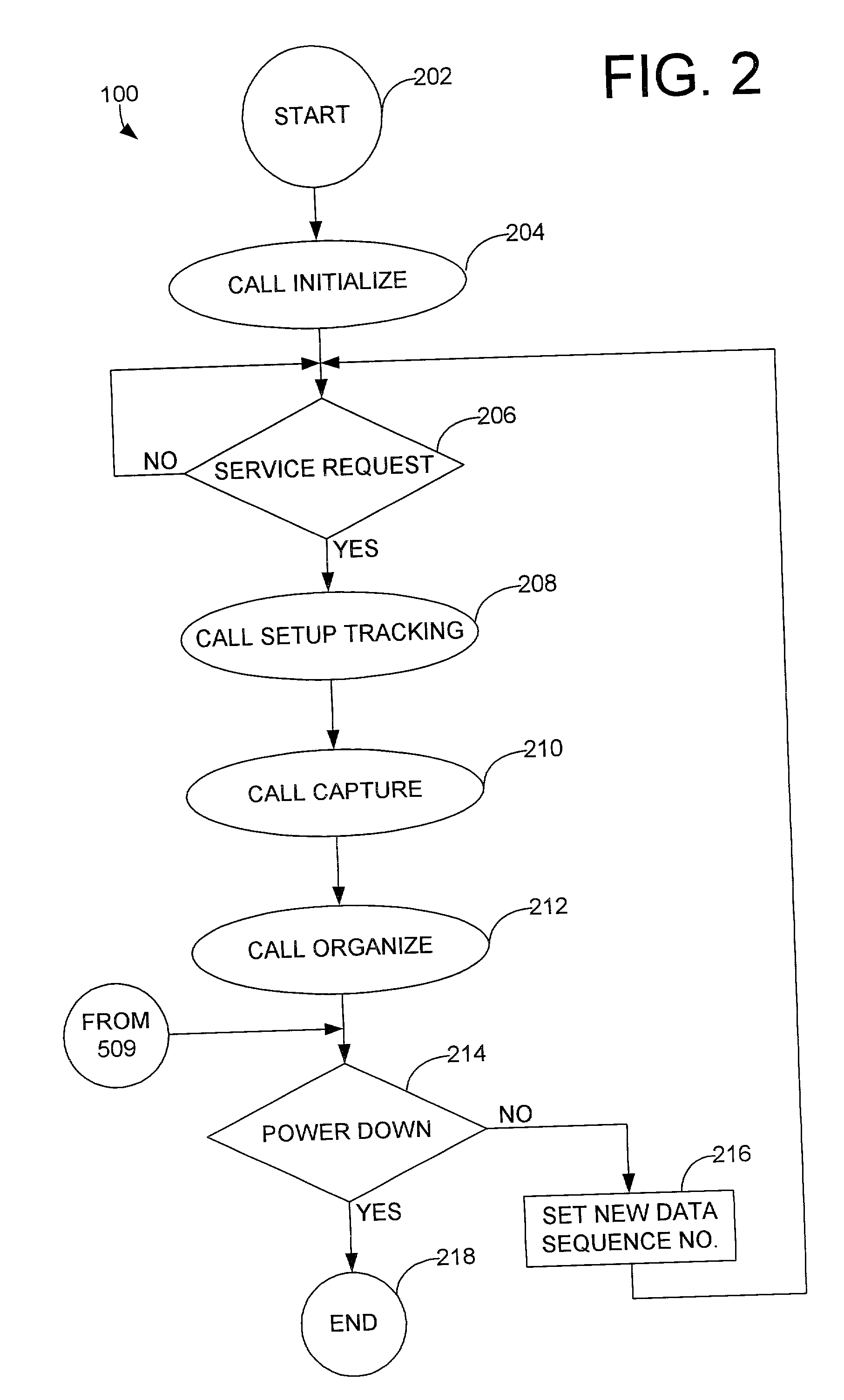
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
131 results about "Chain of custody" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
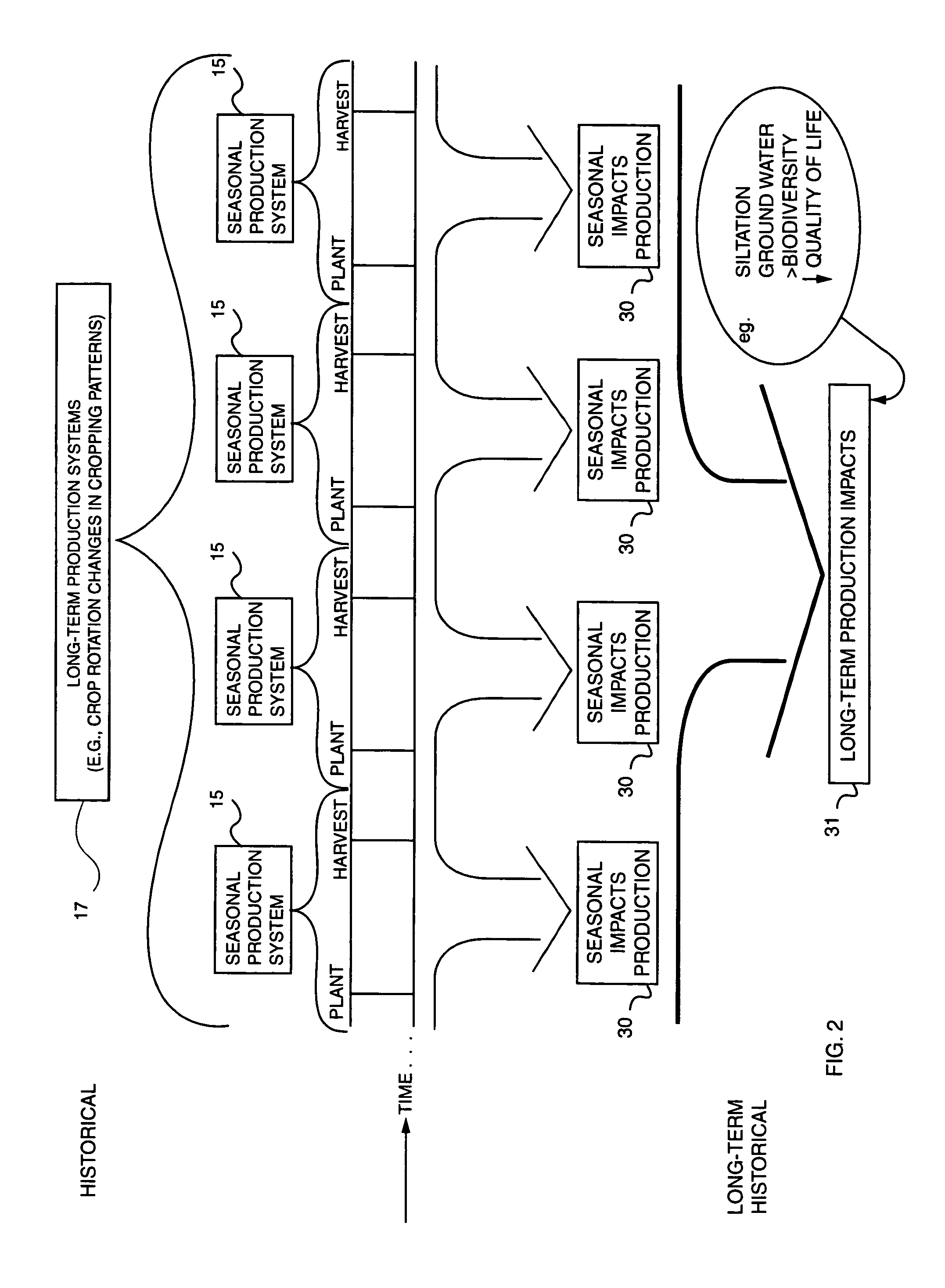
Chain of custody (CoC), in legal contexts, is the chronological documentation or paper trail that records the sequence of custody, control, transfer, analysis, and disposition of physical or electronic evidence. Of particular importance in criminal cases, the concept is also applied in civil litigation—and sometimes more broadly in drug testing of athletes, and in supply chain management, e.g. to improve the traceability of food products, or to provide assurances that wood products originate from sustainably managed forests. It is often a tedious process that has been required for evidence to be shown legally in court. Now however, with new portable technology that allows accurate laboratory quality results from the scene of the crime, the chain of custody is often much shorter which means evidence can be processed for court much faster.
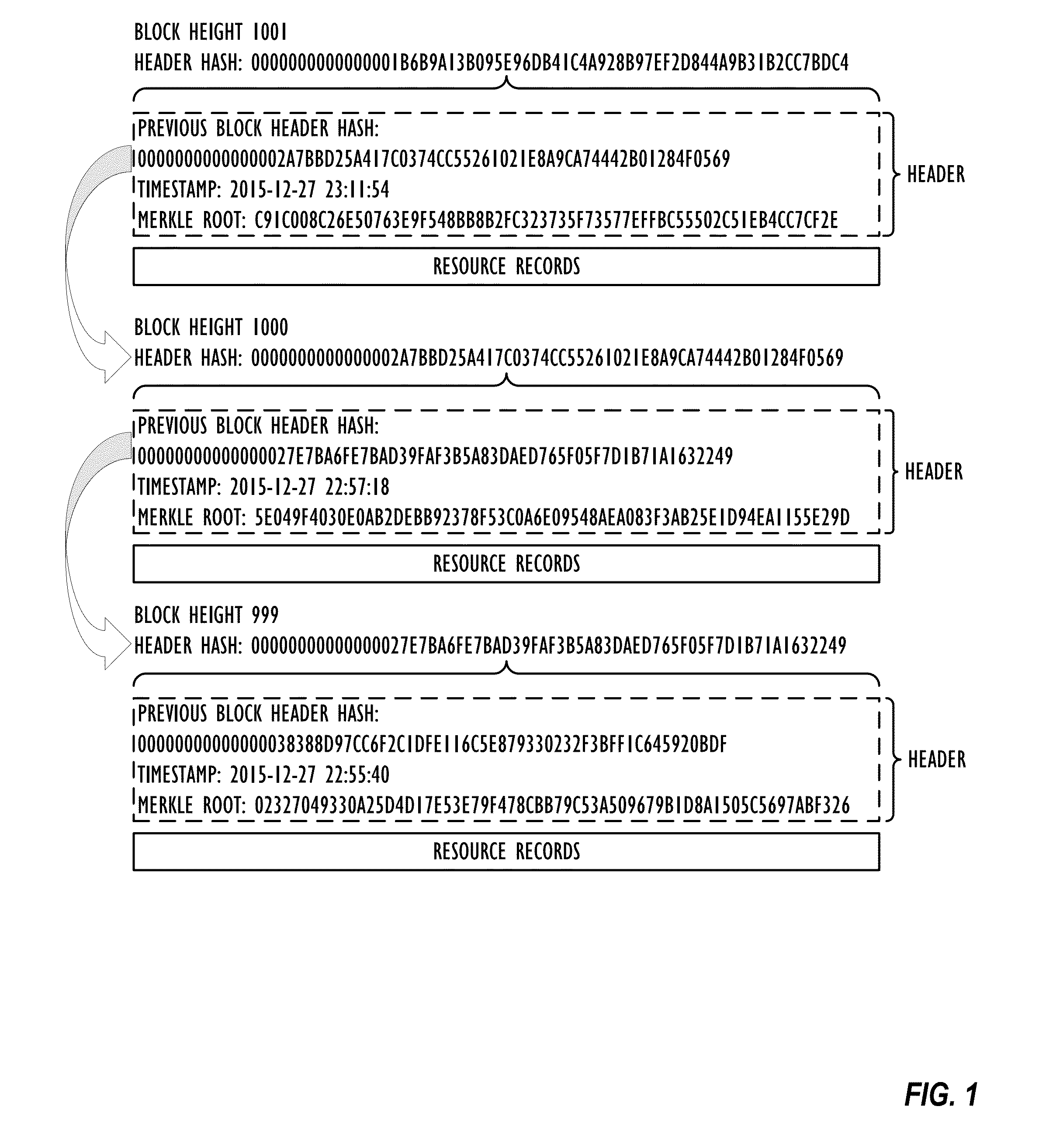
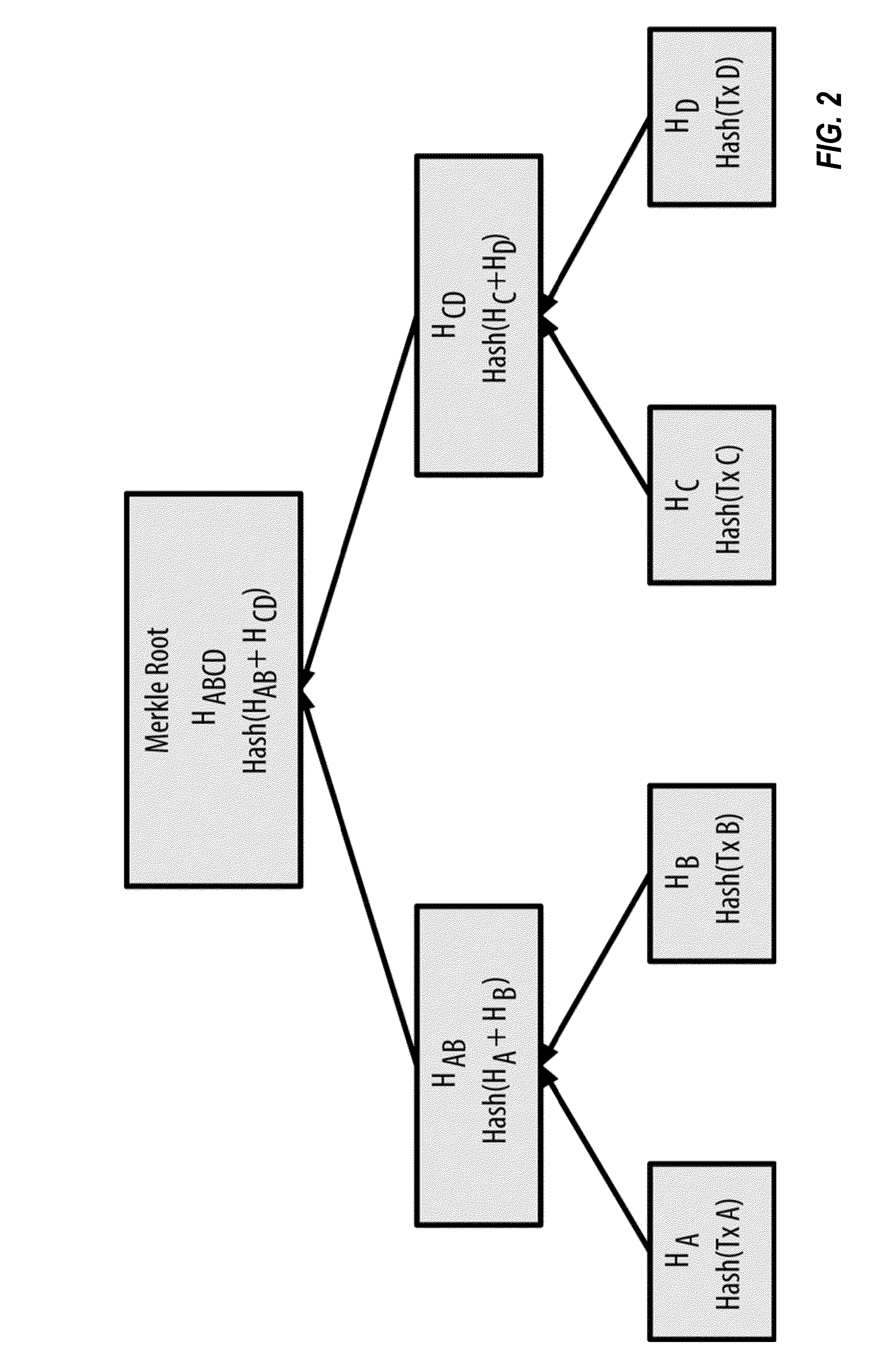
Authentication and verification of digital data utilizing blockchain technology
InactiveUS20160283920A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesDigital dataHuman interaction
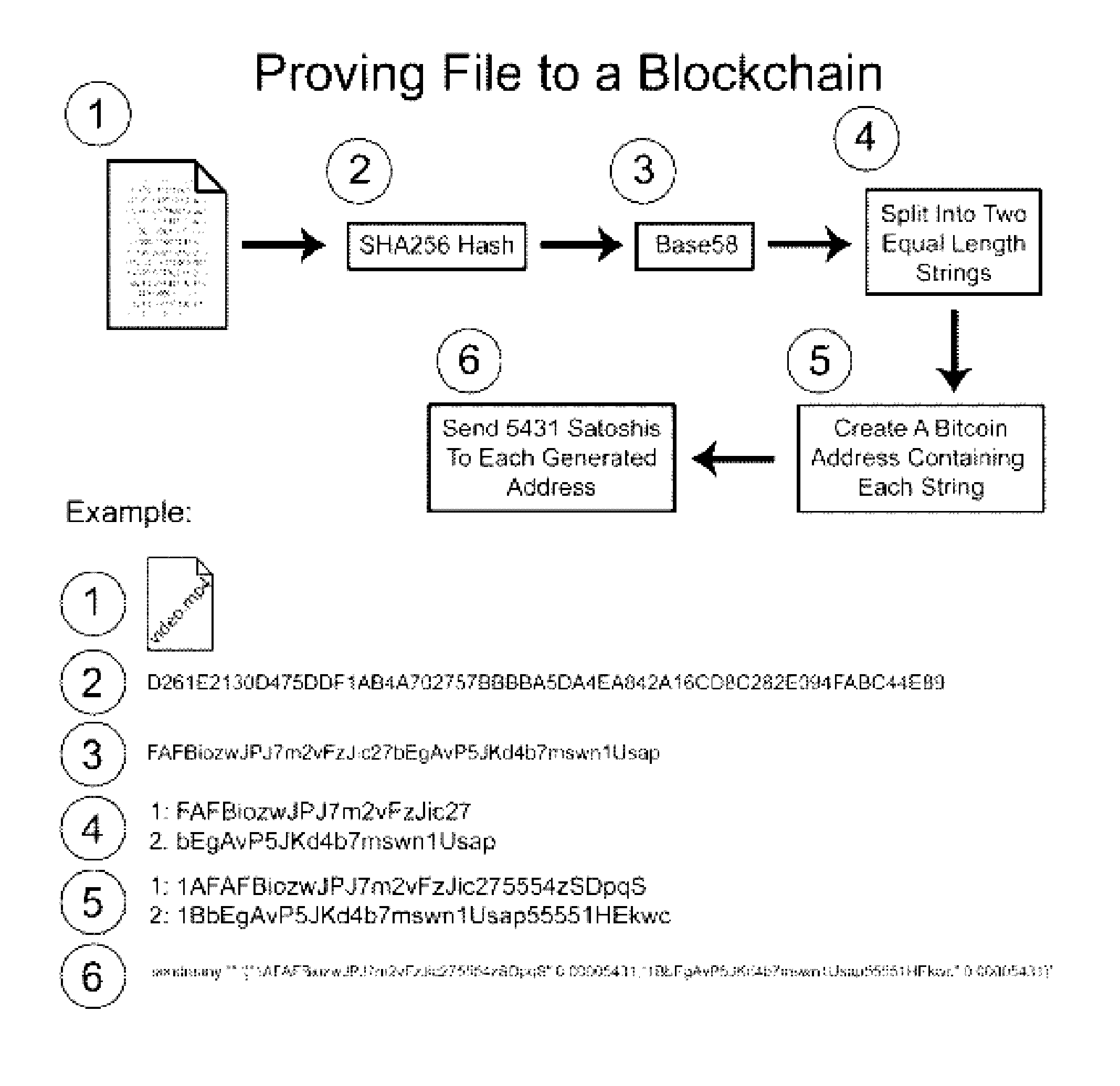
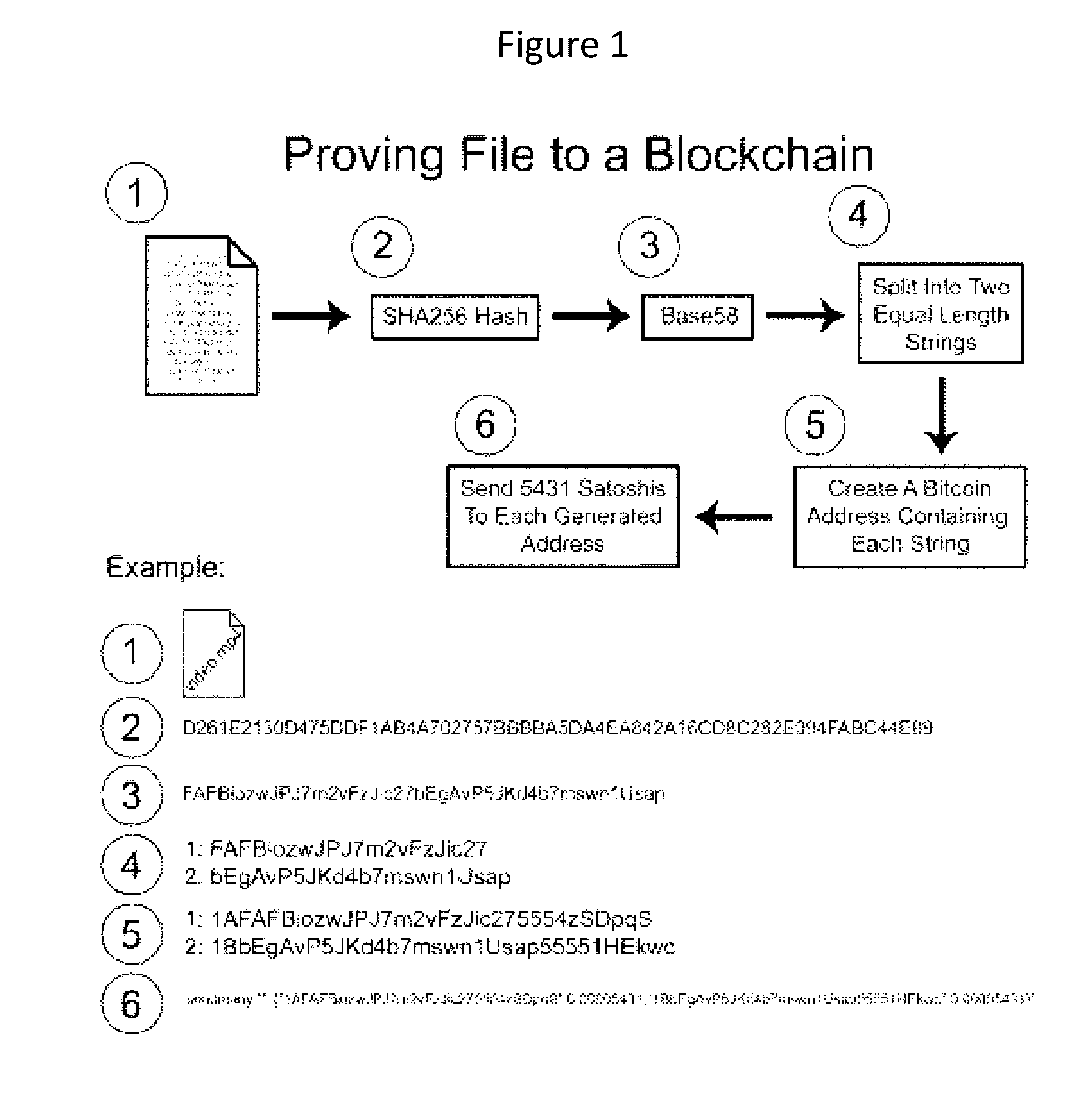
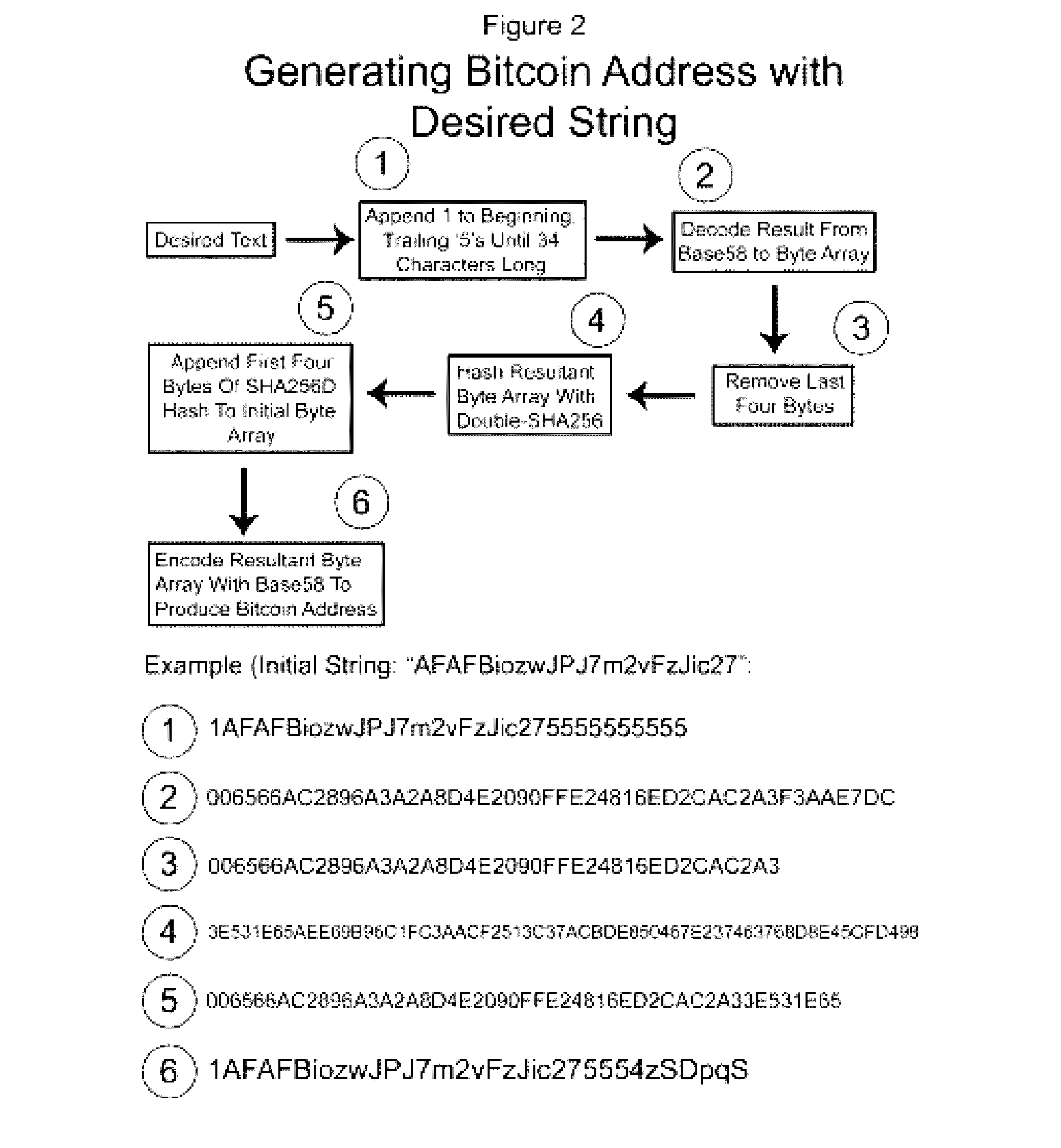
