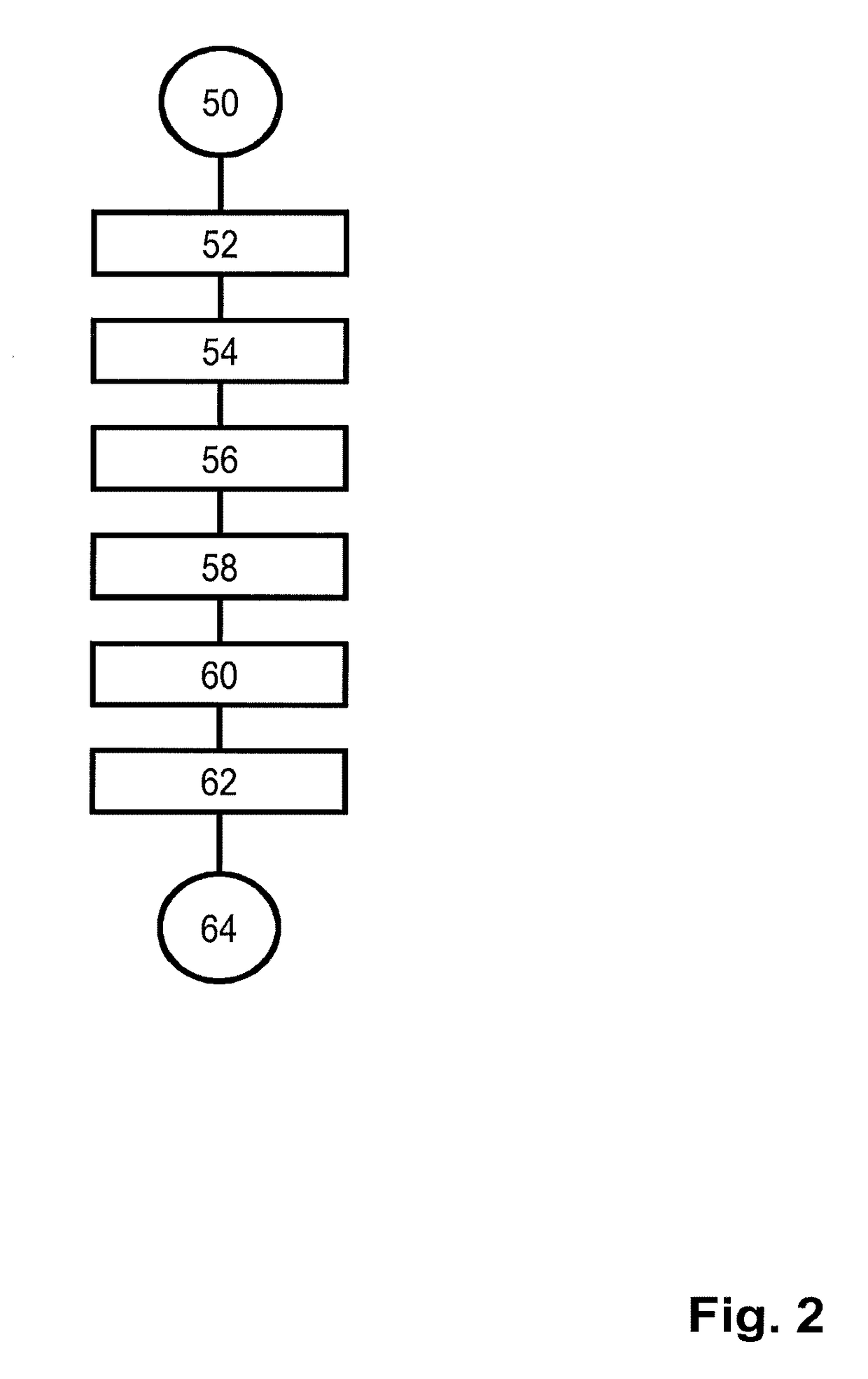
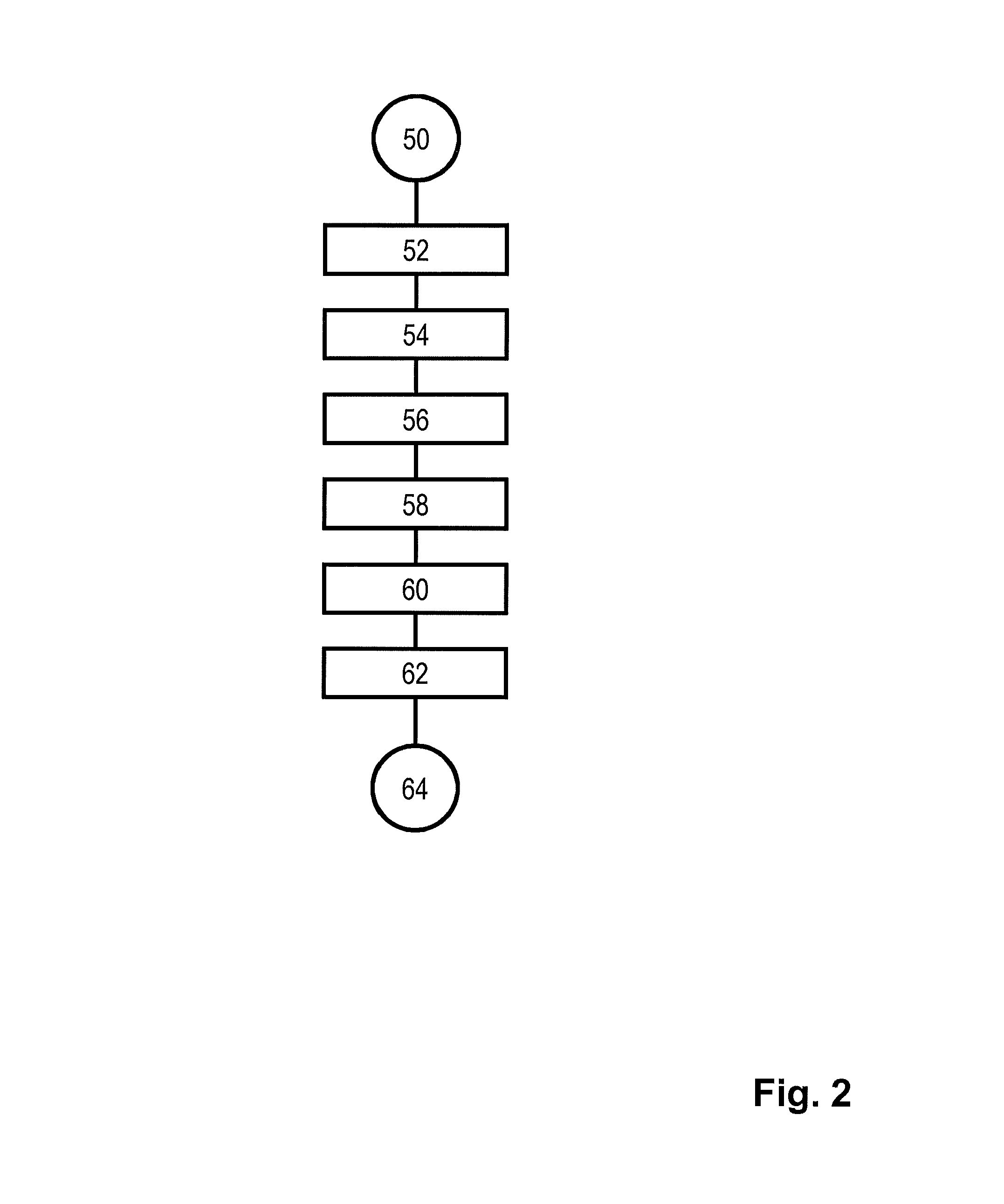
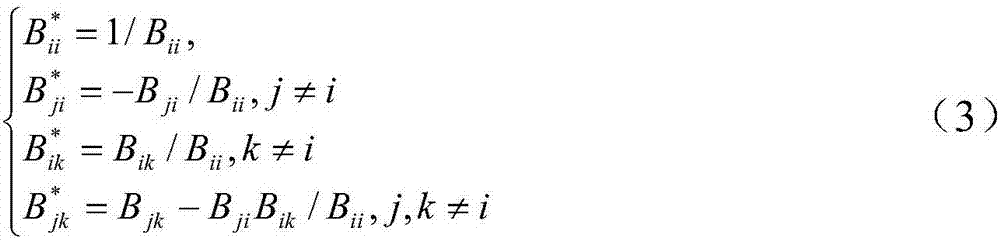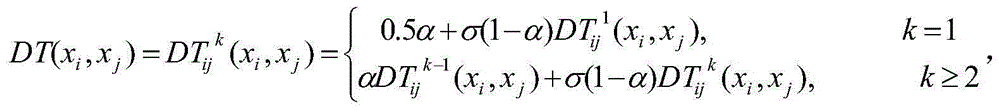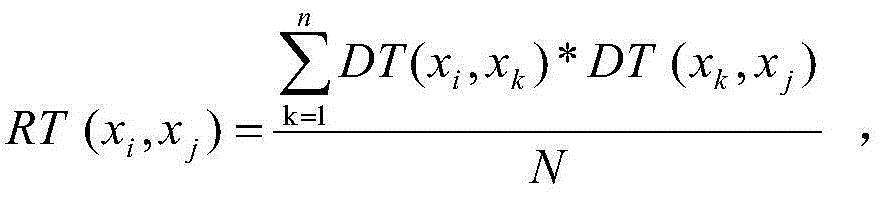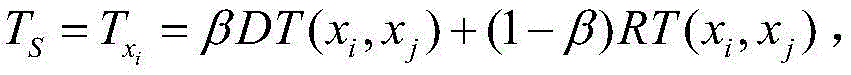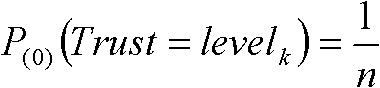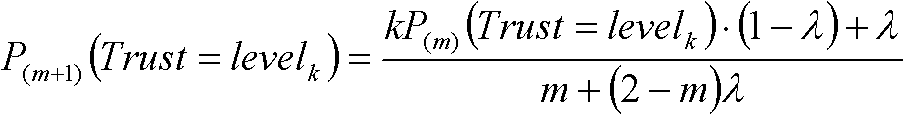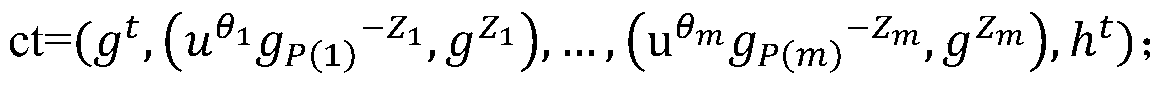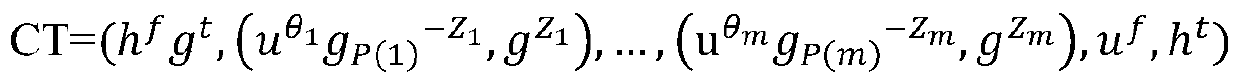Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
45 results about "Attribute-based access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
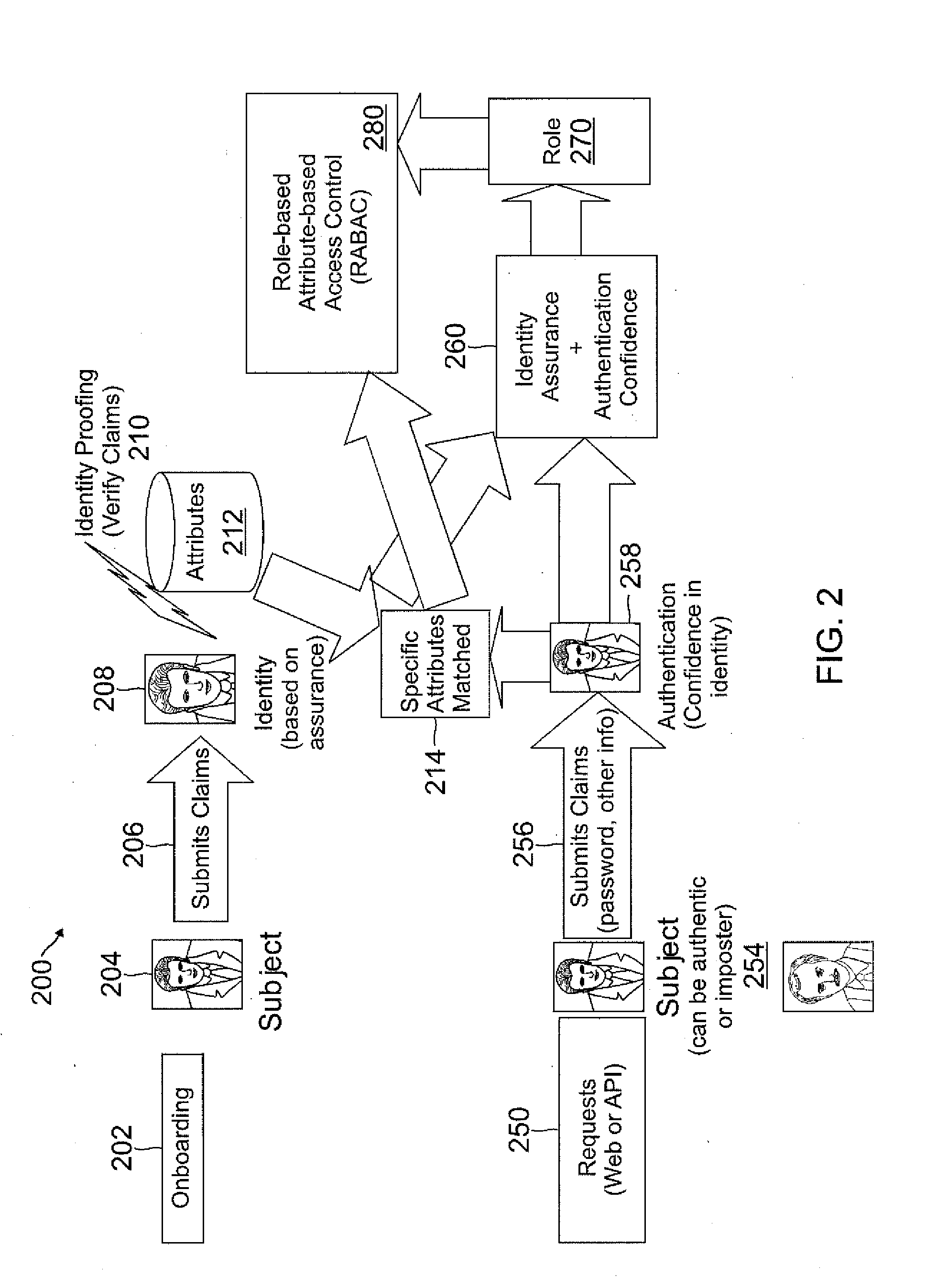
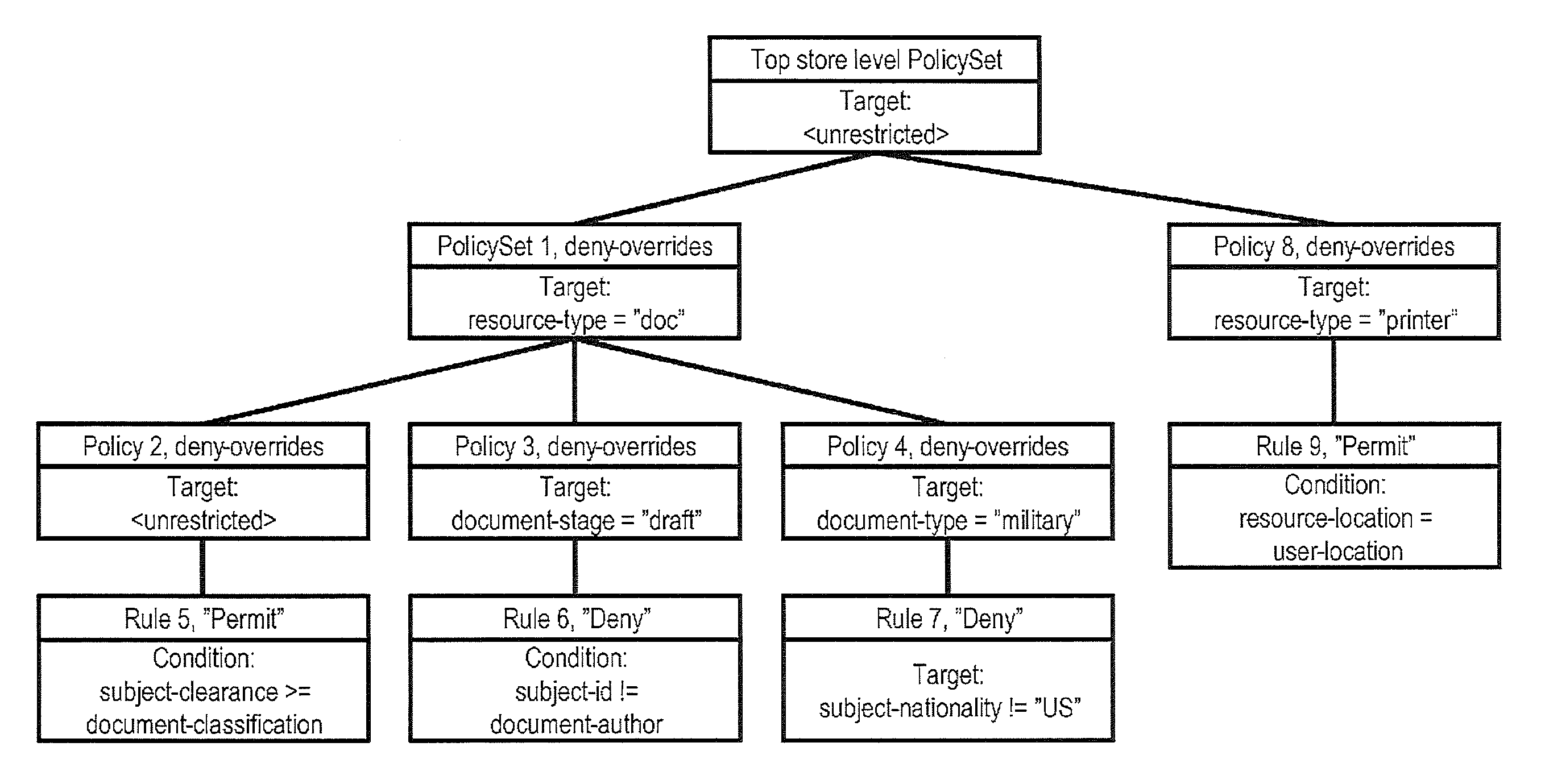
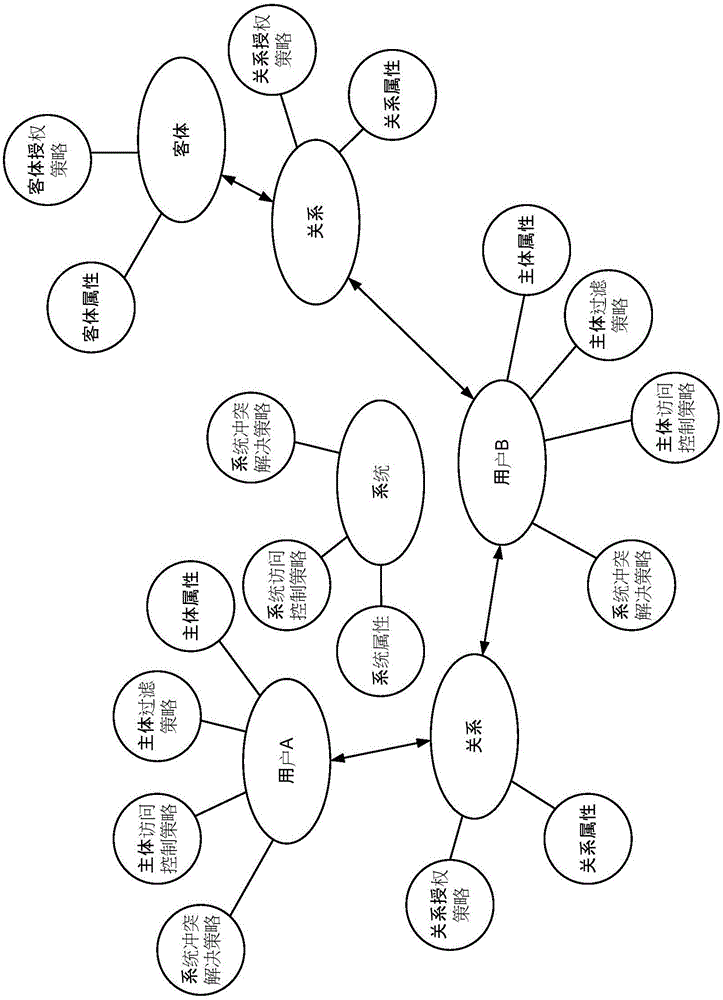
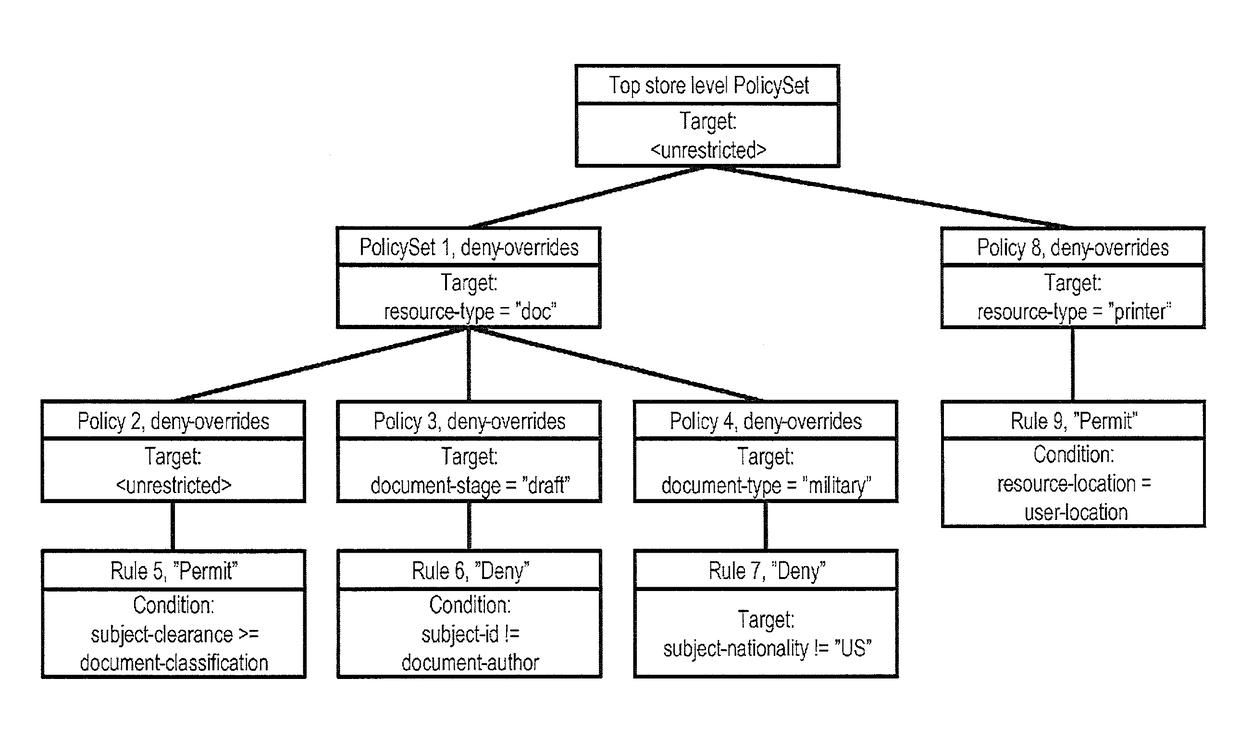
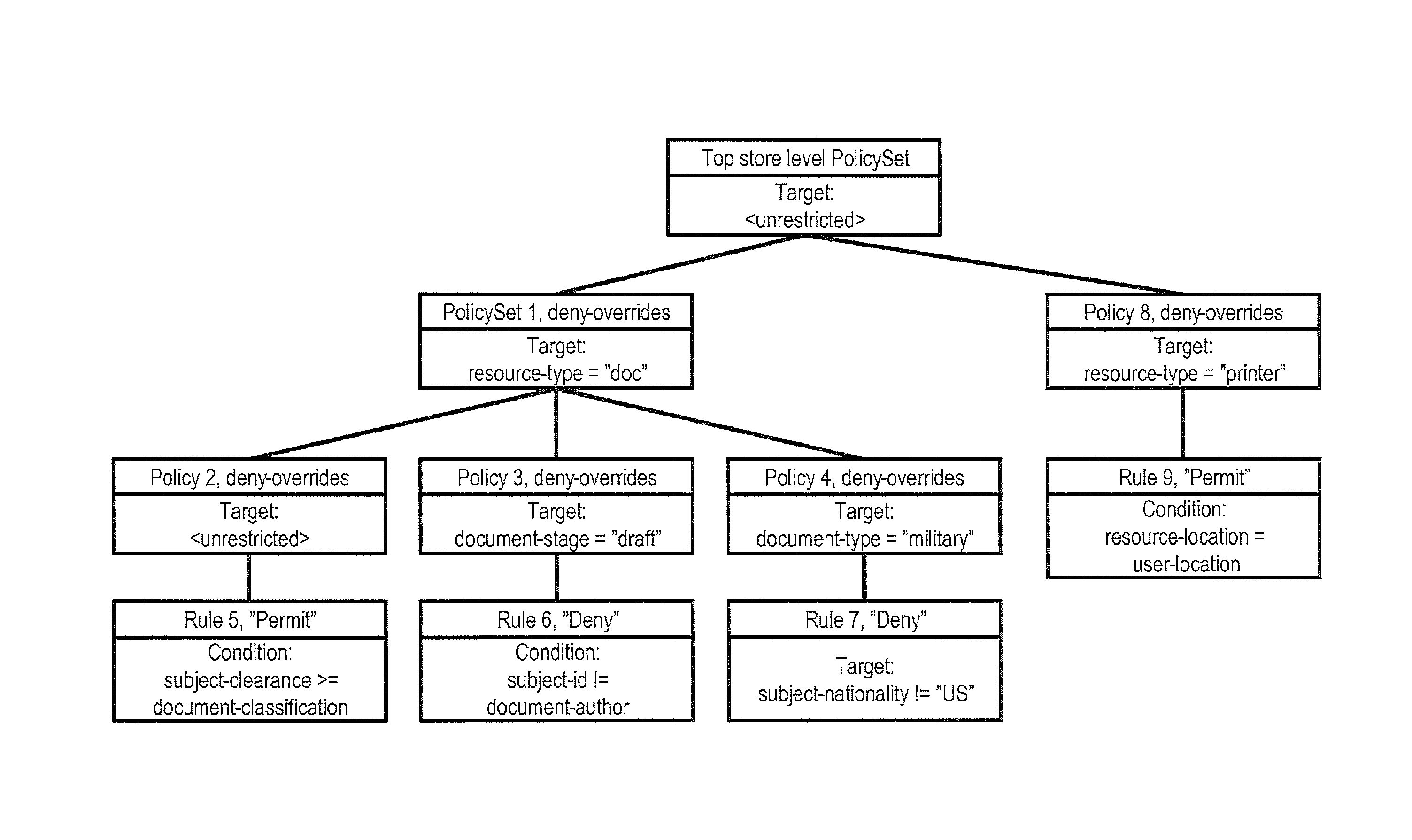
Attribute-based access control (ABAC), also known as policy-based access control, defines an access control paradigm whereby access rights are granted to users through the use of policies which combine attributes together. The policies can use any type of attributes (user attributes, resource attributes, object, environment attributes etc.). This model supports Boolean logic, in which rules contain "IF, THEN" statements about who is making the request, the resource, and the action. For example: IF the requestor is a manager, THEN allow read/write access to sensitive data.
