Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
842 results about "Message authentication code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
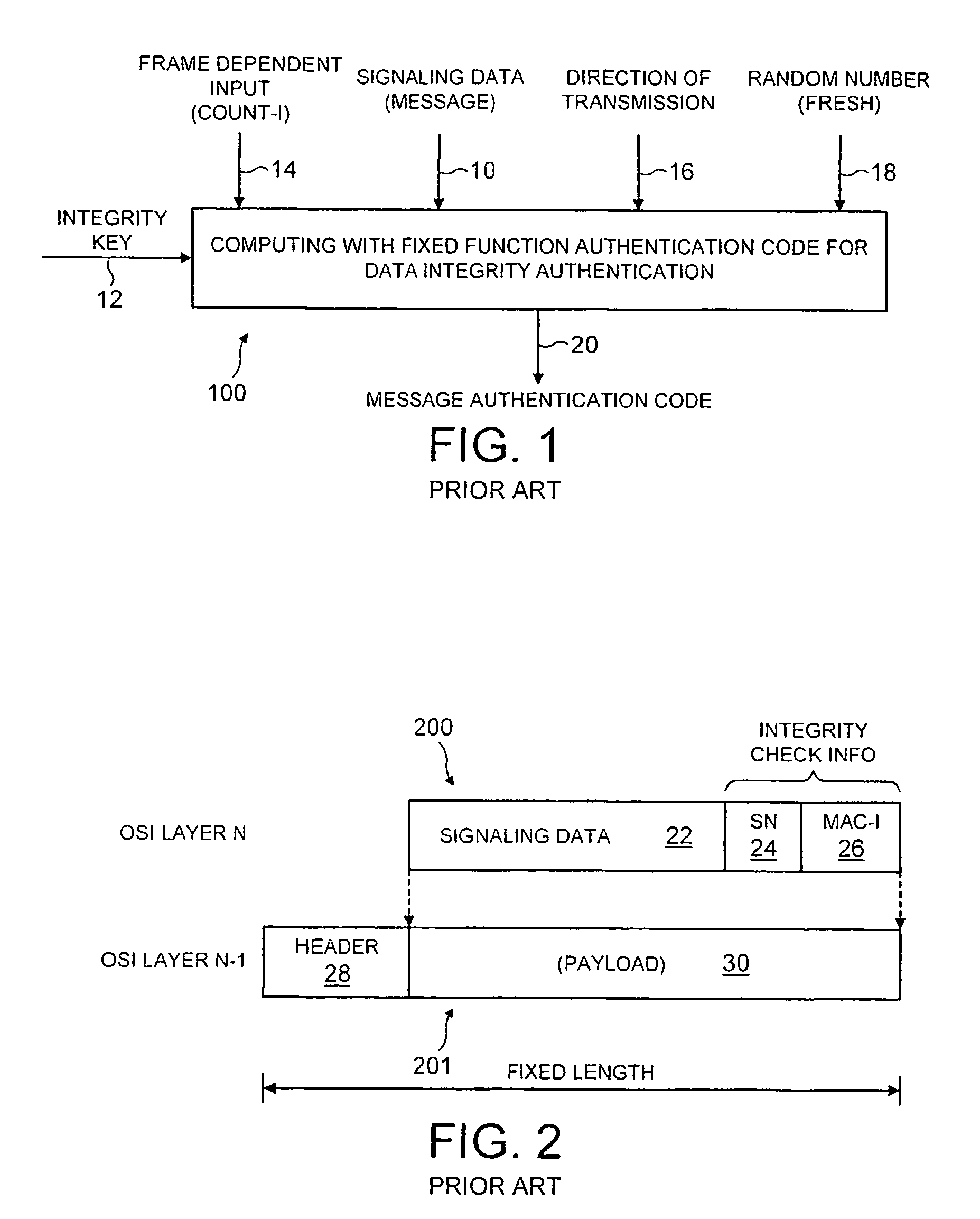
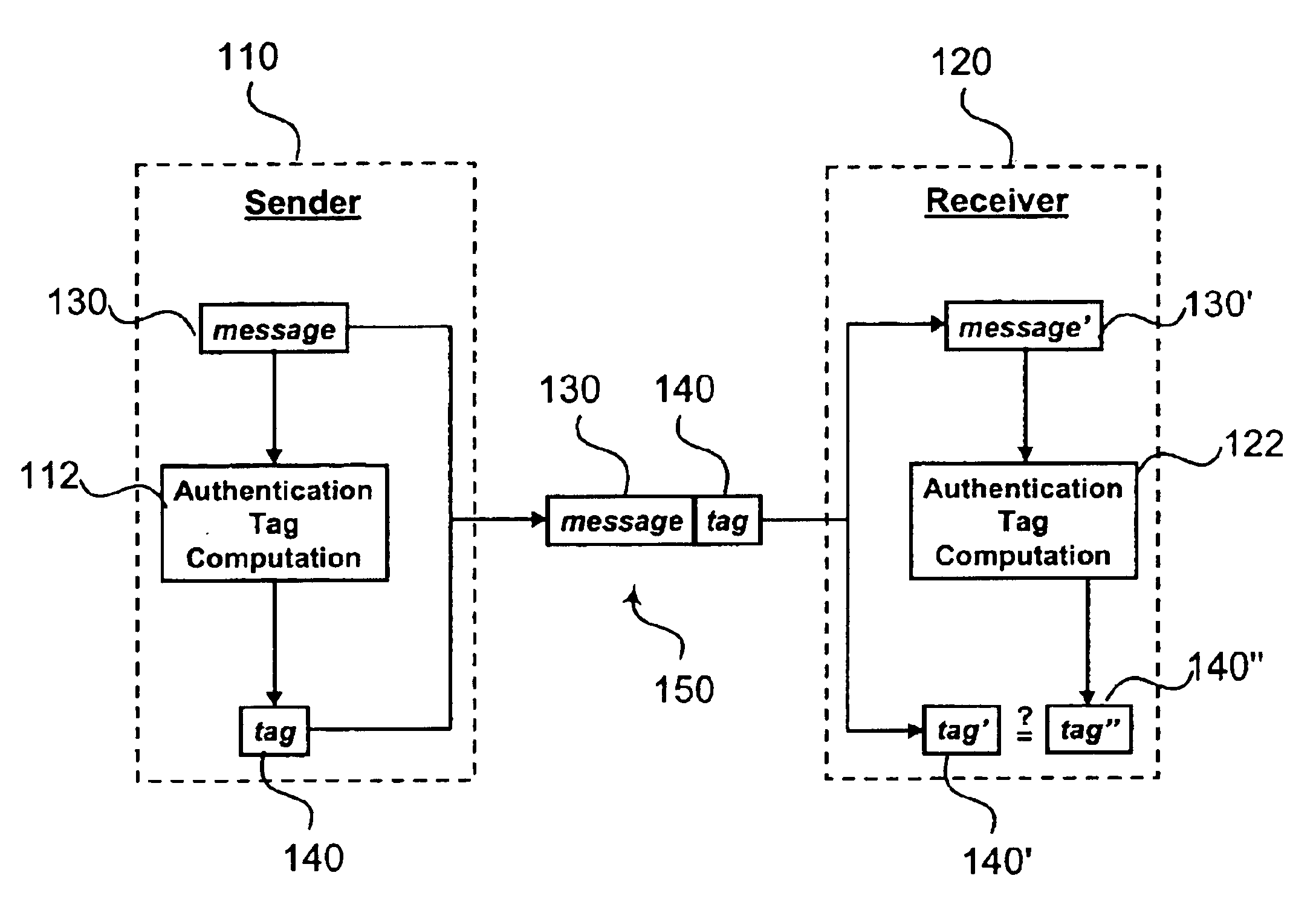
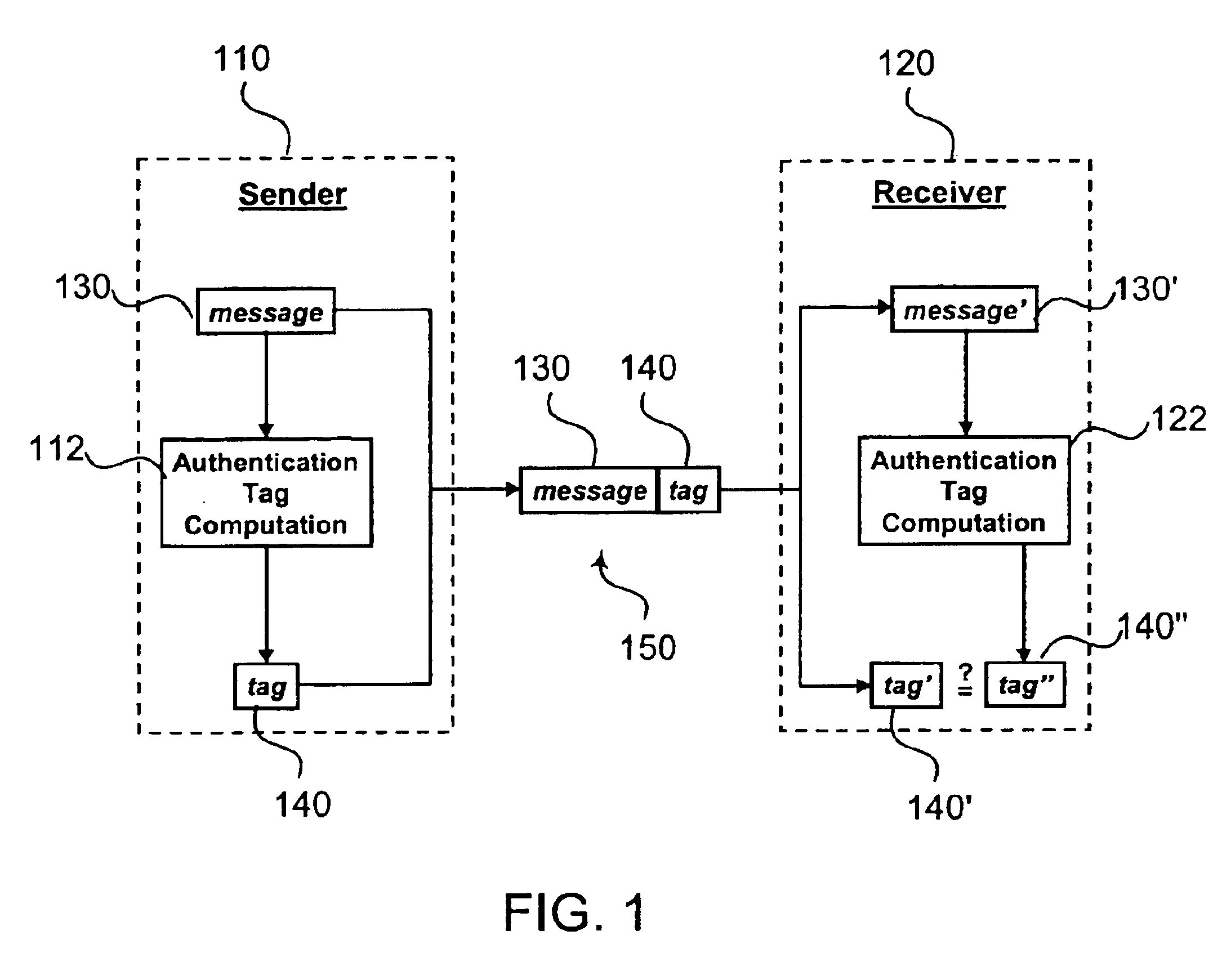
In cryptography, a message authentication code (MAC), sometimes known as a tag, is a short piece of information used to authenticate a message—in other words, to confirm that the message came from the stated sender (its authenticity) and has not been changed. The MAC value protects both a message's data integrity as well as its authenticity, by allowing verifiers (who also possess the secret key) to detect any changes to the message content.
Message authentication
InactiveUS20050033960A1Reduce bandwidth usageUser identity/authority verificationComputer hardwareCommunications system
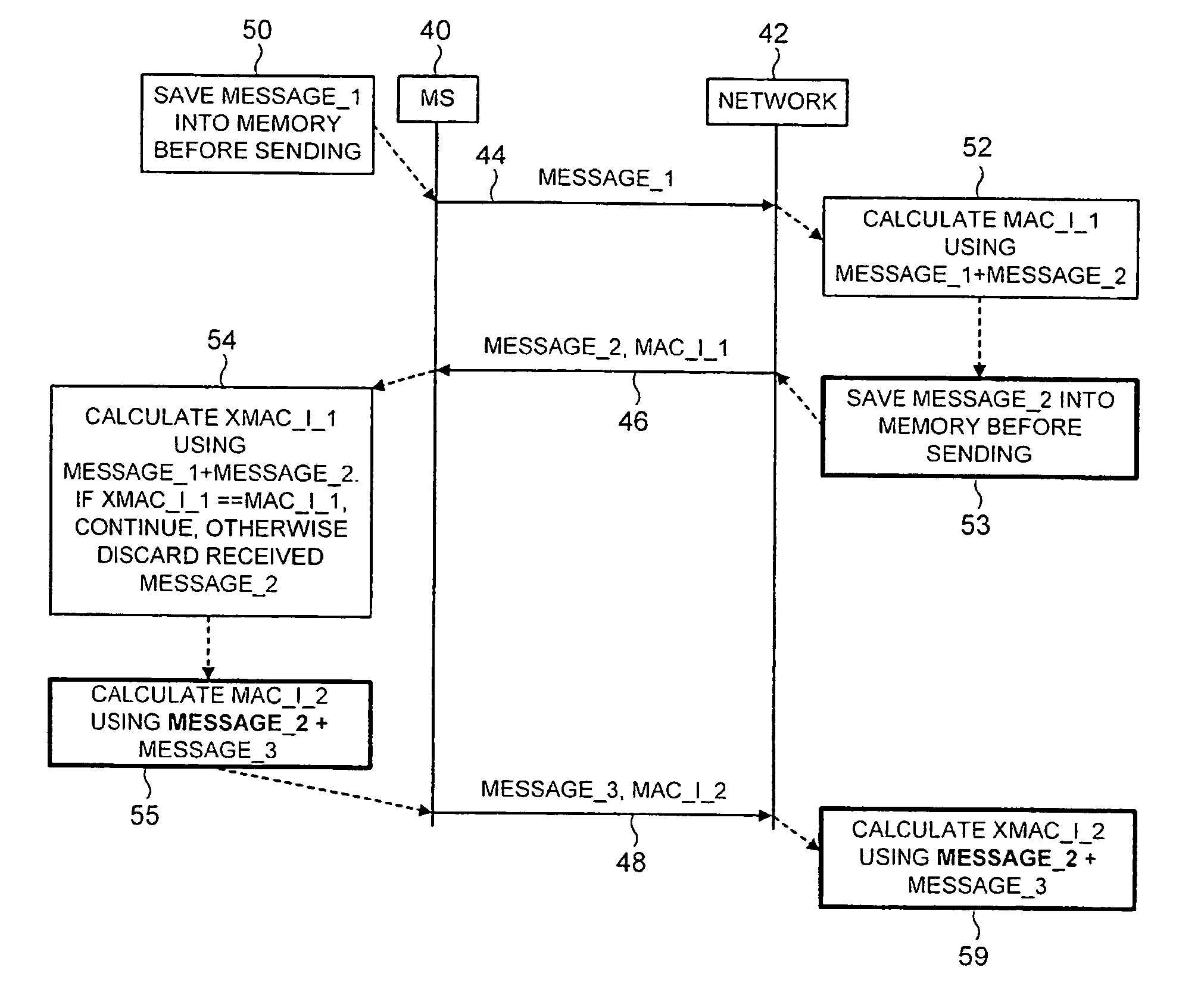
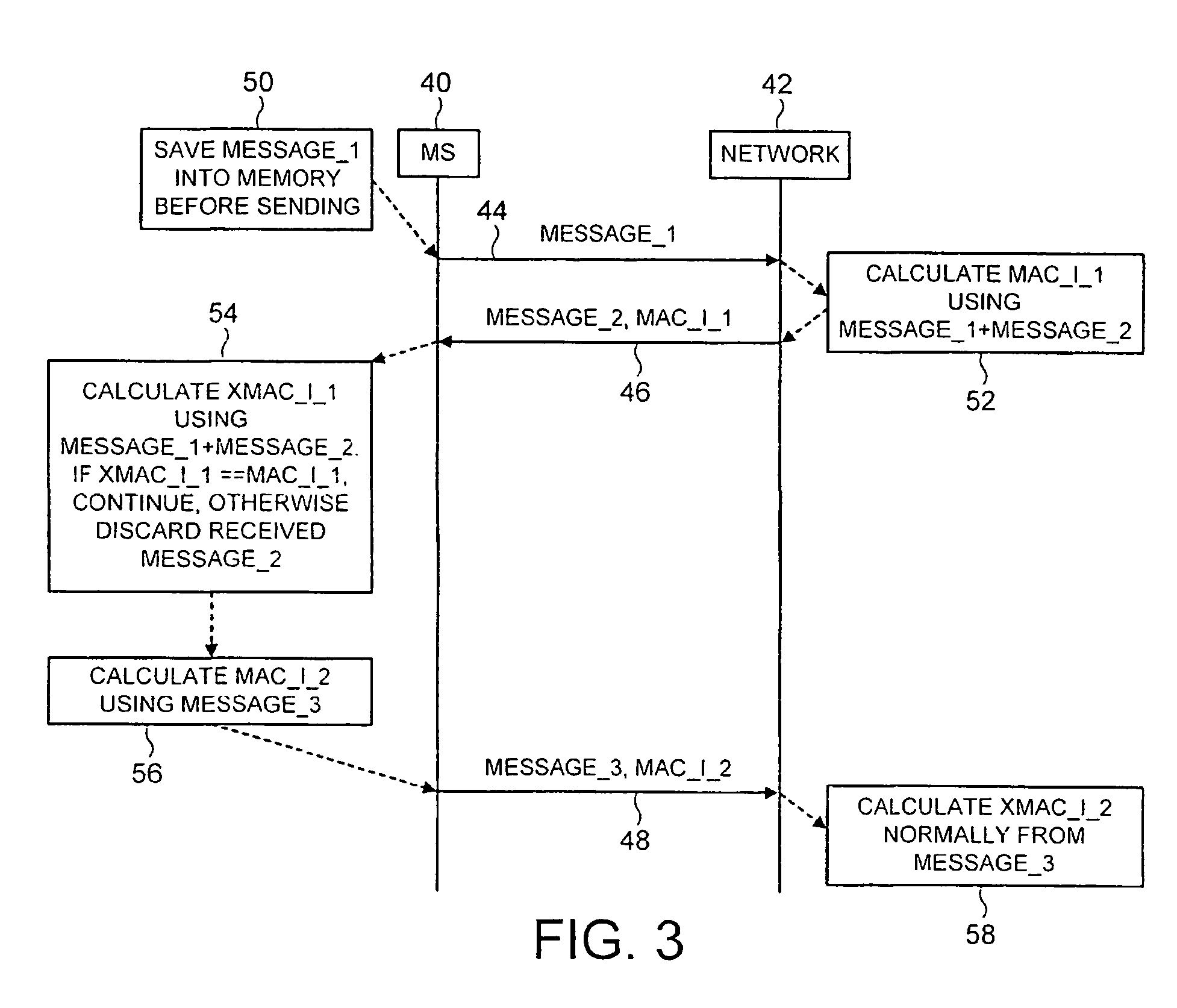
There is disclosed a technique of providing message authentication in a communication system comprising the steps of: transmitting a first message from a first device to a second device; transmitting a second message from the second device to the first device, the second message including a message authentication code determined using said first and second messages; transmitting a third message from the first device to the second device, the third messages including a message authentication code determined using the third message. The message authentication code of the third message may be additionally based on the second or the second and first messages.
