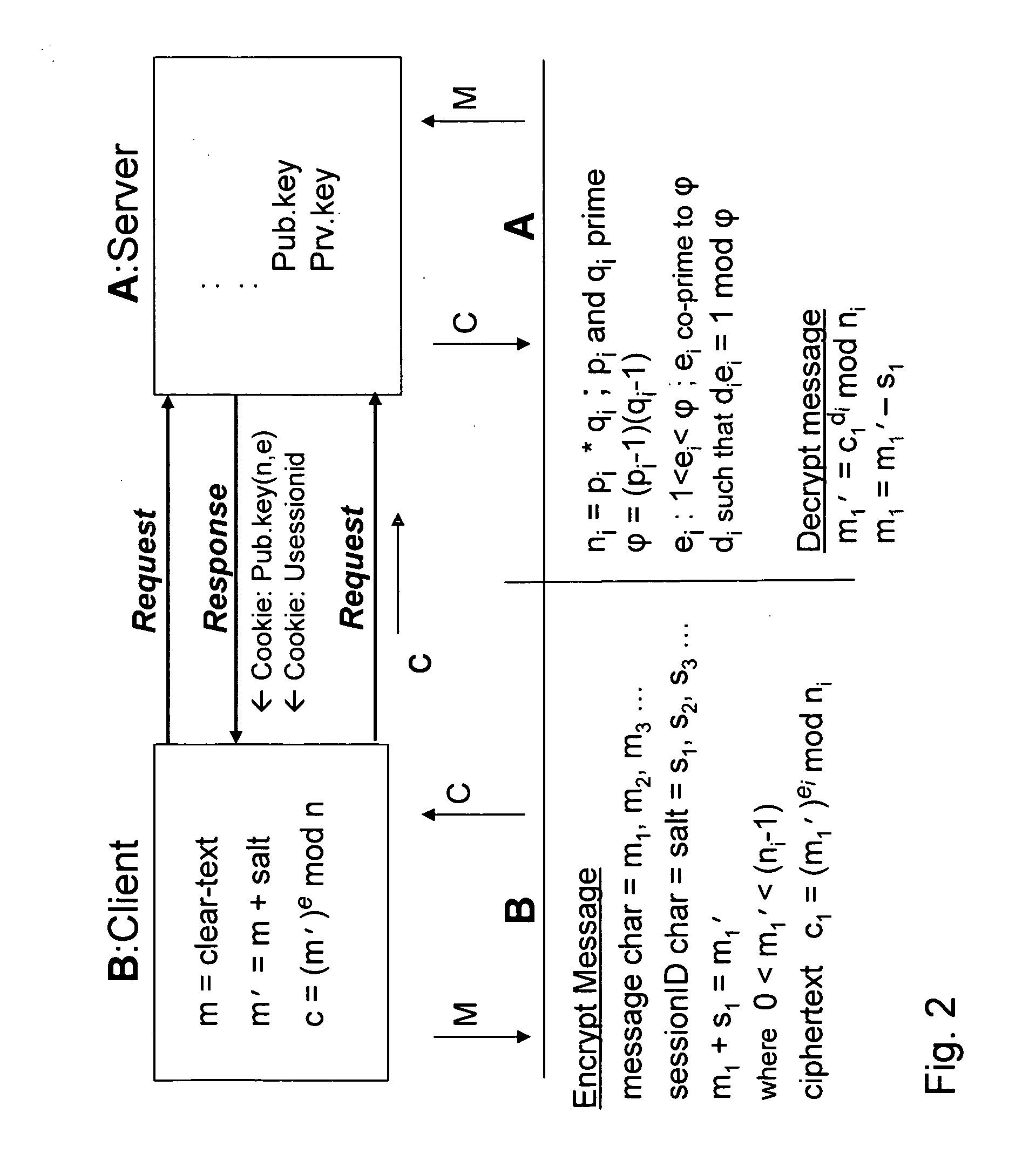
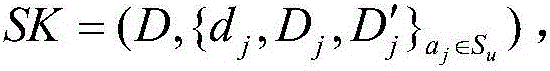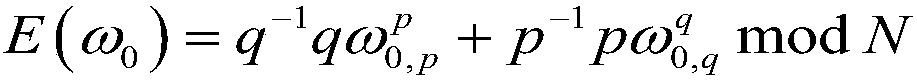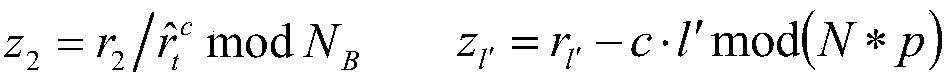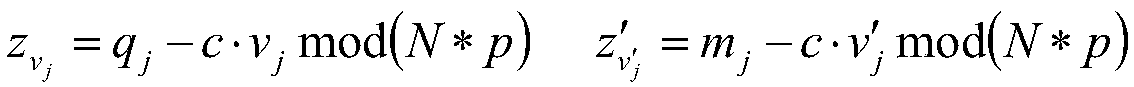Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
10508 results about "Ciphertext" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
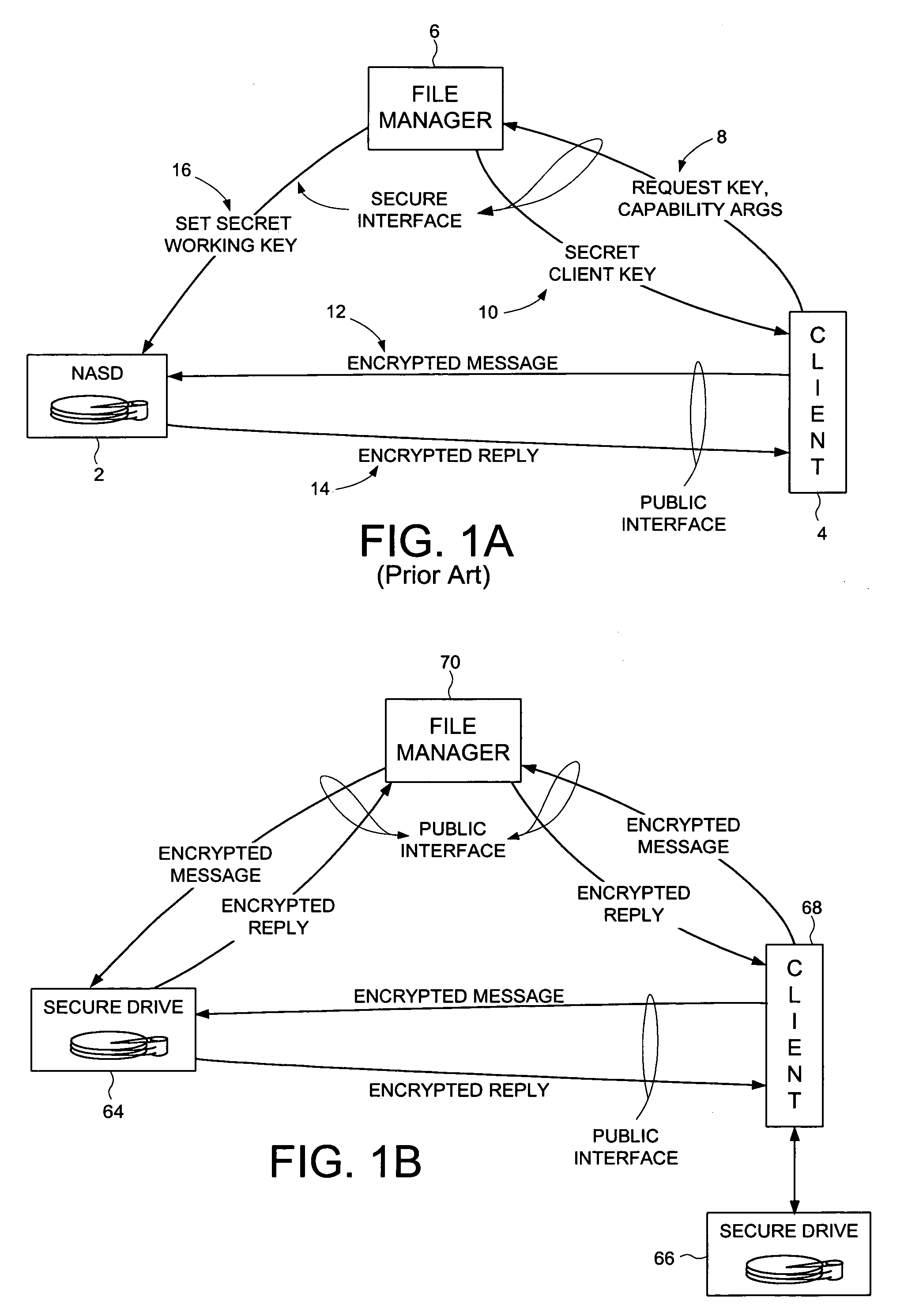
In cryptography, ciphertext or cyphertext is the result of encryption performed on plaintext using an algorithm, called a cipher. Ciphertext is also known as encrypted or encoded information because it contains a form of the original plaintext that is unreadable by a human or computer without the proper cipher to decrypt it. Decryption, the inverse of encryption, is the process of turning ciphertext into readable plaintext. Ciphertext is not to be confused with codetext because the latter is a result of a code, not a cipher.
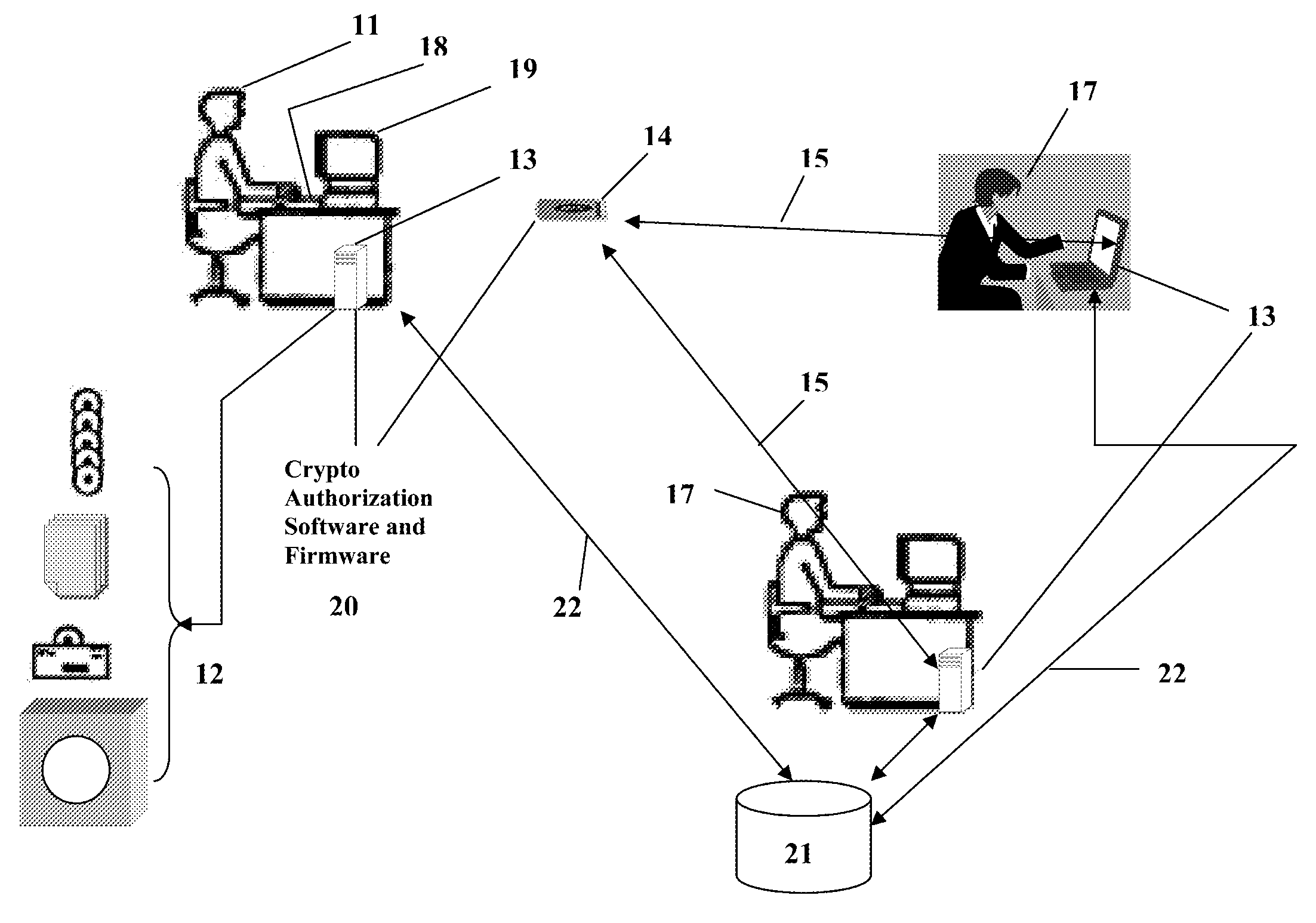
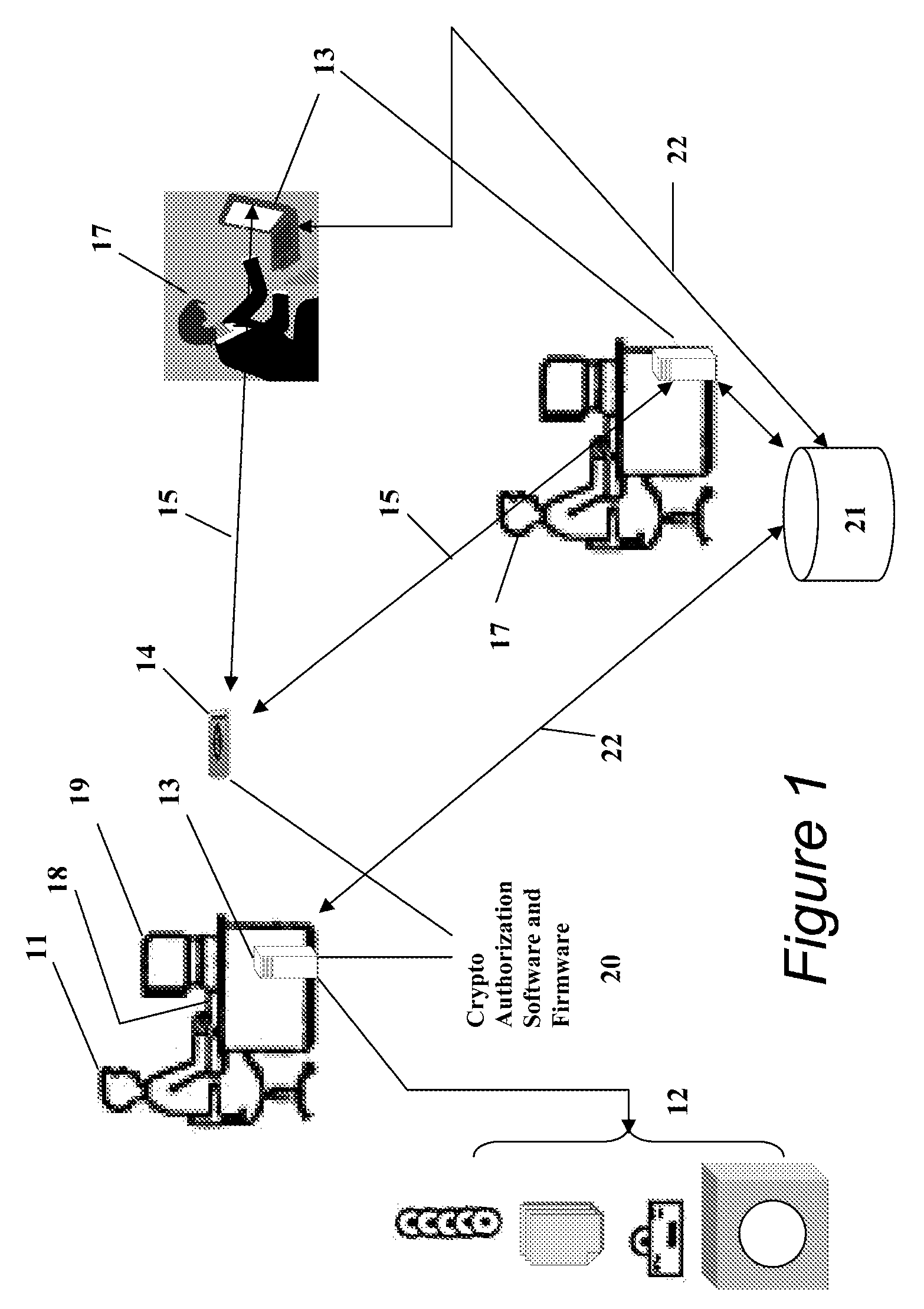
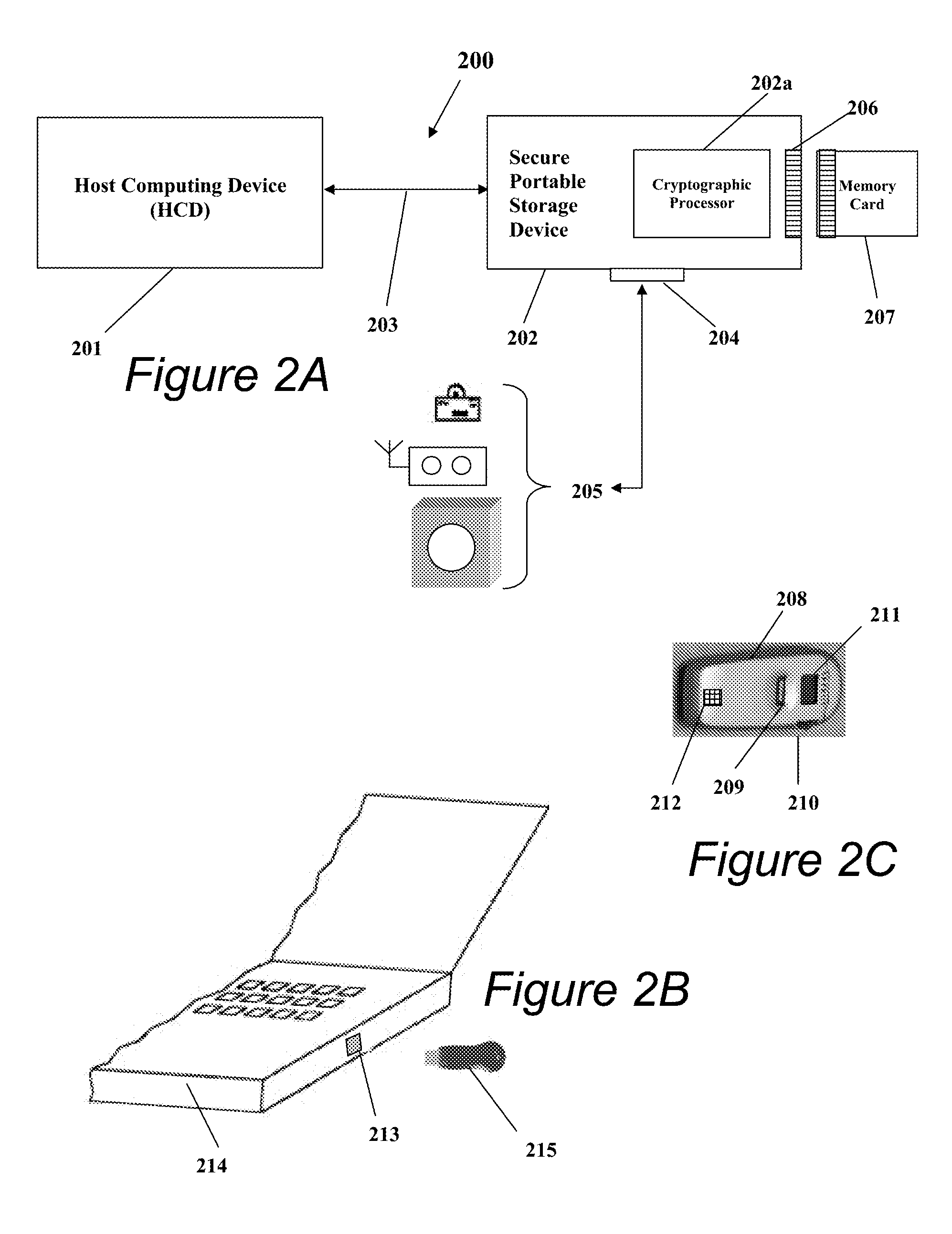
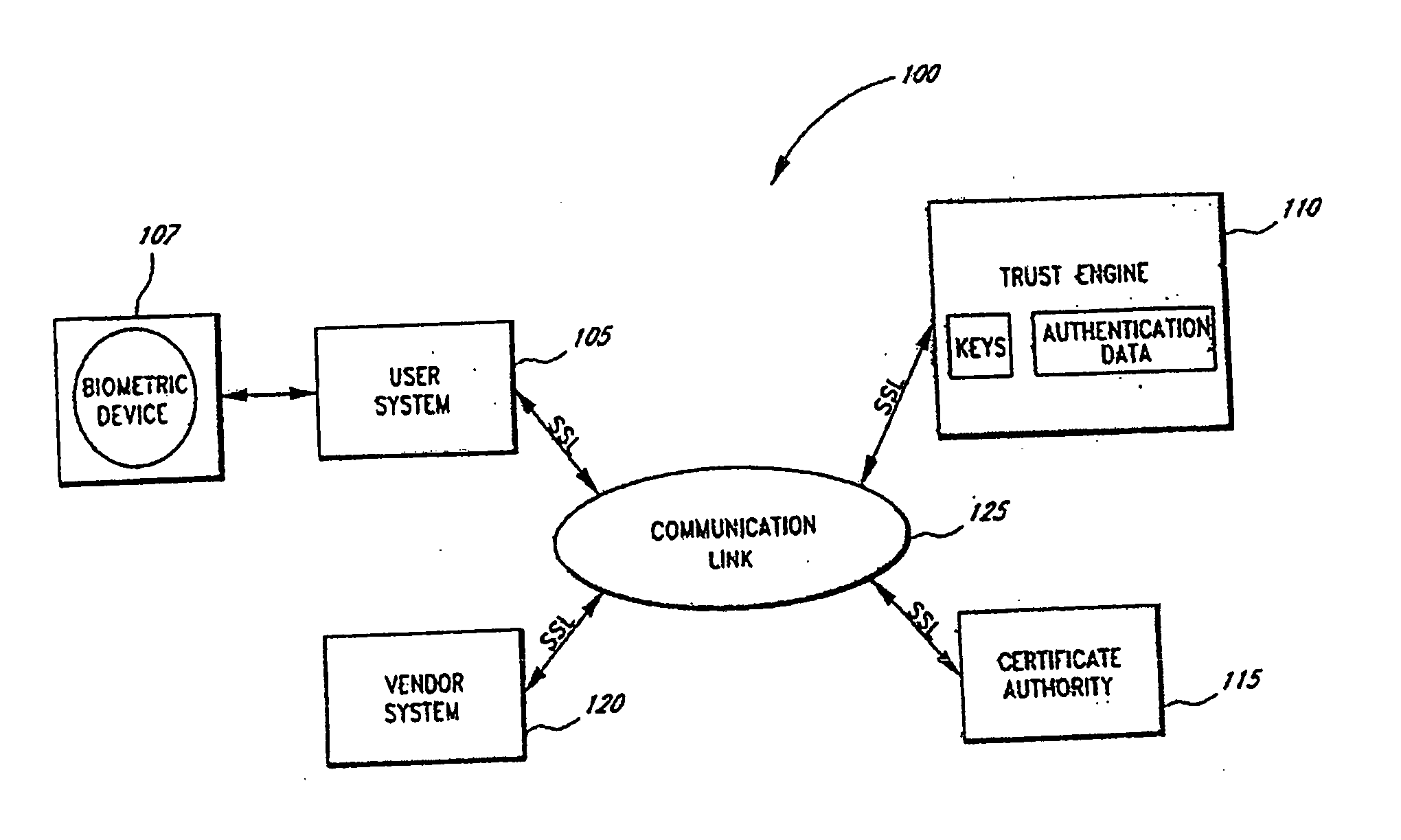
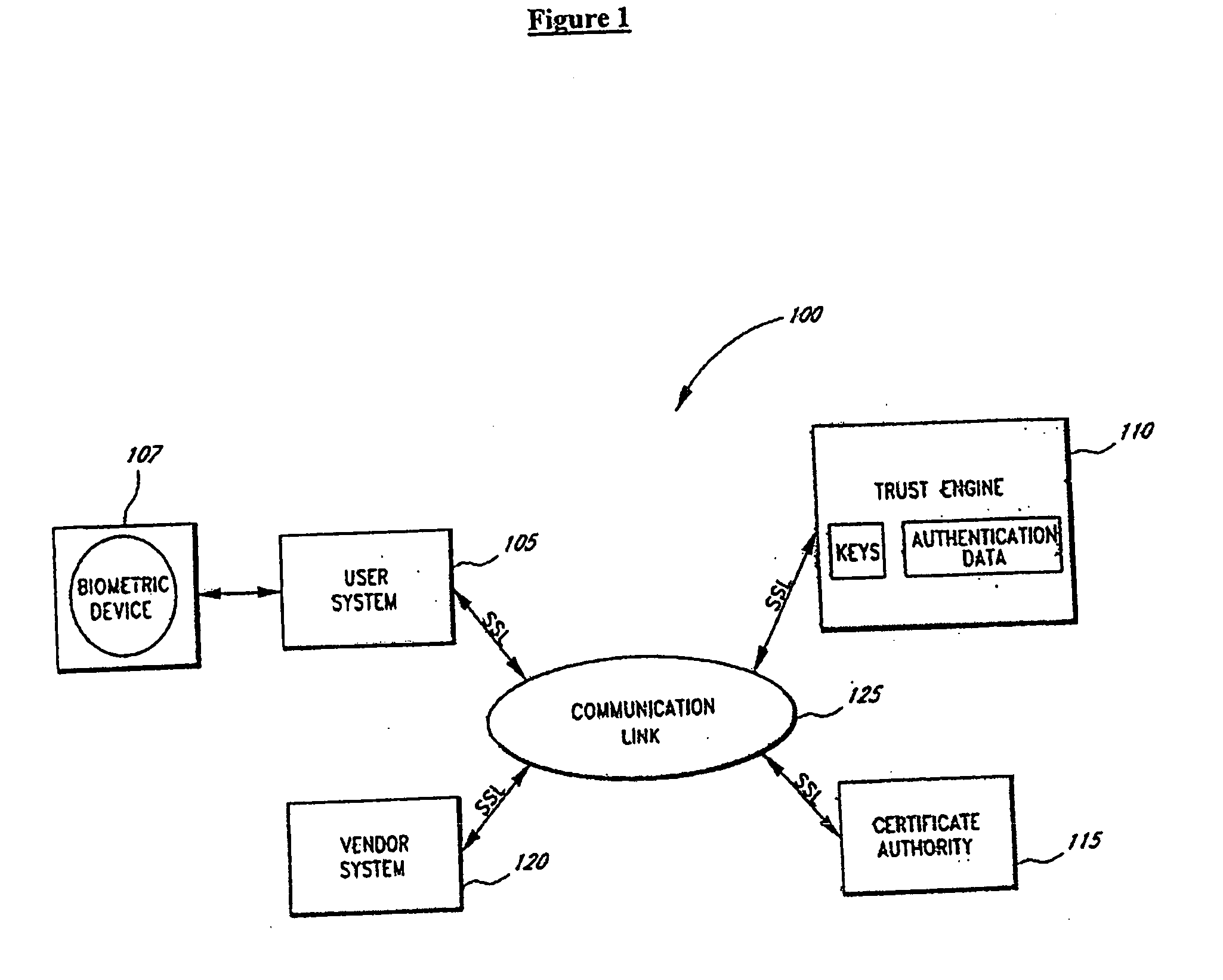
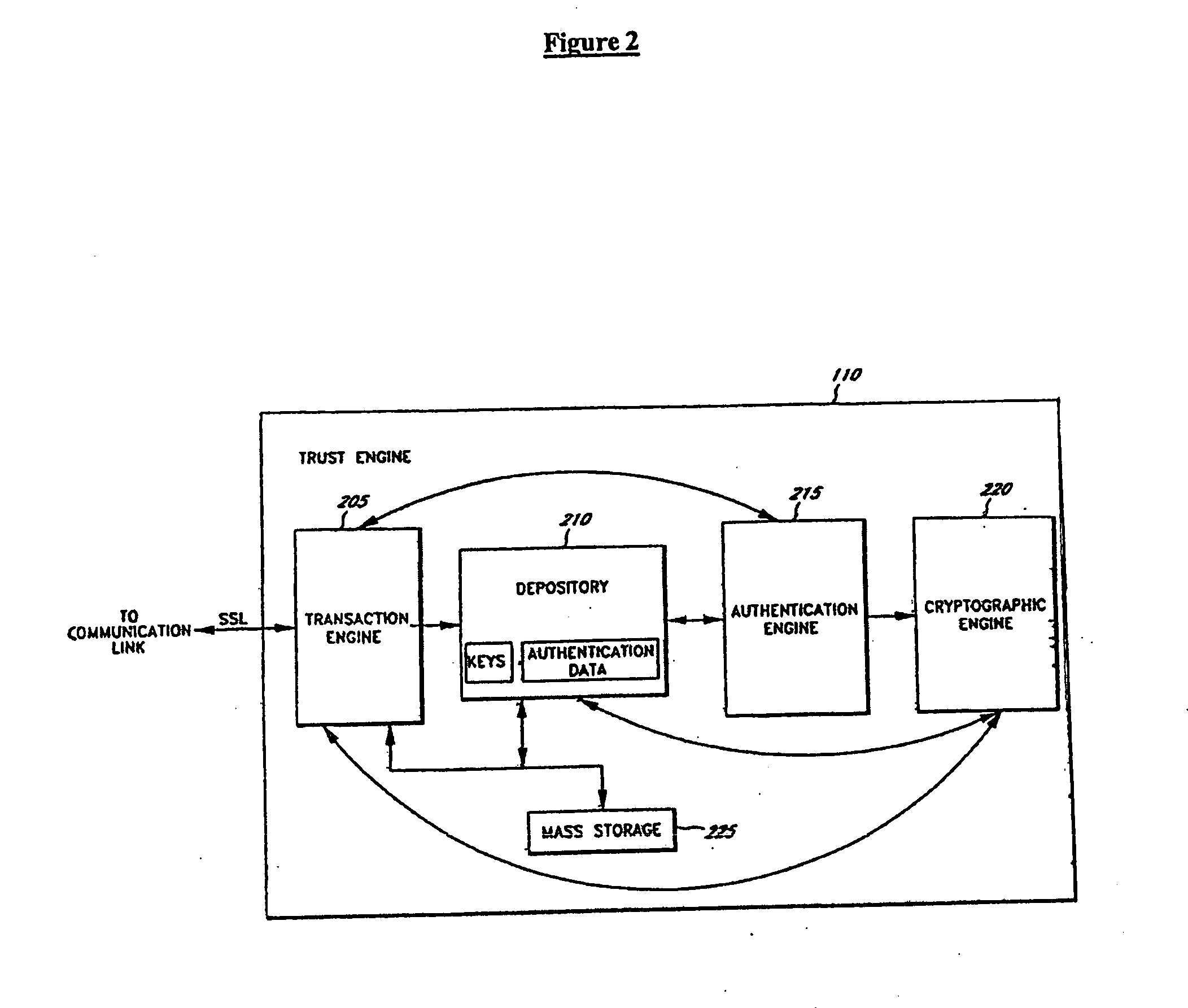
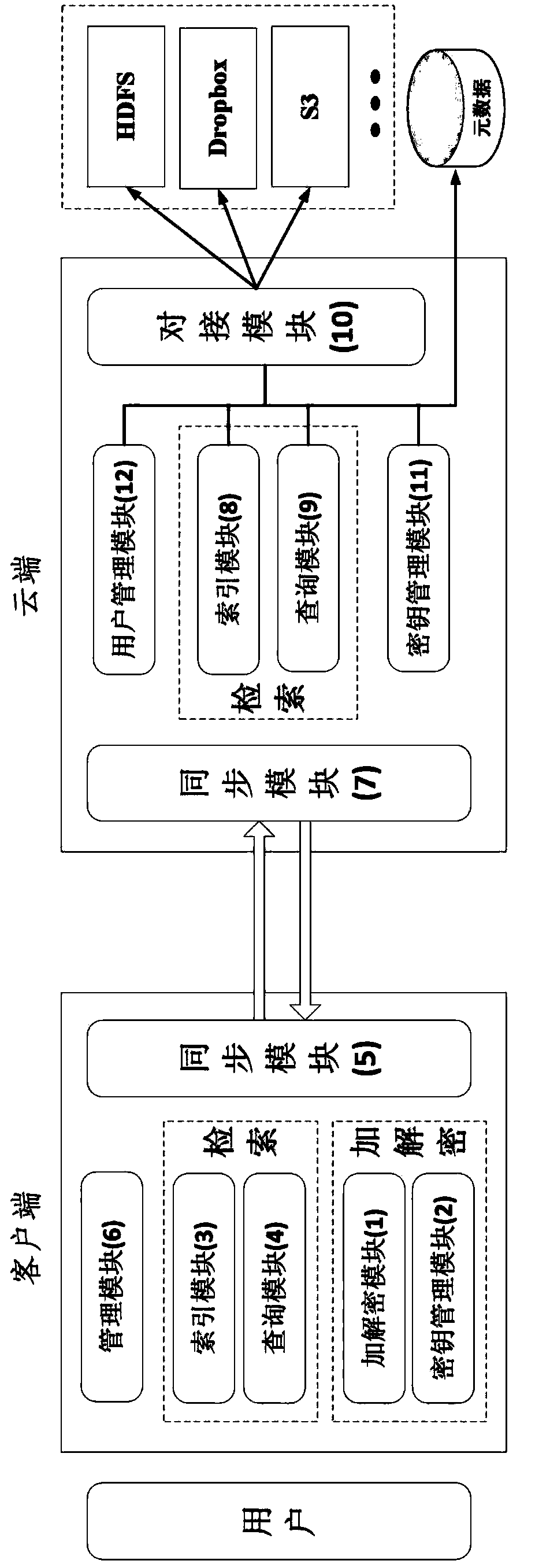
Portable Data Encryption Device with Configurable Security Functionality and Method for File Encryption
InactiveUS20080263363A1Mitigates and eliminates vulnerabilityUser identity/authority verificationInternal/peripheral component protectionComputer hardwarePlaintext
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
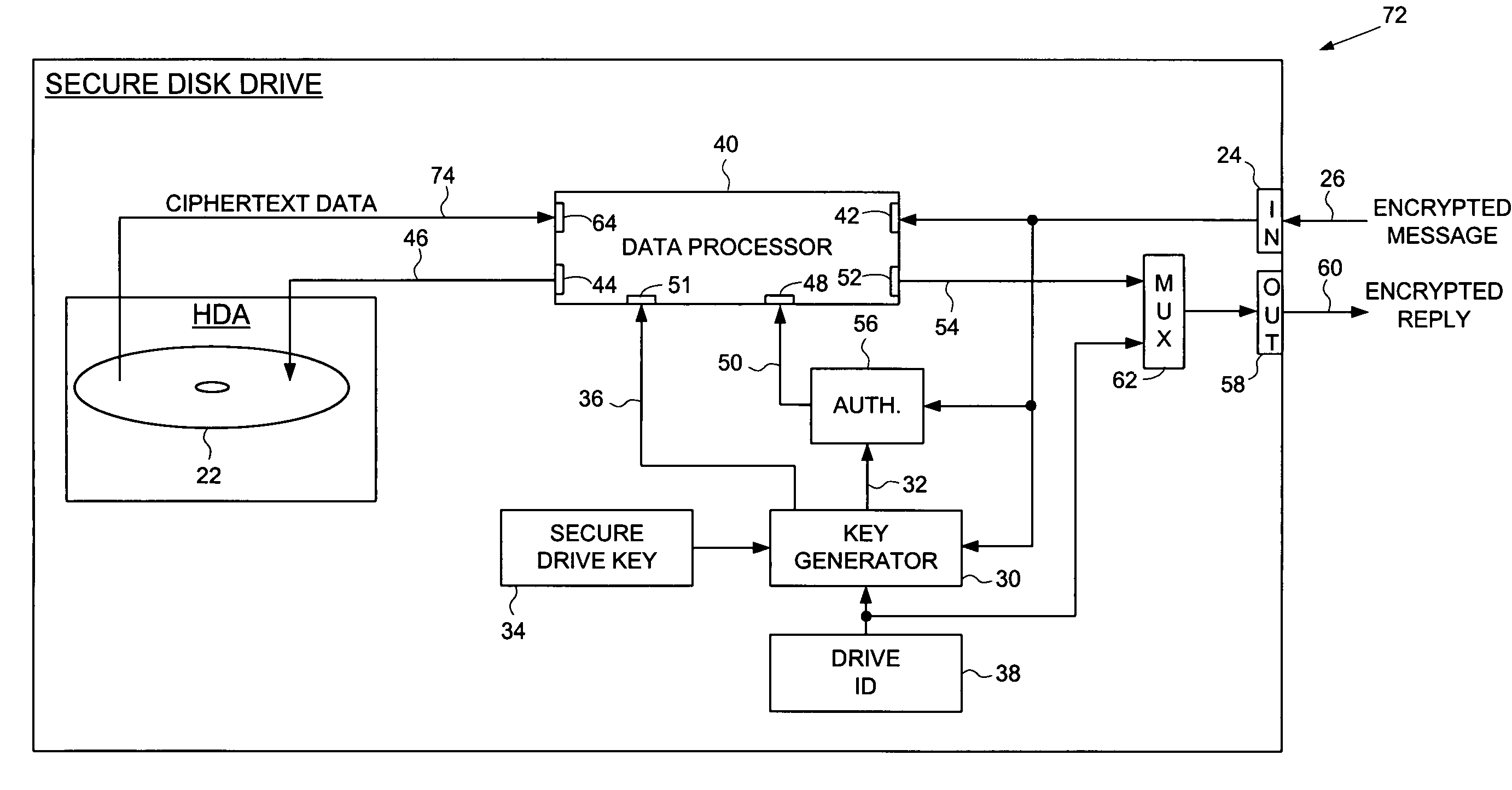
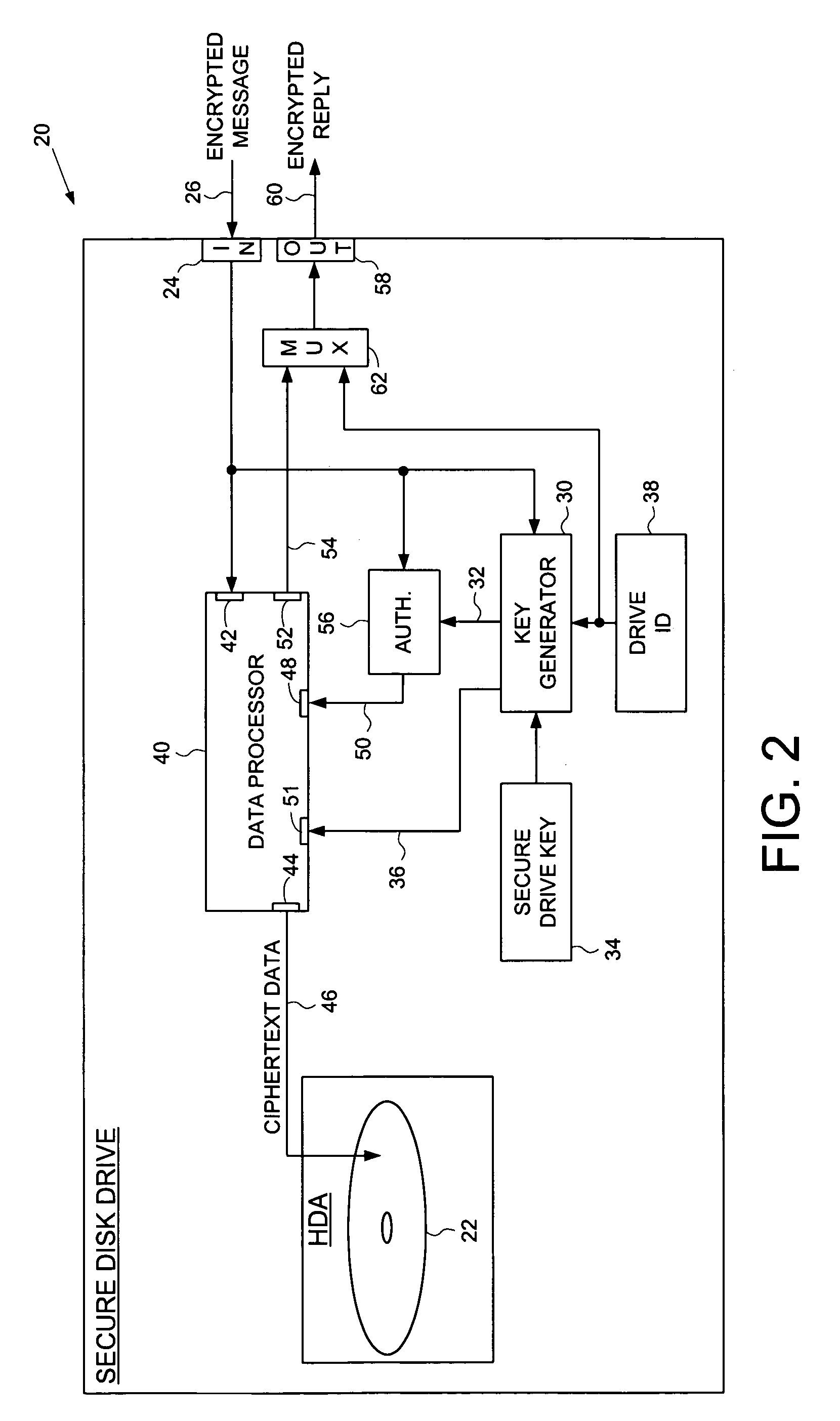
Secure disk drive comprising a secure drive key and a drive ID for implementing secure communication over a public network
InactiveUS7215771B1Volume/mass flow measurementUser identity/authority verificationSecure communicationCiphertext
A secure disk drive is disclosed comprising a disk for storing data, and an input for receiving an encrypted message from a client disk drive, the encrypted message comprising ciphertext data and a client drive ID identifying the client disk drive. The secure disk drive comprises a secure drive key and an internal drive ID. A key generator within the secure disk drive generates a client drive key based on the client drive ID and the secure drive key, and an internal drive key based on the internal drive ID and the secure drive key. The secure disk drive further comprises an authenticator for verifying the authenticity of the encrypted message and generating an enable signal, the authenticator is responsive to the encrypted message and the client drive key. The secure disk drive further comprises a data processor comprising a message input for receiving the encrypted message from the client disk drive, and a data output for outputting the ciphertext data to be written to the disk. The data processor further comprises an enable input for receiving the enable signal for enabling the data processor, and a key input for receiving the internal drive key, the internal drive key for use in generating a message authentication code. The data processor outputs reply data comprising the message authentication code. The secure disk drive outputs a reply to the client disk drive, the reply comprising the reply data and the internal drive ID.
Owner:WESTERN DIGITAL TECH INC
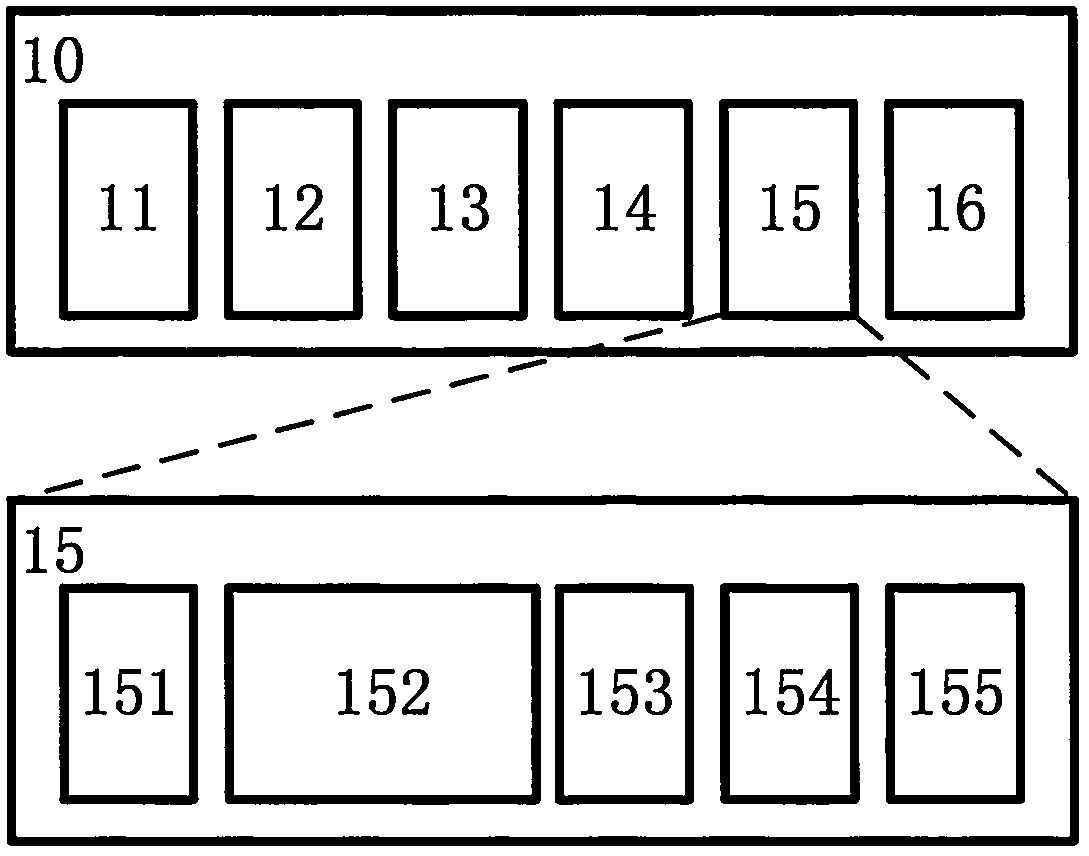
Internet of things communication protocol capable of being encrypted dynamically
InactiveCN104052742AImprove securityReduce the risk of decipheringTransmissionCiphertextThe Internet
