Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1309 results about "Request distribution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Request For Distribution. Following is/are the item (s) or service (s) for which a distribution is requested. A receipt, purchase order or like must be attached. If additional information is needed, requester will be notified.
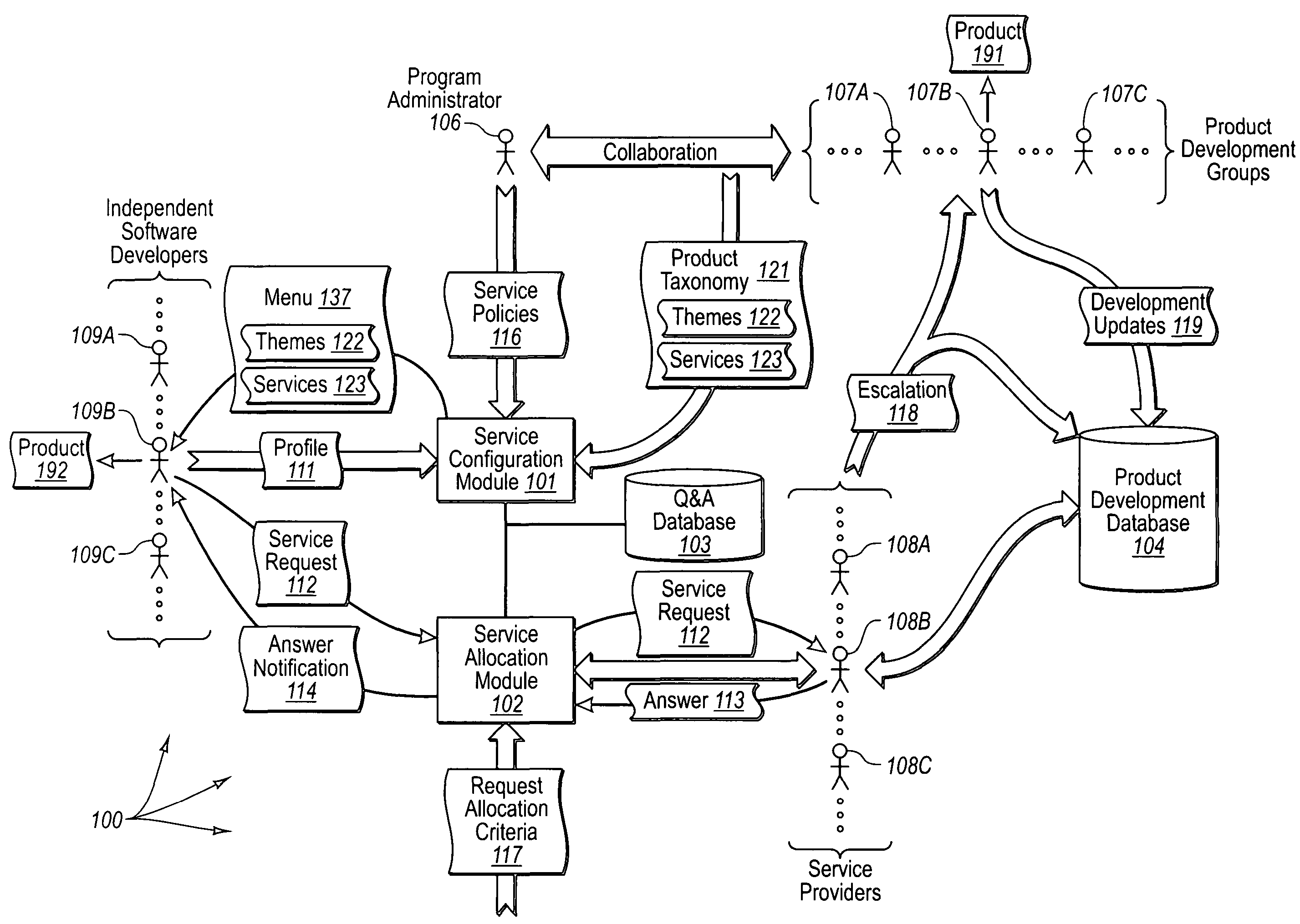
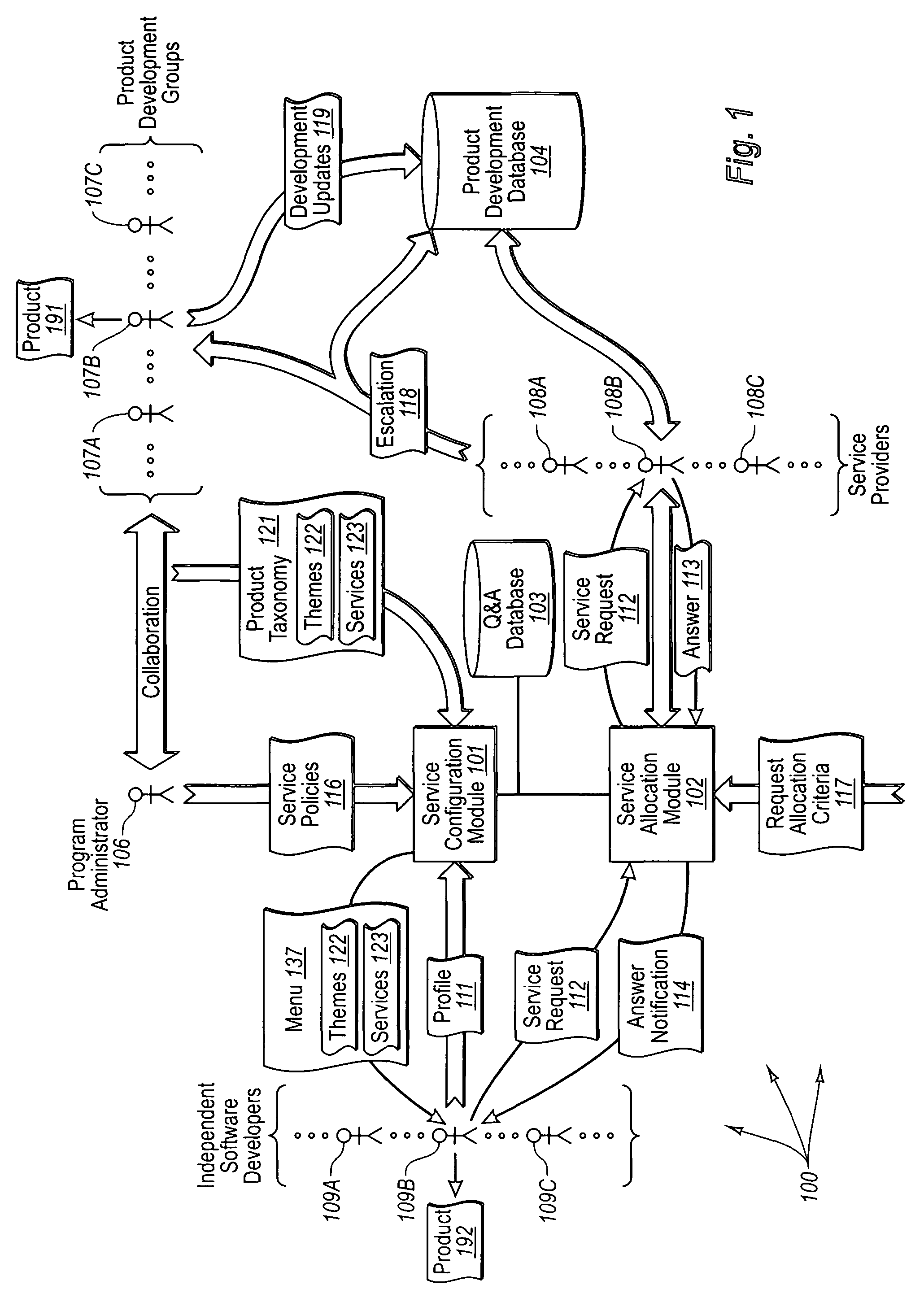
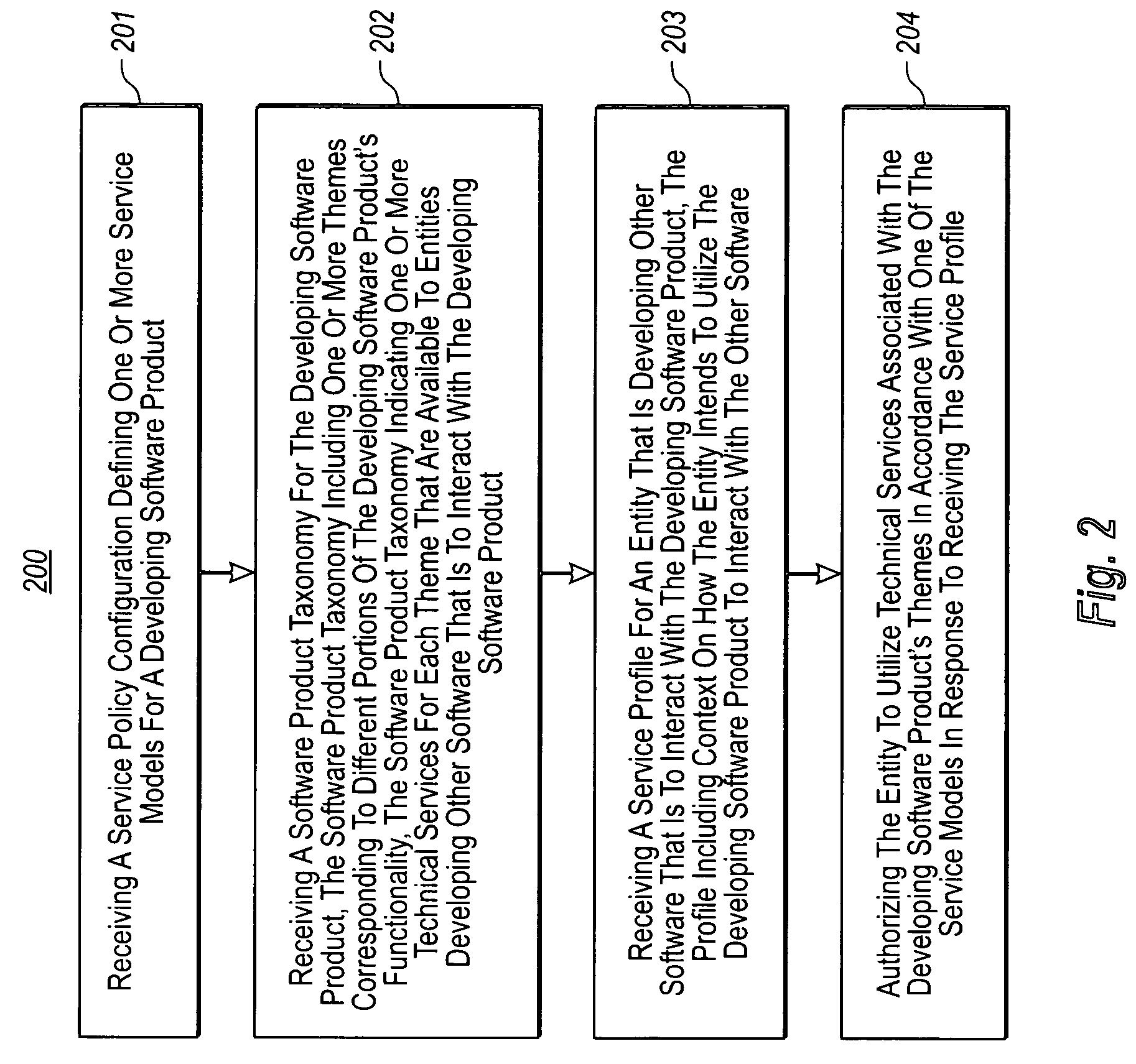
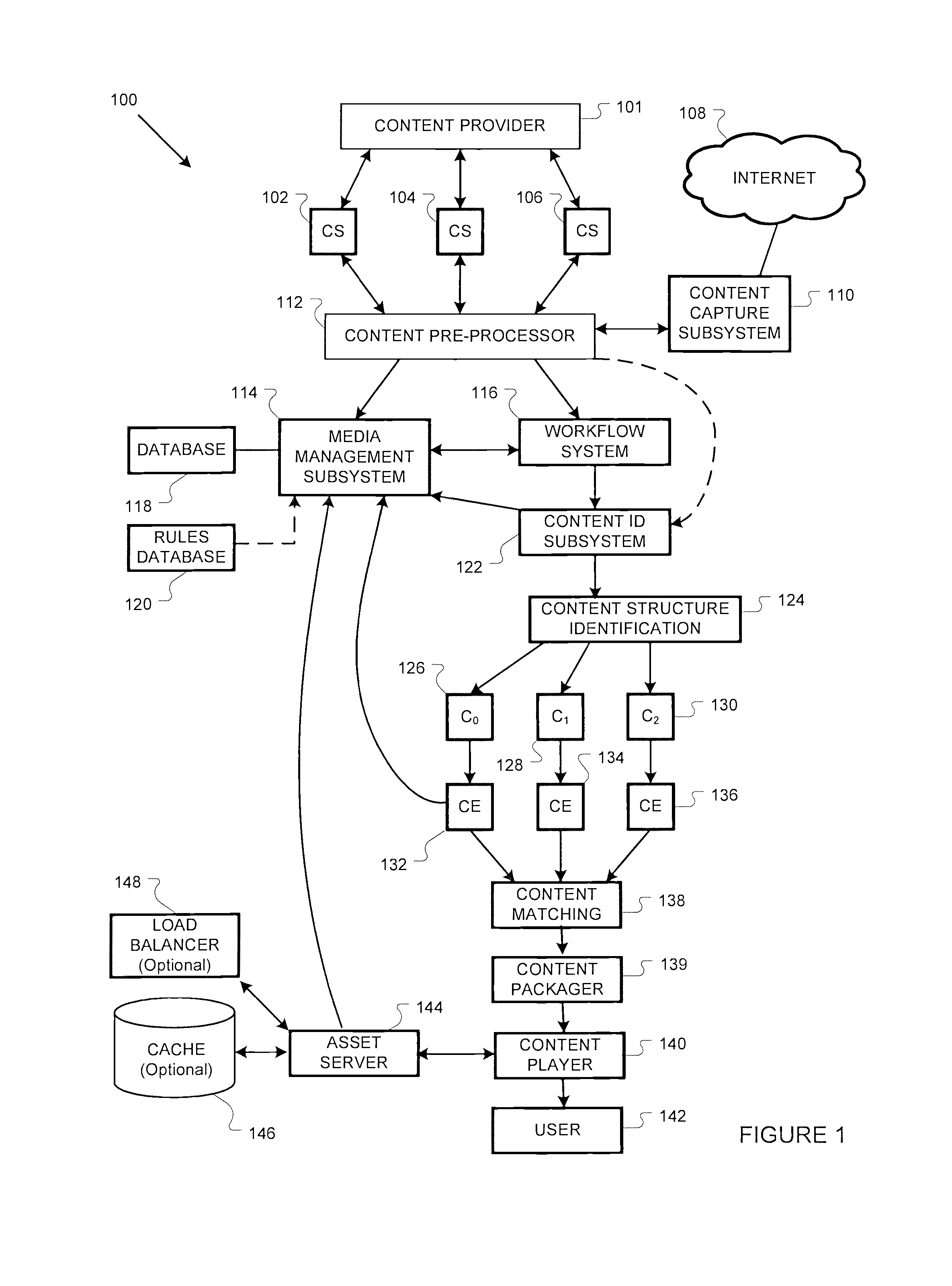
Configuring and allocating software product technical services
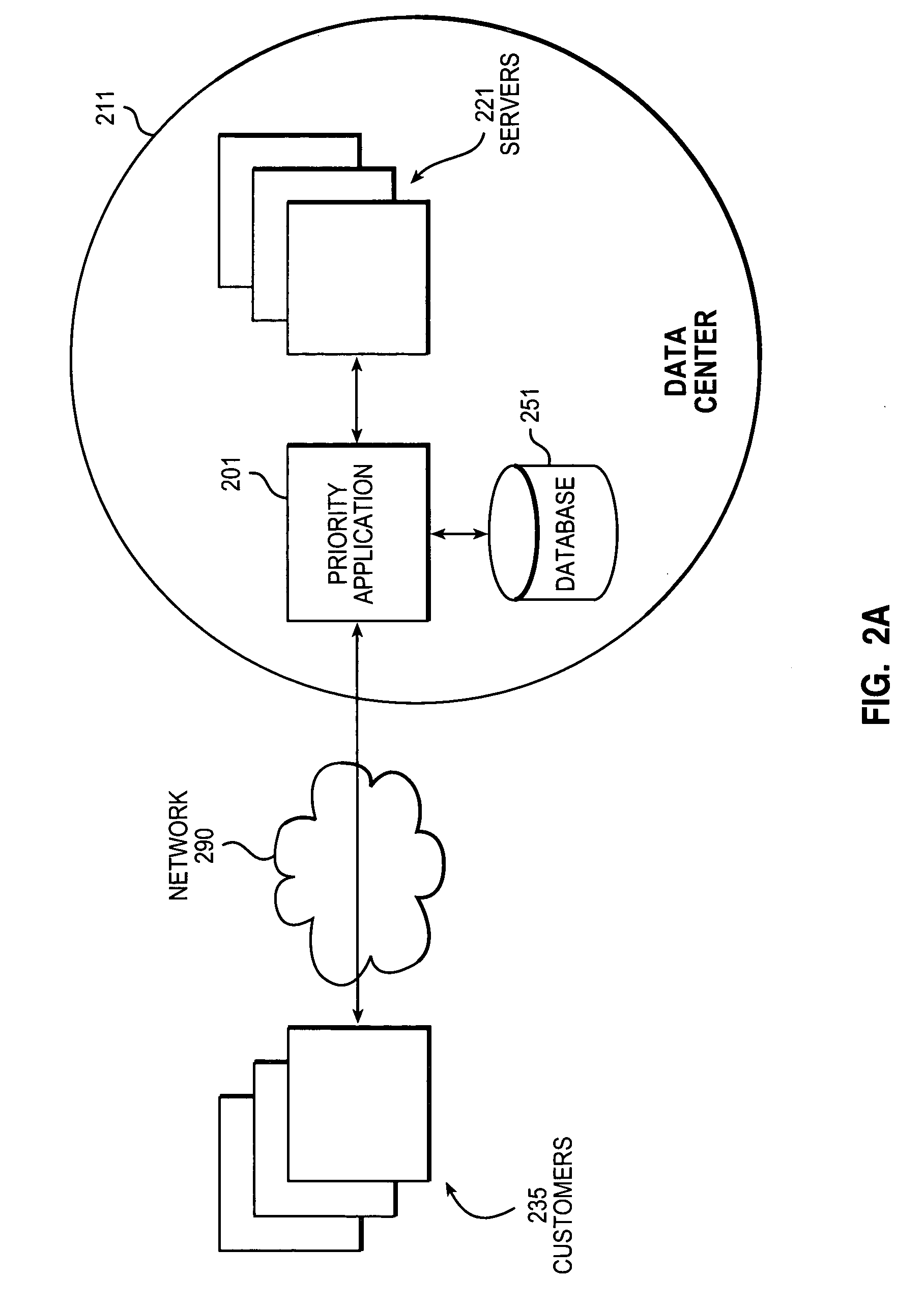
The present invention extends to methods, systems, and computer program products for configuring and allocating software product technical services. A service policy configuration defining one or more service models for the developing software product is received. A software product taxonomy, including one or more themes and corresponding technical services, for the developing software product is received. A service profile, including context on how the entity intends to utilize the developing software product, is received. The entity is authorized to utilize technical services associated with the developing software product in accordance with one of the service models in response to receiving the service profile. In other embodiments, a service request selection is made from a menu that lists themes and technical services associated with a software product. The service request is allocated to the identified service provider based on request allocation criteria. An entity is at least notified of a received answer.
Owner:MICROSOFT TECH LICENSING LLC
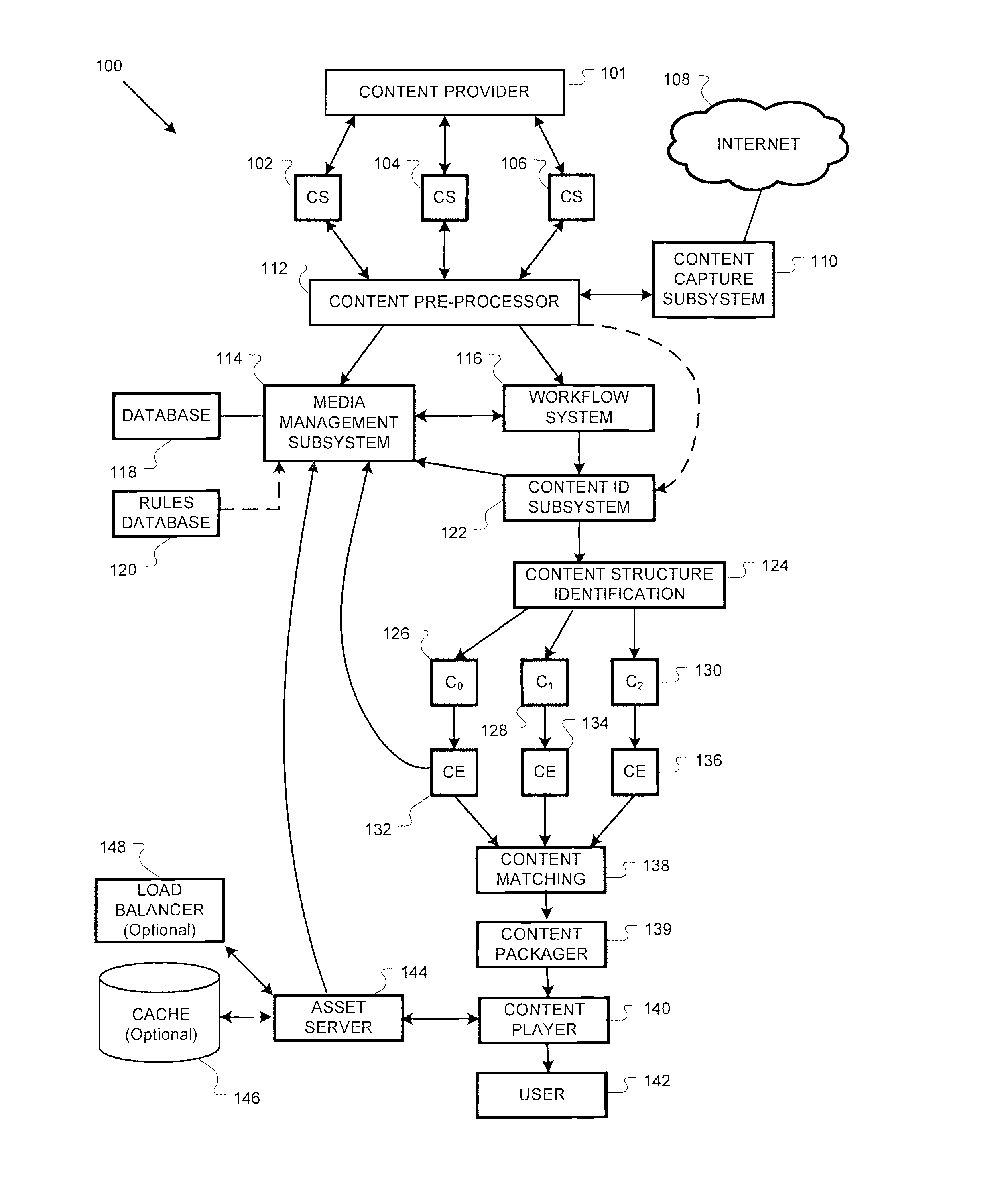
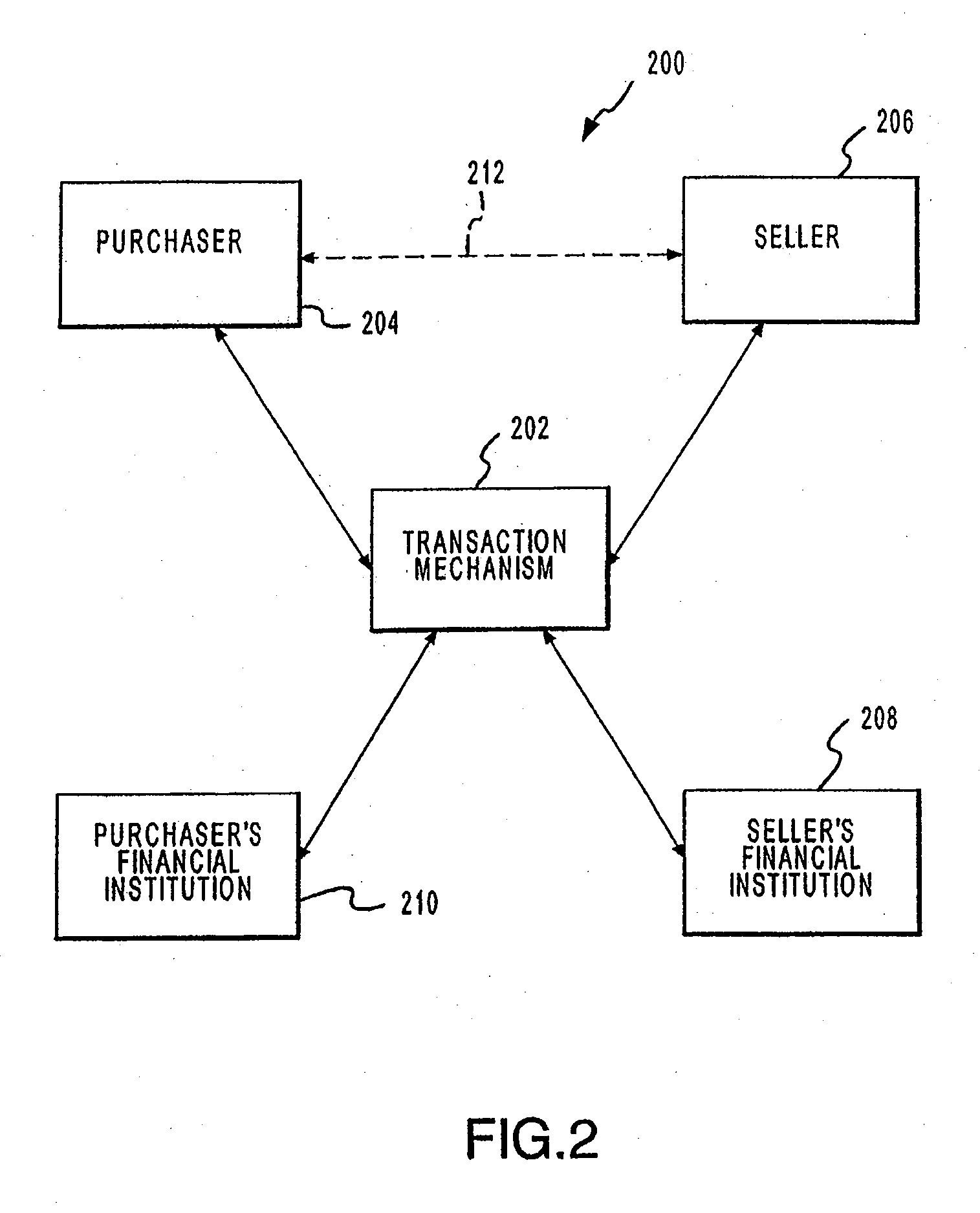
System and method for collecting and distributing content
InactiveUS20070288518A1Metadata multimedia retrievalSpecial data processing applicationsSystems approachesDistributor
A system method is provided for virally distributing content. One or more items of content may be received from a content provider, and the received content items may be packaging in a container. At least one of the packaged content items may be a viral content item associated with a mashing option, where the container of packaged content may be distributed to a distributor. The packaged content may be presented by the distributor using a player application, which displays the mashing option when playing the viral content. The viral content may then be distributed to a user when the user selects the displayed mashing option, wherein additional users can request distribution of the viral content from the distributor or the user by selecting the mashing option.
Owner:VOXANT
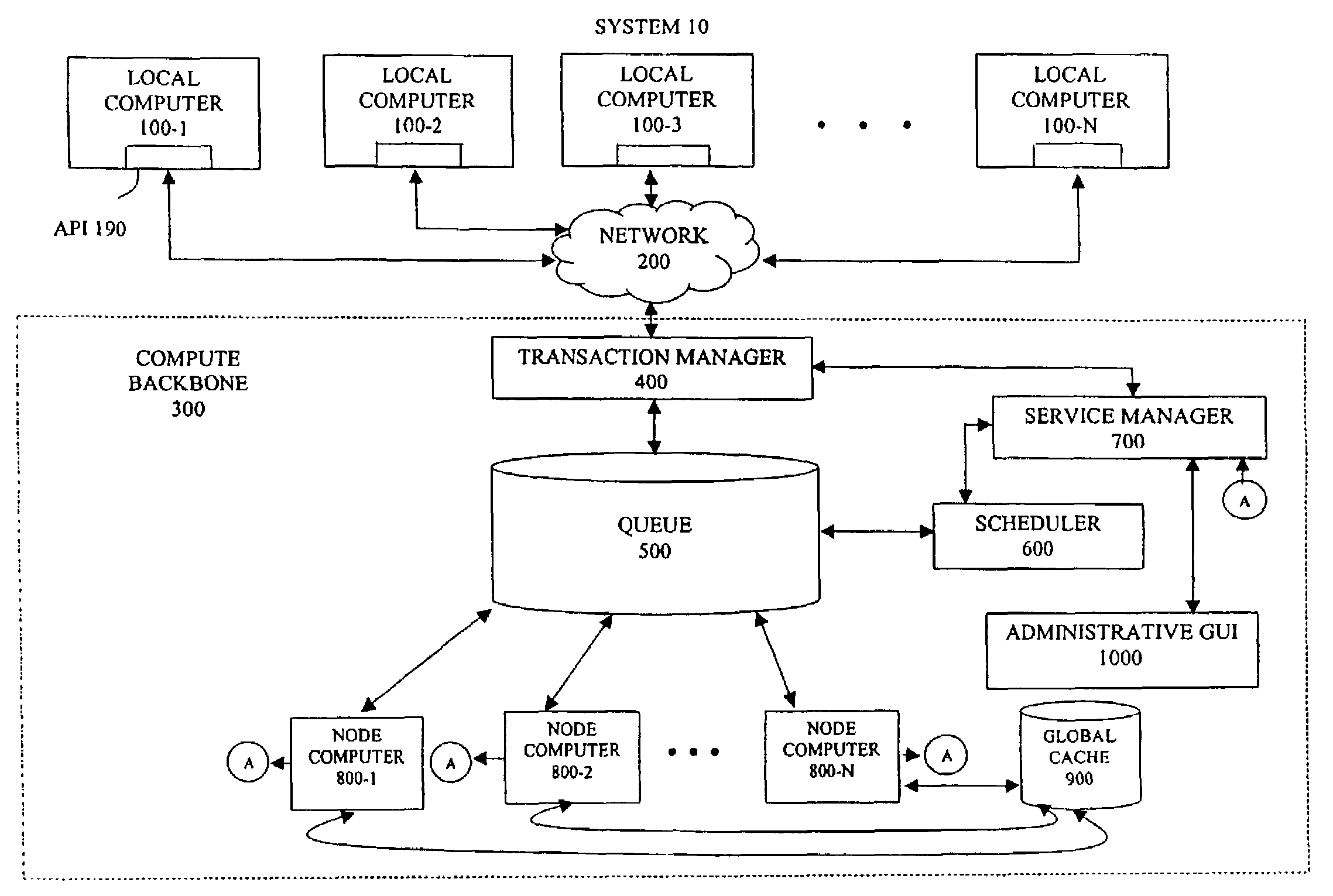
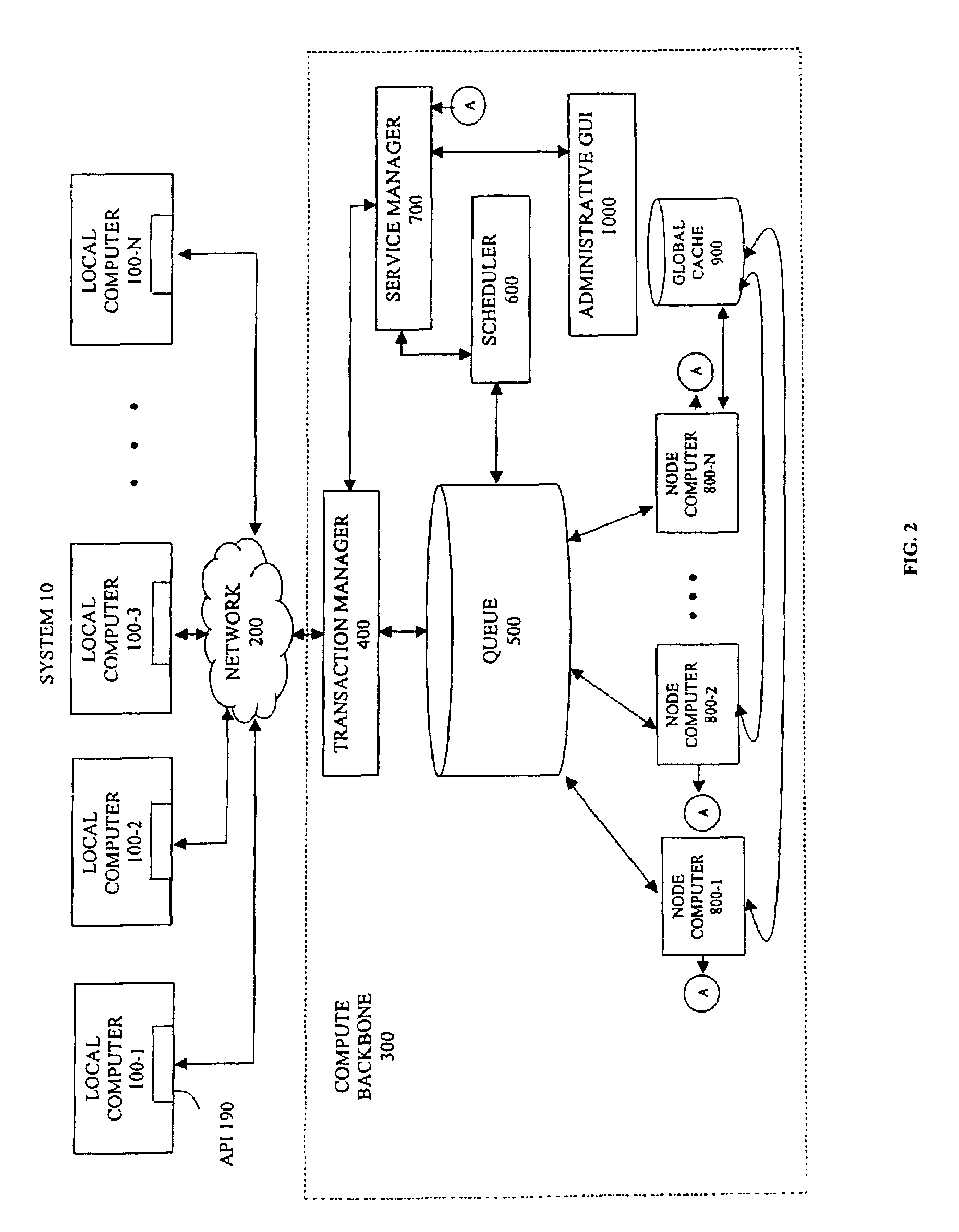
System and method for allocating computing resources of a distributed computing system
In certain aspects, the invention features a system and method for (1) receiving reservations for a first subset of computing resources of a distributed computing system (DCS), wherein each of the reservations specifies a time period, (2) allocating the first subset according to the reservations, (3) receiving requests for use of at least a second subset of the DCS's computing resources, wherein each of the requests specifies a time period, (4) determining whether enough unallocated resources are available to fulfill all of the requests, wherein the unallocated resources include the DCS's resources not allocated according to the reservations, (5) allocating resources according to the requests, if there are enough unallocated resources available, and (6) allocating resources in accordance with an allocation criteria if there are not enough unallocated resources available.
