Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1517results about How to "Achieve consistency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Three-dimensional enhancing realizing method for multi-viewpoint free stereo display
ActiveCN102568026ARealisticAchieve consistencySteroscopic systems3D-image renderingViewpointsDisplay device
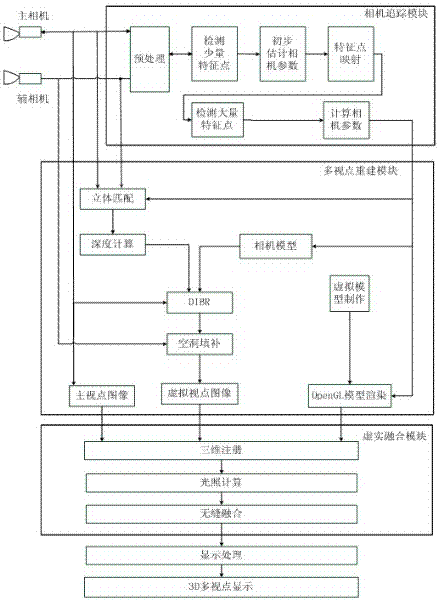
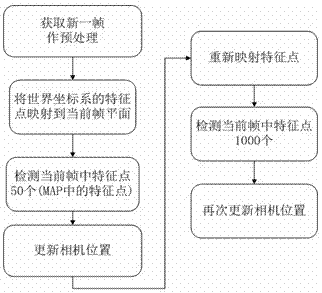
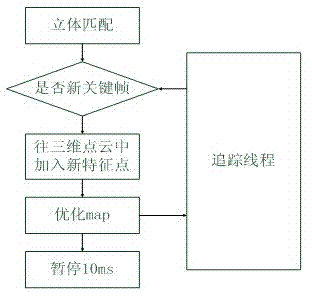
The invention discloses a three-dimensional enhancing realizing method for multi-viewpoint free stereo display, which comprises the following steps: 1) stereoscopically shooting a natural scene by using a binocular camera; 2) extracting and matching a characteristic point of an image of a main camera, generating a three-dimensional point cloud picture of the natural scene in real time, and calculating a camera parameter; 3) calculating a depth image corresponding to the image of the main camera, drawing a virtual viewpoint image and a depth image thereof, and performing hollow repairing; 4) utilizing three-dimensional making software to draw a three-dimensional virtual model and utilizing a false-true fusing module to realize the false-true fusing of the multi-viewpoint image; 5) suitably combining multiple paths of false-true fused images; and 6) providing multi-viewpoint stereo display by a 3D display device. According to the method provided by the invention, the binocular camera is used for stereoscopically shooting and the characteristic extracting and matching technique with better instantaneity is adopted, so that no mark is required in the natural scene; the false-true fusing module is used for realizing the illumination consistency and seamless fusing of the false-true scenes; and the multi-user multi-angle naked-eye multi-viewpoint stereo display effect is supplied by the 3D display device.
Owner:万维显示科技(深圳)有限公司
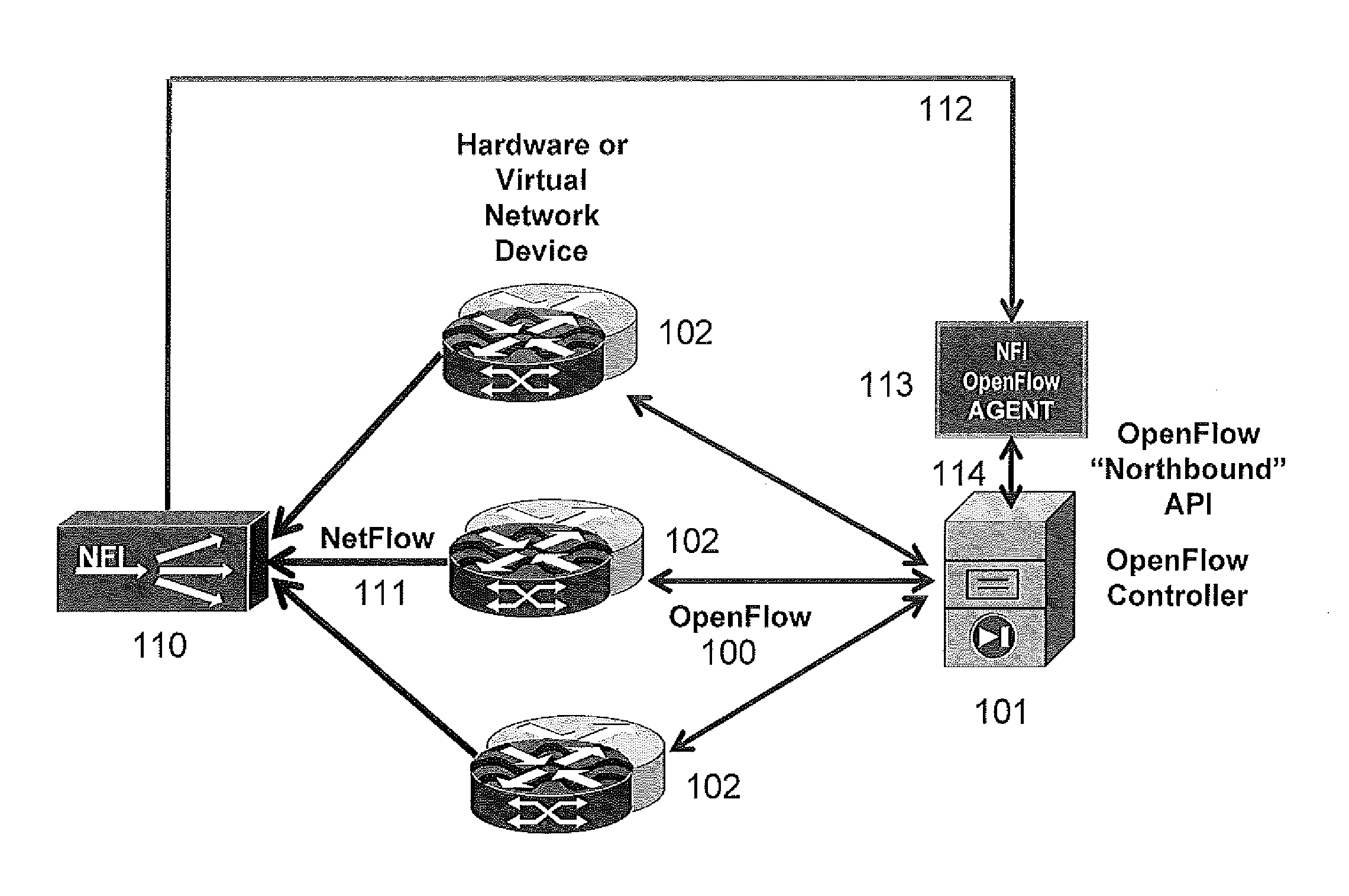
Streaming Method and System for Processing Network Metadata
InactiveUS20140075557A1Easy to deployImprove system throughputMemory loss protectionError detection/correctionInternet trafficTemplate based
An improved method and system for processing network metadata is described. Network metadata may be processed by dynamically instantiated executable software modules which make policy-based decisions about the character of the network metadata and about presentation of the network metadata to consumers of the information carried by the network metadata. The network metadata may be type classified and each subclass within a type may be mapped to a definition by a unique fingerprint value. The fingerprint value may be used for matching the network metadata subclasses against relevant policies and transformation rules. For template-based network metadata such as NetFlow v9, an embodiment of the invention can constantly monitor network traffic for unknown templates, capture template definitions, and informs administrators about templates for which custom policies and conversion rules do not exist. Conversion modules can efficiently convert selected types and / or subclasses of network metadata into alternative metadata formats.
Owner:NETFLOW LOGIC
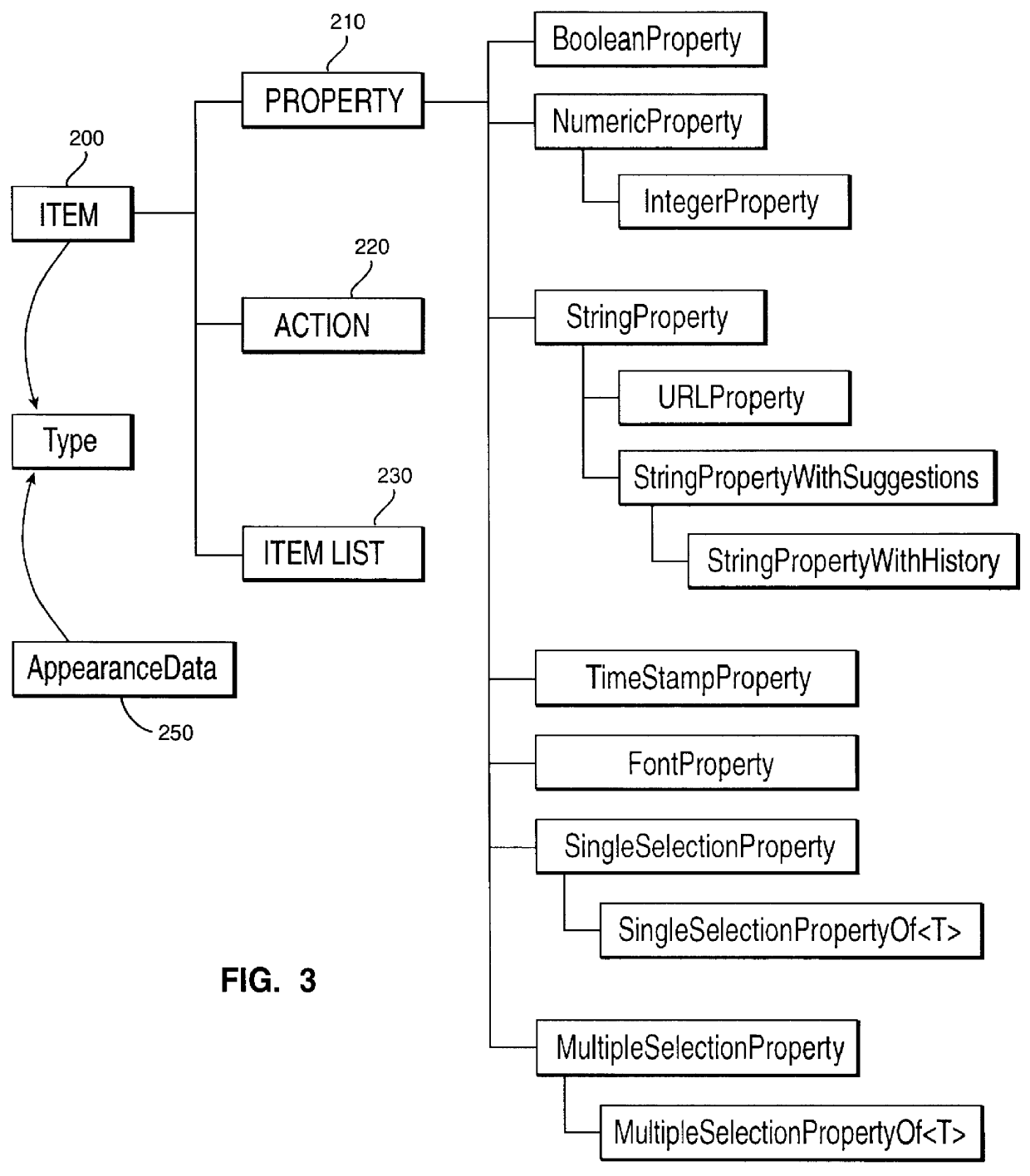
Supporting modification of properties via a computer system's user interface
InactiveUS6100885ASimplify application program developmentSave development timeSoftware engineeringSpecific program execution arrangementsObject ClassComputerized system
A set of object classes provide a framework supporting user modification of user interface properties. The classes include a properties class which is a template for creation of property objects encapsulating property values and the view attributes (GUI information) required for creating views of the property via a user interface. Property objects provide a single mechanism for representing a particular property, allowing a number of different views to be open on the same property. User interactions with different views of a property via the user interface result in messages being sent to the same property object. If a property value is changed, then the chance is propagated back to all associated applications having views for the object and so view concurrency is automatically achieved.
Owner:IBM CORP
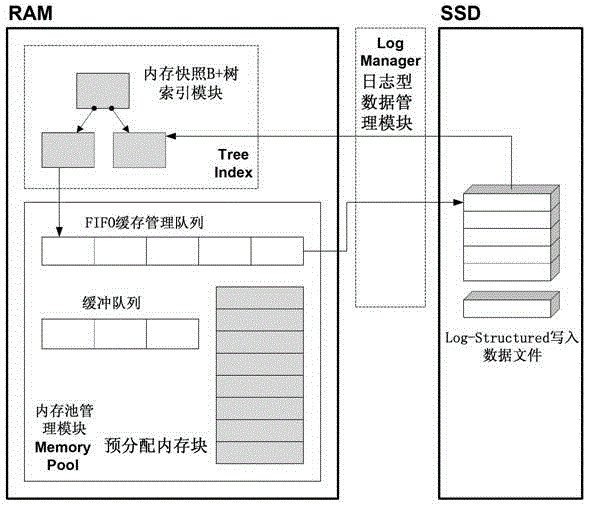
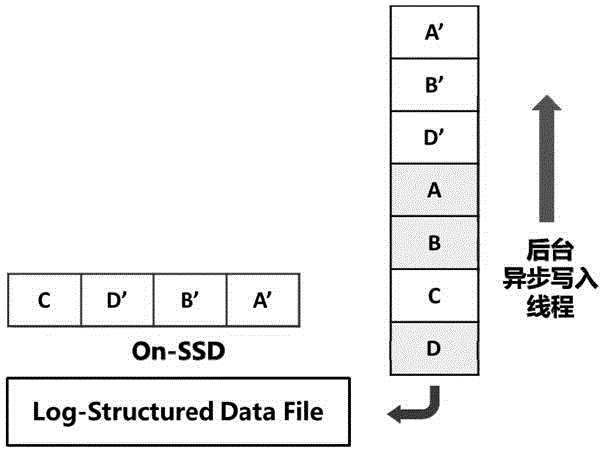
Key-Value local storage method and system based on solid state disk (SSD)
ActiveCN102722449AEasy to wearRealize read-write separationDigital data information retrievalMemory adressing/allocation/relocationSolid-state driveFifo queue
The invention discloses a Key-Value local storage method and a Key-Value local storage system based on a solid state disk (SSD). The method comprises the following steps of: 1, performing read-write separation operation of a memory on data by adopting a memory snapshot B+ tree index structure; 2, performing first in first out (FIFO) queue management and caching on the indexed data aiming at a B+ tree; and 3, performing read-write operation on the data. Mapping management of logical page number and physical position is realized through an empty file mechanism in the log type additional write-in data.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI +1
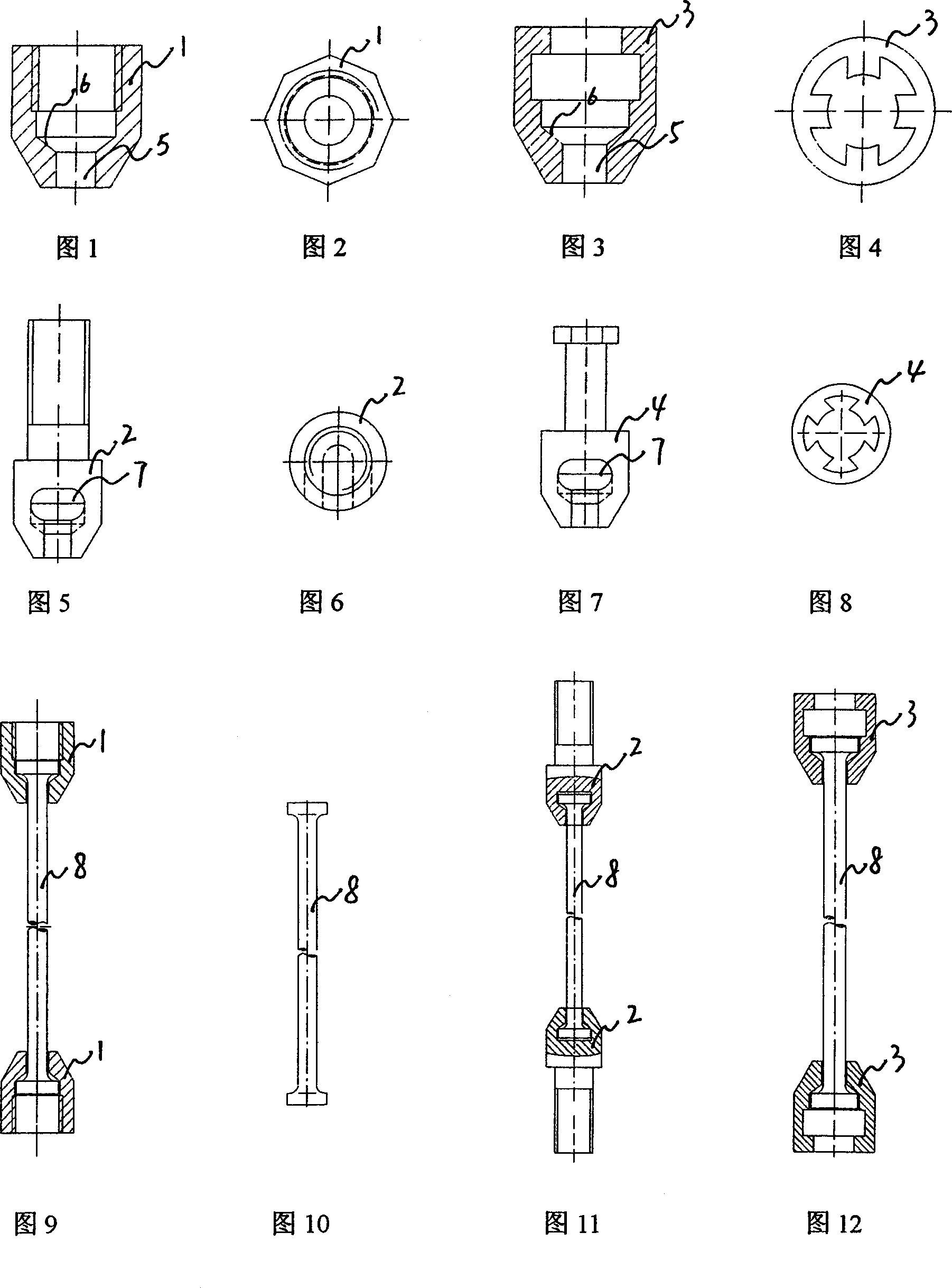
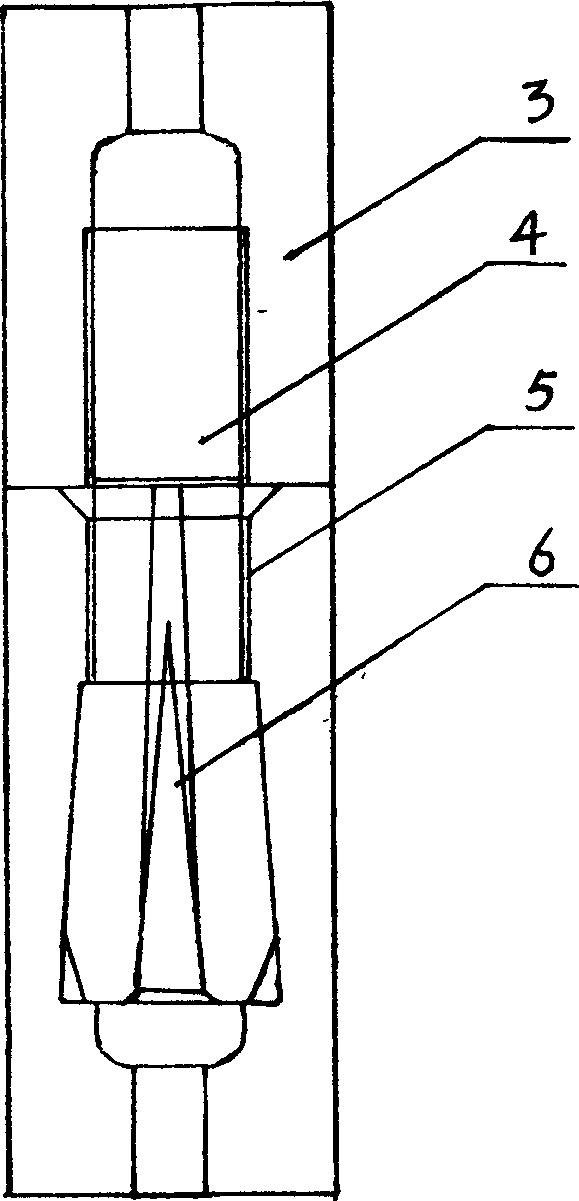
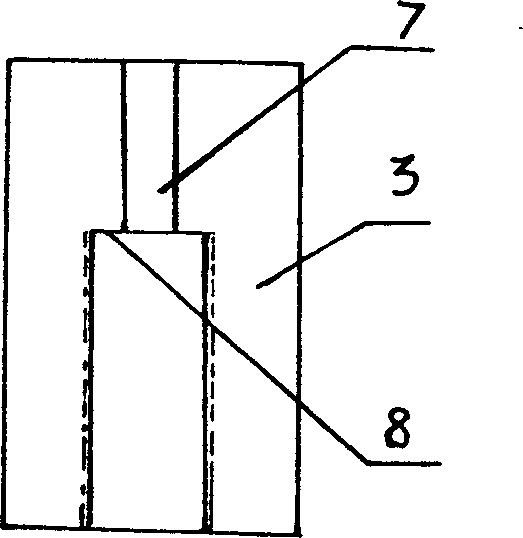
Pile connecting buckle and its prefabricated unit
InactiveCN100348803CReduce manufacturing costAchieve consistencyBuilding constructionsBulkheads/pilesPre stressRebar
The present invention relates to one kind of powerful buckle for prefabricated unit, prefabricated unit with the buckle and it forming process. The powerful buckle has screw thread connecting or bayonet jointing structure with steel bar hole in the center and upset steel bar head clamping stage around the steel bar hole. The prefabricated pre-stressed unit has reinforcing rib skeleton comprising longitudinal ribs and ring ribs and the each end of its longitudinal ribs are bayonet jointed to the upset steel bar head clamping stage. After the powerful buckle has the end fixed onto the fixing board and expanding board and set inside formwork, and concrete is deposited and the expanding board is drawn to set pressure, to form centrifugal pile and obtain prefabricated pre-stressed unit.
Owner:周兆弟
Upper screw lower connecting pile fastener and precast member
InactiveCN1603523AReduce manufacturing costAchieve consistencyBuilding constructionsBulkheads/pilesNosePre stress
The invention involves a kind of tube column to meet the buckle, as well as uses with the time mouth constitution pre-stressed high strength pre- workpiece and -odd in view of the fact that with the between between connection structure and the connection method, is the pre- workpiece to meet buckles with the pre- workpiece manufacture domain. On under the spiral goes against pile extension buckles by pulls the cap nut, inflates the screw and goes against pulls the cap nut constitution, pulls the cap nut screw together in the spiral which inflates the screw wire shorts, inflates the screw the inflation measure expansion in to go against pulls in the cap nut in the inflation cavity, when pile extension, demands the collection attire two maybe certain to pull the cap nut with the between nose minute to buckle goes against pulls the cap nut mouth which corresponds with the prefabrication, inflates the screw the spiral wire shorts screw together in pulls the cap nut screw thread in, Inflates the screw the inflation to carefully examine like goes against pulls the cap nut the inflation cavity also the inflation sells under the function in its nose to inflate in goes against pulls the cap nut in the inflation cavity, completes docking between the pre- workpiece and pre- workpiece.
