Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
45 results about "Low confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
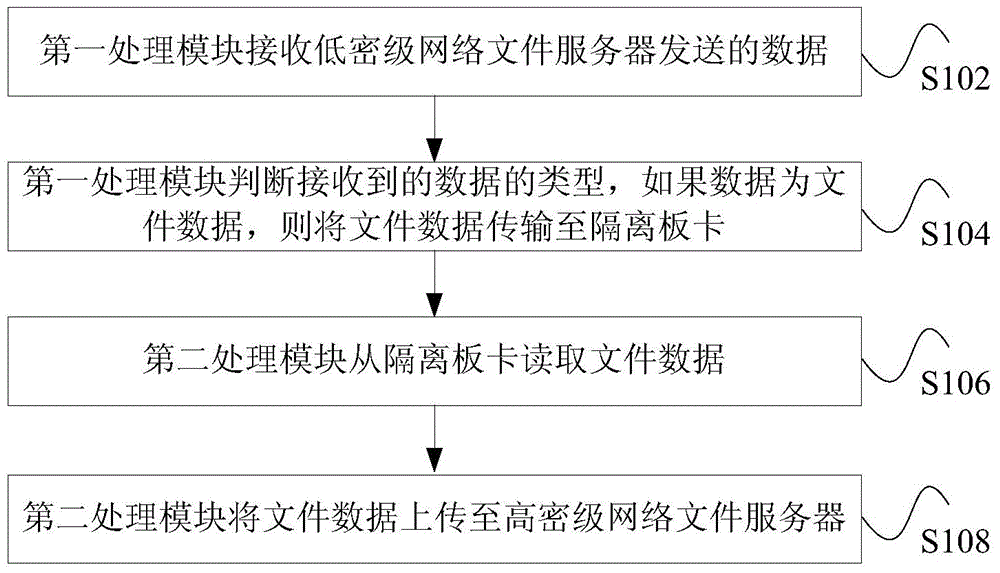
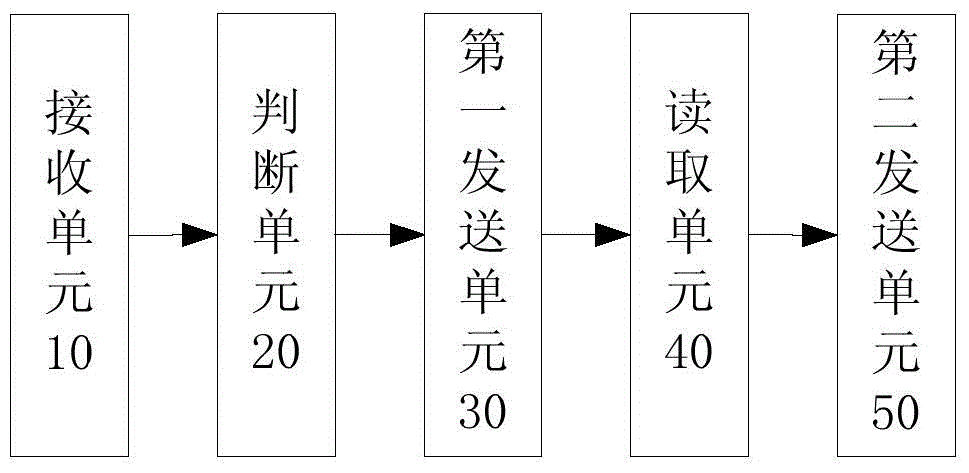
File transmission method and device based on one-way safety isolation gap
The invention discloses file transmission method and device based on an one-way safety isolation gap. The method comprises the steps of receiving data by a first processing module from a low-confidentiality-level network server; determining the type of the received data through the first processing module; transmitting the file to an isolation plate card if the data are the file data; reading the file data through a second processing module from the isolation plate card; uploading the file data to a high-confidentiality-level server through the second processing module. With the adoption of the method, the problem that a file is inconvenient to be transferred from the low-confidentiality-level network server to the high-confidentiality-level network server through the client in the prior art can be solved.
Owner:QI-ANXIN LEGENDSEC INFORMATION TECH (BEIJING) INC
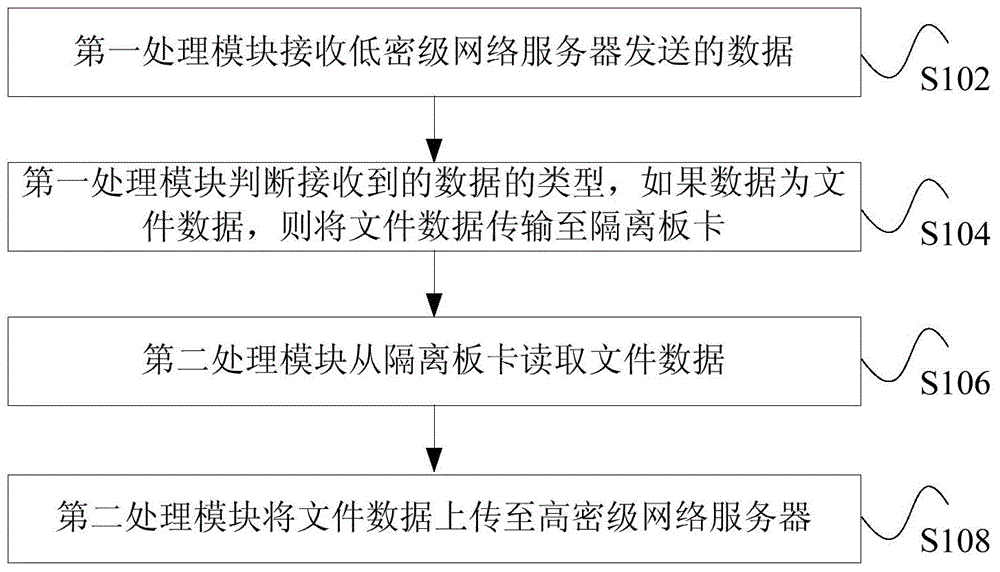
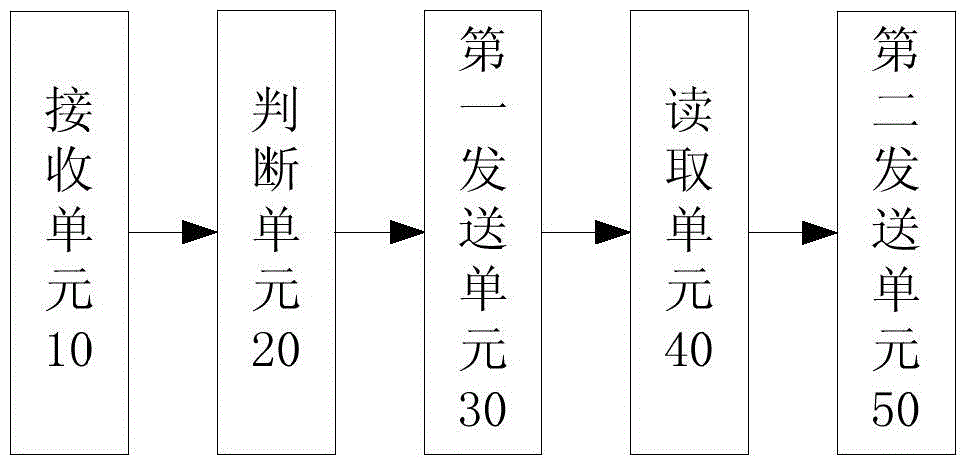
File transmission method and device based on one-way safety isolation gap
InactiveCN104601703ASolve the inconvenient problem when ferrying to a high-density network serverTransmissionLow confidentialityFile transmission
The invention discloses file transmission method and device based on an one-way safety isolation gap. The method comprises the steps of receiving data by a first processing module from a low-confidentiality-level network server; determining the type of the received data through the first processing module; transmitting the file to an isolation plate card if the data are the file data; reading the file data through a second processing module from the isolation plate card; uploading the file data to a high-confidentiality-level server through the second processing module. With the adoption of the method, the problem that a file is inconvenient to be transferred from the low-confidentiality-level network server to the high-confidentiality-level network server through the client in the prior art can be solved.
Owner:QI-ANXIN LEGENDSEC INFORMATION TECH (BEIJING) INC
Communication system based on ultra-wideband spread spectrum chaos carrier and communication method
ActiveCN107231227AChange structureEasy to implementElectromagnetic transmission optical aspectsSecuring communication by chaotic signalsUltra-widebandExternal cavity laser
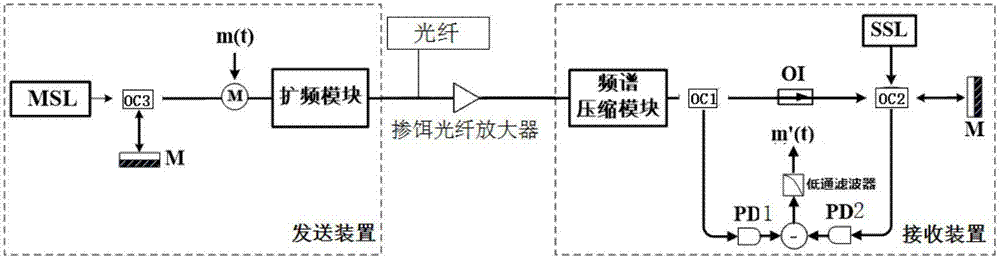
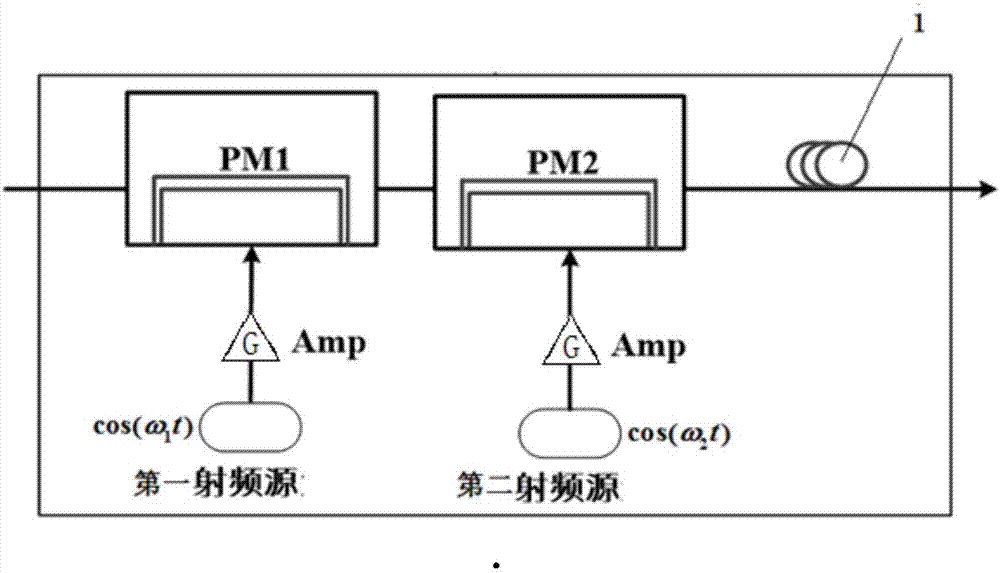
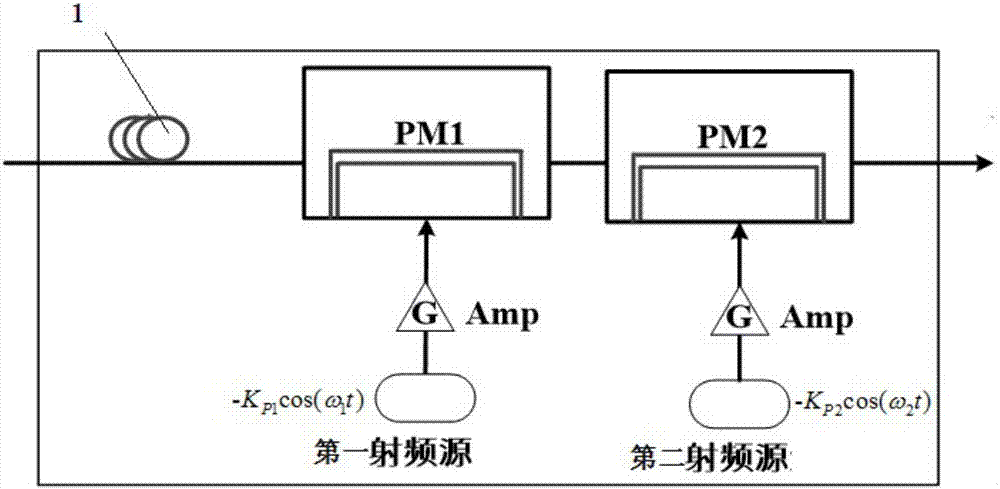
The invention relates to a communication system based on ultra-wideband spread spectrum chaos carrier and a communication method and mainly solves the technical problem of low confidentiality in the existing technology. The problem is well solved through adoption of a technical scheme as follows: a receiving device comprises a frequency spectrum compression module and a first optical coupler OC1 connected to the frequency spectrum compression module, wherein the output of the first optical coupler OC1 is divided into two paths, one path is directly connected to a chaos synchronization unit and the other path is connected to a first connection end of the chaos synchronization unit through a photovoltaic conversion unit; a sending device comprises a chaos external cavity laser, an MZ modulator connected to the chaos external cavity laser and a spread spectrum module connected to the MZ modulator; and parameters of the frequency spectrum compression module and the spread spectrum module are opposite, and the technical scheme can be used for a communication system of the chaos carrier.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
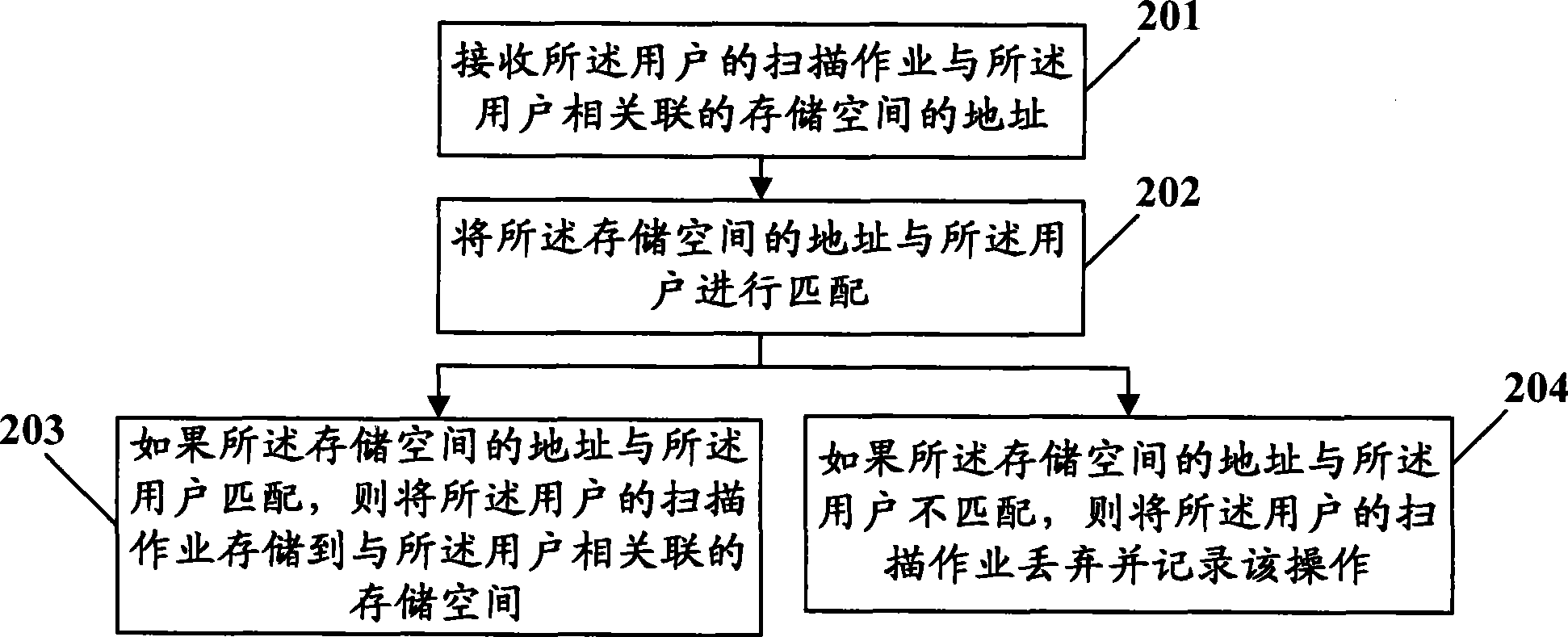
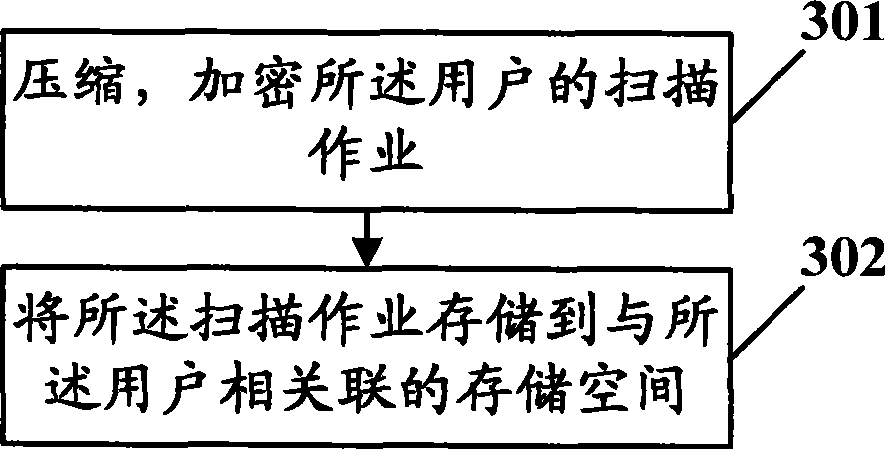
Management method, device and system for scanning operation
InactiveCN101394455ASafe and orderly managementImprove utilization efficiencyPictoral communicationLow confidentialityComputer science
