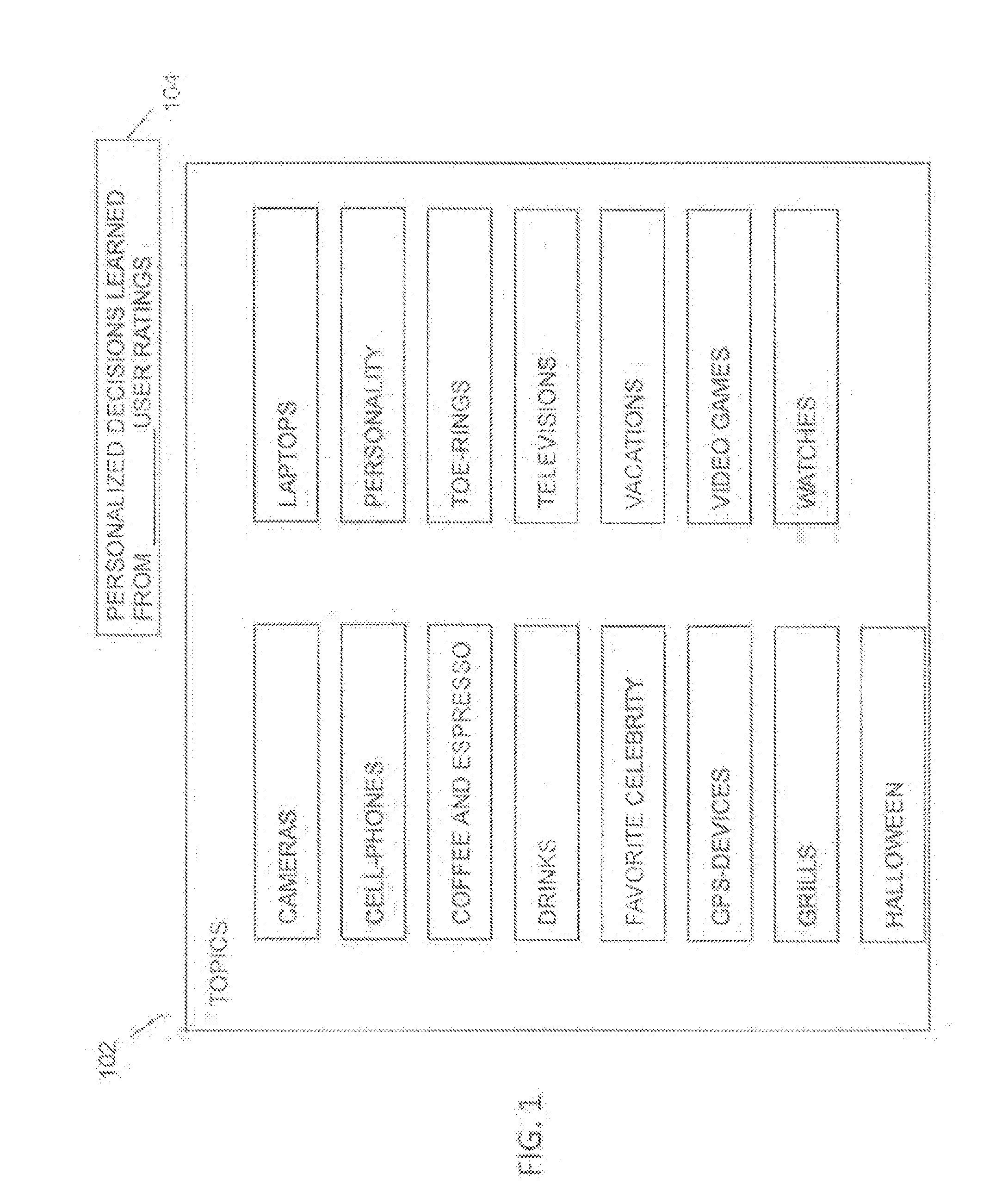
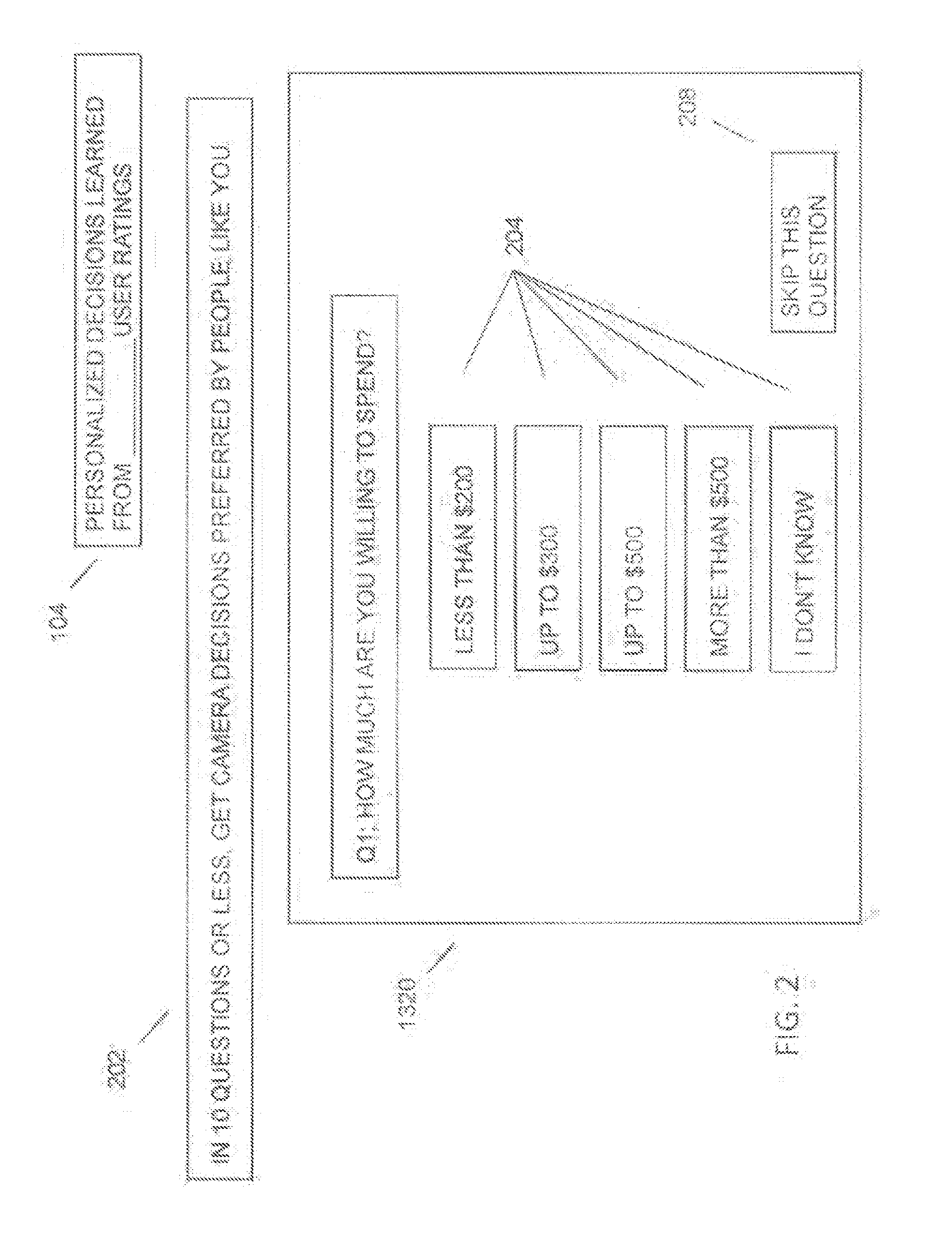
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2681results about "Fuzzy logic based systems" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
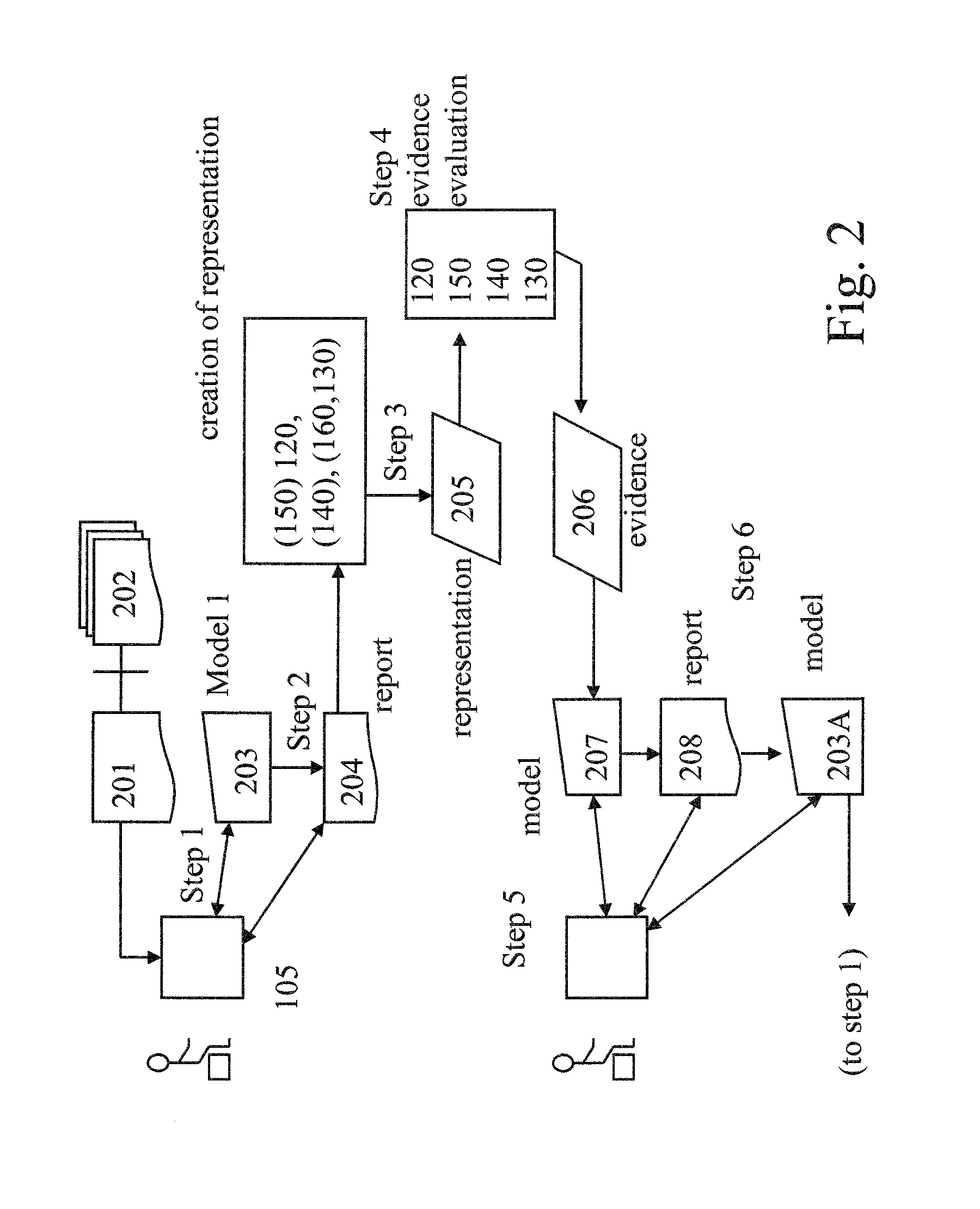
Evidence evaluation system and method based on question answering
An evidence evaluation method and system based on question answering converts a report of analyzed information and / or a model of information into a collection of questions, determines answers for the collection of questions. A fact in the report is marked as being supported if one or more of the answers for the collection of questions support the fact. A fact in the report of analyzed facts is marked as being refuted if one or more of the answers for the collection of questions refute the fact. The method and system also may collect the answers as evidence and add the evidence to the model of information to create an updated model of information. The steps may be repeated using the updated report and updated model.
Owner:IBM CORP
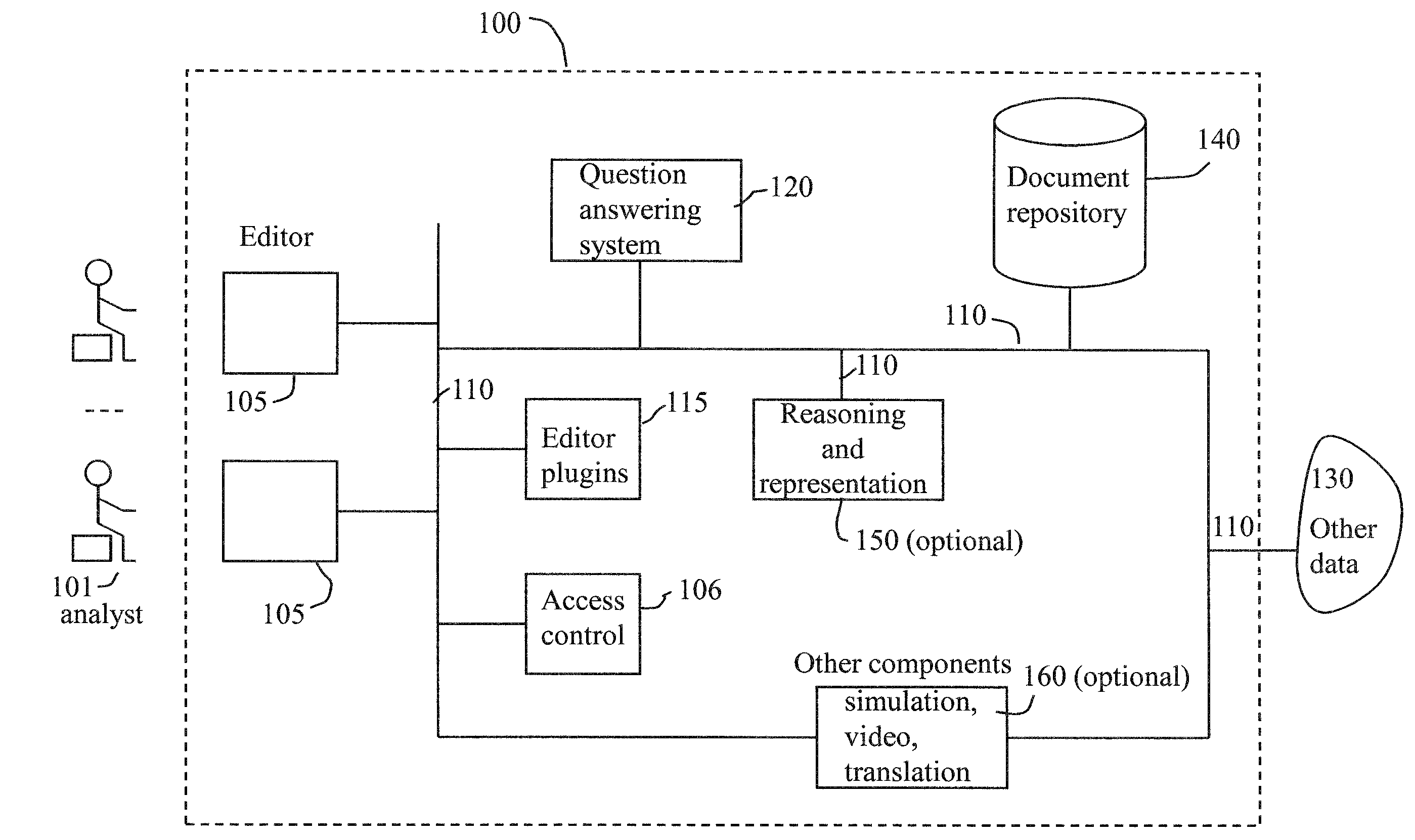
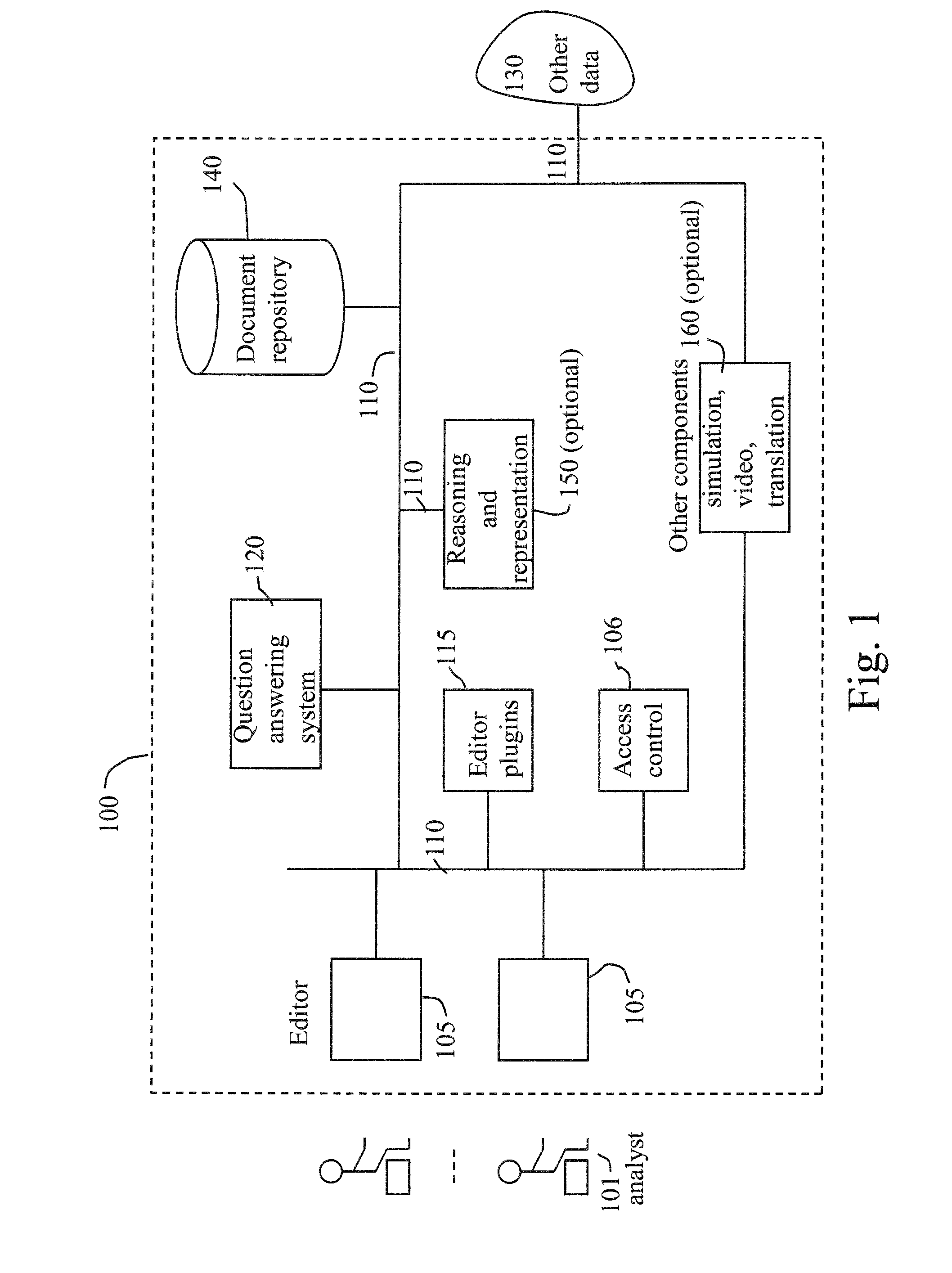
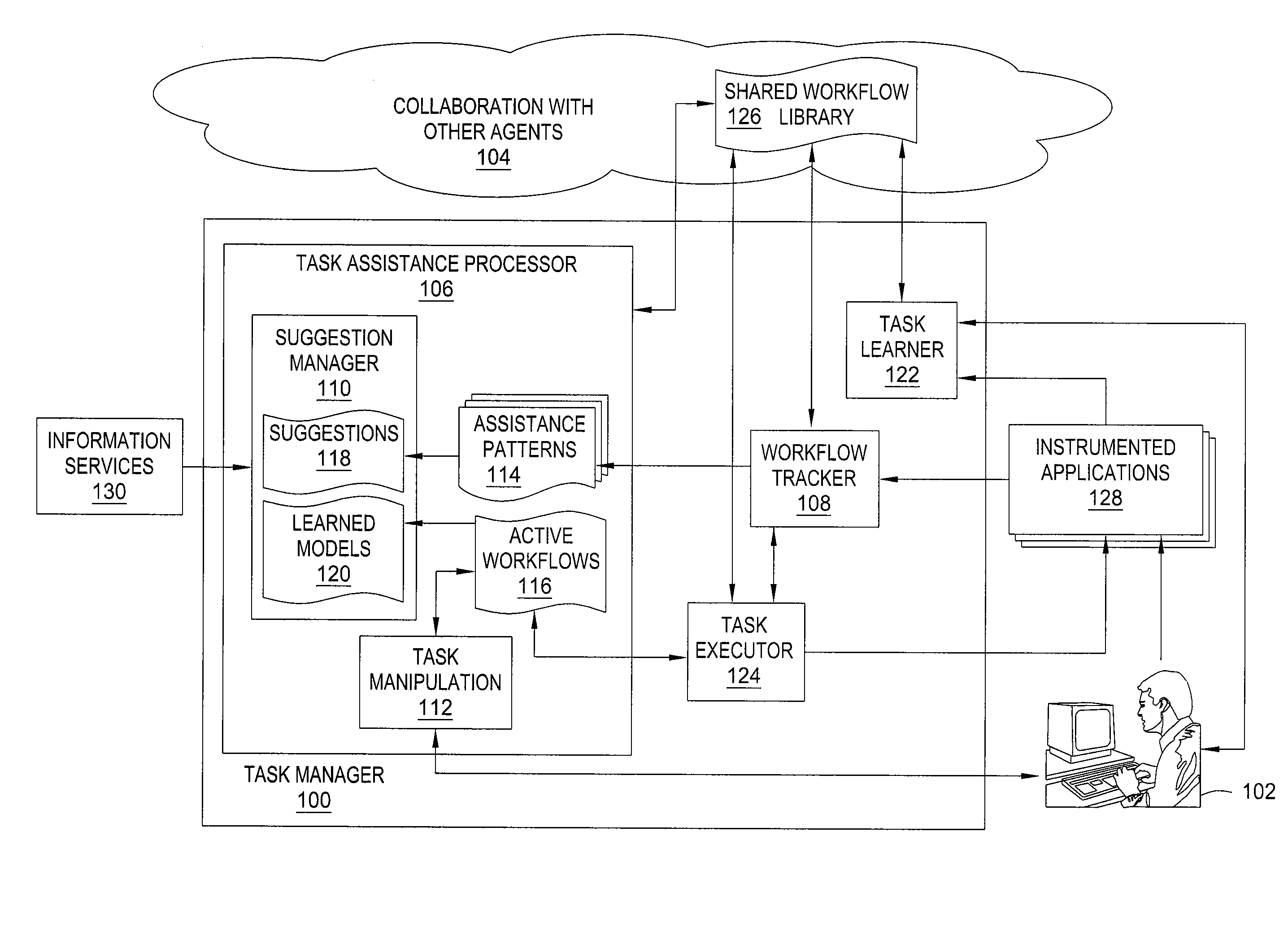
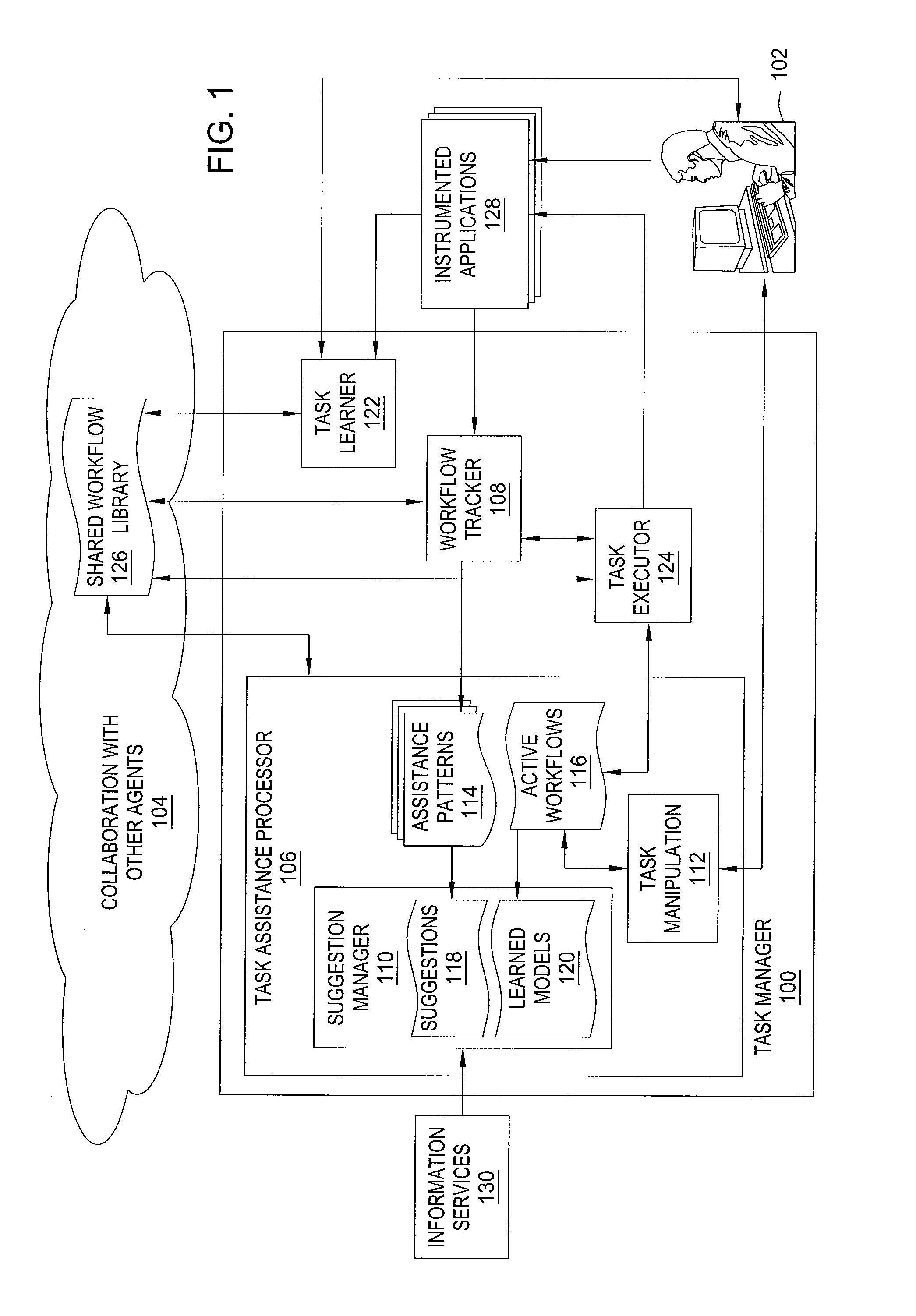
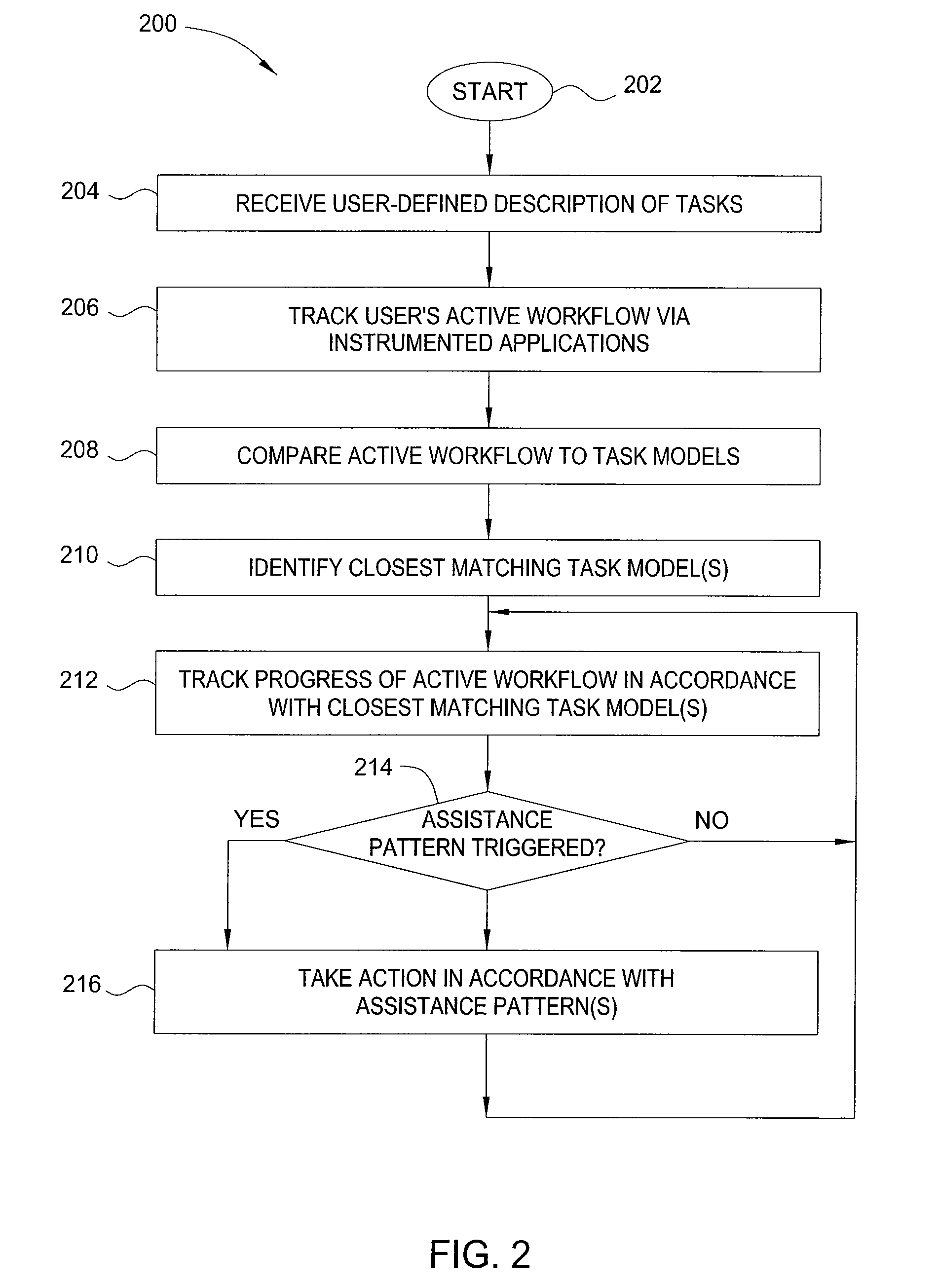
Method and apparatus for automated assistance with task management
ActiveUS20090307162A1Digital computer detailsMultiprogramming arrangementsCoprocessorApplication software
The present invention relates to a method and apparatus for assisting with automated task management. In one embodiment, an apparatus for assisting a user in the execution of a task, where the task includes one or more workflows required to accomplish a goal defined by the user, includes a task learner for creating new workflows from user demonstrations, a workflow tracker for identifying and tracking the progress of a current workflow executing on a machine used by the user, a task assistance processor coupled to the workflow tracker, for generating a suggestion based on the progress of the current workflow, and a task executor coupled to the task assistance processor, for manipulating an application on the machine used by the user to carry out the suggestion.