Owner:周兆弟
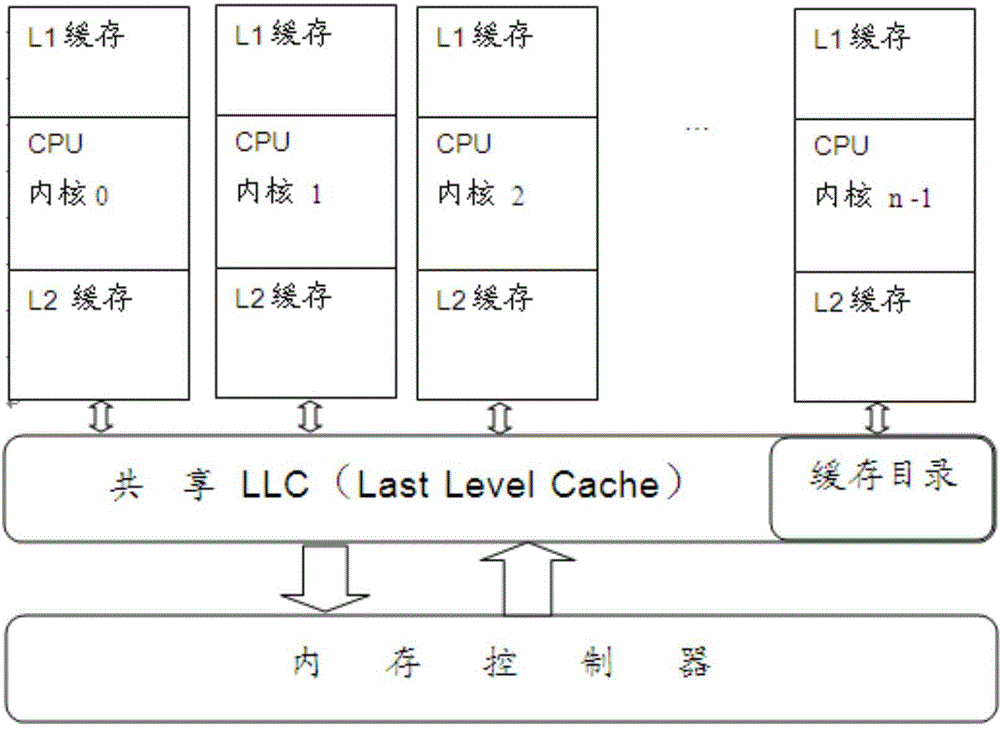
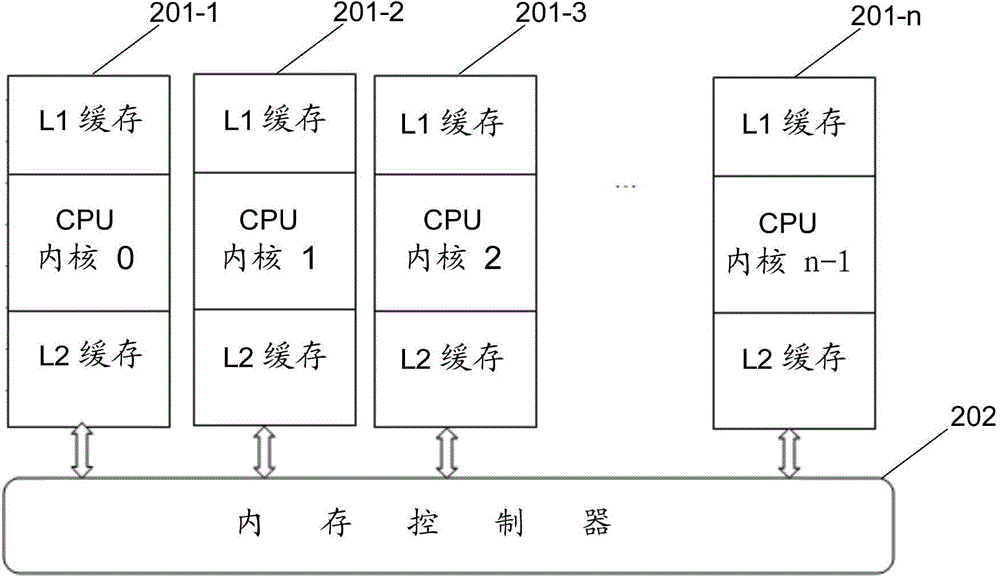
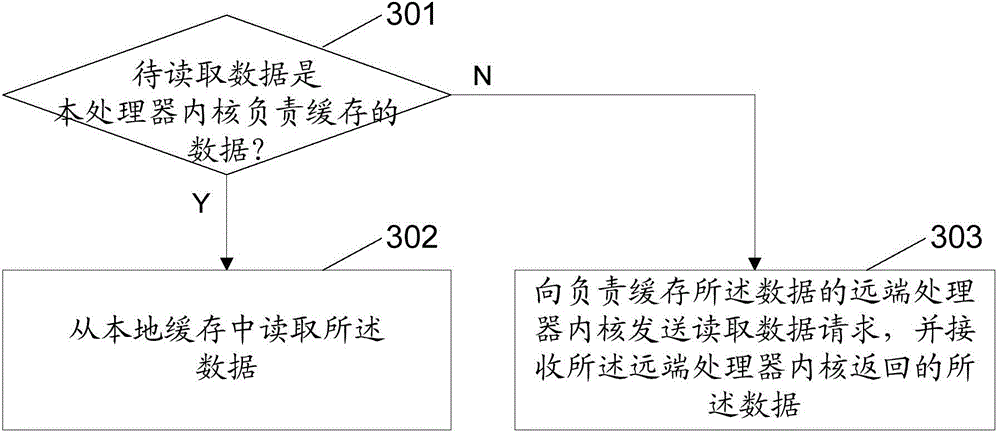
Multi-core processor supporting cache consistency, reading and writing methods and apparatuses as well as device
ActiveCN105740164AAchieve consistencyImprove performanceMemory architecture accessing/allocationMemory adressing/allocation/relocationDistribution methodCache consistency
The invention discloses a multi-core processor supporting cache consistency, a data reading method and apparatus based on the multi-core processor, a data writing method and apparatus based on the multi-core processor, a memory allocation method and apparatus based on the multi-core processor, and a device. The multi-core processor supporting cache consistency comprises a plurality of processor cores and local caches corresponding to the processor cores respectively, wherein the local caches of different processor cores are used for caching data in memory spaces of different address ranges respectively; and each processor core accesses the data in the local caches of other processor cores through an interconnection bus. According to the technical scheme provided by the invention, a new thought of removing a cache directory and shared caches from a conventional multi-core processor framework is provided, so that the cache consistency is realized, private caches are shared, and the overall performance of the processor is improved while the conflicts between the private caches and the shared caches are eliminated.
Owner:ALIBABA GRP HLDG LTD
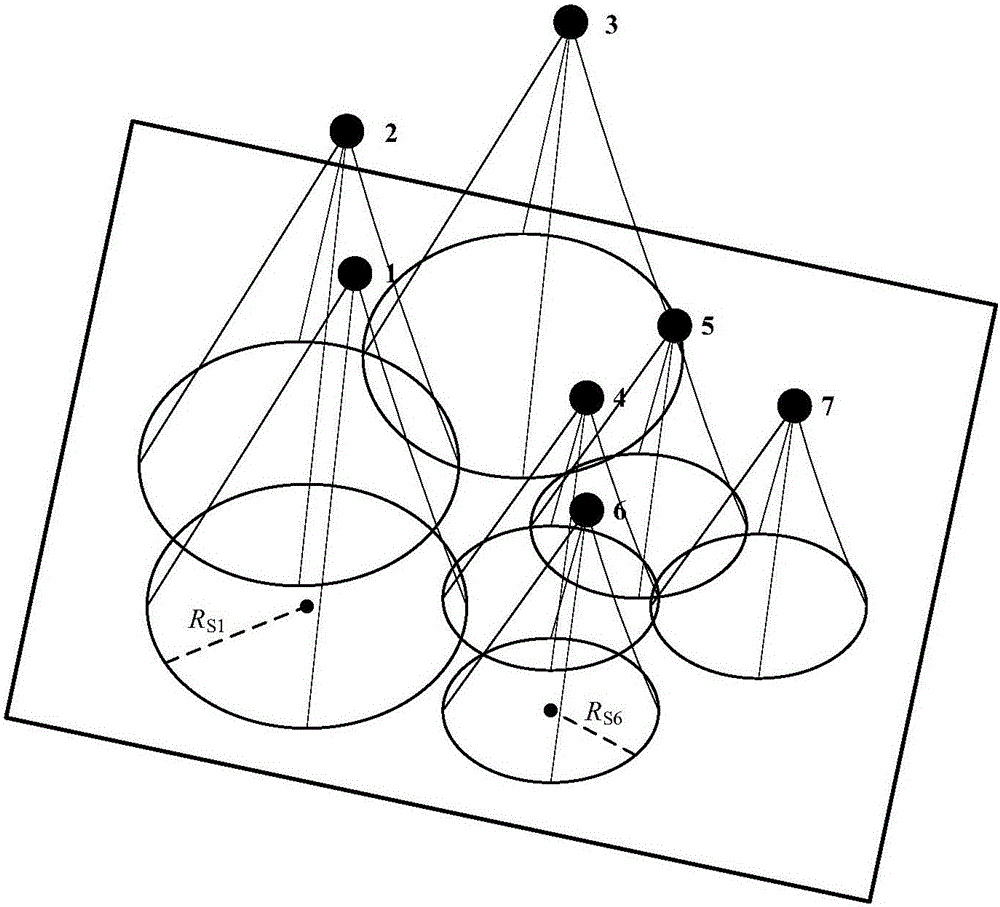
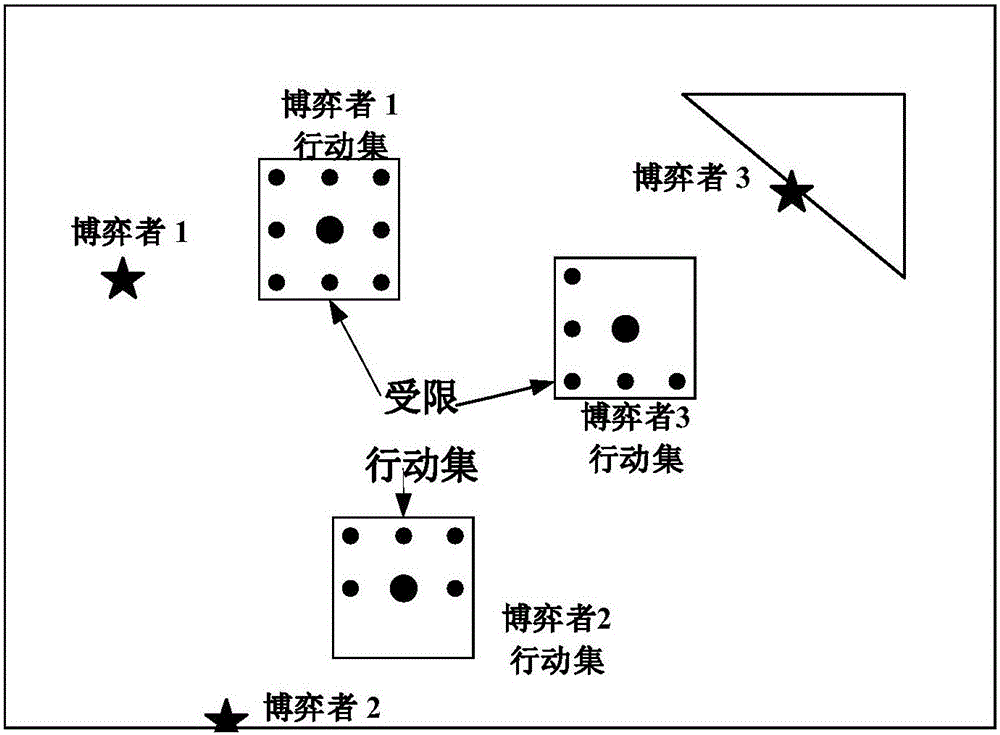
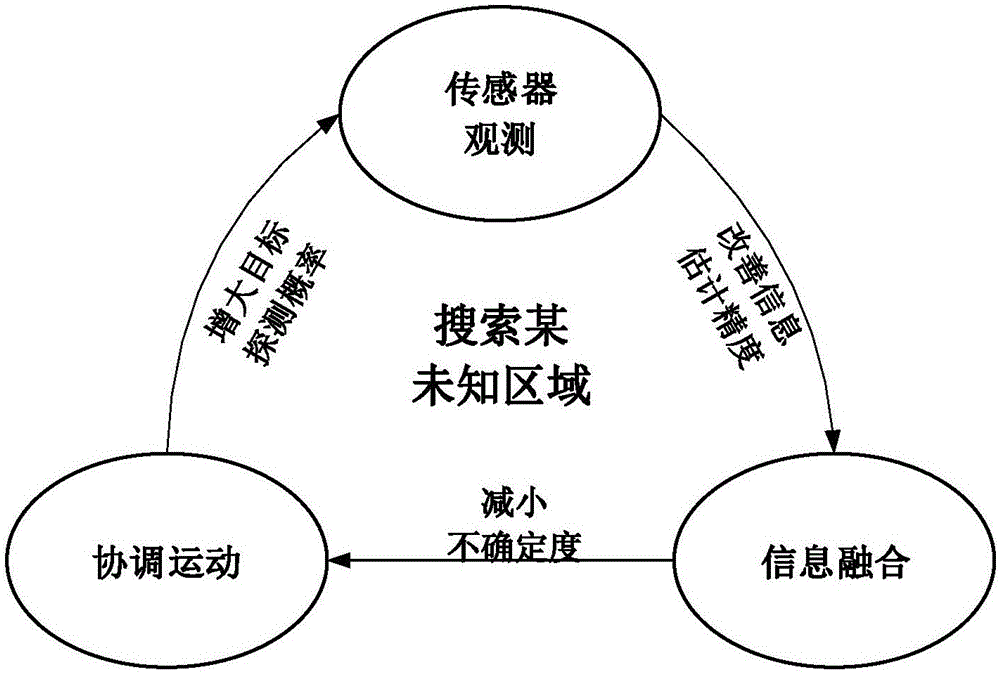
Potential game-based multi-unmanned aerial vehicle cooperative search method
ActiveCN105700555AOvercome localityAchieve consistencyTarget-seeking controlAdaptive controlSearch problemControl manner
The invention discloses a potential game-based multi-unmanned aerial vehicle cooperative search method. The method comprises steps: 1, modeling of a multi-unmanned aerial vehicle cooperative search problem is carried out; 2, potential game modeling for a multi-unmanned aerial vehicle cooperative motion and potential game solution in a double log-linear learning method are carried out; 3, a probability map is updated according to sensor detection information, information fusion is carried out on the updated probability map, and a target existence probability is acquired; and 4, uncertainty is updated according to the target existence probability, and multi-unmanned aerial vehicle cooperative search is carried out. The method of the invention can realize multi-unmanned aerial vehicle cooperative search, and comprises steps of cooperative motion based on the potential game, updating of the probability map, information fusion and the like, and due to the self distributed control mode, the calculation is simple, the robustness is strong, and external disturbance can be effectively handled.
Owner:BEIHANG UNIV
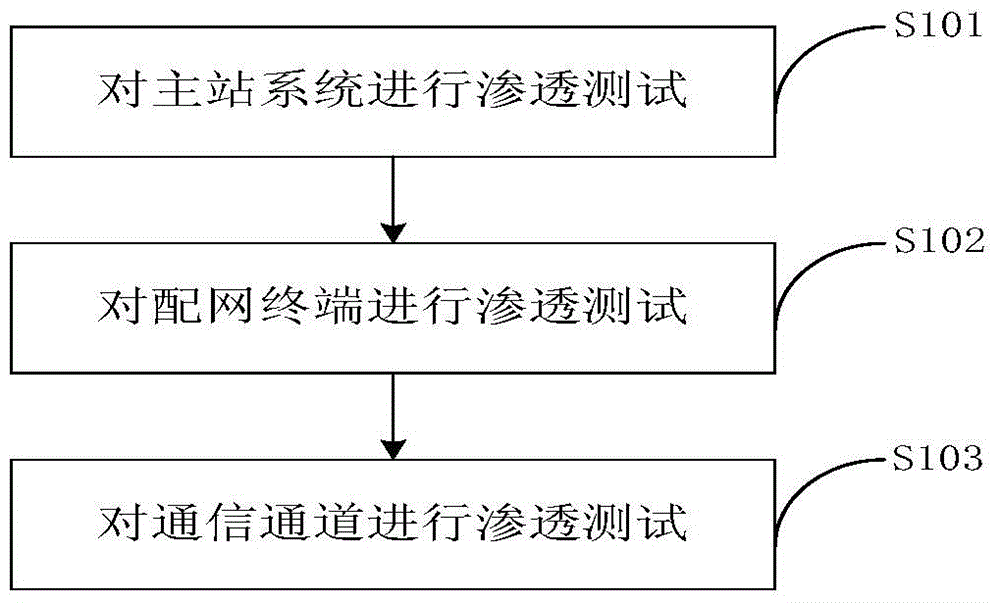
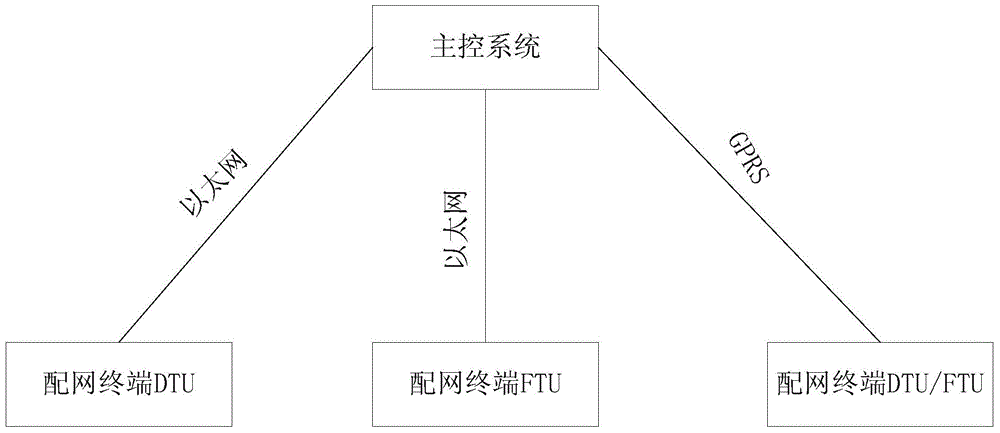
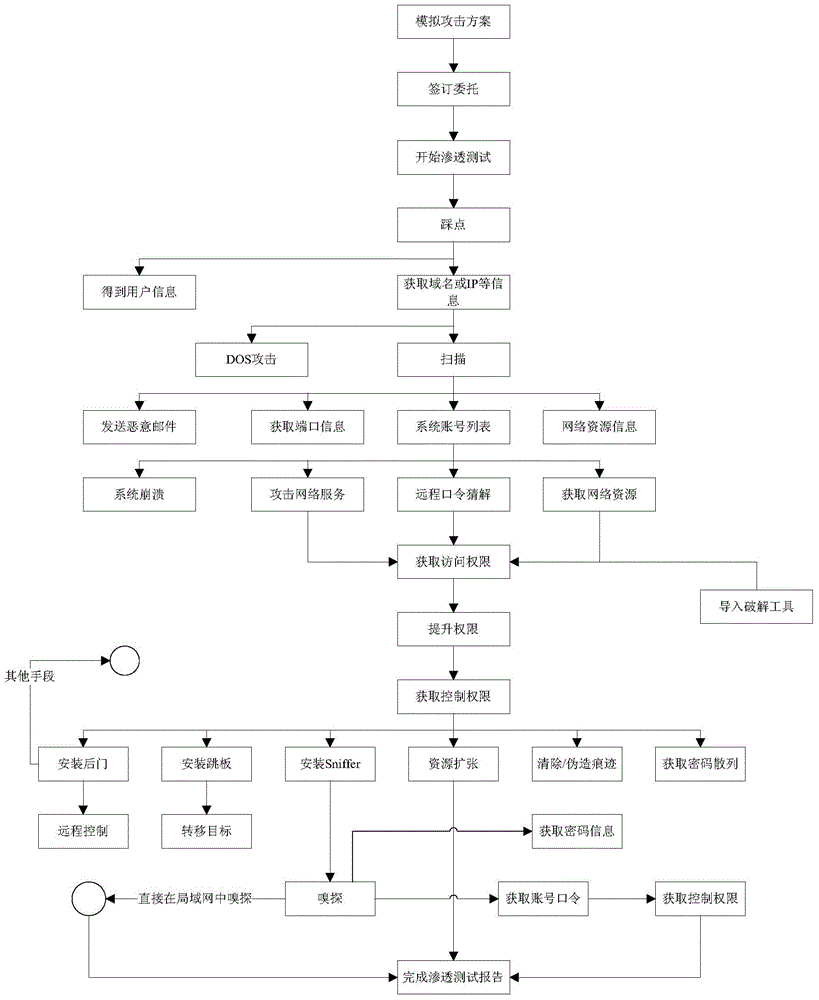
Information safety penetration testing method for distribution automation system
ActiveCN104468267AAchieve consistencyImplementations should be consistent withData switching networksThe InternetMaster station
The invention discloses an information safety penetration testing method for a distribution automation system. Penetration testing is carried out on a master station system, a distribution network terminal and a communication channel, the information system vulnerability penetration testing technology is fully used, the safety of the distribution automation system is evaluated by simulating the attack method of a hacker, and the information safety penetration testing method includes the active analysis for any weakness, technical defects or loopholes of the master station system, the communication circuit and the distribution network terminal. The information safety penetration testing method for the distribution automation system can be used for safety risk analysis work before the distribution automation system is connected to the internet, guidance is provided for finishing problem rectification and reformation and retest work of manufacturers with safety risks, and the method is high in pertinence and wide in test range. Compared with a traditional penetration testing method, the test time can be largely shortened, offline repairing events caused by safety problem failures after equipment is on line are reduced, the information safety penetration testing for the distribution automation system is realized, and the information safety penetration testing method can be applied to industrial control systems inside and outside the industry.