A method for authenticating a chain of custody utilizing blockchain technology, whereby digital evidence or other digital content is acquired and then hashed to produce a hash fingerprint / signature and then immediately or instantly submitting said hash fingerprint / signature to the blockchain using the blockchain network protocol, forming an immediate verifiable chain of custody without human interaction or requiring a trusted third party.
Owner:FISHER JUSTIN +1
Out-of-band validation of domain name system records
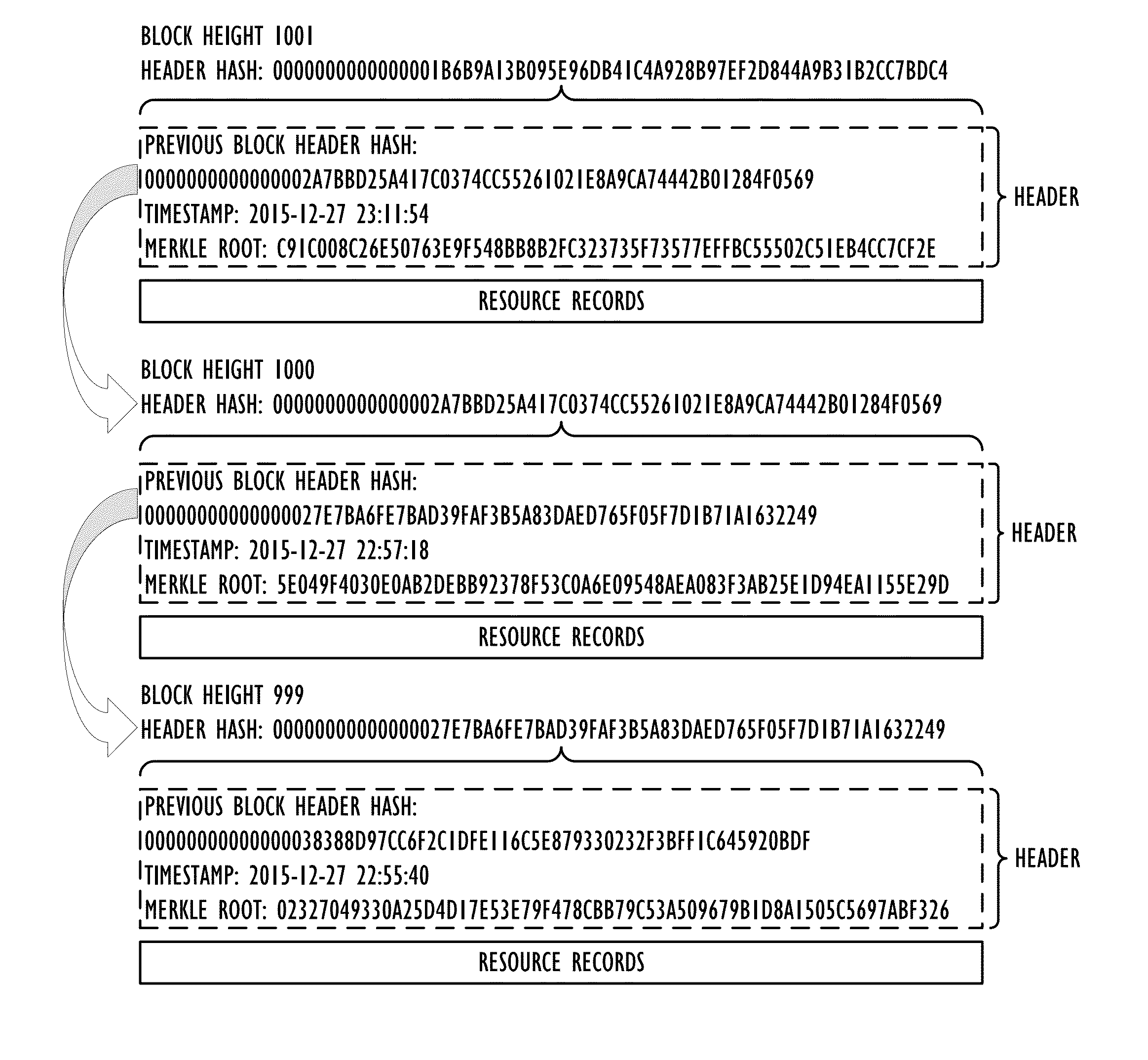
An out-of-band Domain Name System (DNS) security technique uses a cryptographic blockchain for securing and validating DNS data in a chain of custody that exists outside the DNS namespace, allowing validated access to cached DNS information without requiring real-time access to root servers.
Owner:MANNING WILLIAM
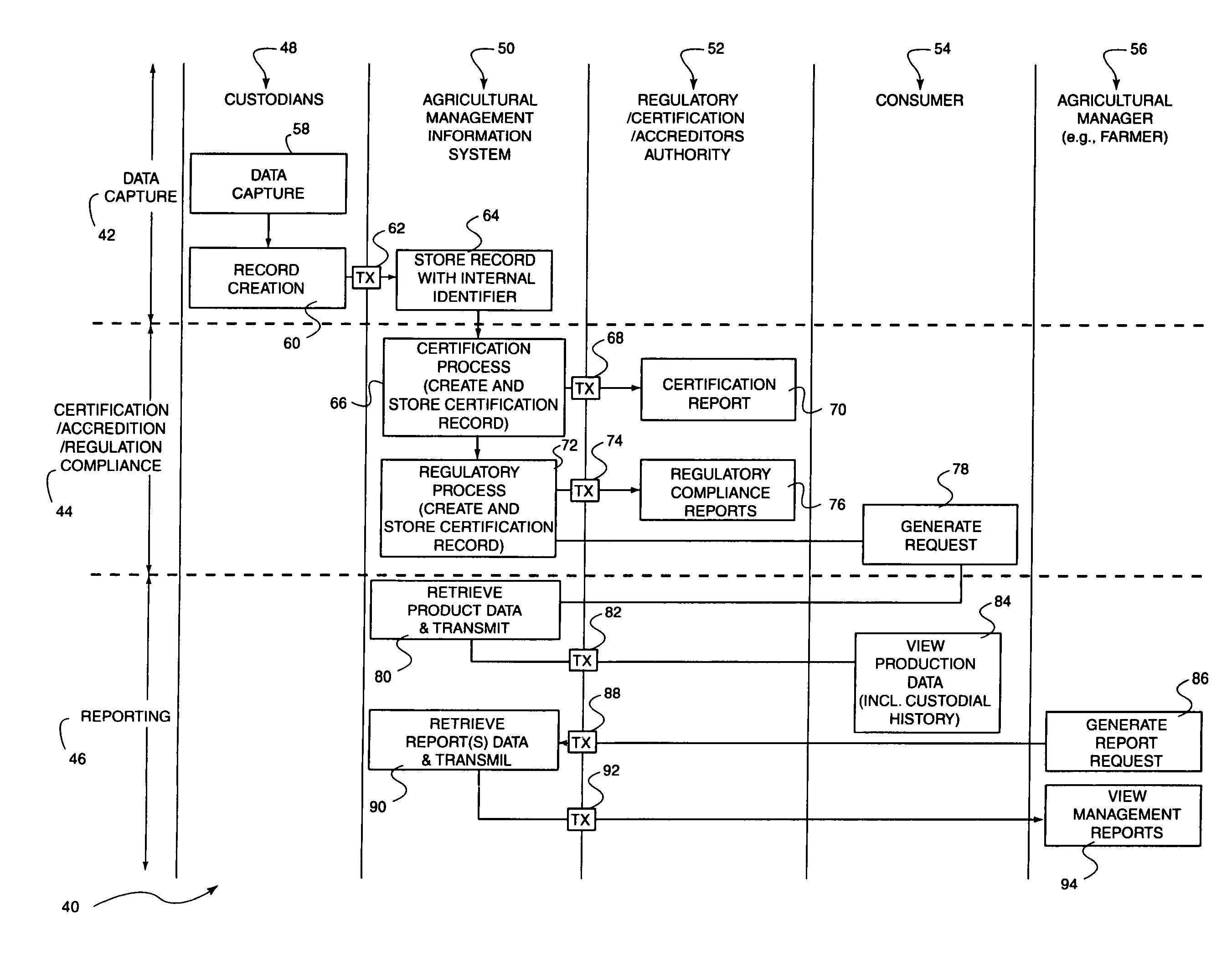
Method and system to communicate agricultural product information to a consumer
InactiveUS7440901B1Digital data processing detailsCustomer communicationsThe InternetProduct Identifier
A method to communicate agricultural product information to a user includes receiving, at a management information system, a request for agricultural product information. The request includes an agricultural product identifier. An agricultural product record, identified utilizing the agricultural product identifier, is then accessed and retrieved from a database at the management information system. The agricultural product record includes agricultural product data collected on the chain of custody of the agricultural product. The agricultural product data, as contained within the record, is then communicated to a user responsive to the request. The communication of the request, and the response, may be performed via the Internet as web-based communications.
