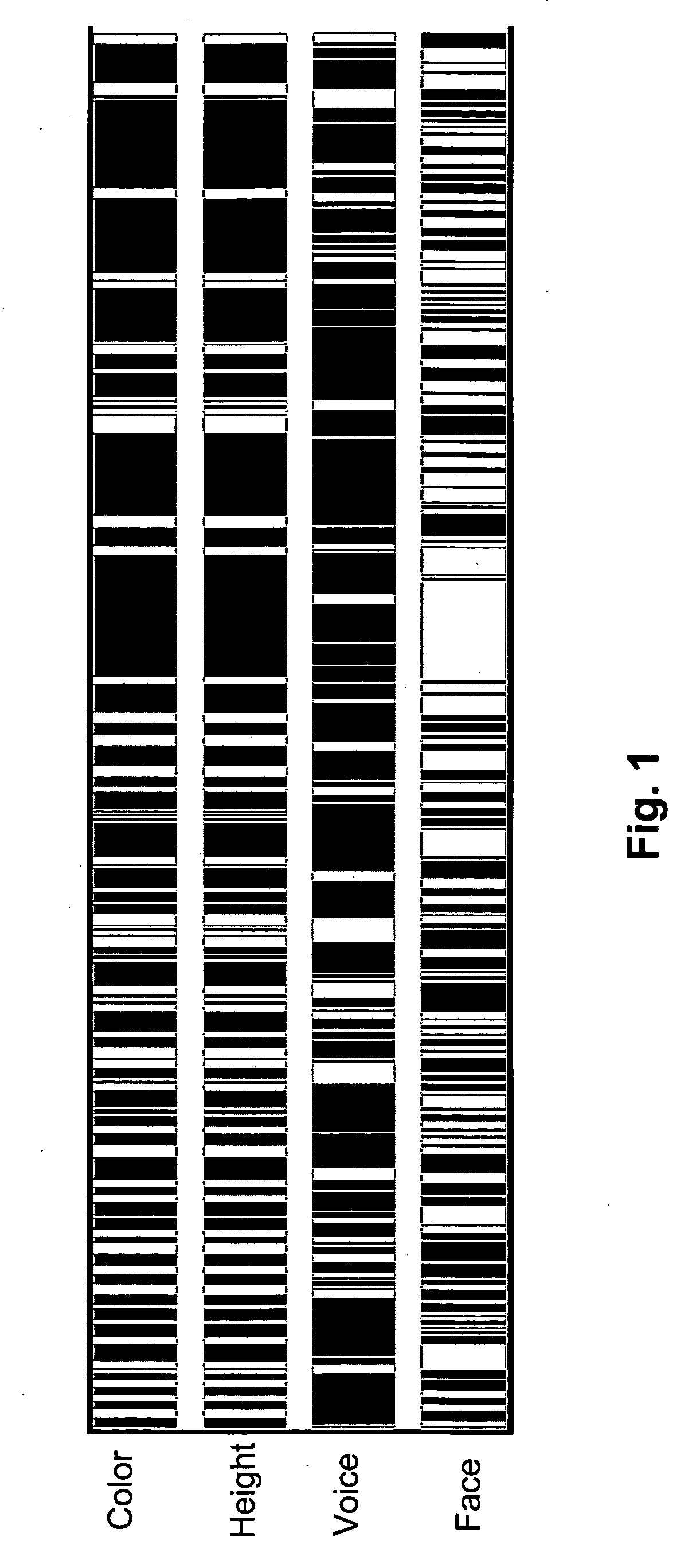
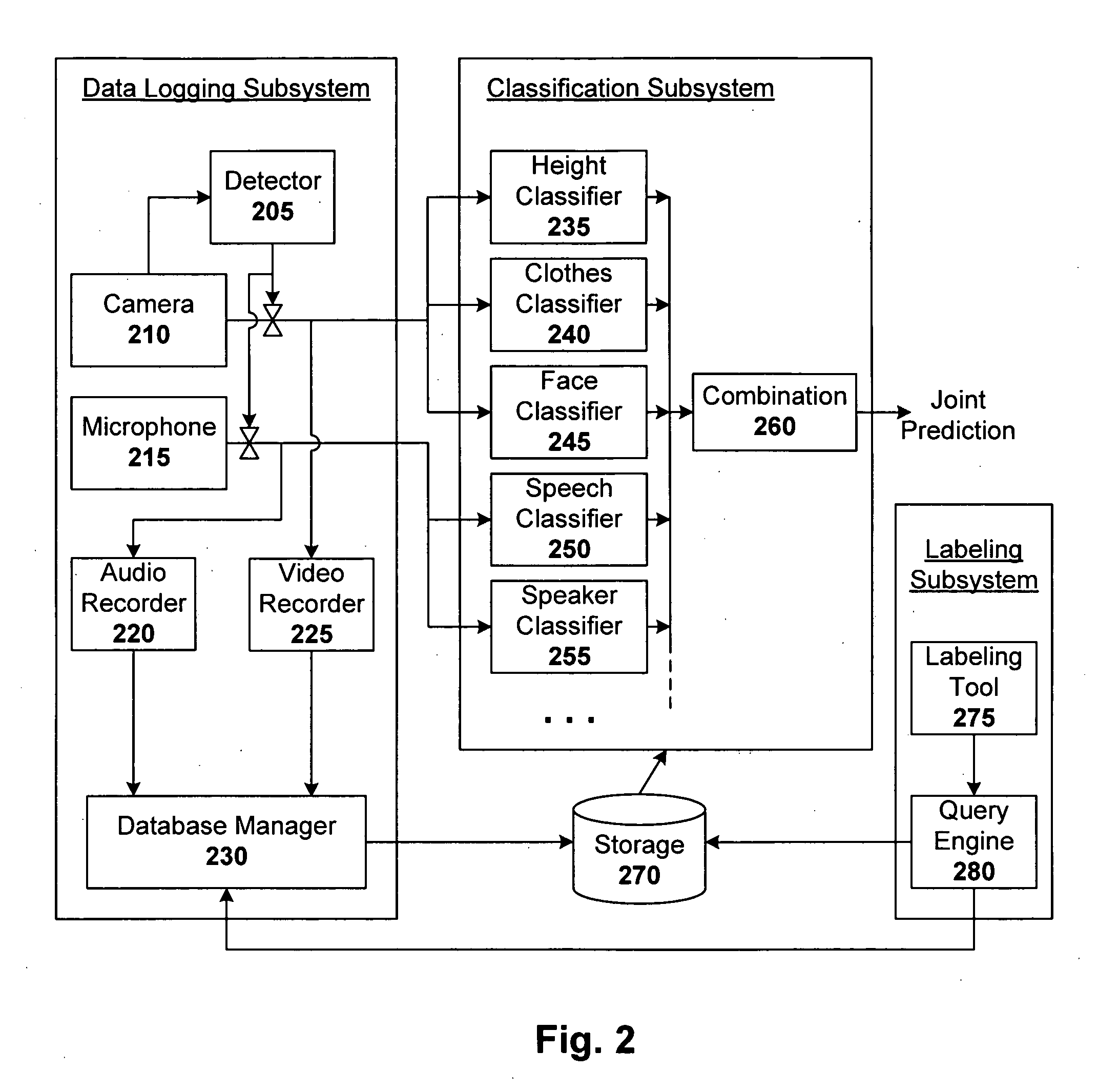
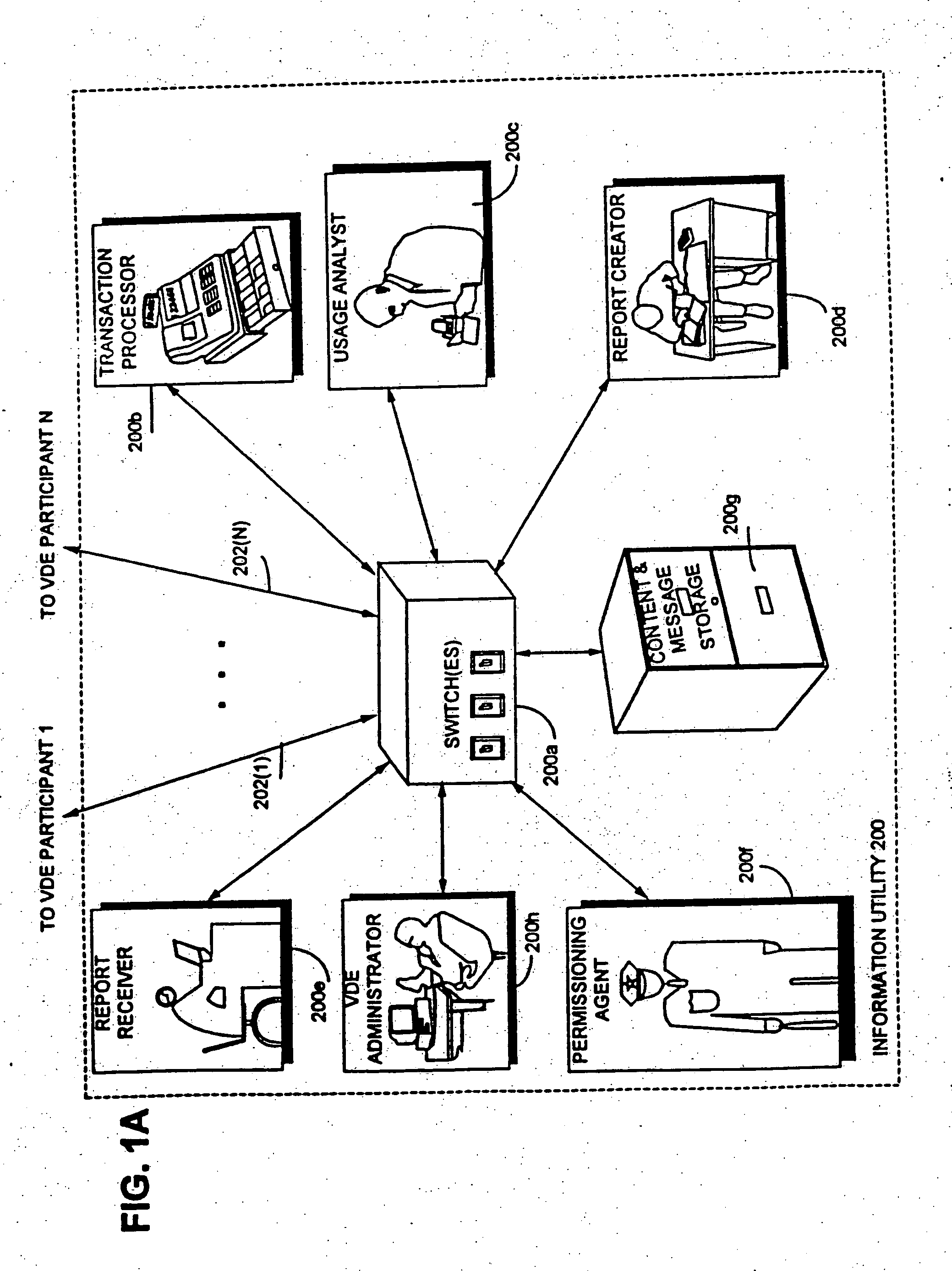
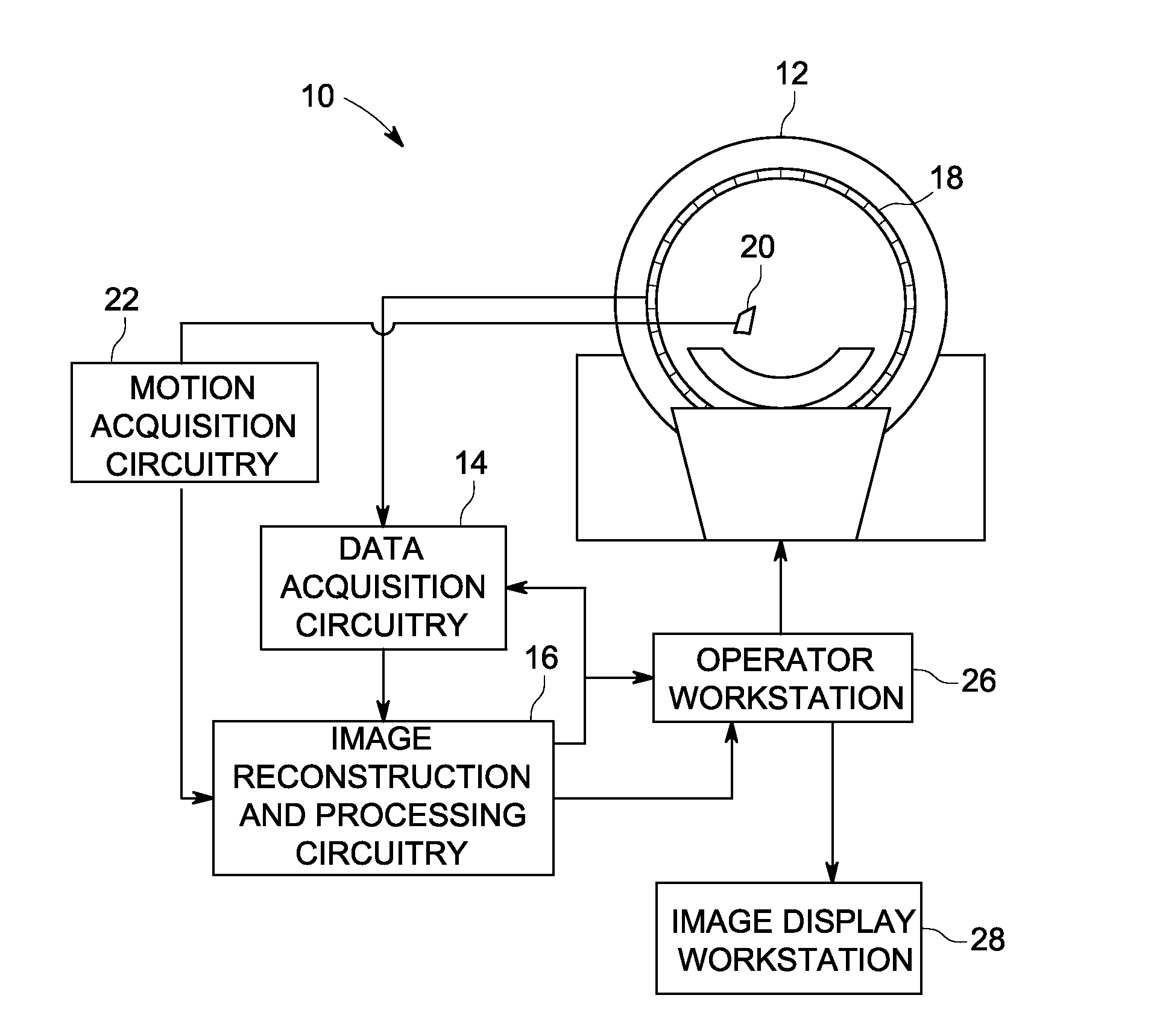
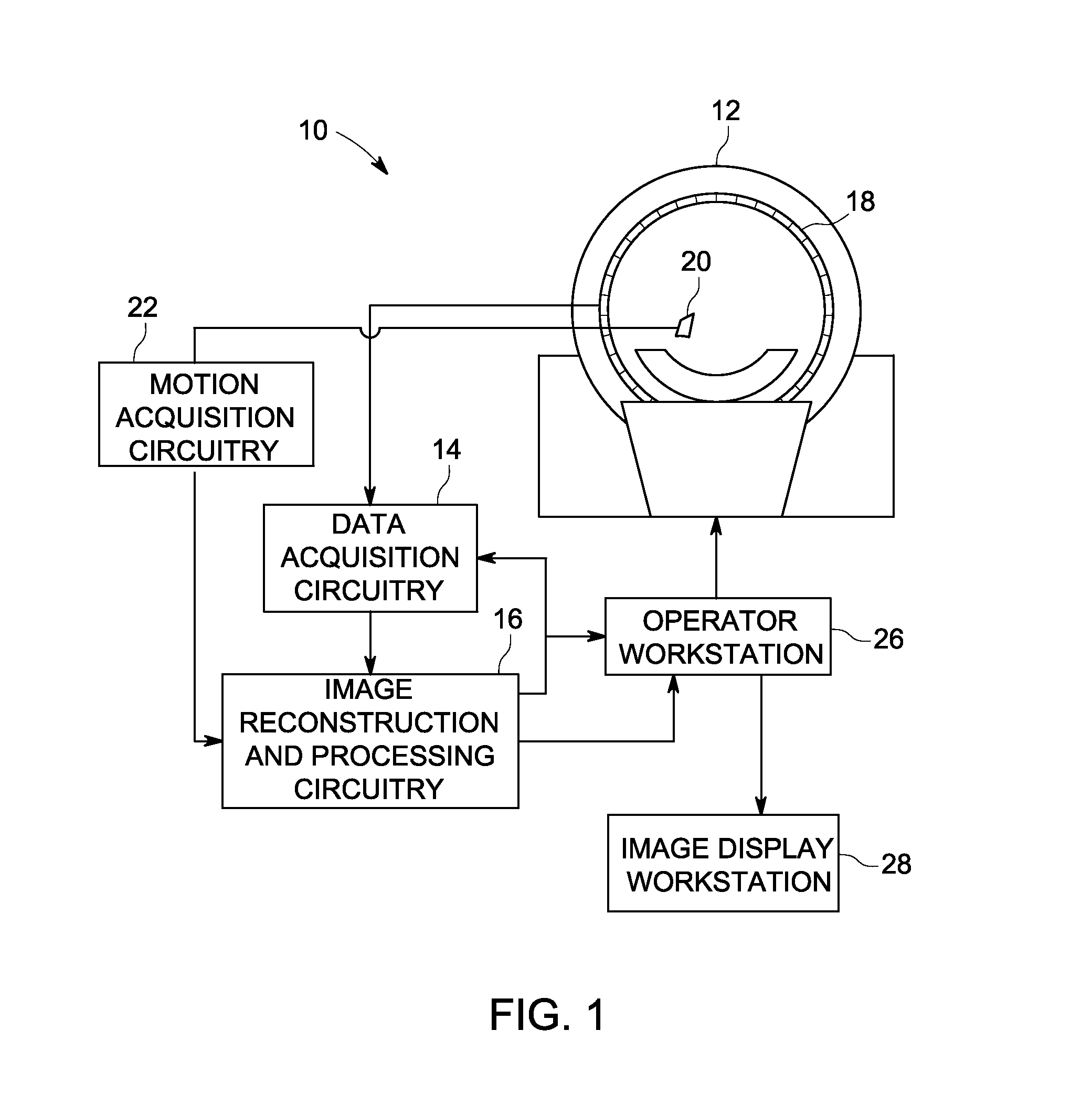
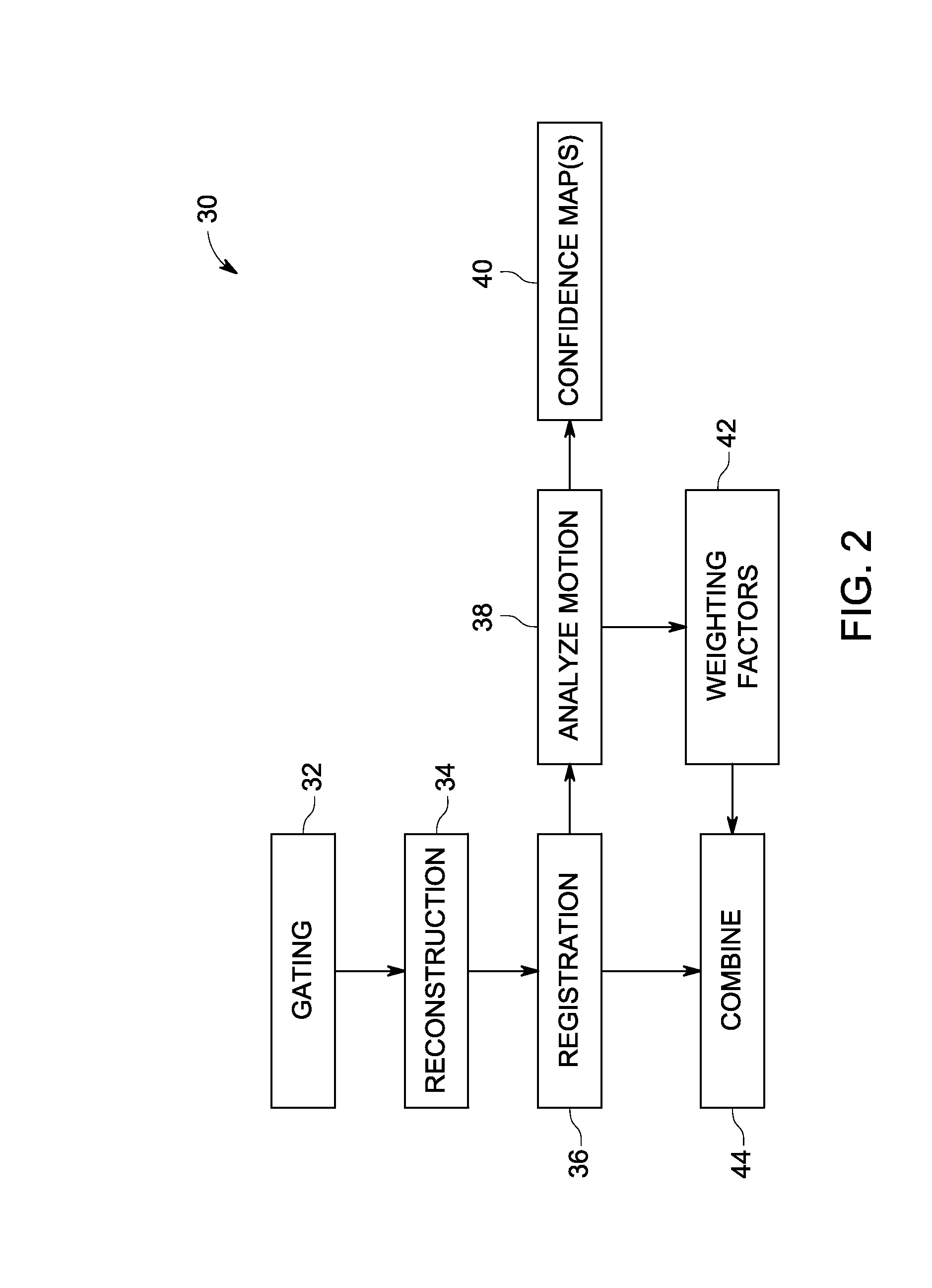
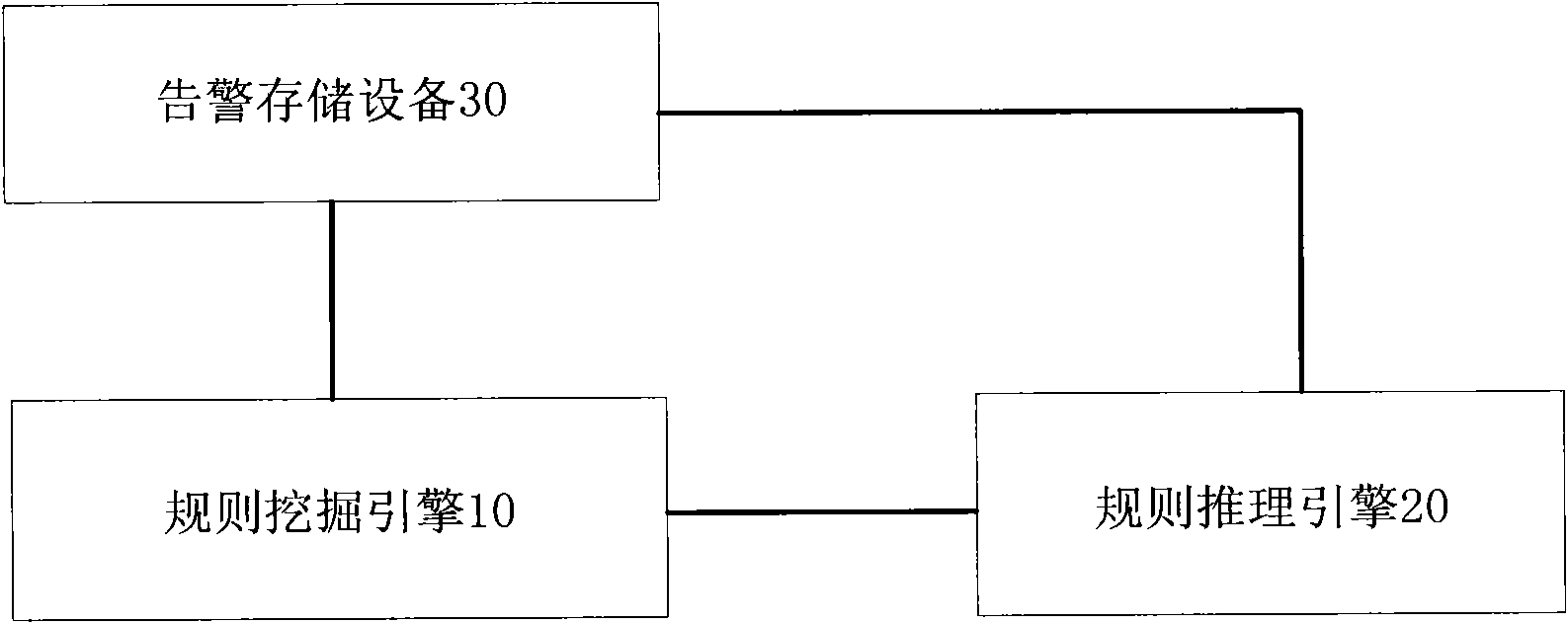Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
184 results about "Degree of confidence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
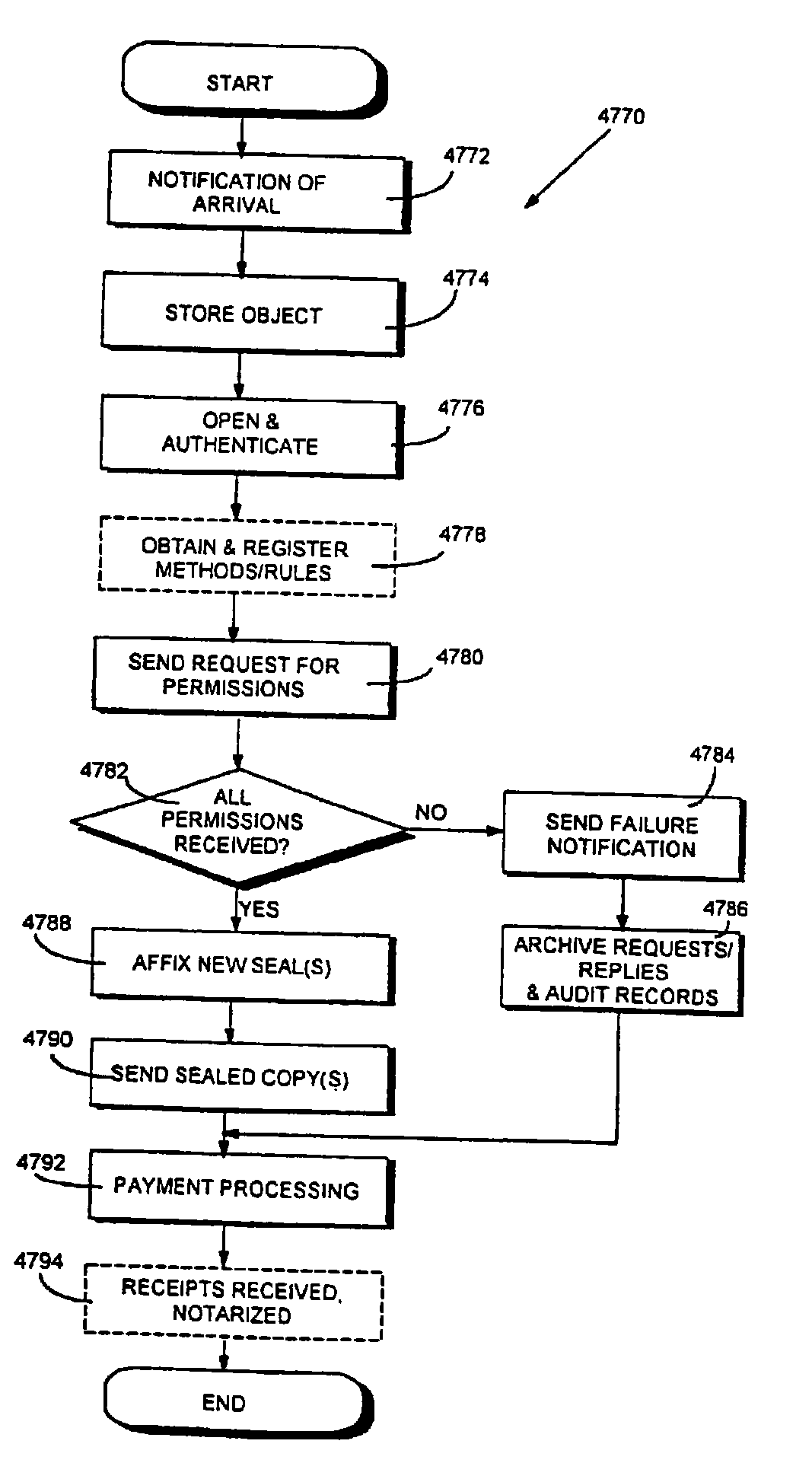
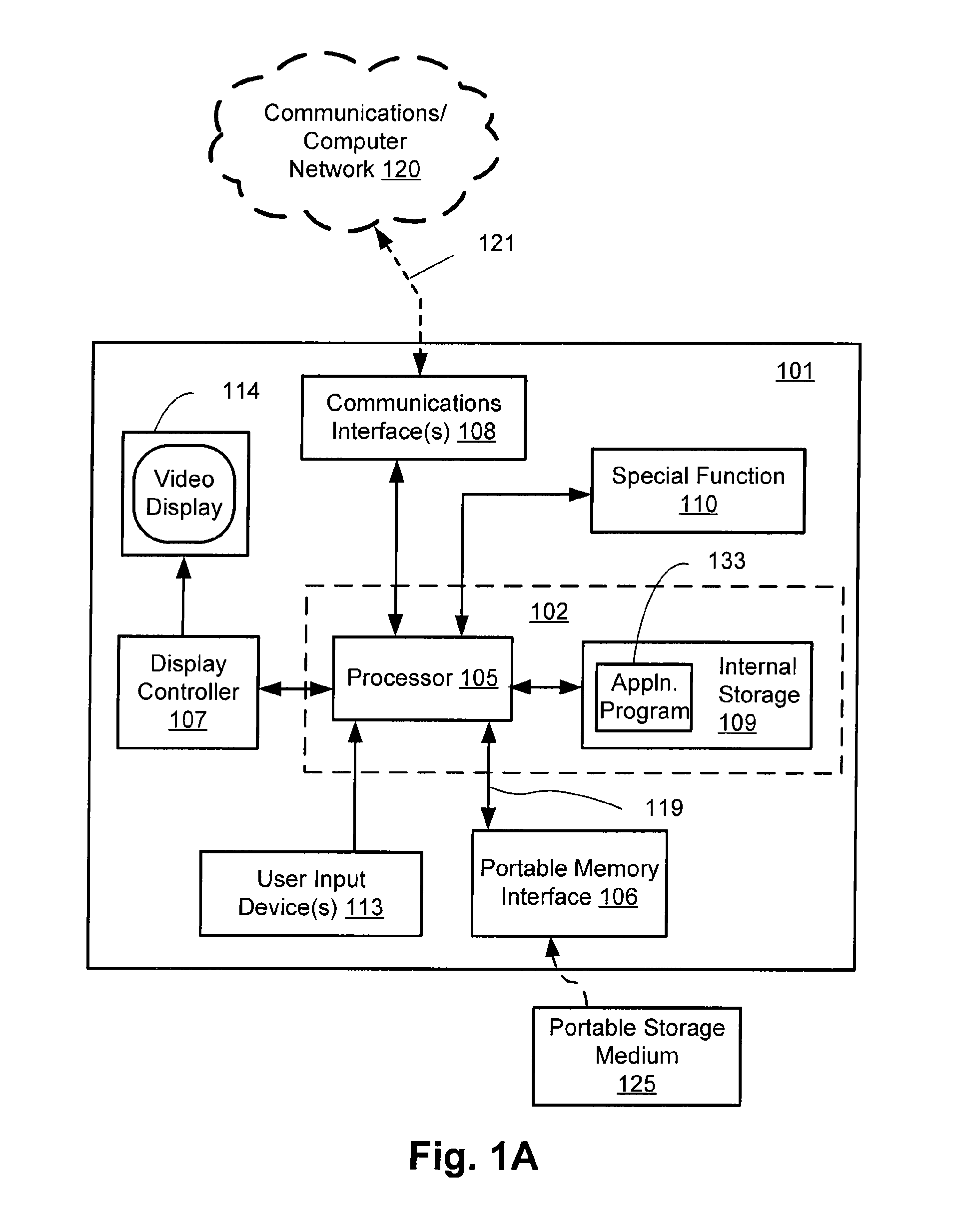
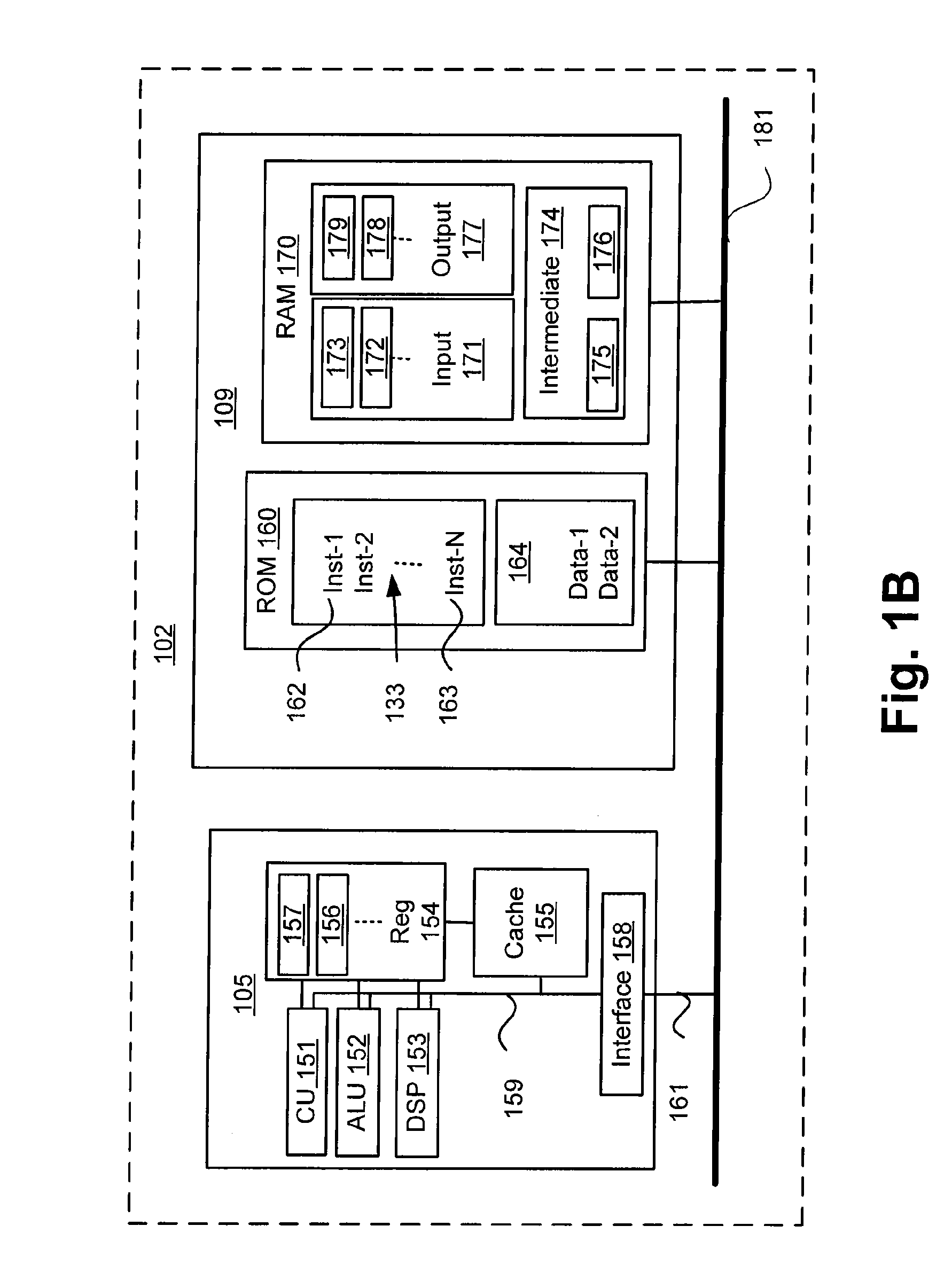
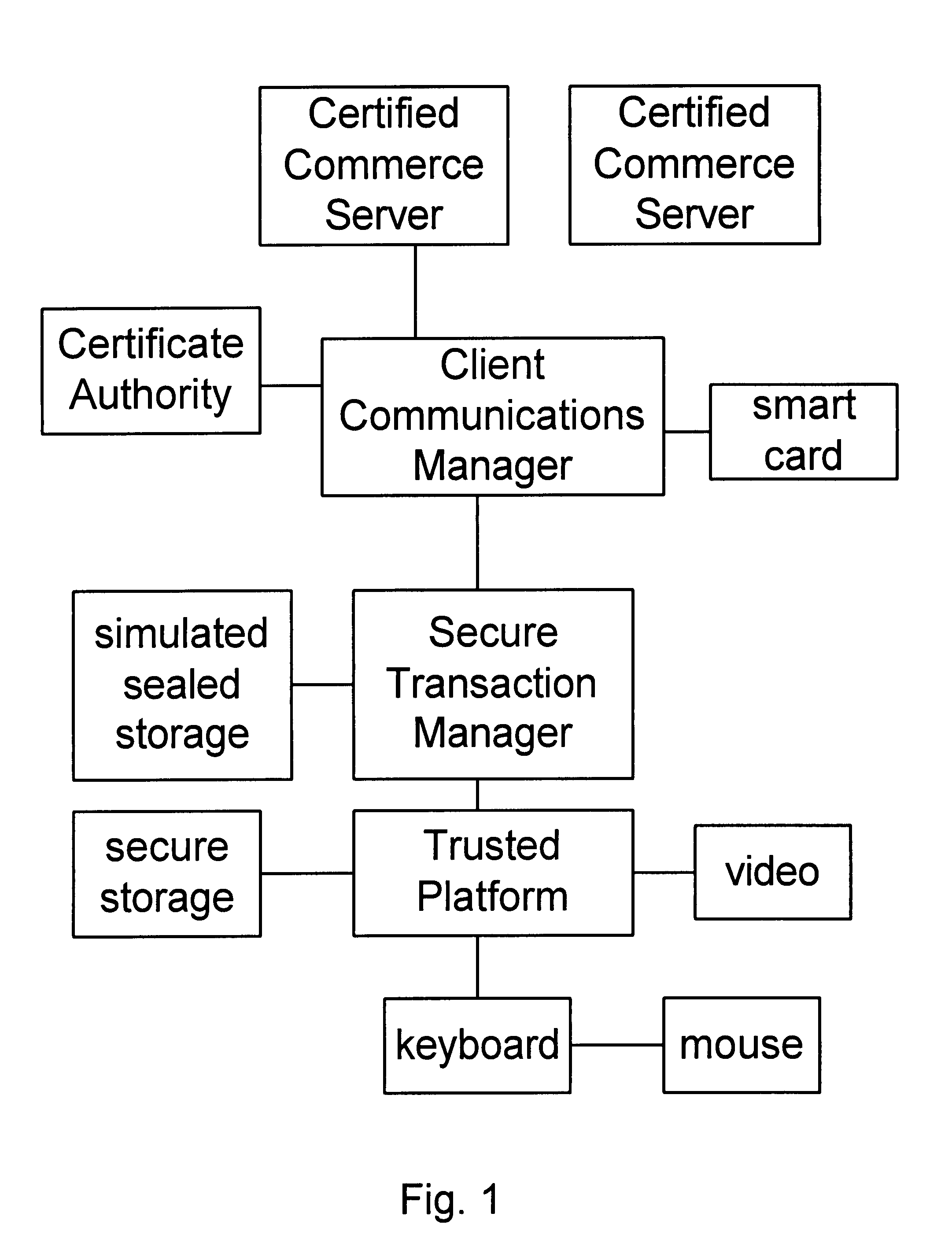
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS6185683B2Avoid deletionEasy to identifyTelevision system detailsPulse modulation television signal transmissionDocumentation procedureDocument preparation
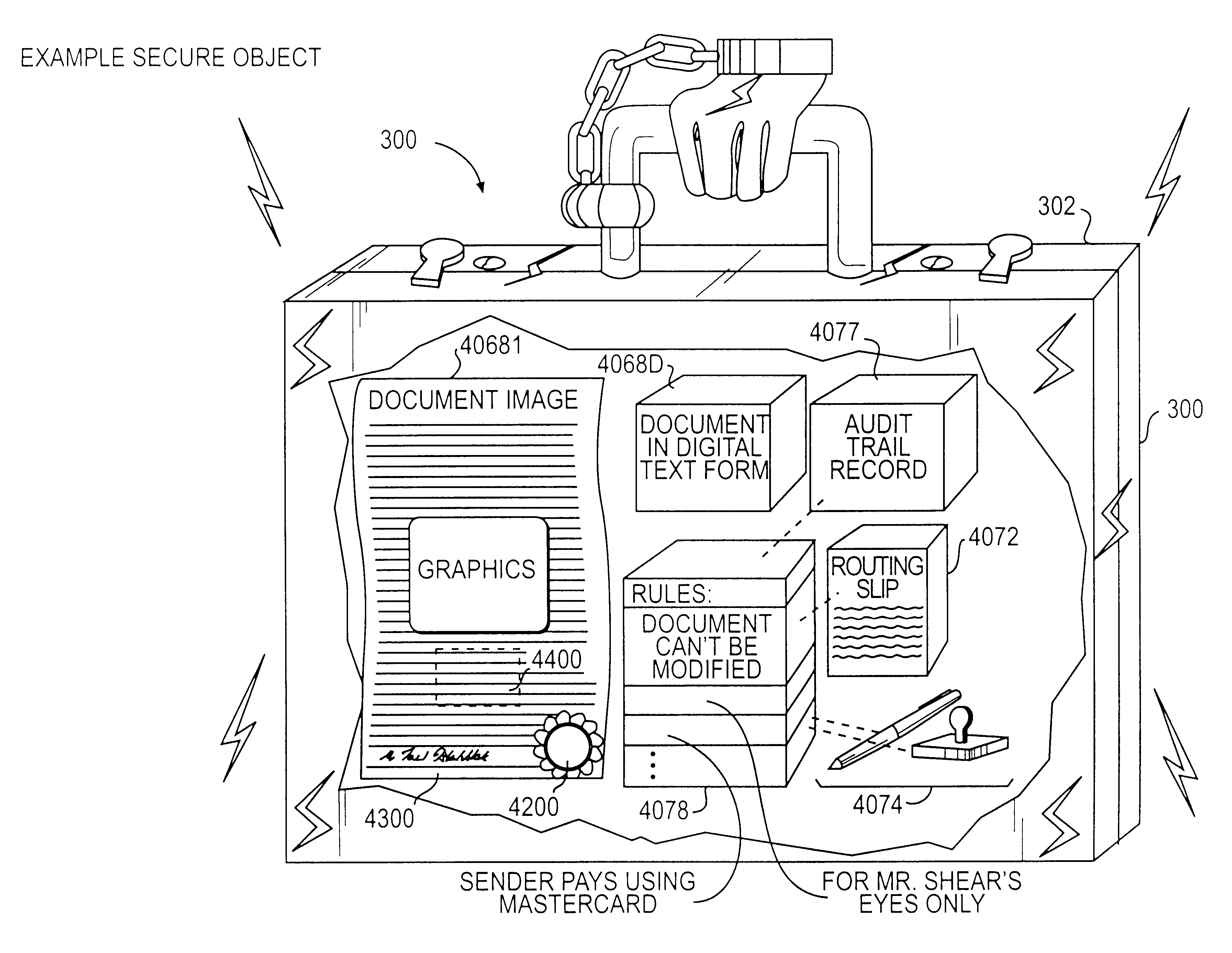
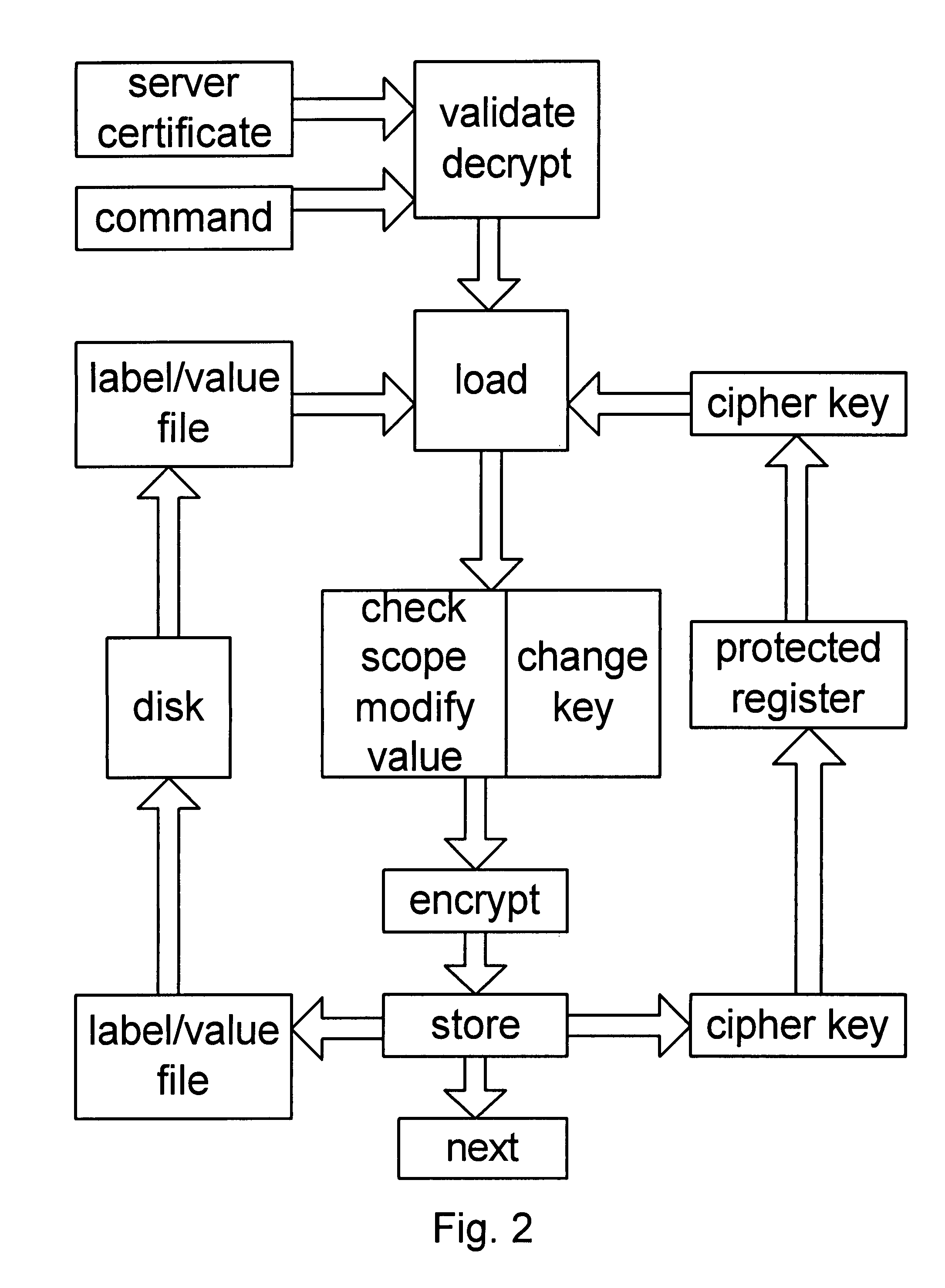
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, "trusted" virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
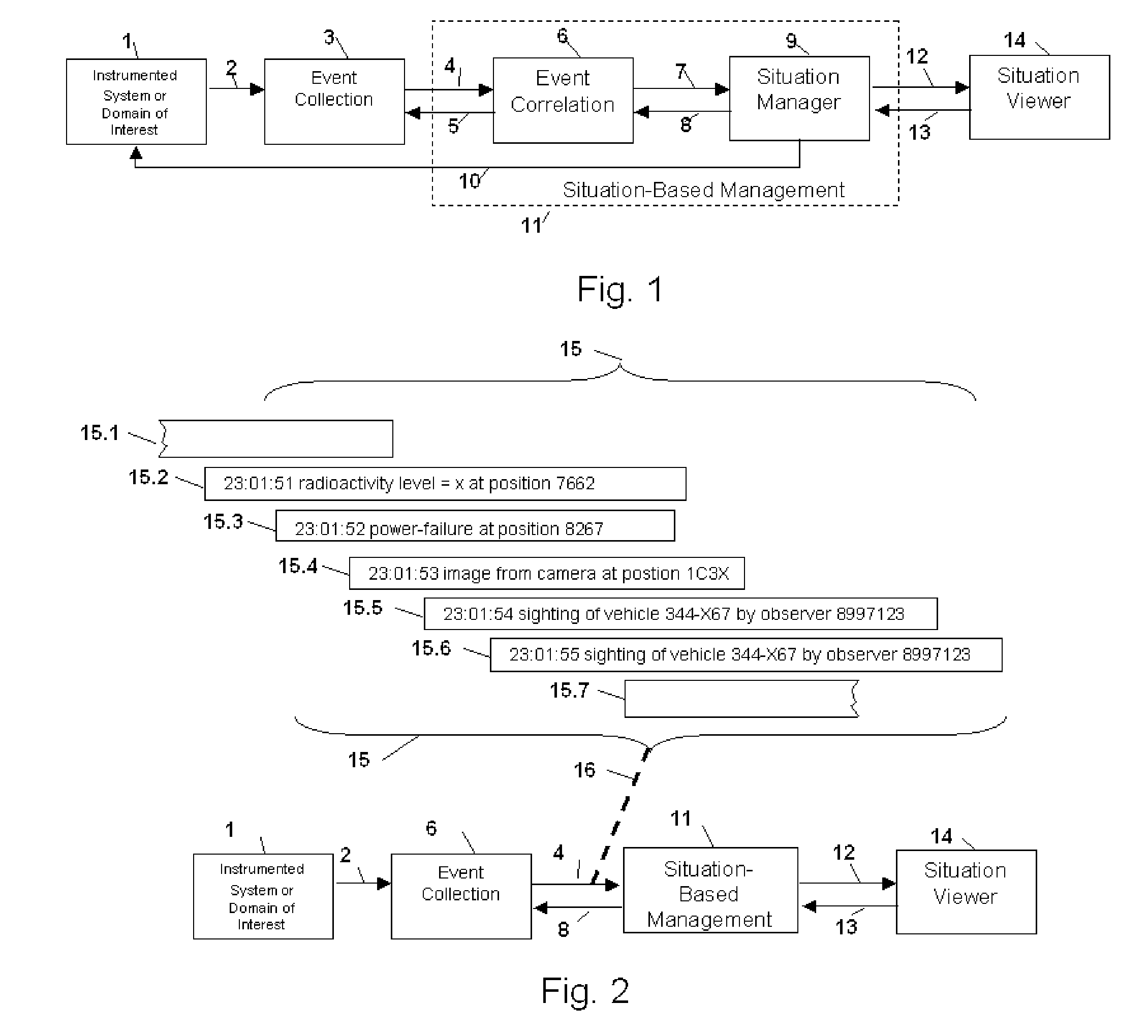
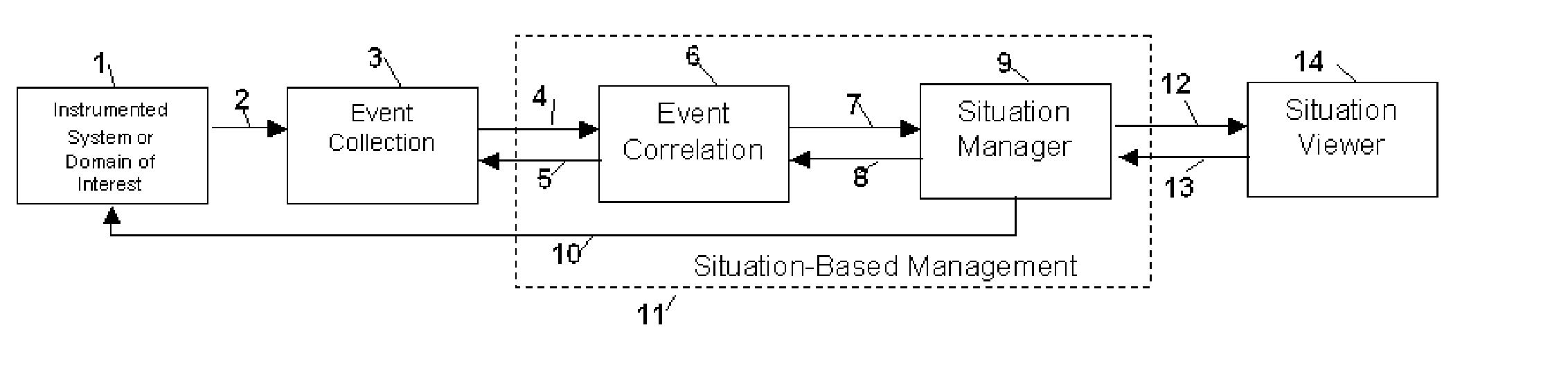
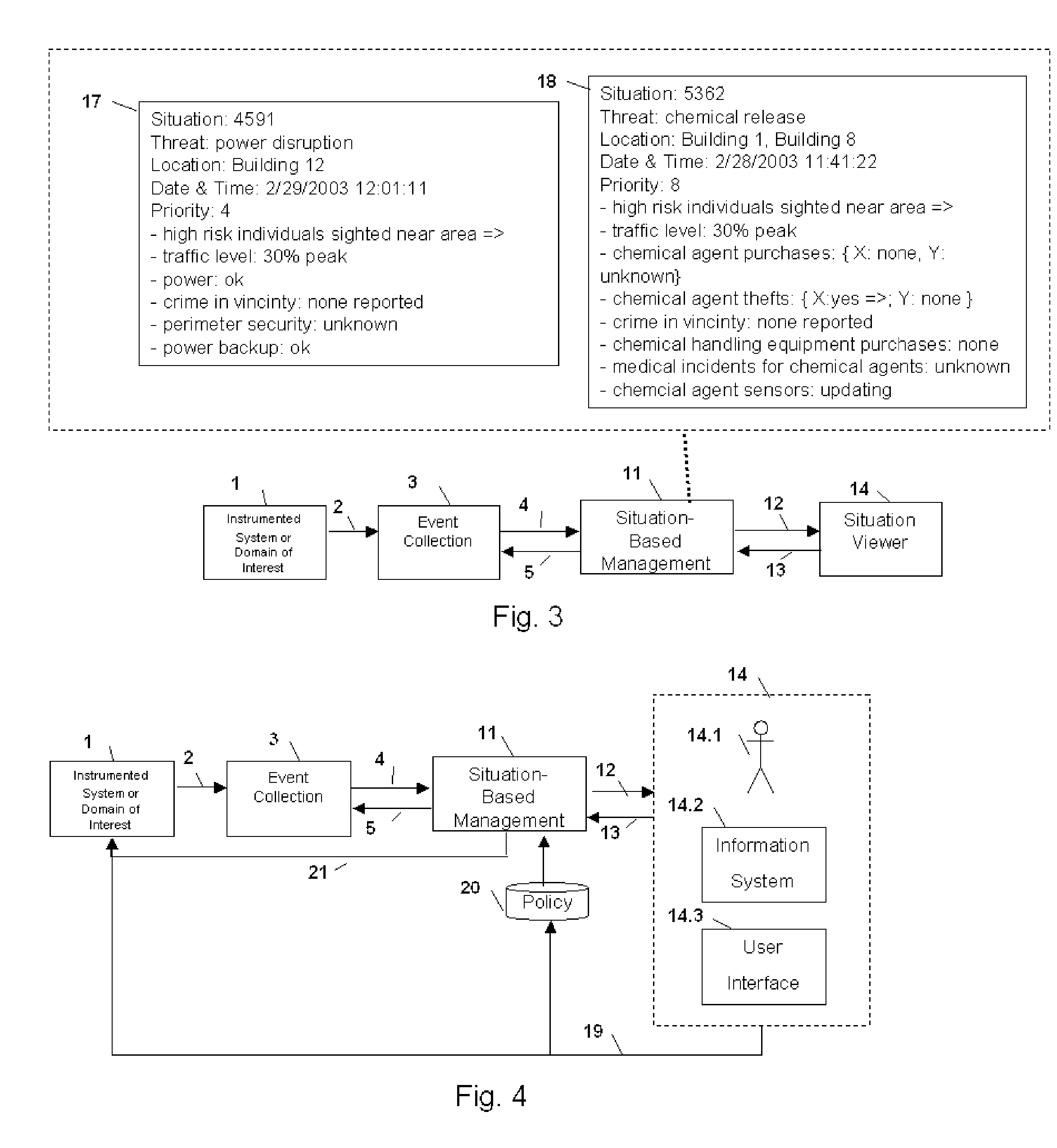
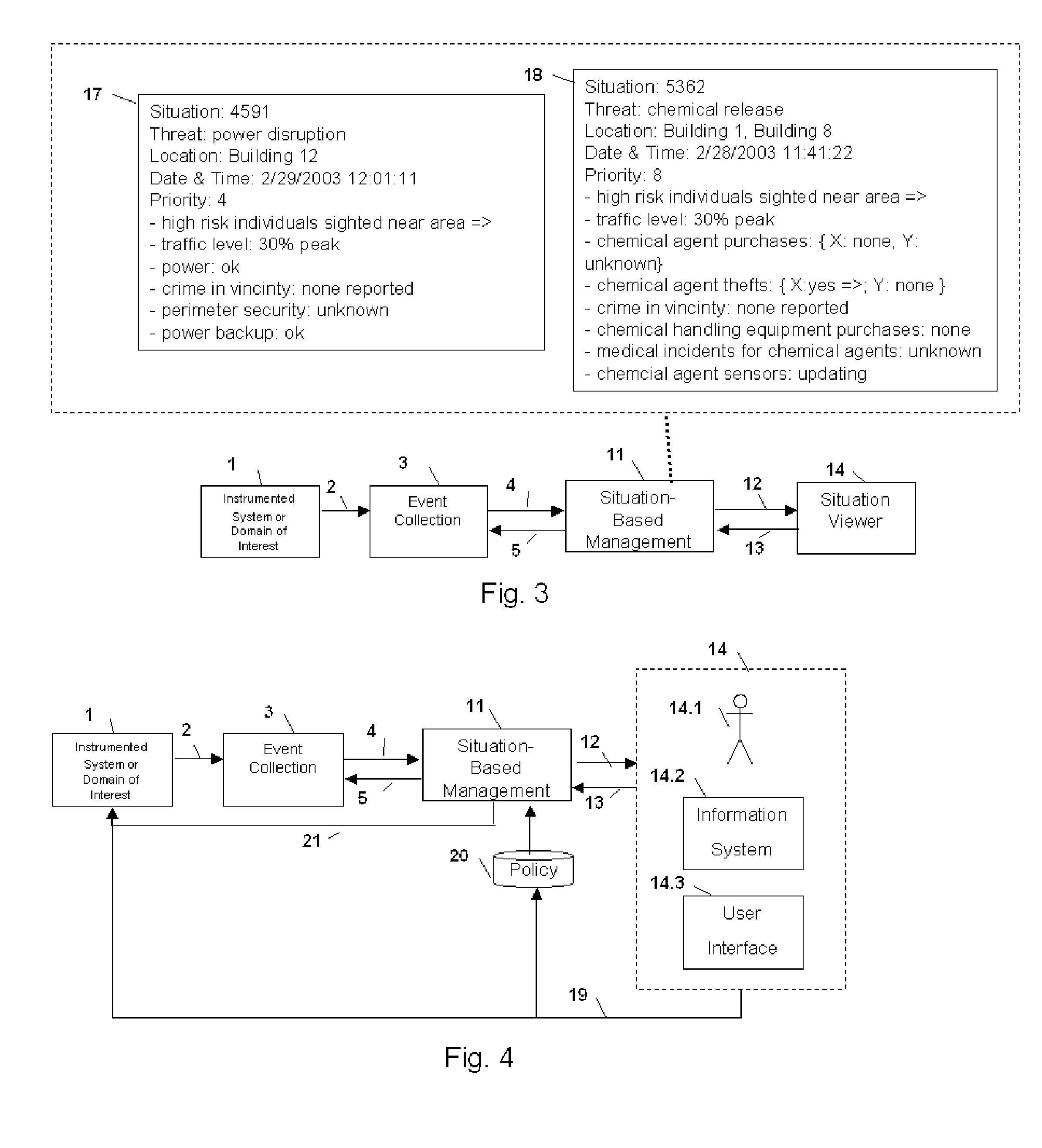
Method and Apparatus for Situation-Based Management
InactiveUS20050228763A1Guaranteed normal transmissionRemove redundant informationDigital computer detailsResourcesArtificial systemsComputer science
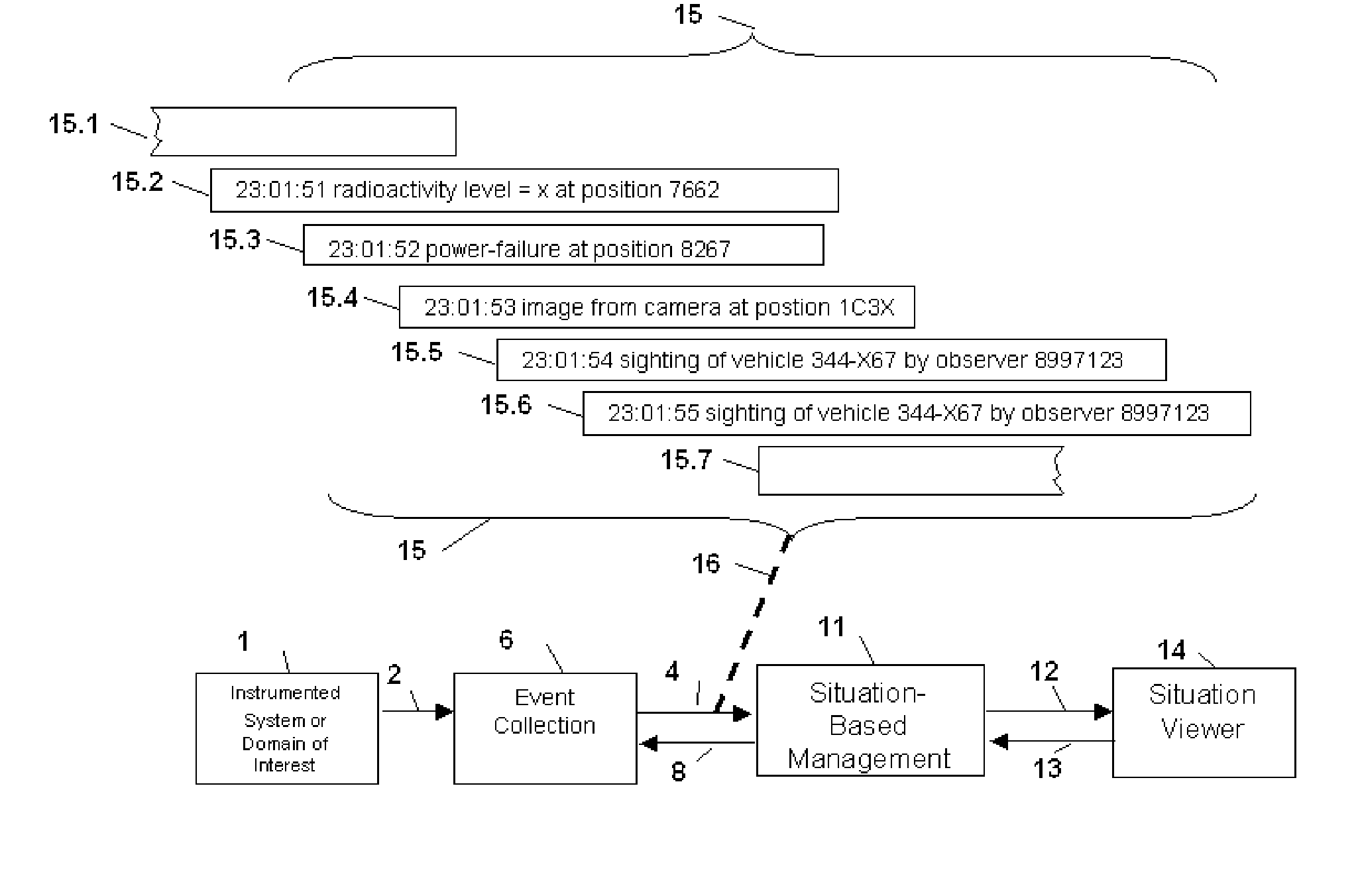
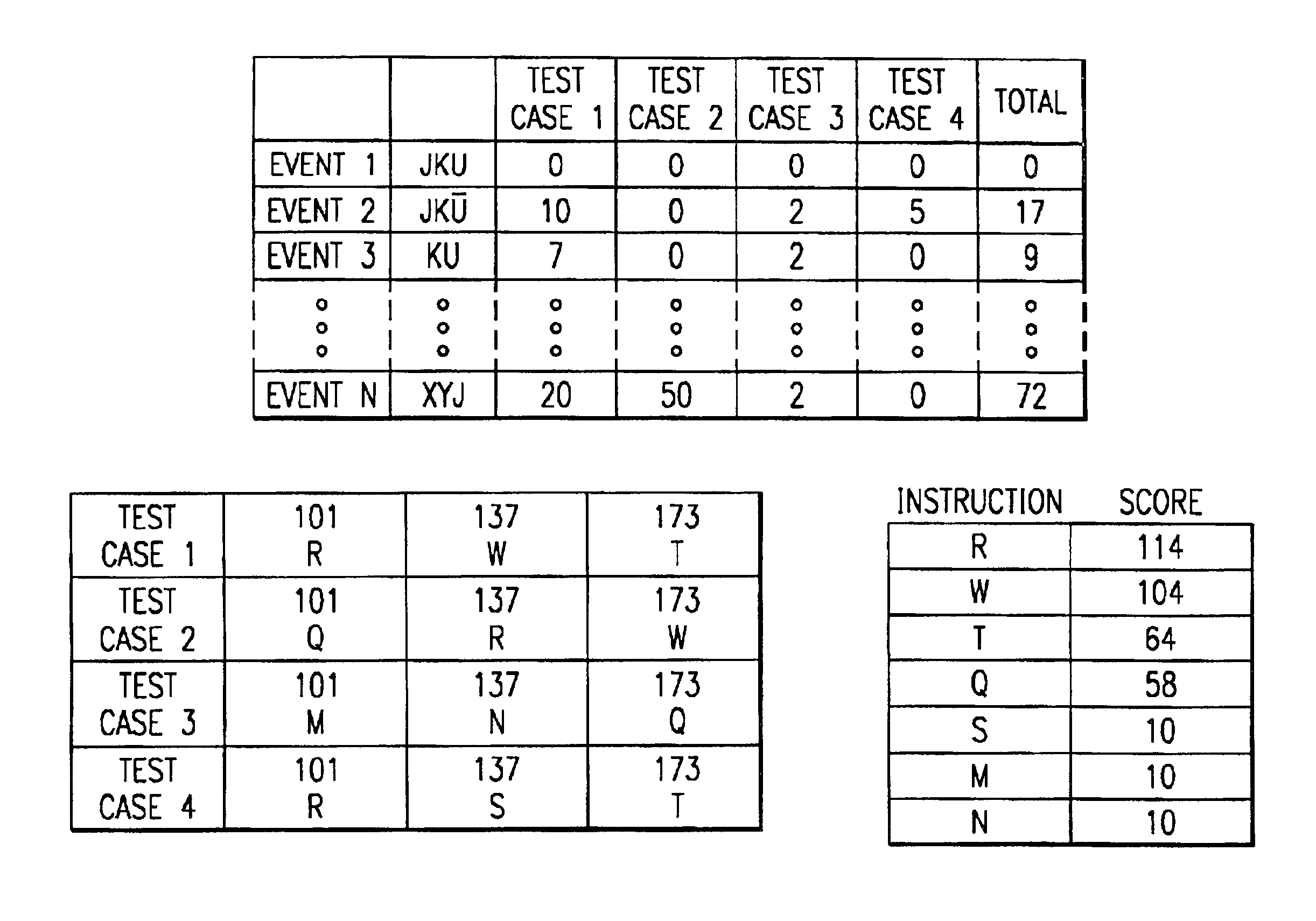
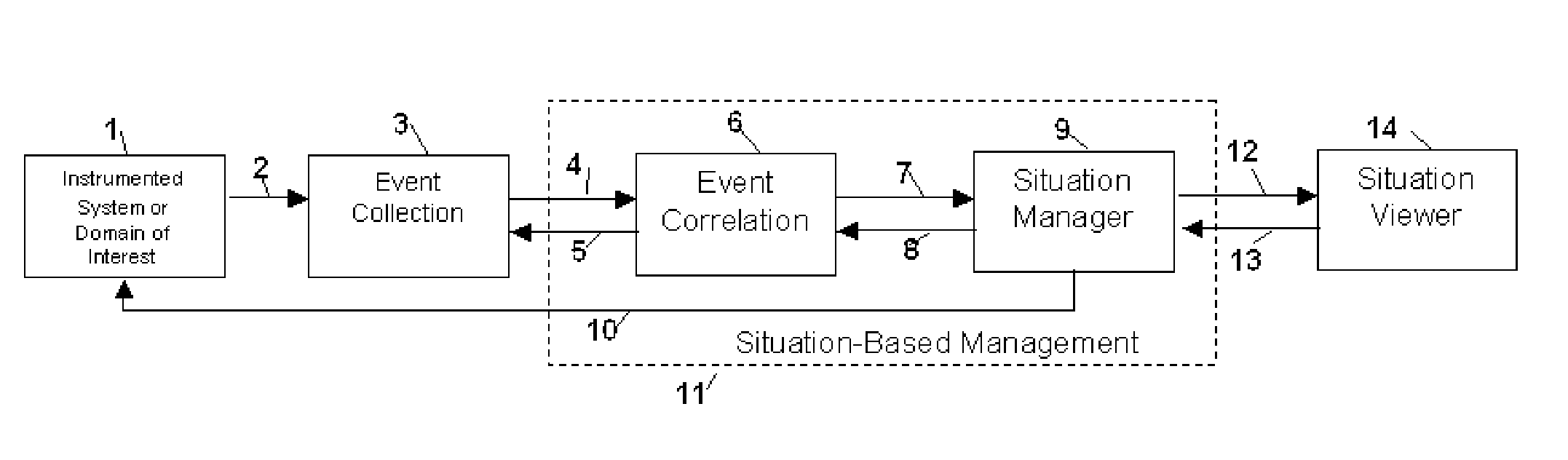
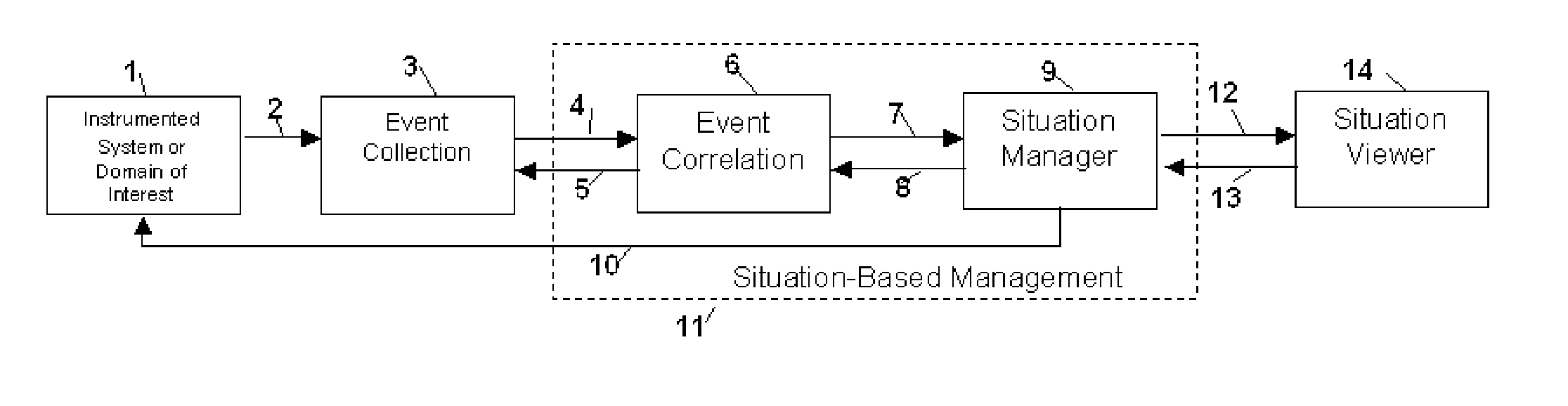
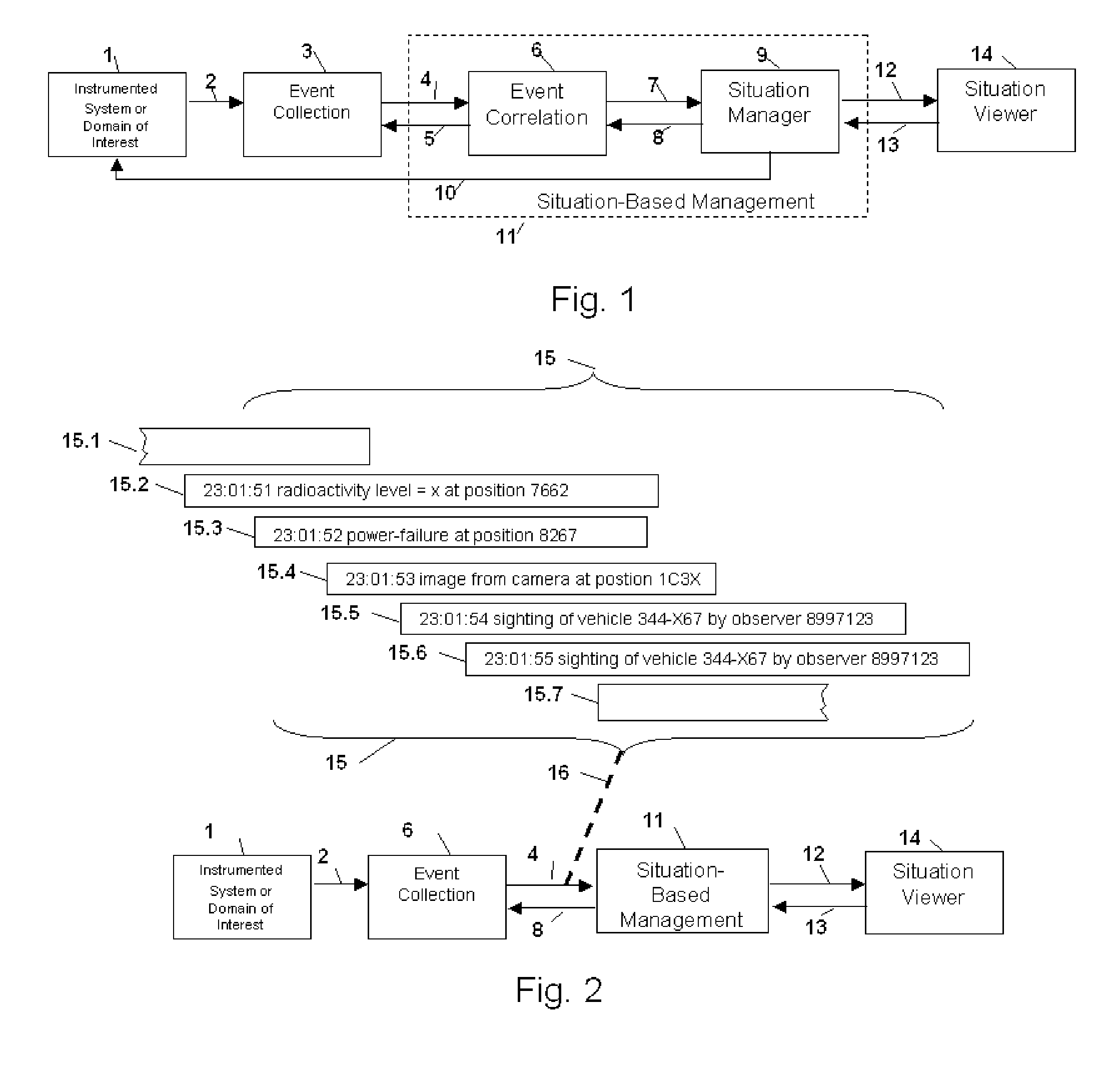
