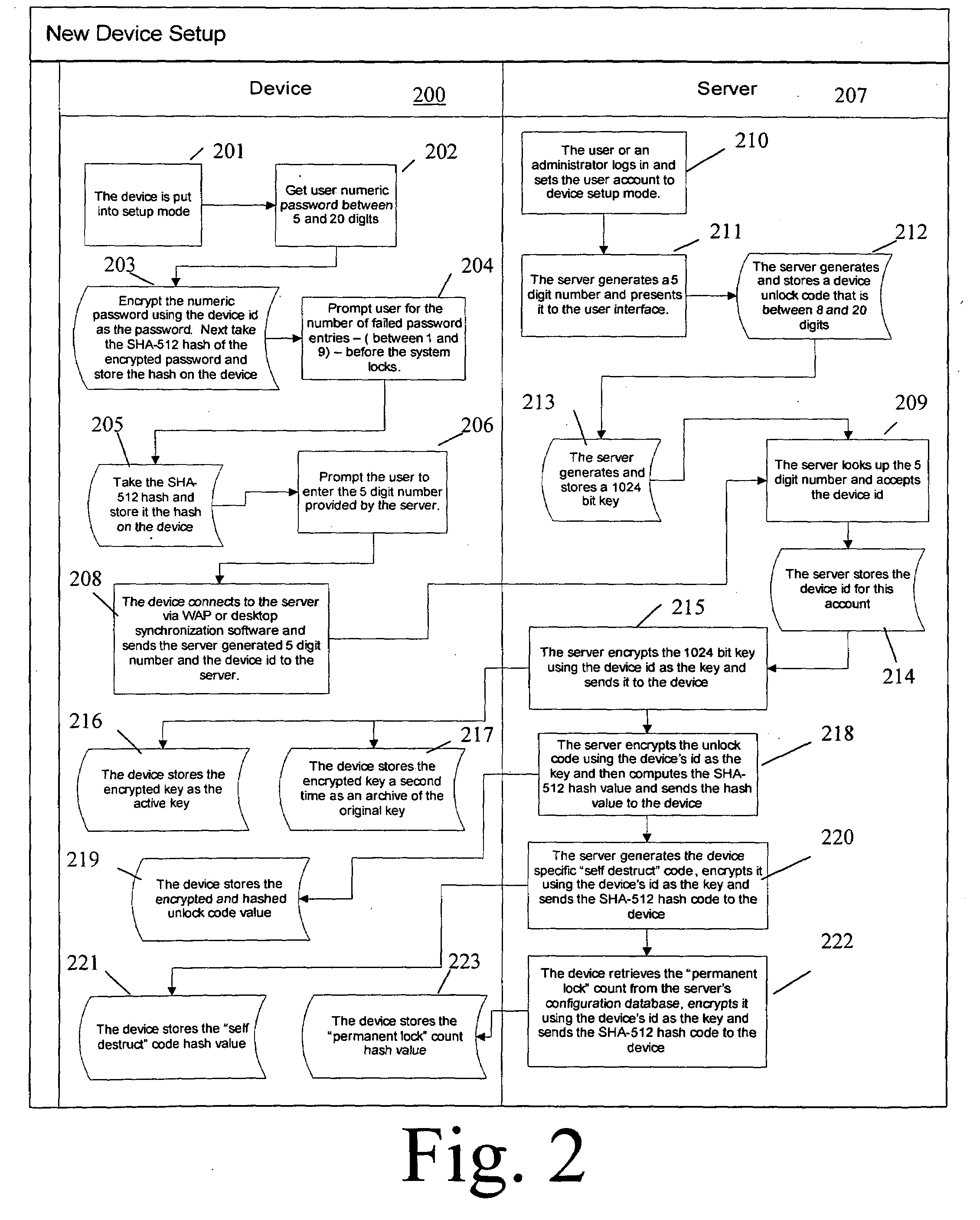
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
186results about How to "Convenient access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
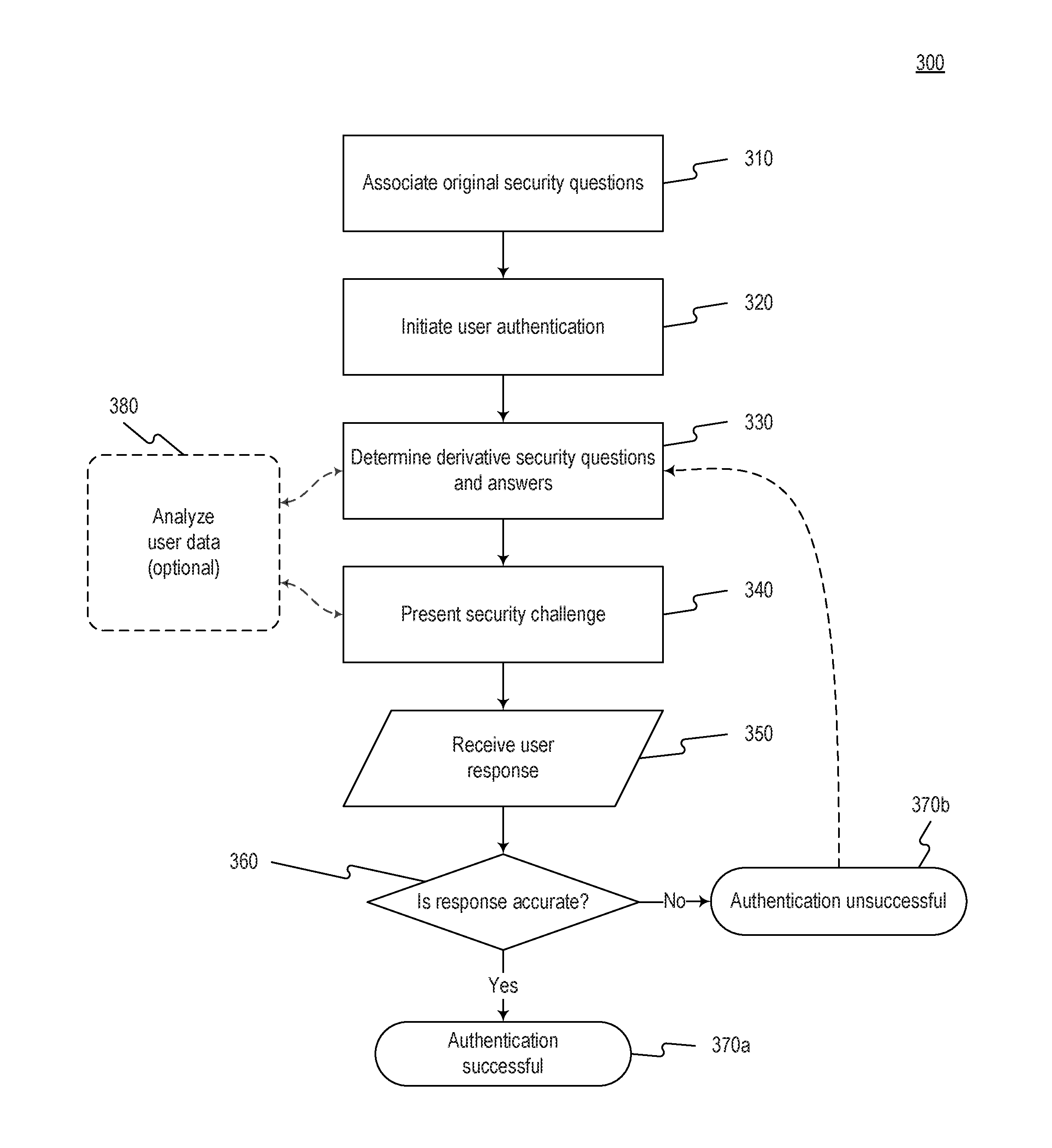
Systems and methods for derivative fraud detection challenges in mobile device transactions
InactiveUS20160381560A1Improve identification and verificationImprove experienceDigital data processing detailsMultiple digital computer combinationsInternet privacyMobile transaction
The disclosed embodiments include systems, methods, and computer-readable media configured to provide mobile device transaction security. The techniques described in the disclosed embodiments may be used to verify a mobile device user by providing derivative fraud protection challenges. Thus, the techniques may be used to improve identification and verification of users during mobile transactions. As a result, the disclosed embodiments improve mobile security and user experience as well as enhance access control.
Owner:OFFLA SELFSAFE
Device social-control system
InactiveUS20070214264A1Convenient access controlDigital computer detailsElectric digital data processingComputer networkControl system
A device social-control system includes: providing a computer system; and connecting the computer system to a network for: facilitating set up of an access right and an access level to control a device through the network; determining the access right from another computer system and the access level from an online social network system; and facilitating control of the device based on the access right from the another computer system and the access level from the online social network system.
Owner:68TECH PTE
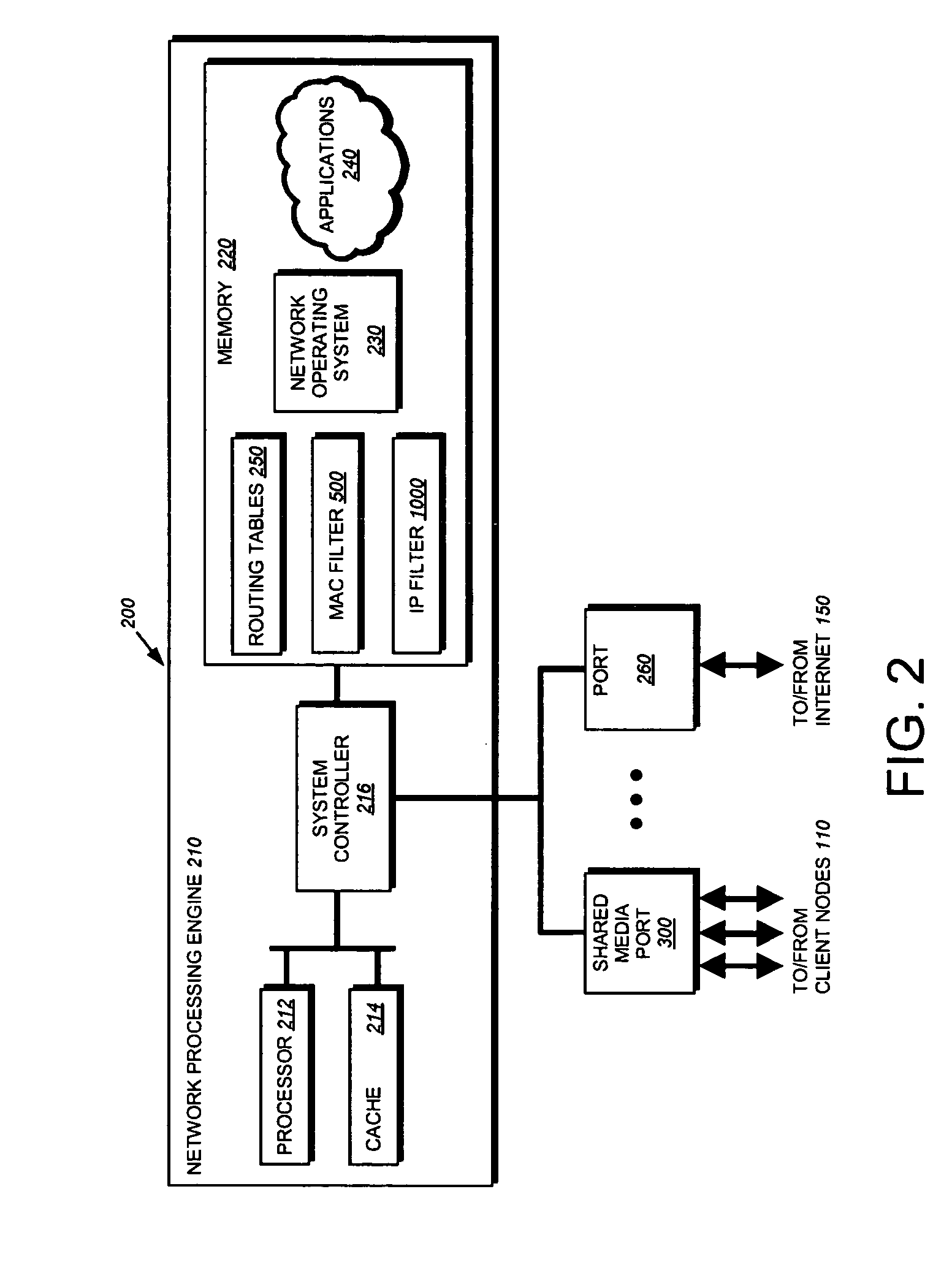
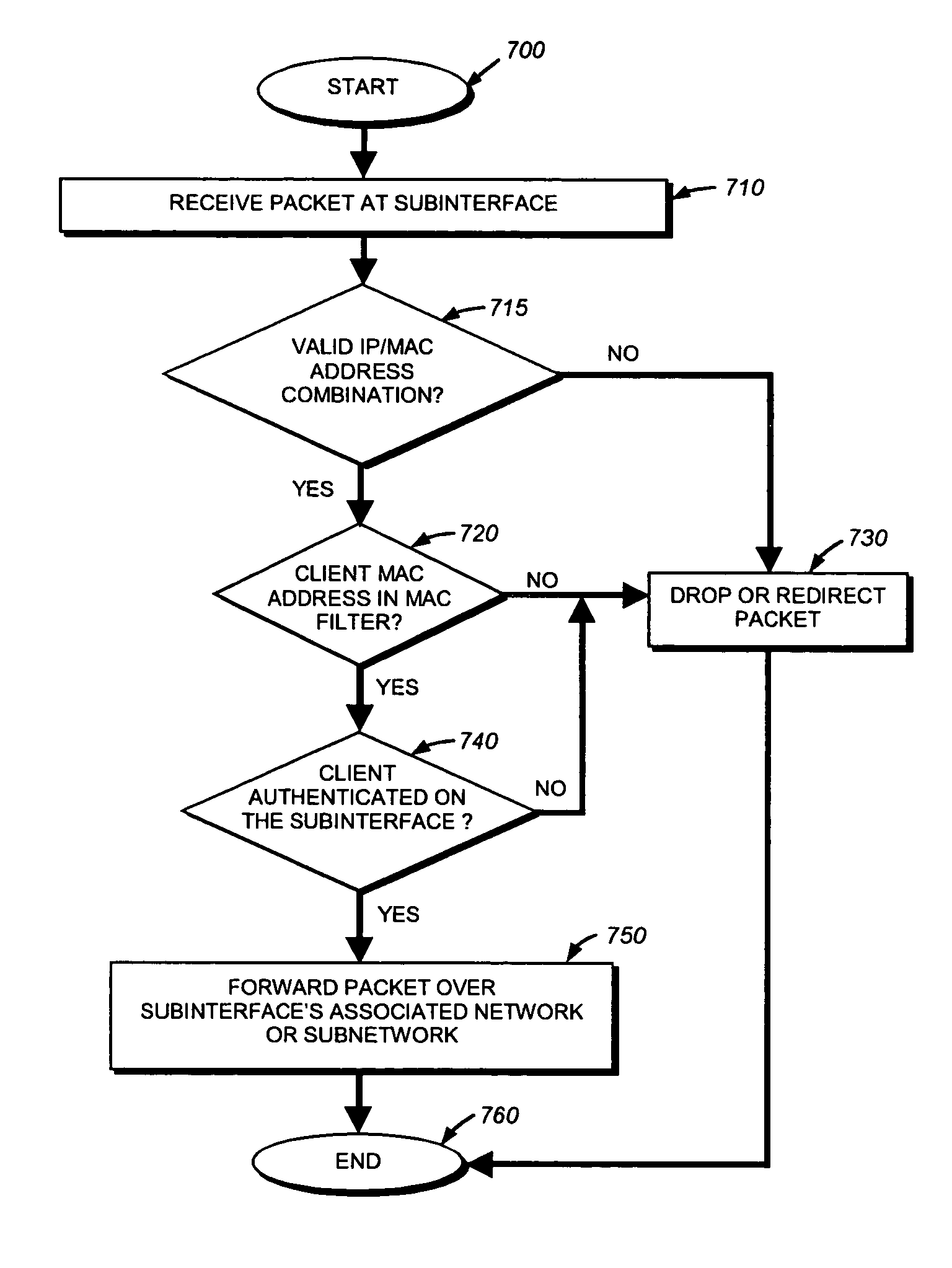
802.1X authentication technique for shared media
ActiveUS20050125692A1Increase network-access securityConvenient access controlDigital data processing detailsUser identity/authority verificationClient-sideNetwork Access Control
The present invention provides a technique for securely implementing port-based authentication on a shared media port in an intermediate node, such as a router. To that end, the invention provides enhanced port-based network access control that includes client-based control at the shared media port. Unlike previous implementations, the port does not permit multiple client nodes to access a trusted subnetwork as soon as a user at any one of those nodes is authenticated by the subnetwork. Instead, port-based authentication is performed for every client node that attempts to access the trusted subnetwork through the shared media port. As such, access to the trusted subnetwork is not compromised by unauthenticated client nodes that “piggy-back” over the shared media port after a user at another client node has been authenticated by the trusted subnetwork.
Owner:CISCO TECH INC
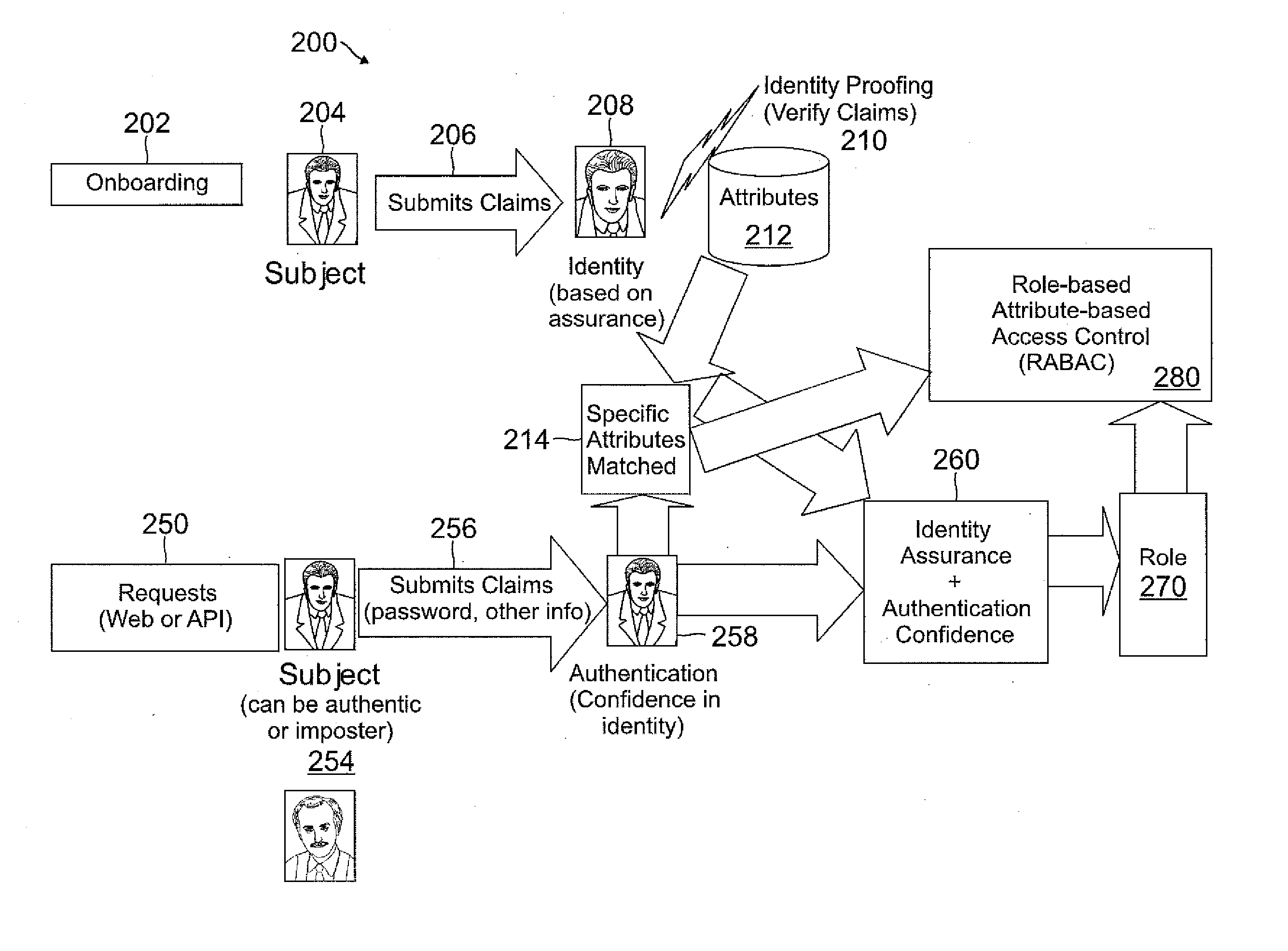
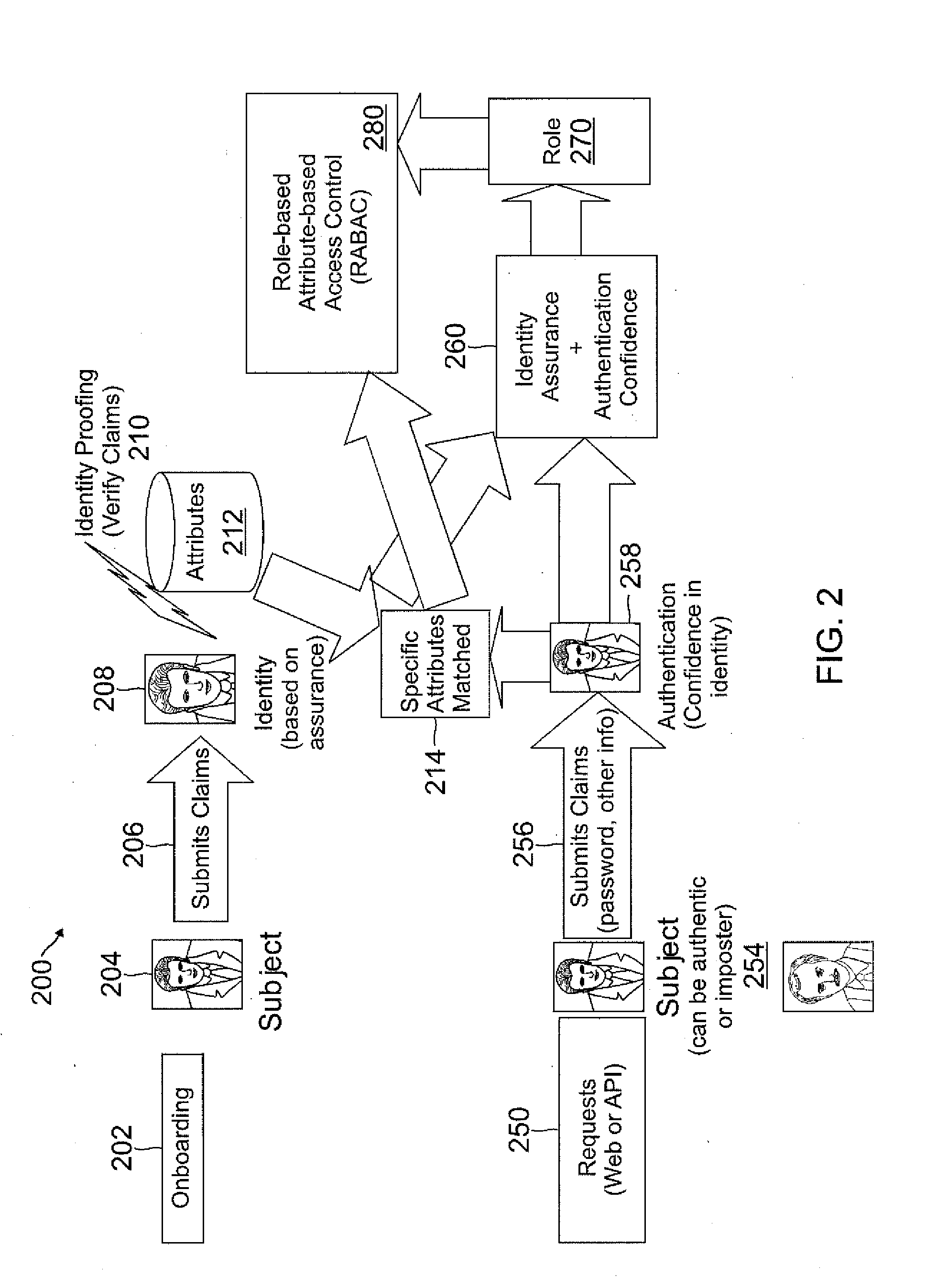
Role-based attribute based access control (RABAC)
ActiveUS20120060207A1Enhanced access control securityConvenient access controlDigital data processing detailsDigital data protectionUser deviceMedia access control
Systems and methods are disclosed for receiving an access request from a user device, the access request including an identity claim for a user; evaluating a risk of access based on matching an attribute of the user device with attributes stored in a user information database; authenticating the access request based on the identity claim and the risk evaluation to determine an authentication confidence level; generating a token based on the confidence level and the attribute matched; producing an authorization response based on inputs from the token, a risk based access control, a role based access control, and an attribute based access control, in which the authorization response determines whether to allow access to a system, deny access to the system, or request additional input from the user device.
