Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
111 results about "Safety policy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safety Policy. Definition - What does Safety Policy mean? An organization's safety policy is a recognized, written statement of its commitment to protect the health and safety of the employees, as well as the surrounding community.
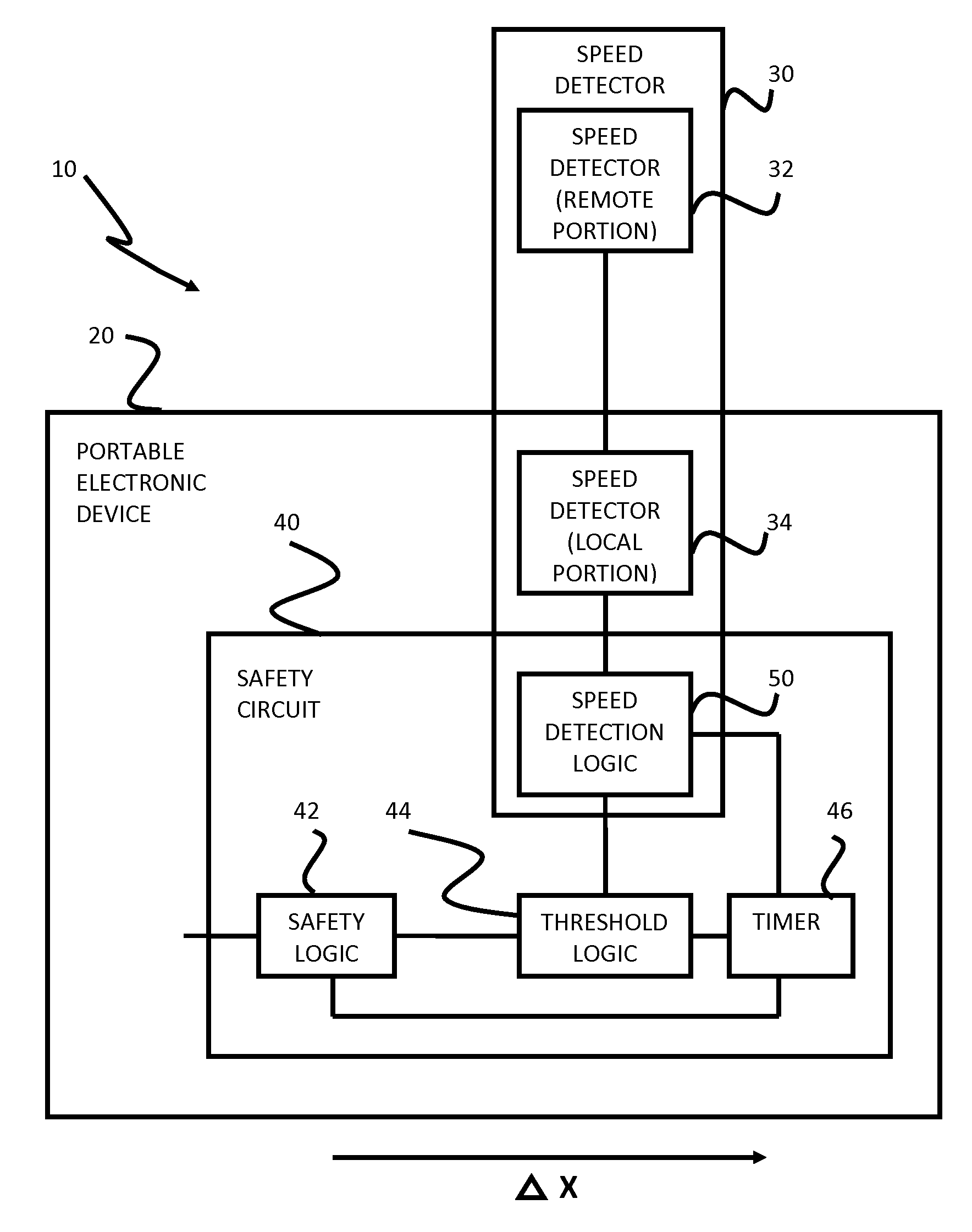
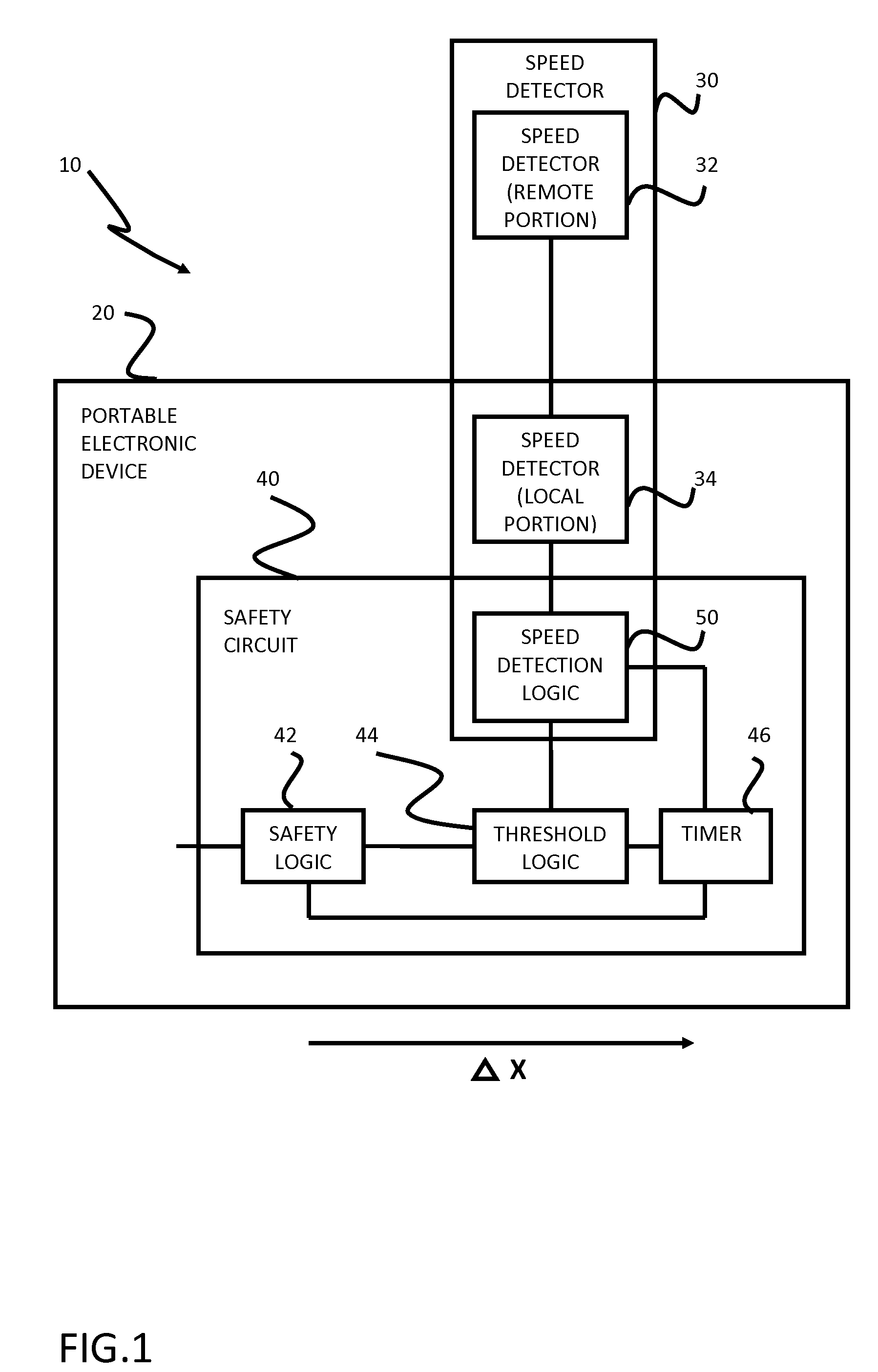
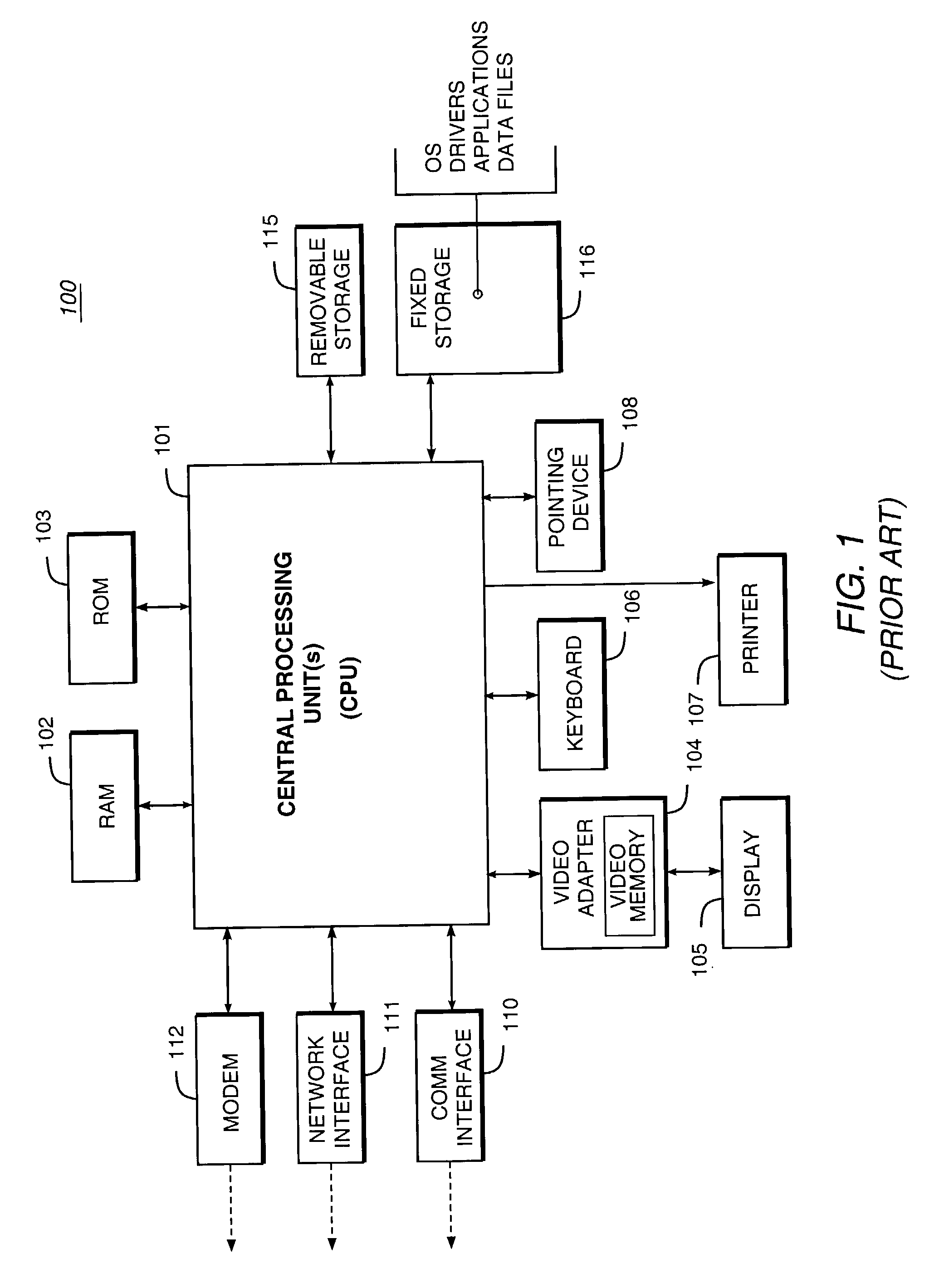
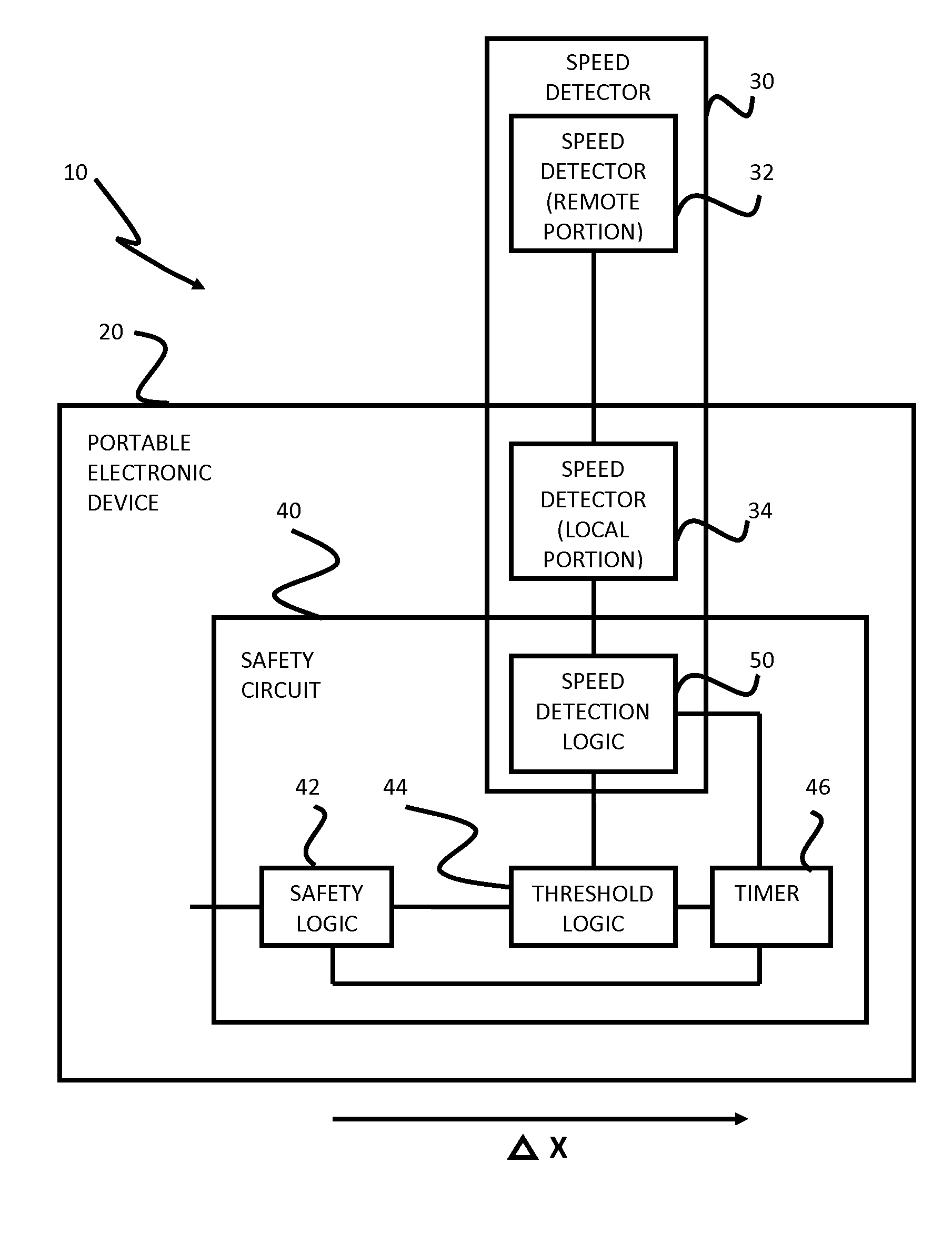
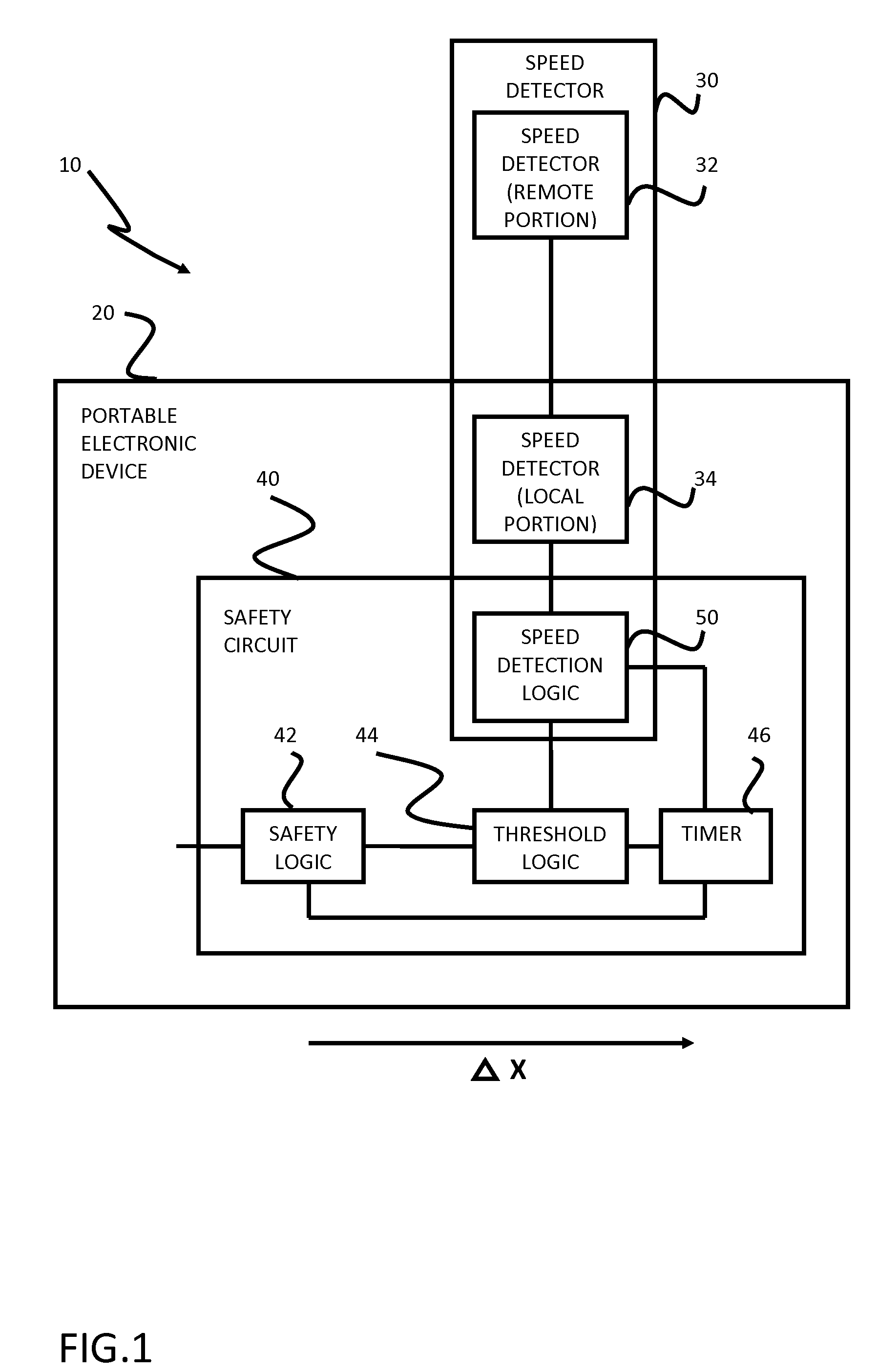
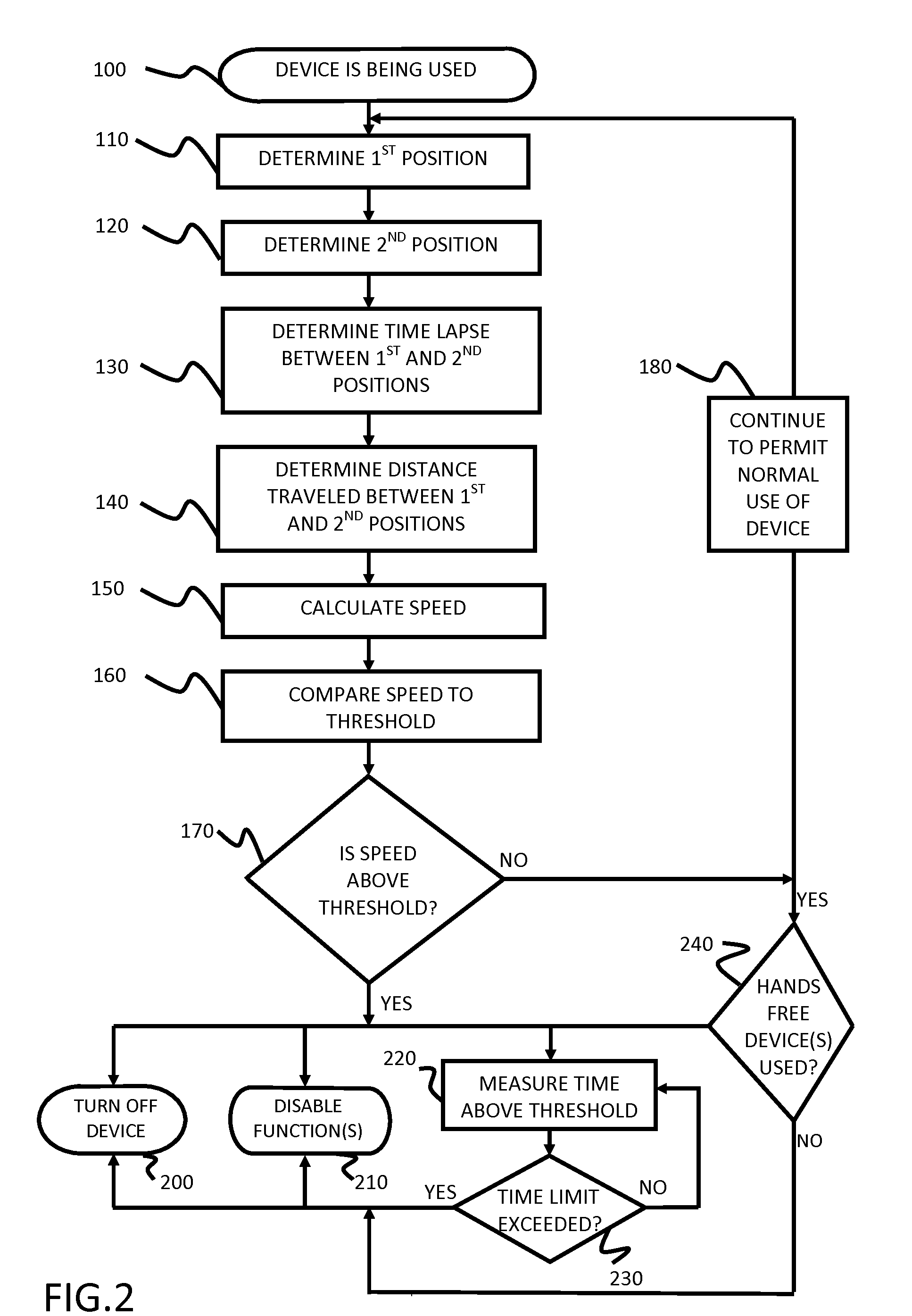
Safety features for portable electronic device
ActiveUS20100216509A1Unauthorised/fraudulent call preventionDevices with sensorHands freeSecurity policy
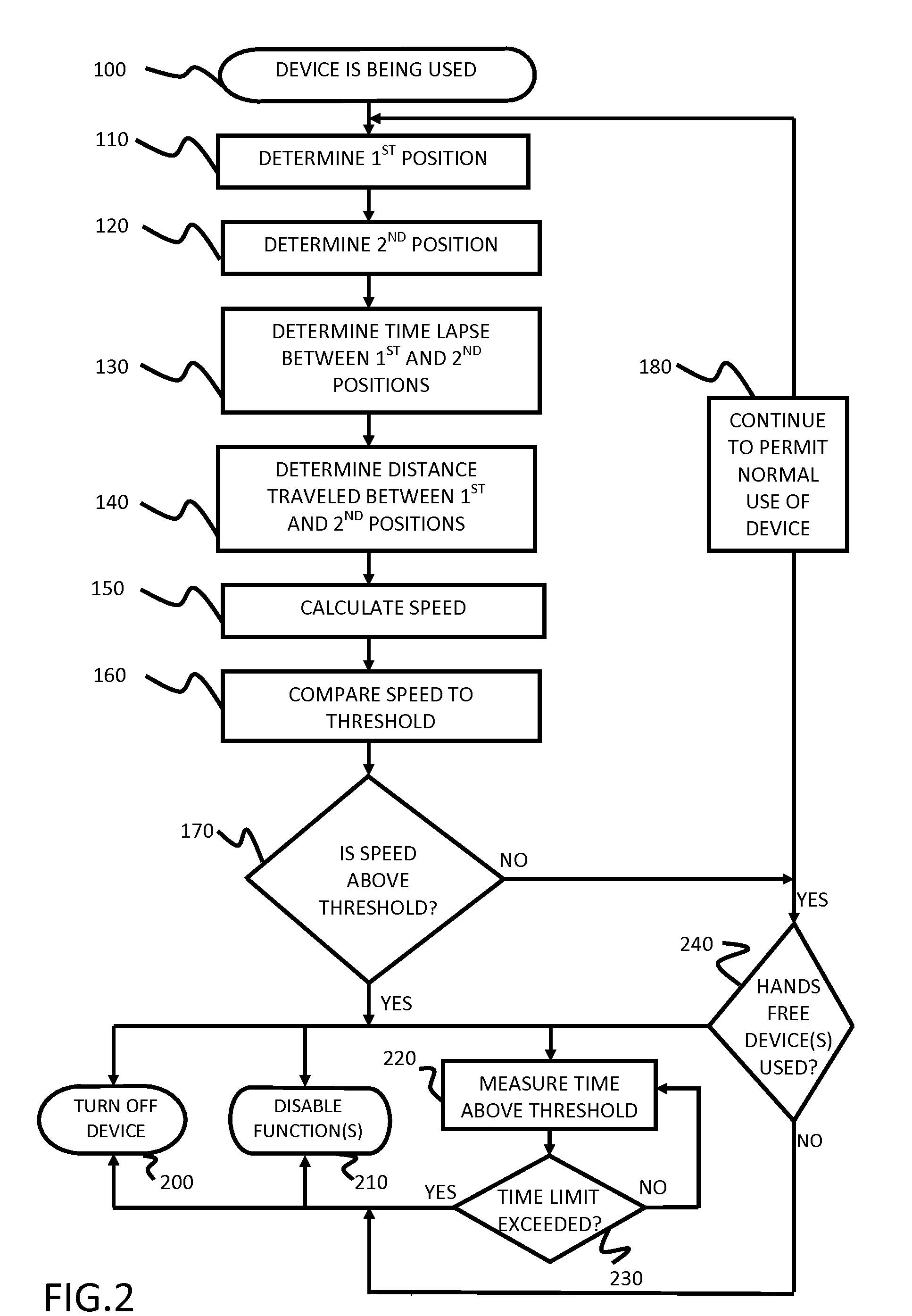
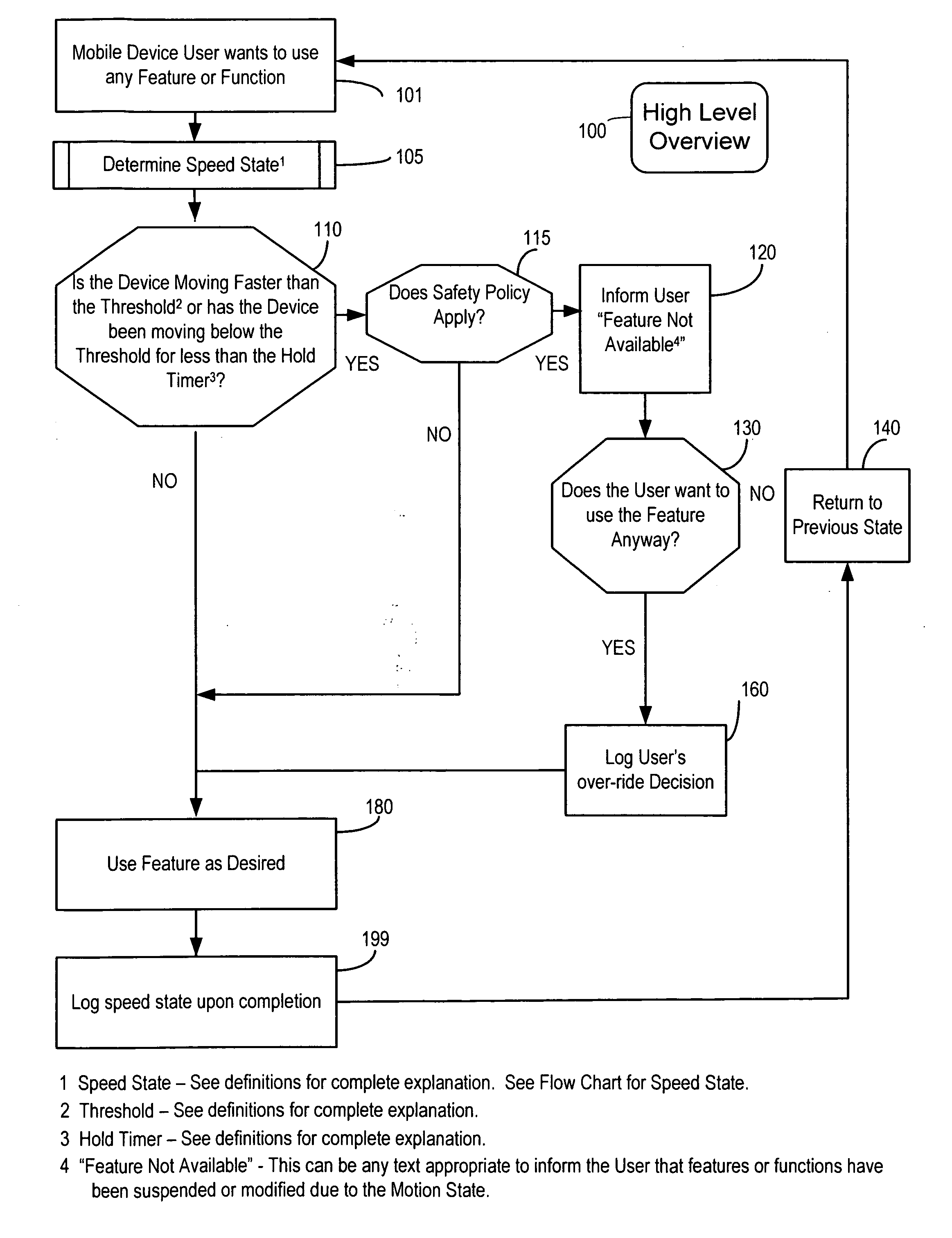
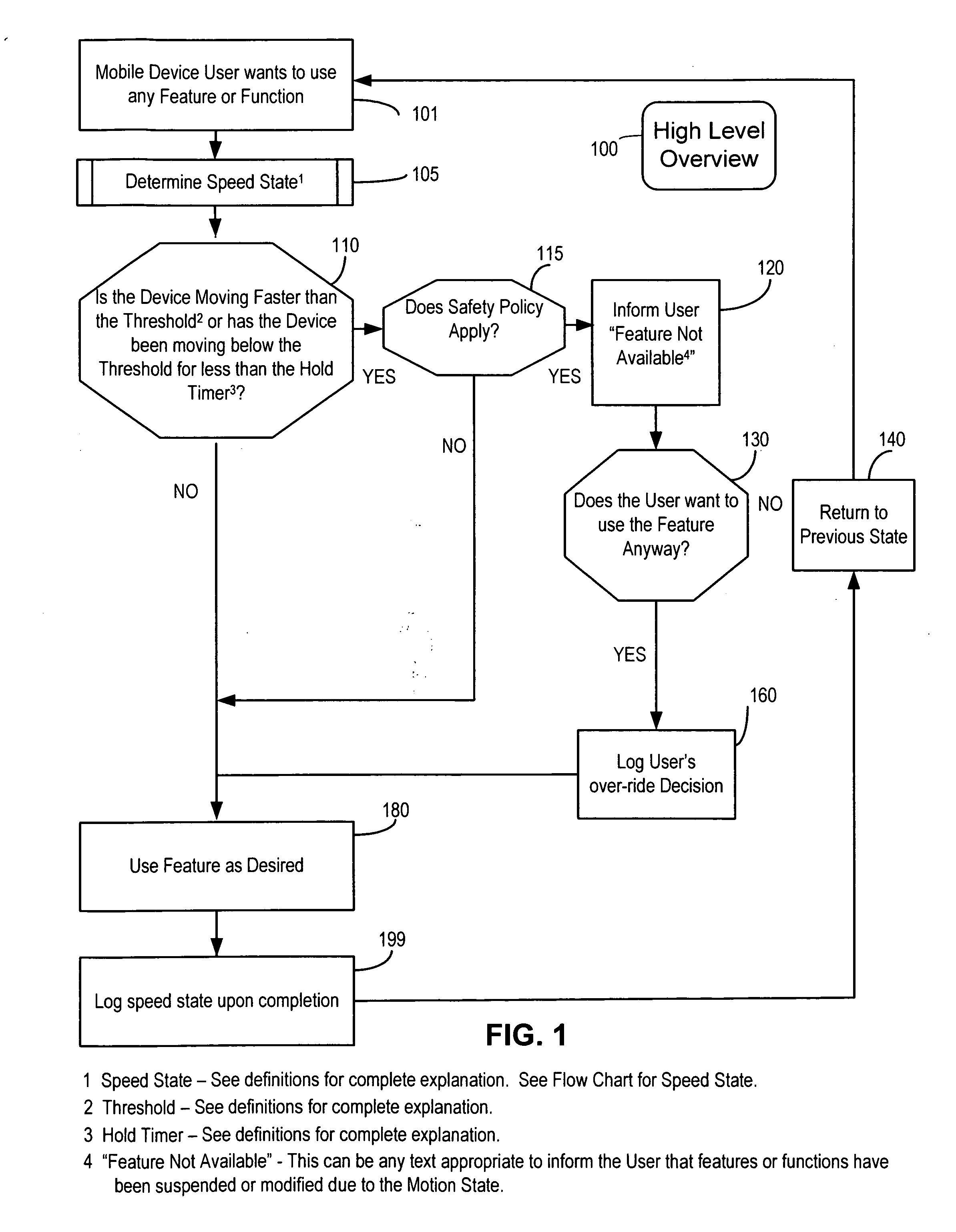
A portable device includes a safety feature that prevents some forms of use when the device is moving. The device may detect its speed or movement, compare that to a threshold, and provide a response or blocking function upon exceeding that threshold. The device may be a cell phone configured to disable transmission and reception of voice / text, conceal its display screen, and disable incorporated features and functions, if the cell phone is moving faster than walking speed or the movement is uncharacteristic of walking. The blocking function may be partially overridden based on a safety policy, which can be managed and customized. The introduction of hands-free devices may serve to override a blocking function and enable other functions.
Owner:AI-CORE TECH LLC
System and methodology for security policy arbitration
ActiveUS20030177389A1Multiple digital computer combinationsProgram controlComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
Safety features for portable electronic device
ActiveUS8270933B2Unauthorised/fraudulent call preventionDevices with sensorHands freeSecurity policy
A portable device includes a safety feature that prevents some forms of use when the device is moving. The device may detect its speed or movement, compare that to a threshold, and provide a response or blocking function upon exceeding that threshold. The device may be a cell phone configured to disable transmission and reception of voice / text, conceal its display screen, and disable incorporated features and functions, if the cell phone is moving faster than walking speed or the movement is uncharacteristic of walking. The blocking function may be partially overridden based on a safety policy, which can be managed and customized. The introduction of hands-free devices may serve to override a blocking function and enable other functions.
Owner:AI CORE TECH LLC
System and methodology for security policy arbitration
ActiveUS7546629B2Multiple digital computer combinationsSecret communicationComputer networkSecurity policy
A system providing methods for a device to apply a security policy required for connection to a network is described. In response to receipt of a request from a device for connection to a particular network, a current policy to apply to said device for governing the connection to this particular network is determined from a plurality of available security policies available to the device. This current policy to apply to said device is generated by merging a plurality of security policies available for governing connections. After said current policy is applied to the device, the connection from the device to this particular network is allowed to proceed.