Method and apparatus for situation-based management of natural and artificial systems using event correlation and a situation manager. Input is provided from multiple sources in the form of a collection of events. A first level of processing performs event correlation over the collection of events and infers new events and new qualities of events. A second level of processing manages situations based on the collection of events, where situations are recognized, maintained, and given a degree of confidence. Situations are periodically updated based on incoming events. The assertion of a situation may call for information from external sources, provide information for external sources, and provide control instructions to external sources. Given a current situation, past, and possible future situations are inferred. Additionally, a method and apparatus for bi-directional communication between the event correlator and situation manager.
Owner:ALTUSYS
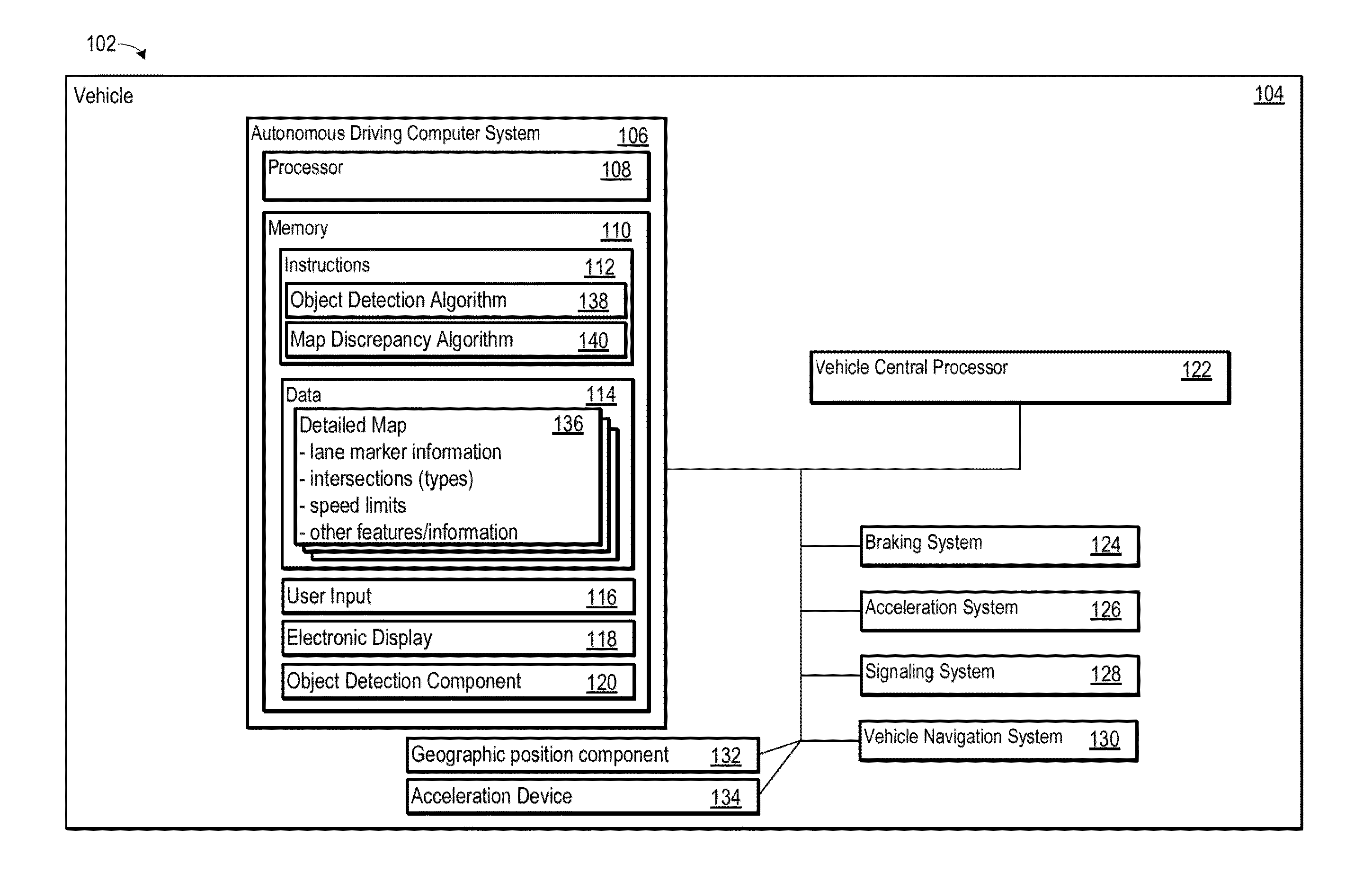
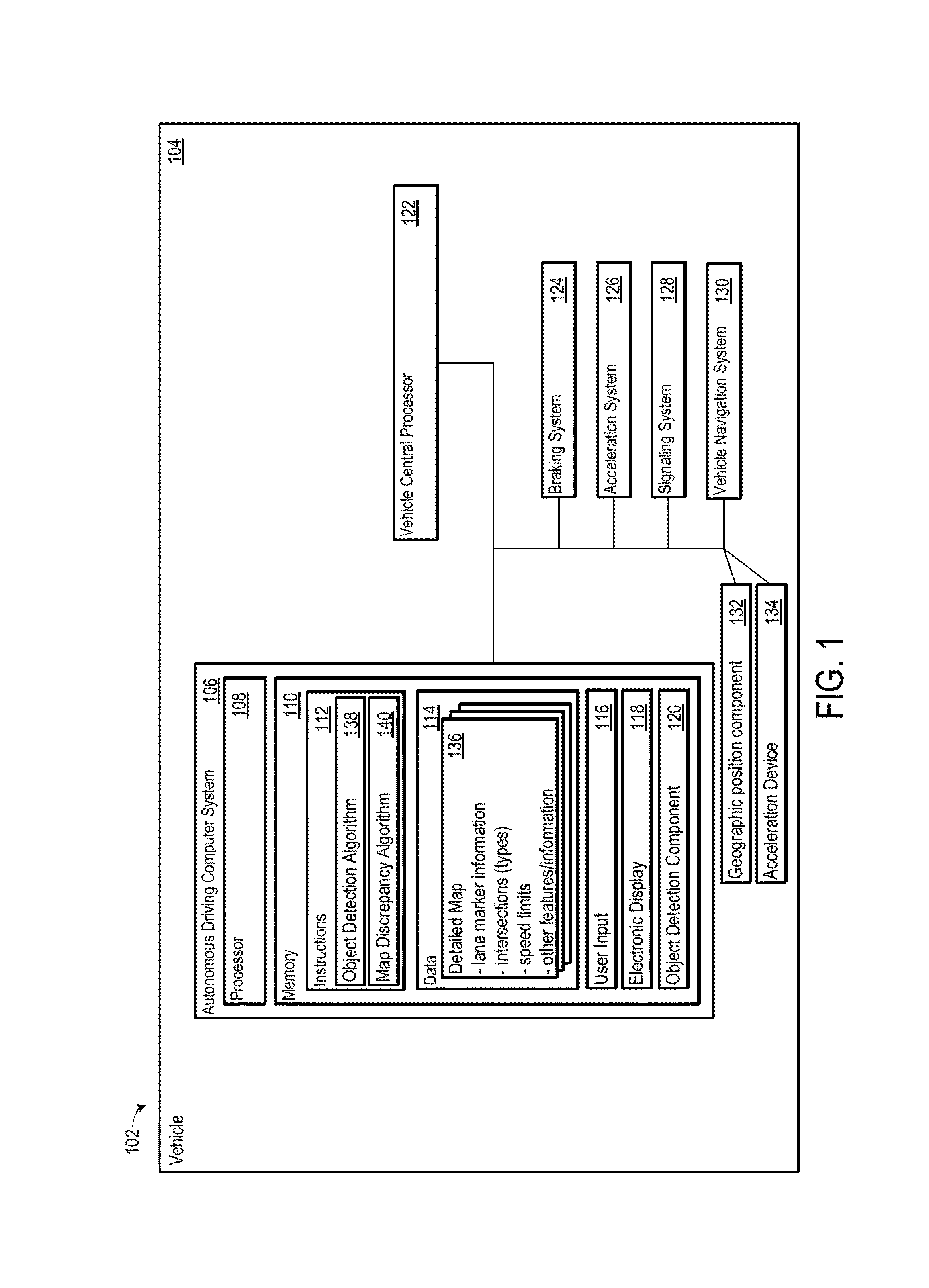
Systems and methods for determining whether a driving environment has changed
ActiveUS8949016B1Anti-collision systemsOptical signallingComputerized systemHuman–computer interaction
A autonomous driving computer system determines whether a driving environment has changed. One or more objects and / or object types in the driving environment may be identified as primary objects. The autonomous driving computer system may be configured to detect the primary objects and / or object types, and compare the detected objects and / or object types with the previous known location of the detected object and / or