Owner:NOKIA SOLUTIONS & NETWORKS OY
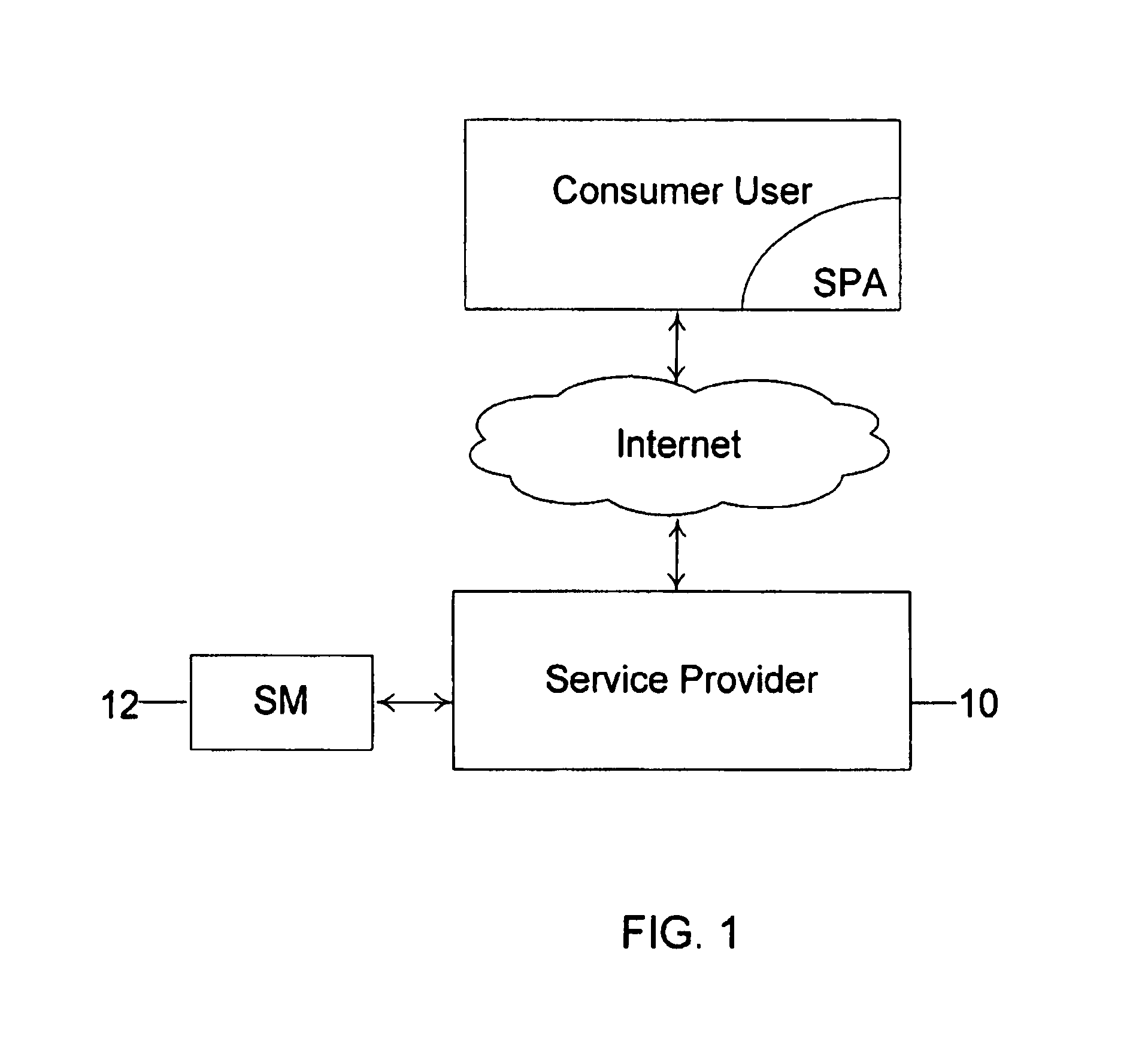
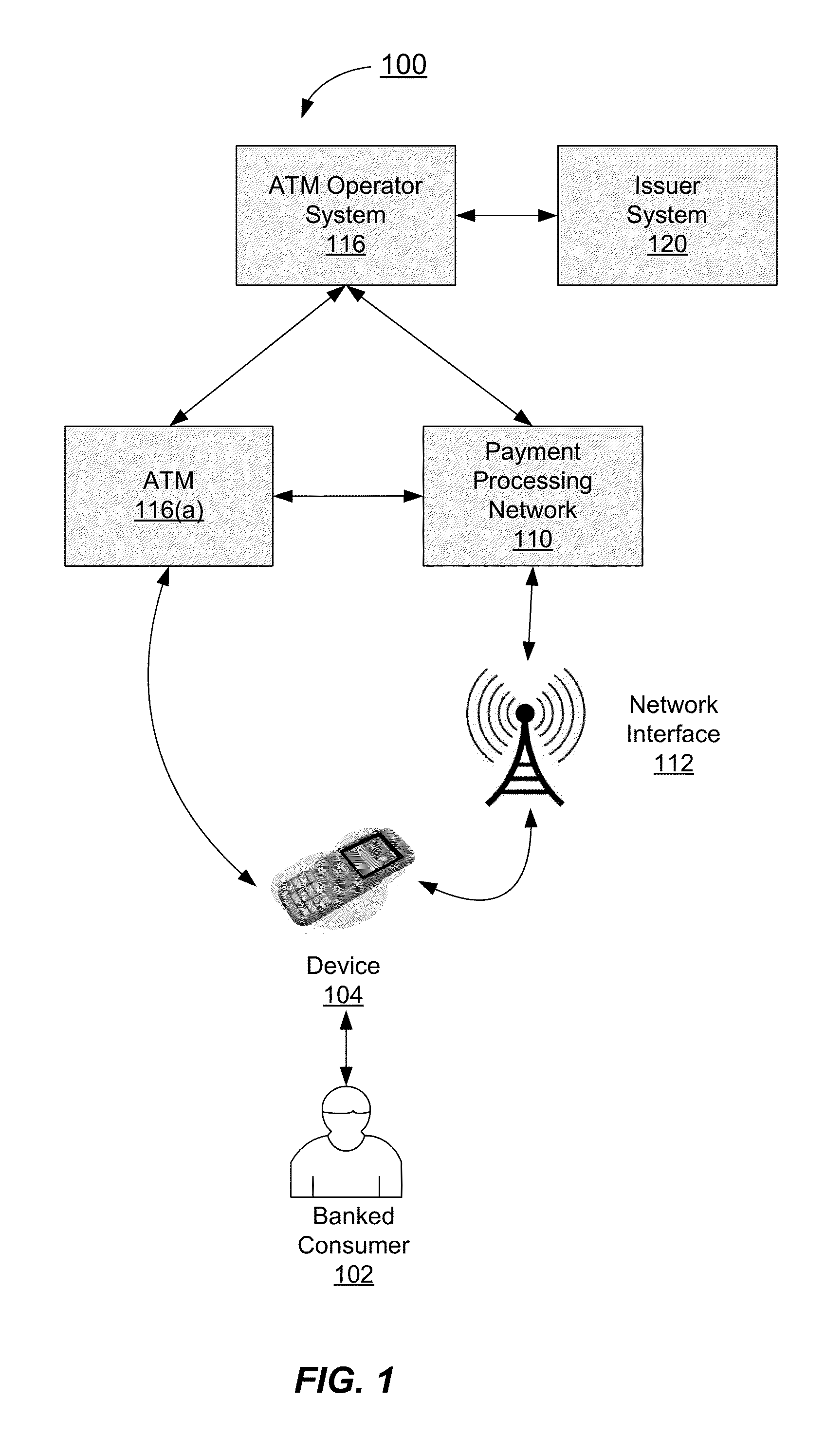
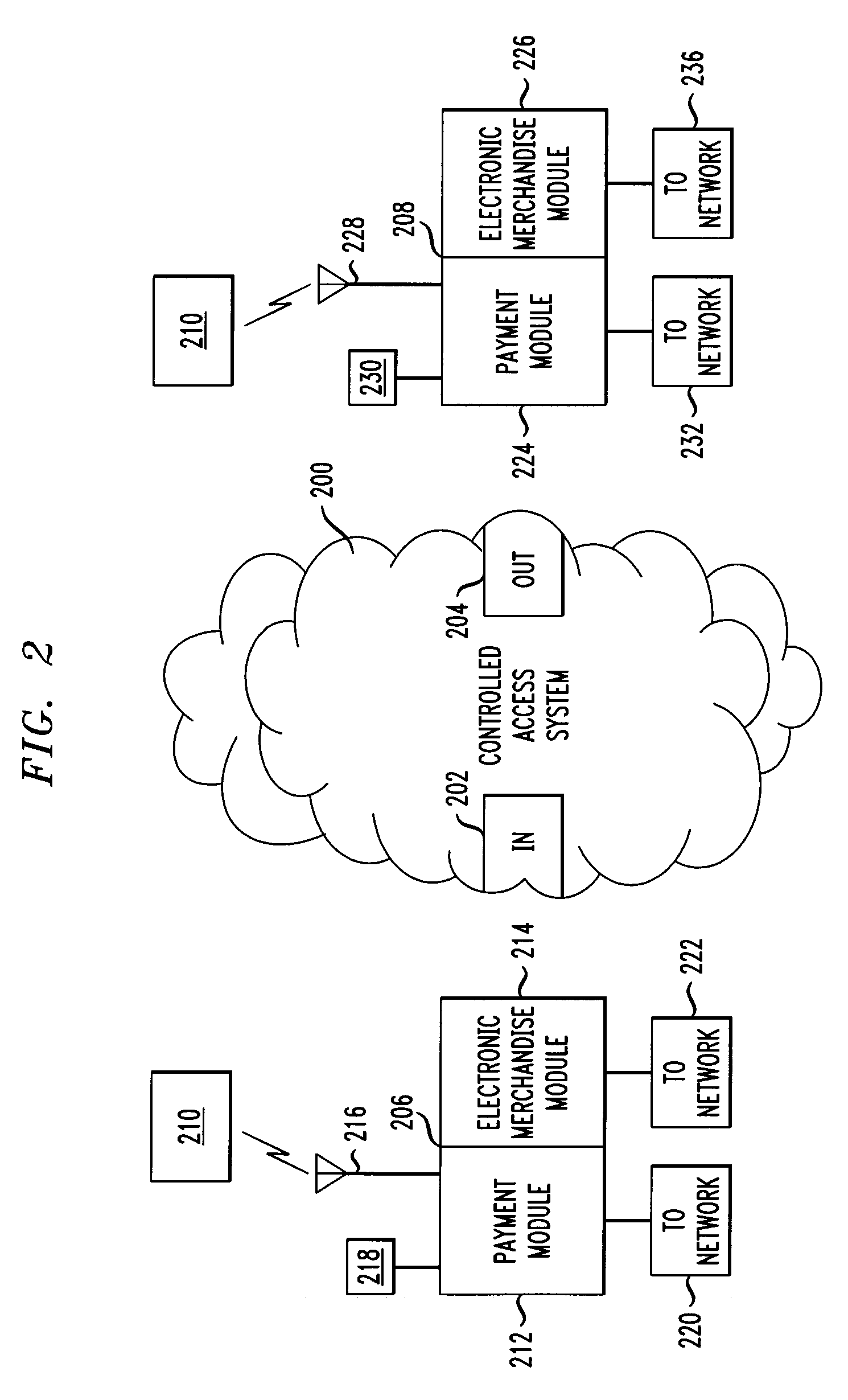
Method and system for conducting secure payments over a computer network without a pseudo or proxy account number
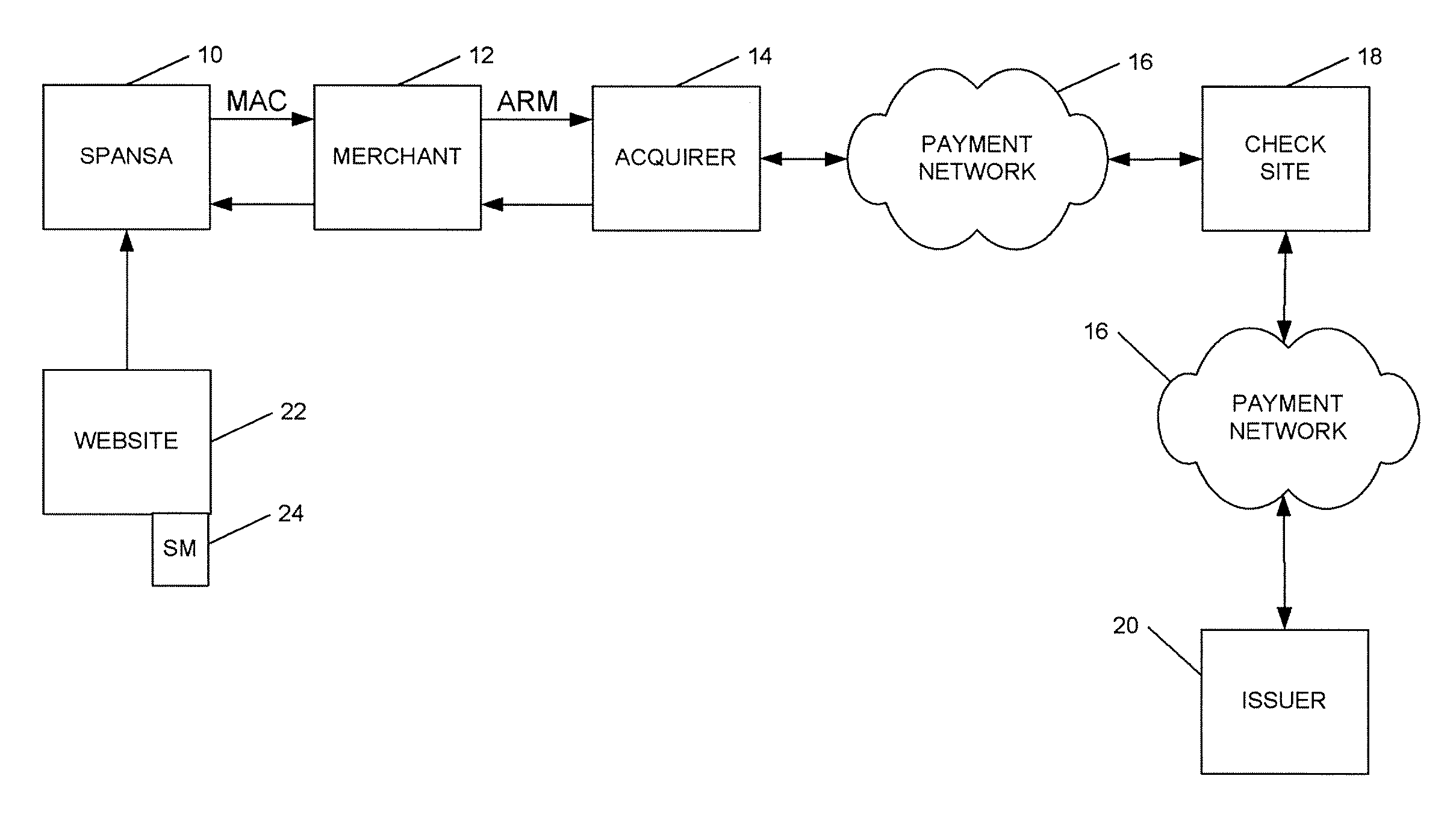
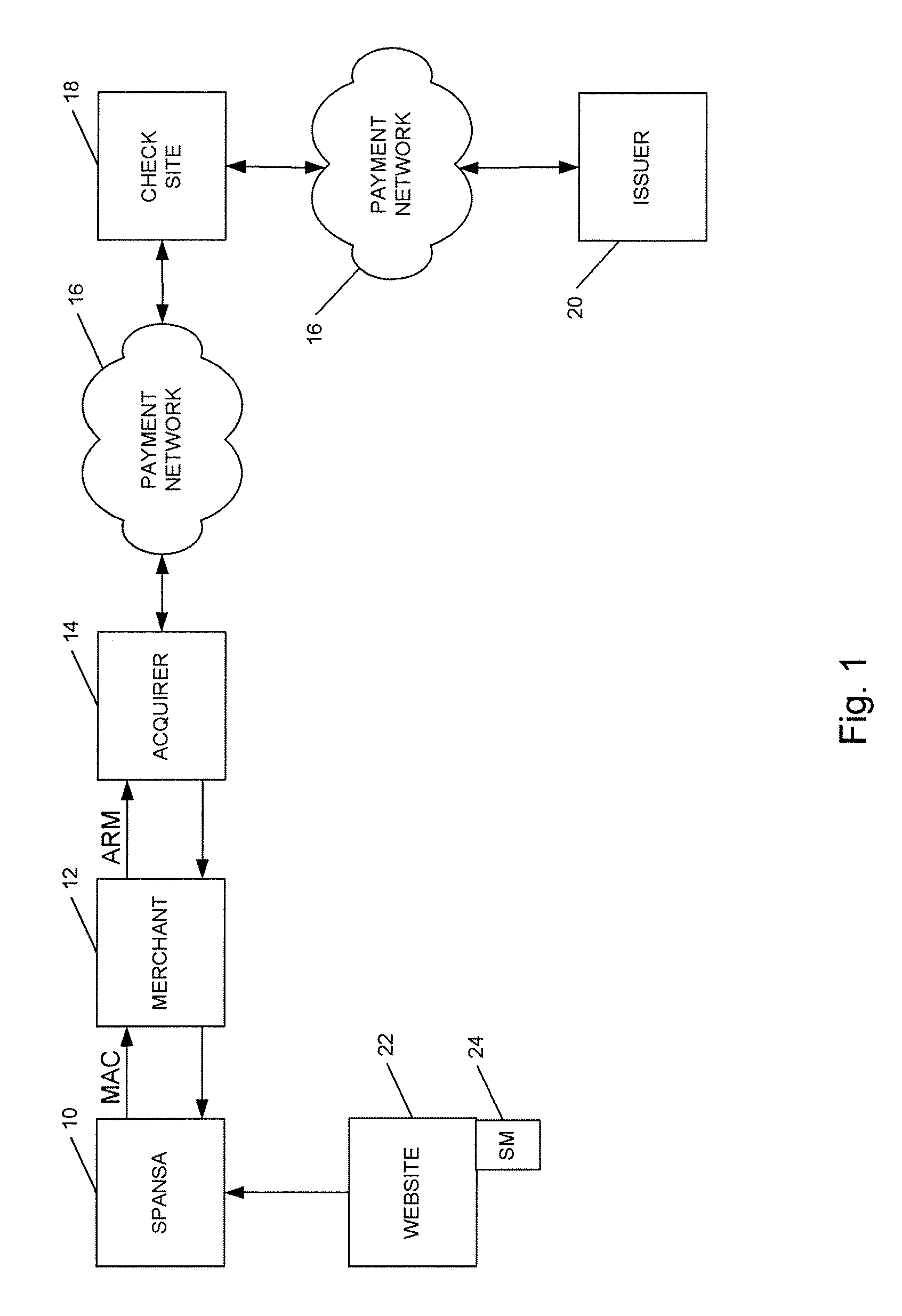
A method is provided for conducting an electronic transaction with a payment account number having a certain amount of available funds, using a payment network and a “check site”. The method comprises the following steps: (a) generating a secret key associated with the payment account number; (b) using the secret key to generate a message authentication code (“MAC”) specific to the transaction; (c) generating an authorization request message including the message authentication code; (d) forwarding the authorization request message over the payment network to the check site for verifying the authenticity of the MAC; (e) verifying the message authentication code by the check site using the secret key; (f) responding to the authorization request message over the payment network based on the available funds and the transaction amount.
Owner:MASTERCARD INT INC
Method and system for conducting secure payments over a computer network
A method is provided for conducting a financial transaction by a purchaser with a merchant having an acquirer bank, over a communications network. The method includes the steps of sending a first authorization request using a pseudo account number associated with a real account number to a service provider which forwards a second authorization request to the issuer using the real account number and preferably a pseudo acquirer code associated with the service provider such that the response to the second request is based on the real account number and sent back to the service provider who preferably forwards a response to the first request preferably to the “real” acquirer. A message authentication code is further provided which includes transaction data, and where the authorization request is formatted as a standard payment card track having one or more fields including a discretionary field in which the message authentication code is placed.
Owner:MASTERCARD INT INC
Method and system for conducting secure payments over a computer network
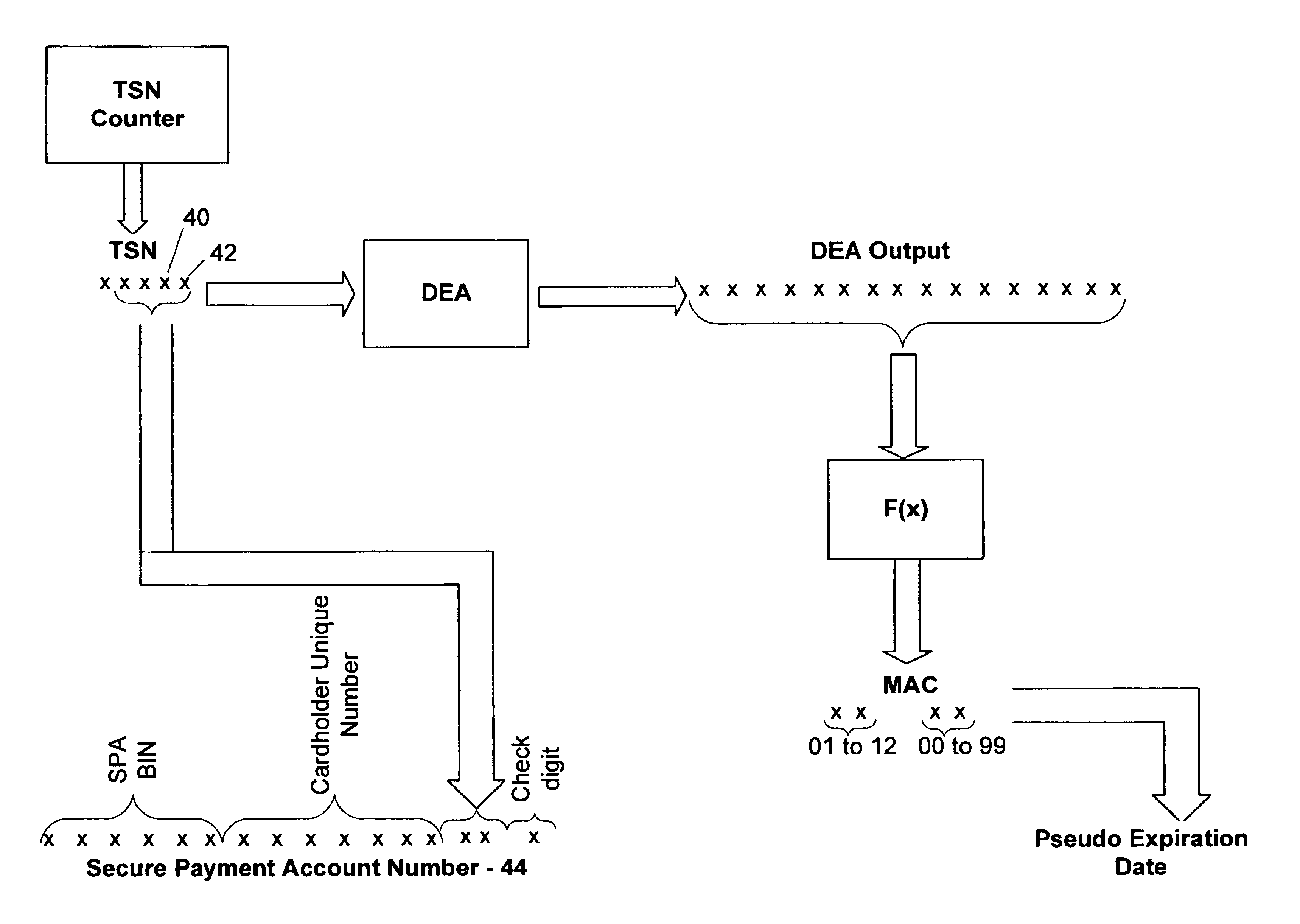
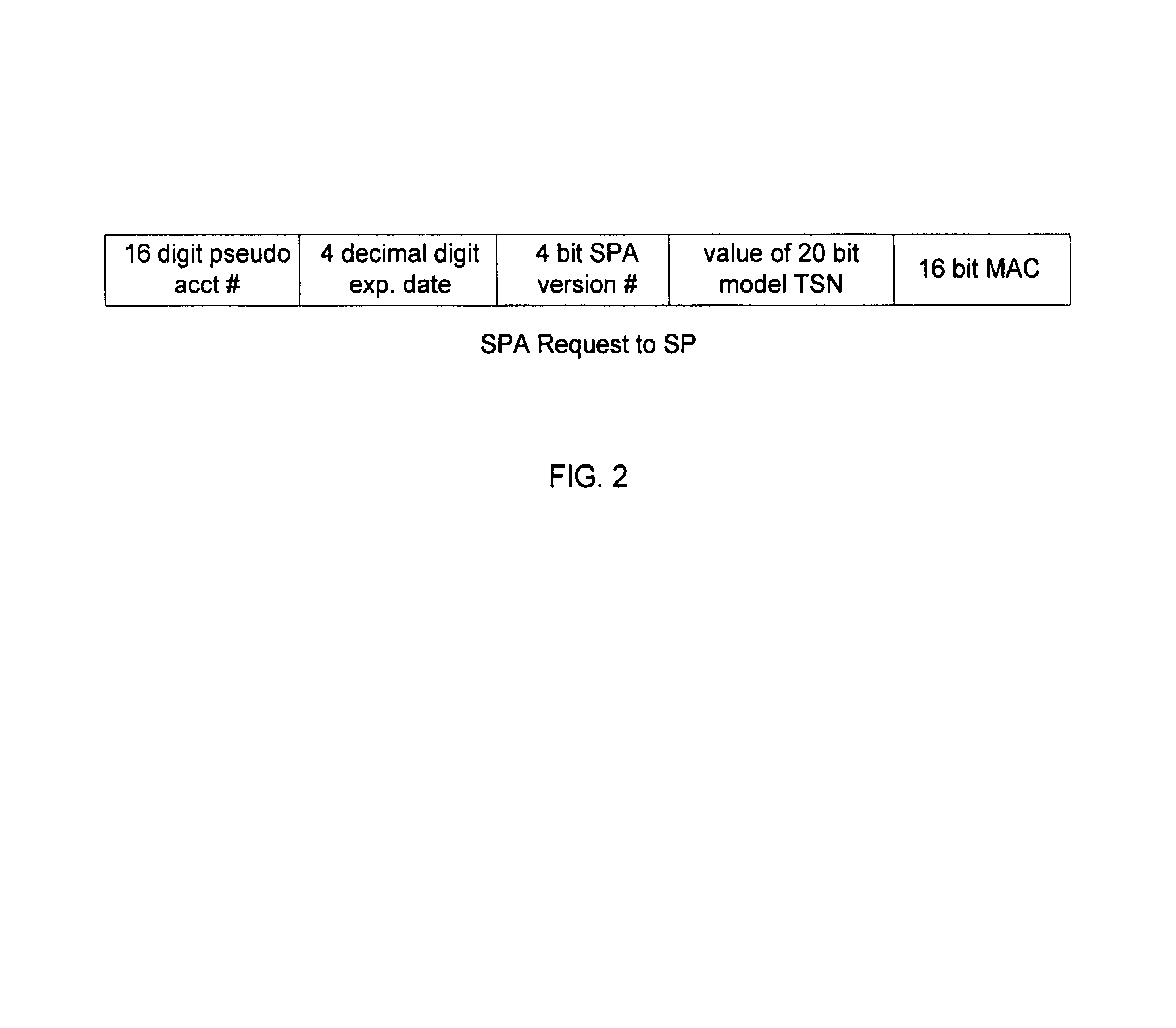
A secure method of conducting an electronic transaction over a public communications network is provided which utilizes a pseudo-expiration date in the expiration date field of an authorization request. One of the preferred methods comprises:generating a per-card key associated with an account number;generating a message authentication code using the per-card key;converting the message authentication code into a pseudo expiration date;generating an authorization request for the transaction, the request having an expiration date field containing the pseudo expiration date; andverifying the message authentication code based on the pseudo expiration date.Another embodiment of the invention includes a method of conducting an electronic transaction over a public communications network, with a payment account number having an associated pseudo account number, comprising:(a) providing the pseudo account number with a control field indicating one of a plurality of key-generation processes to be used to generate an authentication key;(b) generating an authentication key associated with the pseudo account number using one of the plurality of key-generation processes indicated in the control field of the pseudo account number;(c) using the authentication key to generate a message authentication code specific to the transaction;(d) generating an authorization request message including the message authentication code and the pseudo account number; and(e) verifying the message authentication code using the indicated key-generation process and the authentication key.
