Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
842results about How to "Avoid prolonged use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
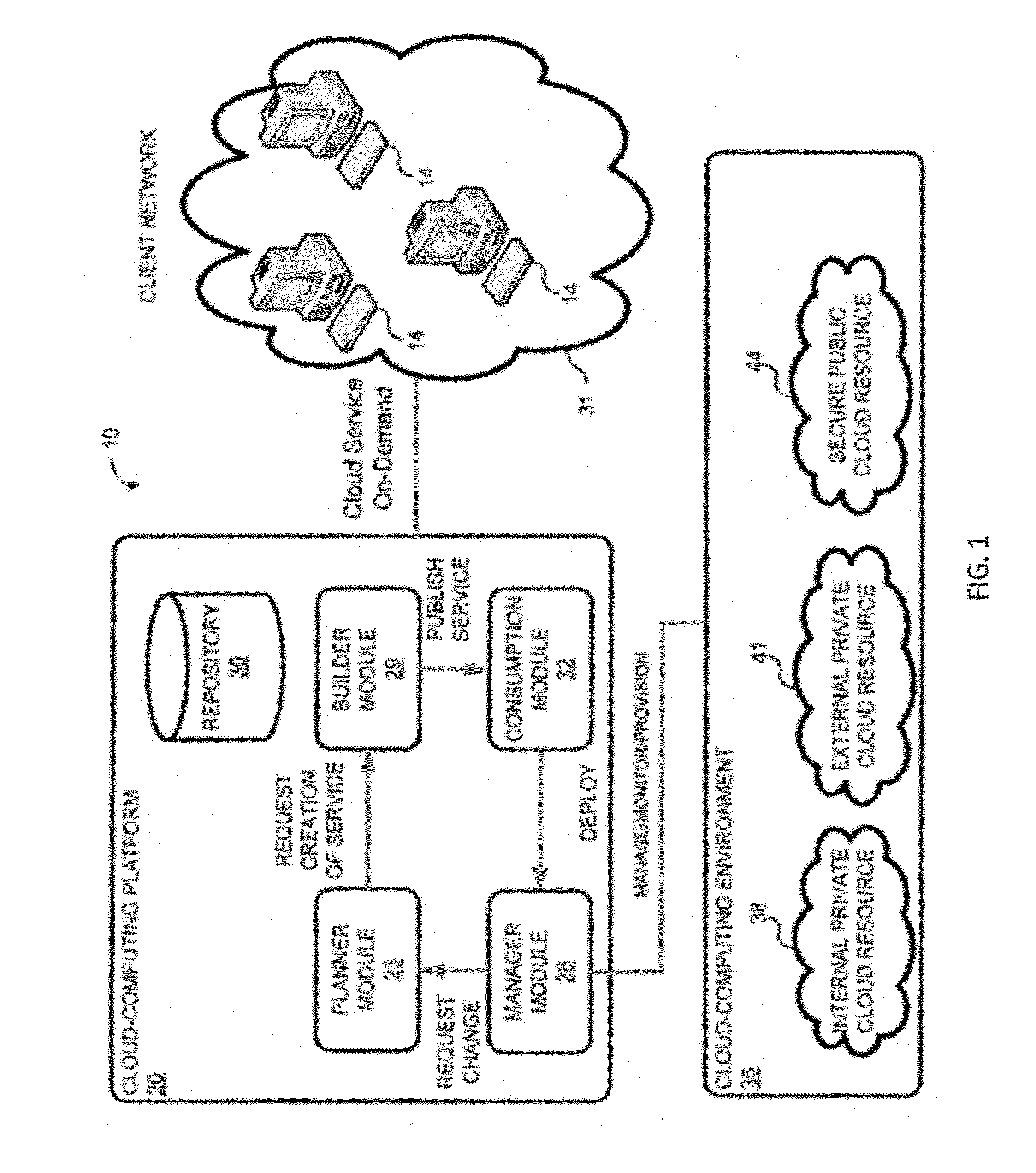
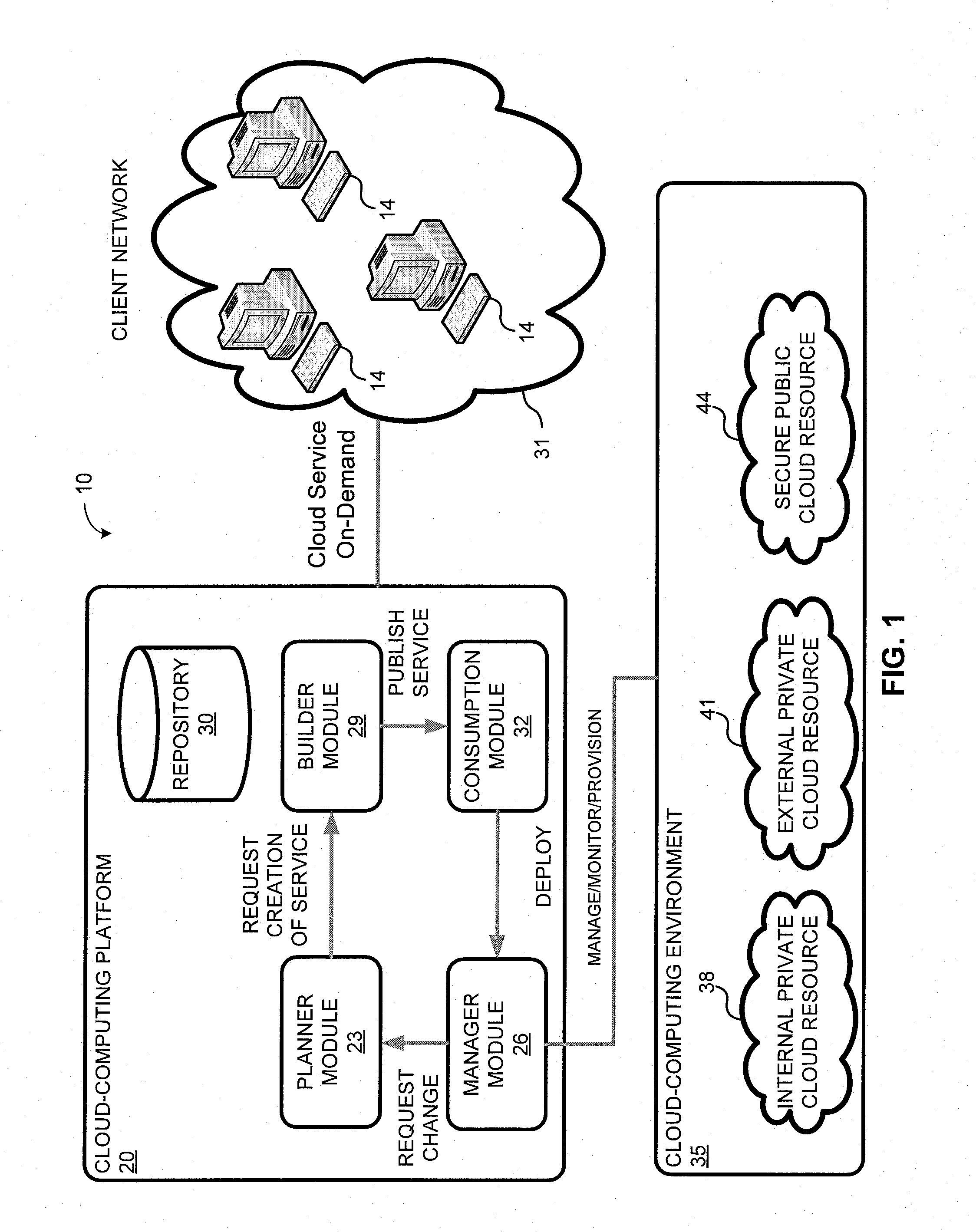
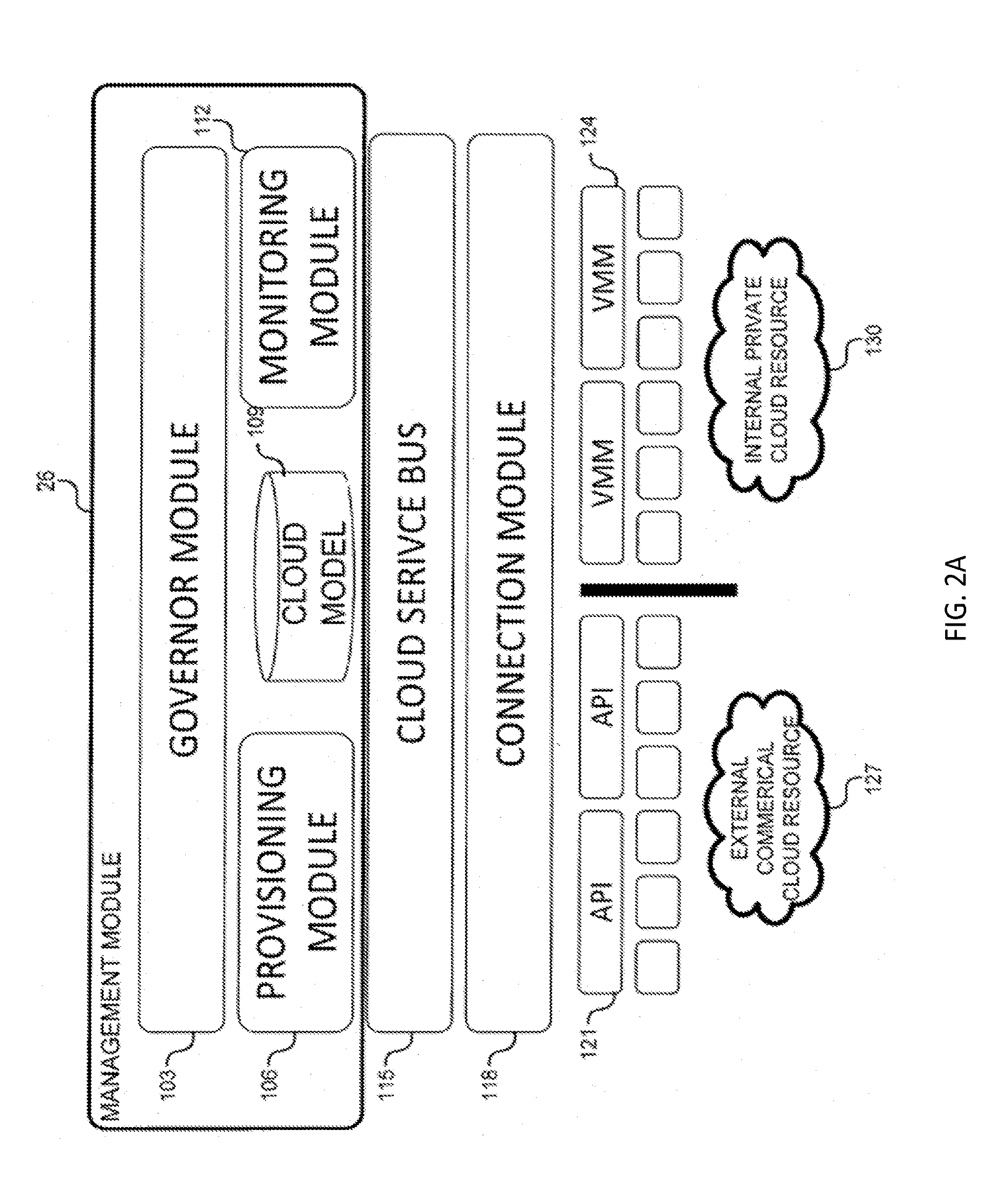
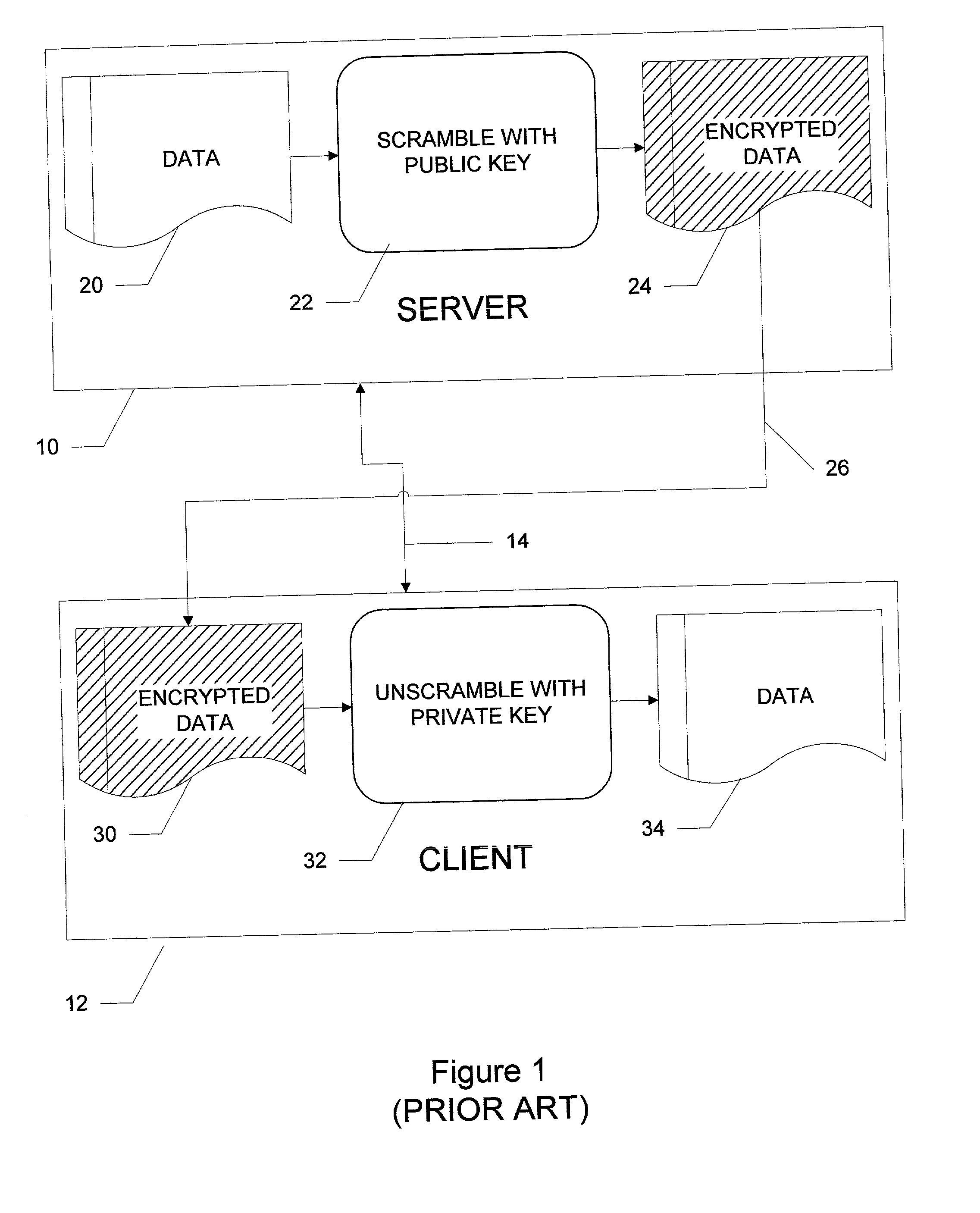
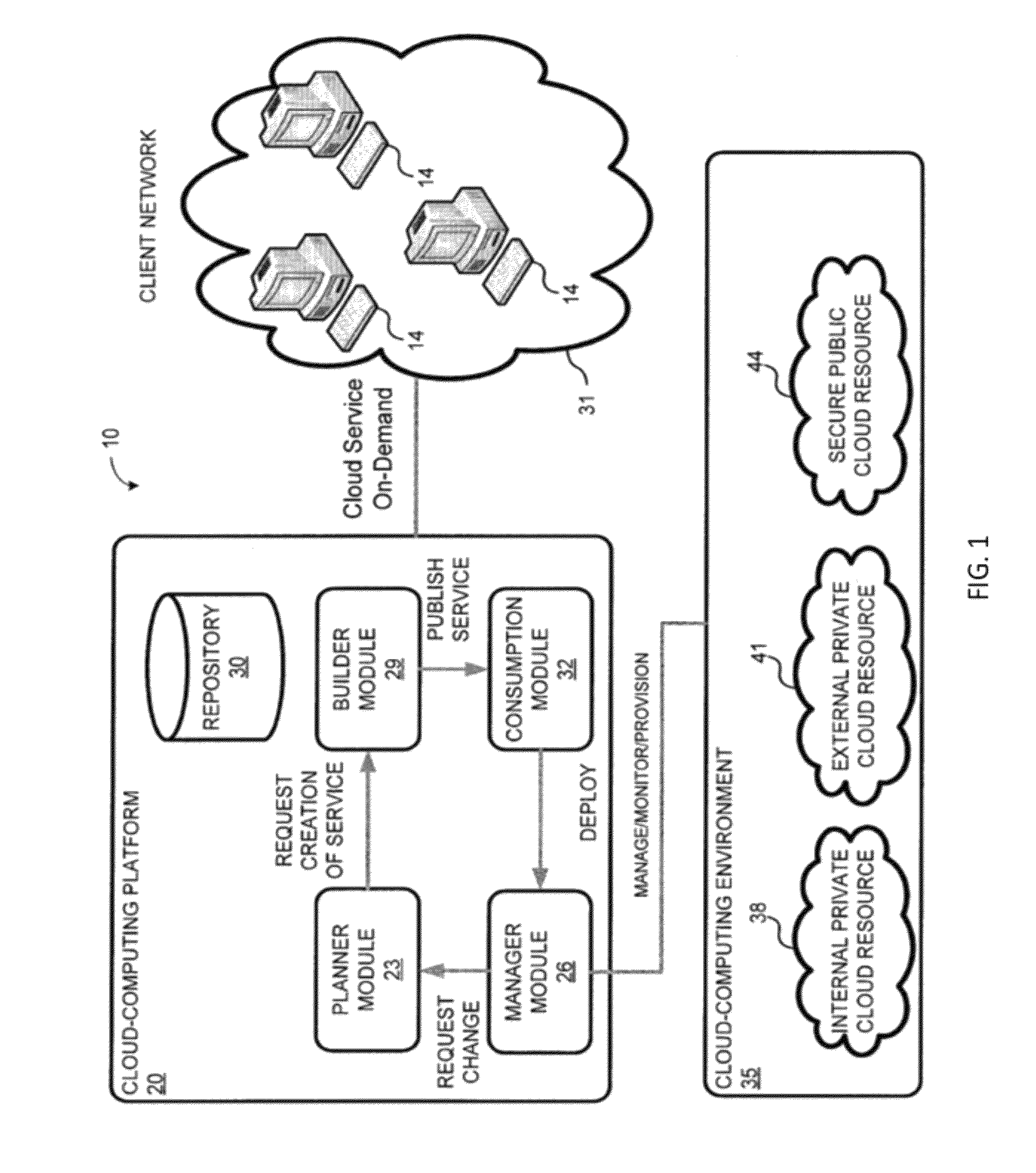
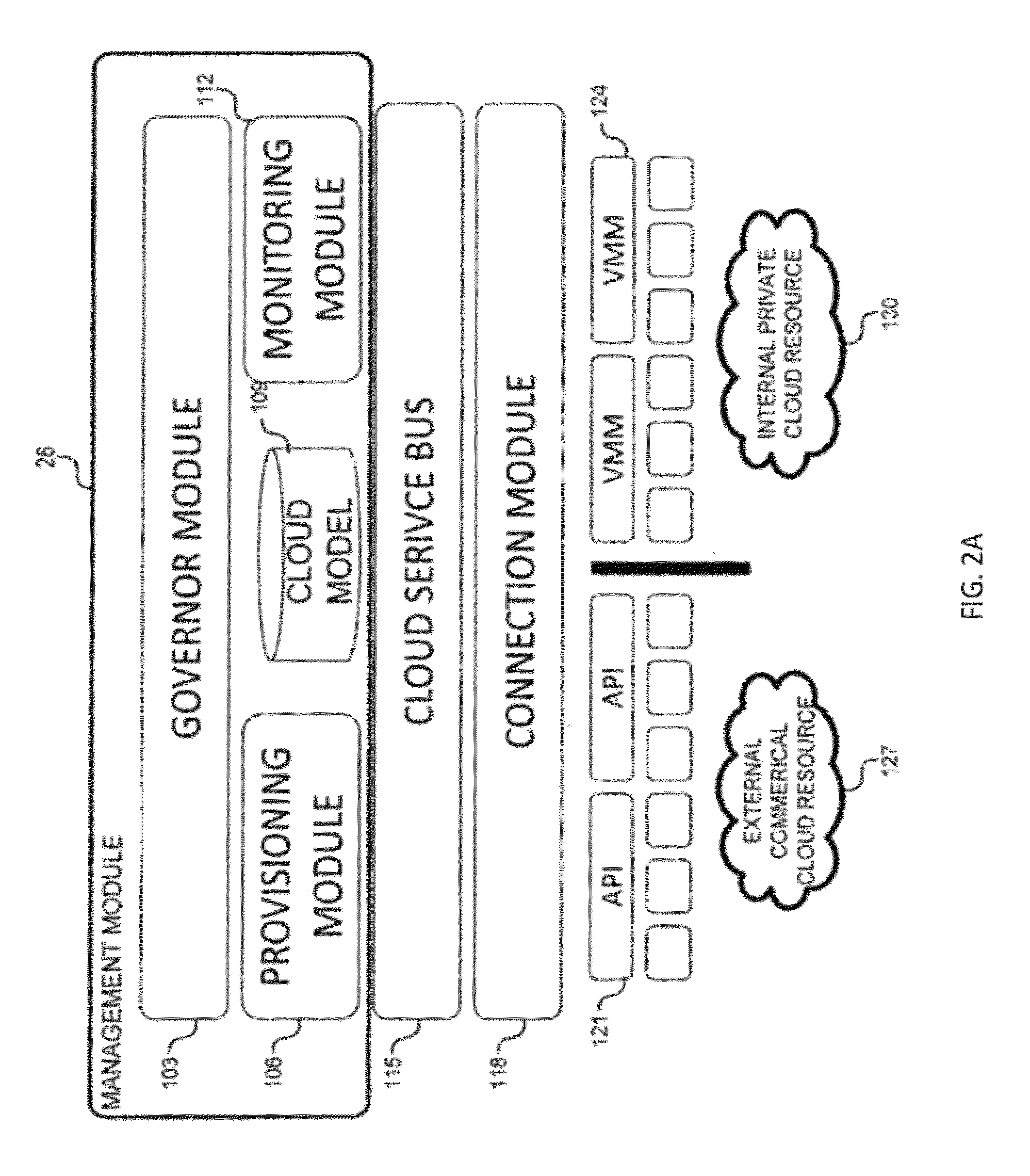
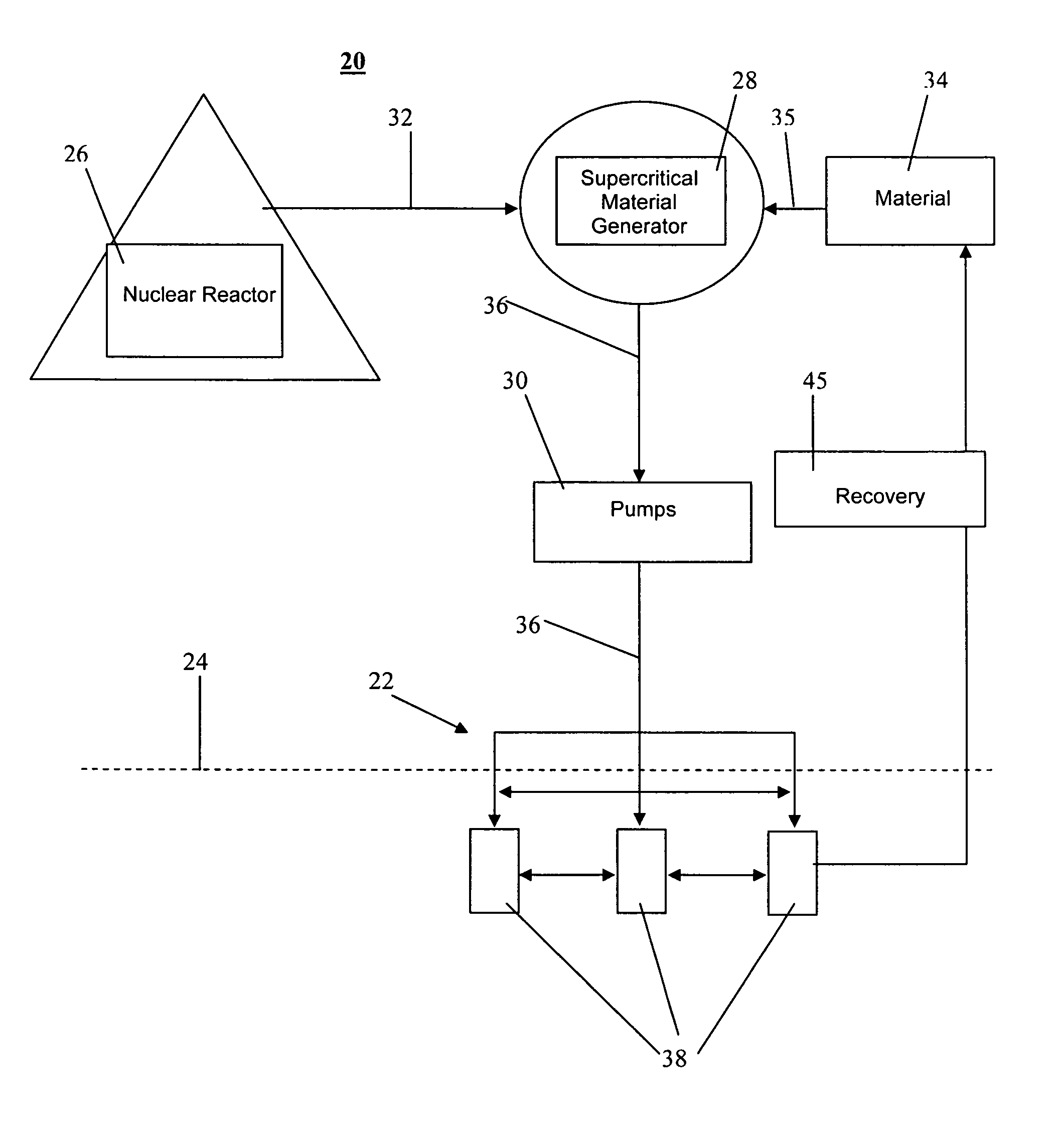
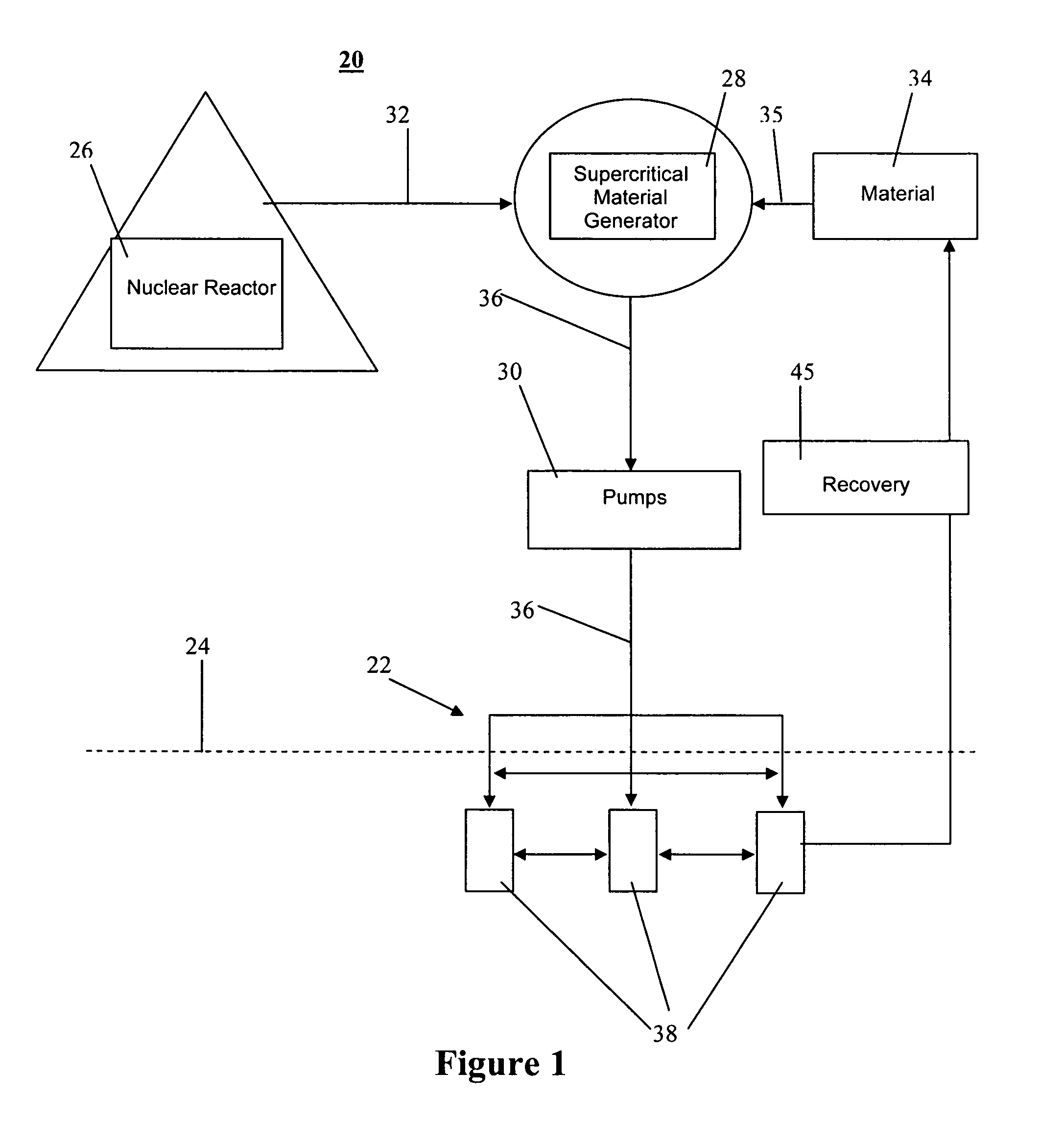
System and method for a cloud computing abstraction layer with security zone facilities
ActiveUS20120185913A1Rapid and dynamic deployment and scalingShorten the timeComputer security arrangementsHybrid transportVirtualizationAbstraction layer
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload. This allows a developer to define a security zone and to apply at least one type of security policy with respect to the security zone including the type of security zone policy in the metamodel framework such that the type of security zone policy can be associated with the software workload upon development of the software workload, and if the type of security zone policy is associated with the software workload, automatically applying the security policy to the software workload when the software workload is deployed within the security zone.