Owner:PAYPAL INC
Distributive access controller
ActiveUS20040025052A1Provide securityConvenient access controlDigital data processing detailsUnauthorized memory use protectionComputer resourcesComputerized system
A device for securely controlling communications among or within computers, computer systems, or computer networks, comprising: (a) a primary access port to which an "owner" computer program, computer, computer system, or computer network is connectable to access shared computer resources; (b) a secondary access port to which a non-owner computer program, computer, computer system, or computer network is connectable to access the shared computer resources; (c) a transfer port to which a shared computer resource is connectable to provide controlled access to that computer resource from computer programs, computers, computer systems, or computer networks connected to the access ports; and (d) a separate physical communication path to and from each access port and each transfer port, where access permissions and restrictions for each communication path are set by the owner of the device through the primary access port.
Owner:SECUREEDEN LLC
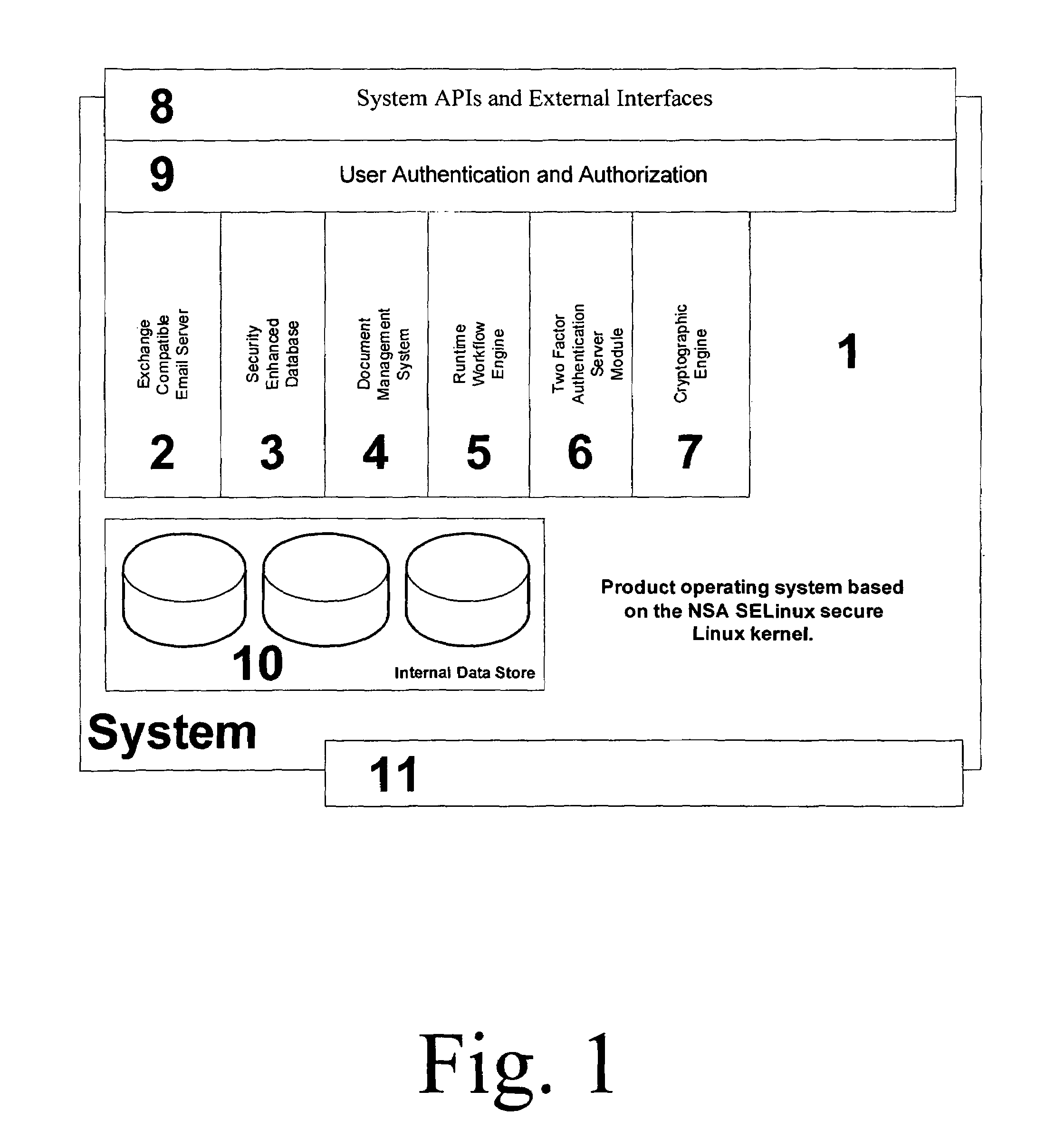
Security Enhanced Data Platform
InactiveUS8161527B2Improve securityConvenient access controlDigital data processing detailsUnauthorized memory use protectionUser PrivilegeInternet privacy
The security enhanced data platform is comprised of two primary subsystems and a host of supporting subsystems. The first primary subsystem is a document management system. A set of client side tools provides the user a way to specify classifications and compartments for selected areas of a document, and a way to save the document in the format required by the system in order to allow the system to enforce the rules and privileges dictated to the system. The second subsystem is a security enhanced database management system. In documents the system allows different user privilege requirements on the document as a whole as well as on pages, paragraphs, sentences, words, and / or letters of a word. A history of document changes is maintained to provide an audit trail after the fact of who did what changes, where those changes were made and when those changes were made.
Owner:CURREN EDWARD
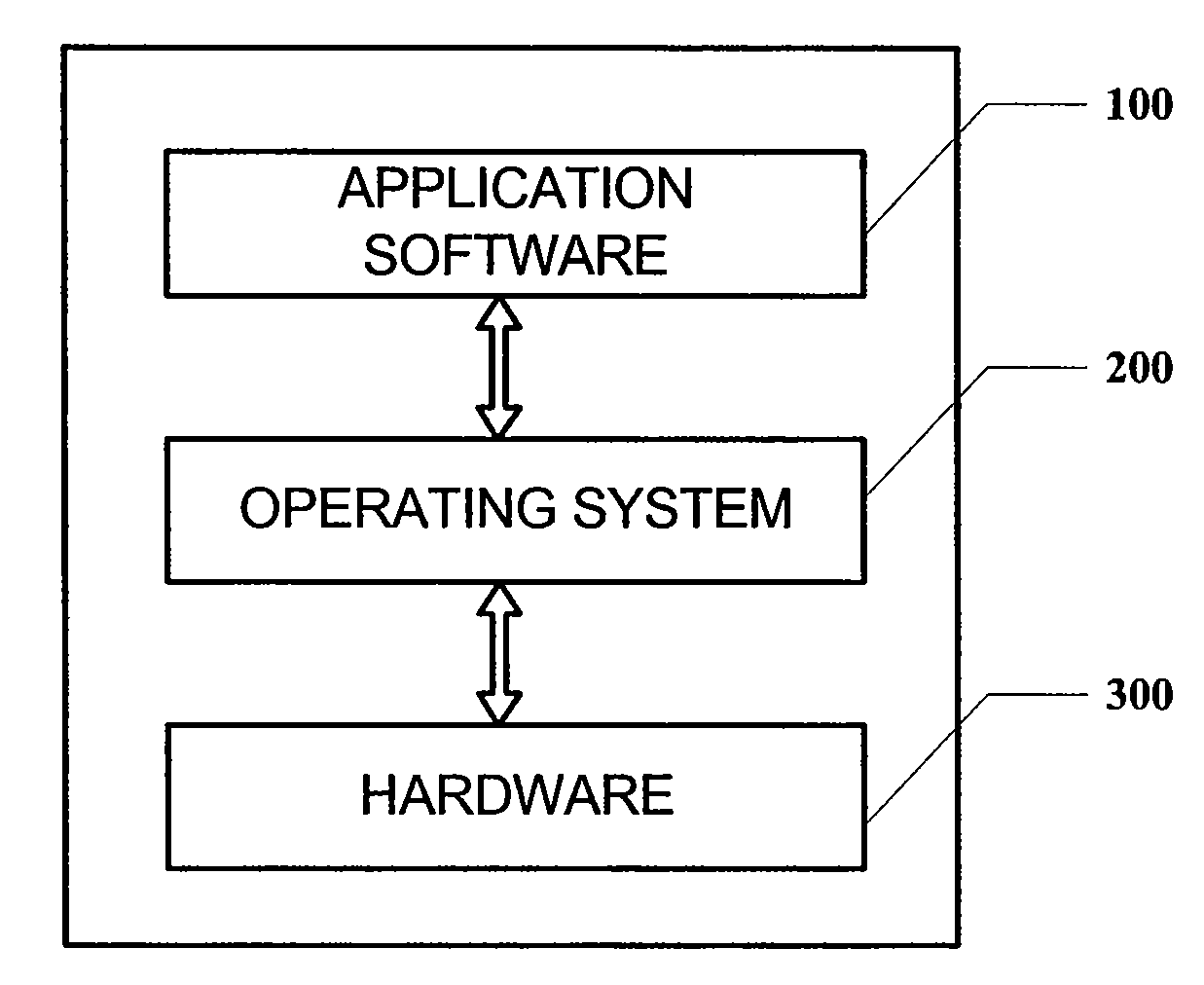
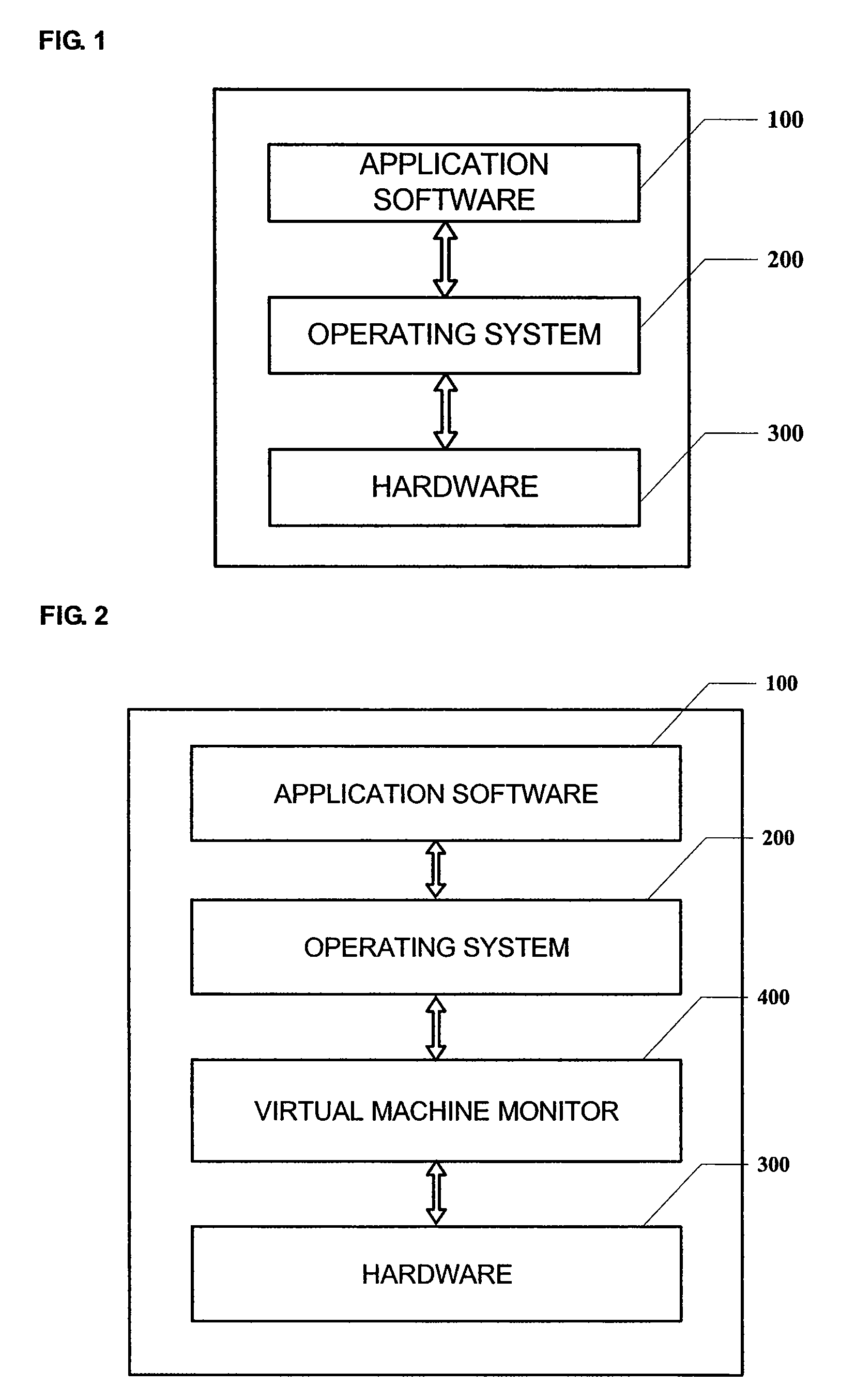
System and method for hardware access control
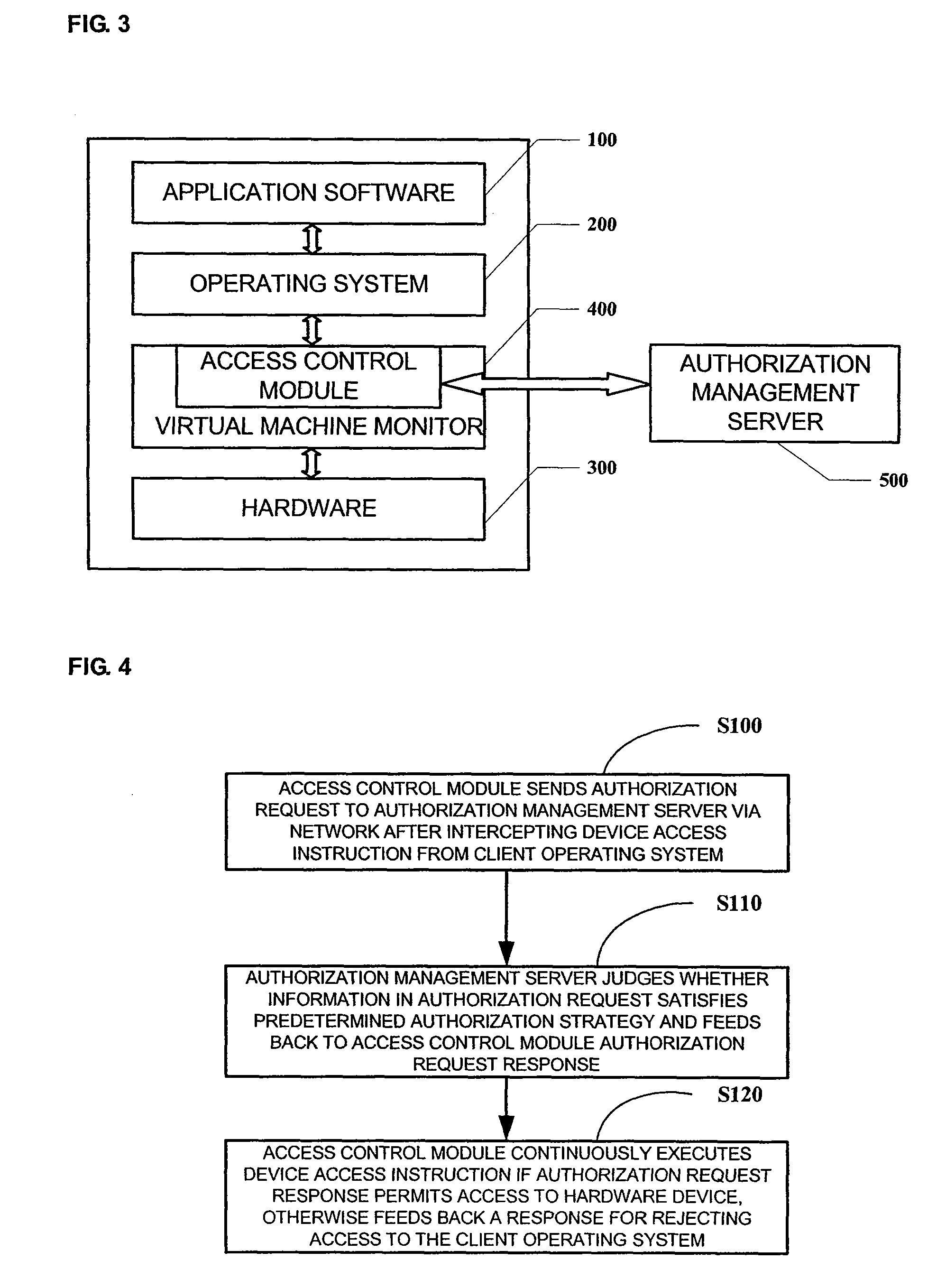
InactiveUS20080022376A1Effective controlImprove hardware access controlDigital data processing detailsUser identity/authority verificationOperational systemControl system
The present invention provides a system and method for hardware access control comprising a virtual machine system including a client operating system, a virtual machine monitor and a hardware device, the system further comprises: an access control module provided in the virtual machine monitor and configured to send an authorization request via a network after intercepting a device access instruction from the client operating system; and an authorization management server configured to receive the authorization request from the access control module, judge whether the authorization request satisfies a predetermined authorization strategy and feed back a response corresponding to the authorization request to the access control module; wherein the access control module determines whether the client operating system is permitted to access the hardware device based on the feedback from the authorization management server. With the present invention, the access to the hardware device from the client operating system can be effectively controlled, and thus legal data copy can be guaranteed while prohibiting any illegal data copy.