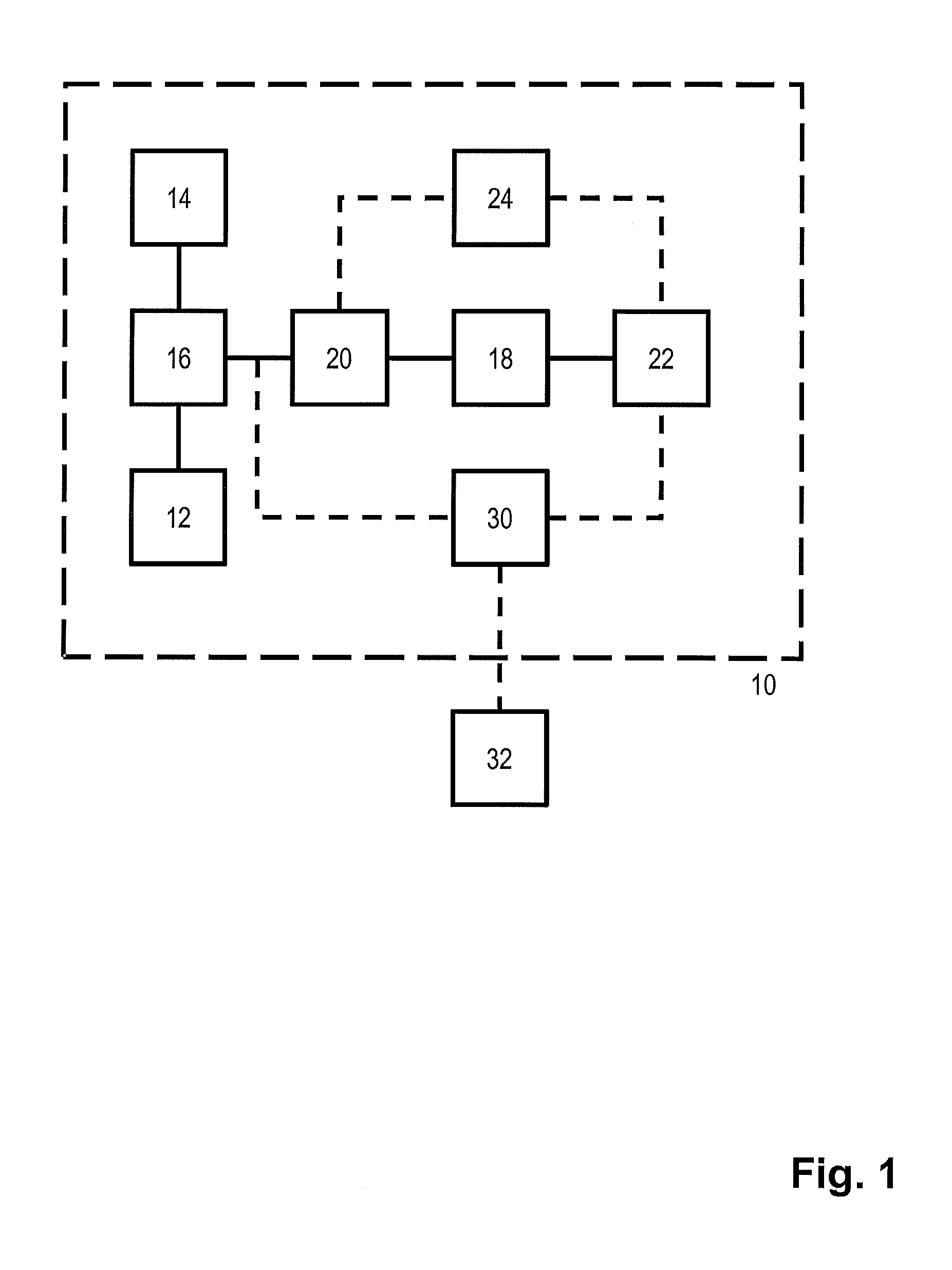
Method and system for the specification and enforcement of arbitrary attribute-based access control policies
InactiveUS20090205018A1Computer security arrangementsSpecial data processing applicationsData setControl system
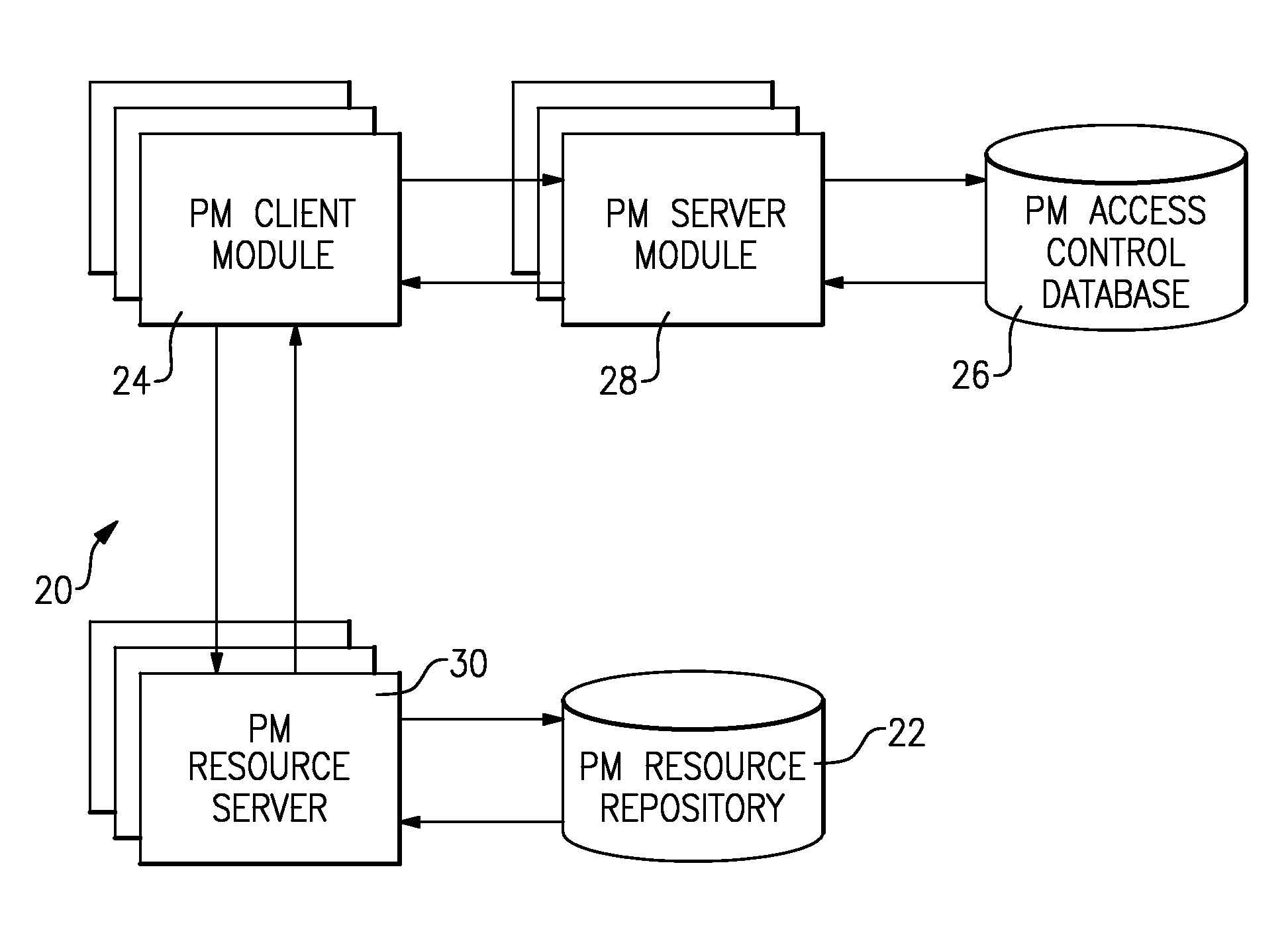
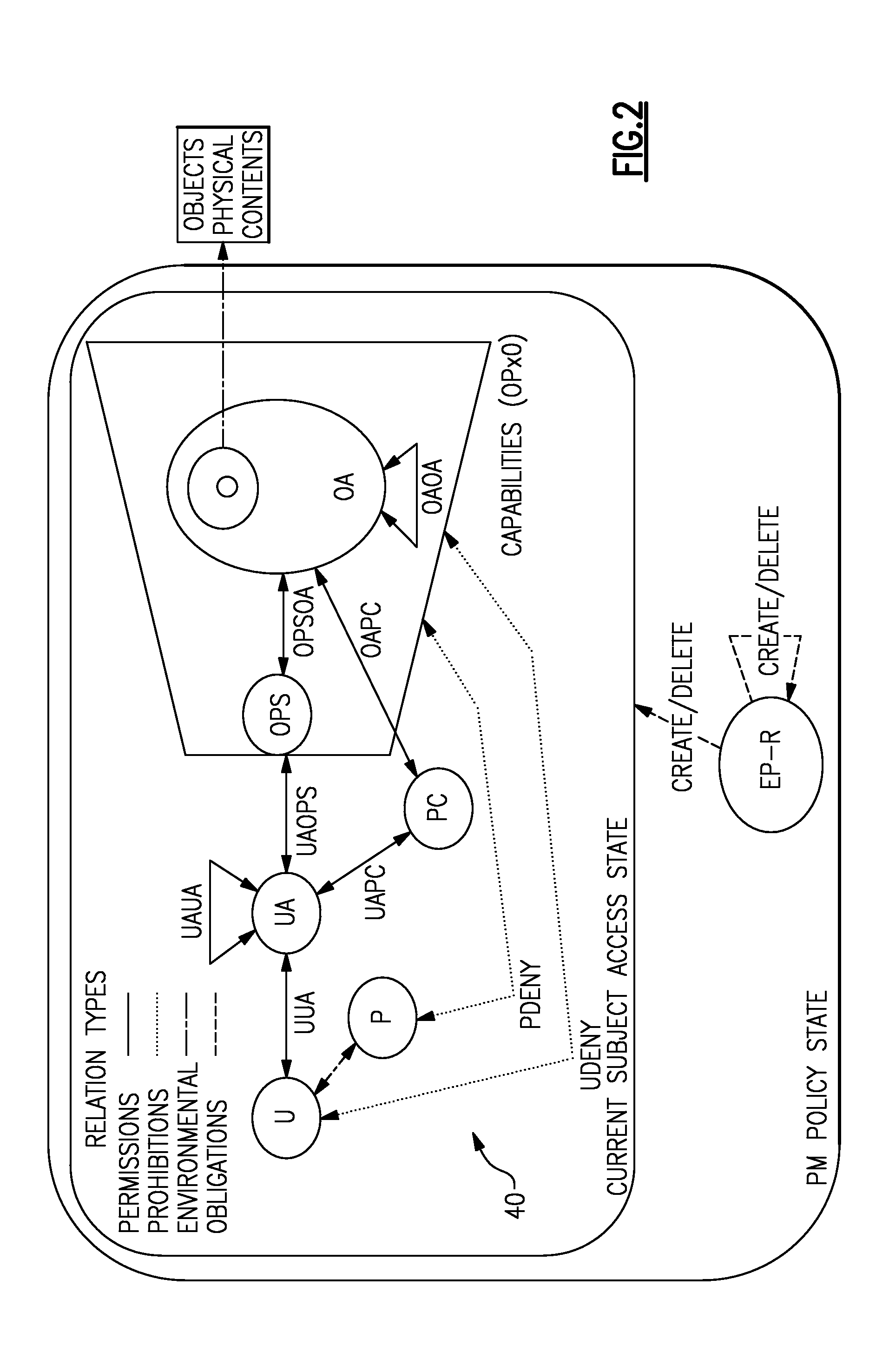
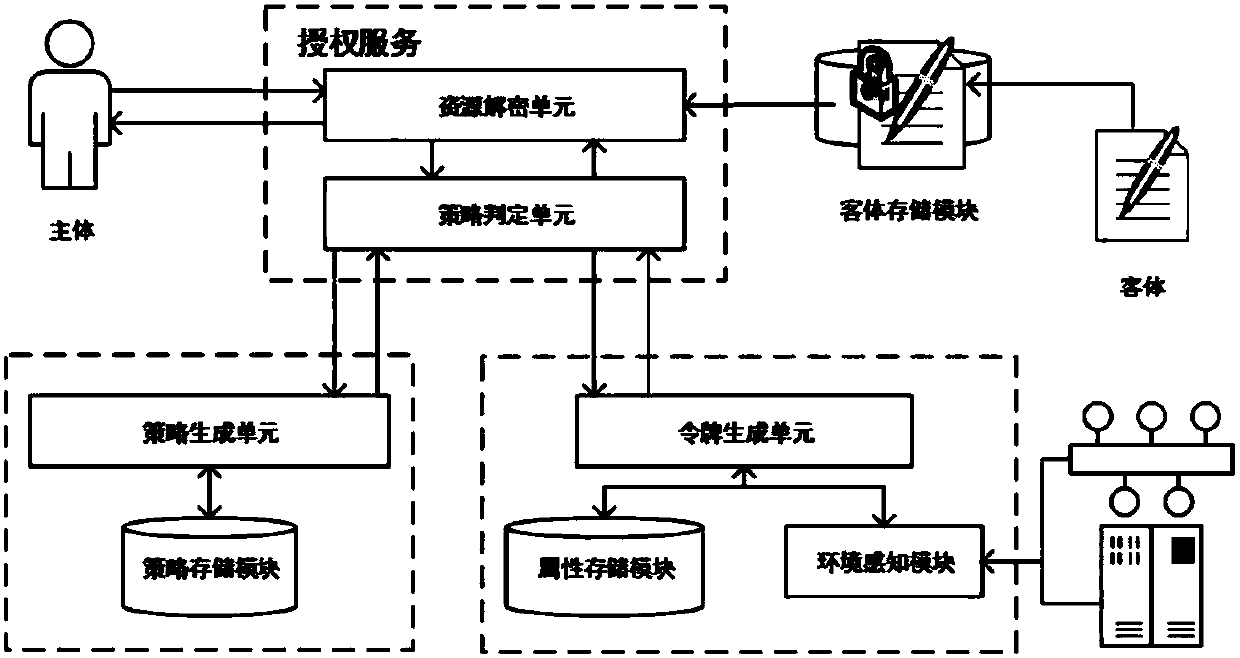
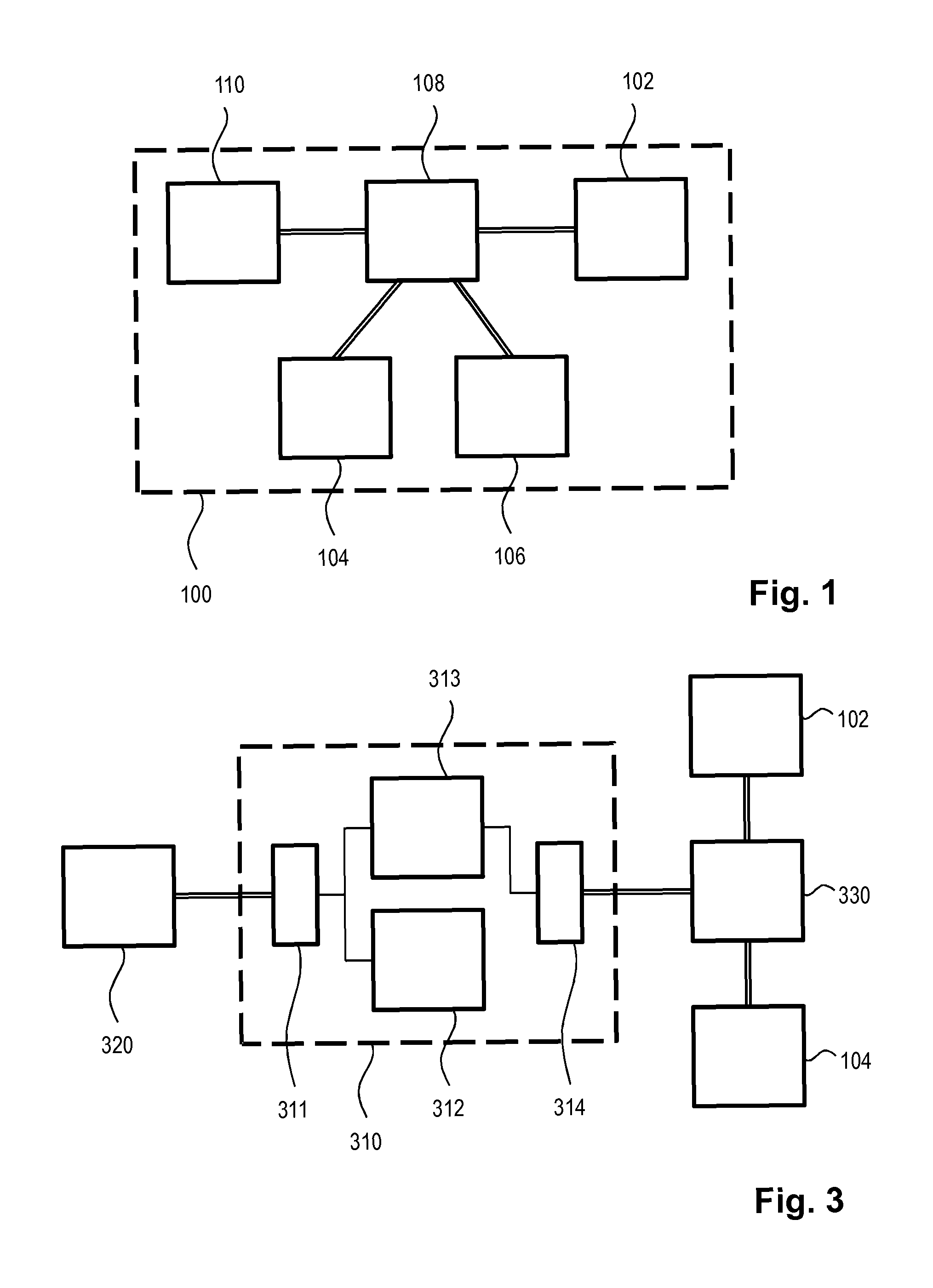
A general attribute-based access control system includes at least one resource server, at least one client module, an access control database including basic data sets and basic relations between the basic data sets, at least one server module including an access decision sub-module that computes a decision whether to grant or deny access to computer-accessible resources referenced by objects, an event processing sub-module that processes events, and an administrative sub-module that creates, deletes, and modifies elements of the basic data sets and the basic relations.
