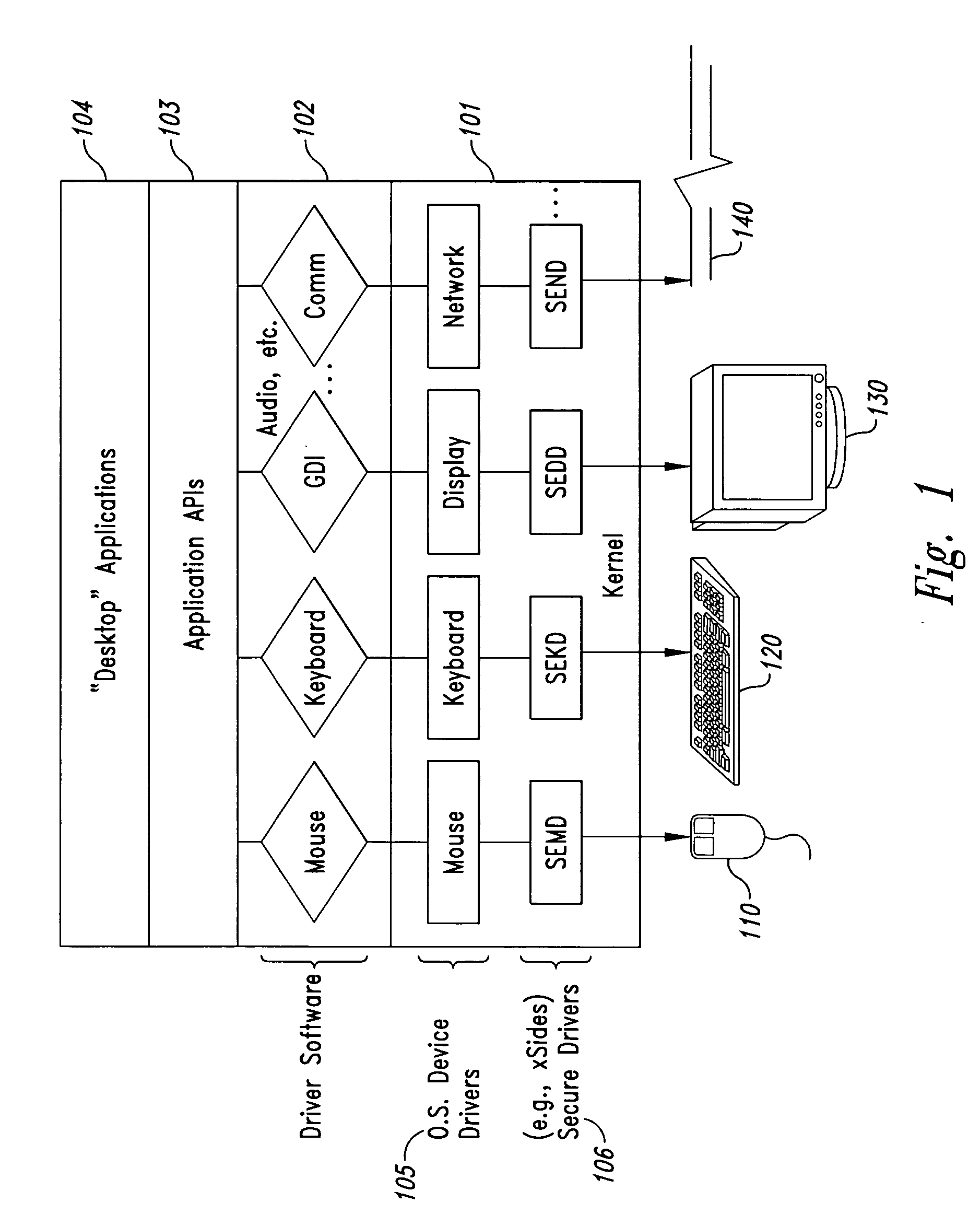
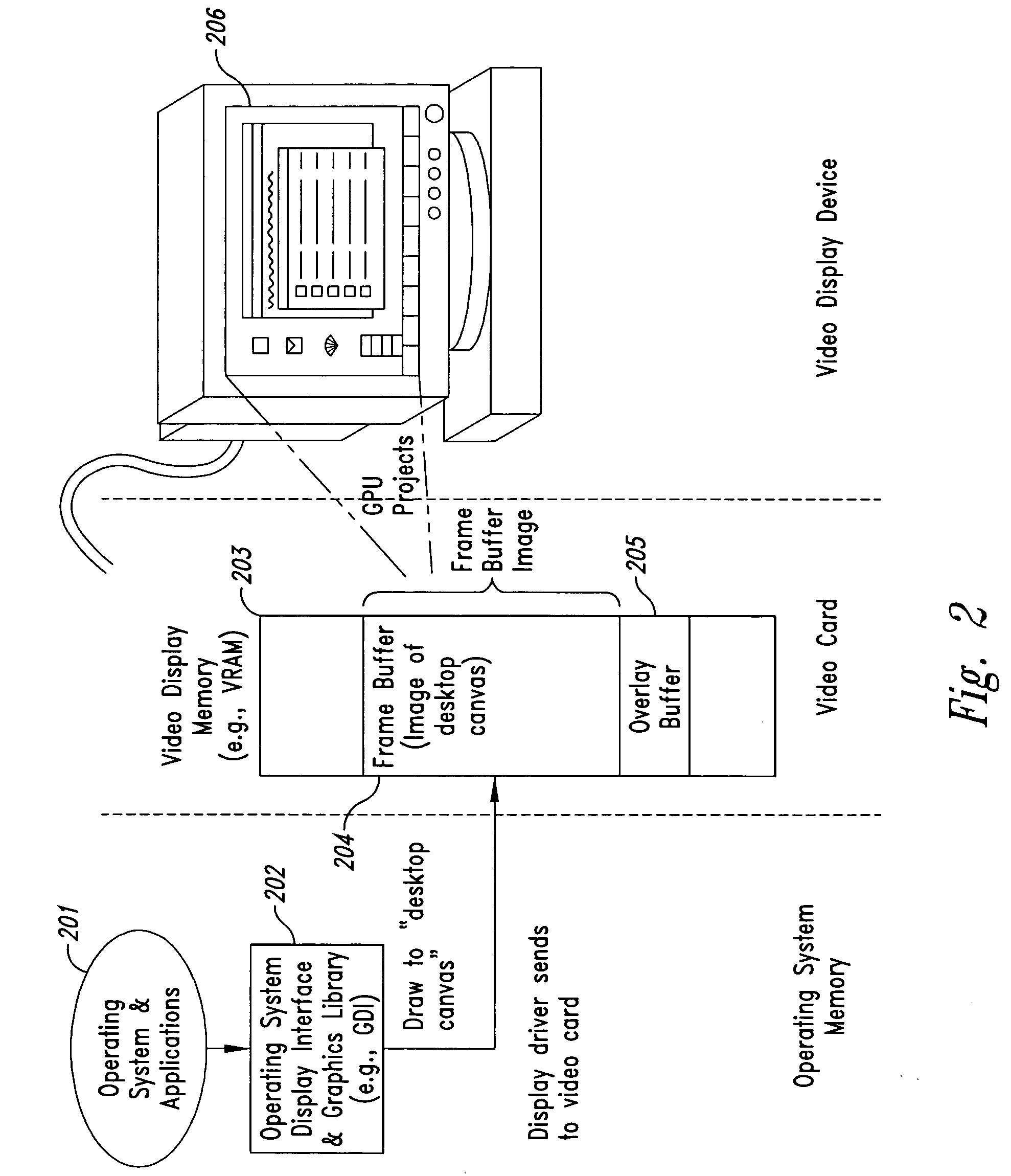
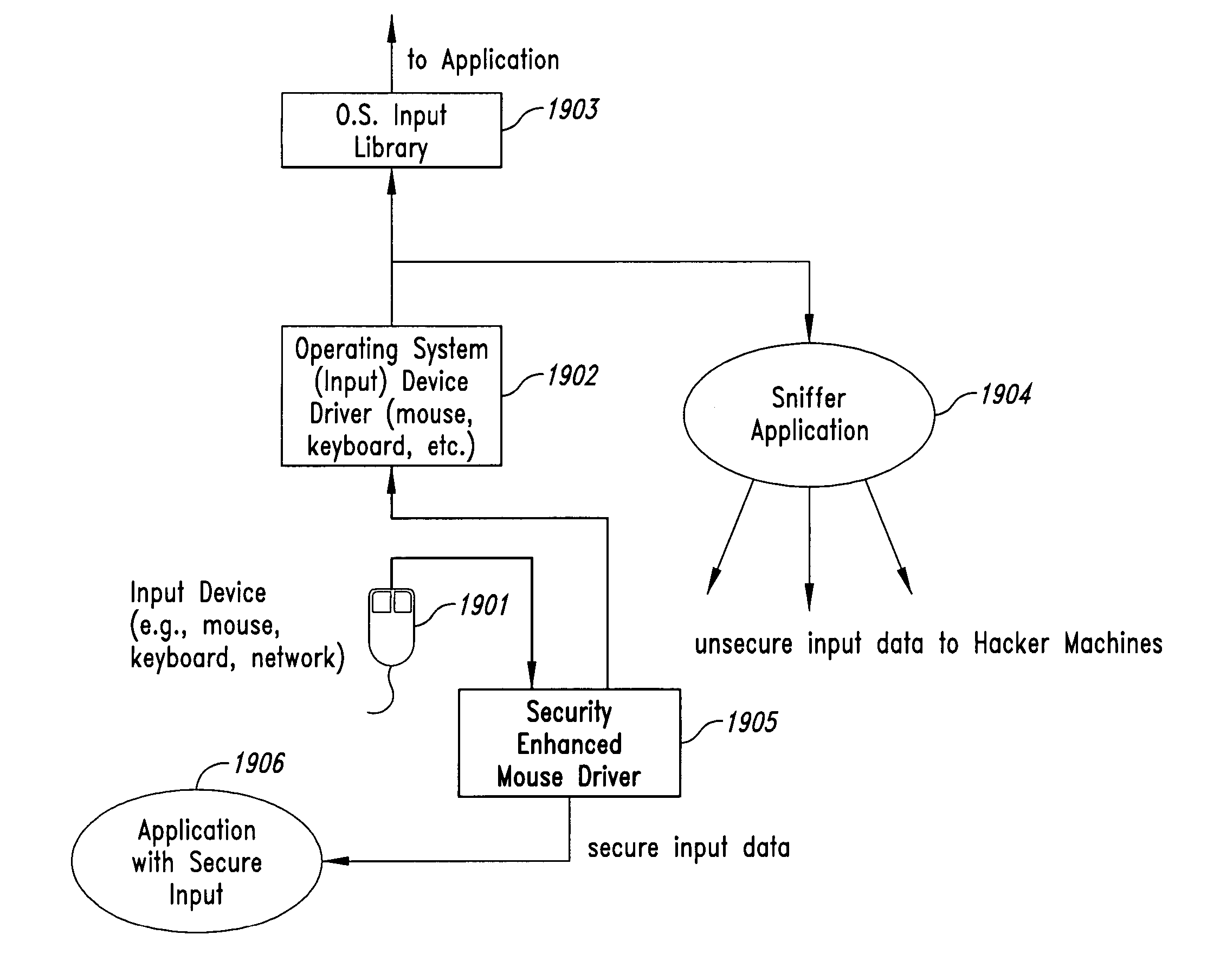
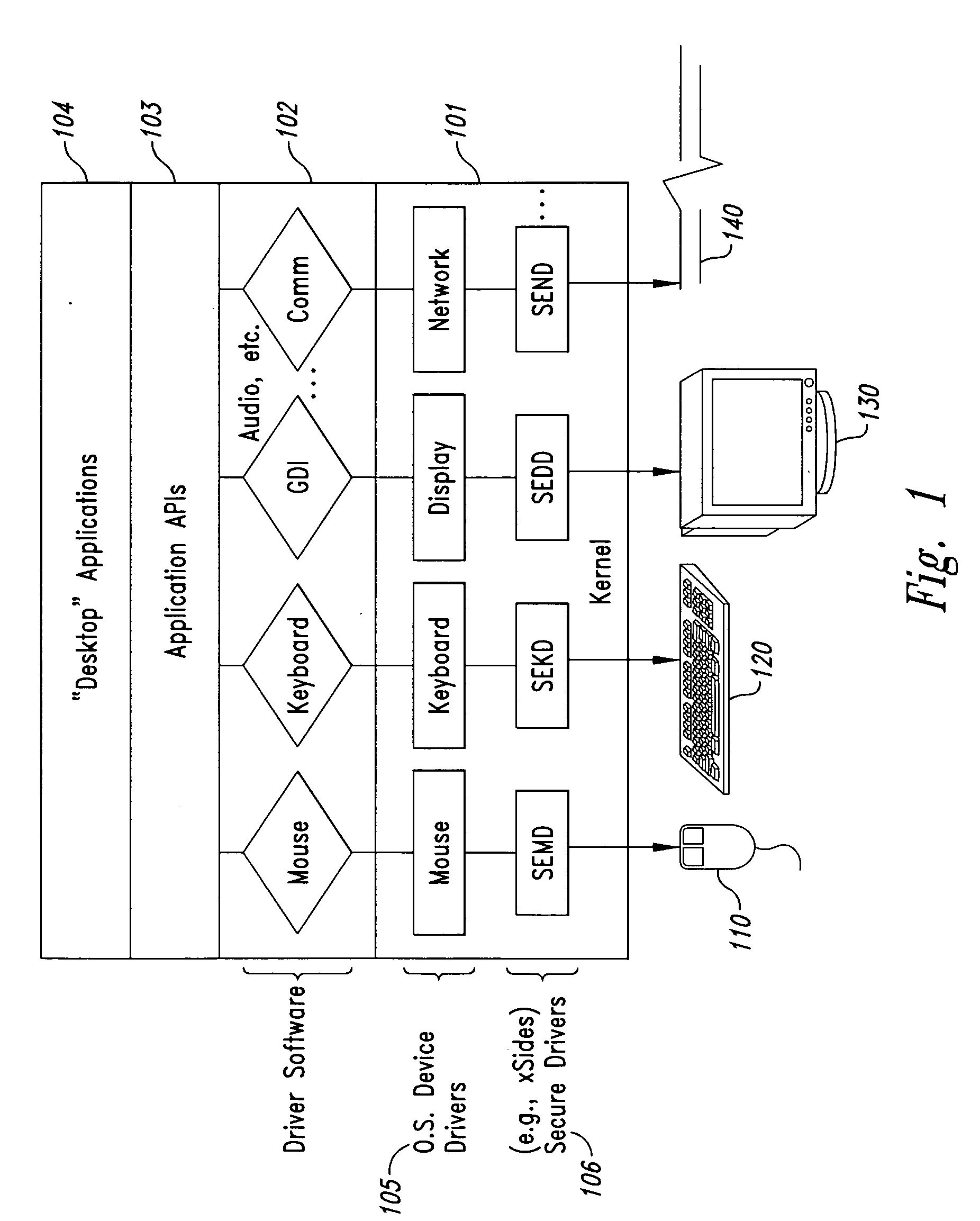
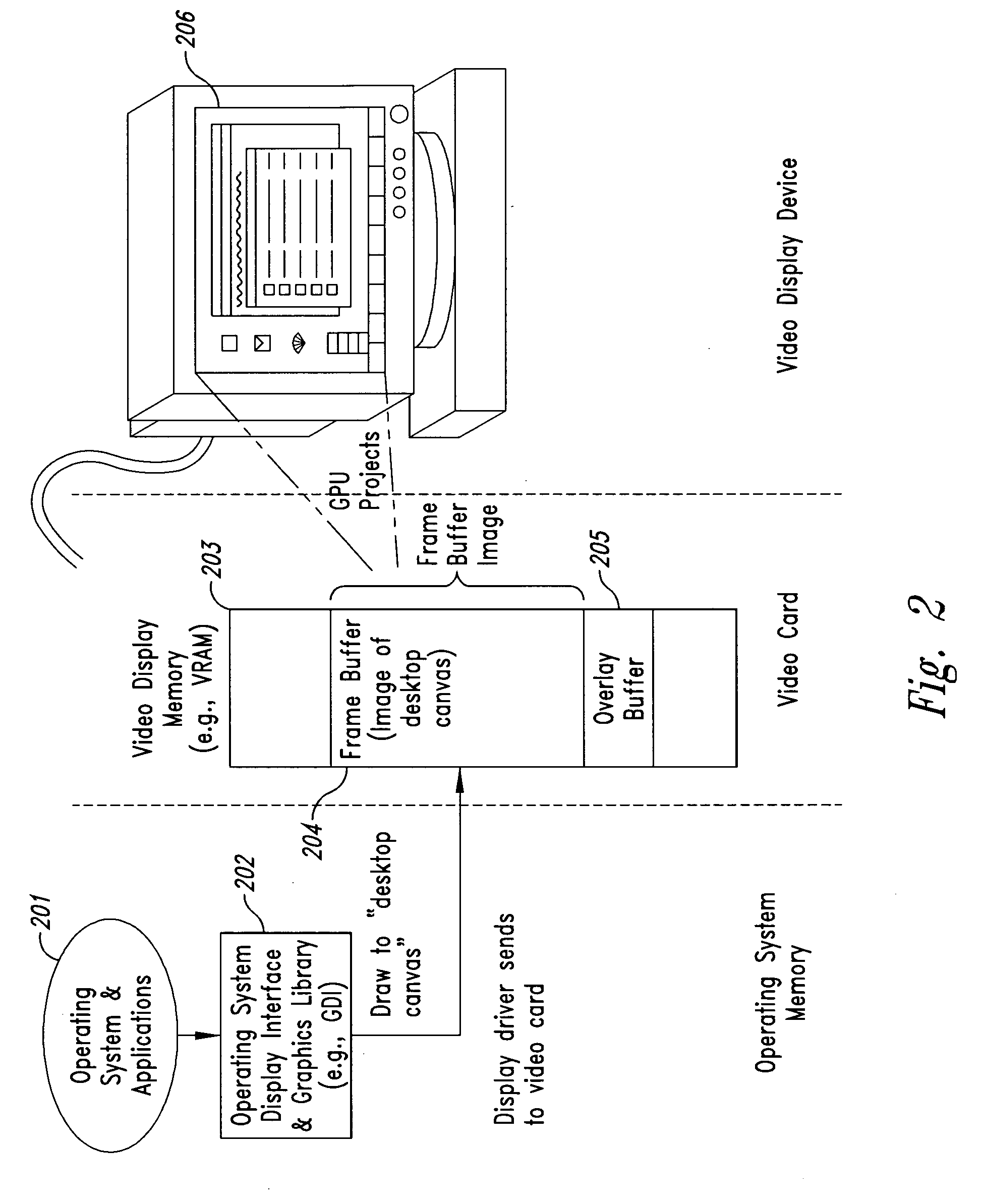
InactiveUS20050102264A1Improve data securityProhibit and frustrate attemptData processing applicationsDigital data processing detailsObfuscationClient-side
Methods and systems for enhancing the security of data during input and output on a client computer system are provided to prevent attempts by unauthorized code to access, intercept, and / or modify data. Example embodiments provide a plurality of obfuscation techniques and security enhanced drivers that use these obfuscation techniques to prohibit unauthorized viewing / receiving of valid data. When the drivers are used together with the various obfuscation techniques, the security enhanced drivers provide mechanisms for “scheduling” the content of the storage areas used to store the data so that valid data is not available to unauthorized recipients. When unauthorized recipients attempt to access the “data,” they perceive or receive obfuscated data. The obfuscation techniques described include “copy-in,”“replace and restore,” and “in-place replacement” de-obfuscation / re-obfuscation techniques. In one embodiment, a security enhanced display driver, a security enhanced mouse driver, a security enhanced keyboard driver, and a security enhanced audio driver are provided. To complement the security enhancements, the methods and systems also provide for a watchdog mechanism to ensure that the driver is functioning as it should be and various user interface techniques for denoting security on a display device.
Owner:XSIDES
Method and system for maintaining secure data input and output
InactiveUS20050102266A1Improve data securityProhibit and frustrate attemptData processing applicationsDigital data processing detailsObfuscationProgram security
Methods and systems for enhancing the security of data during input and output on a client computer system are provided to prevent attempts by unauthorized code to access, intercept, and / or modify data. Example embodiments provide a plurality of obfuscation techniques and security enhanced drivers that use these obfuscation techniques to prohibit unauthorized