Owner:SRI INTERNATIONAL
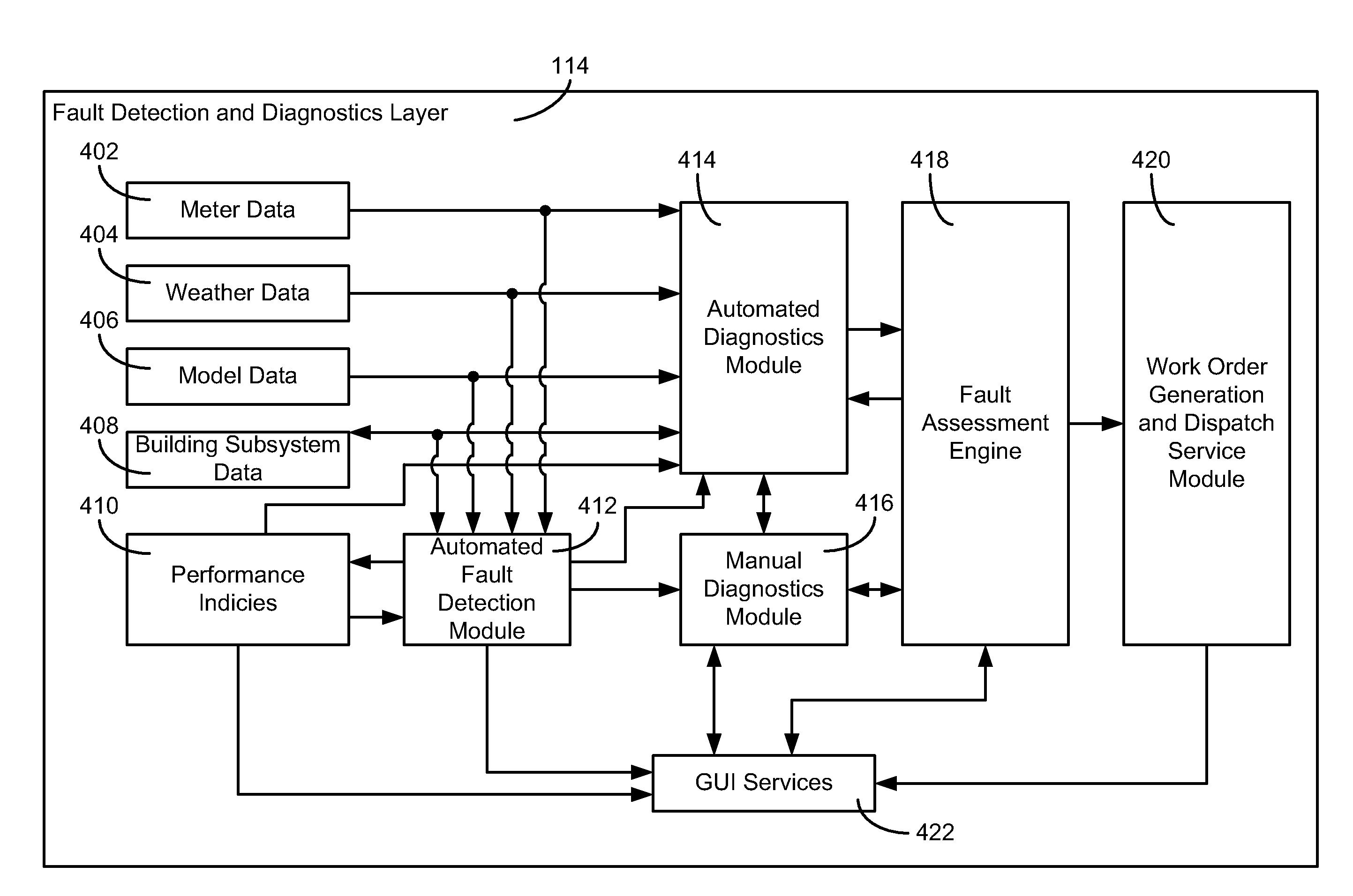
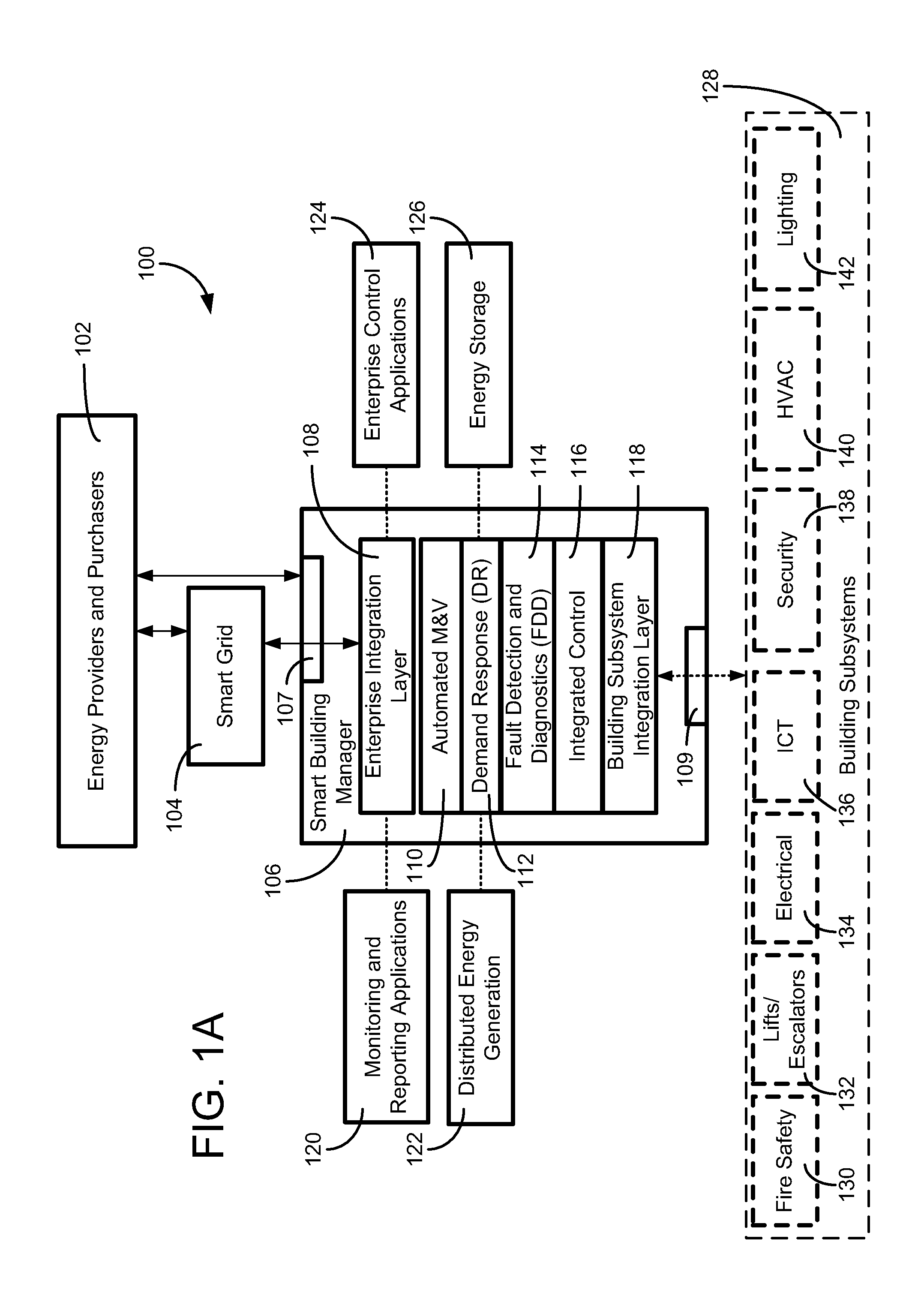
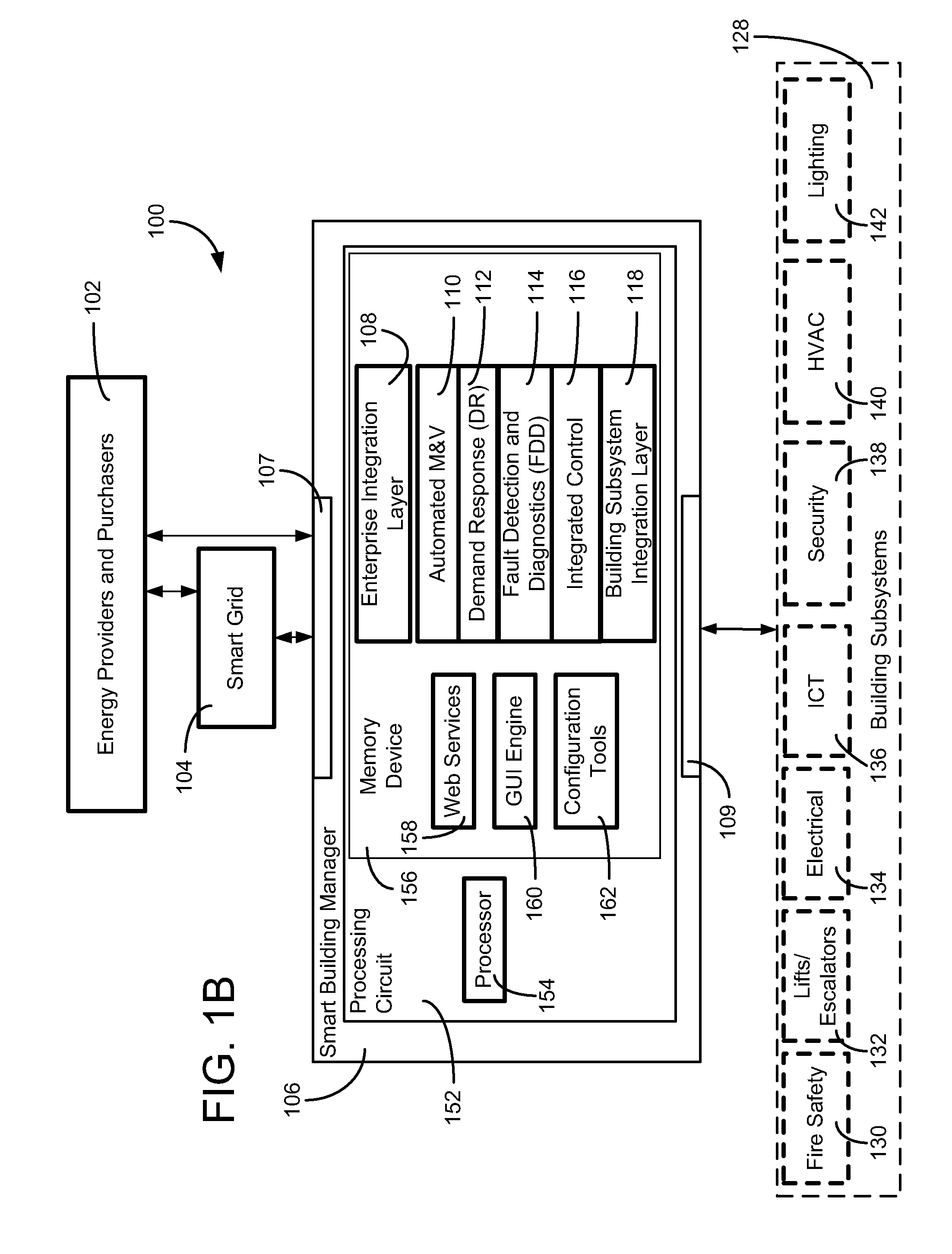
Building management system with fault analysis
ActiveUS20110178977A1Enhance data loggingTechnology managementFuzzy logic based systemsEngineeringFault analysis
Owner:JOHNSON CONTROLS TECH CO
Simple and dynamic configuration of network devices
ActiveUS20050108369A1Reduce the burden onFunction increaseData processing applicationsDigital computer detailsOperational systemPersonal computer
The present invention relates to a system and method for configuring and managing network devices. The arrival (and departure) of devices on a network can be detected by a monitor. Upon detection, network devices can be simply and dynamically configured with little or no end-user intervention, for instance by automatically loading device drivers and allocating resources for the devices. Furthermore, network devices can be associated with other network devices such as a personal computer to facilitate seamless integration of network devices with a computer operating system.
Owner:MICROSOFT TECH LICENSING LLC
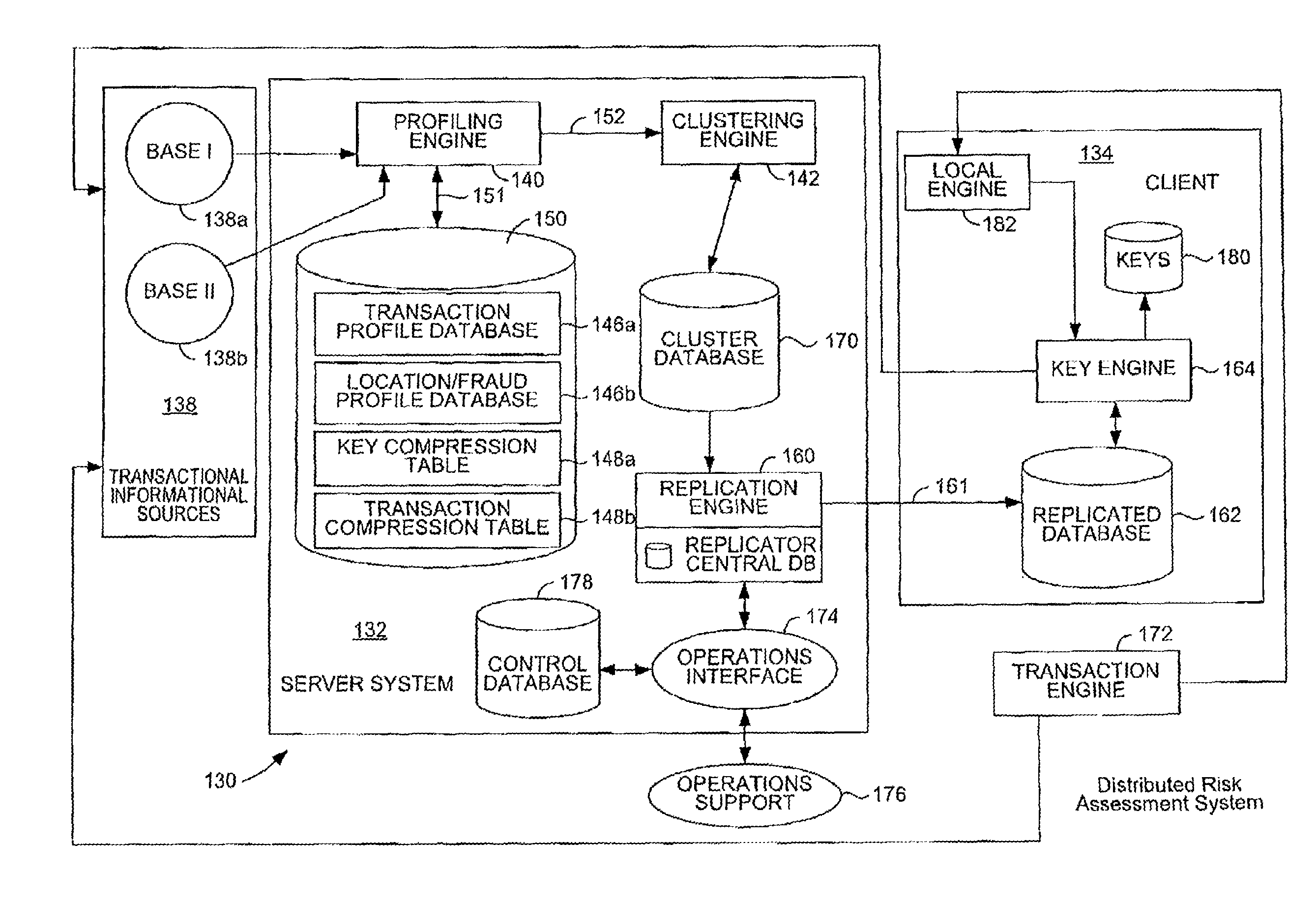
Distributed Quantum Encrypted Pattern Generation And Scoring
InactiveUS20100057622A1Informed decisionPrivacy protectionFinancePublic key for secure communicationPattern generationClient-side
Transaction scoring is performed in a distributed manner across a client-server computing system. A computing system for processing a transaction includes a server system and a client system. The server system is arranged to process information associated with the transaction, while the client system communicates with the server system and includes a key engine which is arranged to generate keys. The client system and the server system are arranged to cooperate to make probabilistic determinations associated with the transaction. The client is arranged to send the keys generated by the key engine as a transaction to the server system.
Owner:VISA USA INC (US)
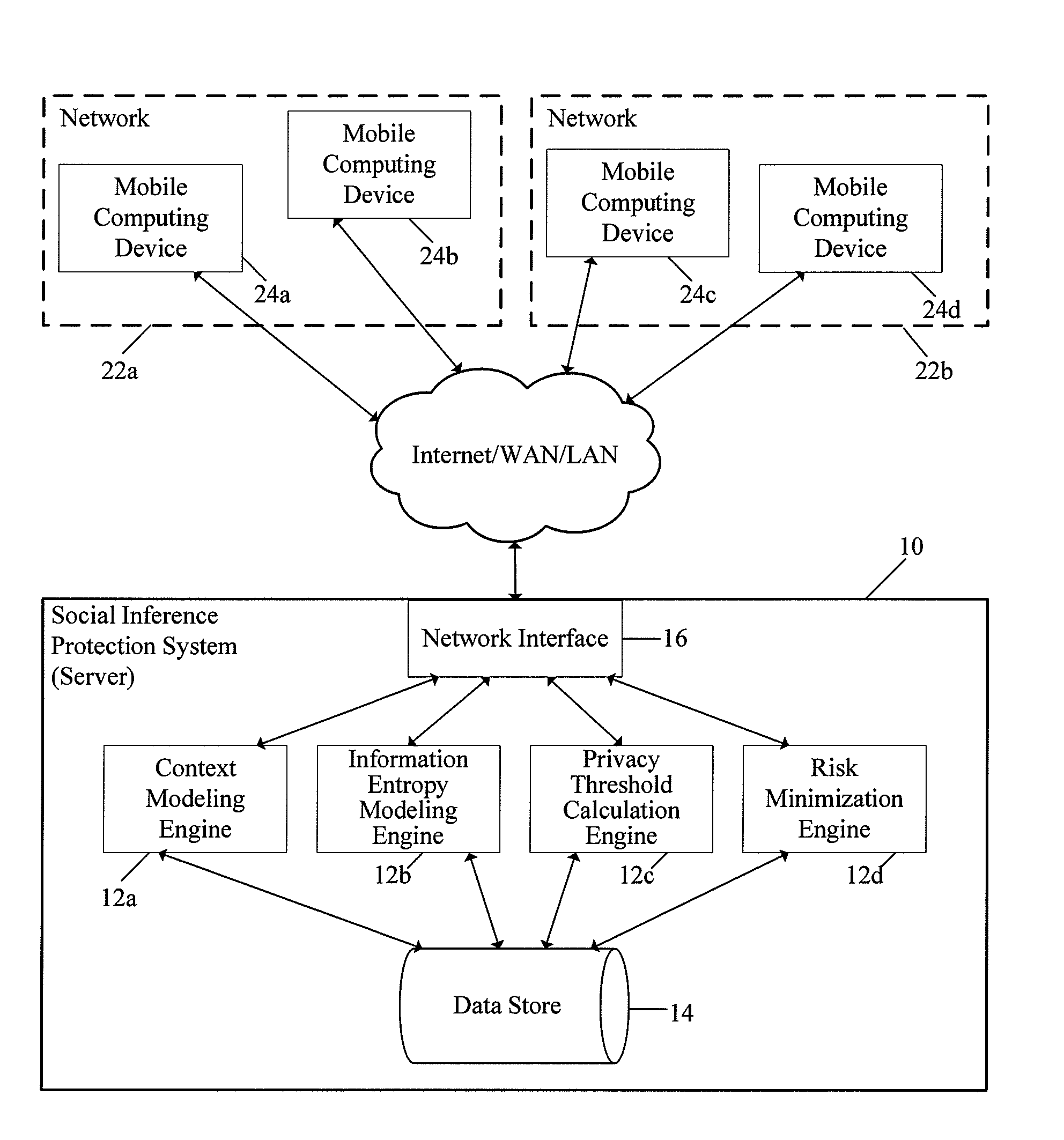
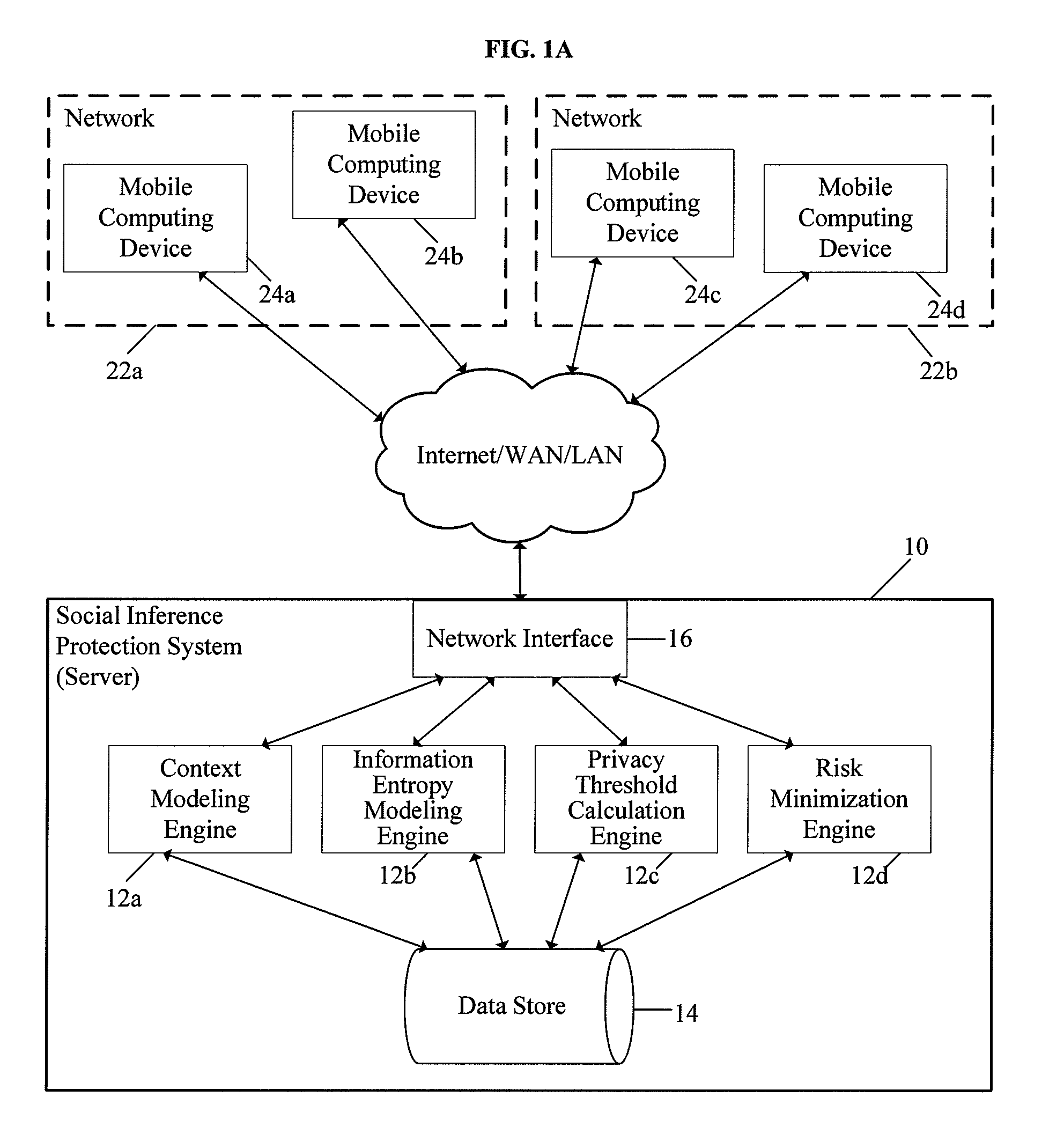
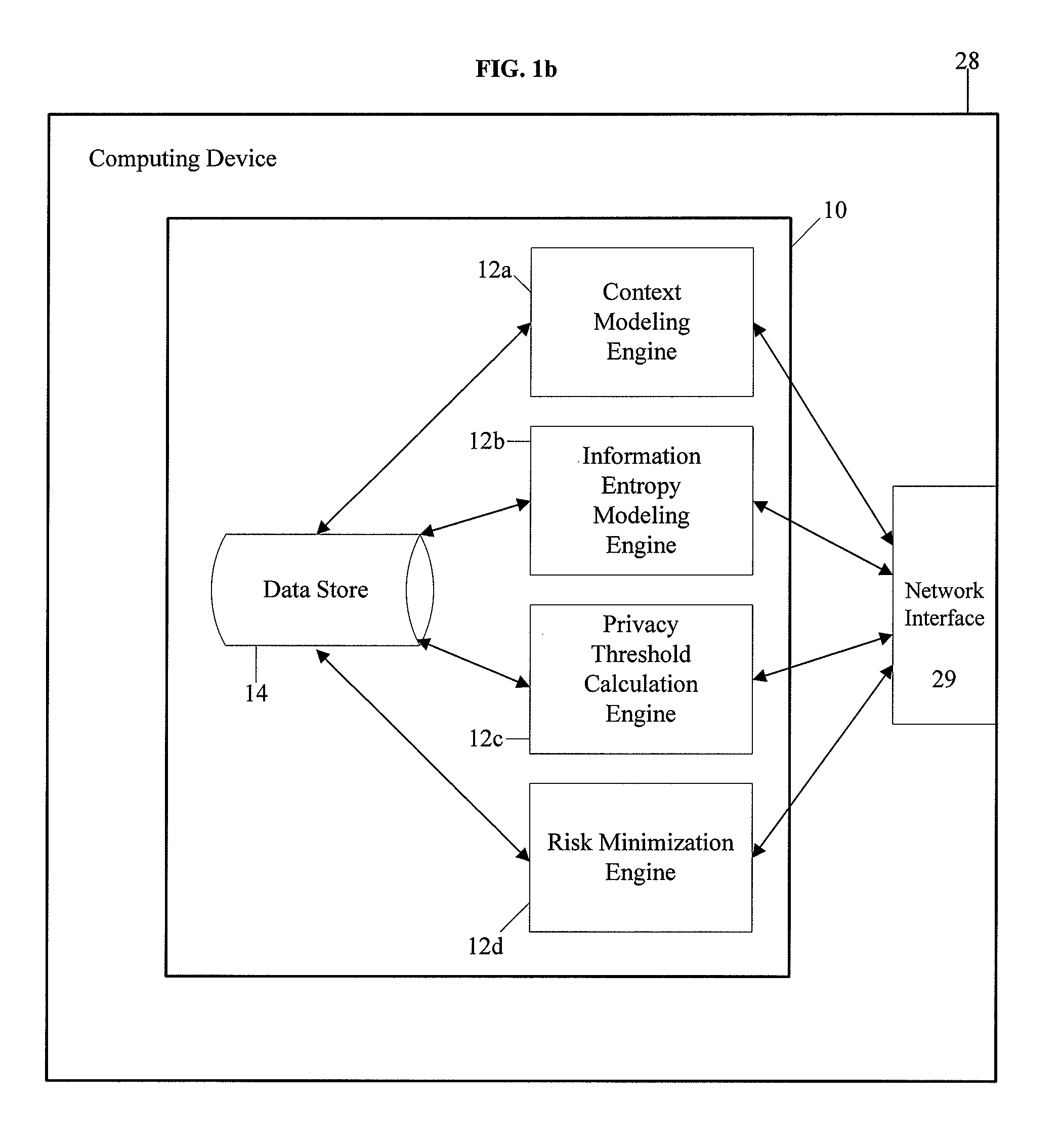
System and method for protecting user privacy using social inference protection techniques
InactiveUS8504481B2Minimize privacy riskInhibit exchangeDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyUser privacy
A system and method for protecting user privacy using social inference protection techniques is provided. The system executes a plurality of software modules which model of background knowledge associated with one or more users of the mobile computing devices; estimate information entropy of a user attribute which could include identity, location, profile information, etc.; utilize the information entropy models to predict the social inference risk; and minimize privacy risks by taking a protective action after detecting a high risk.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
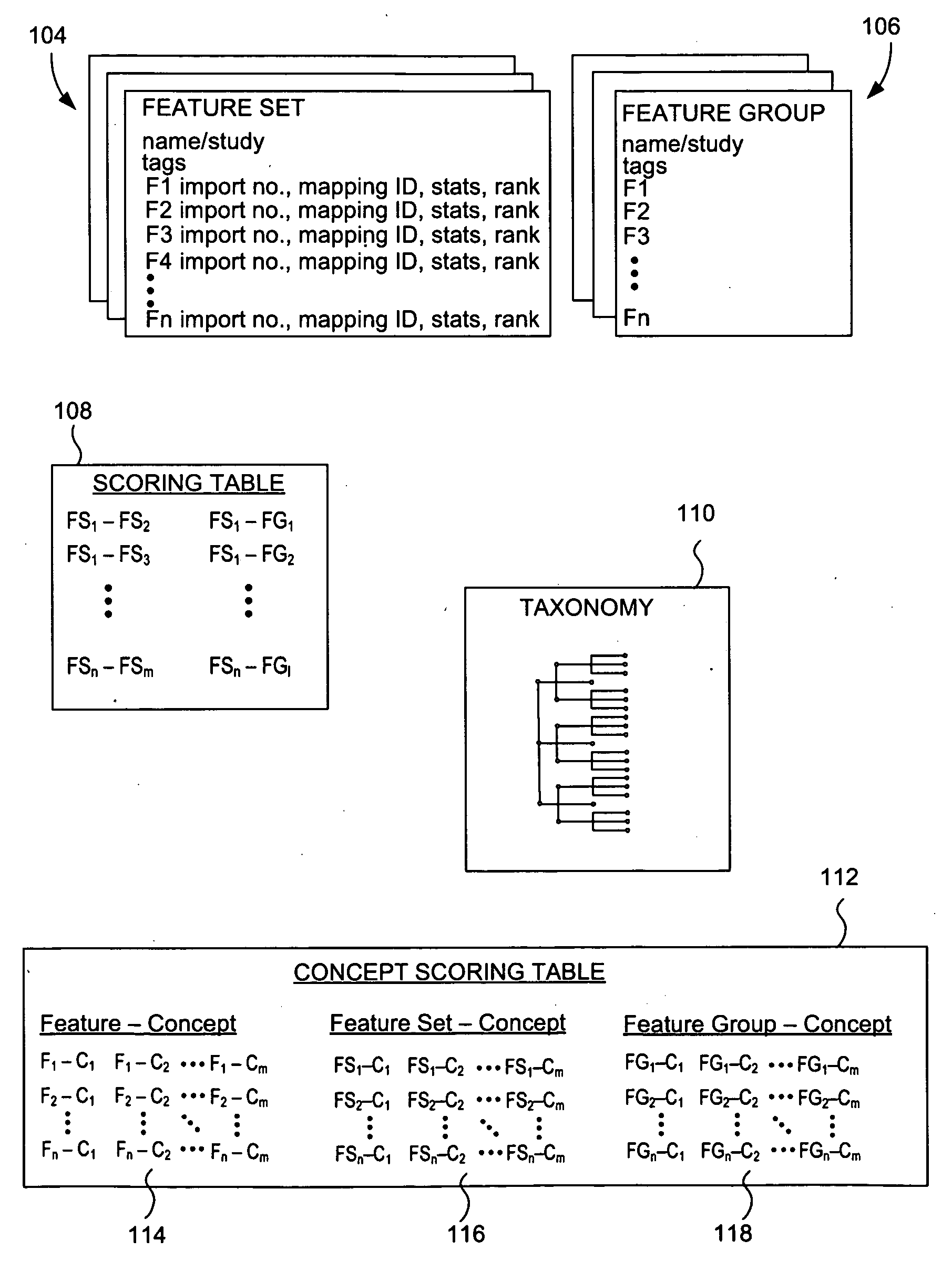
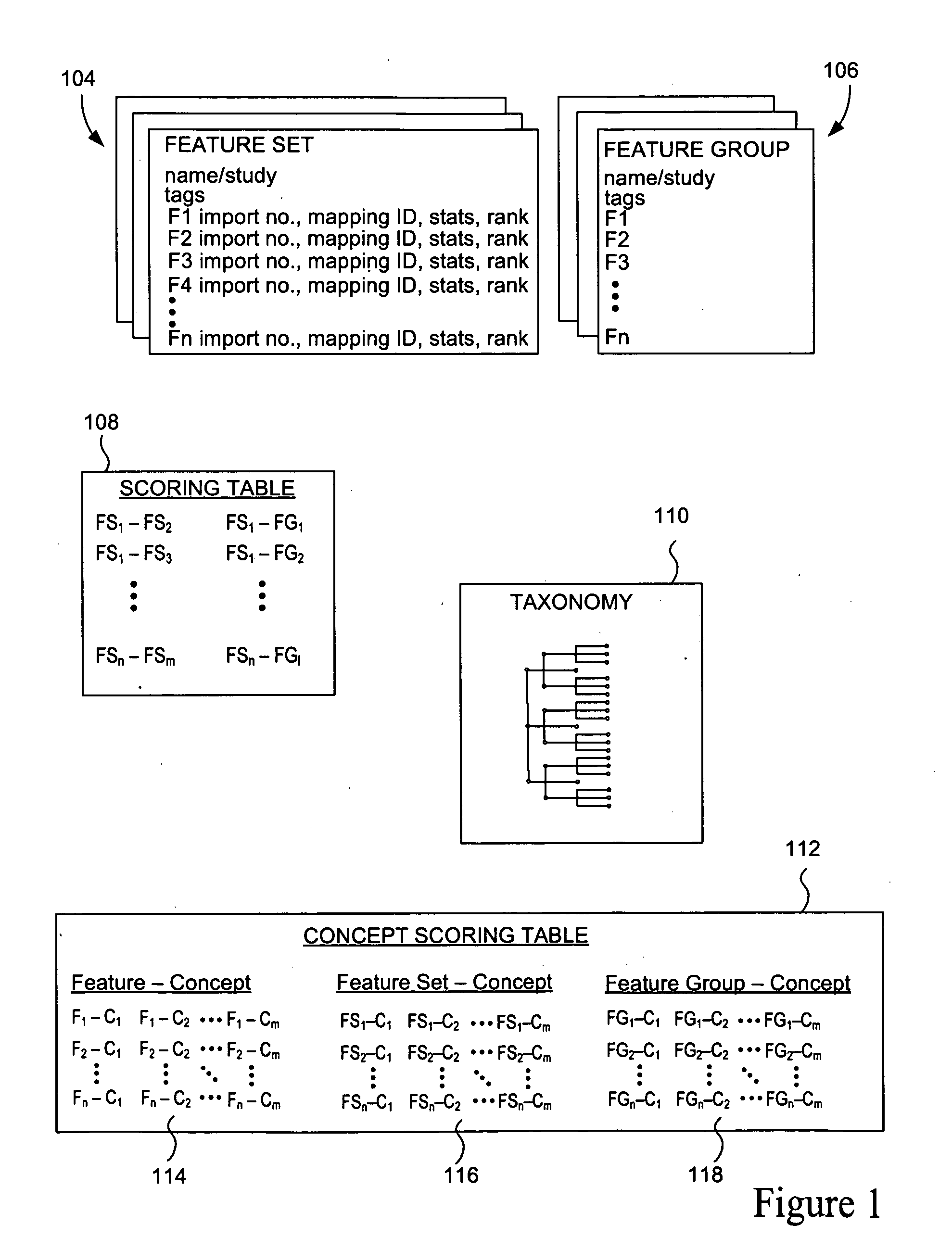
Categorization and filtering of scientific data
ActiveUS20090222400A1Improve efficiencyChaos modelsNon-linear system modelsBiological bodyMeta-analysis
The present invention relates to methods, systems and apparatus for capturing, integrating, organizing, navigating and querying large-scale data from high-throughput biological and chemical assay platforms. It provides a highly efficient meta-analysis infrastructure for performing research queries across a large number of studies and experiments from different biological and chemical assays, data types and organisms, as well as systems to build and add to such an infrastructure. According to various embodiments, methods, systems and interfaces for associating experimental data, features and groups of data related by structure and / or function with chemical, medical and / or biological terms in an ontology or taxonomy are provided. According to various embodiments, methods, systems and interfaces for filtering data by data source information are provided, allowing dynamic navigation through large amounts of data to find the most relevant results for a particular query.
