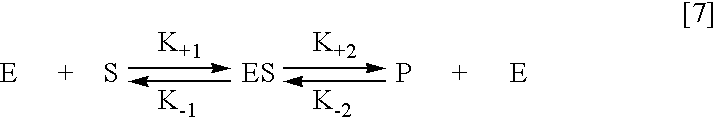Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1169results about How to "Reliable identification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
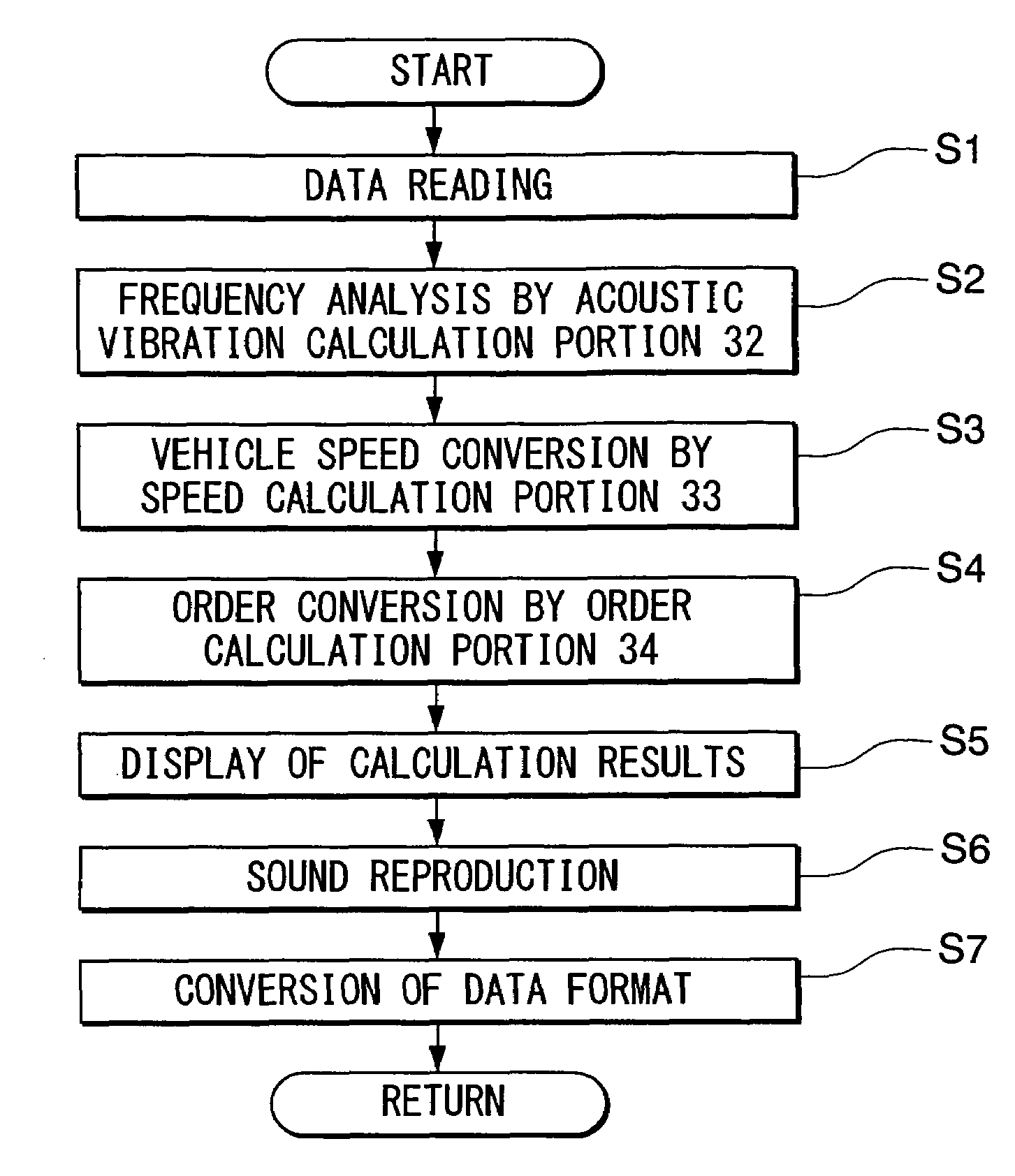
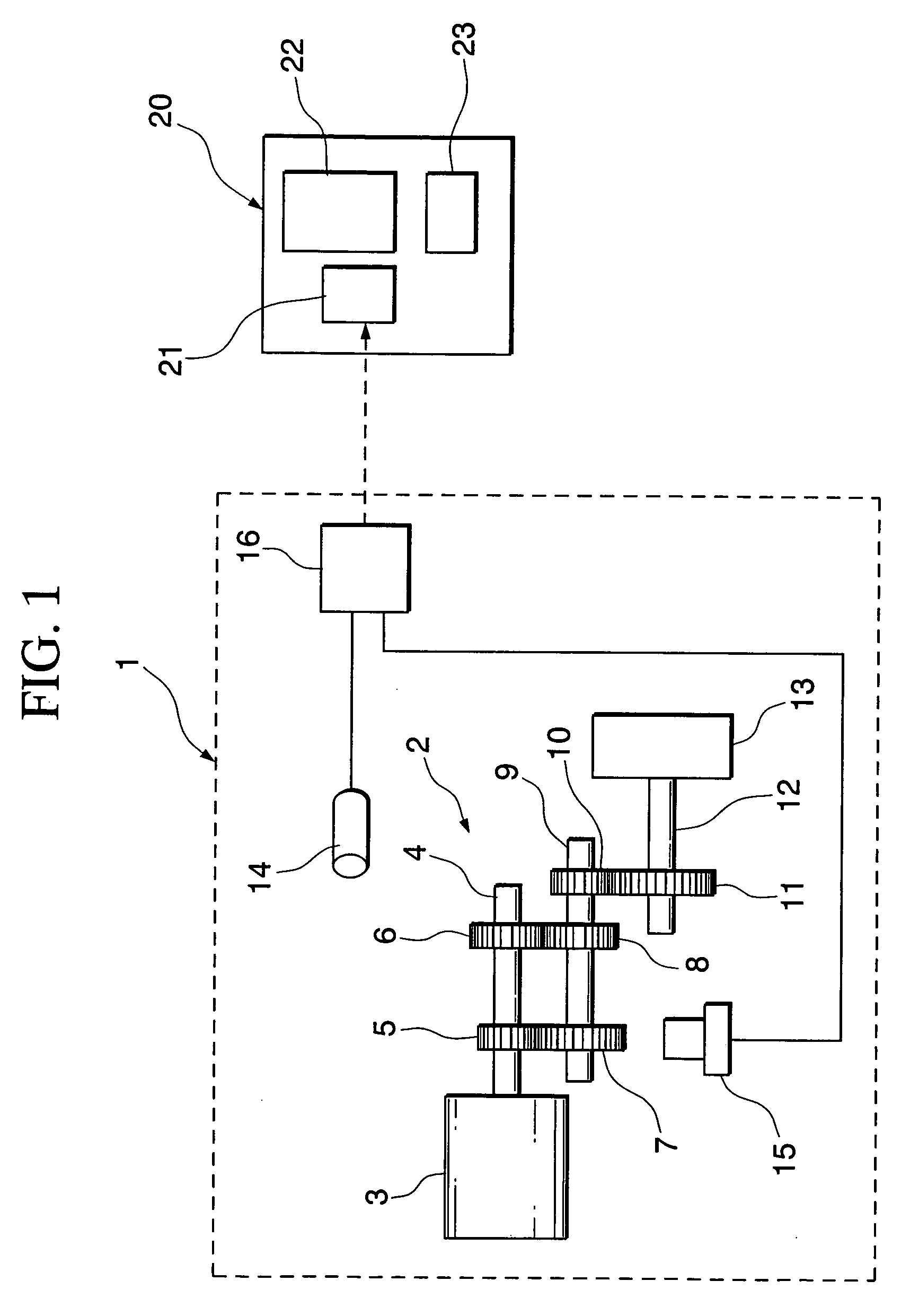
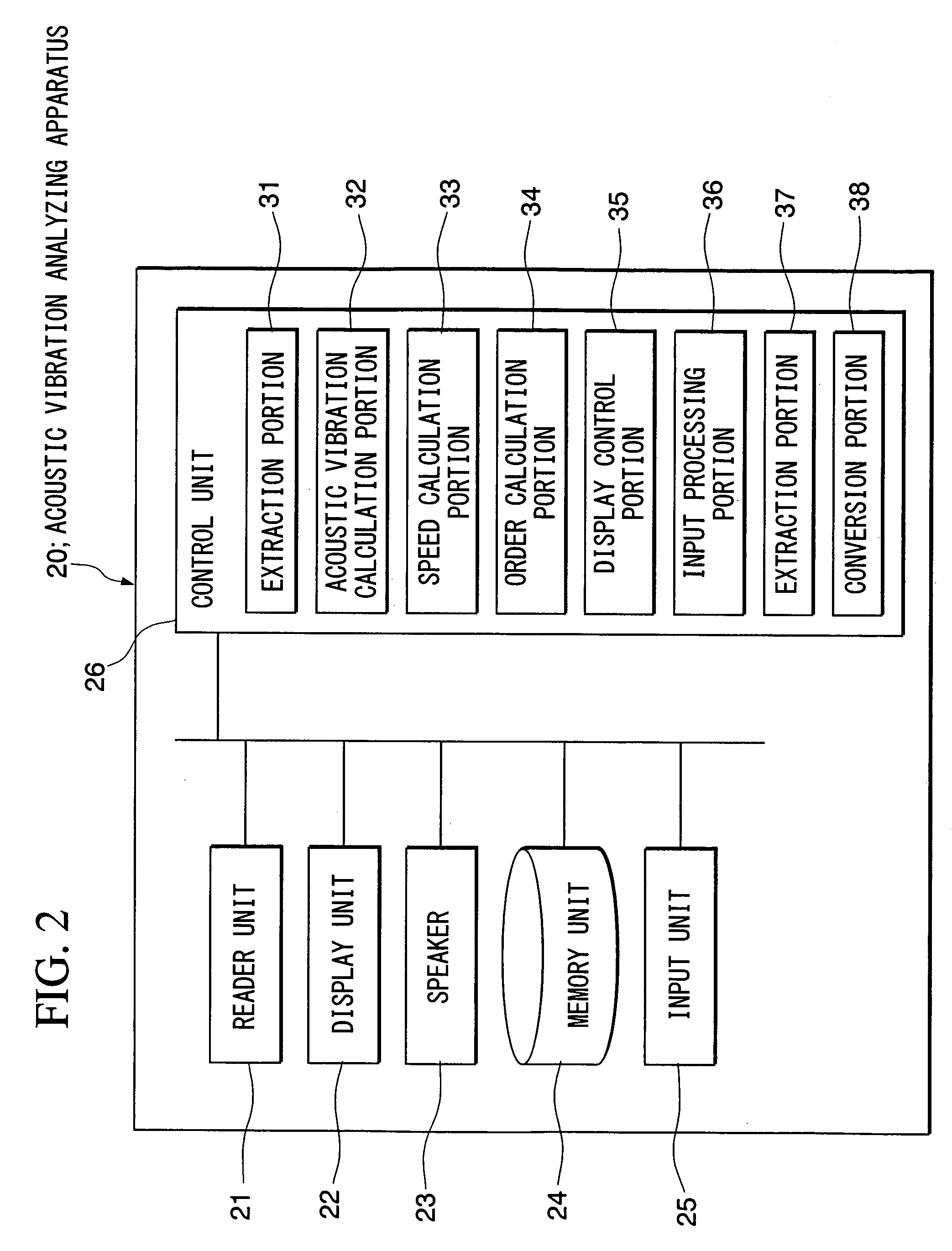
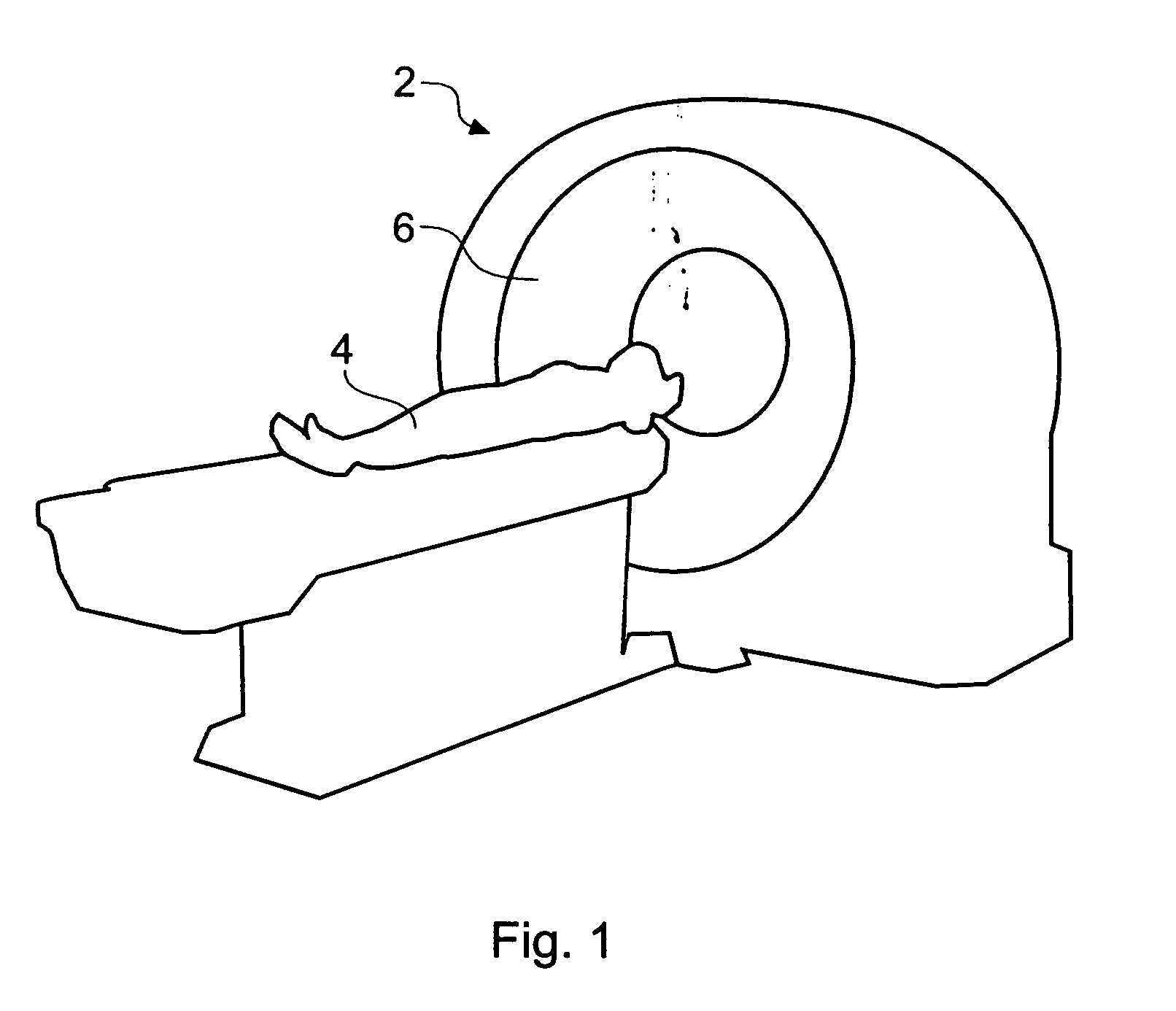
Acoustic vibration analyzing apparatus and acoustic vibration analyzing method, program for analyzing acoustic vibration, and recording medium, readable by computer, on which program for analyzing acoustic vibration is stored
ActiveUS7401000B2Easy to carryReduce in quantityVibration measurement in solidsVehicle testingAnalysis methodAcoustics
The present invention provides an acoustic vibration analyzing apparatus for carrying out acoustic vibration analysis by picking up data of sounds generated due to rotation of a plurality of gears and data of the number of revolutions of a gear selected from a plurality of gears when a transmission of a vehicle having the plurality of gears operates. The acoustic vibration analyzing apparatus comprises an acoustic vibration calculation portion for analyzing acoustic data in terms of frequency, an order calculation portion for calculating an order in compliance with the specifications of a plurality of gears, a speed calculation portion for calculating the speed of a vehicle, and a display unit for displaying acoustic pressure levels with the order and vehicle speed associated therewith.