viewing / receiving of valid data. When the drivers are used together with the various obfuscation techniques, the security enhanced drivers provide mechanisms for “scheduling” the content of the storage areas used to store the data so that valid data is not available to unauthorized recipients. When unauthorized recipients attempt to access the “data,” they perceive or receive obfuscated data. The obfuscation techniques described include “copy-in,”“replace and restore,” and “in-place replacement” de-obfuscation / re-obfuscation techniques. In one embodiment, a security enhanced display driver, a security enhanced mouse driver, a security enhanced keyboard driver, and a security enhanced audio driver are provided. To complement the security enhancements, the methods and systems also provide for a watchdog mechanism to ensure that the driver is functioning as it should be and various user interface techniques for denoting security on a display device.
Owner:XSIDES
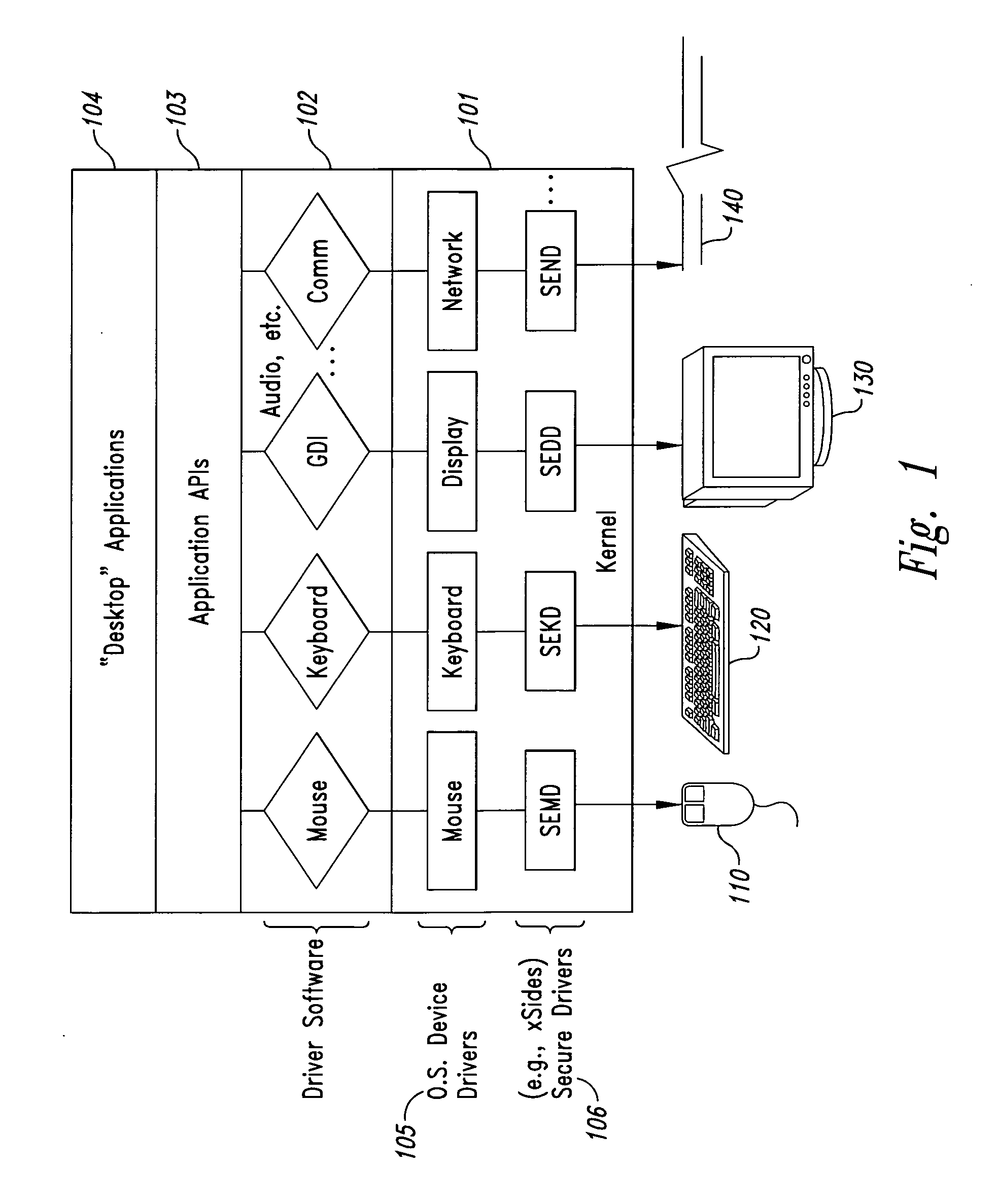
Security enhanced network device and method for secure operation of same
ActiveUS8402267B1Digital data processing detailsUnauthorized memory use protectionCommunication controlSecurity enhancement
A security enhanced network device includes a processor, a memory, and a communication controller operably connected to form a processing device. A microkernel provides a partitioning between a communication address space, a security enforcement address space, and a protected operations address space. The communication address space contains communications threads for interacting with a network. The protected operations address space contains protected operations threads for performing protected operations. The security enforcement address space contains security threads for providing secure isolation of the protected operations address space from the communication address space. A method of secure operation of the network device includes: partitioning the network device into the communication address space, the security enforcement address space, and the protected operations address space; interacting with the network; providing secure isolation of the protected operations address space from the communication address space; and performing protected operations.