object types. The autonomous driving computer system may obtain several different metrics to facilitate the comparison. A confidence probability obtained from the comparison may indicate the degree of confidence that the autonomous driving computer system has in determining that the driving environment has actually changed.
Owner:WAYMO LLC
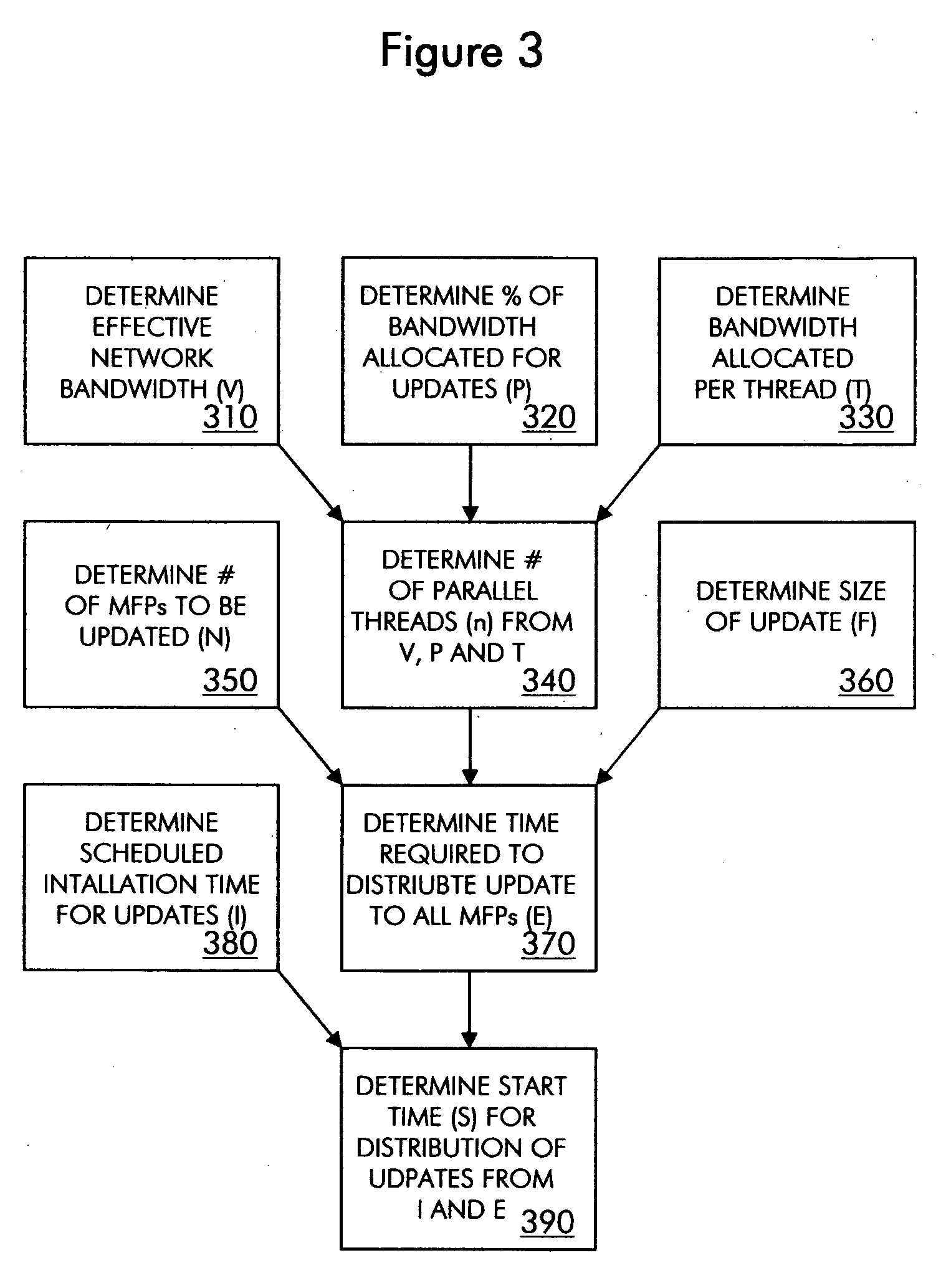
Method and system for updating the software of multiple network nodes
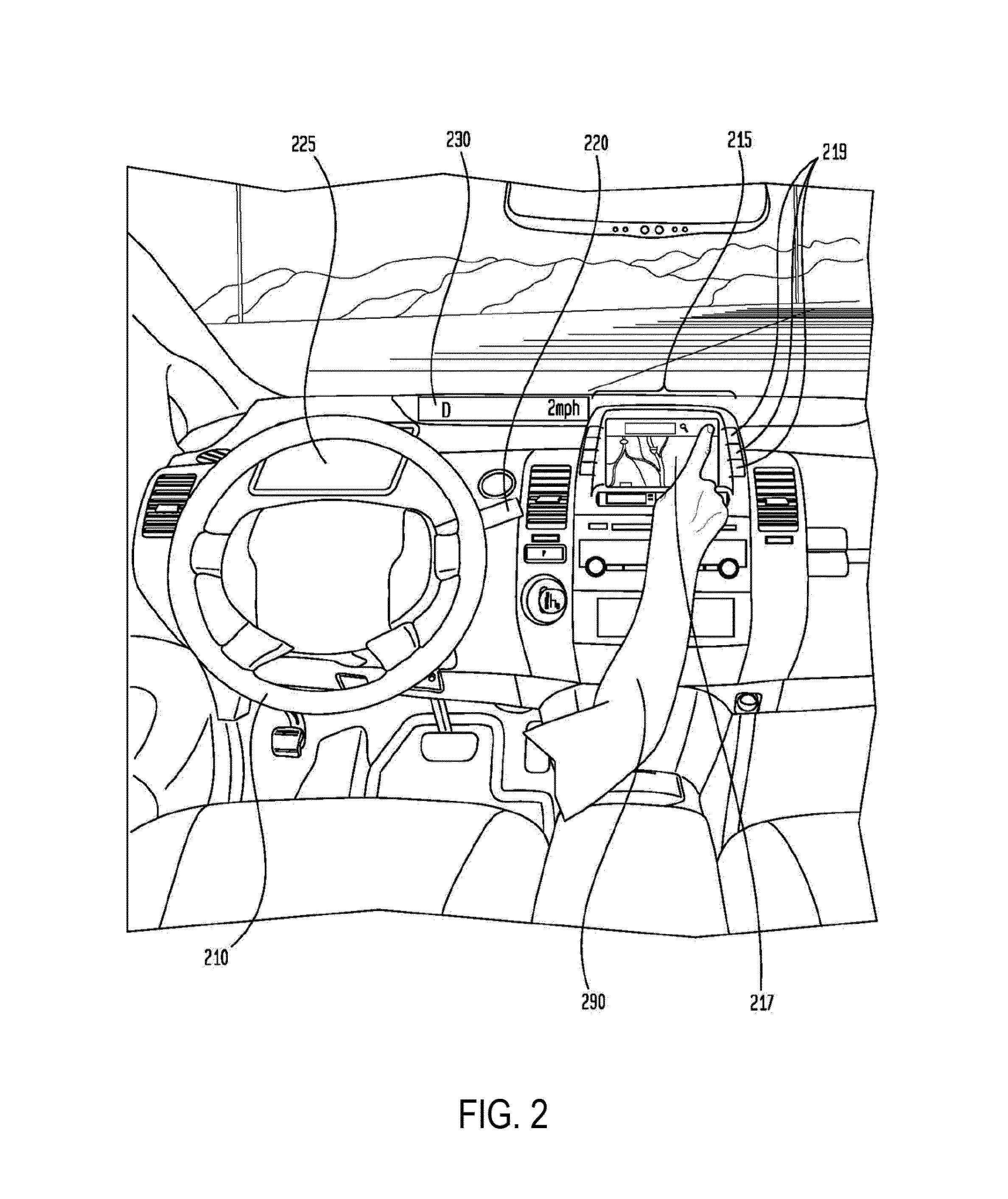
ActiveUS20090150878A1Improve network performanceHigh degreeMultiple digital computer combinationsSpecific program execution arrangementsCompletion timeStart time
A method and system for updating a group of network nodes, such as a group of MFPs, with replacement software in a manner that improves network performance and the predictability of a completion time for installation of the replacement software involves throttling distribution of a software update package to avoid resource oversubscription while time-bounding distribution so that installation of the software update on all of the network nodes can be completed by a certain time and, in some embodiments, further involves determining a start time for distribution of the software update package based at least in part on a scheduled installation time selected by a network administrator, which provides a high degree of confidence that installation of the software update across the entire group of network nodes will be completed around a scheduled time (e.g. during “off hours”) notwithstanding the staggered distribution of the software update package.
