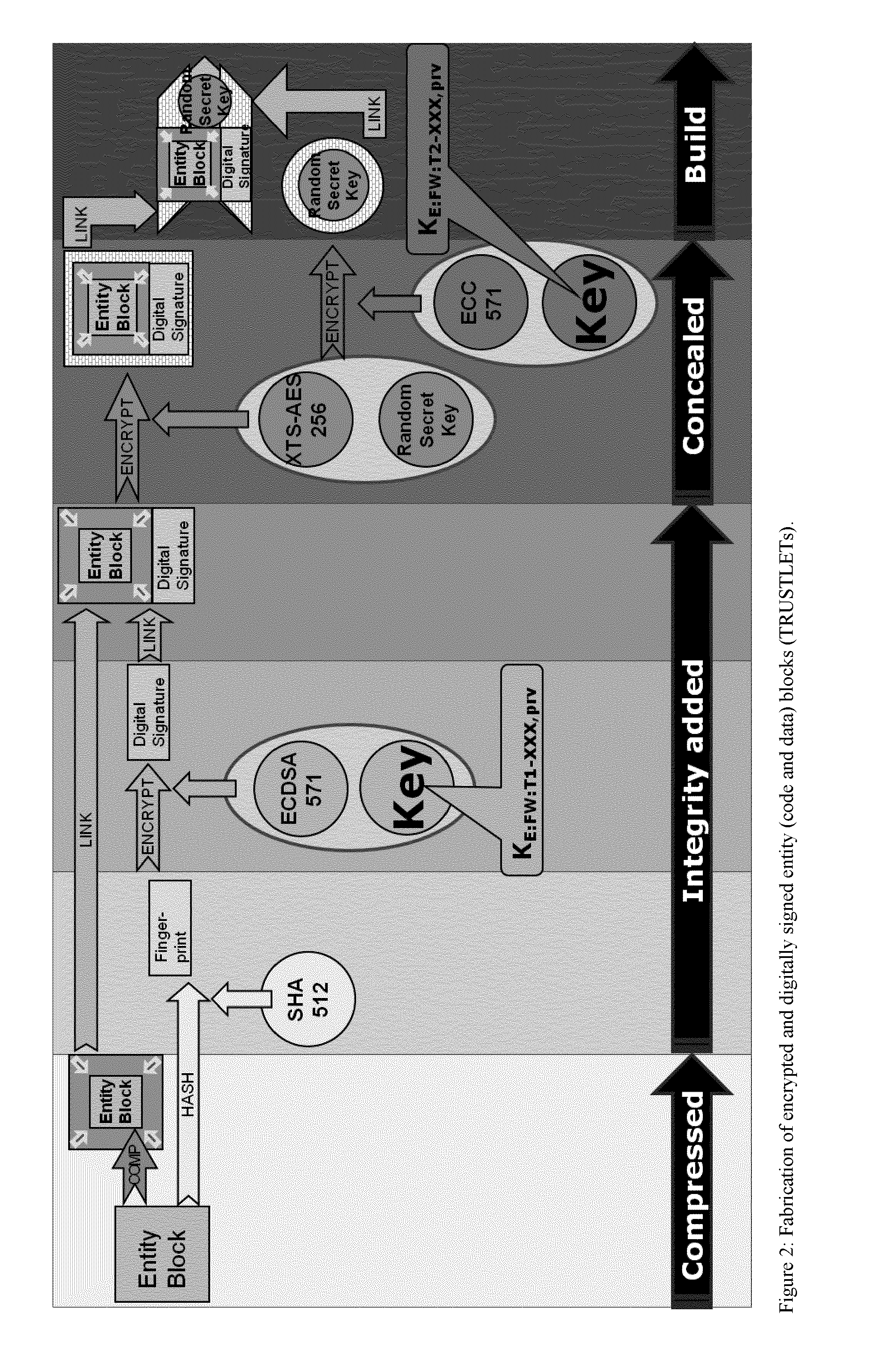
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
423results about How to "Preventing execution" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
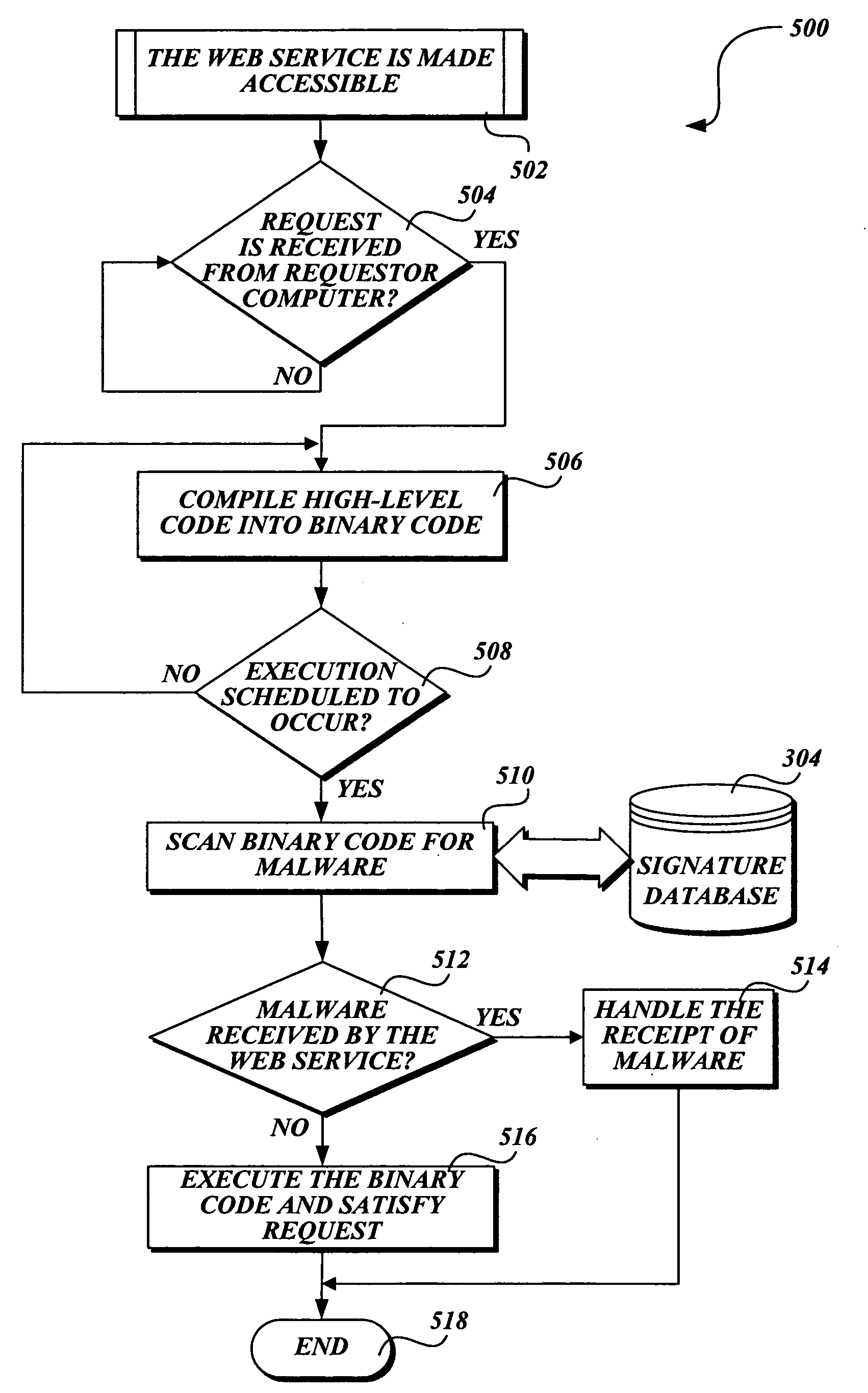
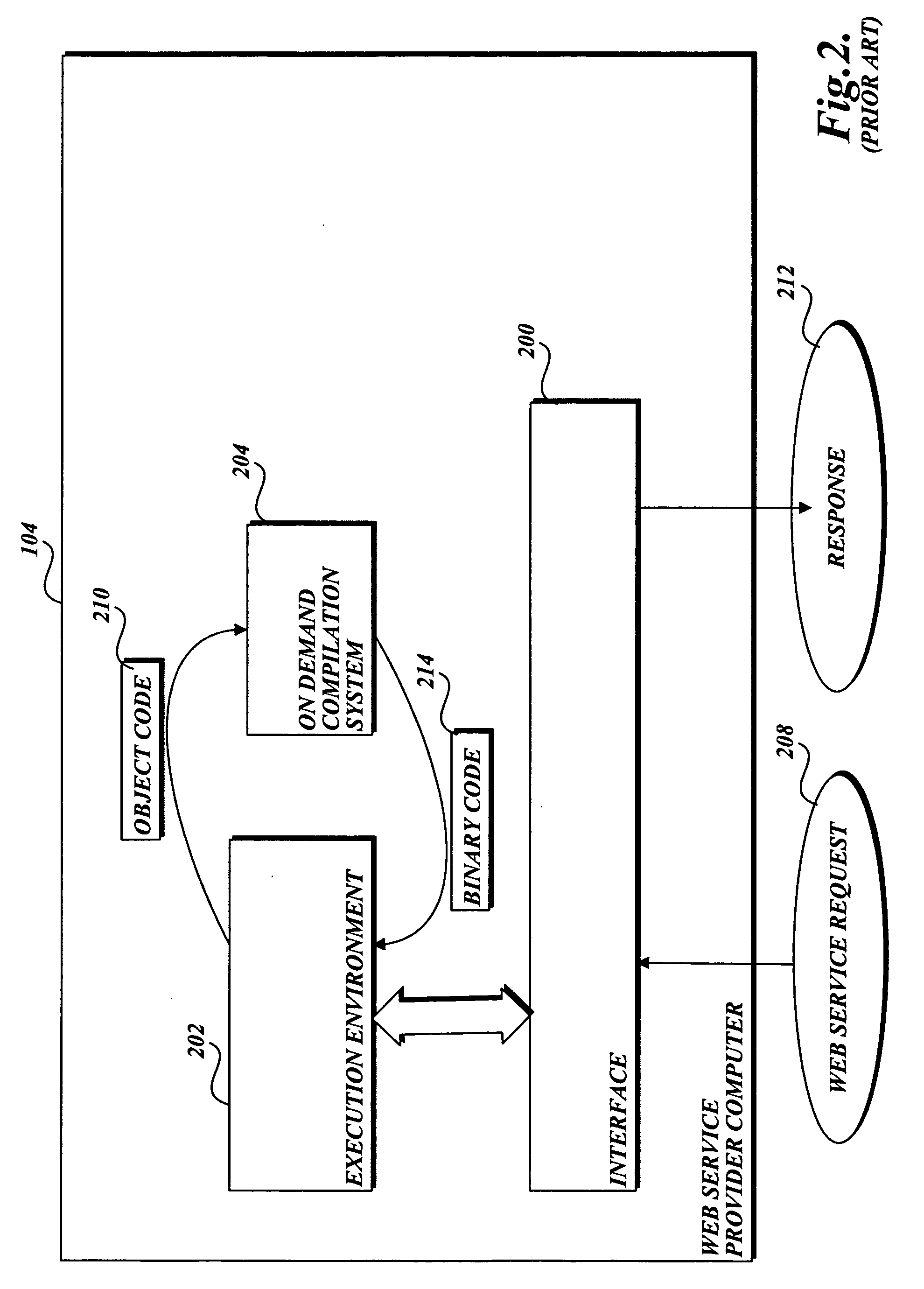
Protecting a computer that provides a Web service from malware
InactiveUS20060242709A1Preventing executionMemory loss protectionError detection/correctionWeb serviceSoftware design
In accordance with the present invention, a system, method, and computer-readable medium for identifying malware in a request to a Web service is provided. One aspect of the present invention is a computer-implemented method for protecting a computer that provides a Web service from malware made in a Web request. When a request is received, an on-demand compilation system compiles high-level code associated with the request into binary code that may be executed. However, before the code is executed, antivirus software designed to identify malware scans the binary code for malware. If malware is identified, the antivirus software prevents the binary code associated with the request from being executed.
Owner:MICROSOFT TECH LICENSING LLC
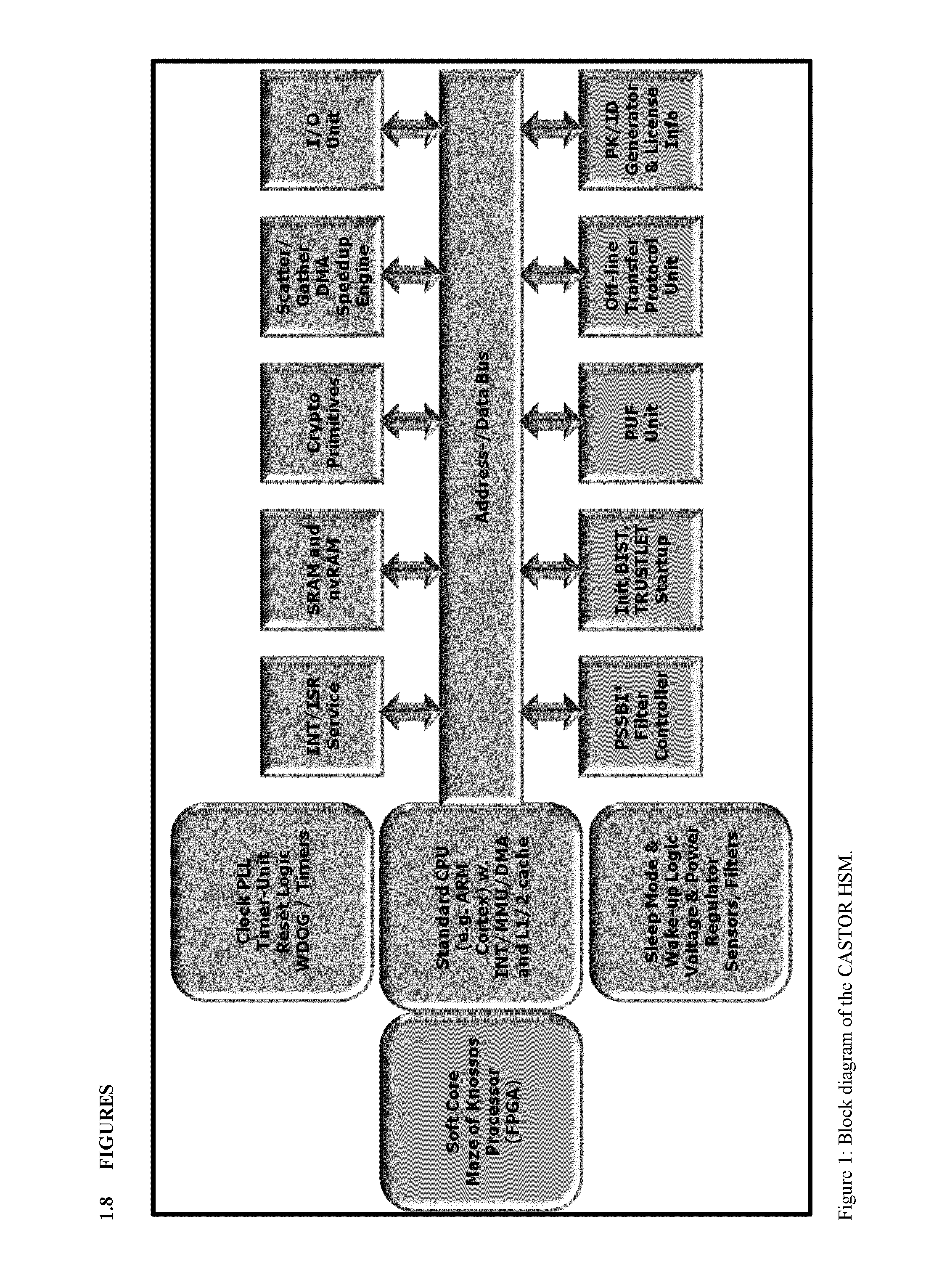
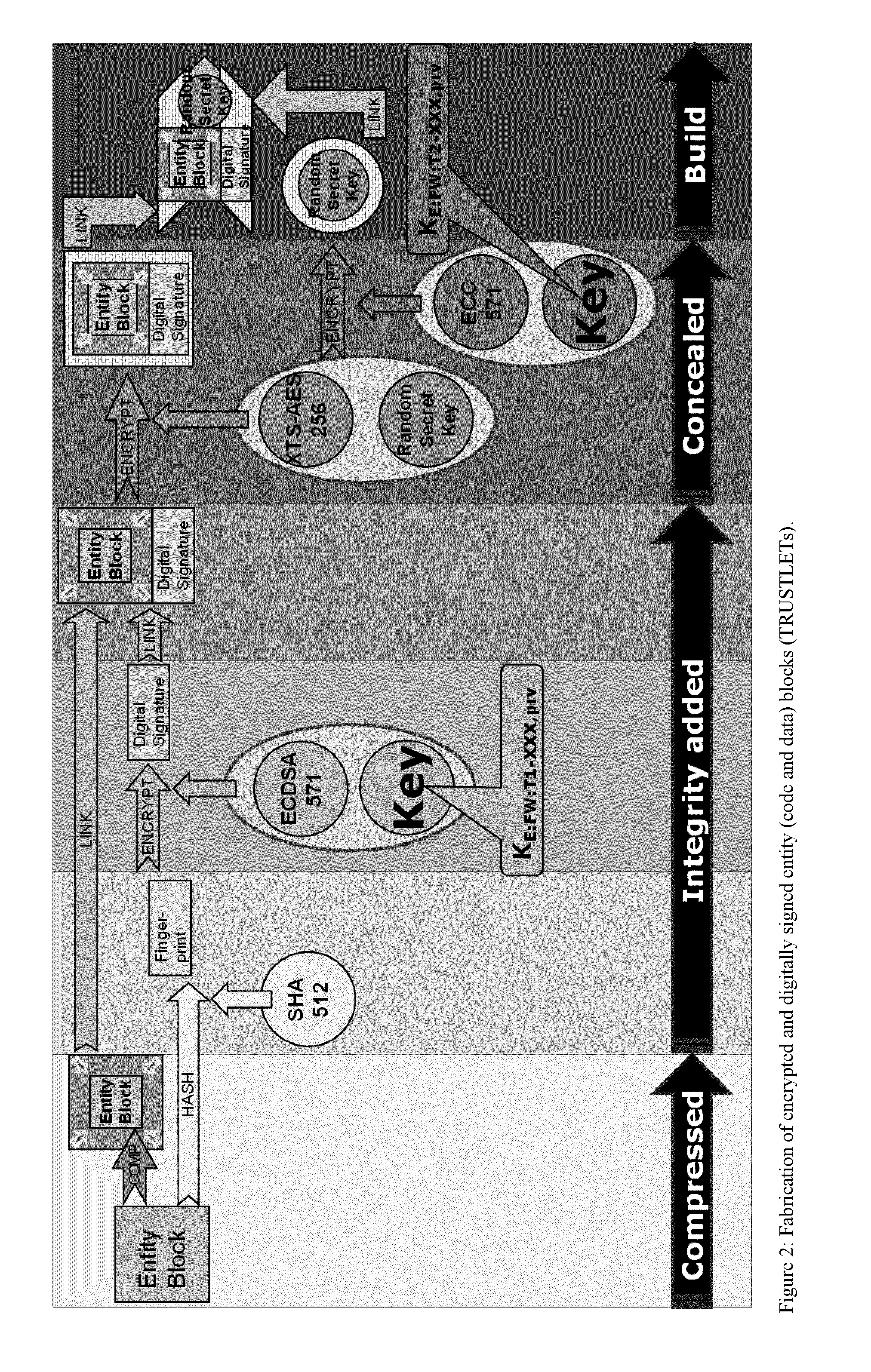
Tamper-protected hardware and method for using same
ActiveUS20140108786A1Execution of malicious code is preventedPreventing executionKey distribution for secure communicationMultiple keys/algorithms usageTamper proof hardwareComputer module
One of the various aspects of the invention is related to suggesting various techniques for improving the tamper-resistibility of hardware. The tamper-resistant hardware may be advantageously used in a transaction system that provides the off-line transaction protocol. Amongst these techniques for improving the tamper-resistibility are trusted bootstrapping by means of secure software entity modules, a new use of hardware providing a Physical Unclonable Function, and the use of a configuration fingerprint of a FPGA used within the tamper-resistant hardware.
