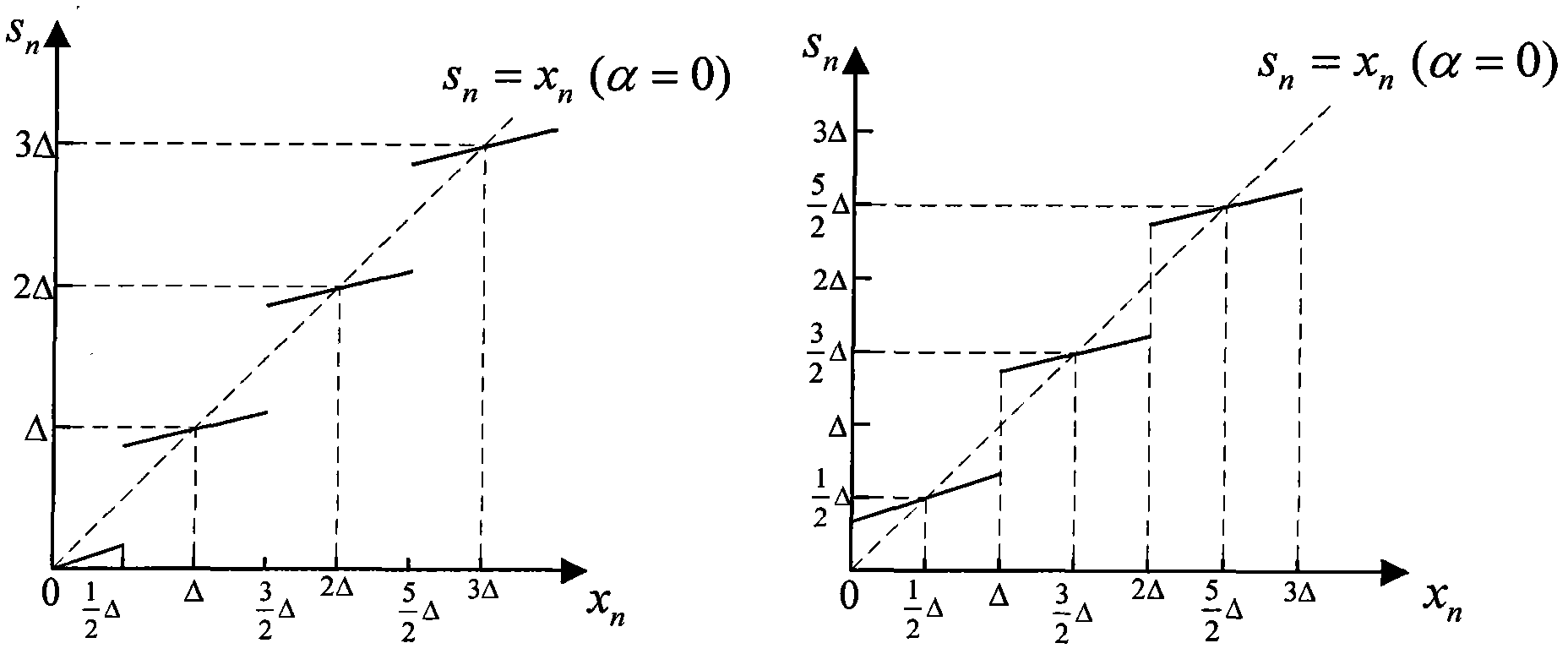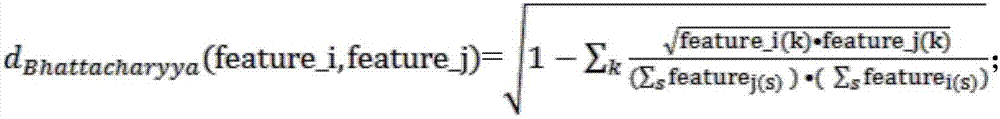Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1077 results about "Information hiding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, information hiding is the principle of segregation of the design decisions in a computer program that are most likely to change, thus protecting other parts of the program from extensive modification if the design decision is changed. The protection involves providing a stable interface which protects the remainder of the program from the implementation (the details that are most likely to change).
Mobile ticketing via information hiding
InactiveUS20070017979A1Reduce riskBuying/selling/leasing transactionsVerifying markings correctnessBarcodeInformation hiding
A information-hidden mobile ticketing system, having a ticket purchasing device, an mobile ticket issuance management system, a embedded mobile ticket, a mobile communication device, and a ticket verification device. The user can purchase a mobile ticket from the mobile ticket issuance management system via the ticket purchasing device. Once the purchasing information is provided, the mobile ticket can be sent in the form of a message, a multi-medium message or other wireless form to a mobile communication device assigned by the purchaser. The information hiding method is used to embed the barcode representing the mobile ticket in a digital image. By a program specified by the mobile communication device, the digital image can be retrieved. Thereby, the risk of being decoded and stolen can be alleviated.
Owner:CHUNGHWA TELECOM CO LTD
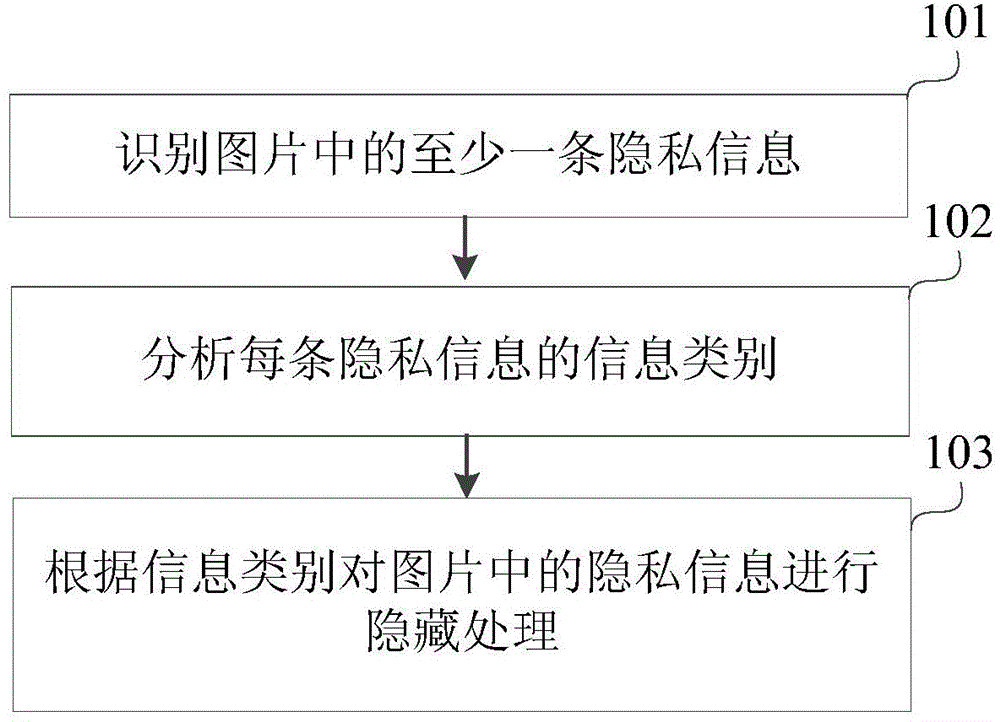
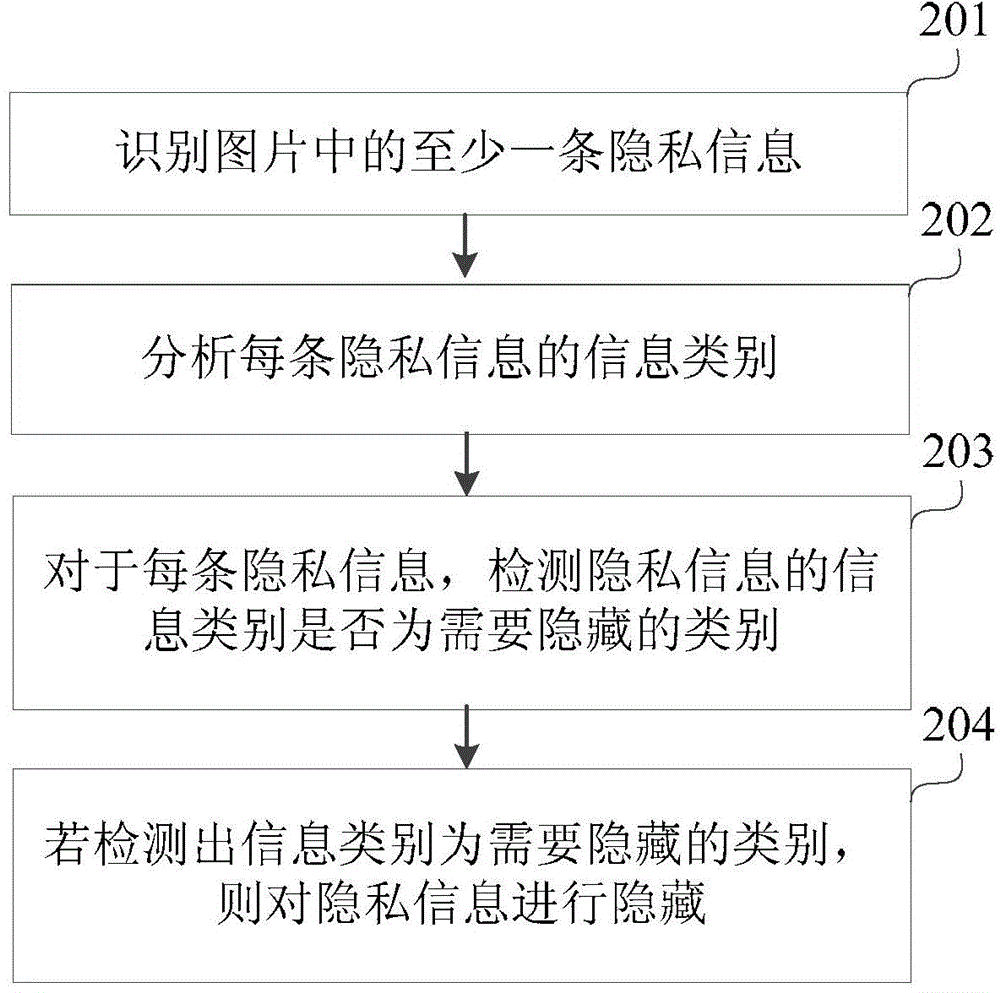
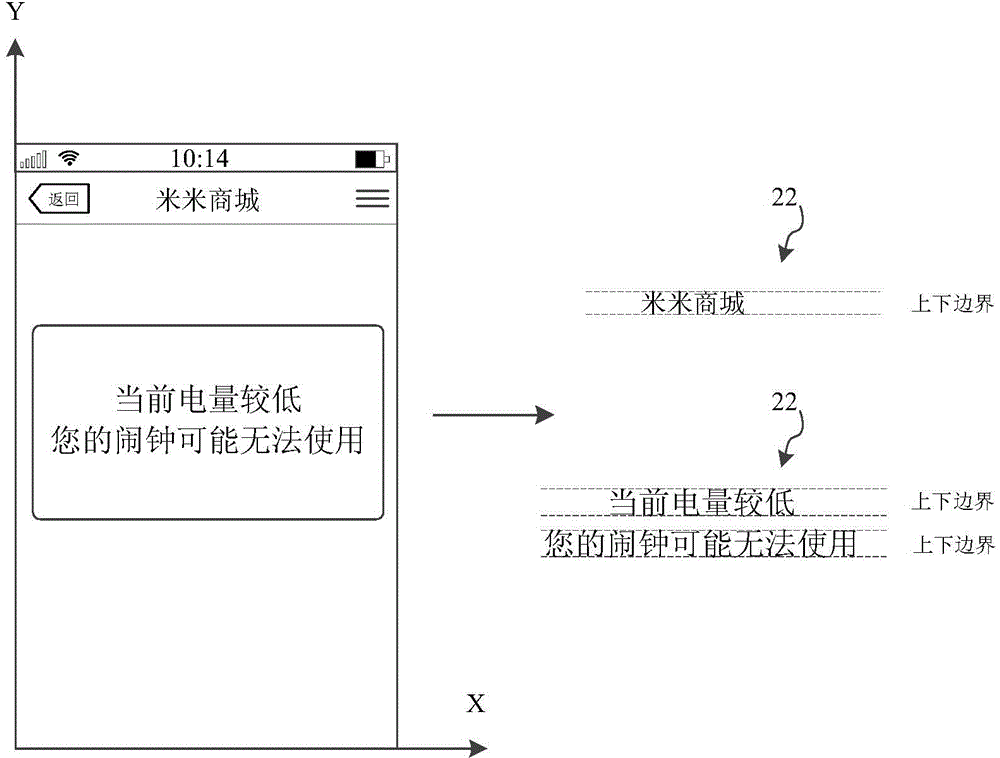
Privacy-information hiding method and device
ActiveCN104021350ASolve processing problemsAchieve the hidden effectTelevision system detailsImage enhancementInformation typeInformation processing
The invention relates to a privacy-information hiding method and device, and belongs to the field of image processing. The privacy-information hiding method comprises the following steps of identifying at least one piece of privacy information in an image, analyzing the information type of each piece of privacy information, and hiding the privacy information in the image according to the information types. According to the privacy-information hiding method and device, the problem that privacy-information processing cannot be carried out on images of which not all character information is privacy information needing to be hidden in related technologies is solved; according to the information types of the privacy information, the privacy information is hidden in different processing modes.