Owner:STATE GRID CORP OF CHINA +1
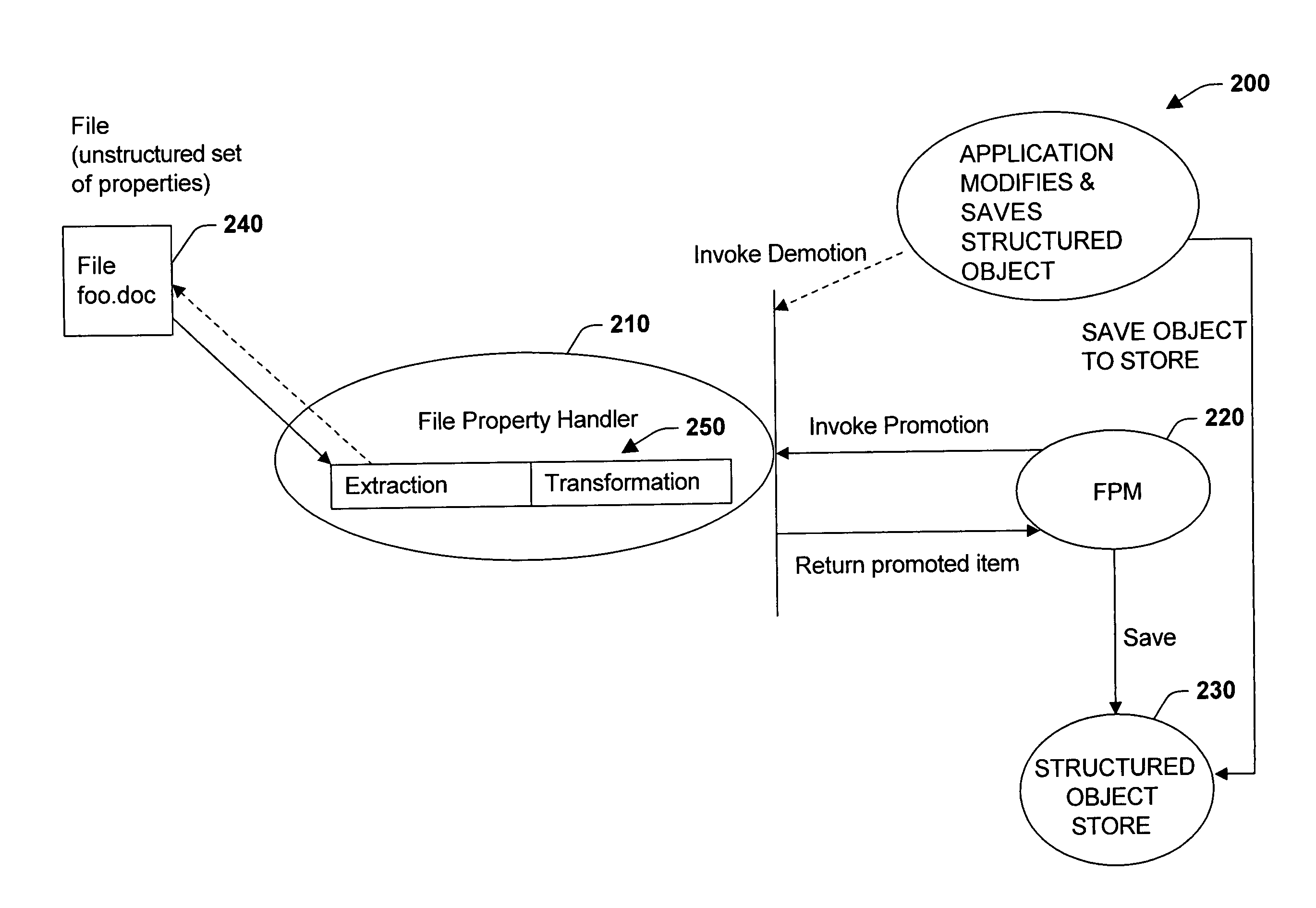
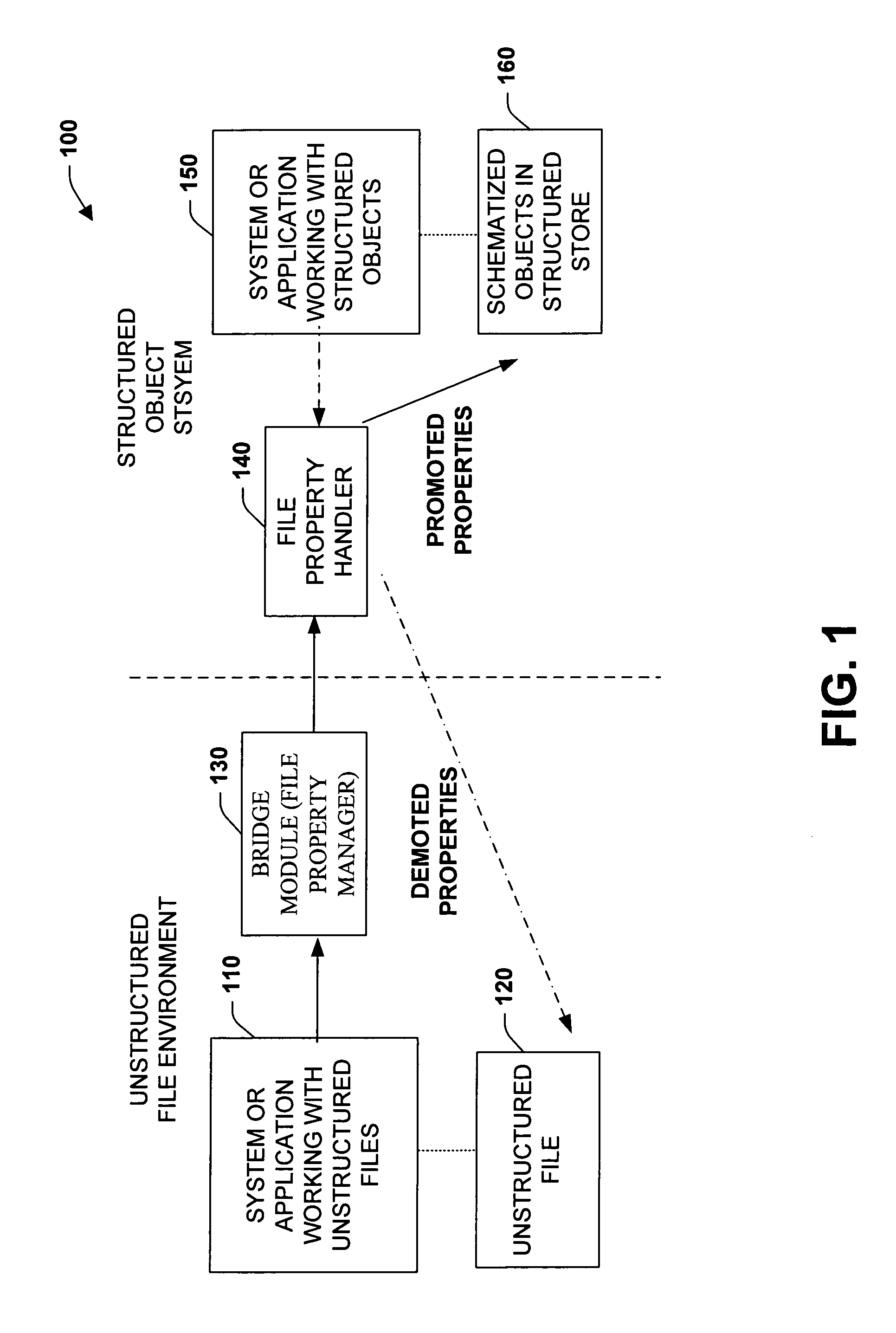
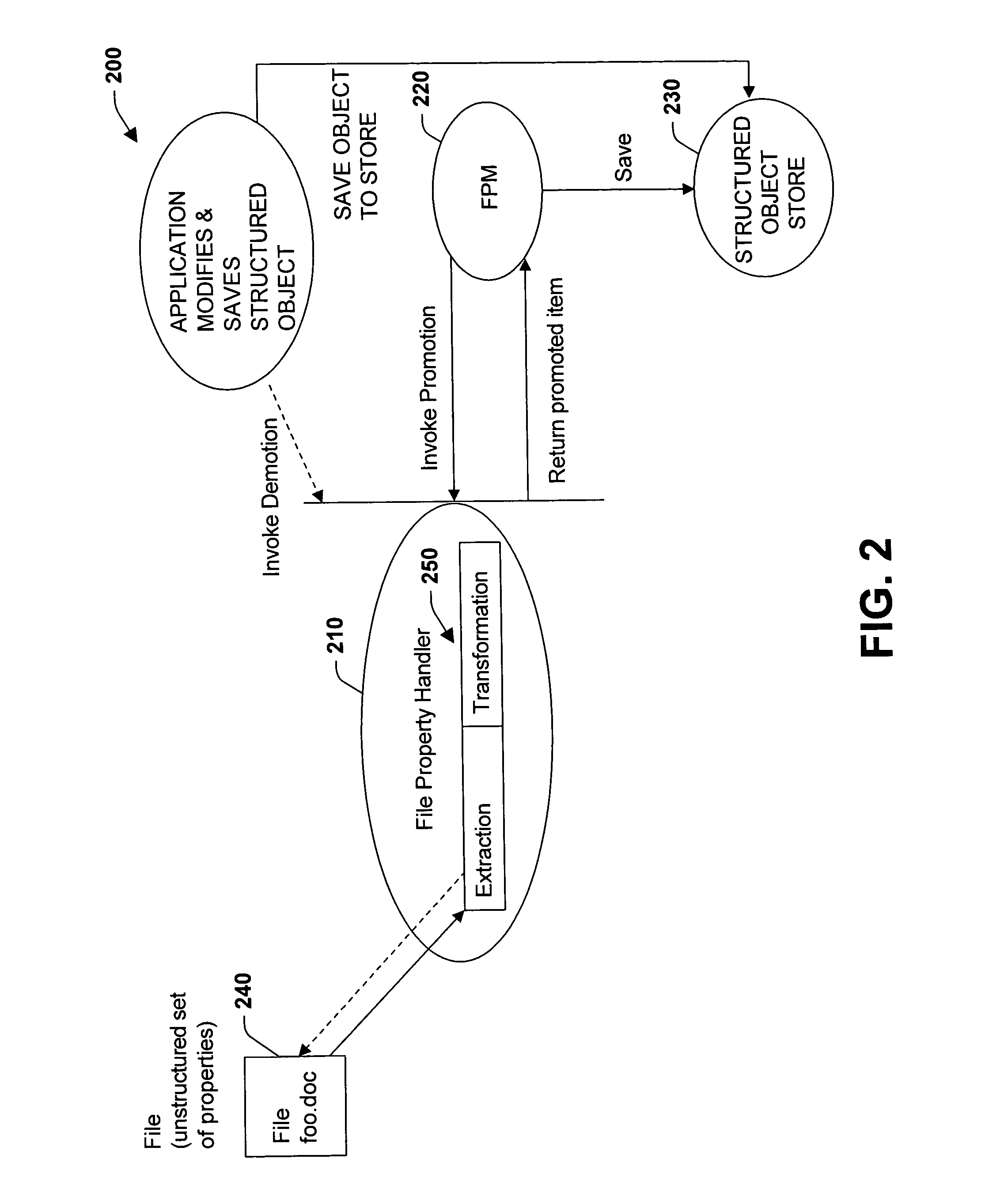
Promotion and demotion techniques to facilitate file property management between object systems
ActiveUS7155444B2Facilitate file manipulationAchieve consistencyAcutation objectsData processing applicationsComputer compatibilityObject store
The present invention relates to a system and methodology to facilitate interoperability and compatibility between disparate data systems. In one aspect, a file transformation system is provided having at least one file associated with one or more unstructured properties. A file property handler manipulates the unstructured properties in accordance with one or more structured properties associated with a structured object store environment. If an unstructured file is to be operated in the context of a structured object store environment, a promotion operation is performed to update unstructured properties in the file with structured properties suitable for operation in the structured object store environment. If a promoted item were to be manipulated in the structured object store environment, a demotion operation or reverse transformation is performed to update properties in the file.
Owner:MICROSOFT TECH LICENSING LLC
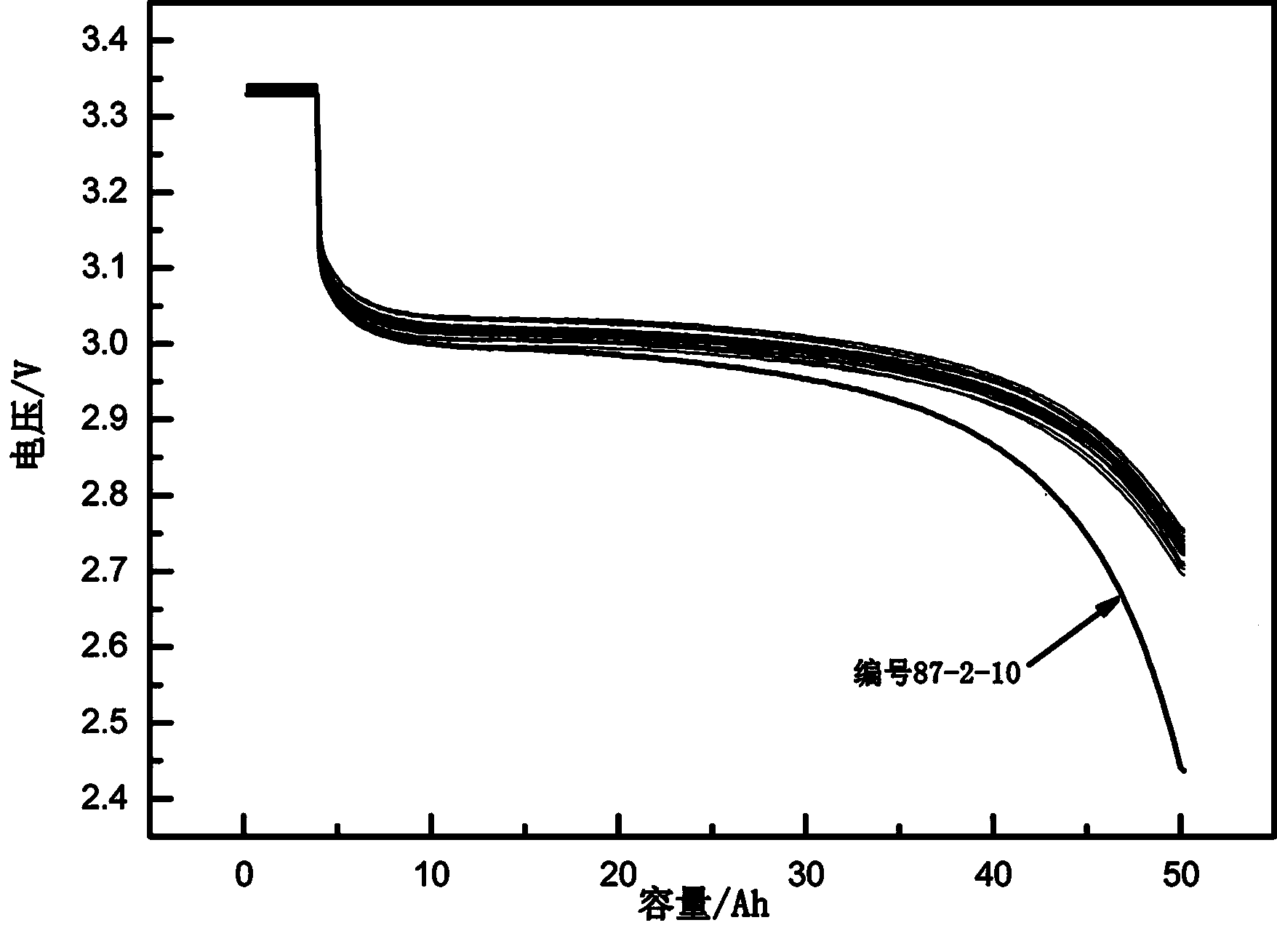
Lithium iron phosphate power battery consistency matching screening method
InactiveCN103611692AAchieve consistencyAchieve electrochemical polarizationElectrical testingSortingInternal resistanceElectrical battery
A disclosed lithium iron phosphate power battery consistency matching screening method comprises the steps: evaluating lithium iron phosphate power batteries according to the performance parameters of the batteries, preliminarily screening the lithium iron phosphate power batteries into a group; performing heavy-current test on the lithium iron phosphate power batteries to reject batteries with abnormal voltage in the battery group; and finally performing self discharging rate screening test on the lithium iron phosphate power batteries to reject batteries with reduced voltage and further to screen out batteries with relatively good consistency. The method helps to realize the consistency of parameters such as battery capacity, static-state internal resistance, open-circuit voltage and the like of the lithium iron phosphate power battery group, also helps to realize the consistency of electrochemical polarization of the lithium iron phosphate power battery group during heavy-current discharging, and also helps to realized the consistency of the self discharging rate of the lithium iron phosphate power battery group.
Owner:XIAMEN CHL NEW ENERGY +1
Method for maintaining consistency and performing recovery in a replicated data storage system
ActiveUS7103884B2Slow recoveryAchieve consistencyDigital data information retrievalData processing applicationsData storage systemDistributed computing
A recovery process allows a recovering replica in a replicated data storage system to recover from a current replica the changes to the data that it has missed during a failure while, at the same time, the system is processing new requests issued by the source. Sequence numbers, assigned by the source to write requests and stored by each replica in association with the data item that the write request modifies, are used by the recovery process to determine when a replica has missed one or more write requests and requires recovery. During recovery, the recovering replica ignores all requests directly received from the source, and replaces the contents of a data item with the data received from the current replica only if the newly received data item has a higher sequence number than the corresponding sequence number of the data item already stored in the recovering replica. It also updates data items in response to new write requests that are forwarded to it by the current replica. At the same time, the current replica continues to receive requests from the source, performs those requests, and forwards those write requests to the recovering replica. It also scans its data items and sends to the recovering replica those data items and associated sequence numbers that have a sequence number higher than the sequence number of the last consecutive write request sent by the source that the recovering replica received before missing a write request.
Owner:ALCATEL LUCENT SAS
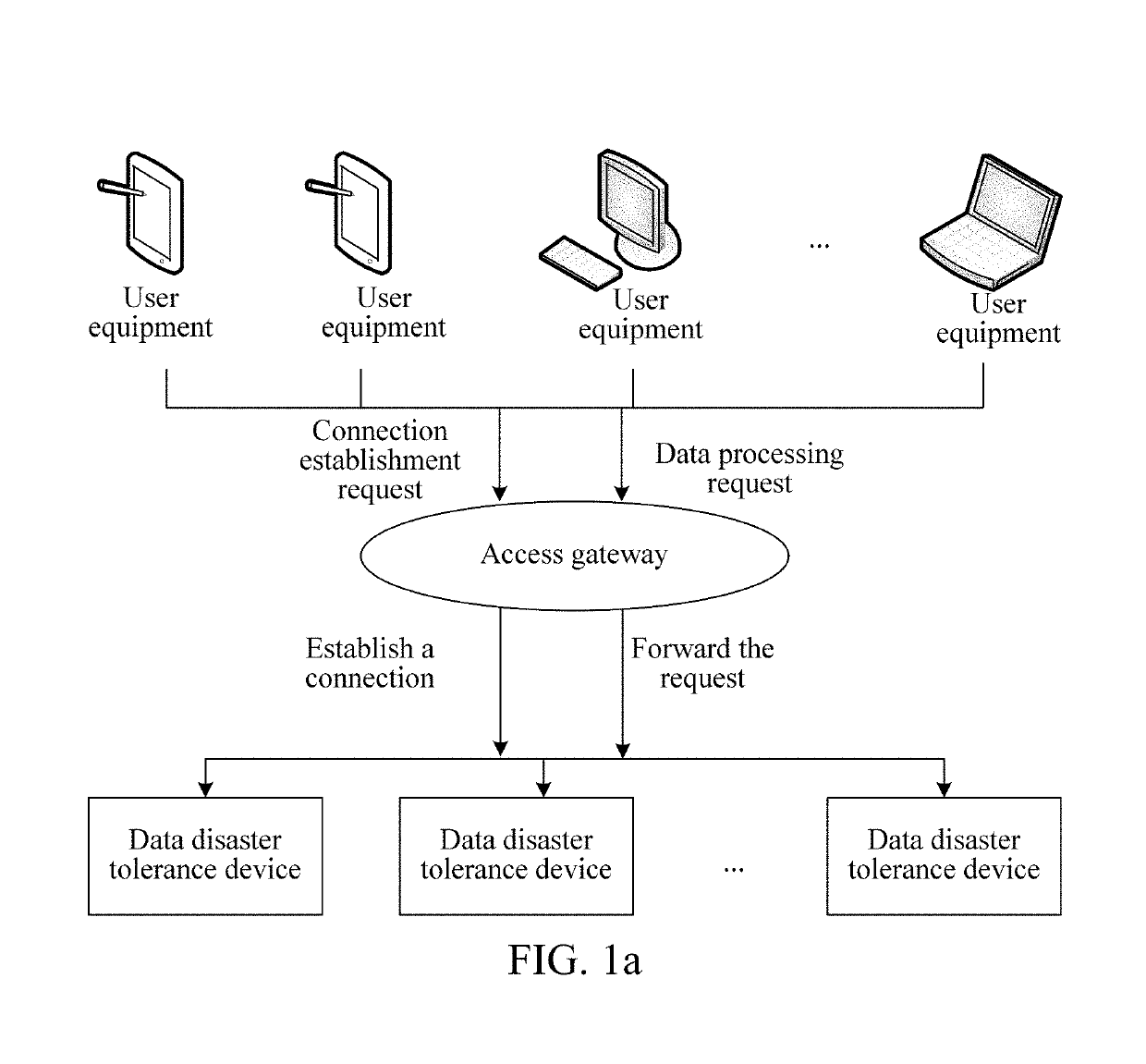
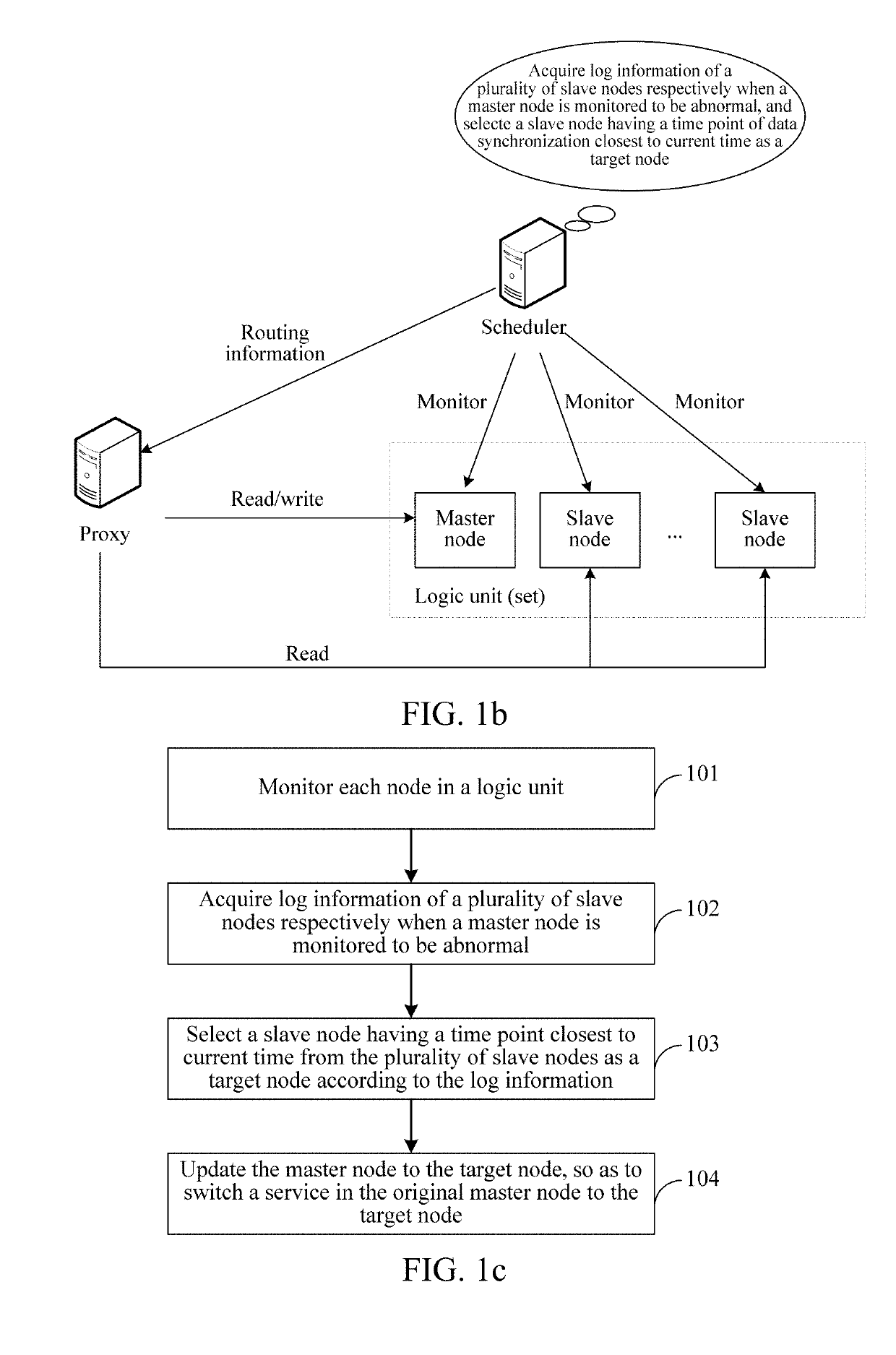
Data disaster recovery method, device and system
ActiveUS20190095293A1Simple to implementHigh availability of systemNon-redundant fault processingTransmissionCurrent timeReal-time computing
A data disaster tolerance method, device and system is disclosed. Each node in a logic unit including a single master node and two or more slave nodes is monitored. If the master node is abnormal, the server acquires log information of the plurality of two or more slave nodes separately, the log information of the two or more slave nodes includes respective time points of data synchronization between the slave nodes and the master node A respective slave node of the two or more slave nodes having the time point of data synchronization closest to a current time is selected as a target node. A master-slave relationship in the logic unit is updated to change a role of the target node to that of the master node.