Owner:EMSYCON
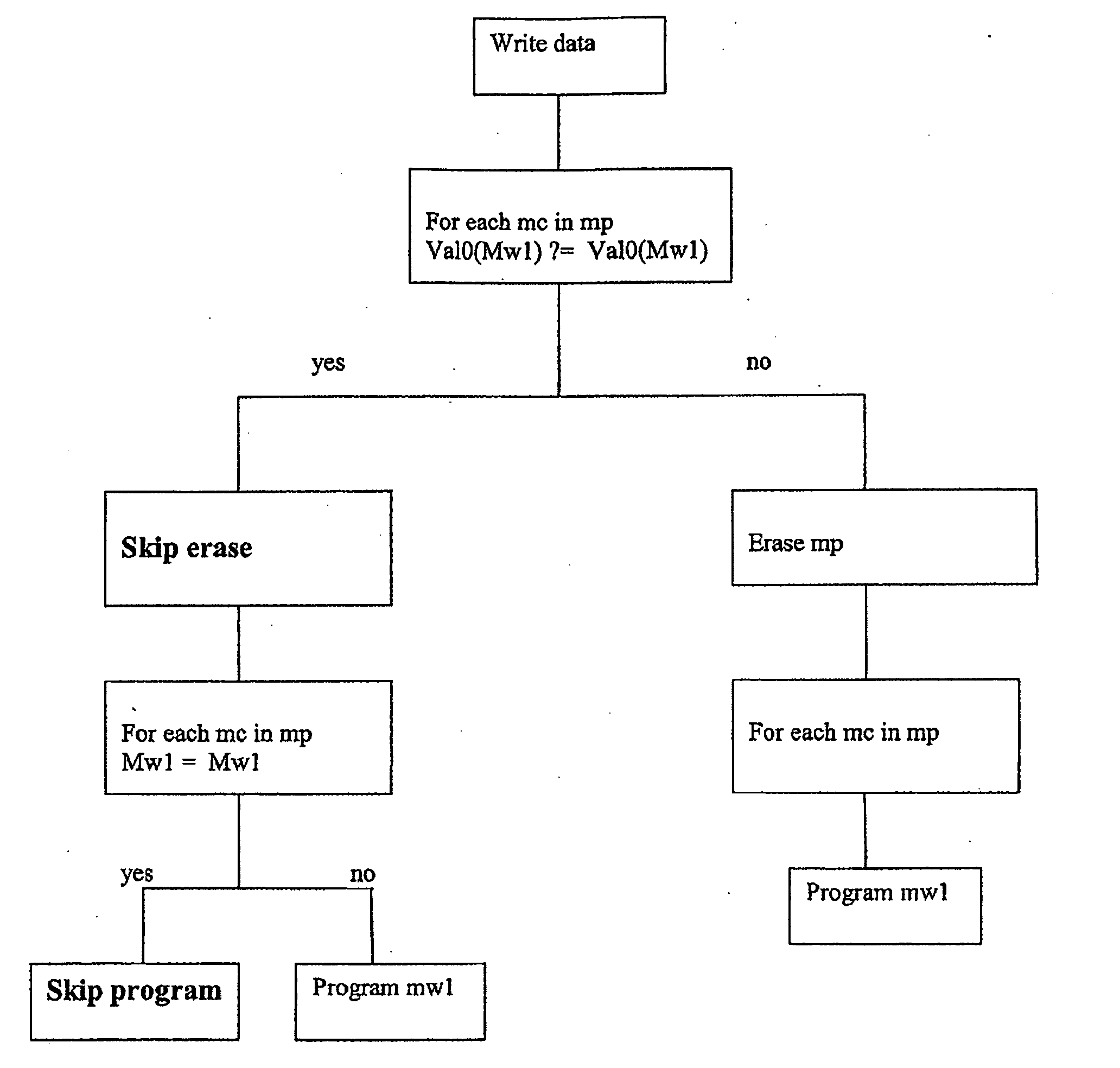
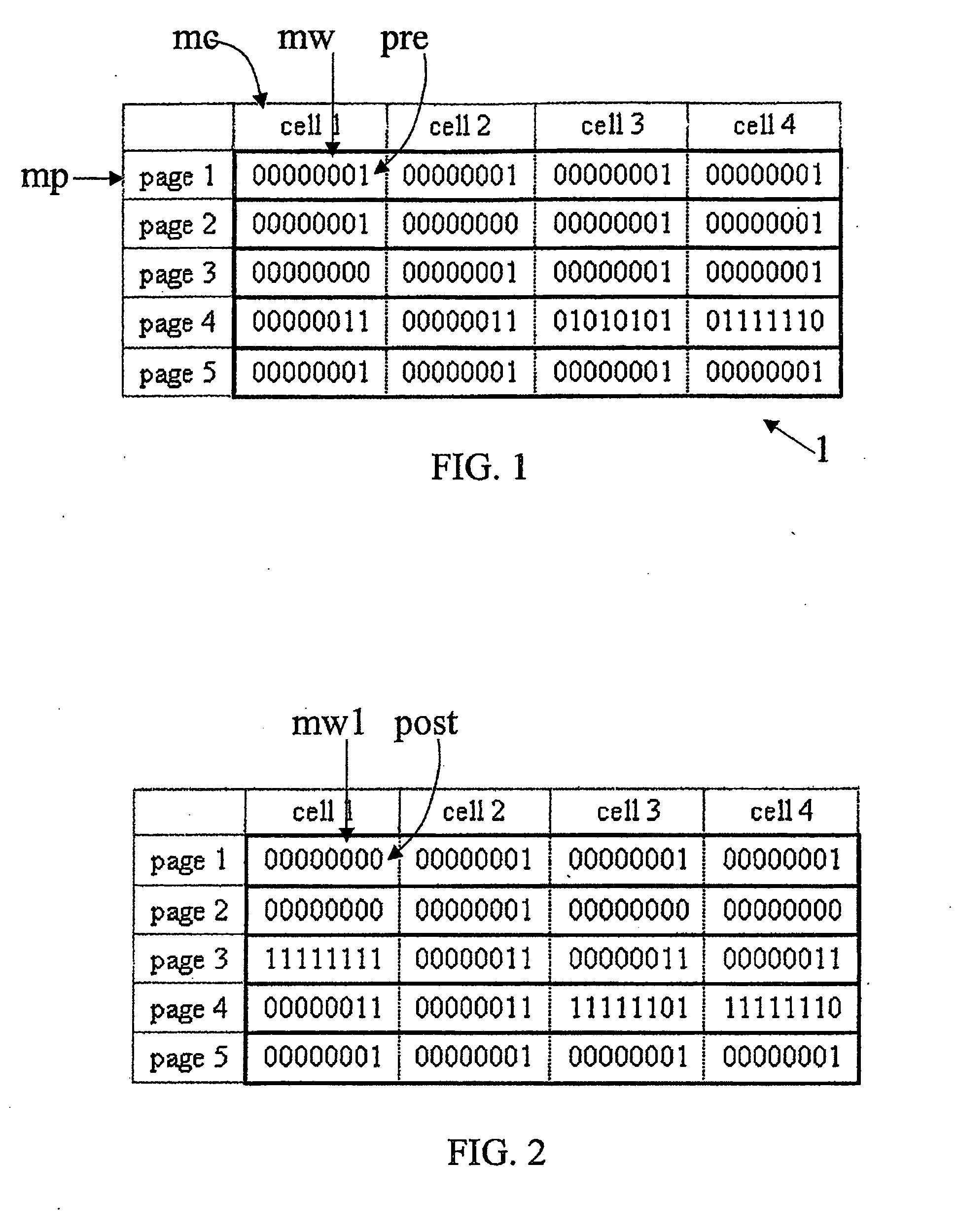
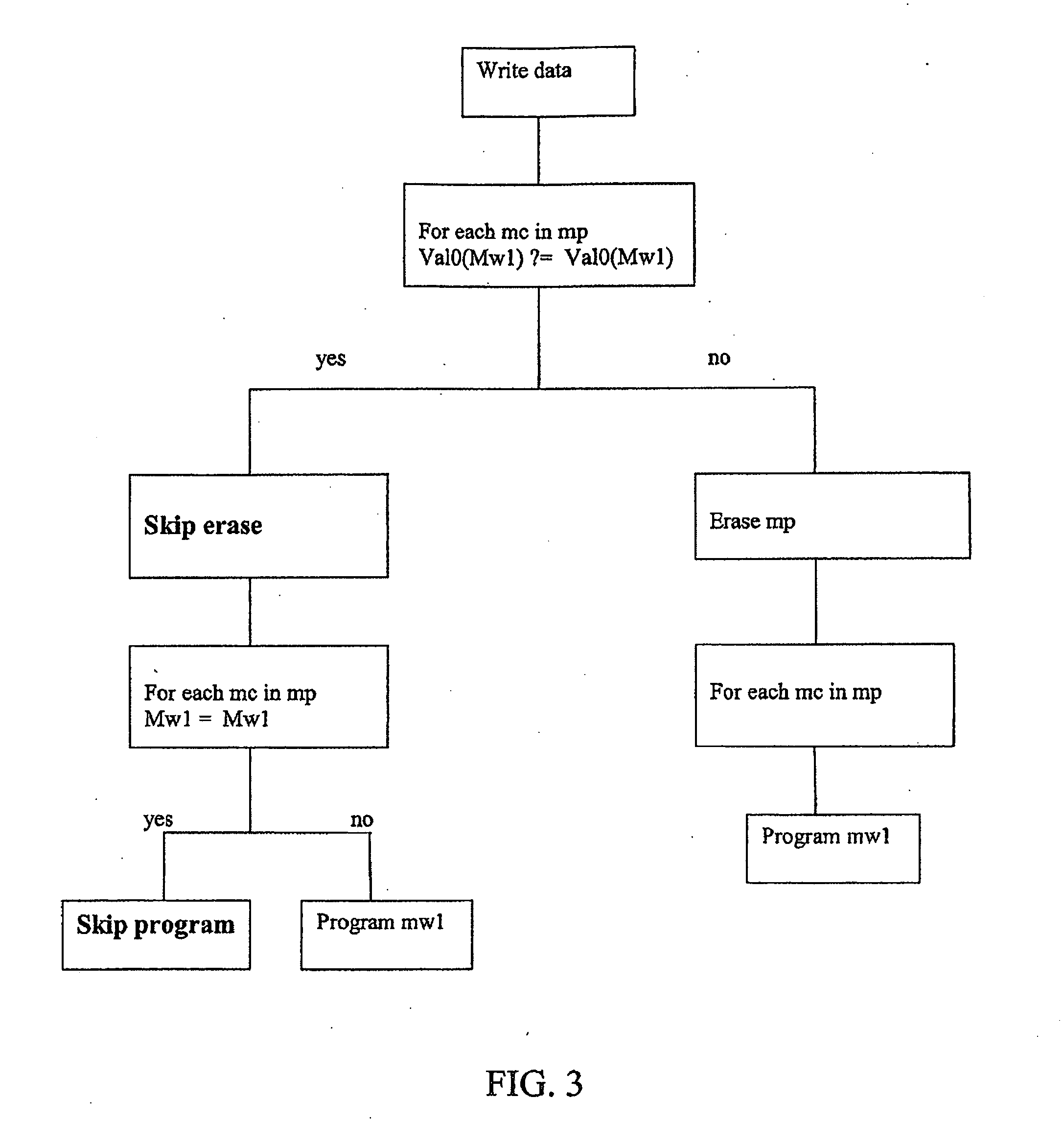
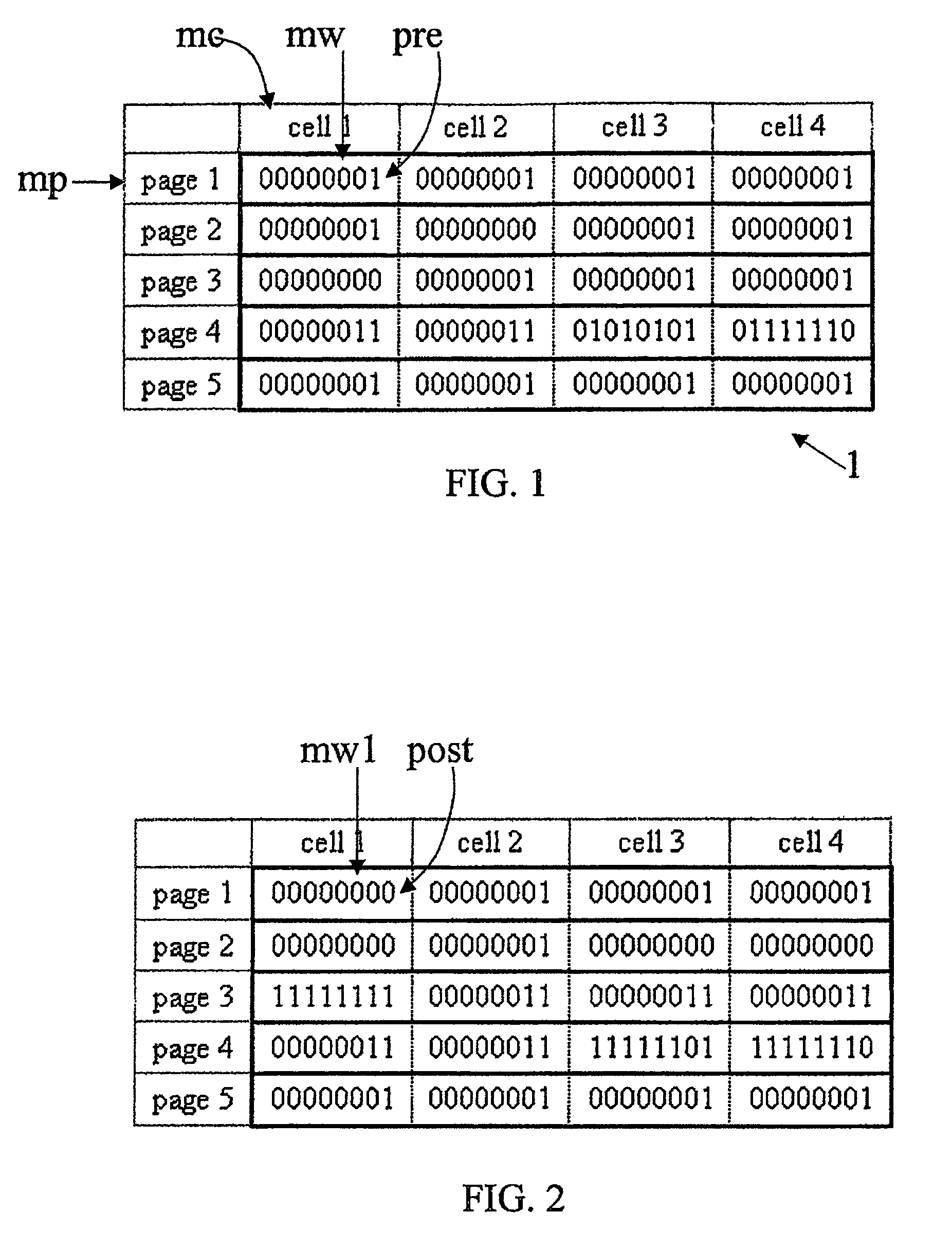
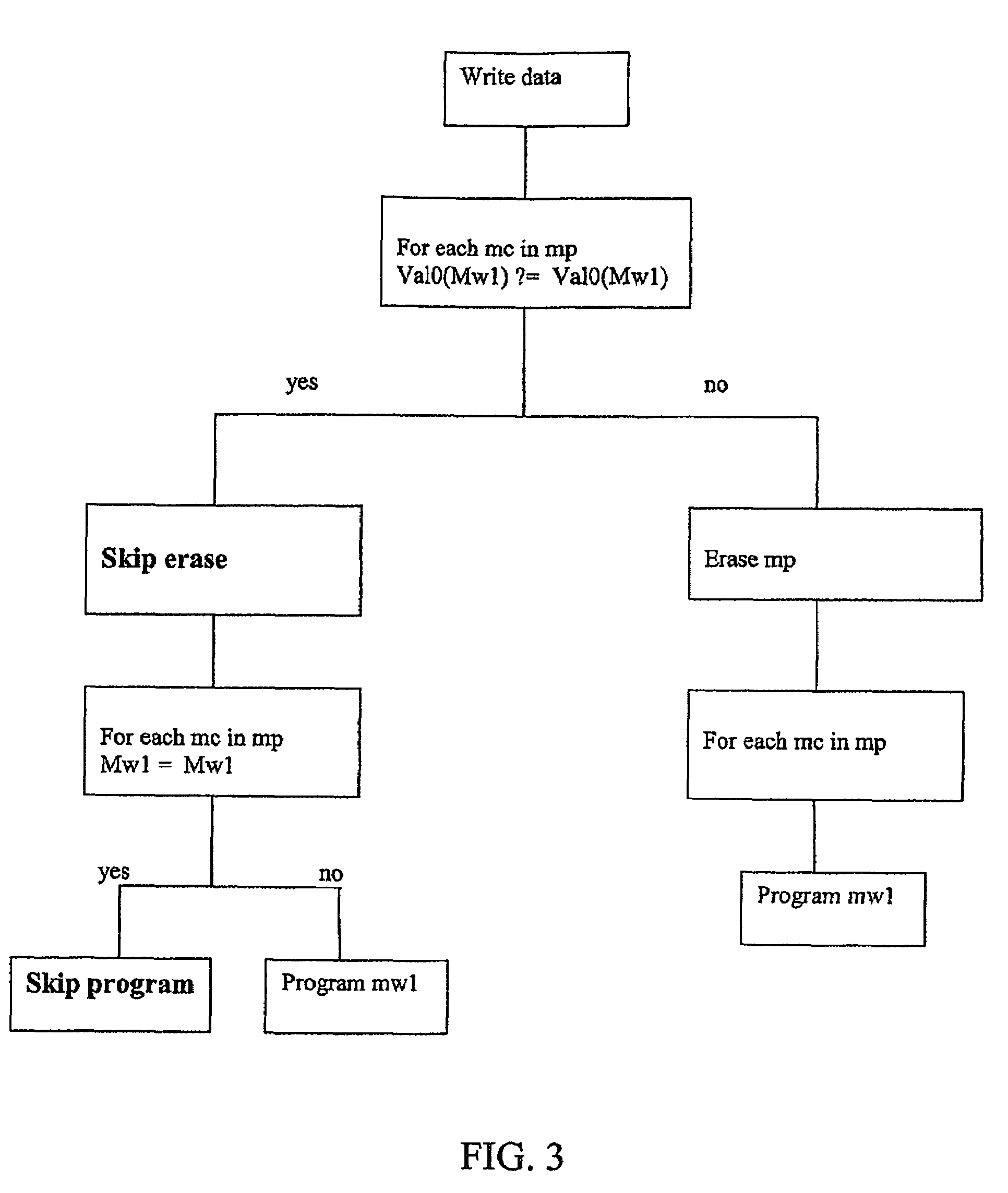
Method for writing data in a non volatile memory unit
ActiveUS20090046522A1Reduce in quantityExtended service lifeRead-only memoriesDigital storageComputer scienceNon-volatile memory
A method for writing data in a non volatile memory unit having memory pages includes a predetermined number of memory cells storing a memory word being a predetermined sequence of digital values. An erase operation erases the memory words in the memory page, setting the predetermined sequence of digital values to a sequence of complementary values. A program operation stores in the memory cell a word and sets a sequence of a word to be stored. For the memory cells of the memory page, the memory word is compared with the word to be stored. A positive check is returned if complementary values of the sequence correspond to complementary values of the predetermined sequence. If the check is negative, the erase operation is executed. The memory word is compared with the word to be stored and the program operation is executed if the word to be stored is different.
Owner:STMICROELECTRONICS INT NV
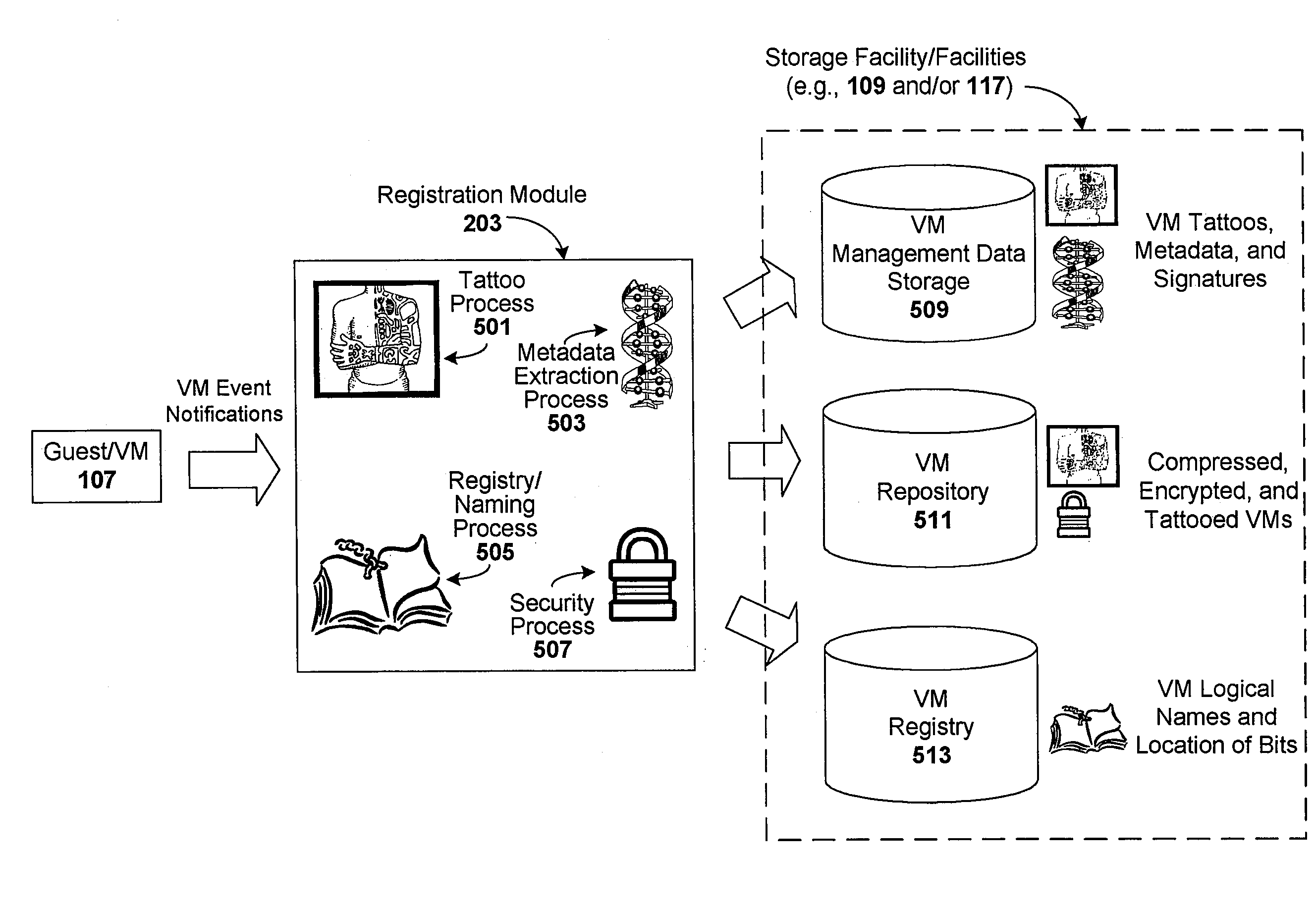
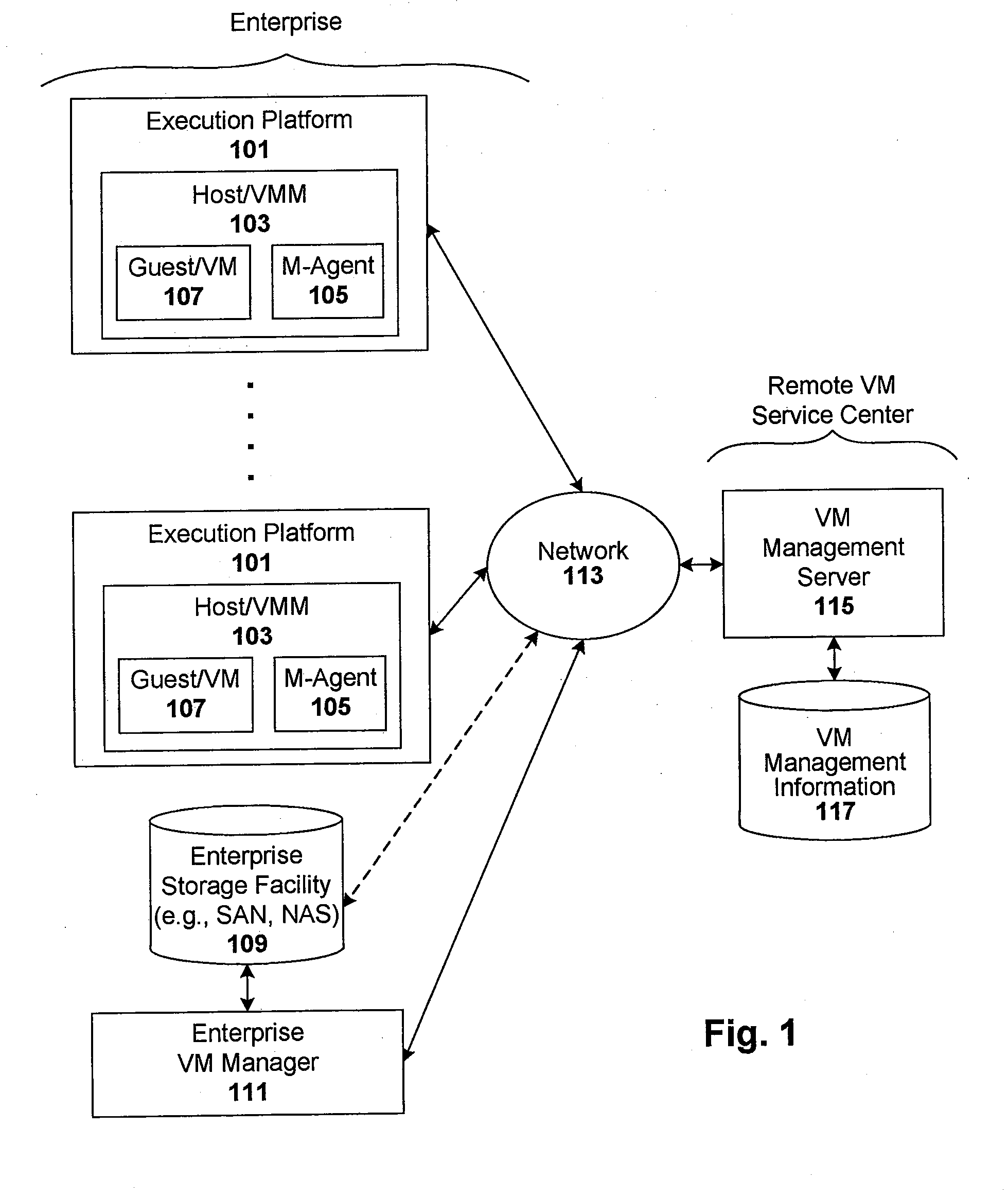
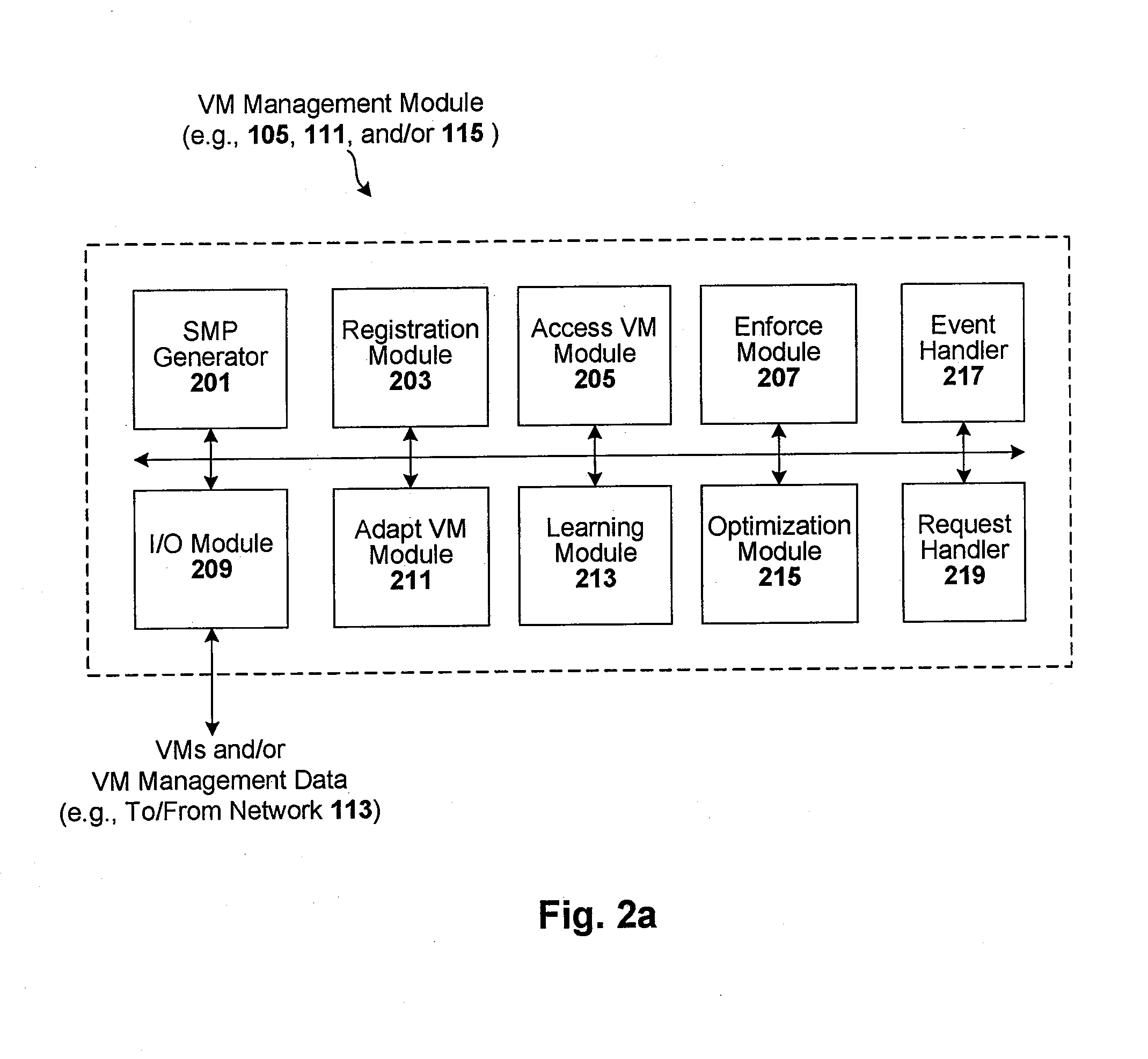
Enforcement of compliance policies in managed virtual systems
ActiveUS20080134176A1Preventing executionNon-redundant fault processingSoftware simulation/interpretation/emulationSystems managementMetadata
Techniques are disclosed for controlling and managing virtual machines and other such virtual systems. VM execution approval is based on compliance with policies controlling various aspects of VM. The techniques can be employed to benefit all virtual environments, such as virtual machines, virtual appliances, and virtual applications. For ease of discussion herein, assume that a virtual machine (VM) represents each of these environments. In one particular embodiment, a systems management partition (SMP) is created inside the VM to provide a persistent and resilient storage for management information (e.g., logical and physical VM metadata). The SMP can also be used as a staging area for installing additional content or agentry on the VM when the VM is executed. Remote storage of management information can also be used. The VM management information can then be made available for pre-execution processing, including policy-based compliance testing.
Owner:RED HAT
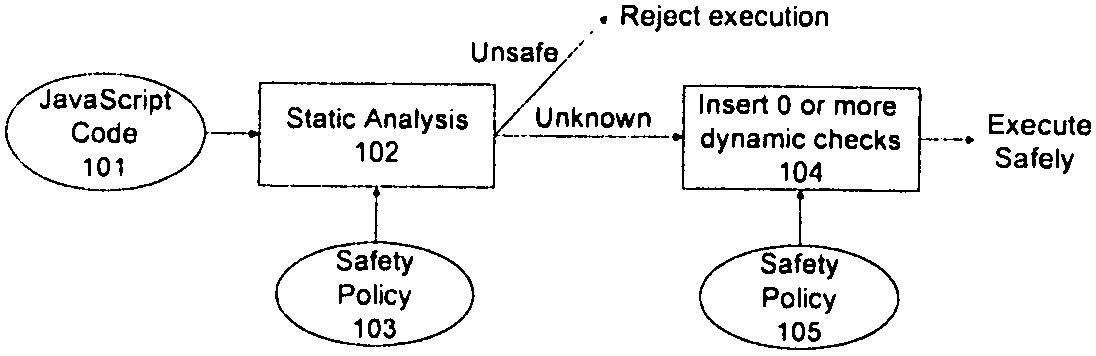
Method and apparatus for detecting and preventing unsafe behavior of javascript programs
InactiveUS20070107057A1Detecting and preventing unsafe behaviorPreventing executionMemory loss protectionError detection/correctionSecurity policySafety policy
A method and apparatus is disclosed herein for detecting and preventing unsafe behavior of script programs. In one embodiment, a method comprises performing static analysis of a script program based on a first safety policy to detect unsafe behavior of the scrip program and preventing execution of the script program if a violation of the safety policy would occur when the script program is executed.