Owner:UNIV OF LOUISVILLE RES FOUND INC
Hardware/software partitioning for encrypted WLAN communications
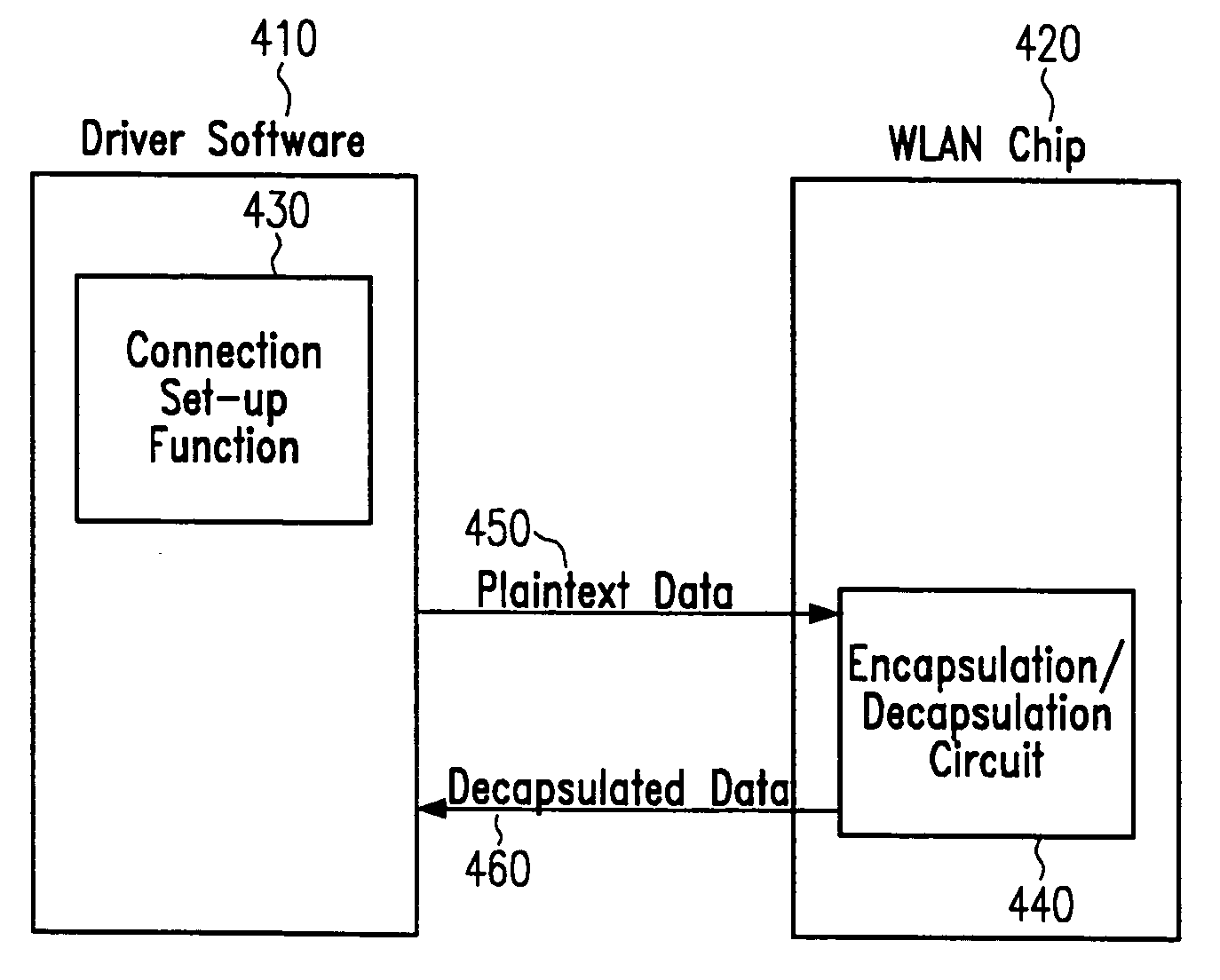
ActiveUS20050172119A1Overcome disadvantagesData stream serial/continuous modificationUser identity/authority verificationComputer hardwareSoftware architecture
A method of performing encrypted WLAN communication is provided that comprises the steps of performing a connection set-up for the encrypted WLAN communication and performing data frame encapsulation and / or decapsulation during the encrypted WLAN communication. The connection set-up is performed by executing software-implemented instructions, and the data frame encapsulation and / or decapsulation is performed by operating single-purpose hardware. In embodiments, corresponding single-purpose hardware devices, integrated circuit chips, computer program products and computer systems are provided. The embodiments may provide an improved hardware / software architecture for 802.11i security enhancement.
Owner:ADVANCED MICRO DEVICES INC
Method and system for maintaining secure data input and output
InactiveUS20050086666A1Improve data securityProhibit and frustrate attemptData processing applicationsDigital data processing detailsObfuscationProgram security
Methods and systems for enhancing the security of data during input and output on a client computer system are provided to prevent attempts by unauthorized code to access, intercept, and / or modify data. Example embodiments provide a plurality of obfuscation techniques and security enhanced drivers that use these obfuscation techniques to prohibit unauthorized viewing / receiving of valid data. When the drivers are used