Owner:ILLUMINA INC
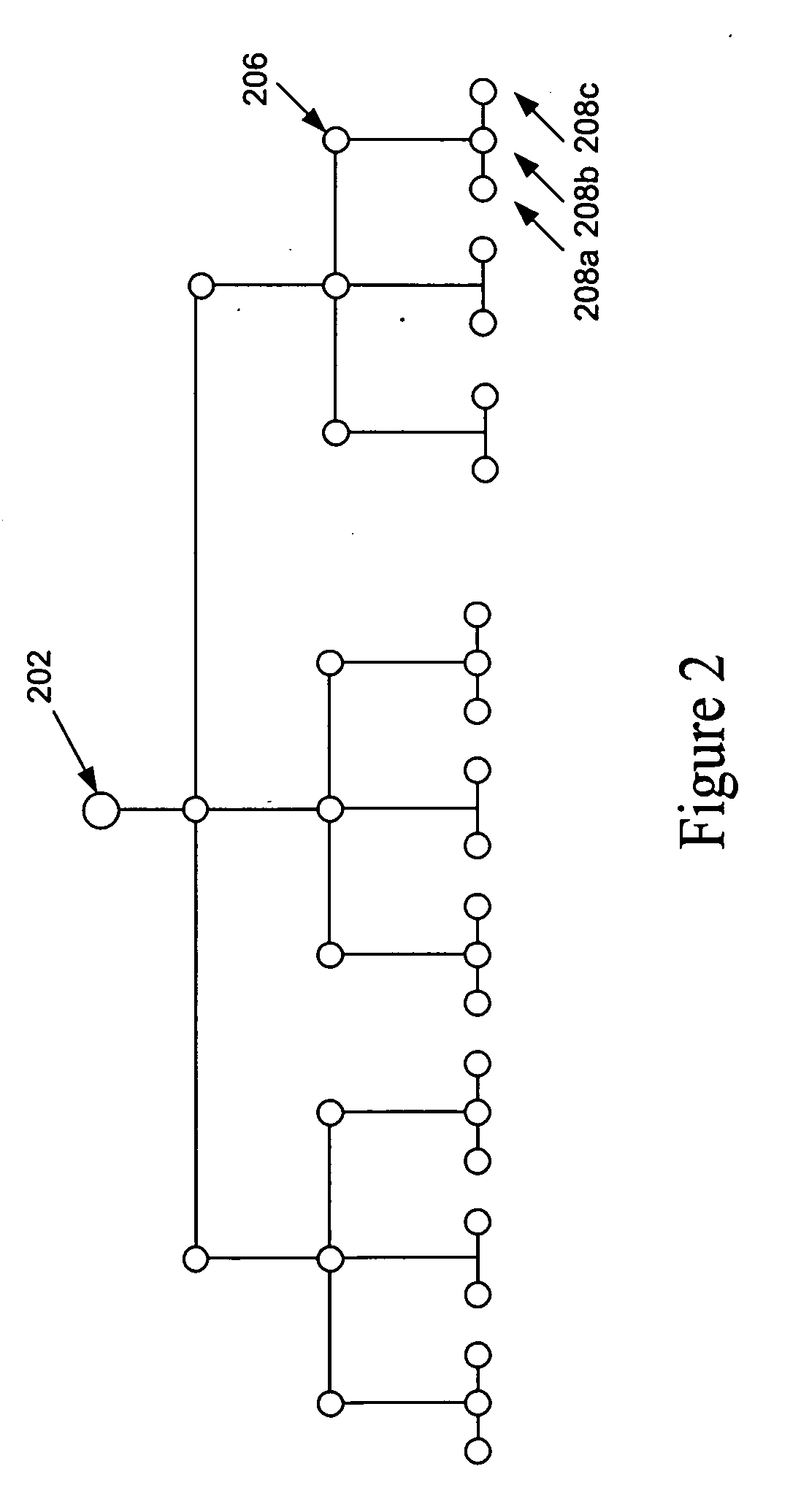
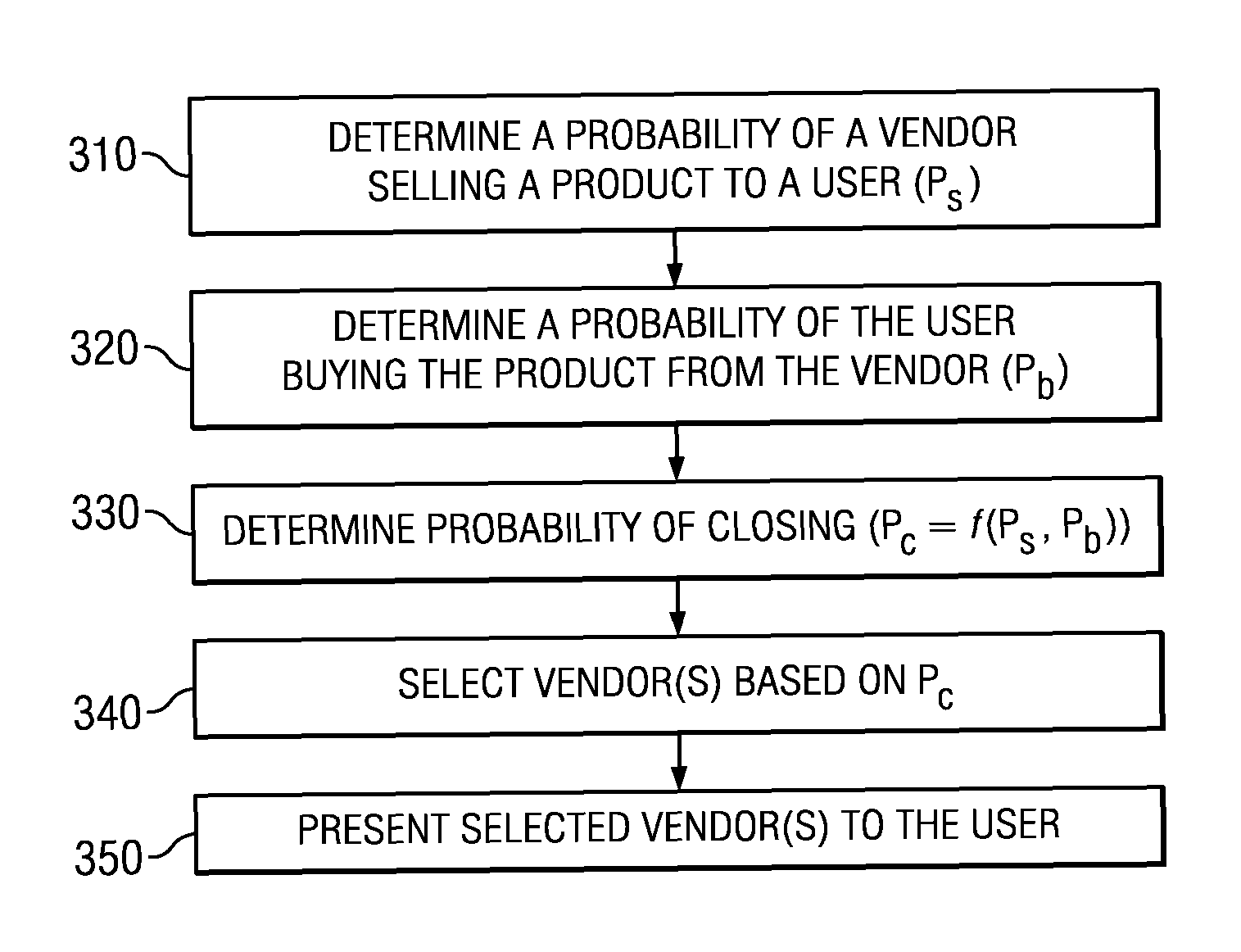
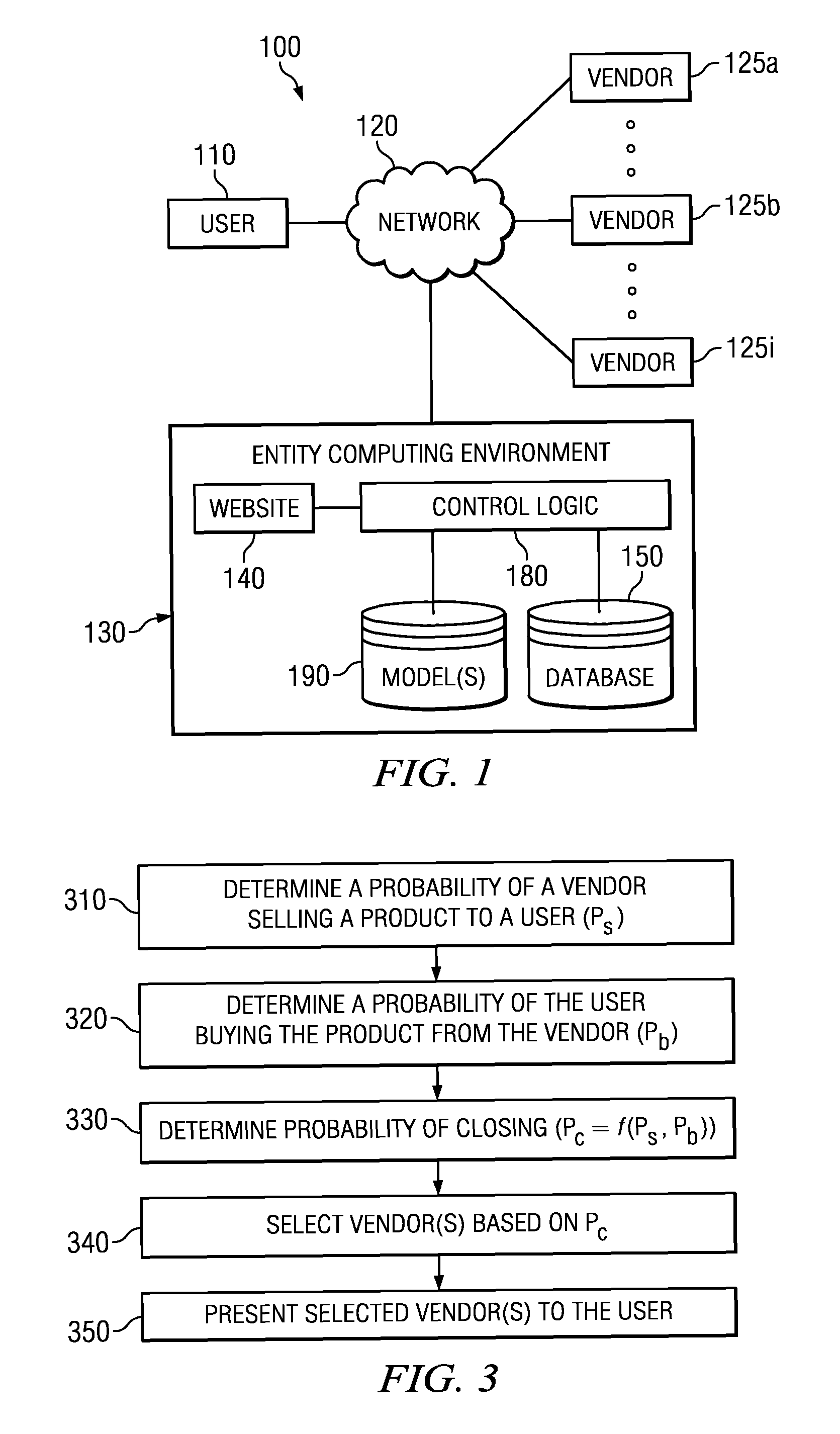
Method and system for selection, filtering or presentation of available sales outlets
ActiveUS20130006916A1Efficient identificationIncrease probabilityFuzzy logic based systemsKnowledge representationHigh probabilityComputer science
Owner:TRUECAR
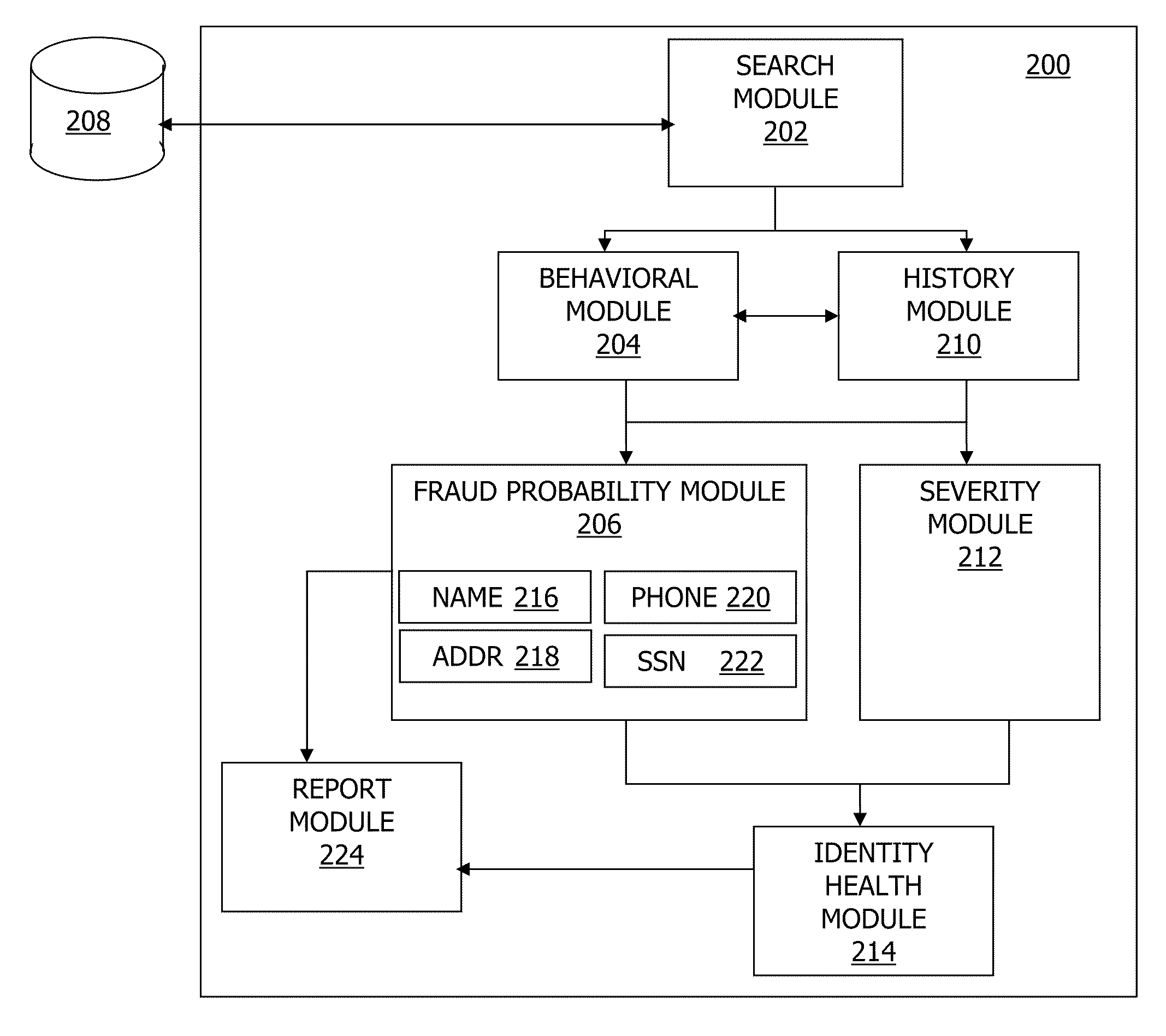
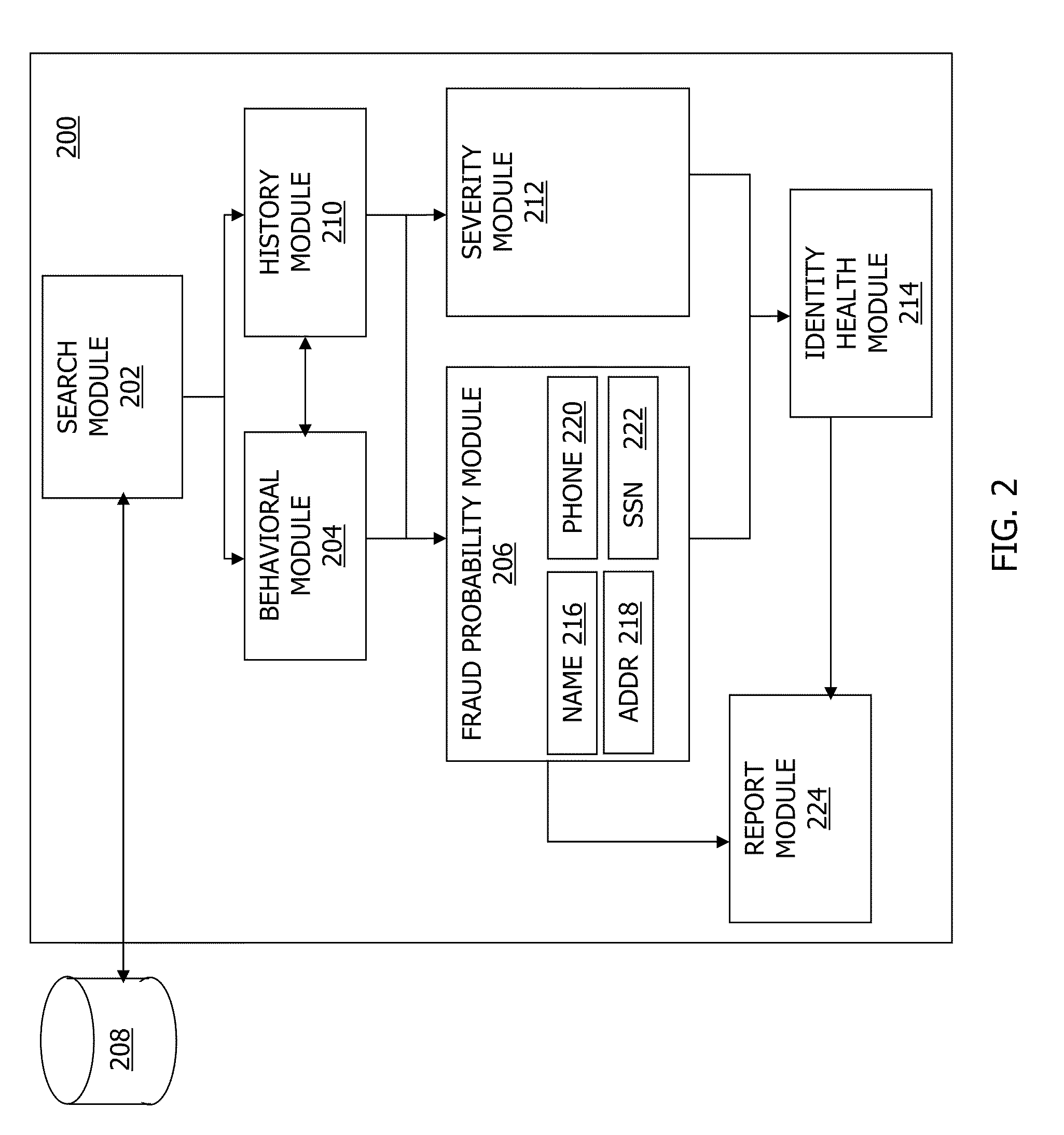
Systems, methods, and apparatus for determining fraud probability scores and identity health scores
In general, in one embodiment, a computing system that evaluates a fraud probability score for an identity event relevant to a user first queries a data store to identify the identity event. A fraud probability score is then computed for the identity event using a behavioral module that models multiple categories of suspected fraud.
Owner:IDENTITYTRUTH
Design of computer based risk and safety management system of complex production and multifunctional process facilities-application to fpso's
InactiveUS20120317058A1Strong robust attributeStrong robust attributesDigital computer detailsFuzzy logic based systemsProcess systemsNerve network
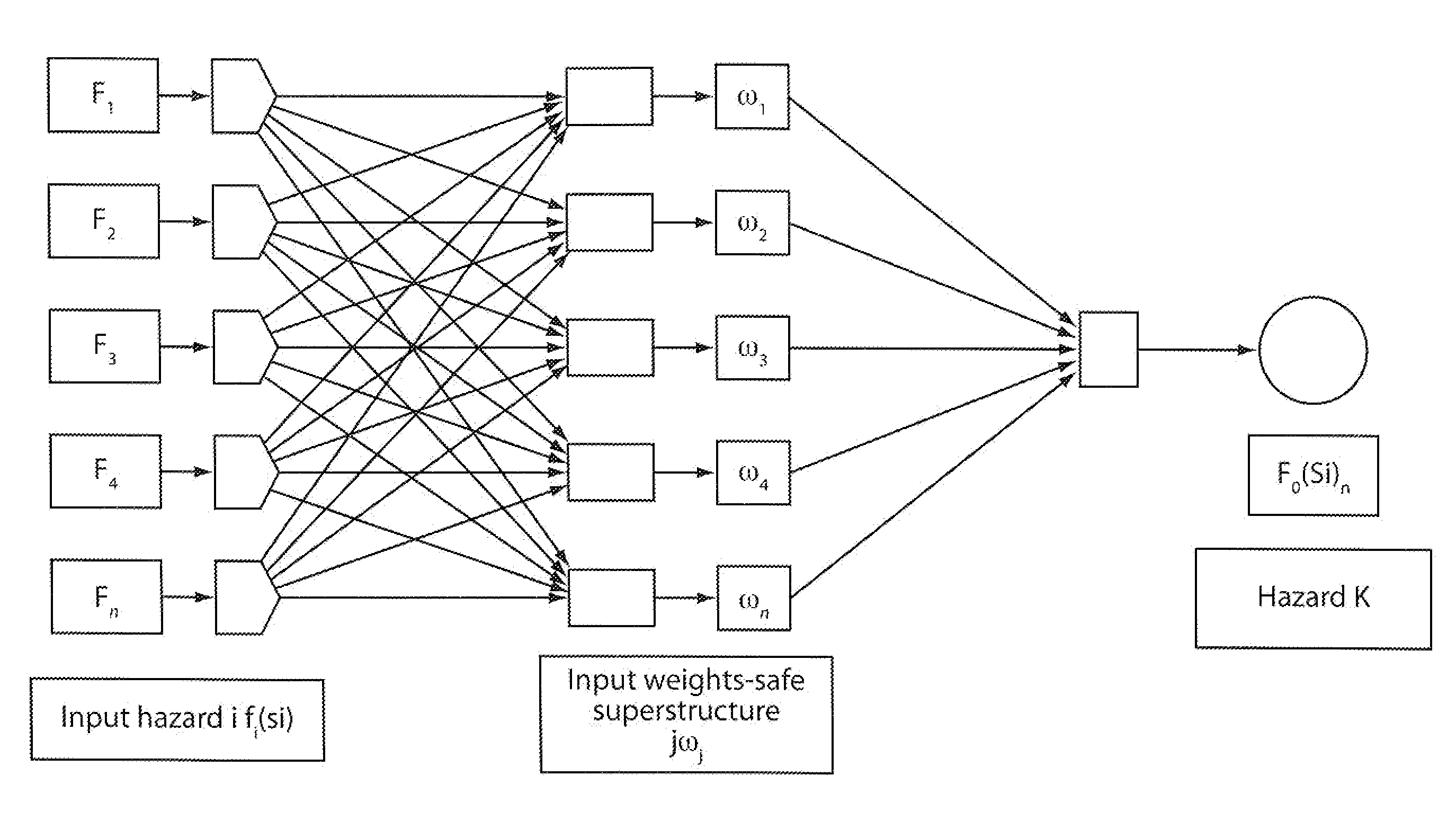
A method for predicting risk and designing safety management systems of complex production and process systems which has been applied to an FPSO System operating in deep waters. The methods for the design were derived from the inclusion of a weight index in a fuzzy class belief variable in the risk model to assign the relative numerical value or importance a safety device or system has contain a risk hazards within the barrier. The weights index distributes the relative importance of risk events in series or parallel in several interactive risk and safety device systems. The fault tree, the FMECA and the Bow Tie now contains weights in fizzy belief class for implementing safety management programs critical to the process systems. The techniques uses the results of neural networks derived from fuzzy belief systems of weight index to implement the safety design systems thereby limiting use of experienced procedures and benchmarks. The weight index incorporate Safety Factors sets SFri {0, 0.1, 0.2 . . . 1}, and Markov Chain Network to allow the possibility of evaluating the impact of different risks or reliability of multifunctional systems in transient state process. The application of this technique and results of simulation to typical FPSO / Riser systems has been discussed in this invention.
Owner:ABHULIMEN KINGSLEY E
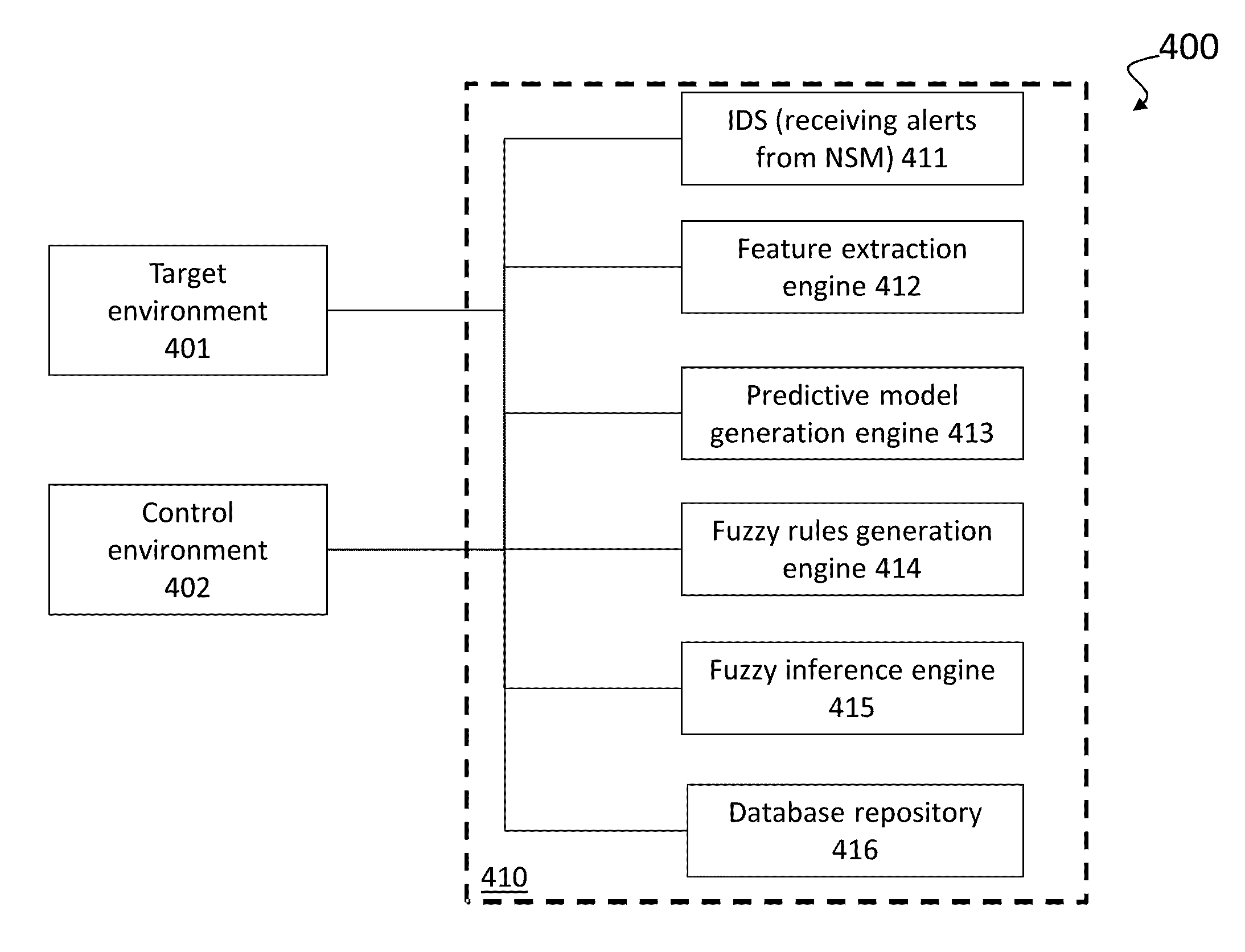
Profiling cyber threats detected in a target environment and automatically generating one or more rule bases for an expert system usable to profile cyber threats detected in a target environment
InactiveUS20150163242A1Efficiently presentedEasy to identifyMemory loss protectionError detection/correctionSecurity information and event managementSecurity information
A computer implemented method of profiling cyber threats detected in a target environment, comprising: receiving, from a Security Information and Event Manager (SIEM) monitoring the target environment, alerts triggered by a detected potential cyber threat, and, for each alert: retrieving captured packet data related to the alert; extracting data pertaining to a set of attributes from captured packet data triggering the alert; applying fuzzy logic to data pertaining to one or more of the attributes to determine values for one or more output variables indicative of a level of an aspect of risk attributable to the cyber threat.
