Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3930results about "Payments involving neutral party" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
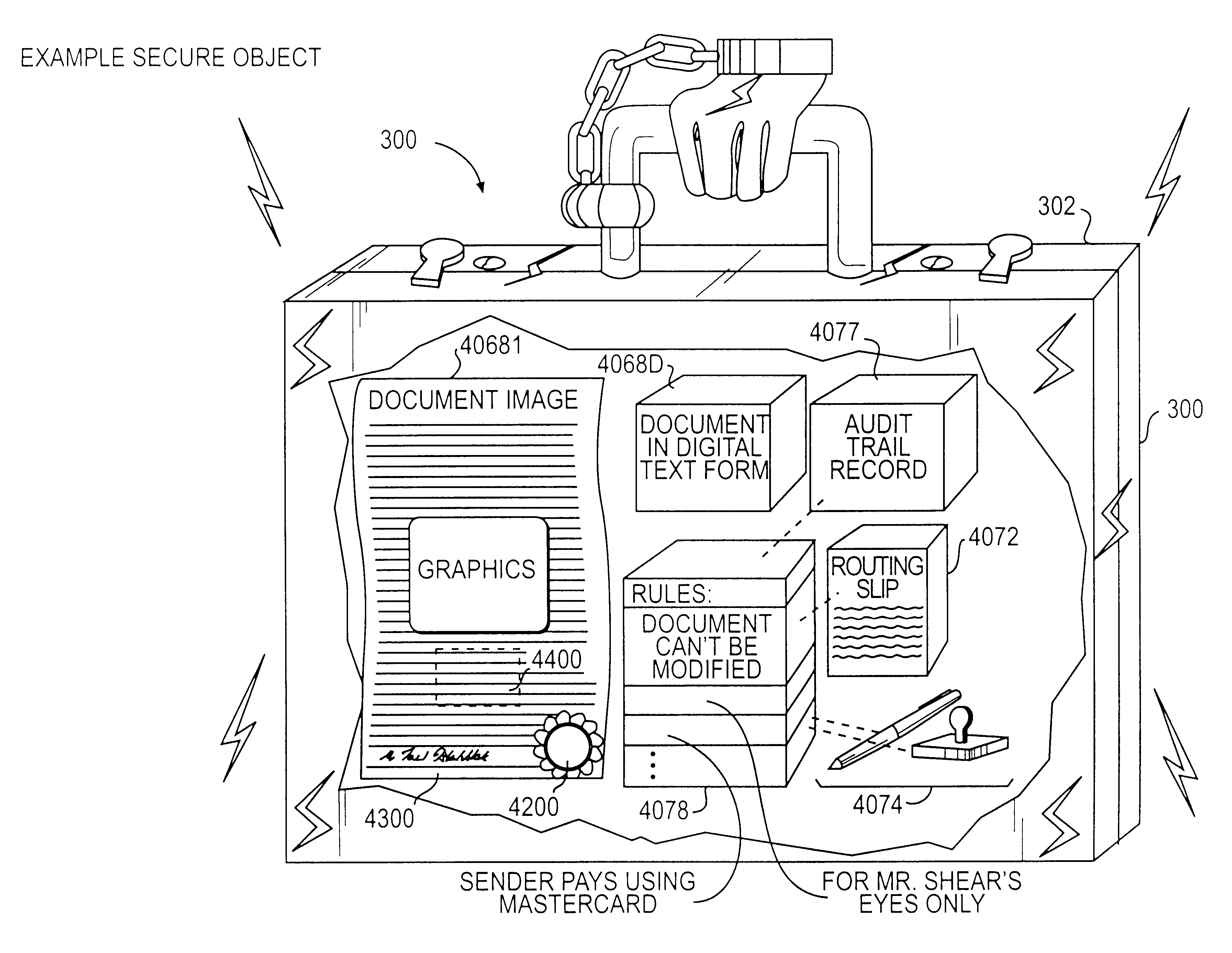
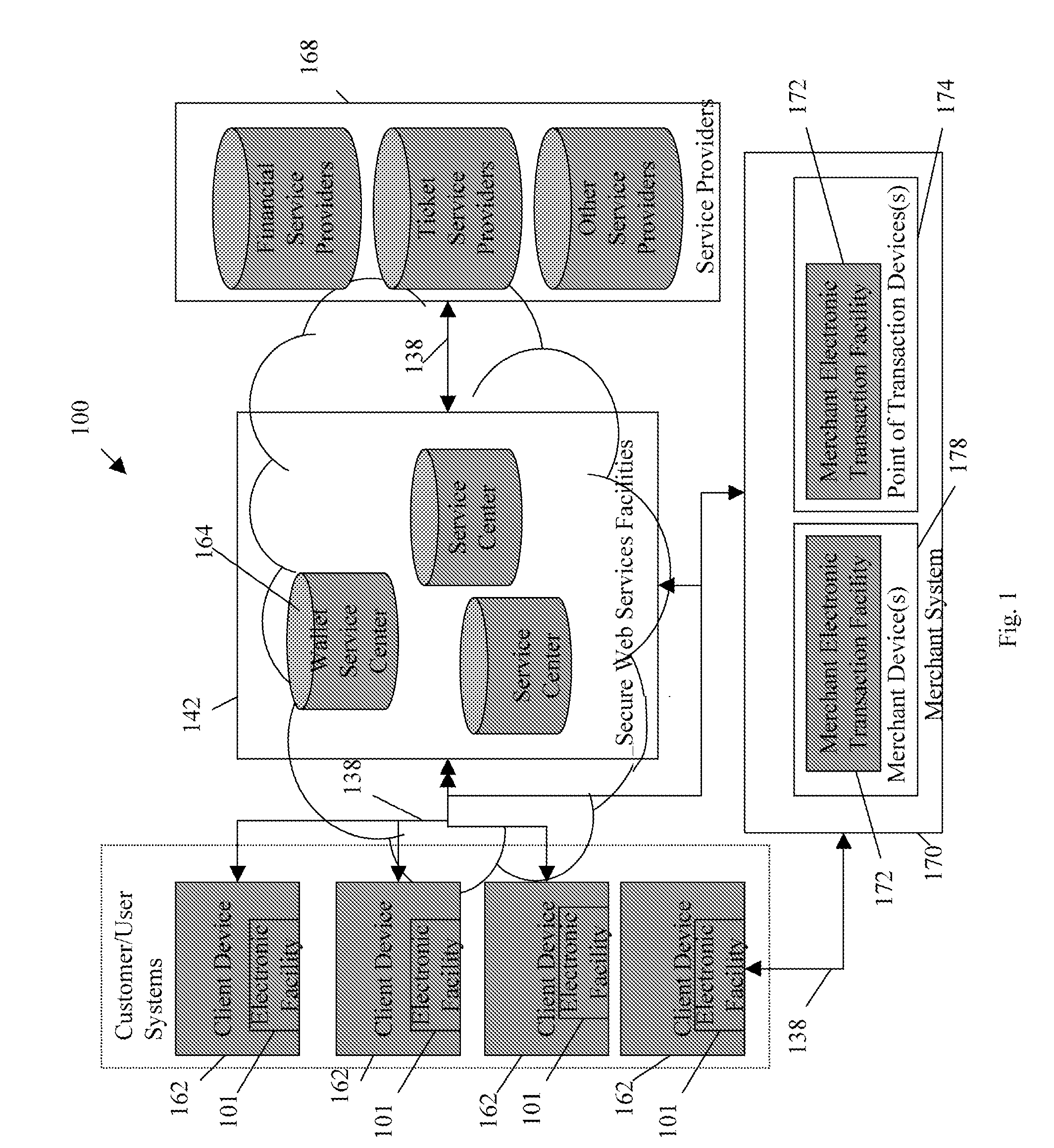
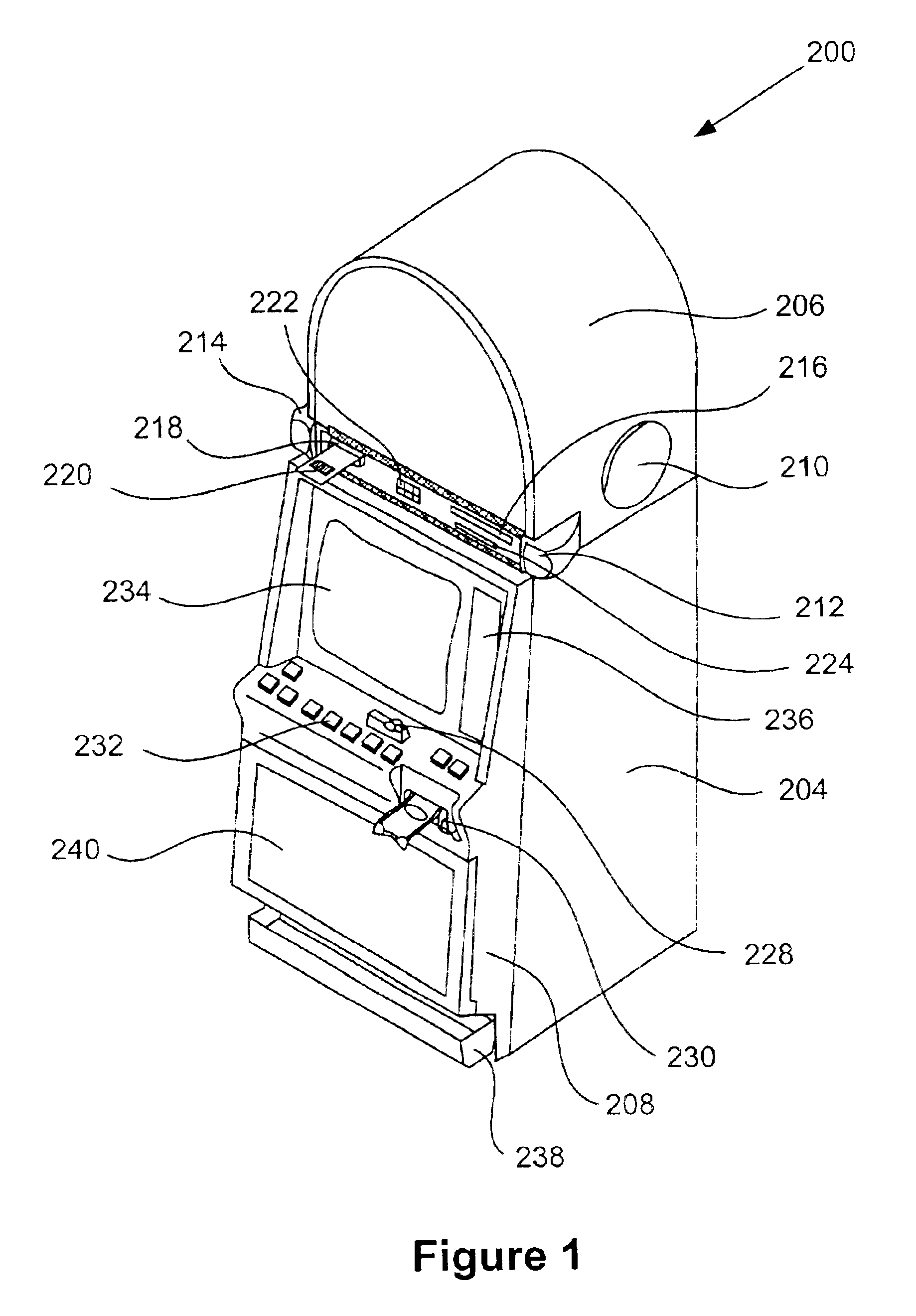
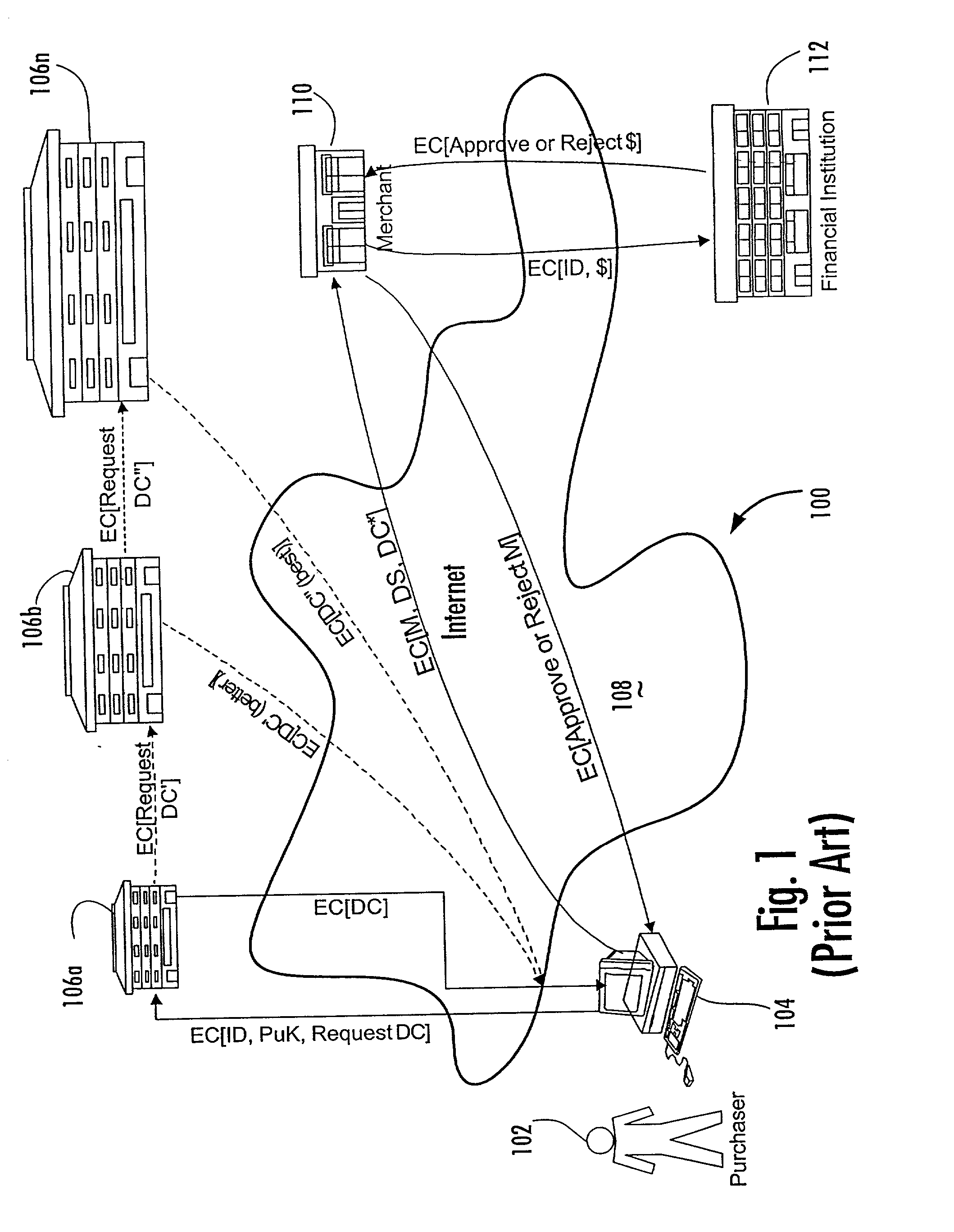
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
Transactional services
InactiveUS20070198432A1High level of throughputHigh level of efficiencyCryptography processingComputer security arrangementsTransaction serviceDatabase
Owner:MASTERCARD MOBILE TRANSACTIONS SOLUTIONS
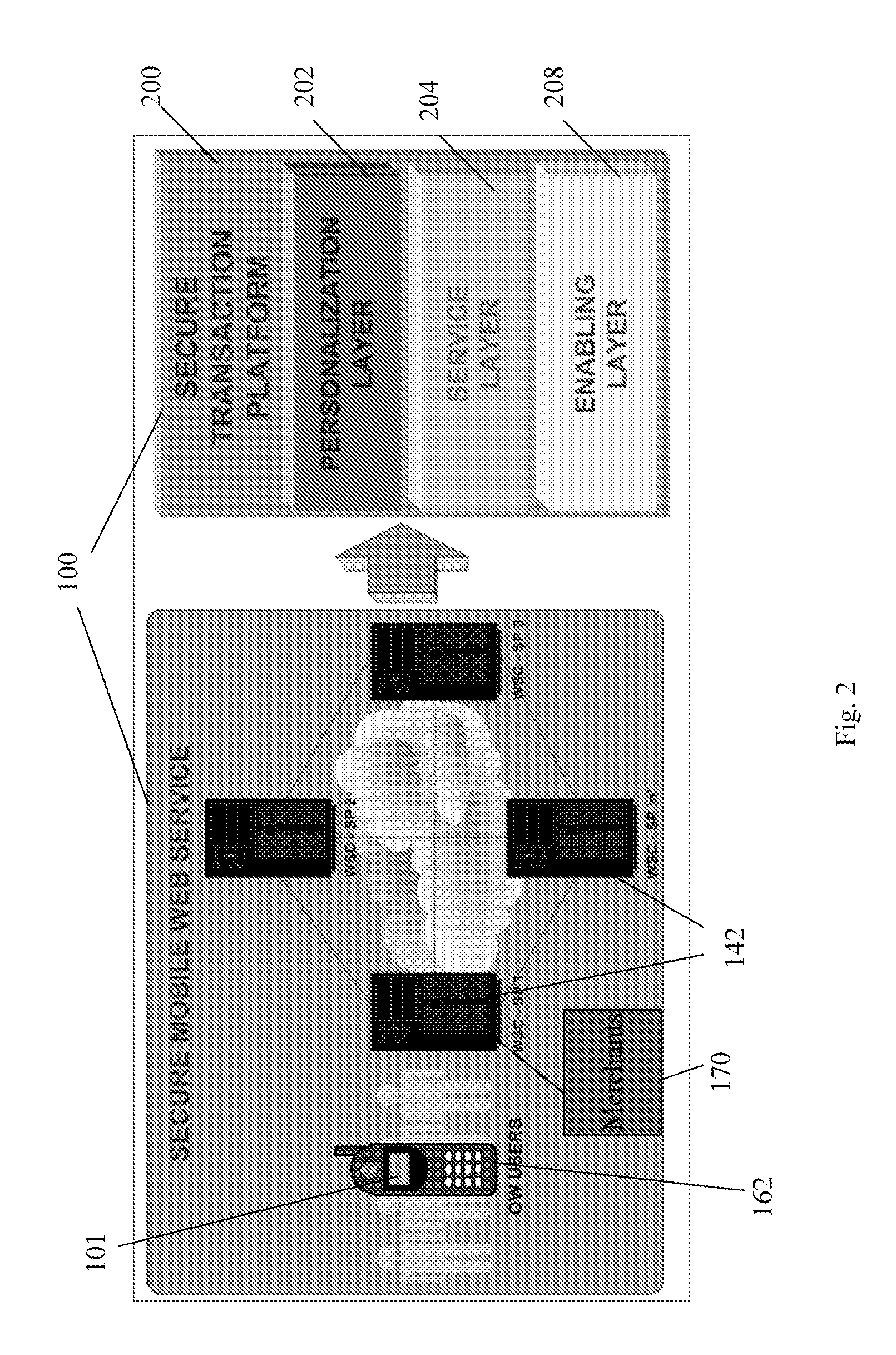
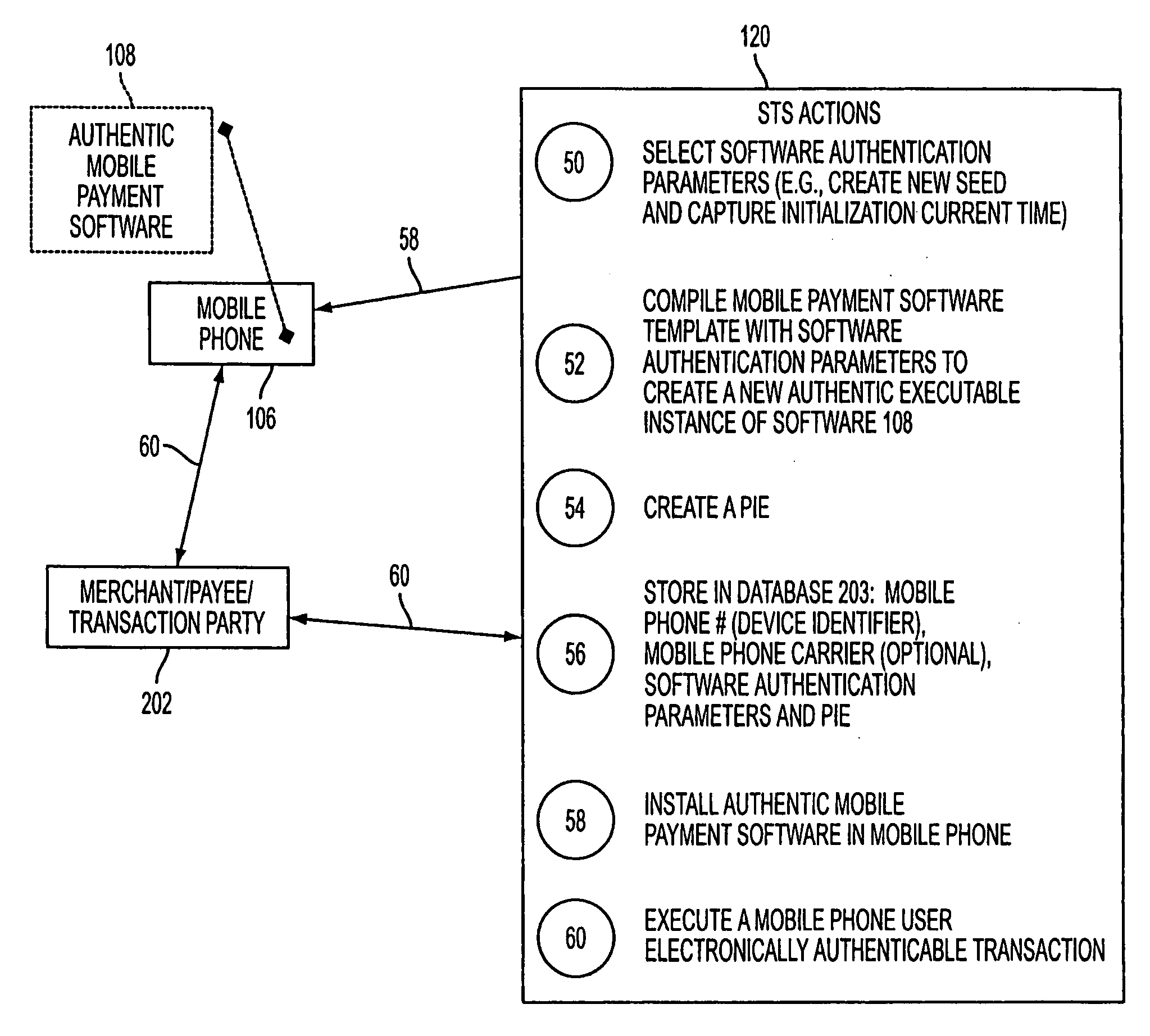
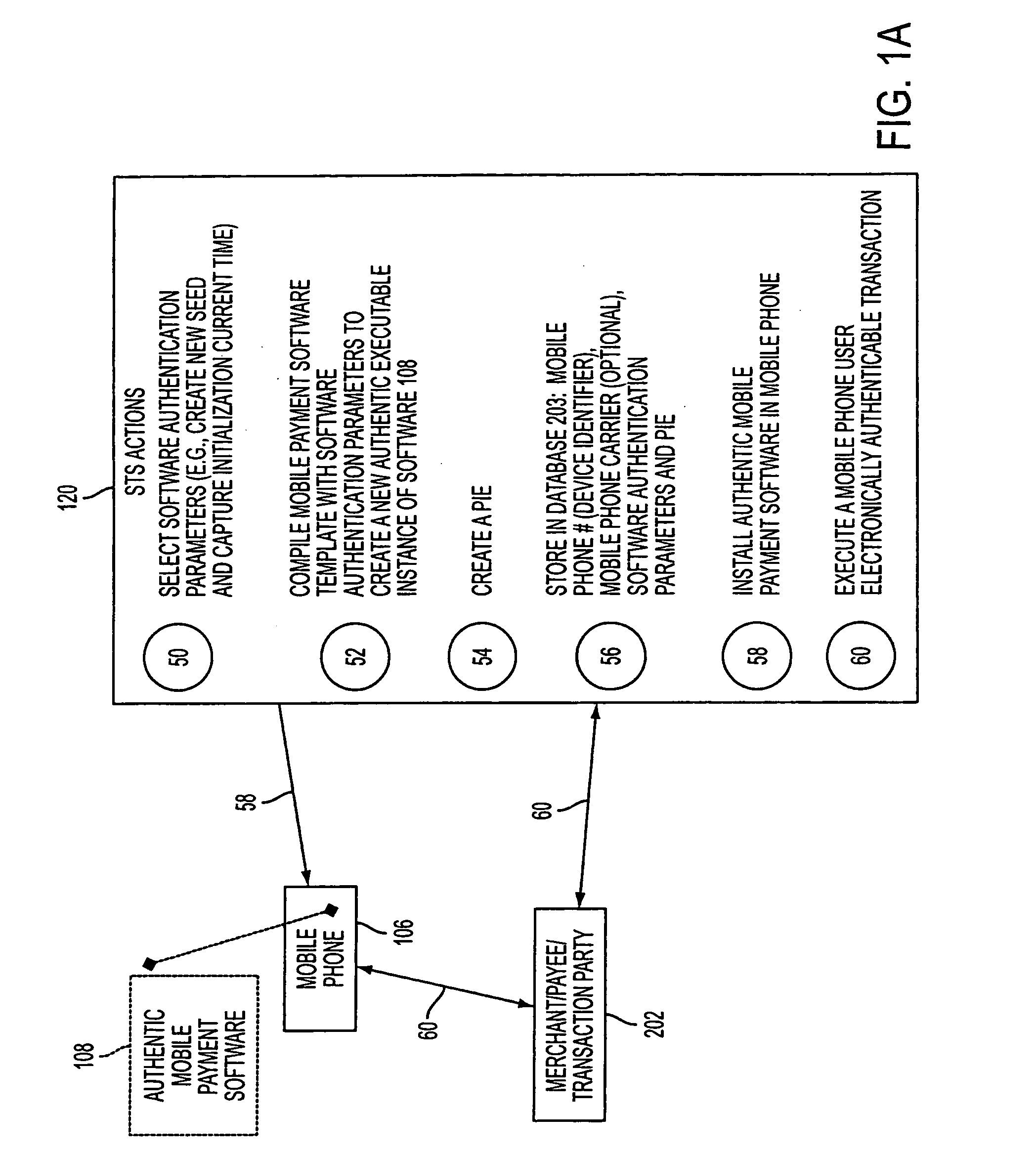
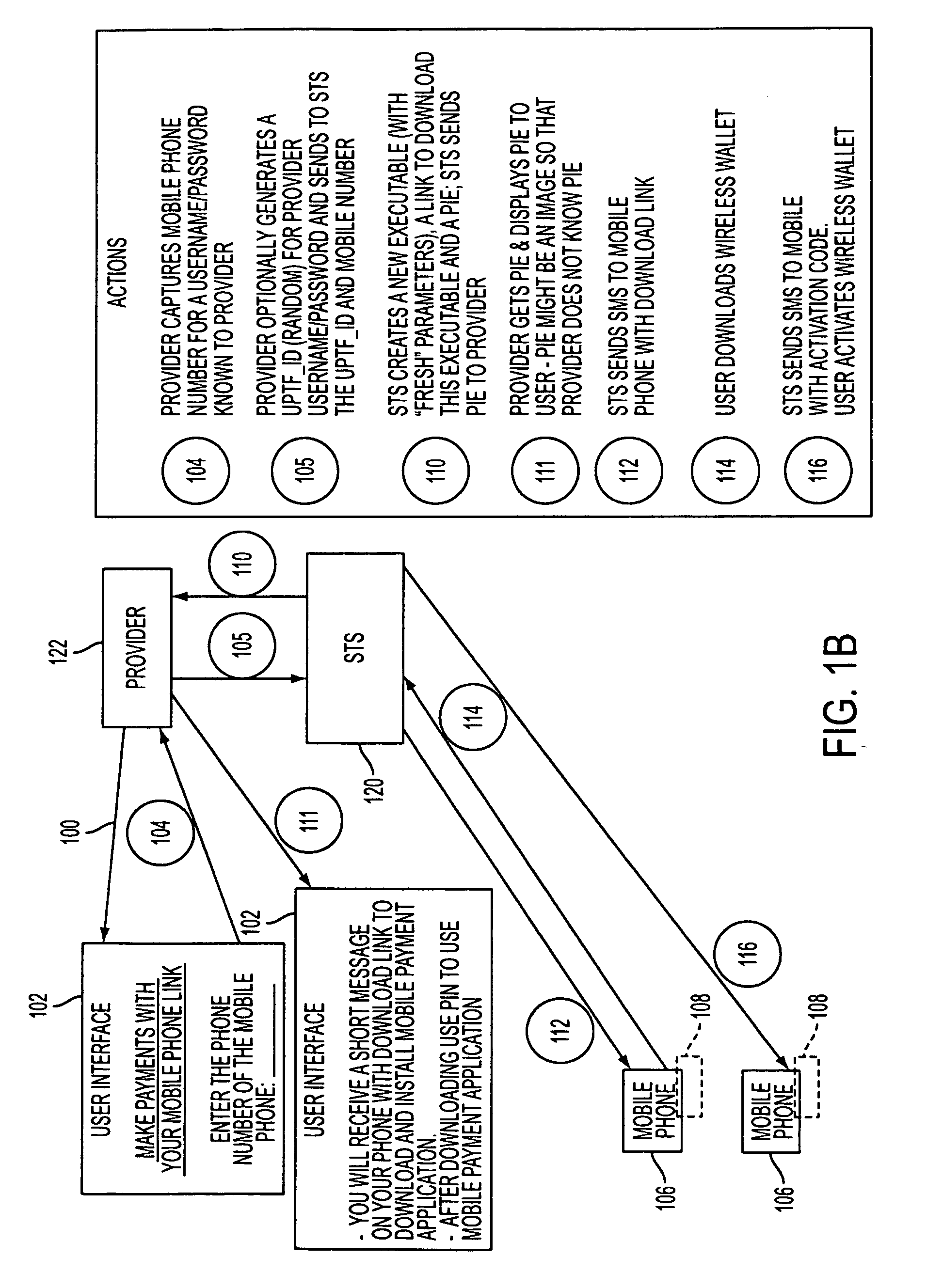
Wireless wallet
A mobile phone system and method of initializing, at a secure transaction server (STS), a mobile payment software with a software authentication parameter, as an authentic mobile payment software; providing an STS correlation between a personal identification entry (PIE) and the authentic mobile payment software; installing, in a mobile phone, the authentic mobile payment software; and inputting, by a user, the PIE to the installed authentic mobile payment software to generate according to the PIE and the software authentication parameter a transformed secure authenticable mobile phone cashless monetary transaction over the mobile phone network, as a mobile phone wireless wallet of the user of the mobile phone. The mobile phone authenticable cashless monetary transaction is performed according to an agreement view(s) protocol.