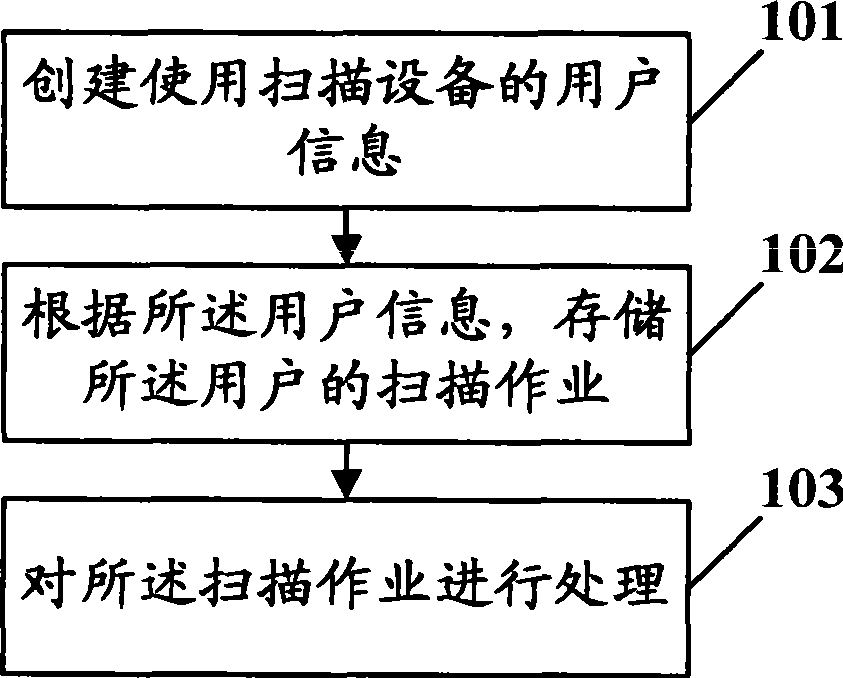
The invention discloses a management method, a device and a system of scanning operations and relates to the technical field of the electric numeral data processing, and the invention solves the problems of the low utilization efficiency of scanning devices, the low confidentiality of the scanning operation content and the disordered management of scanning operations in the prior art. The management method of the scanning operations provided by the invention comprises the following steps: creating the information of a user who uses the scanning devices; storing the scanning operations of the user according to the user information; and processing the scanning operations. The invention can improve the utilization efficiency of the scanning devices and the security of the scanning operations, so that the management of the scanning operations can be safe and orderly.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
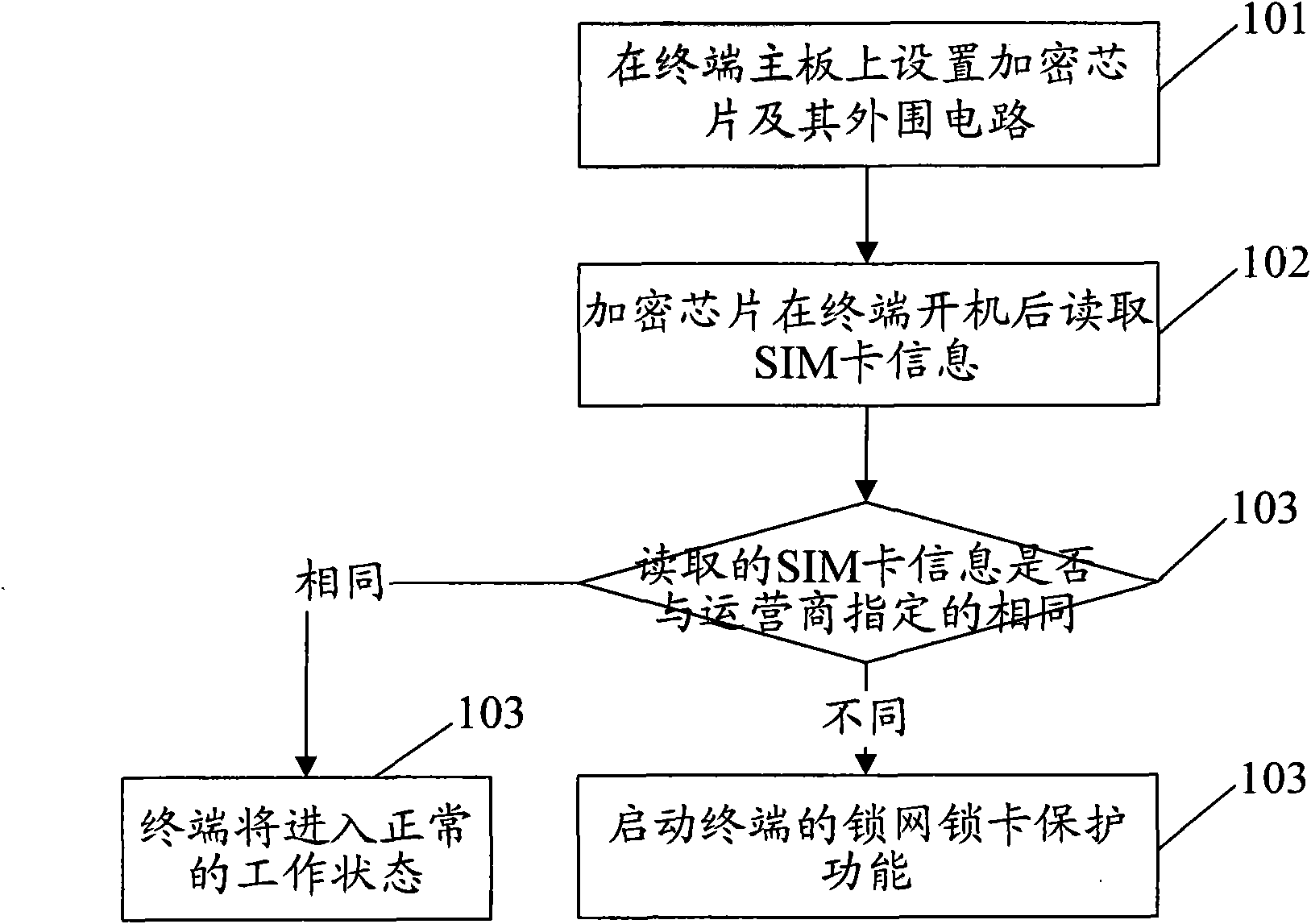
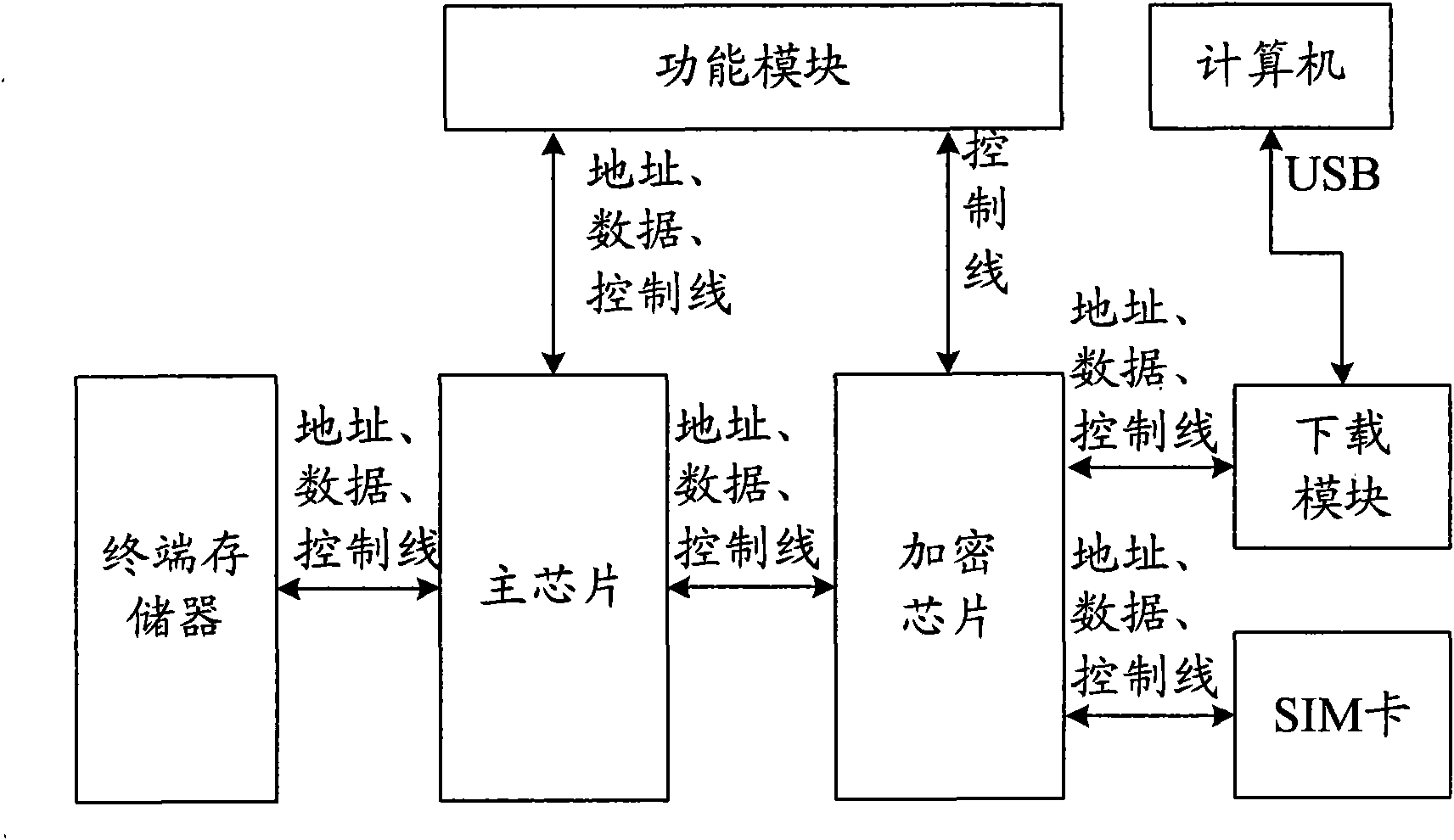
Method for realizing network and card locking function of terminal and terminal
InactiveCN102104864AAvoid situations of low confidentialityImprove confidentialityNetwork data managementLow confidentialitySubscriber identity module
The invention discloses a method for realizing a network and card locking function of a terminal, which comprises that: an encryption chip is arranged on a mainboard of the terminal; and the encryption chip reads subscriber identity module (SIM) card information after the terminal is started, judges whether the read SIM card information is the same as the SIM card information specified by an operator and stored per se or not, and enables the network and card locking protection function of the terminal when determining the read SIM card information is different from the stored SIM card information. Simultaneously, the invention also discloses the terminal capable of realizing the network and card locking function. By the method and the terminal, the condition of low confidentiality of the software-based network and card locking function of the terminal can be avoided, and the confidentiality of the network and card locking function of the terminal is improved.
Owner:ZTE CORP
Communication method combining chaos and MIMO
ActiveCN104410487AOvercome the disadvantage of low code rateImprove robustnessSpatial transmit diversitySecuring communicationLow confidentialityCommunications system
The invention relates to a communication method combining chaos and MIMO (Multiple Input Multiple Output) and belongs to the technical field of communication. According to the method, for the defects of low transmission rate, high error rate and low confidentiality of a correlation delay shift keying (CDSK) chaotic communication scheme, a frequency modulated signal is dispersed in multiple channels for transmission, a delayed signal is equally divided into M sections by a segmentation cyclic shifter, and the M signal sections are cyclically shifted right for n sections according to information code elements and added into an original chaotic signal to form an output signal. Therefore, the confidentiality is remarkably improved and the information transmission rate is remarkably increased in comparison with an FM-CDSK scheme; under the same error rate, the signal-noise ratio is greatly improved in comparison with the FM-CDSK scheme; an improved chaotic confidential communication system adopting the method has wide application prospects in the fields of images, military confidential information and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Anti-crawling method, device, terminal and readable medium for live broadcast room data
ActiveCN109067805AImprove cracking strengthEnsure safetyKey distribution for secure communicationObfuscationLow confidentiality
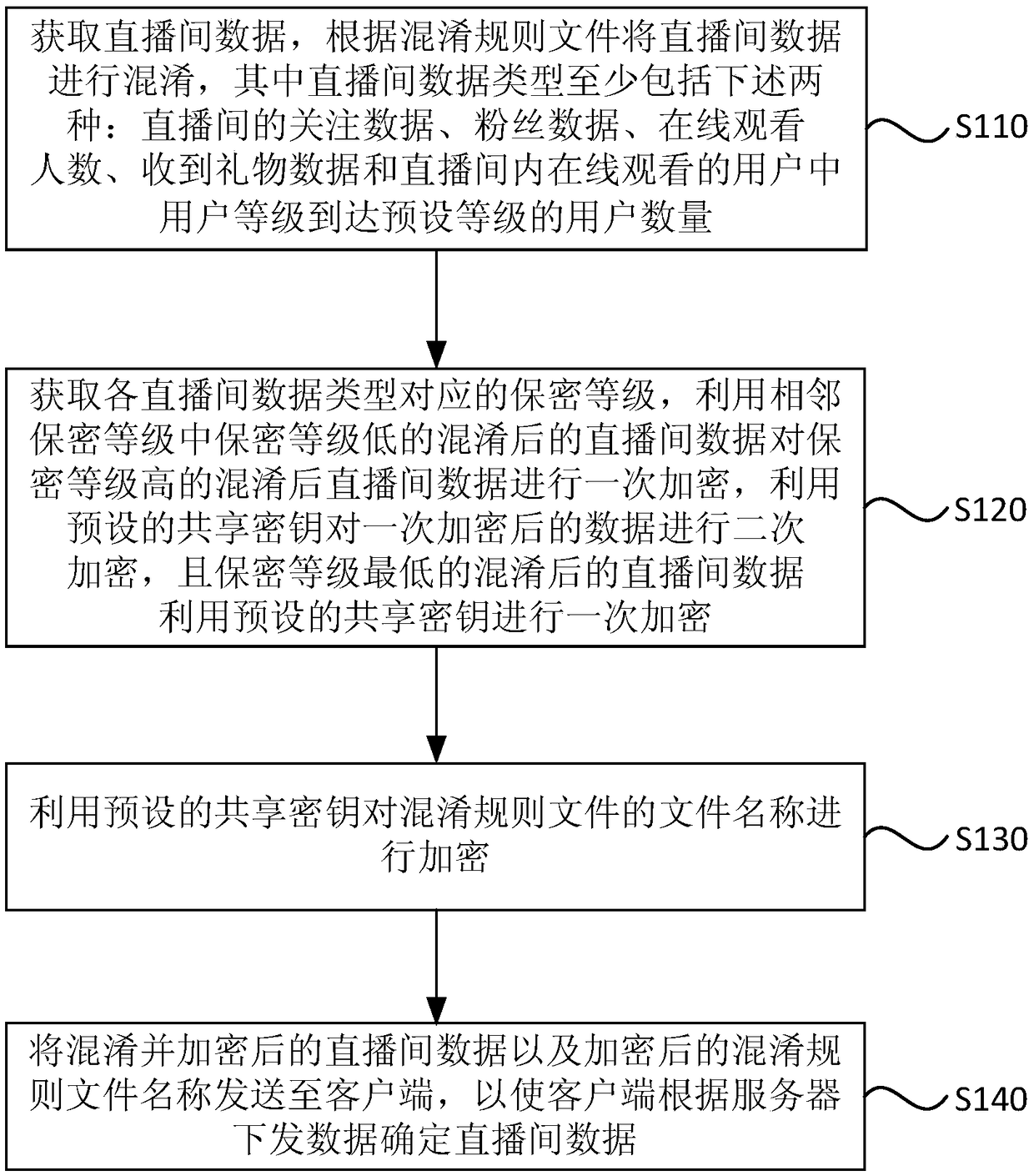
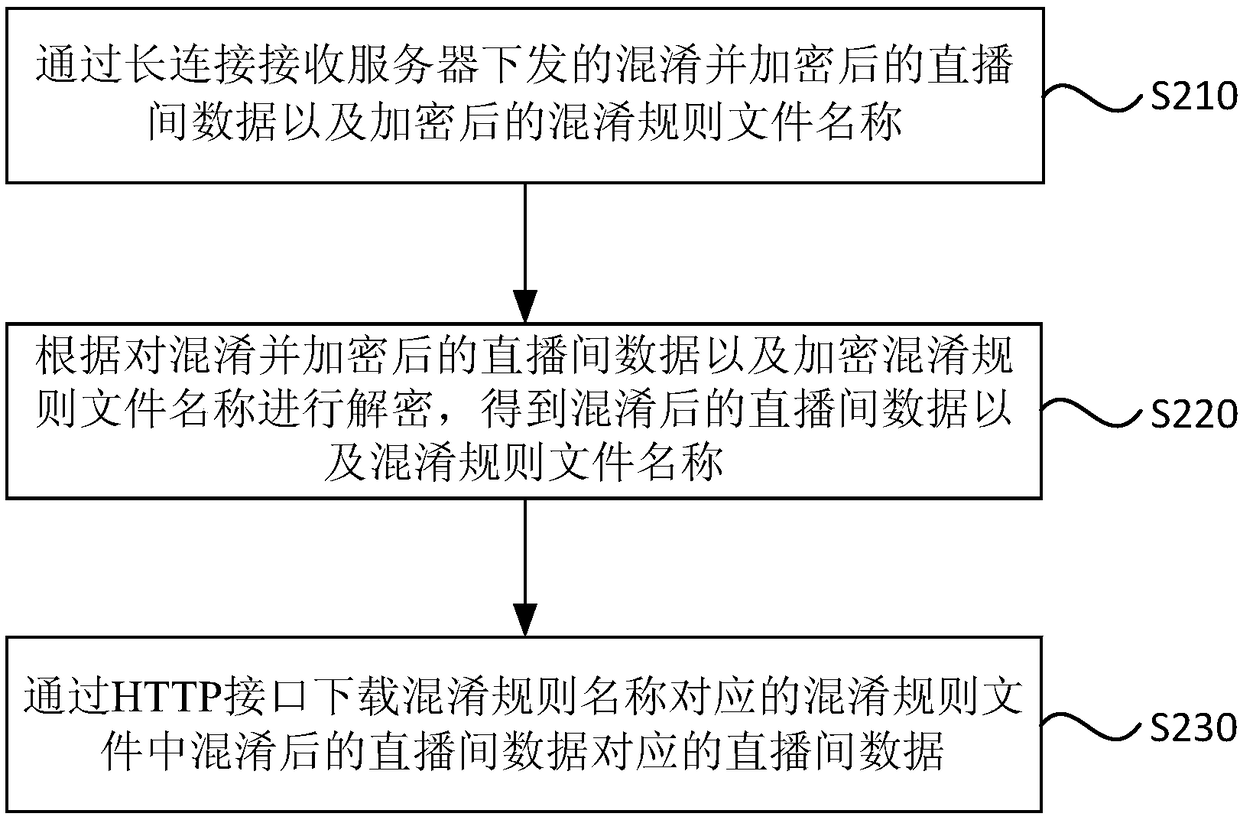
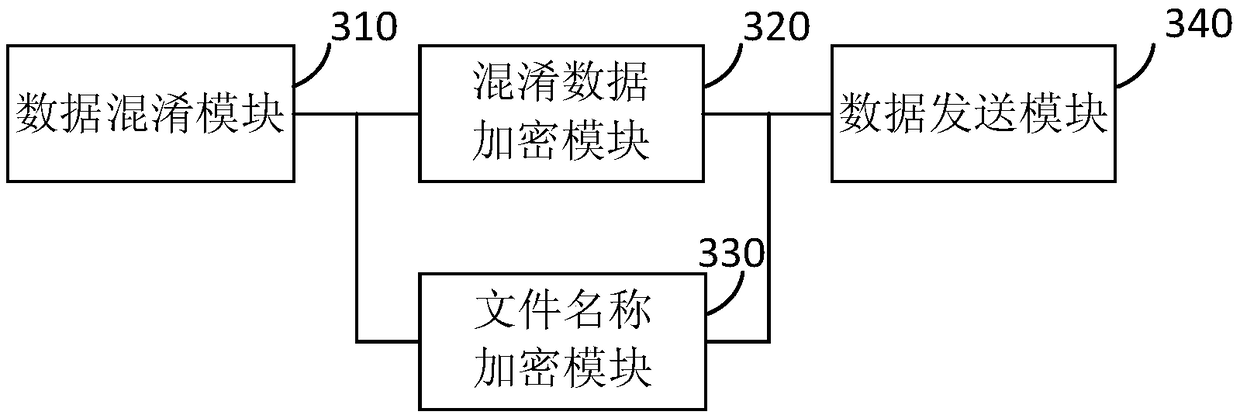
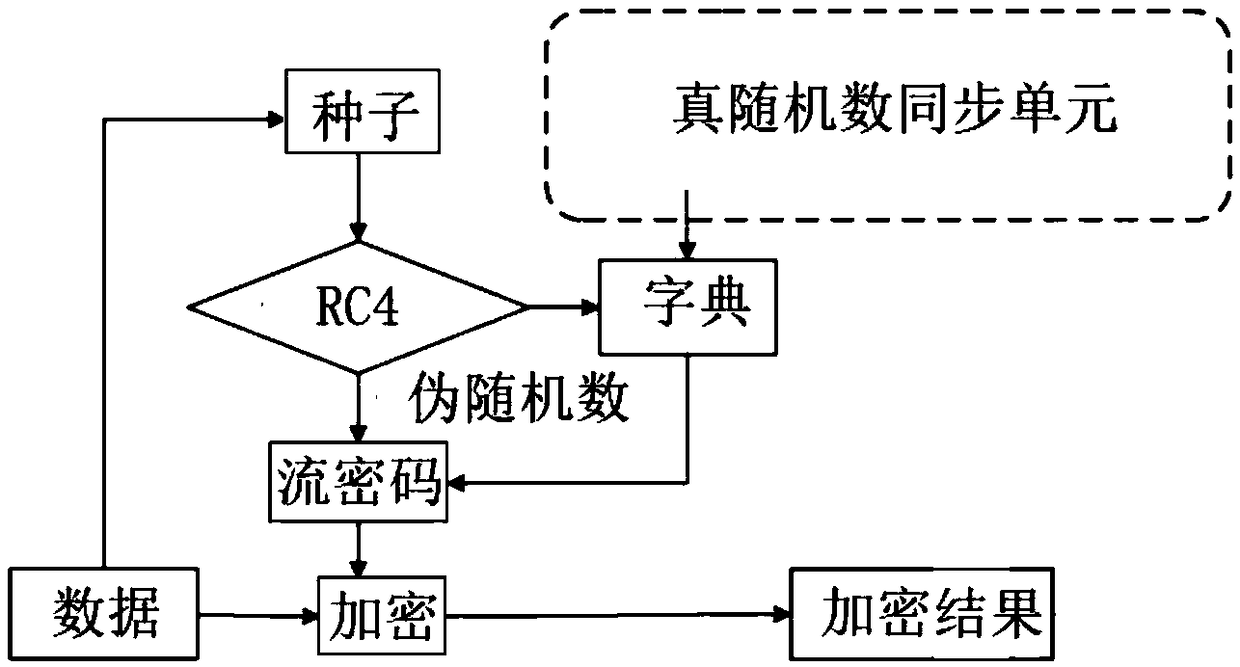