Owner:CYBERLYTIC
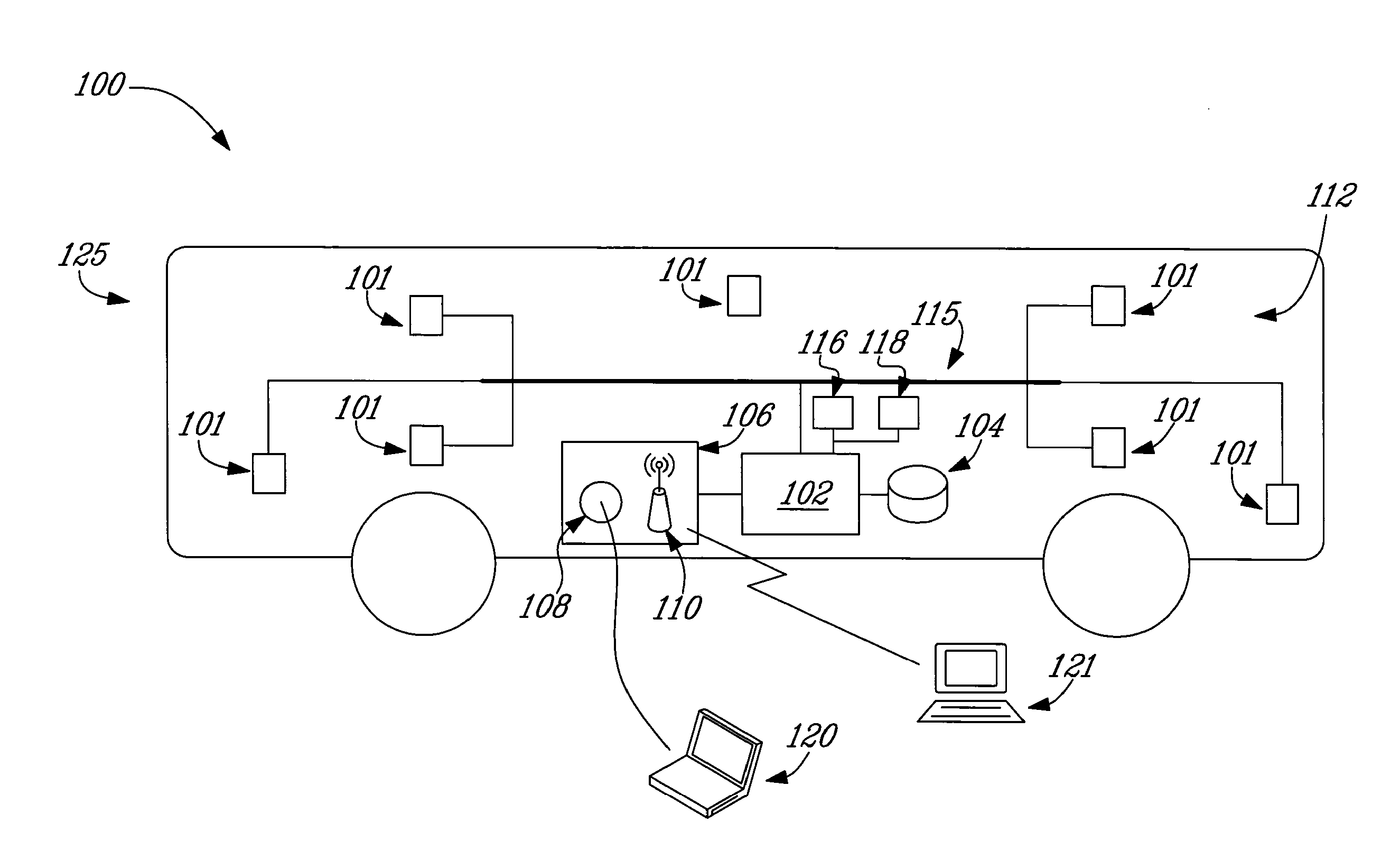
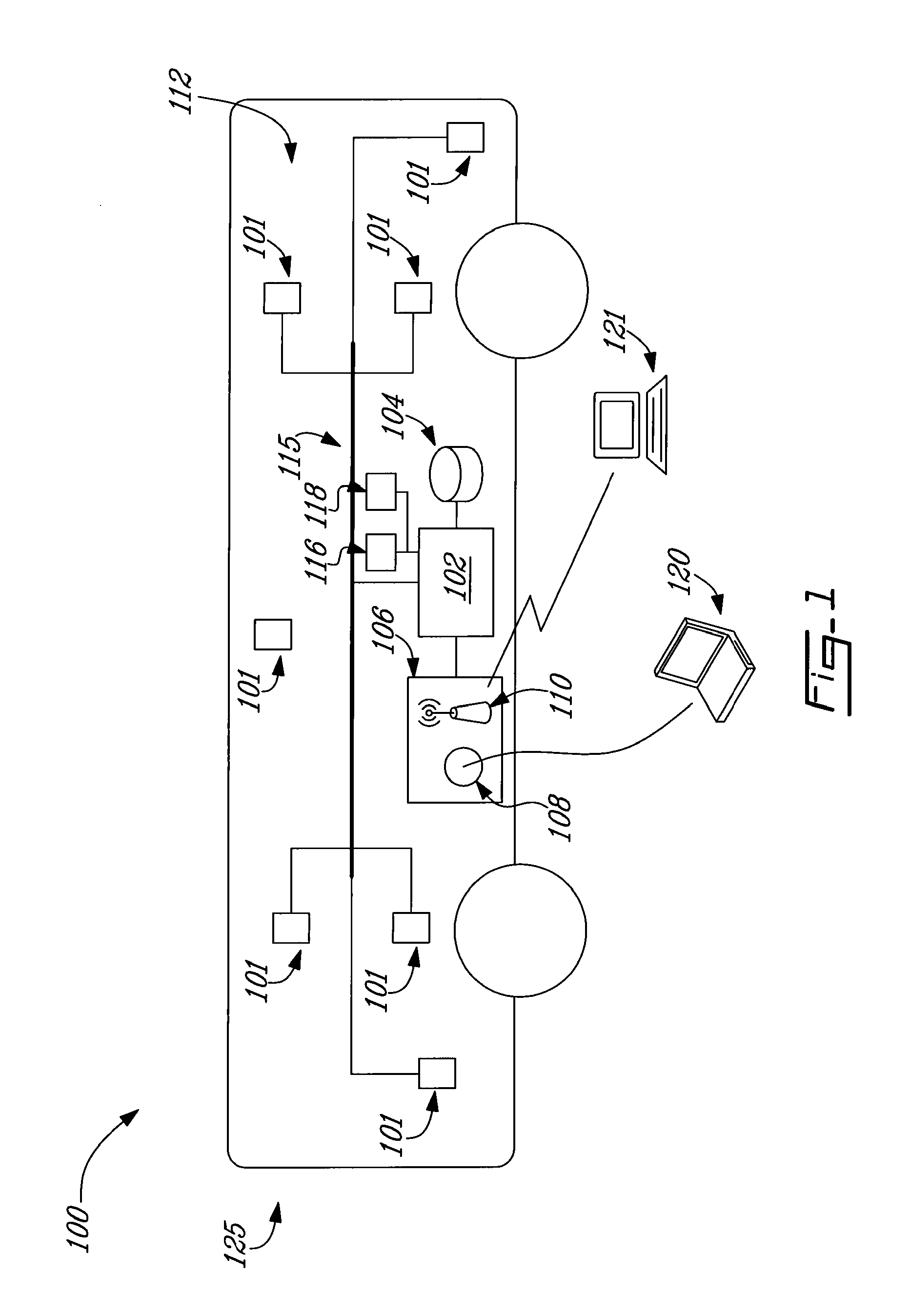
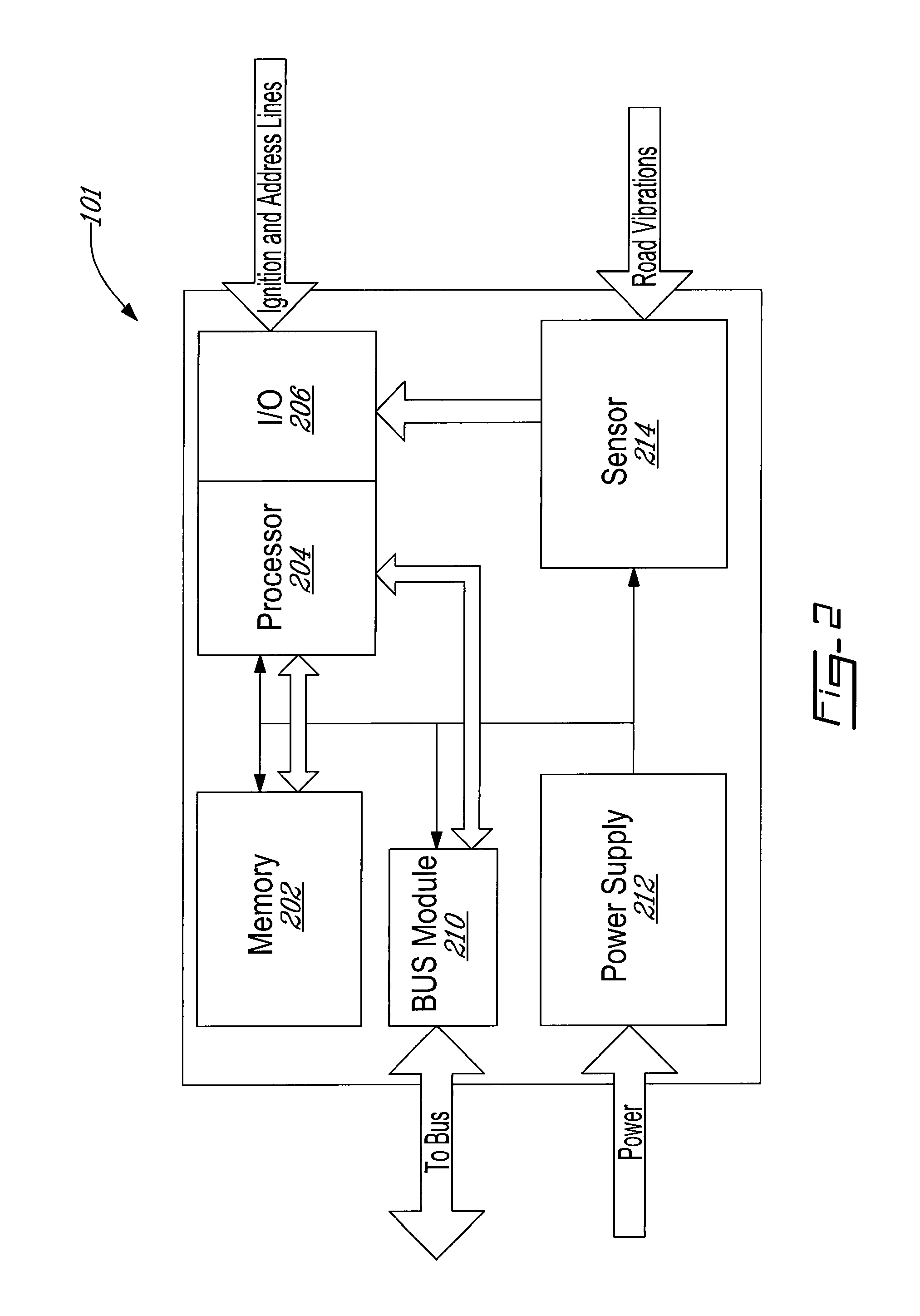
System and method for monitoring operation of vehicles
ActiveUS20100174576A1Data can be usedVehicle testingRegistering/indicating working of vehiclesCommunications systemAccelerometer
Systems, methods, devices, and computer programming products useful for the gathering and use of data relating to structural loading and other operational use of transit and other vehicles, and their systems. Systems according to the invention can, for example, comprise one or more data acquisition devices such as strain gauges, accelerometers, or other sensors; data processors; memories; and communications systems. Such systems, methods, and programming are useful in a wide variety of ways, including, for example, monitoring the structural status and use of vehicles and their systems, including fatigue other operational analyses; gathering and applying data useful in the maintenance of such vehicles and the routes they travel; monitoring the use / abuse of such vehicles by operators and other individuals; reporting traffic events or anomalies; and routing transit and other vehicles around such events or anomalies. Rainflow, level-crossing and other peak-counting or event-counting algorithms are applied to advantage, such that required data storage is greatly reduced, and life-long monitoring is feasible.
Owner:NEW FLYER INDS CANADA ULC
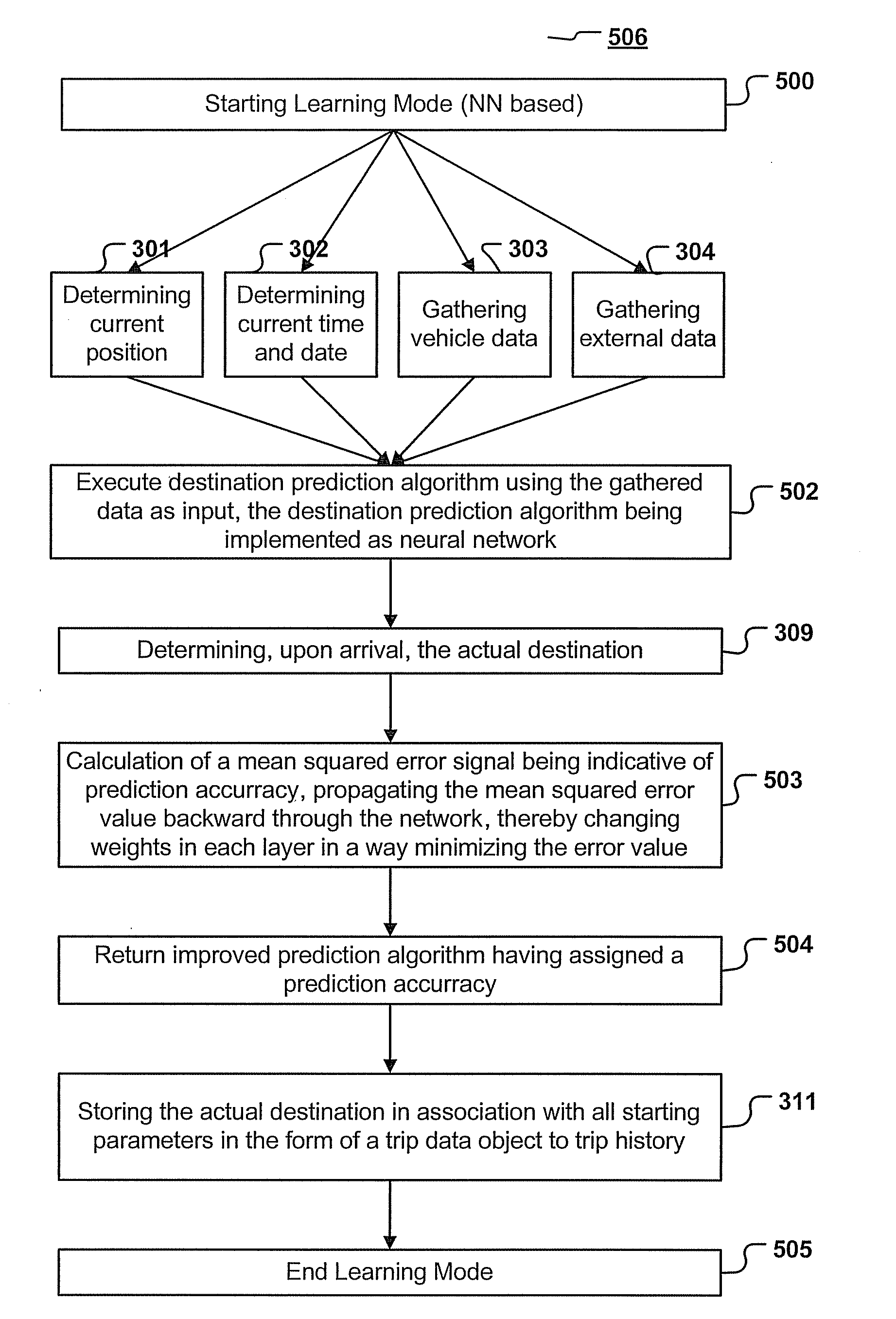
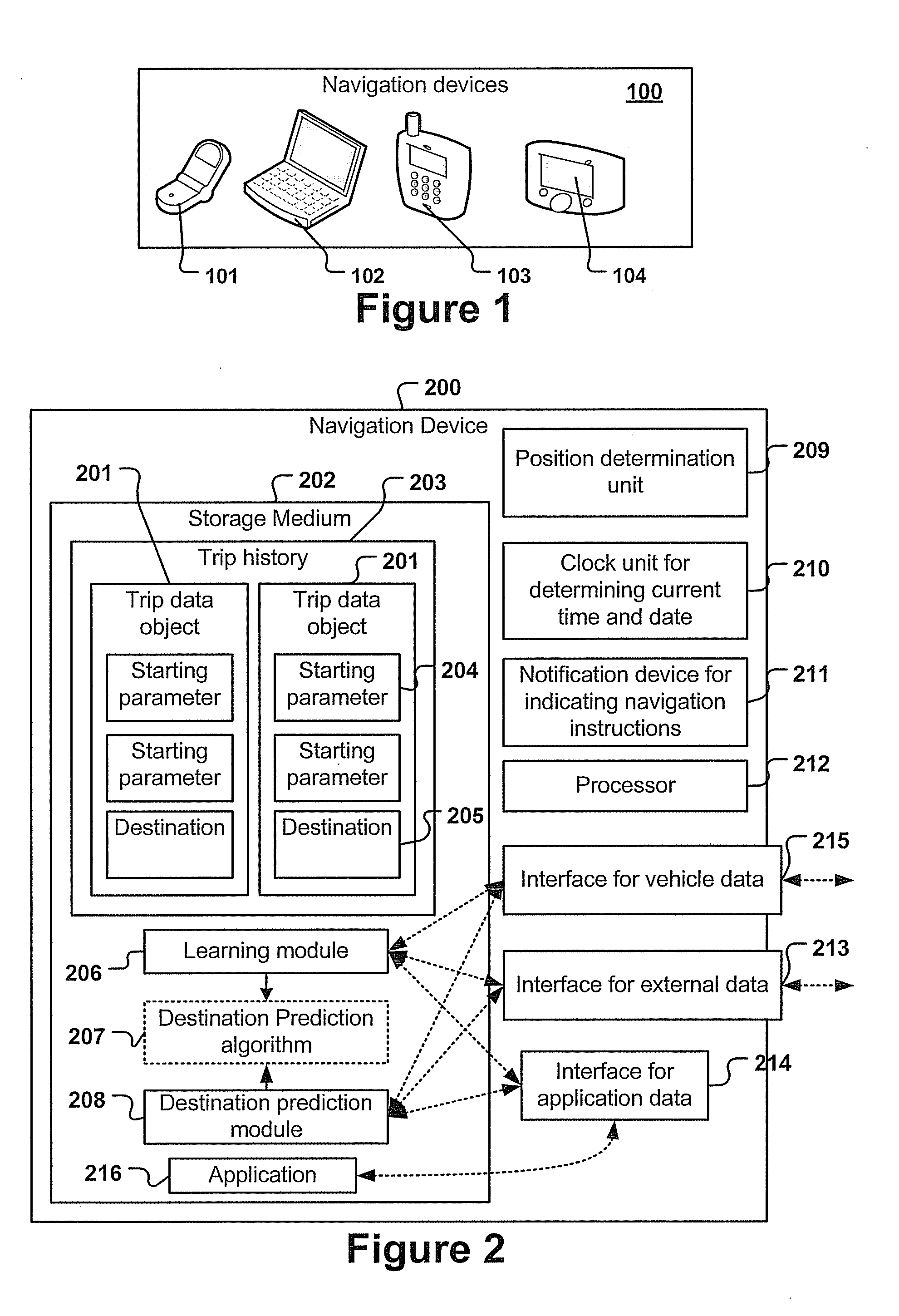
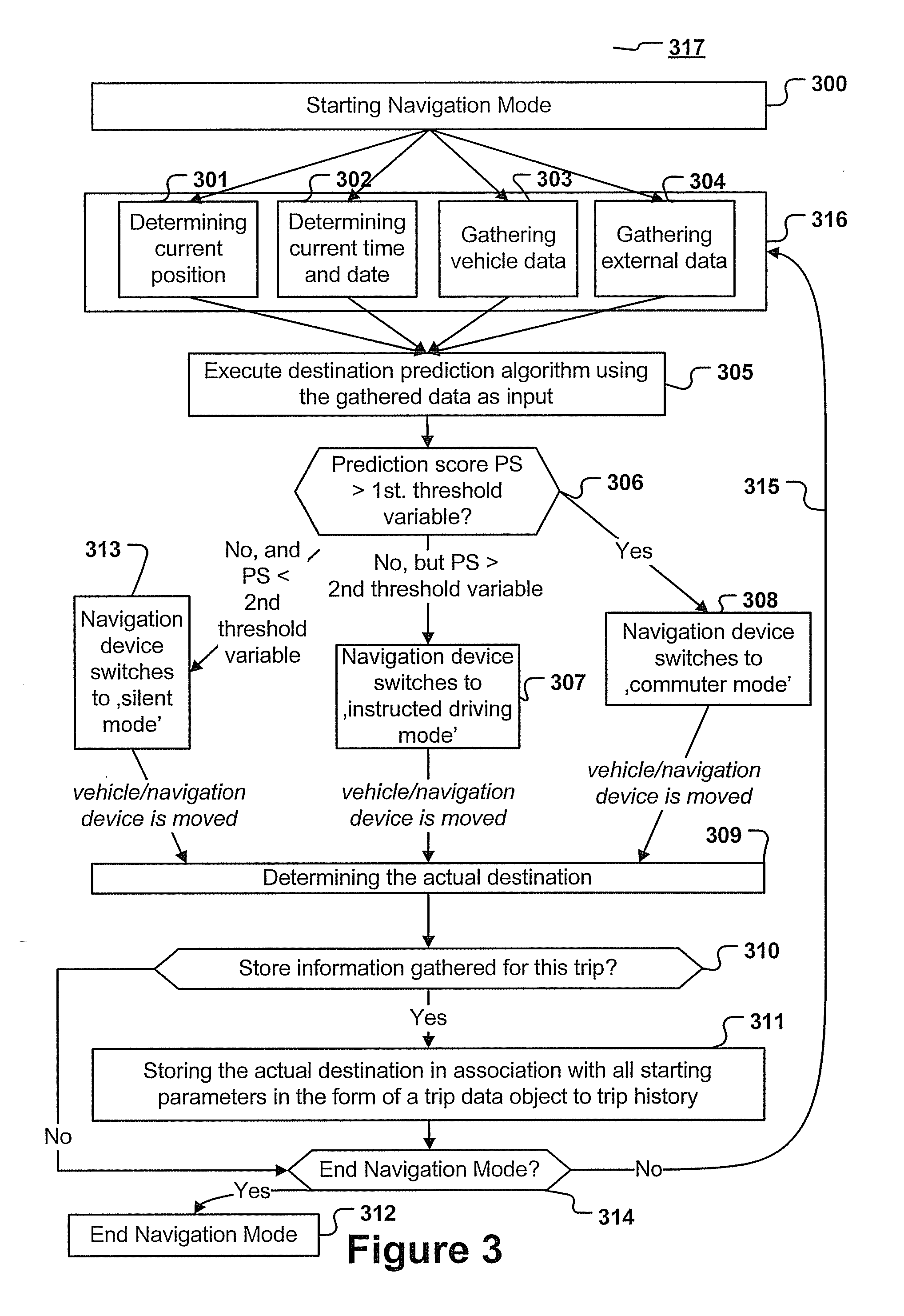
Navigation device and method for predicting the destination of a trip
ActiveUS20110238289A1Improve efficiencyImprove accuracyInstruments for road network navigationDigital data processing detailsStart timePrediction algorithms
A navigation device and computer implemented method for predicting the destination of a trip, the method being executed by a navigation device, the method comprising the steps of: determining starting parameters, the starting parameters comprising at least the starting point, starting time and date of the trip, executing a destination prediction algorithm, the destination prediction algorithm taking the starting parameters as input and predicting a destination, wherein the destination prediction algorithm is generated by using information of a trip history; determining, upon arrival at the predicted or another destination, the actual destination.
Owner:SAP AG
Analyte measurement and management device and associated methods
Owner:LIFESCAN INC
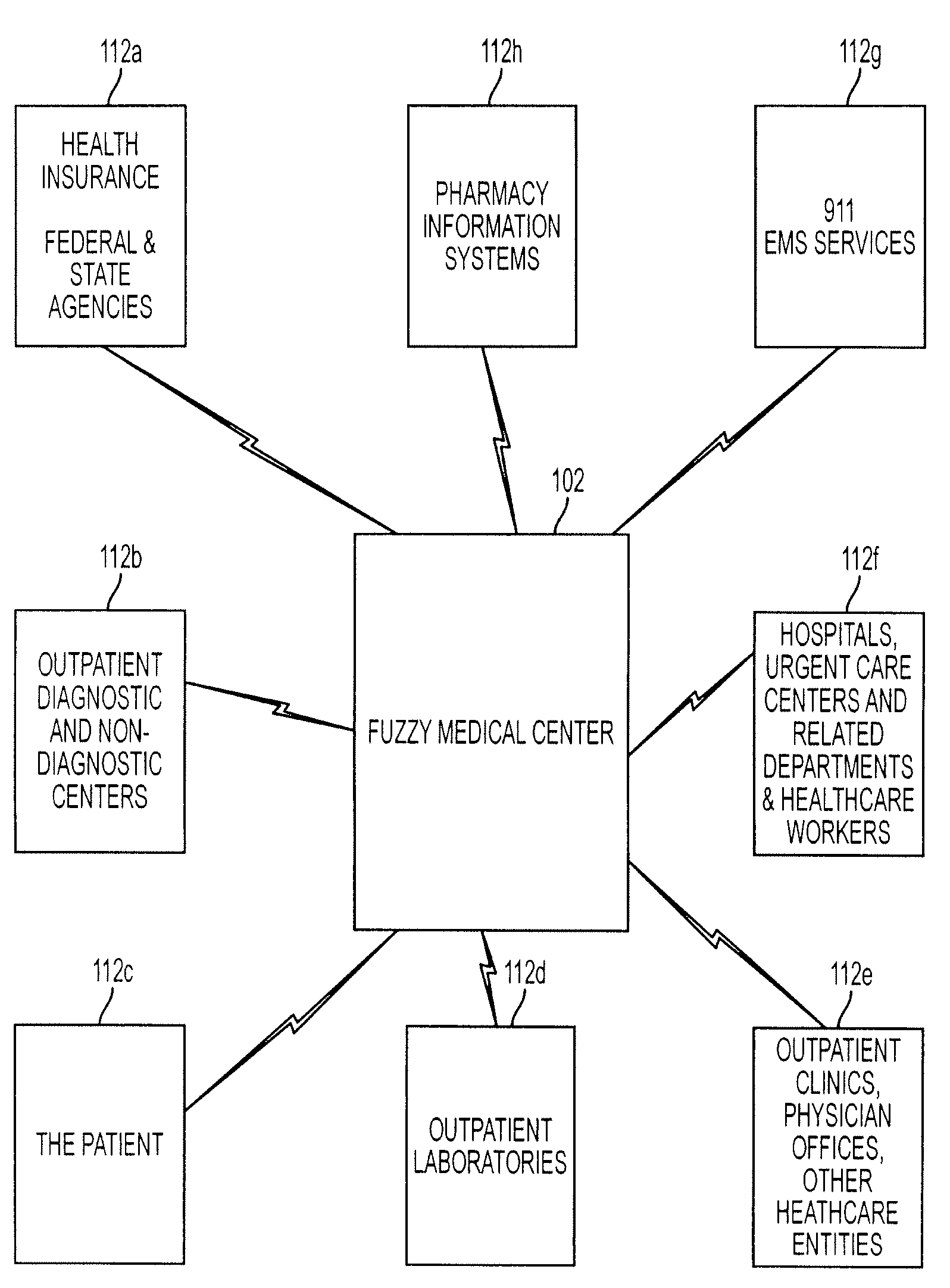
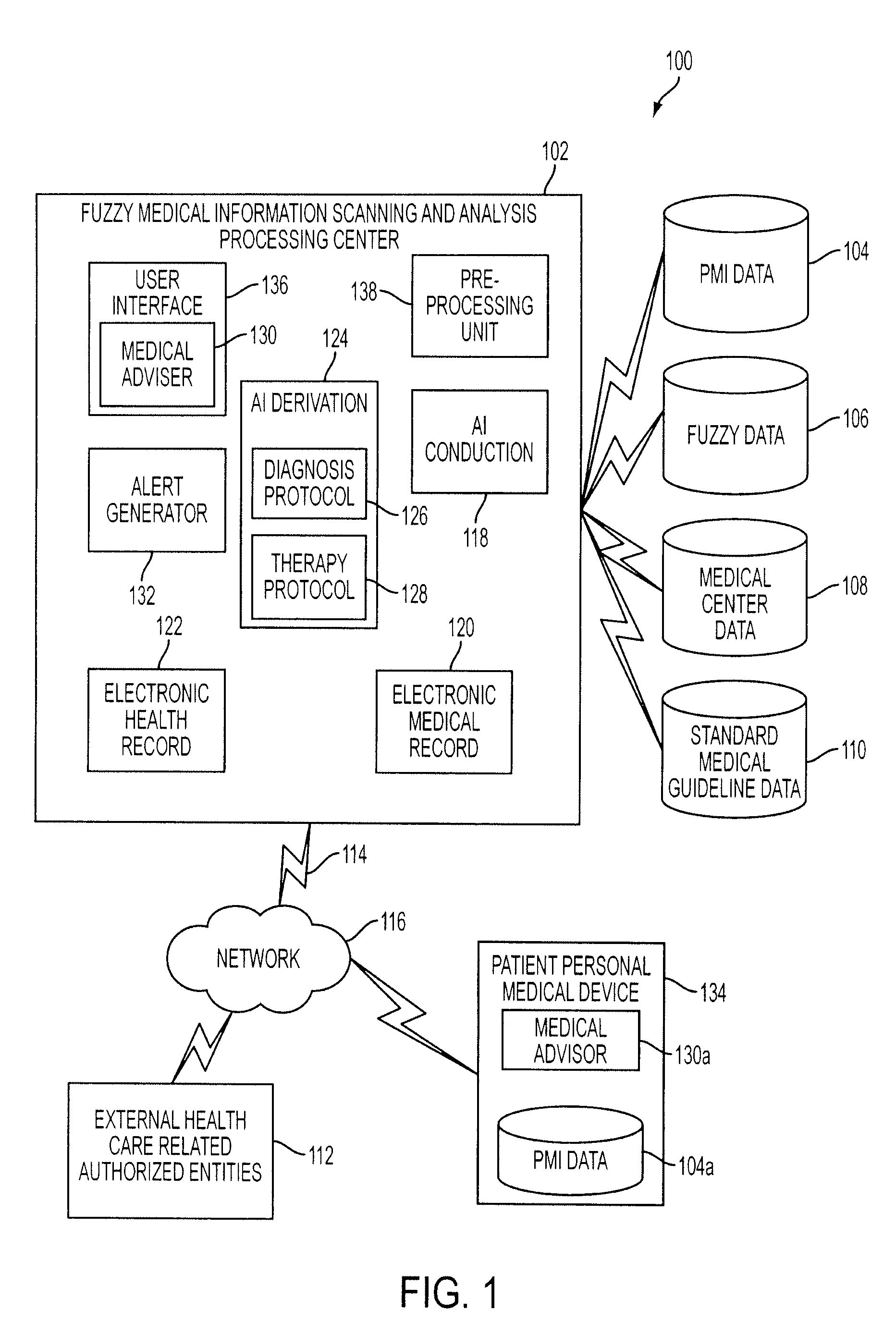
System, method, and device for personal medical care, intelligent analysis, and diagnosis
ActiveUS20090177495A1Reduce needAvoid testingData processing applicationsMedical automated diagnosisComputer scienceMedical treatment
A system for personal medical care, intelligent analysis and diagnosis may include: at least one source of medical information; at least one source of personal medical data for at least one patient; and one or more servers, where the medical information and the personal medical data are accessible to the server(s). The server(s) may include: an artificial intelligence (AI) component for analyzing the personal medical data with the medical information and identifying at least one issue requiring follow-up by the patient or by at least one external authorized entity; and at least one real-time communication link for bi-directional communication with at least one external authorized entity.
Owner:FUZZMED
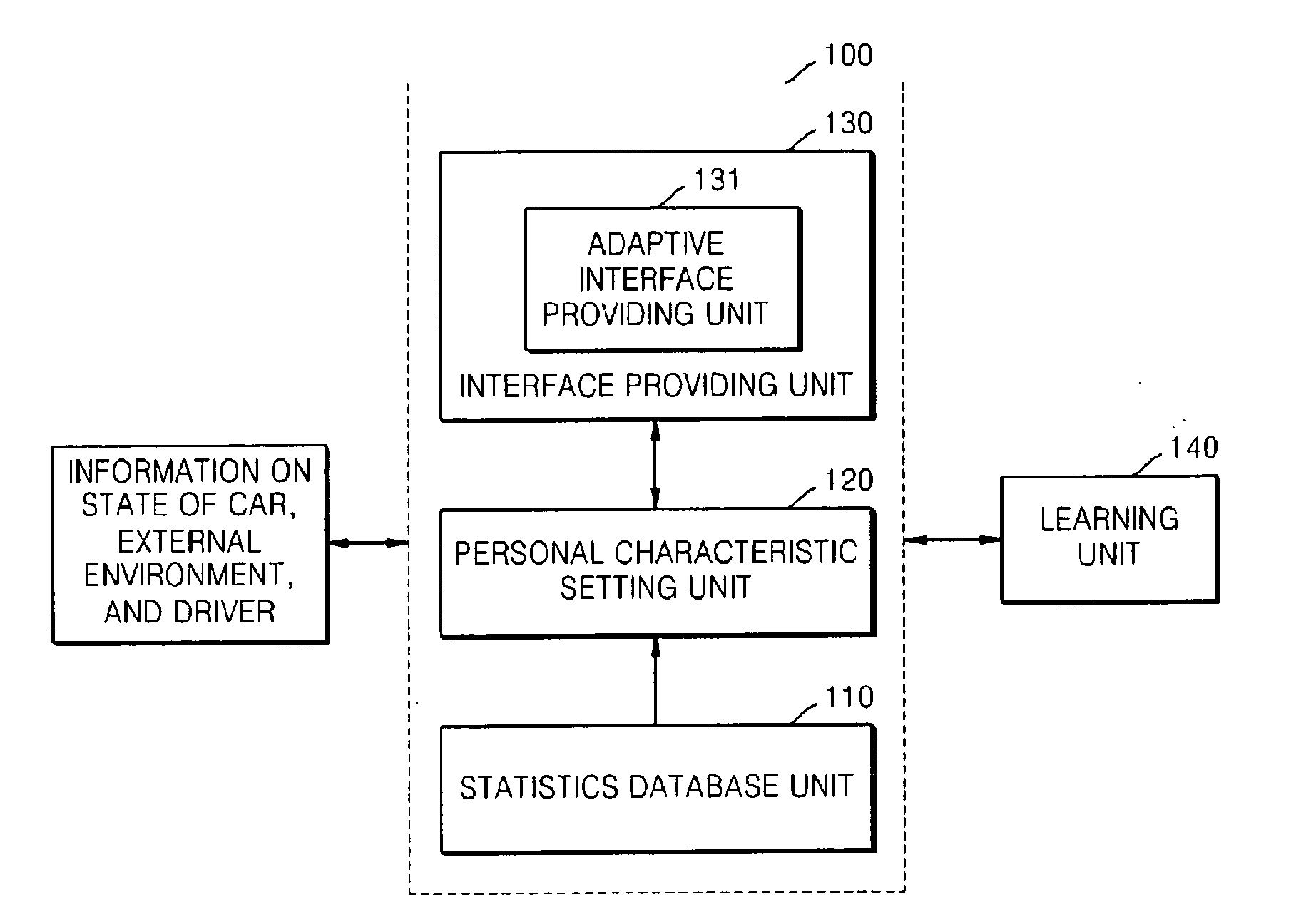
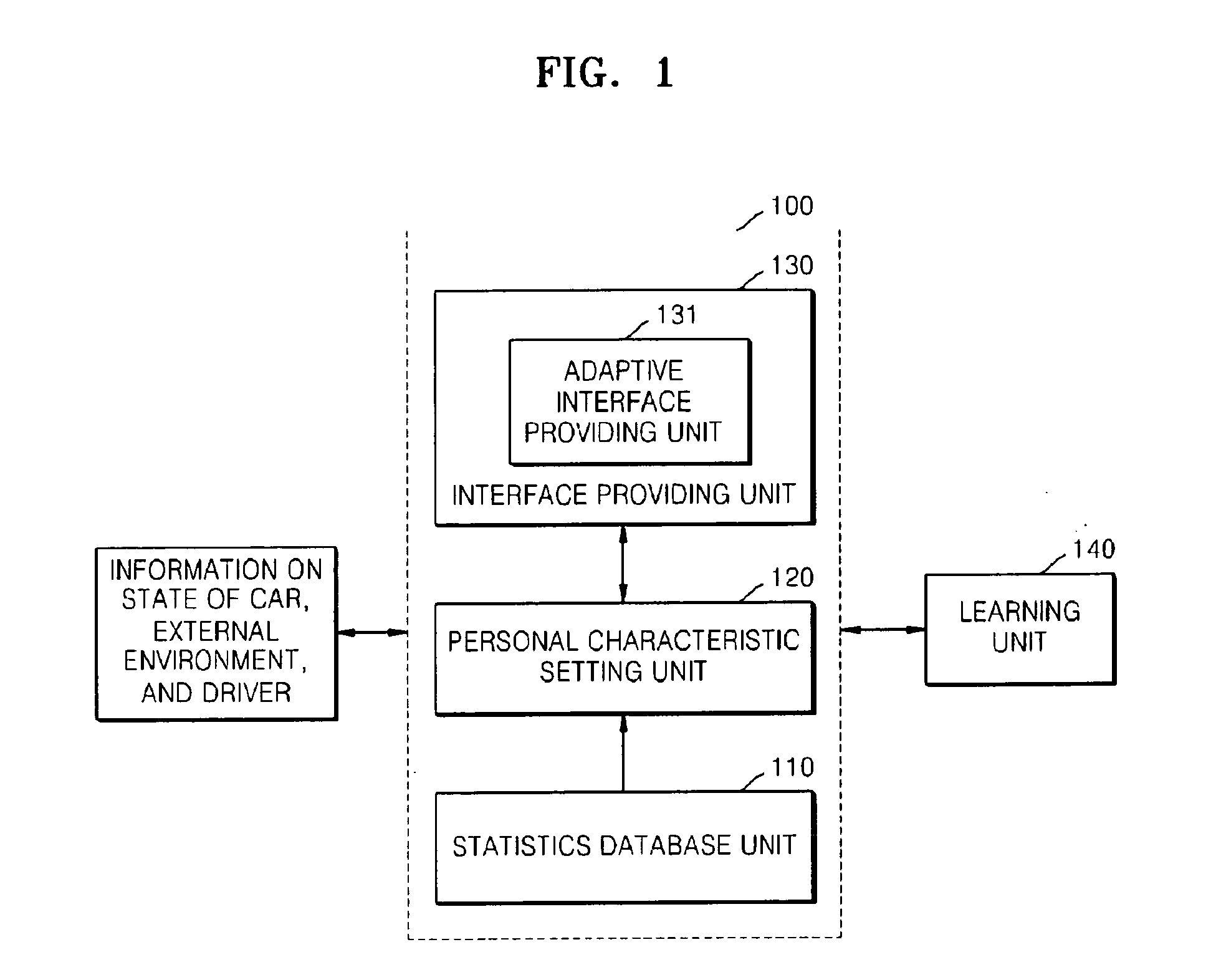
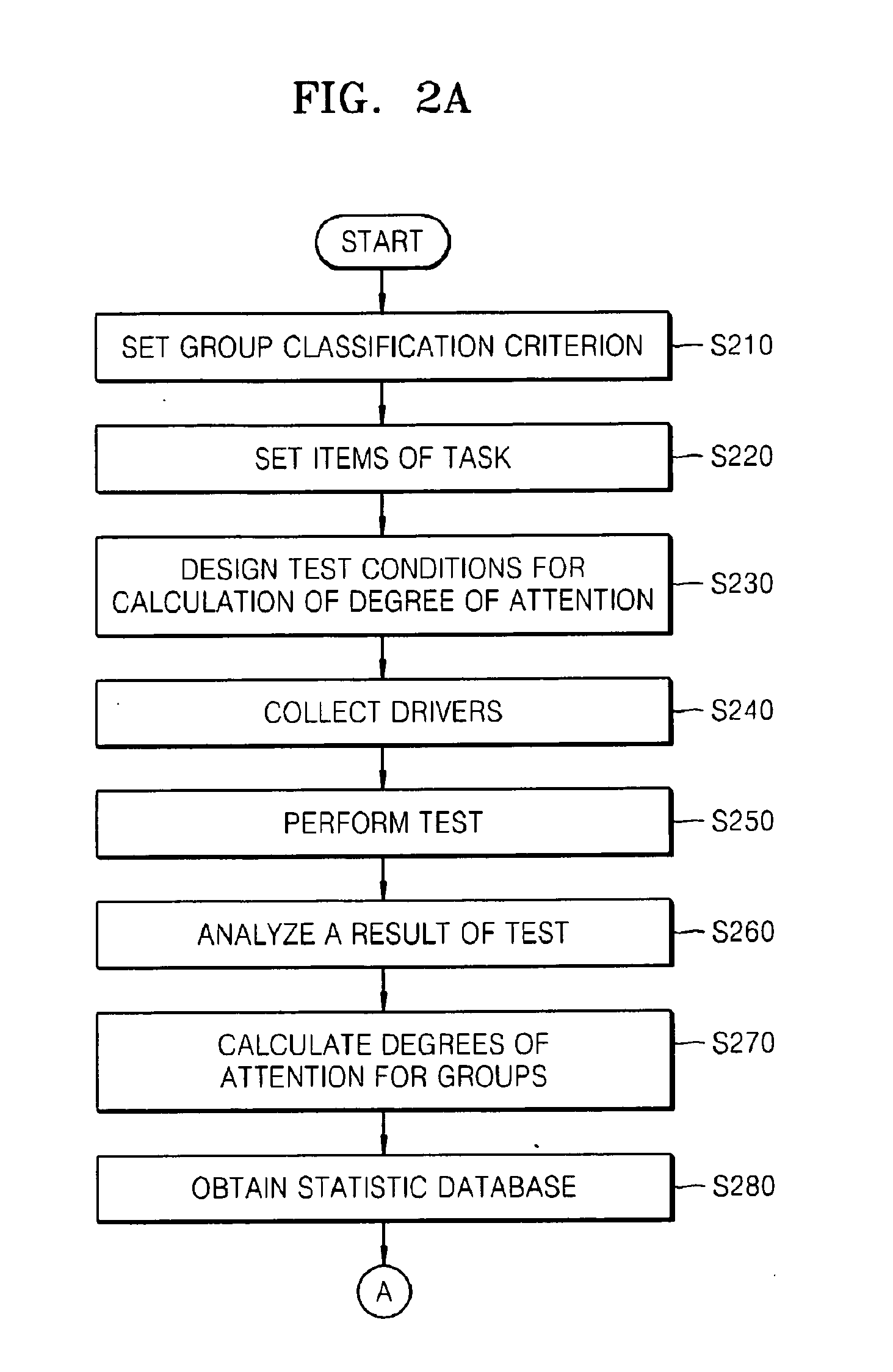
Adaptive drive supporting apparatus and method
InactiveUS20100179932A1Overcome limitationsReduce decreaseRoad vehicles traffic controlDigital computer detailsPersonalizationStatistical database
Provided are an adaptive drive supporting apparatus and method that provide a personalized telematics user interface capable of supporting safe driving and convenient use. The adaptive drive supporting apparatus includes: a statistics database unit which stores and manages information on an average degree of attention required when a driving operation, a state of a car, or an external environment changes, information on degrees of attention required for manipulations of interfaces of the car, and a similarity between the functions of the interfaces; a personal characteristic setting unit which sets an individual degree of attention for each driver based on the average degree of attention according to a change in at least one of the driving operation, the state of the car, and the external environment; and an interface providing unit which determines whether or not a sum of the individual degree of attention and the degree of attention required when each driver manipulates a requested interface is larger than a predetermined threshold degree of attention required for safe driving.