Owner:LENOVO (BEIJING) LTD
Security system for access control using smart cards
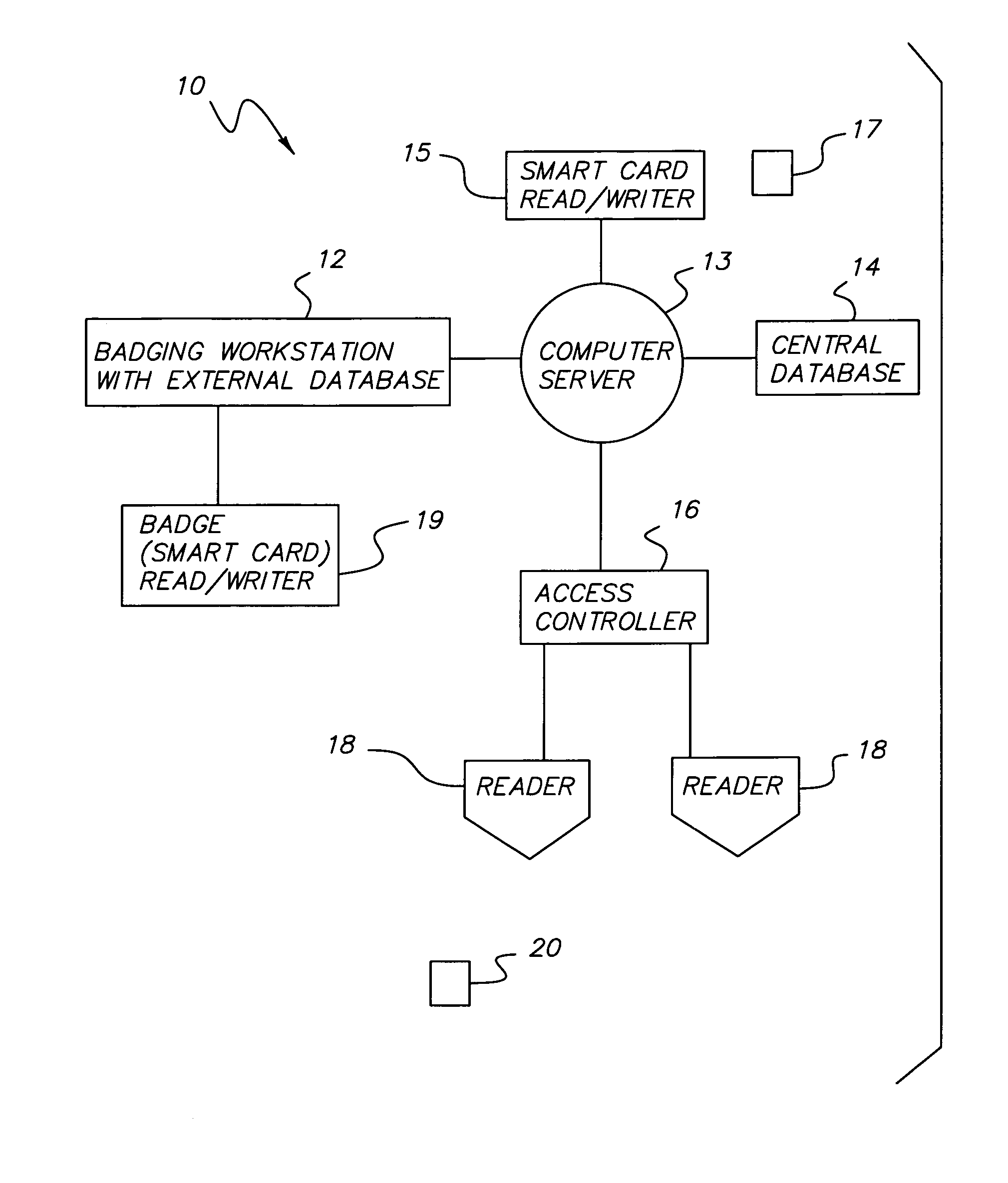
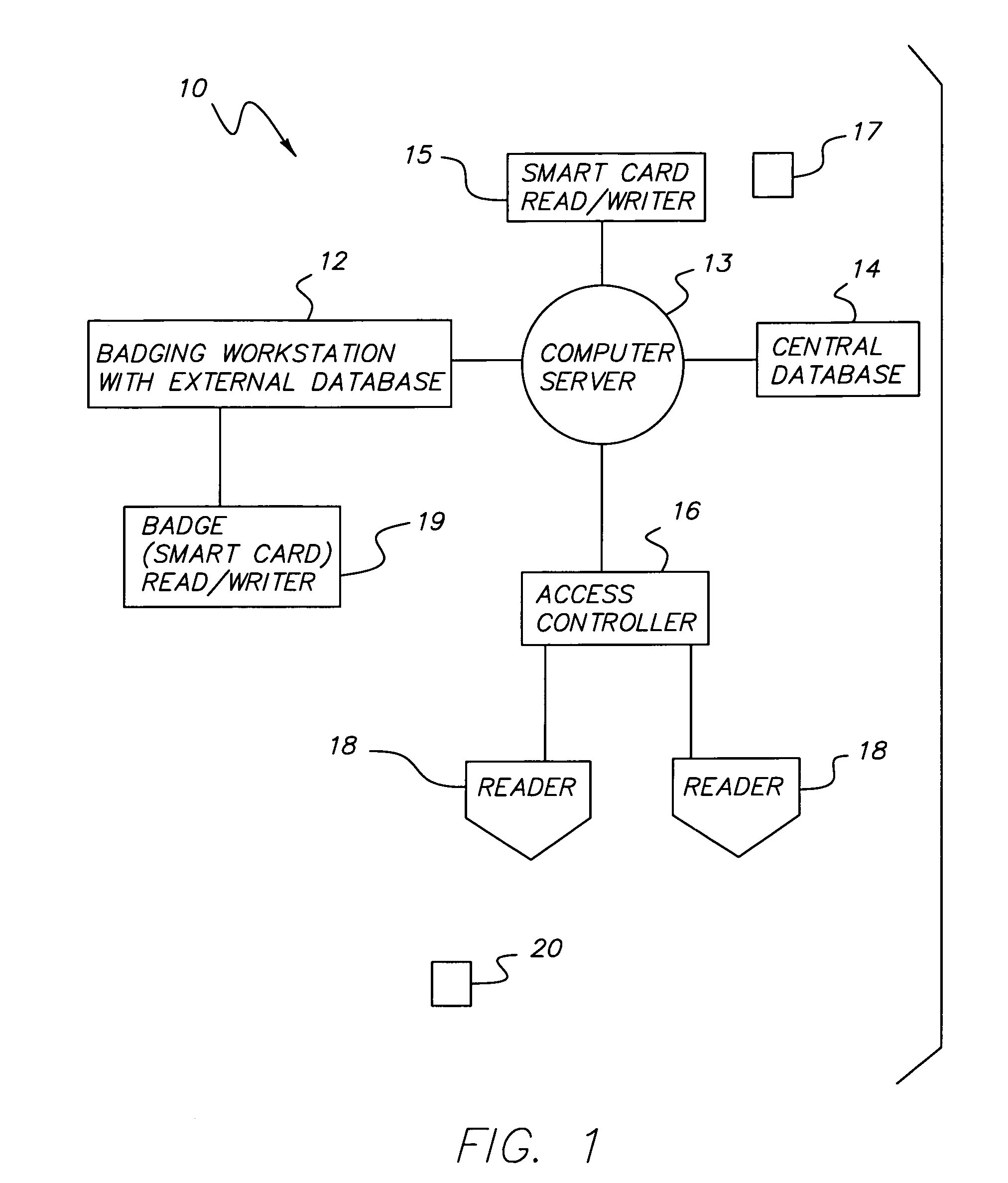
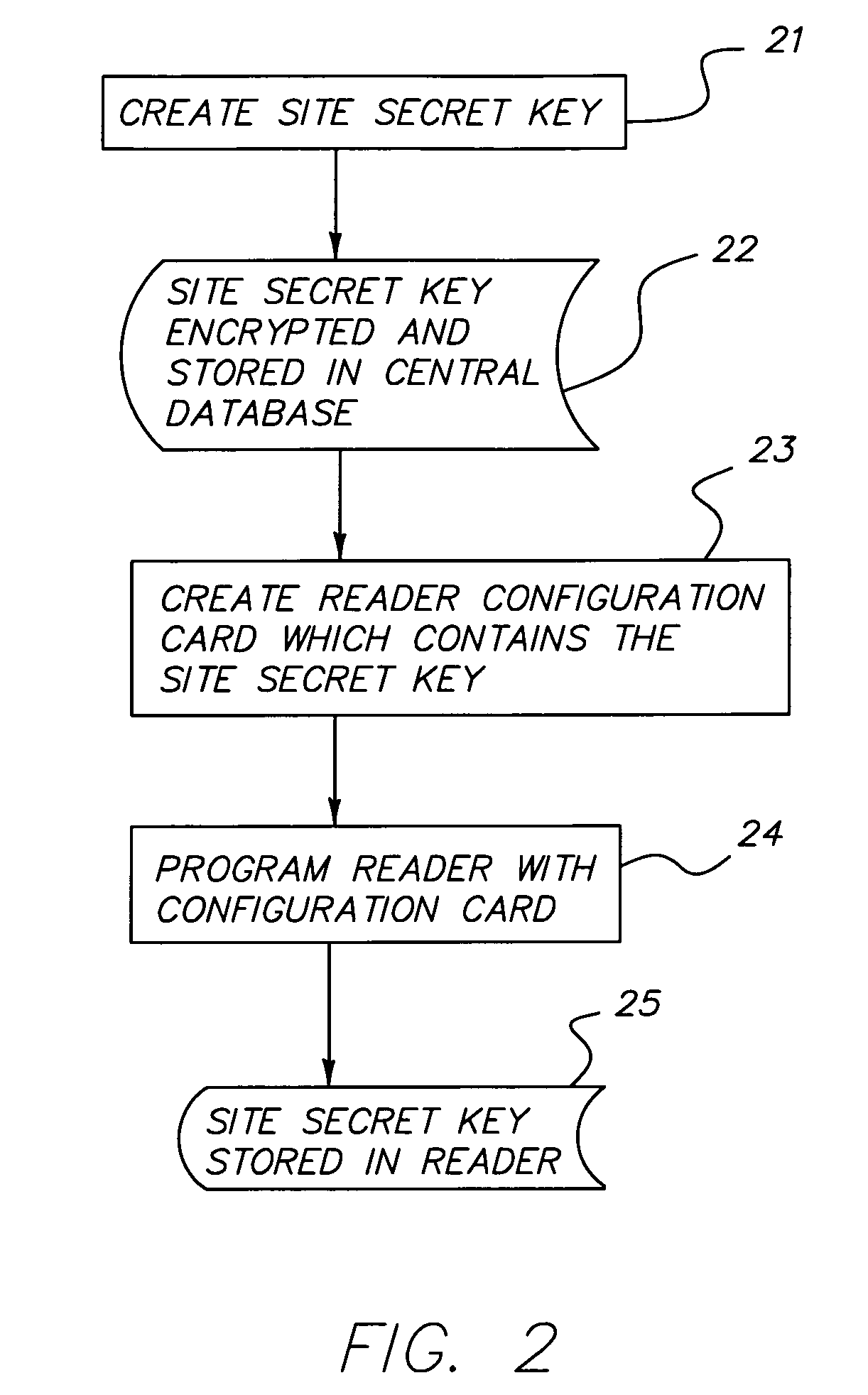
InactiveUS7475812B1Enhanced authenticationConvenient access controlIndividual entry/exit registersVerifying markings correctnessSmart cardKey generation
An improved security system for access control using smart card badges and readers, and one or more access controllers coupled to the readers. Each access controller has a database storing for each badge at least a Credential Identifier and an encrypted Authorization Code as badge number and issue code, respectively, and access privileges data for the cardholder. Each badge has memory storing a Credential Identifier and unique Smart Card Serial Number. The Authorization Code is encrypted using a badge's Credential Identifier and unique Smart Card Serial Number using a Site Secret Key. Each reader can read a badge's Credential Identifier and Smart Card Serial Number and generate an encrypted Authorization Code using the read Credential Identifier and Smart Card Serial Number, and the Site Secret Key. The access controller receives from the reader a request having at least the read Credential Identifier and generated Authorization Code as a badge number and issue code, respectively, and uses such in determining whether the cardholder has access at the reader.
Owner:UTC FIRE & SECURITY AMERICAS CORPORATION INC
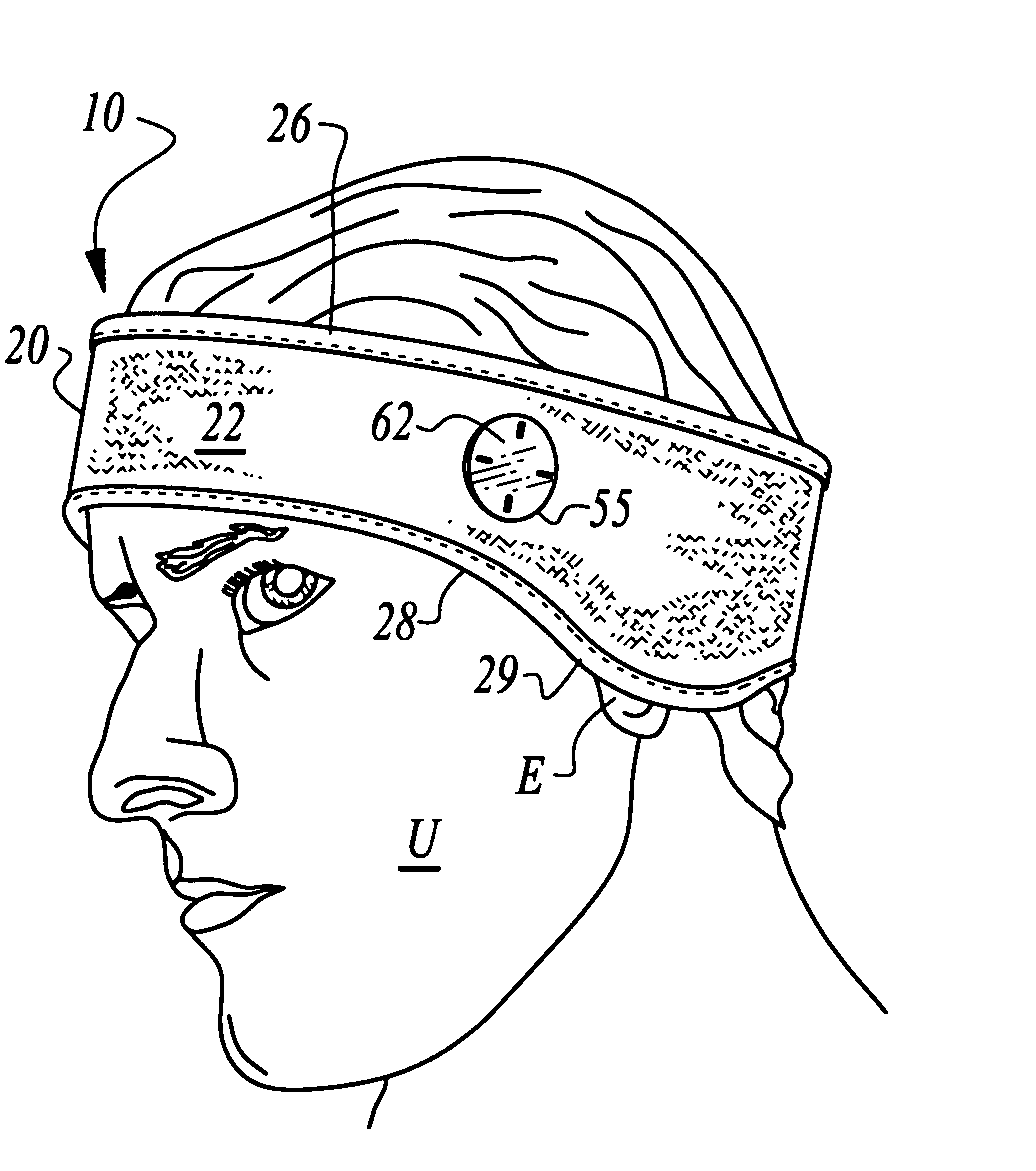
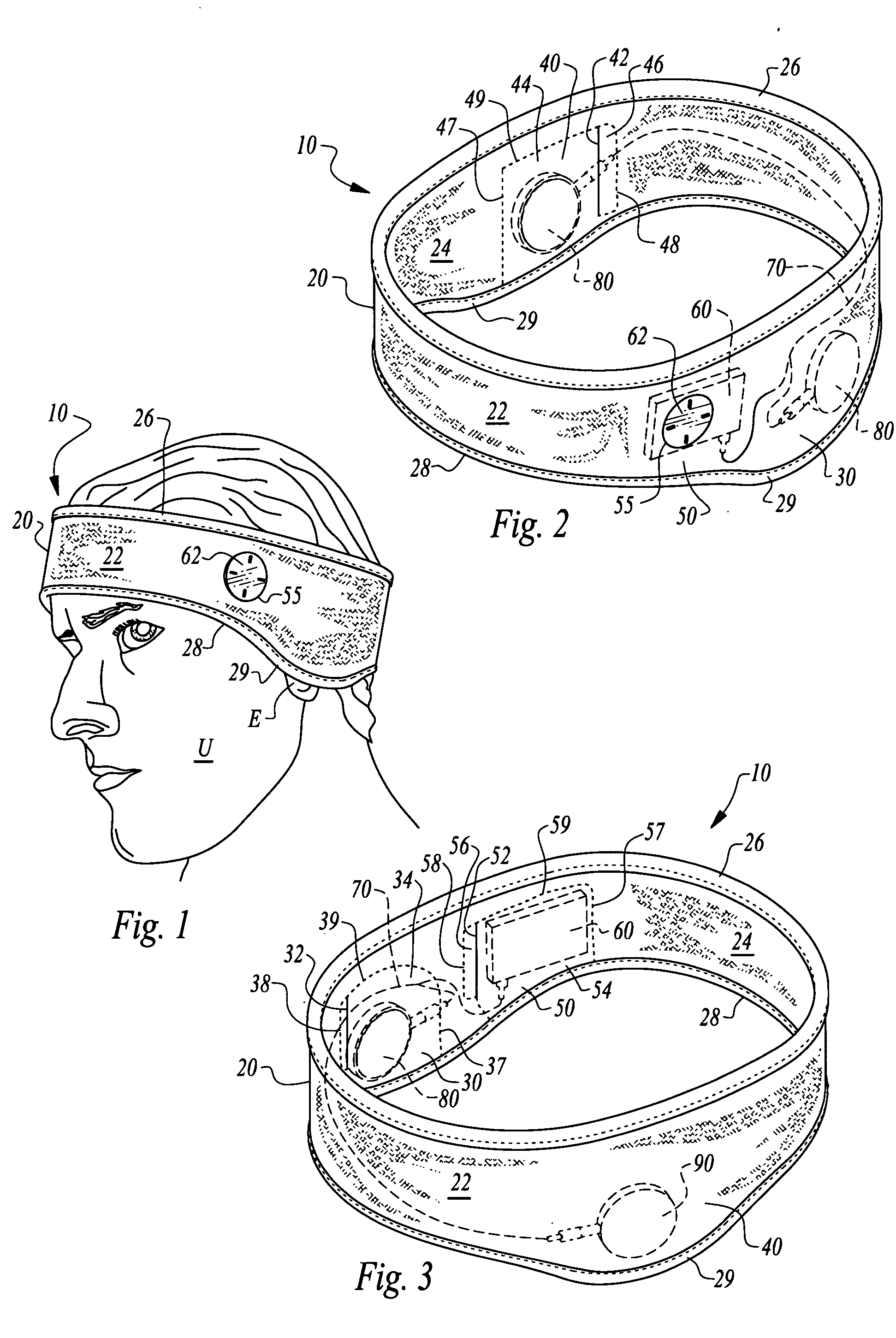
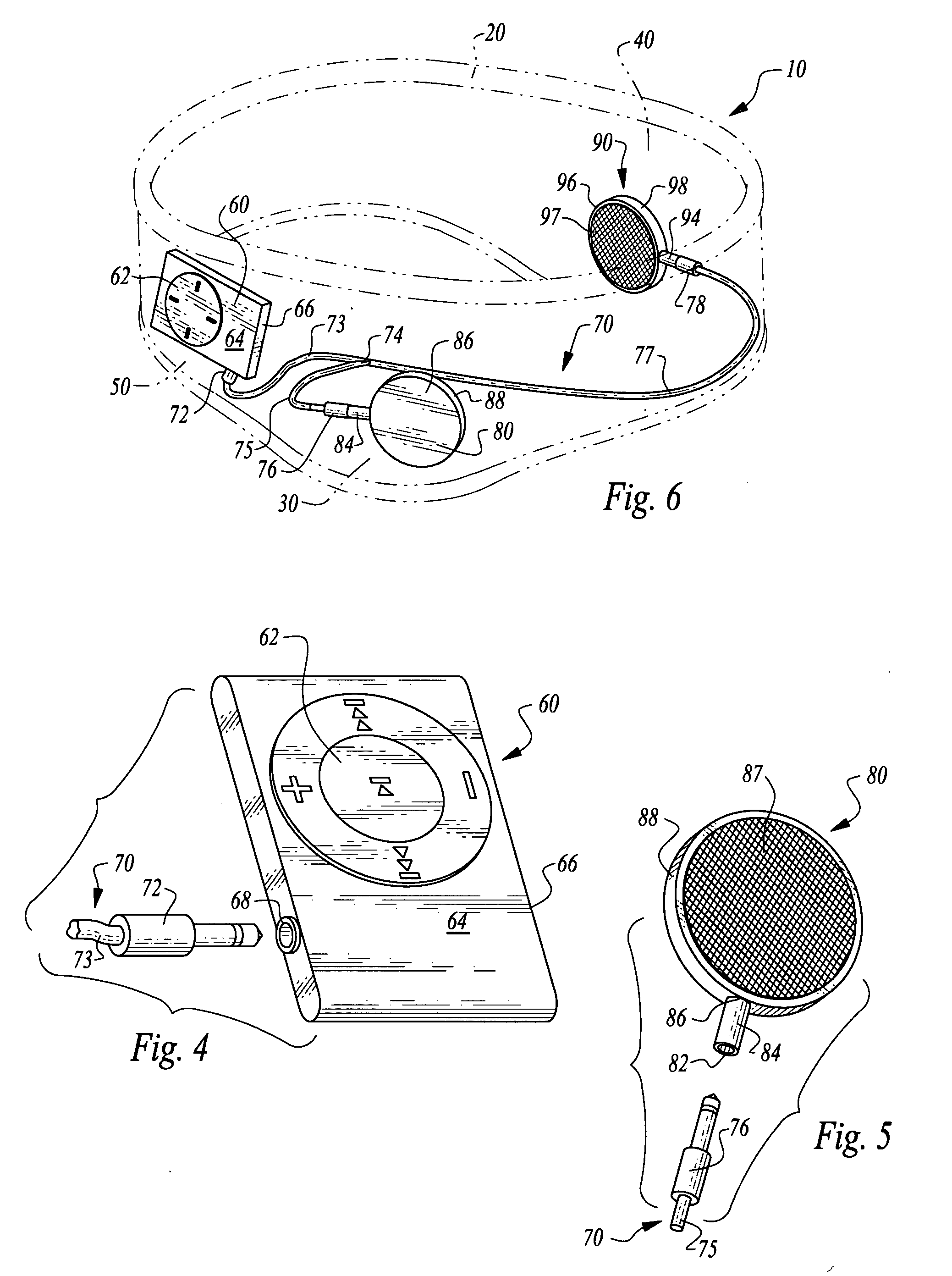
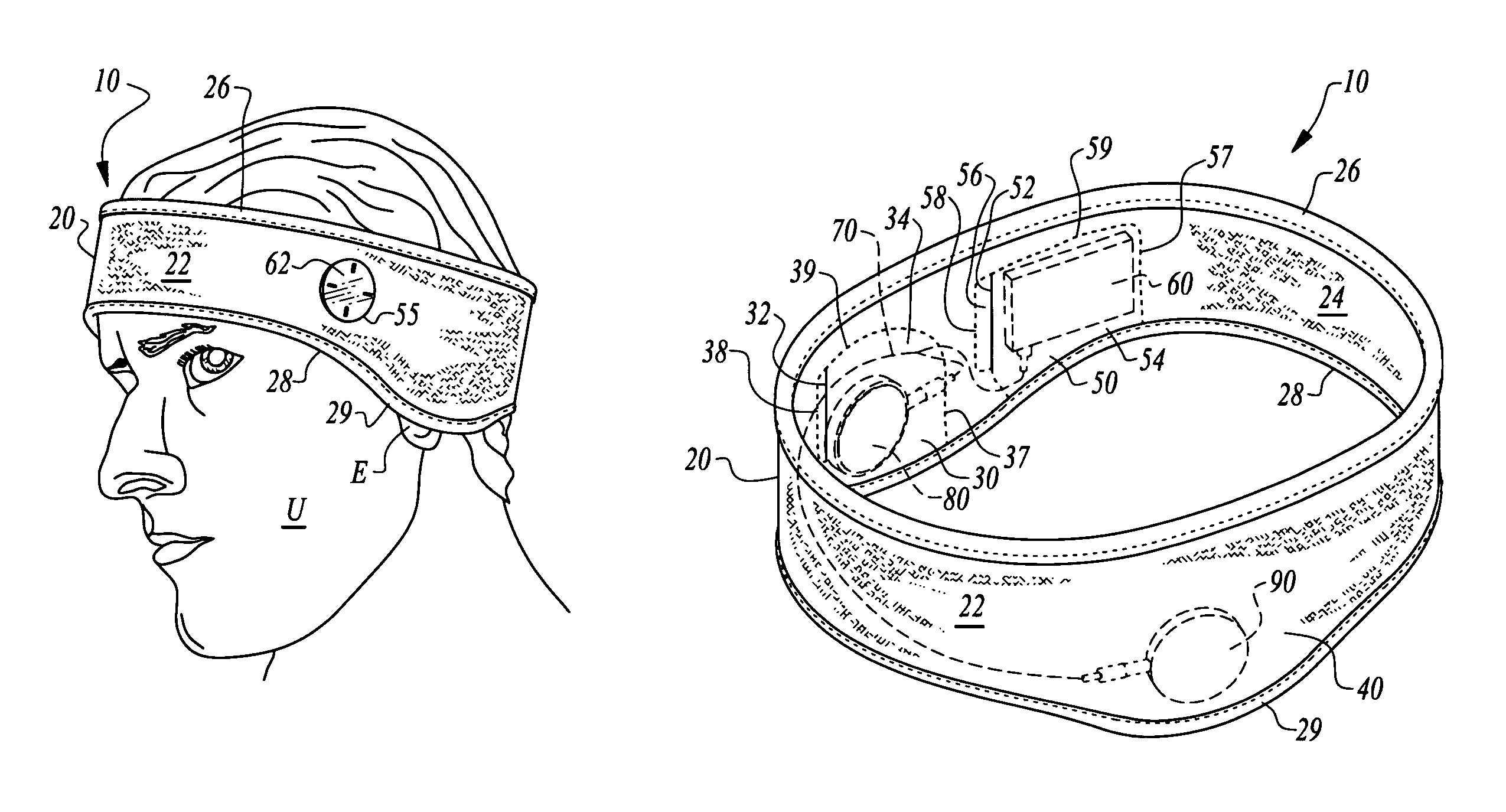
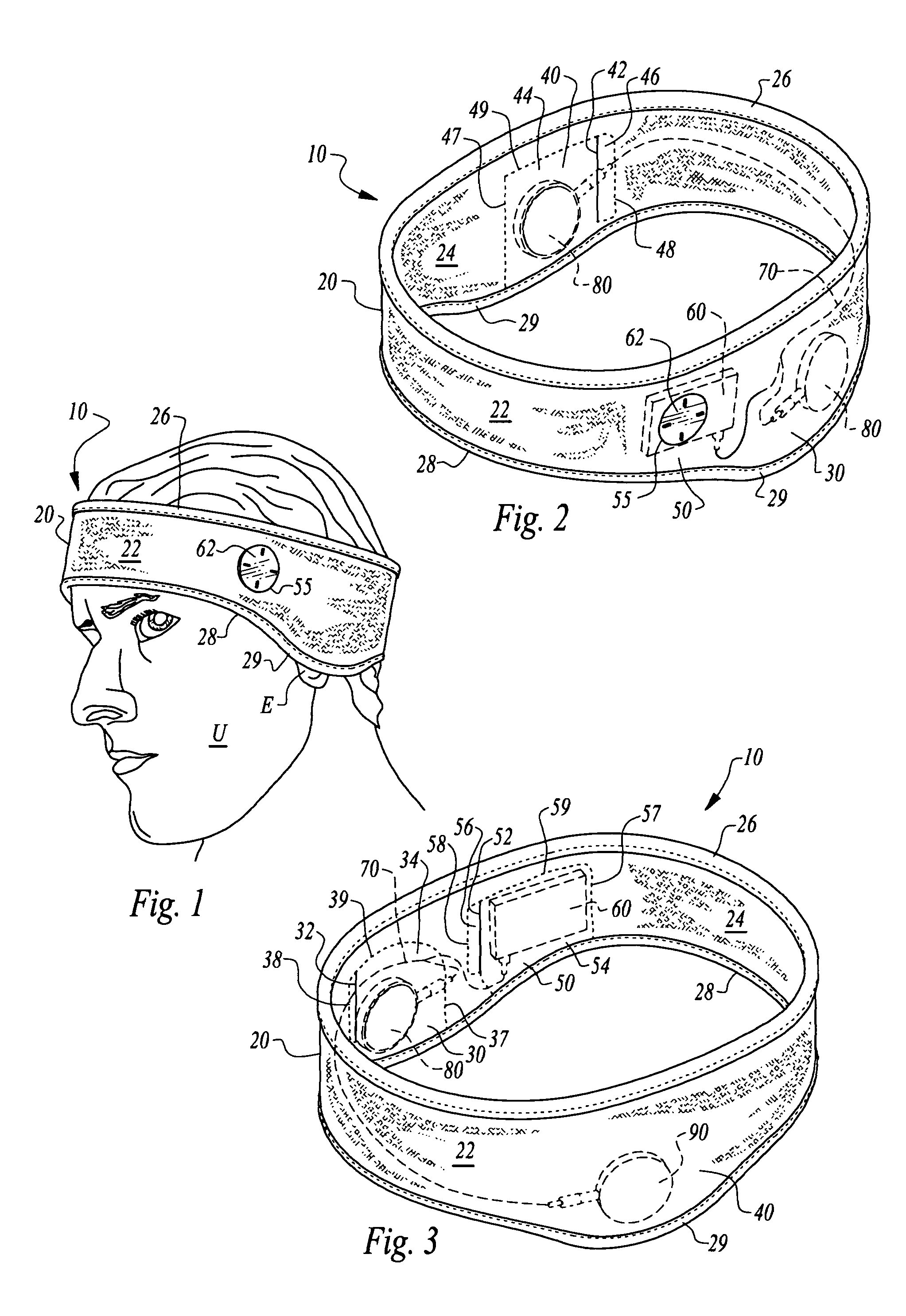
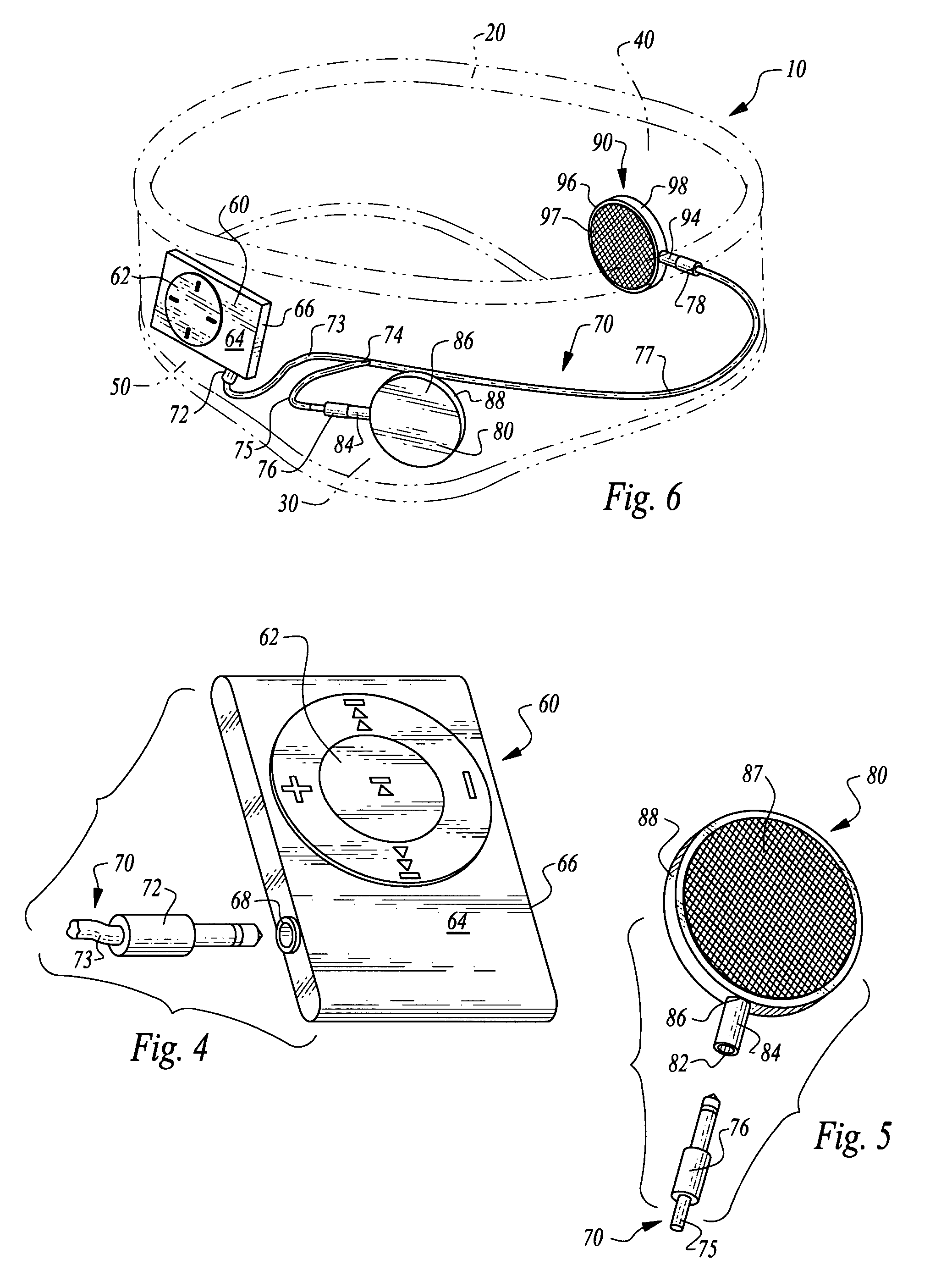
Headgear and integrated music player
A headgear assembly is provided with an integrated music or other sound player supportable therein. The headgear assembly includes a headband or cap with pouches therein for various portions of the music player. In particular, a left speaker pouch is provided for a left speaker, a right speaker pouch is provided for a right speaker and a player pouch is provided for a sound player. A wire harness is also provided to preferably removably attach the speakers to the sound player. The headband or cap with the pouches therein holds the player and speakers directly adjacent a head of the user, and with the speakers directly over ears of the user. Controls on the player are accessed through a window in an outer panel of the headband or cap to allow user access. The player, wire harness and speakers are all substantially concealed within the headgear assembly.
Owner:PHILLIPS AARON M
System and method for real-time cloud simulation on Internet of things sensing device
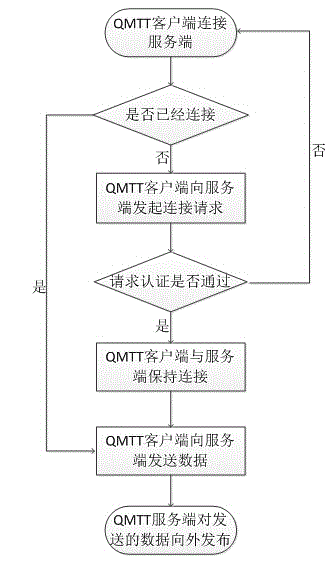
The invention discloses a system and a method for real-time cloud simulation on an Internet of things sensing device. The system comprises the Internet of things sensing device, an Internet of things gateway device, a cloud device simulation center and an MQTT (Message Queuing Telemetry Transport) server; the Internet of things sensing device is an intelligent sensing device which is accessed to a sensing network; the Internet of things gateway device is used for providing the access for a heterogeneous sensing