together with the various obfuscation techniques, the security enhanced drivers provide mechanisms for “scheduling” the content of the storage areas used to store the data so that valid data is not available to unauthorized recipients. When unauthorized recipients attempt to access the “data,” they perceive or receive obfuscated data. The obfuscation techniques described include “copy-in,”“replace and restore,” and “in-place replacement” de-obfuscation / re-obfuscation techniques. In one embodiment, a security enhanced display driver, a security enhanced mouse driver, a security enhanced keyboard driver, and a security enhanced audio driver are provided. To complement the security enhancements, the methods and systems also provide for a watchdog mechanism to ensure that the driver is functioning as it should be and various user interface techniques for denoting security on a display device.
Owner:XSIDES
Database safety access control method based on independent authorization
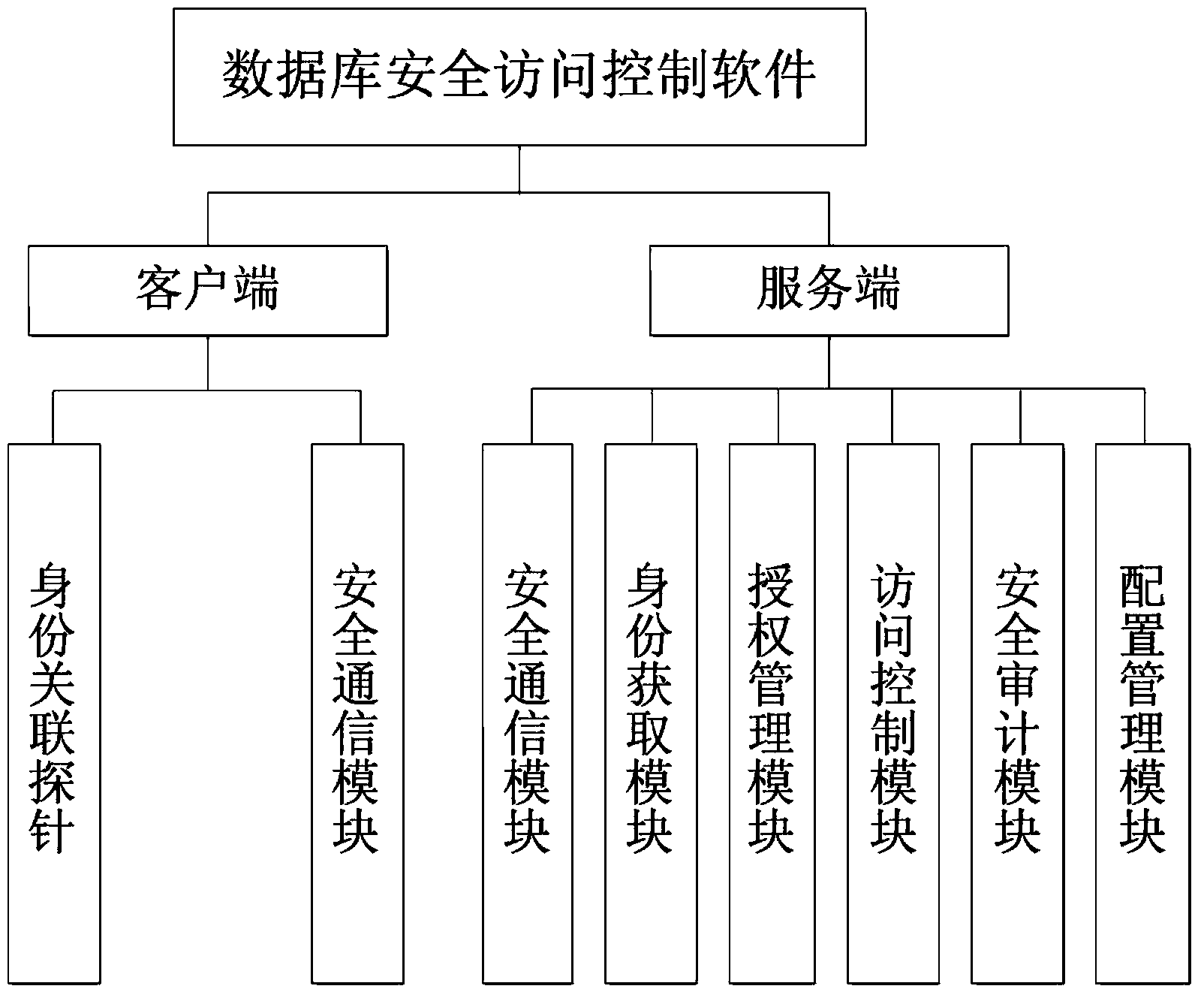
ActiveCN104166812AImprove securityDigital data authenticationSpecial data processing applicationsLoose couplingDatabase security
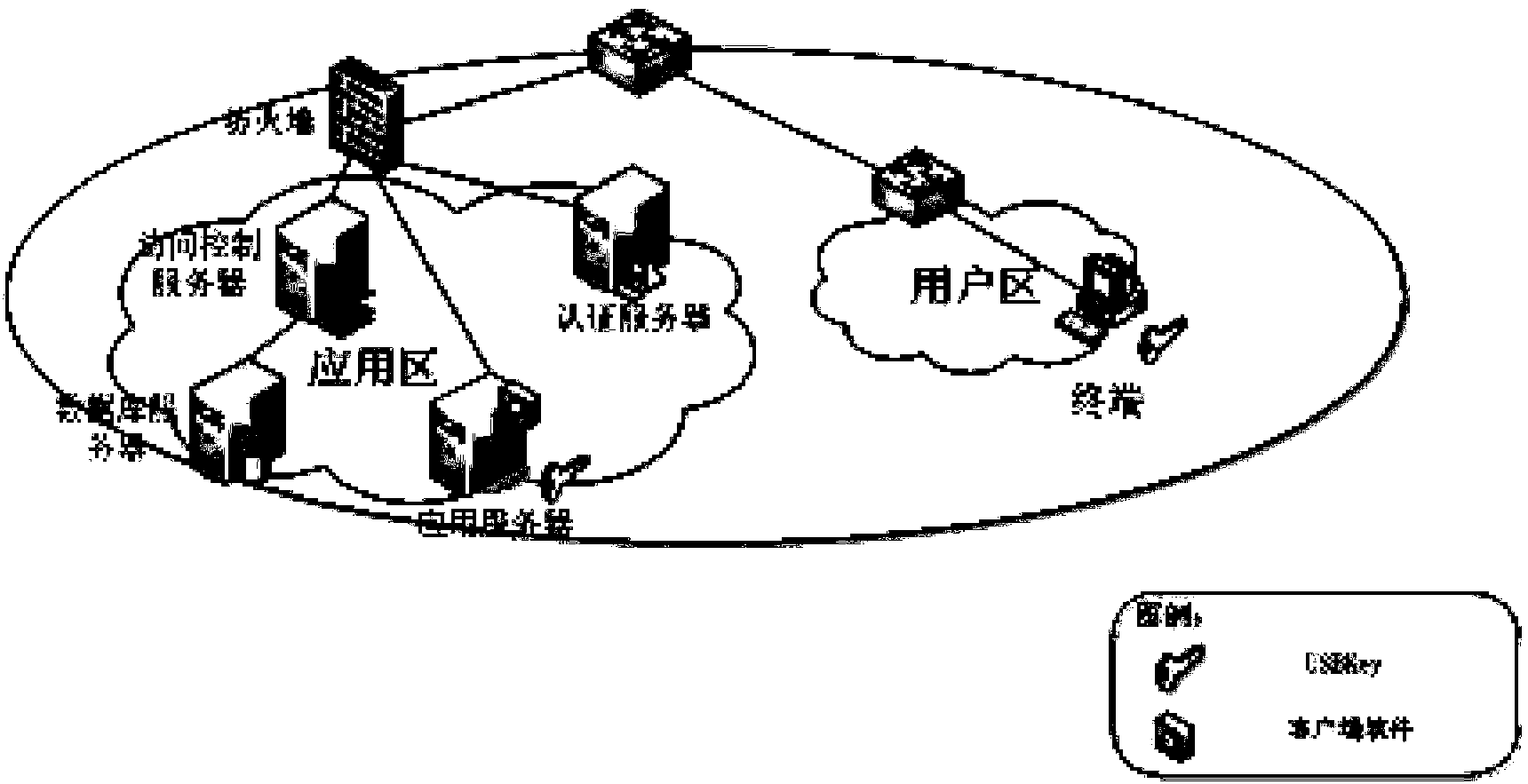
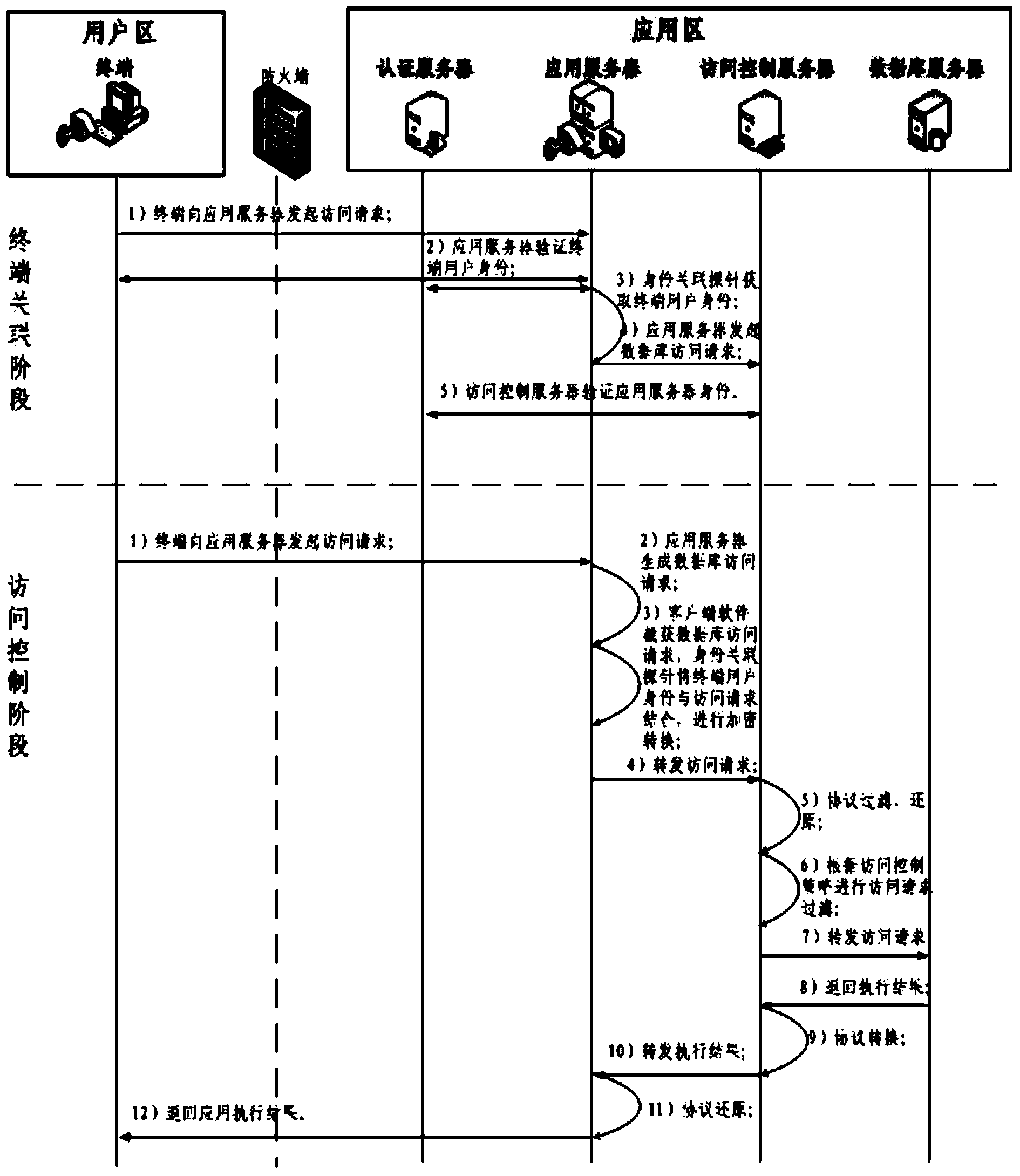
The invention discloses a database safety access control method based on independent authorization, and belongs to the field of database safety. The designing thought that the method is in loose coupling with a database system is adopted, access control on the basis of users instead of database accounts is realized by binding database access behaviors with a USBKey, and control and audit can be conducted on behaviors of terminal users by correlating the