Owner:HONDA MOTOR CO LTD
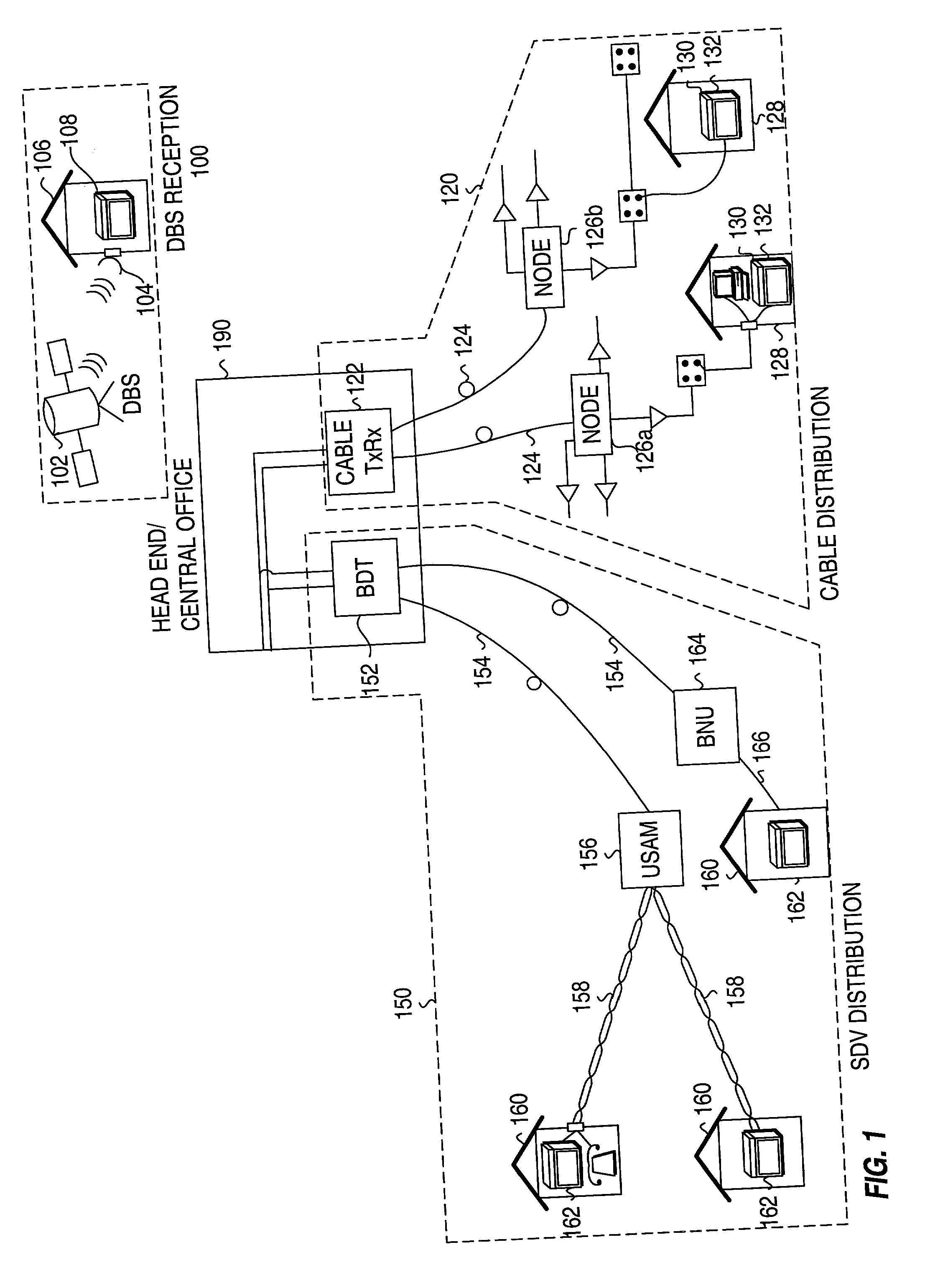
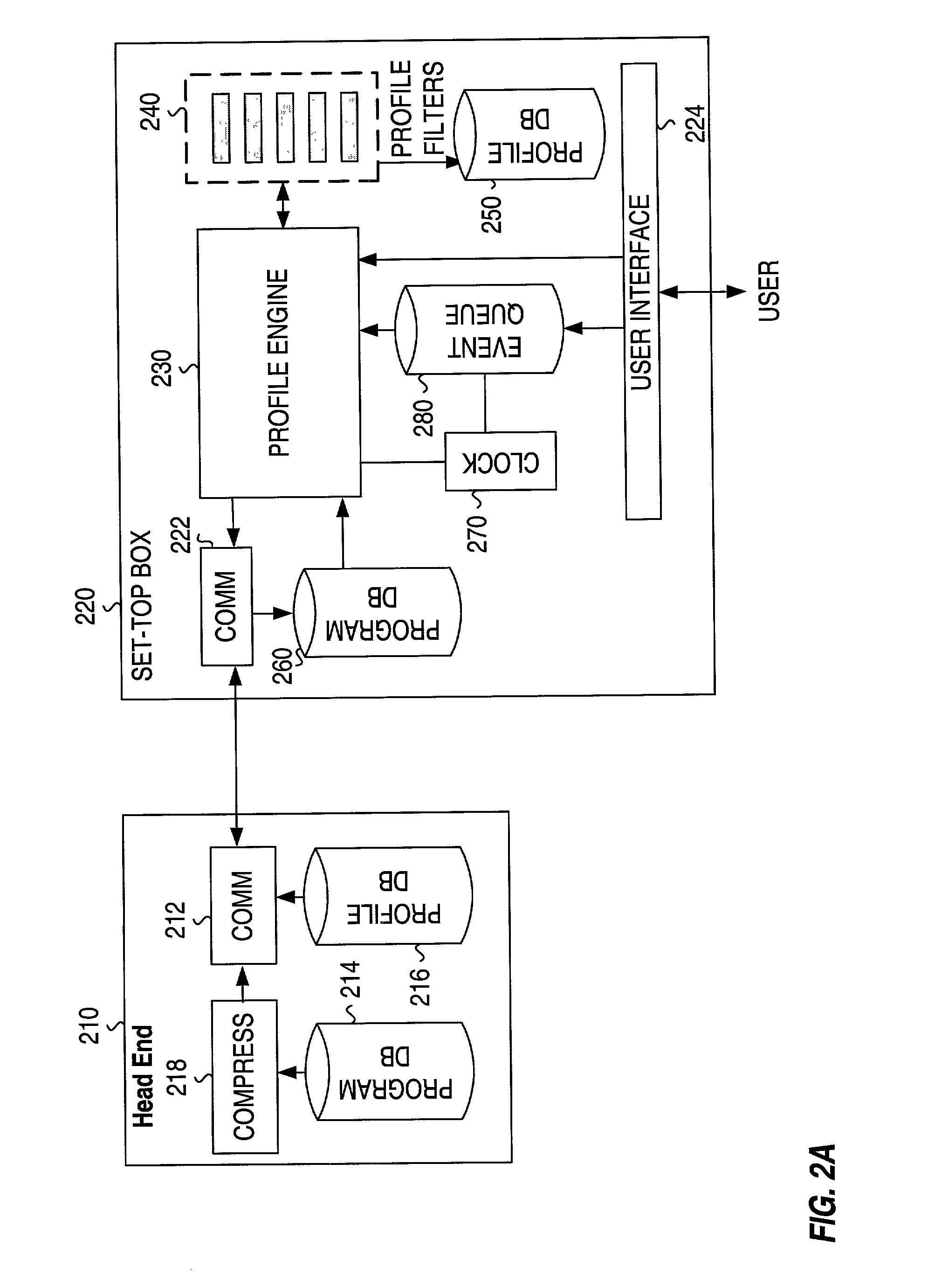
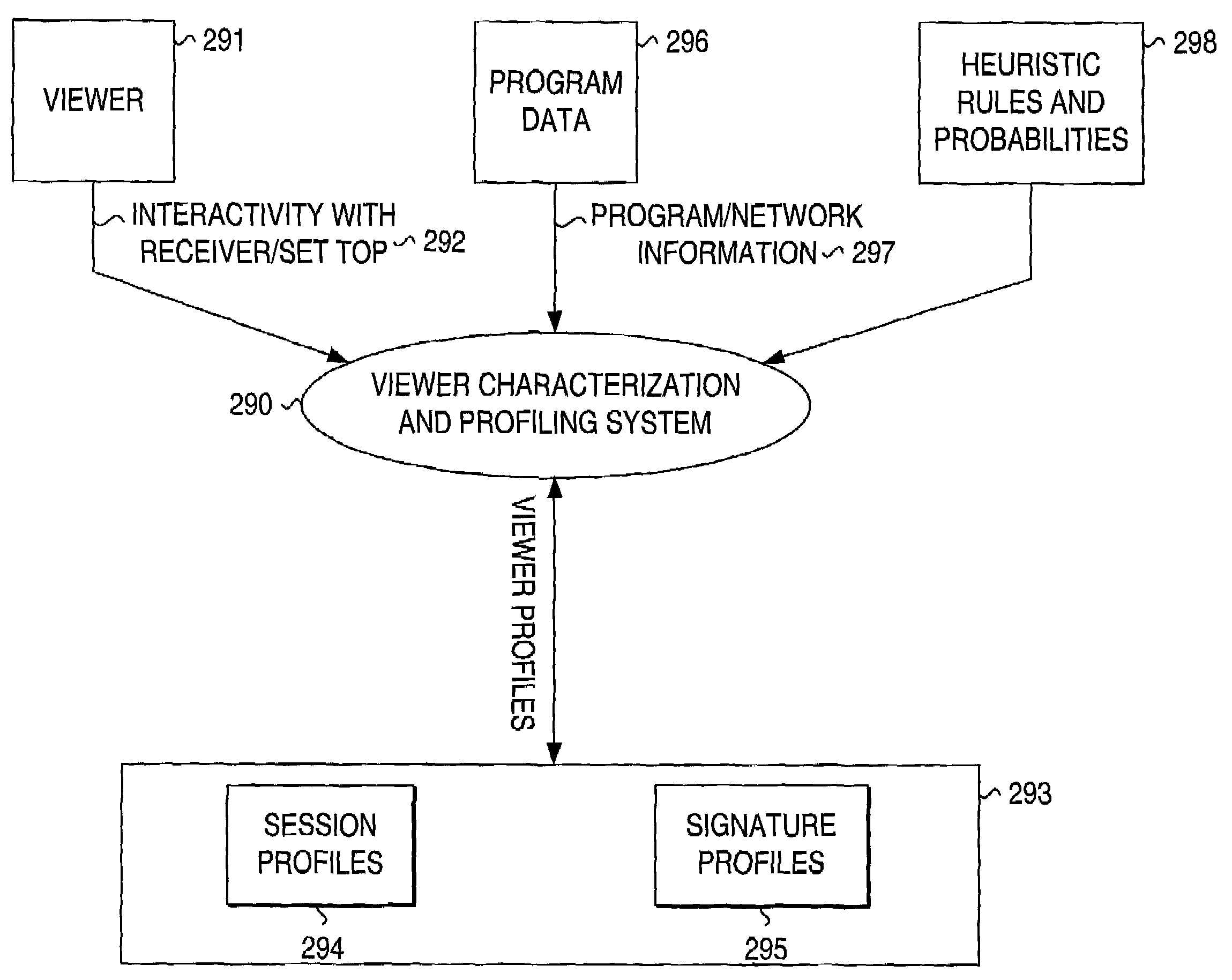
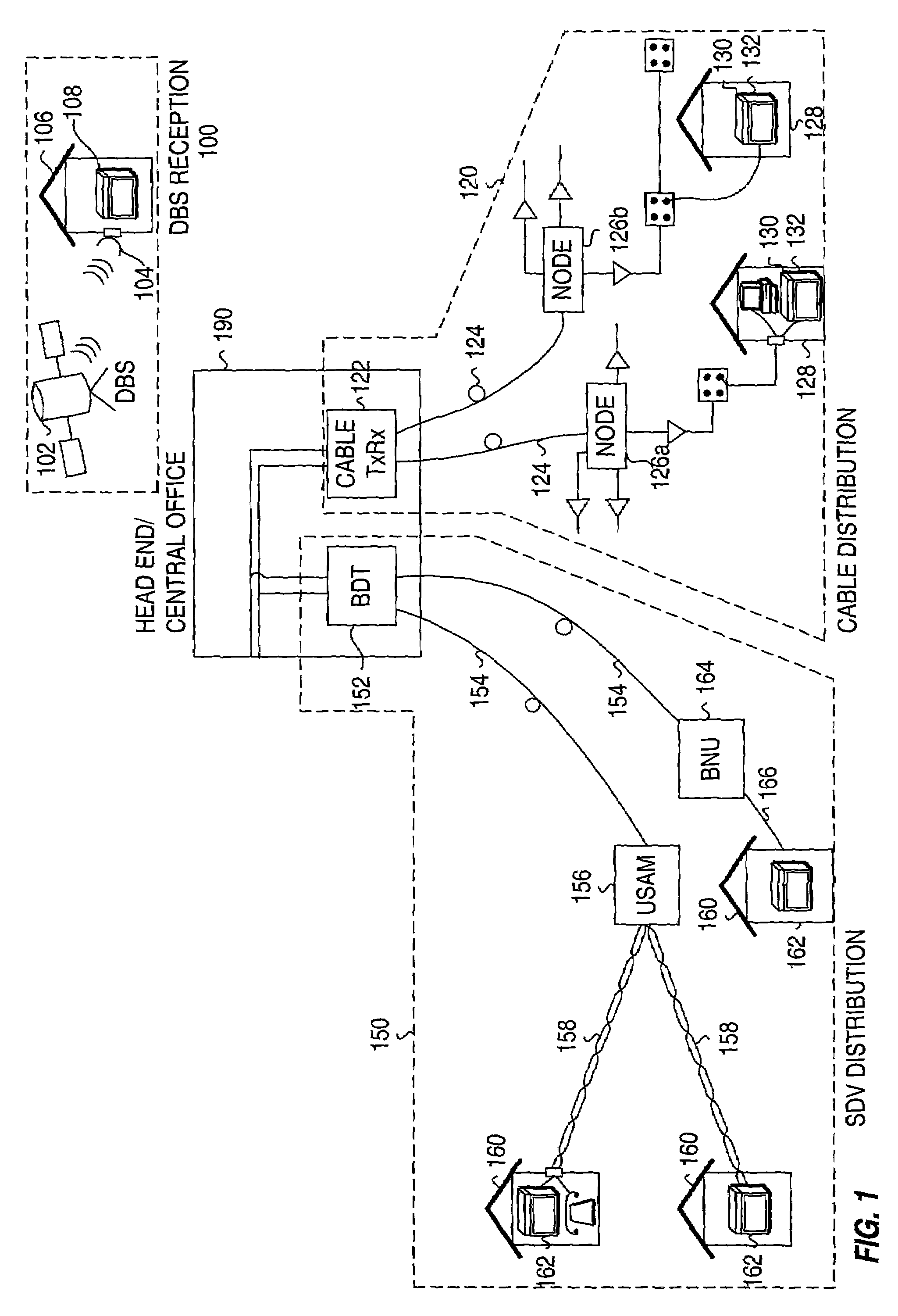
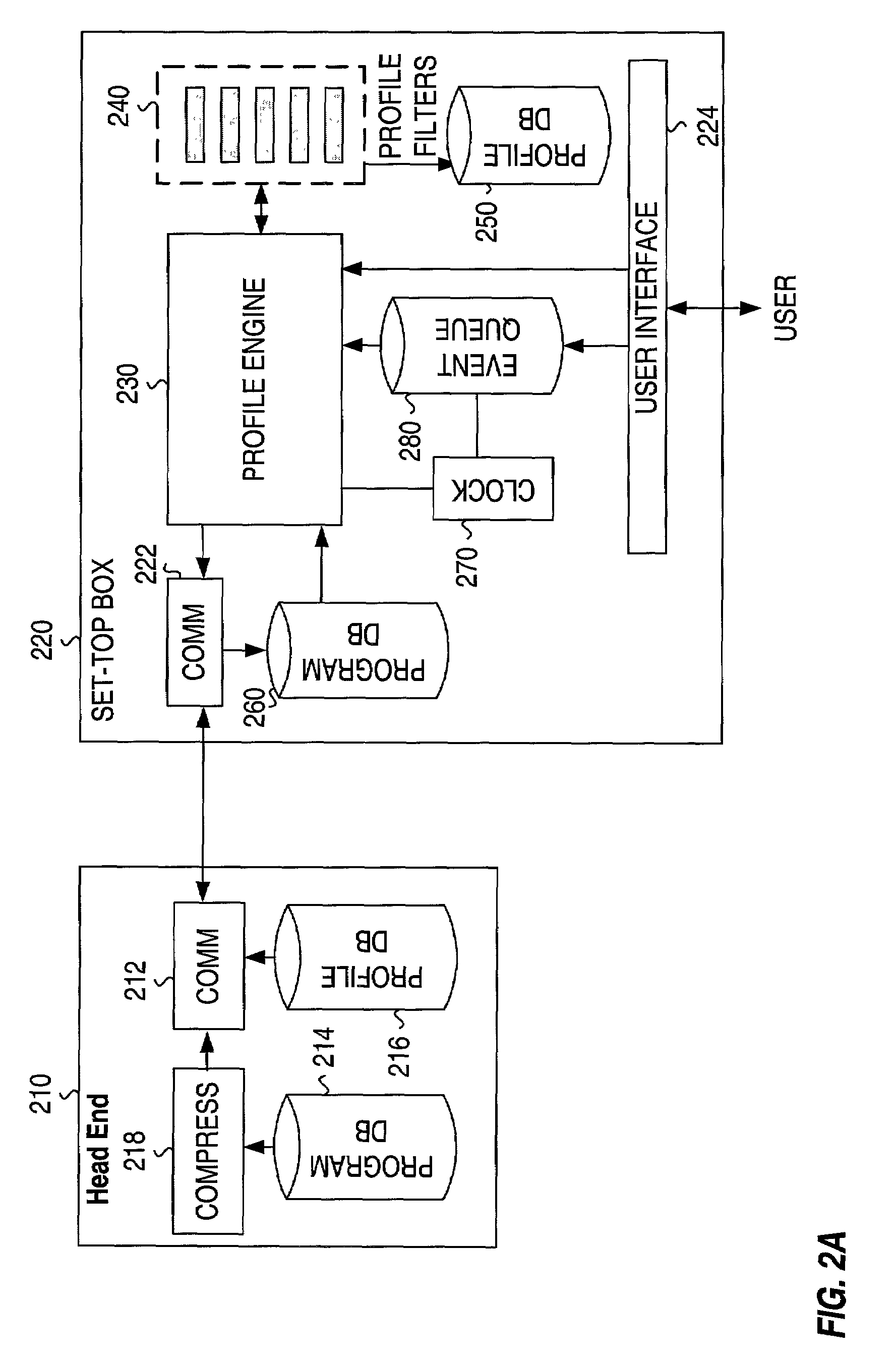
Profiling and identification of television viewers
ActiveUS20020129368A1Reliable identificationTelevision system detailsBroadcast system return channelsRemote controlTargeted advertising
Profiling a television viewer by monitoring and processing, locally at a television viewing environment, the viewer's interactivity (e.g., via a remote control unit) with the television viewing environment. Generating one or more profiles for each viewer based on one or more of the multitude of interactions of each viewer and on, in general, the viewing habits and preferences of the viewer. Automatically and reliably, detecting or inferring at a particular time, which specific individual or individuals, are actually interacting with the TV in household comprising more than one individual. Such viewer identification and profile generation can be used to facilitate the delivery of targeted content, including targeted advertising.
Owner:PRIME RES ALLIANCE E LLC
Profiling and identification of television viewers
ActiveUS7260823B2Reliable identificationTelevision system detailsBroadcast system return channelsRemote controlHabit