Owner:TENCENT TECH (SHENZHEN) CO LTD
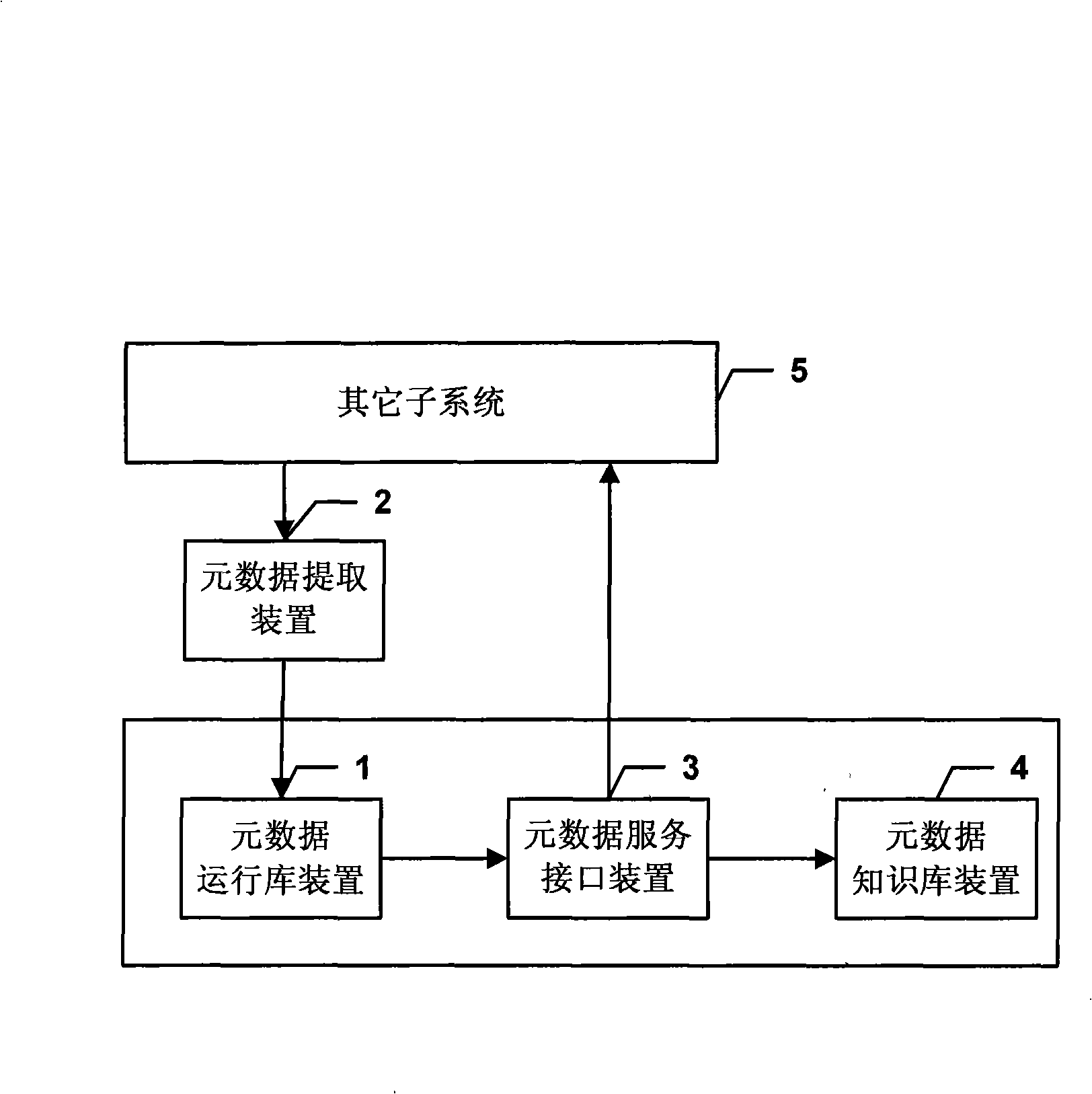
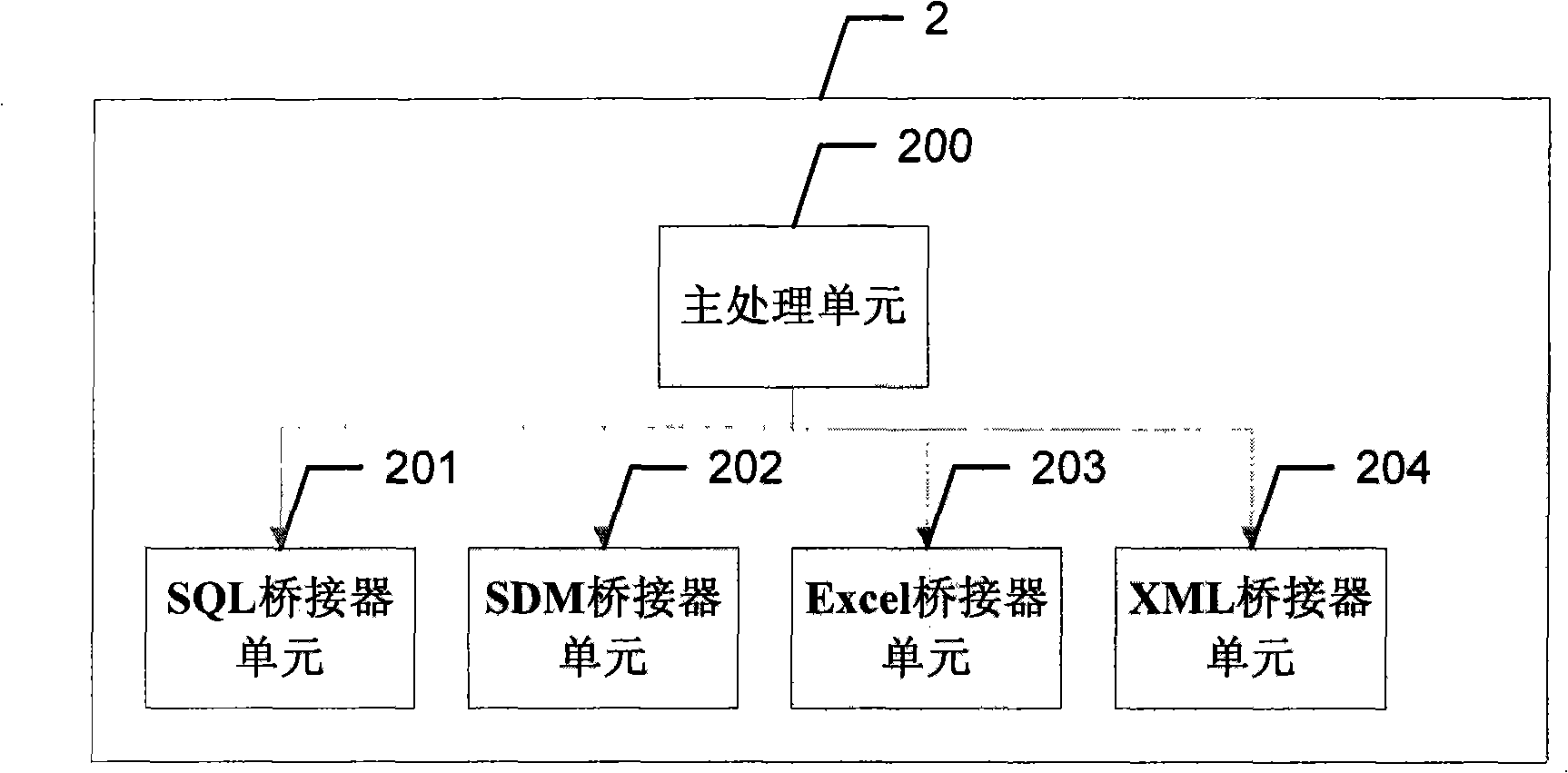
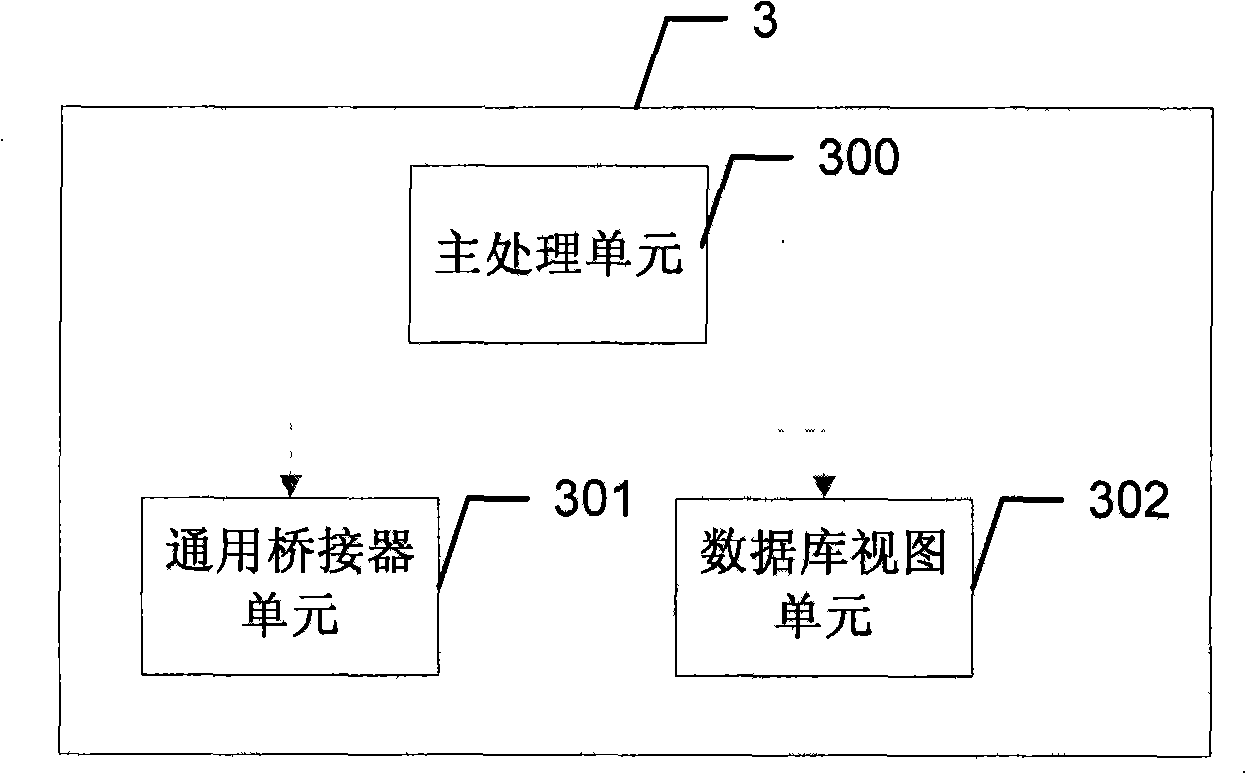
Metadata management system with bidirectional interactive characteristics and implementation method thereof
ActiveCN101515290AReduce management difficultyGuaranteed accuracySpecial data processing applicationsForm analysisMetadata management
The invention discloses a metadata management system with bidirectional interactive characteristics and an implementation method thereof. A metadata data extraction device extracts the metadata of all subsystems of an EDW to a metadata runtime library device, and a universal relational metadata model stores the metadata; a conventional bridge extracts the metadata of the relational metadata model to a metadata knowledge base device of an object metadata model to form analysis results for inquiry by a user; a database view supplies the needed metadata information to other subsystems. The invention uses a bidirectional metadata management system framework, can support the metadata extracted from other subsystems of the EDW to be stored into the metadata management system, and meanwhile, supports providing the needed metadata information to other subsystems of the EDW, solves the running management problem of the metadata and the EDW, reduces the management difficulty of the EDW, guarantees the accuracy of the metadata and causes the subsystems to efficiently communicate and stably run.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
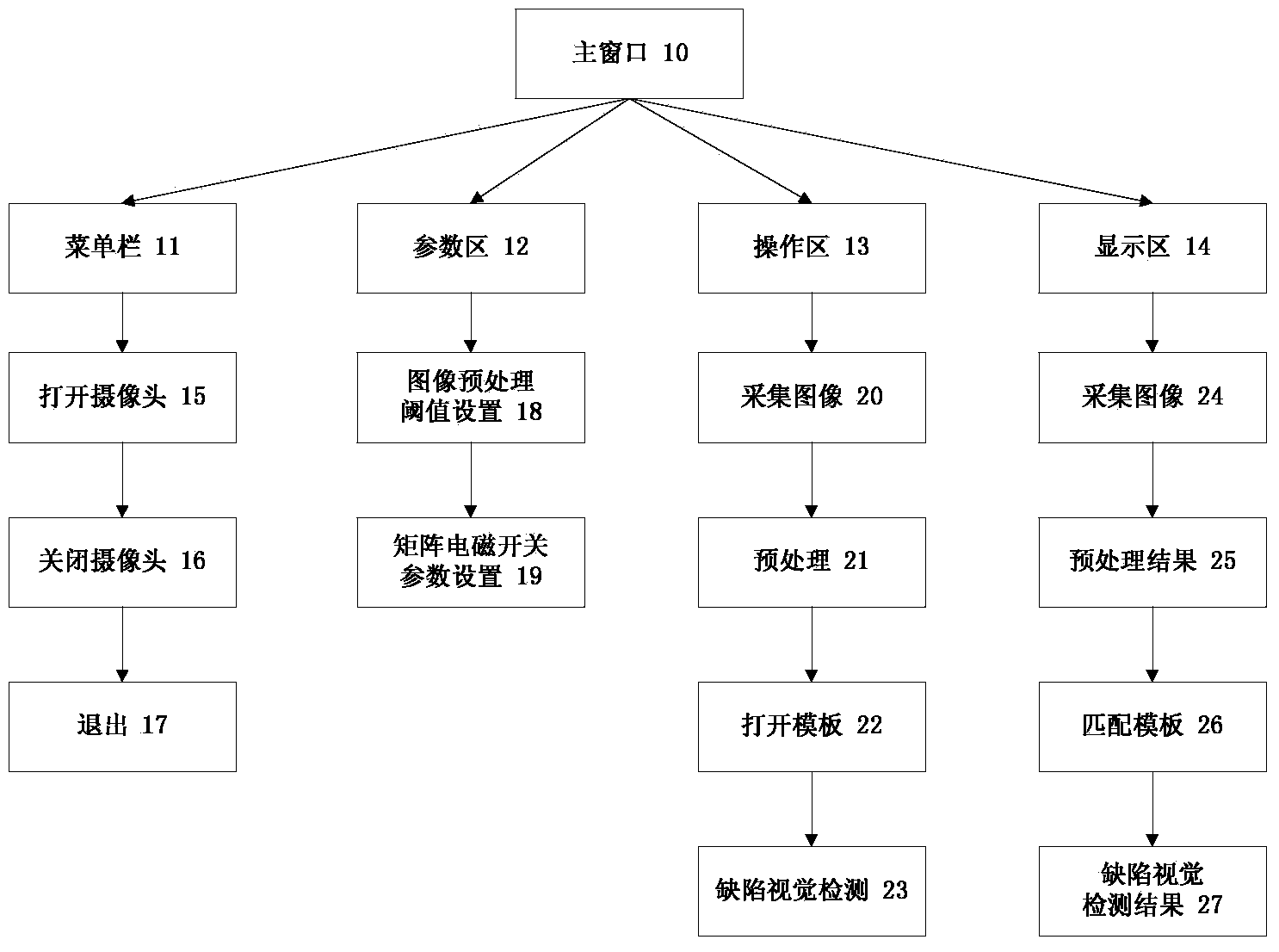
Visual detection method and device for defects of liquid crystal display screen
InactiveCN104360501AAchieve consistencyAchieve efficiencyStatic indicating devicesNon-linear opticsTemplate matchingColor image
The invention relates to a visual detection method and device for defects of a liquid crystal display screen. The method comprises the following steps: adjusting positions of buttons of button disks of a matrix electromagnetic switch according to the arrangement situation of keys of a sample to be detected, so as to enable the positions of the buttons to be fit with the arrangement of the keys of the sample to be detected; collecting a template image of each button in an off-line manner; collecting the image of the liquid crystal display screen in real time by using a CCD (charge coupled device) and a lens which are connected with an embedded processor; catching one frame of an image to be detected, and performing four steps of preprocessing operation of color image graying, binaryzation, median filtering and positioning by a projection method on the image; performing template matching calculation on the preprocessed image and the template images by a sliding template matching method, obtaining a visual detection result of the defects, and performing character recognition on the result without defects. The invention also provides a corresponding system device. The method provided by the invention has the advantages of high speed and high accuracy, overcomes the defects of low manual defect detection efficiency of the liquid crystal display screen, high cost and poor consistency, and meanwhile, realizes integration of detection and recognition.