Owner:PCMS HOLDINGS INC
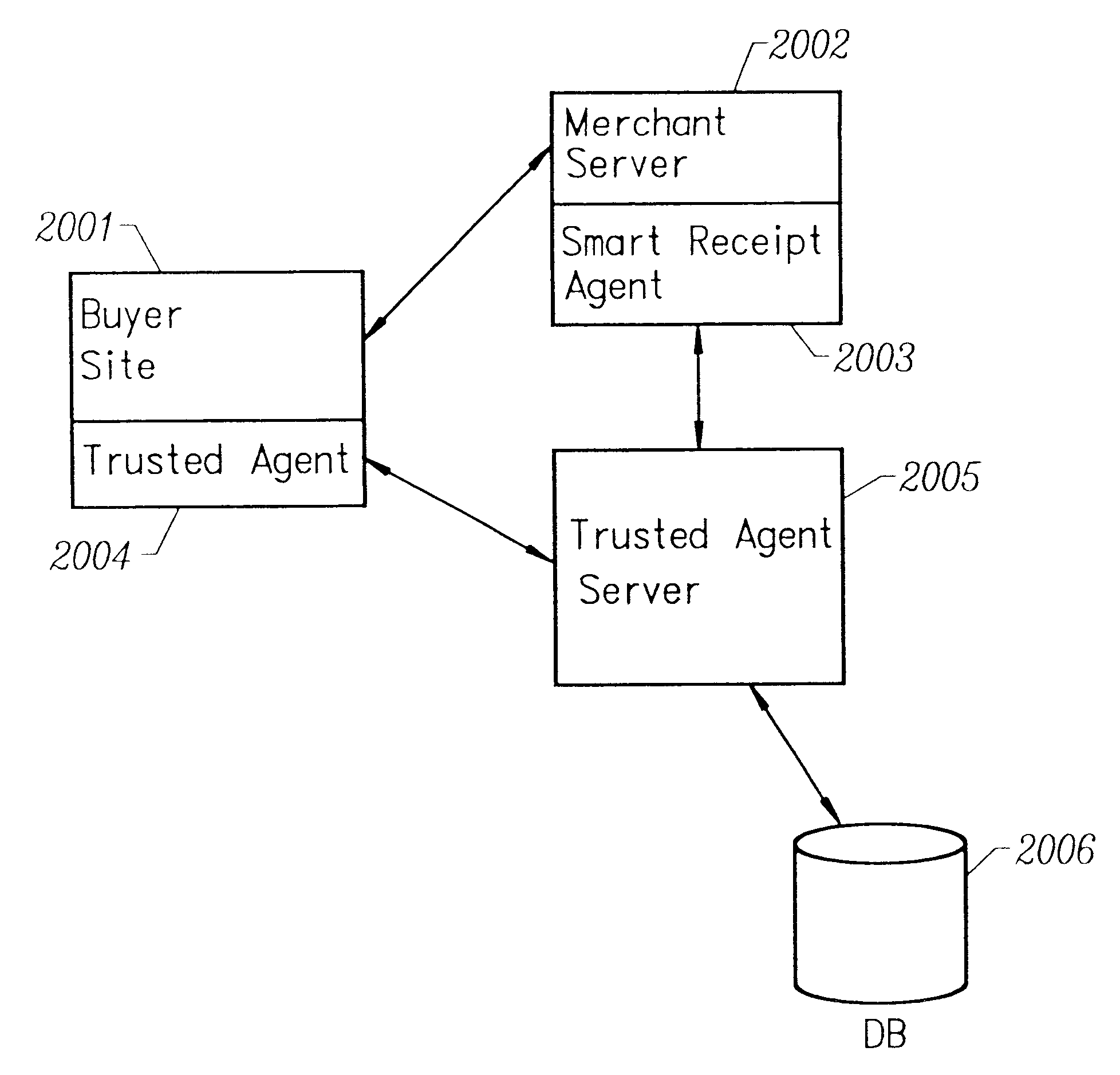
Smart electronic receipt system
A smart electronic receipt system that provides intelligent receipts, called Smart Receipts, that electronically document a transaction between two parties and maintains a persistent connection between the two parties following a successful online transaction. A Trusted Agent on the Buyer's client system creates an order record which is stored in a database on a Trusted Agent Server and starts the transaction process with the merchant. A Smart Receipt is delivered by a Smart Receipt Agent over a secure connection from the merchant to the Trusted Agent Server upon successful completion of a purchase and reflects the details of the transaction. It is stored in a secure database on the Trusted Agent Server and is made available to the Buyer (user) through a Trusted Agent located on his machine. The Trusted Agent Server compares the order record Limited Edition Digital Objects (LEDOs) stored in database with the Smart Receipt's LEDO to find the corresponding order record. The Smart Receipt provides the customer with detailed information about an online purchase in a standardized format. Hyperlinks embedded in the Smart Receipt enable the customer to access customer service and order status. The merchant may also embed addition-al services within the Smart Receipt, including special offers for future purchases. Offers provided in a Smart Receipt can be personalized to a user's preferences which are stored on the Trusted Agent Server. Each Smart Receipt is comprised of a chain of LEDOs with each LEDO object having a unique owner. A Smart Receipt is a dynamic entity and is continuously updated until the Buyer deletes it from the Trusted Agent Server.
Owner:THE BRODIA GROUP
Methods and Systems For Making a Payment Via A Stored Value Card in a Mobile Environment
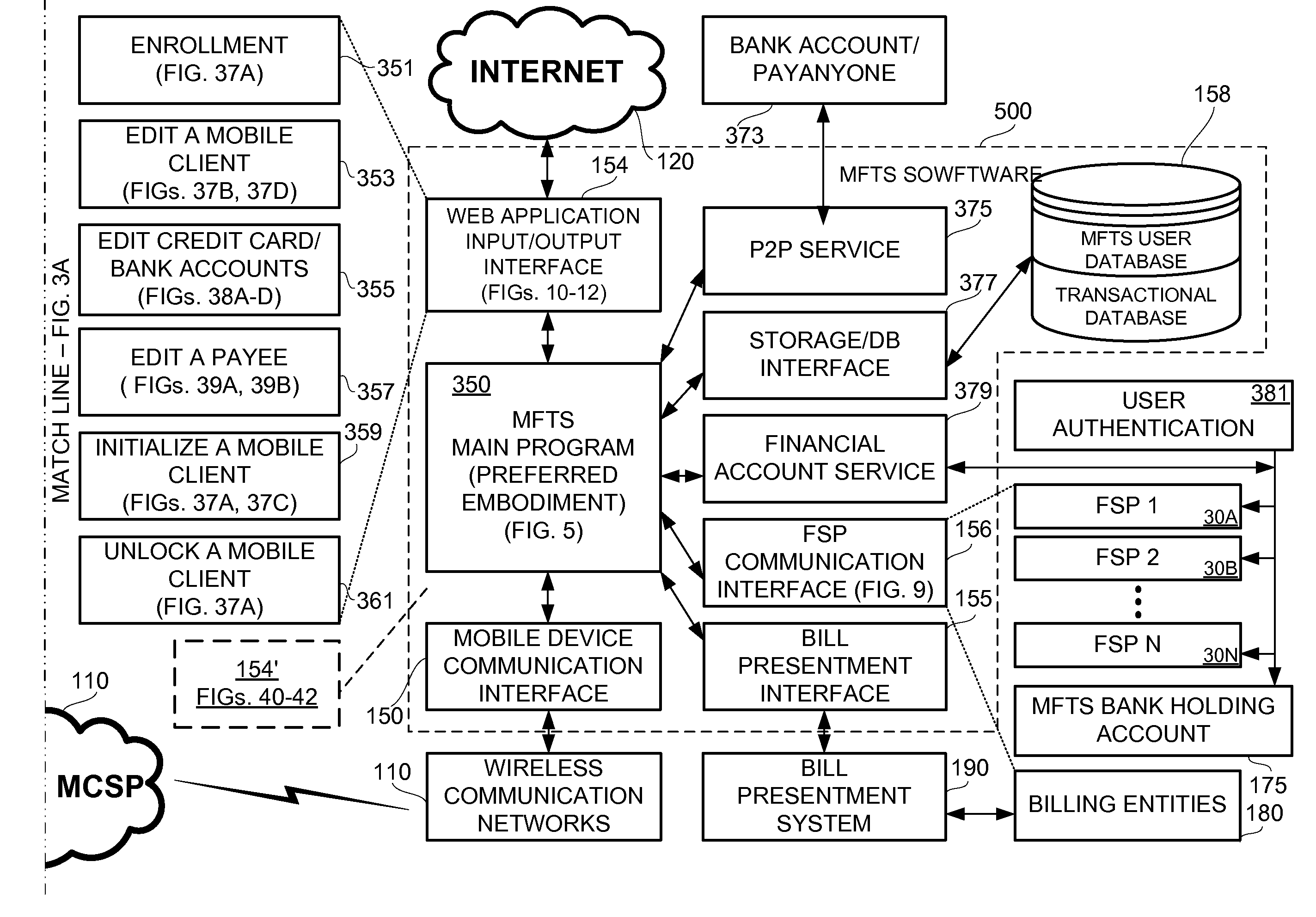
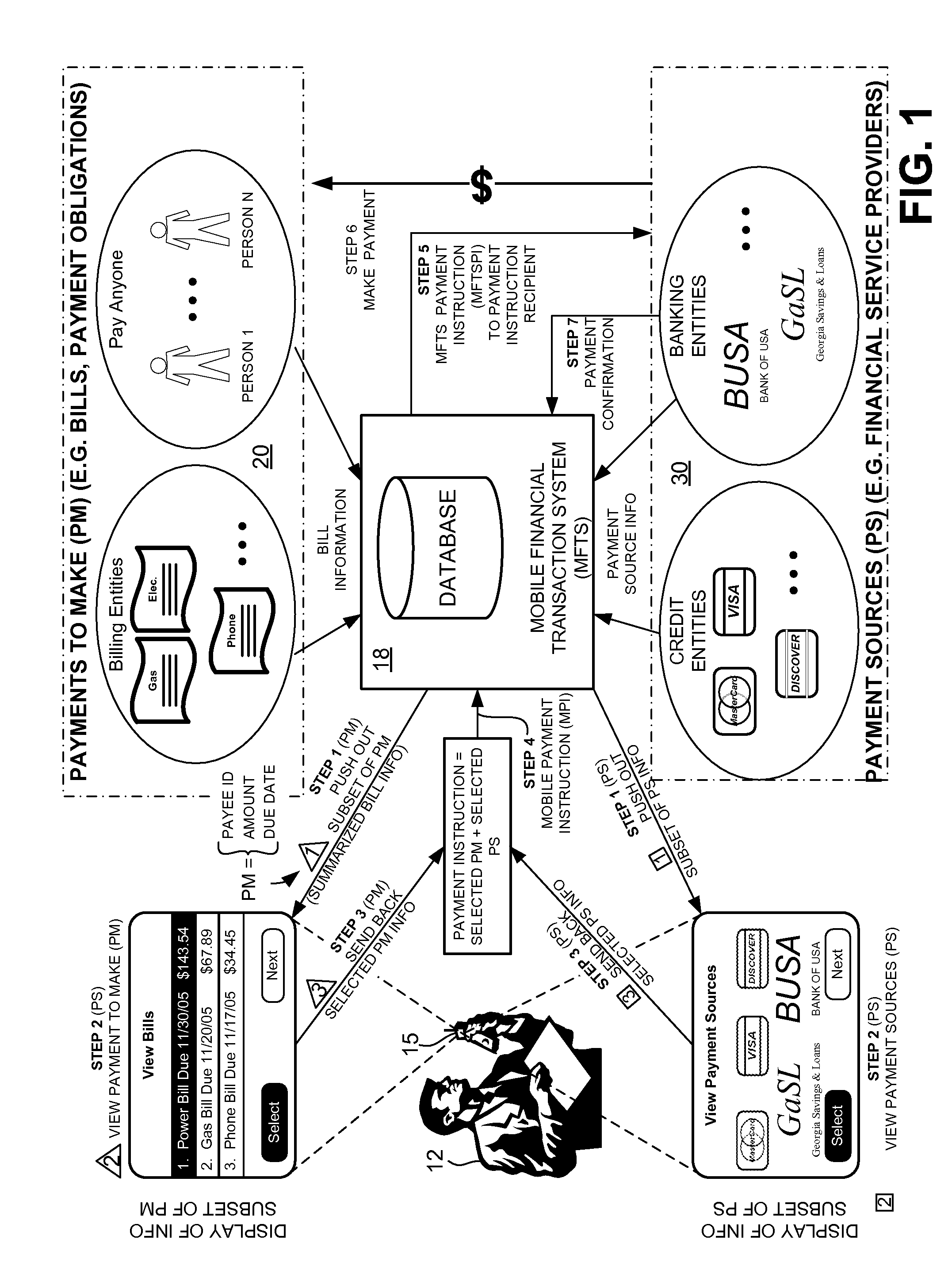
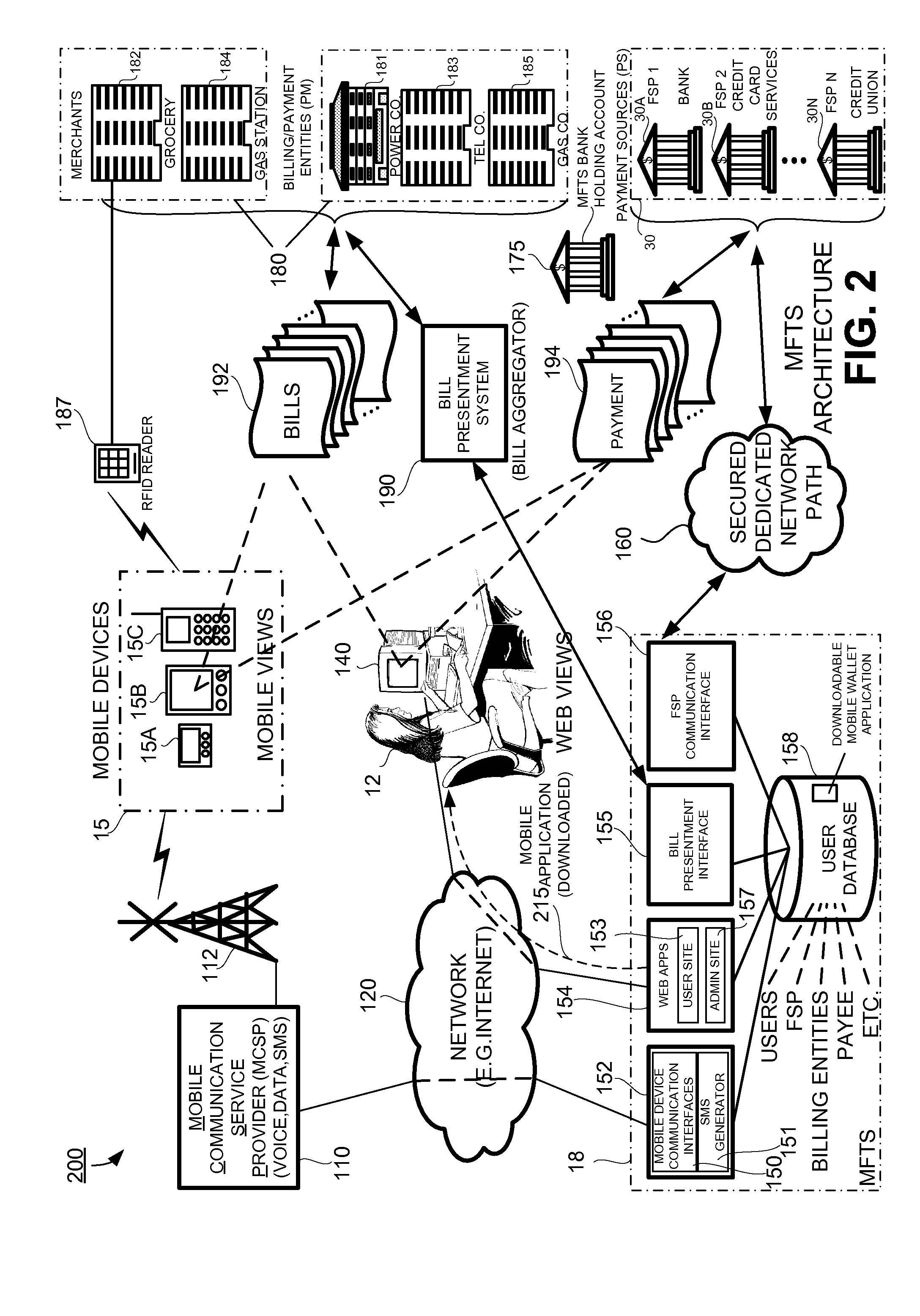
ActiveUS20080040265A1Unprecedented convenienceUnprecedented flexibilityFinanceBilling/invoicingFinancial transactionMobile context
Methods and systems for making a financial payment to a payee via a stored value (SV) card utilizing a mobile device such as a mobile telephone (cellphone) or wireless connected personal digital assistant (PDA). The mobile device communicates wirelessly with a mobile financial transaction system (MFTS) that stores user information and transaction information. A user enters information via the mobile device identifying a payee and indicating a stored value card payment method. The mobile device generates a mobile payment instruction that includes information corresponding to the identified payee and indicating a stored value card payment method. The mobile payment instruction is wirelessly communicated to the MFTS. The MFTS generates an MFTS payment instruction to a payment instruction recipient that can issue a new stored value card and / or reload funds onto a pre-existing stored value card. The MFTS communicates the MFTS payment instruction to the payment instruction recipient, which arranges for payment to the identified payee by issuing a new stored value card or reloading funds onto a pre-existing stored value card.
Owner:QUALCOMM INC
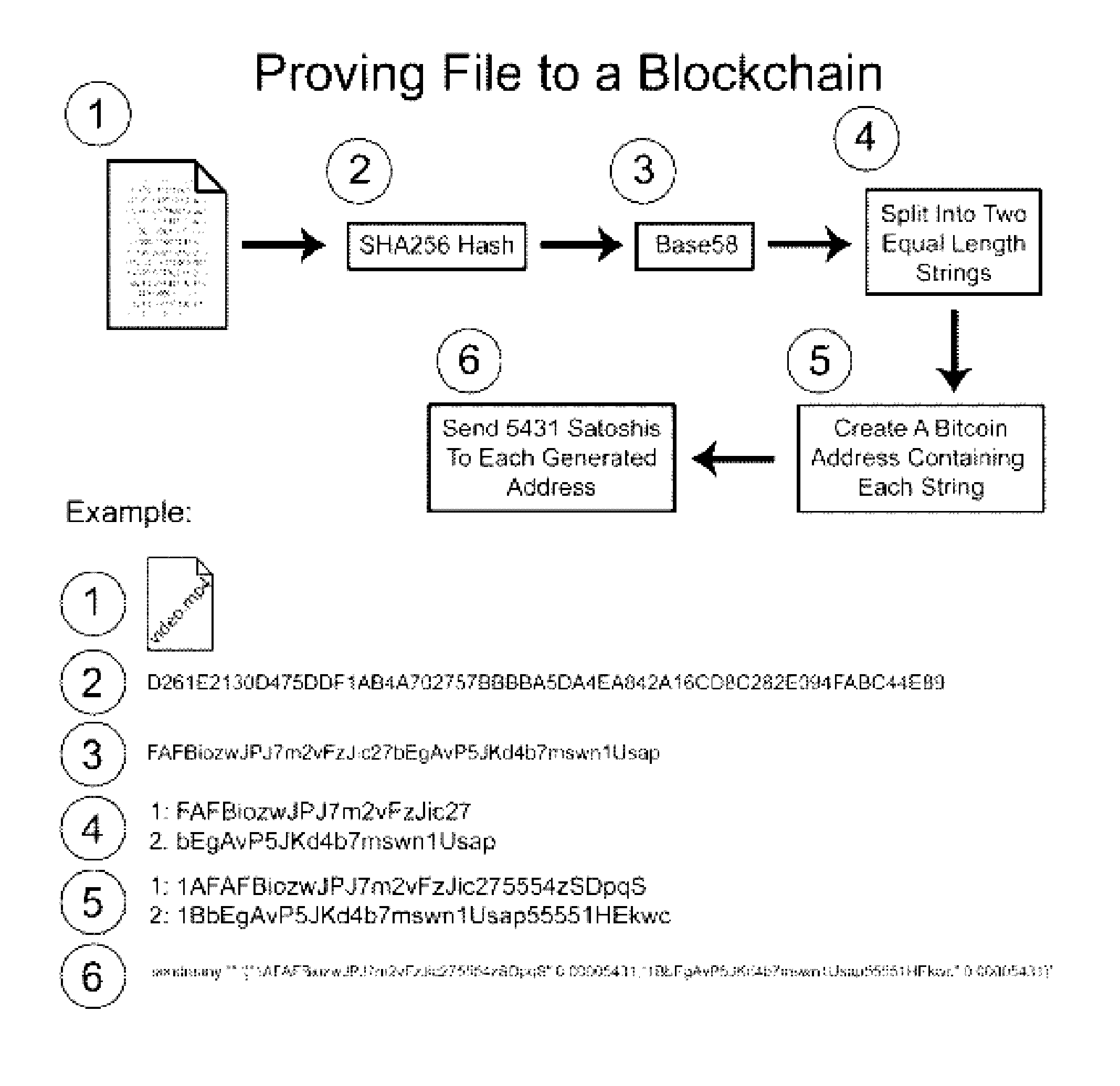
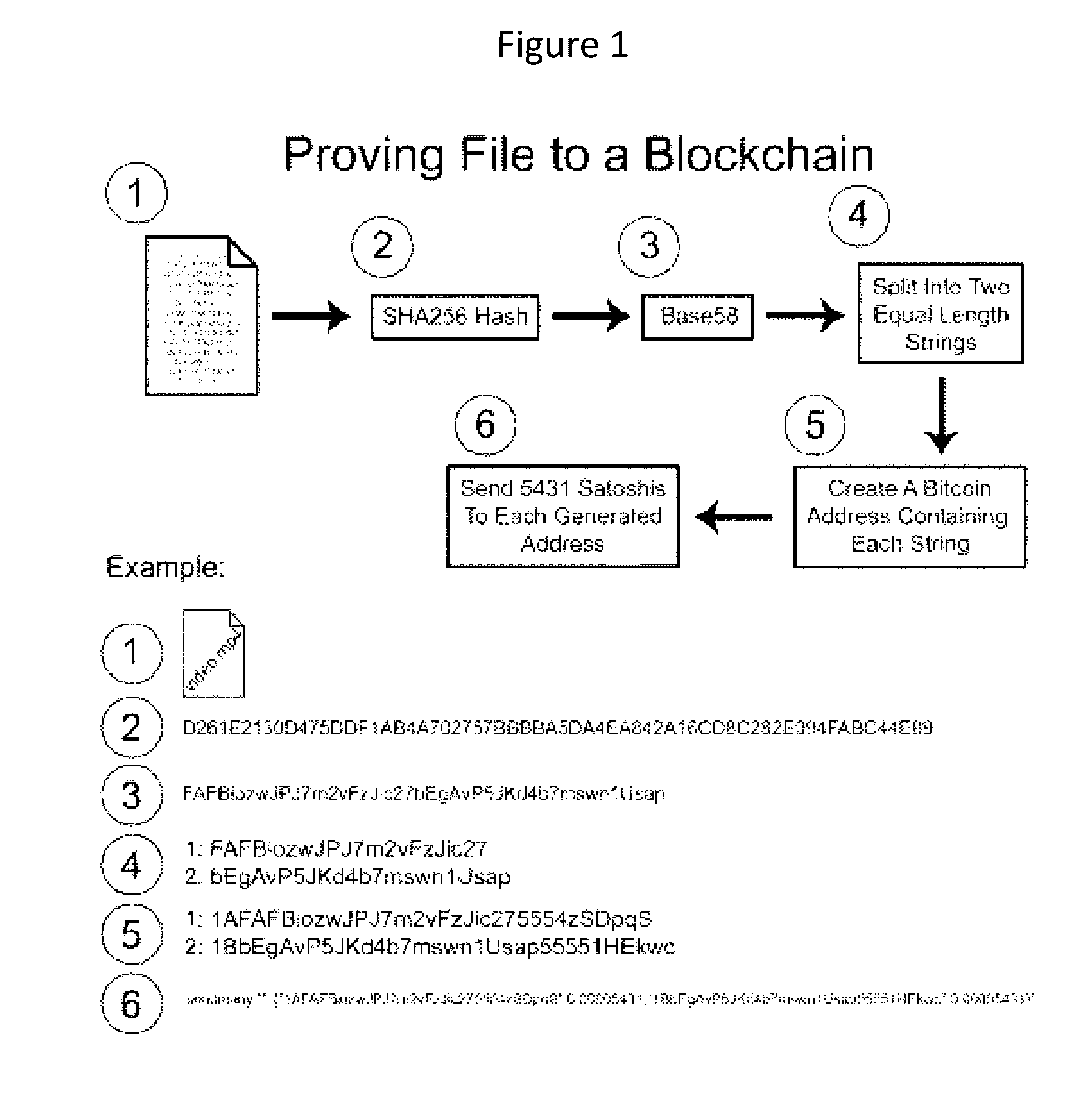
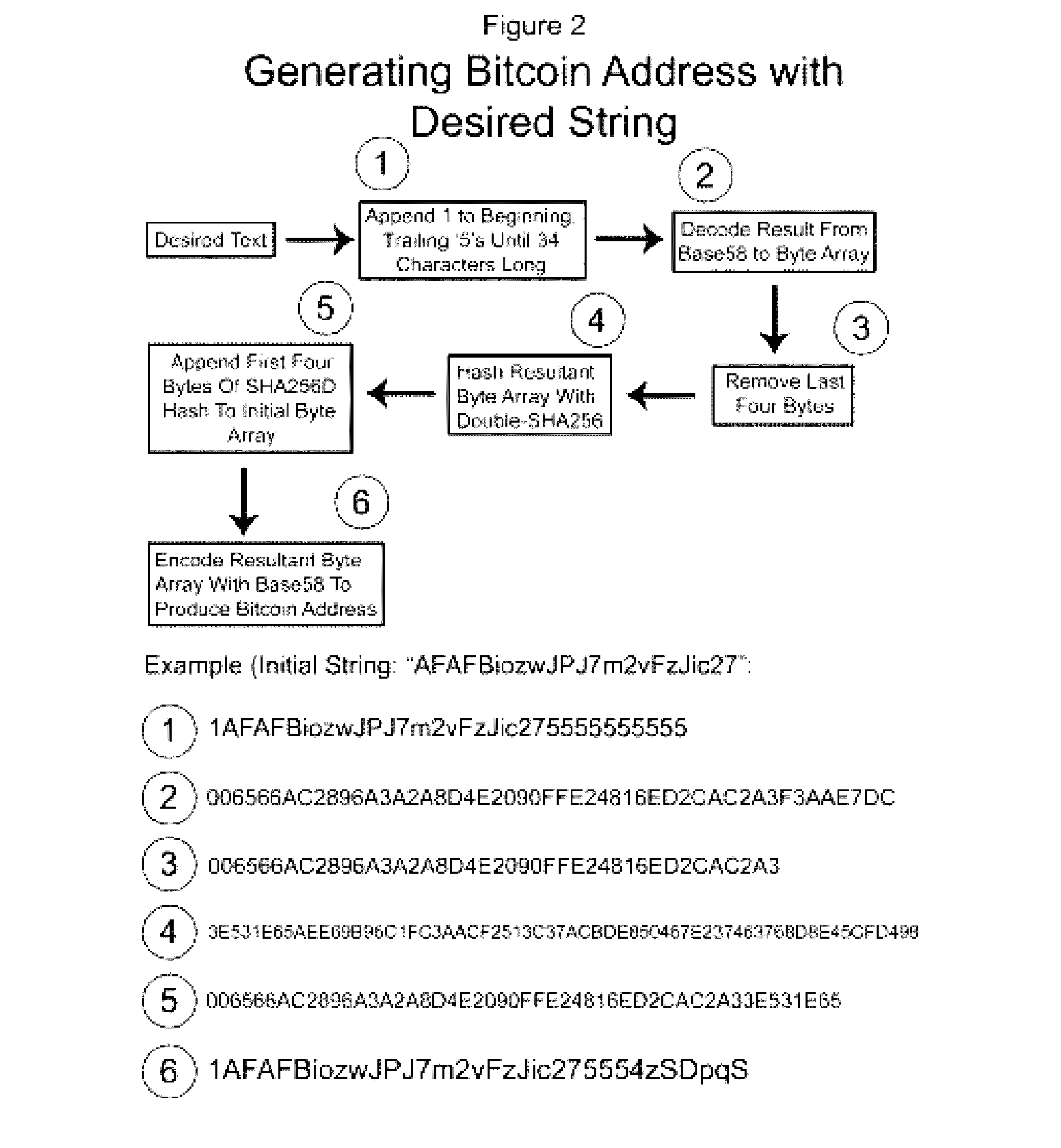
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
Methods for purchasing of goods and services
InactiveUS7349871B2Risk minimizationReducing credit card fraudPayment circuitsElectronic credentialsThird partyPurchasing
Owner:PCMS HOLDINGS INC
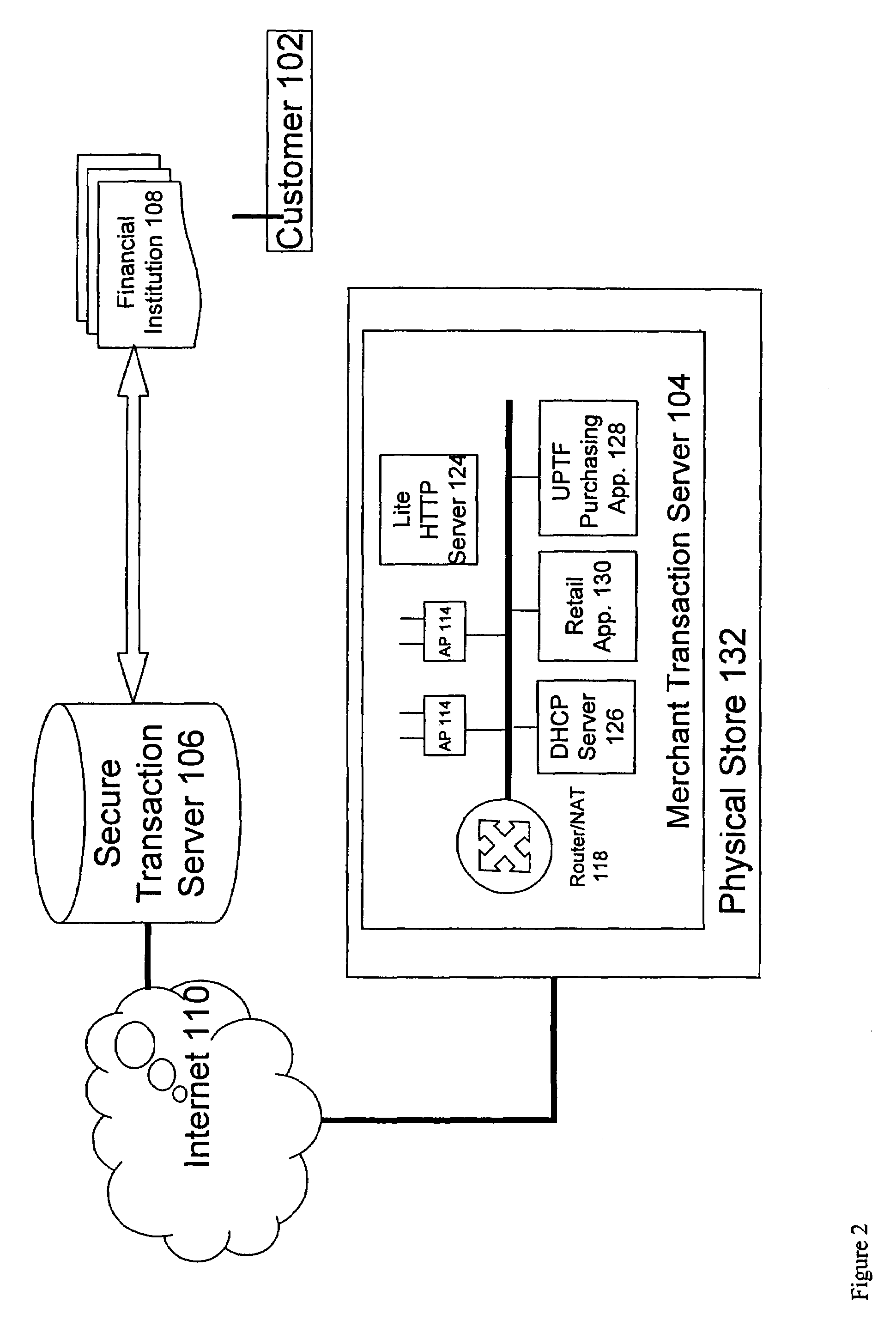
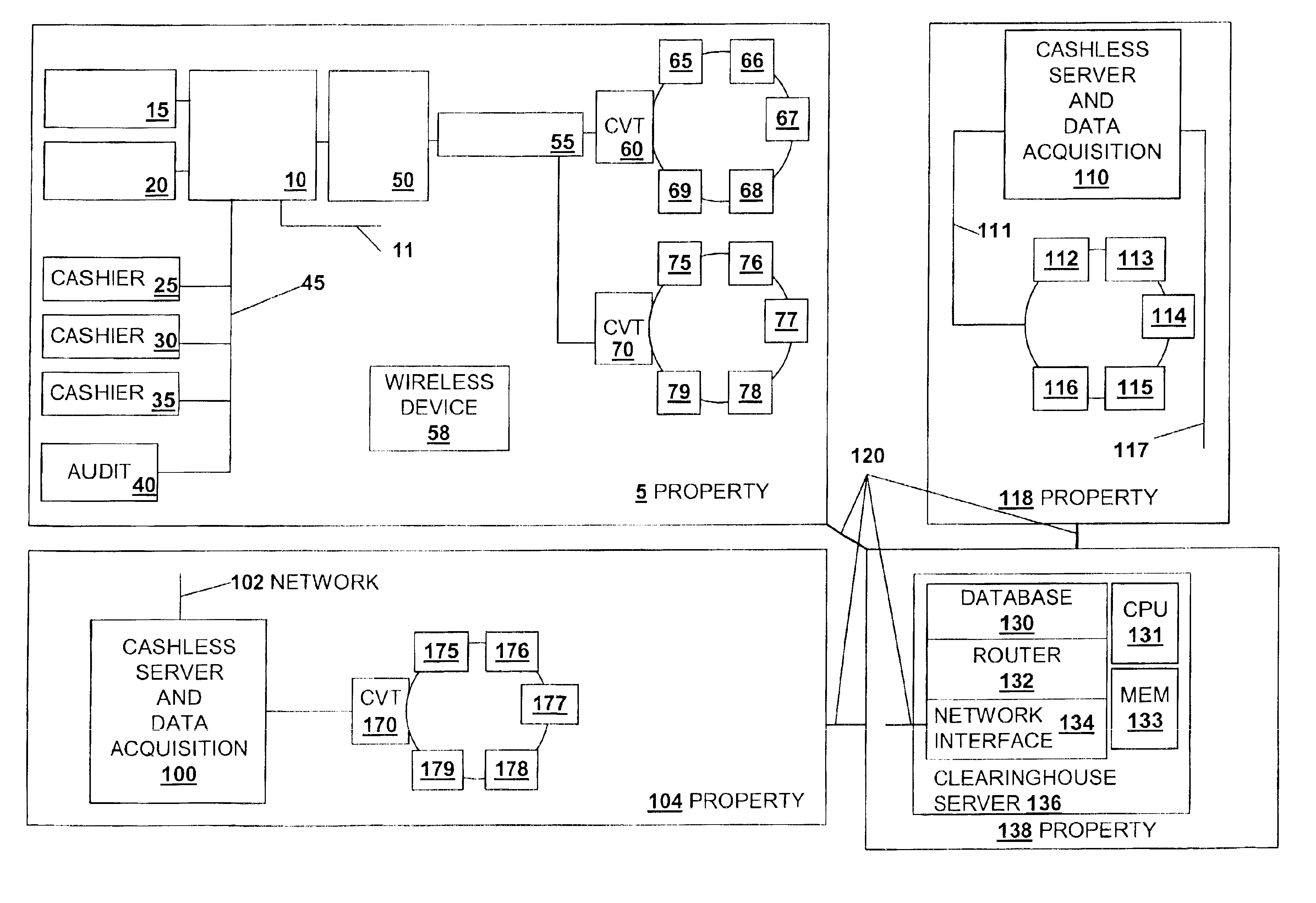
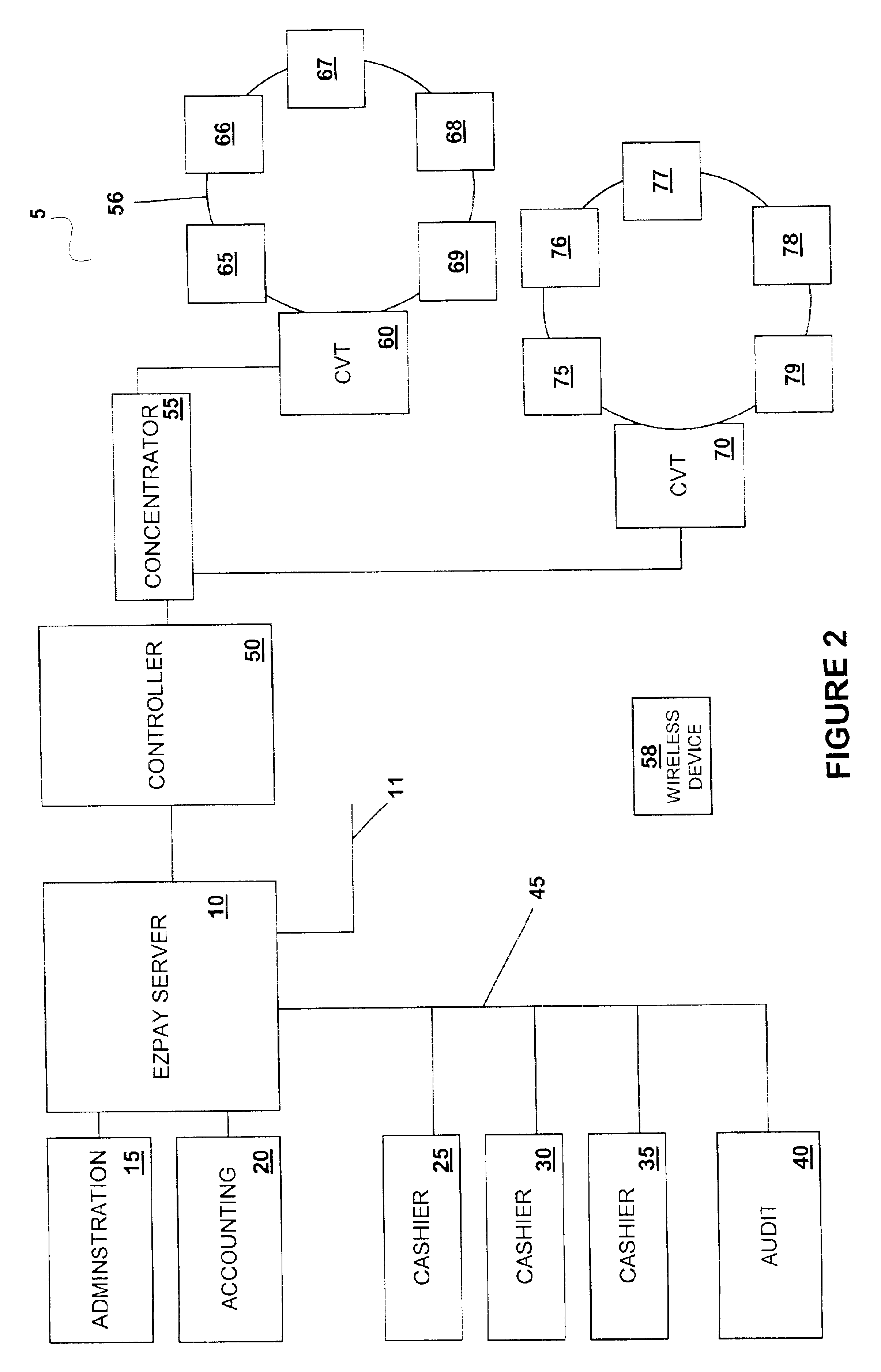
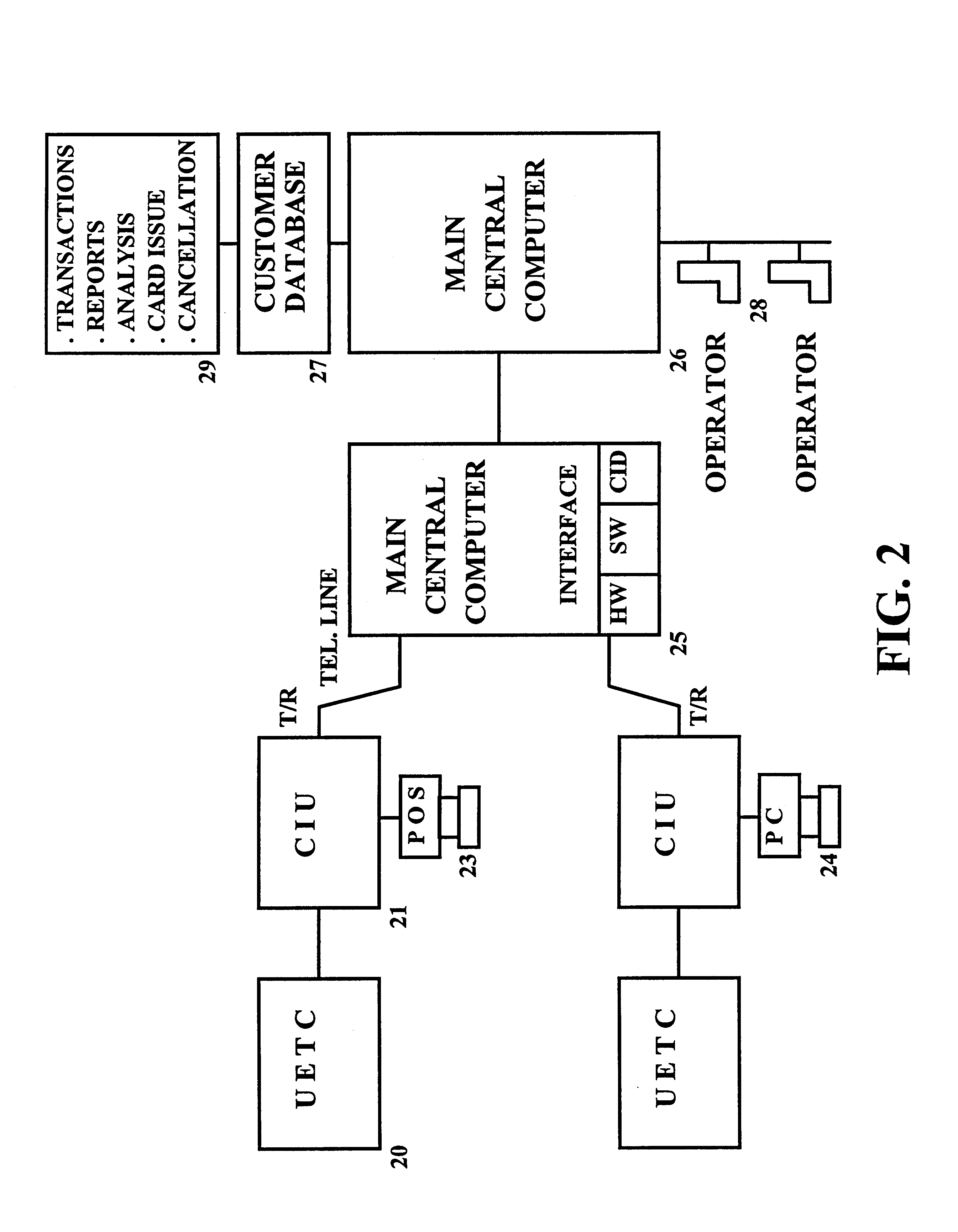
Cashless transaction clearinghouse
InactiveUS6866586B2Reduce the possibilityApparatus for meter-controlled dispensingPre-payment schemesEngineeringFinancial transaction
A disclosed cashless instrument transaction clearinghouse provides clearinghouse server including a network interface allowing the cashless instrument transaction clearinghouse to communicate with a number of gaming properties and a processor configured to enable the validation of cashless instruments at a gaming property different from where the cashless instrument was generated. Methods are provided that allow a plurality of cashless gaming devices located at different gaming properties to communicate with one another via the cashless instrument transaction clearinghouse in a secure manner using symmetric and asymmetric encryption techniques. Further, to reduce the possibilities of theft and fraud, the methods allow a receiver of a message to authenticate an identity of a sender of a message.