Owner:DXC US AGILITY PLATFORM INC
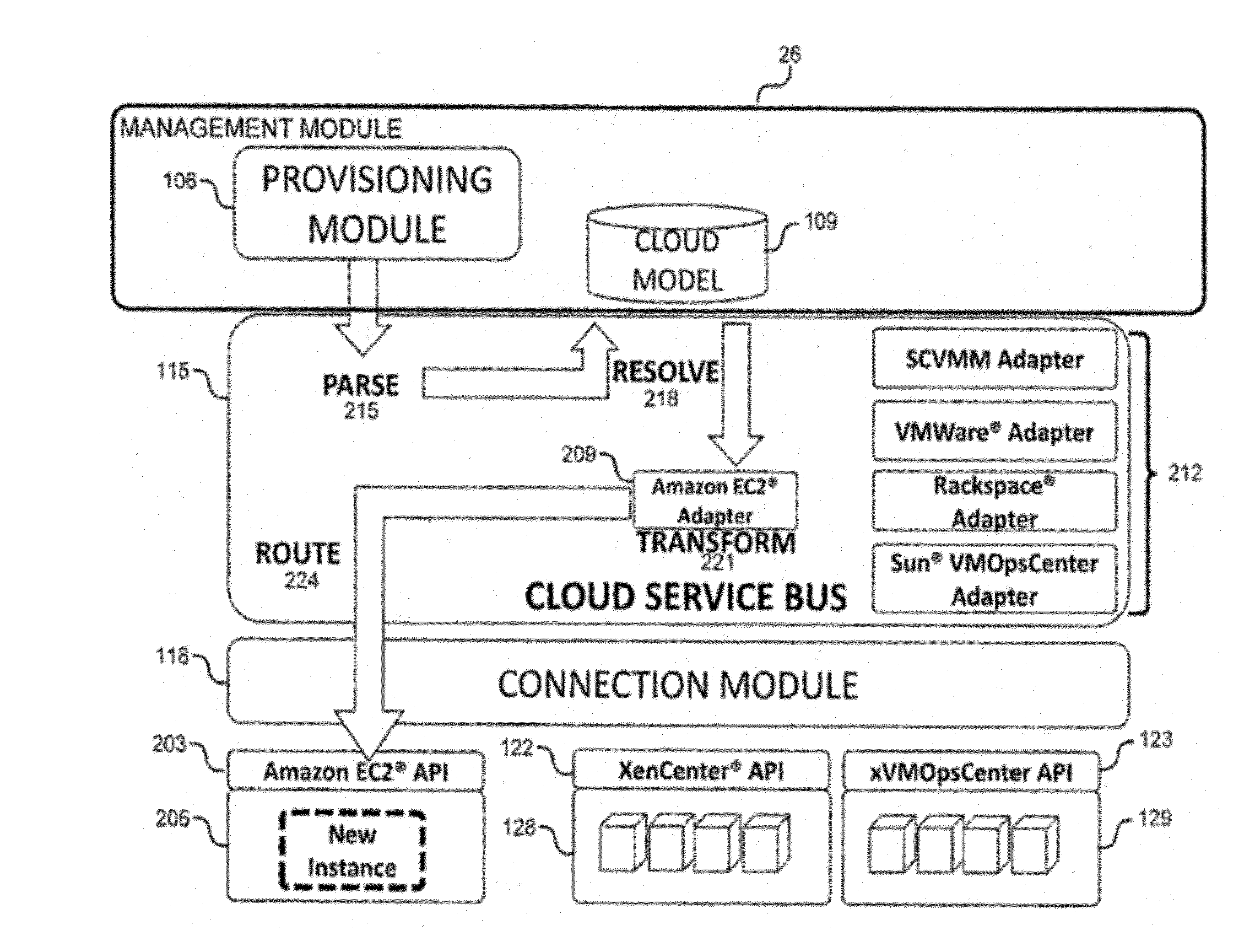
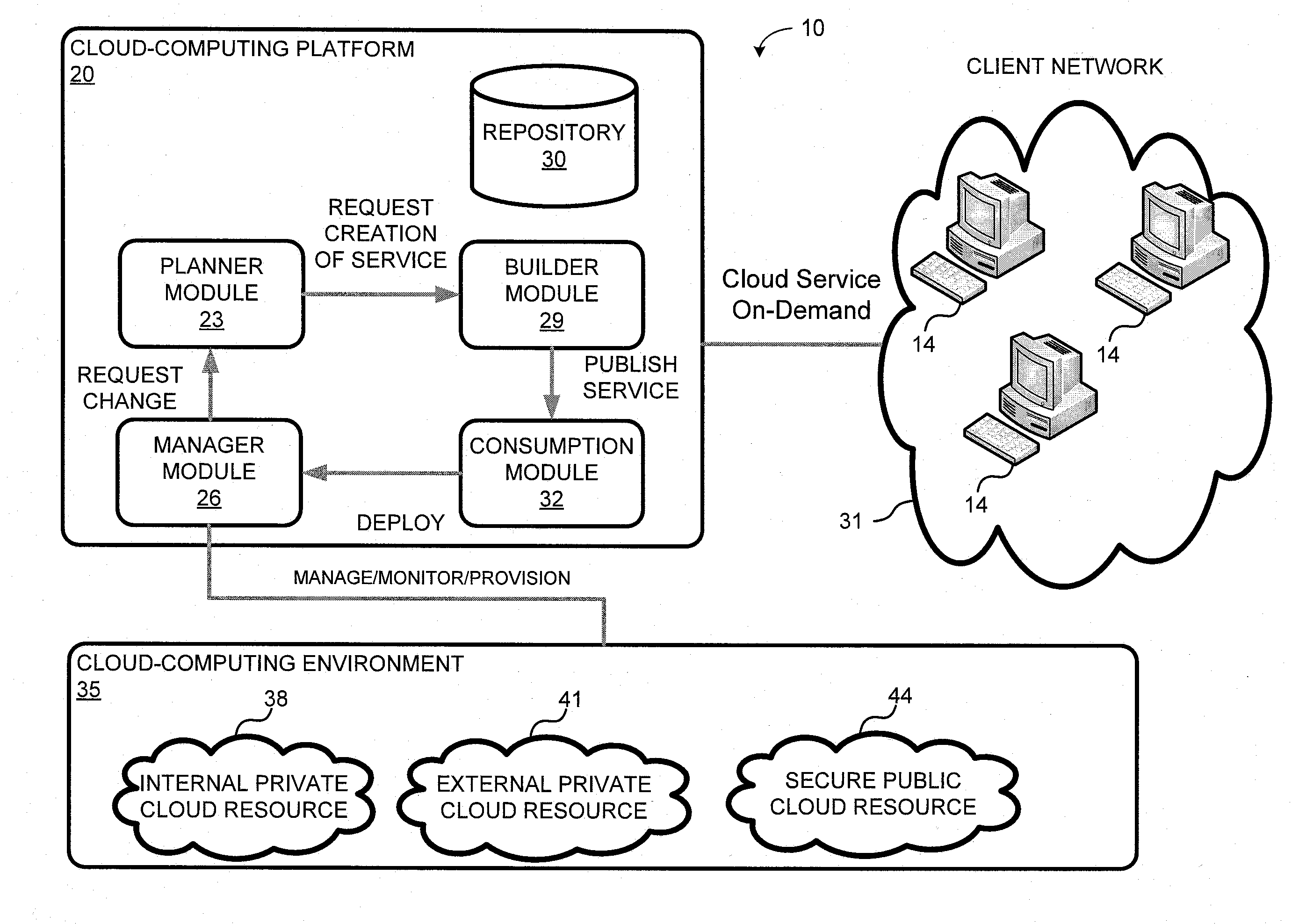
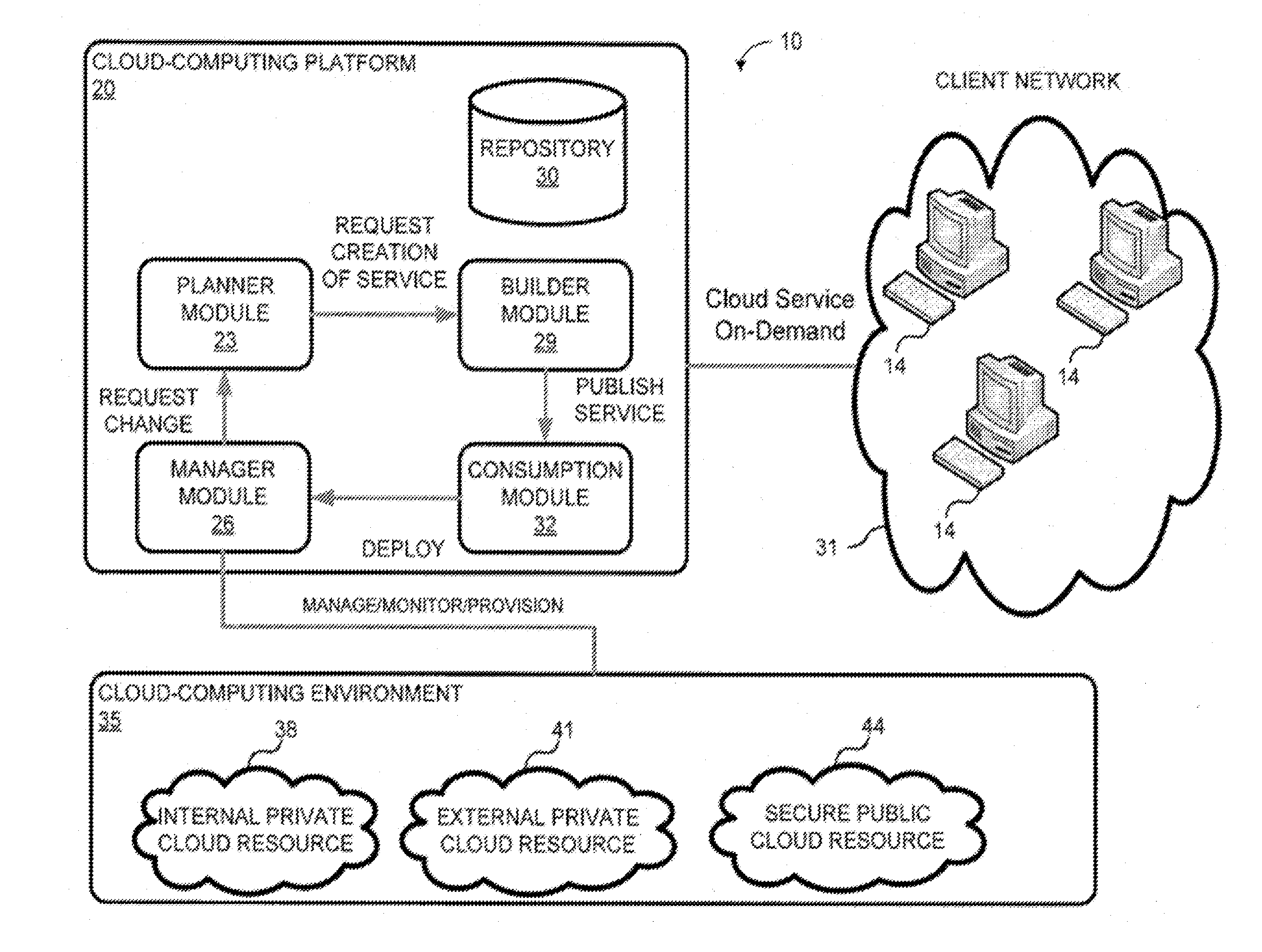
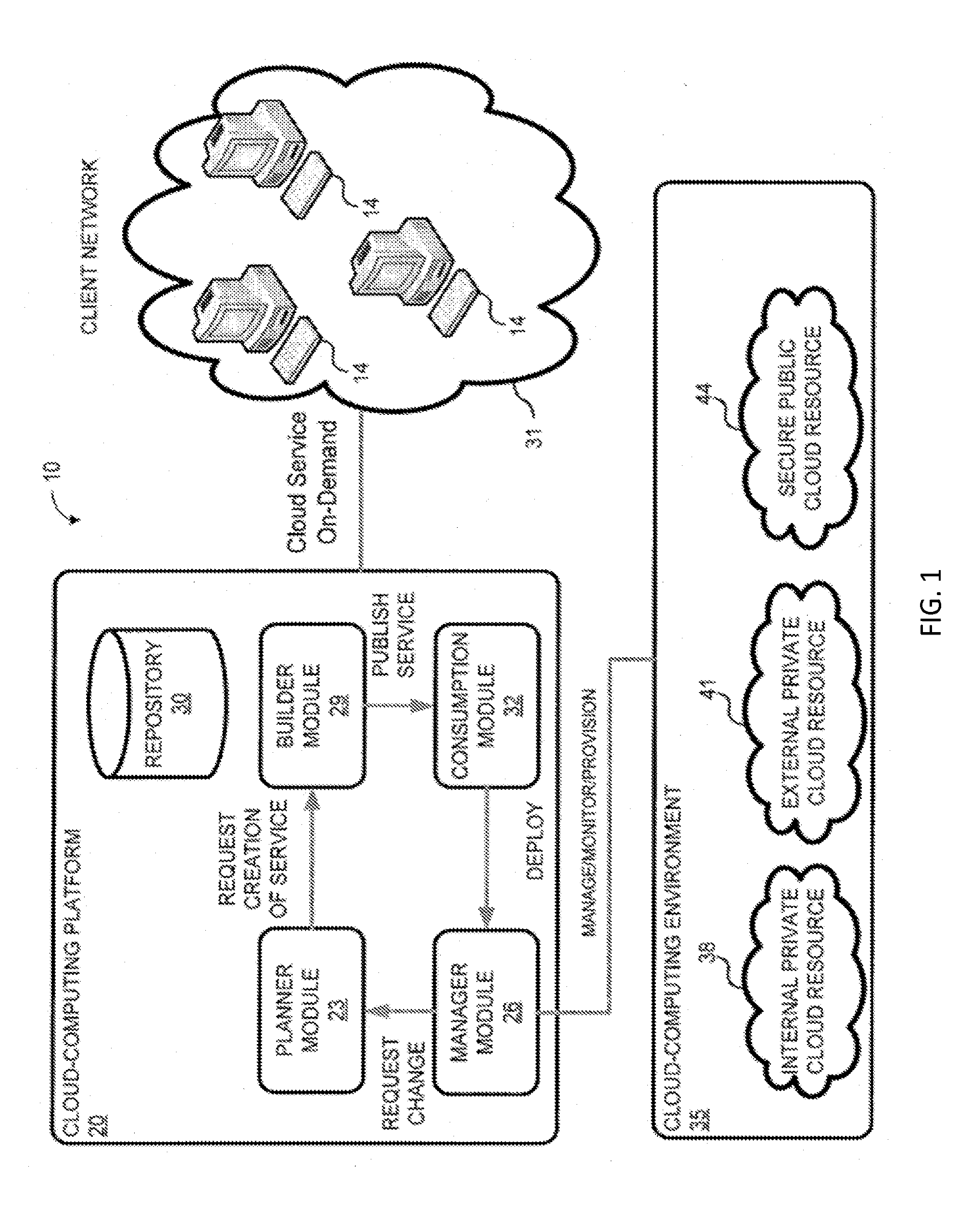
System and method for a cloud computing abstraction layer
ActiveUS20110231899A1Rapid and dynamic deployment and scalingShorten the timeDigital computer detailsComputer security arrangementsAbstraction layerWorkload
According to one system of the invention, the system provides a cloud-computing service from a cloud-computing environment comprising a plurality of cloud-computing resources. The system may comprise: a management module configured to manage a cloud-computing resource of the plurality of cloud-computing resources as a cloud-computing service, wherein the cloud-computing service performs a computer workload; an adapter configured to connect to the cloud-computing resource to the system and translate a management instruction received from the management module into a proprietary cloud application program interface call for the cloud-computing resource; a cloud service bus configured to route the management instruction from the management module to the adapter; a consumption module configured to allow a user to subscribe the cloud-computing service; a planning module configured to plan the cloud-computing service; and a build module configured to build the cloud-computing service from the cloud-computing resource and publish the cloud-computing service to the consumption module.
Owner:DXC US AGILITY PLATFORM INC
Method and kit for imaging and treating organs and tissues
InactiveUS6331175B1High resolutionStrong specificityElectrotherapyNanomedicineMammalHypoplastic genitalia
Provided are methods and compositions for detecting and treating normal, hypoplastic, ectopic or remnant tissue, organ or cells in a mammal. The method comprises parenterally injecting a mammalian subject, at a locus and by a route providing access to above-mentioned tissue or organ, with an composition comprising antibody / fragment which specifically binds to targeted organ, tissue or cell. The antibody / fragment may be administered alone, or labeled or conjugated with an imaging, therapeutic, cytoprotective or activating agent.
Owner:IMMUNOMEDICS INC
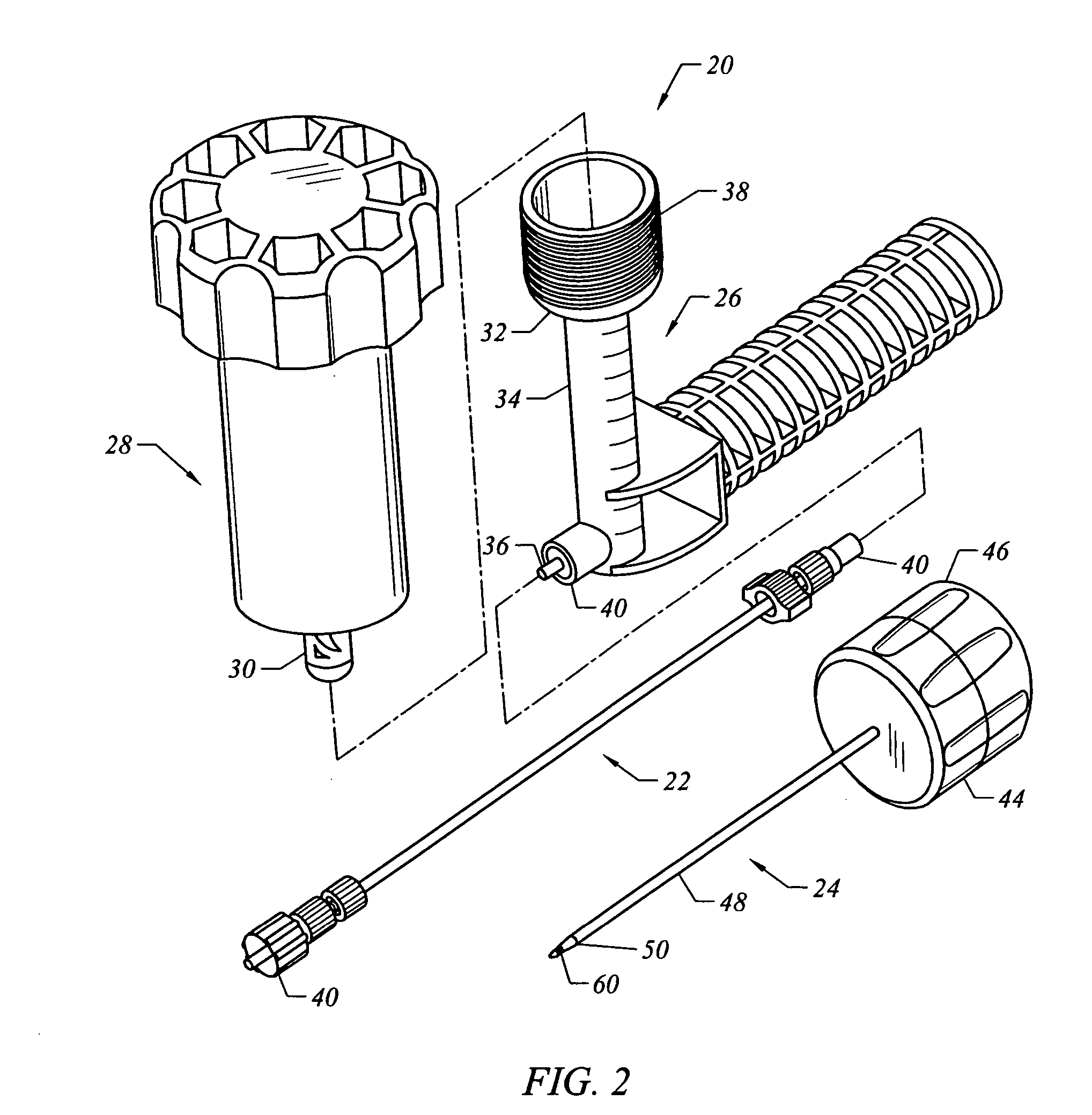
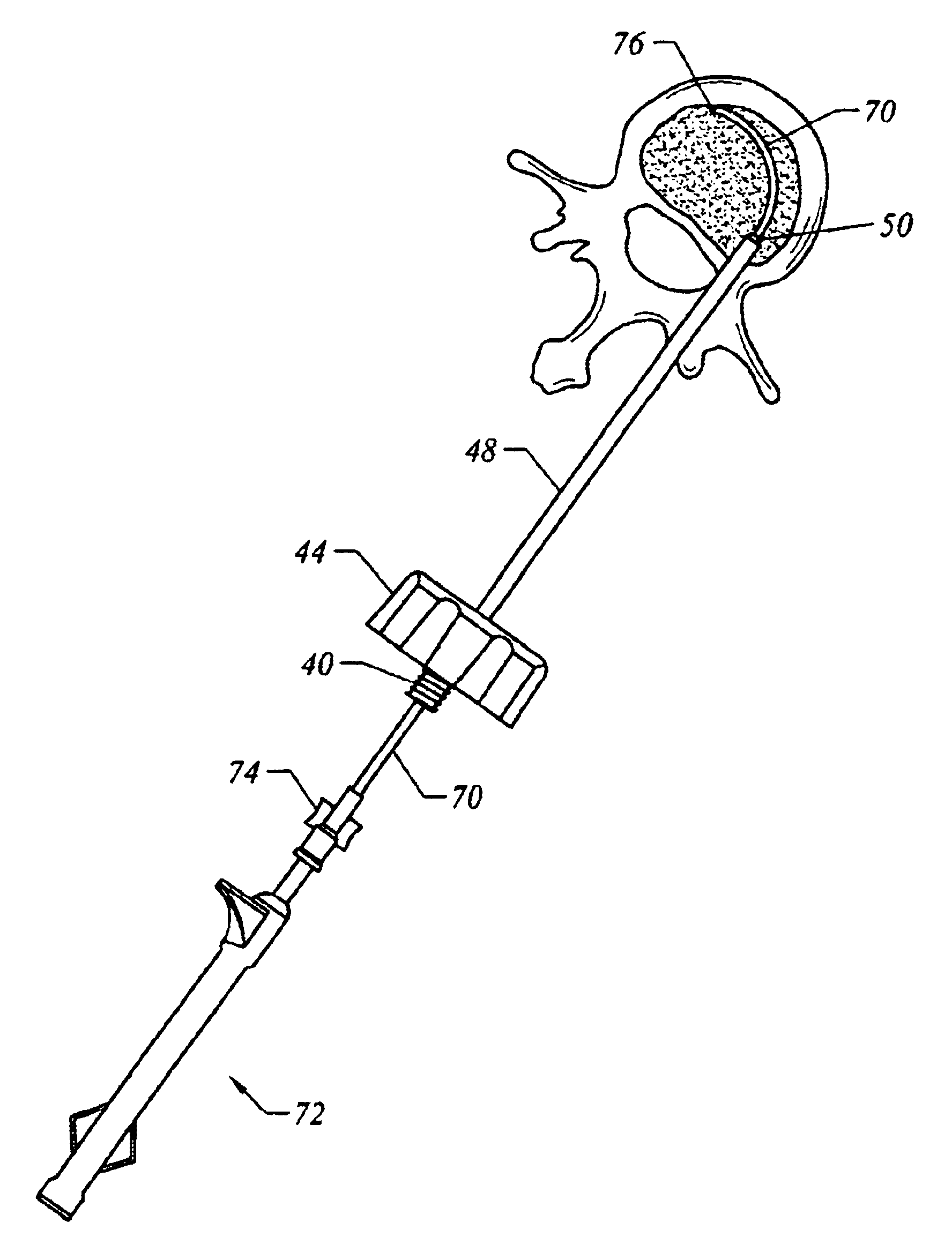
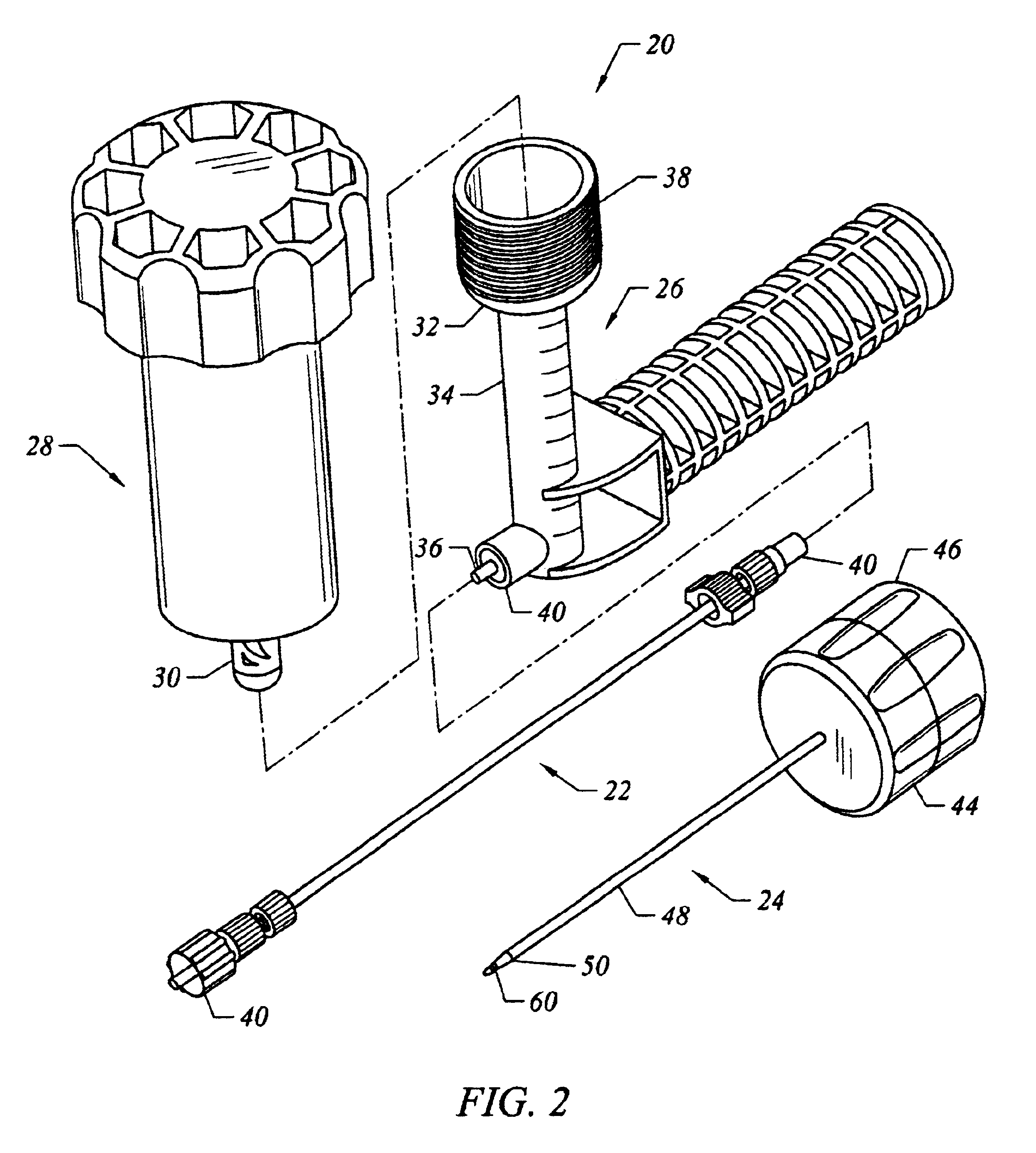
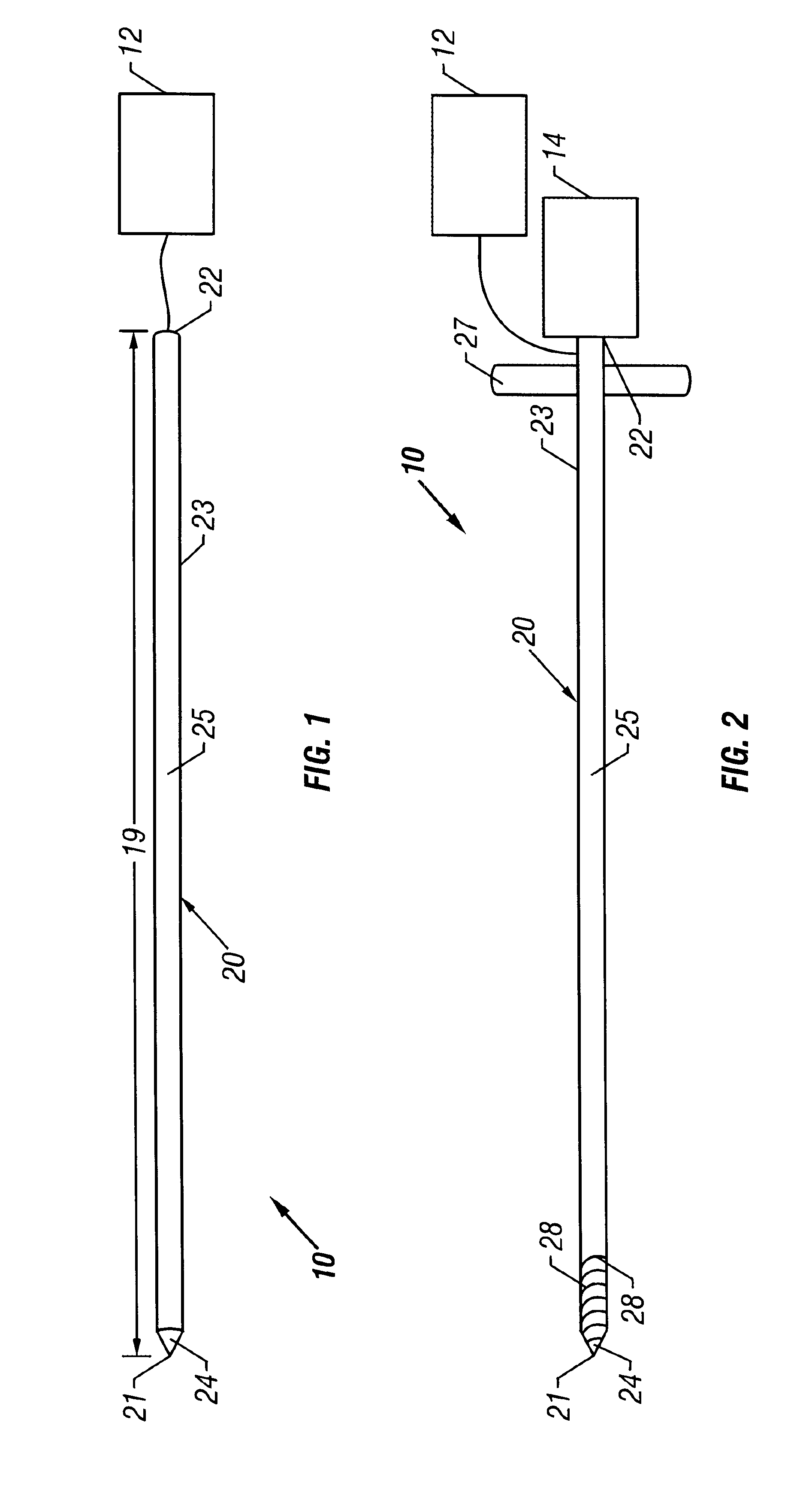