Owner:SUREHARVEST SERVICES LLC
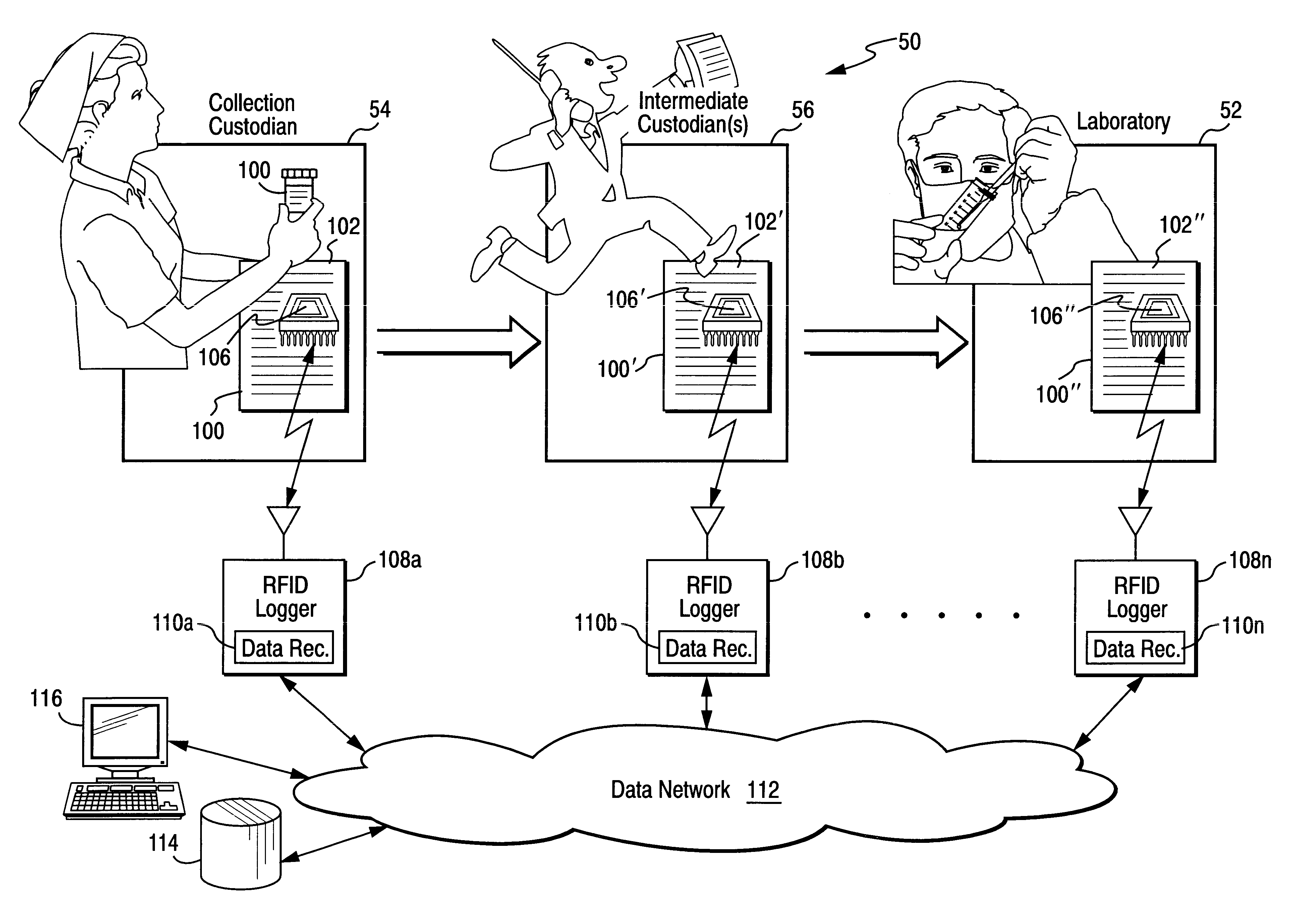
Chain of custody business form with automated wireless data logging feature
InactiveUS6535129B1Reduce consumable costsReliable identificationElectric signal transmission systemsDigital data processing detailsThird partyWireless data
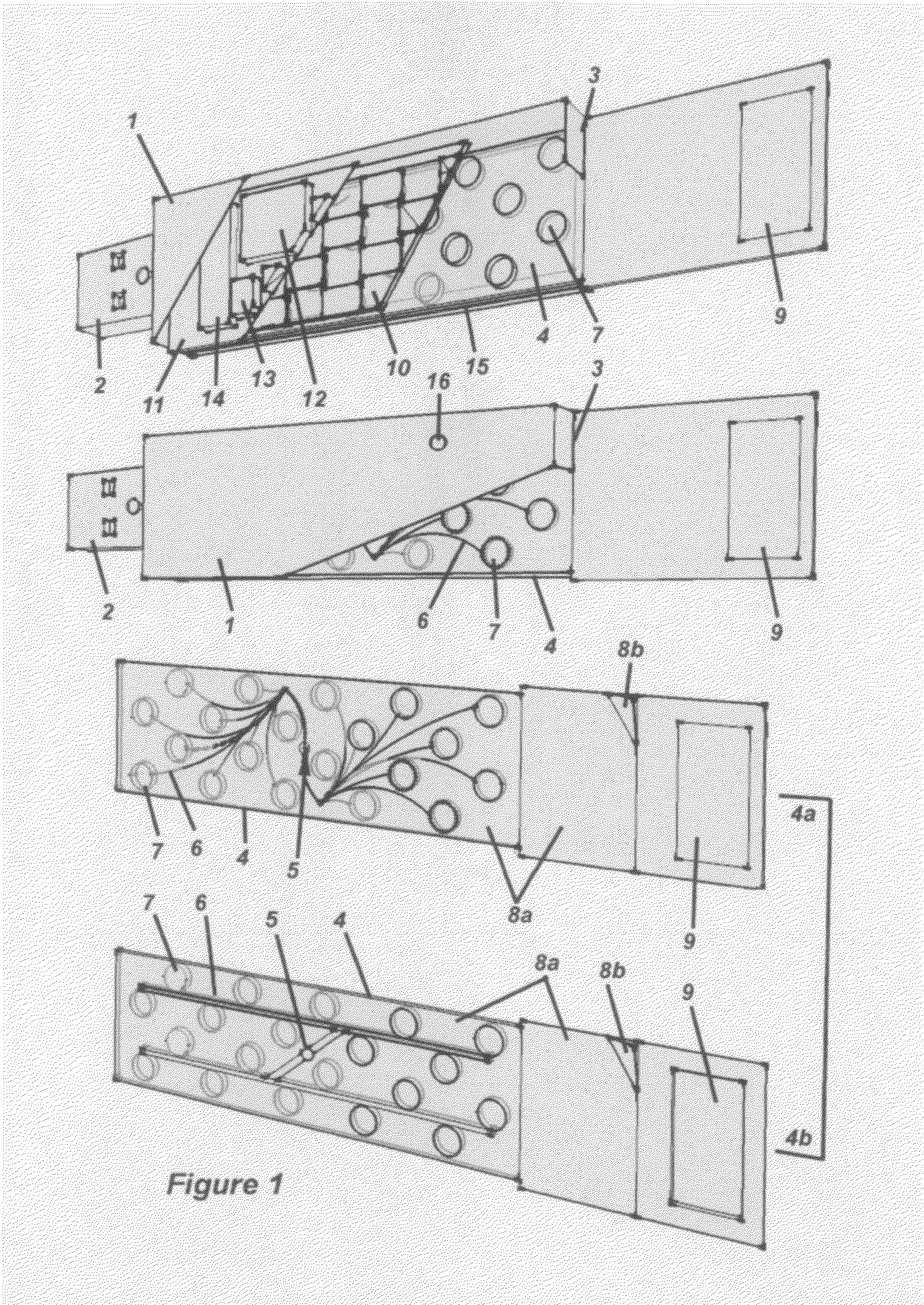
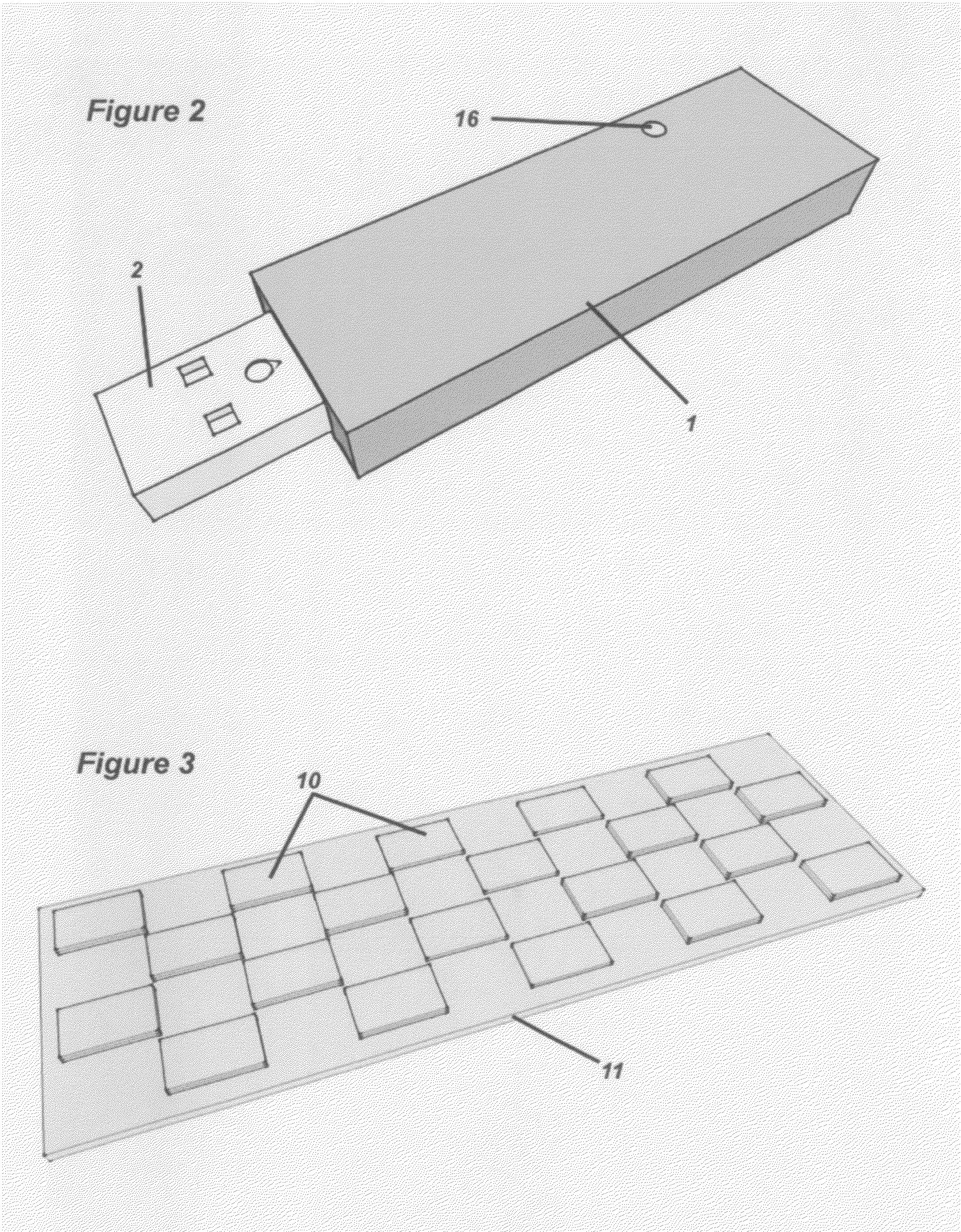
A chain of custody form with an associated wireless (e.g., RFID) chip results in data being monitored and filed electronically, minimizes the need for a multi-part form and results in reduced consumable costs to the customer. Samples are no longer lost in transit or within a testing laboratory, as the RFID chip allows for complete tracking of the specimen. Positive location identification is always available. All data may be tracked using the RFID chip which may prompt the collector or other custodian to correctly enter data. The chain of custody is always accurate and is never broken. All data may be shared with all parties electronically including, for example, an employer, a collection site, a medical review officer, a third party administrator, etc. No re-keying of the information is necessary, eliminating multiple steps, reducing the potential for error, and providing increased efficiencies and decreased processing time at reduced costs.
Owner:MOORE NORTH AMERICA INC
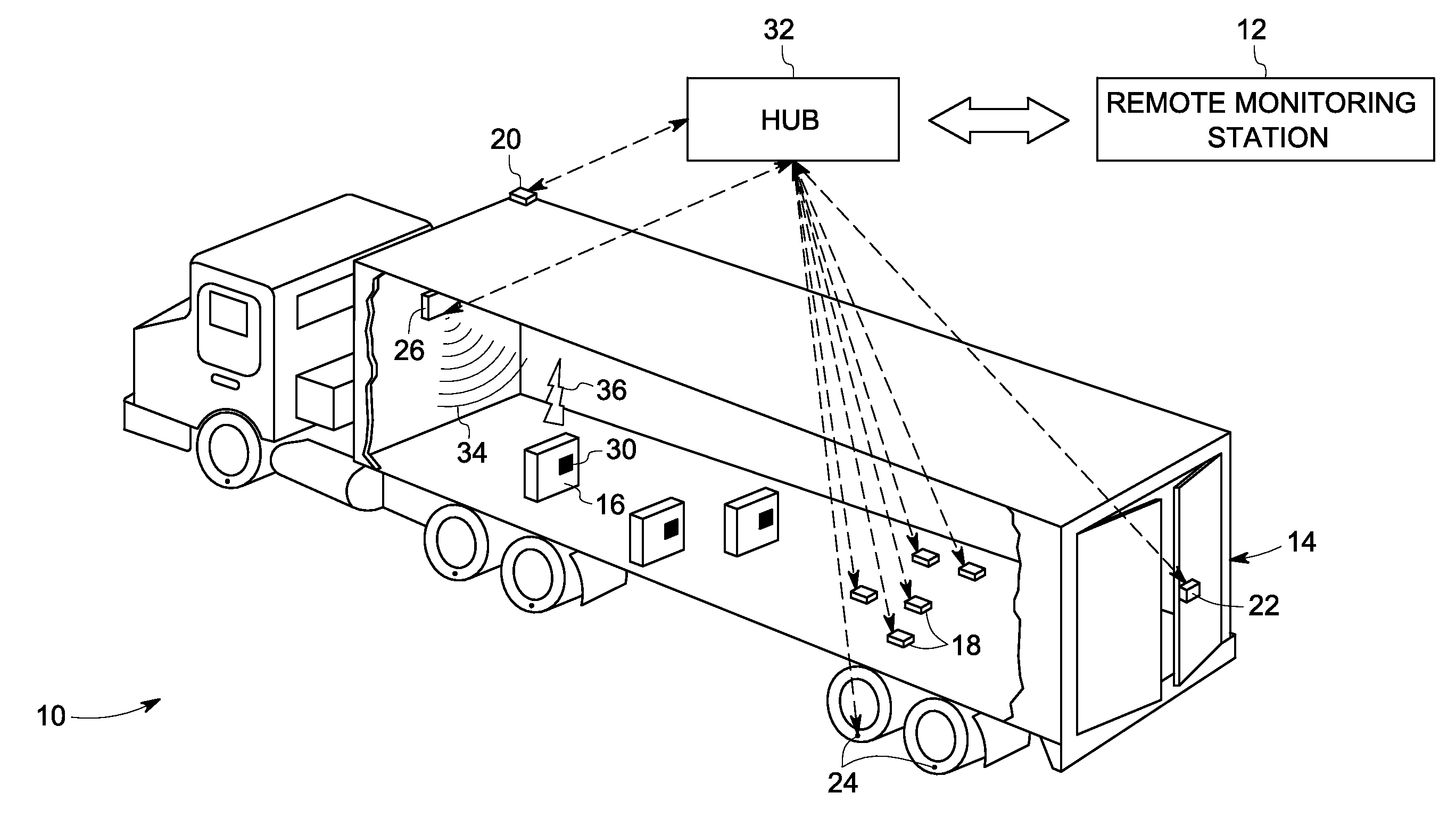
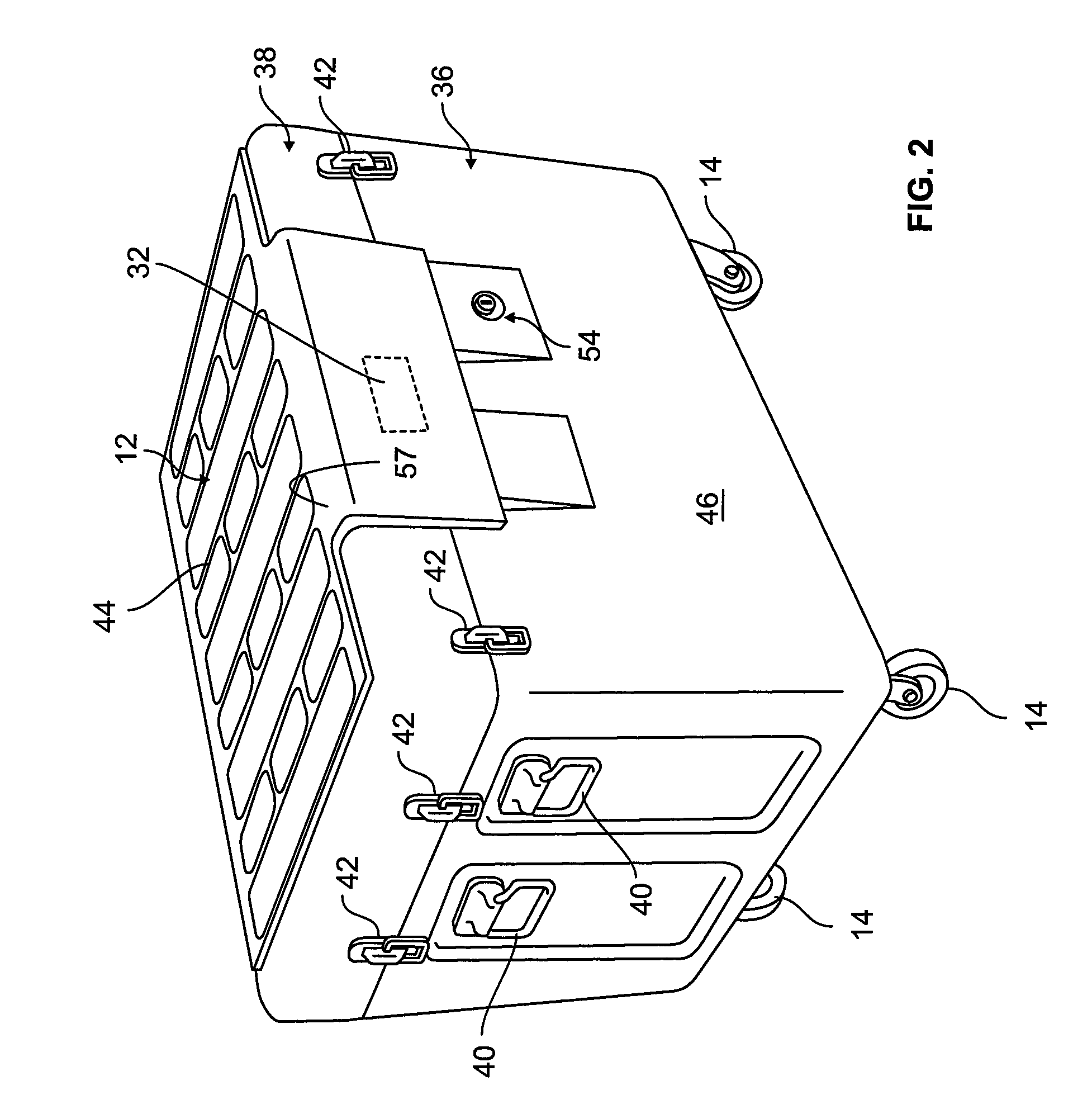
System for maintaining security of evidence throughout chain of custody
ActiveUS20100265068A1Improve tamper resistancePrevent insertionPosition fixationSatellite radio beaconingEngineeringApplication specific
An evidence chain of custody system that is application-specific auditable and trackable secure smart mobile containers (SMC) for securely storing evidence items that are collected at crime scenes and search locations pursuant to subpoenas or warrants. Each SMC includes a electronics package that can read RF tags applied to evidence bags or totes placed in the SMC or for oversized items, associated with the event or scene, that are tagged with active RF tags. The electronics package also includes condition sensors and an RF transmitter module to permit remote reporting and monitoring of GPS / RSSI location and condition. The SMC includes an electronic lock that provides access security and an audit trail of all opening, closing, and other events.