database access behaviors and the terminal users. Advanced access control is introduced for conducting analyzing and monitoring on database access statements, therefore, database attack behaviors are shielded, insider operation behaviors are controlled and audited, and information loss caused by the database attacking behaviors can be reduced. By repackaging database access requests, monitoring and sniffing attacks are avoided. According to the technology, by adding the means of identity authentication, access control and safety transmission which are independent from a database management system, safety enhancing of a heterogeneous database management system under multiple platforms is realized on the premise that the usage mode of an existing application system is not changed.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND +1
Method and system for extending selinux policy models and their enforcement
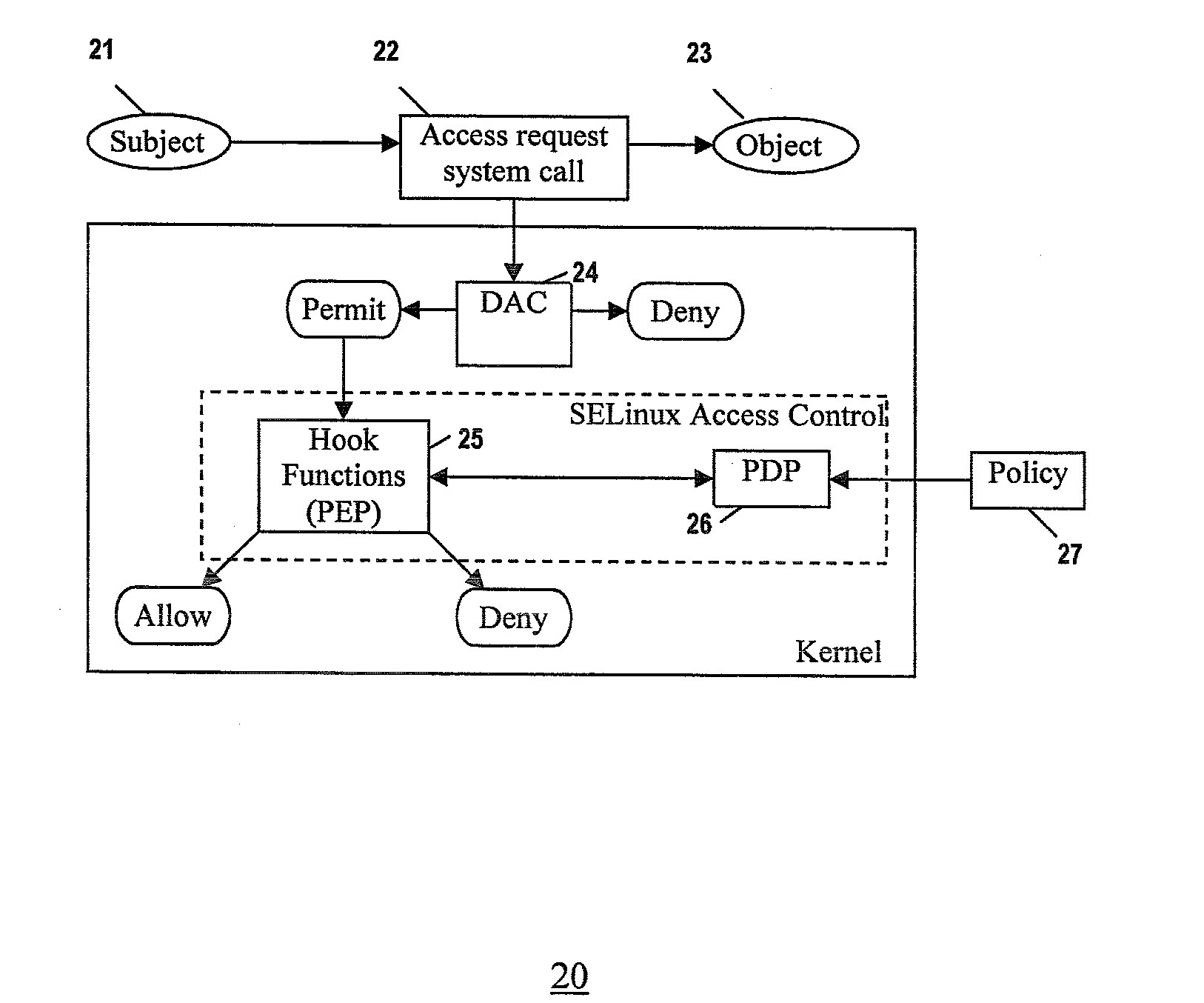
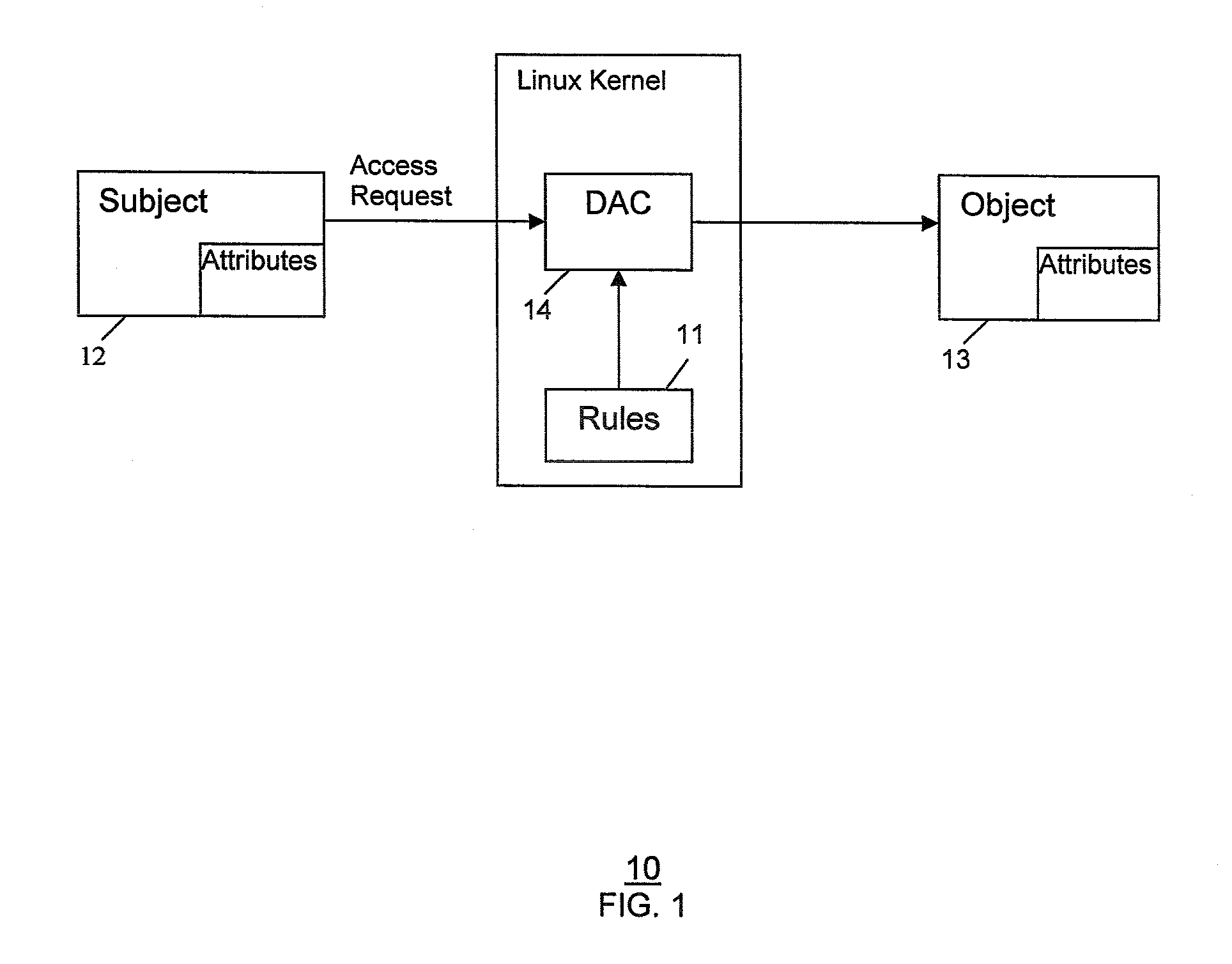
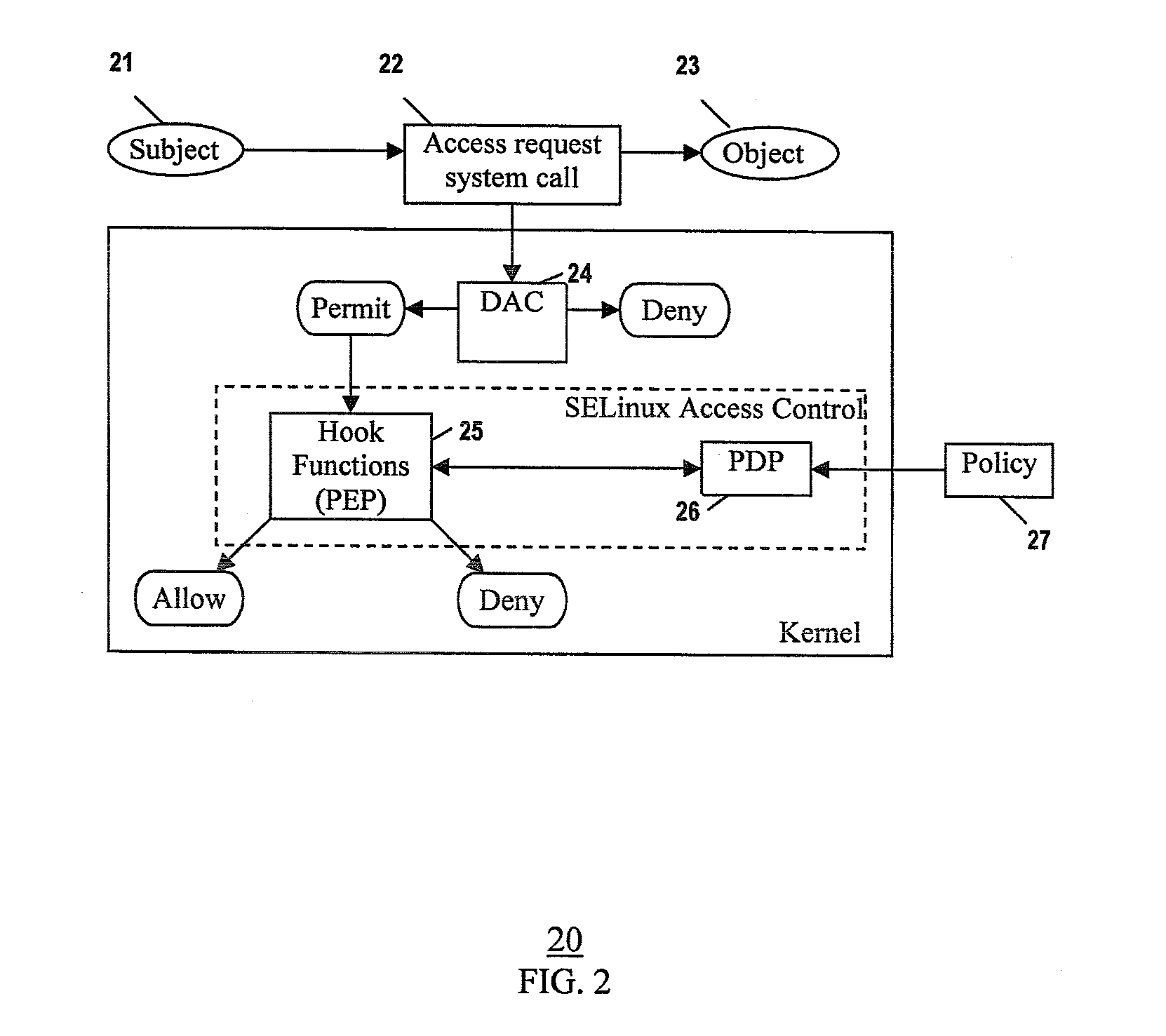
InactiveUS20080184335A1Digital computer detailsPlatform integrity maintainanceGNU/LinuxSecurity enhancement
A Security Enhanced Linux (SELinux) system implementing extended policy models and method for their enforcement, is provided. Extended attributes are defined to specify extended policies. The SELinux policy model is extended to include the extended policies. The extended policies are enforced in addition to SELinux Type Enforcement. In one implementation, defining extended attributes involves defining TC-related attributes to specify TC-related policies. Further, extending the SELinux policy model includes extending the SELinux policy model to include the TC-related policies, in addition to SELinux Type Enforcement. Furthermore, enforcing the extended policies includes enforcing the TC-related policies in addition to SELinux Type Enforcement.