Owner:MASTERCARD INT INC
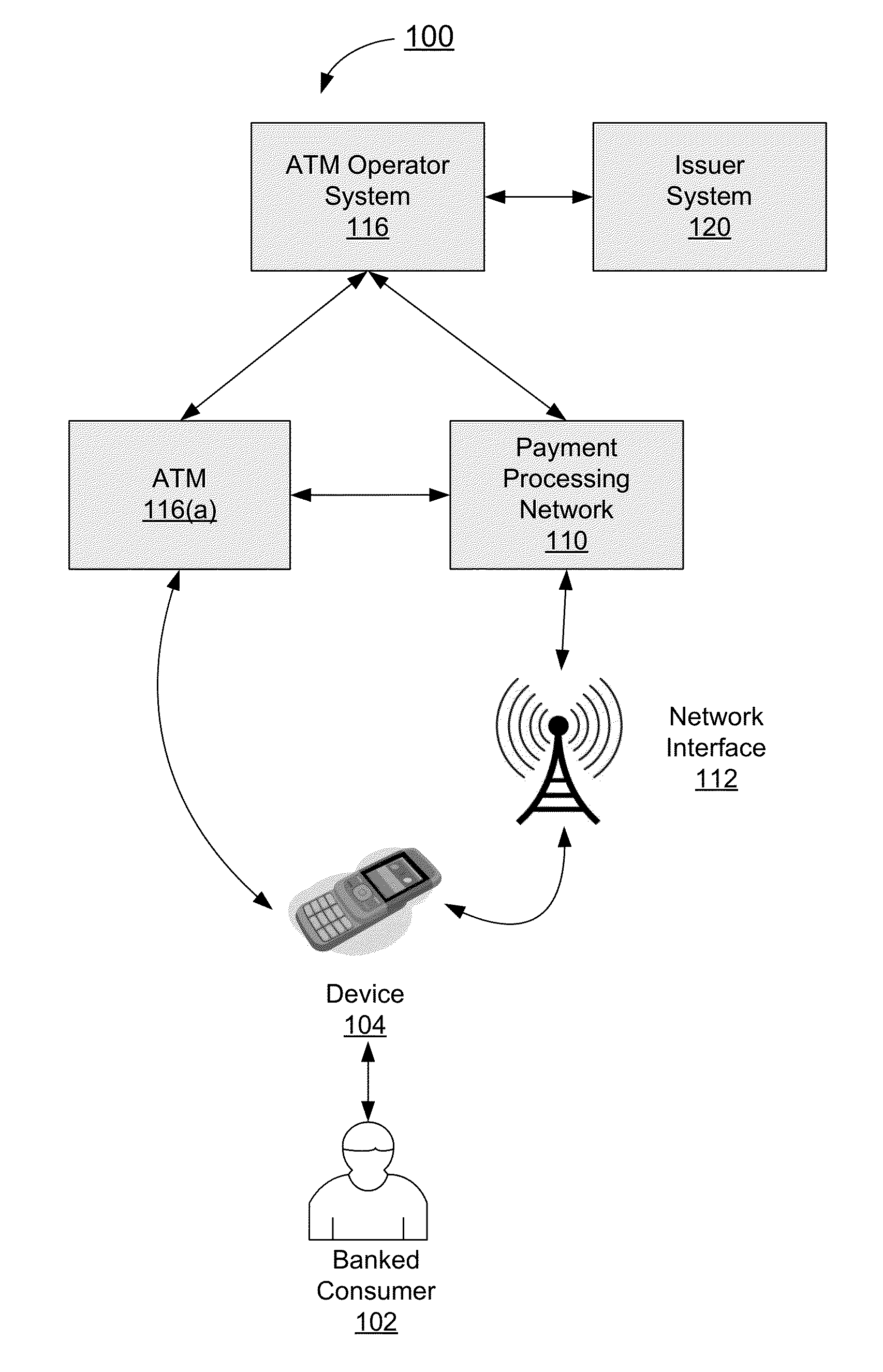
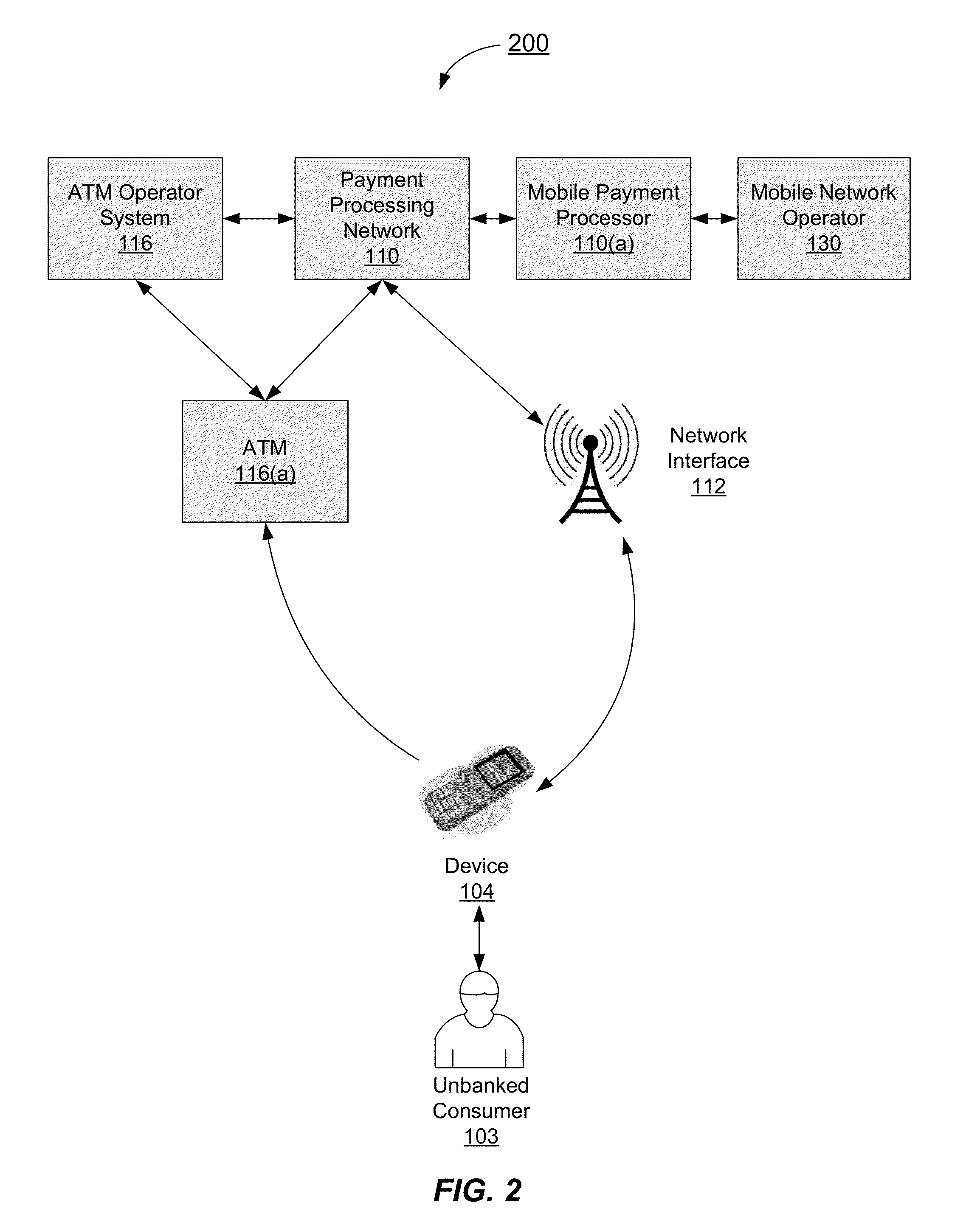
Authentication process for value transfer machine
InactiveUS20130226799A1Prolong transaction processComplete banking machinesFinanceComputer hardwareMessage authentication code
Embodiments of the invention are directed towards improved transaction processing methods and systems with transaction apparatuses, including a value transfer machine, using a device identifier instead of a value transfer machine card to process a transaction. One embodiment of the transaction may be directed to a transaction apparatus and a method including receiving an authentication code from a consumer, sending the authentication code to a first server computer, wherein if the received authentication code matches a generated authentication code, the first server sends a confirmation message. The method continues by receiving the confirmation message from the first server, receiving a secret token from the consumer, and sending an authorization request message to a second server computer. Thereafter, the transaction apparatus receives an authorization response message from the second server, indicating whether the secret token matches an expected token. Other embodiments are directed to first and second servers and corresponding methods.
Owner:VISA INT SERVICE ASSOC
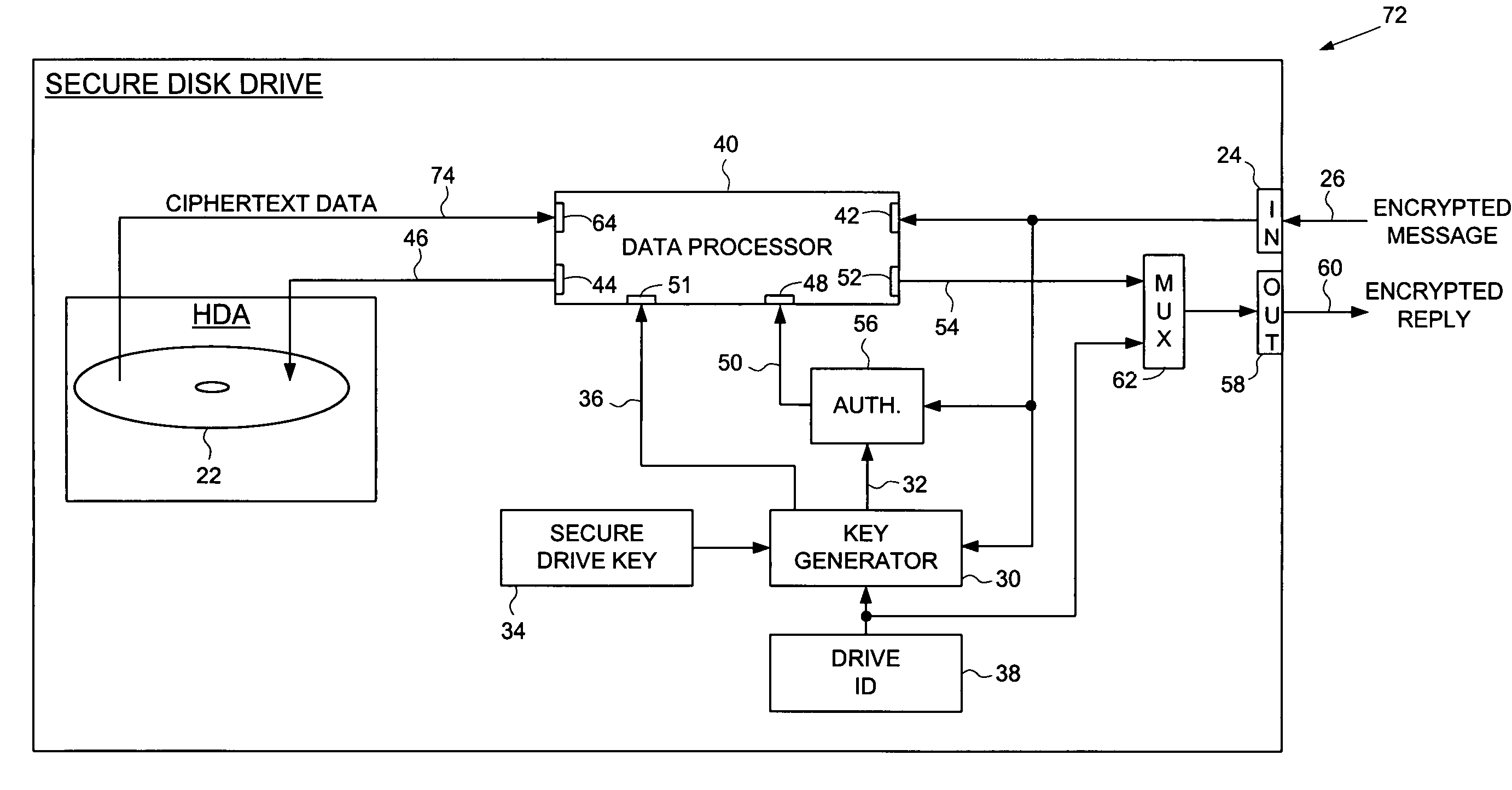
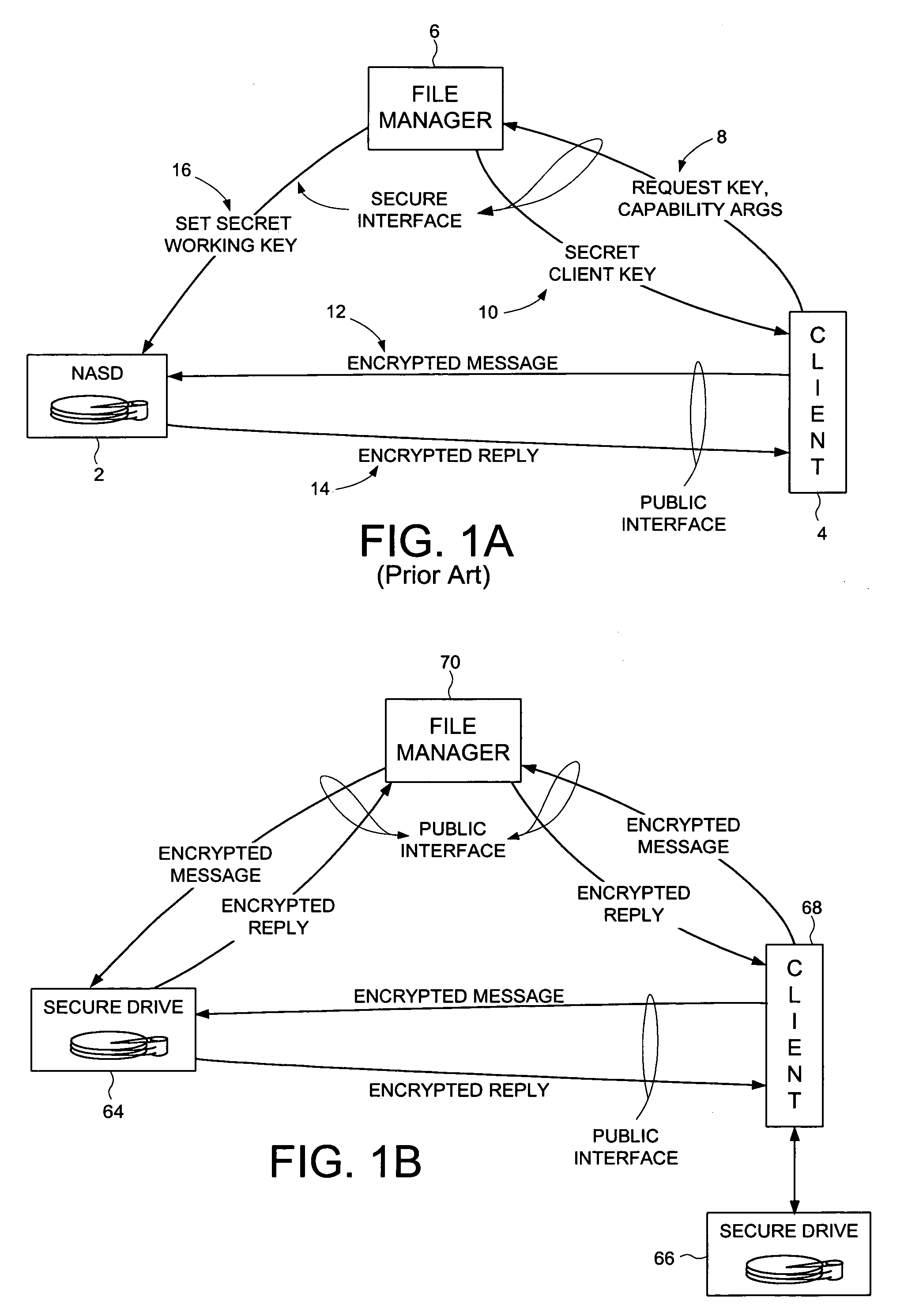
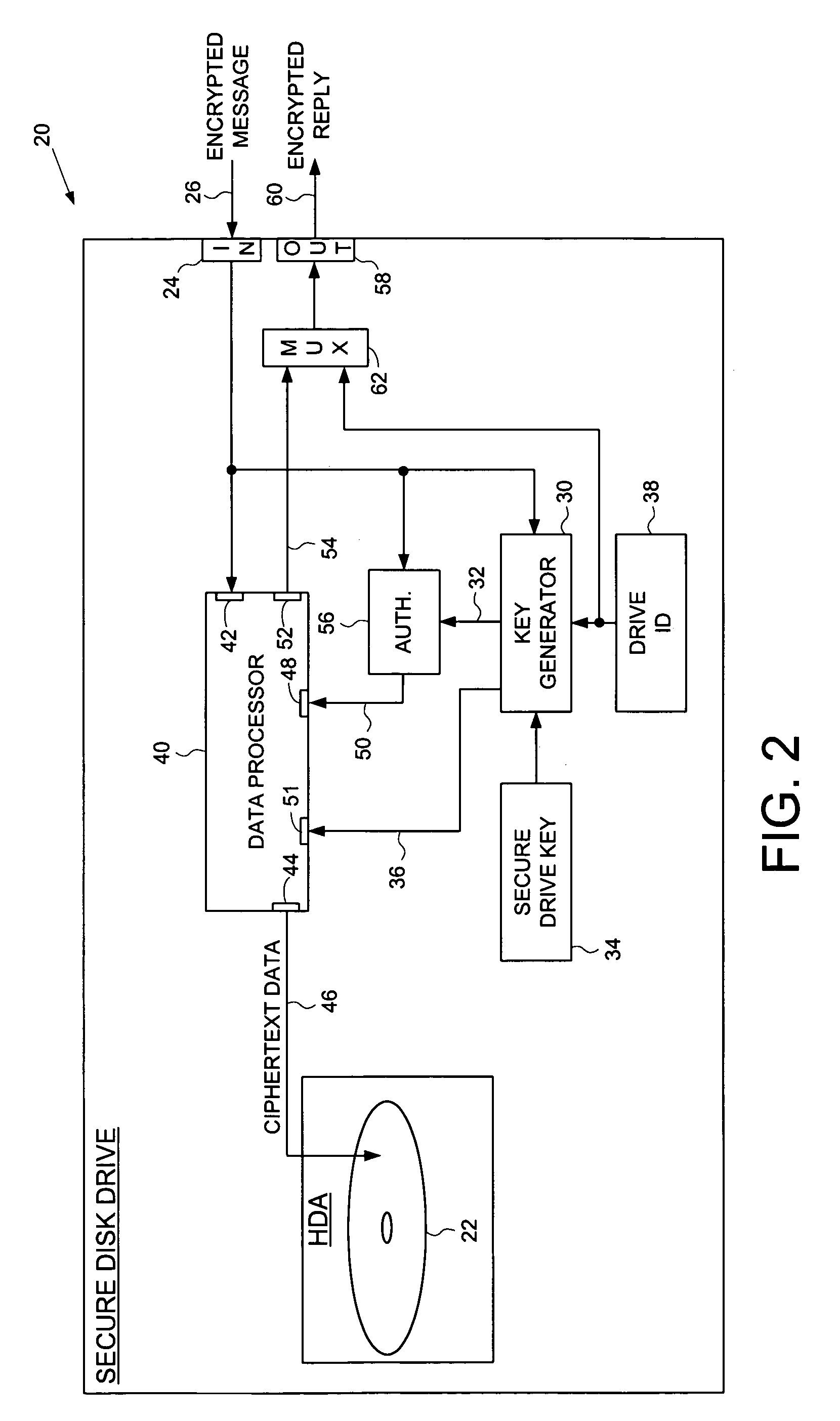
Secure disk drive comprising a secure drive key and a drive ID for implementing secure communication over a public network
InactiveUS7215771B1Volume/mass flow measurementUser identity/authority verificationSecure communicationCiphertext
A secure disk drive is disclosed comprising a disk for storing data, and an input for receiving an encrypted message from a client disk drive, the encrypted message comprising ciphertext data and a client drive ID identifying the client disk drive. The secure disk drive comprises a secure drive key and an internal drive ID. A key generator within the secure disk drive generates a client drive key based on the client drive ID and the secure drive key, and an internal drive key based on the internal drive ID and the secure drive key. The secure disk drive further comprises an authenticator for verifying the authenticity of the encrypted message and generating an enable signal, the authenticator is responsive to the encrypted message and the client drive key. The secure disk drive further comprises a data processor comprising a message input for receiving the encrypted message from the client disk drive, and a data output for outputting the ciphertext data to be written to the disk. The data processor further comprises an enable input for receiving the enable signal for enabling the data processor, and a key input for receiving the internal drive key, the internal drive key for use in generating a message authentication code. The data processor outputs reply data comprising the message authentication code. The secure disk drive outputs a reply to the client disk drive, the reply comprising the reply data and the internal drive ID.
Owner:WESTERN DIGITAL TECH INC
Method and system for conducting secure payments over a computer network
A method is provided for conducting a financial transaction by a purchaser with a merchant having an acquirer bank, over a communications network. The method includes the steps of sending a first authorization request using a pseudo account number associated with a real account number to a service provider which forwards a second authorization request to the issuer using the real account number and preferably a pseudo acquirer code associated with the service provider such that the response to the second request is based on the real account number and sent back to the service provider who preferably forwards a response to the first request preferably to the “real” acquirer. A message authentication code is further provided which includes transaction data, and where the authorization request is formatted as a standard payment card track having one or more fields including a discretionary field in which the message authentication code is placed.
Owner:HOGAN EDWARD J +1
Remote authentication and transaction signatures
InactiveUS20140189359A1Simple ideaUser identity/authority verificationCommunication interfaceSmart card
Authentication devices and methods for generating dynamic credentials are disclosed. The authentication devices include a communication interface for communicating with a security device such as a smart card. A dynamic credential such as a one-time password (OTP) or a message authentication code (MAC) may be generated by receiving from a server an encrypted initialization seed encrypted with an asymmetric encryption algorithm using a public key of a public / private key pair, submitting the encrypted initialization seed to a security device, decrypting at the security device the encrypted initialization seed with a private key of the public / private key pair, returning the decrypted initialization seed to the authentication device, deriving at the authentication device a secret credential generation key from the decrypted initialization seed, and generating the dynamic credential by combining a dynamic variable with the secret credential generation key using a symmetric cryptographic dynamic credential generation algorithm.
Owner:ONESPAN NORTH AMERICA INC
Authenticated Communication Between Security Devices
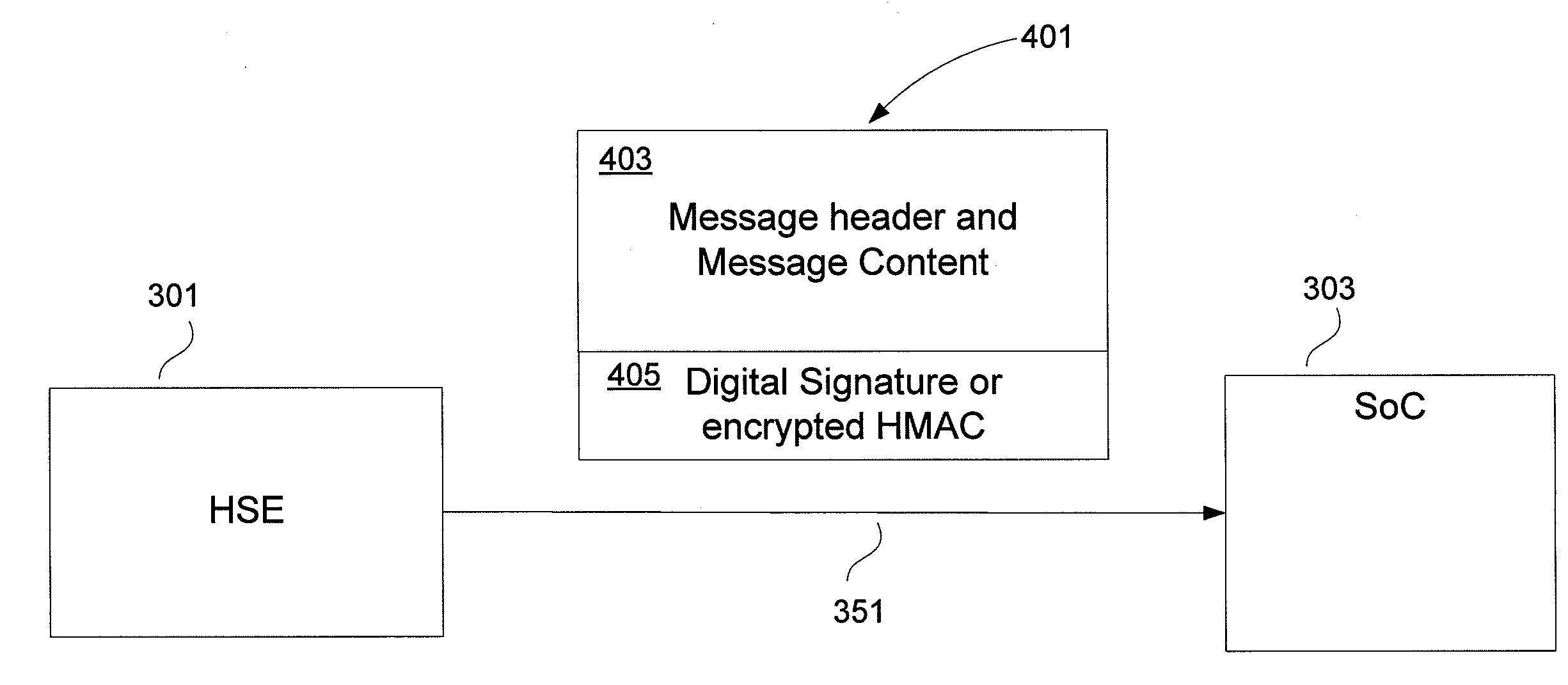
ActiveUS20100217985A1User identity/authority verificationTelevision systemsConditional access systemsDigital signature
Apparatuses, computer readable media, and methods establishing and maintaining trust between security devices for distributing media content are provided. Two security devices bind to establish an initial trust so that security information can be exchanged. Subsequently, trust is refreshed to verify the source of a message is valid. In an embodiment, the security devices may comprise a security processor and a system on a chip (SoC) in a downloadable conditional access system. Trust may be refreshed by a security device inserting authentication information in a message to another security device, where authentication information may assume different forms, including a digital signature (asymmetric key) or a hash message authentication code (HMAC). Trust may also be refreshed by extracting header information from the message, determining state information from at least one parameter contained in the header information, and acting on message content only when the state information is valid.
Owner:COMCAST CABLE COMM LLC
Method and apparatus for authentication of data streams with adaptively controlled losses
InactiveUS20060136728A1Easy to adaptAvoid calculationUser identity/authority verificationUnauthorized memory use protectionData streamDigital signature
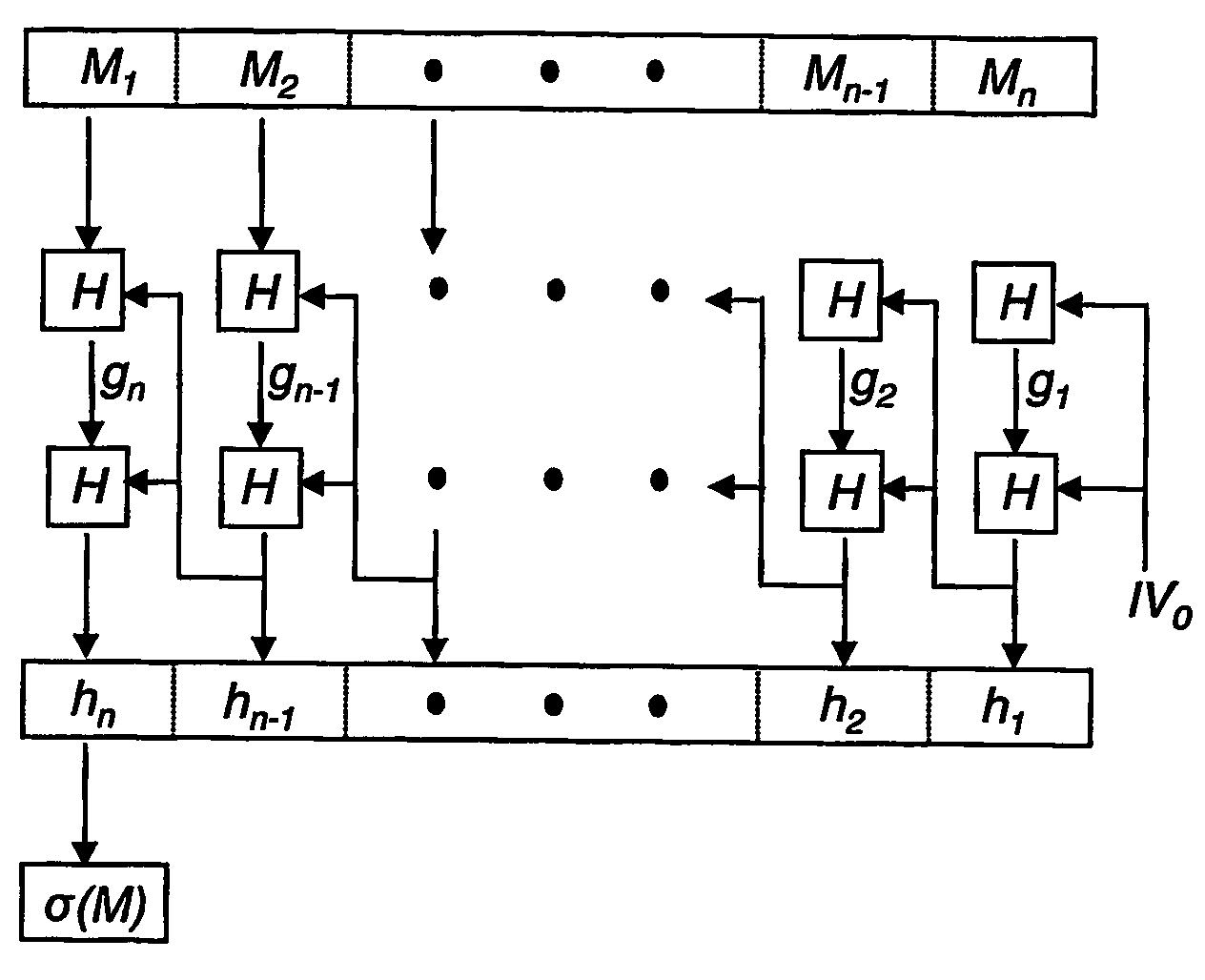
Methods, components, and systems for efficient authentication, either through a digital signature or message authentication codes, and verification of a digital stream sent from a source to a receiver via zero or more intermediaries, such that the source or intermediary (or both) can remove certain portions of the data stream without inhibiting the ability of the ultimate receiver to verify the authenticity and integrity of the data received. According to the invention, a source may sign an entire data stream once, but may permit either itself or an intermediary to efficiently remove certain portions of the stream before transmitting the stream to the ultimate recipient, without having to re-sign the entire stream. Applications may include the signing of media streams which often need to be further processed to accommodate the resource requirements of a particular environment. Another application allows an intermediary to choose an advertisement to include in a given slot.