Owner:JPMORGAN CHASE BANK NA
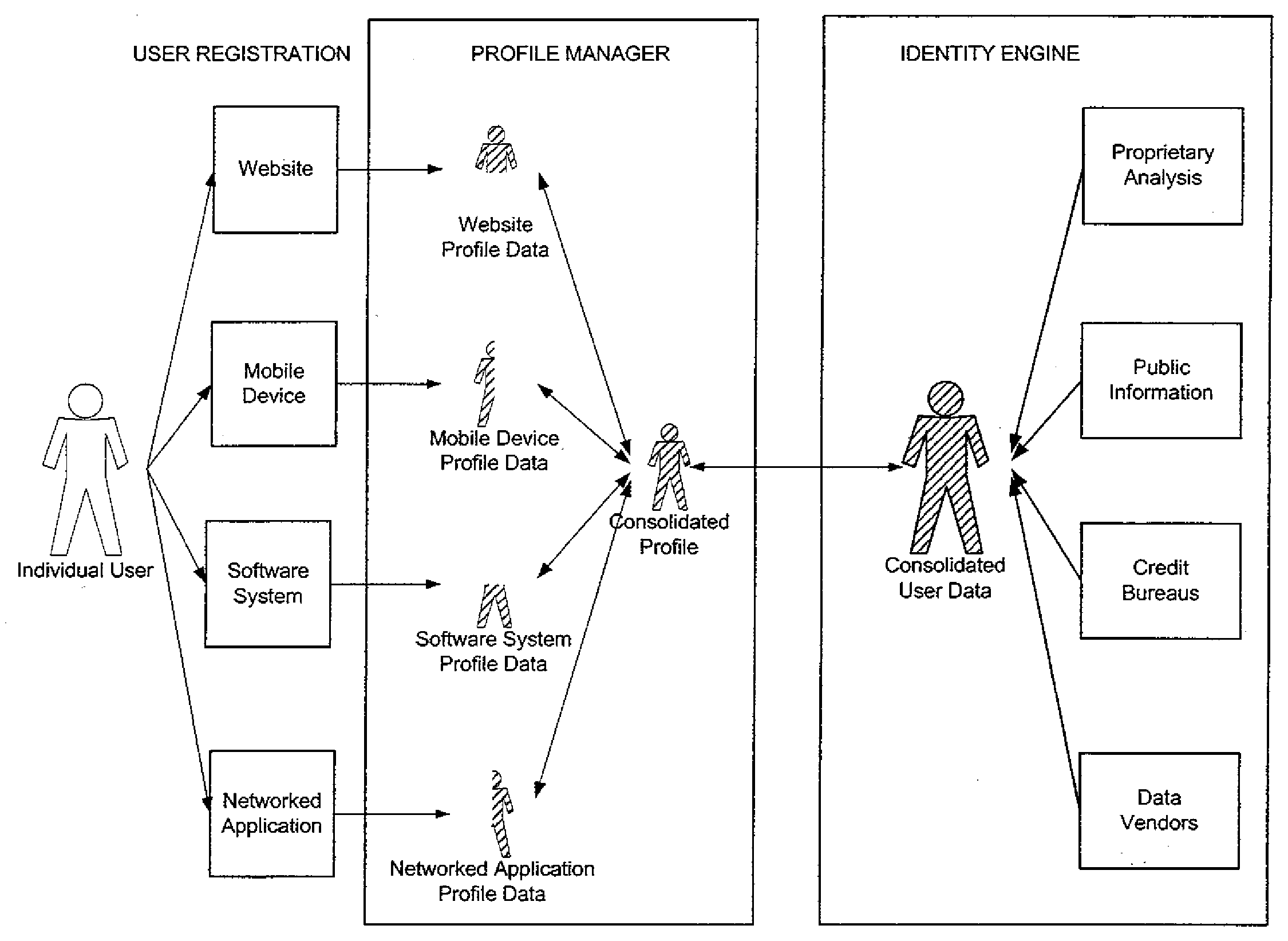
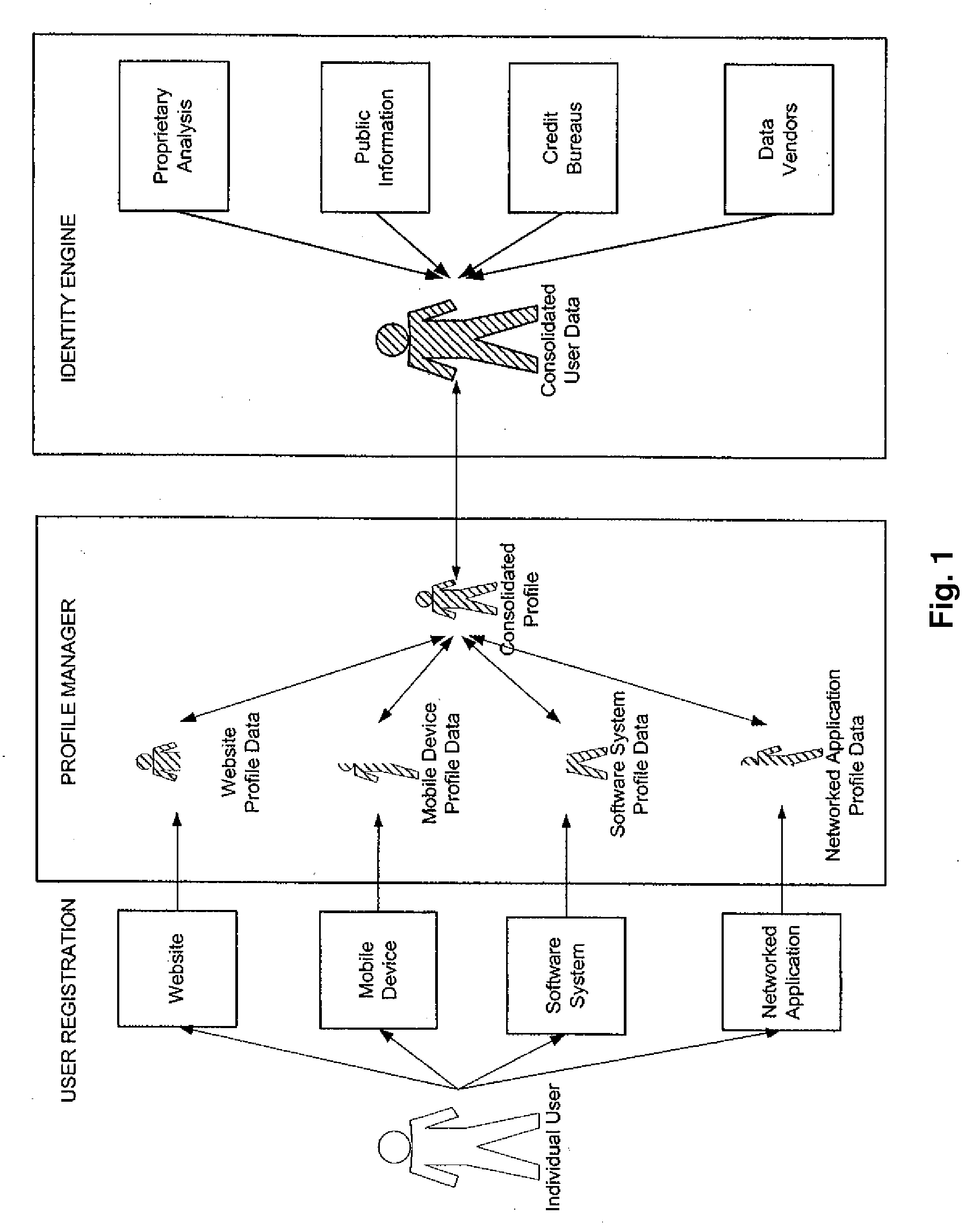
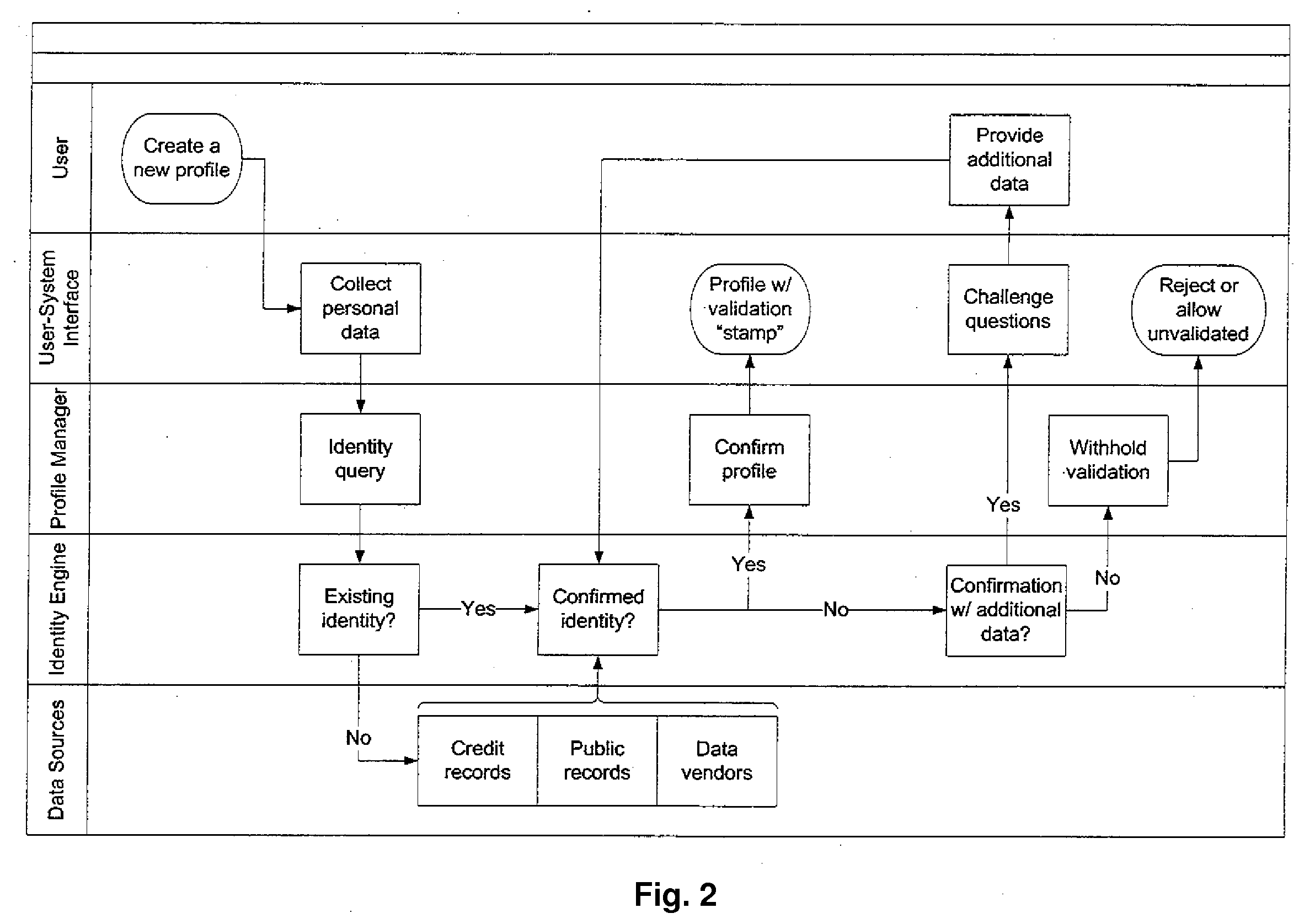
Online Identity Management and Identity Verification
InactiveUS20090119299A1Digital data information retrievalDigital data processing detailsInternet privacyUser authentication
A user identity verification apparatus and method comprising, via one or more processors, collecting in a computer database consolidated user data comprising information about a method user from a plurality of sources comprising credit bureau information, information from data vendors, and public information, generating a profile of the method user comprising a plurality of subsets of the consolidated user data corresponding to a plurality of access levels, receiving a validation request from a third party source at an unknown user's request; assigning an access level to the validation request; requesting information from the unknown user, matching returned information from the unknown user to that in the subset of the consolidated user data corresponding to the assigned access level, and verifying to the third party source that the unknown user is the method user.
Owner:RHODES HUE
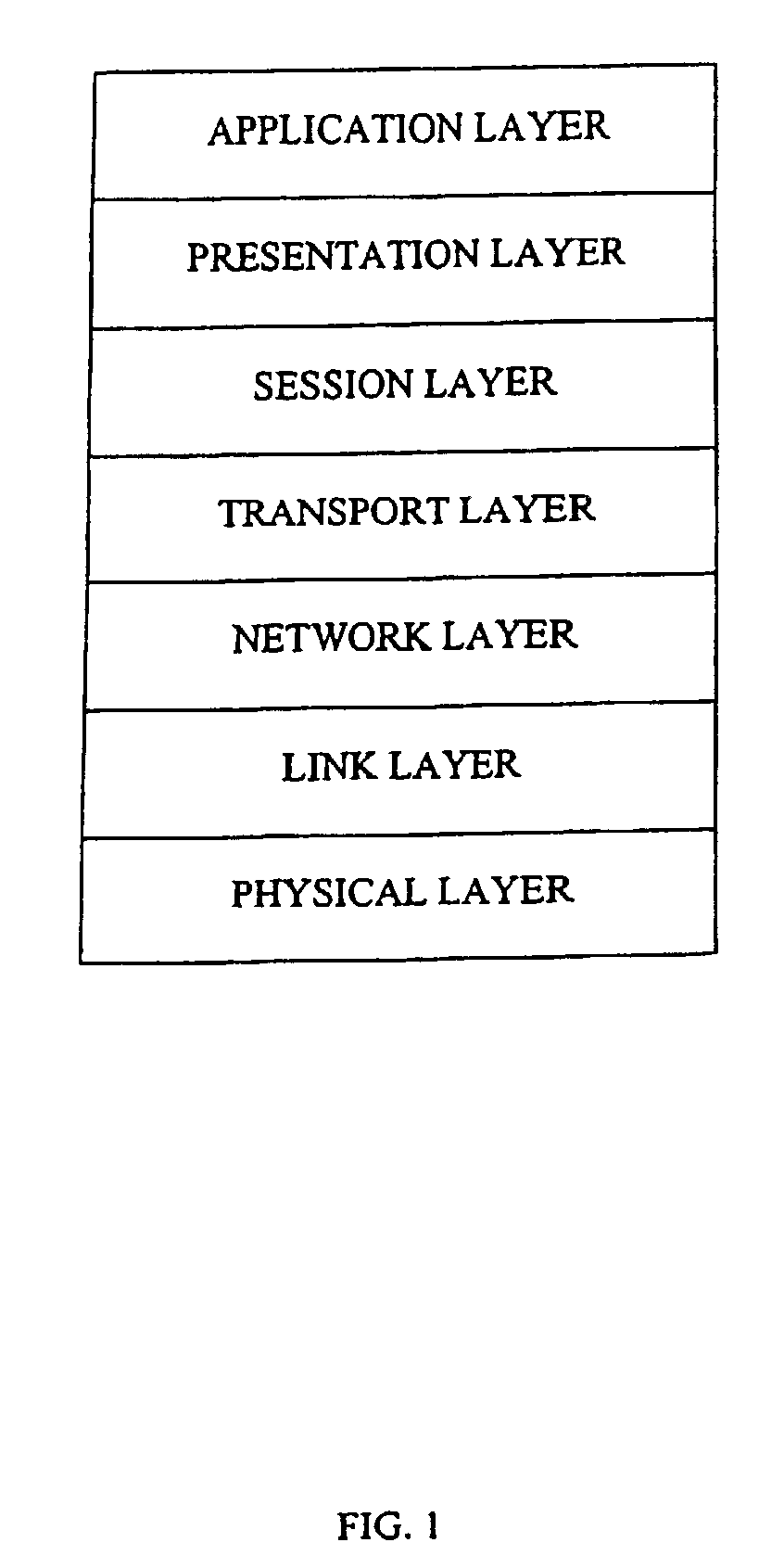
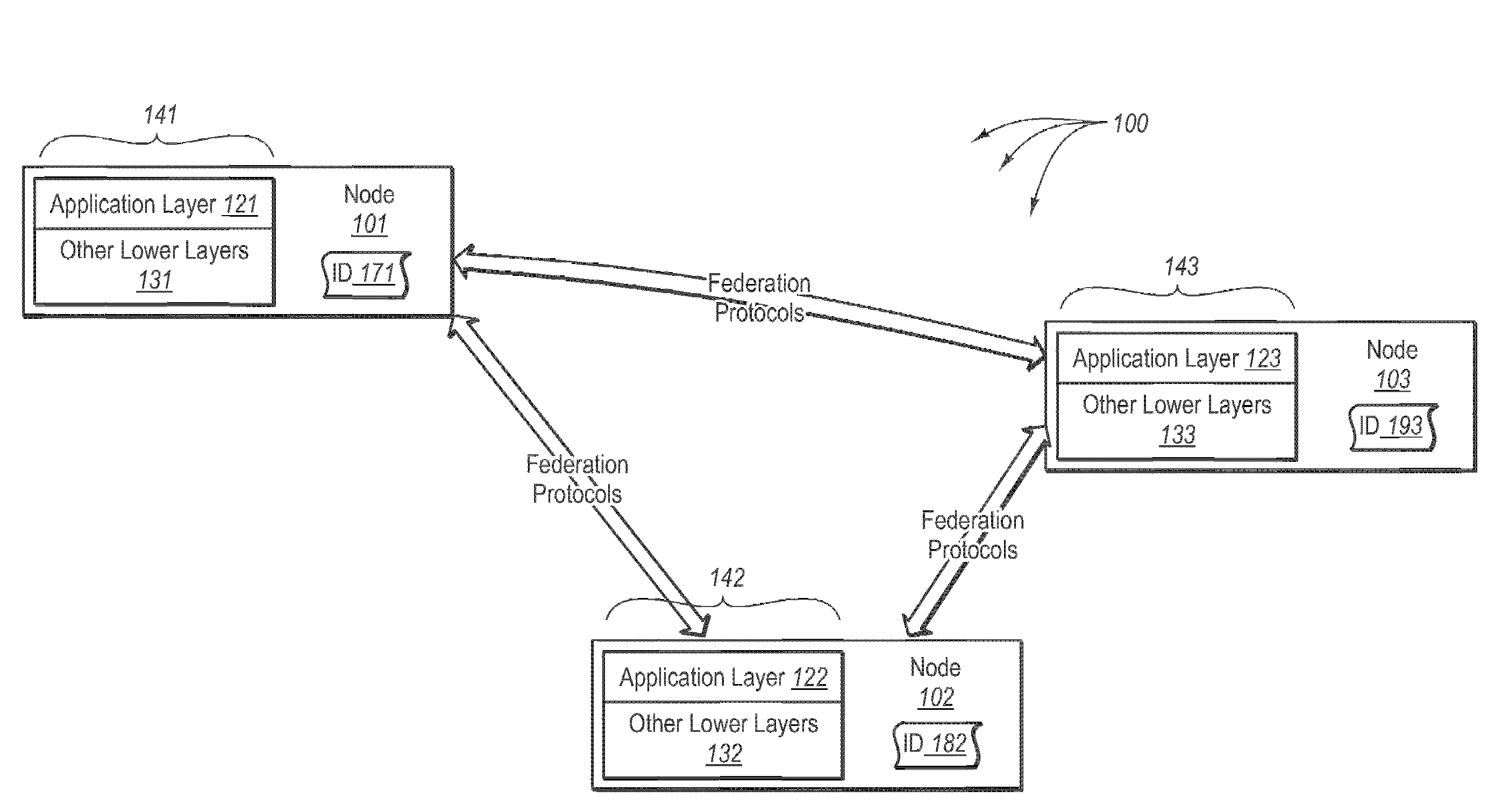
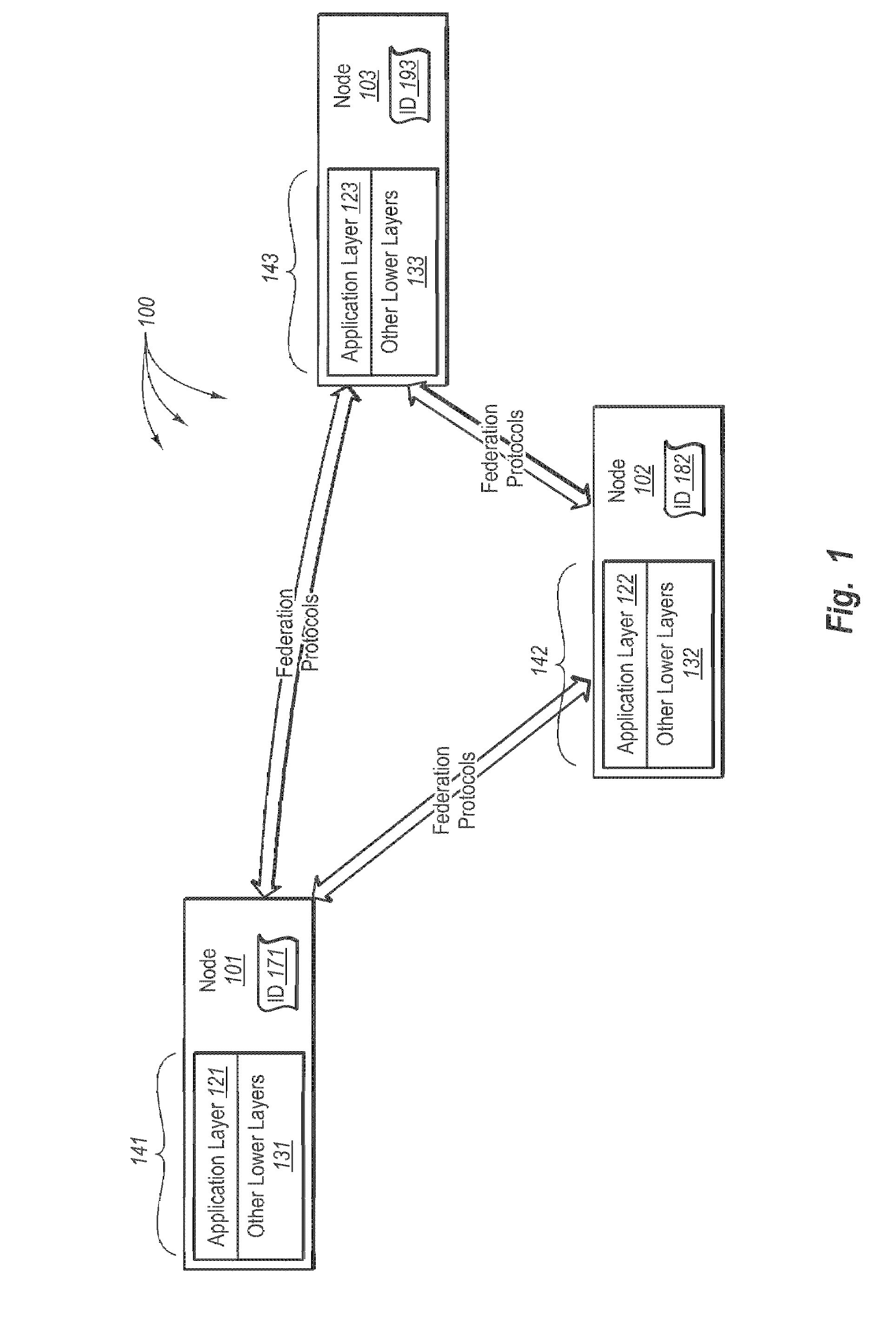
Data consistency within a federation infrastructure
InactiveUS20080288646A1Well formedDigital data information retrievalInput/output to record carriersClient dataClient-side
In some embodiments, it is determined that a primary node has been elected from among a plurality of nodes in a replica set of nodes. The primary node accepts and processes client data access requests. The replica set includes the primary node and other secondary nodes. The primary node receives client data access requests. The primary node assigns a data sequence number to each client data access request that mutates state in the order the client data access requests are received. The data sequence numbers include a linearized processing order that is to be followed by each of the nodes in the replica set. The primary node sends the mutating client data access requests including any corresponding data sequence numbers to the secondary nodes. The primary node receives, from a threshold number of secondary nodes, an acknowledgement indicating reception of the client data access request. The primary node commits the data mutating access request.