Owner:VERDASEE SOLUTIONS
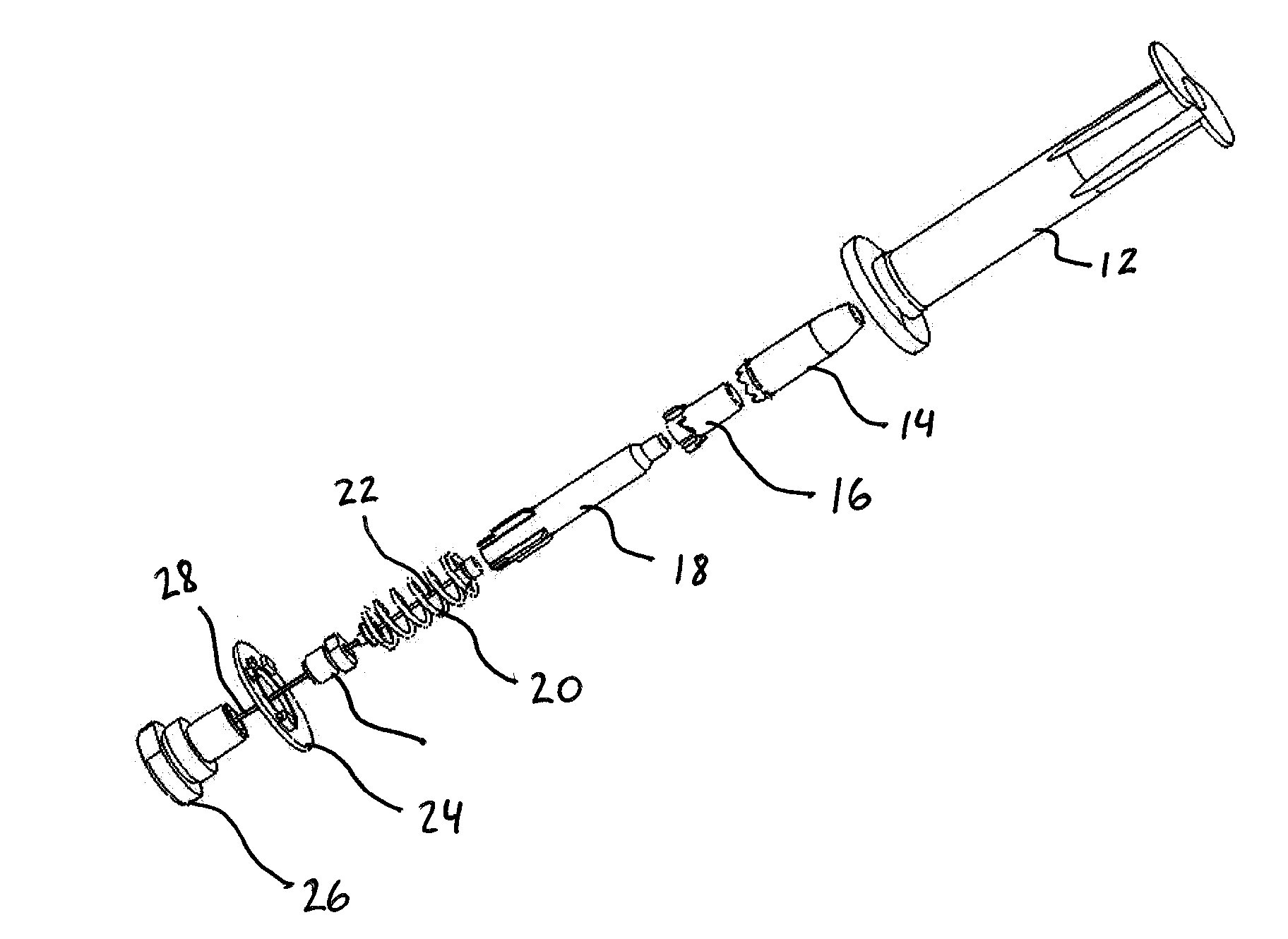
Single-hand operated syringe-like device that provides electronic chain of custody when securing a sample for analysis
A syringe-like device (hereinafter “syringe”) that is operable by a single hand, wherein the syringe includes a plunger for ejecting and then retracting a fiber or filament used for the collection of solids, solids in suspensions and liquids, wherein the syringe includes a microchip embedded in the syringe housing, and wherein the microchip enables electronic chain of custody tracking of a sample from a point of origin through final analysis.
Owner:BRIGHAM YOUNG UNIV
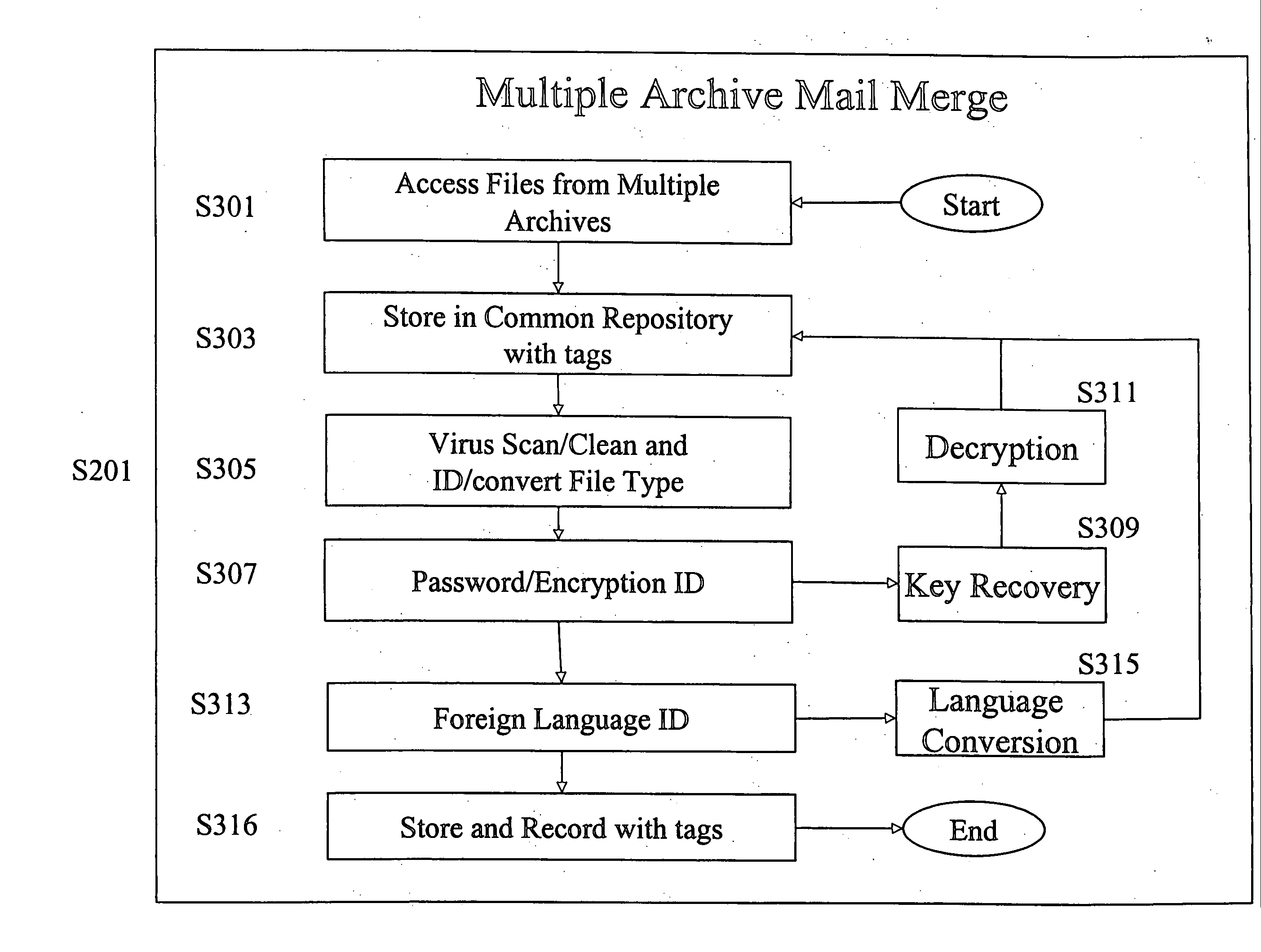
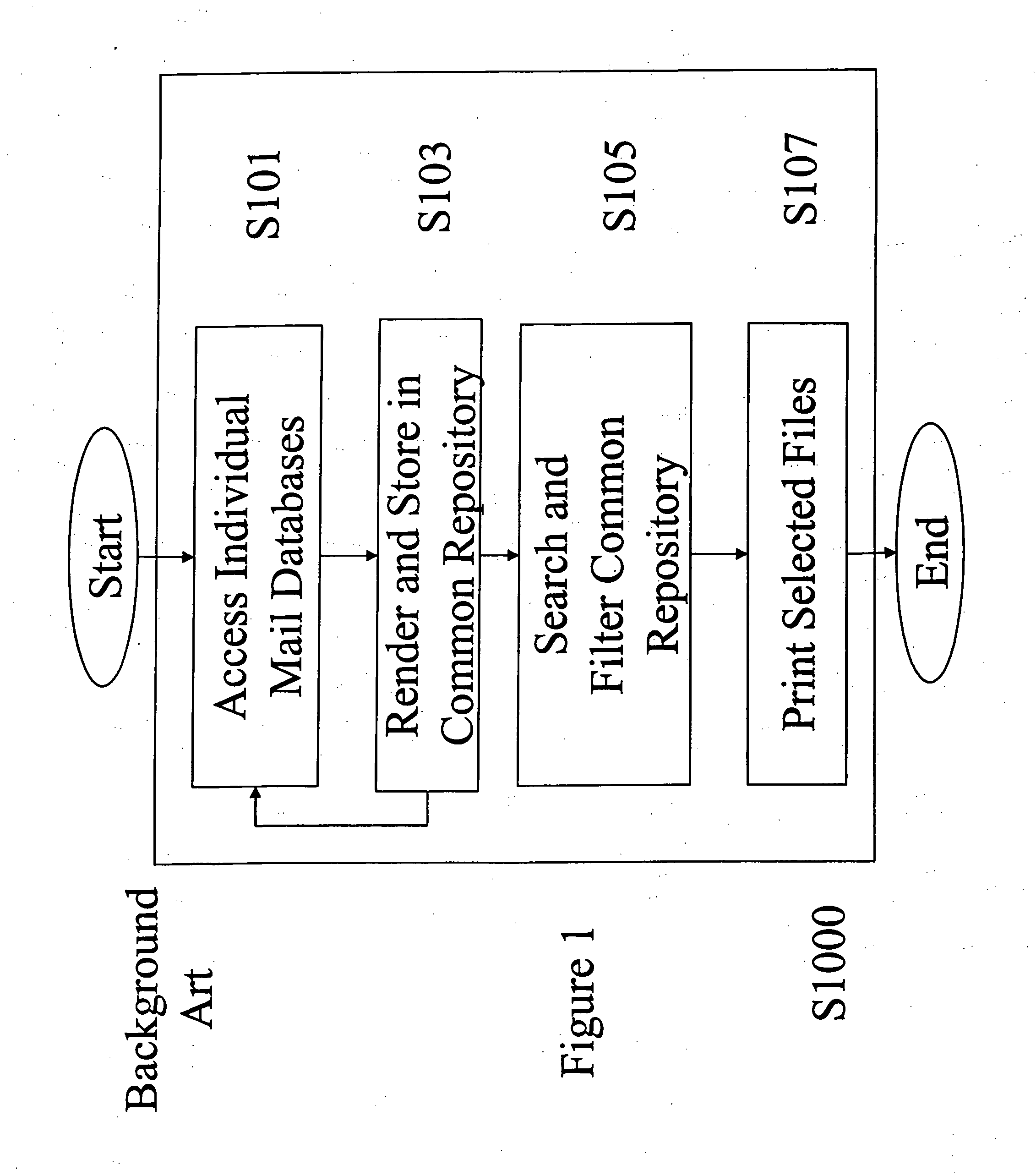
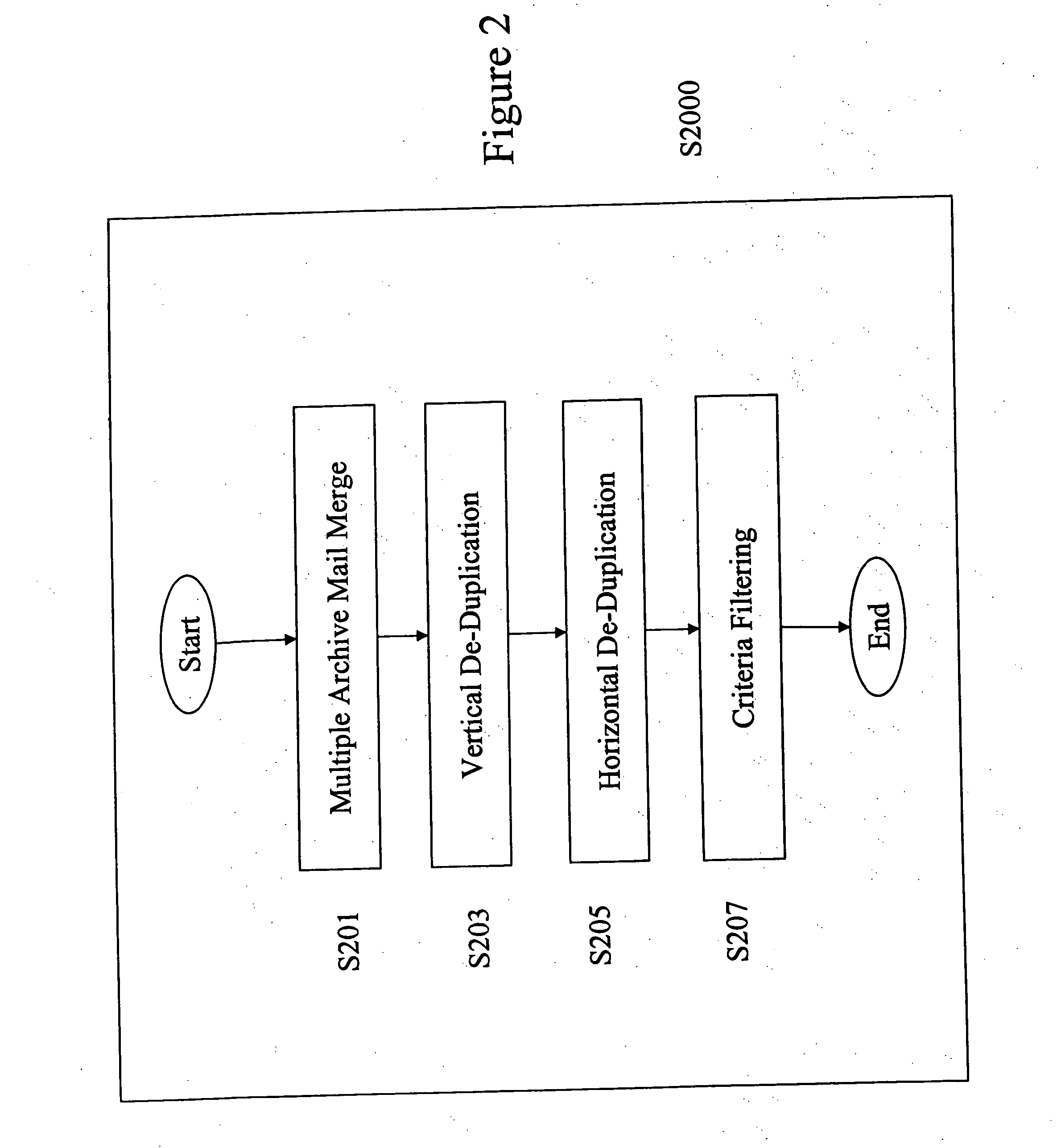
Electronic archive filter and profiling apparatus, system, method, and electronically stored computer program product
InactiveUS20050066190A1Low costEasy to handleDigital data processing detailsHardware monitoringTagged Image File FormatConfigfs
A software-based electronic data discovery tool which accesses multiple electronic archives; copies files and their meta-data into a common repository; vertically de-duplicates and tags the files; horizontally de-duplicates and tags the files; filters and tags the files against a one or more sets of predetermined compliance and privileged criteria identified by one or more parties associated with a specific electronic data discovery procedure; profiles and tags select results; and produces a variety of reports and excerpts. Production is at least one of printing on paper, transferring to magnetic media, or other processes. Files that are selected for profiling and production are then rendered in TIFF or another related format and stored in a common file. All files are identified with a digital “finger print” and complete chain-of-custody information.
Owner:CRICKET TECH
System and method for monitoring and tracking inventories
A technique is provided for monitoring and tracking inventories within one or more assets. The technique includes sensing a plurality of parameters associated with each of the one or more assets. The plurality of parameters includes a positional information of the asset. The technique further includes activating RFID tags attached to the inventories and generating a response based upon the responses received from the RFID tags, and monitoring and tracking inventories based on the sensed parameters and the generated response to ensure integrity and validate a chain of custody of the asset or the inventories during a supply chain process.
Owner:GENERAL ELECTRIC CO
Security for blister packs
Various RFID based blister pack embodiments are provided for improving the ability to detect and prevent tampering and counterfeiting of blister packs and / or facilitating the chain of custody tracking of blister packs during manufacture. Some embodiments employ an RFID chip network on the blister pack and some embodiments employ an RFID strap network on the blister pack, wherein the integrity of the network (or lack thereof) is used to indicate the possibility of tampering. Other embodiments determine the possibility of tampering based on the frequency of an RF signal that is received from a chip provided on the blister pack, which will vary depending on whether the associated antenna has been detuned as a result of some type of tampering.
Owner:UNIVERSITY OF PITTSBURGH
System for maintaining security of evidence throughout chain of custody
An evidence chain of custody system that is application-specific auditable and trackable secure smart mobile containers (SMC) for securely storing evidence items that are collected at crime scenes and search locations pursuant to subpoenas or warrants. Each SMC includes a electronics package that can read RF tags applied to evidence bags or totes placed in the SMC or for oversized items, associated with the event or scene, that are tagged with active RF tags. The electronics package also includes condition sensors and an RF transmitter module to permit remote reporting and monitoring of GPS / RSSI location and condition. The SMC includes an electronic lock that provides access security and an audit trail of all opening, closing, and other events.