Owner:SAMSUNG ELECTRONICS CO LTD
System and methods for firearm safety enhancement
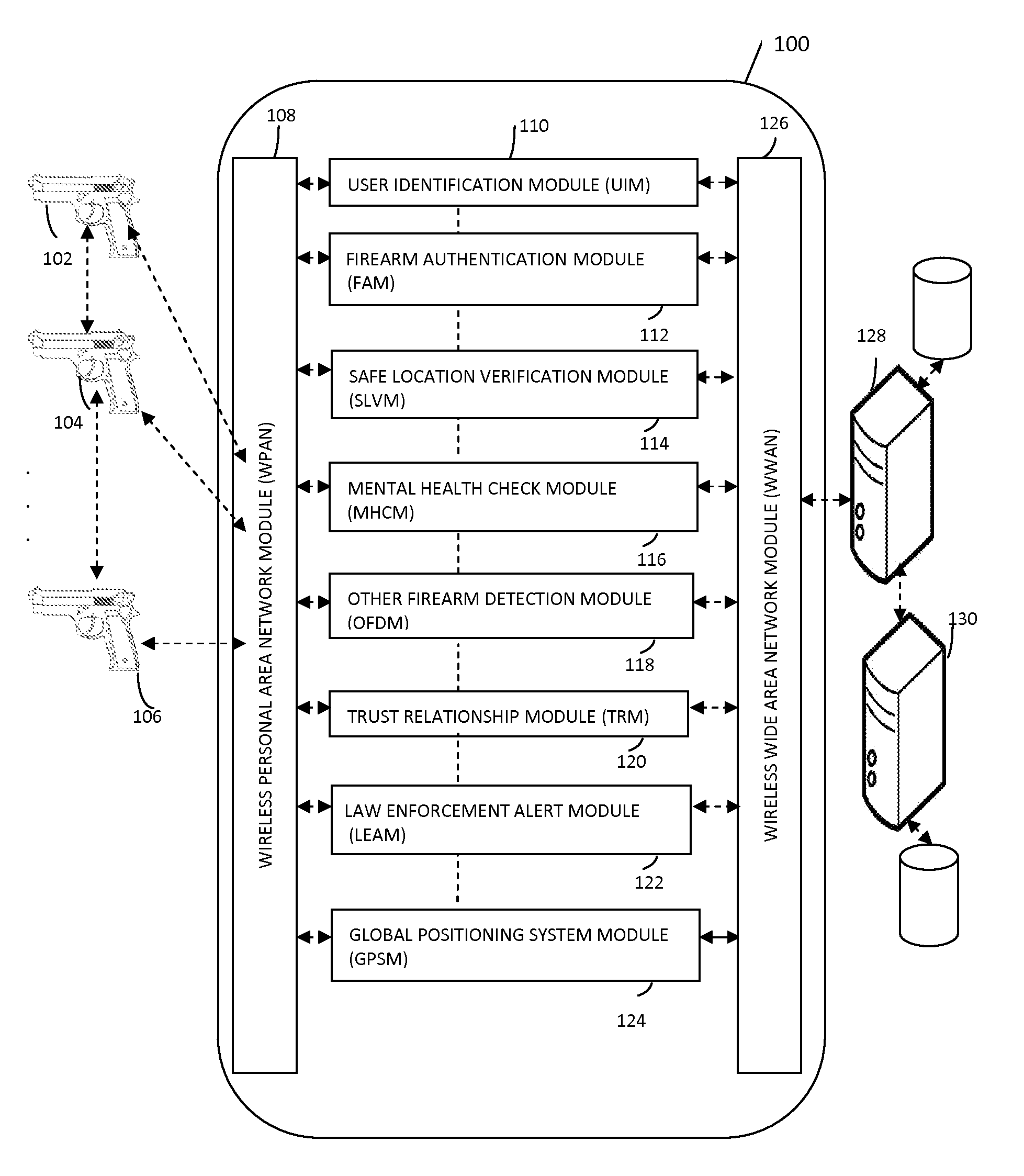
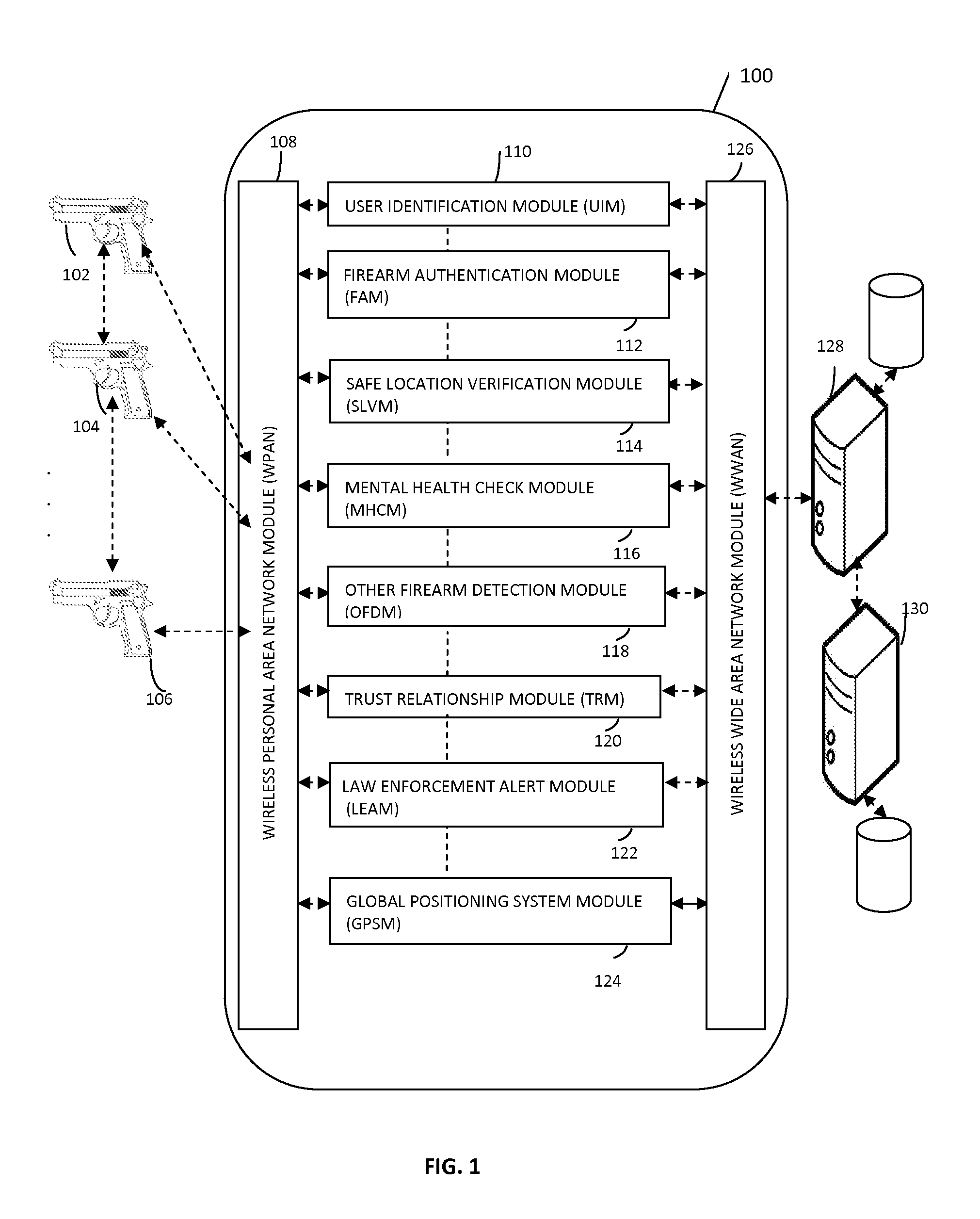
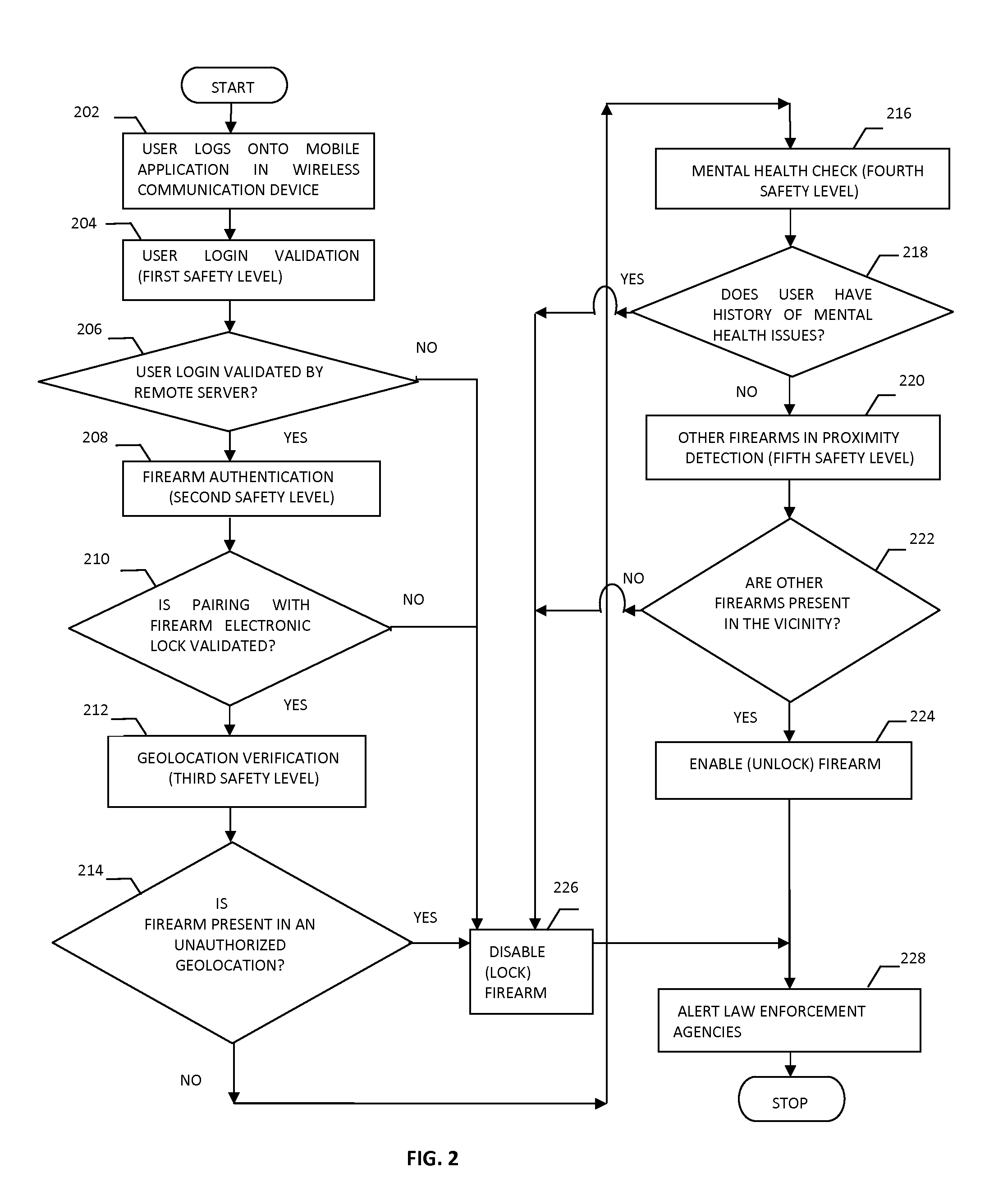
InactiveUS20140366421A1Compromise safetyImprove security featuresSafety arrangementEngineeringSecurity enhancement
The present invention relates to system and methods for providing enhanced firearm safety by utilizing an electronic firearm locking device present in the firearm, in communication with a mobile application of a wireless mobile communication device and a remote firearm management server that provides five levels of safety for selective and dynamic enabling and disabling of the firearm based on real time situations along with several value added features.
Owner:ARIF ADEEL +1
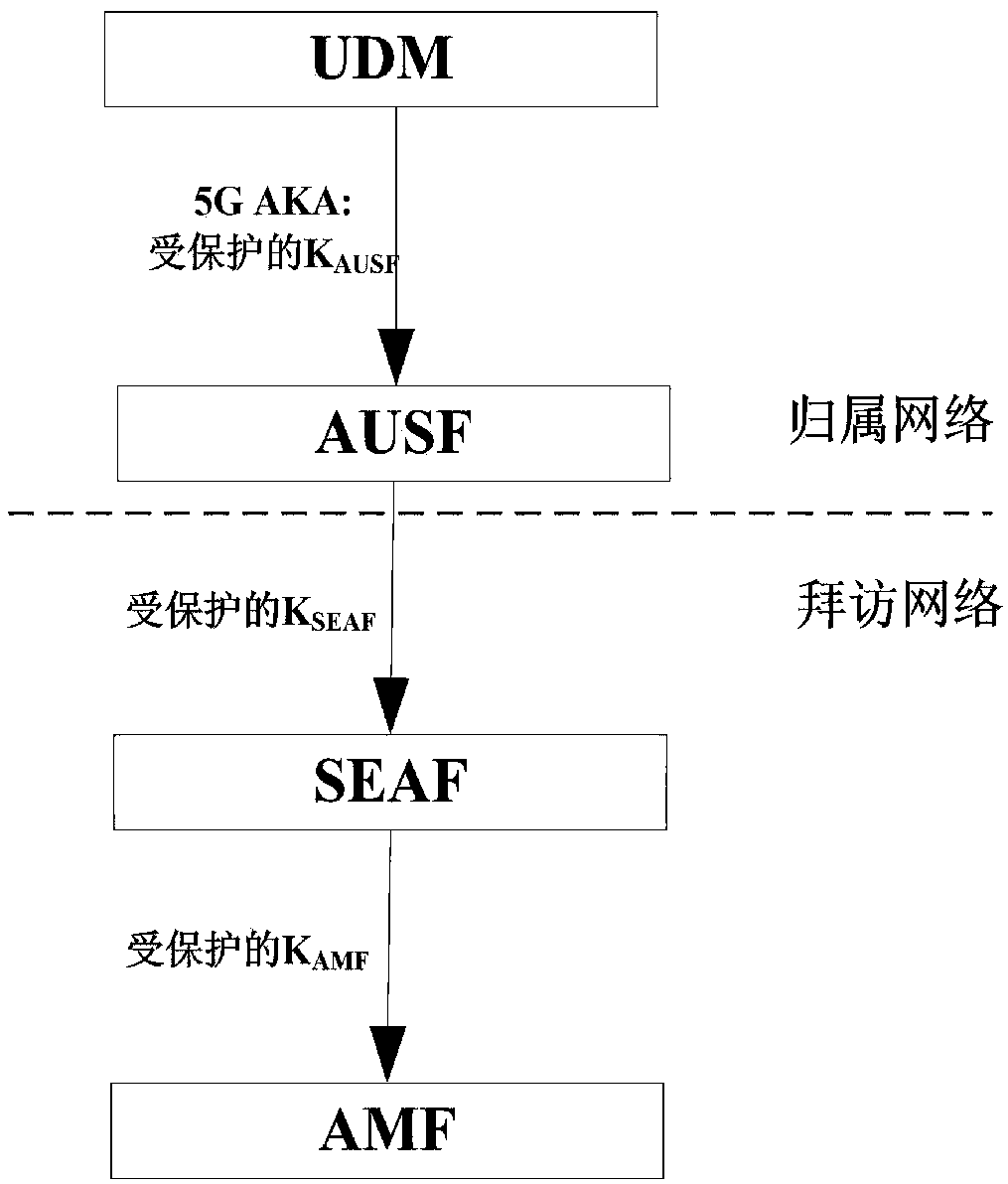
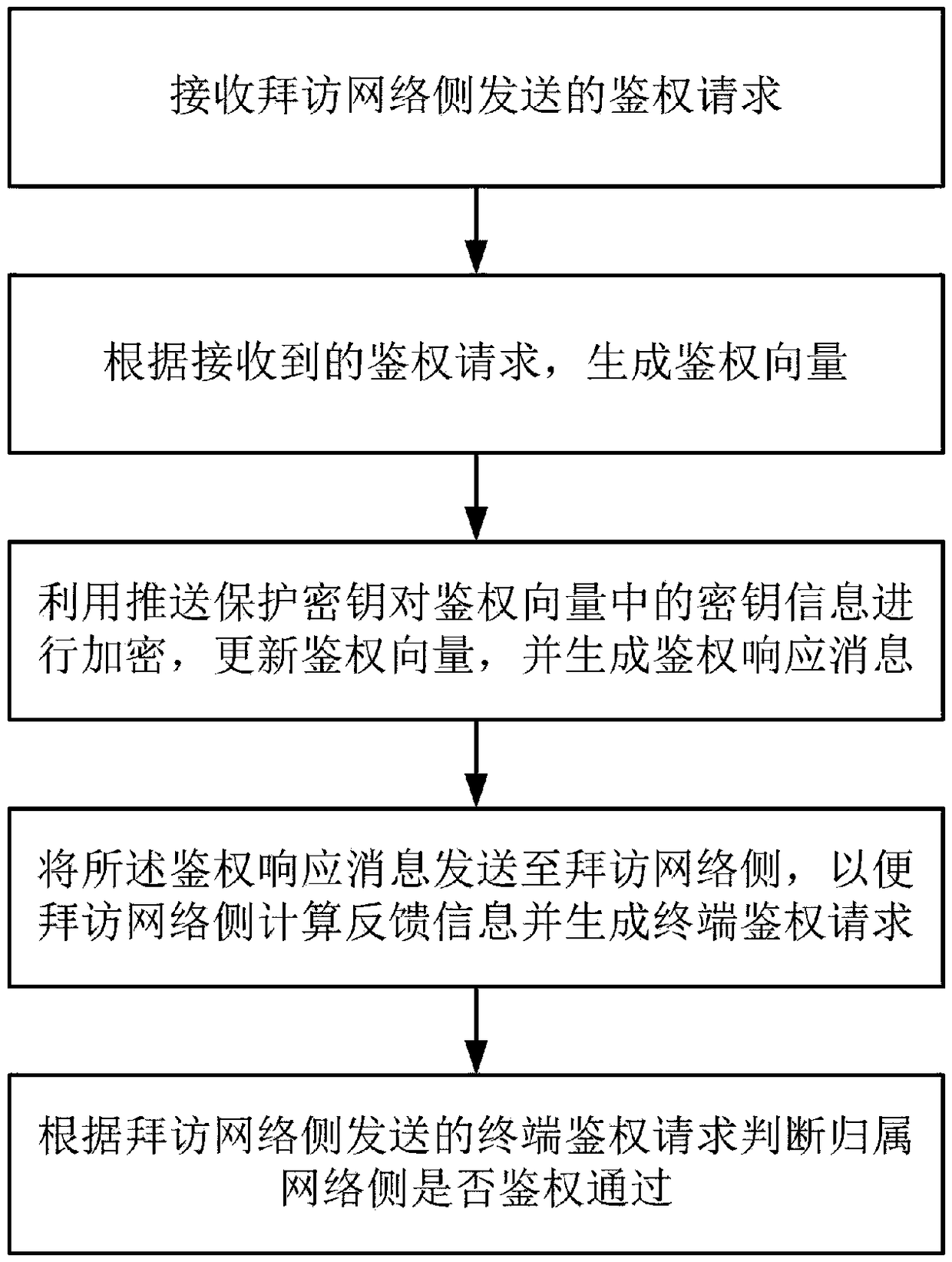
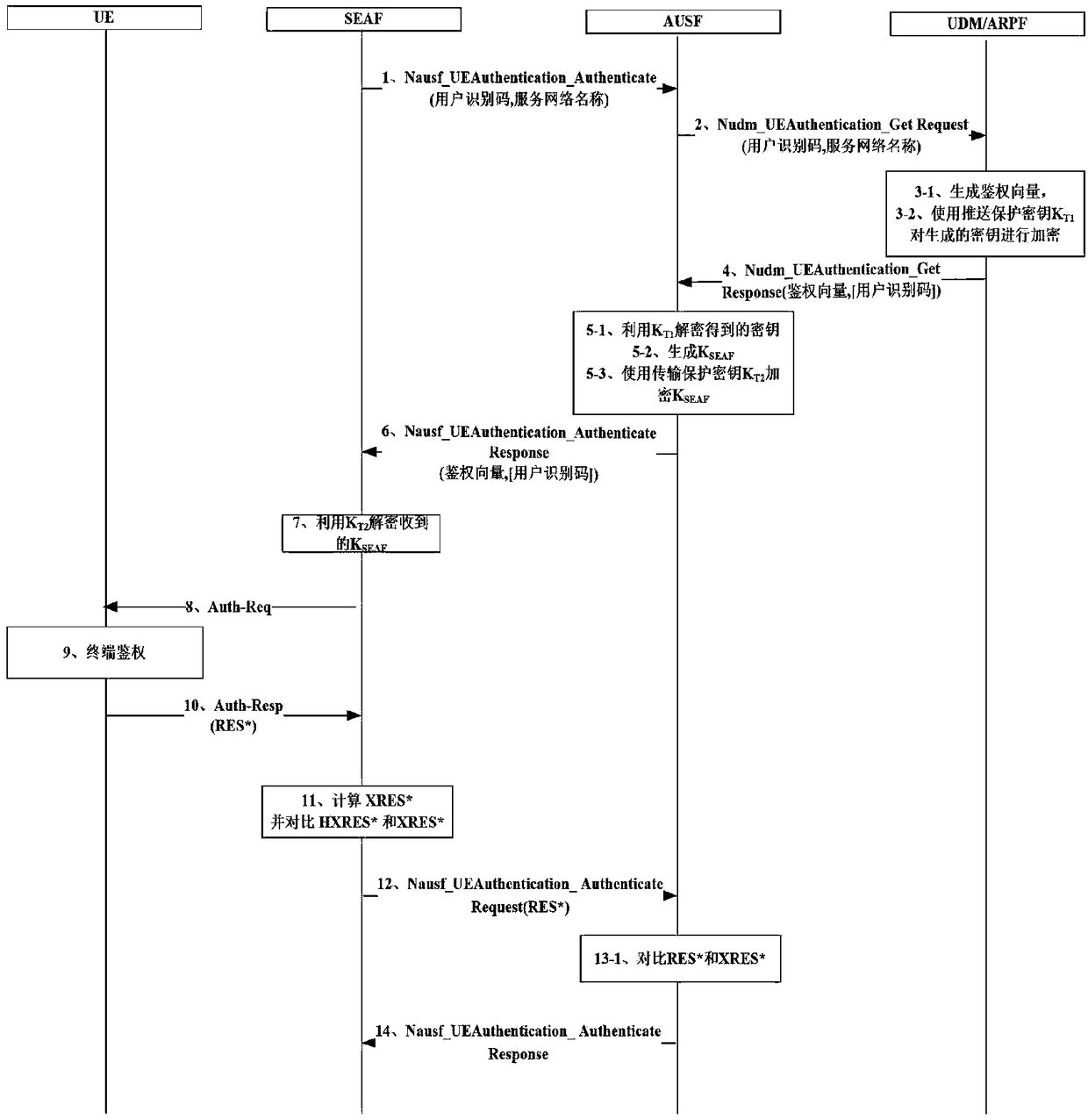
A method for enhancing security of authentication process between network elements of core network based on 5G AKA
ActiveCN109041057AImplement negotiated updatesPrevent leakageSecurity arrangementComputer terminalSecurity enhancement
The invention relates to a method for enhancing the security of authentication process between core network elements based on 5G AKA, belonging to the technical field of mobile communication, which solves the problem that key information such as key, user identity and the like caused by the prior plaintext transmission mode are