Owner:NTT DOCOMO INC
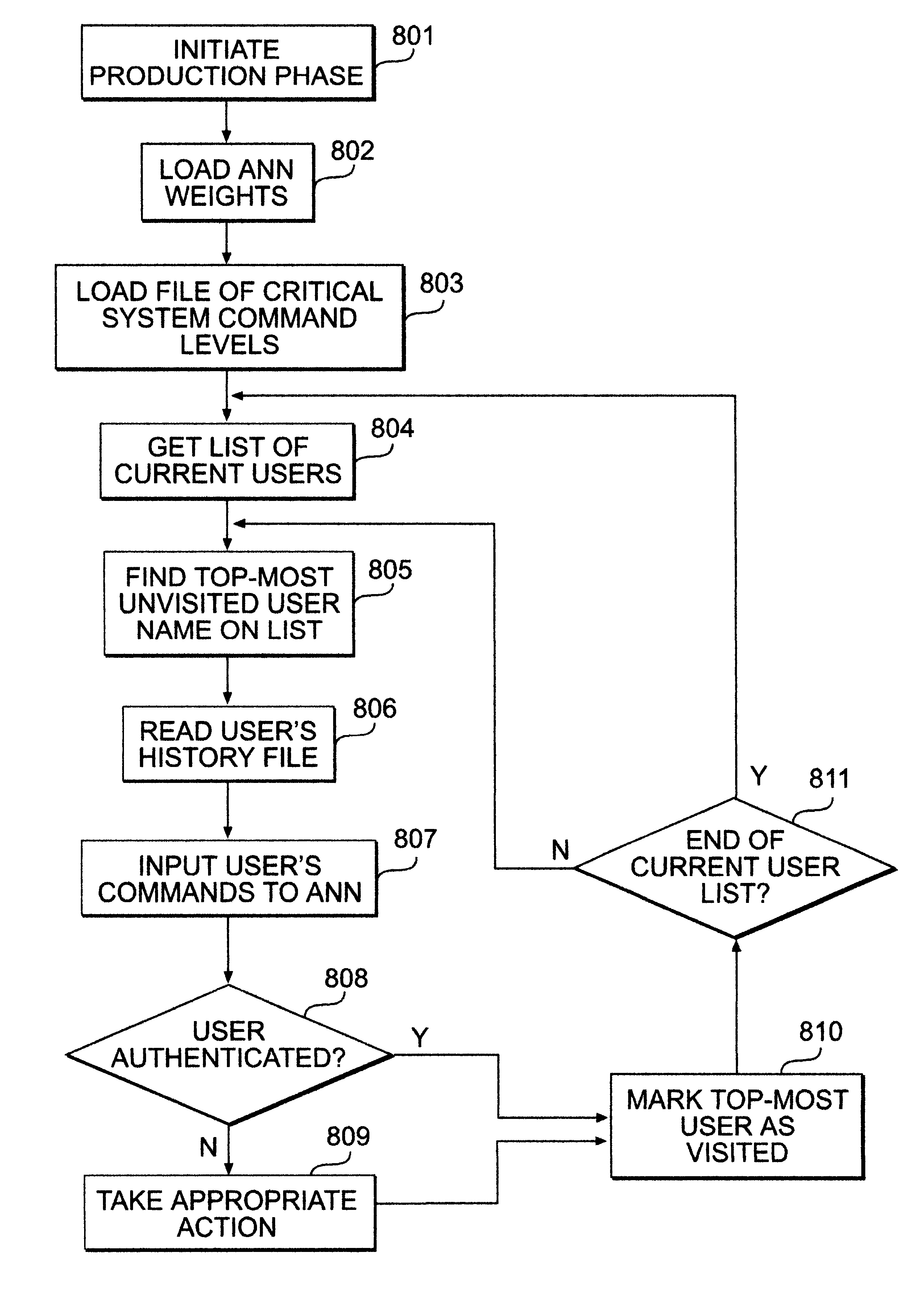
Usage pattern based user authenticator
InactiveUS6334121B1Control damagePreventing executionDigital computer detailsComputer security arrangementsOperational systemOperating system level
A usage based pattern authenticator for monitoring and reporting on user usage patterns in an operating system using a set of security rules and user usage patterns. This computer system security tool authenticates users at the operating system level in multi-user operating systems. It supports system administrators in limiting the ability of unauthorized users to disrupt system operations using a neural network and set of rules to track usage patterns and flag suspicious activity on the system. The data collection mode collects and stores usage patterns of authenticated users. The training mode trains an artificial neural network and sets the interconnection weights of the network. The production mode monitors and reports on usage patterns, and optionally performs automatic responses when confronted with non-authenticated users.
Owner:VIRGINIA COMMONWEALTH UNIV
Method for controlling the execution of an applet for an IC card
ActiveUS20080288699A1Preventing executionAvoid business lossInternal/peripheral component protectionComponent plug-in assemblagesOperating systemJava Card
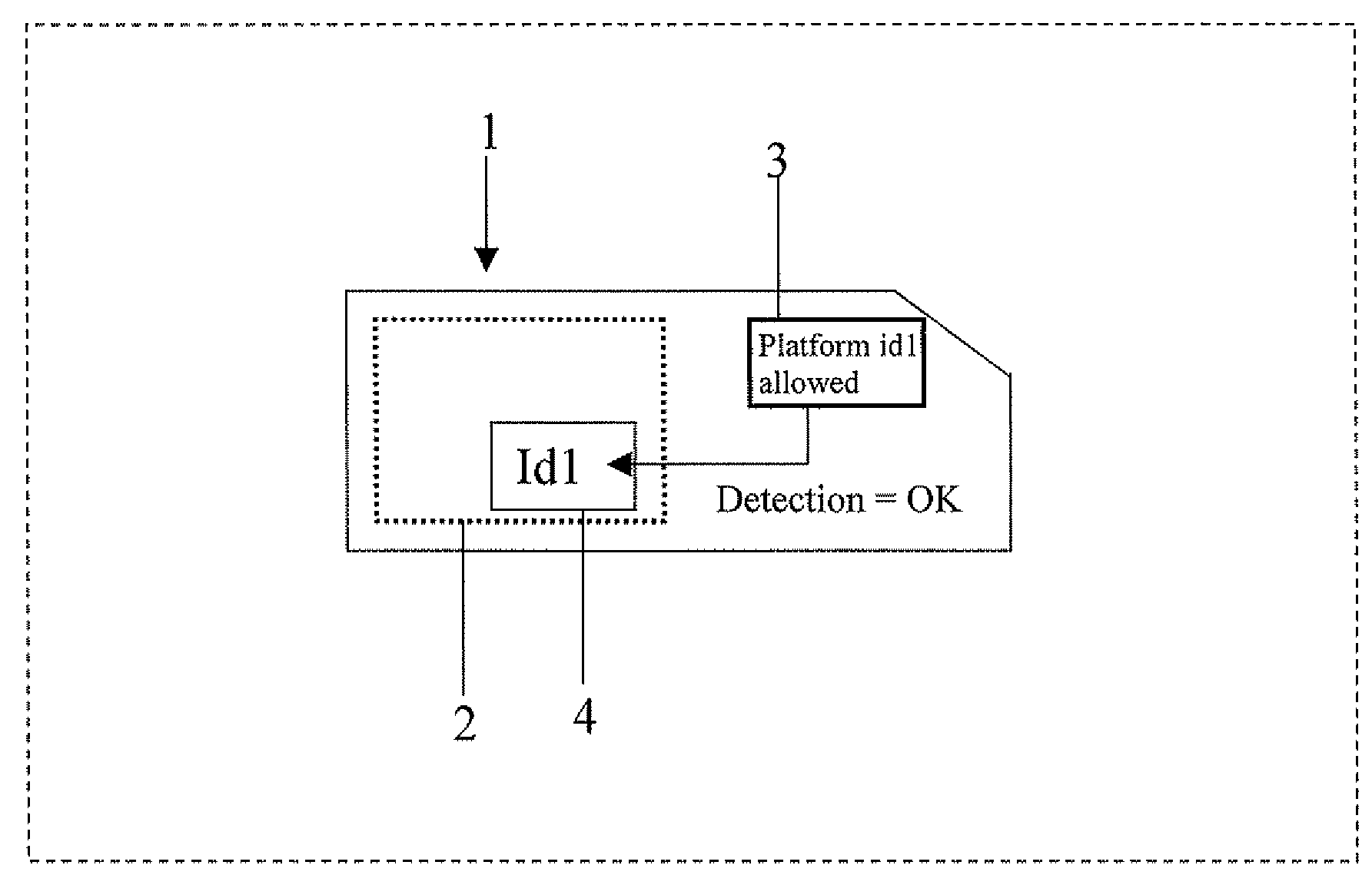
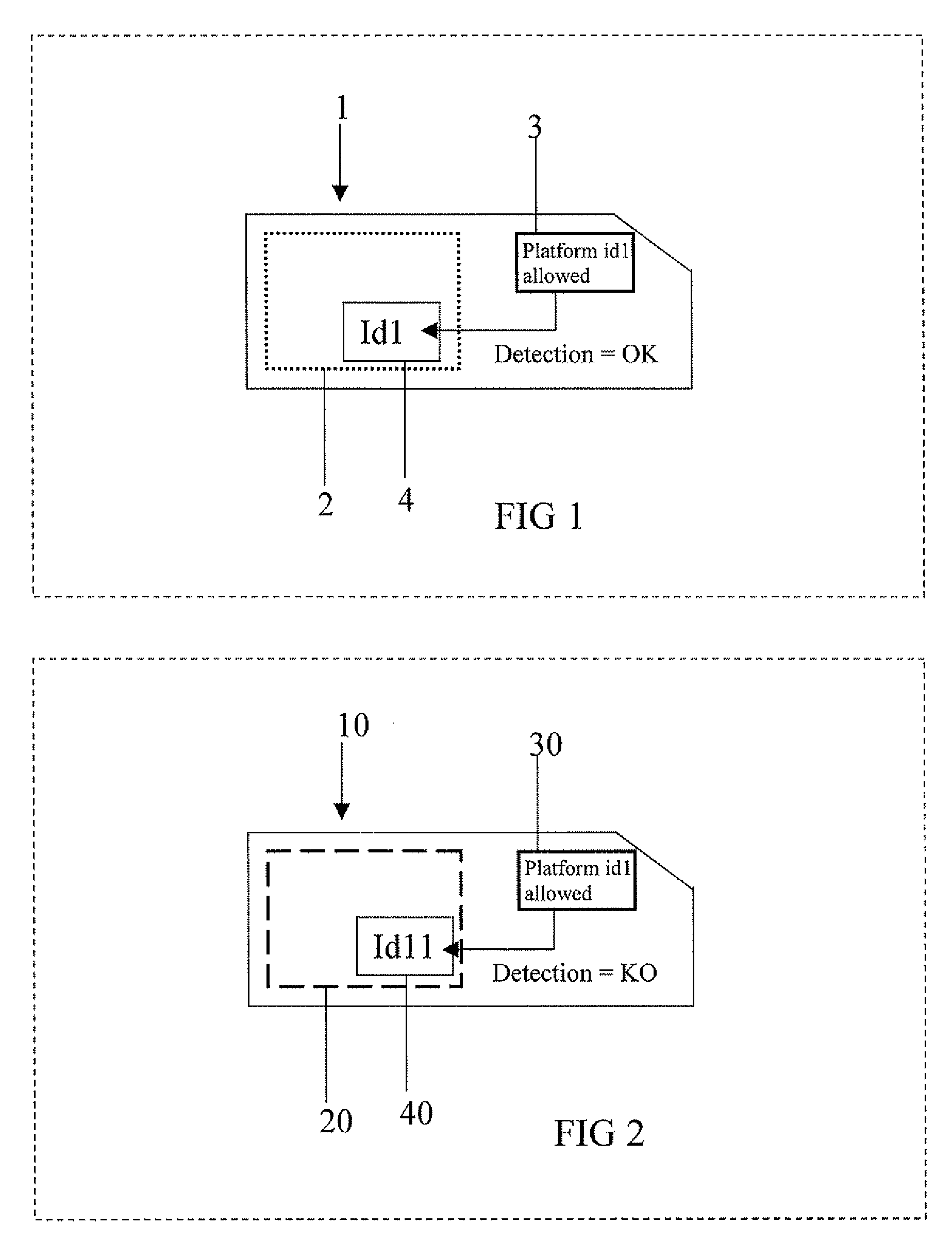
A method for controlling the execution of an applet for an IC Card including a java card platform, includes a phase for downloading the applet inside the IC Card, a phase for executing the applet through the java card platform and a phase for storing an identification platform number inside a memory portion of the IC Card. The phase for executing the applet has a first step for detecting the identification platform number to perform the phase for executing the applet with or without restrictions, respectively if the identification platform number is not or is detected by the step for detecting. The applet is a java card applet or a SIM toolkit applet.
Owner:STMICROELECTRONICS INT NV
Method for writing data in a non volatile memory unit
ActiveUS7639537B2Reduce in quantityExtended service lifeRead-only memoriesDigital storageComputer scienceNon-volatile memory
A method for writing data in a non volatile memory unit having memory pages includes a predetermined number of memory cells storing a memory word being a predetermined sequence of digital values. An erase operation erases the memory words in the memory page, setting the predetermined sequence of digital values to a sequence of complementary values. A program operation stores in the memory cell a word and sets a sequence of a word to be stored. For the memory cells of the memory page, the memory word is compared with the word to be stored. A positive check is returned if complementary values of the sequence correspond to complementary values of the predetermined sequence. If the check is negative, the erase operation is executed. The memory word is compared with the word to be stored and the program operation is executed if the word to be stored is different.
Owner:STMICROELECTRONICS INT NV
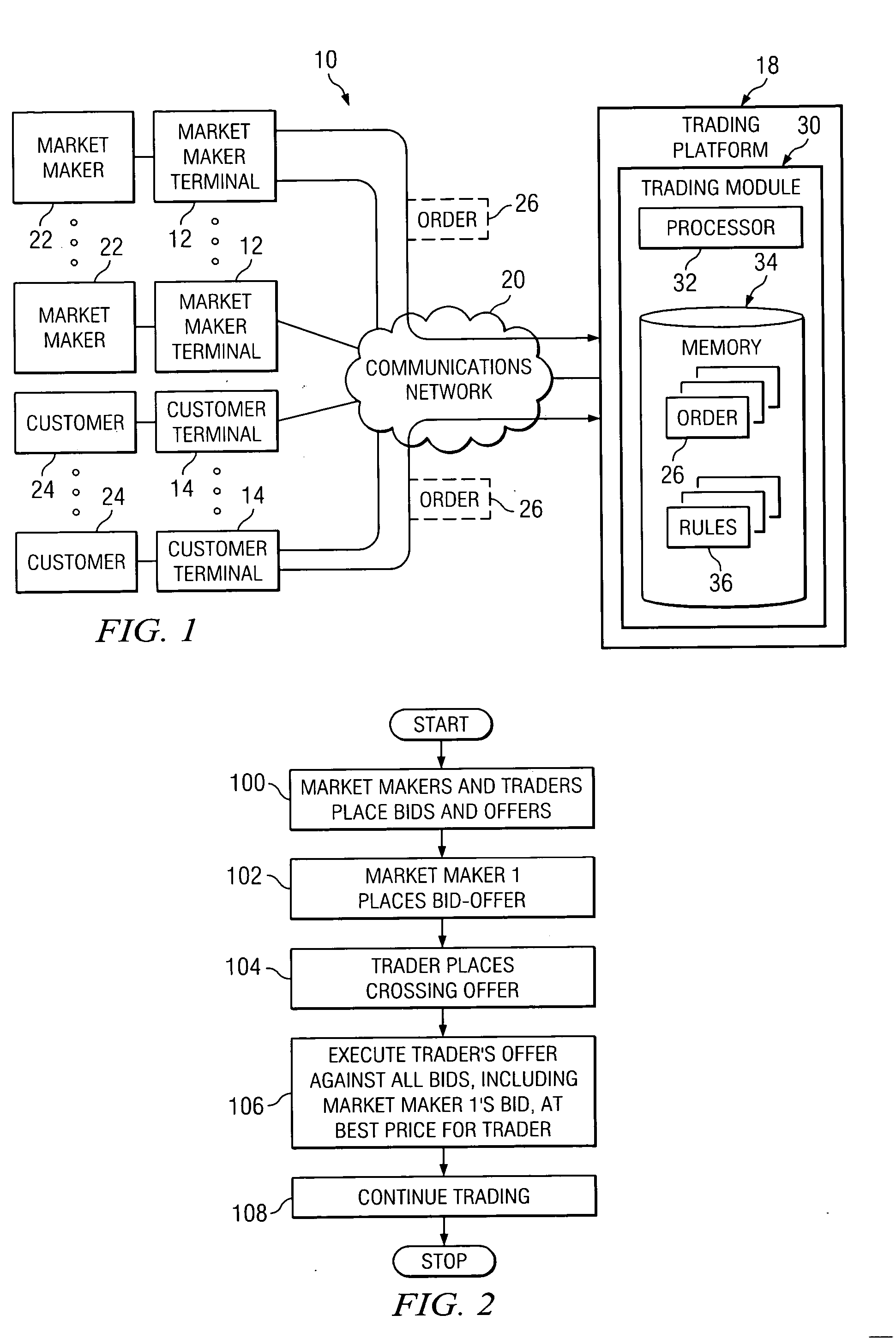
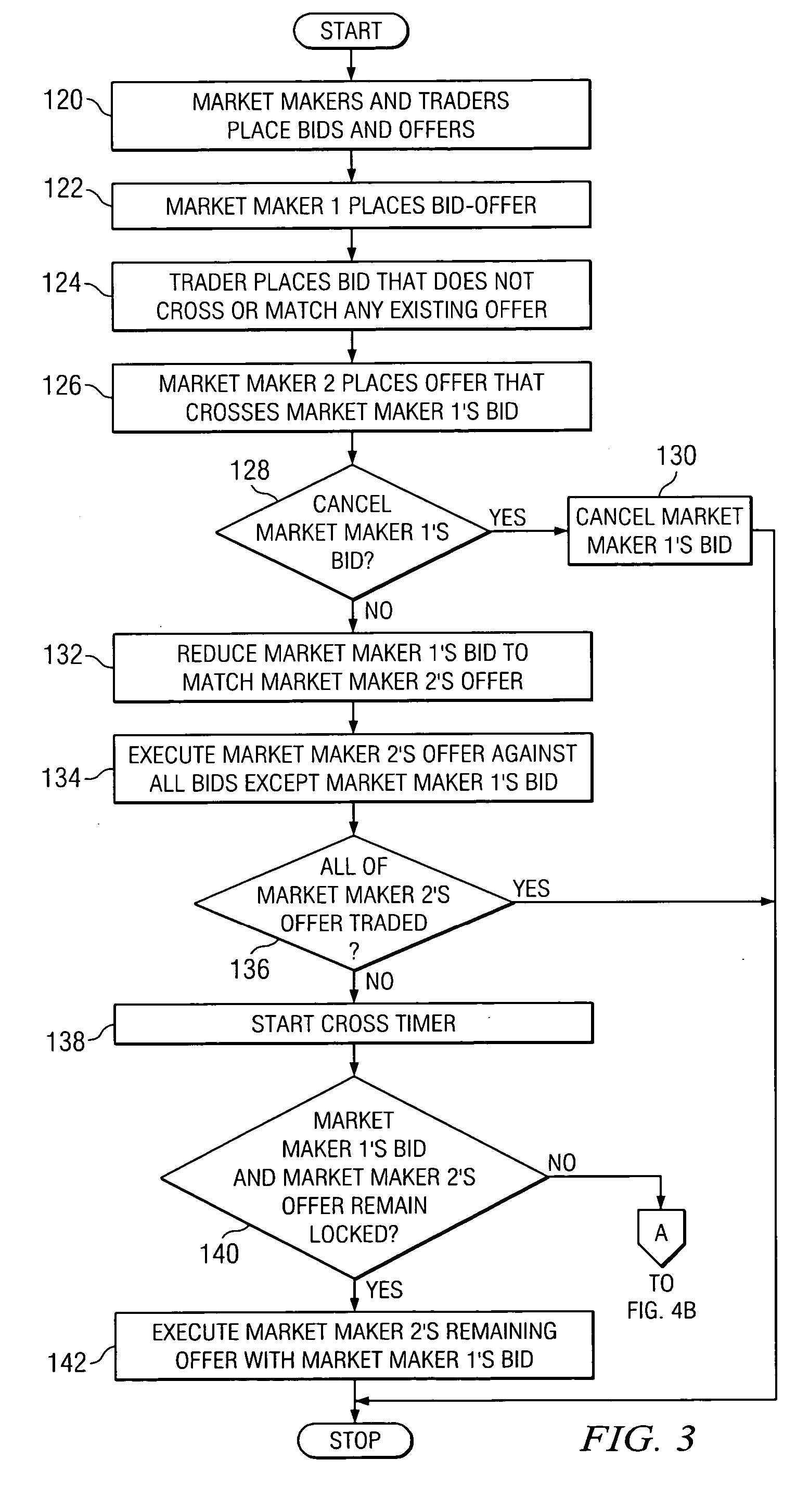
System and method for managing trading orders received from market makers
Owner:BGC PARTNERS LP
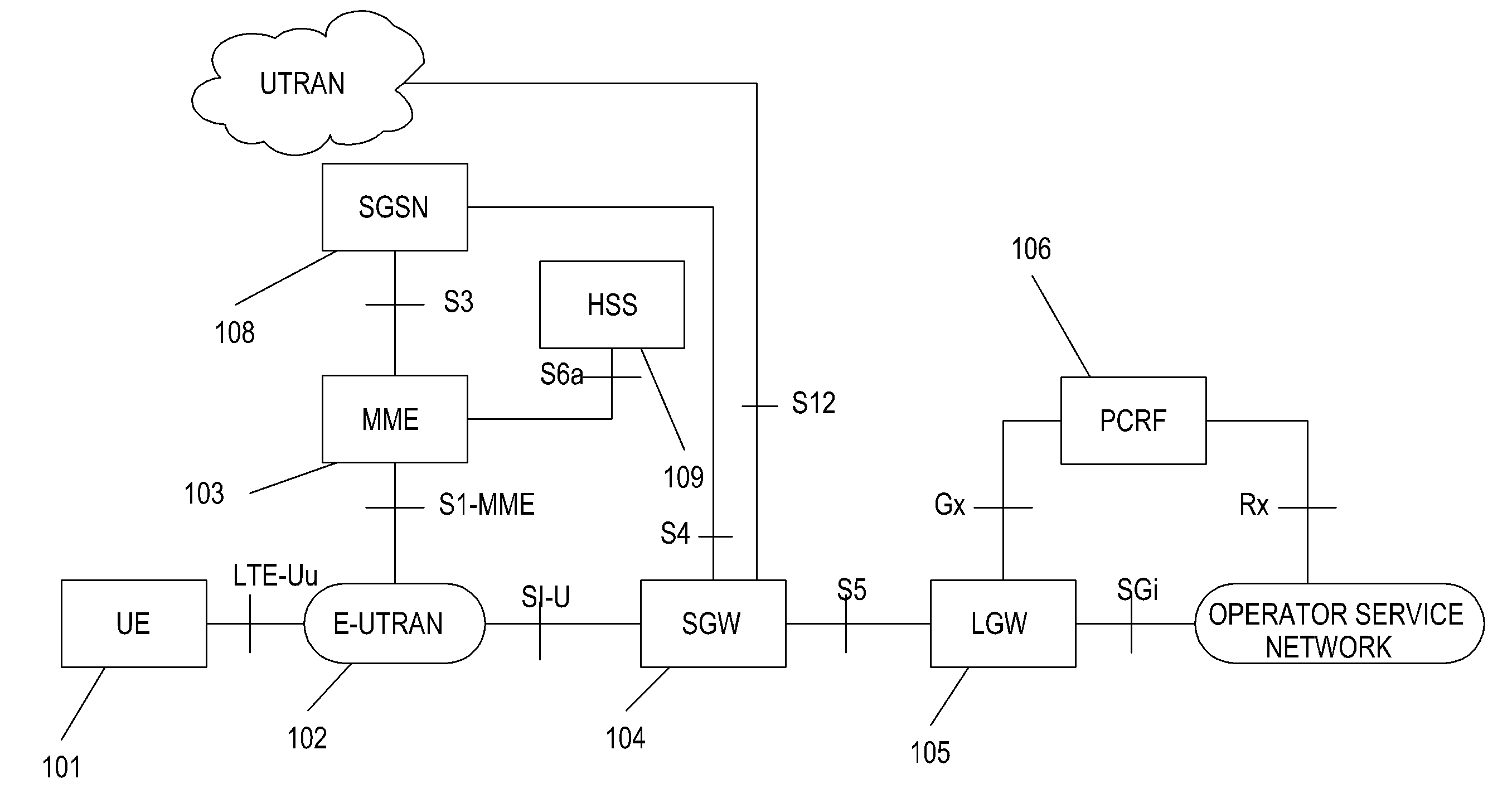
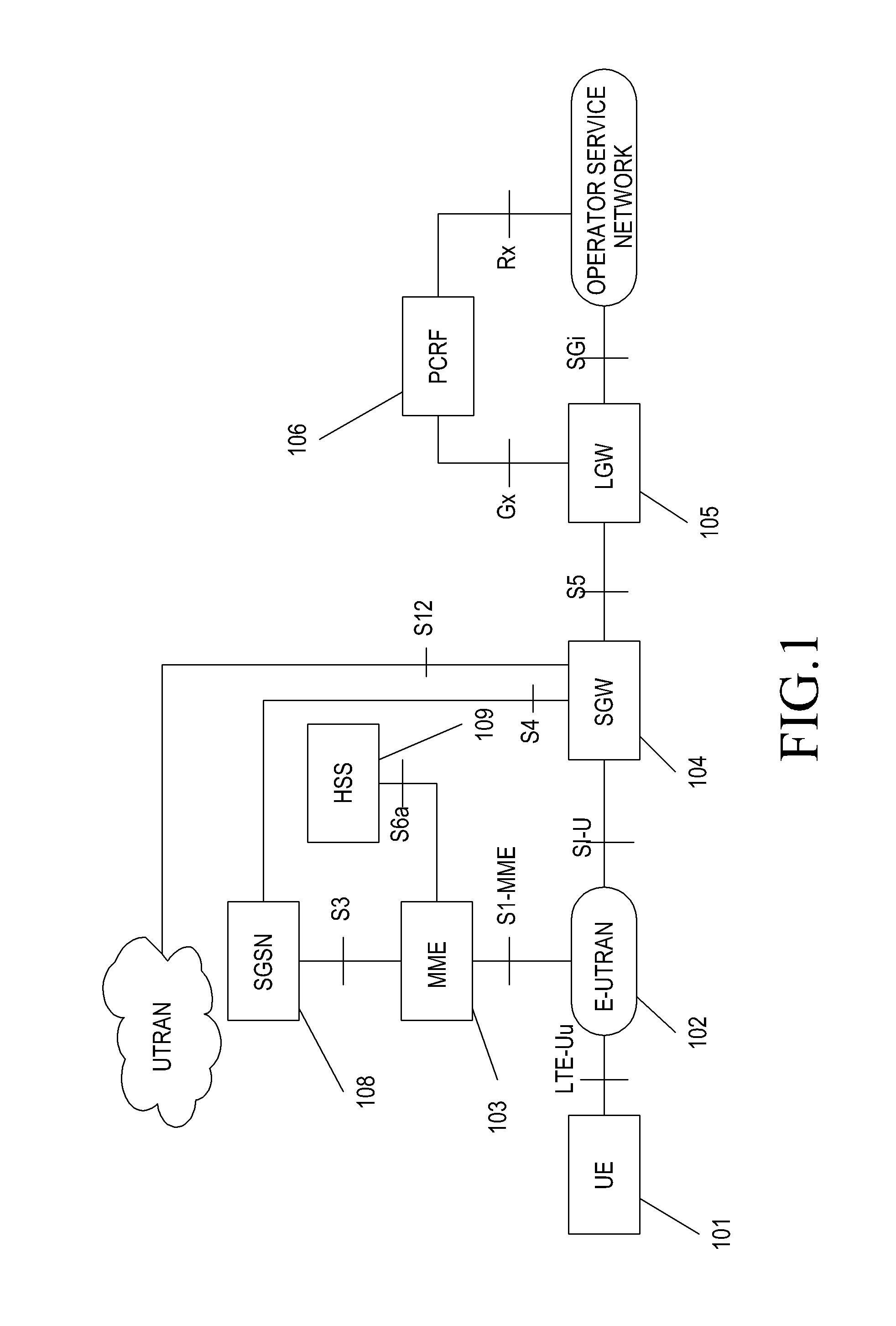
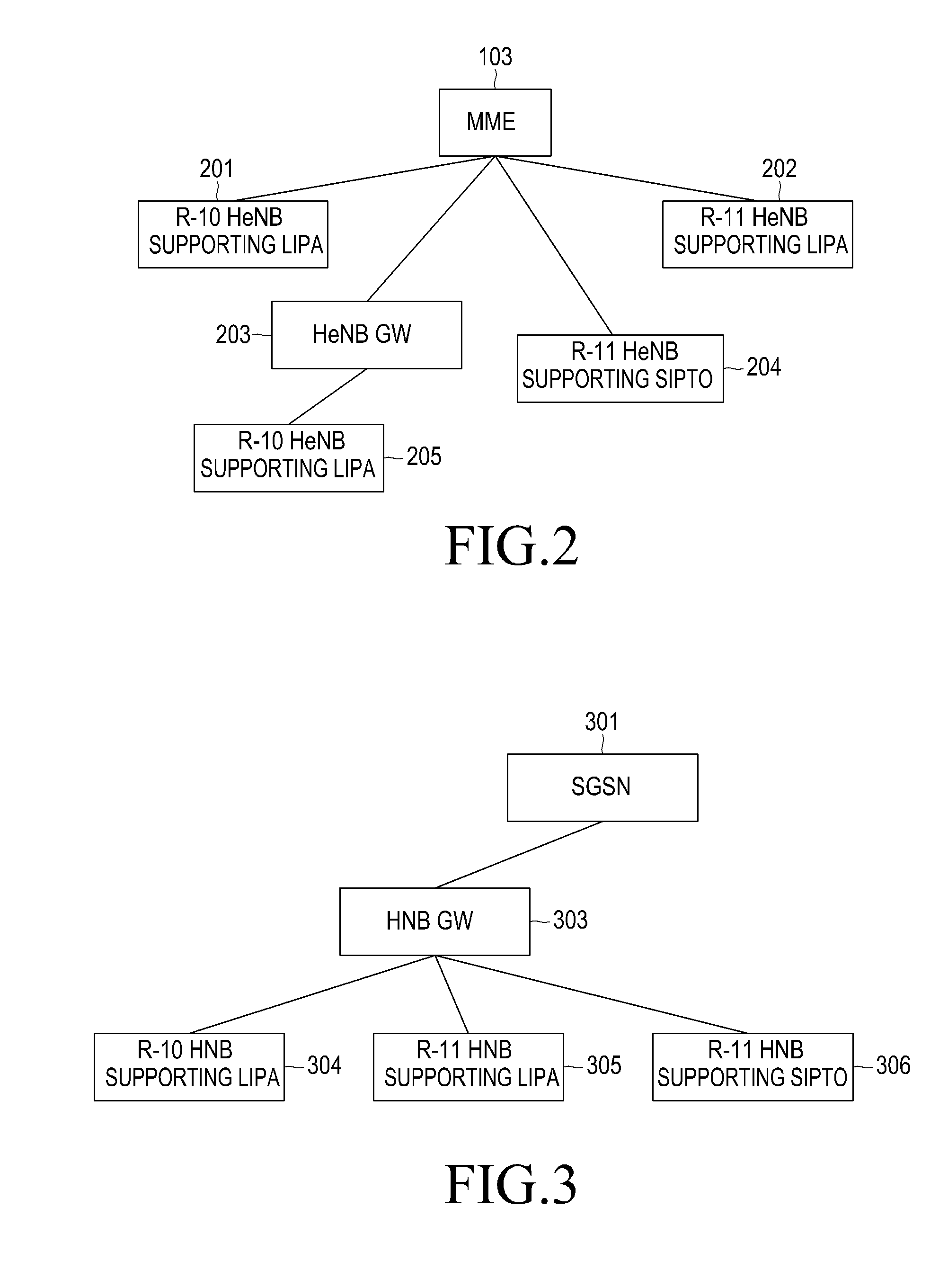
Method and apparatus for supporting user equipment mobility in a wireless communication system
ActiveUS9307388B2Effective supportEffective mobilityAssess restrictionNetwork topologiesCommunications systemIp address
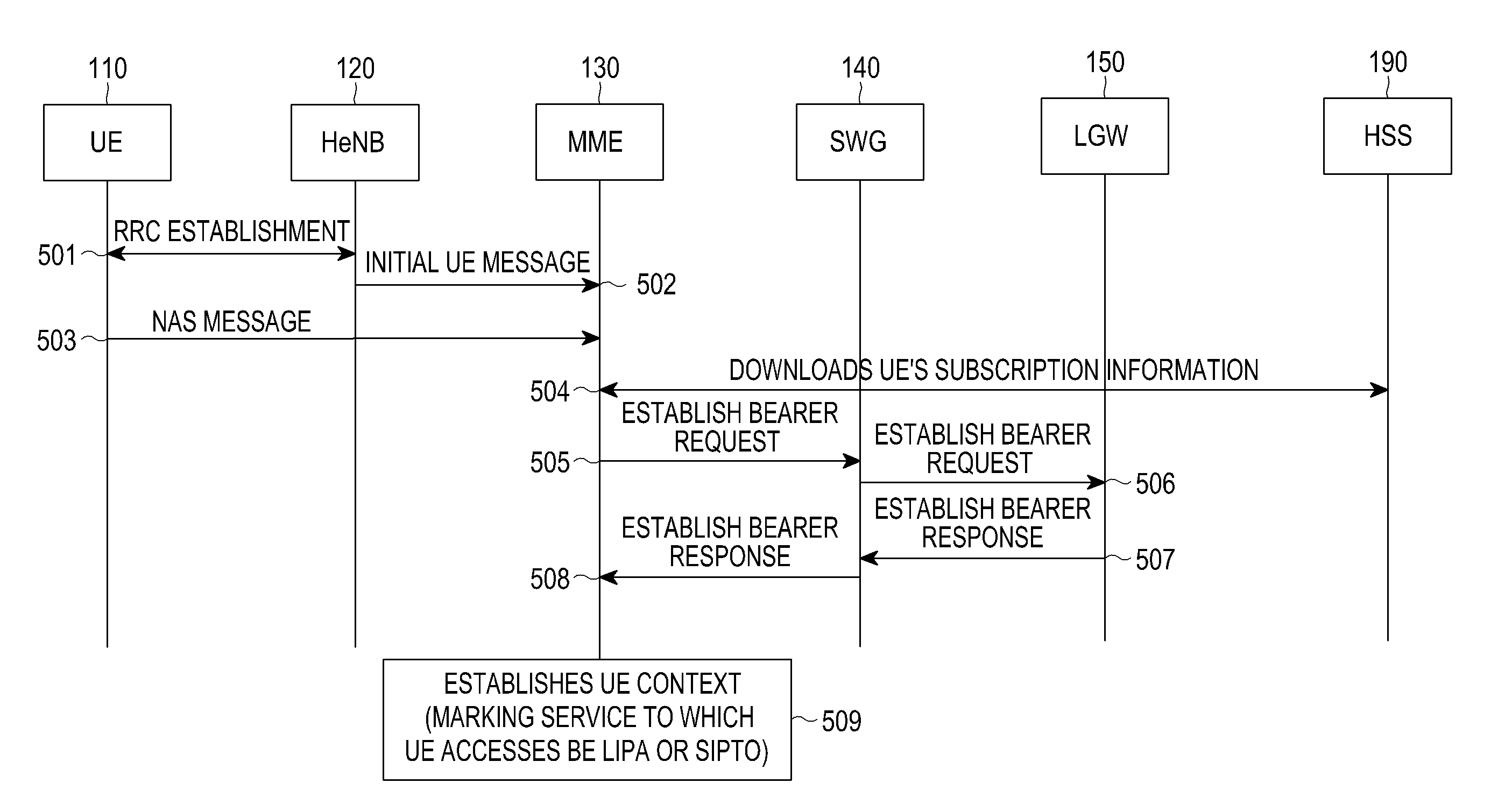
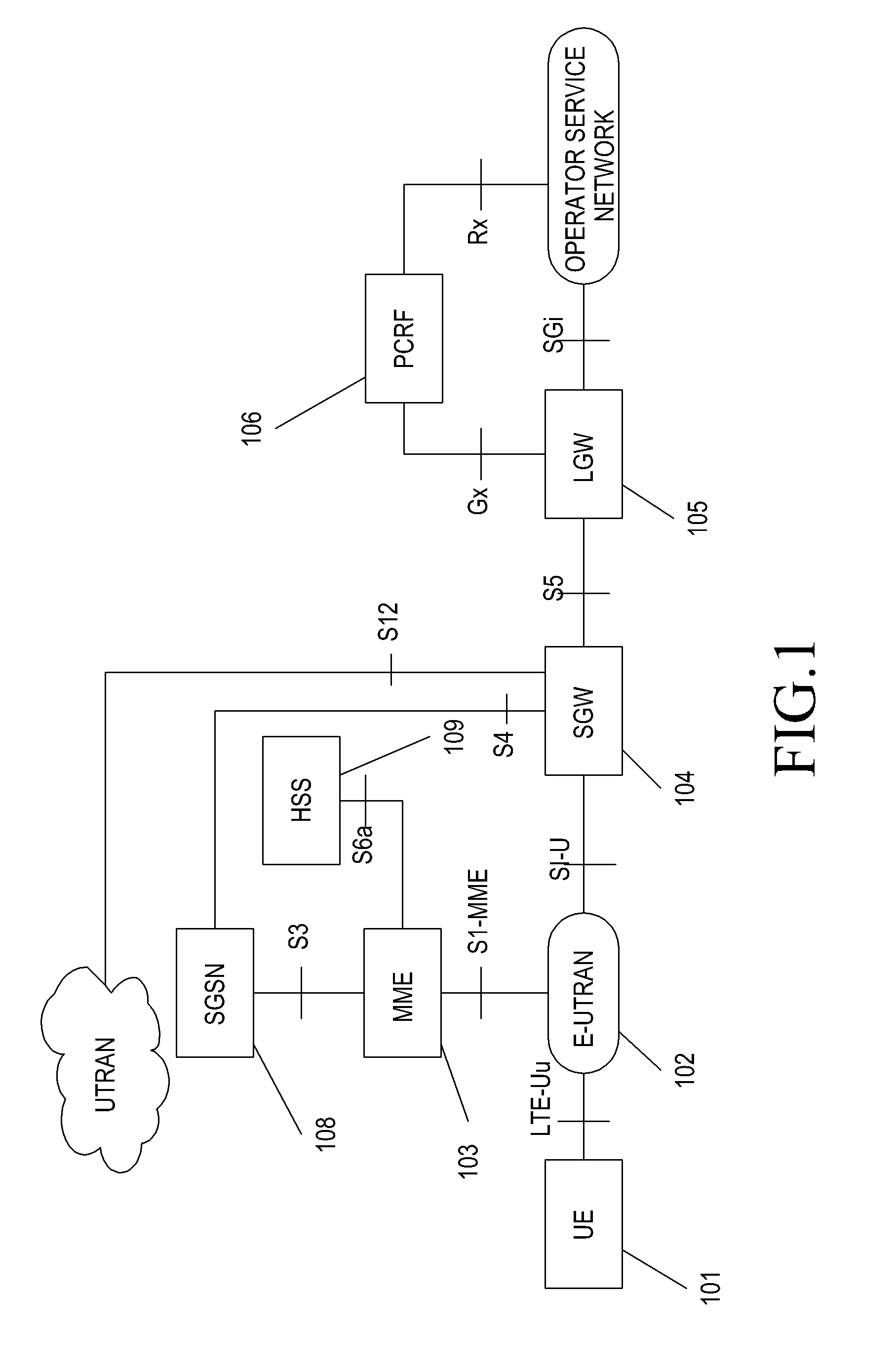