The invention discloses an Internet of things communication protocol capable of being encrypted dynamically, and relates to the Internet of things and the technical field of communication. The Internet of things communication protocol capable of being encrypted dynamically is proposed for solving the ineffective data encryption and no encryption problems which are ubiquitous in Internet of things communication. The Internet of things communication protocol capable of being encrypted dynamically is characterized by comprising a communication frame (10) supporting dynamic encryption, a server-side dynamic encryption and decryption module (30) and a client-side dynamic encryption and decryption module (40). The Internet of things communication protocol capable of being encrypted dynamically has the advantages that encryption keys and an encryption algorithm change randomly and dynamically, the risk that communication ciphertext in the network is broken is lowered greatly, and communication safety is enhanced.
Owner:SHANGHAI KANGXU INTELLIGENT TECH
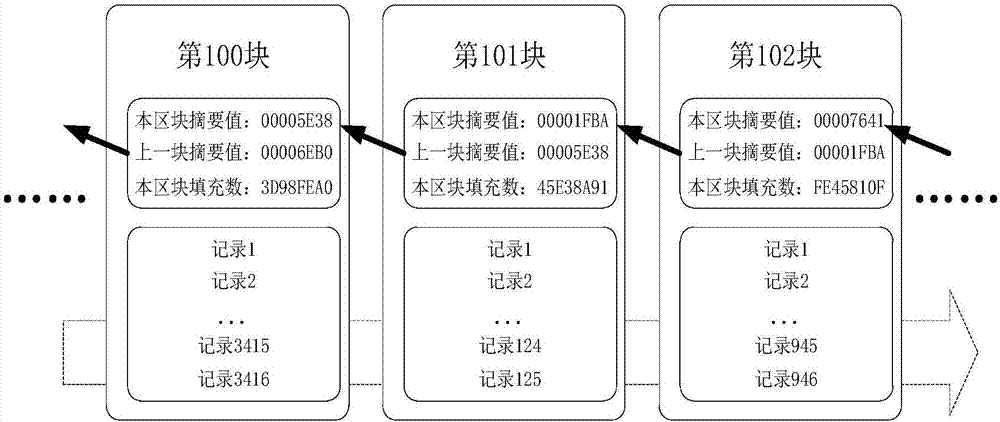
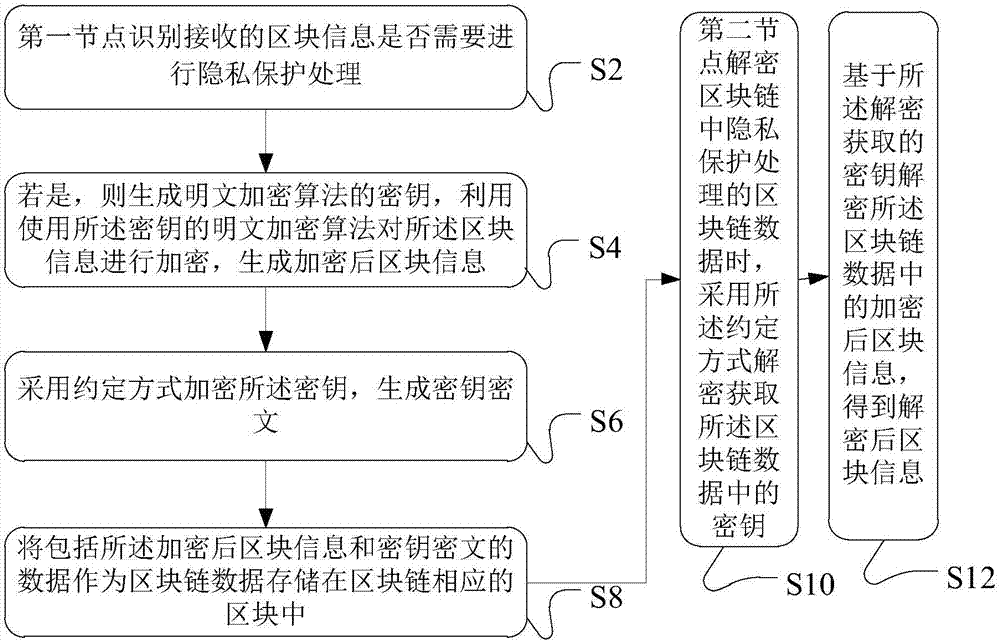
Blockchain data processing method, device and system
InactiveCN107294709ATo achieve the purpose of privacy protectionPrivacy protection is safe and reliableKey distribution for secure communicationCiphertextPrivacy protection
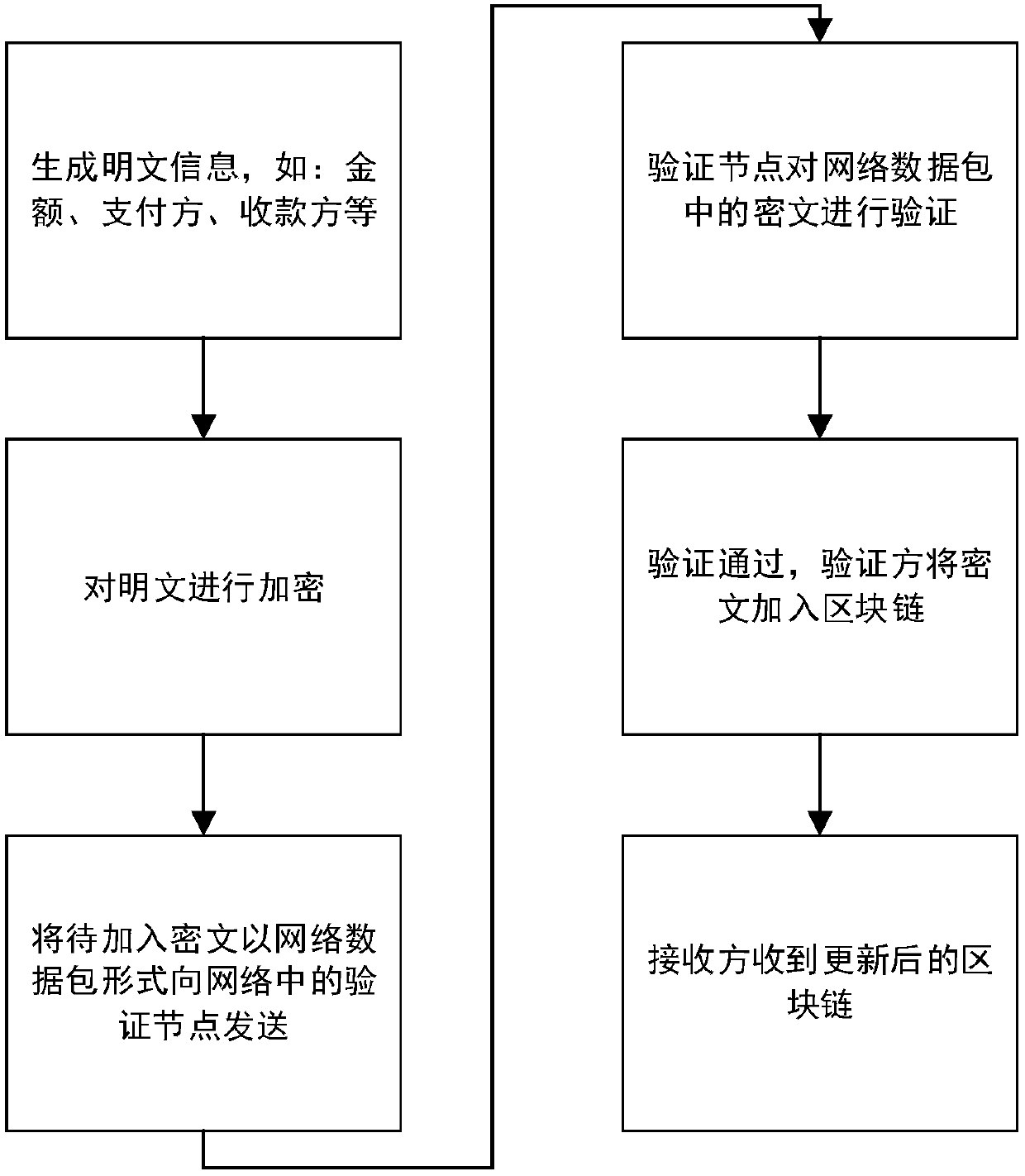
The invention discloses a blockchain data processing method, device and system. The blockchain data processing method comprises that a first node identifies whether received block information needs privacy protection processing; if the received block information needs privacy protection processing, a secret key of a plaintext encryption algorithm is generated, the block information is encrypted by means of the plaintext encryption algorithm employing the secret key, and encrypted block information is generated; the secret key is encrypted in a stipulated way, a secret key ciphertext is generated, the stipulated way comprises an algorithm through which a second node associated with the first node in the first node and the blockchain encrypts and decrypts the secret key ciphertext according to a preset mode; and data including the encrypted block information and the secret key ciphertext is stored a corresponding block of the blockchain as blockchain data. According to each embodiment of the invention, information data stored in the blockchain can be encrypted, so that only specific members can decrypt and check the information data, and the aim of carrying out privacy protection on special transaction information is achieved.
Owner:ADVANCED NEW TECH CO LTD
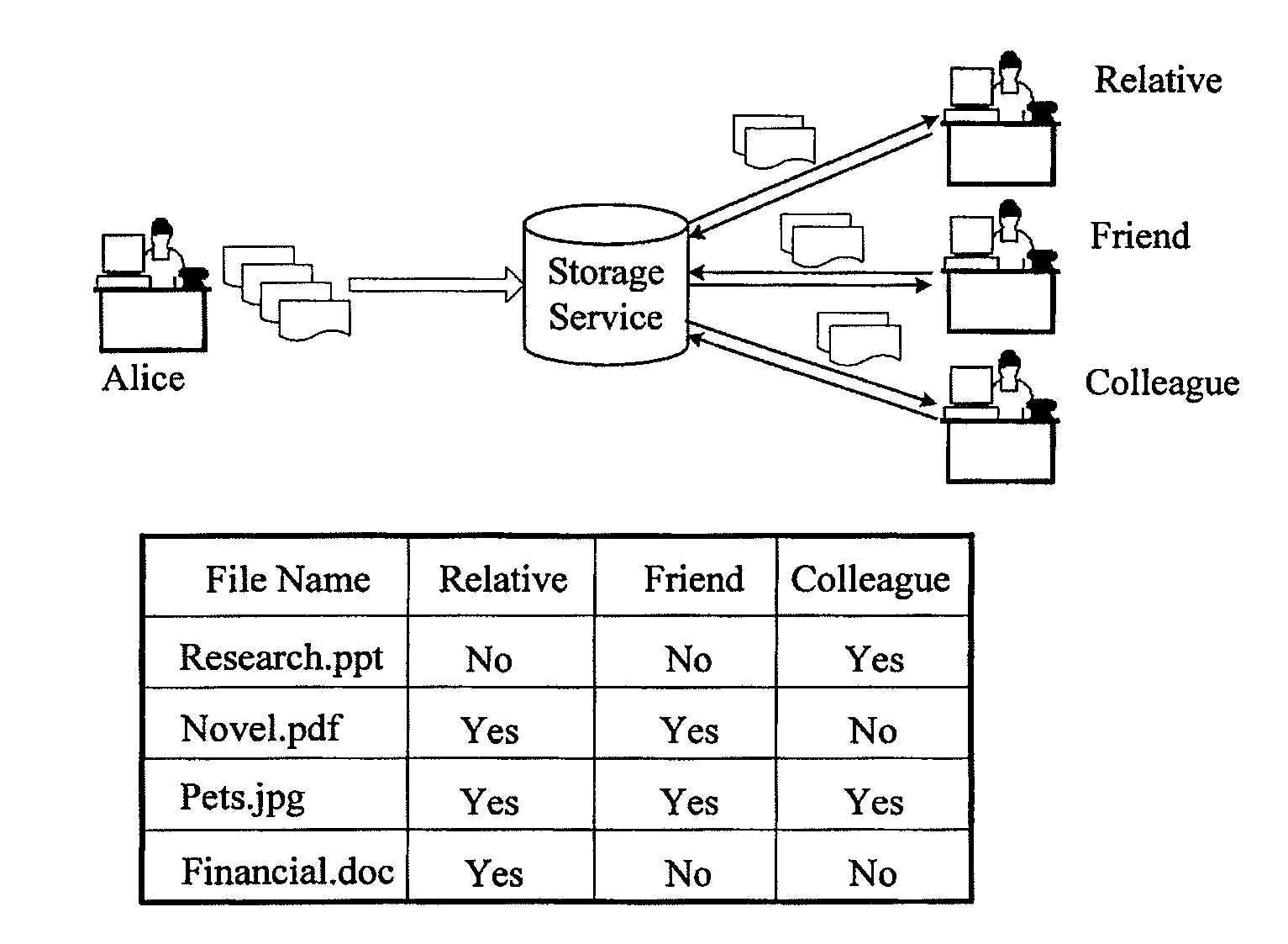
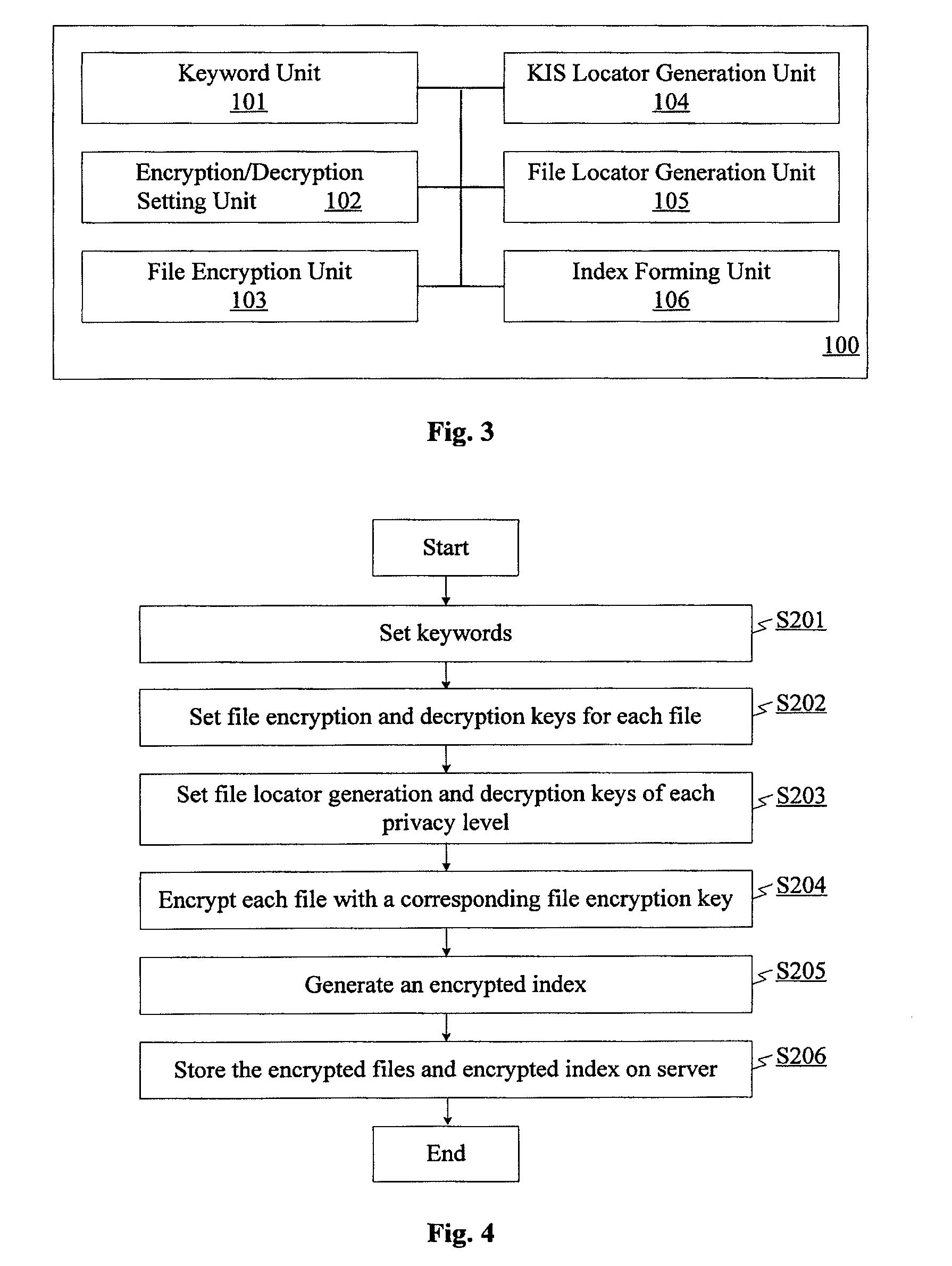
Fast searchable encryption method
InactiveUS20090300351A1Efficient and viable solutionReduce impactKey distribution for secure communicationWeb data indexingCiphertextDatabase
The present invention provides a method, apparatus and system for fast searchable encryption. The data owner encrypts files and stores the ciphertext to the server. The data owner generates an encrypted index according to each keyword of the files, and stores the encrypted index to the server. The index is composed of keyword item sets each being identified by a keyword item set locator and containing at least one or more file locators of the files associated with the corresponding keyword. Each file locator contains ciphertext of information for retrieval of an encrypted file and only with the correct file locator decryption key can the ciphertext be decrypted. Data owner issues a keyword item set locator as well as file locator decryption key to a searcher to enable the searcher to search on the encrypted index and retrieve files related to a certain keyword.