Owner:CHECK POINT SOFTWARE TECH INC
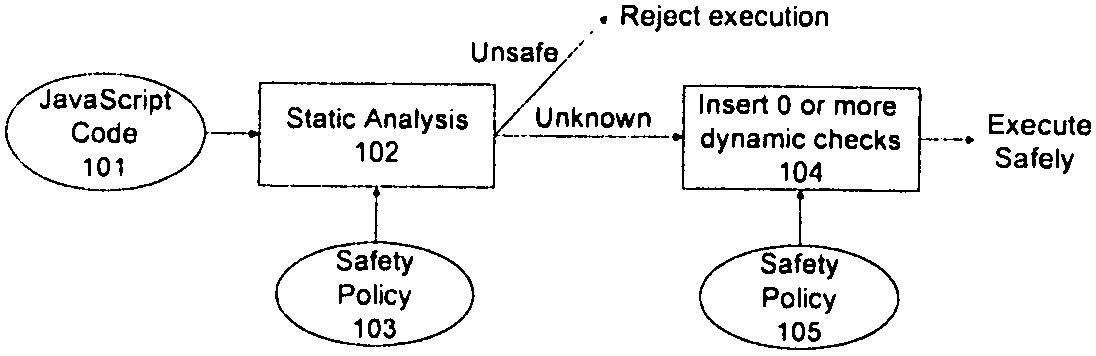
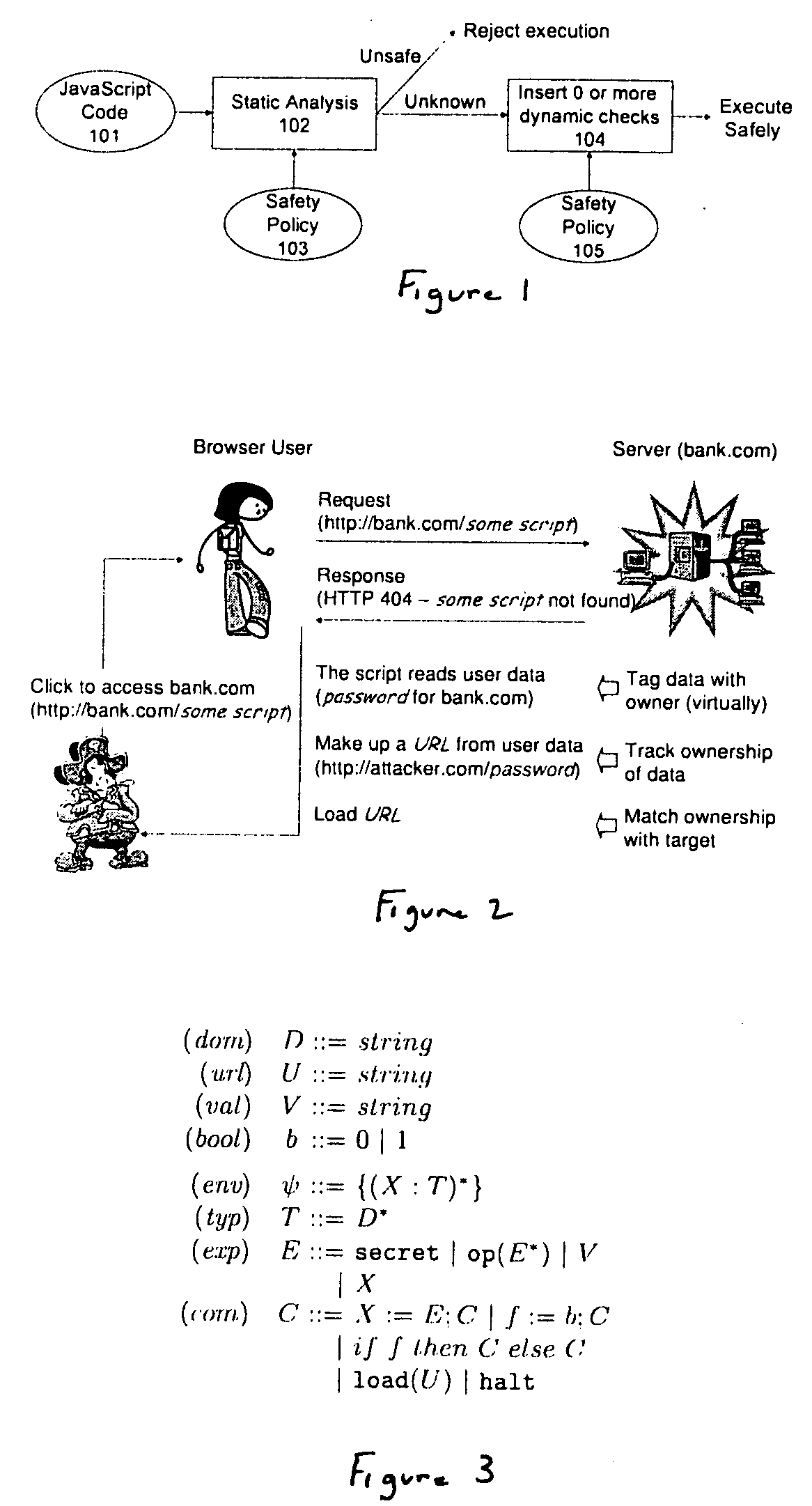
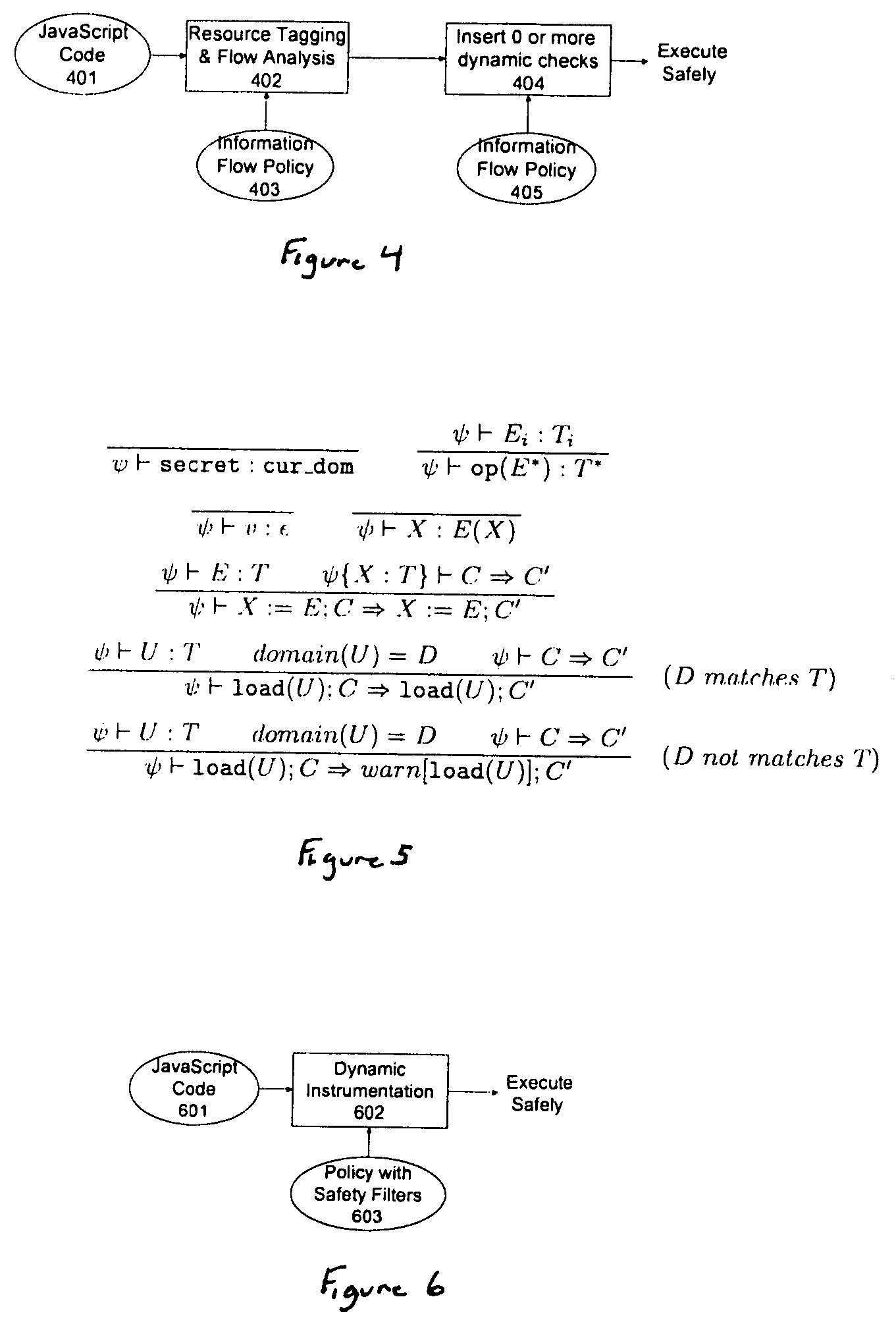
Method and apparatus for detecting and preventing unsafe behavior of javascript programs
InactiveUS20070107057A1Detecting and preventing unsafe behaviorPreventing executionMemory loss protectionError detection/correctionSecurity policySafety policy
A method and apparatus is disclosed herein for detecting and preventing unsafe behavior of script programs. In one embodiment, a method comprises performing static analysis of a script program based on a first safety policy to detect unsafe behavior of the scrip program and preventing execution of the script program if a violation of the safety policy would occur when the script program is executed.
Owner:NTT DOCOMO INC
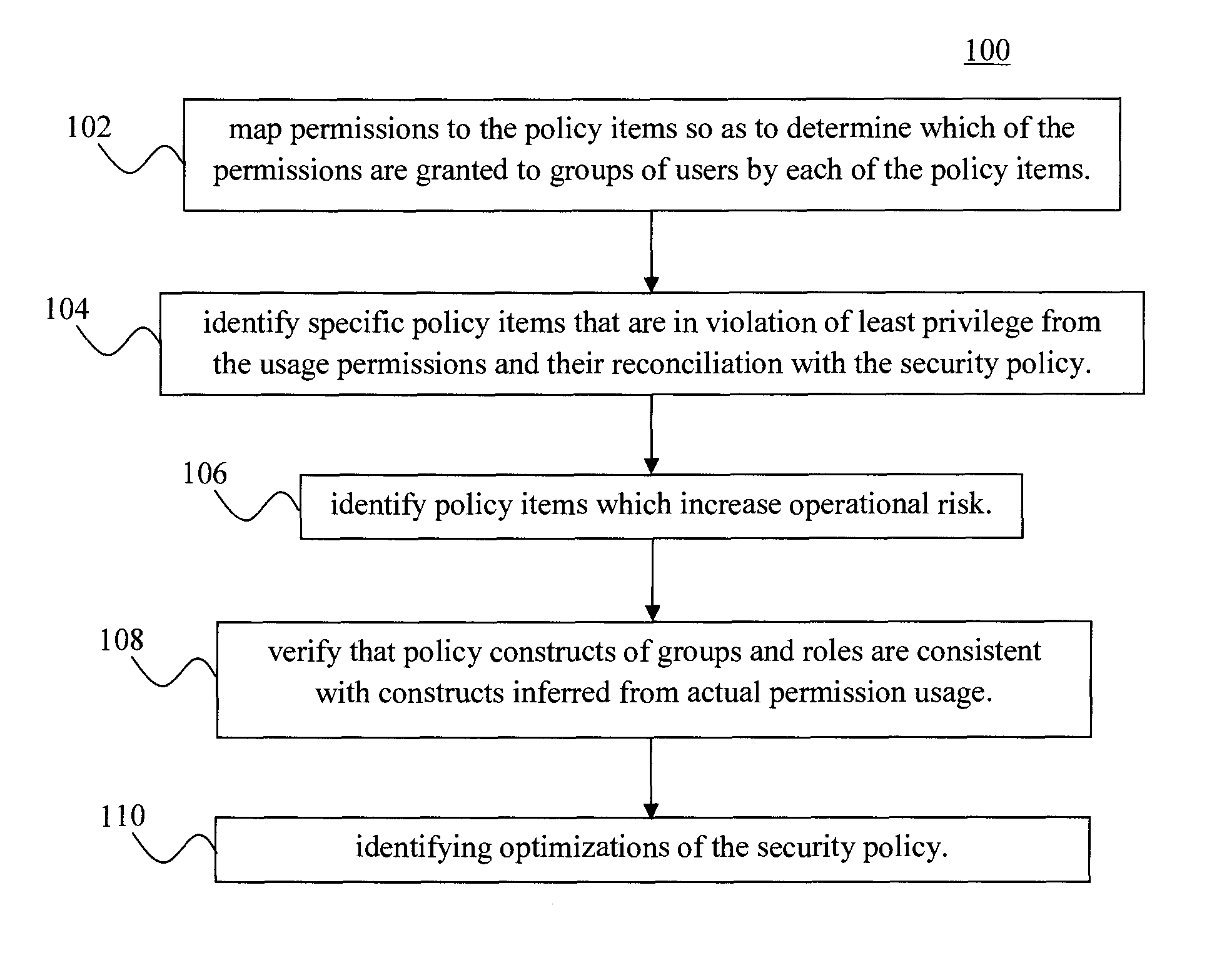
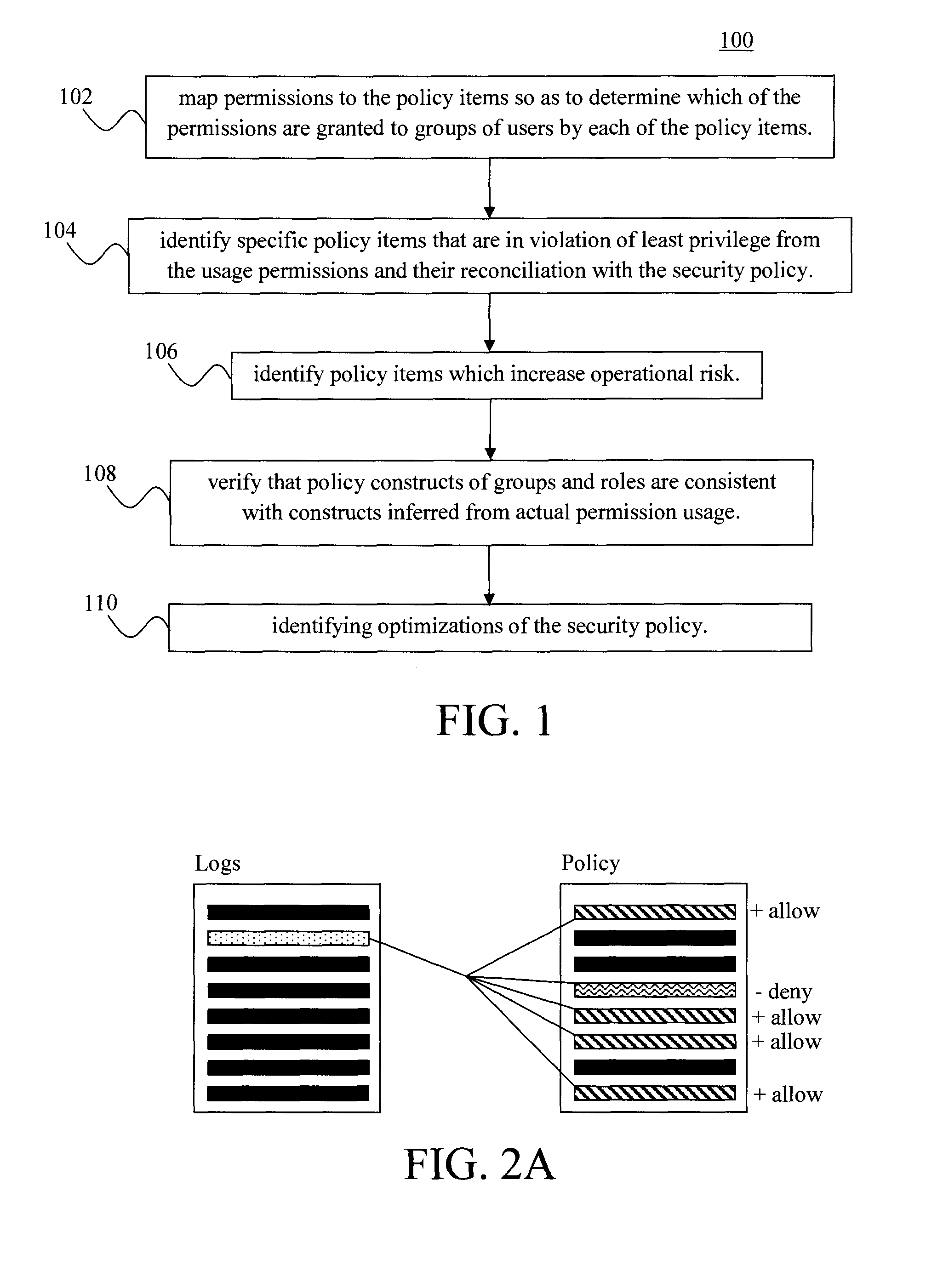
Techniques for Reconciling Permission Usage with Security Policy for Policy Optimization and Monitoring Continuous Compliance
ActiveUS20140359695A1Reduce riskIncreased surgical riskDigital data authenticationTransmissionStructure of Management InformationSecurity policy
In one aspect, a method for managing a security policy having multiple policy items includes the steps of: (a) mapping permissions to the policy items which apply to usage of the permissions so as to determine which of the permissions are granted to groups of users by each of the policy items; (b) identifying at least one of the policy items mapped in step (a) that is in violation of least privilege based on a comparison of an actual permission usage with the security policy; (c) identifying at least one of the policy items mapped in step (a) that increases operational risk; (d) verifying that policy constructs in the security policy are consistent with policy constructs inferred from the actual permission usage; and (e) identifying optimizations of the security policy based on output from one or more of steps (a)-(d).
Owner:SAILPOINT TECH HLDG INC
System and method for insider threat detection
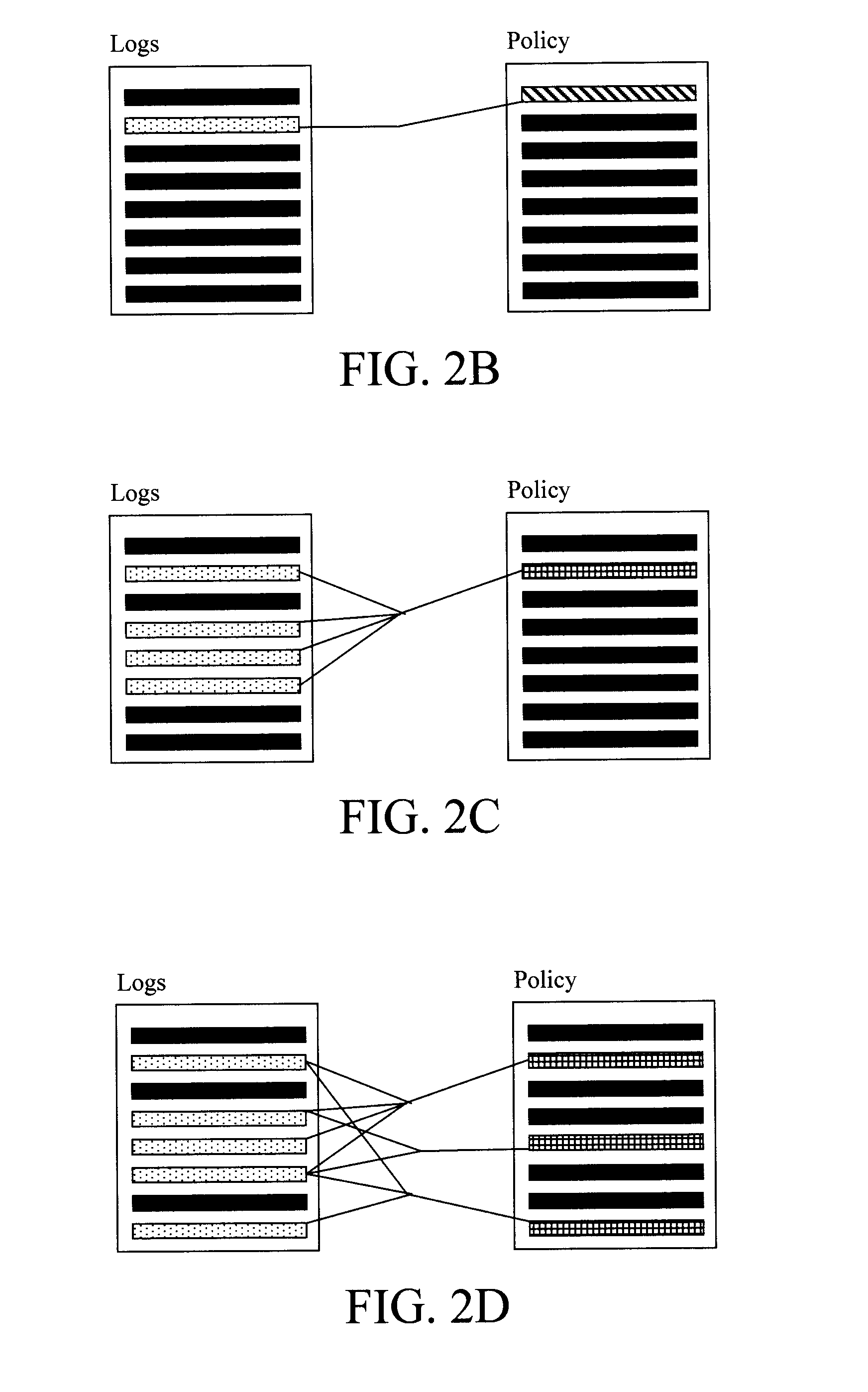
Described is a system for detecting insider threats in a network. In detecting the insider threat, the system receives data from the network relevant to network activity and extracts observable actions from the data relevant to a mission. The observable actions are combined to provide contextual cues and reasoning results. Based on the observable actions and reasoning results, proposed security policy updates are proposed to force insiders into using more observable actions. Finally, the system detects potential insider threats through analyzing the observable actions and reasoning results.