Owner:IGT
Secure network commercial transactions
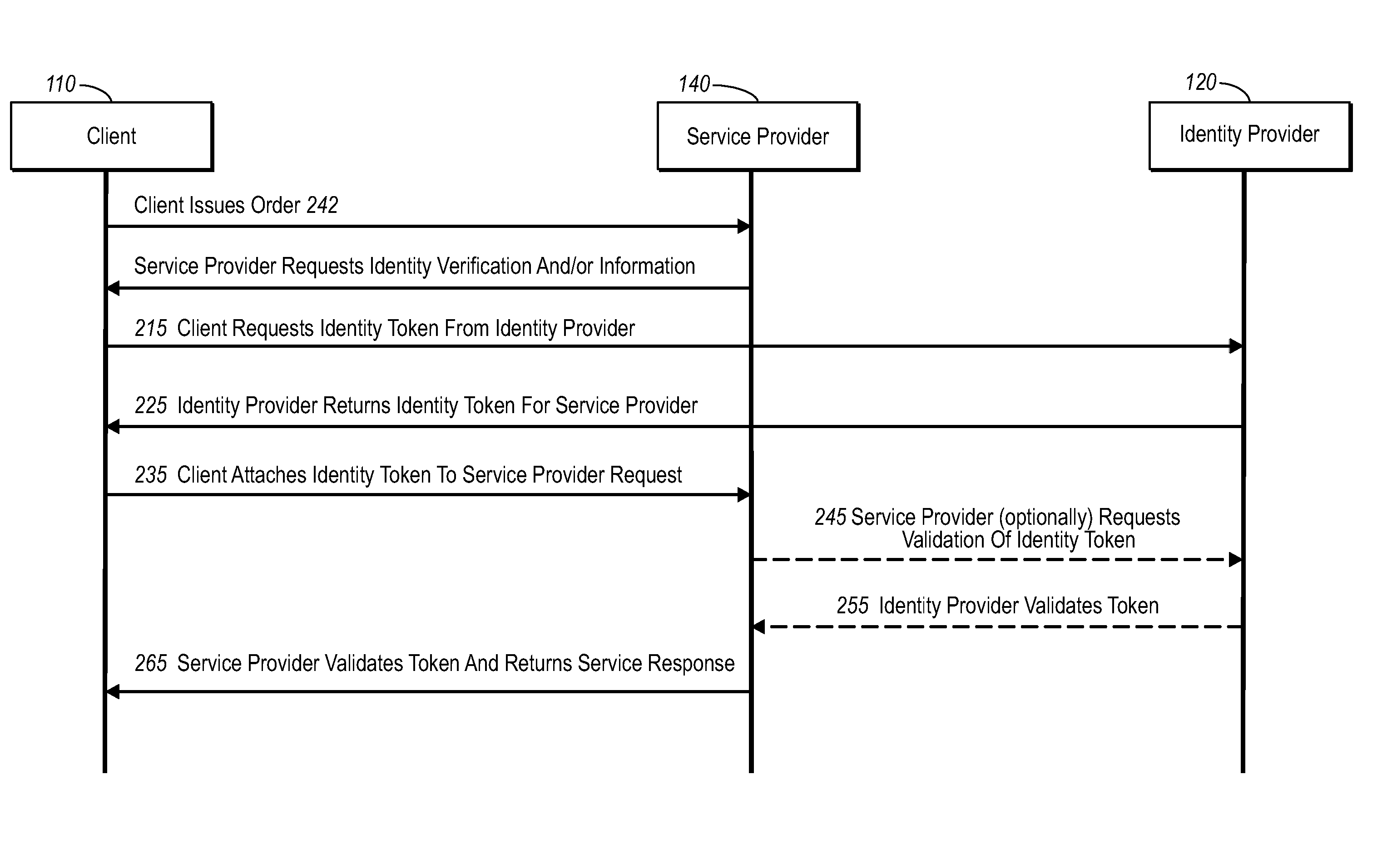
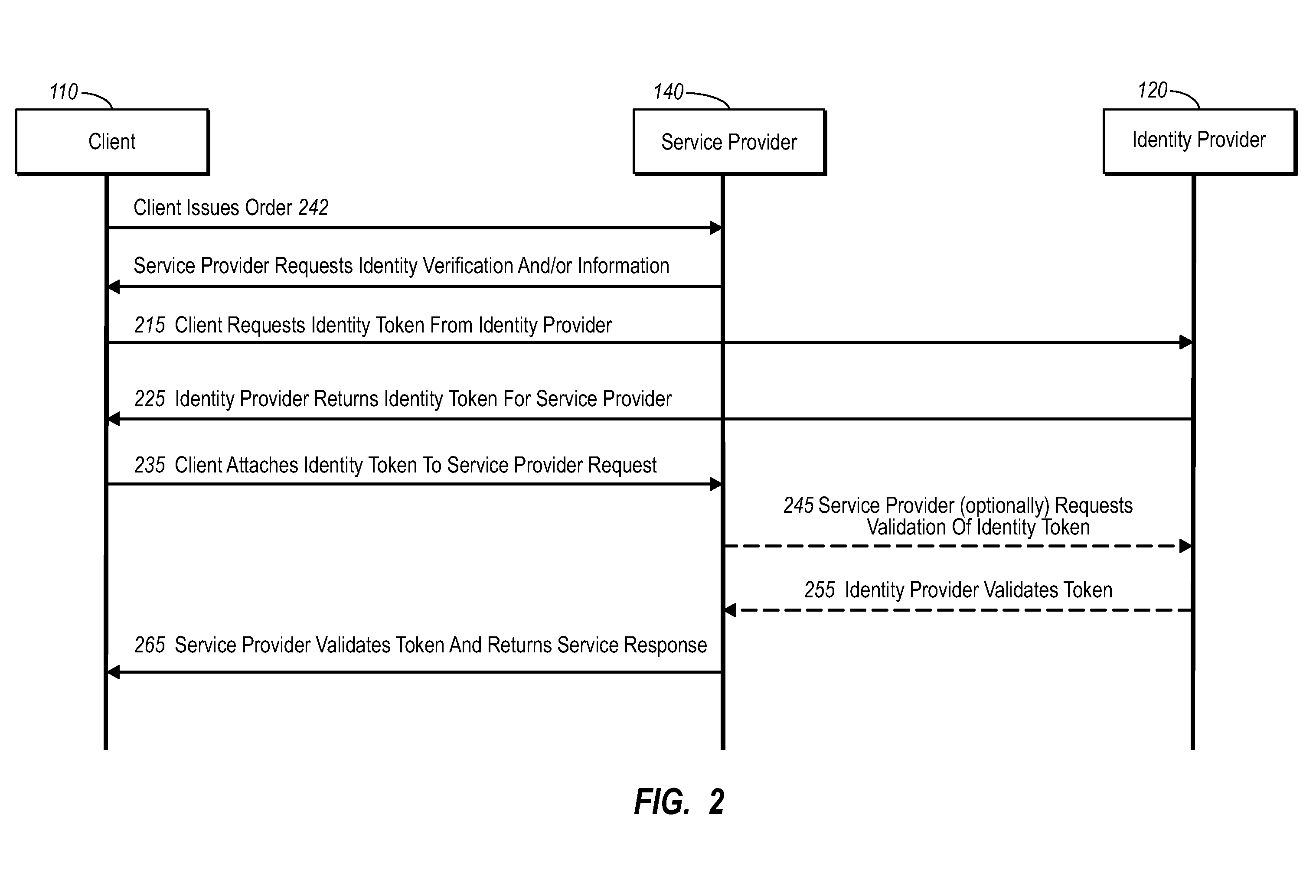
InactiveUS20060235795A1Reduce the burden onSimpler and more secure online commercial transactions frameworkFinanceBuying/selling/leasing transactionsPaymentSecure communication
Current embodiments provide for authorization and payment of an online commercial transaction between a purchaser and a merchant including verification of an identity of the purchaser and verification of an ability of the purchaser to pay for the transaction, where the identity provider and the payment provider are often different network entities. Other embodiments also provide for protocols, computing systems, and other mechanisms that allow for identity and payment authentication using a mobile module, which establishes single or multilevel security over an untrusted network (e.g., the Internet). Still other embodiments also provide for a three-way secure communication between a merchant, consumer, and payment provider such that sensitive account information is opaque to the merchant, yet the merchant is sufficiently confident of the consumer's ability to pay for requested purchases. In yet another embodiment, electronic billing information is used for authorization, auditing, payment federation, and other purposes.
Owner:MICROSOFT TECH LICENSING LLC
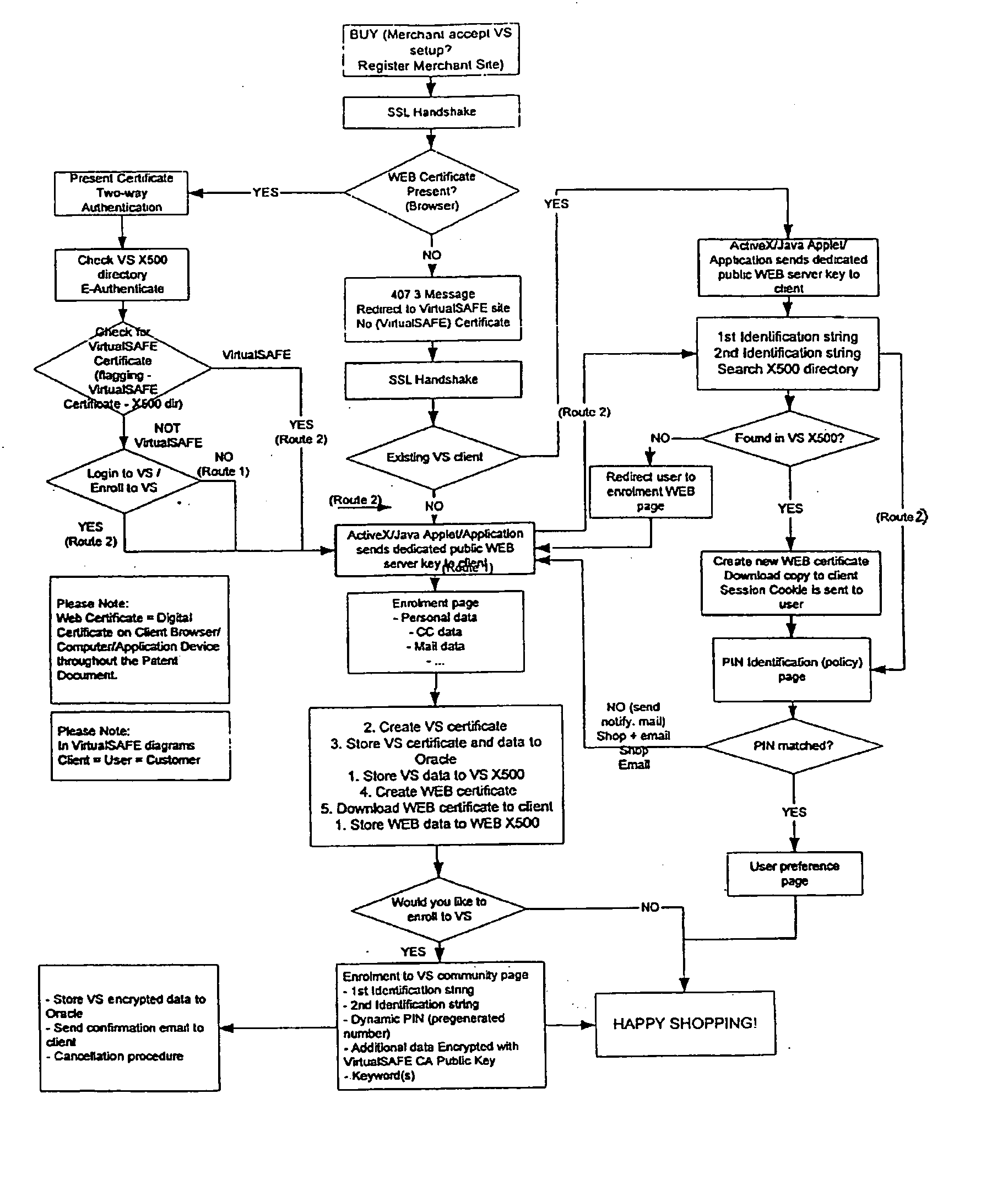
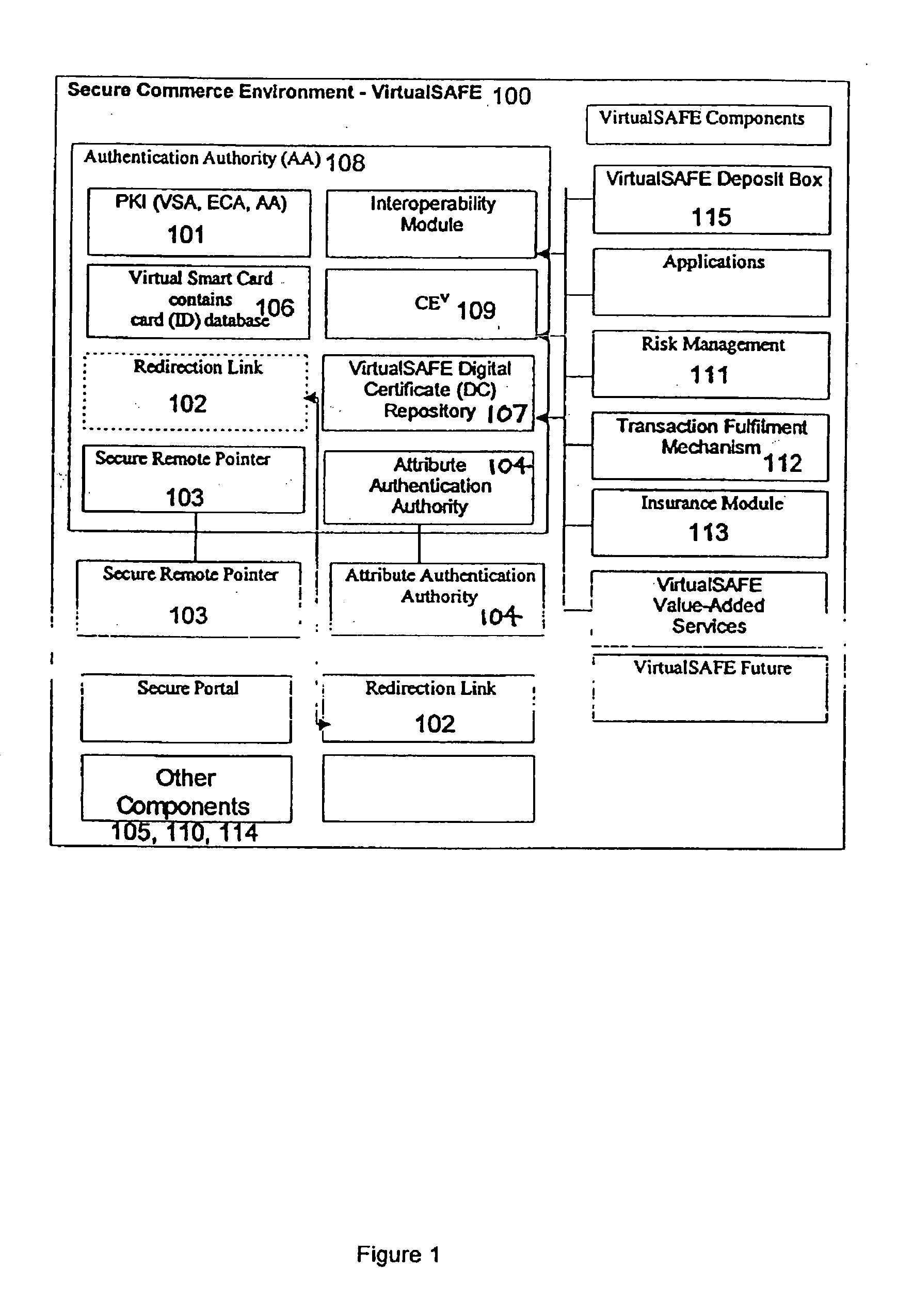
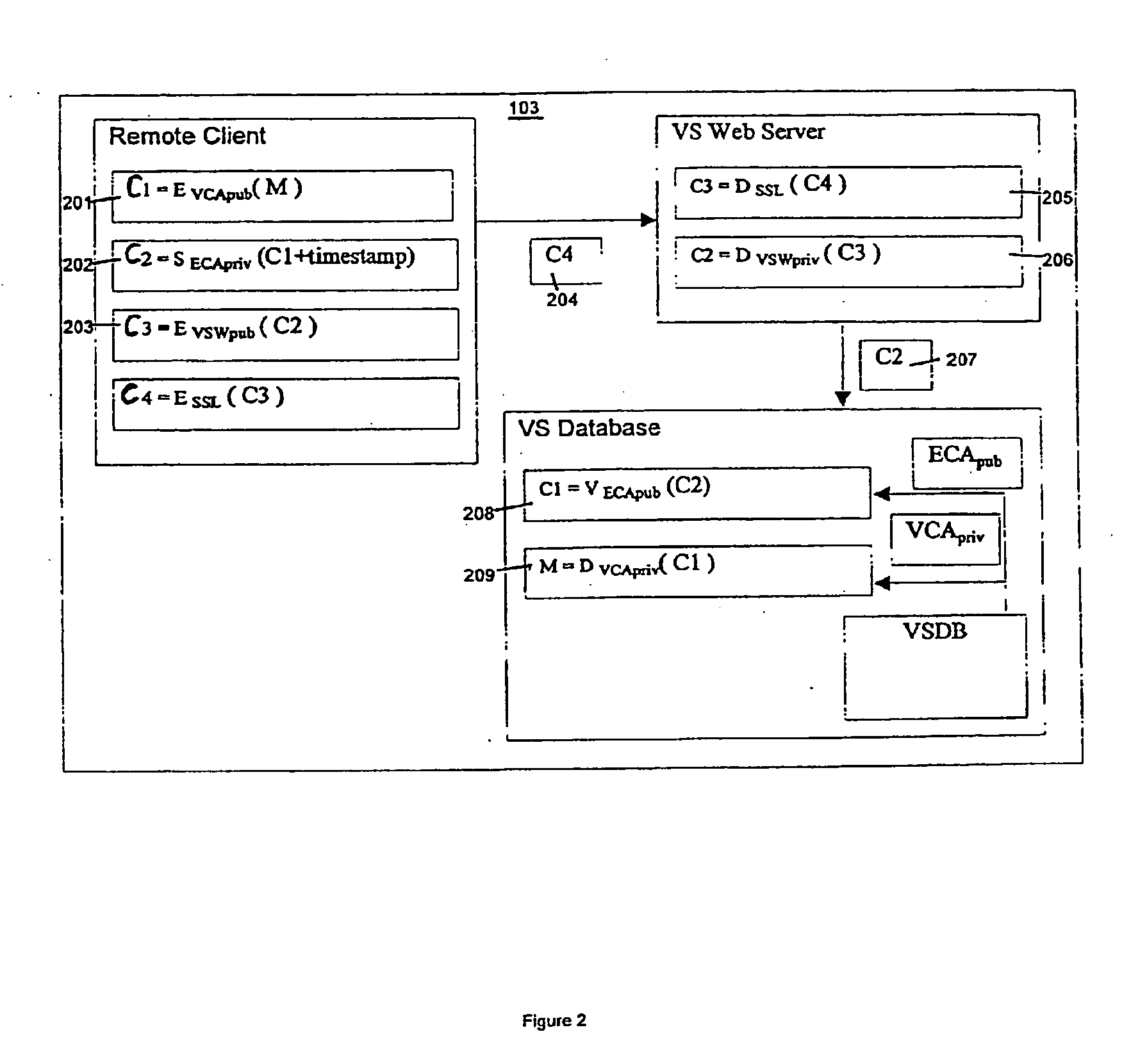
Method and system for a virtual safe
Owner:SARCANIN BRANKO
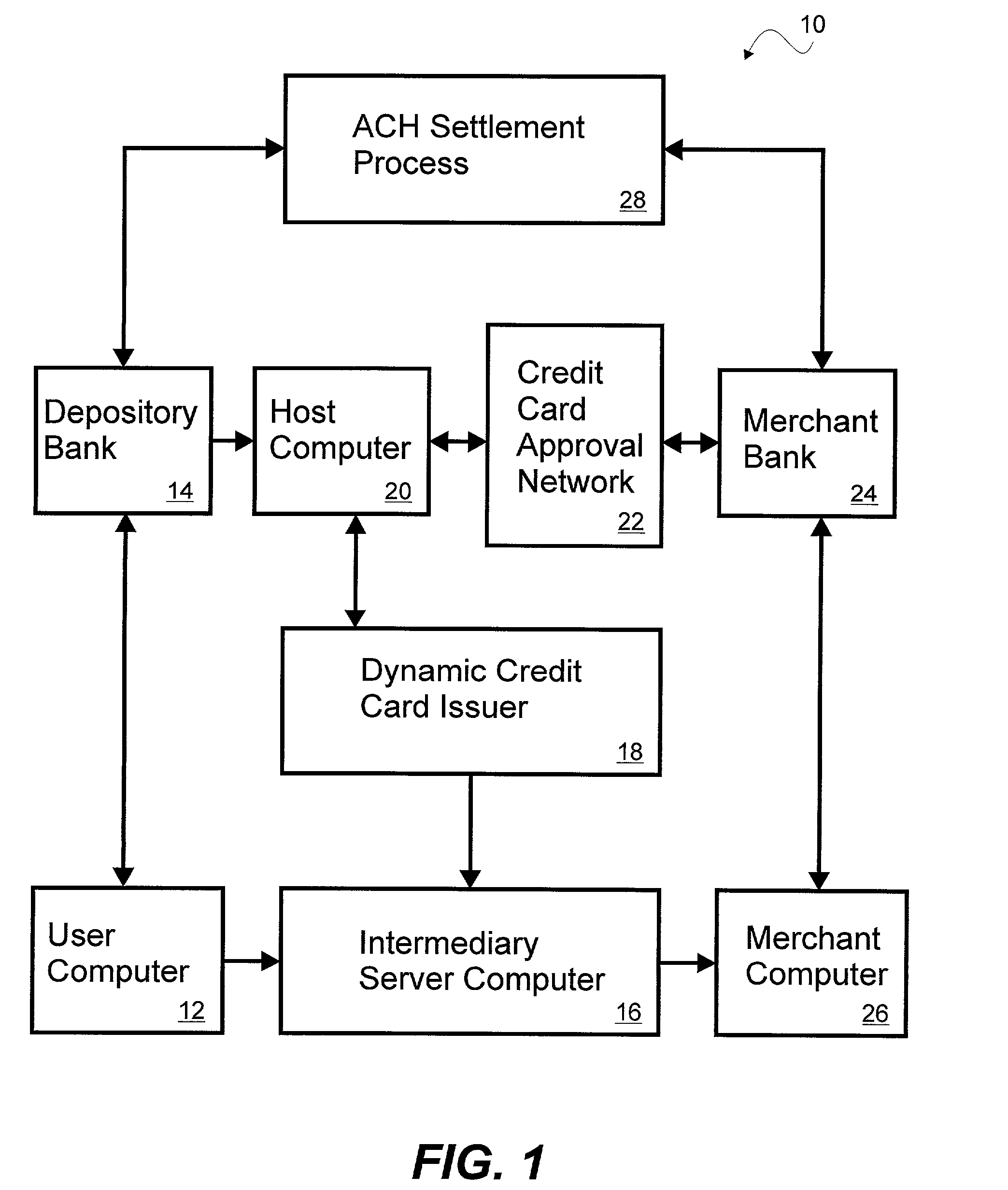
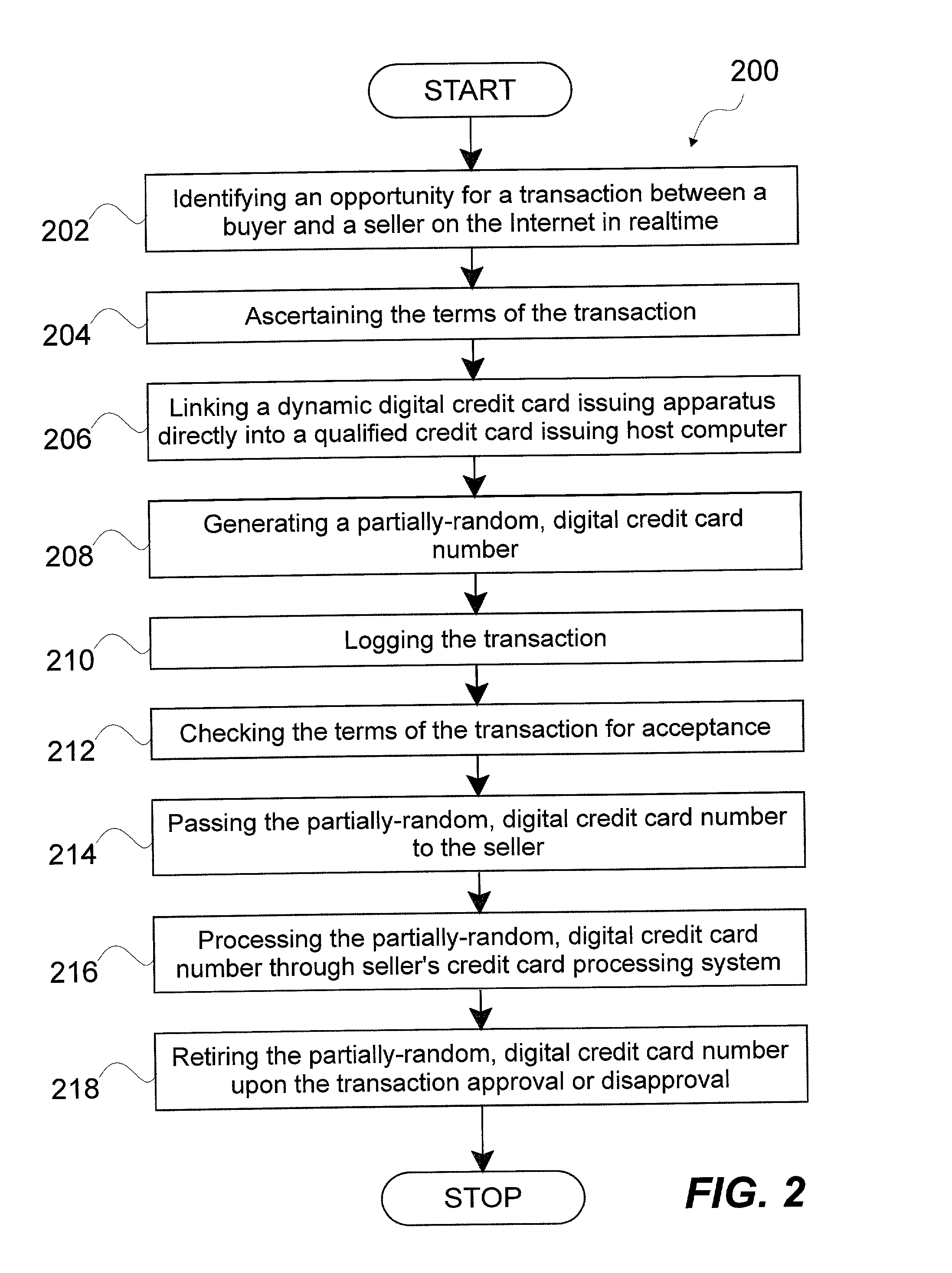
System and method for dynamically issuing and processing transaction specific digital credit or debit cards
A system and method of dynamically issuing credit card numbers and processing transactions using those credit card numbers is disclosed. A method according to the invention includes digitally recognizing a transaction opportunity on the Internet in real-time, recognizing the terms of the transaction, linking a dynamic digital credit card issuing apparatus directly into a qualified credit card issuing host, generating a partially random digital credit card number, logging the transaction, checking the terms of the transaction for acceptance, passing the dynamically issued digital credit card number to the merchant, processing the digital credit card number through the merchant's card processing system, receiving the transaction approval request, participating in credit card validity checking systems, processing the approval request in real-time, sending the requesting party a legitimate authorization code, and retiring the digital credit card number immediately upon transaction approval or disapproval. A system according to the invention implements the method of the invention.