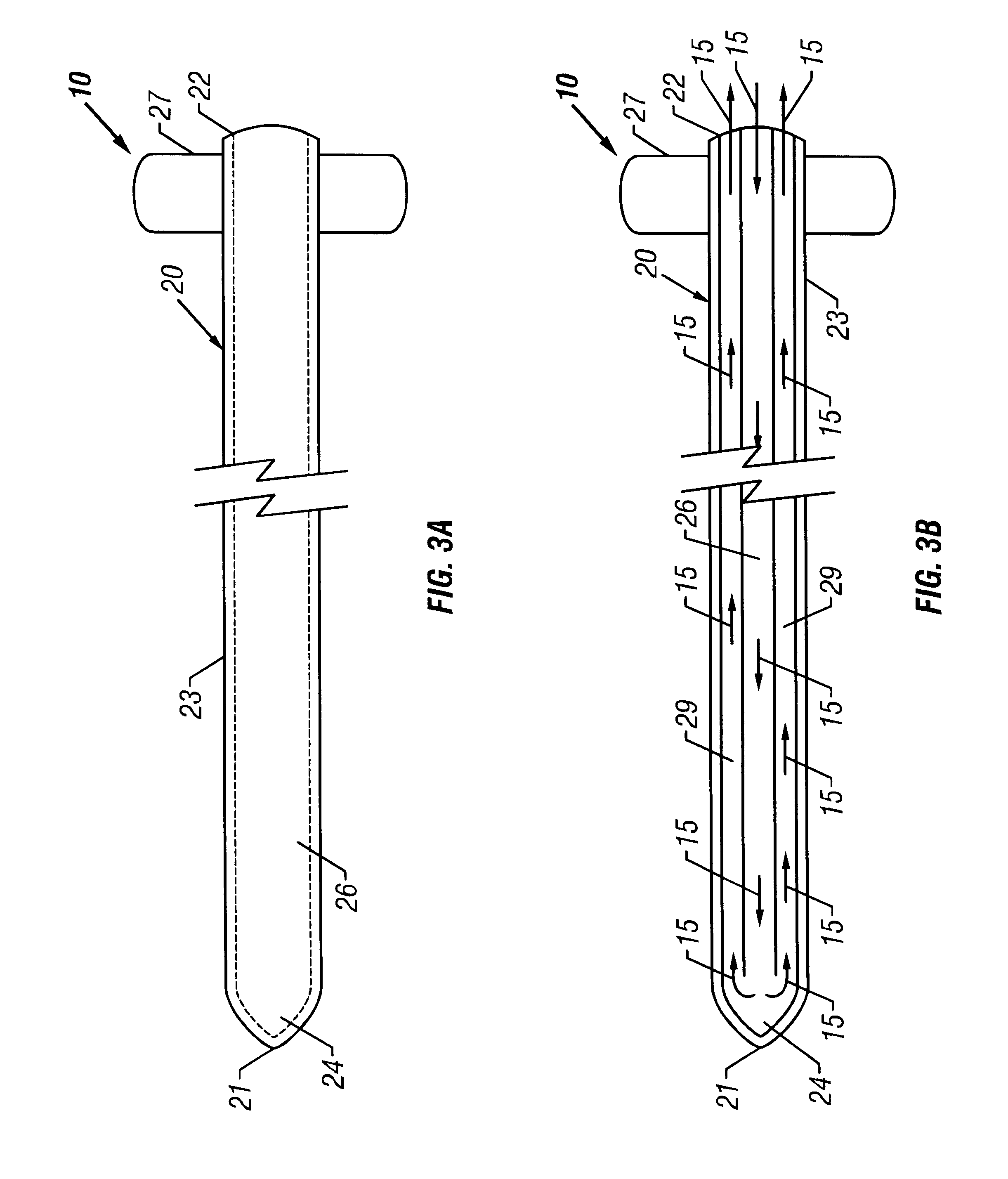
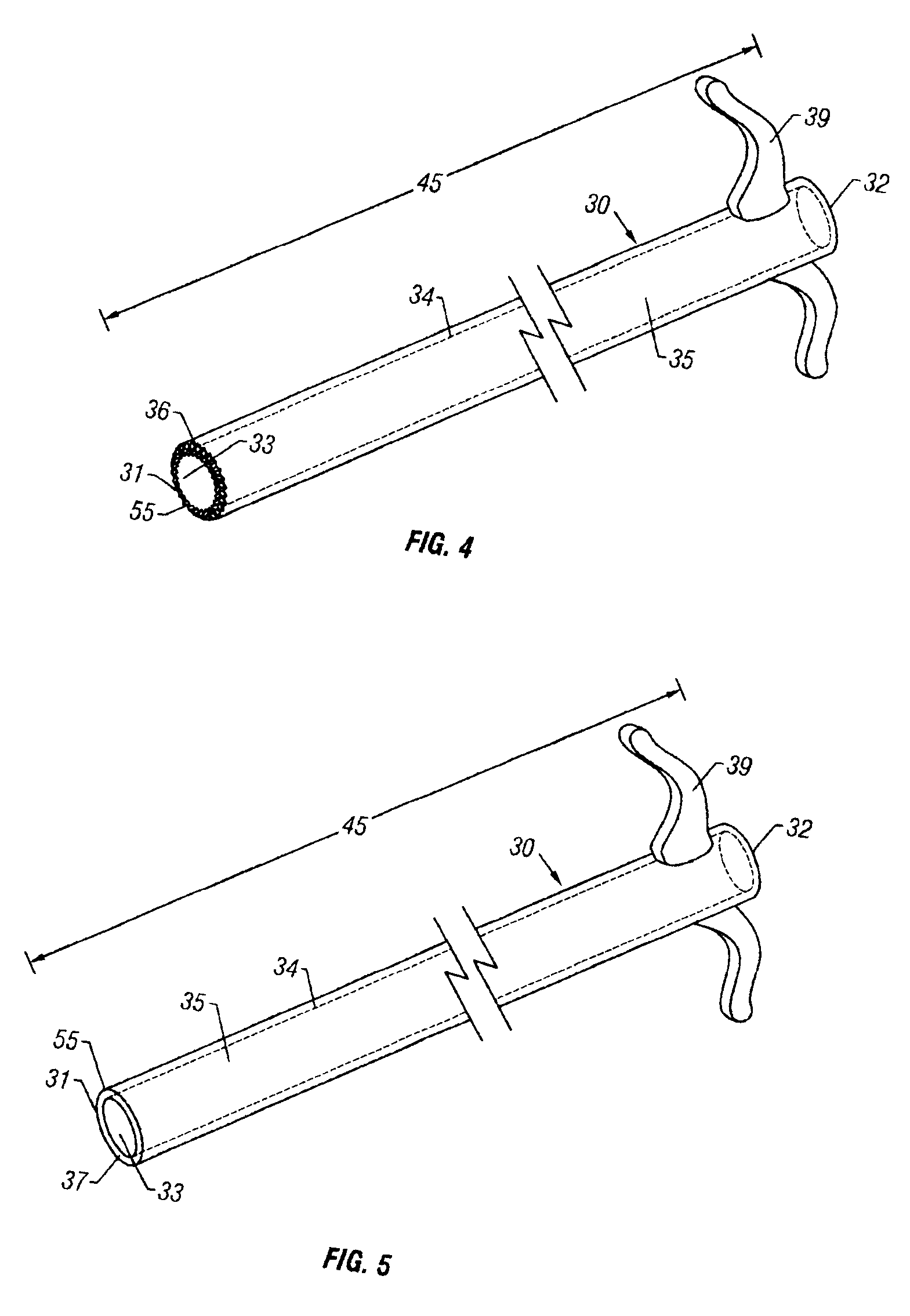
Bone access system
InactiveUS20060064101A1Reduce riskLow stiffnessSurgical needlesSurgical instruments for heatingBone tissueCatheter
Instruments and methodology for nonlinear access to bone tissue sites are described. Embodiments disclosed include a conduit for delivering material or a medical device to a site and a core member that is able to steer the conduit and allow the combination to be advanced thorough cancellous bone. A cannula and stylet may be provided to first advance through hard bone. The core member includes a curved tip that may be straightened by the cannula or an actuator sheath to vary sweep of the curve. An obturator may be included in the system. This instrument may include a flexible portion as well. Each of the obturator and conduit may be provided with any of a variety of active tips. The systems may be used to perform hard tissue site implantation, for example, in connection with a high pressure injection system.
Owner:ARTHROCARE
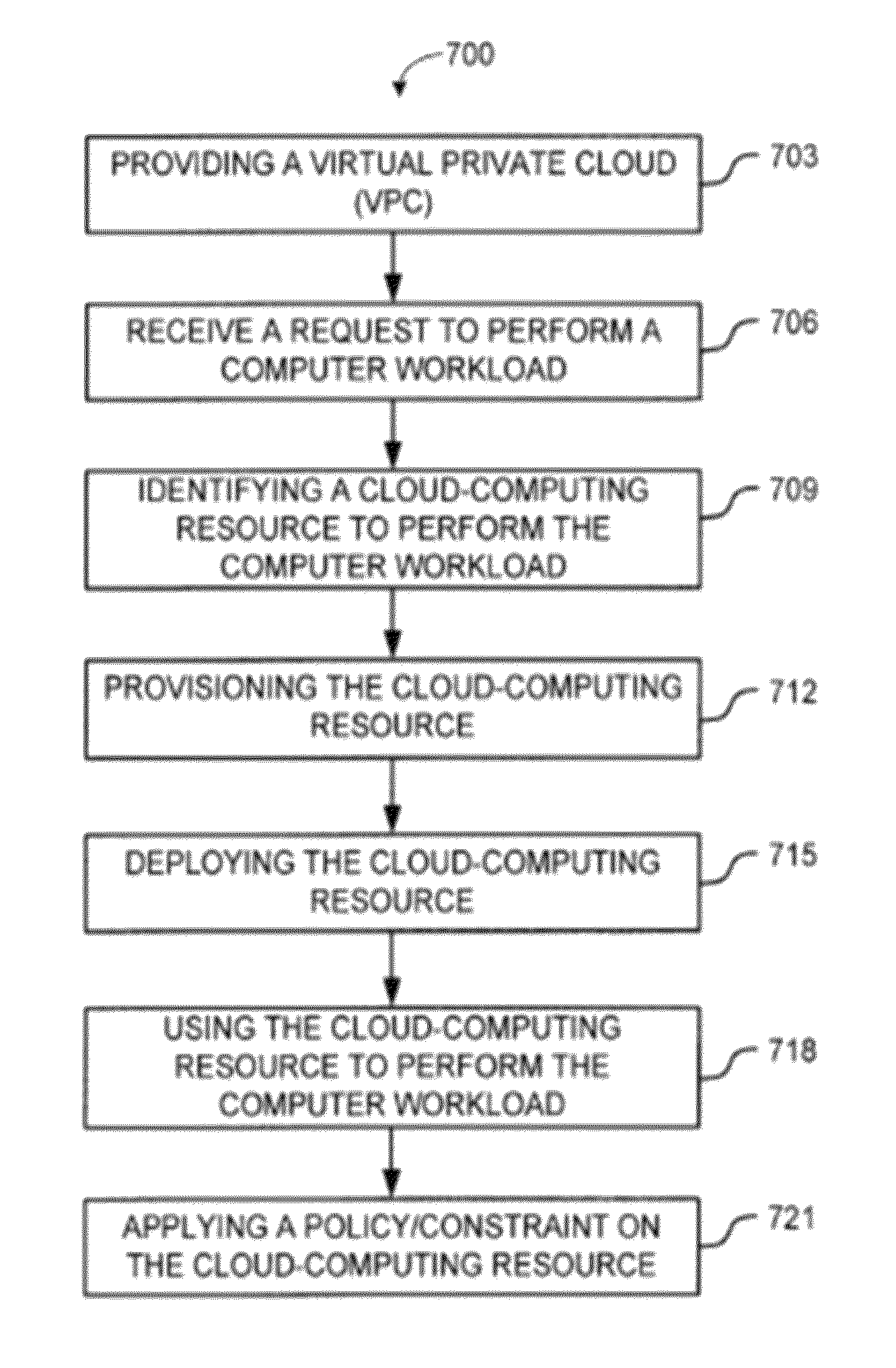
System and method for a cloud computing abstraction with multi-tier deployment policy
ActiveUS20140280961A1Increase and decrease numberScaling downDigital computer detailsData switching networksVirtualizationWorkload
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload.
Owner:CSC AGILITY PLATFORM INC
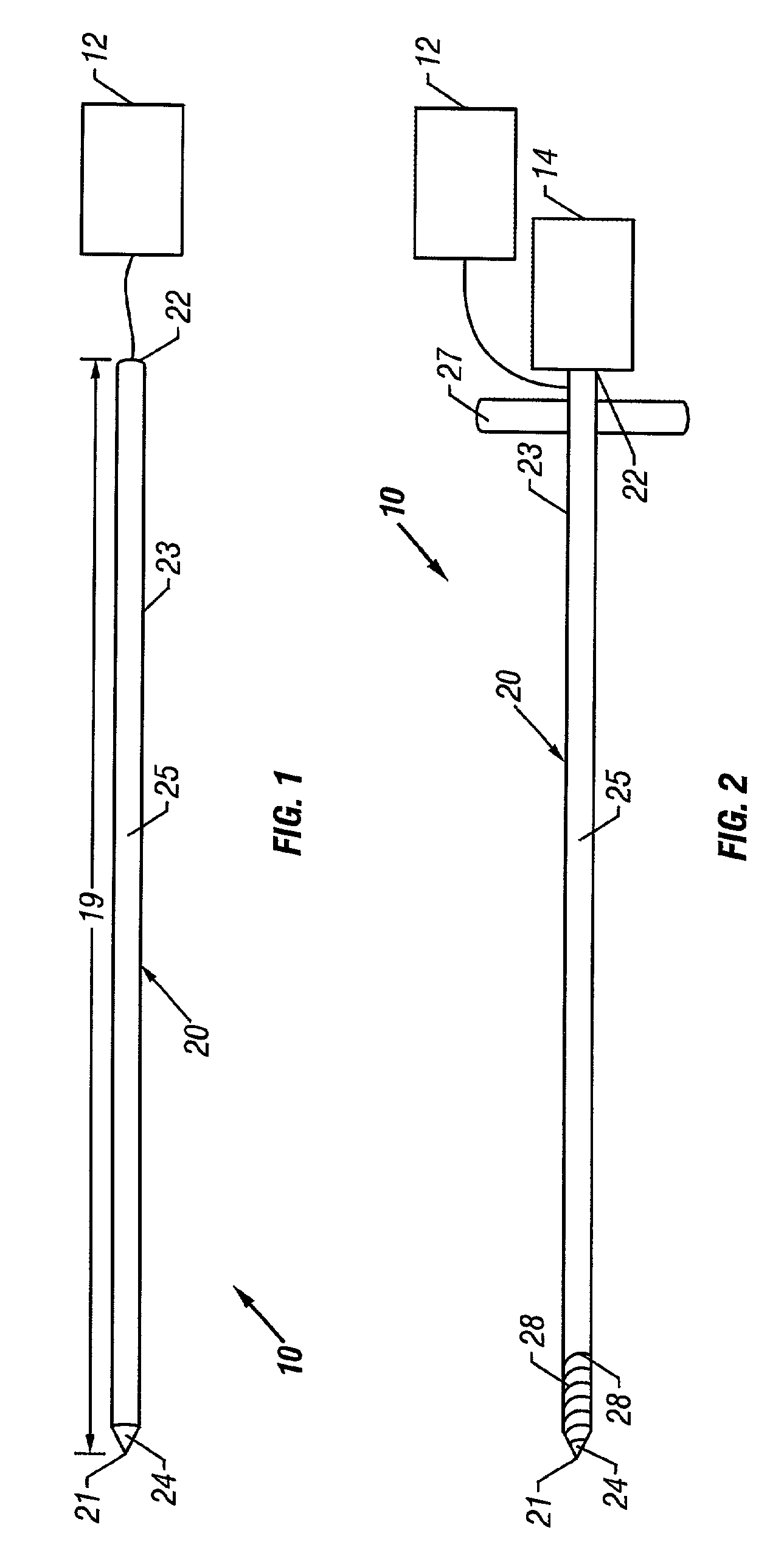
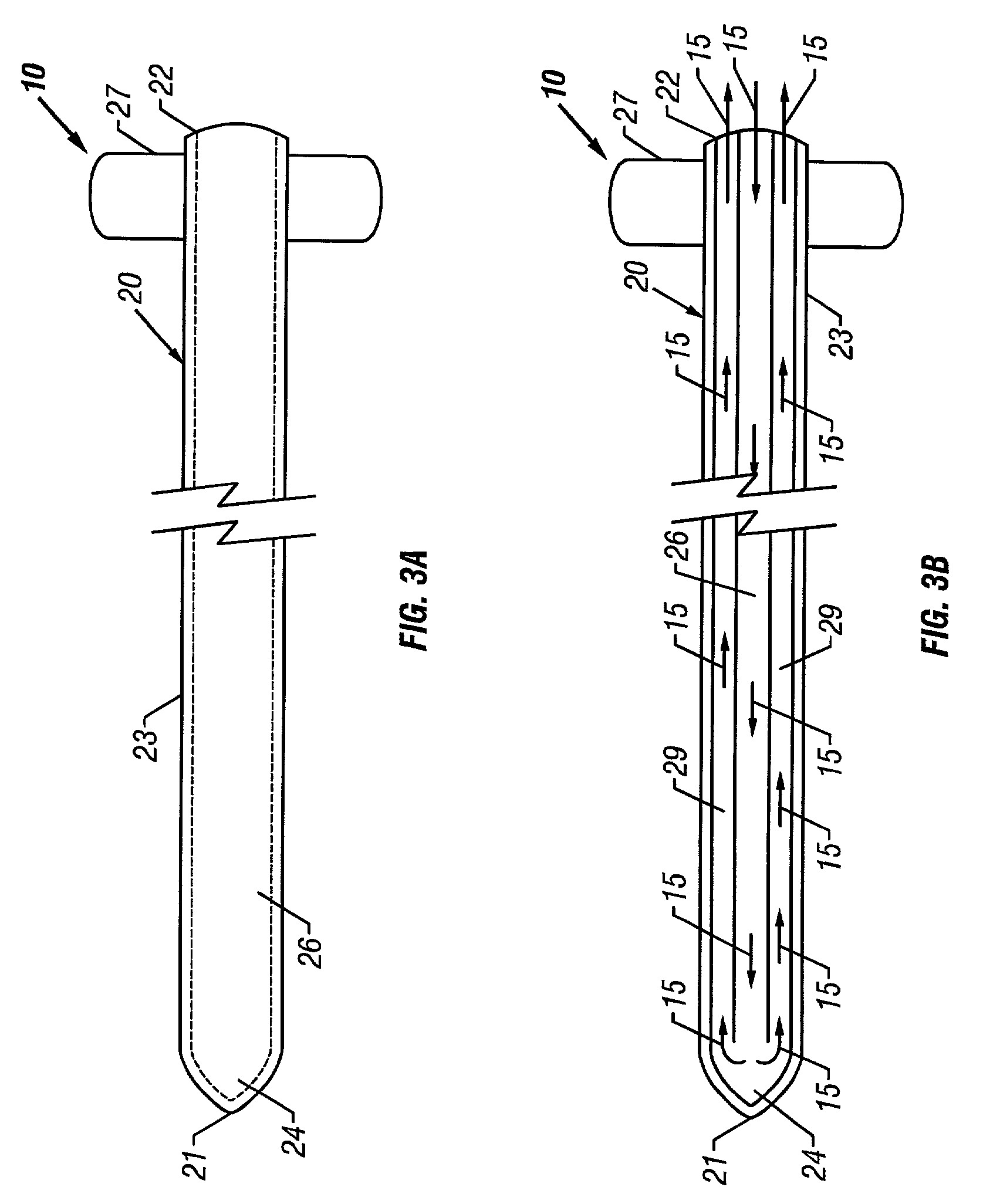
Bone access system
InactiveUS6875219B2Reduce riskLow stiffnessSurgical needlesVaccination/ovulation diagnosticsBone tissueCatheter
Instruments and methodology for nonlinear access to bone tissue sites are described. Embodiments disclosed include a conduit for delivering material or a medical device to a site and a core member that is able to steer the conduit and allow the combination to be advanced thorough cancellous bone. A cannula and stylet may be provided to first advance through hard bone. The core member includes a curved tip that may be straightened by the cannula or an actuator sheath to vary sweep of the curve. An obturator may be included in the system. This instrument may include a flexible portion as well. Each of the obturator and conduit may be provided with any of a variety of active tips. The systems may be used to perform hard tissue site implantation, for example, in connection with a high pressure injection system.