Methods are provided for supporting mobility of a UE in a system without an HeNB GW. An S1 setup request message is sent to an MME by an HeNB. The S1 setup request message includes version information of the HeNB. An RRC connection is established between the UE and the HeNB. An initial UE message is sent from the HeNB to the MME. An NAS message is sent from the UE to the MME. An establish bearer request message is sent from the MME to a corresponding SGW based on an IP address of an LGW. The IP address of the LGW is obtained by the MME through the S1 setup request message. An establish bearer response message is sent from the LGW to the SGW in response to the establish bearer request message. The establish bearer response message is sent from the SGW to the MME.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for supporting user equipment mobility in a wireless communication system
ActiveUS20120177005A1Avoid network executing errorReduce wasteNetwork traffic/resource managementAssess restrictionCommunications systemIp address
Methods are provided for supporting mobility of a UE in a system without an HeNB GW. An S1 setup request message is sent to an MME by an HeNB. The S1 setup request message includes version information of the HeNB. An RRC connection is established between the UE and the HeNB. An initial UE message is sent from the HeNB to the MME. An NAS message is sent from the UE to the MME. An establish bearer request message is sent from the MME to a corresponding SGW based on an IP address of an LGW. The IP address of the LGW is obtained by the MME through the S1 setup request message. An establish bearer response message is sent from the LGW to the SGW in response to the establish bearer request message. The establish bearer response message is sent from the SGW to the MME.
Owner:SAMSUNG ELECTRONICS CO LTD
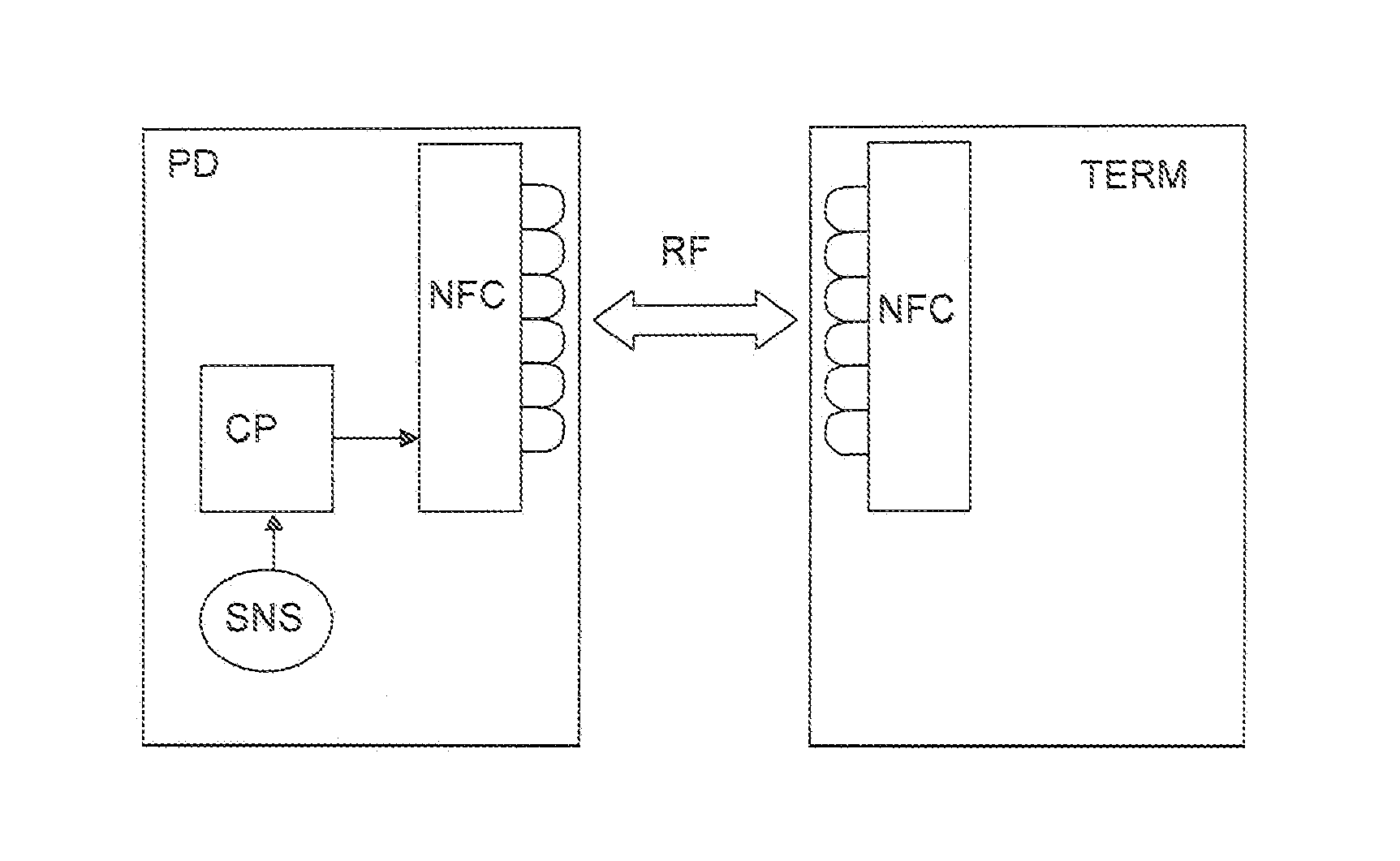
Portable near-field communication device
InactiveUS20140101056A1Preventing executionSimple and cheap solutionFinanceDevices with sensorComputer hardwareComputer terminal
An embodiment of the present invention may be deployed in a mobile payment device configured to communicate with a payment terminal via an RF near-field communication channel. The payment device comprises a sensor to detect and log usage parameters corresponding to behaviors of the user of the payment device. Sensors may take the form of any from movement sensors, light sensors or orientation sensors for example. In order to prevent inadvertent execution of a payment instruction from the terminal, the log of parameters created due to the user's behaviors is compared with a predetermined set of parameters compatible with a user's expected behaviors should he be intentionally performing payment behaviors and payment is only authorized if a match is achieved.
Owner:NAGRAVISION SA
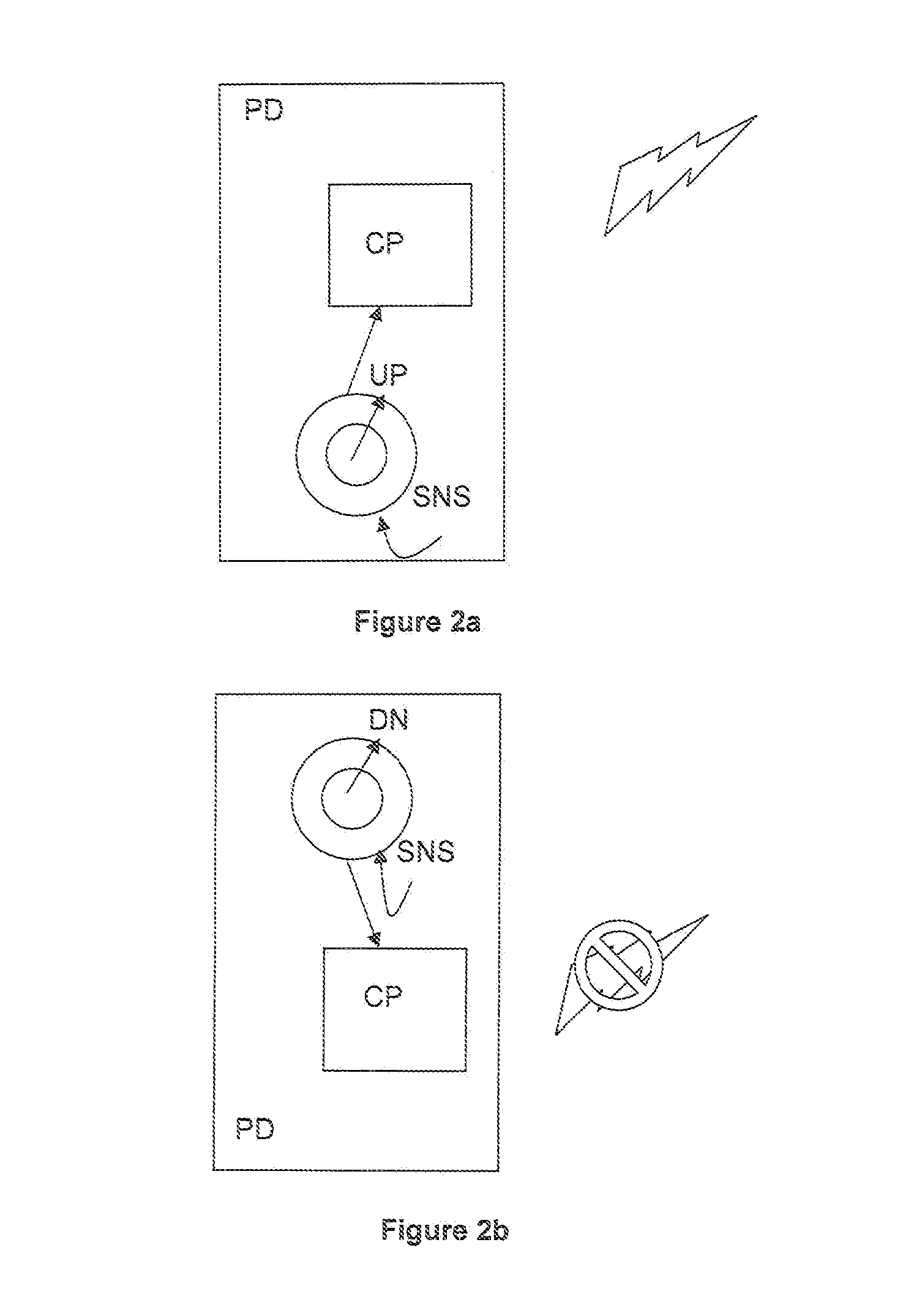
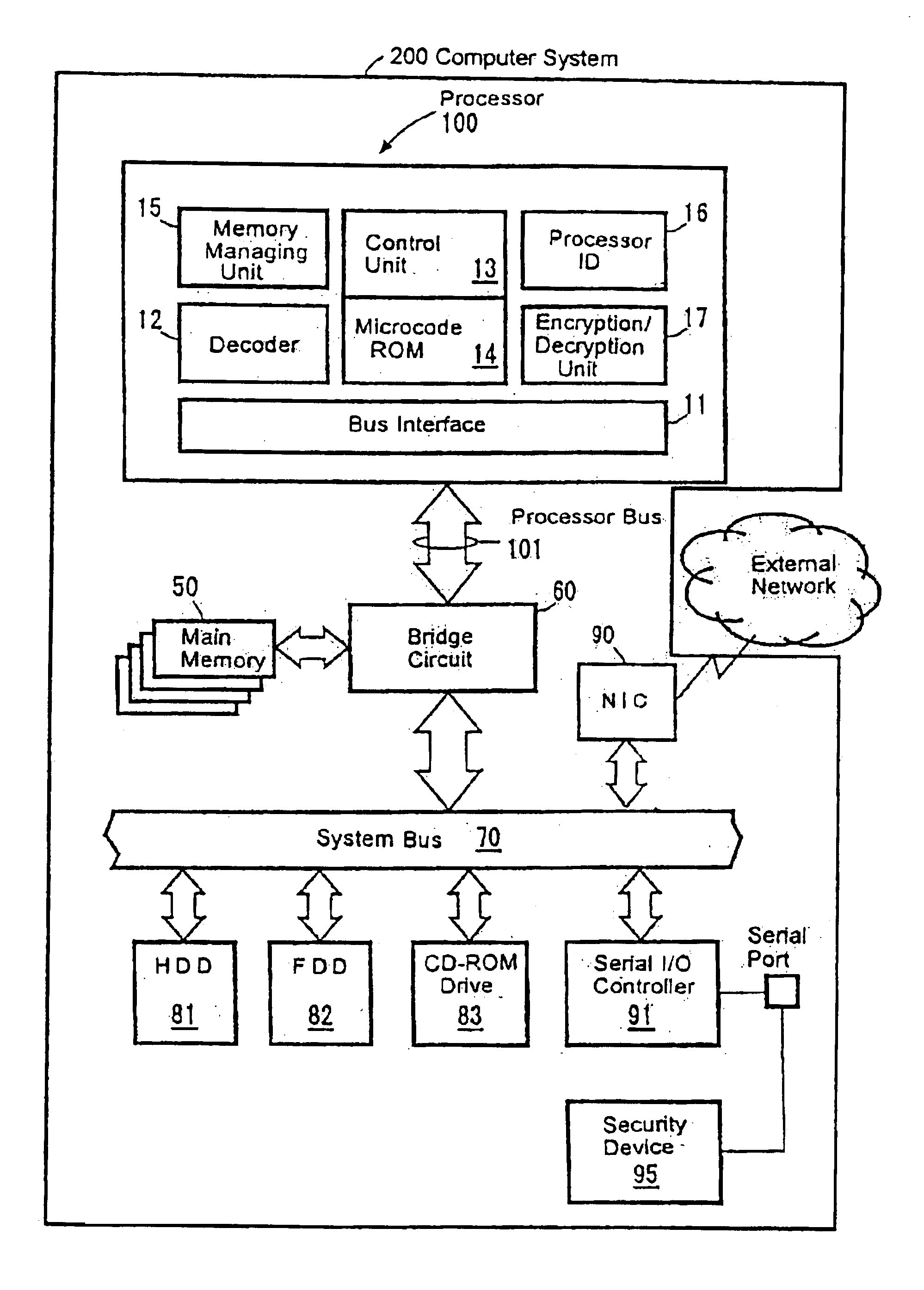
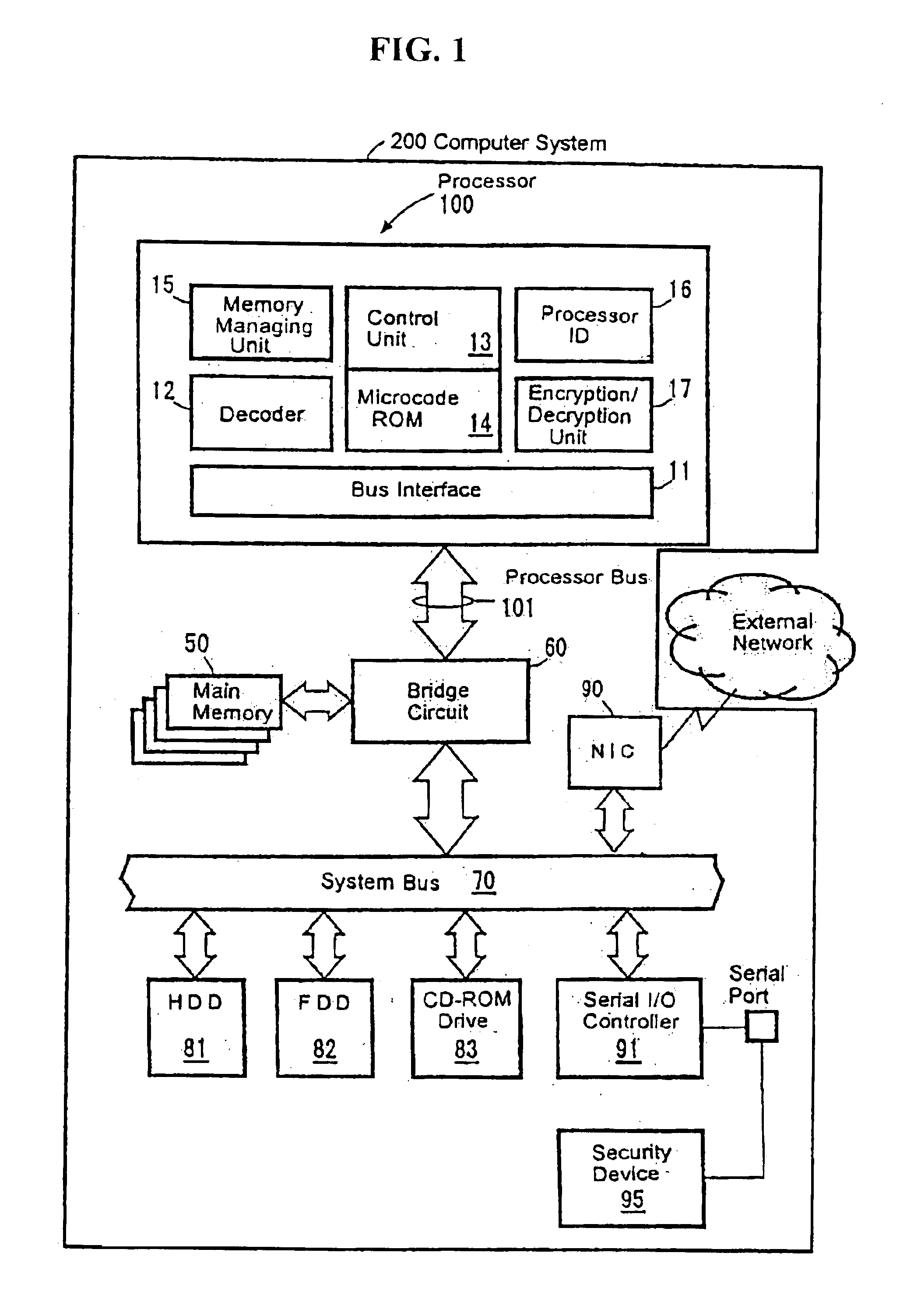
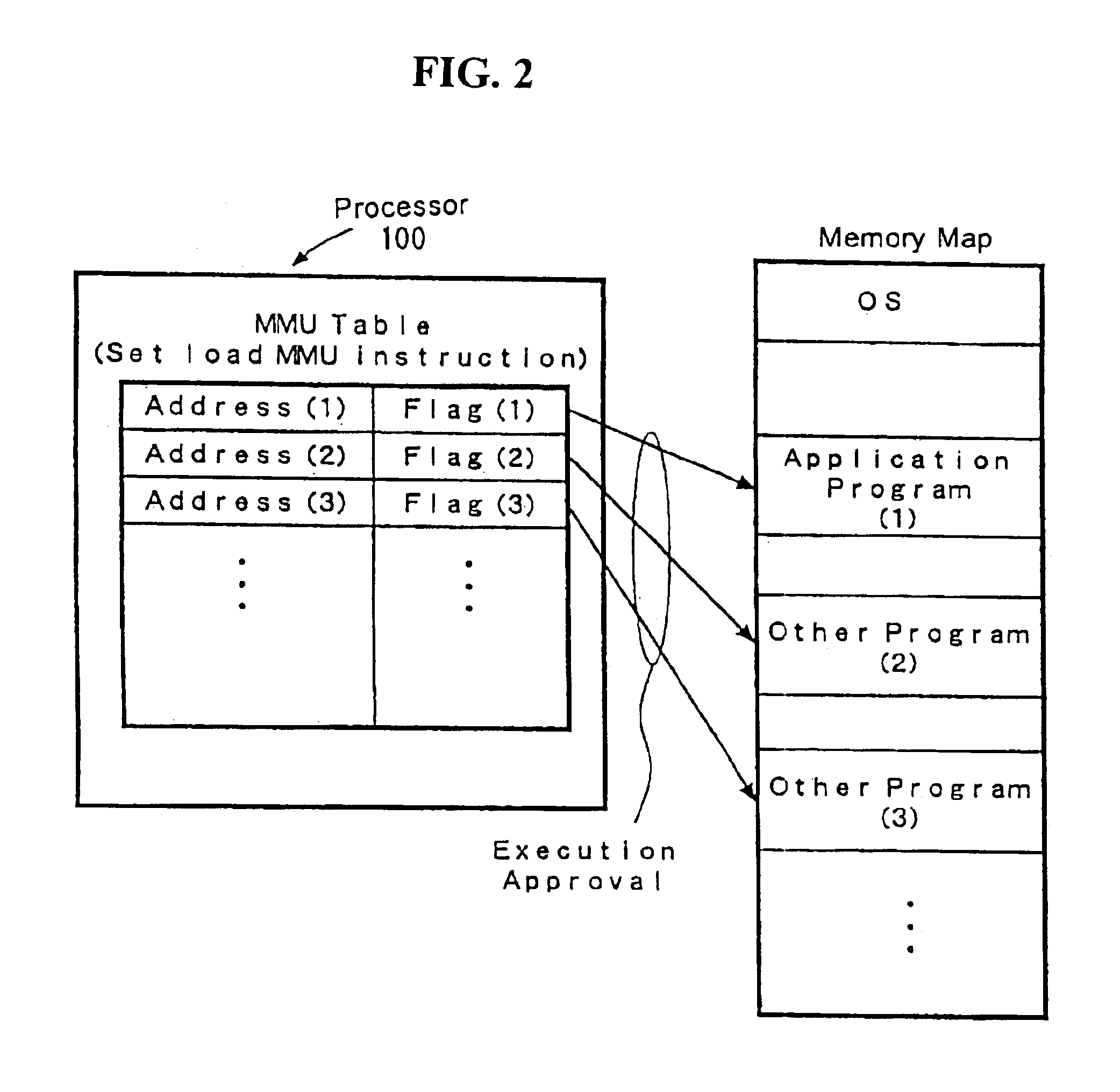
Processor with a function to prevent illegal execution of a program, an instruction executed by a processor and a method of preventing illegal execution of a program
InactiveUS6704872B1Prevent executionAvoid prolonged useUnauthorized memory use protectionHardware monitoringManagement unitComputerized system
The present invention provides an improved technology of preventing illegal use and execution of a software program provided to a computer system. More particularly, the present invention is directed to a Processor of a type in which a memory managing unit is installed therein to manage storing operation of code / data in main memory and includes, as one of instruction set, an execution permitting instruction to permit execution of a program code (application) in the main memory. The procedure of execution permitting instruction is defined by a microprogram and includes an authentication procedure for authenticating the right to use the program beside a procedure for setting predetermined data in the memory managing unit in this invention. Execution of the software program is permitted only when the authentication processing is completed successfully. Because the authentication operation is performed within the processor, it is almost impossible to monitor or detect it from the exterior. Also, by using a processor ID unique to the processor chip as identification information for use in the authentication processing, the right to use a specific software program can be limited to a single processor.