Owner:SHARP KK
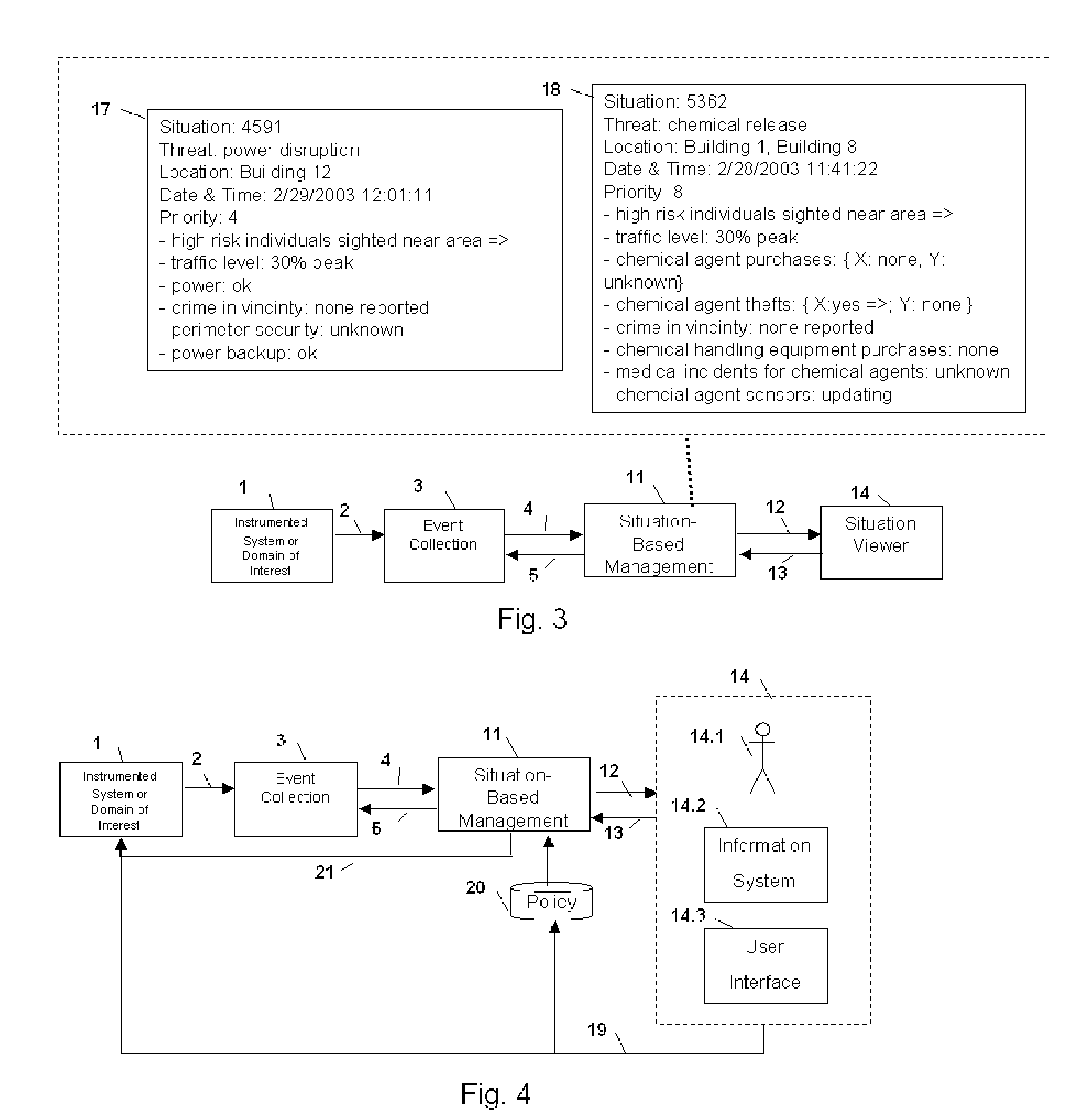
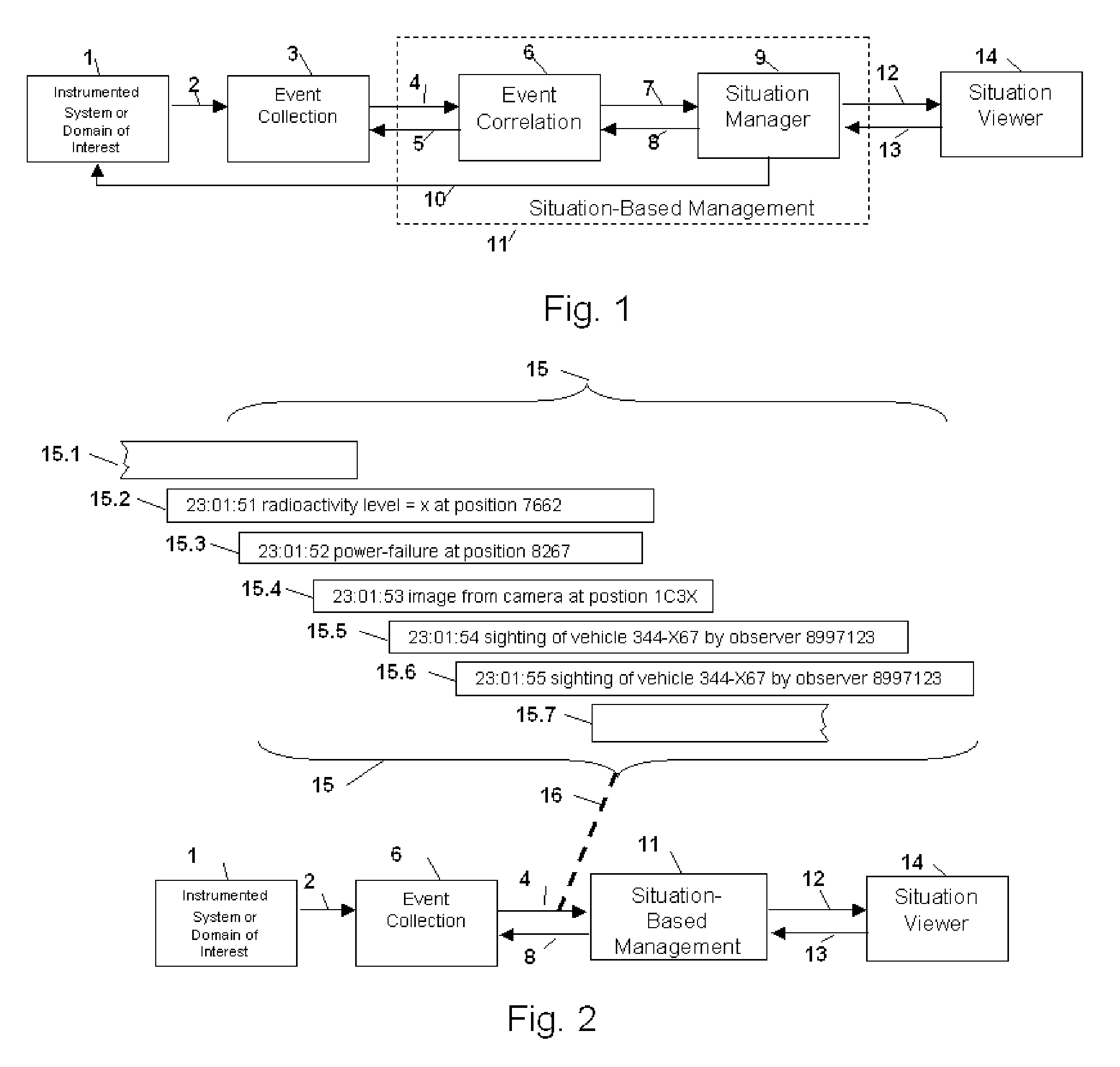
Method and Apparatus for Context-Sensitive Event Correlation with External Control in Situation-Based Management
InactiveUS20050222811A1Efficient processingDigital computer detailsNuclear monitoringArtificial systemsTwo-way communication
Method and apparatus for situation-based management of natural and artificial systems using event correlation and a situation manager. Input is provided from multiple sources in the form of a collection of events. A first level of processing performs event correlation over the collection of events and infers new events and new qualities of events. A second level of processing manages situations based on the collection of events, where situations are recognized, maintained, and given a degree of confidence. Situations are periodically updated based on incoming events. The assertion of a situation may call for information from external sources, provide information for external sources, and provide control instructions to external sources. Given a current situation, past, and possible future situations are inferred. Additionally, a method and apparatus for bi-directional communication between the event correlator and situation manager.
Owner:ALTUSYS
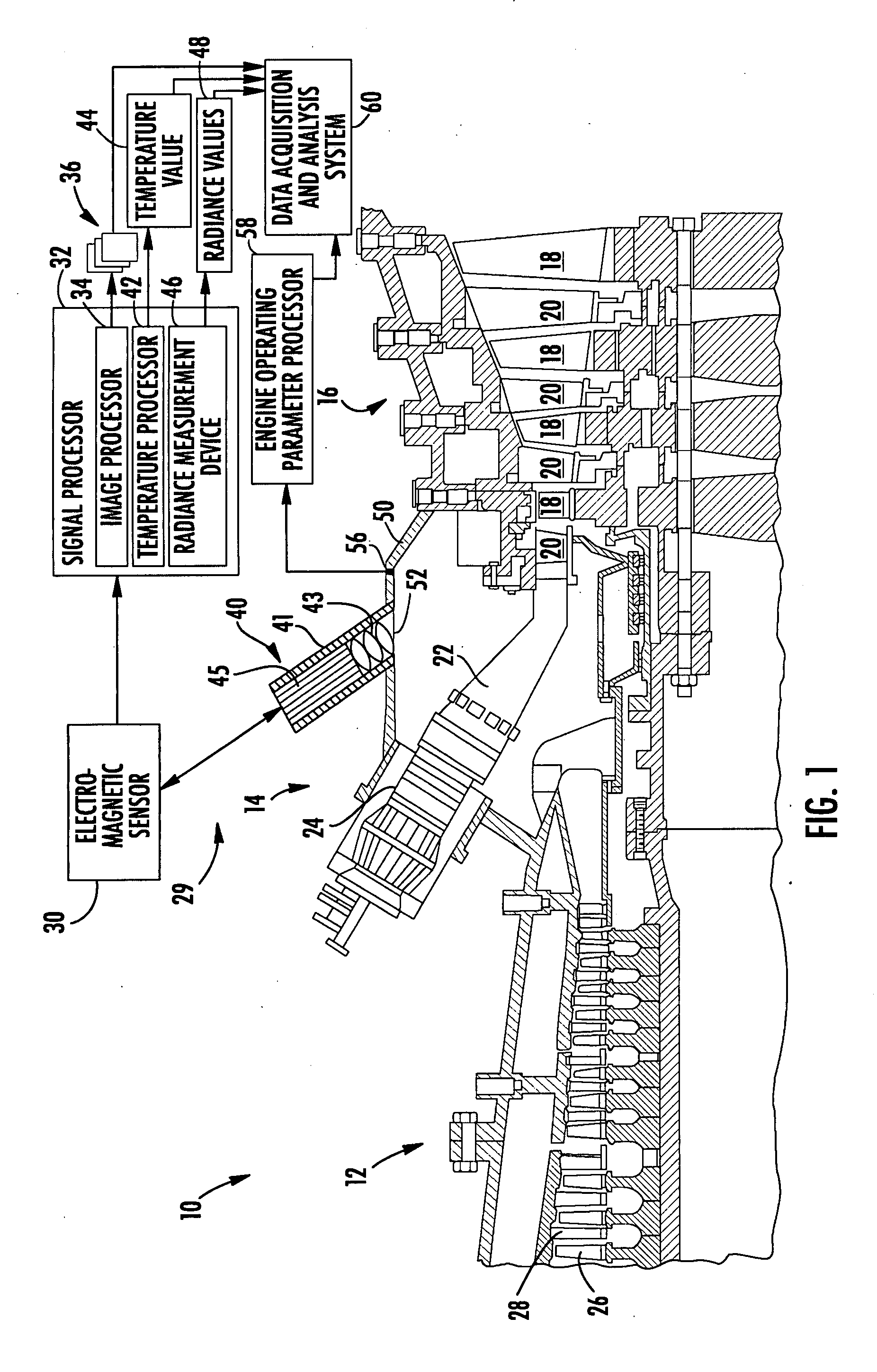
System and method of evaluating uncoated turbine engine components
InactiveUS20080101683A1Gas-turbine engine testingMaterial analysis by optical meansNon destructiveVision based systems
Aspects of the invention are directed to a visual-based system and method for non-destructively evaluating an uncoated turbine engine component. Aspects of the invention are well suited for high speed, high temperature components. Radiant energy emitted from an uncoated turbine engine component can be captured remotely and converted into a useful form, such as a high resolution image of the component. A plurality of images of the component can be captured over time and evaluated to identify failure modes. The system can also measure and map the temperature and / or radiance of the component. The system can facilitate the non-destructive evaluation of uncoated turbine components during engine operation without disassembly of the engine, thereby providing significant time and cost savings. Further, the system presents data to a user with sufficient context that allows an engine operator can evaluate the information with an increased degree of confidence and certainty.
Owner:SIEMENS ENERGY INC
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS20080141033A1Highly cost-effectiveHigh of confidenceDigital data processing detailsUser identity/authority verificationDocumentation procedureDocument preparation
Documents and other items can be delivered electronically from sender to recipient with a level of trustedness approaching or exceeding that provided by a personal document courier. A trusted electronic go-between can validate, witness and / or archive transactions while, in some cases, actively participating in or directing the transaction. Printed or imaged documents can be marked using handwritten signature images, seal images, electronic fingerprinting, watermarking, and / or steganography. Electronic commercial transactions and transmissions take place in a reliable, “trusted” virtual distribution environment that provides significant efficiency and cost savings benefits to users in addition to providing an extremely high degree of confidence and trustedness. The systems and techniques have many uses including but not limited to secure document delivery, execution of legal documents, and electronic data interchange (EDI).
Owner:INTERTRUST TECH CORP
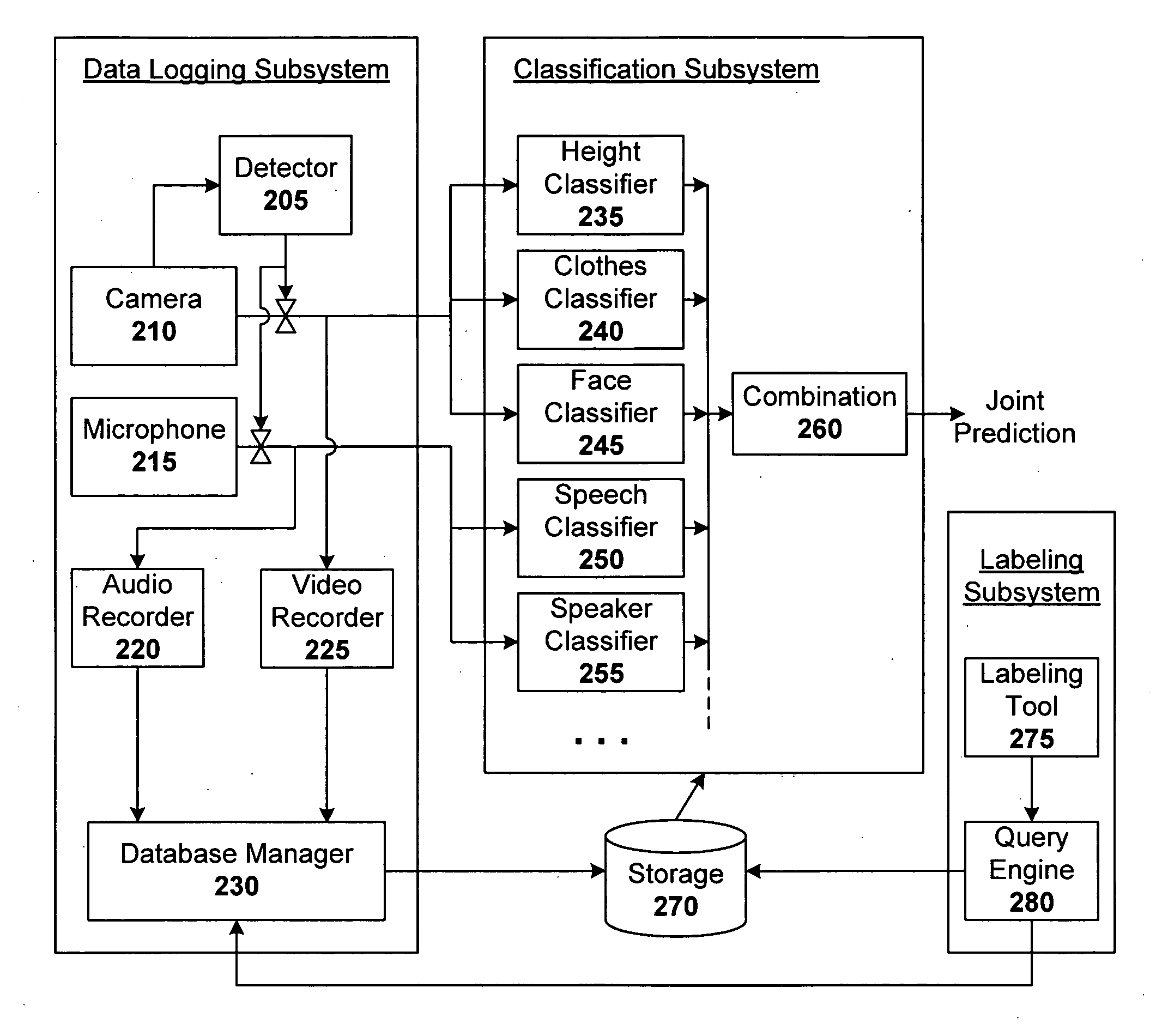
Confidence weighted classifier combination for multi-modal identification
ActiveUS20060120609A1Improves identification system performanceImprove recognition rateCharacter and pattern recognitionSpeech recognitionEnsembles of classifiersMachine learning
Techniques are disclosed for multi-modal identification that utilize a classifier combination framework. One embodiment of the present invention provides a multi-modal identification system that includes a collection of classifiers that classify feature streams derived from audio and / or video sources. A classifier combination scheme is used to combine the classifier outputs having varying degrees of confidence, but in a robust way by using a confidence-based weighting scheme that operates on a “per-class” basis, rather than (or in addition to) the traditional “per-classifier” basis. The system can be distributed across several machines running independent feature classifiers on the subscription basis.
Owner:HONDA MOTOR CO LTD
System and method for identification of automated browser agents
Disclosed herein are methods and systems for evaluating web browser behavior to report on human versus non-human activity, based on varying analyses of detectable properties. By passively detecting the code of a webpage engaged by a browsing user, the present invention evaluates the browsing user's activity in order to predict the type of user with a degree of confidence. The predictions are formed by acquiring information on how a user loads, navigates, and interacts with a webpage and comparing that information with known and unknown properties in various control groups. If the prediction yields a high likelihood of automated activity, additional active detection may be performed. Reports are compiled by analysis servers and made available to the operators of webpages. By compiling performance metrics and informing operators of fraudulent versus normal activity, the invention combats malicious automated traffic directed at any aspect of a given webpage.
Owner:HUMAN SECURITY INC
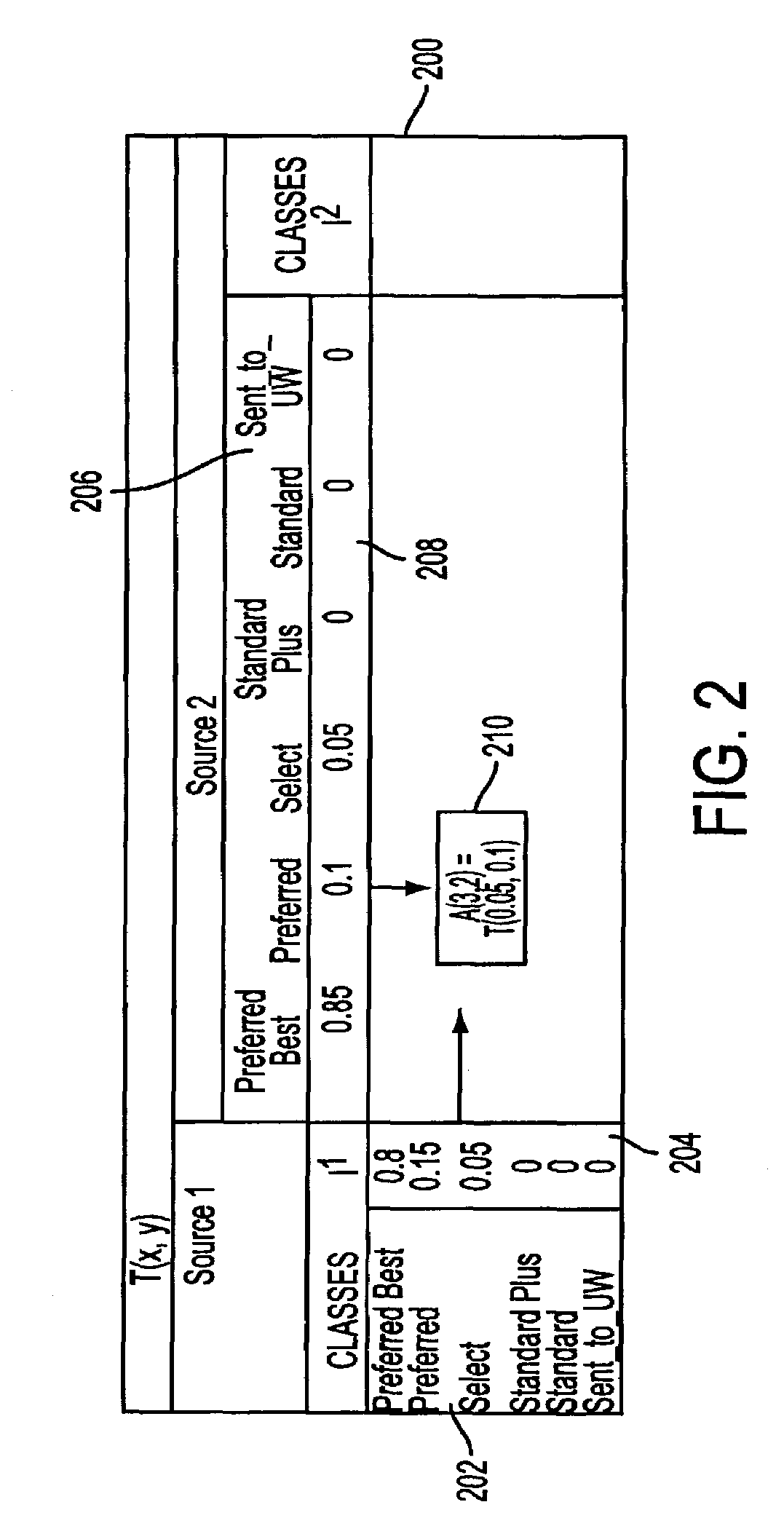
Purchasing system using object matching
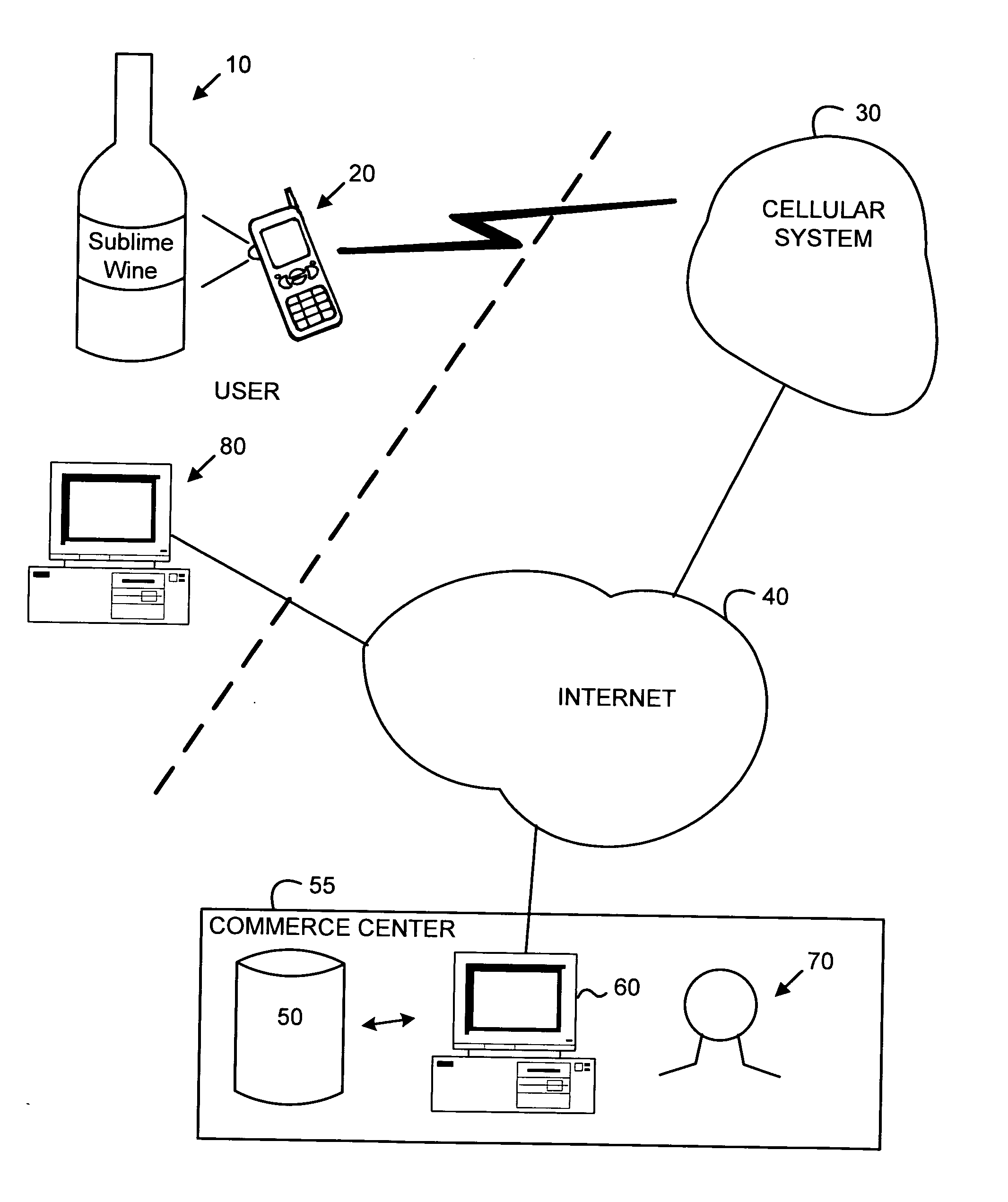
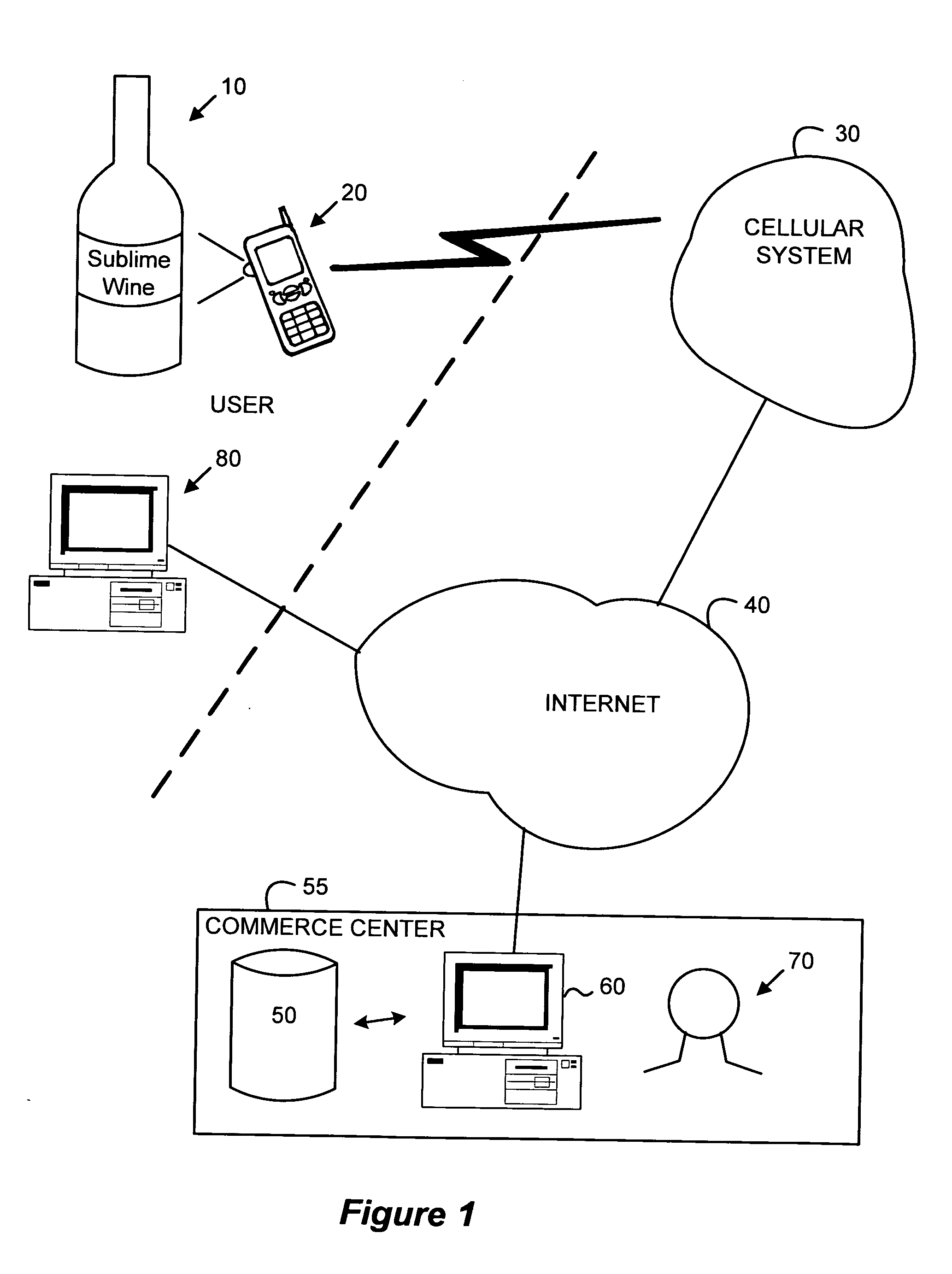
InactiveUS20050252966A1Visual presentationBuying/selling/leasing transactionsCredit cardEmail address
Embodiments of the invention allow a consumer to make an online purchase of an encountered item. In one embodiment the encountered item to be purchased is photographed by a camera in, e.g., a cell phone. The image is sent via the cellular phone network to the Internet where it is received by a commerce center. The commerce center includes automated and manual image-matching tools. If the image is matched (i.e., identified with a predetermined degree of confidence) a message is sent back to the consumer's cell phone to indicate the cost to purchase the image from the commerce center or from another source. The consumer indicates whether and how many of the item type to purchase. Assuming the consumer has registered with the commerce center to provide transaction information such as a name, credit card number, shipping address, etc., the commerce center completes the transaction. Transaction options are available, such as allowing the consumer to request more information to be sent to the consumer's personal computer email address, have hardcopy information mailed, allowing the consumer to specify the item delivered to another party, selecting the item as a gift, obtaining information on related items, etc.
