Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3804 results about "Information needs" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The term information need is often understood as an individual or group's desire to locate and obtain information to satisfy a conscious or unconscious need. Rarely mentioned in general literature about needs, it is a common term in information science. According to Hjørland (1997) it is closely related to the concept of relevance: If something is relevant for a person in relation to a given task, we might say that the person needs the information for that task.
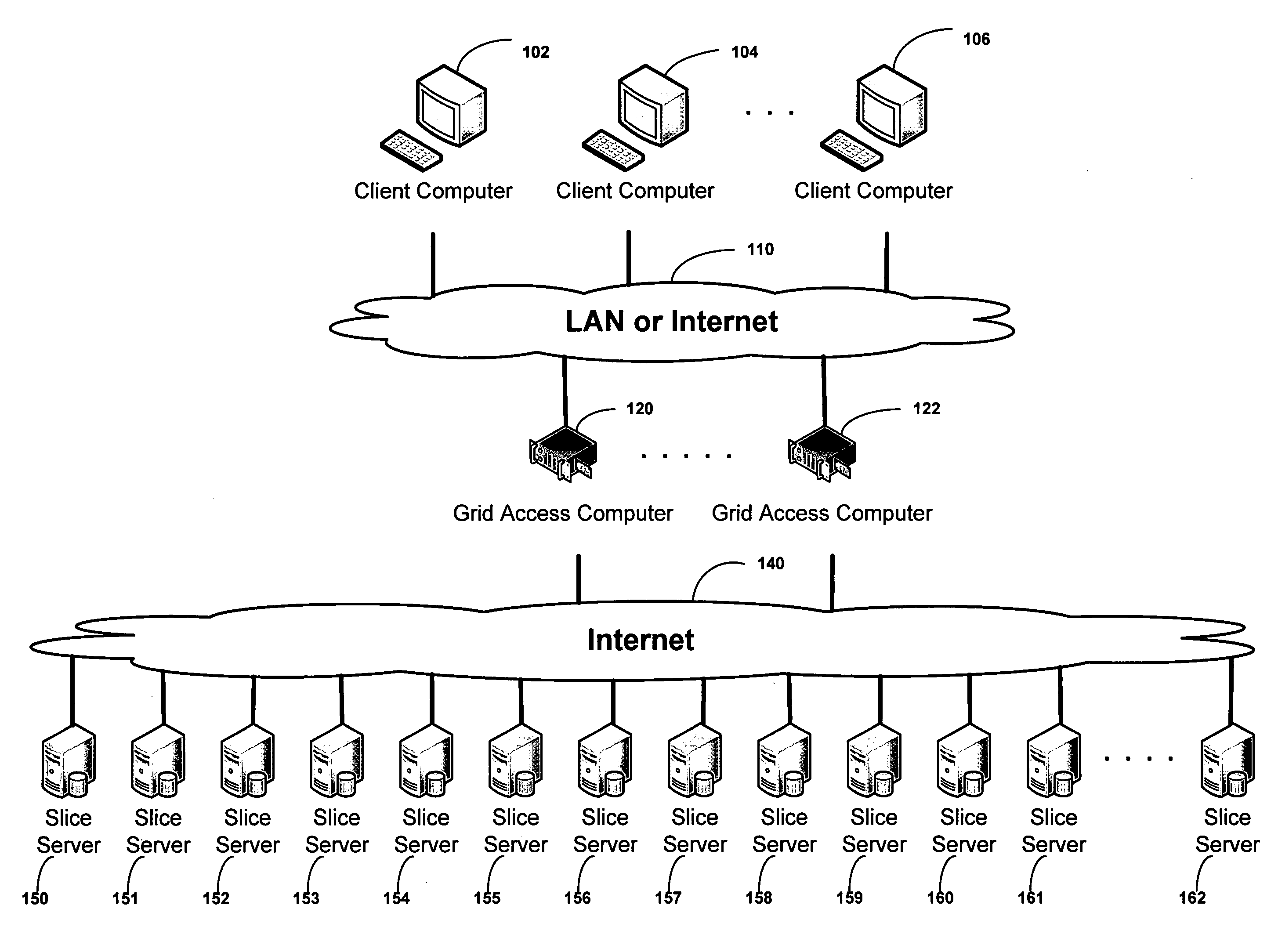
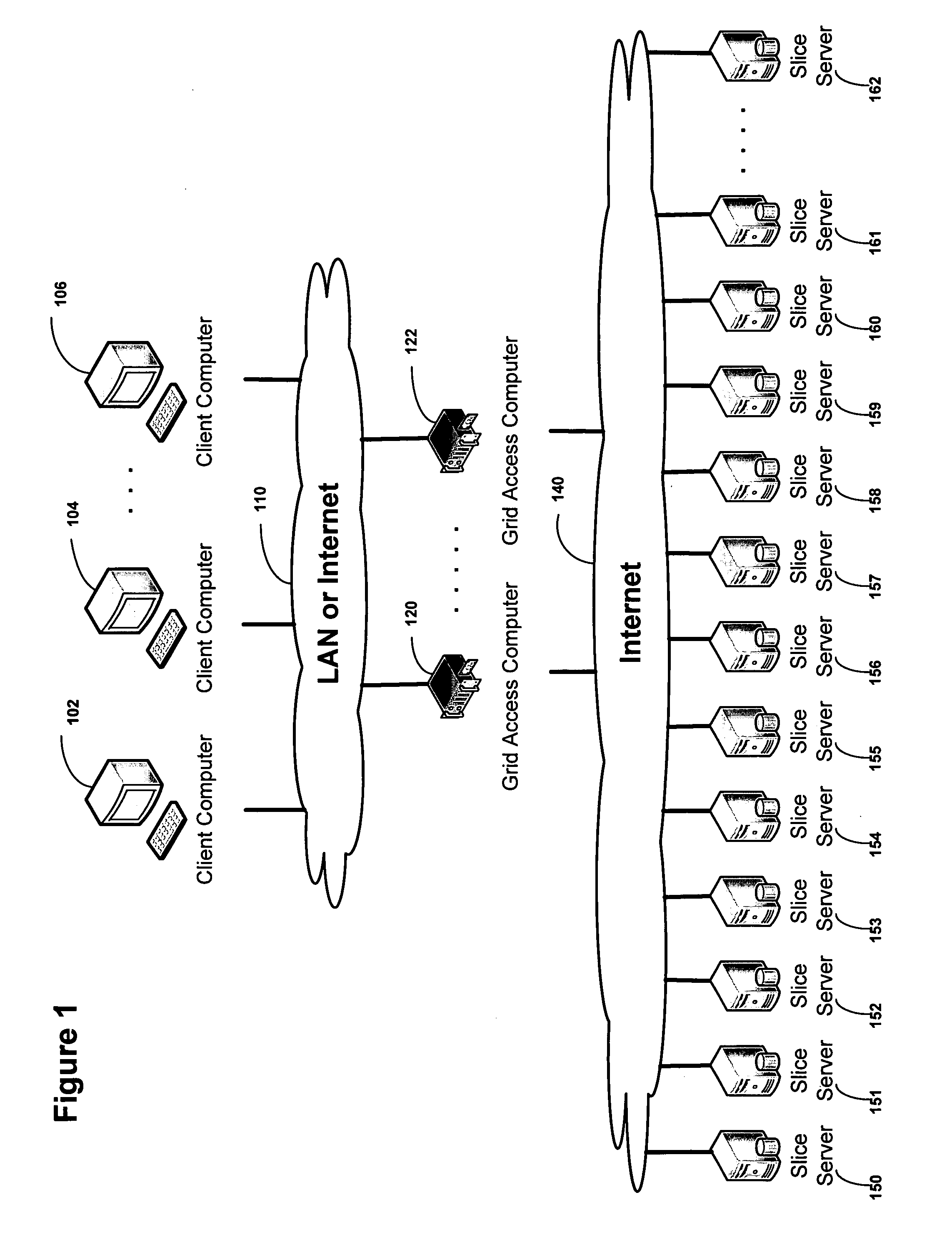
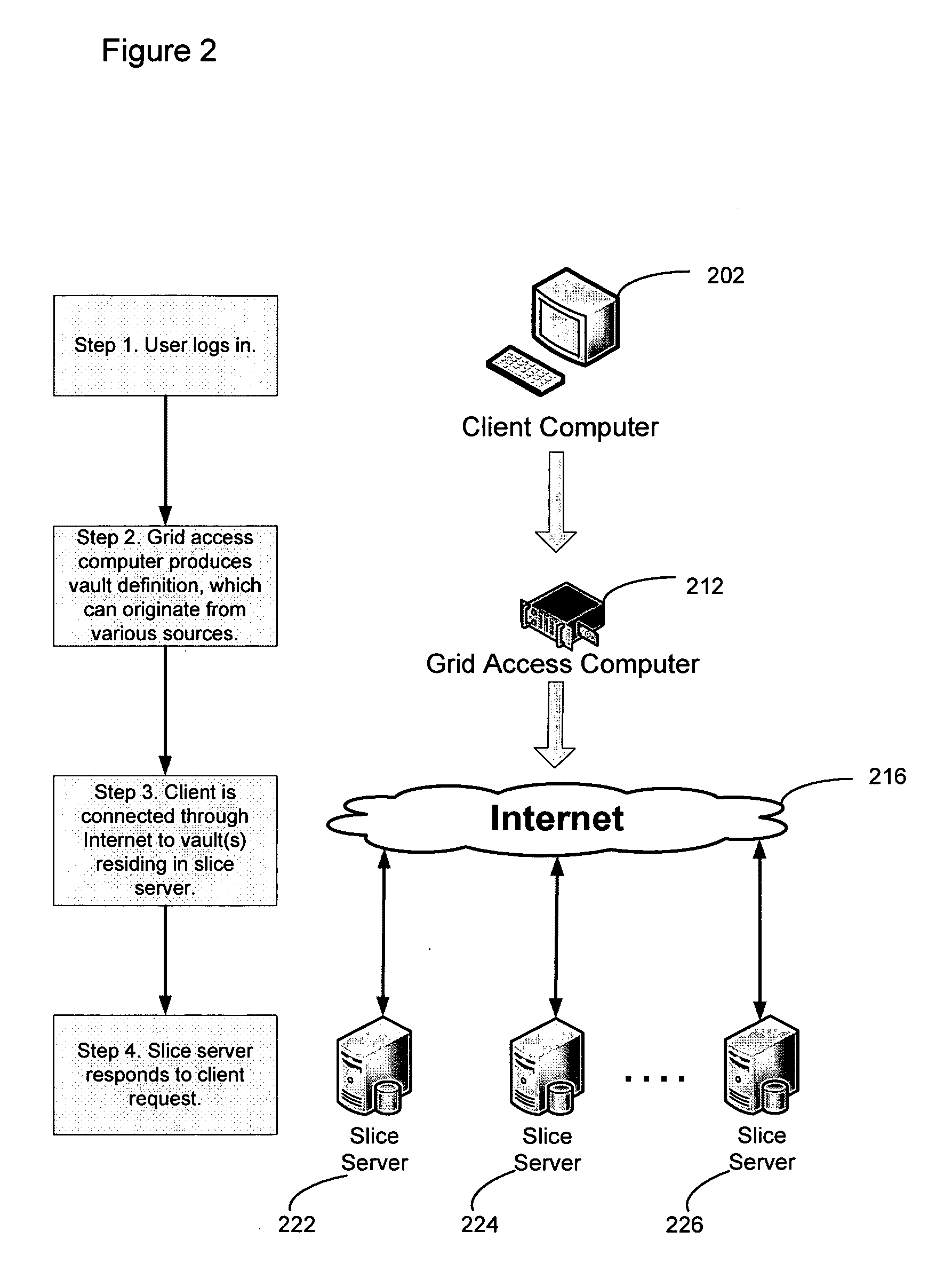
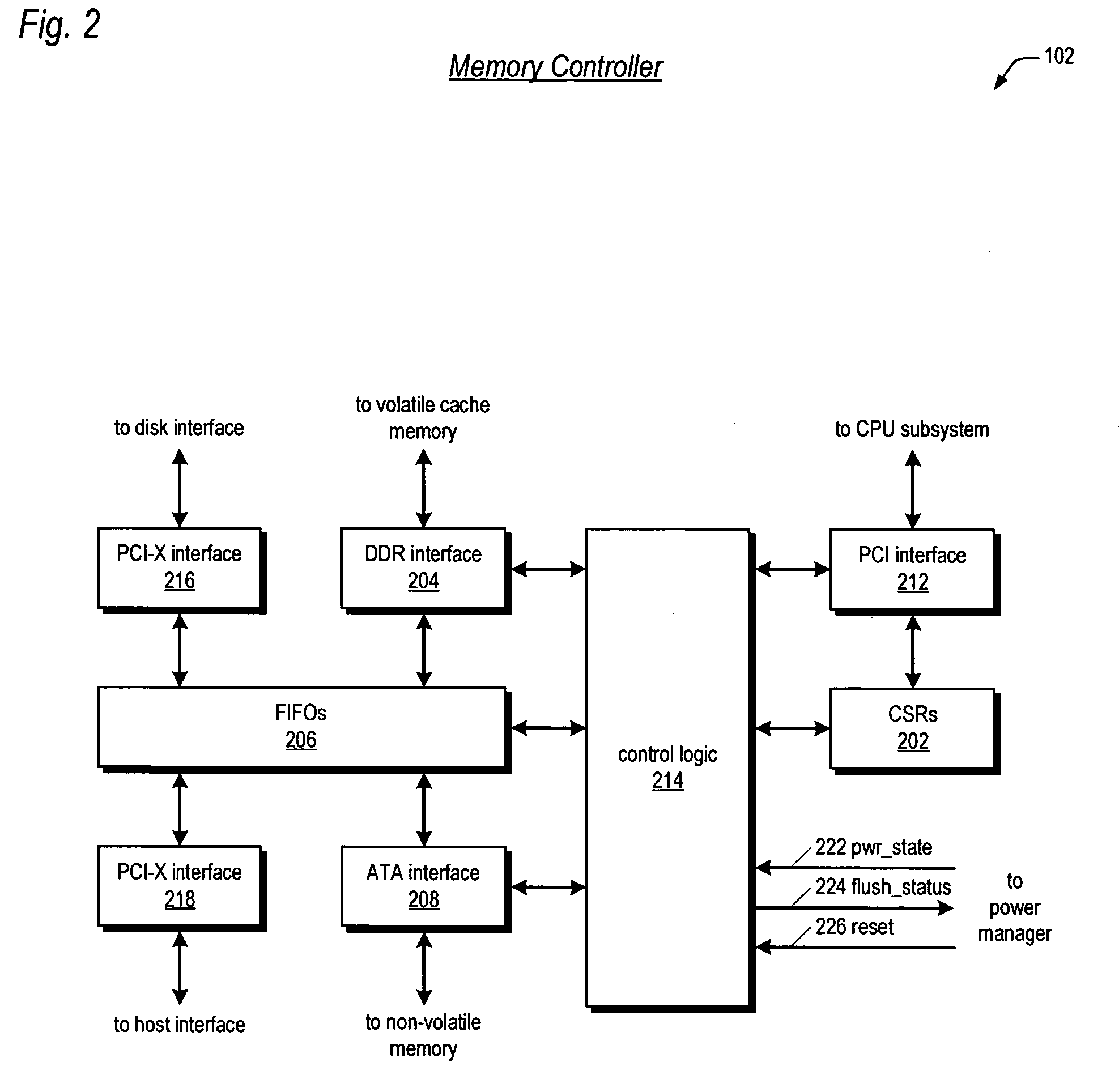
Virtualized data storage vaults on a dispersed data storage network
ActiveUS20090094251A1Efficient managementData processing applicationsDigital data processing detailsInformation dispersalVirtualization
A system, method, and apparatus for implementing a plurality of dispersed data storage networks using a set of slice servers are disclosed. A plurality of information records are maintained, with each information record corresponding to a dispersed data storage network. The information record maintains what slice servers are used to implement the dispersed data storage network, as well as other information needed to administer a DDSN, such as the information dispersal algorithm used, how data is stored, and whether data is compressed or encrypted.
Owner:PURE STORAGE
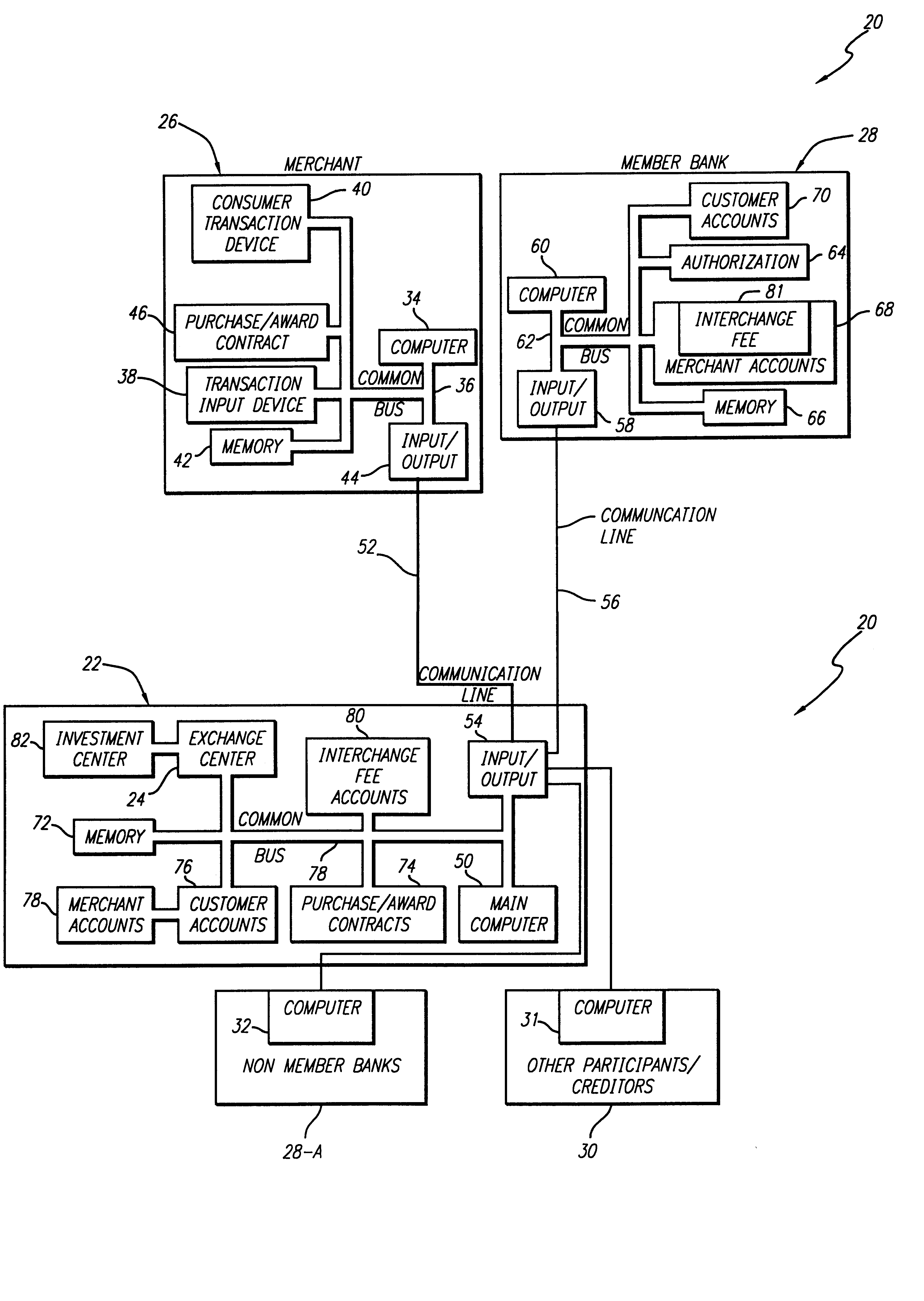
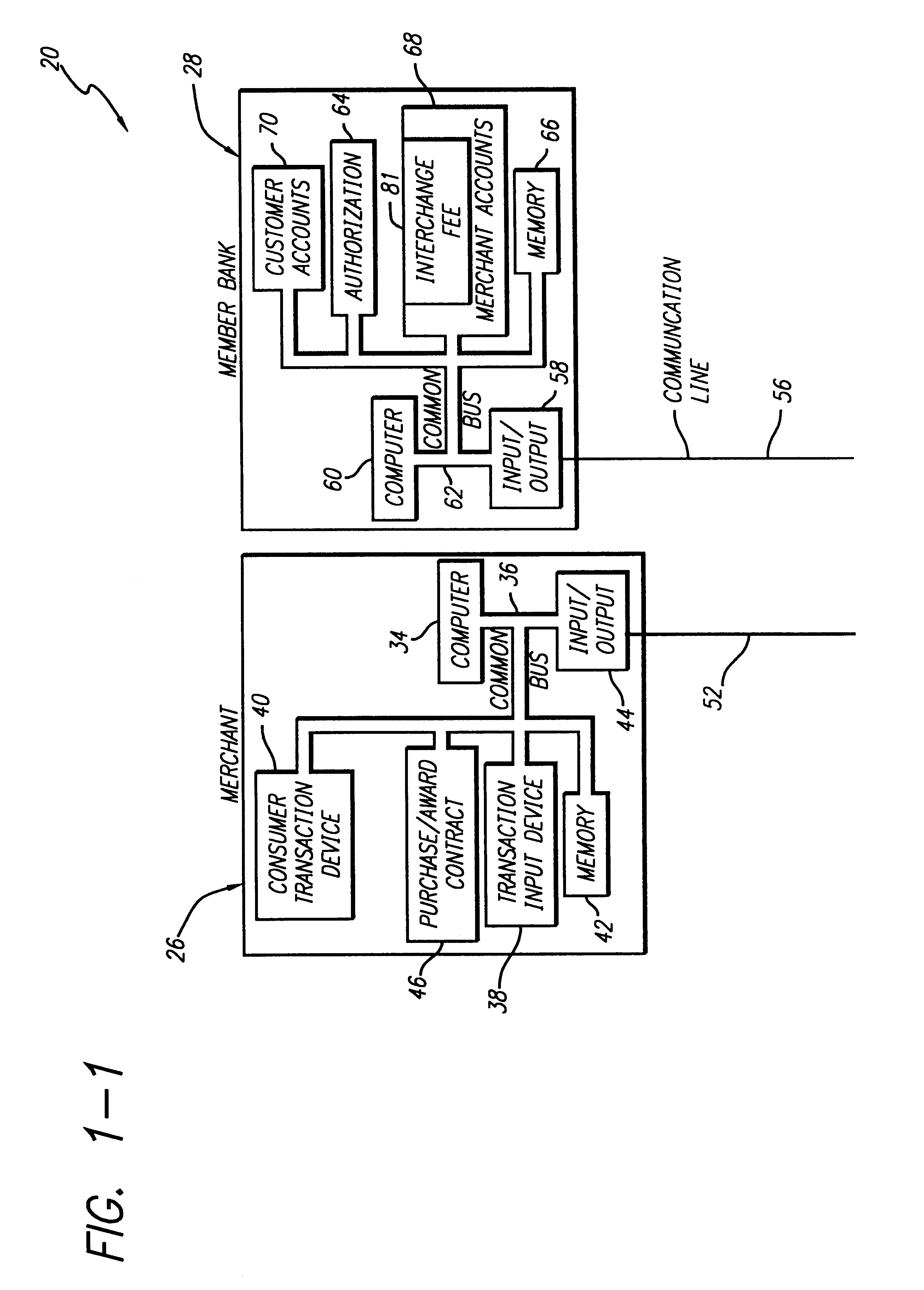
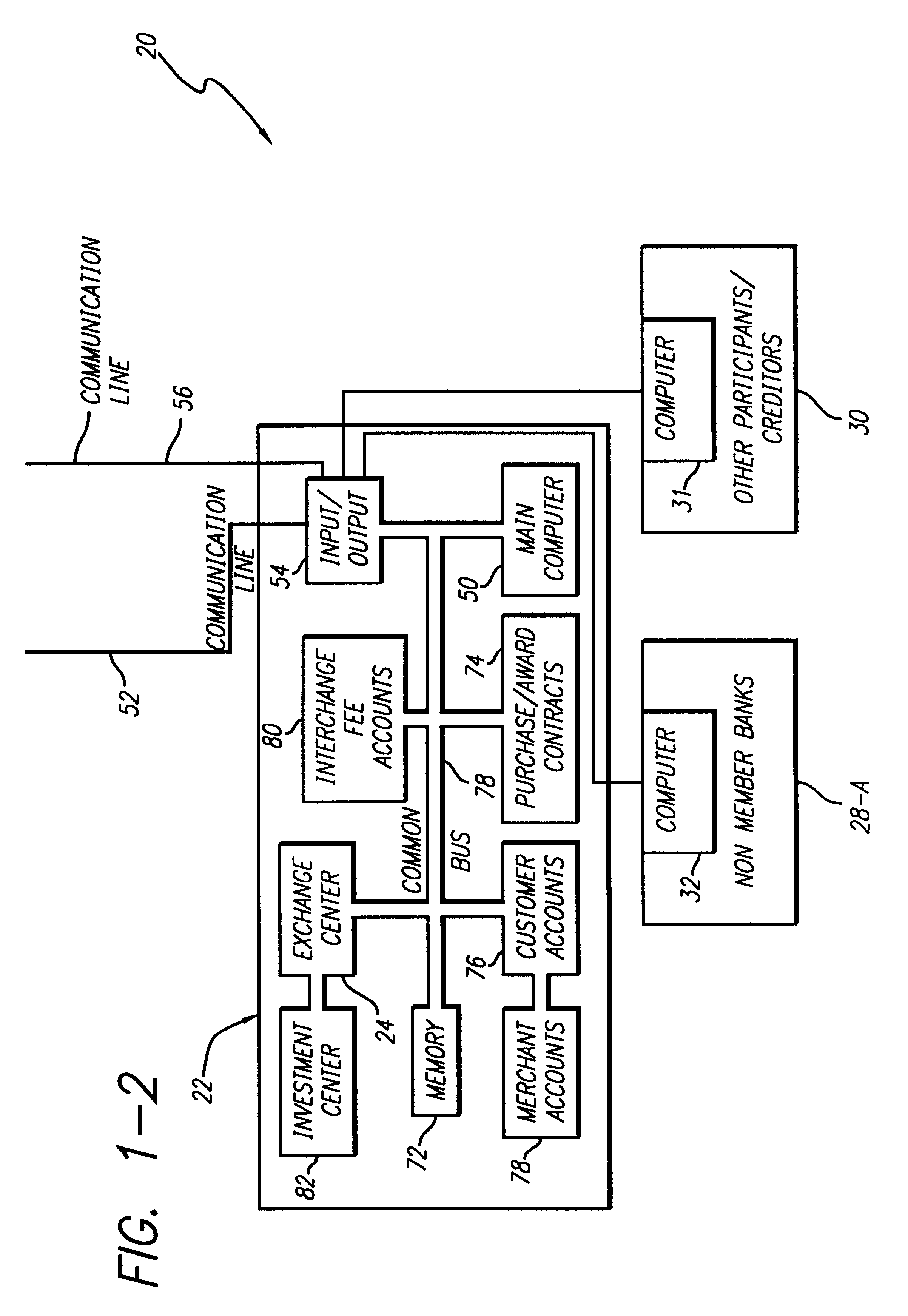
Internet-based credit interchange system of converting purchase credit awards through credit exchange system for purchase of investment vehicle
An Internet-based purchase credit award interchange center is described which interfaces with a credit award exchange center for conversion of any form of merchant or purchase credit award resulting from customer purchase of goods or services to investment in a mutual fund and / or investment vehicle utilizing computer data processing methods. Preassigned purchase credit accumulations earned by a consumer are exchanged from a merchant or creditor through or combination of credit cards, co-branded credit cards, PIN cards, debit and smart cards, coupons, stamps, proof of purchase, rebates, or any form of purchase award of merchant or creditors choice for an investment in a mutual fund or other investment vehicle. A specific implementation is described wherein a credit card account having investment credit awards is issued through the Internet to a customer. While inputting information through the Internet necessary for establishing the credit card account, the customer also provides any information needed to authorize the purchase of investment vehicles on his or her behalf. Any forms that need to be signed by the customer to authorize purchase of the investment vehicles may be printed out by the customer. The customer may also select, via the Internet, particular investment vehicles out of a group of possible investment vehicles. Subsequent use of the credit card by the customer automatically results in accrual of credit award accumulations in the selected investment vehicle.
Owner:KALINA DYAN T
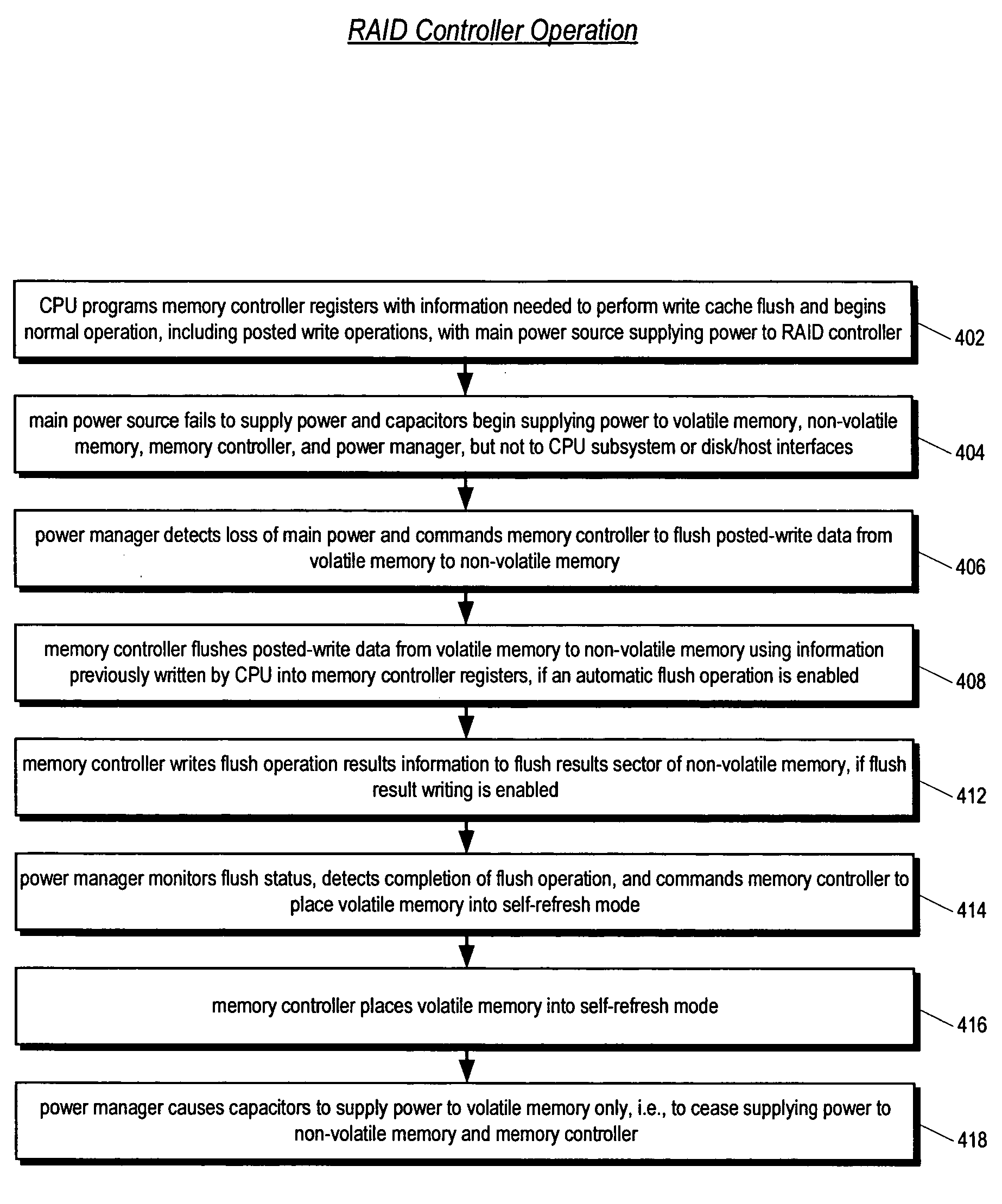
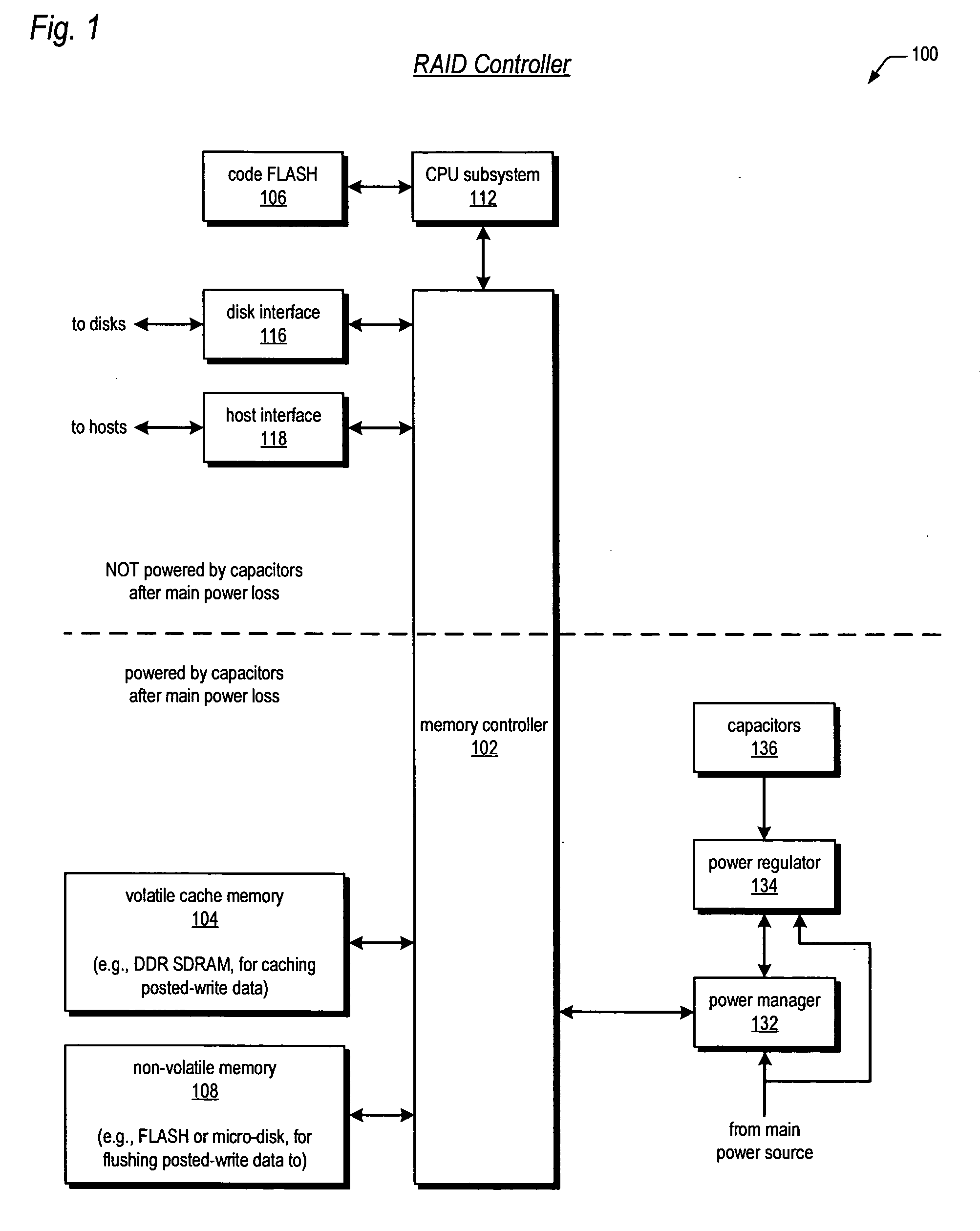
Raid controller using capacitor energy source to flush volatile cache data to non-volatile memory during main power outage
InactiveUS20060015683A1Reduces amount of energy storage capacity requirementLess expensiveEnergy efficient ICTMemory loss protectionRAIDStored energy
A write-caching RAID controller is disclosed. The controller includes a CPU that manages transfers of posted-write data from host computers to a volatile memory and transfers of the posted-write data from the volatile memory to storage devices when a main power source is supplying power to the RAID controller. A memory controller flushes the posted-write data from the volatile memory to the non-volatile memory when main power fails, during which time capacitors provide power to the memory controller, volatile memory, and non-volatile memory, but not to the CPU, in order to reduce the energy storage requirements of the capacitors. During main power provision, the CPU programs the memory controller with information needed to perform the flush operation, such as the location and size of the posted-write data in the volatile memory and various flush operation characteristics.