Owner:HRL LAB
Enforcement of compliance with network security policies
ActiveUS7249187B2Digital data processing detailsMultiple digital computer combinationsNetwork addressingNetwork address
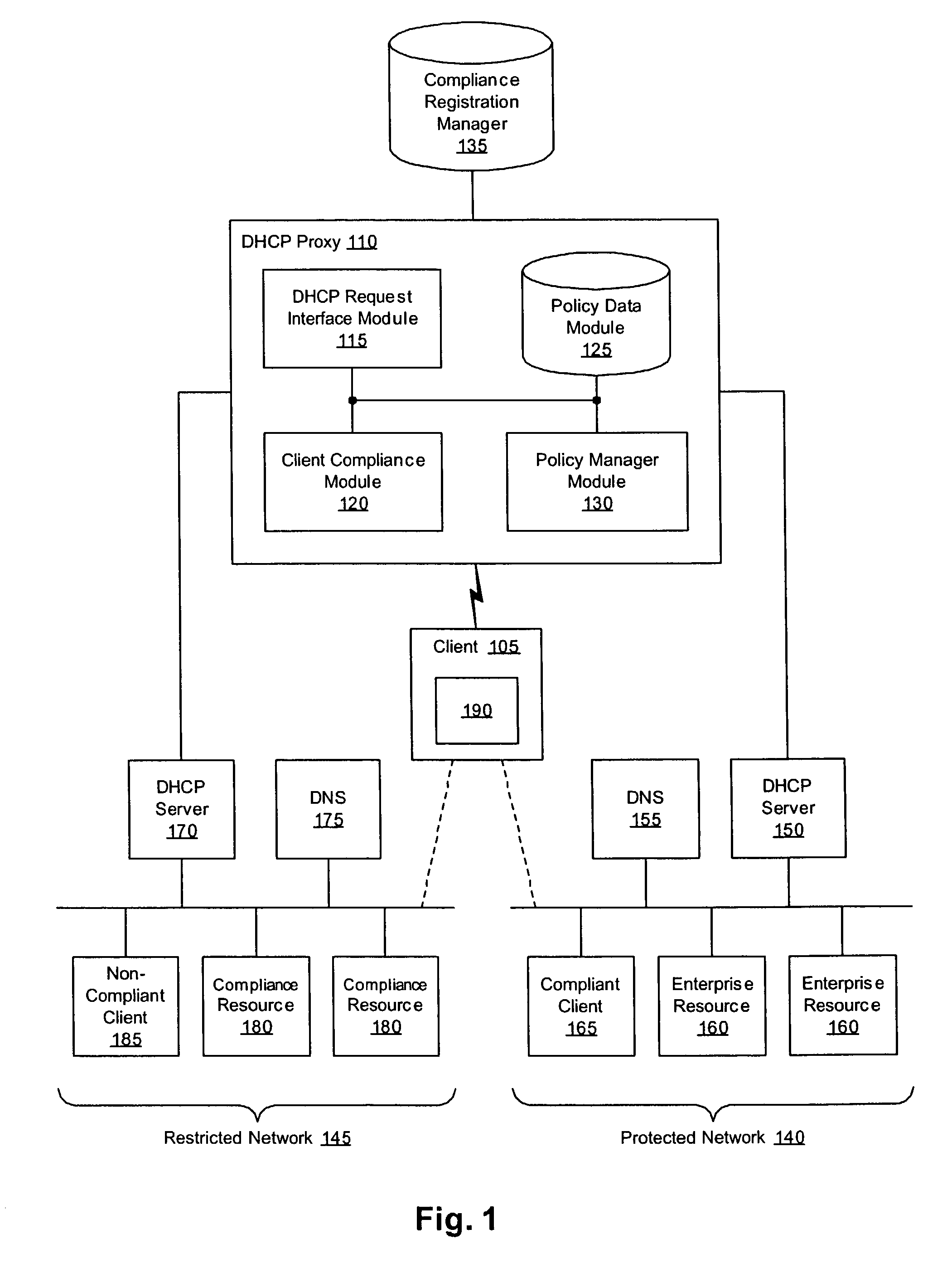
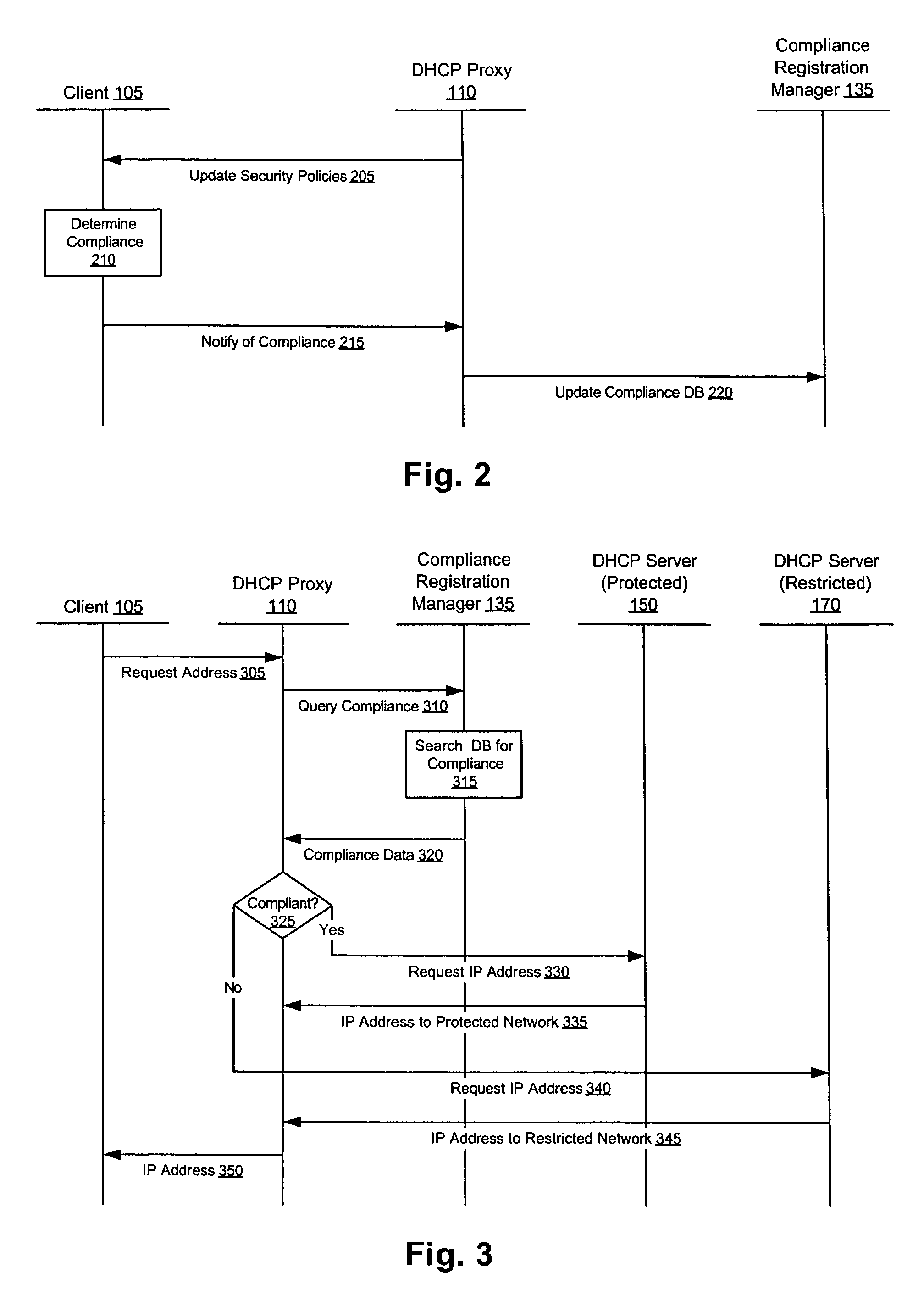
Methods, apparati, and computer program products enforce computer network security policies by assigning network membership to a client (105) based on the client's compliance with the security policies. When a client (105) requests (305) a network address, the DHCP proxy (110) intercepts the request and assigns (350) that client (105) a logical address on the protected network (140) if the client (105) is in compliance with the security policies. If the client (105) is not in compliance with the security policies, in various embodiments, the DHCP proxy (110) assigns (350) the client (105) an address on a restricted network (145) or no network address at all.
Owner:CA TECH INC
Medthod And Apparatus For Controlling Use Of Mobile Phone While Operating Motor Vehicle
InactiveUS20090221279A1Discourage non-emergency useMaintain securitySubstation equipmentAutomatic exchangesAccelerometerHuman–machine interface
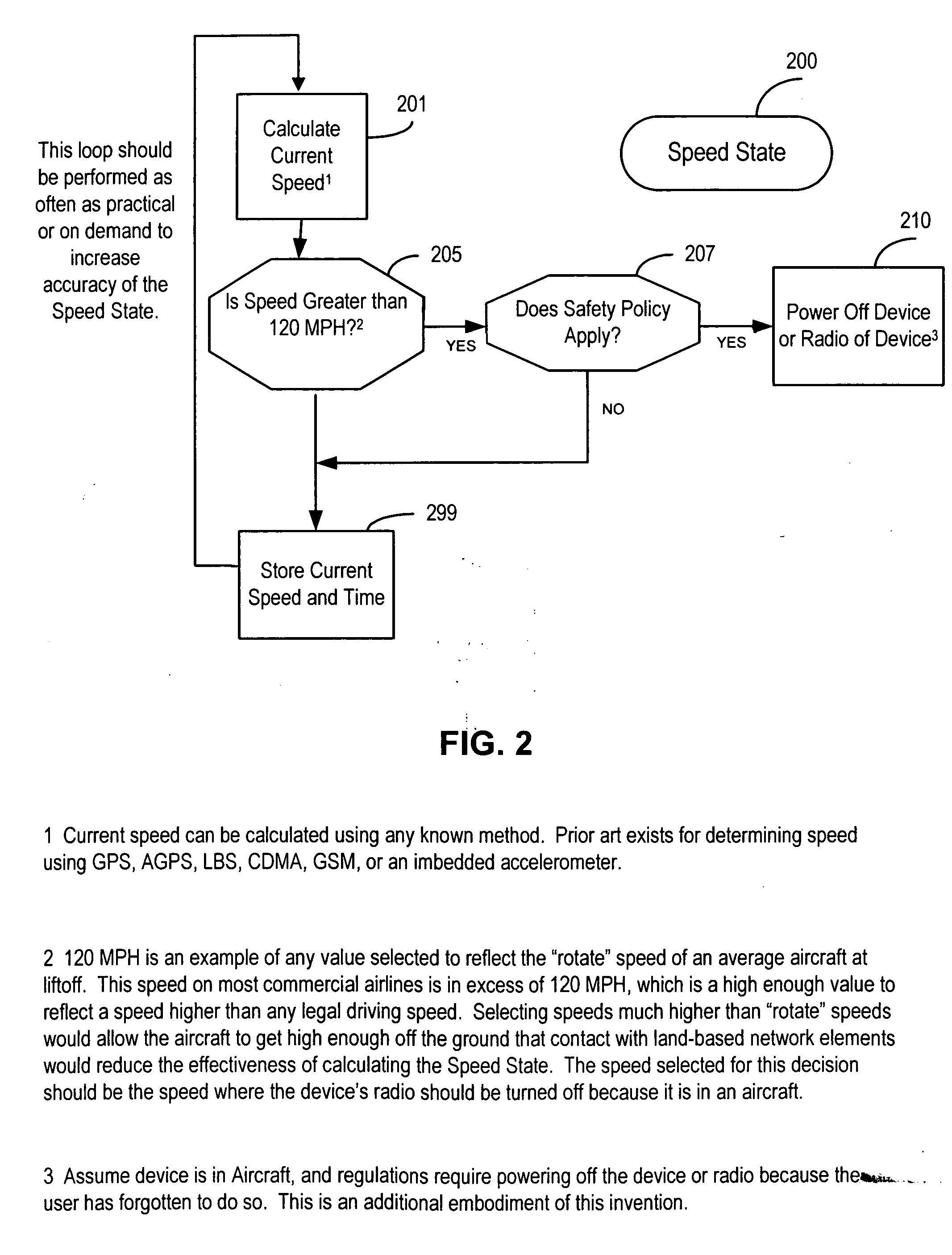
A method and apparatus for controlling use of mobile communication device while operating a vehicle, wherein the mobile communication device (MS) uses one or more ways to determine its speed while moving in order to alter the default behavior of the device based on a stored safety policy. Using existing technologies such as Global Positioning System (GPS), Assisted GPS (AGPS), Location-Based Services (LBS), Global System for Mobile (GSM), Code Division for Multiple Access (CDMA), or an accelerometer, a MS determines the current or last known state of motion to modify the behavior of the MS based on its speed and a stored safety policy. The human interface of the MS is altered to inform the user of the modification, features and functions can be disabled and enabled, the user is prompted to change their behavior, and automatic functions take place. The logging functions of the MS can be enhanced to record the motion state of the MS while using any feature of the MS.
Owner:RUTLEDGE DOUGLAS A
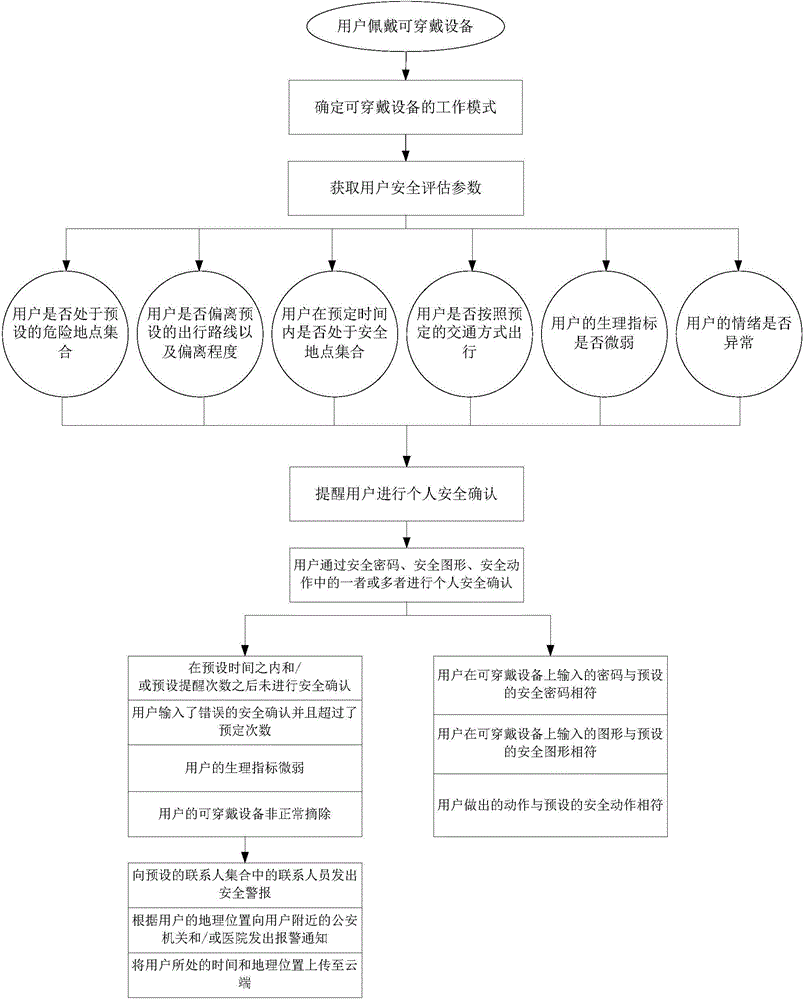
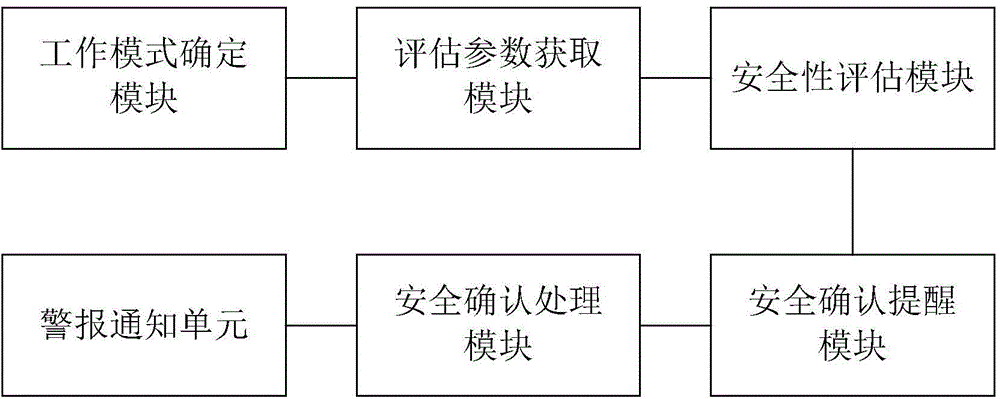
Wearable device-based smart personal security system and implementation method thereof
ActiveCN104900006AImprove intelligenceImprove timelinessDiagnostic recording/measuringSensorsSafety statusComputer science
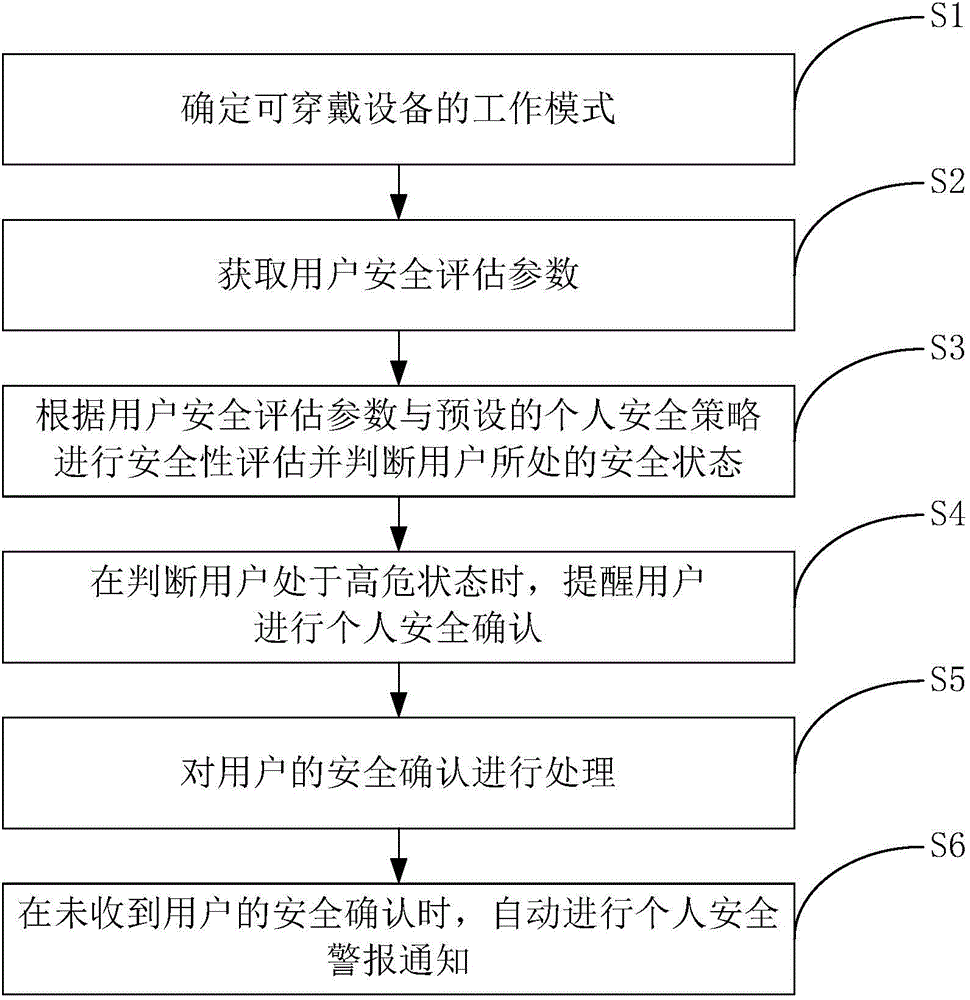
The invention discloses a wearable device-based smart personal security system and an implementation method thereof. The implementation method includes the following steps that: user safety assessment parameters are obtained; safety assessment is performed according to the user safety assessment parameters and preset personal safety policies, and a safety status of a user is judged; when it is judged that the user is in a high dangerous status, the user is prompted to perform personal safety confirmation; and when safety confirmation of the user is not received, personal safety warning notification is performed. According to the method of the invention, based on safety assessment, safety confirmation and warning notification, the intelligence of dangerous condition detection and timeliness of help seeking can be improved, and people can be assisted to pay attention to dangerous conditions and improve safety awareness, and personal safety warning notices can be automatically transmitted when the people encounter dangers.