The embodiment of the invention discloses an anti-crawler method, a device, a terminal and a readable medium for the data between live broadcasts. The method comprises the following steps: obtaining the data between live broadcasts; obtaining the data between live broadcasts; obtaining the data between live broadcasts according to the obfuscation rule file; obfuscating the data between live broadcasts. The confusion data with low confidentiality level in the adjacent confidentiality level is used to encrypt the confusion data with high confidentiality level once, the data encrypted once is used to encrypt twice by using the shared key, and the confusion data with the lowest confidentiality level is used to encrypt once by using the preset shared key. Encrypting the file name of the obfuscation rule file by using a shared key. The encrypted confused data and the file name are distributed to the client, so that the client can determine the live broadcast data according to the data distributed by the server. The anti-crawling method, the device, the terminal and the readable medium of the live broadcasting room data provided by the embodiment of the invention improve the data breakingstrength of the live broadcasting room, prevent the crawler from climbing to obtain the correct live broadcasting room data, and ensure the safety of the data of the live broadcasting room.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Method for implementing optimal confidentiality throughput and high-efficiency energy collection in SWIPT (Simultaneous Wireless Information and Power Transfer) system
ActiveCN108736989AEfficient collectionReduce overheadTransmission monitoringSecurity arrangementLow confidentialitySelf adaptive
The invention discloses a method for implementing an optimal confidentiality throughput and high-efficiency energy collection in a SWIPT (Simultaneous Wireless Information and Power Transfer) system.According to the method for implementing the optimal confidentiality throughput and high-efficiency energy collection in the SWIPT system, a confidentiality throughput of a legal user is calculated, athreshold is set to judge whether confidentiality interruption occurs so as to calculate a confidentiality interruption probability, and by regulating a target confidentiality rate and a power distribution ratio of a transmitting terminal, the optimal confidentiality throughput is obtained; and a receiving terminal adaptively regulates a power distribution coefficient according to received powerand information decoding sensitivity and only provides power which meets the decoding requirement for information decoding, and other power is all used for energy collection. The method solves the problems of low confidentiality throughput and low energy collection efficiency when an eavesdropper exists in an existing SWIPT system.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
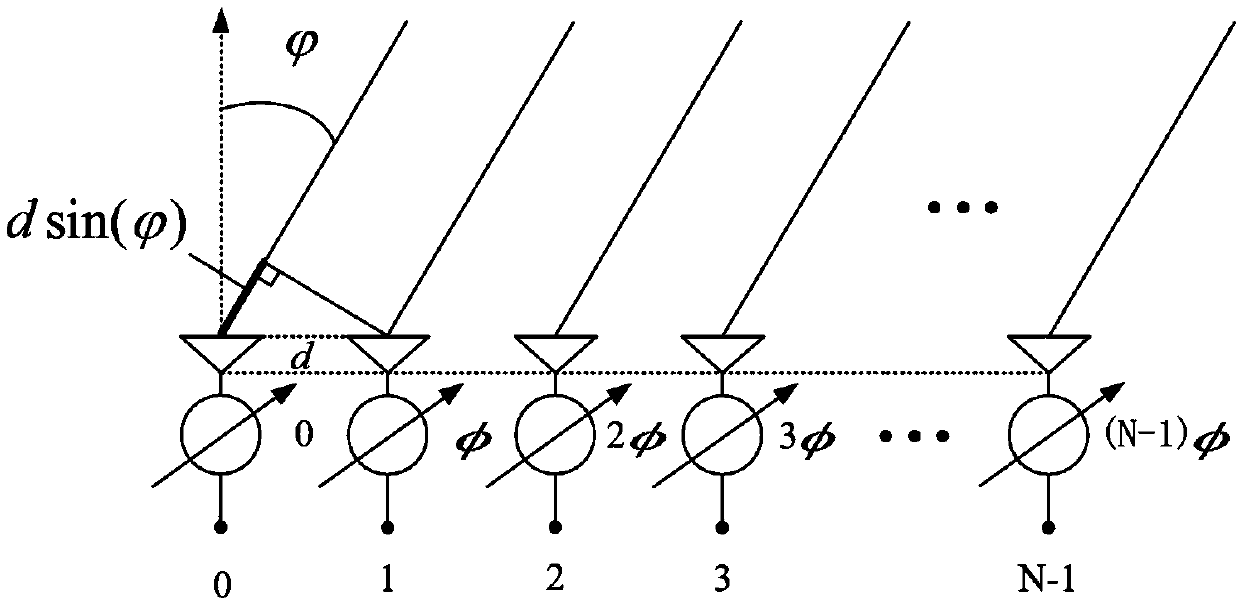
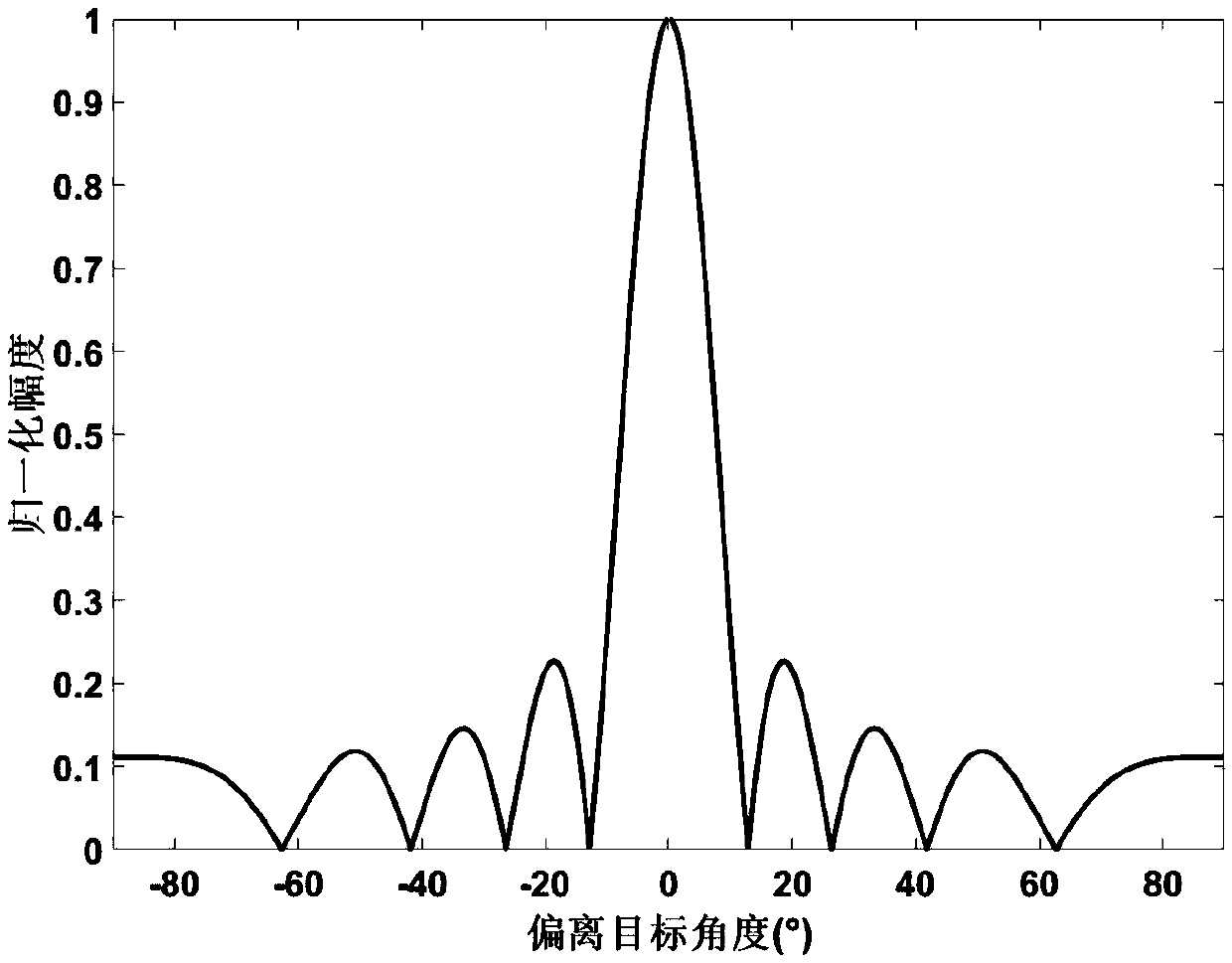
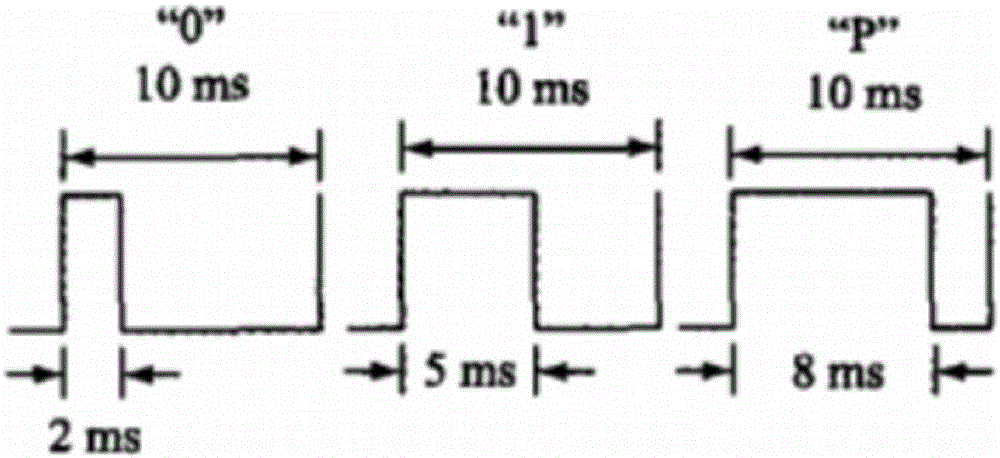
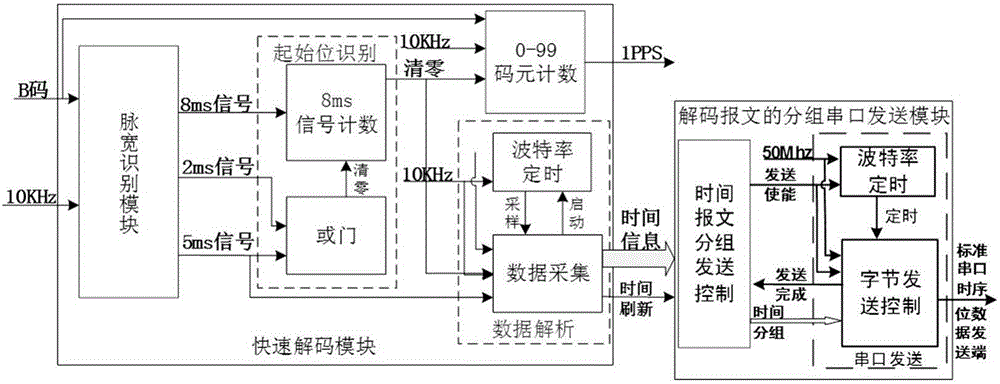
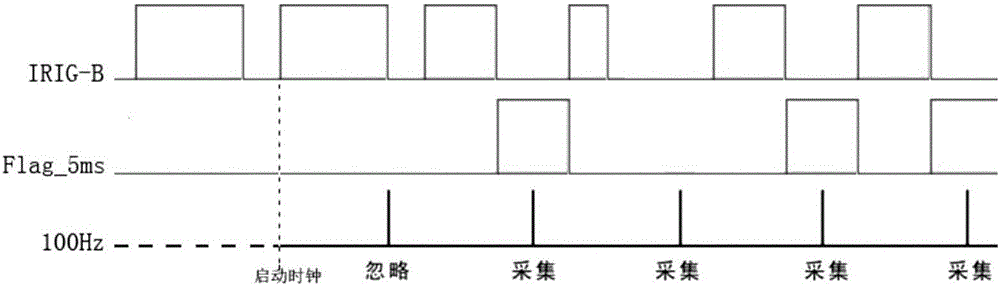
FPGA-based IRIG-B(DC) fast decoding method
InactiveCN105763199ASave resource redundancyImprove performancePulse conversionDecoding methodsCircuit complexity
An FPGA-based IRIG-B(DC) fast decoding method is disclosed and the method comprises an IRIG-B(DC) fast decoding step and a step of sending decoding messages via serial ports after the decoding messages are packeted. According to the FPGA-based IRIG-B(DC) fast decoding method, via use of FPGA technologies, on-line data monitoring technologies, serial port communication technologies and the like, defects of a conventional IRIG-B code time unification system developed via use of discrete elements can be address, wherein the defects of the conventional IRIG-B code time unification system is are circuit complexity, low integration level, difficult-to-debug characteristic, large size, high cost, low confidentiality and the like; most requirements for precision can also be met by the FPGA-based IRIG-B(DC) fast decoding method.