network; the cloud device simulation center comprises a simulation data processing module and a simulation node module, wherein the simulation data processing module is used for receiving, pushing and processing simulation data, the simulation node module is used for establishing cloud simulation nodes, and the cloud simulation nodes and the Internet of things sensing device are maintained to be synchronized; the MQTT server is an interaction intermediary of the Internet of things sensing device and the cloud simulation node which is corresponding to the Internet of things sensing device. According to the system and the method for the real-time cloud simulation on the Internet of things sensing device, the cloud simulation node which is corresponding to the Internet of things sensing device is established at the position of a cloud according to real-time data sent from the Internet of things sensing device to enable the functions of the cloud simulation node to be as same as the functions of the Internet of things entity sensing device and accordingly the access of the cloud application service to the entity sensing device and the operation of the cloud application service on the entity sensing device are convenient.
Owner:河南金路网络科技股份有限公司
Headgear and integrated music player
InactiveUS8111859B2Decoupling of the wire harness from the speakers and the player is facilitatedEasy to decoupleMicrophonesLoudspeakersEngineeringMusic player
Owner:PHILLIPS AARON M
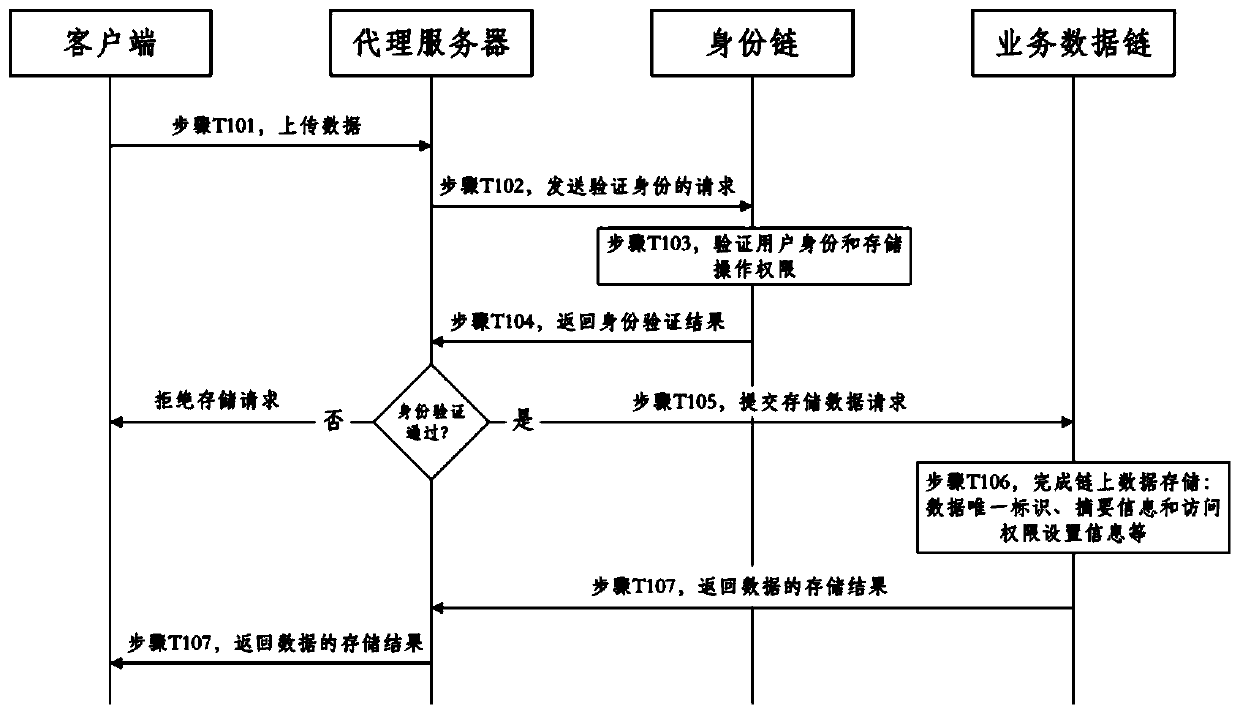
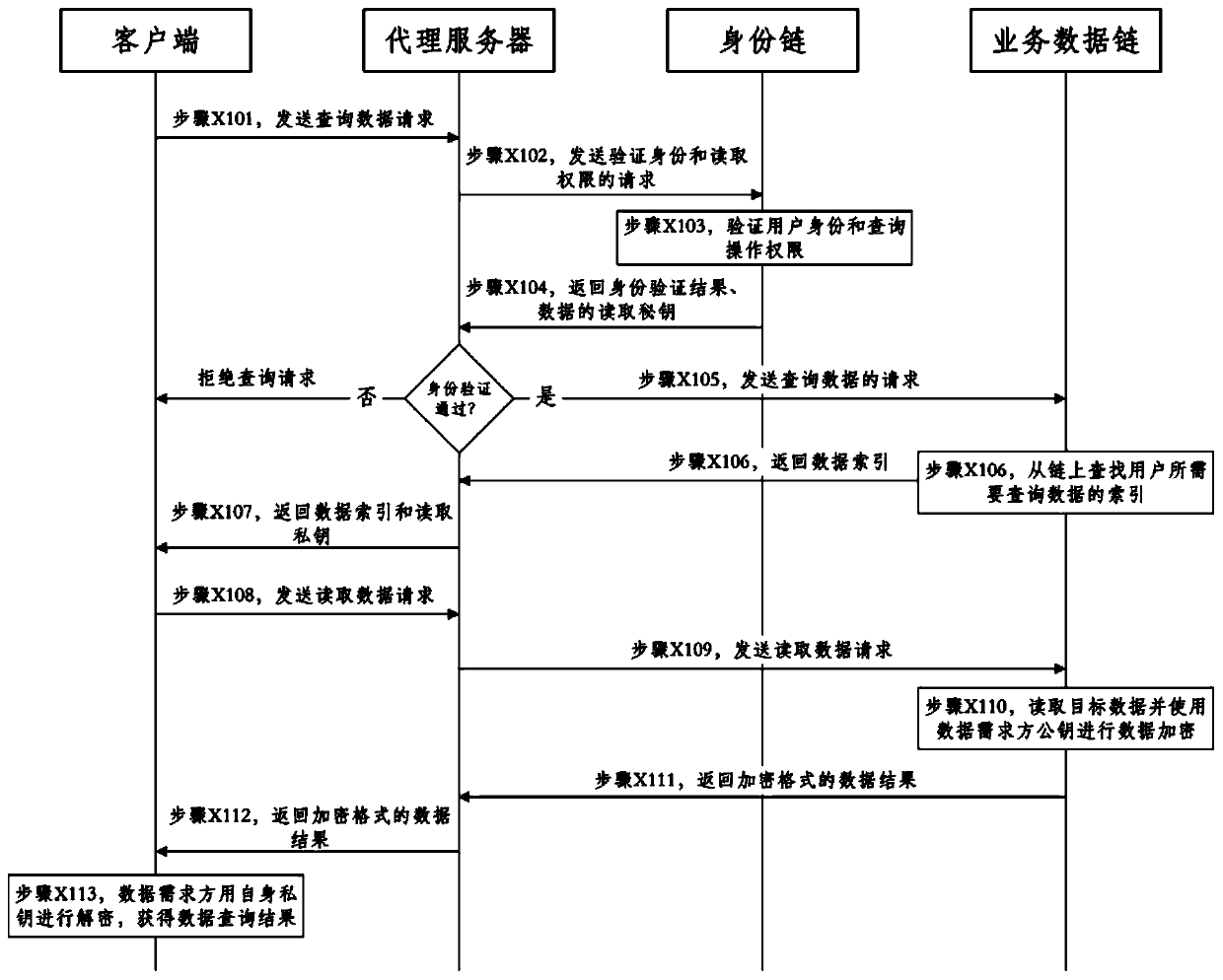
Government affair data storage and query method and system based on block chain double-chain structure
ActiveCN110109930AEnsure safetyGuaranteed controllableData processing applicationsDigital data protectionStructure of Management InformationClient-side
The invention provides a government affair data storage and query method and system based on a block chain double-chain structure. The government affair data storage method based on the block chain double-chain structure comprises the steps that a client uploads the data to a proxy server; the proxy server sends a data storage request to the identity chain and verifies the user identity and the data storage request; the identity chain verifies the identity of the user who makes the request and the storage operation authority, and returns a verification result to the proxy server; if the verification does not pass, the proxy server sends a data storage rejection request to the client; if the verification passes, the proxy server submits a data storage request to a service data chain, and the service data chain completes a consensus process according to the data storage request of the client and stores the data related information in a block chain system state database; and the service data chain feeds back a storage result to the client through the proxy server.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
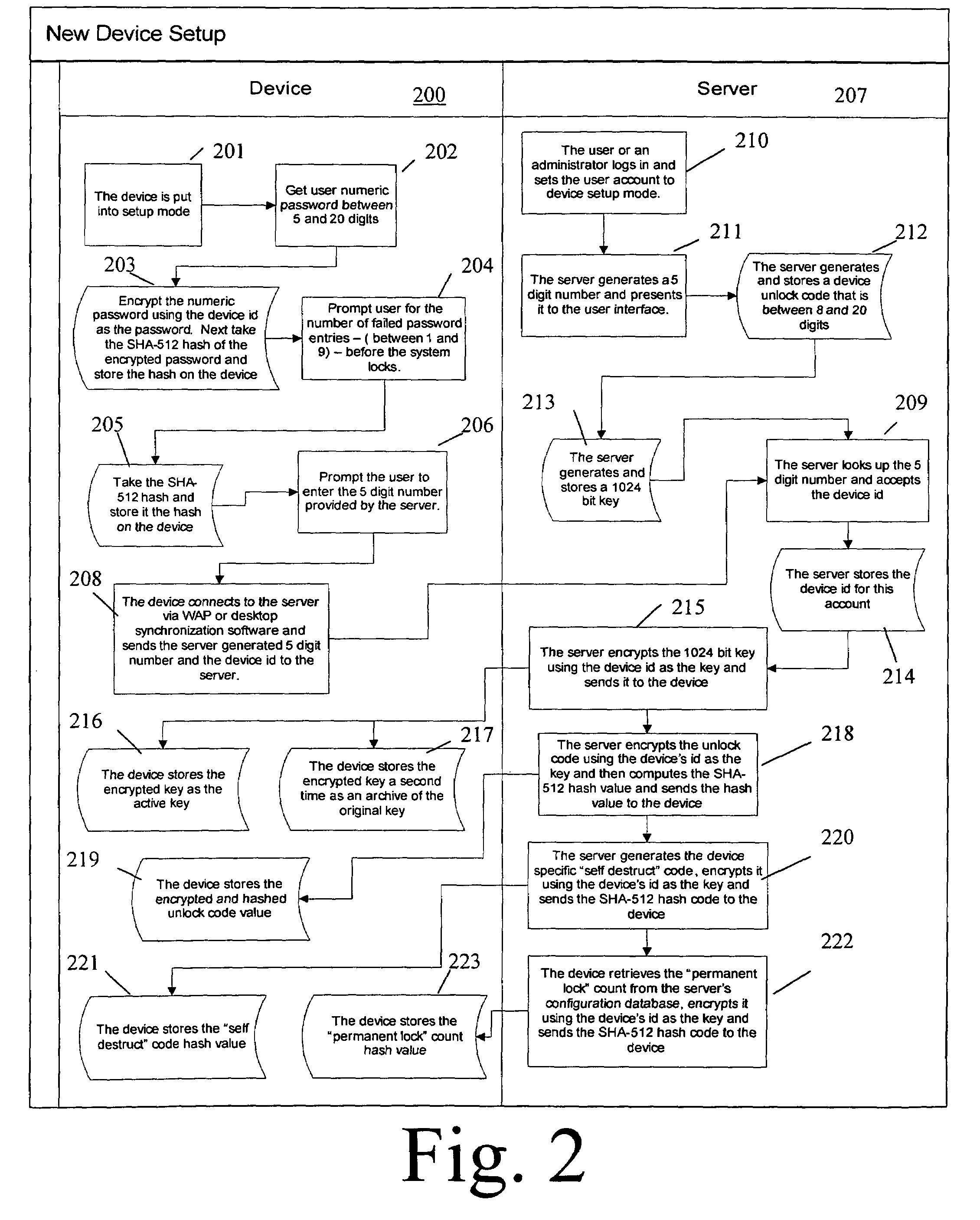
Method to use secure passwords in an unsecure program environment
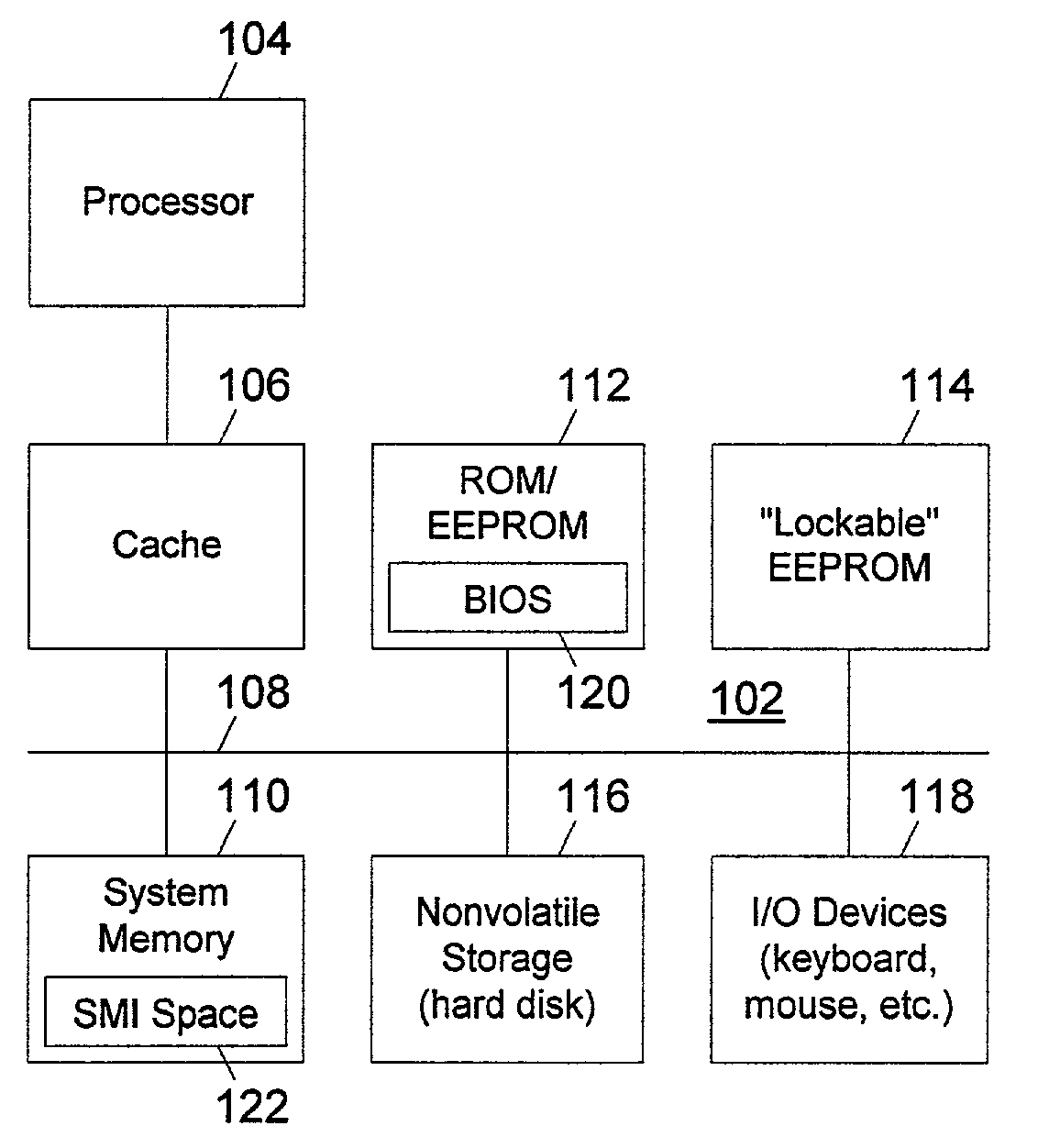
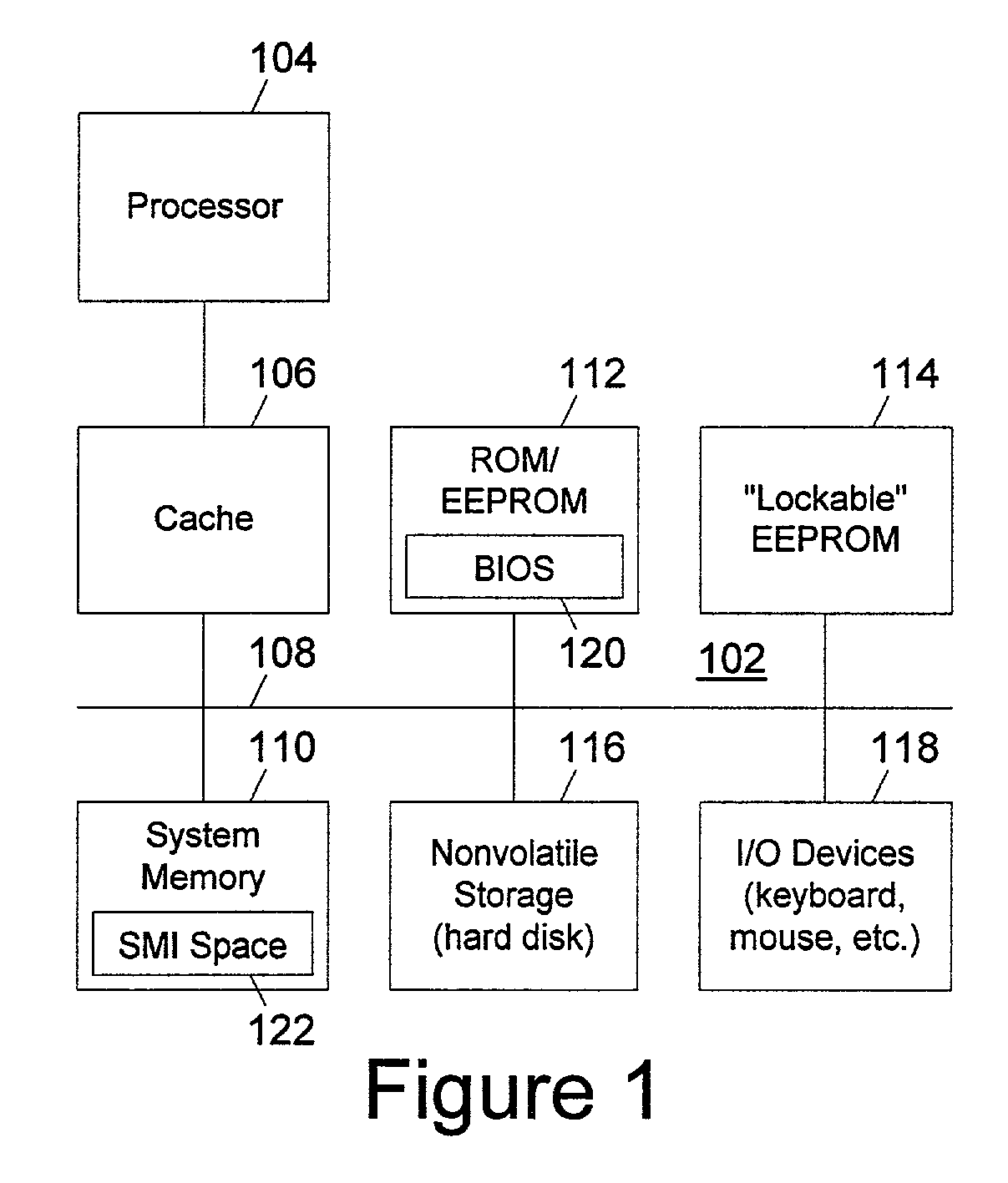
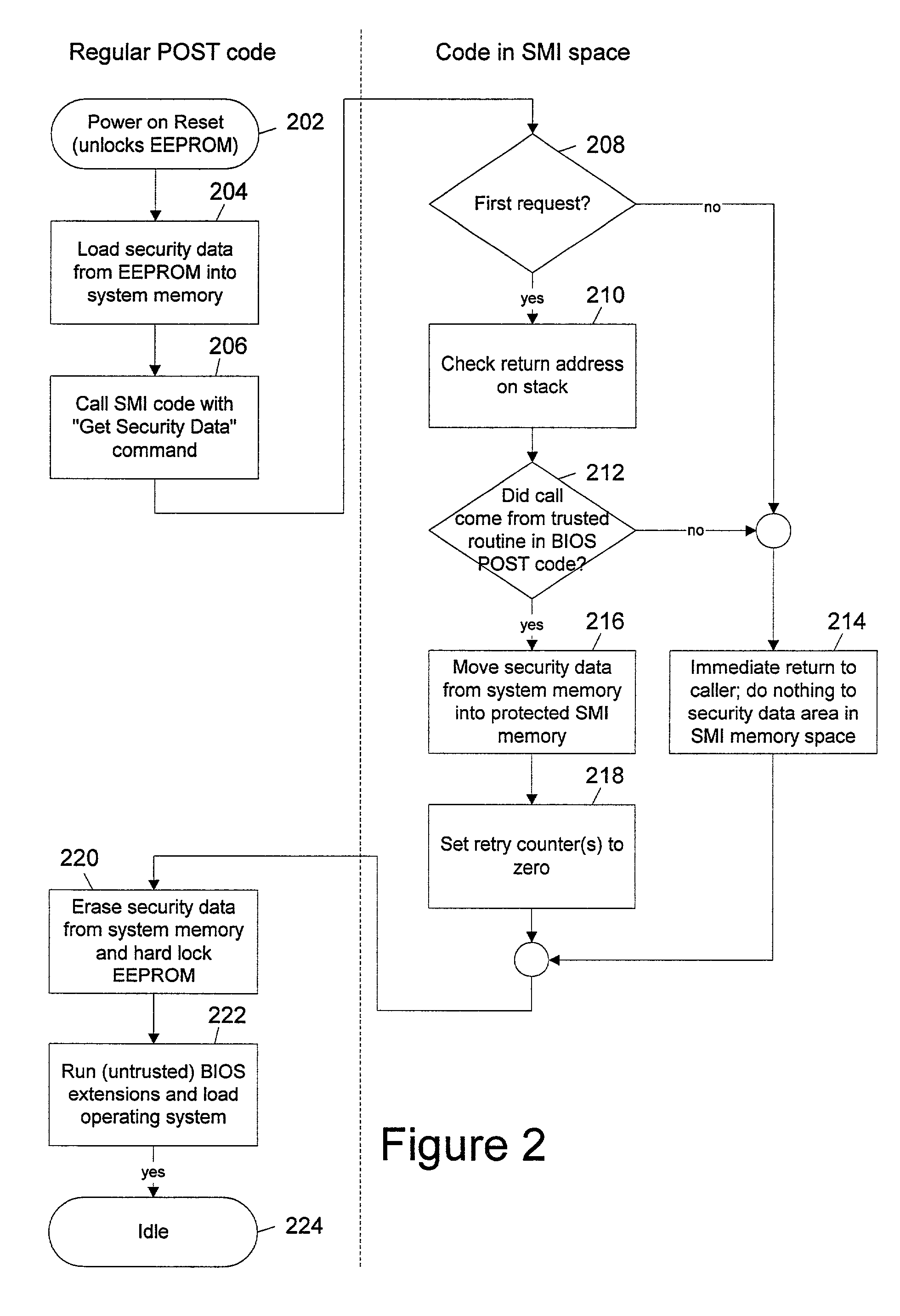
InactiveUS7200761B1Easy to optimizeConvenient access controlDetecting faulty hardware by power-on testProgram control using stored programsElectricityComputer hardware