Owner:MICROSOFT TECH LICENSING LLC
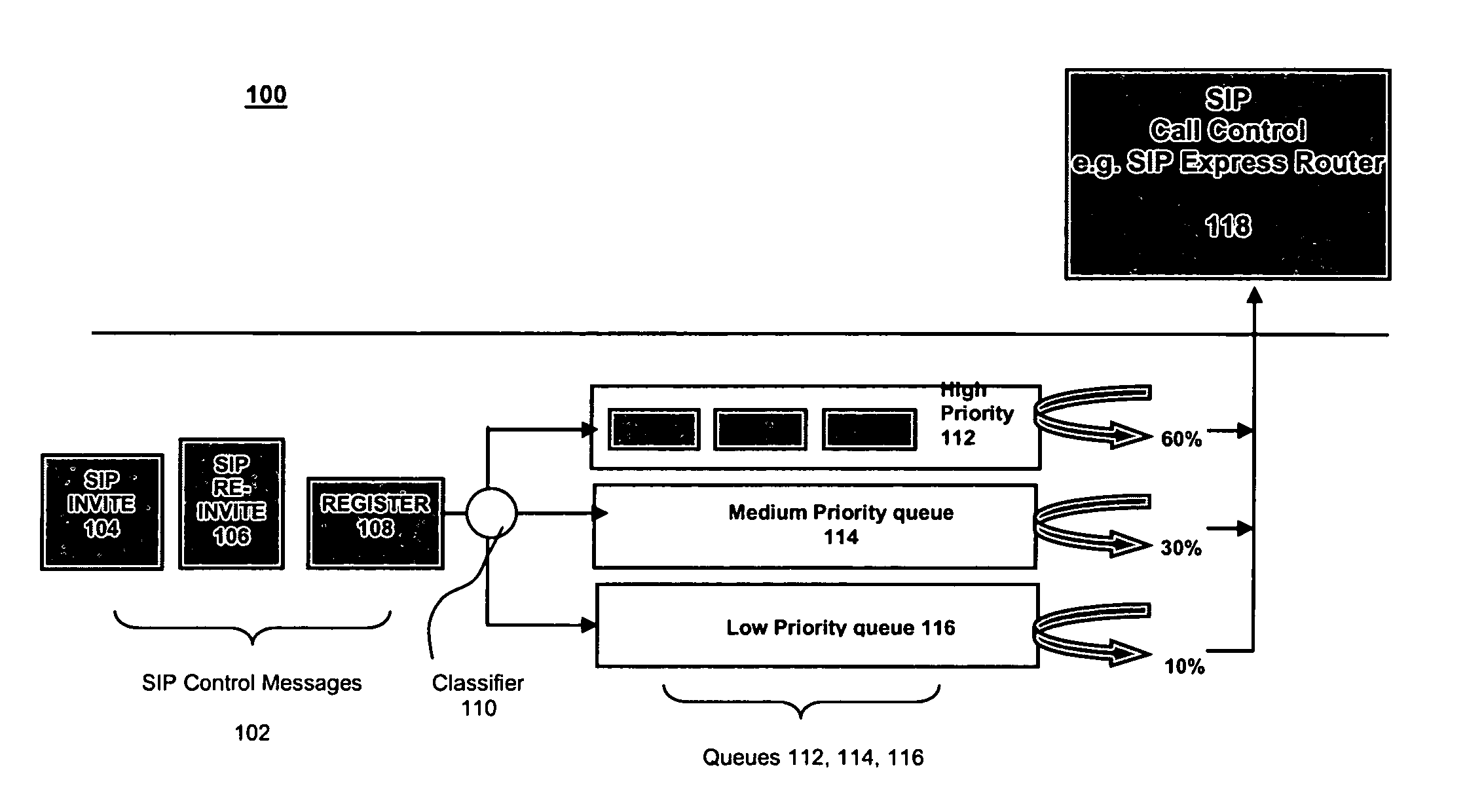
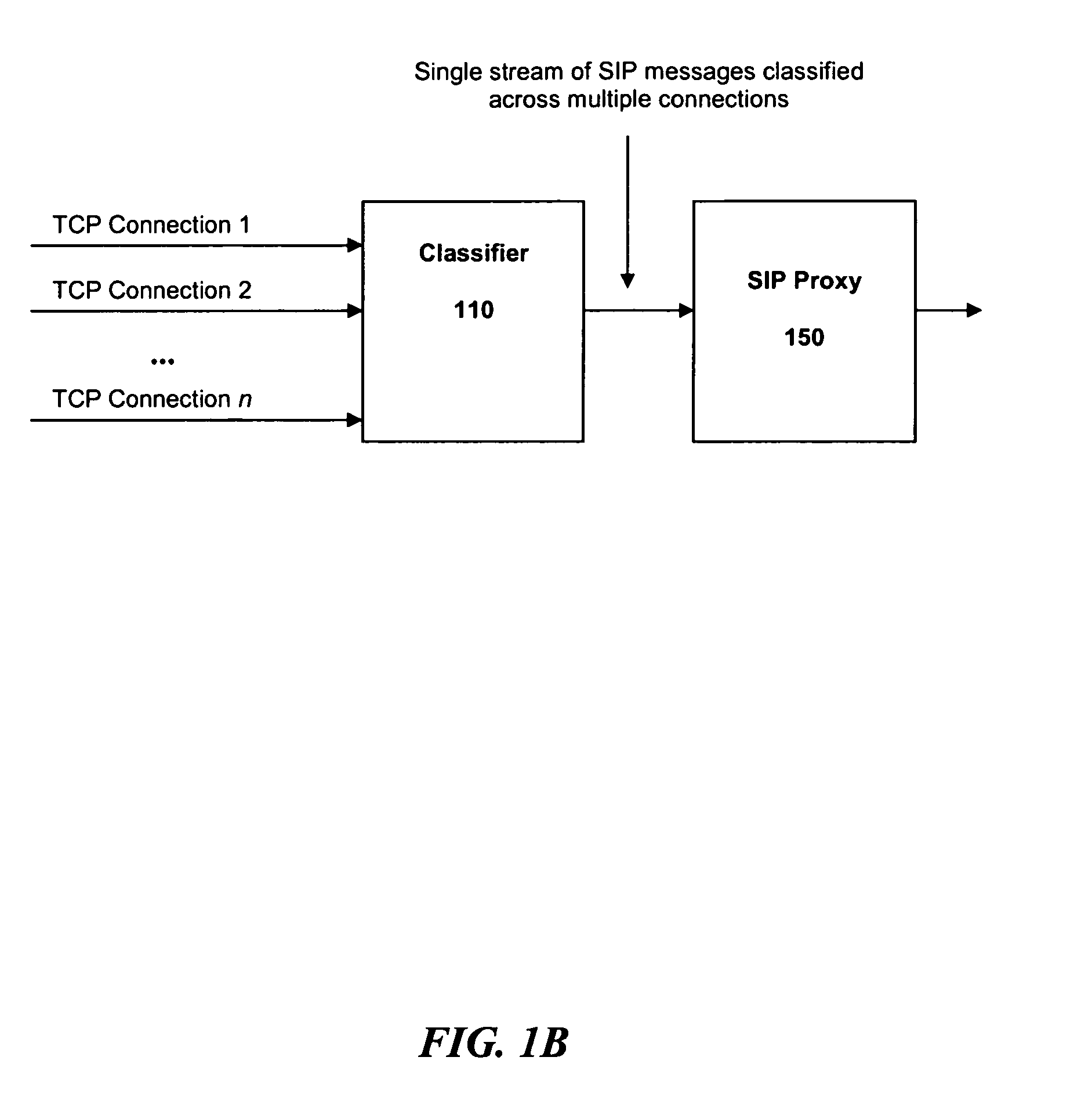
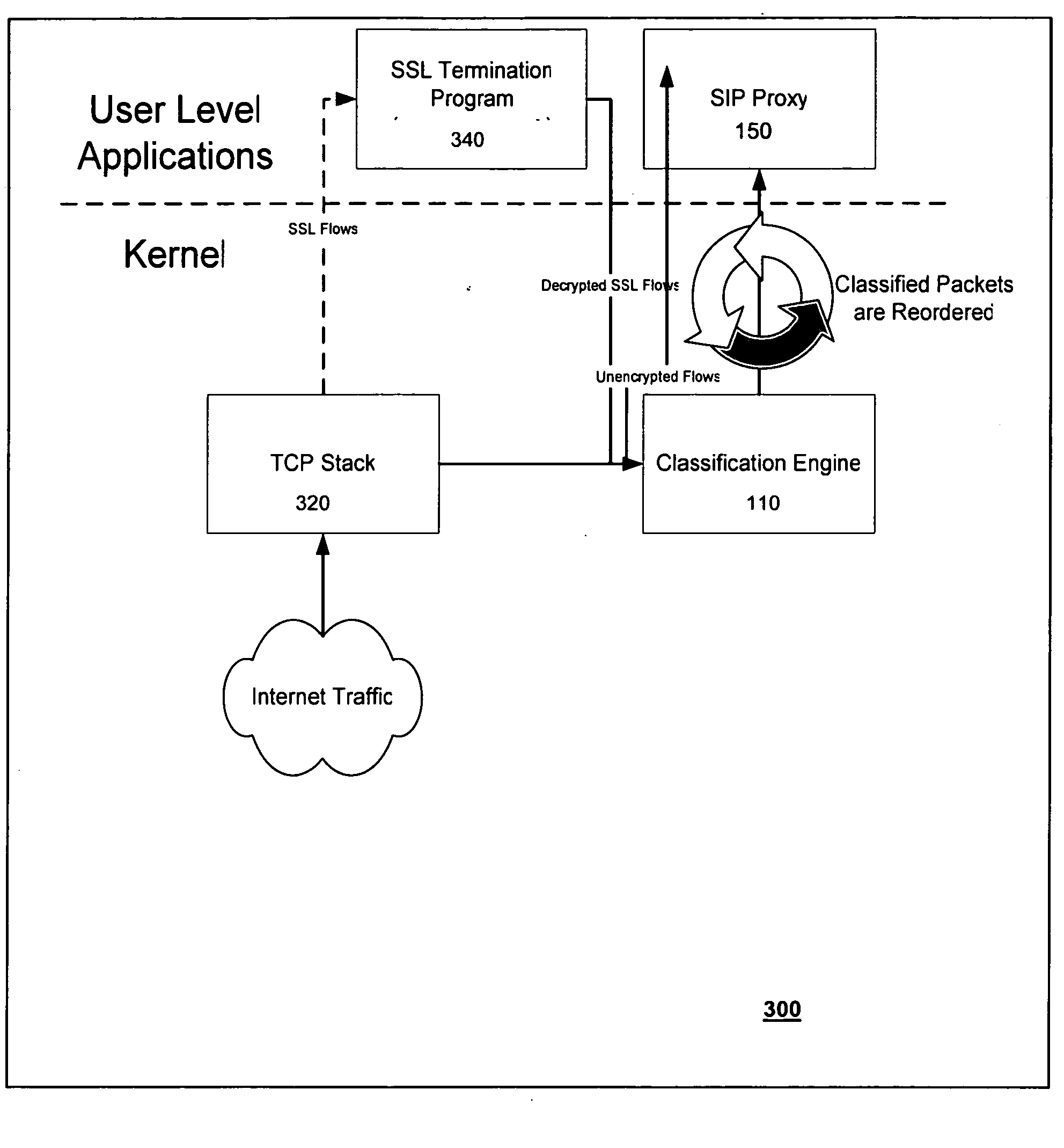
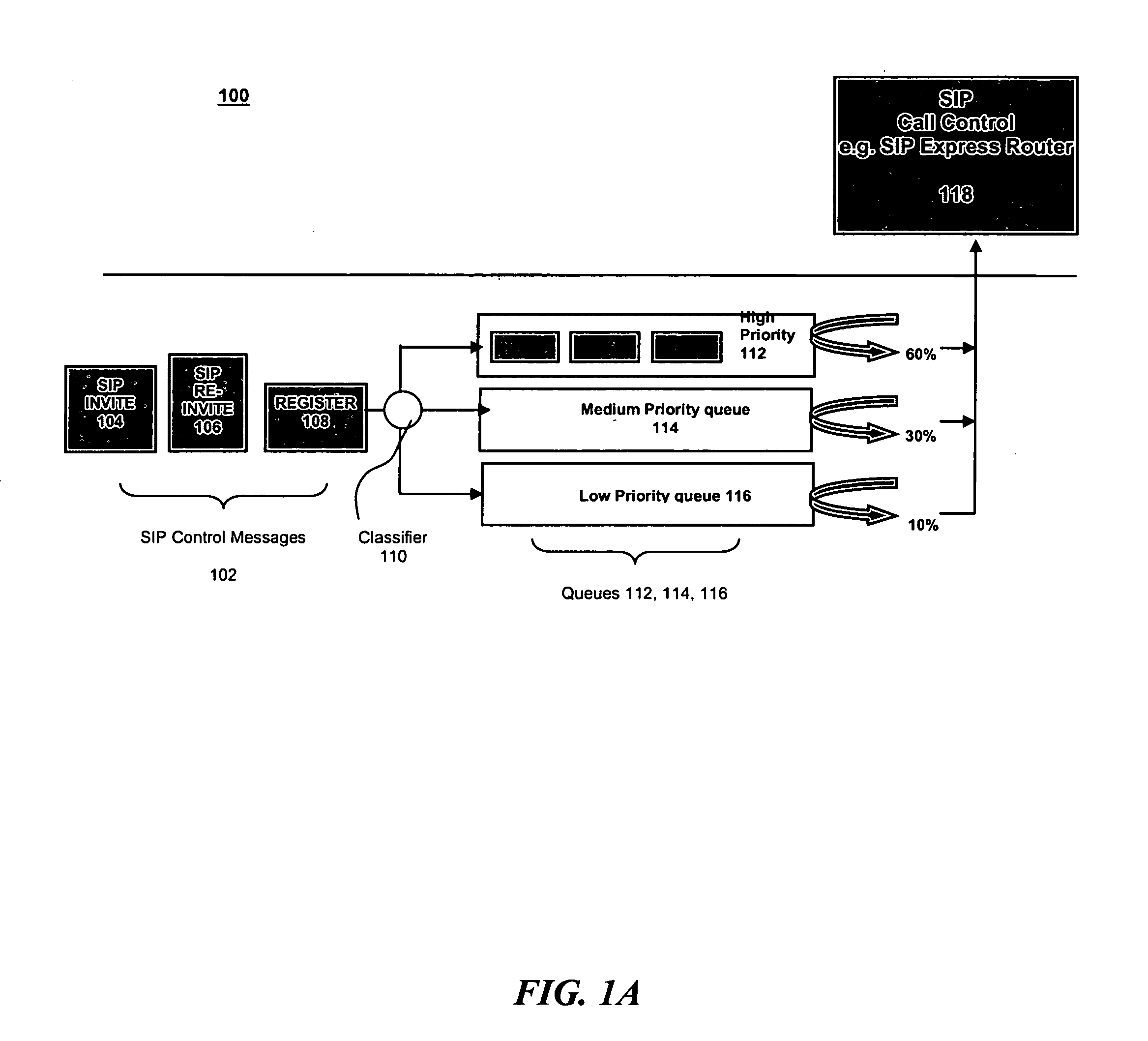
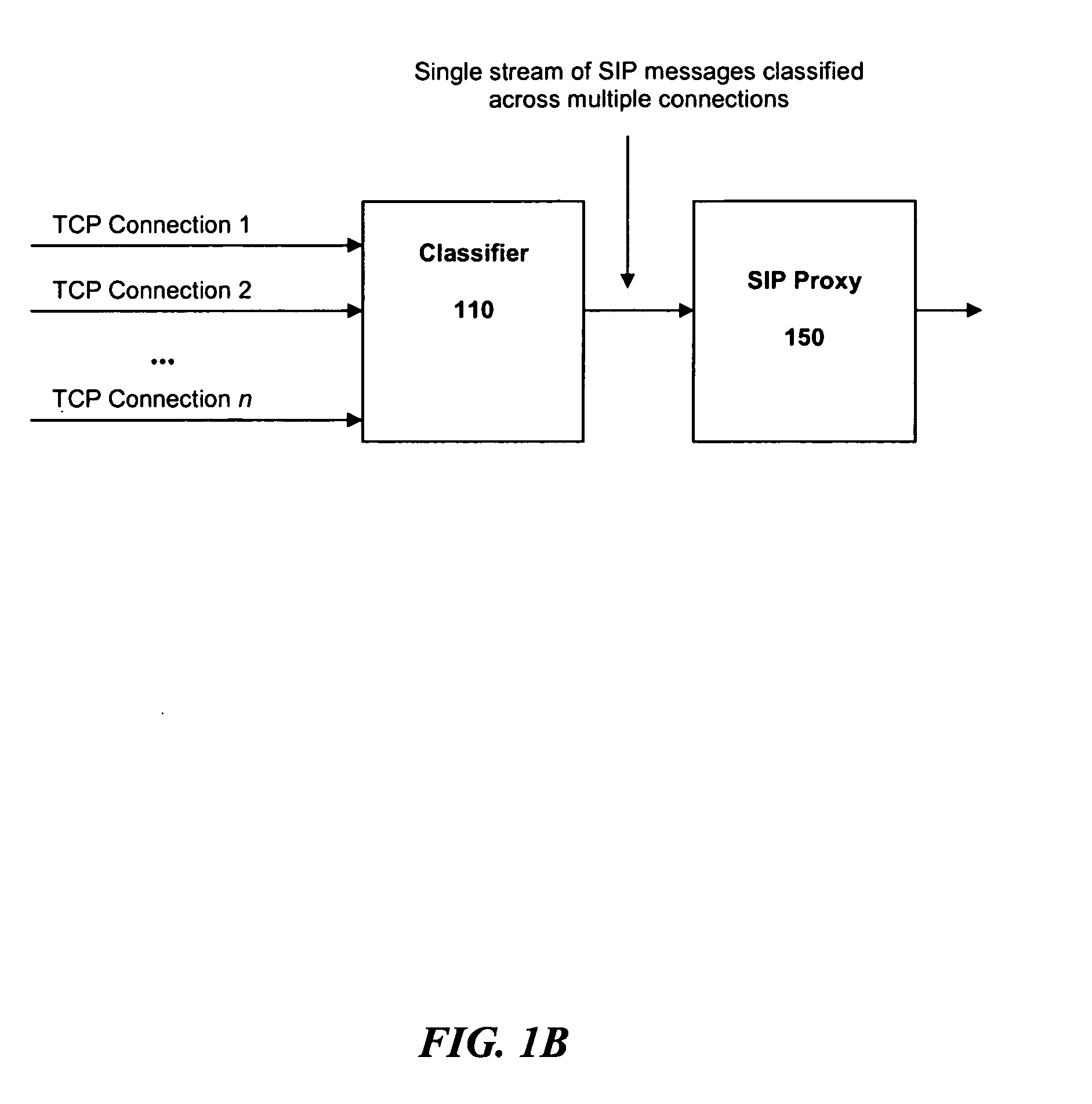
Overload protection for SIP servers
InactiveUS7522581B2Data switching by path configurationNetwork connectionsComputer scienceDistributed computing
A method for operating a server having a maximum capacity for servicing requests comprises the following steps: receiving a plurality of requests; classifying each request according to a value; determining a priority for handling the request according to the value, such that requests with higher values are assigned higher priorities; placing each request in one of multiple queues according to its priority value; and dropping the requests with the lowest priority when the plurality of requests are received at a rate that exceeds the maximum capacity. The server operates according to a session initiation protocol.Classifying each request comprises running a classification algorithm. The classification algorithm comprising steps of: receiving a rule set, each rule comprising headers and conditions; creating a condition table by taking a union of all conditions in the rules; creating a header table by extracting a common set of headers from the condition table; extracting the relevant headers from the header table; determining a matching rule; creating a bit vector table; selecting the matching rule according to data in the bit vector table; and applying the rule to place the message in the appropriate queue.
Owner:INT BUSINESS MASCH CORP
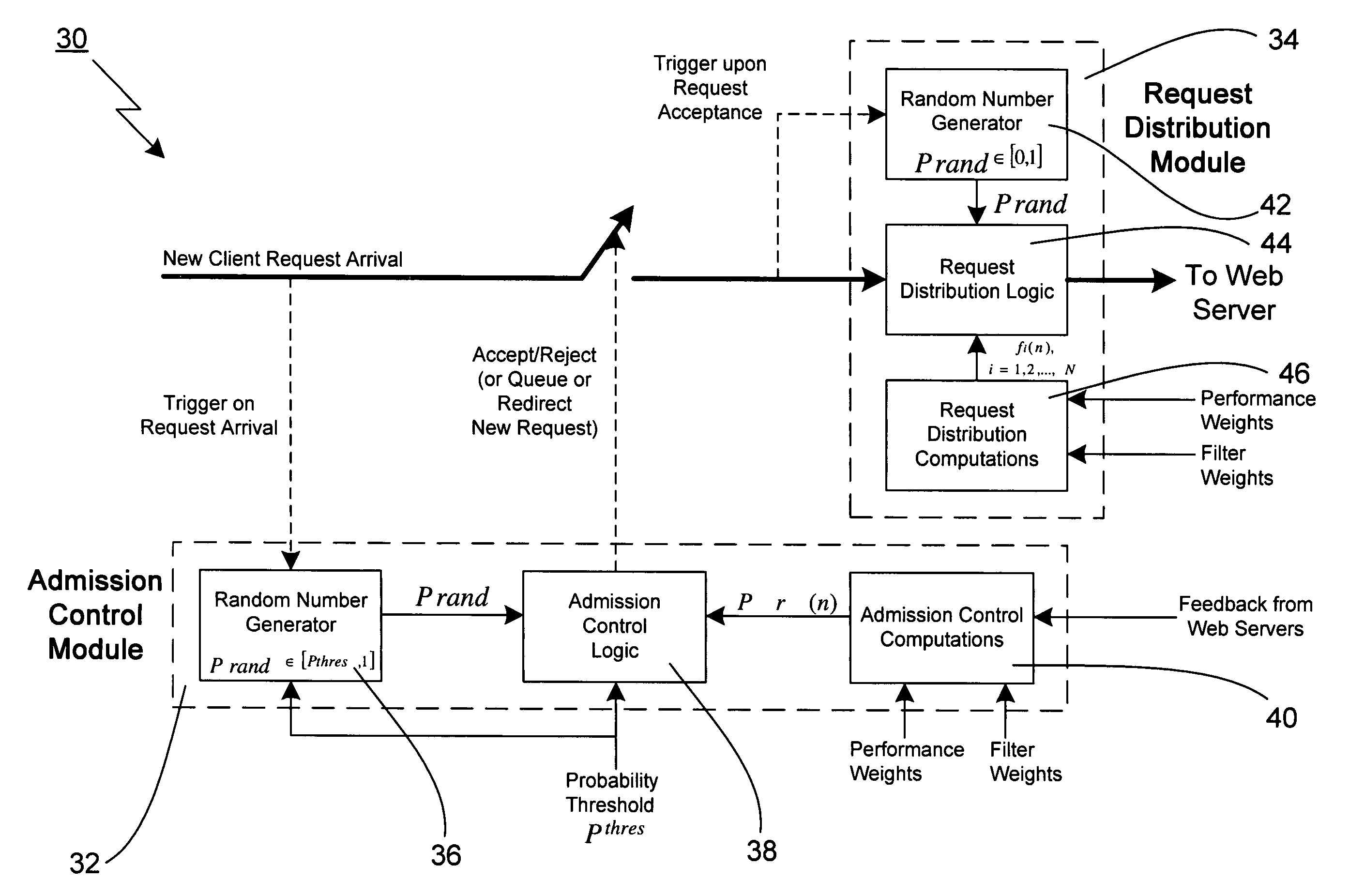
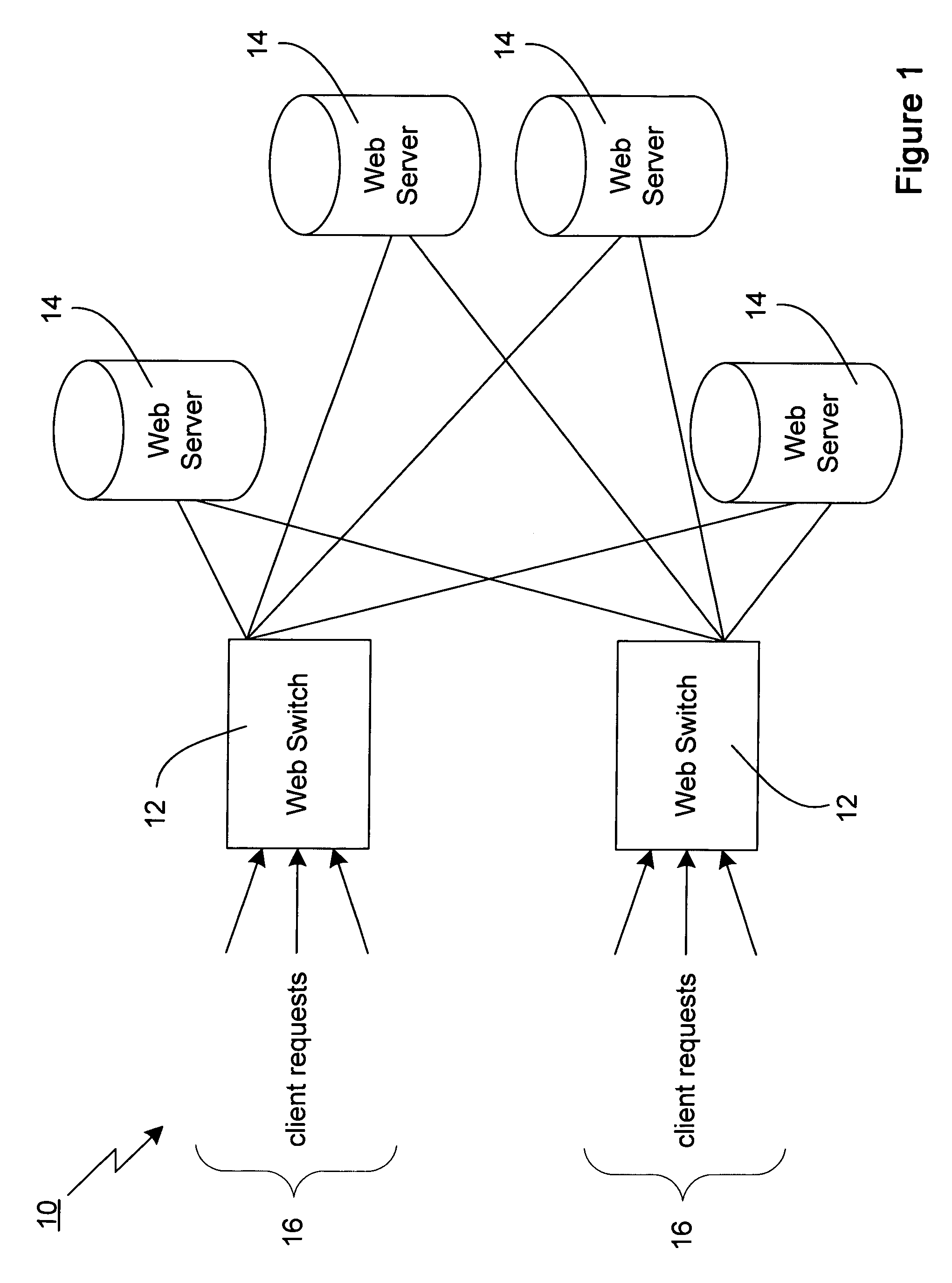
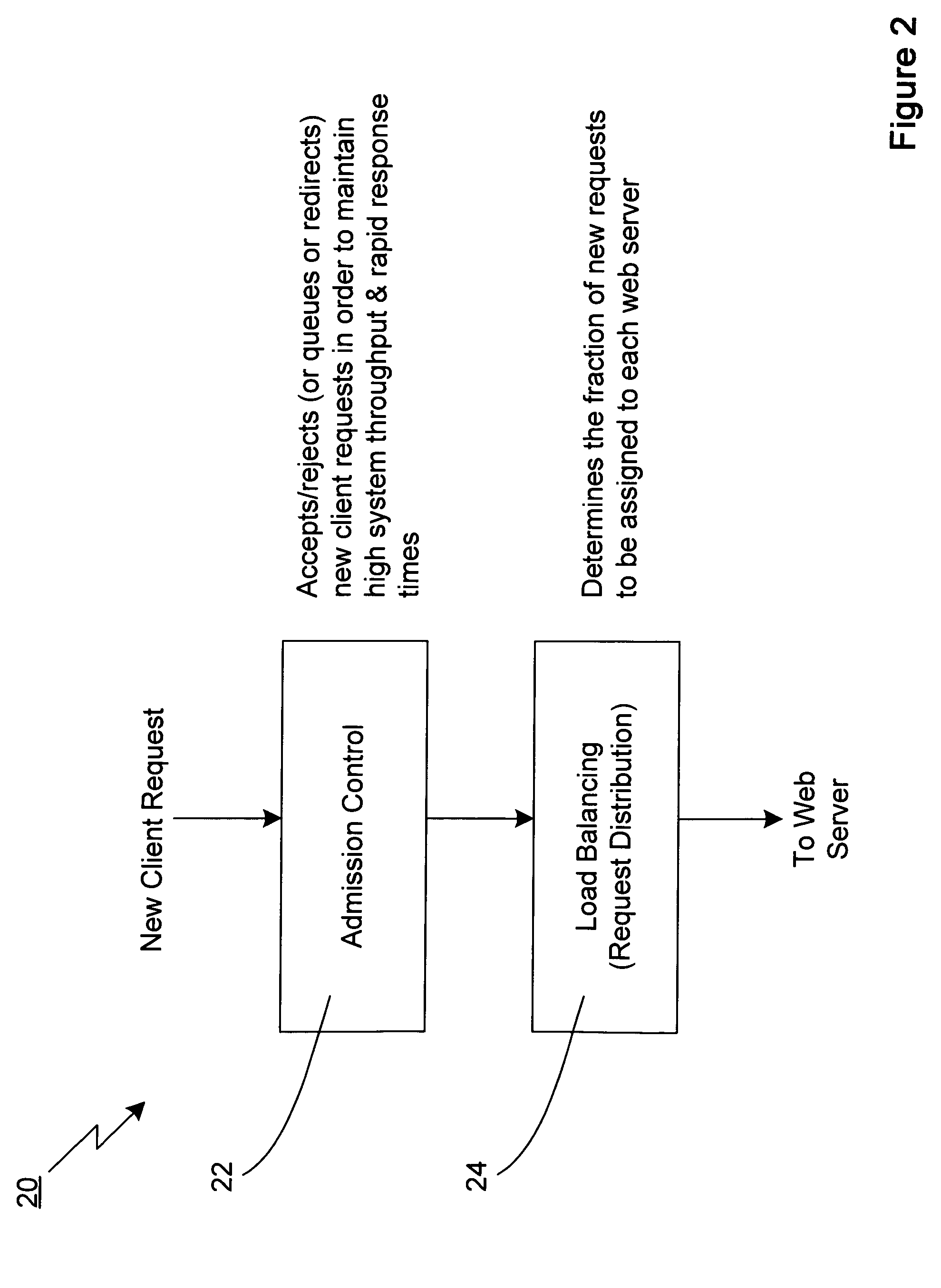
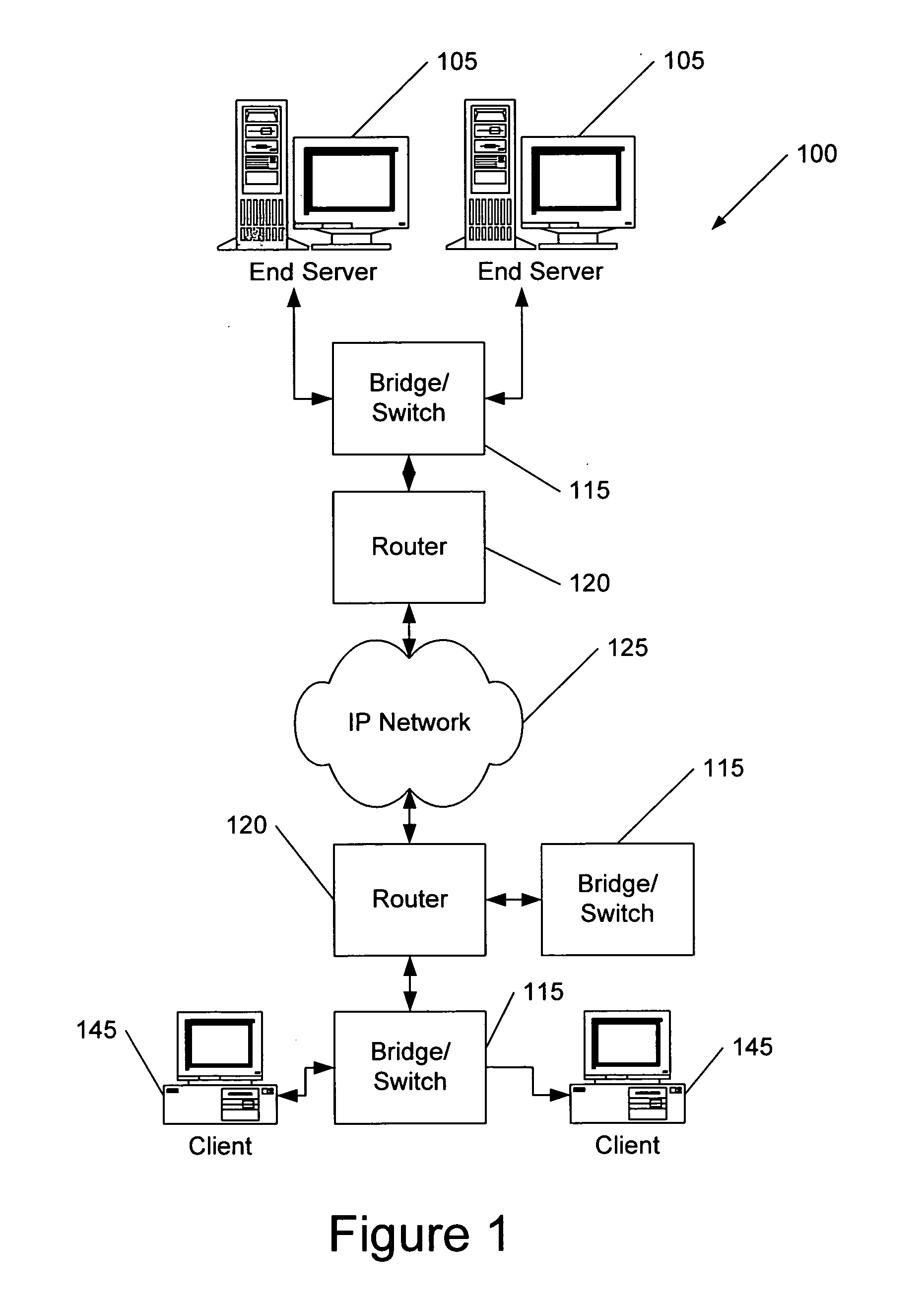
Technique for adaptively distributing web server requests
A technique for adaptively distributing a web server request in a system having a plurality of web servers is disclosed. In one embodiment, the technique is realized by first generating a web server request distribution function for each of the plurality of web servers based upon performance measures of each of the plurality of web servers, wherein each of the plurality of web servers is assigned a respective probability range based upon each respective web server request distribution function. A random probability number is then generated for a web server request. The particular probability range encompassing the random probability number is then determined so as to identify the corresponding web server to which the web server request is to be distributed.