Owner:YUNNAN POWER GRID CO LTD ELECTRIC POWER RES INST +1
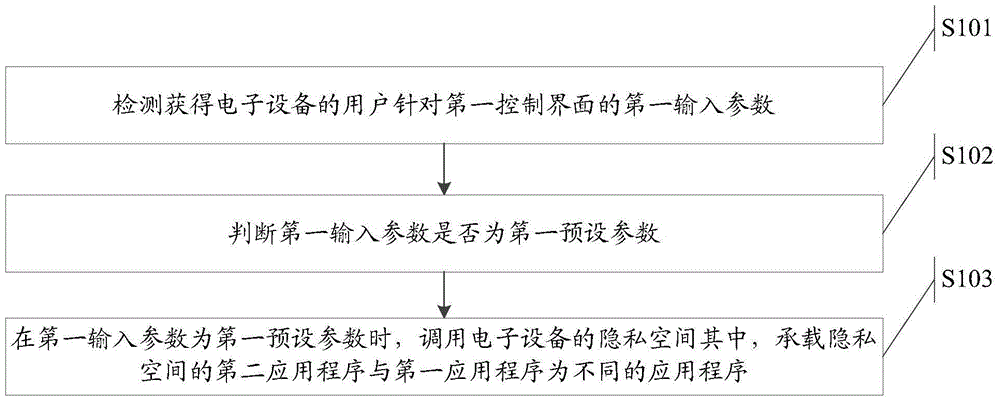
Information retrieval method and electronic equipment
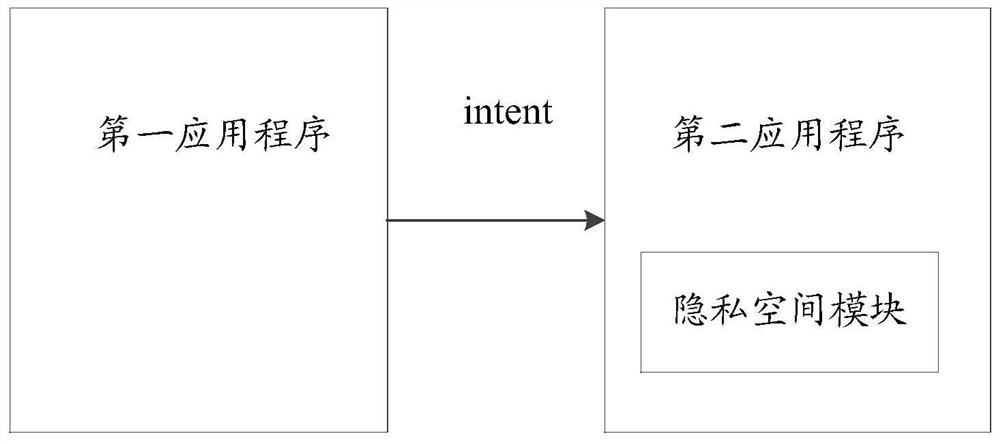
ActiveCN106156646AImprove confidentialityImprove securityDigital data protectionLow confidentialityInformation security
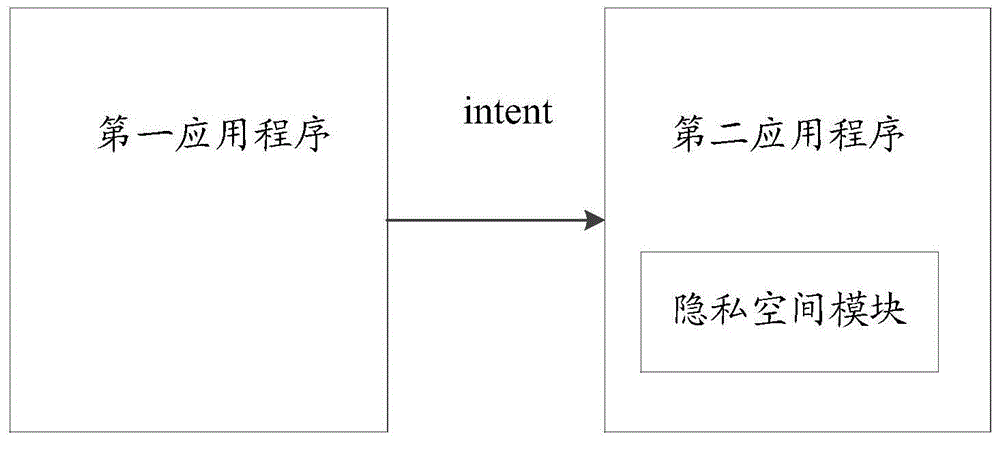
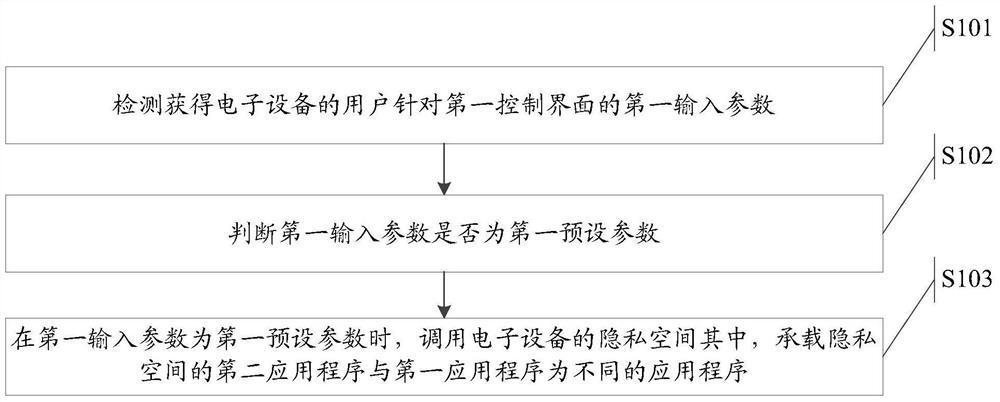
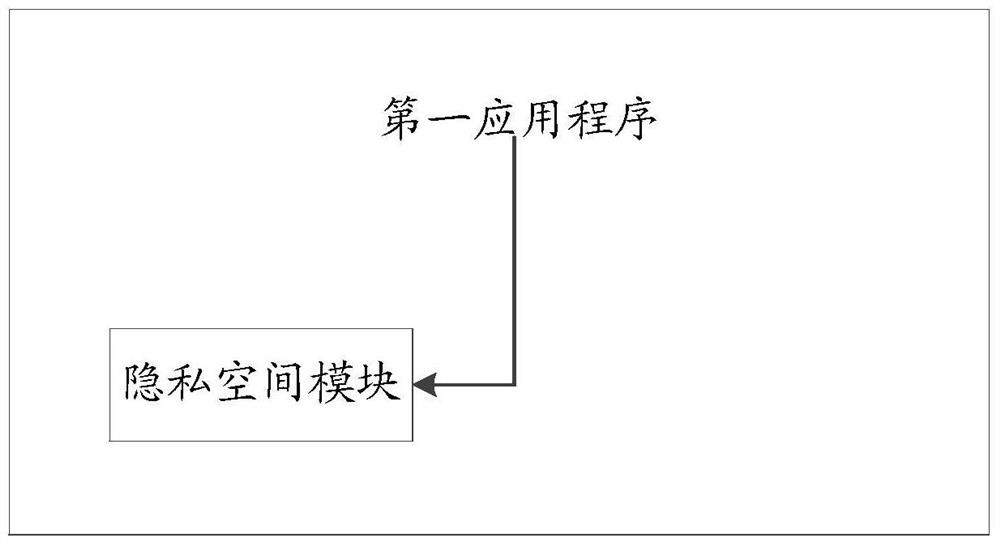
The invention relates to the field of information security, discloses an information retrieval method and electronic equipment, and aims to solve the technical problem of lower confidentiality of information in the prior art. The method is applied to the electronic equipment, a first control interface of a first application program is displayed on the electronic equipment, the method comprises the steps of acquiring a first input parameter of a user of the electronic equipment for the first control interface through detection; judging whether the first input parameter is a first preset parameter or not; retrieving a privacy space of the electronic equipment when the first input parameter is the first preset parameter, wherein a second application program loading the privacy space and the first application program are different application programs. The technical effect of improving the confidentiality of the privacy space is achieved.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Intelligent detection method and system
InactiveCN109547960AIntegrity guaranteedSolve the prone to fraudParticular environment based servicesWireless architecture usageLow confidentialityData integrity
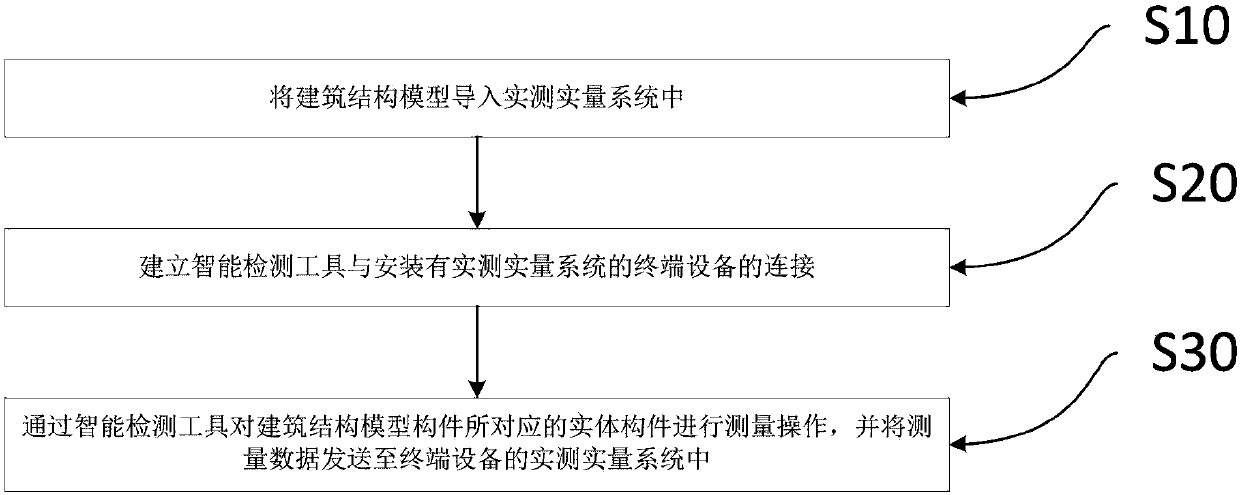
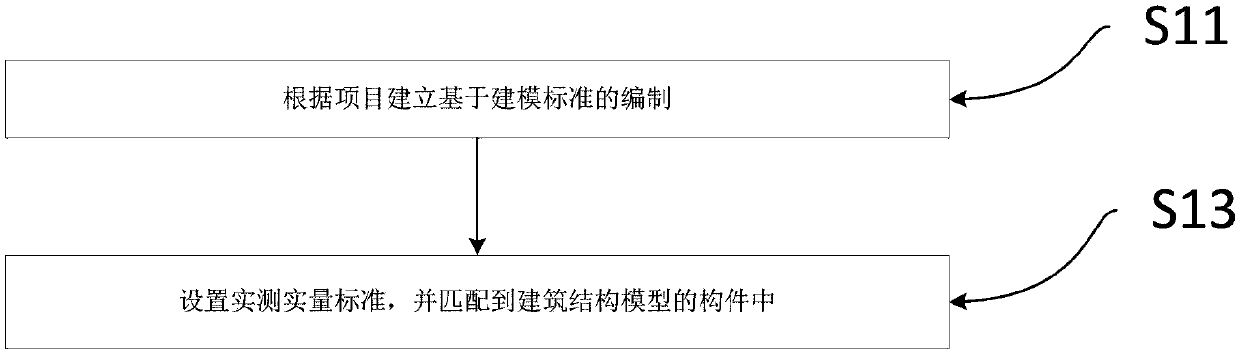
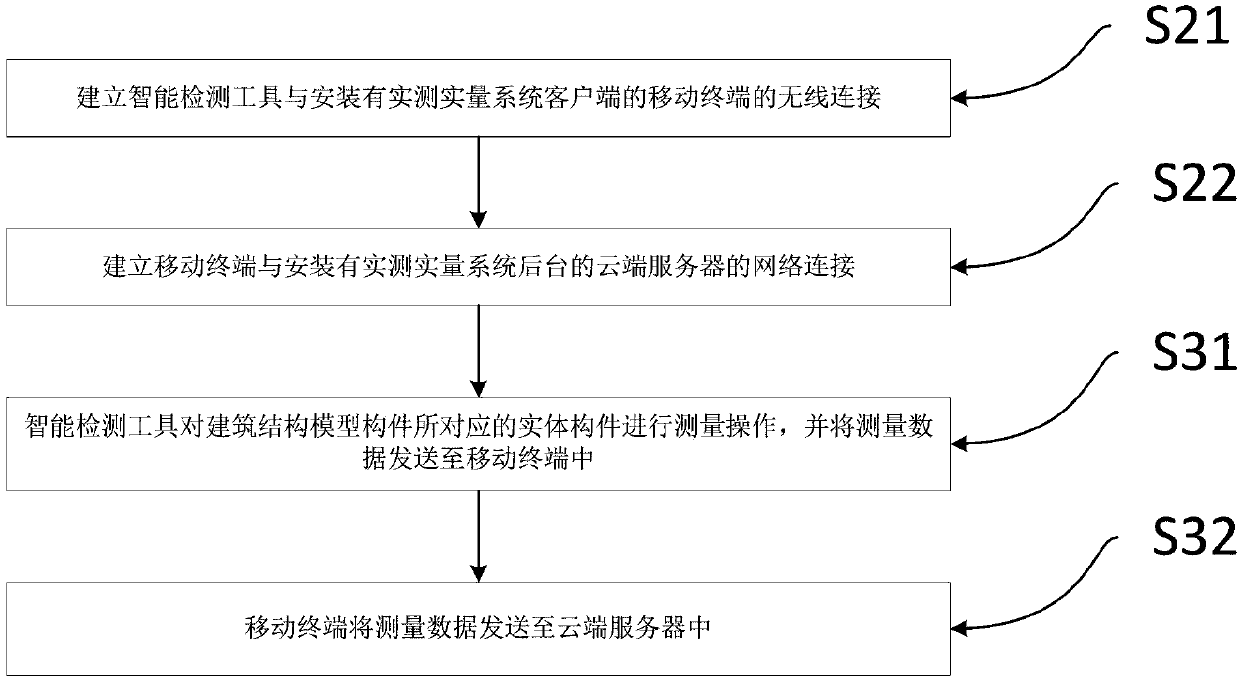
The invention relates to the field of building detection, and specifically relates to an intelligent detection method and system. The intelligent detection method comprises a setting step, a connection step and a measurement step, wherein the setting step is to create a building structure model, import the building structure model into a real measurement system, the building structure model comprises multiple components, the connection step is to establish a connection between an intelligent detection tool and a terminal device with the real measurement system, the measurement step is to measure a physical component corresponding to the building structure model component by the intelligent detection tool and send measurement data to the real measurement system of the terminal device. The existing measurement method is easy to cause falsification, has high fill-in error rate, has low confidentiality, is hard to save data, and is easy to cause repeat measurement. The intelligent detection method solves the above problems, improves detection accuracy and efficiency, guarantee accuracy and truth, prevents cheating and tampering, guarantees data integrity and protects data from losing.