Owner:ORANGATANGO
Transaction system
InactiveUS6236981B1Improve securityImprove the level ofUser identity/authority verificationComputer security arrangementsService provisionThe Internet
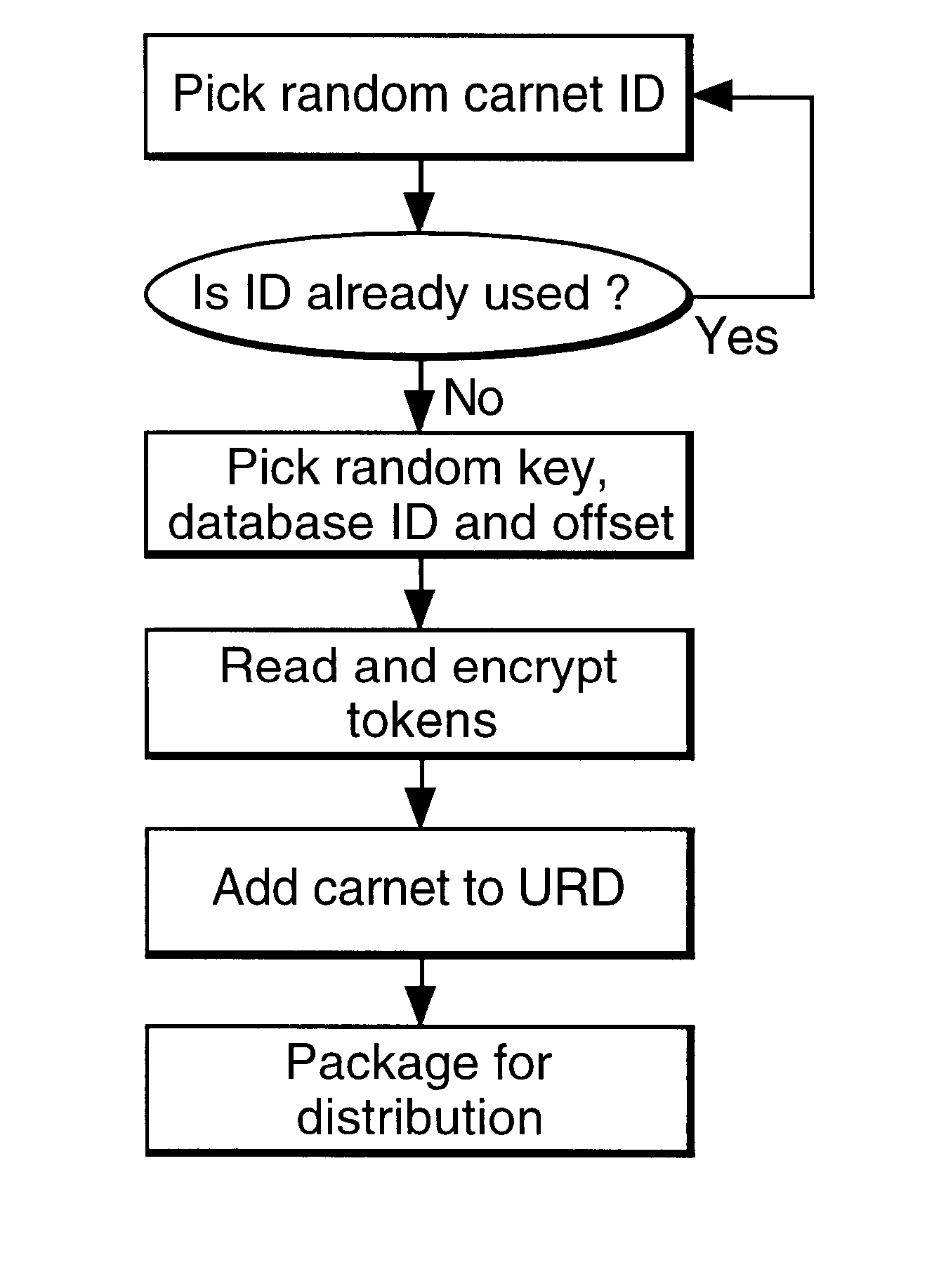
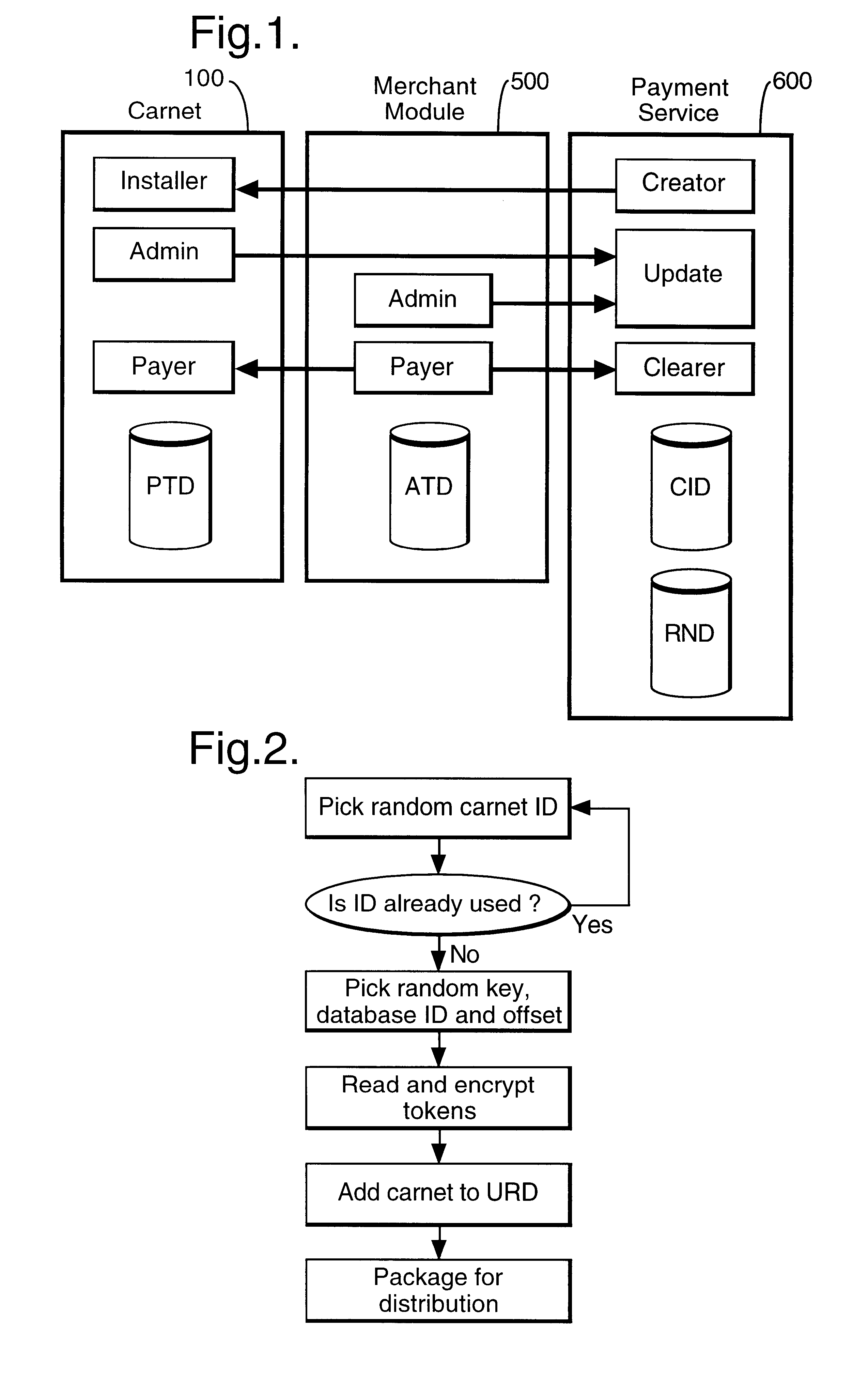
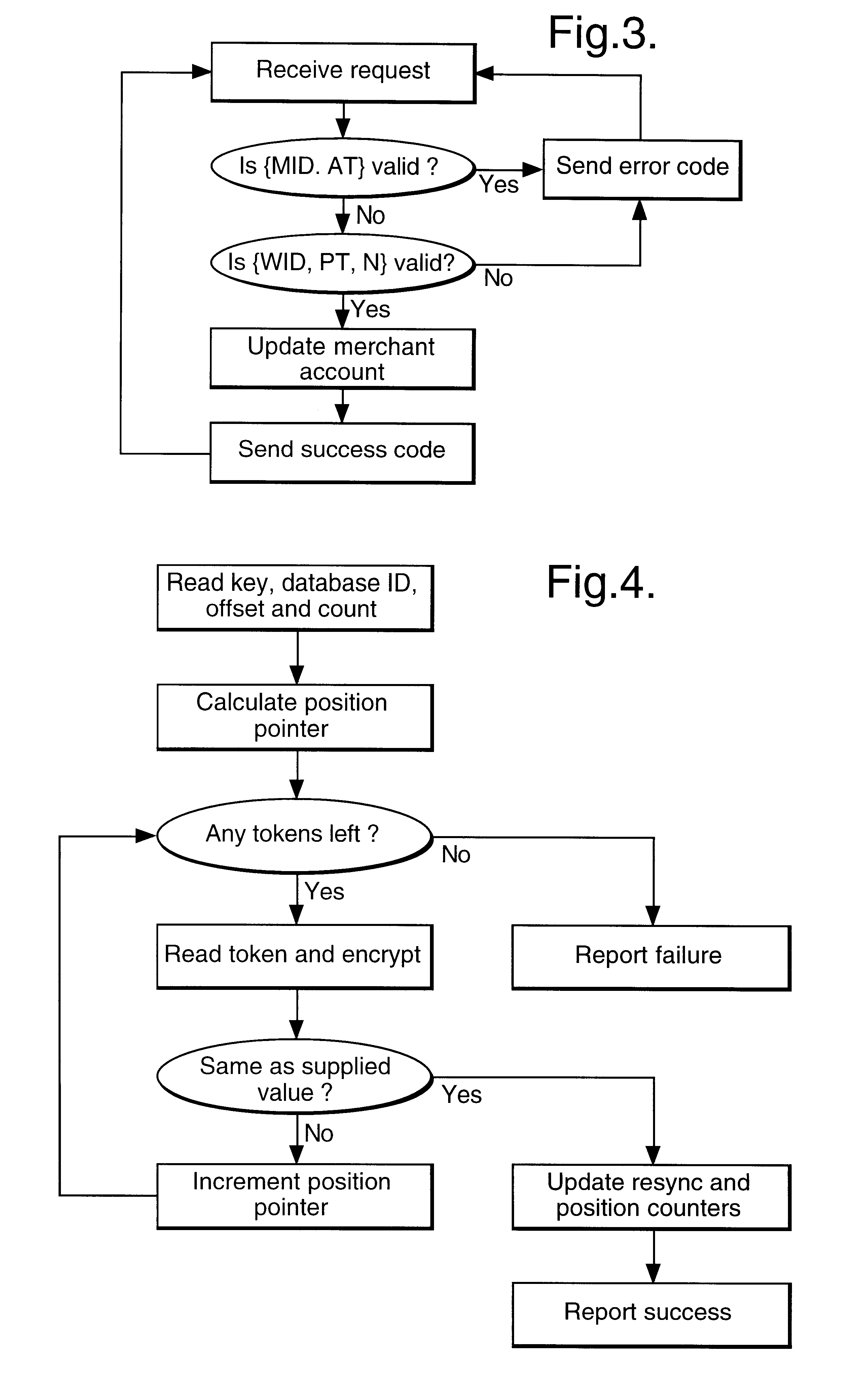
In a digital payment system, a sequence of random numbers is stored at a payment service. A set of digitally encoded random numbers derived from the stored sequence is issued to the user in return for payment. The tokens are stored in a Carnet. The user can then spend the tokens by transferring tokens to a merchant, for example, to an on-line service provider. The merchant returns each token received to the payment server. The payment server authenticates the token and transmits an authentication message to the merchant. The merchant, payment server and user may be linked by internet connections.
Owner:BRITISH TELECOMM PLC
Account-based digital signature (ABDS) system
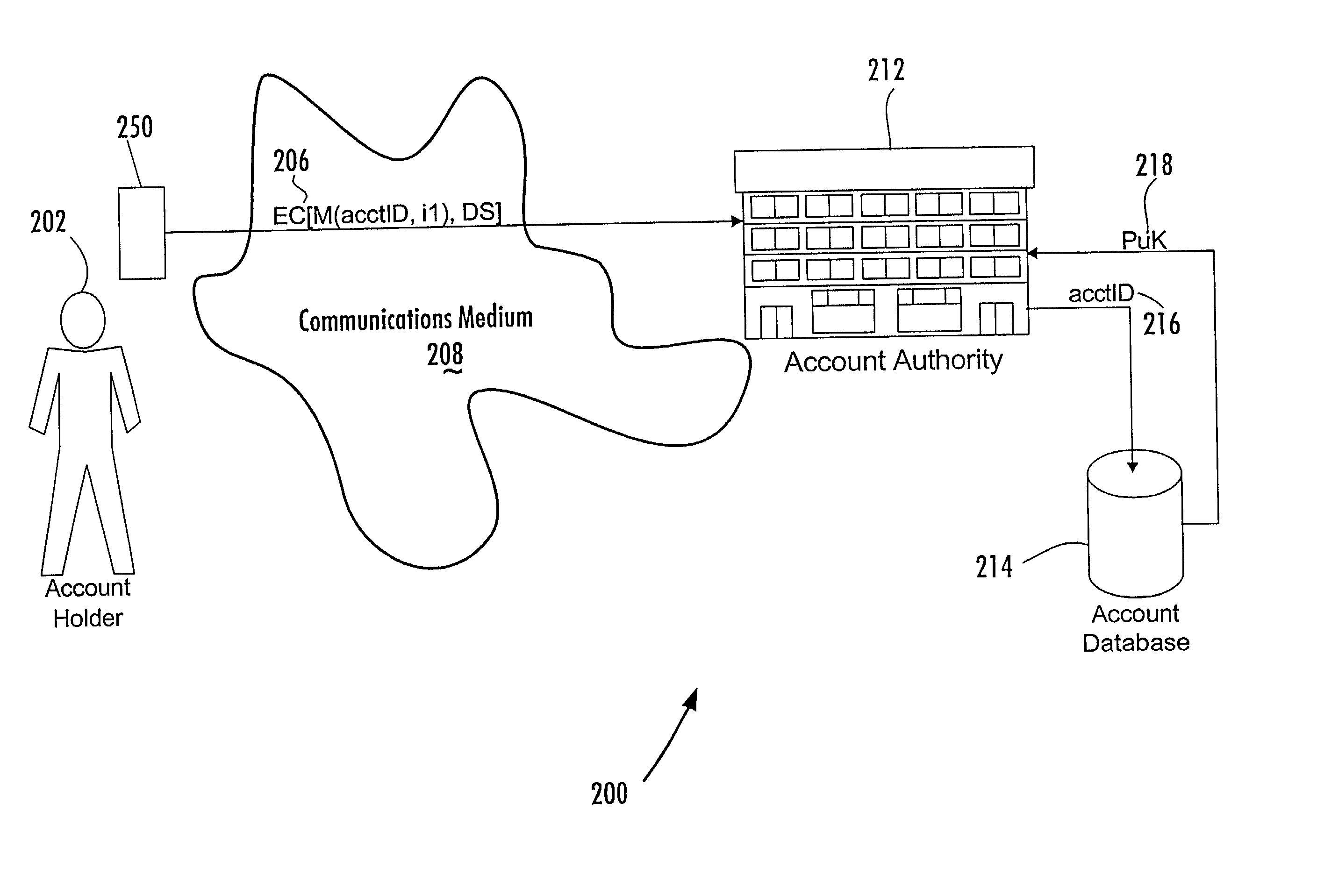
InactiveUS20020026575A1Key distribution for secure communicationFinanceDigital signatureElectronic communication
A method of authenticating an entity by a receiving party with respect to an electronic communication that is received by the receiving party and that includes both a unique identifier associated with an account maintained by the receiving party and a digital signature for a message regarding the account, consists of the steps of, before receipt of the electronic communication, first associating by the receiving party a public key of a public-private key pair with the unique identifier and, thereafter, only conducting message authentication using the digital signature received by the receiving party in the electronic communication and the public key associated with the account identifier.
Owner:FIRST DATA
Dispensing digital objects to an electronic wallet
A configuration system and method is disclosed that includes a unified and integrated configuration that is composed of a payment system, an advertising system, and an identity management system such that the unified system has all of the benefits of the individual systems as well as several additional synergistic benefits. Also described are specific configurations including the system's access point architecture, visual wallet simulator user interface, security architecture, coupon handling as well as the system's structure and means for delivering them as targeted advertising, business card handling, membership card handling for the purposes of login management, receipt handling, and the editors and grammars provided for customizing the different types of objects in the system as well as the creation of new custom objects with custom behaviors. The configurations are operable on-line as well as through physical presence transactions.
Owner:GOOGLE LLC
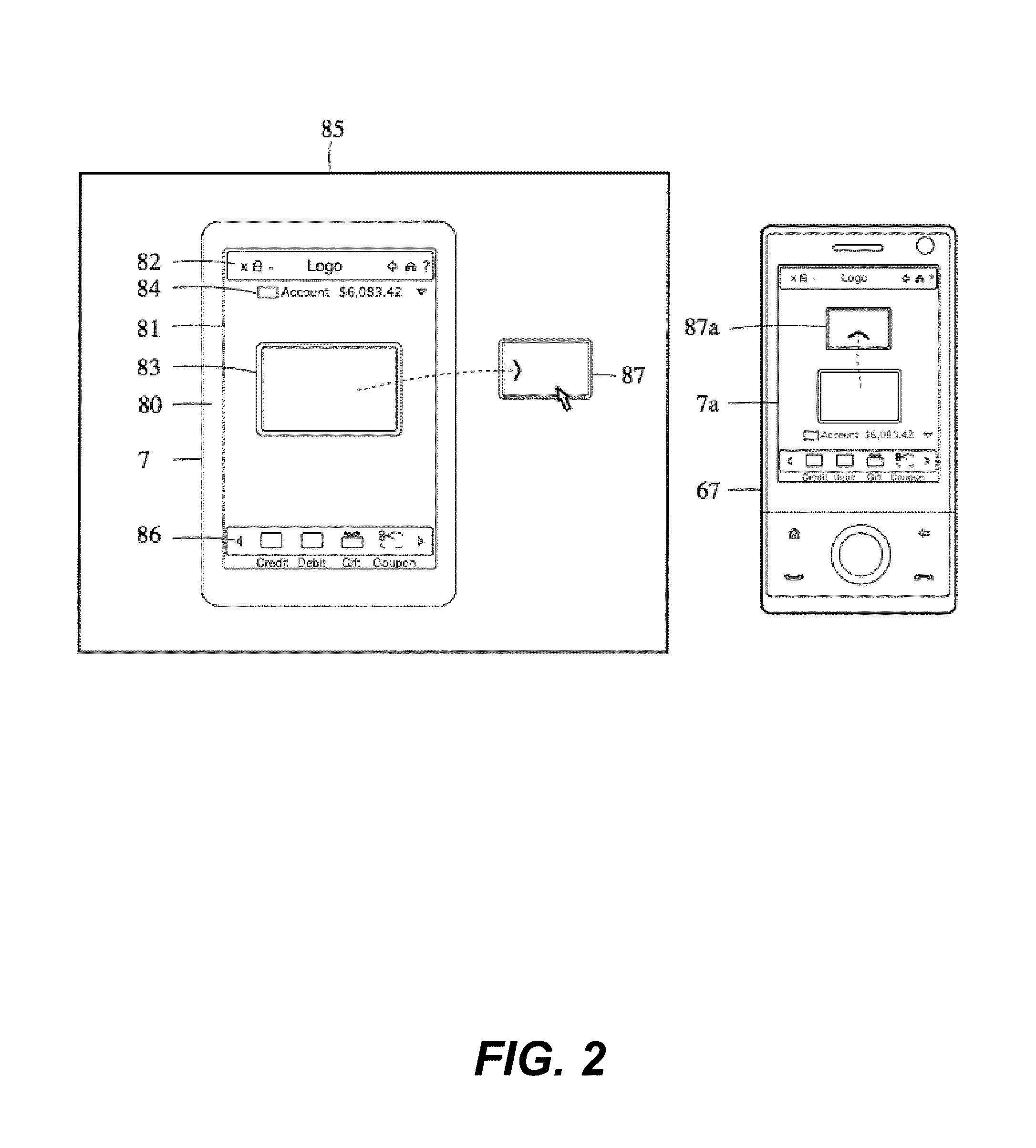
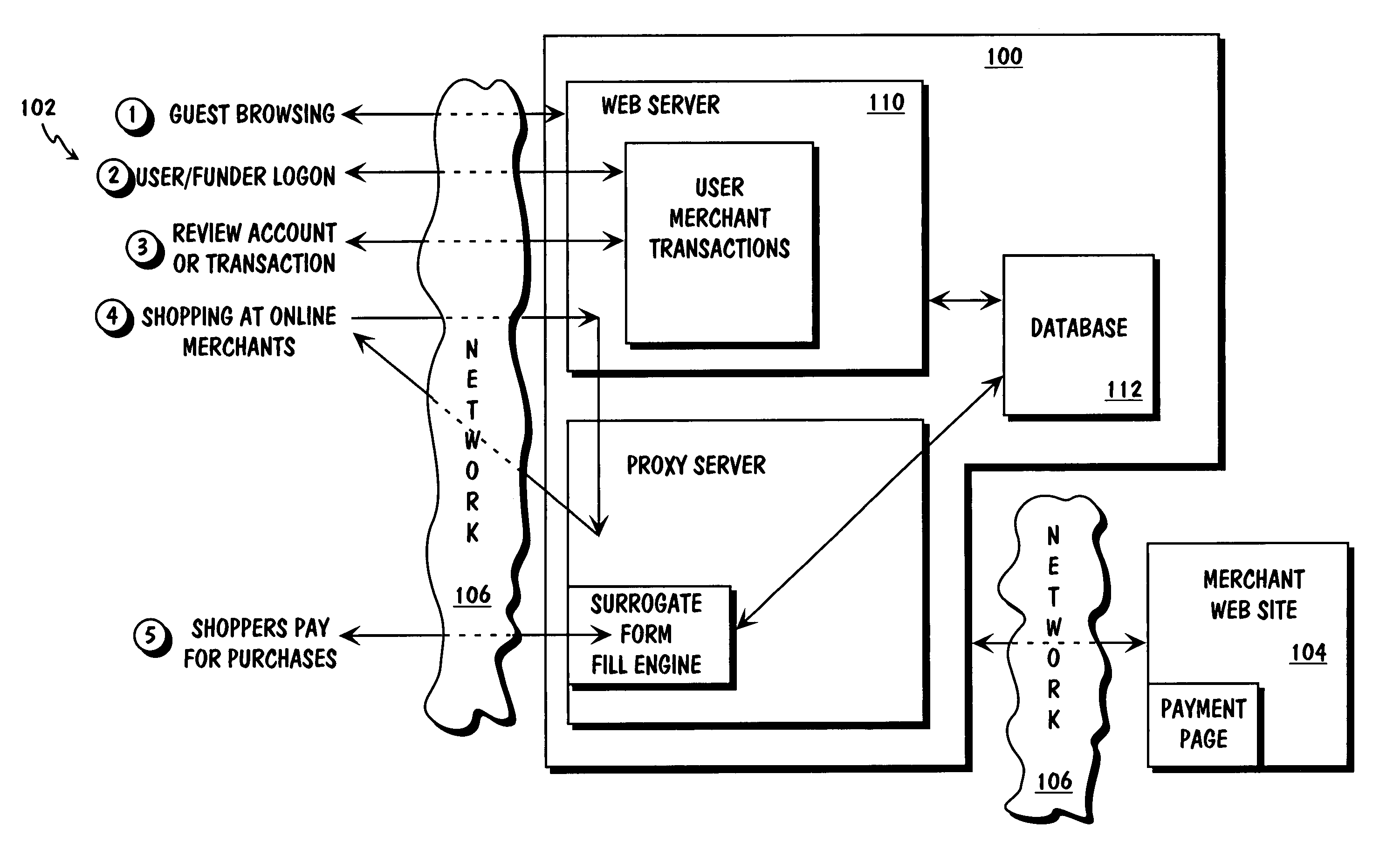
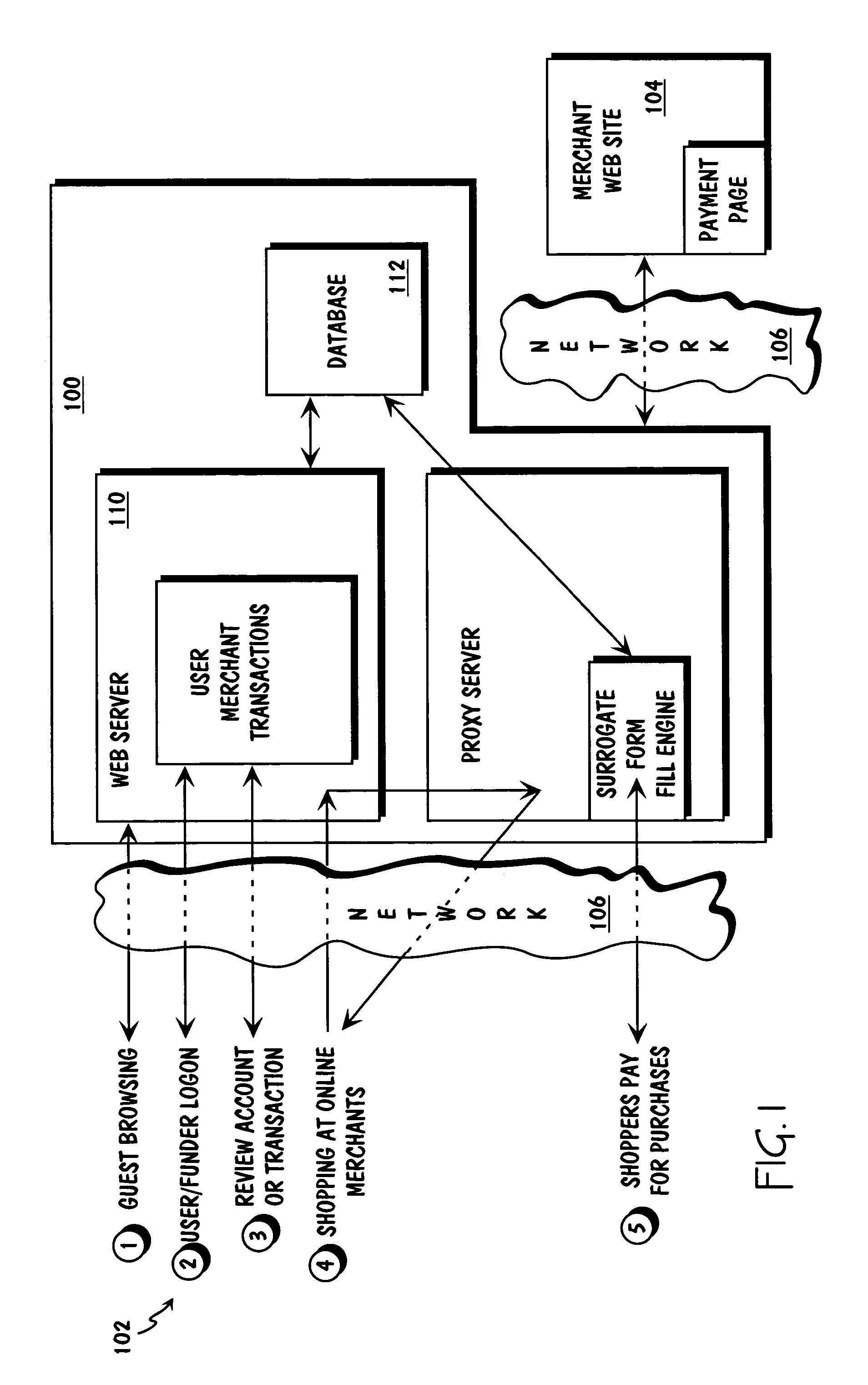
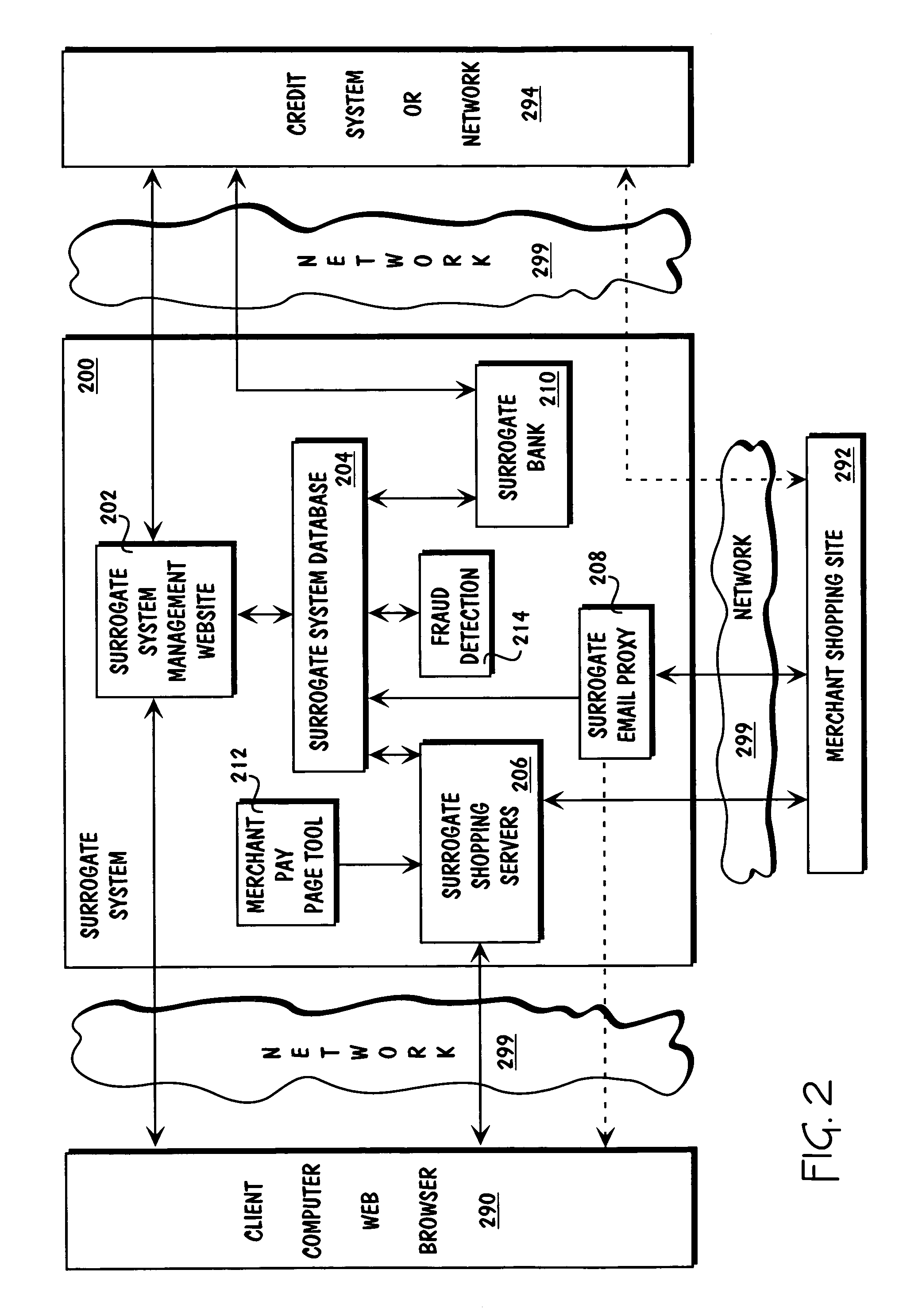
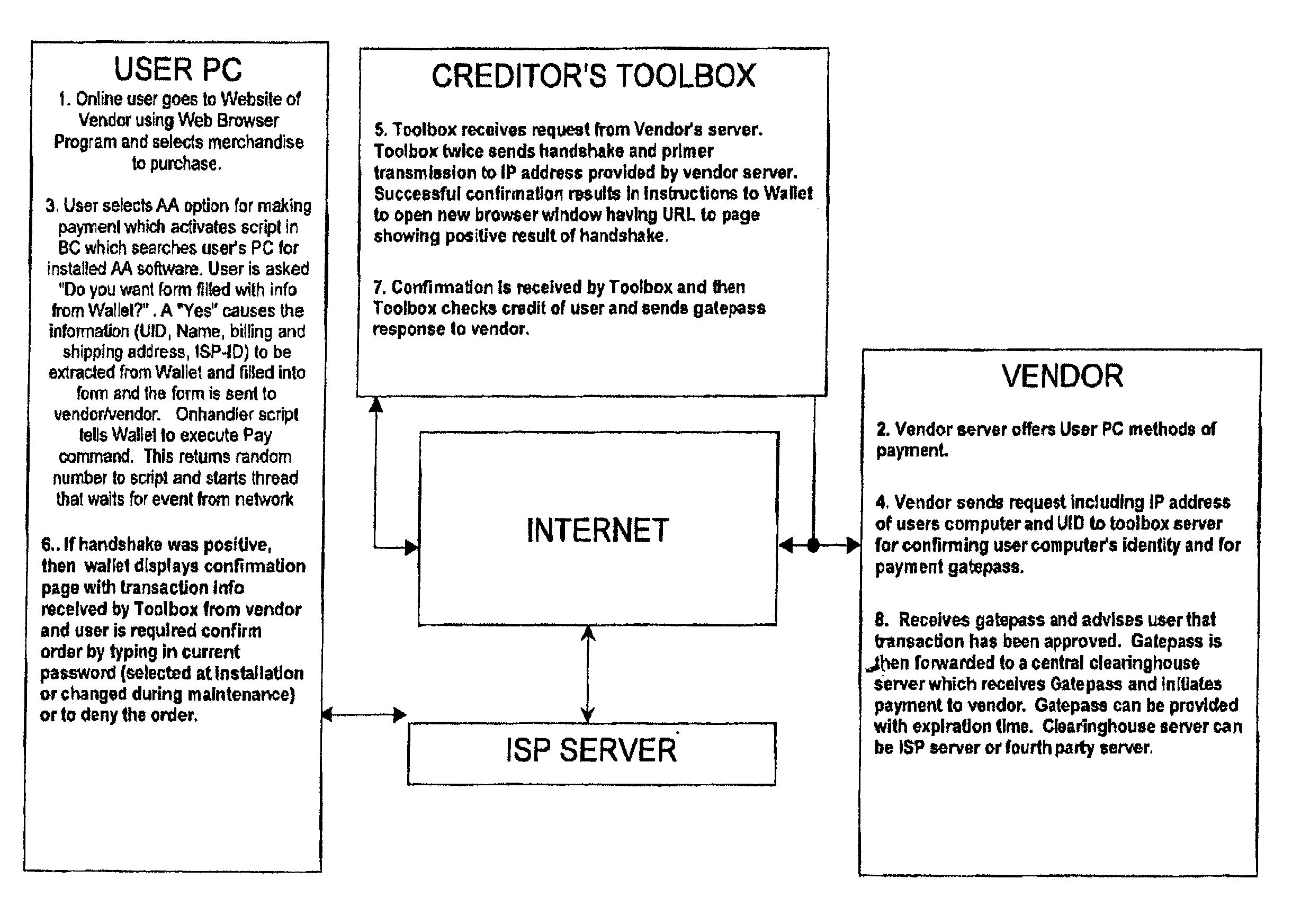
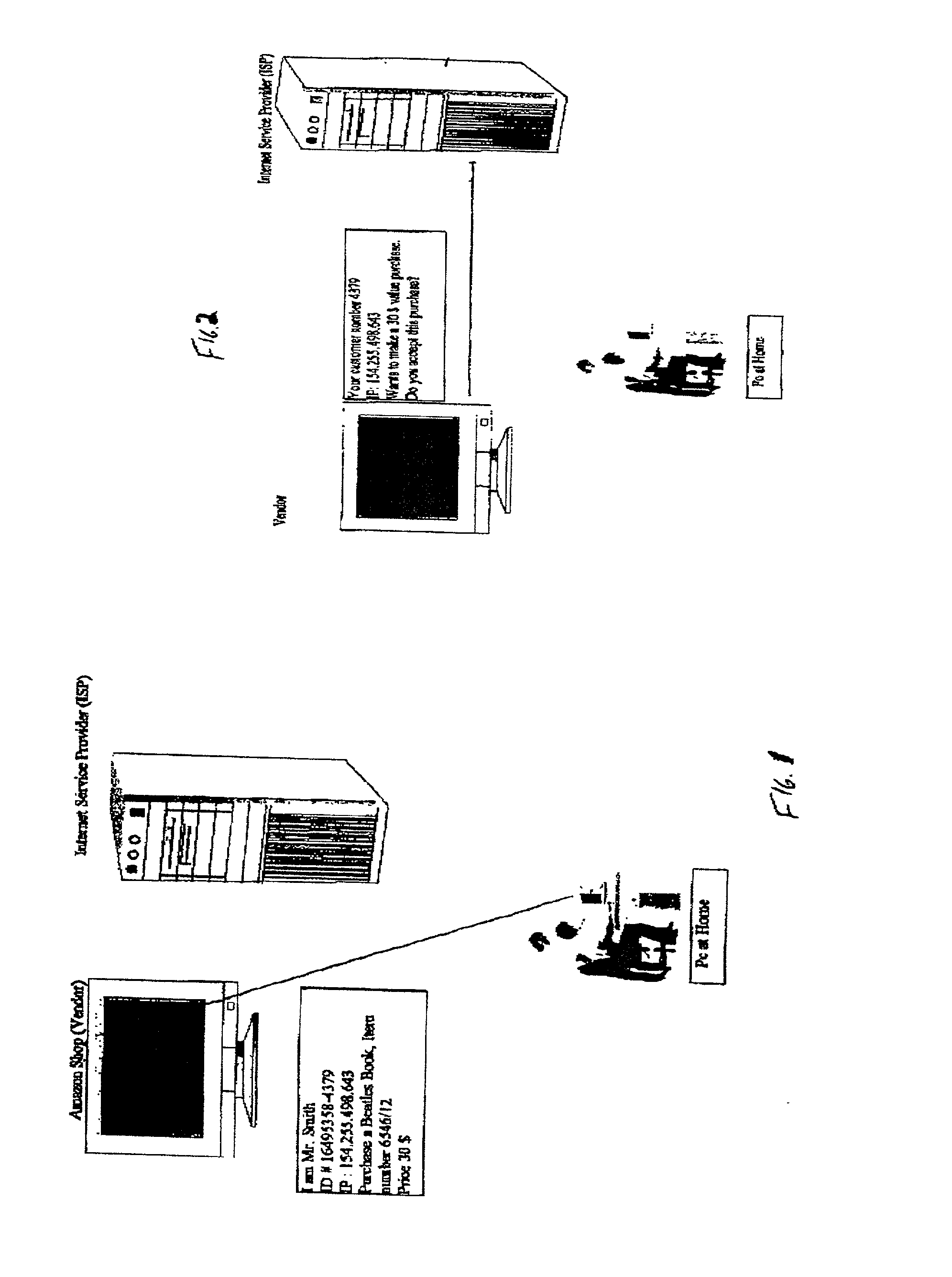
Method and apparatus for surrogate control of network-based electronic transactions
A surrogate system for the transparent control of electronic commerce transactions is provided through which an individual without a credit card is enabled to shop at online merchant sites. Upon opening an account within the surrogate system, the account can be funded using numerous fund sources, for example credit cards, checking accounts, money orders, gift certificates, incentive codes, online currency, coupons, and stored value cards. A user with a funded account can shop at numerous merchant web sites through the surrogate system. When merchandise is selected for purchase, a purchase transaction is executed in which a credit card belonging to the surrogate system is temporarily or permanently assigned to the user. The credit card, once loaded with funds from the user's corresponding funded account, is used to complete the purchase transaction. The surrogate system provides controls that include monitoring the data streams and, in response, controlling the information flow between the user and the merchant sites.
Owner:THE COCA-COLA CO
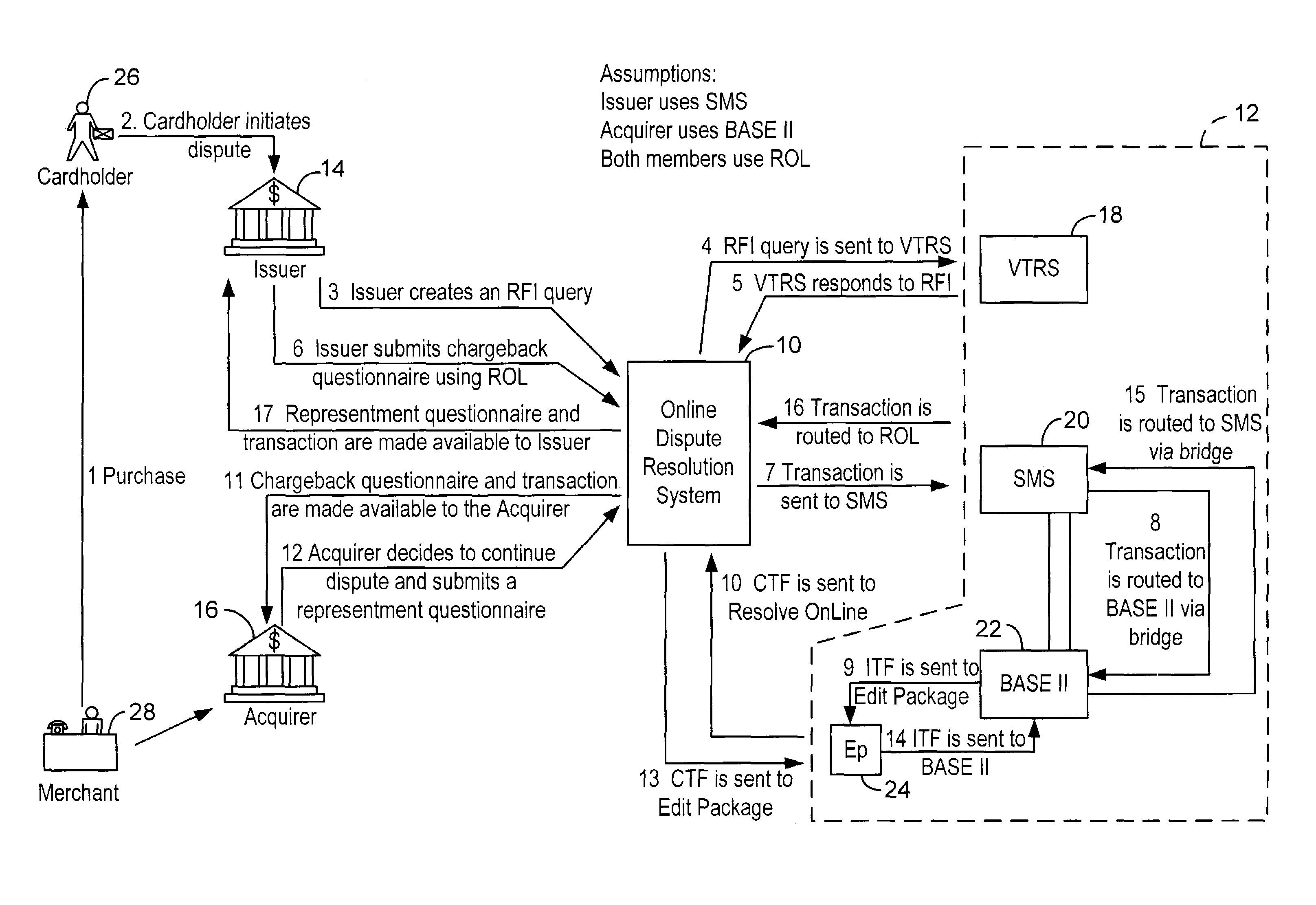
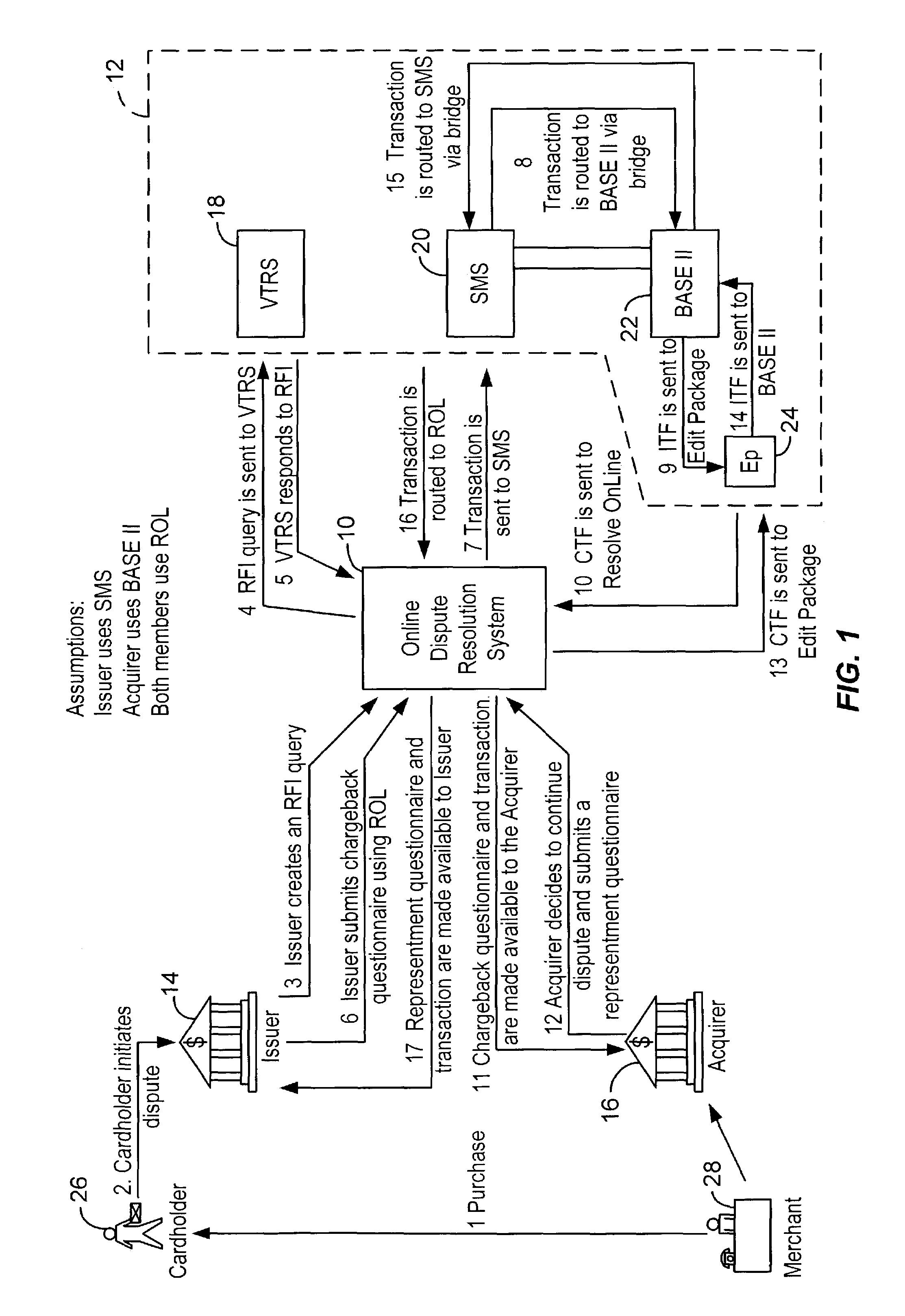