During power up initialization, security data such as passwords and other sensitive data which are stored in a lockable memory device are read and copied to protected system management interrupt (SMI) memory space, subject to verification by code running in the SMI memory space that the call to write the security data originates with a trusted entity. Once copied to SMI memory space, the security data is erased from regular system memory and the lockable storage device is hard locked (requiring a reset to unlock) against direct access prior to starting the operating system. The copy of the security data within the SMI memory space is invisible to the operating system. However, the operating system may initiate a call to code running in the SMI memory space to check a password entered by the user, with the SMI code returning a “match” or “no match” indication. The security data may thus be employed after the lockable memory device is hard locked and the operating system is started.
Owner:IBM CORP
Digital video surveillance
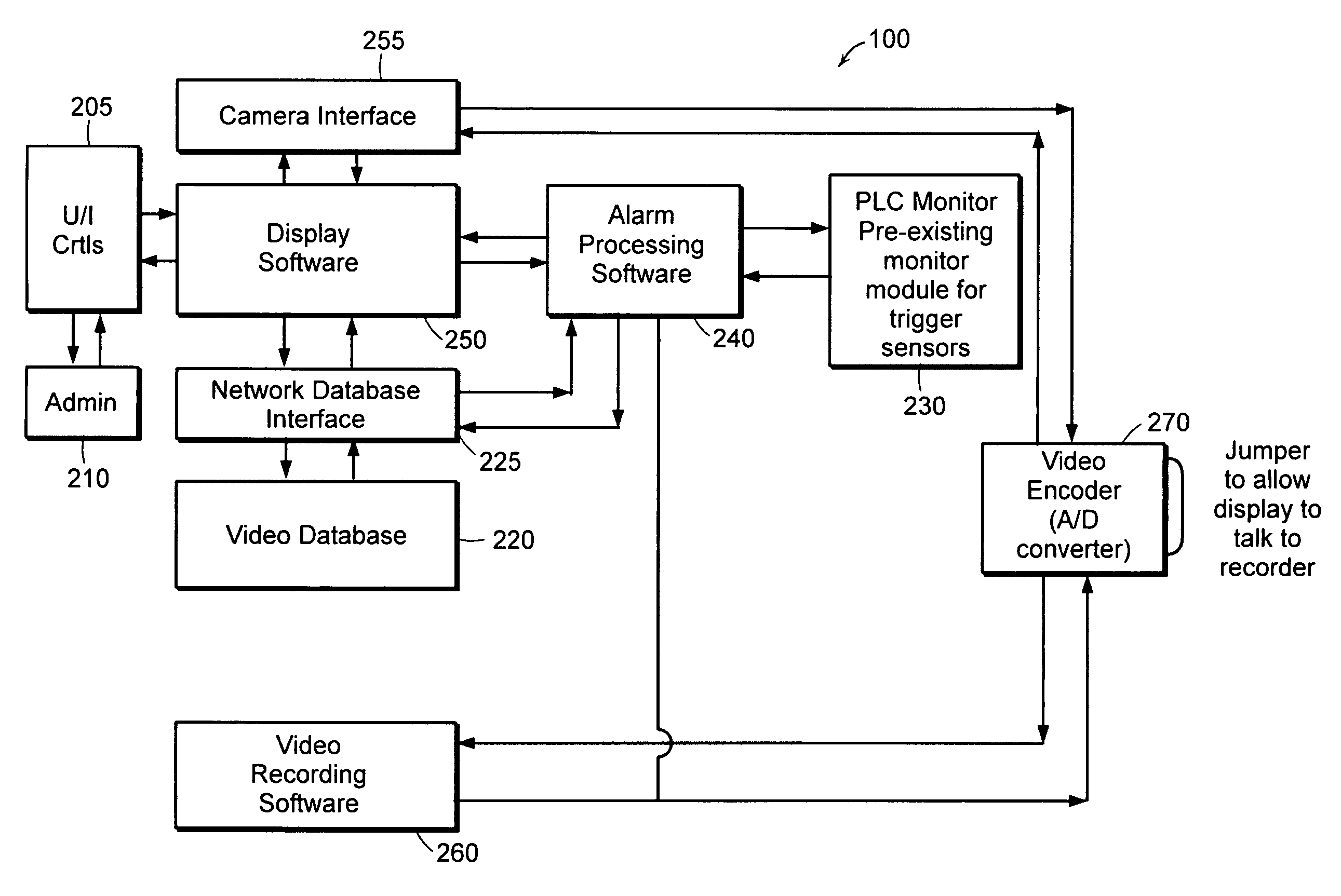
InactiveUS20050162268A1Reduce needConvenient access controlFrequency-division multiplex detailsTime-division multiplexDigital videoDigital data
A control system for use with one or more video surveillance cameras forming a video surveillance system. The control system includes a video database module wherein a database entry includes at least one sensor condition defining an alarm state for each camera. Additionally, there is an alarm condition module that receives one or more sensor signals from one or more sensors associated with a camera and retrieves the sensor condition defining an alarm state for the camera. The alarm condition module outputs an alarm signal if the alarm condition module determines that the one or more sensor signals meets the one or more sensor conditions. The control system is modular and may be distributed in a network environment. The control system also monitors the network bandwidth and can adjust the throughput of digital data representing the digital images in order to avoid any bandwidth limitations.
Owner:INTERGRAPH SOFTWARE TECH
Security Enhanced Data Platform
InactiveUS20100189251A1Improve securityConvenient access controlDigital data processing detailsUser identity/authority verificationUser PrivilegeDocumentation procedure
The security enhanced data platform is comprised of two primary subsystems and a host of supporting subsystems. The first primary subsystem is a document management system. A set of client side tools provides the user a way to specify classifications and compartments for selected areas of a document, and a way to save the document in the format required by the system in order to allow the system to enforce the rules and privileges dictated to the system. The second subsystem is a security enhanced database management system. In documents the system allows different user privilege requirements on the document as a whole as well as on pages, paragraphs, sentences, words, and / or letters of a word. A history of document changes is maintained to provide an audit trail after the fact of who did what changes, where those changes were made and when those changes were made.