Owner:NEUROTHERM
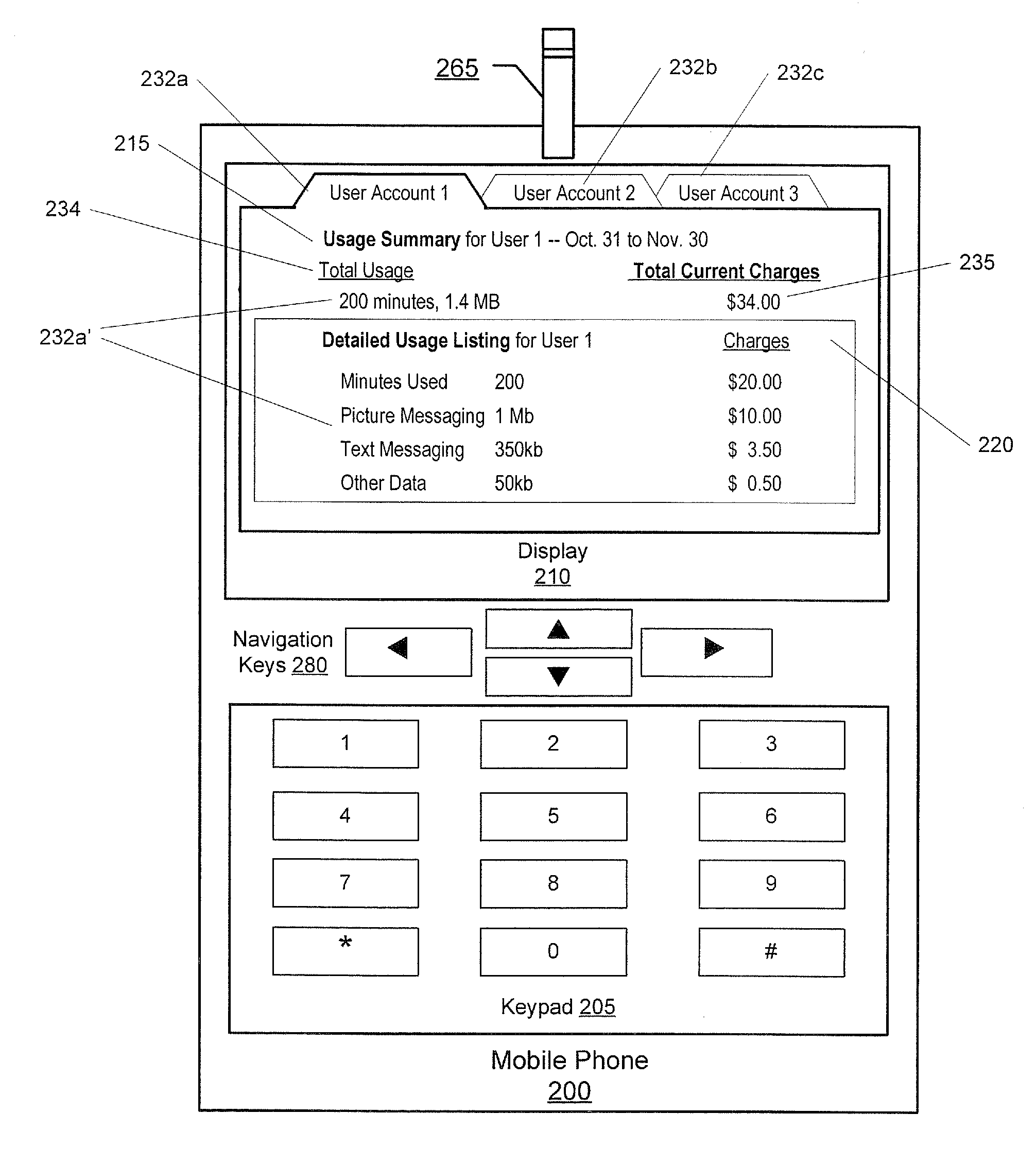
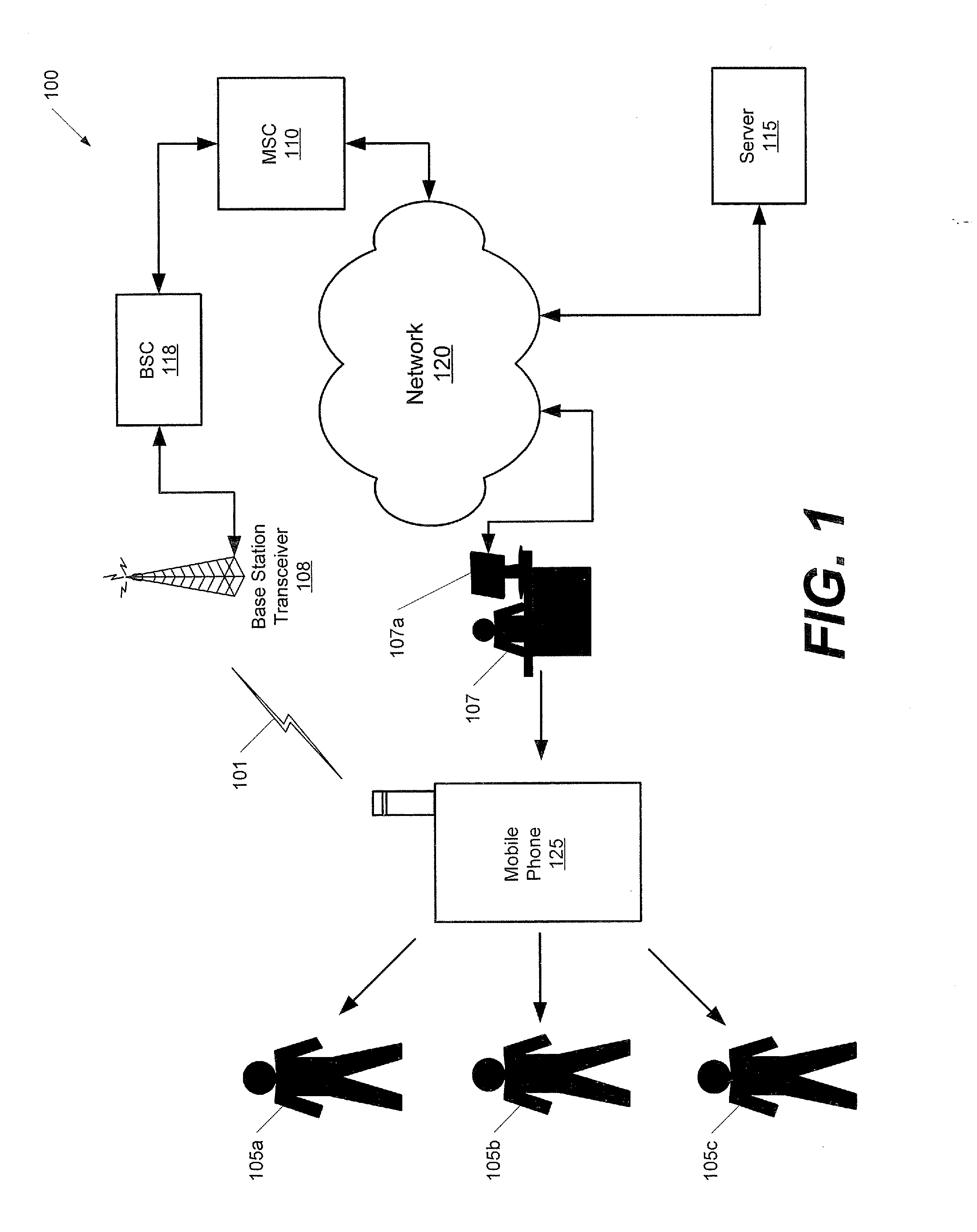
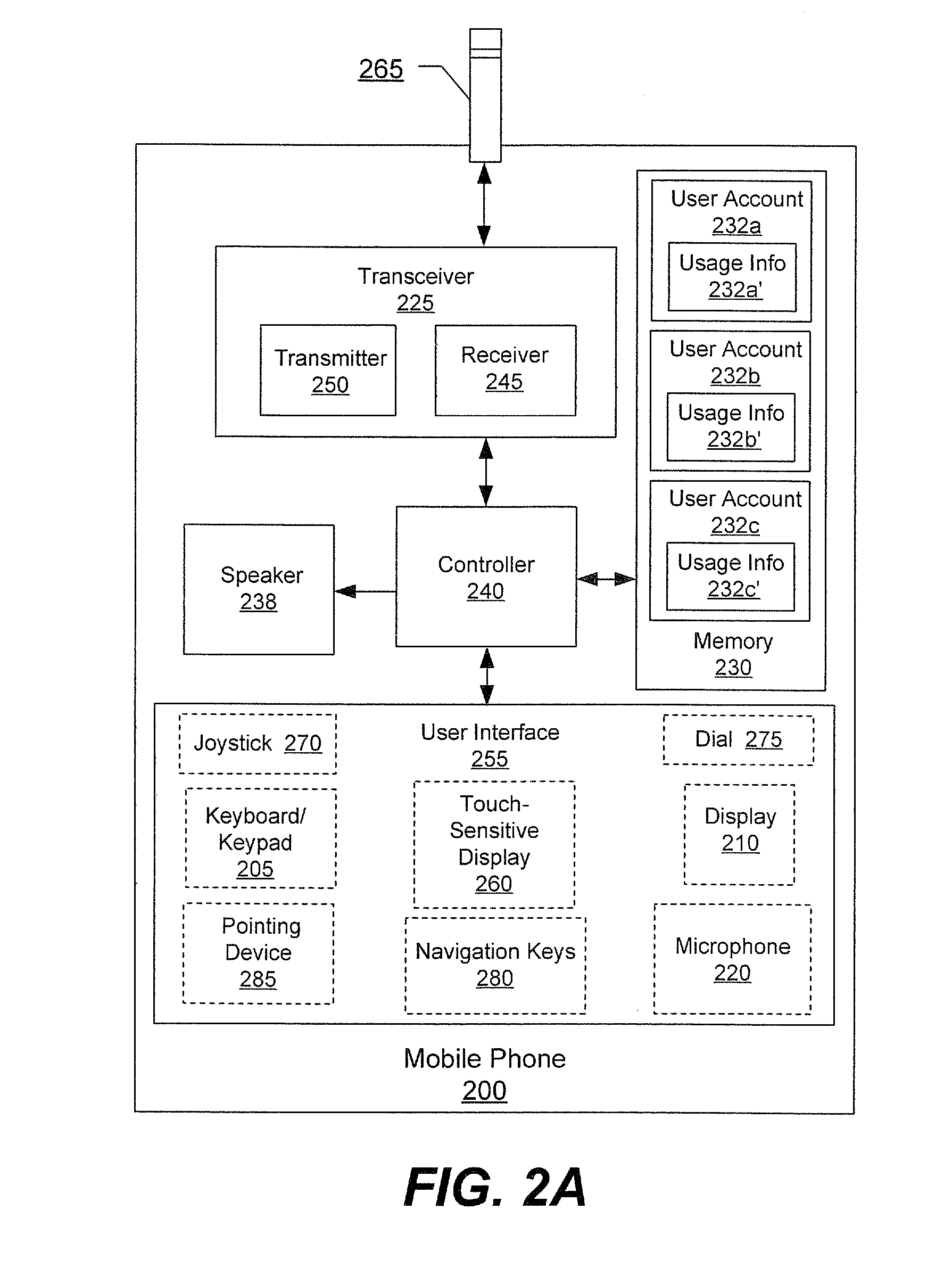
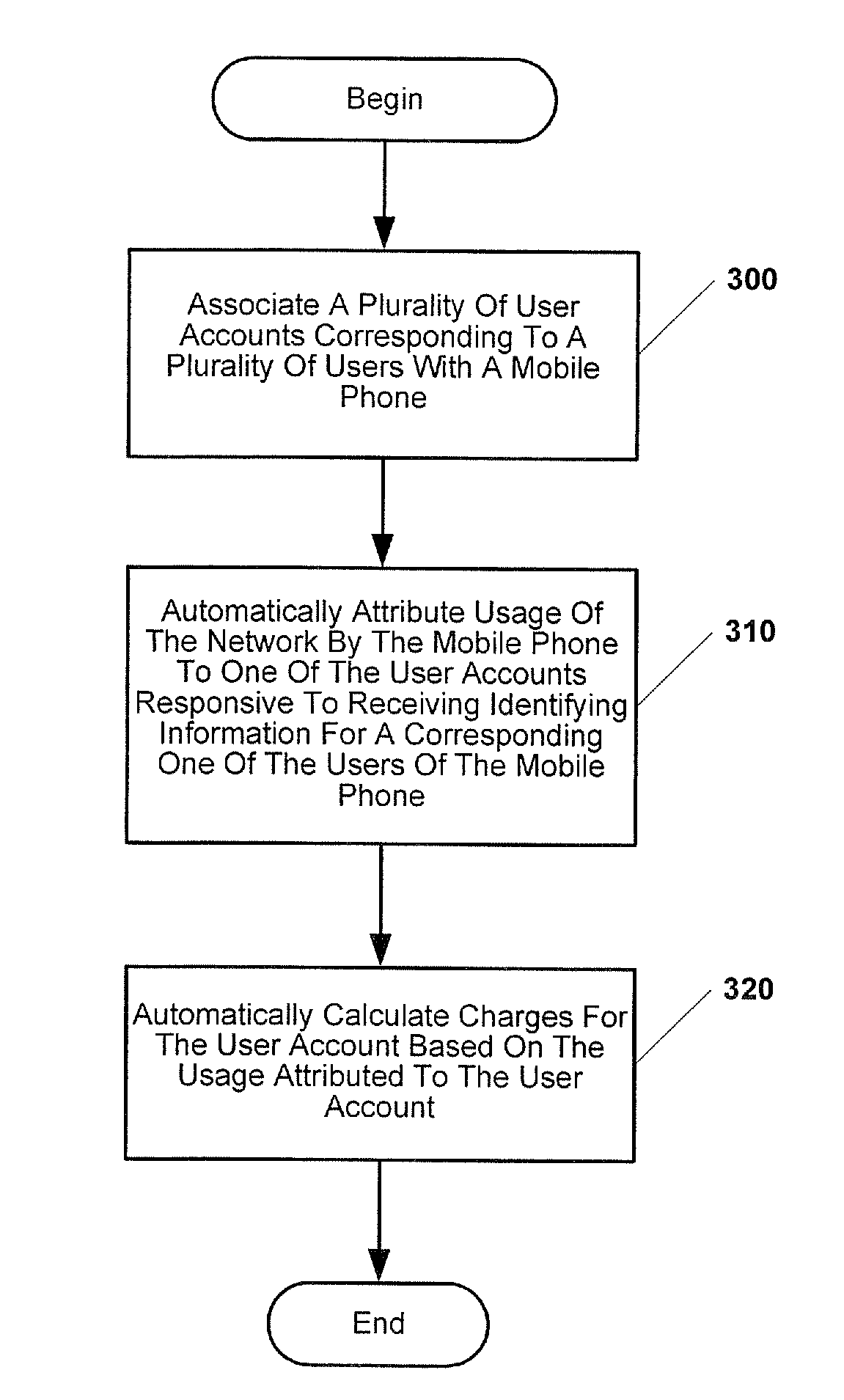
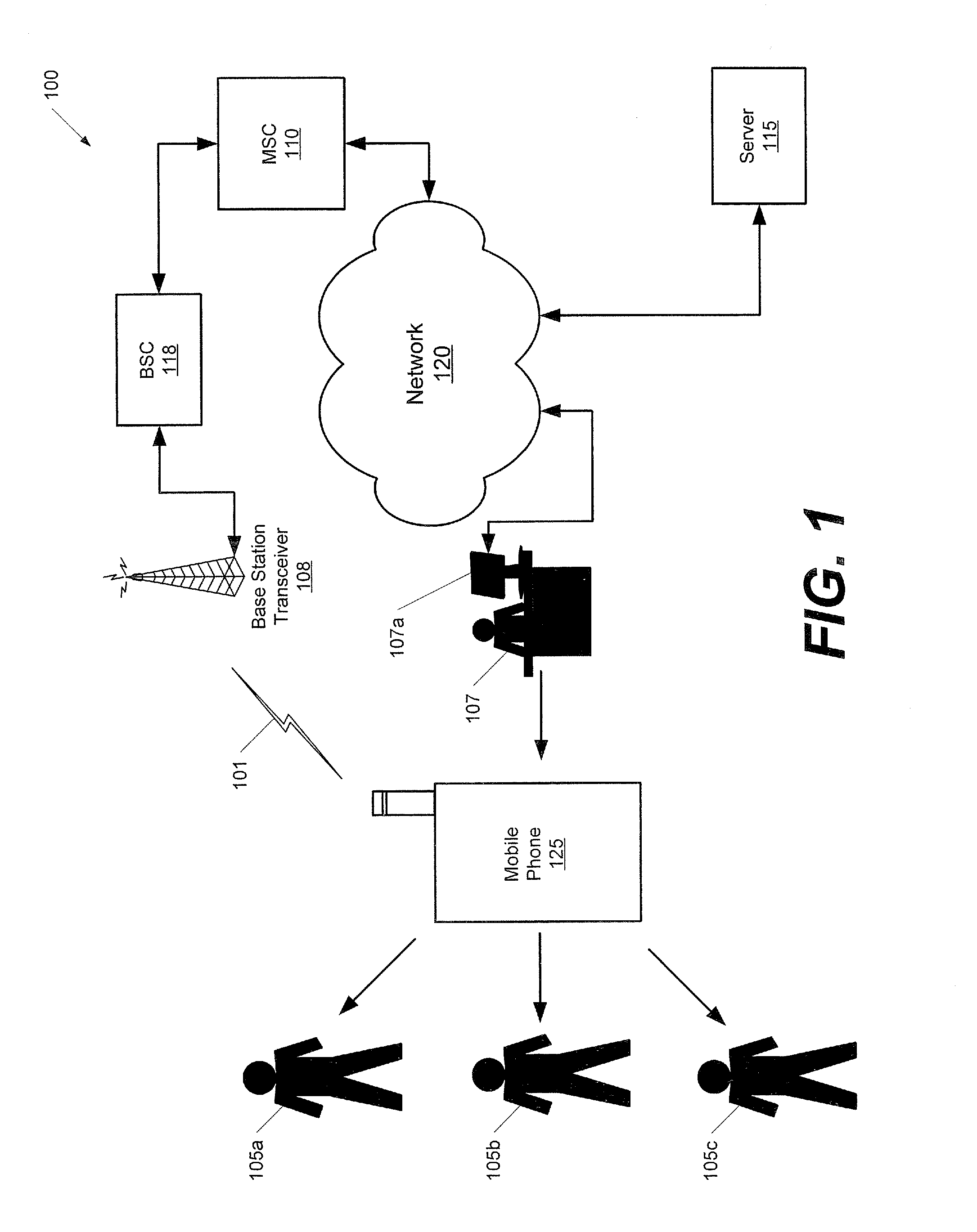
Methods, devices and computer program products for tracking usage of a network by a plurality of users of a mobile phone
InactiveUS20080132201A1Reduce usageAvoid prolonged usePayment architectureAutomatic exchangesWorld Wide WebMobile telephony
Methods for tracking usage of a network by a plurality of users of a mobile phone include associating a plurality of user accounts with the mobile phone, where ones of the plurality of user accounts correspond to ones of the plurality of users of the mobile phone. Usage of the network by the mobile phone is automatically attributed to one of the plurality of user accounts responsive to receiving identifying information for a corresponding one of the plurality of users of the mobile phone. Charges for the one of the plurality of user accounts are calculated based on the usage attributed to the one of the plurality of user accounts. Related devices and computer program products are also discussed.
Owner:SONY ERICSSON MOBILE COMM AB
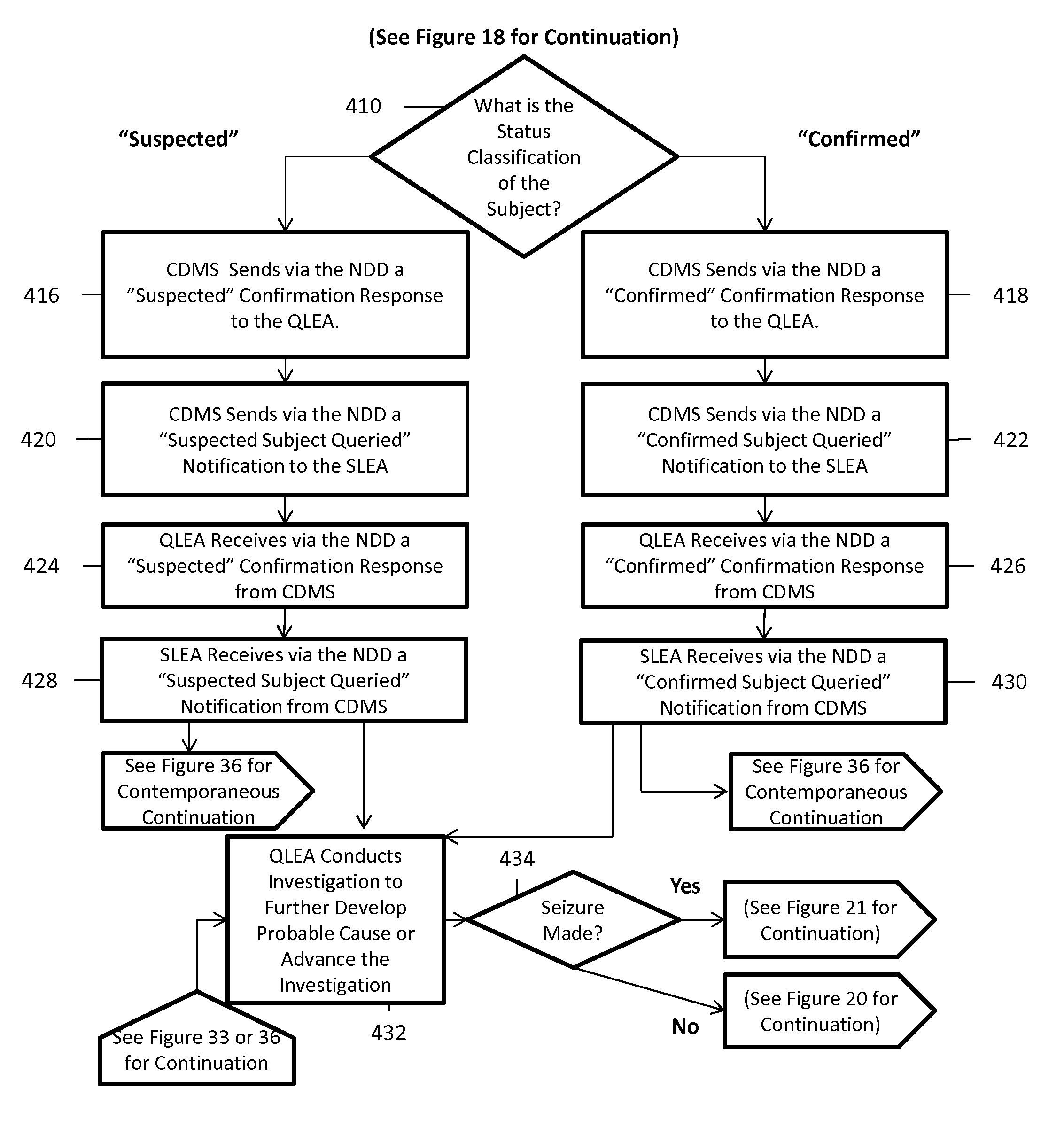
System and method for facilitating the execution of law enforcement duties and enhancing anti-terrorism and counter-terrorism capabilities
ActiveUS8742934B1Easy to grabAvoid prolonged useData processing applicationsDigital data processing detailsElectronic systemsComputer science
A system and method for facilitating the execution of law enforcement duties and enhancing anti-terrorism and counter-terrorism capabilities is disclosed. More particularly, according to one aspect of the invention, an electronic system and associated method is configured to facilitate the performance of law enforcement duties by quasi-instantaneously providing actionable intelligence to its users, such as front-line law enforcement officers, in response to a real-time query. According to another aspect of the invention, a system implements a set of automated status classifications for subjects with suspected or confirmed involvement in criminal and / or terrorist activities. The status classifications specifically and concisely establish the subject's involvement in criminal and / or terrorist activities. According to yet another aspect of the invention, a system executes a streamlined electronic process for asset forfeiture actions so as to ensure that criminal and / or terrorist assets are efficiently and effectively seized.
Owner:SUBJECT PACKET SOLUTIONS LLC
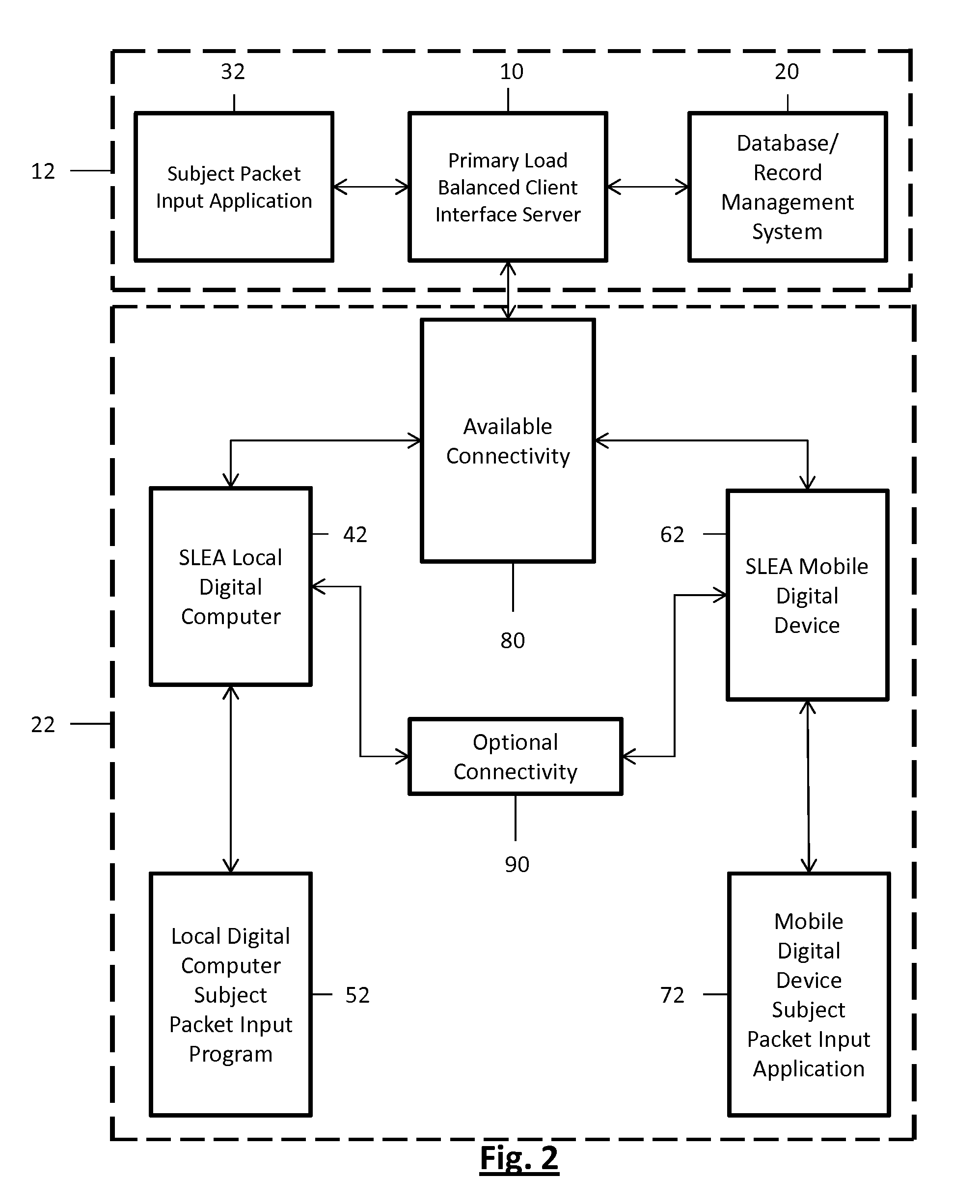
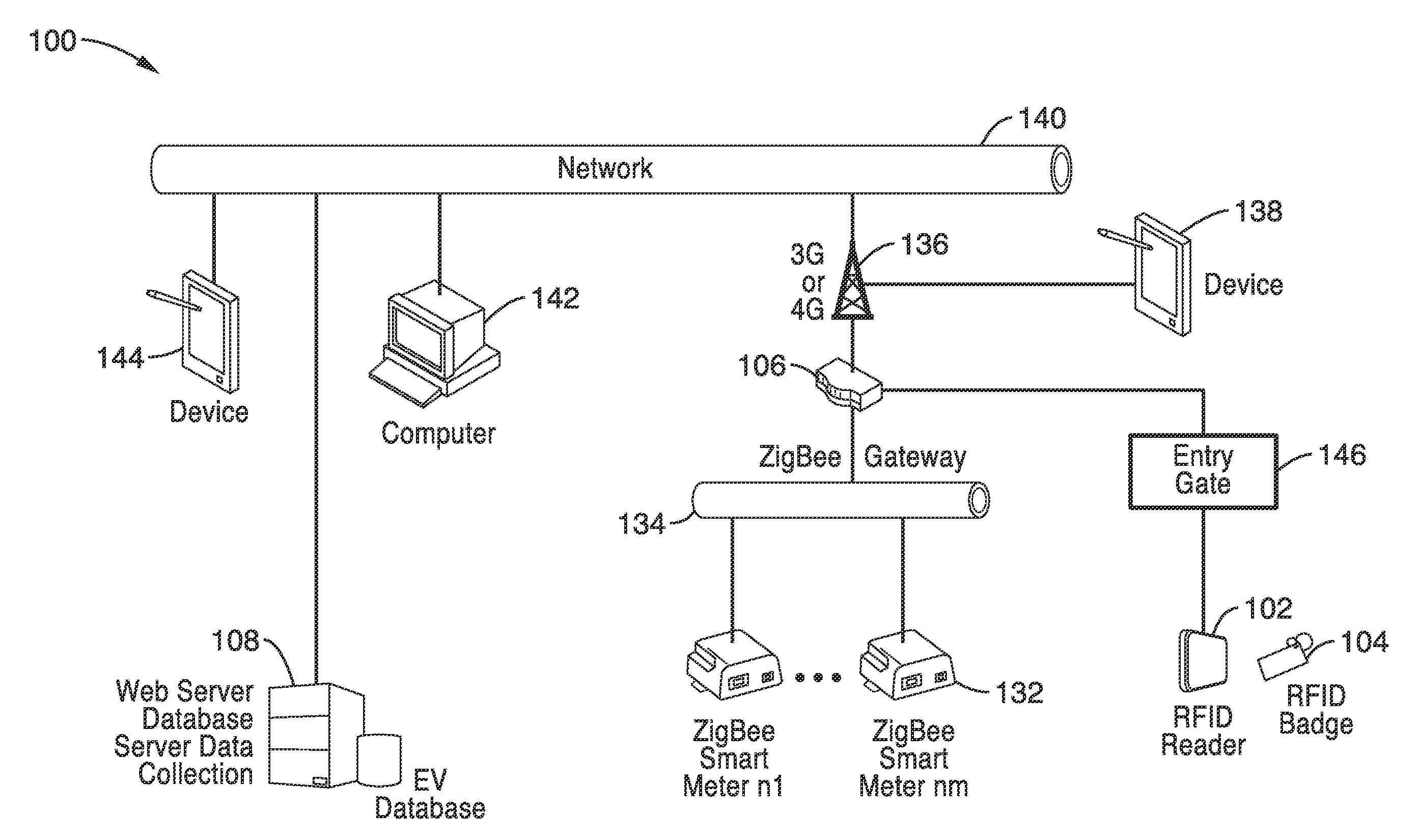
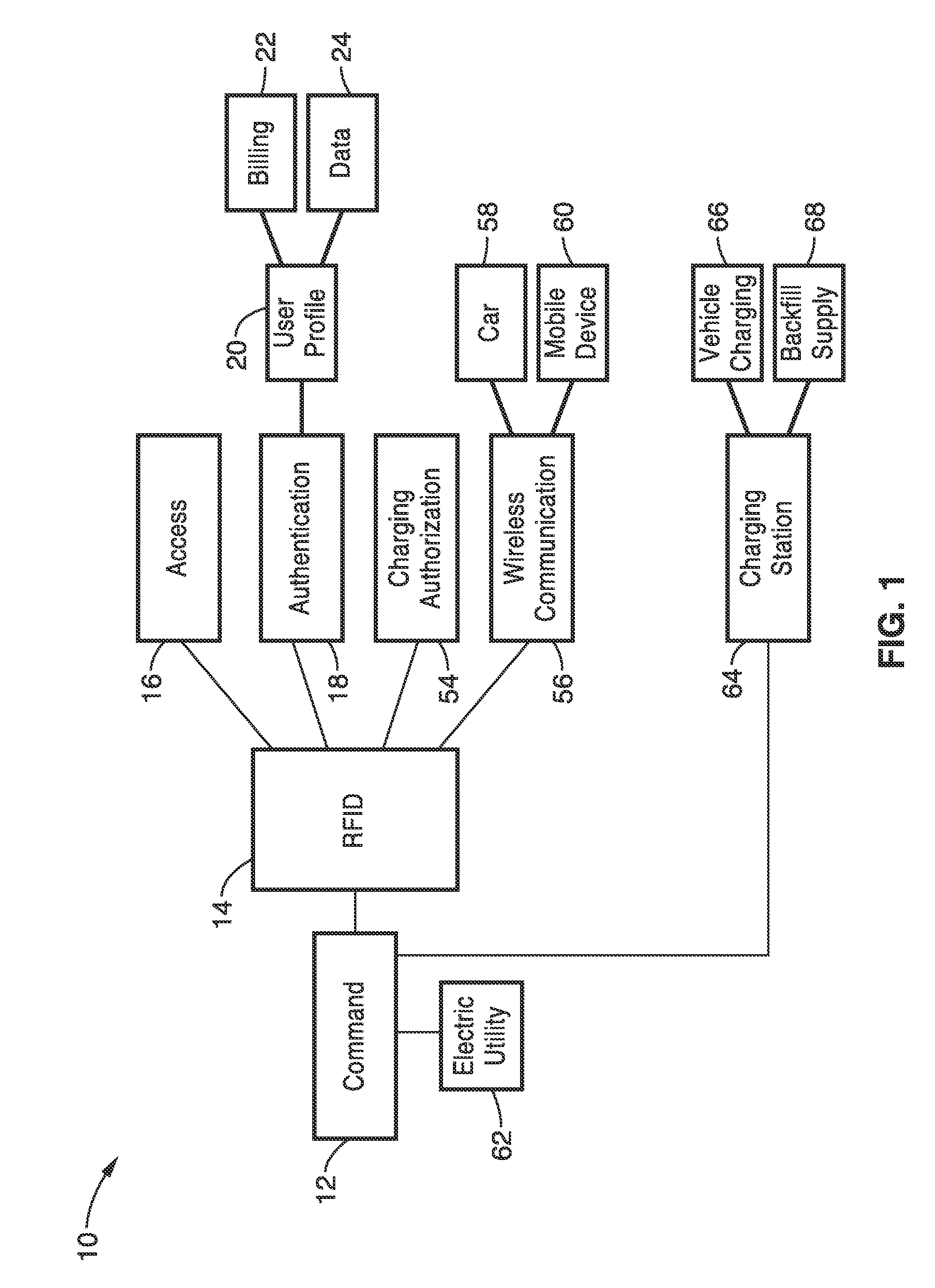
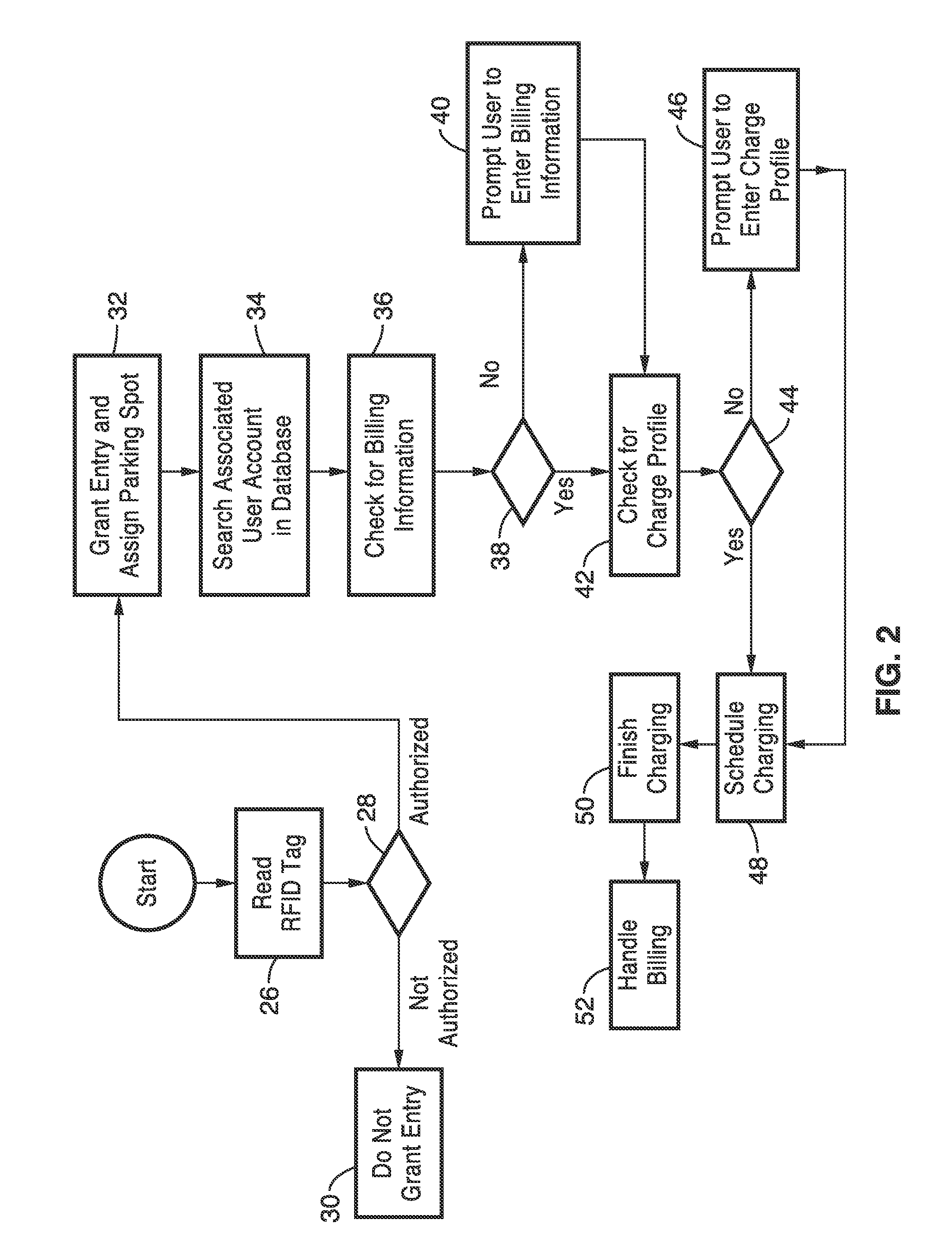
Intelligent electric vehicle charging system
InactiveUS20140203077A1Reduce energy costsAvoid prolonged useCircuit authenticationCircuit monitoring/indicationTelecommunications linkElectrical battery
A battery charging system for an electric vehicle in which an addressable RFID tag, an RFID receiver, an electrical charger, and a controller operate to charge the battery of an electric vehicle according to a user profile and a charging profile in response to a signal received by the RFID reader from the RFID tag. In an interconnected system, multiple charging stations are connected to the electrical power grid and communicate with a central controller through communications links. A grid converter can be provided to allow for backfilling power from an electric vehicle to the power grid in response to a command from the central controller.