Owner:NEC (CHINA) CO LTD
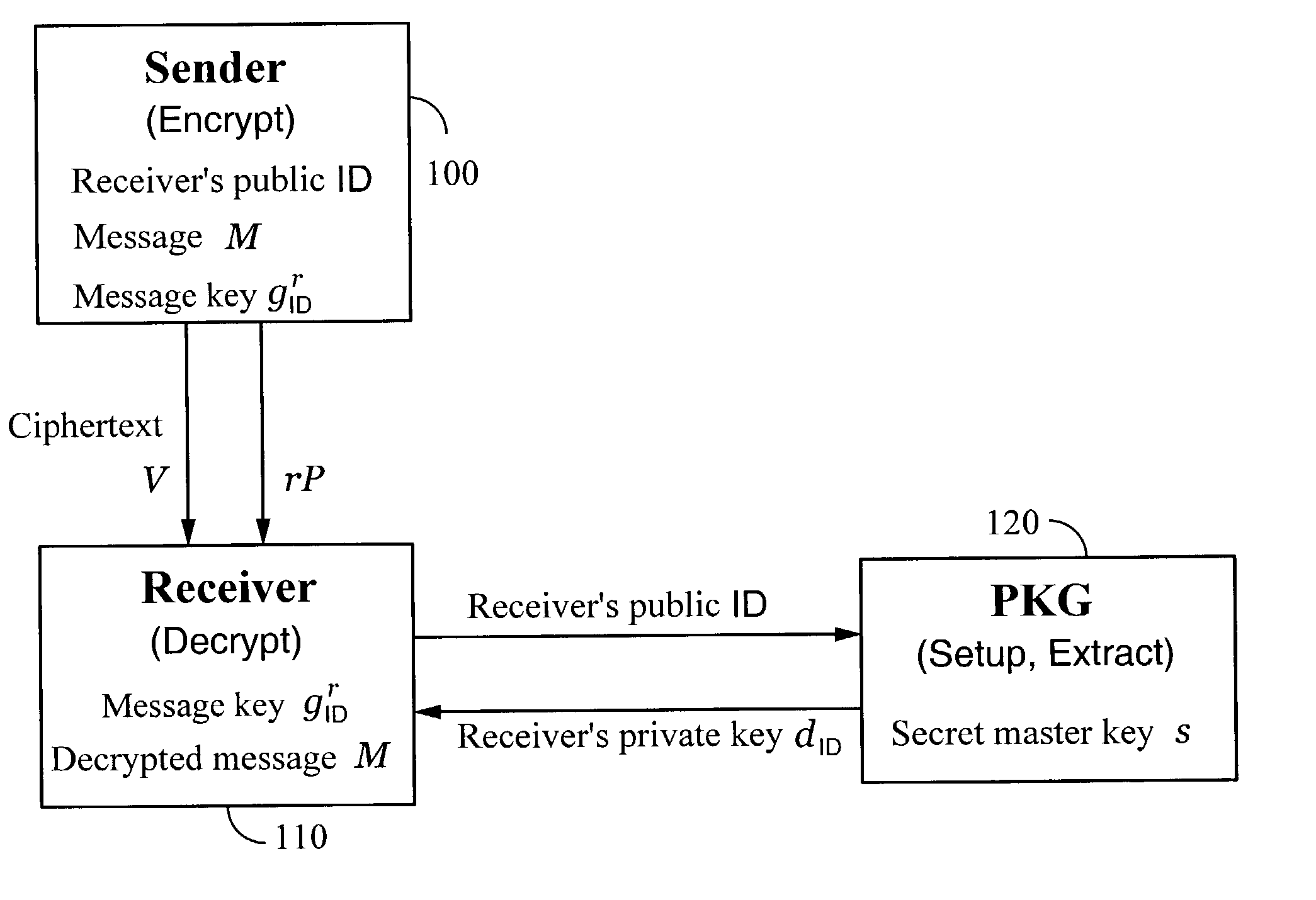
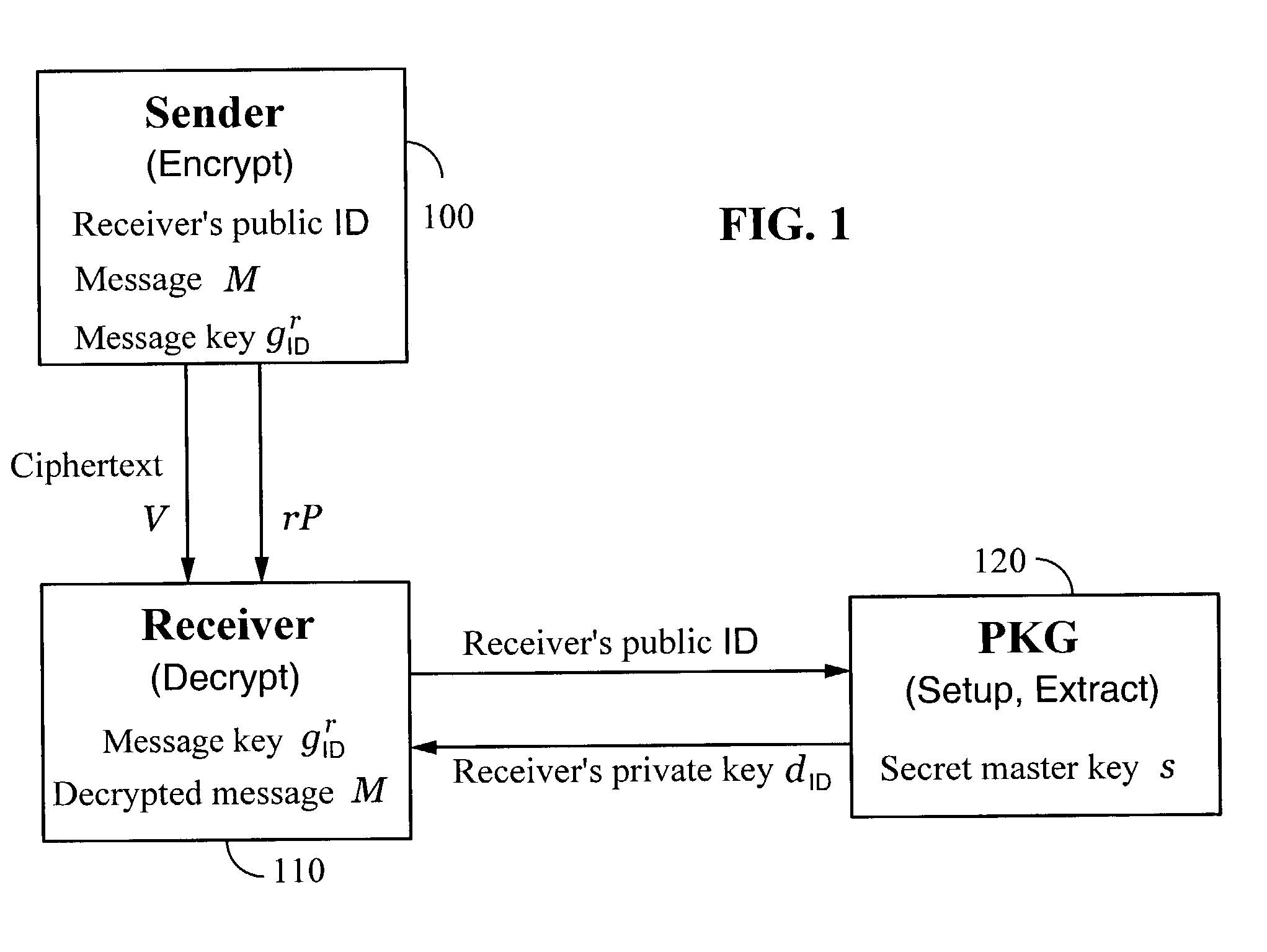
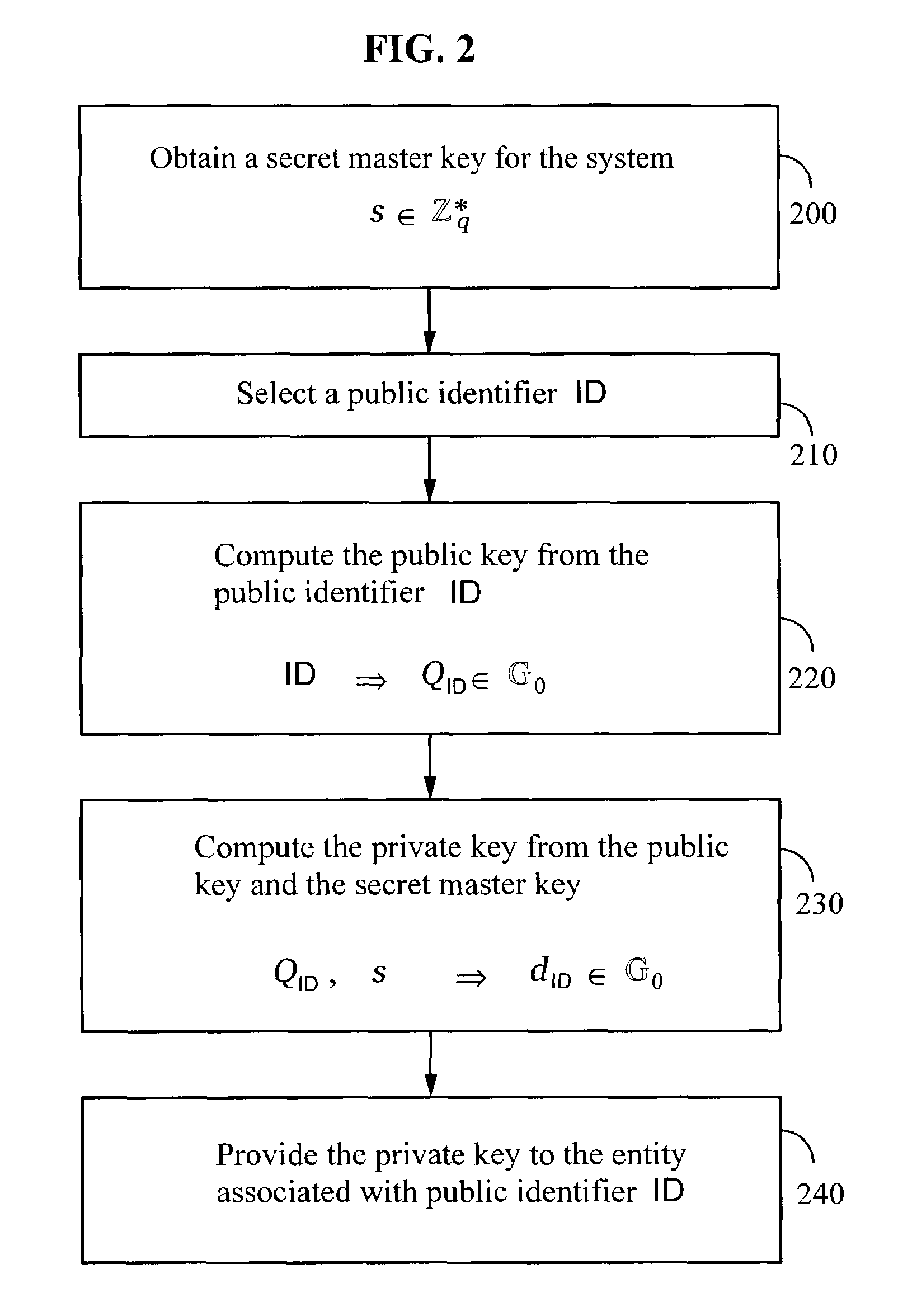
Systems and methods for identity-based encryption and related cryptographic techniques
ActiveUS7113594B2Key distribution for secure communicationPublic key for secure communicationEmail addressCiphertext
A method and system for encrypting a first piece of information M to be sent by a sender [100] to a receiver [110] allows both sender and receiver to compute a secret message key using identity-based information and a bilinear map. In a one embodiment, the sender [100] computes an identity-based encryption key from an identifier ID associated with the receiver [110]. The identifier ID may include various types of information such as the receiver's e-mail address, a receiver credential, a message identifier, or a date. The sender uses a bilinear map and the encryption key to compute a secret message key gIDr, which is then used to encrypt a message M, producing ciphertext V to be sent from the sender [100] to the receiver [110] together with an element rP. An identity-based decryption key dID is computed by a private key generator [120] based on the ID associated with the receiver and a secret master key s. After obtaining the private decryption key from the key generator [120], the receiver [110] uses it together with the element rP and the bilinear map to compute the secret message key gIDr, which is then used to decrypt V and recover the original message M. According to one embodiment, the bilinear map is based on a Weil pairing or a Tate pairing defined on a subgroup of an elliptic curve. Also described are several applications of the techniques, including key revocation, credential management, and return receipt notification.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV +1
Portable data encryption device with configurable security functionality and method for file encryption
ActiveUS9049010B2Mitigates and eliminates vulnerabilityKey distribution for secure communicationUser identity/authority verificationPlaintextComputer hardware
A portable encryption device with logon access controlled by an encryption key, with an on board cryptographic processor for reconstituting the encryption key from a plurality of secrets generated by a secret sharing algorithm, optionally shrouded with external secrets using an invertible transform resistant to quantum computing attacks. Another embodiment provides file decryption controlled by a file encryption key, with the on board cryptographic processor reconstituting the file encryption key from a version of the file encryption key which has been shrouded with a network authorization code. A method for encryption of a plaintext file by hashing, compressing, and encrypting the plaintext file, hashing the ciphertext, hashing the plaintext hash and the ciphertext hash, and sealing the ciphertext together with the resulting hash. A portable encryption device for performing the method is also disclosed.
Owner:SPYRUS
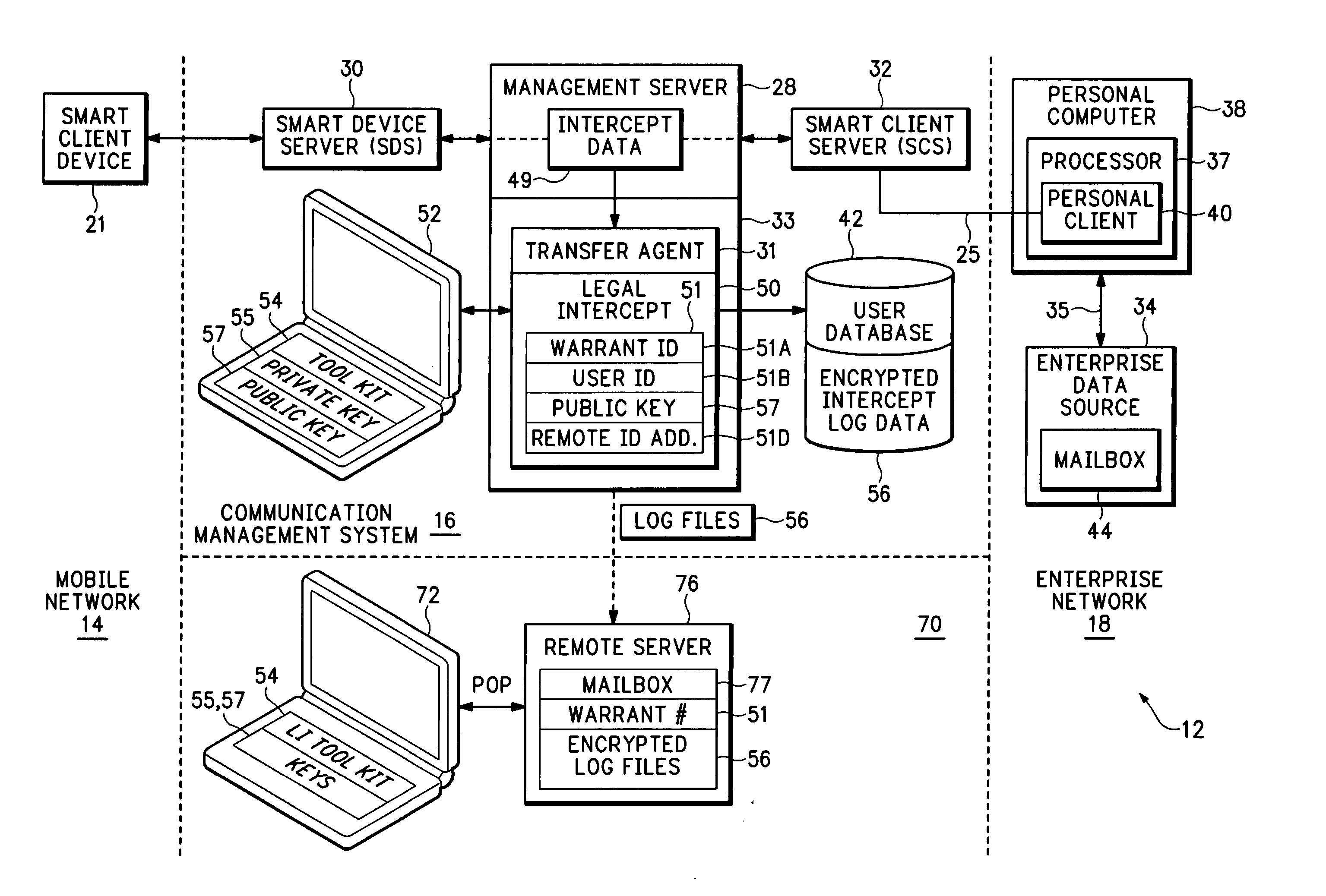
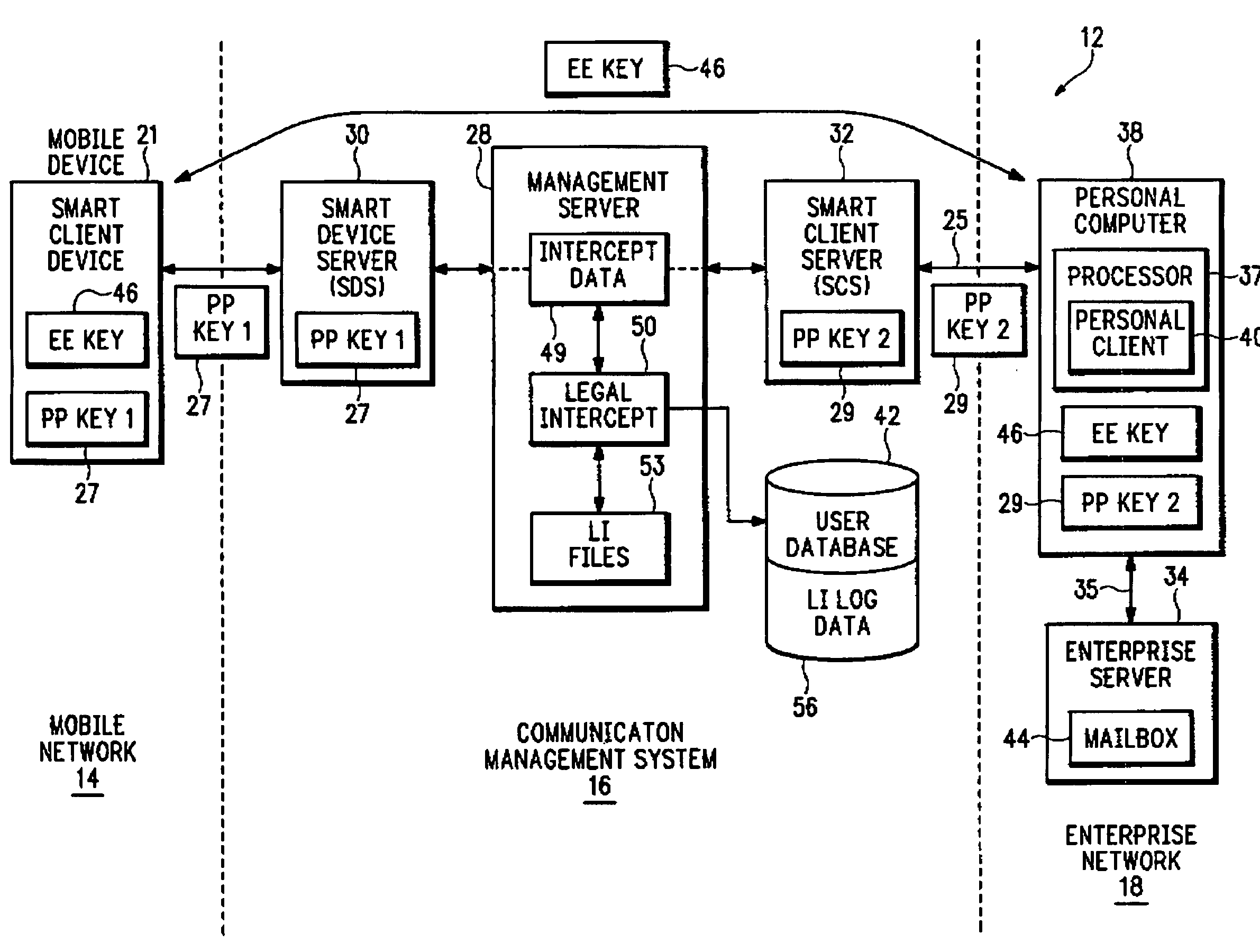
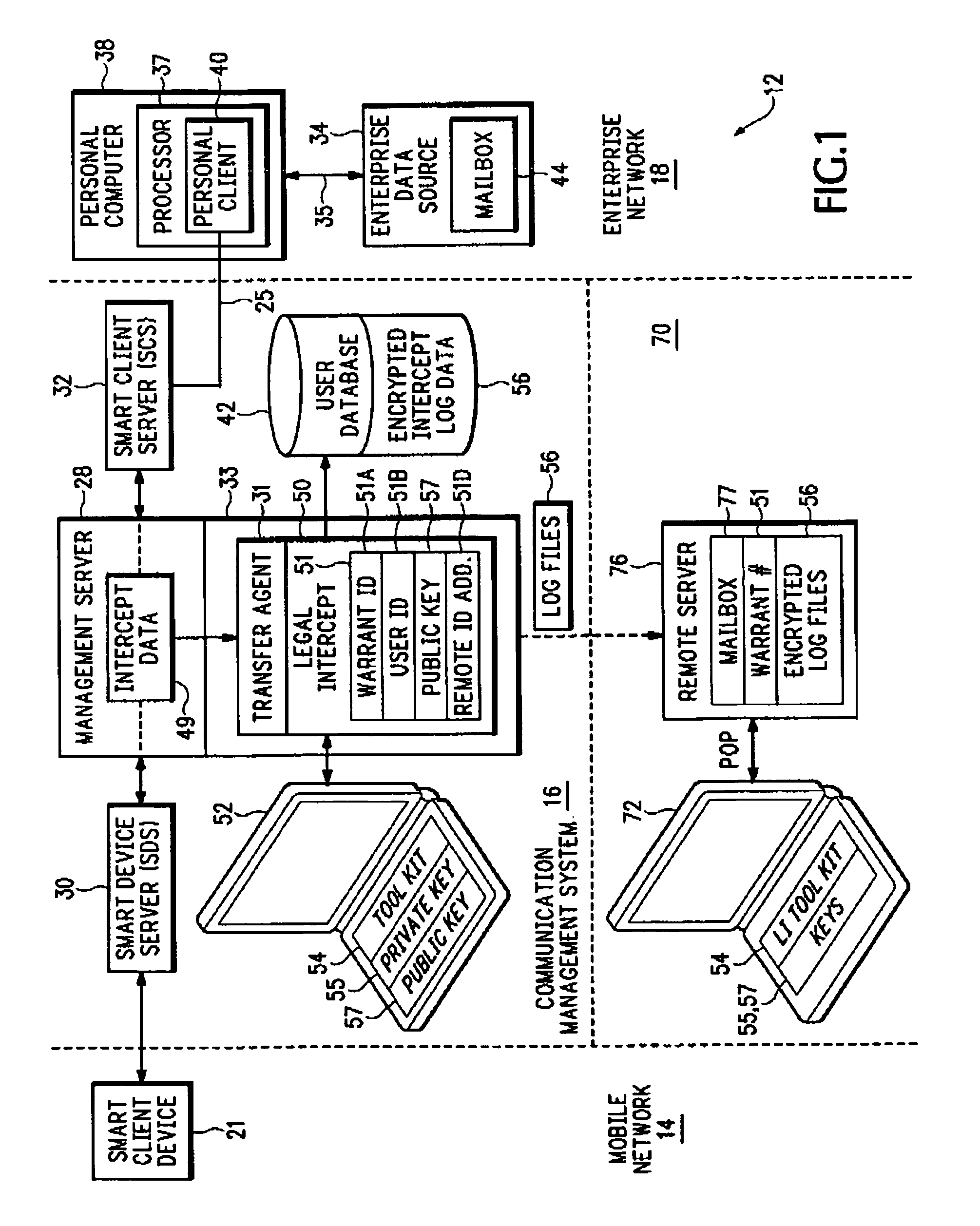
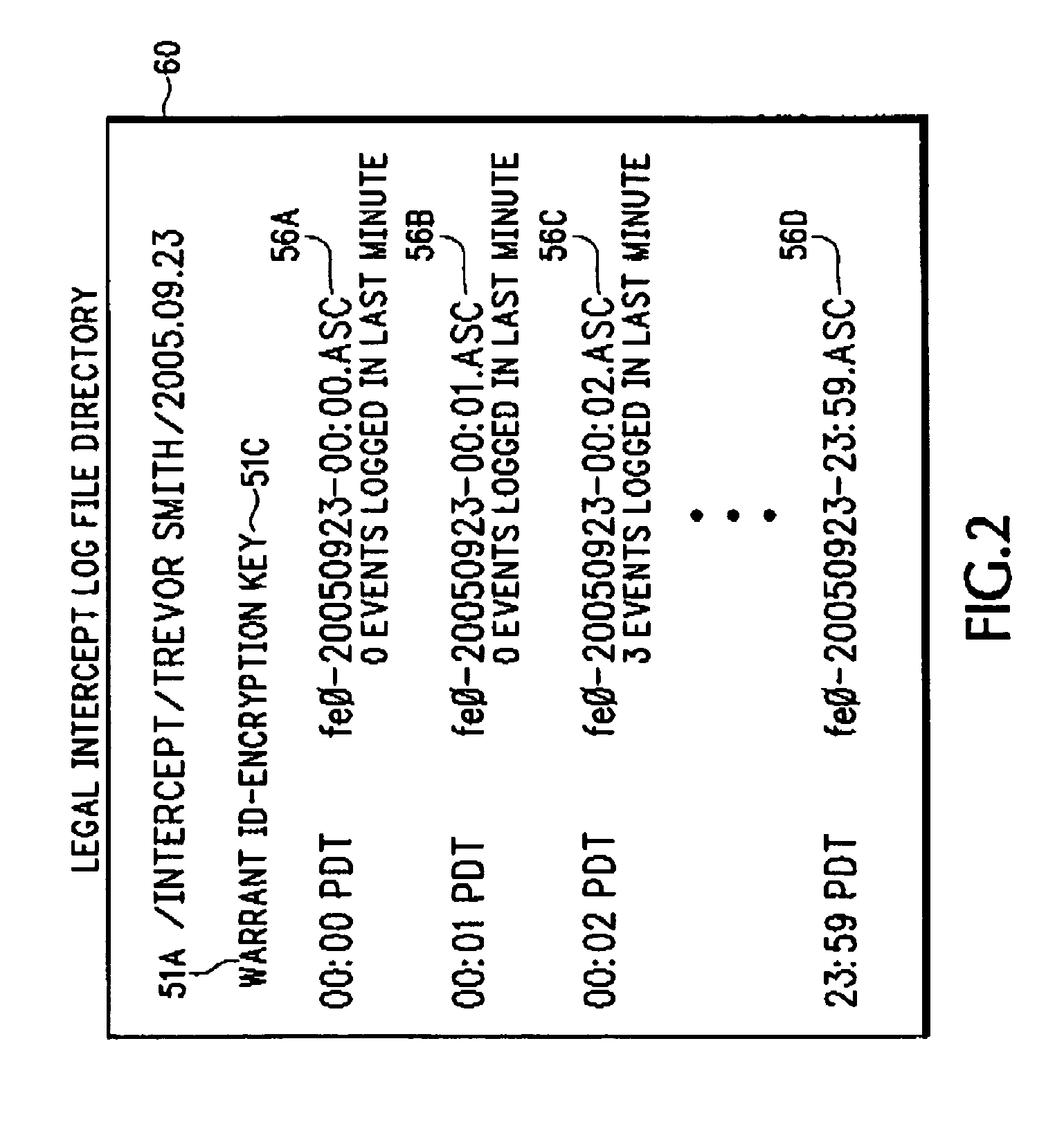
Method and apparatus for intercepting events in a communication system
InactiveUS20060093135A1Effective and efficient complianceMemory loss protectionError detection/correctionCommunications systemCiphertext
An intercept system provides more effective and more efficient compliance with legal intercept warrants. The intercept system can provide any combination of operations that include near-real-time intercept, capture of intercepted data in structured authenticated form, clear text intercept for communications where there is access to encryption keys, cipher text intercept for communications where there is no access to encryption keys, provision of transactional logs to the authorized agency, interception without altering the operation of the target services, and encryption of stored intercepted information.