Owner:KULAS CHARES J
Ranging system and method
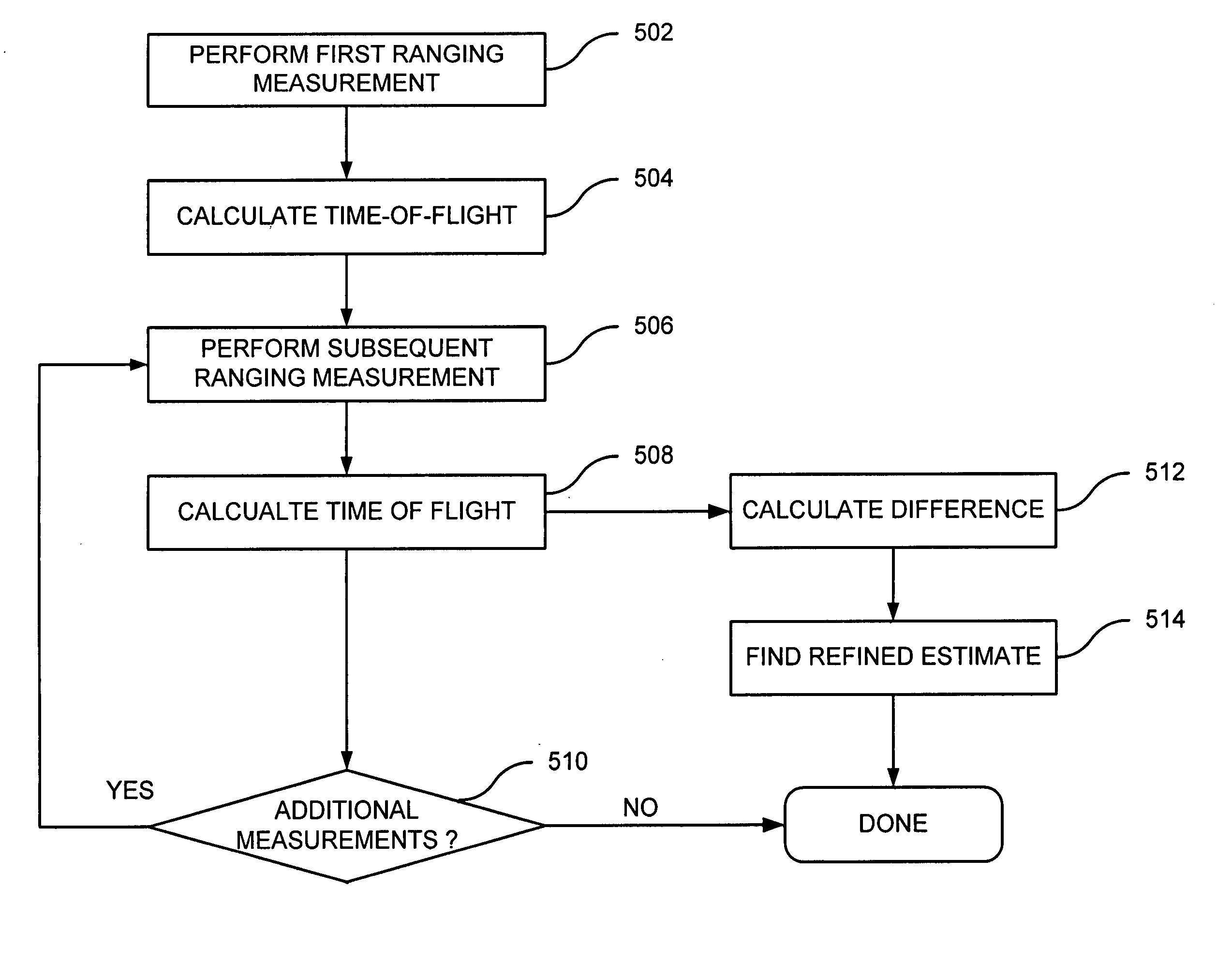
ActiveUS20070200759A1Improve accuracyAccount for uncertaintyDirection finders using radio wavesBeacon systemsClock driftImage resolution
A system and method for estimating the range between two devices performs two or more ranging estimates with subsequent estimates performed using a clock that is offset in phase with respect to a prior estimate. The subsequent estimate allows estimate uncertainties due to a finite clock resolution to be reduced and can yield a range estimate with a higher degree of confidence. In one embodiment, these additional ranging estimates are performed at n / N (for n=1, . . . N−1, with N>1 and a positive integer) clock-period offset introduced in the device. The clock-period offset can be implemented using a number of approaches, and the effect of clock drift in the devices due to relative clock-frequency offset can also be determined. To eliminate the bias due to clock-frequency offset, a system and method to estimate the clock-frequency offset is also presented.
Owner:SAMSUNG ELECTRONICS CO LTD
Trusted and secure techniques, systems and methods for item delivery and execution
InactiveUS20050182956A1Highly cost-effectiveHigh of confidenceDigital data processing detailsAnalogue secracy/subscription systemsDocument preparationDocumentation
Owner:INTERTRUST TECH CORP
Motion compensation in image processing
ActiveUS20120051664A1Image enhancementReconstruction from projectionPattern recognitionImaging processing
Methods and systems for processing a set of images are described. In accordance with this disclosure, images are registered and an analysis is performed in view of one or more constraints (such as constraints based upon anatomical or physiological considerations). Weighting factors are determined based on the analysis. The weighting factors are used in subsequent processing of the registered (and / or unregistered) images and / or to formulate a visualization that conveys the degree of confidence in the motion estimation used in the registration process.
Owner:GENERAL ELECTRIC CO
Method and apparatus for generating transaction-based stimulus for simulation of VLSI circuits using event coverage analysis
InactiveUS6859770B2Improve trustElectronic circuit testingAnalogue computers for electric apparatusSpecific testAlgorithm
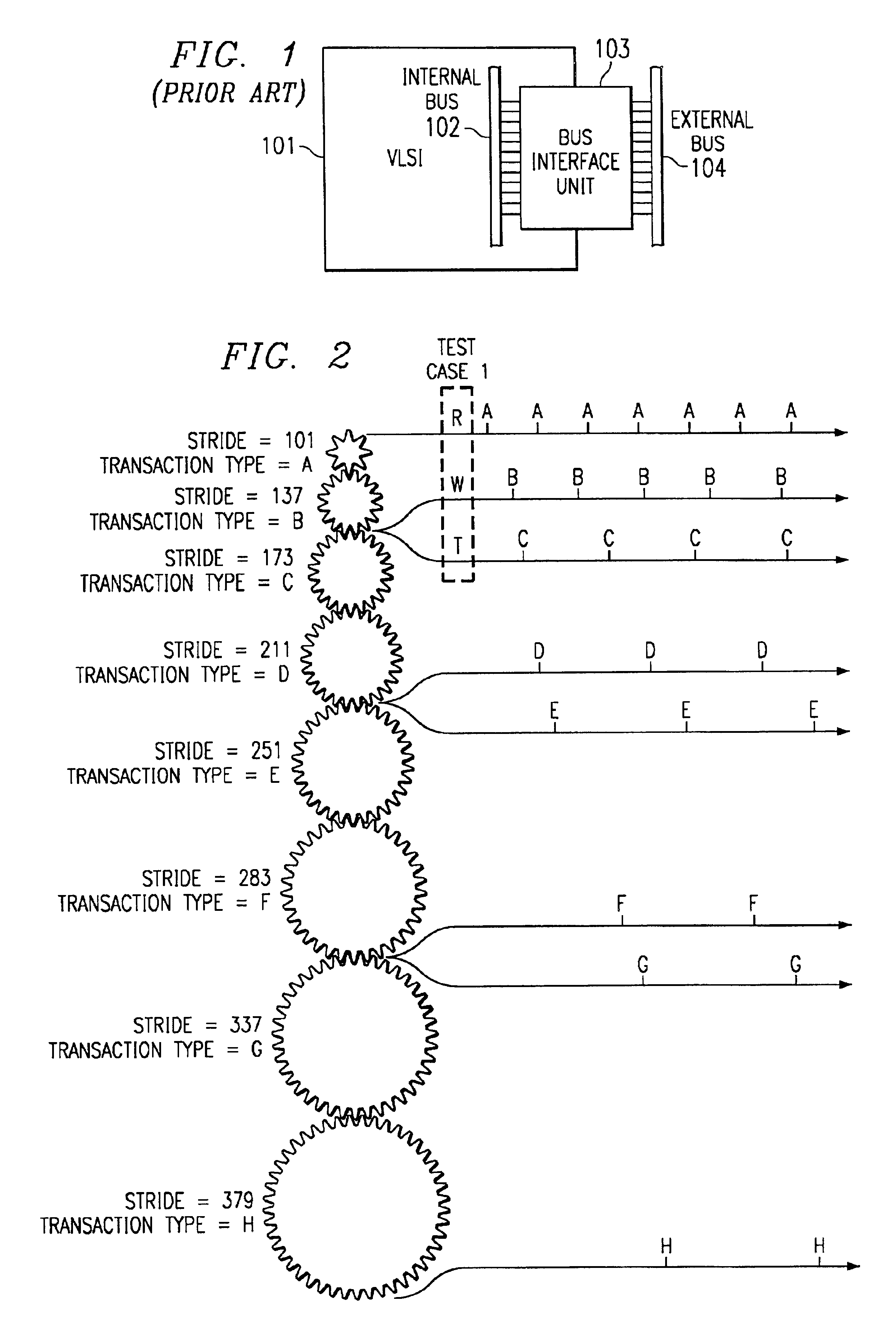
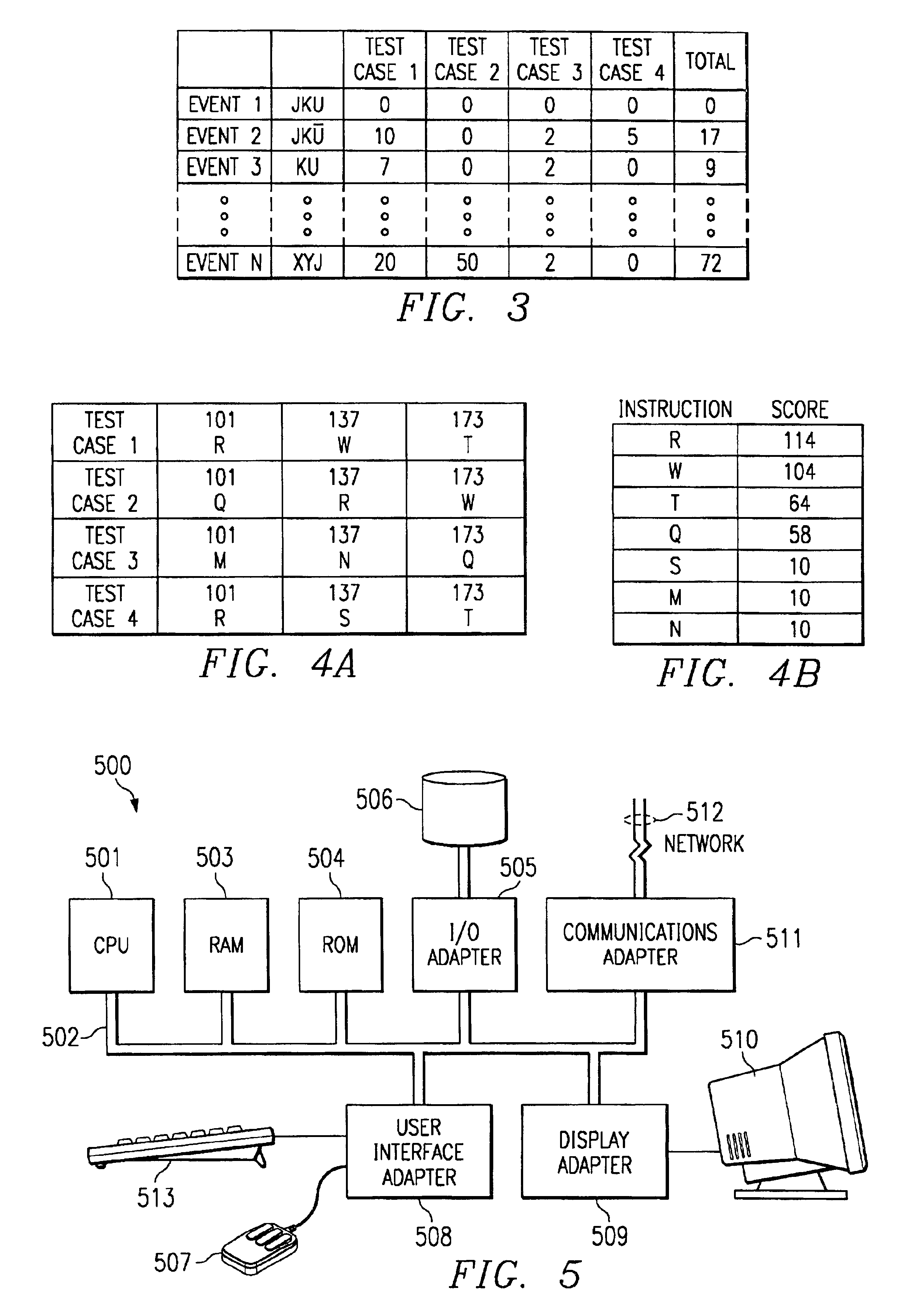
The present invention applies genetic algorithmic generation of test cases the simulation of VLSI logic circuit blocks. The present invention generates a number of original test cases. This aggregate of solutions is provided to a circuit simulator. The results of the simulator are maintained in a matrix or table. The results detail the number of times that particular logic states or events associated with the VLSI block have been stimulated by particular test cases. The aggregate of solutions and the simulation results are then analyzed by the genetic algorithm. The genetic algorithm preferably identifies states associated with the circuit simulation that have not been produced by the original test cases. The genetic algorithm then combines characteristics of various test cases to generate new test cases. The new test cases are provided to the circuit simulator thereby providing a higher degree of confidence that the entire VLSI chip design has been simulated.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and Apparatus for Coordination of a Situation Manager and Event Correlation in Situation-Based Management
InactiveUS20050222810A1Guaranteed normal transmissionRemove redundant informationNuclear monitoringDigital computer detailsArtificial systemsData science
Method and apparatus for situation-based management of natural and artificial systems using event correlation and a situation manager. Input is provided from multiple sources in the form of a collection of events. A first level of processing performs event correlation over the collection of events and infers new events and new qualities of events. A second level of processing manages situations based on the collection of events, where situations are recognized, maintained, and given a degree of confidence. Situations are periodically updated based on incoming events. The assertion of a situation may call for information from external sources, provide information for external sources, and provide control instructions to external sources. Given a current situation, past, and possible future situations are inferred. Additionally, a method and apparatus for bi-directional communication between the event correlator and situation manager.
Owner:ALTUSYS
Alarm association rule mining method, and rule mining engine and system
InactiveCN101937447AReduce false rulesDegree of strong associationSpecial data processing applicationsRule miningResult set
The embodiment of the invention discloses an alarm association rule mining method, an alarm association rule mining engine and an alarm association rule mining system. The method comprises the following steps of: acquiring an alarm sequence, wherein the alarm sequence comprises multiple pieces of alarm; calculating support of each k-item set to obtain a k-item frequency item set aggregate; generating a k+1-item frequency item set aggregate from the k-item frequency item set aggregate; calculating maximum degree of confidence of the k+1-item frequency item set aggregate according to the maximum value in the support of k+1 1-item sets included in the k+1-item frequency item set and the support of the k+1-item frequency item set for each k+1-item frequency item set in the k+1-item frequency item set aggregate; adding the k+1-item frequency item set with the maximum degree of confidence no less than minimum degree of confidence into an association rule result set as an association rule; and thus a false rule produced due to the influence of the parameter of the degree of confidence is reduced and the false rule in the association rule result set is effectively reduced during the mining of the alarm association rule.
Owner:HUAWEI TECH CO LTD
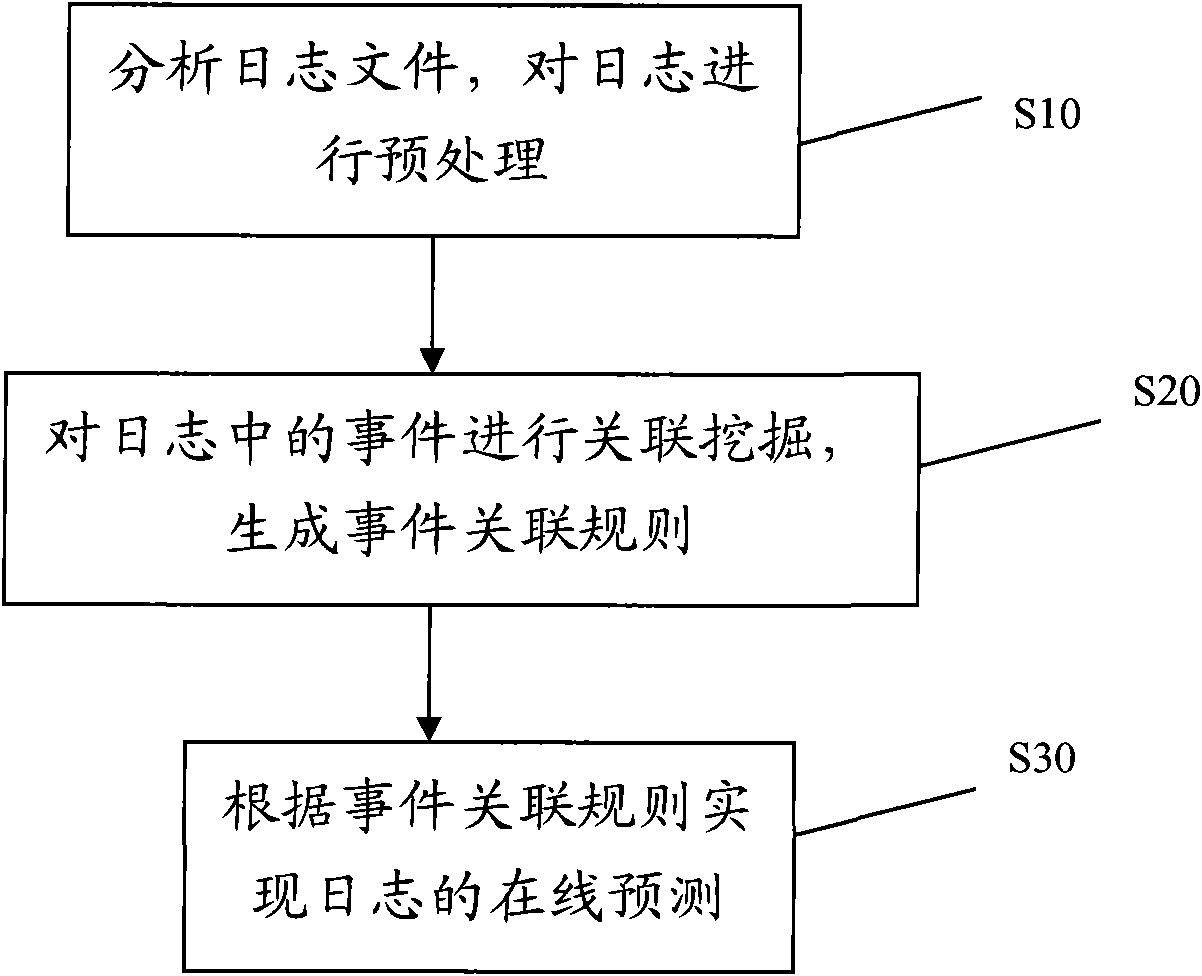
Online log analysis method
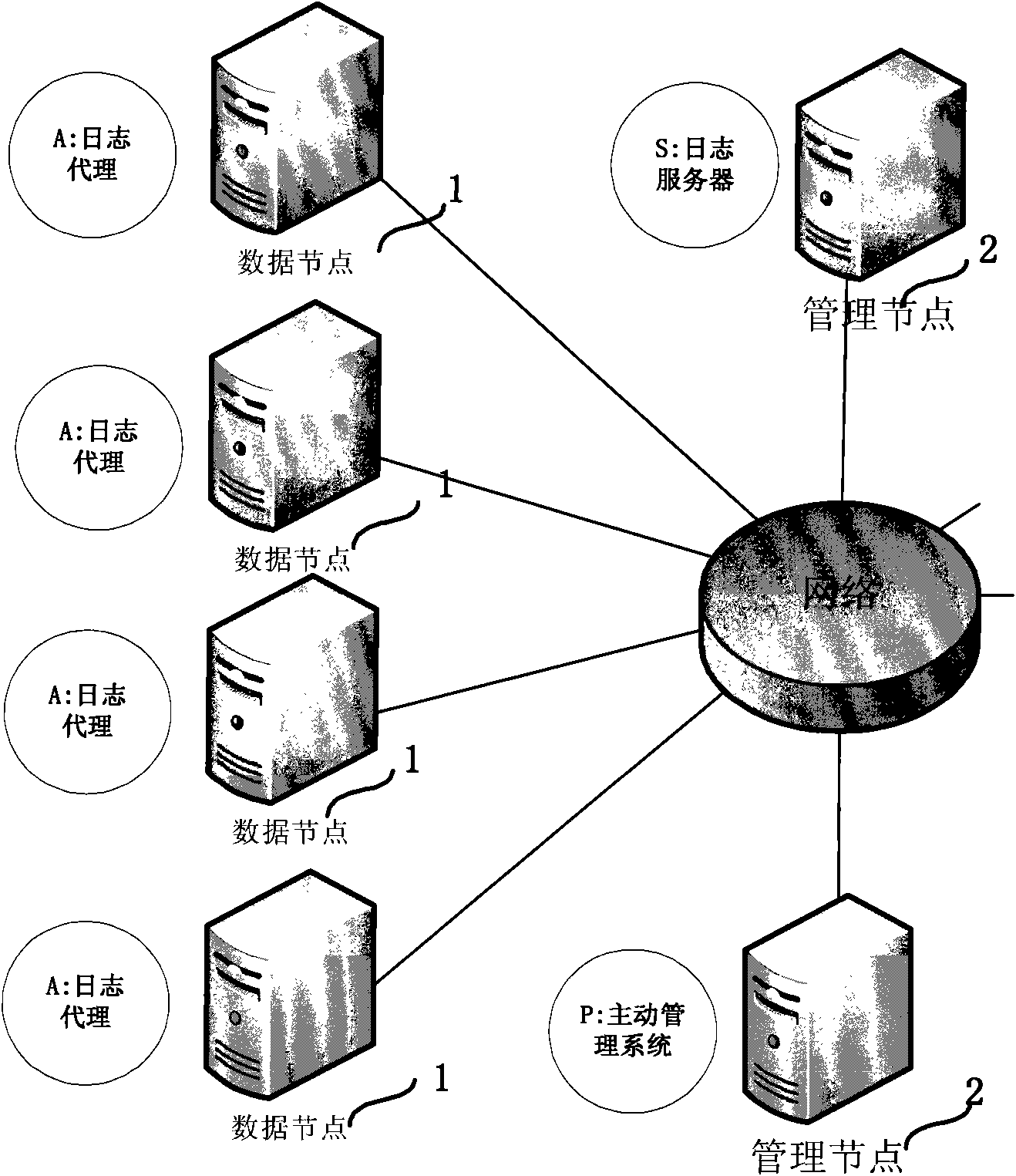
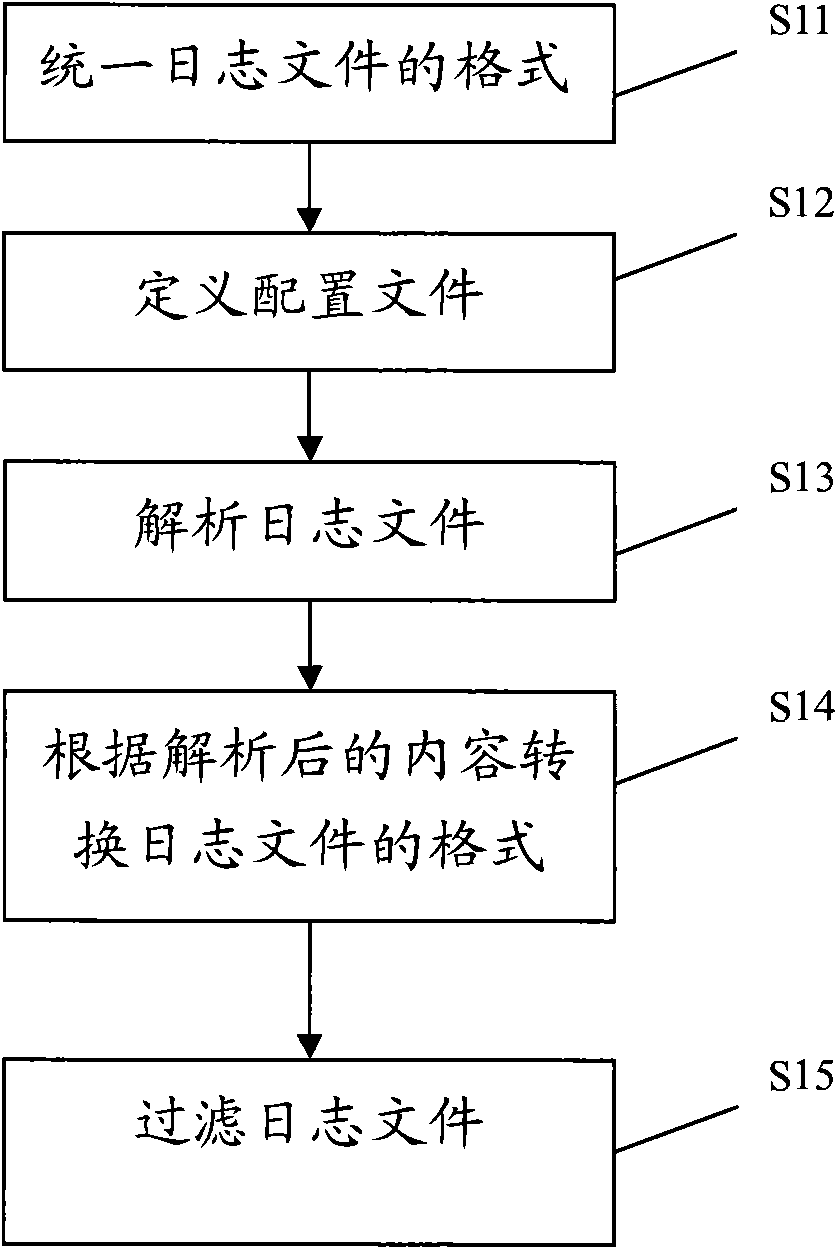
InactiveCN101888309AImprove behaviorImprove productivityData switching networksCluster systemsApproximate computing
The invention provides an online log analysis method, which comprises the following steps of: acquiring a log file from each node of a cluster system on line; defining an event sequence and an event correlation rule according to the log file, counting unitary event sequences, searching out a frequent unitary event sequence set, and obtaining a binary frequent event sequence candidate set C (2); performing statistics on support degree counting and posterior degree counting of the candidate binary frequent event sequence in the C (2), and calculating the degree of confidence and posterior degree; generating a binary frequent event sequence set F (2) and a binary rule set R (2); repeating the process until F(k) and R(k) are obtained, performing join operation on k-element frequent event sequences in the F(k), and generating an F(k+1)-element frequent event sequence set; performing approximate calculation on attribute values of elements which are not in R(k+1) but in F(k+1), until all frequent event sequences are generated; finding the event correlation rule according to the frequent event sequences; and predicting events in the log according to the event correlation rule on line.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method, apparatus and system for detecting a supporting surface region in an image
ActiveUS20140119604A1Image analysisCharacter and pattern recognitionPattern recognitionImage capture
A method of detecting a supporting surface region in an image captured by a camera is disclosed. An object in the image is detected. One or more regions of the image in which a lower part of the detected object exists are determined. A degree of confidence for each of the regions is determined. The degree of confidence indicates likelihood of a corresponding region being a supporting surface region. One or more of the regions are selected based on each corresponding degree of confidence. Similarity of other regions in the image to at least one of the selected regions is determined. The supporting surface region is detected based on the determined similarity.