Profiling a television viewer by monitoring and processing, locally at a television viewing environment, the viewer's interactivity (e.g., via a remote control unit) with the television viewing environment. Generating one or more profiles for each viewer based on one or more of the multitude of interactions of each viewer and on, in general, the viewing habits and preferences of the viewer. Automatically and reliably, detecting or inferring at a particular time, which specific individual or individuals, are actually interacting with the TV in household comprising more than one individual. Such viewer identification and profile generation can be used to facilitate the delivery of targeted content, including targeted advertising.
Owner:PRIME RES ALLIANCE E LLC
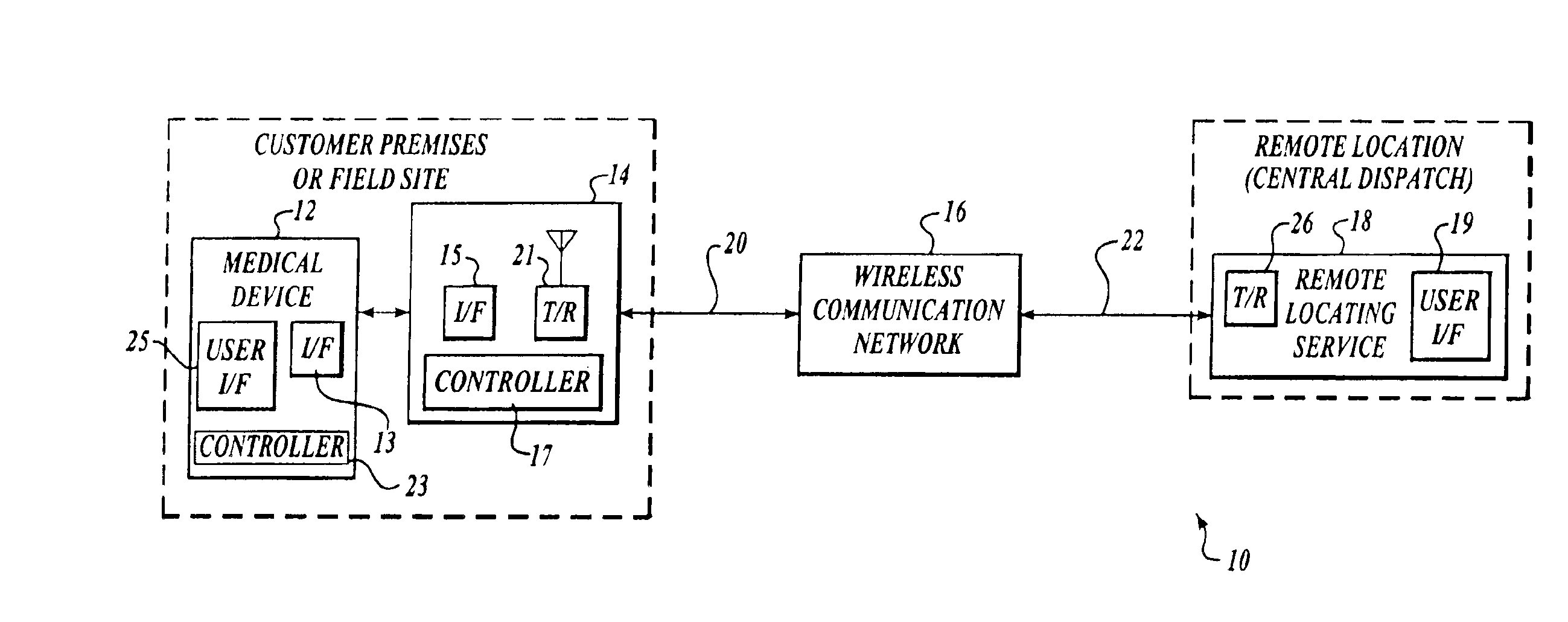
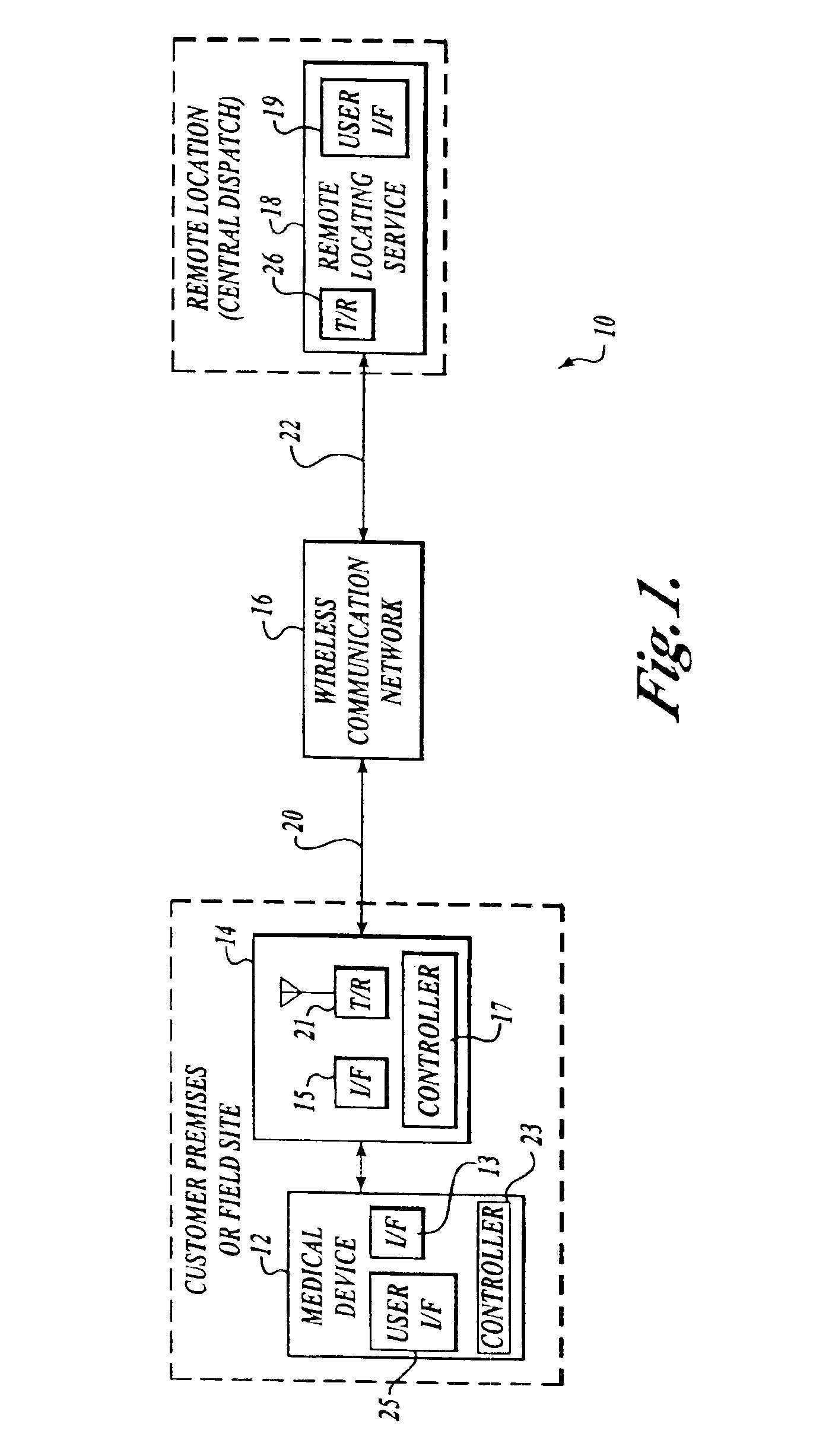
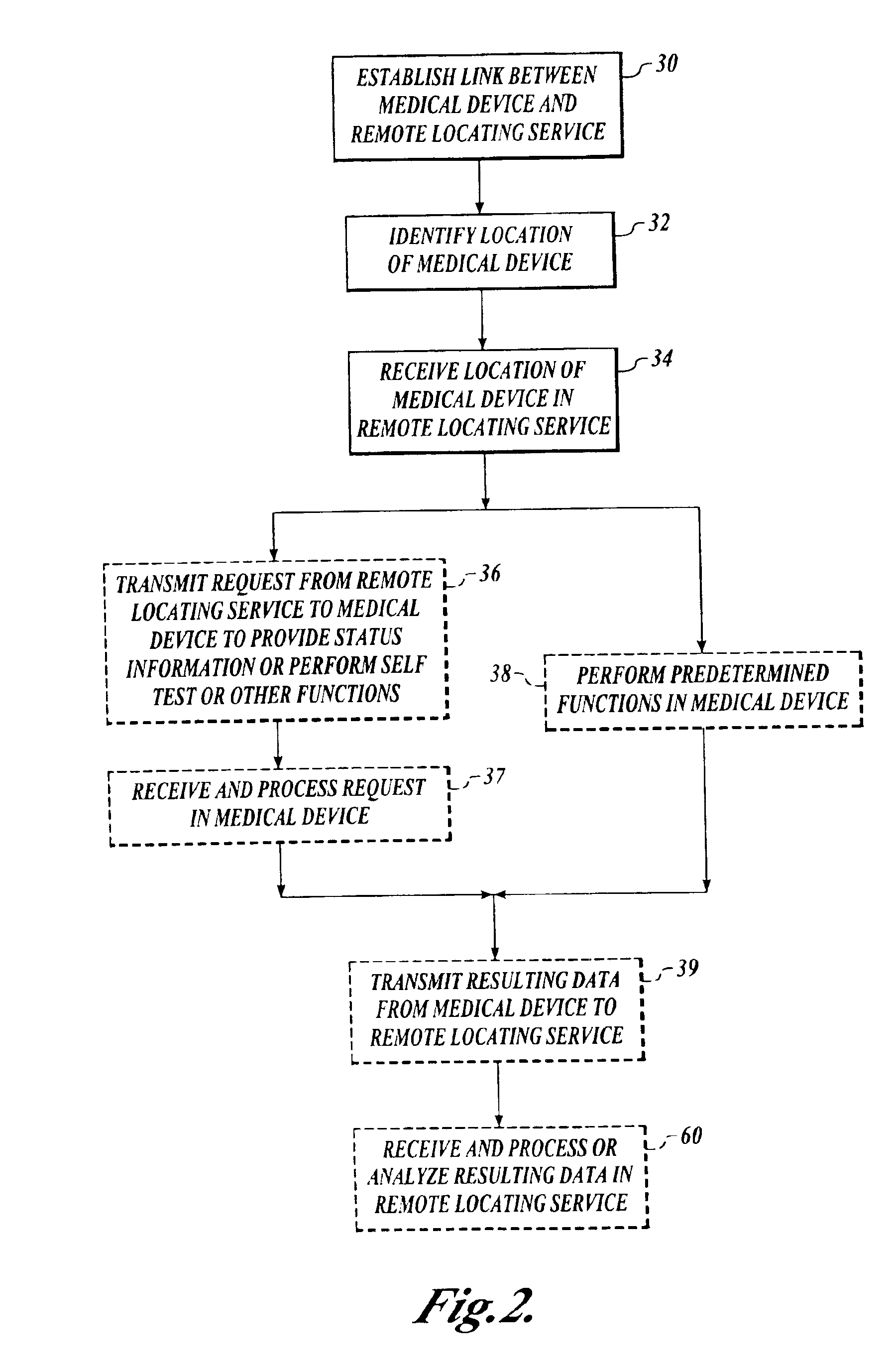
Method and system for locating a portable medical device
InactiveUS6937150B2Located reliablyOvercome problemsFrequency-division multiplex detailsHeart defibrillatorsWireless dataSystem identification
The invention provides a wireless automatic location identification (ALI) capable system (10), including a medical device (12) having a wireless data communicator (14), a wireless communication network (16), and a remote locating service (18) for remotely locating and monitoring one or more medical devices over the wireless communication network. When the medical device is linked to the remote locating service over the communication network, the ALI-capable system identifies the location of the medical device and relays the location information