Owner:INST OF ADVANCED TECH UNIV OF SCI & TECH OF CHINA
Techniques for reconciling permission usage with security policy for policy optimization and monitoring continuous compliance
ActiveUS9246945B2Reduce riskIncreased surgical riskDigital data protectionDigital data authenticationStructure of Management InformationSecurity policy
In one aspect, a method for managing a security policy having multiple policy items includes the steps of: (a) mapping permissions to the policy items which apply to usage of the permissions so as to determine which of the permissions are granted to groups of users by each of the policy items; (b) identifying at least one of the policy items mapped in step (a) that is in violation of least privilege based on a comparison of an actual permission usage with the security policy; (c) identifying at least one of the policy items mapped in step (a) that increases operational risk; (d) verifying that policy constructs in the security policy are consistent with policy constructs inferred from the actual permission usage; and (e) identifying optimizations of the security policy based on output from one or more of steps (a)-(d).
Owner:SAILPOINT TECH HLDG INC
Method and apparatus for detecting and preventing unsafe behavior of javascript programs
InactiveUS20100257603A1Preventing unsafe behavior of script programsPreventing executionMemory loss protectionError detection/correctionSecurity policySafety policy
A method and apparatus is disclosed herein for detecting and preventing unsafe behavior of script programs. In one embodiment, a method comprises performing static analysis of a script program based on a first safety policy to detect unsafe behavior of the script program and preventing execution of the script program if a violation of the safety policy would occur when the script program is executed.
Owner:CHANDER AJAY +1
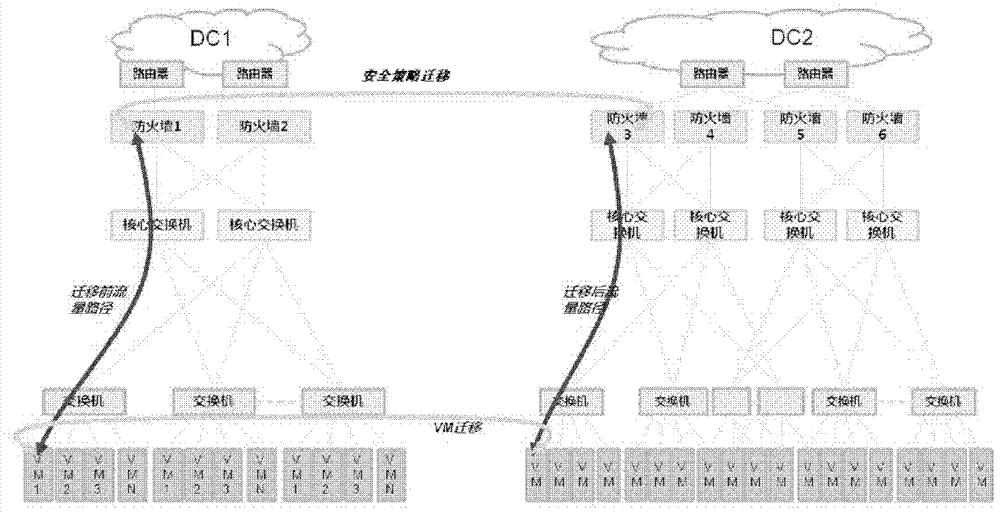
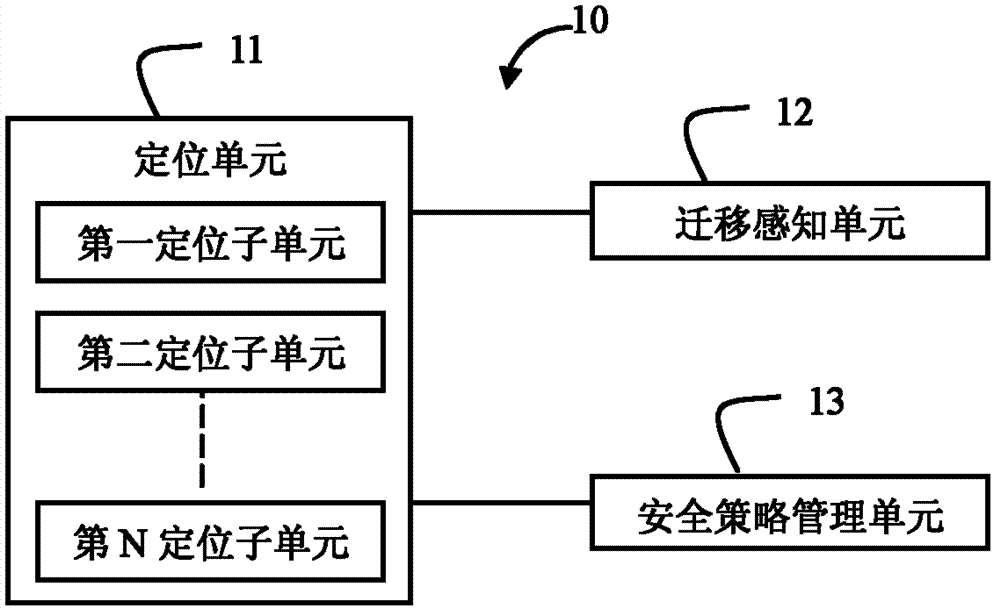
Method and device for migrating virtual machine safety policy
ActiveCN102739645AEliminate manual configuration operationsProgram controlData switching networksManagement unitData center
The invention discloses a virtual machine safety policy migrating device which is applied in a safety management server in a data center and comprises a migration sensing unit, a positioning unit and a safety policy management unit, wherein the migration sensing unit is used for receiving a virtual machine migration report from a virtual machine management device; the report contains location parameters of the virtual machine; the positioning unit is used for determining an original safety device to which the virtual machine belongs before the migration according to the location parameters of the virtual machine, and a new safety device to which the virtual machine belongs after the migration; the safety policy management unit is used for obtaining the safety policy of the virtual machine configured on the original safety device, and transmitting the safety policy to the new safety device. By utilizing the virtual machine safety policy migrating device, the automatic seamless migration of the safety policy of the safety device on the virtual machine along with the migration of the virtual migration is realized; and the manual configuration operation of a manager on the safety device because of the migration of the virtual machine is avoided, which means a lot for a large data center in which the virtual machine migrates often.
Owner:NEW H3C TECH CO LTD
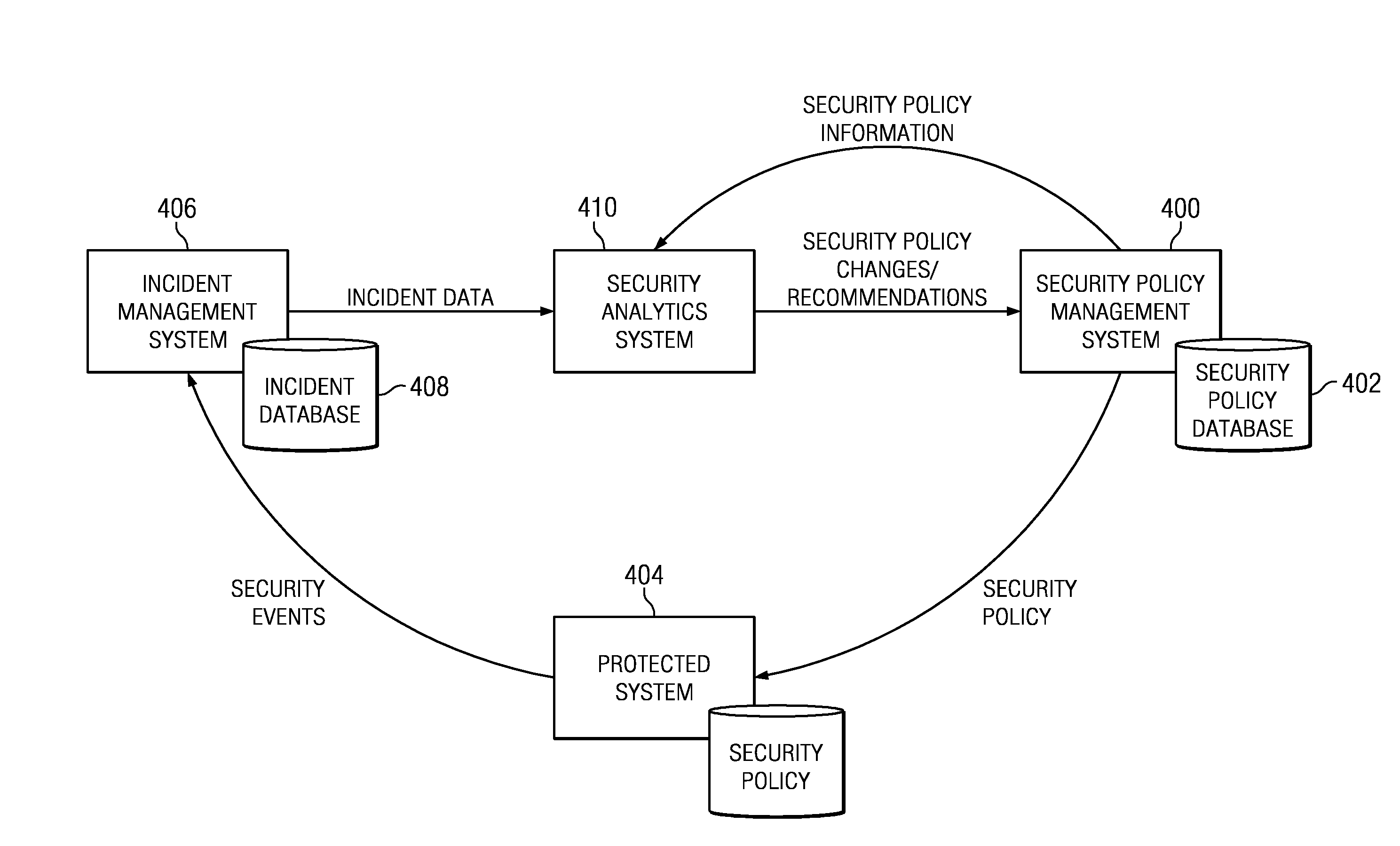
Security policy management using incident analysis
InactiveUS20130179938A1Understand perceived and measured effectiveness and costReduce in quantityError detection/correctionForecastingData setIncident analysis
A security analytics system receives incident data (from an incident management system) and security policy information (from a security policy management system). The security analytics system evaluates these data sets against one another, preferably using a rules-based analysis engine. As a result, the security analytics system determines whether a particular security policy configuration (as established by the security policy management system) needs to be (or should be) changed, e.g., to reduce the number of incidents caused by a misconfiguration, to increase its effectiveness in some manner, or the like. As a result of the evaluation, the security analytics system may cause a policy to be updated automatically, notify an administrator of the need for the change (and the recommendation), or take some other action to evolve one or more security policies being enforced by the security policy management system.
Owner:IBM CORP
Techniques for Reconciling Permission Usage with Security Policy for Policy Optimization and Monitoring Continuous Compliance
ActiveUS20140359692A1Reduce riskIncreased surgical riskDigital data authenticationTransmissionStructure of Management InformationSecurity policy
In one aspect, a method for managing a security policy having multiple policy items includes the steps of: (a) mapping permissions to the policy items which apply to usage of the permissions so as to determine which of the permissions are granted to groups of users by each of the policy items; (b) identifying at least one of the policy items mapped in step (a) that is in violation of least privilege based on a comparison of an actual permission usage with the security policy; (c) identifying at least one of the policy items mapped in step (a) that increases operational risk; (d) verifying that policy constructs in the security policy are consistent with policy constructs inferred from the actual permission usage; and (e) identifying optimizations of the security policy based on output from one or more of steps (a)-(d).
Owner:SAILPOINT TECH HLDG INC
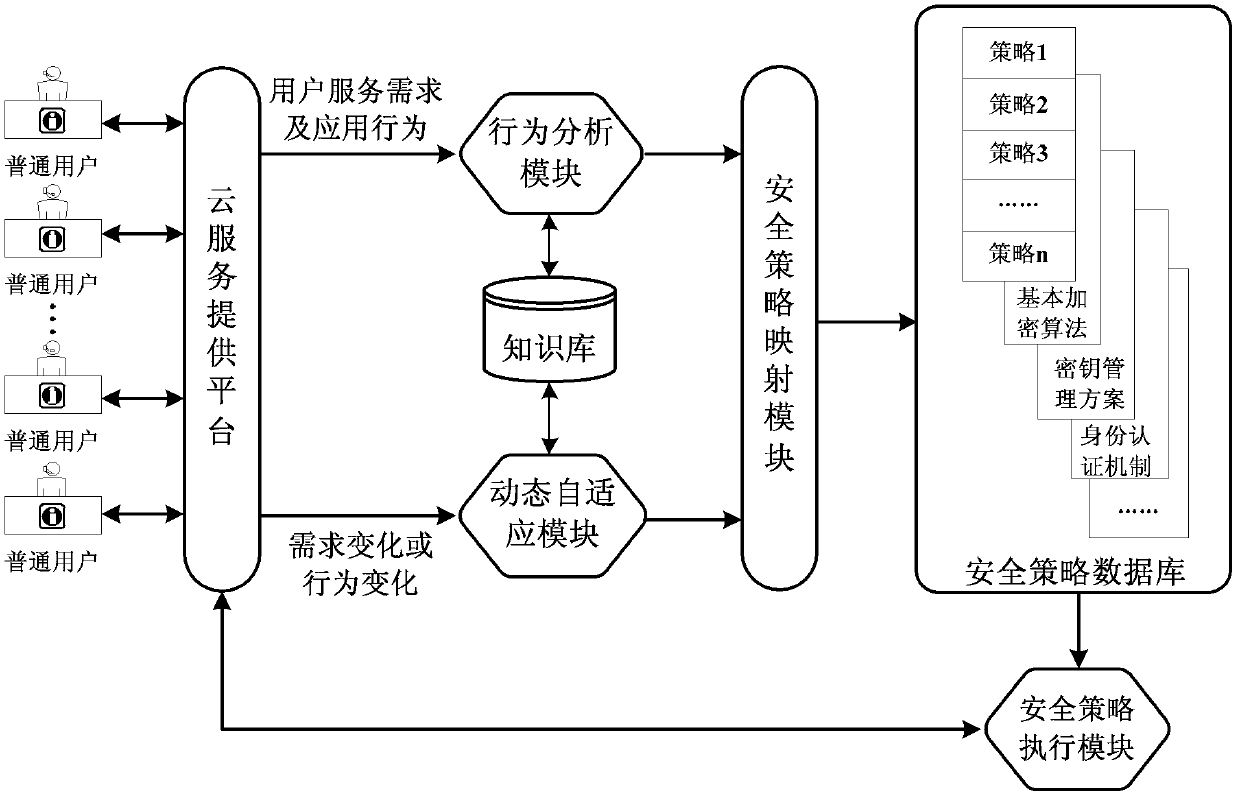
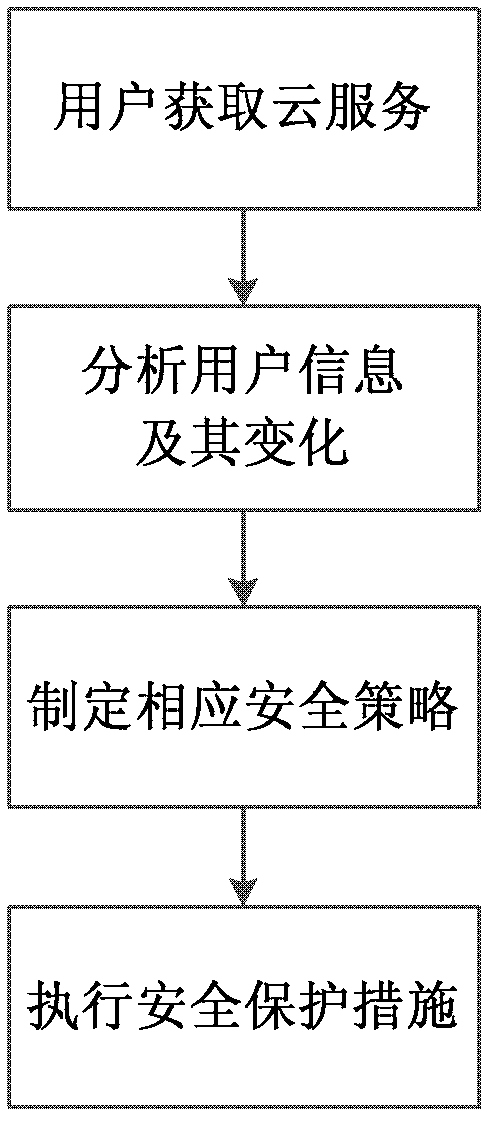
Dynamic adaptive method of safety of cloud service under mobile internet environment
The invention discloses a dynamic adaptive method of the safety of cloud service under a mobile internet environment. The method comprises the following steps that: a user applies to a cloud service provider for purchasing of the cloud service; 2, a cloud service providing platform checks user information and provides appropriate cloud service for the user; 3, the cloud service providing platform analyzes the user information and the change of the user information; 4, a safety policy mapping module makes a corresponding safety policy; 5, a safety policy execution module executes safety protection measures; 6, the cloud service providing platform observes and records the change of user requirements and user behaviors; 7, the step is similar to the step 3; and 8, the step is the same as the steps 4 and 5. The dynamic adaptive method of the safety of the cloud service under the mobile internet environment has the advantages that: according to the change of the user requirements or using behaviors, the safety policy can be updated in a dynamic adaptive mode, and the safety protection measures are adjusted. Based on a cloud computation safety system structure, with the characteristics of the cloud service in mobile internet, the method has high efficiency, reasonableness and advancement.