Owner:INT COMMITTE FOR INFORMATION TECH STANDARDS INCITS
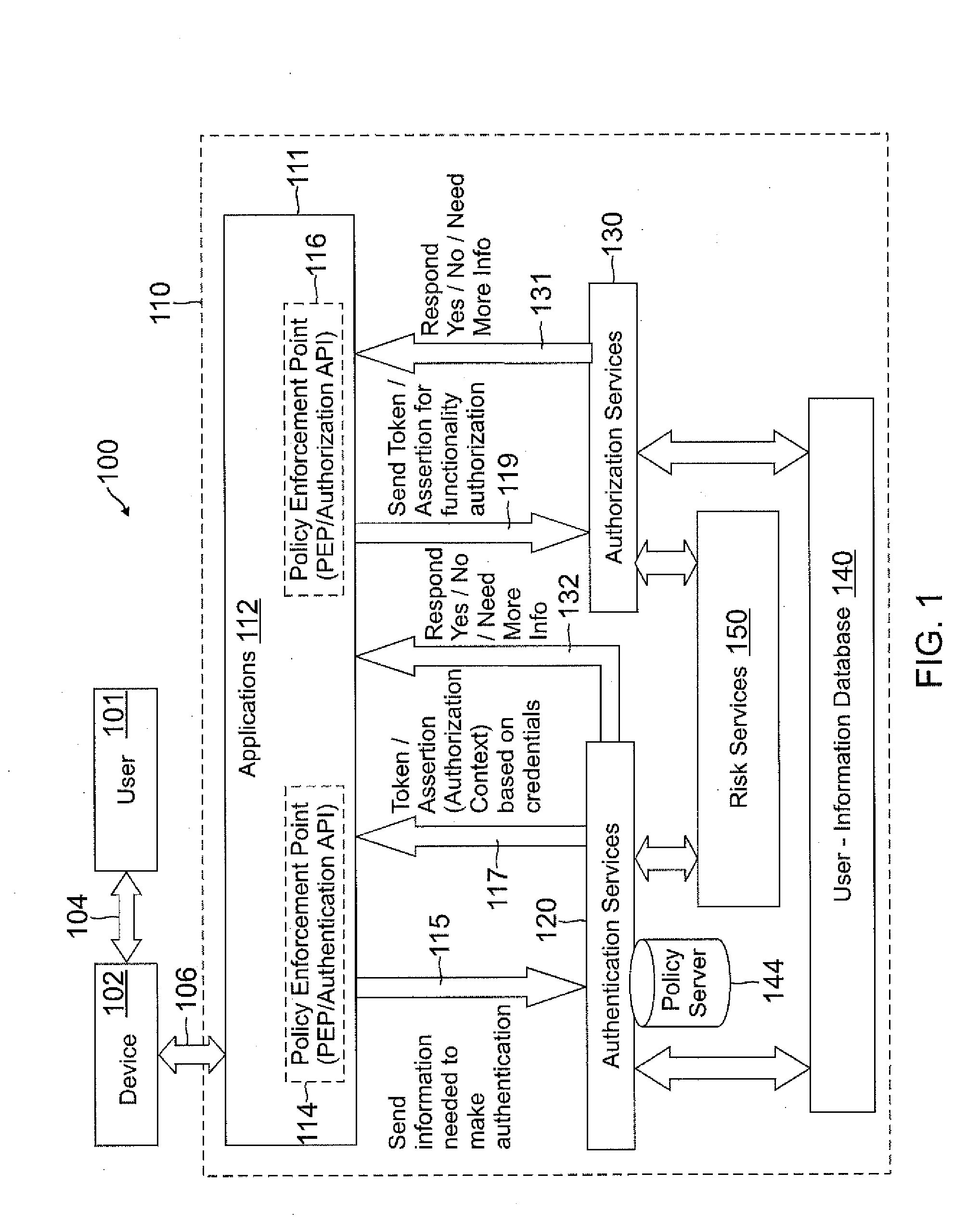
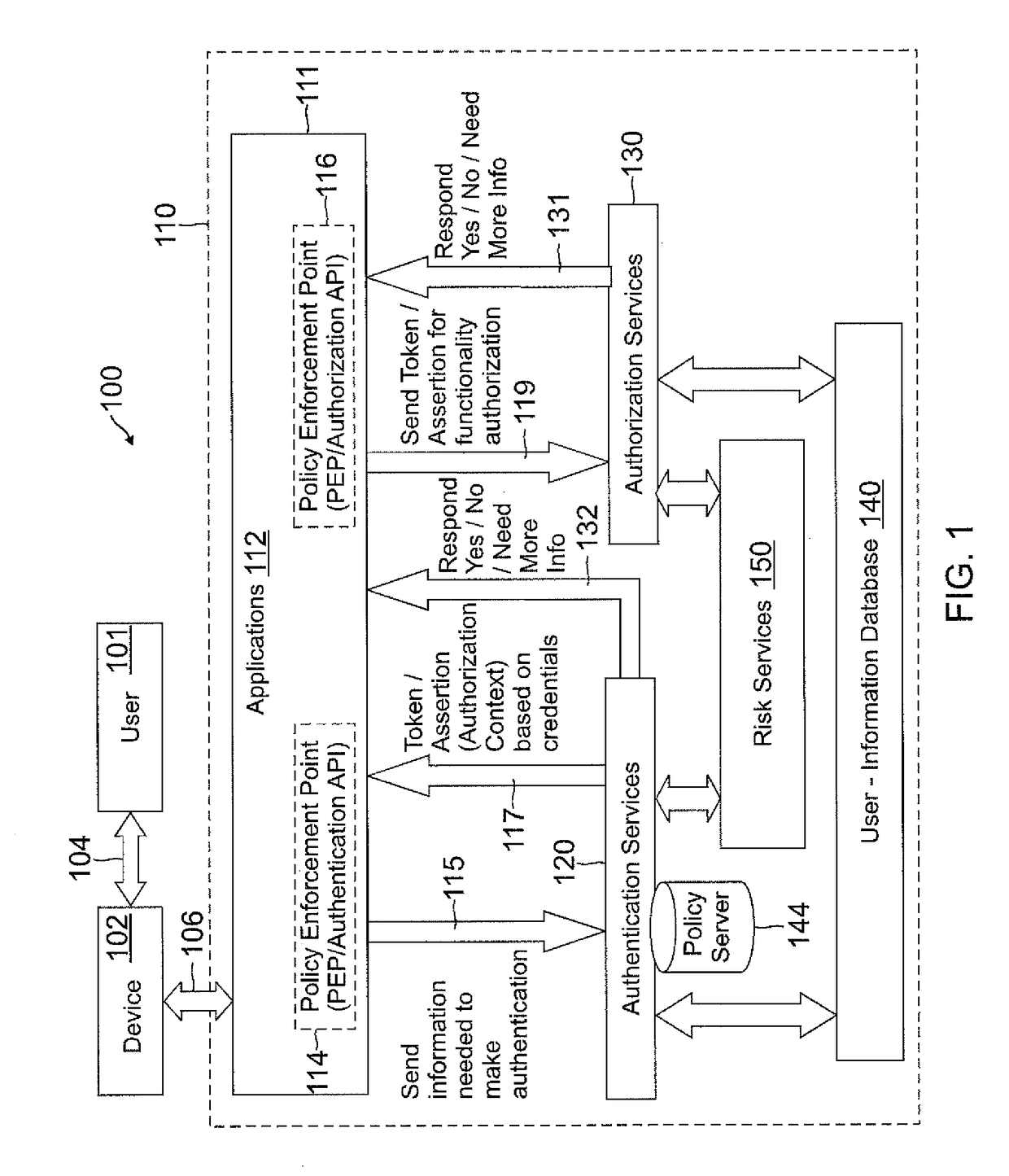
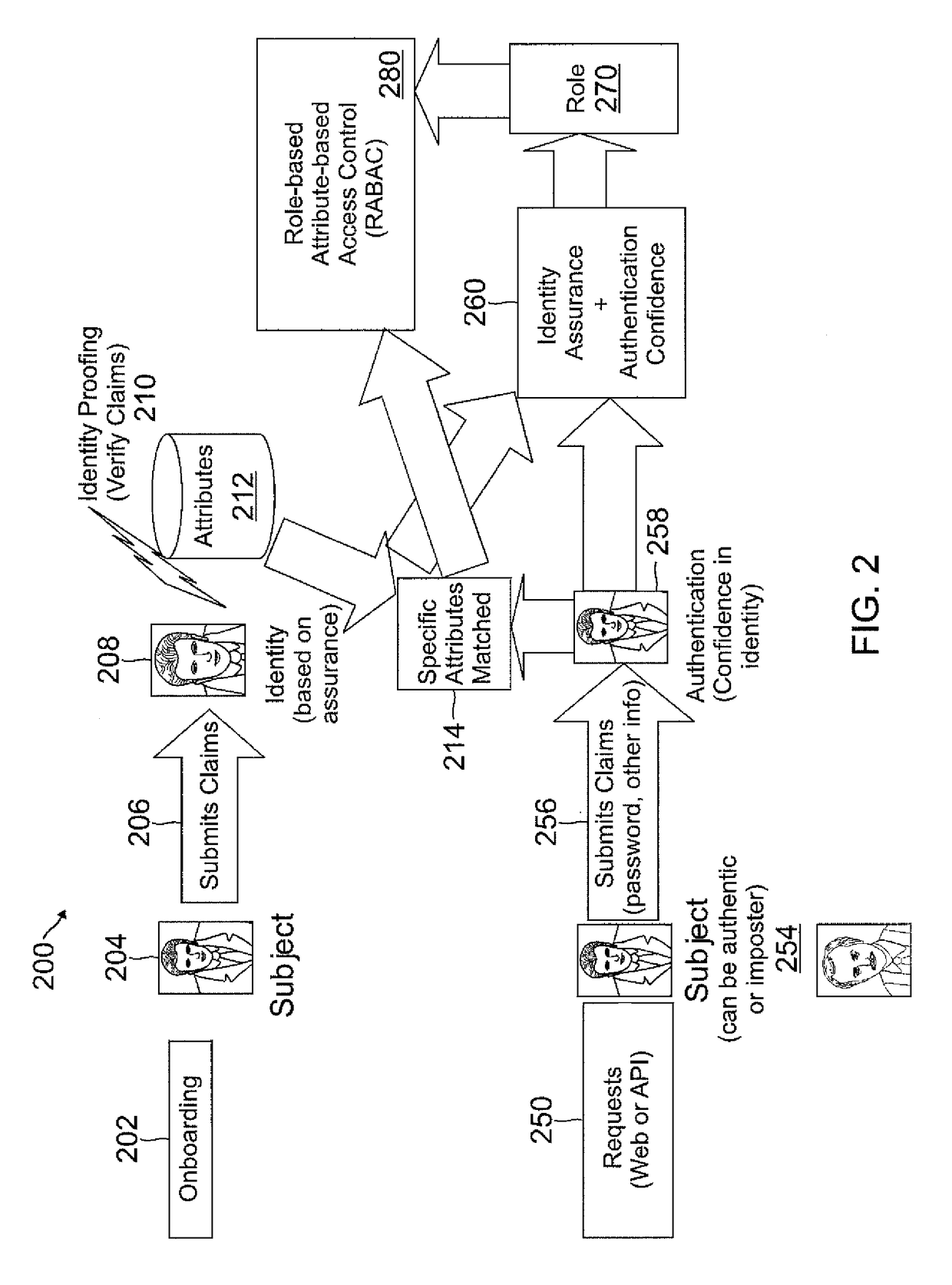
Role-based attribute based access control (RABAC)
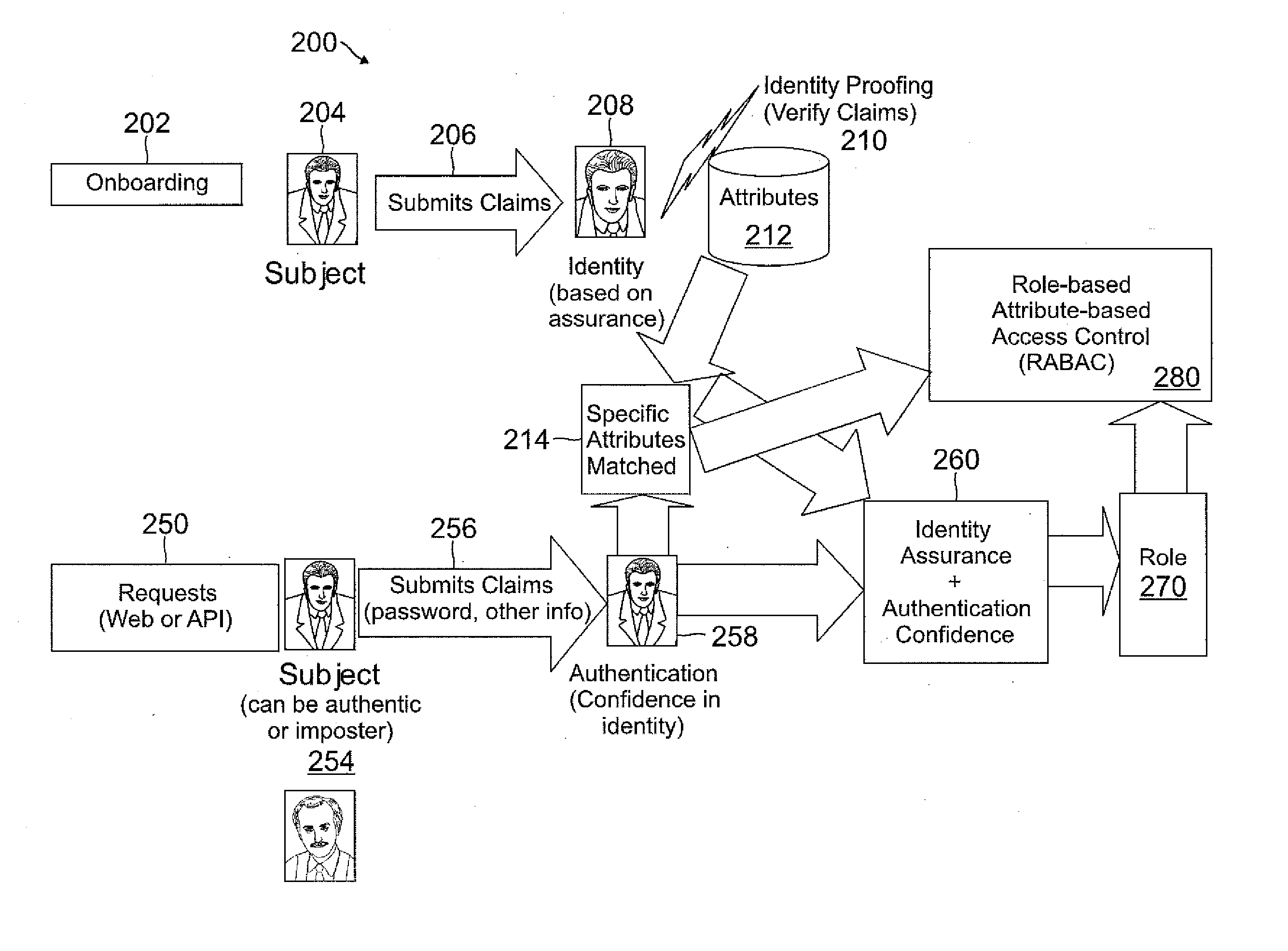
ActiveUS20120060207A1Enhanced access control securityConvenient access controlDigital data processing detailsDigital data protectionUser deviceMedia access control
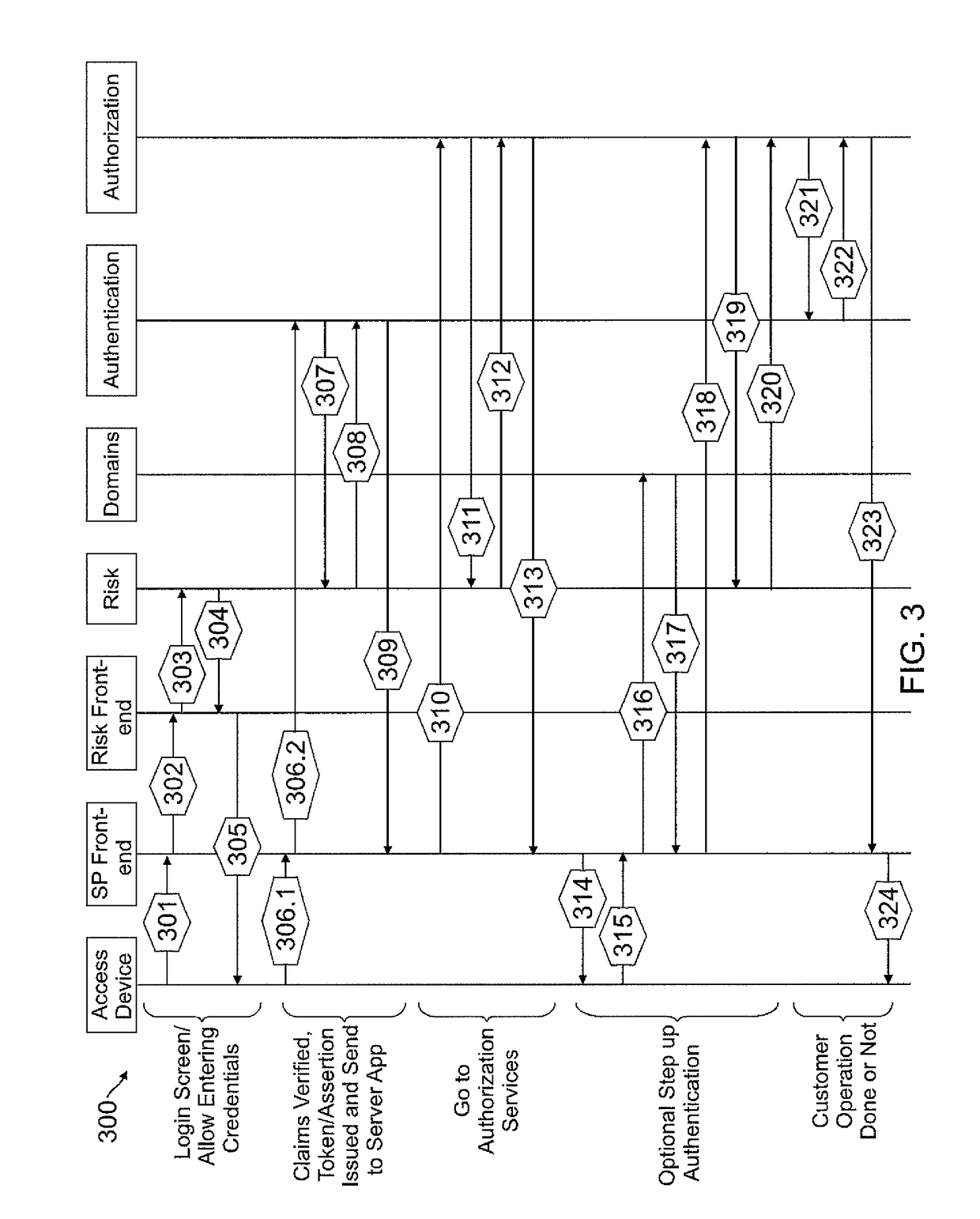
Systems and methods are disclosed for receiving an access request from a user device, the access request including an identity claim for a user; evaluating a risk of access based on matching an attribute of the user device with attributes stored in a user information database; authenticating the access request based on the identity claim and the risk evaluation to determine an authentication confidence level; generating a token based on the confidence level and the attribute matched; producing an authorization response based on inputs from the token, a risk based access control, a role based access control, and an attribute based access control, in which the authorization response determines whether to allow access to a system, deny access to the system, or request additional input from the user device.
Owner:PAYPAL INC
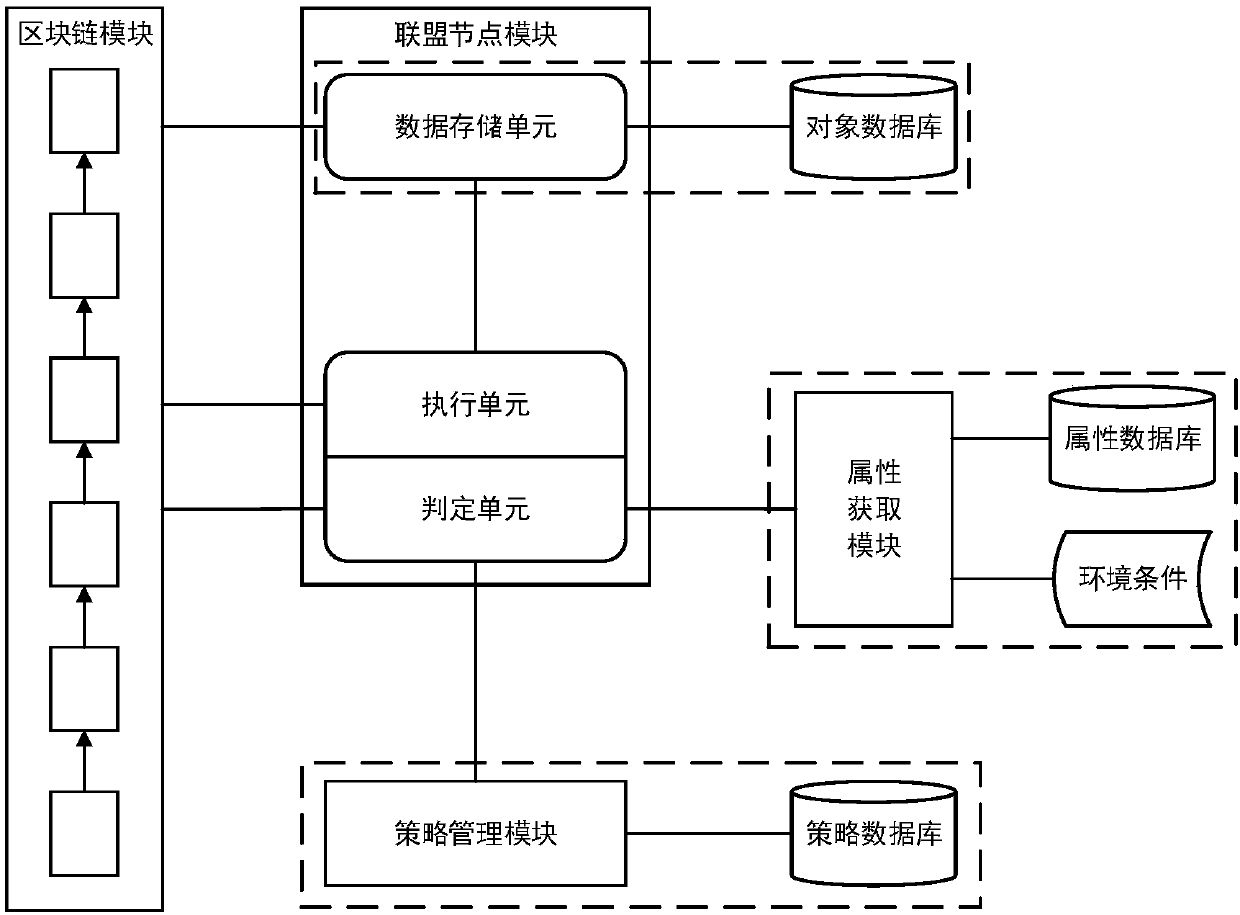
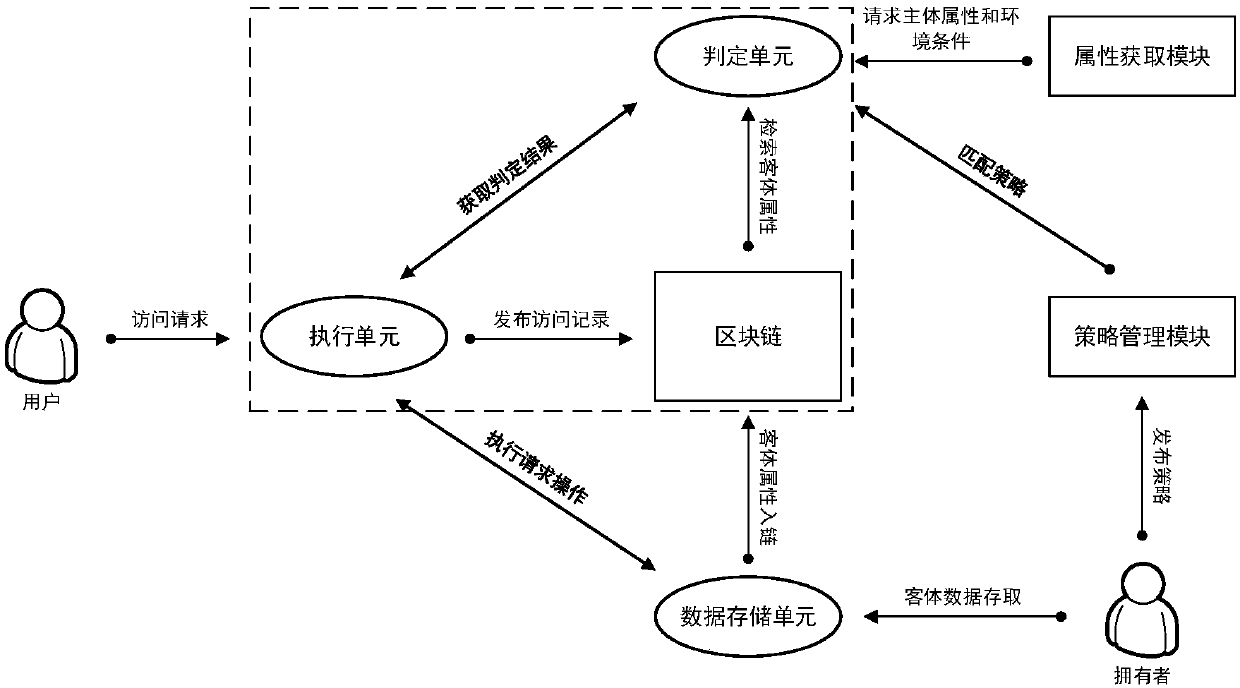
Access control method and system based on block chain technology
ActiveCN108123936AResistance to failureResist being attackedFinancePayment protocolsAuthorization ModeData privacy protection
The invention provides an access control method and system based on block chain technology. The block chain technology is combined with attribute-based access control in the method, and the method comprises the following steps: adding an object in a chain, binding a judgment process of attribute and strategy on all block chain nodes with reference to the strategy. The access authorization is converted from a centralized manner into a distributed manner, the consistency check of the judgment results in the whole network is achieved by using a consensus mechanism of the block chain, and the authorized operations for accessing the recorded transactions are permanently recorded on the block chain. The method has the advantages of anti-single point failure, flexible authorization mode, accurateaccess boundary, and record auditability. The access control method and system provided by the invention are applicable to operating environments such as enterprises and governments that have the need of data privacy protection and realize multi-branch cooperation work based on a block chain platform, the access permissions of users in the system can be dynamically and scalably managed, fine-grained permission management is achieved for the strategy and the attribute, and the access control method and system are of important practical significance for protecting the security of information systems in a distributed network environment.