Owner:RGT UNIV OF CALIFORNIA
Methods, devices and computer program products for tracking usage of a network by a plurality of users of a mobile phone
InactiveUS8229394B2Avoid prolonged useReduce usagePayment architectureCocot systemsWorld Wide WebMobile phone
Methods for tracking usage of a network by a plurality of users of a mobile phone include associating a plurality of user accounts with the mobile phone, where ones of the plurality of user accounts correspond to ones of the plurality of users of the mobile phone. Usage of the network by the mobile phone is automatically attributed to one of the plurality of user accounts responsive to receiving identifying information for a corresponding one of the plurality of users of the mobile phone. Charges for the one of the plurality of user accounts are calculated based on the usage attributed to the one of the plurality of user accounts. Related devices and computer program products are also discussed.
Owner:SONY ERICSSON MOBILE COMM AB
Systems and methods for predicting weather performance for a vehicle
ActiveUS20150166072A1Avoid prolonged useLow costRoad vehicles traffic controlDigital data processing detailsVehicle behaviorEngineering
Systems and methods for obtaining data about road conditions as they pertain to an individual vehicle, using this information to build a model of vehicle behavior as a function of its environment, and aggregating information concerning multiple vehicles along with data from other sources in order to predict vehicle behavior in future environments.
Owner:FATHYM INC
Systems and Methods for Providing Percutaneous Electrical Stimulation
ActiveUS20130096641A1Easy to implementReduce riskElectrotherapyArtificial respirationTreatment painPeripheral neuron
Systems and methods according to the present invention relate to a novel peripheral nerve stimulation system for the treatment of pain, such as pain that exists after amputation.
Owner:SPR THERAPEUTICS
Method and system for combined energy therapy profile
ActiveUS20080221491A1Increase temperatureLess energy useUltrasonic/sonic/infrasonic diagnosticsUltrasound therapyEffective treatmentEnergy Therapy
A method and system for treating tissue with a combined therapy profile is disclosed. In one exemplary embodiment, ultrasound energy is used to treat numerous depths of tissue within a region of interest and the spatial and temporal properties of the ultrasound energy are varied for more effective treatment. The method and system of the present invention are configured to treat all of the tissue from the surface on down and not spare intervening tissue.
Owner:GUIDED THERAPY SYSTEMS LLC
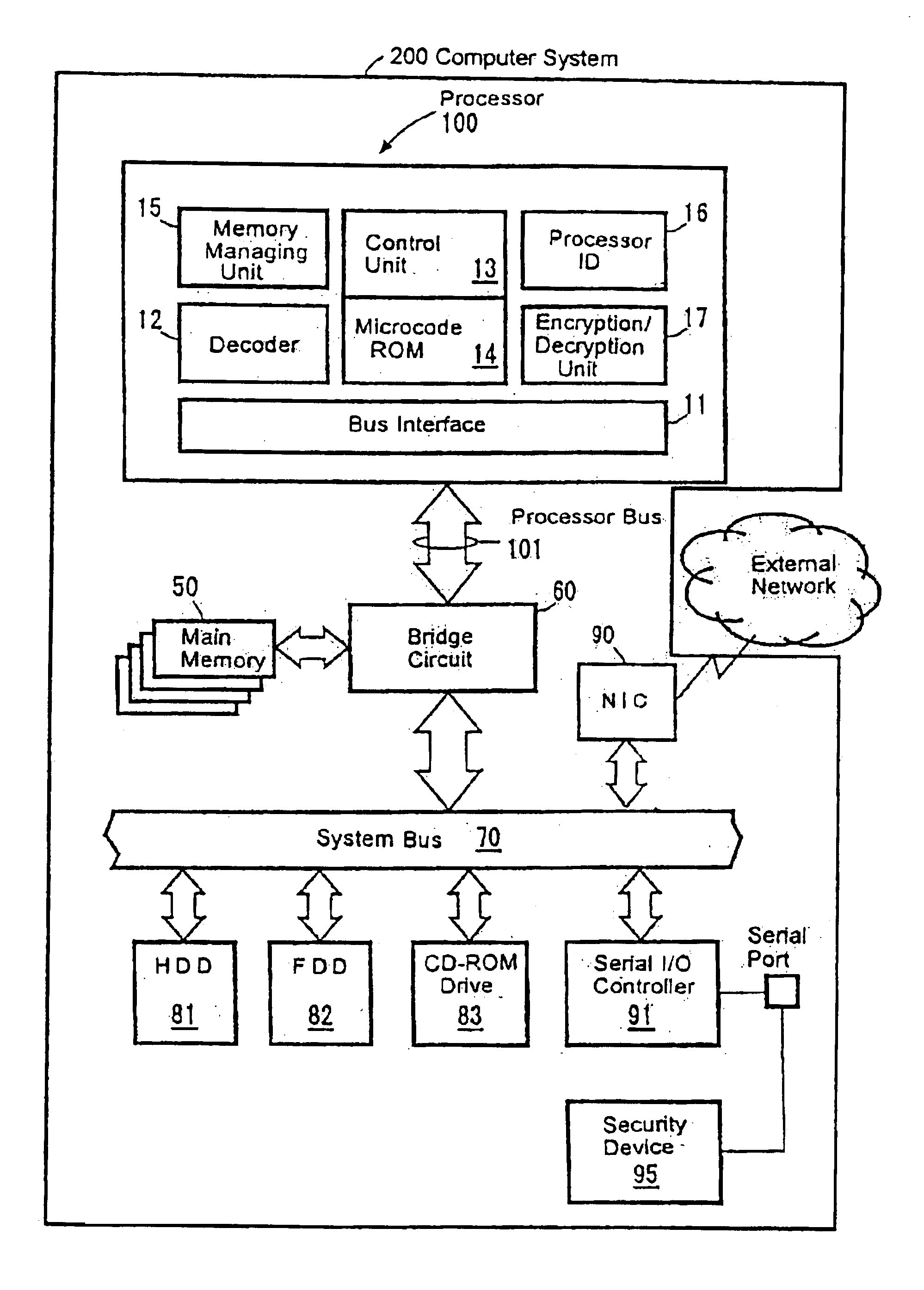
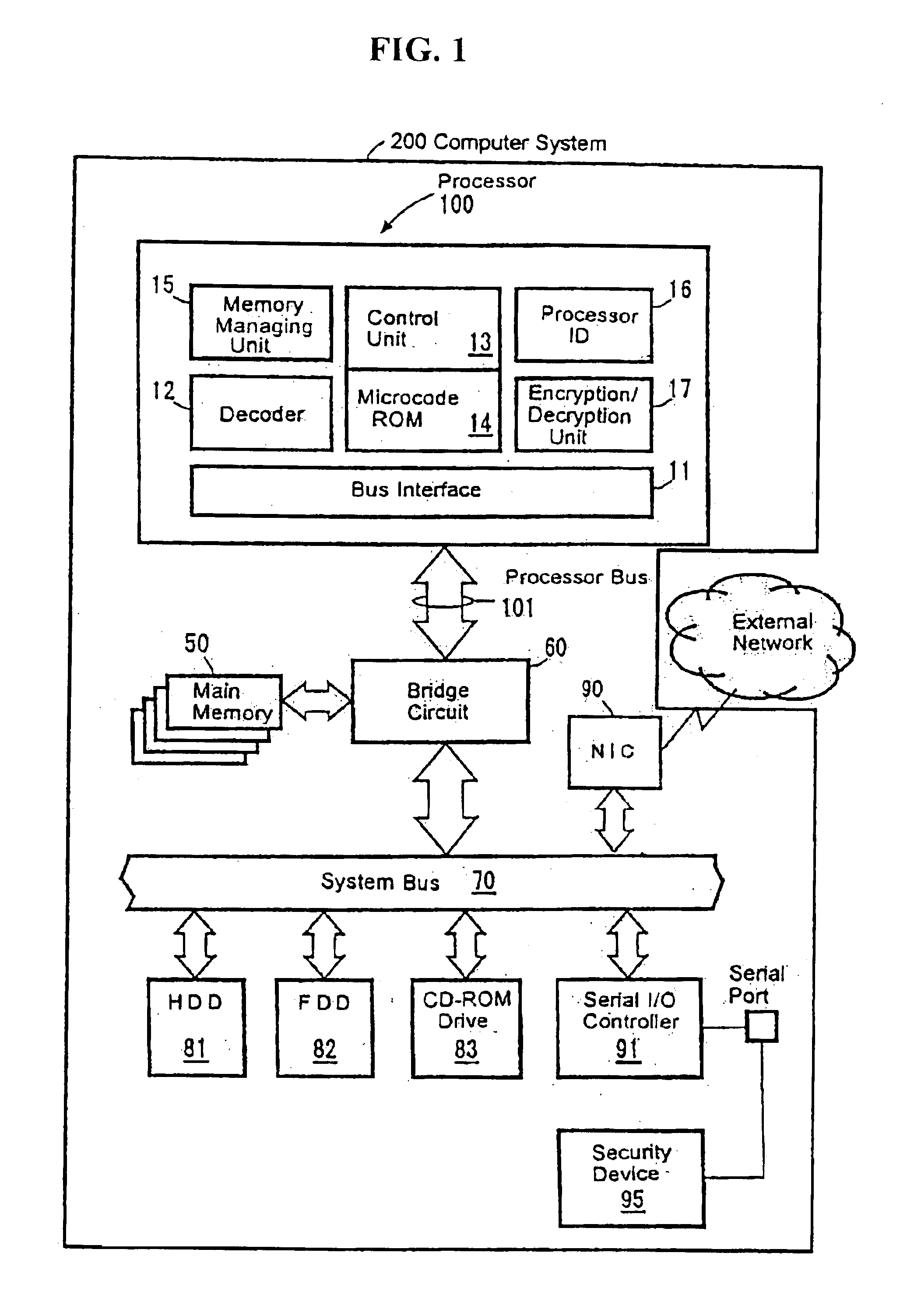
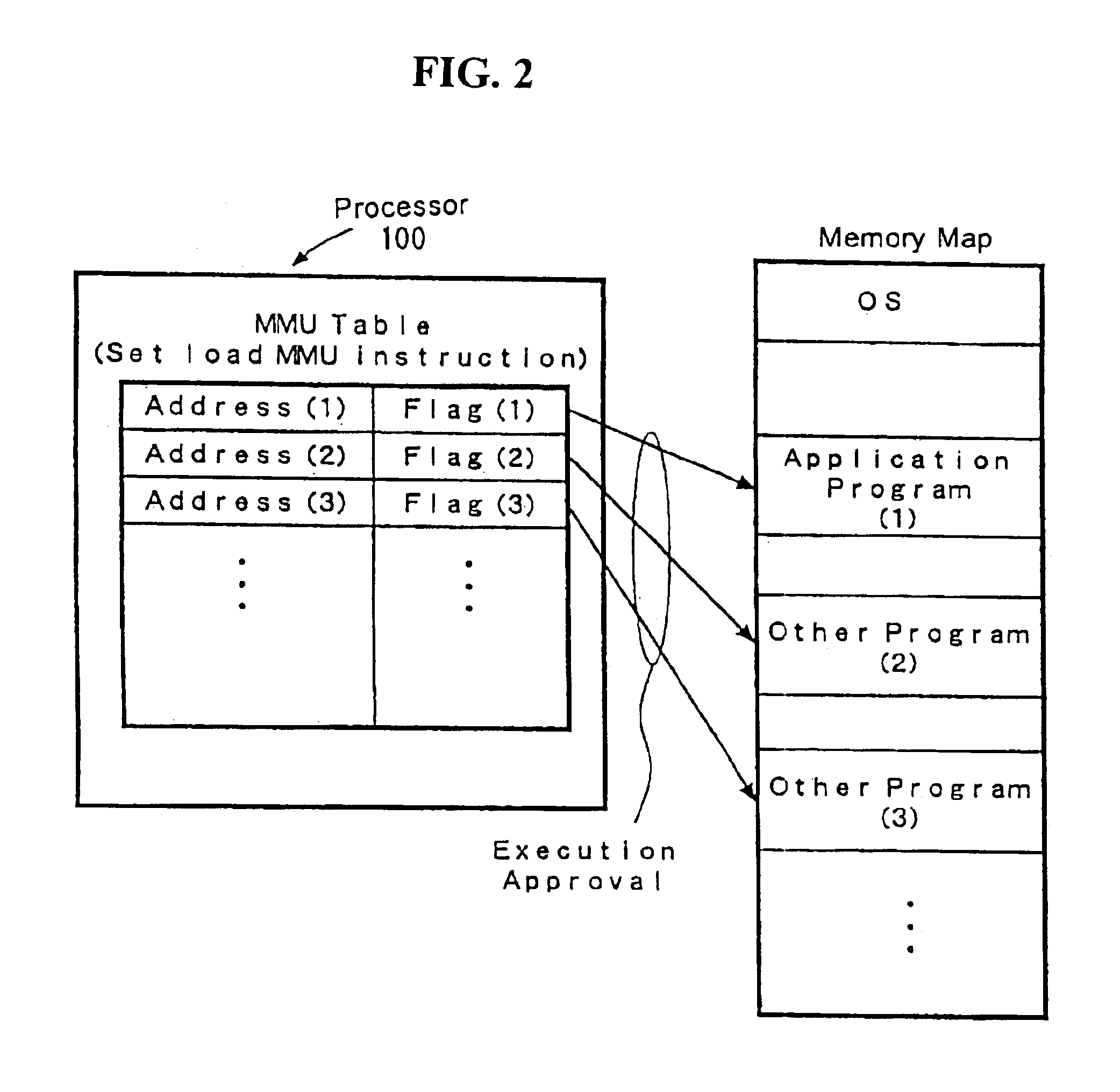
Processor with a function to prevent illegal execution of a program, an instruction executed by a processor and a method of preventing illegal execution of a program
InactiveUS6704872B1Prevent executionAvoid prolonged useUnauthorized memory use protectionHardware monitoringManagement unitComputerized system
The present invention provides an improved technology of preventing illegal use and execution of a software program provided to a computer system. More particularly, the present invention is directed to a Processor of a type in which a memory managing unit is installed therein to manage storing operation of code / data in main memory and includes, as one of instruction set, an execution permitting instruction to permit execution of a program code (application) in the main memory. The procedure of execution permitting instruction is defined by a microprogram and includes an authentication procedure for authenticating the right to use the program beside a procedure for setting predetermined data in the memory managing unit in this invention. Execution of the software program is permitted only when the authentication processing is completed successfully. Because the authentication operation is performed within the processor, it is almost impossible to monitor or detect it from the exterior. Also, by using a processor ID unique to the processor chip as identification information for use in the authentication processing, the right to use a specific software program can be limited to a single processor.
Owner:GOOGLE LLC
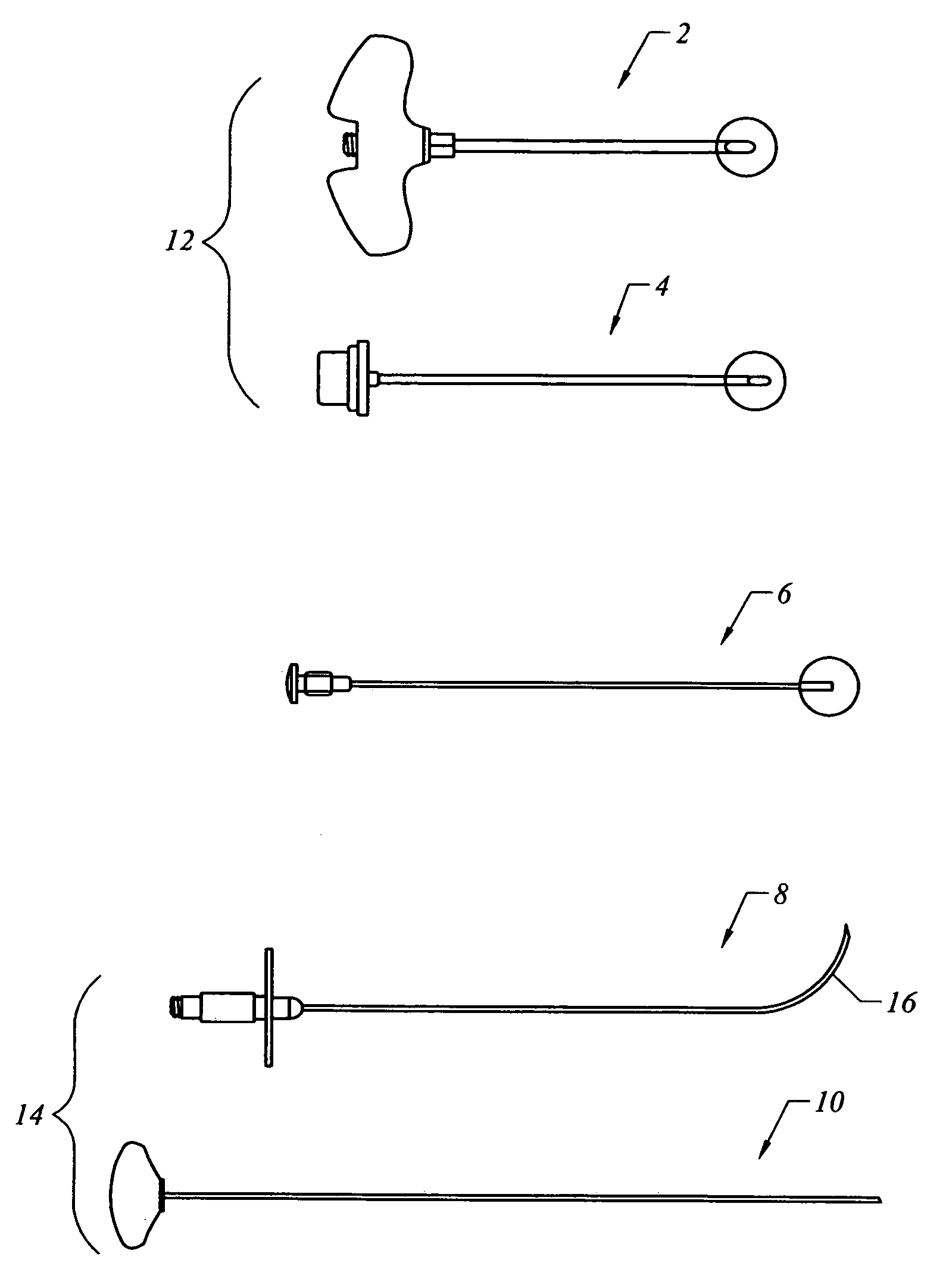
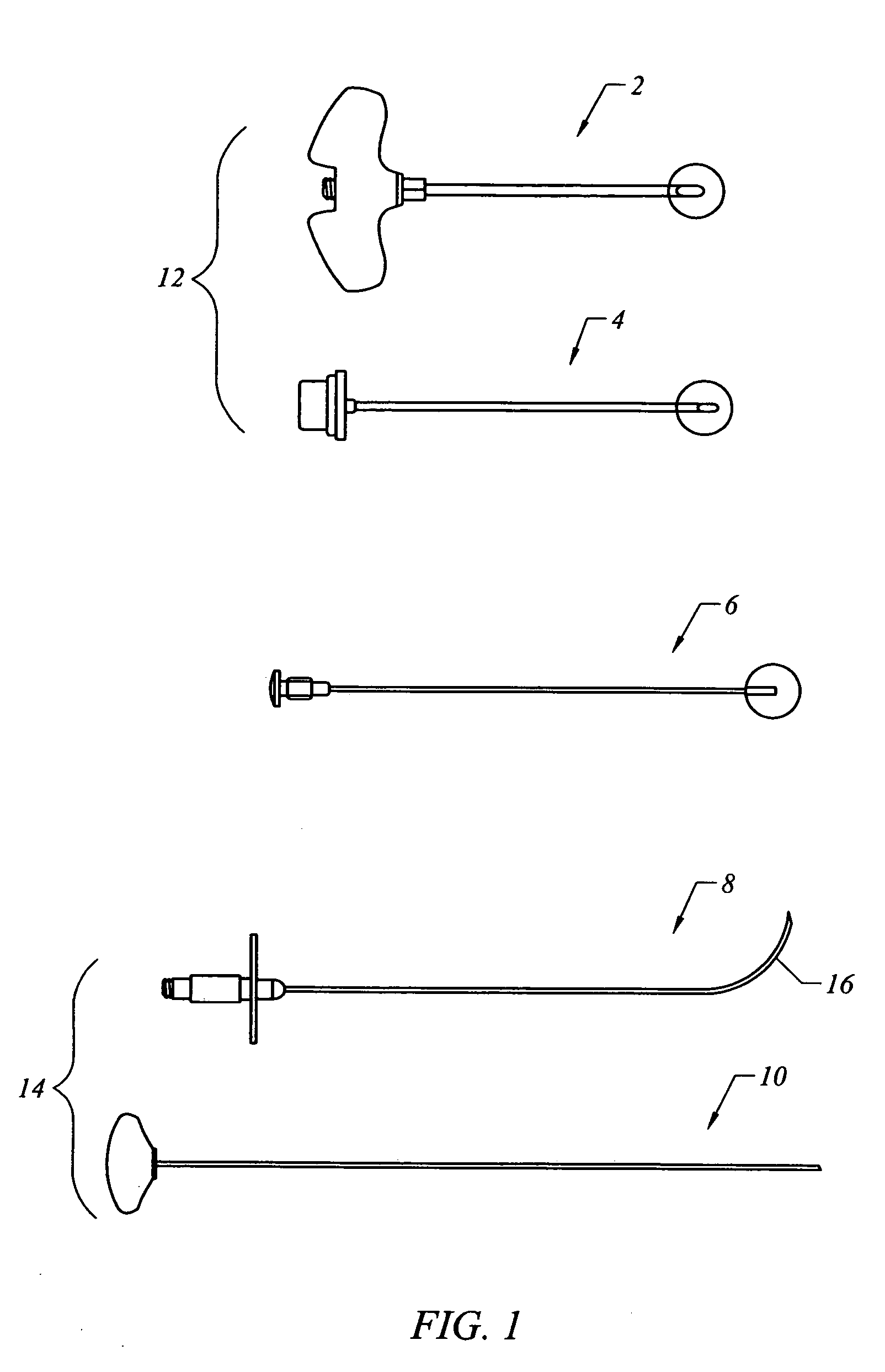
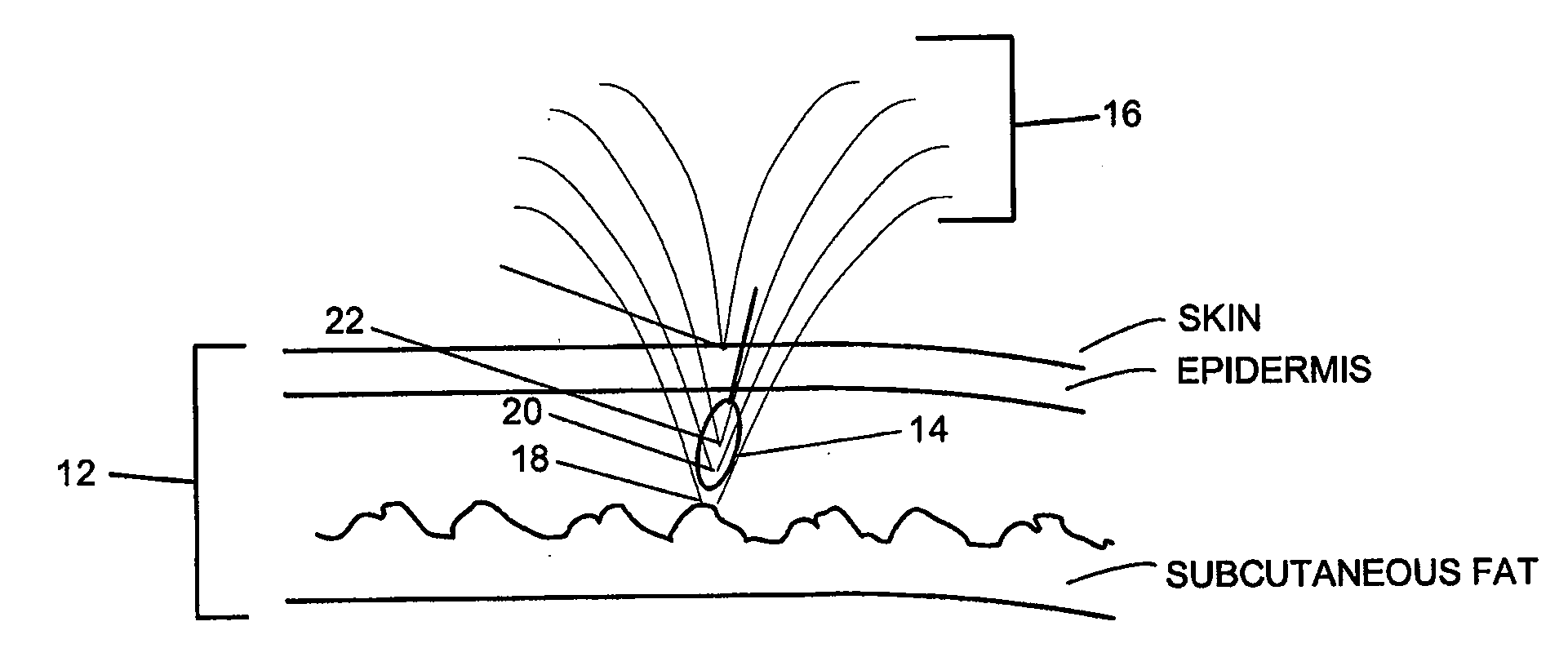
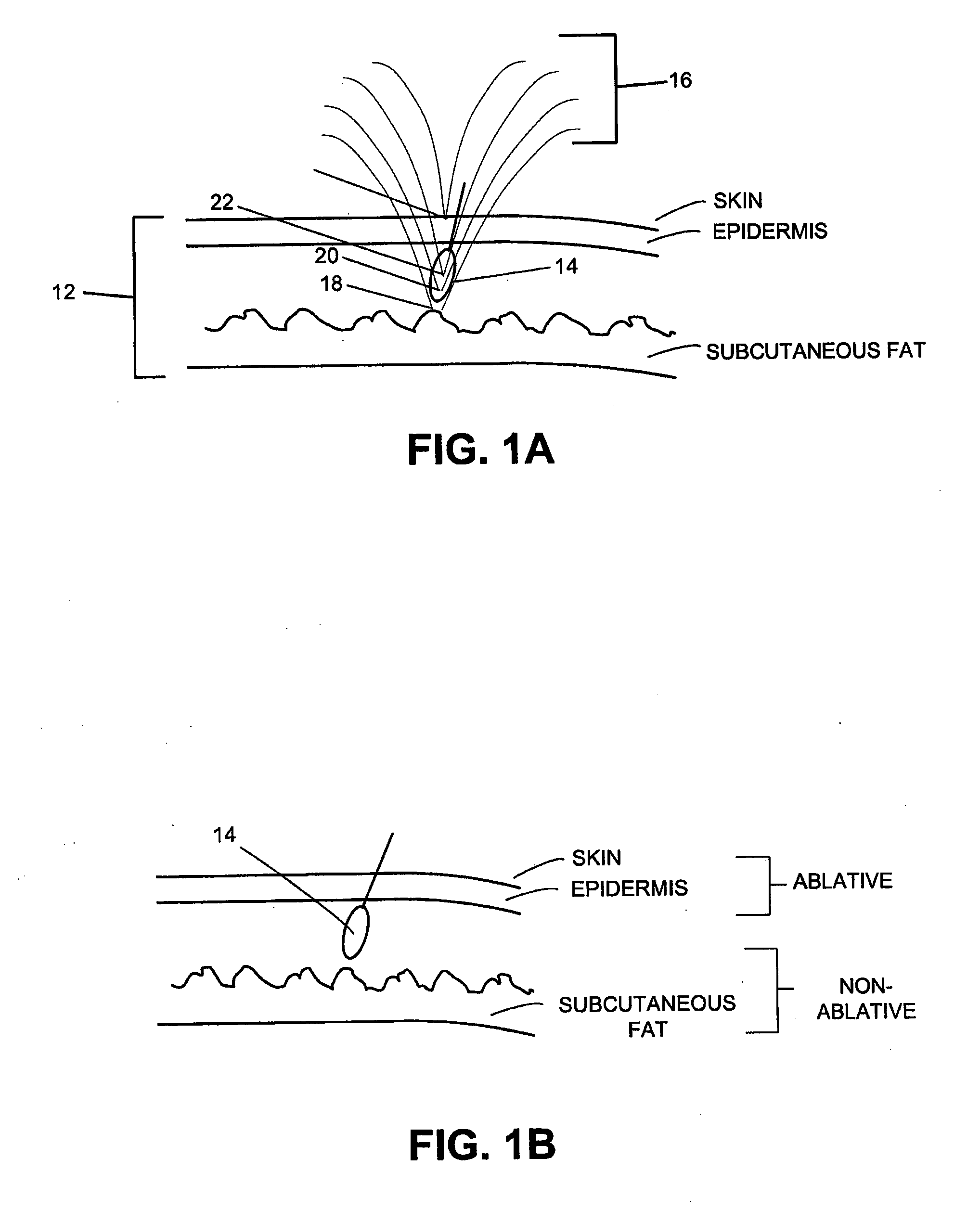
Methods and devices for intraosseous nerve ablation
InactiveUS6699242B2Low costAvoid prolonged useSurgical instruments for heatingSurgical instruments for coolingSurgical departmentSurgical device
Owner:BAYLOR COLLEGE OF MEDICINE
Methods and devices for intraosseous nerve ablation
InactiveUS20010047167A1Limited its pharmaceutical useOvercome disadvantagesSurgical instruments for heatingSurgical instruments for coolingSurgical departmentSurgical device
The invention relates to surgical devices, and in particular, ablating probes for ablating, or severing, intraosseous nerves. The ablating probes are used to ablate or sever the pathway of intraosseous nerves after the ablating probe contacts, or is positioned in close proximity to, the intraosseous nerve. Access to the intraosseous nerve may be provided by the ablating probe or another instrument. The invention is also directed to a surgical system for ablating intraosseous nerves that comprises at least one nerve ablating device, e.g., the ablating probes of the invention, and at least one sleeve through which the ablating probe is passed to contact the intraosseous nerve, or the area in close proximity to the intraosseous nerve, thereby facilitating ablation of the intraosseous nerve. Methods of ablating intraosseous nerves are also disclosed.