Owner:XIAOMI INC
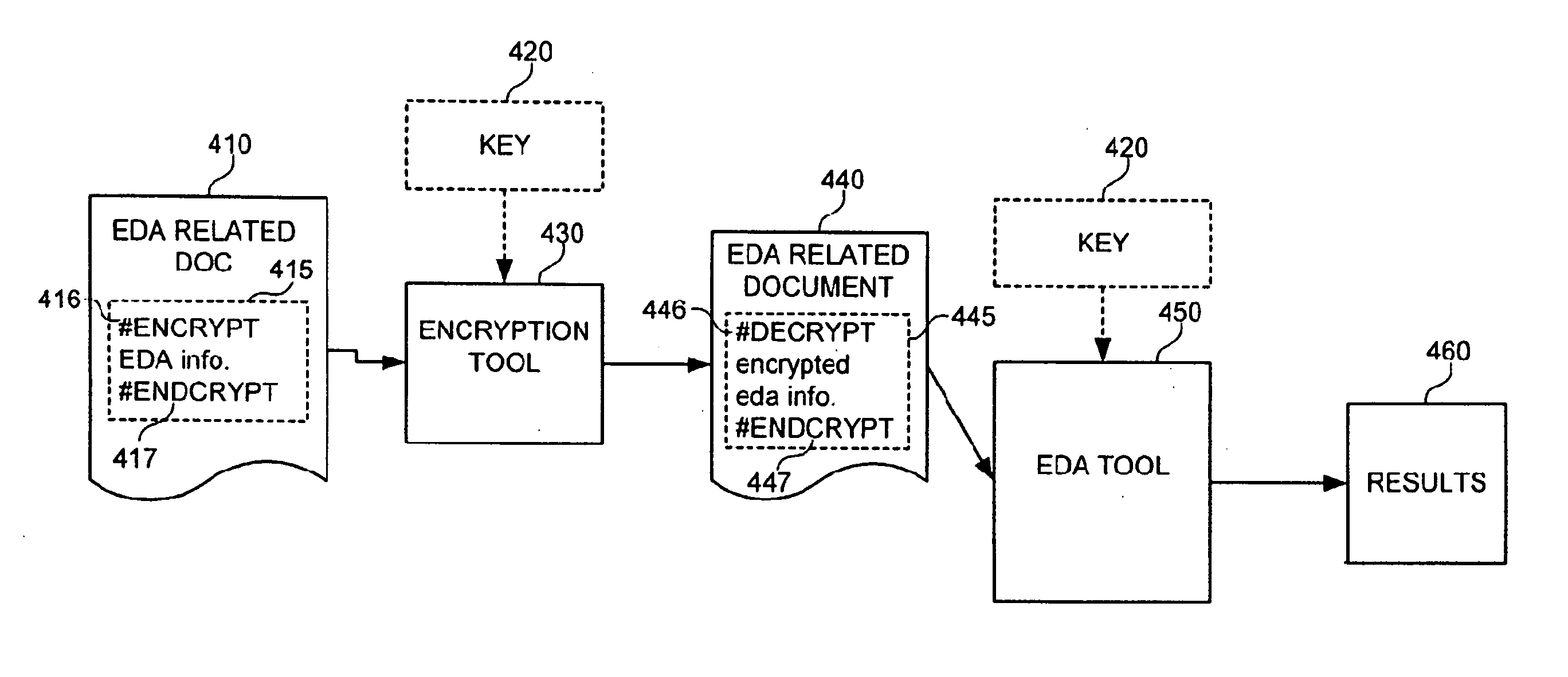
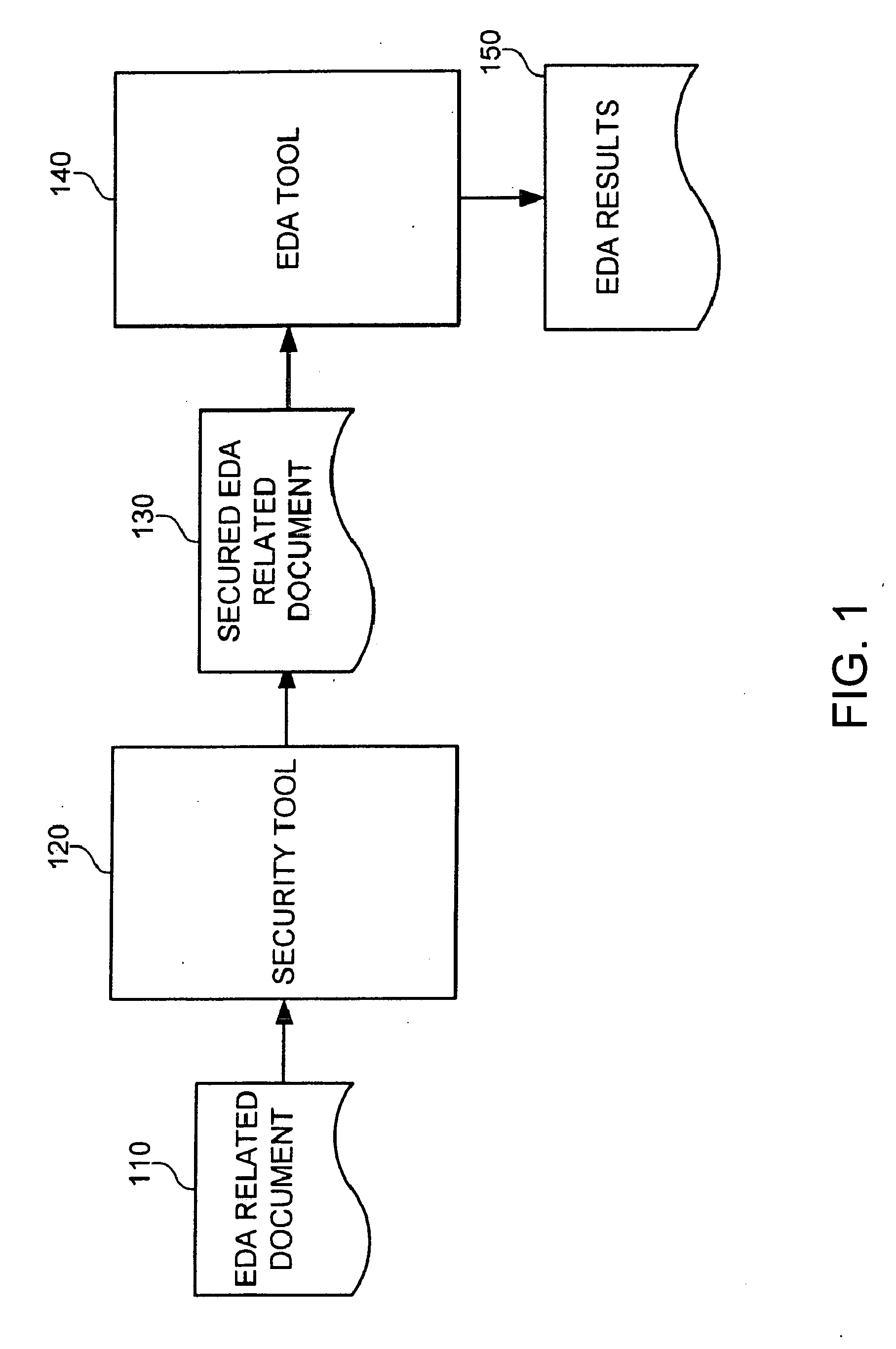
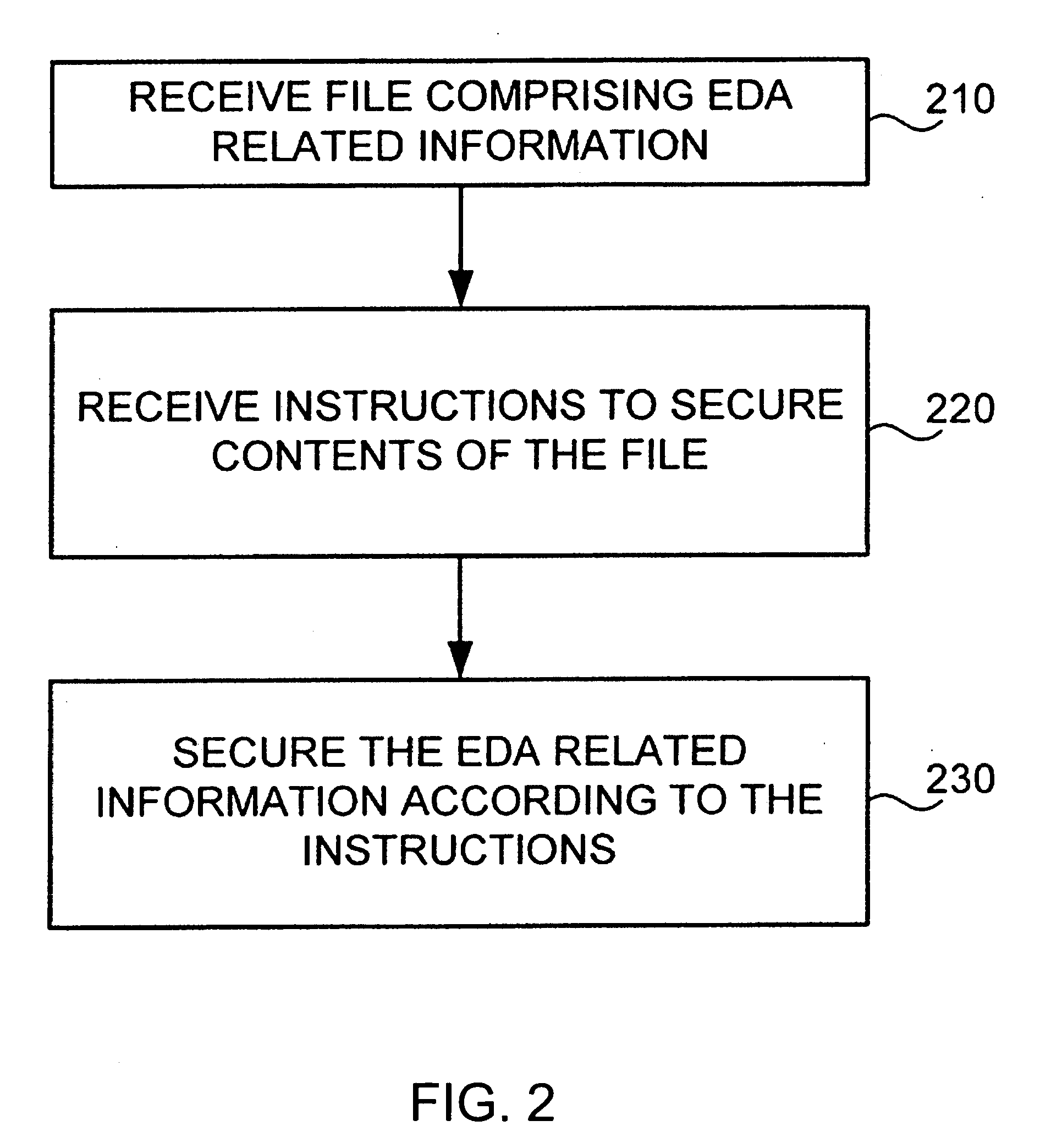
Concealment of information in electronic design automation
InactiveUS20070055892A1Digital data processing detailsUser identity/authority verificationEngineeringInformation hiding
An electronic design automation tool may receive information related to electronic design automation that contains secured information, such as physically secured information, and annotations to indicate the secured portions of the information. Upon receiving such information, the electronic design automation tool may identify those portions of the information comprising secured information related to electronic design automation, and unlock the secured information for processing. The electronic design automation tool may process at least some of the secured electronic design automation information without revealing that secured information to unauthorized persons, tools, systems, or otherwise compromising the protection of that secured information. That is, the design automation tool may process the secured electronic design automation information so that the secured information is concealed both while it is being processed and by the output information generated from processing the secured information.
Owner:MENTOR GRAPHICS CORP
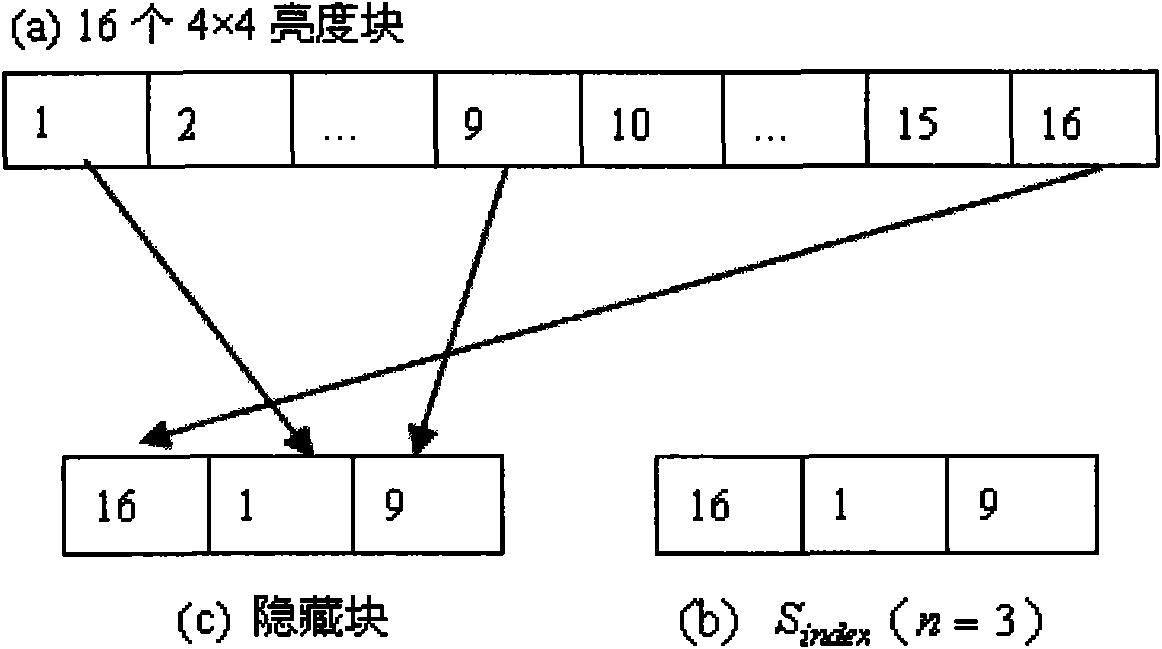
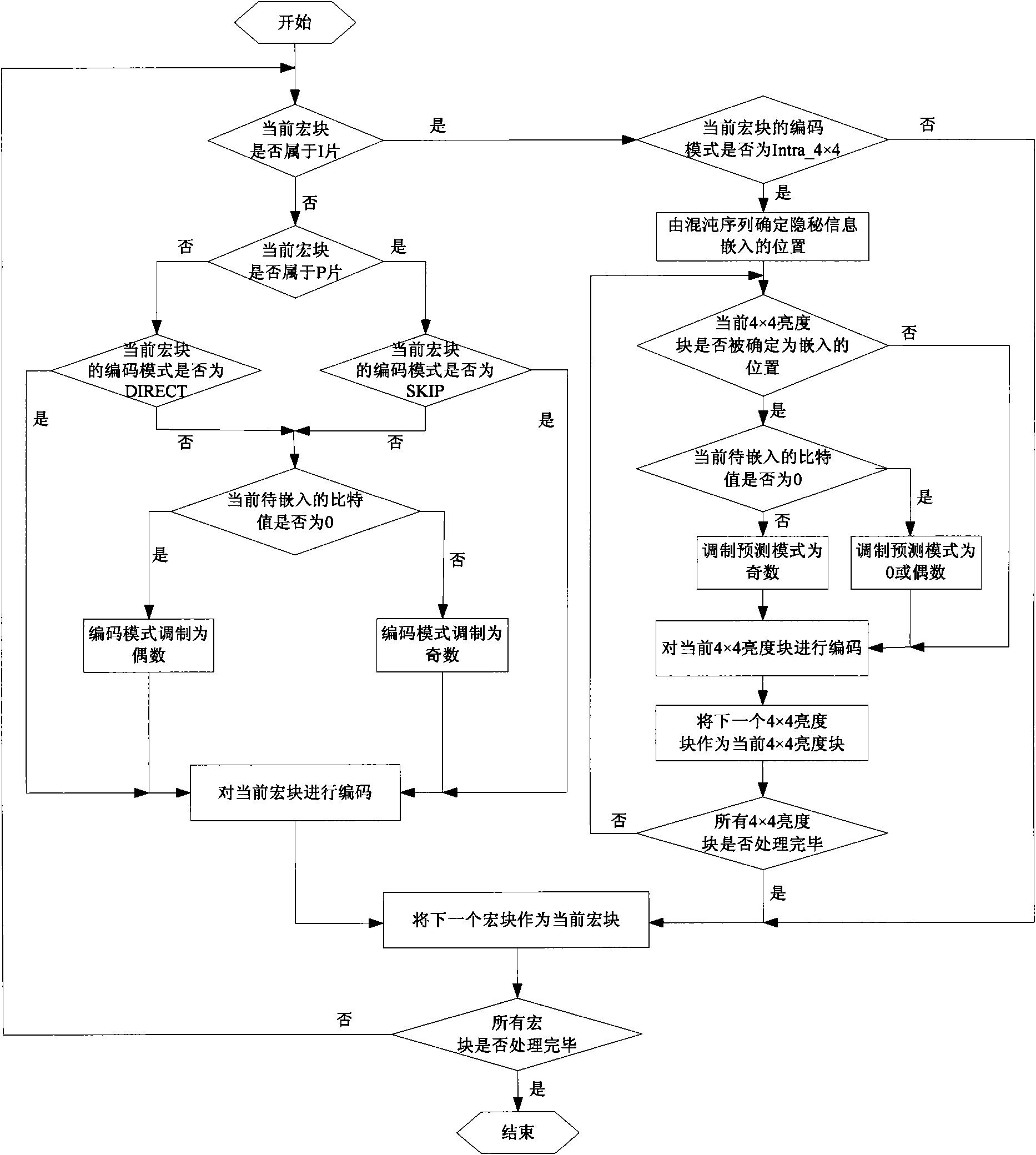
H.264/AVC video information hiding method based on predictive mode
InactiveCN101621692AAchieve hiddenReduce the impact of objective qualityTelevision systemsDigital video signal modificationObjective qualityComputer architecture
The invention discloses an H.264 / AVC video information hiding method based on a predictive mode. For a macro block whose coding mode is Intra_4*4 in an I chip, a predictive mode of a 4*4 luma block is modulated to a suboptimal predictive mode from an optimal predictive mode under the circumstance that the predictive mode of the 4*4 luma block needs to be changed, and for macro blocks whose coding modes are marked not by 0 in a P chip and a B chip, a coding mode of a macro block is modulated to a suboptimal predictive mode from an optimal predictive mode under the circumstance that the predictive mode of the macro block needs to be changed; the impact on the objective quality of a video, caused by the change of the predictive mode or the coding mode, can be reduced as much as possible under the circumstance of ensuring that the secret information can be effectively hidden at the same time; on the other hand, due to the fact that the secret information not only can be embedded in the macro block whose coding mode is Intra_4*4 in the I chip but also can be embedded in the macro blocks whose coding modes are marked not by 0 in the P chip and the B chip, the higher hiding capacity can be obtained.