Owner:UNIV OF SCI & TECH BEIJING
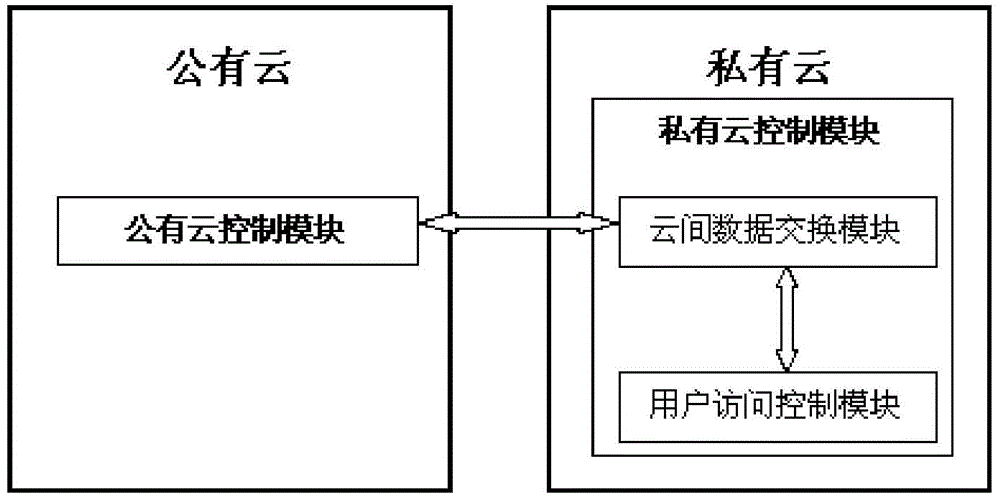
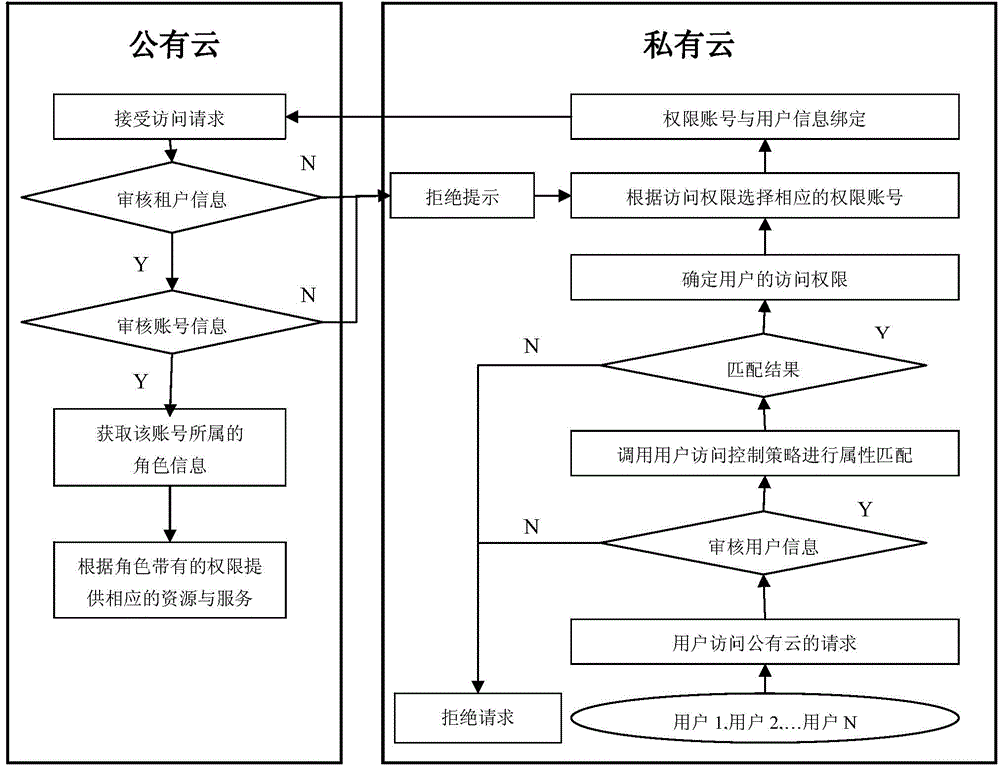
Access control system and access control method between public cloud and private cloud
ActiveCN103067406AControl Access Request ManagementEnsure safetyTransmissionControl systemCloud data
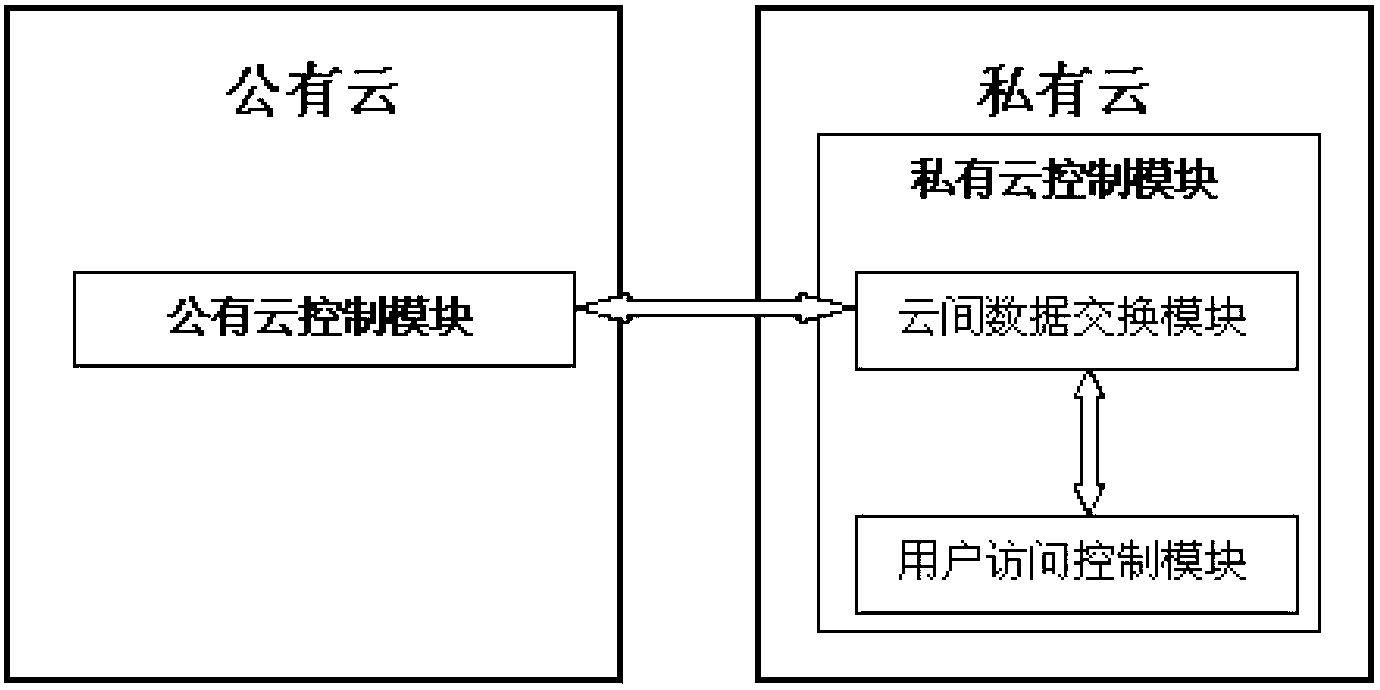
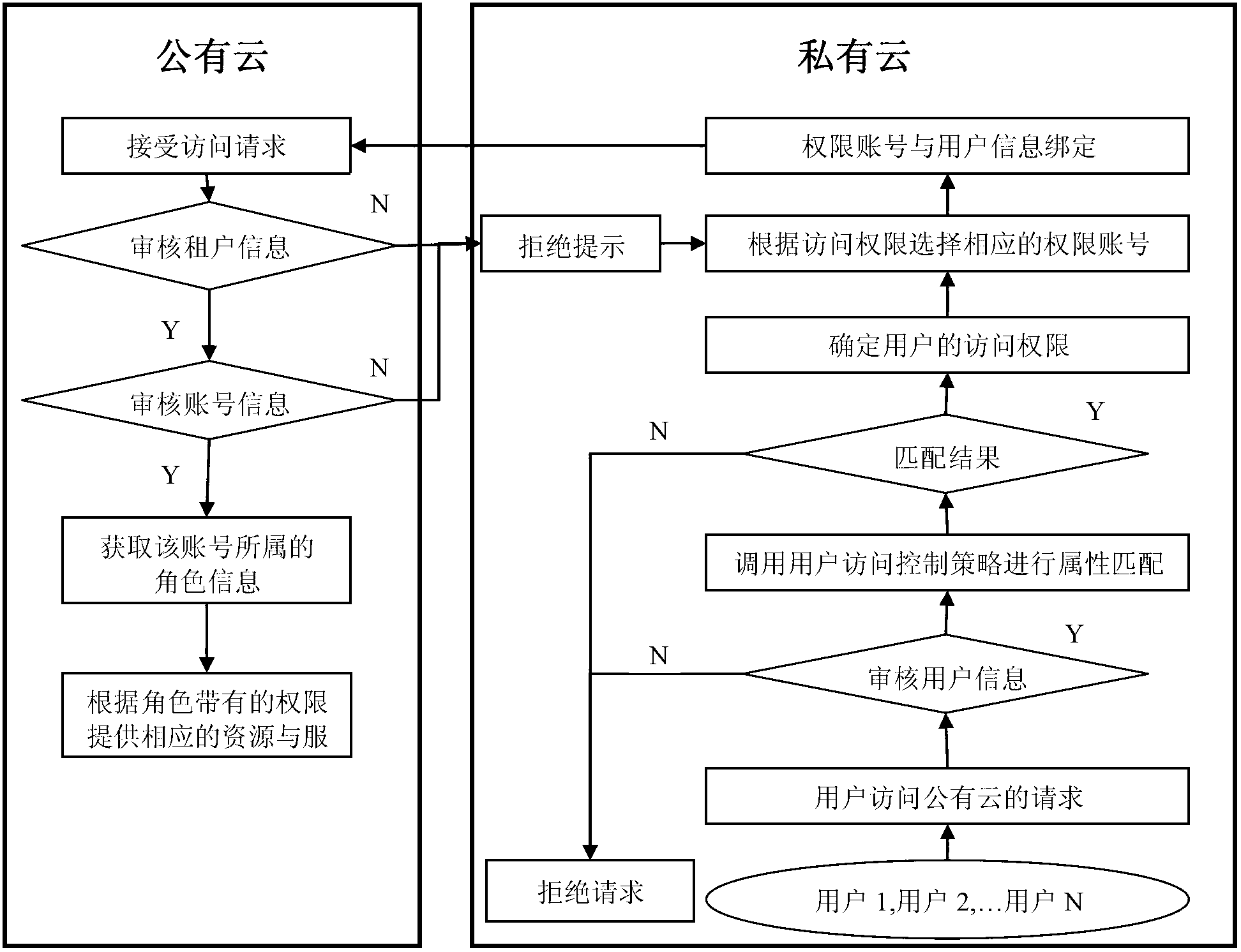
The invention discloses an access control system and an access control method between a public cloud and a private cloud. The access control system includes a private cloud control module at a private cloud end, and a public cloud control module at a public cloud end. The private cloud control module comprises an inter-cloud data exchange module and a user access control module. The inter-cloud data exchange module is respectively connected with the user access control module and the public cloud control module through a network. The access control method combines role-based access control and attribute-based access control, an attribute-based access control mode is adopted in the private cloud, and a role-based access control mode is adopted when the private cloud accesses the public cloud. Due to the fact that the access control system limits the access right of users of the private cloud to resources or services of the public cloud, the access control system has the advantages of being quite high in inter-cloud data exchange safety.
Owner:JINAN UNIVERSITY
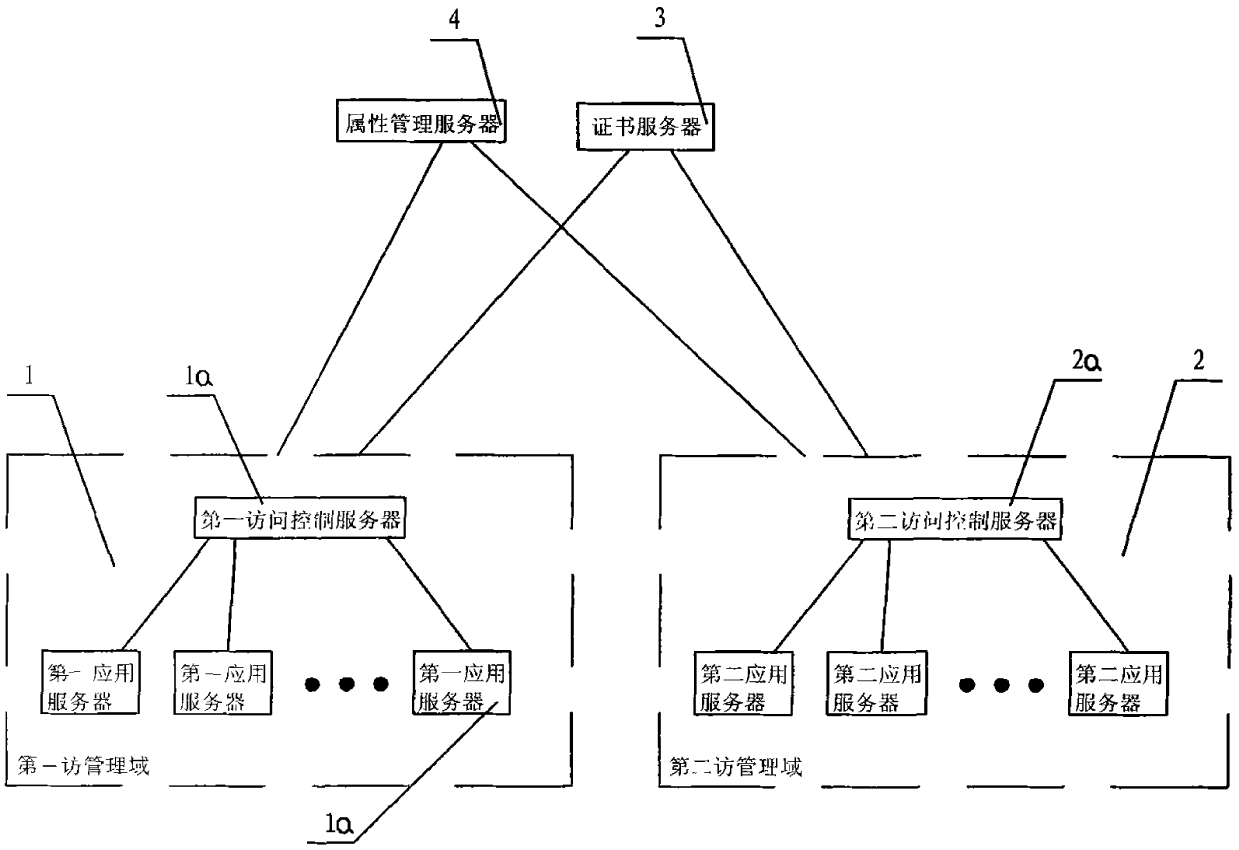
Attribute-based access control model and cross domain access method thereof
InactiveCN101997876ASolve the efficiency problem of user-role-permission assignmentImprove convenienceTransmissionAccess methodAdministrative domain
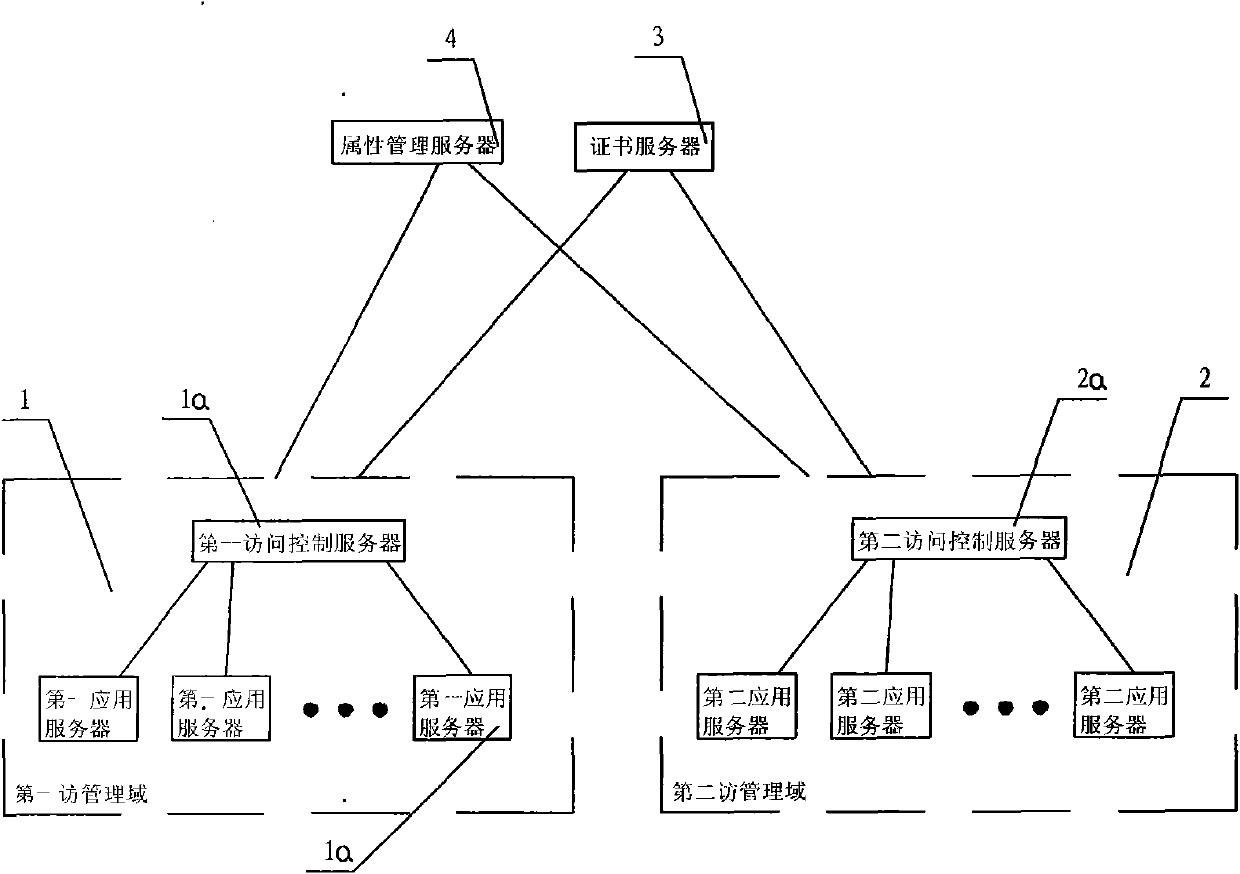
The invention discloses an attribute-based access control model and a cross domain access method thereof. The attribute-based access control model comprises a first management domain and a second management domain, and is characterized by comprising certificate servers and attribute management servers. The cross domain access method of the system comprises the following steps: the certificate servers are respectively used for awarding a server certificate for the first management domain and the second management domain; a user downloads an attribute certificate to a local disk for storage by logging on the first management domain; the user submits the attribute certificate to the second management domain; a second access control server verifies the attribute certificate; and the second access control server extracts an attribute value to judge the operation validity of the user. The attribute-based access control model and the cross domain access method thereof of the invention have the obvious advantages that the role of the user and the management domains can be considered as a single attribute of the user, the efficiency problem of user-role-authority valuation under the condition of complex role in a role-based access control (RBAC) model can be effectively solved, and the corresponding access control method is provided for an anonymous user in an open network environment.