Owner:CURREN EDWARD
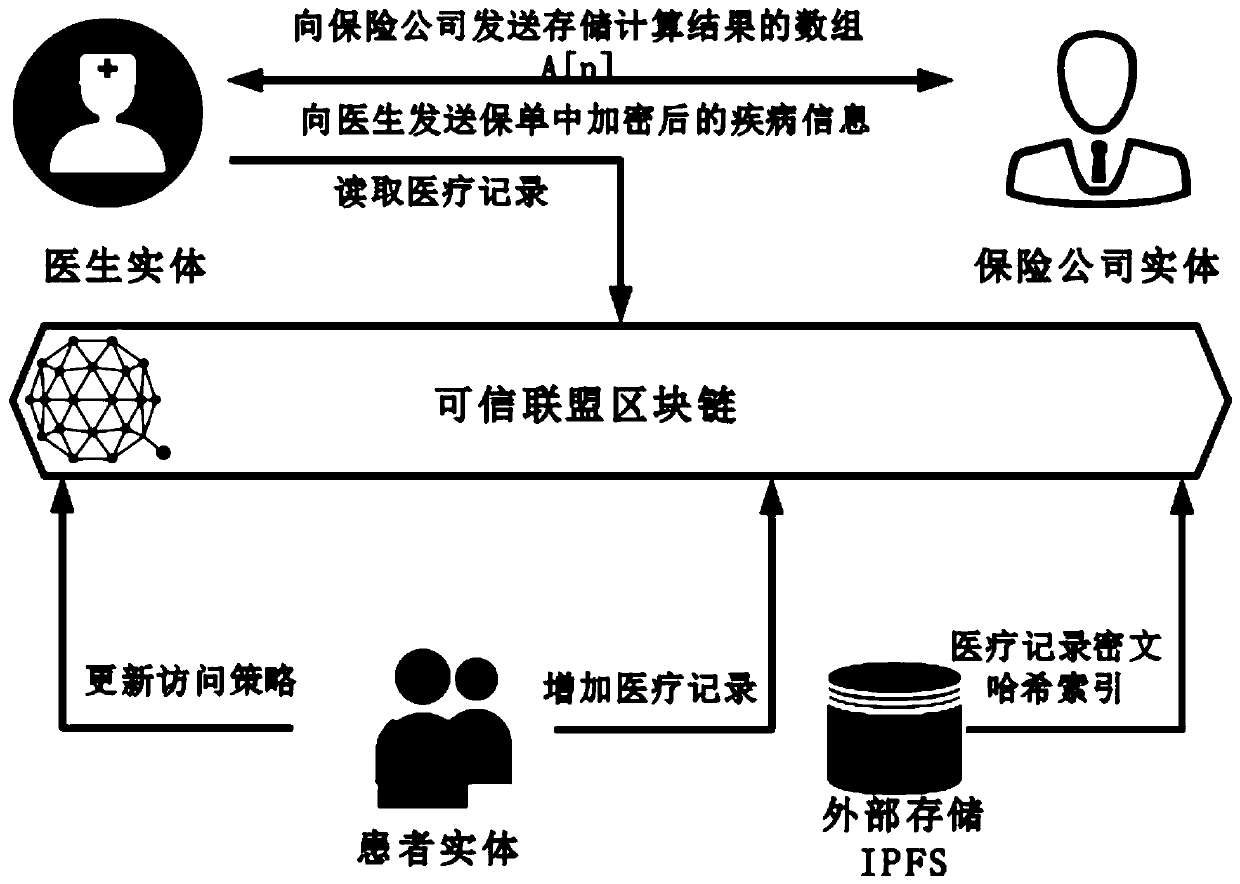
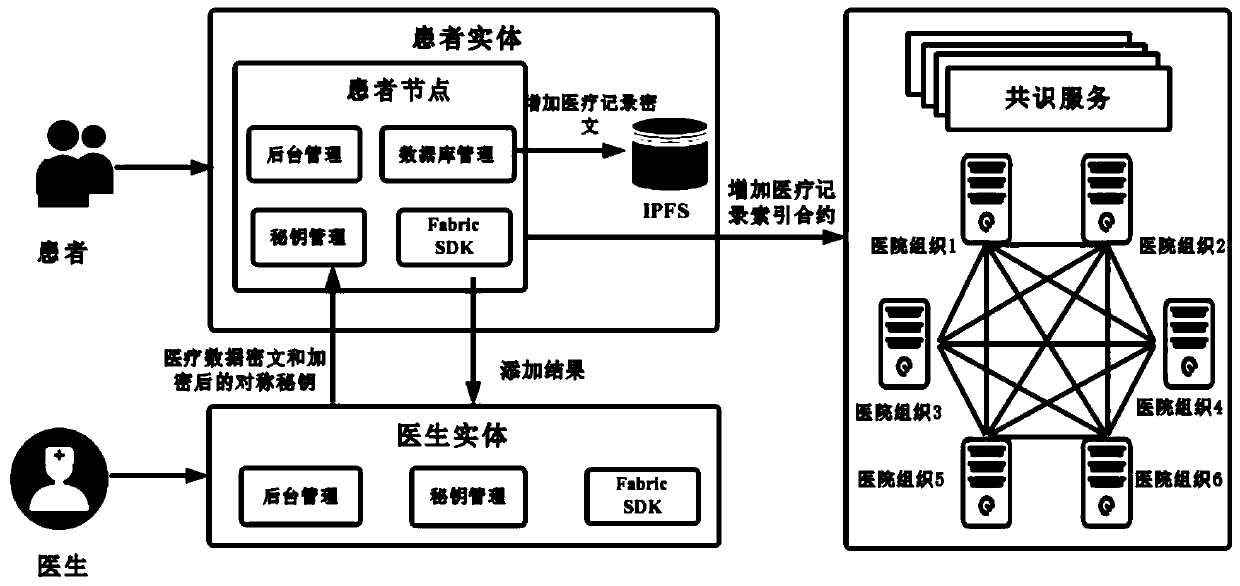
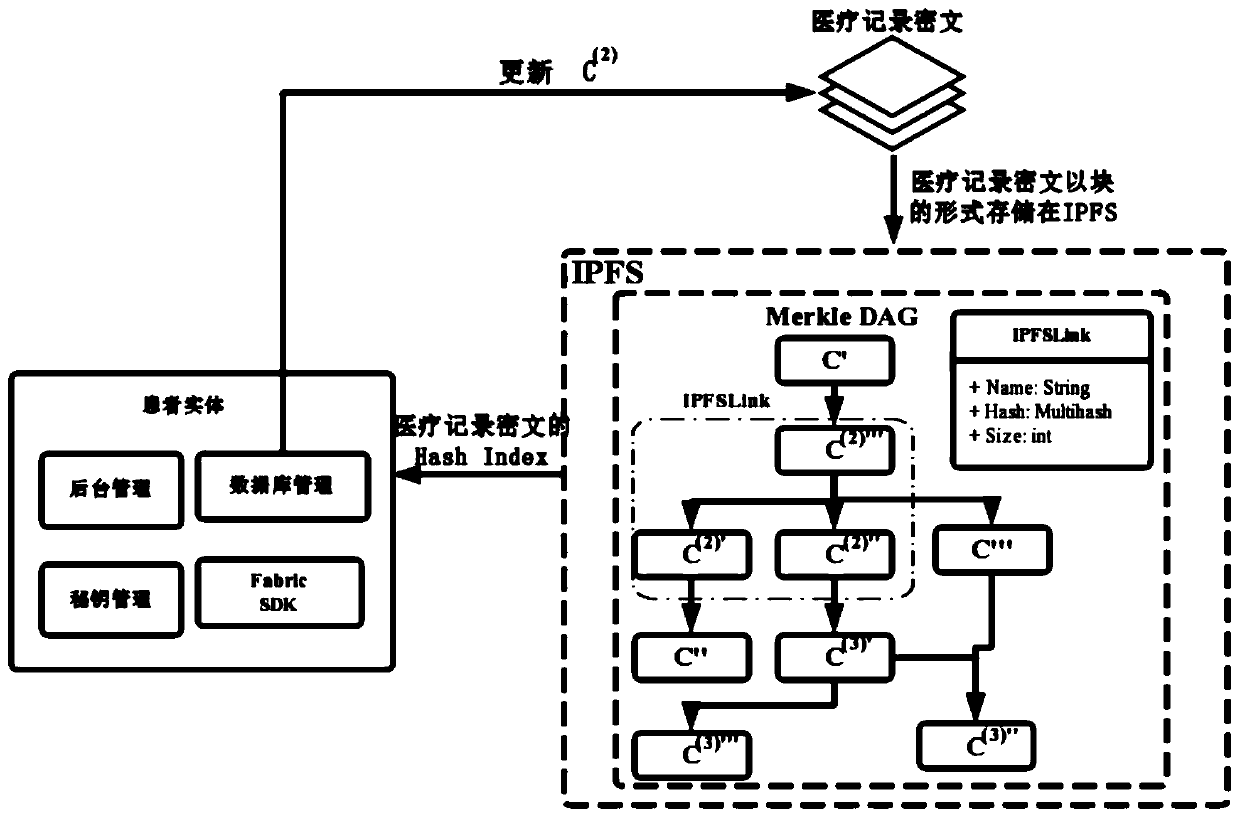
Medical record storage, sharing and security claim settlement model and method based on a block chain
ActiveCN110008746AGuaranteed privacyIncrease resistanceDigital data protectionPatient healthcareMedical recordThird party
The invention belongs to the technical field of medical data management, and relates to a medical record storage, sharing and security claim settlement model and method based on a block chain. Firstly, credible sharing of medical data of patients among medical institutions is achieved through the blockchain technology, and a lifelong medical record is established for the patients; based on a Hashchain type storage structure, the medical data cannot be tampered; secondly, an improved CP-ABE-based cryptographic primitive SHDPCPC-CP-ABE is proposed, security encryption and fine-grained access control on the medical data are realized, and a patient can conveniently and efficiently access and authorize a medical institution to read the medical data; and finally, a Paillier homomorphic encryption technology is utilized to realize safe medical insurance claim settlement, and the privacy of the patient is protected when the patient interacts with a third-party non-medical institution. According to the invention, security, confidentiality, reliability and integrity of medical data can be realized, and confidential sharing of private data is supported.
Owner:DALIAN UNIV OF TECH
Method and system for limiting access rights within a building
ActiveUS8813917B2Convenient access controlAvoid accessElectric signal transmission systemsTicket-issuing apparatusControl systemTerminal equipment
Owner:KONE CORP
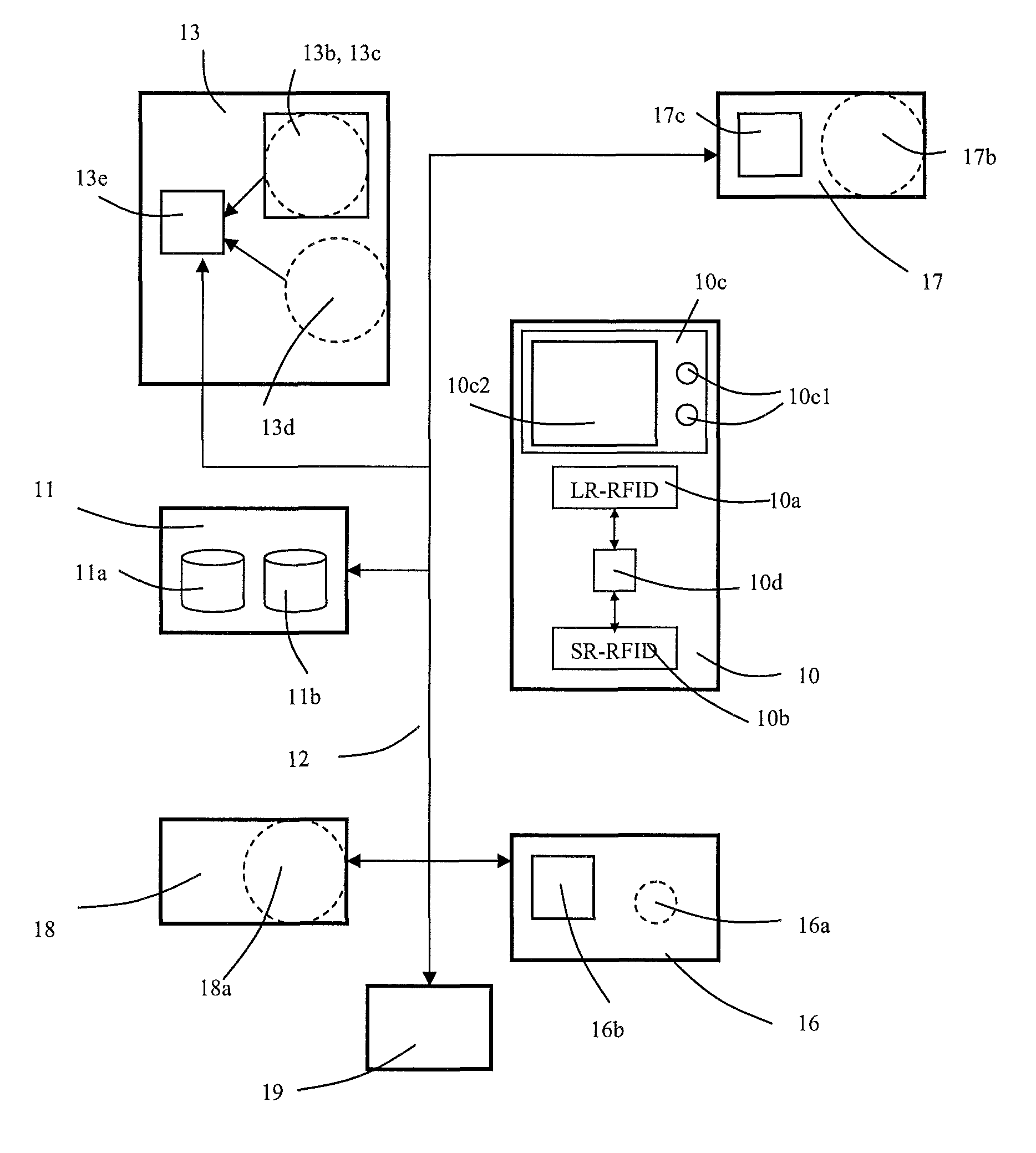
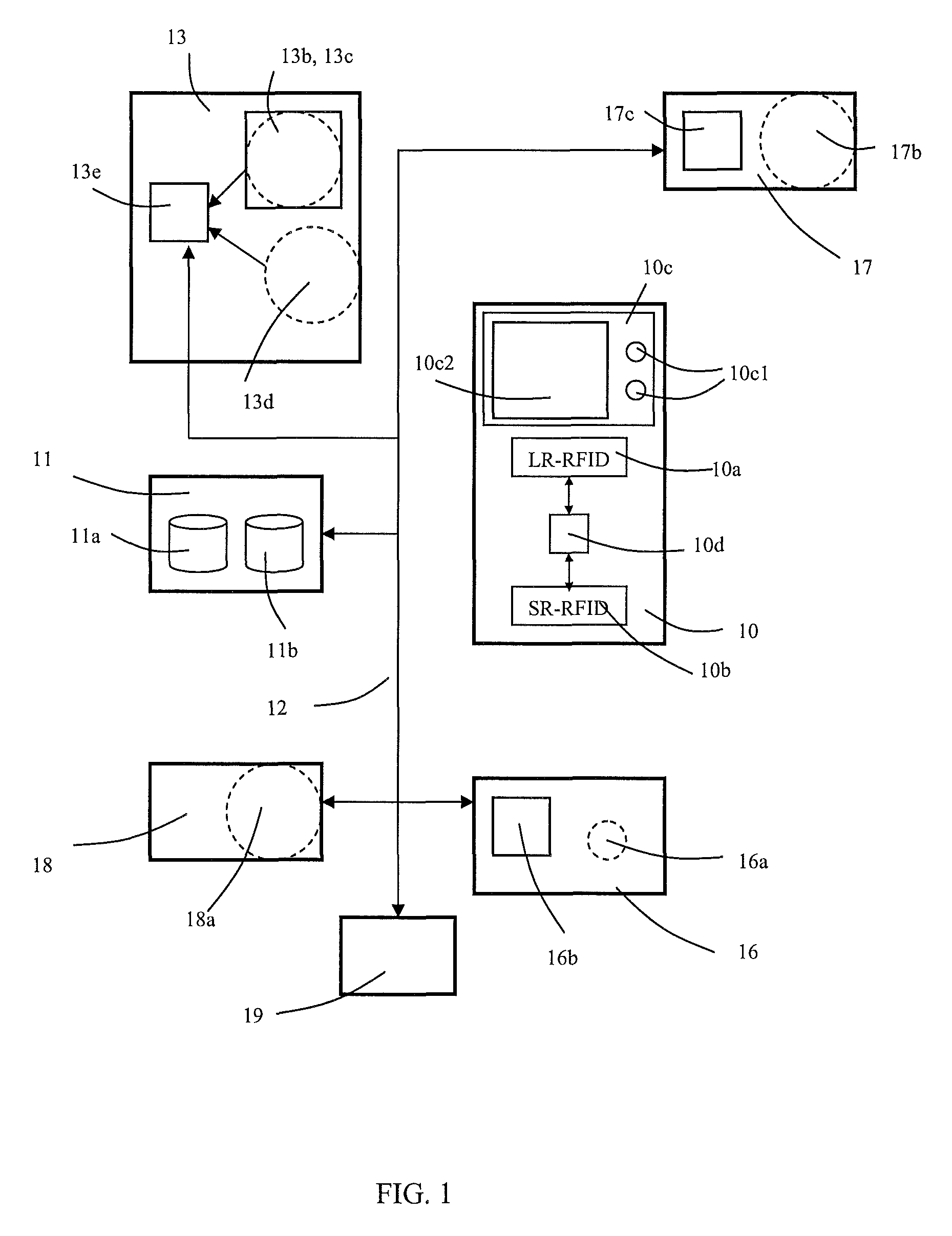
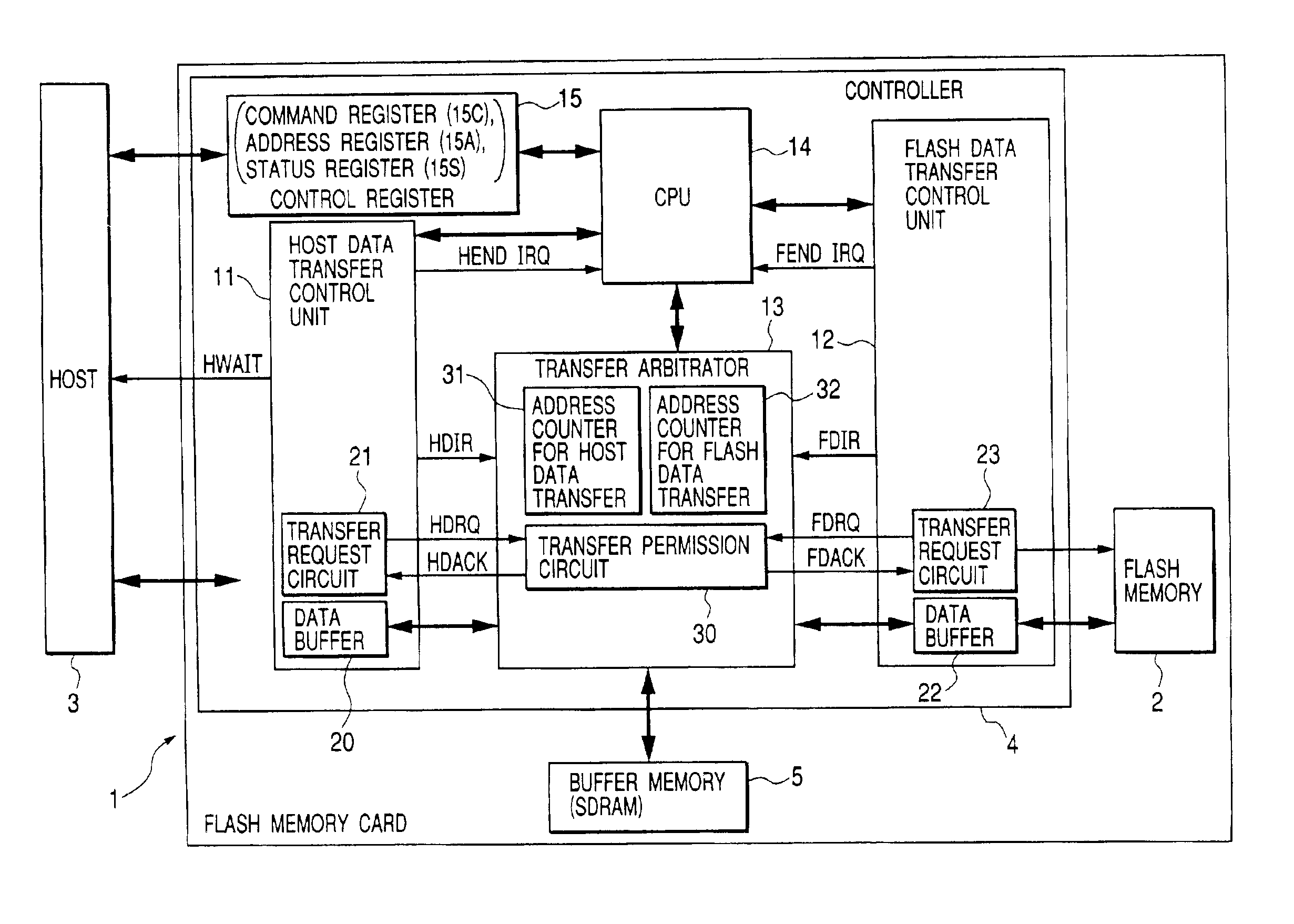
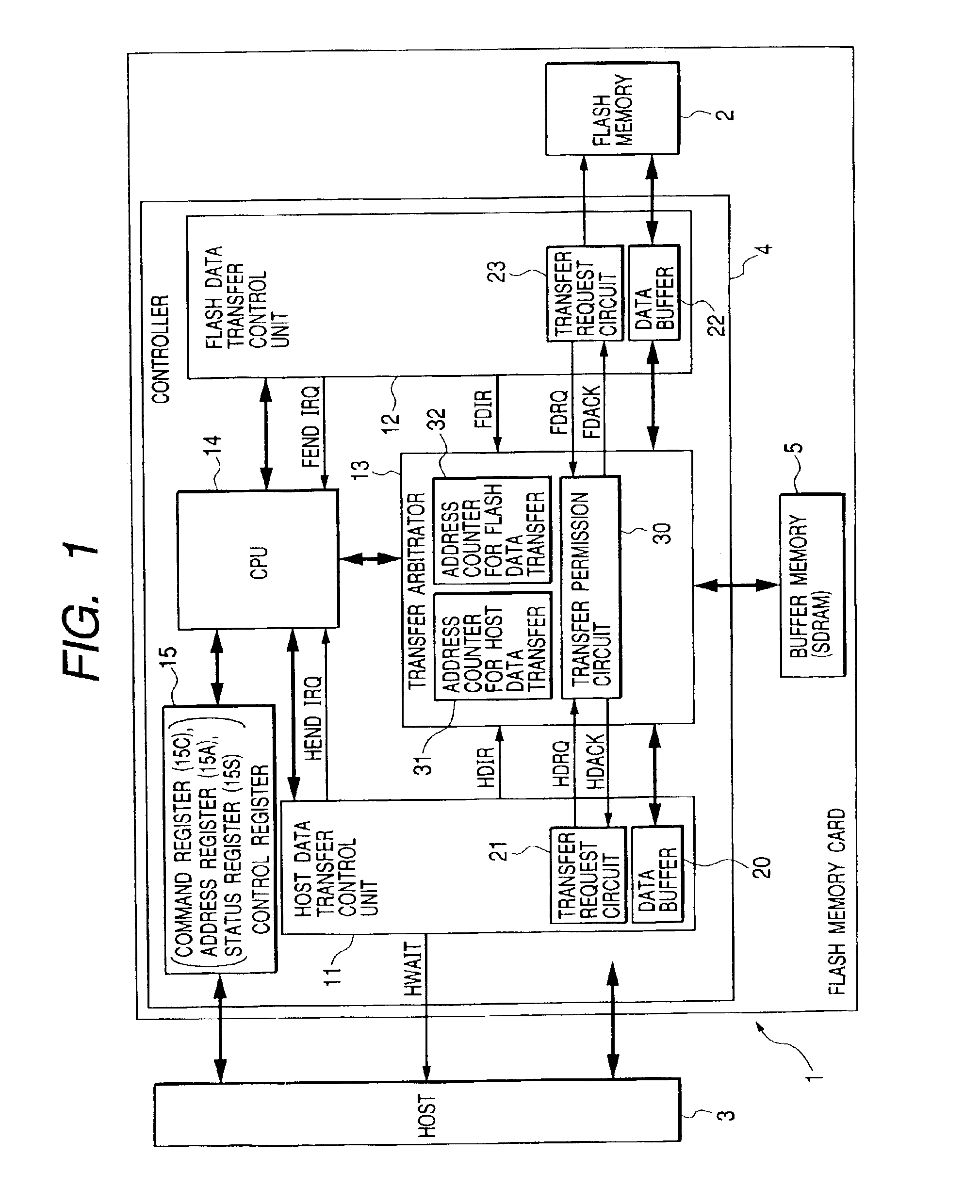
Memory system with improved efficiency of data transfer between host, buffer and nonvolatile memory
InactiveUS6882568B2Increase speedConvenient access controlMemory architecture accessing/allocationInput/output to record carriersTime-sharingData treatment
The present invention provides a memory system which contributes to improvement in efficiency of a data process accompanying a memory access. A memory system has a rewritable nonvolatile memory, a buffer memory, and a controller. The controller controls, in response to an access request from an external apparatus, first data transfer between the controller and the external apparatus, second data transfer between the controller and the nonvolatile memory, and third data transfer between the controller and the buffer memory, controls transfer from the controller to the buffer memory in the third data transfer and transfer from the buffer memory to the controller in a time sharing manner, and enables the first data transfer or the second data transfer to be performed in parallel with the transfer carried out in the time sharing manner.