Owner:BEIHANG UNIV
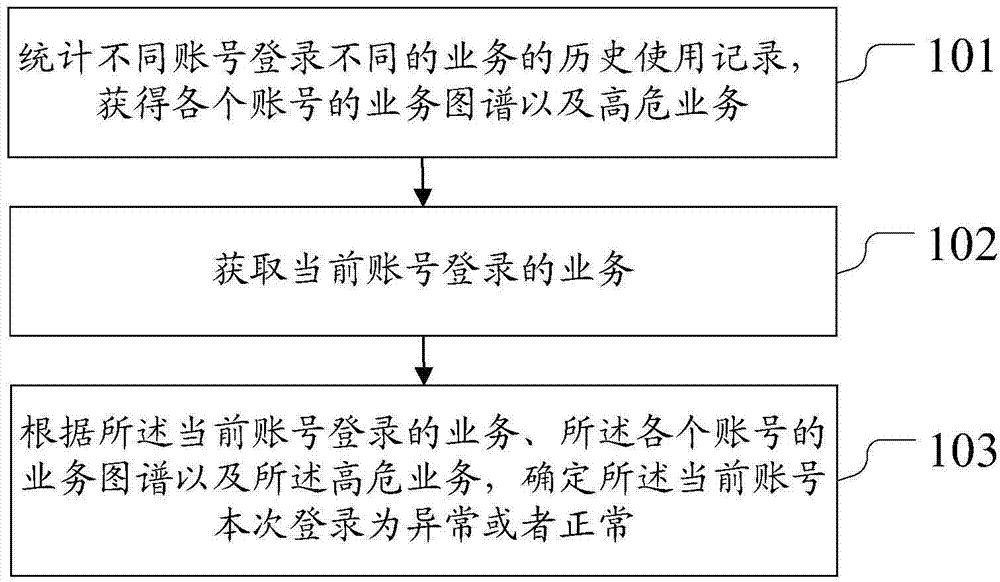
Internet account safety policy and system
ActiveCN104519032AExceptionally timely and effectiveImprove accuracyUser identity/authority verificationThe InternetInformation security
The present invention relates to the technical field of information security. Disclosed are a security policy and system for an Internet account, which can improve accuracy of determining account exception. In an embodiment of the present invention, statistics on historical use records indicating that different accounts log in to different services are collected; a service map of each account and at least one high-risk service are determined, the service map comprising the different services that are logged in to by the accounts and use frequencies of the different services; a service that is logged in to by a current account is acquired; and it is determined, according to the service that is logged in to by the current account, the service map of the current account, and the high-risk service, whether the current login of the current account is exceptional or unexceptional. The embodiment of the present invention is used for determining whether an account is exceptional.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
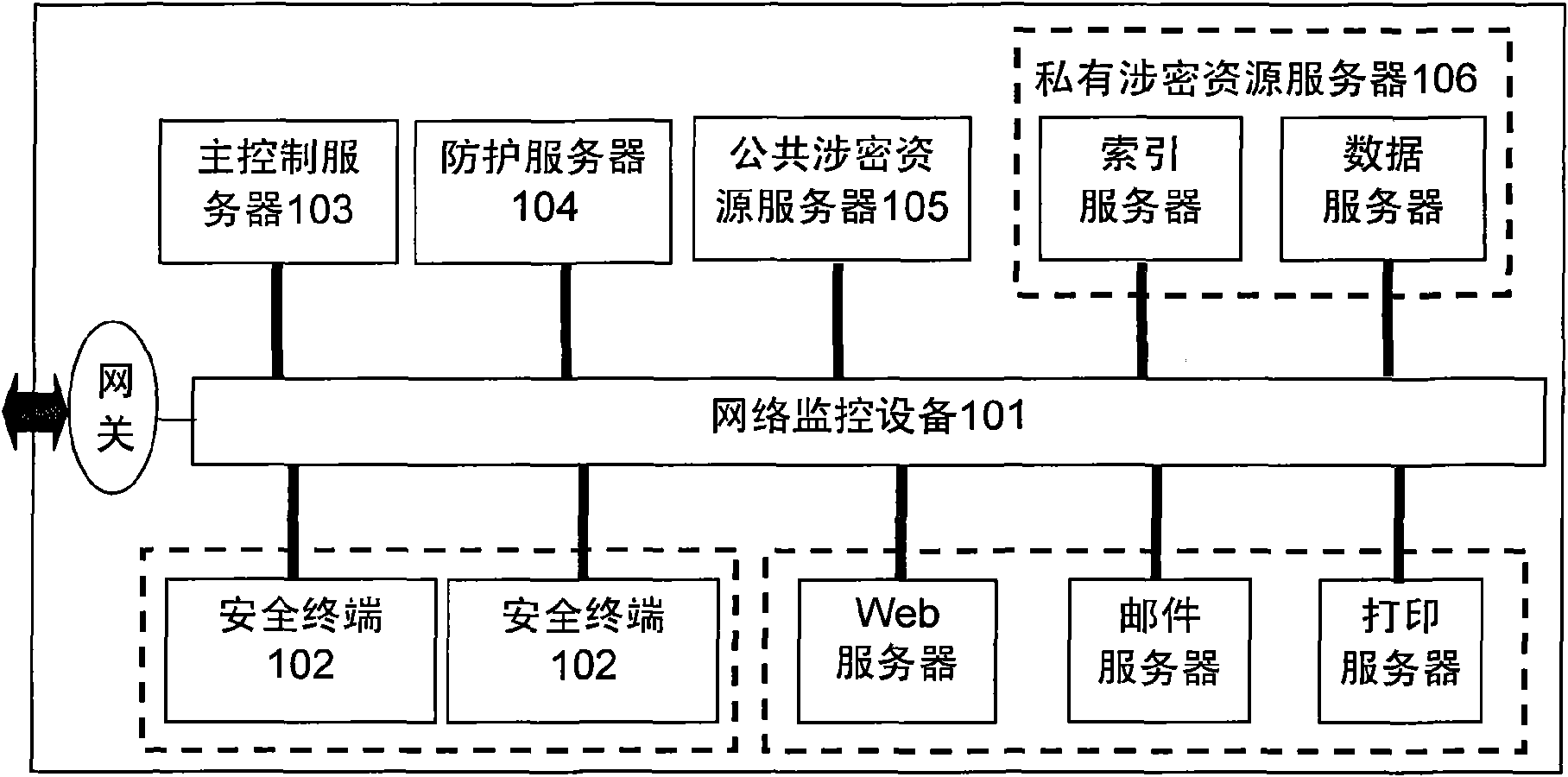
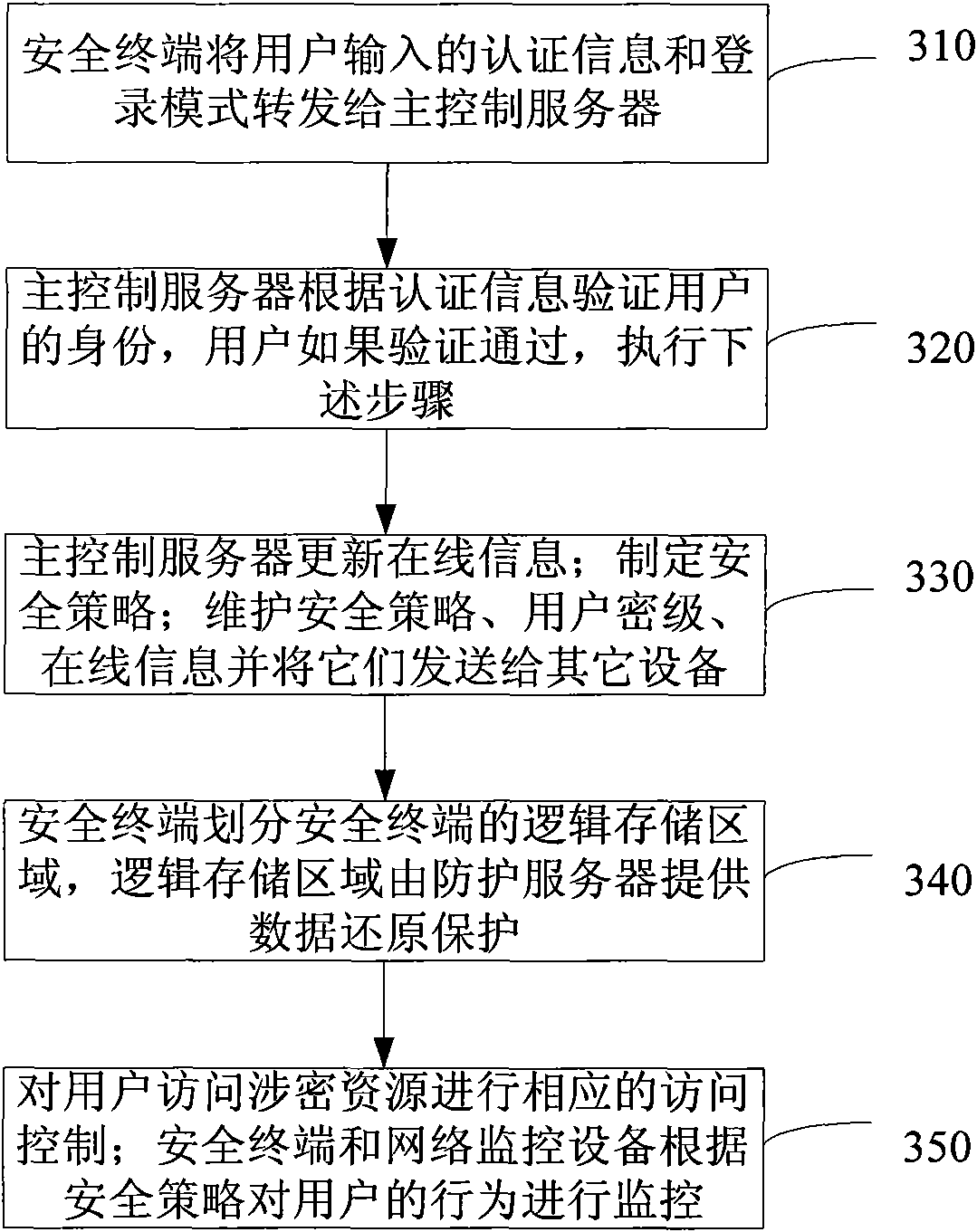
Local area network system and method for maintaining safety thereof
InactiveCN101594360AImprove securityImprove convenienceData switching by path configurationMonitor equipmentInformation security
The invention discloses a local network system and a method for maintaining the safety thereof and belongs to the field of network safety. The system comprises network monitoring equipment, a safety terminal, a main control server, public / private secret-associated source servers and a protective server, wherein the safety terminal, the main control server, the public / private secret-associated source servers and the protective server are connected with the network monitoring equipment; the network monitoring equipment monitors data switching and forwarding; the safety terminal performs local monitoring; the main control server verifies identity and maintains safety policies; the public secret-associated source server monitors accesses to the public secret-associated sources; the private secret-associated source server monitors the accesses to private secret-associated sources; and the protective server provides data reduction protection. The method comprises the following steps that: the safety terminal inputs authentication data and input modes; and the main control server verifies the identity of a user; and if the user passes through the verification, the main control server, the network monitoring equipment, the public secret-associated source server, the private secret-associated source server, the protective server and the safety terminal jointly maintain the safety of the network. The system and the method improve network access safety.
Owner:WUXI RES INST OF APPLIED TECH TSINGHUA UNIV +1
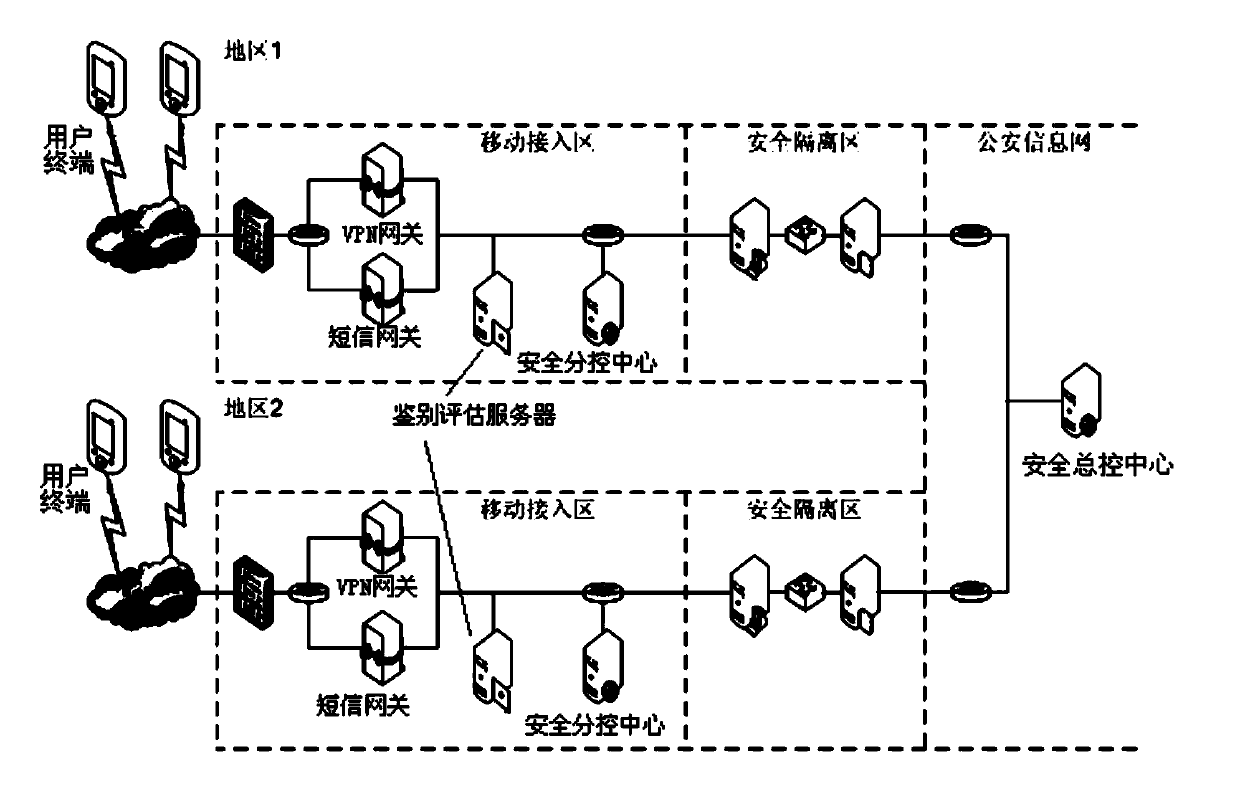
Mobile-police-terminal safety management and control system
ActiveCN103442354AGuaranteed safe operationReduce dependenceNetwork traffic/resource managementTransmissionControl systemSecurity information
The invention discloses a mobile-police-terminal safety management and control system including user terminals, subordinate safety control centers and a chief safety control center, which are set up through a wireless access platform. The subordinate safety control centers are arranged in mobile access areas and used for acquiring information of local user terminals. The chief control center is arranged in a public-security information network and used for acquiring user-terminal information, acquired by the subordinate safety control centers of different areas. The user terminals access the mobile access areas through mobile communication networks. The chief safety control center formulates unified basic safety policies and sends the policies to the subordinate safety control centers of the different areas. The subordinate safety control centers generate subordinate control center safety policies in a customized manner based on the basic safety policies and send the subordinate control center safety policies to the user terminals. The mobile-police-terminal safety management and control system is flexible in deployment, convenient and fast in management and capable of realizing safety, unified policies, controllable system and centralized monitoring and management of the user terminals and supporting storage and processing of data in large quantity and ensuring safe operation of mobile police terminals.
Owner:SHANGHAI CHENRUI INFORMATION TECH
Method and device for matching security policy
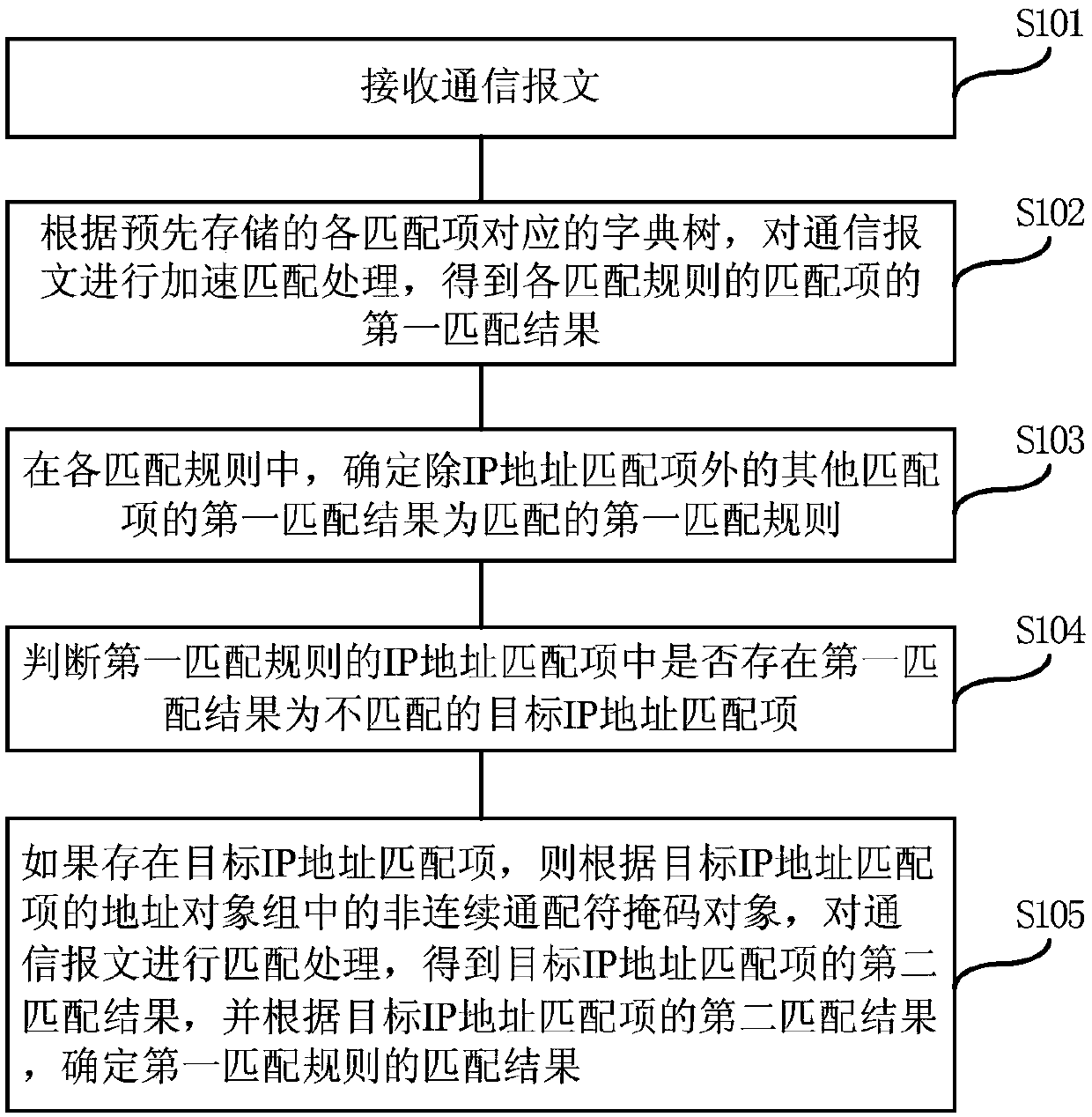
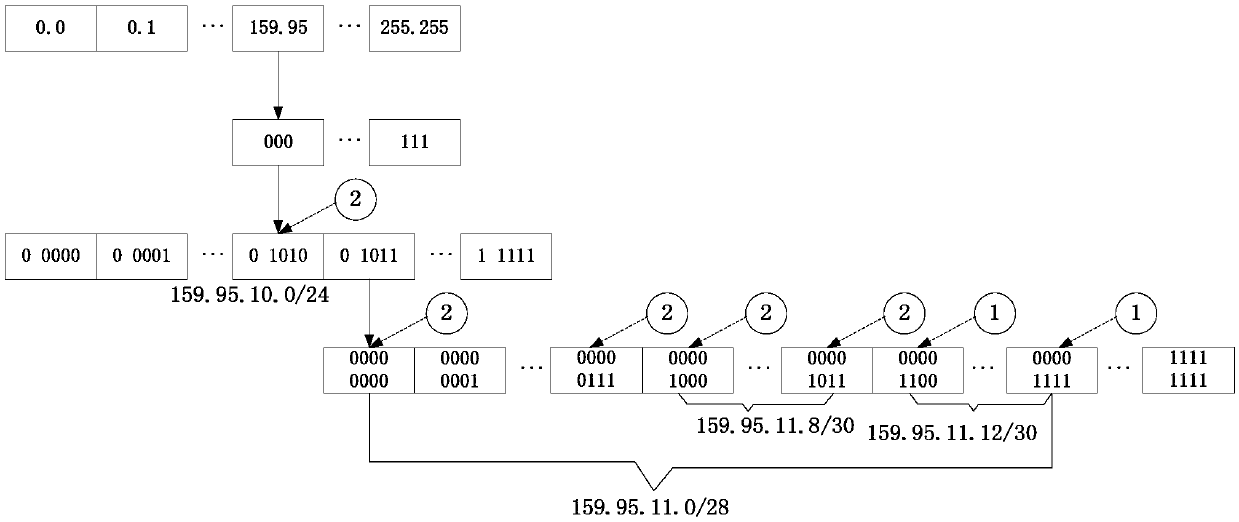
ActiveCN109617927AAccelerate matchingImprove matching efficiencyTransmissionTheoretical computer scienceWildcard character
The embodiment of the invention provides a method and device for matching a security policy, and relates to the technical field of the network security. The method comprises the following steps: receiving a communication message; performing accelerated matching processing on the communication message according to a dictionary tree corresponding to various pre-stored matching items, thereby obtaining a first matching result of various matching items of various matching rules; in various matching rules, determining that the first matching result of other matching items except the IP address matching item is the matched first matching rule; if the condition that the first matching result is an unmatched target IP address matching item is existent in the IP address matching item of the first matching rule, performing matching processing on the communication message according to discontinuous wildcard character mask objects in an address object group of the target IP address matching item,thereby obtaining a second matching result of the target IP address matching item, and determining the first matching result of the first matching rule according to the second matching result of the target IP address matching item. The matching efficiency of the safety policy can be improved by adopting the method disclosed by the application.