Owner:CHONGQING UNIV
Provisioning authorization claims using attribute-based access-control policies
InactiveUS20130227638A1Efficient annotationReduce in quantityDigital data protectionDigital data authenticationComputerized systemAuthorization
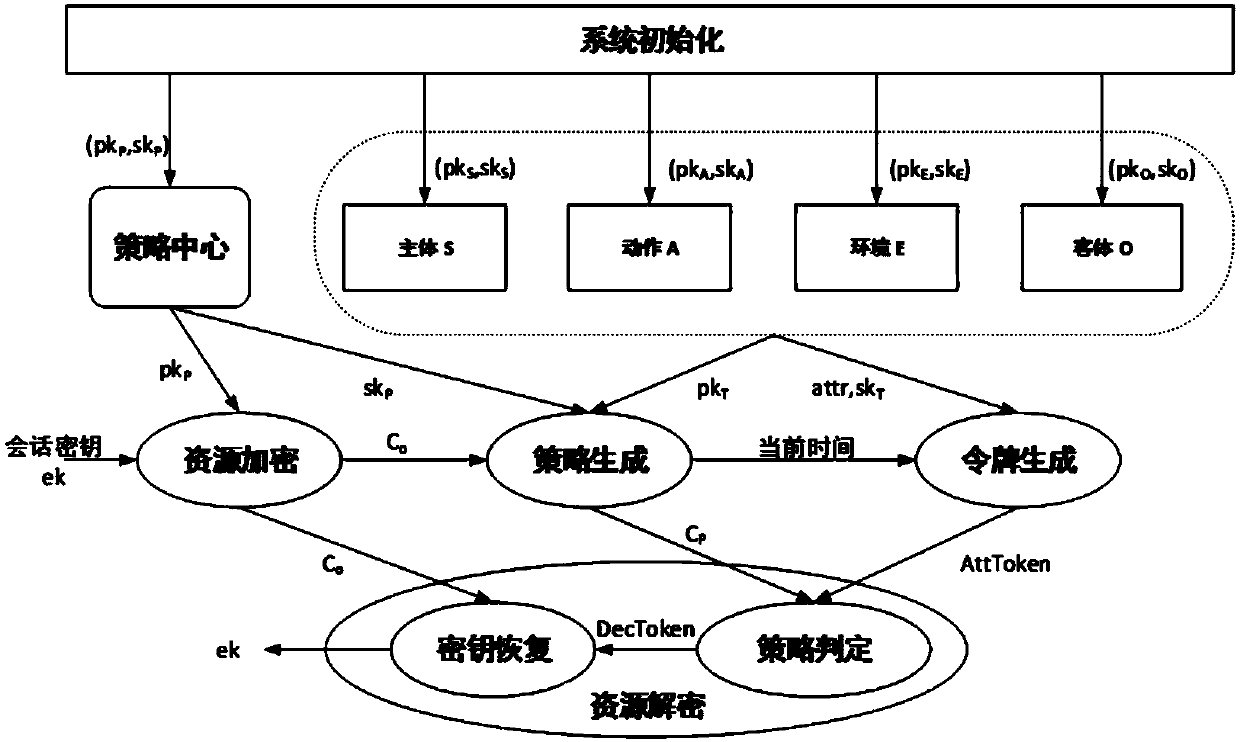
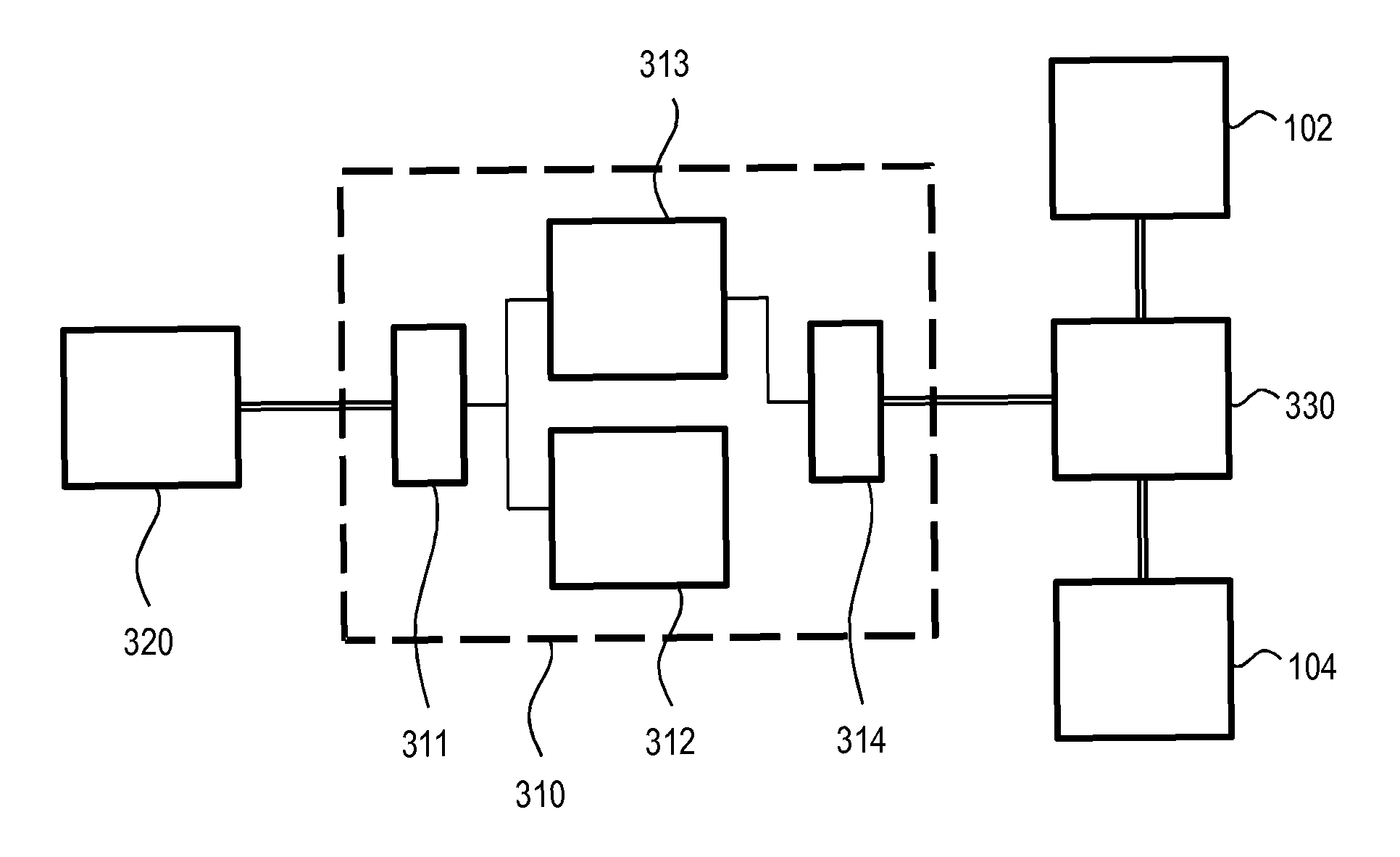
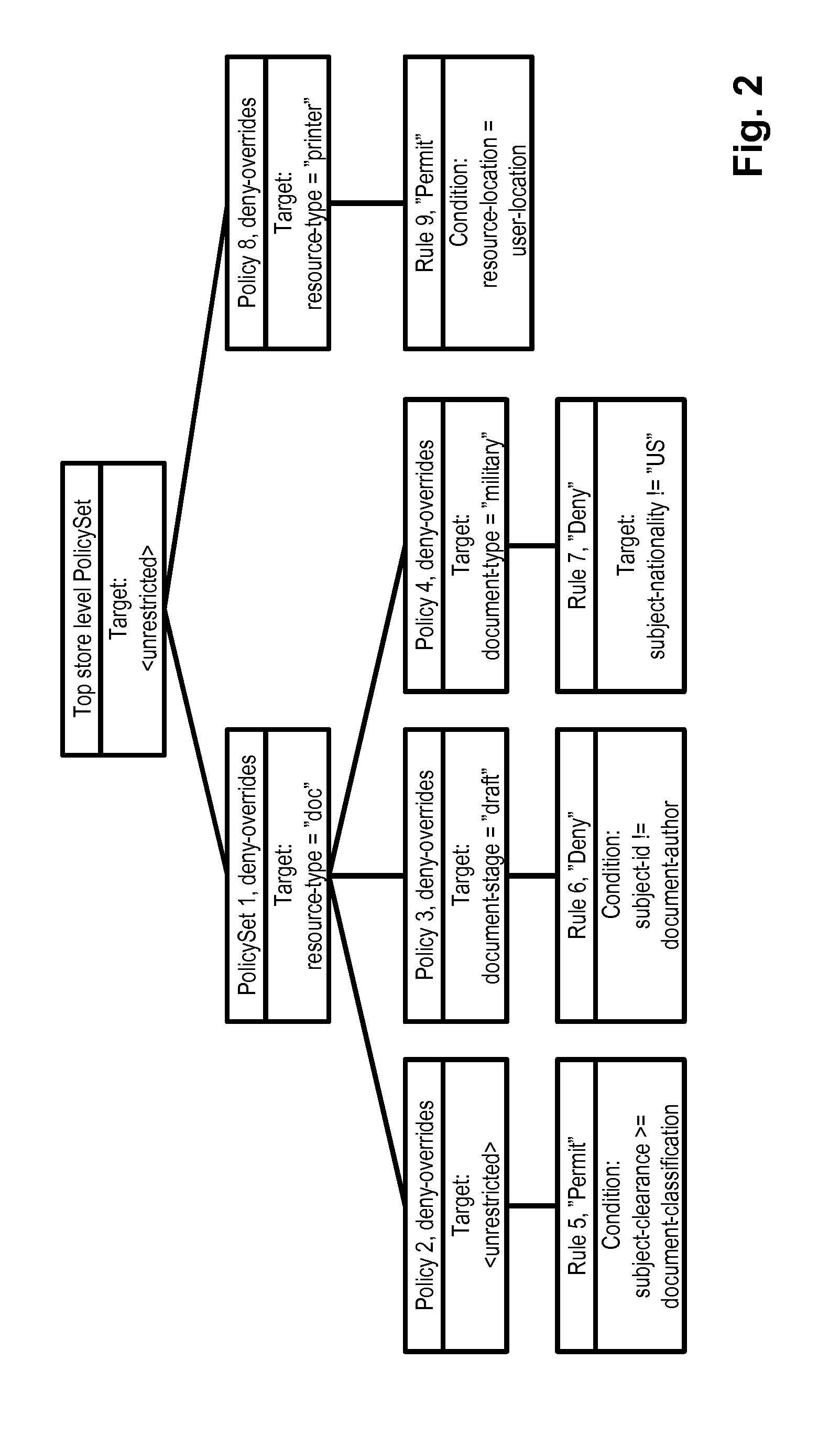
Disclosed are methods and devices for provisioning authorization claims, which are enforced to control access of users to objects (resources) in a computer system (330), and which are to be equivalent to an attribute-based access control (ABAC) policy. A policy converter according to the invention includes a policy processor (310) processing the policy by partial evaluation against attribute values of the users, objects or permission levels in the system and outputting simplified policies, which are subject to reverse evaluation in a reverse policy evaluator (320), whereby users, objects and permission levels to be associated by way of a single authorization claim are obtained. Responsible for the defining of the authorization claim and its distribution in the computer system are an authorization claim generator (330) and an authorization claim distribution interface (340). The invention may be so configured as to return a single authorization claim for each combination of an object and a permission level.
Owner:AXIOMATICS
Access control method based on attribute-based access control policy
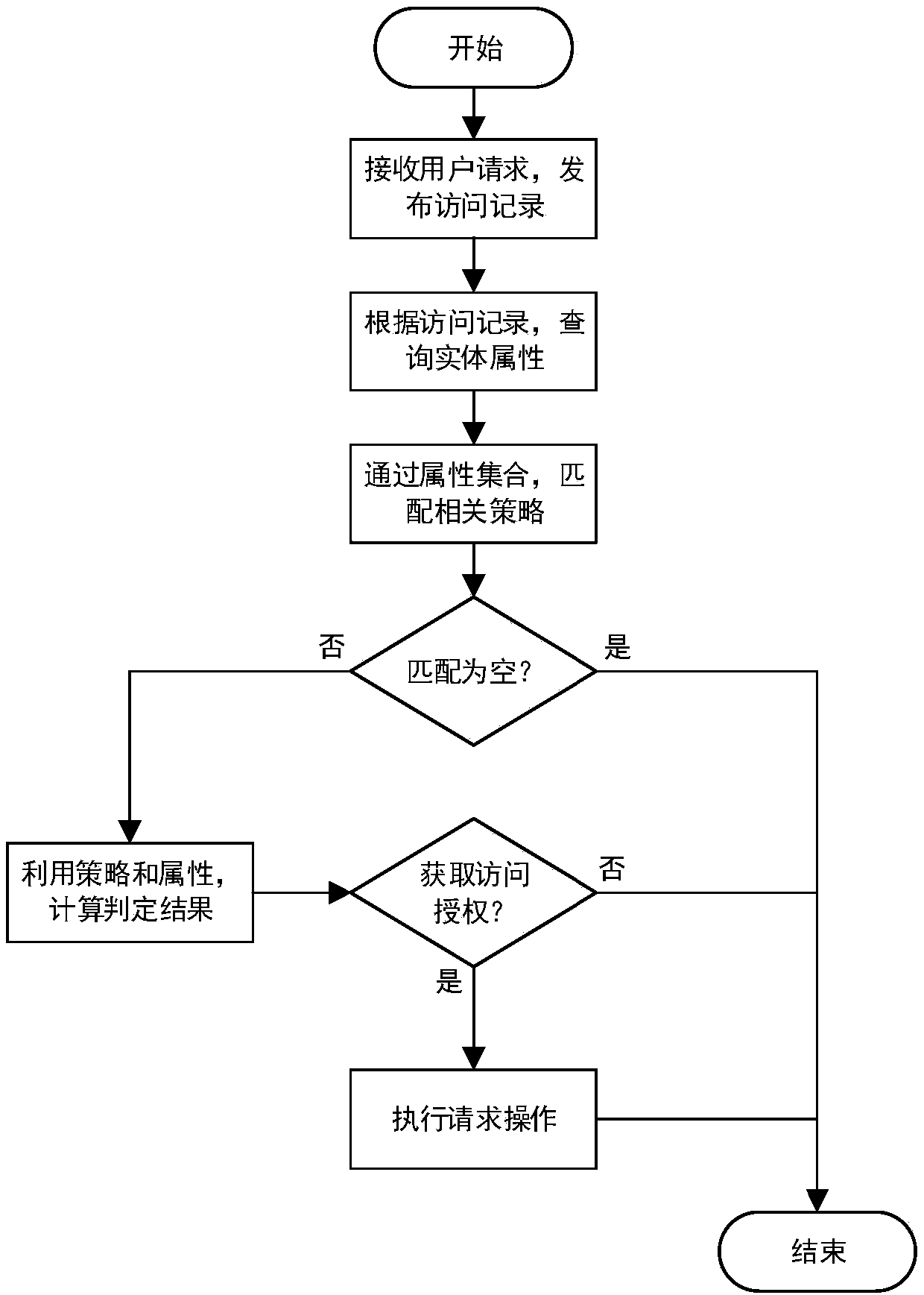
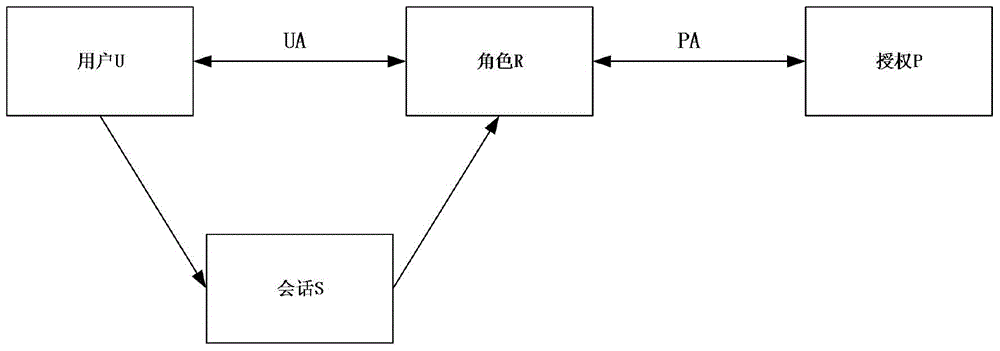
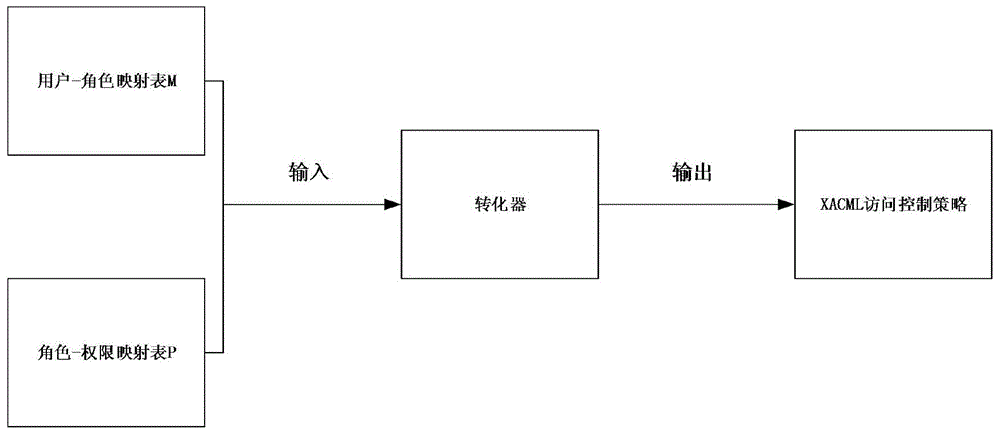
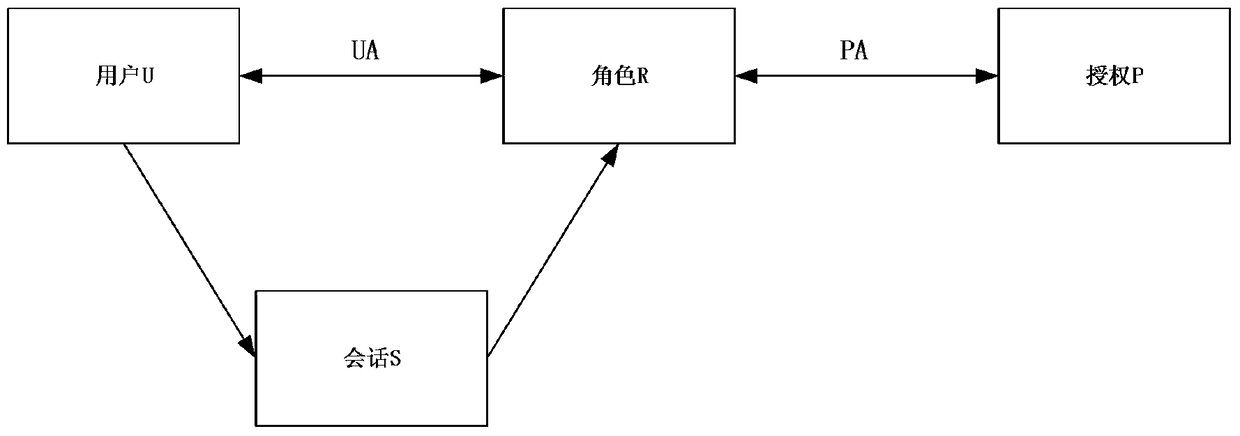
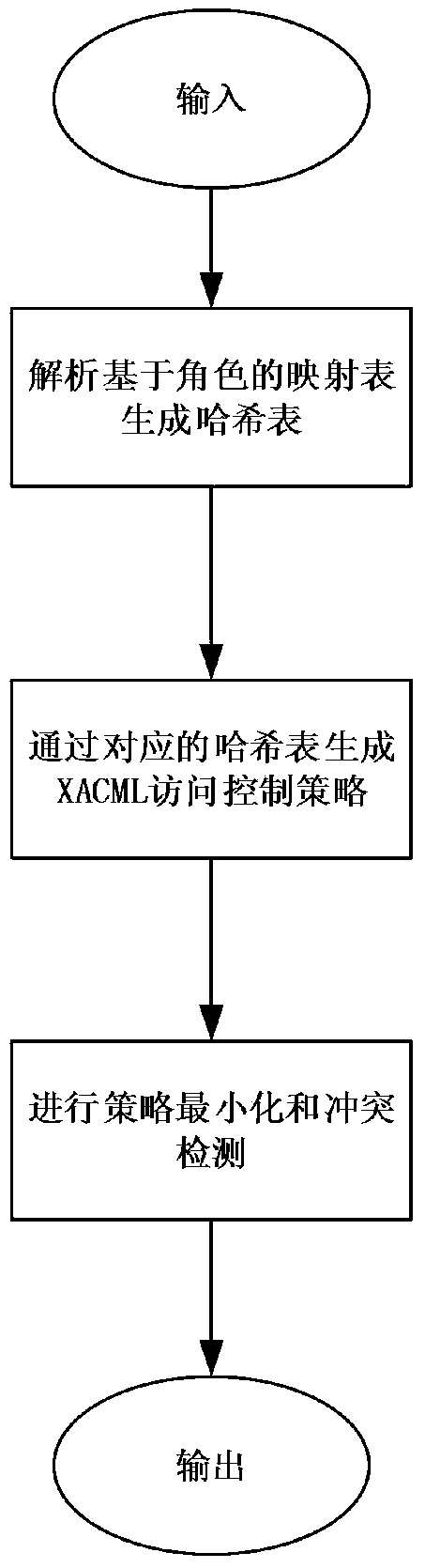
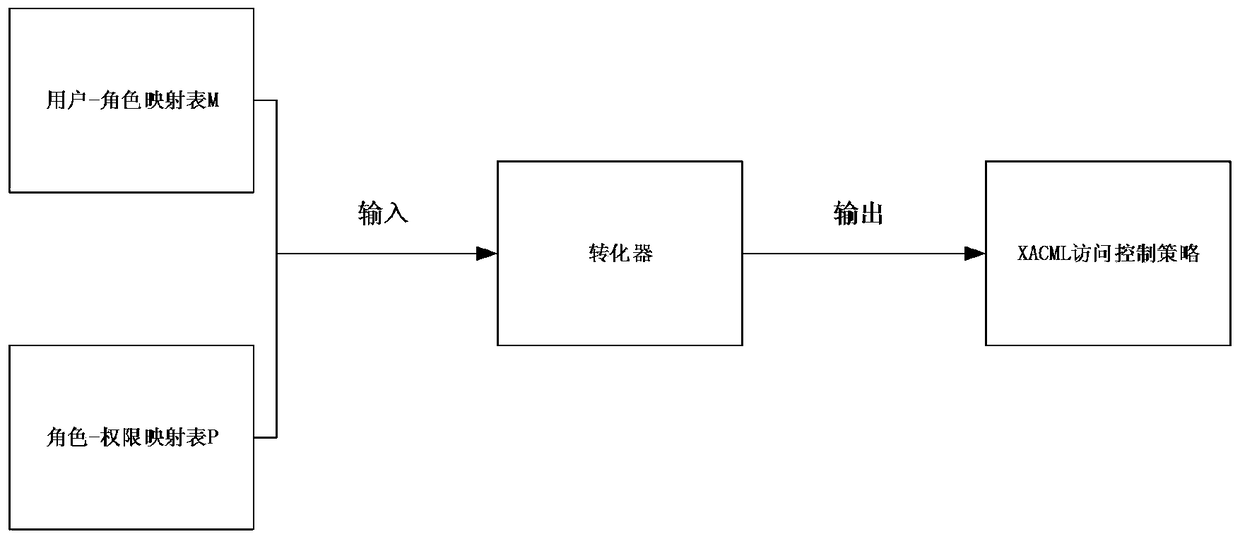
The invention discloses an access control method based on an attribute-based access control policy. The method is characterized by 1) extracting attribute information of a user-role table and a role-authority table in a database and generating a user-role-authority access control relation Hash table; 2) generating an access control policy according to the access control relation Hash table: carrying out iteration traversal on the access control relation Hash table to obtain key value pairs, that is, an attribute set of each user and authority thereof, and then, generating an access control policy rule of the user according to the authority attribute of the user; and 3) for each received access request, an internet-of-thing search engine judging the access request according to the access control policy rule to determine whether access is allowed. The method can give a quick response to the search request, thereby greatly improving efficiency of the internet-of-thing search engine.