to the remote locating service. The system permits reliable determination of the location of the medical device wherever the medical device is situated. The medical device may further be configured to transmit signals indicative of its status, condition, or self-test results, to the remote locating service. This feature allows the remote locating service to centrally monitor the status or condition of a plurality of medical devices.
Owner:PHYSIO CONTROL INC
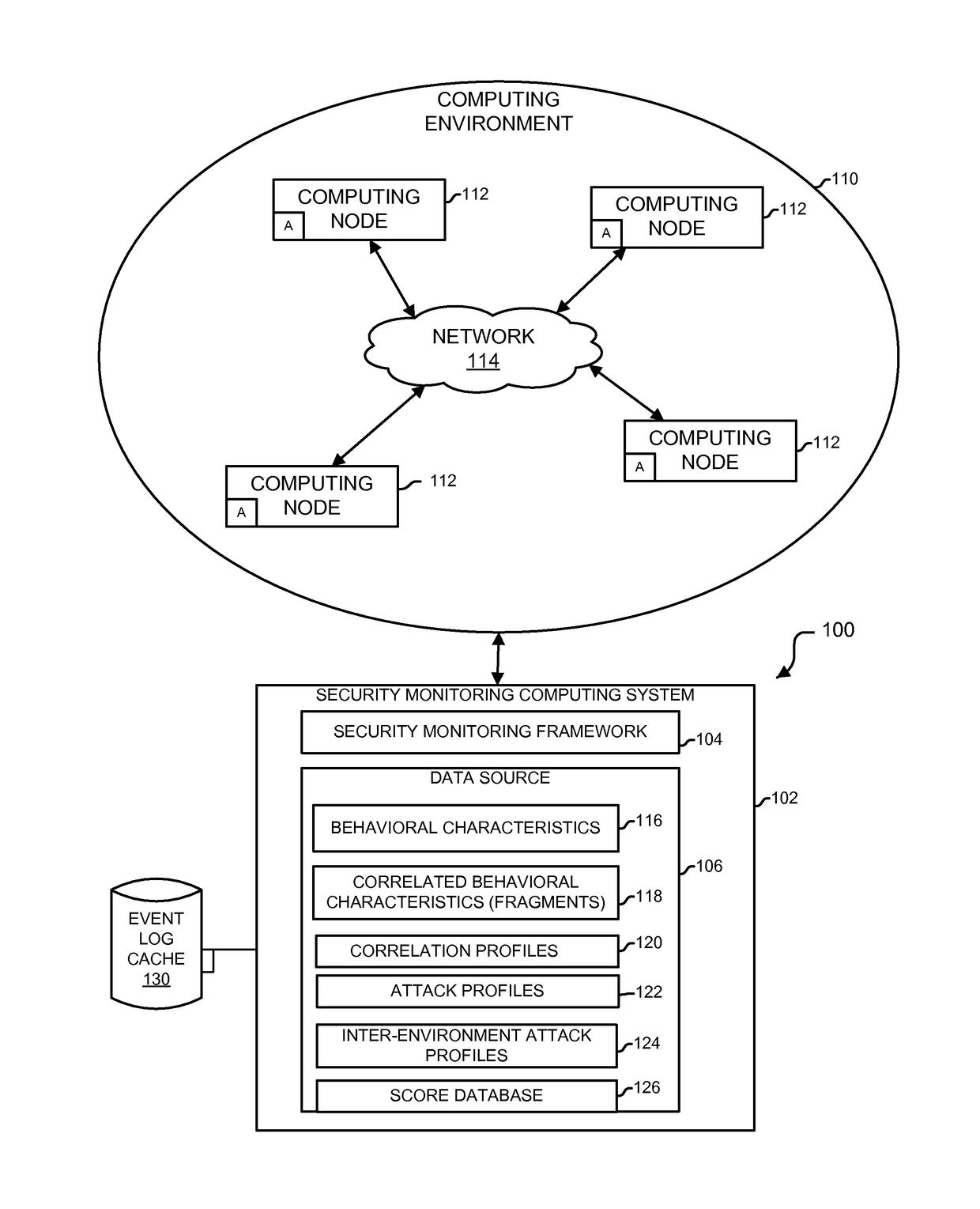
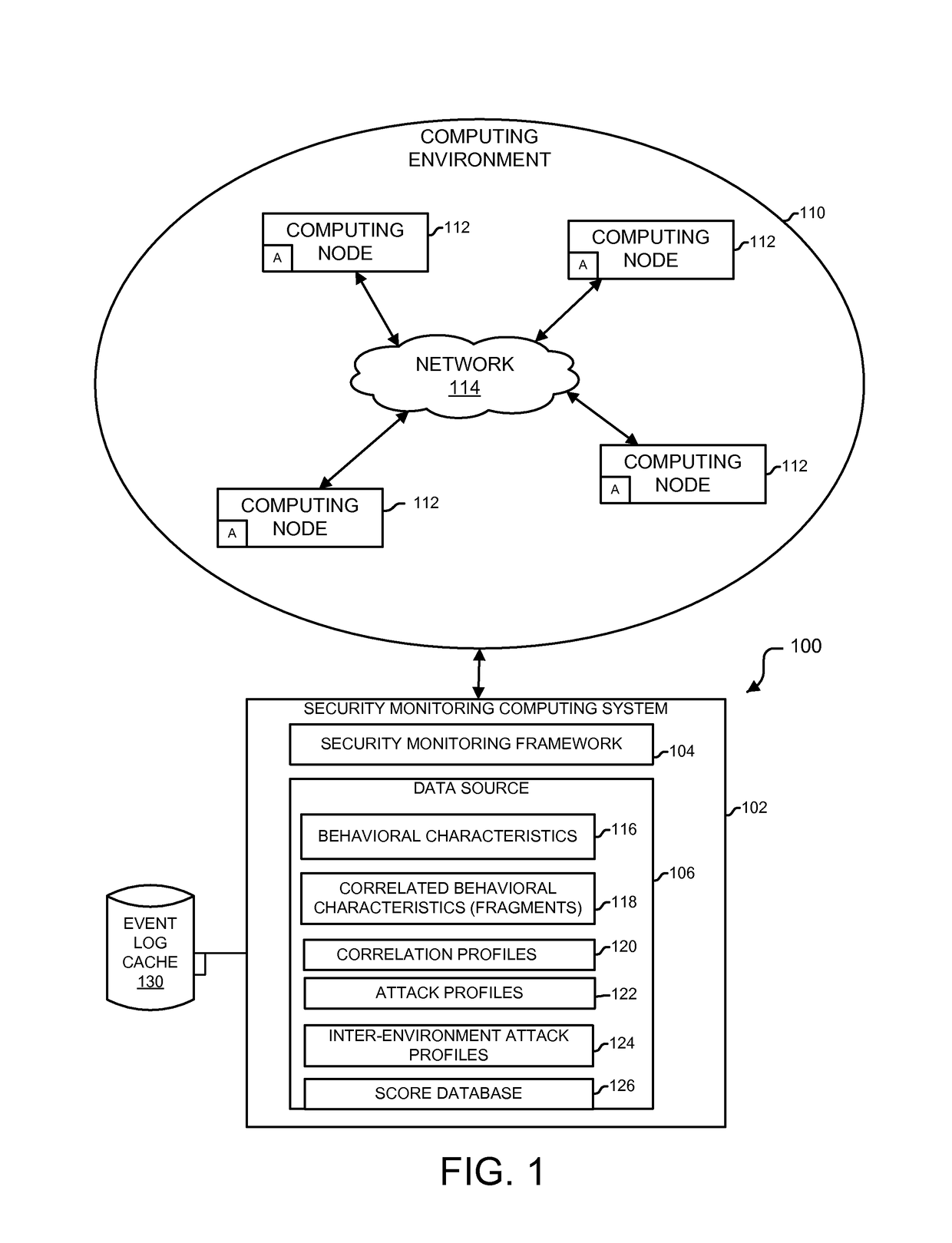
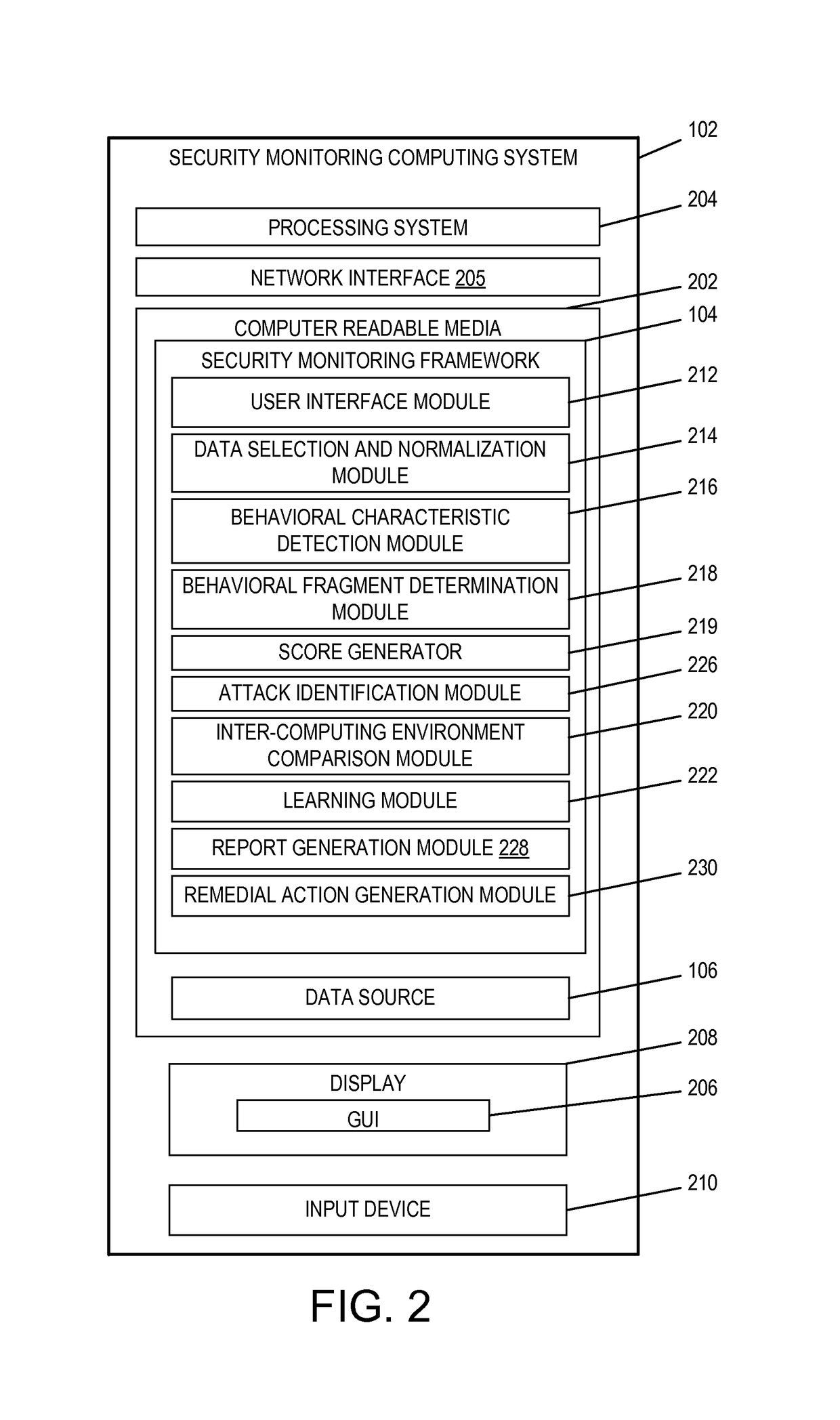
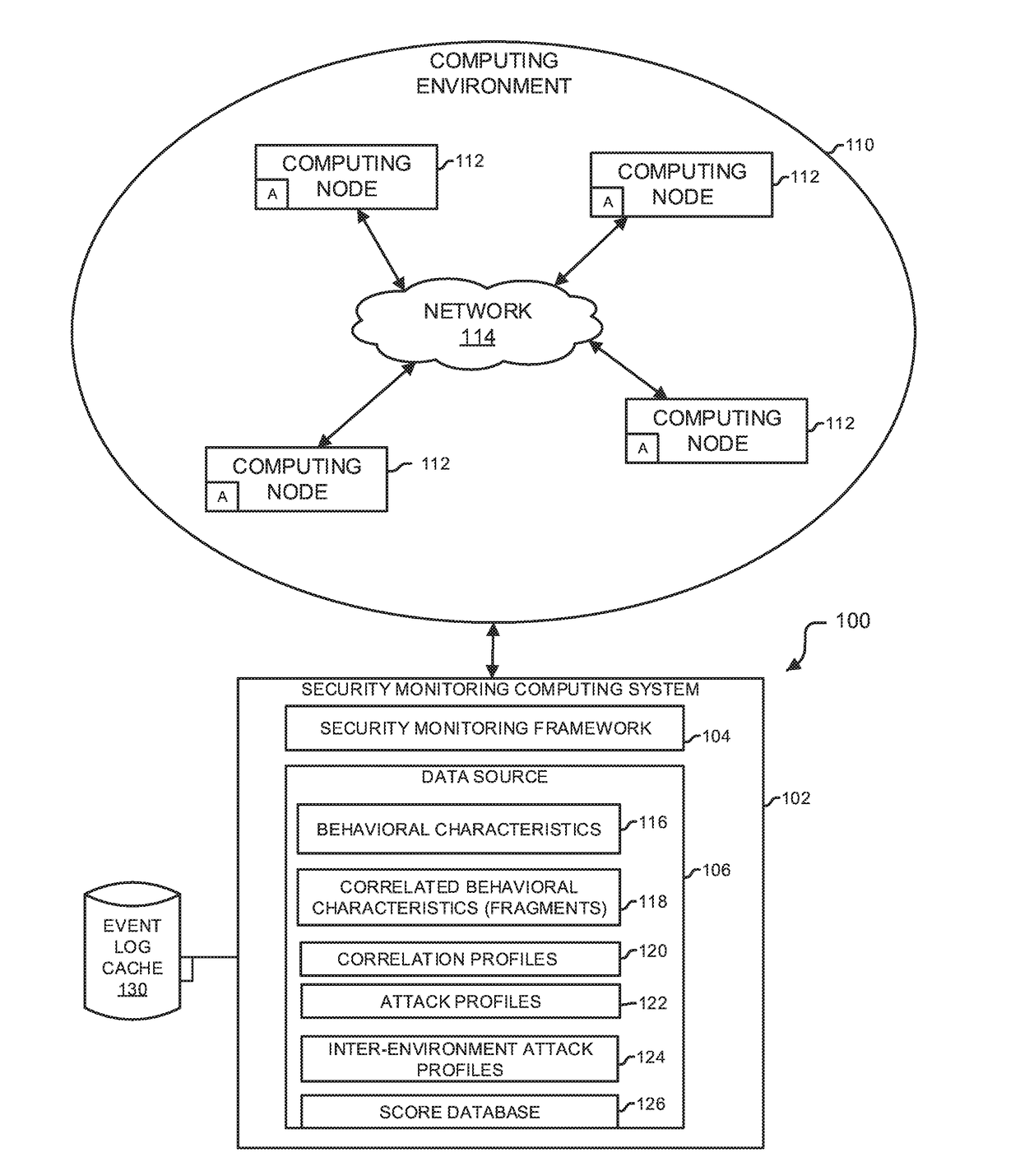
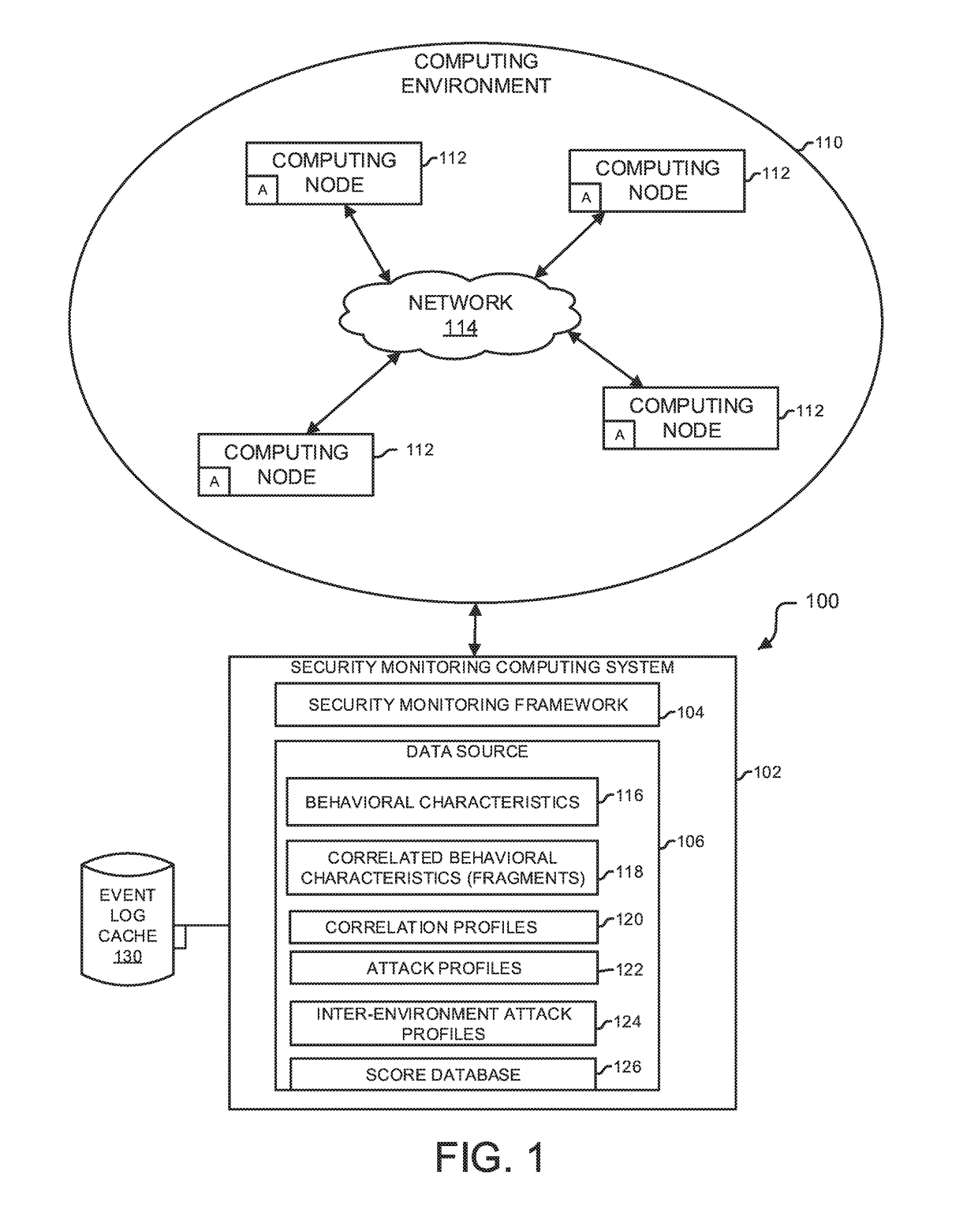
Analytics-based security monitoring system and method
ActiveUS9654485B1Reduce size (quantity)Easy to analyzeMemory loss protectionError detection/correctionRemedial actionSecurity monitoring
An analytics-based security monitoring system includes instructions that may be executed by a computing system to receive data in the form of event logs from one or more network devices transferred through a computing environment, detect a plurality of behavioral characteristics from the received event logs, identify behavioral fragments composed of related behavioral characteristics, and identify an attack by correlating the behavioral fragments against patterns of known malicious attacks. The analytics-based security monitoring system may then perform a learning process to enhance further detection of attacks and perform one or more remedial actions when an attack is identified.