Owner:DOT HILL SYST
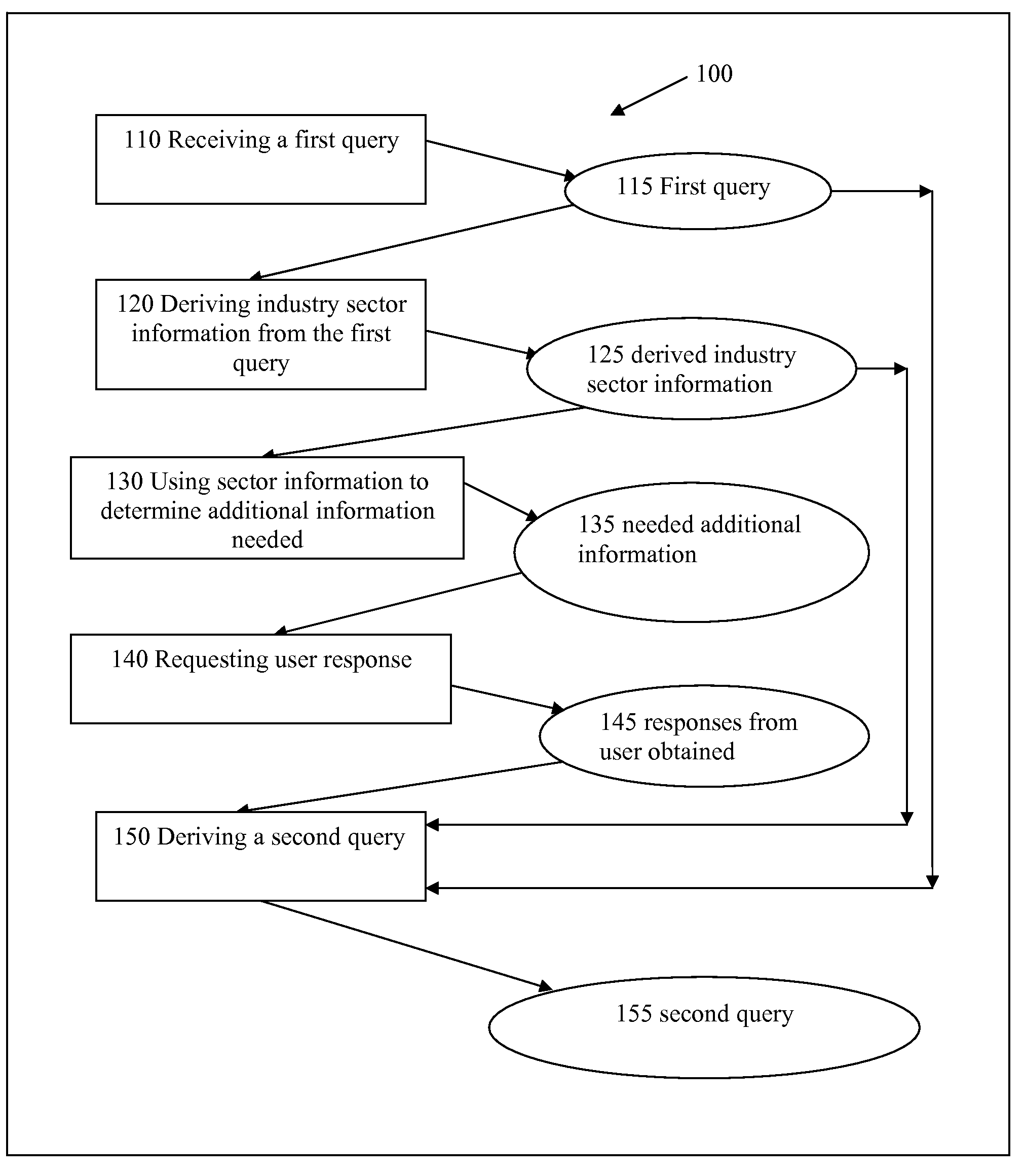
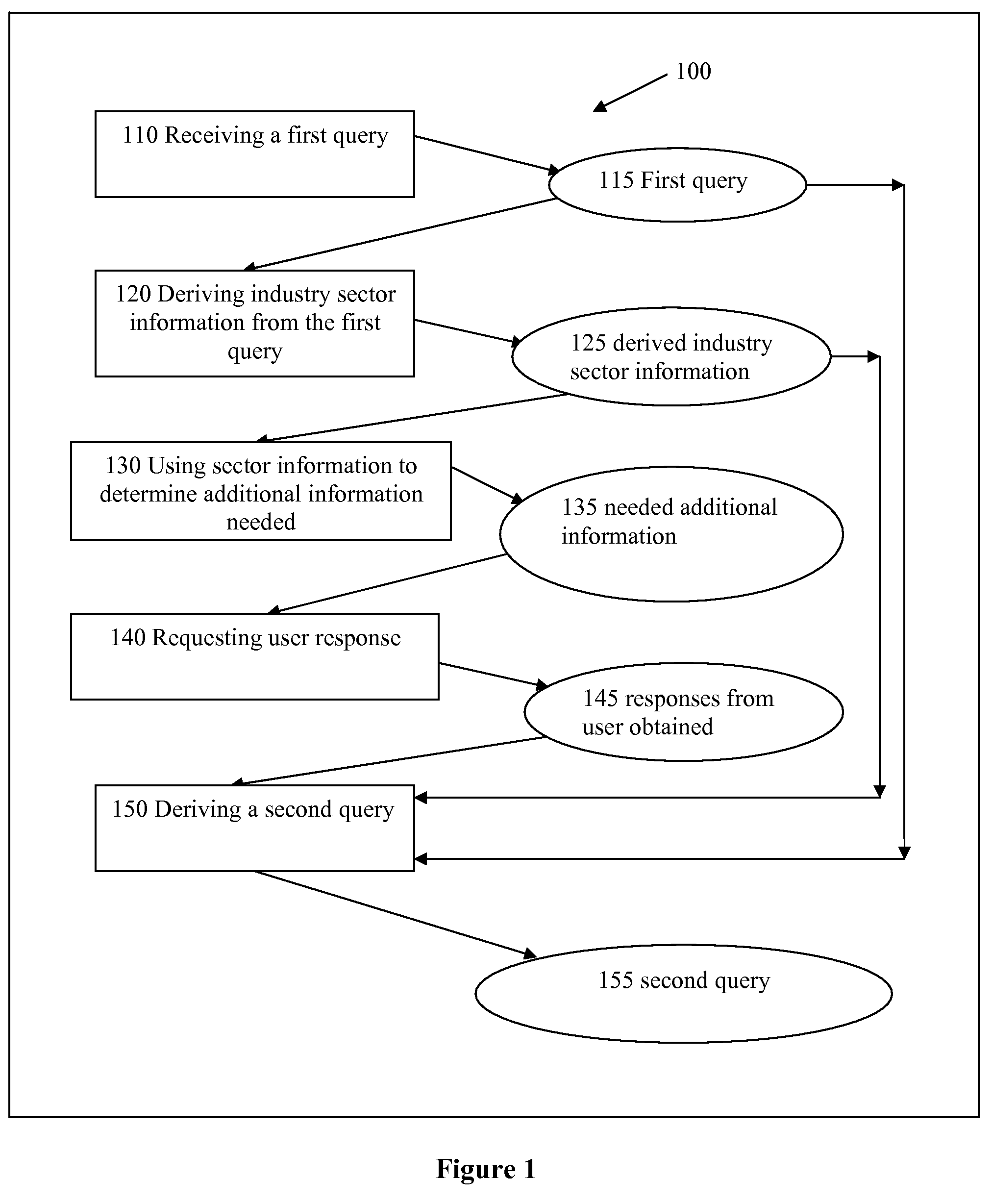
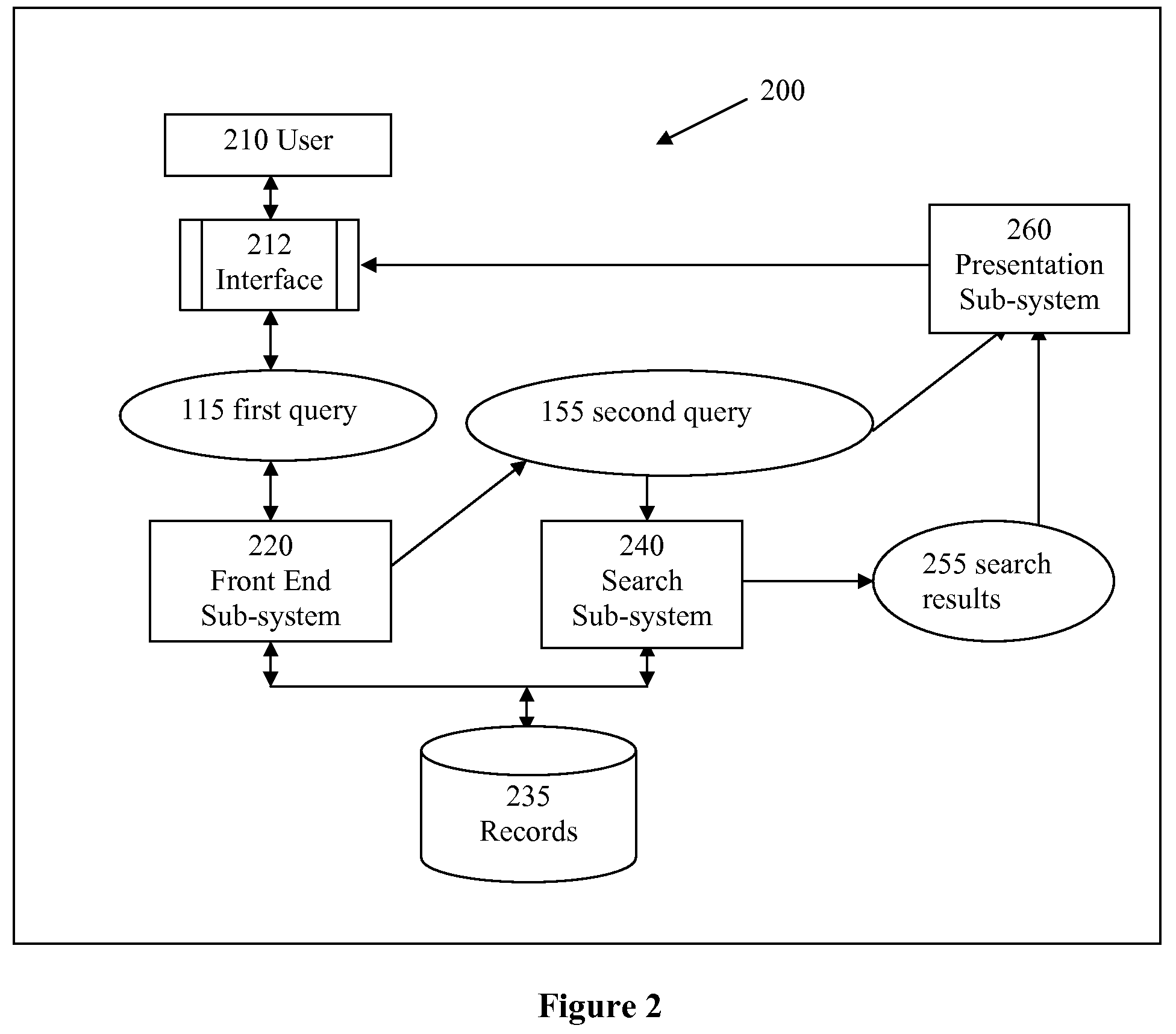
Methods and apparatus for entity search
Owner:TAMIRAS PER PTE LTD LLC
Methods and Apparatus for Entity Search
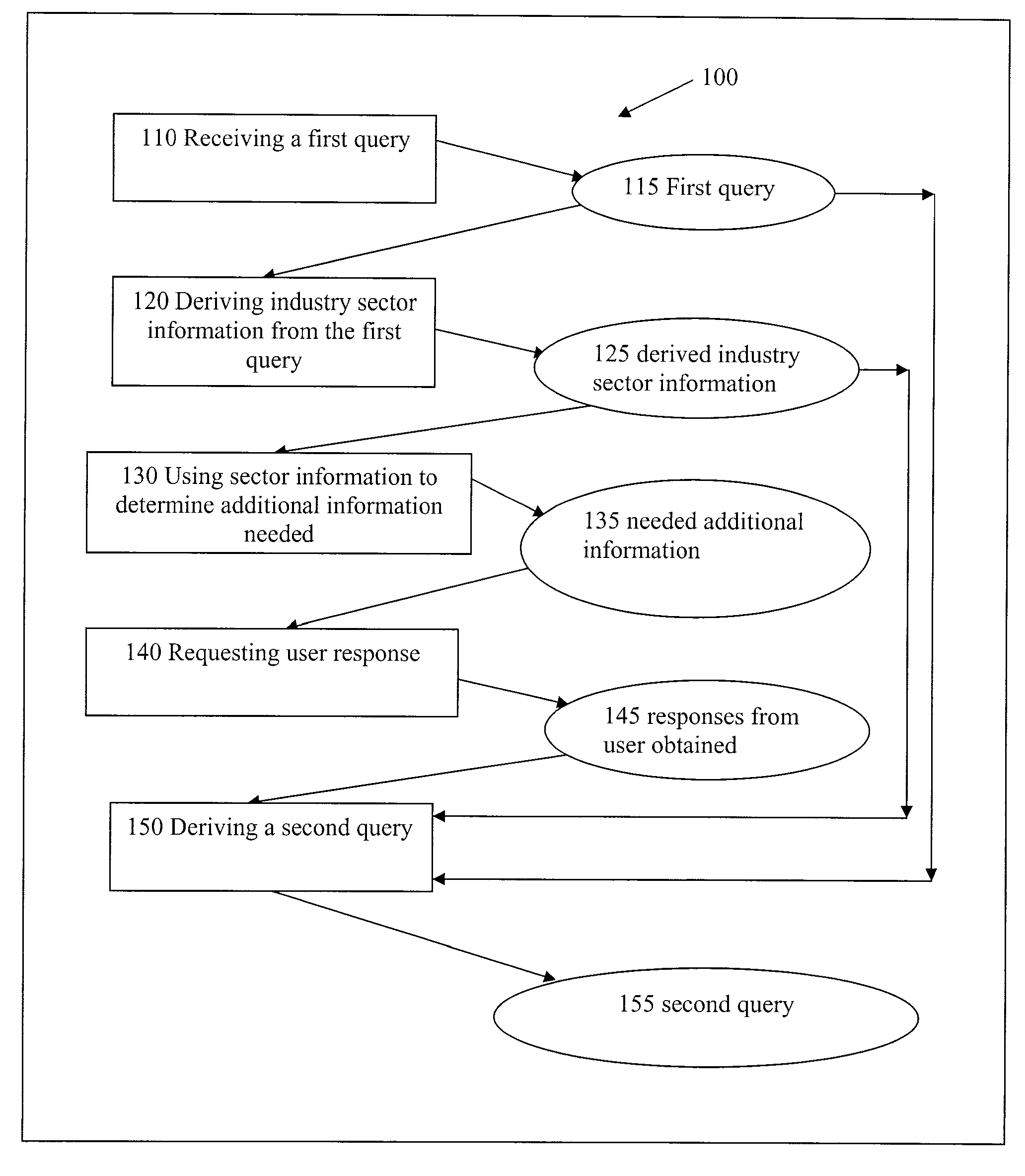
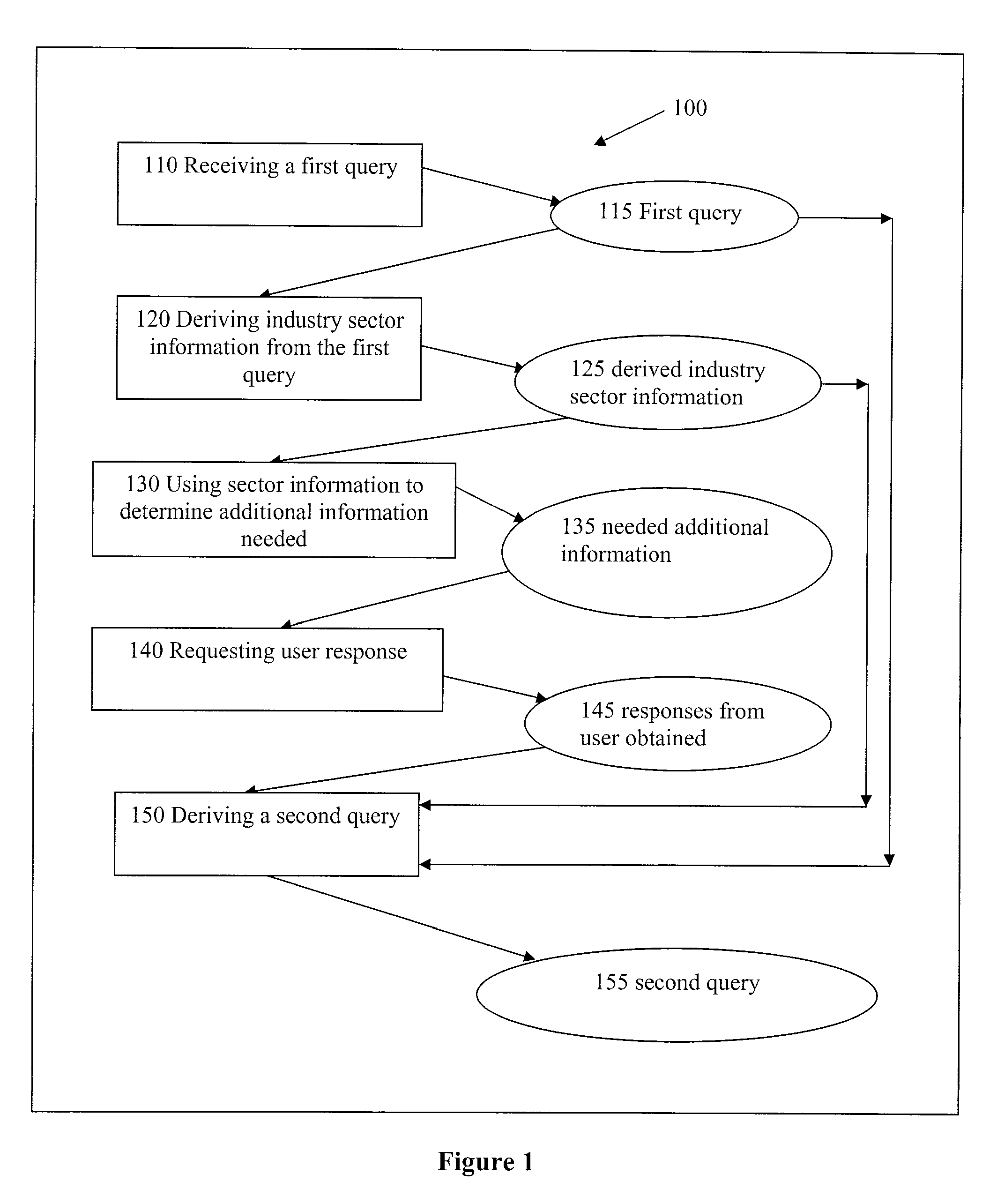
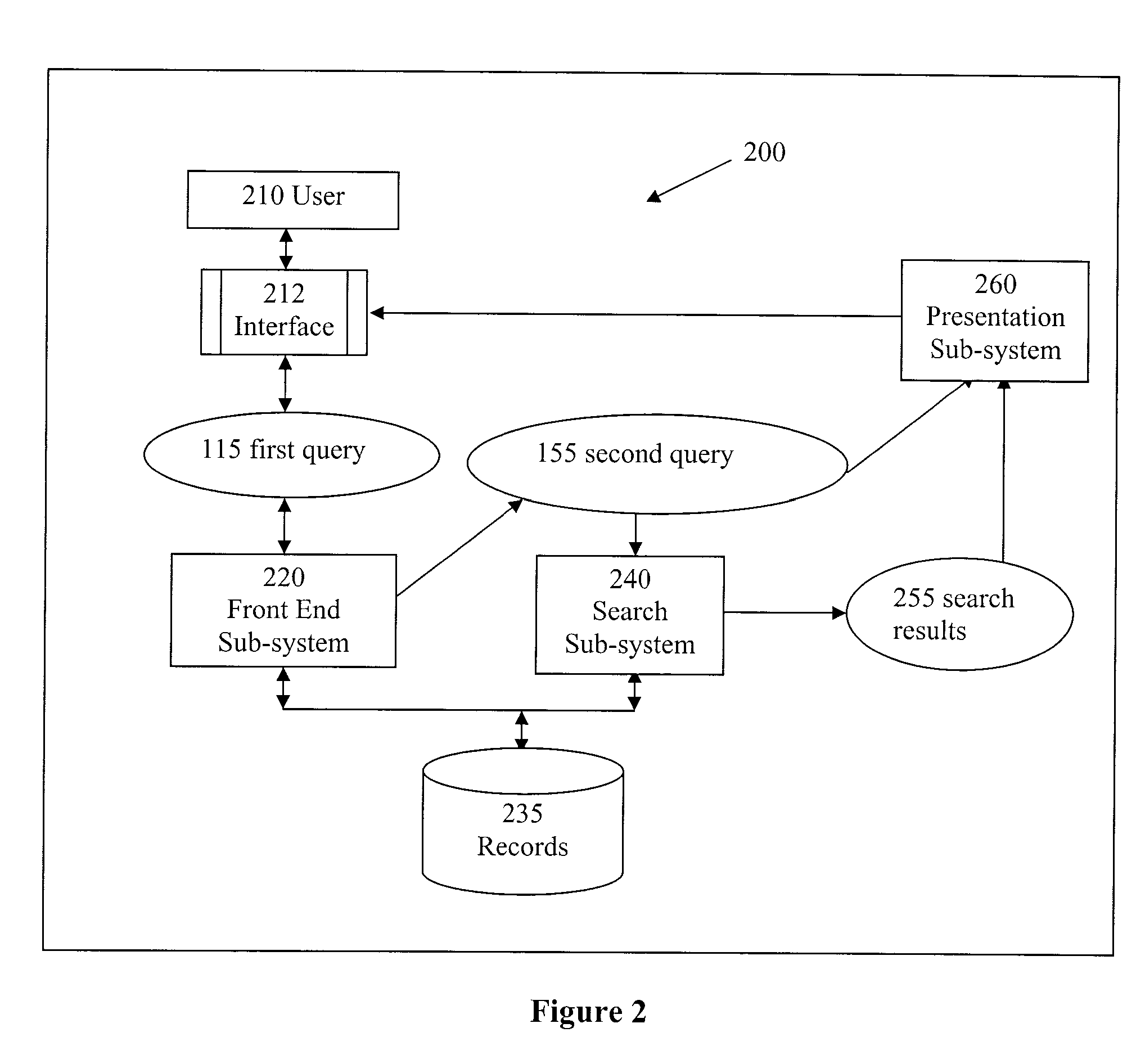
Methods and apparatus that deliver a searching experience that is substantially akin to consultation with a human expert, and that satisfies a user's information need in fulfilling projects such as purchasing, shopping, procurement, bartering, requesting for quotes, in online retail, traditional retail, wholesale, health care, travel, real estate, restaurant-going, entertainment, logistics, and sourcing are disclosed. Search results often contain entities that provide services and products. Records being searched are associated with industry sectors in a broad sense. Industry sector information is first derived from a user query; and is used in determining relevant and adequate additional questions for a searcher, and in matching, ranking, and presenting search results.
Owner:TAMIRAS PER PTE LTD LLC
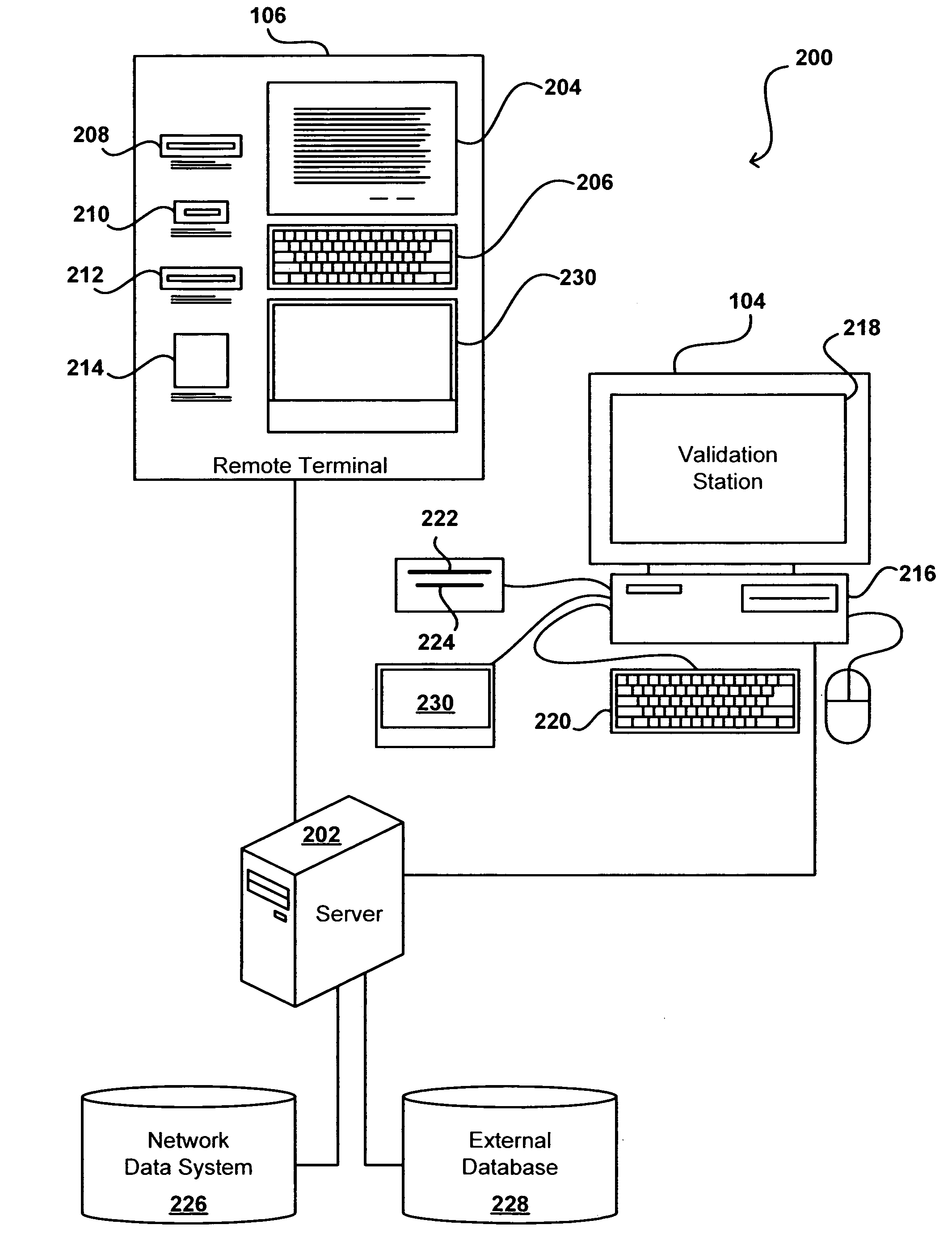
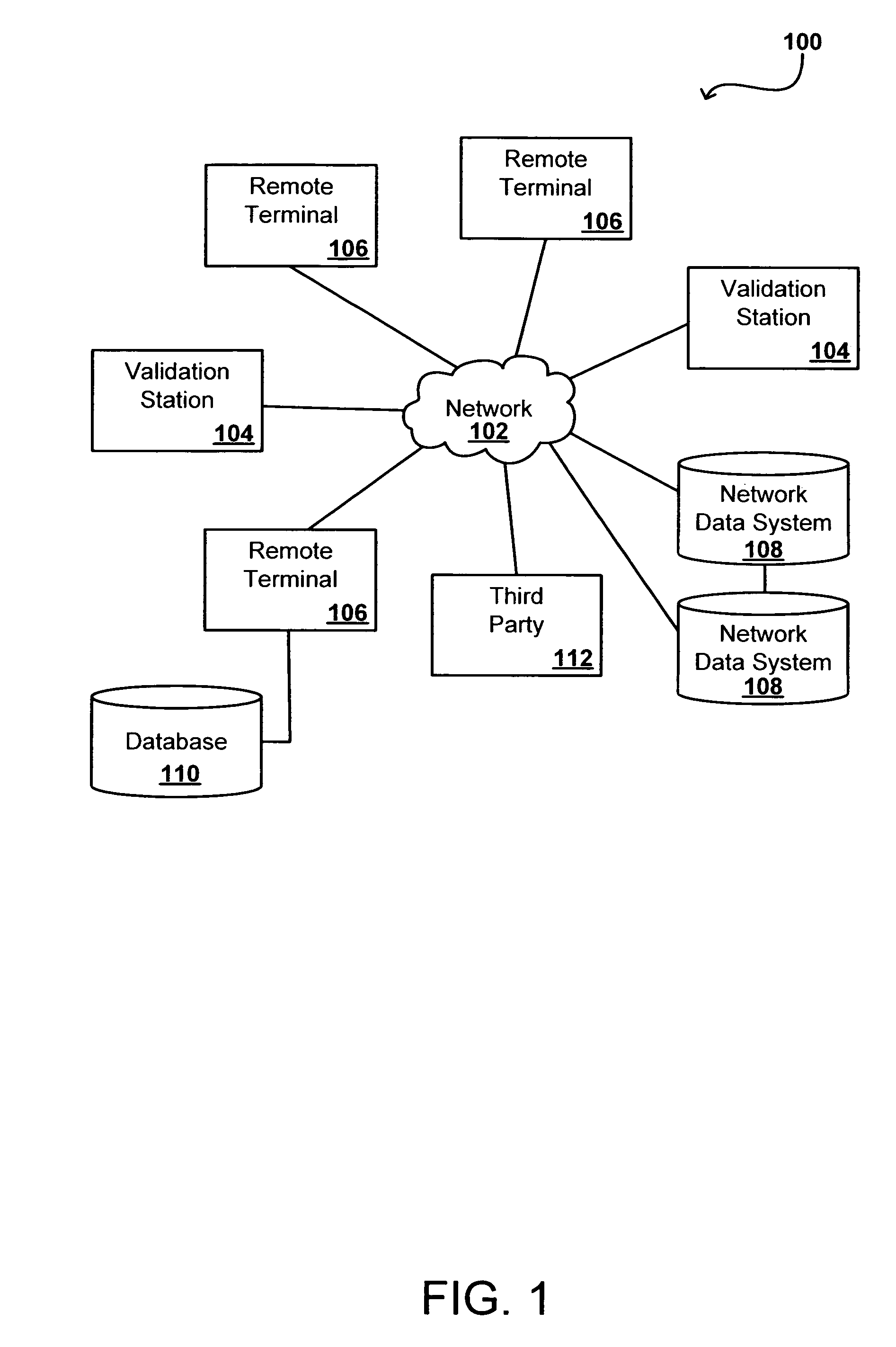
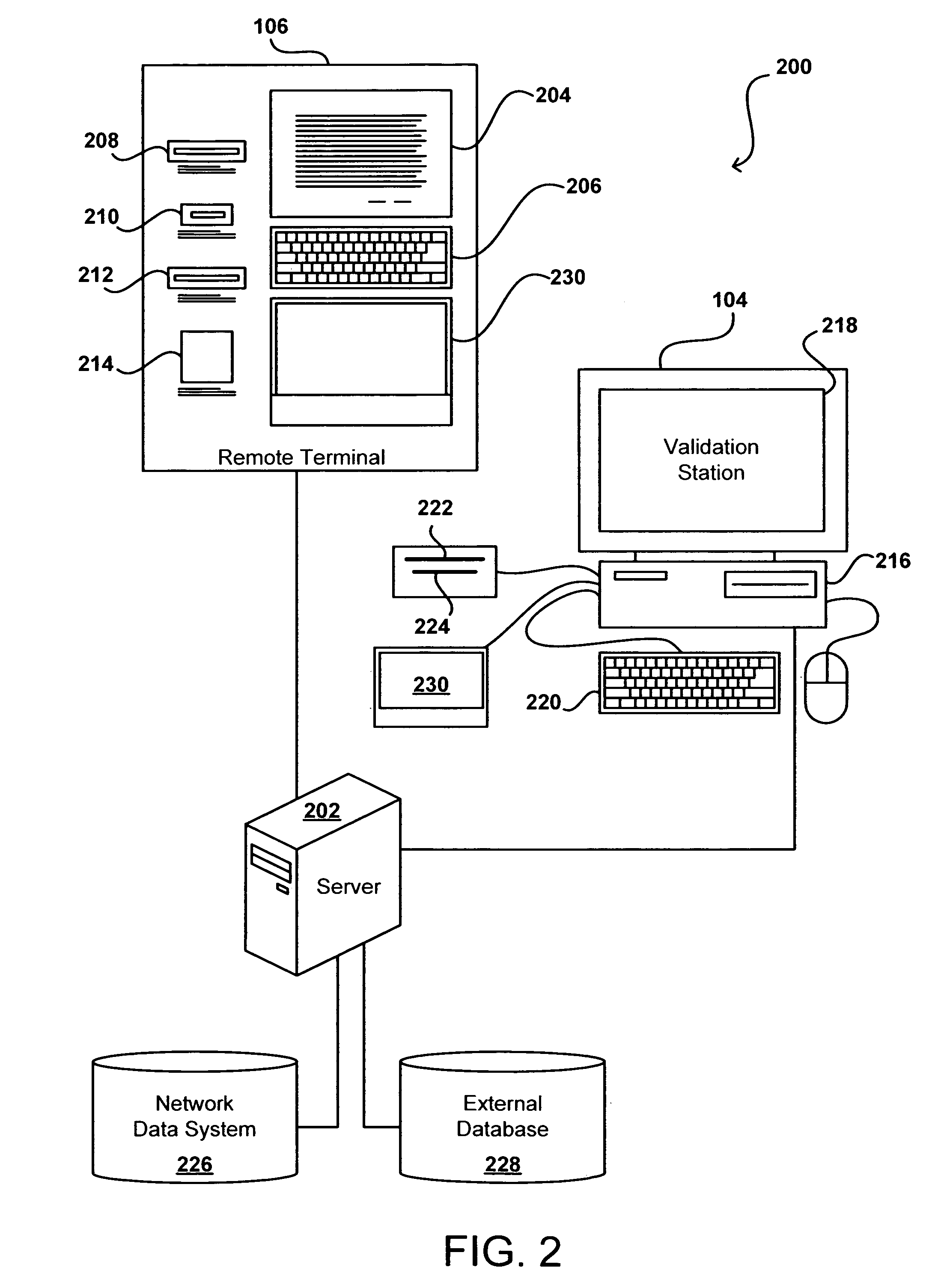
Remote validation system useful for financial transactions
A financial services and transaction network including multiple networked validation stations and remote terminals allows users to access a number of financial services and transactions. A user visiting a remote terminal indicates a desired service or transaction. The user provides any currency or funding information needed for the selected service, after which the remote terminal issues the user a transaction voucher. The user can take this transaction voucher to any of the validation stations in order to authenticate the user's identity and activate the voucher. Once the voucher is activated, the user or a recipient of the voucher can present the voucher at any remote terminal to receive funding or otherwise complete the transaction or service, subject to recipient authentication. The user provides necessary information using the remote terminal or validation station, or supplies the information using the voucher, which is collected upon performance of the requested service or transaction.