Owner:NTT DOCOMO INC
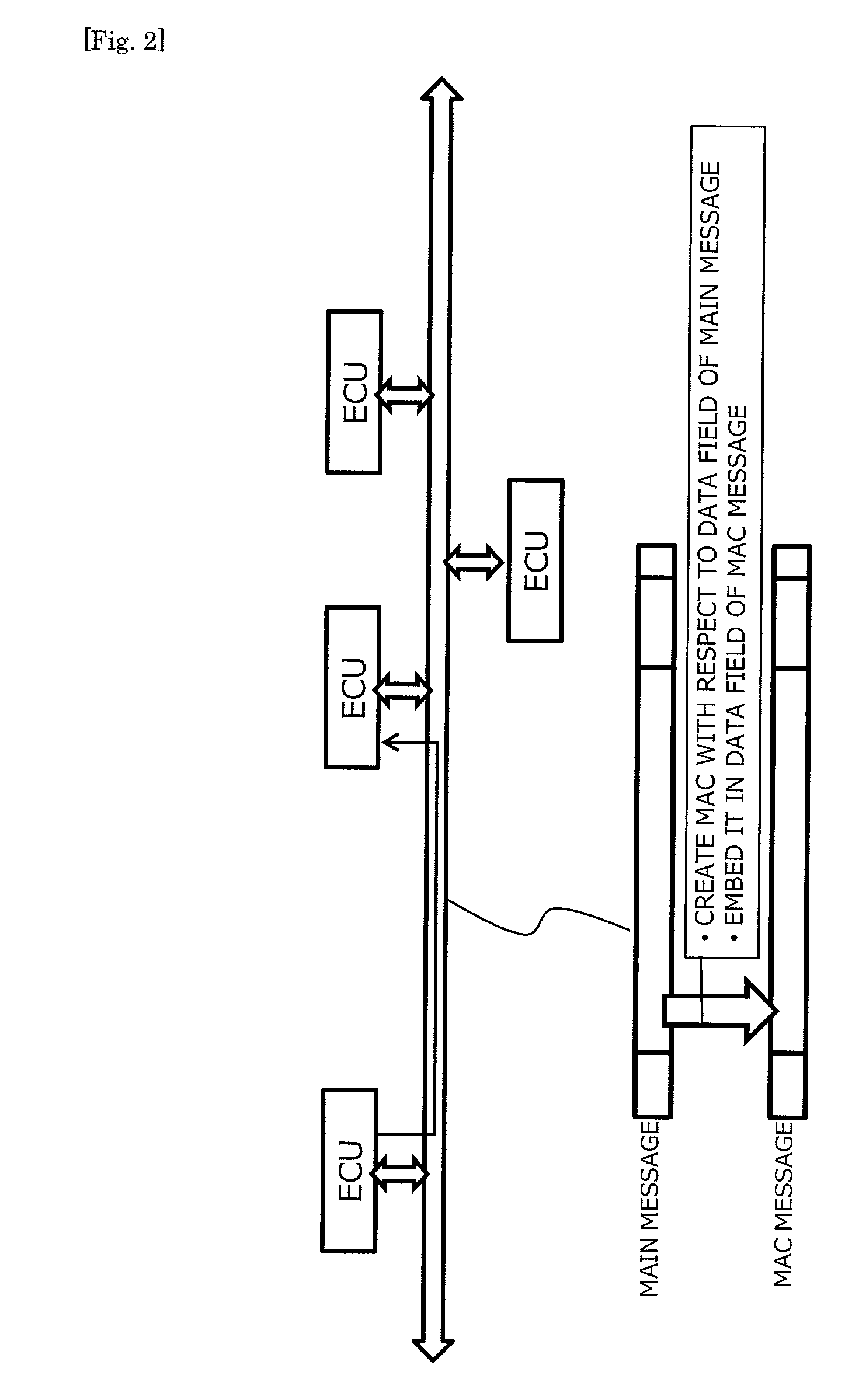
Message authentication method in communication system and communication system
ActiveUS20140310530A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationComputer hardwareCommunications system
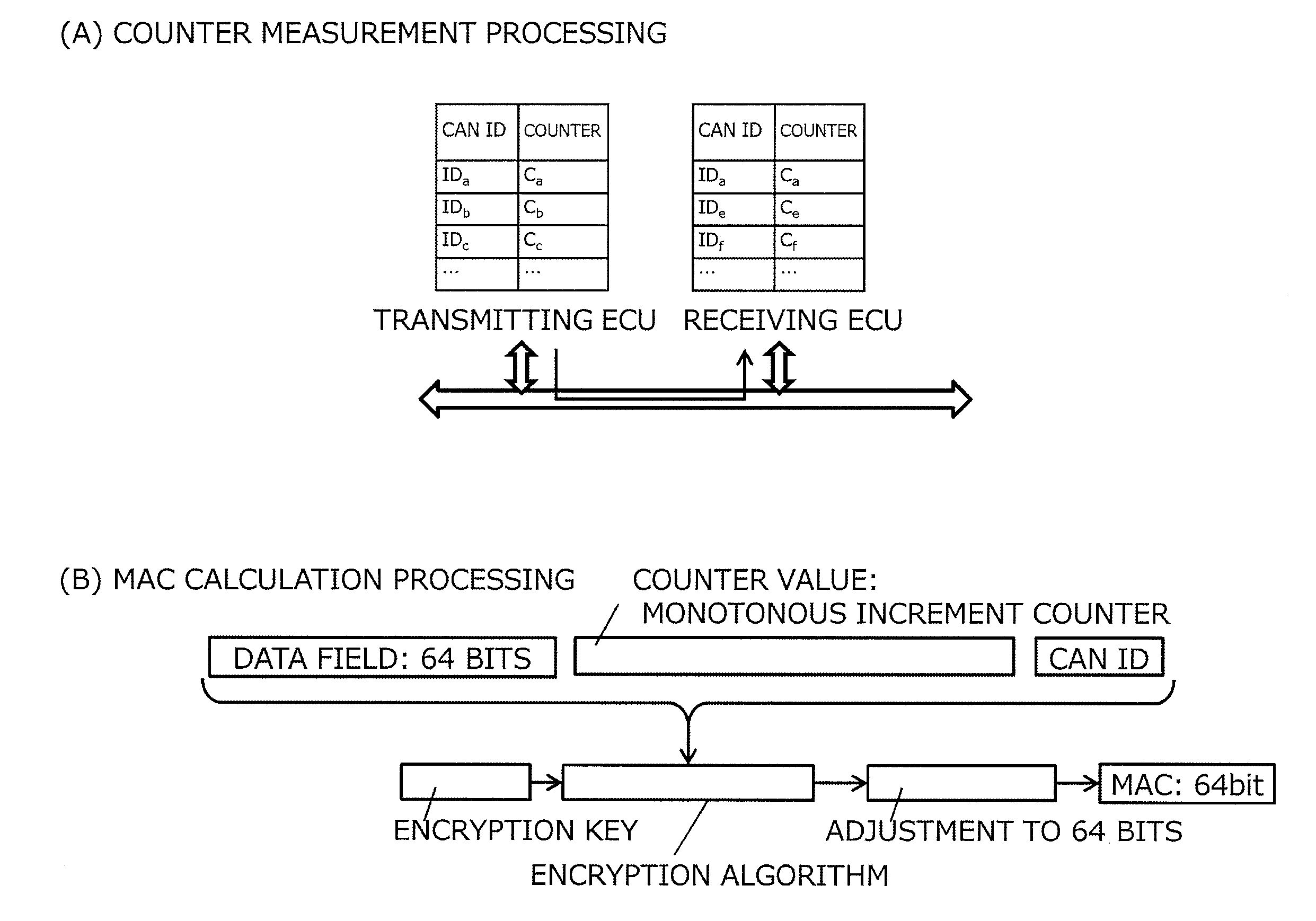
Each of ECUs counts the number of messages transmitted for each of CAN IDs. A transmission node that has transmitted a main message produces an MAC from a data field and the CAN ID in the main message and a counter value corresponding to the CAN ID, and transmits the MAC as an MAC message. A reception node that has received the main message produces an MAC from the data field and the CAN ID contained in the main message and the counter value corresponding to the CAN ID, and determines whether the MAC matches the MAC contained in the MAC message. By so doing, verification whether the main message is valid or not can be made. According to this configuration, message authentication by the MAC can be made without changing a CAN protocol.
Owner:TOYOTA JIDOSHA KK +1
System and method for selectively authenticating data
InactiveUS6842860B1Lower-strength authenticationSave a lot of timeSynchronising transmission/receiving encryption devicesUser identity/authority verificationMessage authentication code
A high-speed, low-strength authentication mechanism is disclosed. This mechanism is based on a partial message authentication code, wherein a message authentication code is applied only to some portion of the message. By applying an authentication algorithm only to selected parts of the message, significant time can be saved while maintaining acceptable security.
Owner:MCAFEE LLC
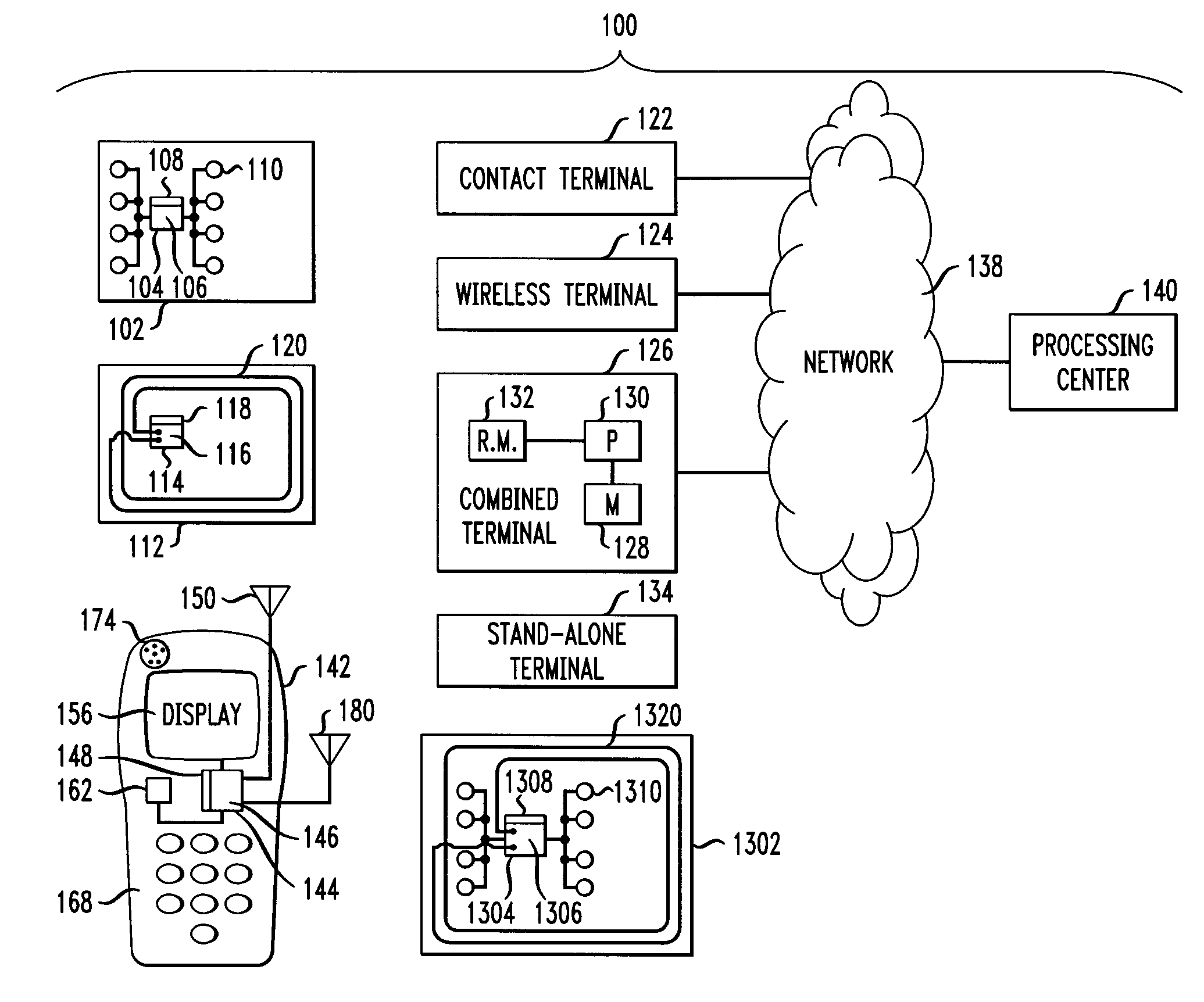
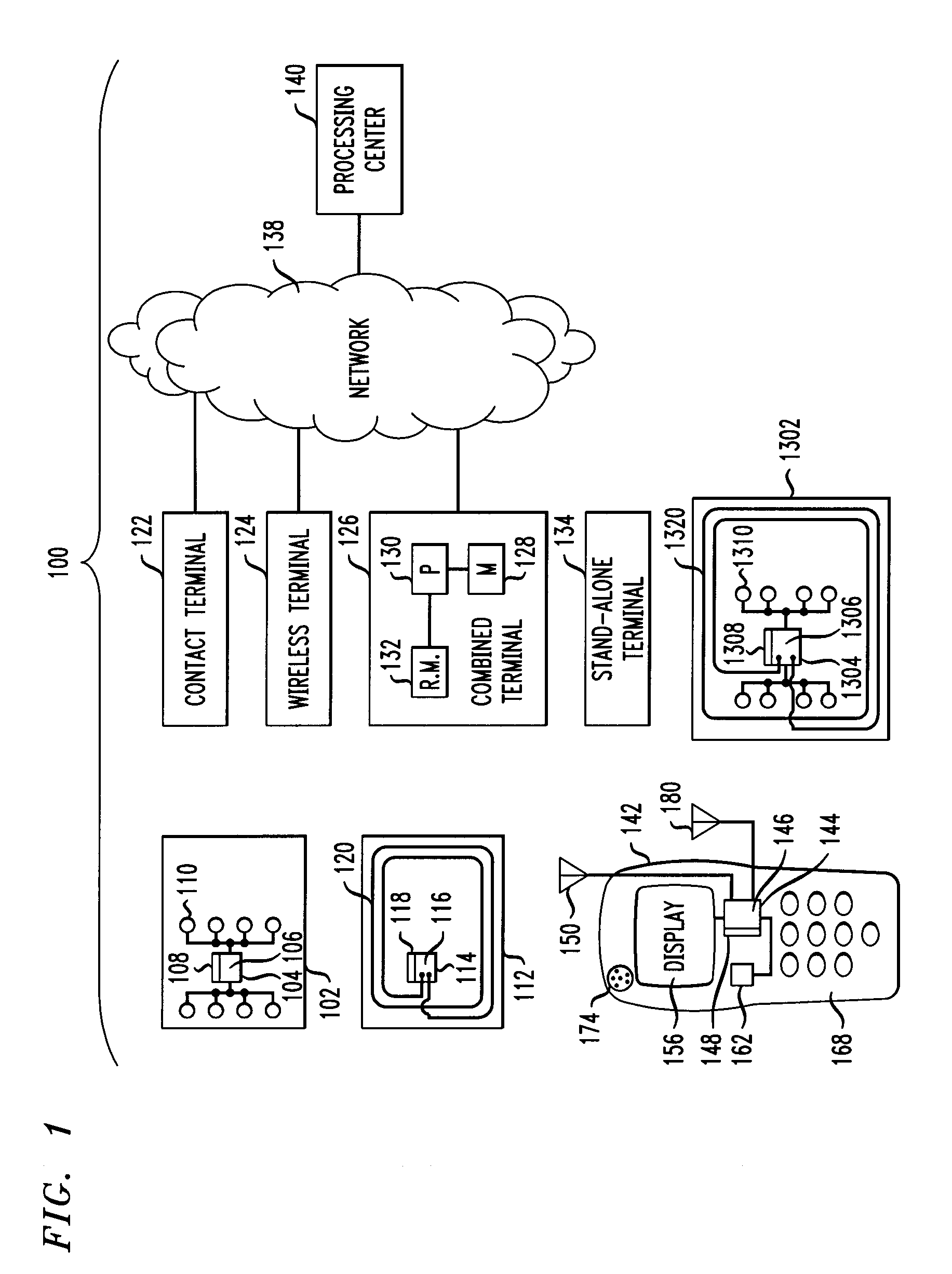
Apparatus and method for integrated payment and electronic merchandise transfer
ActiveUS20100252624A1Efficient combinationEasy transferTransportation facility accessFinanceRelevant informationSummary data
Interrogation of an electronic device by a first terminal is facilitated, to obtain an account number associated with the electronic device. The electronic device is configured according to a payment specification. The first terminal has a first terminal payment module configured according to the payment specification and a first terminal electronic merchandise module configured according to the electronic merchandise infrastructure and coupled to the first terminal payment module to permit transfer of non-payment e-merchandise related information from the first terminal electronic merchandise module to the first terminal payment module. The interrogation of the electronic device is performed by the first terminal payment module. Generation of non-payment e-merchandise related information by the first terminal electronic merchandise module is facilitated. Transfer of the non-payment e-merchandise related information from the first terminal electronic merchandise module to the electronic device via the first terminal payment module, within a transaction between the electronic device and the first terminal payment module that is conducted in accordance with the payment specification, is also facilitated. The non-payment e-merchandise related information is stored on the electronic device in accordance with the payment specification. The electronic device and the first terminal independently calculate a summary data item. The first terminal calculates a first message authentication code based on the non-payment e-merchandise related information and a terminal-calculated value of the summary data item. The non-payment e-merchandise related information is stored on the electronic device together with an electronic device-calculated value of the summary data item and the first message authentication code.
Owner:MASTERCARD INT INC
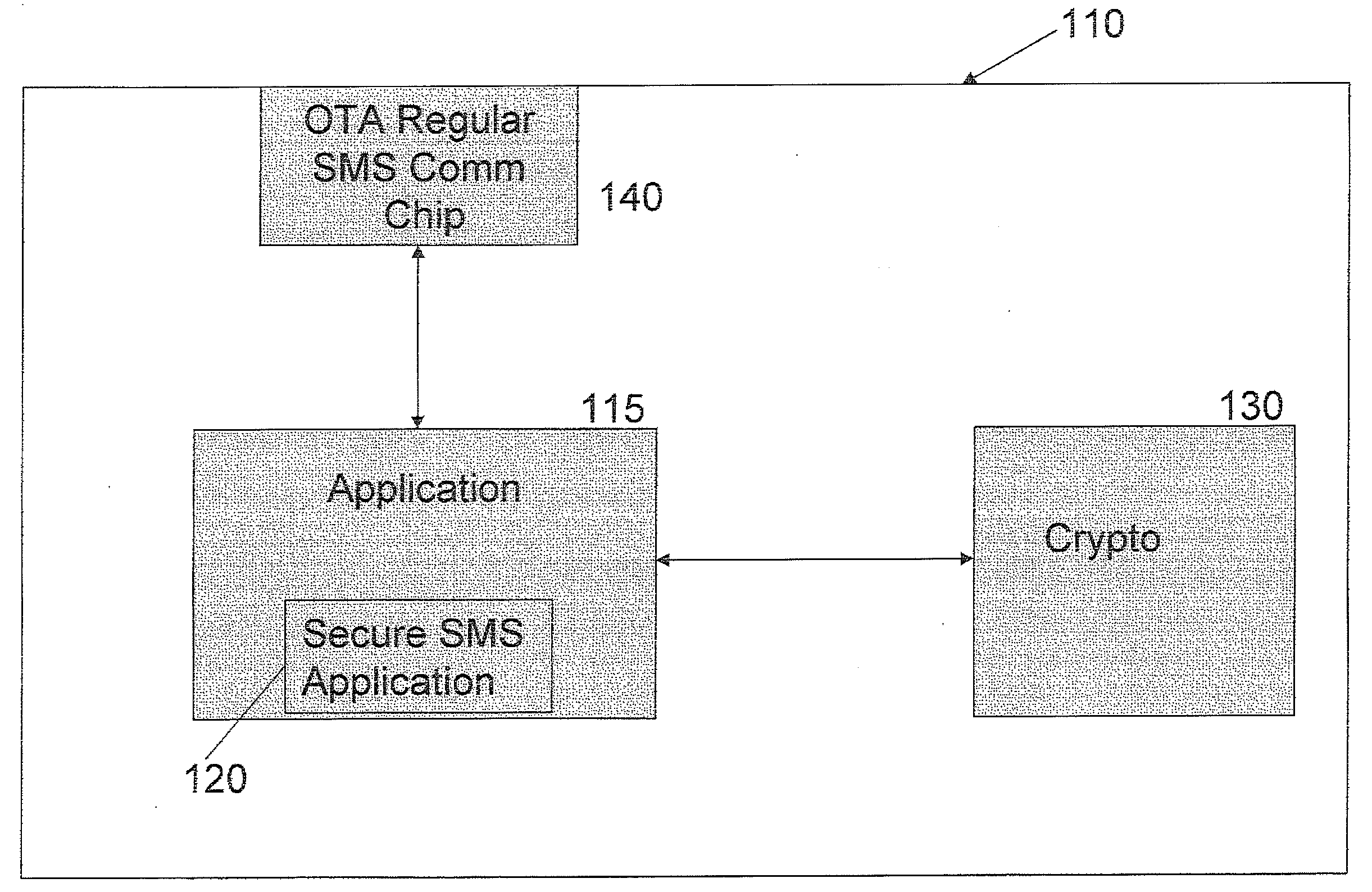
Secure short message service (SMS) communications
ActiveUS20090305673A1Unauthorised/fraudulent call preventionMultiple keys/algorithms usageTimestampClient-side
Embodiments of the present disclosure provide systems and methods for secure Short Message Service (SMS) communications. According to an embodiment, a method of providing secure Short Message Service (SMS) communications comprises requesting that SMS data to be sent from a client device to a remote location be encrypted. The method also comprises encrypting the SMS data by processing the SMS data with a Message Authentication Code (MAC) and a timestamp and / or counter along with second factor authentication information. The method further comprises sending the encrypted SMS data to the remote location by a secure SMS application via a regular SMS channel of the client device.
Owner:PAYPAL INC
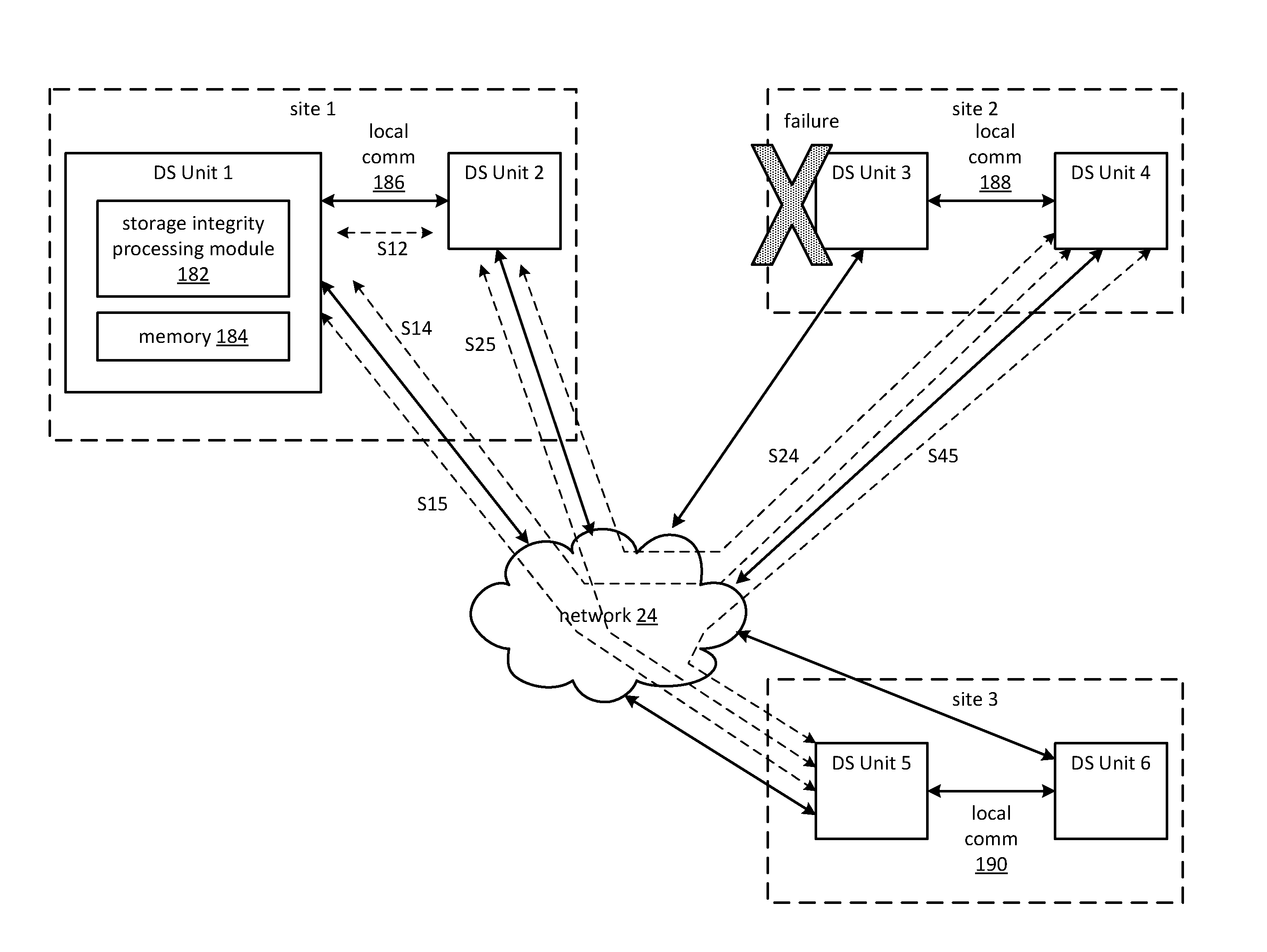
Dispersed storage network data slice integrity verification
InactiveUS20110126295A1Digital data information retrievalError detection/correctionData segmentSecret share
A method begins with a processing module issuing a retrieval request, receiving secret shares of a set of secret shares to produce received secret shares, and receiving encoded data slices of a set of encoded data slices. The method continues with the processing module decoding the received secret shares to recapture a message authentication key when a threshold number of the secret shares is received. The method continues with the processing module identifying a received encoded data slice of the received encoded data slices having an authentication code associated therewith when a threshold number of the encoded data slices is received. The method continues with the processing module verifying the authentication code based on the message authentication key and the received encoded data slice. The method continues with the processing module decoding the received encoded data slices to recapture a data segment when the authentication code is verified.