Owner:NEW H3C SECURITY TECH CO LTD
Information interaction safety protection system and operation realization method thereof
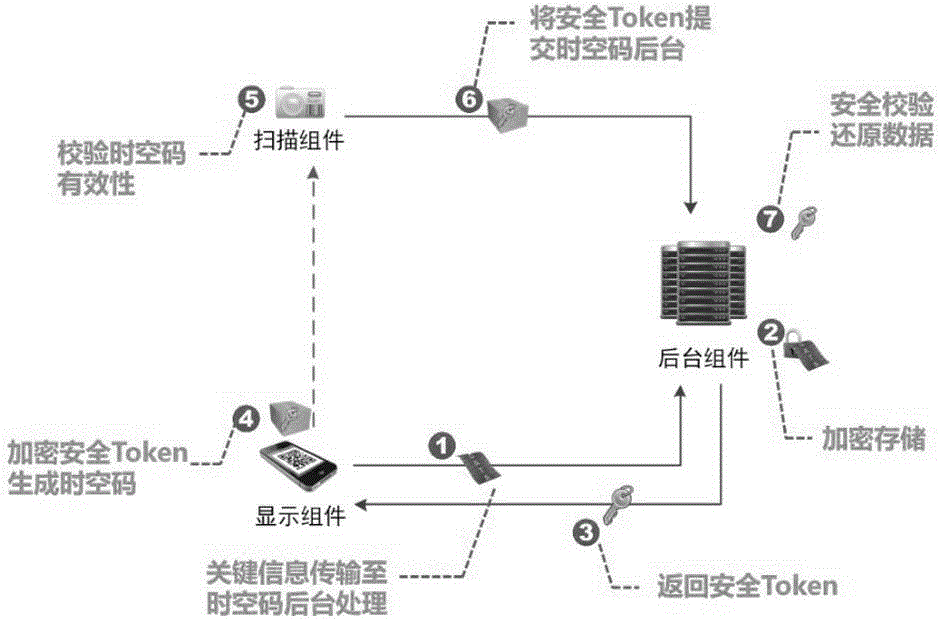
ActiveCN104573547AProtection securitySignificantly progressiveDigital data protectionPayment architectureNumbering systemOpen platform
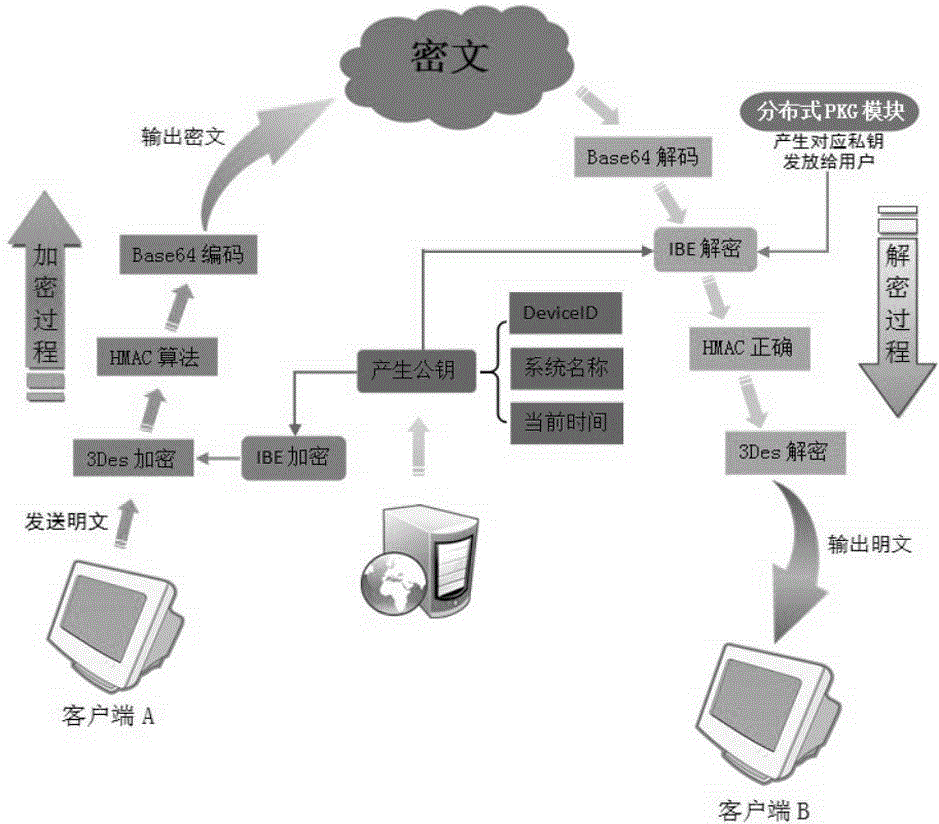
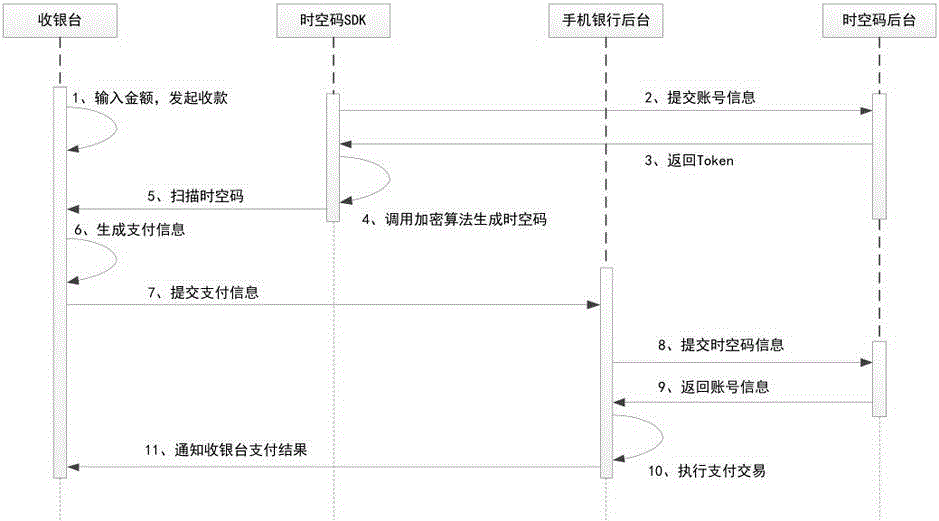
The invention discloses an information interaction safety protection system and an operation realization method thereof. According to the scheme, a space-time code system containing a display component, a scanning component and a background component is adopted and the system is used for generating and interacting cross-browser and cross-application space-time codes on each piece of corresponding Internet equipment; the background component is used for integrating multi-factor operation comprising equipment fingerprints, logic encryption, dynamic analysis, P2P checking, behavior factors, space factors and time factors and providing a background server defined by safety policies and rules, and is integrated with a corresponding business system; the display component and the background component are communicated by a pipe protection channel based on an IBE encryption mechanism and a double-certificate encryption mechanism of an account number certificate and an equipment certificate; the background component is communicated with a safety cloud platform and is sharing a dynamic algorithm with the cloud platform. With the adoption of the safety protection system and the scheme disclosed by the invention, the safety of close-range and remote certificate information is effectively protected, and an invisible account number system is created for an open platform with a complete flow protection.
Owner:JIANGSU PAYEGIS INFORMATION SECURITY TECH CO LTD
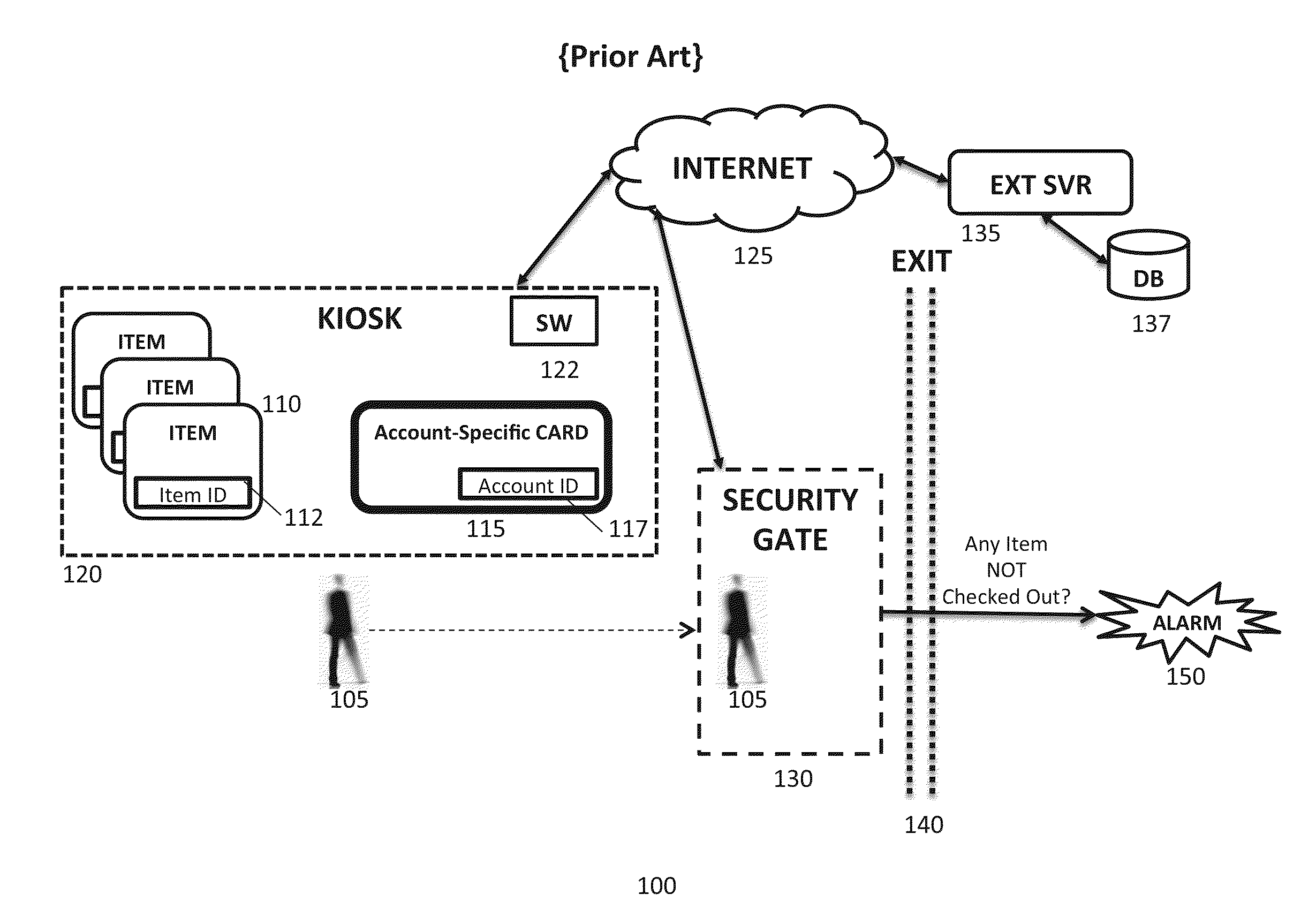
Account-based checkout
InactiveUS20140172610A1Speed up the processMaximum flexibilityCommerceProtocol authorisationSecurity policyDatabase
The present invention leverages the account-creation process that necessarily precedes any account-based transaction. The process of creating an account is enhanced to include the pre-association of various “ID Factors” that can be employed in combination to identify that account. Permitted combinations of ID Factors are those that comply with the account provider's security policy. Subsequently, at the time of a transaction in which a customer desires to check out items, the customer need only present an acceptable combination (i.e., one which meets the provider's security policy) of the ID Factors which have been pre-associated with the customer's account. In one embodiment, such an account-identification mechanism is coupled with a product-identification mechanism to enable a flexible and secure automated self-checkout system.
Owner:BOOPSIE INC
Communication safety protection method for by means of wireless public network
InactiveCN104243437AImprove the strength of security protectionGuaranteed safe operationCircuit arrangementsTransmissionReliable transmissionElectric power system
The invention discloses a communication safety protection method by means of a wireless public network. The method comprises the steps that a master station is isolated from a public network through a serial port power proprietary protocol; dispatch digital certificate authentication and transmission encryption are achieved on the master station and a substation; a safety gateway is additionally arranged; data received by the wireless public network are transmitted to an SCADA system through a communication interface. Meanwhile, a safety policy is adopted to limit the access range and resources. The TCP / IP network communication technology, the IPSEC safety tunnel technology and the USBKET encryption authentication technology are integrated, emergency recovery, temporary debugging and safety access with no power communication conditions are achieved on the condition that power system communication is abnormal, and a safe and reliable transmission channel is provided for power grid dispatch automation real-time data transmission. Safe running of a power system is ensured on the condition that existing application environment and software do not need to be changed. The communication safety protection method has the advantages that the step design is reasonable, safety protection measures are competent, working performance is stable and reliable, and the method is suitable for being popularized for industries.
Owner:STATE GRID CORP OF CHINA +1
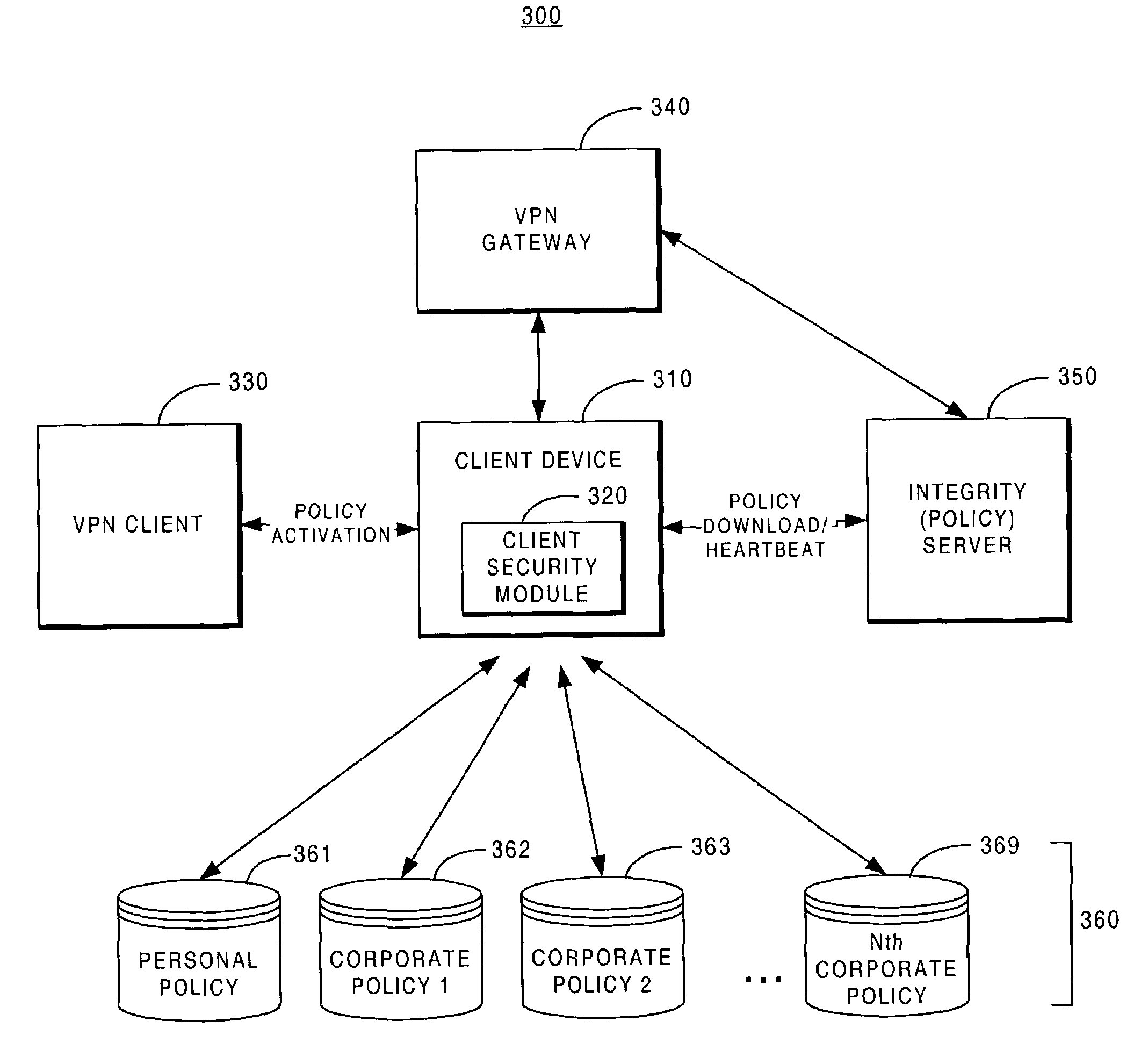
Distribution of security policies for small to medium-sized organizations
A security policy distribution system encapsulates parameters for a security policy and instructions for applying the parameters to a corresponding security program into a self-contained configuration file. When the self-contained configuration file is executed on behalf of a computer, the corresponding security program on the computer is updated with the parameters, thus distributing the security policy to the computer.