Owner:CUCINOTTA ROBERT
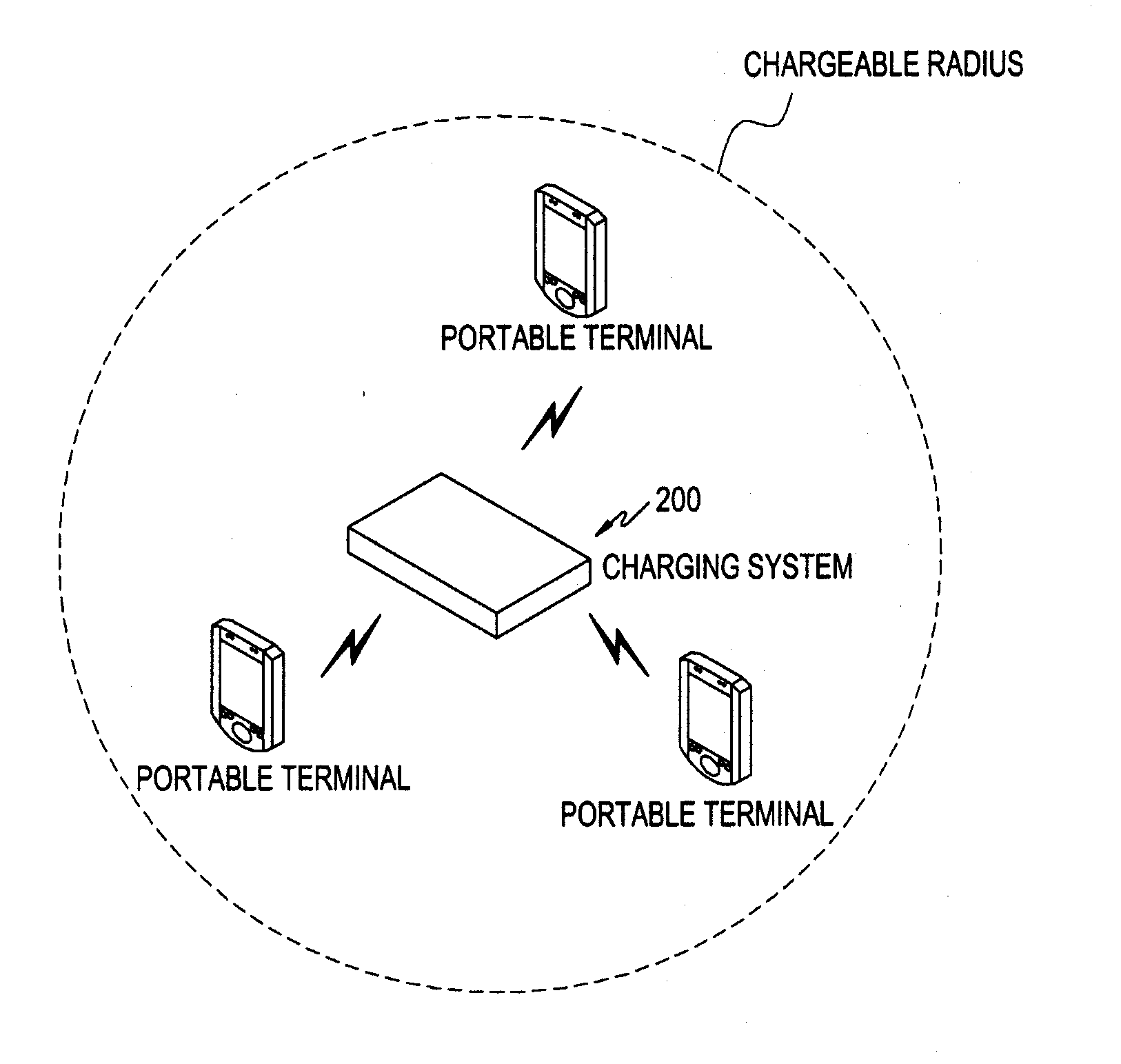
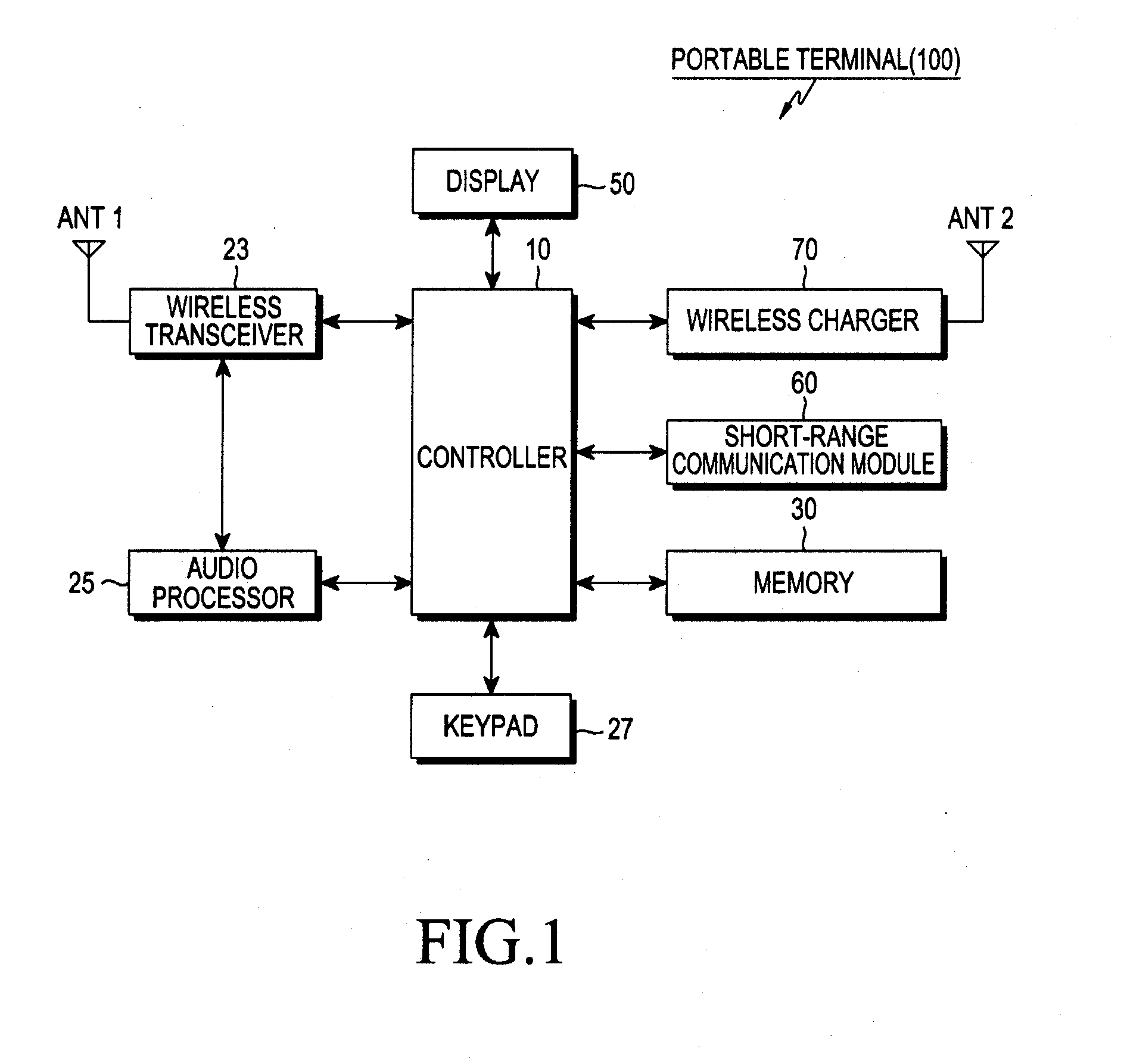
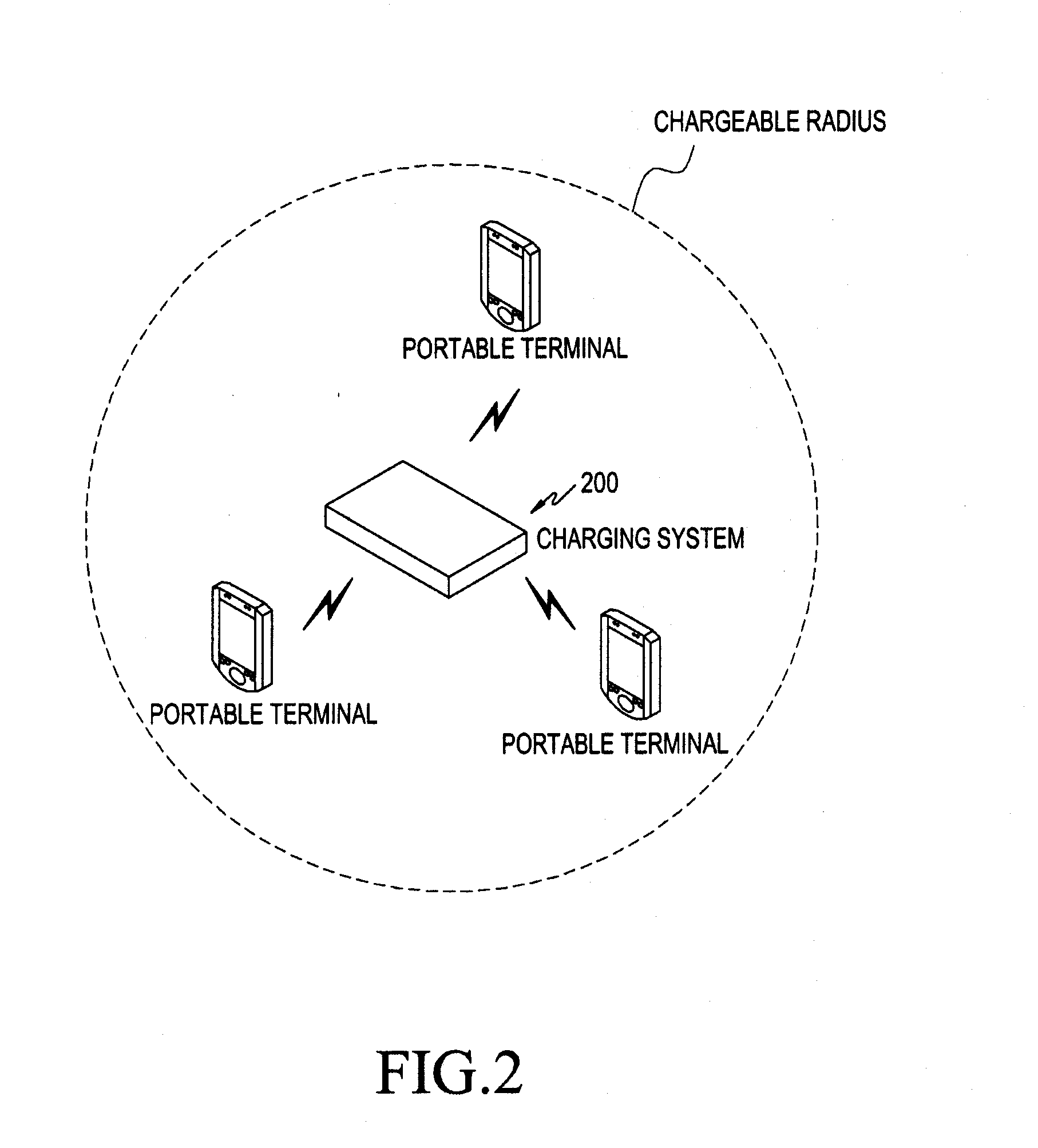
Method and system for wireless charging in a portable terminal
ActiveUS20120249051A1Circuit authenticationCircuit monitoring/indicationRadio frequencyInductive charging
A method for wirelessly charging a portable terminal using a Radio Frequency (RF) is provided. A charging system detects one or more portable terminals within a predetermined area, and preferably requests information needed for charging to the one or more portable terminals via short-range communication, receives the information in response needed for charging from each of the one or more portable terminals. A portable terminal to be wirelessly charged from among the one or more portable terminals is selected, based on the received information needed for charging, and the charging system transmits a predetermined RF for charging to the selected portable terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
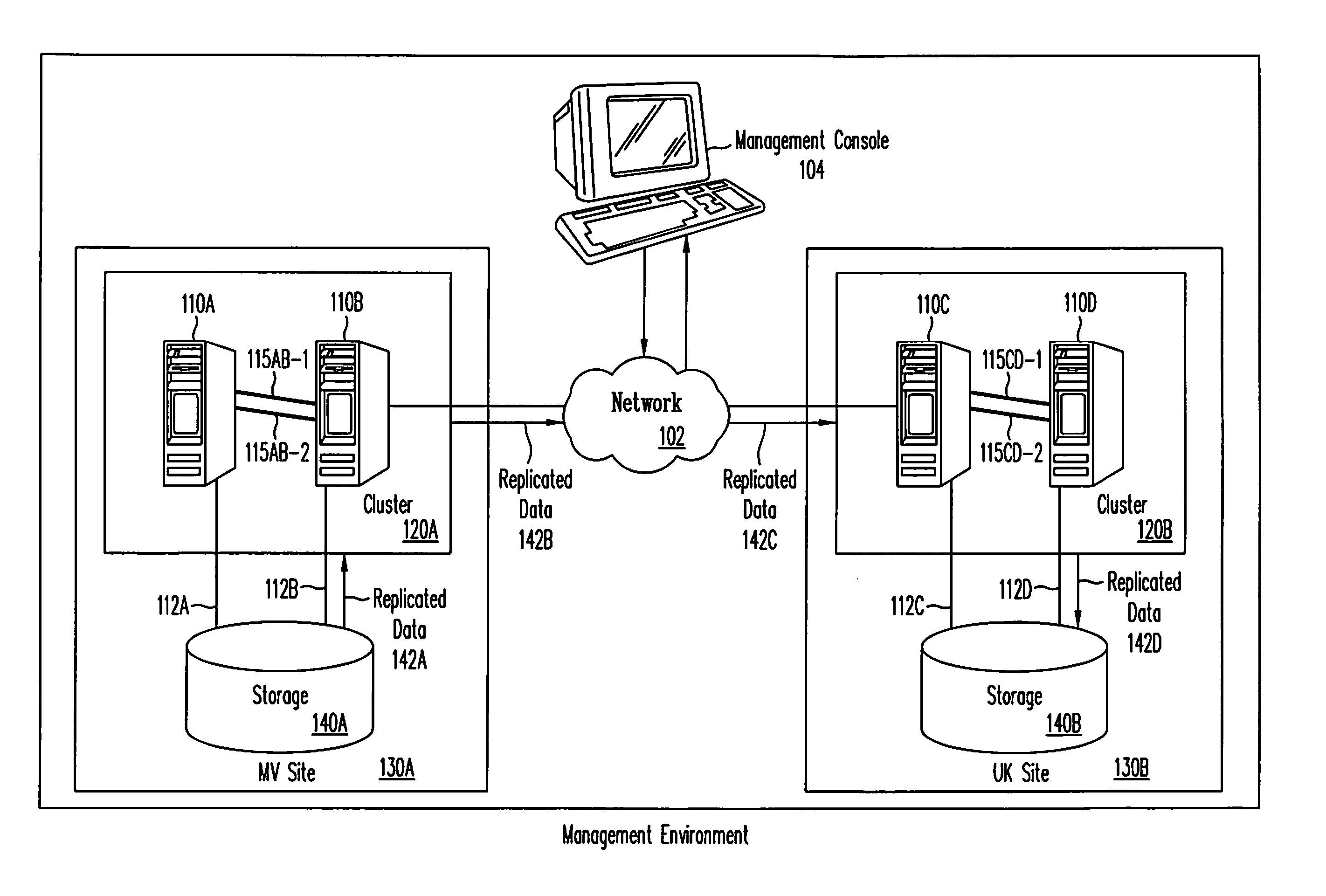
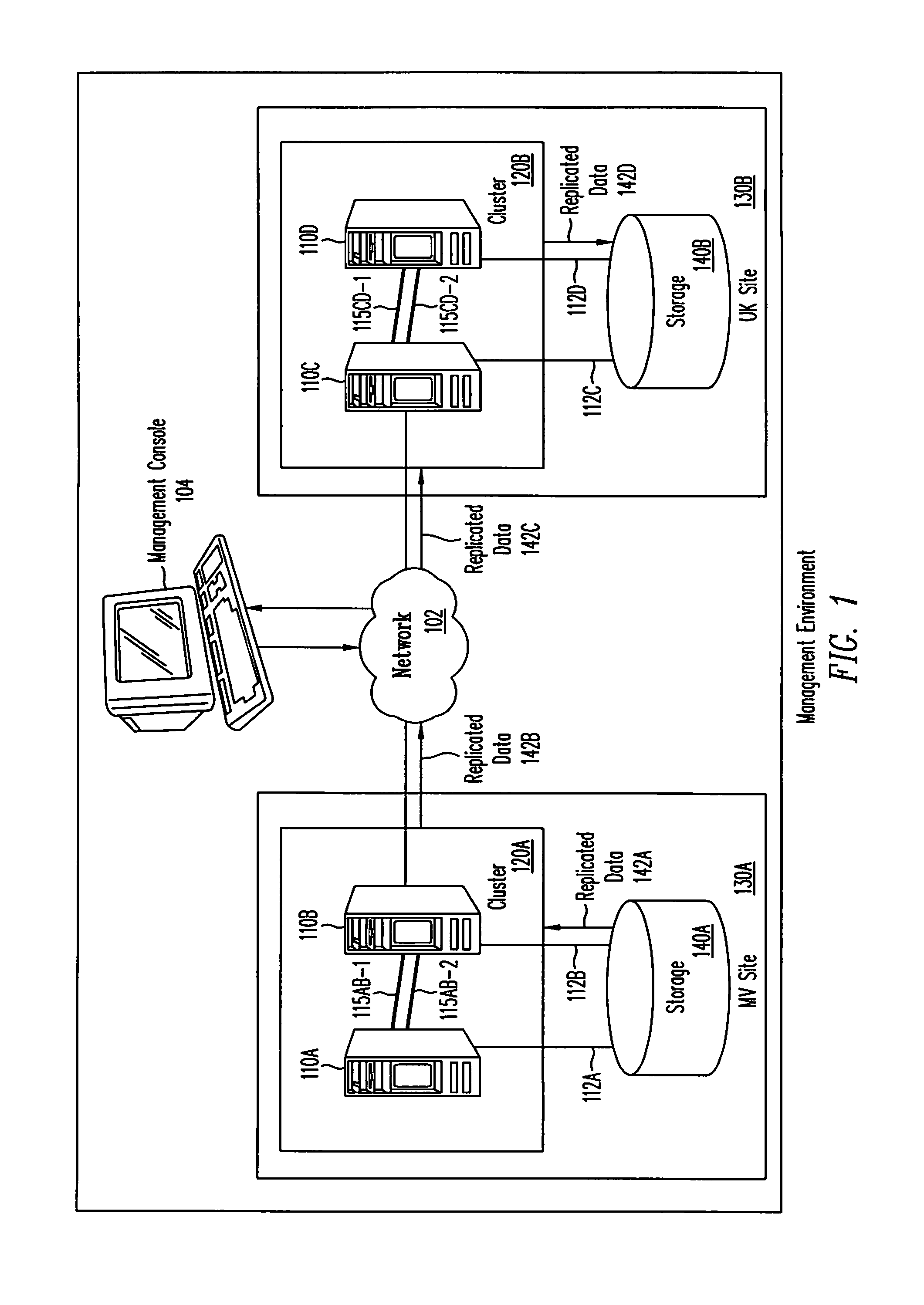
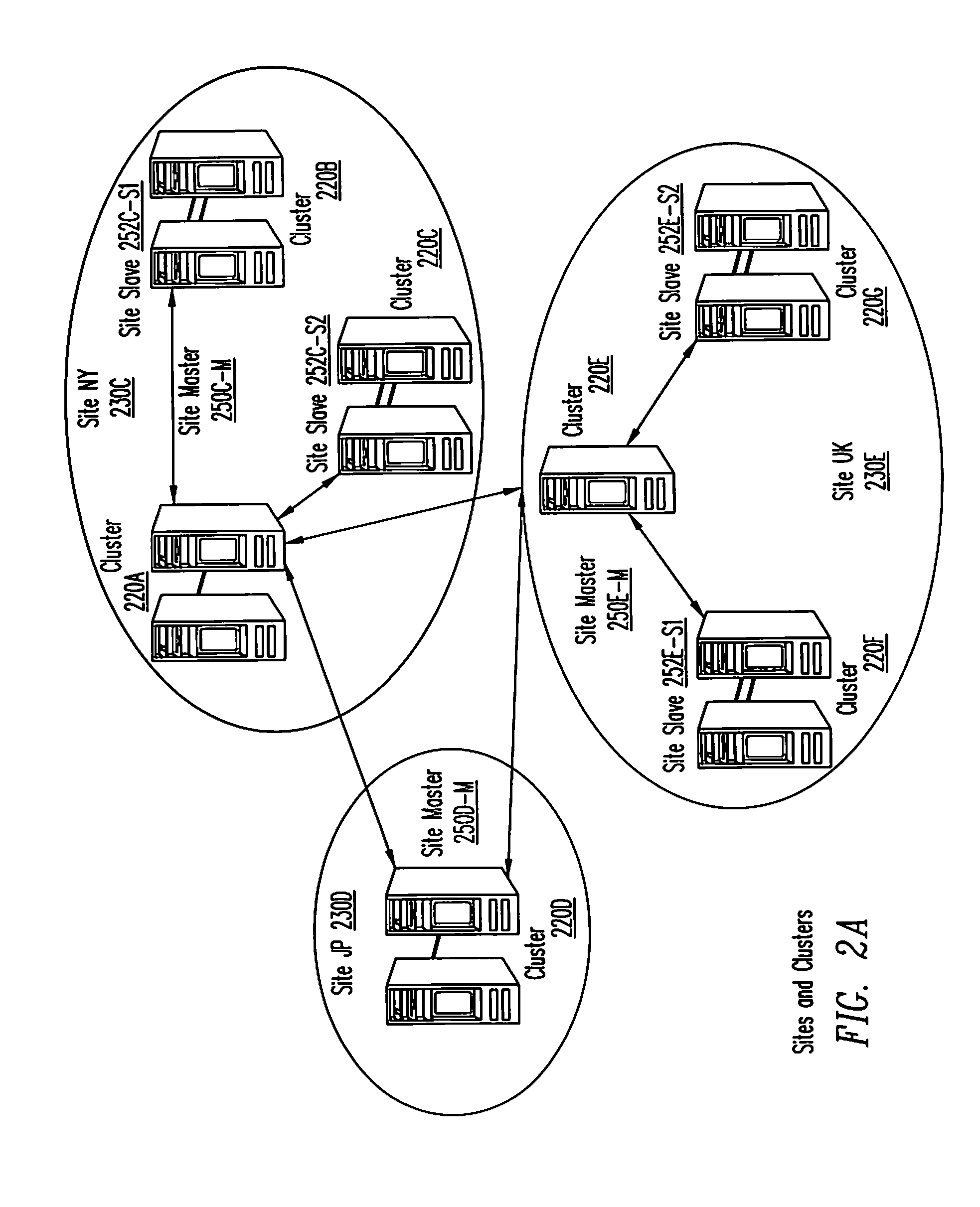
Framework for managing clustering and replication
The present invention provides a framework for managing both clustering and data replication in a software system distributed across multiple nodes. The framework includes at least one agent running at nodes comprising the distributed system. The framework also includes a master to coordinate clustering and replication operations. The framework further includes a library of software programs, called primitives, that are used by agents to communicate with the master. The agent(s) obtain cluster status information and replication status information, which are used by the master to manage clustering and replication operations. The framework is designed to work with existing cluster management applications and data replication facilities. The framework provides status information needed for coordinating clustering and replication operations to ensure that applications and data remain in a consistent state for disaster recovery purposes.
Owner:SYMANTEC OPERATING CORP
System for fulfilling an information need
InactiveUS6859800B1Efficient and fast processingData processing applicationsDigital data information retrievalRelevant informationDocument preparation
The invention offers new approaches to fulfilling an information need, in particular to finding a result for a query based on a large body of information such as a collection of documents. The invention accepts a query containing an unspecified portion that expresses the information need. The invention locates matches for the query within a body of information and returns the matches or portions thereof in addition to or instead of identifiers for documents in which the matches are found. The invention ranks the matches in order to provide the most relevant information. One preferred method of ranking considers the number of instances of a match among a plurality of documents. The invention further defines a new type of index that includes contexts in which terms occur and provides methods of searching such indices to fulfill an information need.
Owner:GLOBAL INFORMATION RES TECH
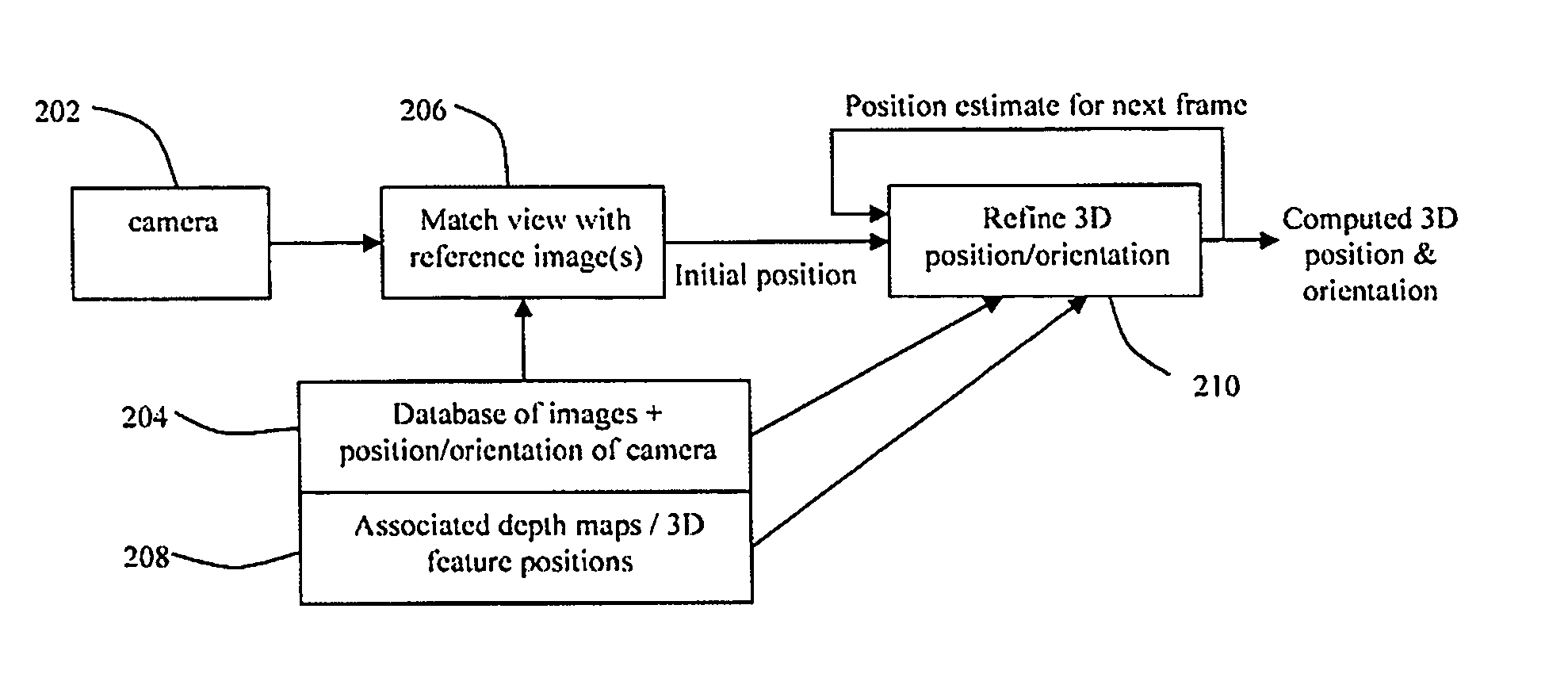
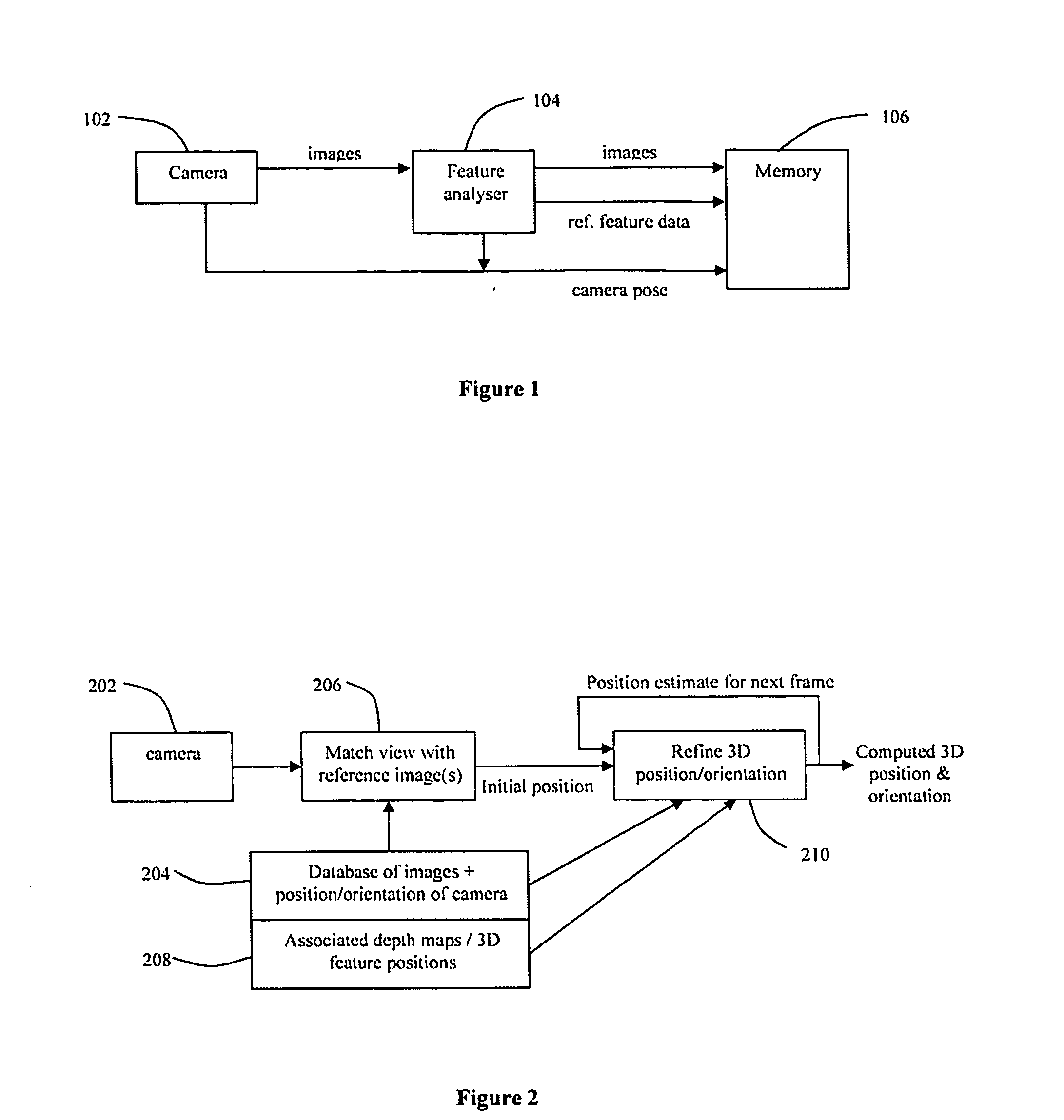
System and method for position determination
A method for determining the position and orientation of a camera, which may not rely on the use of special markers. A set of reference images may be stored, together with camera pose and feature information for each image. A first estimate of camera position is determined by comparing the current camera image with the set of reference images. A refined estimate can be obtained using features from the current image matched in a subset of similar reference images, and in particular, the 3D positions of those features. A consistent 3D model of all stored feature information need not be provided.
Owner:BRITISH BROADCASTING CORP
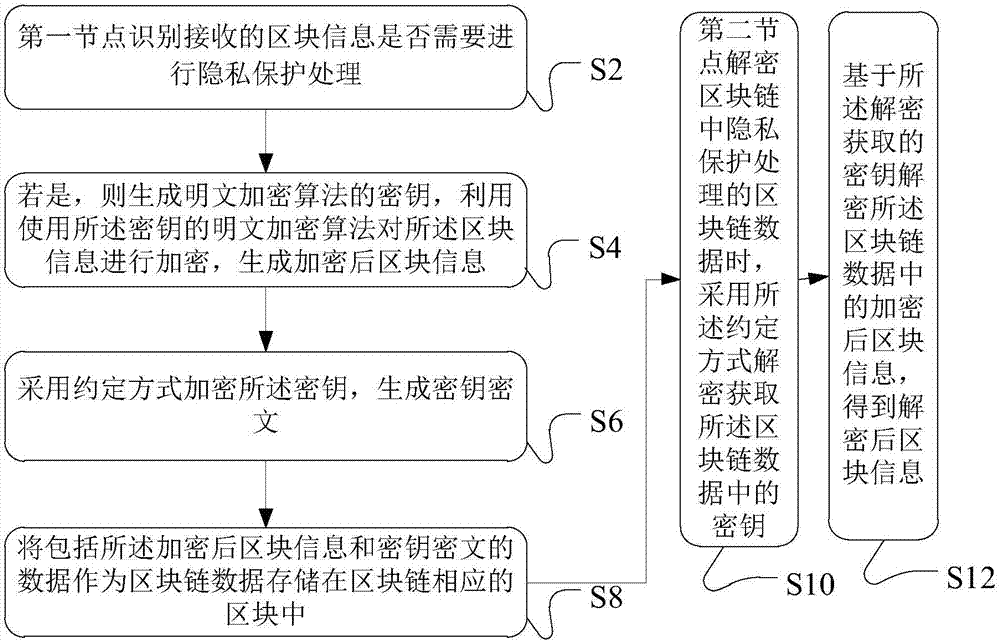
Blockchain data processing method, device and system
InactiveCN107294709ATo achieve the purpose of privacy protectionPrivacy protection is safe and reliableKey distribution for secure communicationCiphertextPrivacy protection
The invention discloses a blockchain data processing method, device and system. The blockchain data processing method comprises that a first node identifies whether received block information needs privacy protection processing; if the received block information needs privacy protection processing, a secret key of a plaintext encryption algorithm is generated, the block information is encrypted by means of the plaintext encryption algorithm employing the secret key, and encrypted block information is generated; the secret key is encrypted in a stipulated way, a secret key ciphertext is generated, the stipulated way comprises an algorithm through which a second node associated with the first node in the first node and the blockchain encrypts and decrypts the secret key ciphertext according to a preset mode; and data including the encrypted block information and the secret key ciphertext is stored a corresponding block of the blockchain as blockchain data. According to each embodiment of the invention, information data stored in the blockchain can be encrypted, so that only specific members can decrypt and check the information data, and the aim of carrying out privacy protection on special transaction information is achieved.