Owner:AVAYA INC
Wireless network user tracking
InactiveUS20100228625A1Facilitate profilingEasy to trackDigital data processing detailsFuzzy logic based systemsDistributed computingRequest distribution
Owner:APPLE INC
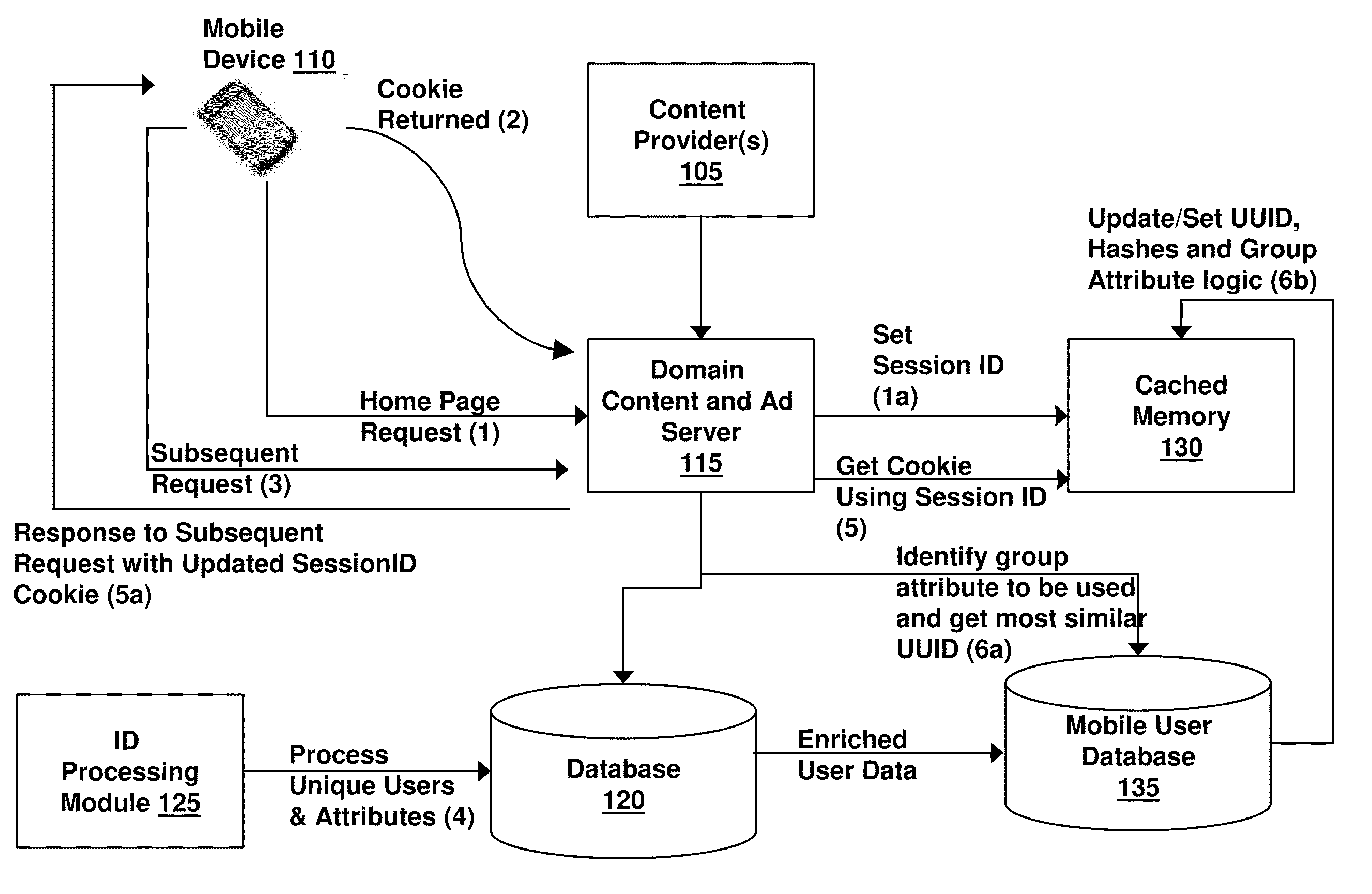
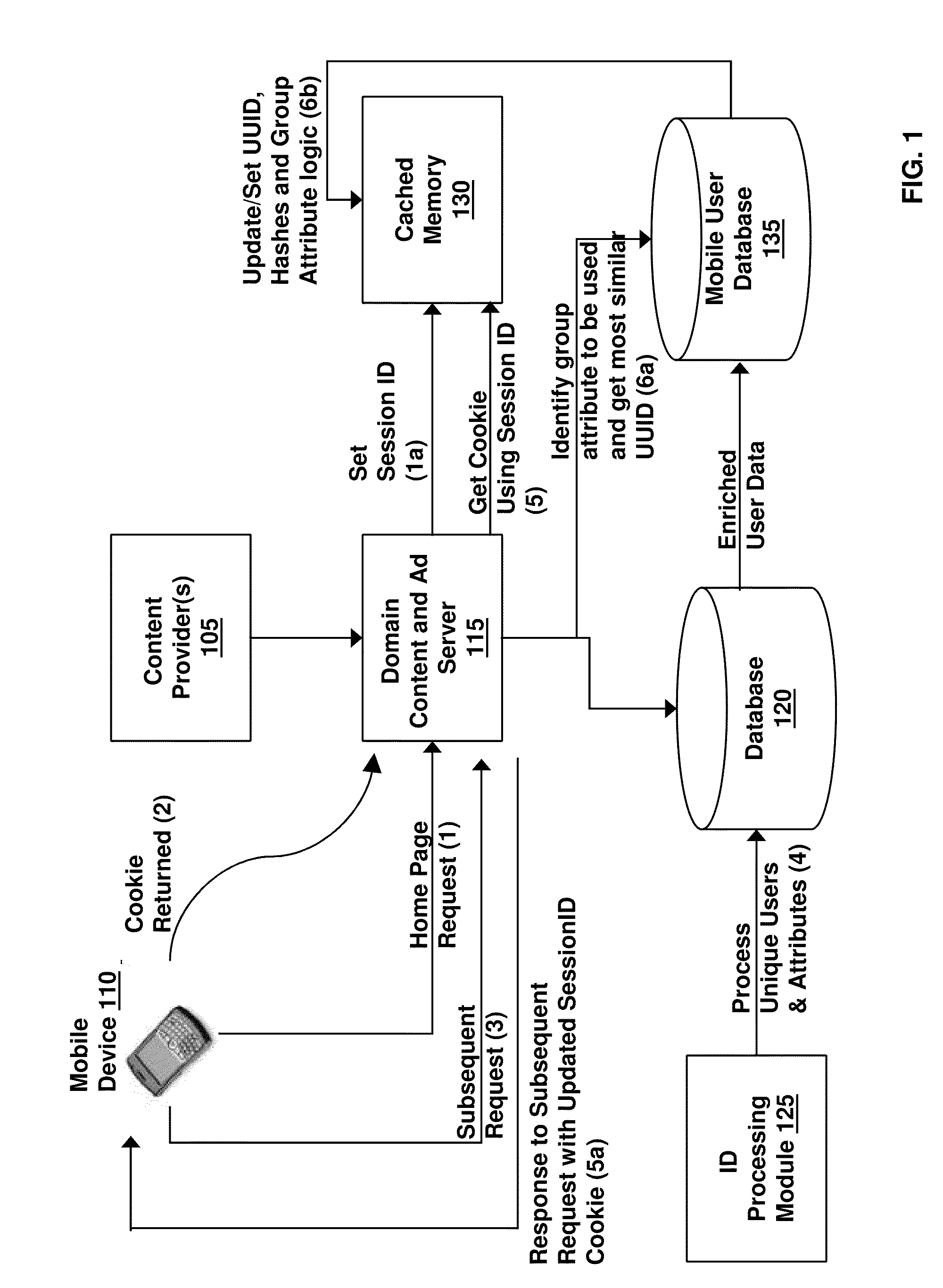
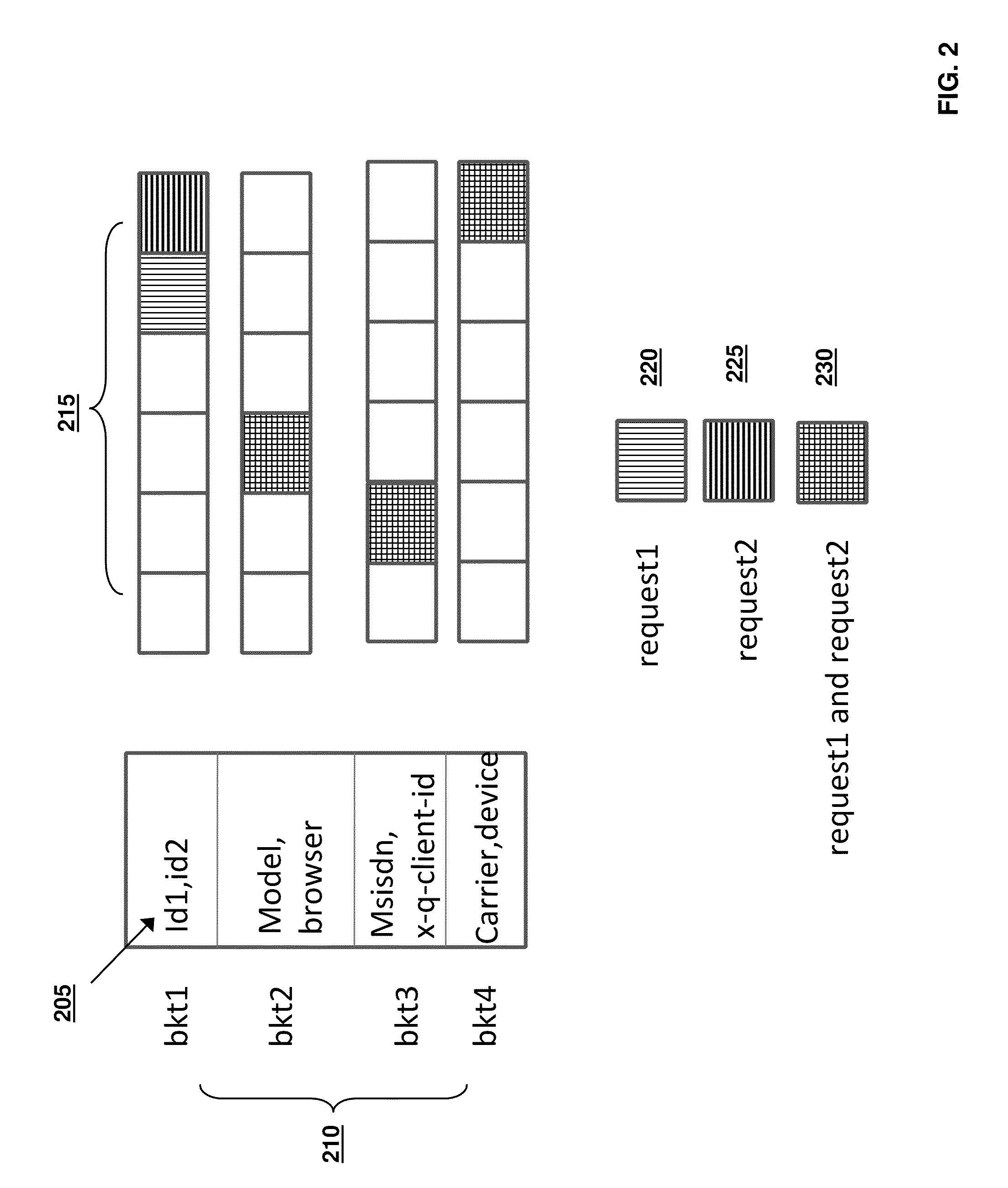
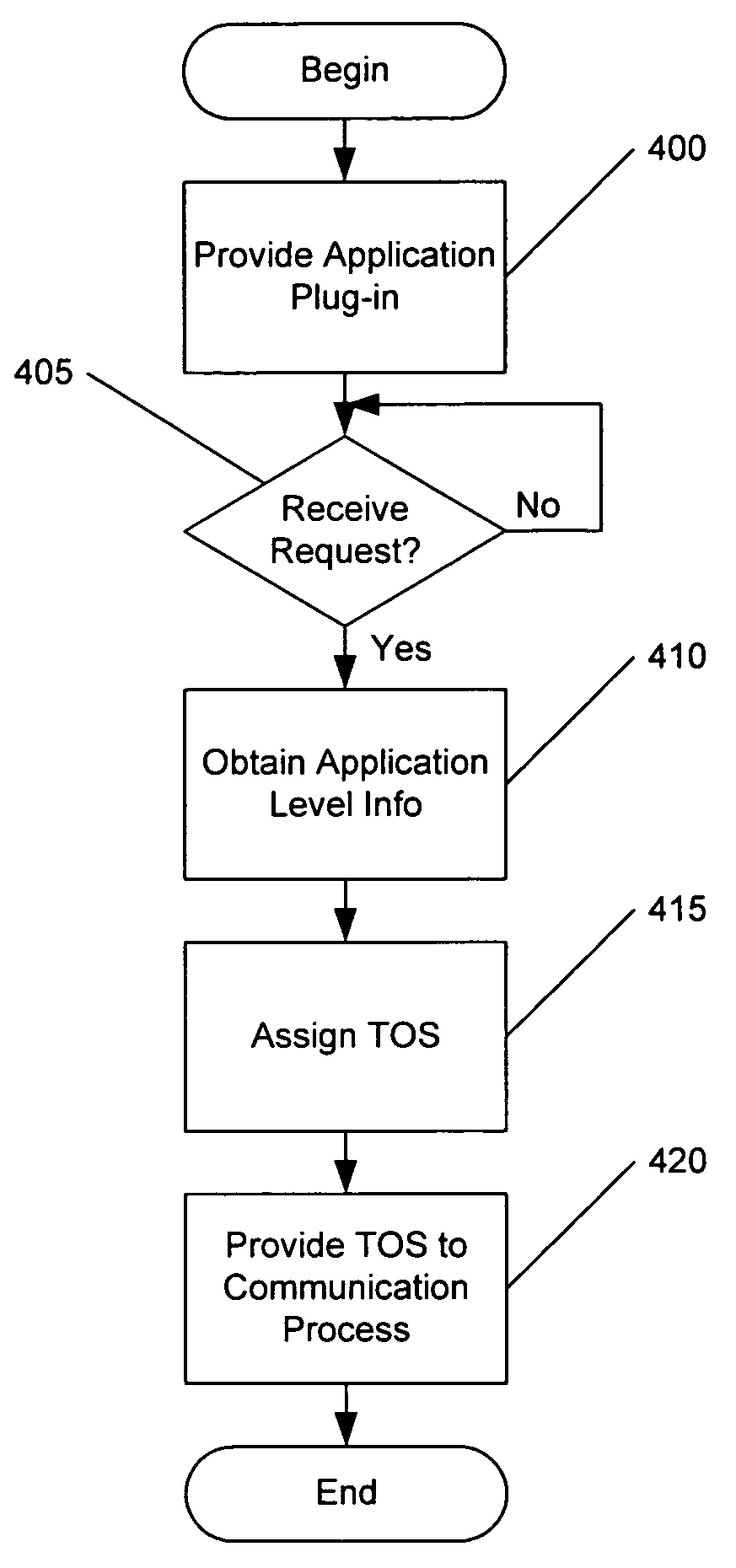
Methods, systems and computer program products for server based type of service classification of a communication request
InactiveUS7089294B1Multiple digital computer combinationsData switching networksOperational systemApplication software
Methods, systems and computer program products are provided for type of service classification of a communication request for an application executing on a server. An application plug-in associated with the application is provided in an operating system kernel of the server. The application plug-in receives the communication request and obtains application level information from the received communication request. The application plug-in further assigns a type of service classification to the received communication request based on the obtained application level information and provides the assigned type of service classification information for the communication request to a process executing on the server for processing communications from the server responsive to the communication request.
Owner:IBM CORP
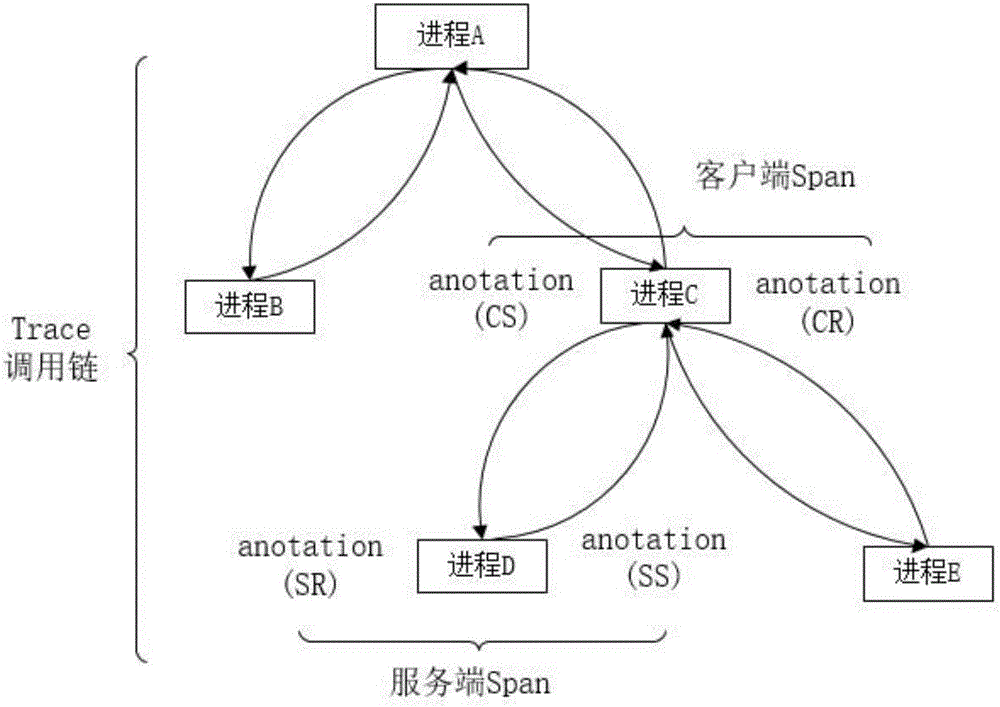
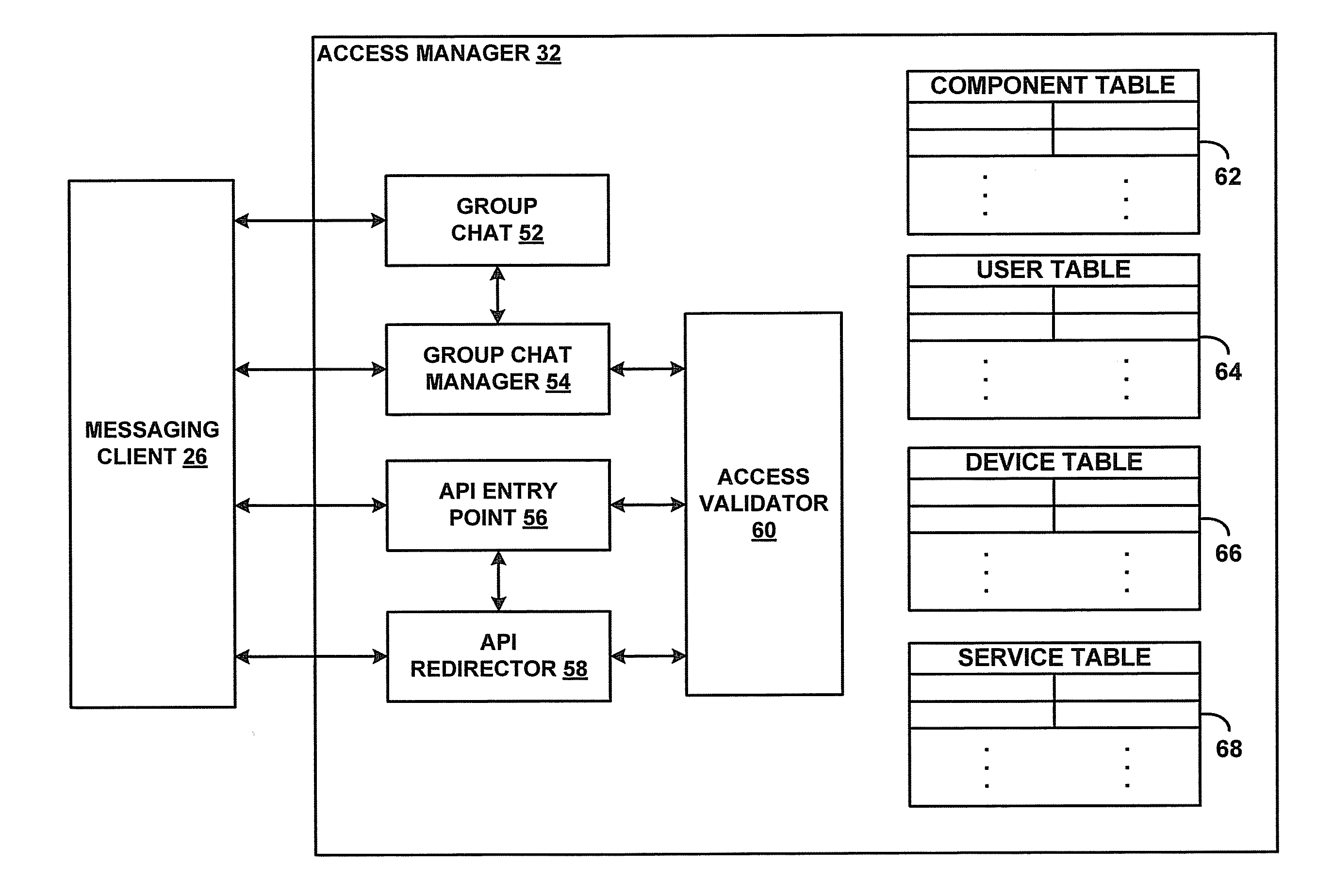
Distributed service tracking implementation method
The present invention provides a distributed service tracking implementation method. When a front-end request arrives at a server, before an application container performs actual service processing, the embedded logic of Cicada is executed first, the embedded logic distributes a global unique call chain ID which is called as TraceId for the front-end request, the embedded logic places the TraceId into a calling context object Span, a calling context object is stored into ThreadLocal, the ThreadLocal can carry out data storage and reading based on a thread, and information can be transmitted among multiple local processing methods of a same time of request. The calling context can be transmitted transparently, the system behavior is understood, a back end calling relation is cleared, the call chain tracking is realized, the path analysis is called, the service personnel is helped to position a performance bottleneck and investigate a fault reason, at the same time, the method needs to be transparent to the user, and the invasion to a business code is reduced.
Owner:优赛恒创科技发展(北京)有限公司
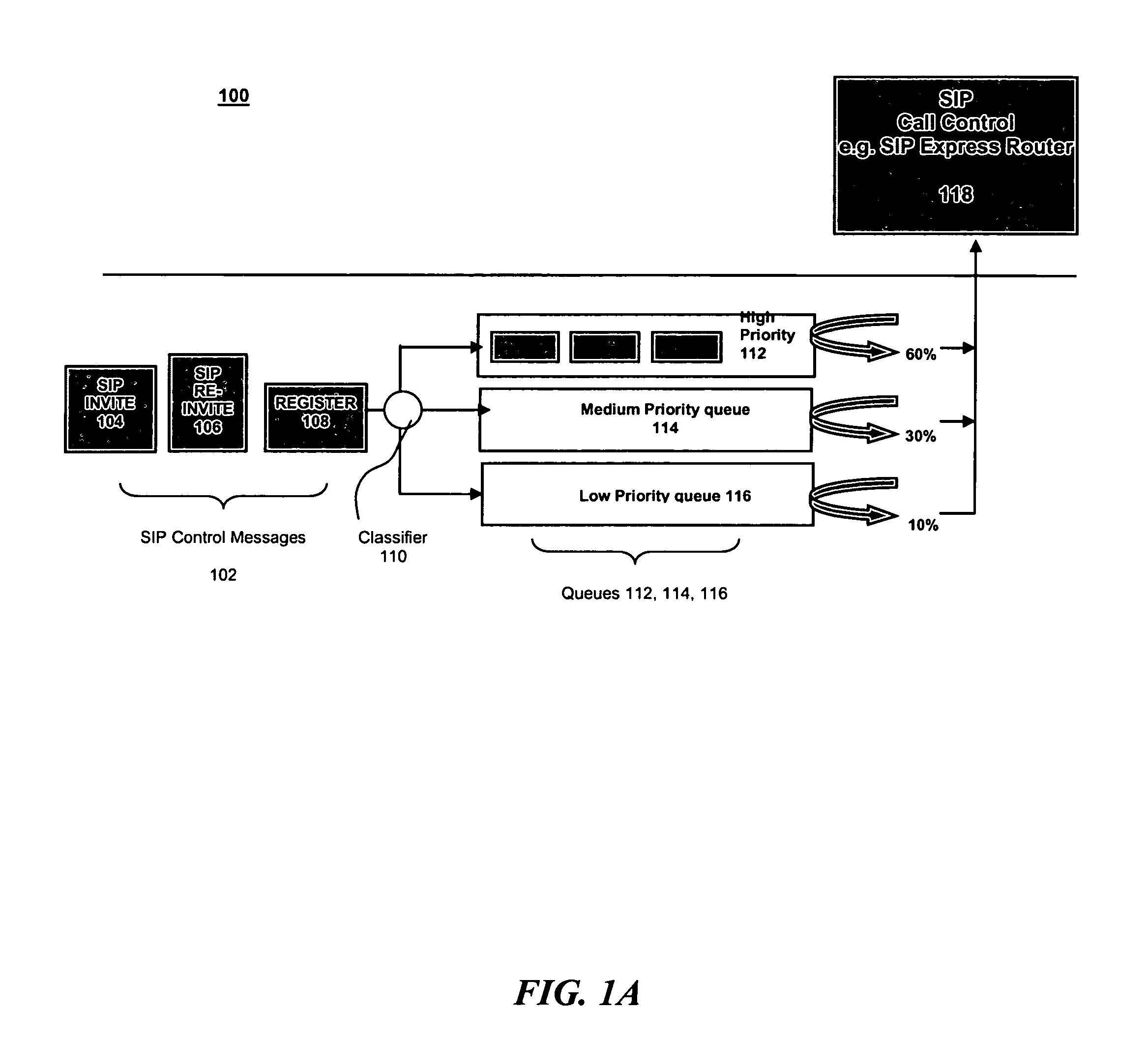
Overload protection for SIP servers
InactiveUS20080031258A1Data switching by path configurationDistributed computingRequest distribution
A method for operating a server having a maximum capacity for servicing requests comprises the following steps: receiving a plurality of requests; classifying each request according to a value; determining a priority for handling the request according to the value, such that requests with higher values are assigned higher priorities; placing each request in one of multiple queues according to its priority value; and dropping the requests with the lowest priority when the plurality of requests are received at a rate that exceeds the maximum capacity. The server operates according to a session initiation protocol.Classifying each request comprises running a classification algorithm. The classification algorithm comprising steps of: receiving a rule set, each rule comprising headers and conditions; creating a condition table by taking a union of all conditions in the rules; creating a header table by extracting a common set of headers from the condition table; extracting the relevant headers from the header table; determining a matching rule; creating a bit vector table; selecting the matching rule according to data in the bit vector table; and applying the rule to place the message in the appropriate queue.
Owner:IBM CORP
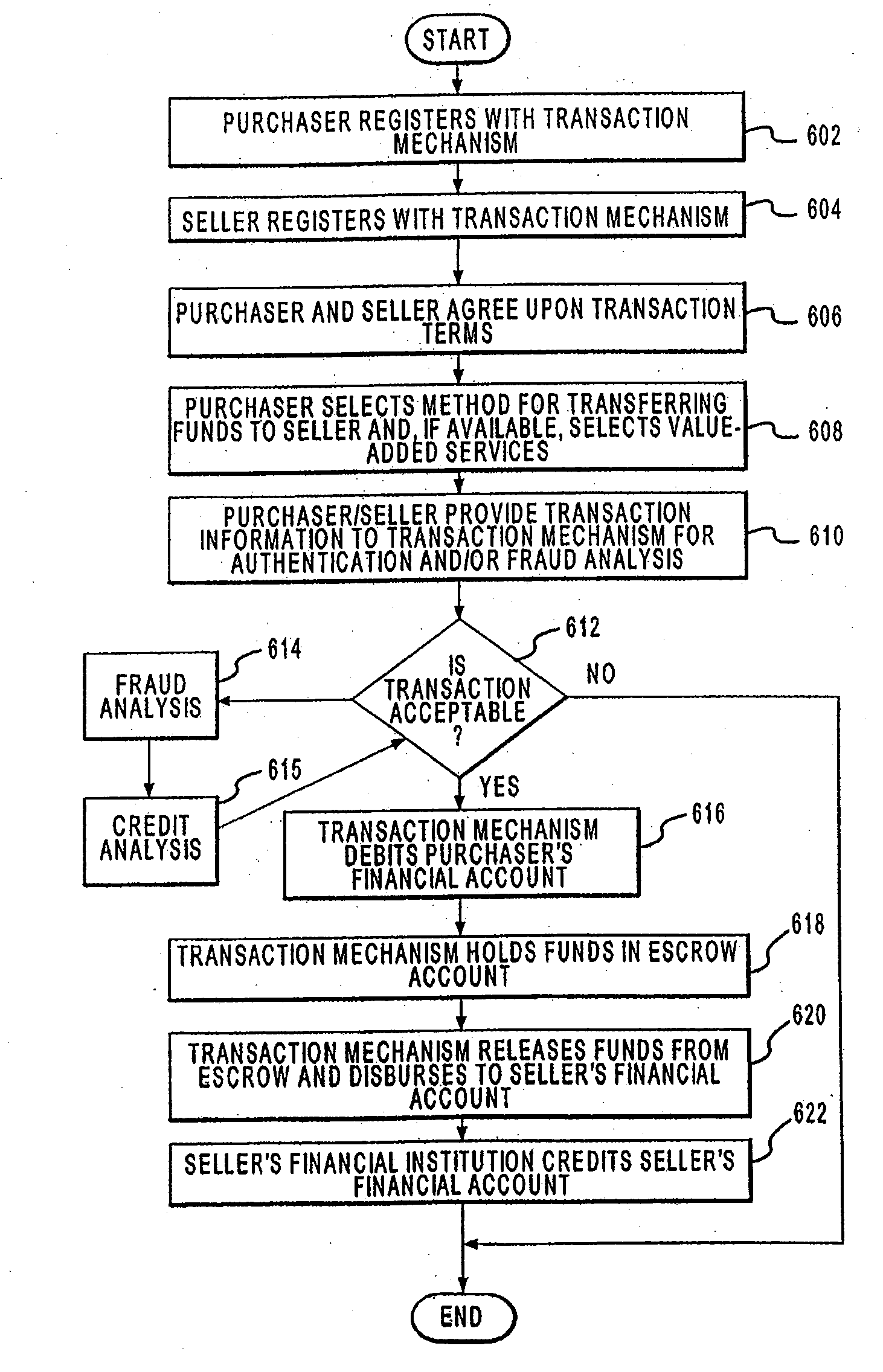
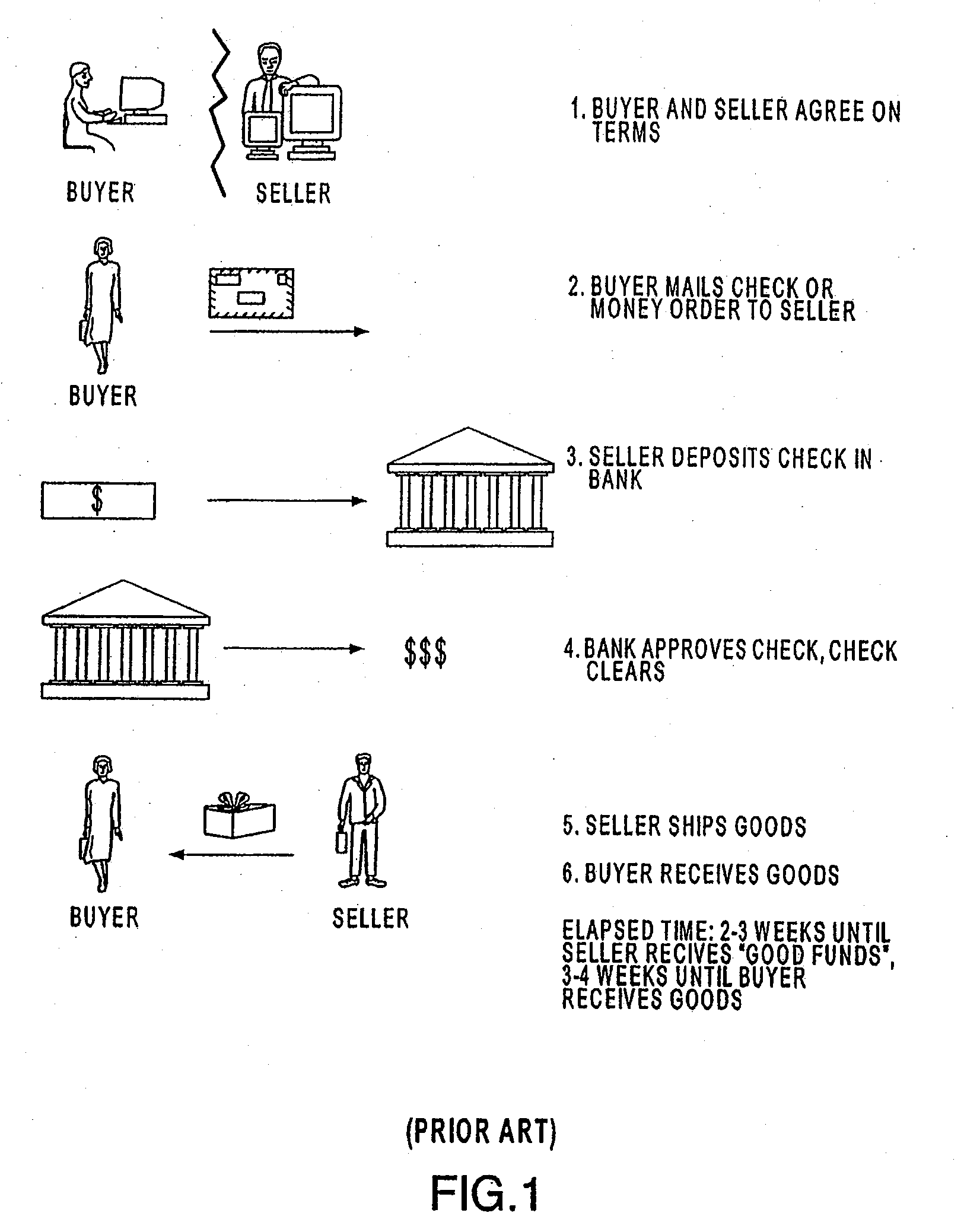
Systems and Methods for Allocating a Payment Authorization Request to a Payment Processor
InactiveUS20090157518A1Easy to identifyEasy to calculateHand manipulated computer devicesFinanceThird partyIssuing bank
A point of sale (POS) device may be configured to locate a payment system and transmit a payment authorization request from a remote location to a payment system, either directly, or via a payment system directory and / or a SSL Gateway. The invention also includes inserting third party account information into an encrypted portion of the payment request, so the payment request appears as a normal request to the issuing bank, but the third party account information may be used by the third party to bill the customer. The payment system directory is further configured to determine one or more payment processors to direct a payment authorization request, such that a single transaction may me allocated among multiple payment processors for authorization. Moreover, the payment system directory is able to format alternative payment methods into a format that is able to be processed over existing payment networks.