Owner:SEVEN NETWORKS INC
User identity verification method, apparatus and system based on block chain
InactiveCN107579817AImprove securityImprove accuracyKey distribution for secure communicationUser identity/authority verificationCiphertextUser authentication
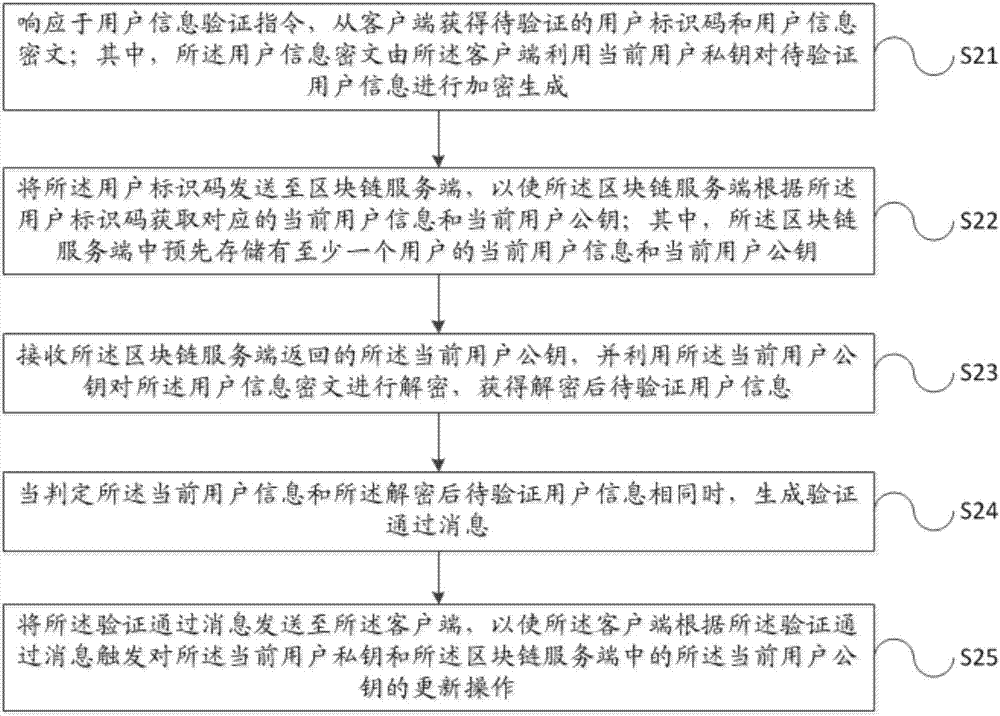
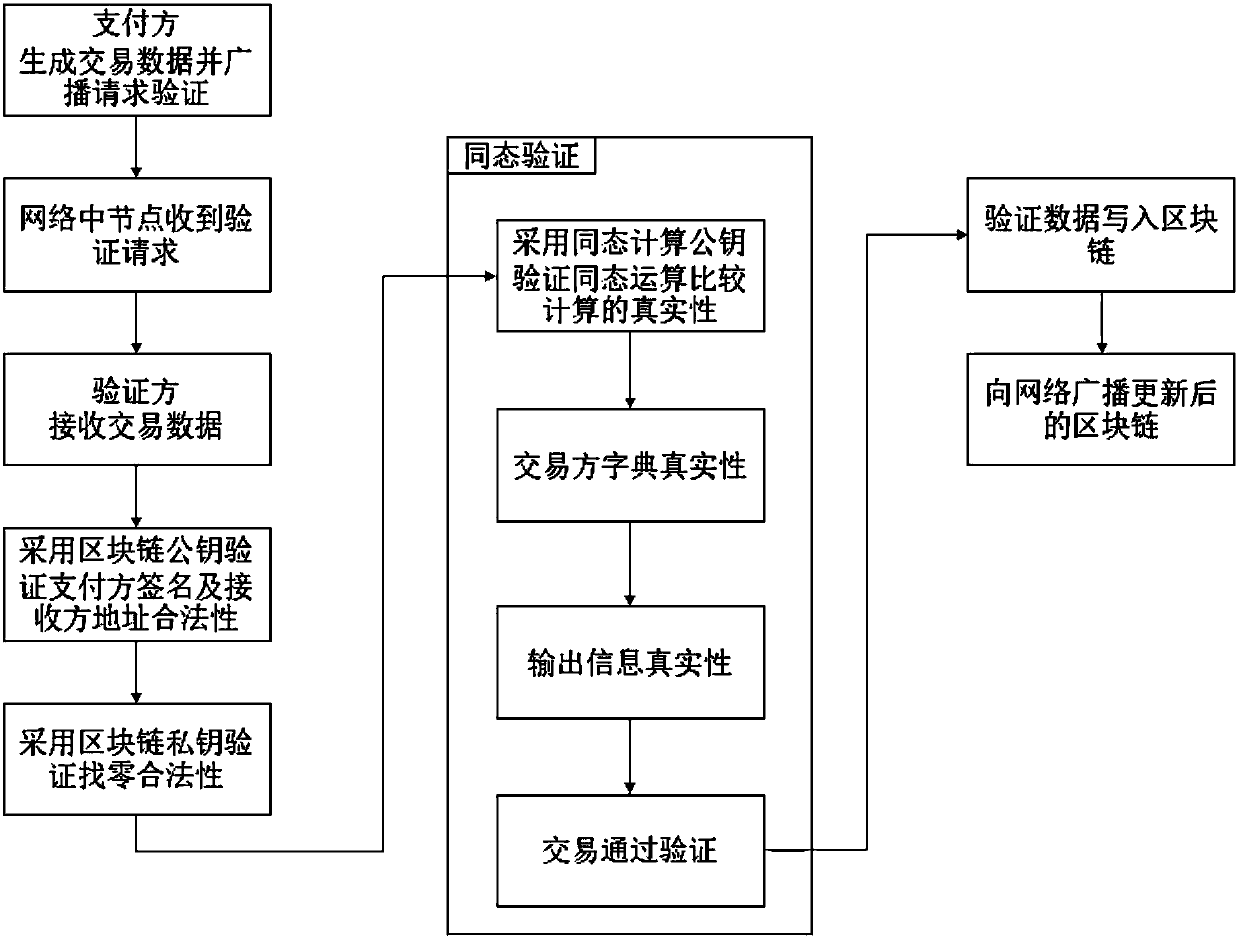
The invention discloses a user identity verification method, apparatus and system based on a block chain. The user identity verification method comprises the following steps: obtaining a user identification code and a user information ciphertext from a client, wherein the user information ciphertext is generated by encrypting to-be-verified user information by using a current user private key; sending the user identification code to a block chain server, so that the block chain server obtains corresponding current user information and a current user public key; decrypting the user informationciphertext by using the current user public key returned by the block chain server to obtain decrypted to-be-verified user information; when it is judged that the current user information is the sameas the decrypted to-be-verified user information, generating a verification pass message; and triggering the updating operation of the current user private key and the current user public key according to the verification pass message by the client. By adoption of the user identity verification method, apparatus and system, the security of user identity verification process can be improved, and the accuracy of a user identity verification result can be improved.
Owner:GRG BAKING EQUIP CO LTD
Block chain privacy data access control method based on attribute encryption
ActiveCN106503994AAddress privacy breachesRealize privacy protectionKey distribution for secure communicationDigital data protectionAttribute-based encryptionCiphertext
The invention discloses a block chain privacy data access control method based on attribute encryption, which mainly solves a problem in the prior art that the real identity of a user in the block chain is anonymously protected but the and transaction privacy information is not encrypted so as to cause privacy leakage. The method comprises the steps that 1. a system is initialized; 1, a user registers to obtain attribute information; 3, an authoritative center, according to the user attribute information, distributes a user private key; 4 a transaction party encrypts transaction privacy data and uploads the transaction privacy data to a block chain; 5, an accountant verifies the transaction information and performs the transaction; 6, a supervisory center is authorized to use the authorized private key to decrypt and check the transaction ciphertext. The method encrypts the transaction privacy information, avoids the leakage of data privacy and can be used for privacy protection of the virtual asset transaction data in the block chain.
Owner:XIDIAN UNIV
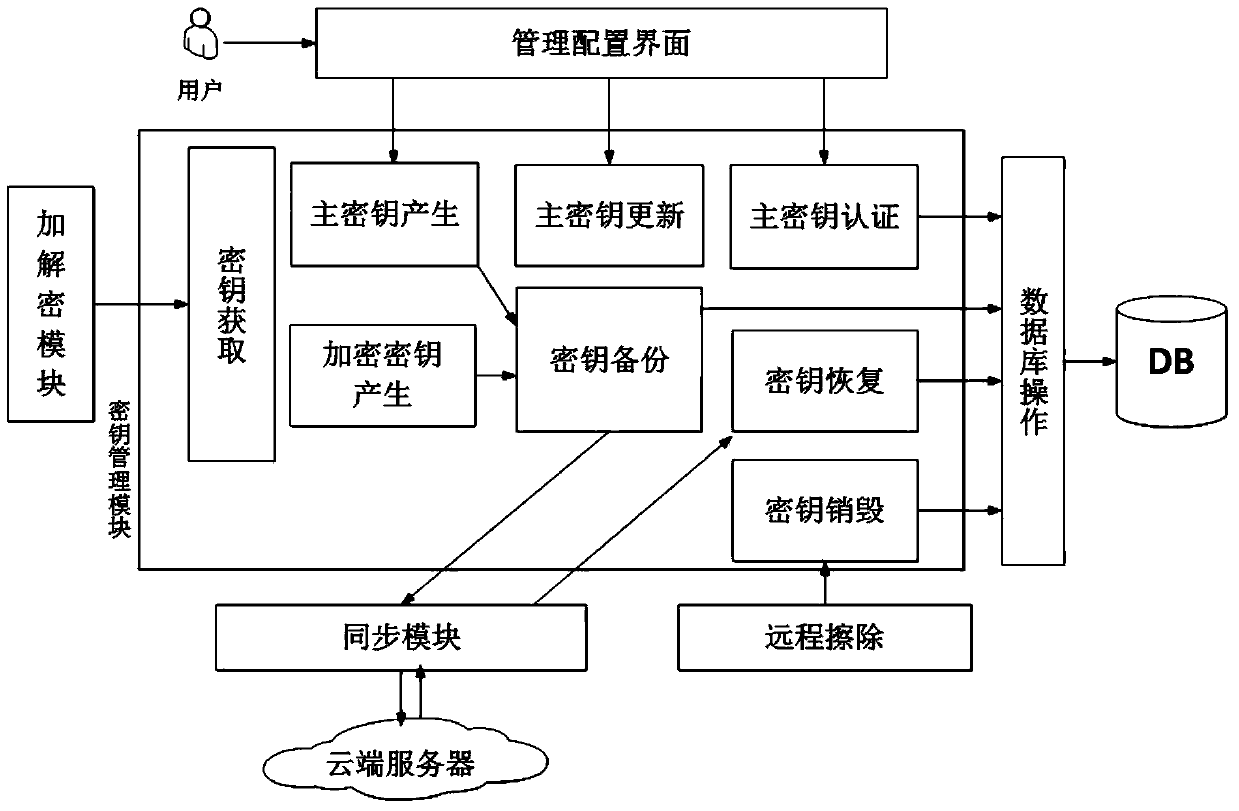
Method for implementing safe storage system in cloud storage environment
ActiveCN102014133AGuaranteed confidentialityTimely detection of damage, etc.TransmissionConfidentialityCiphertext
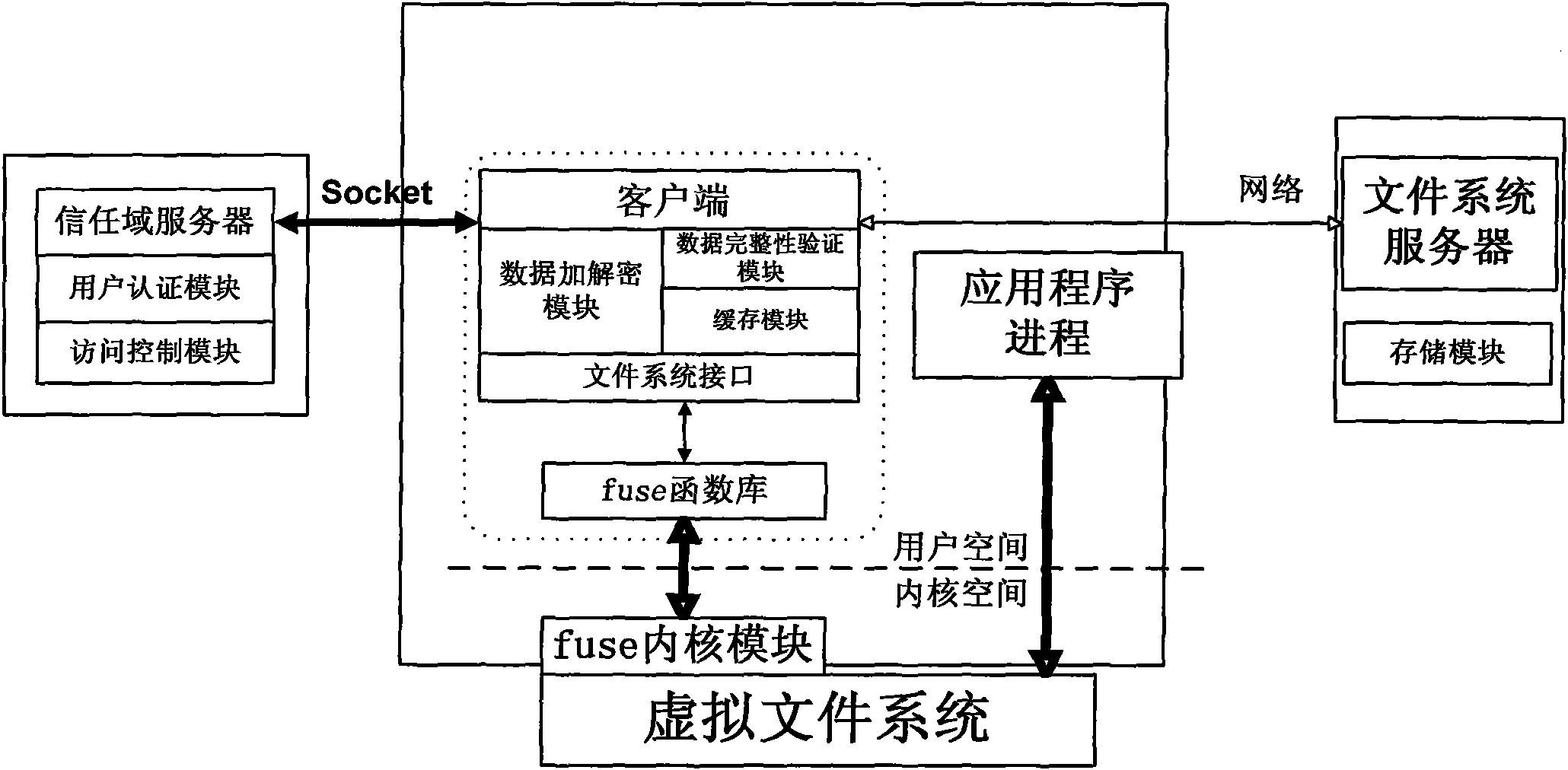
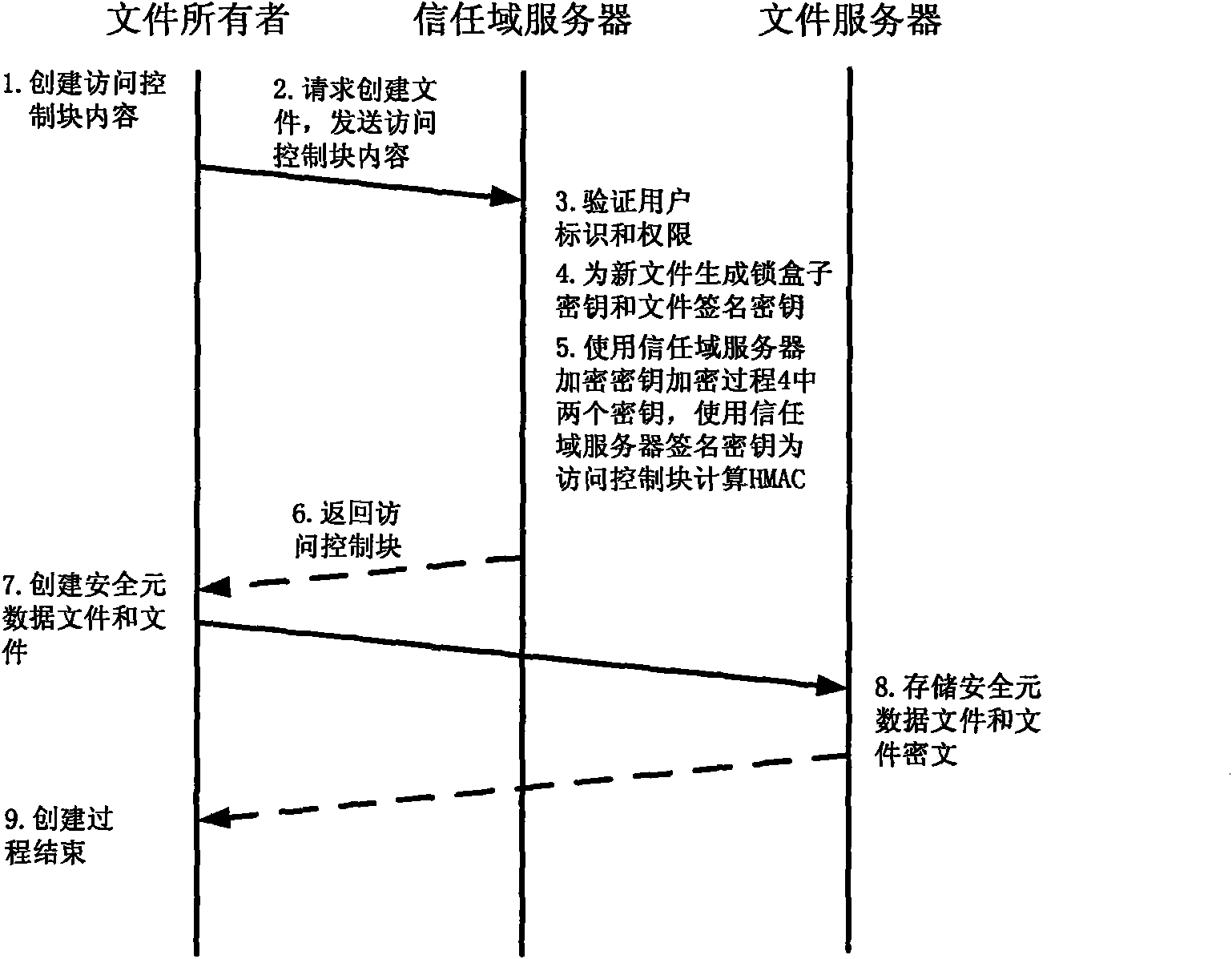
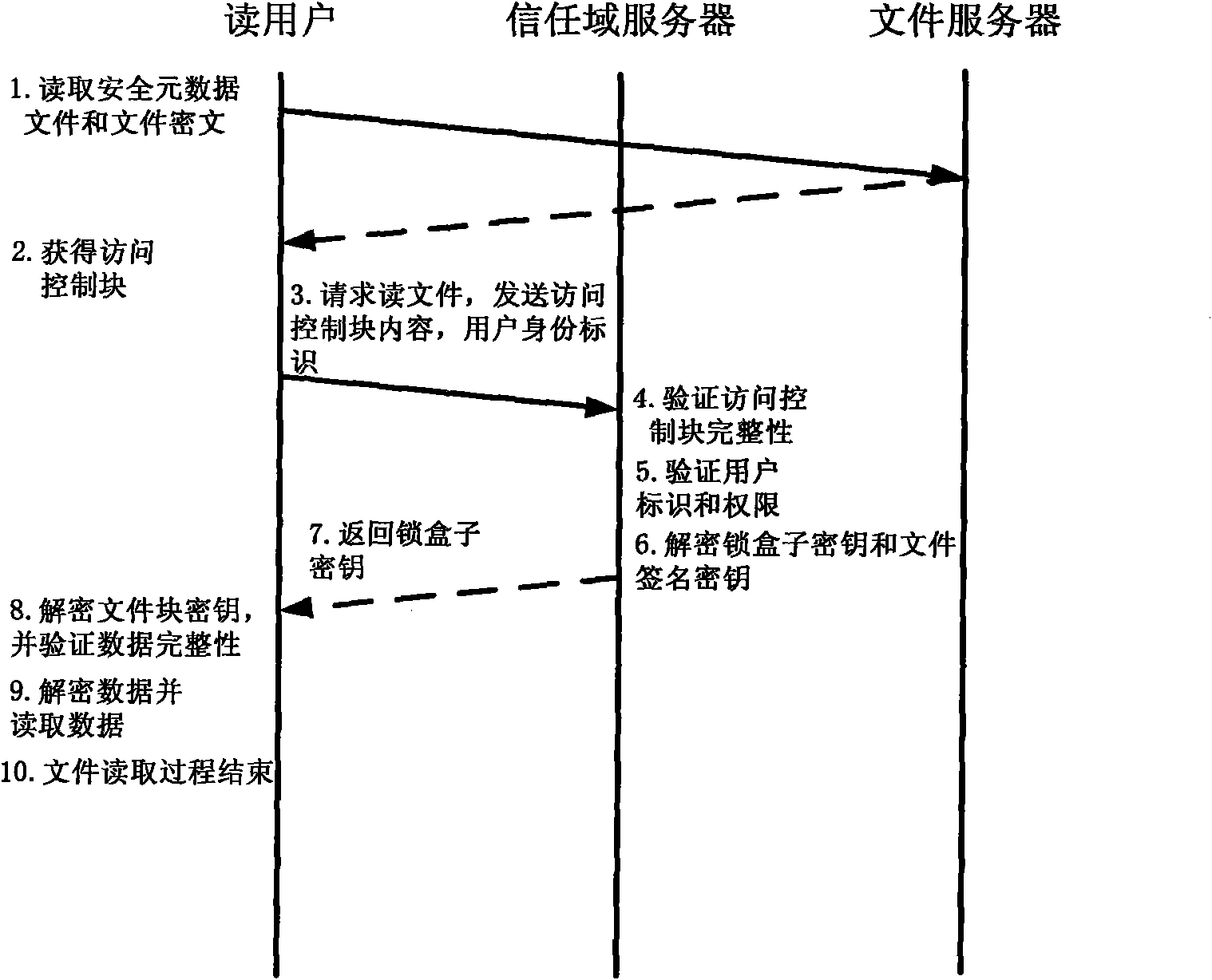
The invention relates to a method for implementing a safe storage system in a cloud storage environment and belongs to the technical field of storage safety. The method is characterized in that a trust domain is established in a server according to the requirements of a user; in the trust domain, identity authentication is performed by using an public key infrastructure (PKI); the independence between the storage system and a bottom layer system is realized by utilizing a filesystem in user space (FUSE); a hash value of a file is calculated by utilizing a secure hash algorithm (SHA1) and taking a block as a unit, a file block is encrypted by utilizing a key and an advanced encryption standard (AES) algorithm of a symmetric encipherment algorithm and taking a block as a unit, and a file cipher text is uploaded to a file server in a cloud storage area so as to guarantee the confidentiality and integrity of the file; a filer owner postpones encrypting the file again when permission is revoked by designating a user with the permission of accessing the file and the permissions thereof in an access control list; and only when the user modifies the content of the file, the user encrypts the file block in which the modified content is positioned again and the system implements three layers of key management, namely a file block key, a safe metadata file key and a trust domain server key so that not only the safety of the file is guaranteed when the permission is revoked, but also the management load of the system is not increased.
Owner:TSINGHUA UNIV
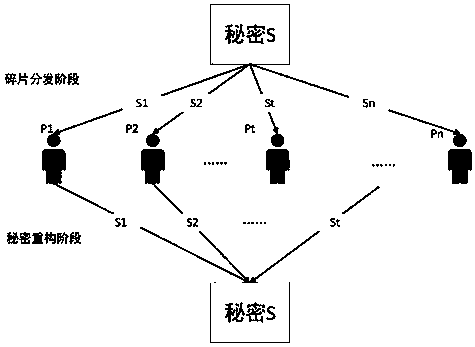
Systems and methods for distributing and securing data
ActiveUS20080137857A1Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
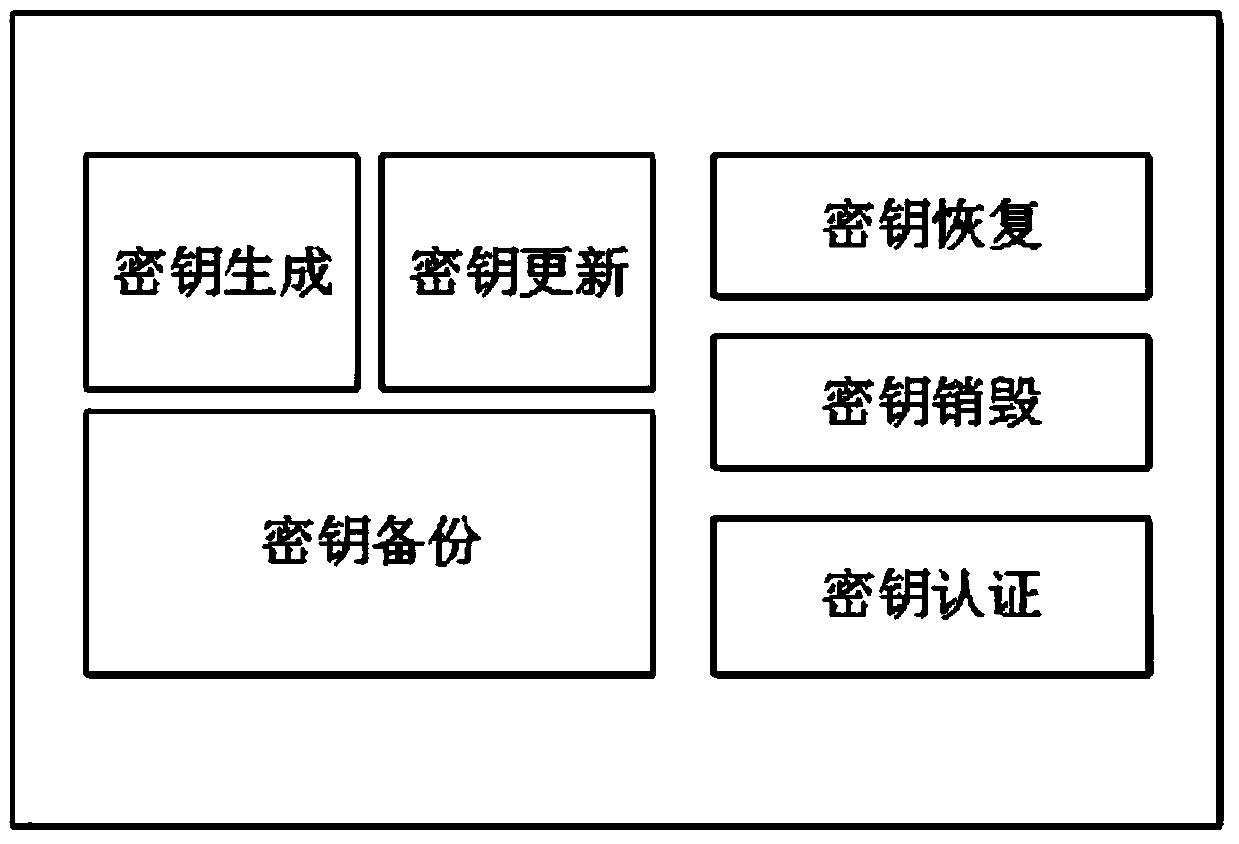
Block chain key trusteeship and recovery method and device based on secrecy sharing technology
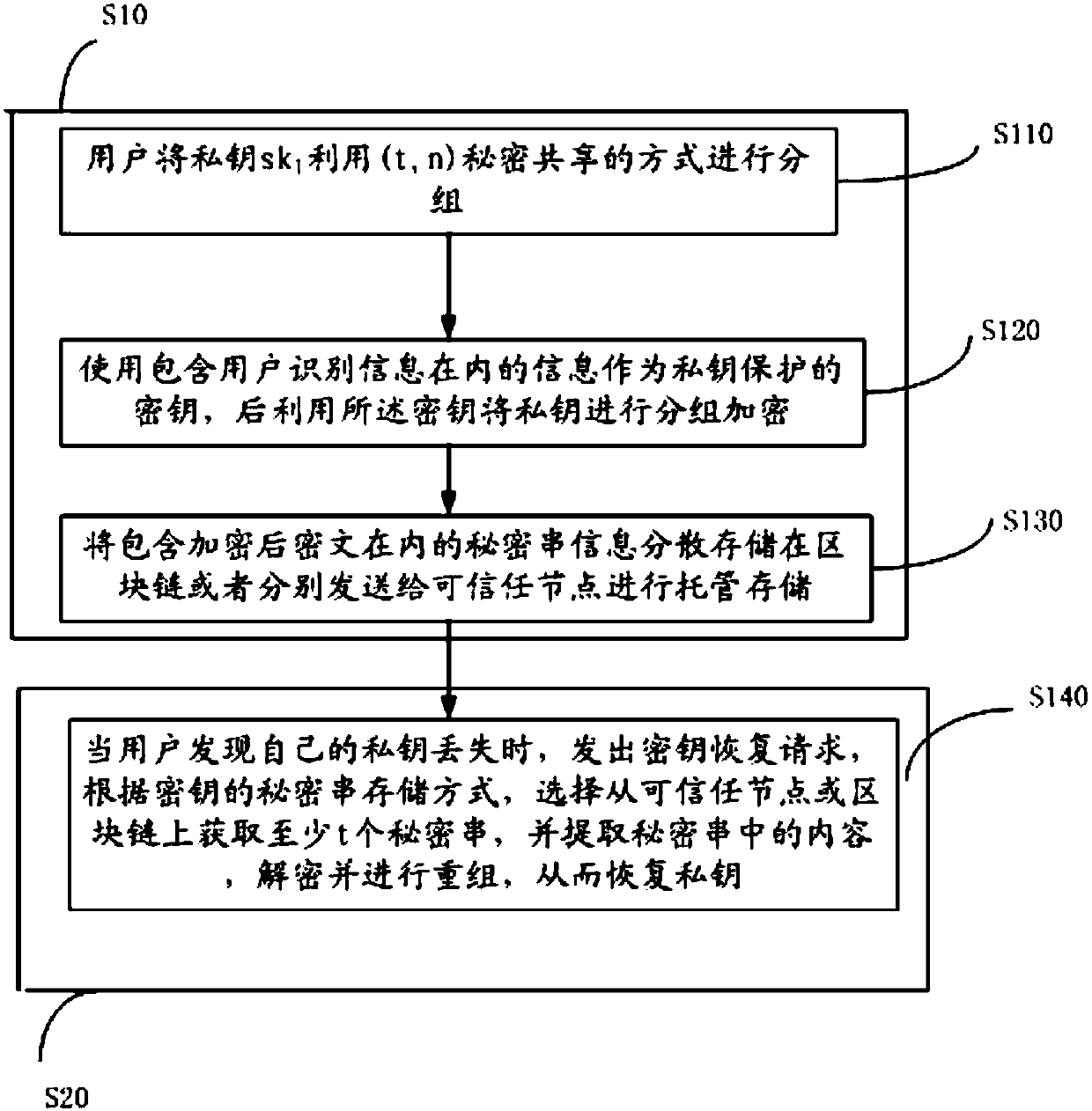
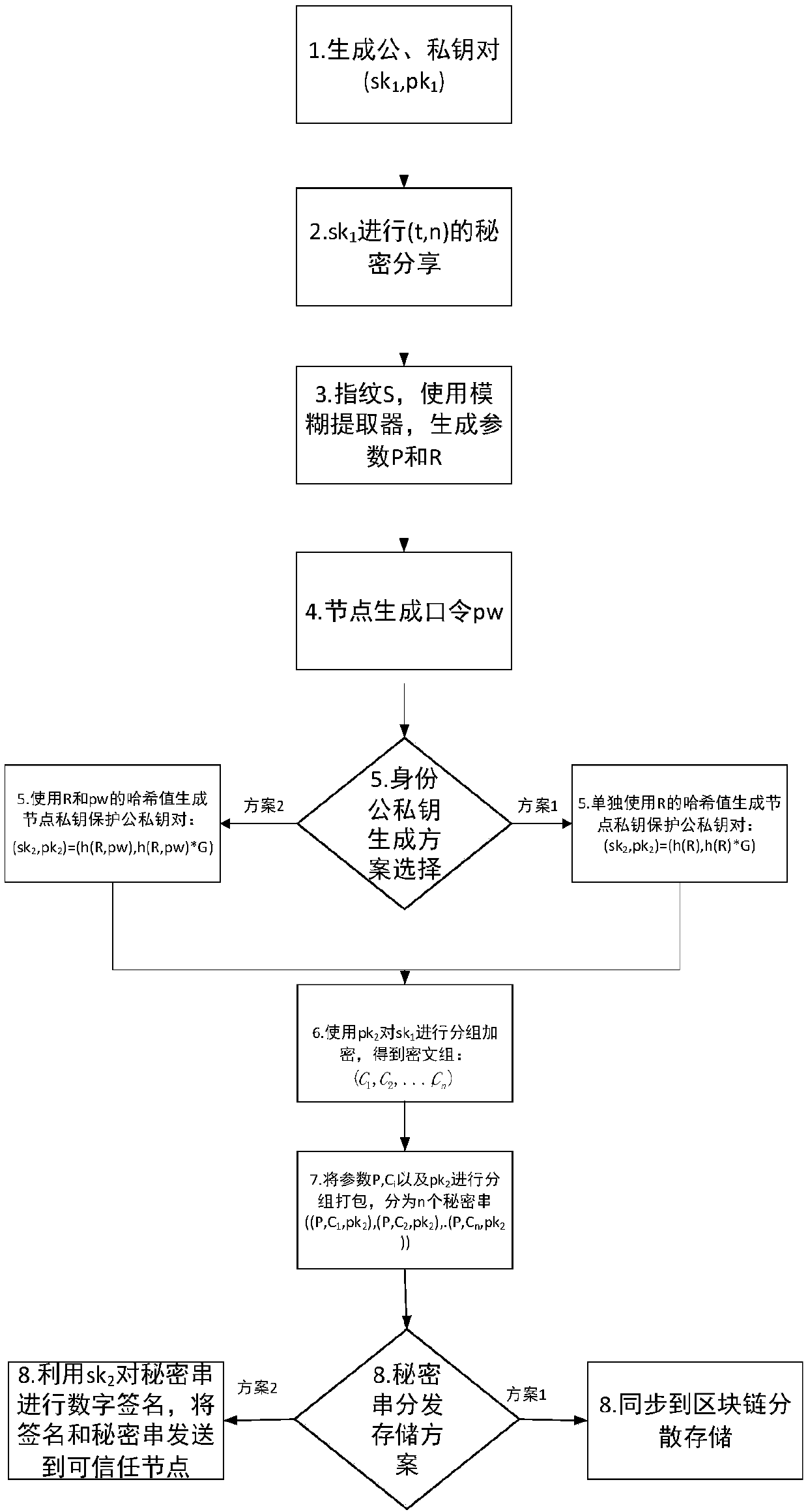
InactiveCN107623569ASafekeepingSafe recoveryKey distribution for secure communicationRecovery methodRestoration method
The invention discloses a block chain key trusteeship and recovery method and device based on a secrecy sharing technology. The method comprises the steps that A1, a user groups a private key sk1 in a(t, n) secrecy sharing mode, wherein the n is the number of fragments of shared secrecies obtained by splitting the private key, the t is the minimum number of the fragments for recovery of the private key, and the t is greater than or equal to 2 and is smaller than or equal to the n; A2, information containing user identification information is taken as a private key protection key, and then grouping encryption is carried out on the private key through utilization of the key; and A3, secrecy string information containing encrypted ciphertexts is dispersely stored to a block chain or is sentto trusted nodes for trusteeship and storage, when the user discovers that own private key is lost, a key recovery request is generated, at least t secrecy strings are obtained from the trusted nodesor the block chain in a secrecy string storage mode of the key, and the content in the secrecy strings is extracted, decrypted and recombined, so the private key is recovered. According to the methodand the device, the secrecy sharing technology is applied to a block chain scene for the first time, thereby solving the private key trusteeship and recovery security problem.