Owner:ADVANCED NEW TECH CO LTD
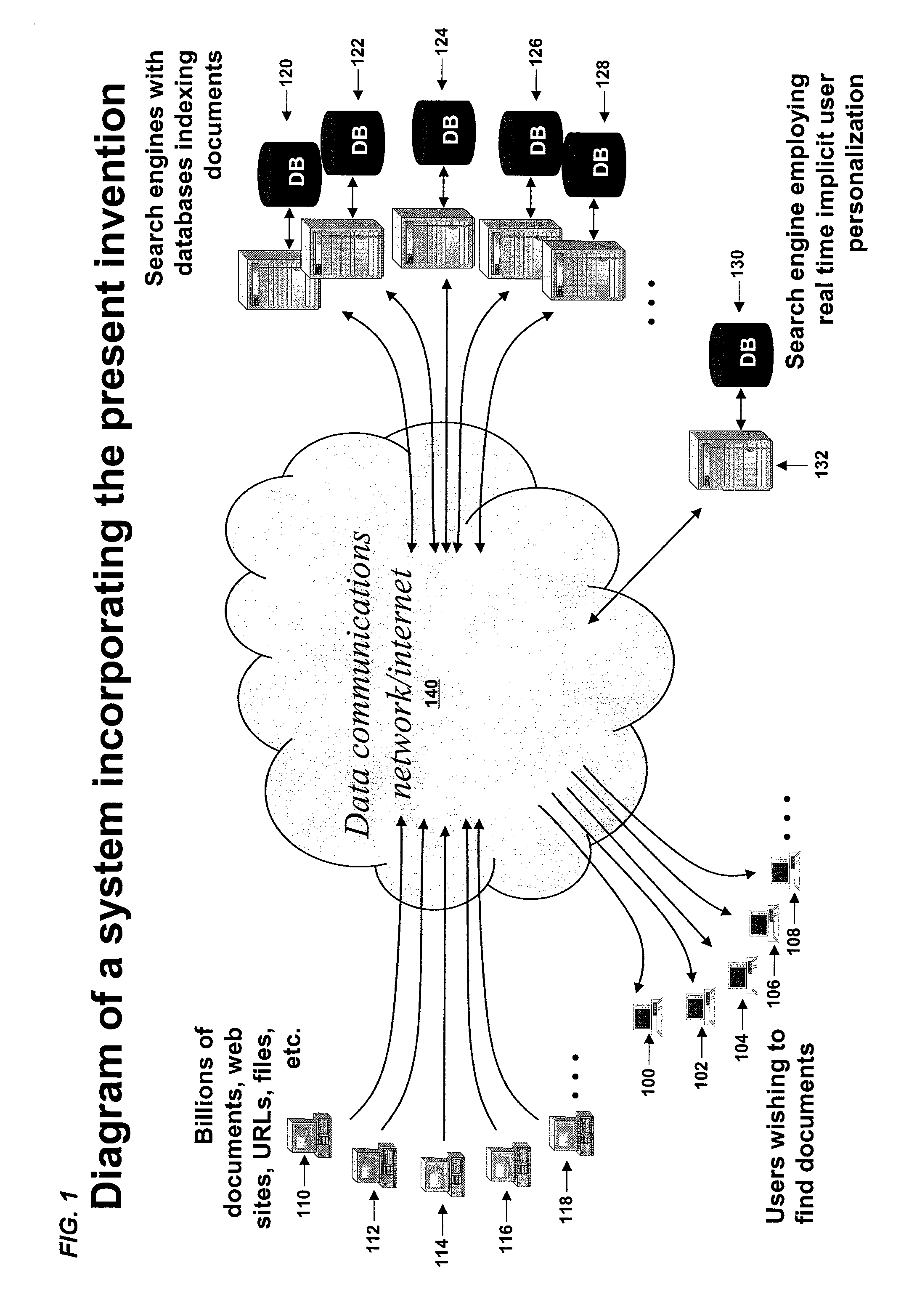
Real time implicit user modeling for personalized search
ActiveUS20080114751A1Improve search capabilitiesSimple equipmentDigital data information retrievalDigital data processing detailsPersonalized searchResult set
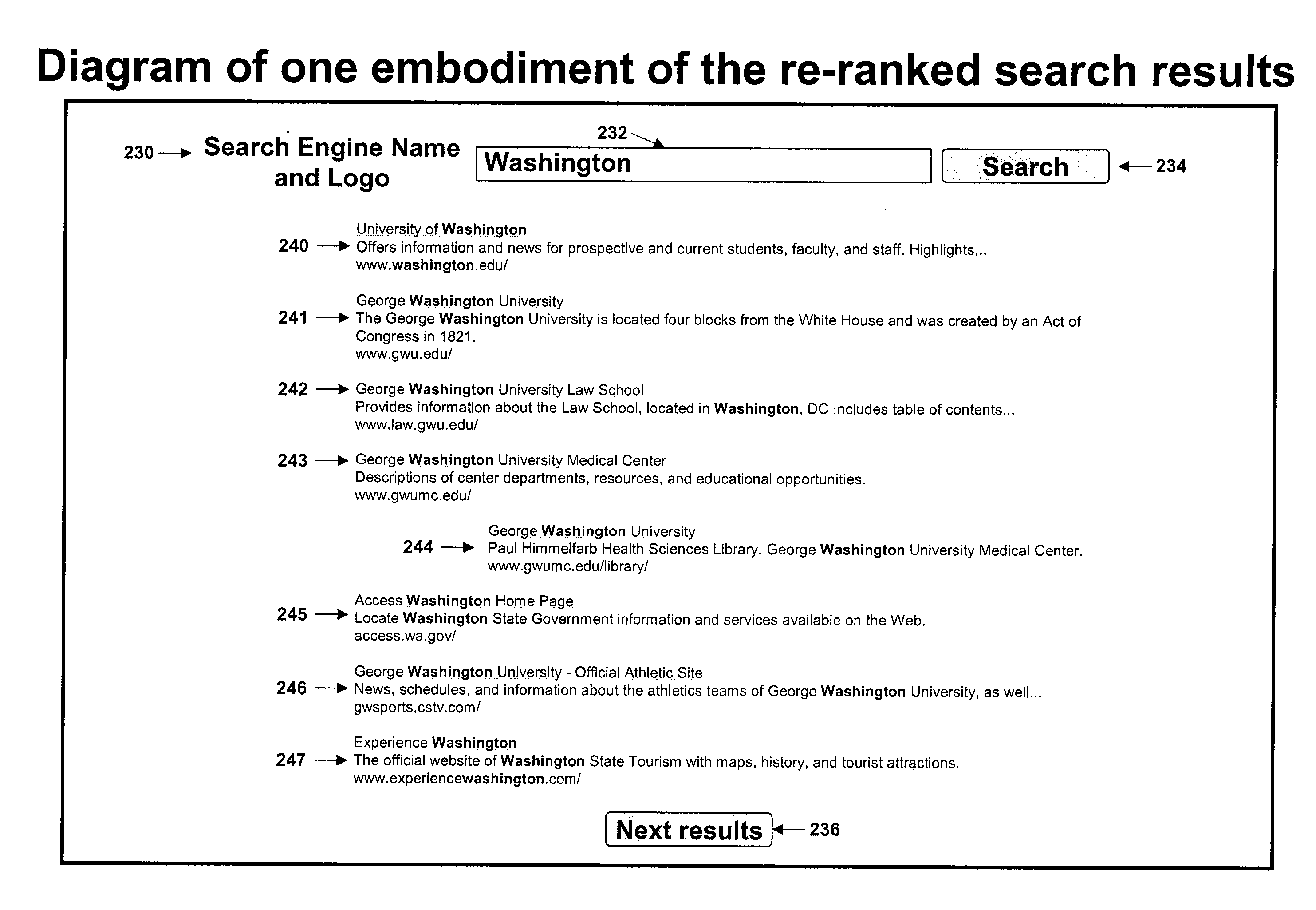
A method and apparatus for utilizing user behavior to immediately modify sets of search results so that the most relevant documents are moved to the top. In one embodiment of the invention, behavior data, which can come from virtually any activity, is used to infer the user's intent. The updated inferred implicit user model is then exploited immediately by re-ranking the set of matched documents to best reflect the information need of the user. The system updates the user model and immediately re-ranks documents at every opportunity in order to constantly provide the most optimal results. In another embodiment, the system determines, based on the similarity of results sets, if the current query belongs in the same information session as one or more previous queries. If so, the current query is expanded with additional keywords in order to improve the targeting of the results.
Owner:SURF CANYON +1
Visual recognition and positioning method for robot intelligent capture application
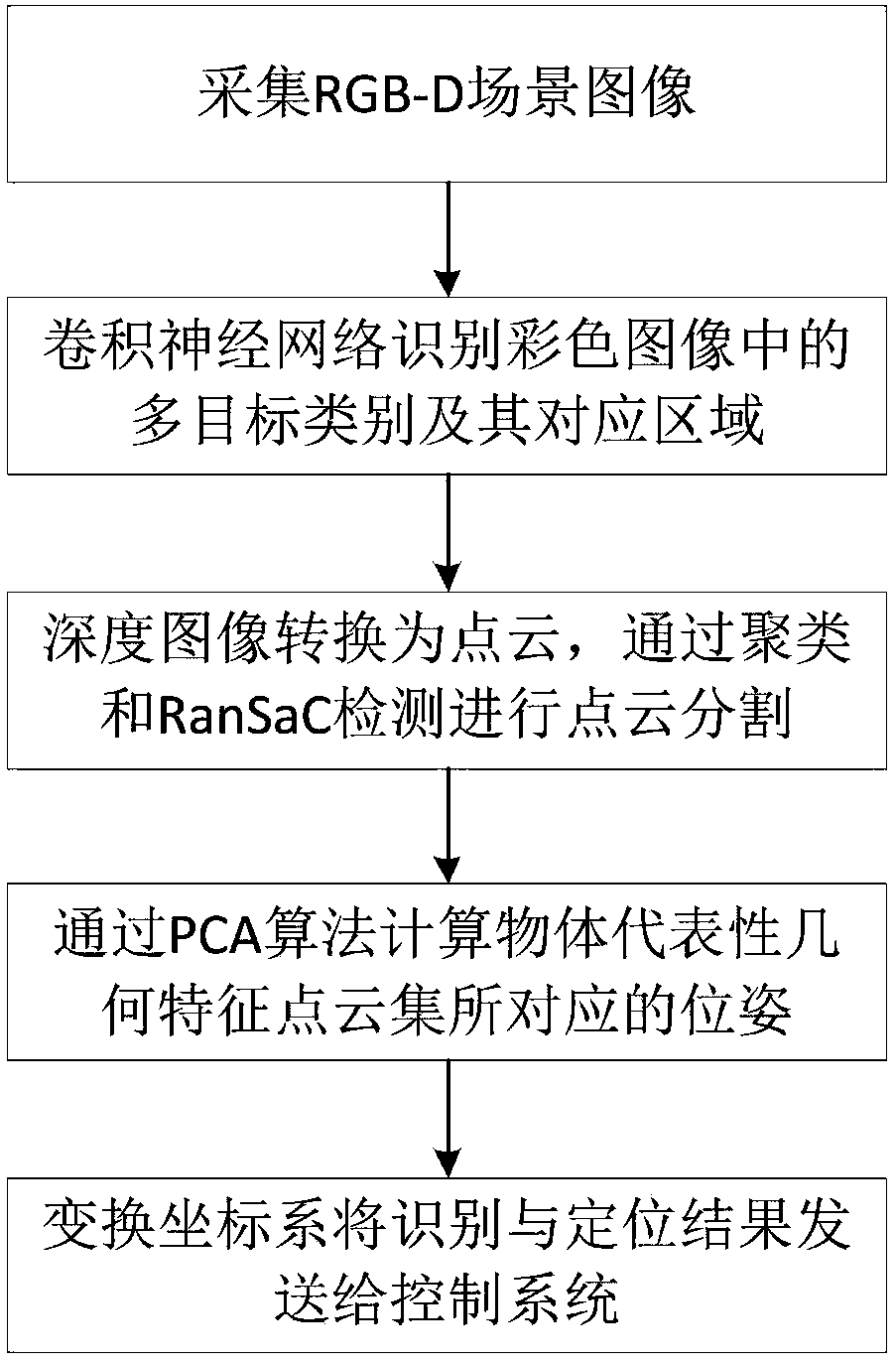
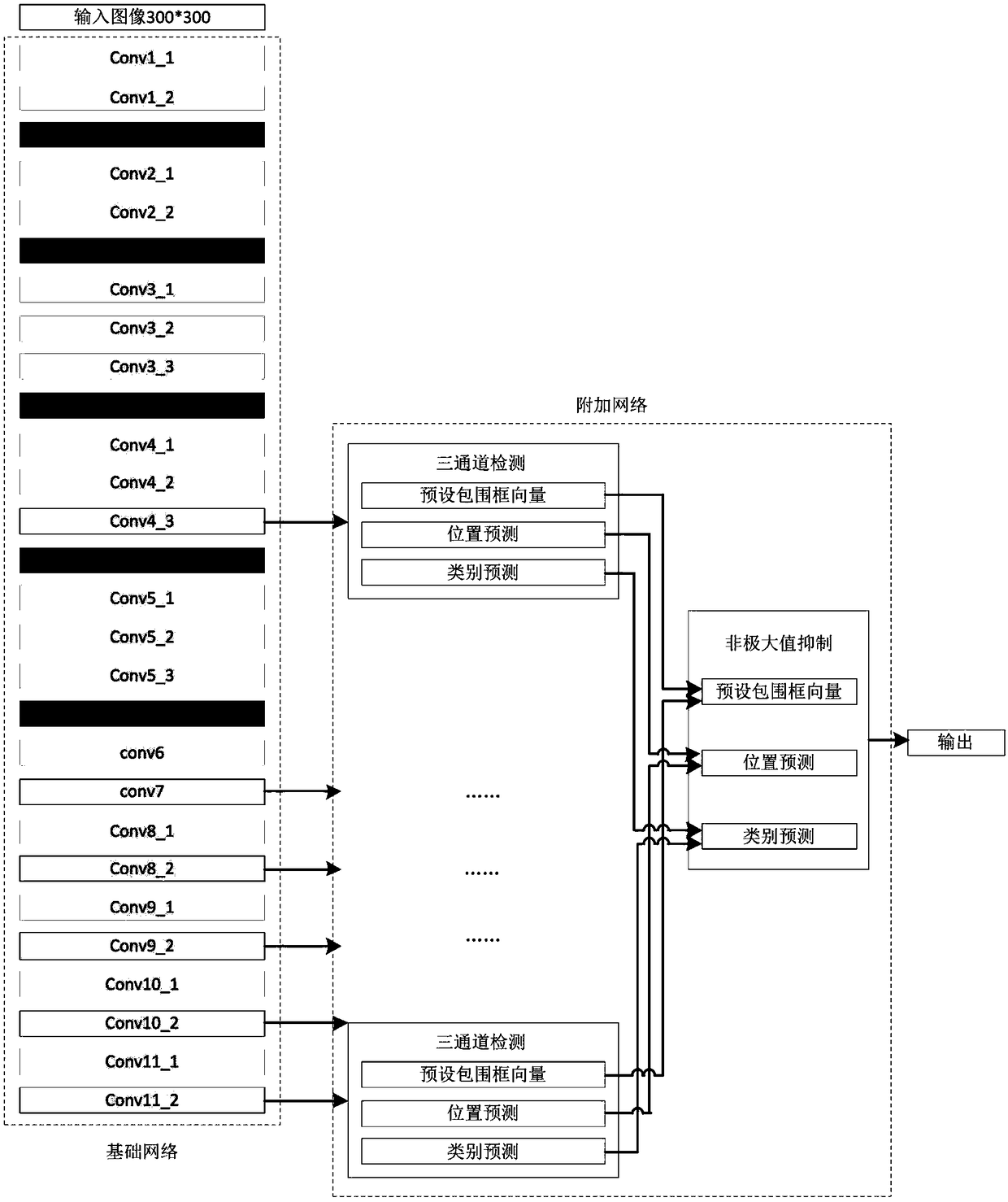
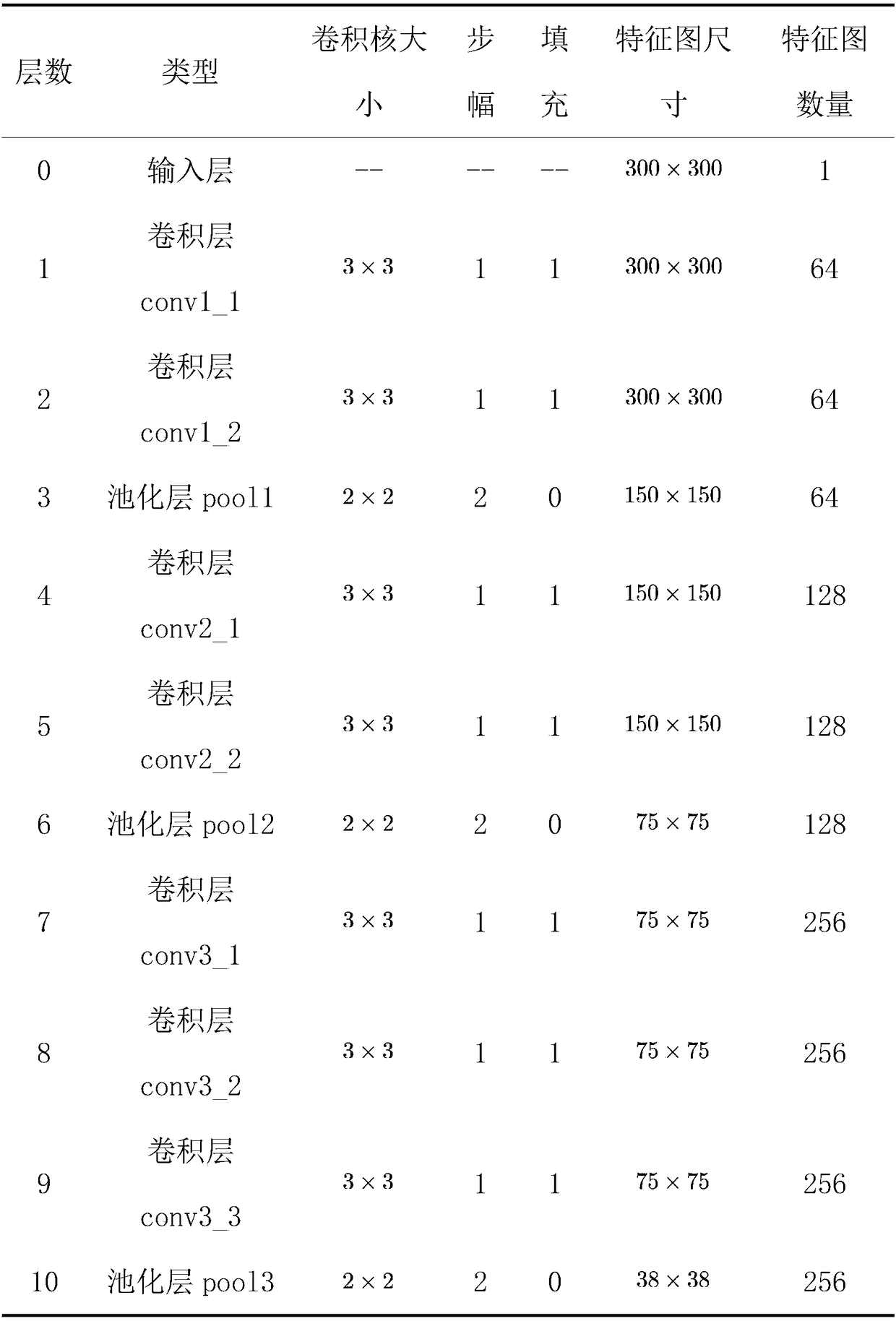
The invention relates to a visual recognition and positioning method for robot intelligent capture application. According to the method, an RGB-D scene image is collected, a supervised and trained deep convolutional neural network is utilized to recognize the category of a target contained in a color image and a corresponding position region, the pose state of the target is analyzed in combinationwith a deep image, pose information needed by a controller is obtained through coordinate transformation, and visual recognition and positioning are completed. Through the method, the double functions of recognition and positioning can be achieved just through a single visual sensor, the existing target detection process is simplified, and application cost is saved. Meanwhile, a deep convolutional neural network is adopted to obtain image features through learning, the method has high robustness on multiple kinds of environment interference such as target random placement, image viewing anglechanging and illumination background interference, and recognition and positioning accuracy under complicated working conditions is improved. Besides, through the positioning method, exact pose information can be further obtained on the basis of determining object spatial position distribution, and strategy planning of intelligent capture is promoted.
Owner:合肥哈工慧拣智能科技有限公司
Method and system for situation tracking and notification
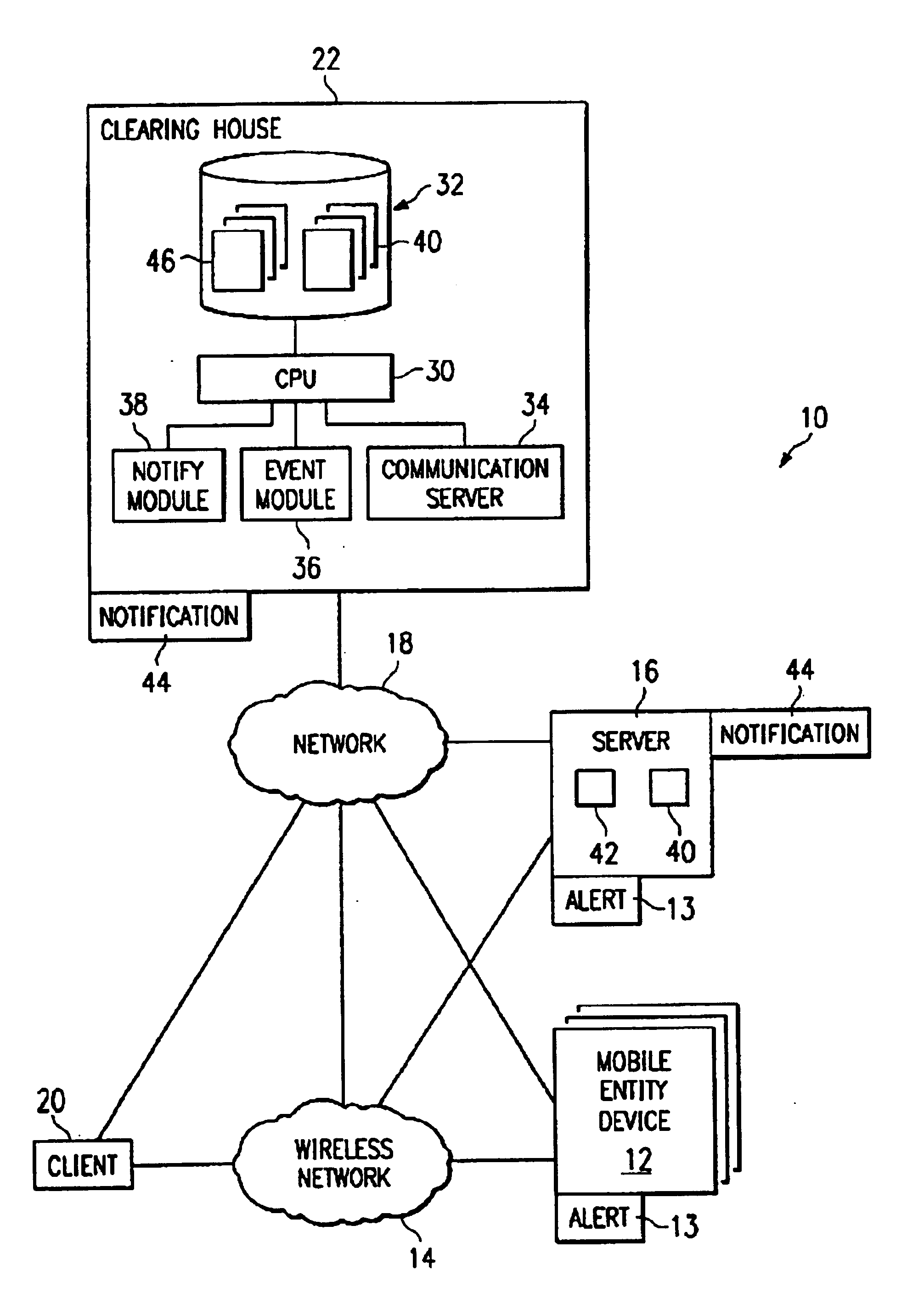
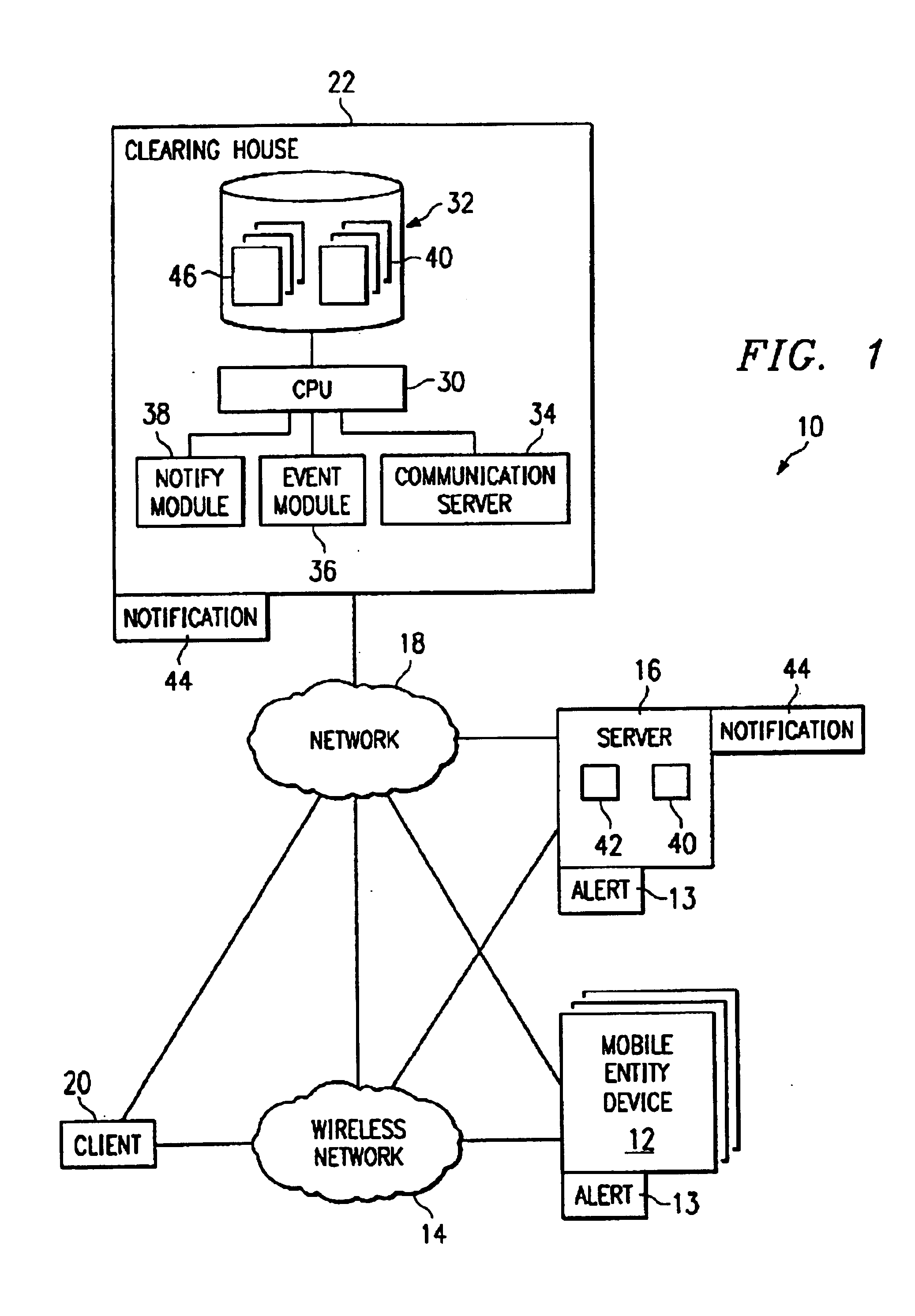
InactiveUS6842774B1Telephonic communicationElectric/electromagnetic visible signallingMobile entityComputer science
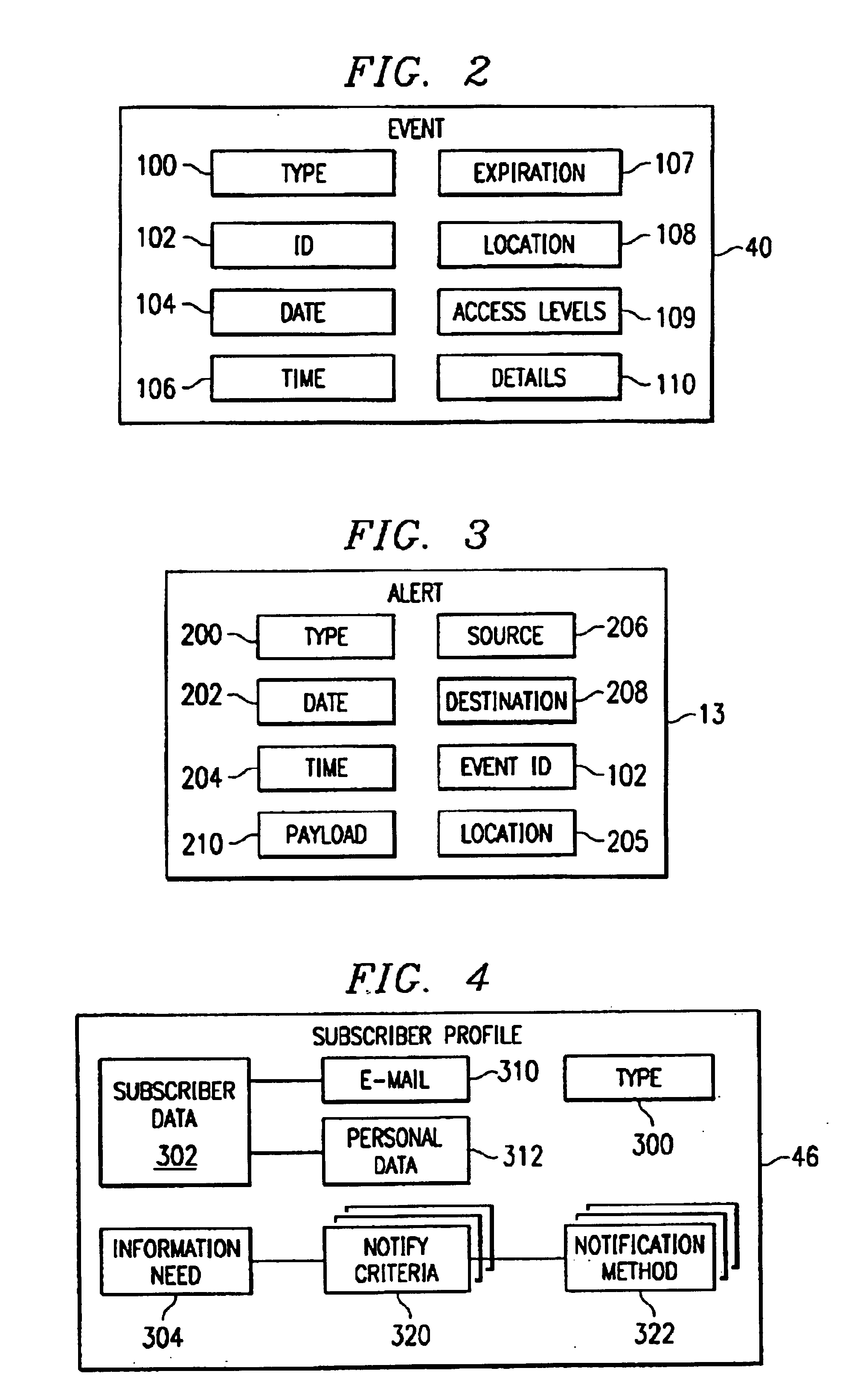
Alerts (13) are generated at mobile entity devices (12) and servers (16). The alerts are examined at the servers and handled by the server and / or forwarded to a clearing house (22). At the clearing house, emergency events (40) are created in response to the alerts by an event module (36). A notify module (38) compares events to an information need (304) associated with a subscriber profile (46) to determine whether a subscriber associated with the subscriber profile should be notified about events. The notify module also handles interactive search requests from a client (20) for the events.