Owner:GOOGLE LLC
Method and apparatus for detecting legitimate computer operation misrepresentation
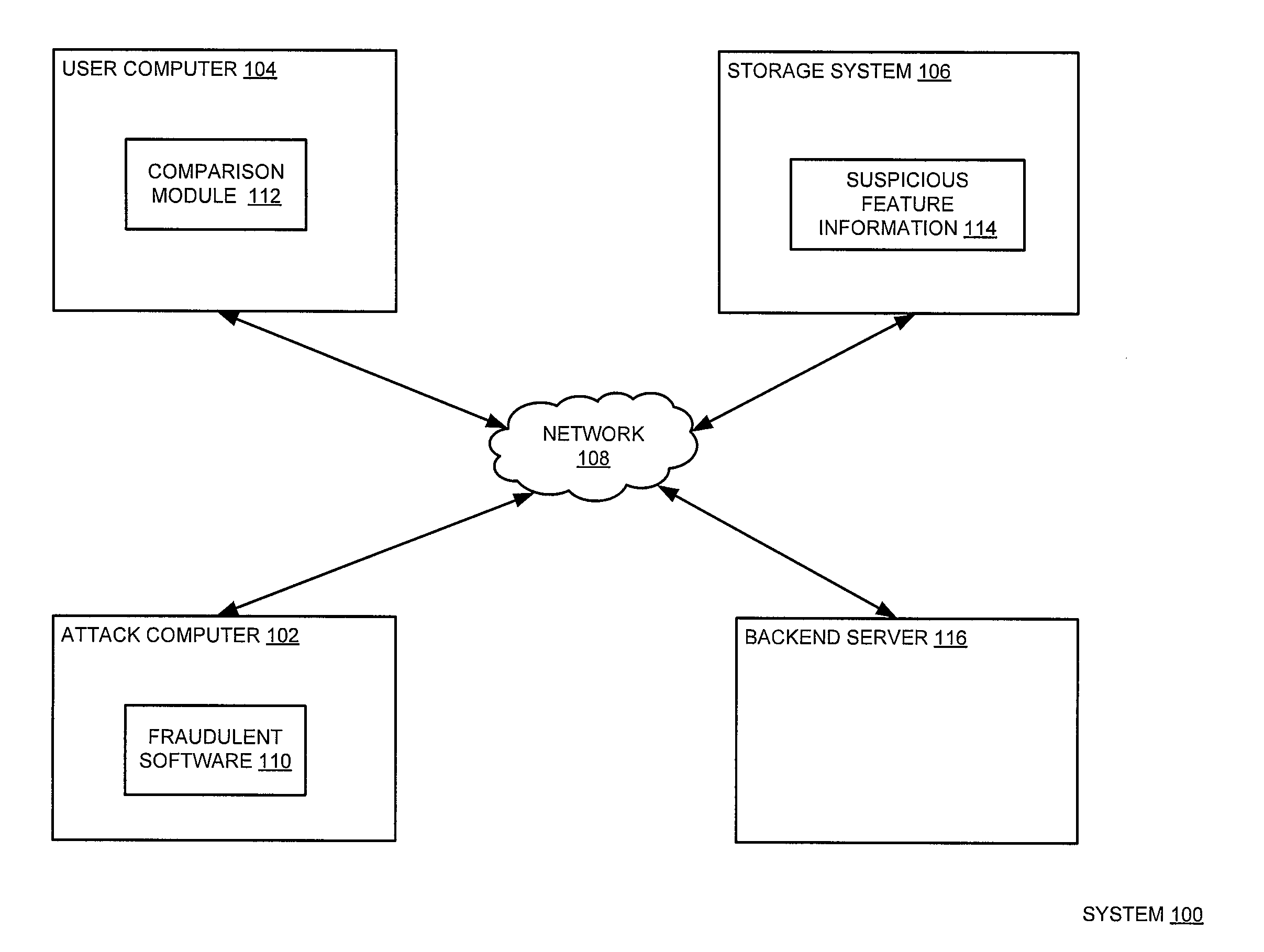
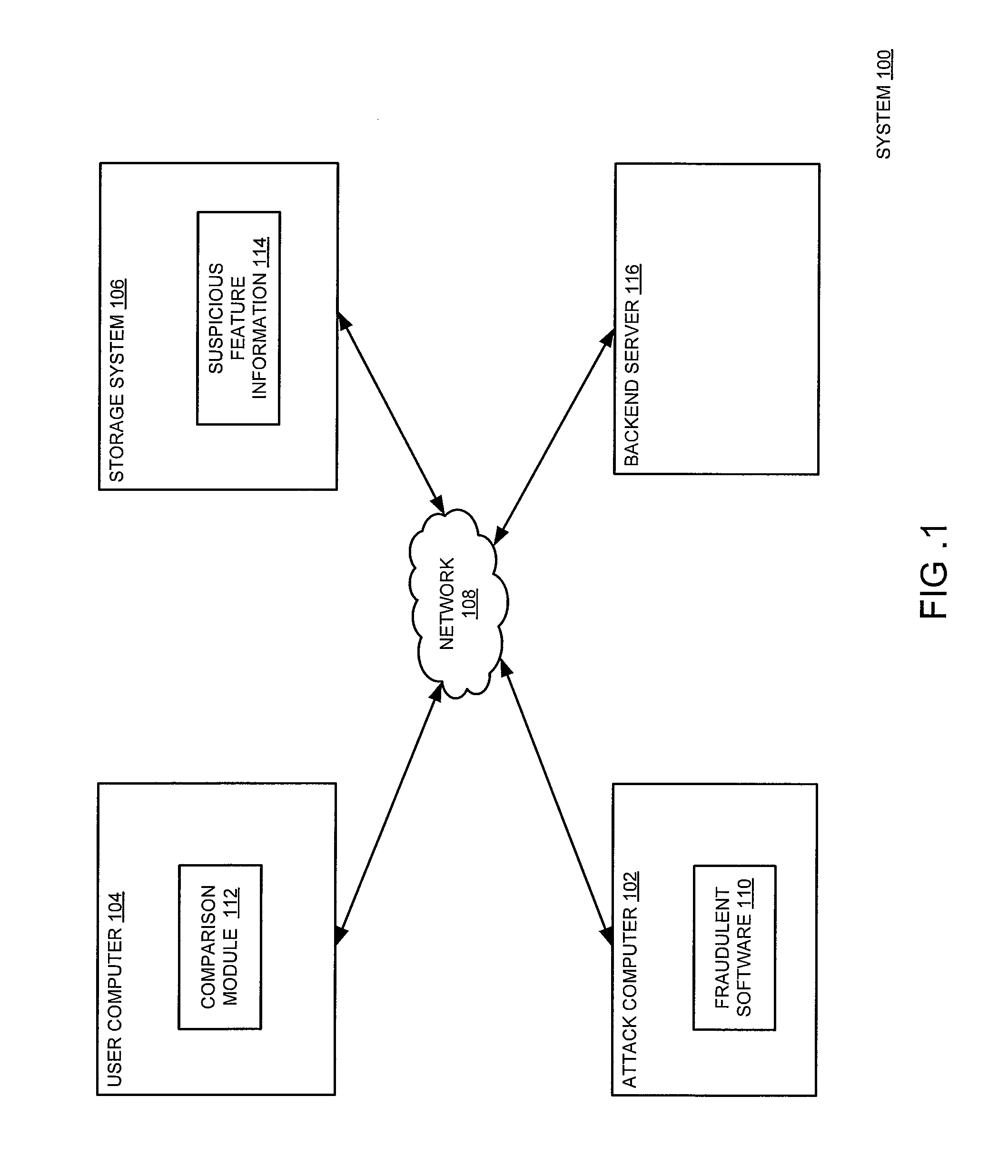
ActiveUS8578496B1Preventing executionAvoid spreadingMemory loss protectionDigital data processing detailsThe InternetImage identification
A method for detecting legitimate computer operation misrepresentation is provided. In some embodiments, the method comprises monitoring internet activity associated with a user computer, comparing the internet activity with suspicious feature information to produce a comparison result, wherein the suspicious feature information comprises at least one image that misrepresents at least one legitimate computer operation, identifying fraudulent software based on the comparison result, wherein the comparison result indicates a portion of the internet activity that misrepresents the at least one legitimate computer operation and mitigating activities associated with the identified fraudulent software.
Owner:GEN DIGITAL INC
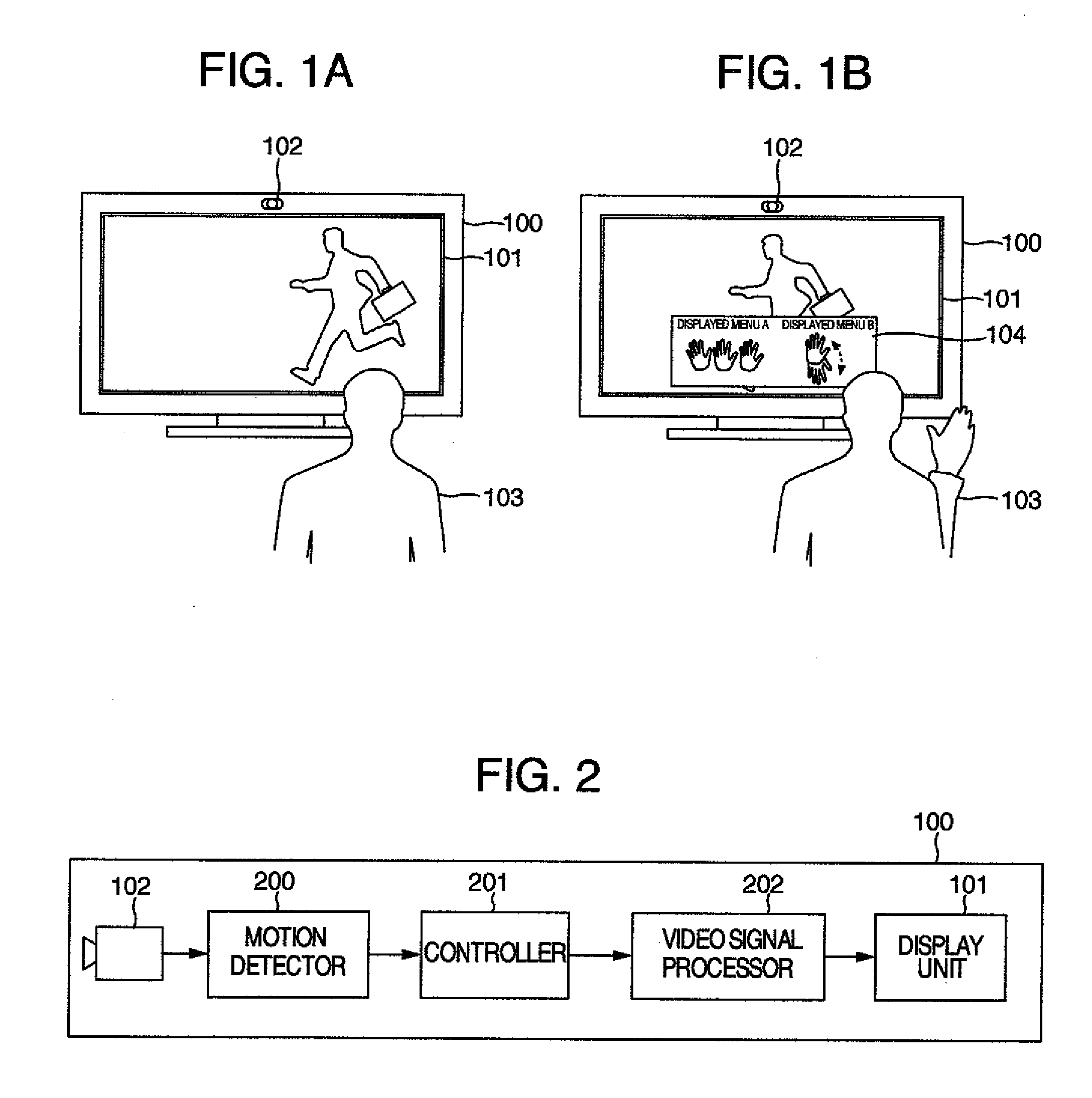
Input device
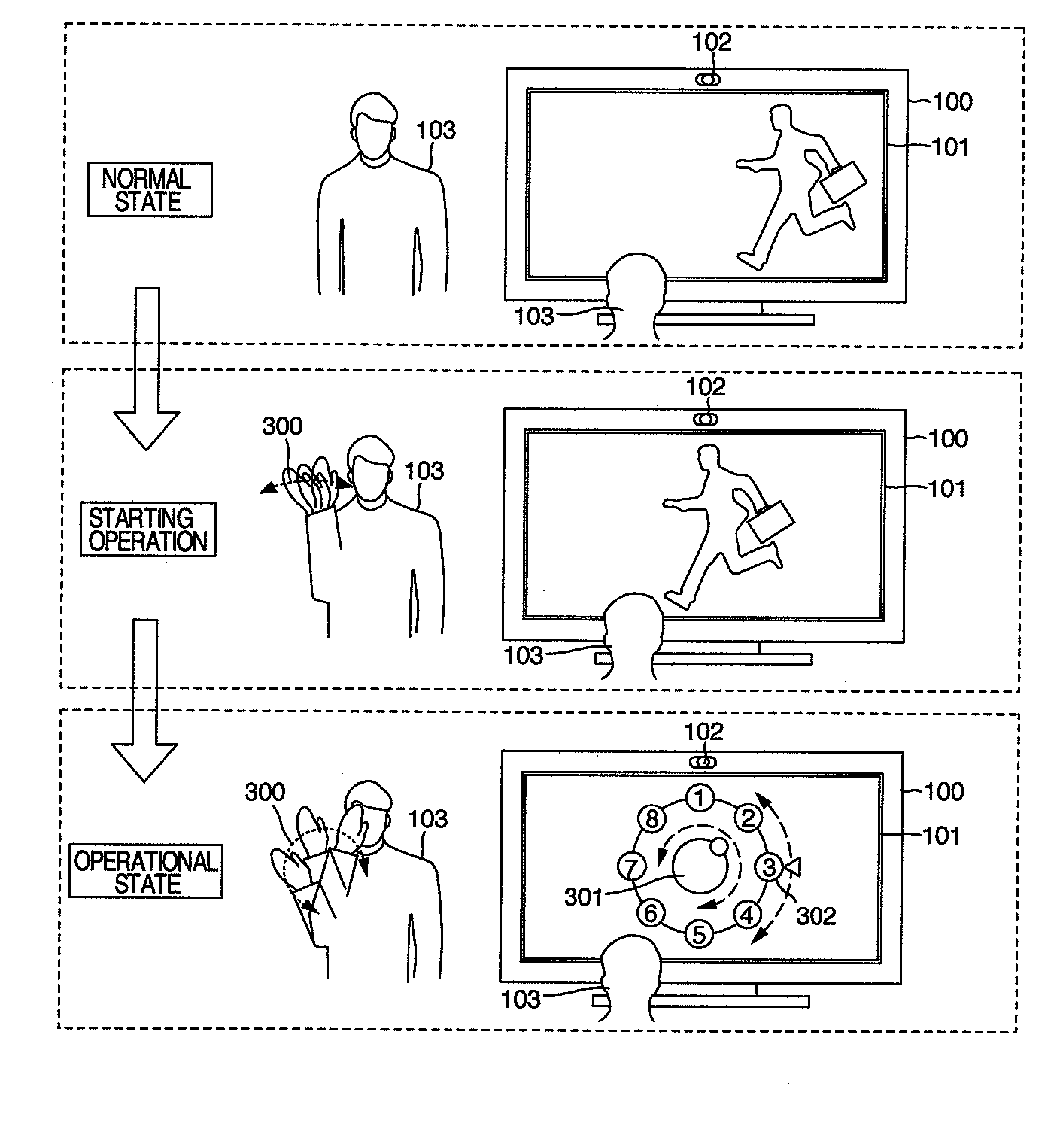
ActiveUS20100275159A1Easy to knowEasy to operateInput/output processes for data processingMotion detectorComputer science
An input device includes an input unit for inputting a predetermined motion image signal, a motion detector for detecting a motion on the basis of the motion image signal inputted into the input unit, a video signal processor for outputting a predetermined video signal, and a controller. The controller controls the video signal processor so that, when a motion detector detects a first motion, the video signal processor outputs a video signal to explain a predetermined second motion to be next detected by the motion detector after the detection of the first motion to a user.
Owner:MAXELL HLDG LTD
System and method for assigning responsibility for trade order execution
InactiveUS20090112775A1Simple processEasy to controlFinanceKnowledge managementSponsoring Organization
An embodiment of the present invention provides a system and method for a sponsoring organization to: (1) utilize a rules-based computer system to capture trade orders from sub-advisors (money management firms) in order to implement a pre trade compliance review process, thereby enabling the sponsoring organization to prevent the execution of trade orders by a sub advisor that violates securities laws and / or account restrictions; and (2) determine and assign, based on expected market impact of a trade order to buy or sell securities, whether responsibility (discretion over the decisions related to how, when and with whom a trade order is executed) for executing the trade order is assigned to the money management firm for an investment portfolio or to the sponsoring organization of that portfolio. Trade orders are categorized in real-time as “high touch” (significant effort and market impact) or “low touch” (insignificant effort and market impact).