Owner:JUZIX TECH SHENZHEN CO LTD
Fully Homomorphic Encryption
InactiveUS20130170640A1Reduce noise levelGrowth inhibitionPublic key for secure communicationSecret communicationRoundingNoise level
In one exemplary embodiment of the invention, a method and computer program include: receiving first and second ciphertexts having first and second data encrypted per an encryption scheme, the encryption scheme has public / secret keys and encryption, decryption, operation and refresh functions, the encryption function encrypts data, the decryption decrypts ciphertext, the operation receives ciphertexts and performs operation(s) on them, the refresh operates to prevent growth of the magnitude of noise for a ciphertext while reducing the modulus of the ciphertext without using the secret key, utilizing a modulus switching technique that involves transforming a first ciphertext c modulo q into a second ciphertext c′ modulo p while preserving correctness, the technique includes scaling by p / q and rounding, p<q; using the operation function(s), performing operation(s) on them to obtain a third ciphertext; and reducing a noise level of the third ciphertext using the refresh function.
Owner:IBM CORP
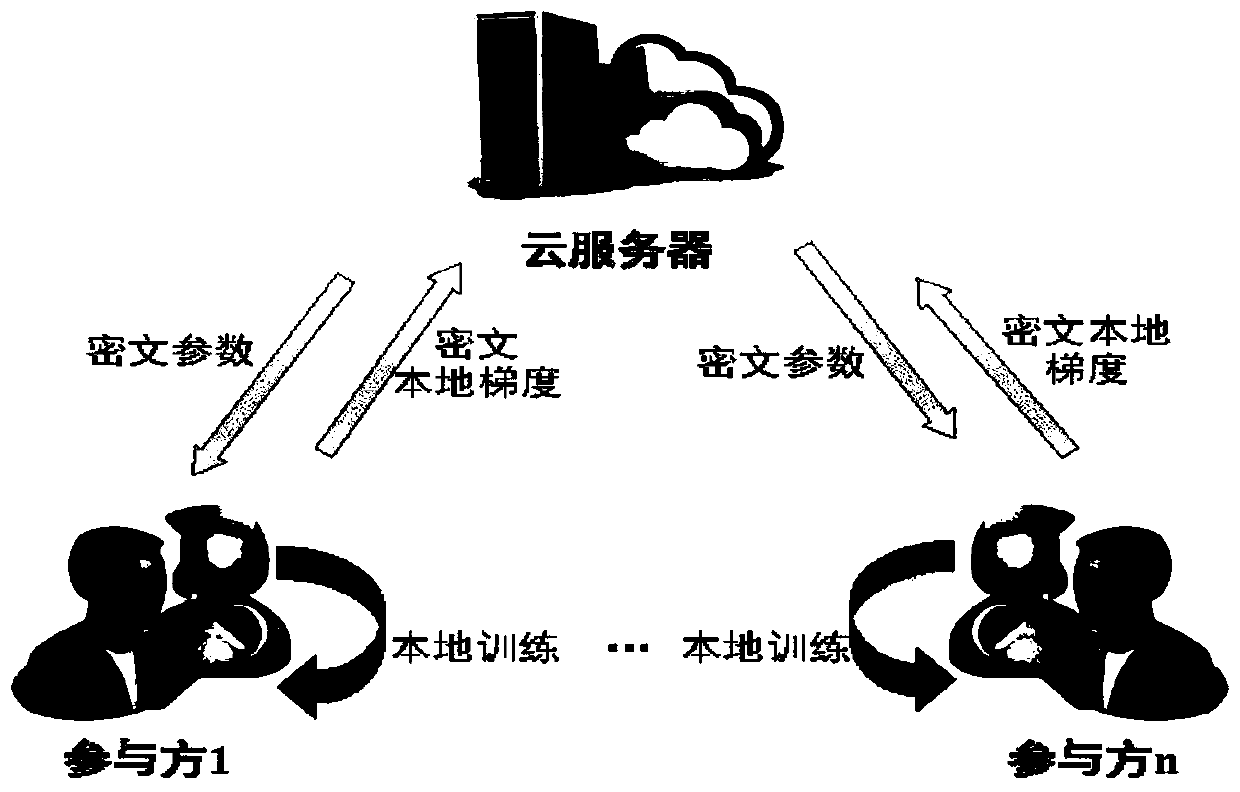
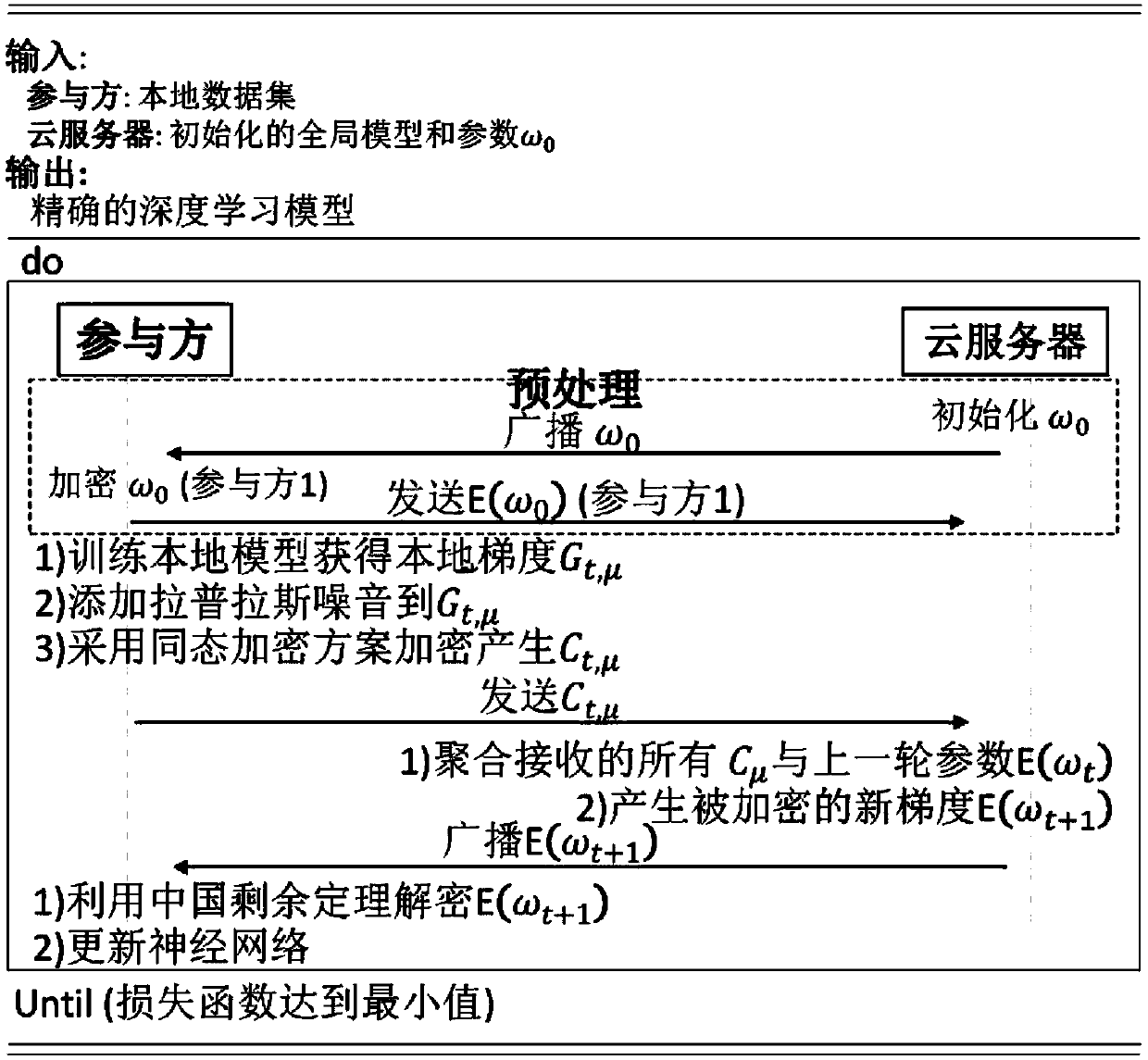
A combined deep learning training method based on a privacy protection technology
ActiveCN109684855AAvoid gettingSafe and efficient deep learning training methodDigital data protectionCommunication with homomorphic encryptionPattern recognitionData set
The invention belongs to the technical field of artificial intelligence, and relates to a combined deep learning training method based on a privacy protection technology. The efficient combined deep learning training method based on the privacy protection technology is achieved. In the invention, each participant first trains a local model on a private data set to obtain a local gradient, then performs Laplace noise disturbance on the local gradient, encrypts the local gradient and sends the encrypted local gradient to a cloud server; The cloud server performs aggregation operation on all thereceived local gradients and the ciphertext parameters of the last round, and broadcasts the generated ciphertext parameters; And finally, the participant decrypts the received ciphertext parameters and updates the local model so as to carry out subsequent training. According to the method, a homomorphic encryption scheme and a differential privacy technology are combined, a safe and efficient deep learning training method is provided, the accuracy of a training model is guaranteed, and meanwhile a server is prevented from inferring model parameters, training data privacy and internal attacksto obtain private information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Ciphertext cloud storage method and system
InactiveCN103595730AWon't leakDoes not affect survivalTransmissionComputer hardwareData synchronization
The invention relates to a ciphertext cloud storage method and system. In the ciphertext cloud storage method system composed of at least one client terminal and a cloud terminal server, the ciphertext cloud storage method comprises the steps that (1) a user adopts a ciphertext and / or a plaintext to conduct data synchronism on the client terminal in the process of data storage and selects an encryption algorithm for the ciphertext; (2) authentication parameters provided based on the identity of the user is used for generating a master key, synchronous data of the ciphertext are encrypted on the client terminal through two-level keys comprising the master key and an encryption and decryption key, and the master key is backed up; (3) the ciphertext and a ciphertext index are synchronized on the client terminal and a cloud terminal, or a plaintext index is established after synchronous data of the plaintext are synchronized on the cloud terminal and the client terminal; (4) the plaintext and / or ciphertext is / are stored in a local private cloud storage server or in a storage server of a cloud storage provider according to a mount point requested by the user. By the adoption of the ciphertext cloud storage method and system, the data cannot be lost when the terminal is lost, if protection is inappropriate, only the ciphertext form of a file is damaged, and the ciphertext cloud storage system can dock with multiple cloud server providers.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
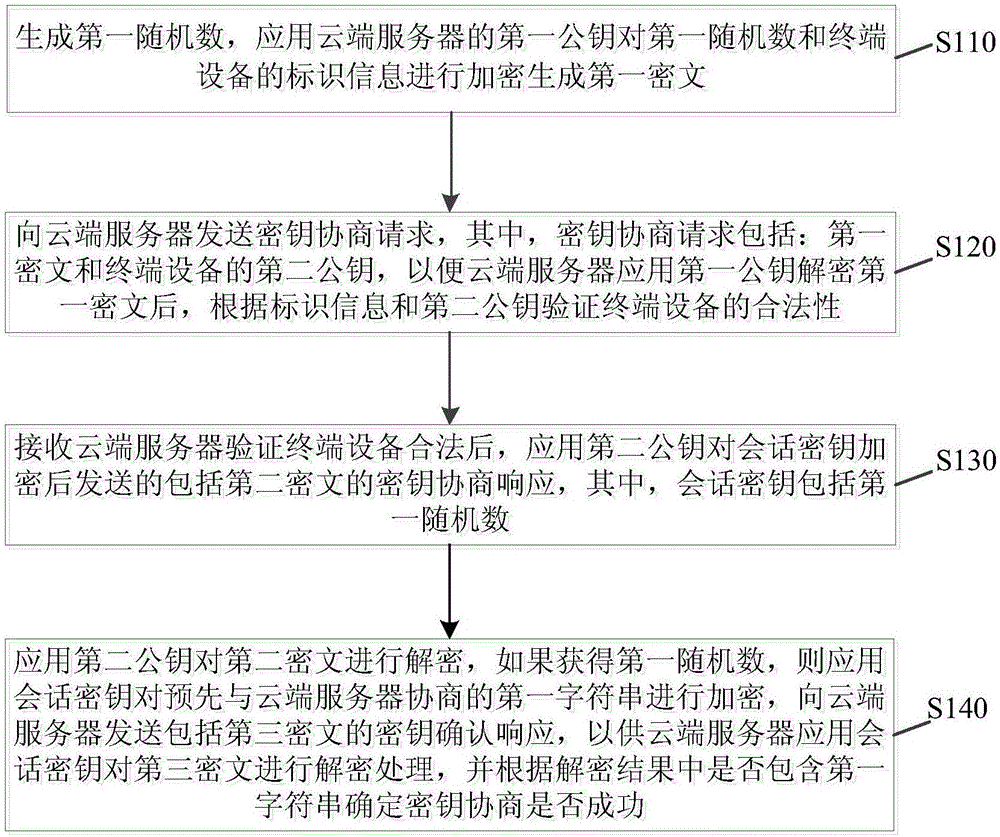
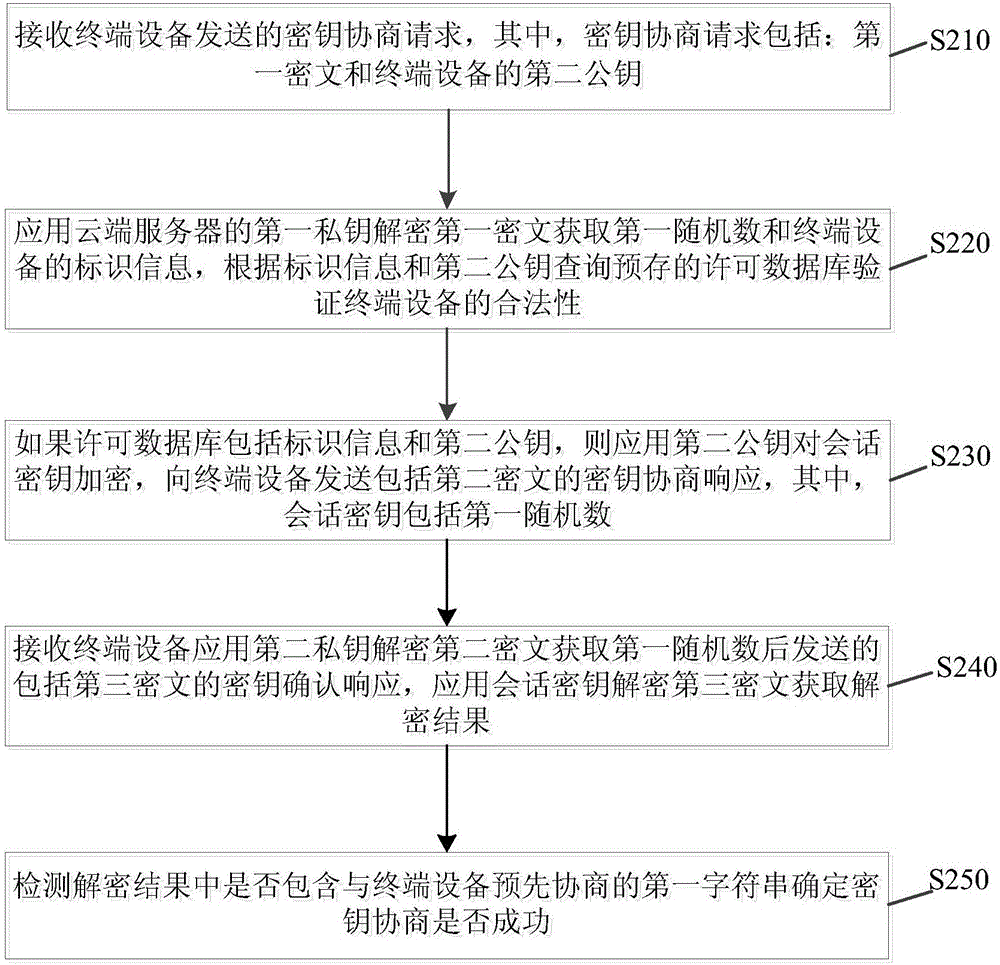
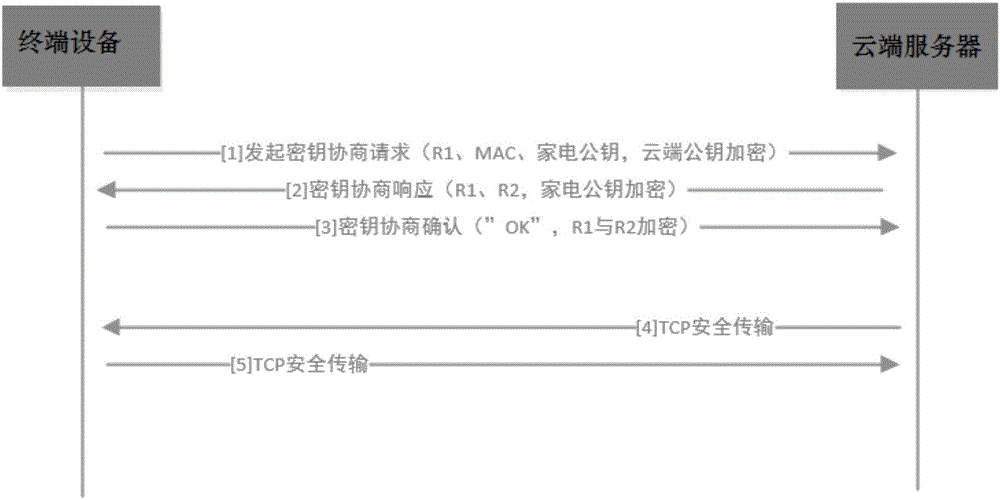
Secret key negotiation method and device
ActiveCN106603485AImprove securityReliable and secure connectionKey distribution for secure communicationUser identity/authority verificationCiphertextTerminal equipment
The invention discloses a secret key negotiation method and a secret key negotiation device. The secret key negotiation method comprises the steps of: generating a first random number, encrypting the first random number and identification information of terminal equipment by using a first public key of a cloud server to generate a first ciphertext; sending a secret key negotiation request containing the first ciphertext and a second public key of the terminal equipment to the cloud server; receiving a secret key negotiation response containing a second ciphertext sent after the cloud server verifies that the terminal equipment is legal and a session key containing the first random number is encrypted by using the second public key; decrypting the second ciphertext by using a second private key, encrypting a first character string which negotiates with the cloud server in advance by using the session key when the first random number is obtained, and sending a secret key confirmation response containing a third ciphertext to the cloud server. The secret key negotiation method can complete the bidirectional identity authentication of the terminal equipment and the cloud server, establishes reliable and secure connection, reduces cost, improves security of data transmission, and is high in efficiency.
Owner:MIDEA SMART TECH CO LTD +1
Bcencryption (BCE) - a public-key based method to encrypt a data stream
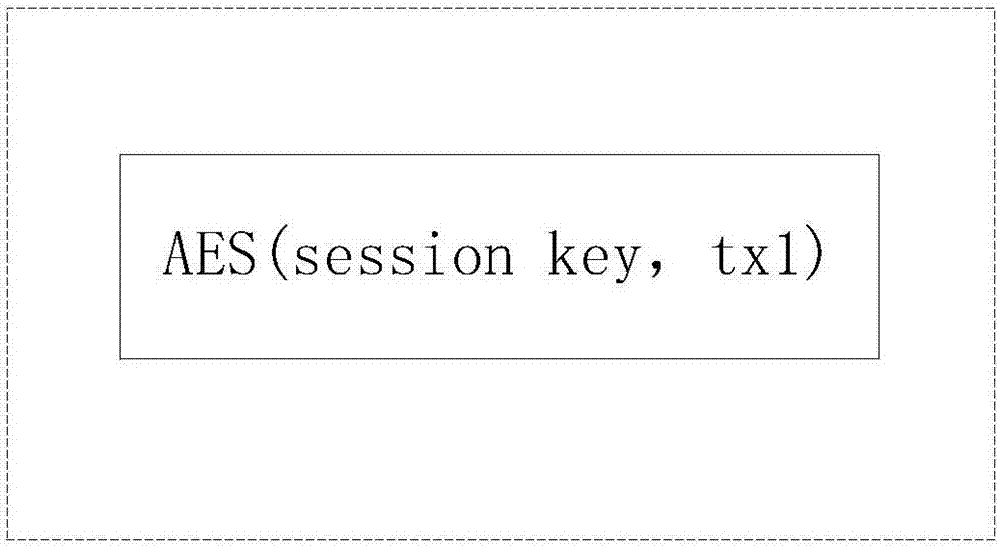
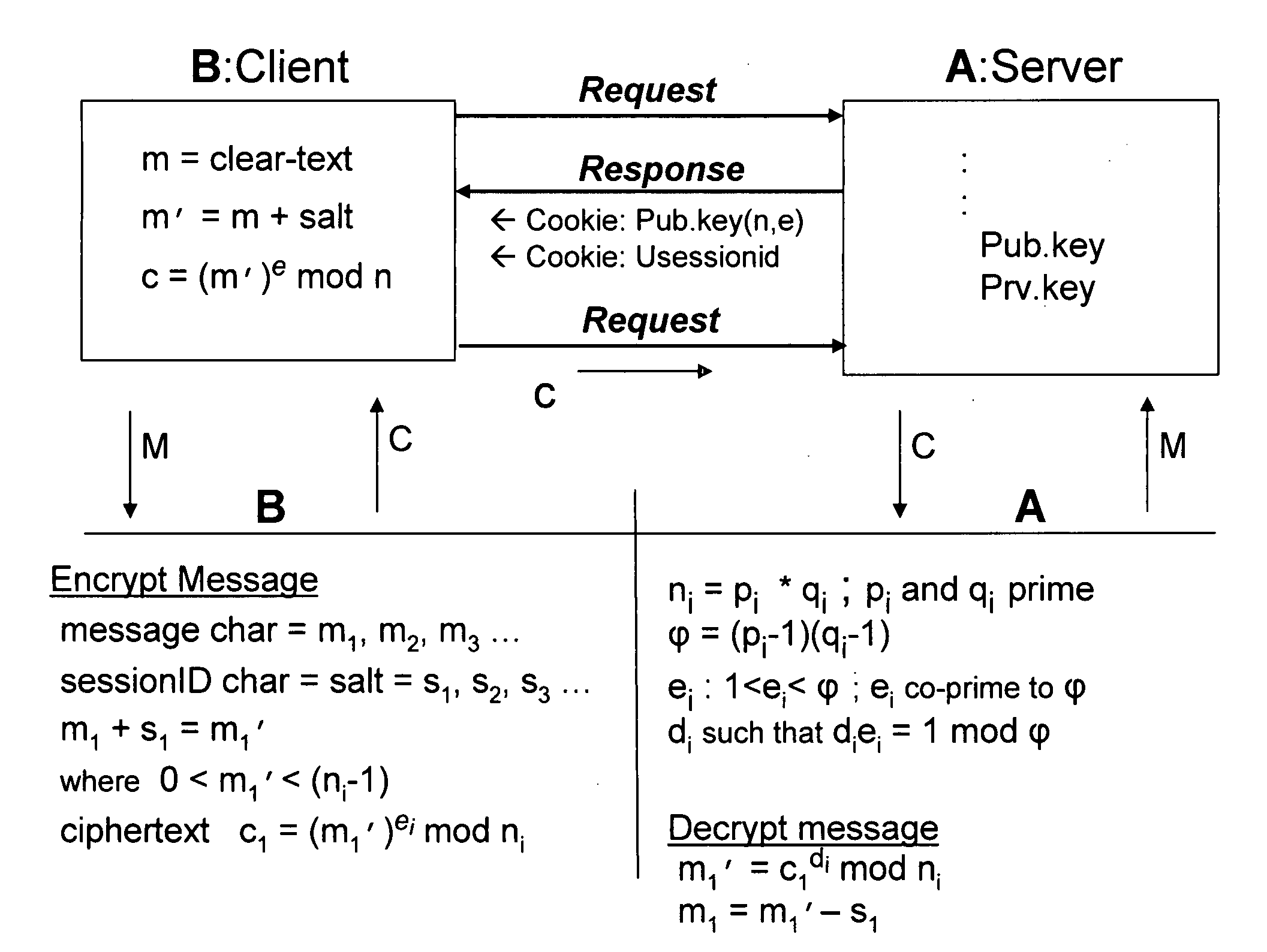
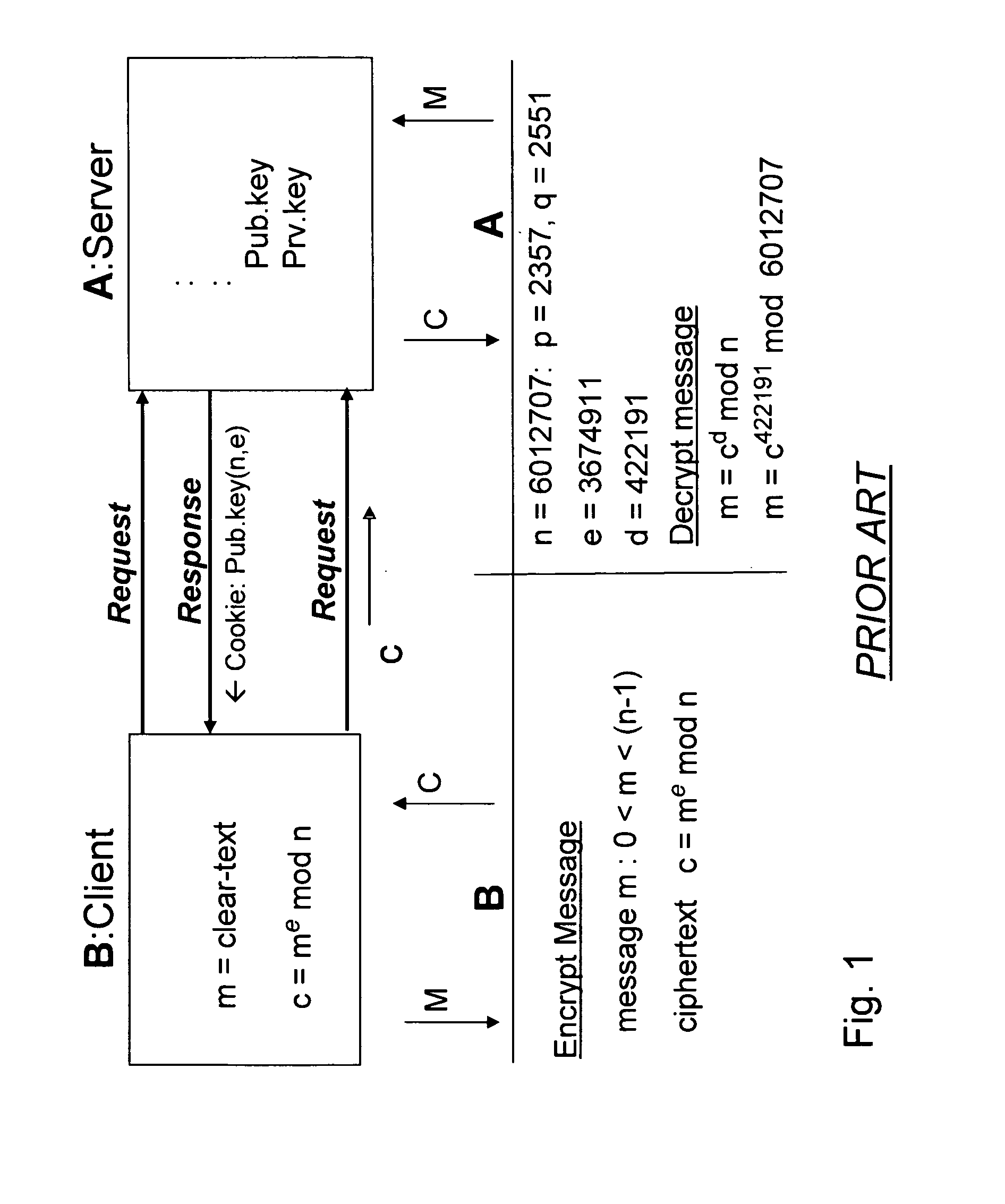
ActiveUS20070180230A1Increase safetyReduce loadData stream serial/continuous modificationUser identity/authority verificationClient-sideSession ID
A system and method for a web browser to convert an unencrypted character string into a cipher-text string combines a public-key encryption algorithm with a unique and constantly changing salt key. A private “server-key”, a public “client-key” and a server session ID are generated by the server, and the client-key and the session ID are sent to the browser with the code used to encrypt the message. The session-based string can be a randomly generated set of characters which changes between established user sessions and the salt key can be formed from the server session ID string. The server contains the matching code necessary to decrypt the stream using the private key.