Owner:TECHRADIUM
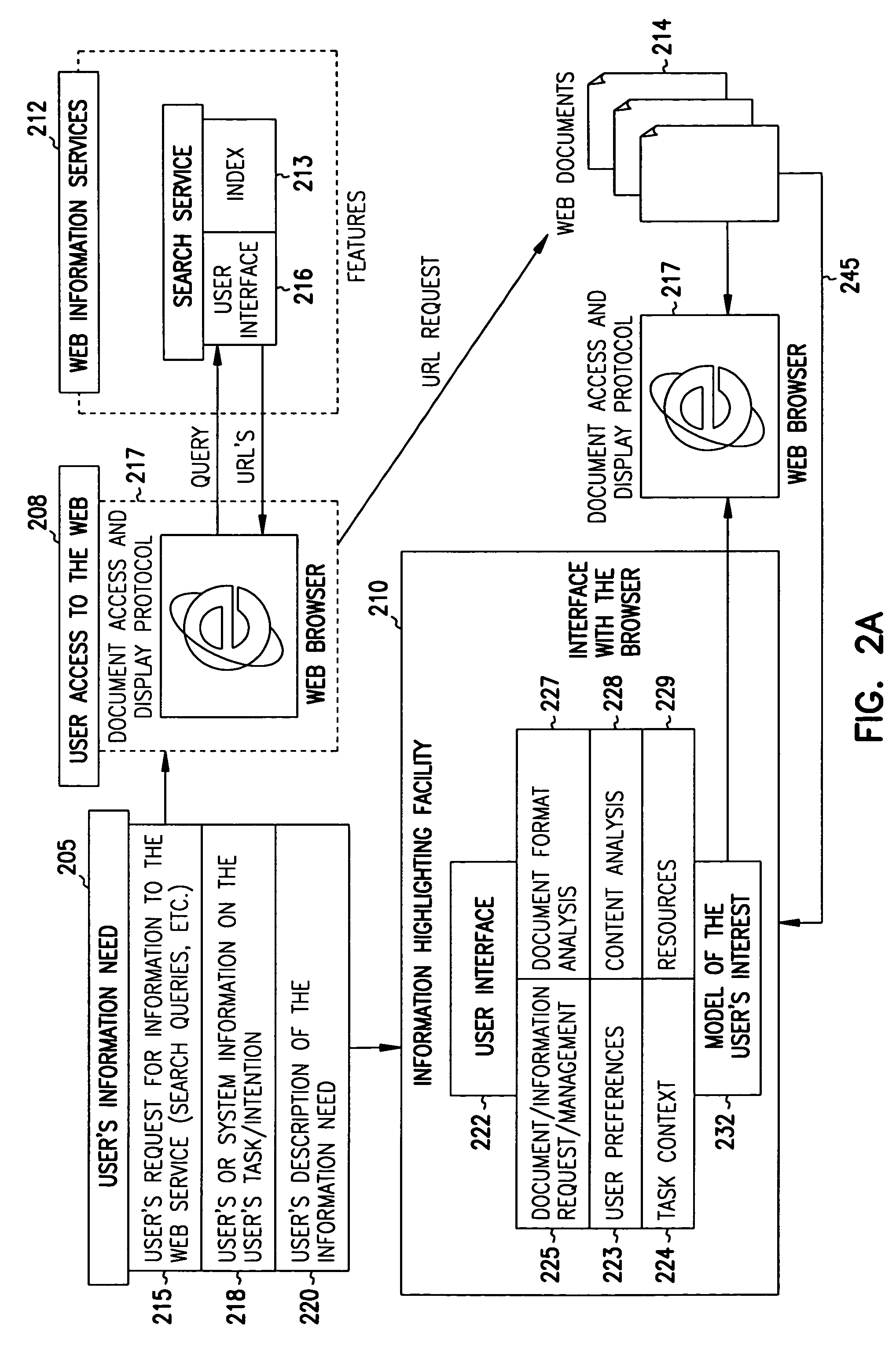
Facility for highlighting documents accessed through search or browsing
InactiveUS6968332B1Easy to spotRich representationData processing applicationsDigital data information retrievalThumbnailDocument preparation
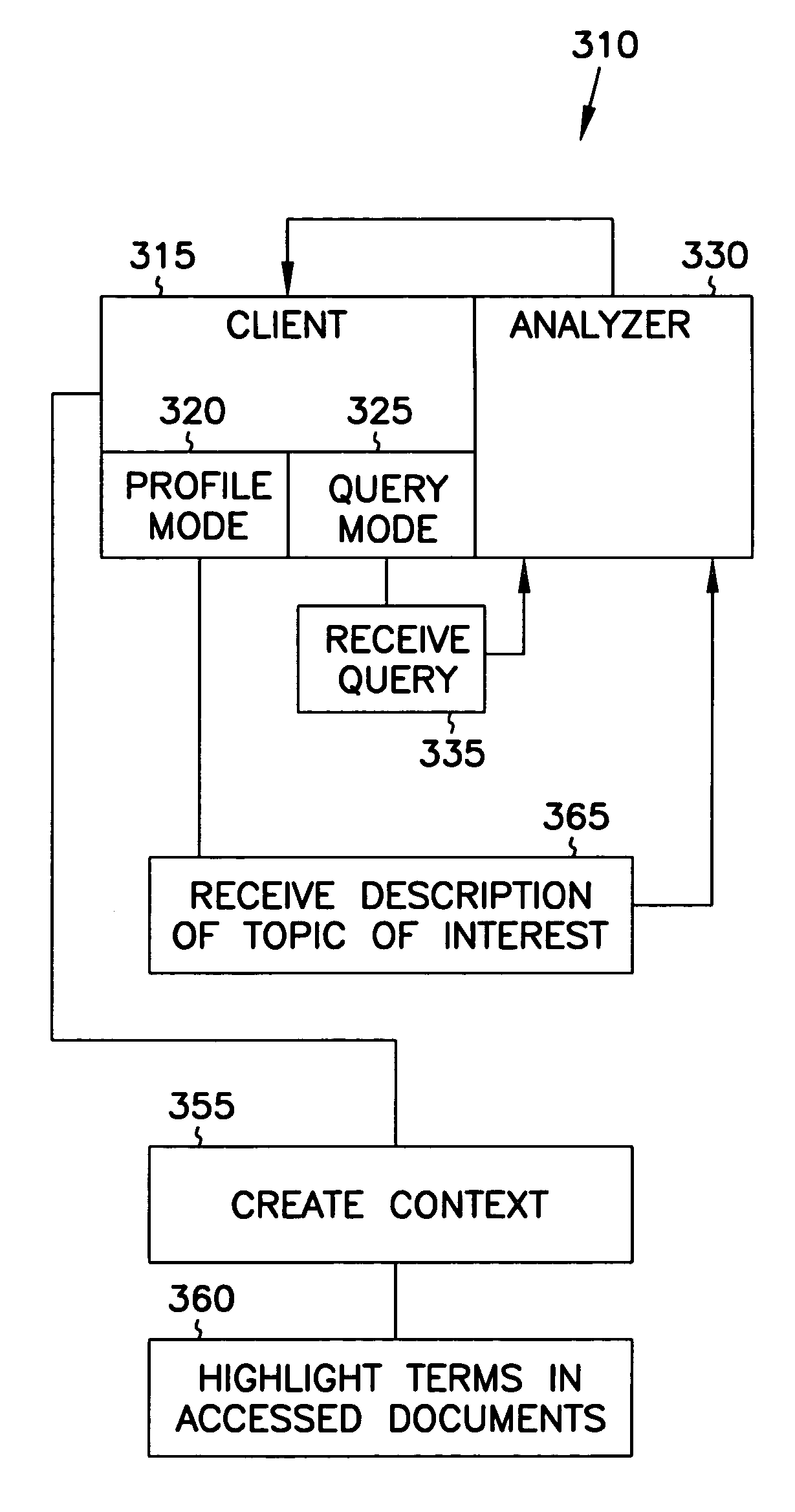
An Information highlighting facility assists the user in evaluating relevance of accessed documents to the user's information need. The accessed documents may, for example, be identified by a search engine in response to a user query. When accessing documents identified as relevant by a search engine from other networked computers, the facility provides information highlighting to assist the user in determining whether the document is relevant. A model of the user's interest, which may include an augmented set of search terms is used to take into account the general interest of the user as captured by an interest profile and context of use of the computer by the user, or a combination thereof. The model of the user's interest is applied to the document text as the document is accessed from its source. The highlighting of information about the document content may include highlighting of the terminology in the text, scrolling of the document to the relevant passages, identification of entity names and entity relations, creation of a document summary and a document thumbnail, etc. In addition, the model can be applied to a set of documents accessed by the user, e.g., to re-rank the top scoring documents from the result set provided to the user by a search engine or some other information providing services.
Owner:MICROSOFT TECH LICENSING LLC
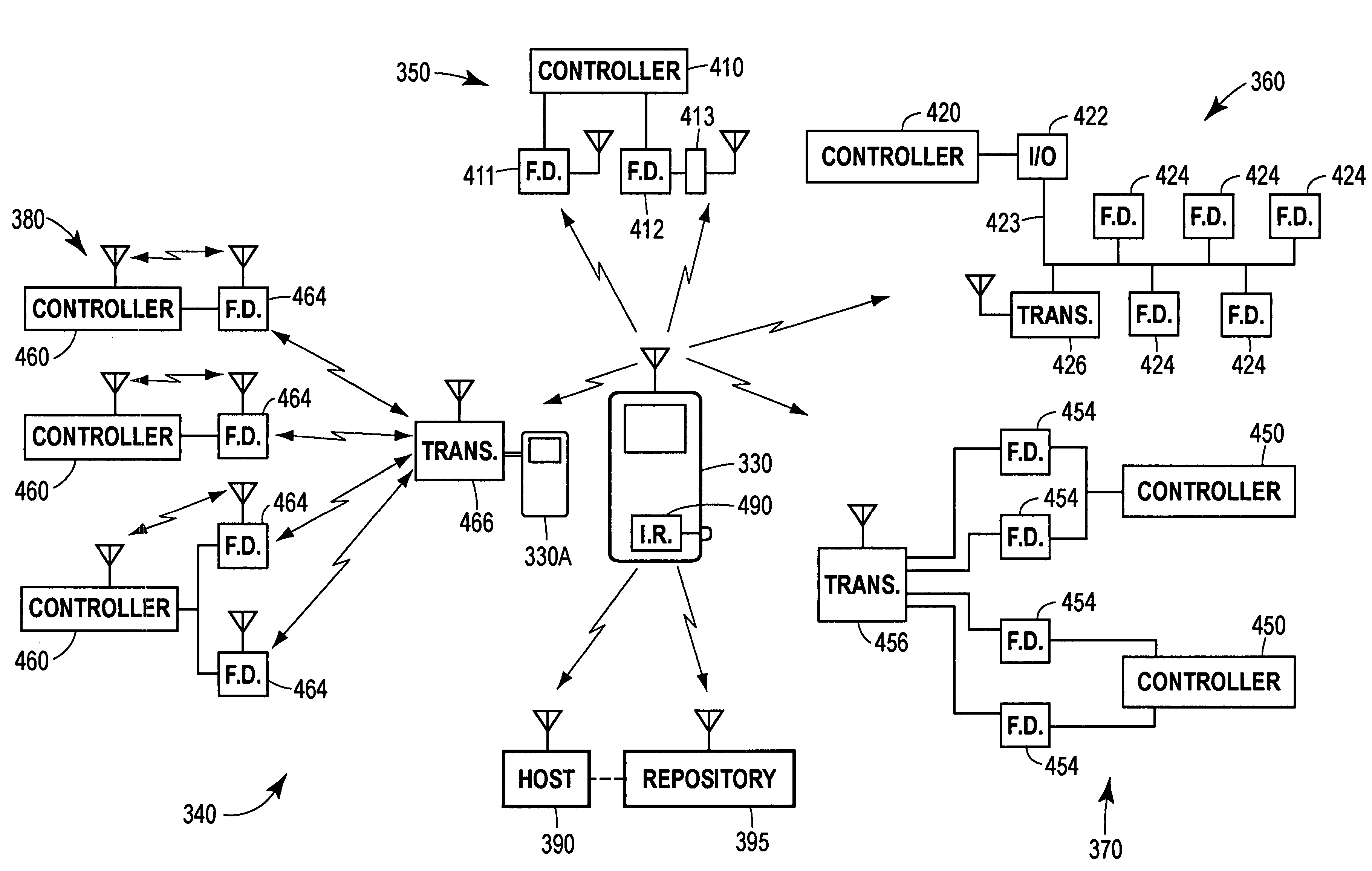
Wireless handheld communicator in a process control environment
A handheld communicator wirelessly interfaces or communicates with individual devices in a process control system, such as field devices, controllers, etc., to wirelessly perform monitoring, maintenance, configuration and control activities with respect to those devices. The wireless handheld communicator includes a housing adapted for handheld operation, a processing unit disposed within the housing, a computer readable memory disposed within the housing and coupled to the processing unit and a display, a keypad and a radio frequency transceiver. The handheld communicator may be adapted to communicate with a host system to receive information needed to communicate with various field devices in the process plant and may then be used to wirelessly communicate with each of the various field devices directly while in close proximity to the field devices to perform monitoring and configuration activities with respect to the field devices. Thereafter, information obtained from the field devices may be wirelessly communicated to the host system or to a repository, such as a data historian or a configuration database.
Owner:FISHER-ROSEMOUNT SYST INC
Relevance clause for computed relevance messaging
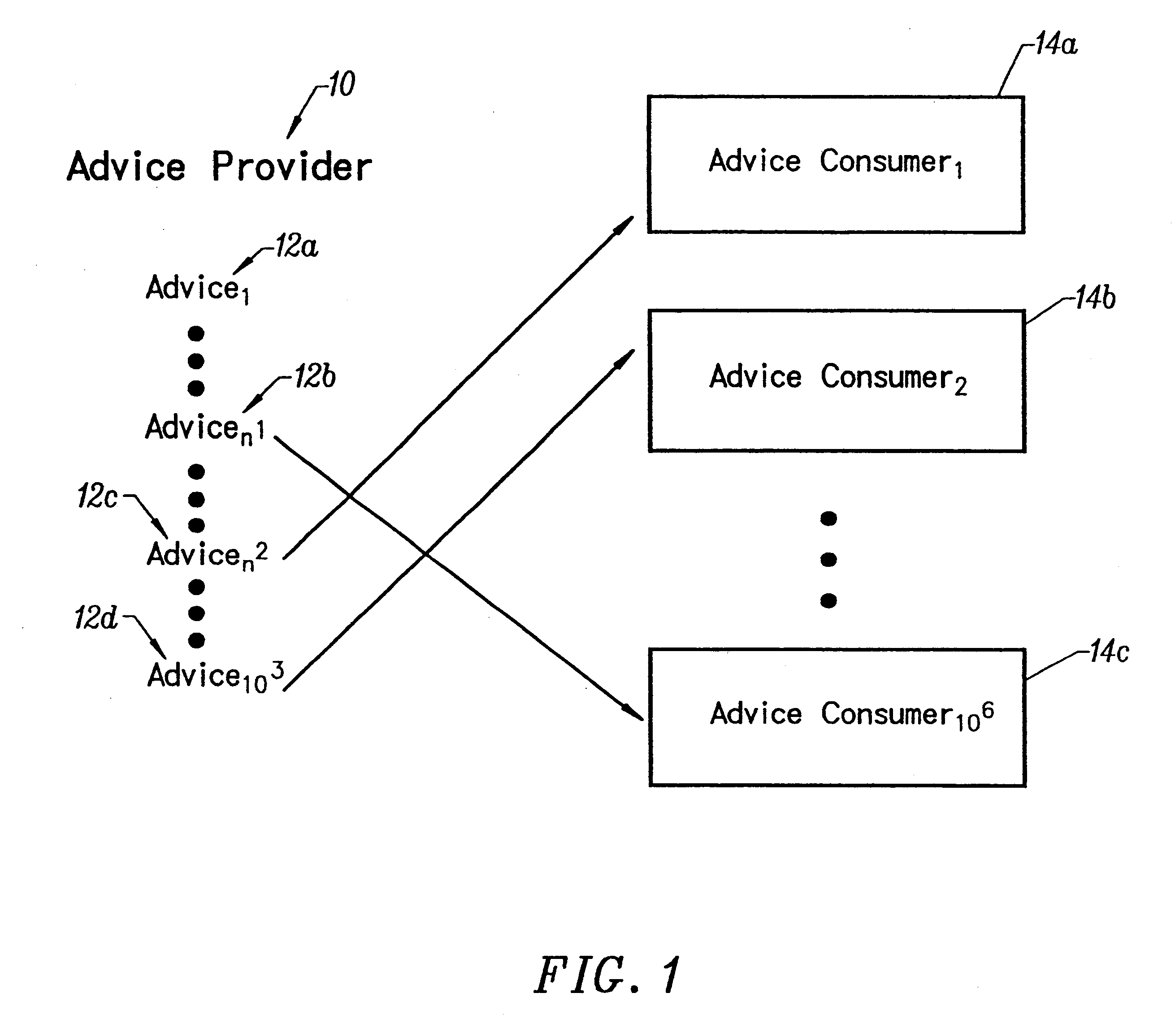
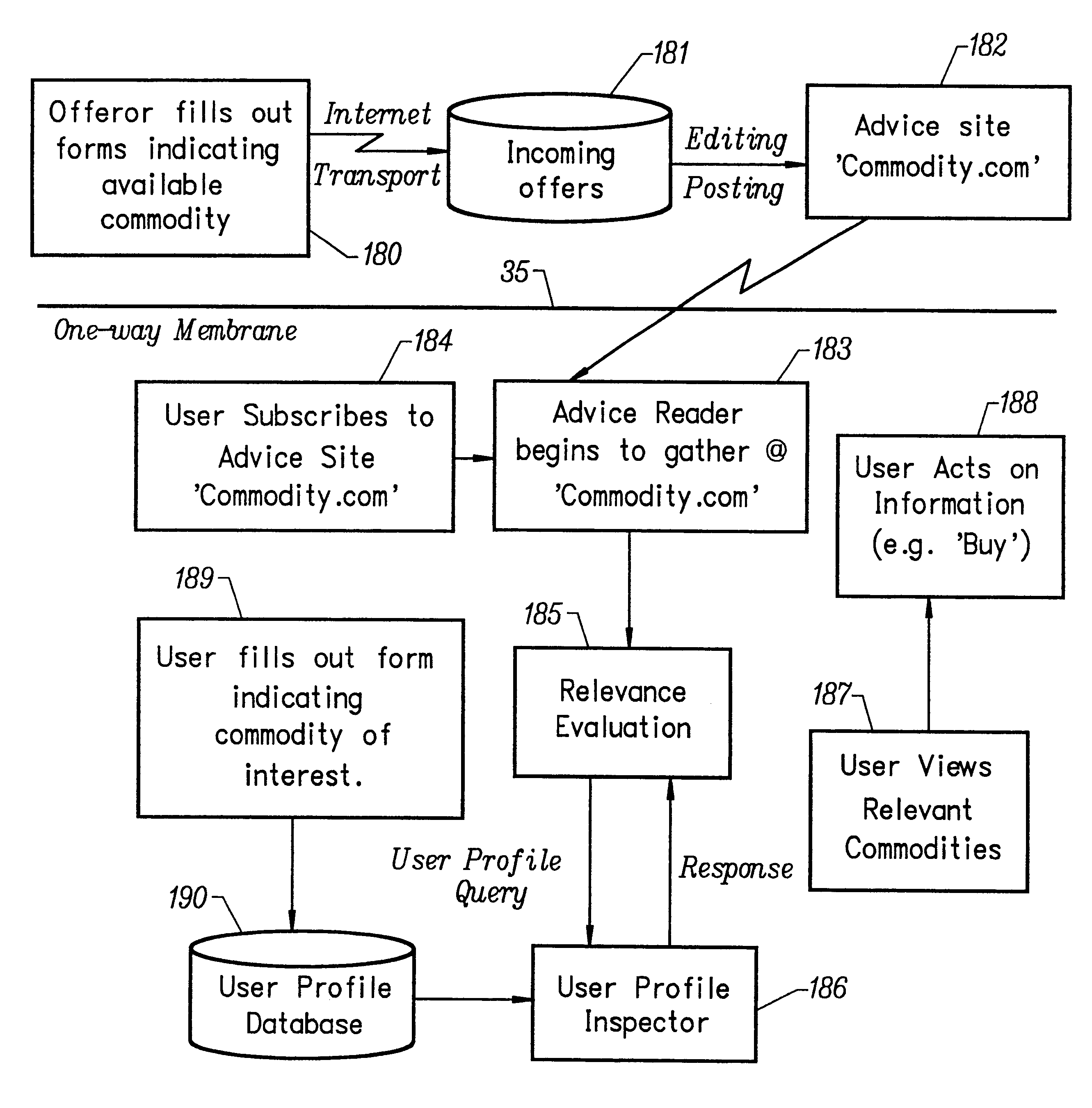
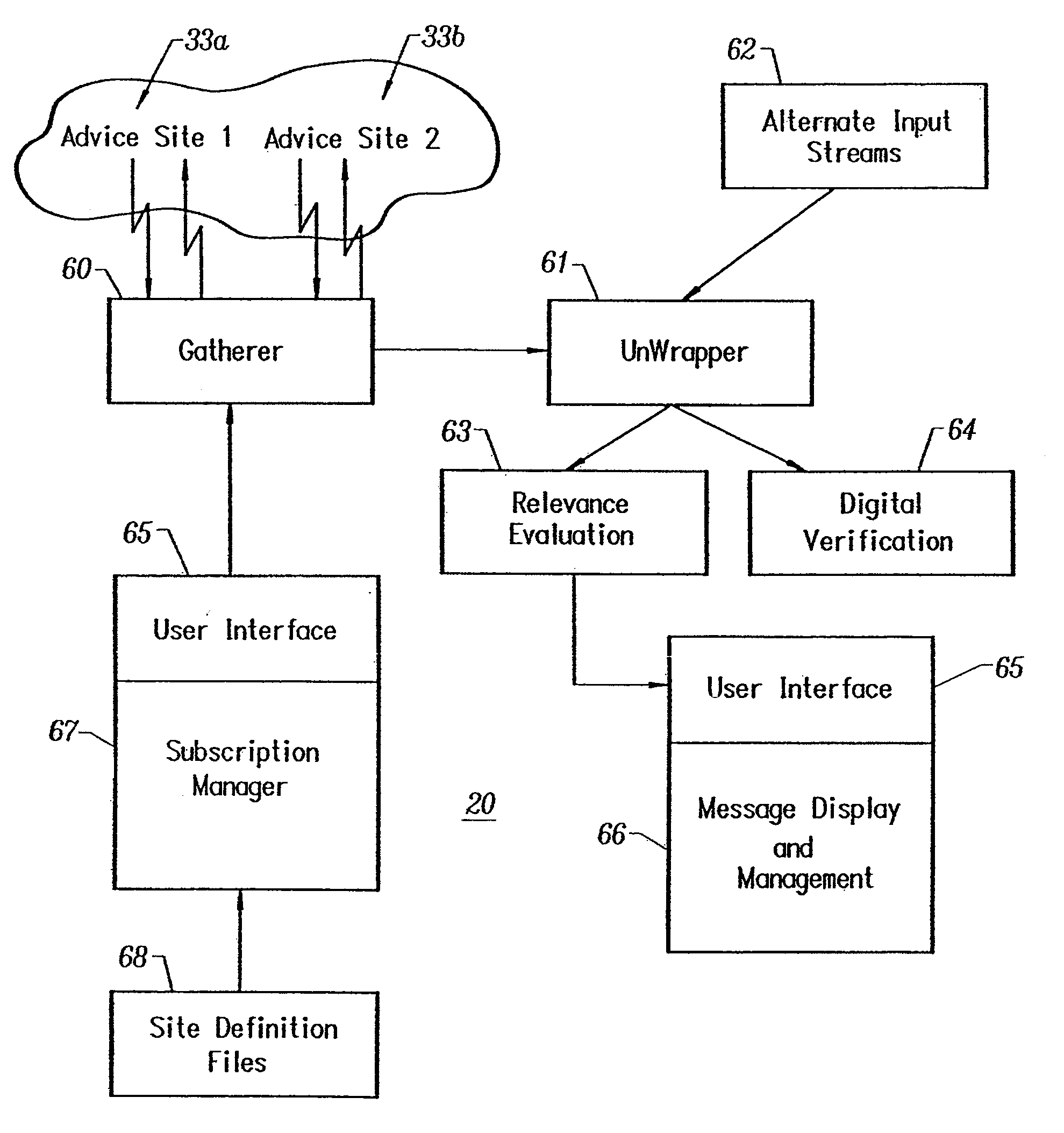
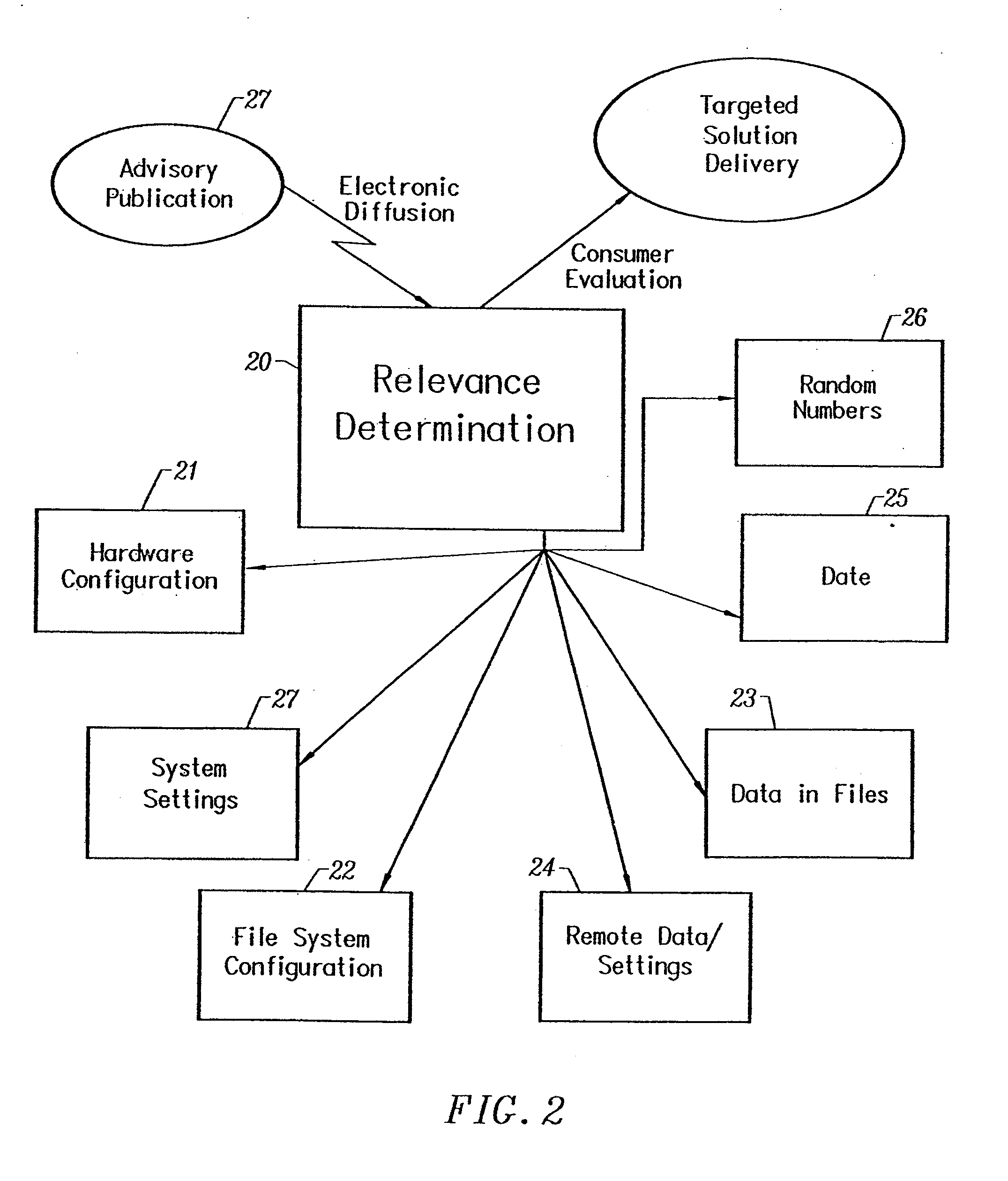
InactiveUS6356936B1Special service provision for substationMultiple digital computer combinationsTime elementInformation needs
The invention disclosed herein enables a collection of computers and associated communications infrastructure to offer a new communications process which allows information providers to broadcast information to a population of information consumers. The information may be targeted to those consumers who have a precisely formulated need for the information. This targeting may be based on information which is inaccessible to other communications protocols. The targeting also includes a time element. Information can be brought to the attention of the consumer precisely when it has become applicable, which may occur immediately upon receipt of the message, but may also occur long after the message arrives. The communications process may operate without intruding on consumers who do not exhibit the precisely-specified need for the information, and it may operate without compromising the security or privacy of the consumers who participate.
Owner:IBM CORP
Inspector for computed relevance messaging
InactiveUS6263362B1Accurate understandingSpecial service provision for substationMultiple digital computer combinationsTime elementMessage passing
The invention disclosed herein enables a collection of computers and associated communications infrastructure to offer a new communications process which allows information providers to broadcast information to a population of information consumers. The information may be targeted to those consumers who have a precisely formulated need for the information. This targeting may be based on information which is inaccessible to other communications protocols. The targeting also includes a time element. Information can be brought to the attention of the consumer precisely when it has become applicable, which may occur immediately upon receipt of the message, but may also occur long after the message arrives. The communications process may operate without intruding on consumers who do not exhibit the precisely-specified need for the information, and it may operate without compromising the security or privacy of the consumers who participate.
Owner:IBM CORP
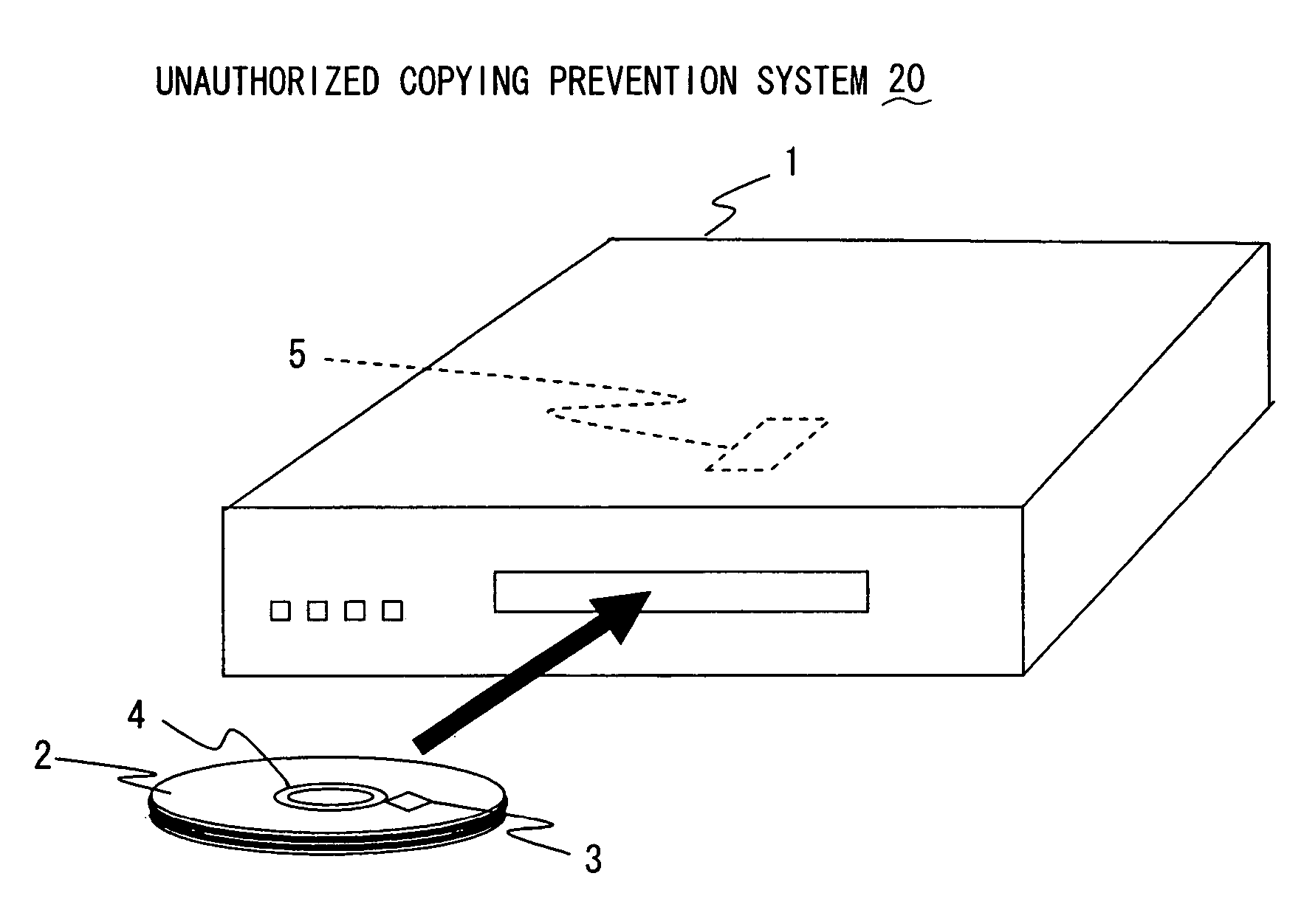
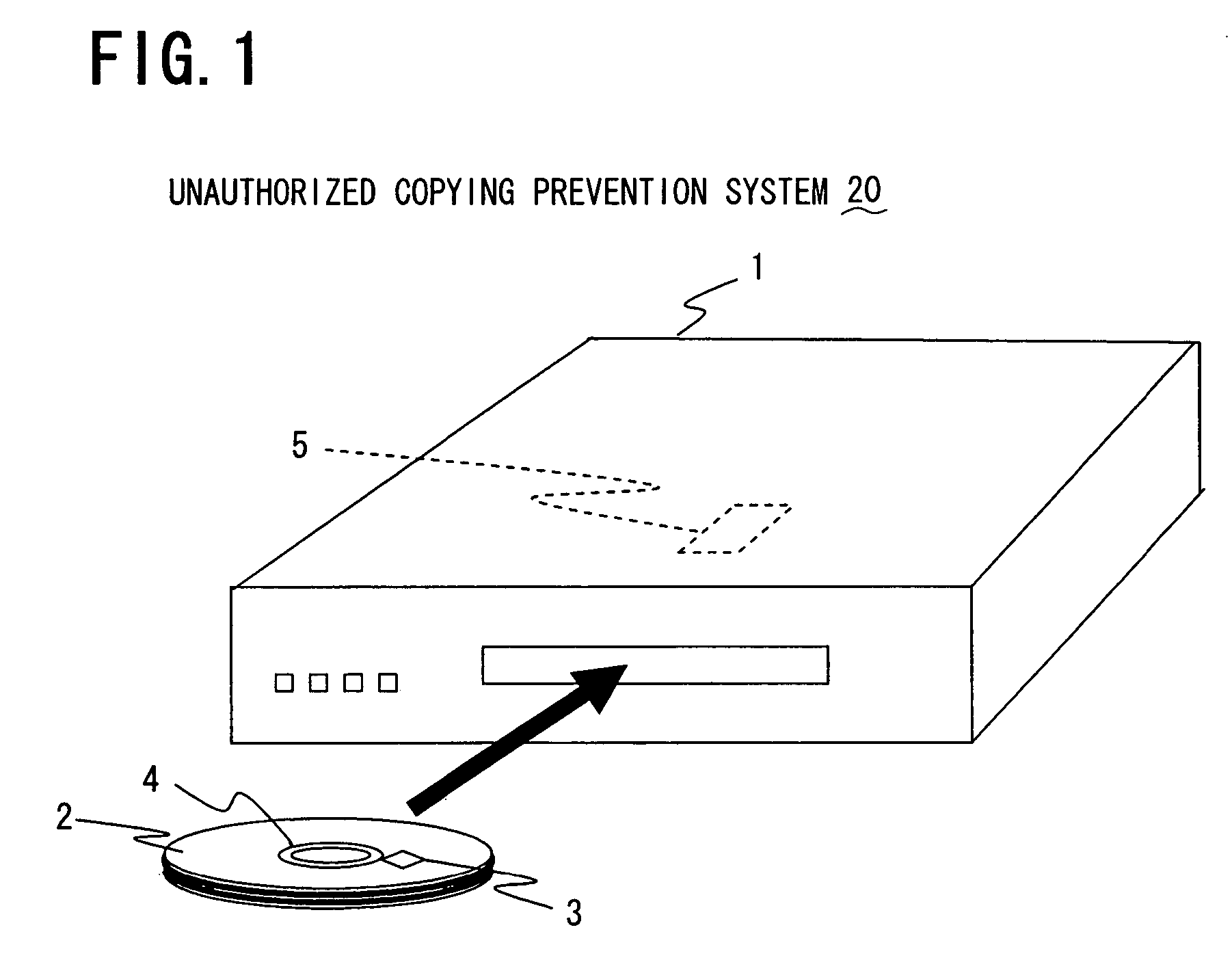
Optical disc having RFID tag, optical disc apparatus, and system for preventing unauthorized copying
InactiveUS7317396B2Reliable preventionInhibitory contentDigital data processing detailsMechanical recordingSecret codeInformation needs
In an optical disc having an RFID tag, disc control information needed for control of reproduction of the content recorded in the disc body of the optical disc is stored in the RFID tag. Thereby, even if the content recorded in the disc body is illegally copied in some way, common optical disc apparatus incapable of reading RFID tags cannot read and copy the disc control information stored in the RFID tag. Accordingly, unauthorized copying of the content recorded on the optical disc can be reliably prevented without the use of special cryptographic technology.