Owner:LIBERTY PEAK VENTURES LLC
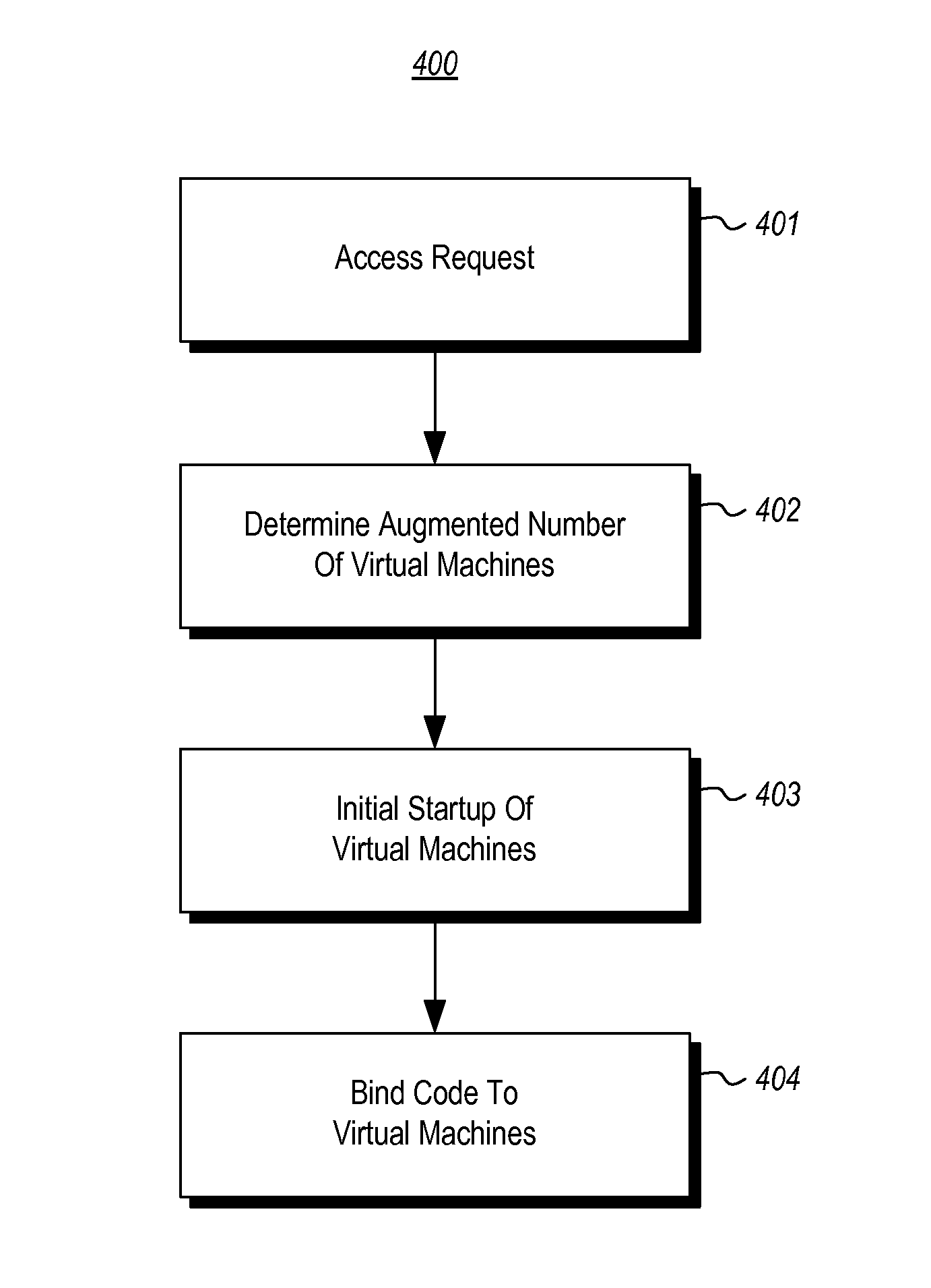
Augmented allocation of virtual machines for application
ActiveUS20140109088A1Software simulation/interpretation/emulationMemory systemsStart upVirtual machine
The starting up of an application involving multiple virtual machines by overallocating virtual machines. In response to a request to allocate a certain number of virtual machines corresponding to the application, an augmented number of virtual machines is determined to be allocated in response to the request. The augmented number includes both the initially requested number of virtual machines in addition to a surplus number of virtual machines. The virtual machines are then initiated startup if they are not already started up. Before all of the virtual machines are started up, code is bound to the virtual machines. Thus, because more virtual machines were initiated startup than are required for the application, the code may be bound to some of the virtual machines in the application before all of the virtual machine have started up.
Owner:MICROSOFT TECH LICENSING LLC
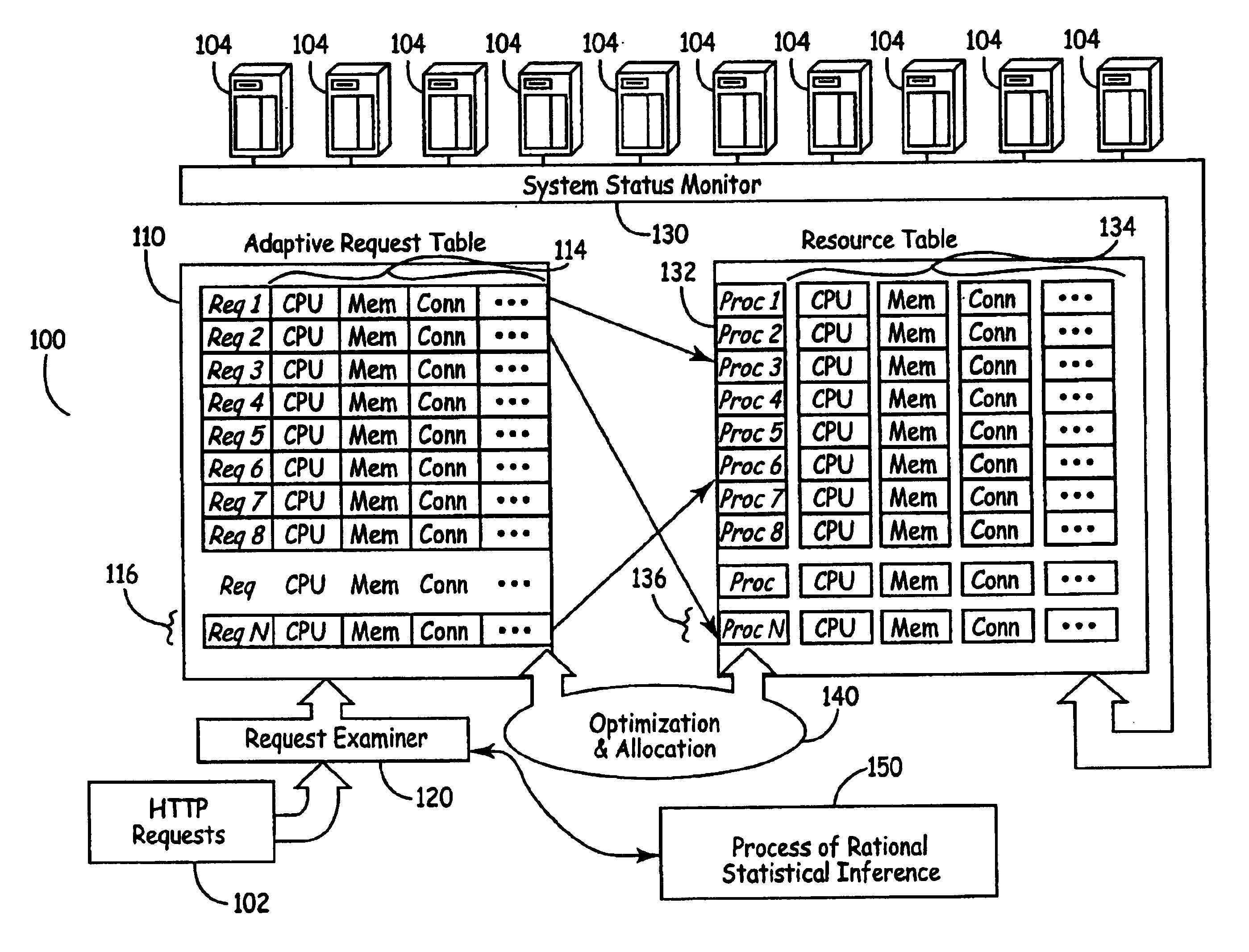
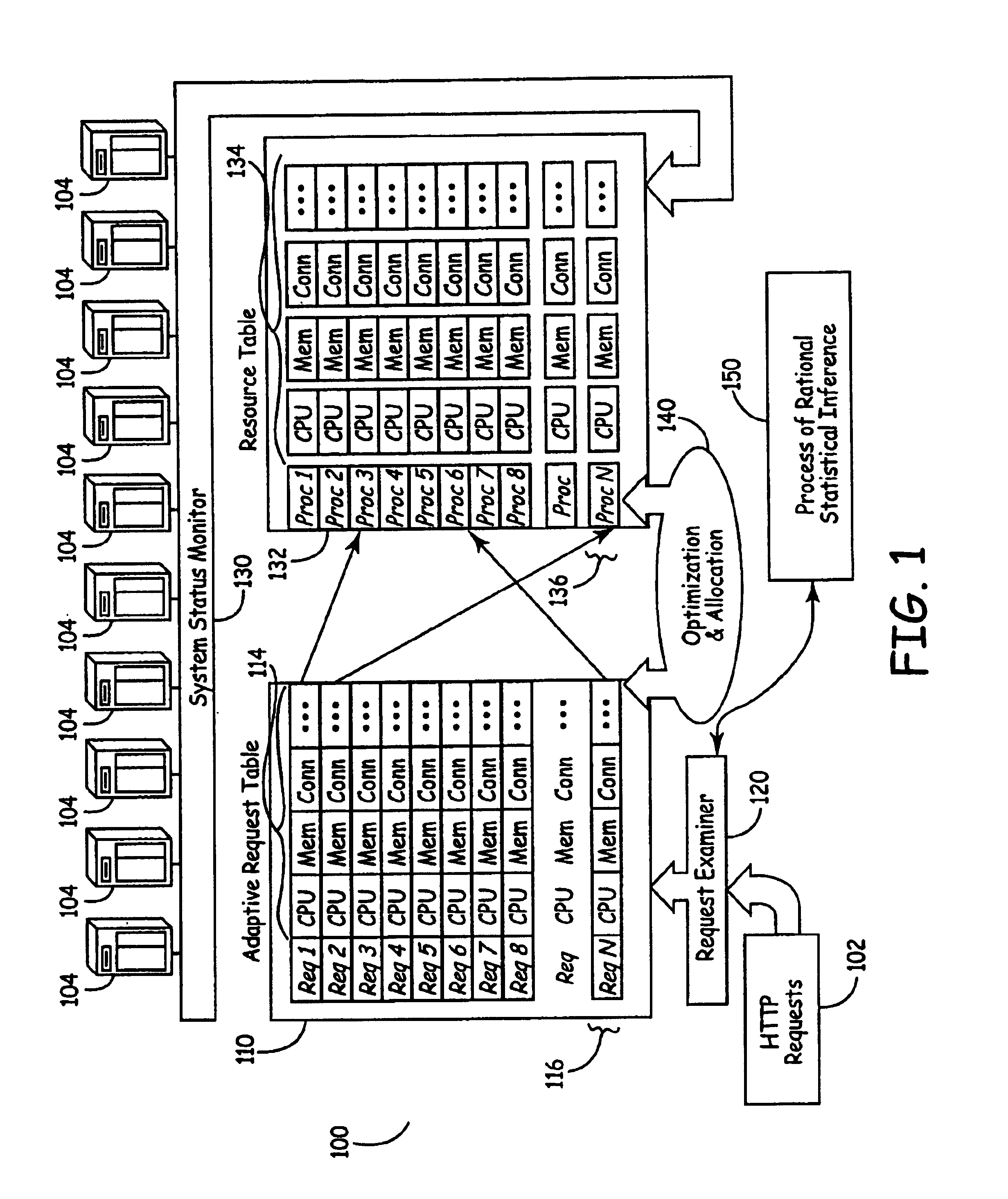
System for balance distribution of requests across multiple servers using dynamic metrics
InactiveUS6938256B2Improve performanceMaximizing numberResource allocationHardware monitoringDynamic metricsRelational database
A system for distributing incoming client requests across multiple servers in a networked client-server computer environment processes all requests as a set that occur within a given time interval and collects information on both the attributes of the requests and the resource capability of the servers to dynamically allocate the requests in a set to the appropriate servers upon the completion of the time interval. Preferably, the system includes a request table to collect at least two requests incoming within a predetermined time interval. A request examiner routine analyzes each collected request with respect to at least one attribute. A system status monitor collects resource capability information of each server in a resource table. An optimization and allocation process distributes collected requests in the request table across the multiple servers upon completion of said time interval based on an optimization of potential pairings of the requests in the request table with the servers in the resource table. The optimization and allocation process preferably analyzes metrics maintained in the request table and resource table as part of a relational database to allocate requests to servers based on a minimization of the metric distance between pairings of requests and servers. Preferably, the request table is part of a dynamic, relational database and a process of statistical inference for ascertaining expected demand patterns involving said the attributes adds predictive information about client requests as part of the request examiner routine.
Owner:RPX CORP +1
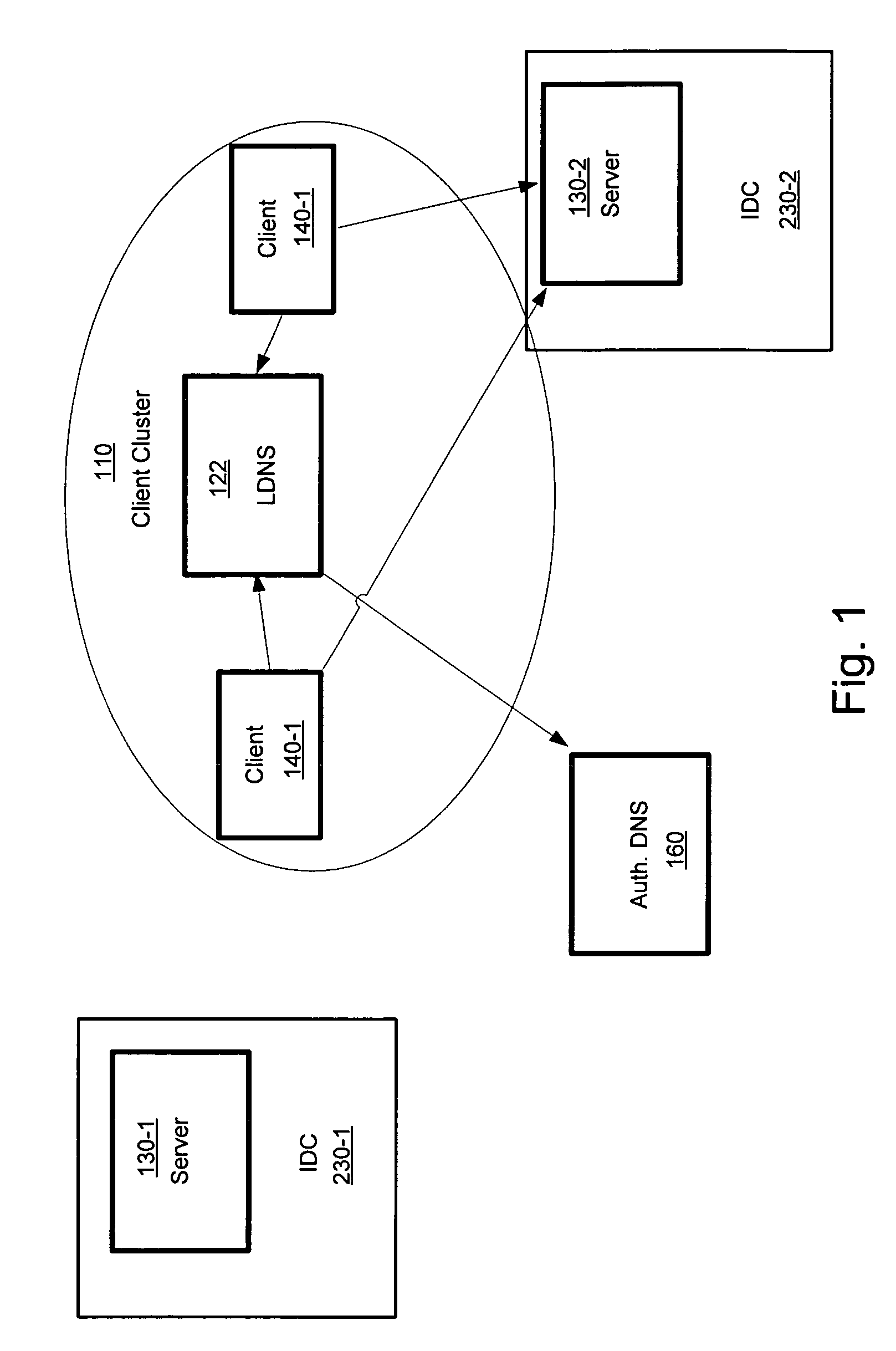
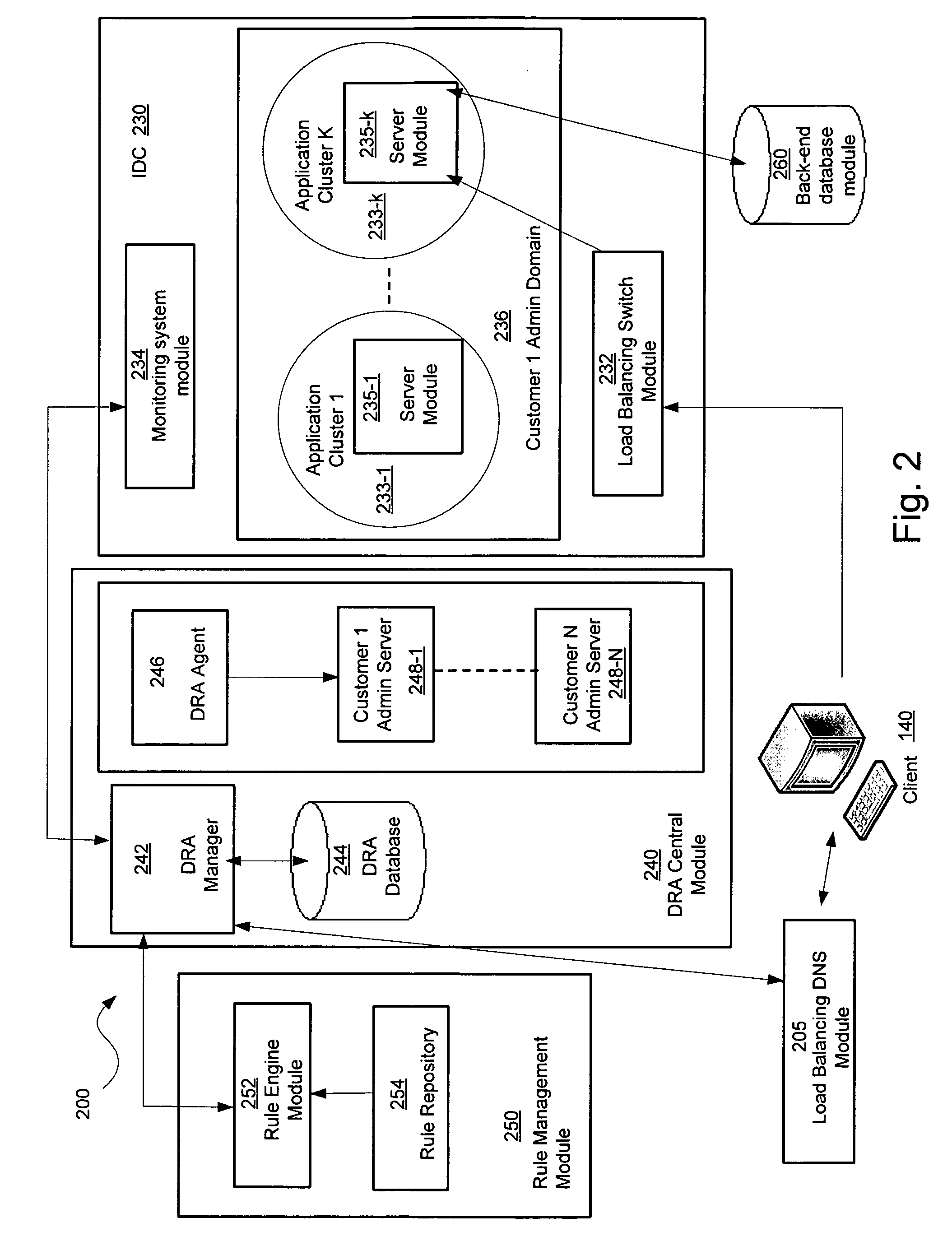
Monitoring for replica placement and request distribution
ActiveUS20060190602A1Digital computer detailsData switching by path configurationDynamic resourceMonitoring system
A platform that may be used to dynamically reallocation resources to support an Internet application is disclosed. In an embodiment, the platform may include two layers of distribution, one at the DNS layer and one at an Internet data center layer. The platform may include a dynamic resource allocation manager that causes instances of applications to be initiated in Internet data centers in response to dynamic conditions and characteristics of the application. A monitoring system module may be provided to keep the dynamic resource allocation manager informed as the health and utilization of instances of the application.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
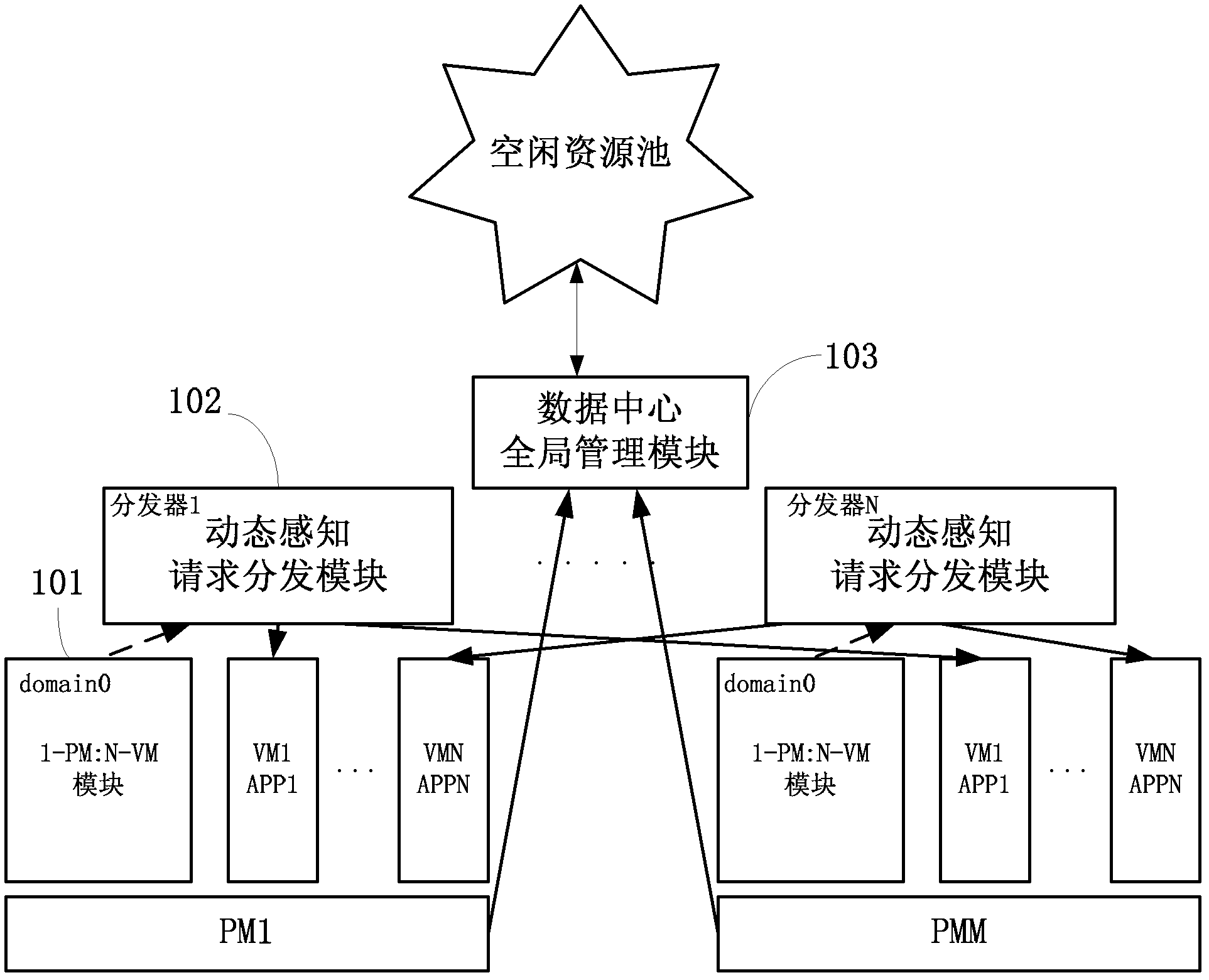
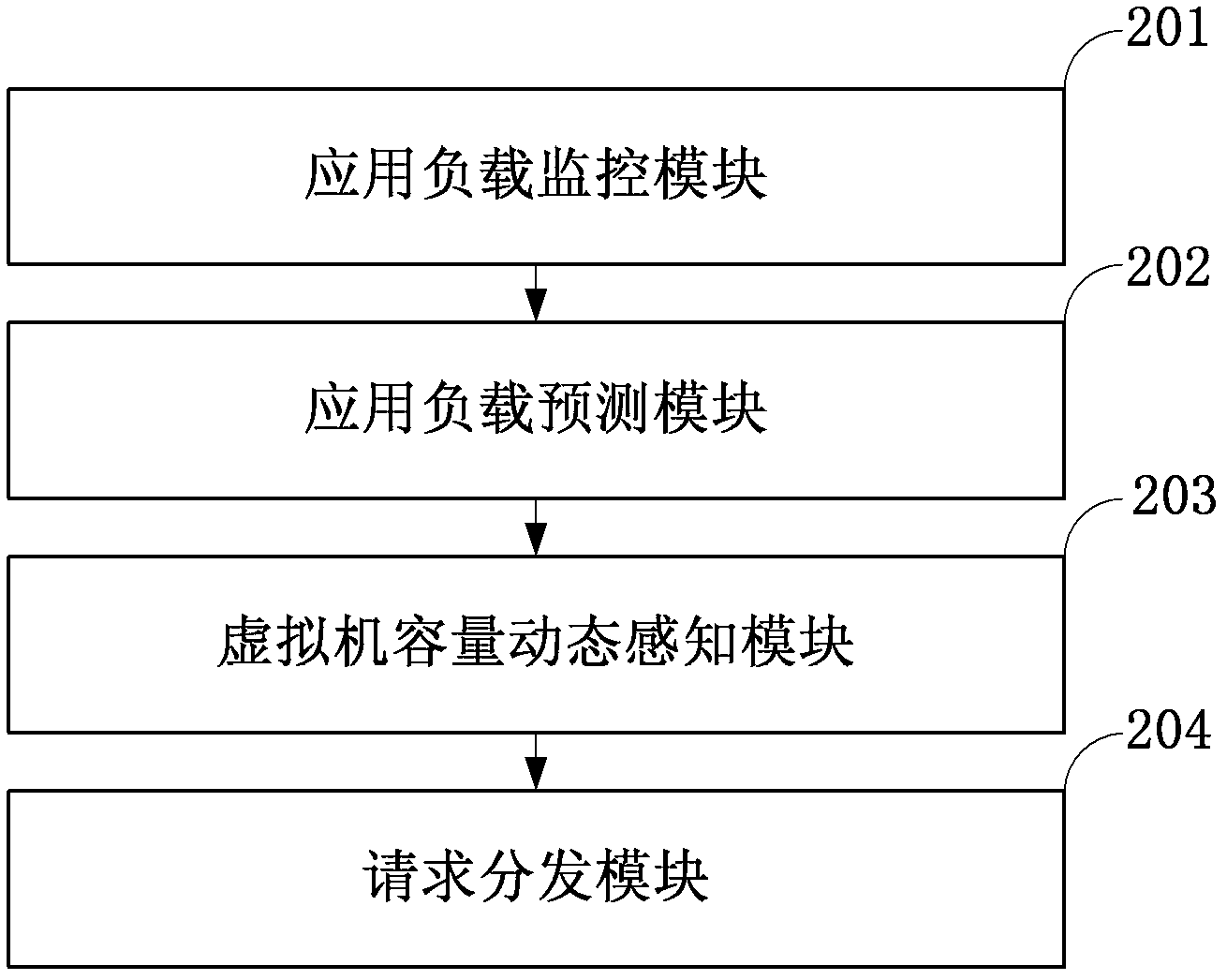
Method and system for self-adaptive on-demand resource allocation in a virtualized environment
ActiveCN102279771AReduce maintenance costsAdaptableProgram initiation/switchingResource allocationVirtualizationResource pool
The invention discloses a system for adaptively allocating resources as required in a virtualization environment. The system comprises a dynamic perception request distribution module, a 1-physical machine (PM):N-virtual machine (VM) module and a data center global management module, wherein the 1-PM:N-VM module allocates the resources on a PM according to user experiences which are collected in real time; the dynamic perception request distribution module distributes loads to proper VMs according to monitored application request load information and VM volume information and responds to requests; and the data center global management module judges whether the VMs are required to migrate between the PMs to be re-placed according to collected PM resource load information, and judges whether a new PM is released or applied to an idle resource pool to quit or enter application service when the PM is excess or insufficient. The invention also discloses a method for adaptively allocating the resources as required in the virtualization environment. The method comprises an adaptive VM dynamic volume perception request distribution strategy, a 1-PM:N-VM resource allocation strategy and a VM migration strategy. The invention has an application prospect in the technical field of computers.
Owner:日照育成科技咨询服务有限责任公司
Optimized Consistent Request Distribution for Balanced Load Distribution in a Content Delivery Network
ActiveUS20140195686A1Optimize allocationImprove distributionDigital computer detailsTransmissionLoad distributionUniform resource locator
Some embodiments provide a proprietary 64-bit consistent distribution scheme that preserves the efficiencies of CARP while providing a significantly more balanced distribution of requests that is on par with schemes reliant on computationally expensive cryptographic hashes. The scheme performs hashing of requested URLs and identifiers of available servers over a 64-bit space while optimizing the hashing to remove computationally expensive operations. Some embodiments provide a variant of the scheme to provide a differentiated distribution on the basis of one or more differentiating factors. A first variant utilizes load factor values to adjust the resulting hashes and to produce a first distribution of differentiated content that varies from a second distribution of undifferentiated content. A second variant identifies requests for differentiated content from requests for undifferentiated content and utilizes a first scheme to distribute the differentiated content and a second altered scheme to distribute the undifferentiated content.