Owner:NINGBO UNIV
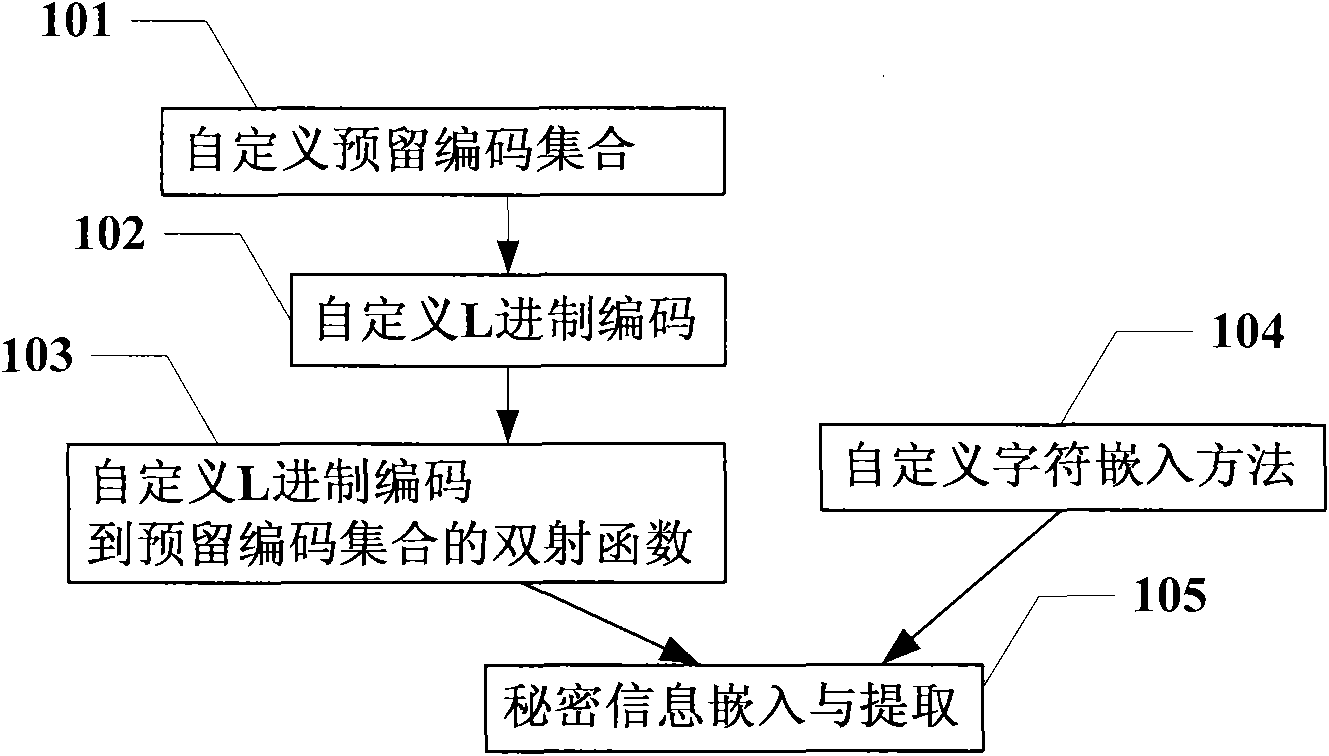
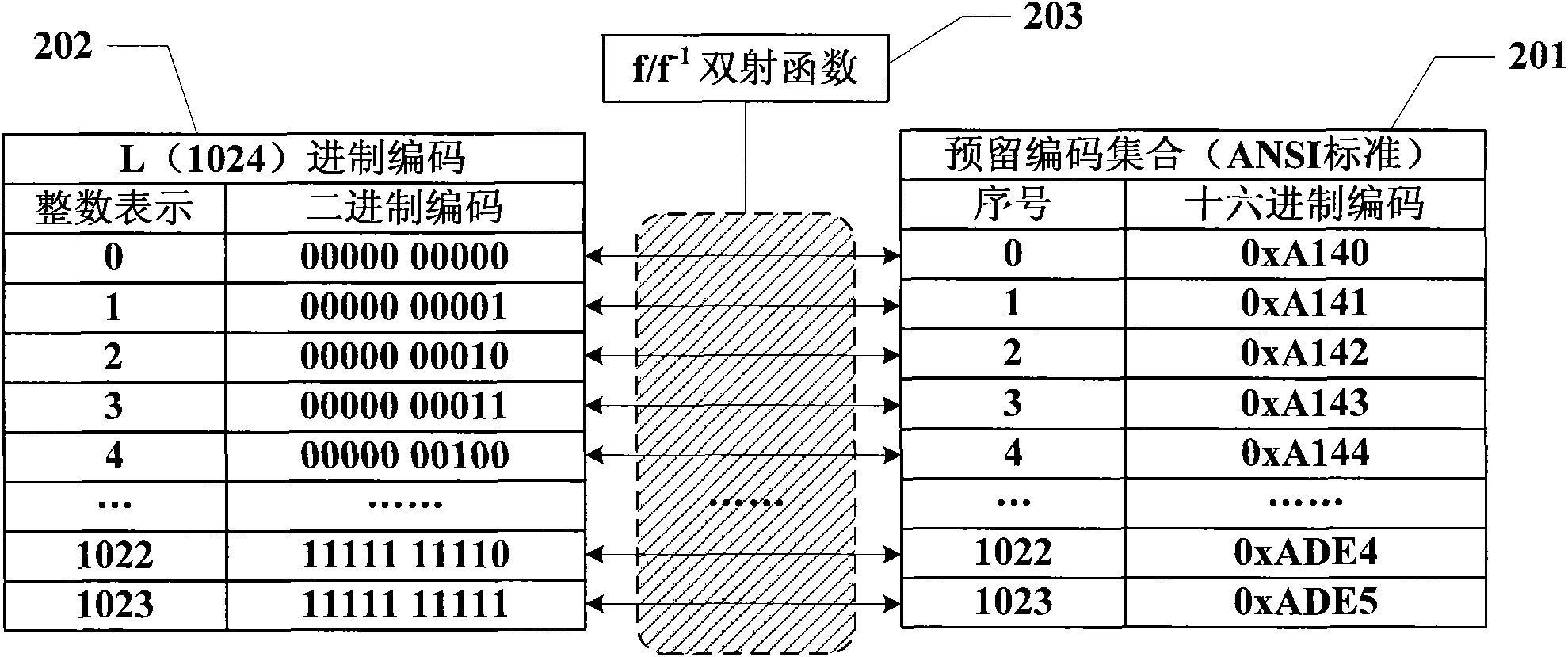
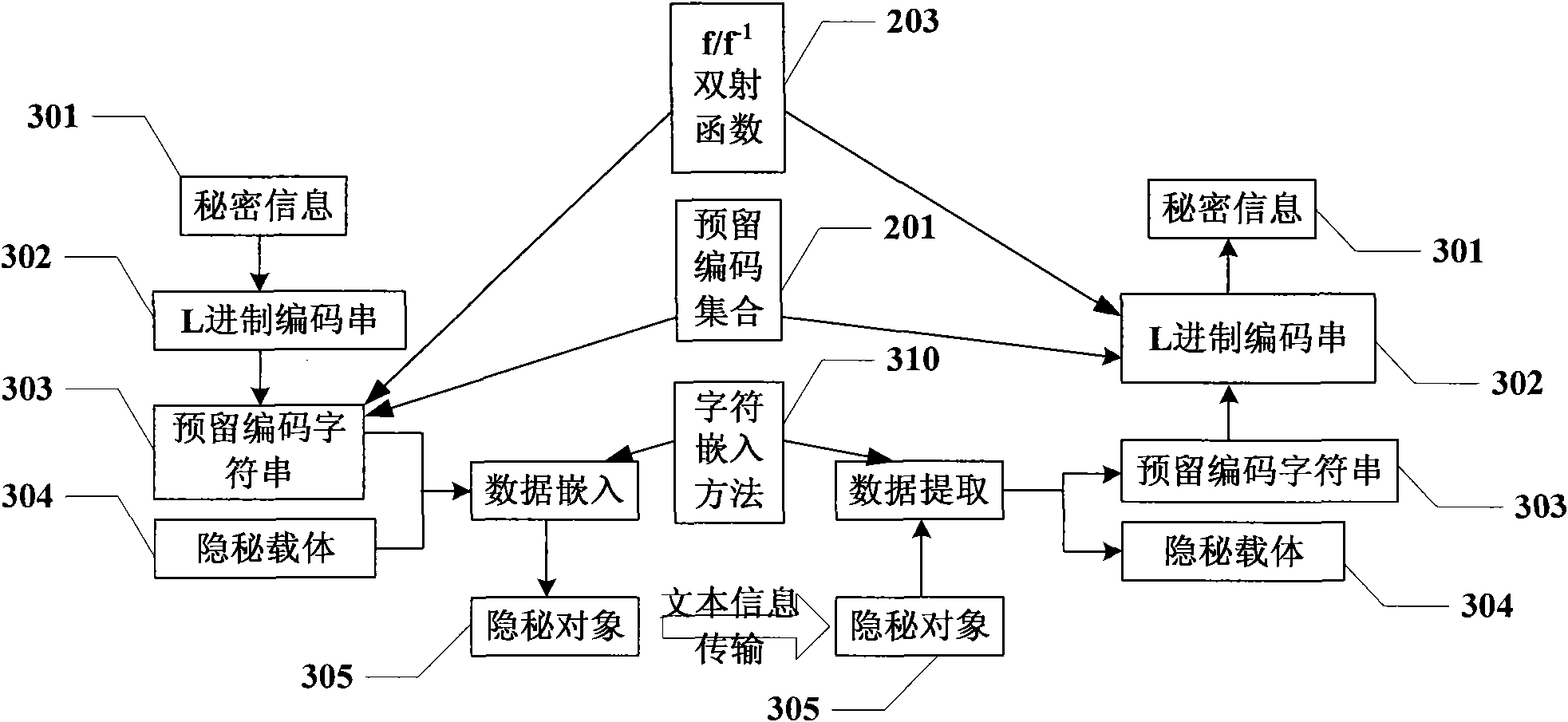
Information hiding method taking text information as carrier
InactiveCN101645061ADoes not affect normal displayHigh coding utilizationComputer security arrangementsSpecial data processing applicationsInformation hidingData transmission
The invention discloses an information hiding method taking text information as a carrier, which is used for providing a hiding channel to secret information in the process of data transmission. The method comprises the following steps: self-defining a reserved code set according to a character coding standard characteristic; self-defining an L scale code according to a base number L of the reserved code set; self-defining a bijective function f of the L scale code to the reserved code set and a reverse function f<-1> thereof; self-defining a method of embedding reserved code character stringsin text information; embedding the secret information to a carrier of the text information and obtaining a secret object; and extracting the secret information from the secret object. The informationhiding technology takes the text information as the carrier and has strong versatility, large hiding capacity, good transparence and strong safety.
Owner:张浩
Covert document system
InactiveUS20070029394A1Improve securityEfficient implementationPaper-money testing devicesPattern printingLatent imageDocument preparation
This invention relates generally to document protection methods and product. More specifically, the present invention relates to a method for hiding information in a document by means of a latent image or message, which is practically invisible to the naked eye and may only be revealed through use of a matching viewing device. The present invention further relates to a method for creating original documents containing latent messages, which are revealed when the document is read by a viewing device. In one embodiment, print elements such as lines, dots, spots, swirls, or images are used to form covert information. The covert information print elements are disposed at an angle to print elements of a background, thus creating a covert document. In another embodiment, print elements of the covert information are used with a solid background.
Owner:DOCUMENT SECURITY SYST
Considerable information hide method using JPEG2000 compression image as carrier
InactiveCN101304522AIncrease hidden capacityNormal decodingPulse modulation television signal transmissionImage codingCoding blockRate distortion
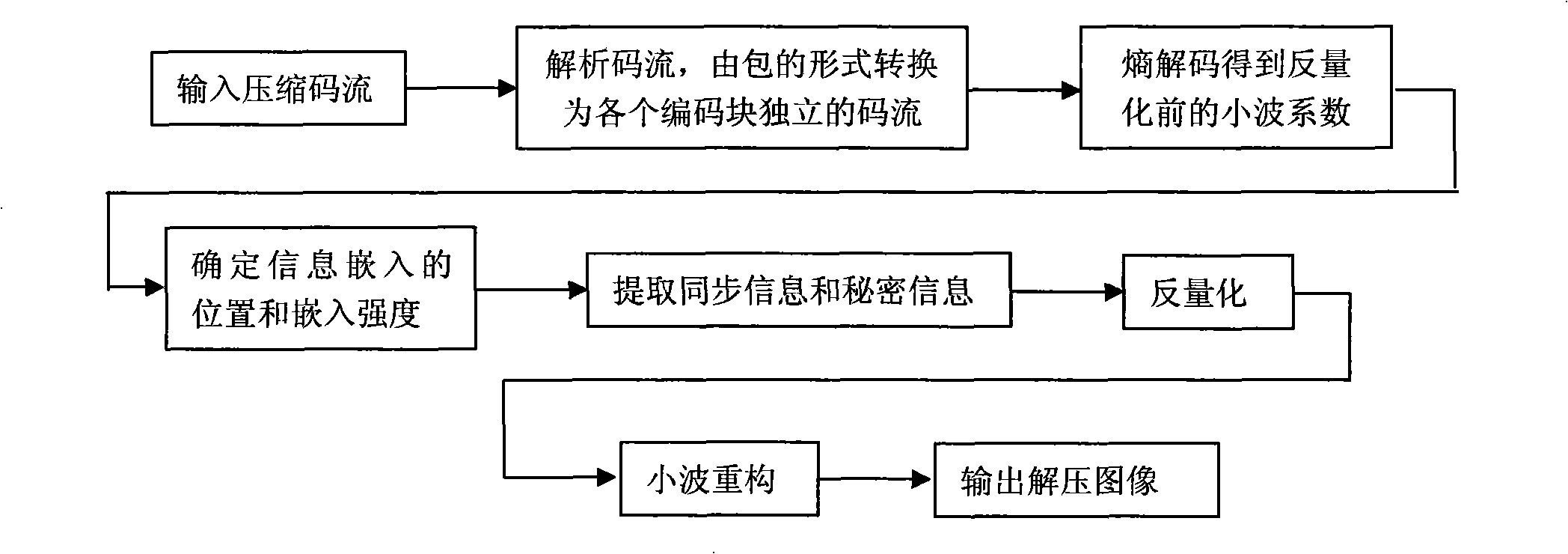
The invention relates to a high capacity information hiding method using JPEG2000 compressing images as the carrier. The operation steps are: applying wavelet decomposition, wavelet coefficients quantification and bit-plane coding to images, and determining the truncation position of the code flow of all coding blocks and the lowest bit-plane of the embeddable information by rate-distortion optimization; primarily choosing a wavelet coefficient which is more than the threshold value as the embedding point, and making a redundancy estimation and adjusting the embedding point and the embedding strength; embedding the synchronous information and the hidden information into the quantified wavelet coefficient in an order of the bit plane from the lowest to the highest starting from the lowest embeddable bit-plane; making a second bit-plane coding and organizing the code flow after embedding the information. The high capacity information hiding method is based on a second coding strategy to determine the embedding position and improves the information hiding volume by self-adaptively choosing the embedding point and adjusting the embedding strength, The high capacity information hiding method has the advantages of being transparent completely for the standard JPEG2000 decoders and being able to be conveniently integrated in the JPEG2000 coders. Meanwhile, the code flow still can decode normally after being embedded with hiding information.
Owner:CIVIL AVIATION UNIV OF CHINA
Real-time speech secret communication system based on information hiding
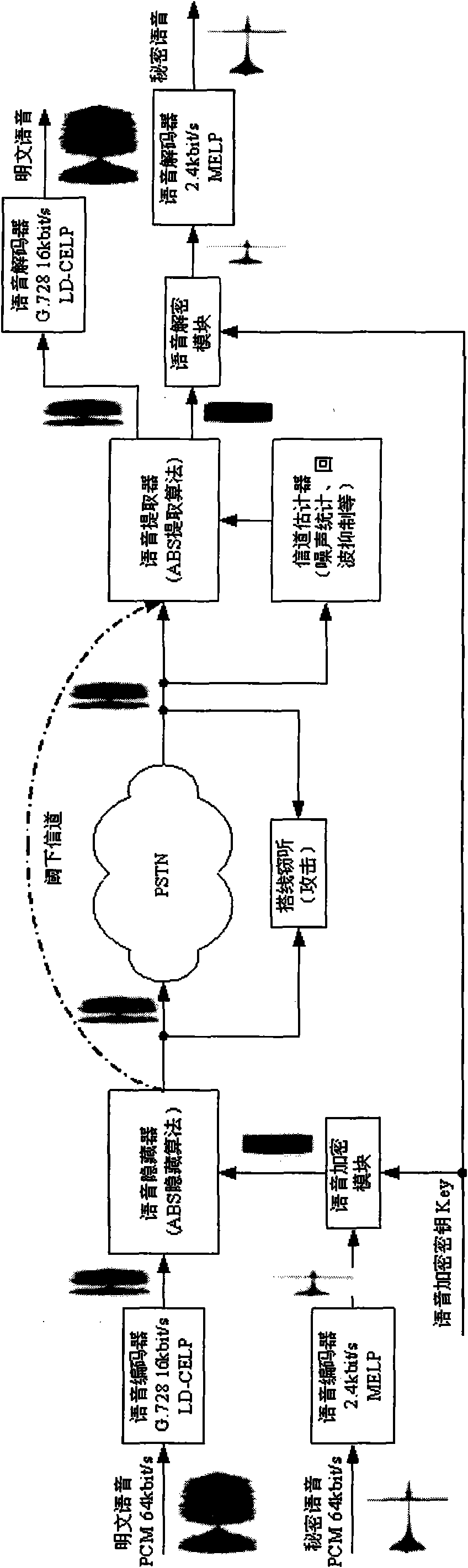
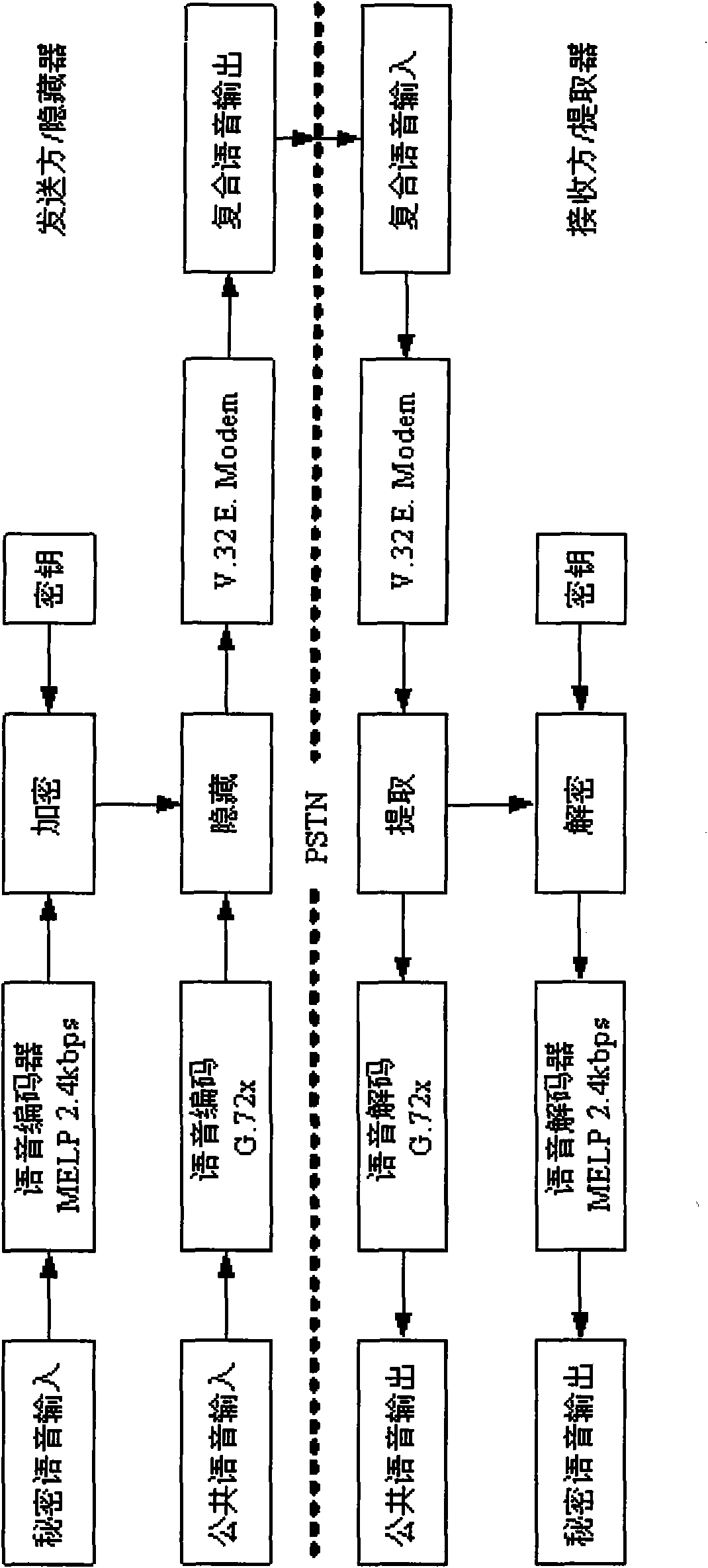
The invention relates to a speech information hiding secret communication system which organically integrates techniques, such as information hiding, passwords, communication, and the like. In the invention, MELP2.4KBps secret speech is hidden in the public speech of G.721, G.728, GSM and G.729 of a code-excited linear prediction code by connecting a public telephone network PSTN, mobile communication GSM / CDMA, videoconferences and a VoIP network and utilizing a speech information hiding and extraction algorithm, and a private channel is established in a public communication channel to carry out the real-time secret communication of secret speech information. The system adopts an embedded type technique based on DSP, and designs corresponding functional modules, such as speech coding and decoding, speech encryption and decryption, speech information hiding and extraction, and the like. Under the condition that a certain communication rate and a certain speech quality are ensured, secret speech real-time communication is carried out on various public channels, and the communication quality reaches the requirement of a communication standard.