Owner:MANDIANT +1
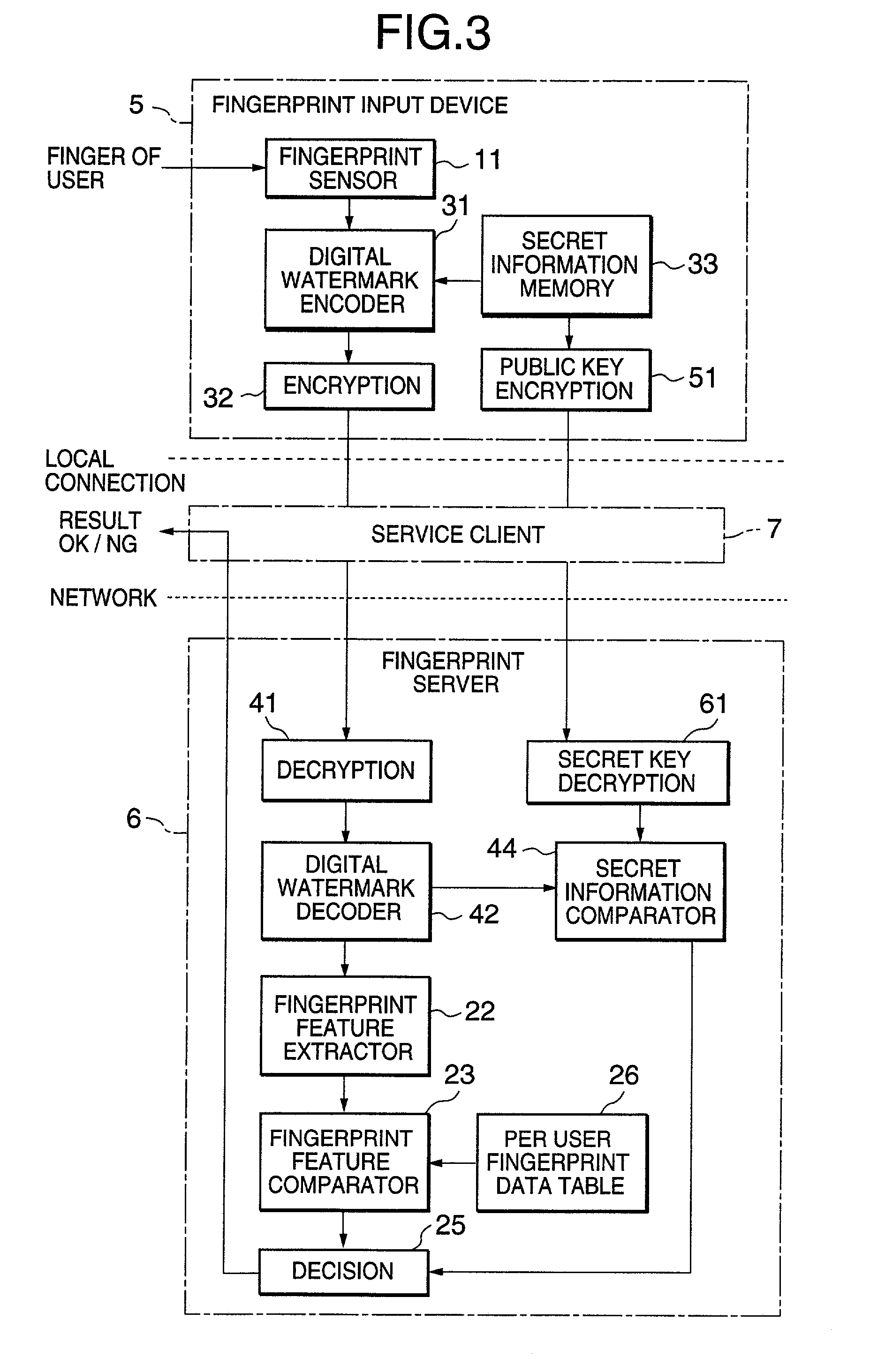
Method and arrangement for reliably identifying a user in a computer system
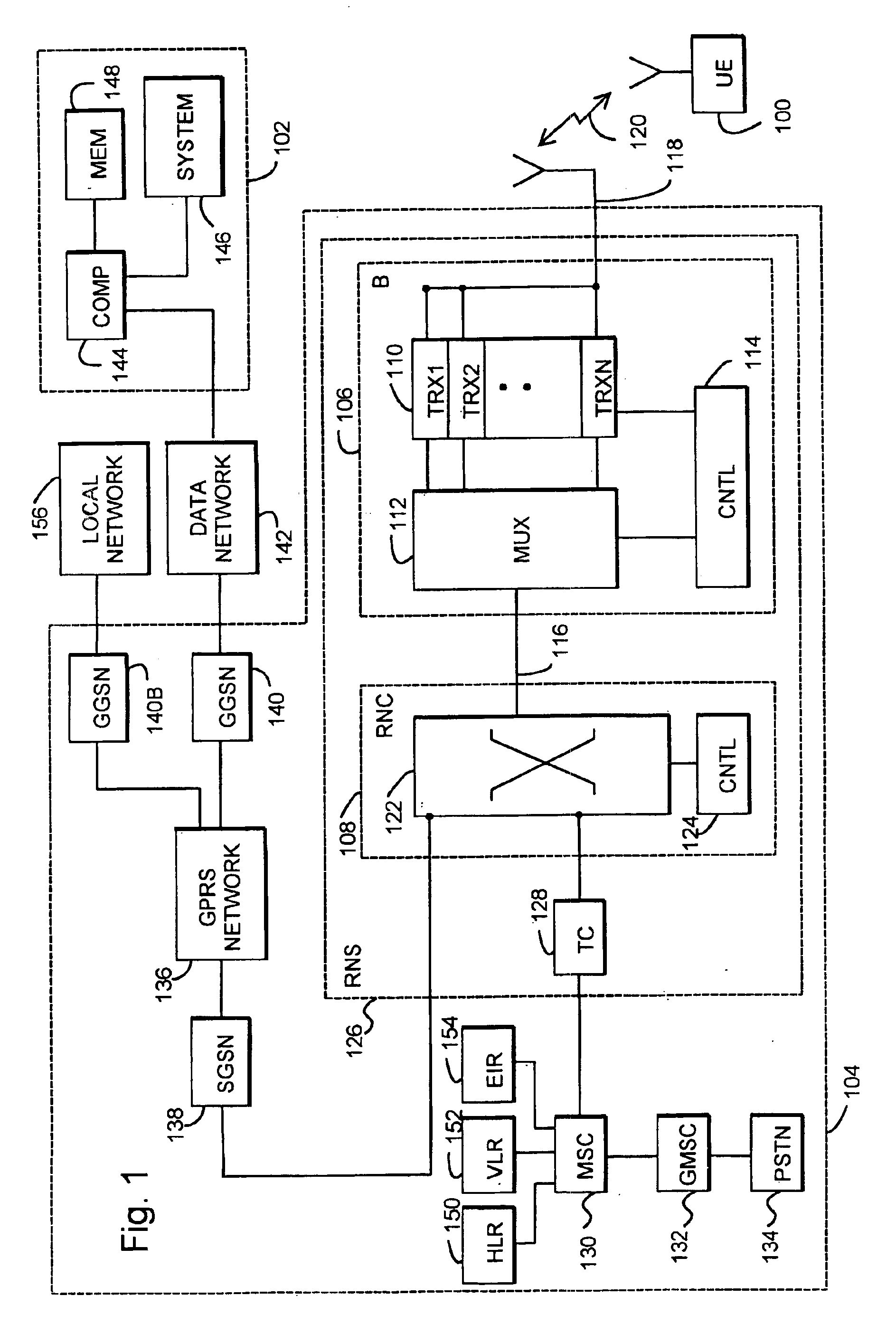
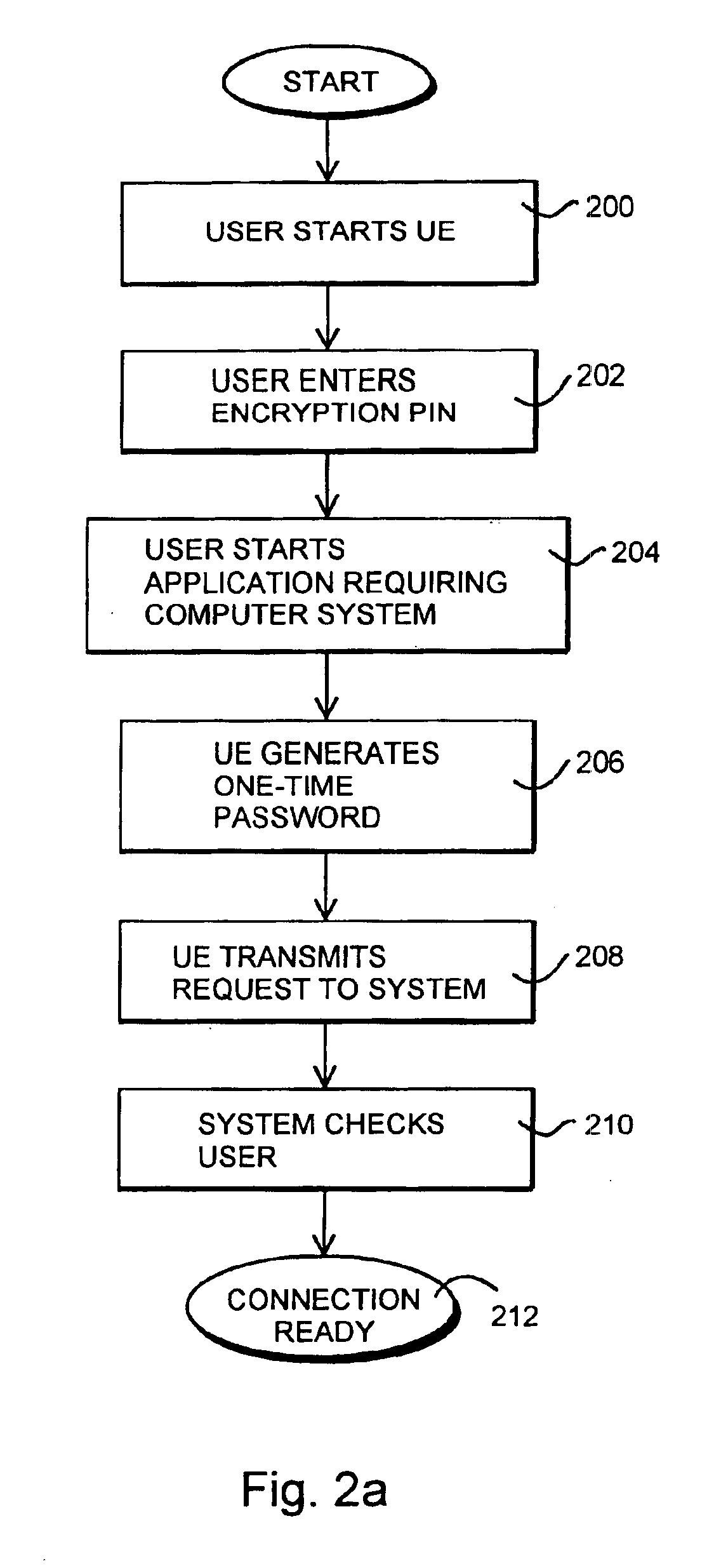
InactiveUS6928558B1Avoid disadvantagesReliable identificationDigital data processing detailsUser identity/authority verificationPersonal identification numberComputerized system
The invention relates to an arrangement and a method for reliably identifying a user in a computer system. The method utilizes a mobile station for communicating with the system. The method comprises generating a first one-time password in the mobile station by utilizing a known algorithm on the basis of the identification number of the user, subscriber-specific identifier, device-specific identifier of the mobile station, and time. The password obtained and the subscriber-specific identifier of the user are encoded and transmitted to an authentication server of the computer system, comprising identifying the user on the basis of the subscriber-specific identifier, searching a database for the personal identifier number of the user and the device-specific identifier of the mobile station associated with the user, generating a second password at the authentication server by utilizing the same predetermined algorithm on the basis of the personal identification number of the user, subscriber-specific identifier, device-specific identifier