Owner:XI AN JIAOTONG UNIV
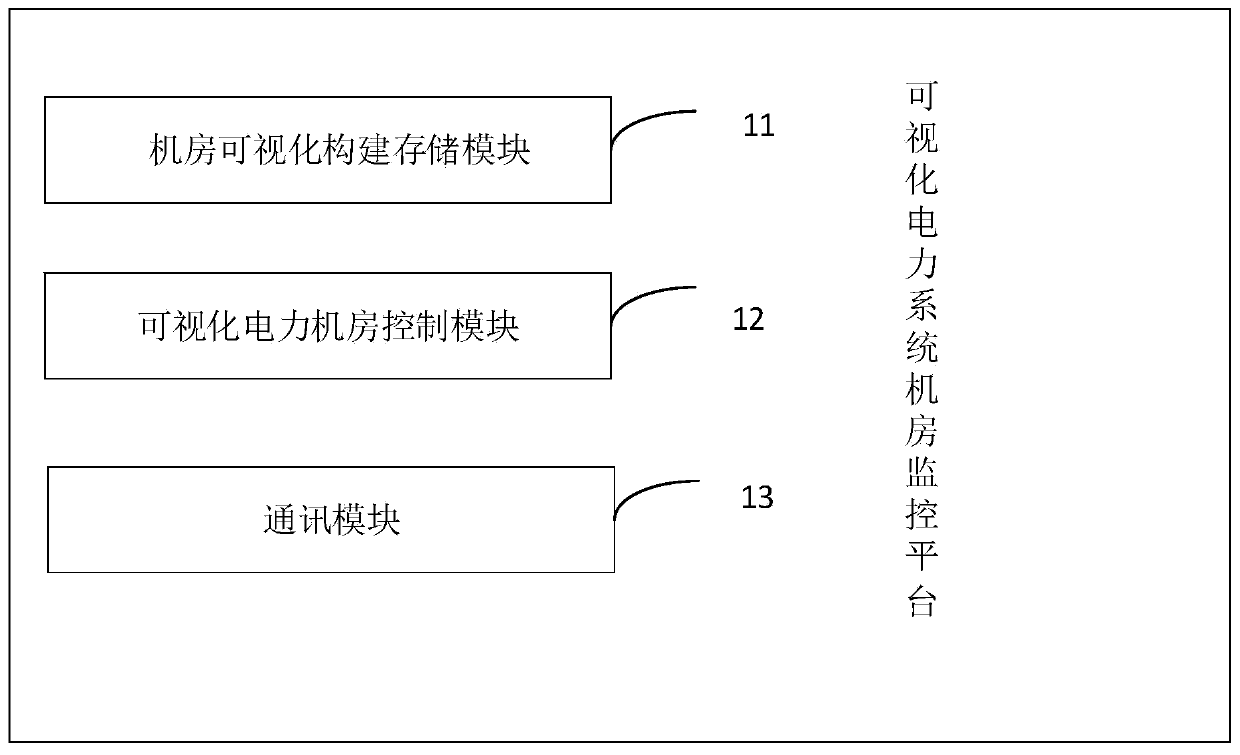
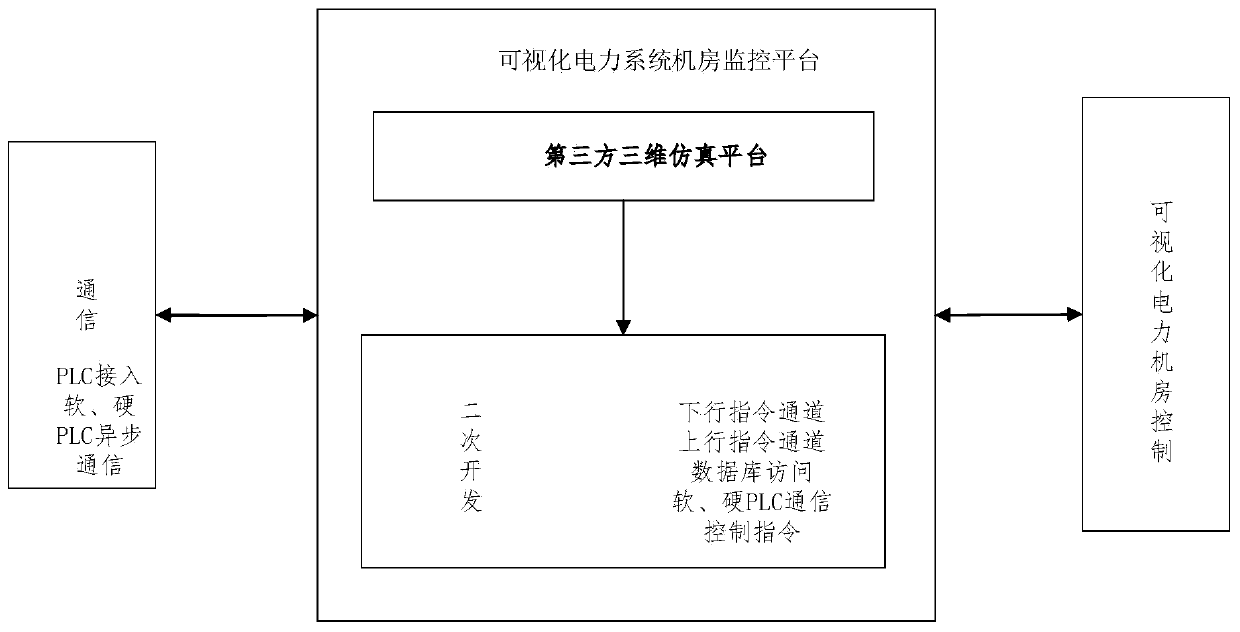
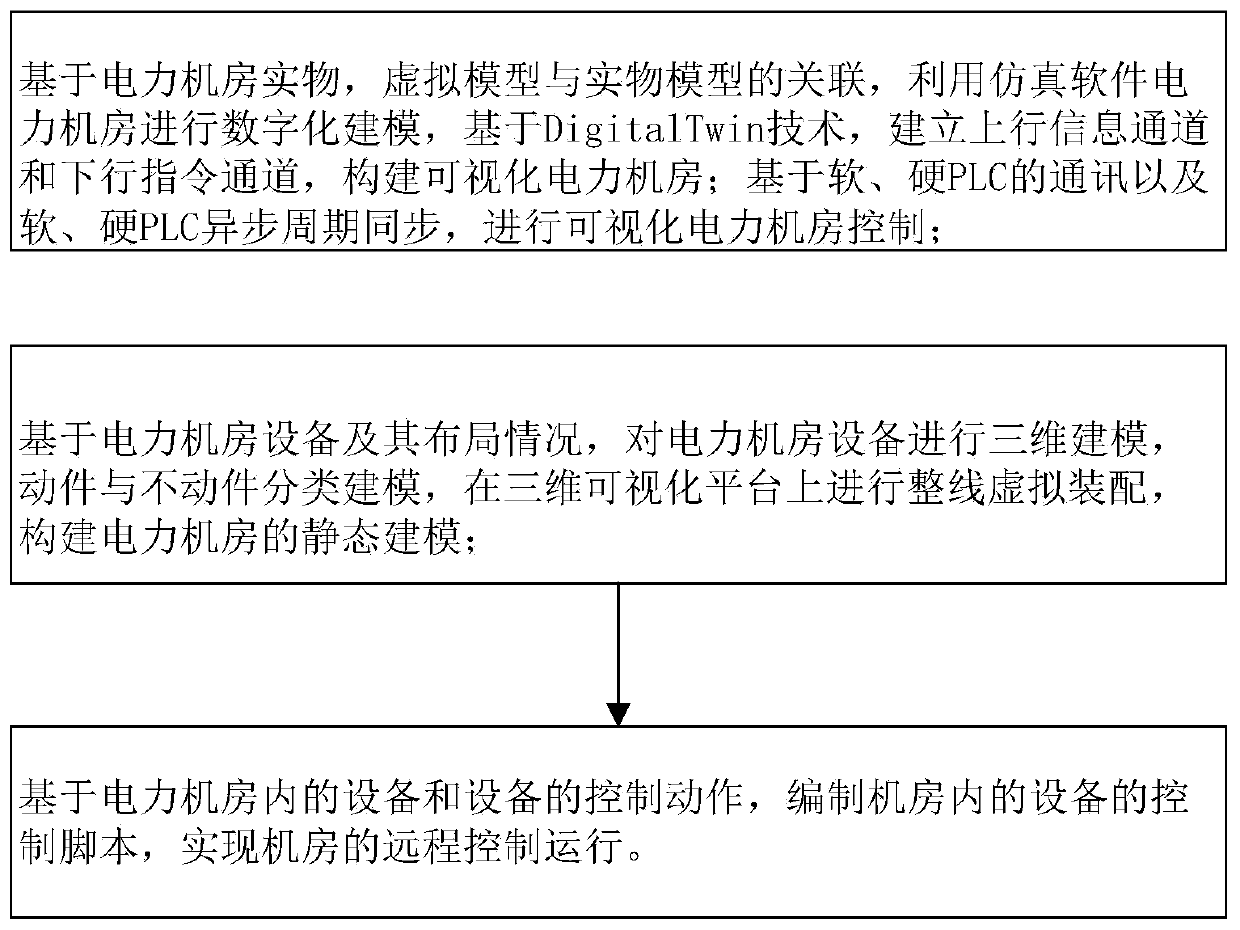
Digital twin-based visual power system machine room monitoring system and method
InactiveCN110083119AEnhance resilienceAchieving Operational Failure PredictionProgramme control in sequence/logic controllers3D modellingElectric power systemUser input
The invention relates to a digital twin-based visual power system machine room monitoring system, which is used for managing at least one machine room and is suitable for the whole main body machine room with a plurality of departments so as to control a company main body or a cross-company main body. The digital twin-based visual power system machine room monitoring system comprises a machine room visual construction storage module, wherein the machine room visual construction storage module is used for providing at least one machine room information, correlated to a plurality of machine rooms, input by a user, each machine room information is corresponding to a department main body, and the machine room information comprises a power machine room simulation platform in conversion with a machine room site according to a proportion. Three-dimensional visual data of power machine room equipment is used as a reference object, a digital twin model with high integration and fusion is built,running fault forecast of the equipment is achieved, the probability of an equipment fault is reduced, and the strain capability of machine room safety is improved.
Owner:INFORMATION & COMM BRANCH OF STATE GRID JIANGSU ELECTRIC POWER +3
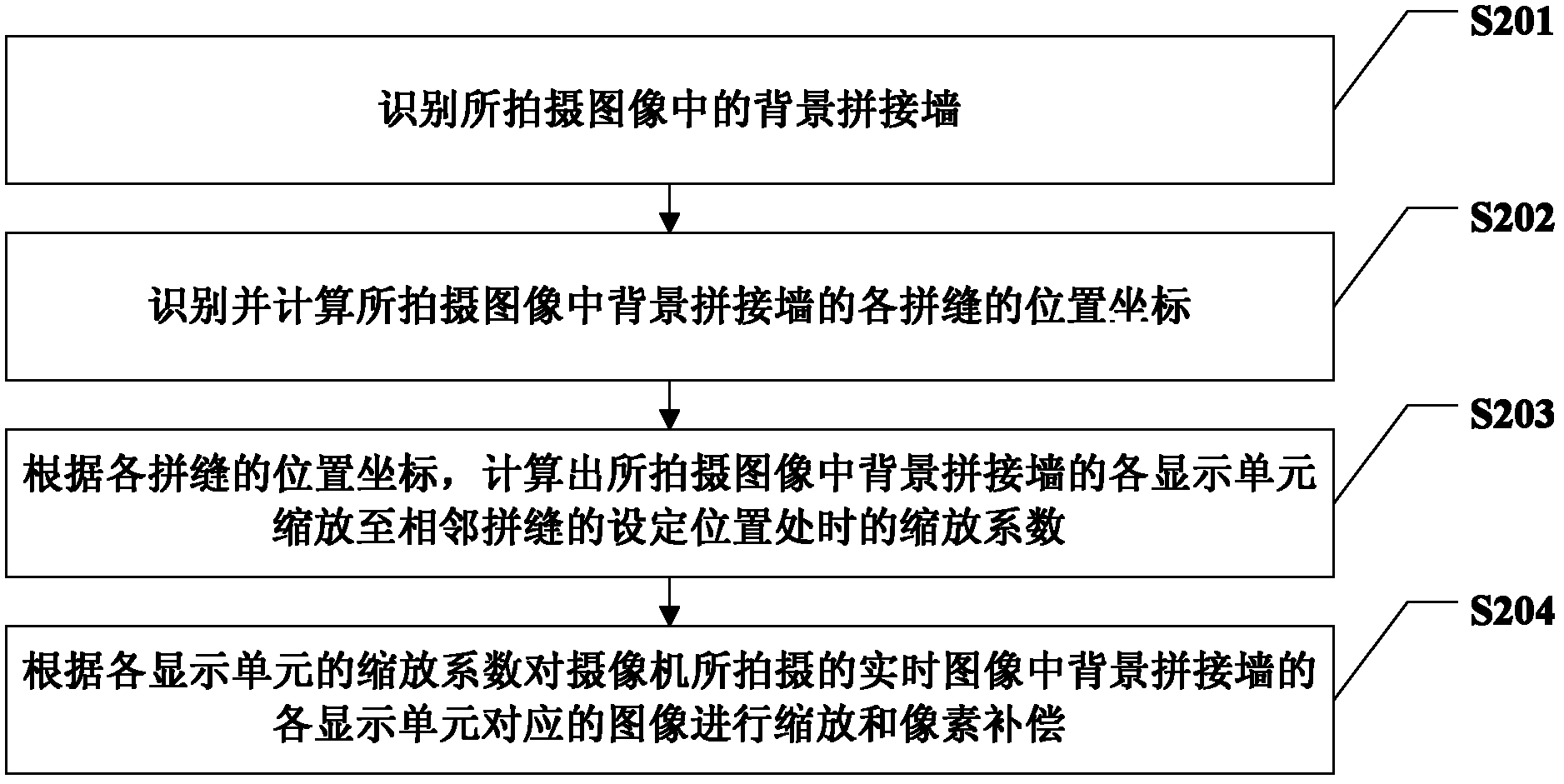
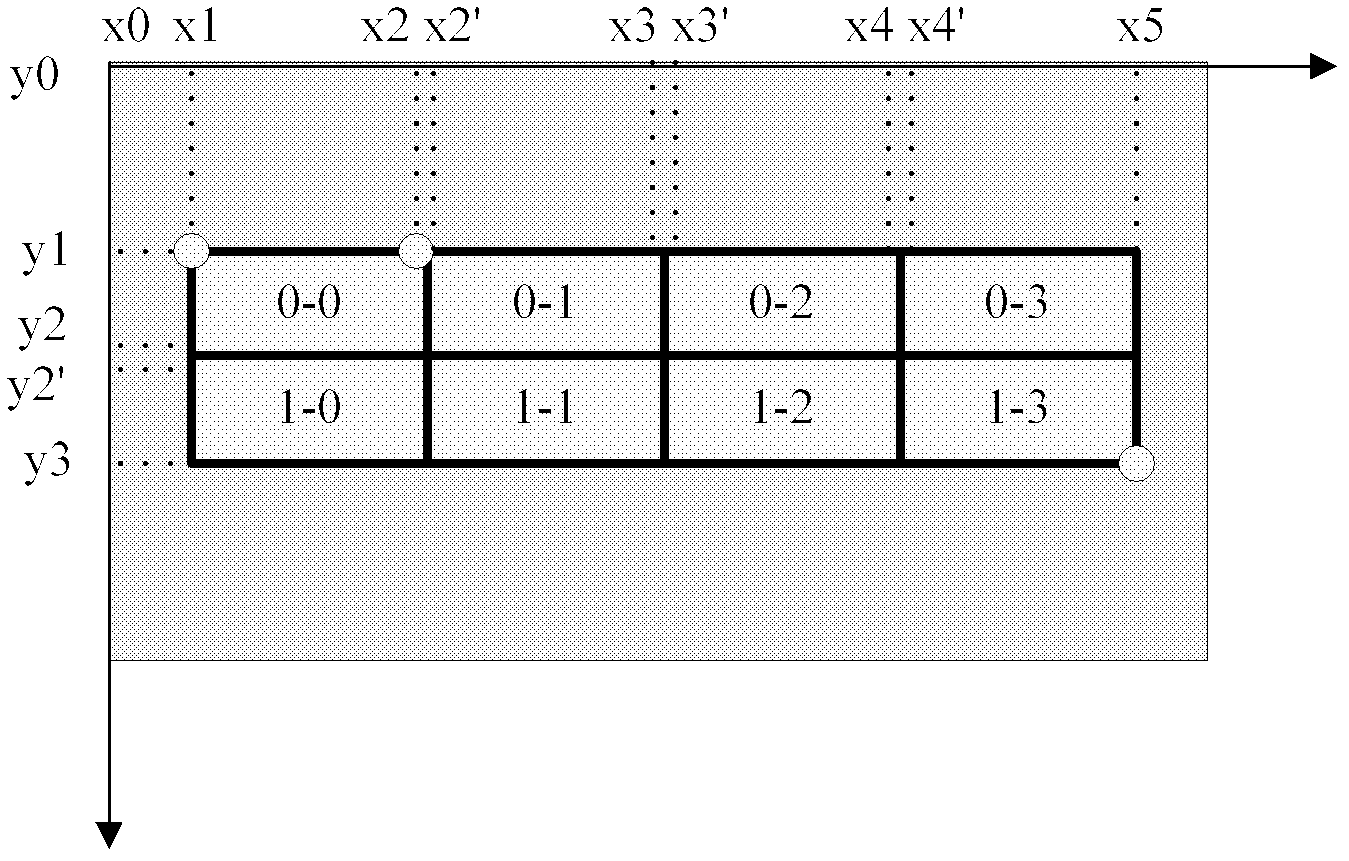
Image processing method, device and system based on background splicing wall
ActiveCN102427504AViewing angle change limitEliminate seamsTelevision system detailsCharacter and pattern recognitionVideo cameraComputer graphics (images)
The invention relates to an image processing method, a device and a system based on a background splicing wall. The method comprises the steps of recognizing the background splicing wall in photographed images; and processing the background splicing wall in the photographed images and eliminating the splicing joints of the background splicing wall in the photographed images. By adopting the technical scheme, since the display edge of the splicing wall in the images photographed by a camera is recognized and the splicing wall in the photographed images is processed to eliminate the splicing joints of the splicing wall in the photographed images, not only can the splicing joints of displayed and output pictures be effectively eliminated, but also no processing is required to be conducted to the splicing display wall, the hardware cost is not increased, the consistency of the images at different observation points can be realized and the limits caused by the change of the visual angles of the camera can be avoided.
Owner:RUGAO TIANAN ELECTRIC TECH
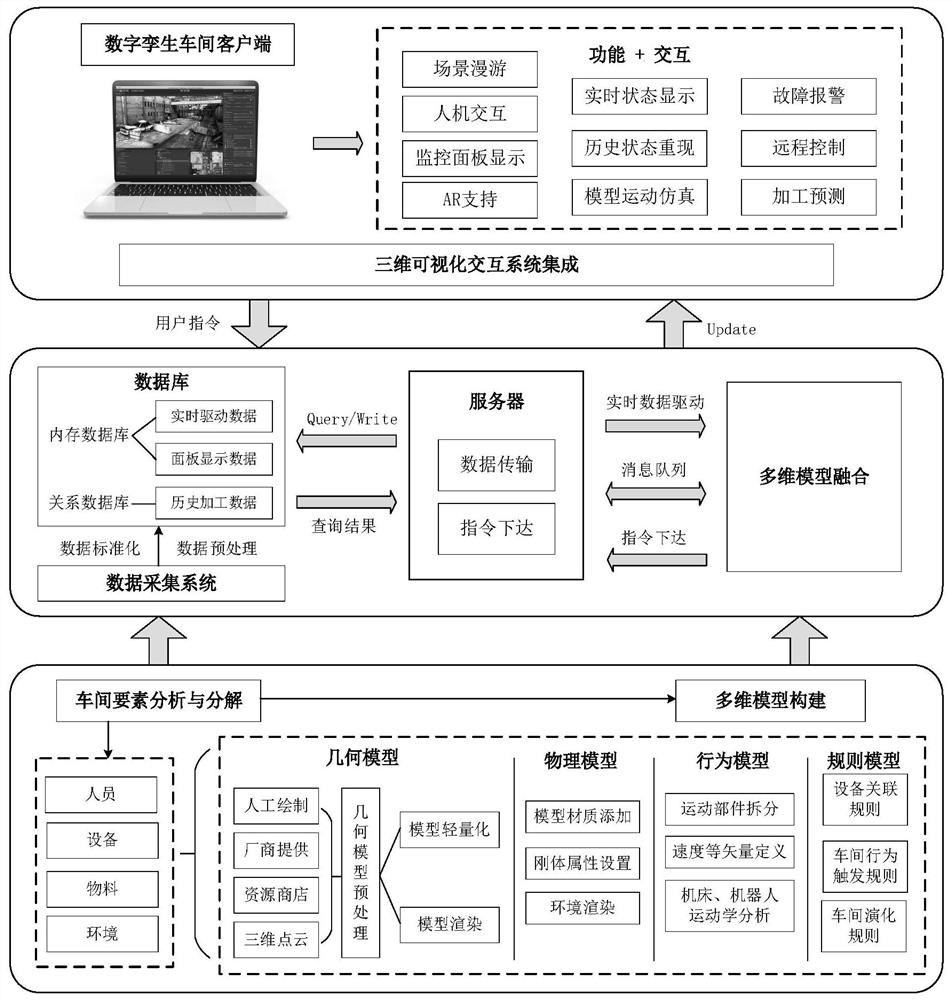
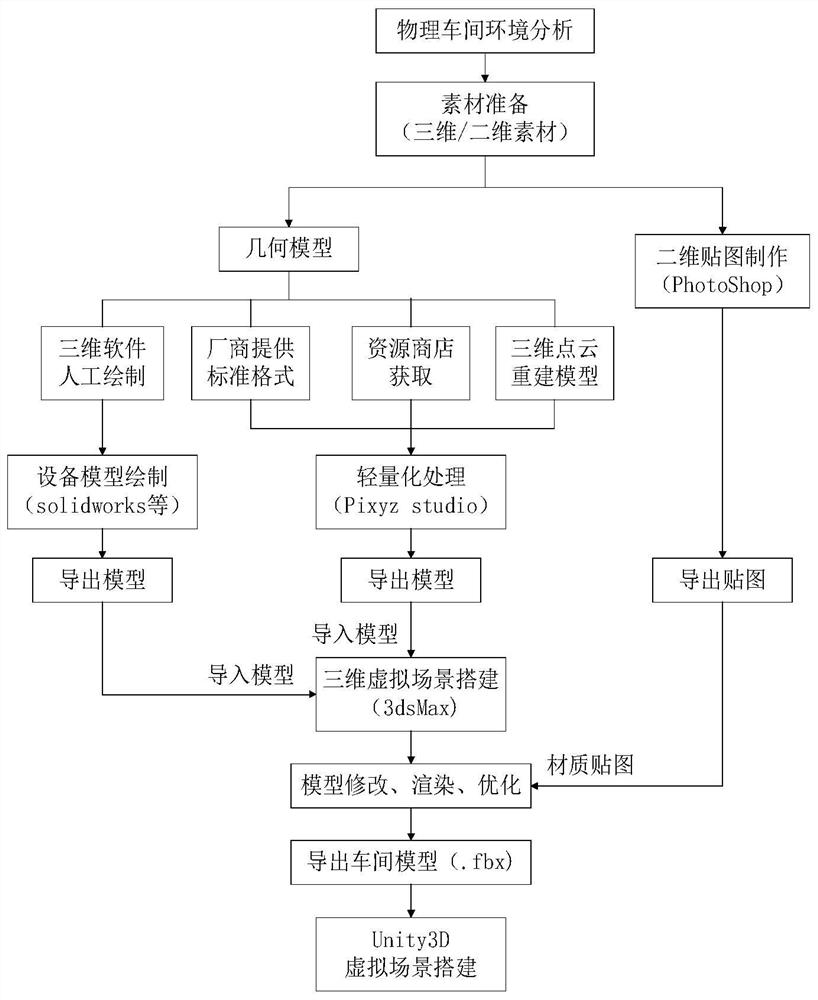
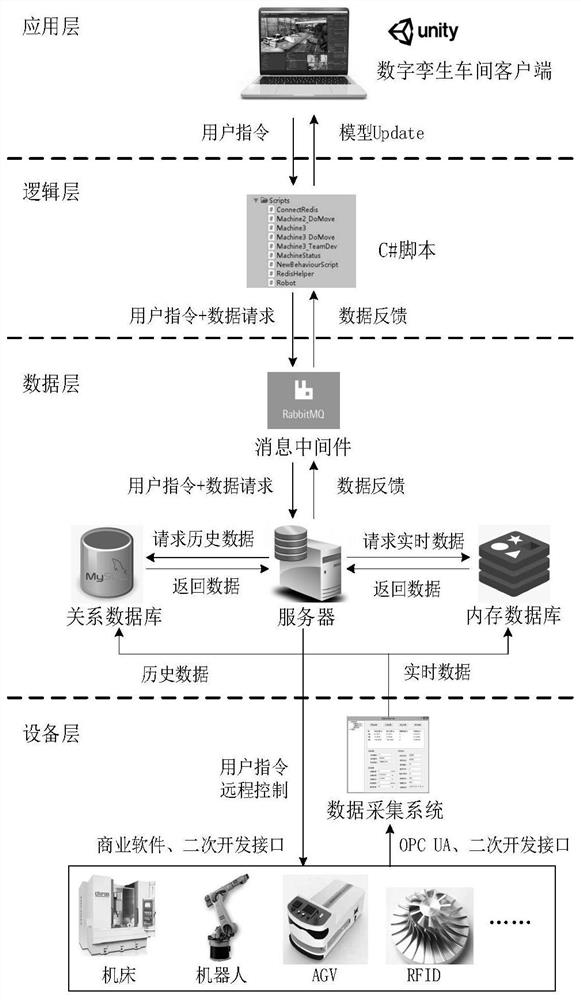
Construction method of intelligent workshop digital twin system
PendingCN112818446AImplement bidirectional mappingRealize remote controlInput/output for user-computer interactionGeometric CADSystem integrationState prediction
The invention discloses a construction method of an intelligent workshop digital twin system, and belongs to the technical field of intelligent manufacturing. The method comprises the following steps: aiming at physical workshop production elements, constructing a workshop total element multi-level twin model to obtain a digital twin workshop model; constructing a data acquisition system to acquire multi-source heterogeneous data of a physical workshop, preprocessing and standardizing the multi-source heterogeneous data, and storing the preprocessed and standardized multi-source heterogeneous data into a database; by adopting the digital twin workshop model as a client and by combination with a server, achieving interaction between the digital twin workshop client and the database so that bidirectional mapping between the digital twin workshop client and the physical workshop is realized; based on three-dimensional visualization system integration, subjecting the physical workshop model and the digital twin workshop model to deep fusion interaction to finish construction of the intelligent workshop digital twin system. Therefore, the functions of real-time state display, historical state reproduction, remote control, fault alarm, state prediction and the like are achieved, and the problems that existing digital workshop data are monotonous in presentation and poor in interaction and immersion are solved.