Owner:吴志军 +1
Development System with Methodology Providing Information Hiding in Executable Programs
InactiveUS20060136875A1Program/content distribution protectionSpecific program execution arrangementsTheoretical computer scienceInformation hiding
A development system providing a method for information hiding in executable programs is described. In one embodiment, for example, a method of the present invention is described for hiding information in computer programs, the method comprises steps of: receiving first input comprising program modules for a computer program being created, the program modules including data and code; receiving second input comprising information to be hidden in the computer program; linking together the program modules to form an executable computer program, including determining pads necessary for aligning data and code; and hiding the second input in the executable computer program by storing portions of the second input at locations in the executable computer program intended for pads.
Owner:BORLAND
Method for hiding high-capacity compression-resisting image information
ActiveCN103414892AImprove performanceSolve hidden capacityTelevision systemsRound complexityInformation hiding
The invention discloses a method for hiding high-capacity compression-resisting image information. According to the method, firstly, a carrier image is sampled and is decomposed to acquire sub-images which are same in size and do not mutually overlap; secondly, several sub-images are preferentially selected from the sub-images and serve as carrier sub-images, and the rest of the sub-images serve as source images used for carrier recovery. Firstly, encoding and scrambling are conducted on embedded information; secondly, one or more digits among four high digits in the carrier sub-images are hidden with a foundational hiding method, and sub-images which contain secret information and sub-images which do not contain secrete information are reconstructed to form an image which contains secret information to be transmitted; received images are decomposed by a receiving end, the secret information is extracted from the sub-images which contain the secret information, and the sub-images which do not contain the secret information are predicted in an interpolation mode to recover carrier images. The method has the advantages of being large in hiding capacity, strong in compression-resisting capability and low in complexity, can recover the secret information and the carrier images in a high-quality mode under the condition of achieving two-time compression to eight-time compression of a JPEG2000 algorithm, wherein the maximum relative hiding capacity can reach one eighth and the typical value of the PSNR of carrier image recovery is 40dB.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
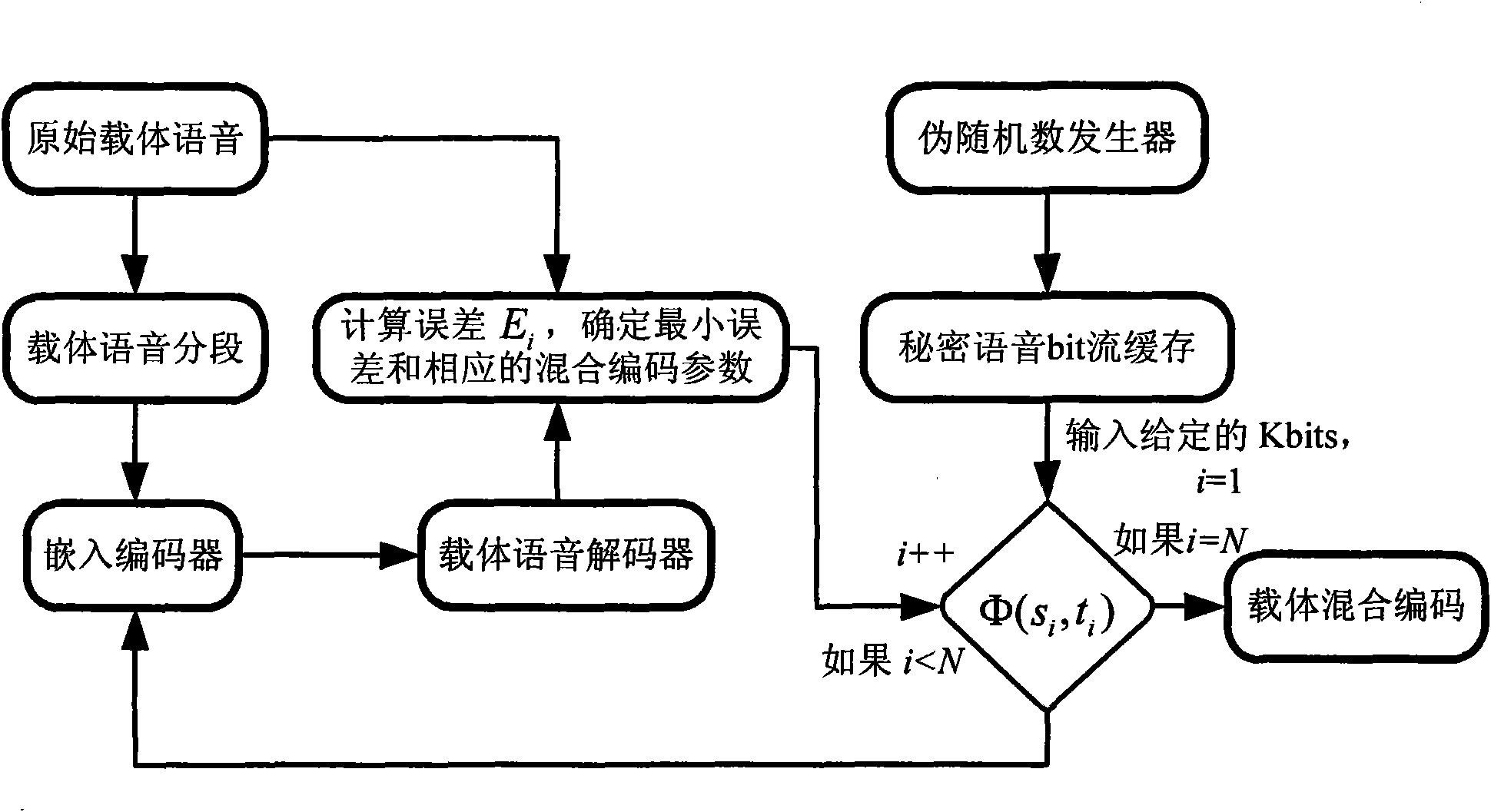
Voice secret communication system design method based on compressive sensing and information hiding
ActiveCN102034478AQuality improvementImprove sparsitySpeech analysisSecret communicationWavelet denoisingVoice communication
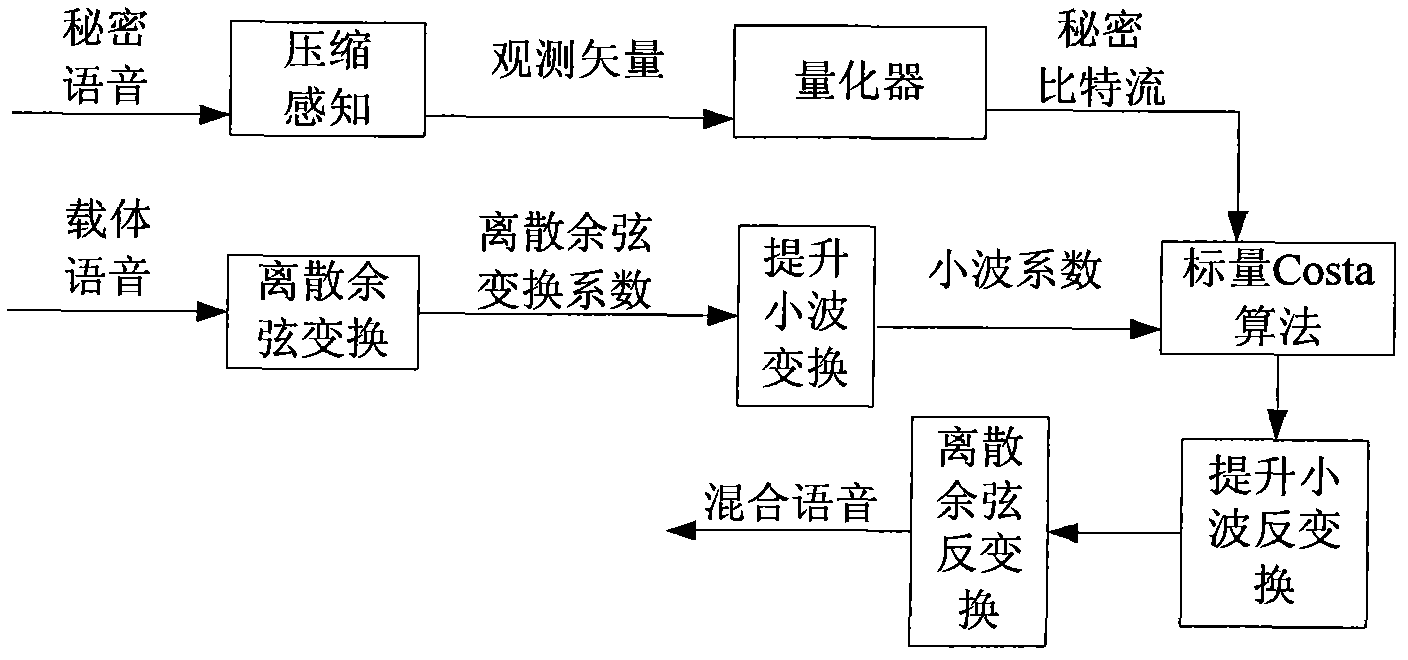
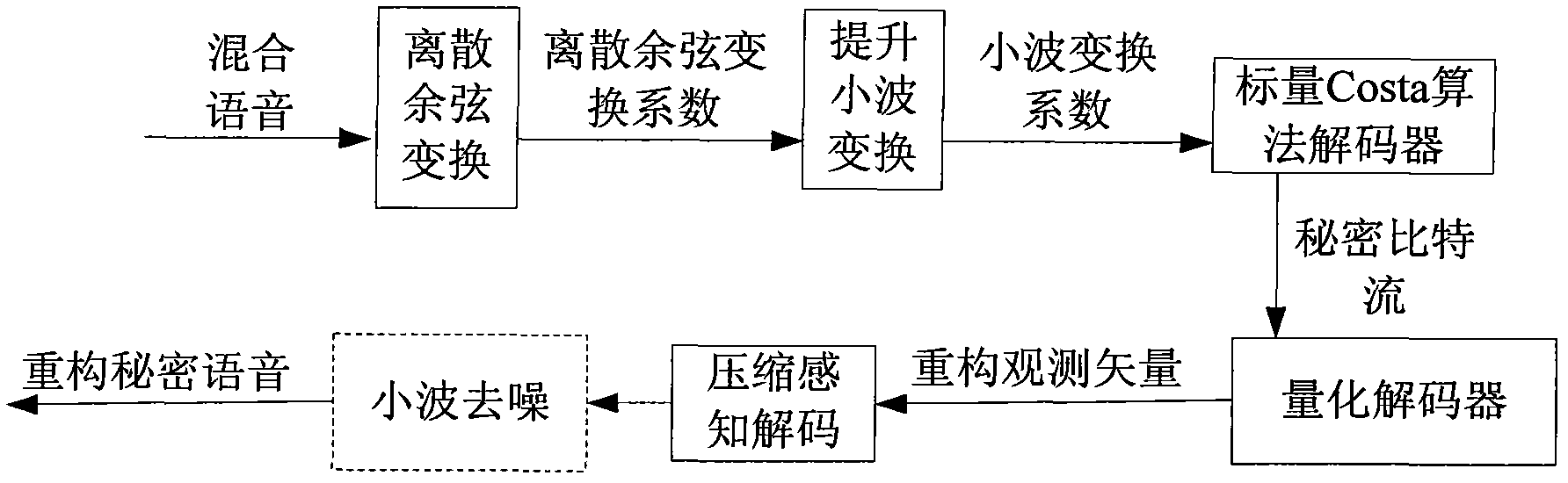
The invention discloses a voice secret communication system design method based on compressive sensing and information hiding, comprising the following steps: embedding secret voice into carrier voice by an embedded system to obtain mixed voice; designing a compressive sensing overcomplete dictionary aiming at the voice signal; sampling the secret voice by a compressive sensing self-adaption observation matrix to obtain a observation vector for reducing dimensions; quantizing the observation vector by an LBG (Linde-Buzo-Gray algorithm) vector, taking the quantized observation vector to serve as secret information to embed into the carrier voice, and carrying out two-stage transform on the carrier voice to obtain mixed voice; extracting the secret voice from the mixed voice by an extraction system; carrying out discrete cosine transform on mixed voice, and improving wavelet transform two-stage transform to obtain a wavelet transform coefficient; obtaining a secret bit stream by a scalar Costa decoding algorithm; obtaining a reconstructing observation vector by an LBG vector quantization decoder; reconstructing the secret voice by a compressive sensing orthogonal matching pursuit algorithm; and improving the quality of the reconstructed secret voice with a wavelet denoising method.
Owner:NANJING UNIV OF POSTS & TELECOMM
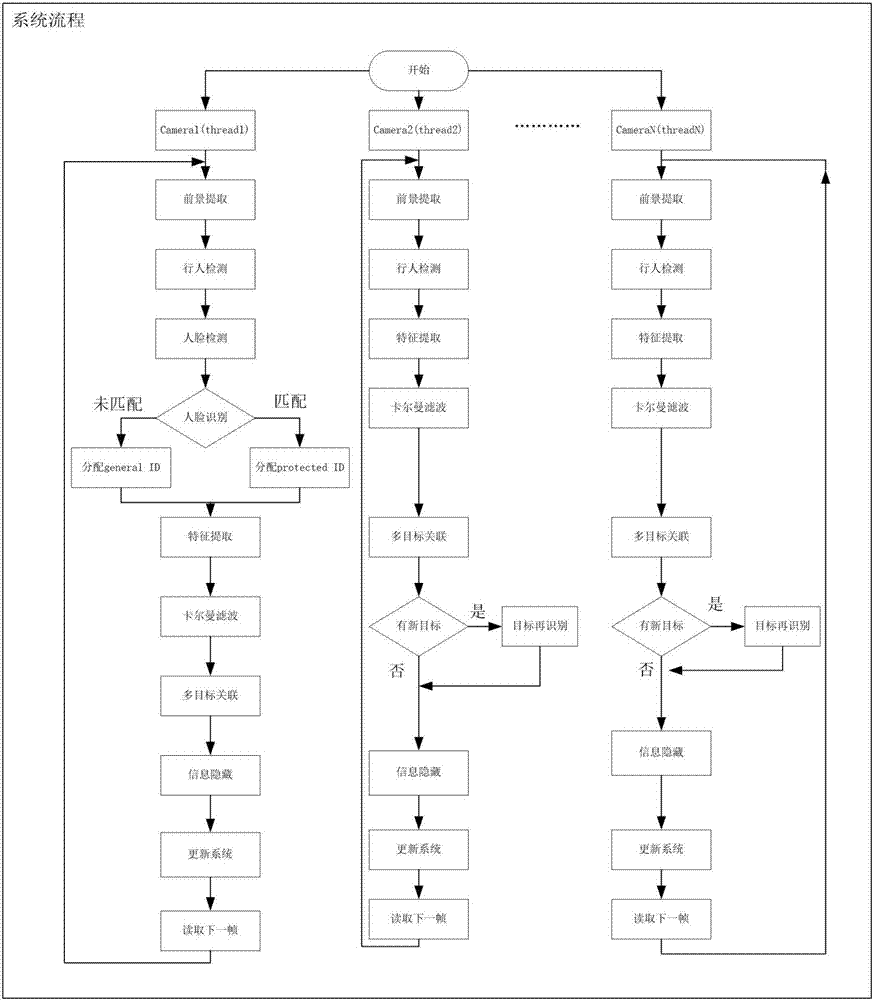
Privacy protection method based on monitoring video multi-target tracking and face recognition
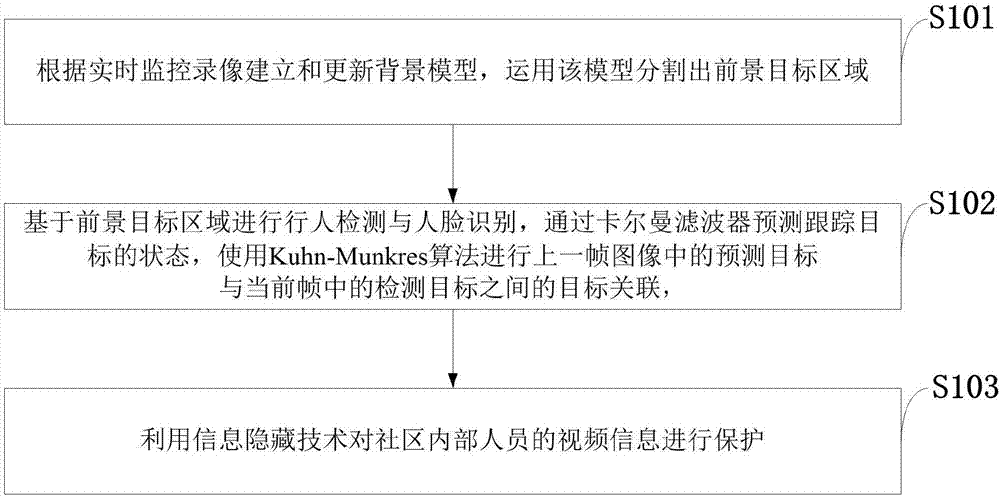
ActiveCN107273822AEnhance expressive abilitySolve occlusionImage analysisCharacter and pattern recognitionPattern recognitionIdentity recognition
The invention belongs to the field of video privacy protection technology and discloses a privacy protection method based on monitoring video multi-target tracking and face recognition. The method comprises the steps that a background model is established and updated according to a real-time monitoring video, and the new background model is adopted to divide a foreground target region; pedestrian detection and face recognition are performed based on the foreground target region, and continuous tracking and identity recognition of community internal personnel and community foreign personnel in a community monitoring video are realized through combination of a Kalman filtering technology and a Hungary algorithm; and video information of the community internal personnel is protected by means of information hiding. According to the method, privacy information of users in a community is protected through face recognition and target tracking technologies, foreign strangers are also monitored, and balance is achieved between maintenance of community safety and protection of user privacy; and the video information of specific users is subjected to privacy protection in combination with target detection, target recognition and multi-target tracking technologies while monitoring system availability is guaranteed.