Owner:CANON KK
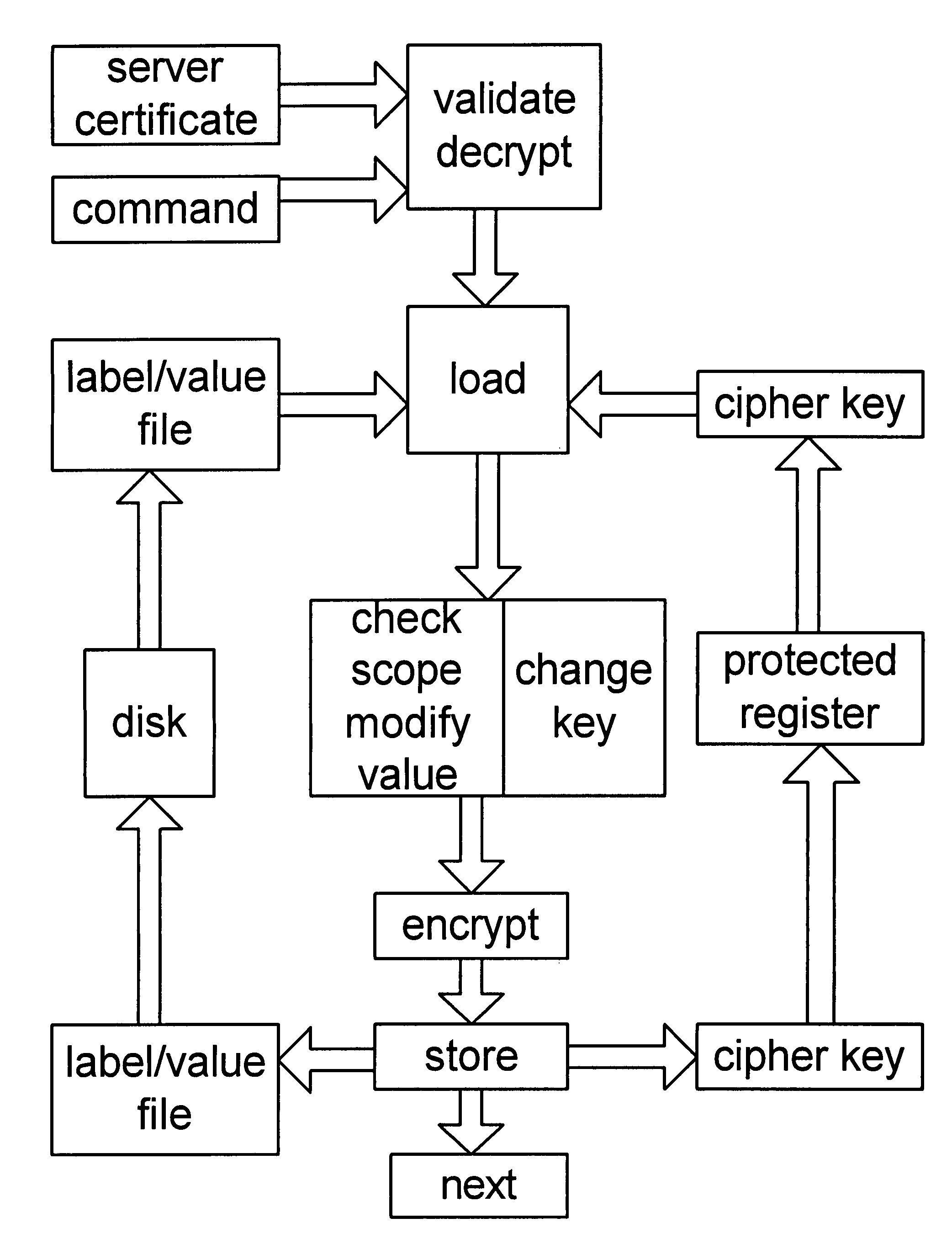
Secure transaction processor
InactiveUS7568114B1User identity/authority verificationUnauthorized memory use protectionDocumentation procedureProcessor register
Owner:SCHLAFLY ROGER
Detecting collusion among multiple recipients of fingerprinted information
InactiveUS7036024B2Improve trustConfidenceTelevision system detailsData processing applicationsDigital contentNumber content
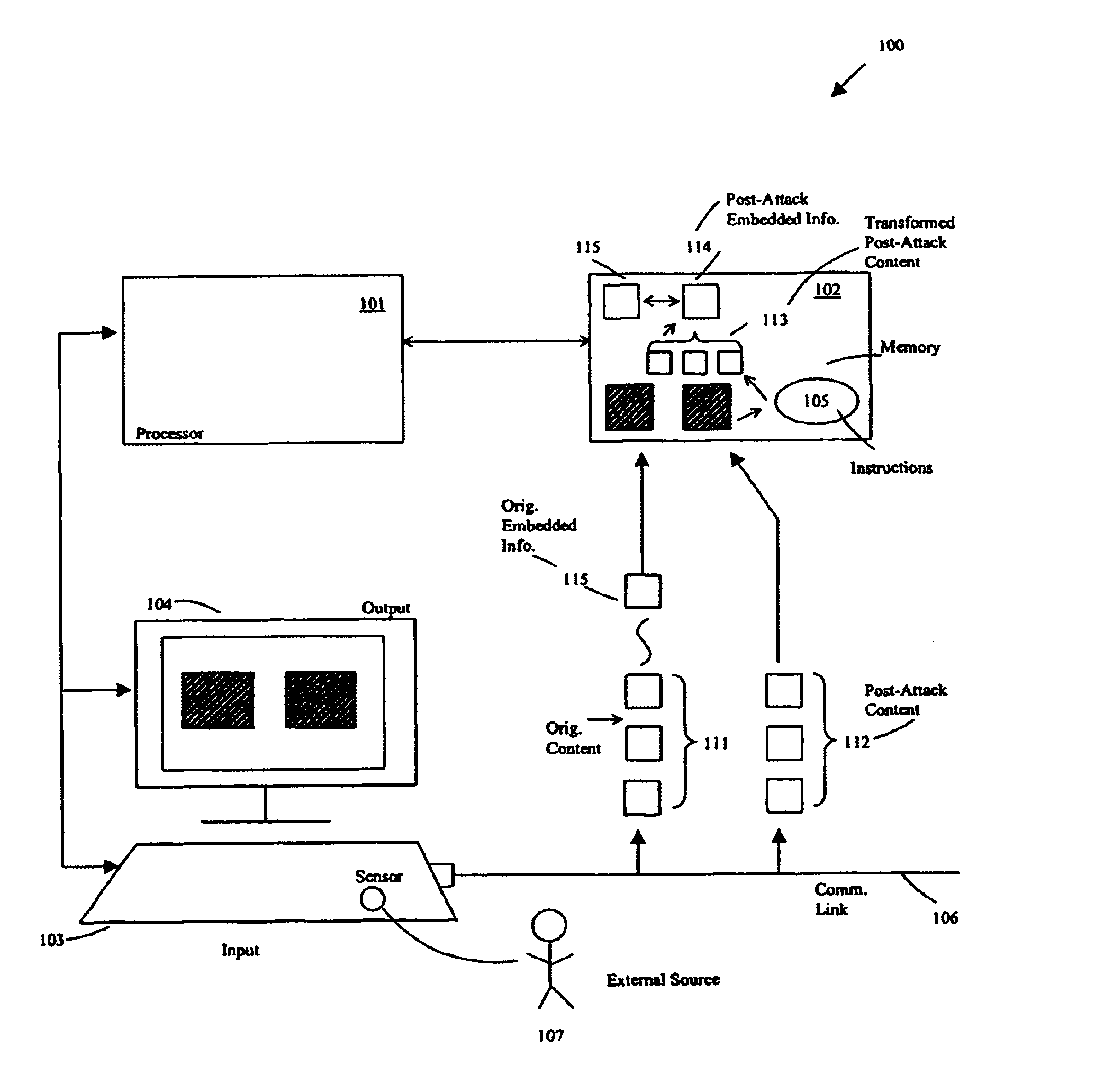
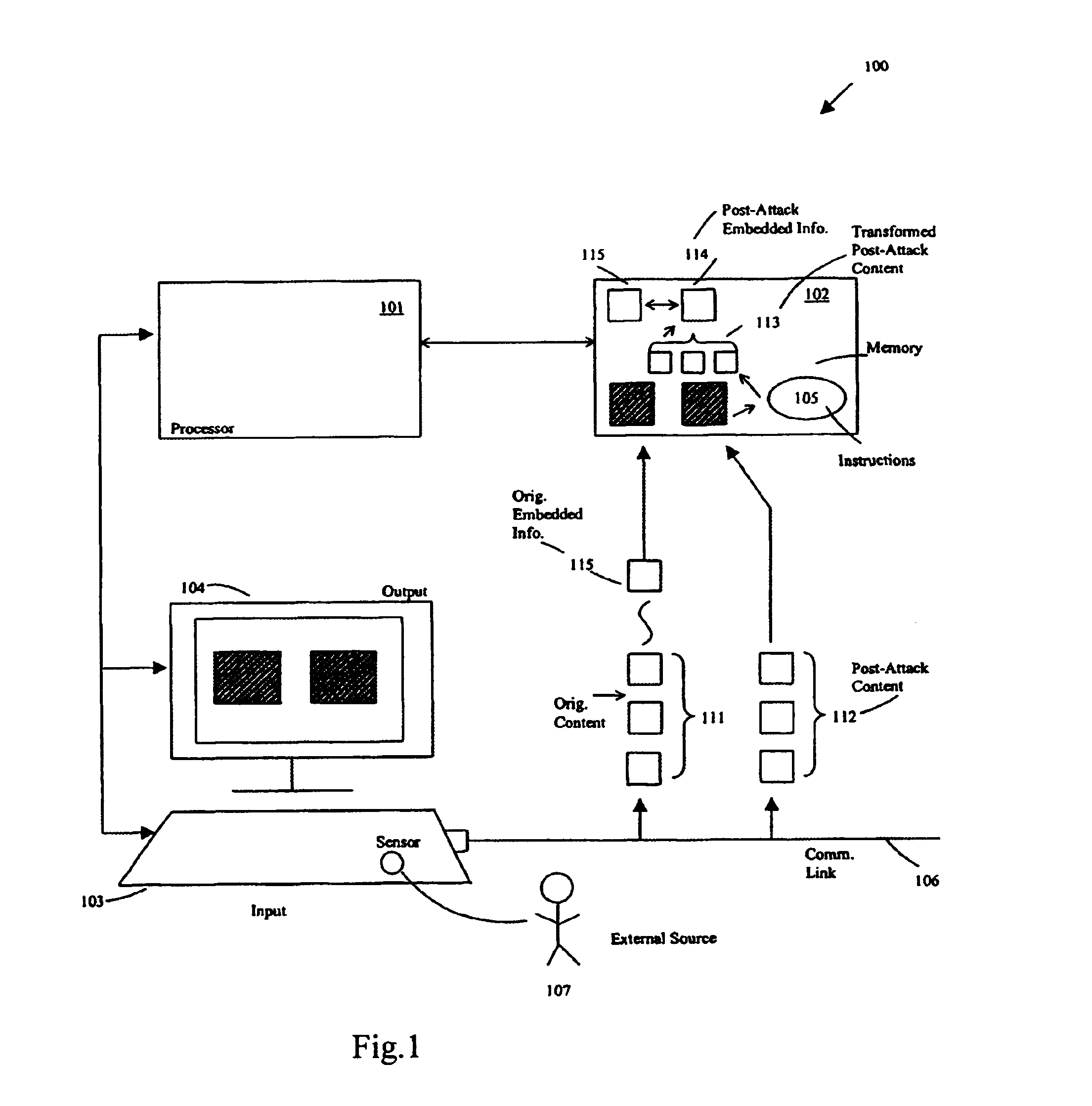
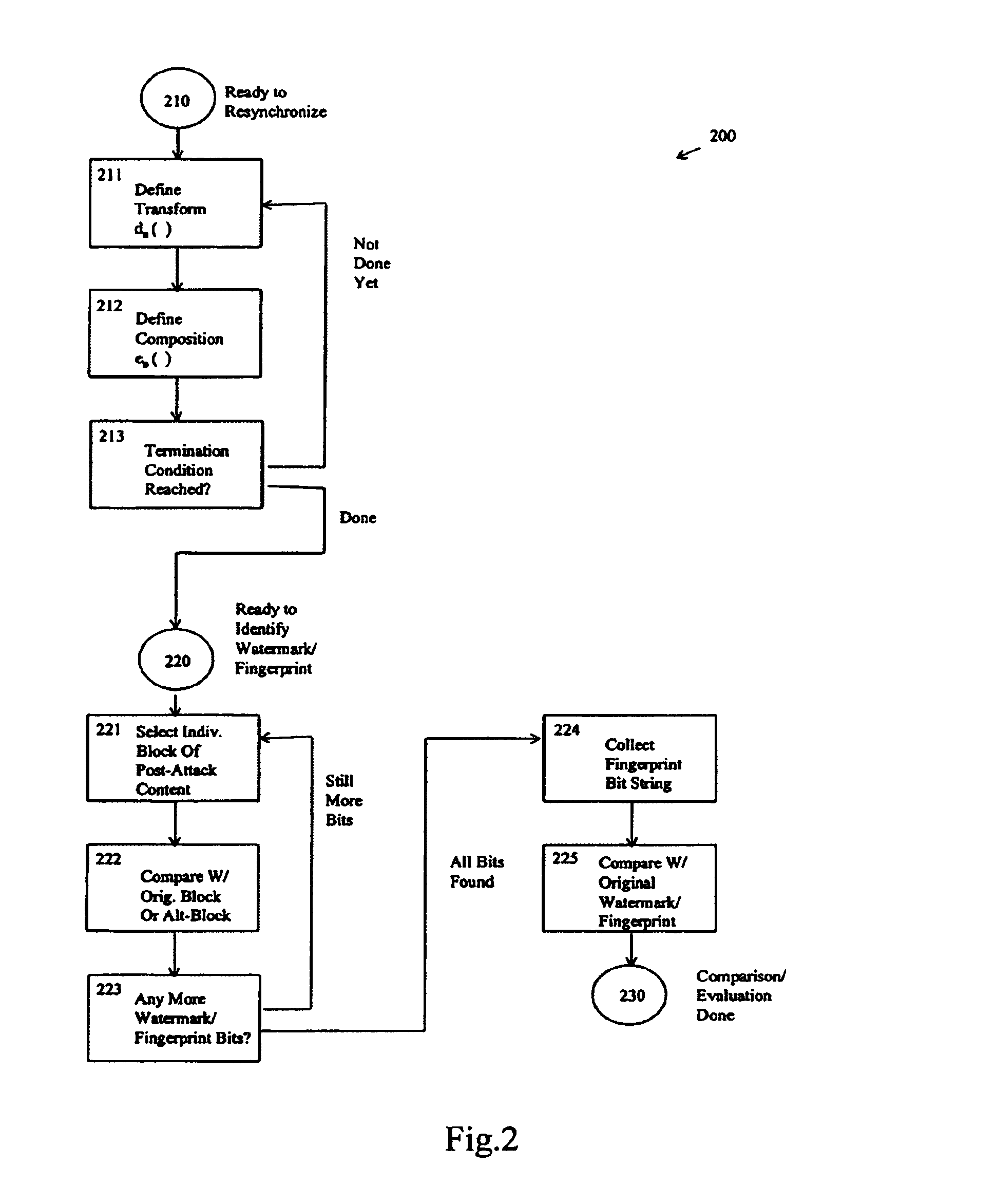
Embedding fingerprinting or watermarking information includes delivering information in-band within digital content representing a media stream, so unauthorized distributors must choose between degrading the media stream, or leaving sufficient information detectable that unauthorized distribution can be detected. For fingerprinting, the method provides a relatively high degree of confidence of both detecting at least one colluding unauthorized distributor, and not falsely accusing any innocent party of being an unauthorized distributor. Embedding fingerprinting or watermarking information includes selecting a sequence of locations within digital content, and embedding information in the form of a sequence of one or more bits at each of those locations, thus representing a set of marking symbols. Marking symbols cannot be readily manufactured without at least one colluding unauthorized distributor having received it, so any distributed digital content includes at least some marking symbols traceable to at least one colluding unauthorized distributor.
Owner:KALEIDESCAPE
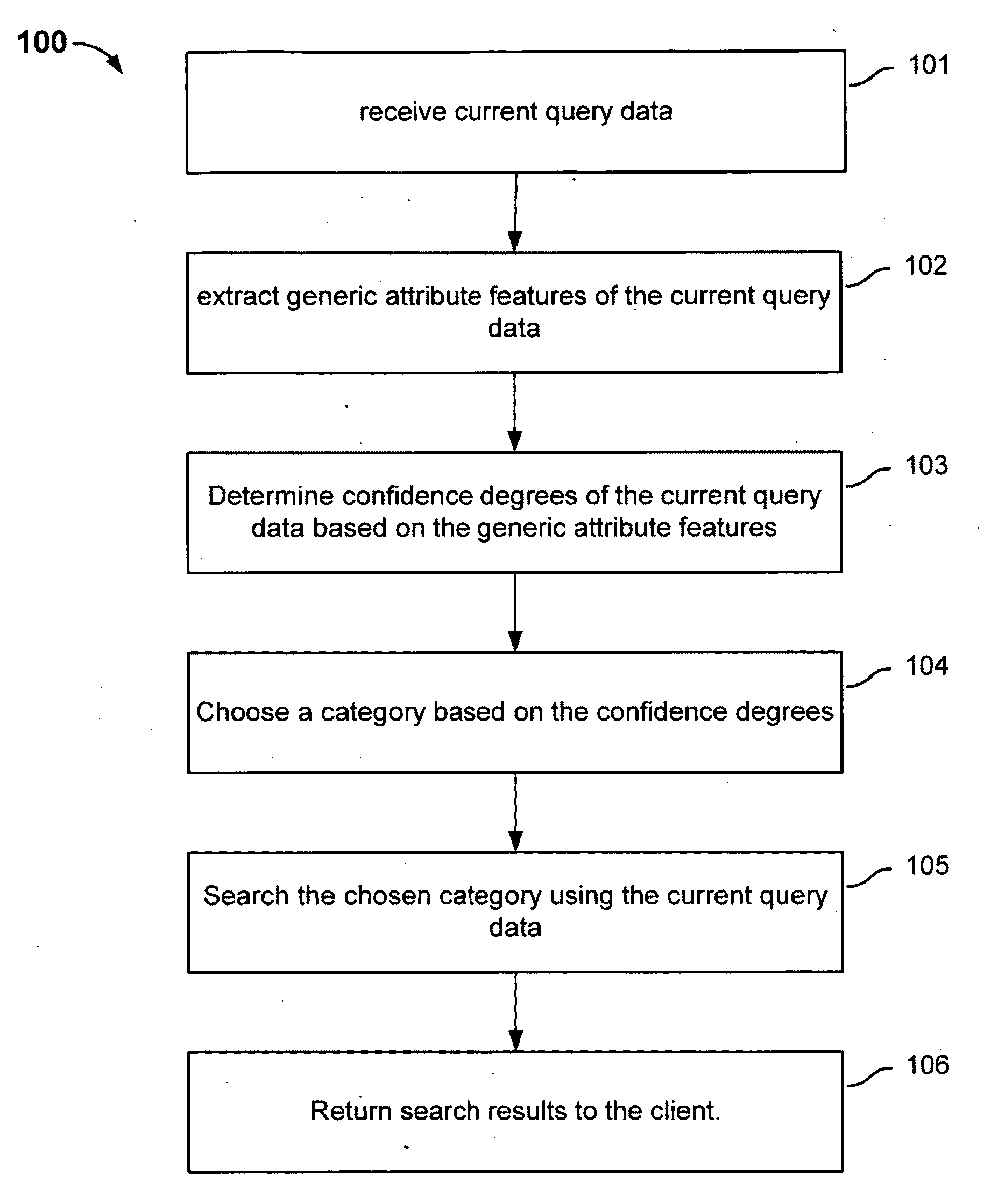
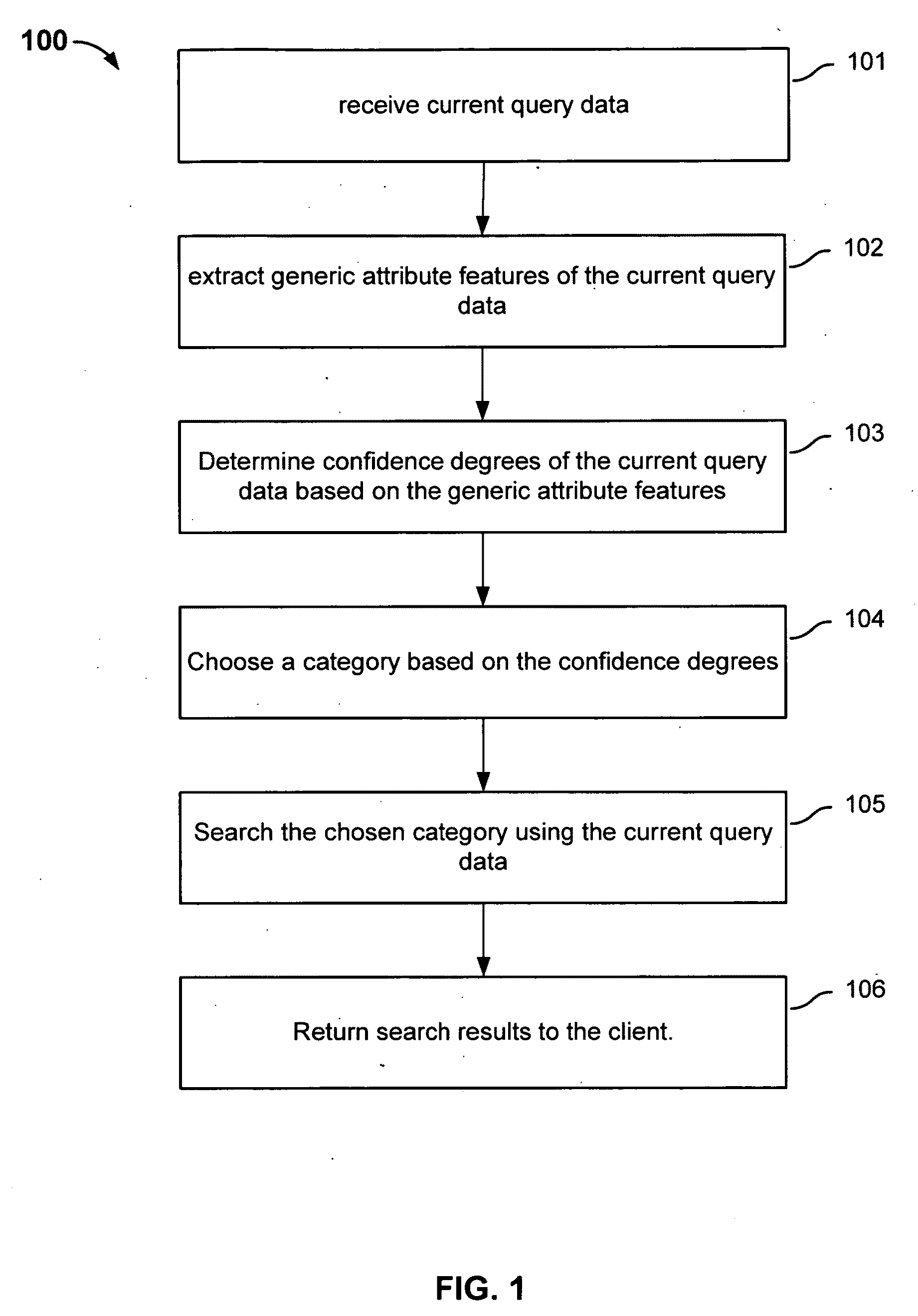
Searching for information based on generic attributes of the query
InactiveUS20110078127A1Improve efficiencyImprove performanceDatabase updatingWeb data indexingDatabaseDegree of confidence
Searching information includes: receiving current query data from a client; extracting generic attribute features of the current query data, wherein the generic attribute features are used for calculating a plurality of confidence degrees of the current query data that correspond to a plurality of categories, each of the confidence degrees indicating a degree of confidence that the current query data belongs to a respective one of the plurality of categories; determining the plurality of confidence degrees of the current query data based at least in part on the generic attribute features; searching in a chosen category for a search result that corresponds to the current query data, the chosen category being one of the plurality of categories and being chosen based at least in part on the plurality of confidence degrees; and returning the search result.
Owner:ALIBABA GRP HLDG LTD
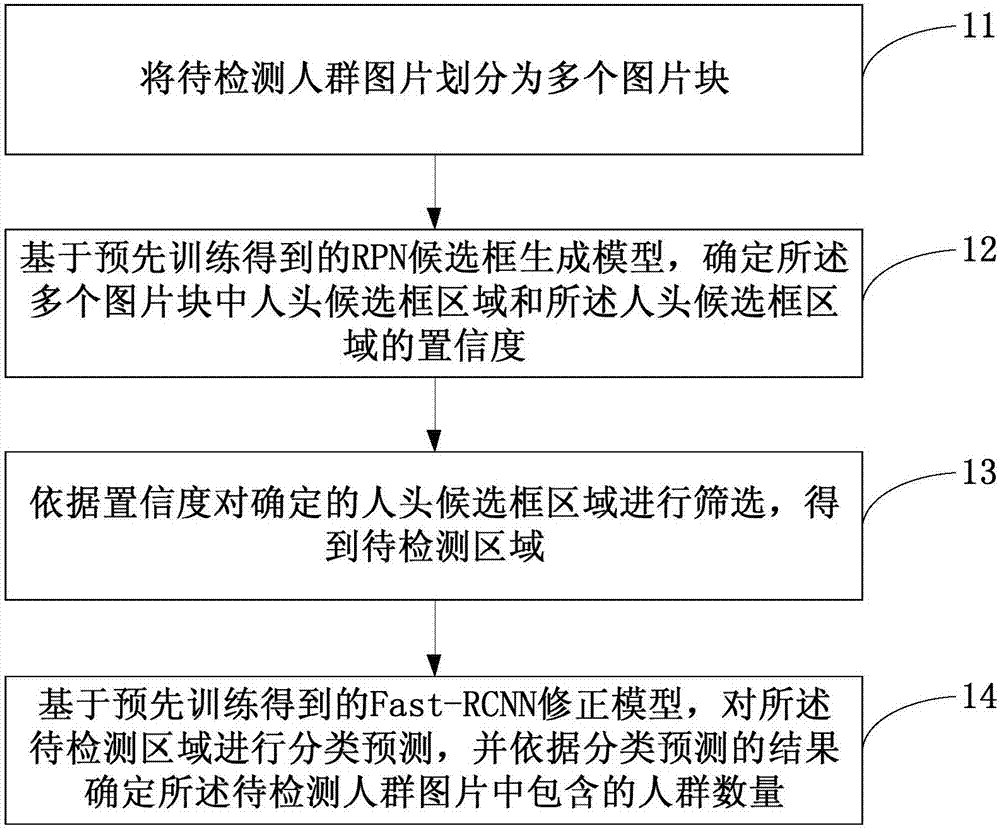
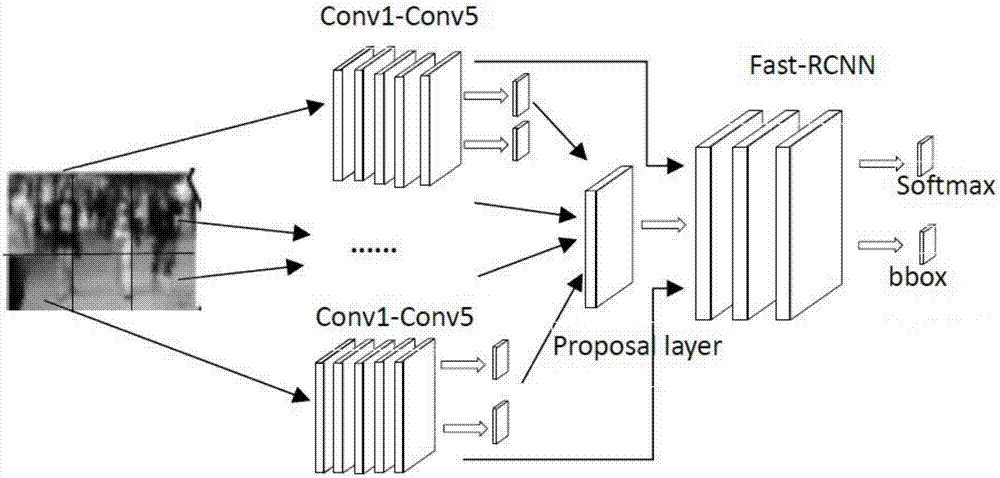
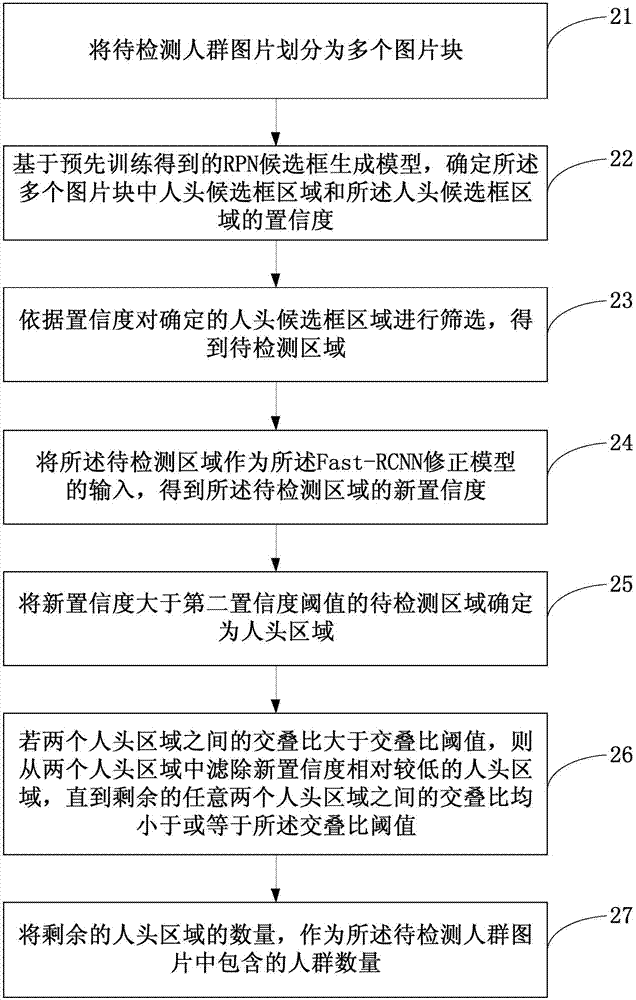
Crowd counting method based on deep learning and apparatus thereof
ActiveCN106960195AImprove accuracyImprove robustnessCharacter and pattern recognitionPattern recognitionCrowd counting
Embodiments of the invention disclose a crowd counting method based on deep learning and an apparatus thereof. The method comprises the following steps of dividing a crowd picture to be detected into a plurality of picture blocks; based on an RPN candidate frame acquired from training in advance, generating a model, and determining head candidate frame areas in the plurality of picture blocks and degrees of confidence of the head candidate frame areas; according to the degrees of confidence, screening the determined head candidate frame areas and acquiring an area to be detected; and based on a Fast-RCNN correction model acquired from the training in advance, carrying out classification prediction on the area to be detected, and according to a classification prediction result, determining a crowd number included in the crowd picture to be detected. In the embodiments of the invention, the crowd counting method under high resolution is provided, and accuracy and robustness of crowd counting are increased.