Owner:FUNAI ELECTRIC CO LTD
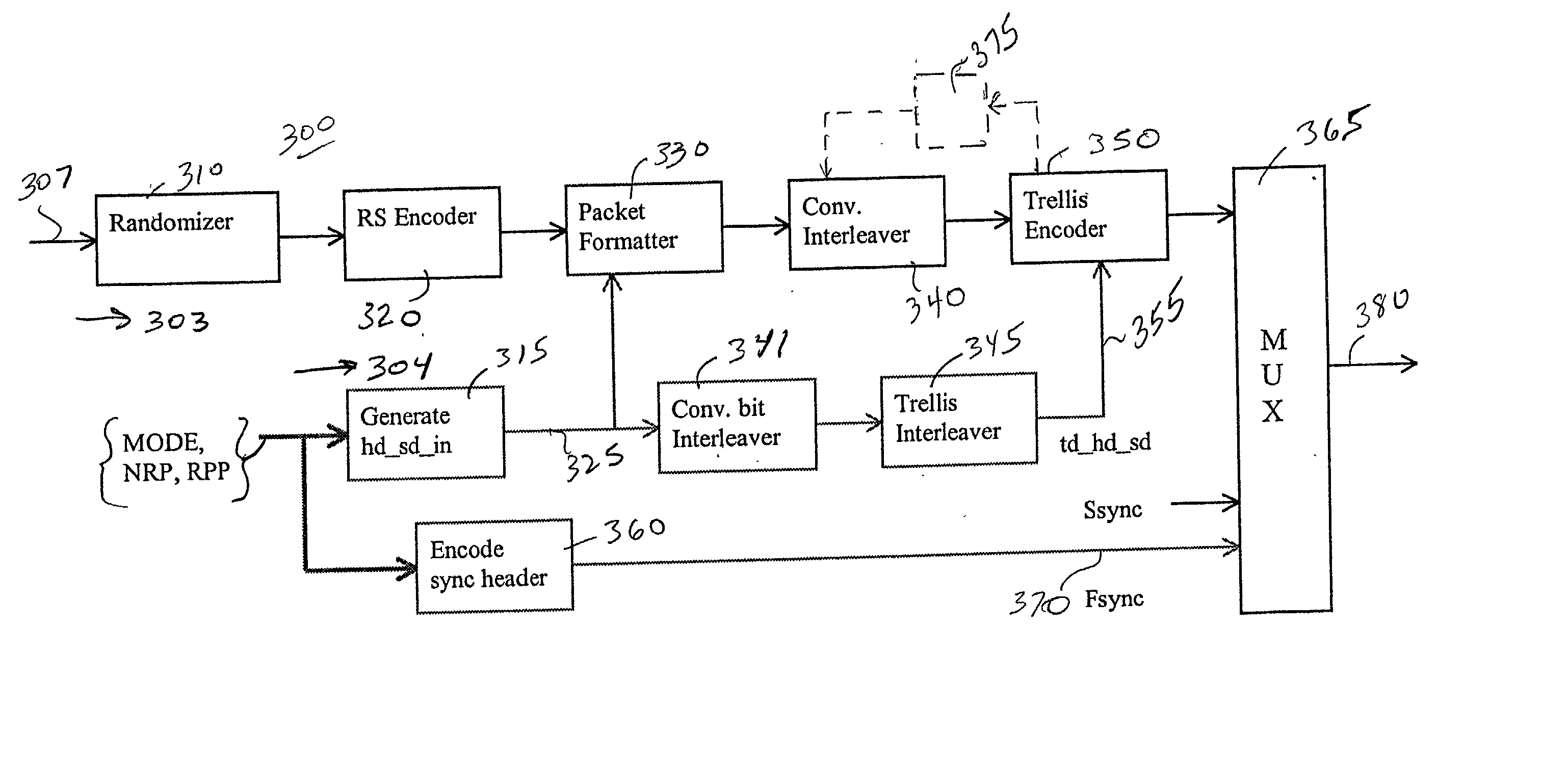
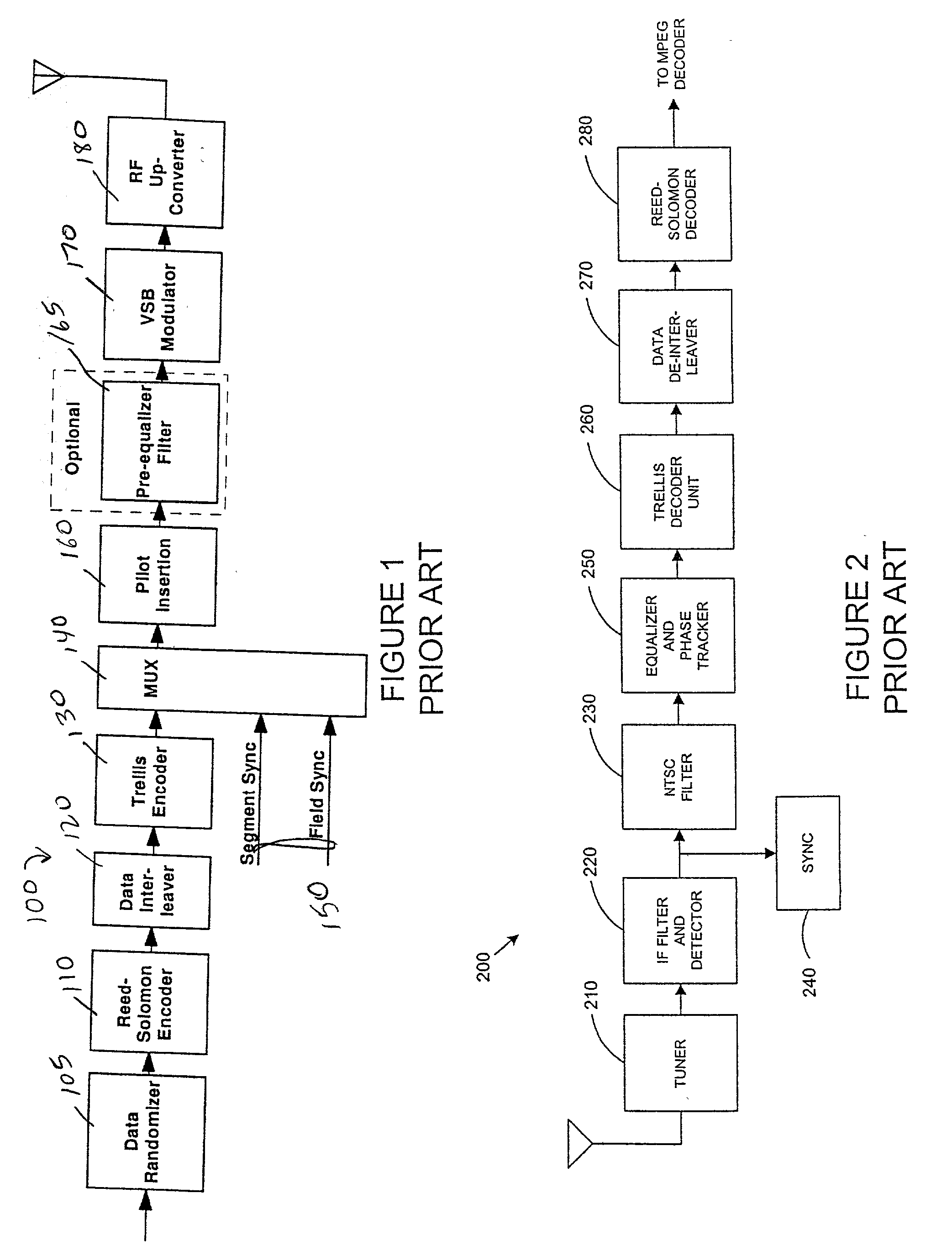
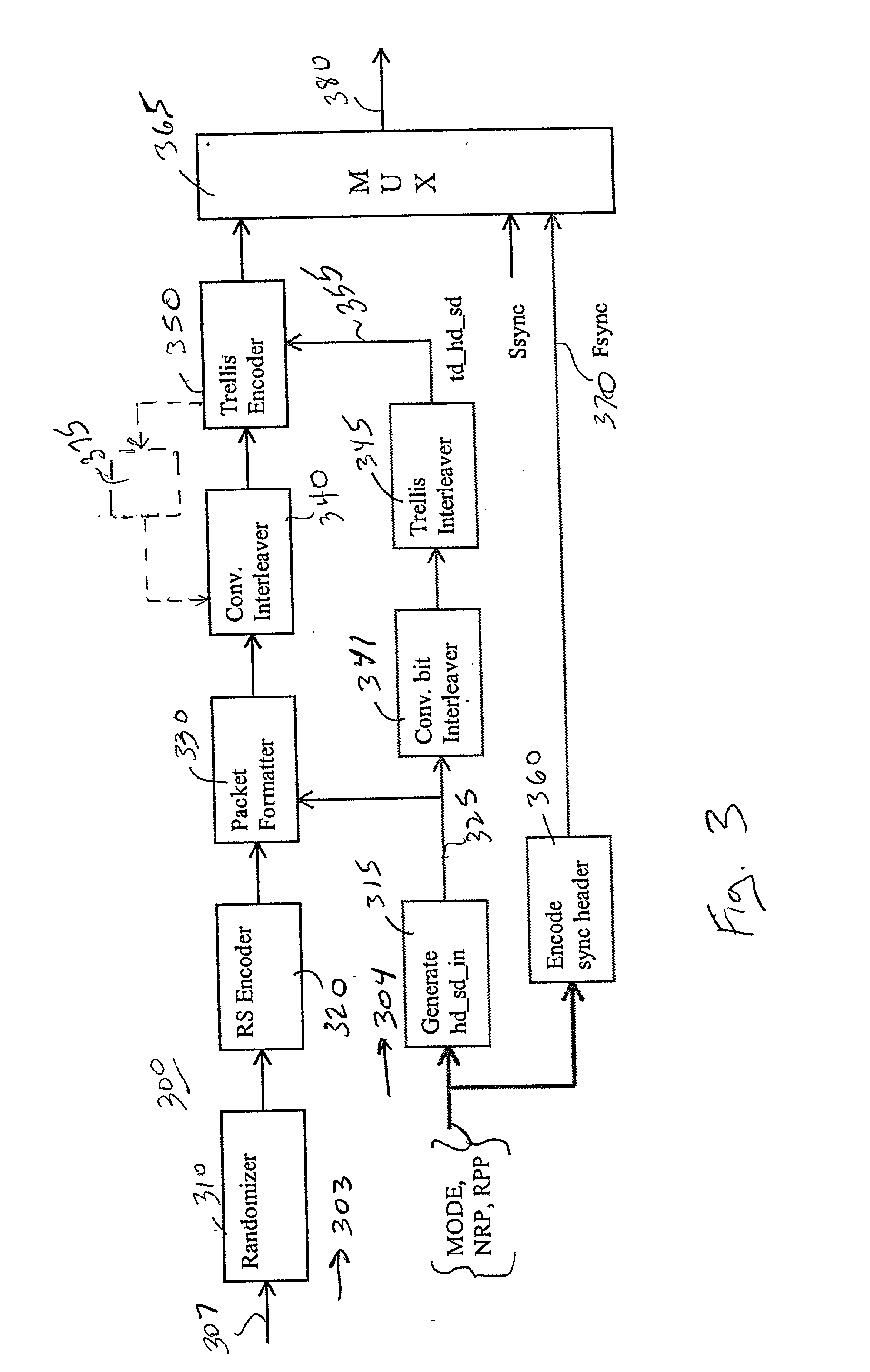
Packet identification mechanism at the transmitter and receiver for an enhanced ATSC 8-VSB system
InactiveUS20020191712A1Reduce payloadModulation with suppressed carrierAmplitude-modulated carrier systemsComputer hardwareTelevision system
A flexible digital transmission system that improves upon the ATSC A / 53 HDTV signal transmission standard. The system includes a digital signal transmitter for generating a first Advanced Television Systems Committee (ATSC) standard encoded 8-VSB bit stream and, for generating an encoded new robust bit stream for transmitting high priority information bits, wherein symbols of the new bit stream are capable of being transmitted according to a transmission mode including: a 2-VSB mode and a 4-VSB transmission mode. The standard 8-VSB bit stream and new bit stream may be simultaneously transmitted over a terrestrial channel according to a broadcaster defined bit-rate ratio. The transmission system includes a control mechanism for generating information needed for encoding robust packets at a transmitter device. It also includes a mechanism for encoding control parameters and multiplexes the generated information with the standard and robust bit-streams for transmission. A receiver architecture is additionally provided to decode standard and robust bit-streams transmitted by the transmitter device.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Hybrid data structures for graphics programs
InactiveUS20080062183A1Increase speedImage data processing detailsElectric digital data processingGraphicsData set
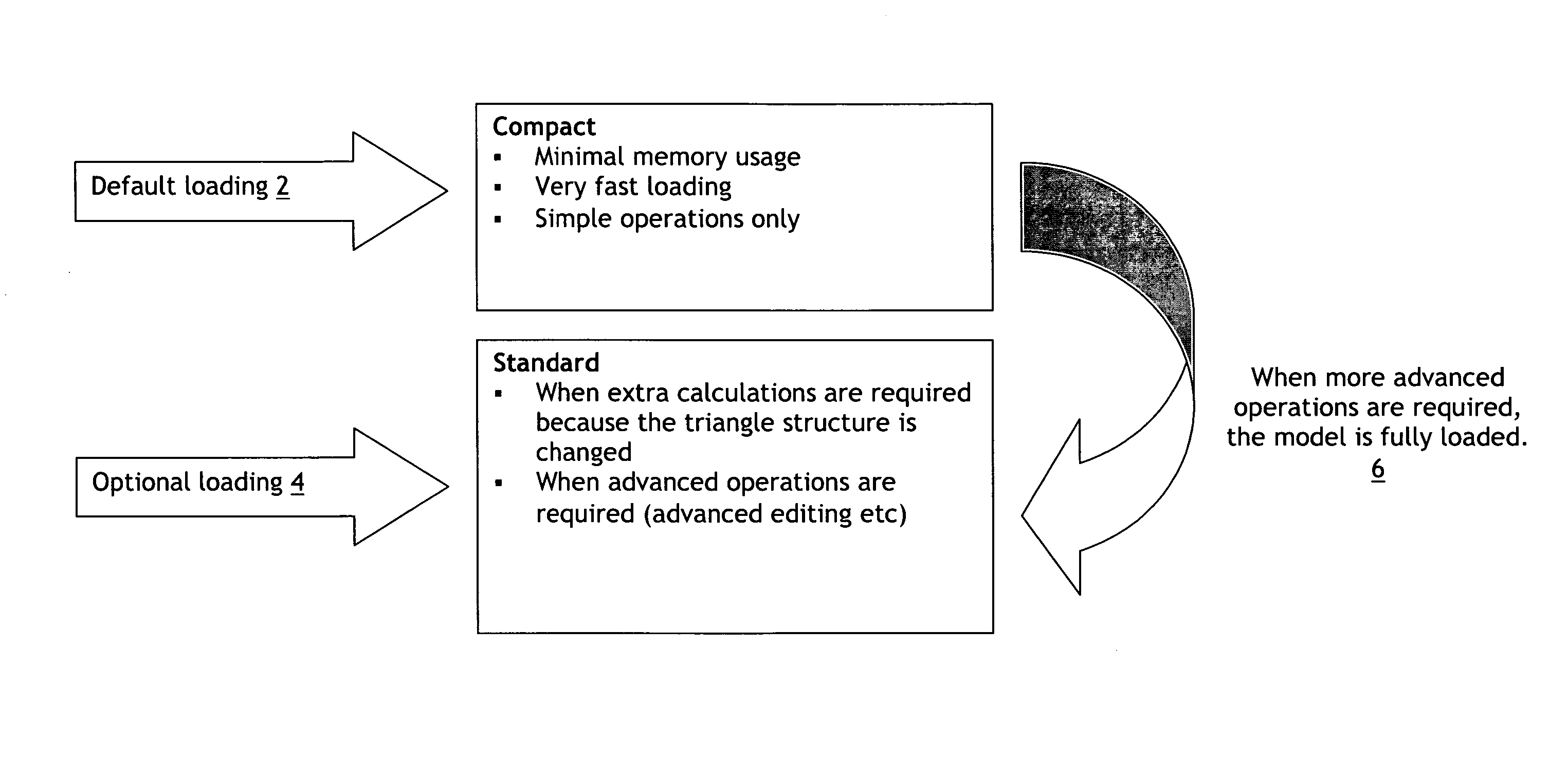
The use of data structures for displaying images is described: A first minimal data structure. In this structure only that information needed to show the data in the form of a 3D image, either wire mesh or rendered, to the user, is loaded into memory, e.g. the RAM memory. No additional information about the data structure is generated. For example, no connectivity data is loaded into memory. Typically this memory state is used for “read-only” purposes. In other words, the data objects are not to be modified. A second Rich (Flexible) data structure. In this structure, information, which a typical application holds to perform operations on the data, will be kept in memory, e.g. a RAM memory. Optional examples of extra information needed are, connectivity data such as neighbor information, some data flags for polygons, e.g. triangles and vertices, references to next and previous vertices and polygons, e.g. triangles, etc. In order to perform complex operations on big datasets in a somewhat efficient way, such extra information is preferred. A third data structure mainly in the non-volatile memory. In this structure the bulk of the data will be put into the non-volatile storage again, but in such a way that it can very easily be converted into one of the other memory structures again that are mentioned above. The structure in RAM will be similar as in 1 or 2, but will contain a reduced version of the data: for instance the 3D model will be described with less polygons, ultimately with only 6 polygons (the bounding box).
Owner:MATERIALISE NV
Route calculation method for a vehicle navigation system
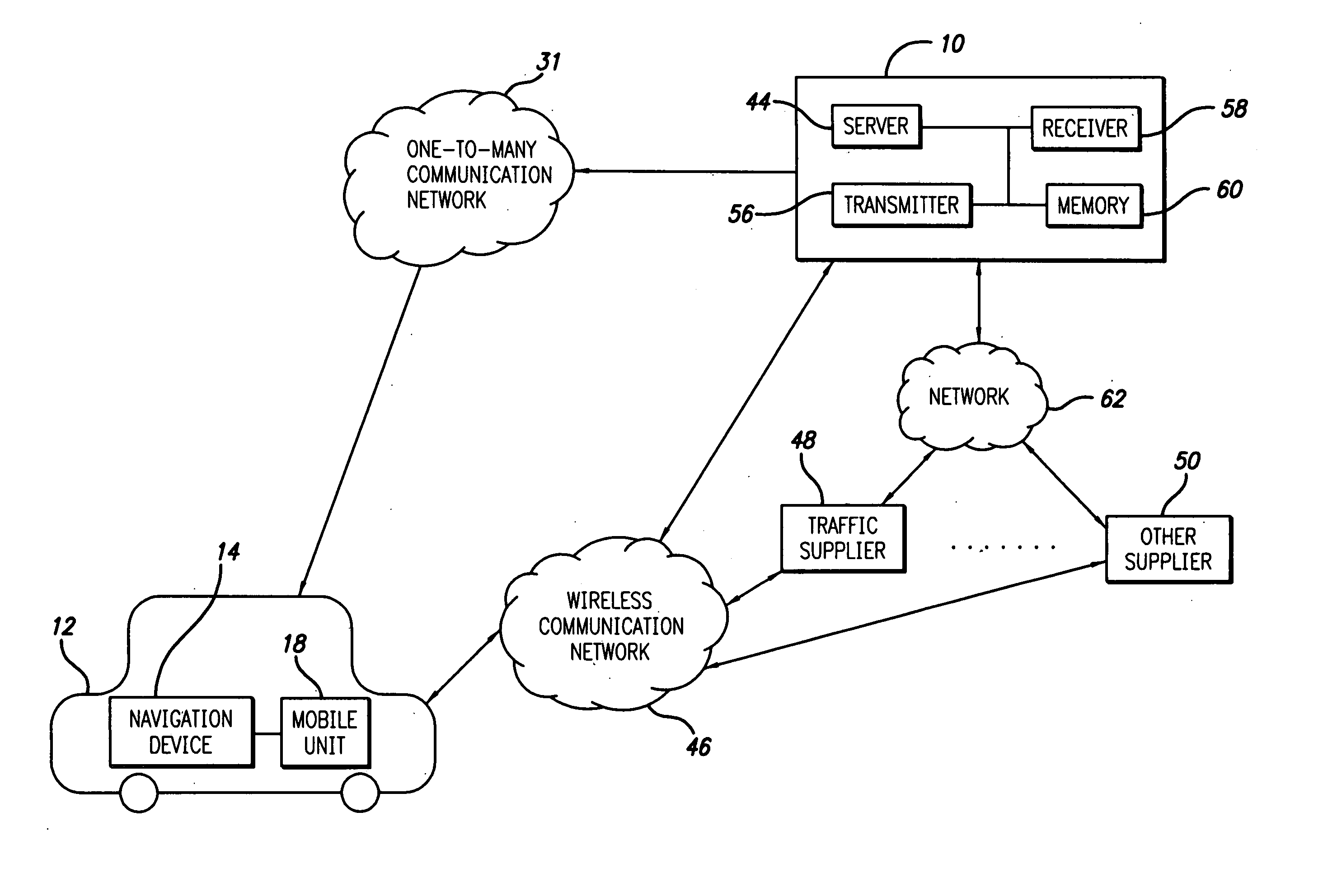
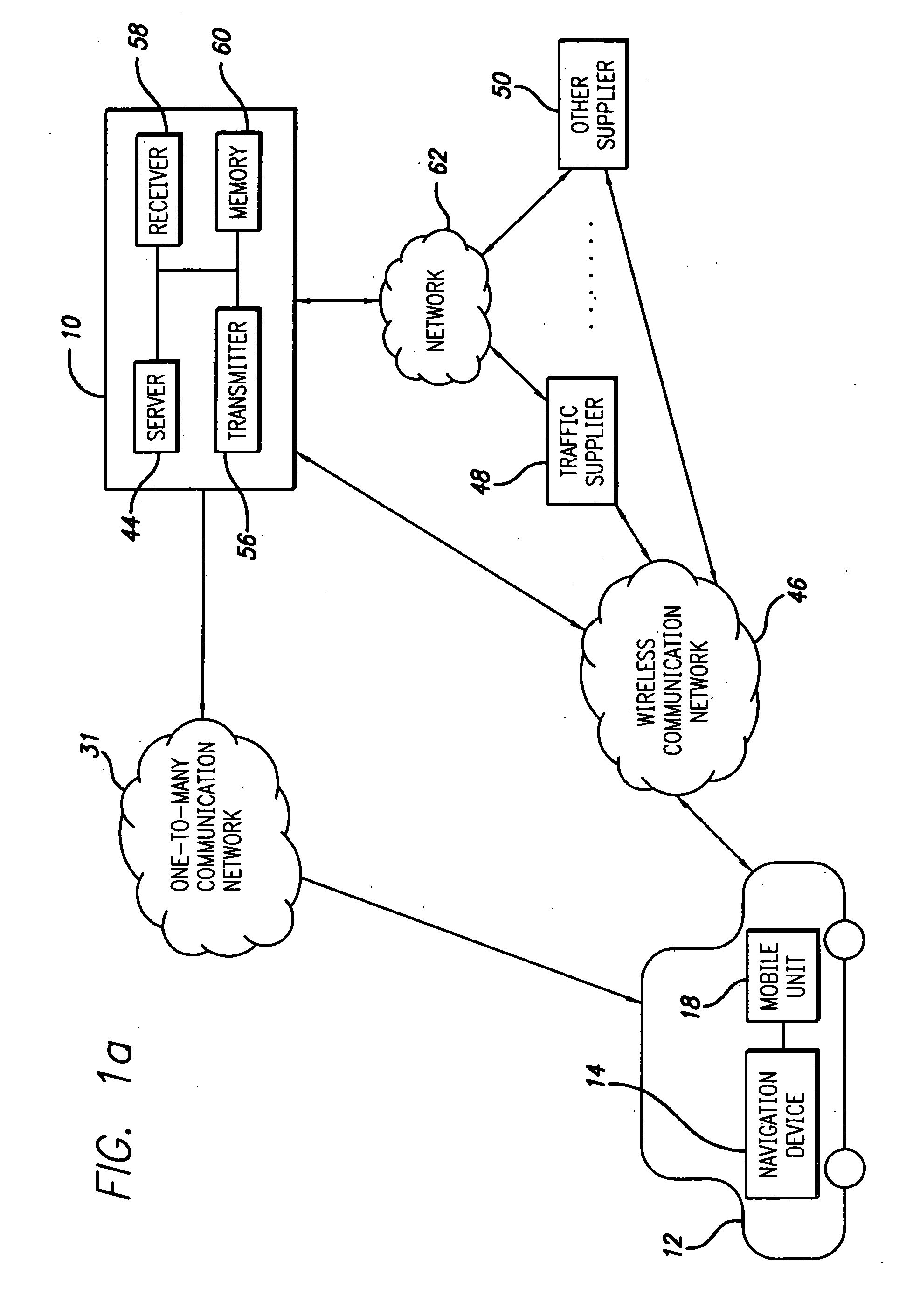
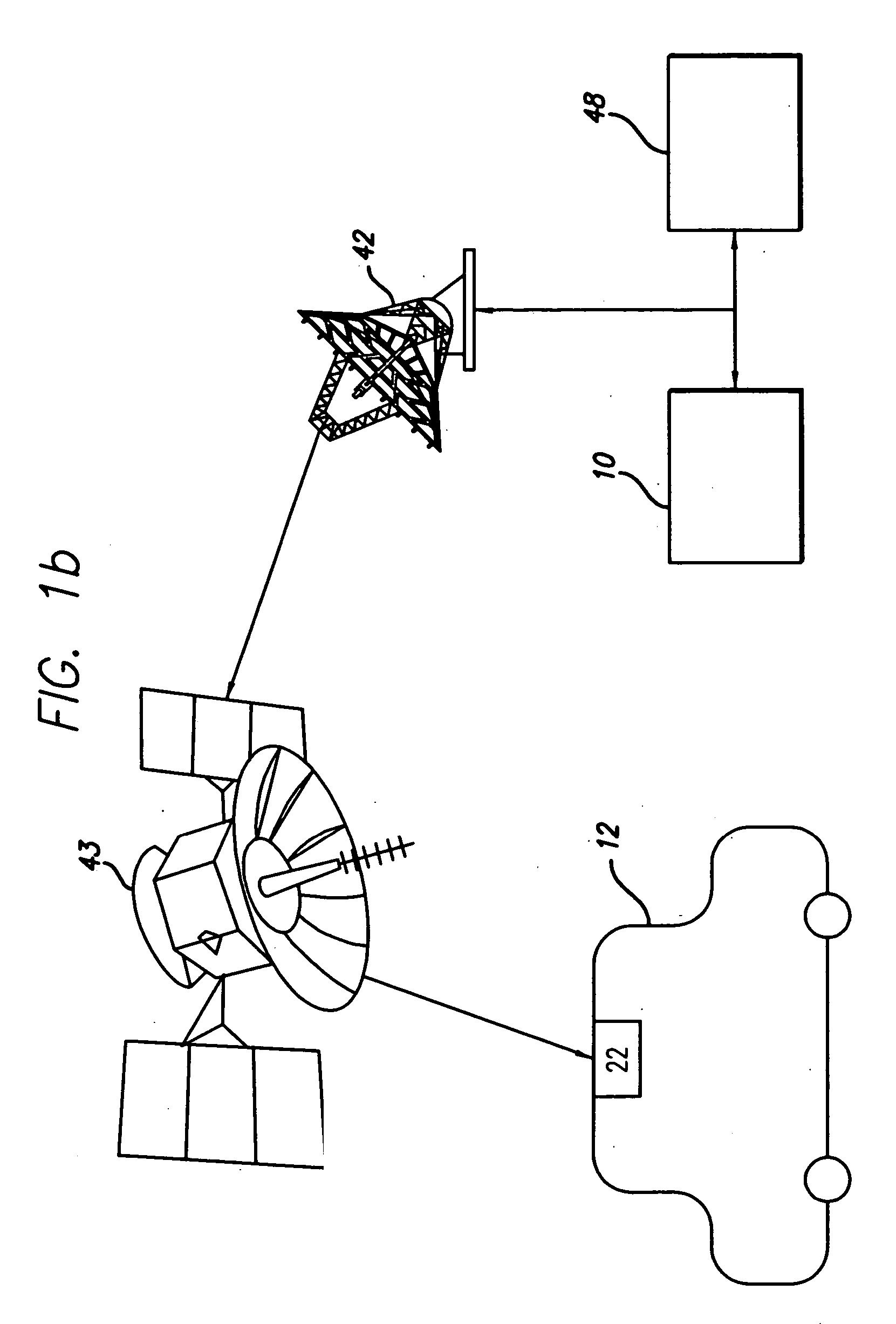
ActiveUS20050222764A1Increase route calculationIncrease and decrease broadcastInstruments for road network navigationRoad vehicles traffic controlNavigation systemReceipt
Traffic information, including flow information and incident information, obtained through a traffic management system for providing and facilitating the exchange of traffic information between a remote location and a vehicle may be used in route calculation by a navigation device. The navigation device may recalculate a route based on anticipated user error. Alternatively, the navigation device may recalculate a route using received traffic information triggered by the receipt of a traffic information update, or triggered by the passage of an amount of time. The broadcast rate of traffic information updates may vary temporally (providing more frequent updates during peak commute times) or geographically (providing more frequent updates to metropolitan areas with increased traffic information needs). If route calculation is triggered by an elapsed amount of time, the amount of time may vary to be shorter during peak commute times. Additional route calculation techniques allow the incorporation of historical traffic information or the use of the most recent traffic information if incomplete traffic information is available. Still further route calculation techniques may calculate a best route by avoiding zigzagging or evaluating an assigned cost of a potential route.