Owner:VERDASEE SOLUTIONS
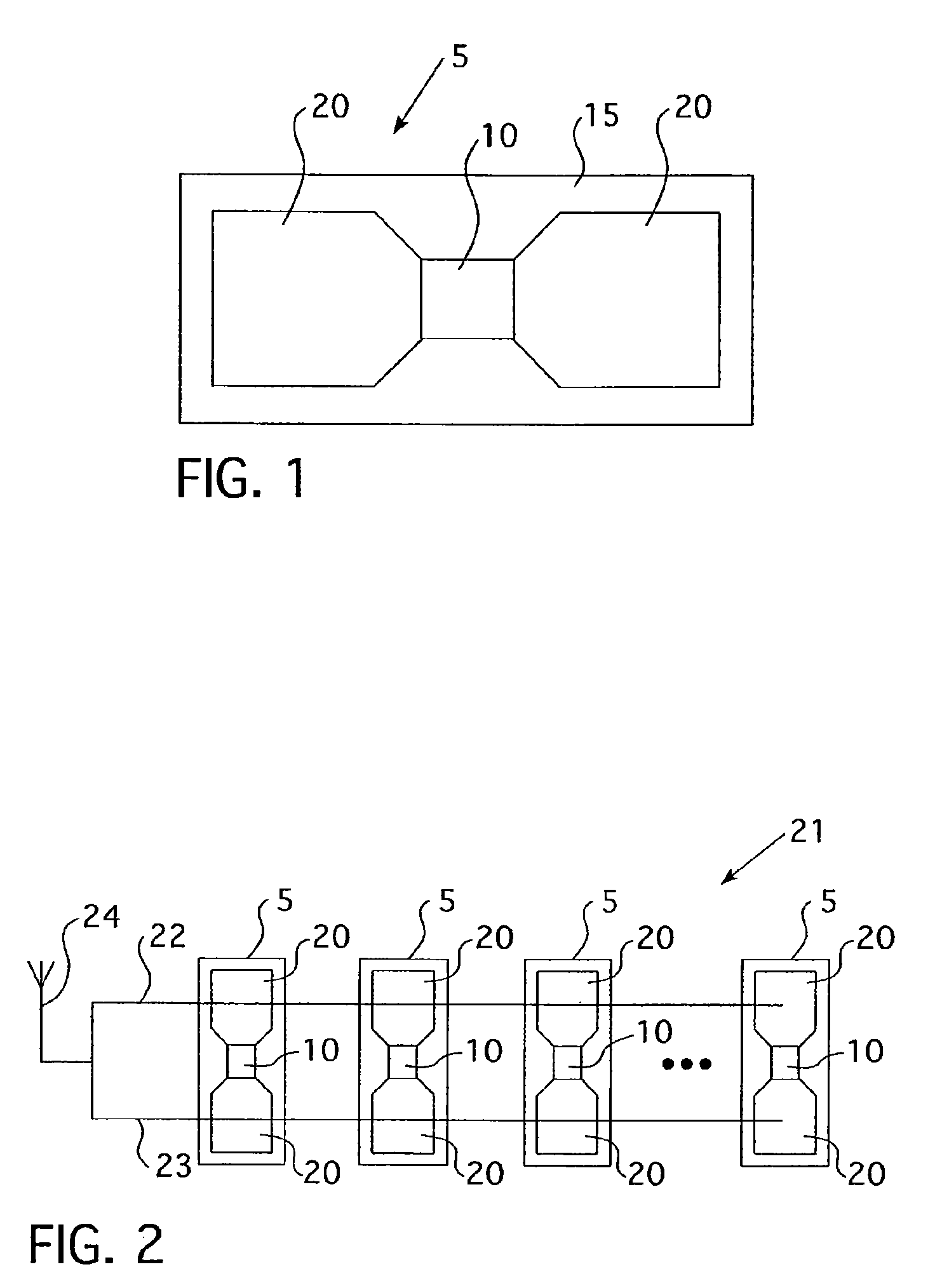
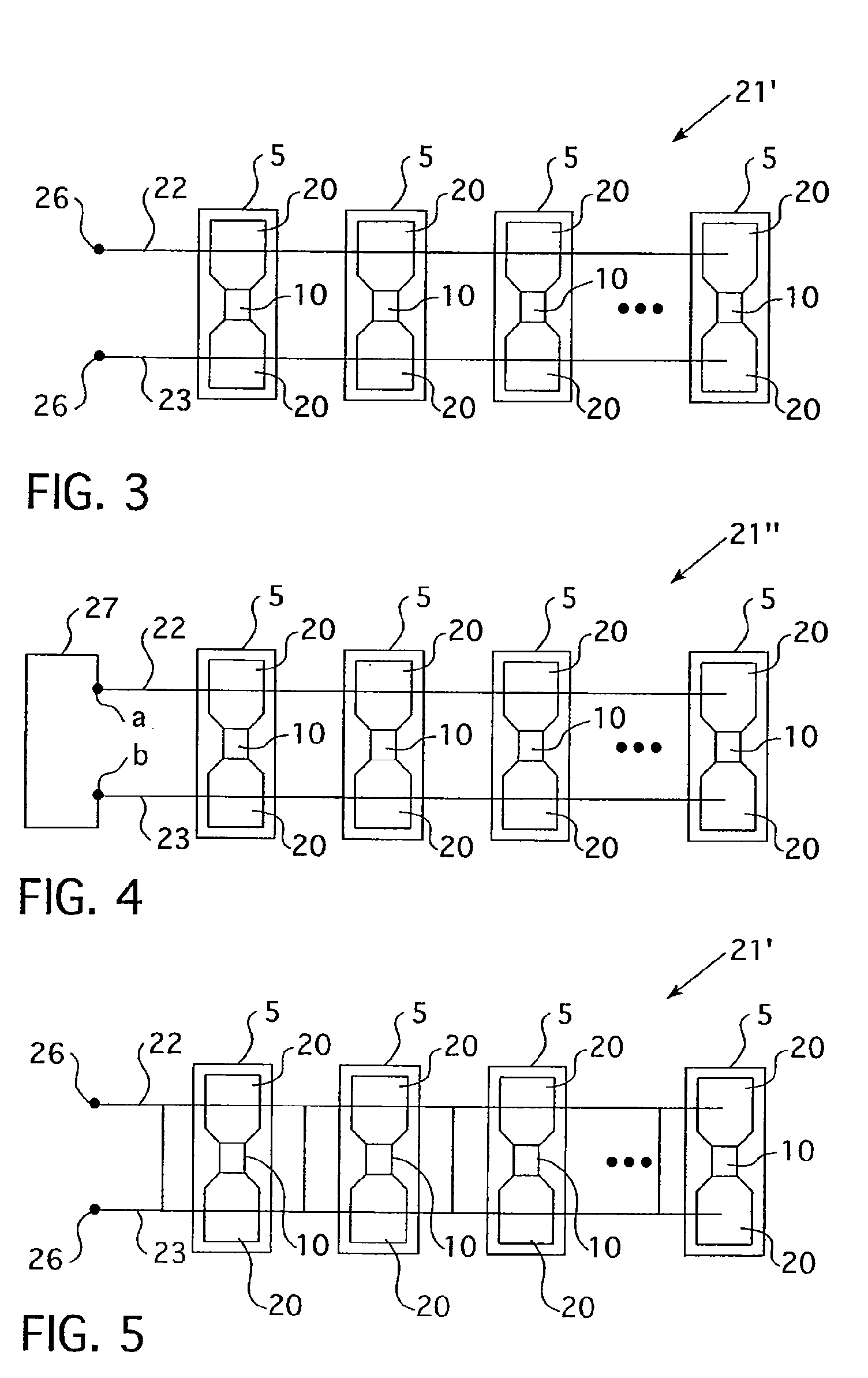
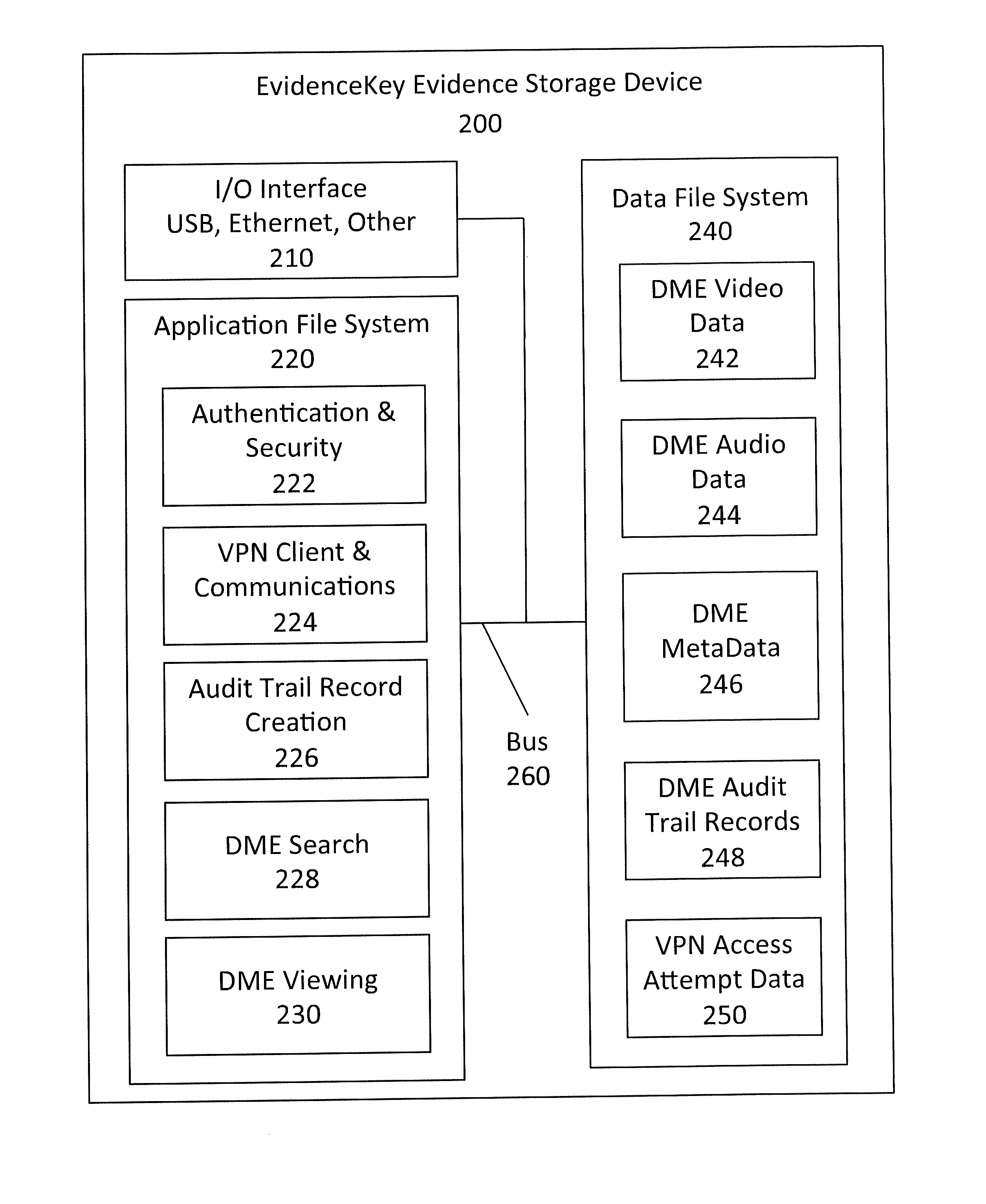
System and Method for Securely Distributing Legal Evidence
ActiveUS20140143545A1Shorten the timeReliable controlDigital data processing detailsUser identity/authority verificationLibrary scienceChain of custody
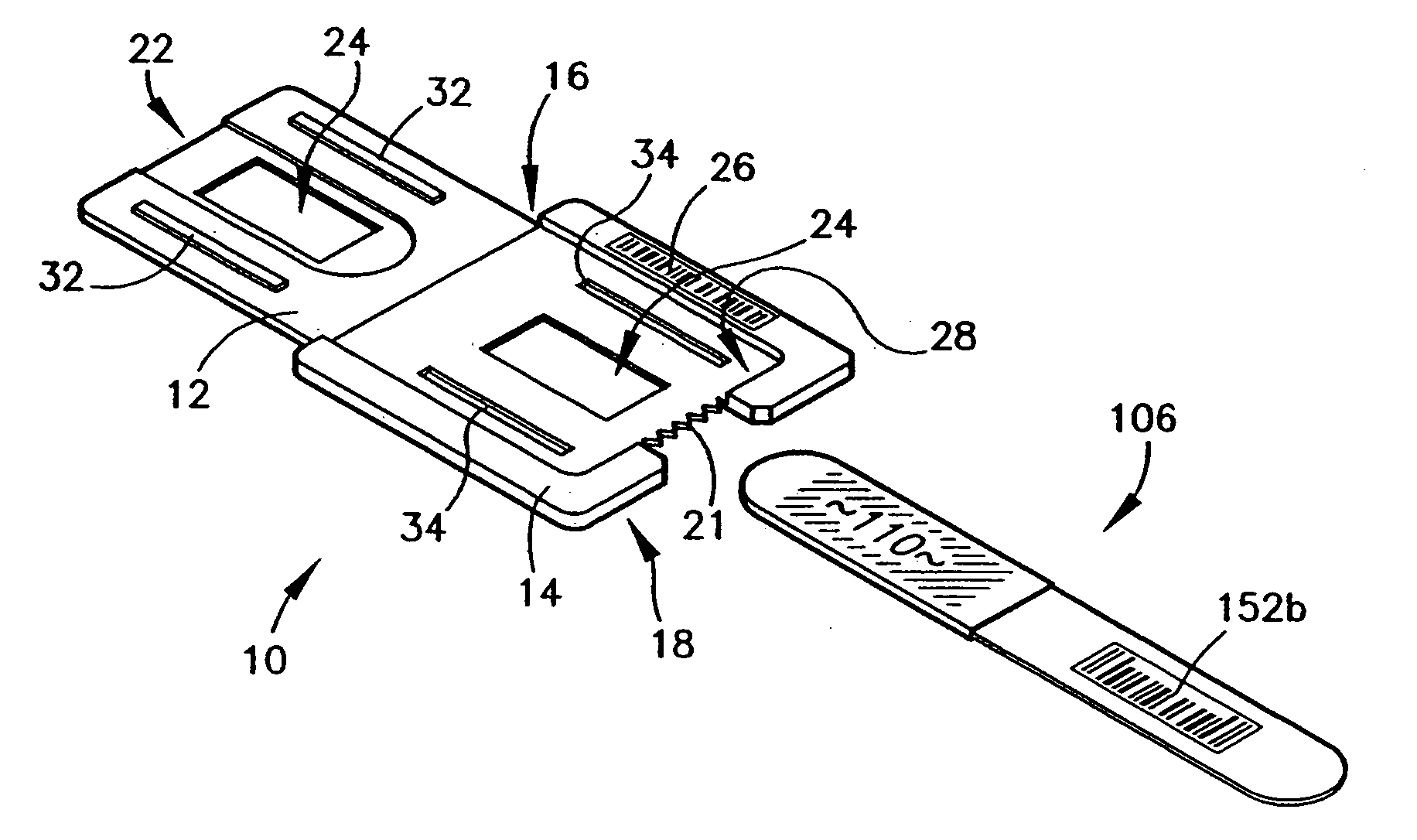
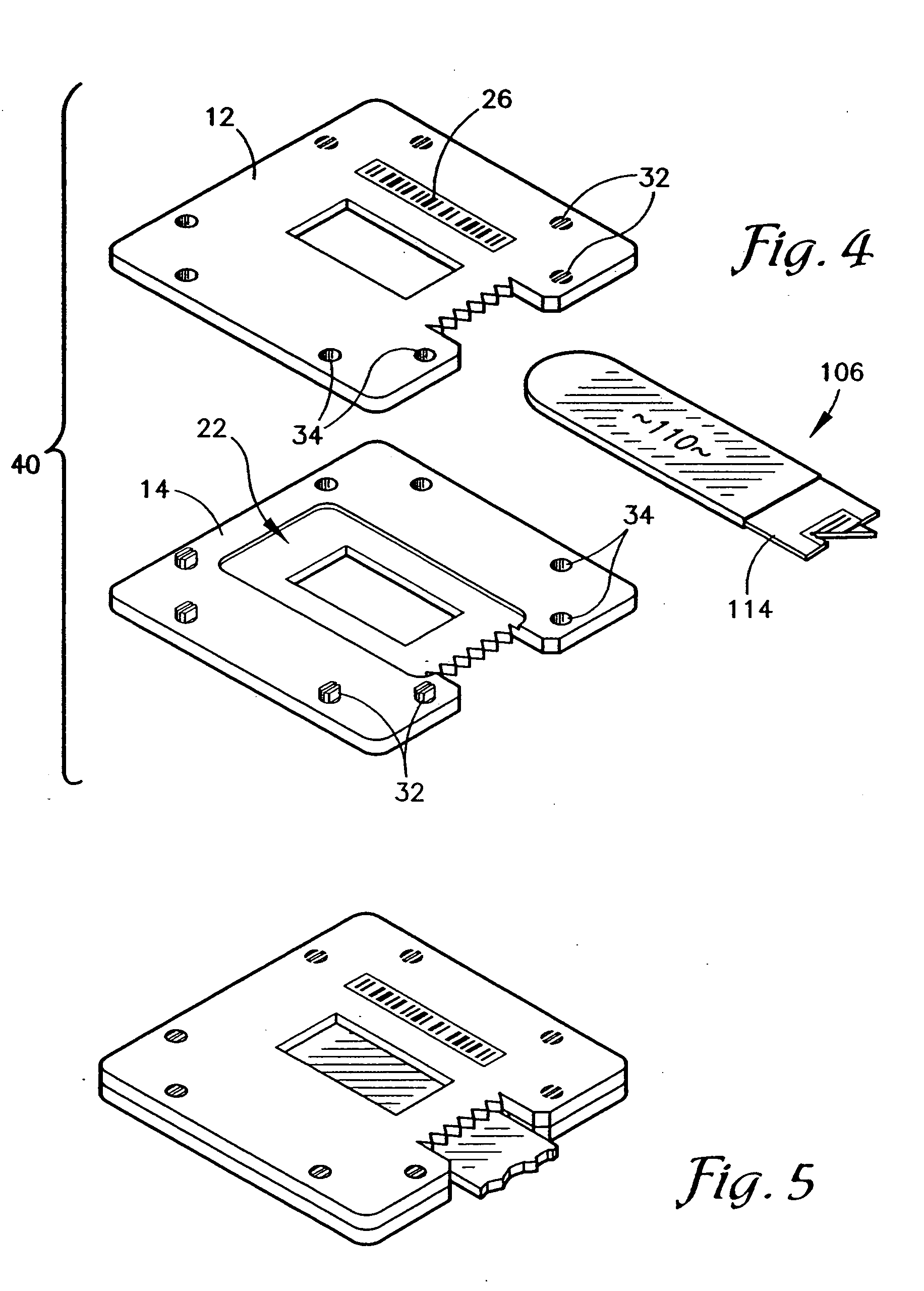
This invention provides a system and method to search for and securely download Digital MultiMedia Evidence (DME) data from a central DME repository to portable USB, smart phone, tablet, laptop, desktop, or other data storage devices, with a clear chain of custody and access control audit trail reporting, so the DME can be used to prepare for and conduct legal proceedings.
Owner:UTILITY ASSOCS
Chain of custody system and method
InactiveUS20030074556A1Facilitate receiving and storingPromote generationUser identity/authority verificationDigital data protectionComputer hardwareAuthentication system
An unimpeachable chain of custody system and method includes a confirmation authentication system that facilitates receiving and storing a communication signal that is indicative of an evidentiary item captured at a determined location and at a determined time. The confirmation authentication system and method further facilitates generating and transmitting a chain of custody confirmation signal to a transportable input system that the communication signal has been authenticated and stored for subsequent retrieval. The transportable input system includes a positioning device and a communication device that cooperate to facilitates generating and transmitting the communication signal in response to receiving the chain of custody confirmation signal. The transportable input system further facilitates generating an authentication signal that the communication signal was generated by the input system at about the determined location and at about the determined time so that the integrity of the received evidentiary item cannot be impeached.
Owner:HEWLETT PACKARD DEV CO LP
Methods and systems for transaction digital watermarking in content delivery network
InactiveUS20110126018A1Easy to detectUser identity/authority verificationPayment architectureMinutiaeChain of custody
Methods and systems for applying a transaction digital watermark to content being downloaded over a content delivery network. The digital watermark carries information about the transaction pursuant to which the content was downloaded, which can be useful in establishing a “chain of custody” that facilitates piracy detection and / or other tracking and monitoring applications. Moreover, the digital watermark is applied by an edge caching server, which enables downstream entities in the content delivery chain, such as Internet service providers, to influence the information carried in the digital watermark and enables transaction details that become known after the content leaves the content provider network to be carried in the digital watermark, but without opening up a security hole at the end user premises.