Owner:KRONOS TECH SYST PARTNERSHIP
Cryptographic apparatus and method
InactiveUS7177424B1Quick implementationEasy to operateEncryption apparatus with shift registers/memoriesUnauthorized memory use protectionPlaintextComputer hardware
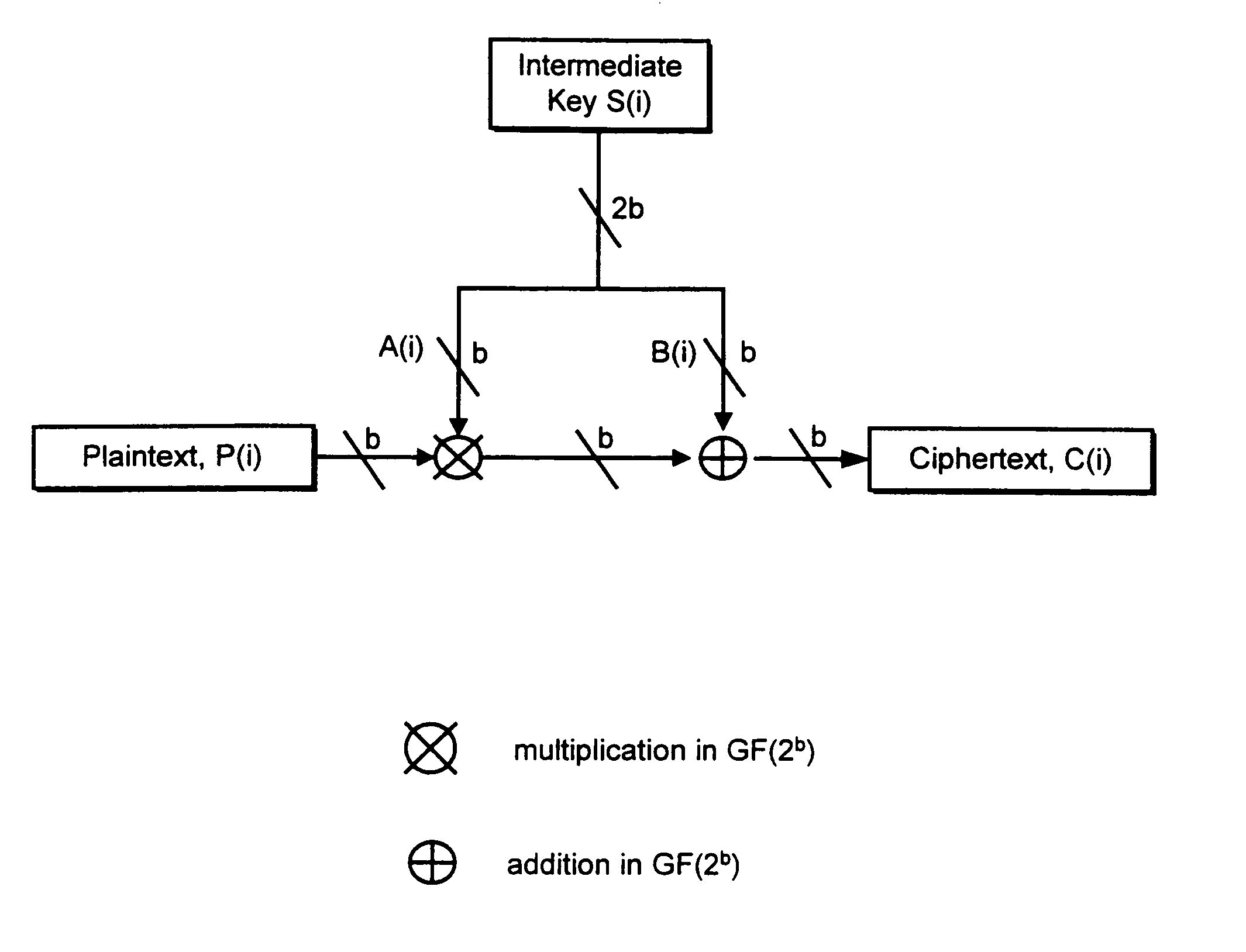
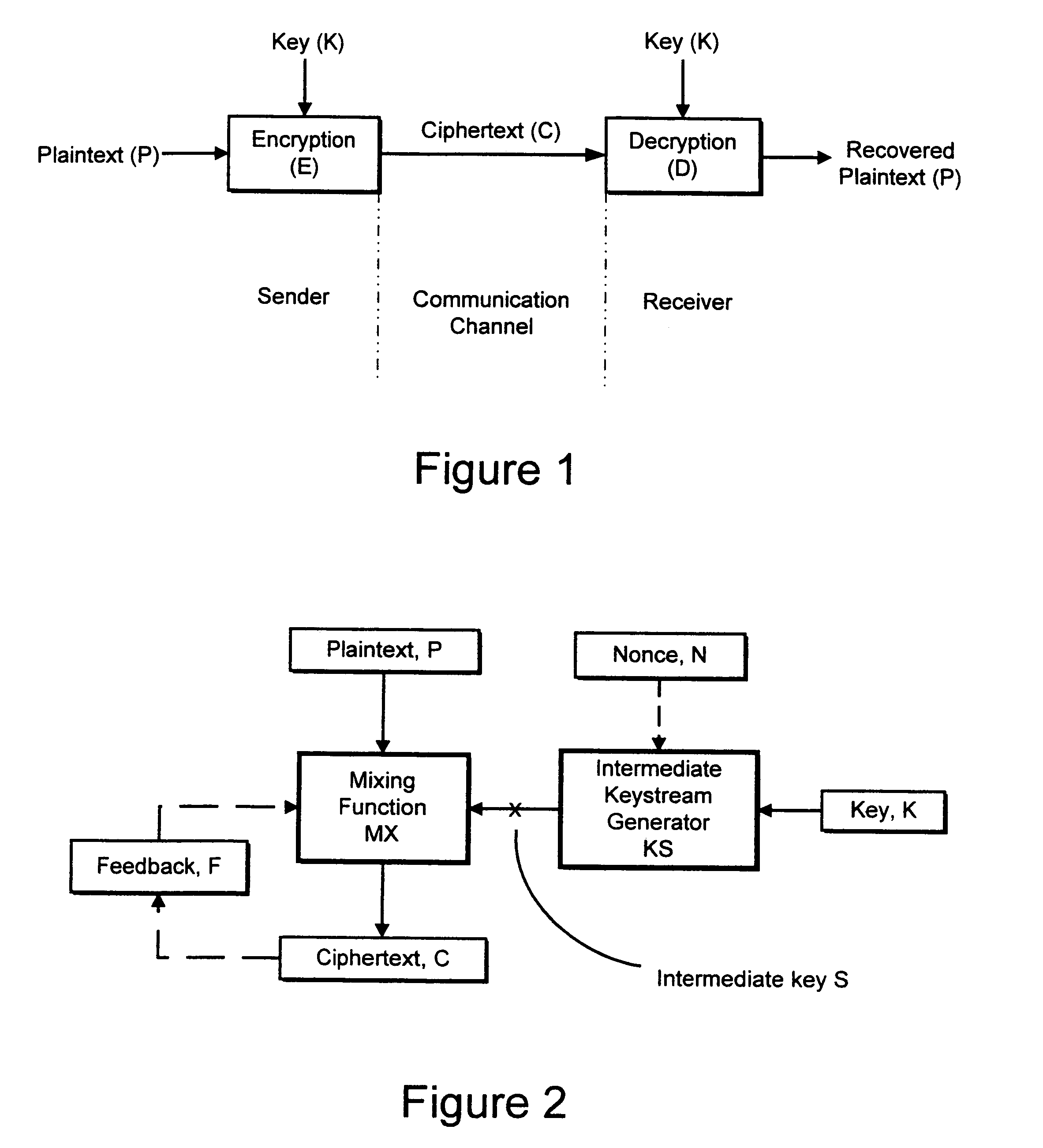
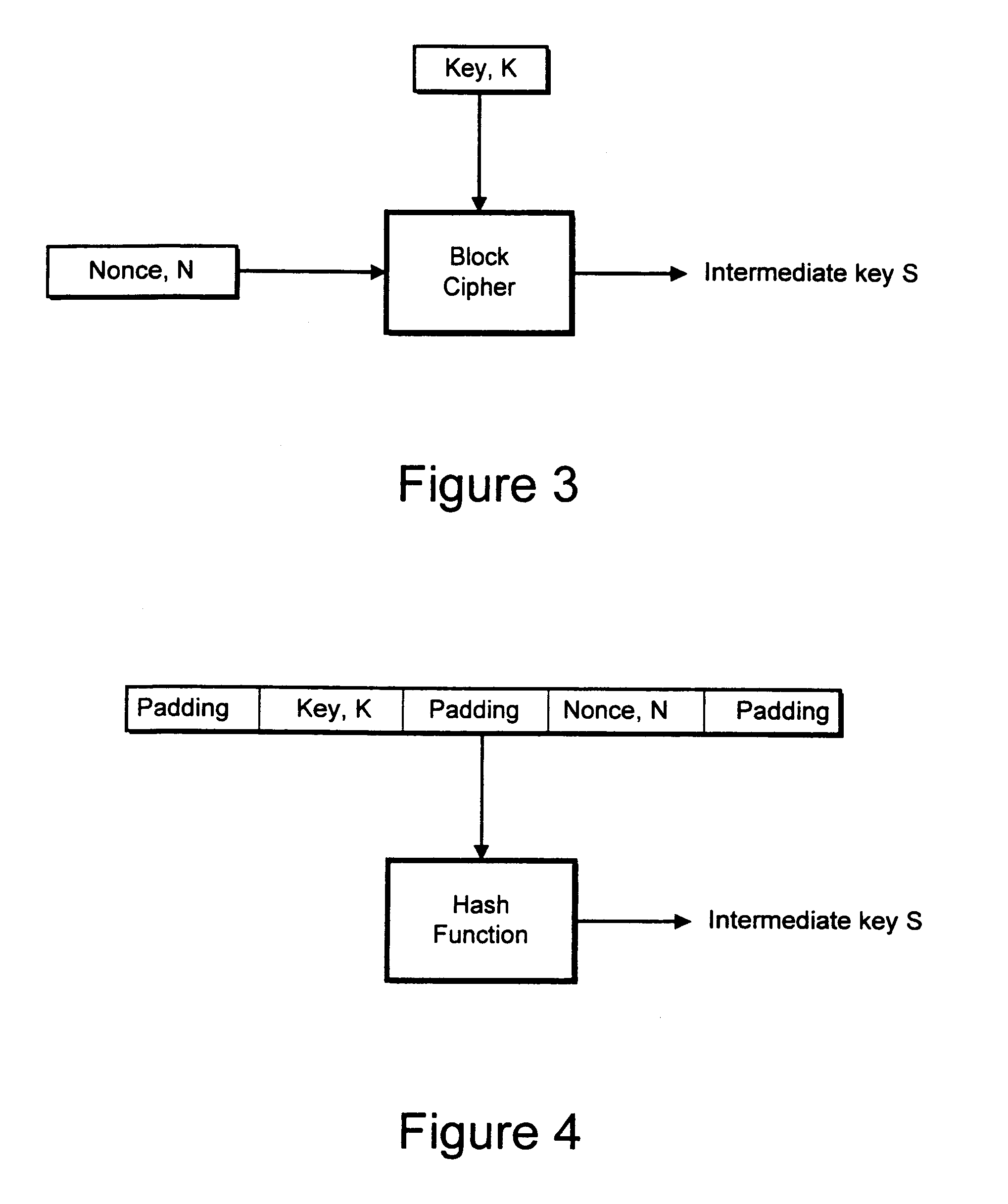
An encryption system comprises a pseudo-random number generator (KS) for generating a long pseudo-random sequence (S) from a shorter encryption key (K) and, if necessary, a nonce value (N), and a mixing function (MX) for combining the sequence with a plaintext message (P) on a block-by-block basis, where successive blocks (S(i)) of 128 bits of the sequence are combined with successive 64-bit blocks of plaintext (P(i)) to produce successive 64-bit blocks of ciphertext. The blockwise use of a long pseudo-random sequence preserves the advantages of a block cipher in terms of data confidentiality and data integrity, as well as benefiting from the speed advantages of a stream cipher.
Owner:HITACHI LTD
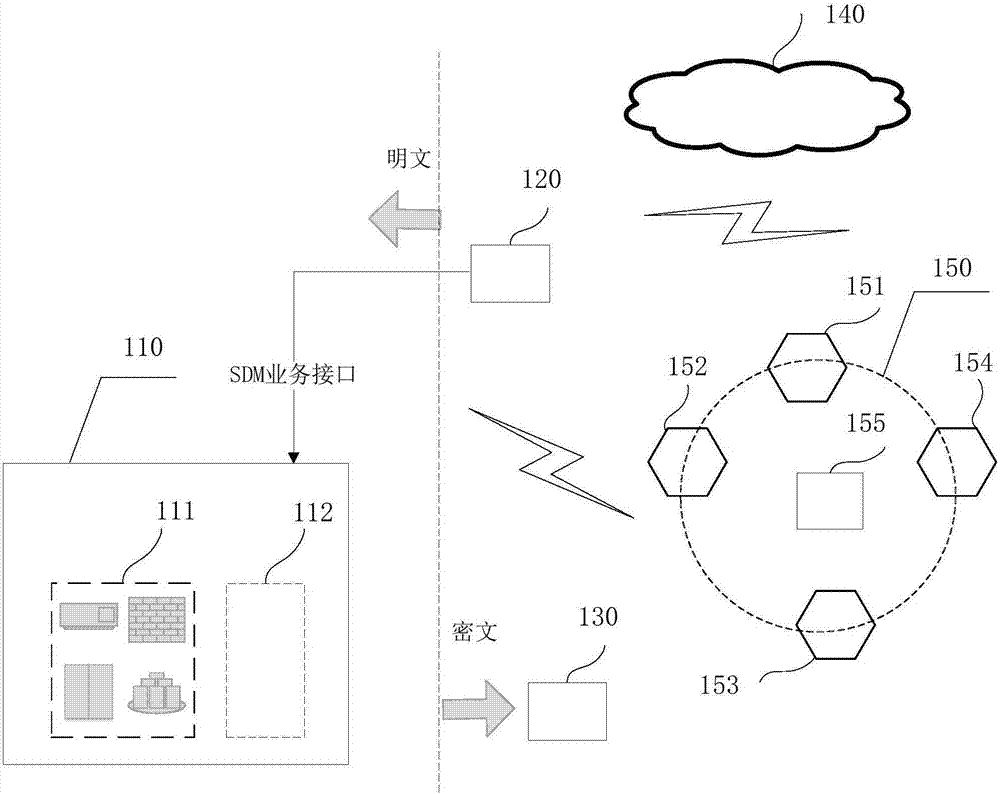
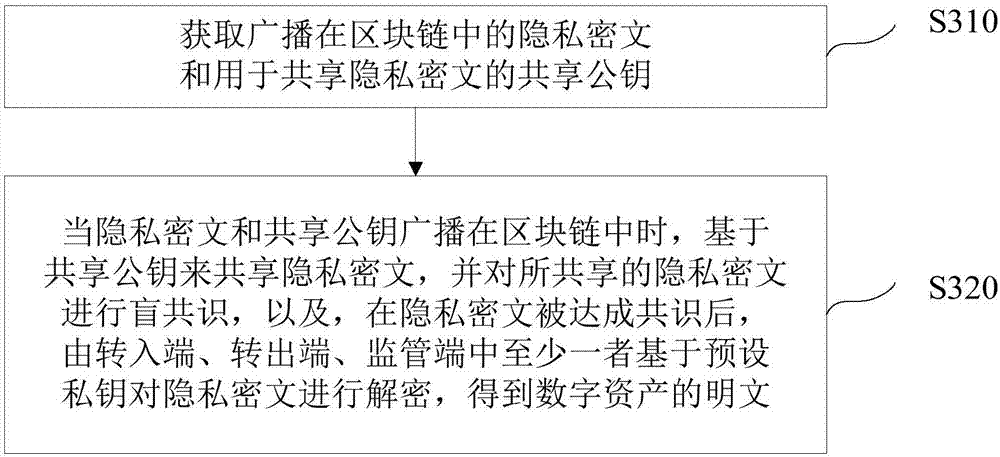
Blockchain-based digital asset processing method and device
ActiveCN106982205AProtection of privacySmooth circulationKey distribution for secure communicationDigital data protectionPlaintextCiphertext
The invention discloses a blockchain-based digital asset processing method and device. The method comprises the following steps: receiving private ciphertext for a digital asset circulated from a sending end to a receiving end through a blockchain, and a preset public key; and obtaining a sharing public key for sharing the private ciphertext based on the preset public key, so that when the private ciphertext and the sharing public key are broadcast in the blockchain, blockchain nodes on the blockchain can share the private ciphertext based on the sharing public key and reach a blind consensus on the shared private ciphertext, and after the consensus on the private ciphertext is reached, the private ciphertext can be decrypted by at least one of three parties, i.e., the sending end, the receiving end and a monitoring end, based on a preset private key to obtain plaintext of the digital asset. The method and device provided by the embodiment of the invention has the advantages that the privacy right of a user is protected; under the premise of privacy protection, the single general digital asset can be smoothly circulated within one blockchain or among multiple blockchains, and a total currency amount remains unchanged; and a monitoring party other than the transaction parties can monitor transaction information at any time.
Owner:中钞信用卡产业发展有限公司杭州区块链技术研究院 +1
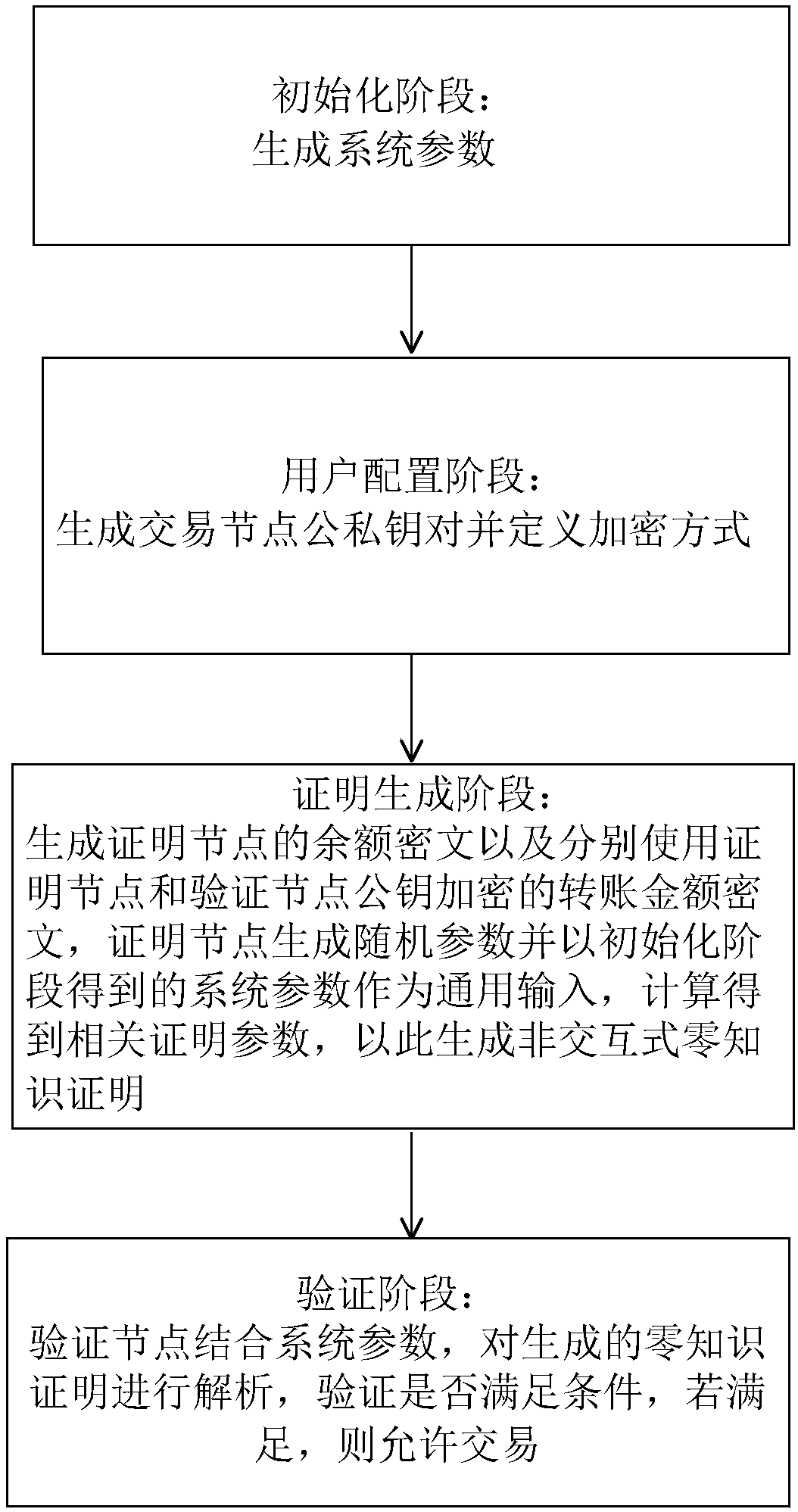
Zero knowledge proving method suitable for protecting privacy of block chain, and medium
ActiveCN108418689AReduce consumptionUser identity/authority verificationProtocol authorisationGeneration processCiphertext
The invention discloses a zero knowledge proving method suitable for protecting the privacy of a block chain, and a medium. UTXO of Bitcoins and a balance model of Ethereum can be supported, and wellcombined with a smart contract, so that the security of the scheme can be further enhanced, the application scene of the scheme can be extended, and aiming at a zero knowledge certificate designed bya specific algebraic structure of a transaction, even a light node can also generate a proving process. The technical scheme is as follows: the method comprises a system parameter in an initializationphase (including a generation process and meaning of the parameter), a specific process of generating the zero knowledge certificate in a certificate generating phase (including ciphertext generatedin the process, and involved formula and parameter), and a verification phase (including verification formula and condition).
Owner:JUZIX TECH SHENZHEN CO LTD +1
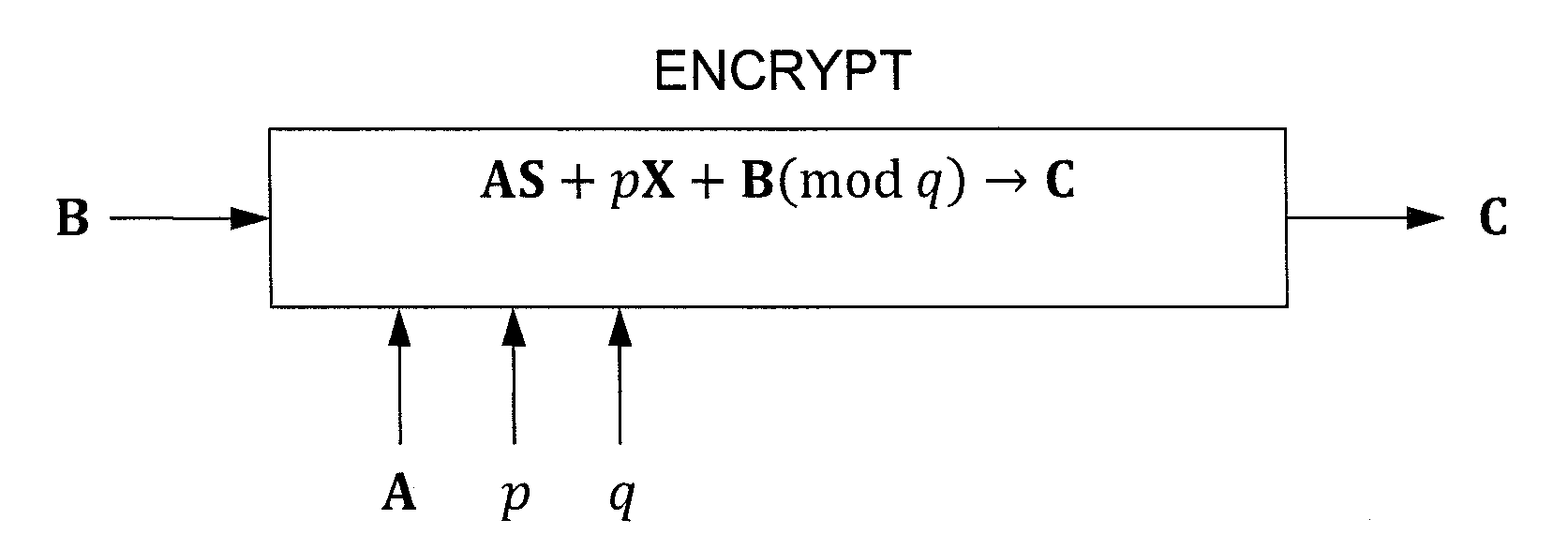
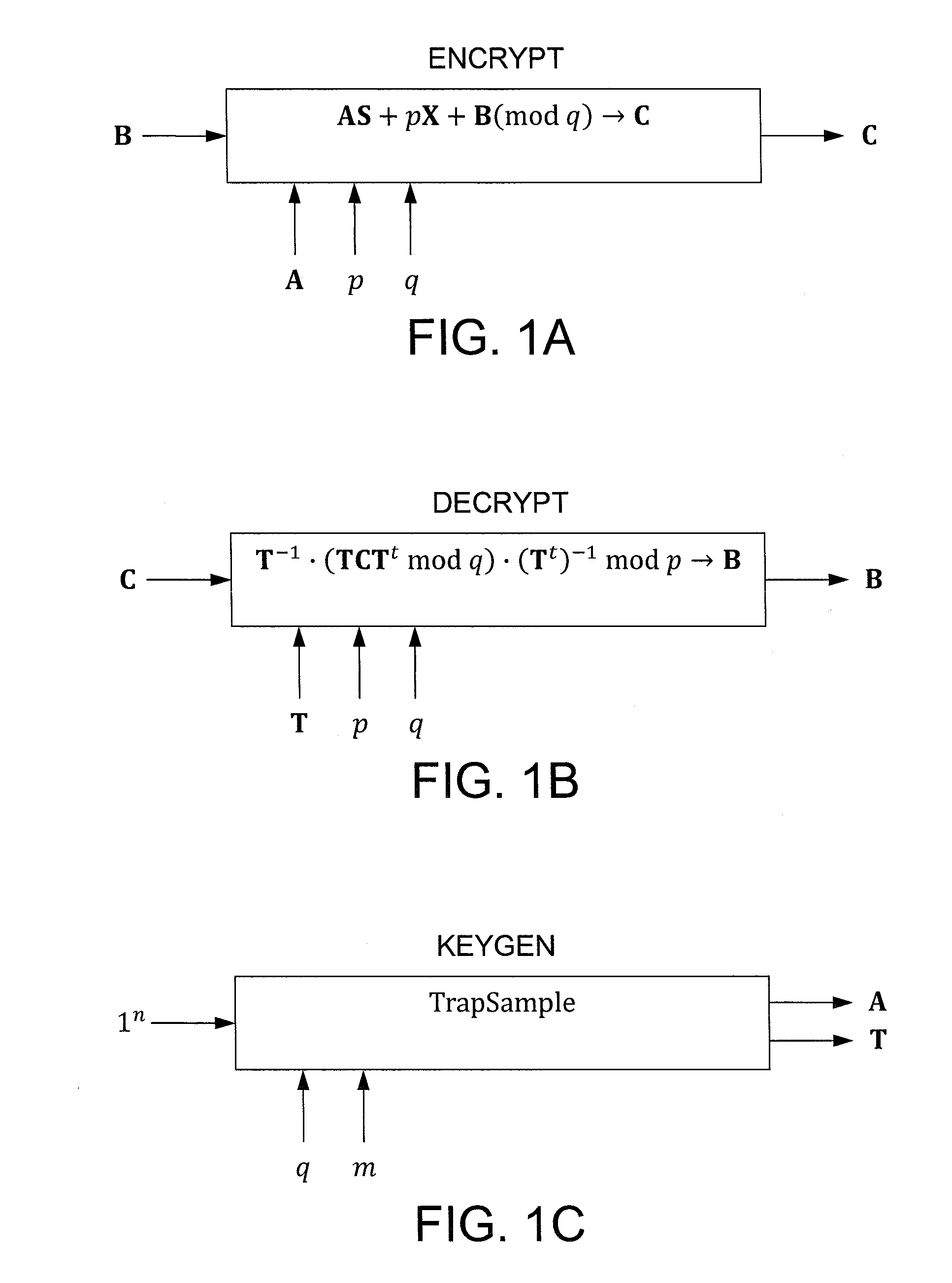
Efficient Homomorphic Encryption Scheme For Bilinear Forms
InactiveUS20110243320A1Public key for secure communicationSecret communicationComputer hardwareCiphertext
In one exemplary embodiment, a computer readable storage medium tangibly embodying a program of instructions executable by a machine for performing operations including: receiving information B to be encrypted as a ciphertext C in accordance with an encryption scheme having an encrypt function; and encrypting B in accordance with the encrypt function to obtain C, the scheme utilizes at least one public key A, where B, C, and A are matrices, the encrypt function receives as inputs A and B and outputs C as C→AS+pX+B (mod q), S is a random matrix, X is an error matrix, p is in integer, q is an odd prime number. In other exemplary embodiments, the encryption scheme includes a decrypt function that receives as inputs at least one private key T (a matrix) and C and outputs B as B=T−1·(TCTt mod q)·(Tt)−1 mod p.