Owner:BAYLOR COLLEGE OF MEDICINE
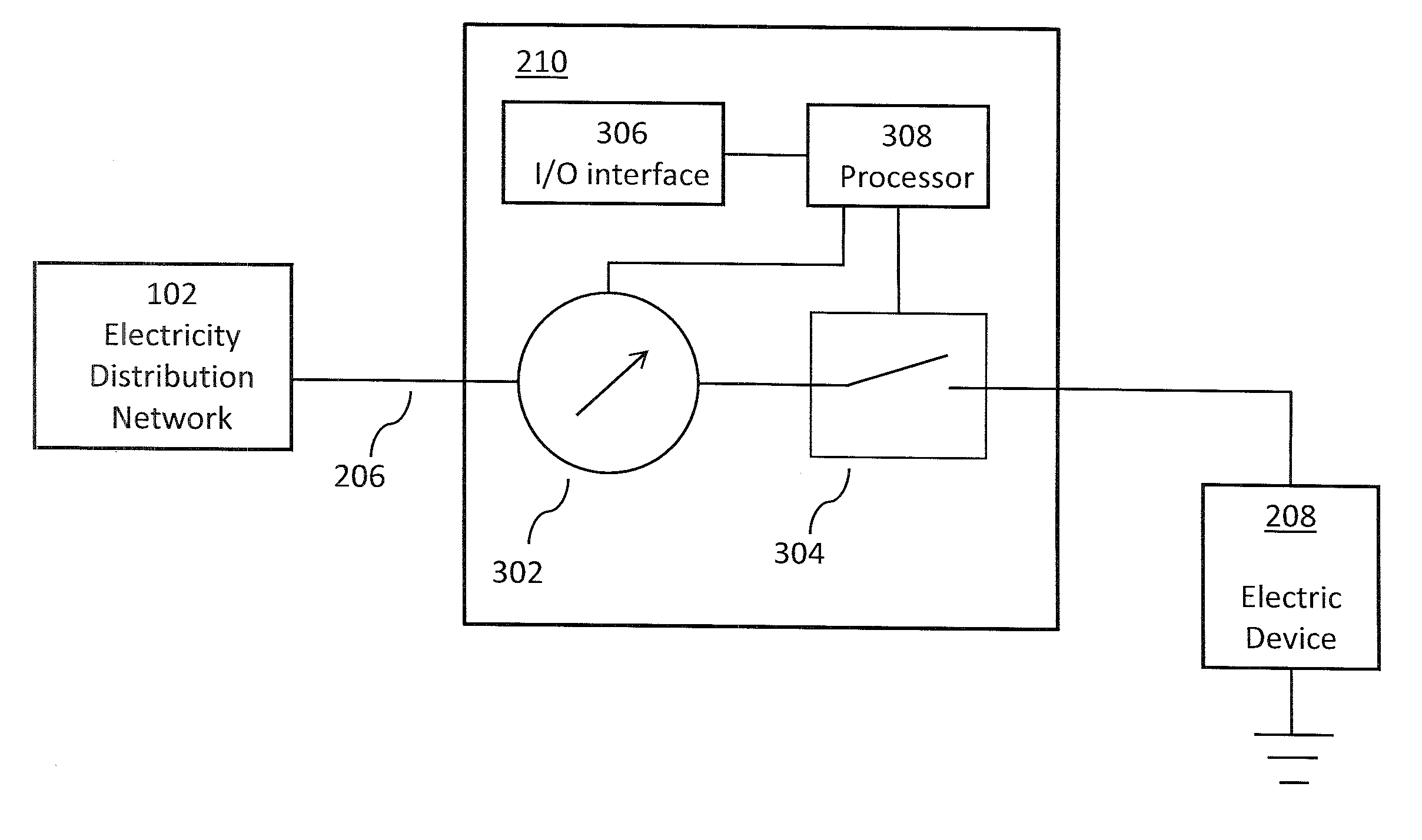
Energy consumption management
ActiveUS20120245752A1Decreasing net amountIncreasing net amountMechanical power/torque controlLevel controlElectric energyElectric devices
Methods, systems, and devices for controlling electrical energy consumption in an electricity distribution network, so as to reduce net energy consumption in a given area during a given time period, are described. In particular, a method of controlling electrical energy consumption within an electricity distribution network is described. The method comprises maintaining a database of information about electric devices, and identifying a time period during which consumption of electrical energy is to be controlled. The method further comprises selecting, based on device profile information stored in the database, groups of electric devices, and associating one or more time intervals with each of the selected groups. Requests are sent to the electric devices of the selected groups to control electrical energy consumption and / or provision by the electric devices. This enables a reduction in net consumption of electrical energy during a respective time interval.
Owner:REACTIVE TECH
Digital data and software security protection
InactiveUS20010034846A1Prevents illegal installation and useAvoid installationDigital data processing detailsUnauthorized memory use protectionDigital dataIntellectual property
The present invention provides for a system method of preserving digital intellectual property data and software security utilizing a network by removing a random chunk of data from executable code and only delivering the proper chunk, size and location upon successful authentication of the user, the computing device environment and previous registration history.
Owner:BEERY PETER
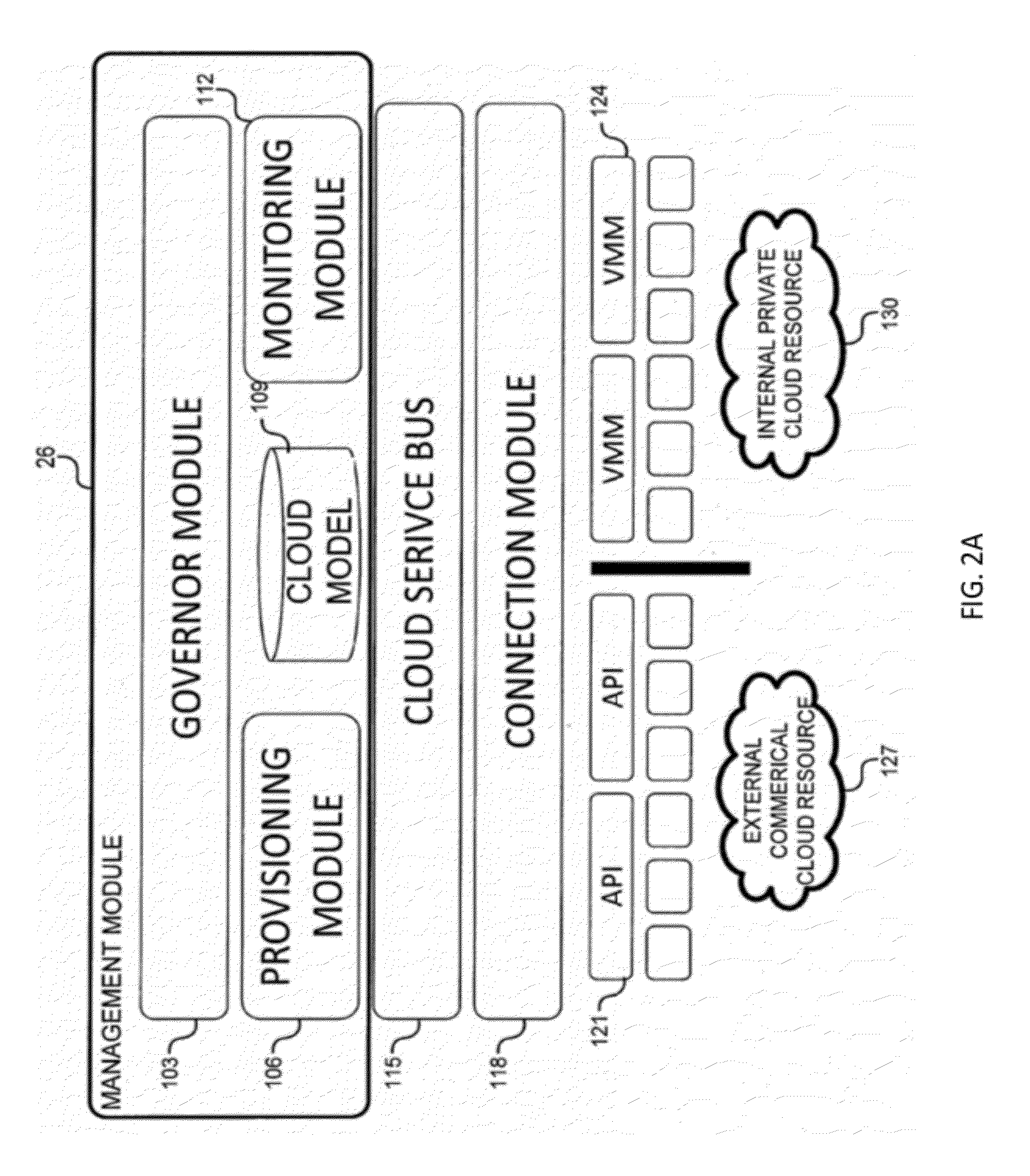
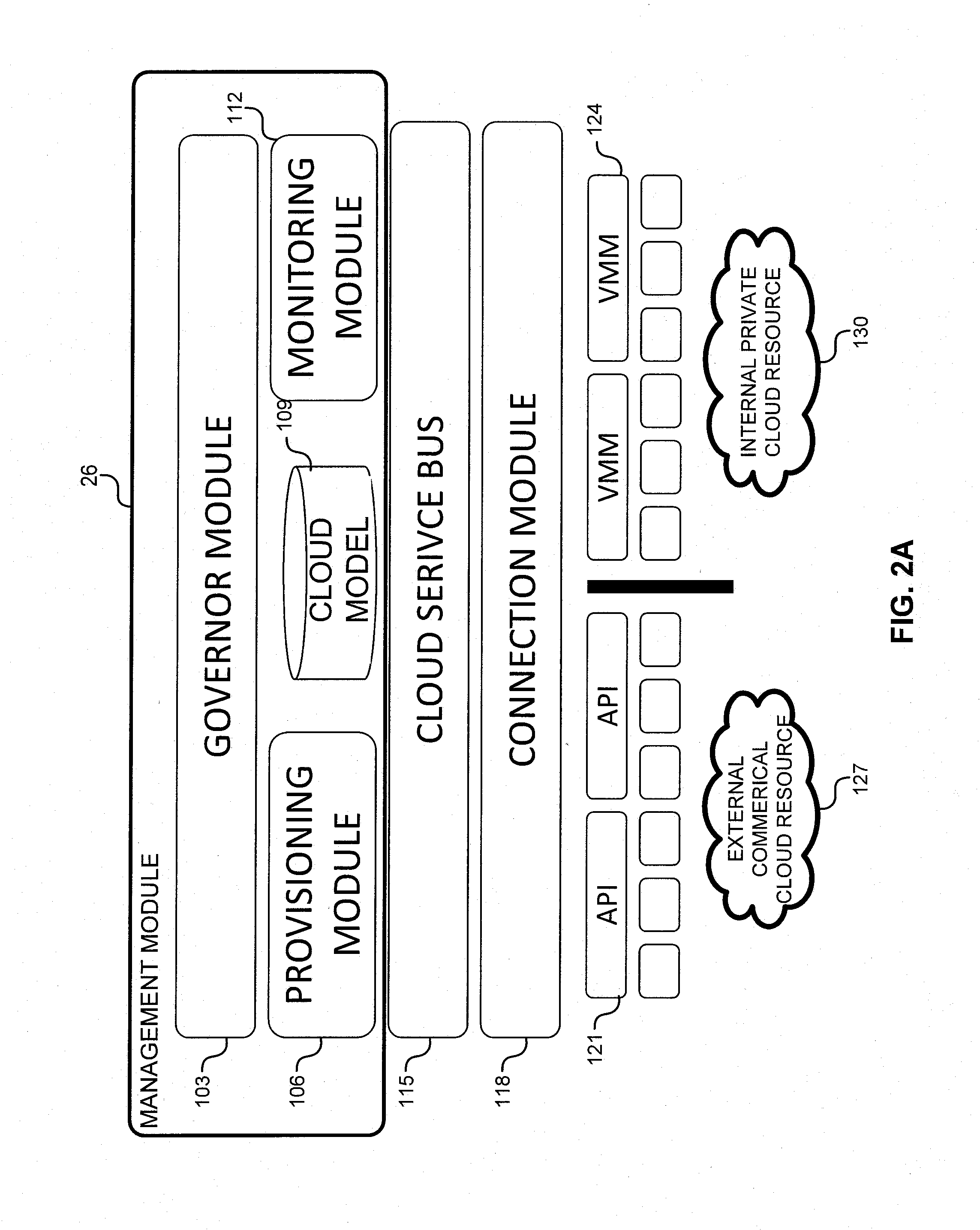
System and method for a cloud computing abstraction layer with security zone facilities
ActiveUS9069599B2Rapid and dynamic deployment and scalingShorten the timeResource allocationHybrid transportVirtualizationAbstraction layer
In embodiments of the present invention improved capabilities are described for a virtualization environment adapted for development and deployment of at least one software workload, the virtualization environment having a metamodel framework that allows the association of a policy to the software workload upon development of the workload that is applied upon deployment of the software workload. This allows a developer to define a security zone and to apply at least one type of security policy with respect to the security zone including the type of security zone policy in the metamodel framework such that the type of security zone policy can be associated with the software workload upon development of the software workload, and if the type of security zone policy is associated with the software workload, automatically applying the security policy to the software workload when the software workload is deployed within the security zone.
Owner:DXC US AGILITY PLATFORM INC
Exhaust gas treatment catalyst
InactiveUS7374729B2Improved coating architectureSacrificing TWC catalyst performanceCombination devicesInternal combustion piston enginesSorbentMetal
Provided are an exhaust treatment catalyst and an exhaust article containing the catalyst. The catalyst comprises:(a) a carrier;(b) a first layer deposited on the carrier, said first layer comprising substantially only at least one refractive metal oxide;(c) a second layer deposited on the first layer, said second layer comprising substantially only at least one oxygen storage component and at least one binder therefor; and(d) a third layer deposited on the second layer, said third layer comprising at least one layer of one or more platinum group metal components supported on a refractory metal oxide support.Optionally, a fourth layer is deposited on the third layer wherein the fourth layer comprises one or more platinum group metal components supported on a refractory metal oxide support. As a further option, an overcoat layer may be deposited on the third or fourth layer wherein the overcoat layer comprises a catalyst poison sorbent. Also provided are methods for preparing the catalyst and methods for monitoring the exhaust storage capacity of an exhaust article containing the catalyst.
Owner:BASF CATALYSTS LLC
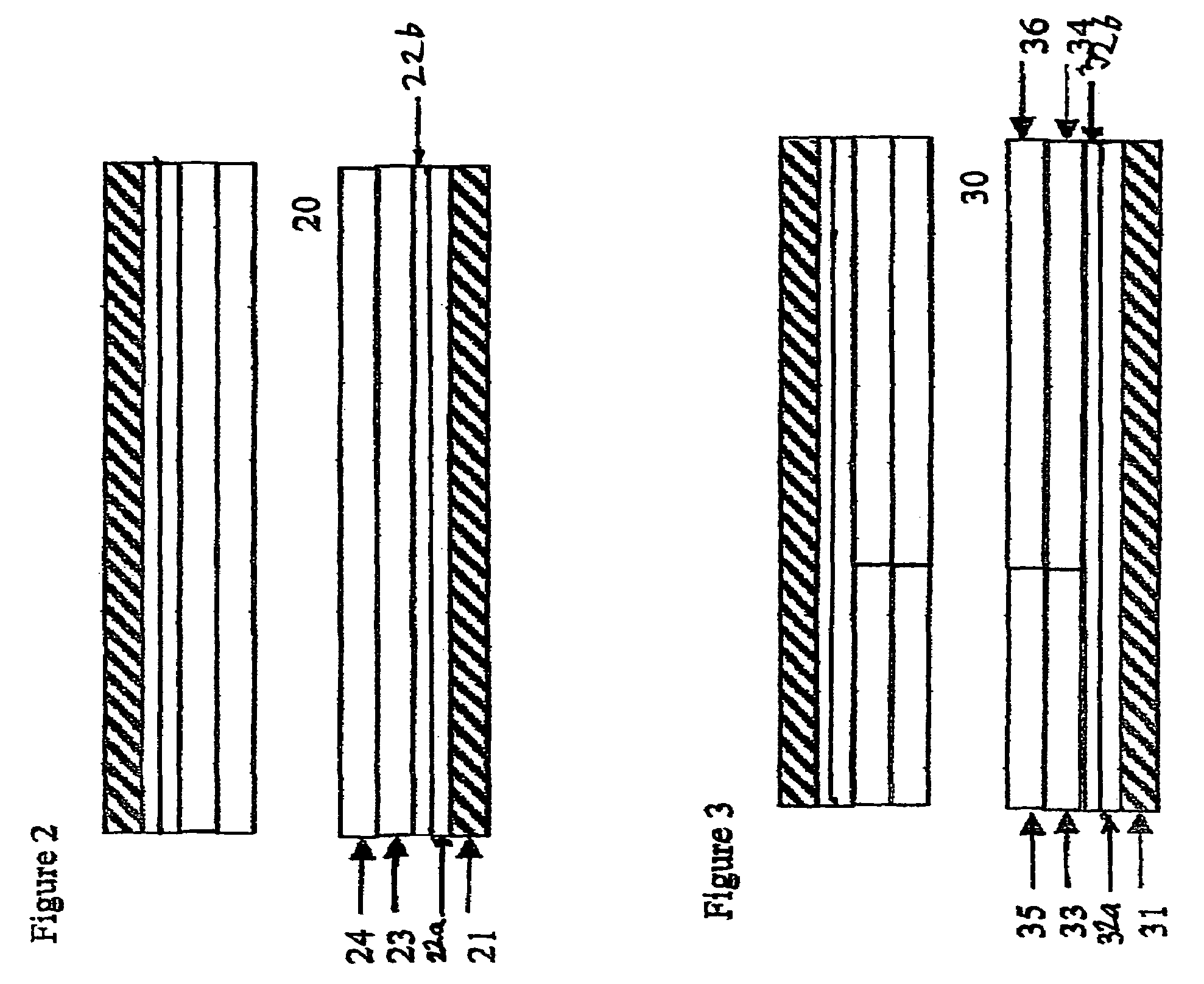
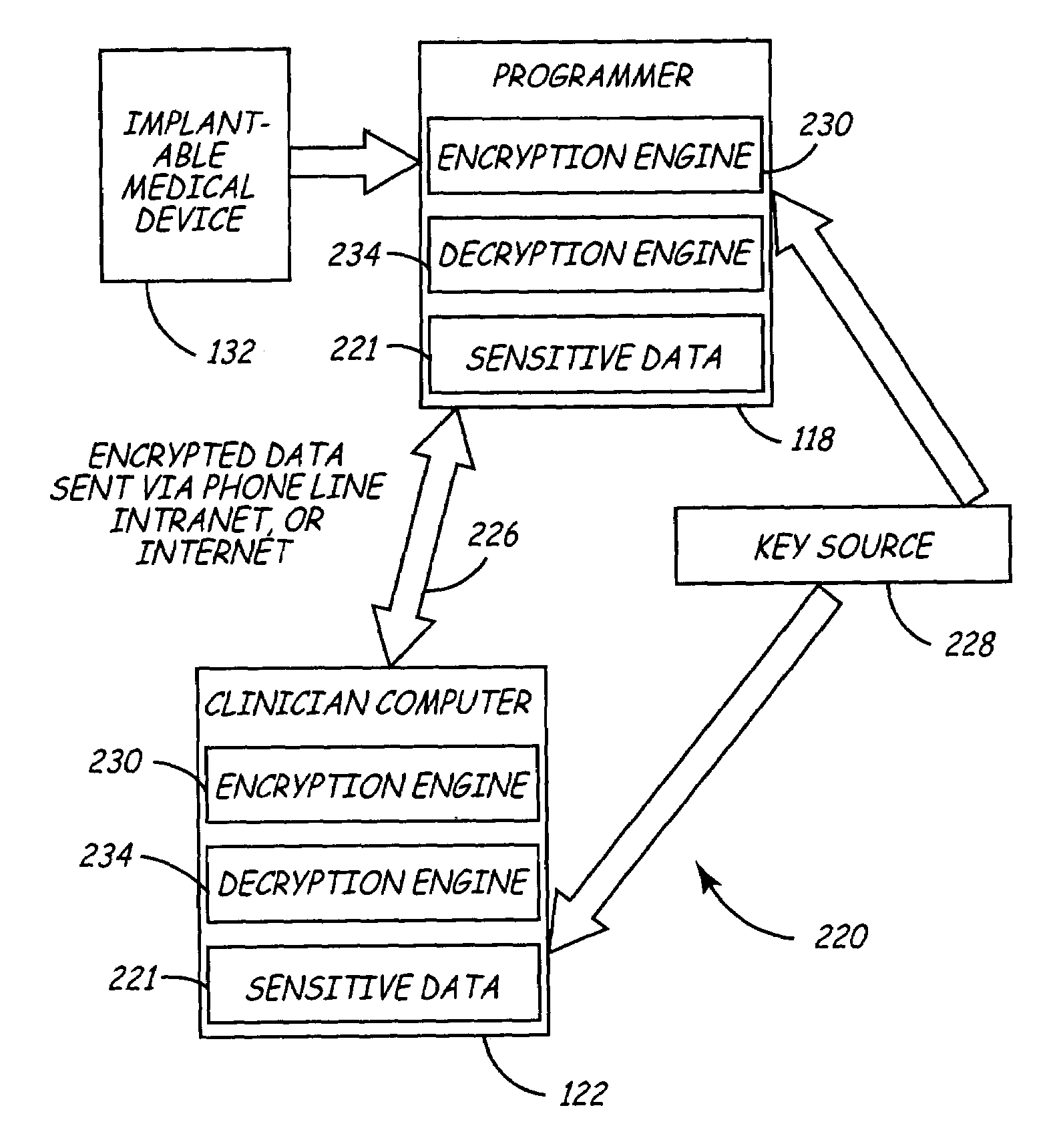