Owner:EDGIO INC
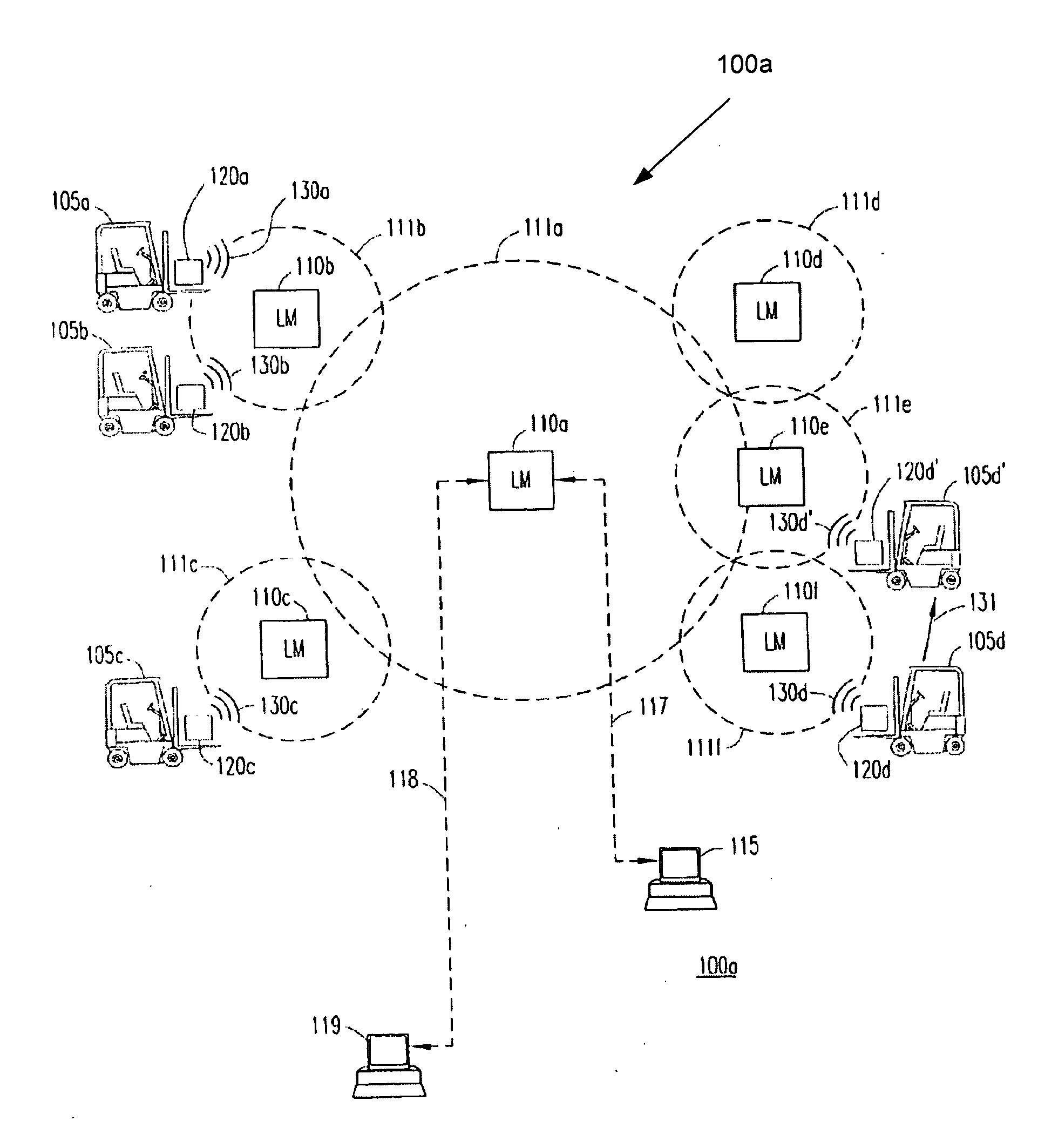
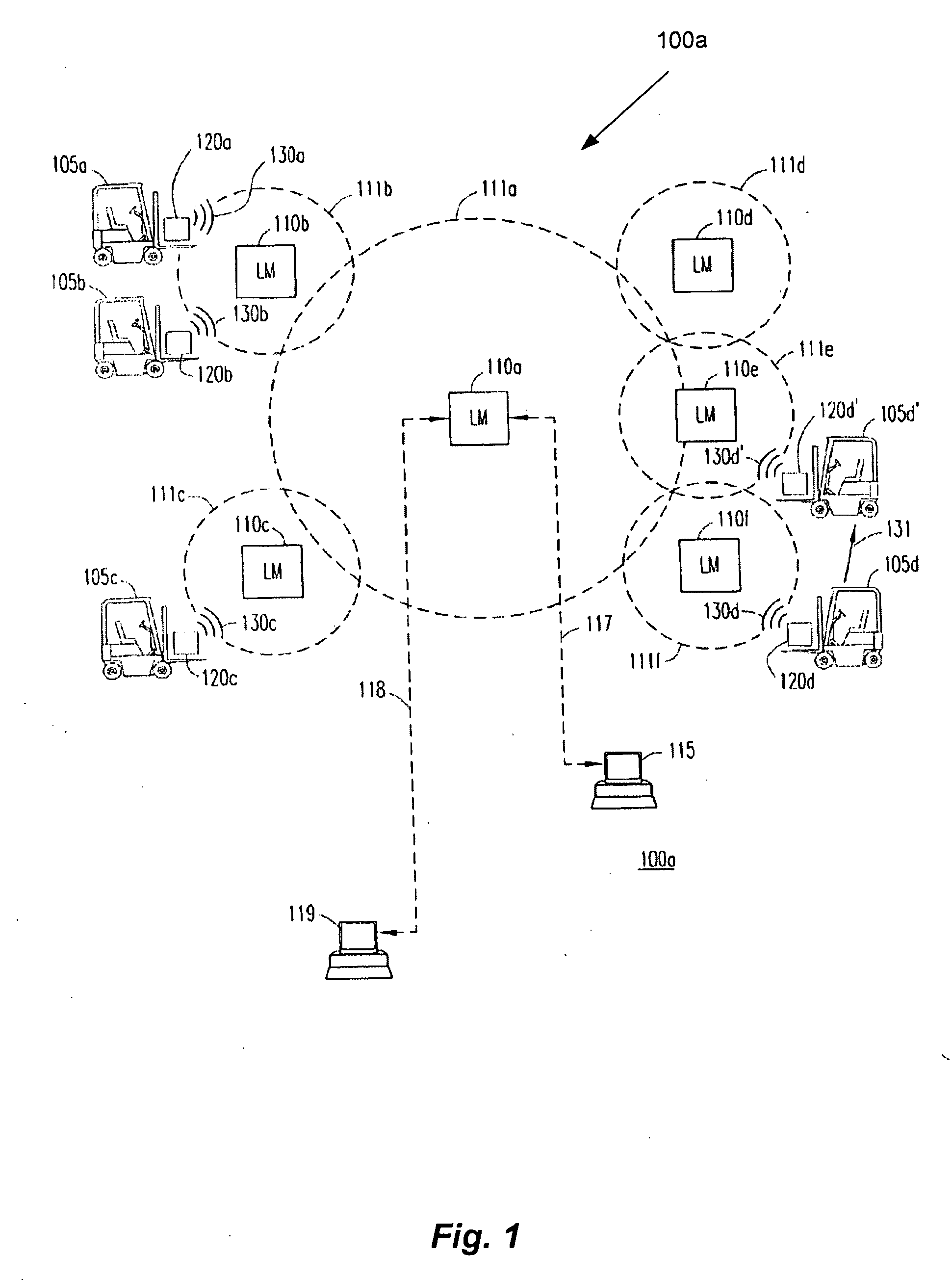
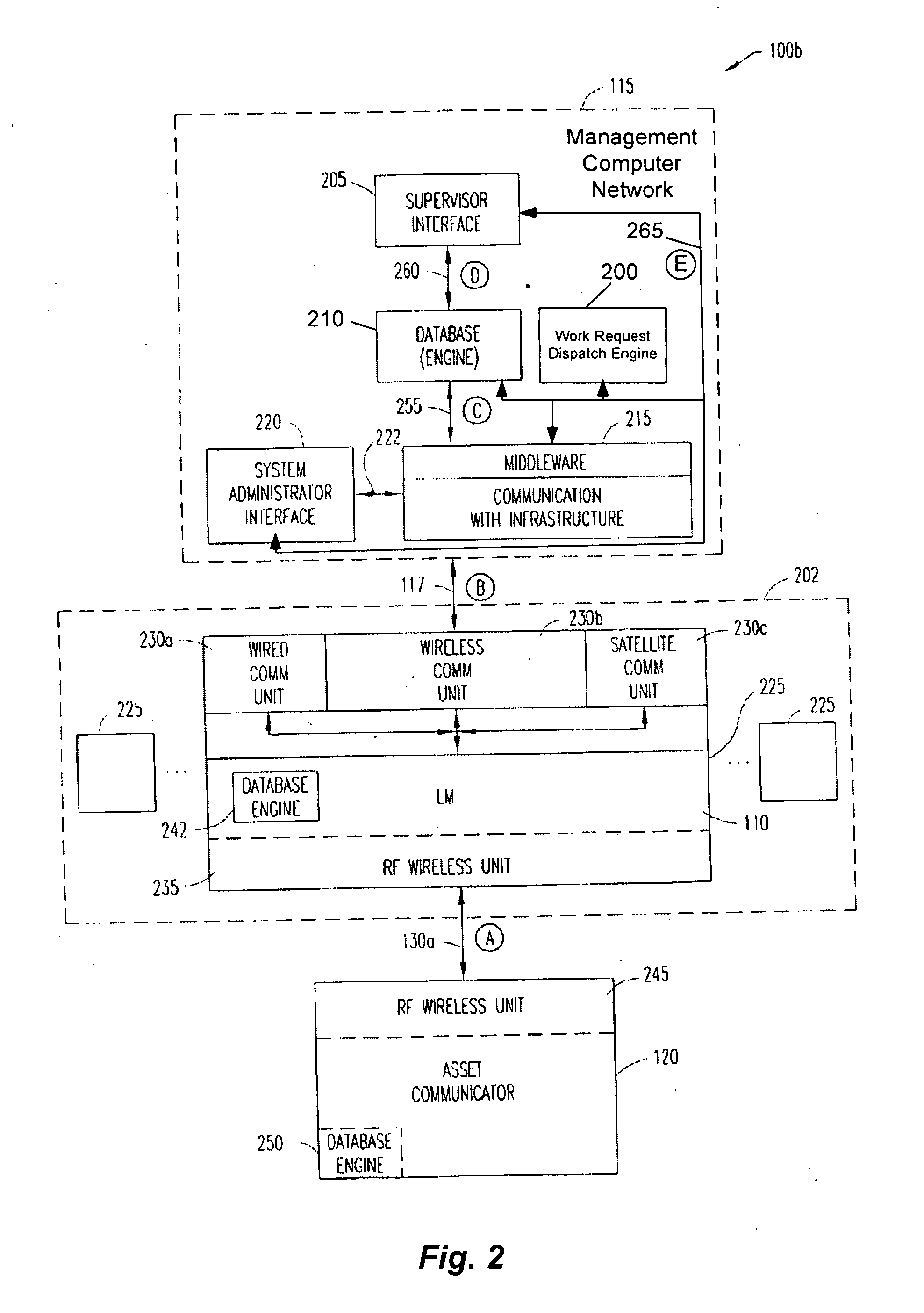
System and method for managing work requests for mobile assets
A system for managing a fleet of mobile assets is disclosed. The system comprises vehicle asset communicators coupled to mobile assets / vehicles, local monitors in wireless communication with the communicators, and a controller in communication with the communicators. The controller comprising logic configured to receive work requests to be completed by the fleet and heuristically determine which mobile asset / vehicle to assign each work request to. The controller can receive real-time operational information related to the fleet to assist in the determination of which mobile asset / vehicle is best suited to complete the work request. The communicators enable the operators of the mobile assets / vehicles to accept or decline the work request, and to cancel the work request after acceptance or report to the system that the work request has been completed.
Owner:I D SYST
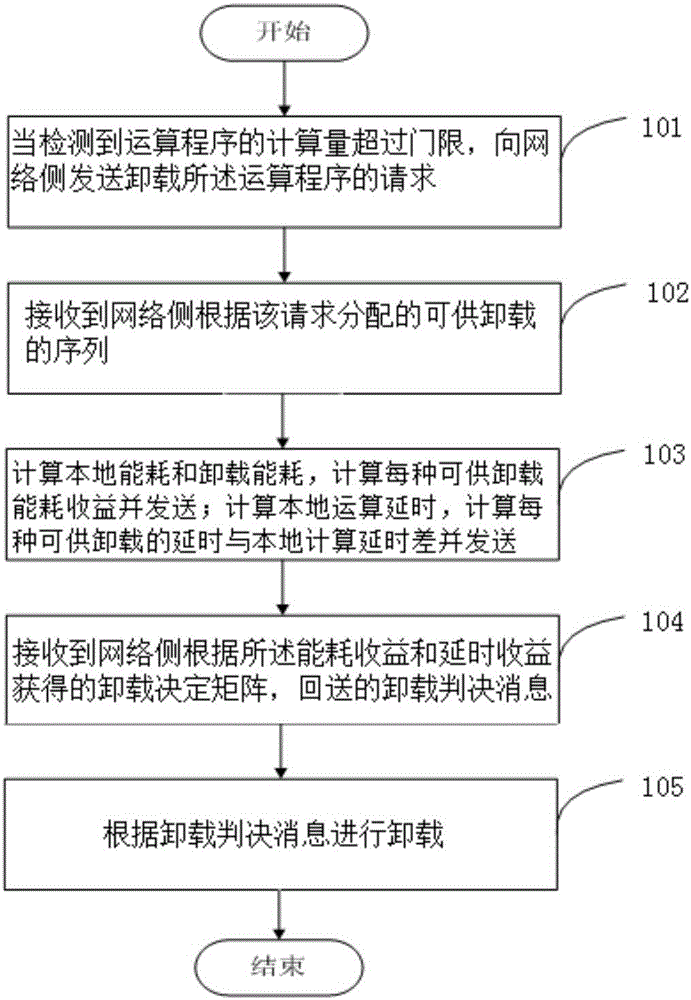
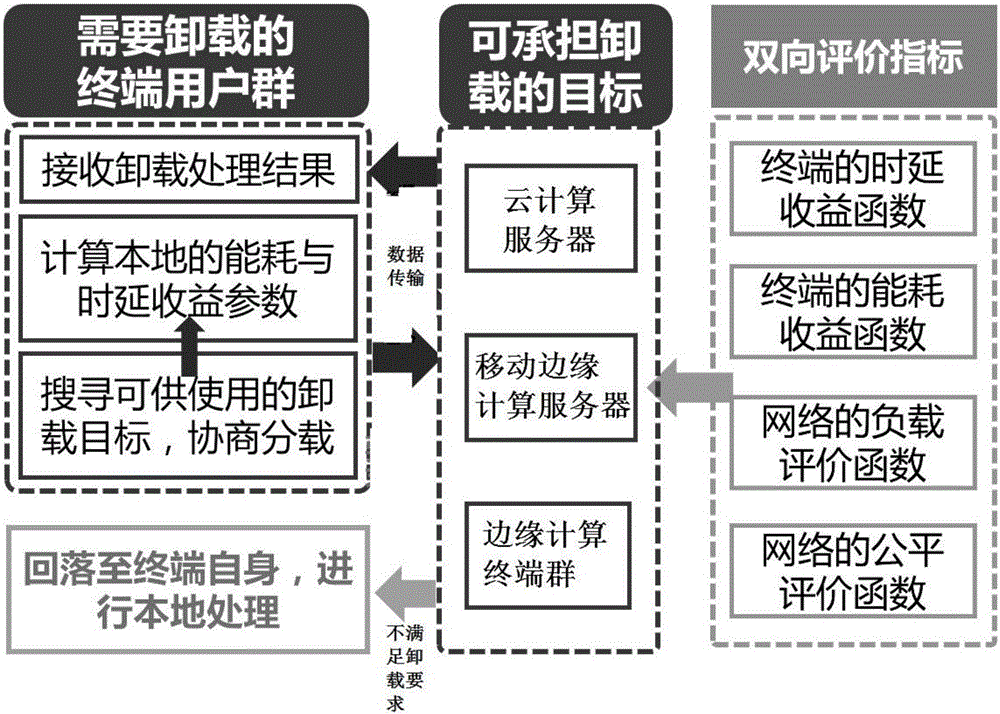
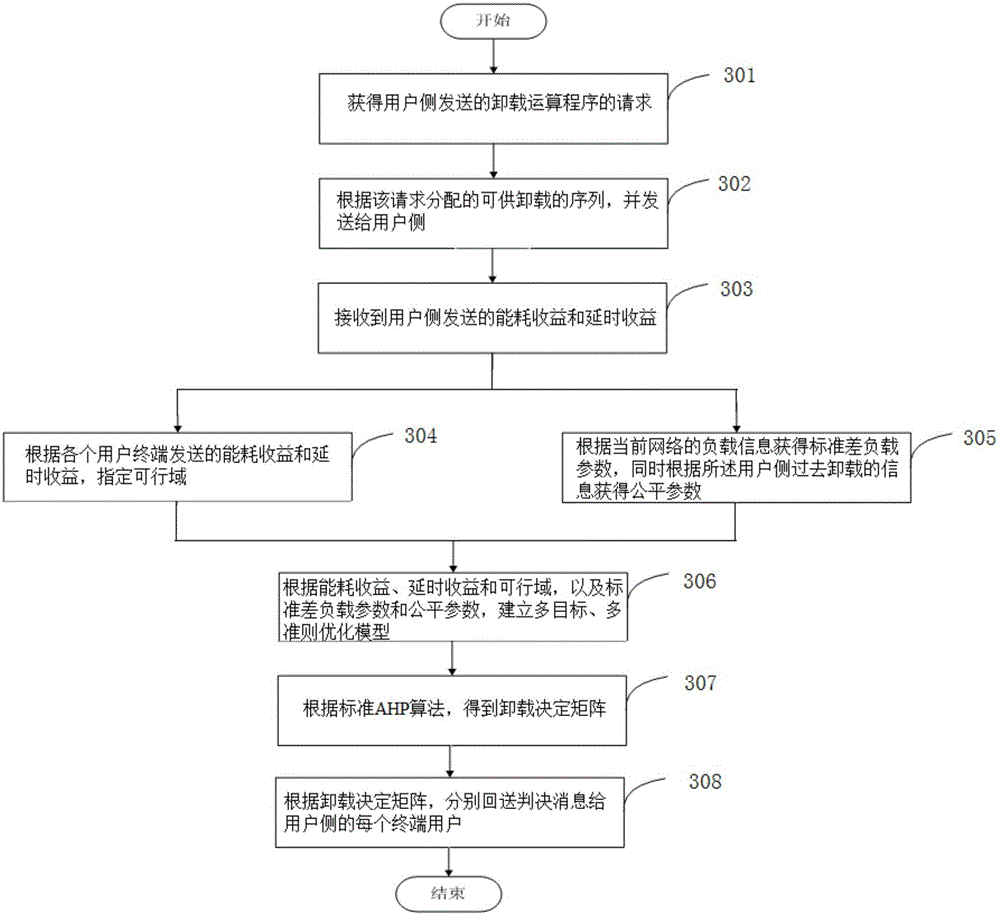
Bidirectional selection computing unloading method based on MEC and MCC
ActiveCN106534333AReduce energy consumptionReduce processing timeProgram loading/initiatingTransmissionComputer terminalAnalytical hierarchy
The invention discloses a bidirectional selection computing unloading method based on MEC and MCC. The method comprises steps of: sending to a network side a request to unload an operation program when it is detected that the computing amount of the operation program exceeds a threshold; receiving a unloading sequence allocated by the network side according to the request; computing local energy consumption and unloading energy consumption based on the received unloading sequence, and further computing each unloading energy consumption benefit and sending the same to the network side; and computing a local operation delay and further computing a difference between each unloading delay and local computing delay and sending the same to the network side; receiving a unloding decision matrix obtained by the network side based on the energy consumption benefit and the delay benefit, and returning a decision message; and performing unloading according to the unloading decision message. Therefore, the bidirectional selection computing unloading method based on MEC and MCC can realize the multi-criterion, multi-objective and bidirectional selection computing amount unloading of terminal linear weighting and network side analytical hierarchy process.
Owner:BEIJING UNIV OF POSTS & TELECOMM
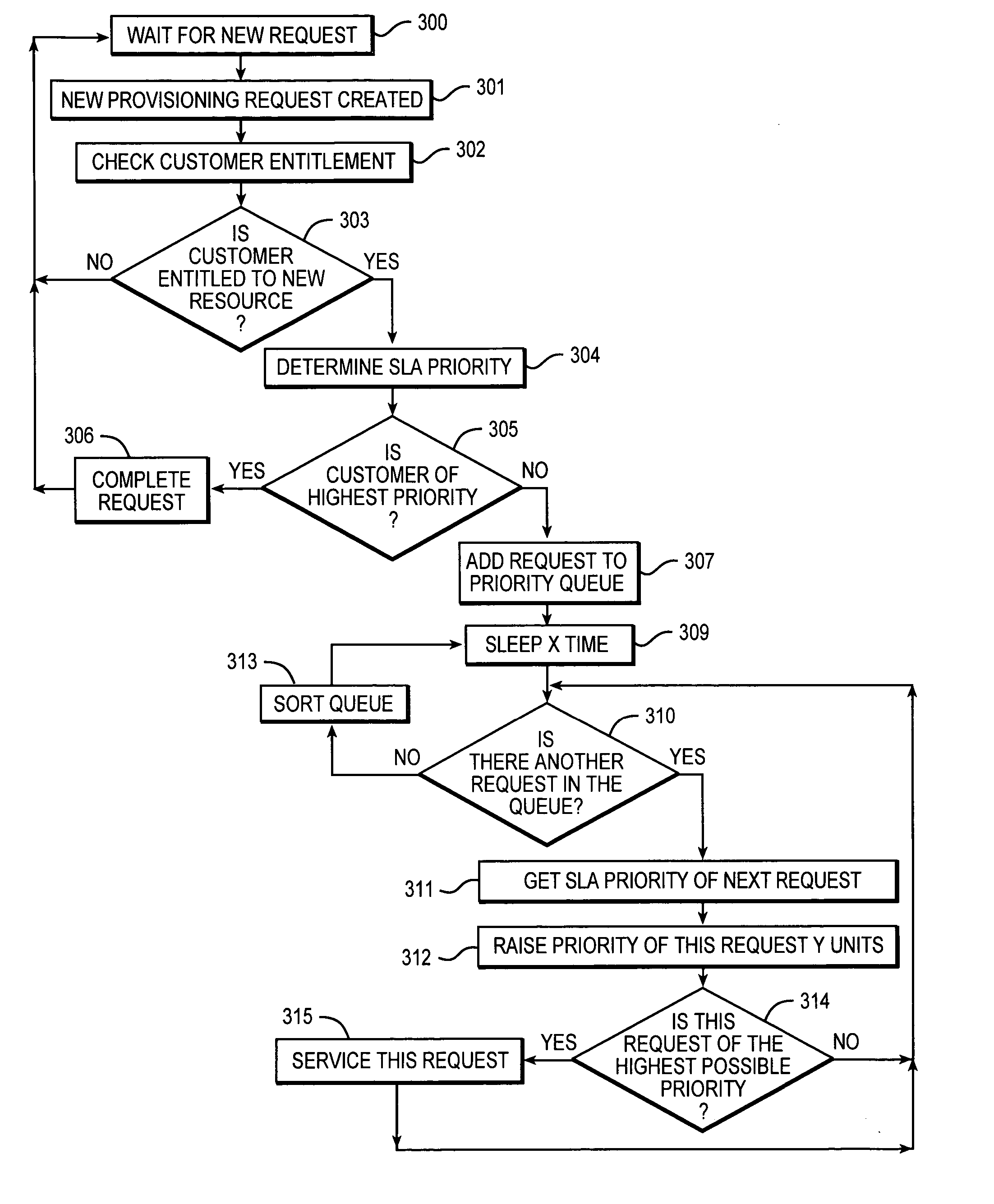
Method and system of ordering provisioning request execution based on service level agreement and customer entitlement
ActiveUS20050198231A1Multiprogramming arrangementsMultiple digital computer combinationsService-level agreementCustomer information
A solution provided here comprises receiving requests for a service from a plurality of customers, responding to the requests for a service, utilizing a shared infrastructure, and configuring the shared infrastructure, based on stored customer information. Another example of such a solution comprises: analyzing at least one provisioning request; assigning a priority to the provisioning request, based on performance data and stored customer information; configuring a shared infrastructure, according to the provisioning request and the priority; and responding to requests for services, utilizing the shared infrastructure.
Owner:IBM CORP
System and Method of Accessing Resources in a Computer Network
InactiveUS20110040814A1Digital data processing detailsDigital computer detailsFile synchronizationUnique identifier
Disclosed herein are system and methods of accessing resources in a computer network. An exemplary method may include (a) receiving into a networking device, from a first client device of a plurality of client devices, a request for a given resource (e.g., a file, directory, or metadata) assigned to a given file service (e.g., a file share service, file sync service, or file search service), (b) verifying that the first client device is allowed to access the given file service, (c) in response to verifying that the first client device is allowed to access the given file service, identifying a second client device having at least one stored resource assigned to the given file service, and (d) sending to the second client device an updated request for the given resource that includes a unique identifier of the at least one stored resource assigned to the given file service.
Owner:WESTELL TECH
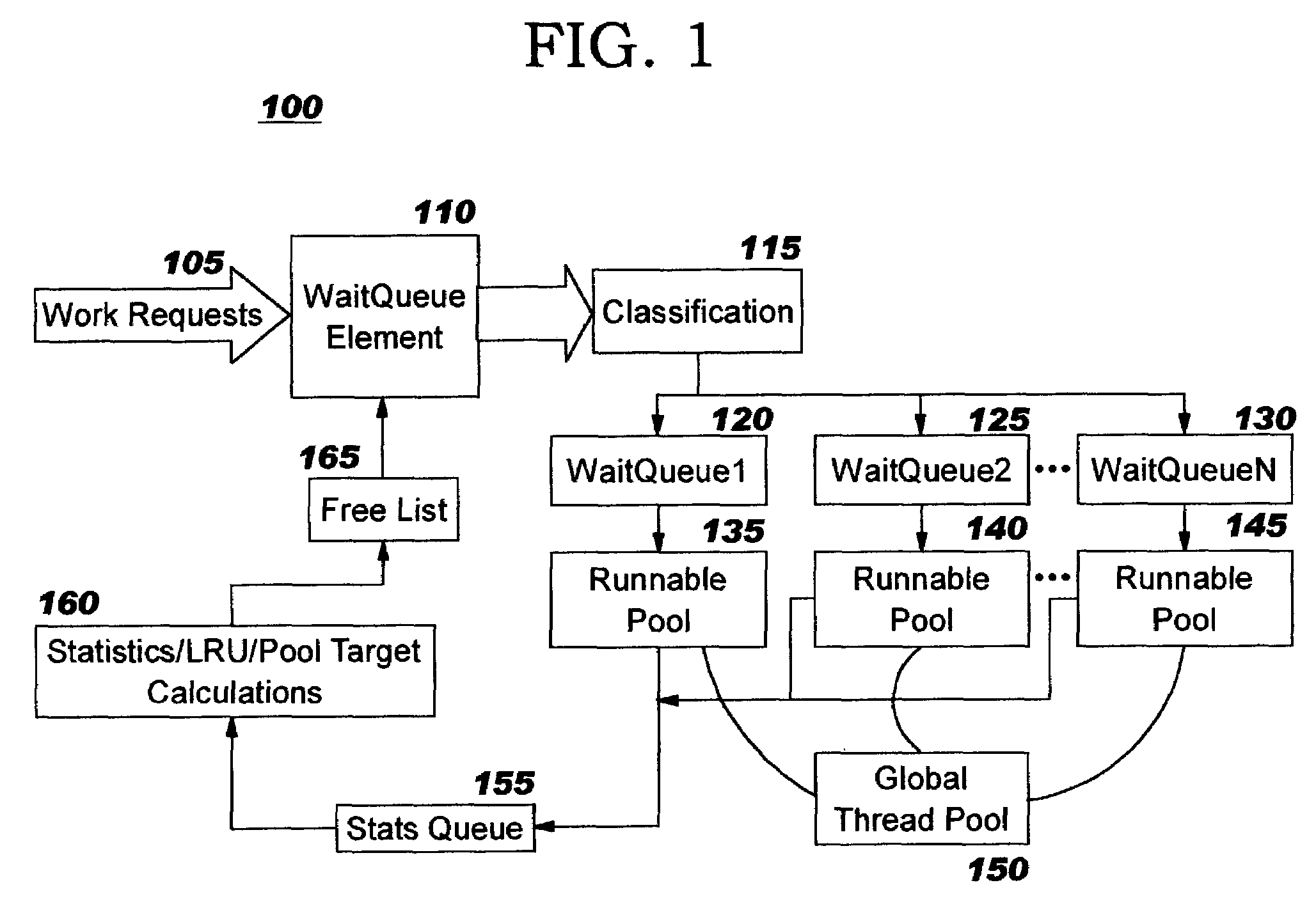
Programmatic response-time based workload distribution techniques
InactiveUS7207043B2Improve performanceSimple technologyProgram initiation/switchingElectric devicesQueue timeWorkload
Workload is programmatically distributed across a set of execution resources. In a multithreaded server environment, response time to end users is improved while increasing the efficiency of software execution and resource usage. Execution time and wait / queued time are tracked, for various types of requests being serviced by a server. Multiple logical pools of threads are used to service these requests, and inbound requests are directed to a selected one of these pools such that requests of similar execution-time requirements are serviced by the threads in that pool. The number and size of thread pools may be adjusted programmatically, and the distribution calculation (i.e., determining which inbound requests should be assigned to which pools) is a programmatic determination. In preferred embodiments, only one of these variables is adjusted at a time, and the results are monitored to determine whether the effect was positive or negative. The disclosed techniques also apply to tracking and classifying requests by method name (and, optionally, parameters).