Owner:XIDIAN UNIV
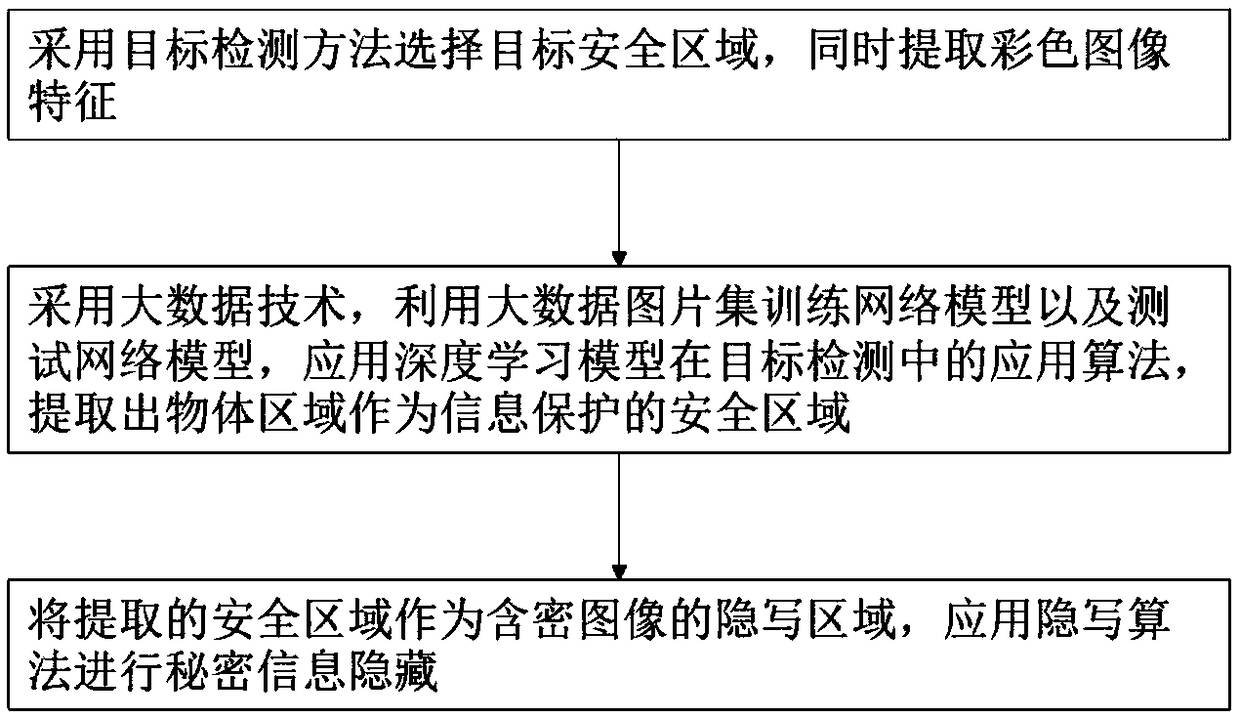
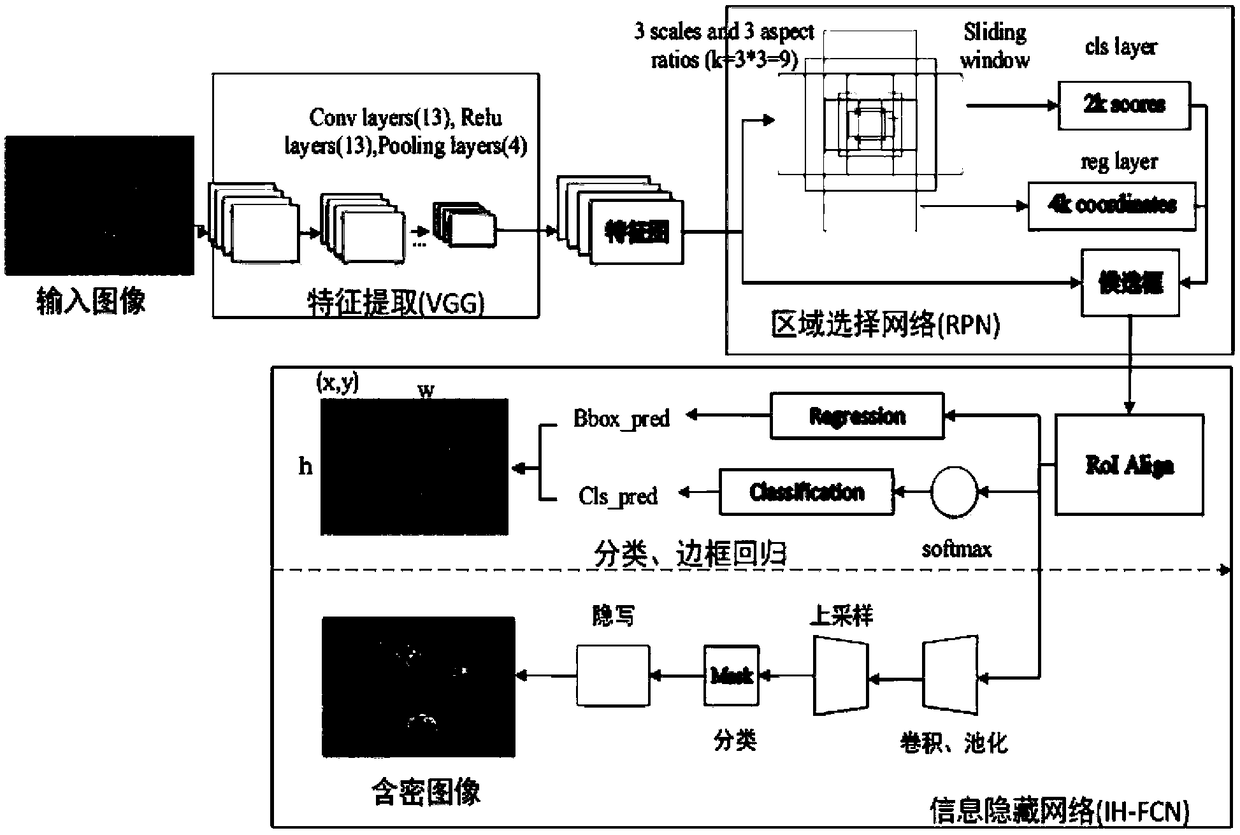
Big data image protection method and system based on a security area
ActiveCN109492416AAchieve hiddenImplement image protectionCharacter and pattern recognitionDigital data protectionColor imagePattern recognition
The invention provides a big data image protection method based on a security area, and the method comprises the steps: S1, selecting a target security area through employing a target detection method, and extracting color image features; s2, a big data technology is adopted, a big data picture set is utilized to train a network model and a test network model, an application algorithm of a deep learning model in target detection is applied, and an object area is extracted to serve as a safety area of information protection; and S3, taking the extracted security area as a steganography area ofthe encrypted image, and carrying out secret information hiding by applying a steganography algorithm. According to the invention, the application algorithm of the deep learning model is applied in the target detection, that is, the Mask R-CNN instance segmentation method, and select the region with complex texture noise in the image, an area with complex texture noise in the image, namely a foreground part, is selected, secret information is accurately hidden in a foreground object, and therefore the purpose of more secret image secret information hiding protection is achieved.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
JPEG image information hiding based private information communication method and system
ActiveCN105426709AHidden efficientLarge capacityImage data processing detailsProgram/content distribution protectionUser inputInformation embedding
The invention relates to a JPEG image information hiding based private information communication method and system. The system comprises a preprocessing module used for converting to-be-transmitted information into binary data, an encryption / decryption module used for generating an information hiding key by a password input by a user, an information hiding module used for embedding the converted binary data into a carrier JPEG image, a transmission module for transmitting and sharing the JPEG image embedded with the binary data information, and an information extraction module used for extracting the binary data in the image embedded with the binary data information, wherein the information hiding module comprises an entropy decoding module, an information embedding module and an entropy encryption module. The invention provides a complete multi-morphological information hiding core algorithm taking an image as a medium and a communication solution. The private information communication method and system have important theoretical and application values.
Owner:FUJIAN NORCA TECH
Information hiding method facing to H.264/AVC (automatic volume control) video
InactiveCN102223540AEnsure safetyIncrease hidden capacityTelevision systemsDigital video signal modificationAutomatic controlMotion vector
The invention discloses an information hiding method facing to an H.264 / AVC (automatic volume control) video. The embedding of watermark information is realized through modifying a data communication terminal (DCT) coefficient of a frame I, but for a frame B and a frame P, the embedding of the hiding information is realized through modifying motion vector data (MVD), thus on one hand, the embedded watermark information can be used for authenticating the integrity of the content of the video streaming, and on the other hand, whether the video is attacked is judged, and whether the extracted information is credible and the like at an information detection end according to the integrity of the extracted watermark information, thus ensuring the safety of the private information; as the frame P and frame B in a video sequence are divided into a motion subblocks from the size range of 16*16 to 4*4; the smaller subblock division provides a large amount of MVD data which can provide for hiding the private information, thus the video has larger information hiding capacity; and the process extracting the information is simple and rapid, does not need an original video file for reference, and only needs to decode the DCT coefficient of the frame I and the MVD data of the frame B and frame P, thereby effectively improving the instantaneity and the practicability.
Owner:NINGBO UNIV
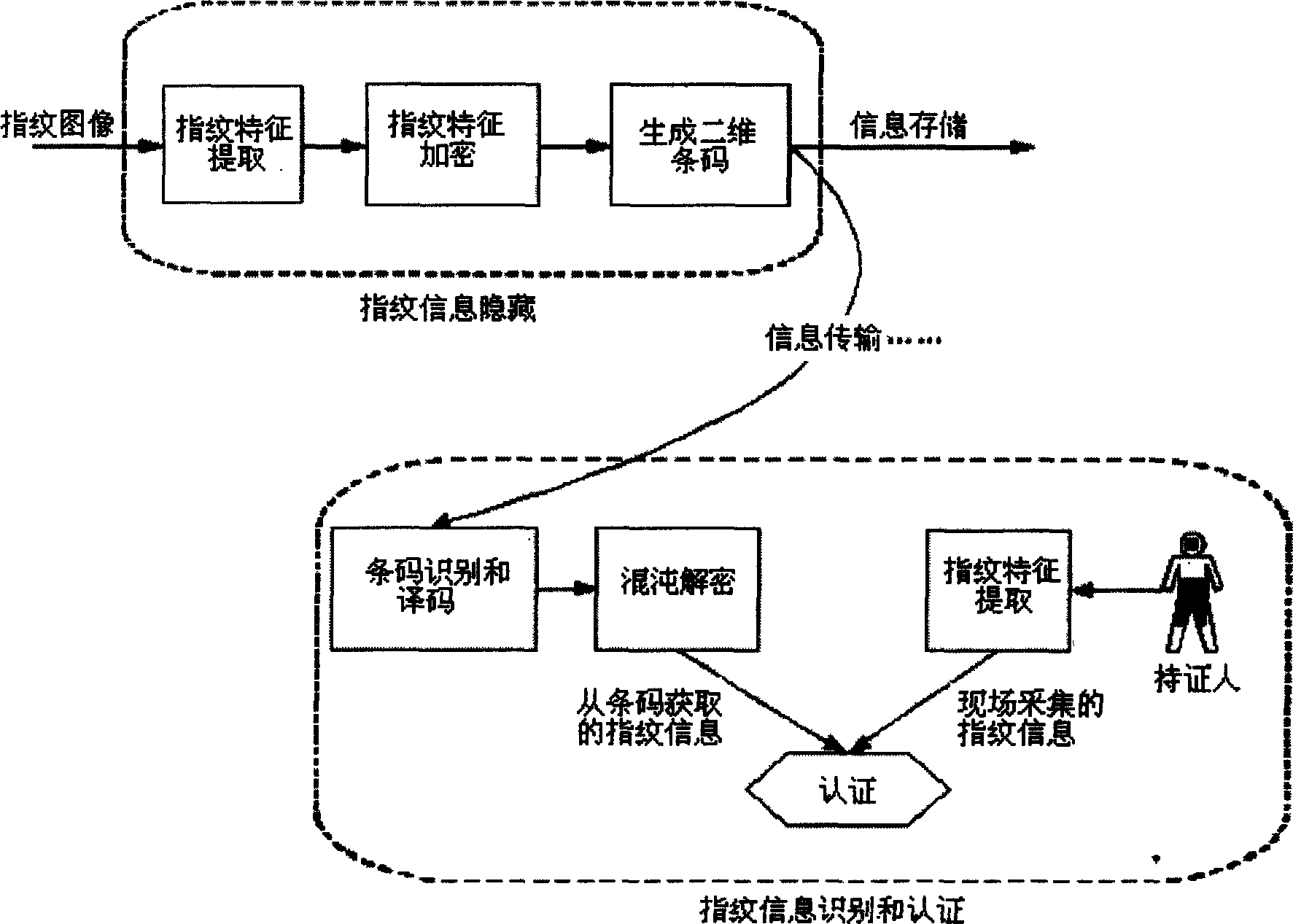
Fingerprint information hiding and verifying method based on two-dimensional bar code
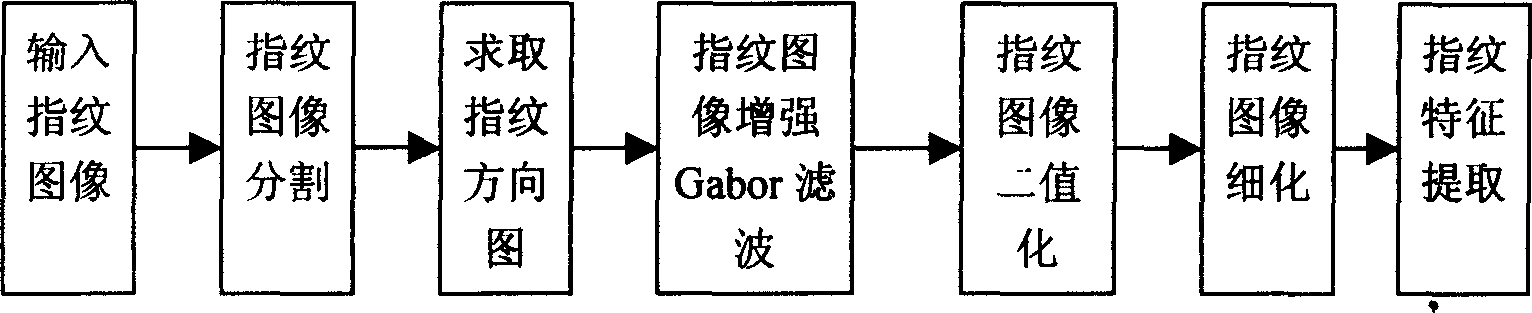
InactiveCN1741043AWith automatic reading functionLarge capacityCo-operative working arrangementsCharacter and pattern recognitionComputer hardwareFeature extraction
The invented method includes the following steps: firstly, collecting fingerprint image, making characteristics extraction, encryption processing, printing it on the two-dimensional bar code, concealing the fingerprint information into two-dimensional bar code; collecting two-dimensional bar code image, making image segmentation, filtering, geometric correction and layered pretreatment, identifying and decoding said bar code image to obtain the loaded encrypted information, deciphering said encrypted information to obtain fingerprint characteristic information loaded in two-dimensional bar code, comparing said information with field fingerprint information, making detection so as to implement anti-false authentication of fingerprint.
Owner:XI AN JIAOTONG UNIV
WWW transformation technology
InactiveCN101526953AOvercoming the Deletion DefectEasy to browseSpecial data processing applicationsHyperlinkClient-side
The invention relates to a method for transforming a WWW web page into a WAP web page. The method is characterized by comprising the steps as follows: step A, a request of a client end for accessing certain URL is received, whether a web page is the WWW web page is judged preliminarily according to the URL; step B, web page content is obtained; step C, the web page which is not the WWW web page probably is judged further to confirm whether the web page is the WWW web page; step D, web page switch is carried out on the WWW web page, firstly, display width is confirmedly, then each block of the web page is rearranged from top to bottom, and the format of the web page content is transformed into the format fit for mobile phone browse and is reduced less than an image with set size, and step E, the transformed web page is returned to the client end. During the transformation, useless and / or secondary information can also be folded and hidden in the web page in a way of establishing a hyperlink. The invention not only can carry out the transformation of WWW web page content, but also can identify which web pages are required to be transformed into the WWW web page, and the invention hides the information which is less concerned by people during the process of the transformation.