Owner:XI AN JIAOTONG UNIV
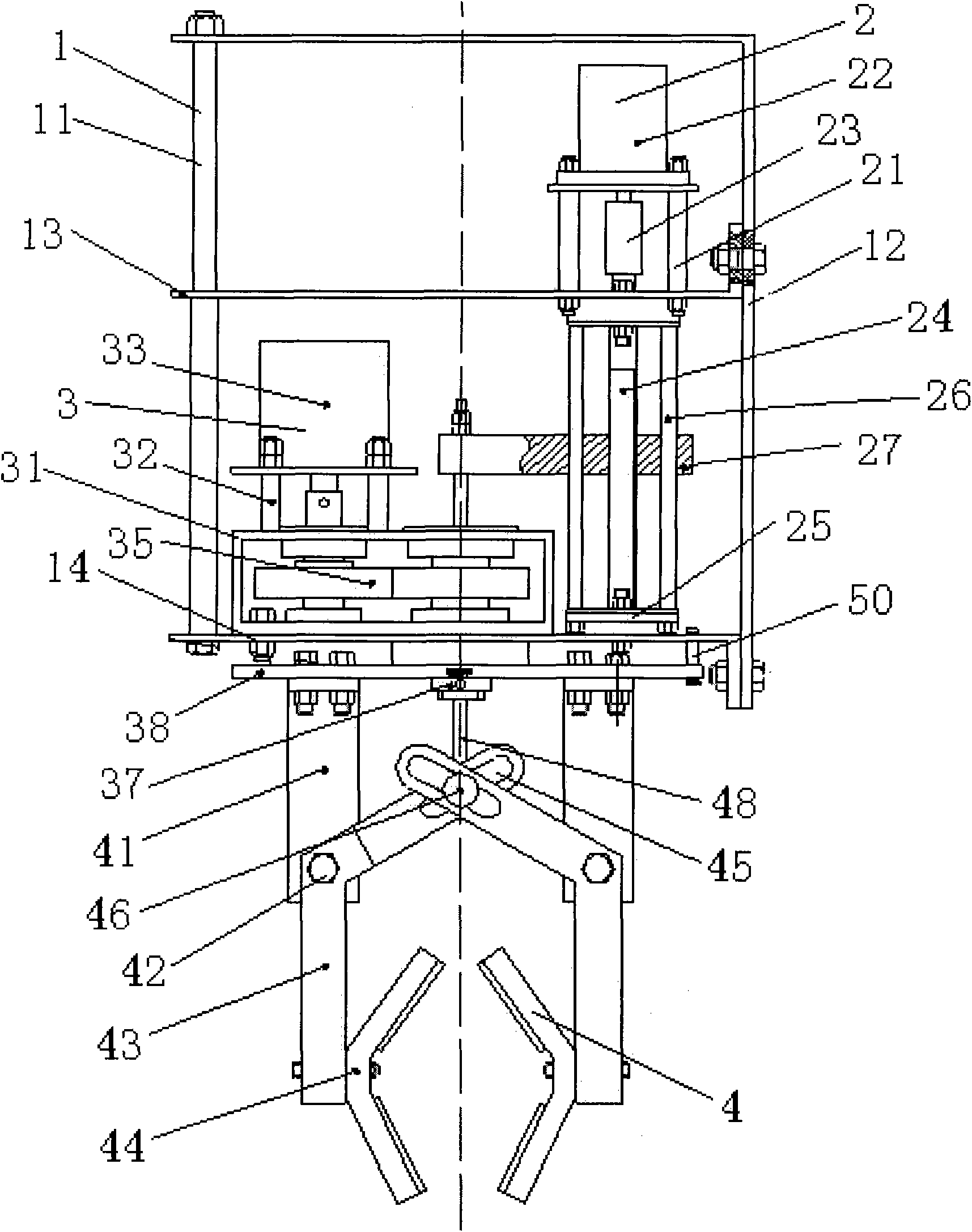
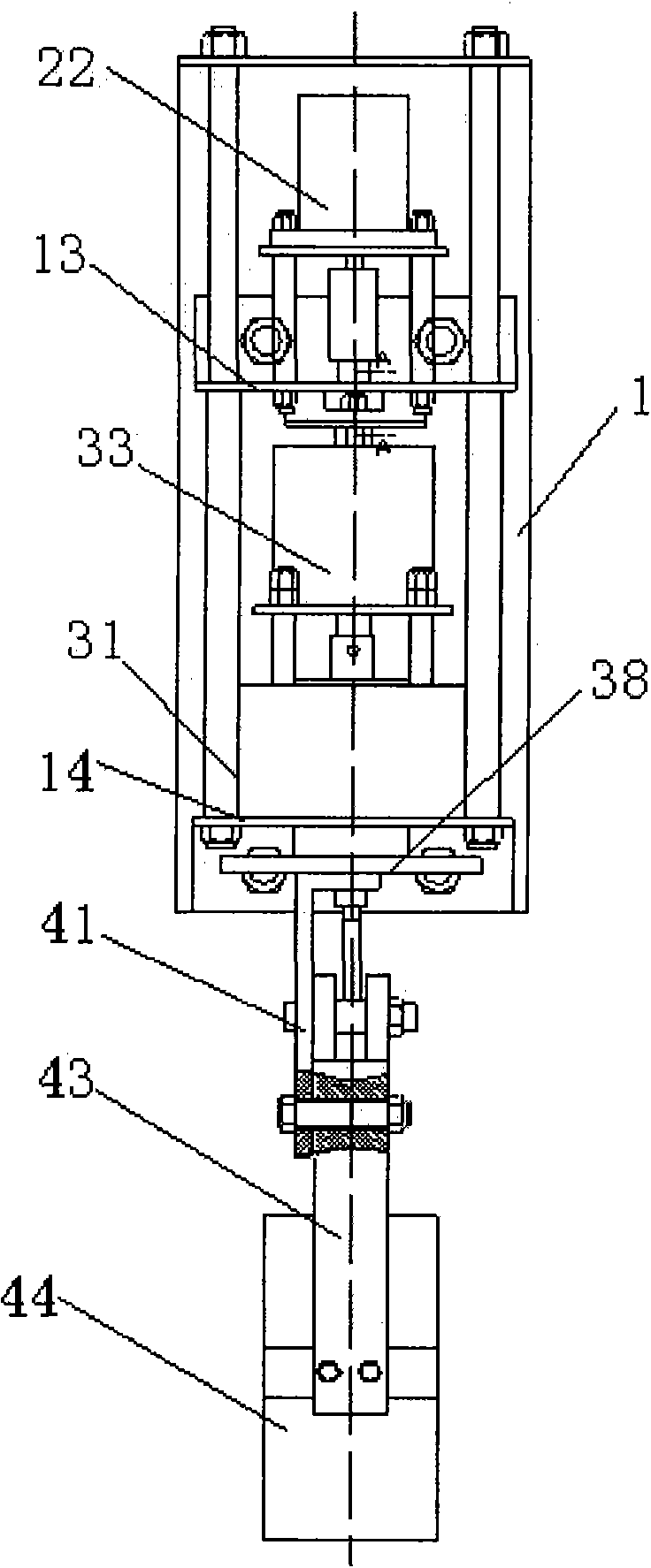
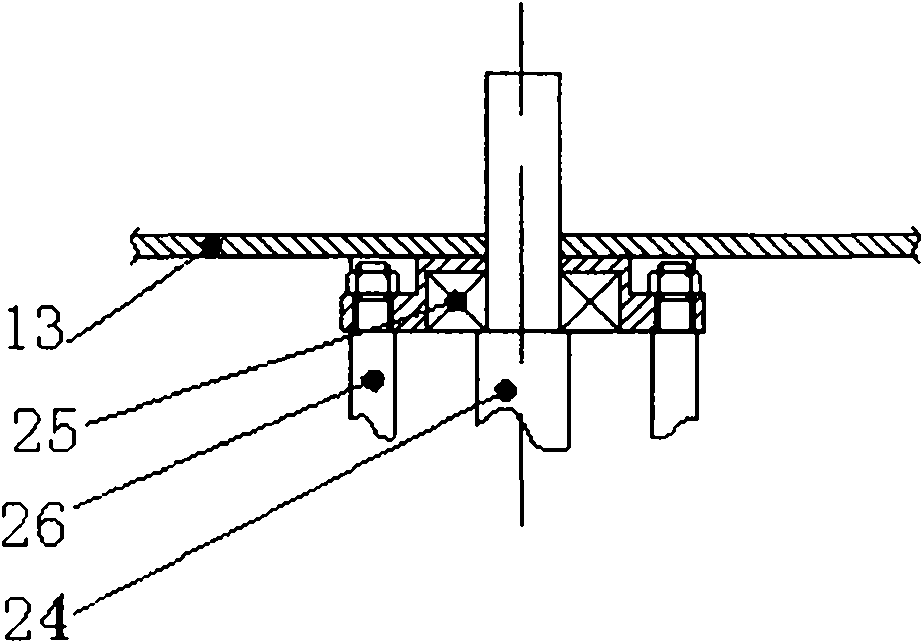
Twist-off picking paw mechanism and picking method thereof
InactiveCN101878699AAccurate and stable gripGuaranteed stabilityPicking devicesEngineeringDrive wheel
Owner:CHINA AGRI UNIV
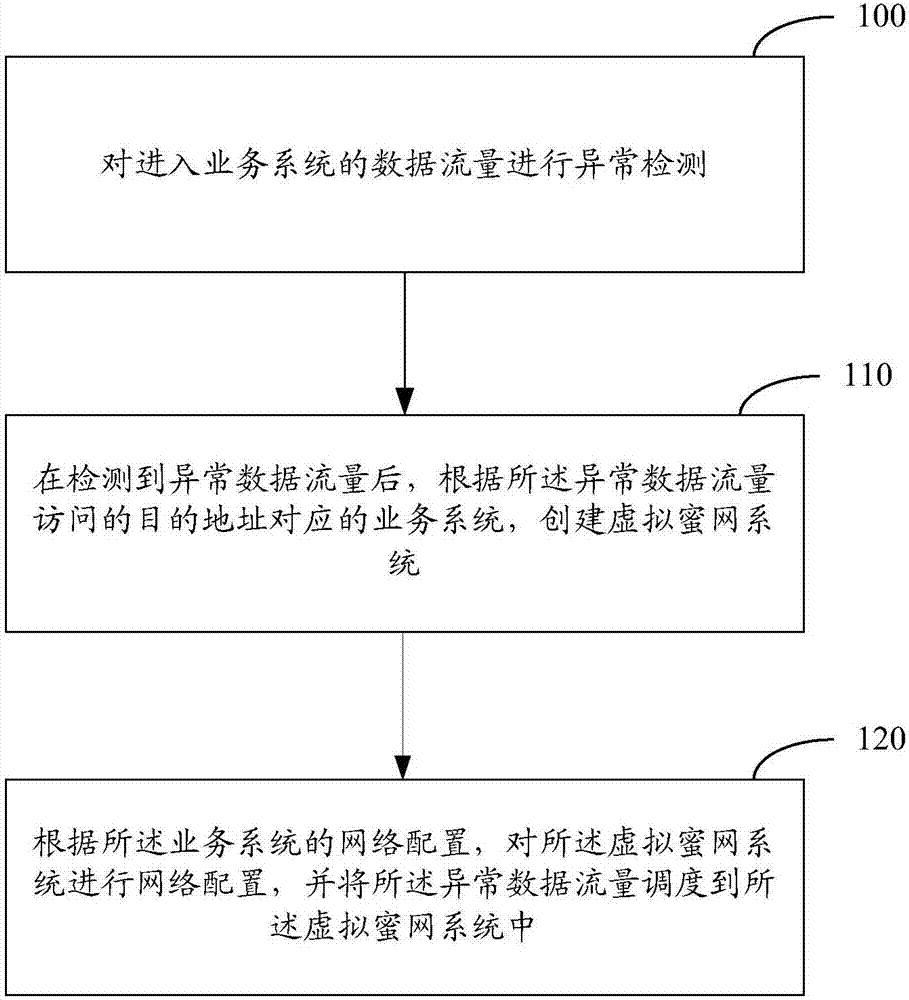
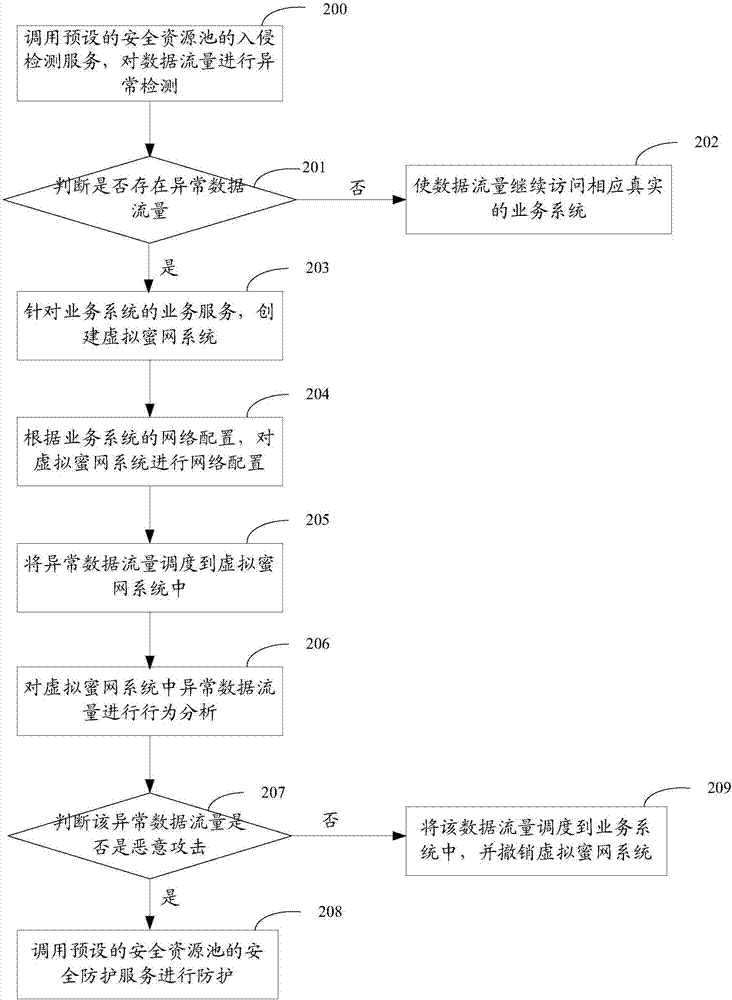
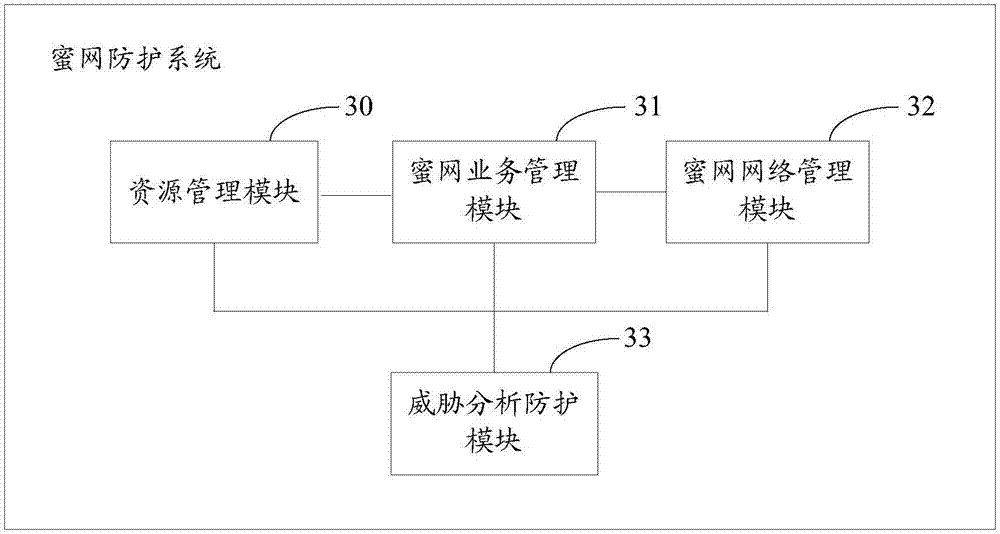
Honeynet protection method and system
ActiveCN107370756AImprove concealmentAchieve consistencyTransmissionAnomaly detectionNetwork overhead
The invention relates to the field of network security, and especially relates to a Honeynet protection method and system. The method includes the following steps: detecting whether the data traffic entering a business system is abnormal; after detecting abnormal data traffic, creating a virtual Honeynet system according to a business system corresponding to a destination address accessed by the abnormal data traffic; and carrying out network configuration on the virtual Honeynet system according to the network configuration of the business system, and scheduling the abnormal data flow to the virtual Honeynet system. The virtual Honeynet system consistent with the business service of the business system is created, and network configuration is carried out on the virtual Honeynet system. The consistency between the virtual Honeynet system and the business system in business logic and network configuration is ensured, the virtual Honeynet system is more concealed, and attack seduction and forensic analysis are more concealed and less detectable to attackers. Moreover, the deployment is relatively simple, and the method and the system can be quickly deployed to an SDN (Software Defined Network) to achieve security protection without increasing the overhead of the business network.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
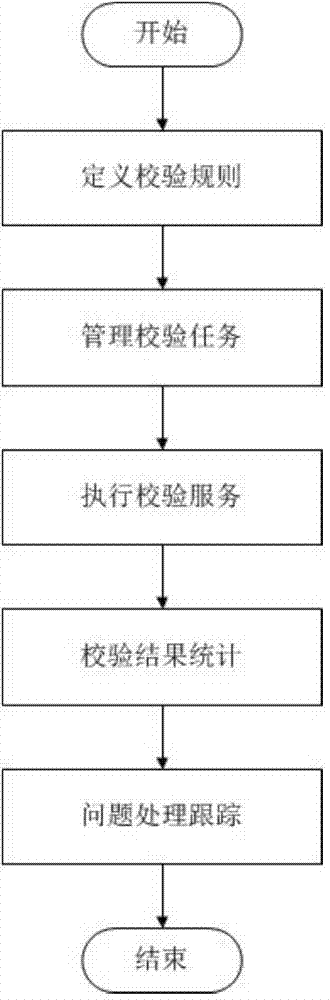
Quality management and control method for electricity transaction data warehouses and management and control system thereof
InactiveCN104766151ARealize timely releaseImplement trackingOffice automationResourcesData setData warehouse
The invention relates to a quality management and control method for electricity transaction data warehouses and a management and control system thereof. The method comprises the following steps: defining checking metadata and checking rules; setting checking tasks; performing checking service; releasing a data checking result; and handling and tracking quality problems. According to the technical scheme of the invention, the rationality, consistency, integrality and timeliness of data are judged by aiming at a data set and through flexible definition of the checking rules, statistical and historical trend analysis is made on four management and control indicators, and a problem handling and tracking feedback mechanism is designed to facilitate quality control measure formulation by management personnel. After implementation, the system, as an important part of an electricity market data warehouse, provides a data quality guarantee for advanced analysis and mining application of the market.
Owner:STATE GRID CORP OF CHINA +4
Wafer packaging construction with array connecting pad and method of manufacturing the same
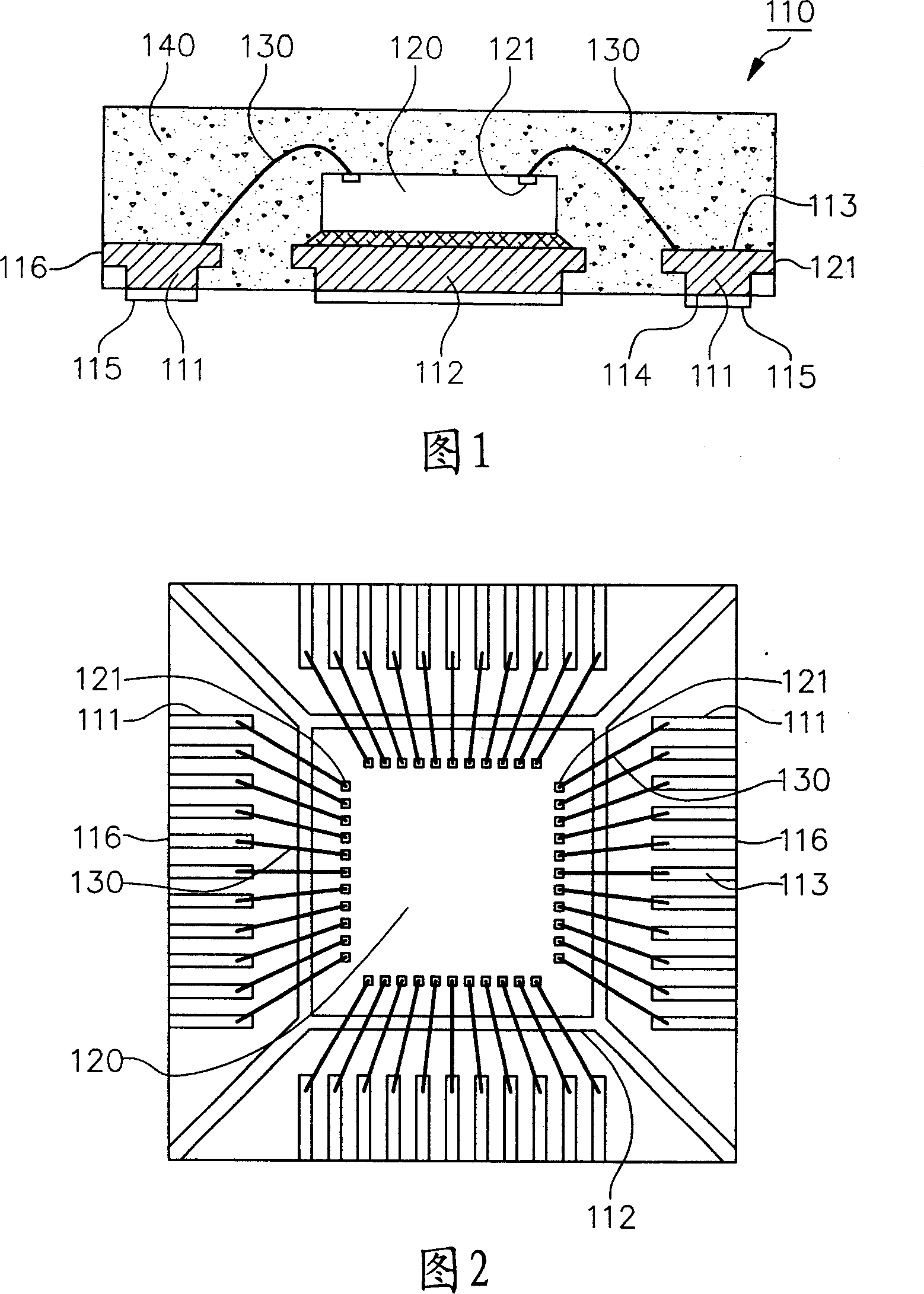
InactiveCN101131980AHigh densityPrevent rustSemiconductor/solid-state device detailsSolid-state devicesHigh densityEngineering
The present invention relates to a wafer packaging with array pads and its processing method. The wafer packaging mainly includes even numbers of wire-bonded pads, a wafer, even numbers of welding line and a sealing colloid. An upper and a lower combination layers are separately formed on cores of the wire-bonded pads, in which materials of the cores include copper. These welding lines electric connect the wafer with the upper combination layer of the wire-bonded pads. The sealing colloid seals these welding lines, cores and upper combination layers, in which only the lower combination layers are exposed out of the sealing colloid. The present invention can solve the former rusting problem of exposed cutting surface of pins in non-external-pin wafer packaging of conductor frame substrate, and has array pads which can achieve high density of wafer packaging. The processing method of the present invention keeps using a rigid conductive mold in packaging process to carry steps of electroforming, wafer attaching, wire bonding and packaging to achieve coherence of the packaging process.