Owner:PURE STORAGE
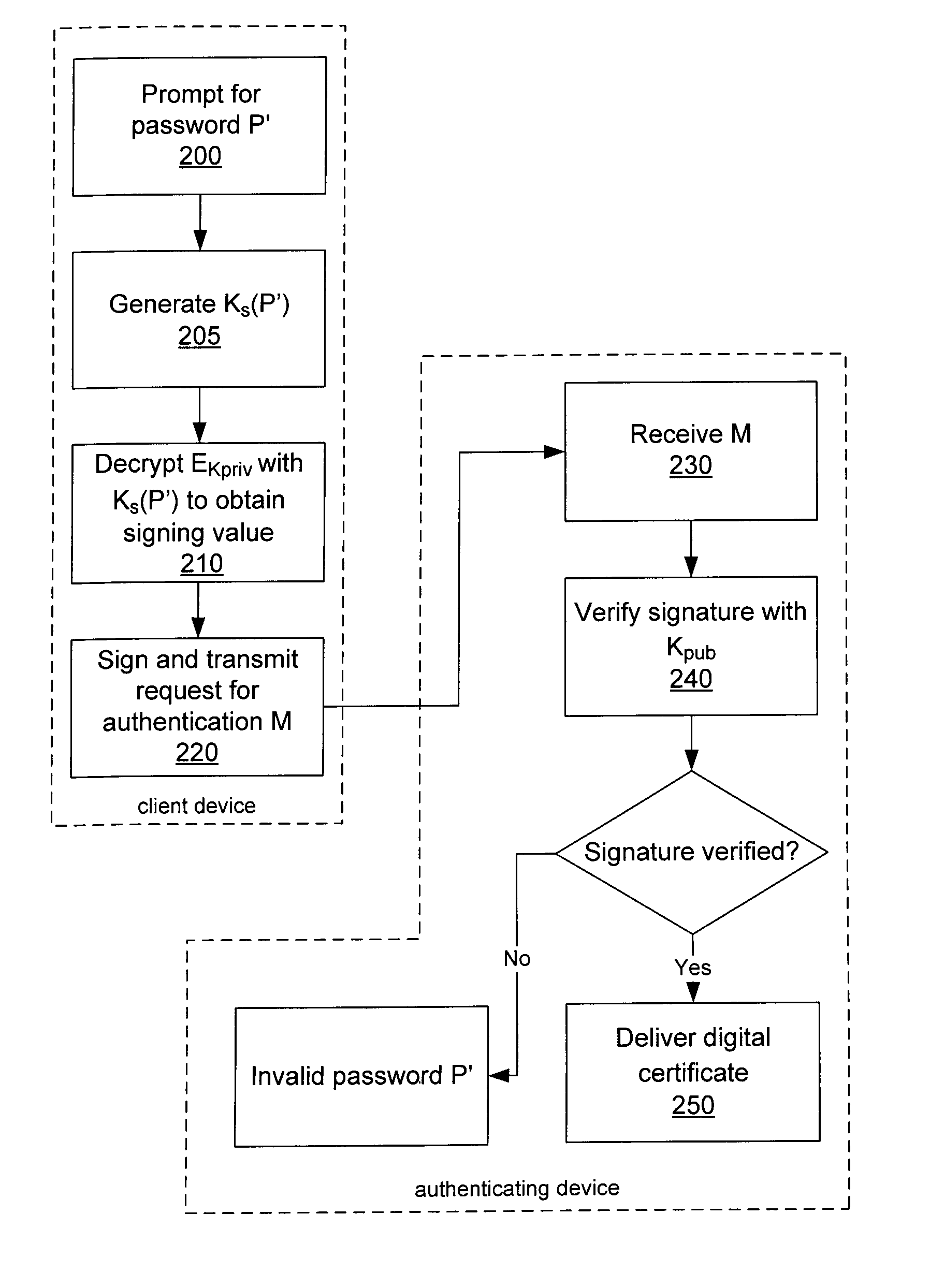
System and method for protecting a password against brute force attacks
ActiveUS20080120504A1User identity/authority verificationCryptographic attack countermeasuresBrute forcePassword
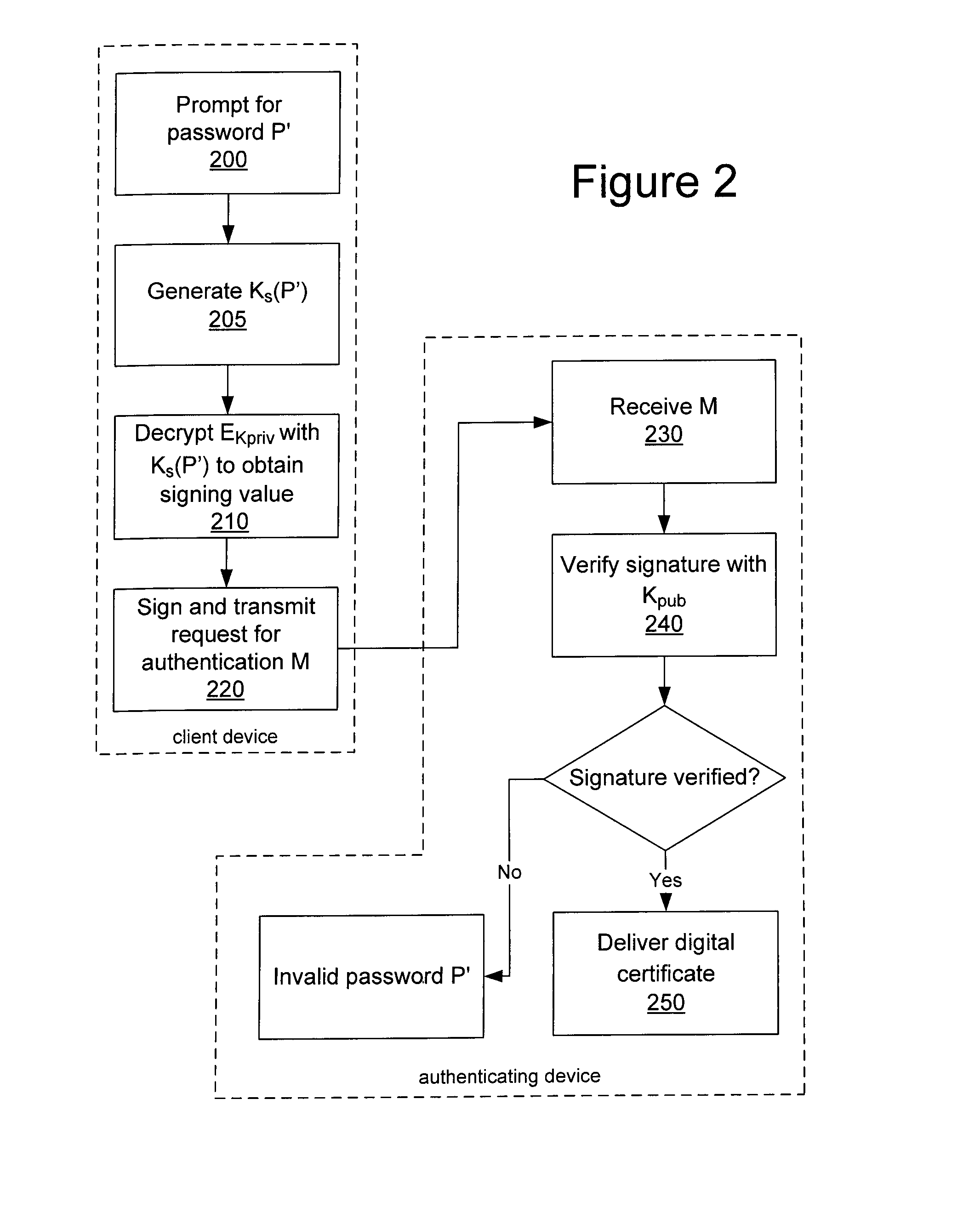
In a system and method for authenticating a client device by an authentication device, the client device user is assigned a PIN generated by the authentication device. The user provides the PIN and a password to the client device, from which the client device generates a symmetric key and further generates a public / private key pair. The private key is encrypted using the symmetric key and stored in encrypted form only. The public key and a message authentication code generated from the PIN are provided to the authentication device, which stores the public key. Subsequently, when the user seeks to be authenticated, the user enters a password at the client device, which is used to generate a symmetric key to decrypt the encrypted private key. A message to the authentication device is signed using the resultant value. The authentication device uses the public key to verify the signature of the message.
Owner:MALIKIE INNOVATIONS LTD
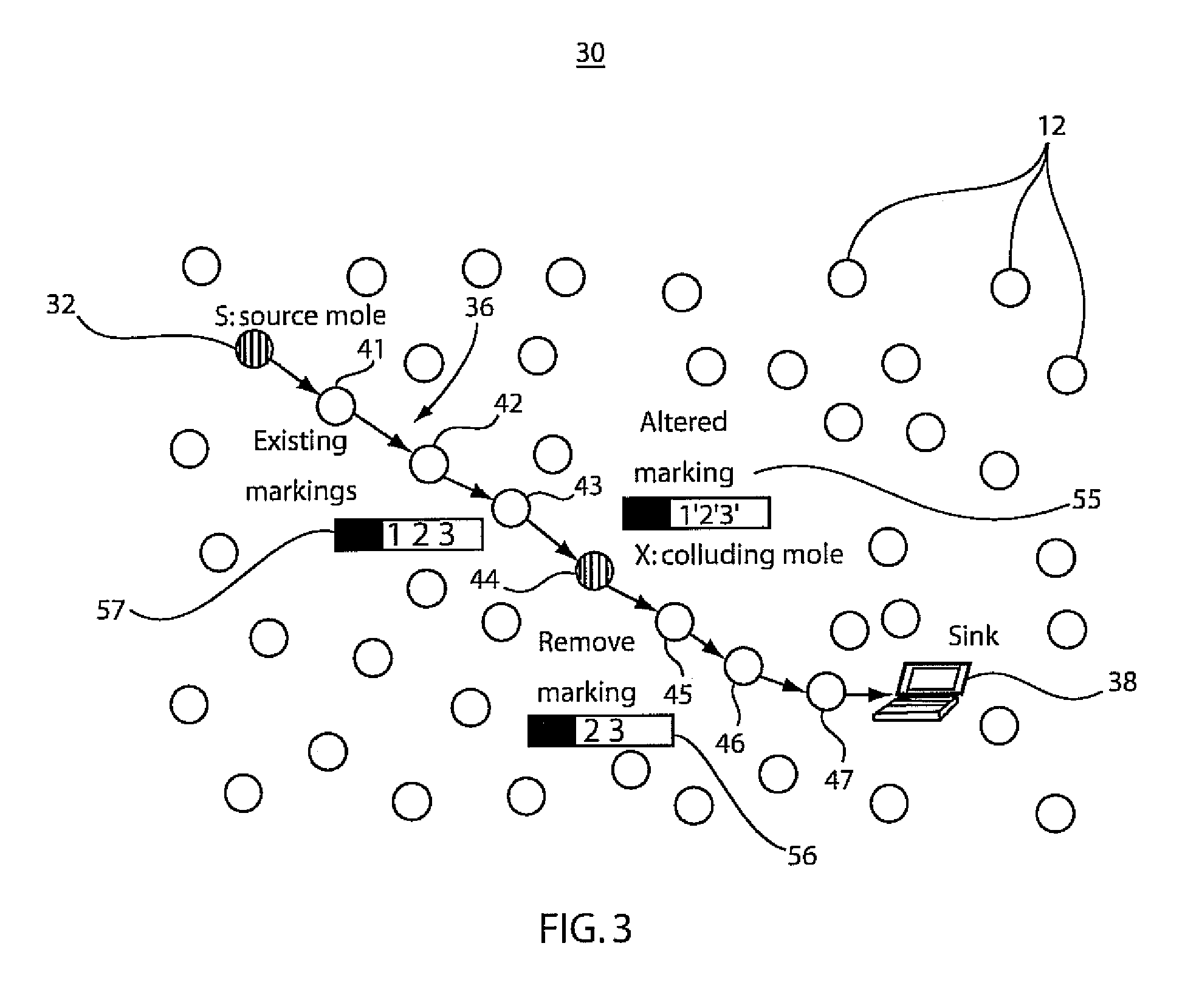
Method and system for resilient packet traceback in wireless mesh and sensor networks
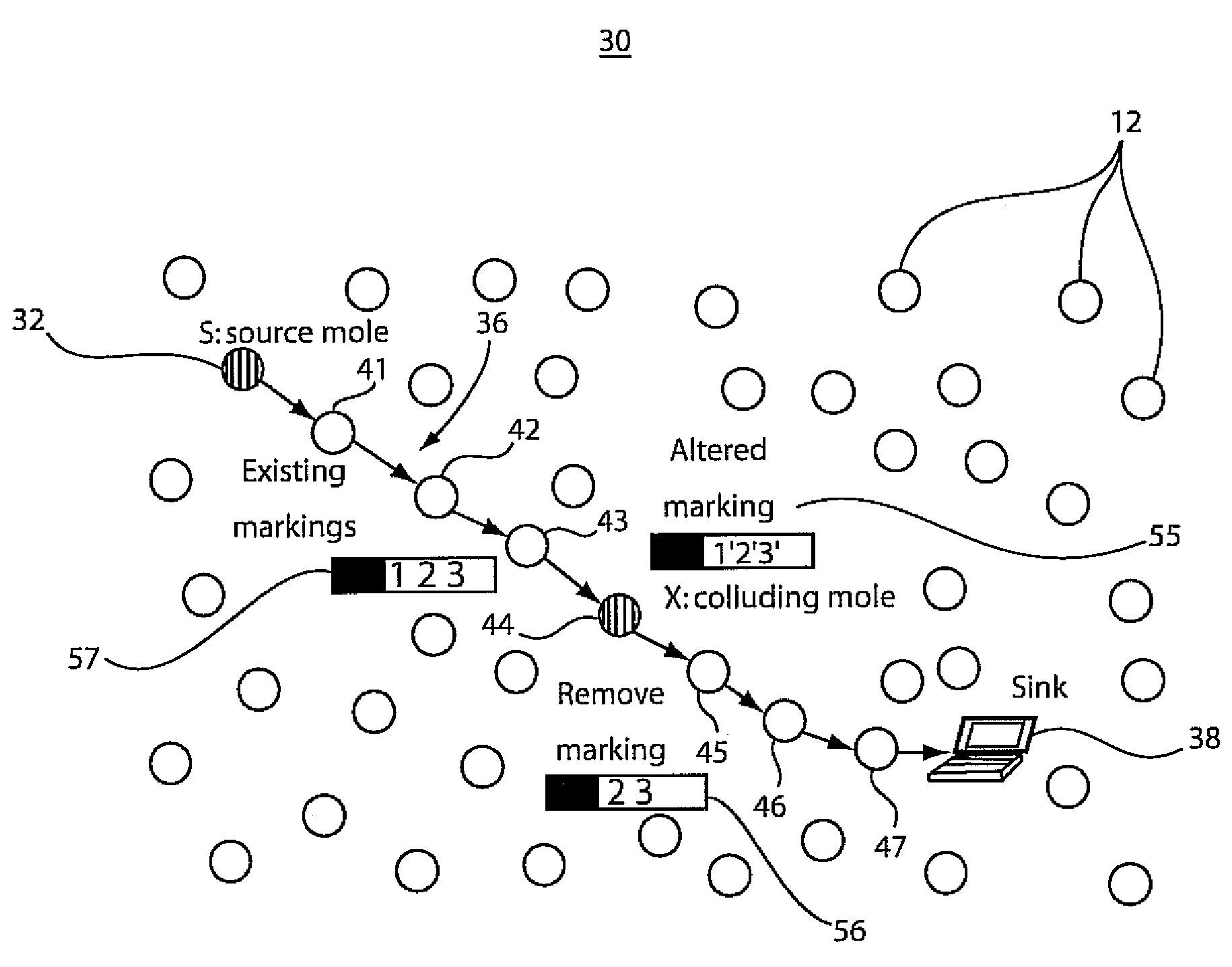
A system and method for packet traceback in a network includes maintaining an identity number (ID) for each node in a network and generating a signature (e.g., a message authentication code (MAC)) using a secret key shared between each node on a forwarding path and a sink. Each forwarding node leaves a mark by appending its ID and a signature in the packet, either in a deterministic manner or with a probability. Upon receiving a packet at the sink, correctness of the signatures included in each packet is verified in the reverse order by which these signatures were appended. A last valid MAC is determined in the forwarding path to determine the locations of compromised nodes that collude in false data injection attacks.
Owner:MARVELL ASIA PTE LTD
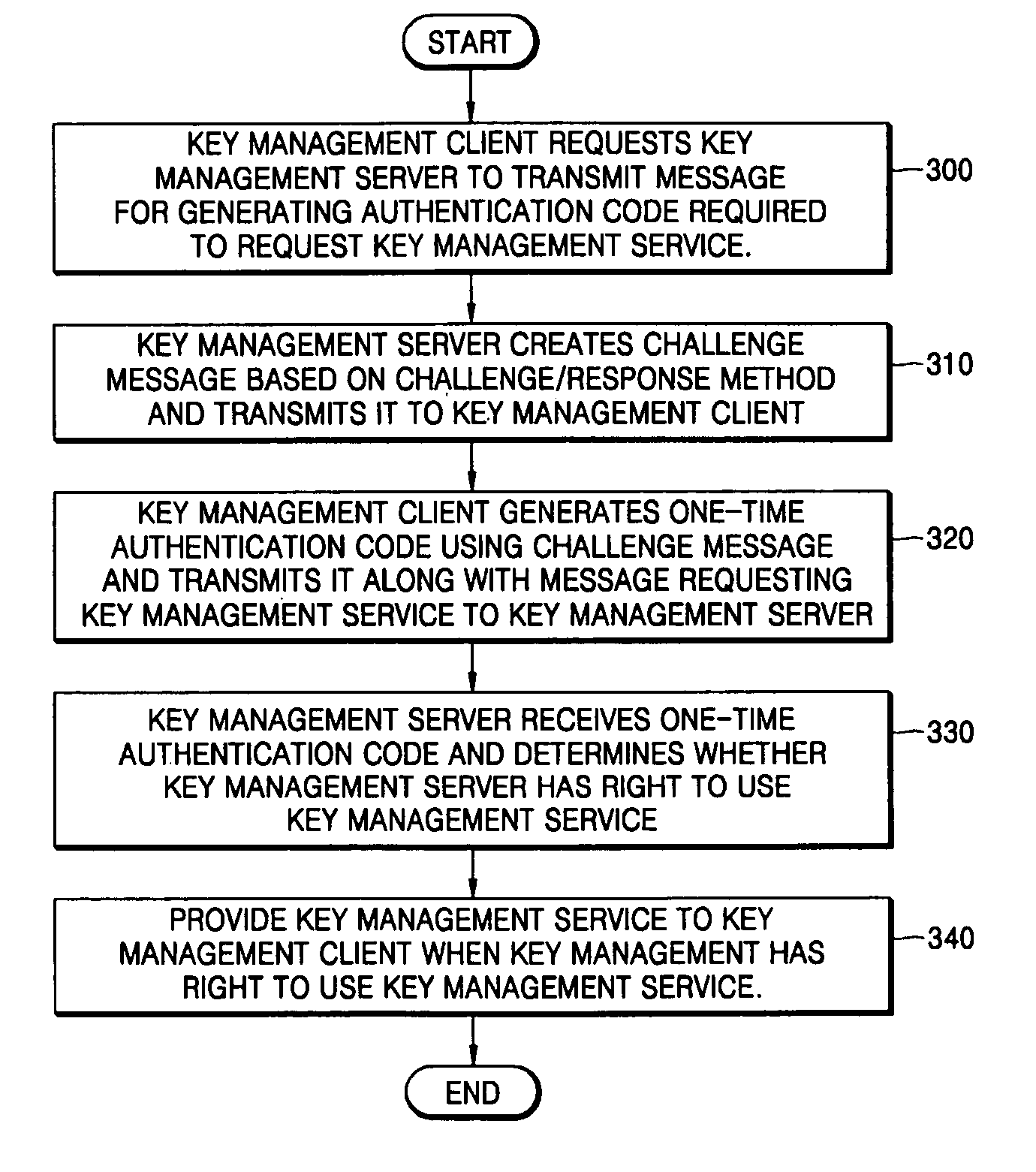
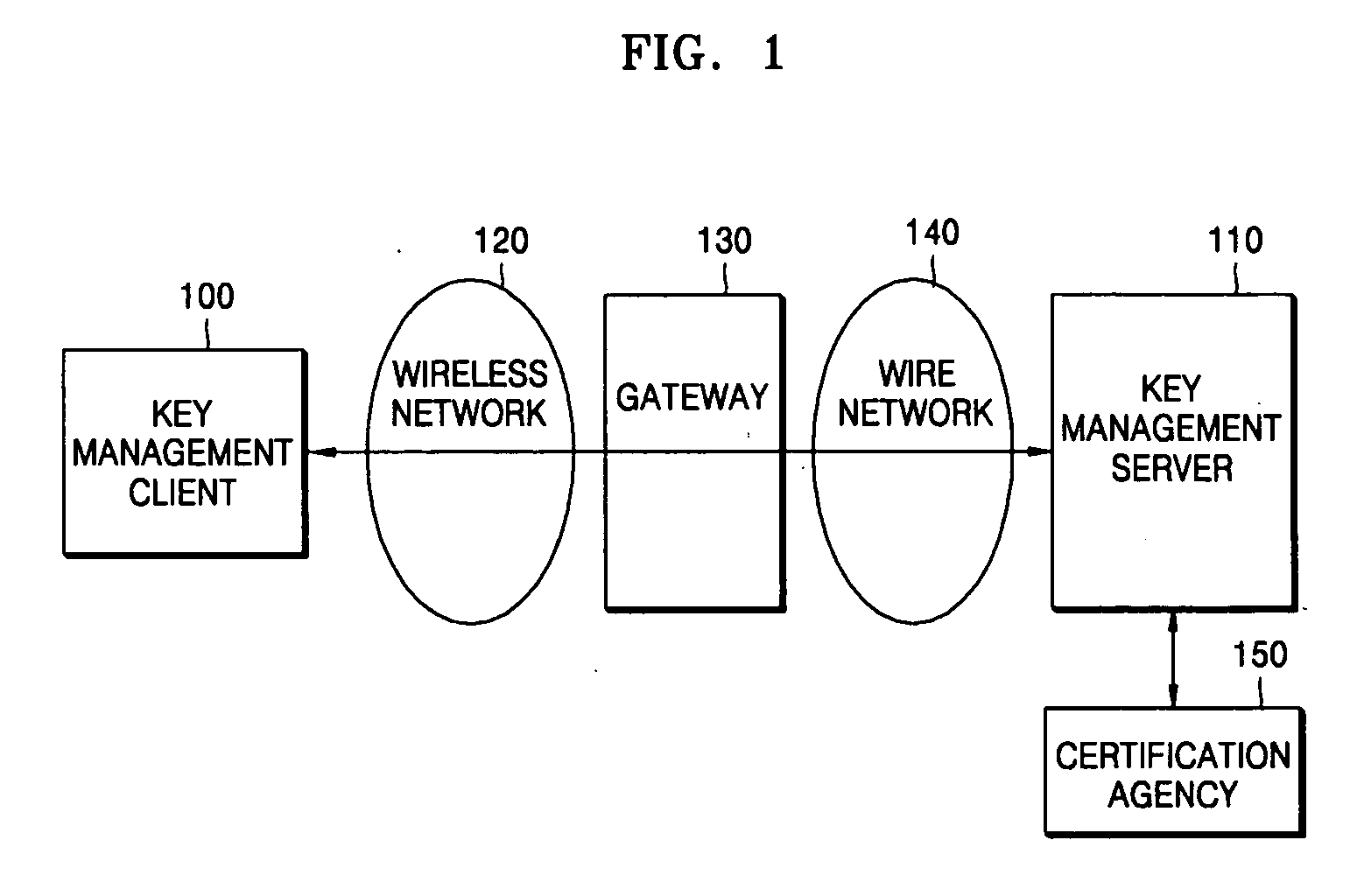
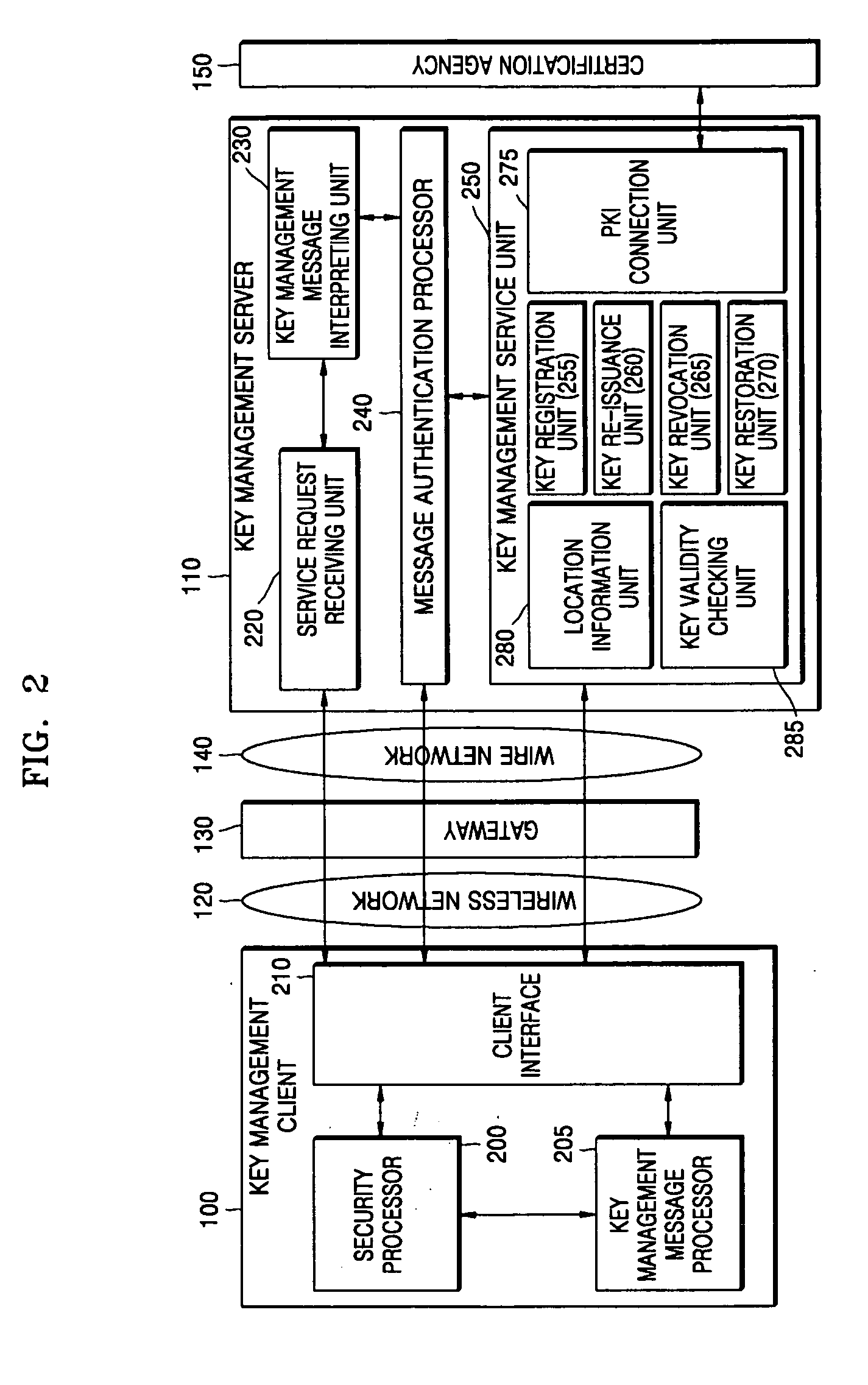
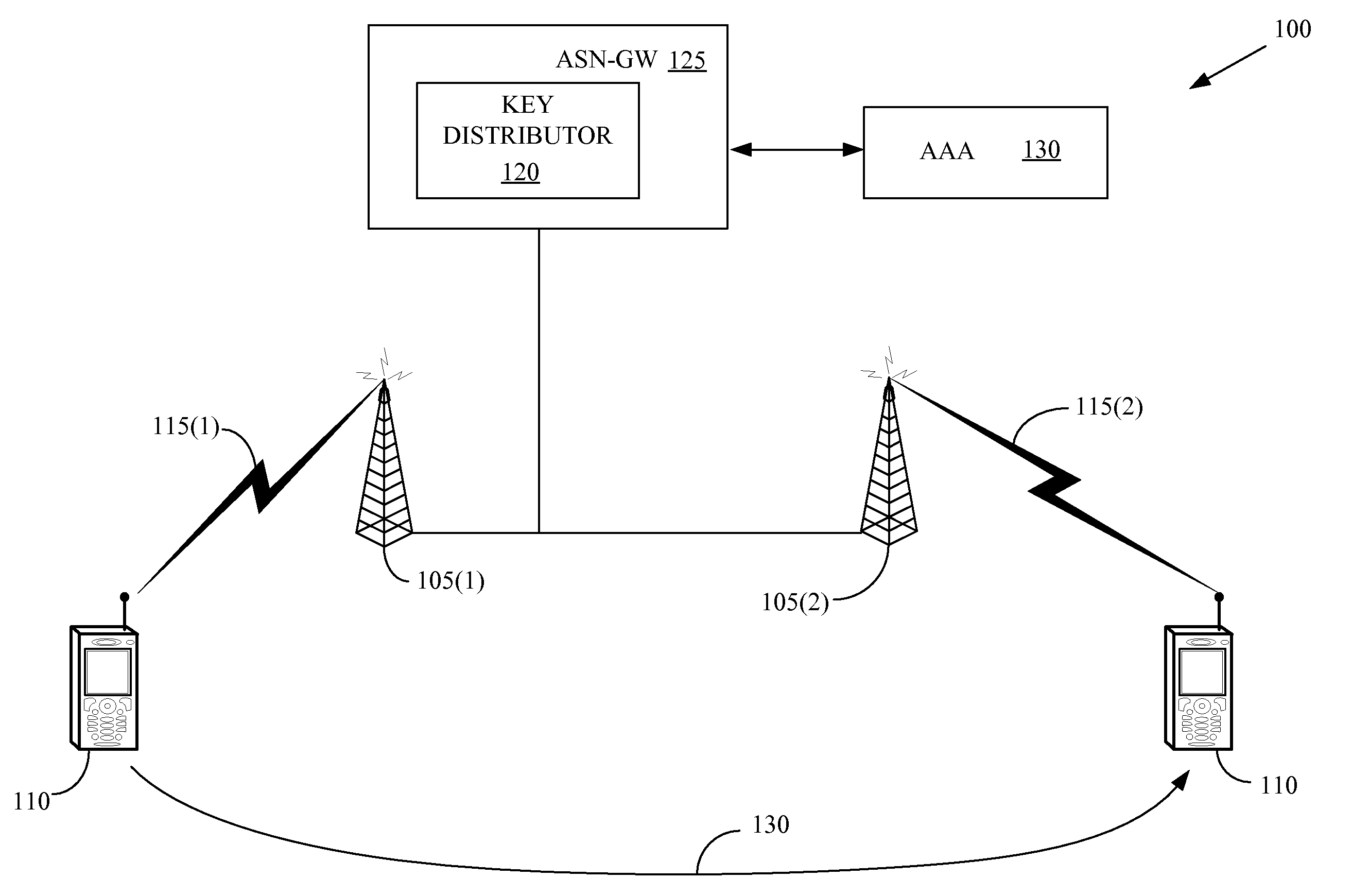
Key authentication/service system and method using one-time authentication code
Provided are a key authentication / service system and method using one-time authentication code. In the system and method, a key management client sends a key management server a message requesting transmission of a message for generating authentication code required to request a key management service. Next, the key management server creates a challenge message based on a challenge / response method using the received message. Next, the key management client generates the one-time authentication code using the challenge message and transmits it along with a message requesting a key management service to the key management server. Next, the key management server receives the one-time authentication code from the key management client and checks whether the one-time authentication code is certified to determine whether the key management client has a right to use the key management service. Then, the key management server provides the key management service to the key management client when it is determined that the key management client has a right to use this service.