Owner:HUAWEI TECH CO LTD
Adaptive H.264 compressed domain video watermark embedding and extracting method
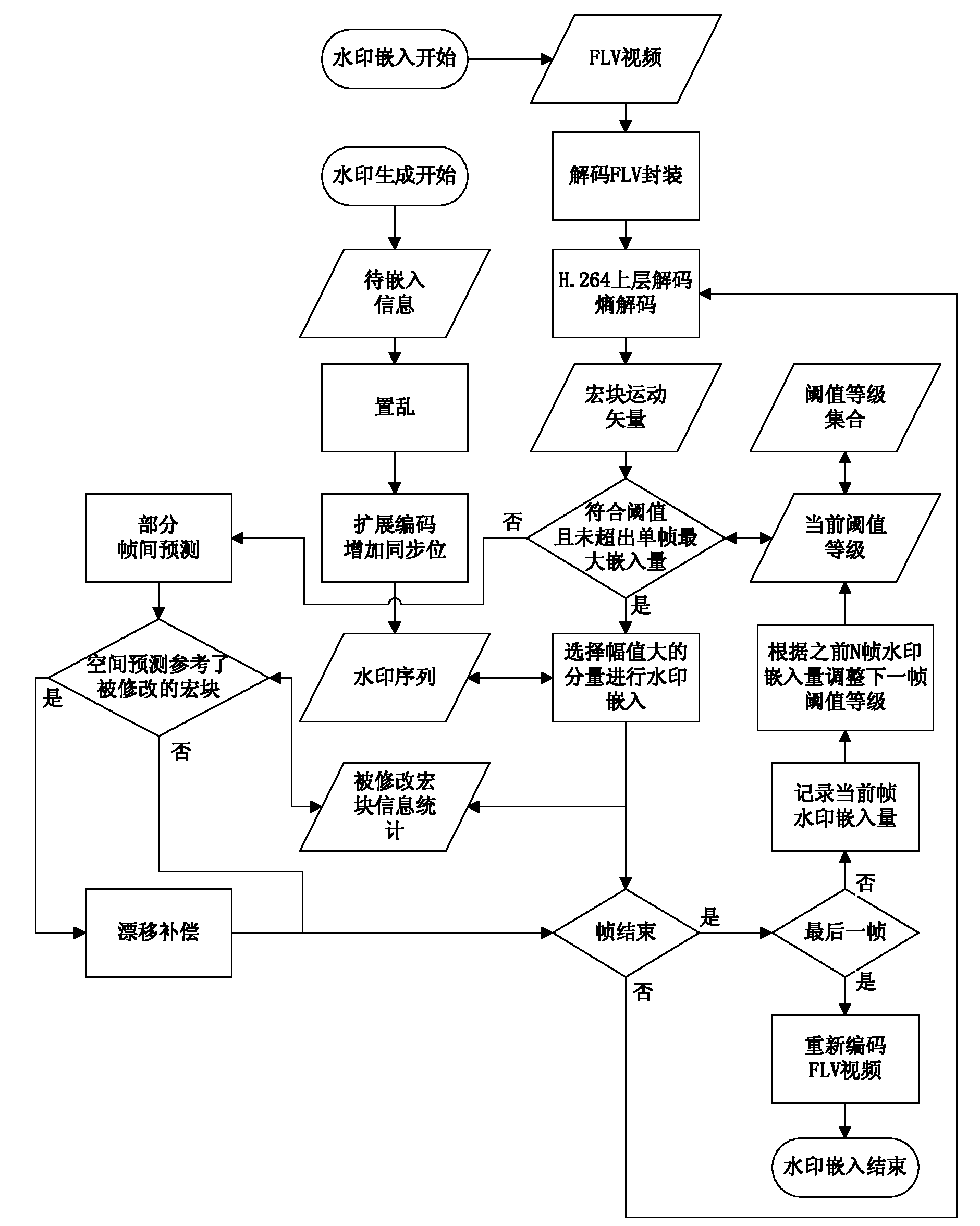
ActiveCN101951520AImprove extraction efficiencyGuaranteed real-timeTelevision systemsImage data processing detailsCompensation effectMotion vector
The invention relates to an adaptive H.264 compressed domain video watermark embedding and extracting method in the technical field of information security, which can realize the real-time operation of video information hiding. The threshold value of a motion vector is adaptively adjusted according to watermark embedding amount statistical data of an adjacent frame, so that watermark capacity is ensured and the requirement of embedding a one-time watermark among a few frames is met; and error diffusion caused by modifying the motion vector is accurately positioned in a partial interframe prediction mode, so that good drift and distortion compensation effects can be achieved.
Owner:SHANGHAI JIAO TONG UNIV
Graph convolutional network gradient-based node information hiding method
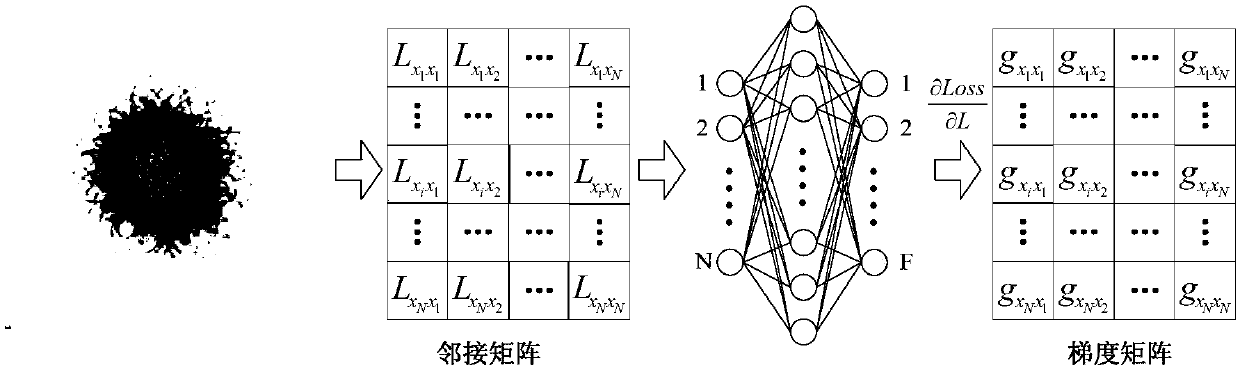
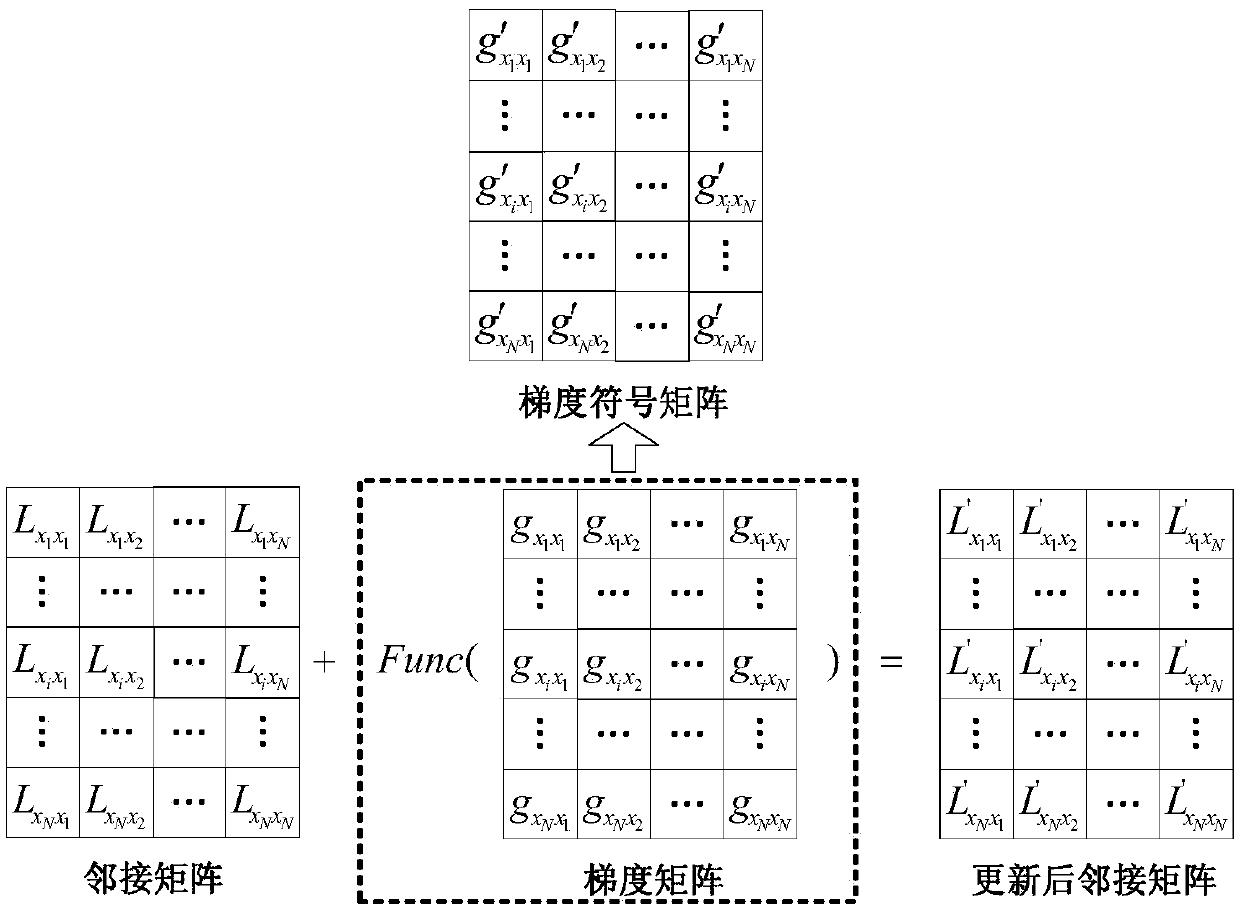
PendingCN108648095AAccurate classificationAchieve hiddenData processing applicationsCharacter and pattern recognitionNODALAlgorithm
The invention discloses a graph convolutional network gradient-based node information hiding method. The method comprises the steps of (1) constructing a network graph, constructing an adjacent matrixaccording to a connected edge set corresponding to the network graph, and preprocessing the adjacent matrix; (2) constructing and training a graph convolutional network model, and determining final weight information of the graph convolutional network model; (3) according to the final weight information, building an objective function based on a goal of ensuring non-target node classification tobe accurate as far as possible and enabling target node classification to be wrong, and calculating a connected edge gradient matrix corresponding to the adjacent matrix by utilizing the objective function; (4) according to a set gradient threshold, symbolizing the connected edge gradient matrix to obtain a connected edge gradient symbol matrix; and (5) updating the adjacent matrix by utilizing the connected edge gradient symbol matrix to hide node information. According to the method, the target node information of a network can be hidden under the condition of slightly changing the structureof the network as far as possible.
Owner:ZHEJIANG UNIV OF TECH
High-capacity steganographic method based on JPEG (Joint Photographic Experts Group) digital image
The invention discloses a method for hiding the information of a JPEG (Joint Photographic Experts Group) digital image based on a modified quantization table, in particular to an improved quantization table 16*16 by changing the method of a traditional quantization table 8*8 in the JPEG standard and embedding 2 bits of information at the 2-LSBs (Least Significant Bit) of each low and medium frequency coefficients in the DCT domain after carrying out DCT (Discrete Cosine Transform) and quantization to the carrier image. On the basis of favorable robustness and invisibility, the method modifies the quantization table so as to fully extract secrete information to be hidden, greatly improve the capacity of the steganographic method in comparison with a traditional Jsteg method and obatin higher hidden image quality.
Owner:周岩
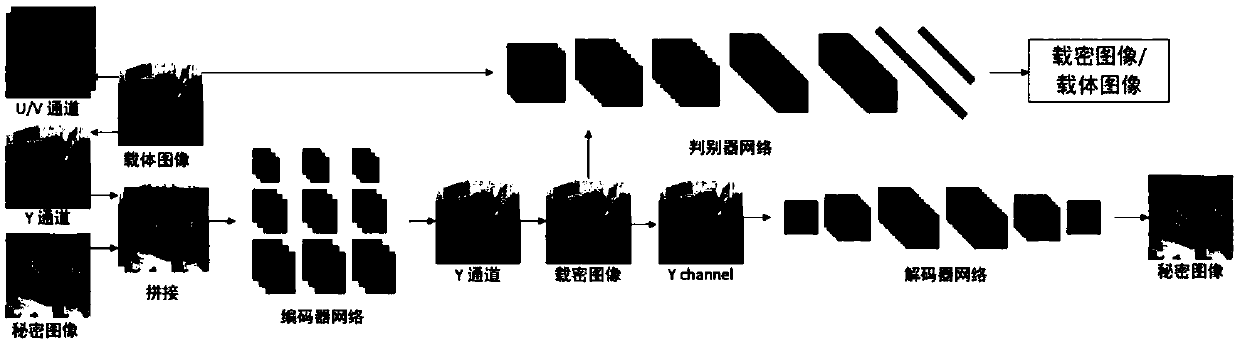
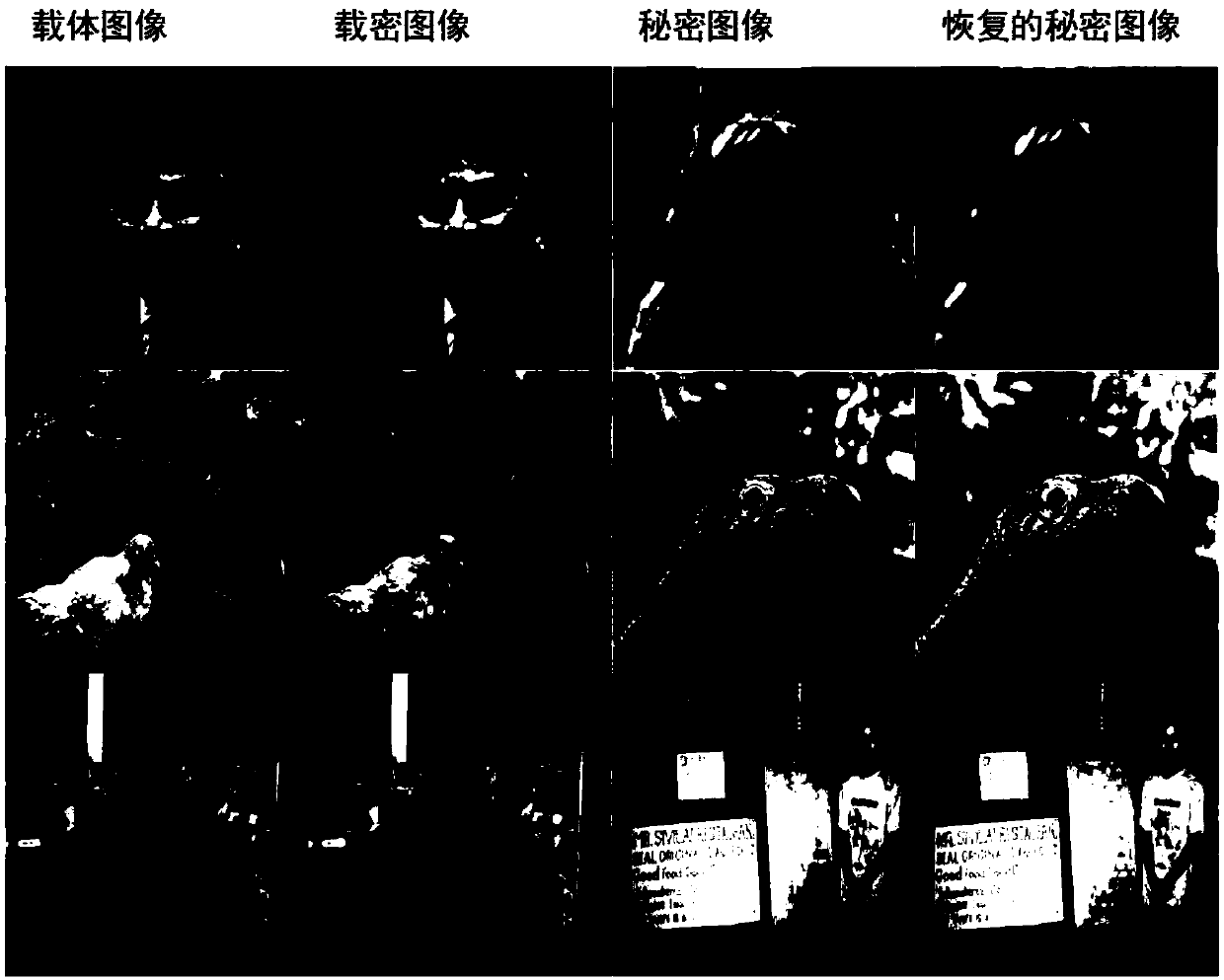
Invisible image steganography based on generative adversarial network
ActiveCN109587372ASolve the problem of color differenceResolve differencesNeural architecturesNeural learning methodsSteganalysisDiscriminator
The invention discloses an invisible image steganography based on a generative adversarial network which can embed a grayscale secret image into a color carrier image to obtain a confidential image and can successfully recover a secret image from the payload image. The invisible image steganography comprises: an encoder network which is responsible for embedding a secret image into a carrier imageto generate a confidential image; a decoder network which is responsible for recovering a secret image from a loaded image; and a discriminator network which is responsible for performing steganalysis of a natural image and a confidential image to adjust the safety of the encoder network and decoder network. The invisible image steganography based on the generative adversarial network provides anew design idea for image information hiding.