Owner:深圳市和巨信息技术有限公司
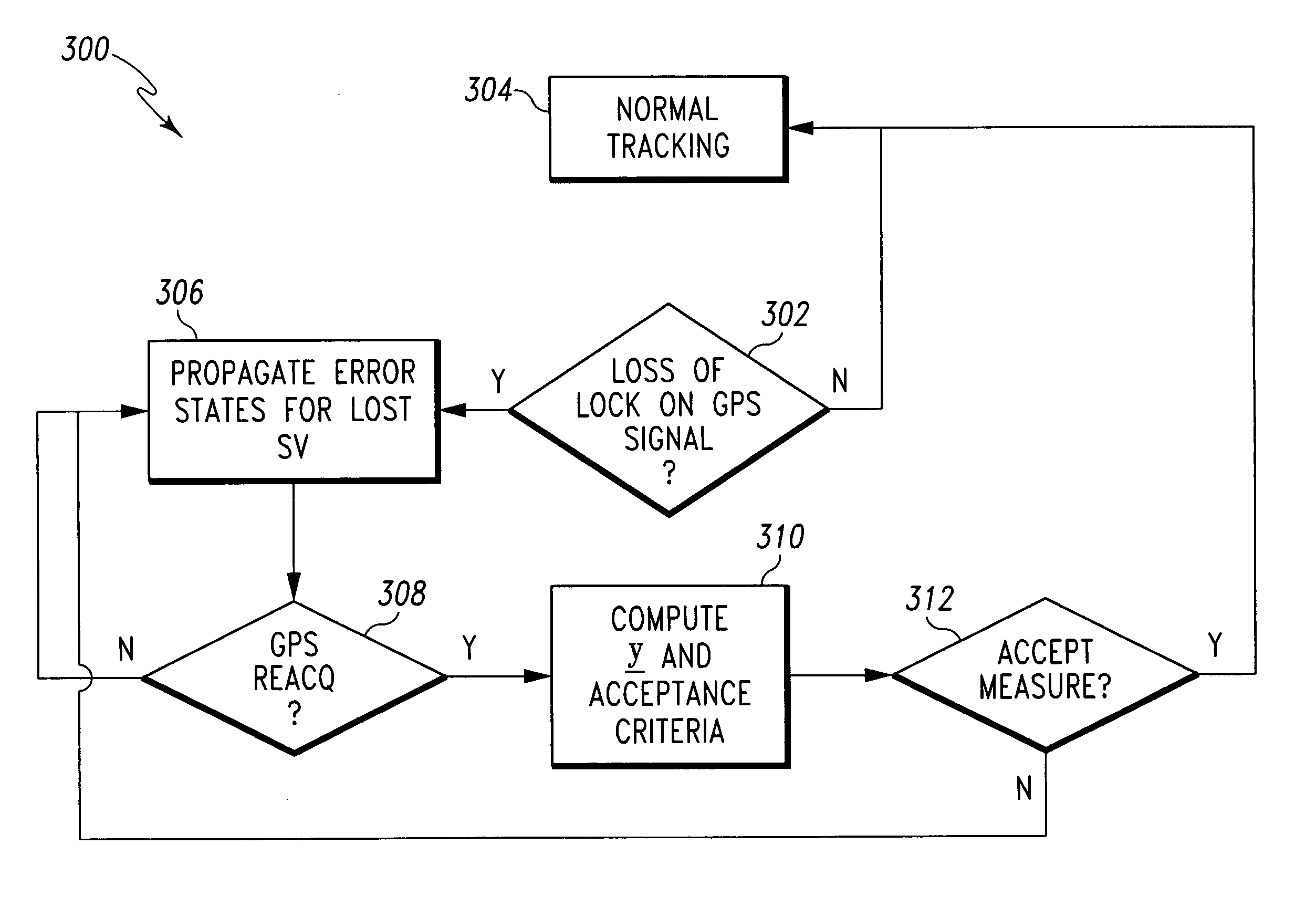
System and method for detecting false navigation signals
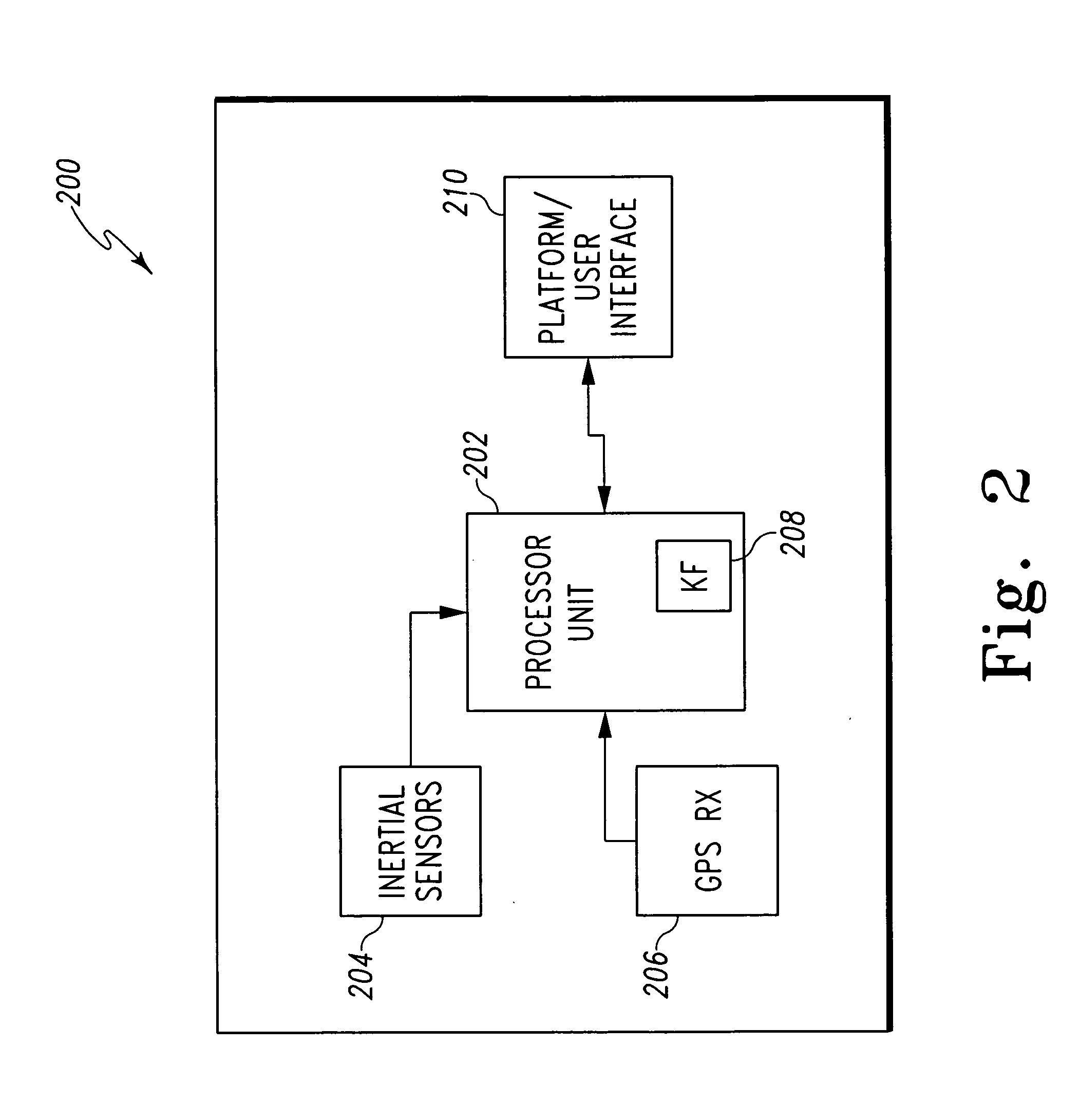
ActiveUS20070194984A1Improve trustPosition fixationSatellite radio beaconingGps measurementKaiman filter
A system and method for detecting and excluding false GPS signals are disclosed, which predict a GPS measurement value with a high degree of confidence, compare the predicted value with measured values, and reject a false measurement based on the comparison results. As one example, a tightly coupled GPS / Inertial Navigation System (GPS / INS) is disclosed, which uses a Kalman filter for comparison of a predicted GPS measurement value with measured values (e.g., the residuals) to form the basis for the rejection of false measurements. This rejection is referred to as a chi-squared reject, and can be extended in time in order to apply the same test to a reacquired signal following the loss of an original validated GPS signal. The Kalman filter propagates the receiver's clock bias rate, and enables the system to predict the GPS measurements at the time of reacquisition. The residuals are compared to a limit defined by the uncertainties of the prediction and the measurement errors expected to be involved.
Owner:HONEYWELL INT INC
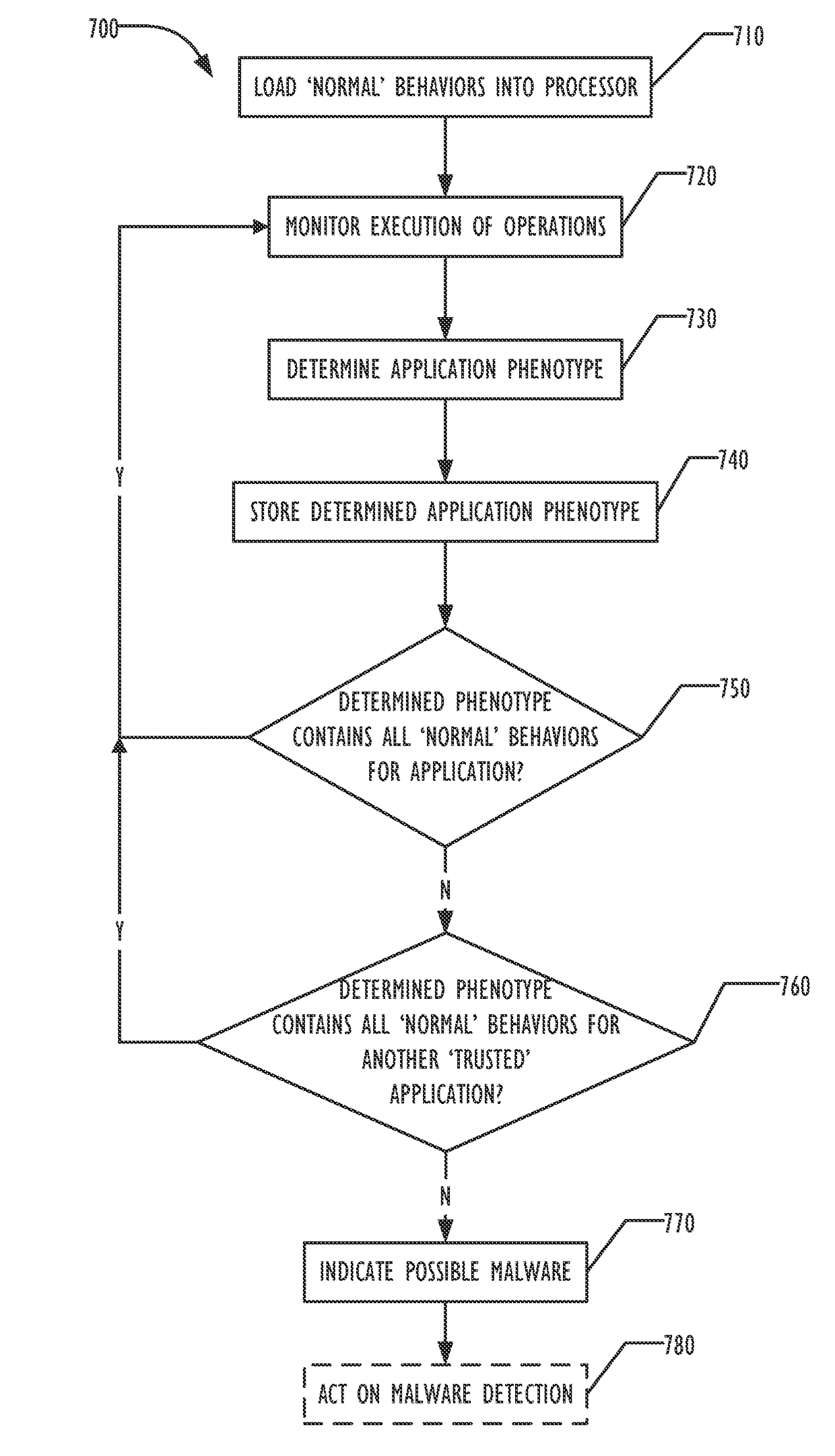
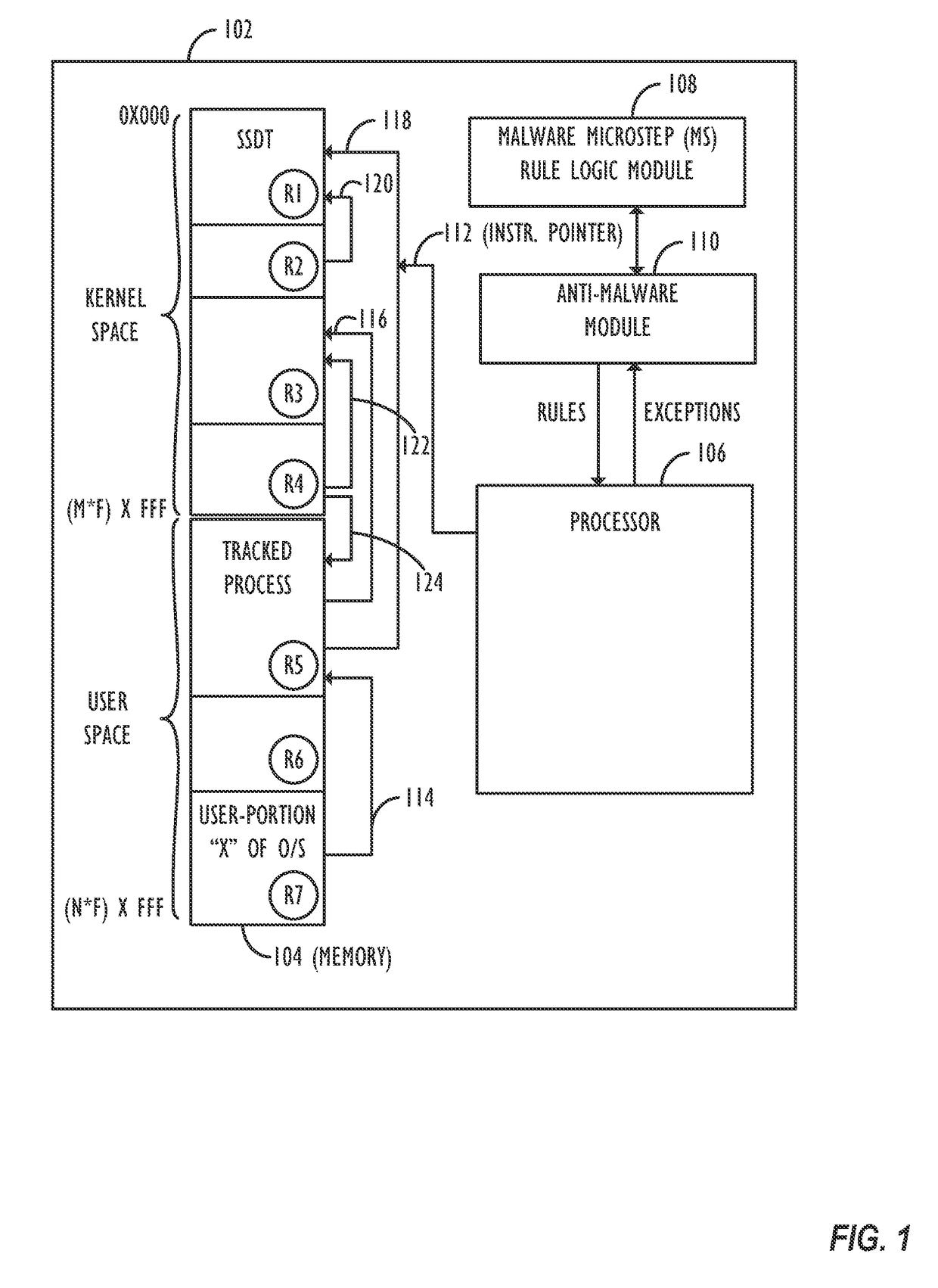
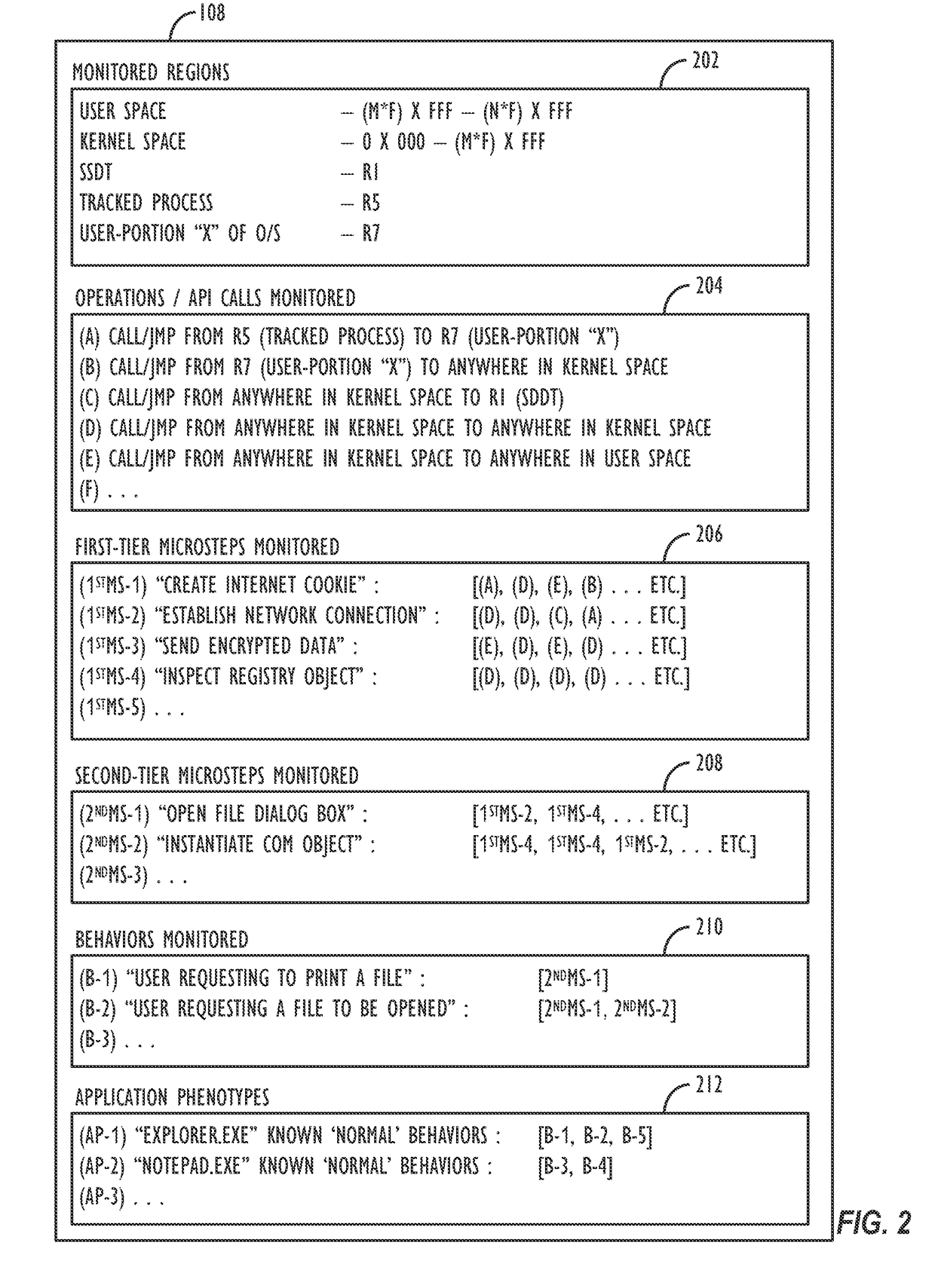
Application phenotyping
ActiveUS20170093897A1Digital data information retrievalComputer security arrangementsUser deviceInternet privacy
A collection of techniques is disclosed to allow for the detection of malware that leverages pattern recognition and machine learning to effectively provide “content-less” malware detection, i.e., detecting a process as being an ‘anomaly’ not based on its particular content, but instead based on comparisons of its behavior to known (and characterized) ‘trusted’ application behaviors, i.e., the trusted applications' “phenotypes” and / or the phenotypes of known malware applications. By analyzing the patterns of normal behavior performed by trusted applications as well as malware applications, one can build a set of sophisticated, content-agnostic behavioral models (i.e., “application phenotypes”)—and later compare the processes executed on a user device to the stored behavioral models to determine whether the actual measured behavior reflects a “good” application, or if it differs from the stored behavioral models to a sufficient degree and with a sufficient degree of confidence, thus indicating a potentially malicious application or behavior.
Owner:MCAFEE LLC
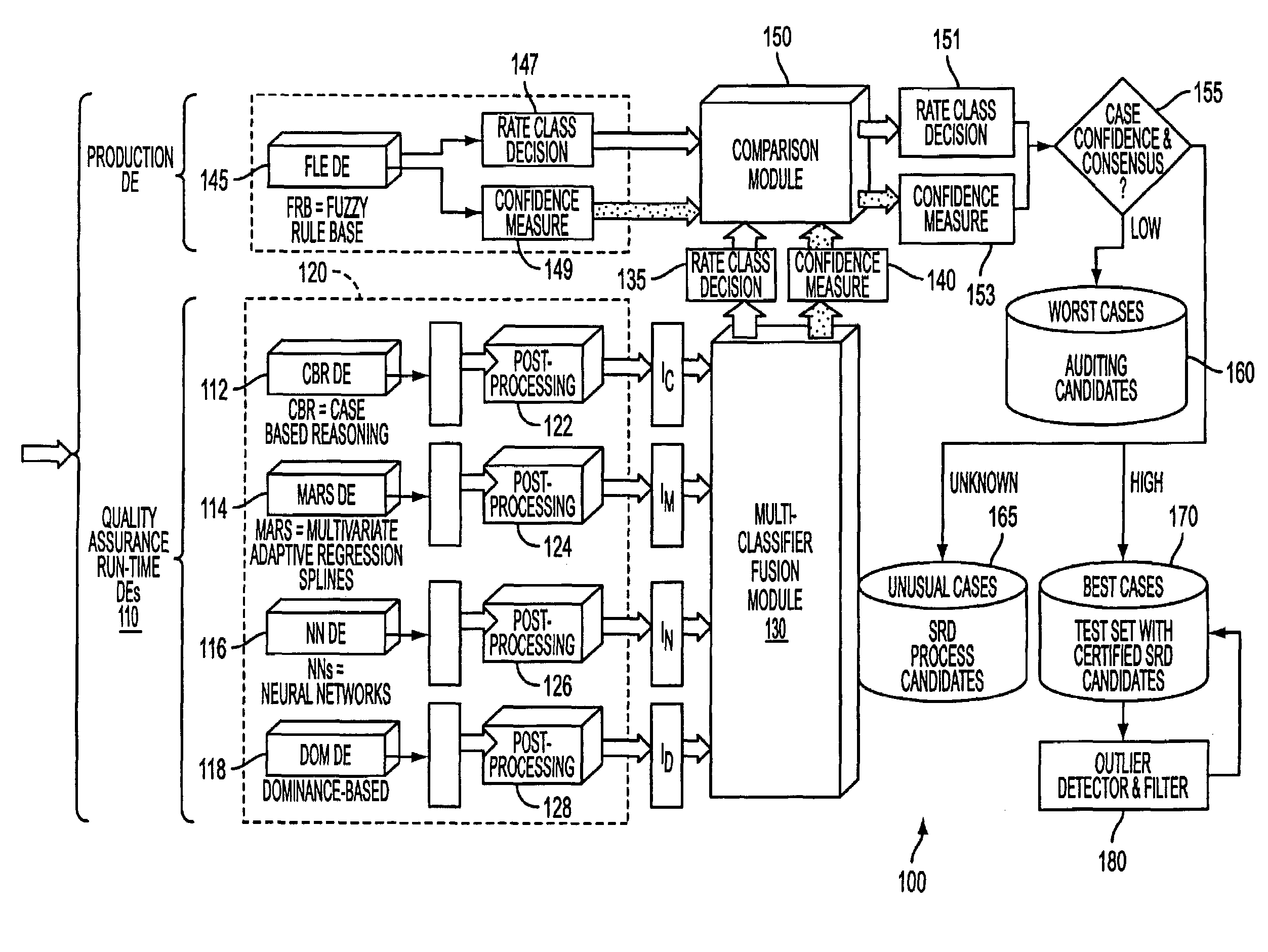
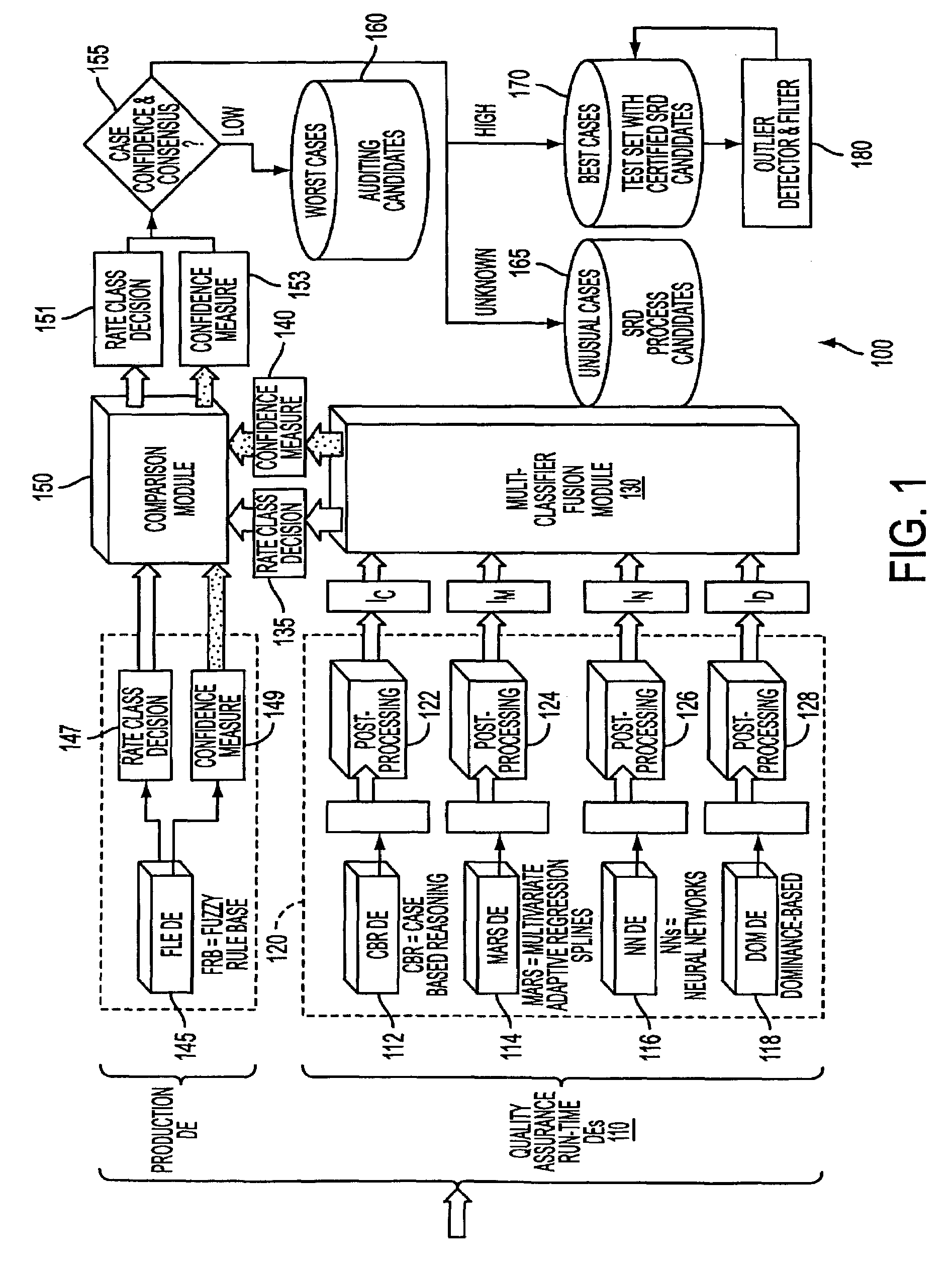
System and process for a fusion classification for insurance underwriting suitable for use by an automated system
A method and system for fusing a collection of classifiers used for an automated insurance underwriting system and / or its quality assurance is described. Specifically, the outputs of a collection of classifiers are fused. The fusion of the data will typically result in some amount of consensus and some amount of conflict among the classifiers. The consensus will be measured and used to estimate a degree of confidence in the fused decisions. Based on the decision and degree of confidence of the fusion and the decision and degree of confidence of the production decision engine, a comparison module may then be used to identify cases for audit, cases for augmenting the training / test sets for re-tuning production decision engine, cases for review, or may simply trigger a record of its occurrence for tracking purposes. The fusion can compensate for the potential correlation among the classifiers. The reliability of each classifier can be represented by a static or dynamic discounting factor, which will reflect the expected accuracy of the classifier. A static discounting factor is used to represent a prior expectation about the classifier's reliability, e.g., it might be based on the average past accuracy of the model, while a dynamic discounting is used to represent a conditional assessment of the classifier's reliability, e.g., whenever a classifier bases its output on an insufficient number of points it is not reliable.