Owner:ELECTRONICS & TELECOMM RES INST
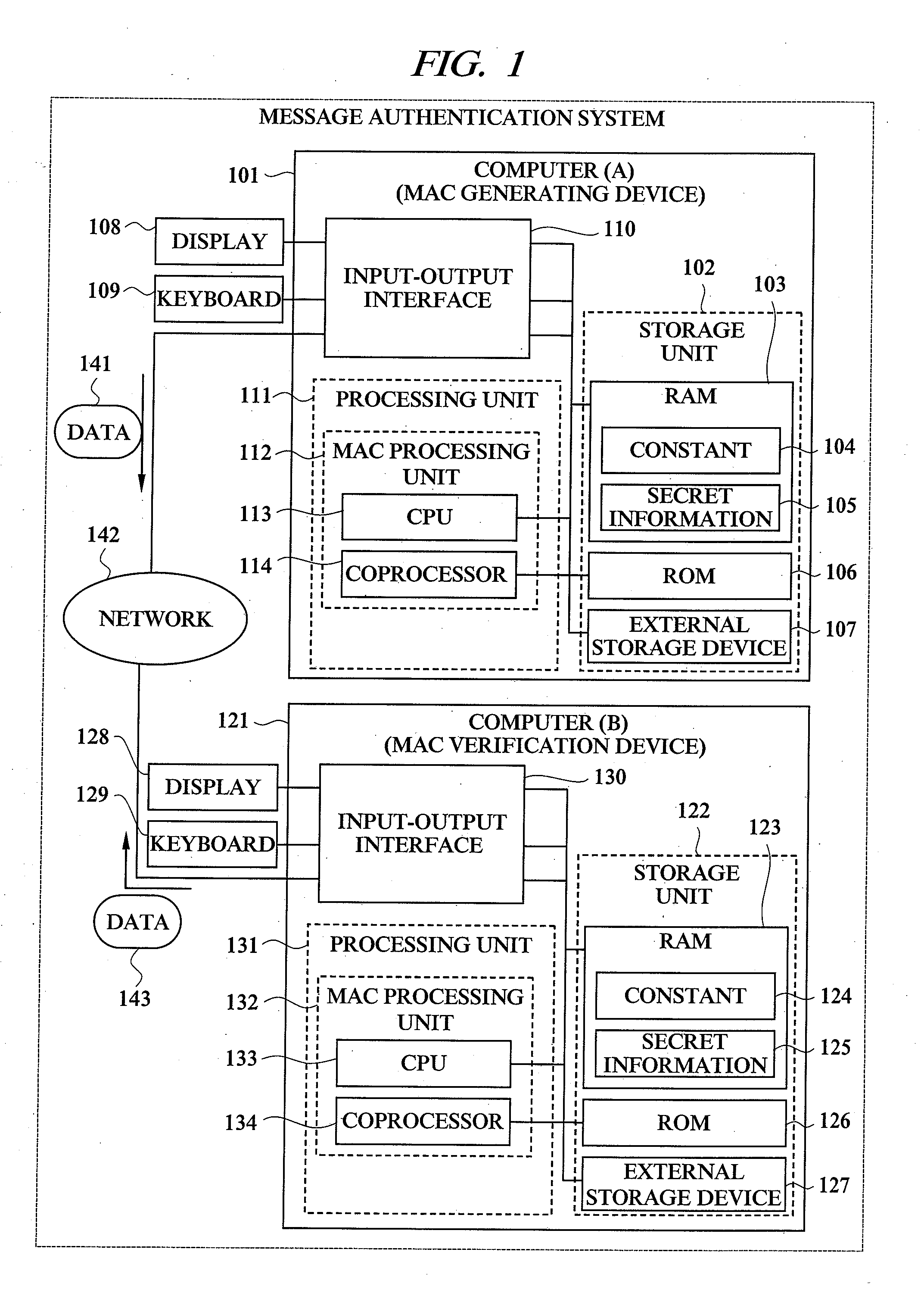
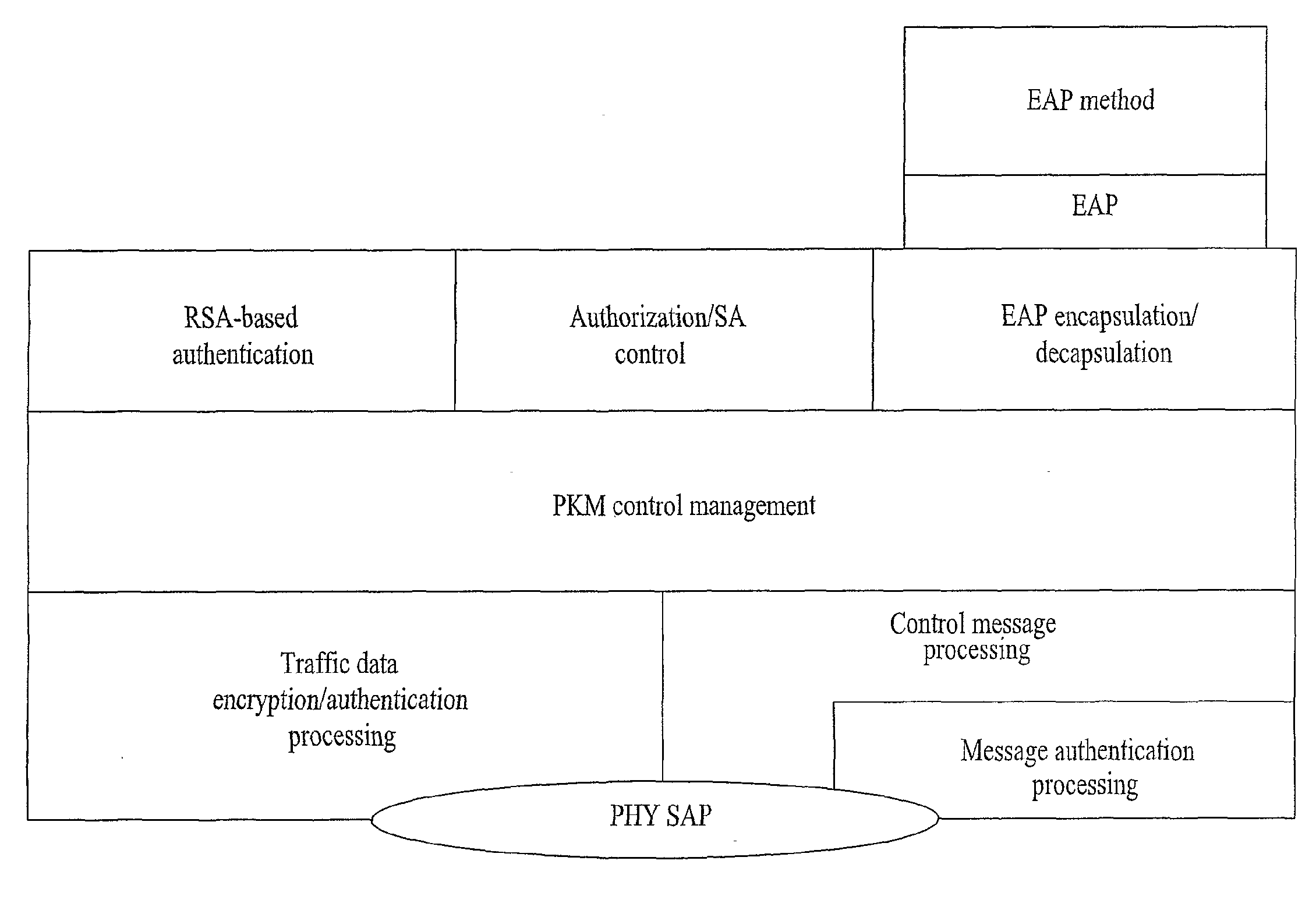
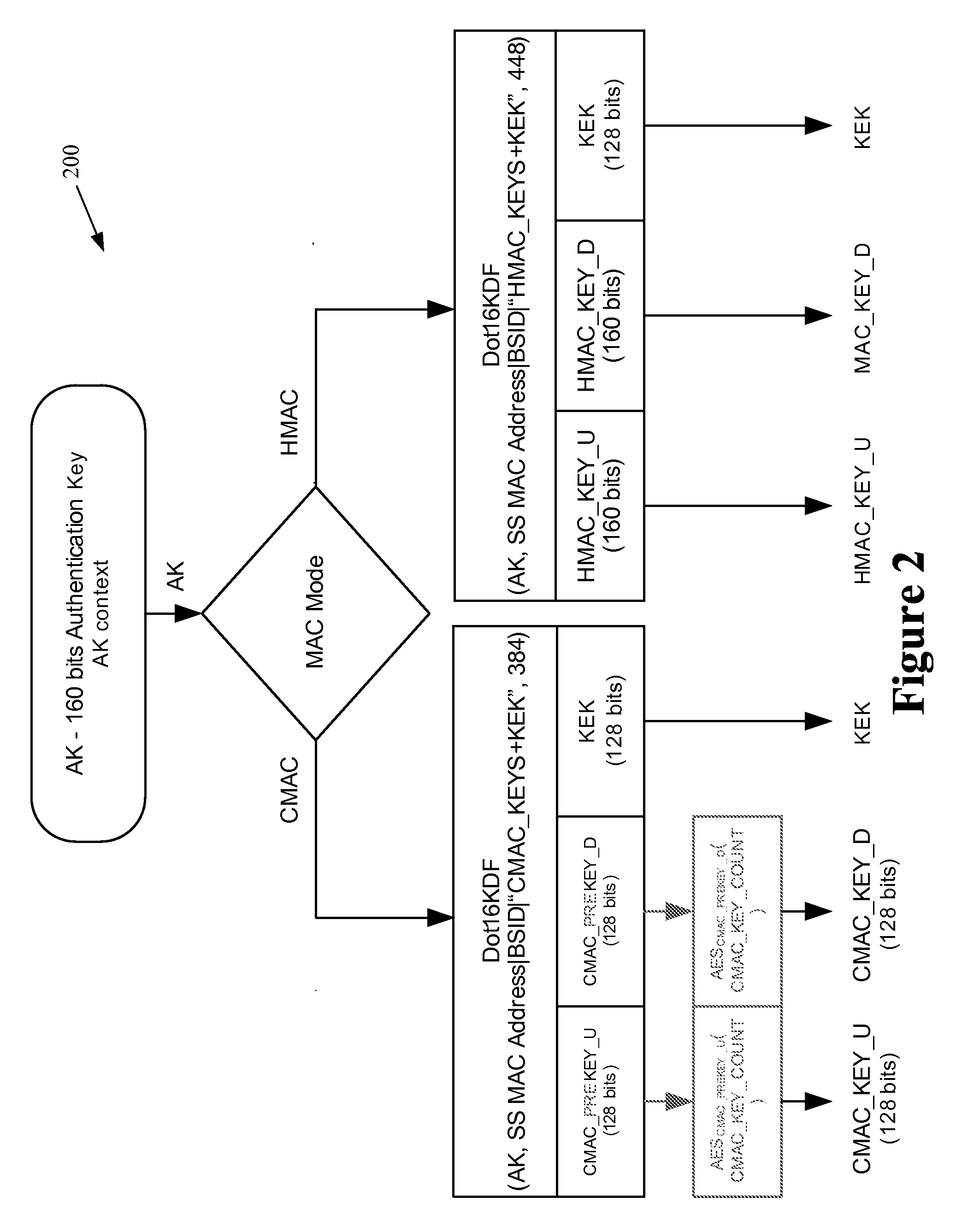
Message authentication code generating device, message authentication code verification device, and message authentication system
InactiveUS20070245147A1User identity/authority verificationMultiple digital computer combinationsComputer hardwareMessage authentication code
A message authentication technology capable of securing against side channel attack is provided. In a message authentication code generating device for calculating a message authentication code for a message from the message, a process in which disturbance information is generated from a temporary use numerical value, a process in which a conversion message is calculated from the message; and a process in which the message authentication code is calculated from the disturbance information and the conversion message are performed. In the process of calculating the message authentication code, process information is disturbed or concealed by the disturbance information. Therefore, the message authentication which is secure against side channel attack can be realized.
Owner:RENESAS ELECTRONICS CORP
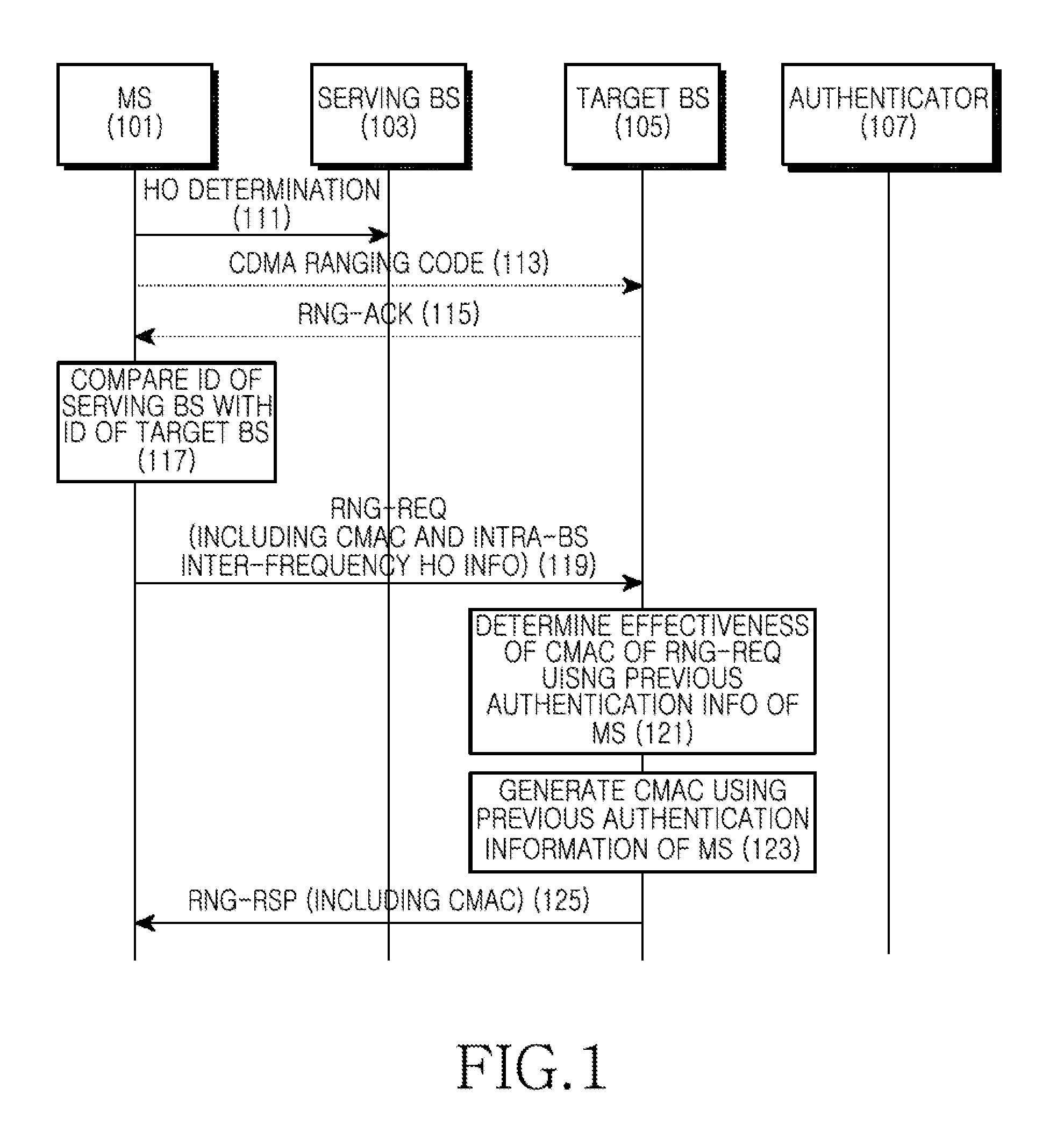
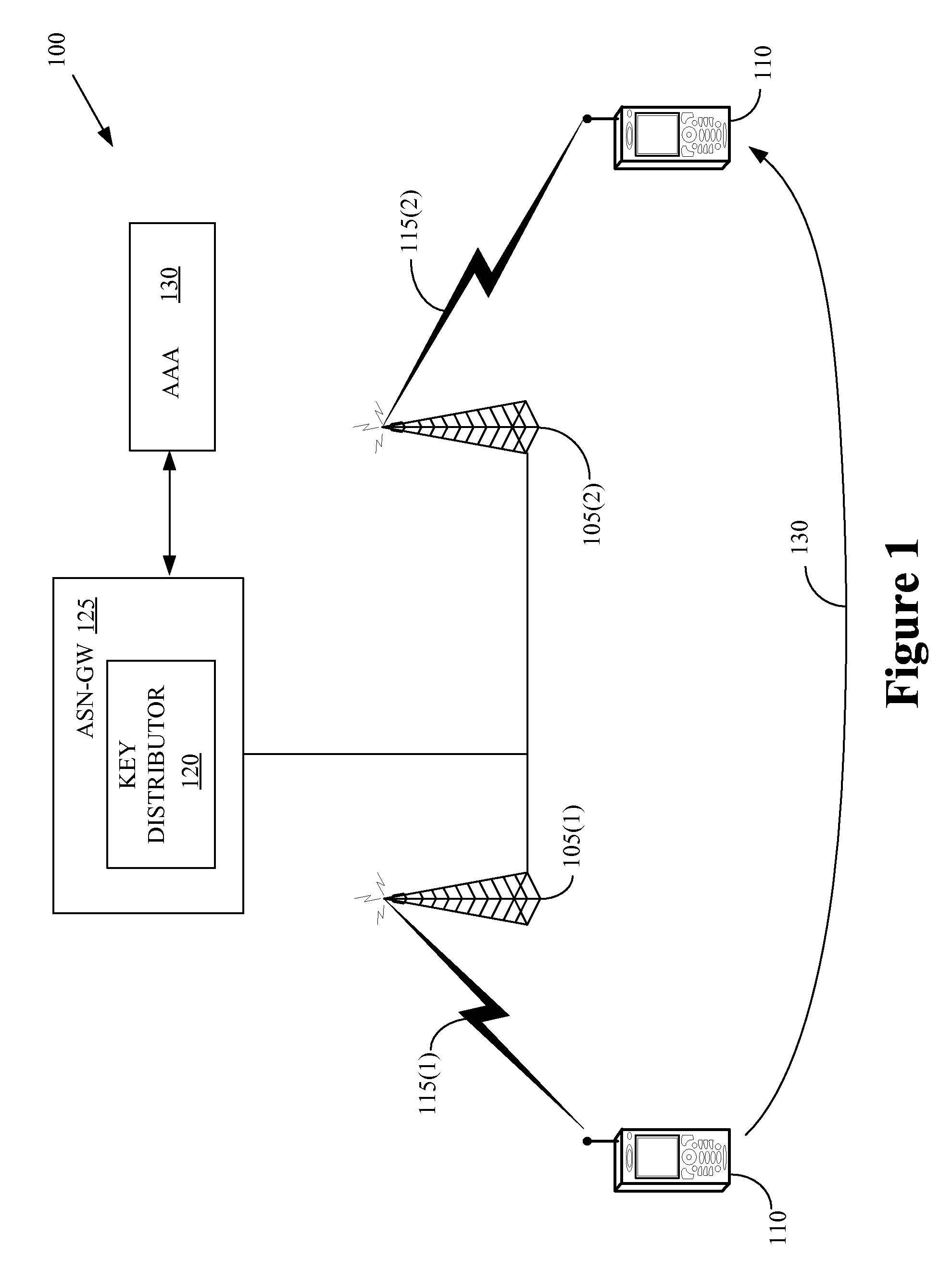
Apparatus and method for handover of ms in wireless communication system
InactiveUS20110128935A1Reduce switching delayWireless commuication servicesSecurity arrangementCommunications systemMobile station
An apparatus and method for handover of a Mobile Station (MS) in a wireless communication system are provided. The method includes, if a ranging request signal is received from the MS attempting access through a handover, determining if the BS and a serving BS of the MS are the same BS based on the ranging request signal, and, if the BS and the serving BS are the same BS, determining the effectiveness of a Cipher-based Message Authentication Code (CMAC) included in the ranging request signal using previous authentication information of the MS. The serving BS denotes a BS from which the MS has been serviced before the handover. The previous authentication information of the MS denotes authentication information that the serving BS has used for authenticating the MS.