Owner:IBM CORP
Method for the addressing of a mobile terminal
InactiveUS20030013467A1Time-division multiplexMultiple digital computer combinationsComputer networkImage resolution
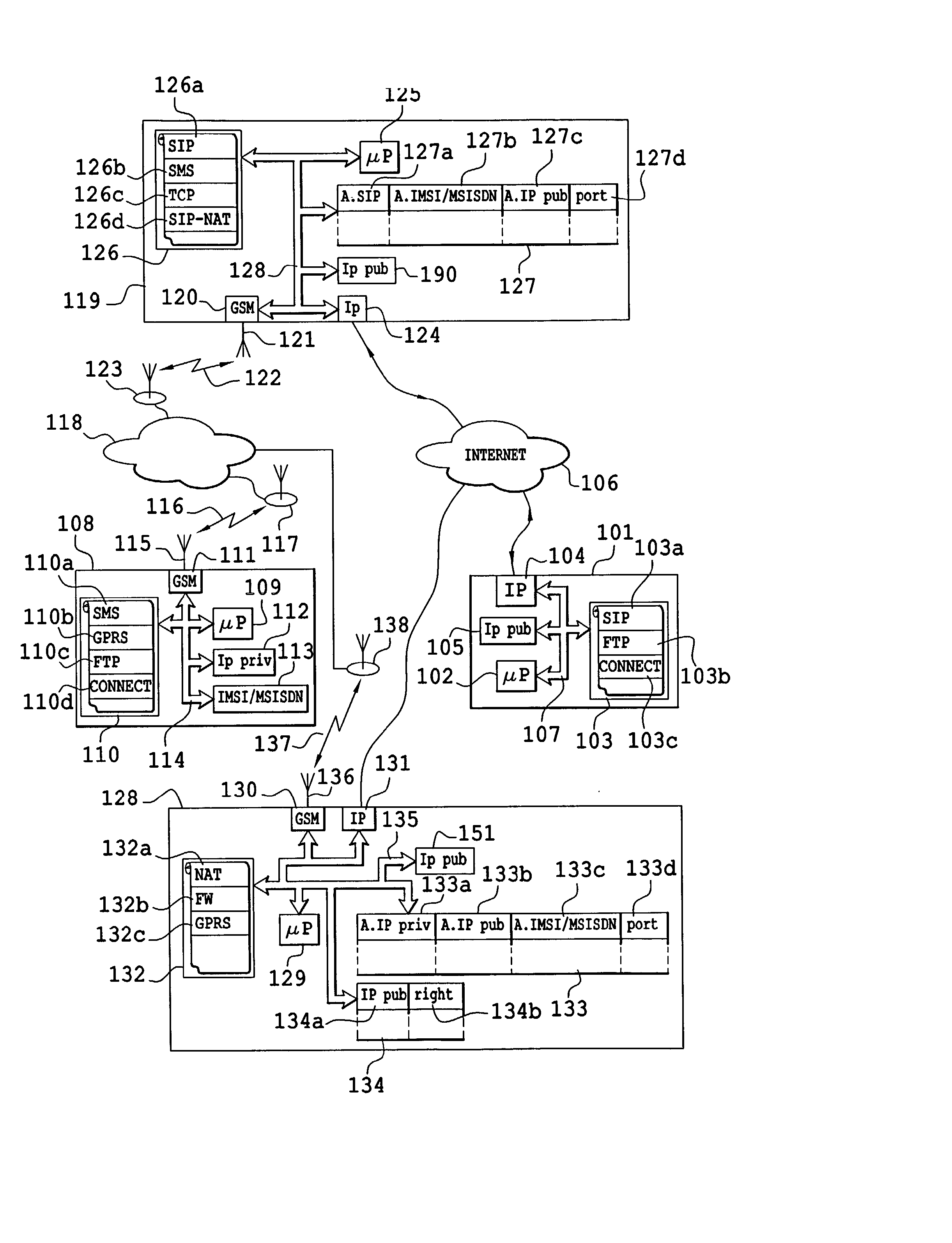
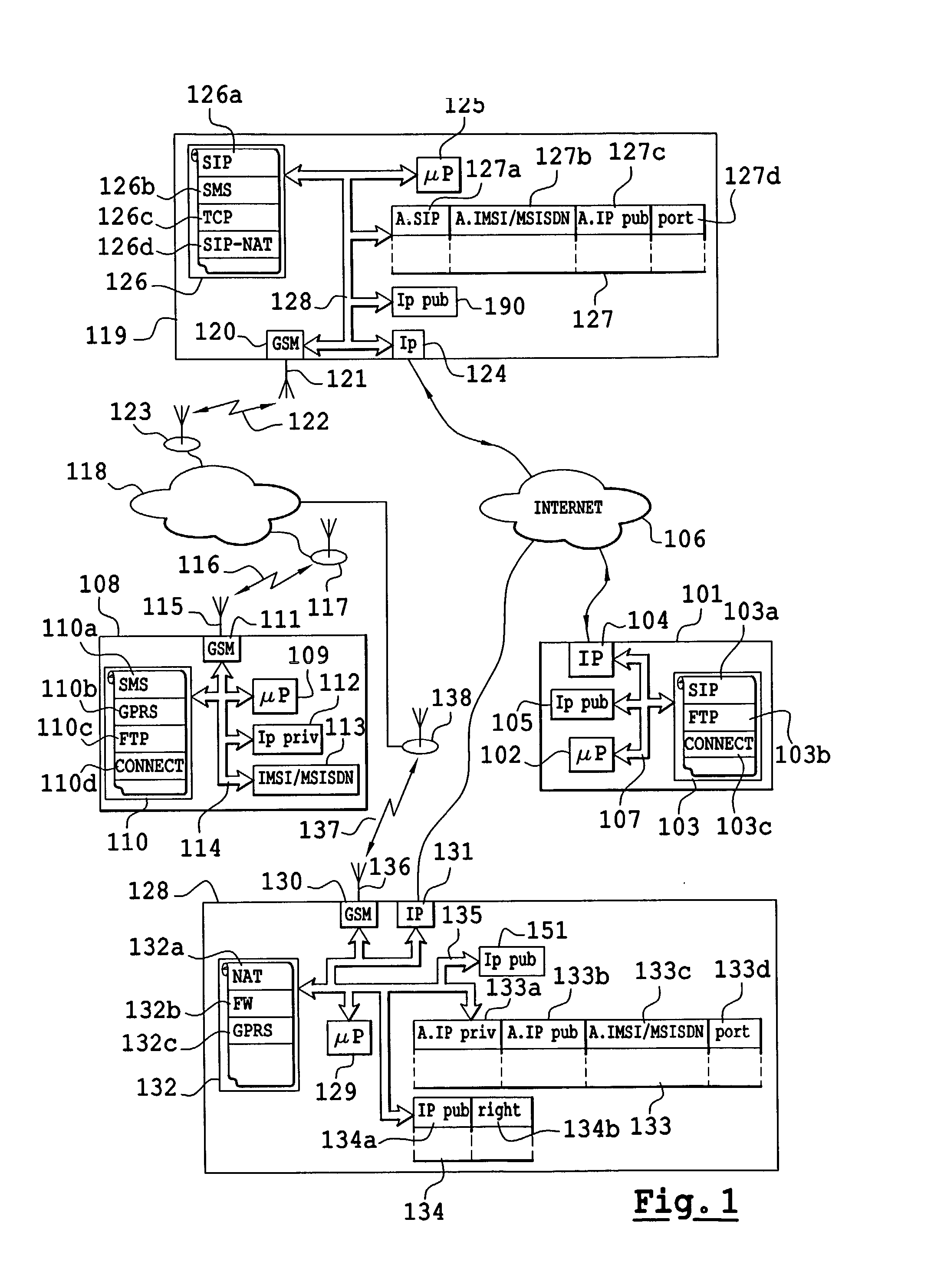
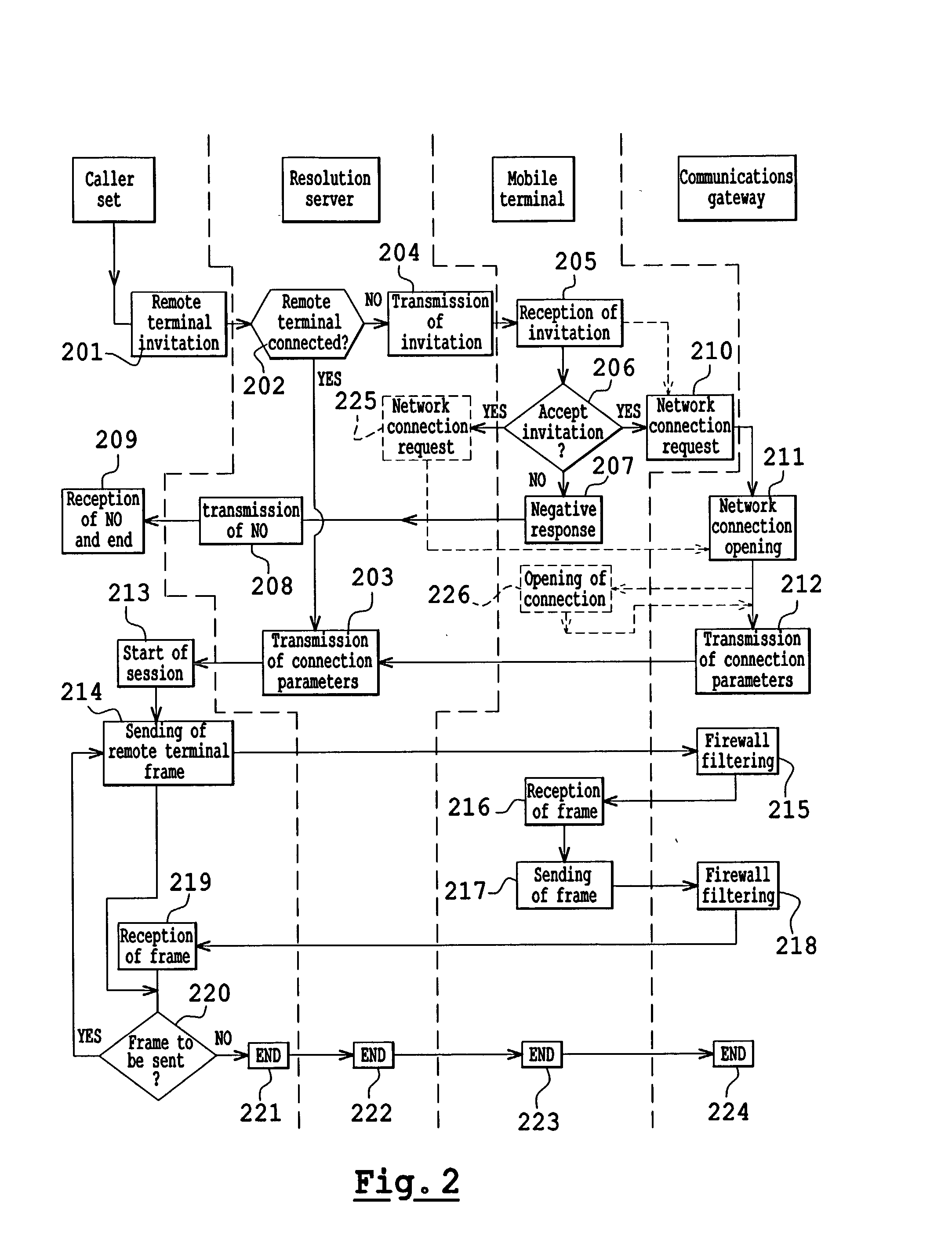
Existing capacities, the SIP protocol (126a), address translation, (126d), short messages (126b) and TCP (126c) are used to implement a resolution server (119) capable of engaging in dialog with a caller set (101), a called mobile terminal (108) and a gateway 128 having to be parameterized to set up a connection between the caller set and the mobile telephone through the Internet network (106). The resolution server accepts connection invitations according to the SIP protocol. These invitations are transmitted, after the resolution of the SIP address, at the mobile terminal in the form of a short message. The mobile terminal accepts or rejects the connection request. In the event of acceptance, the mobile terminal makes a request for the allocation of communications means to the gateway. These allocated means are notified to the caller set through the resolution server.
Owner:VOLUBILL
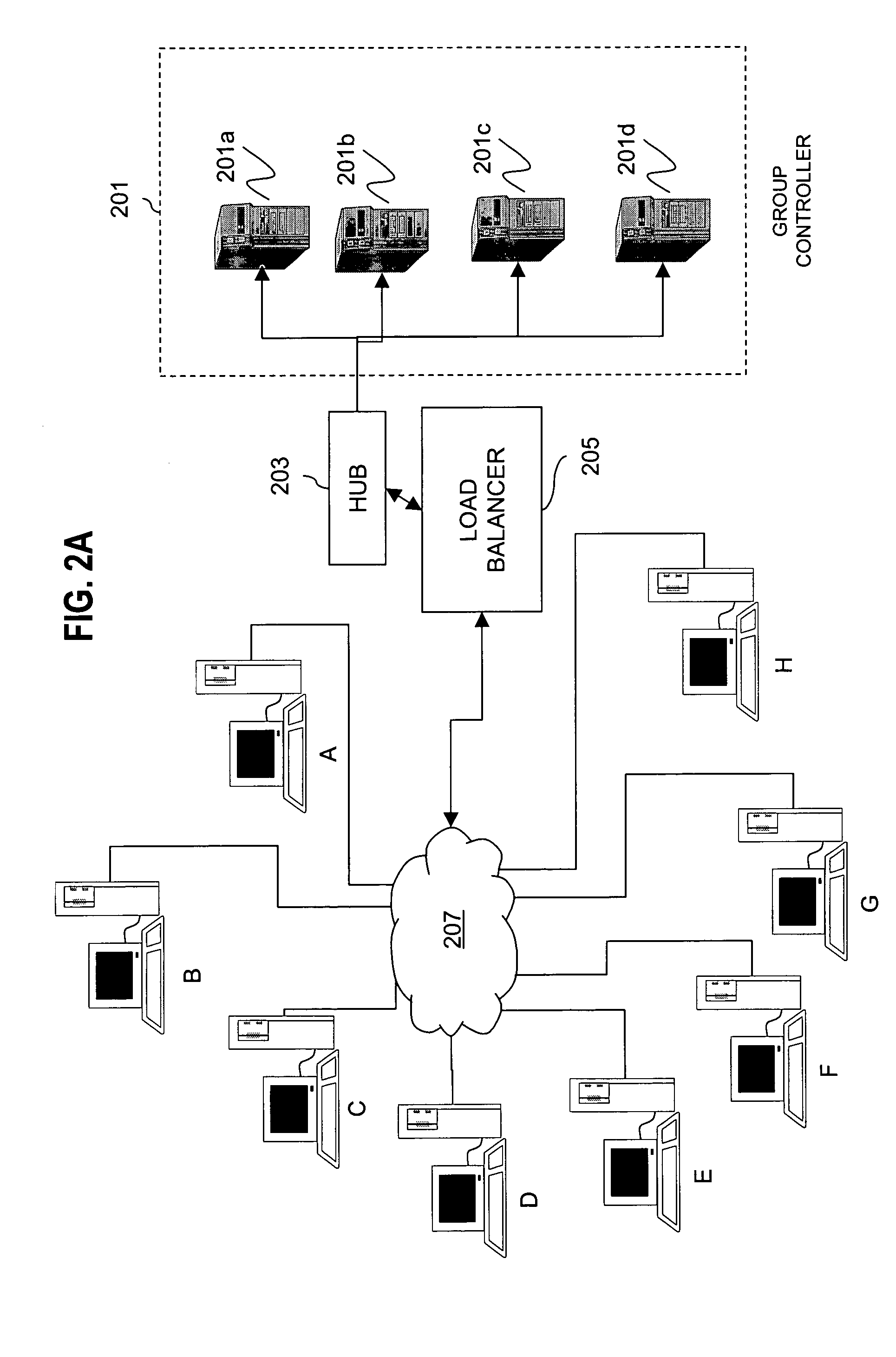
Method for overcoming the single point of failure of the central group controller in a binary tree group key exchange approach
InactiveUS7260716B1Improve scalabilityLess attentionKey distribution for secure communicationSynchronising transmission/receiving encryption devicesComputer networkStructure of Management Information
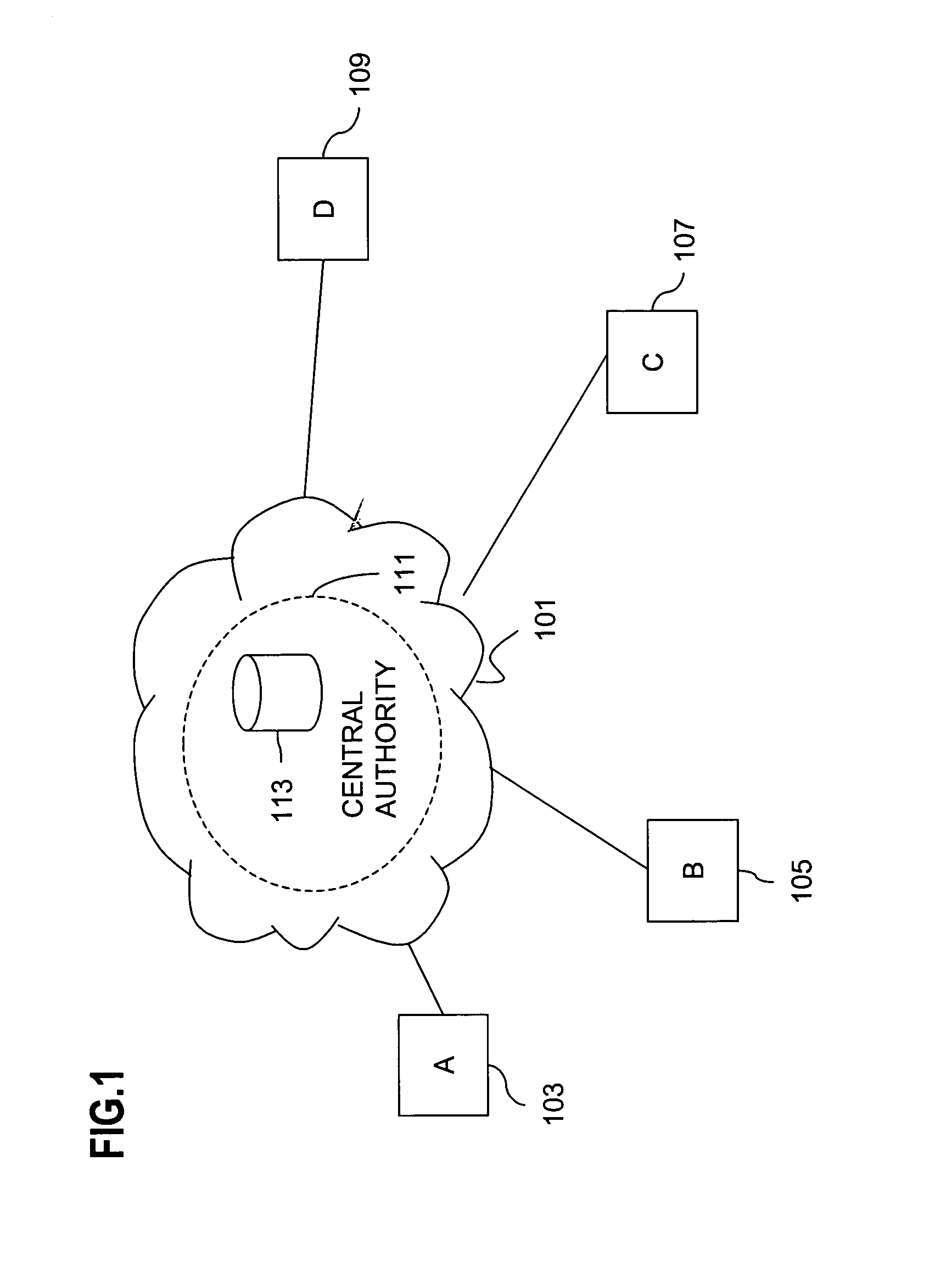
An approach for managing addition or deletion of nodes in a multicast or broadcast group, which avoids introducing a single point of failure at a group controller, certificate authority, or key distribution center, is disclosed. A central group controller utilizes a binary tree structure to generate and distribute session keys for the establishment of a secure multicast group among multiple user nodes. The central group controller is replicated in a plurality of other group controllers, interconnected in a network having a secure communication channel and connected to a load balancer. The secure communication channel is established using a public key exchange protocol. The load balancer distributes incoming join / leave requests to a master group controller. The master group controller processes the join or leave, generates a new group session key, and distributes the new group session key to all other group controller replicas. Each group controller is successively designated as master group controller in real time when a former master group controller crashes or relinquishes its master authority.
Owner:CISCO TECH INC
Programmatic response-time based workload distribution techniques
InactiveUS20040139433A1Improve performanceSimple technologyProgram initiation/switchingElectric devicesQueue timeWorkload
Workload is programmatically distributed across a set of execution resources. In a multithreaded server environment, response time to end users is improved while increasing the efficiency of software execution and resource usage. Execution time and wait / queued time are tracked, for various types of requests being serviced by a server. Multiple logical pools of threads are used to service these requests, and inbound requests are directed to a selected one of these pools such that requests of similar execution-time requirements are serviced by the threads in that pool. The number and size of thread pools may be adjusted programmatically, and the distribution calculation (i.e., determining which inbound requests should be assigned to which pools) is a programmatic determination. In preferred embodiments, only one of these variables is adjusted at a time, and the results are monitored to determine whether the effect was positive or negative. The disclosed techniques also apply to tracking and classifying requests by method name (and, optionally, parameters).
Owner:IBM CORP
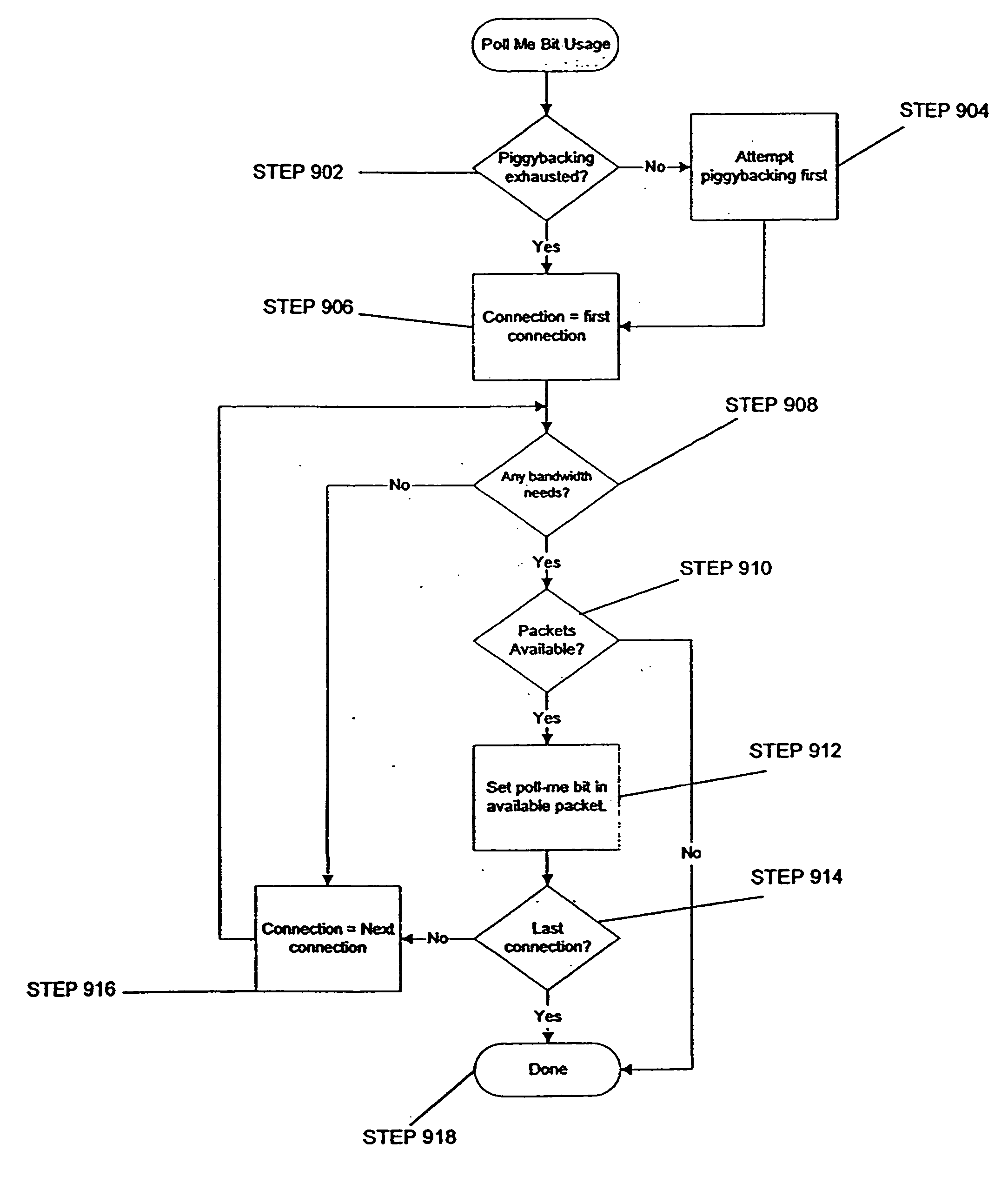
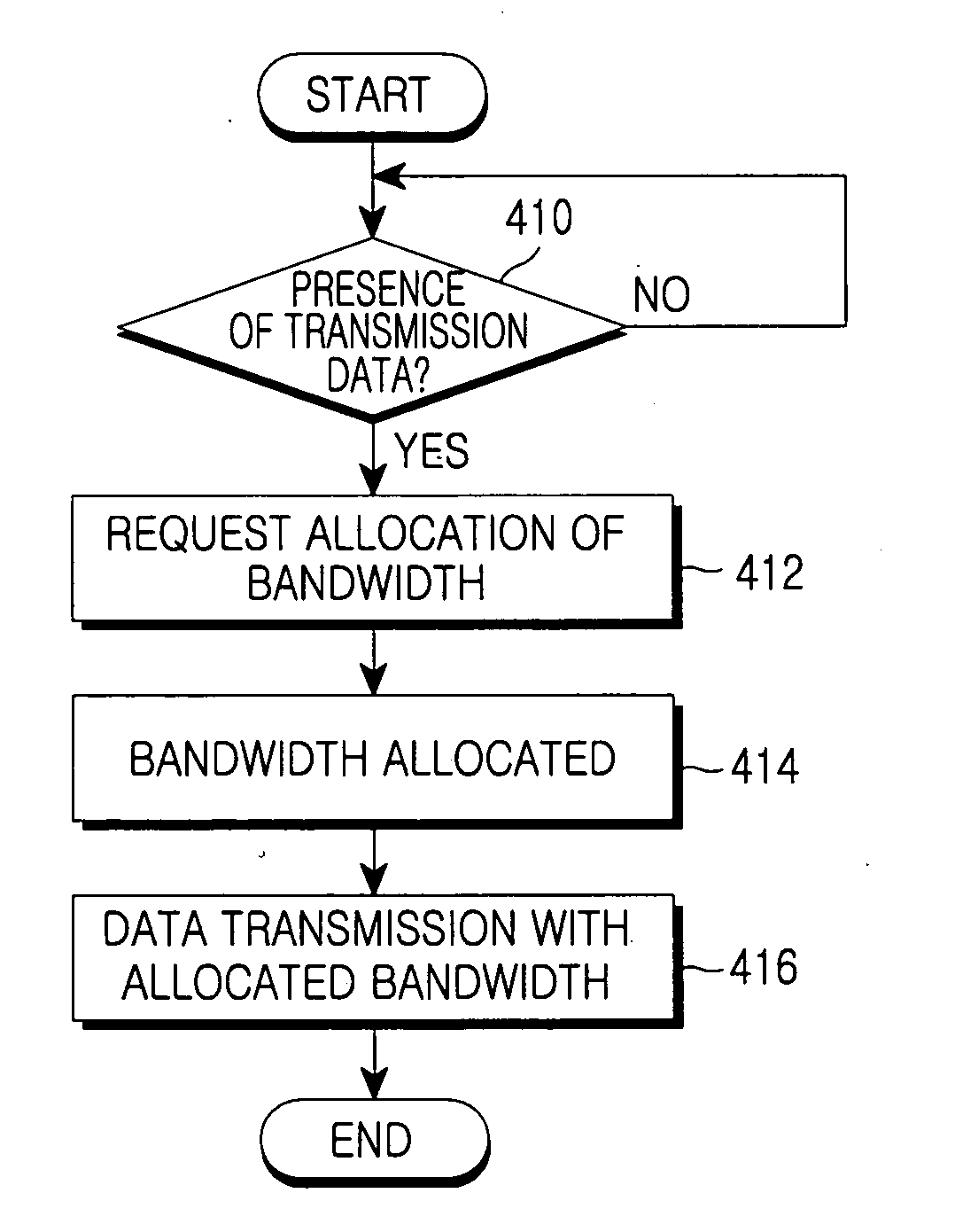
Method and system for adapatively obtaining bandwidth allocation requests
InactiveUS20060146863A1Reduce amountEffective bandwidthNetwork traffic/resource managementTime-division multiplexRate adaptationState parameter
A method and apparatus for adaptively obtaining bandwidth requests in a broadband wireless communication system, The method and apparatus includes dynamically varying technique combinations enabling a plurality of users to efficiently request bandwidth from a shared base station. A user may “piggyback” a new bandwidth request upon, or set a “poll-me bit” within, presently allocated bandwidth. A base station may poll users, individually or in groups, by allocating unrequested bandwidth for new requests. Polling may respond to a “poll-me bit,” and / or it may be adaptively periodic at a rate based on communication status parameters, such as recent communication activity and connection QoS levels Group polling permits a possibility of collisions. Polling policies may be established for dynamically varying user groups, or may be determined for each user. Dynamic selection of appropriate polling techniques makes use of efficiency benefits associated with each technique.