Owner:INST OF INFORMATION ENG CAS
Method and device for generating access controlling policy
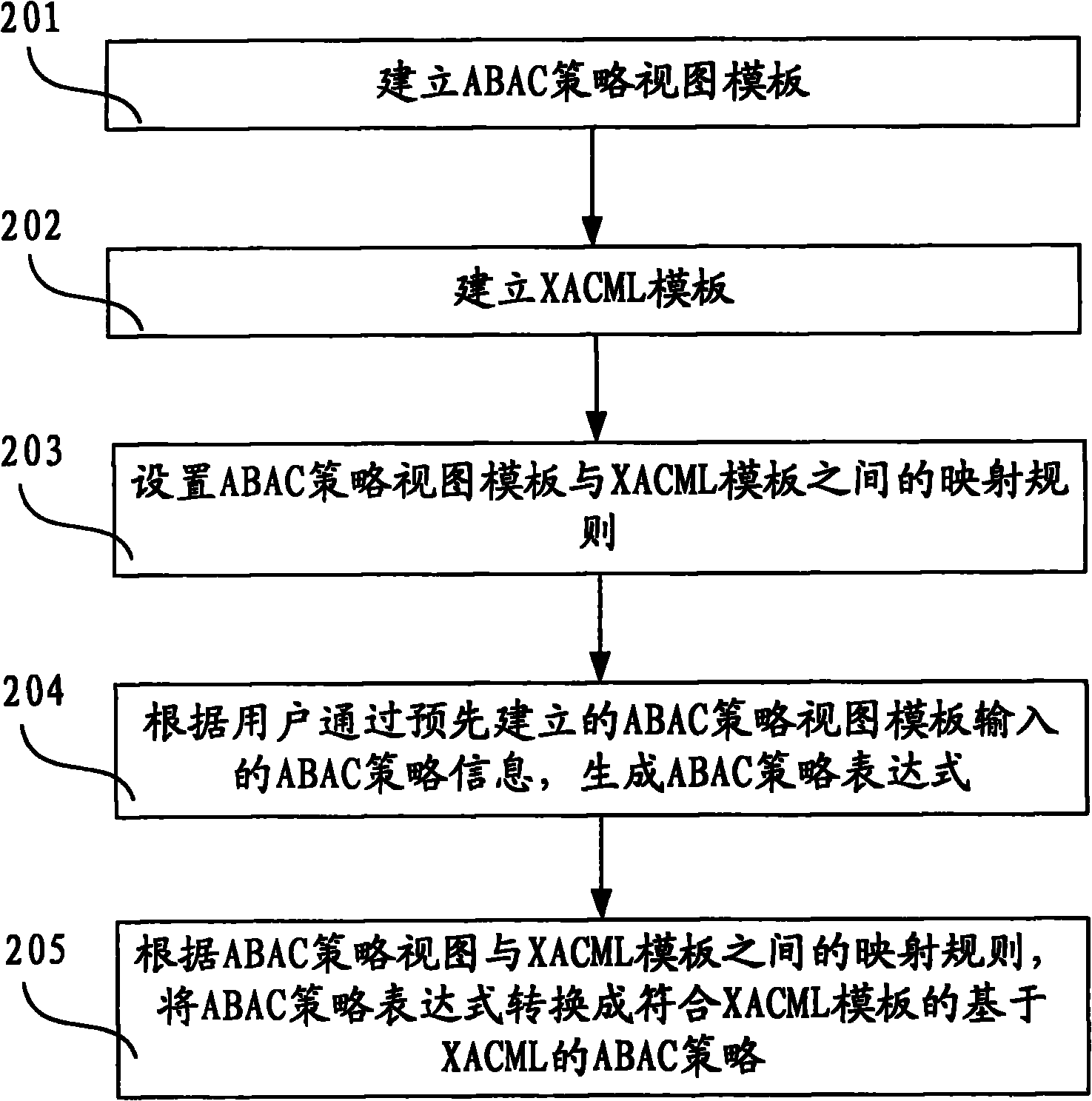
InactiveCN101771683AGuaranteed accuracyReduce the burden onData switching networksSpecial data processing applicationsXACMLWorld Wide Web
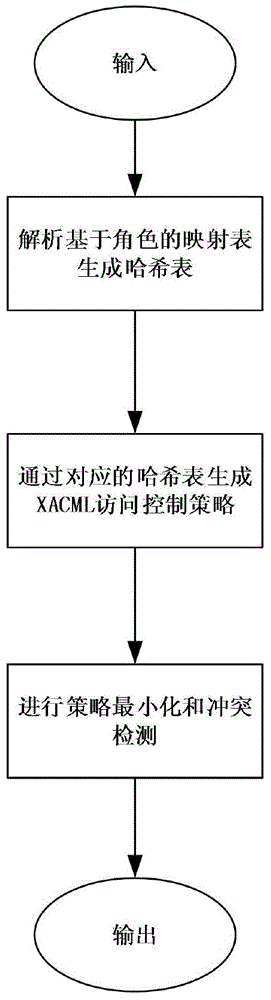
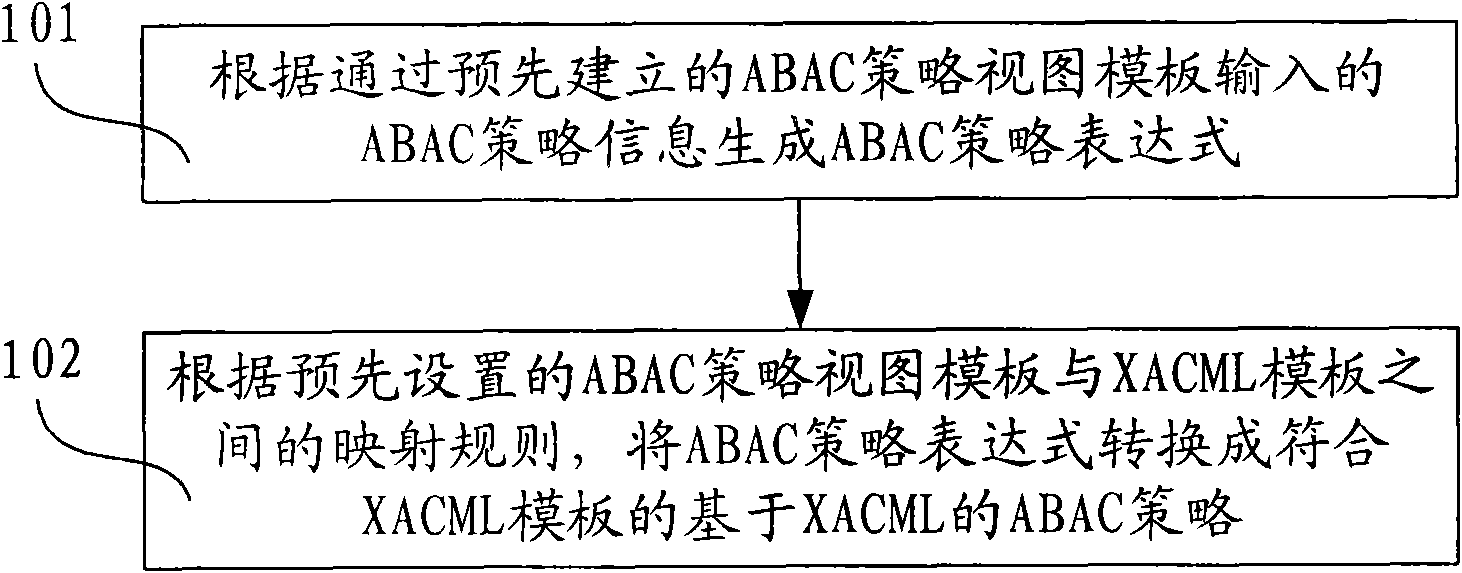
The invention discloses method and device for generating an access controlling policy. The method comprises the following steps of: generating an ABAC policy expression according to ABAC policy information input by a user through a pre-established attribute-based access control (ABAC) policy view template; and converting the ABAC policy expression into an ABAC policy which is based on XACML and conforms to the XACML template according to mapping rules of the preset ABAC policy view template and an extensible access control markup language (XACML) template. In the invention, the user only needs to input some simple ABAC policy information through the ABAC policy view template and does not need to write a complicated ABAC policy based on XACML in a manual mode, therefore, the problem that the user difficultly defines the ABAC policy based on XACML is solved, the problem that errors are made in the process of writing the complicated ABAC policy based on XACML in a manual mode by the useris avoided, and the accuracy of the ABAC policy based on XACML is ensured.
Owner:BEIHANG UNIV
Systems and methods for permissioned blockchain infrastructure with fine-grained access control and confidentiality-preserving publish/subscribe messaging
PendingUS20190394175A1Automatic accessKey distribution for secure communicationCryptography processingConfidentialityData access control
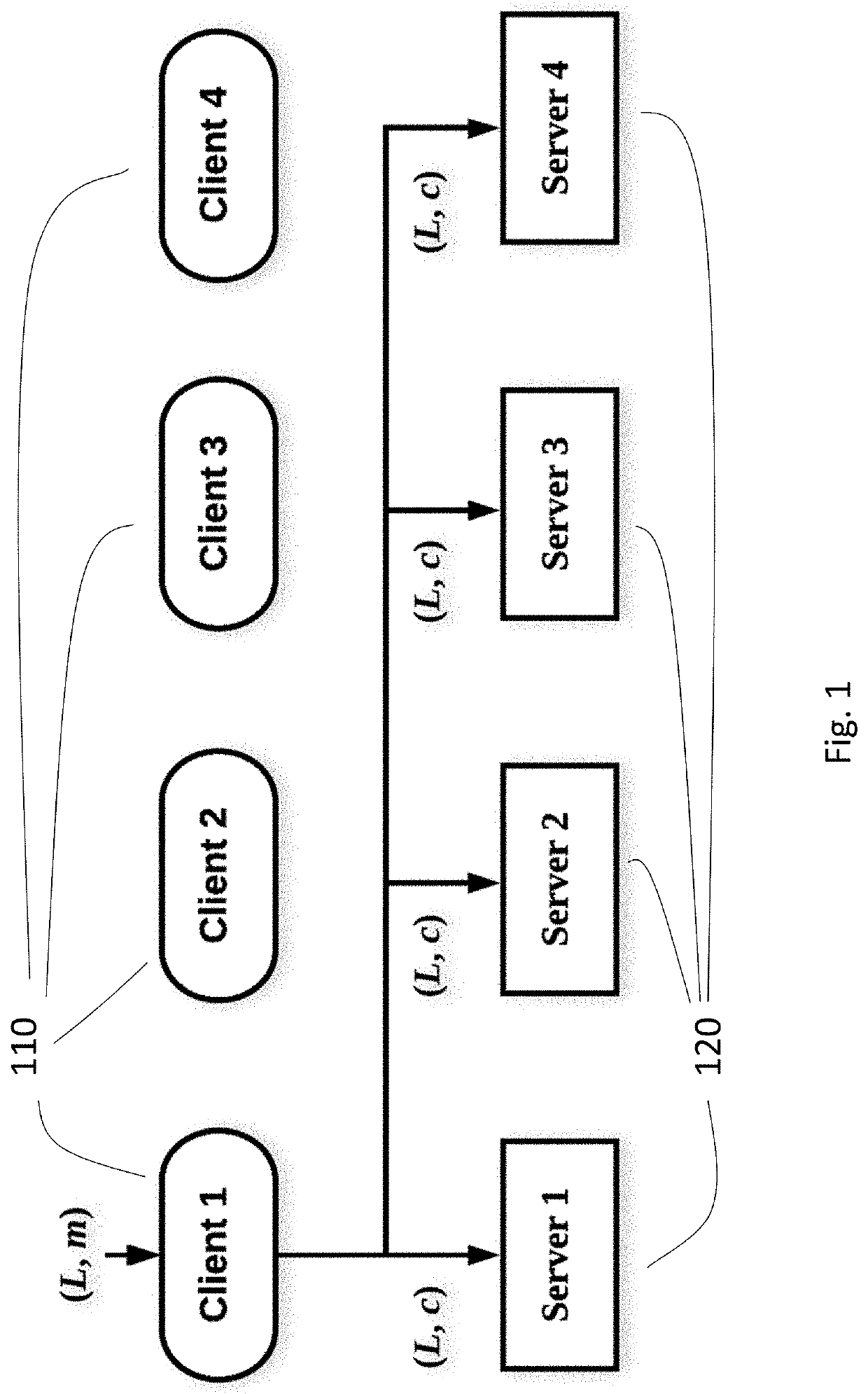
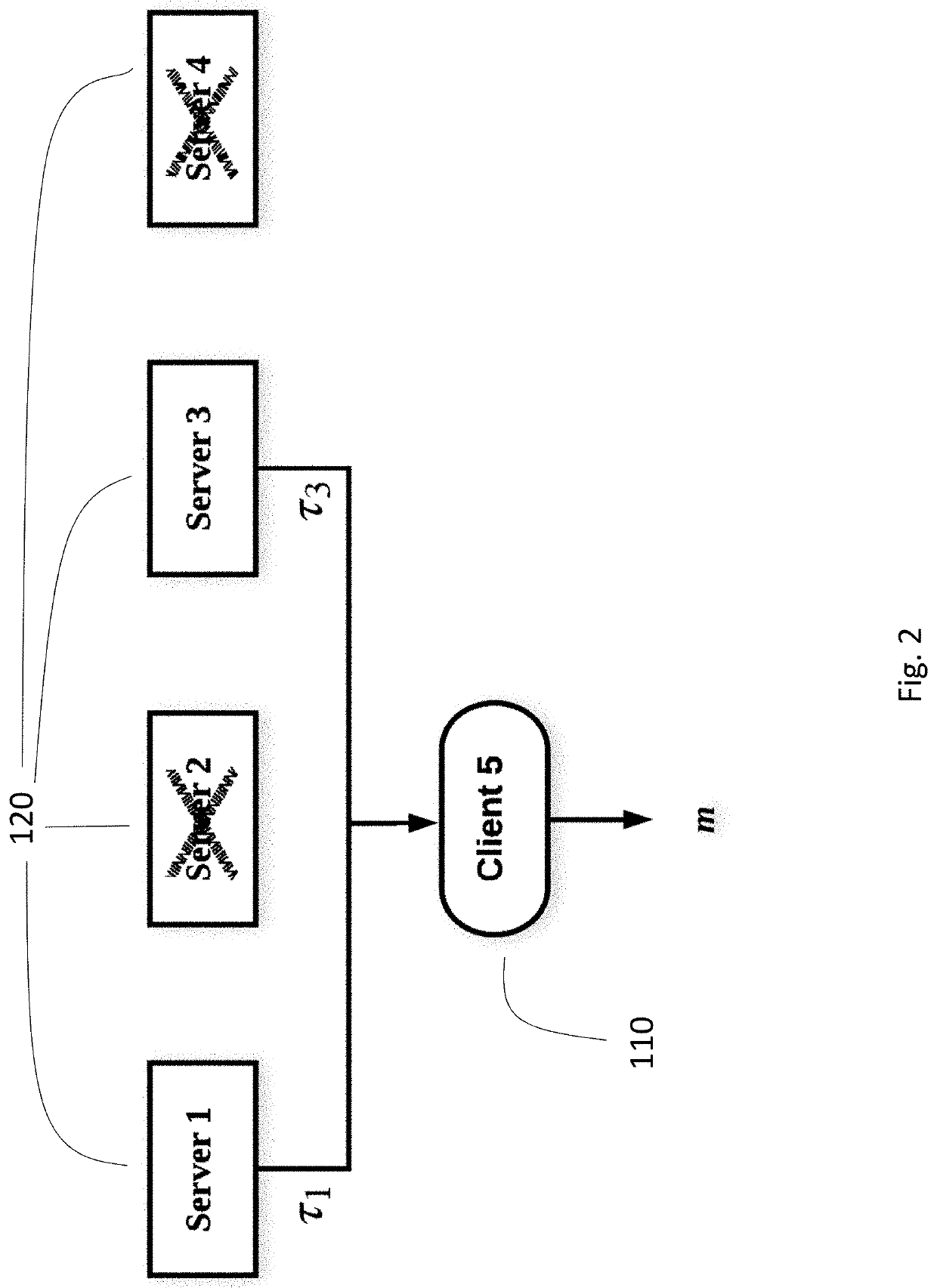
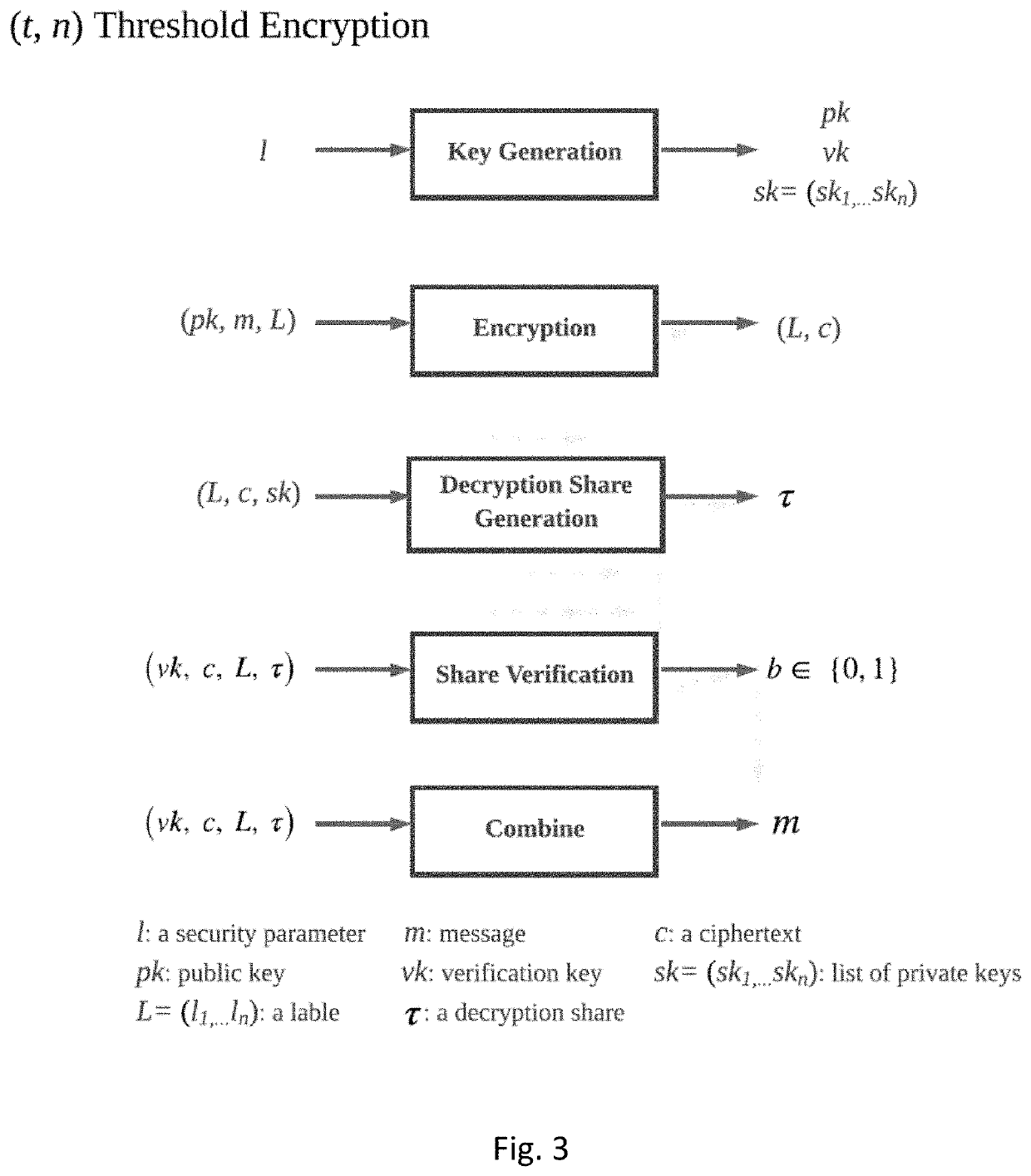
A multitude of systems and methods are provided. An encryption method and system utilizing vector label input threshold encryption is included, enabling decentralized confidentiality and decentralized, fine-grained, and attributed-based access control, enabling clients to define by whom, when, and how their data is accessed. Additionally, the disclosed systems and methods can include publish / subscribe mechanisms while achieving confidentiality-preserving and decoupled publish / subscribe messaging and strong total order for publications even with crytographic access control enforced.
Owner:UNIV OF MARYLAND BALTIMORE COUNTY
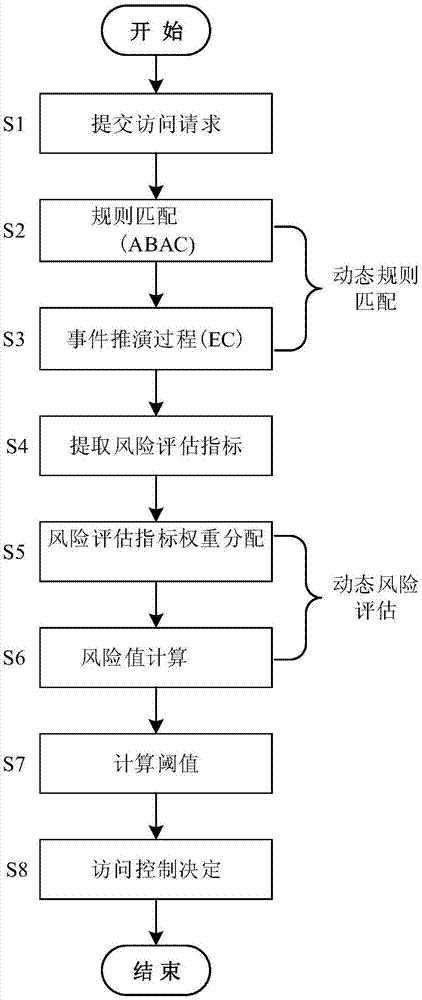
Dynamic risk access control method of cloud platform
ActiveCN107395430AHigh sensitivityImprove dynamic performanceData switching networksMedia access controlSystem safety
The invention provides a dynamic risk access control method of a cloud platform. The control method comprises steps of submitting an access request, implementing a rule matching strategy, carrying out an event deduction process, extracting a risk evaluation index, carrying out risk evaluation index weight distribution, calculating a risk value, calculating a threshold value, and making an access control decision. According to the dynamic risk access control method, an attribute based access control (ABAC) strategy is improved by using an event deduction mechanism with high expressivity and flexibility, thereby enhancing the dynamic and flexible properties during rule matching and thus realizing high adaptability to the complicated cloud environment; and a risk assessment index is constructed by using a system security state and historical behavior information of the user, a mathematic model for calculating a risk assessment index weight is put forward, and a corresponding weight is calculated based on a formula regression algorithm, so that the sensitivity to the access request by the risk value is improved. On the basis of observation of a simulated experiment, the rule is adjusted dynamically based on a change of an access request attribute; and the risk assessment index weights are distributed dynamically in real time and the sensitivity to the risk value by the access request is improved. The method has the good real-time and dynamic performances.