Owner:BEIJING UNIV OF POSTS & TELECOMM
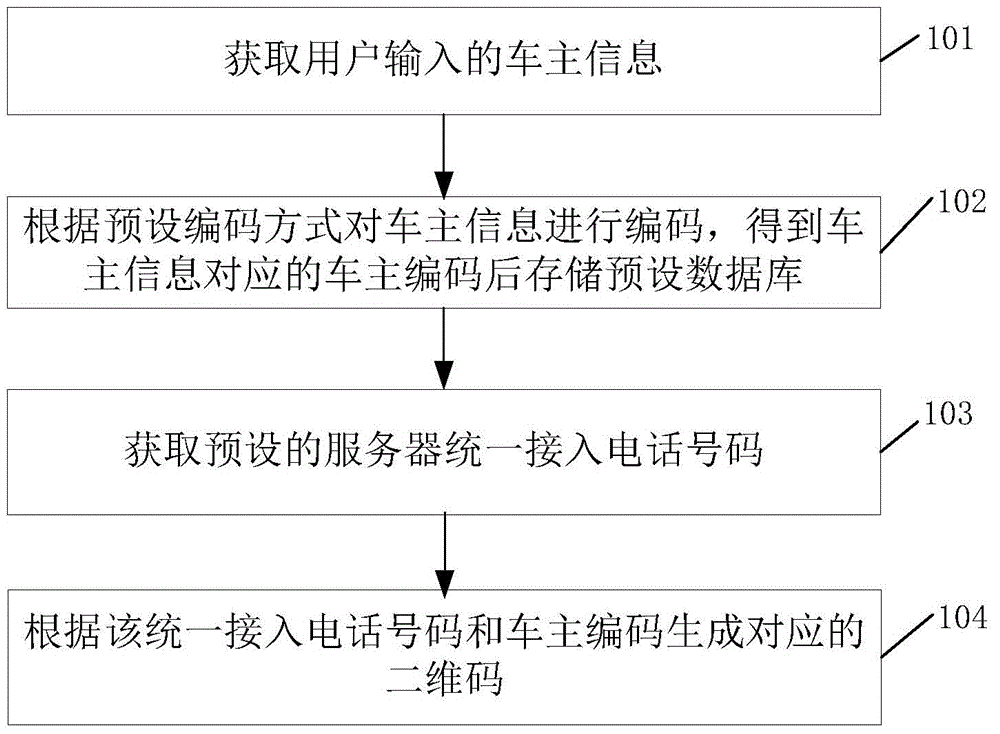
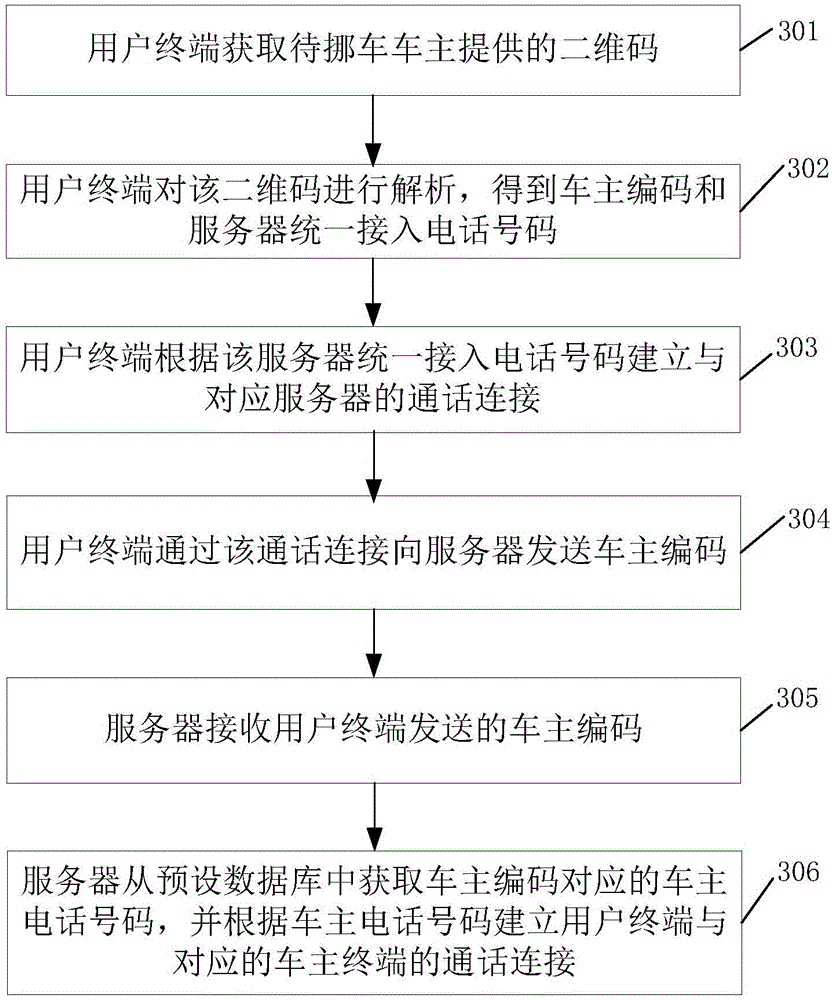
Method for hiding car owner information and contacting car owners
InactiveCN104537109AAchieve hiddenPrevent leakageRecord carriers used with machinesSpecial data processing applicationsState of artUser input
The invention discloses a method for hiding car owner information and contacting car owners, and relates to a communication method. The method aims to solve the problem that phone numbers of the car owners are prone to leakage in the prior art. According to the technical scheme, the method includes the steps that (S10) the car owner information input by users is obtained, wherein the car owner information includes the phone numbers of the car owners; (S20) the car owner information is coded in a preset coding mode to obtain car owner codes corresponding to the car owner information, and the car owner codes are stored in a preset database; (S30) the phone numbers having access to a preset server in a unified mode are obtained; (S40) corresponding two-dimensional codes are generated according to the phone numbers having access to the server in the unified mode and the car owner codes.
Owner:陶晨辰 +1
Hiding ciphertext using a linguistics algorithm with dictionaries
Encrypted communications is made to appear to be normal text so as to avoid undue attention to either the sender or recipient. Information can be hidden or embedded in innocuous documents using steganography wherein the information is masked within a larger document. Other approaches would translate the ciphertext into a form of normal looking text that would in effect be gibberish but would use normal words in at least one native language. There are many tradeoffs and benefits to be considered when attempting any form of encrypted communications.
Owner:GLOBAL INTEGRITY INC
Method and system for protecting the consistency of information in a distributed file system
InactiveUS20060136369A1Improve concurrencyConsistency of protectionDigital data information retrievalDigital data processing detailsInformation sharingFile system
Disclosed are “black-box leases” that protect information consistency and that allow for information sharing in a distributed file system while hiding from a client information about other clients' use of the file system. This information hiding also allows greater concurrency because changes to the file system are permitted as long as they do not affect the leases as observed by the clients. For each data field protected by a black-box lease, a client has a two-value data structure: SelfValue represents the client's intended use of the data field, and OtherValue is an aggregation of the other clients' intended uses of that data field. Knowing only this aggregate OtherValue, but without knowing any specifics of the other clients' usage patterns, the client knows how it may use the data field without adversely affecting the consistency of data in the distributed file system.
Owner:MICROSOFT TECH LICENSING LLC
Method for abstracting graph and text infromation utilizing half-hue image networking hiding
InactiveCN101022499AGuaranteed lossEasy to findPattern printingPictoral communicationHueInformation hiding
A method of utilizing halftone to hide and to pick up alphaphotographic information includes hiding alphaphotographic information effectively in printed manuscript at printing process and simultaneously enabling to use printing film prepared by present invention to easily pick up false proof information hidden in said printed manuscript.
Owner:PEKING UNIV +2
Transmitting/receiving method for secret communication
InactiveCN101277194AImprove concealmentGood secrecySecuring communicationNetworking protocolConfidentiality
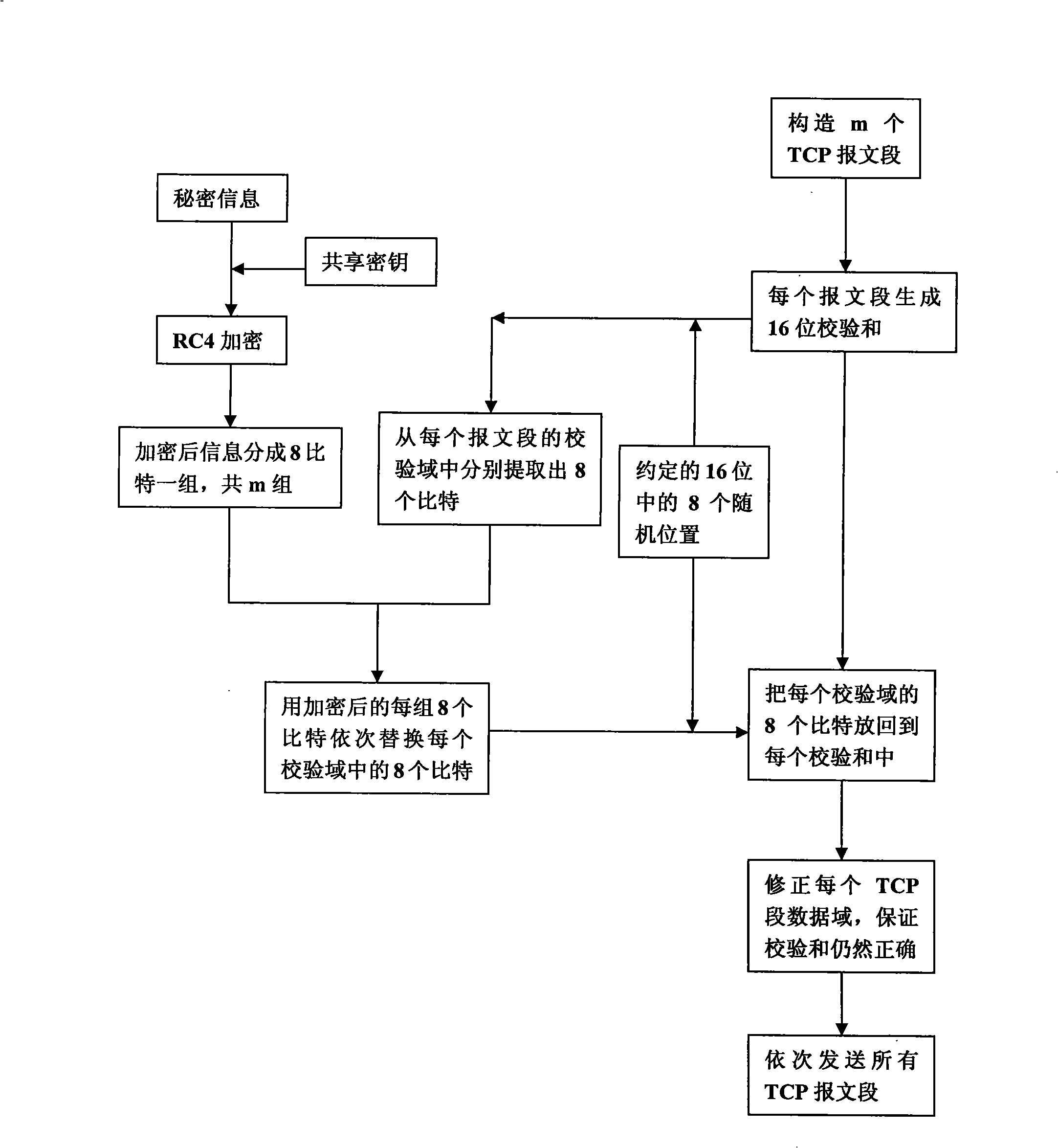
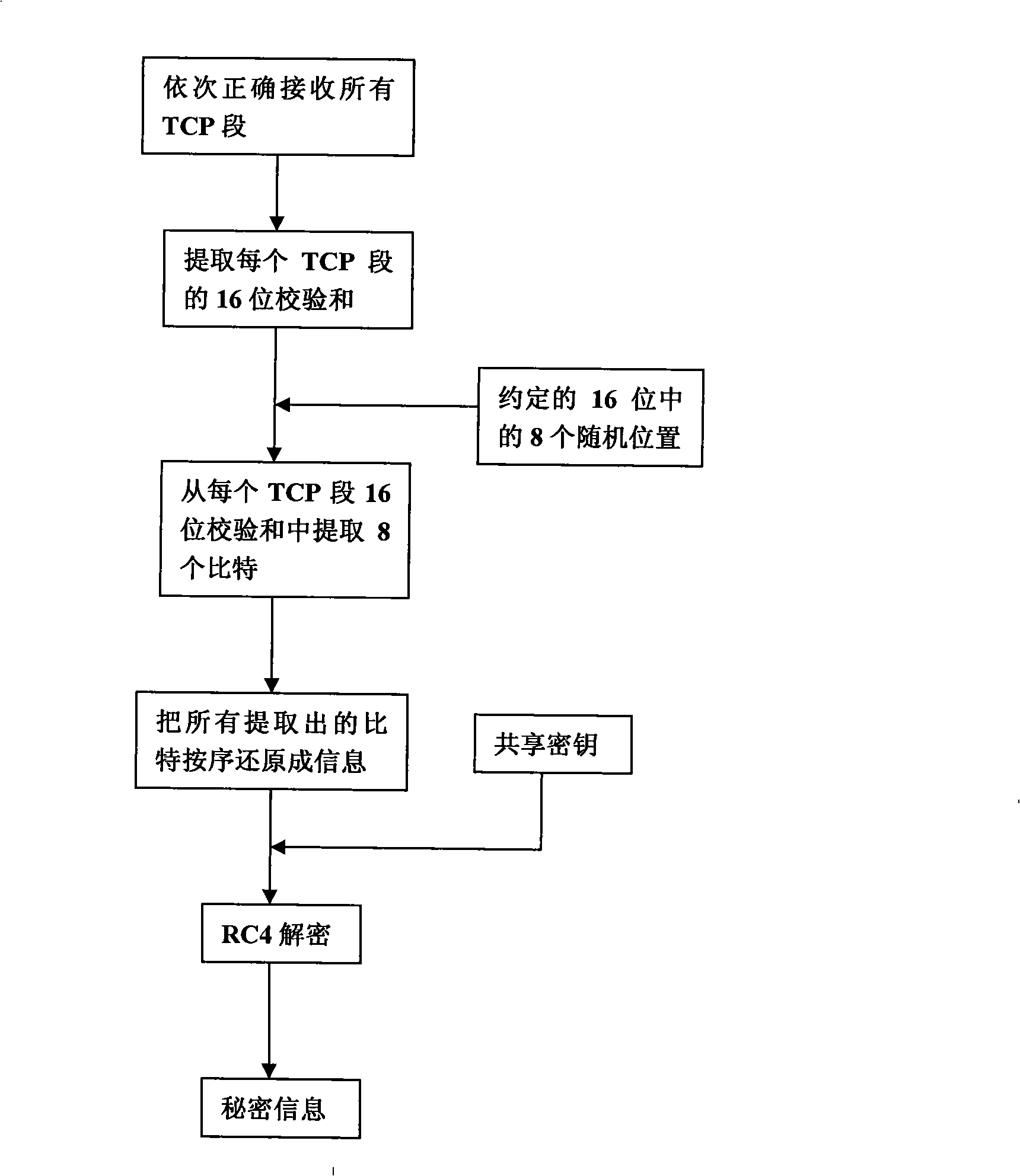
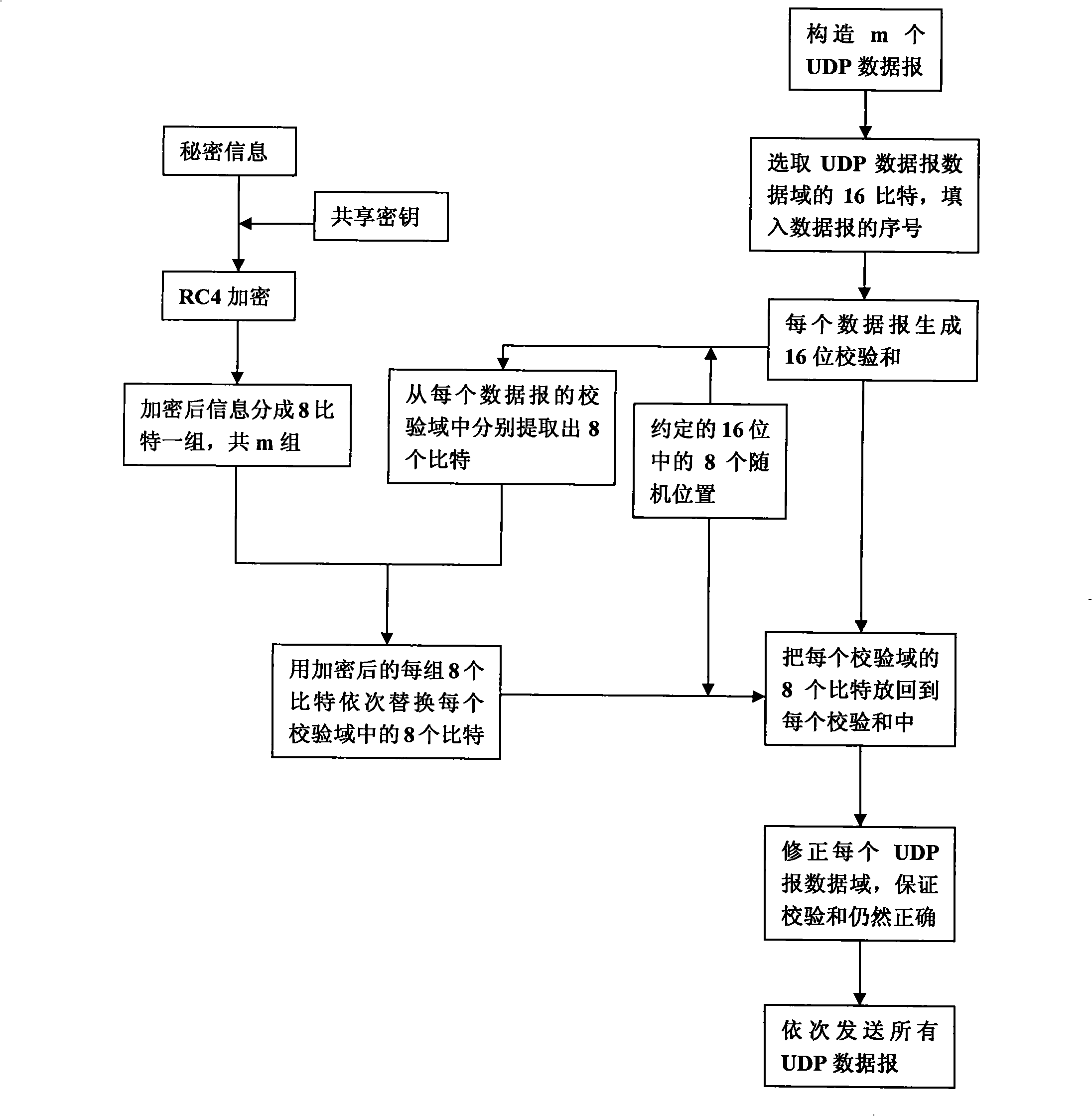
The invention discloses a transmitting / receiving method of covert communication. The method conceals important information waiting convey into a carrier in computer network environment, and important information is unware. When a transmitter transmits network date, a secret information is random embedded into a check field of network protocol date unit (TCP section or UDP) header, and date field is corrected for ensuring check sum right after the secret information is embedded; a receiver extracts the secret information after receiving network protocol date unit from network. The method has better confidentiality and anti-attack by using check and covert information of protocol date unit, and is safely and reliable. The method is especially suitable for convert communication of important information with less date quantity.
Owner:JIANGSU UNIV OF SCI & TECH
Histogram feature based image encryption domain reversible information hiding method
InactiveCN106251278AFull independenceFully reversibleImage data processing detailsCiphertextDigital image
The invention provides a histogram feature based image encryption domain reversible information hiding method, and belongs to the field of digital image encryption and information hiding. The histogram feature based image encryption domain reversible information hiding method comprises the steps that an image owner generates a ciphertext image through carrying out image pixel position scrambling encryption and pixel value encryption, then sends an encryption key and the sub-block size of the ciphertext image to an image receiver, and sends the ciphertext image and the sub-block size thereof to an information hider at the same time; the information hider randomly selects block information embedded information, generates a ciphertext image carrying information, then sends an embedded key, the information containing ciphertext image and the sub-block size to an information receiver, and sends the information containing ciphertext image to the image receiver; the information receiver extracts information according to the embedded key; and the image receiver decrypts and recovers the image according to the encryption key. The method provided by the invention has the beneficial effects that the algorithm is simple and effective, the information can be completely extracted, and the original image can be completely recovered; and the information extracting process, the image decrypting process and the image recovering process are completely independent.