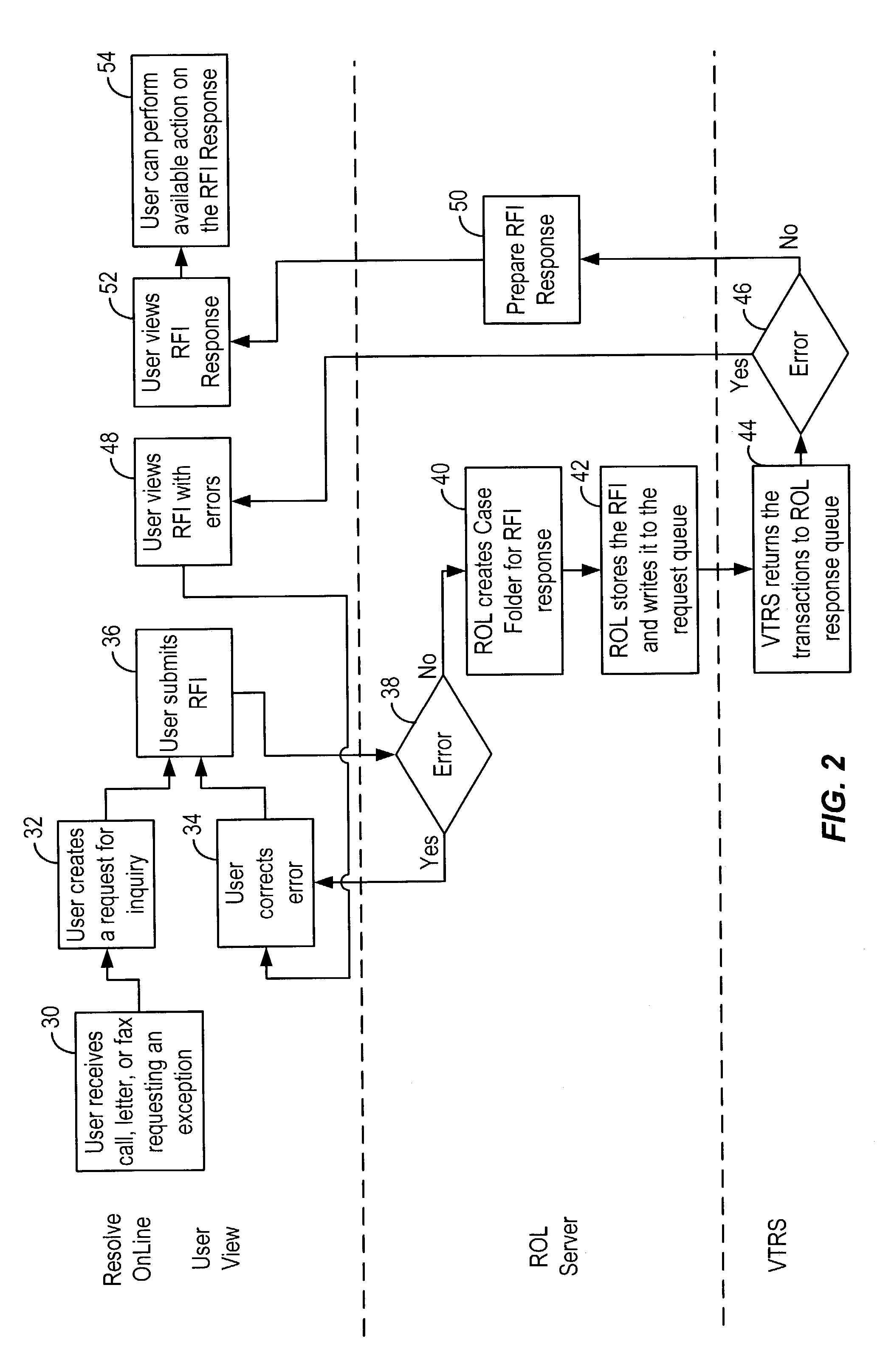
Method and system for facilitating electronic dispute resolution
A system for facilitating payment transaction disputes is provided. According to one aspect of the system, a user, such as an issuer, is allowed to use the system to resolve a disputed transaction. Based on information provided by a cardholder, the issuer is able to use the system to retrieve transactional information relating to the disputed transaction reported by the customer for review. When the issuer uses the system to retrieve information relating to the disputed transaction, a case folder is created. The case folder is a repository for storing all the relevant information and documentation relating to the disputed transaction. Using the information retrieved by the system, the issuer then determines whether to initiate a dispute. Alternatively, the system can also be used by an acquirer to respond to a dispute, usually on behalf of one of its merchant. If a dispute is responded to, a questionnaire is then created by the system. Alternatively, the issuer may decline to initiate a dispute and either seek additional information from the cardholder or deny the cardholder's inquiry. The case folder and the questionnaire are created for a specific disputed transaction. The questionnaire is designed to capture information from the cardholder and / or the issuer relating to the disputed transaction. The questionnaire may be pre-populated with previously retrieved transactional information which is stored in the case folder. Relevant documents in support of the disputed transaction may also be attached as part of the questionnaire. Various parties to the dispute may then provide relevant information (including supporting documentation) to the system. The relevant information provided by the parties is maintained in the case folder. The system then keeps track of the relevant timeframes for the case folder to ensure that each party to the dispute is given the correct period of time to respond during the processing of a dispute. Prior to filing the dispute for arbitration or compliance, the system permits the parties to resolve the dispute amongst themselves without the help of an arbiter through pre-arbitration and pre-compliance. If the parties to the dispute are unable to resolve the dispute on their own, the system also permits the parties to resolve the dispute via arbitration or compliance with the help of an arbiter. The system provides the arbiter with access to the case folder to allow the arbiter to render an informed decision on the dispute.
Owner:VISA USA INC (US)
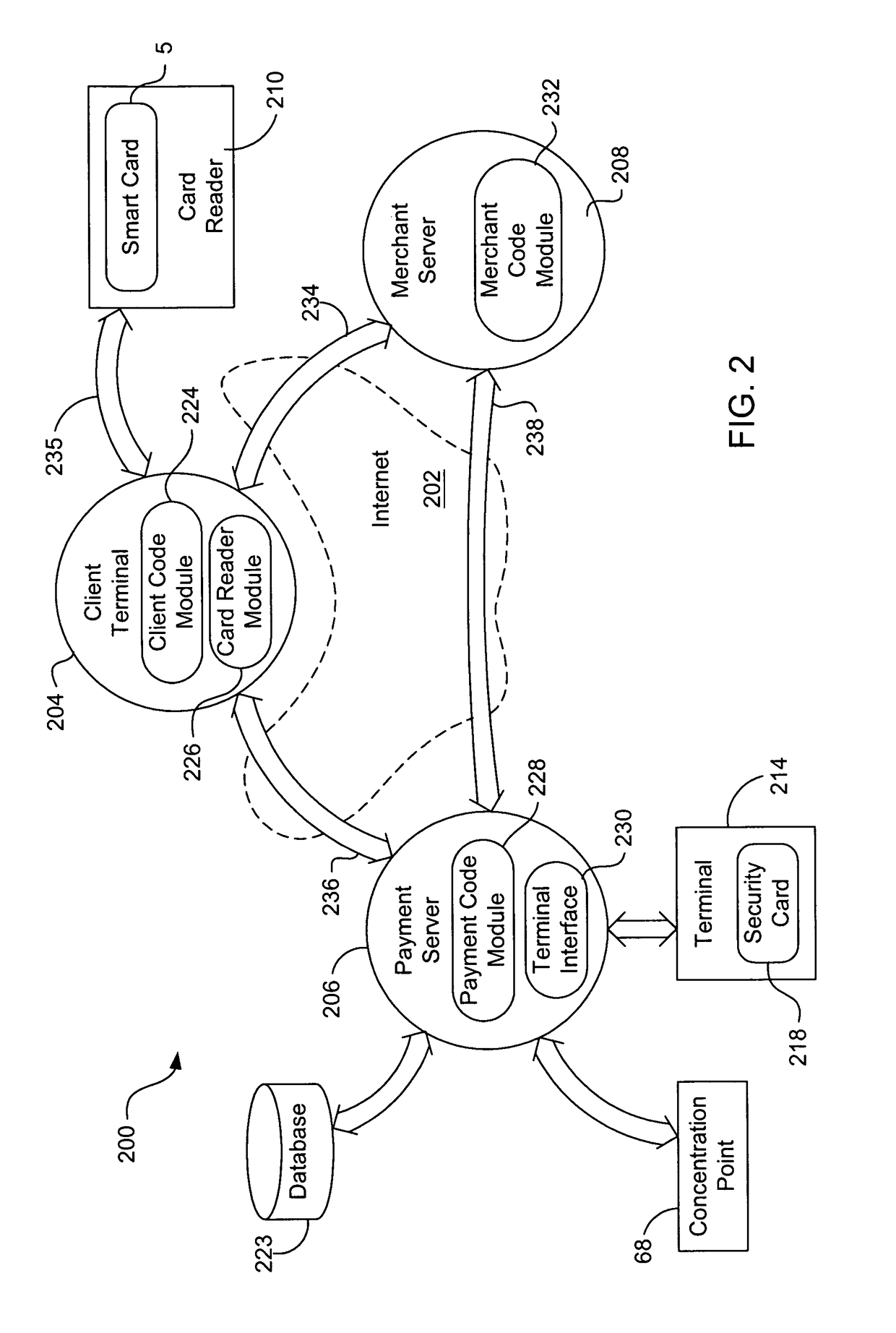
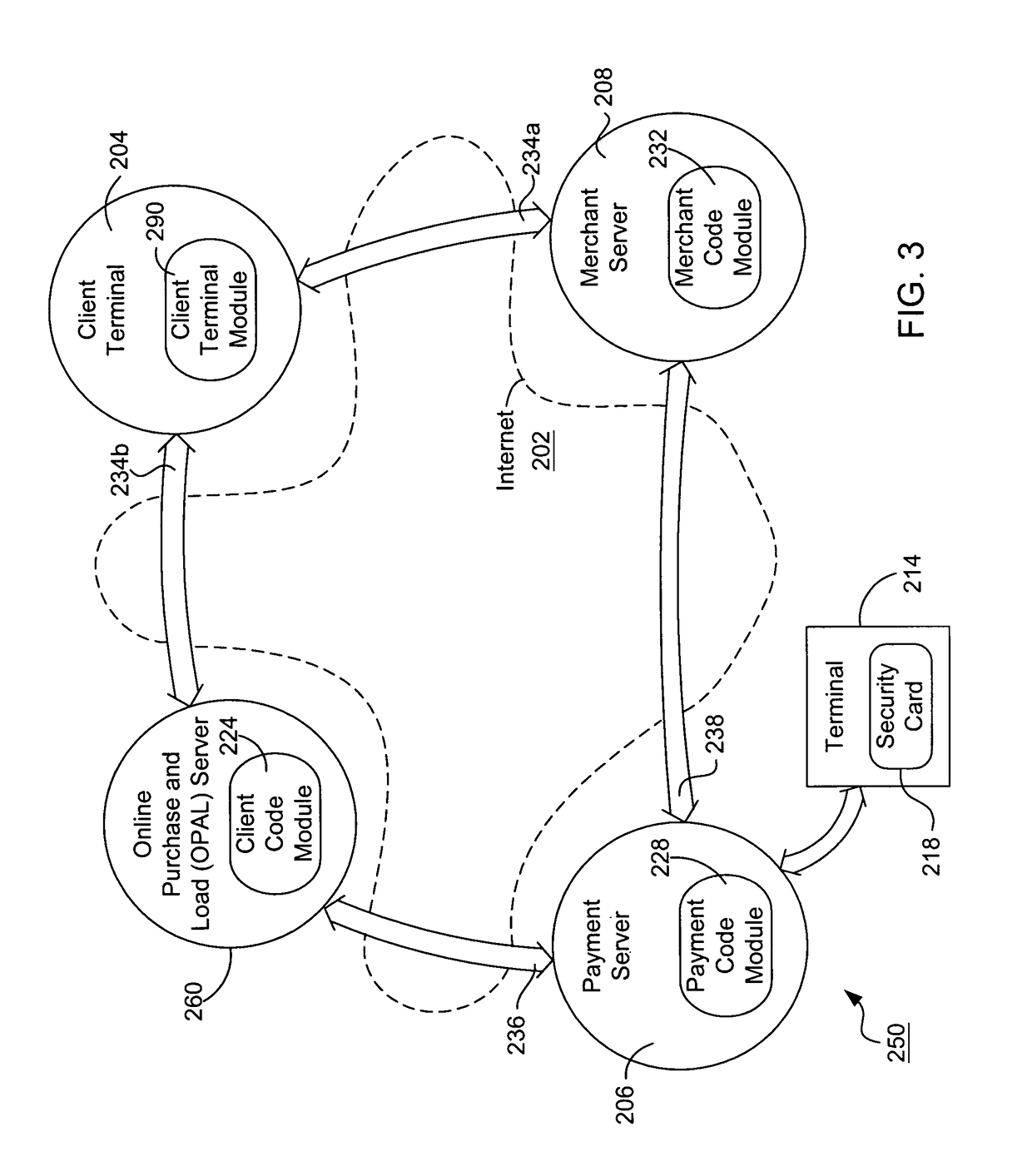
Internet payment, authentication and loading system using virtual smart card
InactiveUS7908216B1Advantageous for small dollar amount transactionMinimal timeFinancePayment circuitsMerchant servicesPayment
A system loads, authenticates and uses a virtual smart card for payment of goods and / or services purchased on-line over the Internet. An online purchase and load (OPAL) server includes a virtual smart card data base that has a record of information for each smart card that it represents for a user at the behest of an issuer. The server includes a smart card emulator that emulates a smart card by using the card data base and a hardware security module. The emulator interacts with a pseudo card reader module in the server that imitates a physical card reader. The server also includes a client code module that interacts with the pseudo card reader and a remote payment or load server. A pass-through client terminal presents a user interface and passes information between the OPAL server and a merchant server, and between the OPAL server and a bank server. The Internet provides the routing functionality between the client terminal and the various servers. A merchant advertises goods on a web site. A user uses the client terminal to purchase goods and / or services from the remote merchant server. The payment server processes, confirms and replies to the merchant server. The payment server is also used to authenticate the holder of a virtual card who wishes to redeem loyalty points from a merchant. To load value, the client terminal requests a load from a user account at the bank server. The load server processes, confirms and replies to the bank server.