of the mobile station and time, comparing the first and the second passwords with each other at the authentication server, and if the passwords match, enabling the telecommunication connection between the mobile station and the computer system.
Owner:NOKIA MOBILE PHONES LTD
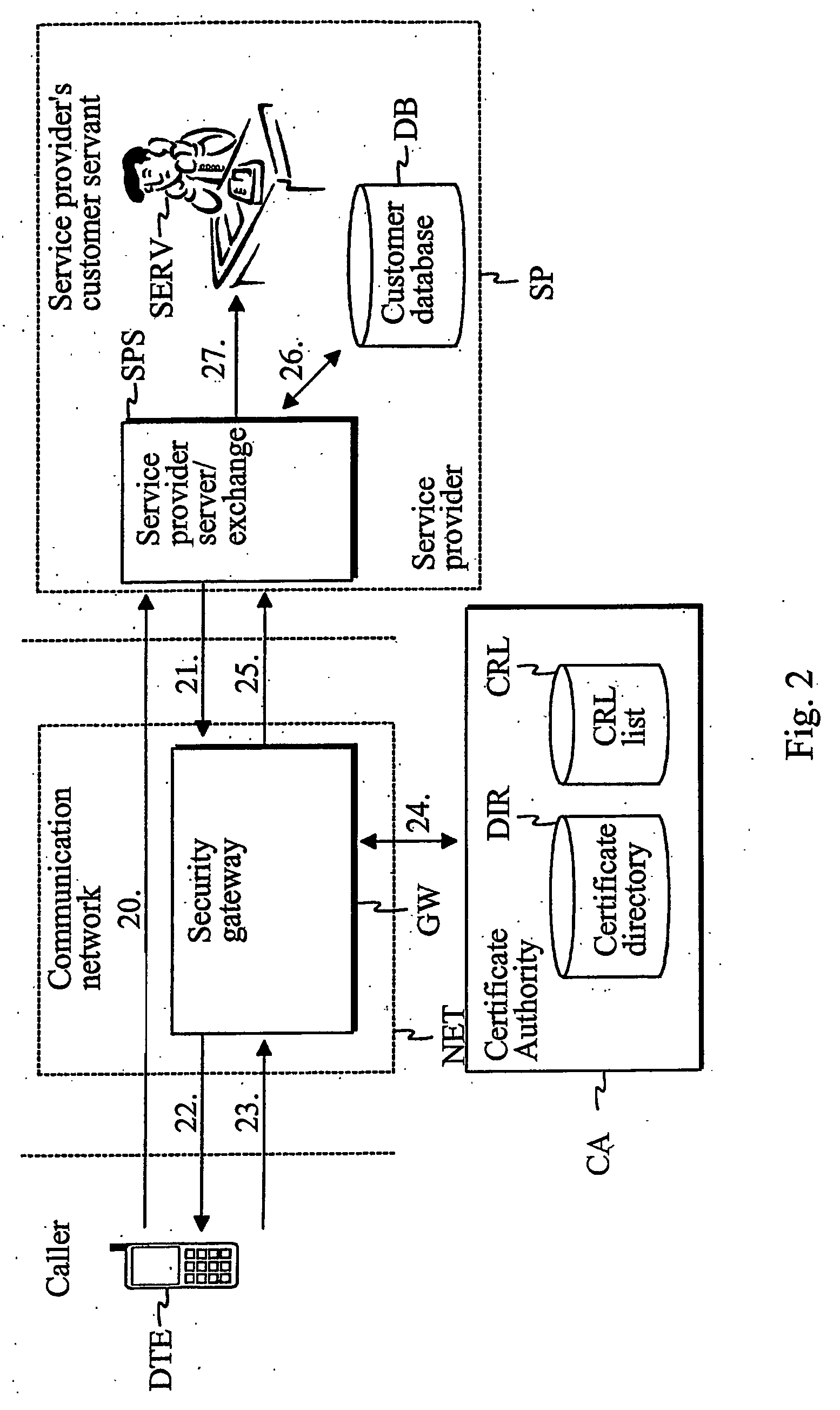
Method and system for identifying the identity of a user
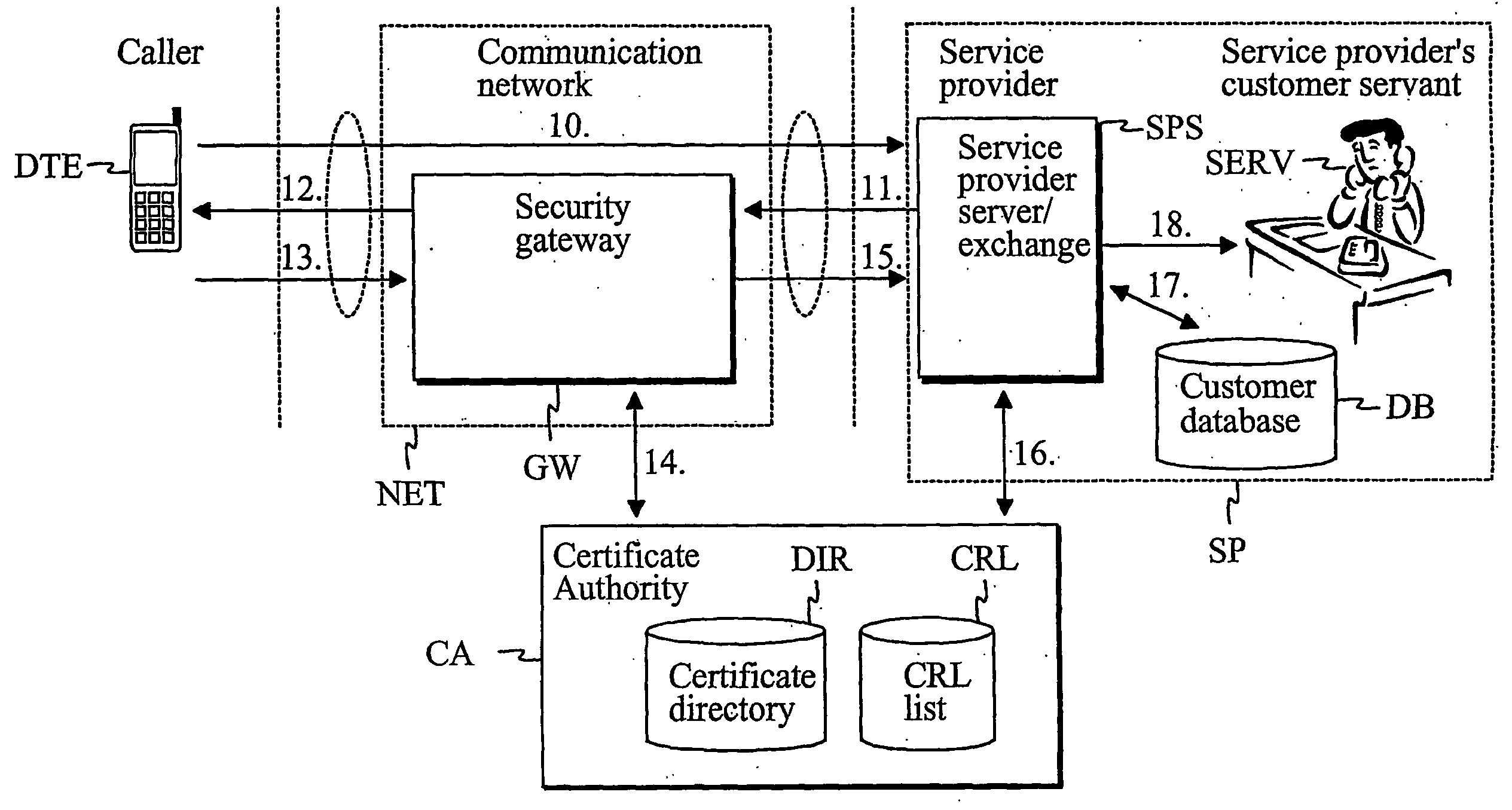
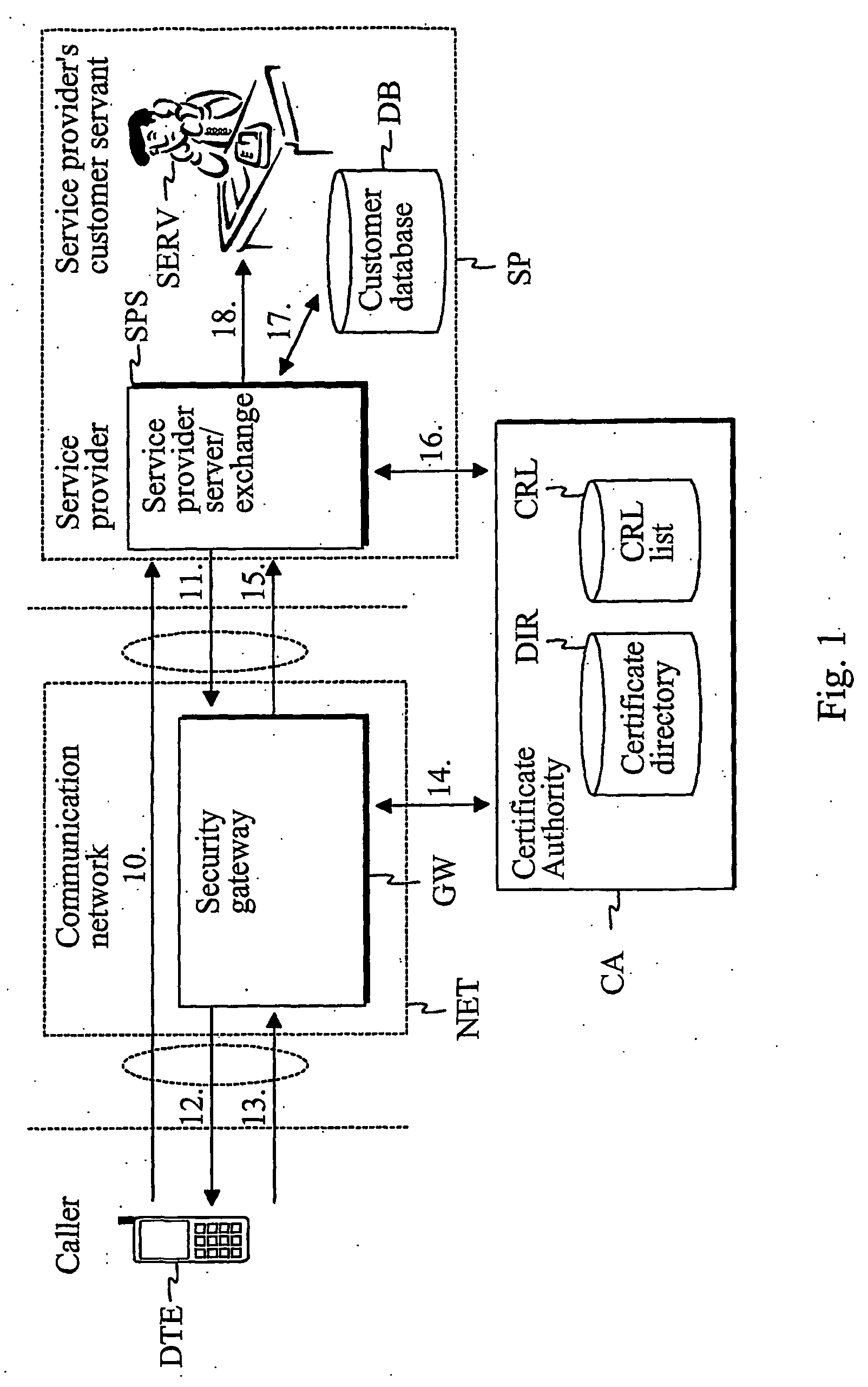
InactiveUS20060262929A1Easy to implementCost efficientSecret communicationTransmissionService providerService provision
The present invention describes a method and system for verifying the identity of a user of a first terminal in a communication system having at least a communication network (NET), a first terminal (DTE) associated with the communication network (NET) and a service provider (SP) associated with the communication network (NET). In the method, a first logical channel is set up via the communication network between the first terminal (DTE) and the service provider (SP). The user of the first terminal is identified after the first logical channel set up via a second logical channel other than the established first logical channel between the service provider and the first terminal prior to providing any services to the caller.
Owner:QITEC TECH GROUP
Method and arrangement for processing a noise signal from a noise source
InactiveUS20050100172A1Reliable identificationSimple and reliable processVibration measurement in fluidEar treatmentSignal characteristicEngineering