Owner:WI LAN INC
Arbitration apparatus for allocating computer resource and arbitration method therefor
InactiveUS20070106796A1Digital computer detailsMultiprogramming arrangementsComputer resourcesResource allocation
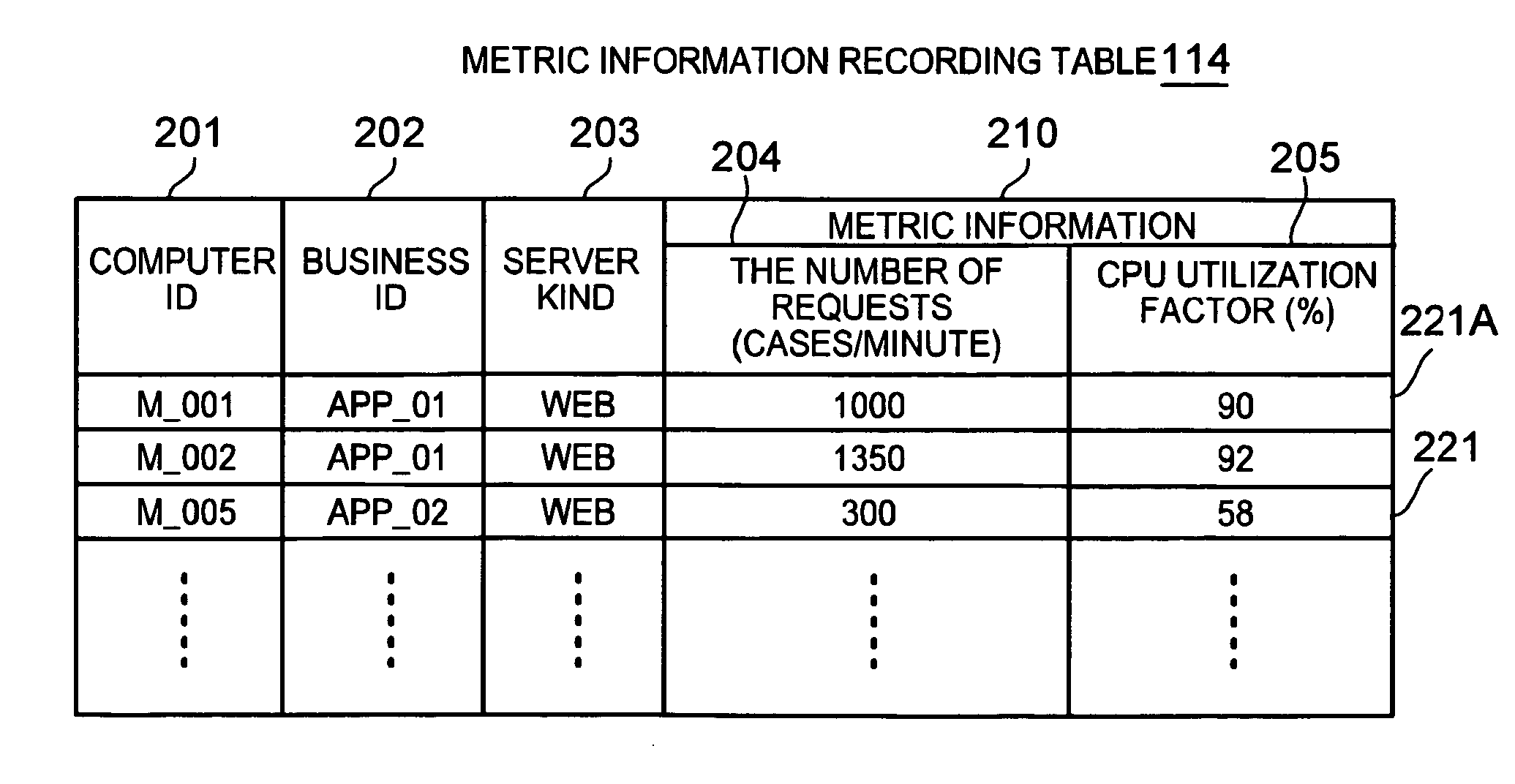
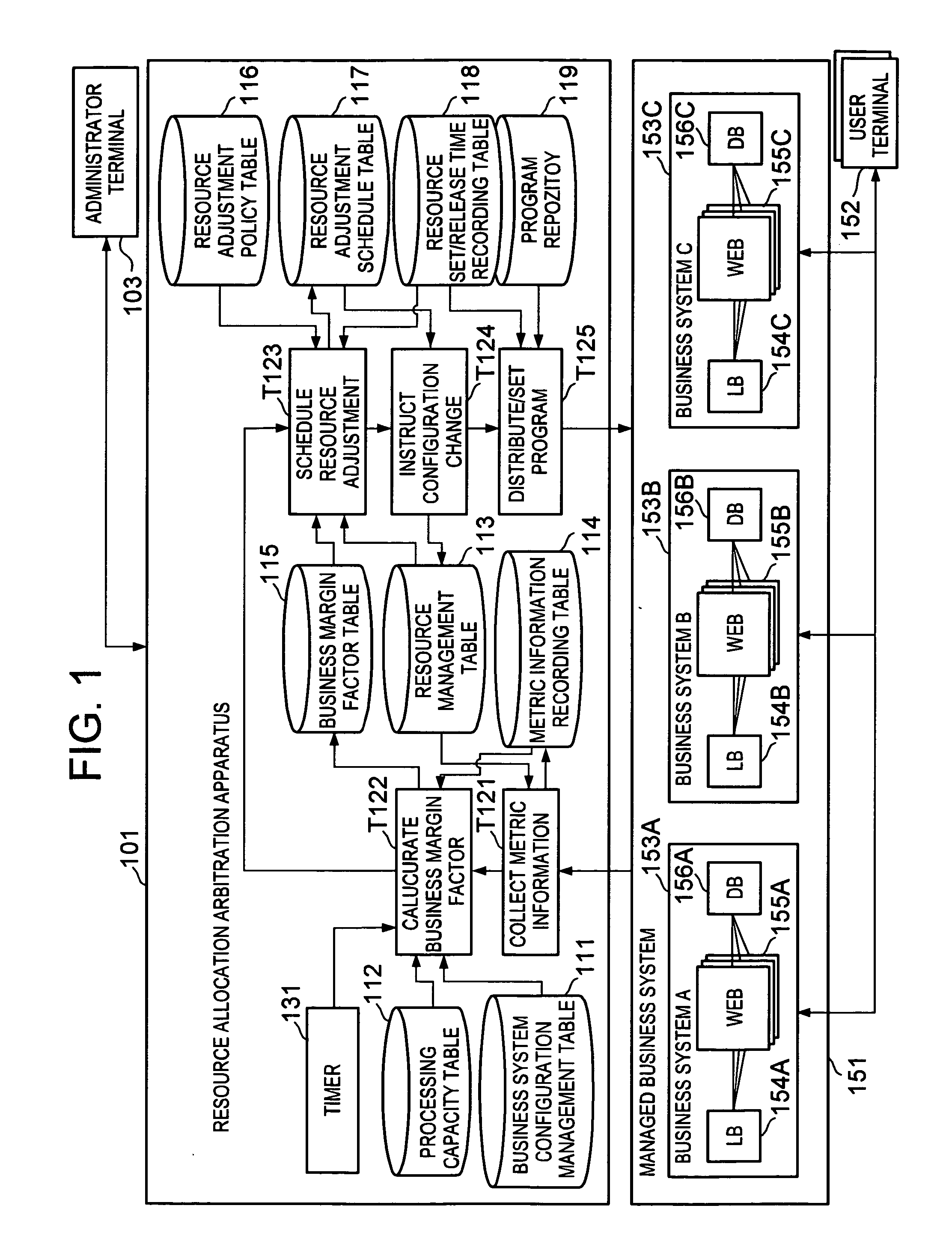
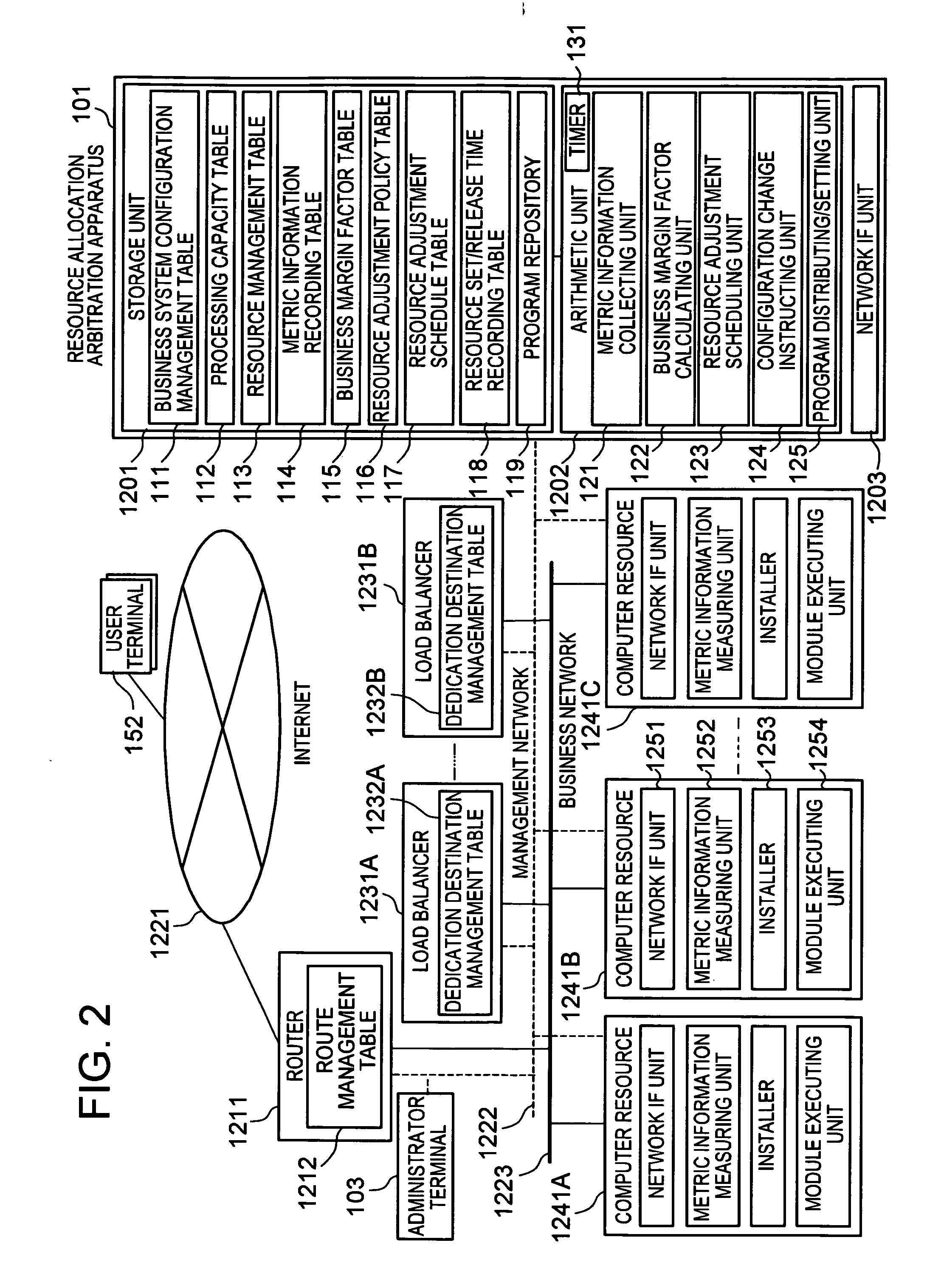
In a business system which allocates a request for one business application to one or more of the computer resources executing such business application, the computer resources are accommodated among the plurality of the business systems so that the load covered by each of the business systems is averaged out. The arbitration apparatus for resource allocation 101 calculates a margin rate for each business system by measuring load for respective business systems, and by calculating a ratio of the measured load and the allowable execution amount allowable under current constitution. When a computer resource 1241 which is not allocated to business system is found, this computer resource is allocated to the business system indicating low margin rate while if such computer resource 1241 is not found, the computer resource 1241 is reallocated by being released from the business system having high margin rate.
Owner:HITACHI LTD
Method and apparatus for a bandwidth broker in a packet network
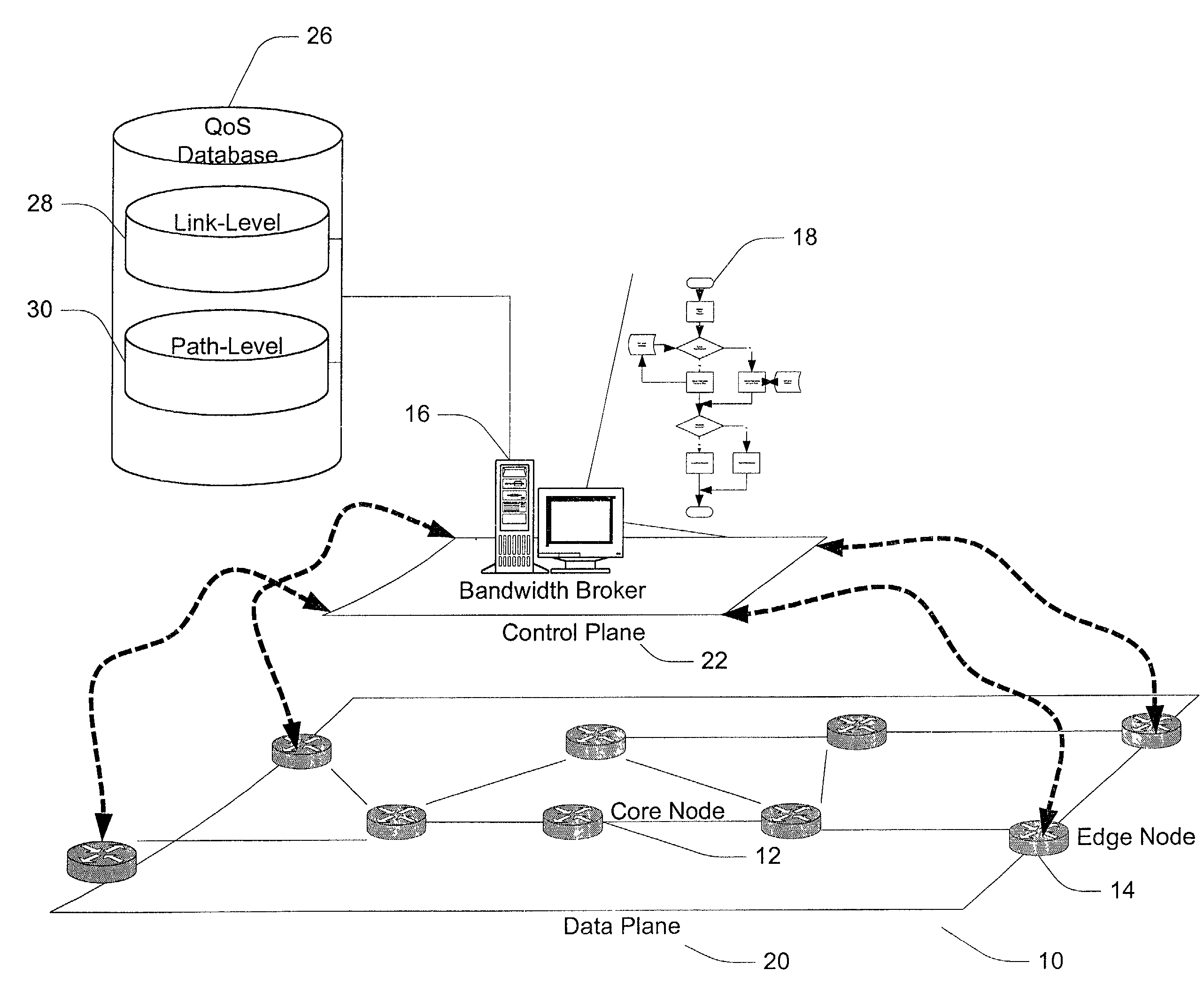
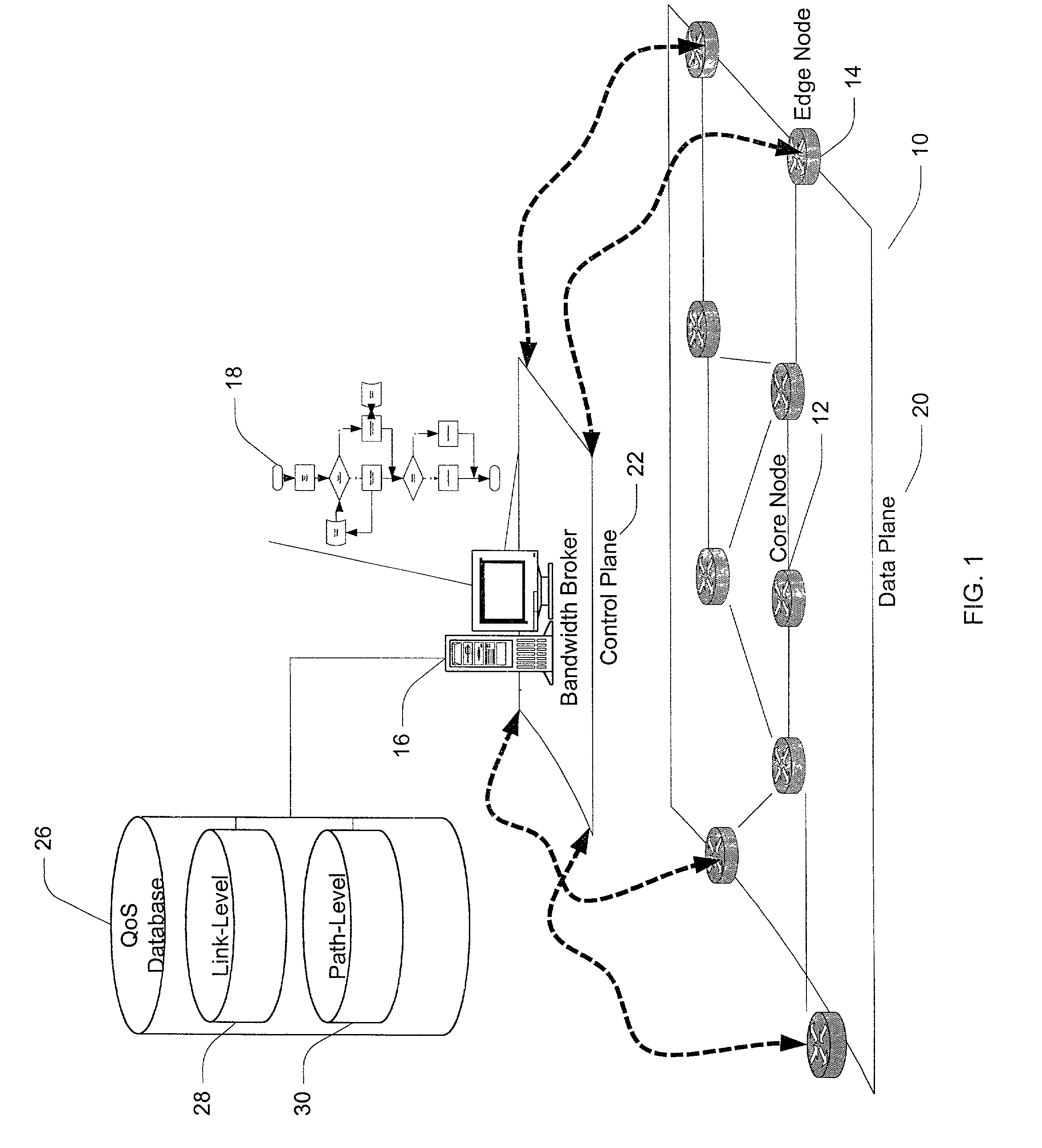
InactiveUS7257632B2Digital computer detailsData switching networksBandwidth BrokerDistributed computing
A method and apparatus for allocating bandwidth within a network domain. A centralized bandwidth broker maintains a link-level database including detailed flow data for individual links in a network domain and a path-level database including summarized flow data for individual paths in the network domain. The bandwidth broker determines bandwidth allocations at a path-level by allocating discrete amounts of bandwidth, termed quotas, based on flow requests. If a flow request cannot be satisfied by allocating quotas, then the bandwidth broker uses the link-level database to recover bandwidth from unused bandwidth by other paths on the same link in order to satisfy the flow request. In another embodiment of a bandwidth broker, the centralized bandwidth broker is replaced by a distributed bandwidth broker including a central bandwidth broker and one or more edge bandwidth brokers. An edge bandwidth broker conducts path-level allocations and requests or releases quotas from and to the central bandwidth broker. The central bandwidth broker conducts link-level allocations and allocates or de-allocates quotas to and from the path maintained by the edge bandwidth broker.
Owner:FUJITSU LTD
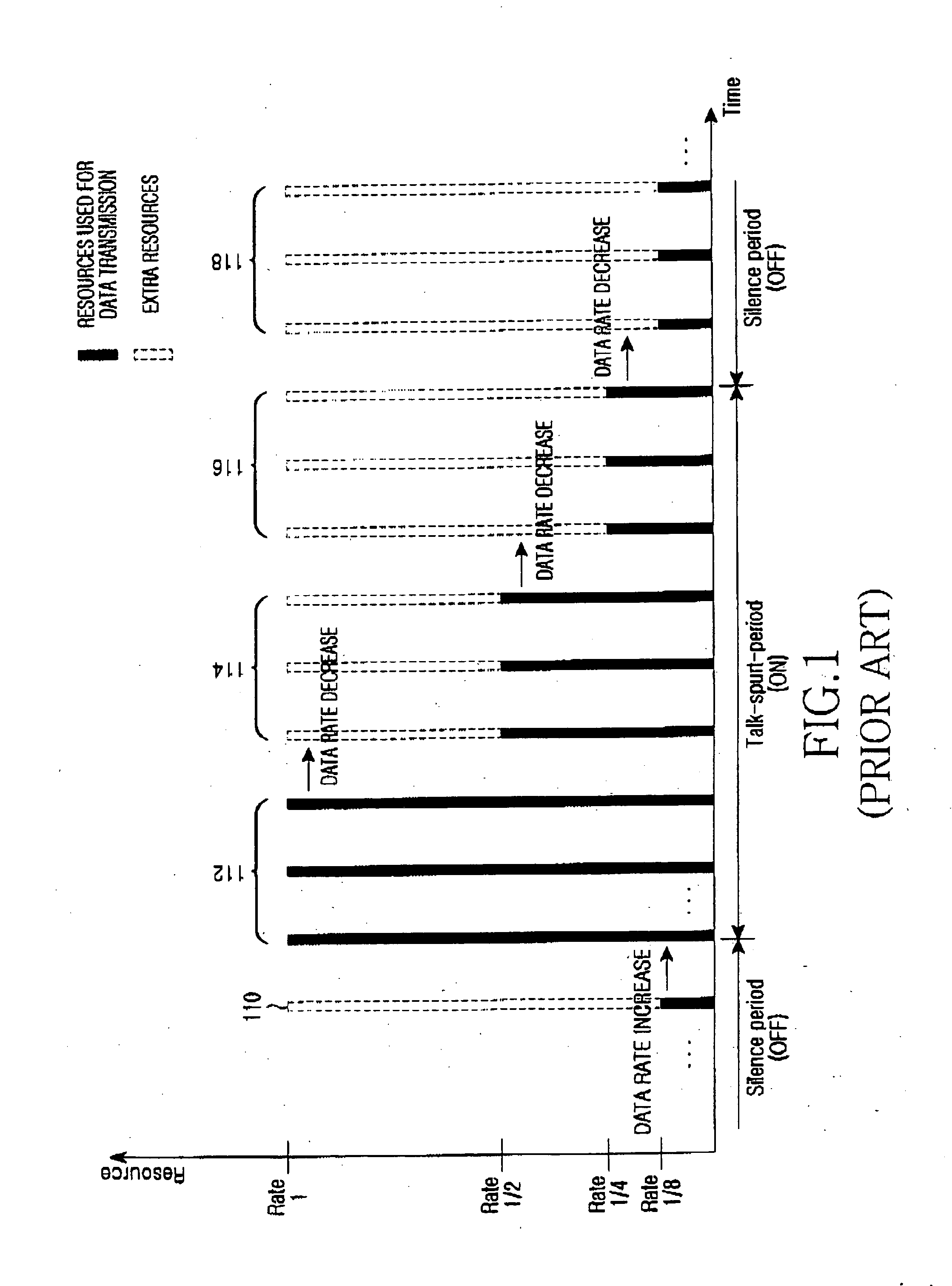
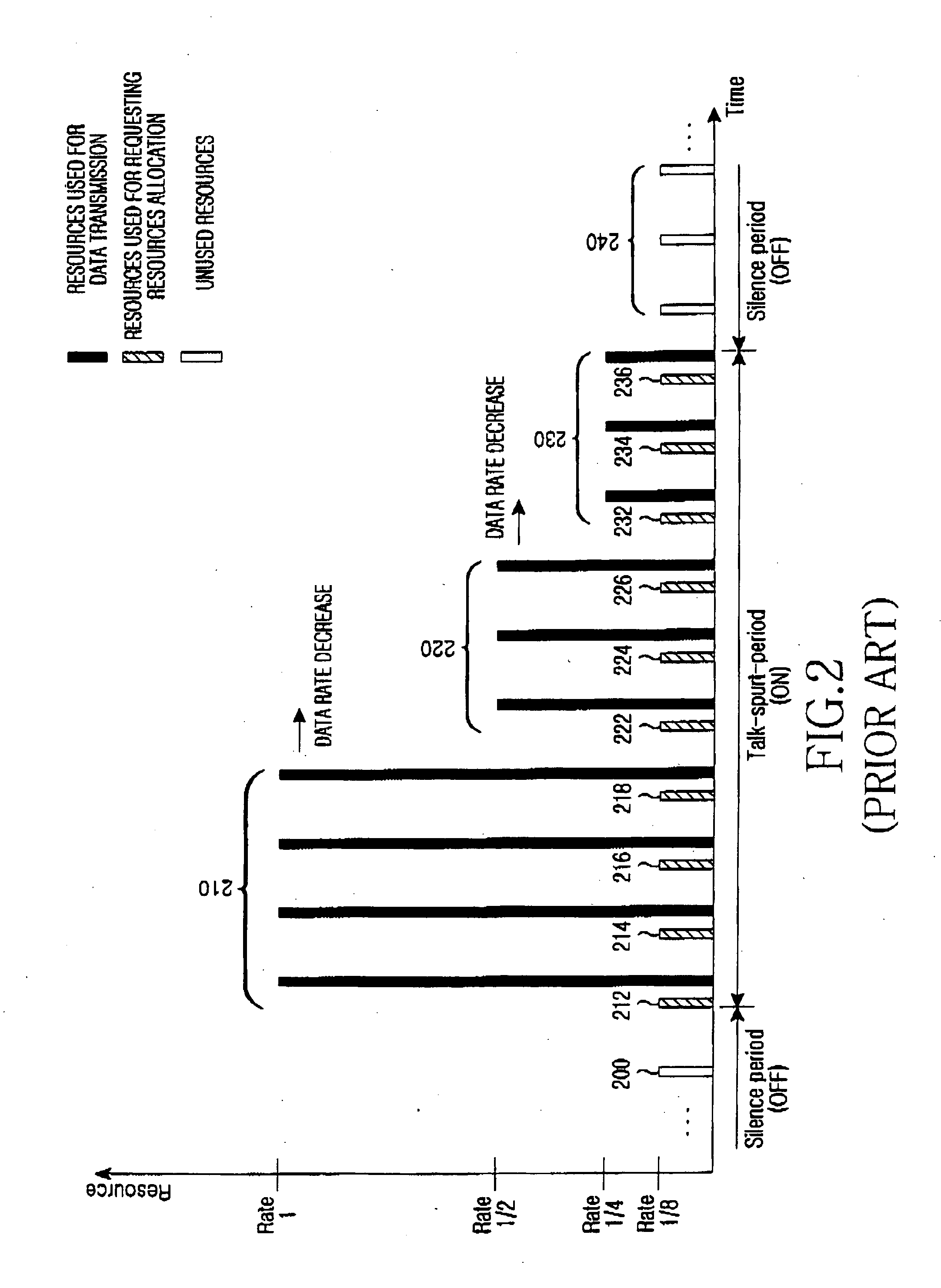
Method of requesting allocation of uplink resources for extended real-time polling service in a wireless communication system
ActiveUS20060245352A1Easy to useFrequency-division multiplex detailsRadio/inductive link selection arrangementsCommunications systemResource consumption
Provided is a device and method for scheduling uplink resources in a wireless communication system supporting VoIP. When its data rate is decreased, an MS notifies a BS of the rate decreased. When increasing its data rate, the MS requests resource allocation to the BS by transmitting a BR header or a CQICH codeword. Compared to the conventional ertPS in which the BS periodically allocates uplink resources to the MS irrespective of the state of the MS, the BS does not allocate uplink resources when the MS transitions form a talk-spurt period to a silence period. Therefore, resources consumption arising from unnecessary bandwidth allocation is reduced.
Owner:SAMSUNG ELECTRONICS CO LTD
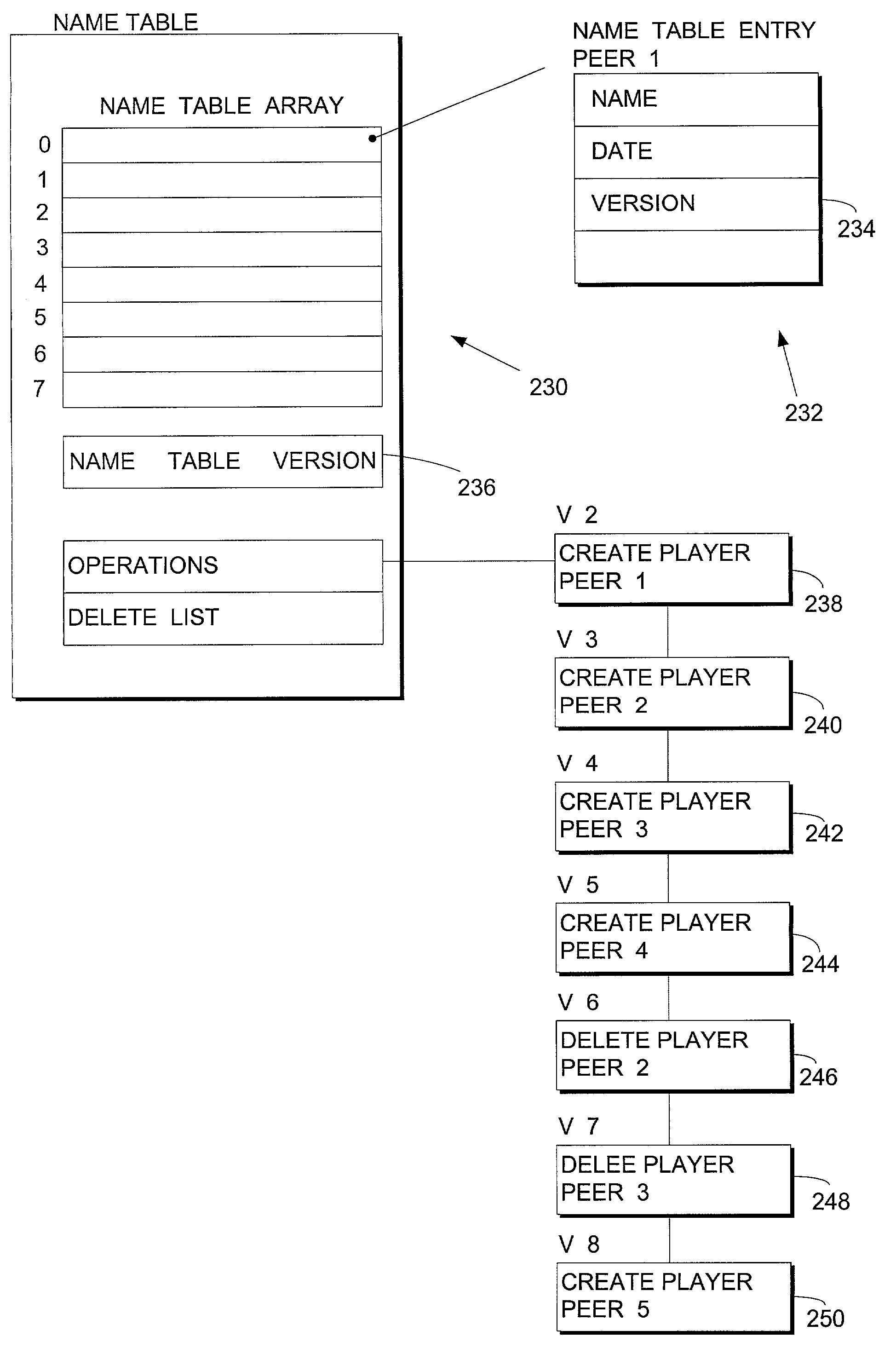
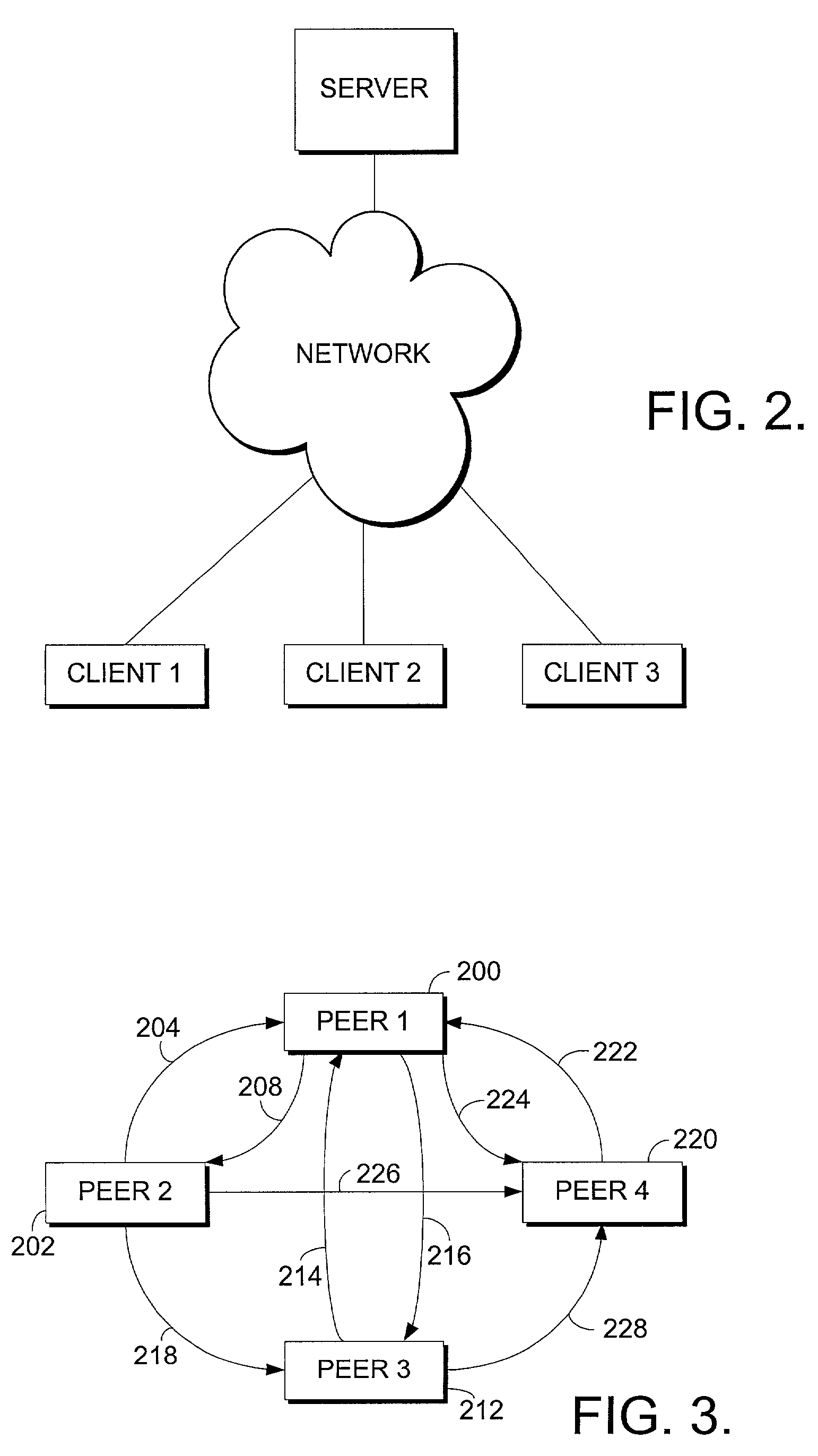
Synchronization and recovery of peers in a peer to peer environment
InactiveUS7177950B2Resource allocationMultiple digital computer combinationsComputerized systemDistributed computing
A method is provided for use in a computer system that is operating in a peer-to-peer environment. The peer-to-peer environment has a host peer and at least one non-host peer. The method of the invention is used to order the operation requests of the peers so that operations are performed only in the order that they are processed by the host peer. The method includes providing a list of recognized operations which may be requested by any of the peers in the session. The host peer then receives at least one operation request from one of the peers, the request being selected from the provided list. The host then assigns a unique version number to the operation request, so that all peers within the session can determine the proper order in which to process orders given by the host peer.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com