Owner:NUMETRA
System and method for automated sample preparation
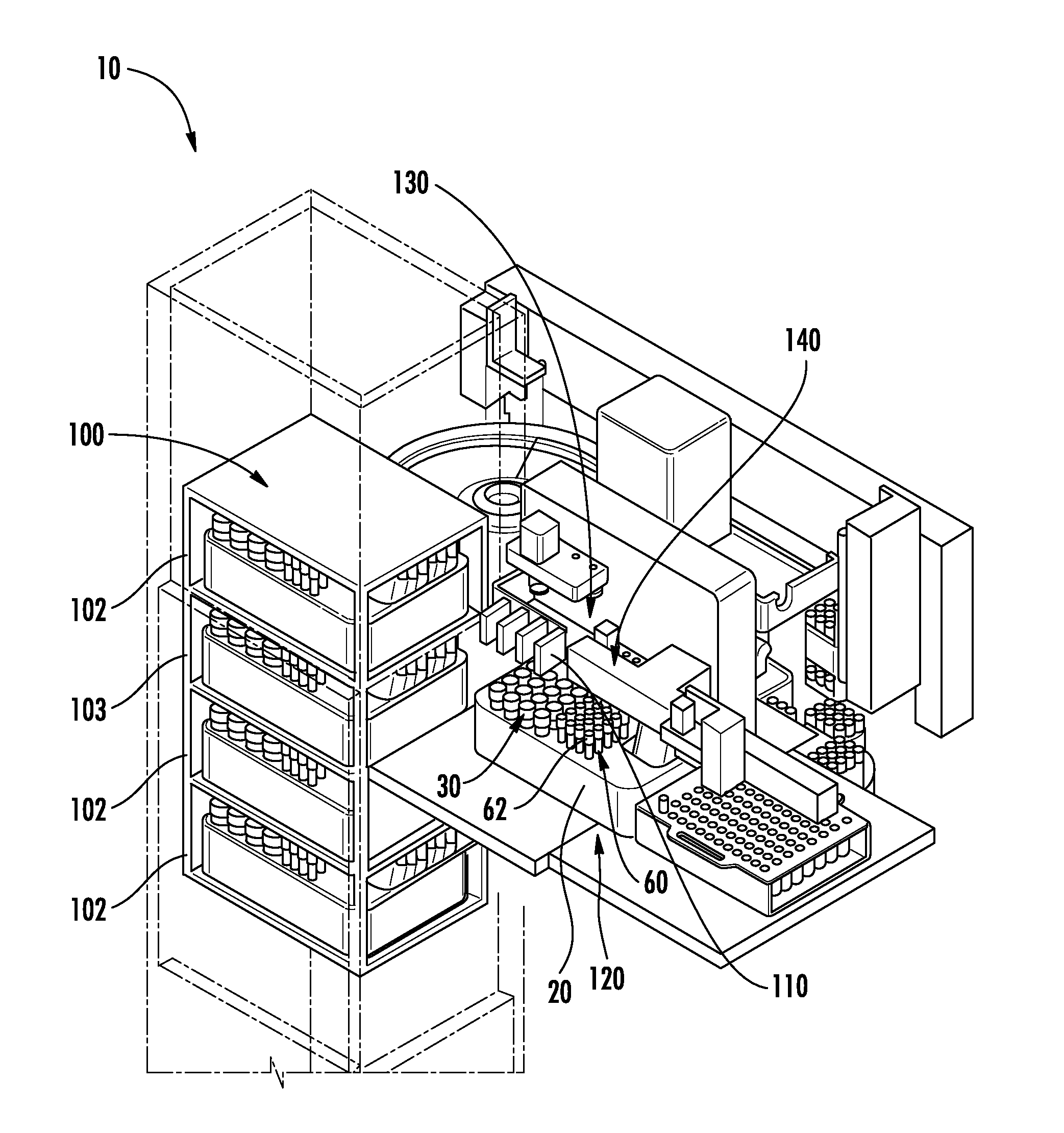
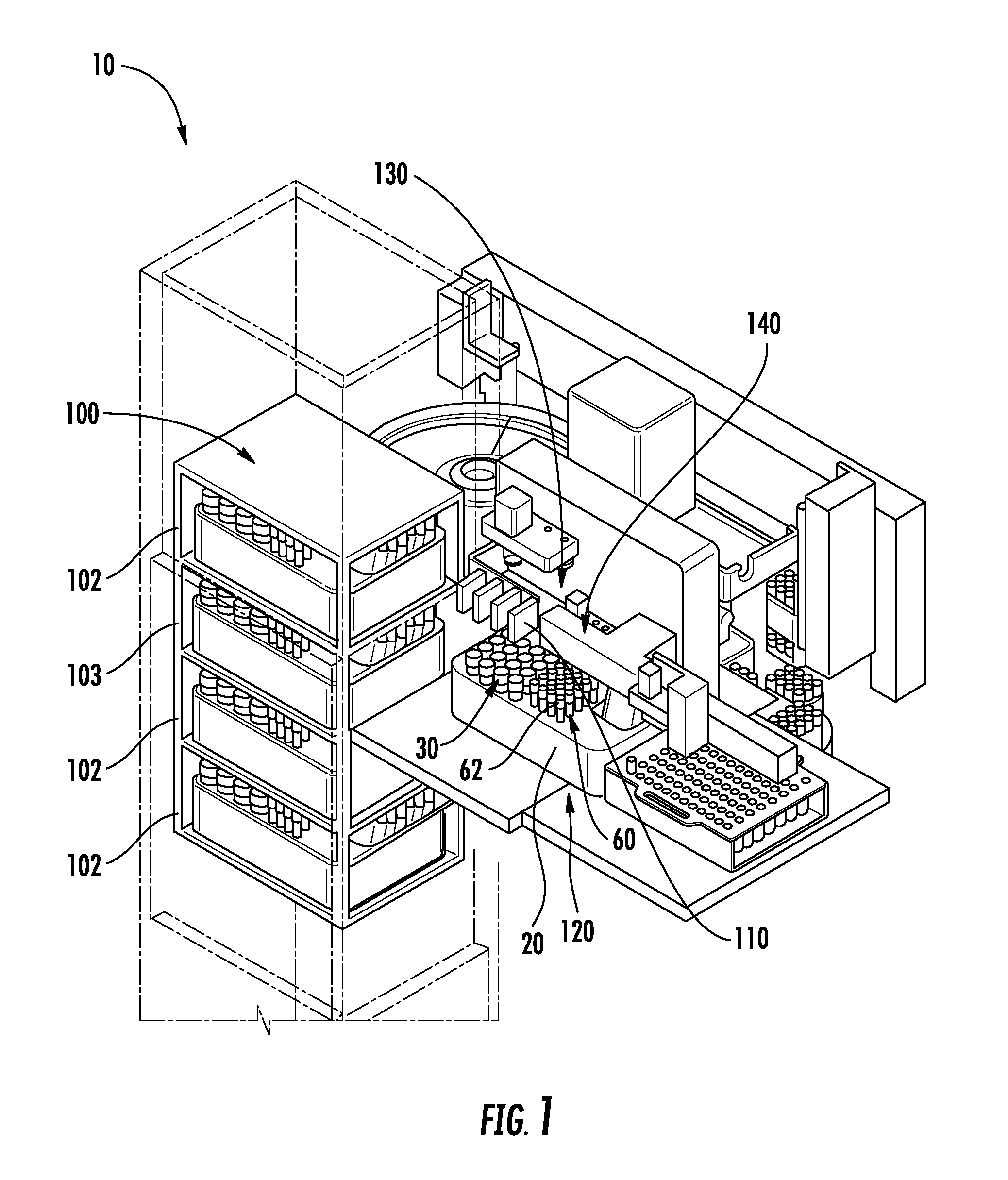
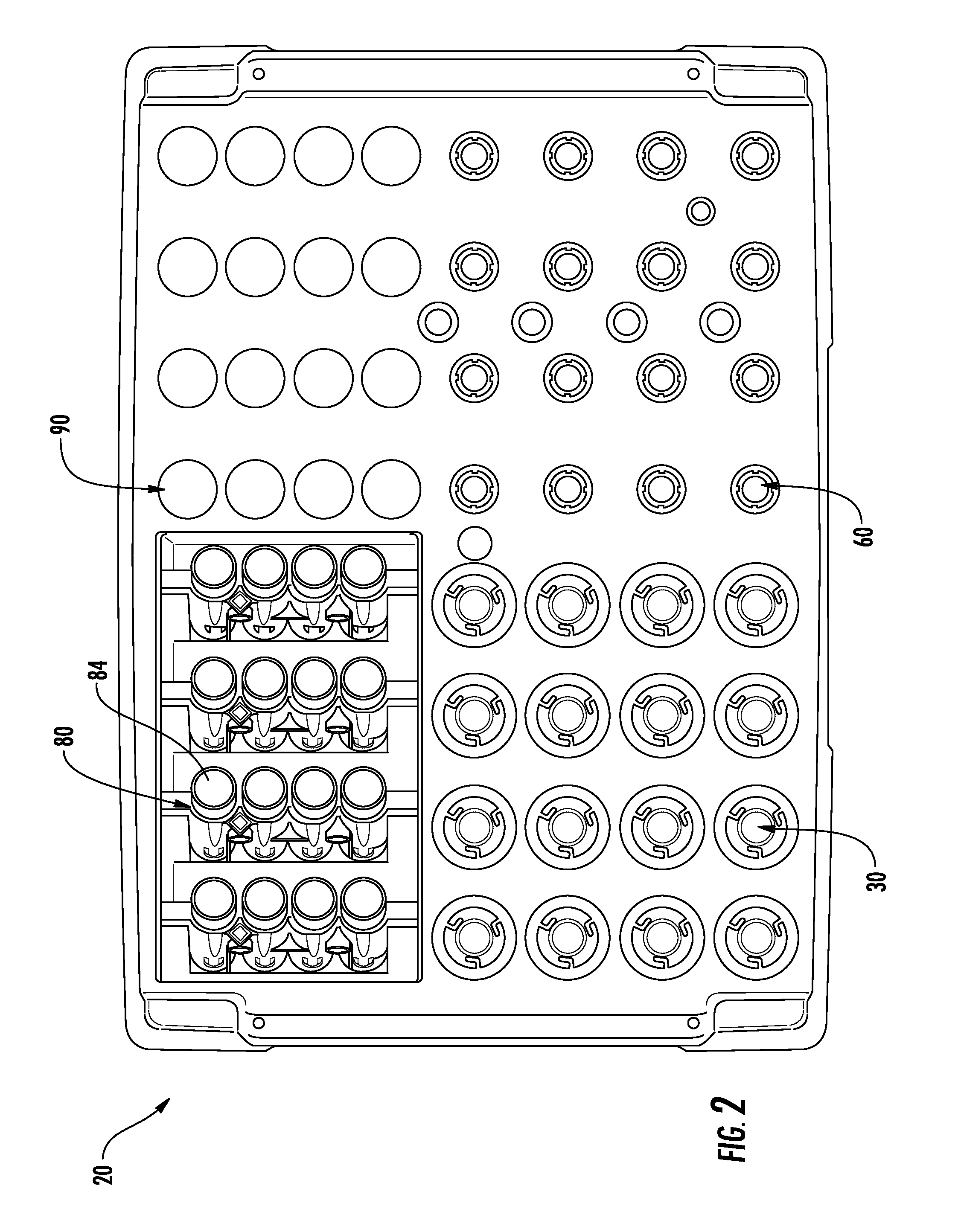
ActiveUS20130116102A1Easy accessDispersed particle separationCentrifugal force sediment separationEngineeringBio-Specimen
A system for automatically processing a biological specimen is provided that includes an elevator comprising a plurality of shelves configured to receive a plurality of sample trays. The trays may comprise a plurality of sample containers containing a sample and having a plurality of respective caps engaged therewith. The trays may further include a plurality of centrifuge tube racks each containing a plurality of centrifuge tubes. The system may include a first transport mechanism, a second transport mechanism and a third transport mechanism. The system may include a chain-of-custody device configured to read identifiers on each of the containers. The system may also include a pipetting device configured to remove a portion from the sample containers and dispense the sample into the centrifuge tubes.
Owner:BECTON DICKINSON & CO
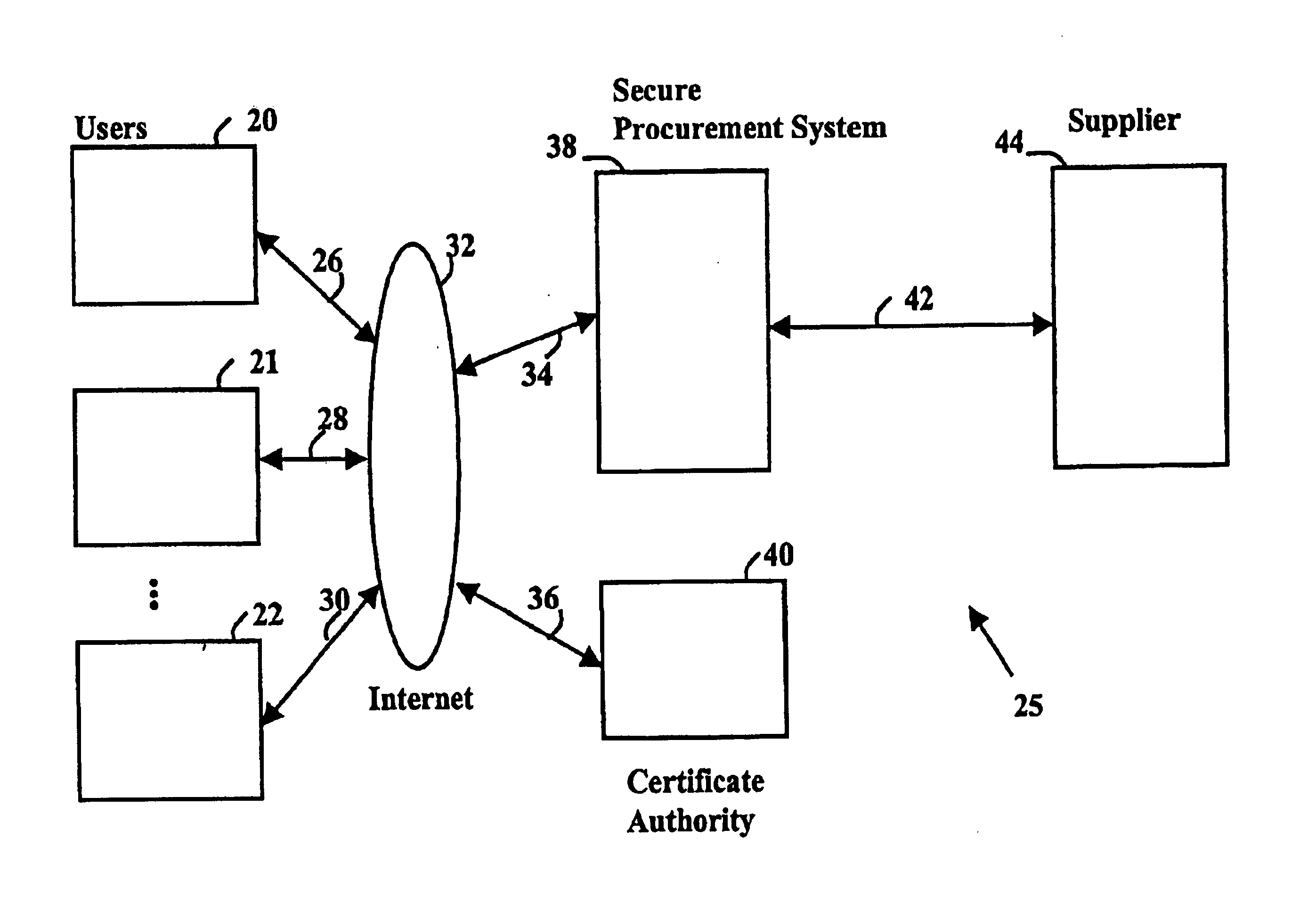
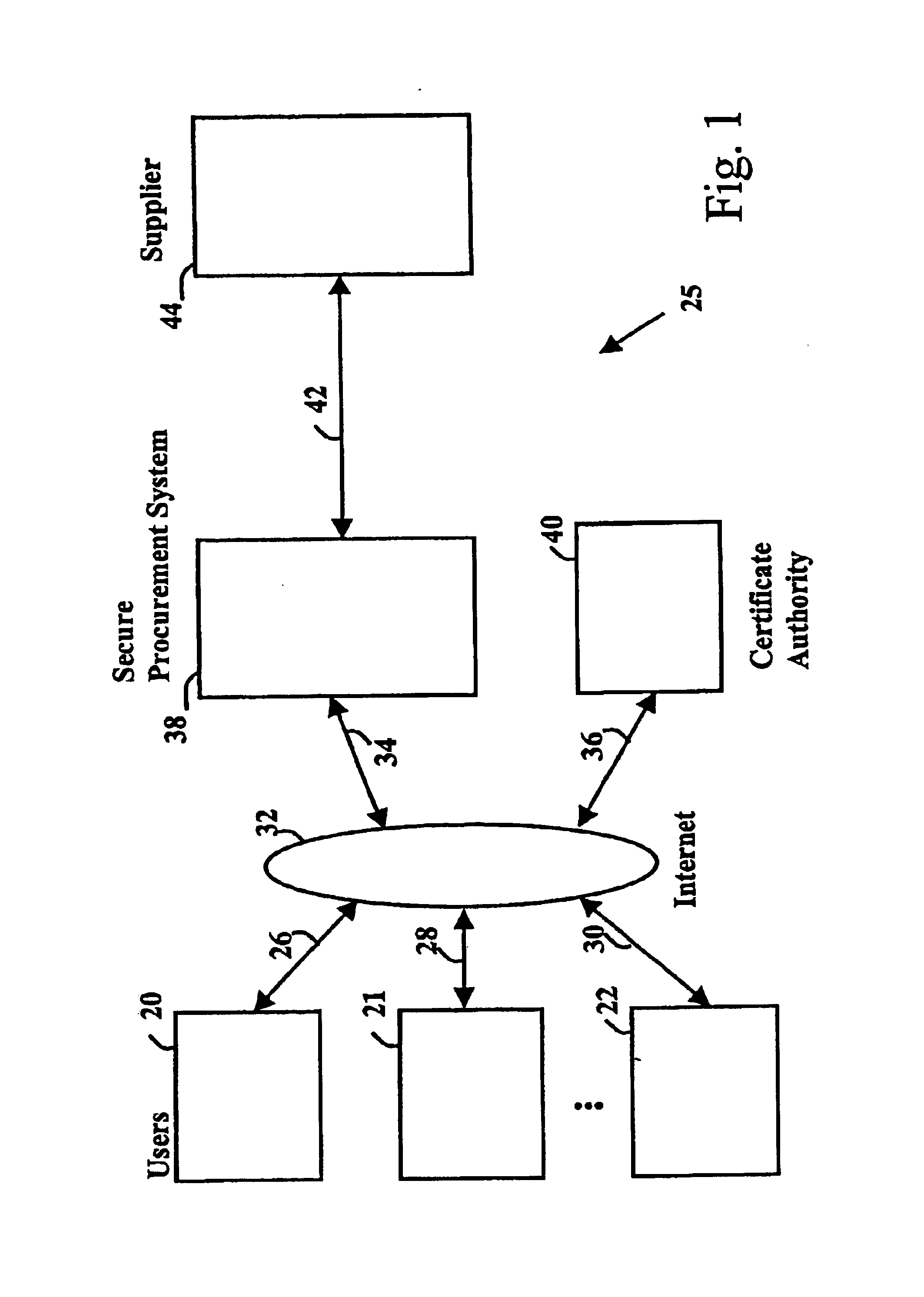
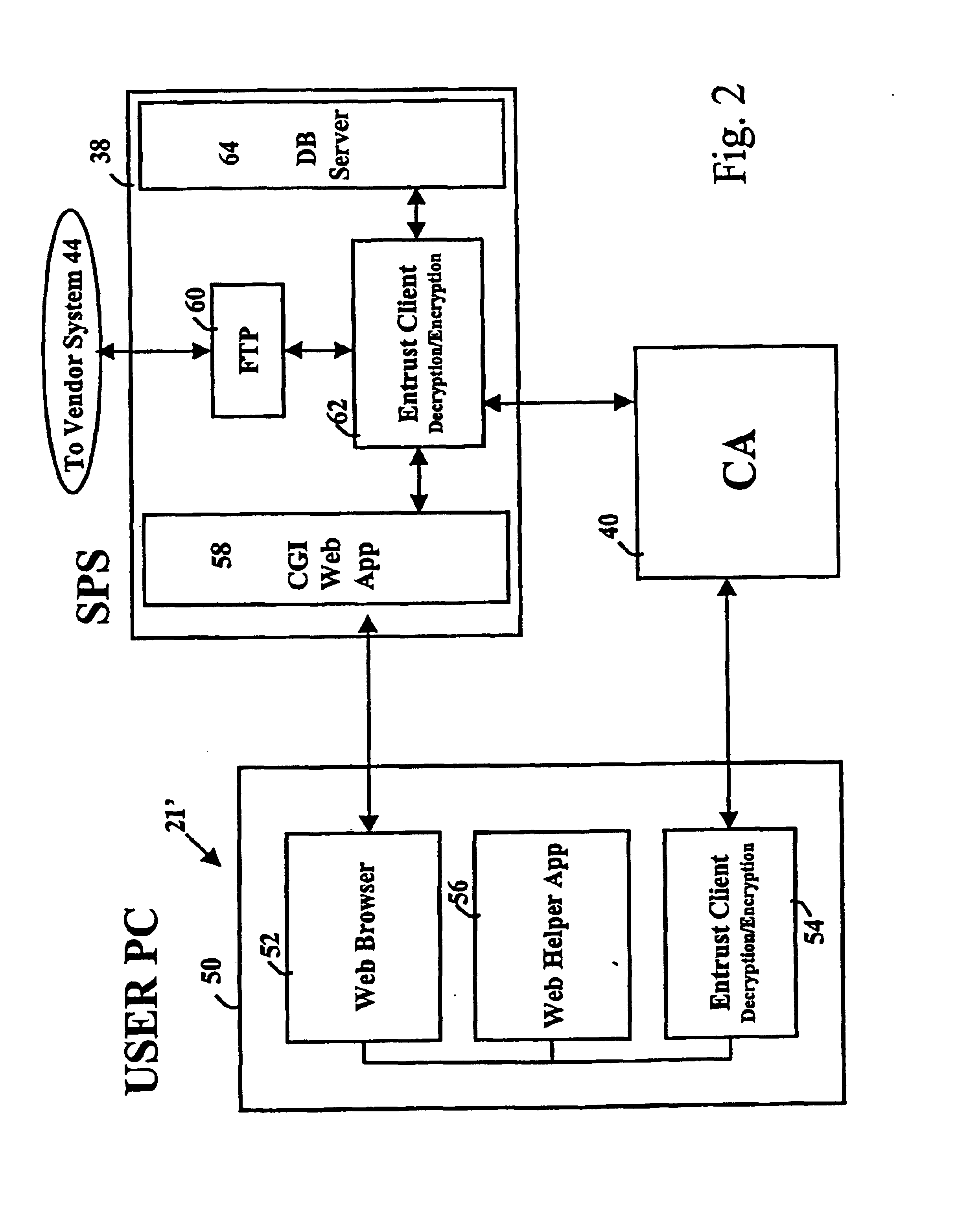
Secure electronic procurement system and method
InactiveUS7054844B2Reduce opportunity diversionReduce lossSpecial service provision for substationHand manipulated computer devicesUser deviceDigital signature
A secure electronic procurement system allows a user (e.g. pharmacist) to order and confirm receipt electronically over a network (e.g. Internet) goods normally subject to a verifiable chain of custody (e.g. narcotics, controlled drugs and substances, other public distribution regulated goods or valuables). The system includes hardware and software for a user device, a secure procurement system, a supplier system and a certificate authority to authenticate communications, particularly user orders and confirmed receipts. The supplier system may be a legacy EDI based order system. Copies of electronic orders, shipping notices and receipts confirming shipment received together with digital signatures are securely stored for audit trail purposes. Business rules within the secure procurement system operate to ensure proper adherence to the chain of custody.