Owner:CHIPMOS TECH INC
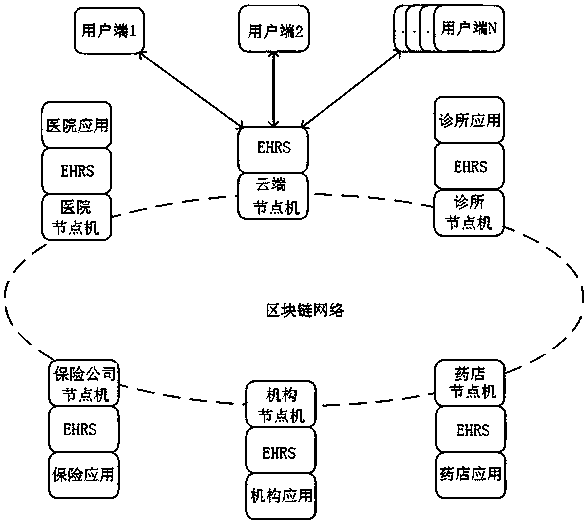
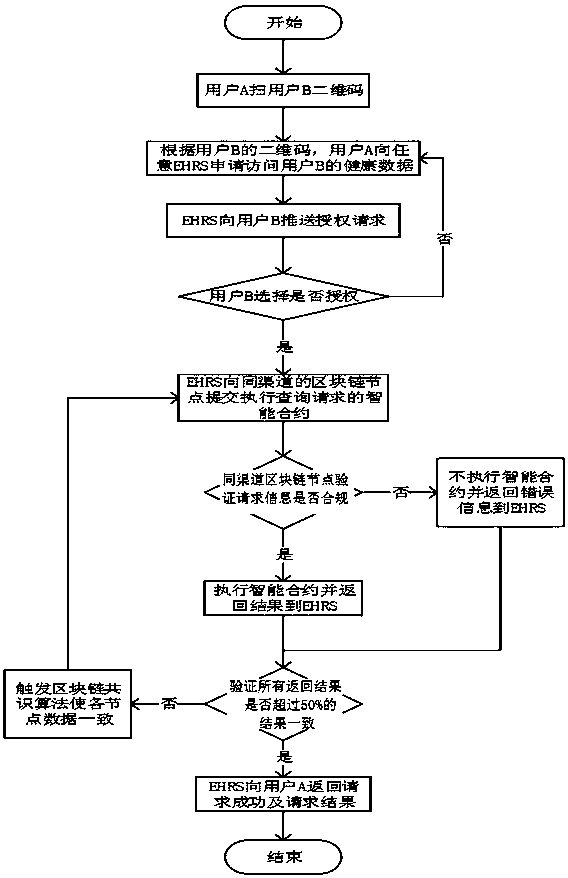
Electronic health record management system and method
InactiveCN108460290AGuaranteed originalityKeep storage safeDigital data protectionPayment protocolsBlockchainManagement system
The present invention relates to an electronic health record management system and method, which solves the technical problem of low confidentiality. The method is characterized in that: by taking a blockchain as a storage underlying layer of a health record system, de-intermediated trust of all nodes is achieved; all data cannot be tampered with, and traceability and consistency of all the data are achieved; and open transparency of non-sensitive data and confidentiality of sensitive and private data are achieved. The technical scheme of the present invention has the following beneficial effects that: the originality and authenticity of health data and operational data are ensured, and the health data and the operational data cannot be tampered with; the storage security of the health data and of the operational data of the health data is ensured; it is ensured that personal privacy and sensitive information cannot be leaked; and the technical scheme for fast sharing of health data and operational data better solve the problem and can be used in medical electronic applications.
Owner:江苏省卫生统计信息中心
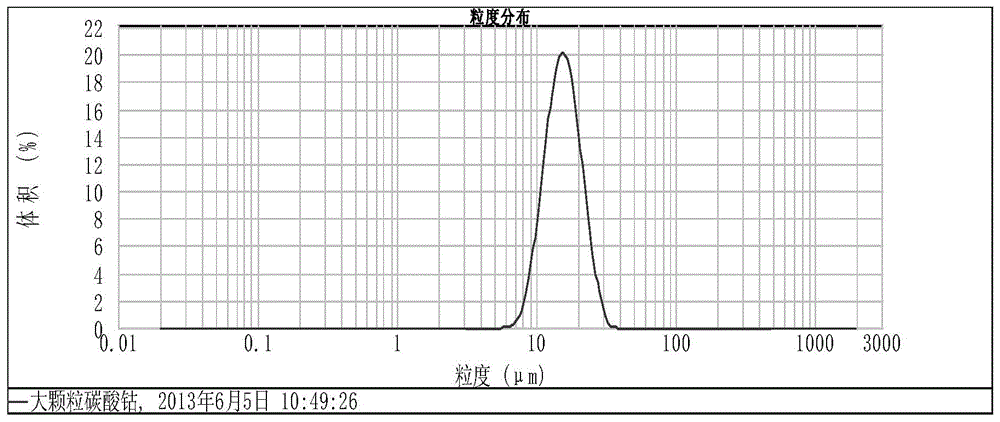
Method for continuously producing large-particle spherical cobalt carbonate
The invention relates to a method for continuously producing large-particle spherical cobalt carbonate. The method comprises the following steps: manufacturing a turbid liquid containing small-particle-size cobalt carbonate seed crystal and manufacturing a turbid liquid containing large-particle spherical cobalt carbonate, stirring the turbid liquid containing the small-particle-size cobalt carbonate seed crystal and the turbid liquid containing large-particle-size cobalt carbonate to form a mixed liquid, carrying out solid-liquid separation, washing and filter pressing to obtain a filter cake as a large-particle cobalt carbonate filter cake, drying the filter cake, and repeatedly operating to obtain the large-particle cobalt carbonate powder. According to the method disclosed by the invention, the small-particle-size cobalt carbonate seed crystal is adopted to control the particle size of the large-particle cobalt carbonate in reaction mother liquor, so that the degree of sphericity of cobalt carbonate produced by continuous production can be ensured to be high, the particle size can be stably controlled within the range of 15+ / -0.5 microns, and the consistency and the stability of the particle size of the large-particle spherical cobalt carbonate through large-scale continuous production can be realized; the method is simple in process, easy to operate and low in cost, and can provide the high-quality raw material for producing high-end lithium cobalt oxide; the carbonate is used as a precipitant, so that the environment can be optimized; the production efficiency can be improved, and the wide application prospect can be achieved.
Owner:CHINA ELECTRONIC TECH GRP CORP NO 18 RES INST
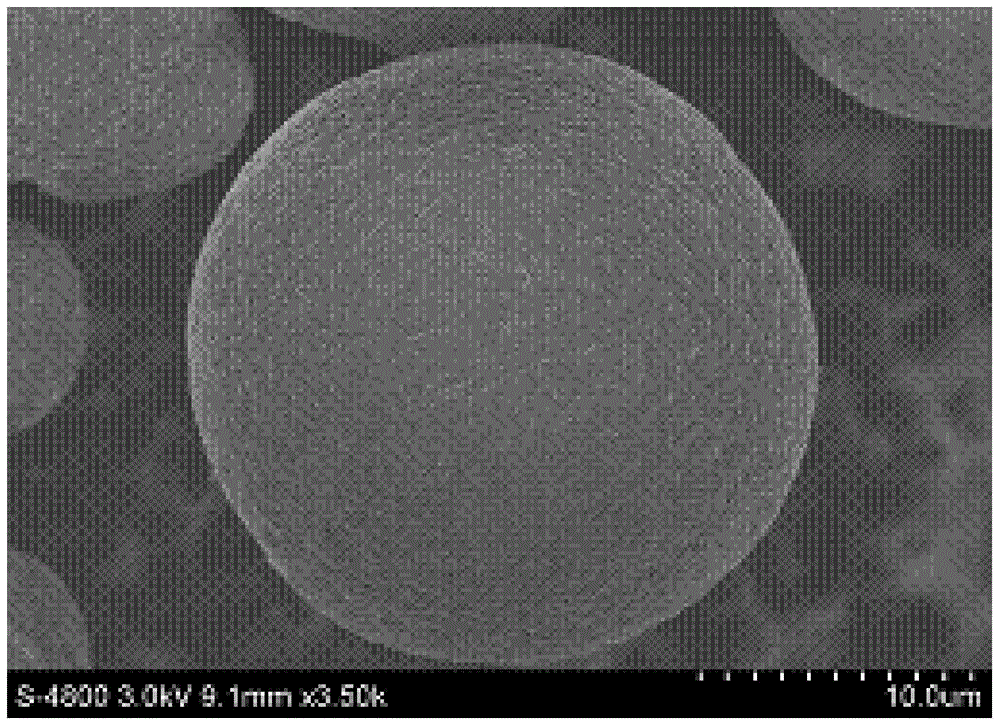
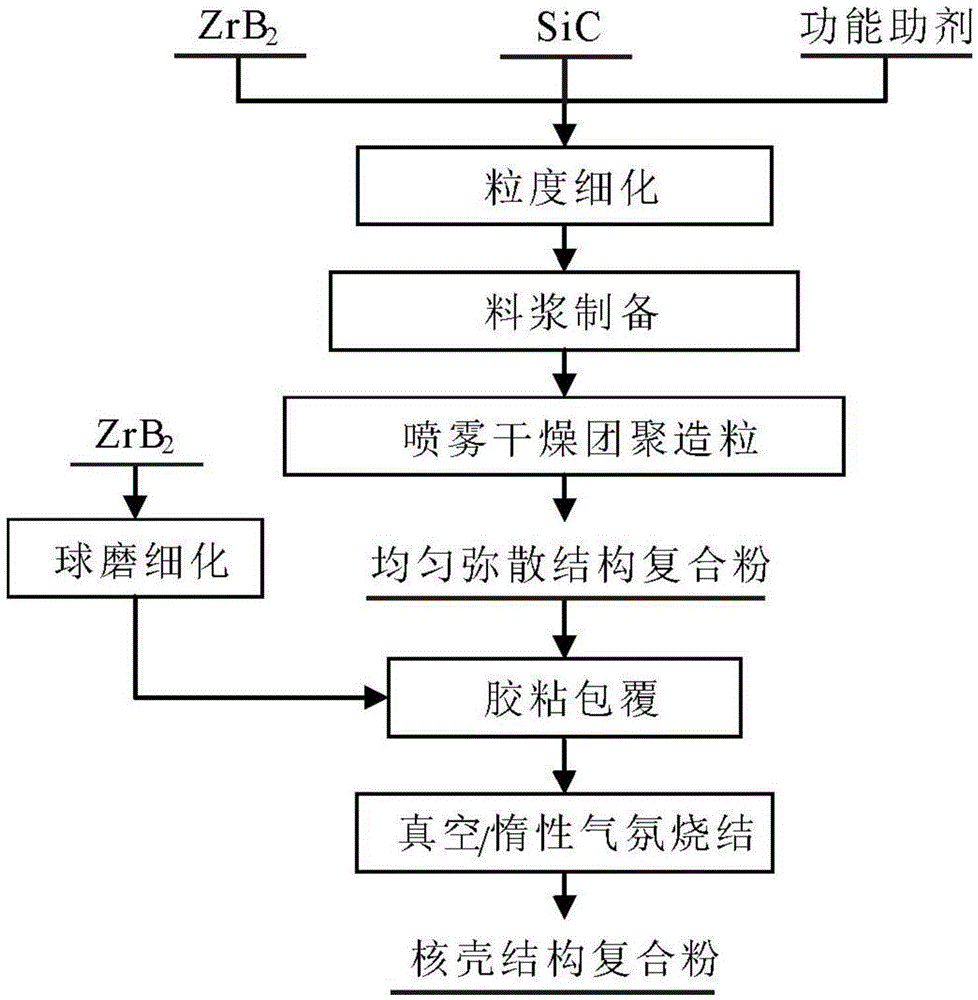
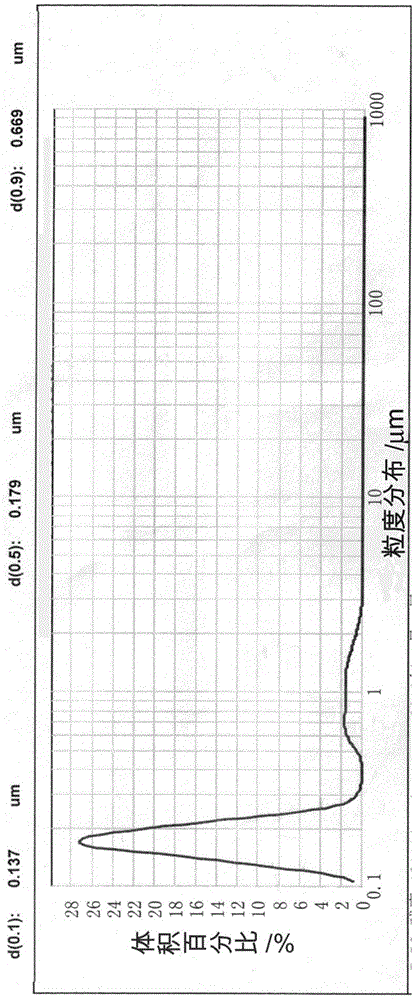
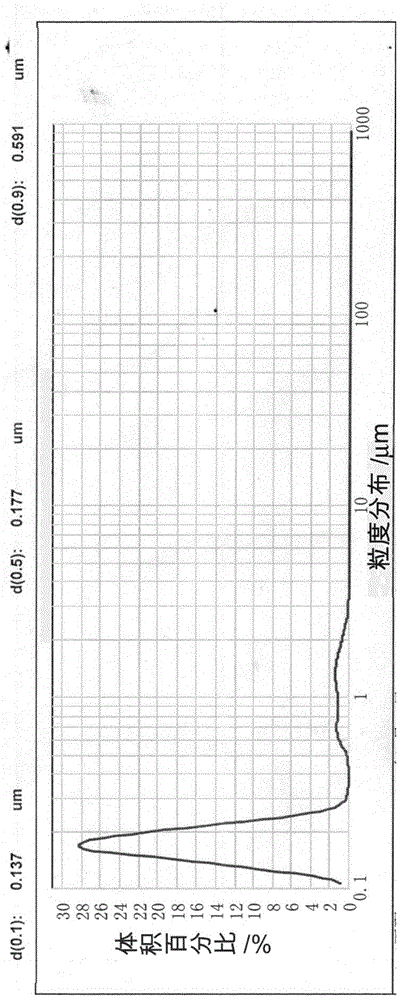
Core-shell-structure ZrB2-SiC/Si composite powder and preparation method thereof
ActiveCN104557050AAvoid decomposition and burningAchieve consistencyCoatingsDecompositionPlasma sprayed
Owner:BEIJING GENERAL RES INST OF MINING & METALLURGY +1
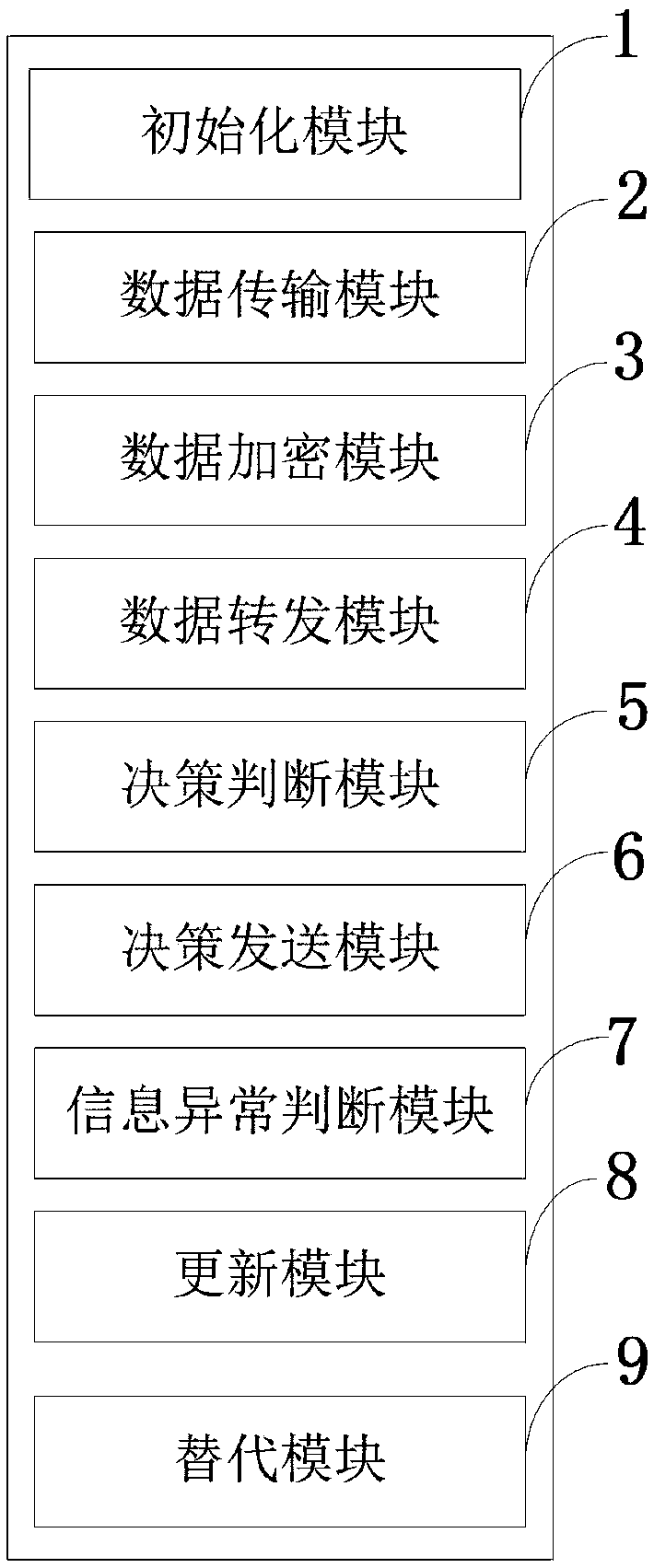
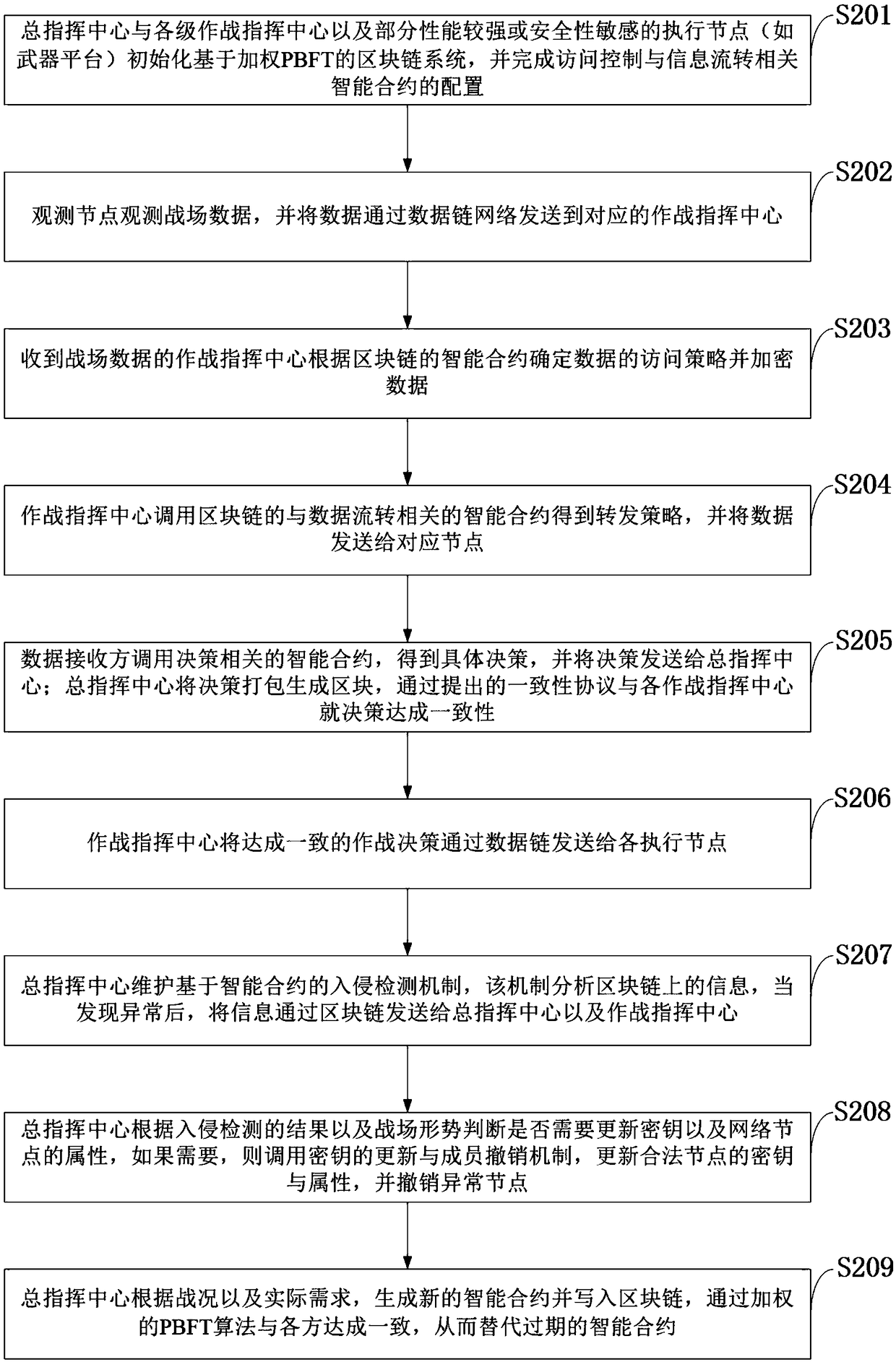
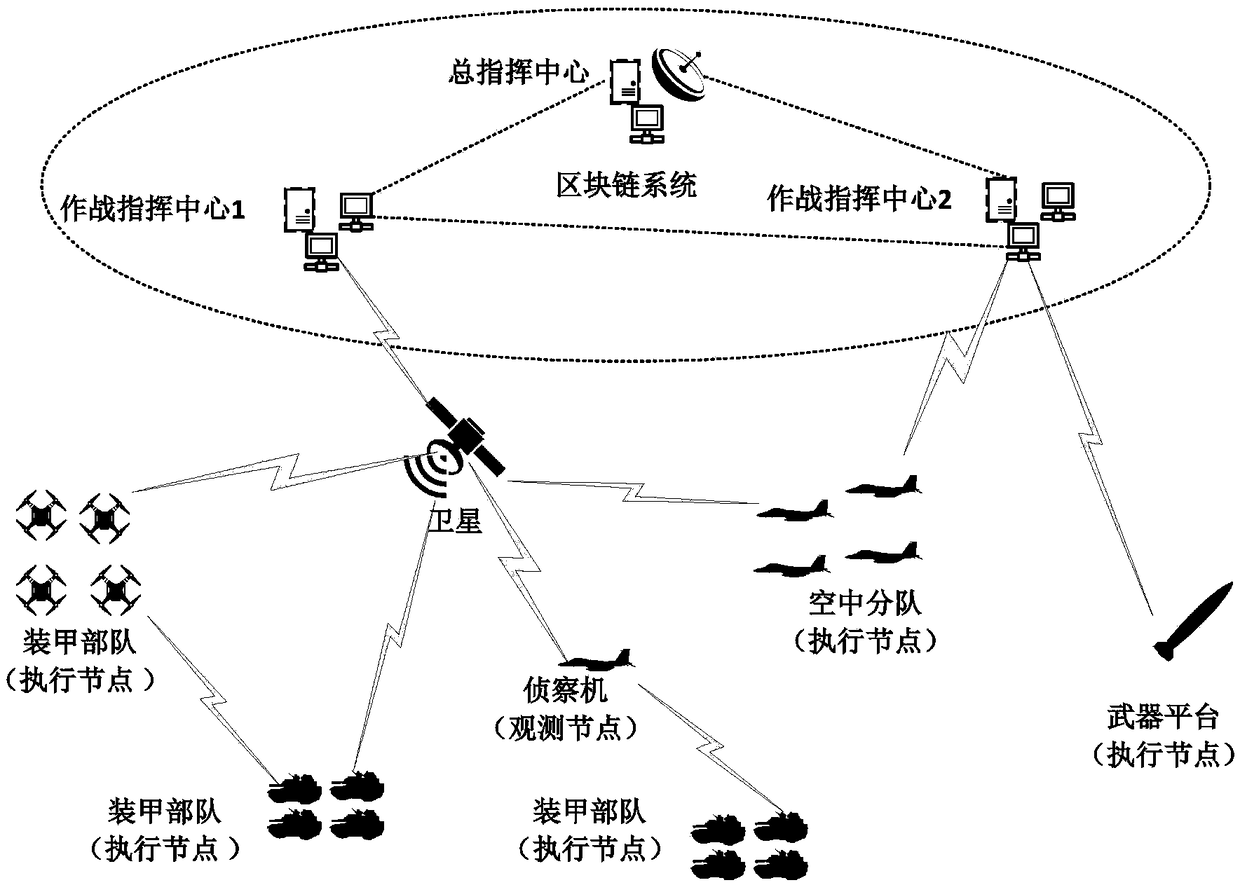
Data chain information circulation control system based on block chain as well as method
ActiveCN109450856AGuaranteed credibilityIncrease flexibilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesTamper resistanceControl system
The invention belongs to the technical field of transmission control procedures such as a data chain stage control procedure and discloses a data chain information circulation control system based ona block chain as well as a method. The system disclosed by the invention is based on a weighted PBFT algorithm, can distribute weights specific to different entity characters of a data chain, fully considers significance of different characters of the data chain as well as influence of the different characters on consistency and has high flexibility; based on an access control scheme of the blockchain, consistency and tampering resistance of the block chain guarantee credibility of a contract self, a smart contract can be automatically executed, characteristics of the block chain are combined, and credibility of an access strategy output by the contract is guaranteed, so that data security is effectively guaranteed; and attribute encryption is combined with symmetrical encryption, data isencrypted by using a symmetrical encryption scheme, and a symmetric key is encrypted by using an attribute encryption algorithm, so that efficient encryption is guaranteed, and flexible access control is supported.