Owner:WANYI TECH
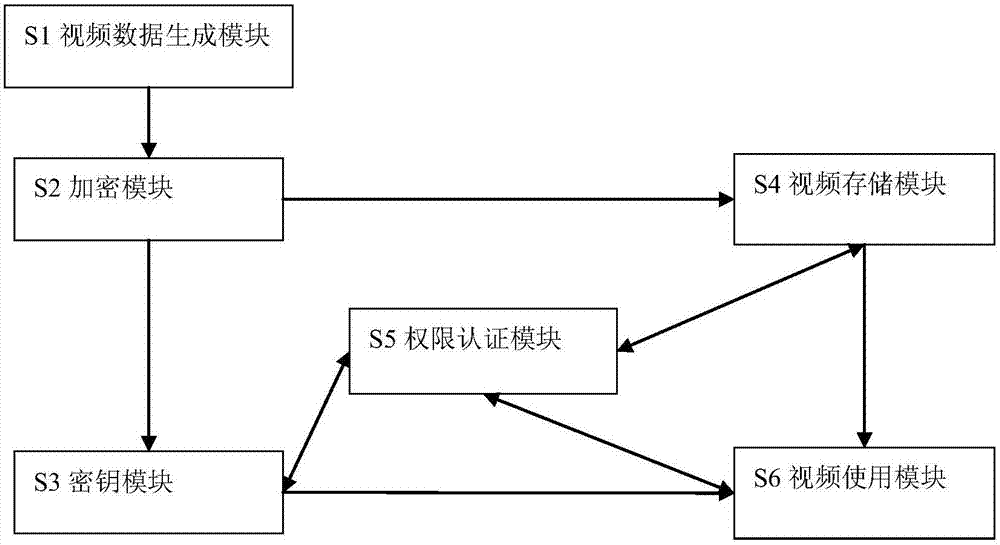
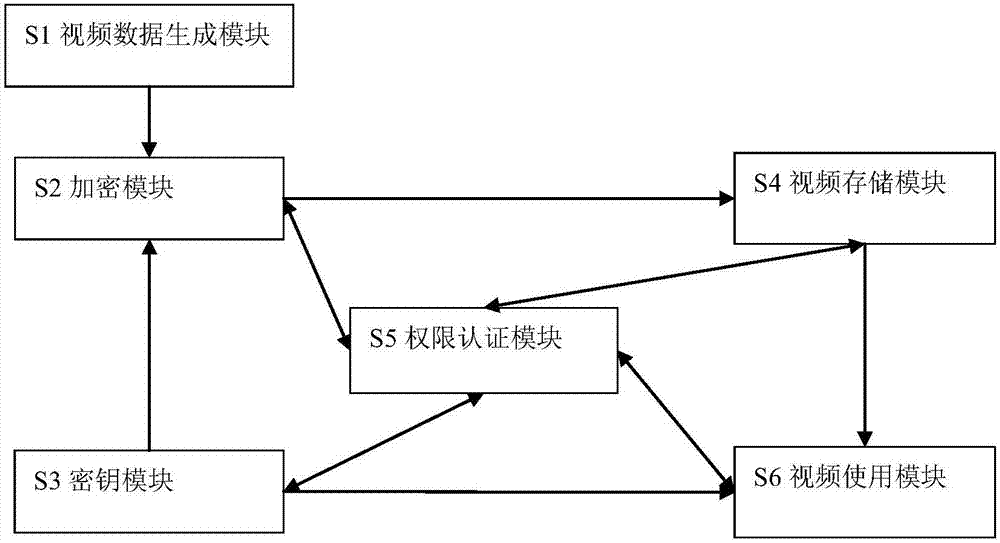
Video data protection system and processing method
PendingCN107426628ALow confidentiality requirementsConstruction cost advantageTransmissionSelective content distributionVideo storageLow confidentiality
The invention relates to a video data protection system and a processing method. The video data protection system comprises a video generating module, a video encrypting module, a key module, a video storage module, a permission authenticating module and a video application module. Specific to a personal user scene, the video generating module, the video encrypting module, the key module, the video storage module and the permission authenticating module are encapsulated into a camera with a function of preventing playing without authorization. Specific to a social scene, the video generating module and the video encrypting module are encapsulated into a social video collection agent; and the permission authenticating module, the key module and the video storage module are encapsulated into a social equipment integrating system. The video data protection system has low confidentiality requirement on the storage and transmission of video data; a used key can be updated on time, so that video breaking difficulty is improved; a file access way is adopted, real-time video data are acquired as the access of ordinary files, so that the real-time video data acquiring difficulty is lowered.
Owner:BEIJING GUOCHUANG KESHI TECH
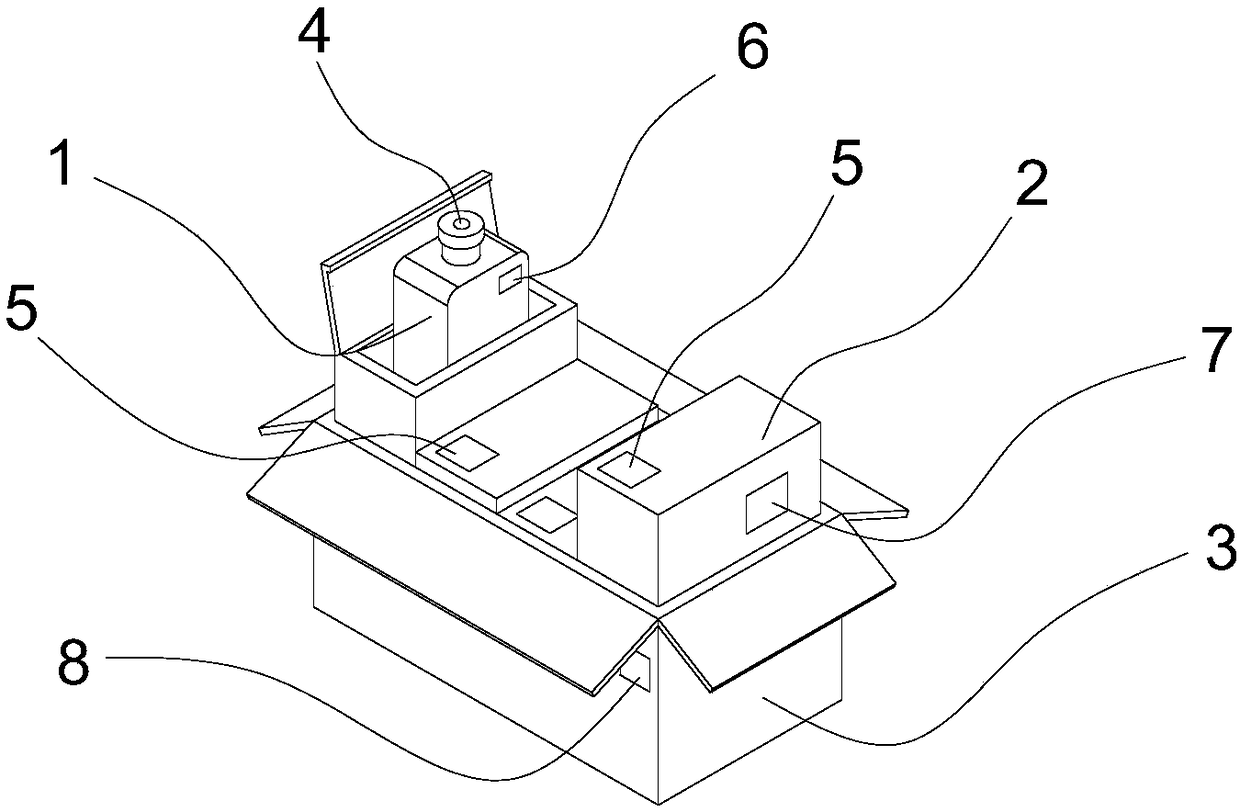
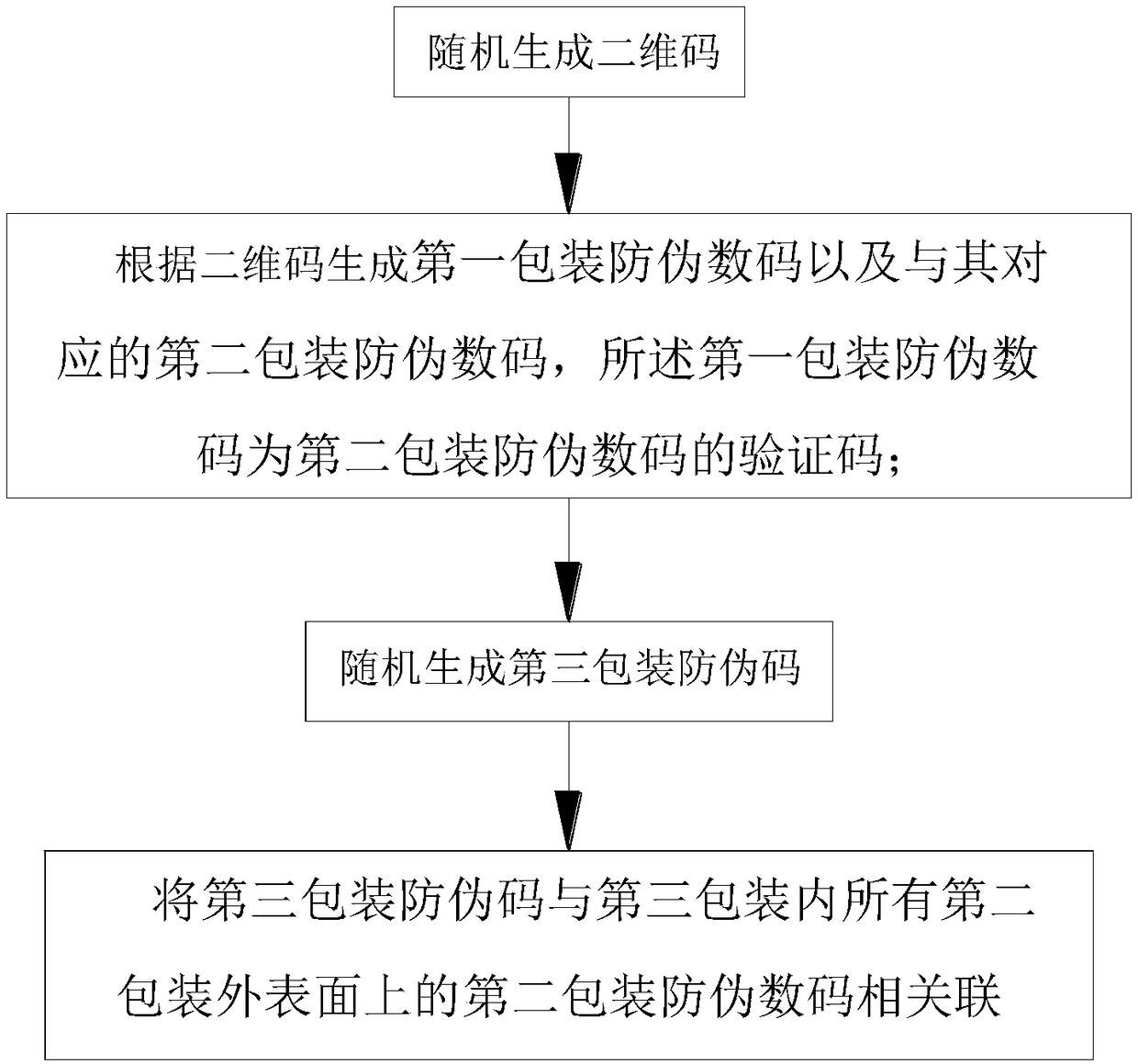
Commodity package and two-dimensional code anti-counterfeiting method thereof
InactiveCN108108780AHigh anti-counterfeiting strengthAnti-counterfeiting realizationCo-operative working arrangementsCommerceComputer hardwareLow confidentiality
The invention relates to a commodity package and a two-dimensional code anti-counterfeiting method thereof. The commodity package and the two-dimensional code anti-counterfeiting method thereof settletechnical problems of low confidentiality, inconvenient searching and complicated production management. The commodity package comprises one or more first packages, one or more second packages and athird package. The two-dimensional code anti-counterfeiting method comprises the steps of utilizing a randomly generated two-dimensional code; generating a first package anti-counterfeiting code and asecond package anti-counterfeiting code according to the two-dimensional code; arranging the two-dimensional code on the external surface of the second package; spraying the second package anti-counterfeiting code on the external surface of the second package, spraying the first package anti-counterfeiting code on the external surface of the first package, randomly generated a third package anti-counterfeiting code, and correlating the third package anti-counterfeiting code with the second package anti-counterfeiting code on the external surfaces of all second packages in the third package; and arranging the third package anti-counterfeiting code on the third package. The commodity package and the two-dimensional code anti-counterfeiting method thereof have advantages of improving counterfeiting difficulty and improving confidentiality grade. The commodity package and the two-dimensional code anti-counterfeiting method thereof can be used in commodity two-dimensional code anti-counterfeiting operation.
Owner:GUIZHOU MOUTAI WINERY GRP XIJIU CO LTD
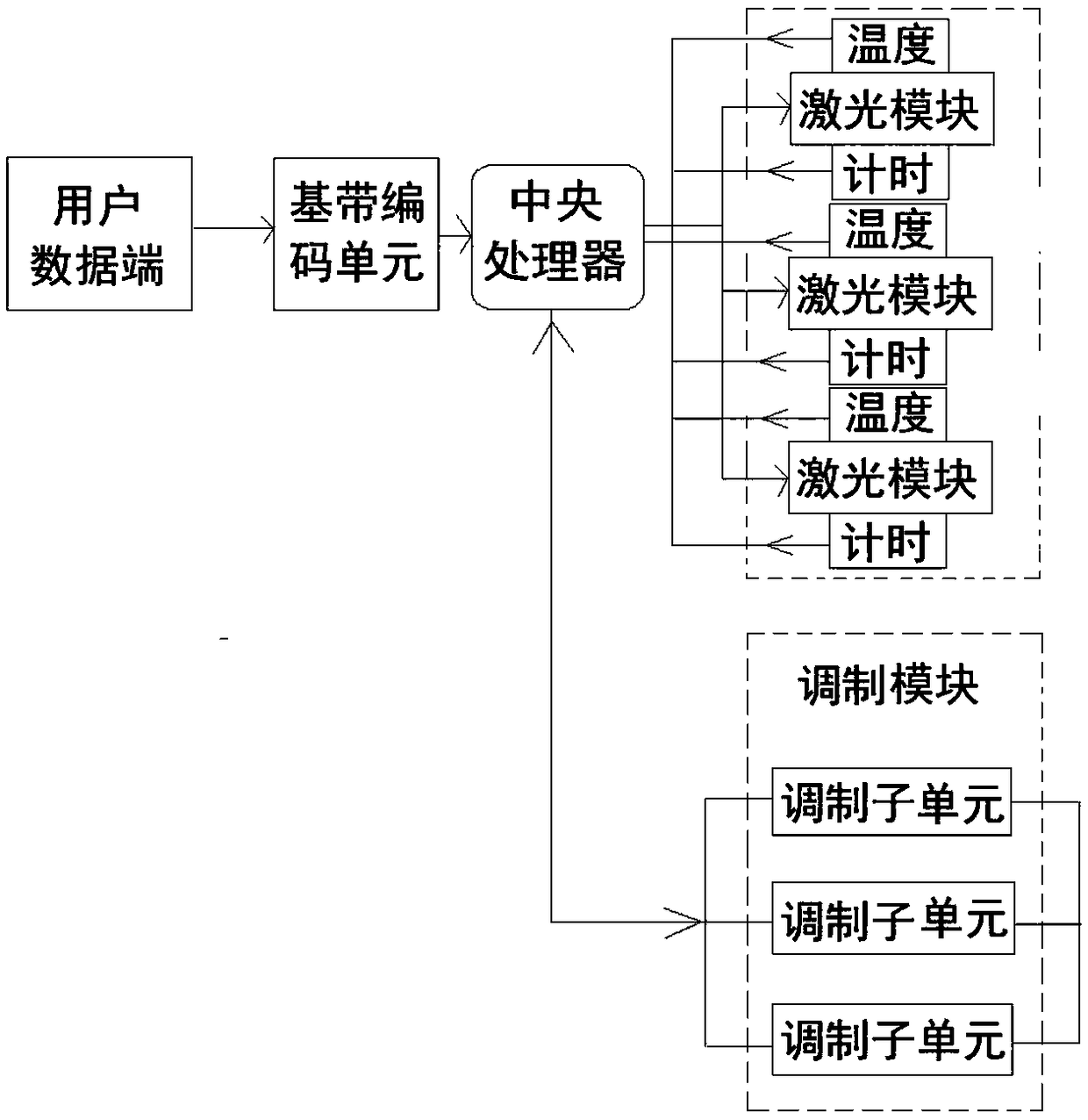
Wireless communication method and system
ActiveCN108736965ADoes not affect suitabilityImprove confidentialityMultiple modulation transmitter/receiver arrangementsModulation type identificationLow confidentialityComputer module
The invention relates to a wireless communication method and system, and aims to solve the technical problems of low confidentiality and low efficiency. A transmitter comprises a baseband coding unitfor converting data into a baseband coding signal, a central processing unit connected with the baseband coding unit, a modulation module connected with the central processing unit, at least two lasermodules, a timing unit and a temperature detection unit, wherein each laser module is provided with an identification code; the central processing unit selects one of the laser modules according to timing parameters of the timing unit and temperature parameters of the temperature detection unit to serve as a laser transmitting module; the laser transmitting module is controlled to transmit a laser signal according to a coding result from the modulation module; the modulation module comprises a plurality of modulation sub-units; each modulation sub-unit corresponds to one modulation method; and the modulation module chooses a corresponding modulation sub-unit according to a modulation identification code of the central processing unit. Through adoption of the wireless communication methodand system, the problem is well solved. The wireless communication method and system can be applied to wireless communication.