Owner:ELECTRONICS & TELECOMM RES INST
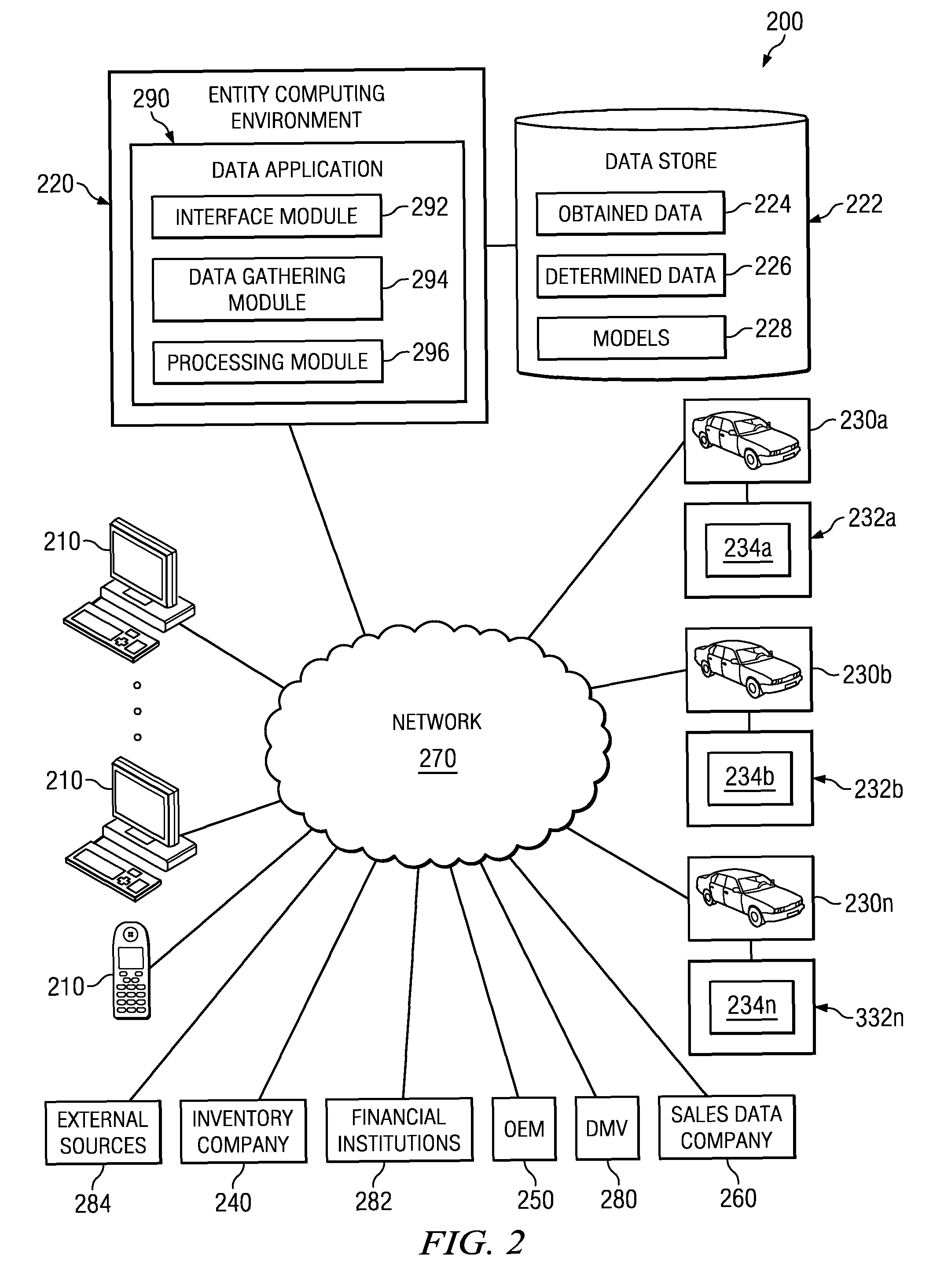
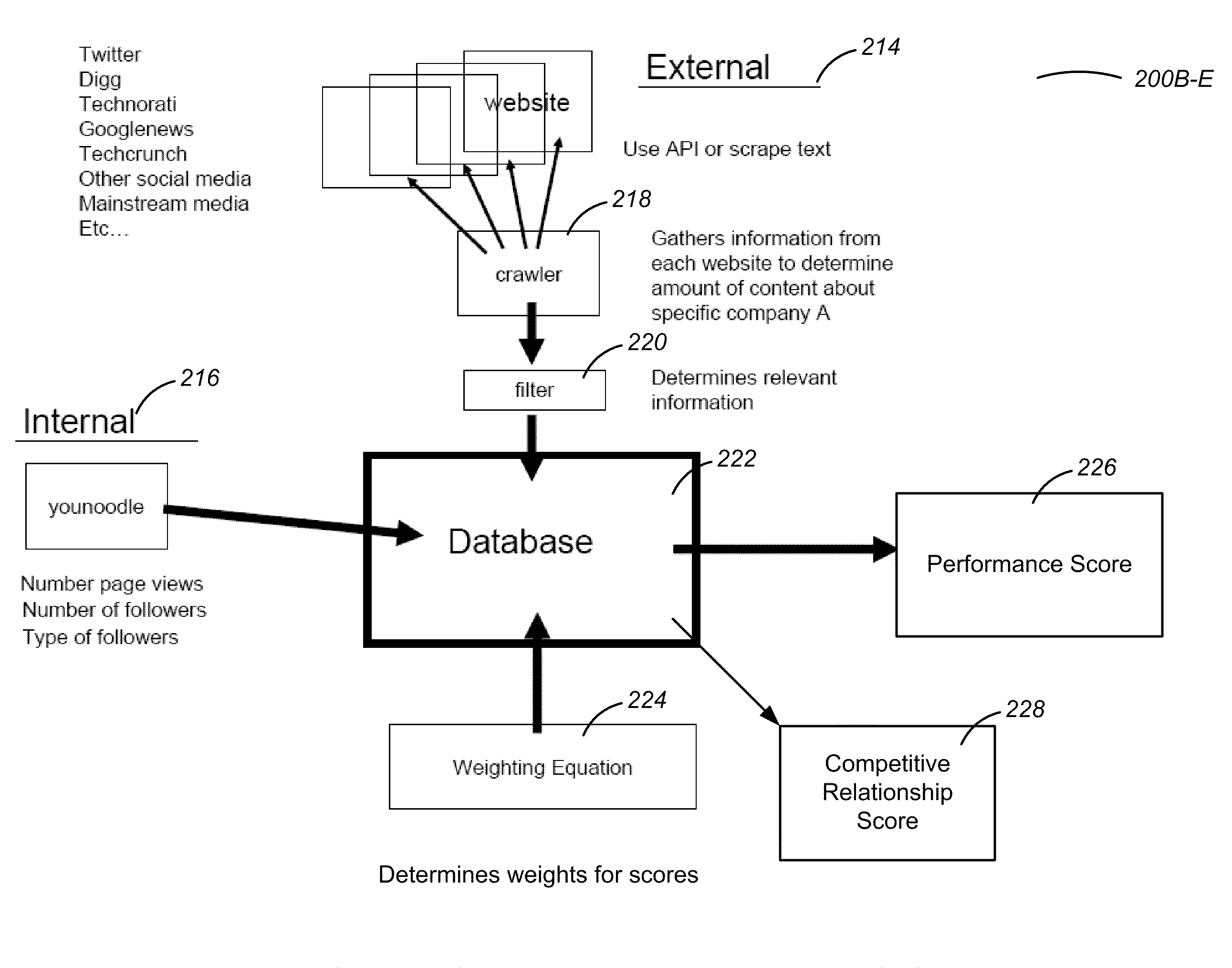
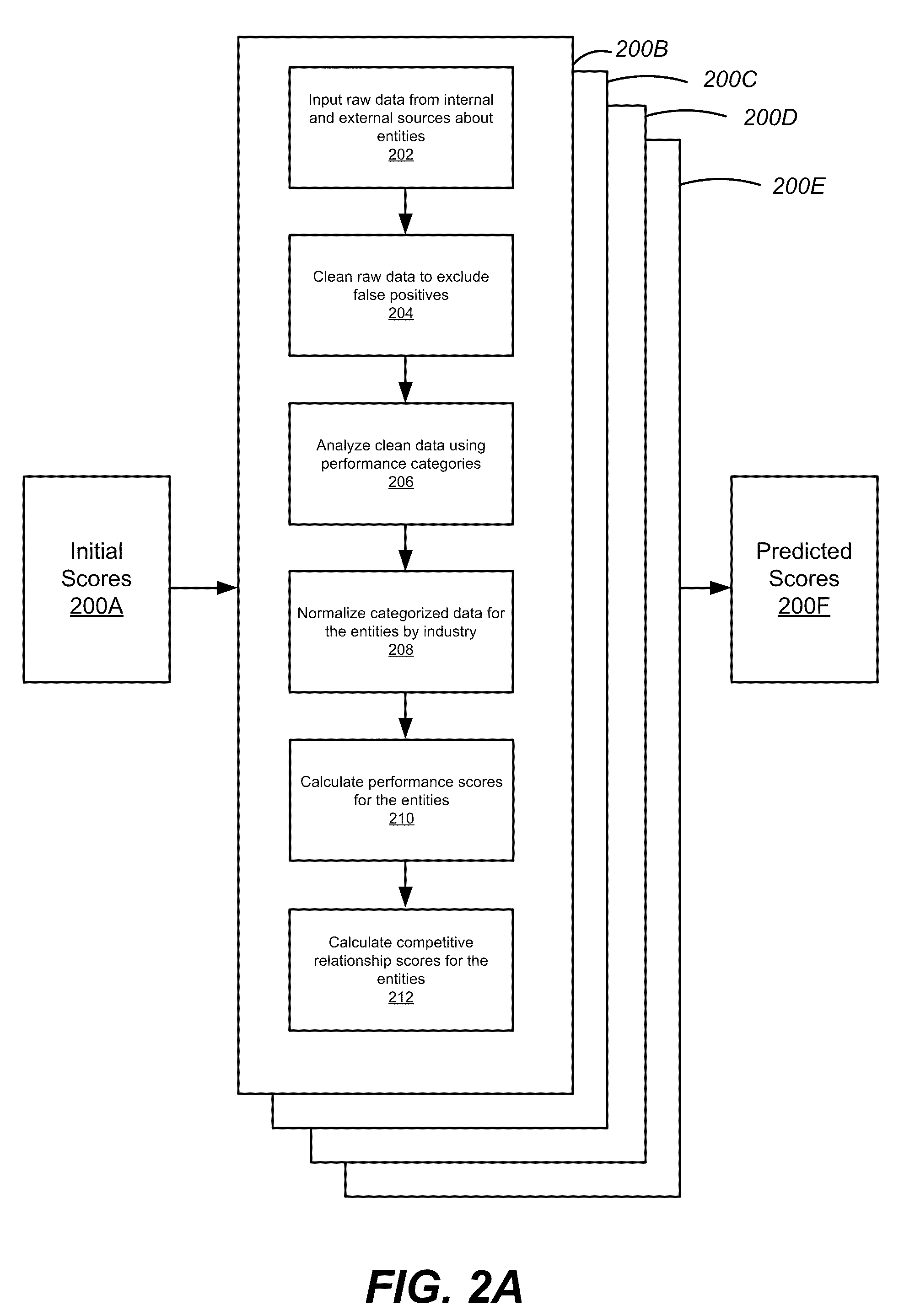
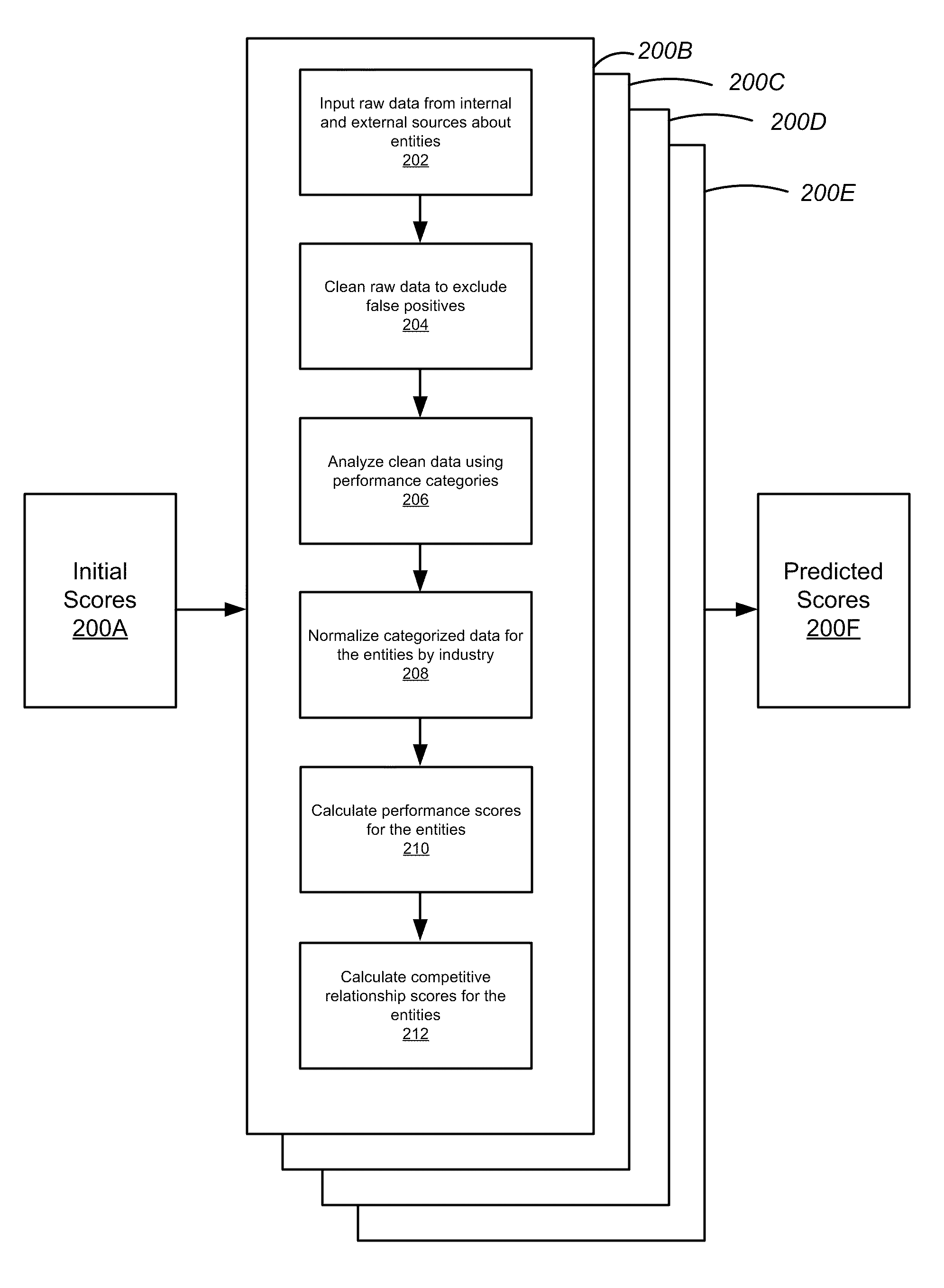
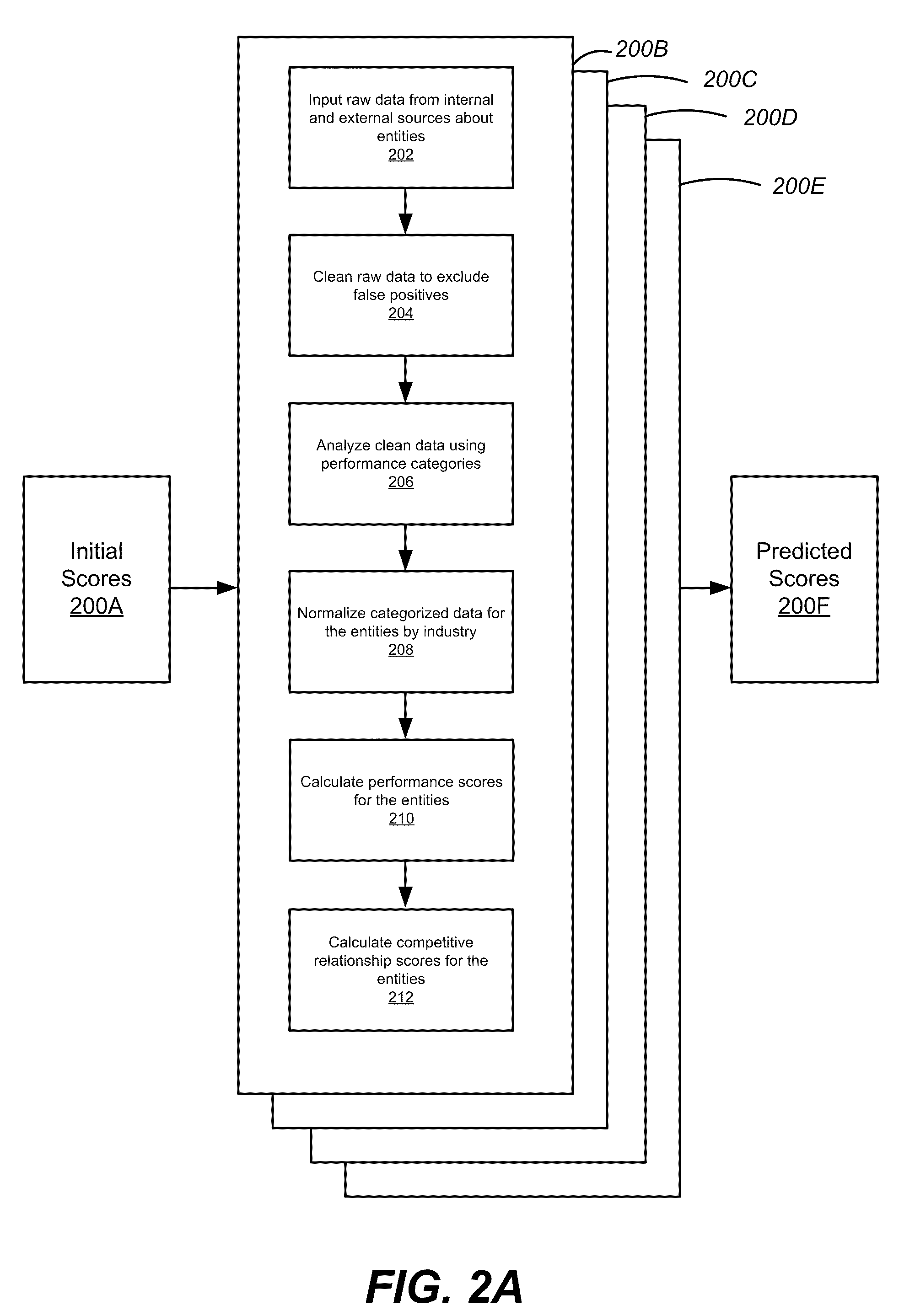
Entity Performance Analysis Engines
A system and method for measuring a performance of an entity and for predicting its future performance is disclosed. Raw information about the entity is collected from internal and external sources. The information is cleaned to exclude false positives. Using performance categories, the information is organized and transformed into meaningful data for the performance analysis engine. The information is normalized by scaling the meaningful data by industry type. A performance score is calculated by the performance analysis engine based on the normalized data. Further, a competitive relationship score is calculated based on the performance score and the normalized data. These scores are reported in a user interface displaying the performance of the entity and are used as inputs, among other factors, to a predictive analysis engine that assesses the future performance of the entities.
Owner:QUID LLC
Affinity Propagation in Adaptive Network-Based Systems
ActiveUS20070203872A1Easy to navigateDigital computer detailsFuzzy logic based systemsComputer basedSelf adaptive
Adaptive applications of affinity propagation are described to facilitate effective and computationally efficient means of clustering computer-based objects such as items of content, and / or to determine exemplars associated with a set of objects. Affinity propagation is also applied by the present invention to define system user affinity groups and / or exemplar users. The present invention applies usage behaviors as a basis for influencing clustering through methods such as initializing exemplar attractor values based on usage behaviors and / or basing similarity values between pairs of objects or users on usage behaviors associated with system objects, or usage behaviors that are associated with, directly or indirectly, specific system users.
Owner:GULA CONSULTING LLC
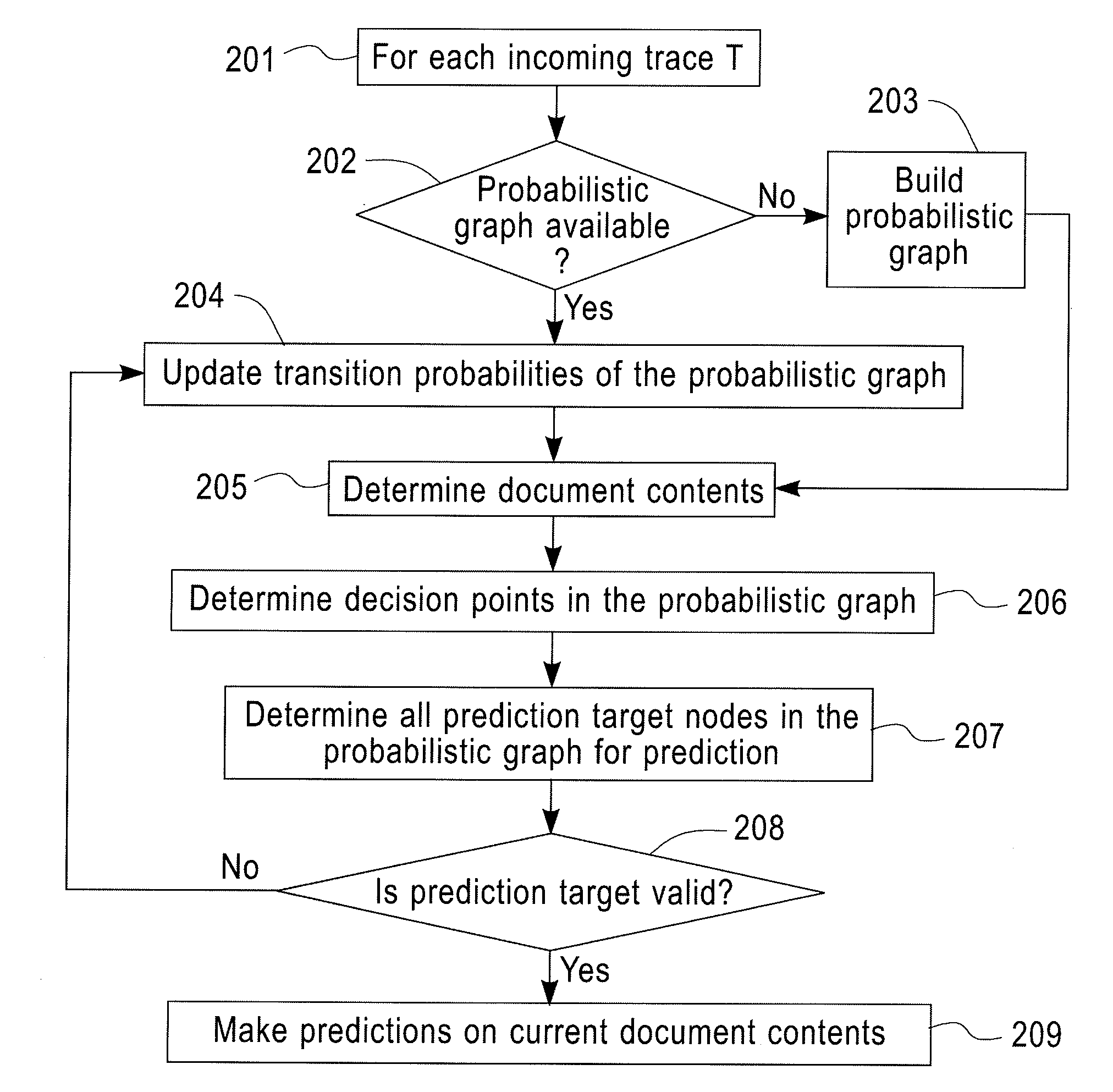
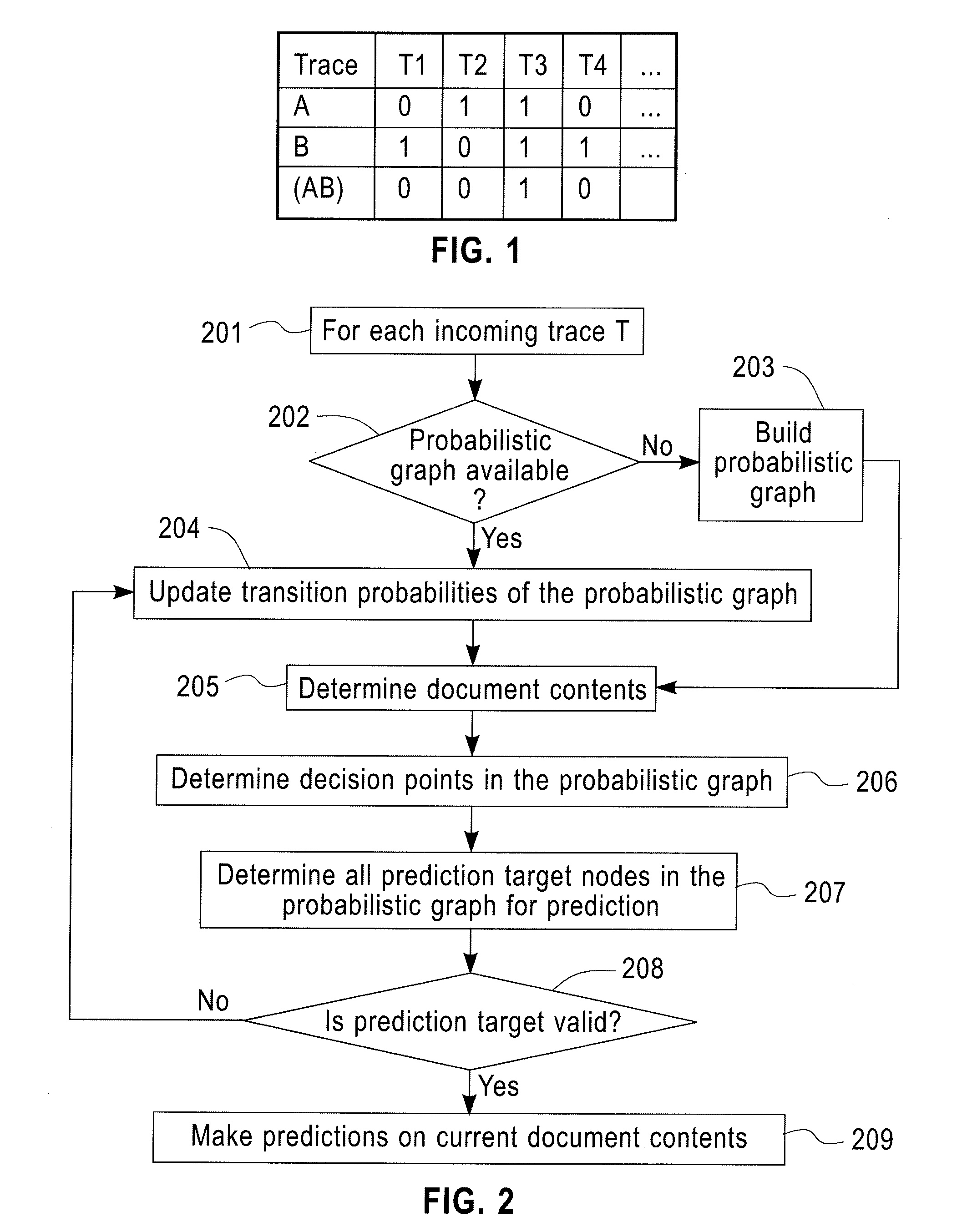
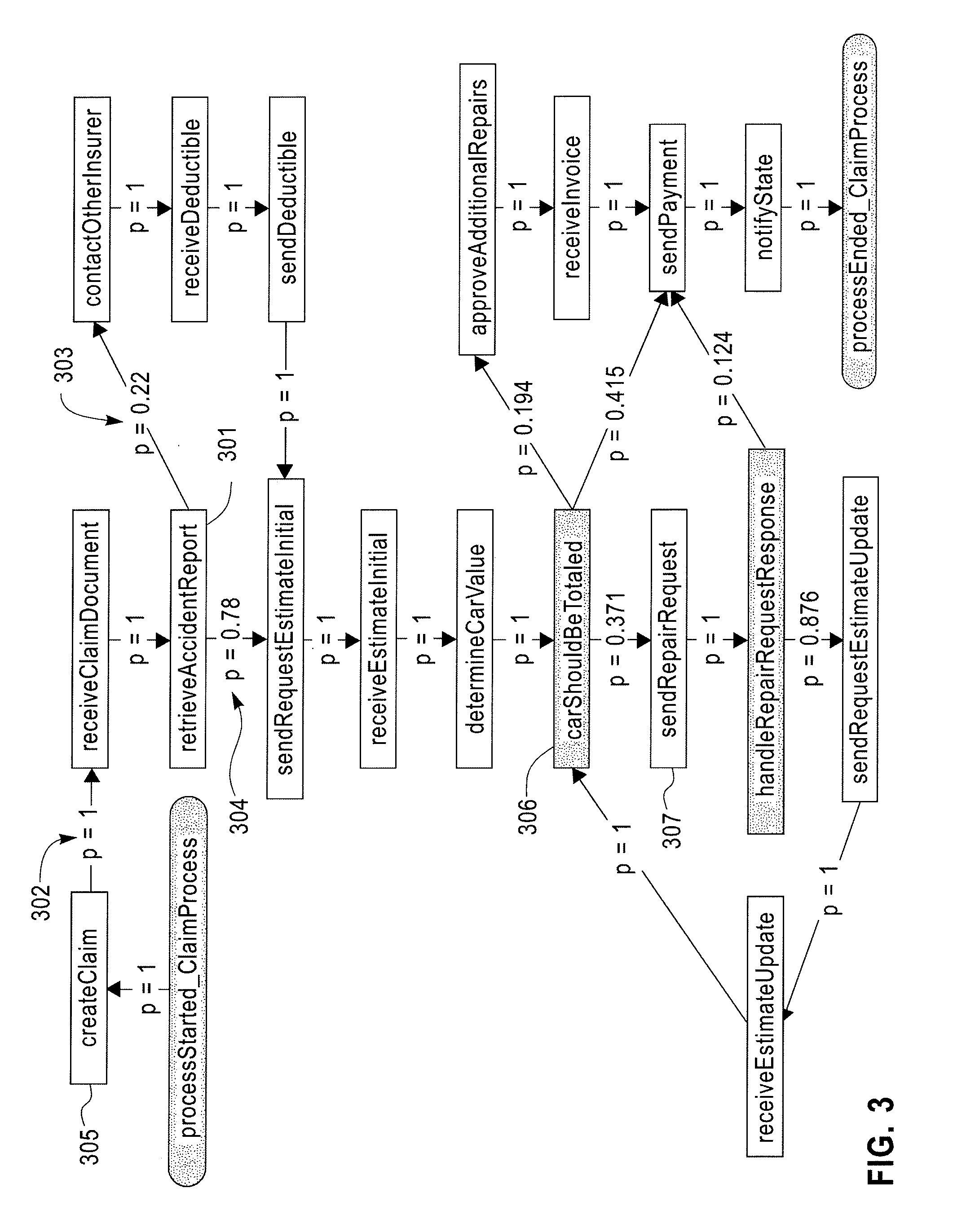
Predictive Analytics for Semi-Structured Case Oriented Processes
InactiveUS20120066166A1Probabilistic networksFuzzy logic based systemsNODALTheoretical computer science
A method for predictive analytics for a process includes receiving at least one trace of the process, building a probabilistic graph modeling the at least one trace, determining content at each node of the probabilistic graph, wherein a node represents an activity of the process and at least one node is a decision node, modeling each decision node as a respective decision tree, and predicting, for an execution of the process, a path in the probabilistic graph from any decision node to a prediction target node of a plurality of prediction target nodes given the content.