Owner:EMERGENCE MEMORY SOLUTIONS LLC
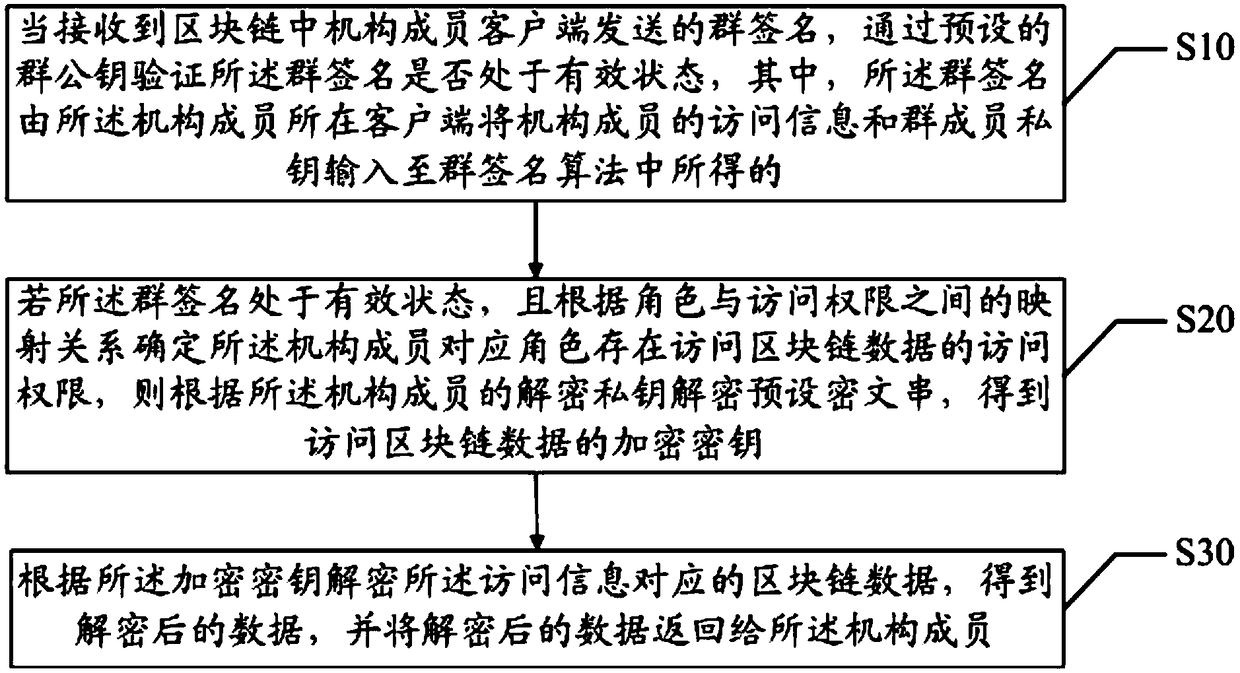
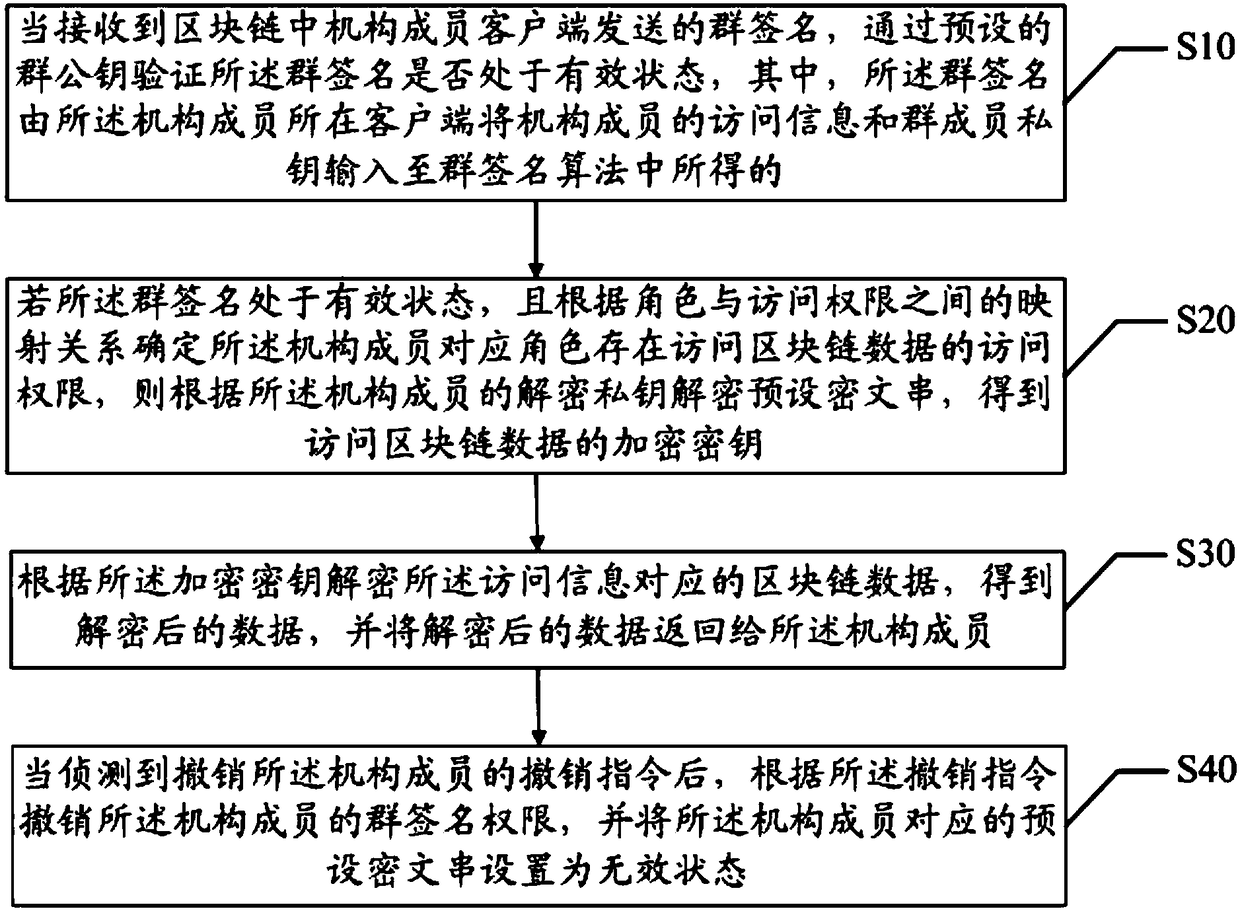
Blockchain access control method, device and computer readable storage medium
ActiveCN108768988AImprove operational efficiencyAchieve accessKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInter agencyRelational database
The invention discloses a blockchain access control method, a blockchain access control device and a computer readable storage medium. The blockchain system provided by the invention completes the identity authentication of a member of a role corresponding institution by a group signature algorithm, and implements the access of encryption data by using a digital envelope technology; through the concept of groups and roles, each group corresponds to a role, and each role may correspond to multiple institutional members, so that the blockchain system supports the scenarios of multi-user data access. Compared to the traditional relational database-based data access system, the blockchain system in the application is strong in scalability, and capable of easily implementing inter-agency accesscontrol. And in this embodiment, the signature operation of the group signature algorithm and the verification time for verifying the group signature are independent of the number of group members, thereby improving the operation efficiency of the blockchain system during data access.
Owner:WEBANK (CHINA)
802.1X authentication technique for shared media
ActiveUS7624431B2Convenient access controlImprove securityDigital data processing detailsUser identity/authority verificationNetwork Access ControlClient-side
The present invention provides a technique for securely implementing port-based authentication on a shared media port in an intermediate node, such as a router. To that end, the invention provides enhanced port-based network access control that includes client-based control at the shared media port. Unlike previous implementations, the port does not permit multiple client nodes to access a trusted subnetwork as soon as a user at any one of those nodes is authenticated by the subnetwork. Instead, port-based authentication is performed for every client node that attempts to access the trusted subnetwork through the shared media port. As such, access to the trusted subnetwork is not compromised by unauthenticated client nodes that “piggy-back” over the shared media port after a user at another client node has been authenticated by the trusted subnetwork.
Owner:CISCO TECH INC
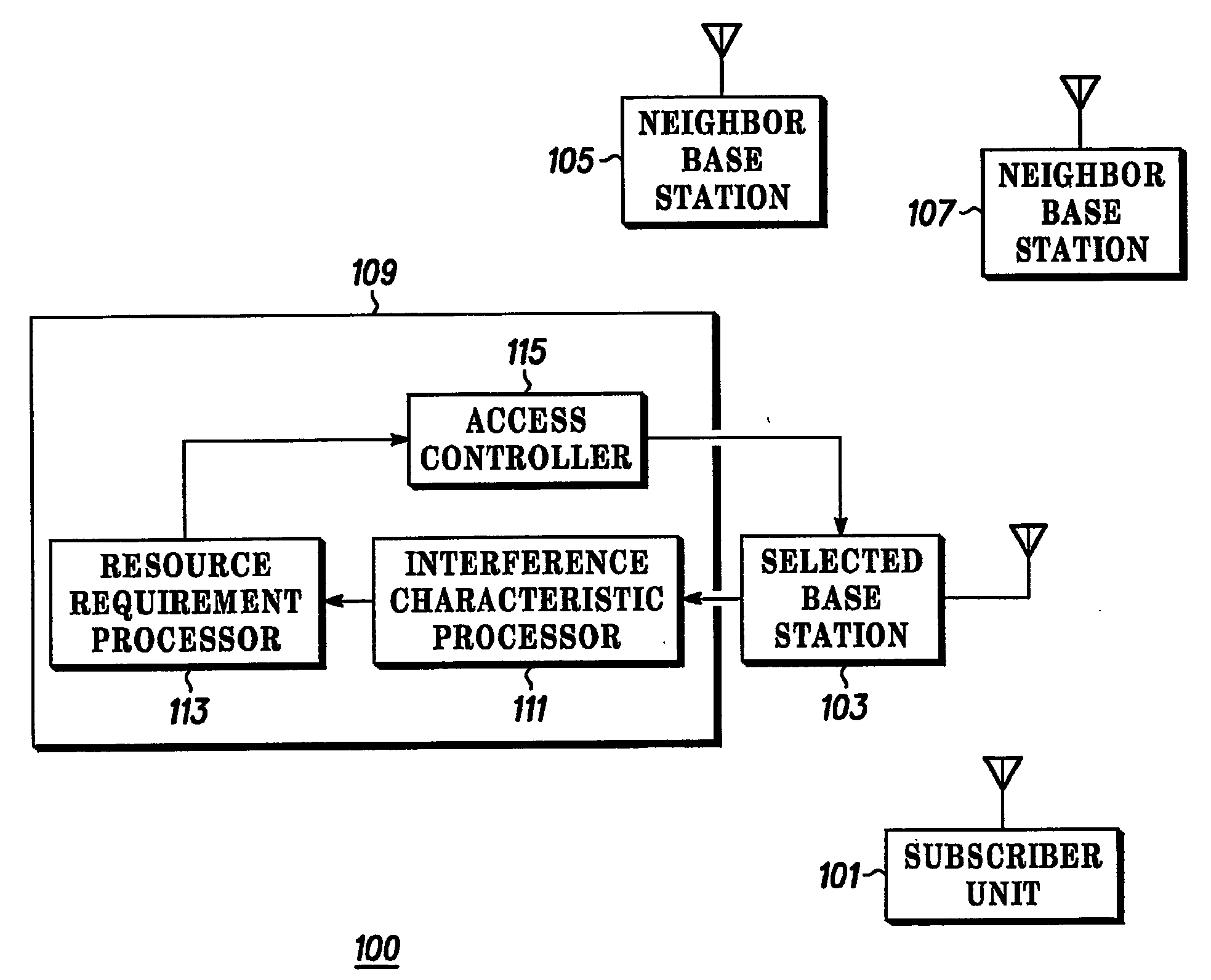
Apparatus and method of radio access management for a radio communication system
ActiveUS20070010270A1Improve accuracyImprove performancePower managementTransmission control/equalisingCommunications systemInterference (communication)
The invention relates to access management in a radio communication system. A subscriber unit (101) transmits an access message to a base station (103). A Radio Access Controller (RNC) (109) receives information of the access request. The RNC (109) comprises an interference characteristic processor (111) which determines an interference characteristic associated with the subscriber unit (101). The interference characteristic may include an inter-cell interference factor and an intra-cell orthogonality factor determined as a function of the distance between the base station and the subscriber unit and / or based on subscriber unit measurements of pilot signals from the selected base station (103) and neighbouring base stations (105, 107). The interference characteristic processor (111) is coupled to a resource requirement processor (113) which determines a resource requirement for achieving a desired signal to interference ratio for the requested service in response to the interference characteristic. The RNC (109) further comprises an access controller (115) which accepts or rejects the request in response to the determined resource requirement.
Owner:GOOGLE TECH HLDG LLC
Attribute-based encryption method for achieving hierarchical certification authority
ActiveCN103647644AFacilitate hierarchical distributionEase of distributed managementKey distribution for secure communicationPublic key for secure communicationCiphertextAttribute-based encryption
The invention discloses an attribute-based encryption method for achieving a hierarchical certification authority. The attribute-based encryption method for achieving the hierarchical certification authority mainly comprises the following steps of 1) initialization of a central authority; 2) initialization of multilayer certification authorities; 3) user registration and certification; 4) extraction and distribution of private keys; 5) encryption; 6) decryption. The attribute-based encryption method for achieving the hierarchical certification authority achieves hierarchical distribution of multiple certification authorities on the basis of an attribute-based encryption system of a ciphertext policy, facilitates management of the central authority to the certification authorities, and is applicable to shared data encryption solution in a large organization structure of hierarchical distribution. Besides, during the extraction and distribution process of the private keys, overlapping among attribute sets of different users is allowed, so that the attribute-based encryption method for achieving the hierarchical certification authority has wider adaptability in practical application.
Owner:BEIHANG UNIV
Access control method and device
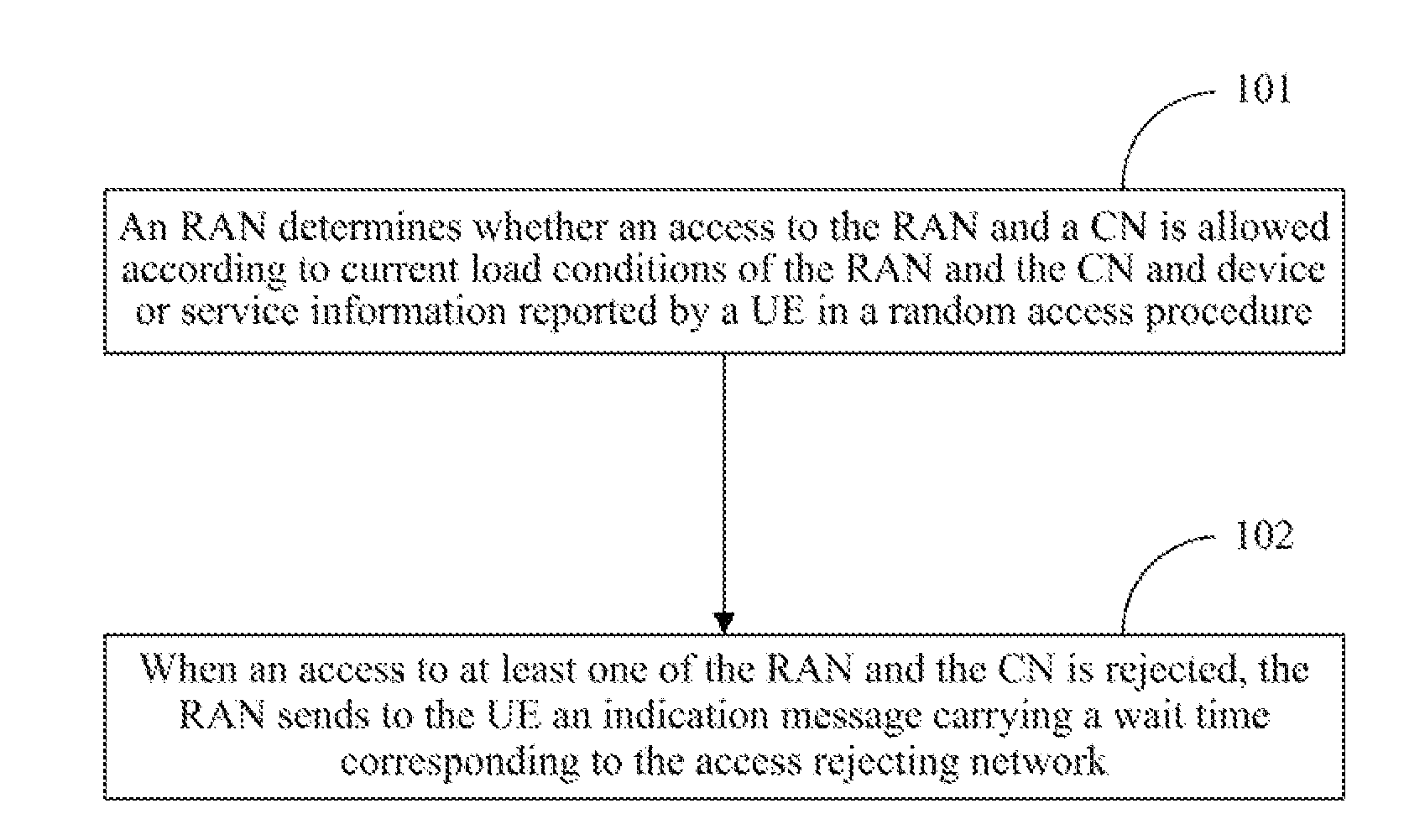
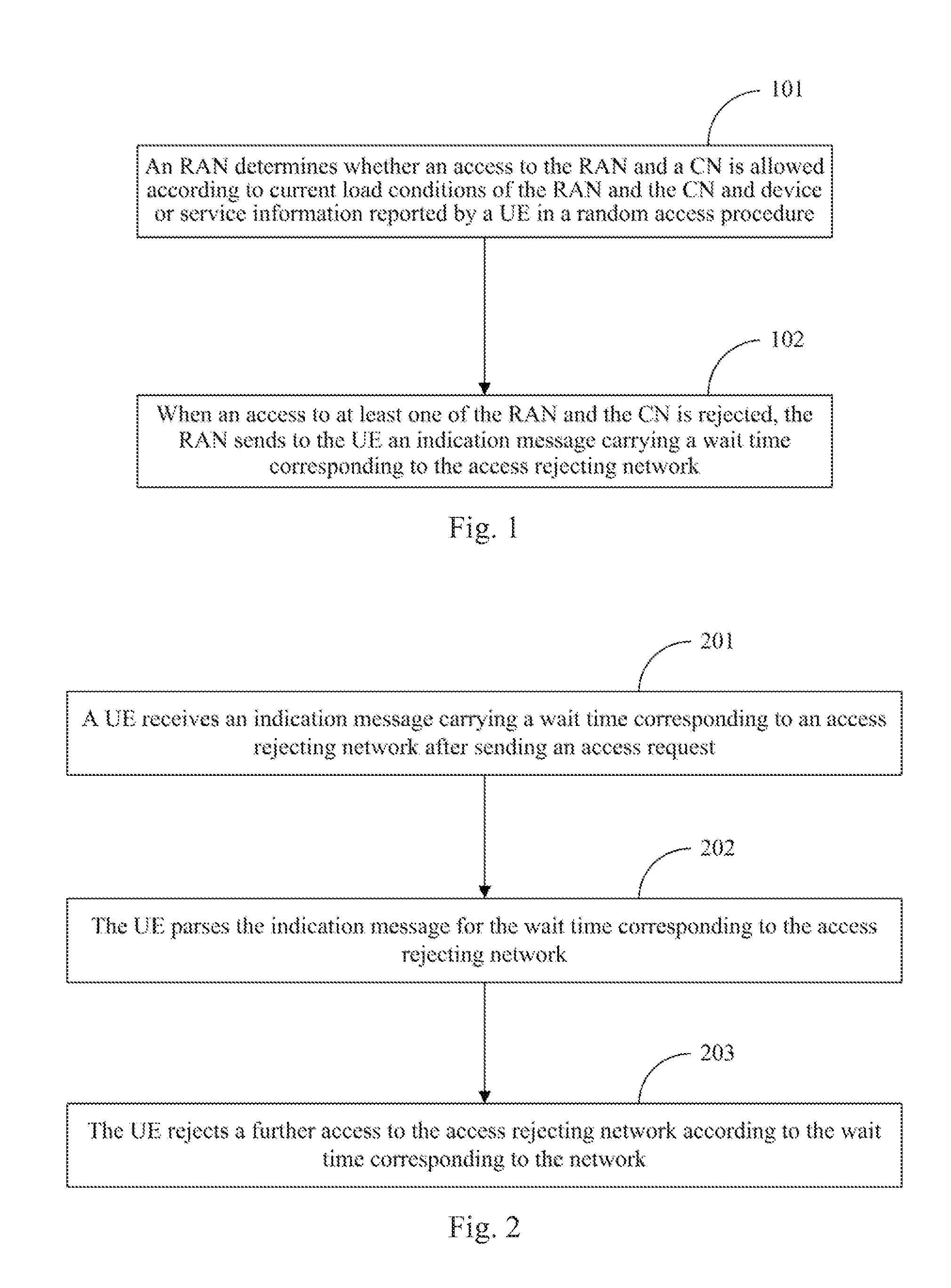
ActiveUS20130279330A1Convenient access controlMuch congestionError preventionTransmission systemsCurrent loadRandom access memory
Disclosed is an access control method, for use in implementing improved access control. The method comprises: during a random access process, on the basis of a current load of a random access network (RAN) and a core network (CN) and of terminal or service information reported by a user equipment (UE), the RAN judging whether or not access to the RAN and to the CN is allowed; when access is denied by at least one network between the RAN and the CN, the RAN transmitting to the UE an instruction message having attached therein a backoff time corresponding to the access denying network. Also disclosed is a device for implementing the method.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Authority control method and device
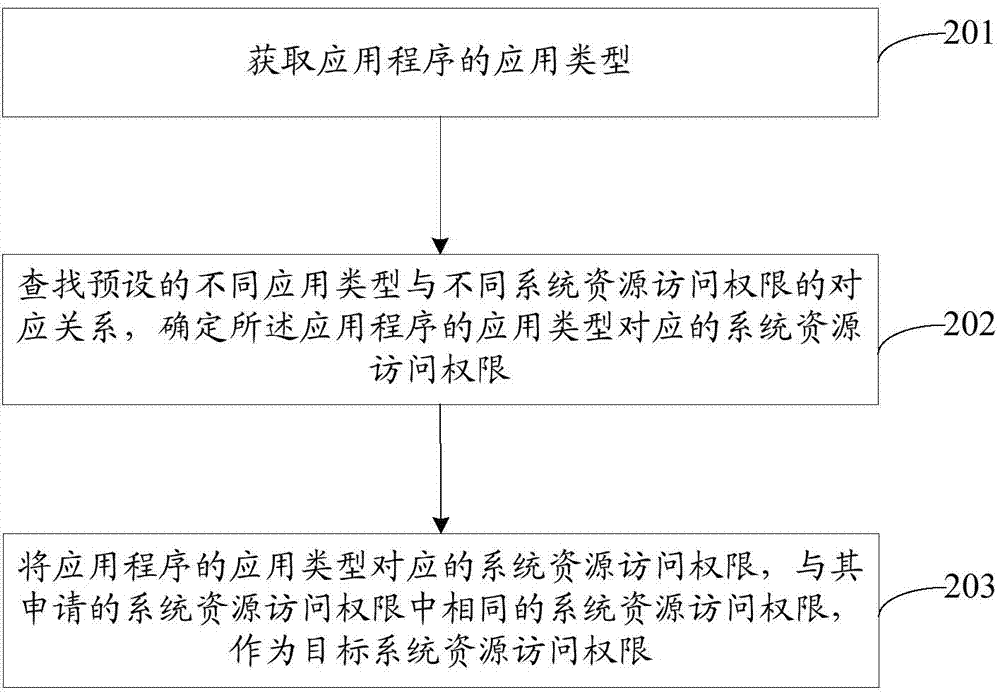
ActiveCN104516783AEasy access controlImprove efficiencySpecific access rightsResource allocationGoal systemAuthority control
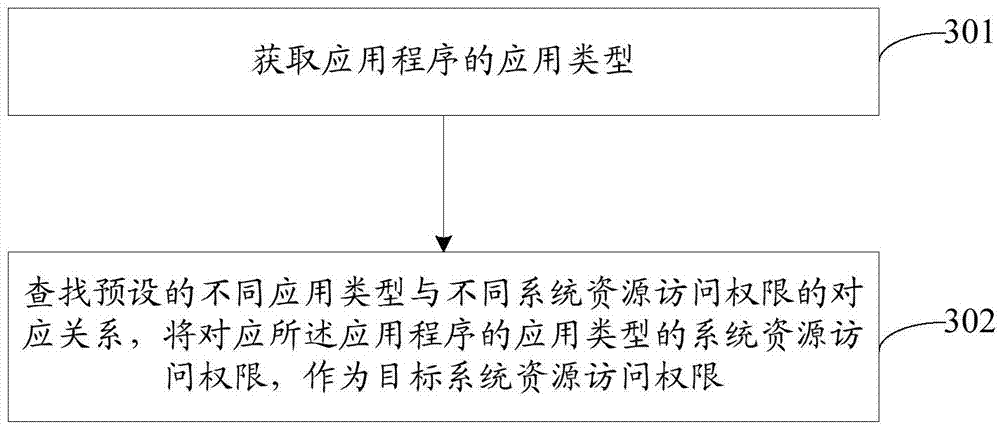
Provided are a permission control method and device. The method comprises: acquiring an application type of an application program; determining, in a system resource access permission corresponding to the application type of the application program, a destination system resource access permission of the application program according to a preset correspondence between different application types and different system resource access permissions, so as to control the access of the application program to the system resource according to the destination system resource access permission. With the embodiments of the present application, it is easy to achieve a permission control, and the permission control efficiency is improved.