stolen. The invention relates to a security enhancement method for enhancing security of authentication process between network elements of core network based on 5G AKA, which is applied to a home network side. The method comprises the following steps: receiving authentication request sent by a visiting network side; generating an authentication vector according to the received authentication request; encrypting the key information in the authentication vector by using the push protection key, updating the authentication vector, and generating an authentication response message; sending the authentication response message to the visiting network side so that thevisiting network side calculates feedback information and generates a terminal authentication request; according to the terminal authentication request sent by the visiting network side, judging whether or not the home network side has passed the authentication. By encrypting the key information transmitted between the network elements of the core network, the security of the authentication process between the network elements of the core network is effectively enhanced.
Owner:XINGTANG TELECOMM TECH CO LTD +1
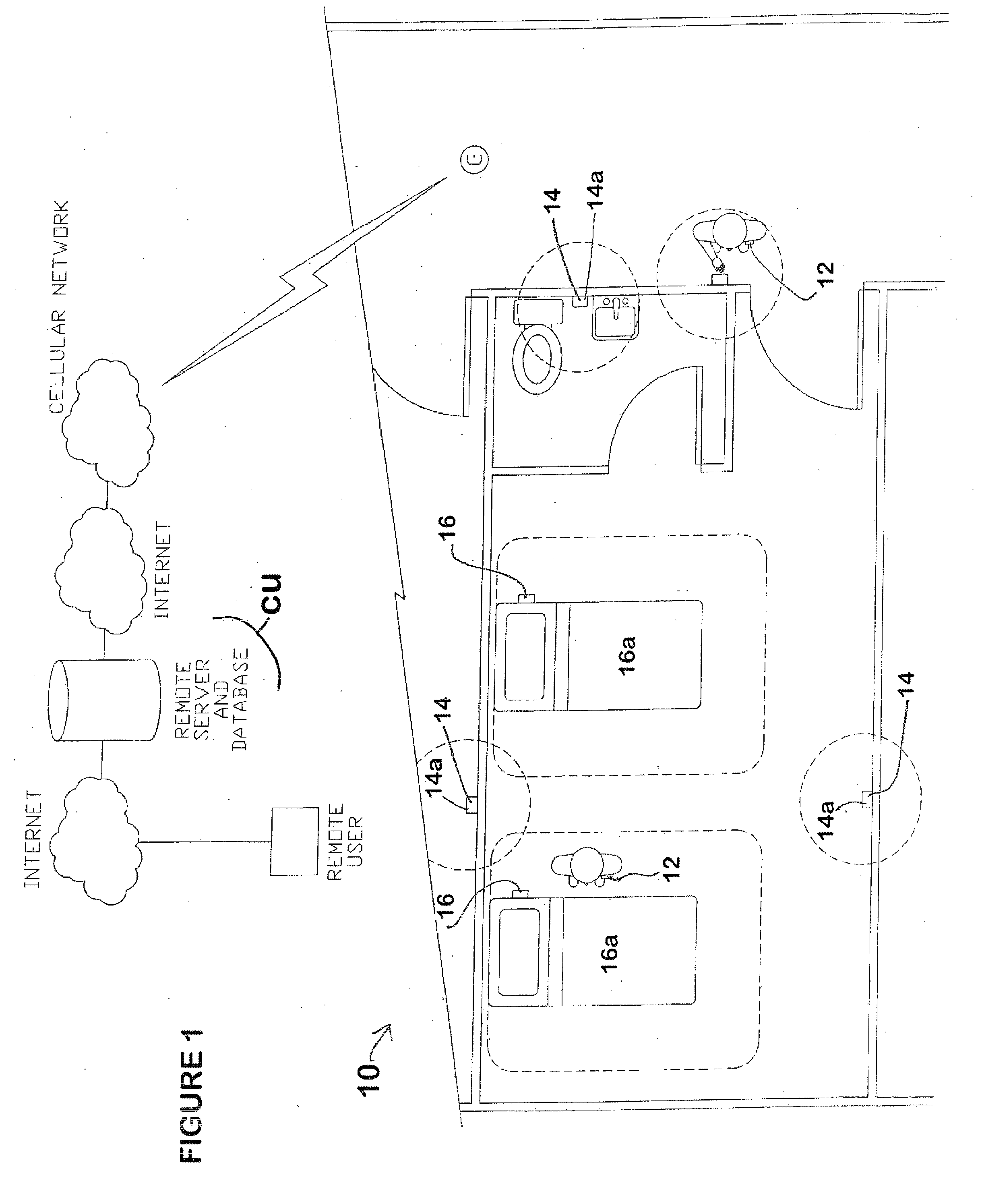
Sanitization compliance monitoring system with security enhancements
InactiveUS20130127615A1Improve securityImprove efficiencyElectric signal transmission systemsDigital data processing detailsCompliance MonitoringCentral unit
A sanitization compliance monitoring system comprises care giver badges, patient bed beacons associated with patient beds, dispenser beacons associated with sanitization dispensers, and a central unit for wirelessly communicating with the badges.