Owner:DAIMLER AG
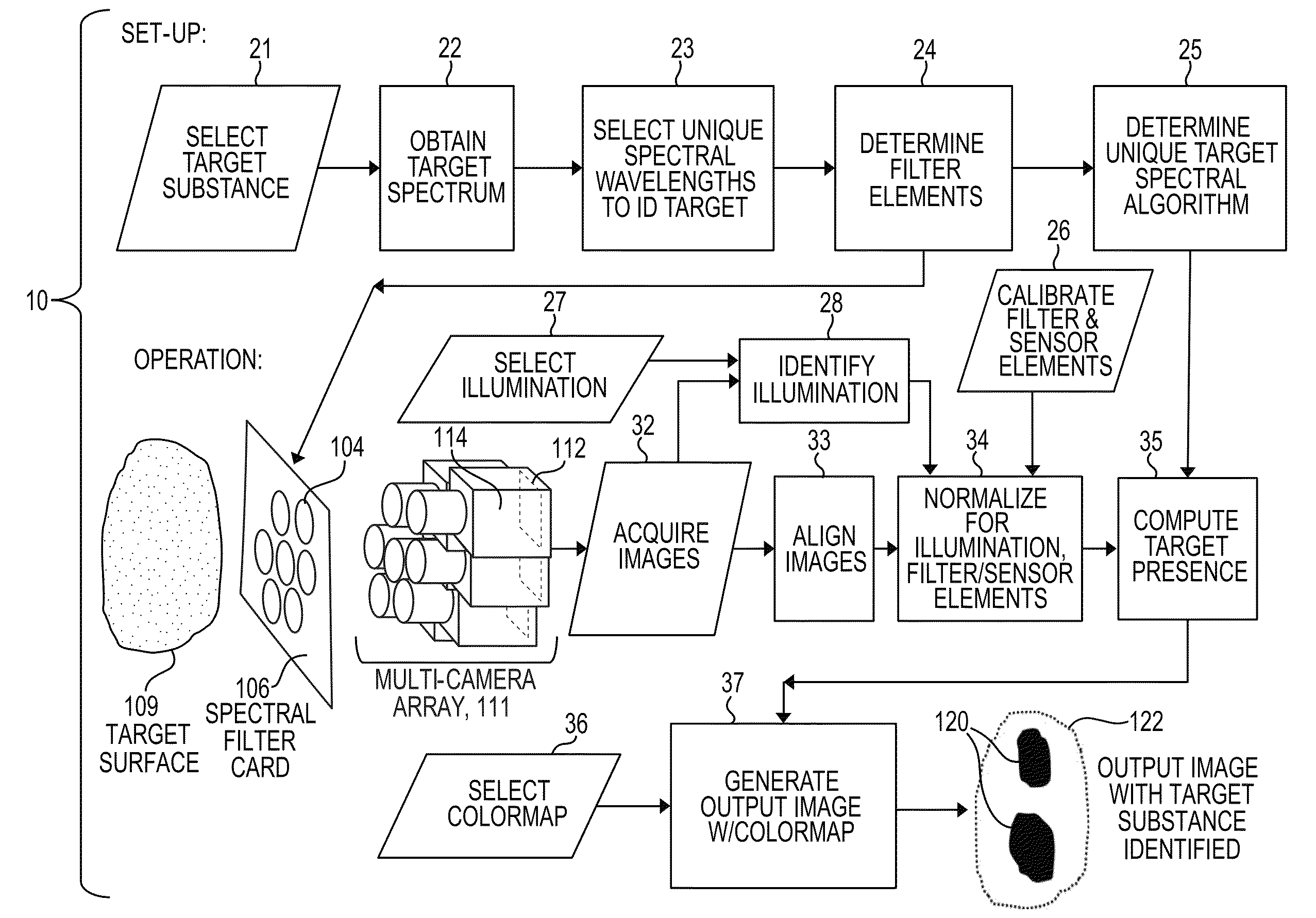
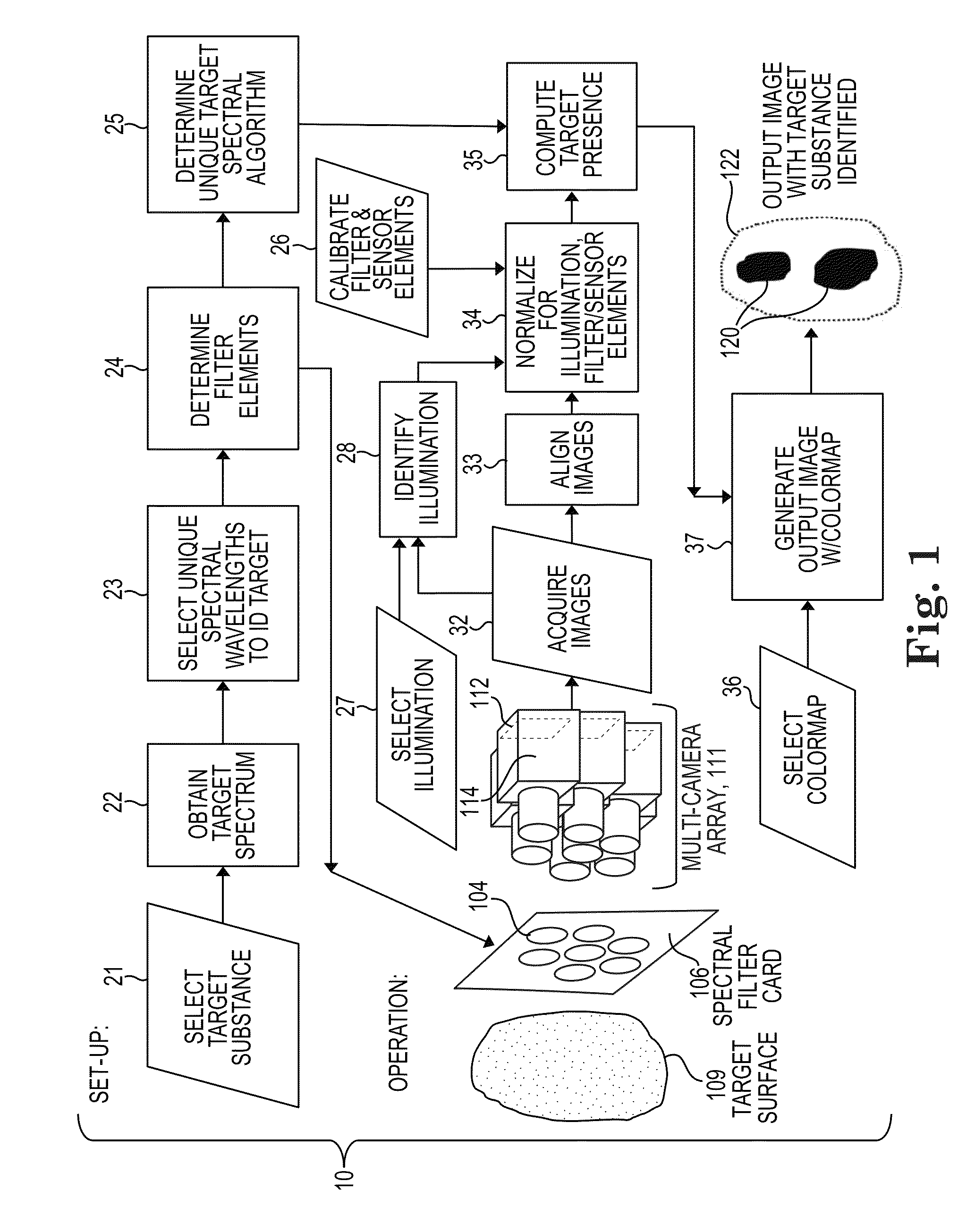
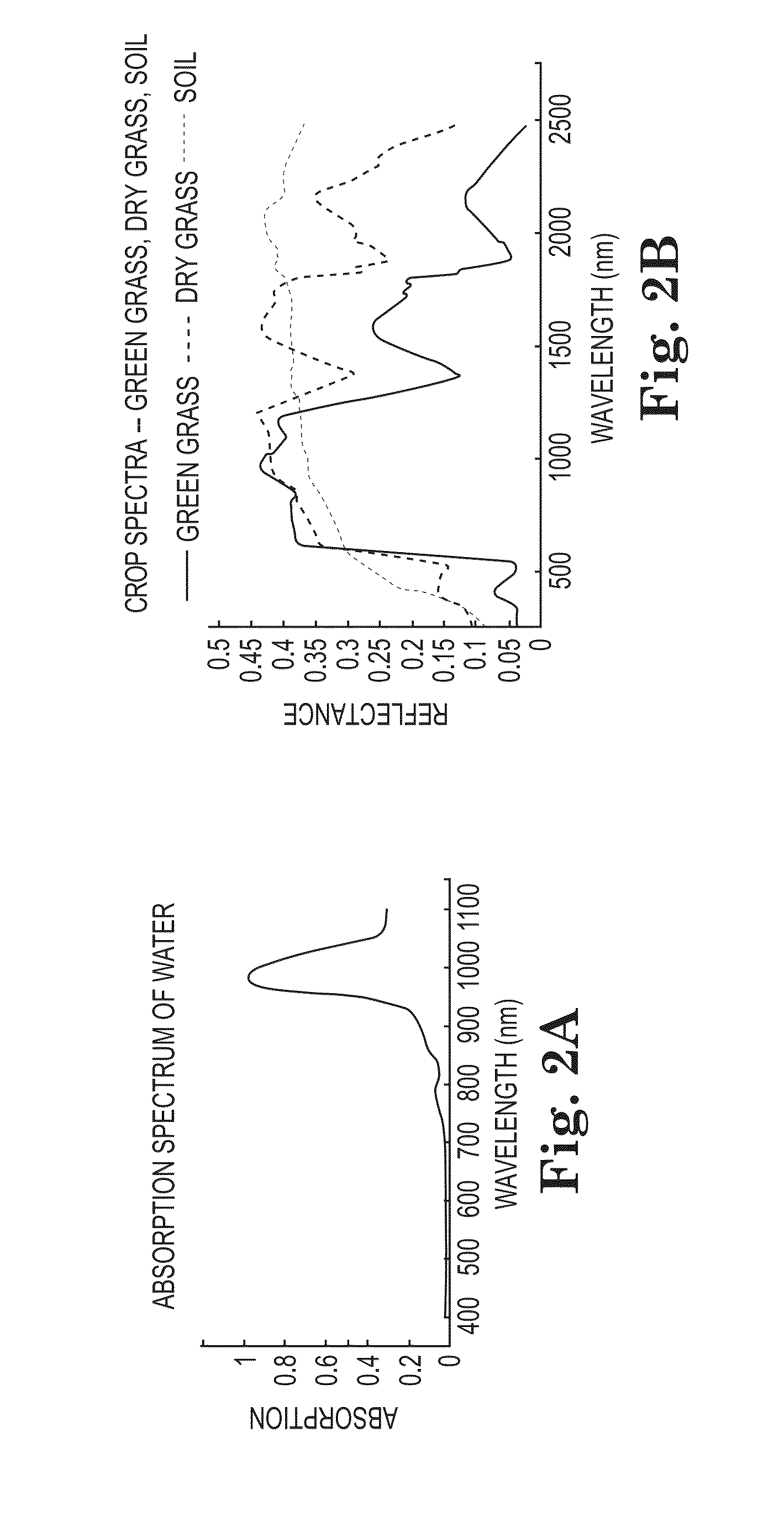
Spectral imaging system for remote and noninvasive detection of target substances using spectral filter arrays and image capture arrays
ActiveUS20160069743A1Reliable identificationEnhance the imageMedical imagingRadiation pyrometryProgram instructionSpectral imaging
An approach to noninvasively and remotely detect the presence, location, and / or quantity of a target substance in a scene via a spectral imaging system comprising a spectral filter array and image capture array. For a chosen target substance, a spectral filter array is provided that is sensitive to selected wavelengths characterizing the electromagnetic spectrum of the target substance. Elements of the image capture array are optically aligned with elements of the spectral filter array to simultaneously capture spectrally filtered images. These filtered images identify the spectrum of the target substance. Program instructions analyze the acquired images to compute information about the target substance throughout the scene. A color-coded output image may be displayed on a smartphone or computing device to indicate spatial and quantitative information about the detected target substance. The system desirably includes a library of interchangeable spectral filter arrays, each sensitive to one or more target substances.