Owner:GE FINANCIAL ASSURANCE HLDG INC A RICHMOND
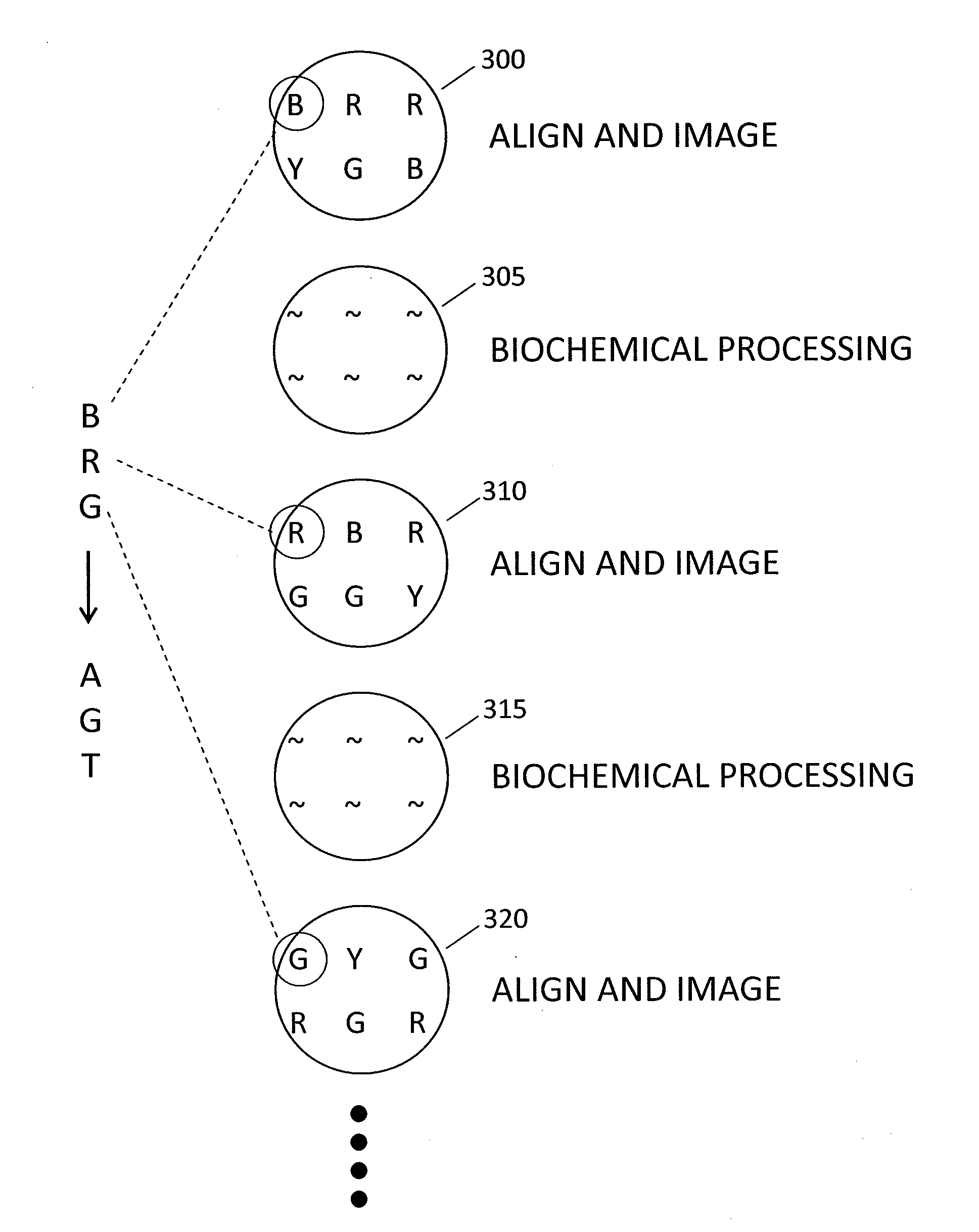
Method and system for accurate alignment and registration of array for DNA sequencing
ActiveUS20110268347A1High precisionImprove trustImage enhancementImage analysisGenomic sequencingPattern matching
In a genome sequencing system and methodology, a protocol is provided to achieve precise alignment and accurate registration of an image of a planar array of nanoballs subject to optical analysis. Precise alignment correcting for fractional offsets is achieved by correcting for errors in subperiod x-y offset, scale and rotation by use of minimization techniques and Moiré averaging. In Moiré averaging, magnification is intentionally set so that the pixel period of the imaging element is a noninteger multiple of the site period. Accurate registration is achieved by providing for pre-defined pseudo-random sets of sites, herein deletion or reserved sites, where nanoballs are prevented from attachment to the substrate so that the sites of the array can be used in a pattern matching scheme as registration markers for absolute location identification. Information can be extracted with a high degree of confidence that it is correlated to a known location, while at the same time the amount of information that can be packed on a chip is maximized.
Owner:COMPLETE GENOMICS INC
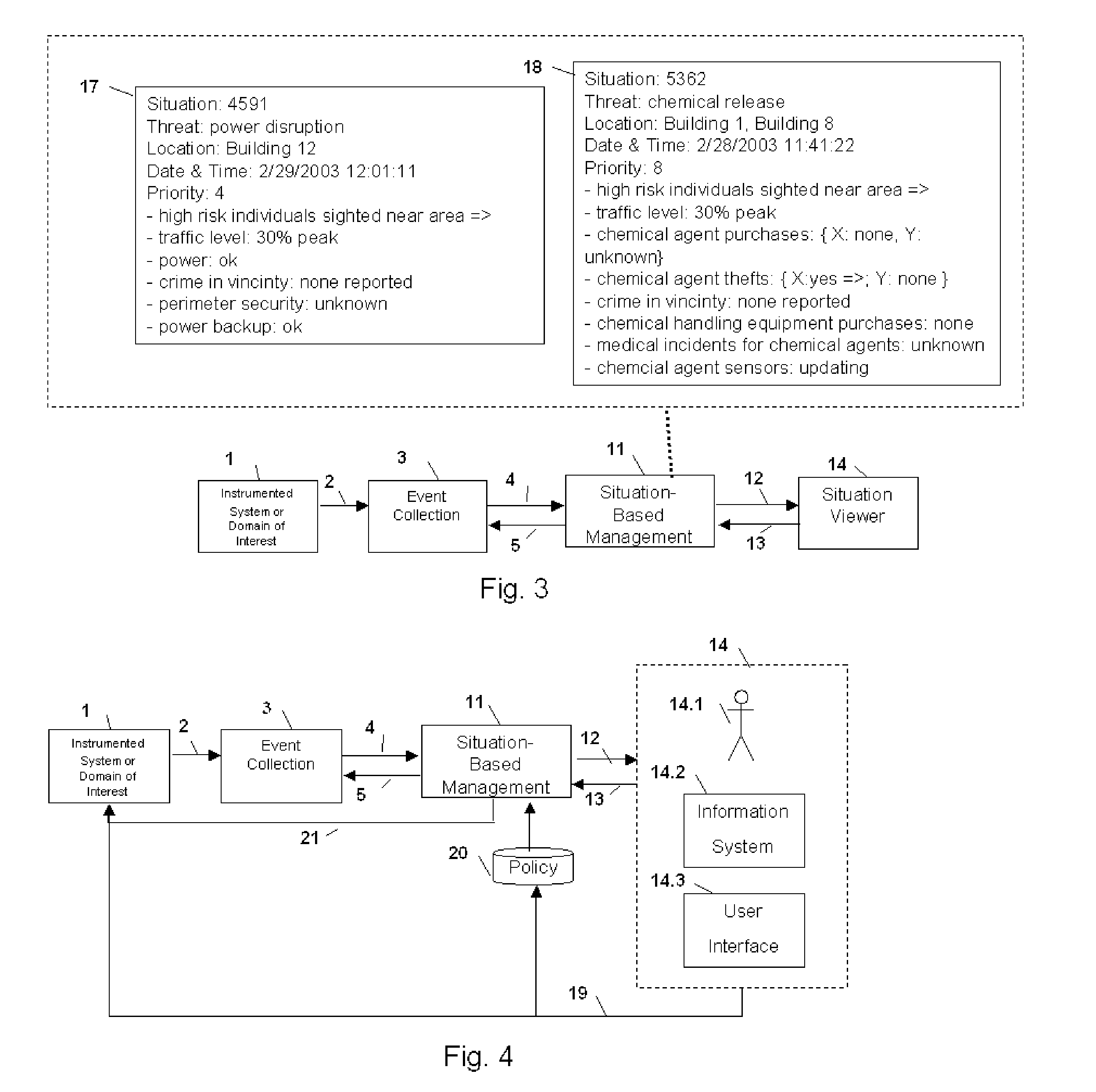
Method and Apparatus for Creating and Using Situation Transition Graphs in Situation-Based Management
InactiveUS20050222895A1Guaranteed normal transmissionRemove redundant informationFinanceResourcesArtificial systemsTwo-way communication
Method and apparatus for situation-based management of natural and artificial systems using event correlation and a situation manager. Input is provided from multiple sources in the form of a collection of events. A first level of processing performs event correlation over the collection of events and infers new events and new qualities of events. A second level of processing manages situations based on the collection of events, where situations are recognized, maintained, and given a degree of confidence. Situations are periodically updated based on incoming events. The assertion of a situation may call for information from external sources, provide information for external sources, and provide control instructions to external sources. Given a current situation, past, and possible future situations are inferred. Additionally, a method and apparatus for bi-directional communication between the event correlator and situation manager.
Owner:ALTUSYS
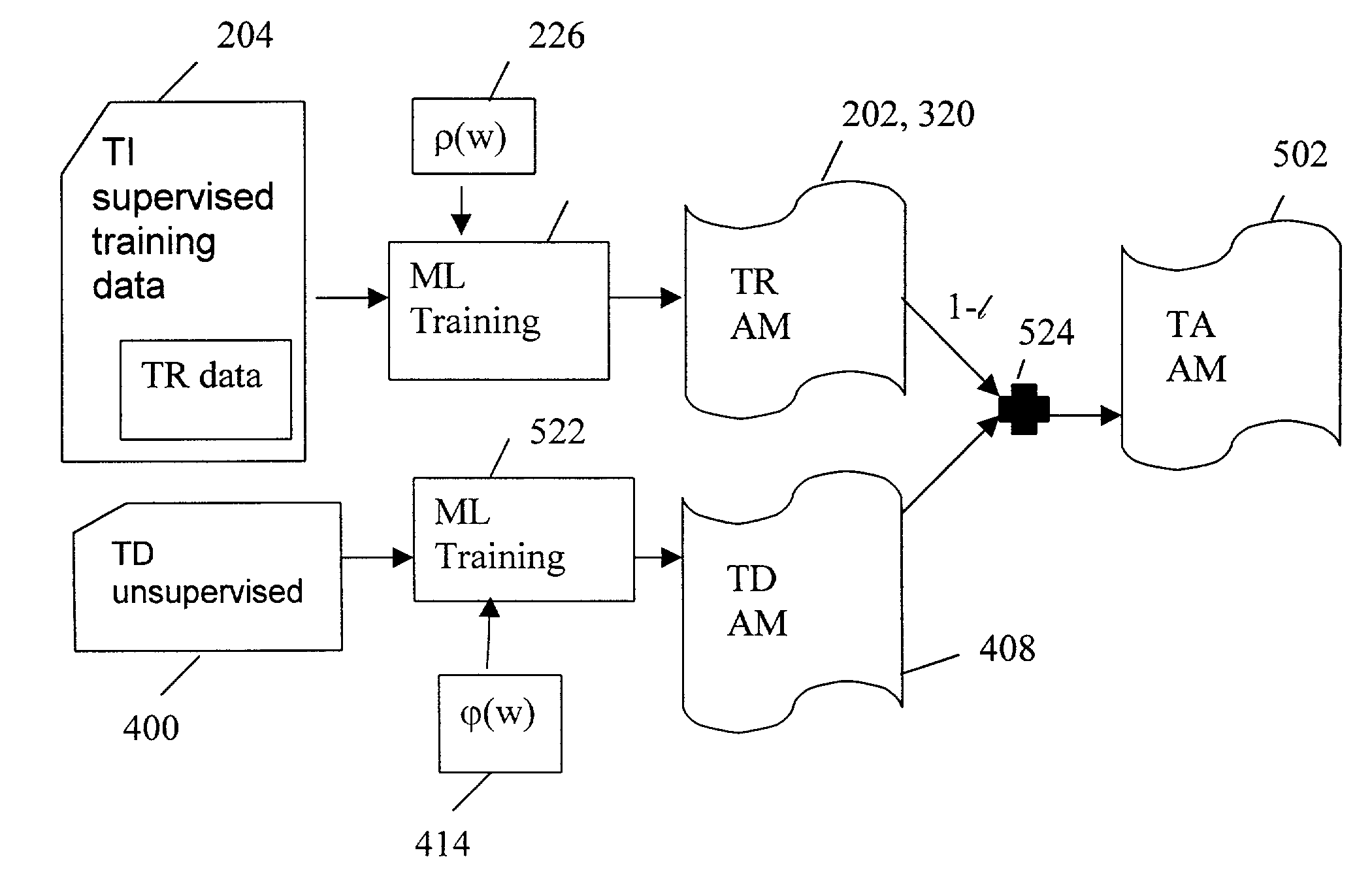
Generating a task-adapted acoustic model from one or more supervised and/or unsupervised corpora
Unsupervised speech data is provided to a speech recognizer that recognizes the speech data and outputs a recognition result along with a confidence measure for each recognized word. A task-related acoustic model is generated based on the recognition result, the speech data and the confidence measure. Additional task independent model can be used. The speech data can be weighted by the confidence measure in generating the acoustic model so that only data that has been recognized with a high degree of confidence will weigh heavily in generation of the acoustic model. The acoustic model can be formed from a Gaussian mean and variance of the data.
Owner:MICROSOFT TECH LICENSING LLC
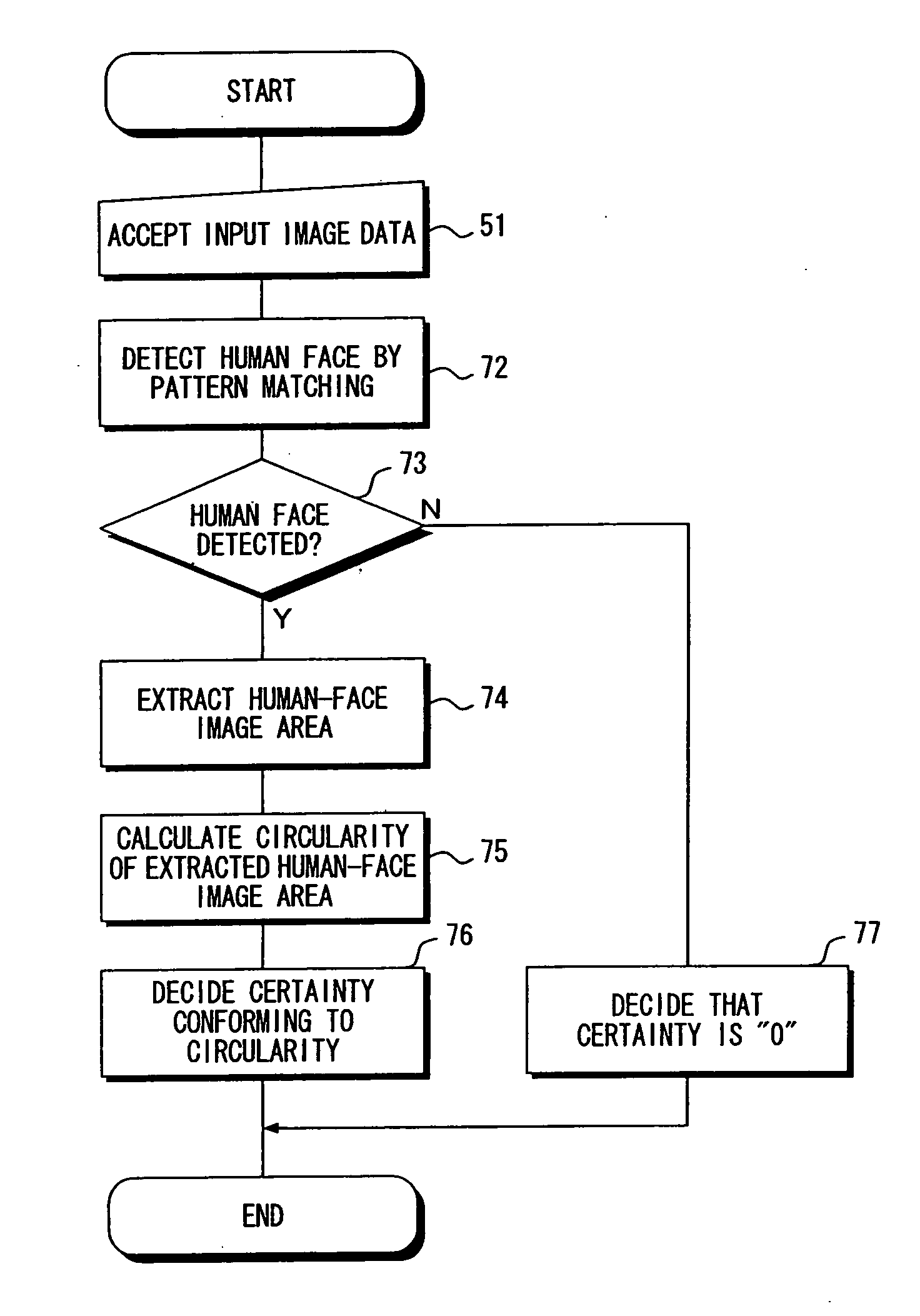
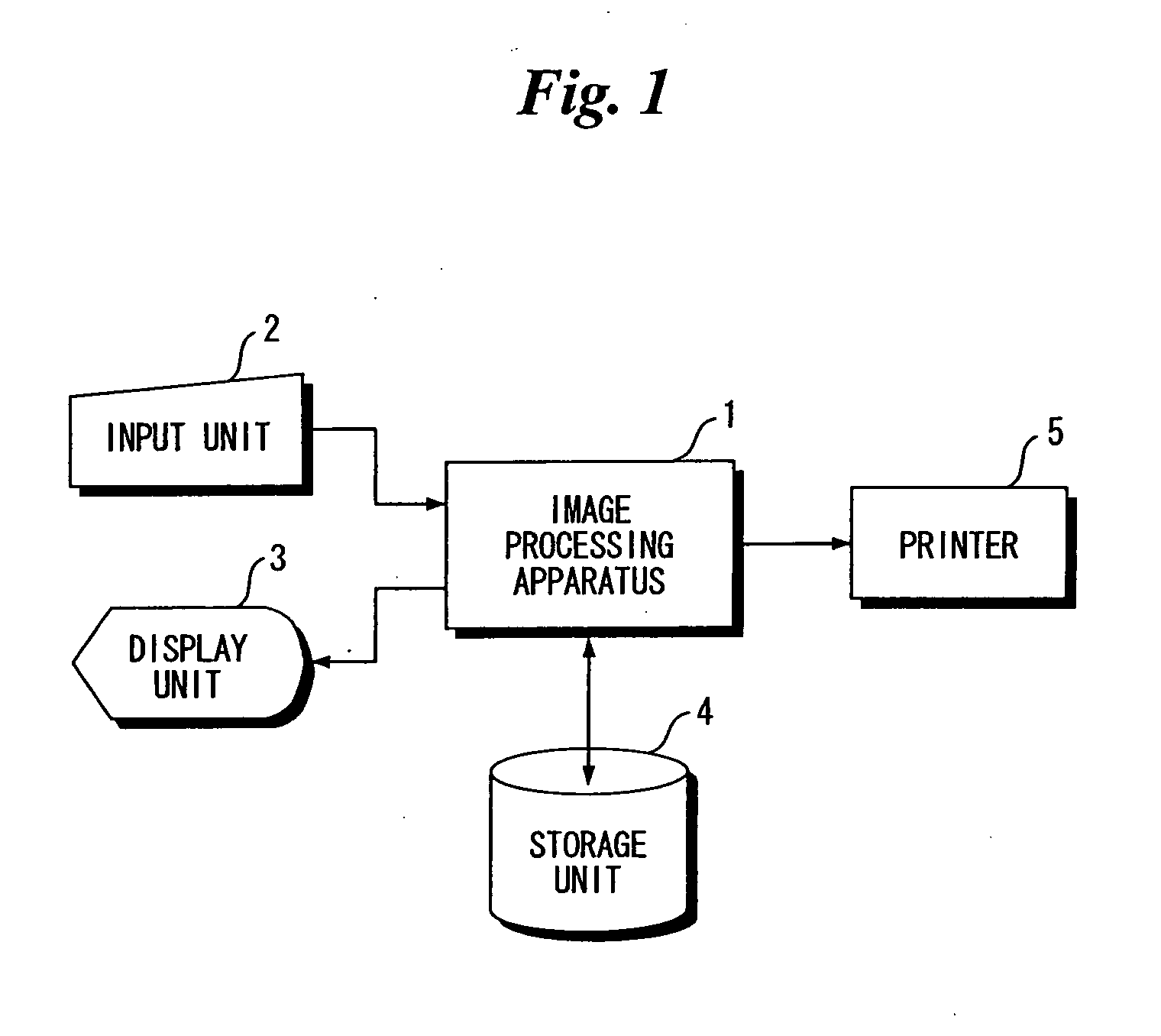
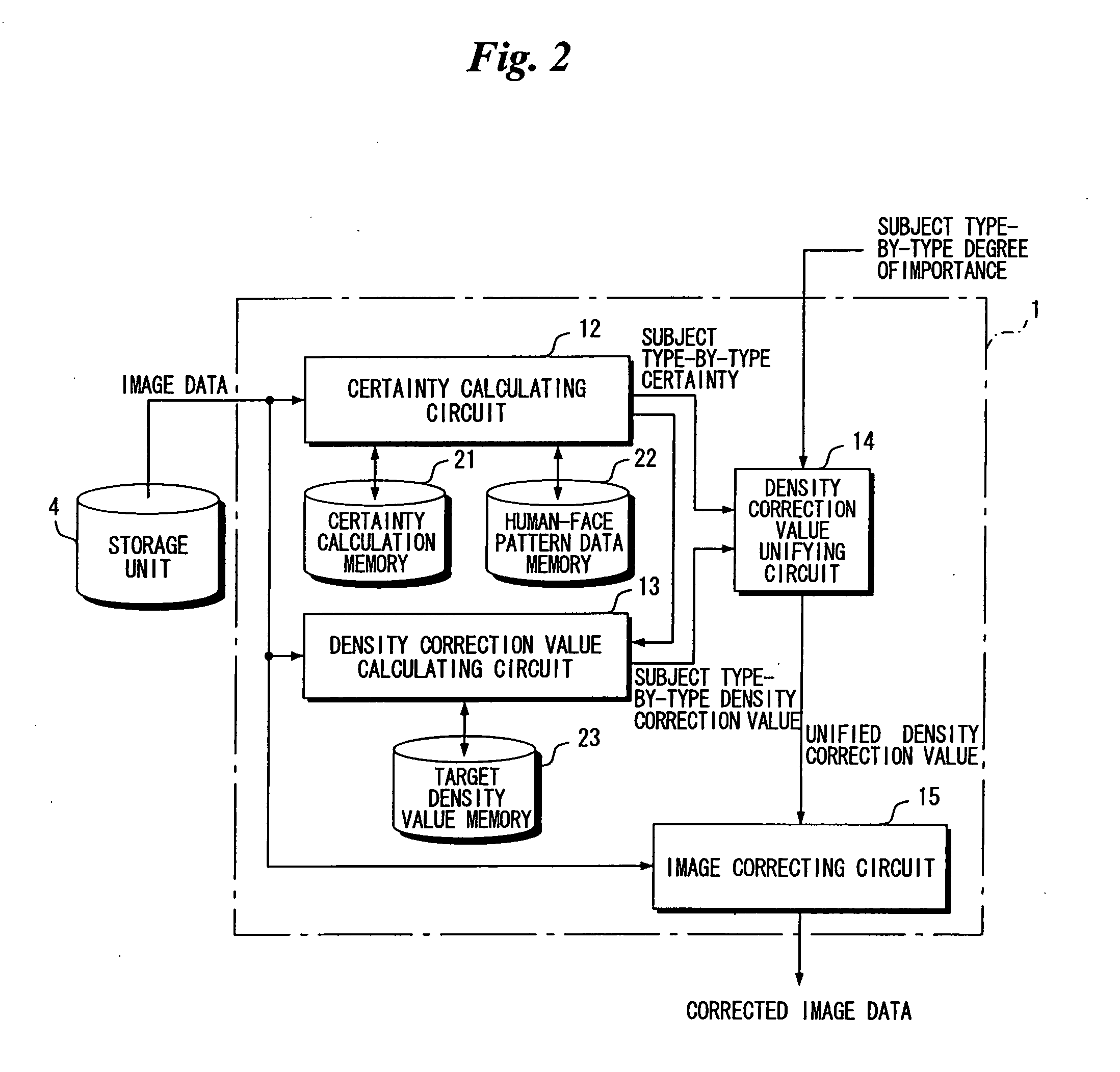
Image Processing Apparatus and Method, and Image Processing Program
ActiveUS20070292038A1Degree of certaintyImprove certaintyImage enhancementCharacter and pattern recognitionImaging processingAlgorithm
Owner:FUJIFILM CORP
High precision ultrasonic corrosion rate monitoring
ActiveUS20110067497A1Analysing solids using sonic/ultrasonic/infrasonic wavesWeather/light/corrosion resistanceUltrasonic testingPulse measurement
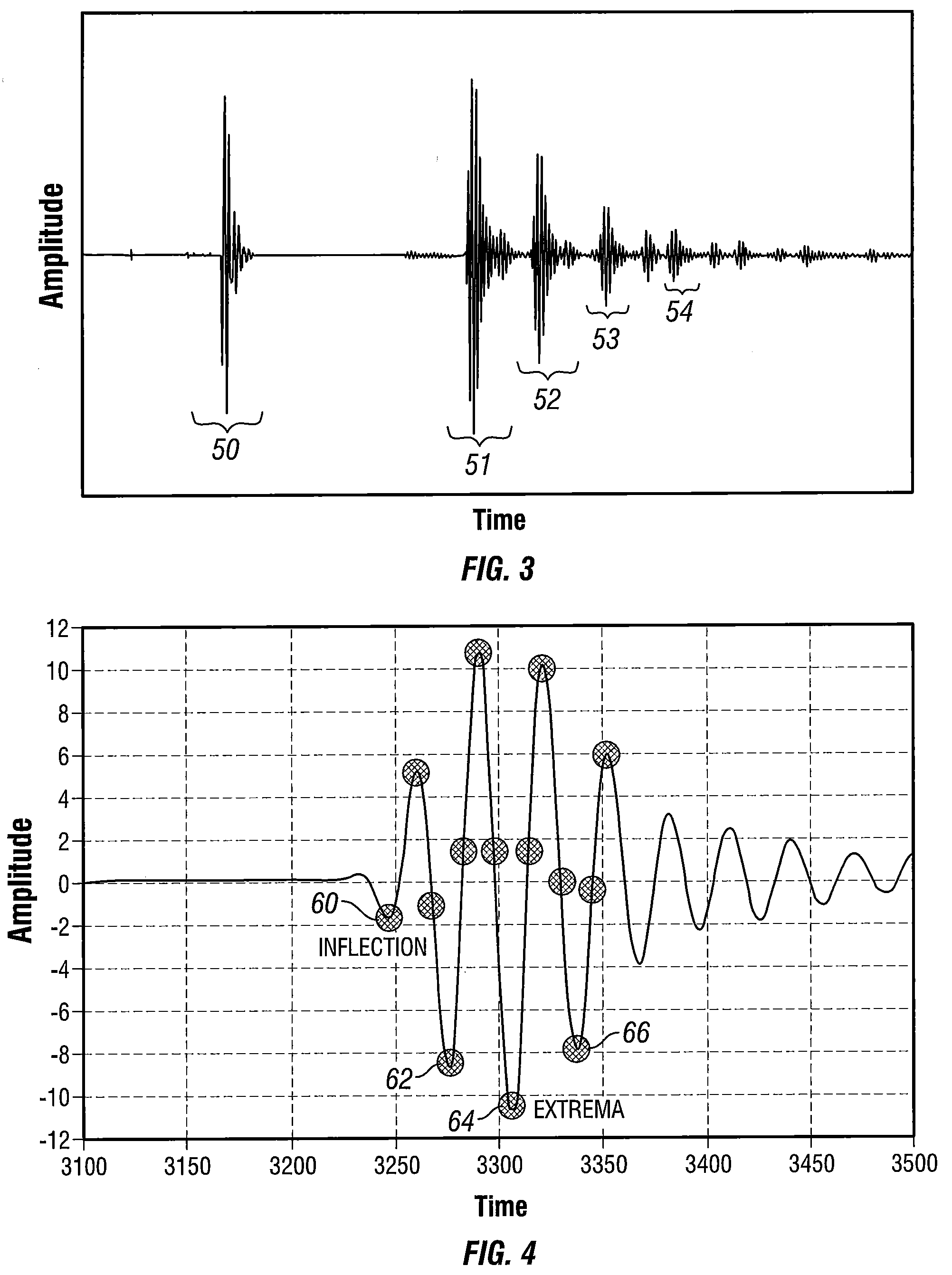
The invention relates to very precisely measuring changes in thickness of pipe walls to determine corrosion rate prior to any significant corrosion loss. The thickness is determined by ultrasonic testing where many measurements of the wall thickness are taken at the same spot by a fixed sensor and errors associated with noise and temperature changes are substantially eliminated. A highly sensitive receiver converts each reflected pulse to waves that are averaged with other pulse measurements. The resulting average wave is analyzed so that each waveform is analyzed to identify the extrema and inflection points of each reflected pulse. The resulting analysis provides a far more accurate determination of the time between reflected pulses. As a result, a far more accurate picture of corrosion at the location of the wall of the pipe can be determined within weeks with a high degree of confidence.
Owner:CONOCOPHILLIPS CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com