Owner:UAT
Roll control device of vehicle manageable of sudden failure of rolling condition detection means
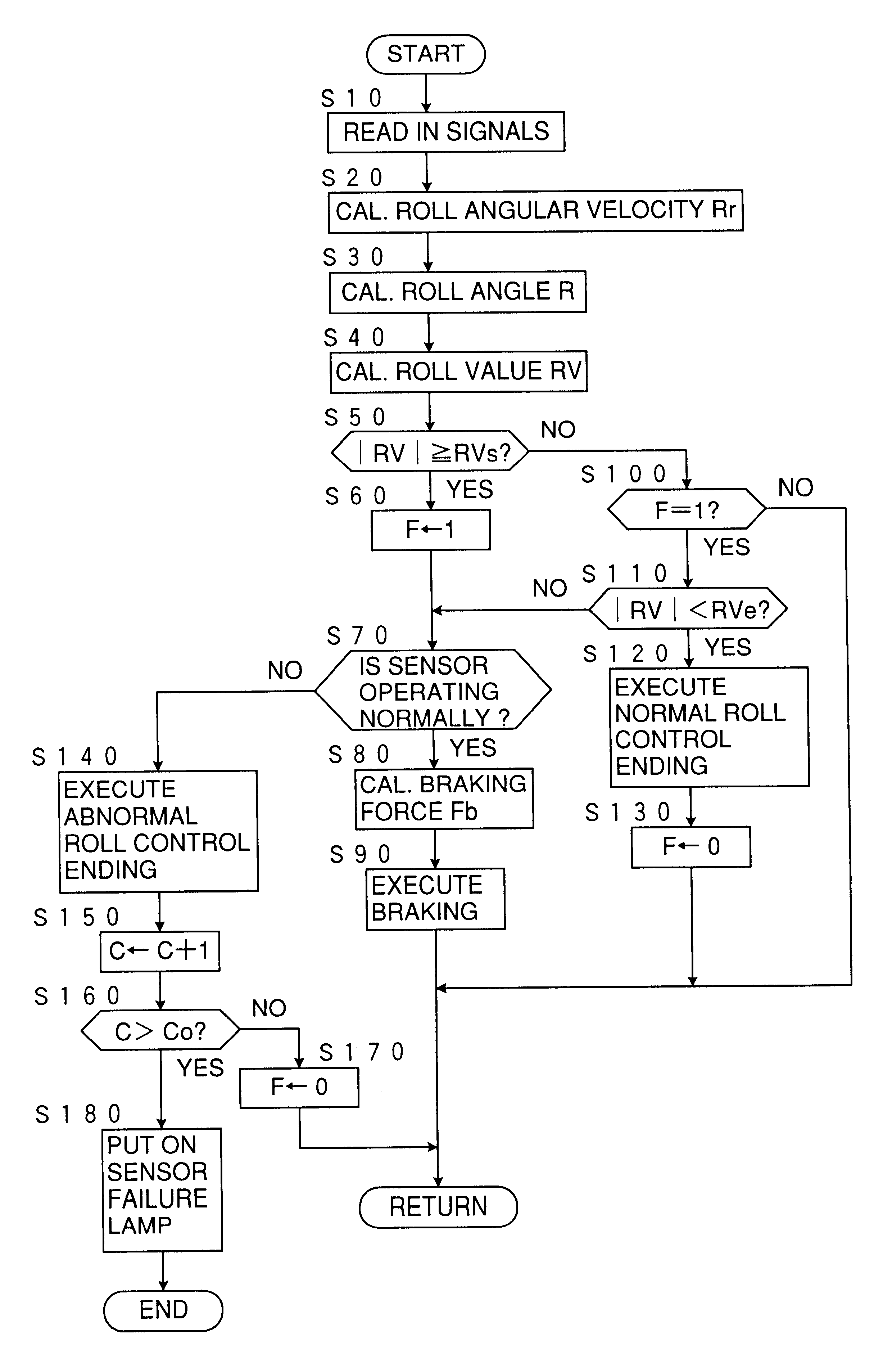
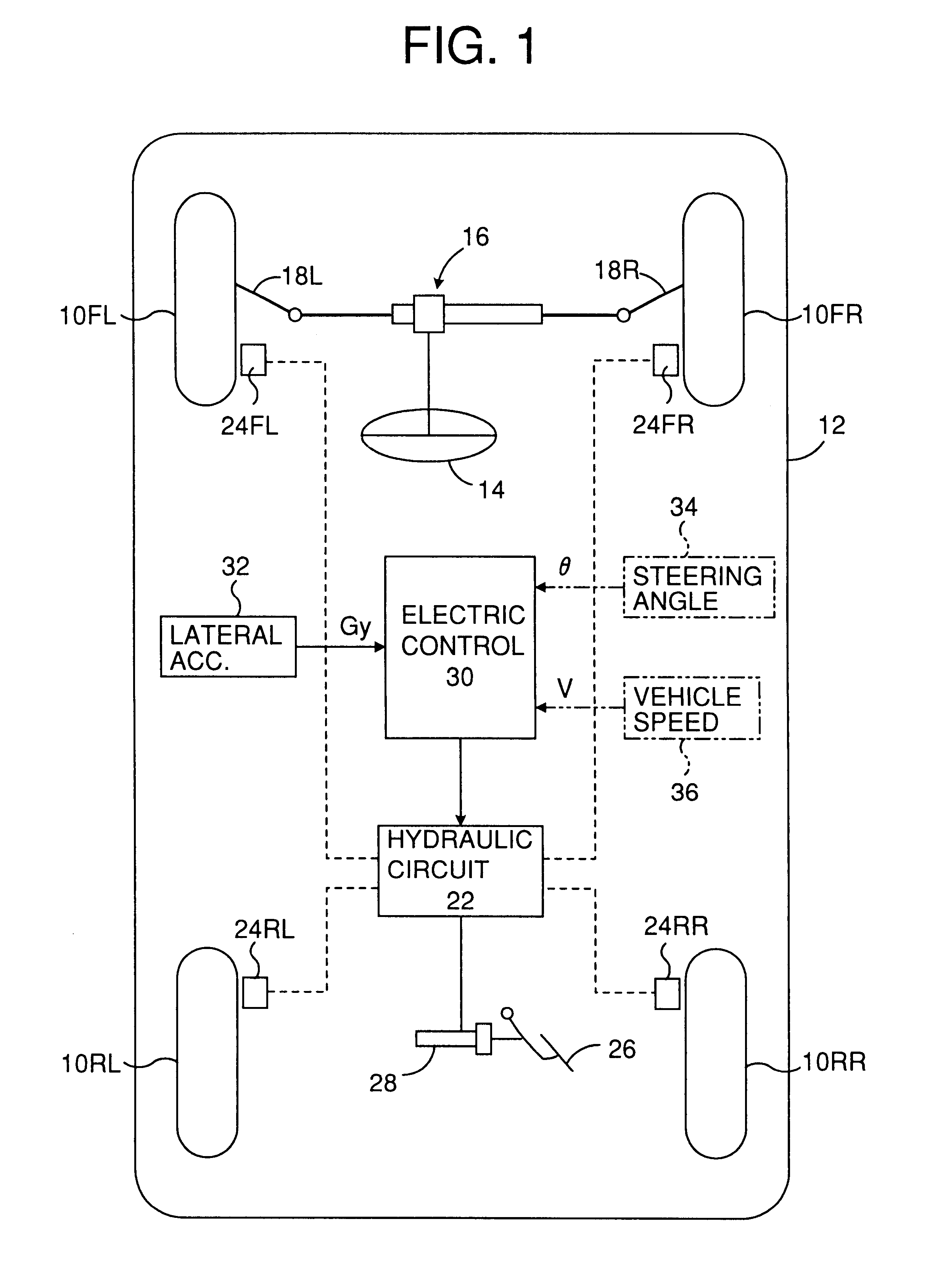
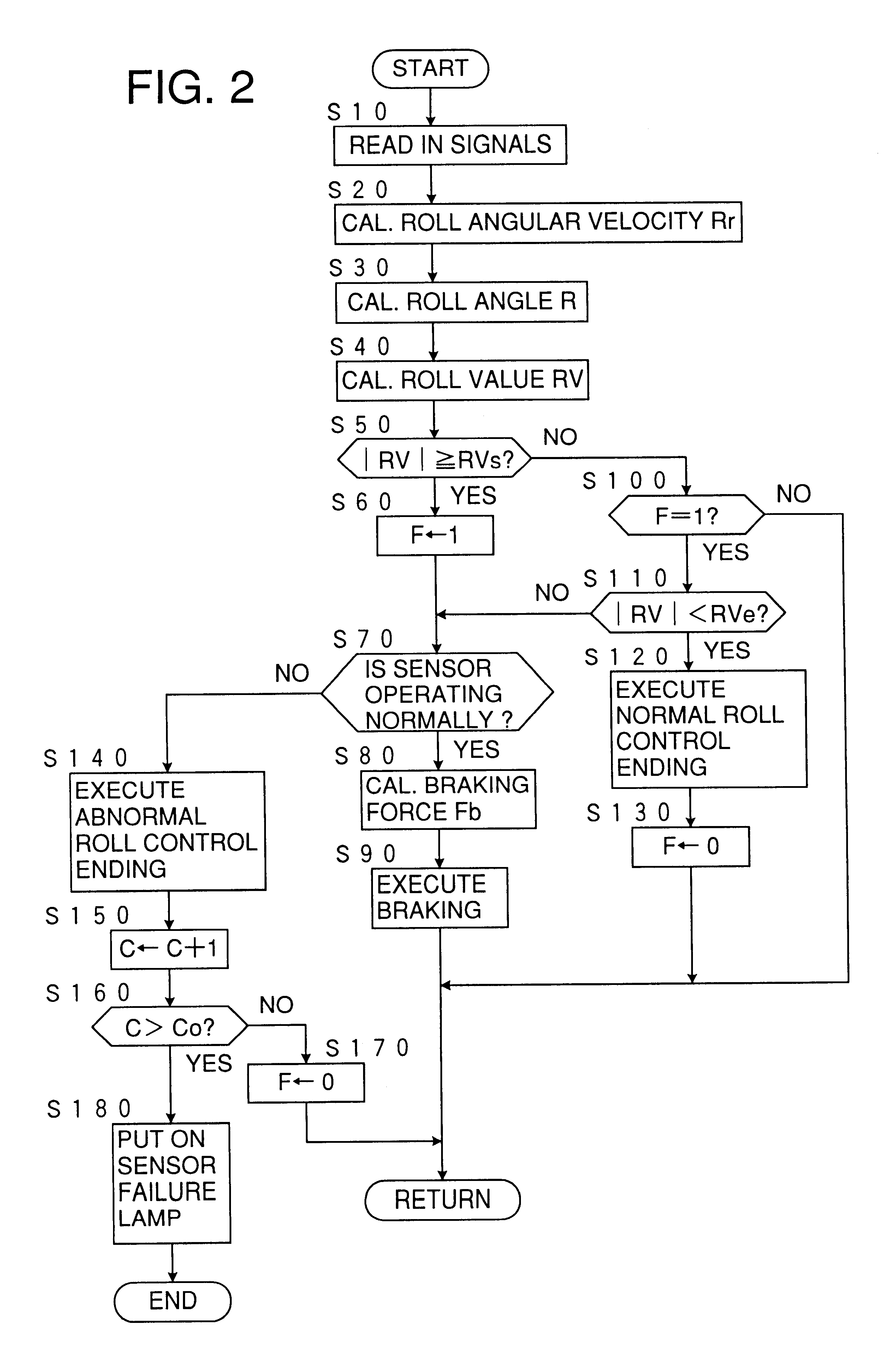
InactiveUS6315373B1Less quicknessPreventing executionBrake control systemsPedestrian/occupant safety arrangementAutomotive engineeringEngineering
A roll control device of a vehicle for executing a roll suppress braking according to a detection of a rolling condition of the vehicle so that the braking is executed when the rolling condition increases beyond a first threshold value and the braking is canceled according to a normal brake ending schedule when the rolling condition subsides below a second threshold value lower than the first threshold value, wherein when an abnormal condition occurs about the detection of the rolling condition, the braking is canceled according to an abnormal brake ending schedule at a less quickness than according to the normal brake ending schedule, even before the rolling condition subsides below the second threshold value.
Owner:TOYOTA JIDOSHA KK
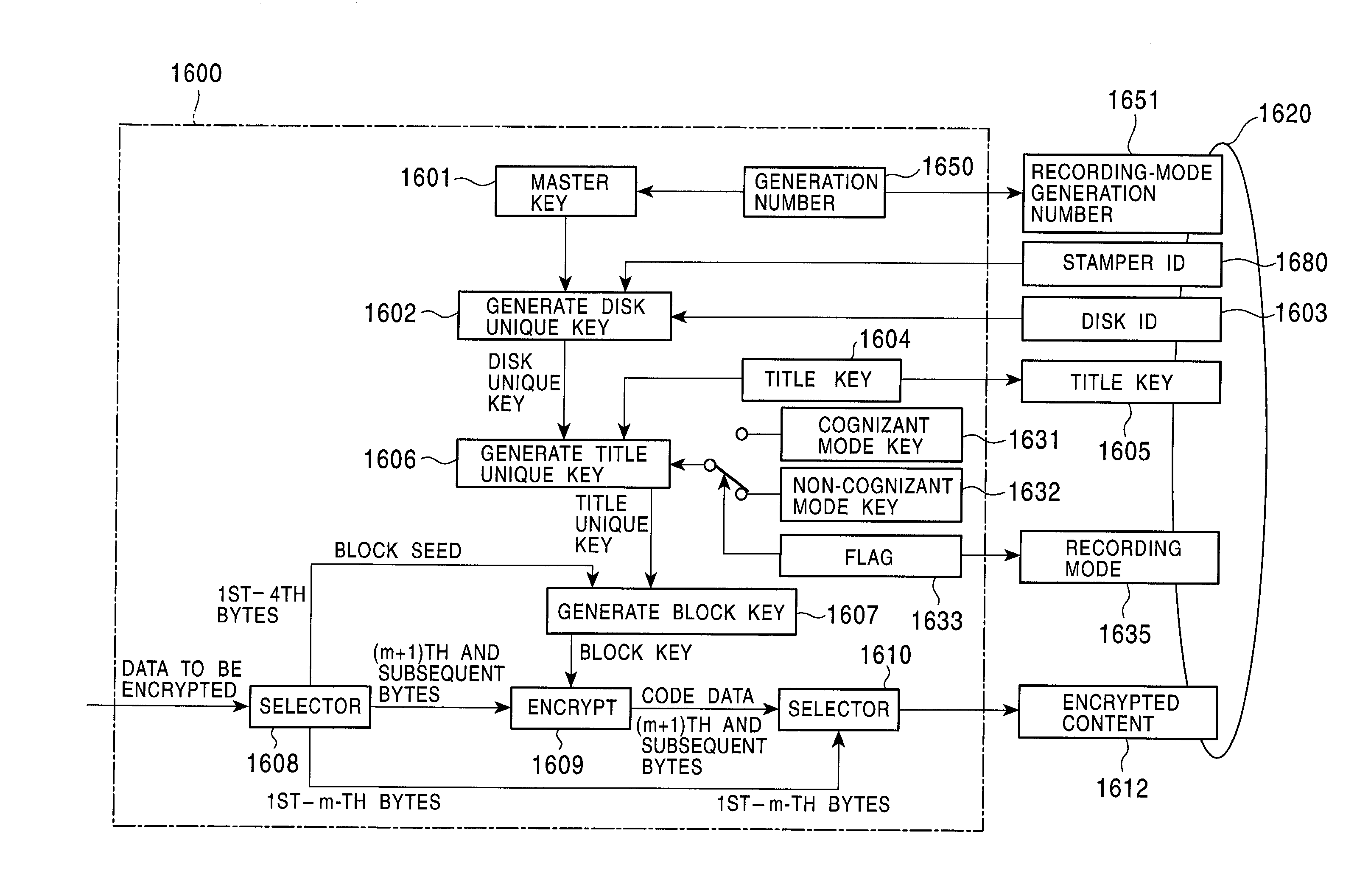
Method and apparatus for selectively executing information recording using a cognizant mode and a non-cognizant mode
InactiveUS7203968B2Reduce usagePreventing executionTelevision system detailsKey distribution for secure communicationCryptographic key generationPattern selection
When the recording mode of an information recording / playback device is a cognizant mode which analyzes embedded copy control information, the information recording / playback device performs content encryption using a content-encryption key generated by using a cognizant key as a content-encryption-key generating key in the cognizant mode. When the recording mode of the information recording / playback device is a non-cognizant mode which does not analyze the embedded copy control information, the information recording / playback device performs content encryption using a content-encryption key generated by using a cognizant key as a content-encryption-key generating key in the non-cognizant mode. By using these techniques, the above two recording modes are clearly distinguished and separately executed. This prevents an encryption mode indicator as copy control information and embedded copy control information from being mismatched.
Owner:SONY CORP
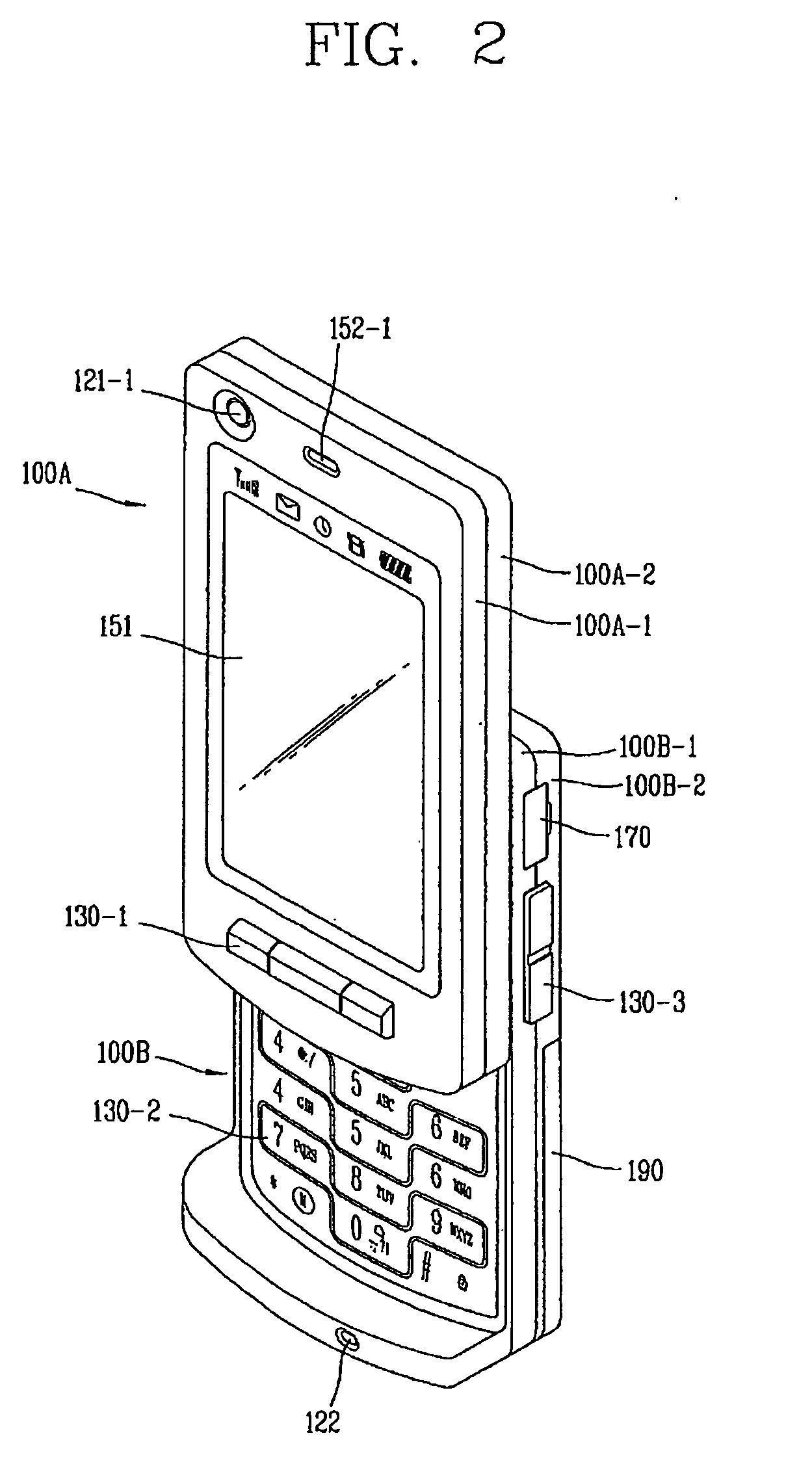
Mobile terminal and touch recognition method therefor
InactiveUS20090061947A1Reduce stepsPreventing executionDigital data processing detailsSubstation equipmentComputer terminalTouchscreen
Owner:LG ELECTRONICS INC
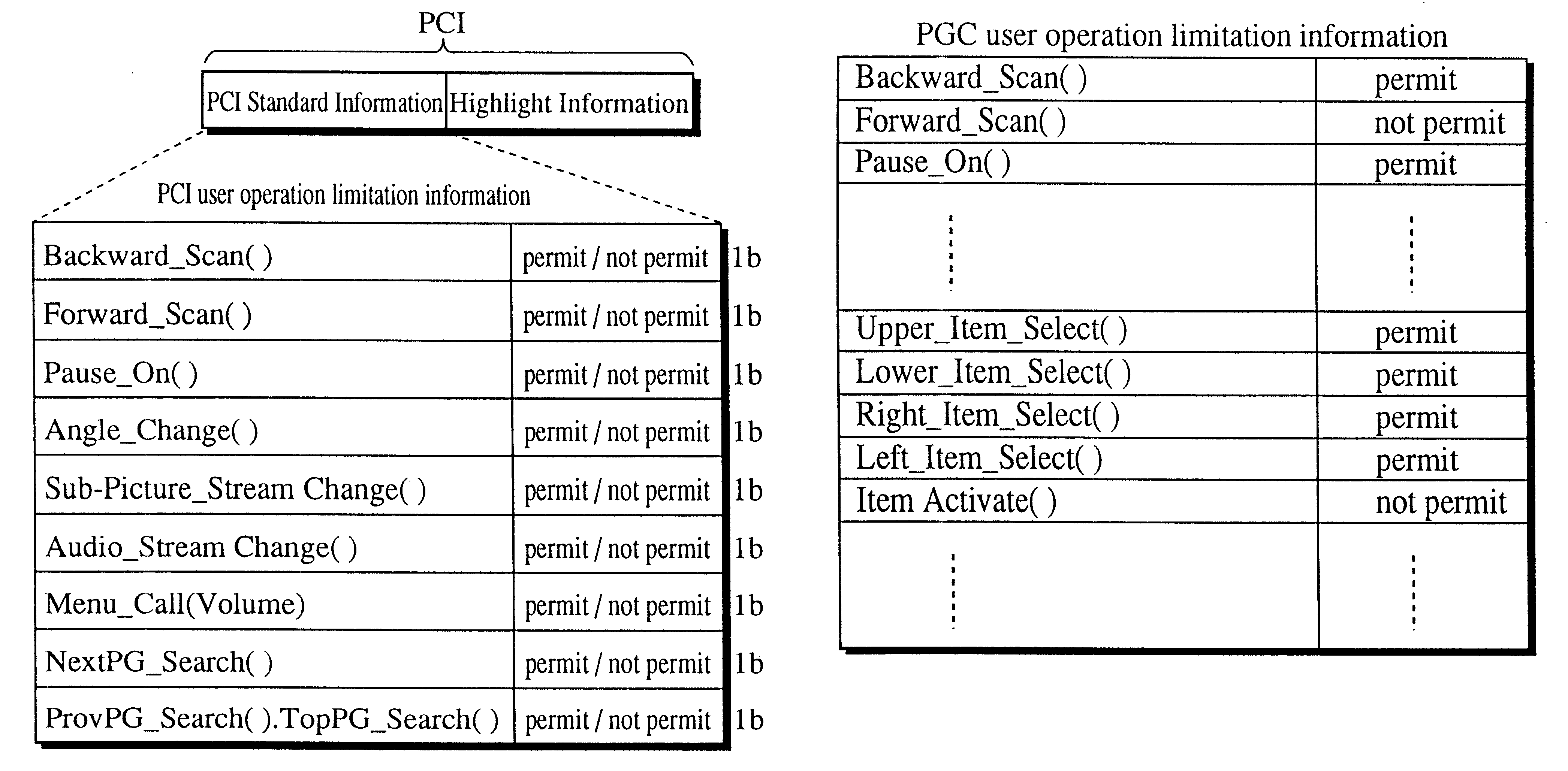
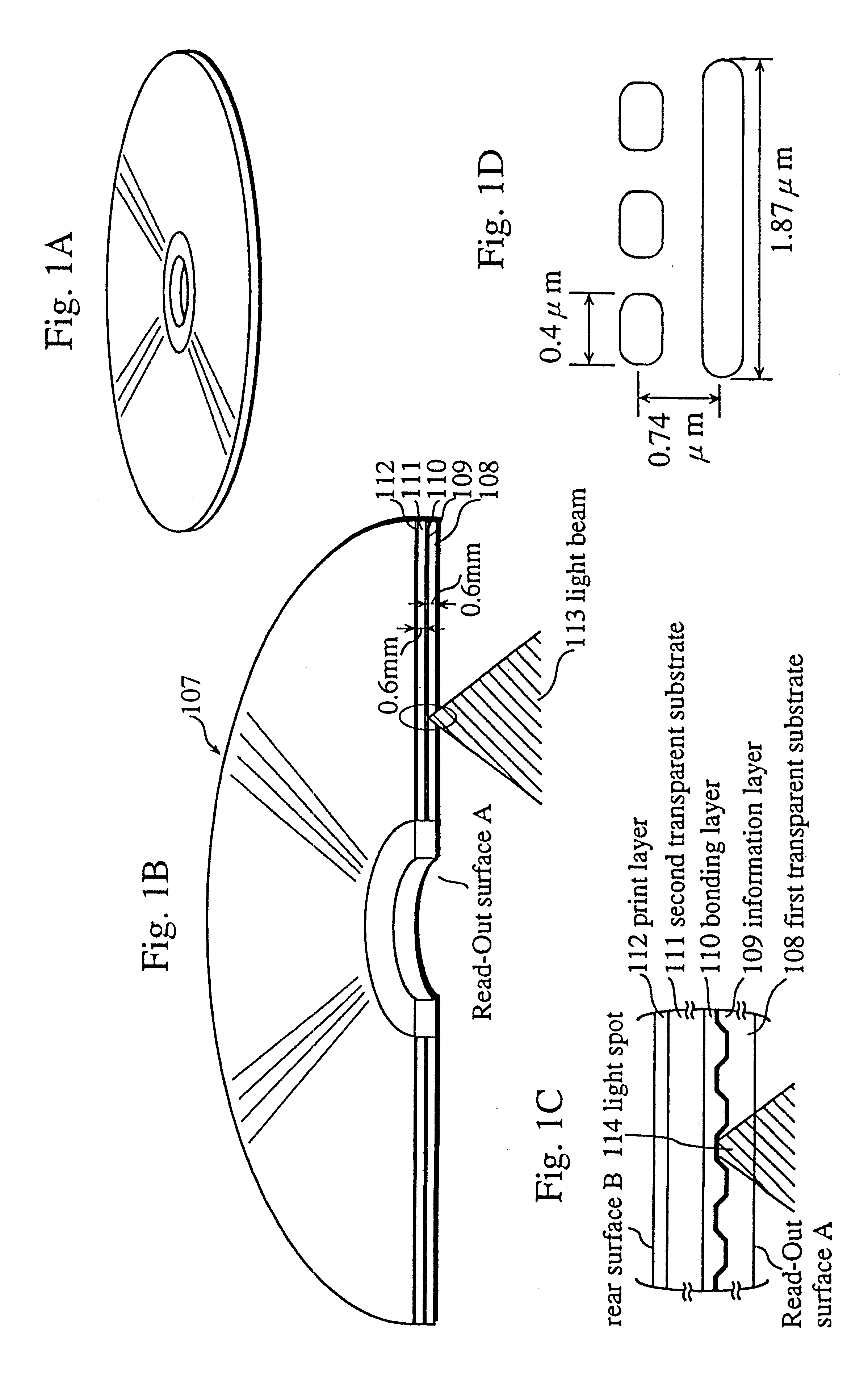
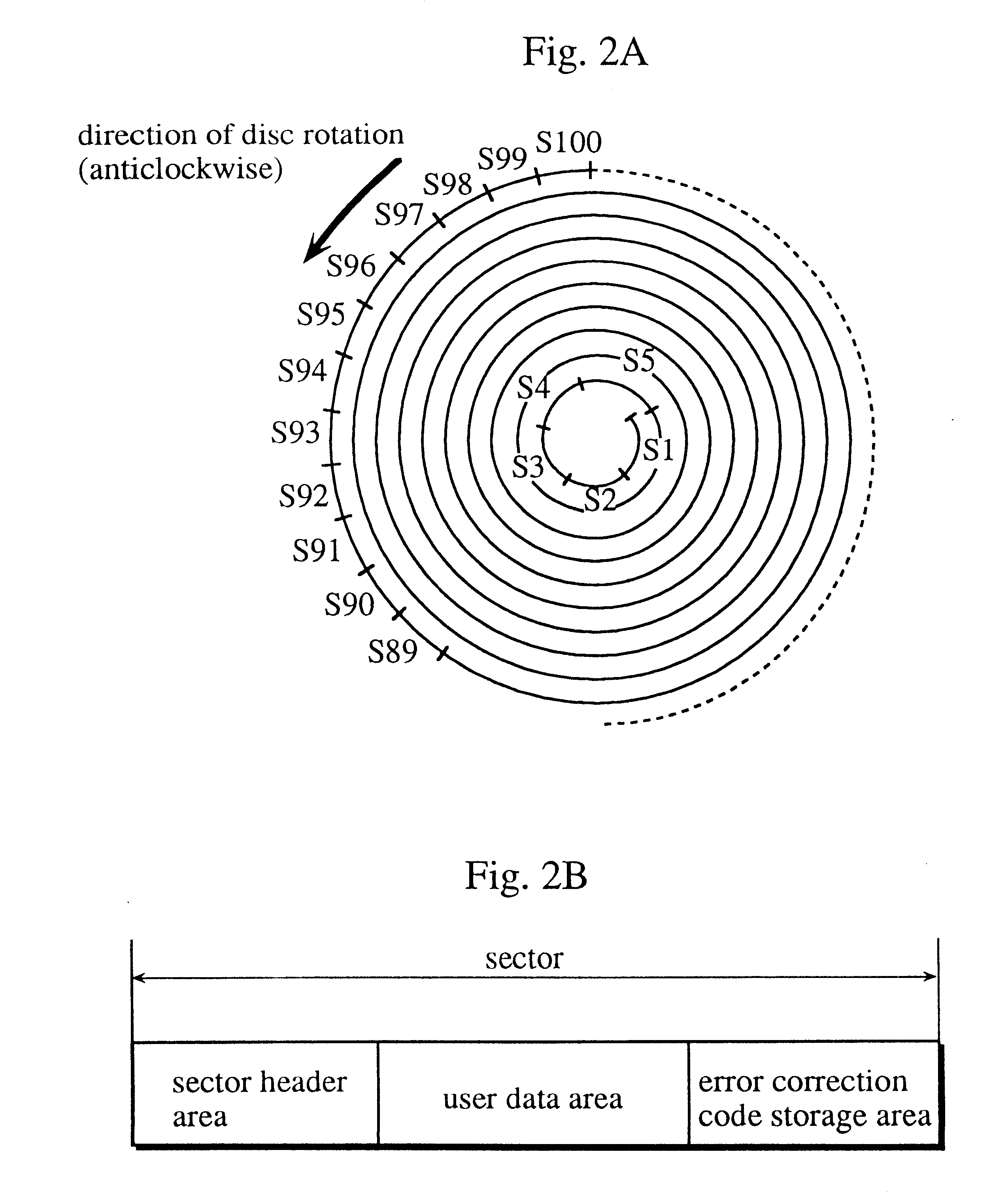
Optical disc for coordinating the use of special reproduction functions and a reproduction device for the optical disc
InactiveUS6553179B1Preventing executionDamage the interactive nature of a titleTelevision system detailsRecord information storageComputer hardwareReproduction function
A multimedia optical disc includes a lot of blocks each of which stores moving picture data, audio data, sub-picture data, and control information. Each piece of moving picture data, audio data, sub-picture data, and control information in the same block has the same reproduction time limit. Each piece of control information includes a mask flag indicating whether to mask a key interrupt requesting a special reproduction such as fast forward, the key interrupt being generated by the user by pressing a key on a remote controller and the like. The mask flag is effective for the key interrupt generated during the reproduction time limit stored in the control information.