Owner:ULTRACLENZ
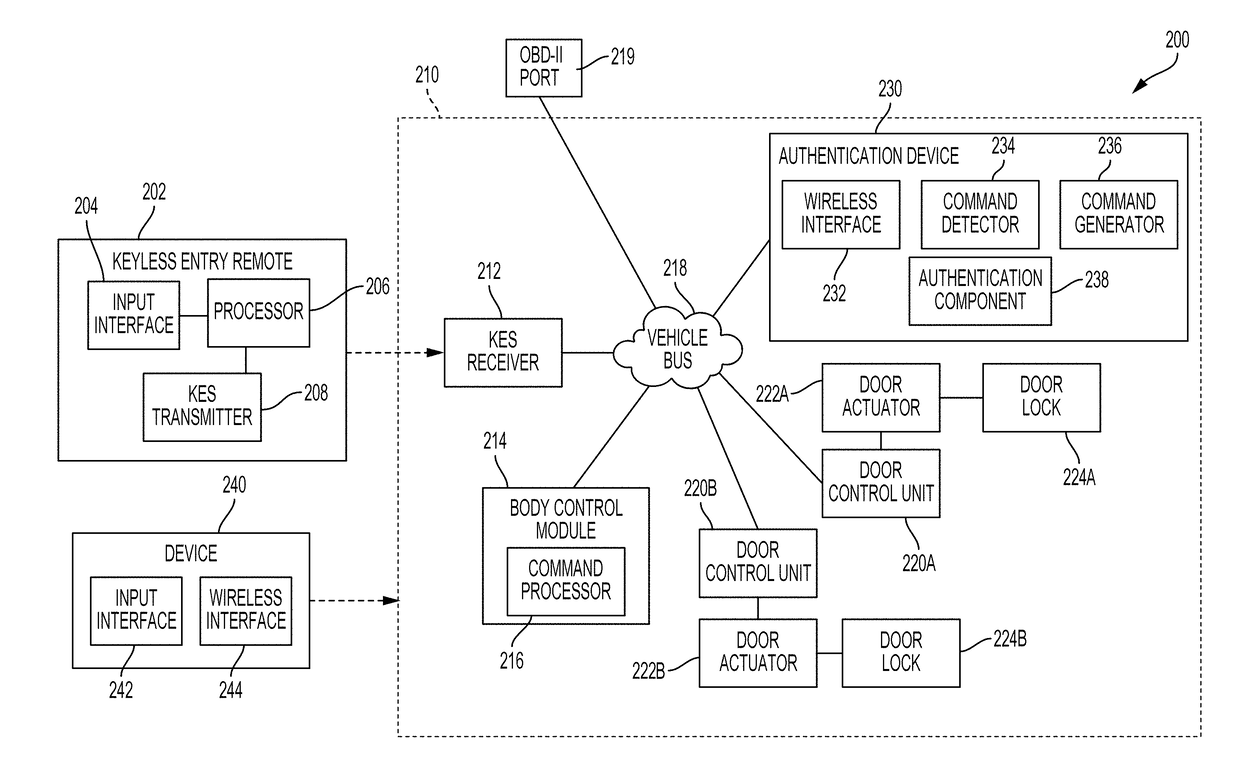
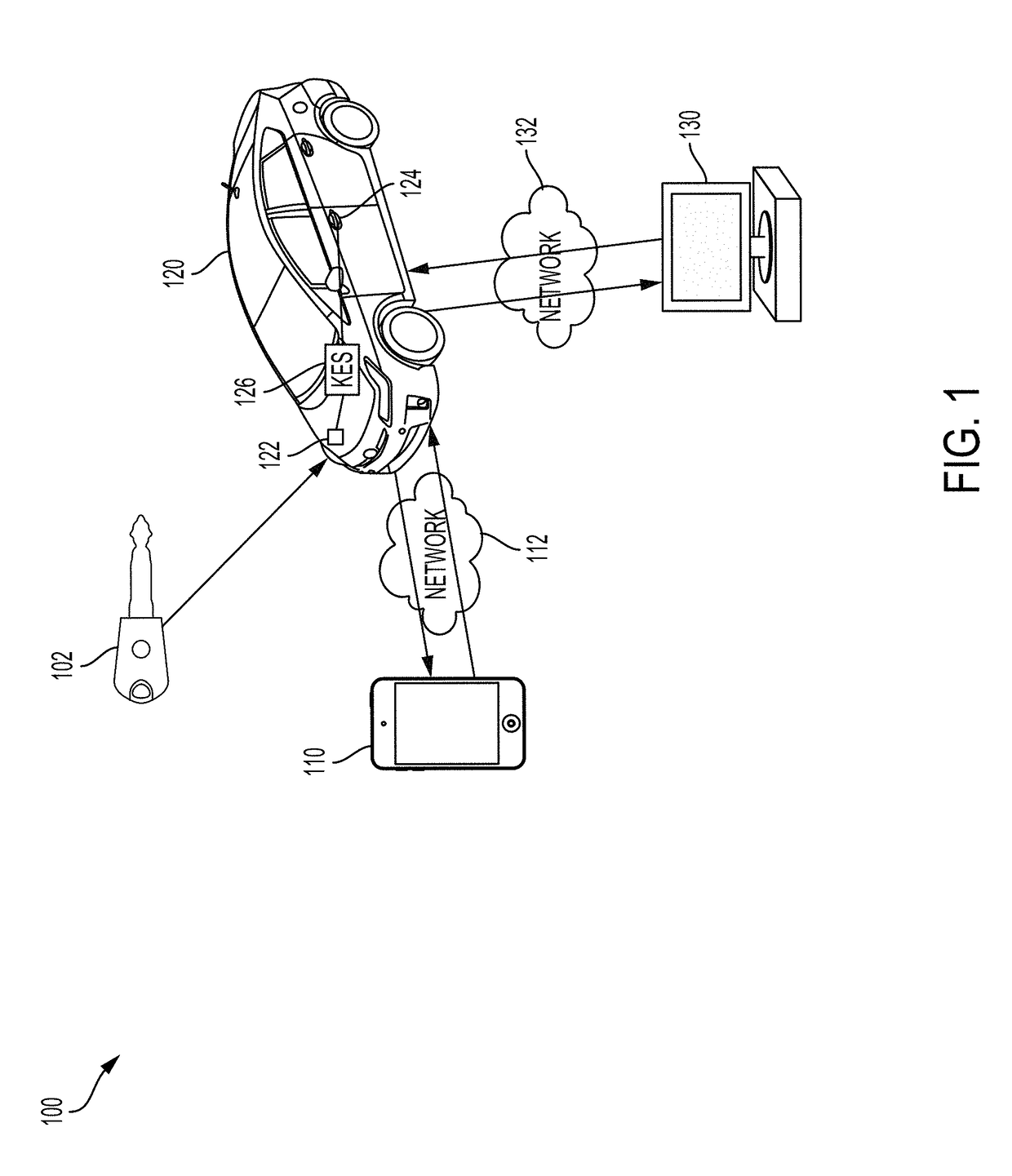
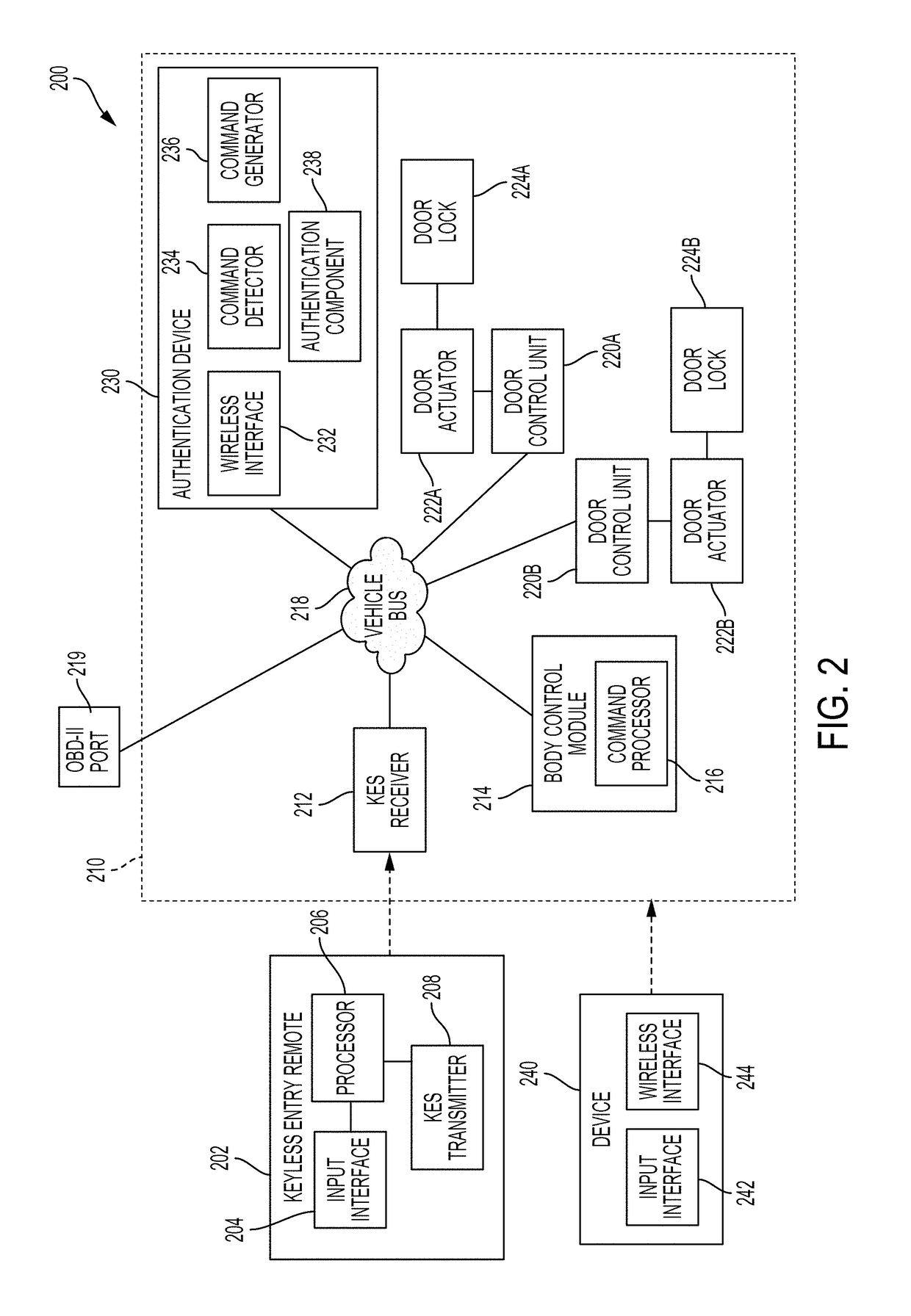
Keyless entry system security enhancement
ActiveUS20180194323A1Improve securityParticular environment based servicesAnti-theft devicesSecurity enhancementEmbedded system
The keyless entry system (KES) controls access to a vehicle's doors, trunk, hood, etc., through a keyless entry device (e.g., a key fob) using wireless communication with the vehicle. The technology described here mitigates vulnerabilities in the KES implementation by employing a device configured to suppress a keyless entry command until an additional means of authentication is verified, at which point the keyless entry command is unsuppressed.
Owner:MITRE SPORTS INT LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com