Owner:广西奕兴信息科技有限公司
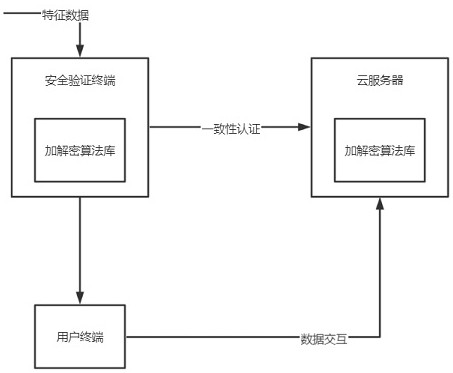
Financial business data cloud interaction method
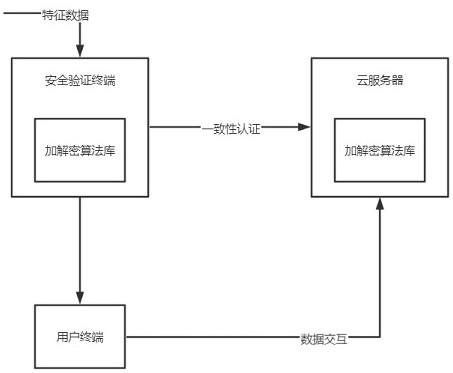
ActiveCN113806725AEfficient Consistency CheckWill not cause errorDigital data protectionDigital data authenticationLow confidentialityEngineering
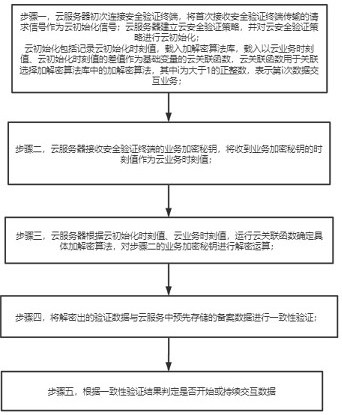
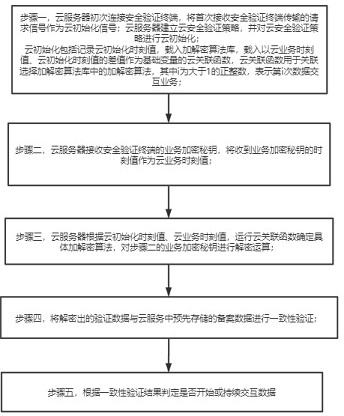
The invention relates to a financial business data cloud interaction method, which solves the technical problem of low confidentiality, and comprises the following steps of: 1, connecting a cloud server with a security verification terminal for the first time, and taking a request signal which is transmitted by the security verification terminal and is received for the first time as a cloud initialization signal; performing cloud initialization on the cloud security verification strategy; 2, receiving a service encryption key of the security verification terminal, and taking a moment value when the service encryption key is received as a cloud service moment value; 3, according to the cloud initialization time value and the cloud service time value, running a cloud correlation function to determine a specific encryption and decryption algorithm, and performing decryption operation on the service encryption key in the step 2; 4, performing consistency verification on the decrypted verification data and pre-stored filing data in the cloud service; and 5, judging whether to start or continuously interact data according to a consistency verification result, so that the problem is well solved, and the method can be applied to financial business data cloud exchange.
Owner:焦成飞
Method and equipment for identifying passwords
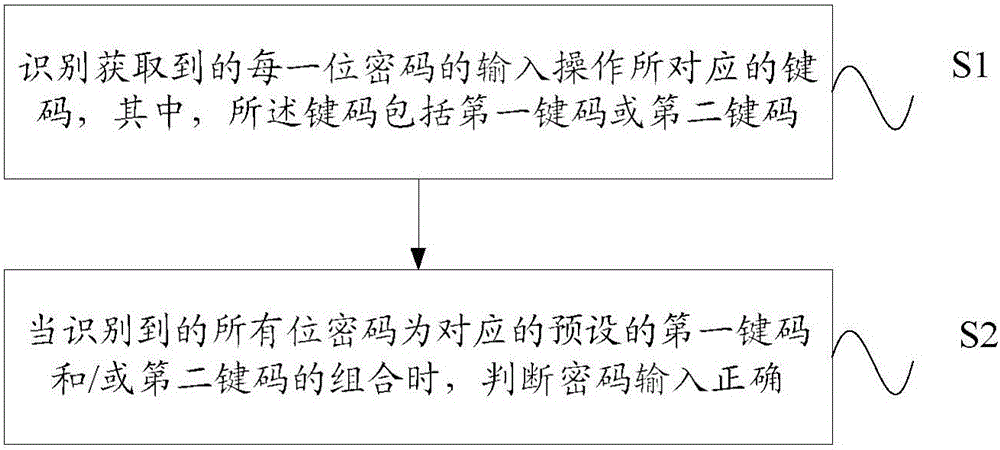
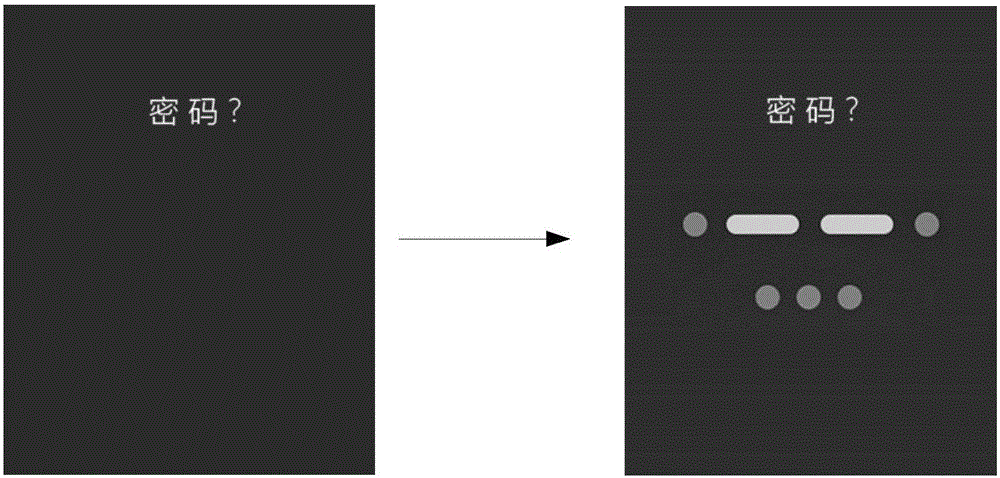
ActiveCN106326727AImprove confidentialitySolve the problem of low confidentialityDigital data authenticationKey pressingLow confidentiality
The invention provides a method and equipment for identifying passwords. The method comprises the following steps of identifying to obtain key codes corresponding to the input of each digit of password, wherein the key codes comprise a first key code or a second key code. The method has the advantages that when all identified digits of password correspond to the preset combination of first key code and / or second key code, the input correctness of the password is judged, so as to solve the problem of false input because multiple press keys corresponding to the key codes are set on the screens, especially smaller screens, the area of each press key is smaller, the user difficultly identifies, and the other press keys are falsely touched; in addition, if the press keys are not set on the screen, the confidentiality of the password is improved, and the problem of low confidentiality of conventional digit and / or aliphatic passwords is solved.
Owner:ALIBABA GRP HLDG LTD
Transmission encryption method and system based on private block chain, medium and electronic equipment
ActiveCN114448736ASolve the costSolve the disadvantages of difficult maintenanceSecuring communicationLow confidentialityEngineering
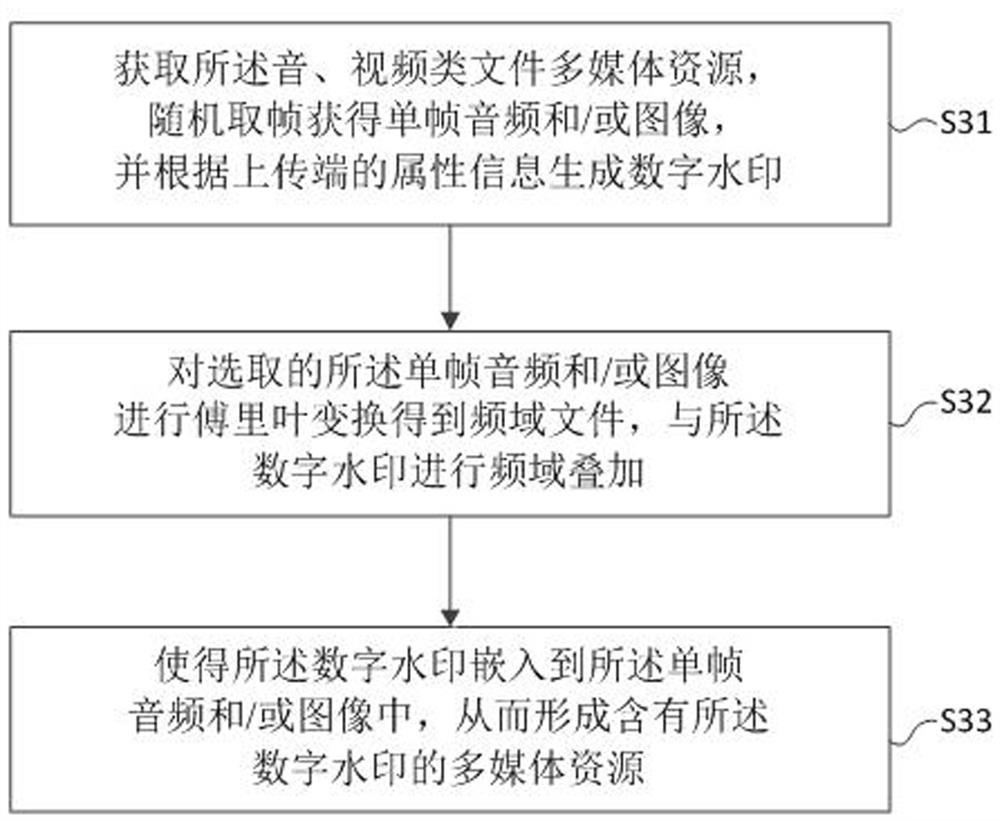
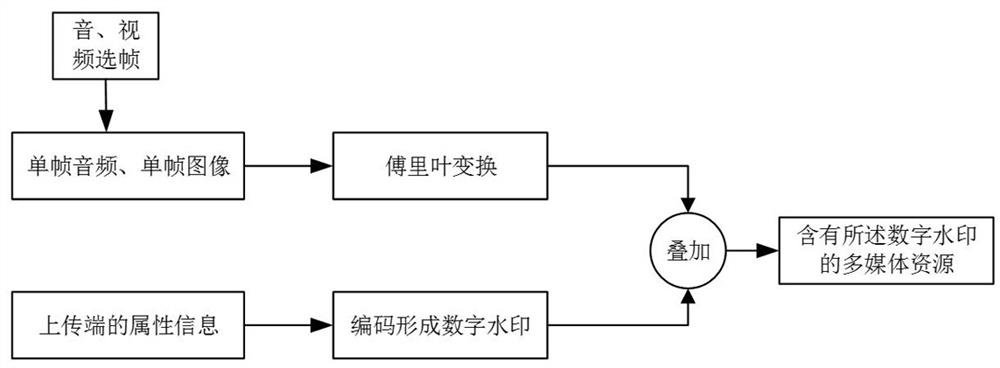
The invention provides a transmission encryption method, device and system based on a private block chain, and electronic equipment, and provides the transmission encryption method and system based on the private block chain, a medium and the electronic equipment according to the confidentiality grade attribute condition of a to-be-uploaded file and the identity, address and uploading time of an uploader. Setting a file confidentiality level, and obtaining a confidentiality level attribute condition of the to-be-uploaded file; according to the attribute condition, not encrypting a low-confidentiality file, and encrypting a high-confidentiality file; the encryption method comprises the step of adding digital watermarks to audio and video files for encryption. According to the private block chain-based transmission encryption method and system, the medium and the electronic equipment, a decentralized and high-security file storage mechanism is formed by using a block chain technology, and in the data transmission process, the risk of leakage of commercial core data can be effectively avoided, core confidentiality can be protected, and stable development of enterprises can be promoted.
Owner:合肥链世科技有限公司
Paper medium destroying system
PendingCN110935533AAvoid the problem of real-time cleaning due to small capacityEffective control of water levelGrain treatmentsLow confidentialityProcess engineering
The invention provides a paper medium destroying system and relates to the paper medium destroying technology field. Technical problems that a paper shredding effect of an existing paper shredding device can only satisfy occasions with a low confidentiality level and the device cannot be applied to the occasions with high confidentiality levels; the existing paper shredding device can automatically shut down for cooling after continuously working for a period of time and is low in working efficiency; and a volume of a paper shredding barrel is limited so that the volume of shredded paper is small in the prior art are solved. The device comprises a shell, a first-stage destroying module and a second-stage destroying module, wherein the first-stage destroying module and the second-stage destroying module are successively arranged in the shell. The first-stage destroying module is located at a top of the second-stage destroying module, the first-stage destroying module comprises a cuttercomponent, and the second-stage destroying module comprises a water inlet control device, a paper liquid adjusting device and a discharging pipeline which are successively arranged. The system is usedfor thoroughly destroying a paper medium.