Owner:PANASONIC CORP
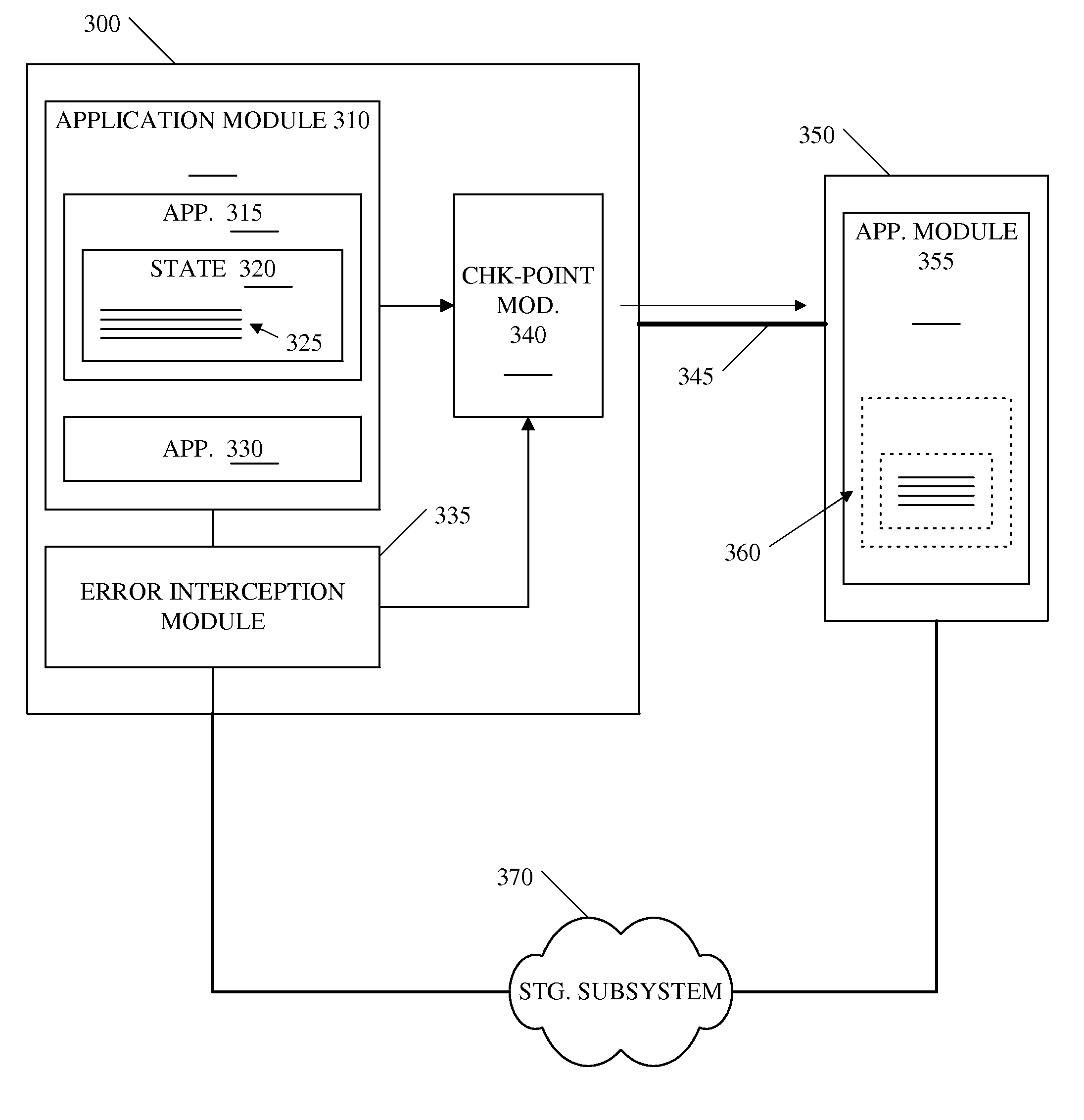
Obviation of Recovery of Data Store Consistency for Application I/O Errors
ActiveUS20120144233A1Preventing executionRedundant hardware error correctionComputer hardwareError prevention
Embodiments comprise a plurality of computing devices that dynamically intercept process application I / O errors. Various embodiments comprise two or more computing devices, such as two or more servers, each having access to a shared data storage system. An application may be executing on the first computing device and performing an I / O operation when an I / O error occurs. The first computing device may intercept the I / O error, rather than passing it back to the application, and prevent the error from affecting the application. The first computing device may complete the I / O operation, and any other pending I / O operations not written to disk, via an alternate path, perform a checkpoint operation to capture the state of the set of processes associated with the application, and transfer the checkpoint image to the second computing device. The second computing device may resume operation of the application from the checkpoint image.
Owner:KYNDRYL INC
Apparatus and method for TOL client boundary protection
InactiveUS7065785B1Preventing executionDigital data processing detailsUnauthorized memory use protectionGraphicsGraphical user interface
A telephony-over-LAN (ToL) system having a graphical user interface (GUI) wherein an authorized or guest user may be locked within a ToL window, having full access to the ToL features, but denied access to other parts of the computer system. In such a system, the terminal user or subscriber may click on a “Guest” button on the ToL client GUI screen before leaving the computer. The ToL guest user may then execute the call normally. According to a first embodiment of the invention, the ToL client locks the user into the ToL client screen. Keystrokes and mouse cursor movements which would allow exiting the ToL client are prevented. According to a second embodiment, of the invention, the ToL client screen is “maximized” and the minimize or resize window functions are blocked. When the terminal subscriber returns, a password is entered to regain full access to the computer.
Owner:ENTERPRISE SYST TECH S A R L
Tamper-protected hardware and method for using same
ActiveUS9071446B2Improve robustnessSuitable for useKey distribution for secure communicationMultiple keys/algorithms usageComputer hardwareTamper proof hardware
Owner:EMSYCON
Automatic threat detection of executable files based on static data analysis
ActiveUS20160335435A1Preventing executionDecompilation/disassemblyKernel methodsStatic timing analysisAnalysis aspect
Aspects of the present disclosure relate to threat detection of executable files. A plurality of static data points may be extracted from an executable file without decrypting or unpacking the executable file. The executable file may then be analyzed without decrypting or unpacking the executable file. Analysis of the executable file may comprise applying a classifier to the plurality of extracted static data points. The classifier may be trained from data comprising known malicious executable files, known benign executable files and known unwanted executable files. Based upon analysis of the executable file, a determination can be made as to whether the executable file is harmful.
Owner:OPEN TEXT CORPORATION
Authenticated program execution method
InactiveUS20050138397A1Guaranteed reputationImprove responsivenessUnauthorized memory use protectionHardware monitoringBiological activationAuthentication
According to a conventional technique, in the case where a program is stored into a non-volatile memory once and then activated, authentication of the program is performed immediately before such activation. However, calculations such as decryption of encrypted values are required before the activation of the program starts, which causes the problem that responsiveness is decreased in proportion to the time required for calculations. In order to solve this problem, authentication of a program is performed immediately before such program is stored, so that no authentication is performed or only a part of the authentication is performed to verify the validity of certificates at program activation time.
Owner:PANASONIC CORP
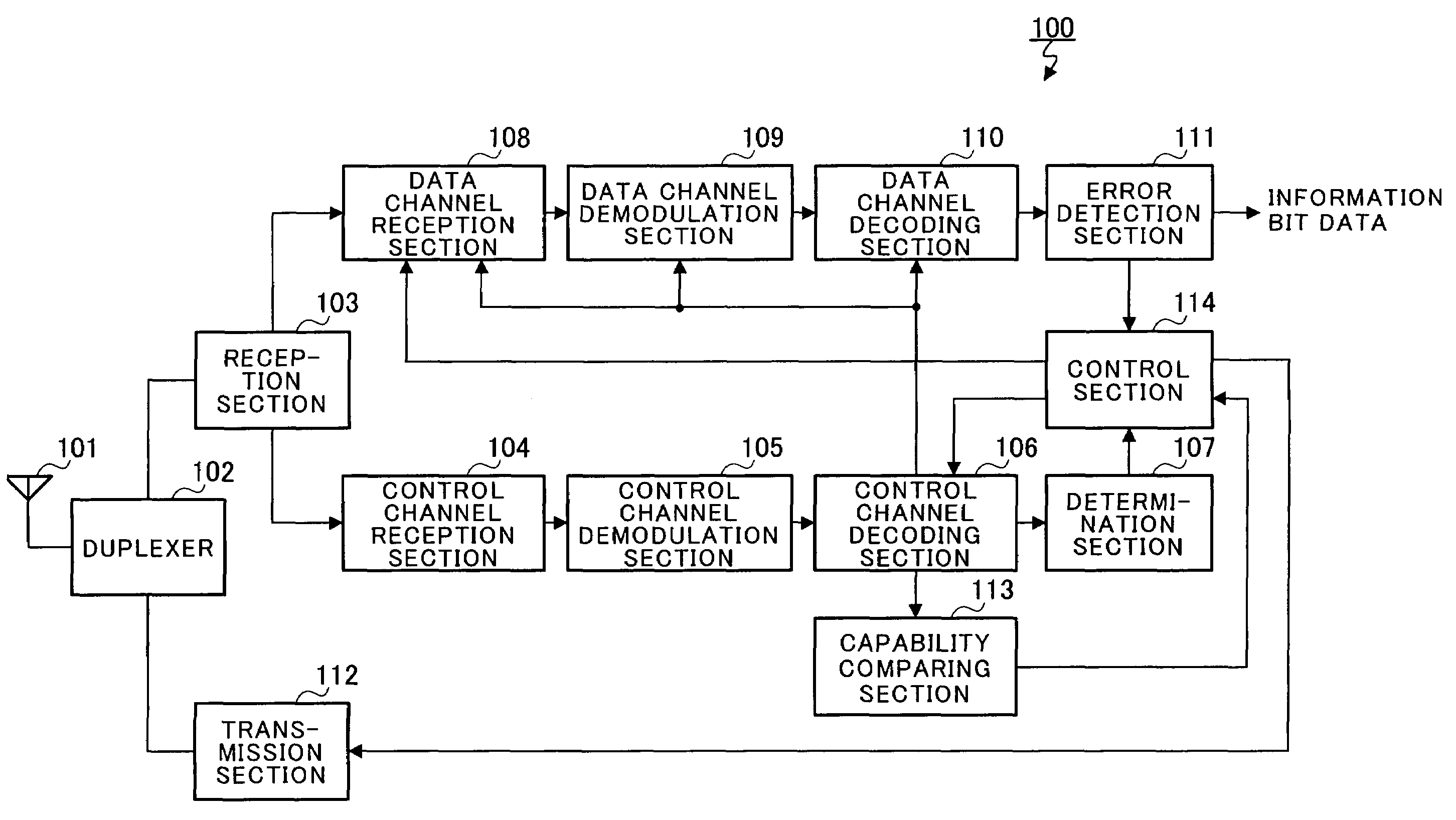
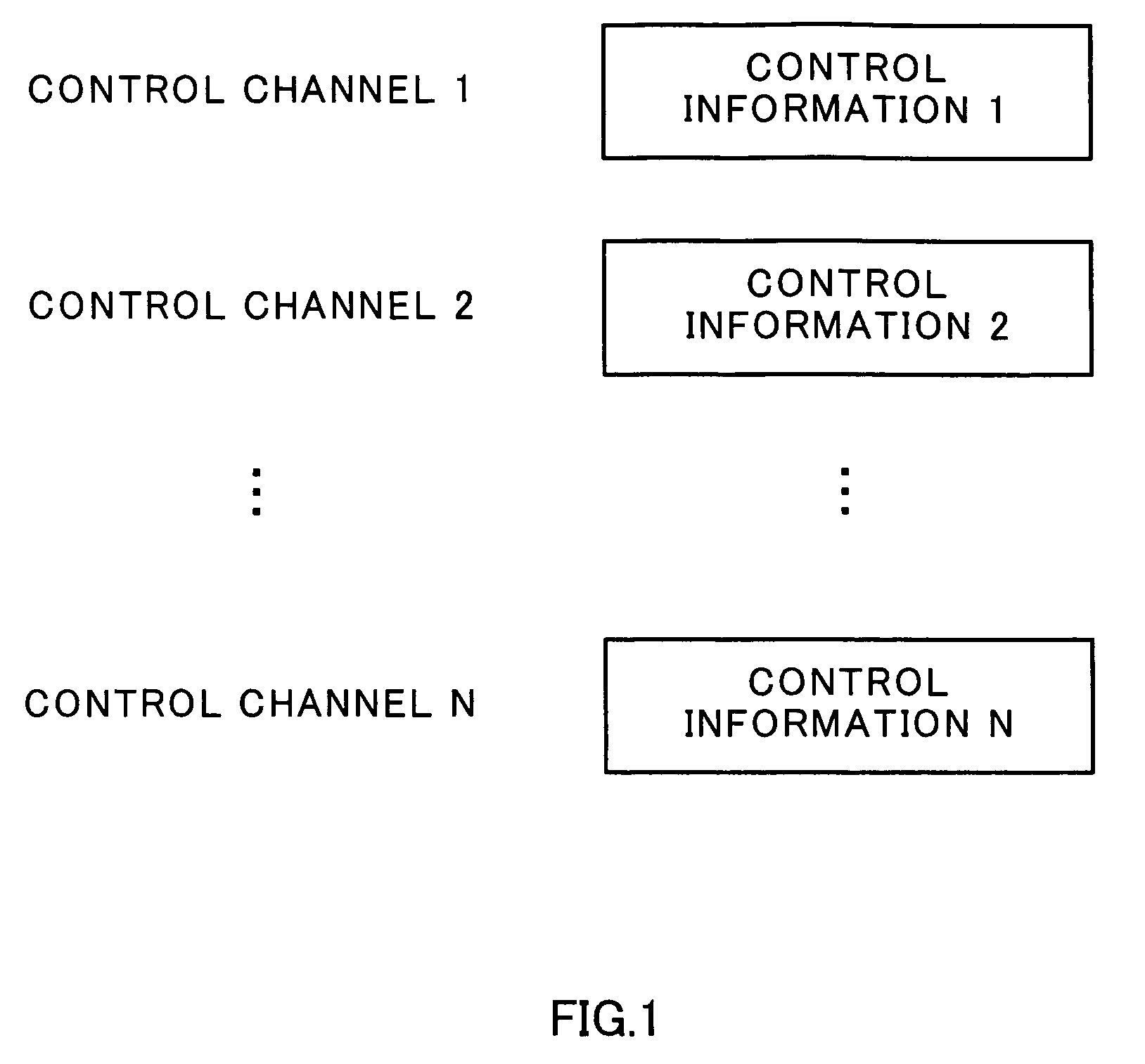
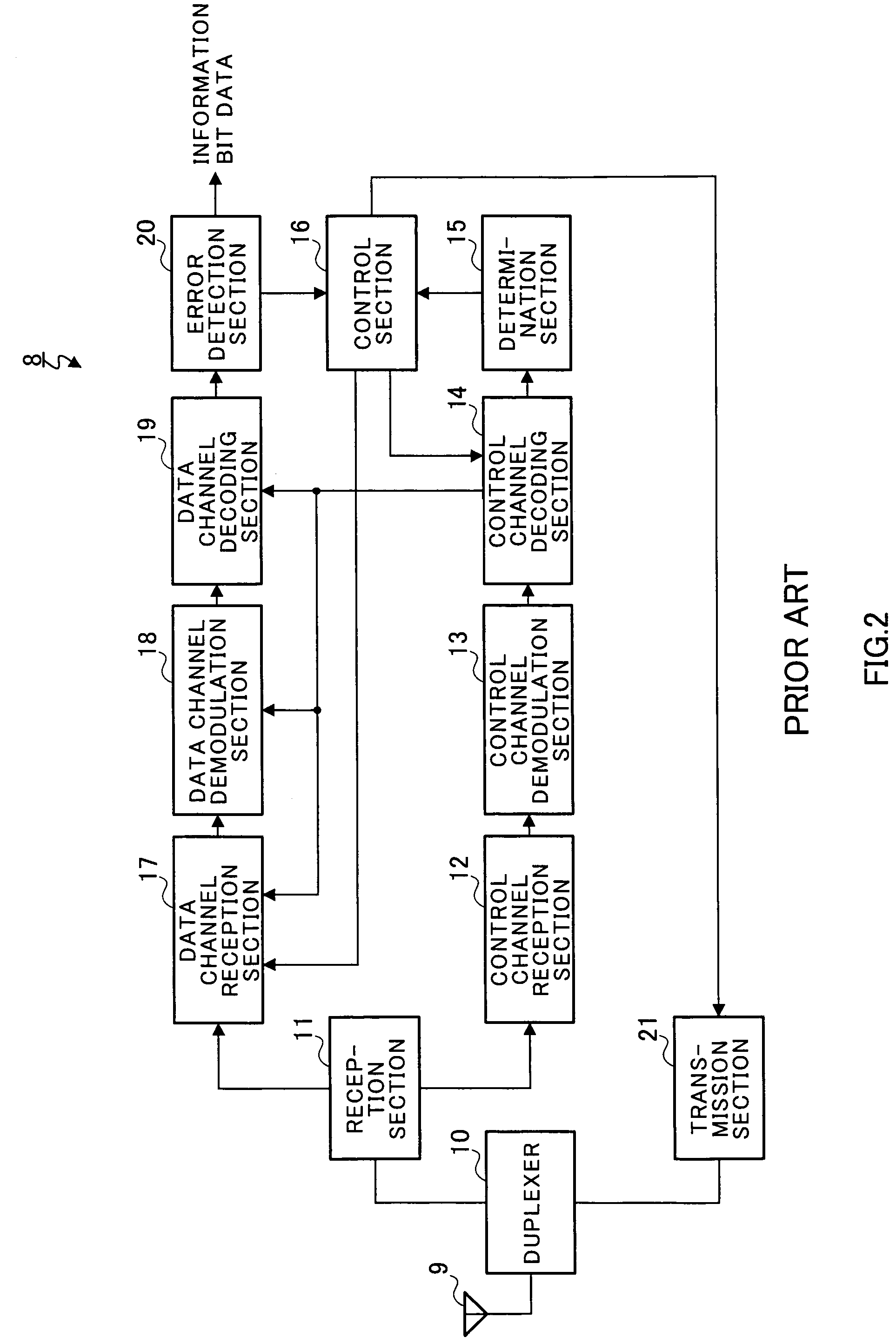
Radio reception system that inhibits transmission of acknowledgment or negative acknowledgment signal for a data channel when control information of a control channel exceeds a reception capability of a receiver
InactiveUS7200788B2Preventing executionError prevention/detection by using return channelNetwork traffic/resource managementTelecommunicationsRadio reception
Owner:PANASONIC CORP
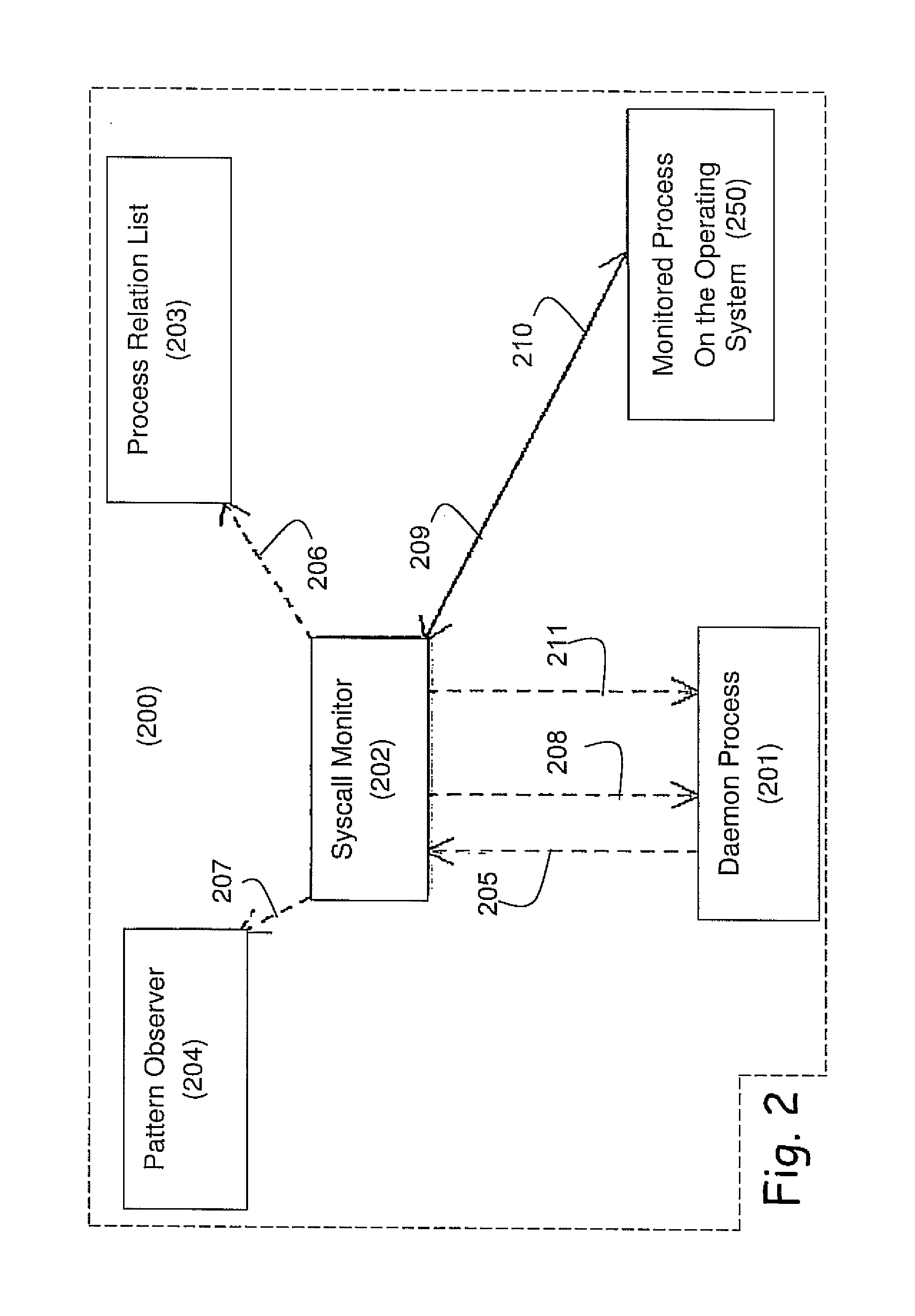
System and method for detection and prevention of host intrusions and malicious payloads
InactiveUS20130347111A1Preventing executionSame effectMemory loss protectionError detection/correctionComputer hardwareComputer science
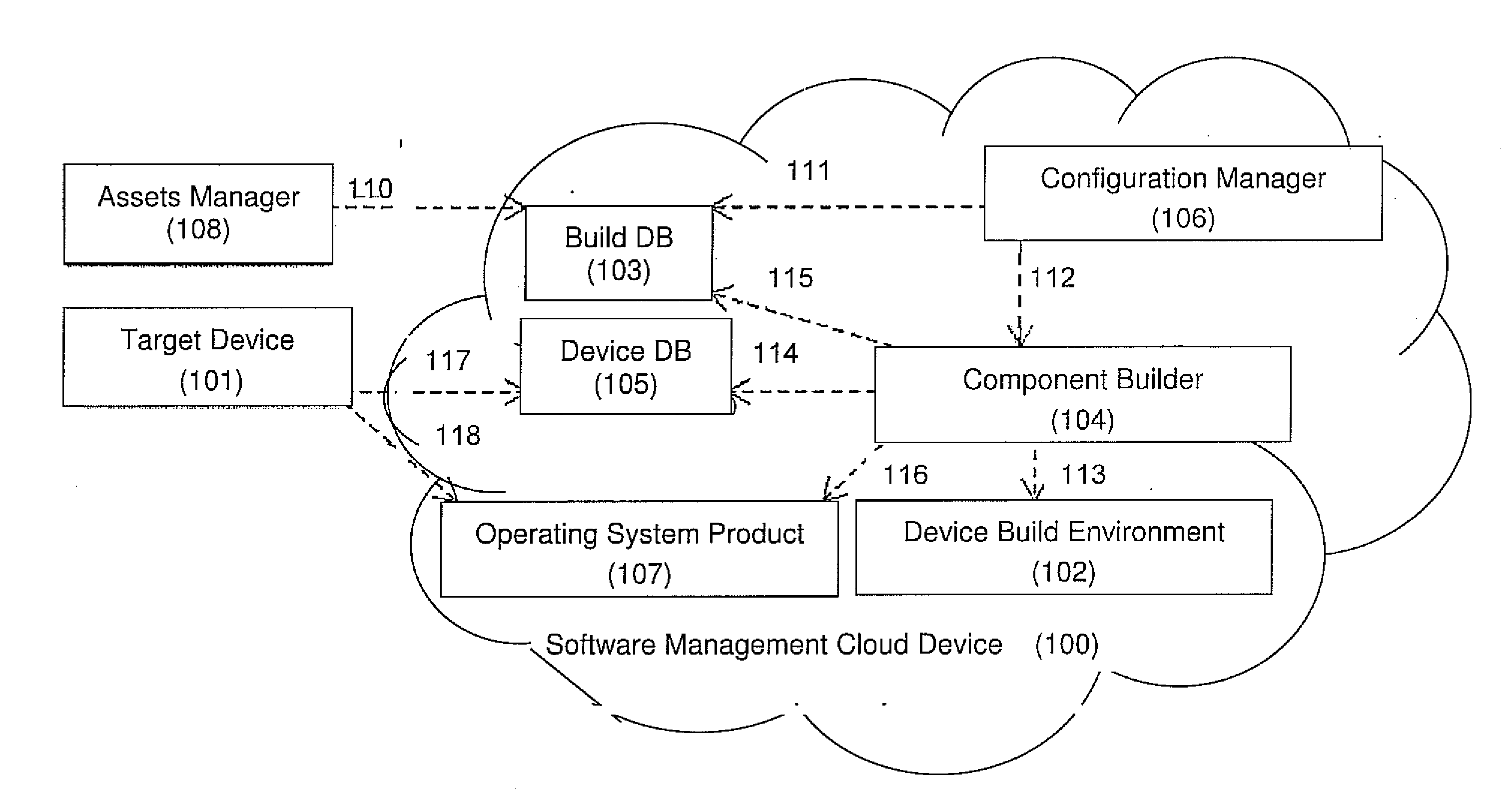
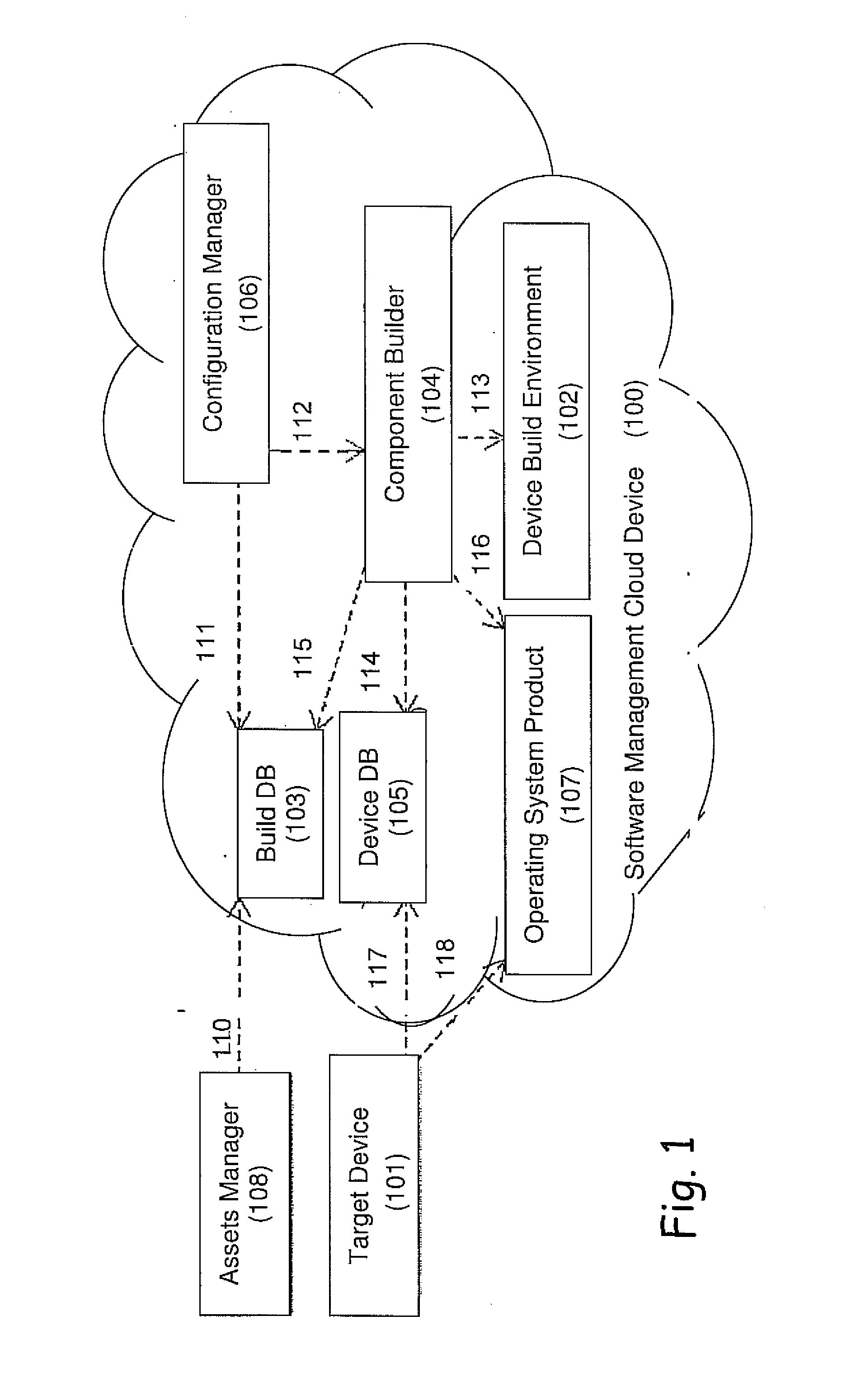
A computerized system for preventing host intrusions on a communication device. The device is wirelessly connected to a wireless communication network. The system includes a computer readable management software module configured to analyze malicious payloads. The management software module includes an asset manager module configured to assign updates to the communication device, a device database module configured to describe the communication device characteristics and a build database module configured to automate software builds of the communication device core operating system. The management software module also includes a component builder module configured to run a plurality of instruction sets to establish a build environment for the communication device according to the communication device characteristics, a configuration manager module configured to build the instruction sets and an operating system product module configured by the build database module as part of a build process triggered by the asset manager module.