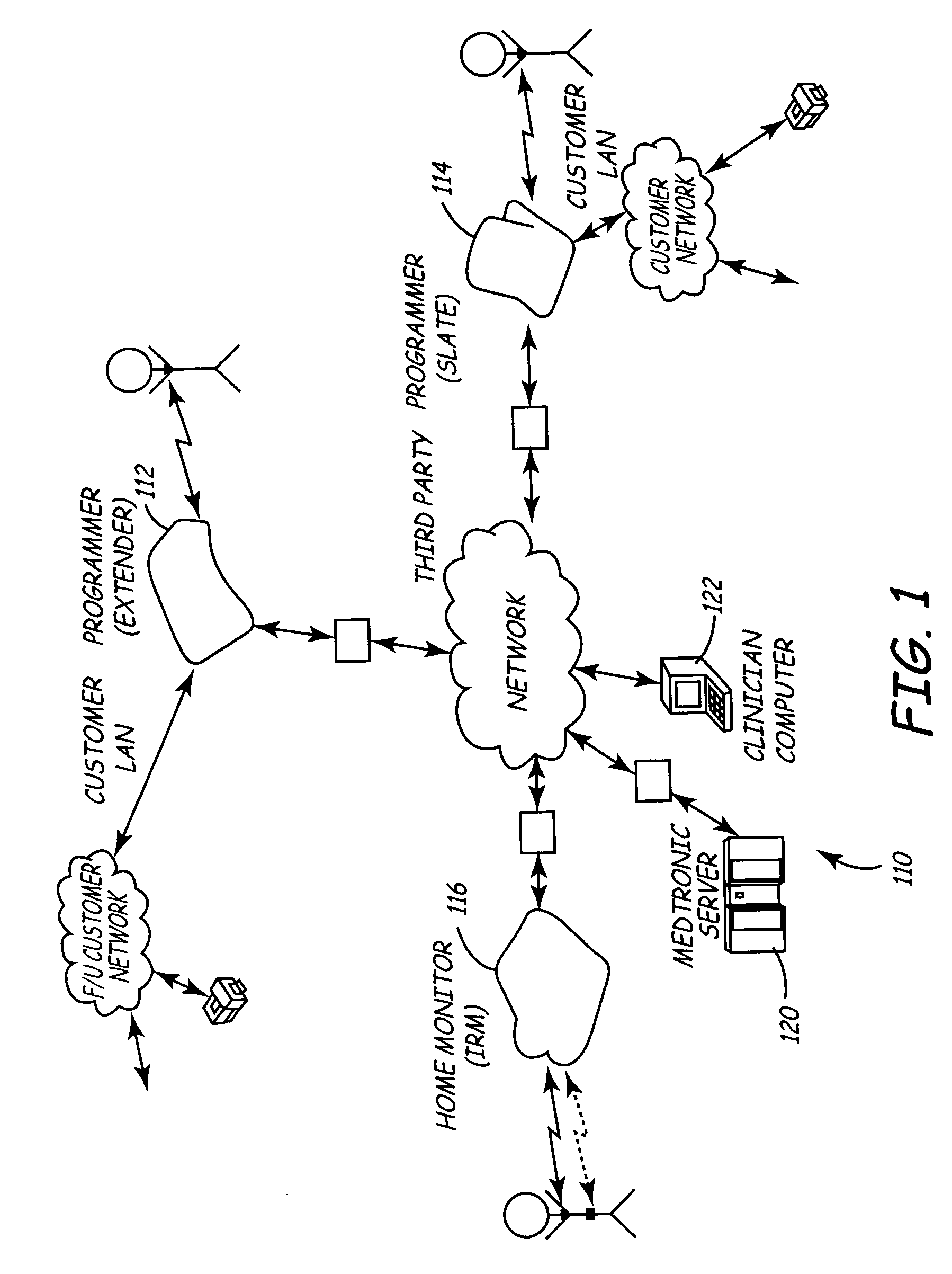
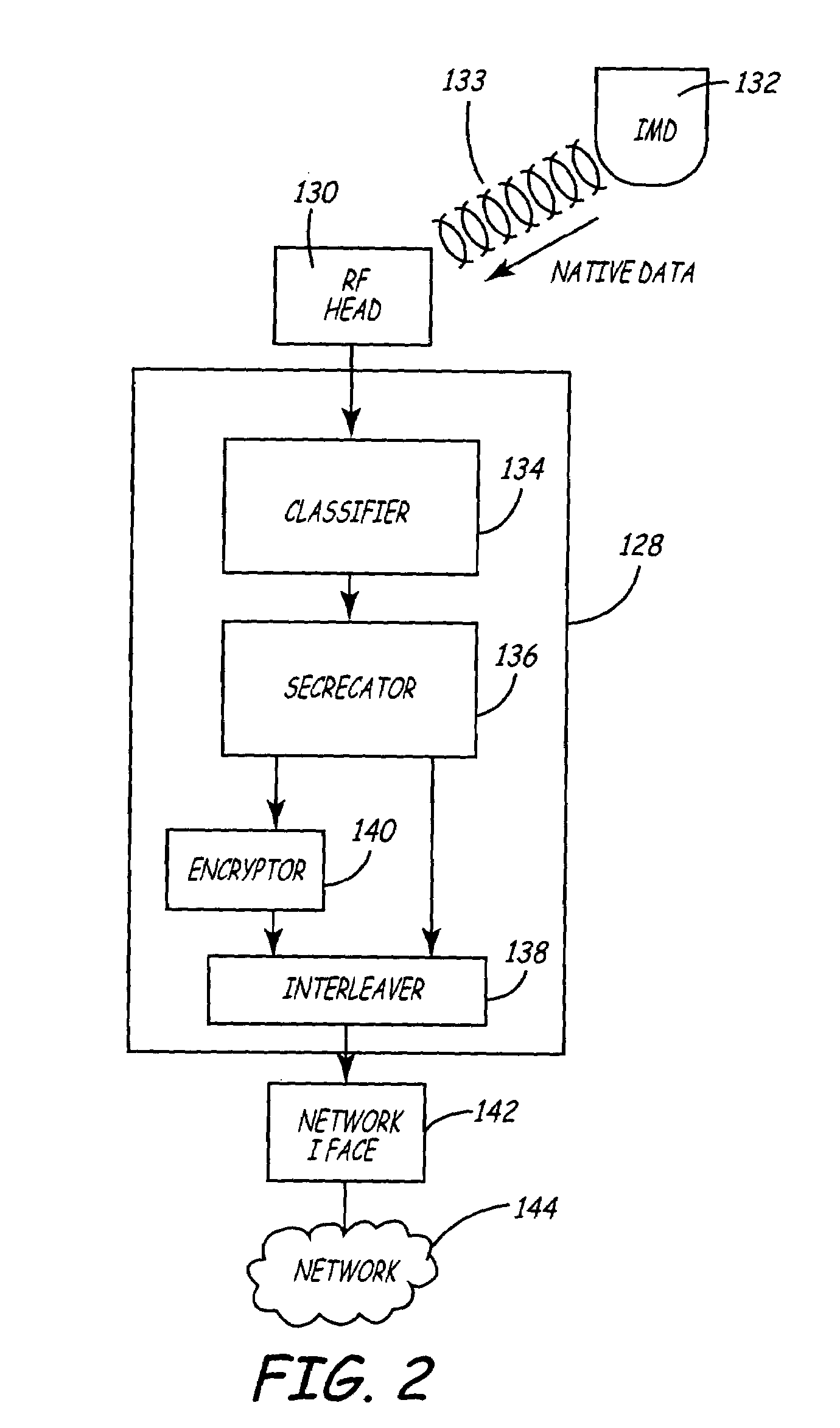
Variable encryption scheme for data transfer between medical devices and related data management systems
InactiveUS7027872B2Ensure authenticityEnsure integrityElectrotherapyData processing applicationsData centerData management
Owner:MEDTRONIC INC
Method and system for extraction of hydrocarbons from oil shale
Owner:ULTRA SAFE NUCLEAR CORP
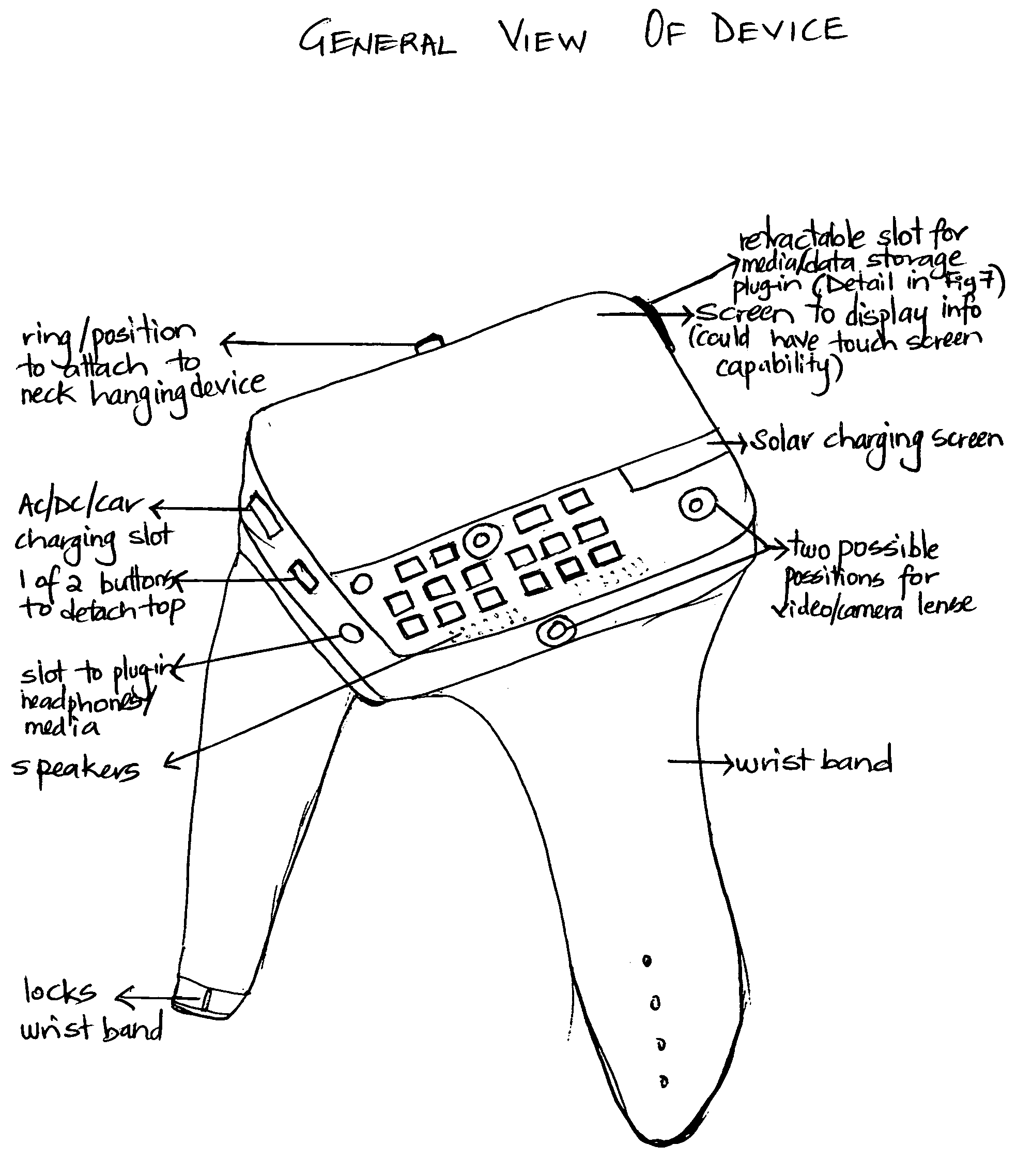
Multifunctional all-in-one detachable wrist wireless mobile communication device
InactiveUS20090280861A1Eliminate stressEliminate timeSubstation equipmentTransmissionHeadphonesLoudspeaker
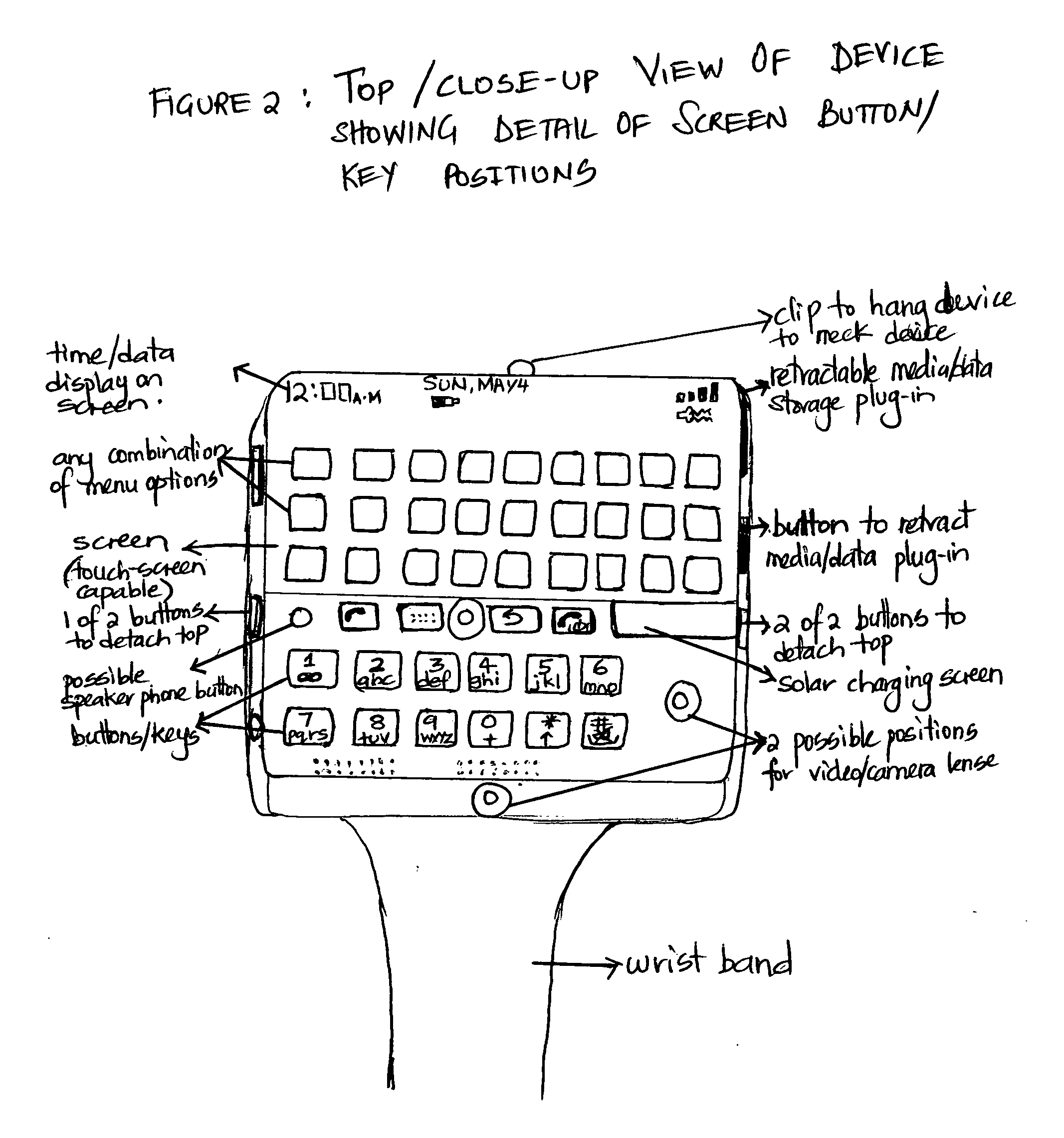
The invention claimed herein is a Multifunctional, All-in-one, Detachable Wrist Wireless Mobile Communication Device, which can be worn on the wrist, and used with a wireless earpiece for wireless communication needs. This device has a screen and / or buttons to operate the device, is detachable from its base if needed to be used like a regular mobile phone. This multifunctional device has all the mobile communication functions / features / capabilities such as audio, video, camera, media playback, secured wireless (or with an option to plug in) media / data storage capability, secured video / audio house / business / child monitoring features, dual solar charging and AC / DC / car charging capabilities, speaker phone capabilities, and GPS and satellite reception capabilities. All the features mentioned above and described in the specifications eliminates the need to carry a separate MP3 player, or headphones, or flash drive, as all this features are built in this device. By wearing this device, the user does not need to carry a separate mobile device that falls and gets damaged, or is lost or stolen or forgotten in cars and at home, and neither does the user need to locate the device in purses, pockets, or retrieve from holders to answer calls like most mobile phones in the market today. The device also comes with an option to be detached and hanged around the neck with the hanging device claimed herein, if preferred over wearing it on the wrist. It is a convenient, practical, all-in-one, next generation communication device that is readily available on the wrist to use, and thus is the all in one solution for all the communication / media / technology needs of today, and tomorrow.
Owner:KHAN ASHANA SABANA NISHA
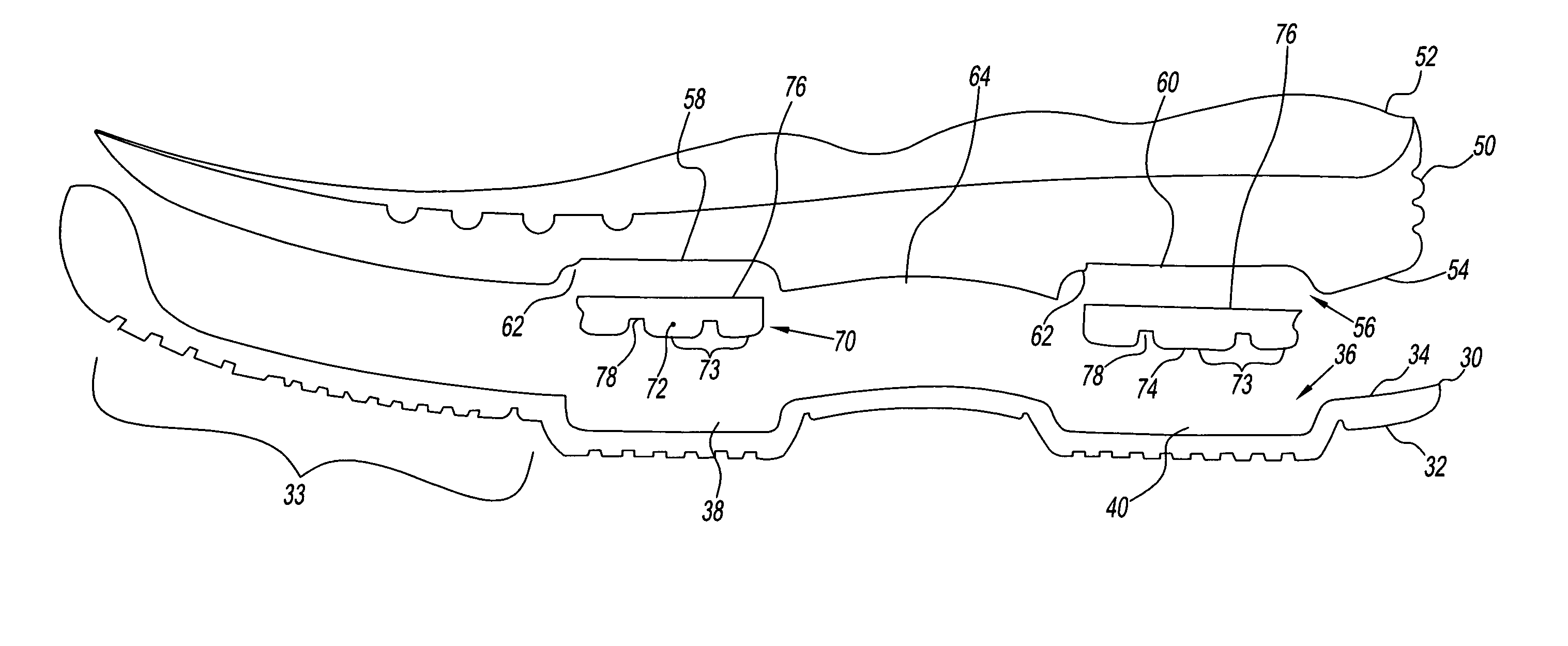
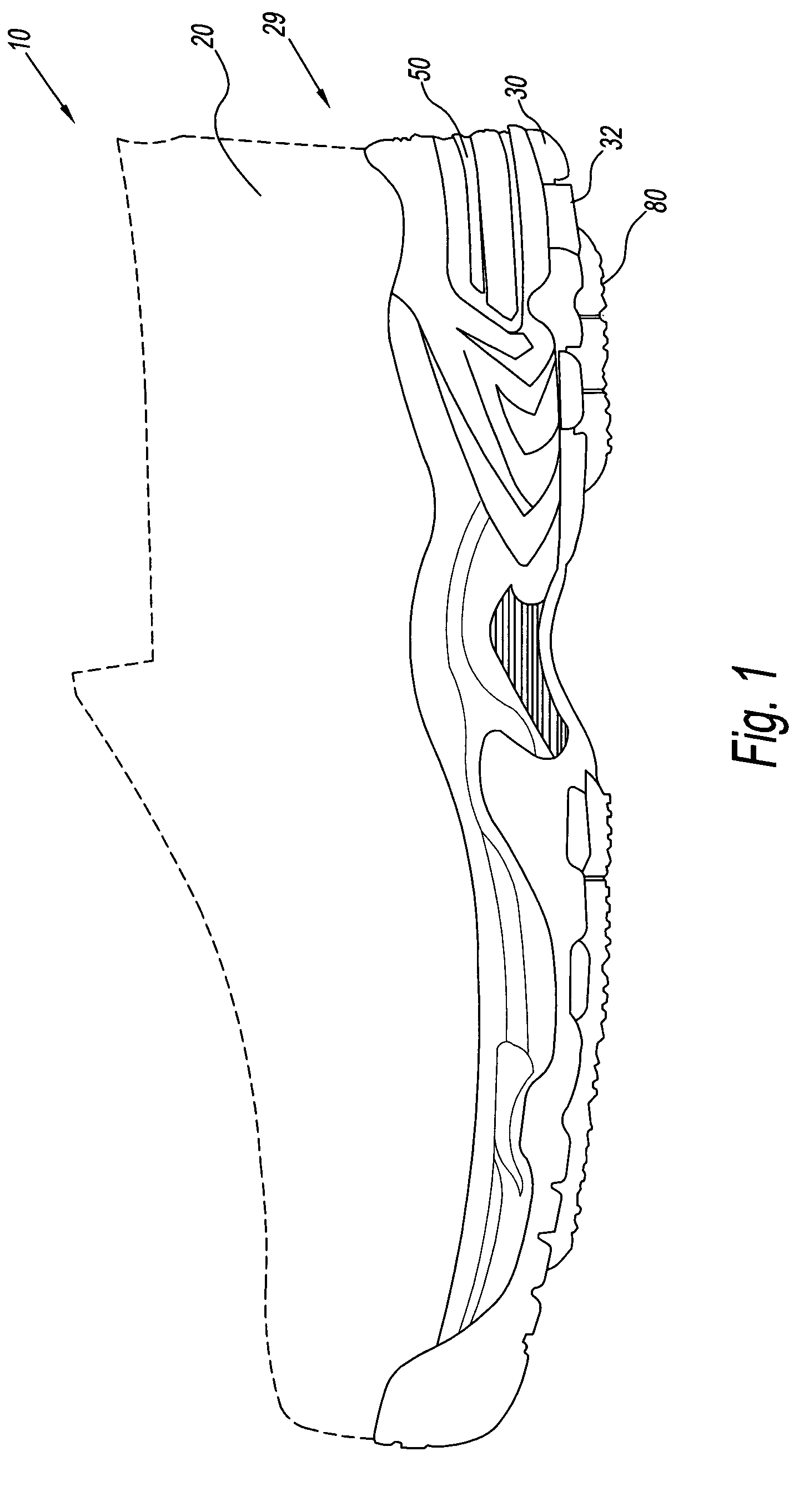
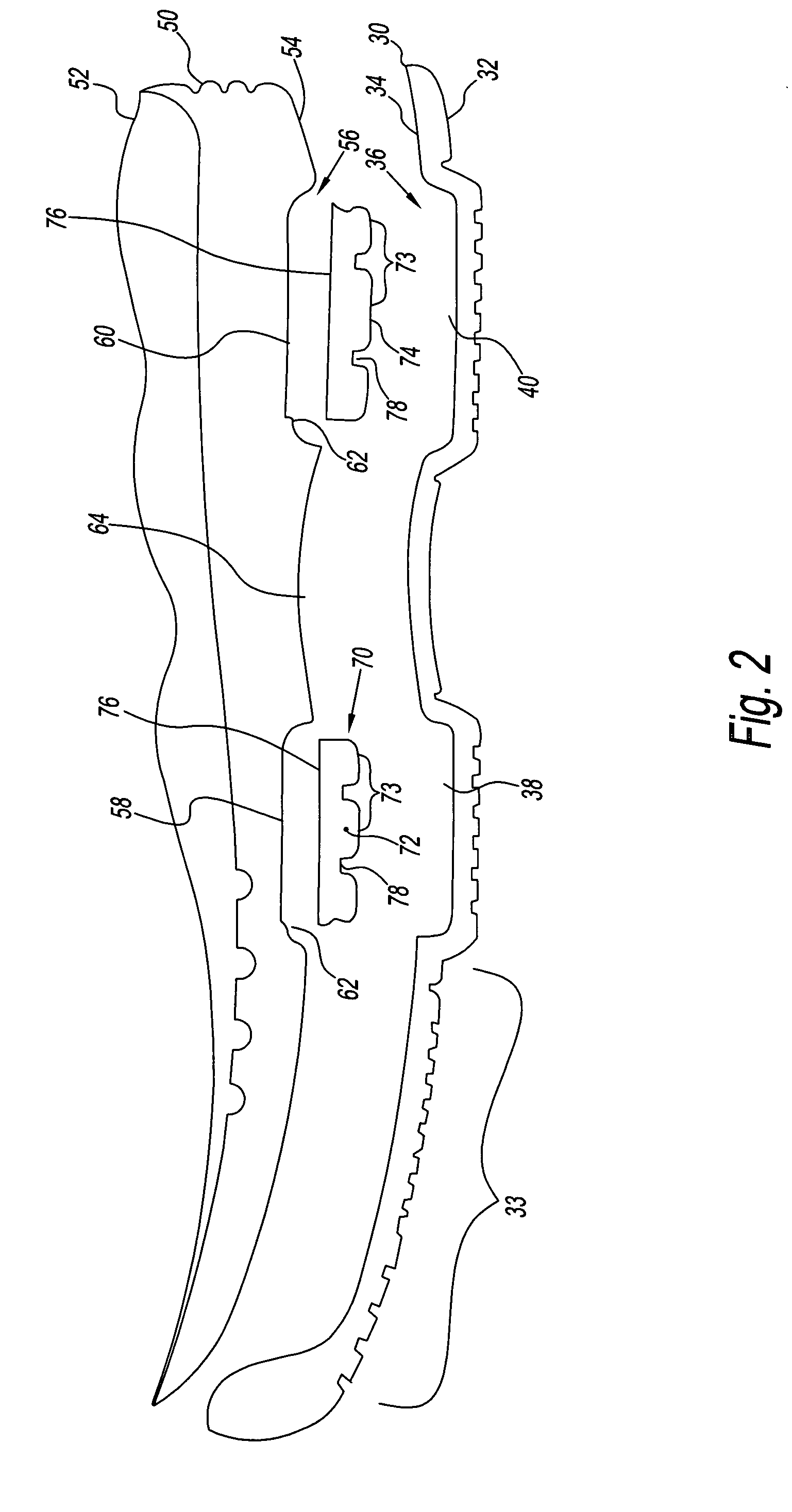
Footwear system
Owner:TRANSFORM SR BRANDS LLC
Exhaust articles for internal combustion engines
InactiveUS7276212B2Improved coating architectureSacrificing TWC catalyst performanceCombination devicesInternal combustion piston enginesCombustionInternal combustion engine
Provided is a base metal undercoat containing catalyst and an exhaust article containing the catalyst. The catalyst contains a base metal undercoat with an oxygen storage component, and at least one catalytic layer. Also provided are methods for preparing the catalyst and methods for monitoring the oxygen storage capacity of an exhaust article containing the catalyst.
Owner:ENGELHARD CORP
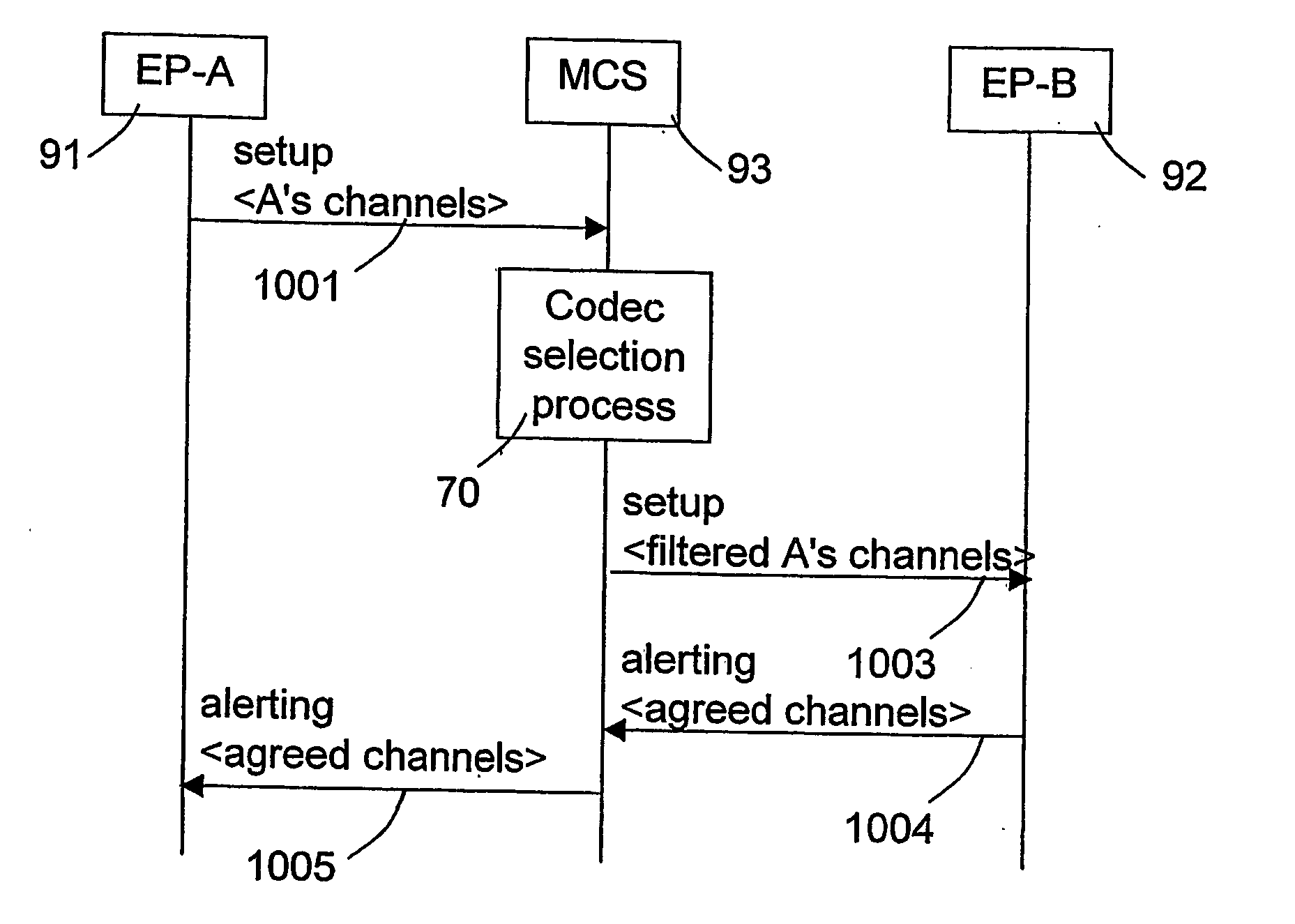
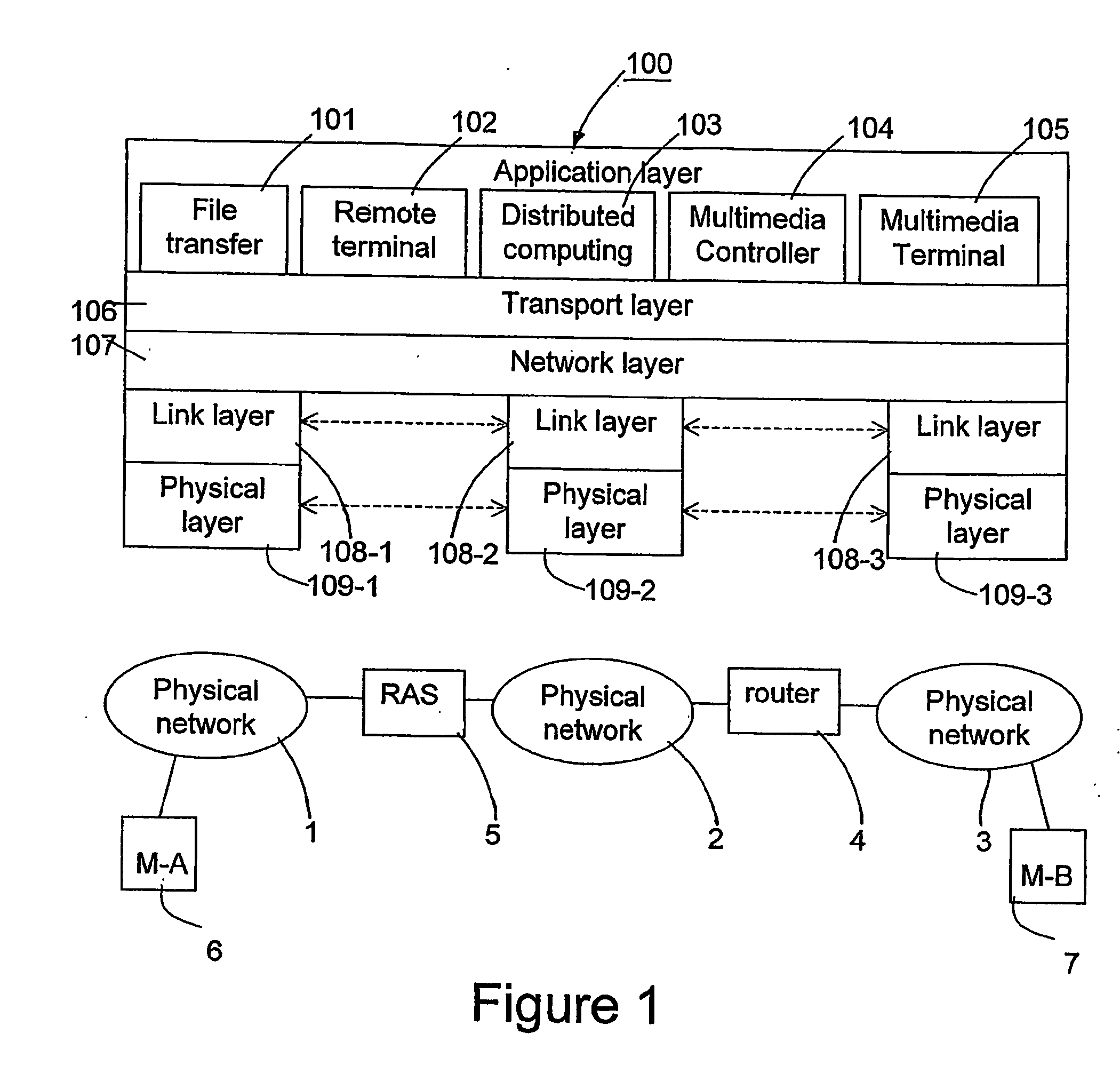
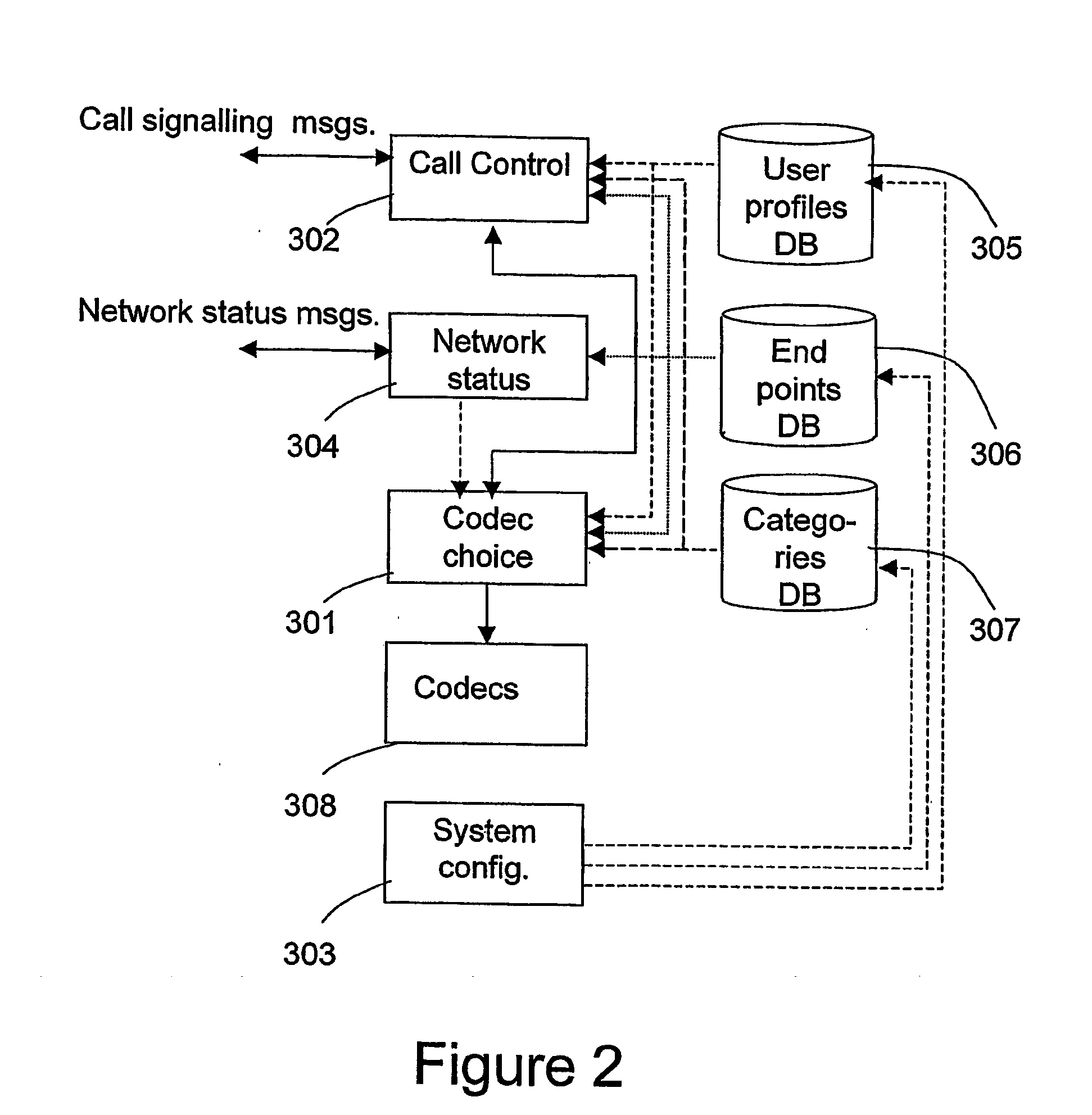
Method and apparatus for codec selection
InactiveUS20060174015A1Limit useLimitation on bandwidth be useMultiple digital computer combinationsTransmissionTelenetNetwork element
A telecommunications system includes a public network, to which a first endpoint device is connected, and a data network, to which second endpoint devices and a multimedia controller are connected. The networks are interconnected via a remote access server which provides data connectivity for the first endpoint device but which has a limited bandwidth. Codecs with corresponding bandwidth are selected for communication between the endpoints. The multimedia controller receives a communication request that comprises information related to the codecs desired by the endpoint device for said communication. The multimedia controller sends an address detection message towards the endpoint device involved in said communication and checks the address information in the answer to said address detection message. Final codecs for the communication are selected depending on if the answer contains an address of a network element, which can limit the bandwidth for said communication.