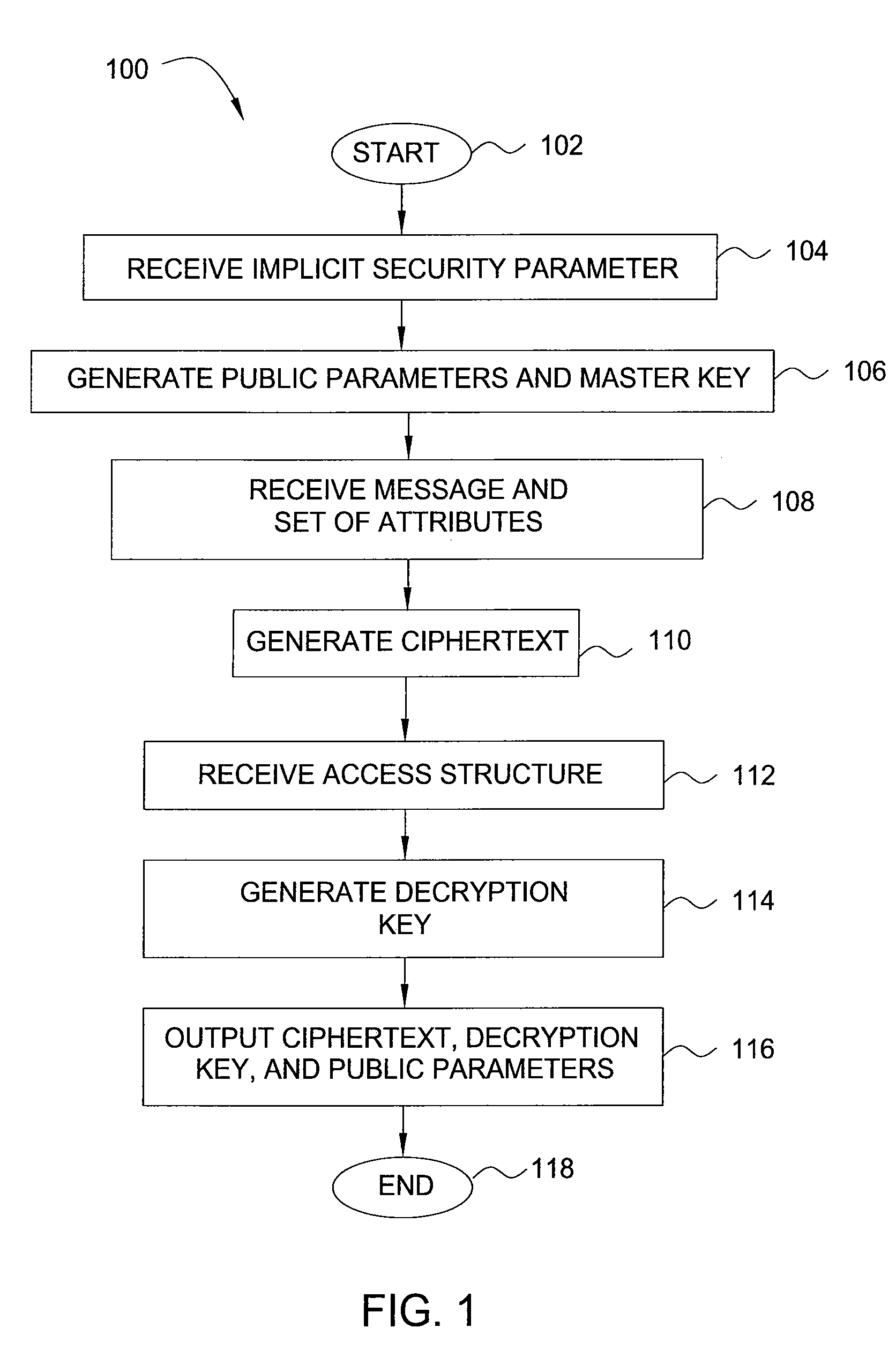
Owner:IBM CORP
Method and apparatus for intercepting events in a communication system
InactiveUS7441271B2Effective and efficient complianceMemory loss protectionError detection/correctionPlaintextCommunications system
An intercept system provides more effective and more efficient compliance with legal intercept warrants. The intercept system can provide any combination of operations that include near-real-time intercept, capture of intercepted data in structured authenticated form, clear text intercept for communications where there is access to encryption keys, cipher text intercept for communications where there is no access to encryption keys, provision of transactional logs to the authorized agency, interception without altering the operation of the target services, and encryption of stored intercepted information.
Owner:SEVEN NETWORKS INC
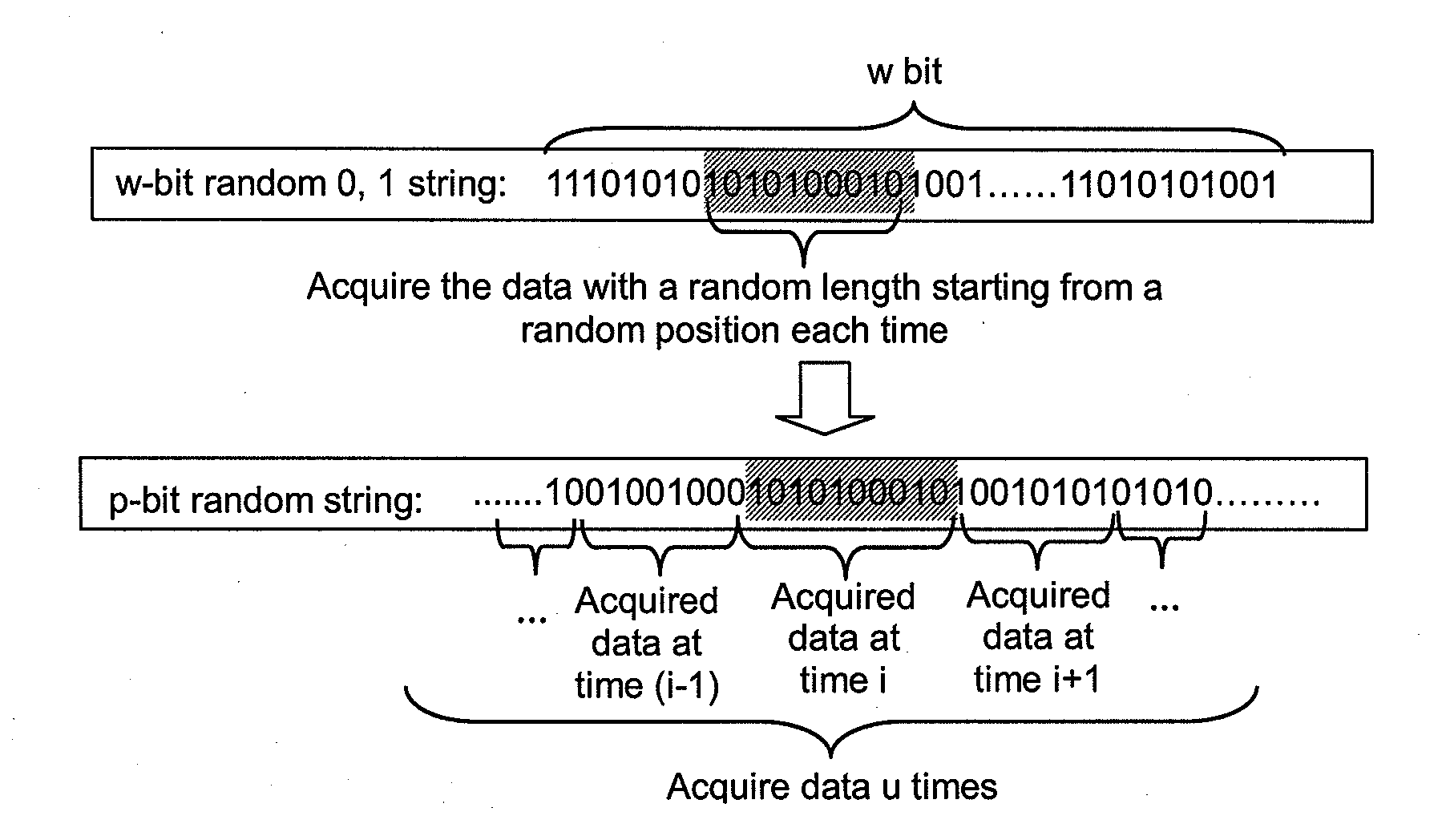
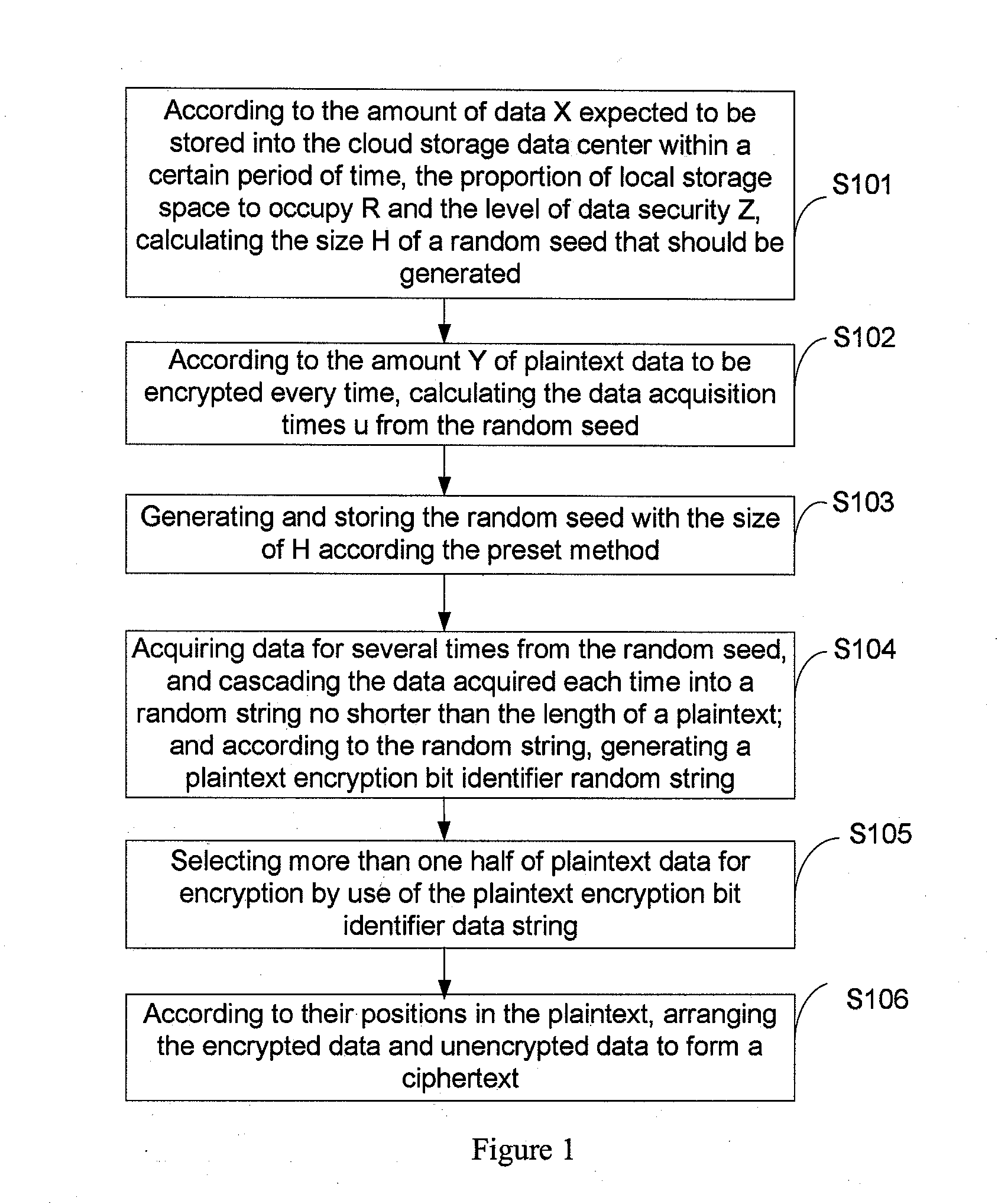
Cloud Storage Data Encryption Method, Apparatus and System
InactiveUS20120134491A1Reduced strengthReduce the amount of dataComputer security arrangementsSecret communicationComputer hardwarePlaintext
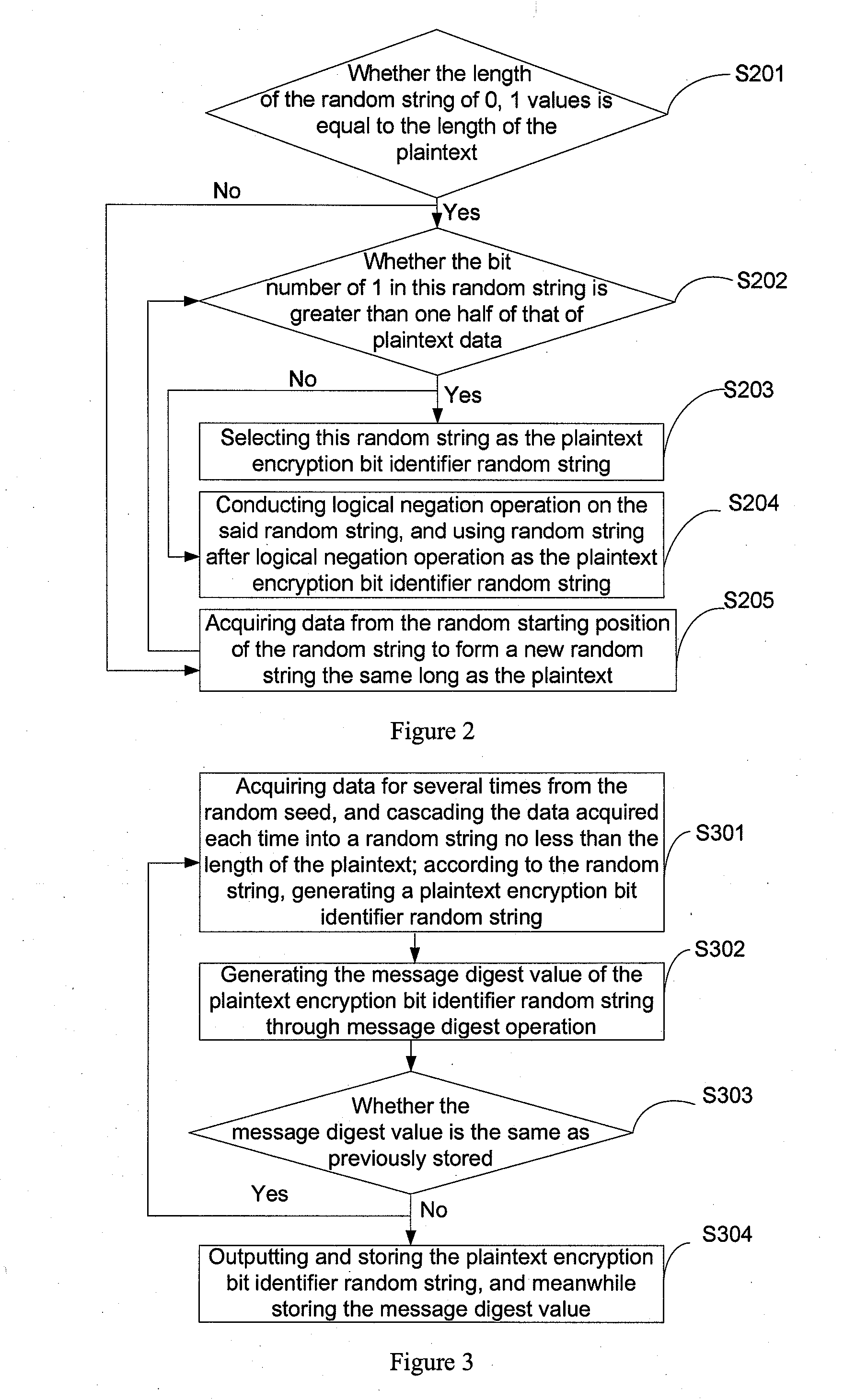
This present application relates to the field of cloud storage security technology, and in particular, relates to a cloud storage data encryption method, apparatus and system. The method comprises: according to the amount of data X expected to be stored within the preset time, the proportion of local storage space R and the security level of data Z, calculating the size H of a random seed that should be generated; according to the amount Y of plaintext data every time, calculating the times u of random seed acquired; according to the times u, acquiring data from the generated random seed with the size of H for several times to generate a plaintext encryption bit identifier data string; by use of the data string, selecting more than one half of the plaintext data for encryption to form a ciphertext. This application also provides a cloud storage data encryption apparatus and system. This invention has reduced the amount of encrypted data to be stored without sacrifice in the degree of data security protection, thus greatly improves the cloud storage data encryption and decryption performance.
Owner:BEIJING Z & W TECH CONSULTING
Method and apparatus for transferring protected content between digital rights management systems
InactiveUS20060282391A1Program/content distribution protectionSelective content distributionCiphertextDigital rights management system
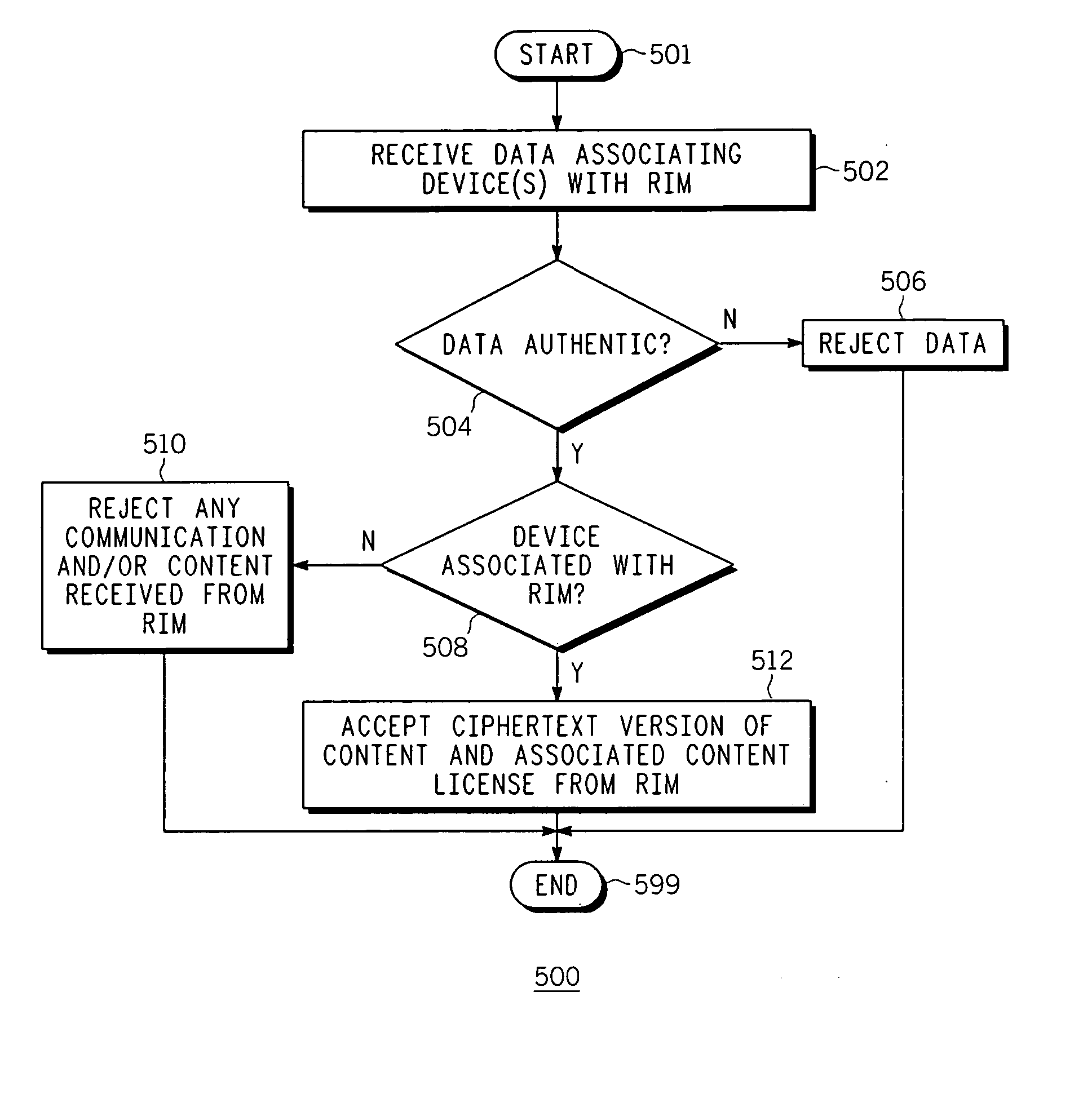
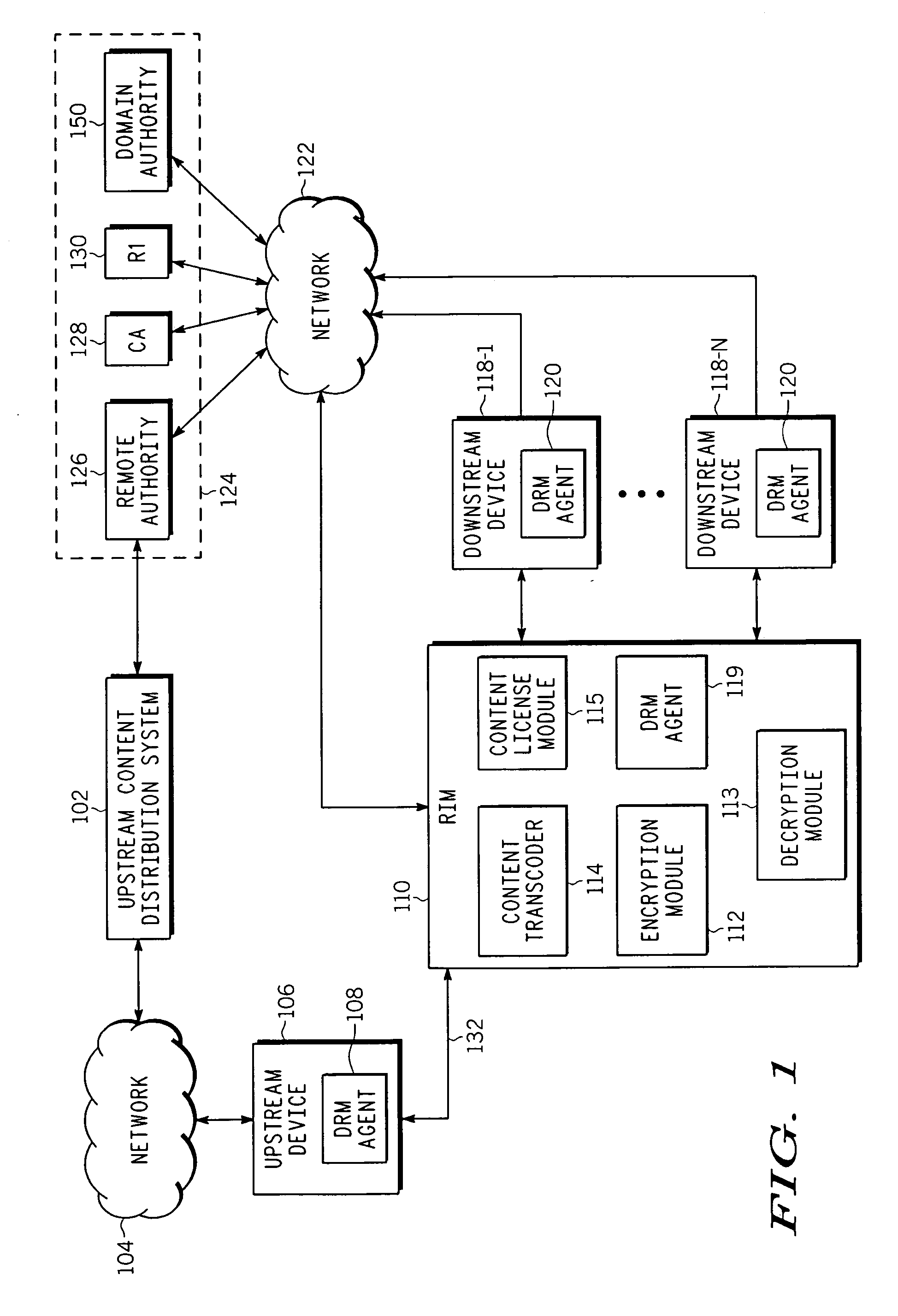
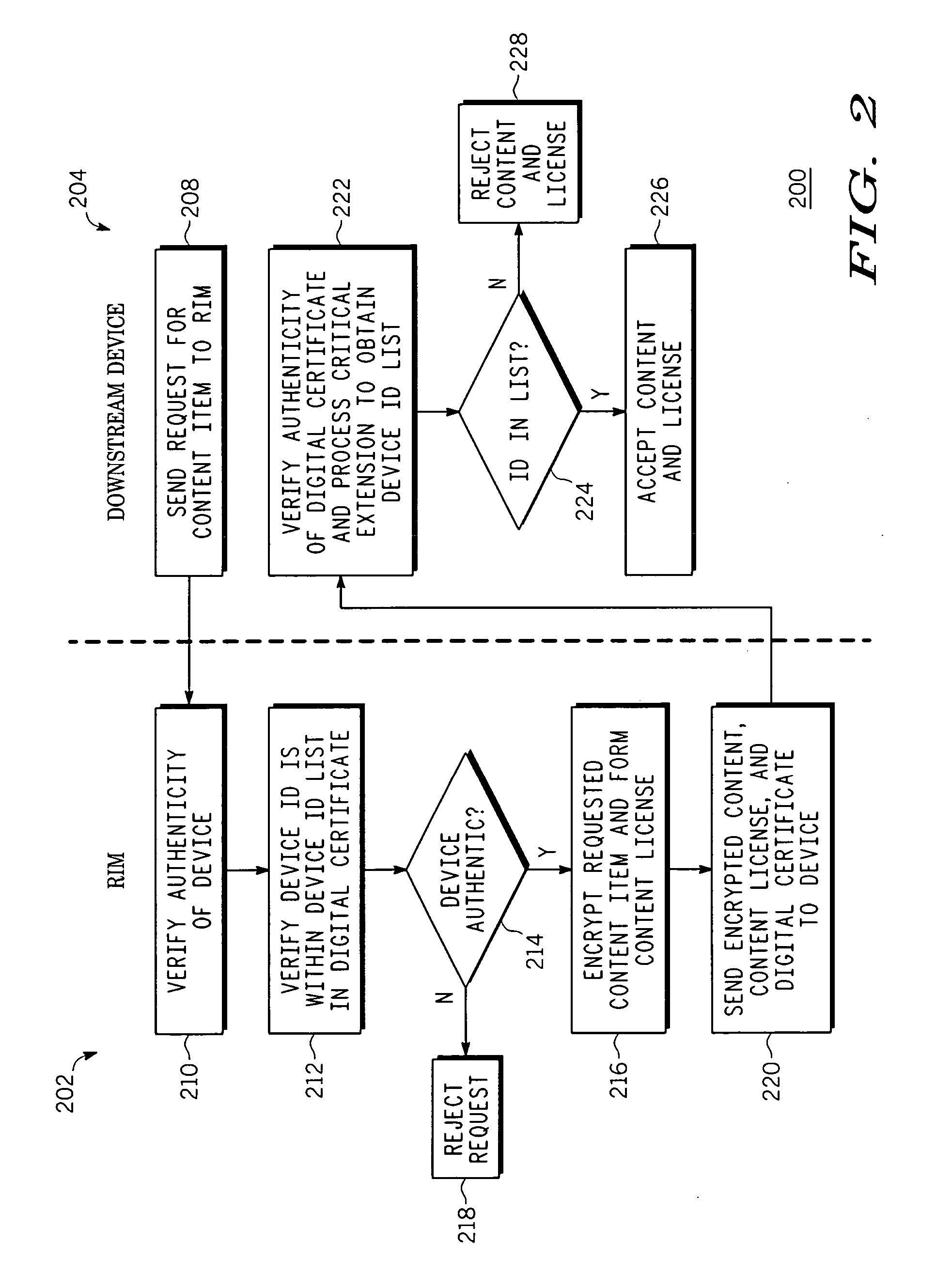
Method and apparatus for transferring protected content between digital rights management systems is described. One aspect of the invention relates to importing content from an upstream digital rights management (DRM) system into a device in a downstream DRM system. Data is received that associates at least one device in the downstream DRM system with a rights issuer module (RIM). Authenticity of the data is verified as originating from an entity in a trust hierarchy of the device. If the data is authentic and the device is one of the at least one device associated with the RIM, a ciphertext version of the content and a corresponding content license is accepted from the RIM.