Owner:VISA INT SERVICE ASSOC
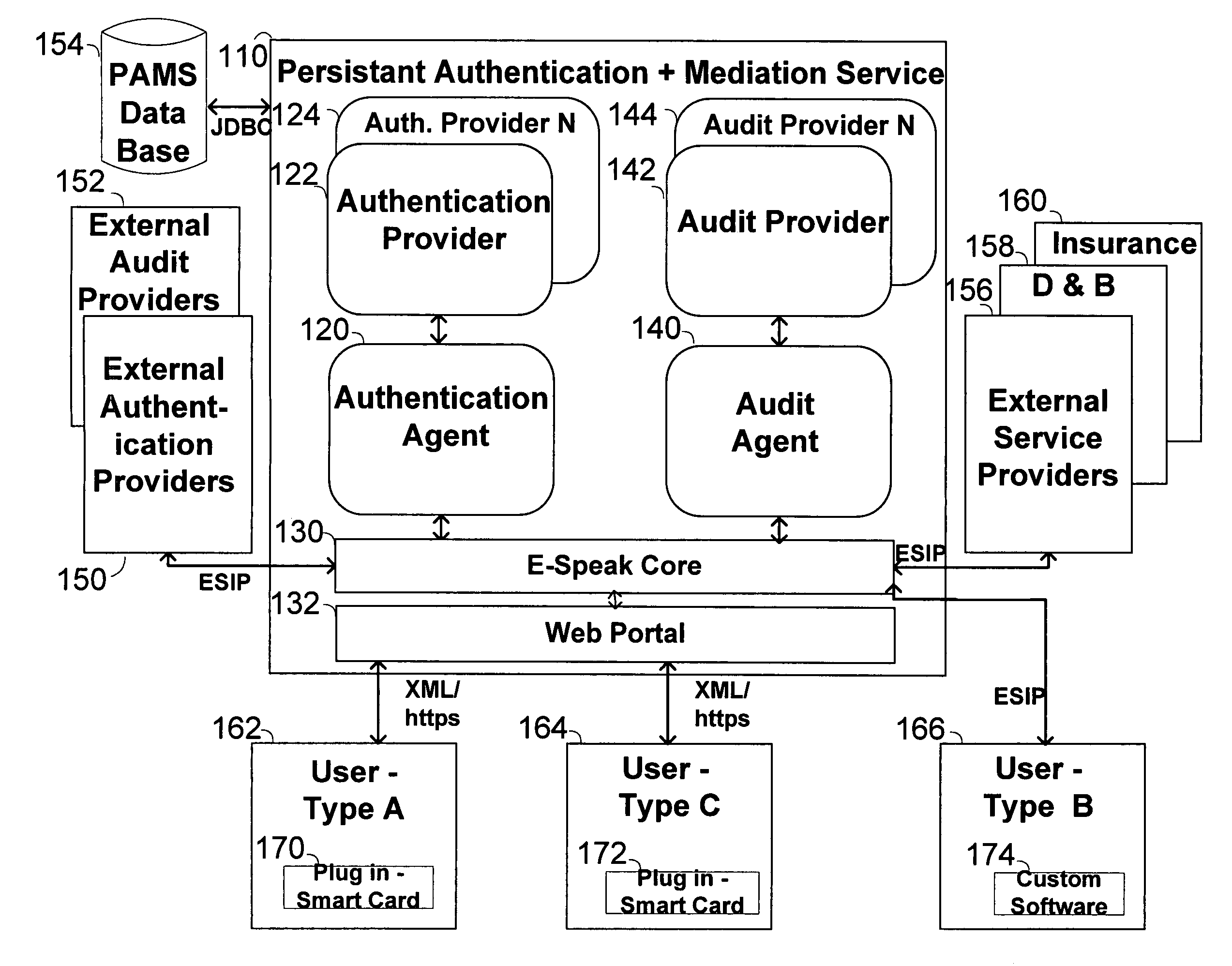
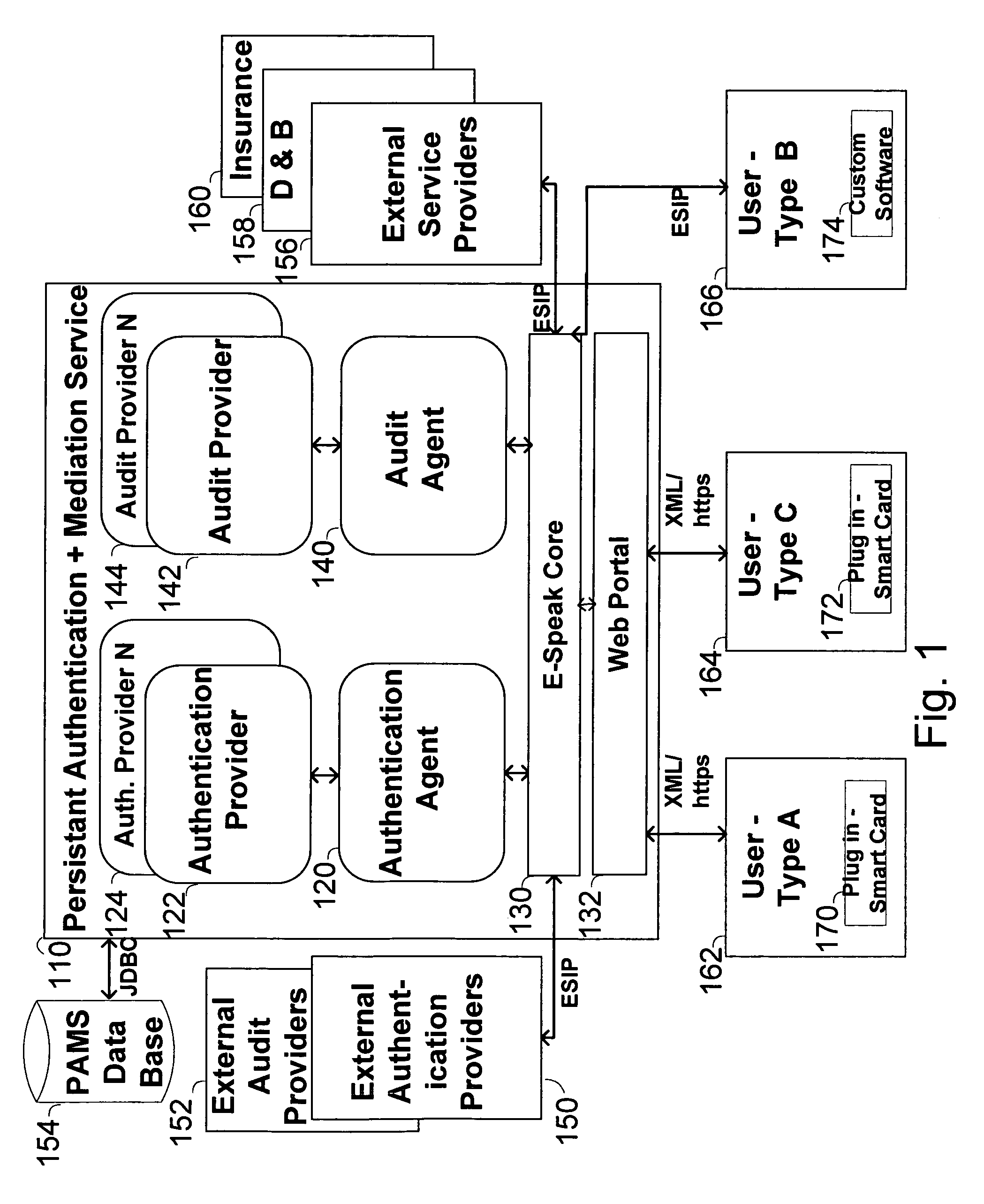
Method, system and service for conducting authenticated business transactions
InactiveUS6957199B1Fast authenticationImprove securityComputer security arrangementsCommerceService provisionThe Internet
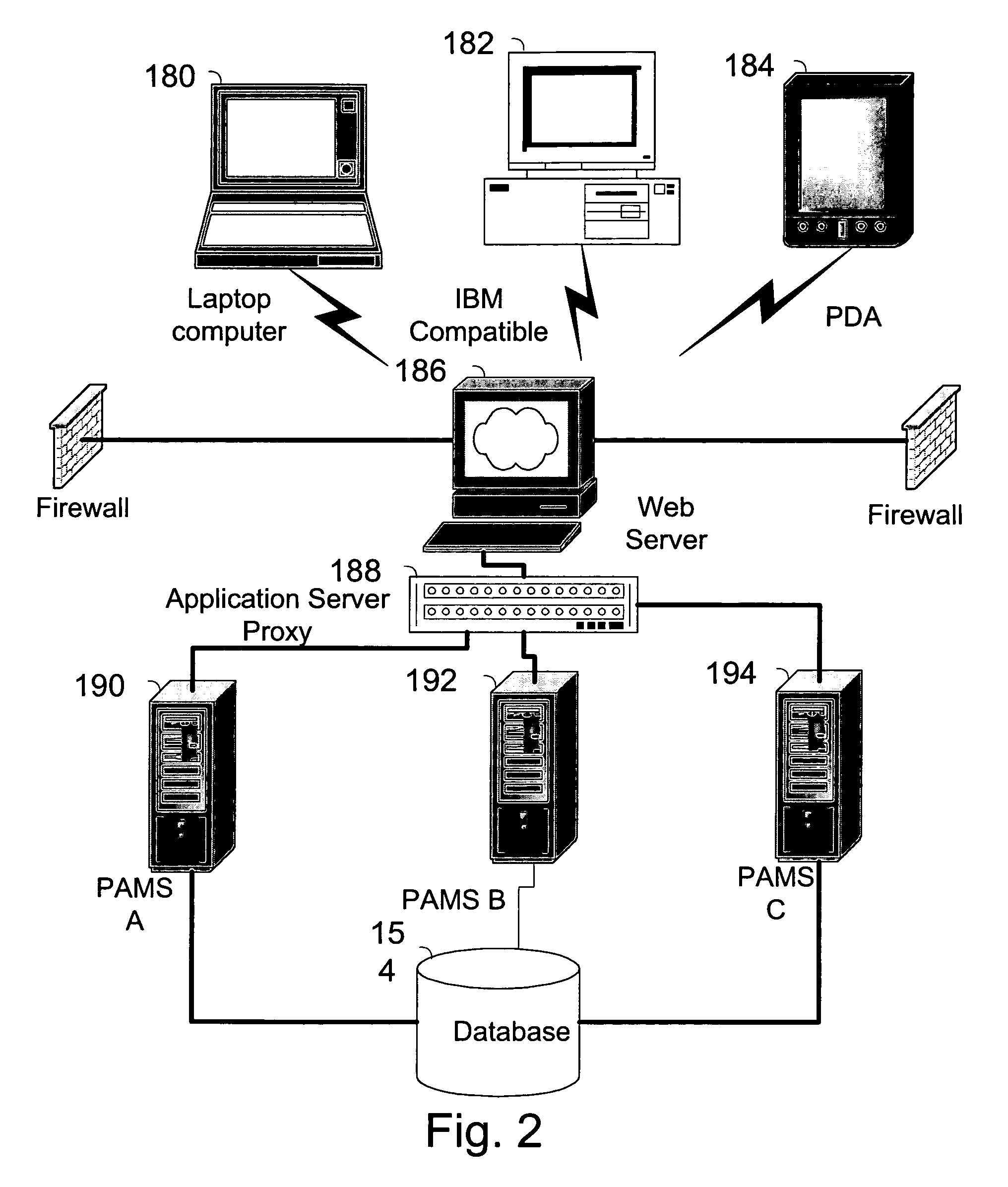
The invention pertains to a method, online service, and system, for creating partnerships based on trust relationships over a public network, authenticating trade partners, infrastructure providers and collaborators to each other, and providing users with an environment suitable for conducting transactions requiring a high level of trust. A service according to the invention is a persistent authentication and mediation service (PAMS) which is provided as an on-line service. One embodiment is a method for conducting authenticated business transactions involving microprocessor equipped devices over the Internet comprising:A. providing an on-line authentication service available on the distributed network;B. authenticating a plurality of users to said on-line authentication service using a closed authentication system to produce a plurality of authenticated users; andC. connecting a group of at least two of said plurality of authenticated users under persistent mediation of said on-line authentication service, producing a connected group of authenticated users.
Owner:FISHER DOUGLAS
Framework and system for purchasing of goods and services
InactiveUS7801826B2Risk minimizationReducing credit card fraudComputer security arrangementsPayment protocolsThird partyPurchasing
A system for conducting an agreement between two parties relying on a trusted a third party includes a first party generating a first view of the agreement and transmitting the first view of the agreement to the third party, a second party independently generating a second view of the agreement and transmitting the second view of the agreement to the third party, a wireless network connecting the first party and the second party, and a wired or wireless network connecting the second party to the third party. The trusted third party, receives the first view of the agreement and the second view of the agreement, verifies conditions including that the identities of the parties that transmitted the agreements and that the independent views of the agreement are consistent with each other, and takes action to execute the agreement if the conditions are satisfied.
Owner:PCMS HOLDINGS INC
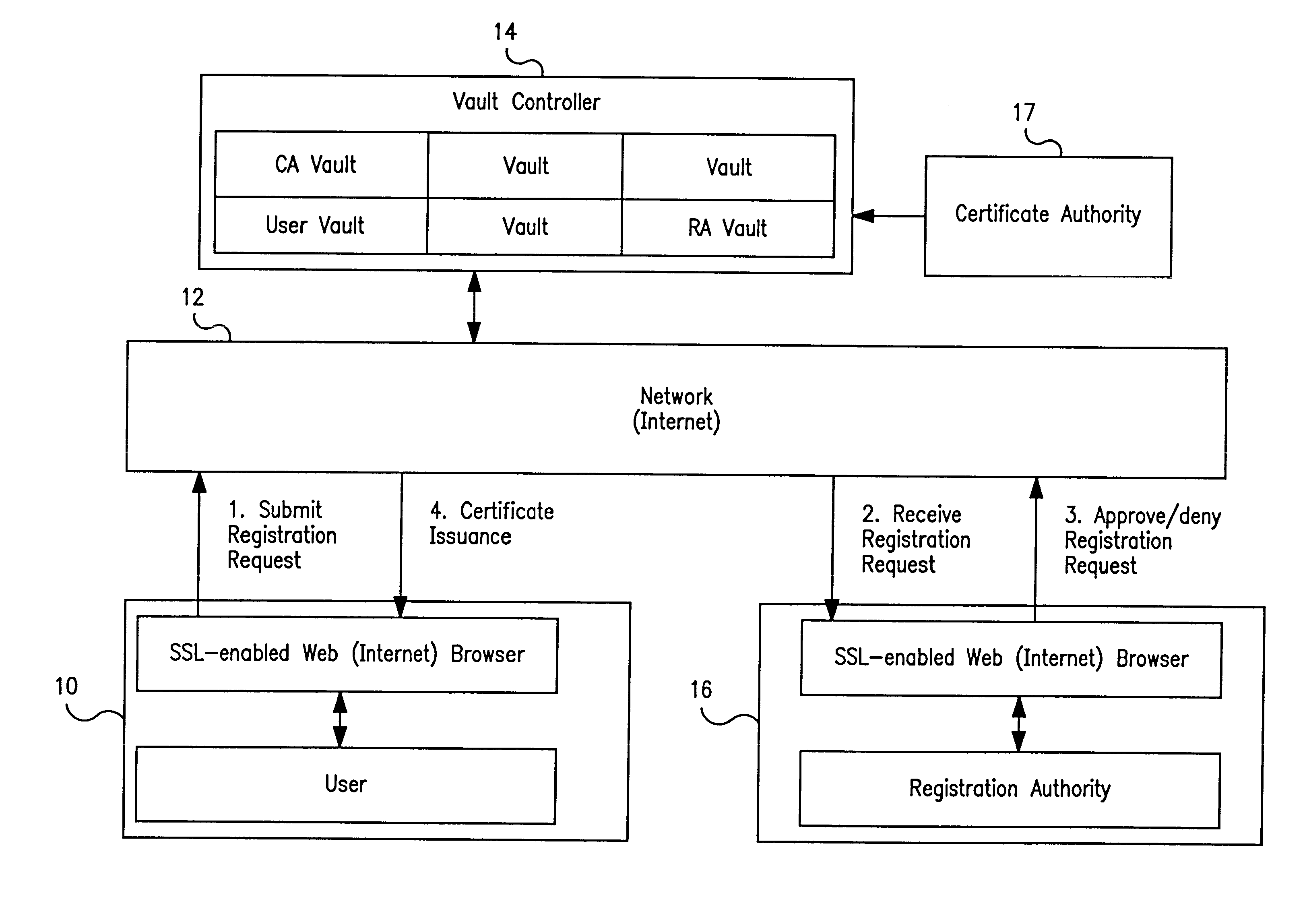
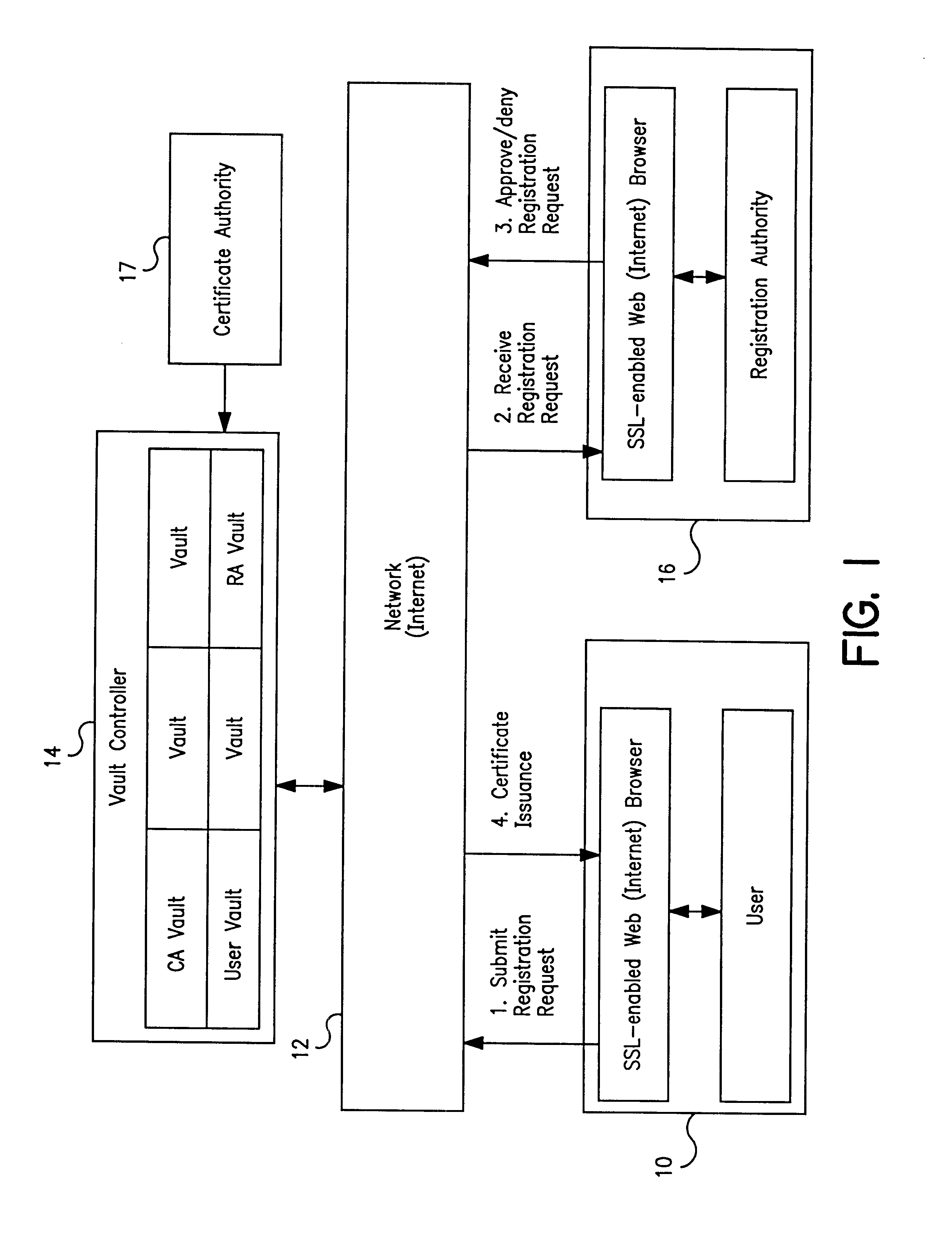
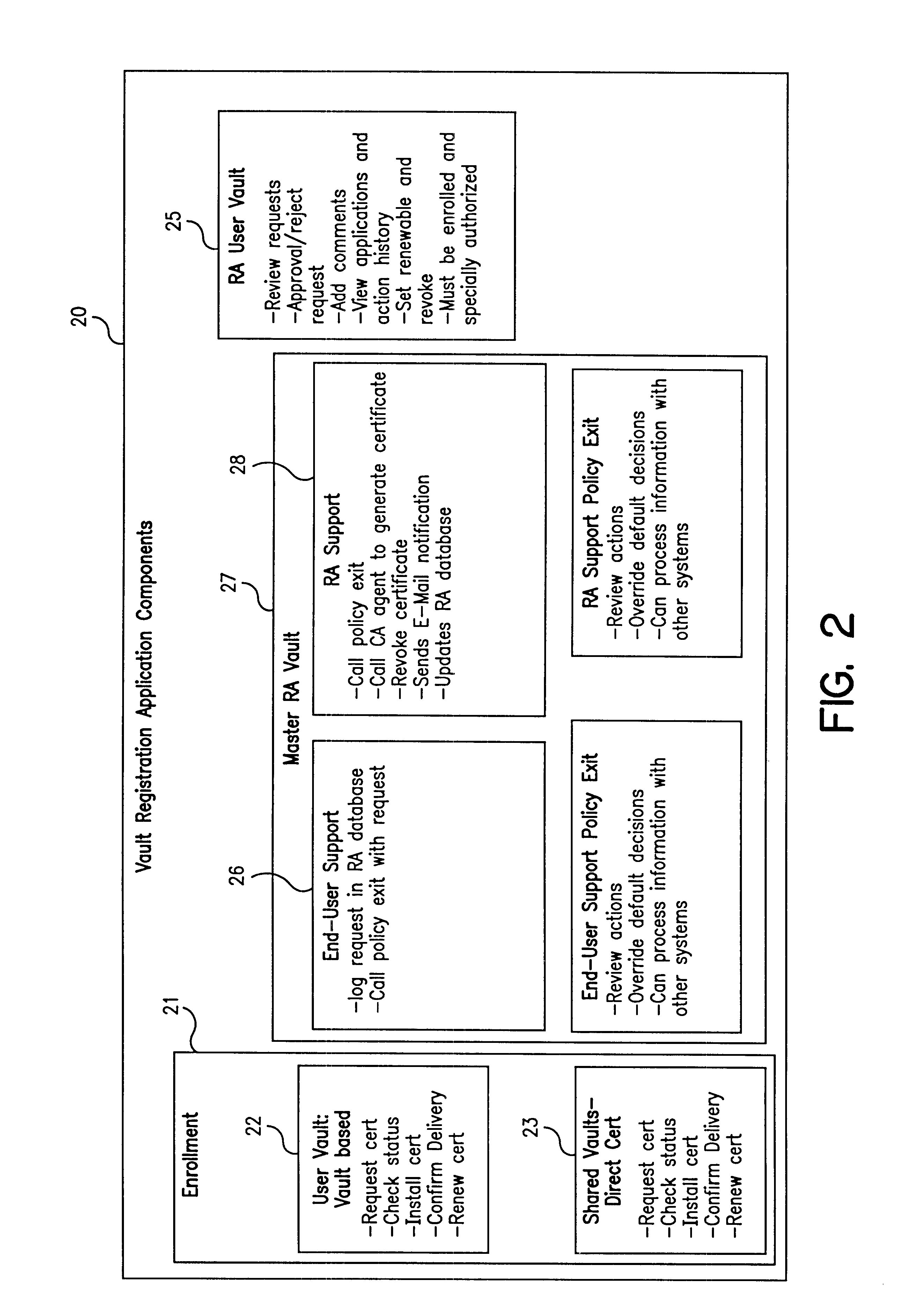
Vault controller based registration application serving web based registration authorities and end users for conducting electronic commerce in secure end-to-end distributed information system
InactiveUS6438690B1FinanceDigital data processing detailsRegistration authorityCommunications system
A secure end-to-end communications system includes a vault controller based registration application for managing the issuance and administration of digital certificates for use in conducting electronic commerce in the system. The system includes an end user terminal and a registration authority terminal coupled to a vault controller through the system. A registration application executable in the controller utilizes SSL and dedicated vaults to process requests for digital certificates from end users on an automated or manual basis. The registration application includes an enrollment module which implements the process of applying for and receiving certificates; an RA desk top module which allows an administrator to review certificate requests and manage certificates; a master Registration Authority (RA) module which conducts the processing of requests and the generation of certificates; and an RA (Registration Authority) database serves as a repository of information about applicants, certificate requests, and their processing history.
Owner:IBM CORP
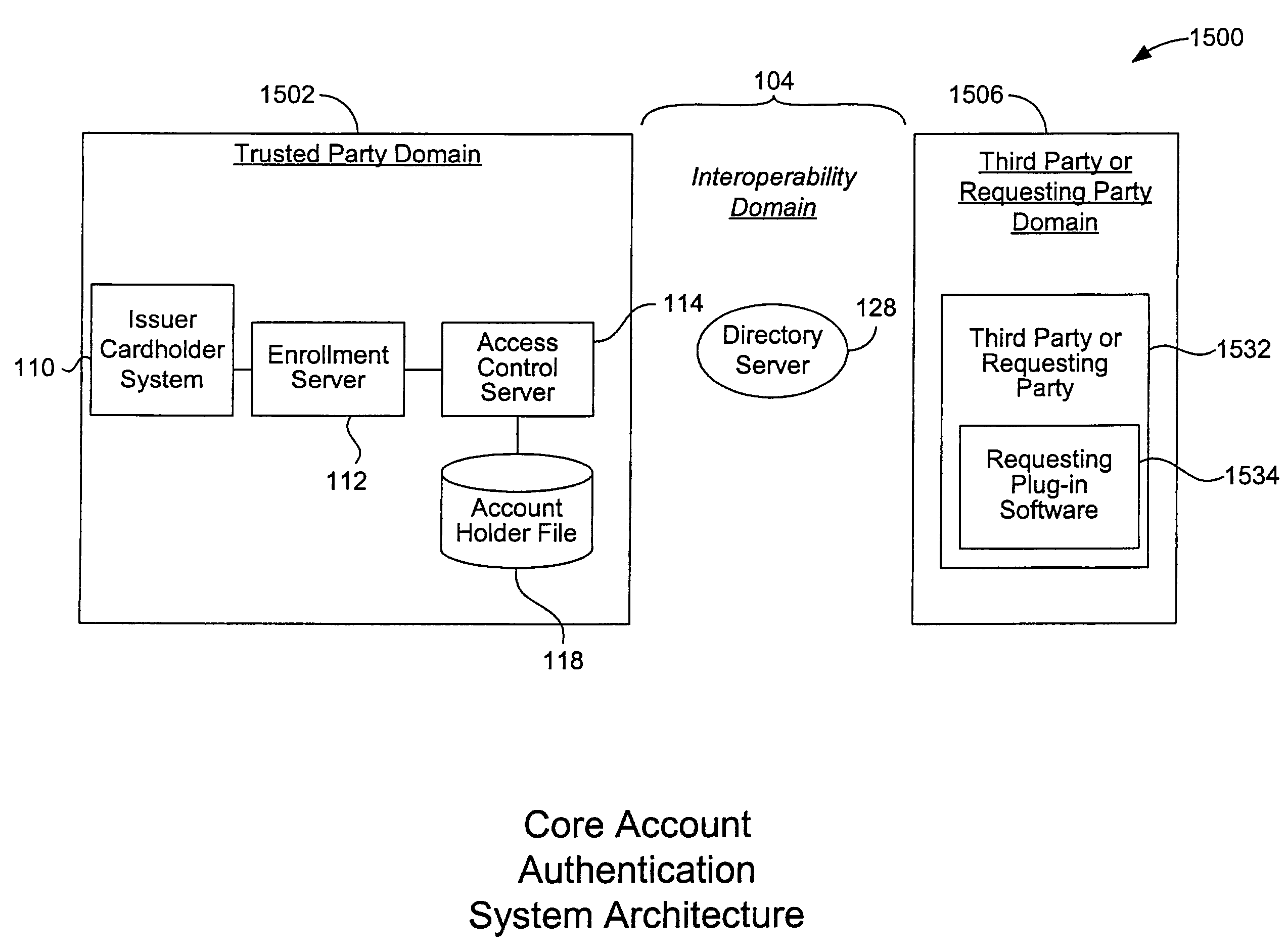
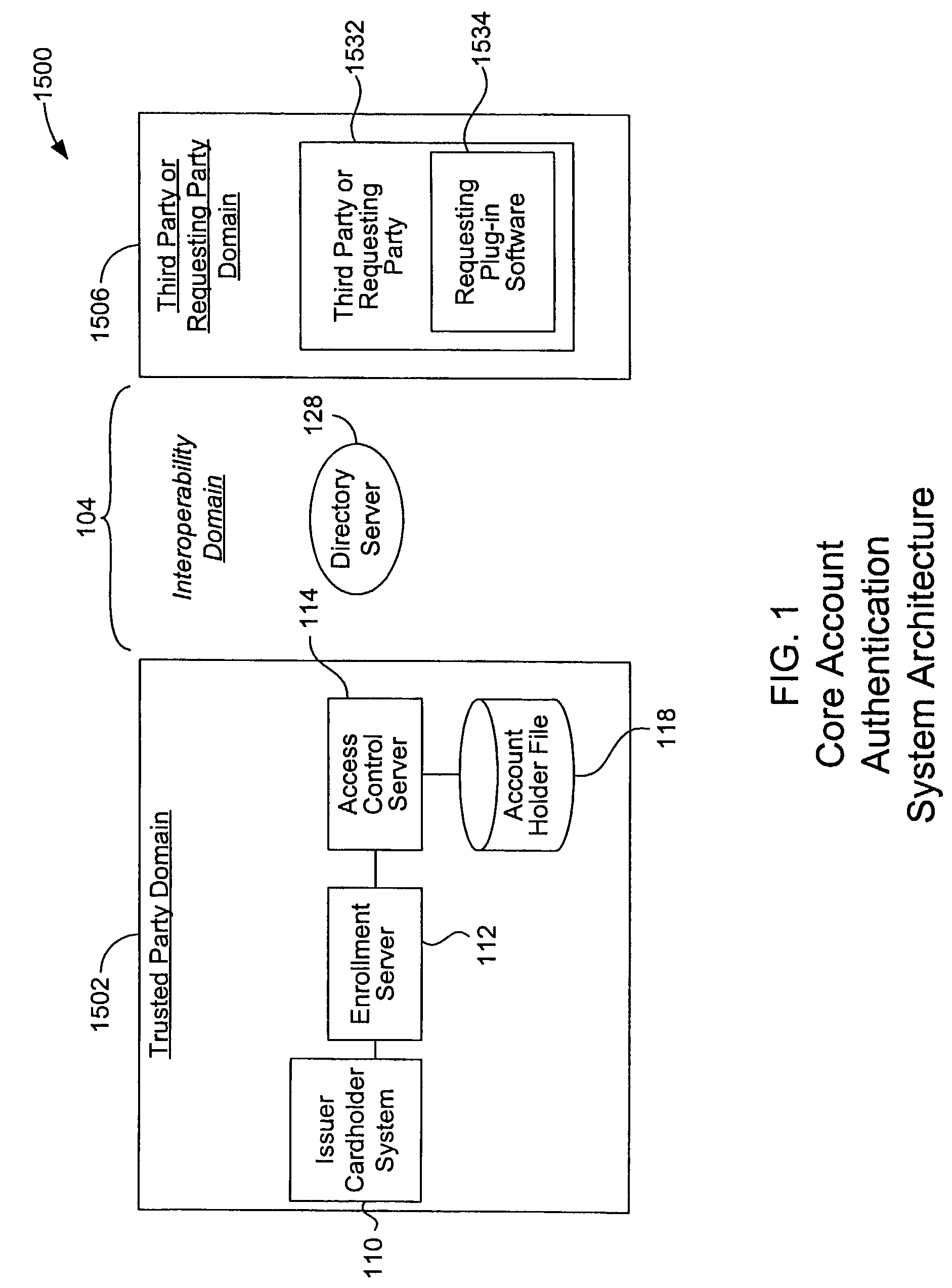
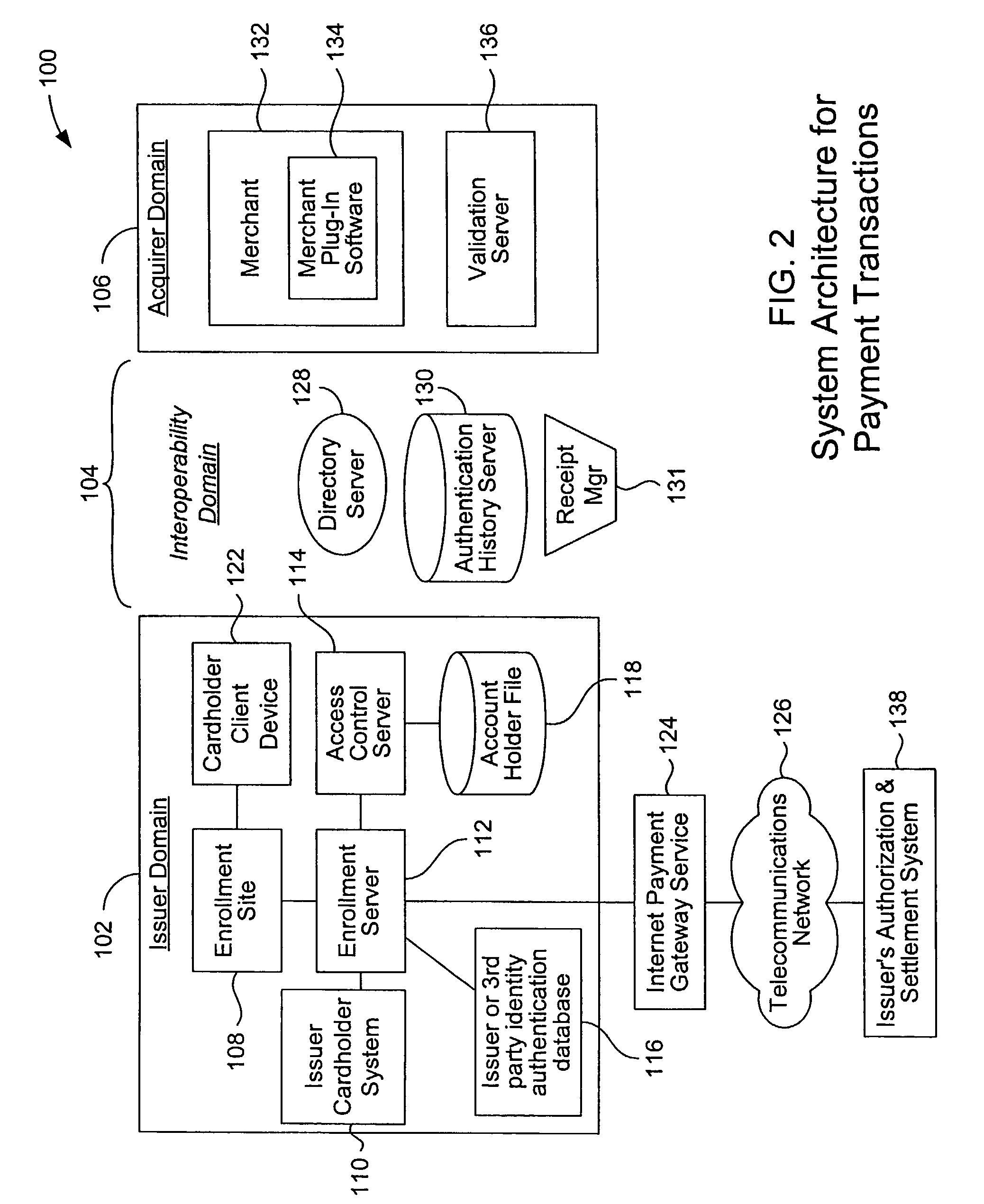
Mobile account authentication service
ActiveUS7707120B2Minimal investmentHigh level of interoperabilityComplete banking machinesFinanceInternet Authentication ServicePayment
A payment authentication service authenticates the identity of a payer during online transactions. The authentication service allows a card issuer to verify a cardholder's identity using a variety of authentication methods, such as with the use of tokens. Authenticating the identity of a cardholder during an online transaction involves querying an access control server to determine if a cardholder is enrolled in the payment authentication service, requesting a password from the cardholder, verifying the password, and notifying a merchant whether the cardholder's authenticity has been verified. Systems for implementing the authentication service in which a cardholder uses a mobile device capable of transmitting messages via the Internet are described. Systems for implementing the authentication service in which a cardholder uses a mobile device capable of transmitting messages through voice and messaging channels is also described.