Owner:廖琪男
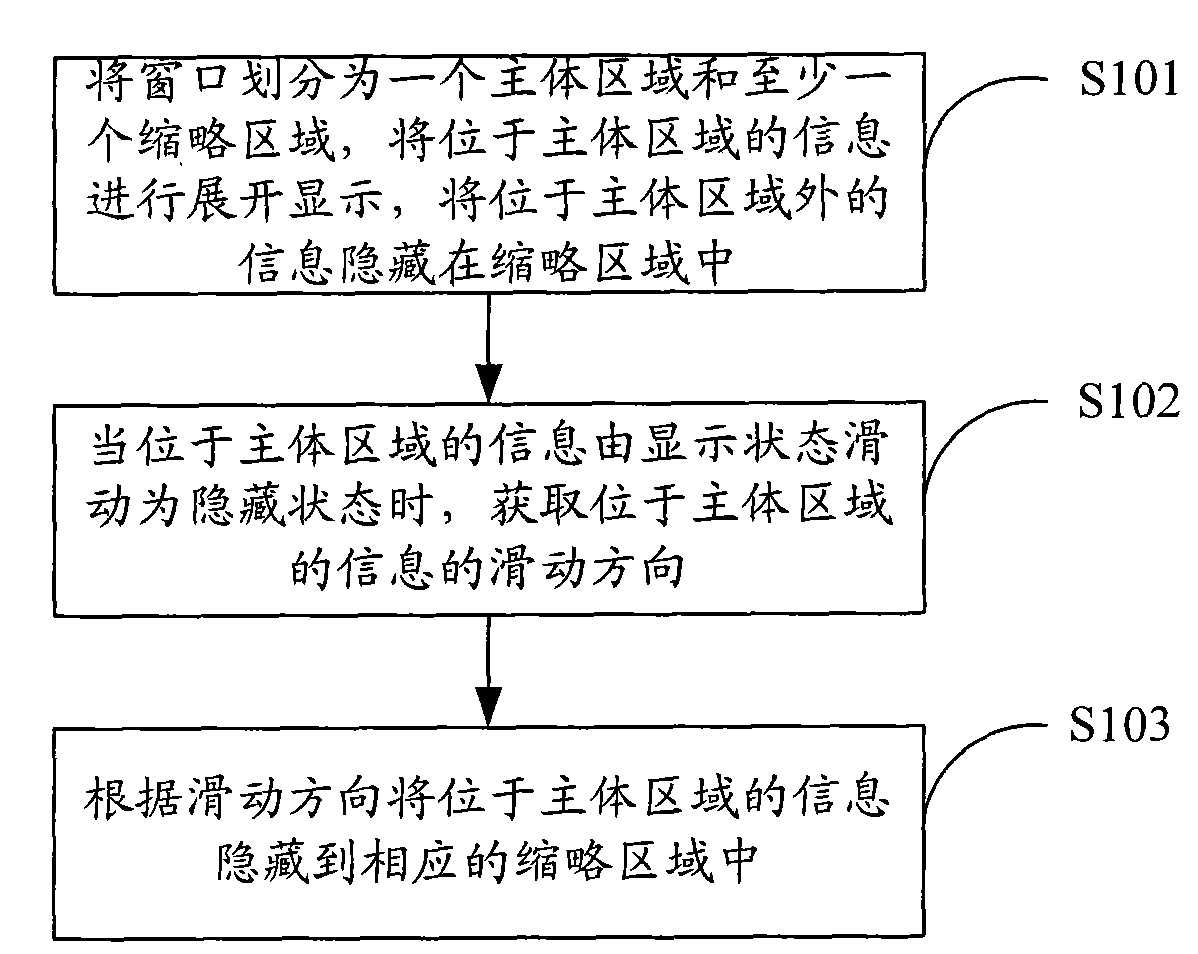
Method for displaying window information, system and display terminal thereof
InactiveCN101661376AQuick ViewEasy to operateInput/output processes for data processingComputer graphics (images)Information hiding
The invention is applicable to the field of display terminals and provides a method for displaying window information, a system and a display terminal thereof. The method comprises the following stepsof dividing a window into a main region and at least one abbreviative region, developing and displaying the information in the main region, and hiding the information outside the main region in the abbreviative region; when the information in the main region is slipped to be a hiding state from a display state, obtaining the slip direction of the information in the main region; and hiding the information in the main region in the abbreviative region according to the slip direction. The invention realizes the quick view of the information at the bottom or top or other positions of the window by synchronously developing and displaying, and hiding and displaying the information in the window. The interface display is visual and vivid, user operation is simple, easy and convenient, and the invention has good operation experience.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Compressive sensing-based adaptive video information hiding method
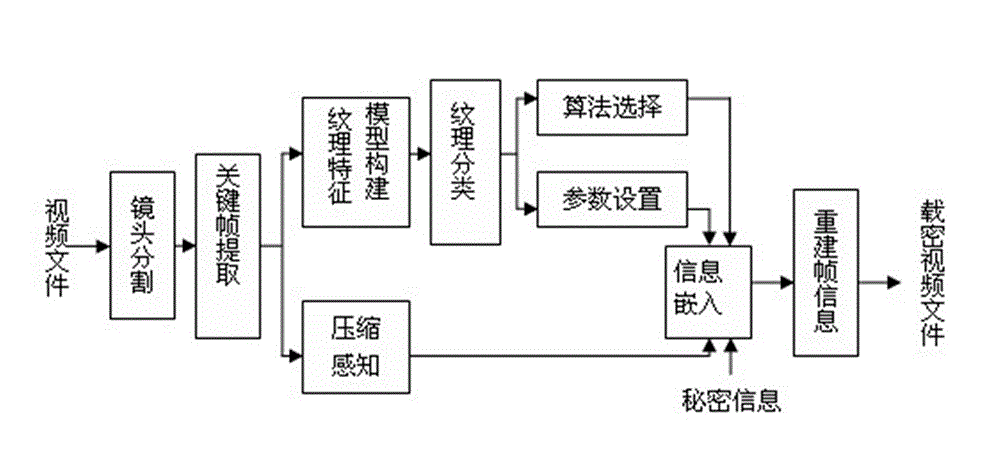
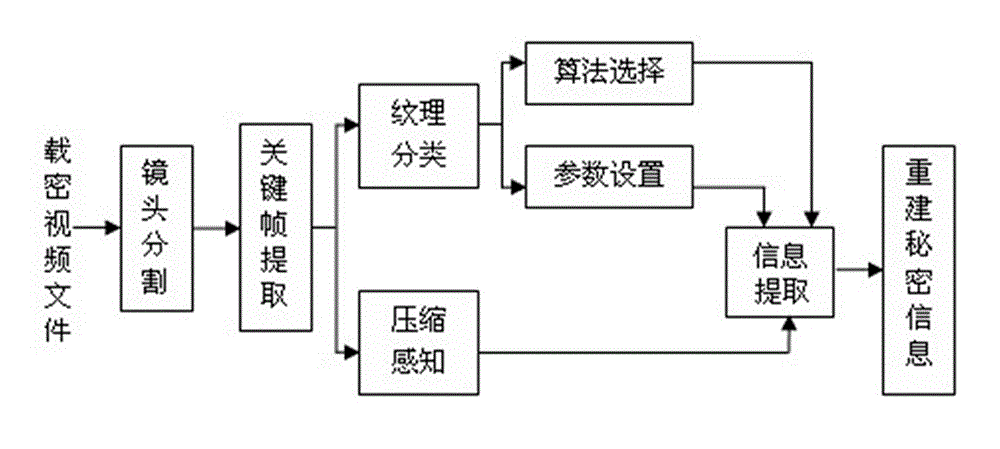
InactiveCN102917227AOrnamental effectSmall amount of calculationTelevision systemsDigital video signal modificationPattern recognitionKey frame
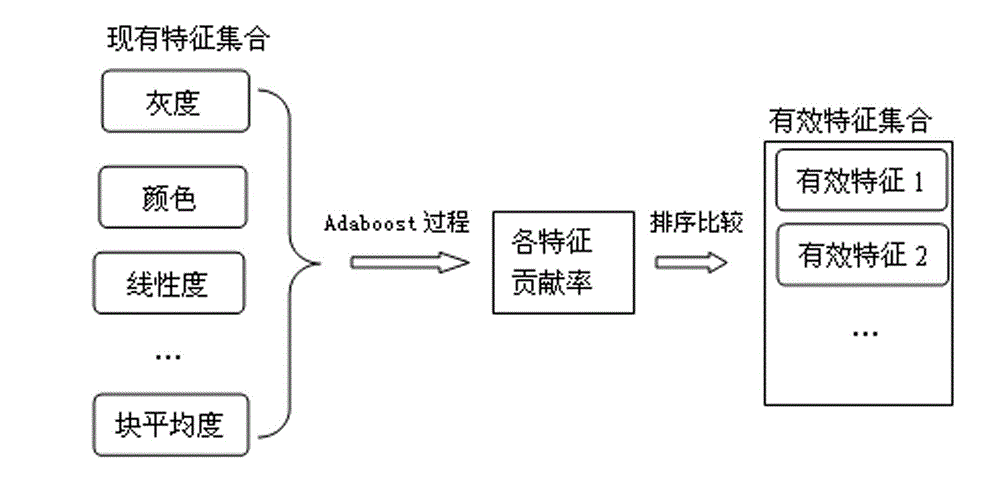
The invention discloses a compressive sensing-based adaptive video information hiding method, which is characterized by comprising the following steps of: a, framing a video file by using shot as a unit; b, taking the first frame of each shot as a key frame; c, establishing an image texture classification model to obtain a texture classification model mark of each key frame; d, determining a texture category of each key frame and determining whether the key frame is a texture region, or a smooth region or between the texture region and the smooth region; e, selecting an algorithm and determining insert depth; f, inserting secret information, i.e., inserting the secret information in a coefficient matrix; and g, synthesizing a video file. According to the video information hiding method, the secret information can be adaptively inserted under the condition that the entire video file is not required to be decompressed, so that the ornamental value of the video is not affected, and the method has the advantages of small amount of calculation, high information steganography efficiency, small influence on the video and good secret information safety. The method can be widely applied to various fields such as copyright authentication, pirate tracking and secure communication.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
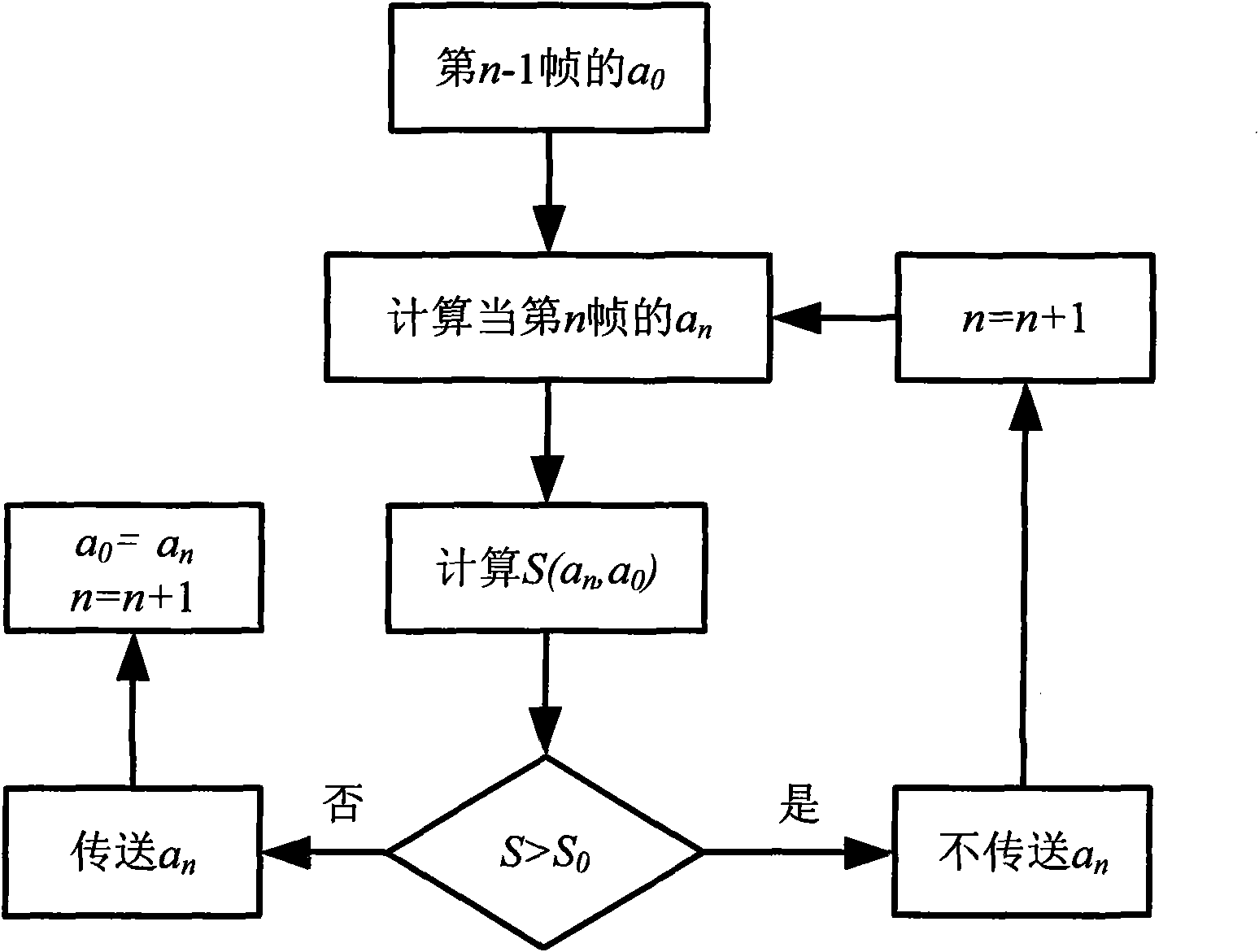
Speech LPC hiding and extraction algorithm based on filter similarity
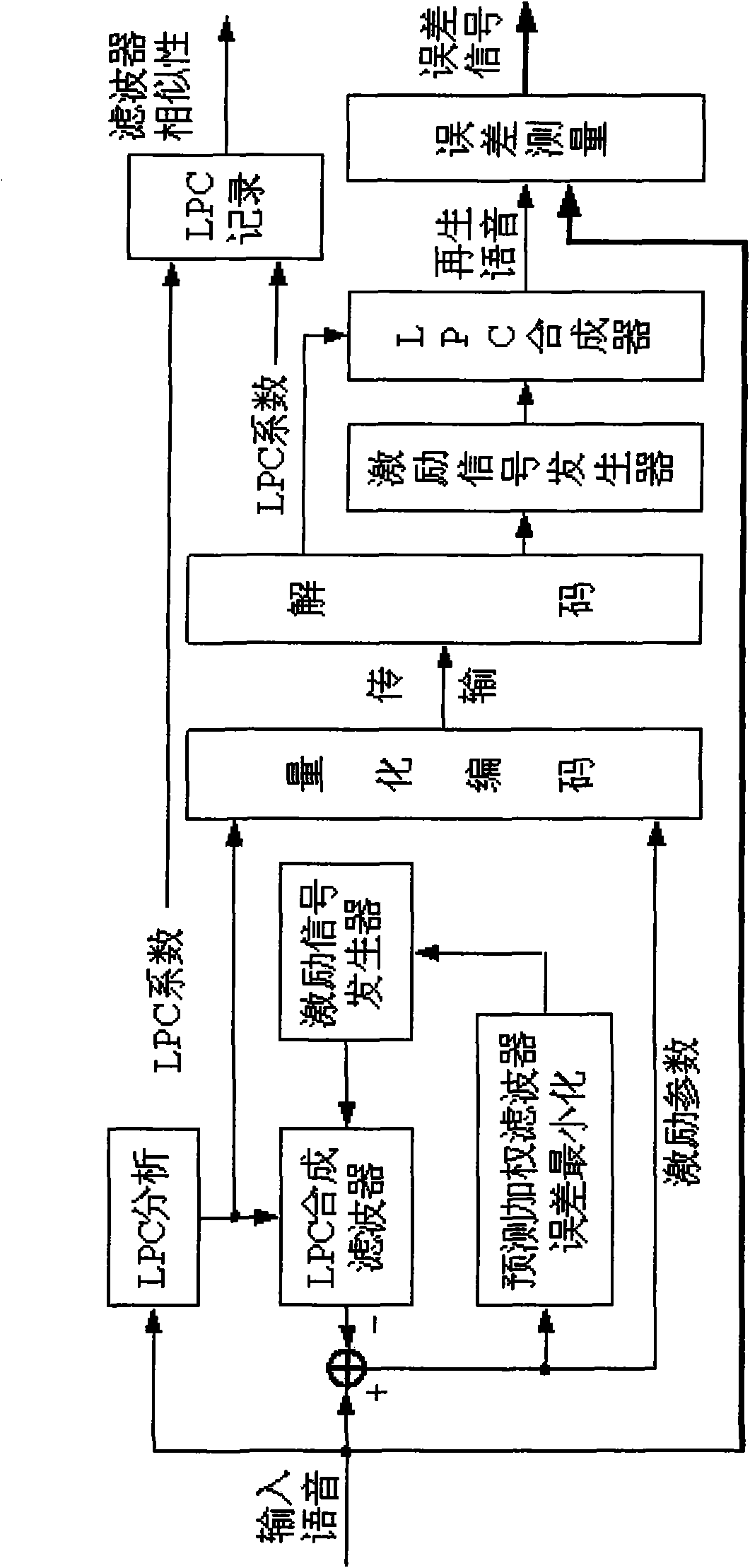
InactiveCN101577605ALight in massGuaranteed continuitySecret communicationSecuring communicationSpeech codeInformation hiding
The invention uses a speech media as a carrier object for speech information hiding and extraction, utilizes the information secret characteristic of information hiding, combines the characteristic ofspeech coding, designs a secret speech information hiding and extraction algorithm, establishes a speech subthreshold channel and realizes a novel real-time speech secret communication mode. The inve ntion comprises the following contents: (1), providing a filter similarity concept and also providing a corresponding definition and a corresponding quantitative calculation method of a filter for determining a speech code LPC parameter used for hiding secret speech information; and (2), providing a speech LPC hiding and extraction algorithm based on filter similarity. After secret speech is embedded into carrier speech, the quality of the carrier speech is not reduced obviously, and the embedded secret speech information can not be detected. Under the condition that the communication rate is ensured, the algorithm can provide enough hiding capacity to ensure the continuity of communication speech and can greatly reduce the code rate.
Owner:吴志军 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com