Owner:GOOGLE TECH HLDG LLC
Storage medium and method and apparatus for separately protecting data in different areas of the storage medium
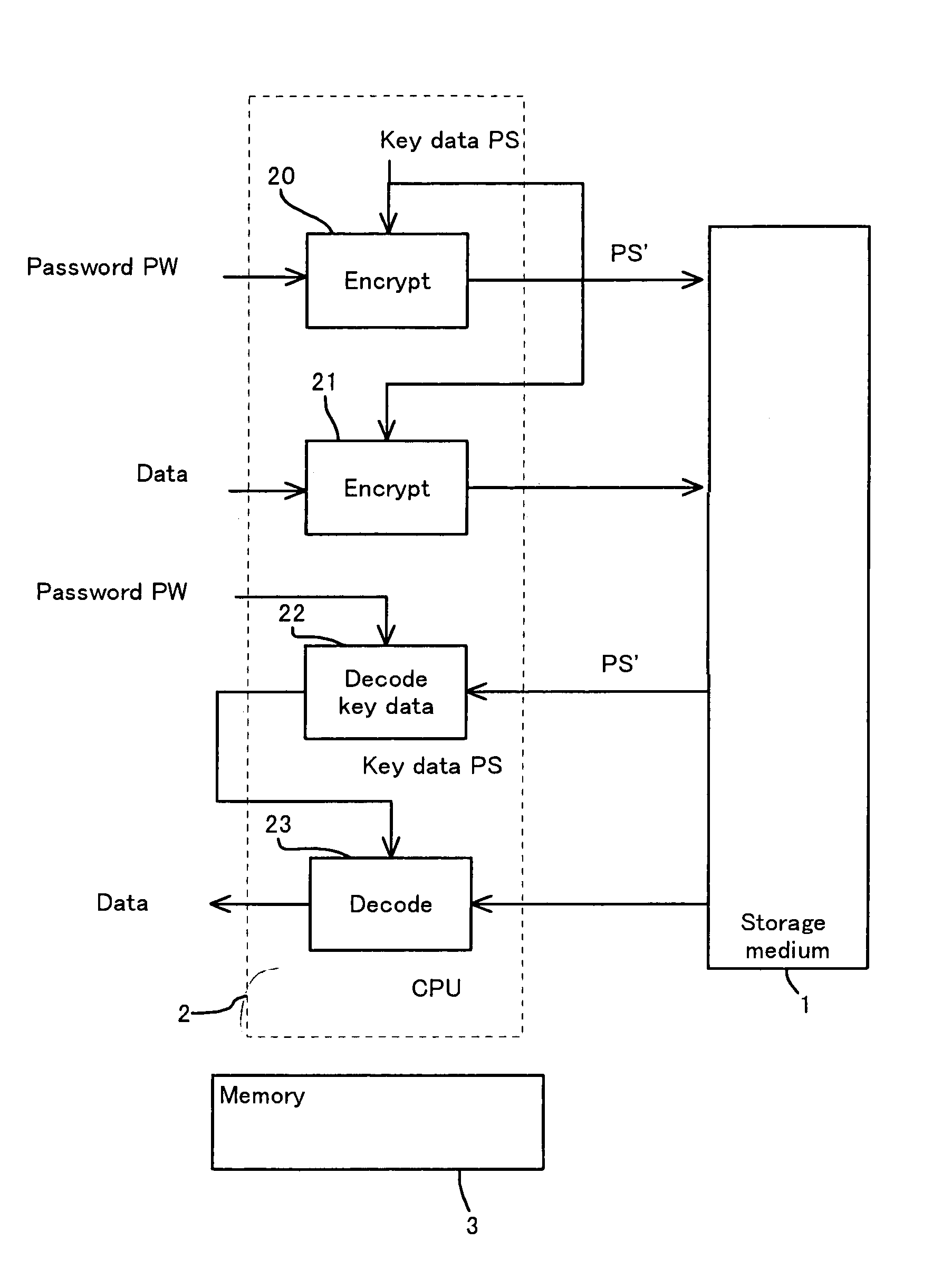
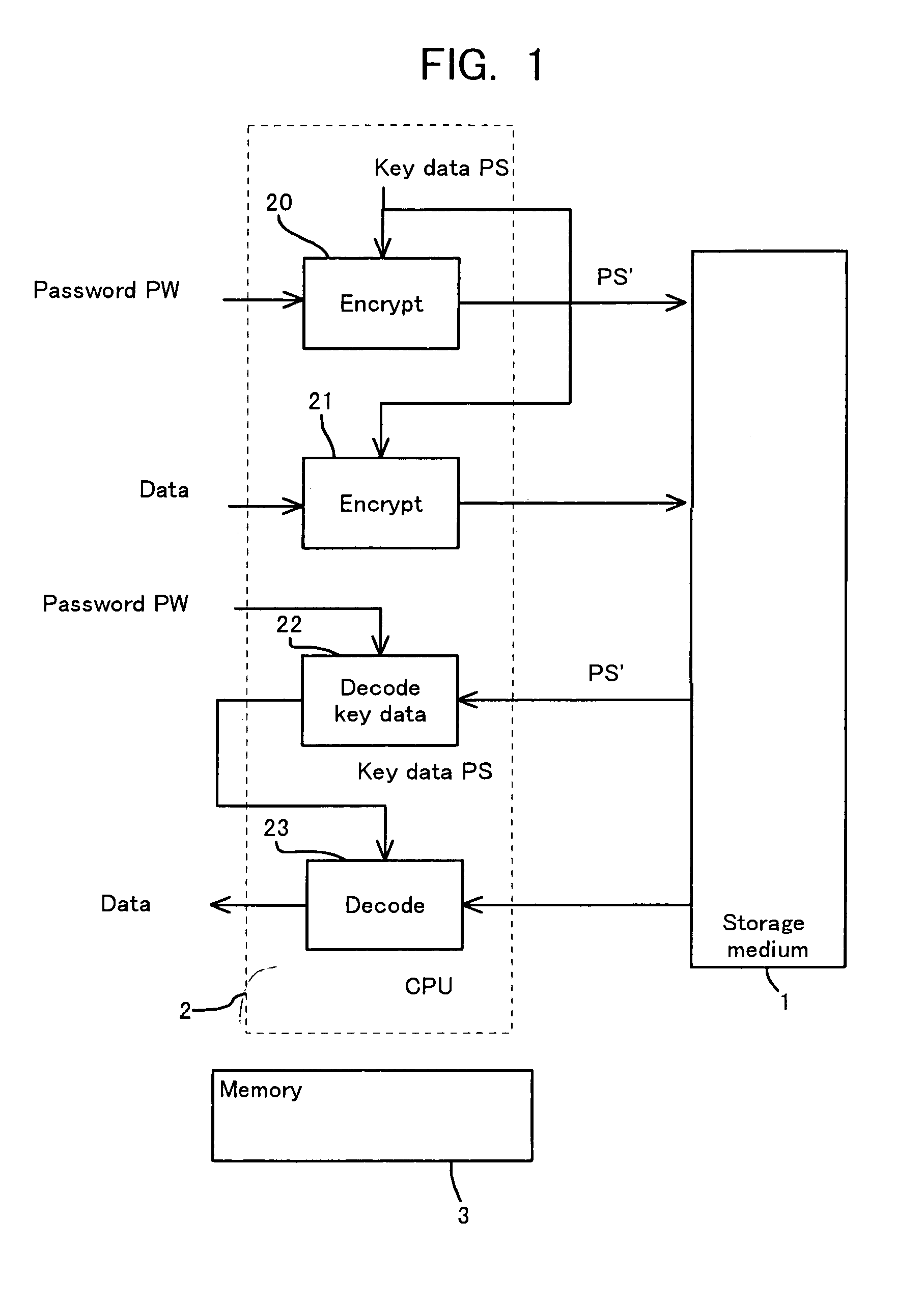
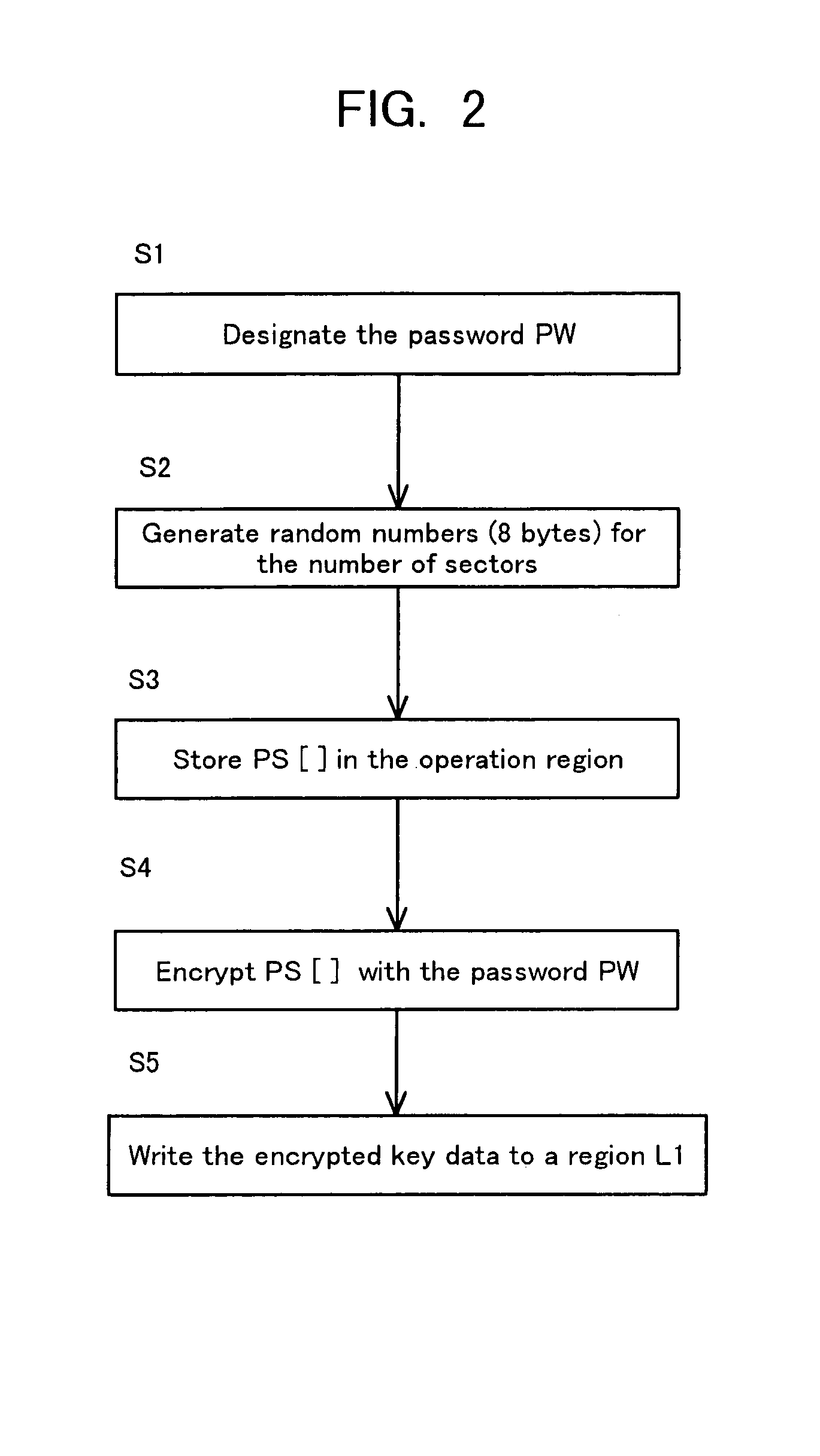
InactiveUS7051213B1Difficult to analyzePrevent decipheringInput/output to record carriersDigital data processing detailsCiphertextPassword
Disclosed are a method and an apparatus for protecting data on a storage medium by encrypting the data to be recorded on the storage medium with a password. This method comprises a step of, generating, for changing key data on each memory unit by one password, the key data, thereafter encrypting the key data with the password and writing the encrypted data to the storage medium, and a step of encrypting the data with the key data and encrypted data to the storage medium. The method further comprises a step of reading the encrypted key data from the storage medium, a step of decoding the encrypted key data with the password, and a step of decoding the data on the storage medium with the decoded key data. The encryption is done by using the key data generated separately from the password, and it is therefore feasible to prevent the password from being analyzed by decoding a cipher text.
Owner:FUJITSU CLIENT COMPUTING LTD
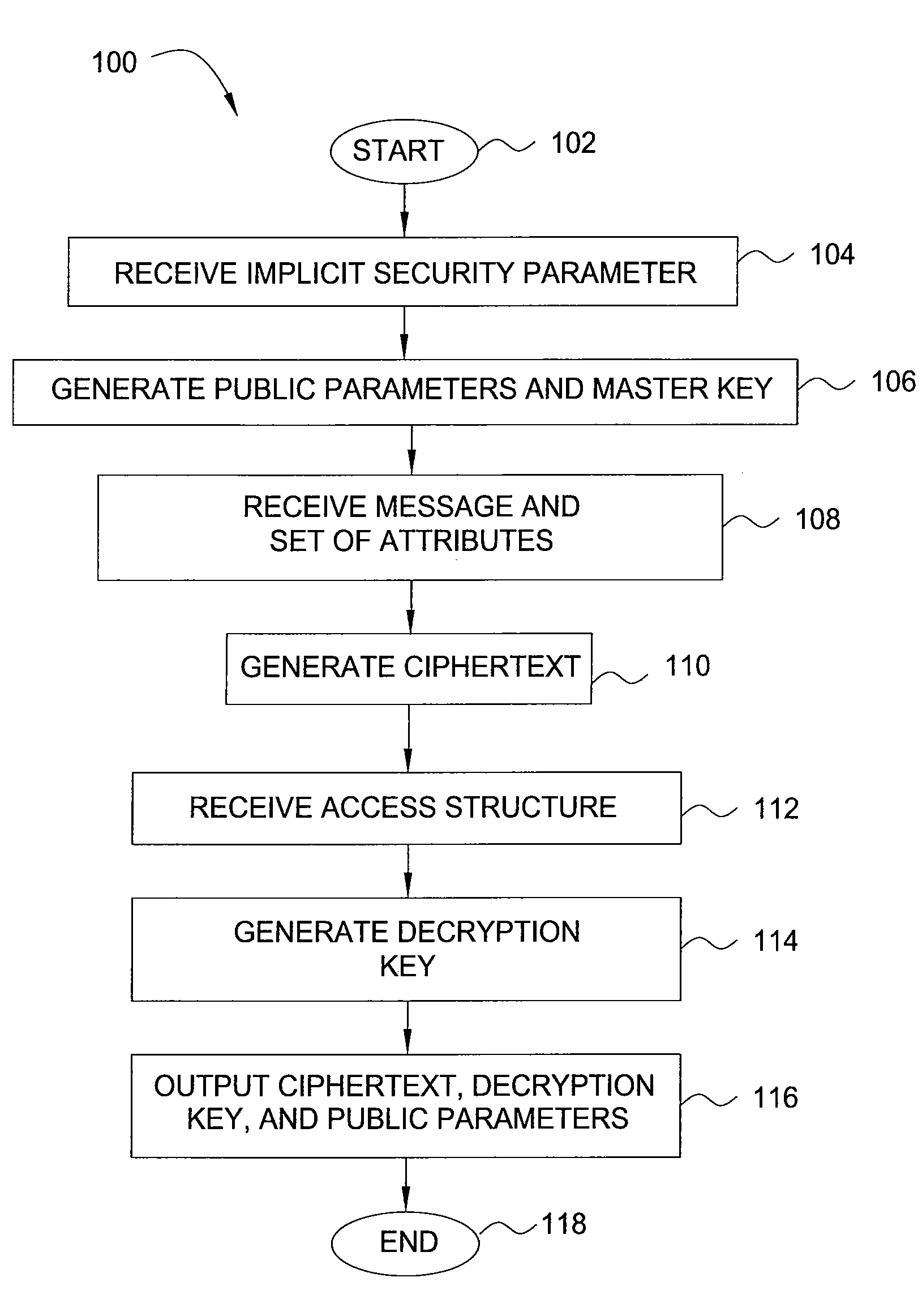
Method and apparatus for encrypting data for fine-grained access control
InactiveUS20090080658A1Encryption apparatus with shift registers/memoriesDigital data processing detailsAccess structureCiphertext
In one embodiment, the present invention is a method and apparatus for encrypting data for fine-grained access control. One embodiment of a method for encrypting data includes encrypting the data as a ciphertext, labeling the ciphertext with a set of one or more descriptive attributes, generating a decryption key for decrypting the ciphertext, associating an access structure with the decryption key, such that the data is recoverable from the ciphertext using the decryption key only if the set of one or more descriptive attributes satisfies the access structure, and outputting the ciphertext and the decryption key.
Owner:RGT UNIV OF CALIFORNIA +1
Method of blockchain information encryption based on complete homomorphic encryption method
ActiveCN107666388AImprove data securityImprove confidentialityUser identity/authority verificationDigital data protectionPlaintextThird party
A method of blockchain information encryption based on a complete homomorphic encryption method comprises: performing complete homomorphic encryption of a plaintext to be encrypted through an information encryption side and then performing signature; publishing a verification request to all the nodes in a network in public through adoption of an encrypted plaintext; respectively employing blockchain public keys by all the nodes to perform blockchain verification of the signature and an information receiving side, and employing complete homomorphic public keys to perform homomorphic encryptionoperation verification of the ciphertext; and after the verification passes, packing the information encryption side information, the information receiving side information and the ciphertext to generate an updated blockchain, performing broadcast of the network, and completing updating operation of the blockchain. The method provided by the invention greatly improve data safety and privacy of theblockchain technology, is more concise in the whole structure and effective, does not need to introduce a trusted third party and greatly extend and improve an original blockchain technology model, and only needs the smallest improvement to reach a secrecy effect.
Owner:郑珂威
Safe storage method based on a plurality of cloud storage systems and system thereof
InactiveCN103118089AImprove fault toleranceAvoid inaccessibilityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCode moduleCiphertext
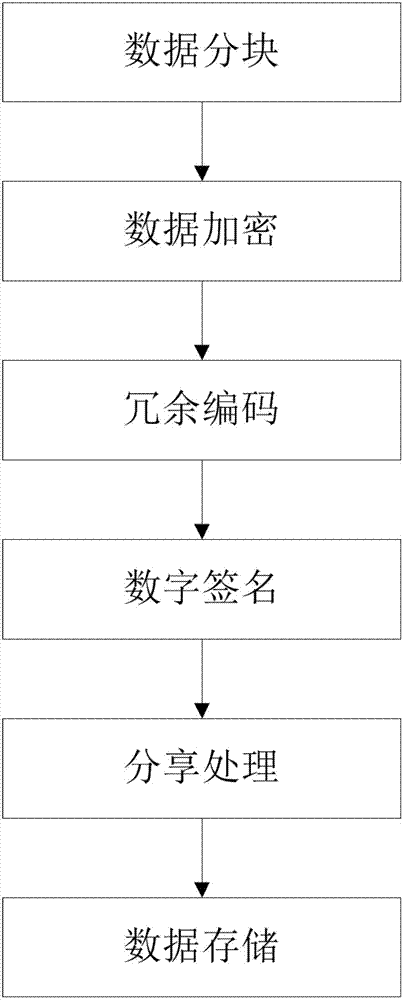
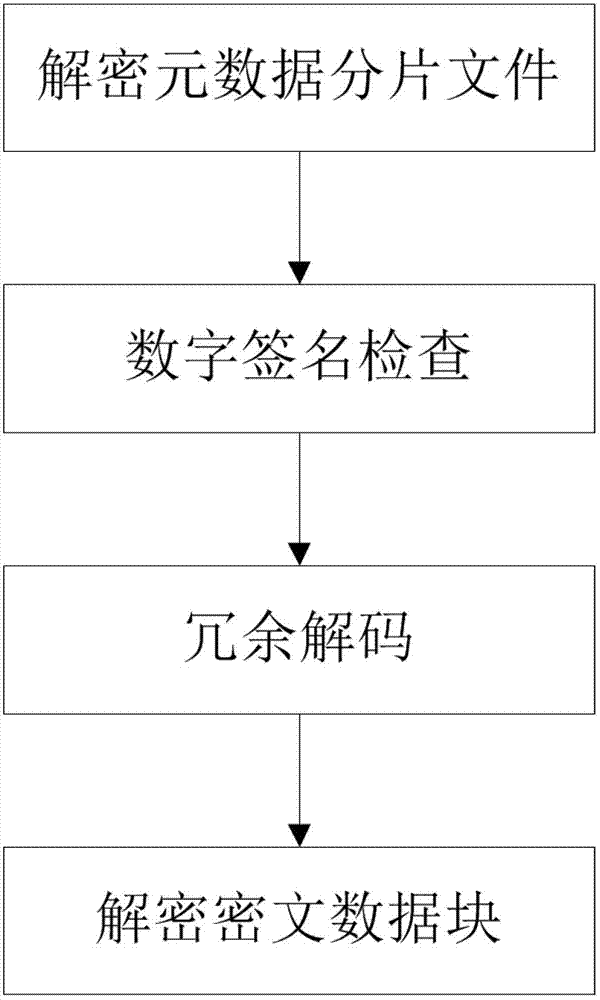
The invention belongs to the technical field of computer storage, and provides a safe storage method based on a plurality of cloud storage systems and a system thereof. The method and the system can achieve the purpose that in the plurality of existing cloud storage systems, safety of data and metadata can be guaranteed at the same time. The safe storage method comprises a step of data writing operation and a step of data reading operation, wherein the step of data writing operation comprises the sub-steps of data partitioning, data encryption, redundancy encoding, digital signature, sharing processing, and data storage. The step of data reading operation comprises the sub-steps of metadata partition file decryption, digital signature inspection, redundancy decoding and cipher text data block decryption. The safe storage system comprises an encryption and decryption coding module, a redundancy encoding module, a secret sharing module and a digital signature module. By means of the method and the system, metadata privacy and high availability can be guaranteed, and meanwhile, a user does not need to store any metadata information for indexing and data query.
Owner:HUAZHONG UNIV OF SCI & TECH
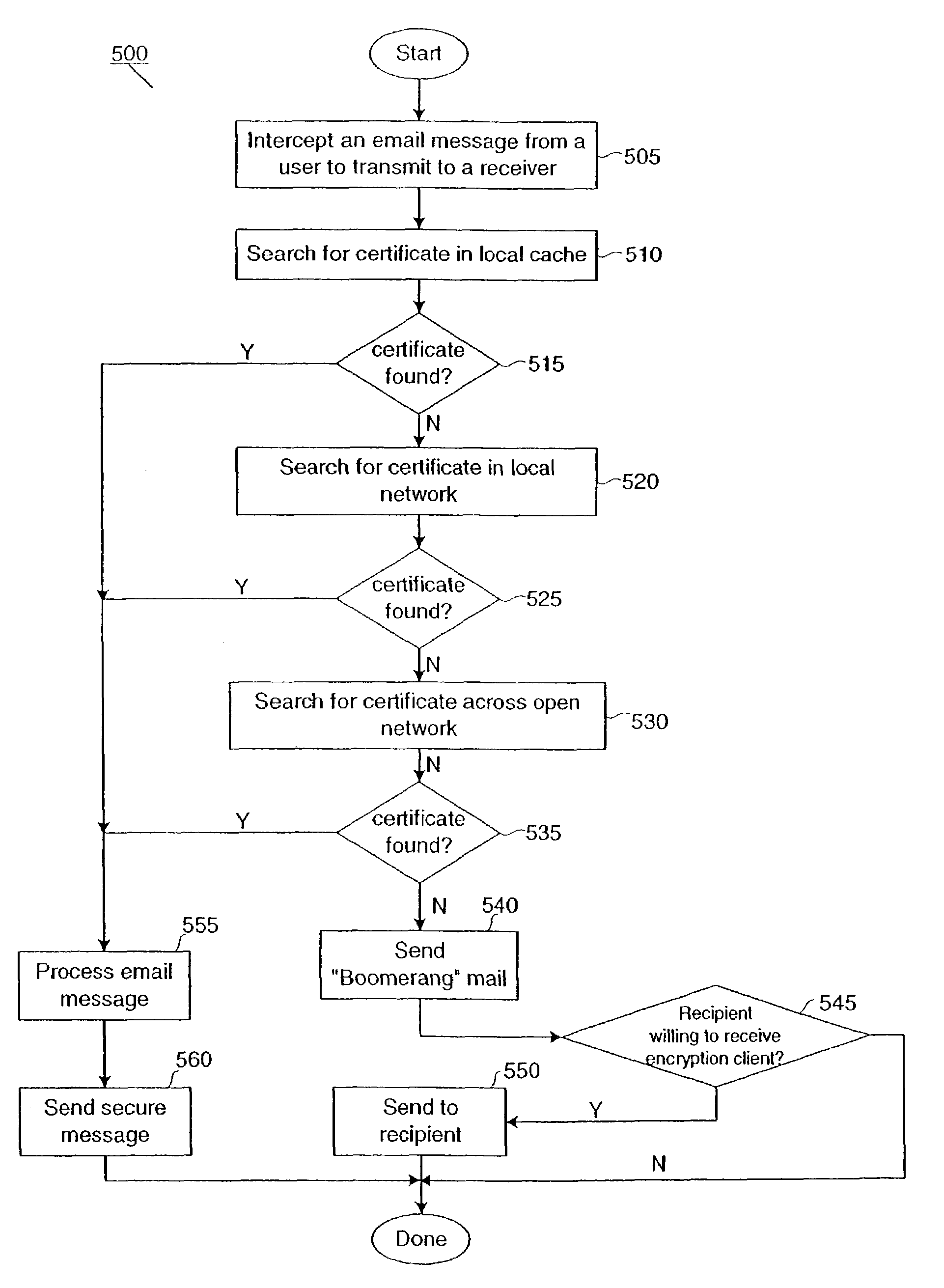
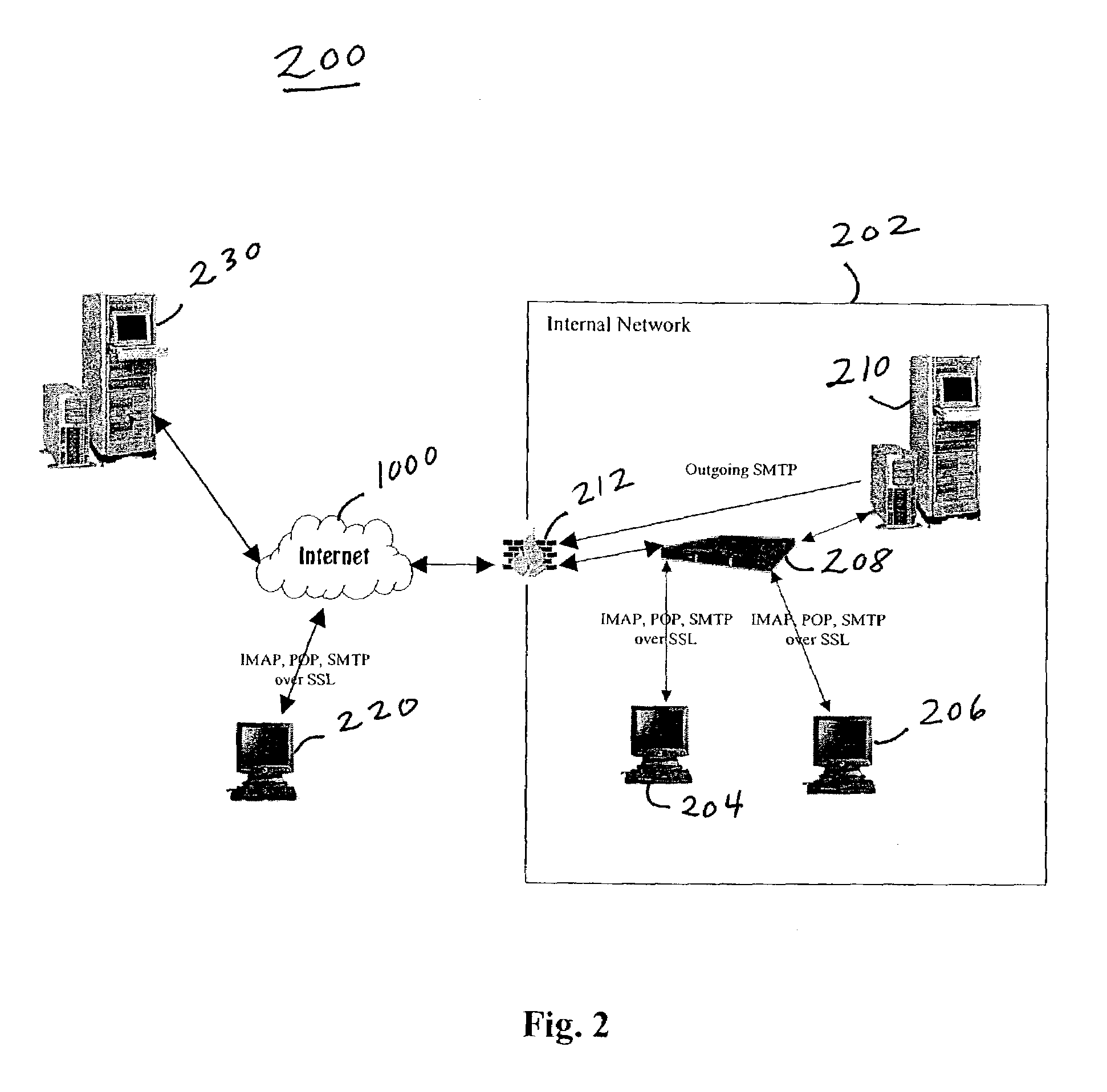
System and method for secure electronic communication in a partially keyless environment
InactiveUS7640427B2Reduce the burden onImprove securityPublic key for secure communicationMultiple digital computer combinationsDigital identityPlaintext
This present invention provides users with secure transparent electronic communication, allowing them to send and receive encrypted and / or signed messages with little or no user involvement. In various embodiments, the present invention provides a user with e-mail security via automated hierarchical techniques for transparently sending and receiving secure messages, and lowers the burden on administrators. Such a system can also manage cryptographic keys and certificates for the users, and creates such keys and certificates for the users when necessary. A server according to the present invention can intercept unsecured messages from a user, automatically transform those messages into secured messages, and transmit those secure messages to the intended recipients. The server can also automatically transform messages after the recipient sends a digital identity to the server and downloads the software necessary for transforming the secured messages back into readable messages (i.e., from ciphertext into plaintext). The server can further intercept an unsecured message from a user, search for a digital identity of the intended recipient, secure the unsecured message upon finding such a digital identity, and transparently send the secured message to the intended recipient.
Owner:CA TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com