Owner:VISA INT SERVICE ASSOC
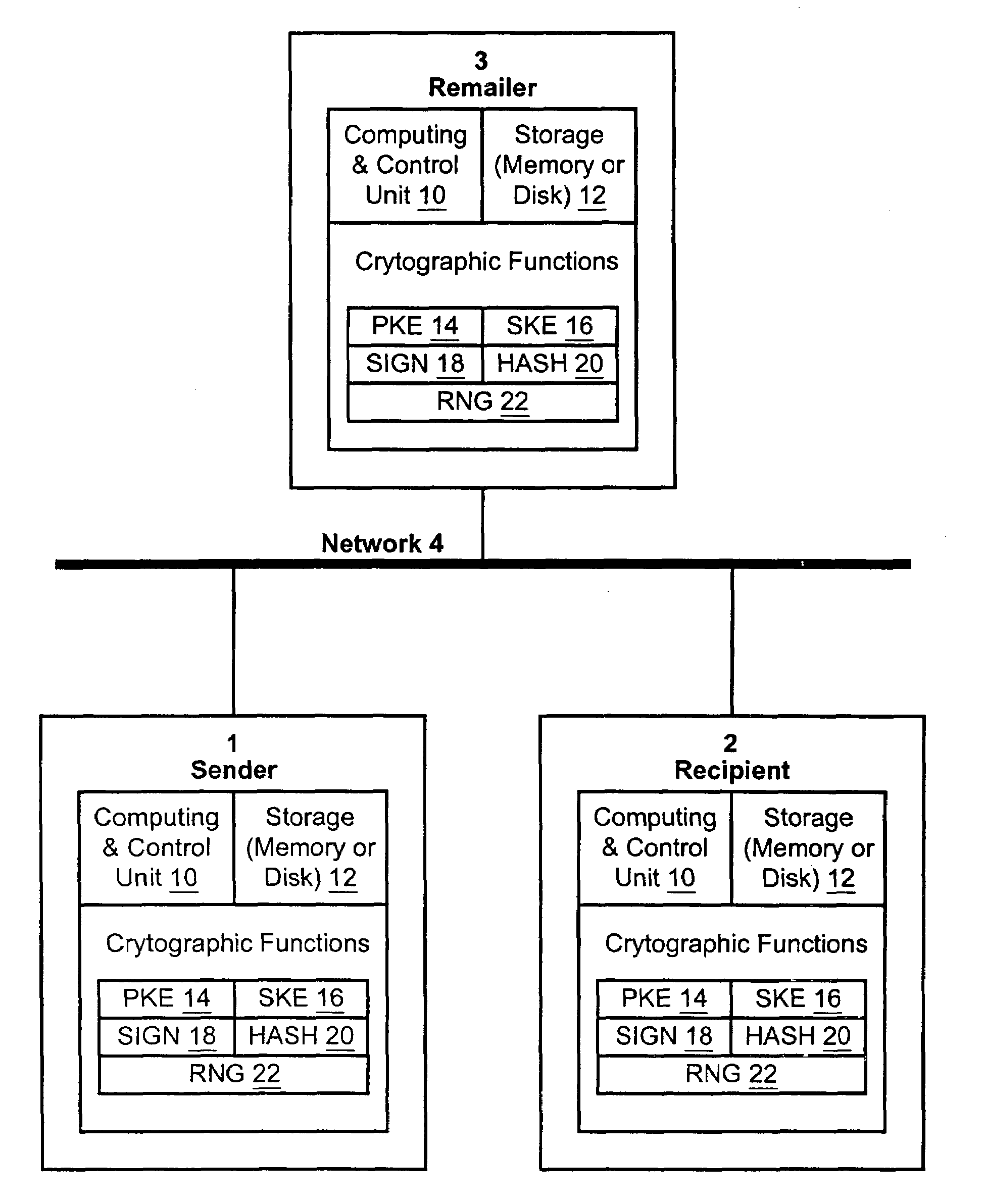
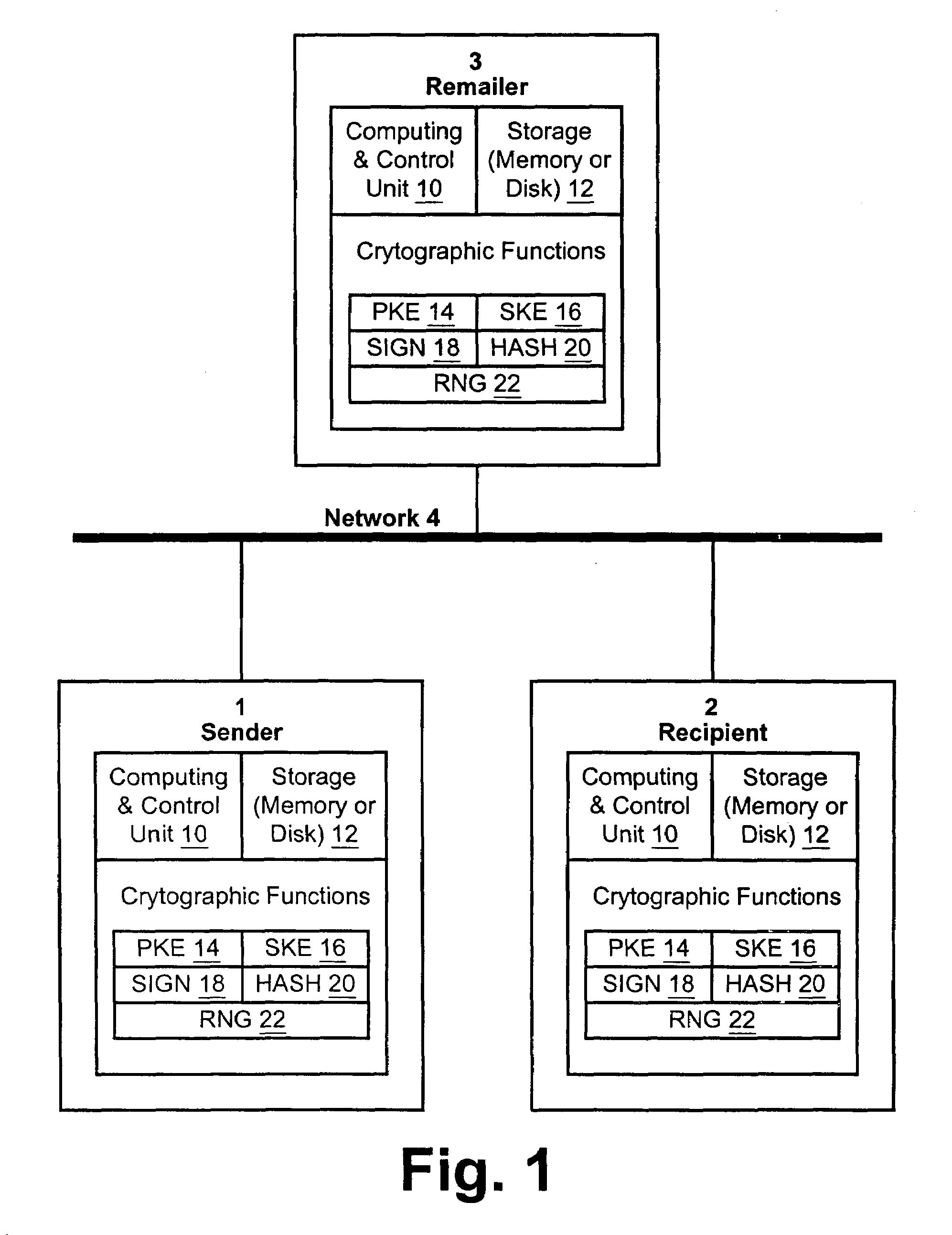
Certified transmission system
InactiveUS7353204B2Improve security featuresKey distribution for secure communicationComputer security arrangementsThird partySymmetric-key algorithm
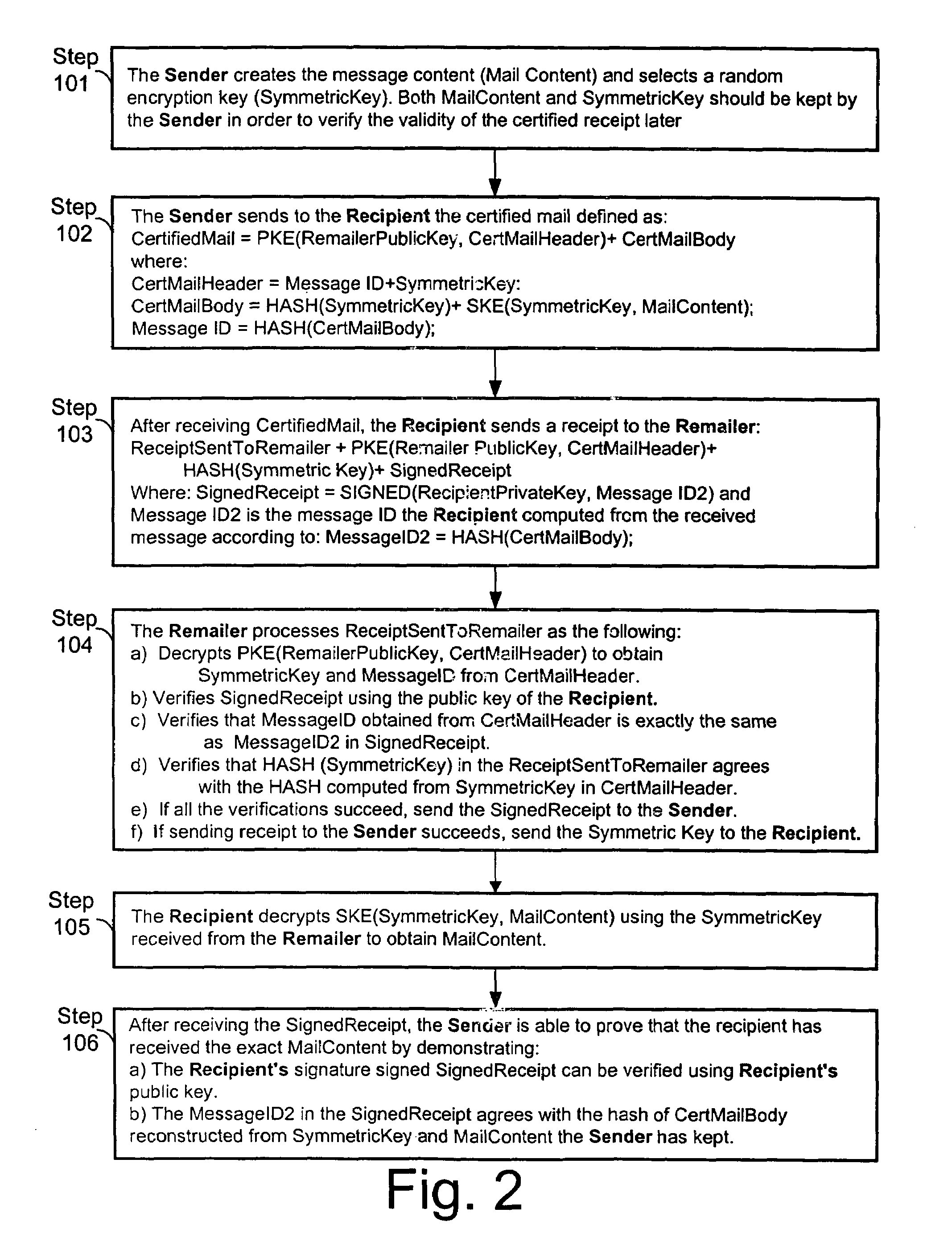
The invention provides a method and apparatus for transmitting a message from a sender to an intended recipient. The method includes encrypting a message using a symmetric key, sending the encrypted message to an intended recipient without the symmetric key and providing the symmetric key to a third party. If the intended recipient signs and returns to the third party a receipt for the message, the method includes transferring, by the third party, the receipt to the sender and providing the symmetric key to the intended recipient.
Owner:ZIX CORP
Secure online commerce transactions
A method of enabling electronic commerce transactions is provided by a service, the service giving to users a disposable credit card or other indicia of credit for a particular transaction or amount. The service receives registration information from the user and authorizes the user. The service establishes an account for the user and issues a disposable (one use) credit card number to the user which has the same format as a permanent credit card number, is acceptable to the user and the institution with whom the user is transacting business. The system incorporates various security features.
Owner:ACEINC PTY LTD
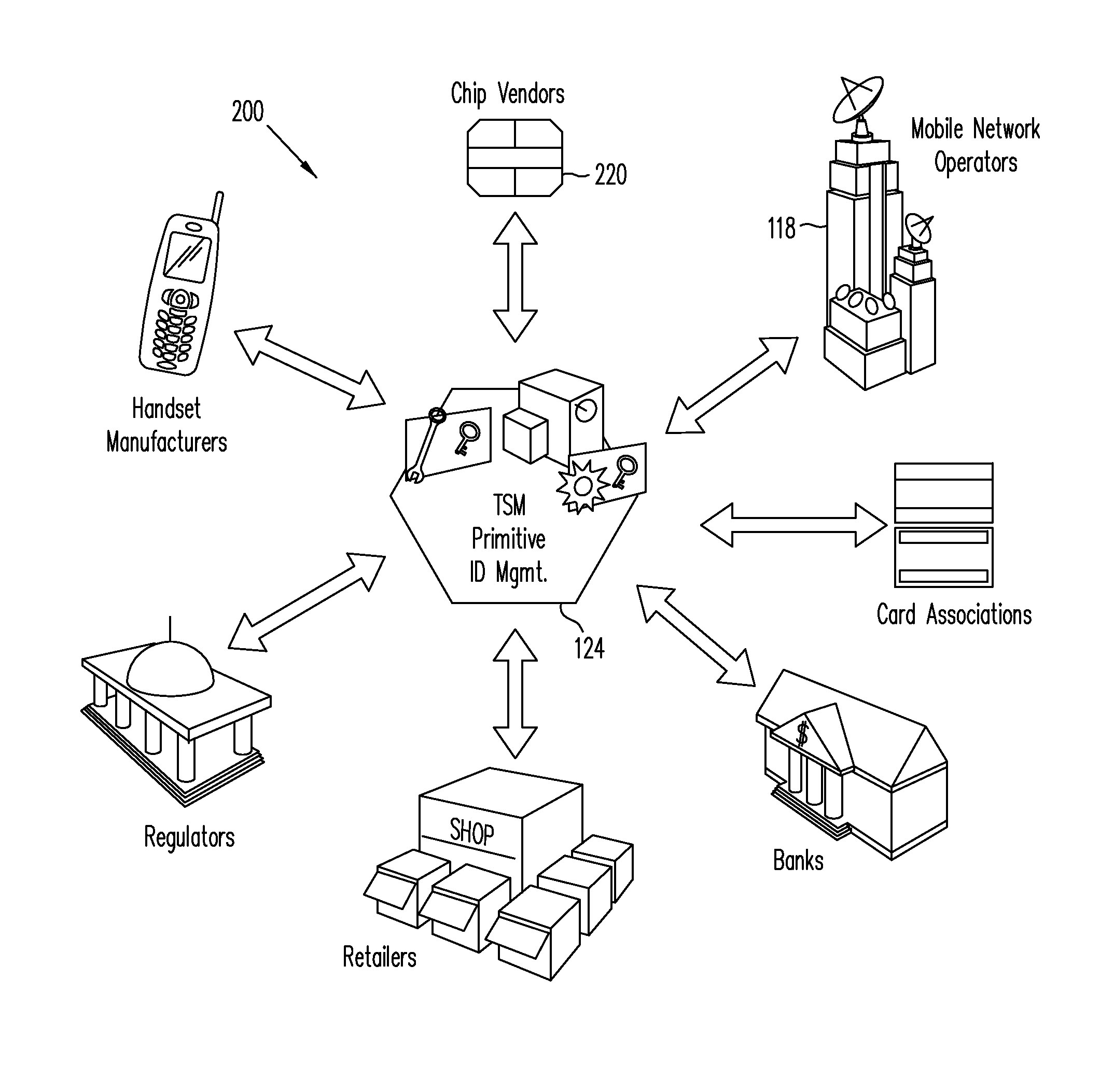
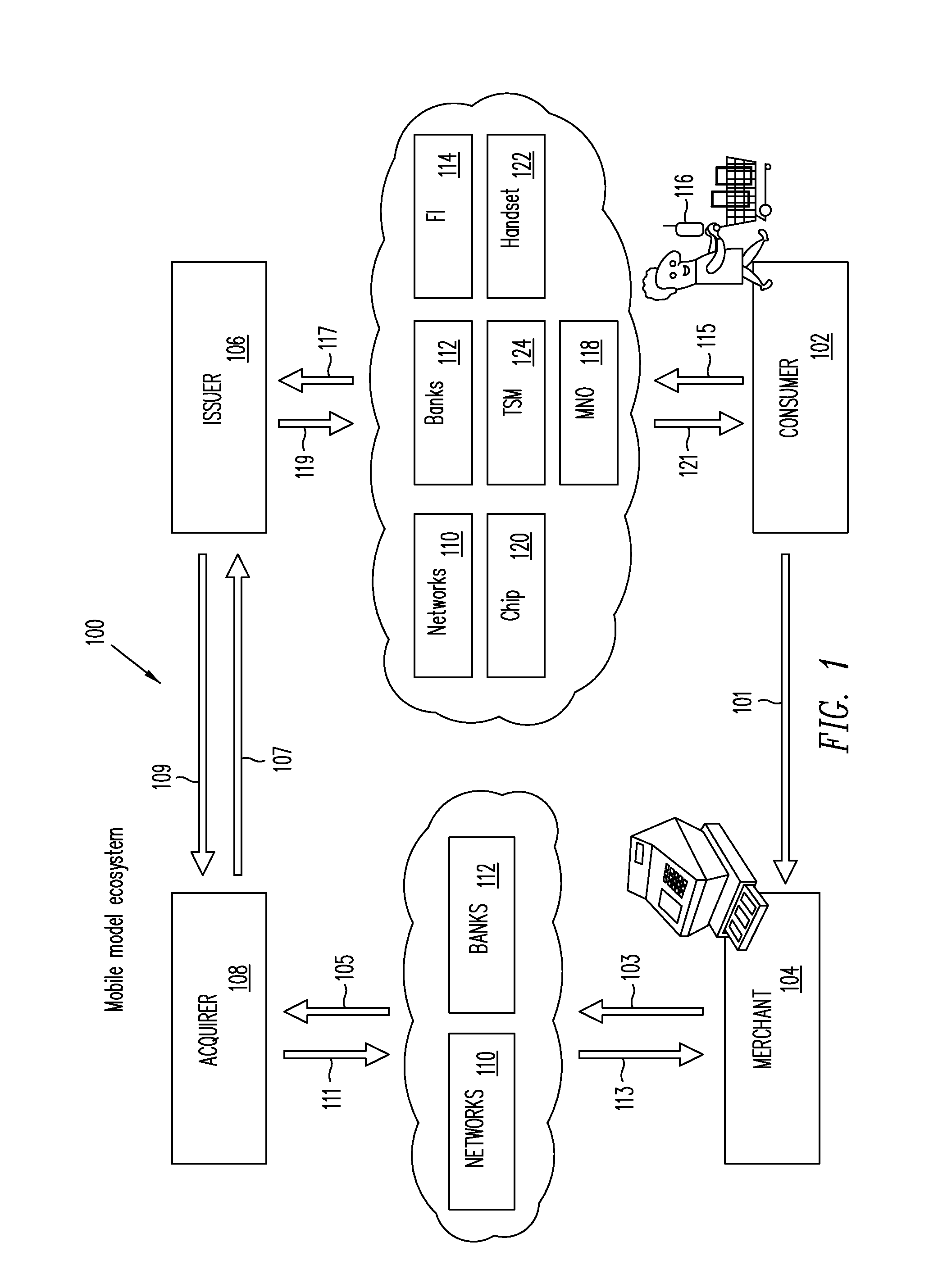
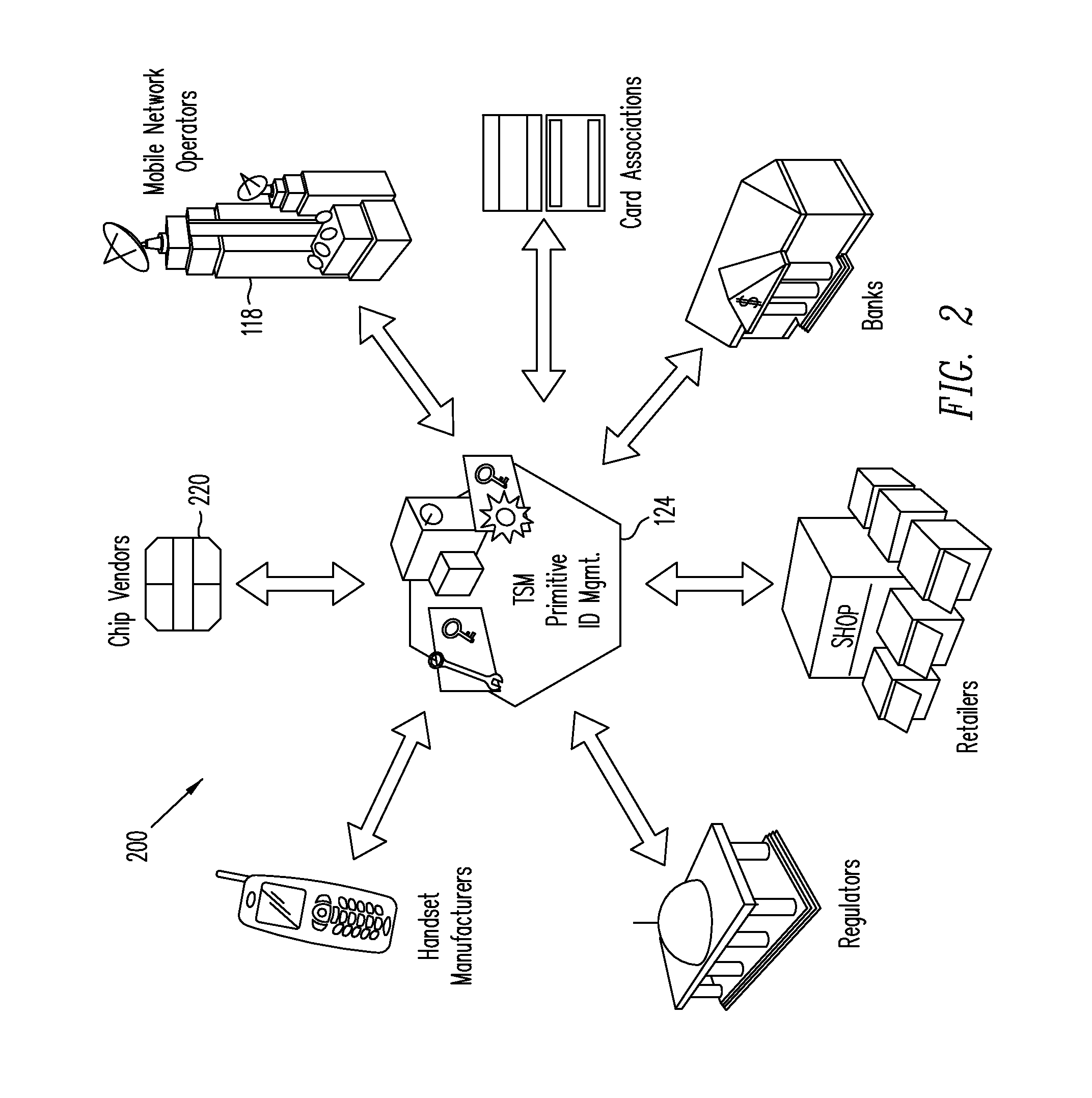
Trusted Integrity Manager (TIM)
A system for use with a trusted service manager (TSM) and a mobile device having a subscriber unique identifying data, according to one embodiment, includes: a server in which the server validates an application against the unique and identifying data of the mobile device and provides the validated application for the mobile device; and a secure element (SE) acting as a client in which the SE is present in the mobile device as client; the validated application from the server is installed in the SE; and the SE is adapted to execute the validated application to perform a service process. The service process includes enablement of payment functions on the mobile device, in which enablement of payment functions includes: providing secure communication between the mobile device and the server; secure provisioning of a payment instrument on the mobile device, wherein authentication and verification for the payment instrument on the mobile device is provided by the server; and binding the payment instruments and the validated application to the mobile device to provide a strong ID management for enhanced user protection and system security and integrity.
Owner:PAYPAL INC
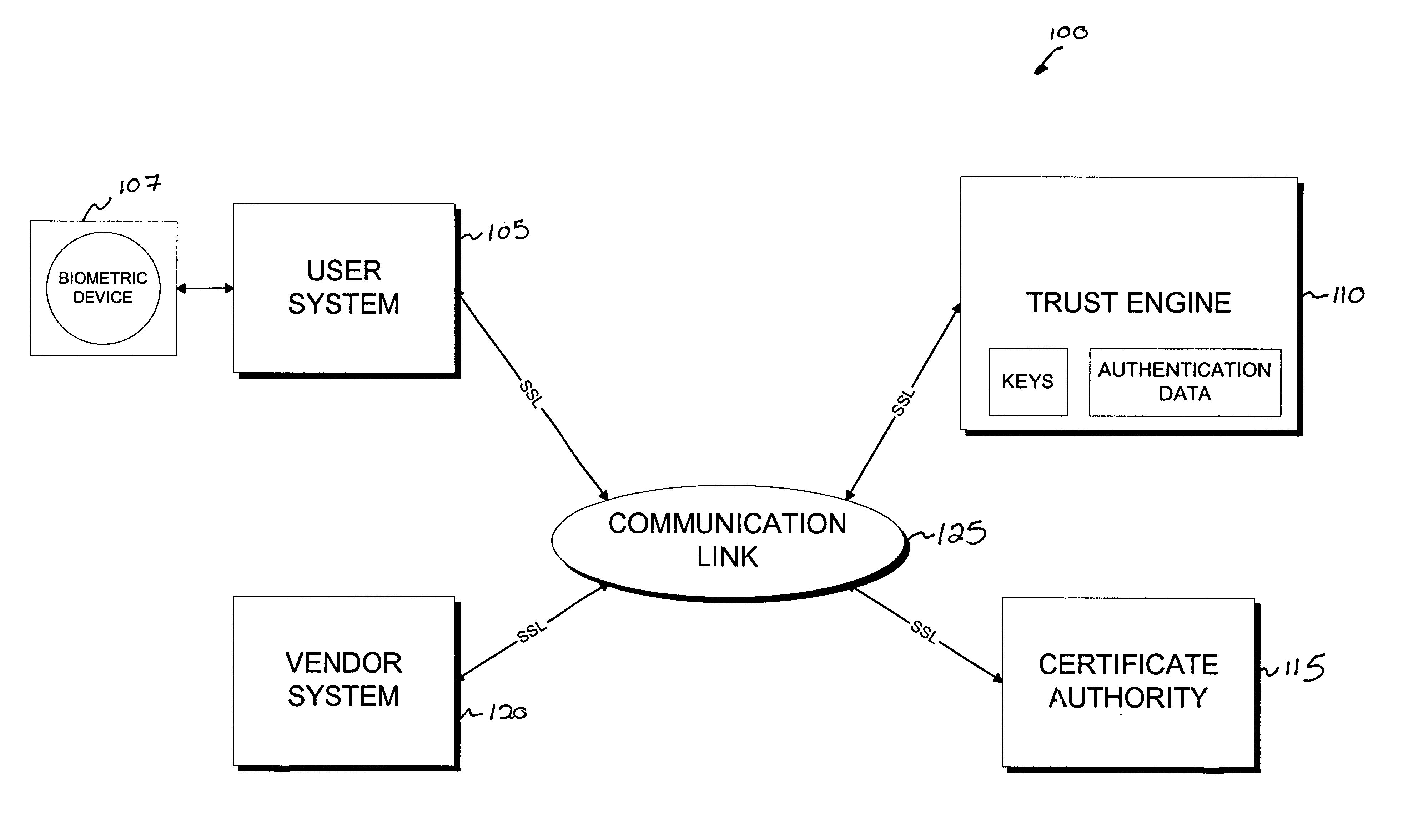
Cryptographic server with provisions for interoperability between cryptographic systems
InactiveUS6853988B1Reduce the number of timesMinimal compute resourceDigital data authenticationBuying/selling/leasing transactionsComputer hardwareKey storage
The invention is a cryptographic server providing interoperability over multiple algorithms, keys, standards, certificate types and issuers, protocols, and the like. Another aspect of the invention is to provide a secure server, or trust engine, having server-centric keys, or in other words, storing cryptographic keys on a server. The server-centric storage of keys provides for user-independent security, portability, availability, and straightforwardness, along with a wide variety of implementation possibilities.