Owner:ANFANG HI TECH ELECTROMAGNETIC SAFETY TECHN BEIJING
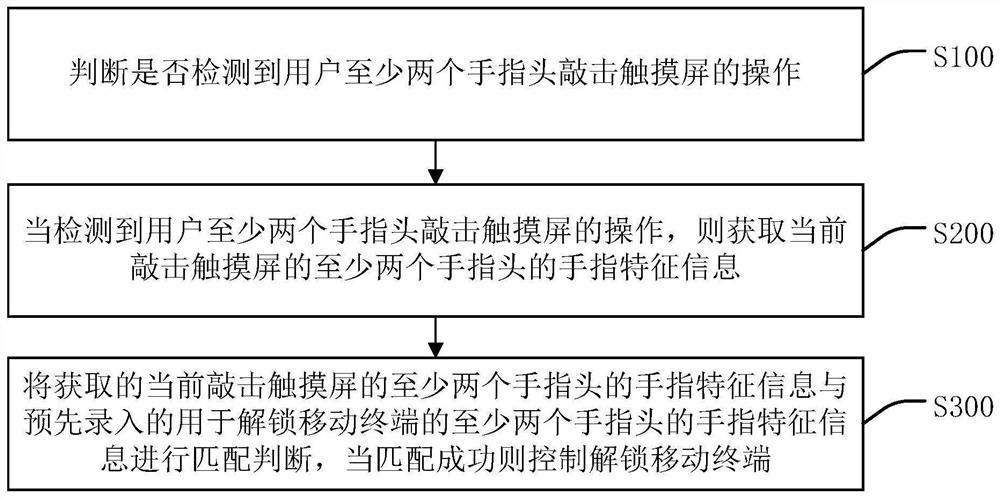
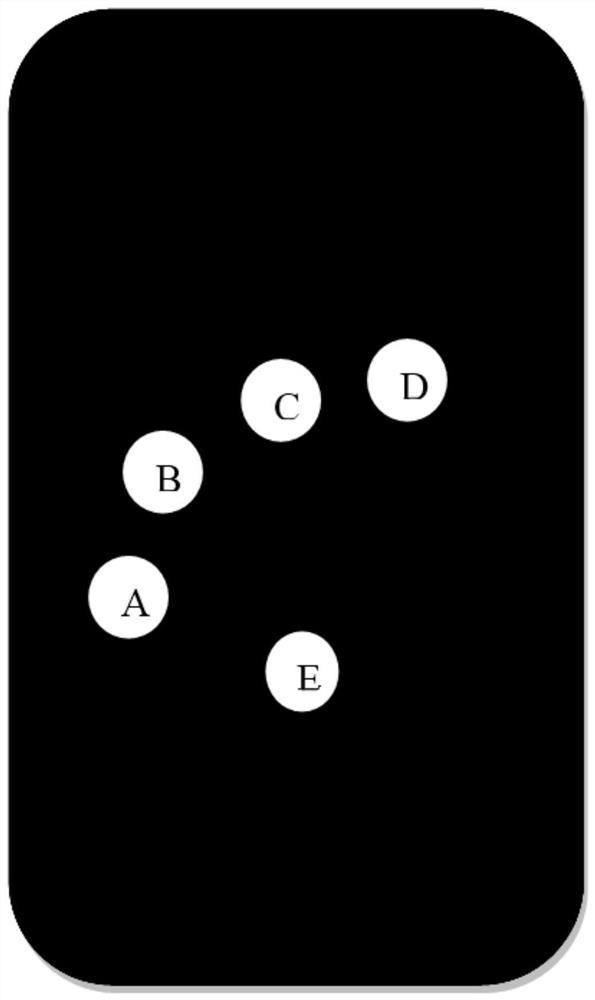
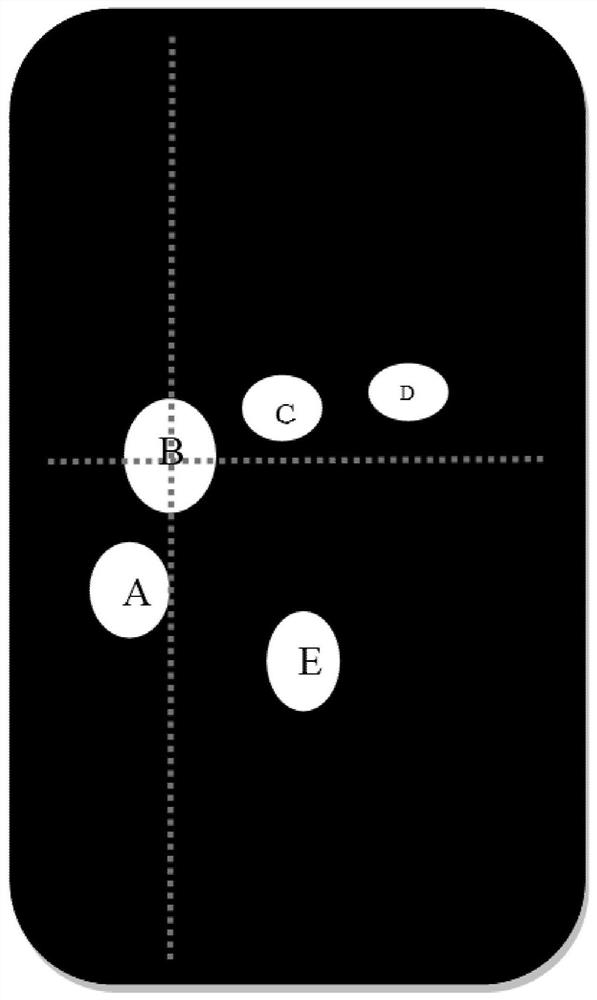
Mobile terminal touch unlocking processing method and device, mobile terminal and storage medium
PendingCN113779531ALow costImprove confidentialityCharacter and pattern recognitionDigital data authenticationComputer hardwareLow confidentiality
The invention discloses a mobile terminal touch unlocking processing method and device, a mobile terminal and a storage medium. The method comprises the following steps: judging whether an operation of knocking a touch screen by at least two fingers of a user is detected or not; when the operation of knocking the touch screen by at least two fingers of the user is detected, obtaining finger feature information of the at least two fingers knocking the touch screen at present; and performing matching judgment on the obtained finger feature information of the at least two fingers currently knocking the touch screen and pre-recorded finger feature information of the at least two fingers used for unlocking the mobile terminal, and controlling to unlock the mobile terminal when matching succeeds. The invention discloses a mobile terminal unlocking method and device and aims to solve the problems of limitation, low confidentiality and high cost of a mobile terminal unlocking scheme in the prior art, so that the mobile terminal supports a user to unlock on a full screen on the basis of not adding hardware, and meanwhile, the mobile terminal has high confidentiality.
Owner:HUIZHOU TCL CLOUD INTERNET CORP TECH CO LTD
A financial business data cloud interaction method
ActiveCN113806725BEfficient Consistency CheckWill not cause errorDigital data protectionDigital data authenticationLow confidentialityBusiness data
The present invention relates to a financial business data cloud interaction method, which solves the technical problem of low confidentiality. By adopting step 1, the cloud server connects to the security verification terminal for the first time, and uses the request signal transmitted by the security verification terminal for the first time as the cloud initialization signal; Perform cloud initialization for the cloud security verification strategy; step 2, receive the business encryption key of the security verification terminal, and use the time value of receiving the business encryption key as the cloud business time value; step 3, according to the cloud initialization time value, cloud business time Value, run the cloud correlation function to determine the specific encryption and decryption algorithm, and decrypt the business encryption key in step 2; step 4, verify the consistency between the decrypted verification data and the pre-stored filing data in the cloud service; step 5, The technical solution of judging whether to start or continue to exchange data based on the consistency verification results can better solve this problem and can be used in financial and commercial data cloud exchanges.
Owner:焦成飞
Intelligent voice recognition module
PendingCN110364167AImprove securityImprove the level ofSpeech recognitionLow confidentialityMiniaturization
The invention relates to an intelligent voice recognition module which solves the technical problems of strong dependence, low confidentiality and low miniaturization degree. The technical scheme is as follows: a housing is provided, the housing is an upper shell and a lower shell which are used in a matched mode, and a PCB, a battery and an NFC module are sequentially arranged between the upper shell and the lower shell from top to bottom; a key is further arranged on the side surface of the PCB; the problem is well solved; and the intelligent voice recognition module can be applied to a voice recognition device.
Owner:深圳市原素盾科技有限公司
Information hiding method and device and computer storage medium
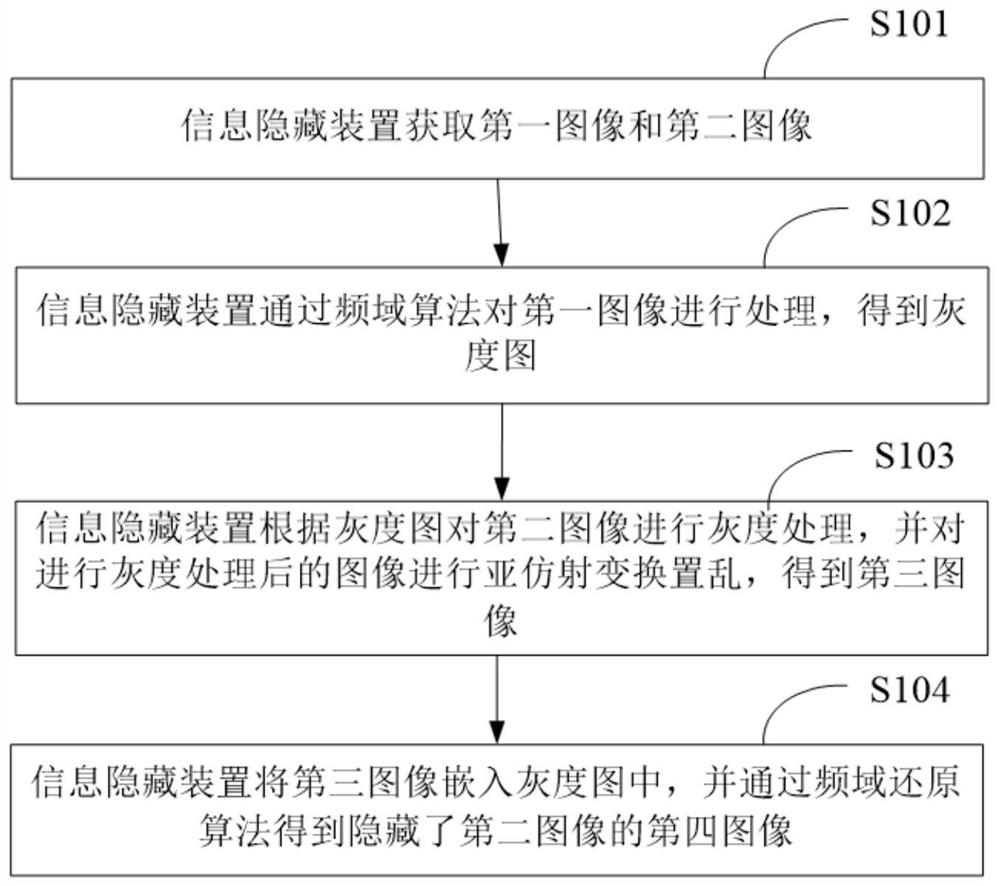
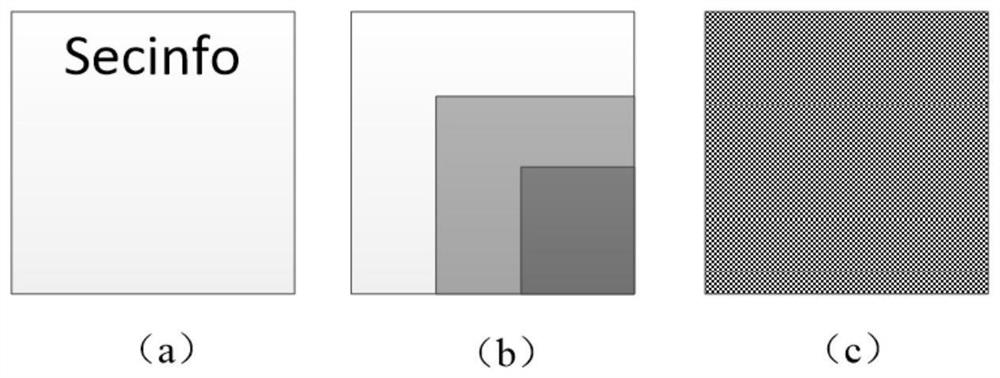
PendingCN113704710AImprove protectionEasy to hideImage data processing detailsDigital video signal modificationPattern recognitionInformation processing
The invention discloses an information hiding method and device and a computer storage medium, relates to the technical field of information processing, and solves the technical problem of low confidentiality of hidden information. The information hiding method comprises the following steps: acquiring a first image and a second image; processing the first image through a frequency domain algorithm to obtain a grey-scale map; carrying out gray processing on the second image according to the gray-scale map, and carrying out sub-affine transformation scrambling on the image subjected to the gray processing to obtain a third image; and embedding the third image into the grey-scale map, and obtaining a fourth image hiding the second image through a frequency domain reduction algorithm.
Owner:SHANGHAI JUNZHENG NETWORK TECH CO LTD
A low temperature storage box
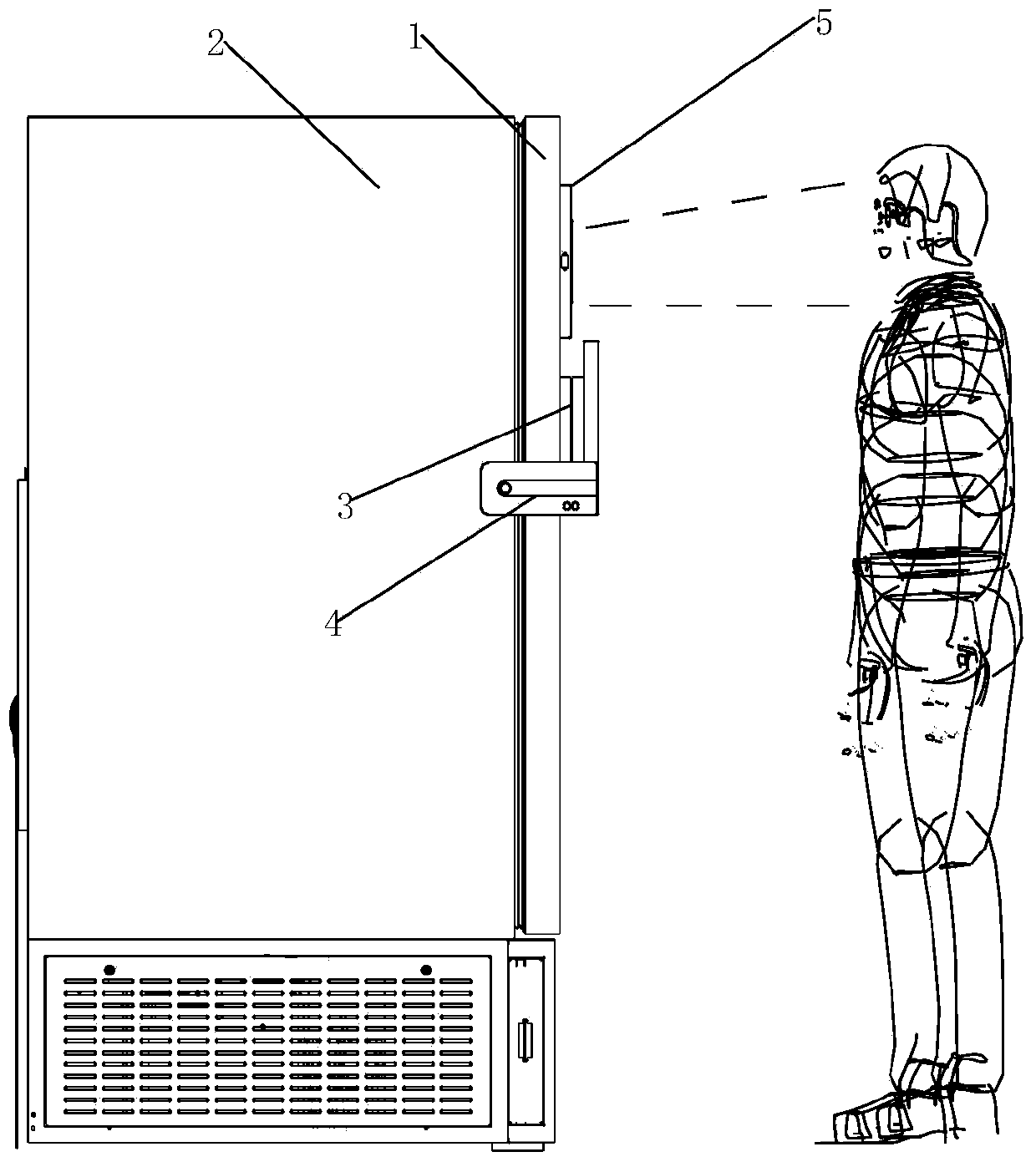
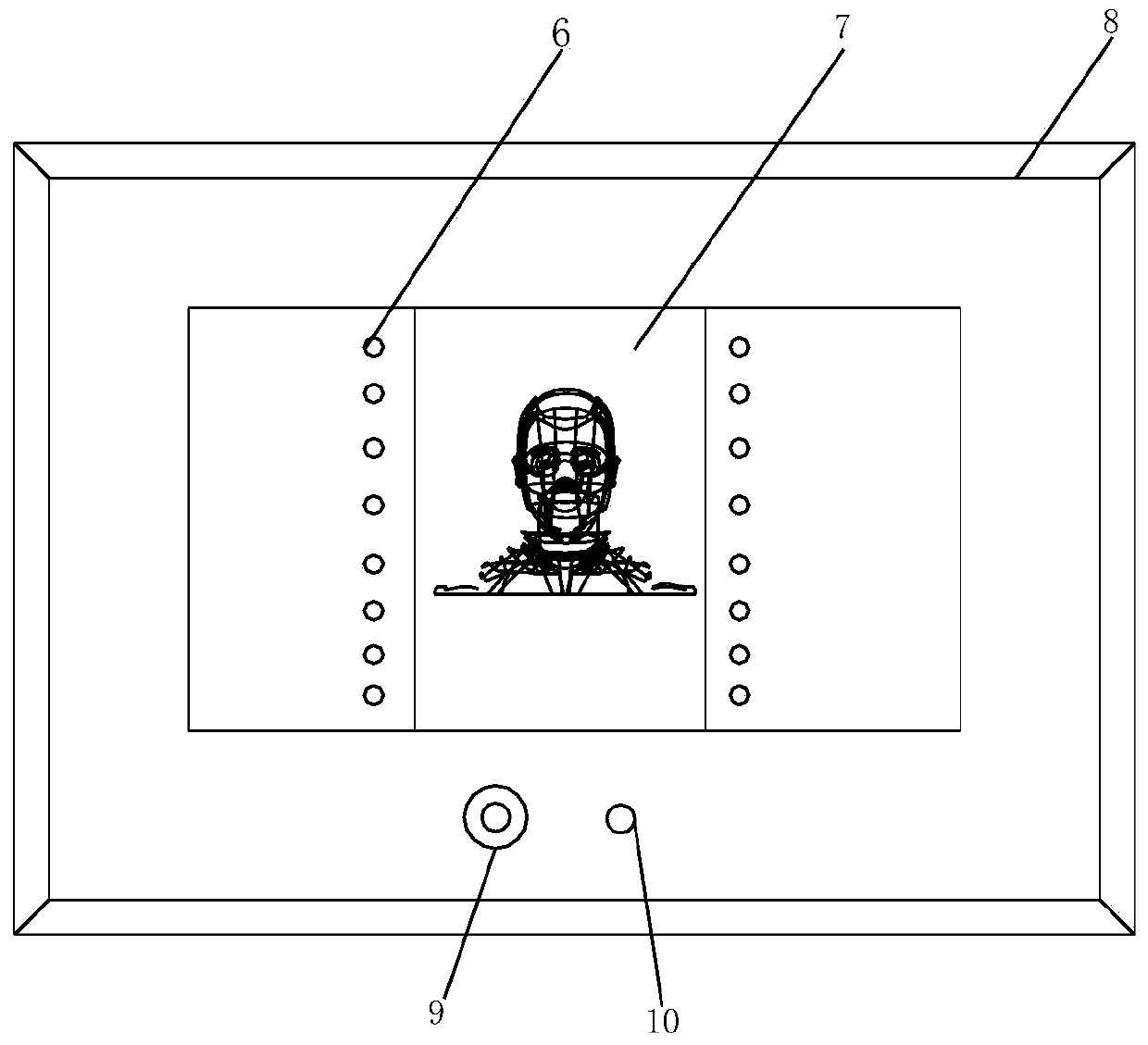
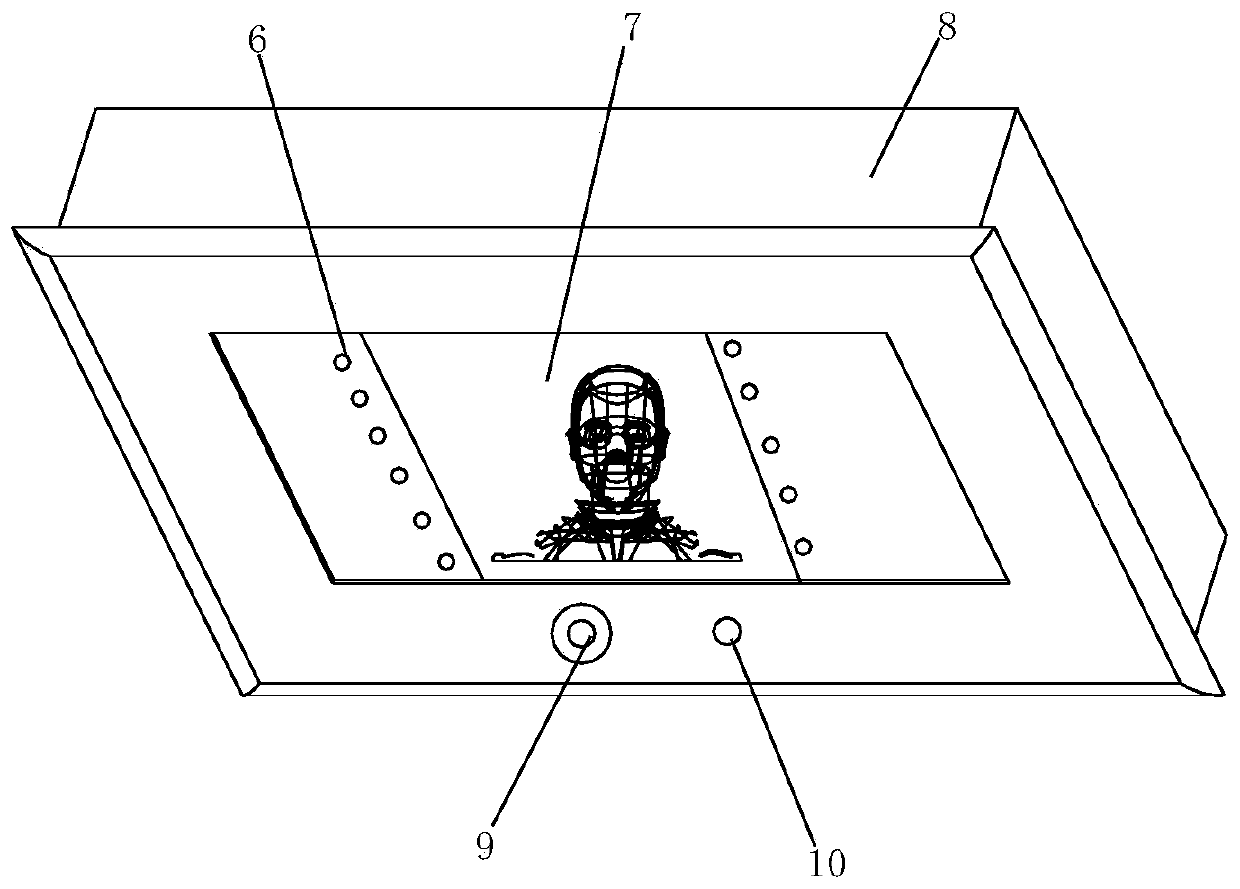
ActiveCN105217147BEasy to useHigh degree of informatizationCharacter and pattern recognitionIndividual entry/exit registersLow confidentialityImaging processing
The invention discloses a novel low-temperature storage box, which belongs to the technical field of storage boxes. It solves the problems that the existing low-temperature storage box can be opened and closed at will, the items in the box are easy to move and extract at will, and the security is low. The new low-temperature storage box includes a door body and a box body, the door body is locked with the box body, and a face recognition system is provided on the door body. The face recognition system includes an image recognition processing module, an electromagnetic switch module and a power supply module; the power supply module and The image recognition processing module and the electromagnetic switch module are connected separately to supply power to the image recognition processing module and the electromagnetic switch module; the image recognition processing module matches the acquired sample image with the image information in the database, and if the matching is successful, the unlocking signal is transmitted to the electromagnetic switch module , the electromagnetic switch module includes a first electromagnetic pole and a second electromagnetic pole that attract each other, and the first electromagnetic pole is located on the door body.
Owner:QINGDAO AUCMA ULTRA LOW TEMPERATURE FREEZING MACHINES
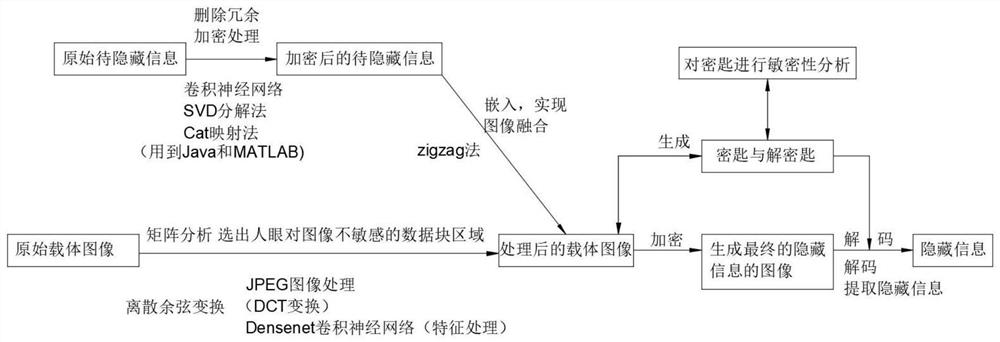
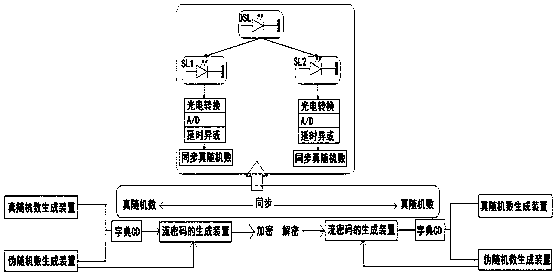
Fusion encryption image information hiding method
PendingCN114598529AImprove securityIncrease freedomKey distribution for secure communicationLow confidentialityInformation transmission