Owner:DND CASH MANAGEMENT SOLUTIONS GP
Methods and compositions for a multipurpose, lab-on-chip device
InactiveUS20140030800A1Sturdy in constructionReduce usageBioreactor/fermenter combinationsBiological substance pretreatmentsDisaster areaTerrain
Methods and compositions for developing a series of microfluidic, USB-enabled, wireless-enabled, lab-on-chip devices, designed to reduce the chain-of-custody handling of samples between sample acquisition and final reporting of data, to a single individual. These devices provide on-the-spot testing for micro- and nanoscale (molecular) analysis of blood, urine, infectious agents, toxins, measurement of therapeutic drug levels, purity-of-sample testing and presence of contaminants (toxic and non-toxic, volatile and non-volatile); and for the identification of individual components and formal compounds—elemental, biological, organic and inorganic—inclusive of foodstuffs, air, water, soil, oil and gas samples. These devices may be relatively inexpensive, ruggedly designed, lightweight and capable of being employed—depending upon the specific application—by individuals with limited training, in remote and extreme environments and settings: including combat zones, disaster areas, rural communities, tropical / arctic / desert and other inhospitable climates and challenging terrains. The device may be comprised of materials that are reclaimed, are re-usable and are recyclable.
Owner:MOSES JONAS +1
Evidence collection holder for sample automation
A device and method of securing the original biological specimen collection absorbent within a holder to permit use of the absorbent within automatic specimen analysis devices and to permit continuance of a chain of custody is provided.
Owner:BODE TECH GROUP
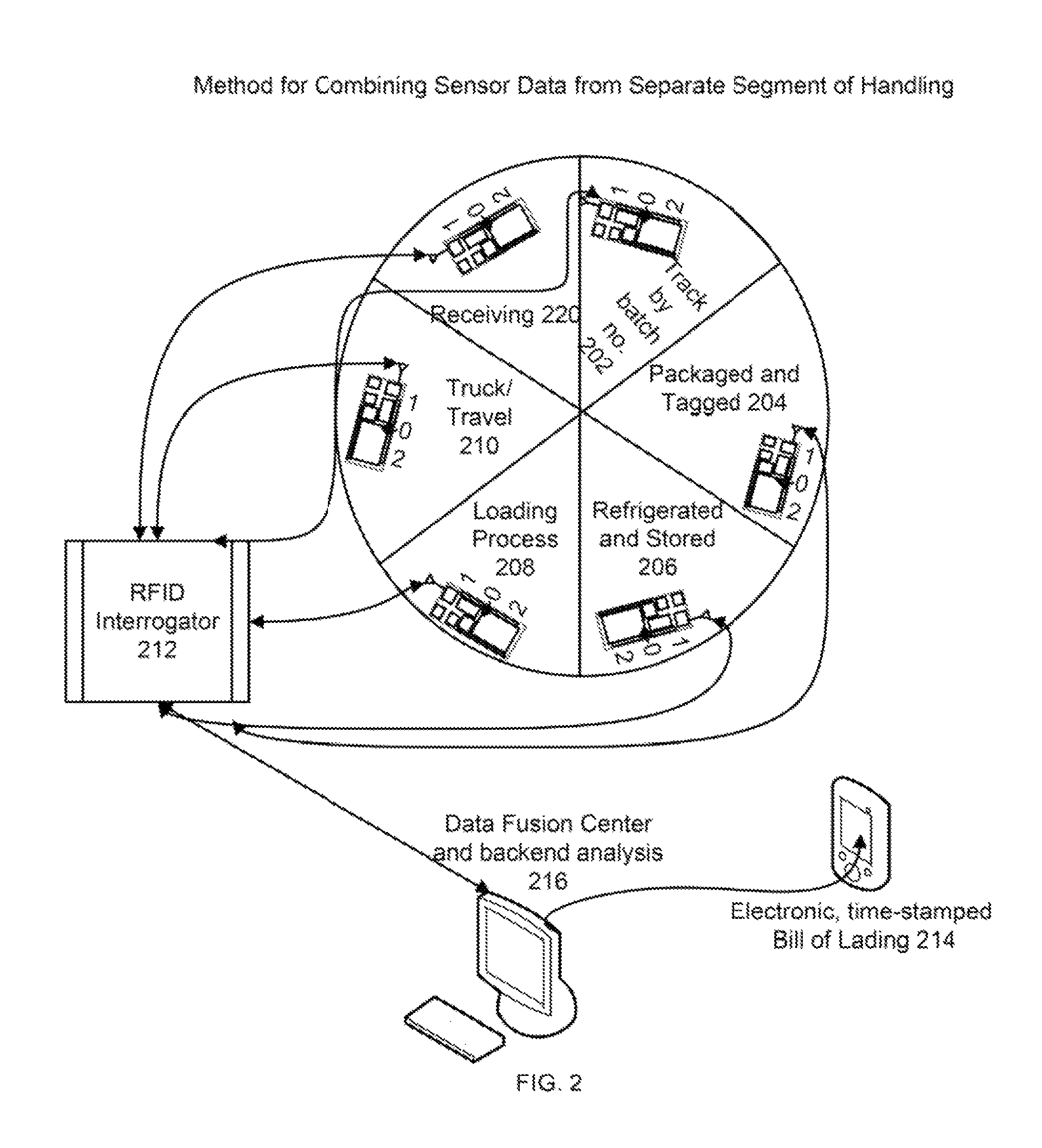
Methods and apparatus for combining temperature data from separate segments of handling
ActiveUS9436853B1Increase awarenessBetter recordkeepingMemory record carrier reading problemsSubscribers indirect connectionEngineeringChain of custody
A system and method for improving supply chain visibility is provided. According to a preferred embodiment, an electronic manifest may be downloaded and linked or attached to an existing purchase order. This electronic manifest is preferably designed to accepted data from RFID devices and other sensors. Further, the electronic manifest is preferably configured to be easily accessed the carriers or others in the chain of custody. According to a further aspect of the present invention, sensor-enabled RFID tags may be employed to track a product through the supply chain, capture temperature data, and to calculate shelf life.
Owner:GLOBALTRAK ACQUISITION
Digital watermarking for workflow
ActiveUS20050249374A1Efficient workflowSpeech analysisRecord information storageVideo playerComputer graphics (images)
Digital watermarking provides a chain of custody for video in movie studios. Several novel improvements in workflow processes for digital watermarking provide chains of custody. In a first implementation, a digital watermark payload includes an embedder ID and time stamp. The embedder ID is associated with a controlling PC user log, including, e.g., the user log being linked to a biometric of the user. In a second implementation, a video player is forced to run a video digital watermark embedder based upon a rights command, where an ID embedded in a watermark payload is determined solely by the embedder. A third implementation encrypts a conglomerate of watermarked segments of video so that a rendering device can decrypt the segments in a manner to produce different results in each usage dependent upon the key. A fourth implementation embeds digital watermarks in DVD disk images during delivery to a duplication house.
Owner:DIGIMARC CORP +1
Fluids Chain-Of-Custody
ActiveUS20050165554A1Electric/magnetic detection for well-loggingSurveyChain of custodyElectronic database
A method of assuring the collection of reliable and quality fluid sample includes the steps of acquiring a fluid sample at a point of acquisition, analyzing physical and chemical properties of the fluid sample at the point of acquisition; recording the point of acquisition sample properties in an electronic database archive, analyzing physical and chemical properties of the fluid sample at a location remote from the point of acquisition, recording the remote location sample properties in the archive, validating the fluid sample through comparison of the point of acquisition sample properties and the remote location sample properties and recording the validated sample properties in the archive.
Owner:SCHLUMBERGER TECH CORP
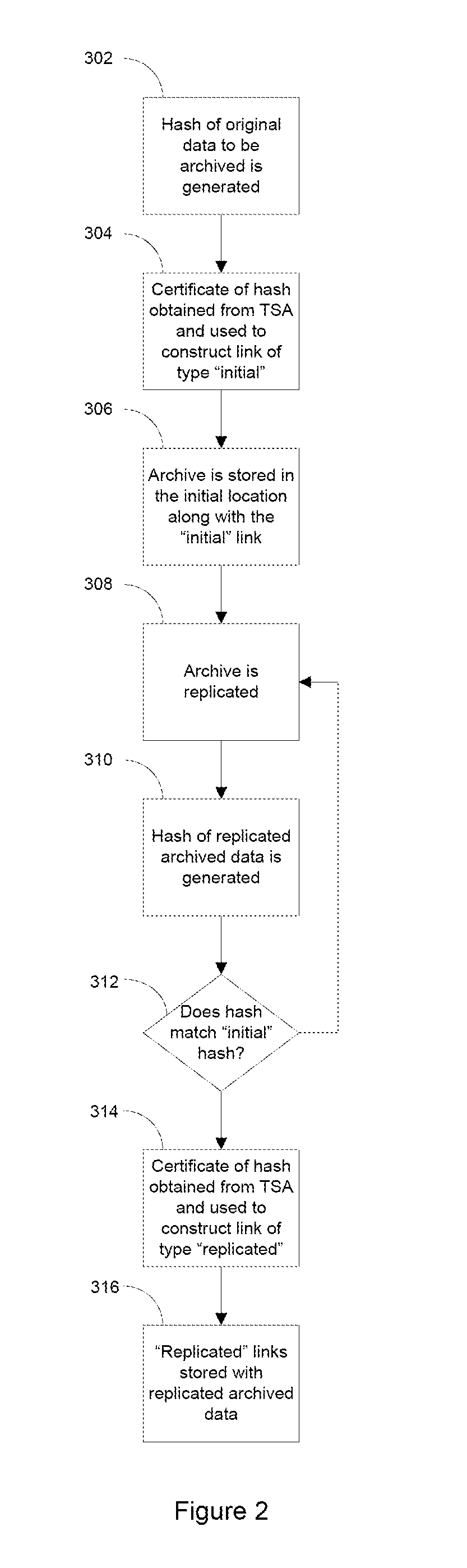
Chain-of-Custody for Archived Data
ActiveUS20110184910A1Overcome limitationsDigital data processing detailsWebsite content managementSchema for Object-Oriented XMLDependability
A method that builds a chain-of-custody for archived data is disclosed to ensure the integrity and reliability of the archived data. In one implementation, by using a certified Time Stamp Authority (TSA), an indelible record of each time the archived data is touched (e.g. created, stored, retrieved, accessed, tested, moved, or transformed) is generated to build verifiable links between events to ensure the custody of the data can be audited and verified that it has remained intact throughout its lifetime. The chain-of-custody, in combination with the storage architecture that ensures archive data has not changed through various software and hardware means (e.g., multiple hash signatures to ensure integrity, timestamp authorities to pinpoint each time the archived data was touched, location information to pinpoint physical location, and coordinated chain of custody on multiple replicas of the digital artifact) validates that the archived data has not changed since it was archived.
Owner:COVAX DATA INC +1
Secure storage systems and methods
ActiveUS20190333304A1Provide limited provisionsPrevent fraudulent useKey distribution for secure communicationMultiple keys/algorithms usageCryptographic protocolChain of custody
Secure storage platforms and their application in secure temporary property storage applications are disclosed and comprise: secure locker systems; secure locker systems comprising emergency access; secure locker systems comprising collapsible lockable compartments; secure storage systems comprising chain of custody management, recording and authentication; redirected delivery including post-delivery redirected delivery, en route delivery and dispatch delivery services comprising chain of custody services; and secure property claim check and car valet systems. A secure storage platform uses a secure protocol to establish challenge code and verification code generators to provide short lived single use access authentication codes to enable secure access and custody management of secured and stored property.
Owner:BINBOX INC
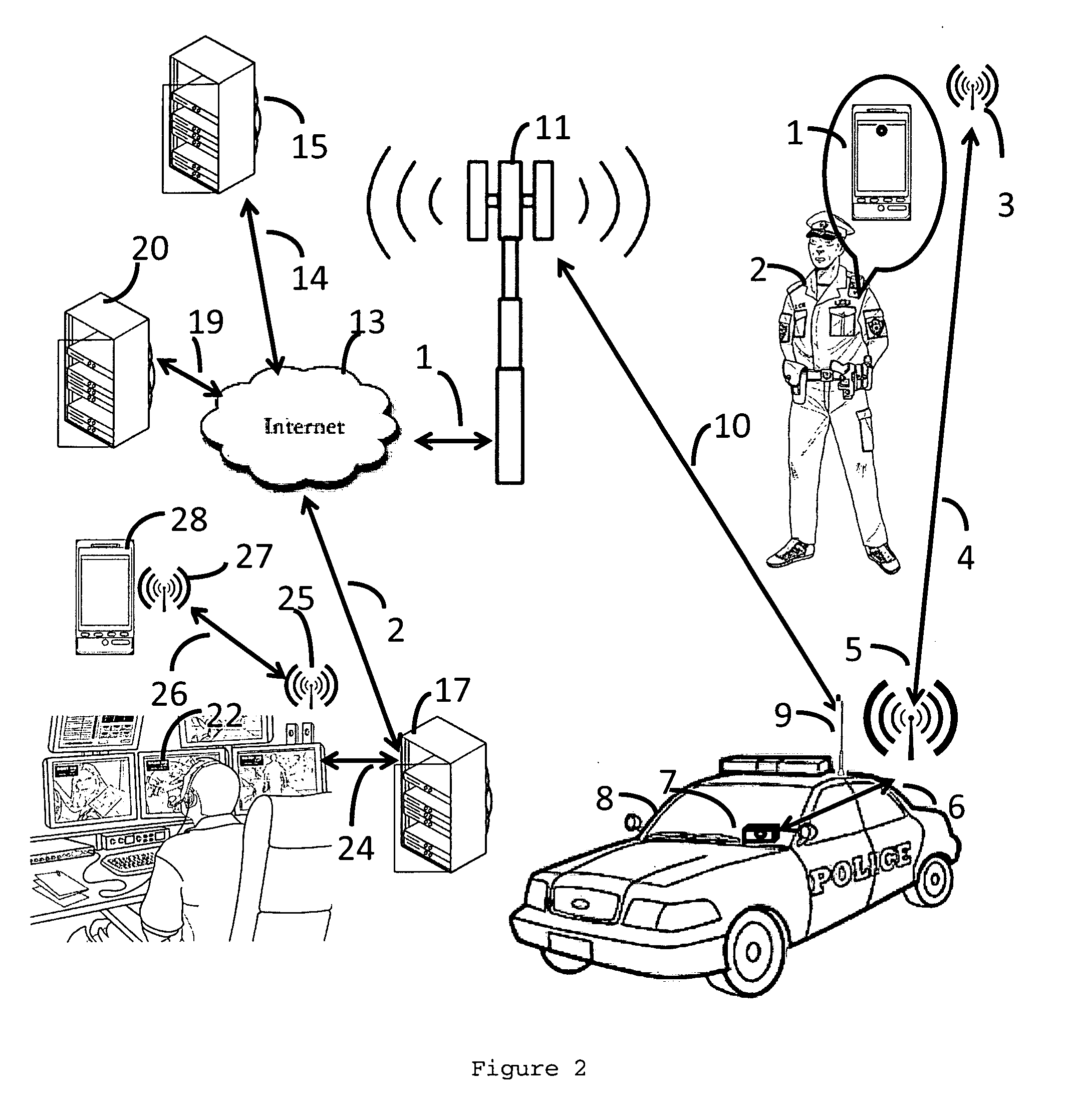
Law enforcement real time digital information chain of custody assurance system and method
InactiveUS20160119667A1Reduce storageReduce the amount requiredTelevision system detailsColor television signals processingEnd to end systemChain of custody
The invention disclosed relates to the end to end system, the methods and apparatuses for delivering real time HD video and audio content using a secure chain of custody method over the ubiquitous cellular network and providing a solution for the lone worker in hazardous environments.
Owner:LAYSON JR HOYT MAC +1
Method, system and program for tracking pharmaceutical samples
InactiveUS20090002173A1Ease of evaluationFacilitate complianceRadio transmissionBurglar alarm by hand-portable articles removalDrug productChain of custody
The invention provides a method, system and machine readable program for tracking pharmaceutical samples. A pharmaceutical sample (such as a batch of pharmaceutical products) is provided to be distributed. The pharmaceutical sample is assigned a unique radio-frequency identification tag. The pharmaceutical sample is then tracked through a chain of custody by scanning the radio-frequency identification tag at one or more points in the chain of custody. Other novel features relating to the invention are described herein.