Owner:CIVIL AVIATION UNIV OF CHINA
Access control strategy composition method based on attribute
InactiveCN104683348AAccess control securityAvoid illegal operationTransmissionAuthorizationStrategy synthesis
The invention discloses an access control strategy composition method based on attribute. When access control of cross-domain resources is achieved, an access control strategy composition method based on attribute is a key technique. According to the access control strategy composition method, by defining authorization of entities through attribute of the entities, the credibility, as an independent attribute predicate, of a main body is added into an attribute authorization item of an access control strategy, so that conventional strategy composition is expanded, the expression capability of strategy composition is improved, and the security of objects in a safety domain is ensured. According to the access control strategy composition method, six strategy composition operators with credibility are defined to achieve access control strategy composition, and whether a strategy synthesis structure can meet the requirements of protecting resources, of different strategy composition parties or not is verified by virtue of attribute of algebras expressed by conventional strategies.
Owner:HENAN POLYTECHNIC UNIV
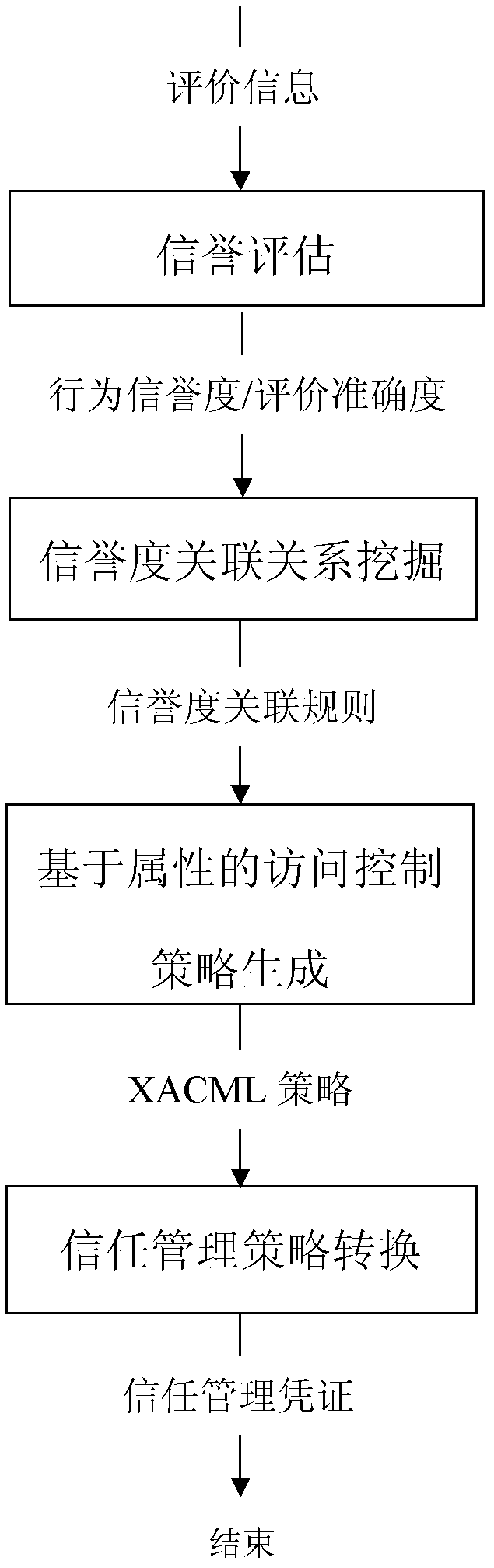
Method for generating cross-domain access control strategy by rising from credit assessment to trust management
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
Provisioning user permissions using attribute-based access-control policies
InactiveUS20130081105A1Computational savingImprove variationDigital data authenticationTransmissionUser PrivilegeTheoretical computer science
An attribute-based access control policy (e.g., XACML policy) for a set of elements depends on attributes carried by elements in one of several predefined categories. In order to evaluate such policy for a set of elements, the invention provides a method including the steps of (I) selecting a primary category; (II) partitioning the elements in the primary category into equivalence classes with respect to their influence on the policy; and (III) using the equivalence classes to replace at least one policy evaluation by a deduction. The result of the evaluation may be represented as an access matrix in backward-compatible format. The efficiency of the policy evaluation may be further improved by applying partial policy evaluation at intermediate stages, by forming combined equivalence classes containing n-tuples of elements and / or by analyzing the influence of each element by extracting functional expressions of maximal length from the policy.
Owner:AXIOMATICS
System and method for evaluating a reverse query
InactiveUS20150295939A1Reduce loadDigital data protectionOther databases queryingDecision takingComputer science
Real-time techniques for determining all access requests to an attribute-based access control policy which evaluate to a given decision, “permit” or “deny”. The policy is enforced to control access to one or more resources in a computer network. In one embodiment, a method includes: (i) receiving a reverse query and a set of admissible access requests, each of which includes one or more attributes in the policy and values of these; (ii) extracting attributes to which all access requests in the set assign identical values; (iii) reducing the ABAC policy by substituting values for the extracted attributes; (iv) caching the policy as a simplified policy; (v) translating the simplified policy and the given decision into a satisfiable logic proposition; (vi) deriving all solutions satisfying the proposition; and (vi) extracting, based on the solutions, all access requests from the set for which the policy yields the given decision.
Owner:AXIOMATICS
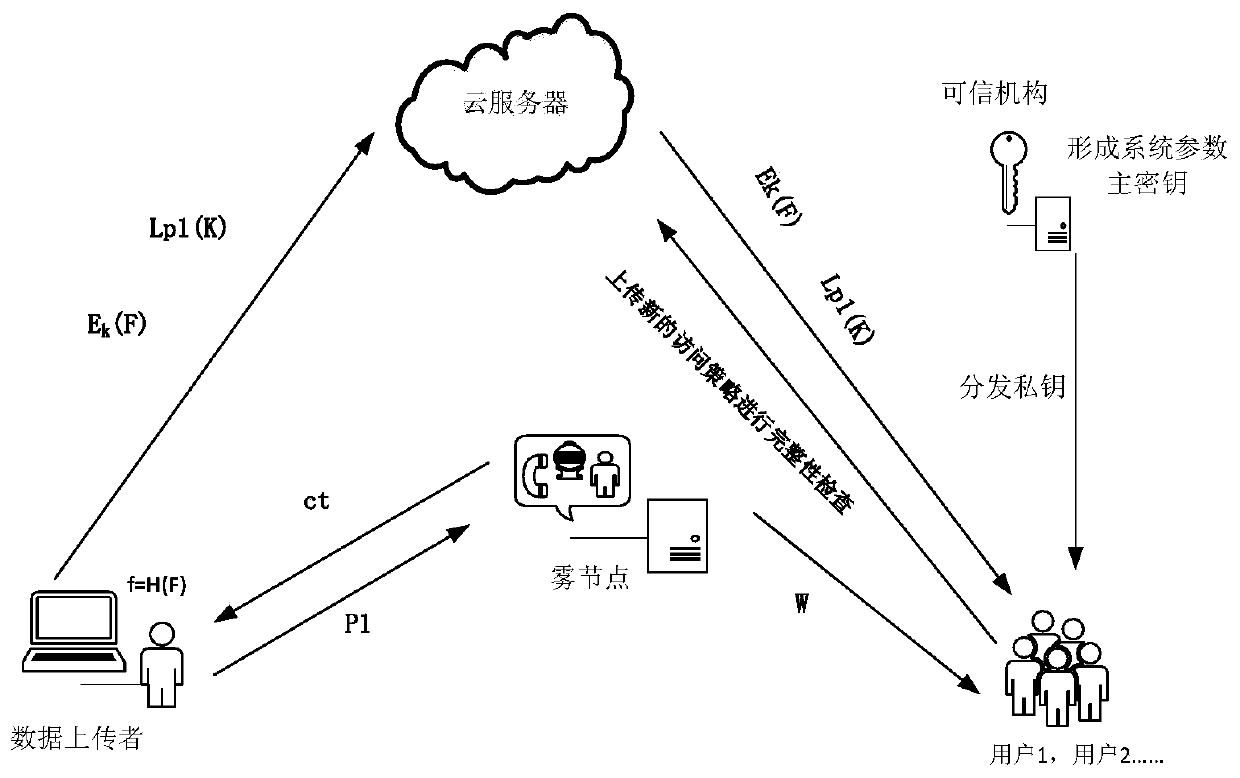
Cryptography attribute-based access control method and system based on dynamic rule
ActiveCN107864139AHigh security requirementsGuaranteed unforgeabilitySecuring communicationExtensibilityUnsafe environment
The invention relates to a cryptography attribute-based access control method and system based on a dynamic rule, mainly belonging to the technical field of information. In the cryptography attribute-based access control system based on the dynamic rule, protected objects are stored in a encrypted form, and only the requests satisfying the requirements of access policies in the attribute-based access control can be authorized to decrypt the objects, therefore, it can be ensured that data in an unsafe environment can be accessed with authorization according to a security policy, and meanwhile,the extensibility of the policies and the dynamic acquisition of the attributes are also supported. The cryptography attribute-based access control method and system based on the dynamic rule are divorced from the traditional encryption system framework, and are a new attribute-based access control model, method and system supporting the cryptography decision. The cryptography attribute-based access control method and system based on the dynamic rule can achieve more secure, diversified, dynamic and flexible access authorization, which are suitable for large-scale organizations or informationsystems, and can be applied to the environments such as cloud computing, grid computing, distributed computing, and so on.
Owner:UNIV OF SCI & TECH BEIJING
System and method for evaluating a reverse query
ActiveUS20130055344A1Reduce loadDigital data protectionTransmissionComputer scienceRequest distribution
Disclosed are real-time techniques for determining all access requests to an attribute-based access control policy which evaluate to a given decision, “permit” or “deny”. The policy is enforced to control access to one or more resources in a computer network. In one embodiment, a method comprises: (i) receiving a reverse query and a set of admissible access requests, each of which comprises one or more attributes in the policy and values of these; (ii) extracting attributes to which all access requests in the set assign identical values; (iii) reducing the ABAC policy by substituting values for the extracted attributes; (iv) caching the policy as a simplified policy; (v) translating the simplified policy and the given decision into a satisfiable logic proposition; (vi) deriving all solutions satisfying the proposition; and (vi) extracting, based on the solutions, all access requests from the set for which the policy yields the given decision.
Owner:AXIOMATICS
Role-based attribute based access control (RABAC)
ActiveUS8474018B2Convenient access controlDigital data processing detailsDigital data protectionUser deviceMedia access control
Systems and methods are disclosed for receiving an access request from a user device, the access request including an identity claim for a user; evaluating a risk of access based on matching an attribute of the user device with attributes stored in a user information database; authenticating the access request based on the identity claim and the risk evaluation to determine an authentication confidence level; generating a token based on the confidence level and the attribute matched; producing an authorization response based on inputs from the token, a risk based access control, a role based access control, and an attribute based access control, in which the authorization response determines whether to allow access to a system, deny access to the system, or request additional input from the user device.
Owner:PAYPAL INC
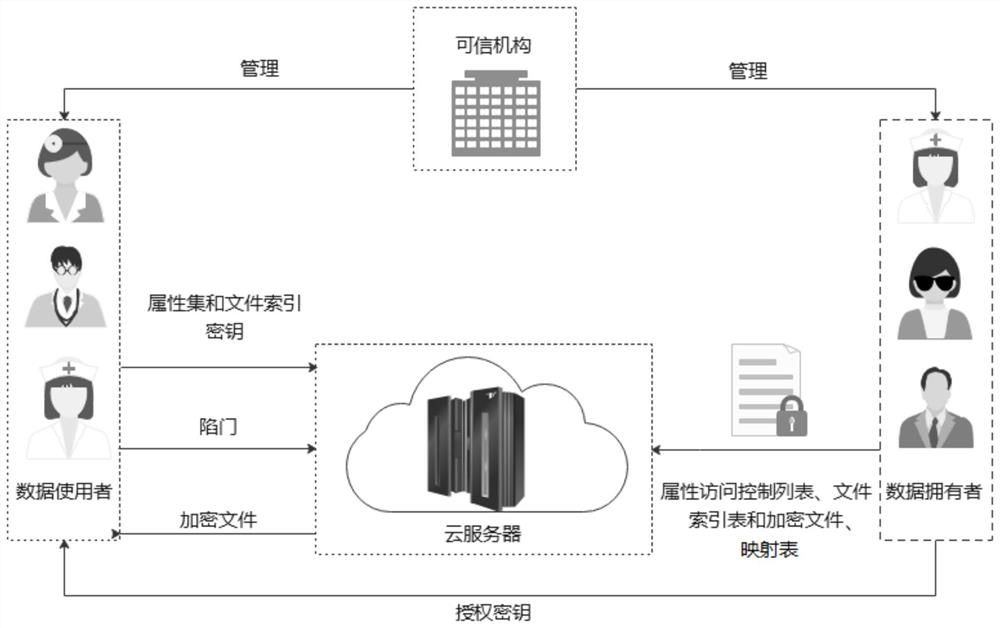
Attribute-based access control method for smart grid based on Bloom Filter
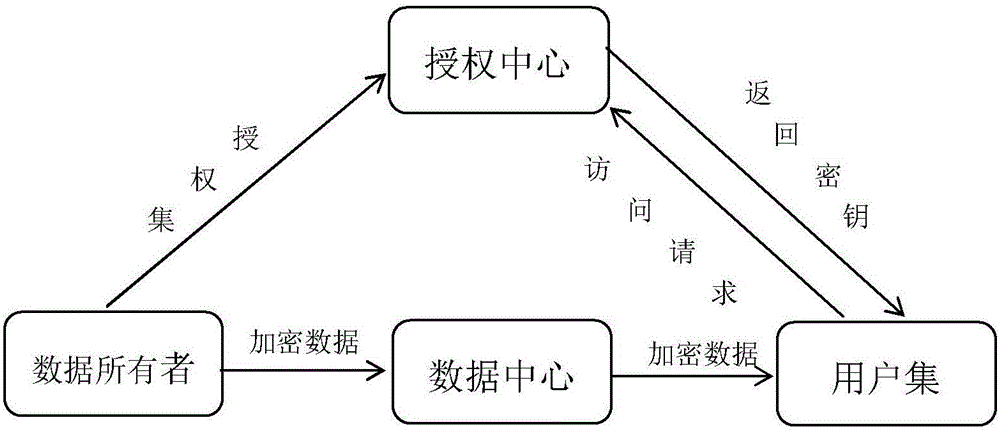
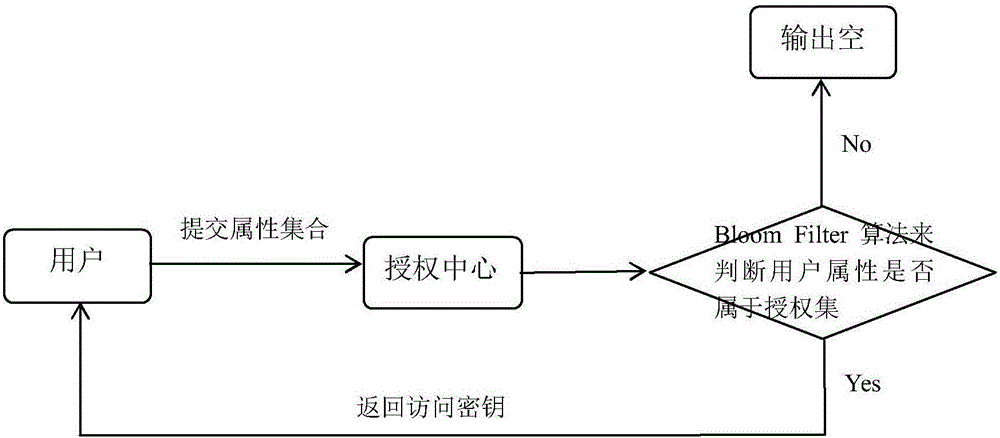
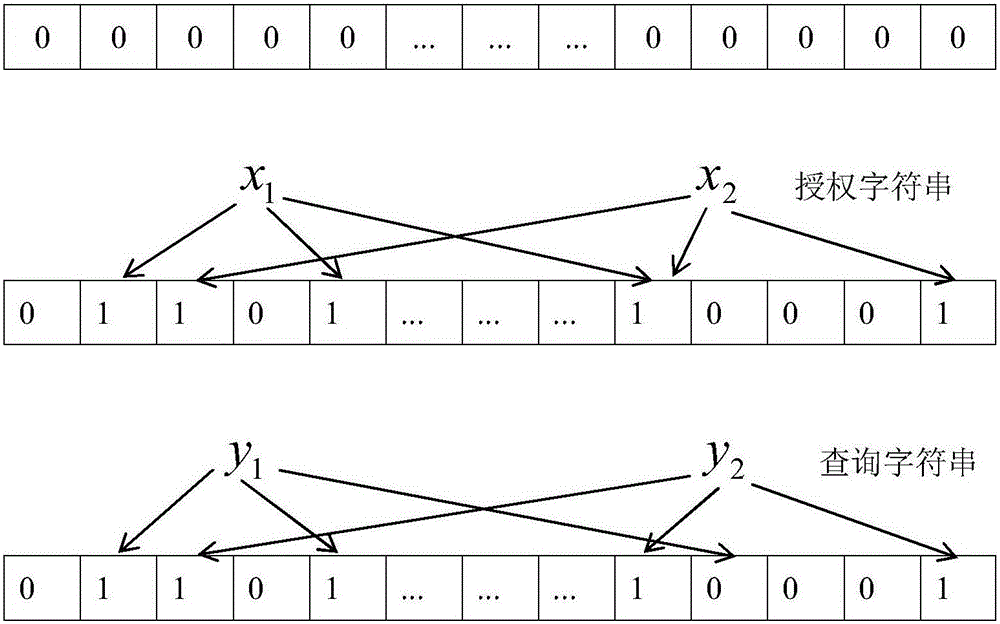
ActiveCN106101093AImprove efficiencyAvoid manipulating access control structuresTransmissionPlaintextData center
The invention discloses an attribute-based access control method for a smart grid based on Bloom Filter. The method comprises the following steps that (1) a data owner stores data into a data center; (2) if a user wants to visit the data, the user submits an access request and an attribute set to the control center; (3) the control center utilizes a Bloom Filter algorithm to judge whether the user belongs to an authorization set; and (4) if judging that the user belongs to the authorization set, a key is obtained and is decrypted to obtain plaintext data, otherwise the data is inaccessible. The method adopts a bit array to represent the attribute set of the user concisely and utilizes the Bloom Filter to carry out quick attribute belonging judgement on the user, so that the efficient attribute-based access control is realized. In comparison with the conventional algorithm, the requirements of a program for the server memory is greatly reduced, and meanwhile, the matching efficiency is improved and the complexity for attribute encryption of mass data in the smart grid is reduced.
Owner:SOUTHEAST UNIV
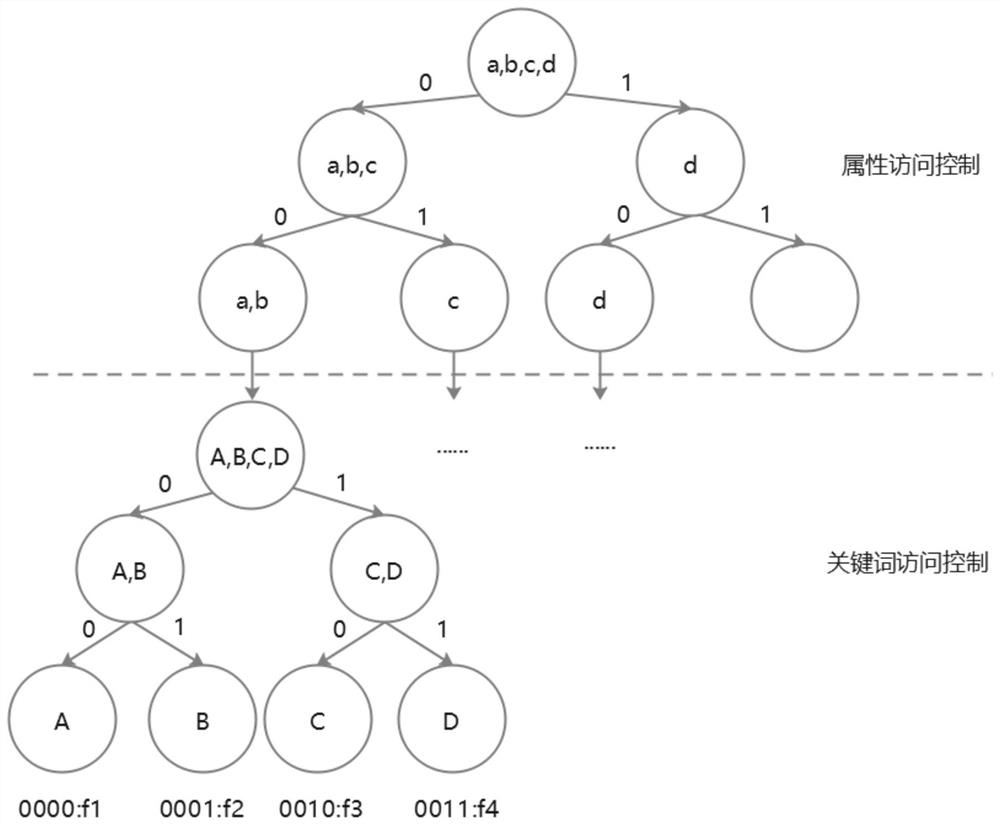
Multi-key searchable encryption method and system based on attribute access control structure
ActiveCN112380553AEfficient access control strategyImprove Access Control EfficiencyDigital data information retrievalDigital data protectionEngineeringCloud storage
The invention discloses a multi-key searchable encryption method and system based on an attribute access control structure, and the method comprises the steps: dividing an attribute set through employing a VBTree under the background of cloud storage, binding the attribute set with the access authority of a file, and effectively determining whether a user is a legal user or not and a file set which can be accessed by the user according to an attribute set submitted by the user. Huge expenditure for traversing all files of a data owner once when the user is verified to be the legal user or notis avoided; meanwhile, combined query of multiple keywords is achieved, so that a query result is more flexible and accurate; and the data owner does not need to generate an authorization key for eachauthorized user and each file which can be accessed by the authorized user, and only needs to generate an authorization key for each authorized user.
Owner:SOUTH CHINA UNIV OF TECH
System and method for performing partial evaluation in order to construct a simplified policy
ActiveUS20140047501A1Faithfully reproducedComputer security arrangementsTransmissionDecision takingComputer science
Methods and devices for constructing a simplified attribute-based access control policy, which more faithfully reproduces not only Permit and Deny decisions but also data relating to errors and quasi-errors resulting from the evaluation. To this end, the simplified policy includes new data fields for storing intermediate results. Further, improved simplification rules allowing partial evaluation to be used in a broader range of situations.