The invention discloses a fusion encryption image information hiding method, and relates to the technical field of image information encryption (communication technology), and the method comprises the steps: S1, preparing original to-be-hidden information; s2, encrypting the hidden information; s3, embedding a hidden file; s4, encrypting an original carrier image; s5, decoding the hidden information; s6, extracting hidden information; the method has the beneficial effects that firstly, by using a multi-layer encryption technology, information with a relatively high confidentiality level is placed in a deep layer, and information with a relatively low confidentiality level is placed in a surface layer, so that authorized personnel of different levels can see encrypted information of corresponding levels, and the security of the encrypted information is improved; compared with the prior art, the method has the advantages that the information transmission safety is improved, meanwhile, the freedom and applicability of watching objects during information encryption are improved, the effective time and the failure time of the information and the key can be set according to the use requirement by adopting the dynamic encryption technology, so that the method is suitable for part of special scenes, and the timeliness of information transmission is improved.
Owner:NORTHEASTERN UNIV
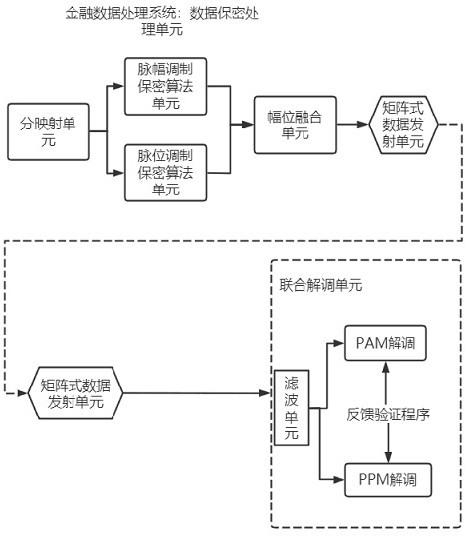
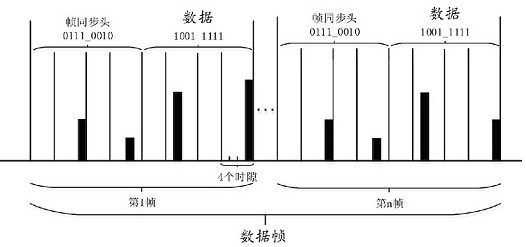
High-confidentiality financial data processing system
ActiveCN113422788AImprove effectivenessRealize high confidentiality data transmissionTransmissionFinancial data processingData processing system
The invention relates to a high-confidentiality financial data processing system, which solves the technical problem of low confidentiality. The high-confidentiality financial data processing system comprises a data confidentiality processing unit, and the data confidentiality processing unit comprises a sub-mapping unit, a pulse amplitude modulation secrecy algorithm unit and a pulse position modulation secrecy algorithm unit which are connected with the sub-mapping unit, the rear ends of the pulse amplitude modulation secrecy algorithm unit and the pulse position modulation secrecy algorithm unit are uniformly connected with an amplitude and position fusion unit, and the amplitude and position fusion unit is connected with a matrix type data transmitting unit; the data confidentiality processing unit further comprises a matrix type data receiving unit corresponding to the matrix type data transmitting unit, and the matrix type data receiving unit is connected with a joint demodulation unit, so that the problem is well solved, and the system can be used for financial data processing.
Owner:焦成飞
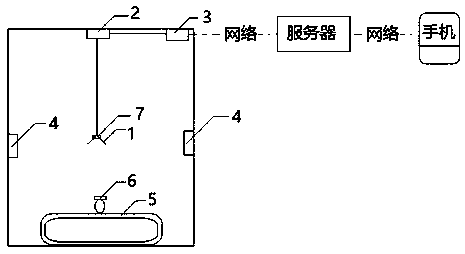
Online doll catching machine for blind
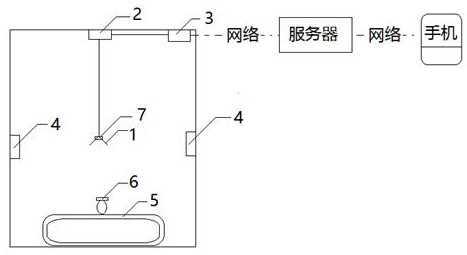
ActiveCN108479056AImprove confidentialityImprove isolationIndoor gamesTransmissionLow confidentialityPassword
The invention relates to an online doll catching machine for the blind. The online doll catching machine for the blind solves the technical problem of low confidentiality. The online doll catching machine for the blind comprises a doll machine, a server connected with the doll machine through a communication network and a mobile terminal connected with the server through a communication network. The doll machine includes a mechanical arm, a mechanical arm control unit and a video image acquisition unit. The mechanical arm control unit and the video image acquisition unit are jointly connectedwith a data transmission unit, and the data transmission unit includes a password generation device. The password generation device is used for generating a password and adding to the data header andthe server for data encryption transmission, and the technical scheme for the mobile terminal to perform data interaction with the server solves the problem better and can be used in the doll machineapplication.
Owner:日照新睿招商发展有限公司
Implementation of Optimal Security Throughput and Efficient Energy Harvesting in Swipt Systems
ActiveCN108736989BEfficient collectionReduce overheadTransmission monitoringSecurity arrangementLow confidentialitySelf adaptive
The invention discloses a method for implementing an optimal confidentiality throughput and high-efficiency energy collection in a SWIPT (Simultaneous Wireless Information and Power Transfer) system.According to the method for implementing the optimal confidentiality throughput and high-efficiency energy collection in the SWIPT system, a confidentiality throughput of a legal user is calculated, athreshold is set to judge whether confidentiality interruption occurs so as to calculate a confidentiality interruption probability, and by regulating a target confidentiality rate and a power distribution ratio of a transmitting terminal, the optimal confidentiality throughput is obtained; and a receiving terminal adaptively regulates a power distribution coefficient according to received powerand information decoding sensitivity and only provides power which meets the decoding requirement for information decoding, and other power is all used for energy collection. The method solves the problems of low confidentiality throughput and low energy collection efficiency when an eavesdropper exists in an existing SWIPT system.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
A kind of online claw machine for the blind
ActiveCN108479056BImprove confidentialityImprove isolationIndoor gamesTransmissionComputer hardwareNetwork connection
Owner:日照新睿招商发展有限公司
An information call method and electronic device
ActiveCN106156646BImprove confidentialityImprove securityDigital data protectionLow confidentialityEngineering
The invention relates to the field of information security, discloses an information retrieval method and electronic equipment, and aims to solve the technical problem of lower confidentiality of information in the prior art. The method is applied to the electronic equipment, a first control interface of a first application program is displayed on the electronic equipment, the method comprises the steps of acquiring a first input parameter of a user of the electronic equipment for the first control interface through detection; judging whether the first input parameter is a first preset parameter or not; retrieving a privacy space of the electronic equipment when the first input parameter is the first preset parameter, wherein a second application program loading the privacy space and the first application program are different application programs. The technical effect of improving the confidentiality of the privacy space is achieved.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Message forwarding method and device
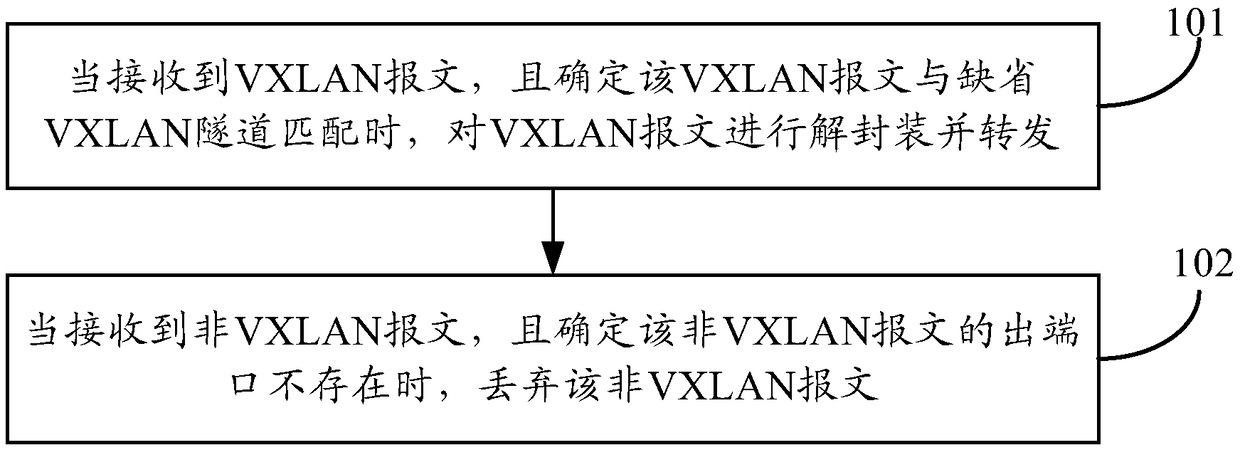
ActiveCN109474507ARealize one-way transmissionEnsure safetyNetworks interconnectionLow confidentialityDistributed computing
The invention provides a message forwarding method and device. The method comprises the steps of: when a VXLAN message is received and the fact that the VXLAN message is matched with a default VXLAN tunnel is determined, performing de-encapsulation and forwarding on the VXLAN message; and, when a non-VXLAN message is received and the fact that the output port of the non-VXLAN message does not exist is determined, abandoning the non-VXLAN message. By adoption of the embodiment of the invention, one-way transmission between high-confidentiality VTEP equipment and low-confidentiality VTEP equipment can be realized; and the data security is ensured.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com