Owner:BERGSTEN JAMES R +3
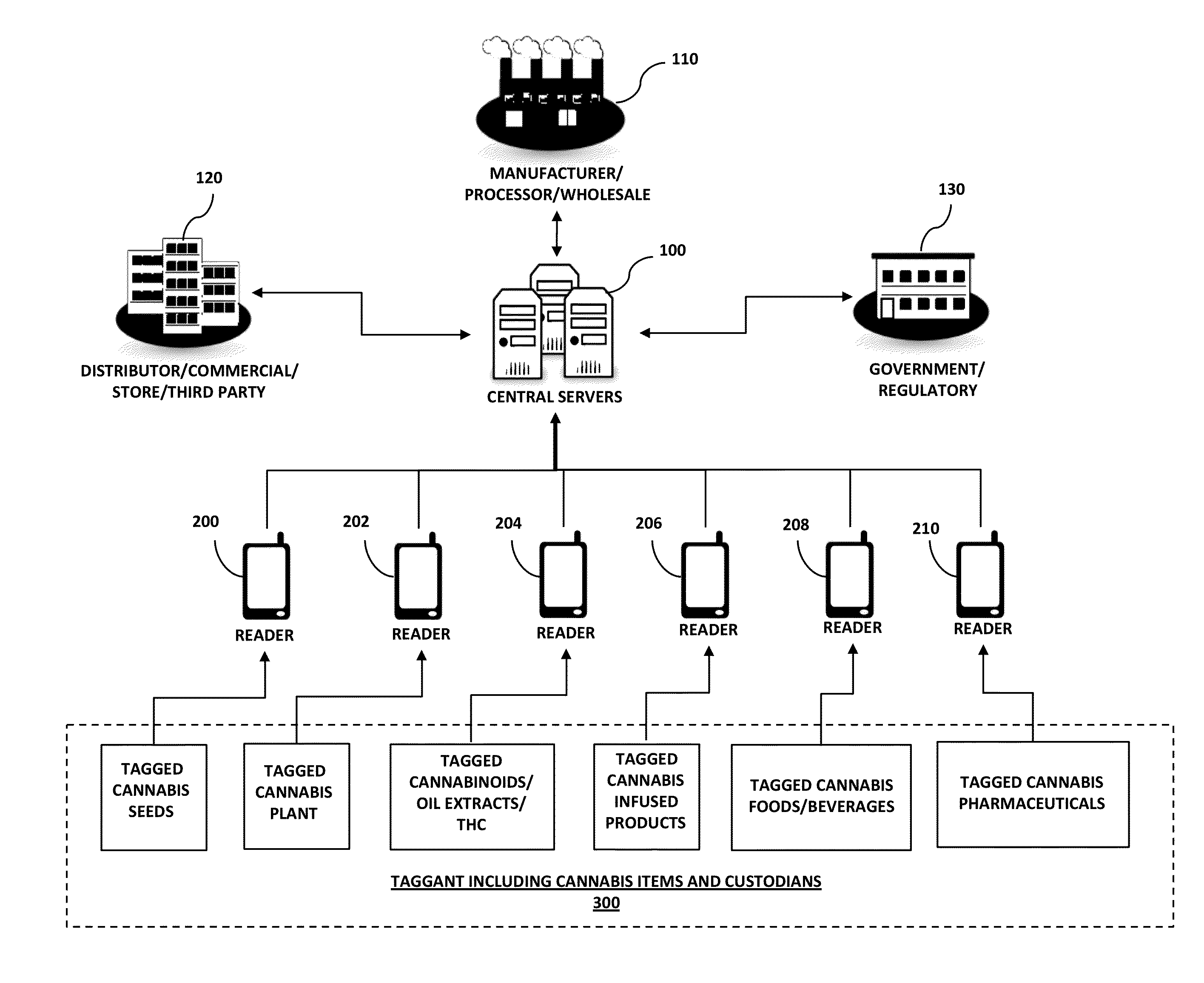
Cannabis chain of custody management
ActiveUS20150278757A1Error minimizationLow costOrganic chemistrySolvent extractionCannabisCannabinoid
A method and system of managing a chain of custody for cannabis is provided that includes depositing one or more identification tags onto the surface of one or more cannabis seeds at a first custodian location, and depositing the identification tags onto the surface of one or more cannabis, wherein the cannabis plants are grown and matured from the cannabis seeds. The method and system further includes receiving the tagged cannabis plants at a second custodian location and extracting cannabinoids from the tagged cannabis plants, wherein the extracted cannabinoids include the one or more identification tags. In addition, the method and system further includes receiving the extracted cannabinoids at a third custodian location, wherein the extracted cannabinoids include the one or more identification tags which may be accumulated from all the prior custodians. Here, the first custodian location can include a seed grower or harvesting facility, the second custodian location can include a processing facility, and the third custodian location can include a distribution, retailer, merchant, sub-manufacturer of food products.
Owner:WALDEN MICHAEL
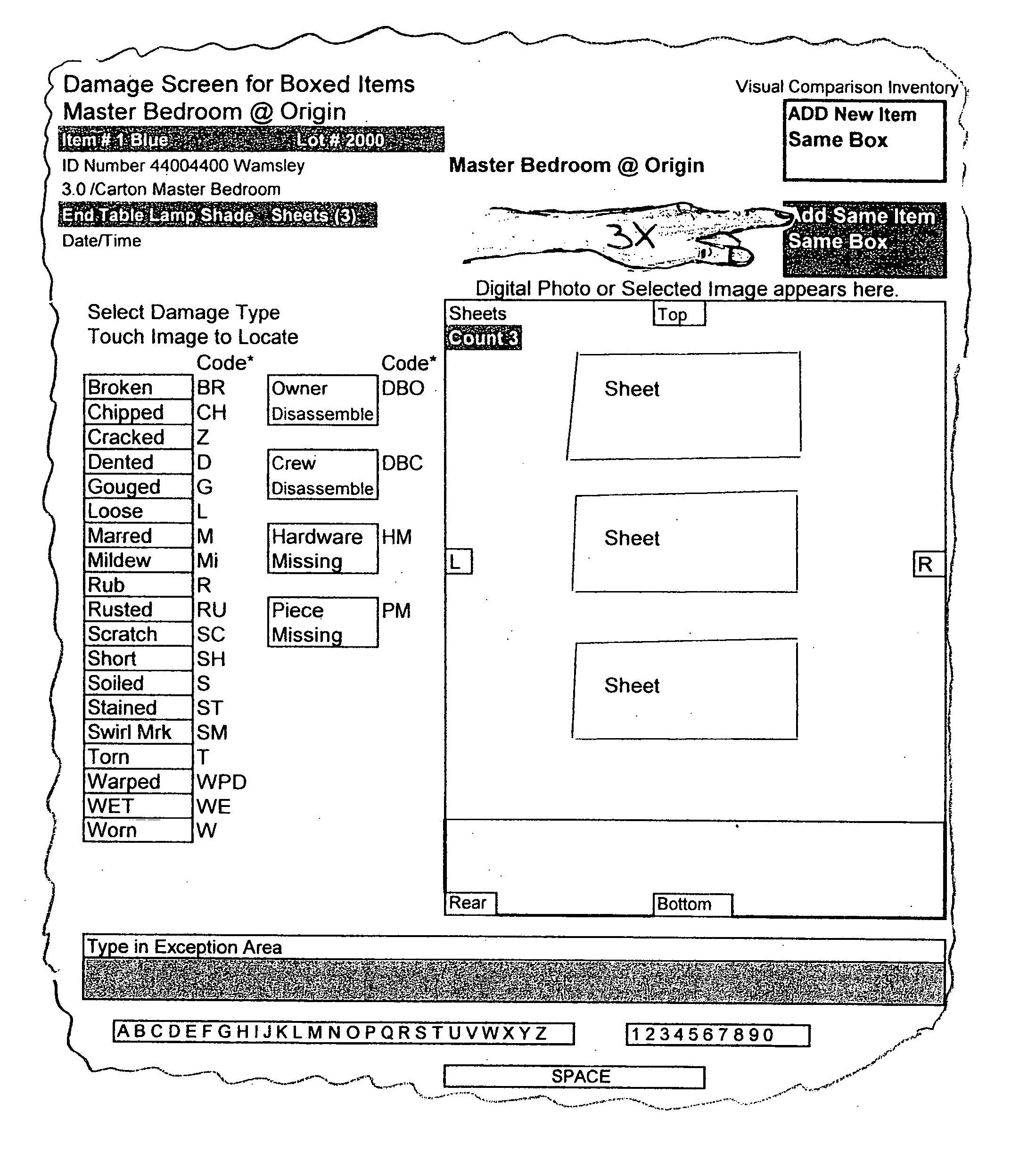
Graphic driven moving personal property tracking system and method
InactiveUS20060106652A1Accurately and easily recordingAccurate monitoringFinanceCathode-ray tube indicatorsGraphicsHand held
A graphic driven moving personal property tracking system that enables the company to monitor and track its customer's personal property during transport and to identify the various parties in the chain of custody. The system uses a hand held device that enables the packing company to accurately inventory and record the initial condition of the personal property prior to packing. Loaded into the memory of the hand held device is a building layout software program that visually presents images of different pieces of the personal property in selected rooms. When a room is selected, a list of personal property normally found in the room is presented. When damage is detected on the personal property prior to packing, the user selects the personal property and records precise location of the damage. When all of the personal property has been recorded, a written report is generated and delivered to the customer who then verifies the information. During the packing stage, an identifying code is assigned to each piece of personal property or to its outer container. When the personal property is moved between the hauling company, the warehouseman, and the unpacker, the handheld device is used to record the chain of custody and the condition of the property.
Owner:WAMSLEY DAVID A
Devices and methods for the collection and detection of substances
InactiveUS20140227796A1Easy to detectSolve the lack of spaceComponent separationWithdrawing sample devicesForensic PharmacyField tests
The present invention provides a single self-contained device for collecting, extracting, on-site testing, and transferring for forensic confirmatory analysis, a wide variety of substances including, but not limited to, drugs of abuse, explosives, weapons of mass destruction, food toxins and industrial wastes. Samples can be obtained from a surface by swabbing a suspect area or the testing of solid materials (pills, capsules, powders), air samples and biological and non-biological fluids by placing the substance in the device. The device includes a swab, a retention well including a wash, and analysis technologies that can be, for example, a lateral flow testing system. The swab is rinsed with a wash prior to testing thereby not compromising the chemistry of the detection technologies and allowing for a wide variety of applications under a number of field conditions. Also, the device is a single self-contained unit instead of having a separate reagent droppers or sprays, making it compact and easy to use. Moreover, the device is designed to not only collect and test samples but to seal the originally target analyte, not affected by testing procedures, in a specially designed cap for shipping under chain of custody documentation to a forensic laboratory for confirmatory testing.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
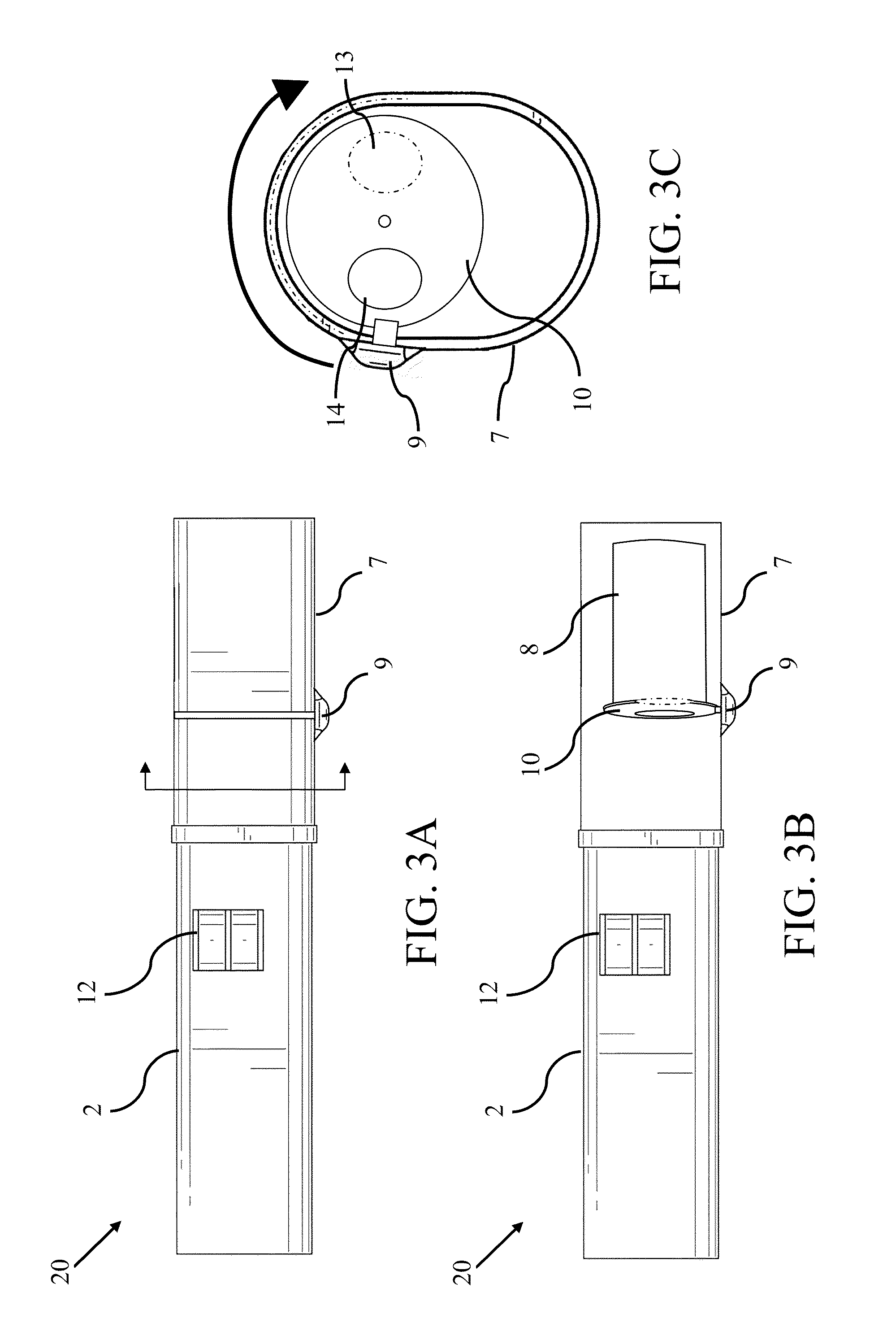
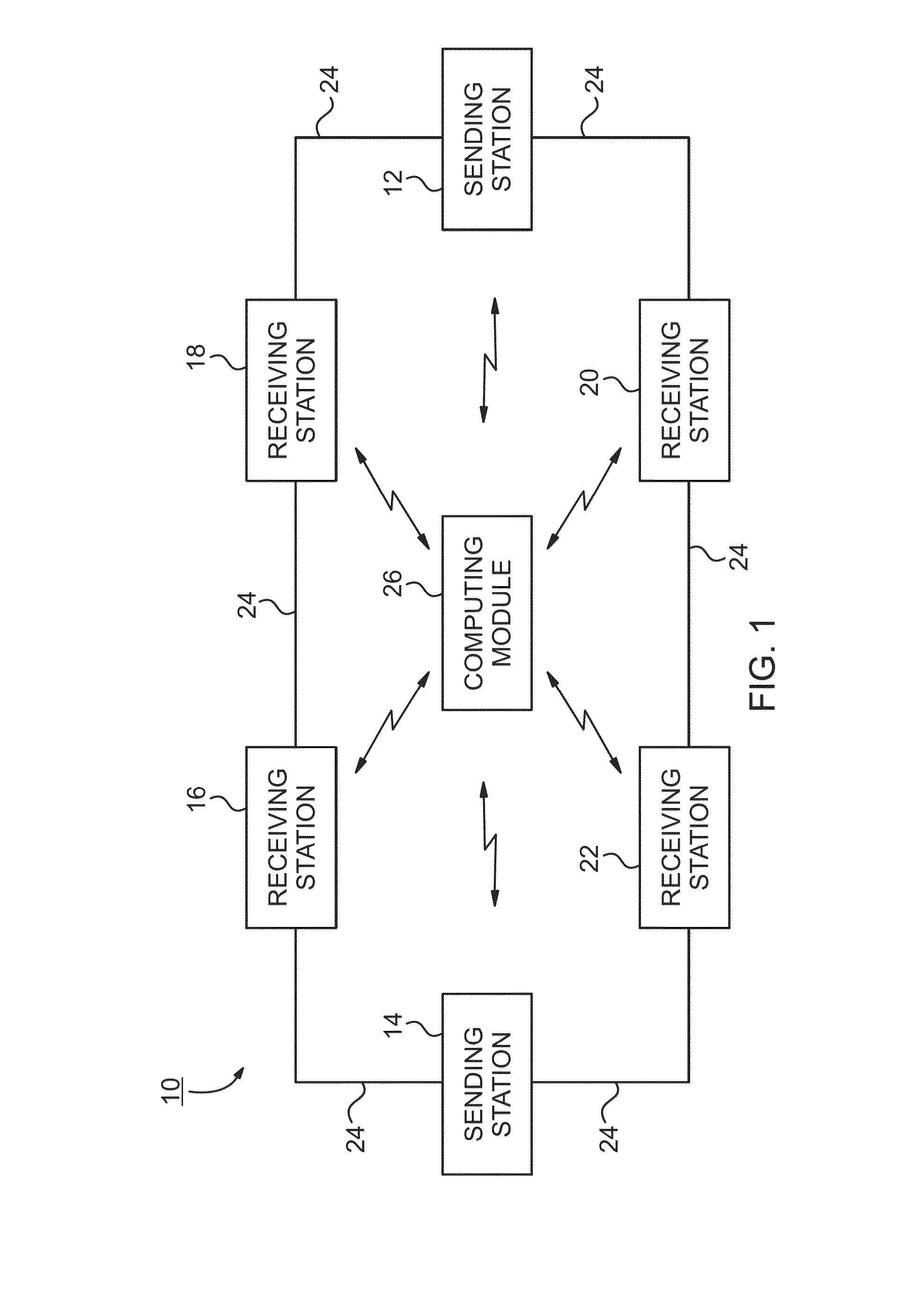
System and Method for Locking a Carrier/Container for Tracking, Controlling Access, and Providing Delivery Confirmation
ActiveUS20140330428A1To offer comfortEasy to collectConveyorsDigital data processing detailsTelecommunicationsCarrier signal
A system and method for tracking / controlling access to transported articles, includes a computing module in signal communication with sending and receiving stations. A first input device at the sending station receives identifying information identifying a carrier (“carrier ID”) and an item (“item ID”) placed within the locked carrier. The carrier ID and the item ID are transmitted to the computing module. A second input device at the receiving station receives the carrier ID for a carrier received at the receiving station and identifying information for an individual (“user ID”) at the receiving station provided access to the locked carrier. The carrier ID and the user ID are transmitted to the computing module, which unlocks the carrier and allows access to the item inside, and records the user ID of the individual provided access and the associated carrier ID and / or item ID to provide chain of custody information for the item.
Owner:CAROLINA LOGISTICS SERVICES LLC
Electronic inventory movement and control device
InactiveUS7113922B2Significant problemHand manipulated computer devicesBuying/selling/leasing transactionsElectronic formBarcode
Disclosed is a method and apparatus to electronically tabulate items marked with a bar code. The system may optionally operate to manage, control and tabulate inventory, produce vendor-correct purchase orders, manage multiple locations, multiple buildings, multiple clients and multiple stores to facilitate efficiency for a wholesaler or retailer or alternatively for a distributor, broker or sales agent. The system may alternatively be used to manage inventory for a manufacturing environment or for tracking evidence or items in a chain of custody environment useful for governmental and scientific functions.
Owner:GENIUS CENT
Methods and systems for labeling labware
ActiveUS20120089490A1Overcome problemsData processing applicationsLaboratory glasswaresMarking outChain of custody
The present invention includes a system for marking labware. The system includes an instruction set with markings to be applied to pieces of labware and the order in which the markings are to be applied to the labware. The system also includes a marking device that receives the instruction set and then places the non-toxic marks on the pieces of labware. The invention also includes methods tracking chain of custody of biological material in a facility. The methods include assigning a unique marking for biological materials, storing that marking in a database, applying a non-toxic marking to a piece(s) of labware and then scanning the marking.
Owner:BLAINE JILL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com