Owner:SAMSUNG ELECTRONICS CO LTD
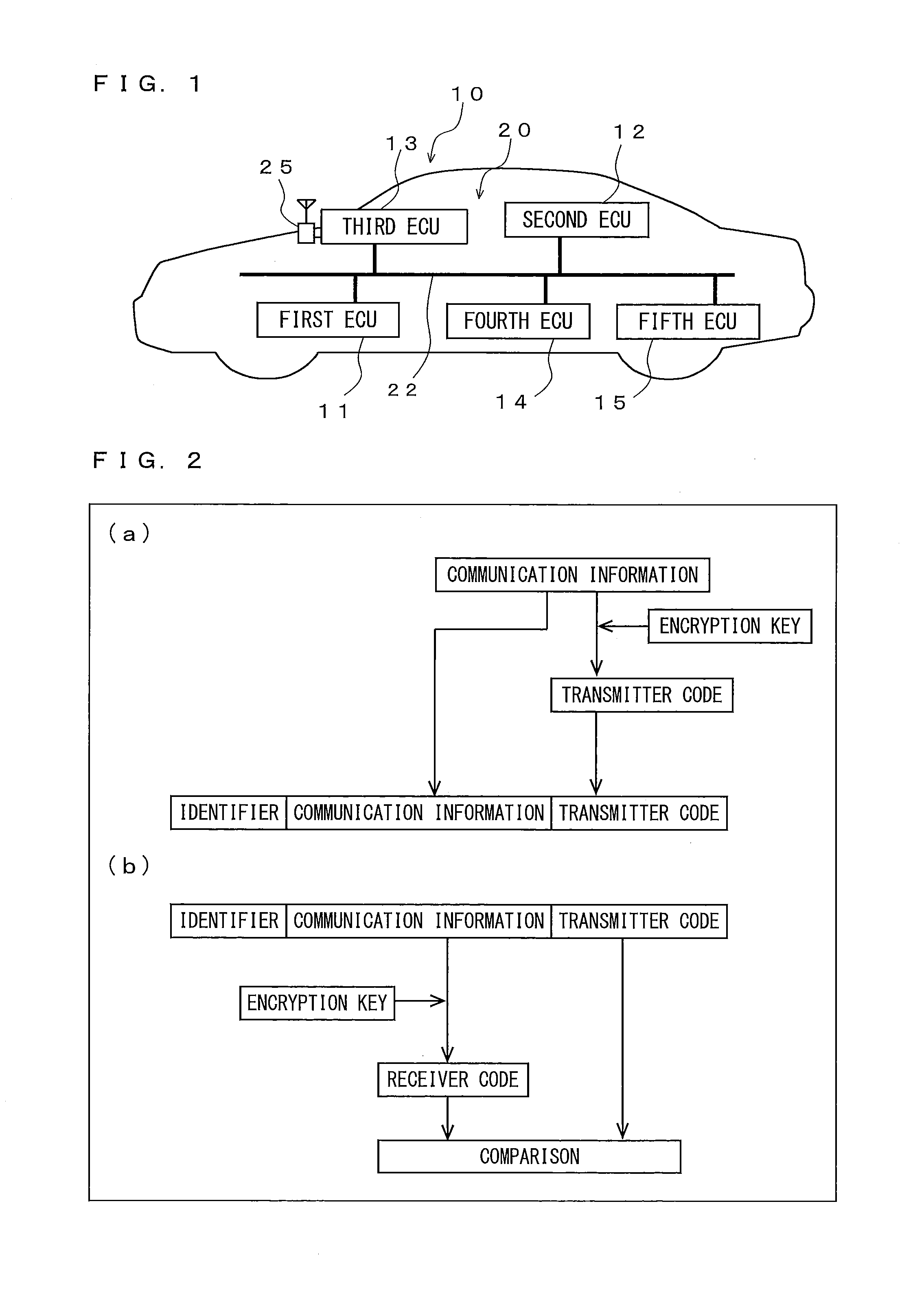
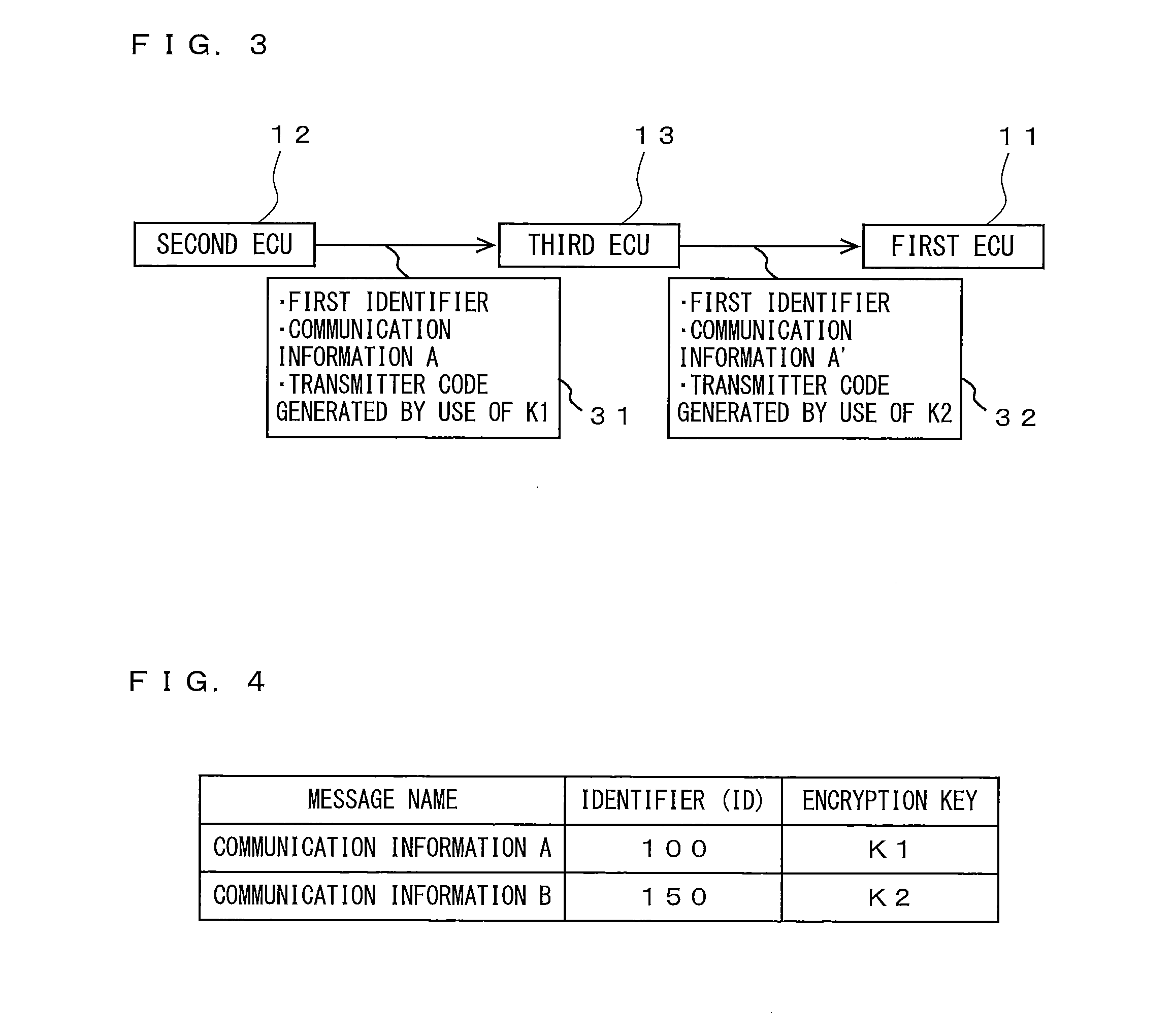
On-vehicle communication system
ActiveUS20160173505A1Public key for secure communicationUser identity/authority verificationCommunications systemMessage authentication code
An on-vehicle communication system, performing message authentication using transmitter and receiver codes that are message authentication codes respectively generated by a communication data transmitter and receiver, includes a first ECU, connected to an on-vehicle network, configured to have, among mutually different first and second encryption keys, only the first one and verify, by using the receiver code generated using the first one, the transmitter code assigned to the communication data received; a second ECU, connected to the on-vehicle network, configured to have at least the first one and transmit communication data to which the transmitter code generated using the first one is assigned; and a third ECU connected to the on-vehicle network and a network outside a vehicle, configured to have only the second one among the first and second ones and generate the transmitter or receiver codes using the second one when making communication over the on-vehicle network.
Owner:TOYOTA JIDOSHA KK
Method of providing security for relay station
InactiveUS20090074189A1Provide securitySafe deliveryKey distribution for secure communicationUnauthorised/fraudulent call preventionComputer hardwareBroadband
A method of providing security of a relay station is disclosed, by which the security can he provided for the relay station in a broadband wireless access system having the relay station. In a mobile communication system to relay a signal transfer between a base station and a mobile station, the present invention includes the steps of performing a relay station authentication from an authentication server using an authentication protocol, receiving a master key from the authentication server, deriving an authentication key from the received master key, deriving a message authentication code (MAC) key using the derived authentication key, and relaying a signal exchanged between the mobile station and the base station using the derived message authentication code key.
Owner:LG ELECTRONICS INC
Method and system for generating ciphertext and message authentication codes utilizing shared hardware
A method and system for generating ciphertext and message authentication codes utilizing shared hardware are disclosed. According to one embodiment, a method is provided of generating ciphertext message data and message authentication codes utilizing shared authenticated encryption unit hardware. In the described embodiment, plaintext message data is received at an authenticated encryption unit which comprises first and second authenticated encryption hardware modules. Thereafter, a first message authentication code (MAC) associated with a first authenticated encryption mode and a second MAC associated with a second authenticated encryption mode are generated. More specifically, the first MAC is generated utilizing the plaintext message data and first authenticated encryption hardware module and ciphertext message data and the second MAC are generated utilizing the plaintext message data and second authenticated encryption hardware module.
Owner:IBM CORP
Method of providing fresh keys for message authentication
ActiveUS20080137853A1Well formedSecret communicationSecuring communicationComputer hardwareCommunications system
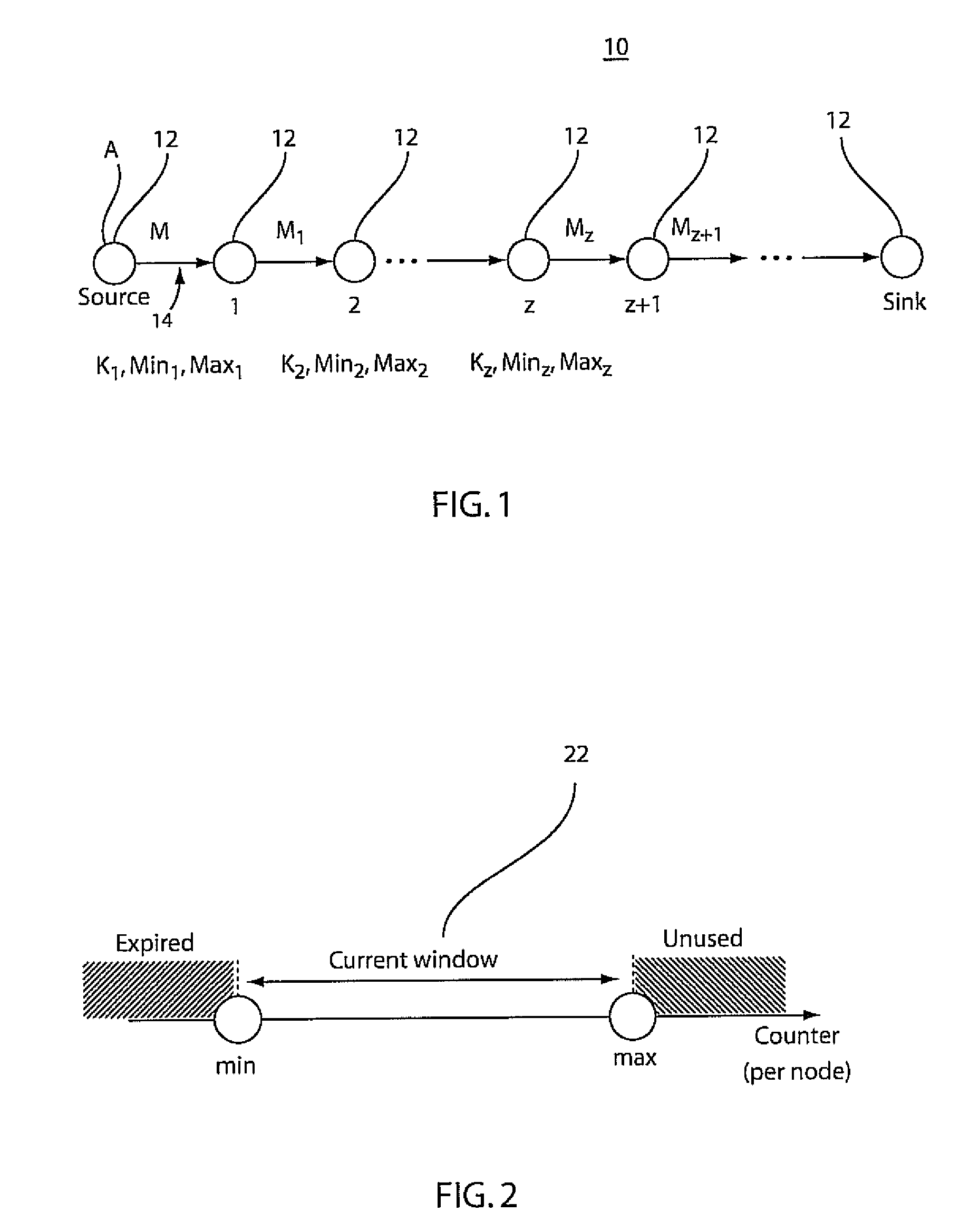
The present invention provides a method of operating a mobile unit in a wireless communication system. Embodiments of the method may include providing access request message(s) including information indicative of a first counter and a message authentication code formed using a first key. The first key is derived from a second key and the first counter. The second key is derived from a third key established for a security session between the mobile unit and an authenticator. The first counter is incremented in response to each access request provided by the mobile unit.
Owner:ALCATEL LUCENT SAS
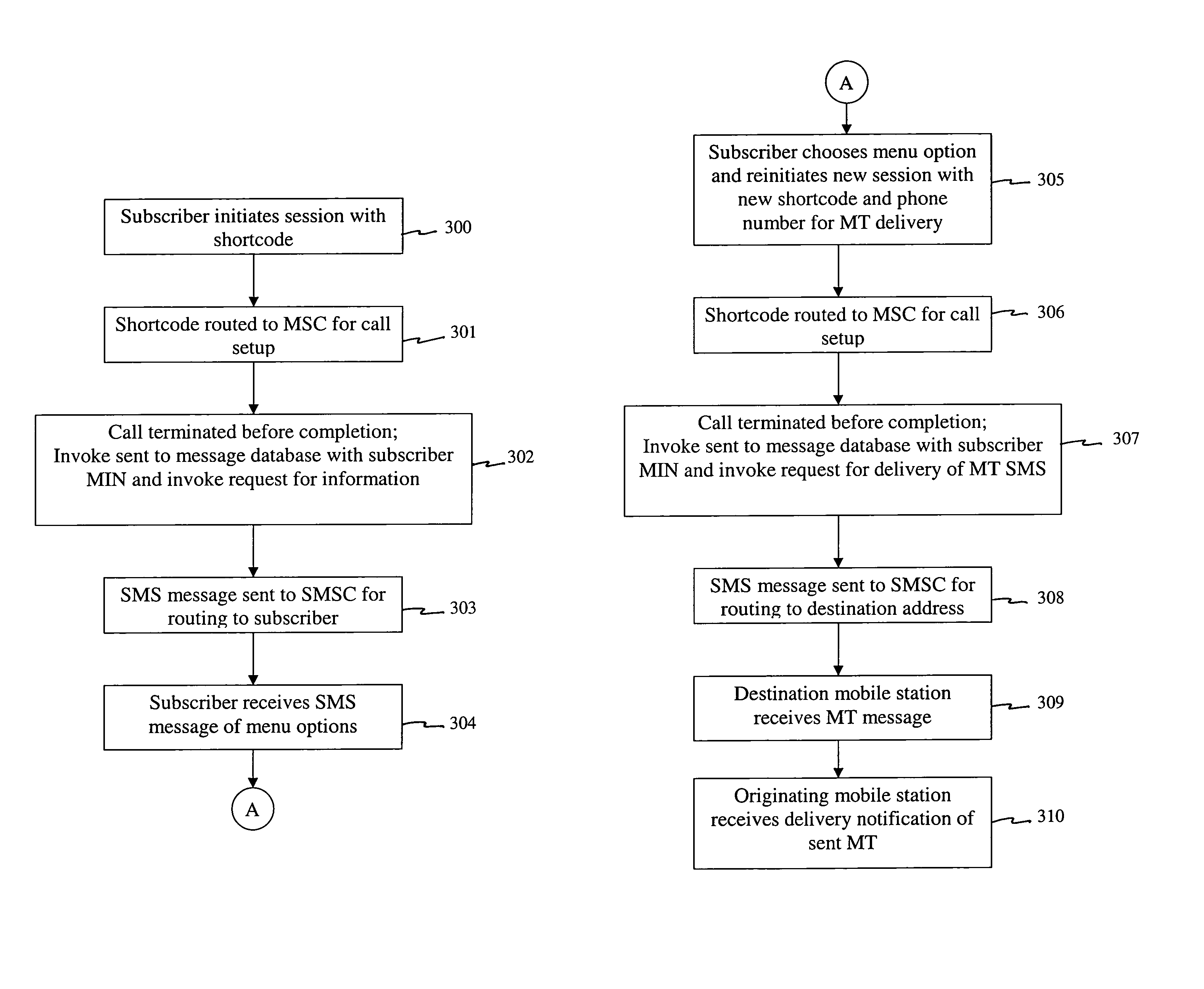
Wireless initiated messaging
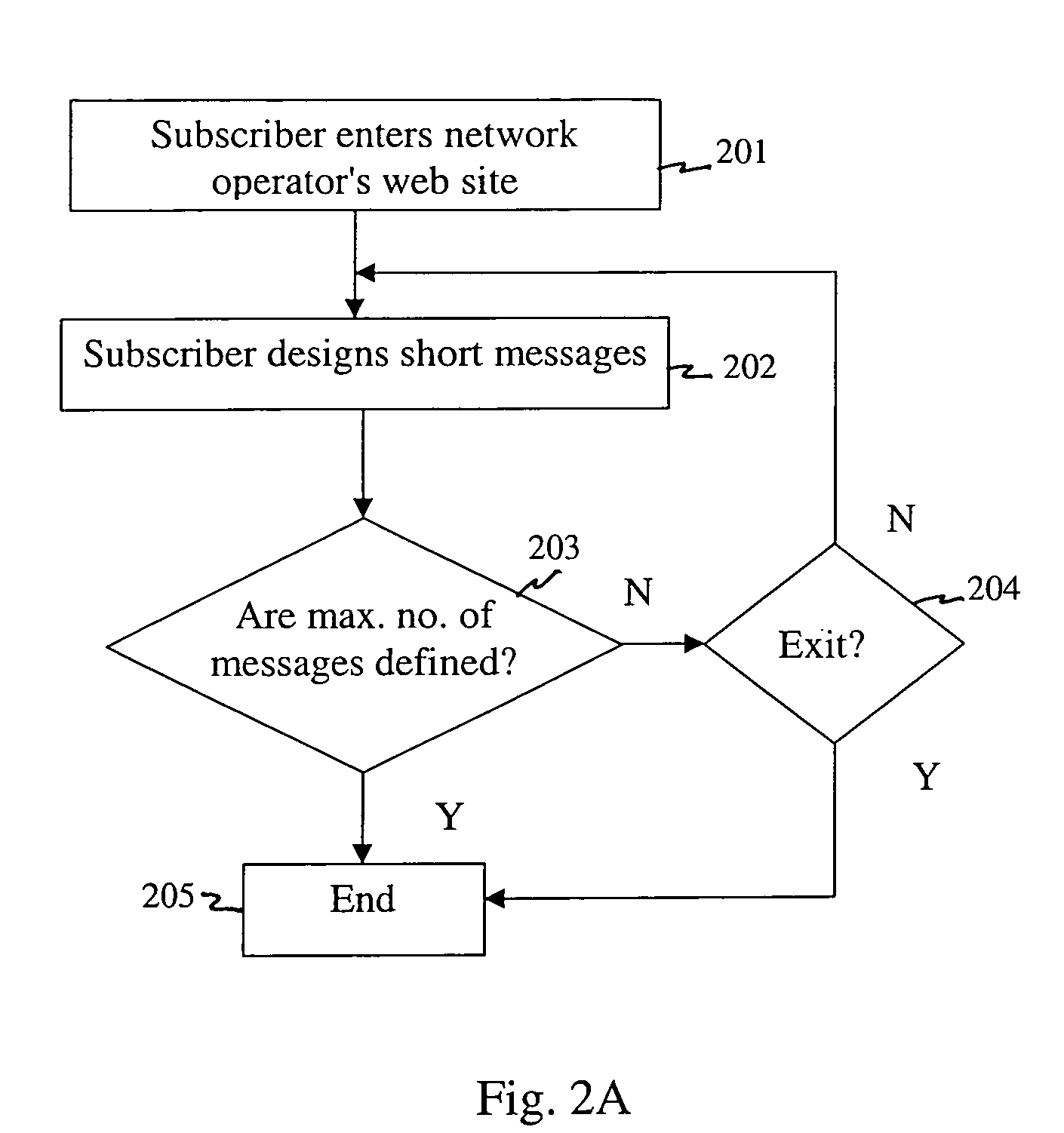
InactiveUS6956831B1Generate additional revenueEasy for to initiate sending short messageSpecial service for subscribersAutomatic call-answering/message-recording/conversation-recordingPersonalizationMessage authentication code
A wireless initiated messaging system includes a personalized message database storing therein messages predefined by or on behalf of a subscriber and in association with the subscriber and a message identifier. The system also includes a call control center coupled to the personalized message database. In response to receiving a signal containing predefined message initiation code, a message identifier identifying one of the predefined messages, and an identifier of a receiving station, the call control center retrieves the predefined message from the personalized message database and sends the retrieved predefined message to the receiving station.