Owner:HONDA MOTOR CO LTD
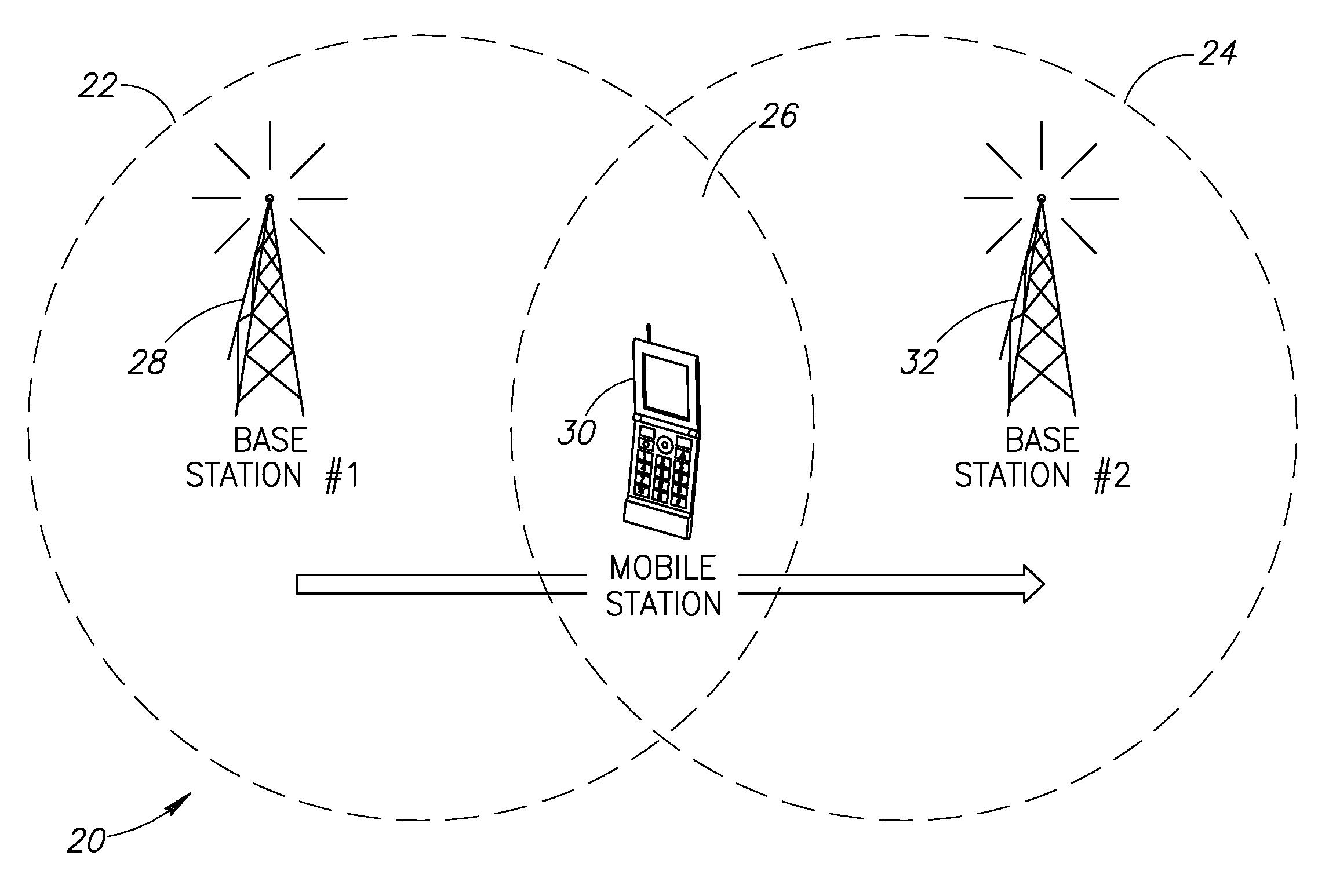
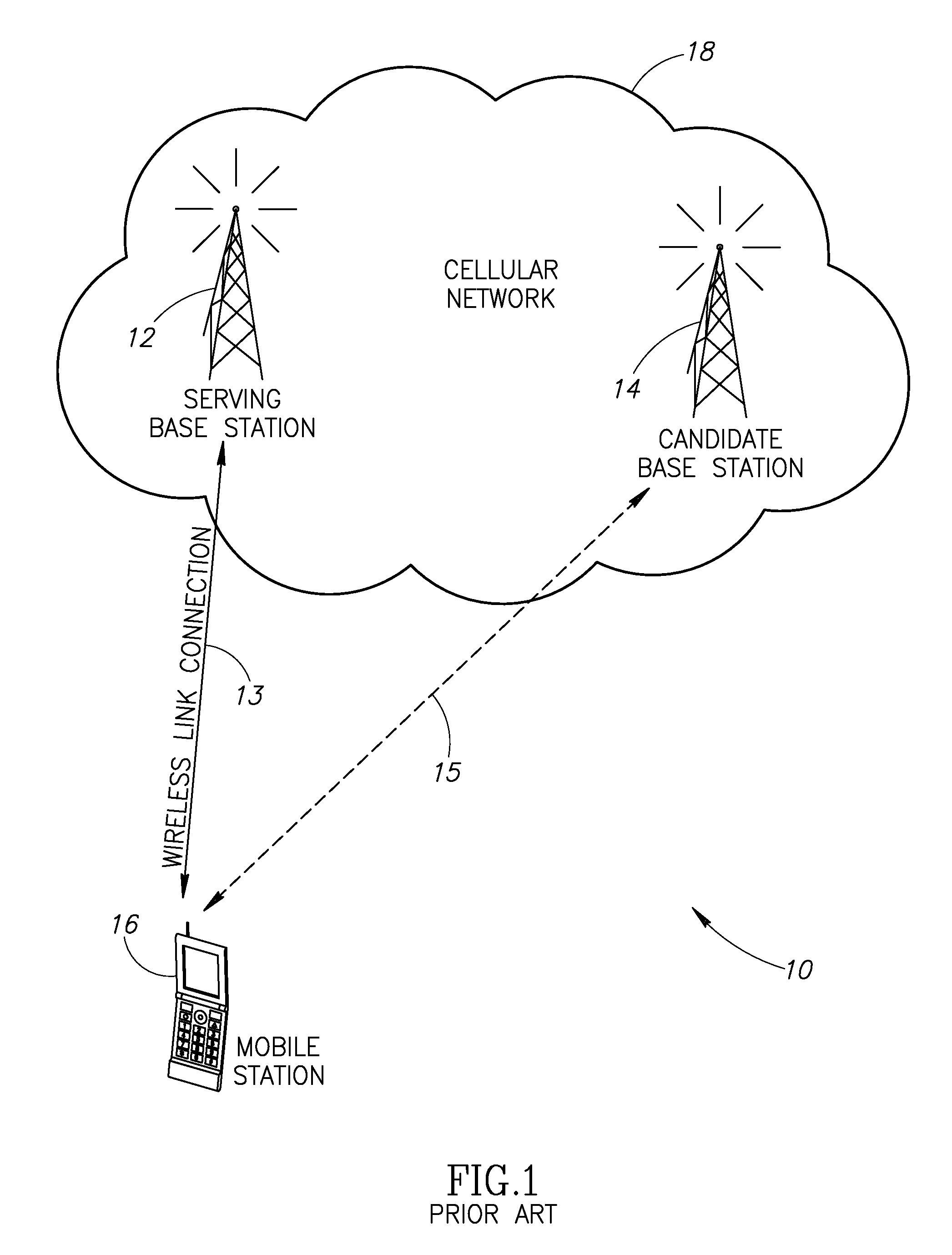
Autonomous anonymous association between a mobile station and multiple network elements in a wireless communication system
InactiveUS20090290555A1Improve service qualityImprove acquisitionServices signallingRadio/inductive link selection arrangementsCommunications systemCellular communication systems
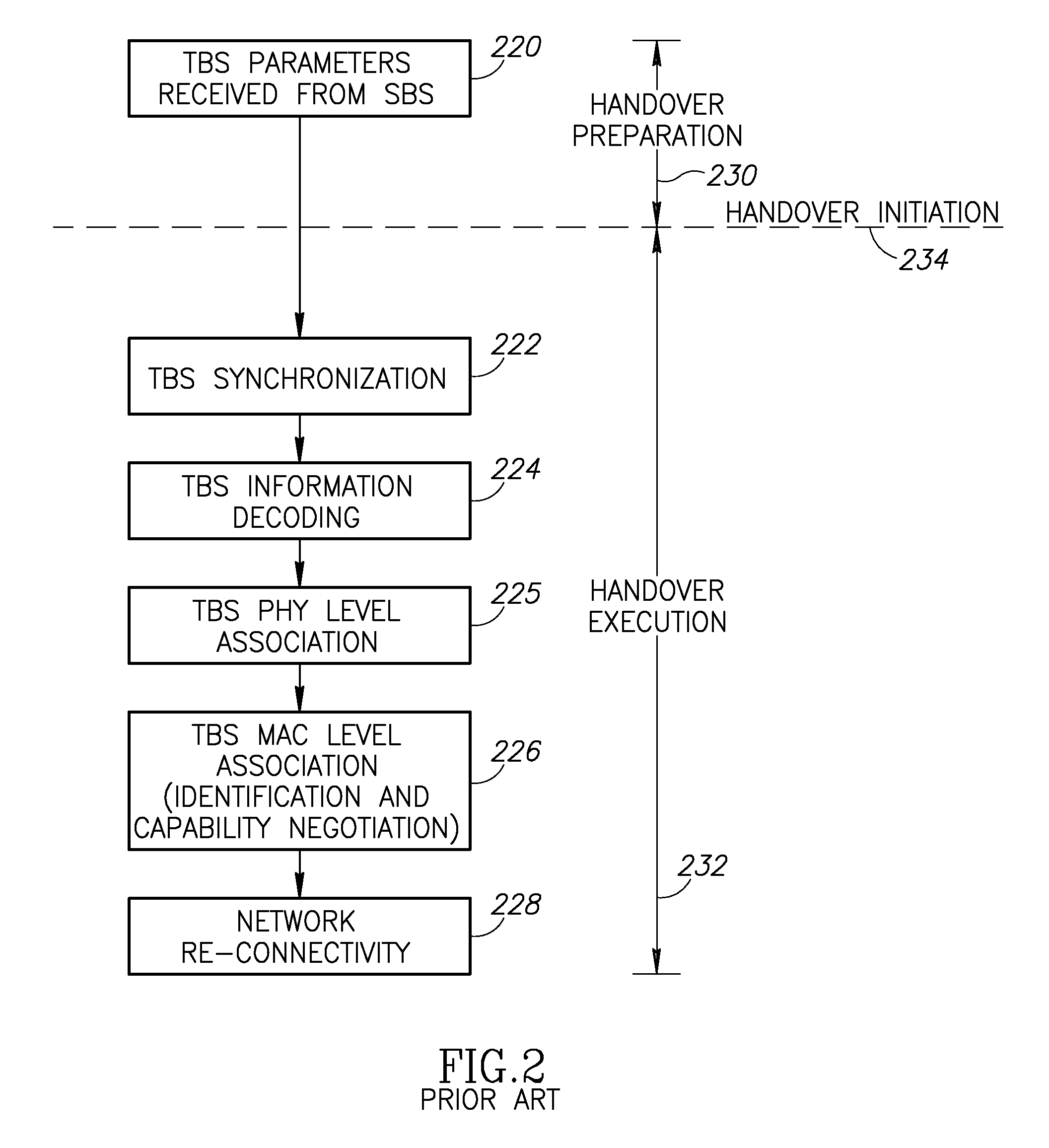
A novel and useful autonomous association mechanism for use in user equipment (UE) network connections in one or more cellular communications systems. The handover process is optimized by improving the selection of target base stations and optimizing the discontinuity period from the time of disconnection from a serving base station and connection to a target base station and by establishing anonymous bidirectional communications with base stations. The mechanism facilitates multiple cell association in a network unaware manner while preserving single endpoint connectivity. The UE does not need to negotiate for or receive pre-allocated opportunities from the network for making associations with neighboring base stations. Association opportunities are created by the UE autonomously in accordance with UE activity patterns. Association opportunities are used to exchange preliminary information needed for handover between the UE and candidate base stations over the same or a plurality of access technologies. The information includes any parameter that can affect the handover process, e.g., link quality, etc.
Owner:COMSYS COMM & SIGNAL PROC
System and method for securely providing a configuration file over and open network
ActiveUS20060174018A1User identity/authority verificationUnauthorized memory use protectionDomain nameNetwork connection
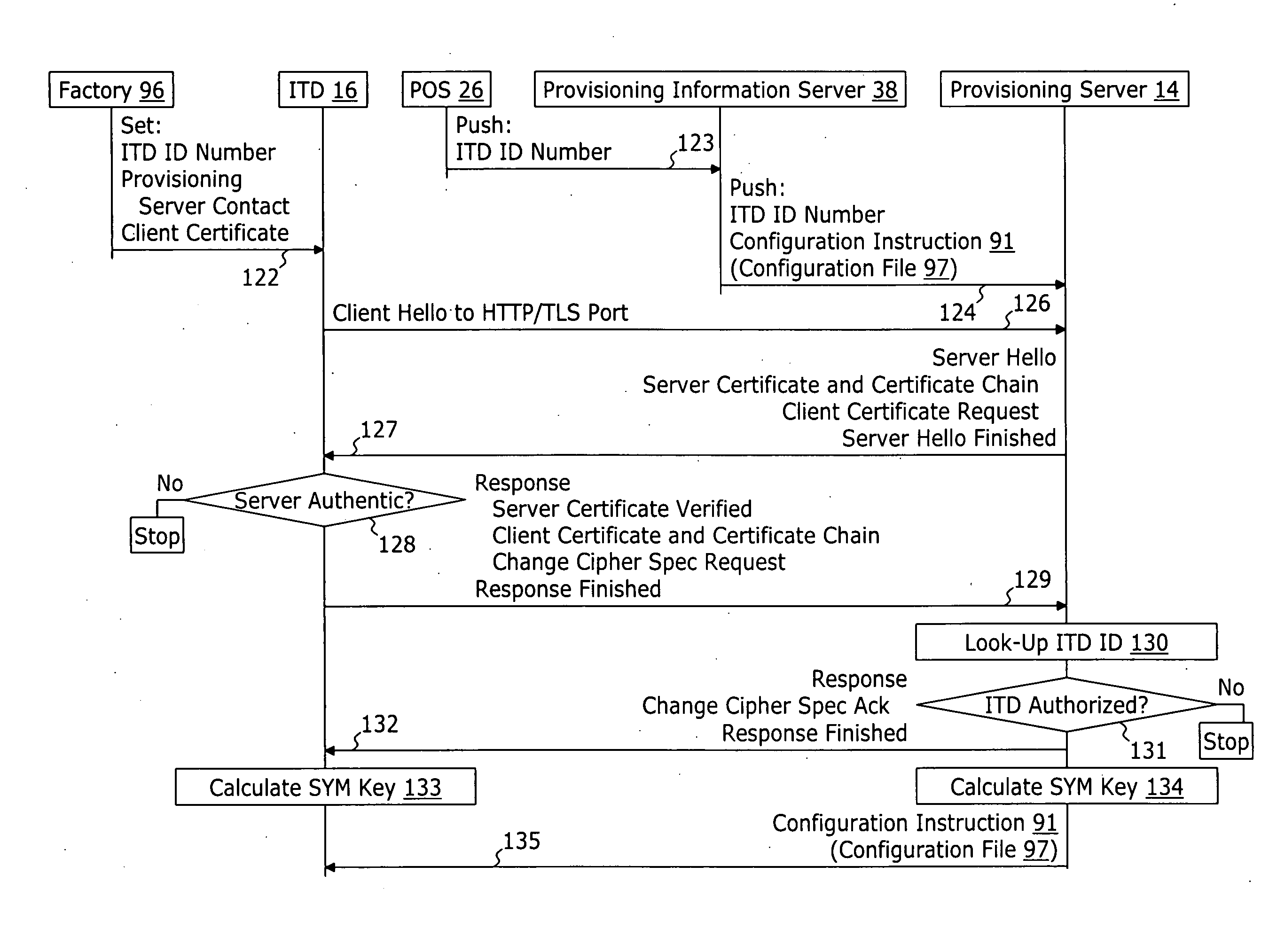
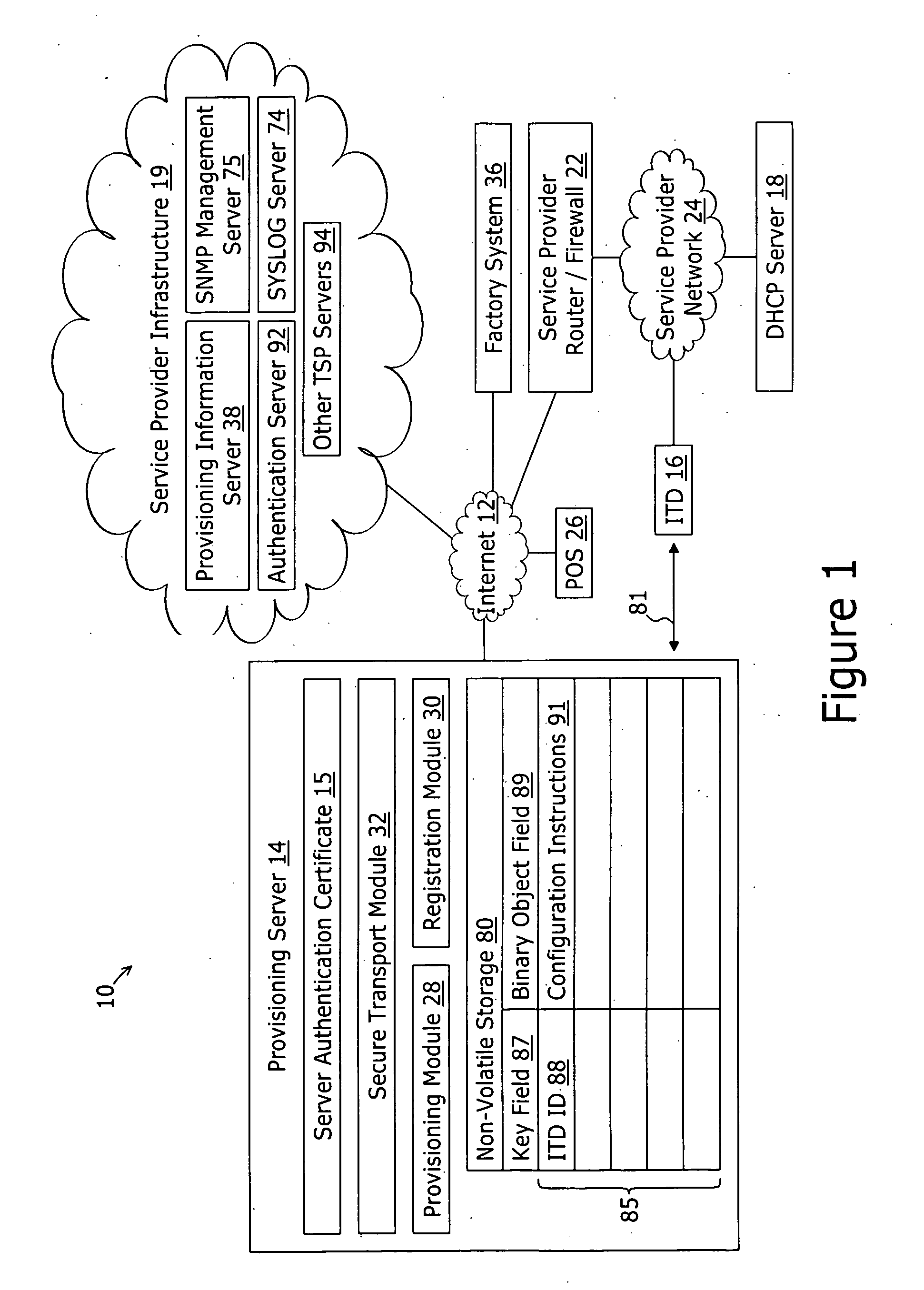
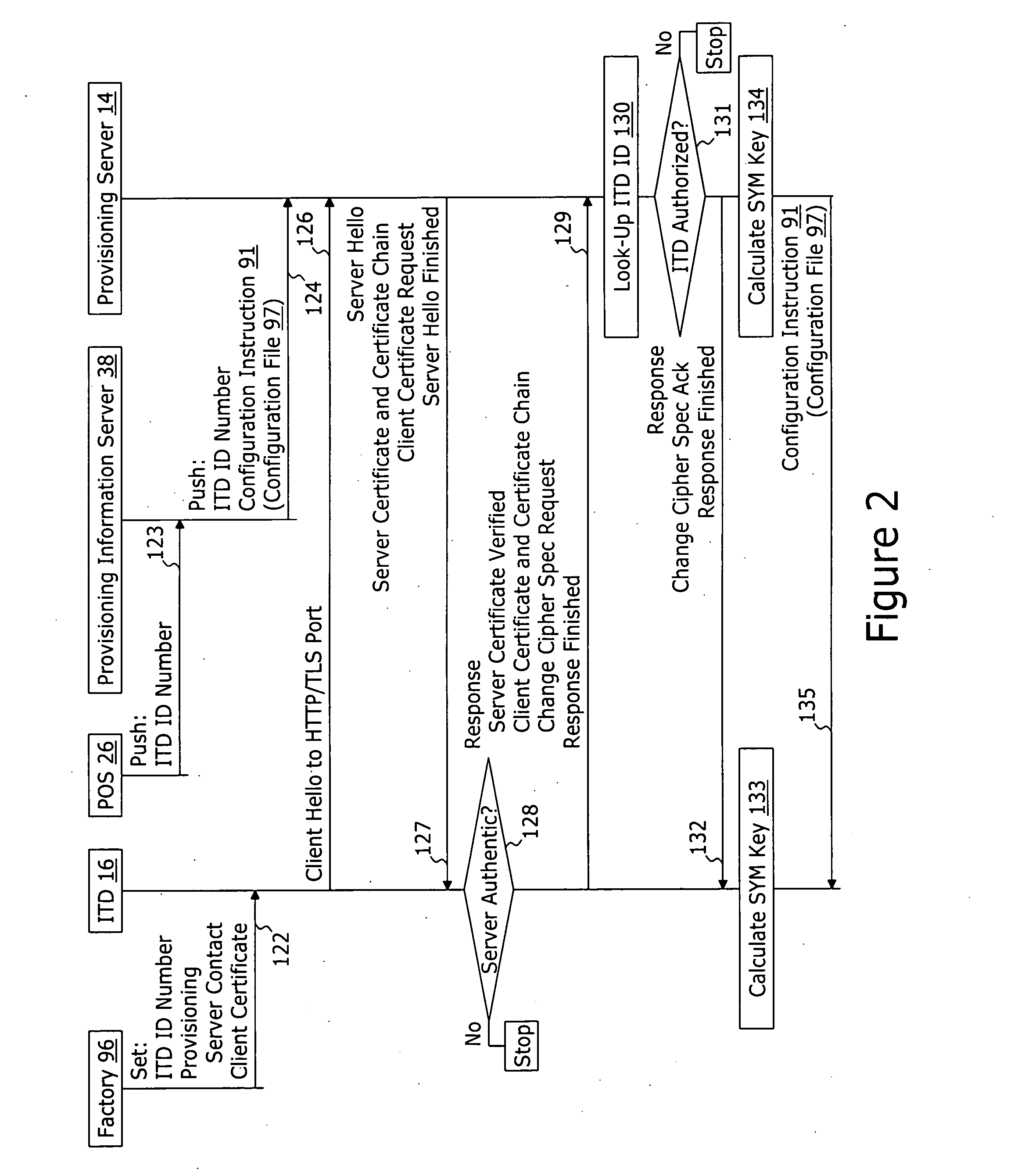
A method for securely provisioning a device for operation within a service provider infrastructure over an open network comprises the device establishing physical and data link layer network connections for communication on at least a subnet of the open network and obtaining a network configuration data such as an IP address and a subnet mask from a provisioning server that responds to a network configuration broadcast request. A device establishes a secure hypertext transport protocol connection to a first provisioning server that corresponds to one of: i) and IP address and port number; and ii) a fully qualified domain name stored in a non-volatile memory of the device. After mutual authentication, the first provisioning server provides at least one of: i) a configuration file; and ii) identification of a second provisioning server and a cipher key through the secure connection. If the first provisioning server provided identification of a second provisioning server, the device establishes a transport connection to the identified second provisioning server. The second provisioning server provides an encrypted file which, when decrypted using the cipher key yields the configuration information needed by the device for operation with the service provider infrastructure.
Owner:INOMEDIA
Advice provided for offering highly targeted advice without compromising individual privacy
InactiveUS7246150B1Compromising securityCompromising privacyDigital data information retrievalMultiple digital computer combinationsTime elementInformation needs
The invention disclosed herein enables a collection of computers and associated communications infrastructure to offer a new communications process which allows information providers to broadcast information to a population of information consumers. The information may be targeted to those consumers who have a precisely formulated need for the information. This targeting may be based on information which is inaccessible to other communications protocols. The targeting also includes a time element. Information can be brought to the attention of the consumer precisely when it has become applicable, which may occur immediately upon receipt of the message, but may also occur long after the message arrives. The communications process may operate without intruding on consumers who do not exhibit the precisely-specified need for the information, and it may operate without compromising the security or privacy of the consumers who participate.
Owner:IBM CORP
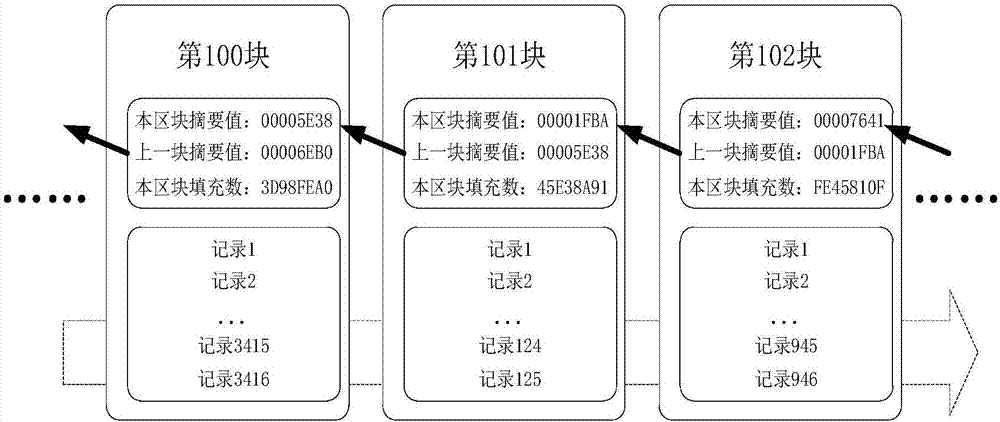
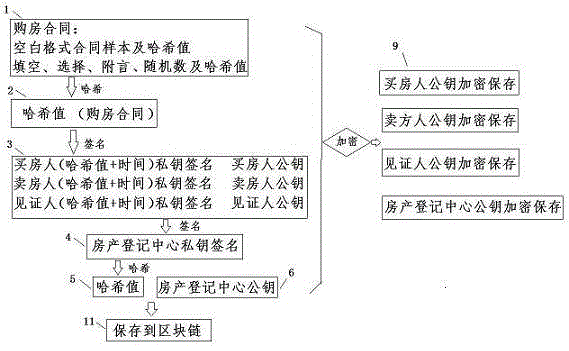
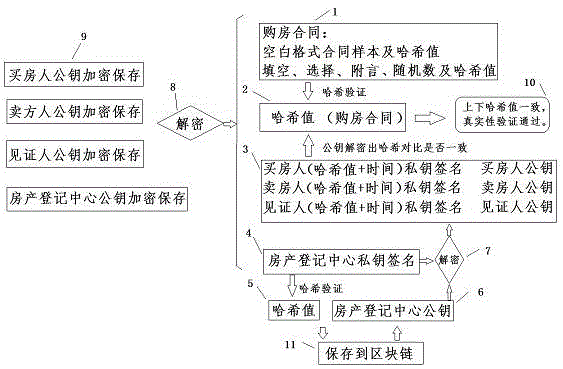
Block chain information archiving and privacy protection method
ActiveCN105610578APrevent tamperingEasy retrievalKey distribution for secure communicationThird partyPrivacy protection
The invention discloses a block chain information archiving and privacy protection method. The block chain information archiving and privacy protection method comprises the steps of adding random number generation Hash values to information needing archiving; then signing by an interest-related person or a eyewitness and generating Hash values; and finally recording at a block chain. Some information needing archiving is formatting and separable formatting information and self-filling information respectively stored and subjected to Hash verification, such as gap-filling information, selection information, postscript information, random number information (for preventing brute force attack). Data which are encrypted by using a public key only can be decrypted by a relevant person who knows the original information by using a private key; a third party verifies true and false of the information; and the encrypted information can be disclosed for a judicial institution if judiciary involvement is needed.
Owner:苏州交链科技有限公司 +1
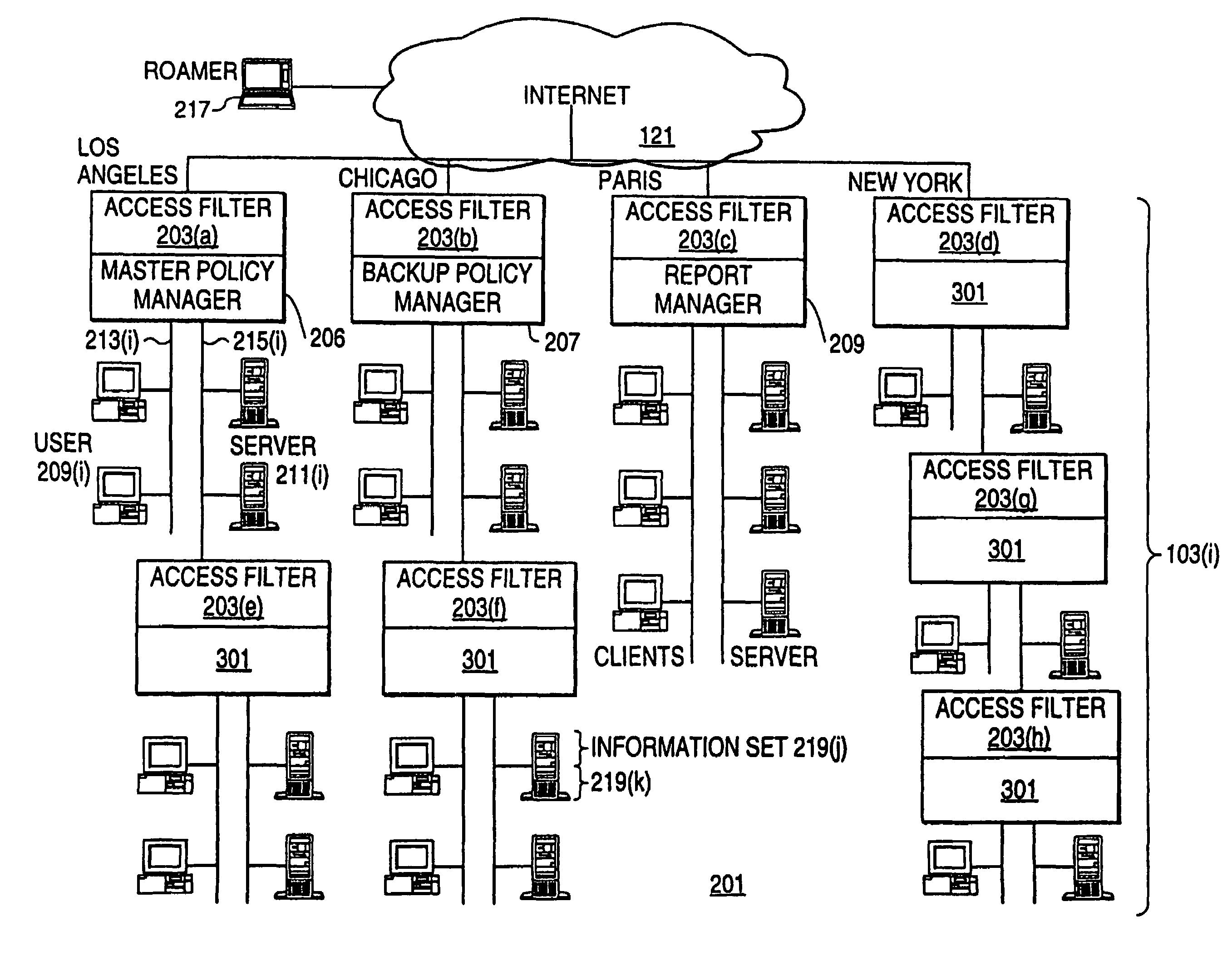
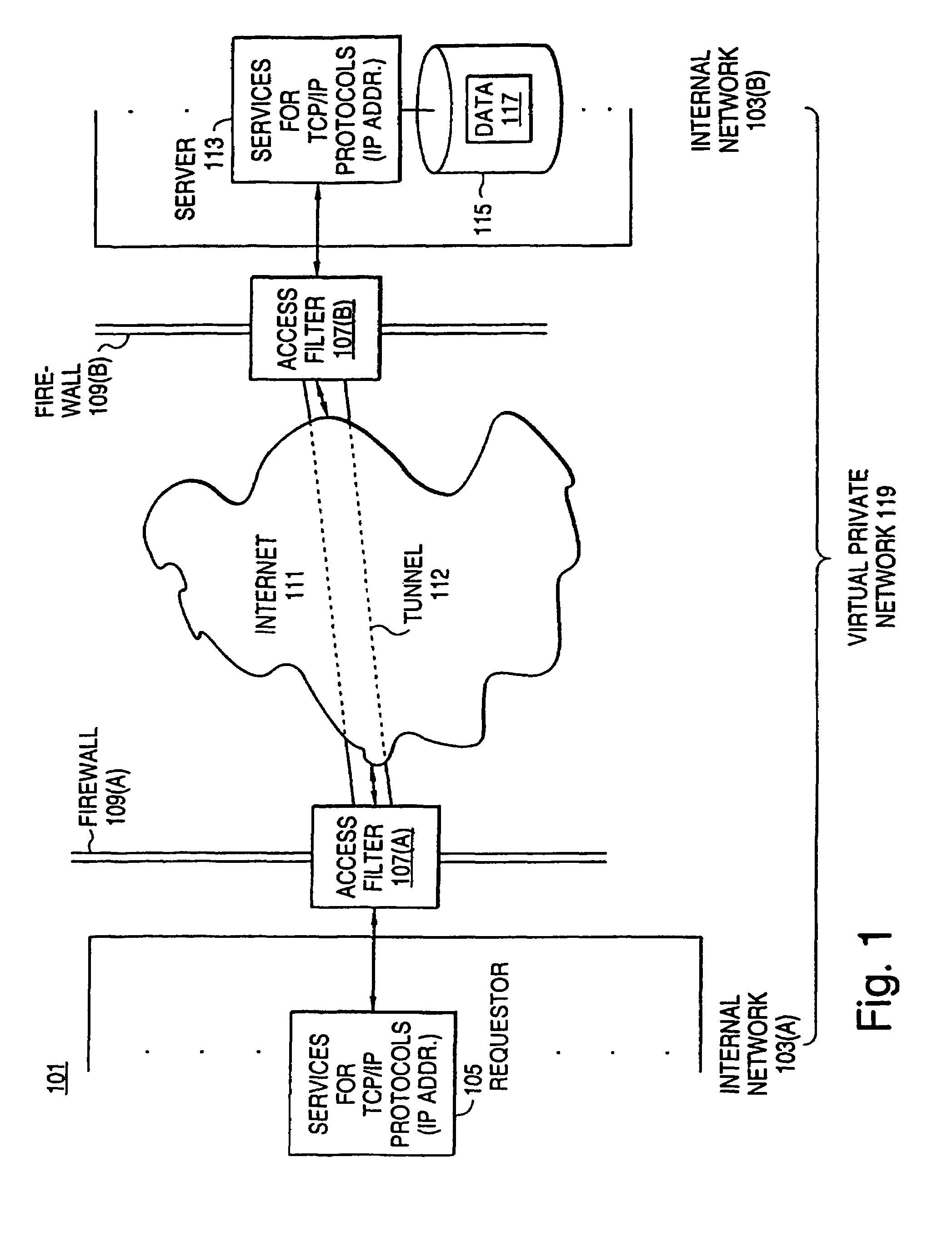
Query interface to policy server
InactiveUS7580919B1Data processing applicationsDigital data information retrievalInformation resourcePrivate network
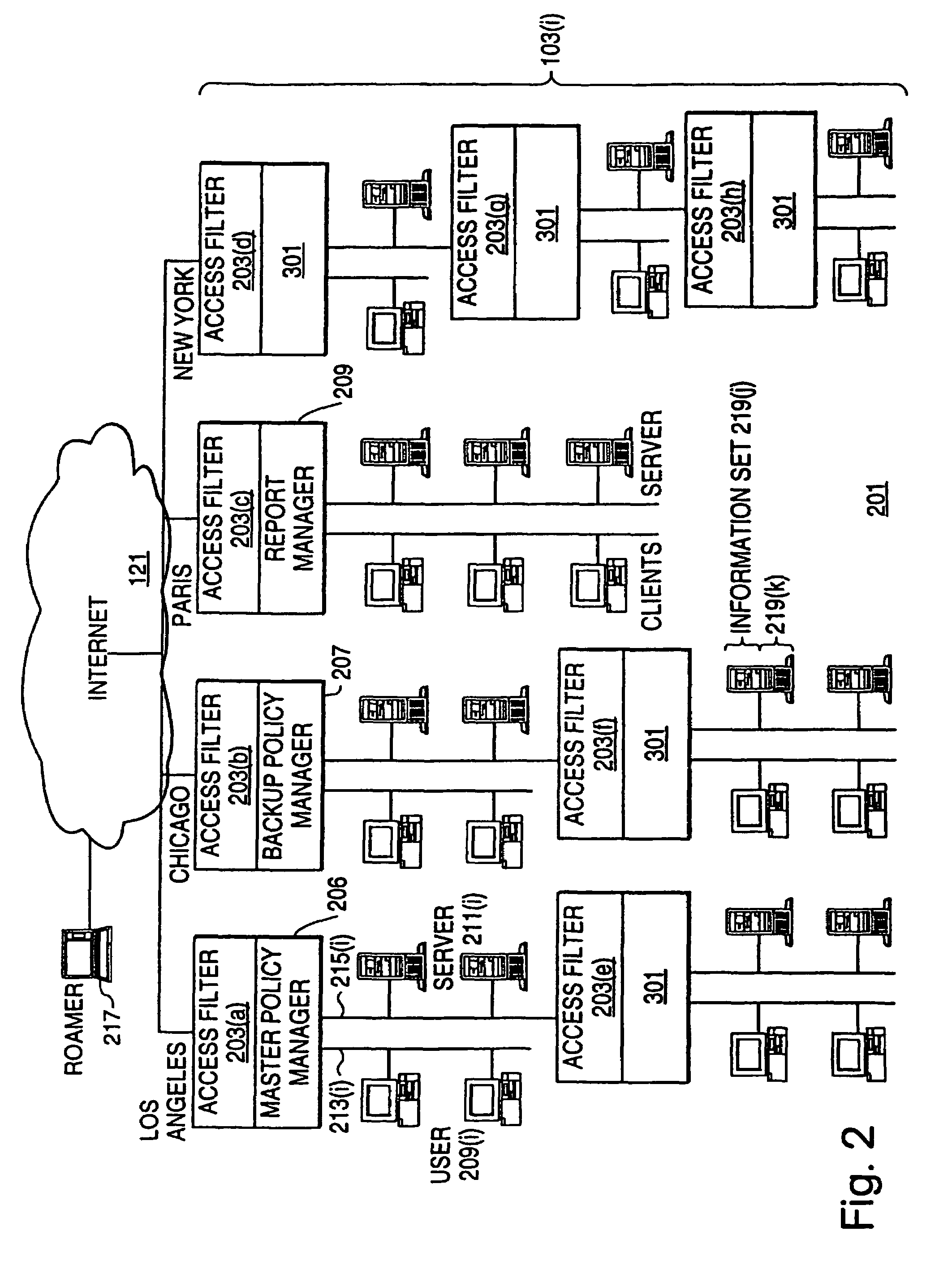
An exemplary scalable access filter that is used together with others like it in a virtual private network to control access by users at clients in the network to information resources provided by servers in the network is disclosed. Each access filter uses a local copy of an access control data base (3845) to determine whether an access request is made by a user. Each user belongs to one or more user groups and each information resource belongs to one or more information sets. Access is permitted or denied according to access policies, which define access in terms of the user groups and information sets. The first access filter in the path performs the access check, encrypts and authenticates the request; the other access filters in the path do not repeat the access check. The interface used by applications to determine whether a user has access to an entity is now an SQL query. The policy server (3811) assembles the information needed for the response to the query from various information sources, including source external to the policy server.