Owner:TELEFON AB LM ERICSSON (PUBL)
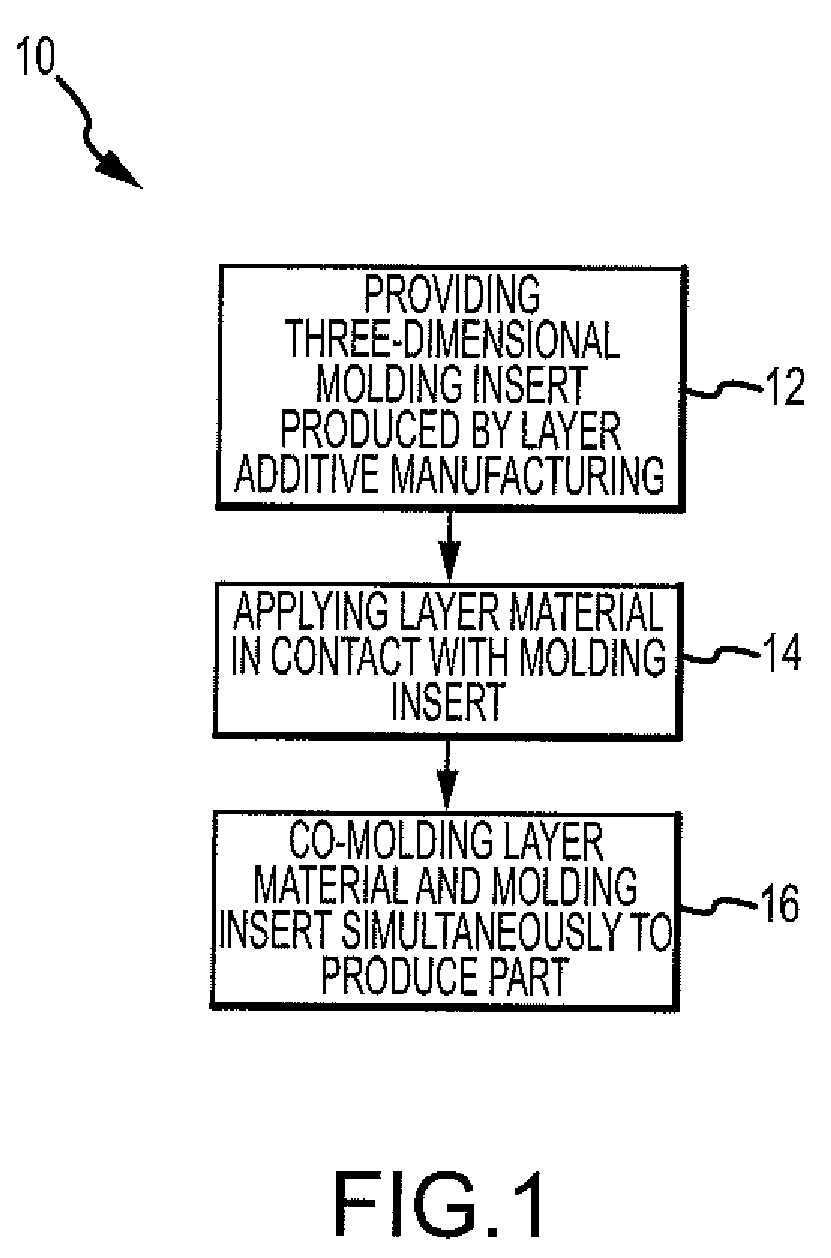
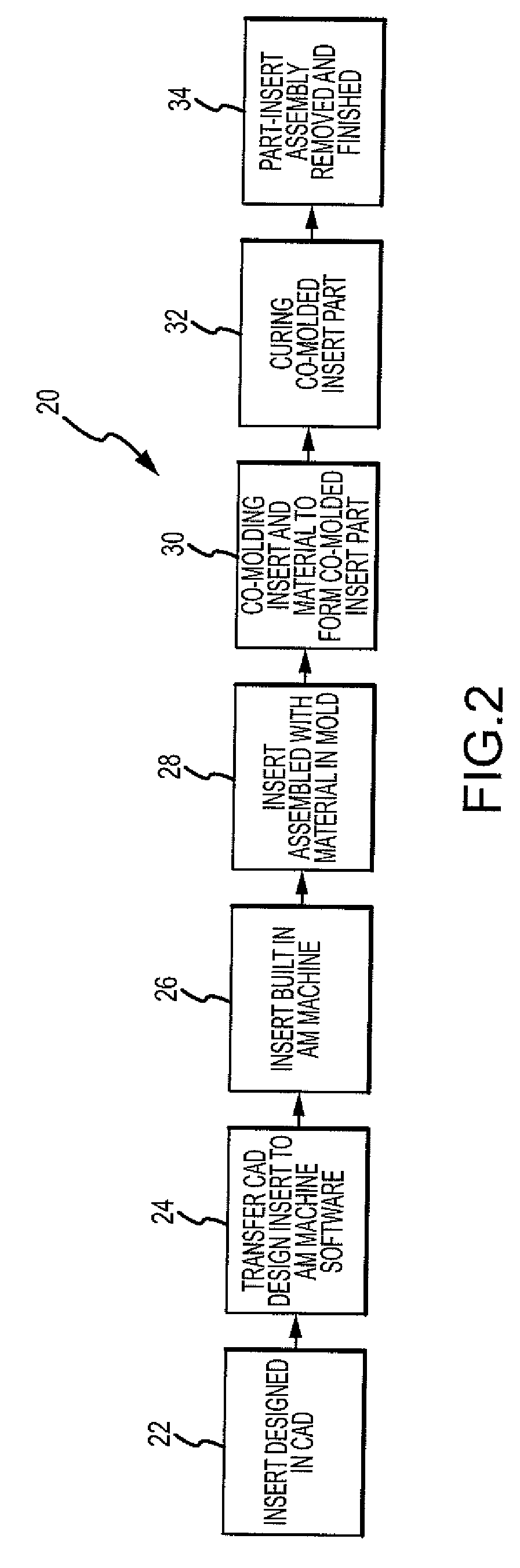
Method of manufacturing co-molded inserts
ActiveUS8383028B2Little costsLittle timeAdditive manufacturing apparatusLamination ancillary operationsMaterials scienceMetal
A method for manufacturing a co-molded insert part for use in composite, plastic, or metal parts is disclosed. The method comprises the step of providing a three-dimensional molding insert produced by a layer additive manufacturing process. The method further comprises the step of applying a layer material in contact with at least a portion of the molding insert. The method further comprises the step of co-molding the layer material and the molding insert simultaneously to produce a co-molded insert part.
Owner:THE BOEING CO
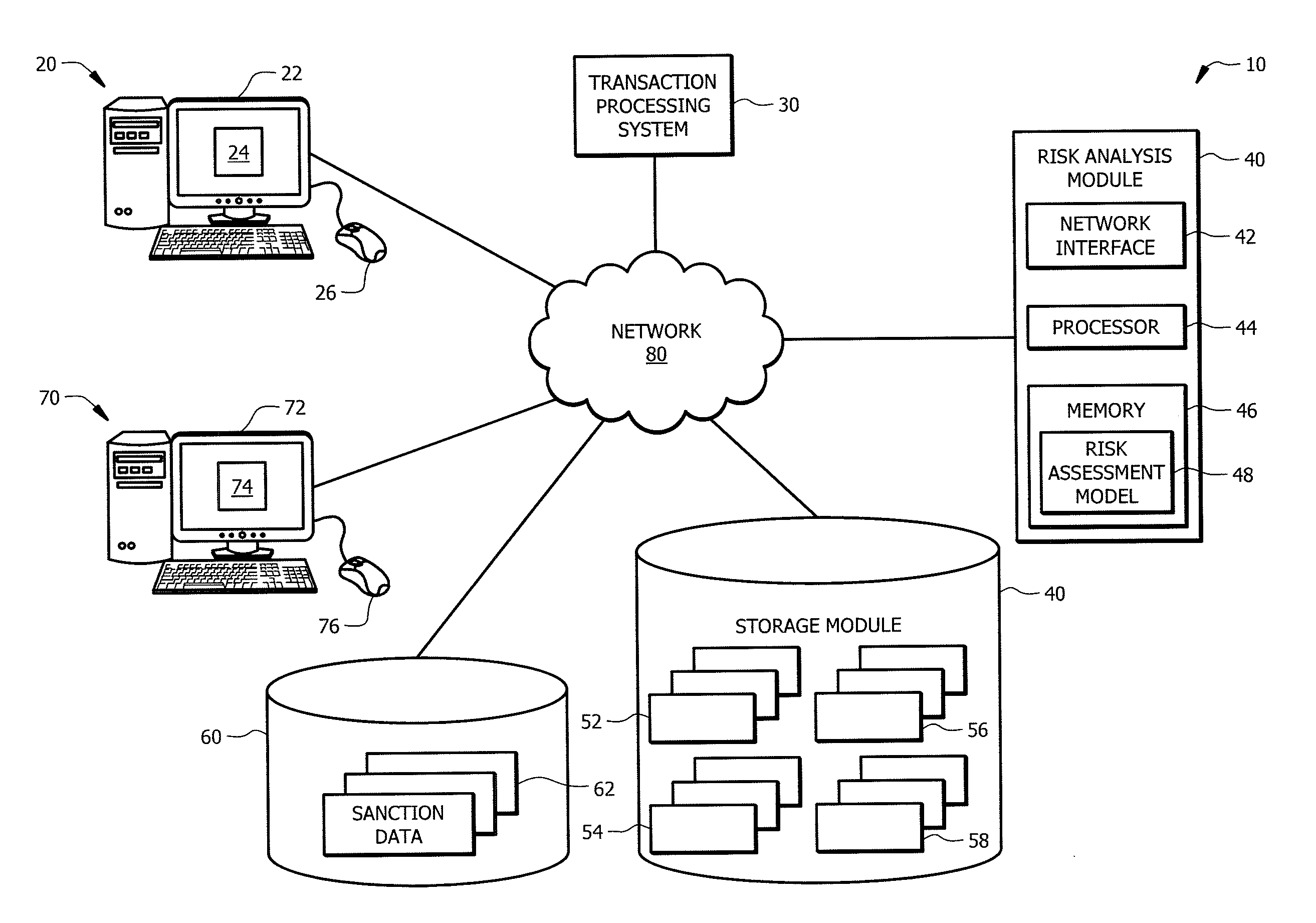
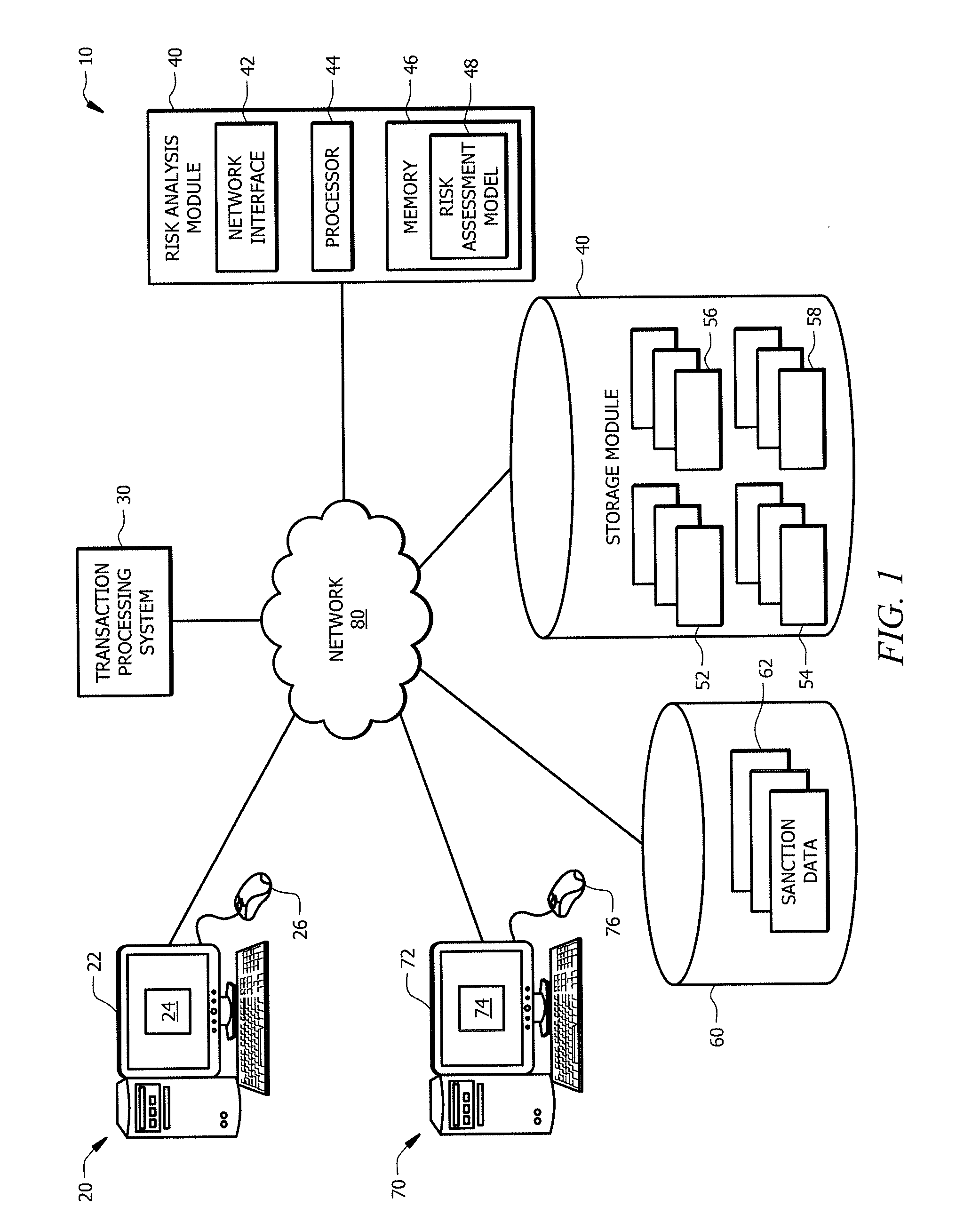
ldentifying Potentially Risky Transactions
ActiveUS20160104163A1Disadvantages can be reduced eliminatedTransactions be reduced eliminatedFinanceWeb data indexingComputer scienceRisk assessment
In certain embodiments, a computer-implemented method includes determining, by a processor, characteristics of a new transaction and processing, by the processor, the characteristics of the new transaction using a risk assessment model. The risk assessment model is generated using an iterative training process that processes, over time, historical transactions to train the risk assessment model based on characteristics of historical transactions and associated risk assessment analysis of the historical transactions. The method includes generating, by the processor, a risk assessment indicator for the new transaction based on processing the characteristics of the new transaction using the risk assessment model. The risk assessment indicator indicates a degree of risk of the new transaction.
Owner:JPMORGAN CHASE BANK NA
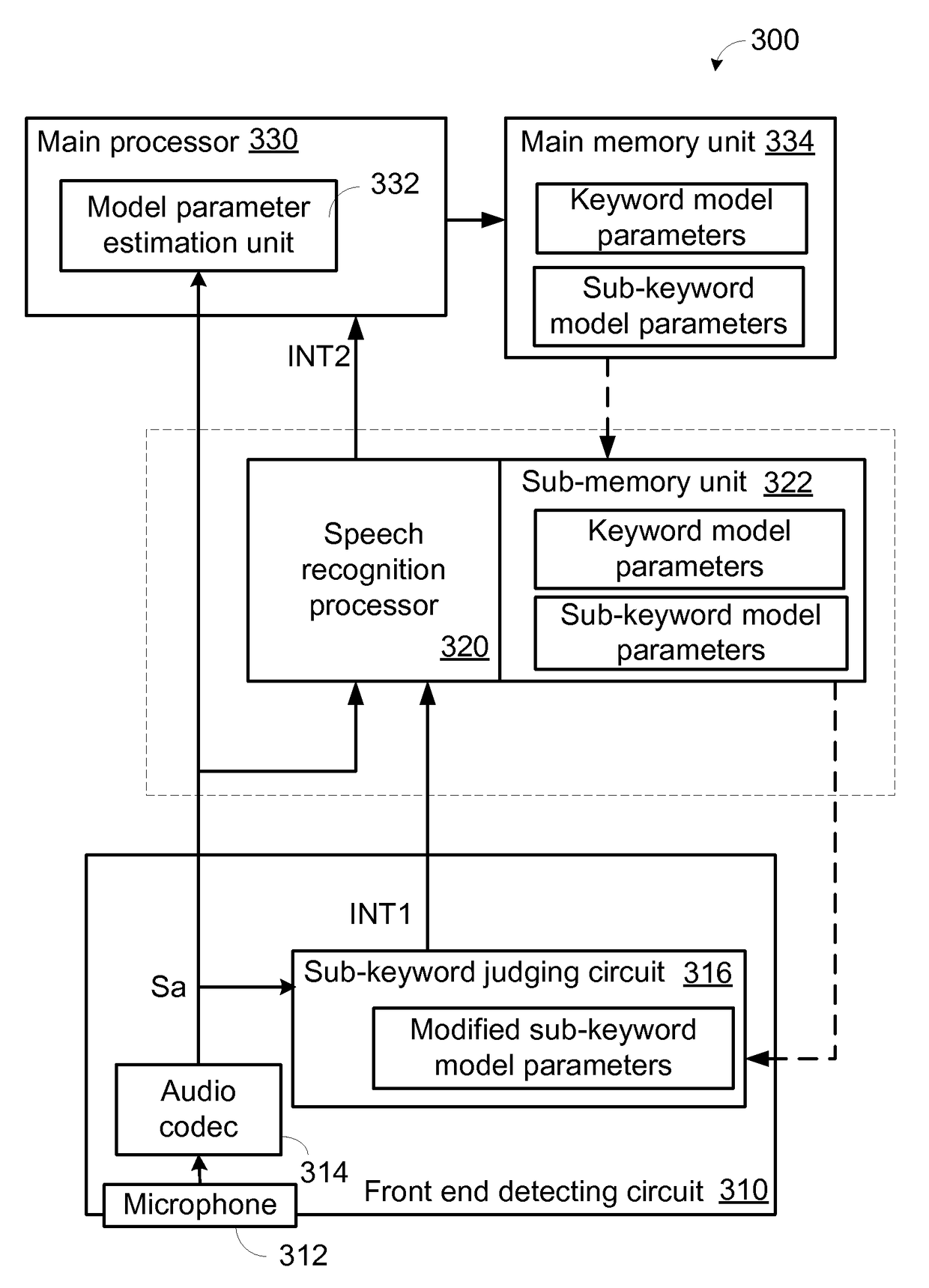
Voice wakeup detecting device and method
ActiveUS9779725B2Avoid prolonged useAccurate identificationPower supply for data processingSubstation equipmentSleep stateSpeech sound
A voice wakeup detecting device for an electronic product includes a front end detecting circuit, a speech recognition processor and a main processor. The front end detecting circuit judges whether a voice signal contains a sub-keyword according to sub-keyword model parameters. If the front end detecting circuit confirms that the voice signal contains the sub-keyword, then it generates a first interrupt signal. In response to the first interrupt signal, the speech recognition processor is enabled to judge whether the voice signal contains a keyword according to keyword model parameters. If the speech recognition processor confirms that the voice signal contains the keyword, then it generates a second interrupt signal. In response to the second interrupt signal, the main processor is enabled. Consequently, the electronic produce is waked up from a sleep state to a normal working state.
Owner:MEDIATEK INC
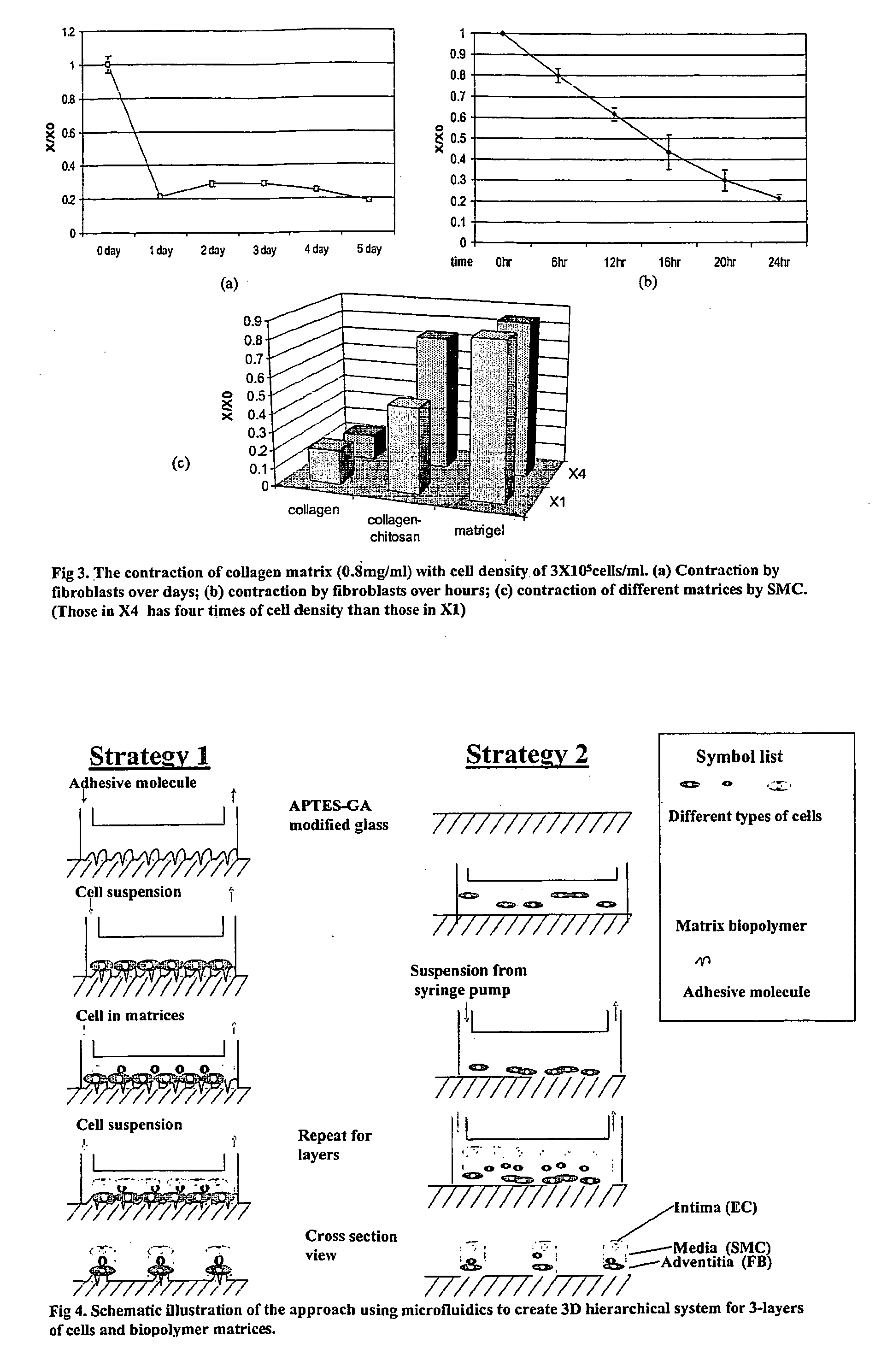
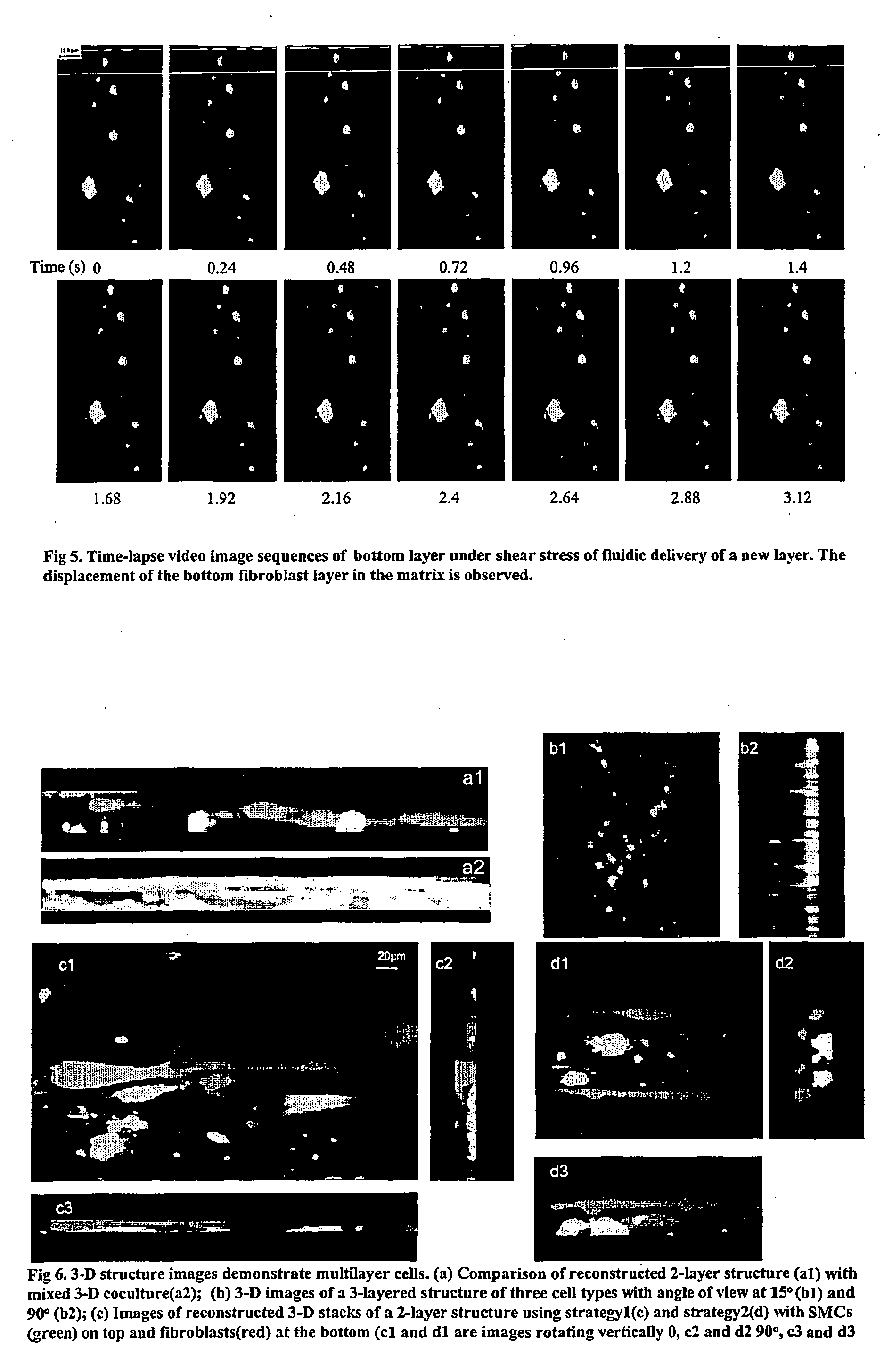
Multilayered microcultures
InactiveUS20060141617A1Accurate mimicFlexible and cost-effectiveBioreactor/fermenter combinationsCompound screeningBiological bodyCell adhesion
A multilayer microculture capable of modeling complex in vitro structures such as mammalian tissues and organ structures is provided, along with methods for producing such a microculture and methods of using such microcultures for assaying for modulators of cell-cell interaction, cell migration, cell proliferation, cell adhesion or cellular or organismal physiology. Further provided are methods of identifying hazardous materials such as environmental toxins and pollutants (e.g., carcinogenic compounds), and methods of monitoring organismal physiology.
Owner:THE BOARD OF TRUSTEES OF THE UNIV OF ILLINOIS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com