Owner:IBM CORP
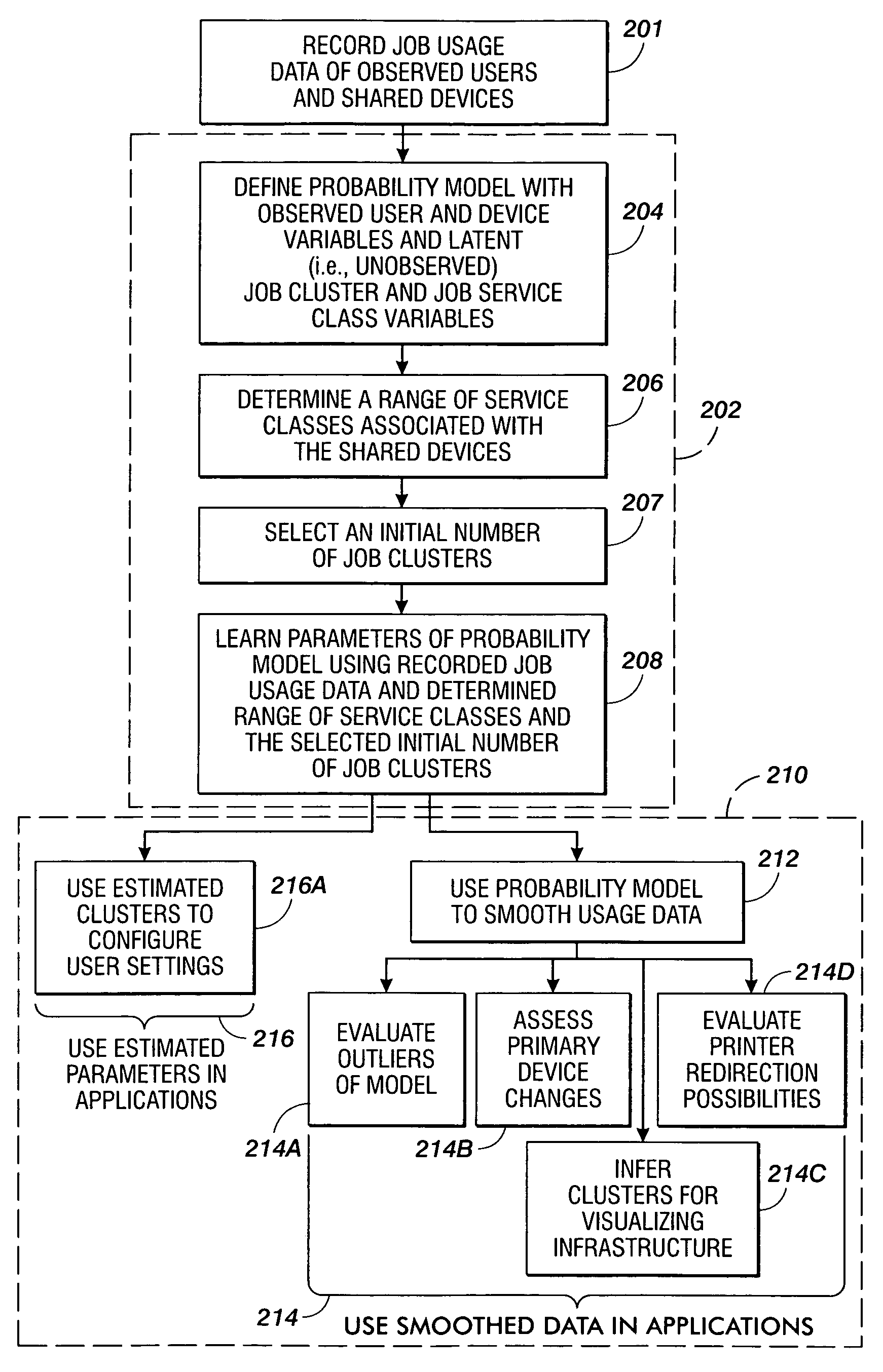
Probabilistic modeling of shared device usage
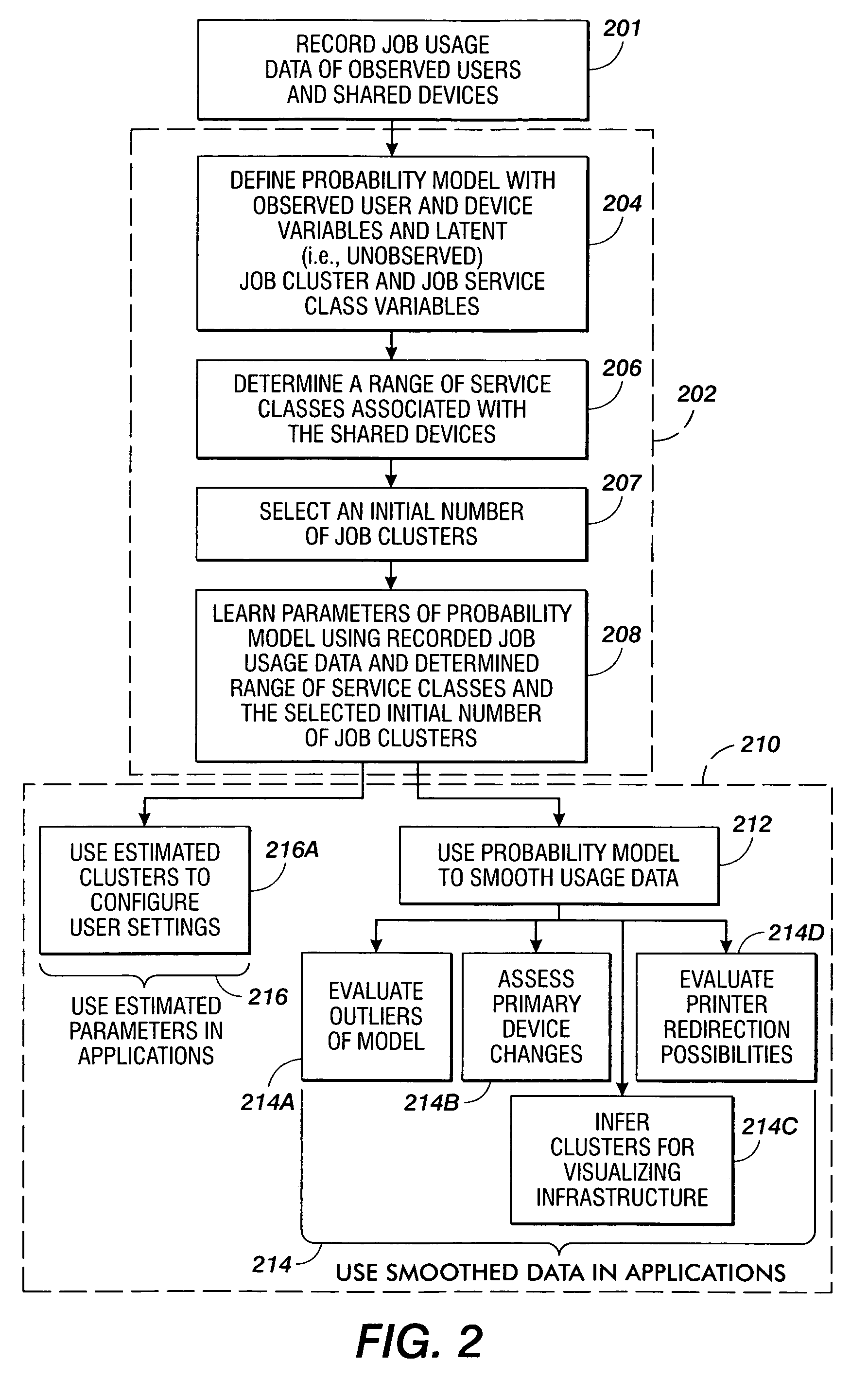
ActiveUS20060206445A1Wide rangeDigital computer detailsCharacter and pattern recognitionClass of serviceModel parameters
Methods are disclosed for estimating parameters of a probability model that models user behavior of shared devices offering different classes of service for carrying out jobs. In operation, usage job data of observed users and devices carrying out the jobs is recorded. A probability model is defined with an observed user variable, an observed device variable, a latent job cluster variable, and a latent job service class variable. A range of job service classes associated with the shared devices is determined, and an initial number of job clusters is selected. Parameters of the probability model are learned using the recorded job usage data, the determined range of service classes, and the selected initial number of job clusters. The learned parameters of the probability model are applied to evaluate one or more of: configuration of the shared devices, use of the shared devices, and job redirection between the shared devices.
Owner:XEROX CORP
Usage pattern based user authenticator
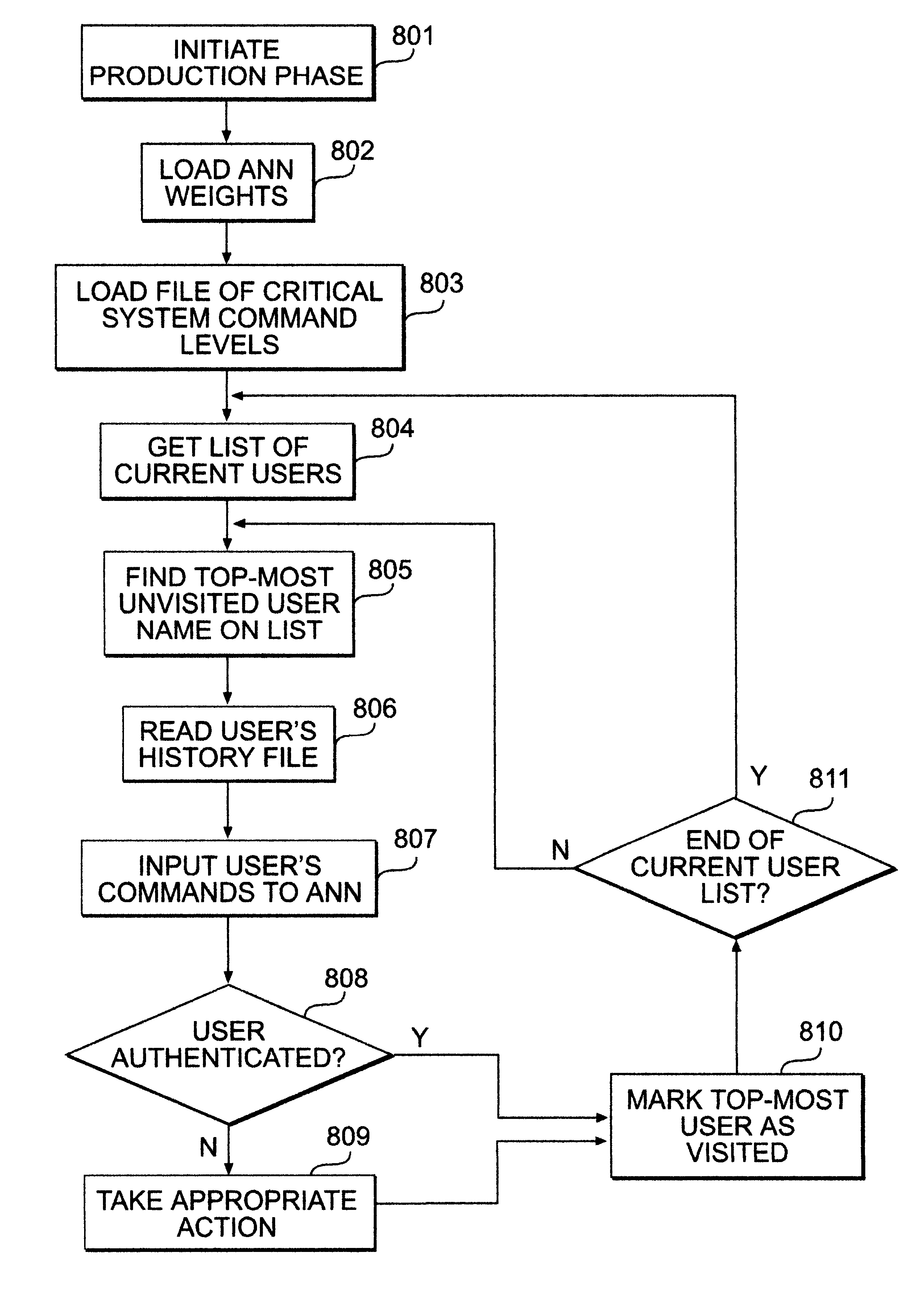
InactiveUS6334121B1Control damagePreventing executionDigital computer detailsComputer security arrangementsOperational systemOperating system level
A usage based pattern authenticator for monitoring and reporting on user usage patterns in an operating system using a set of security rules and user usage patterns. This computer system security tool authenticates users at the operating system level in multi-user operating systems. It supports system administrators in limiting the ability of unauthorized users to disrupt system operations using a neural network and set of rules to track usage patterns and flag suspicious activity on the system. The data collection mode collects and stores usage patterns of authenticated users. The training mode trains an artificial neural network and sets the interconnection weights of the network. The production mode monitors and reports on usage patterns, and optionally performs automatic responses when confronted with non-authenticated users.
Owner:VIRGINIA COMMONWEALTH UNIV
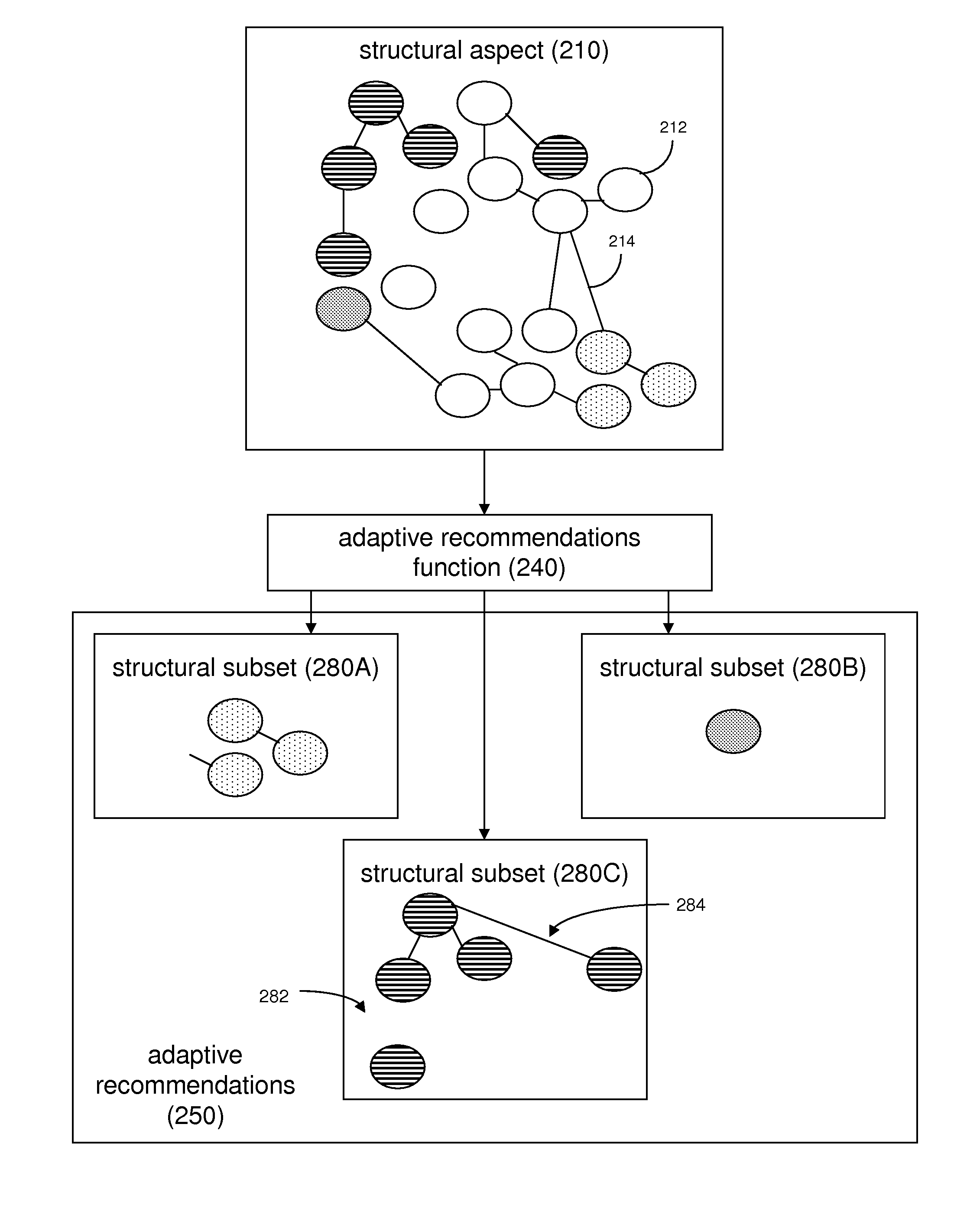
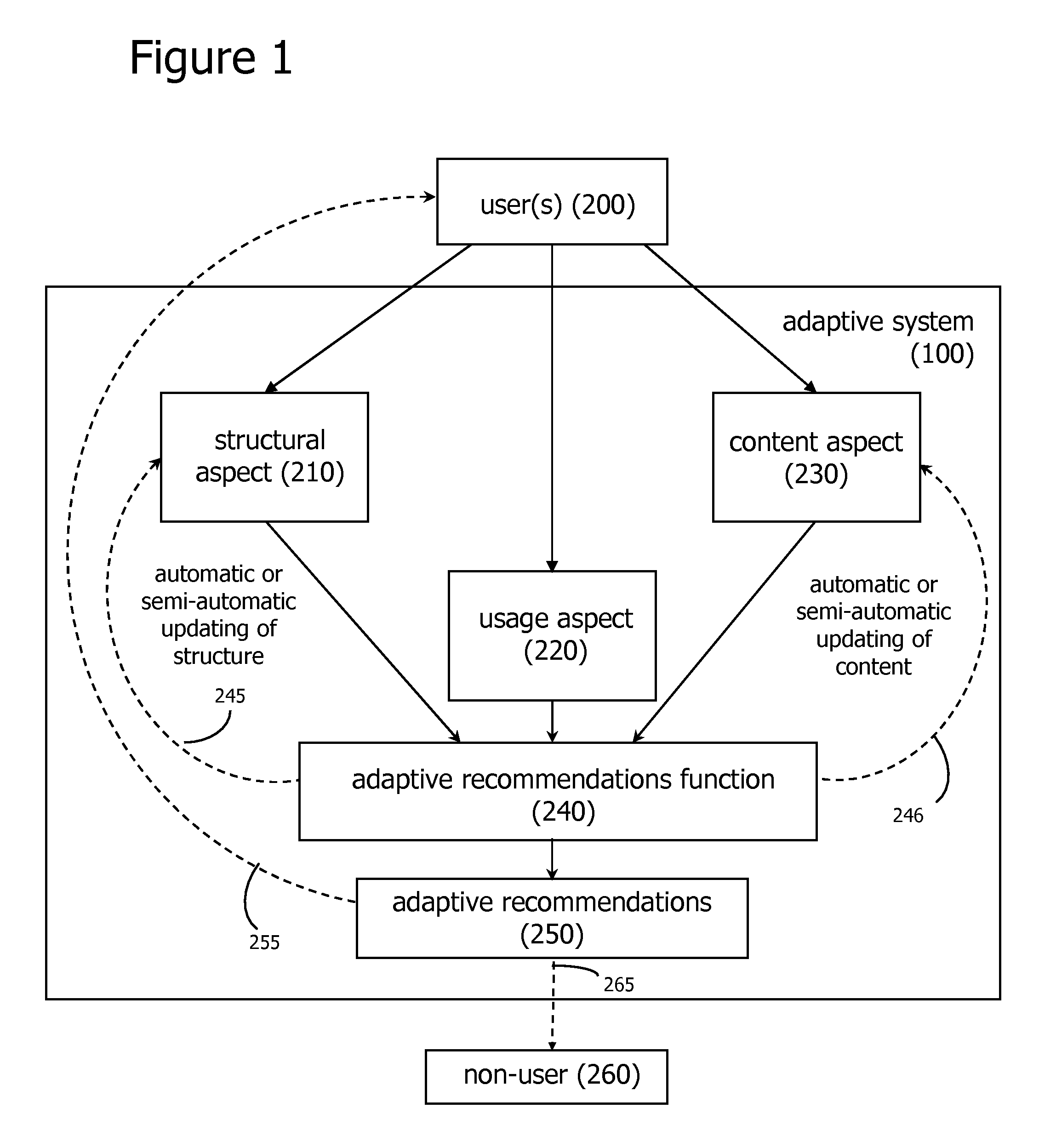
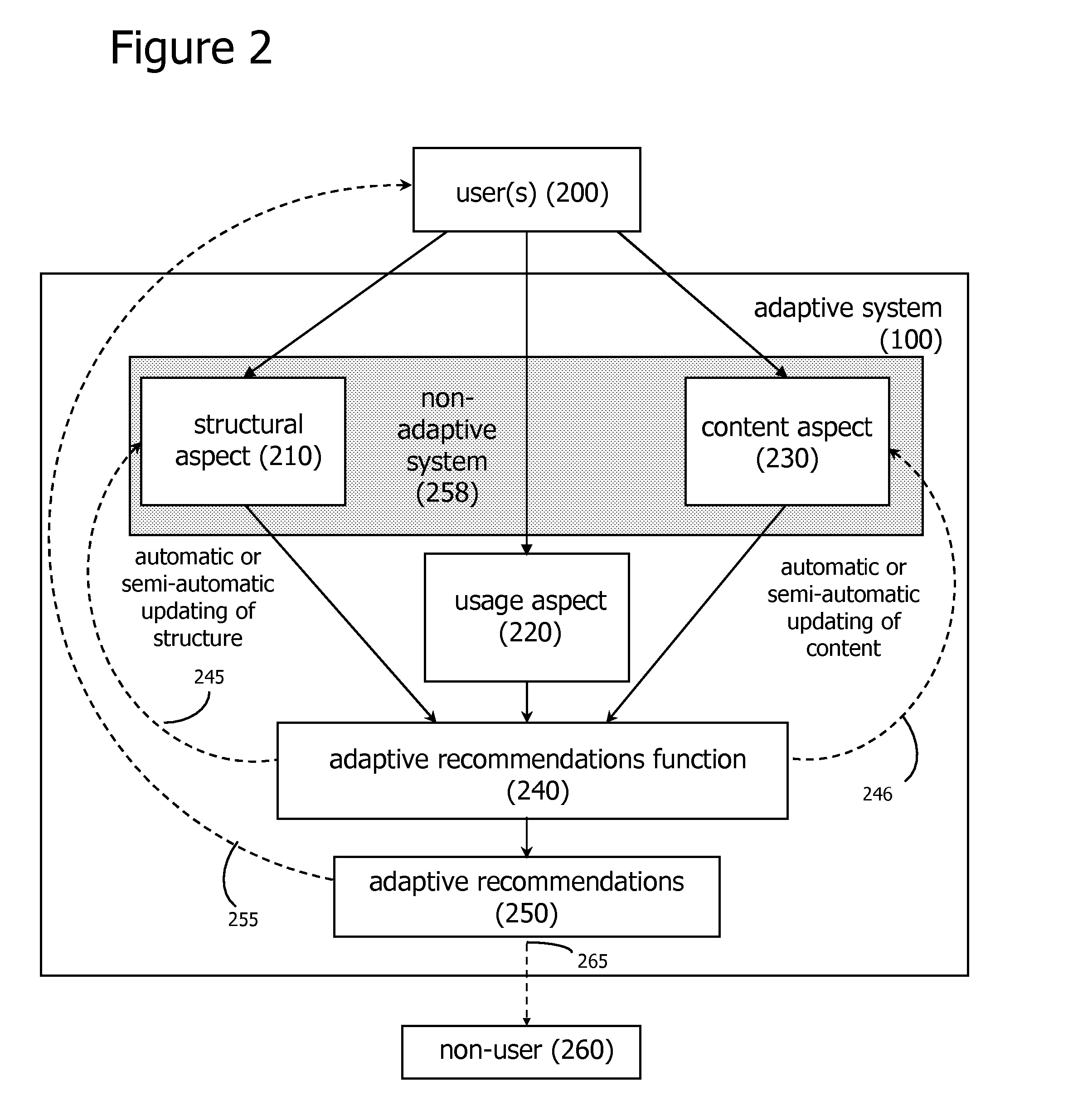
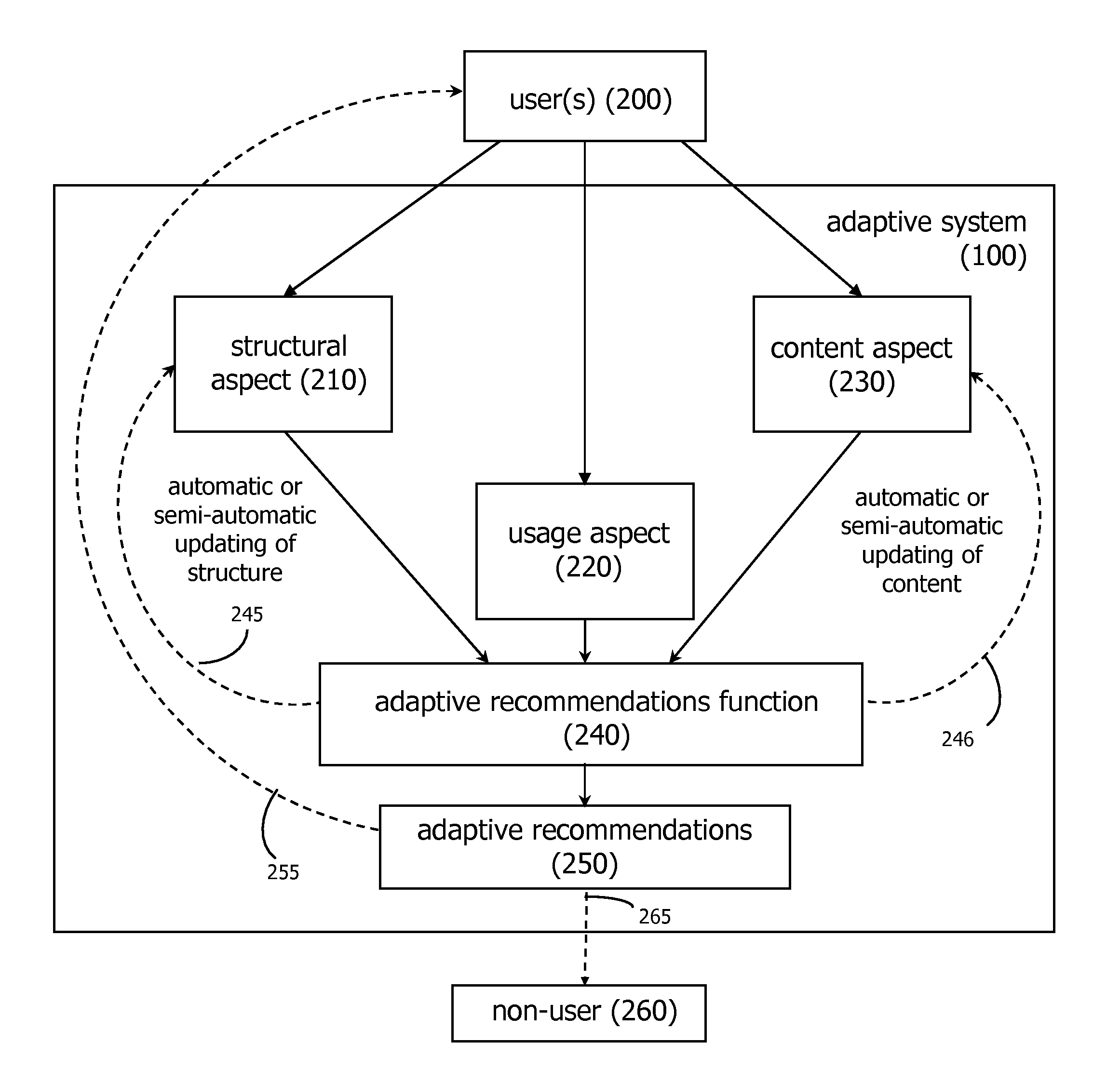
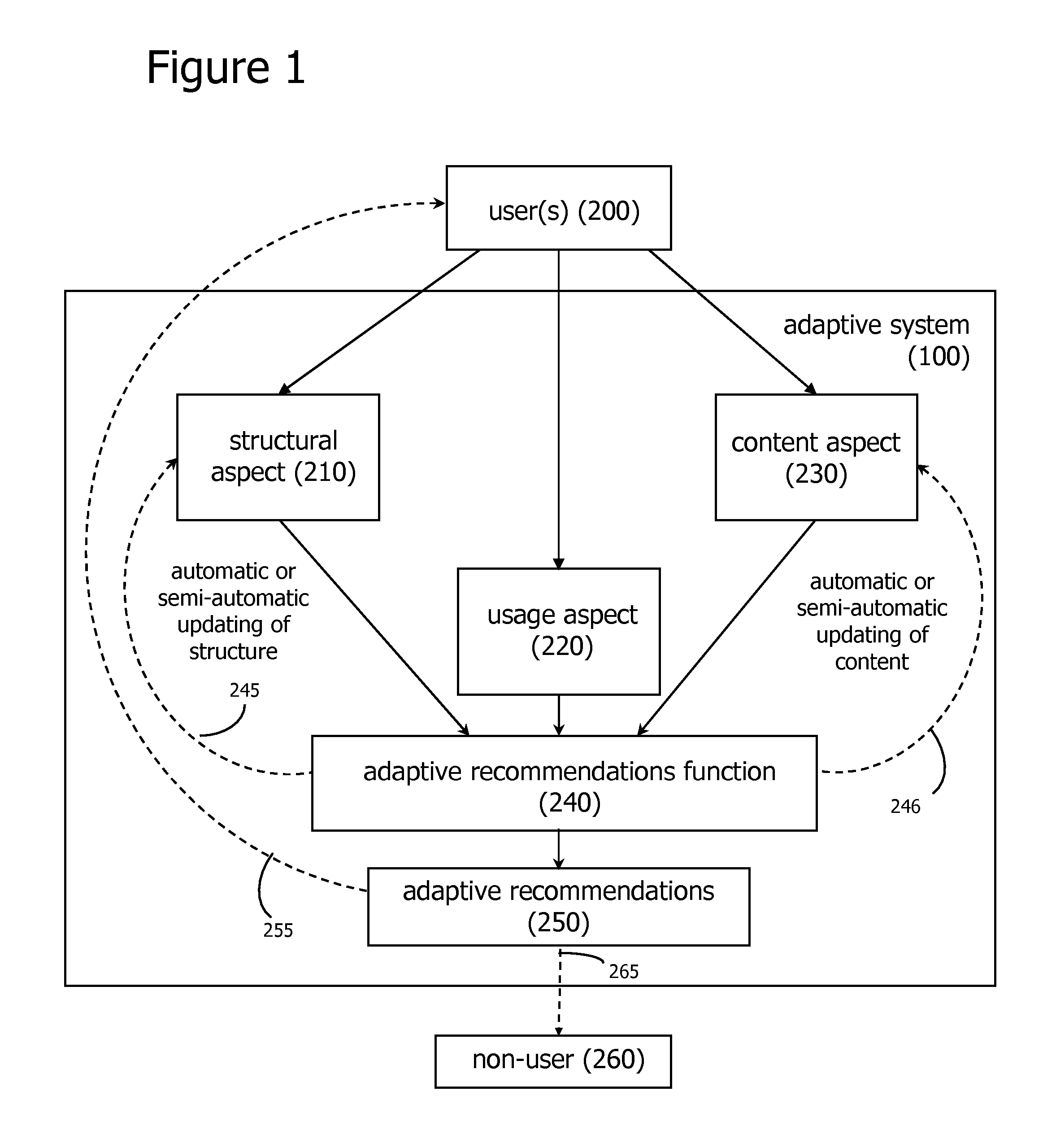
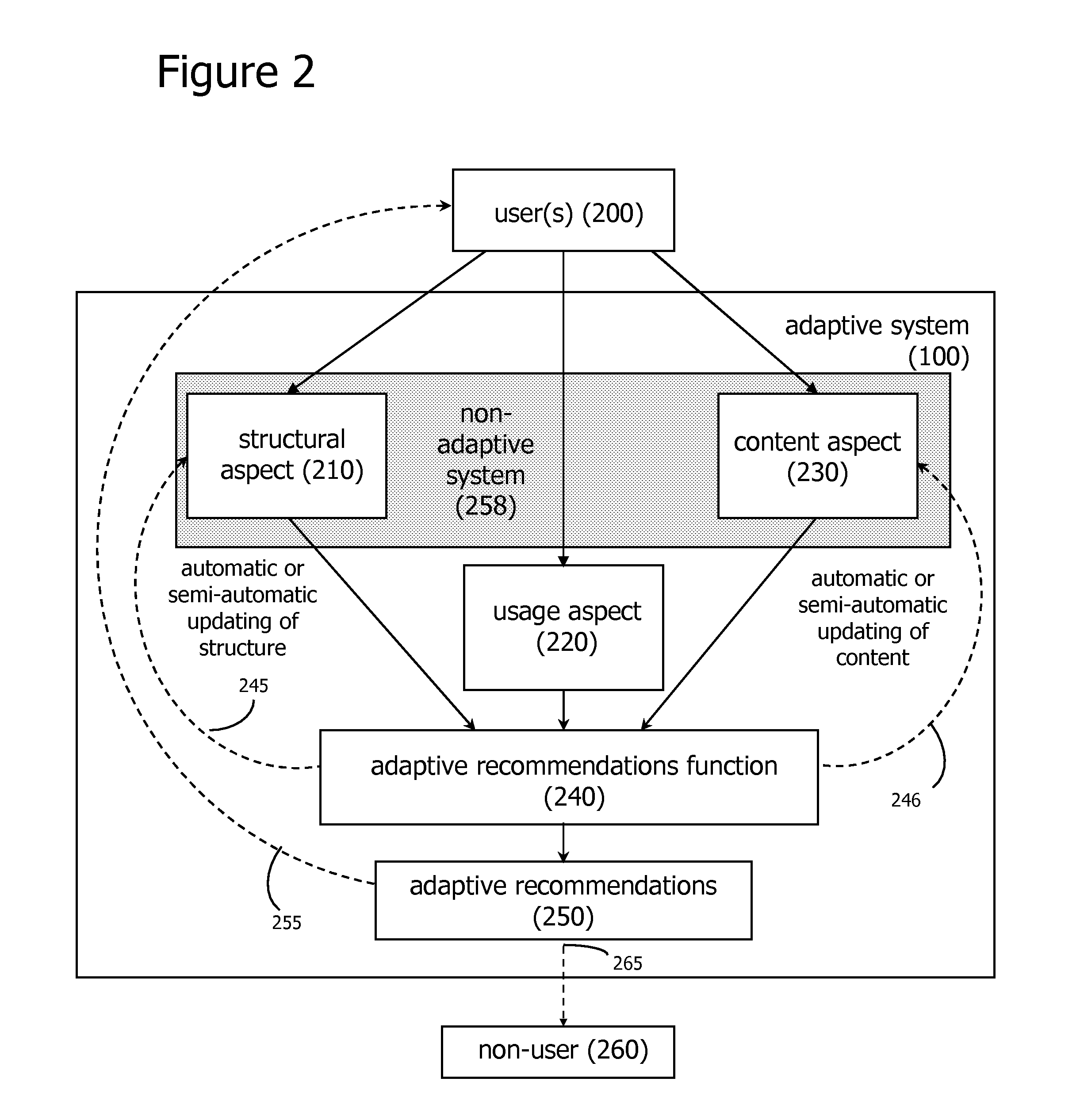
Adaptive Recommendations Systems
ActiveUS20060200432A1Easy to adaptEfficiently navigateDigital computer detailsFuzzy logic based systemsVision basedSelf adaptive
An adaptive recommendation system and a mobile adaptive recommendation system are disclosed. The adaptive recommendation system and the mobile adaptive recommendation system include algorithms for monitoring user usage behaviors across a plurality of usage behavior categories associated with a computer-based system, and generating recommendations based on inferences on user preferences and interests. Privacy control functions and compensatory functions related to insincere usage behaviors can be applied. Adaptive recommendation delivery can take the form of visual-based or audio-based formats.