Owner:XIDIAN UNIV
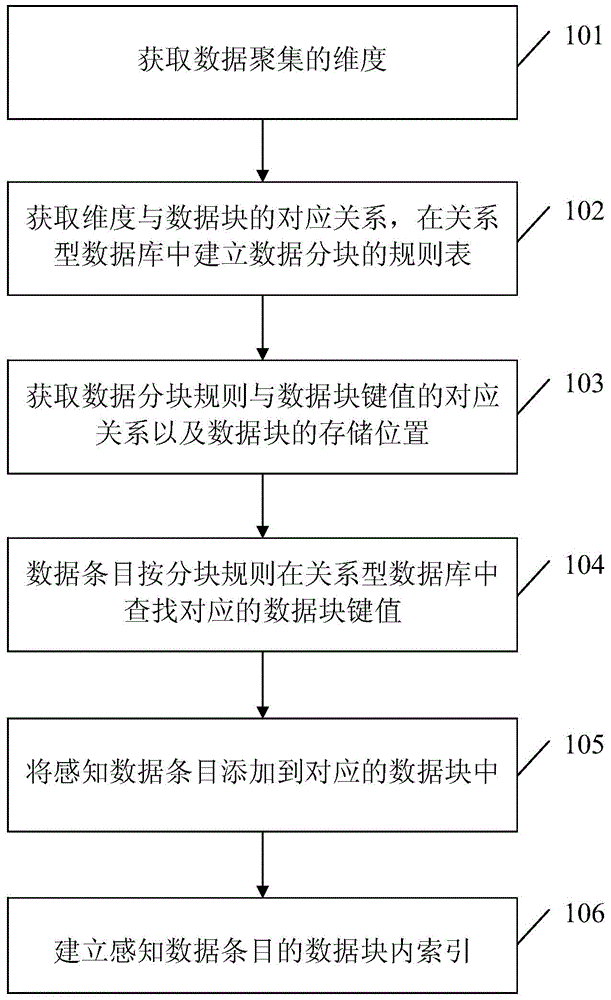
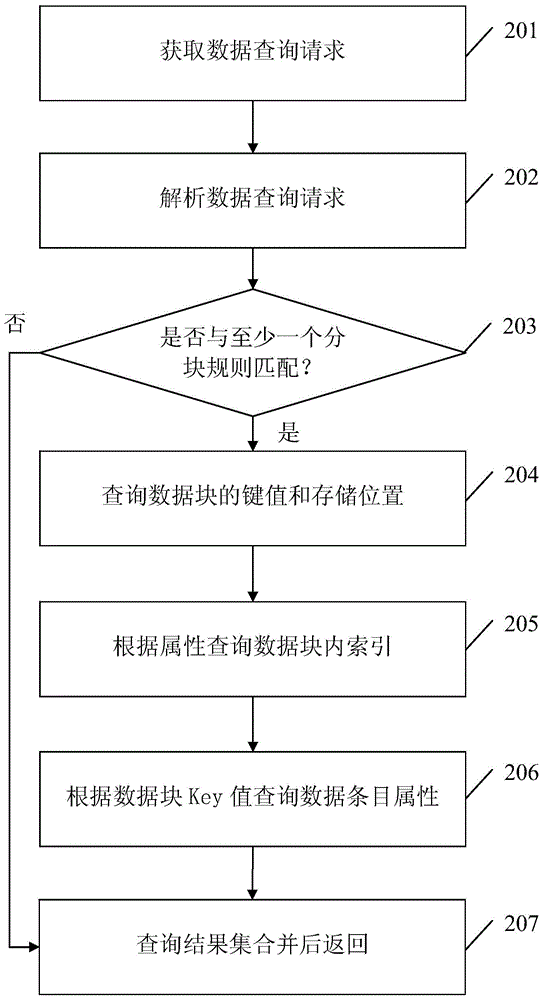
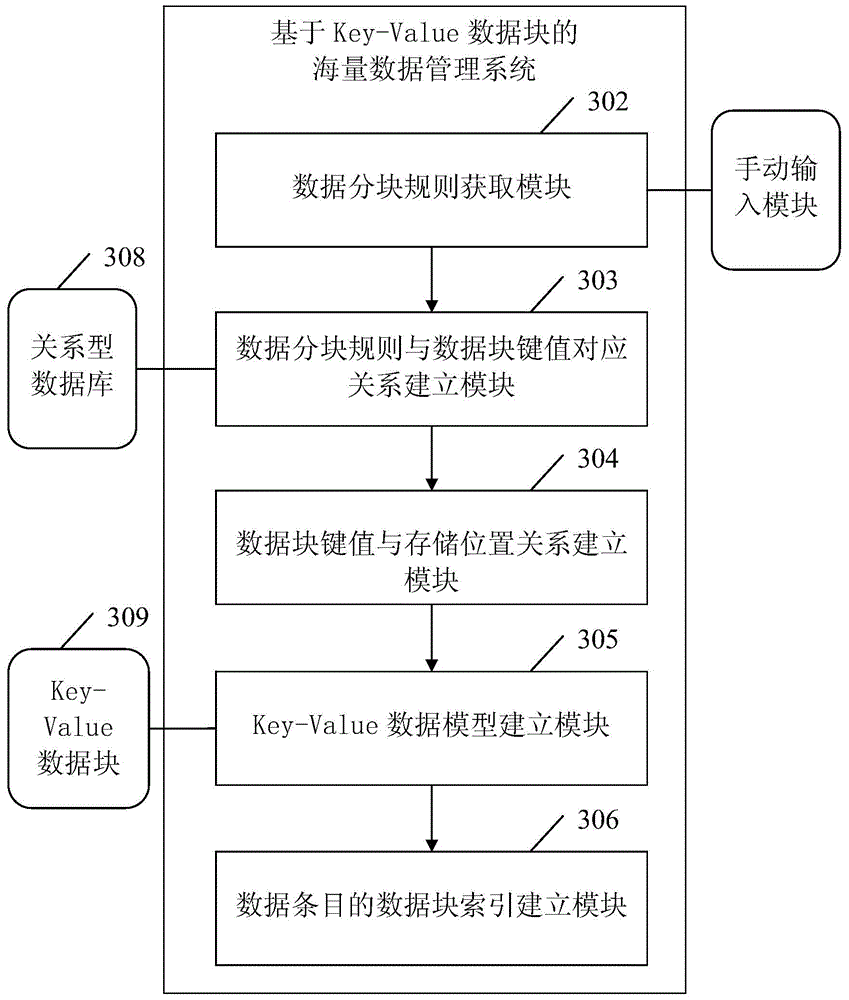
Data query method and system based on Key-Value data blocks
ActiveCN105488043AImprove reading and writing efficiencyImprove query efficiencySpecial data processing applicationsRelational databaseThe Internet
The invention brings forward a data query method and system based on Key-Value data blocks. The method comprises following steps: selecting dimensions of data aggregation based on attributes of perception data, clustering perception data of the same attribute dimension in common, saving perception data to a same data block and utilizing selected data dimensions as attribute information corresponding to data blocks; adopting Key-Value data format to save and manage data in the data blocks; and saving and managing storage positions and corresponding attribute information by adopting a relational database. The data query method and system based on Key-Value data blocks has following beneficial effects: a deluge of perception data on the Internet of Things can be read and written in an efficient manner without using a great number of computers; and the data block is easy to expand according to business scale.
Owner:NANJING UNIV OF SCI & TECH
Device and method for terminal consistency test in mobile communication system
ActiveCN1878373AAchieve consistencyLow costRadio/inductive link selection arrangementsWireless communicationComputer hardwareAsynchronous Transfer Mode
The invention relates to a detecting the consistency of terminal in the mobile communication system and relative method. Wherein, said device comprises a protocol simulator and an improved base station; said protocol simulator comprises a memory storing the protocol stack and executable testing group which can simulate the wireless network controller, the processor of core network and the man-machine interactive input and output units; the processor via the asynchronous transmission mode or the impulse code modulate interface board is connected to the base station; the base station comprises a wireless interface connected to the user terminal; and said method comprises: building the test simulate network, building region, building public signal channel, and sending the system message; the tested terminal, base station and protocol simulator builds calling; relative processor triggers the test sample, to complete the test and record the result; then analyzing the tested result.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Apparatus and method for realizing synchronization between Ethernet chain-like network nodes
InactiveCN101039173AAchieve consistencyOvercome limitationsData switching by path configurationSynchronising arrangementCommunication interfaceNetwork structure
The invention discloses a device and method to achieve synchronization between an ethernet chain network node. The invention solves the problems of high cost when achieving the precise synchronization between every network node in the Ethernet chain network structure without compatibility with products from different producers and increasing using cost. The invention takes advantages of simple structure, convenient operation and excellent compatibility. The structure of the invention is the following: it includes at least a controller and plurality of network node. The controller can enumerate and allocate every network node, and distributes a single nodal number to every network node. The controller contains at least a communication interface, and every node contains at least two communication interfaces. The interfaces of the controller is connected through a data line to the communication interface of a certain node, and then another communication interface of this node is connected through the date line to the communication interface of the next node. With this kind of connection, a chain network structure is formed; every node is provided with a timer.
Owner:山东易码智能科技股份有限公司
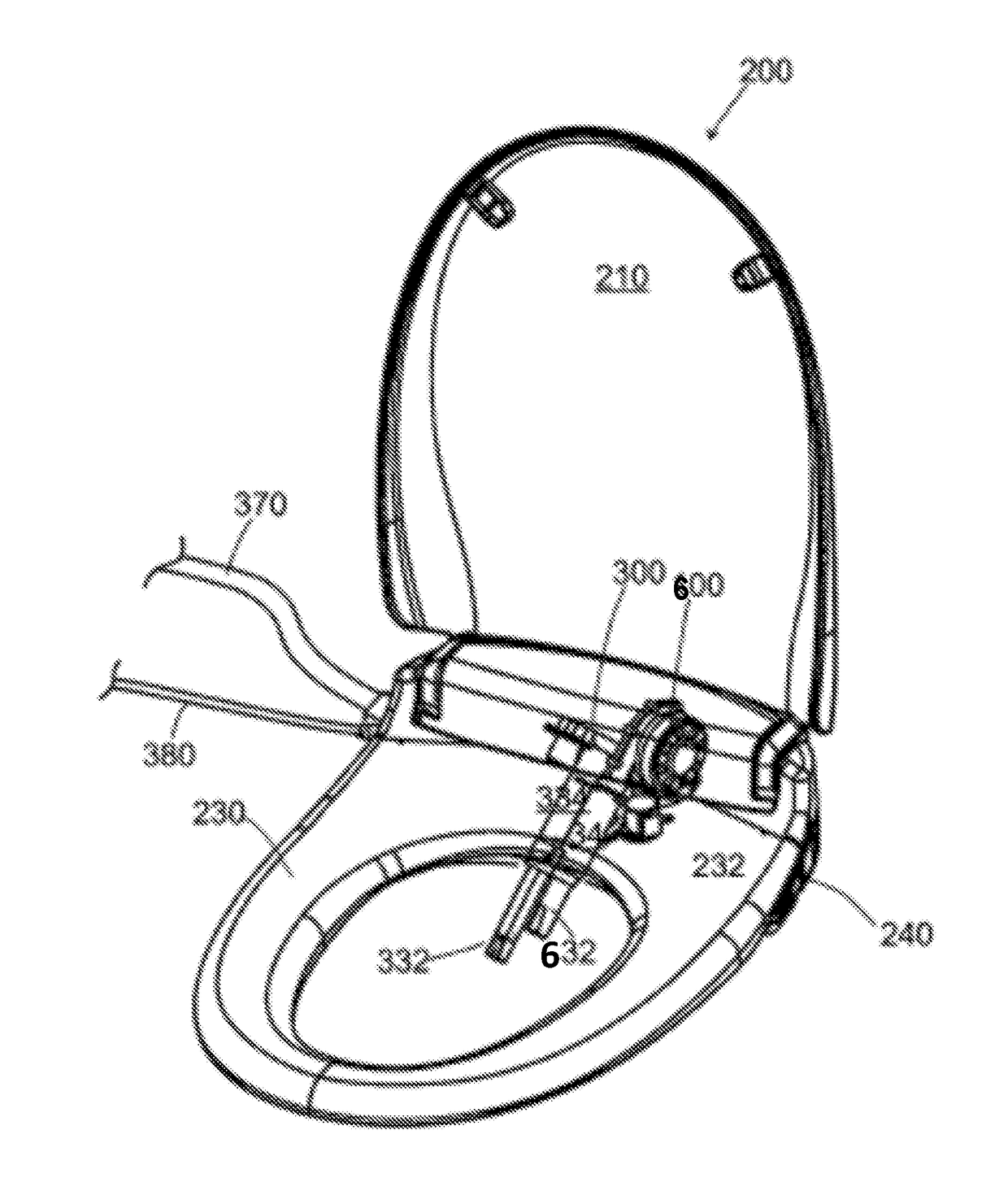
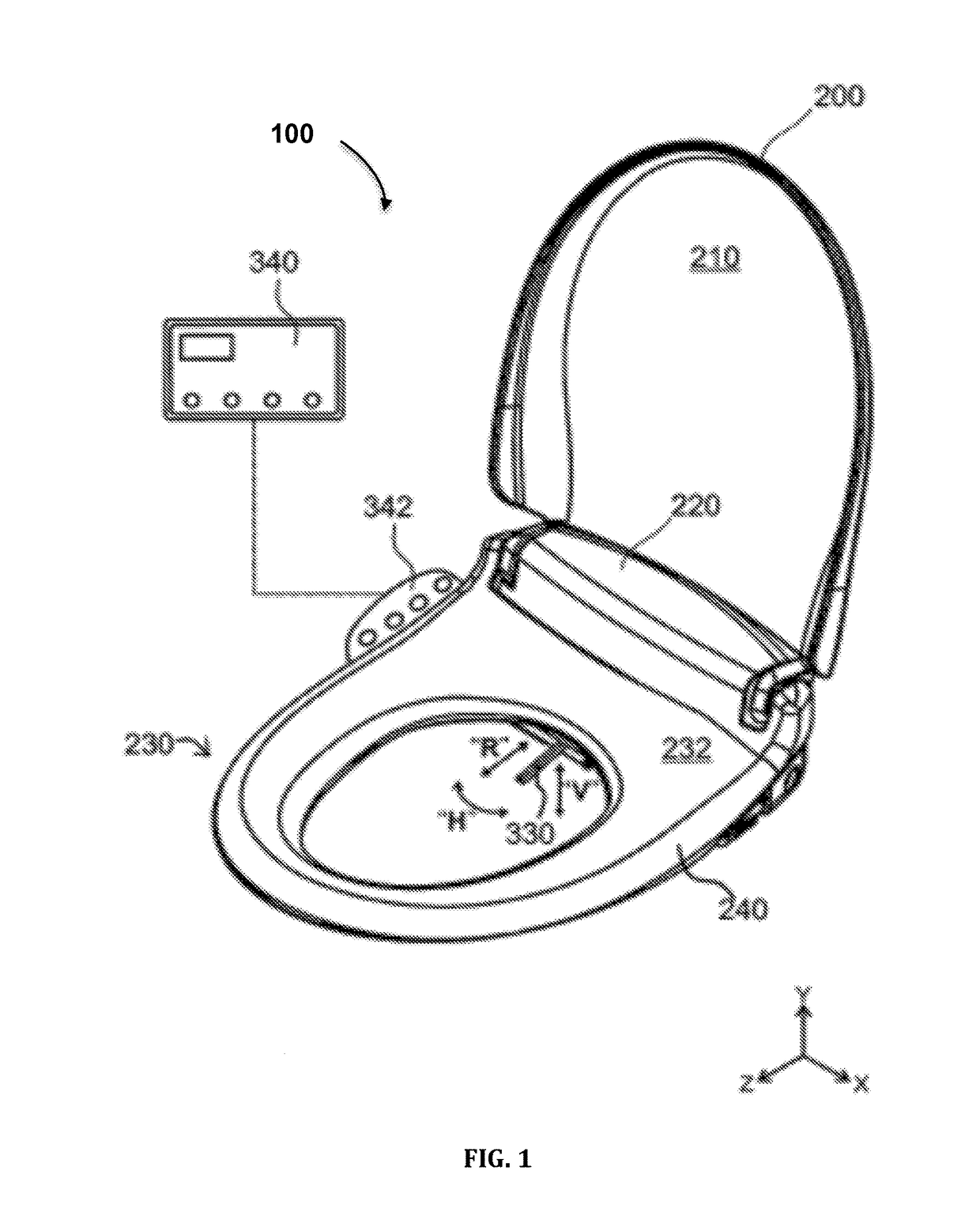
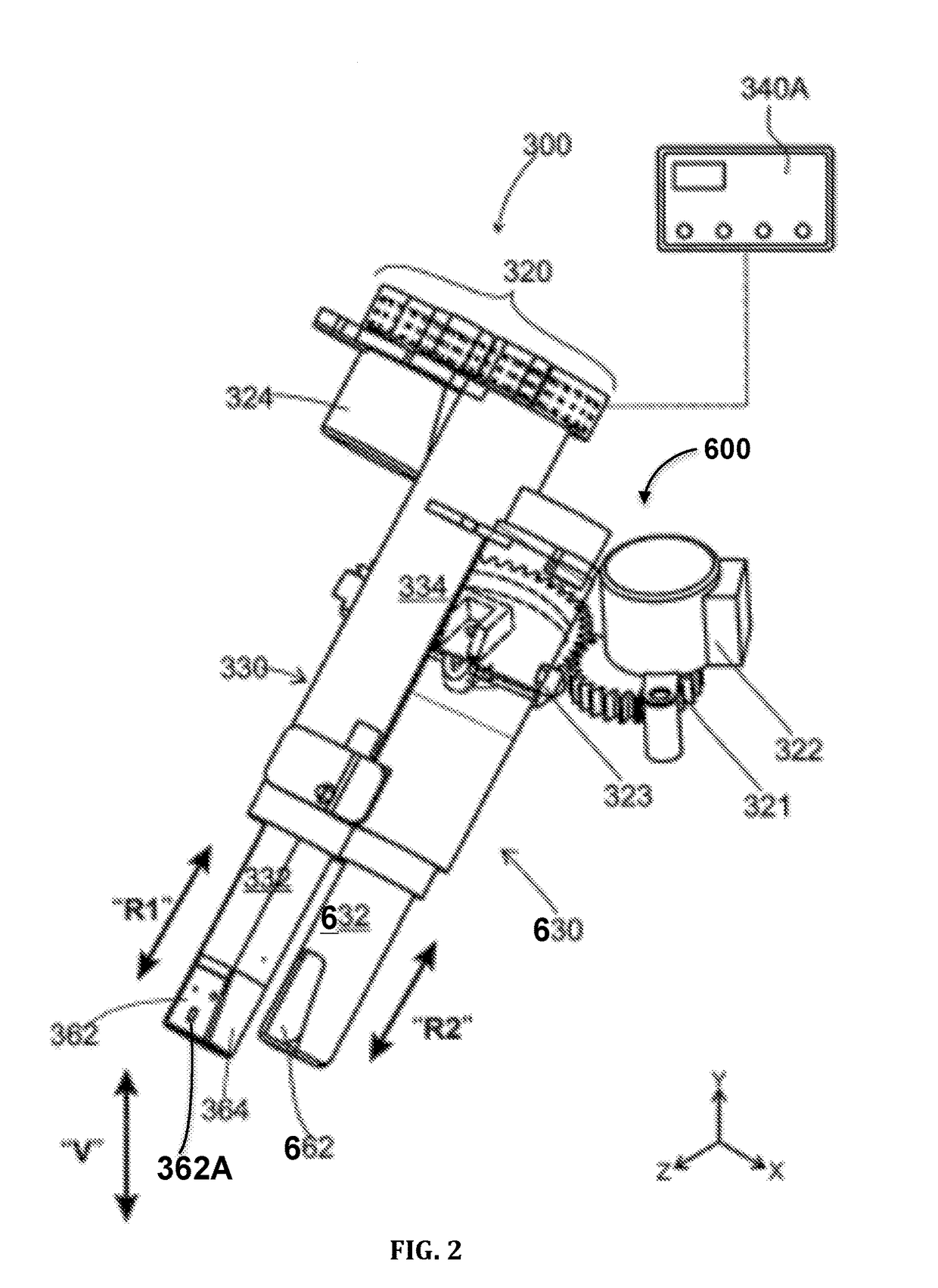
Seat and Cover system with Medical Units
Aspects of the present invention provide a method for using an apparatus to deliver medicine and to wash, clean, and dry a region of a human body. The apparatus include a toilet seat assembly and a medicine delivery assembly. In addition, the apparatus may include a drying nozzle assembly and / or a spraying nozzle assembly. The medicine delivery assembly may include one or more medicine storage cartridges and / or one or more medicine base units, each medicine base unit includes at least a cartridge unit and at least a cartridges slot, wherein the cartridge slot is adapted to match with a medicine storage cartridge. The medicine delivery assembly may include a medicine delivery nozzle, which can be coupled to a spraying nozzle assembly, or may be operated by itself with a medicine delivery nozzle. Finally, the medicine delivery assembly can be controlled by one or more control units.
Owner:BEMIS MANUFACTURING CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com