Owner:MUSARUBRA US LLC
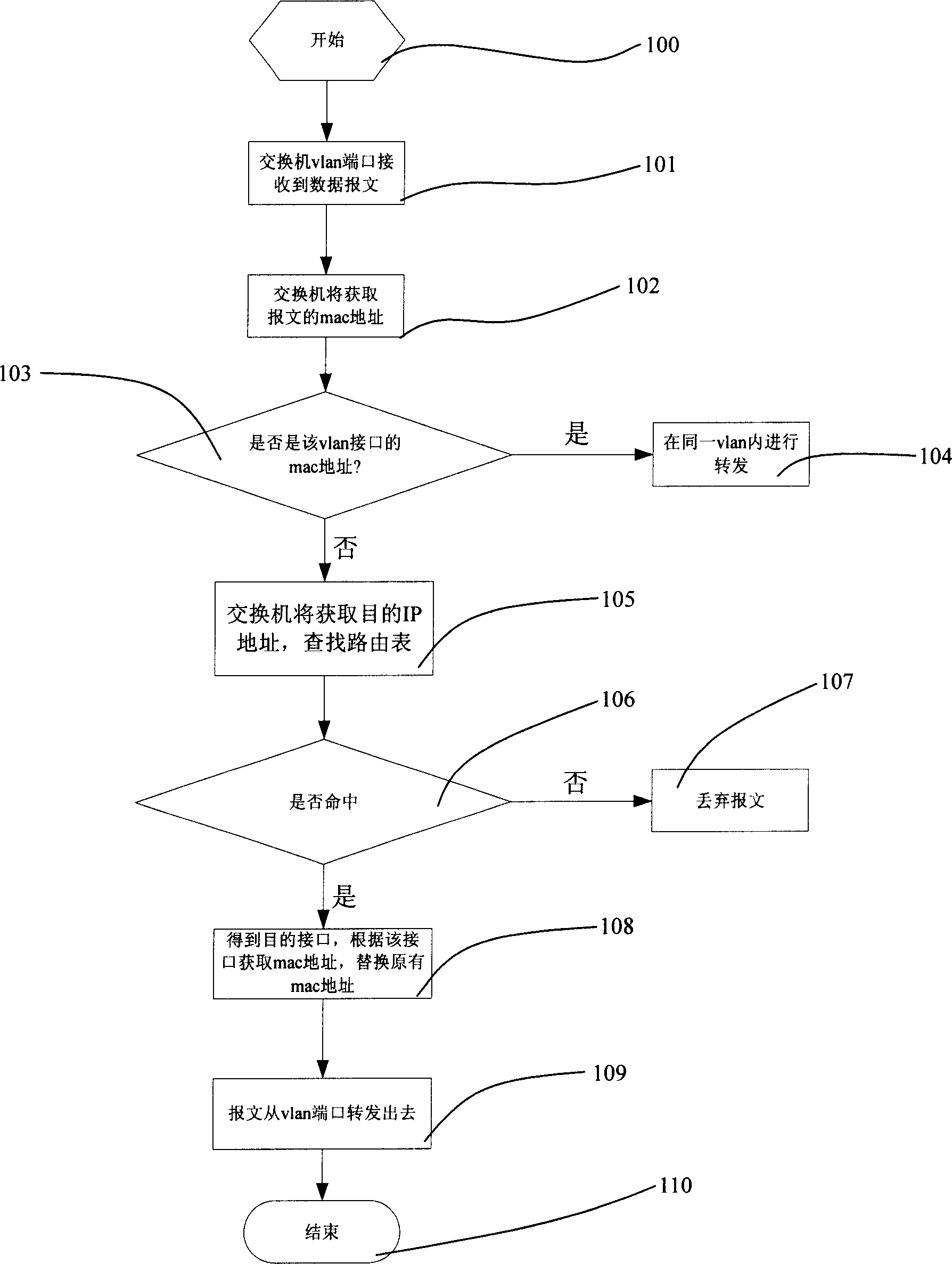
Data transmitting method and apparatus based on virtual LAN
InactiveCN1905528AReserved functionRealize data security communicationNetworks interconnectionSecure communicationVirtual LAN
The invention discloses a VLAN-based data transmitting method and device. And the method comprises: it sets safety grade IDs and safety policies for VLANs and VLAN port receives data message and determines whether to transmit in the same VLAN: if yes, transmitting the data message in the same VLAN and otherwise comparing safety grade ID of a destination VLAN with that of the message-sending VLAN: if the safety grade of the latter is higher or equal to that of the former, directly transmitting the data message and otherwise calling safety policy of the destination VLAN to make safe filtration on the data message. And it implements inter-VLAN safety data communication and assures data safety of high-grade VLAN client machines.
Owner:NEW H3C TECH CO LTD
Method for authentication and assuring compliance of devices accessing external services
ActiveUS9646309B2Digital data processing detailsMultiple digital computer combinationsElectronic communicationSecurity policy
Owner:PULSE SECURE
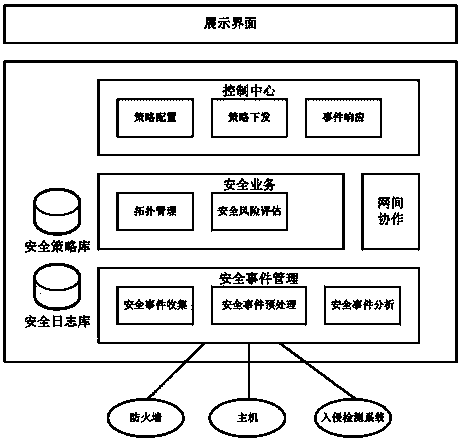
Safety management center capable of conducting collaborative analysis
InactiveCN104378365AReduce security risksReach managementTransmissionSafety management systemsWork task
The invention relates to the technical field of information safety, in particular to a safety management center capable of conducting collaborative analysis. The safety management center is composed of a safety event management module, a safety service module, a control center, a safety policy library, a log database and an internet cooperation module. Whether the collaboration of other safety management centers is needed is judged through the internet cooperation module with the combination of the self working task; if collaboration is needed, communication with other safety management centers is conducted, relevant data are transmitted, and the safety management center capable of conducting collaborative analysis asks the other safety management centers to help the safety management center to complete the tasks such as safety thread conformation. The safety management center capable of conducting collaborative analysis solves the collaborative analysis problem of the safety management center and capable of being used for information safety management.
Owner:GUANGDONG ELECTRONICS IND INST
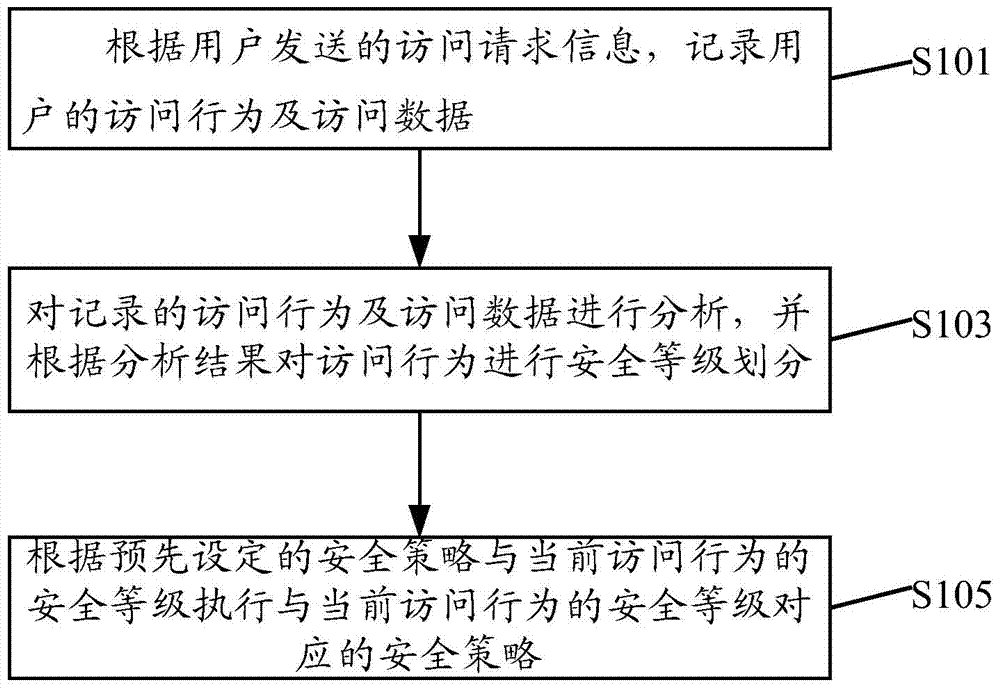
Data processing method and device based on large data platform
ActiveCN104504014AImprove securityComputer security arrangementsSpecial data processing applicationsData platformSecurity policy
The invention discloses a data processing method and a data processing device based on a large data platform. The data processing method comprises the following steps of recording access behaviors and access data of a user according to access request information sent by the user; analyzing the recorded access behaviors and the recorded access data, and performing safety classification on the access behaviors according to an analysis result; executing a safety policy corresponding to a safety class of a current access behavior according to a preset safety policy and the safety class of the current access behavior. According to the method and the device, the access request information of the user is recorded and analyzed, the access request situation of the user is subjected to safety classification, and different user requests are correspondingly processed according to the preset safety policy, so that the problem of low safety of a system caused by the data structure complexity of the large data platform is solved.
Owner:WUXI CITY CLOUD COMPUTING CENT
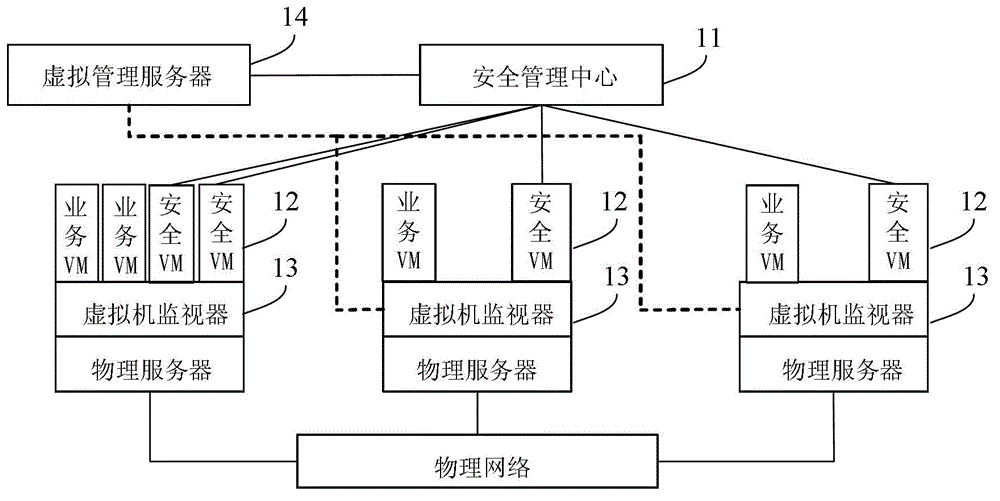
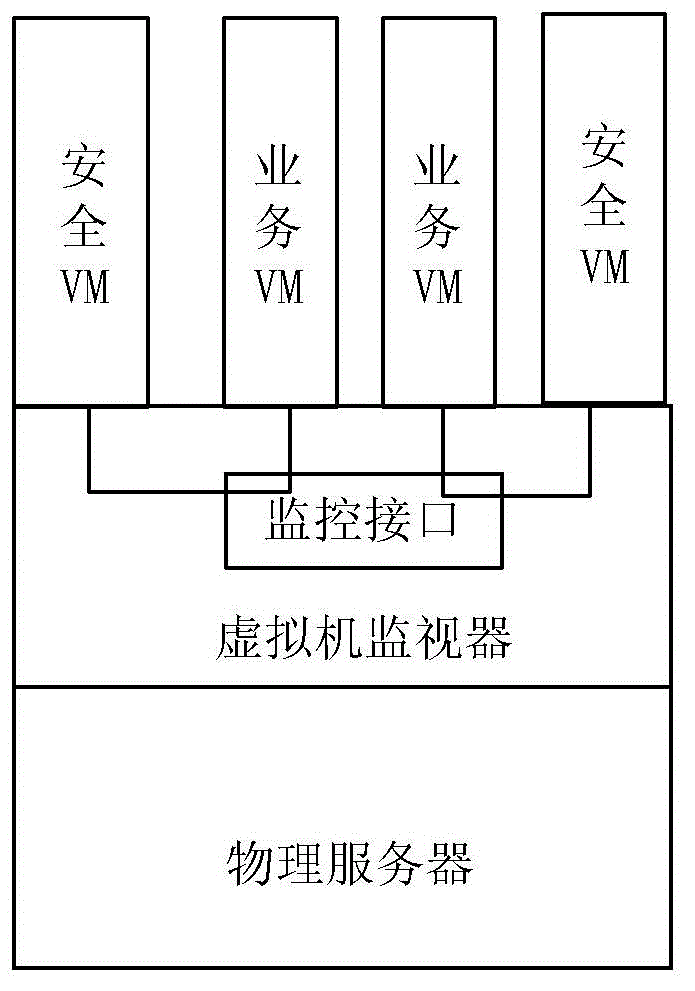
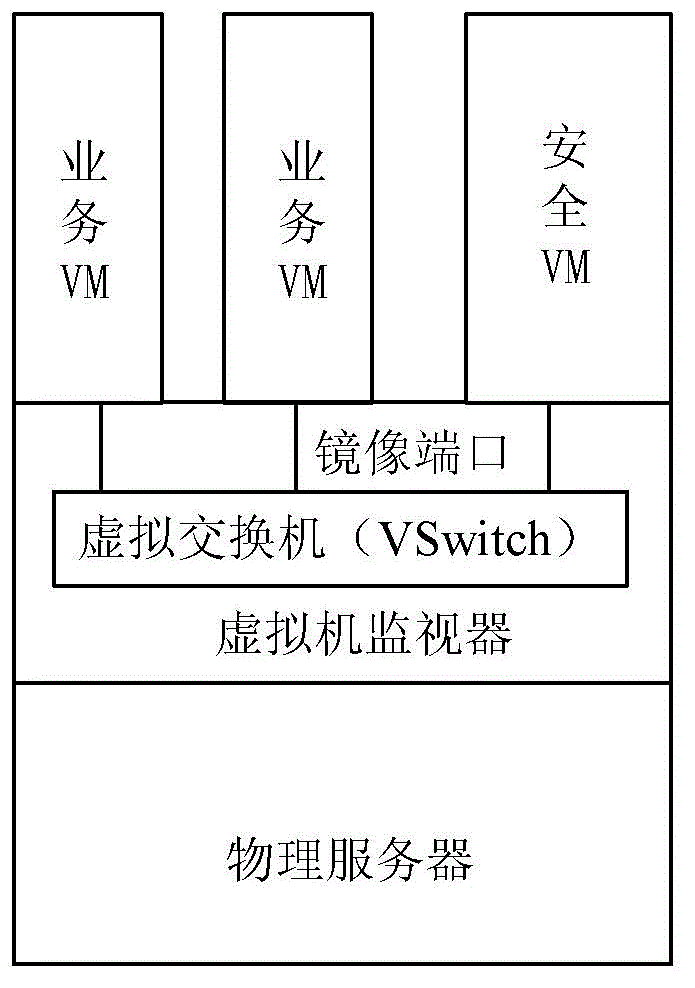
System and method for business virtual machine safety guaranteeing
InactiveCN103067356ARealize continuous monitoringAchieve consistencyData switching networksSoftware simulation/interpretation/emulationVirtualizationSecurity policy
The invention provides a system and a method for business virtual machine safety guaranteeing. The system comprises a safety management center, a business virtual machine and a safety virtual machine. The business virtual machine and the safety virtual machine are arranged on physical servers and correspond in a one-to-one mode. The safety management center is used for acquiring information of a source physical server and a target physical server which the current business virtual machine belongs to before and after moving, the safety virtual machine corresponding to the current business virtual machine is moved to the target physical server in a synchronous mode, and a safety policy is sent to the safety virtual machine corresponding to the current business virtual machine through a virtual management server in a virtual platform. The safety virtual machine is used for receiving the safety policy from the safety management center and carrying out real-time safety monitoring on the corresponding business virtual machine according to the safety policy. When the concerned business virtual machine moves, the corresponding safety virtual machine is moved to the target physical server in a synchronous mode, and ceaseless monitoring on the business virtual machine is achieved.
Owner:BEIJING VENUS INFORMATION TECH +1
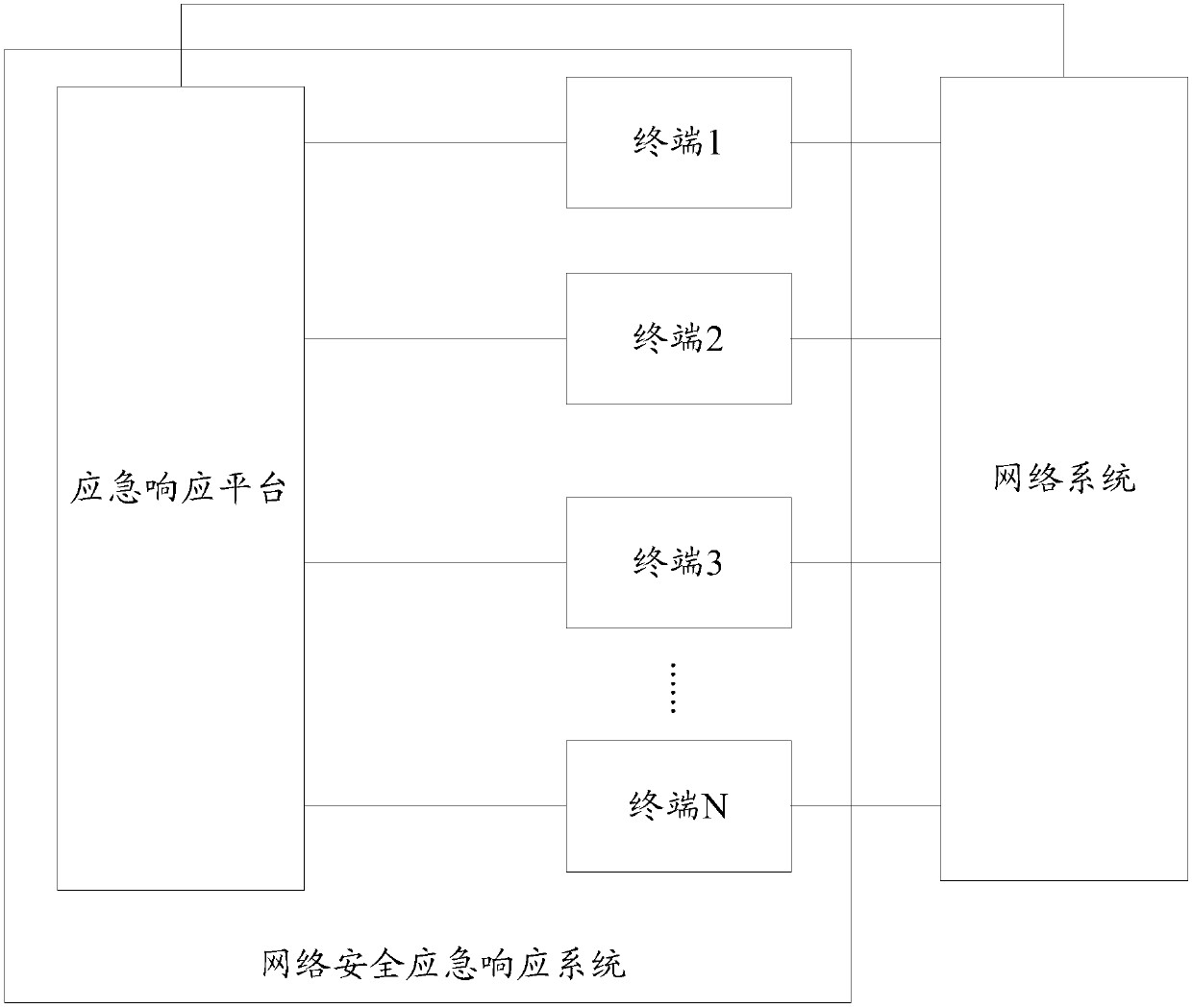
Network safety emergency response method and emergency response platform
The invention discloses a network safety emergency response method and an emergency response platform. The emergency response platform is used for obtaining relevant event information according to thesafety event and determines the terminal which is affected by the relevant event information, and the threat of relevant event information is eliminated, so that the emergency response platform can find the threat in time, the influence range of the threat can be accurately known, the threat can be rapidly and accurately eliminated, and the safety of the network is improved. The method comprisesthe steps that the emergency response platform receives a safety event; the emergency response platform obtains the relevant event information according to the safety event; the emergency response platform determines the target terminal from the terminal according to the relevant event information; the emergency response platform generates a safety policy instruction and sends the safety policy instruction to the target terminal, so that the target terminal eliminates the threat of the relevant event information according to the safety policy instruction.
Owner:SANGFOR TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com