Owner:WORLD ASSETS CONSULTING AG
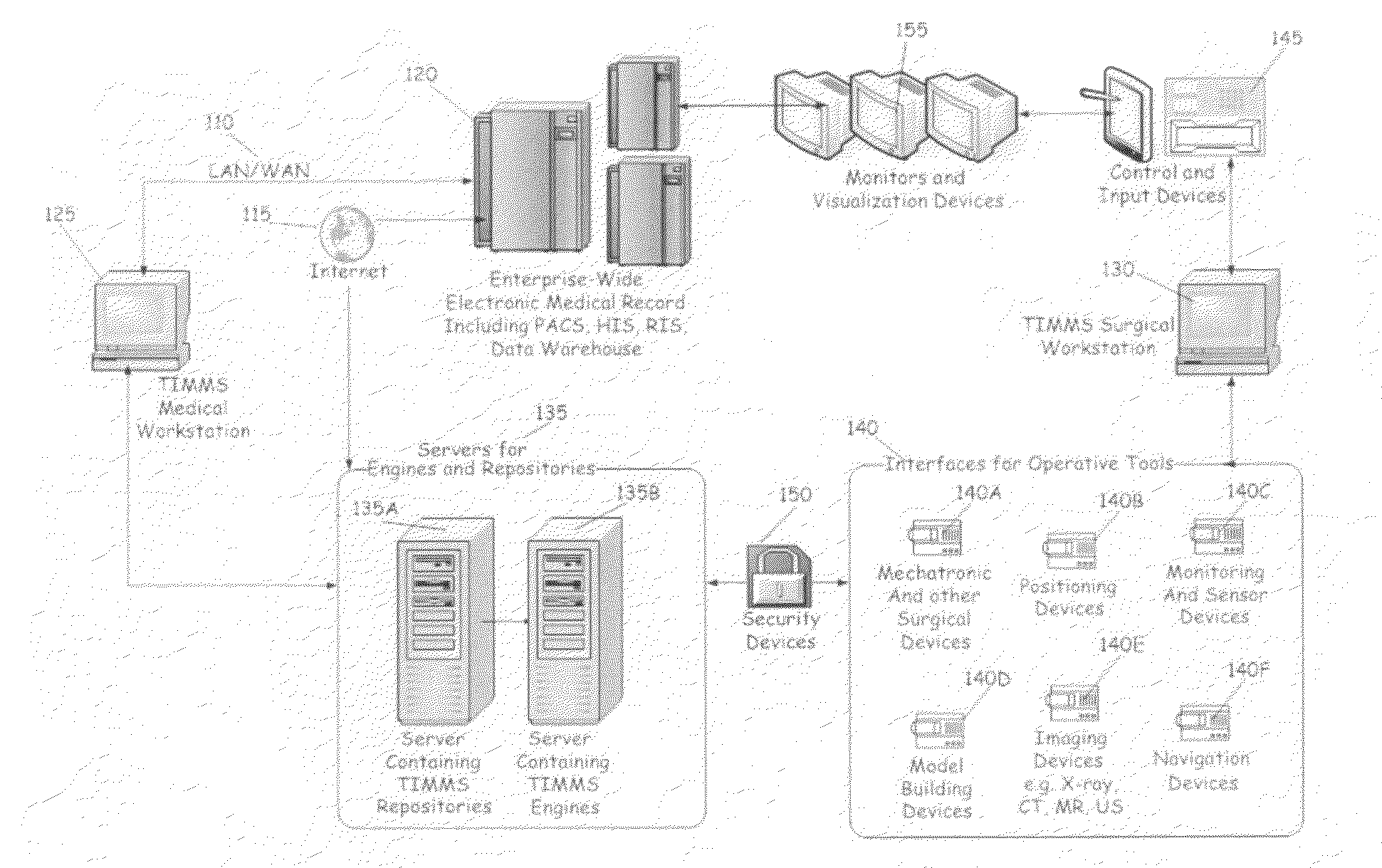
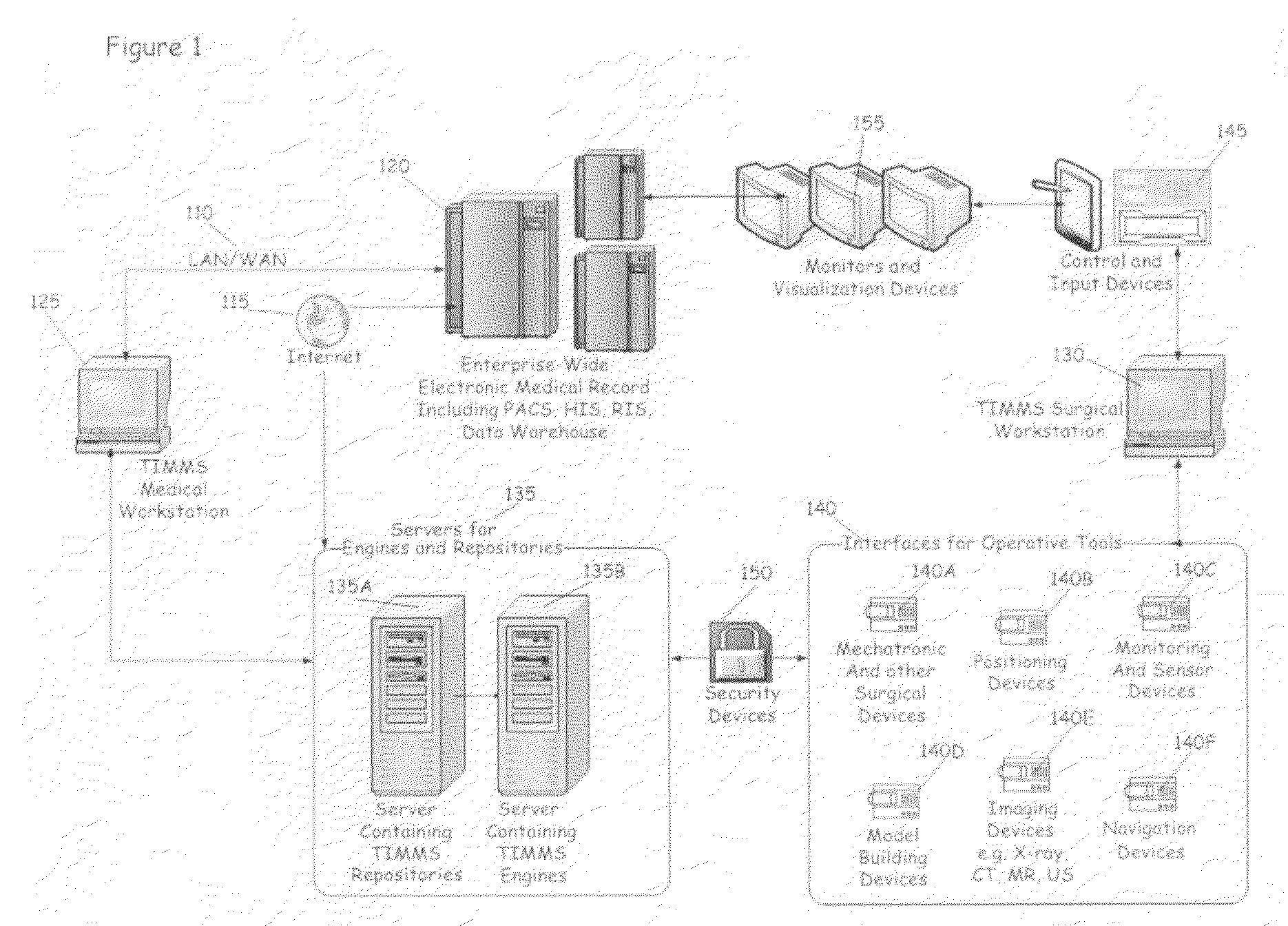
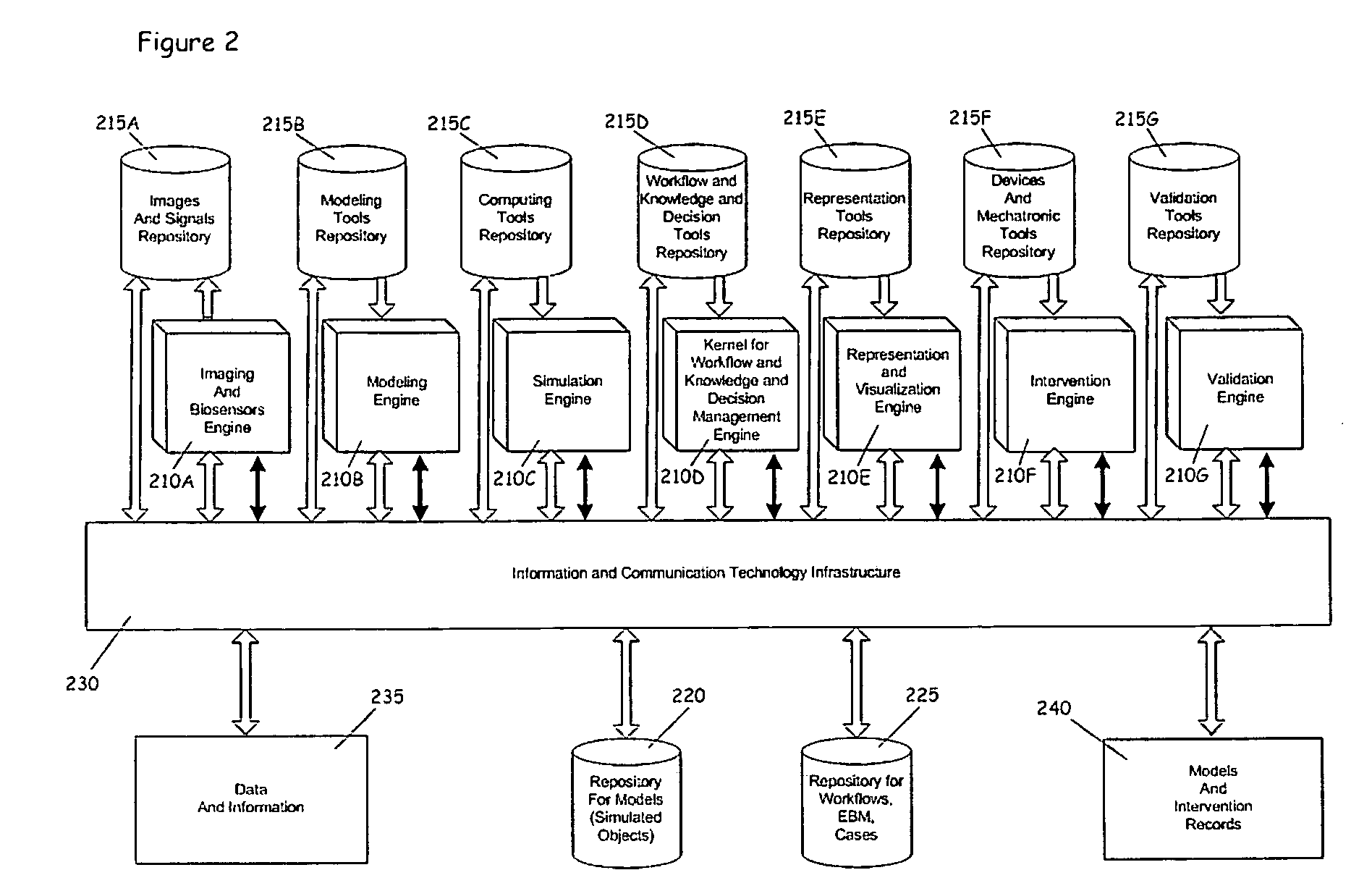
Process for comprehensive surgical assist system by means of a therapy imaging and model management system (TIMMS)
InactiveUS20090326336A1Increase successMechanical/radiation/invasive therapiesDiagnostic recording/measuringModel managementMedical record
This invention provides a process and system for a comprehensive surgical assist system, called a Therapy Imaging and Model Management System (TIMMS), which combines and integrates all of the necessary information and communication technology; workflow analysis, data processing and data synthesis; interactive interfaces between surgeon and mechatronic devices; and, cognitive agents; to provide comprehensive assistance and guidance throughout complex medical and surgical therapies, such as image guided surgery. The components of this invention, which are modular, scalable and may be distributed in location, act synergistically to provide functionality and utility that exceeds the sum of its individual parts.A method of performing surgery on a patient comprising the step of comparing a chosen patient's data to statistical data in a repository of patient data to develop a patient specific model, wherein the data comprises information from two or more sub databases selected from the group consisting of workflow data, electronic medical records, diagnostic data, biological data, measurement data, anatomical data, physiological data, genetic data, molecular data, imaging data, chemical data, clinical laboratory data, simulated data, coordinate data and surgical result and wherein the patient specific model aids in the preoperative, operative or post operative phase of surgery performed in real time on the patient.
Owner:LEMKE HEINZ ULRICH +1
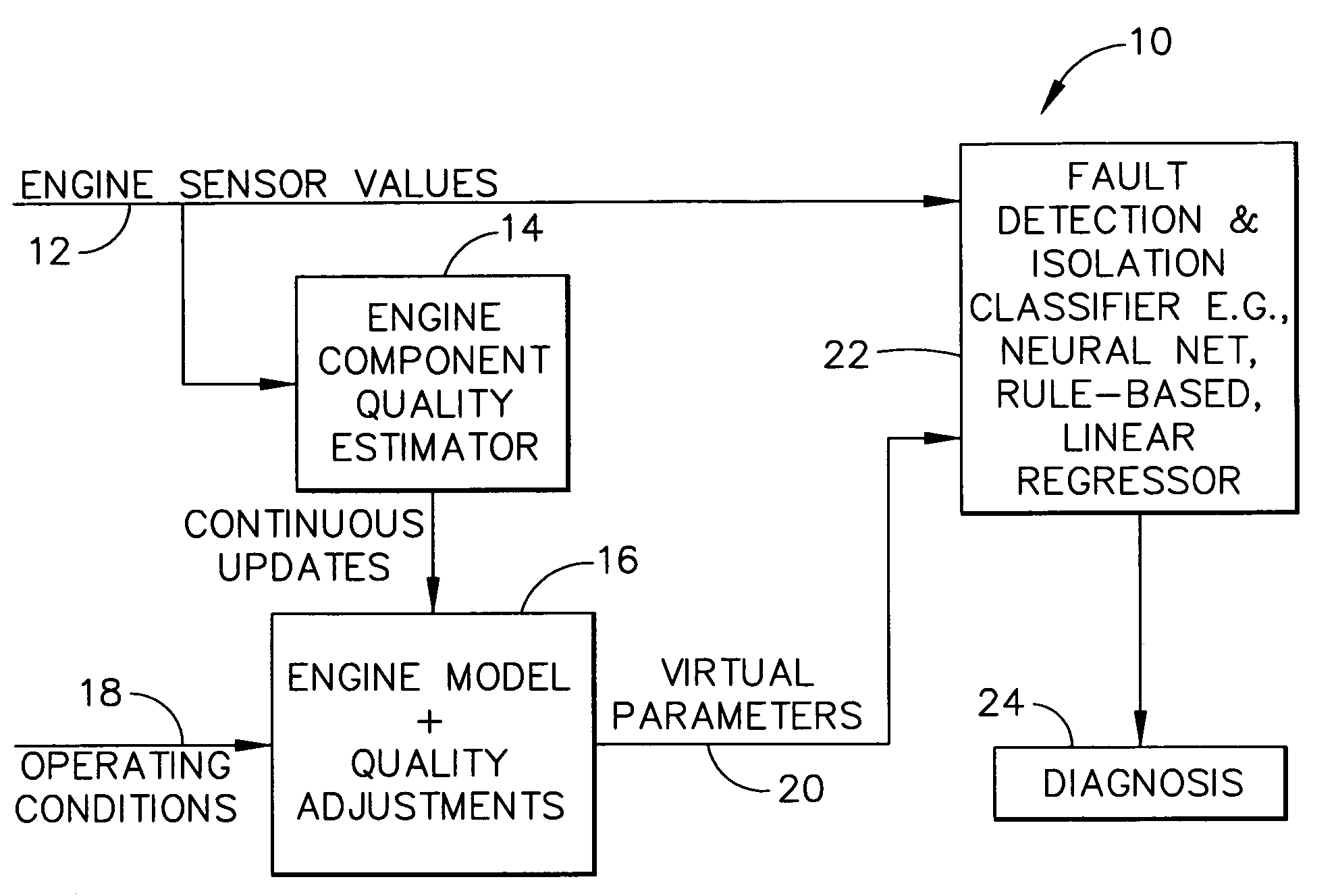
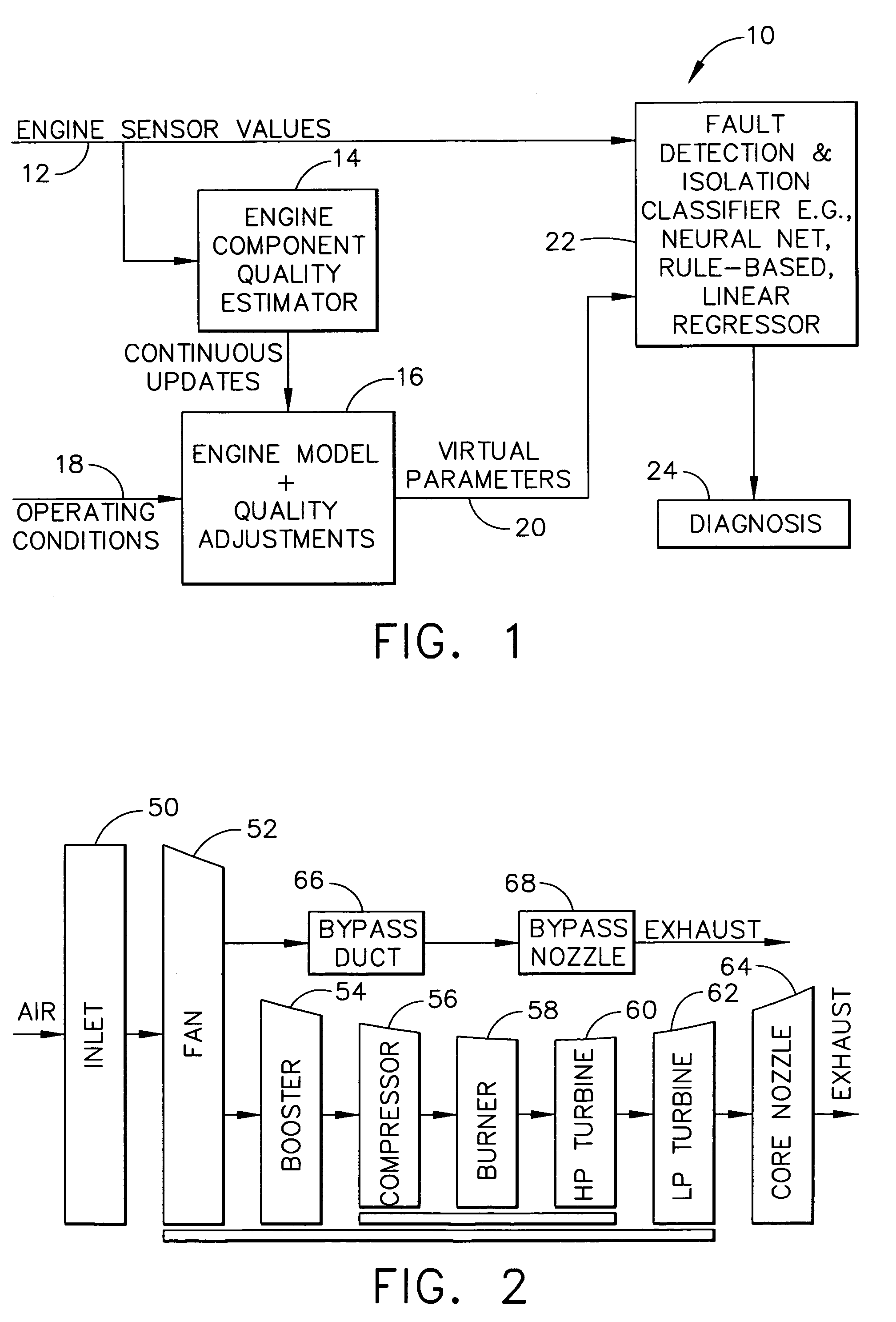
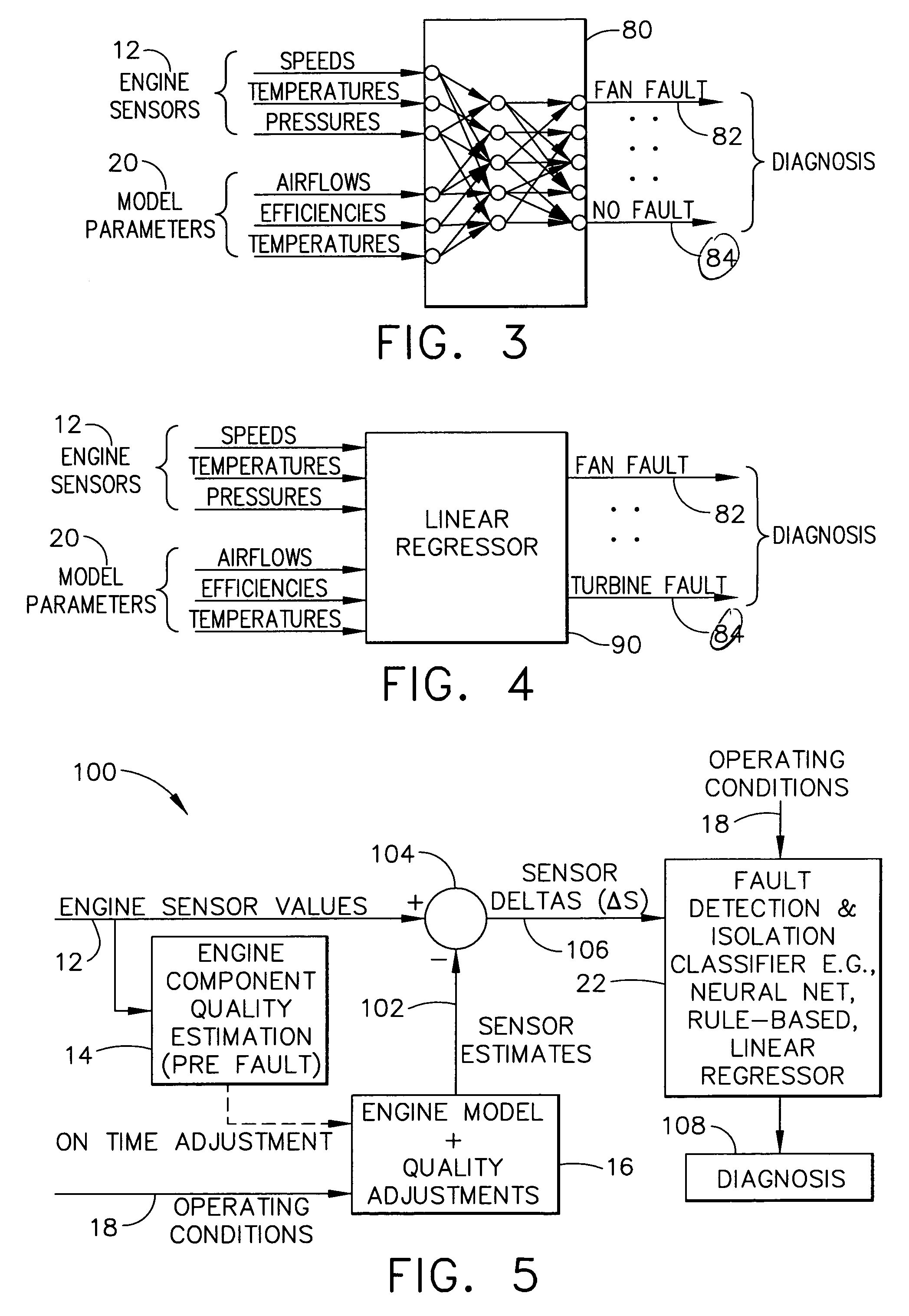
Methods and apparatus for model based diagnostics
Systems and methods for performing module-based diagnostics are described. In an exemplary embodiment, sensor values from an actual engine plant are input to an engine component quality estimator which generates performance estimates of major rotating components. Estimated performance differences are generating by comparing the generated performance estimates to a nominal quality engine. The estimated performance differences, which are indicative of component quality, are continuously updated and input to a real-time model of the engine. The model receives operating conditional data and the quality estimates are used to adjust the nominal values in the model to more closely match the model values to the actual plant. Outputs from the engine model are virtual parameters, such as stall margins, specific fuel consumption, and fan / compressor / turbine efficiencies. The virtual parameters are combined with the sensor values from the actual engine plant in a fault detection and isolation classifier to identify abnormal conditions and / or specific fault classes, and output a diagnosis.