Owner:HUAWEI DEVICE CO LTD
Terminal, server and terminal safety management method
ActiveCN103312676AGuarantee information securityPrevent leakageTransmissionCommunication unitComputer terminal
The invention provides a terminal which comprises a communication unit and a processing unit, wherein the communication unit is used for sending verification request information into a server and receiving permission setting information corresponding to the verification request information from the server; the processing unit is used for configuring the corresponding terminal permission setting according to the permission setting information coming from the communication unit. Correspondingly, the invention also provides the server and a terminal safety management method. After the technical scheme is adopted, the information security problem caused by the mobile terminal can be solved, and information of an area to be protected can be effectively guaranteed to be safe.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
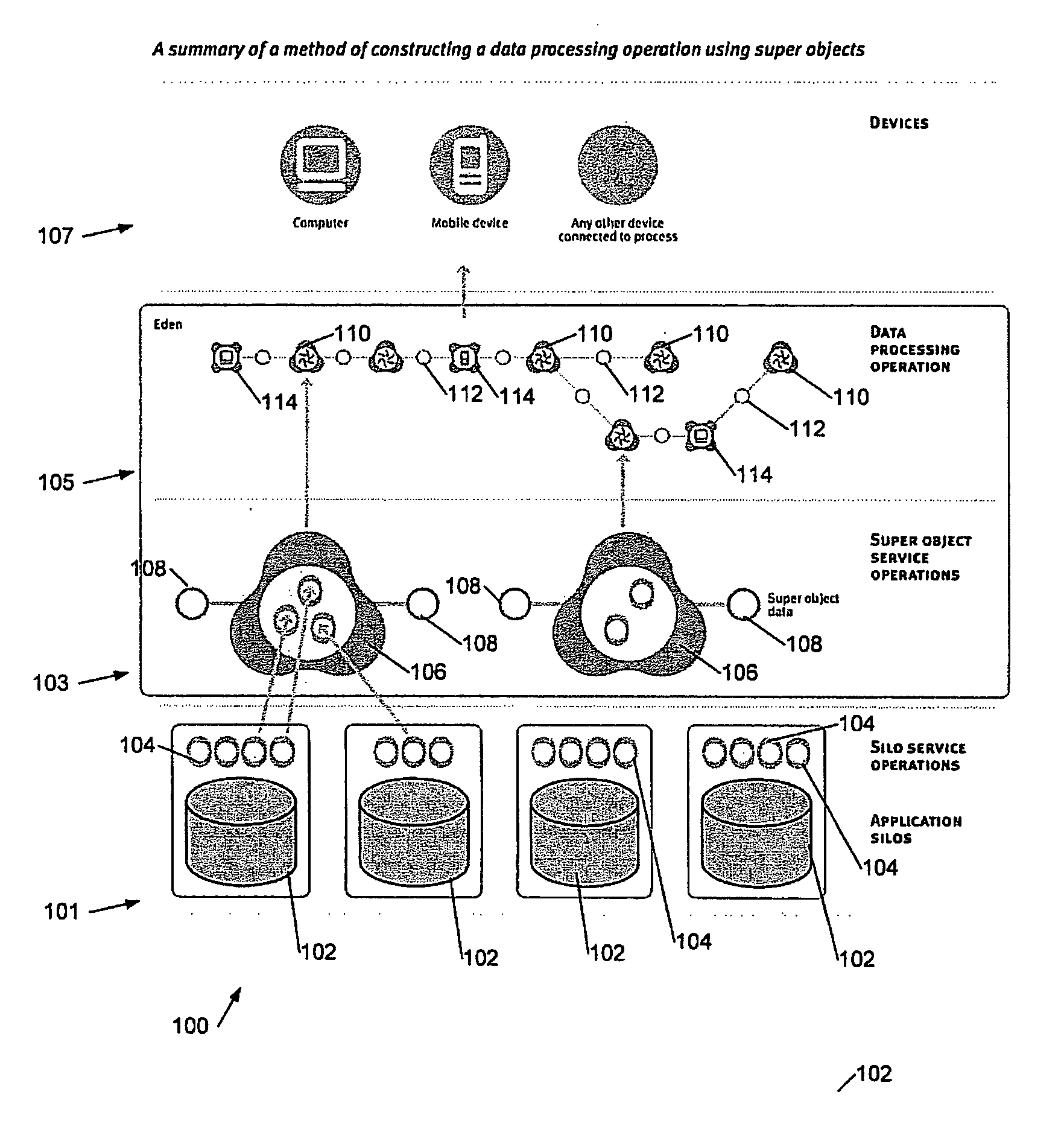
Data processing systems and methods
InactiveUS20050262119A1Convenient queryEasy to implementDigital data processing detailsSoftware designData processing systemPublic interface
This invention generally relates to data processing systems and methods, more particularly to computer systems and related methods for defining unified work flow processors which rely on data and / or services provided by a plurality of disparate underlying systems. A method of constructing a data processing operation, the data processing operation utilising data and / or services provided by a plurality of existing underlying systems, the method comprising: constructing a set of superobjects, a said superobject comprising an aggregation of data and / or services made available by said underlying systems and providing a common interface to said systems; and assembling a plurality of said superobjects to define a workflow for said data processing operation, said workflow comprising a group of linked superobjects defining a processing sequence for the superobjects of said group, to thereby construct said operation.
Owner:MAWDSLEY GARY
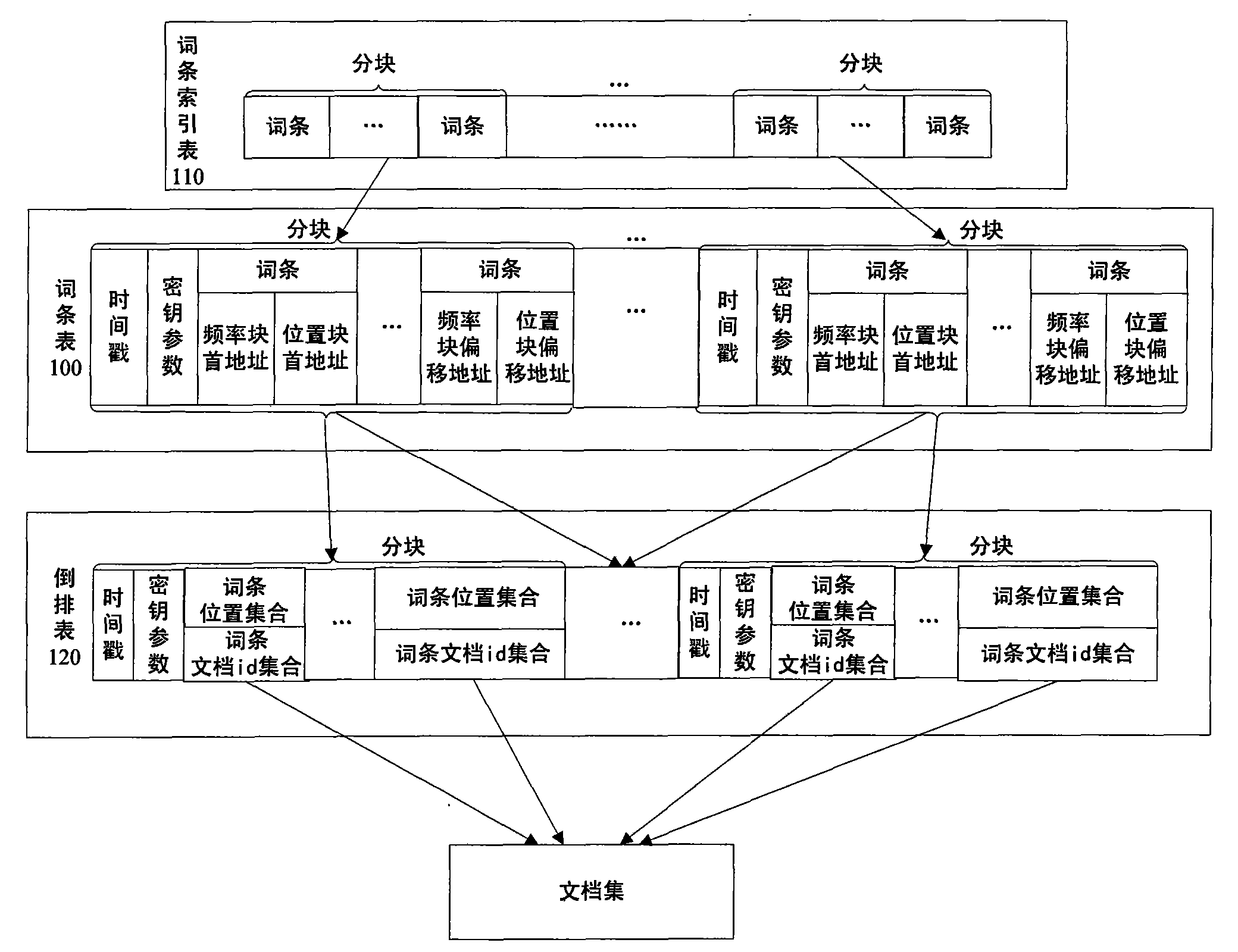
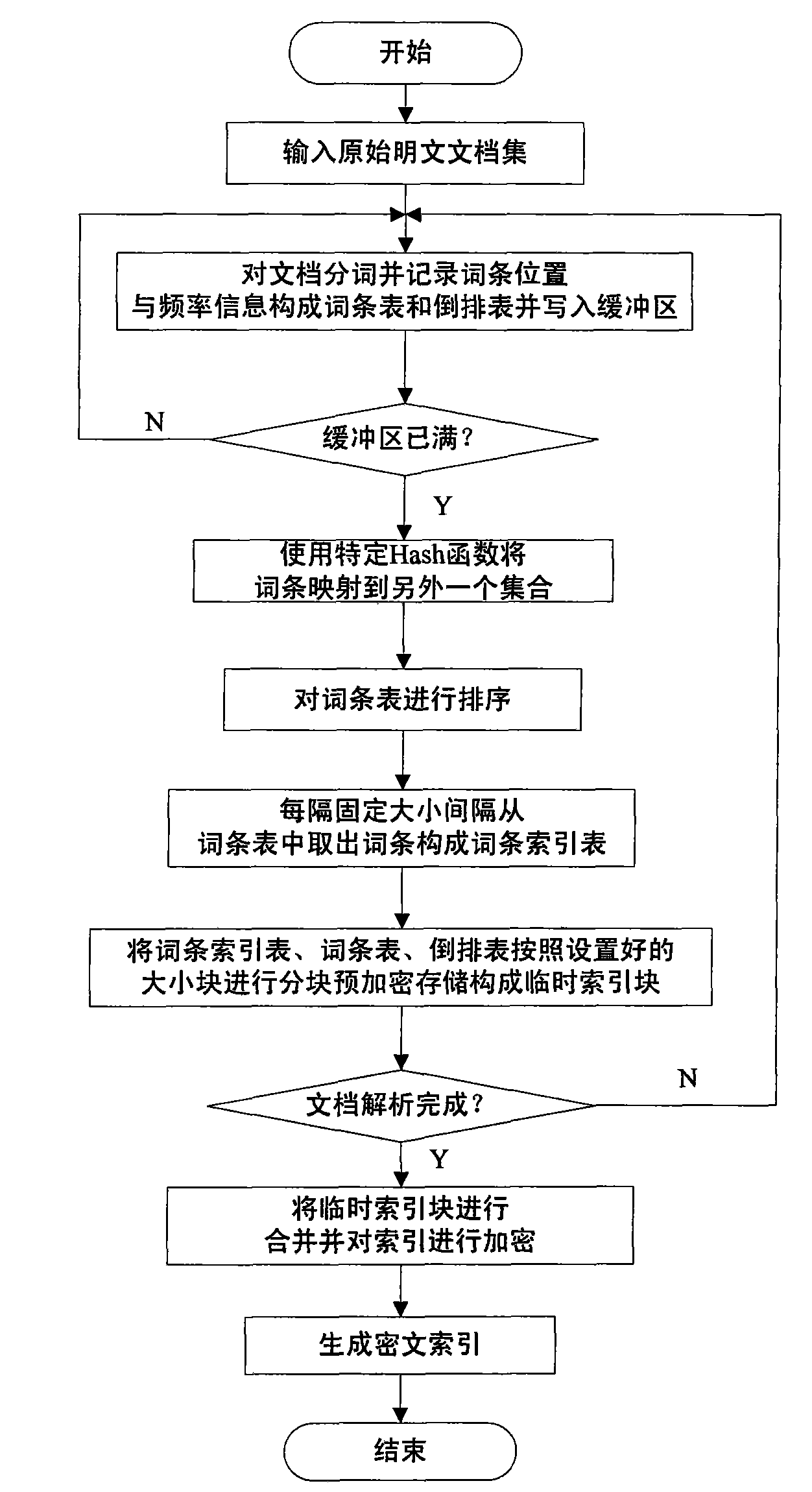
Cryptograph index structure based on blocking organization and management method thereof
InactiveCN101655858AEfficient security structureEfficient security maintenance mechanismDigital data protectionSpecial data processing applicationsInternal memoryTimestamp
The invention discloses a cryptograph index structure based on a blocking organization and a management method thereof. Aiming at a blocking cryptograph index structure, an index establishing mode based on combination is firstly adopted to establish a plain text index when the index is established, and then the plain text index is blocked and encrypted in a unitive way. A maintenance mechanism based on a cryptograph index is divided into the addition, the deletion and the modification of a document in the index. The addition of the document is mainly divided into two conditions of batch addition and littleness addition; in the batch addition, a temporary index is established on a disc; and in the littleness addition, an internal memory index is established. In the deletion of the document,a deletion mark is firstly made on the document to be deleted, and the document is deleted in a unitive way until a proper opportunity. In the modification of the index, an original document is firstly deleted, and then a novel document is anew added. In a key management strategy, stratification management is carried out on an index encryption key, and the update of the key is realized by a timestamp mechanism. In an access control strategy based on the index, access control information is integrated into the index, and the access control of document level granularity is realized.
Owner:HUAZHONG UNIV OF SCI & TECH
Extensible access control architecture
ActiveUS20070016939A1Convenient access controlReduce complexityDigital data processing detailsUser identity/authority verificationUpgradeThird party
Software for managing access control functions in a network. The software includes a host that receives access control commands or information and calls one or more methods. The methods perform access control functions and communicate access control results or messages to be transmitted. The host may be installed in a network peer seeking access to the network or in a server controlling access to the network. When installed in a peer, the host receives commands and exchanges information with a supplicant. When installed in an access control server, the host receives commands and exchanges information with an authenticator. The host has a flexible architecture that enables multiple features, such as allowing the same methods to be used for authentication by multiple supplicants, providing ready integration of third party access control software, simplifying network maintenance by facilitating upgrades of authenticator software and enabling access control functions other than peer authentication.
Owner:MICROSOFT TECH LICENSING LLC
Entrance guard management method and system
InactiveCN105389870AEnable mobilityImplement role hierarchy managementIndividual entry/exit registersEffective timeComputer science
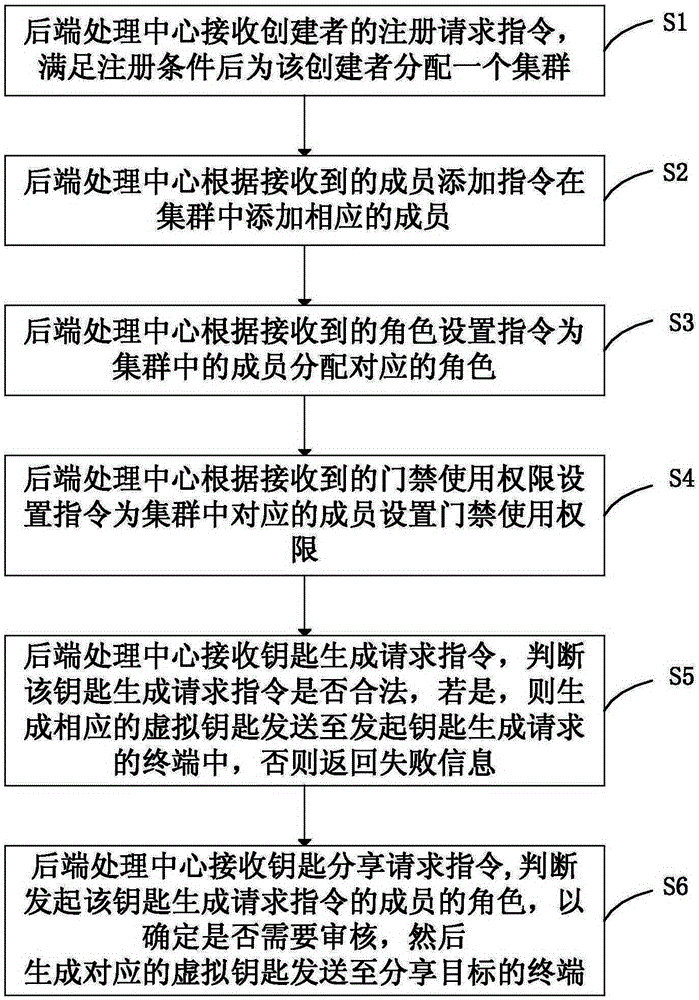
The invention discloses an entrance guard management method and system. The method comprises the steps that a back-end processing center receives a registration request instruction of a creator and allocates a cluster for the creator after registration conditions are met; the back-end processing center adds corresponding members to the cluster according to a received member addition instruction; the back-end processing center allocates corresponding characters to the members in the cluster according to a received character setting instruction; the back-end processing center sets entrance guard use permissions for the corresponding members in the cluster according to a received entrance guard use permission setting instruction, and each entrance guard use permission comprises virtual entrance guard serial number information and effective time information corresponding to the virtual entrance guard serial number information. According to the entrance guard management method and system, mobile management and character hierarchical management of an entrance guard are achieved, an administrator can conveniently conduct permission control on the members in the cluster, each member in the cluster can online generate a virtual key within the entrance guard use permission, the virtual keys can be shared, and great flexibility and real-time performance are achieved.
Owner:GUANGZHOU CHANGLIAN INFORMATION TECH CO LTD
Detecting inappropriate activity in the presence of unauthenticated API requests using artificial intelligence
ActiveUS20200213336A1Efficient discriminationThe result is accurateInterprogram communicationTransmissionWeb applicationBusiness enterprise
Unauthenticated client access to an application (e.g., a SaaS-based web application) that employs unauthenticated API endpoints is monitored and protected by an access control system and method that leverages a neural network. The neural network is trained to recognize user behaviors that should be deemed to be “inappropriate” according to a policy. Using the neural network, the system provides effective discrimination with respect to unauthenticated user behavior, and it enables access controls to be more effectively enforced with respect to users that are not using the application according to an enterprise security policy. By training the neural network to recognize pattern(s) behind regular user behavior, the approach enables robust access control with respect to users that are unauthenticated. More generally, the approach facilitates access control based in whole or in part on API interactions with an application where the identity of the individuals making that access are unknown or necessarily ascertainable.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com