Owner:SECURITY FIRST INNOVATIONS LLC
Micropayment financial transaction process utilizing wireless network processing
InactiveUS7127236B2Unauthorised/fraudulent call preventionEavesdropping prevention circuitsThird partyTransceiver
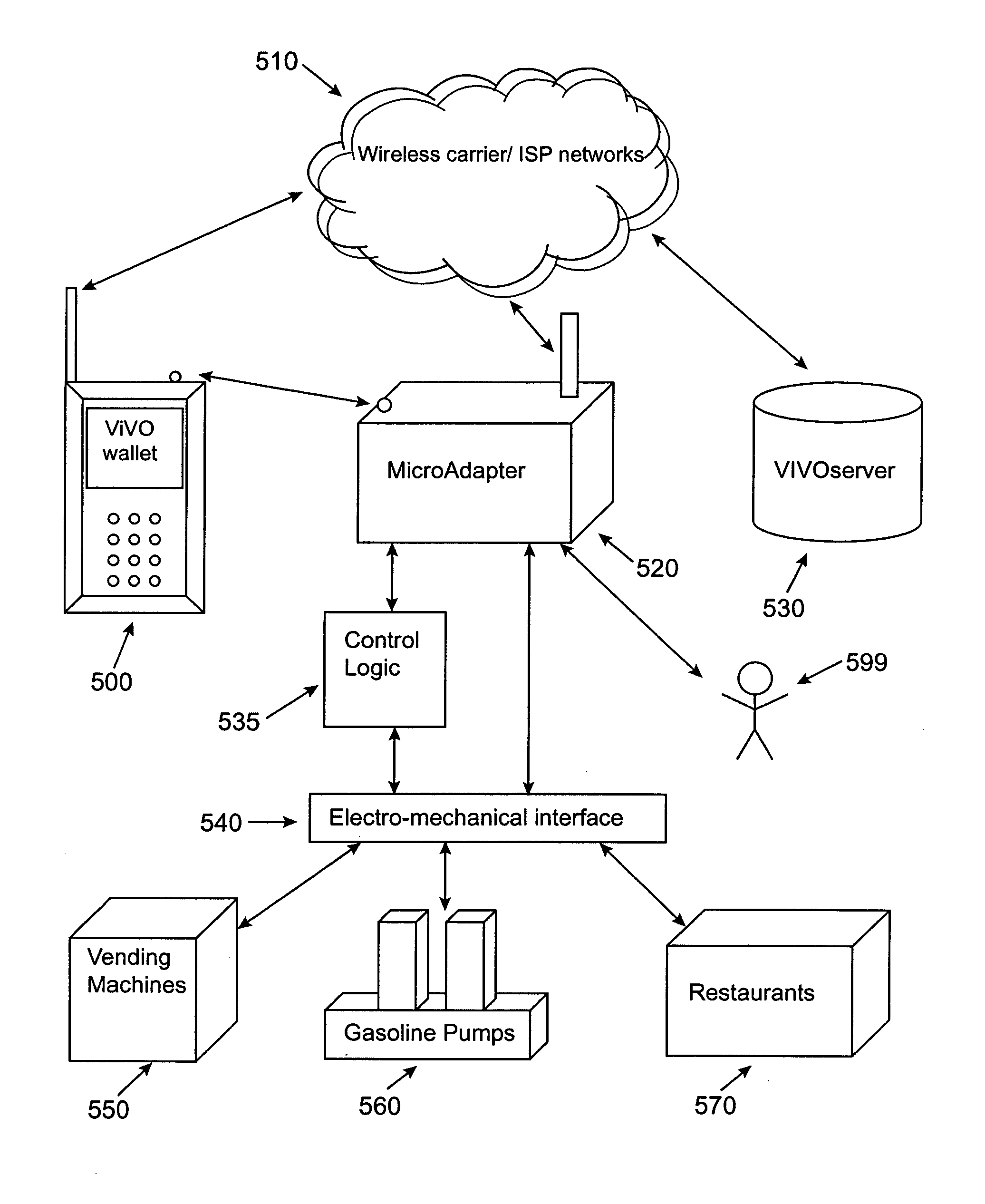
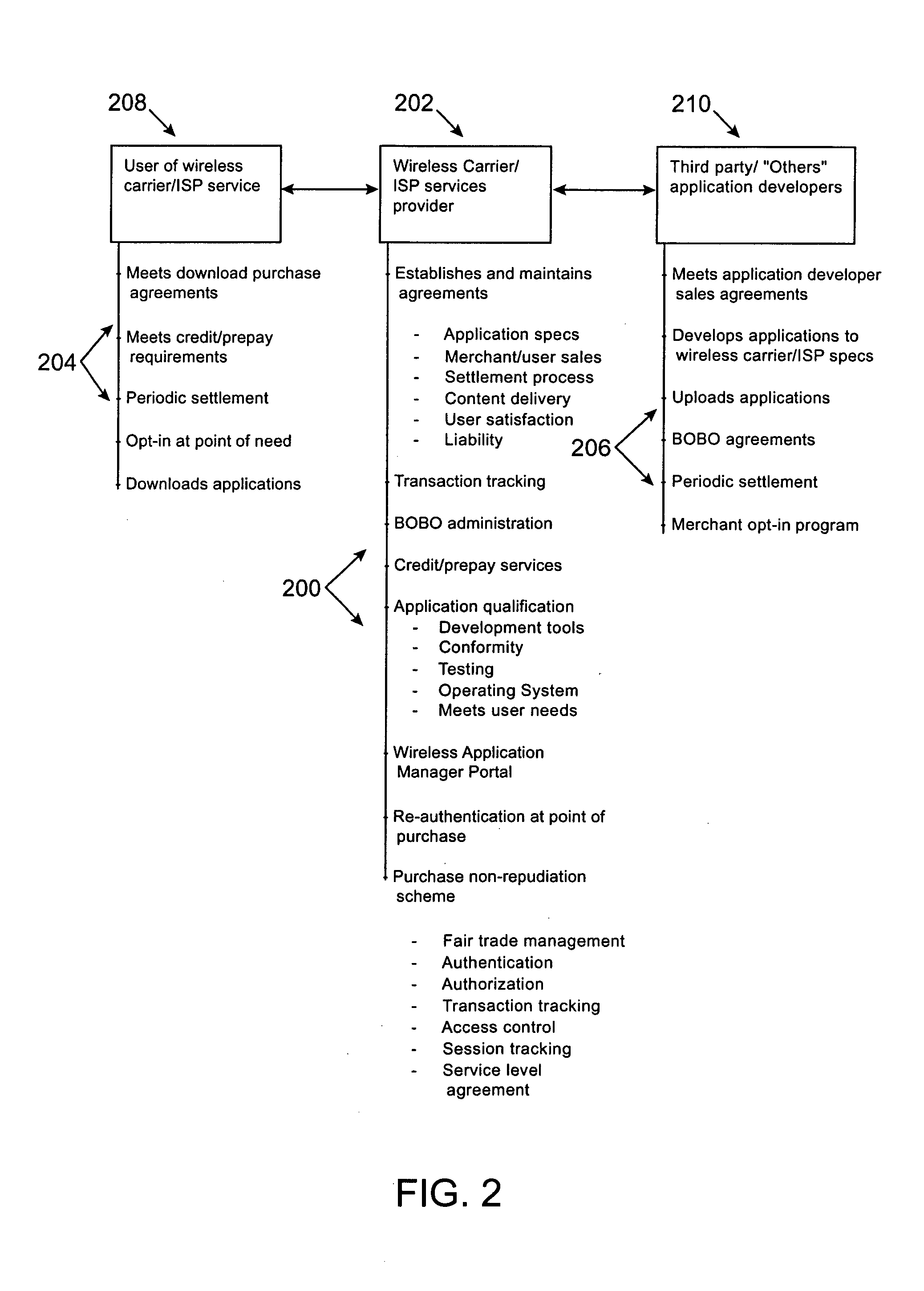
A MicroAdapter device enables payment transactions to be effected through a purchaser's personal trusted device (PTD) without relying upon tokens or prepayment cards. In one embodiment, the MicroAdapter includes a transceiver configured to receive a purchase signal from the PTD including order and payment information. In response, the MicroAdapter communicates via wireless telephony with a transaction authorizer to receive authorization for effectuating the purchase transaction. The MicroAdapter may be particularly suited to effectuate micropayment transactions authorized by a Billing On Behalf of Others (BOBO) program administered through a wireless carrier / ISP or third party.
Owner:MASTERCARD INT INC
Method and system for conducting secure payments over a computer network without a pseudo or proxy account number
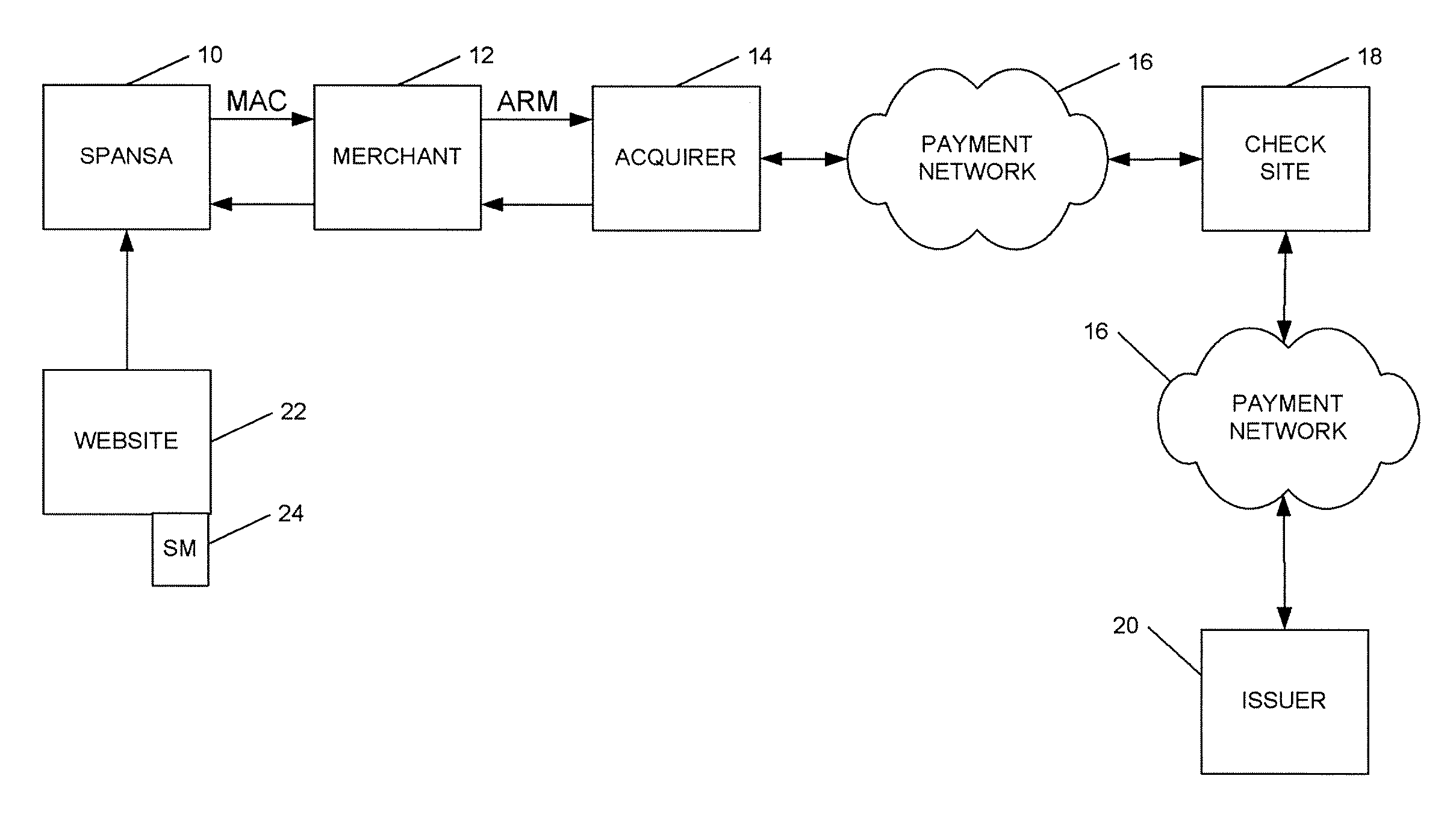
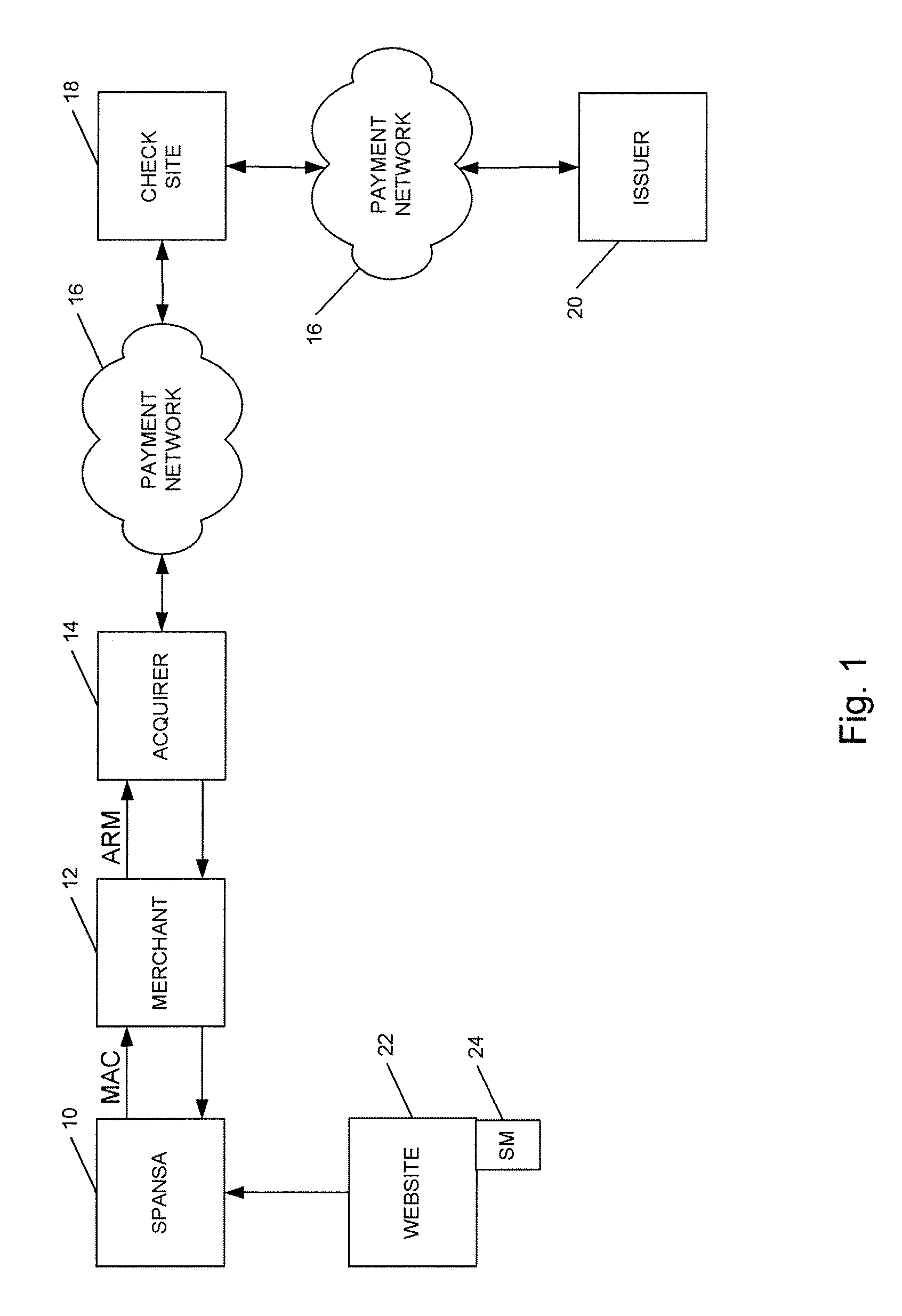
A method is provided for conducting an electronic transaction with a payment account number having a certain amount of available funds, using a payment network and a “check site”. The method comprises the following steps: (a) generating a secret key associated with the payment account number; (b) using the secret key to generate a message authentication code (“MAC”) specific to the transaction; (c) generating an authorization request message including the message authentication code; (d) forwarding the authorization request message over the payment network to the check site for verifying the authenticity of the MAC; (e) verifying the message authentication code by the check site using the secret key; (f) responding to the authorization request message over the payment network based on the available funds and the transaction amount.
Owner:MASTERCARD INT INC
Device, system and methods of conducting paperless transactions
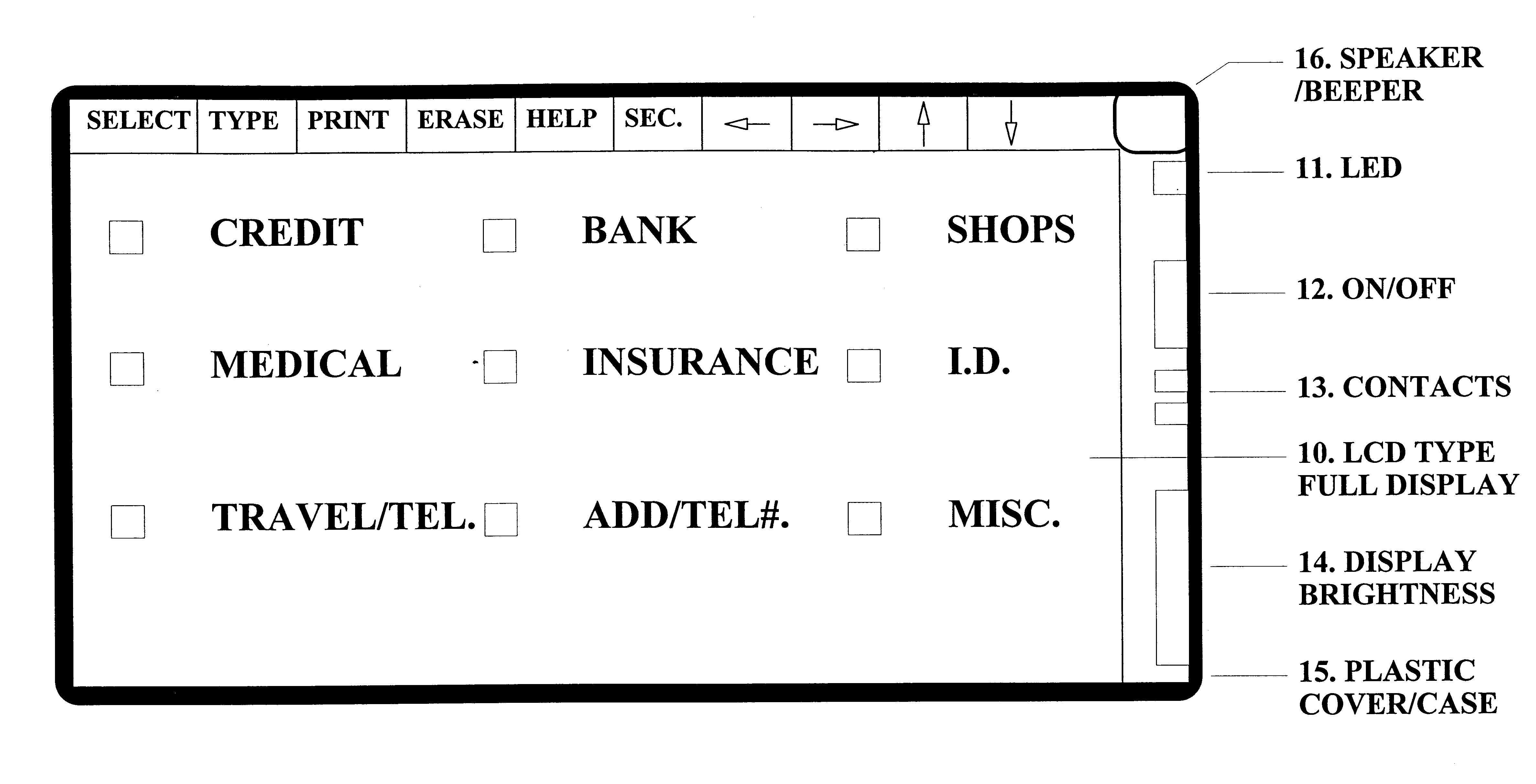
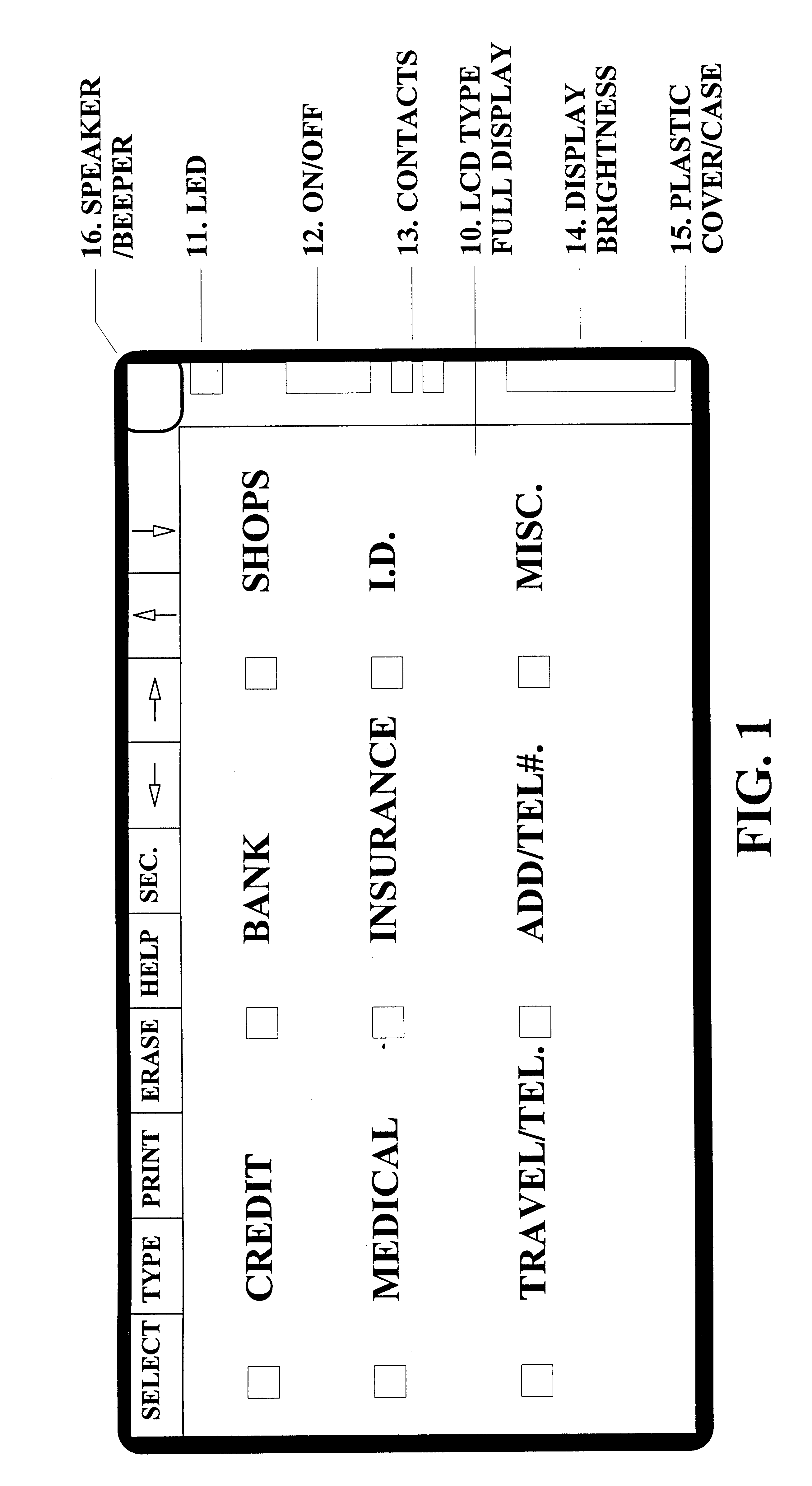
InactiveUS6925439B1Eliminate pointEliminate all paper transactions and billsFinancePayment circuitsPersonal computerComputer terminal
The invention also includes methods of issuing an account authorization to a UET card, a method of transferring transactional and account information between a UET card and a personal computer or a mainframe computer, a method of using the UET card as a remote terminal for a mainframe computer, and a method of conducting an electronic transaction.
Owner:C SAM INC
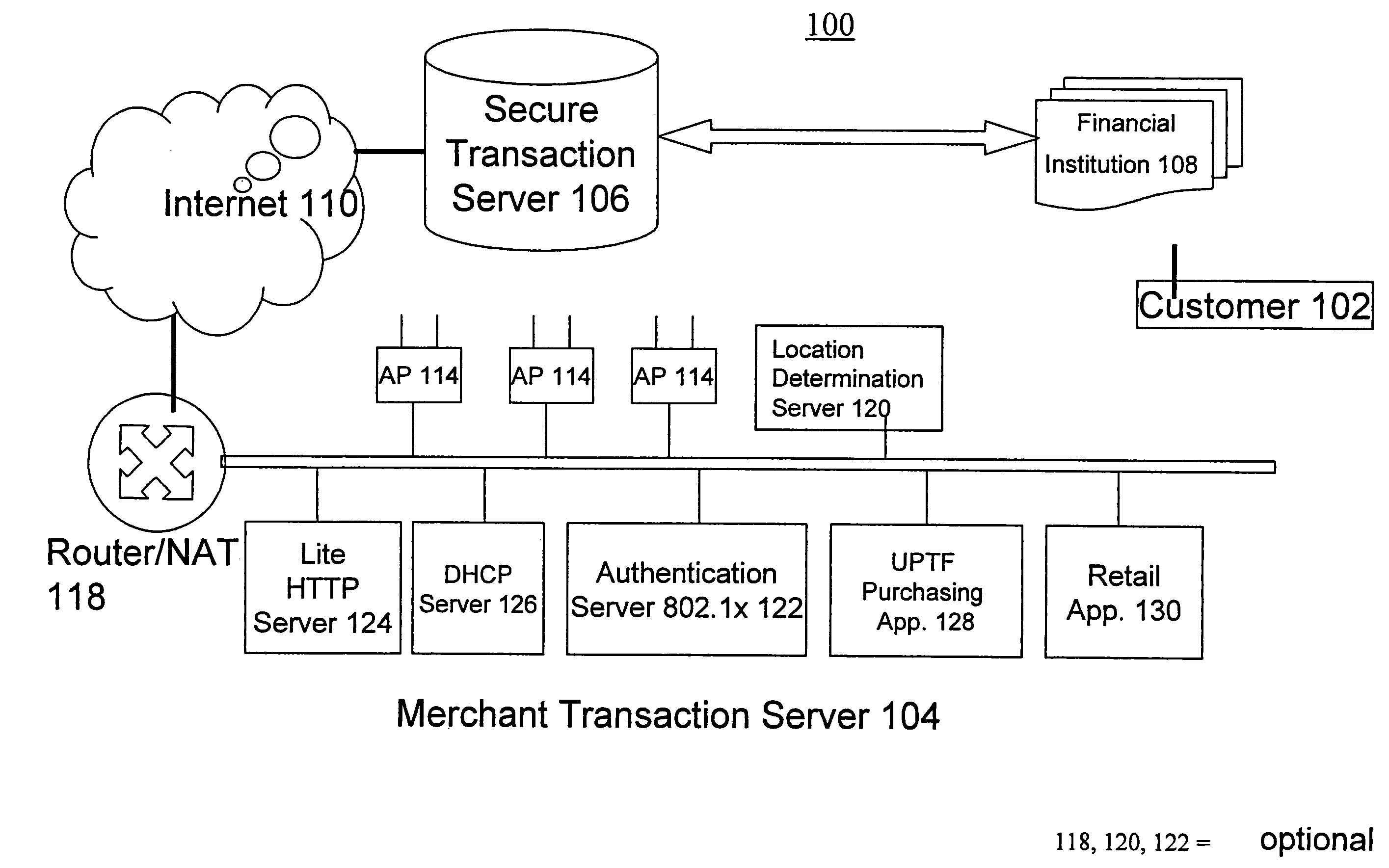
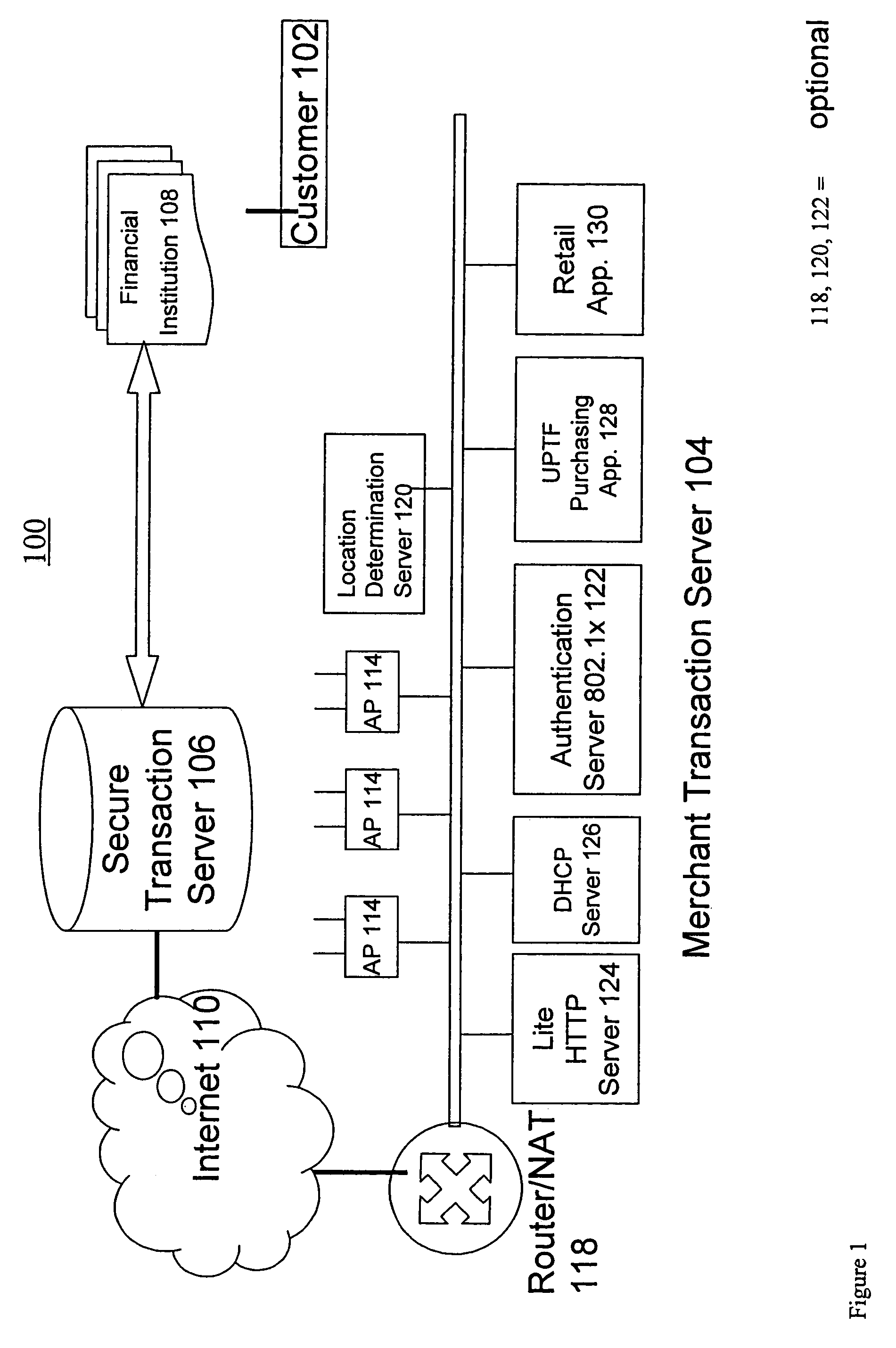
System and method for secure network purchasing
InactiveUS20020073046A1Improve securityCharacter and pattern recognitionDigital data authenticationSecure Electronic TransactionInternet privacy
A system for permitting a secure electronic transaction on a network is disclosed. The network has a user device having a fingerprint, a provider's server and a means for providing verification of user's identity. In response to a request by the provider's server the means for providing verification positively identifies the fingerprint of the user device. It thereupon requests a confirmation from the user device of the transaction and upon receiving the confirmation completes the transaction.
Owner:CHANNEL IP BV
Persistent dynamic payment service
The invention comprises online methods, systems, and software for improving the processing of payments from financial accounts, particularly credit and debit card payments made from consumers to merchants in online transactions. The preferred embodiment of the invention involves inserting a trusted third party online service into the payment authorization process. The trusted third party authenticates the consumer and authorizes the proposed payment in a single integrated process conducted without the involvement of the merchant. The authentication of the consumer is accomplished over a persistent communication channel established with the consumer before a purchase is made. The authentication is done by verifying that the persistent channel is open when authorization is requested. Use of the third party services allows the consumer to avoid revealing his identity and credit card number to the merchant over a public network such as the Internet, while maintaining control of the transaction during the authorization process.
Owner:FISHER DOUGLAS C
Popular searches
Analogue secracy/subscription systems Color television details Internal/peripheral component protection Two-way working systems Program/content distribution protection Selective content distribution Image data processing details Public key infrastructure trust models Payments involving neutral party Securing communication
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com