Owner:GENERAL ELECTRIC CO
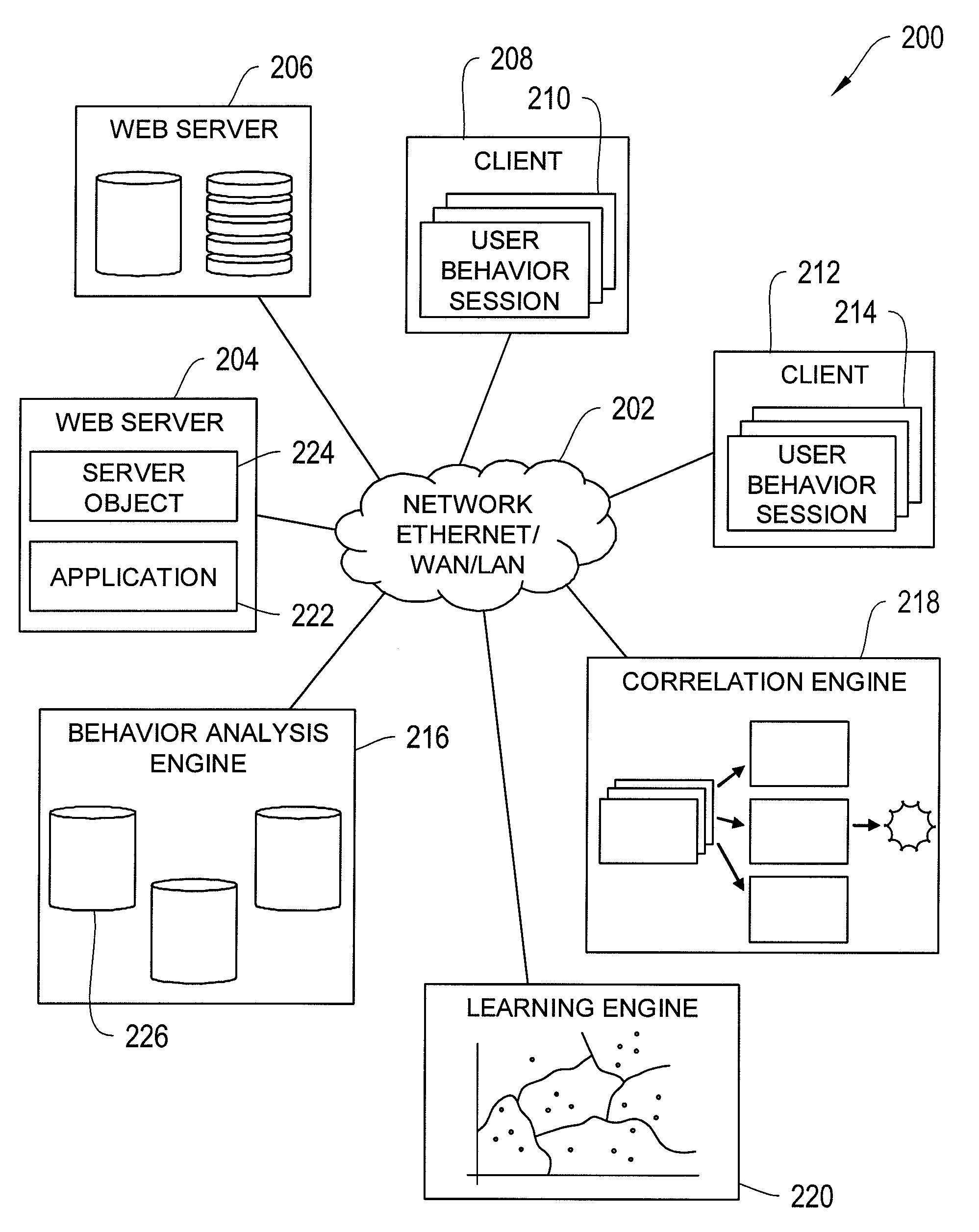
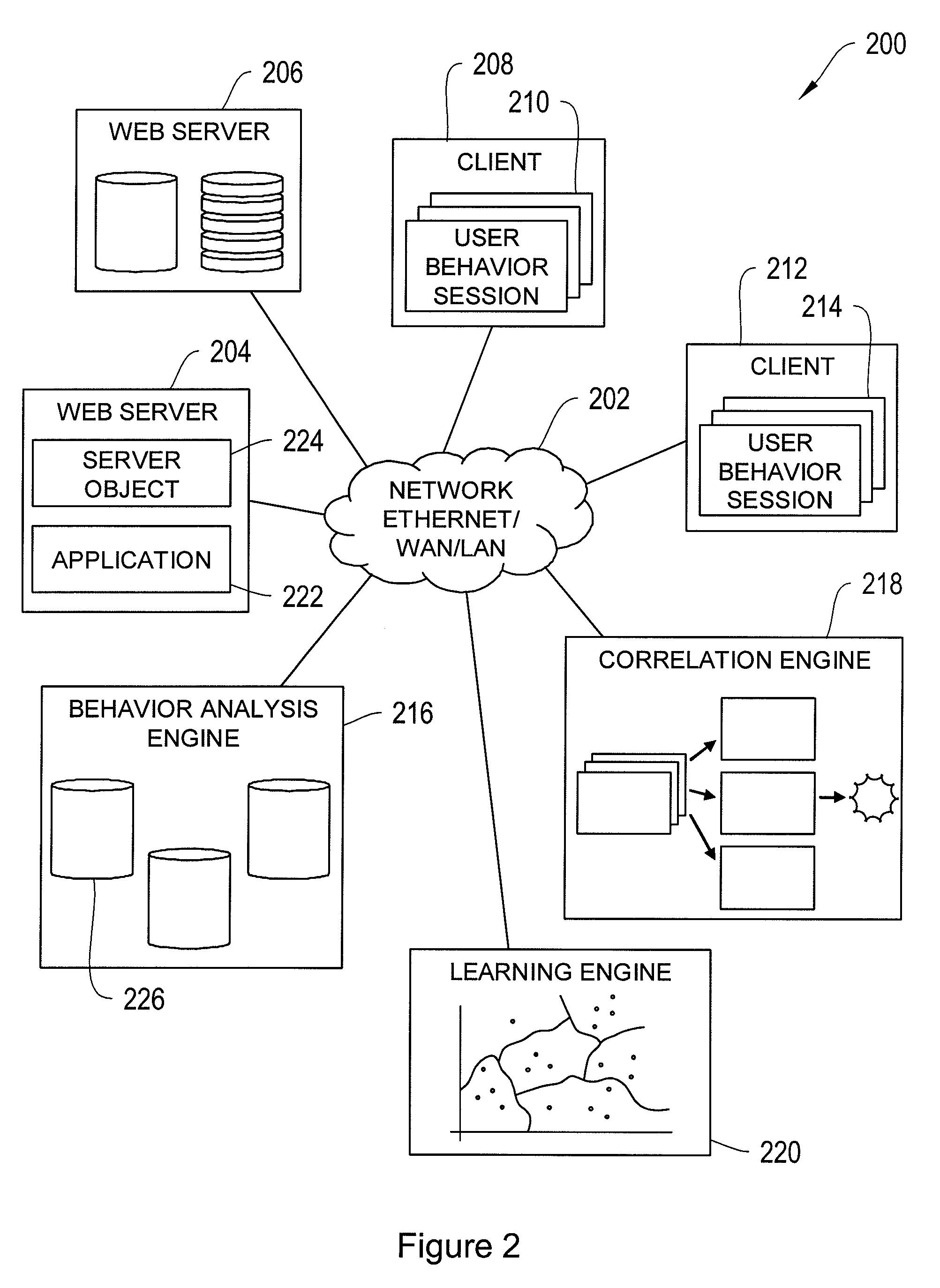
Systems and Methods for Application-Level Security
InactiveUS20100299292A1Easily correlatedReduce settingsMemory loss protectionError detection/correctionInternet privacyBehaviour pattern
A system and method for application-level security is disclosed. Application-level security refers to detecting security threats from functional user behavior. Information about functional user behavior is transformed into a behavior session. The behavior session is transformed into a behavior pattern. The behavior pattern is correlated with evaluation patterns to detect potential security threats. Behavior patterns are collected over time to improve analysis.
Owner:XYBERSHIELD INC
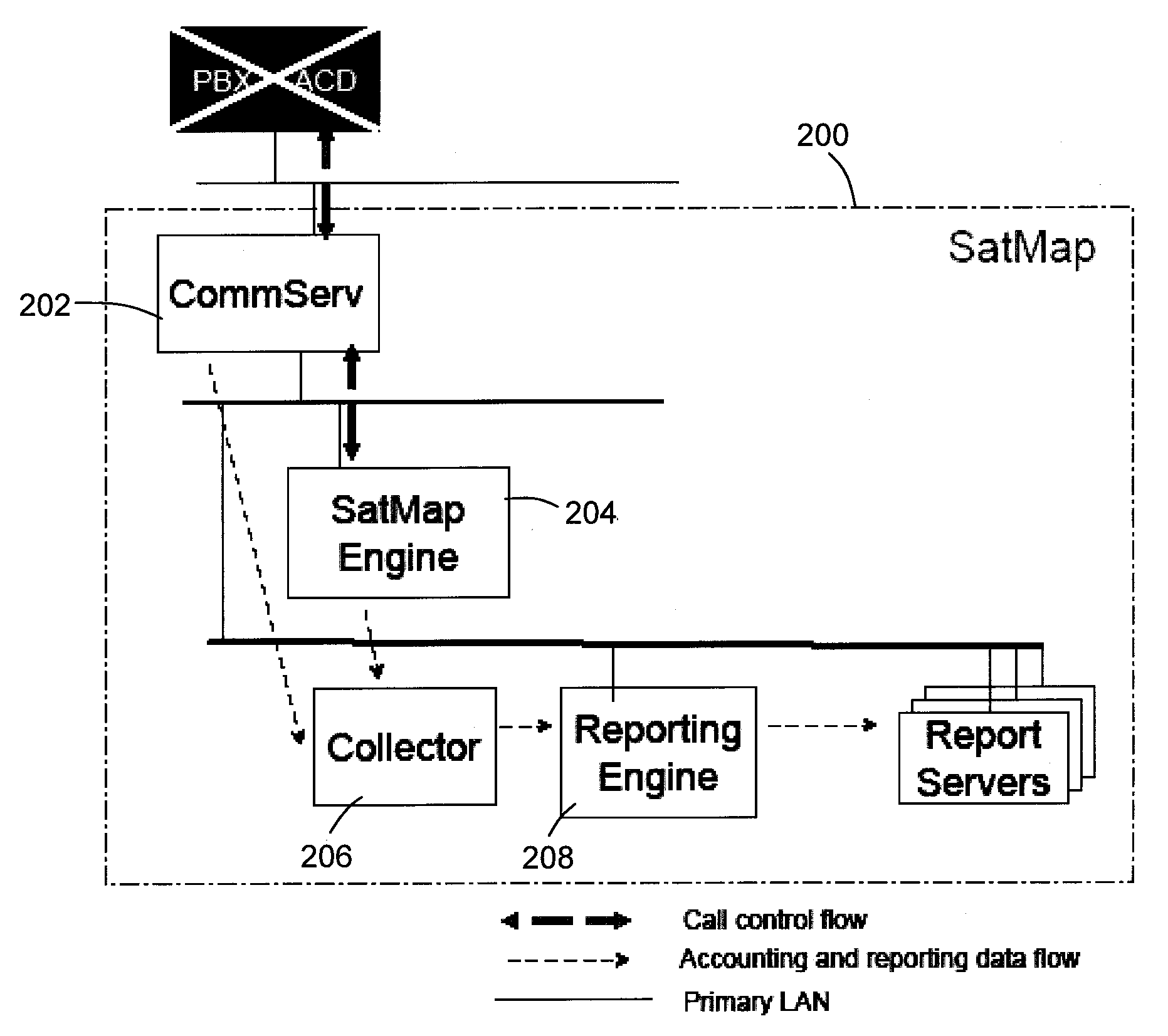
Balancing multiple computer models in a call center routing system
ActiveUS20100111285A1Adjust balanceDigital computer detailsBiological neural network modelsPattern matchingParallel computing
Systems and methods are disclosed for routing callers to agents in a contact center utilizing a multi-layer processing approach to matching a caller to an agent. A first layer of processing may include two or more different computer models or methods for scoring or determining caller-agent pairs in a routing center. The output of the first layer may be received by a second layer of processing for balancing or weighting the outputs and selecting a final caller-agent match. The two or more methods may include conventional queue based routing, performance based routing, pattern matching algorithms, affinity matching, and the like. The output or scores of the two or more methods may be processed be the second layer of processing to select a caller-agent pair and cause the caller to be routed to a particular agent.
Owner:AFINITI LTD
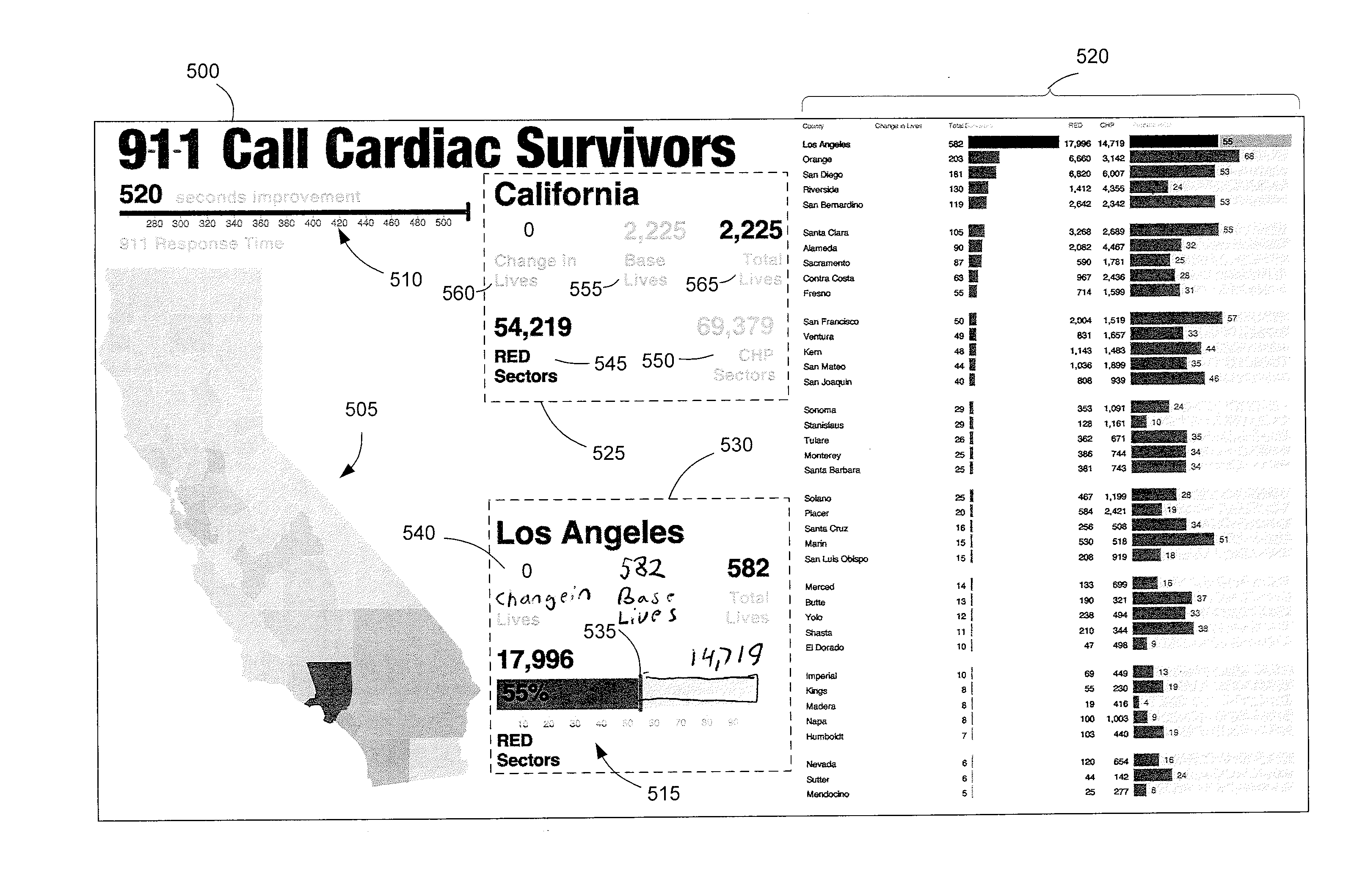
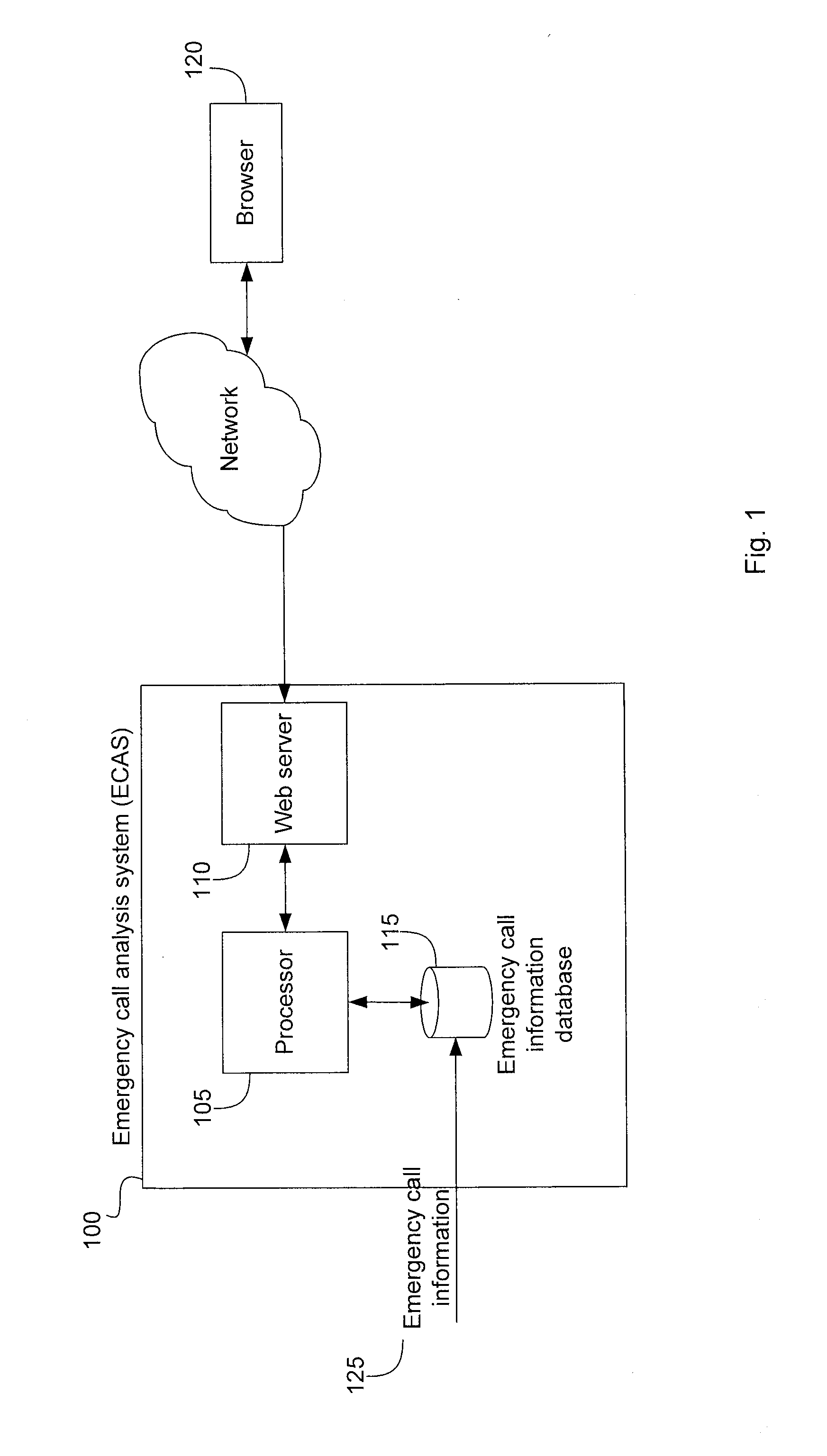
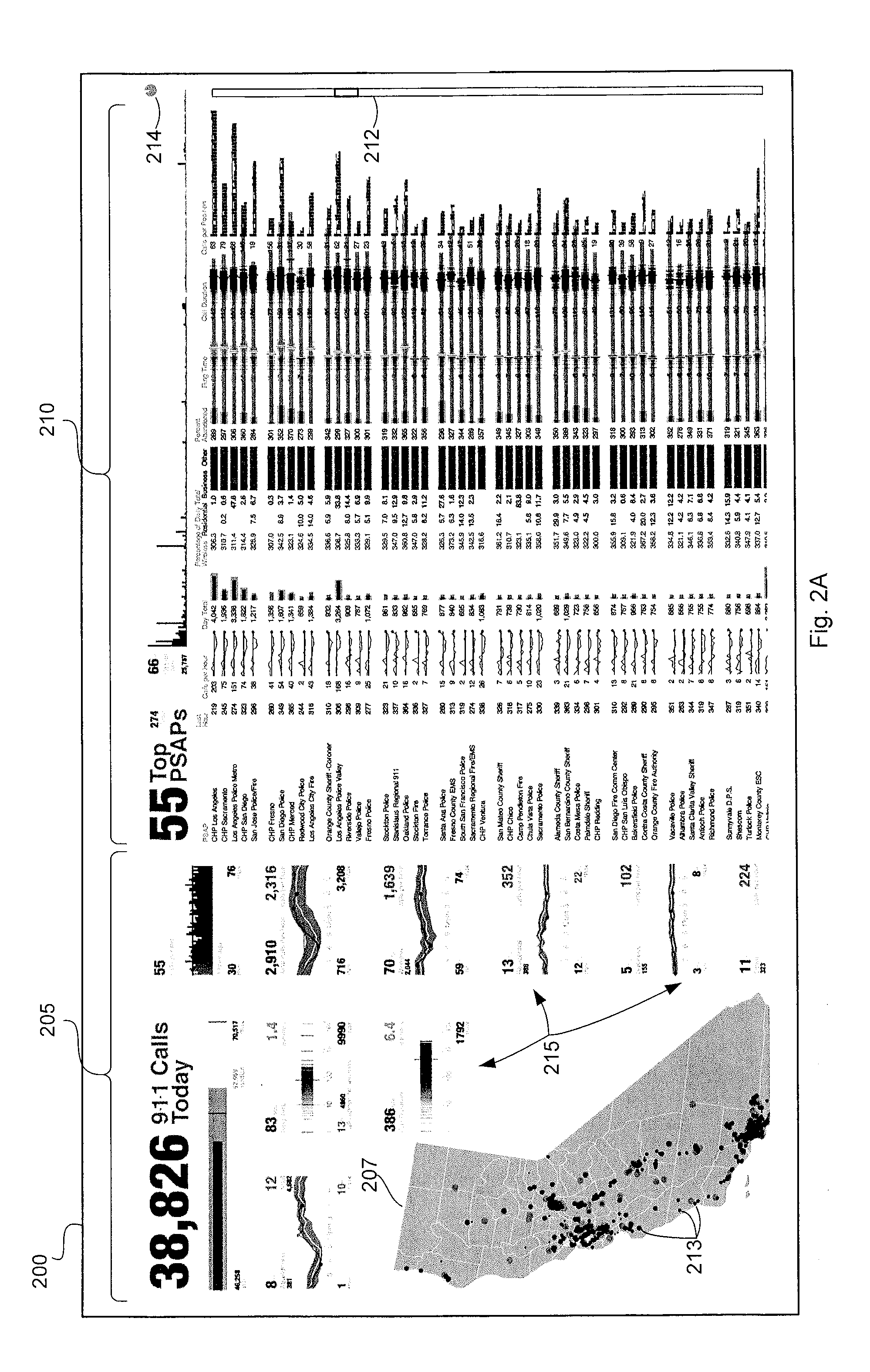
Emergency call analysis system
A method for predicting a survival rate among individuals, where the survival rate depends in part on a responsiveness of emergency personnel, and the responsiveness of the emergency personnel depends in part on an amount of time taken to route an emergency call to a primary emergency response center, includes determining, by a computer system, a number of emergency calls initially routed to a primary emergency response center. The computer system determines a number of emergency calls initially routed to a secondary emergency response center that, in turn, routes the emergency calls to the primary emergency response center. The computer system calculates a survival rate amount individuals according to a function of the determined number of the number of emergency calls initially routed to a primary emergency response center and the number of emergency calls initially routed to a secondary emergency response center. The calculated survival rate is displayed on a terminal.
Owner:REICH DON +1
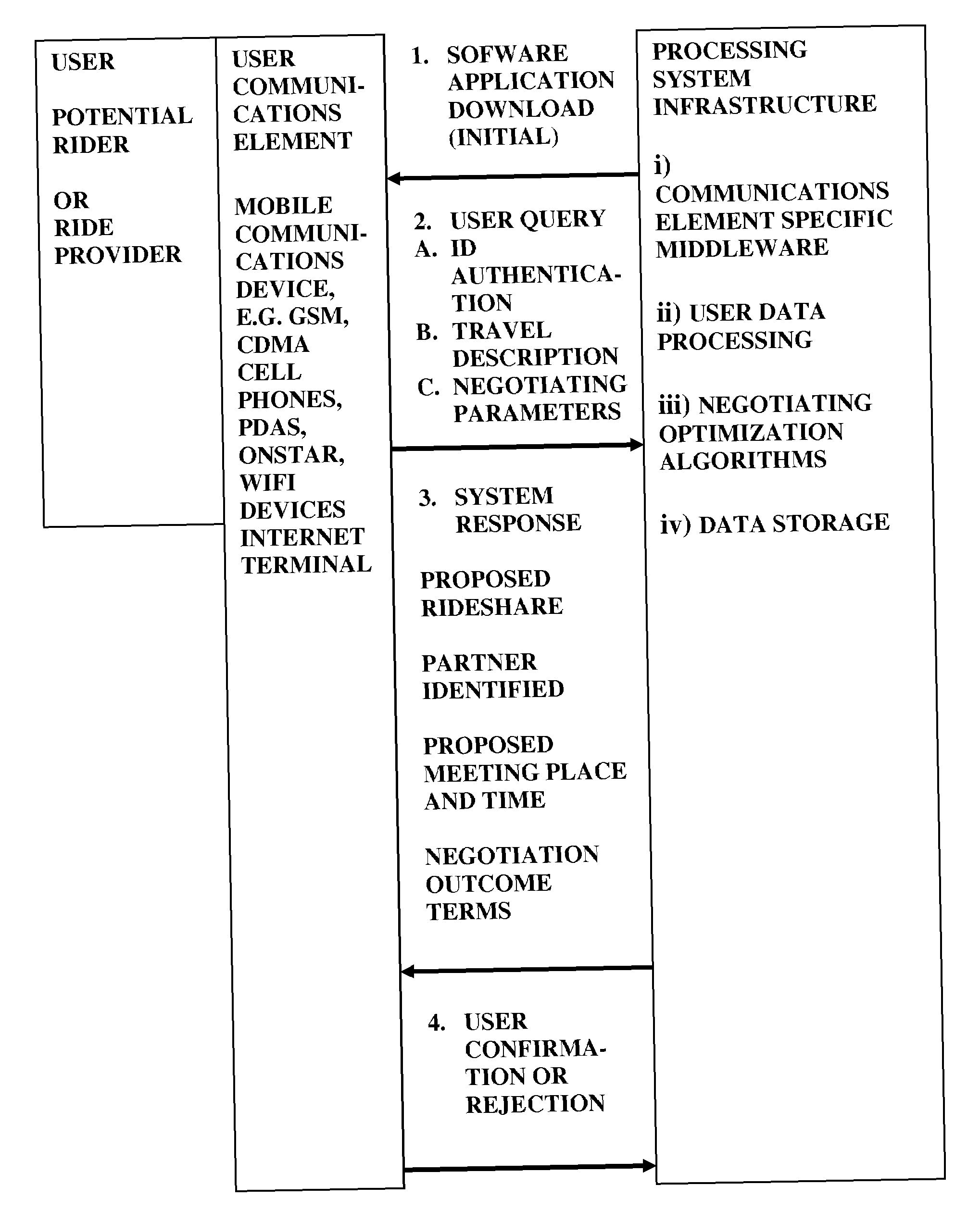
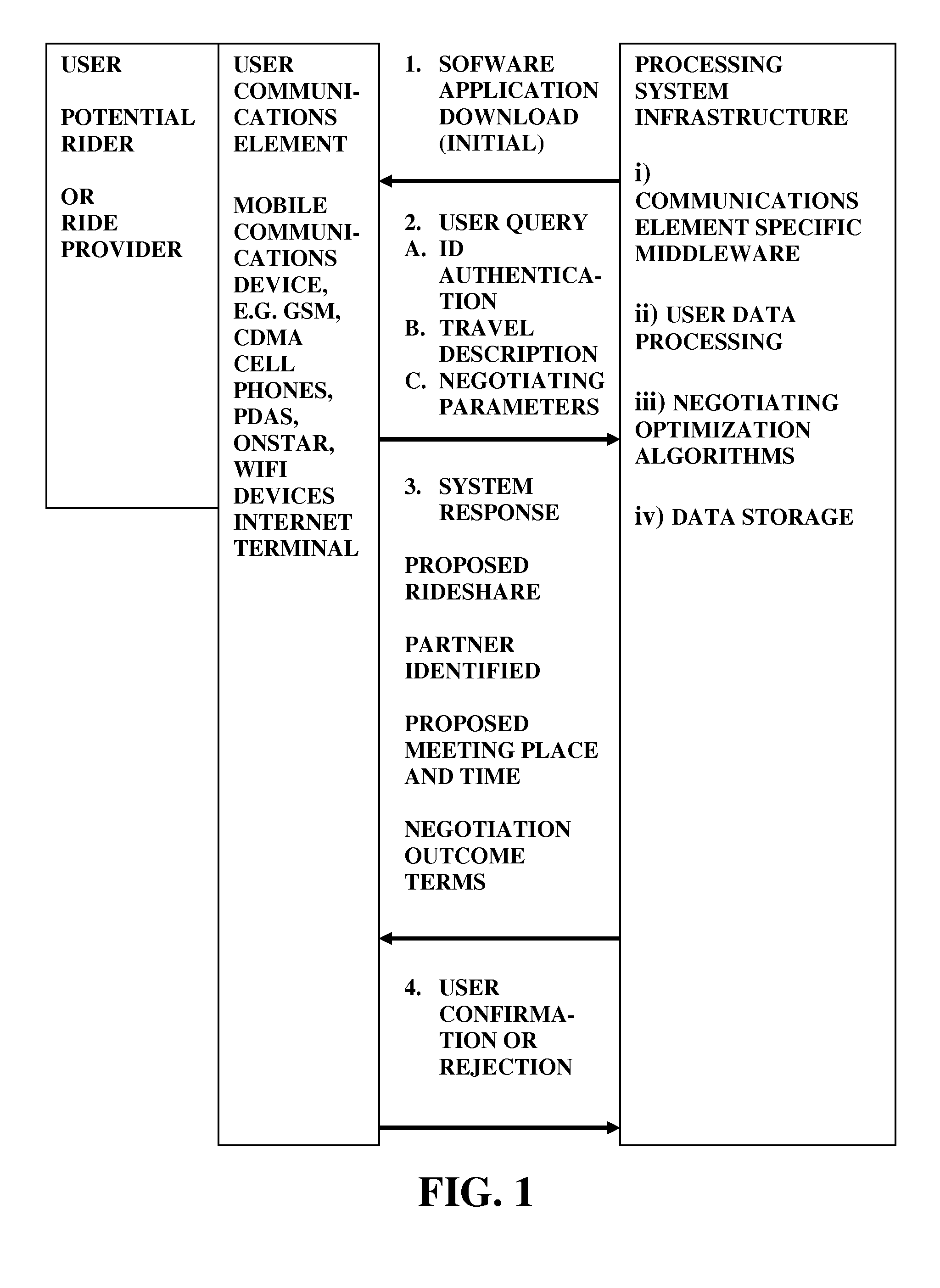
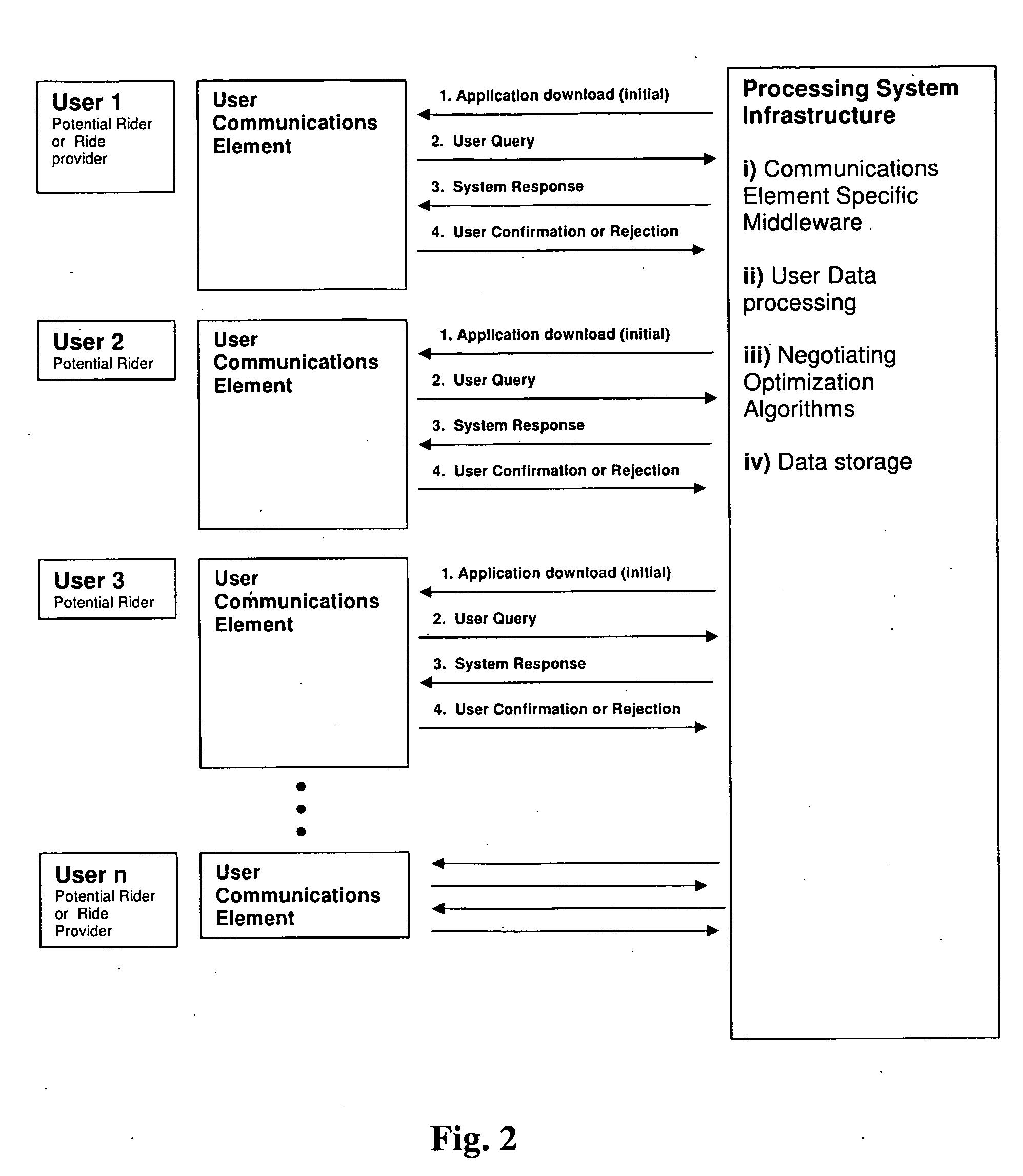
Selectively negotiated ridershare system comprising riders, drivers, and vehicles
InactiveUS20090248587A1Increase widespread proliferationFlexible waysPayment architectureFuzzy logic based systemsRankingSelection criterion
A ridesharing system and method involving selected negotiated participation of riders and ride providers. The ridesharing system in a specific implementation involves a computer-implemented capability for computational matching of potential participants in a ridesharing arrangement, wherein such system is adapted for prioritized ranking of target ridesharing attributes by such potential participants, involving allocation by potential participants of quantitative weight within a quantitative total budget of allocatable value to predetermined selection criteria, with such system having an input capability for inputting the allocations of potential participants, and the system being constructed and arranged for effecting the computational matching based on the allocations, with communication capability for outputting results of the computational matching to the potential participants.
Owner:VAN BUSKIRK PETER C
Entity performance analysis engines
A system and method for measuring a performance of an entity and for predicting its future performance is disclosed. Raw information about the entity is collected from internal and external sources. The information is cleaned to exclude false positives. Using performance categories, the information is organized and transformed into meaningful data for the performance analysis engine. The information is normalized by scaling the meaningful data by industry type. A performance score is calculated by the performance analysis engine based on the normalized data. Further, a competitive relationship score is calculated based on the performance score and the normalized data. These scores are reported in a user interface displaying the performance of the entity and are used as inputs, among other factors, to a predictive analysis engine that assesses the future performance of the entities.
Owner:QUID LLC
Recommendations in a computing advice facility
ActiveUS20130124449A1Digital data information retrievalFuzzy logic based systemsAlgorithmRating matrix
Owner:PAYPAL INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com