Owner:AXIOMATICS
Access control system and access control method between public cloud and private cloud
ActiveCN103067406BControl Access Request ManagementEnsure safetyTransmissionAccess control matrixData access control
Owner:JINAN UNIVERSITY
An extensible access control method for fog computing
ActiveCN109936562AImplement integrity protectionReduce operational overheadTransmissionAccess structureOriginal data
The invention discloses an extensible access control method for fog computing. According to the method, a linear secret sharing matrix is used as an access structure to realize attribute-based accesscontrol, fog nodes are used as edge service nodes, and encryption and decryption operations in the access control are reasonably distributed, so that the operation overhead of a terminal user in the access control is reduced. In addition, on the basis of maintaining the original access strategy, new legal members can be added to form a new access strategy, meanwhile, whether the access user tampers the original data or not when uploading the new access strategy can be detected, and integrity protection of the original data is achieved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Attribute-based access control method with anonymous access capability
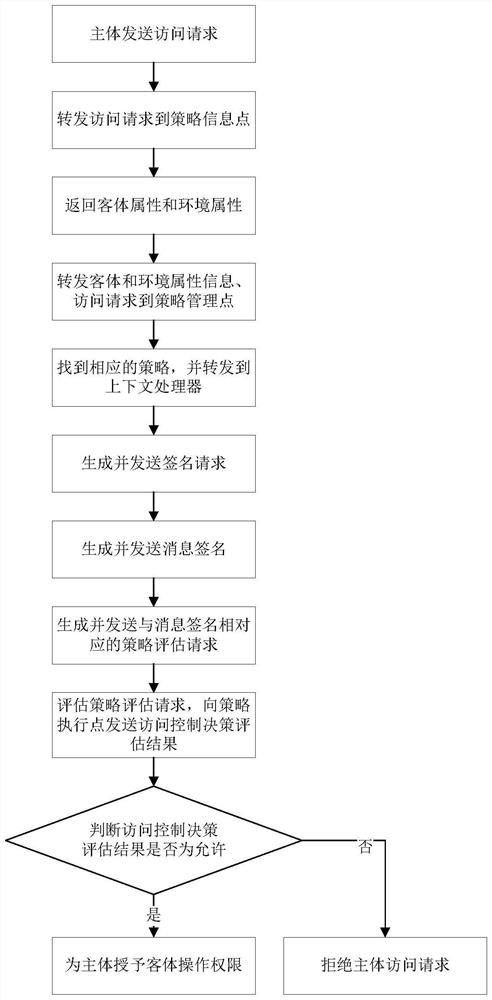
ActiveCN112187800AOvercome leaksAchieve anonymous accessUser identity/authority verificationEvaluation resultEngineering
The invention discloses an attribute-based access control method with anonymous access capability, and mainly solves the problems that privacy of an access request subject is leaked and the subject cannot accurately provide attribute information in the prior art. The implementation scheme is as follows: a subject sending an access request only containing object identity information and operation;sending a signature request to the subject according to the subject attribute required by the strategy corresponding to the access request; and the subject generating a signature of the required subject attribute through the attribute certificate, and participating in strategy evaluation with the access request to obtain an access control decision evaluation result. According to the invention, theleakage of the subject attributes is avoided, the participation of irrelevant subject attributes in the access control decision is reduced, and the decision efficiency of access control is improved while the privacy of the subject is ensured.
Owner:XIDIAN UNIV
Provisioning user permissions using attribute-based access-control policies
InactiveUS8881226B2Computational savingImprove variationDigital data processing detailsUnauthorized memory use protectionUser PrivilegeTheoretical computer science
An attribute-based access control policy (e.g., XACML policy) for a set of elements depends on attributes carried by elements in one of several predefined categories. In order to evaluate such policy for a set of elements, the invention provides a method including the steps of (I) selecting a primary category; (II) partitioning the elements in the primary category into equivalence classes with respect to their influence on the policy; and (III) using the equivalence classes to replace at least one policy evaluation by a deduction. The result of the evaluation may be represented as an access matrix in backward-compatible format. The efficiency of the policy evaluation may be further improved by applying partial policy evaluation at intermediate stages, by forming combined equivalence classes containing n-tuples of elements and / or by analyzing the influence of each element by extracting functional expressions of maximal length from the policy.
Owner:AXIOMATICS
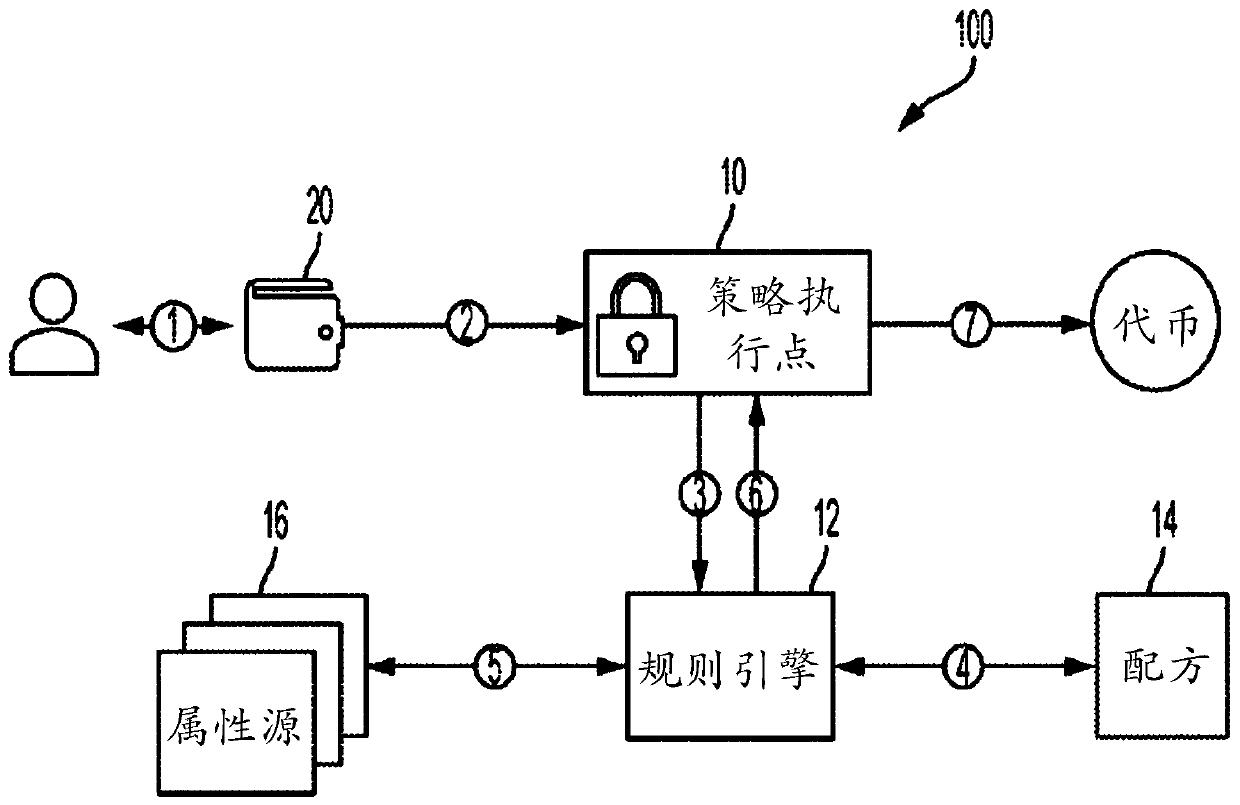
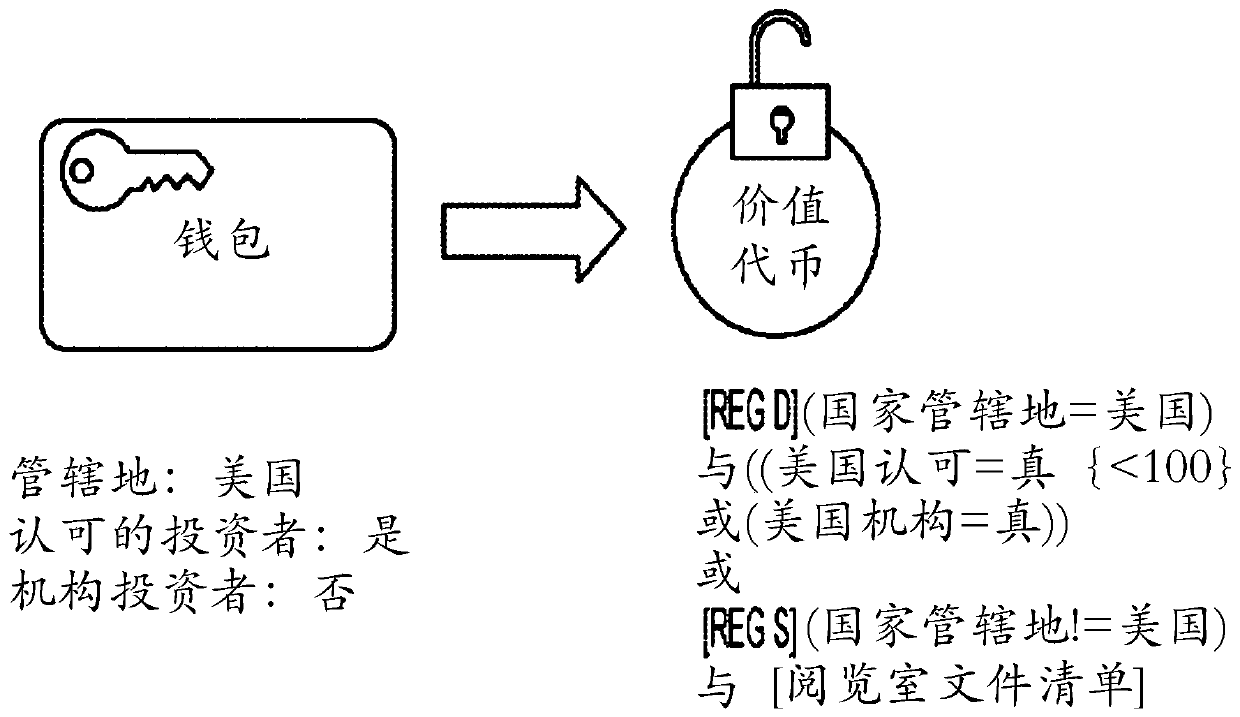
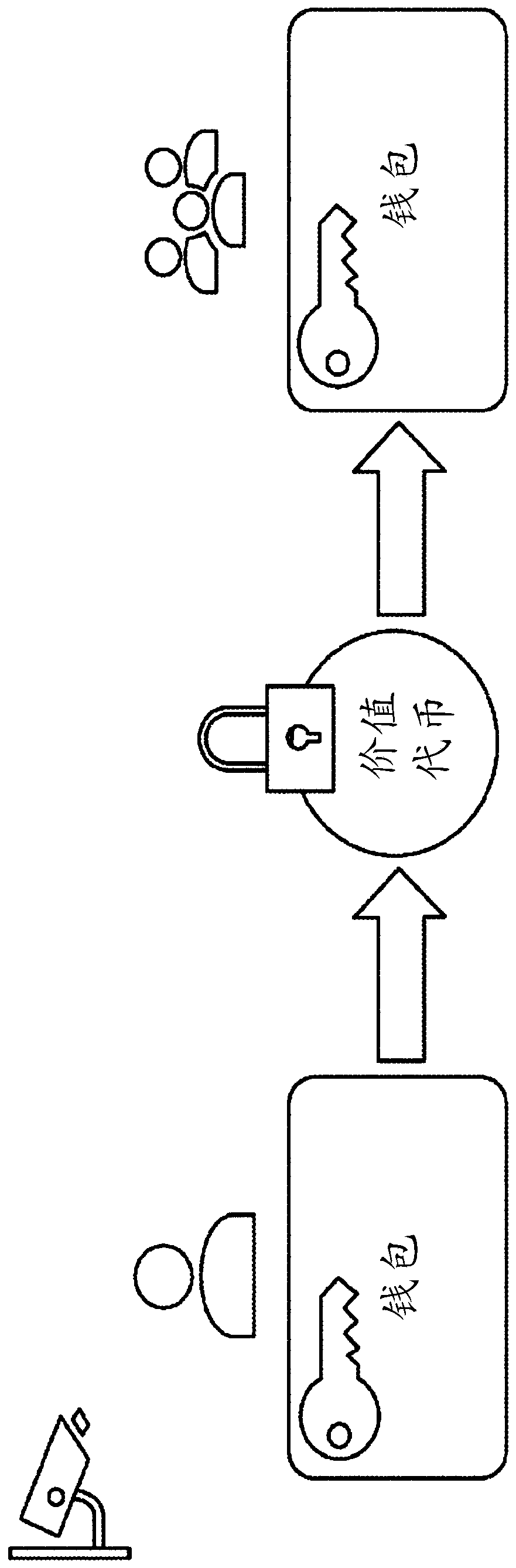
Method, apparatus, and computer-readable medium for compliance aware tokenization and control of asset value
An apparatus, computer-readable medium, and computer-implemented method to facilitate scalable compliance and issuer governance of decentralized financial transactions especially for the trade and transfer of tokenized securities. The resulting Compliance Aware Tokens contain the rulesets to restrict transactions and facilitate regulatory reporting and oversight. The embodied process, includes ofa novel combination of compliance workflows, attribute verification tools, smart contracts and other ledger controls, provides a decentralized Attribute Based Access Control (ABAC) capability. ABAC patterns are extended to govern global financial transactions without the need for an active intermediary.
Owner:赛可润思公司
Attribute based access control method and system
InactiveCN106790119AImprove adaptabilityCreate flexible strategiesTransmissionRights managementDiscretionary access control
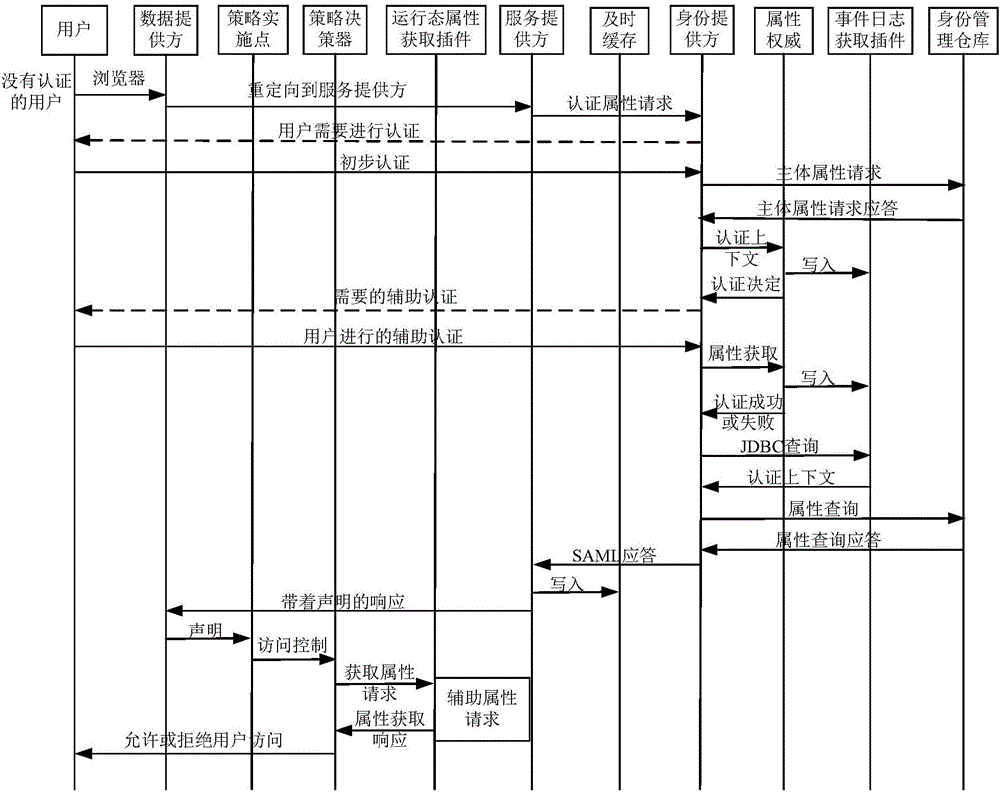
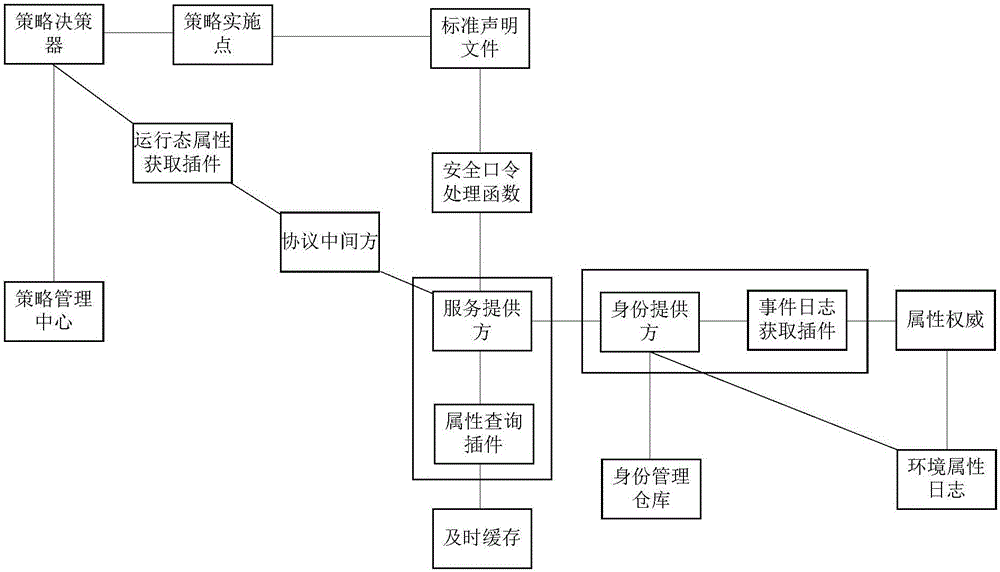
The invention discloses an attribute based access control method and system. The method is implemented through steps as follows: granting and revocation of subject attribute information and a specific subject; collection of environmental attribute information; creation of a strategy; implementation of the strategy; acquisition of running state attributes; determination of a unified data demand response mode of all parts. Access control is realized through control of subjective and objective attribute information and the environmental attribute information, and a series of problems of poor safety, large authority management difficulty, extension difficulty and the like of traditional access control can be solved, so that efficient access control is realized.
Owner:HUAZHONG UNIV OF SCI & TECH
Improved network access control method and device
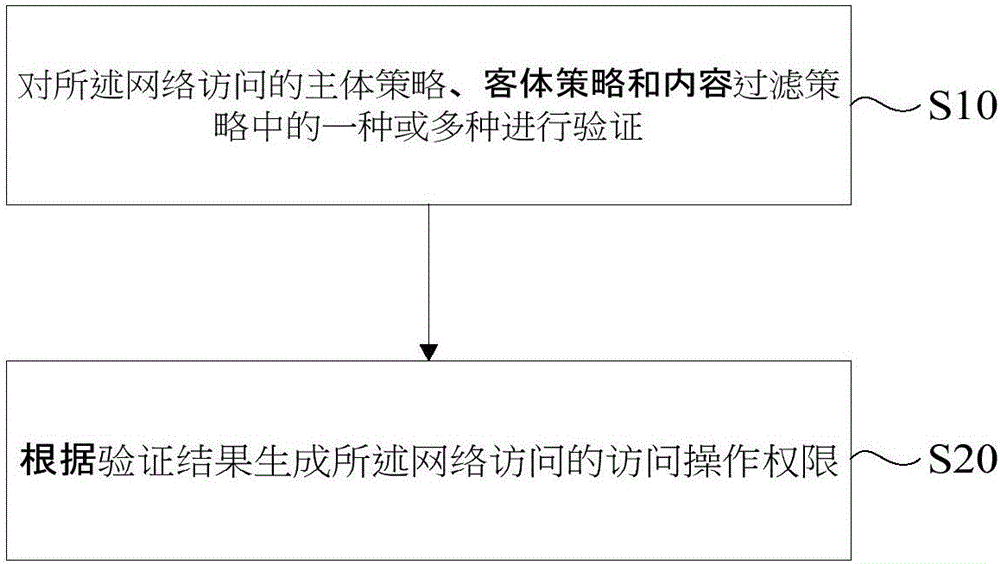
InactiveCN106067885AIncrease flexibilityHigh feasibilityTransmissionNetwork Access ControlAuthorization
The invention discloses an improved network access control method and a device. The method comprises the steps of verifying one or more policies out of a network access subject policy, a network access object policy and a content filtering policy; and generating the access operating authorization based on the above verification result. The network access subject policy comprises at least one or more factors out of the subject attribute, the subject authorization policy, the subject filtering policy and the conflict resolution policy. The network access object policy comprises at least one or more factors out of the object attribute and the object authorization policy. The content filtering policy comprises at least one or more factors out of the subject filtering policy and the object filtering policy. According to the embodiments of the network access control method and the device in the invention, the relation between users, the relation between a user and an object, the relation between objects and the attribute-based access control are integrated. Therefore, the method and the device are better in flexibility and implementation feasibility.
Owner:FOSHAN UNIVERSITY
System and method for evaluating a reverse query
Real-time techniques for determining all access requests to an attribute-based access control policy which evaluate to a given decision, “permit” or “deny”. The policy is enforced to control access to one or more resources in a computer network. In one embodiment, a method includes: (i) receiving a reverse query and a set of admissible access requests, each of which includes one or more attributes in the policy and values of these; (ii) extracting attributes to which all access requests in the set assign identical values; (iii) reducing the ABAC policy by substituting values for the extracted attributes; (iv) caching the policy as a simplified policy; (v) translating the simplified policy and the given decision into a satisfiable logic proposition; (vi) deriving all solutions satisfying the proposition; and (vi) extracting, based on the solutions, all access requests from the set for which the policy yields the given decision.
Owner:AXIOMATICS
System and method for evaluating a reverse query
Real-time techniques for determining all access requests to an attribute-based access control policy which evaluate to a given decision, “permit” or “deny”. The policy is enforced to control access to one or more resources in a computer network. In one embodiment, a method includes: (i) receiving a reverse query and a set of admissible access requests, each of which includes one or more attributes in the policy and values of these; (ii) extracting attributes to which all access requests in the set assign identical values; (iii) reducing the ABAC policy by substituting values for the extracted attributes; (iv) caching the policy as a simplified policy; (v) translating the simplified policy and the given decision into a satisfiable logic proposition; (vi) deriving all solutions satisfying the proposition; and (vi) extracting, based on the solutions, all access requests from the set for which the policy yields the given decision.
Owner:AXIOMATICS
An Access Control Method Based on Attribute Access Control Policy
The invention discloses an access control method based on an attribute-based access control policy. The method is characterized by 1) extracting attribute information of a user-role table and a role-authority table in a database and generating a user-role-authority access control relation Hash table; 2) generating an access control policy according to the access control relation Hash table: carrying out iteration traversal on the access control relation Hash table to obtain key value pairs, that is, an attribute set of each user and authority thereof, and then, generating an access control policy rule of the user according to the authority attribute of the user; and 3) for each received access request, an internet-of-thing search engine judging the access request according to the access control policy rule to determine whether access is allowed. The method can give a quick response to the search request, thereby greatly improving efficiency of the internet-of-thing search engine.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com