Owner:MARSHMAN RES +1
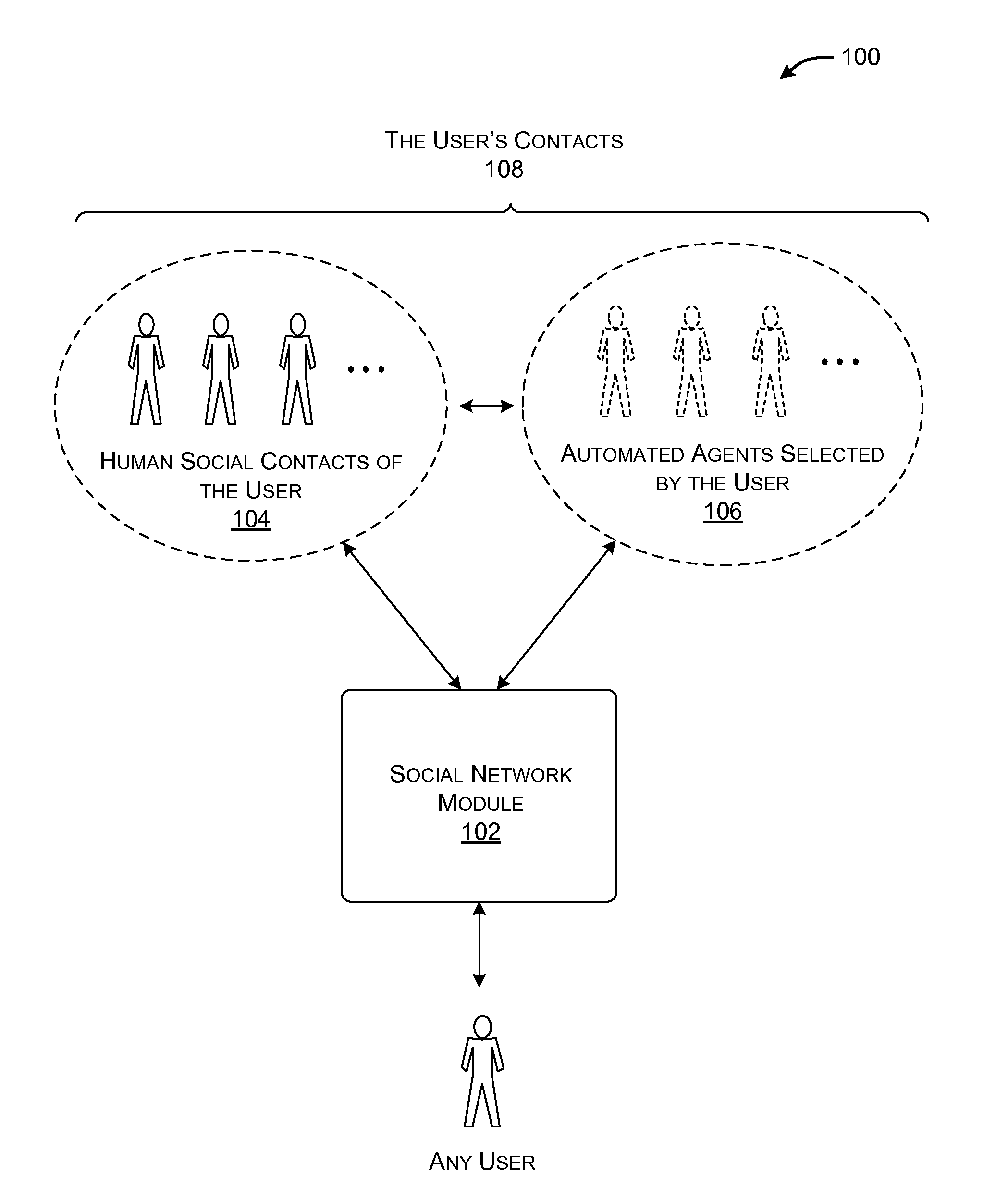
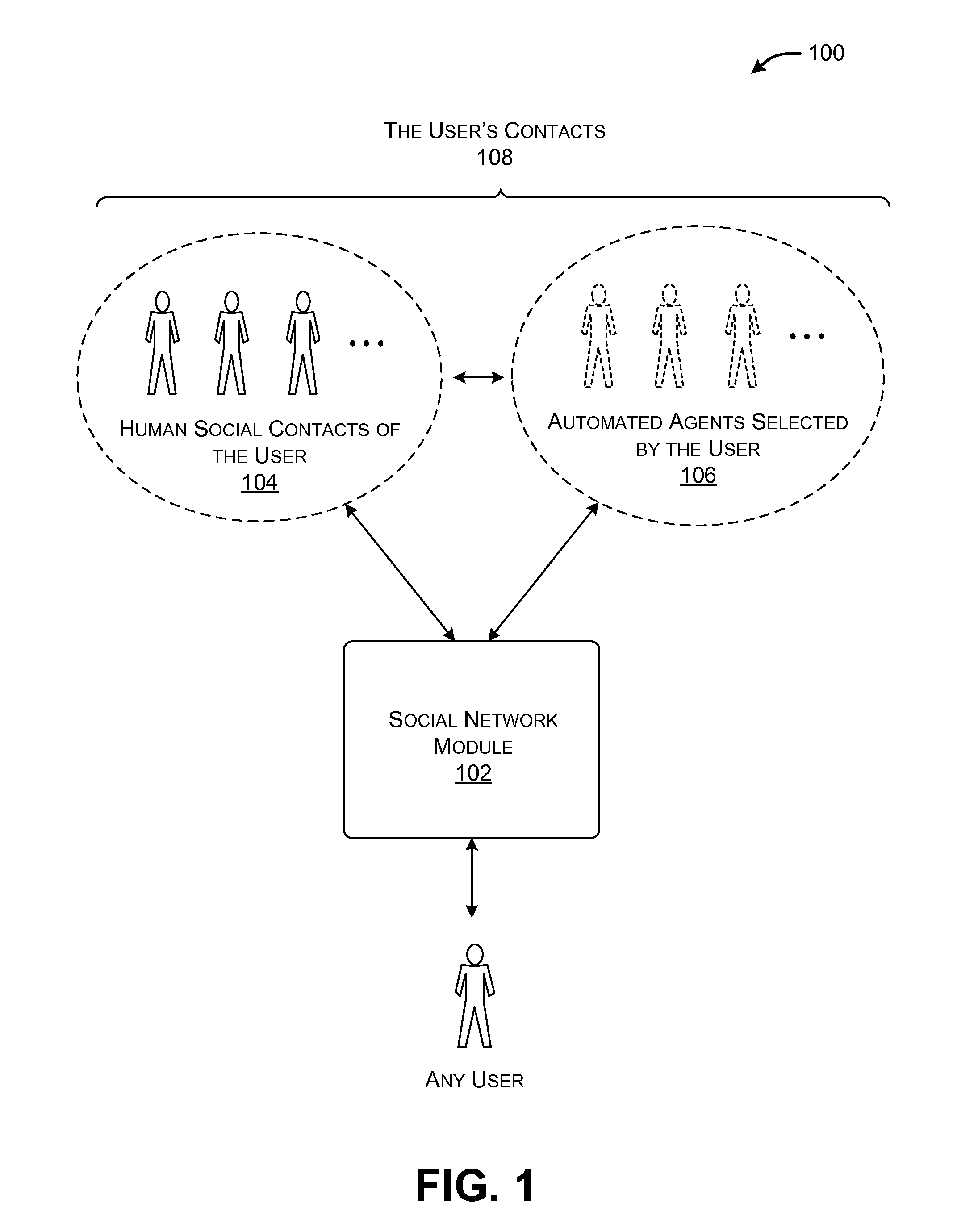
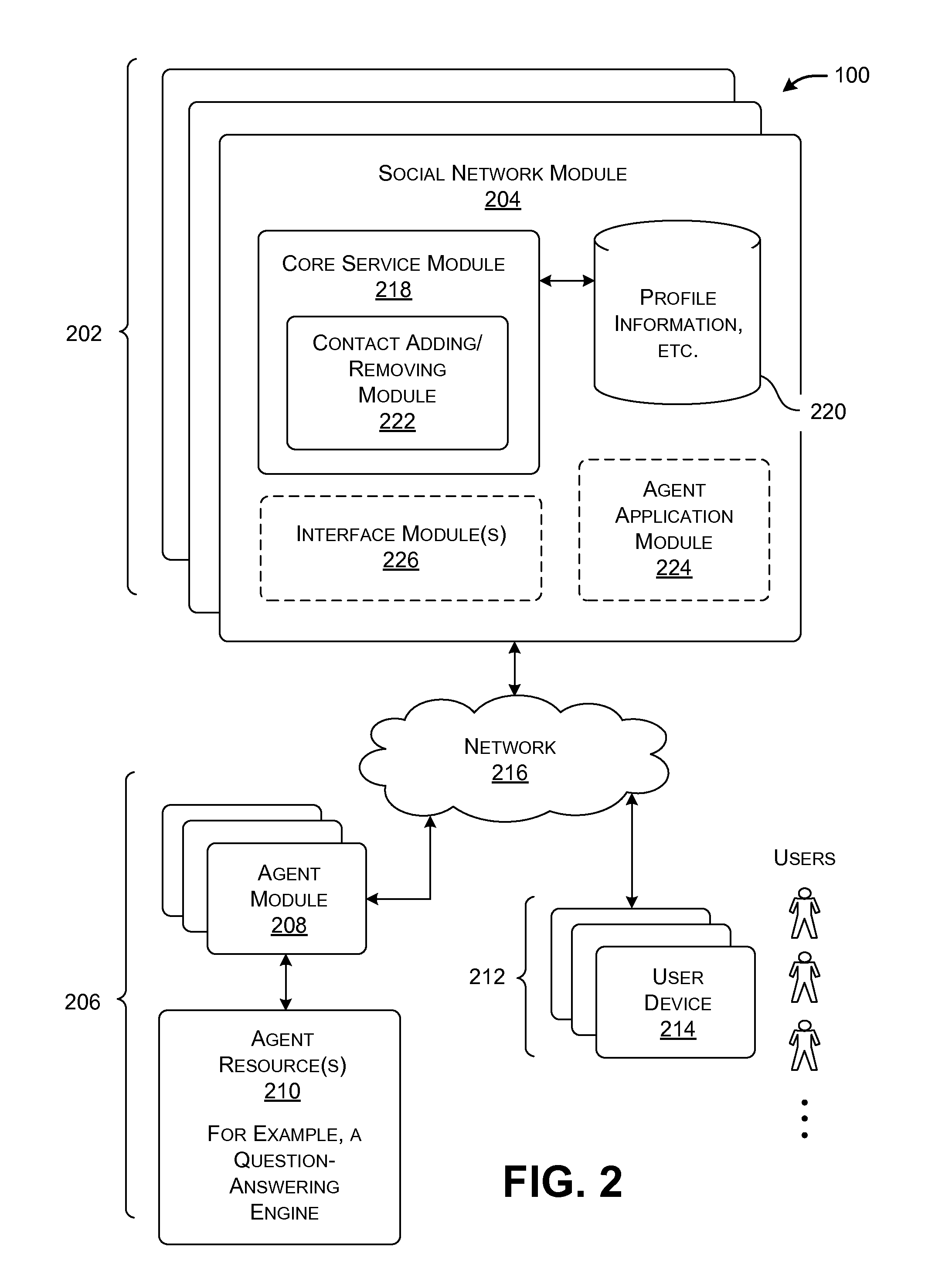
Designating automated agents as friends in a social network service
ActiveUS20110252108A1Multiple digital computer combinationsData switching networksReferral serviceSocial network service
A system is described in which a user can add one or more automated agents as “friends” in a social network service. In operation, an automated agent observes an information need expressed by the user via the social network service, e.g., in the form of an original message posted to the social network service; determines whether it is appropriate to reply to the information need; uses automated functionality to generate a reply message to the information need (if it is deemed appropriate to reply to the information need); and sends the reply message to a target destination, such as a social network page associated with the user. For example, without limitation, one type of automated agent performs a question-answering function. Another type of automated agent performs a social referral service.
Owner:MICROSOFT TECH LICENSING LLC
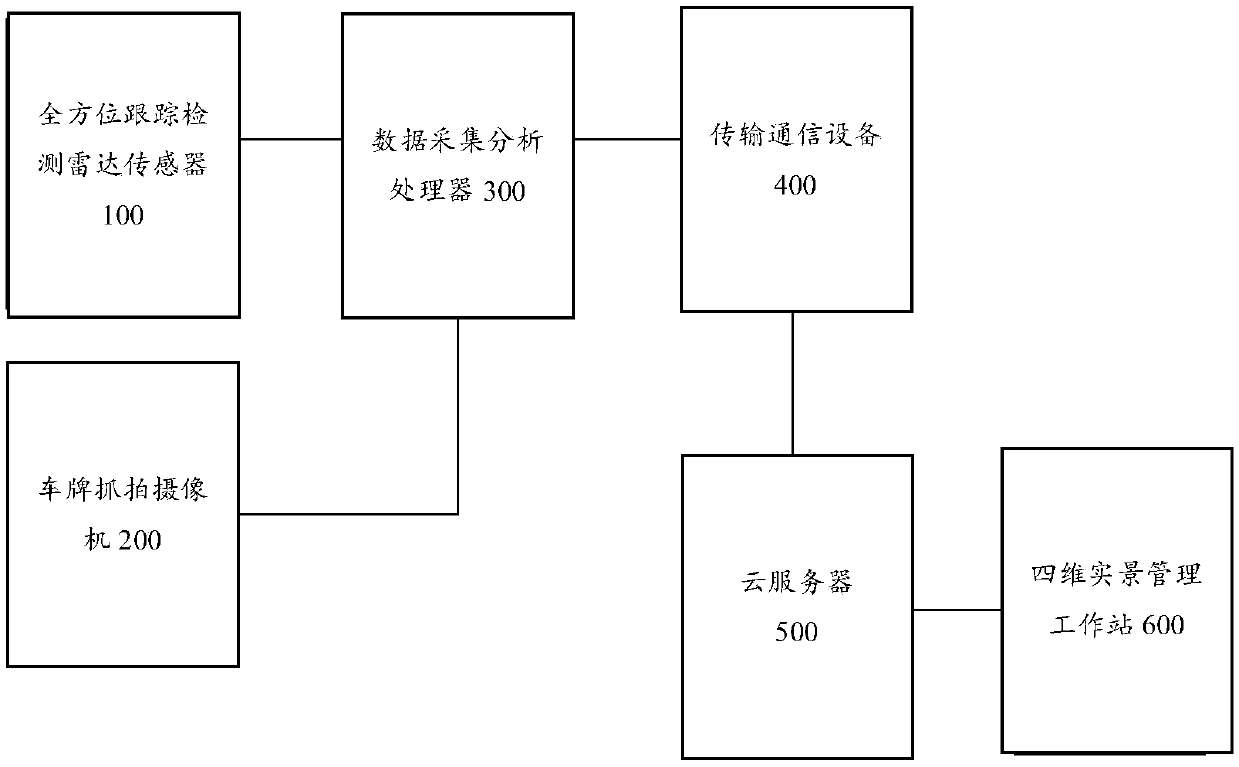
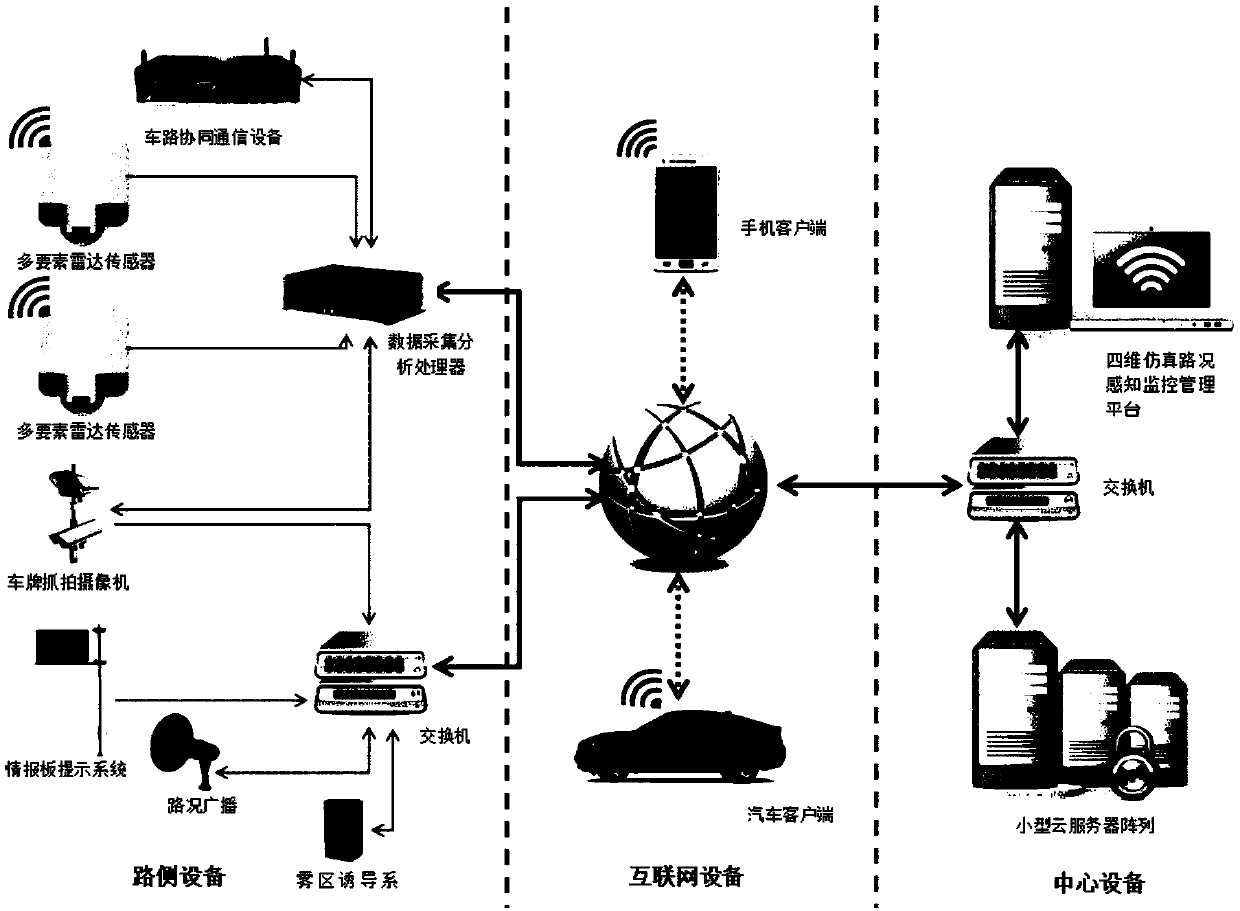
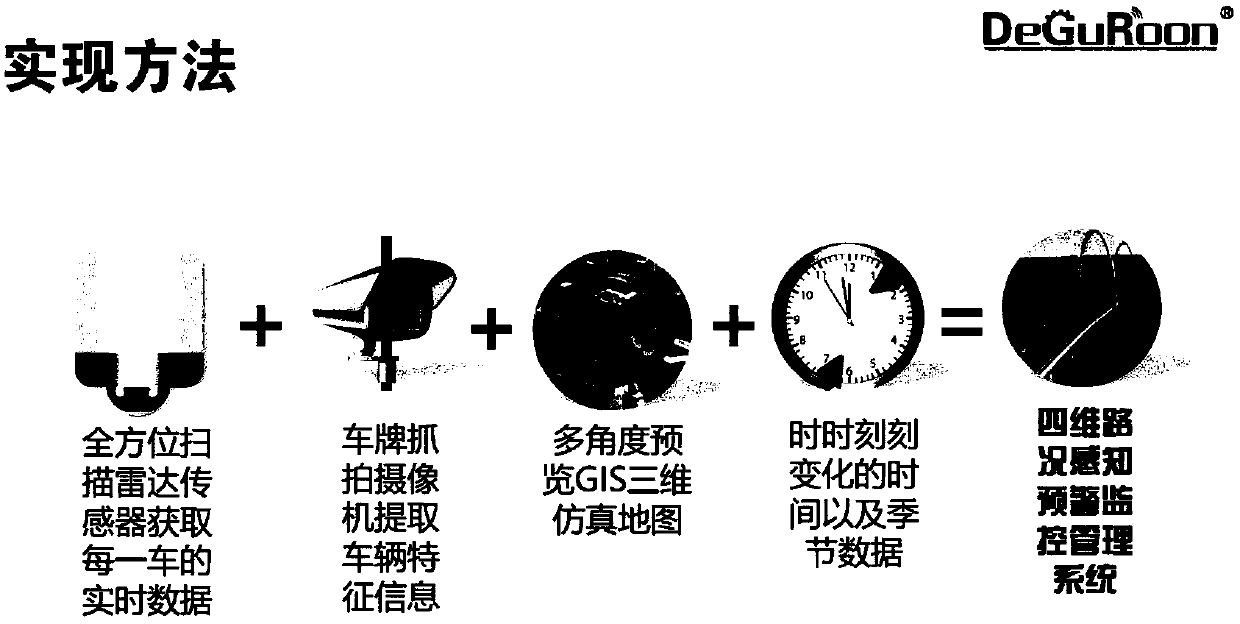
Four-dimensional live-action traffic road condition perceiving and early-warning monitoring management system based on radar tracking and positioning
ActiveCN108922188AEfficient Management ToolsDetection of traffic movementThree dimensional simulationLive action
The invention provides a four-dimensional live-action traffic road condition perceiving and early-warning monitoring management system based on radar tracking and positioning. According to the four-dimensional live-action traffic road condition perceiving and early-warning monitoring management system, a tracking and positioning technology, a license plate snapping technology, a vehicle and pedestrian three-dimensional simulation technology, a road monitoring technology, an early-warning and alarming technology, a traffic condition simulation technology, a network communication technology, a meteorological simulation technology, a computer graphic technology, a video rendering technology, a three-dimensional high-precision GIS map technology, a virtual reality fusion technology, a vehicle-road collaborative technology and a navigation technology are perfectly fused together; and through the system, the various demands of road traffic operation managers for road real-time monitoring orarea monitoring and the information demands of traveling of drivers and passengers for real-time and real traffic conditions are greatly met, and the various drawbacks which are imperfect and cannot be solved in an existing monitoring system are overcome, so that the management efficiency of the road managers is improved, the firm foundation is laid for automatic management of roads, and the important safety guarantee is also provided for traveling vehicles on the road.
Owner:河北德冠隆电子科技有限公司
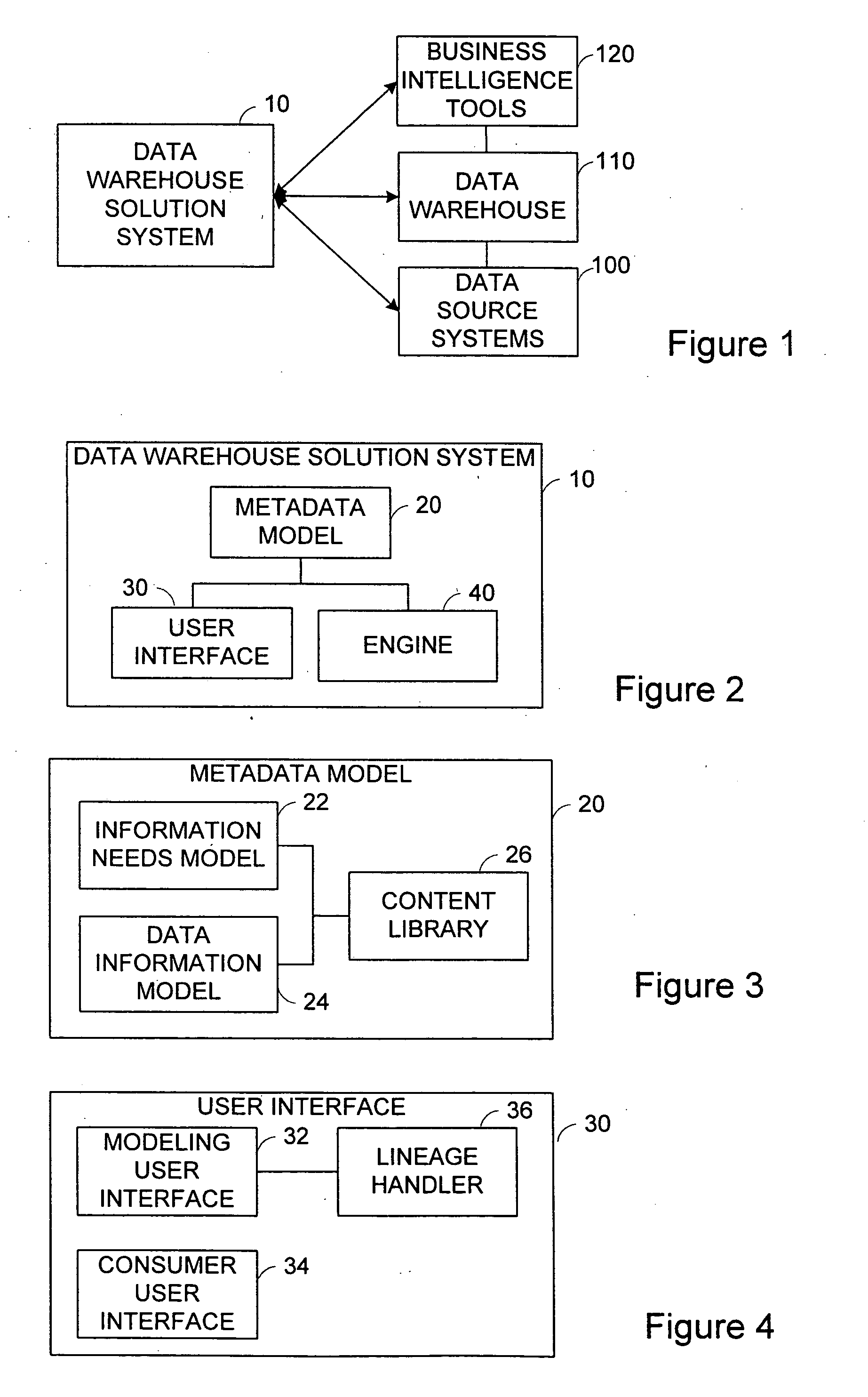
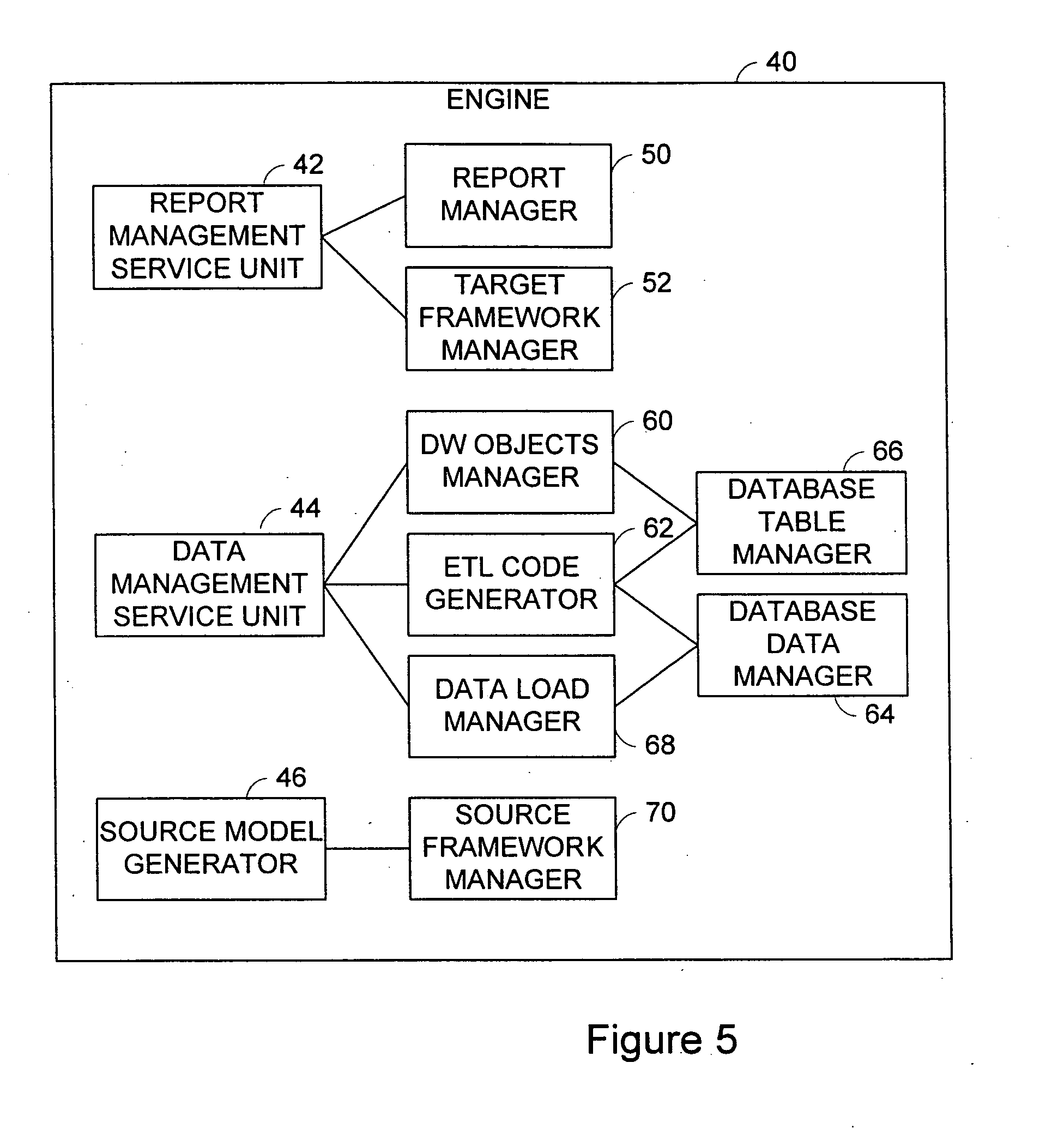
Packaged warehouse solution system
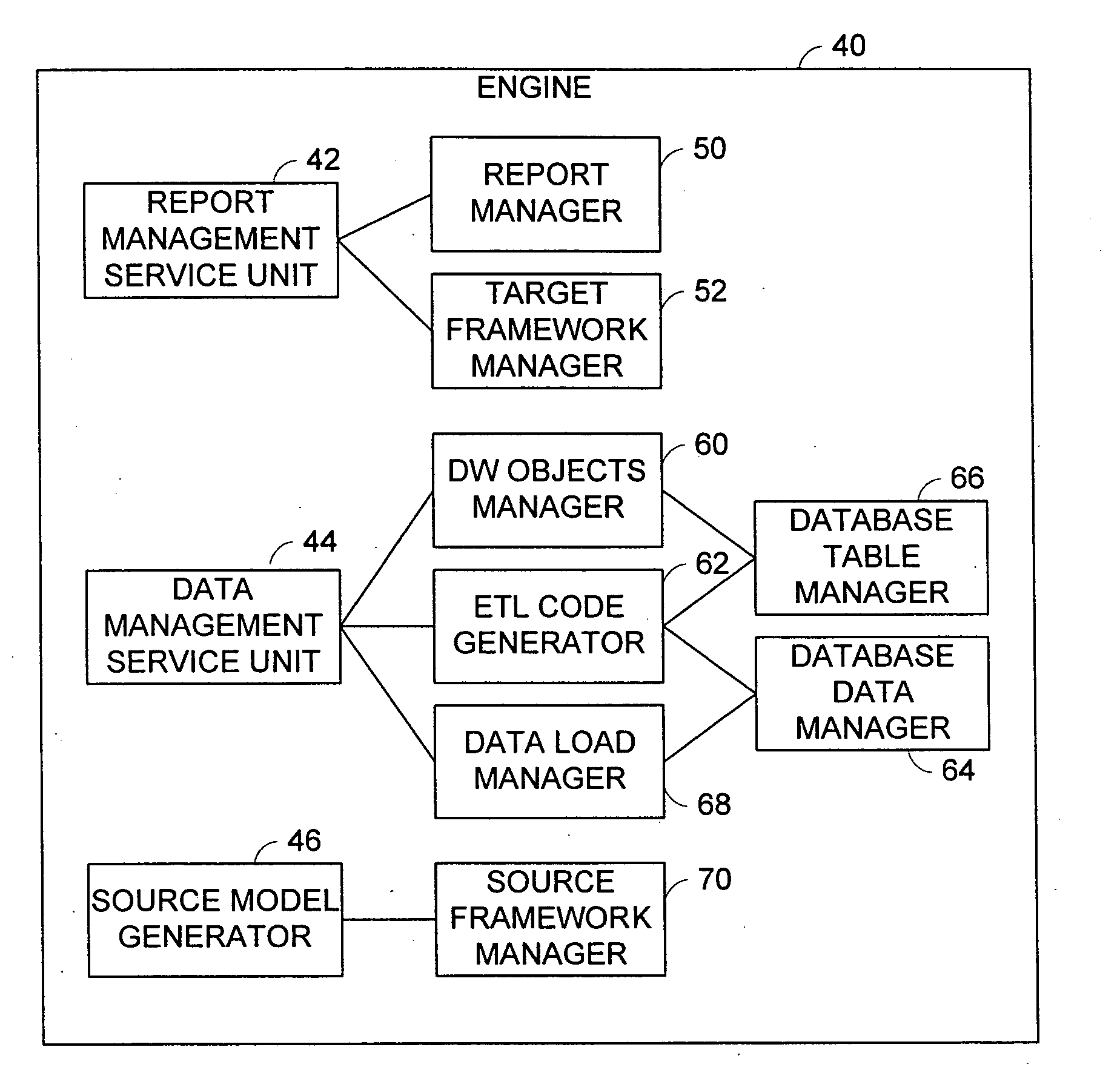
ActiveUS20070239769A1Digital data processing detailsMulti-dimensional databasesData warehouseData information
A data warehouse solution system comprises a metadata model, a user interface and an engine. The metadata model has an information needs model including metadata regarding information needs for building reports by users, and a data information model including metadata describing data that is available for building reports. The user interface has a customer user interface for presenting the information needs model to the users for report generation, and a modeling user interface for presenting the data information model to the users for manipulating data warehouse objects. The engine has a report management service unit for providing report management service using the information needs model, and a data management service unit for providing data management service including generation of a data warehouse using the data information model.
Owner:TWITTER INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com