Owner:COMVERSE
Network safety isolation file transmission control method
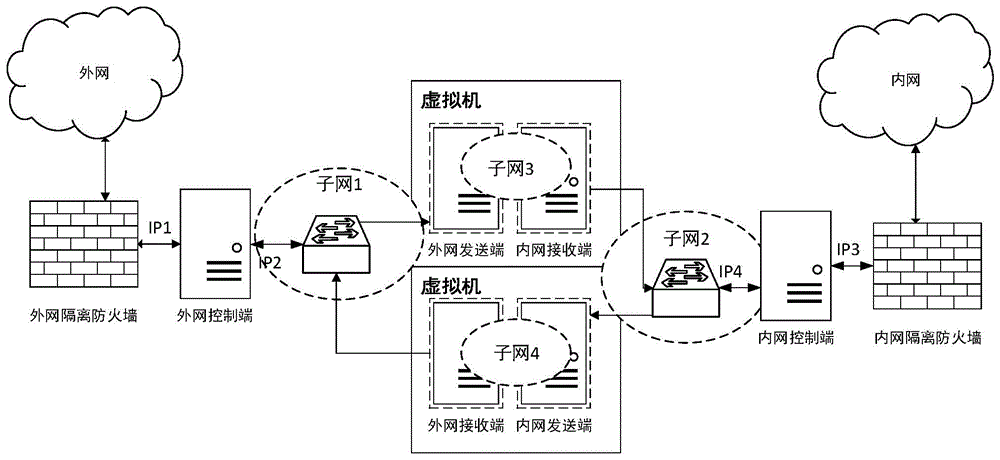
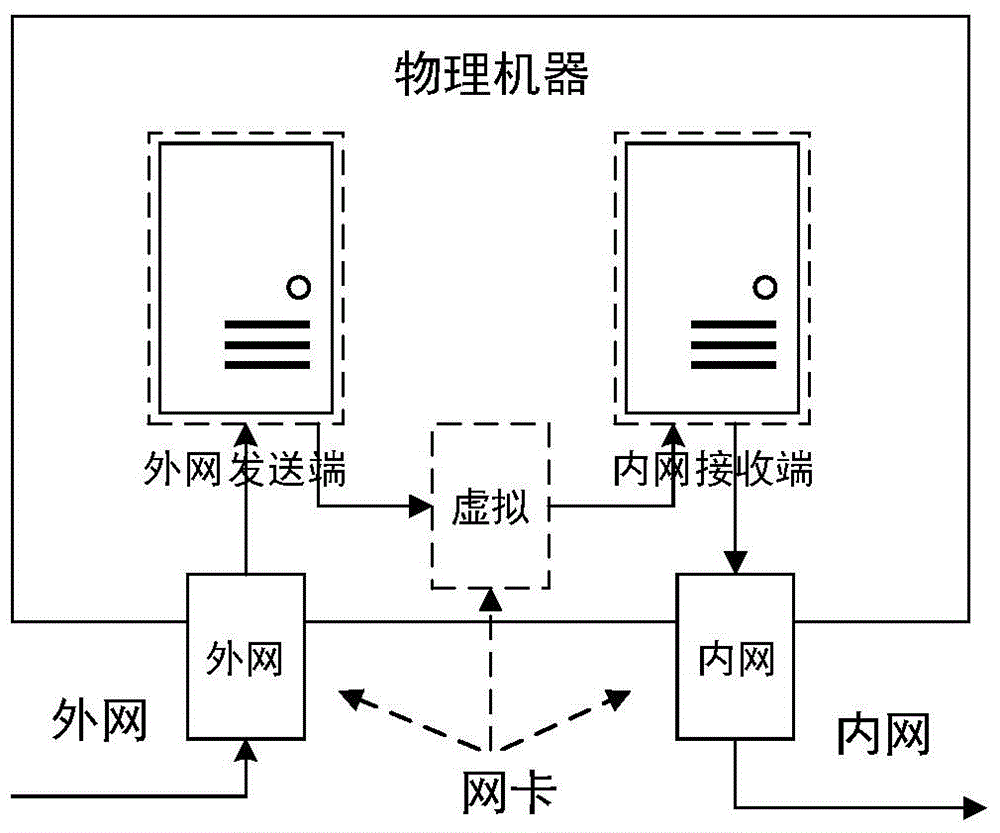
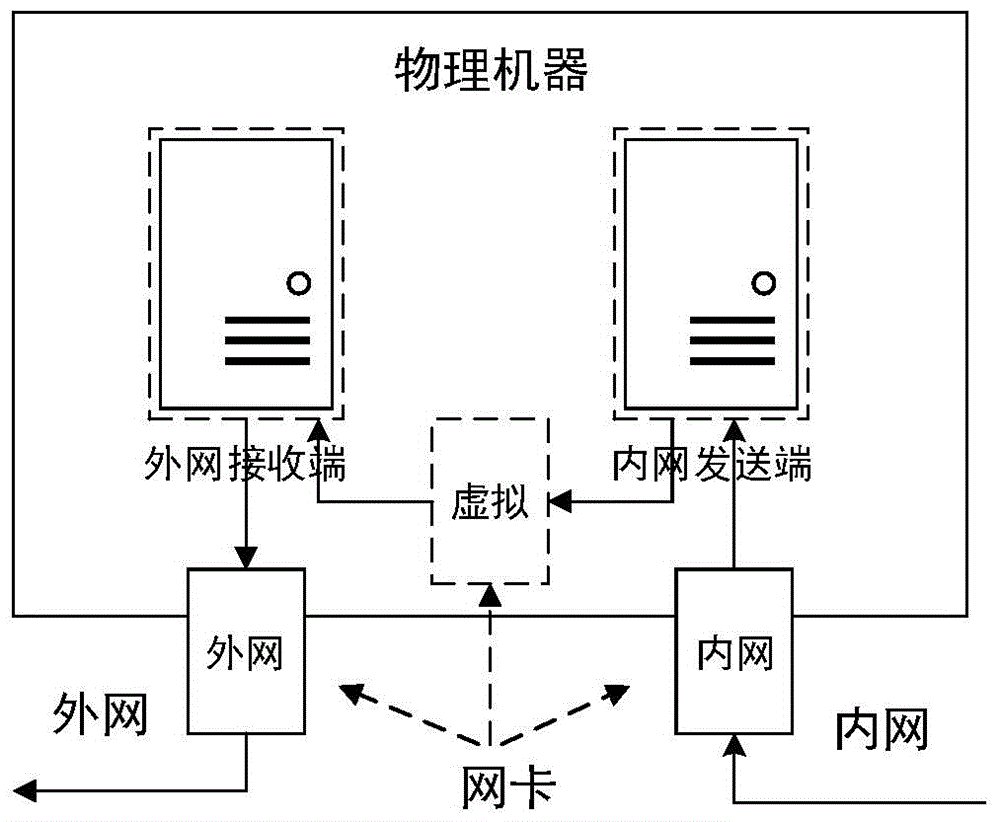
InactiveCN104363221AEnsure safetyKeep Content SafeSecuring communicationComputer hardwareConfidentiality
The invention relates to a safety isolation file transmission control method, in particular to a file transmission control method between taxation network safety isolation systems. A transmission control system comprises an external network isolation firewall, an external network control end, an external network transmitting end, an external network receiving end, an internal network transmitting end, an internal network receiving end, an internal network control end and an internal network isolation firewall. A computer system, a virtual machine system and the isolation firewalls are combined to achieved a relatively universal safety data transmission manner, safe and reliable bidirectional data transmission is achieved by the control method with a special safety protocol, confidentiality, completeness and non-repudiation during information transmission are achieved by safety techniques such as data encryption, digital signatures and information authentication codes, data exchanging performance is increased while safety of internal and external network systems is guaranteed, and the whole system can work reliably and stably.
Owner:QINGDAO WEIZHIHUI INFORMATION
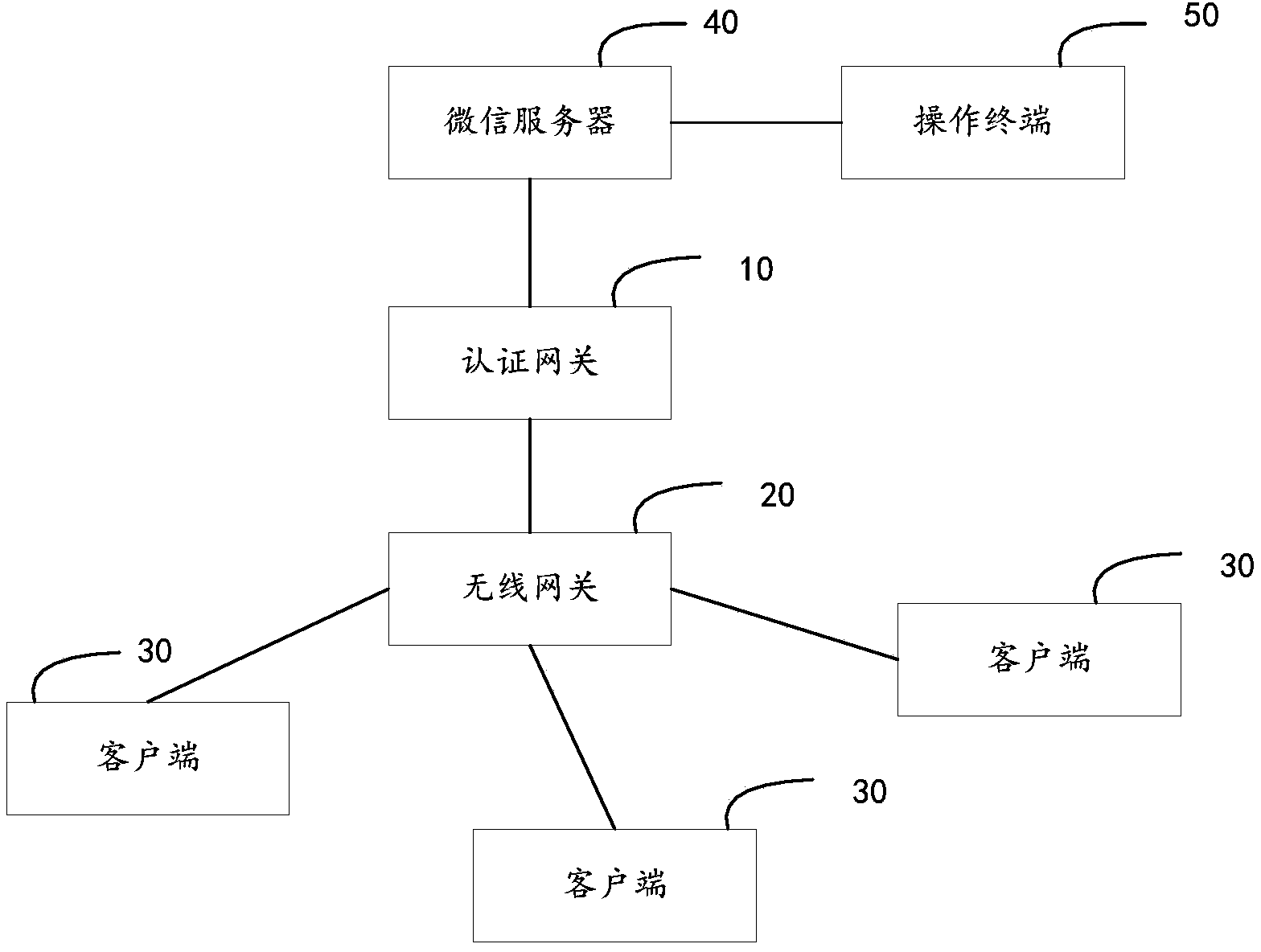
Authentication method and system for public wireless environment Internet access based on micro message
ActiveCN103401884ALow costPrivacy protectionNetwork topologiesTransmissionAuthentication serverInternet access
The invention discloses an authentication method for public wireless environment Internet access based on the micro message, which comprises the following steps: the client side obtains the user identification and an input application authentication instruction, and a corresponding application authentication request is generated through the micro message application and is sent to the micro message sever; the micro message sever receives the application authentication request, and returns the authentication code corresponding to the user identification to the client side and the authentication gateway; the client side obtains the input authentication code, generates an Internet access authentication request through the input authentication code and user identification, and sends the Internet access authentication request to the authentication gateway; the authentication gateway verifies the Internet access authentication request according to authentication code corresponding to the user identification and returned by the micro message server, if the Internet access authentication request passes the verification, the authentication of the Internet access authentication request and the client side corresponding to the user identification is judged to be successful. in addition, the invention further provides an authentication system for public wireless environment Internet access based on the micro message. According to the method and system, a short message platform is not required, so that the cost is reduced.
Owner:SANGFOR TECH INC
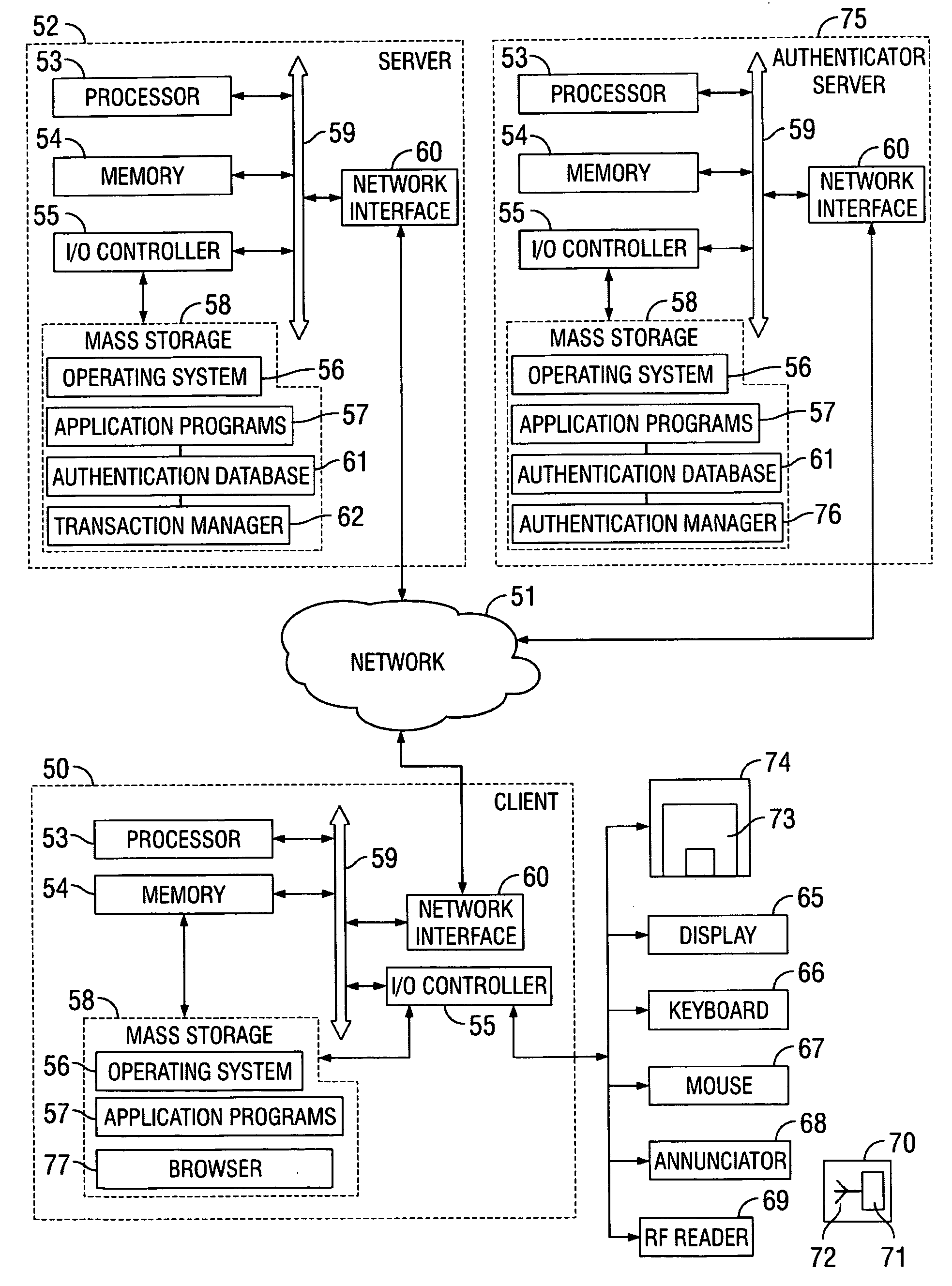
Secure electronic transaction authentication enhanced with RFID
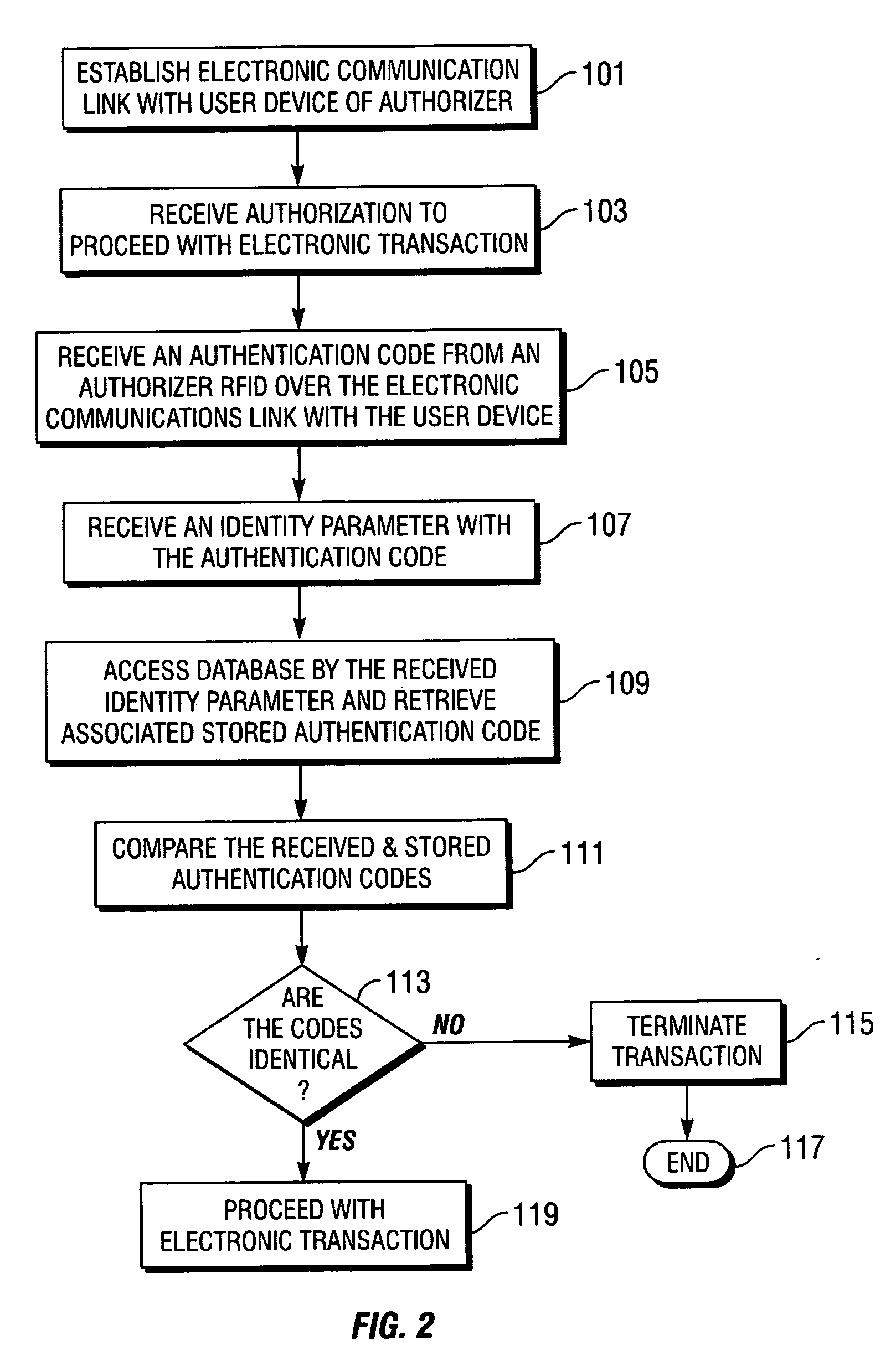
InactiveUS20070094152A1Securing communicationPayments involving neutral partyUser deviceSecure Electronic Transaction
Methods, computer program products and systems for authenticating an electronic transaction conducted over an electronic communications link with a user device of a transaction authorizer. A method includes establishing the electronic communications link with the user device of the authorizer, receiving an authentication code from an authorizer RFID over the electronic communication link, and determining if the received authentication code matches a stored authentication code assigned to the authorizer. The electronic transaction may proceed if the stored authentication code matches the received authentication code. Also included may be the step of determining if one or more required personal attributes match stored personal attributes associated with the stored authentication code assigned to the authorizer. If so, then the method may include proceeding with the electronic transaction if the one or more required personal attributes match the stored personal attributes associated with the stored authentication code assigned to the authorizer.
Owner:IBM CORP
Universal printer chip
A toner cartridge having a microcontroller configured to store data necessary to create a message authentication code required by the printer. The microcontroller contains data values capable of generating acceptable MACs for a plurality of printers. The microcontroller recognizes a variety of unique parameters displayed by the printer's processor to identify the printer being used. Once the printer is identified, the microcontroller loads the data values associated with the printer and generates an acceptable MAC to enable printer operation.
Owner:INNOVATIVE CARTRIDGE TECH
Changing a codec or MAC size without affecting the encryption key in PacketCable communication
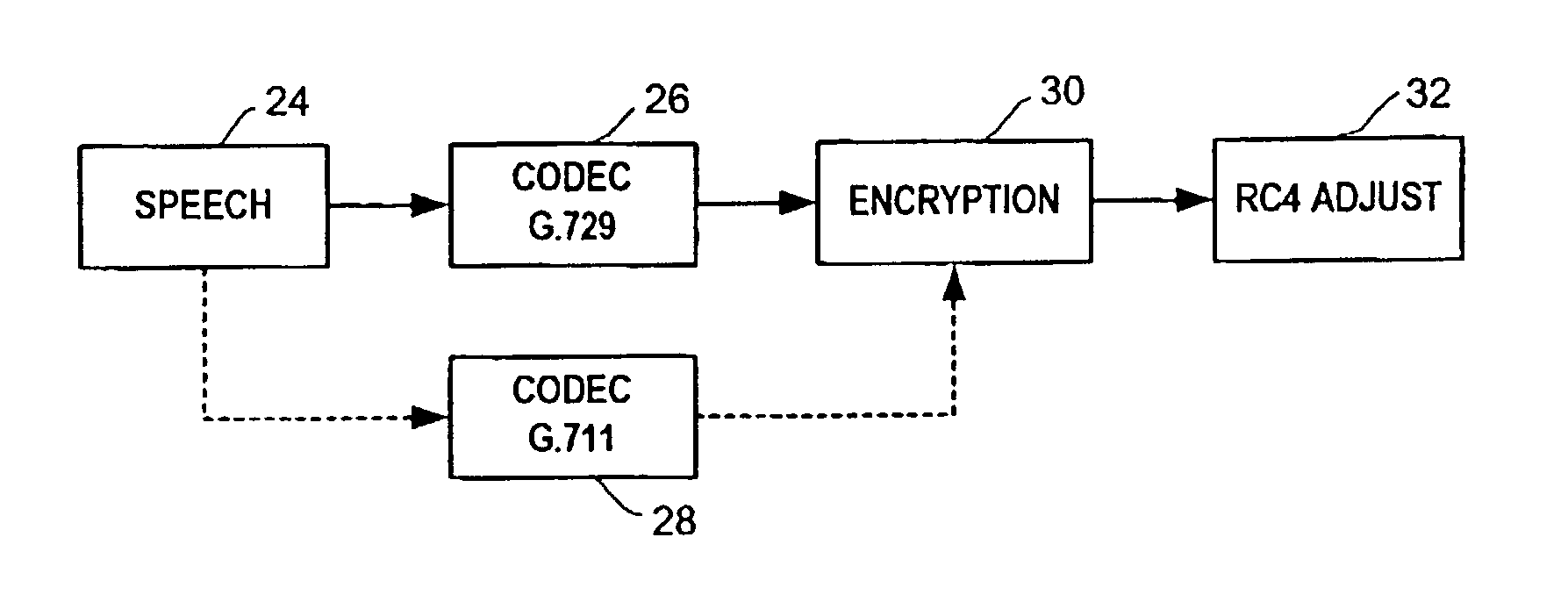
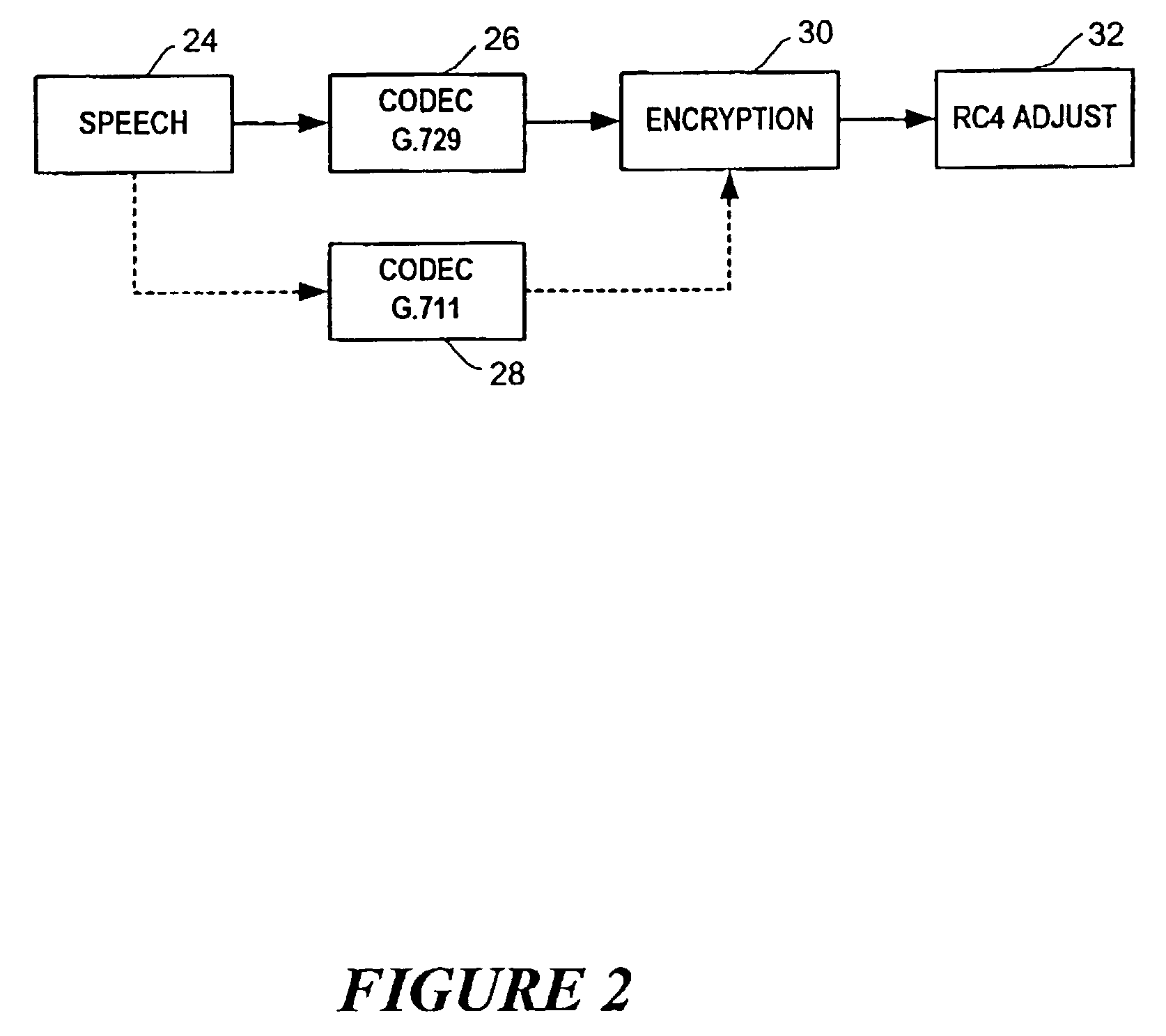
ActiveUS7127604B2Synchronising transmission/receiving encryption devicesError detection/correctionComputer hardwareRC4
A technique is described to change the codec or MAC (message authentication code) size in a packet security unit for PacketCable communications during realtime voice transmissions is described. An algorithm that provides fast RC4 key advancing to prevent MIPS (millions of instruction cycles per second) overflow is used to perform codec or MAC size changes. The invention is performed without changing the keying material, where the sender and receiver must continue the RC4 encryption process from its state prior to the codec or MAC size change. A sender needs to preserve continuity of the timestamp across a codec change, since the timestamp reflects realtime. Changing the codec or MAC size is likely to change the frame parameters. To preserve continuity of the RC4 state and the timestamp across the codec / MAC size change, the sender TX and receiver RX generates a new frame number. The new frame number is applied to the first frame generated by the new codec or MAC size.
Owner:TELOGY NETWORKS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com