Owner:ZIMPERIUM INC
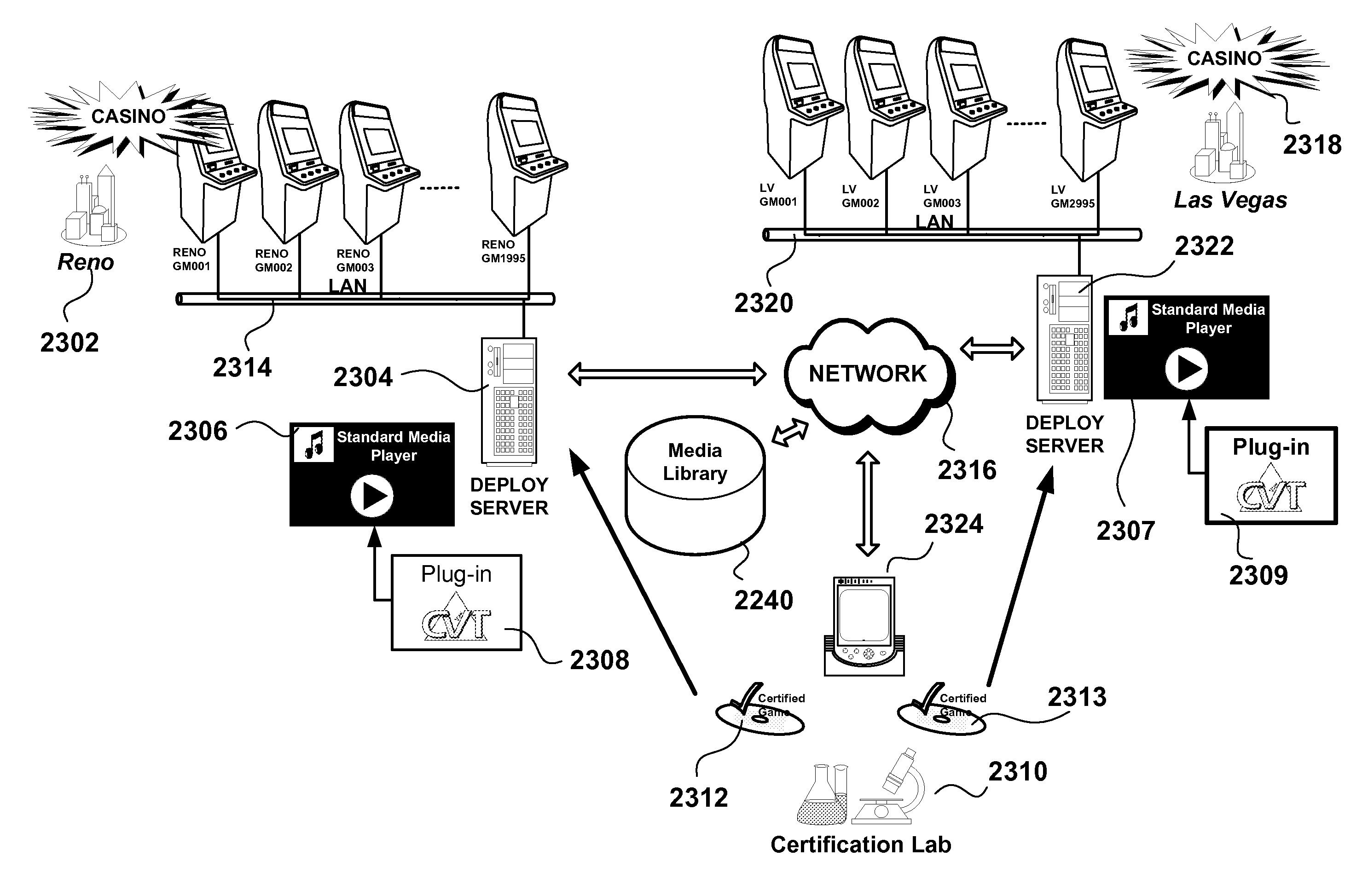
Regulated gaming - agile media player for controlling games
ActiveUS20070191108A1Overcome limitationsPreventing executionUser identity/authority verificationUnauthorized memory use protectionText entryCD-ROM
A method for agile downloading and controlling regulated games in a distributed gaming system, the games being selected from a large library of certified games. A preferred embodiment of the method is a plug-in for the ubiquitous personal media player whereby the regulated games distributed on CD-ROM are catalogued in the media library through a “rip-like” operation and are downloaded to the gaming machines through a “sync-like” operation much like for downloading music, photos and movies to an iPod®. Preventing execution of non authorized games is enforced in the gaming machine through software restriction policy (SRP) much like digital right media (DRM) prevents listening or viewing illegal media files. Other media content such as promotional photos, videos and audio may be downloaded and controlled through the same casino media player. A free-text entry selection accelerator enables rapid selection of media titles, game titles and target gaming machines according to a wide range of indexed embedded information and metadata. Operators already acquainted with downloading media content to portable media player such as the Apple iPod®, Microsoft Zune® and other digital music players will feel immediately at ease with downloading regulated gaming content to gaming machines via the same paradigm, from a control workstation in the central computer room or directly at any location on the floor using a mobile PC.
Owner:IGT
Malware prevention system monitoring kernel events
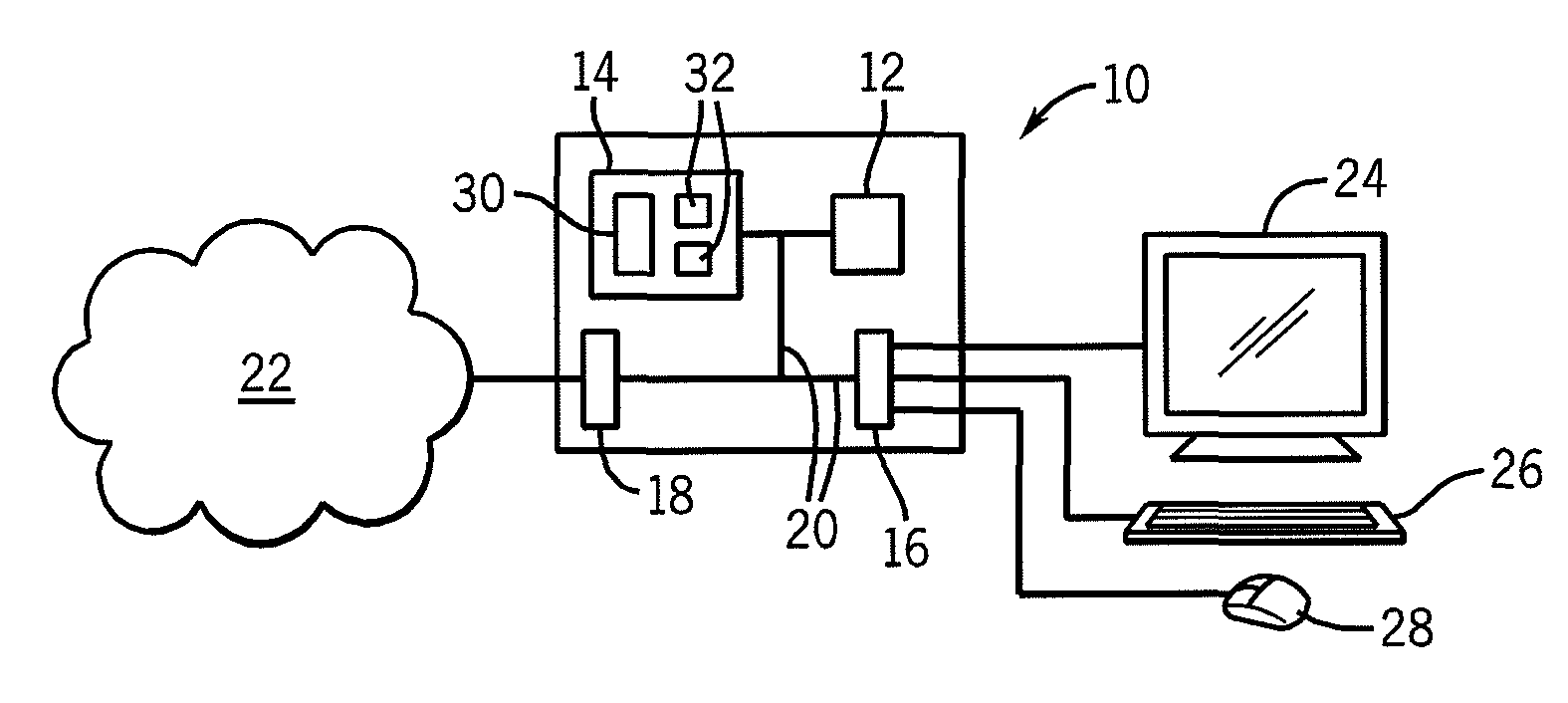
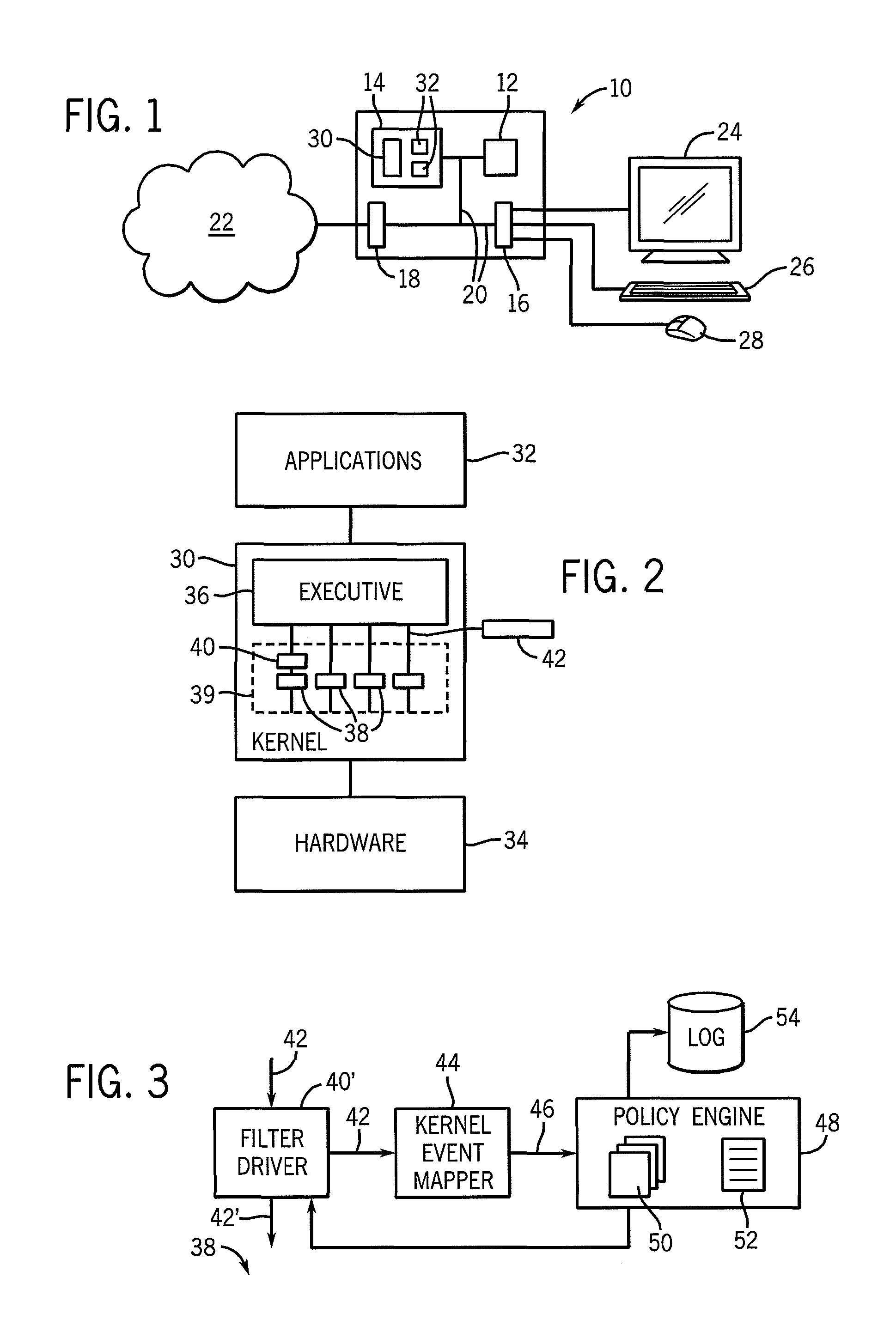
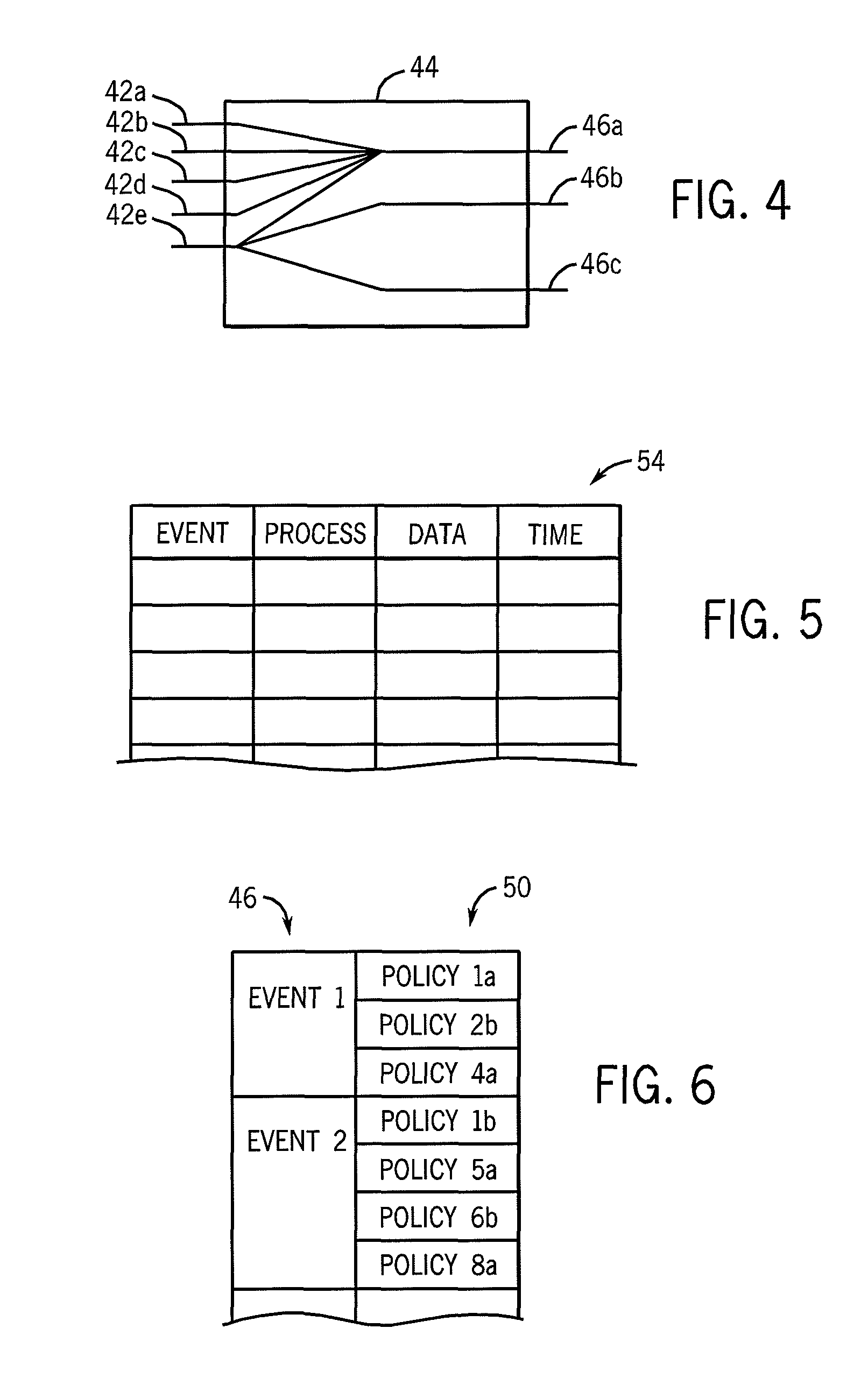
ActiveUS8065728B2Reduce overheadPreventing executionMemory loss protectionError detection/correctionKernel levelMalware
A malware prevention system monitors kernel level events of the operating system and applies user programmable or preprepared policies to those events to detect and block malware.
Owner:WISCONSIN ALUMNI RES FOUND
Updatable firmware having boot and/or communication redundancy
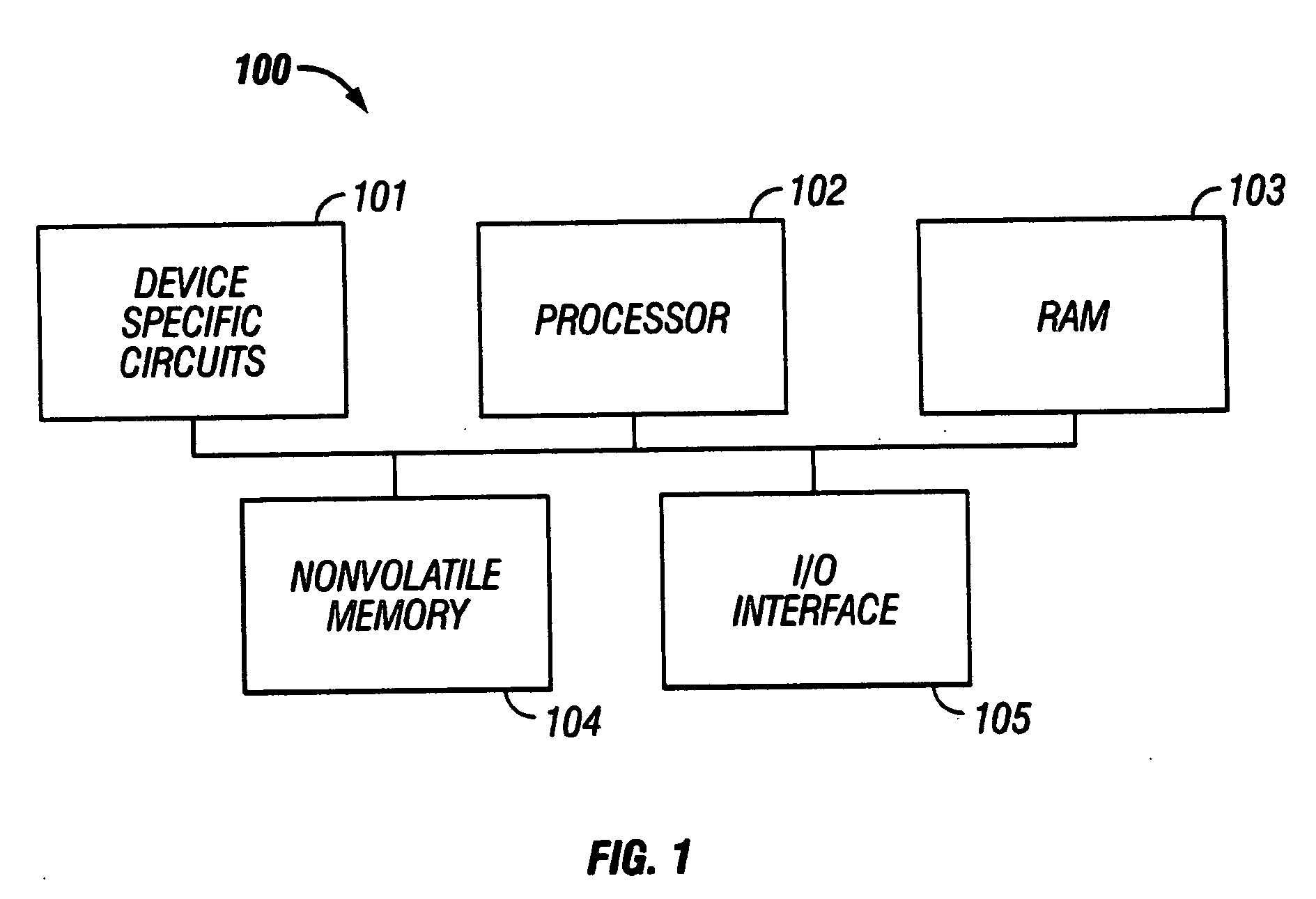
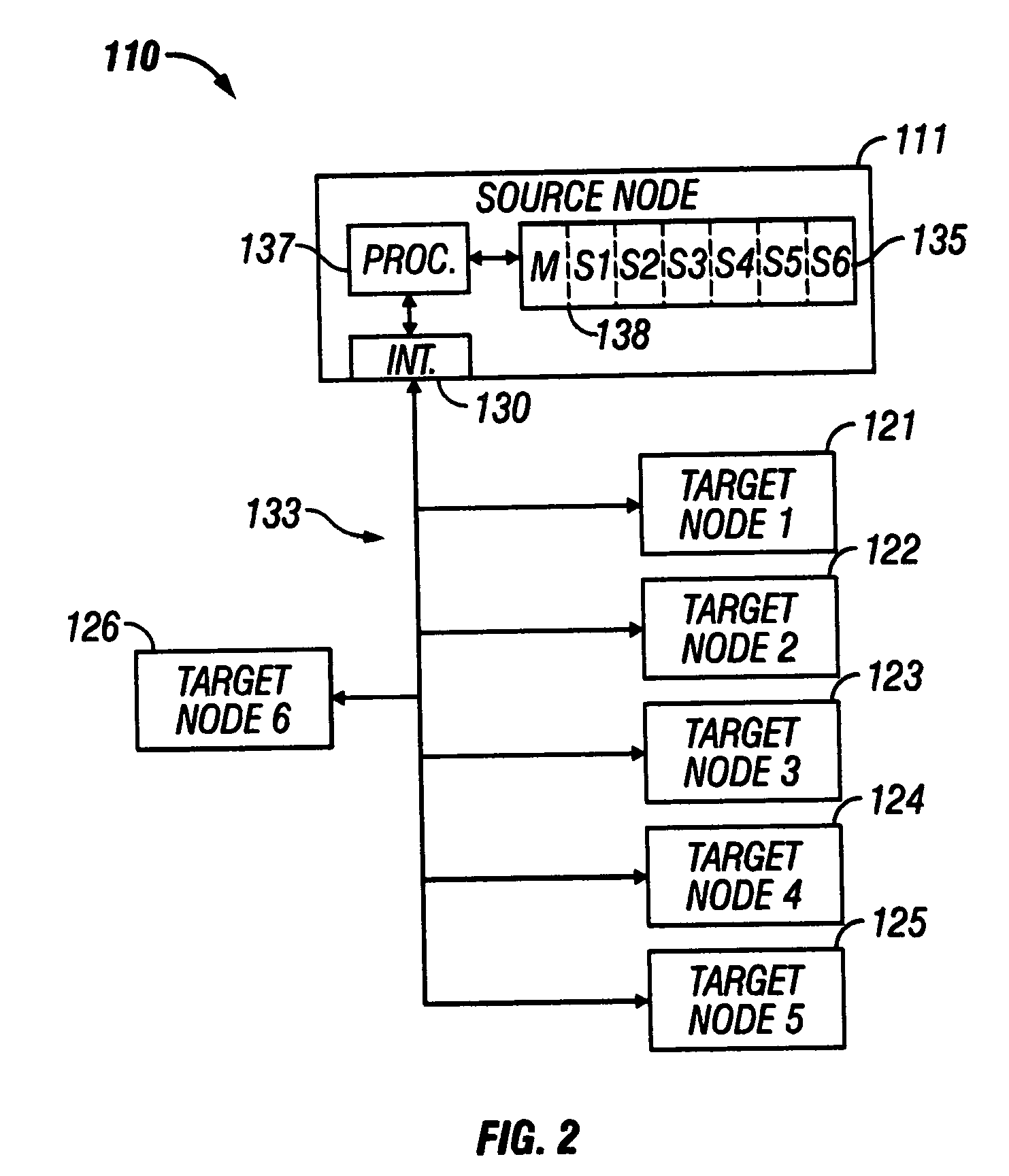
InactiveUS20050251673A1Preventing executionError detection/correctionDigital computer detailsObject codeProcessor node
A distributed nodal system with a source computer processor node storing program code for target node(s). A target node has an updatable firmware memory storing program code for operating a target processor. The target code comprises application code for controlling an embedded device, primary communication code for communicating with a network, backup communication code also having copy code for copying code between portions of the firmware memory, and primary boot code for booting the target processor and having check code. The check code determines whether the primary communication code is corrupted, and if it is corrupted, employs the copy code to overwrite the primary communication code with the backup code. If uncorrupted, the check code determines whether the application code is corrupted, and if corrupted, prevents execution of the code.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com