Owner:INNOPIX
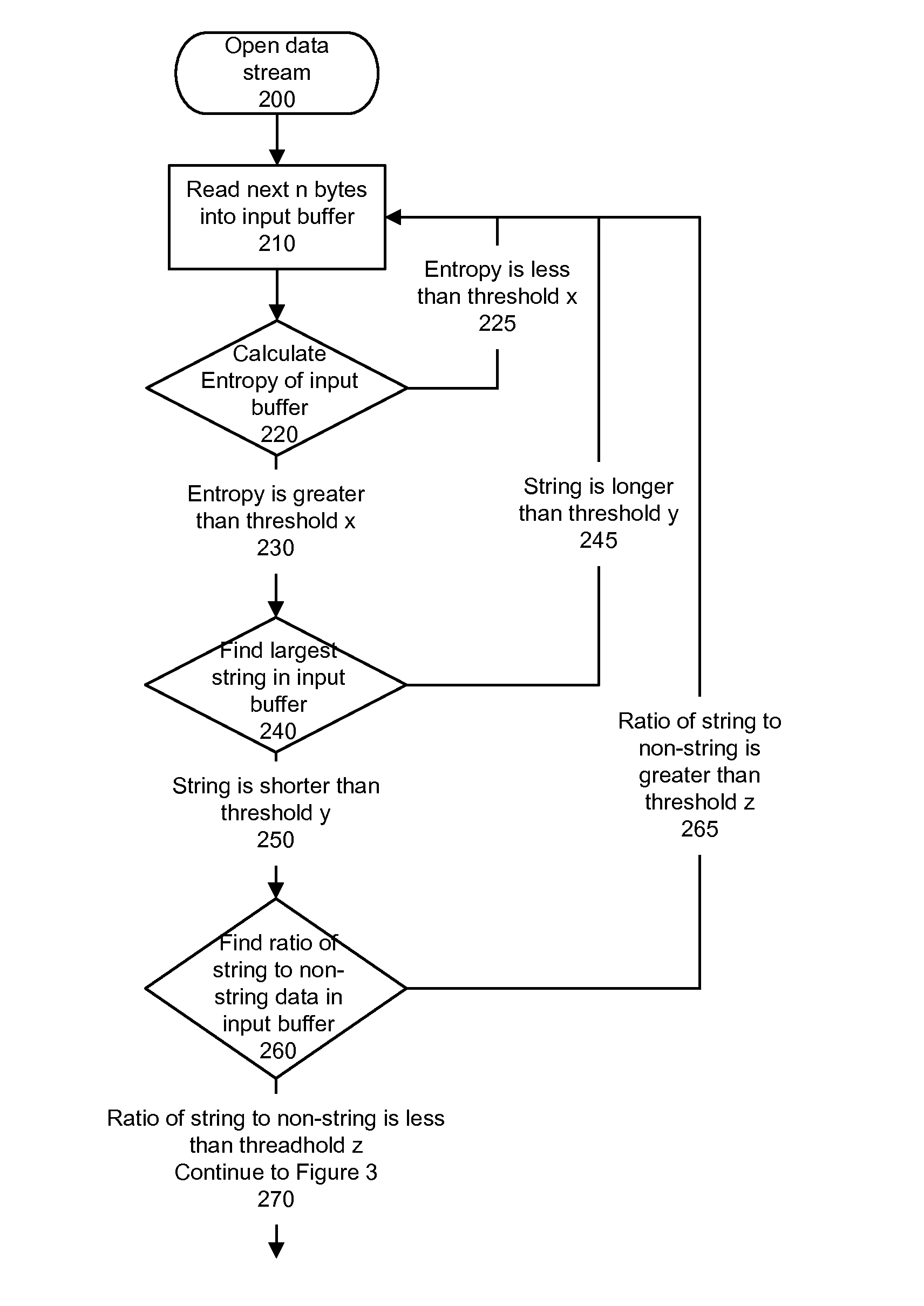
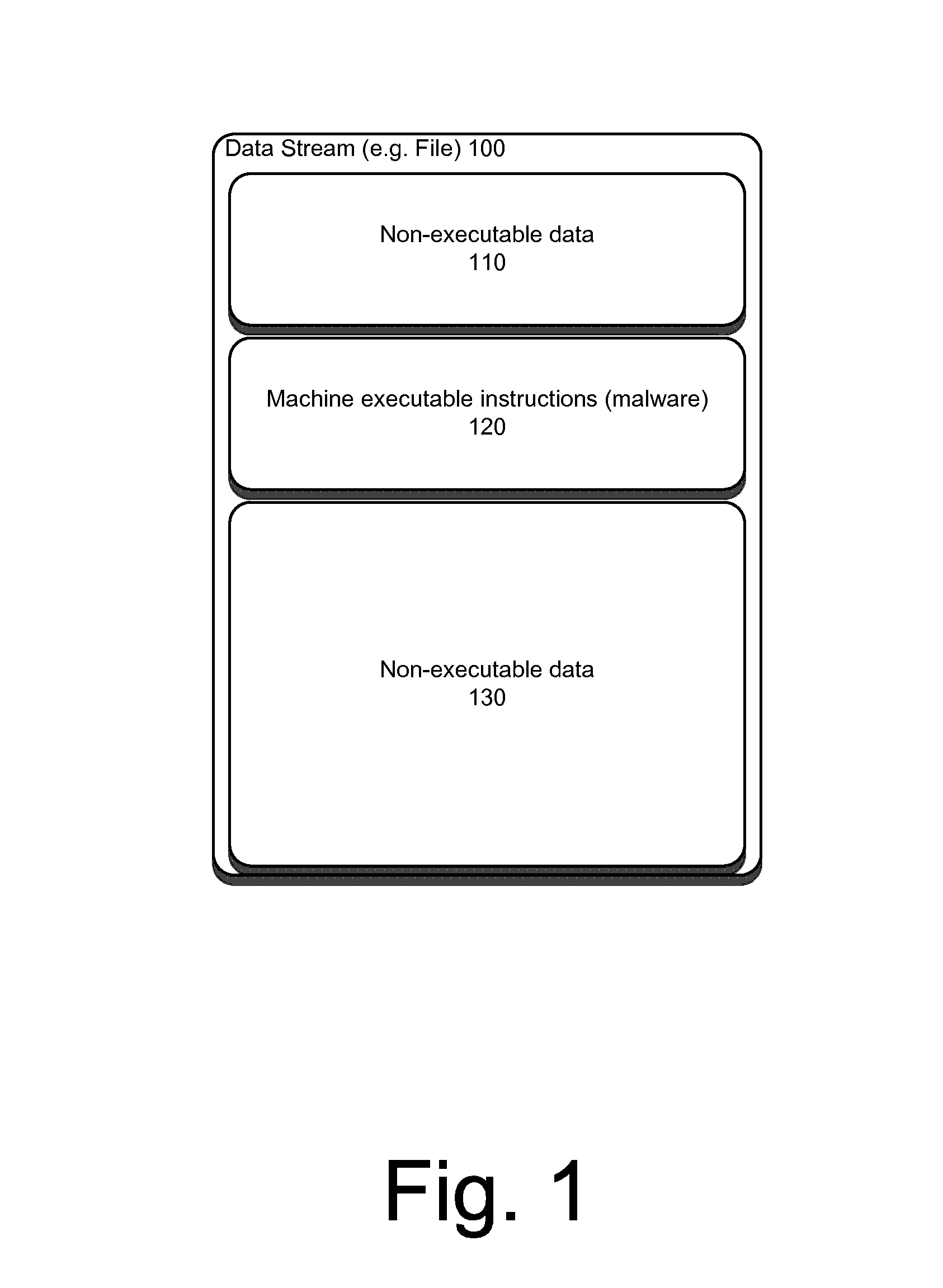
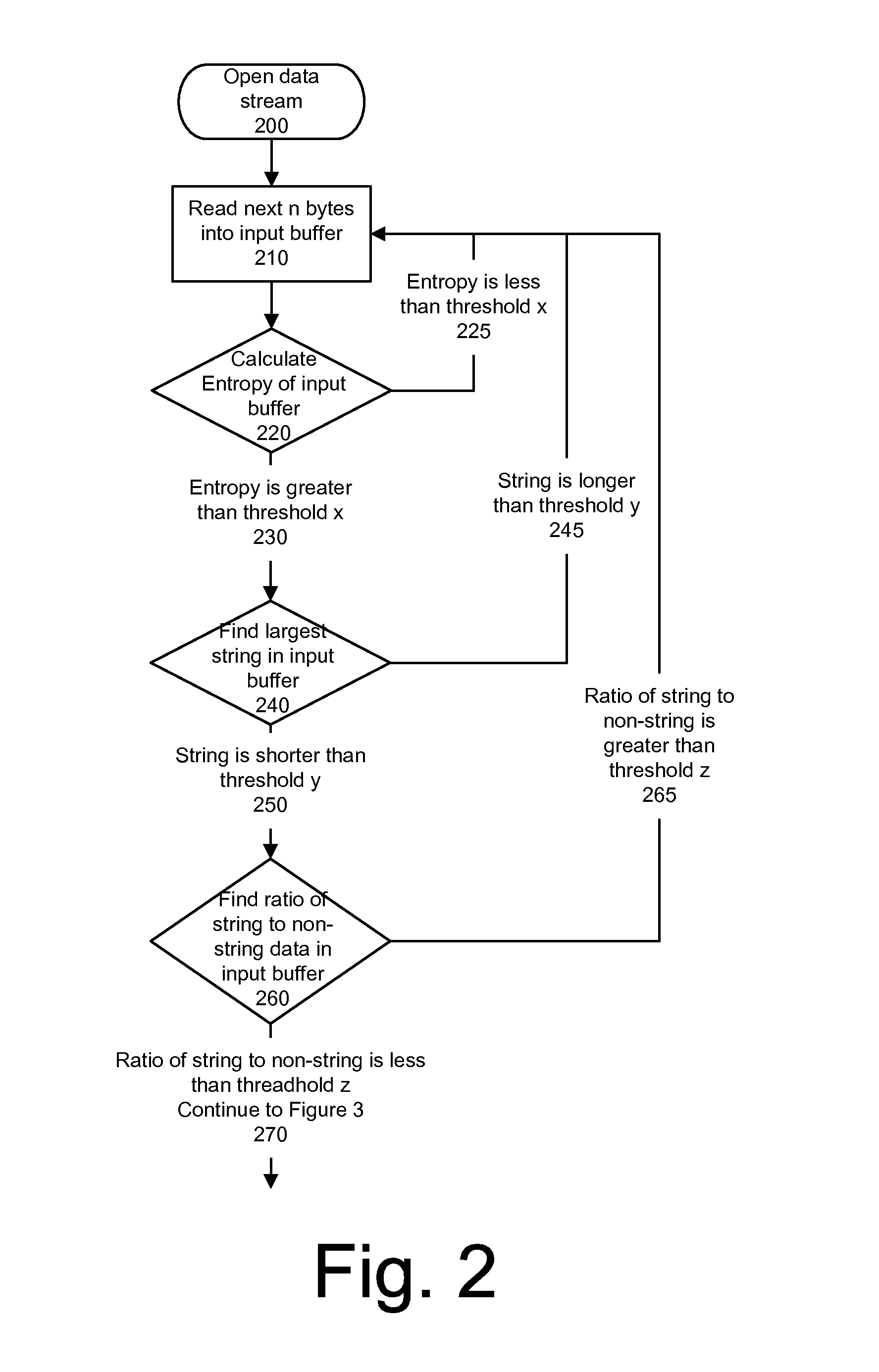
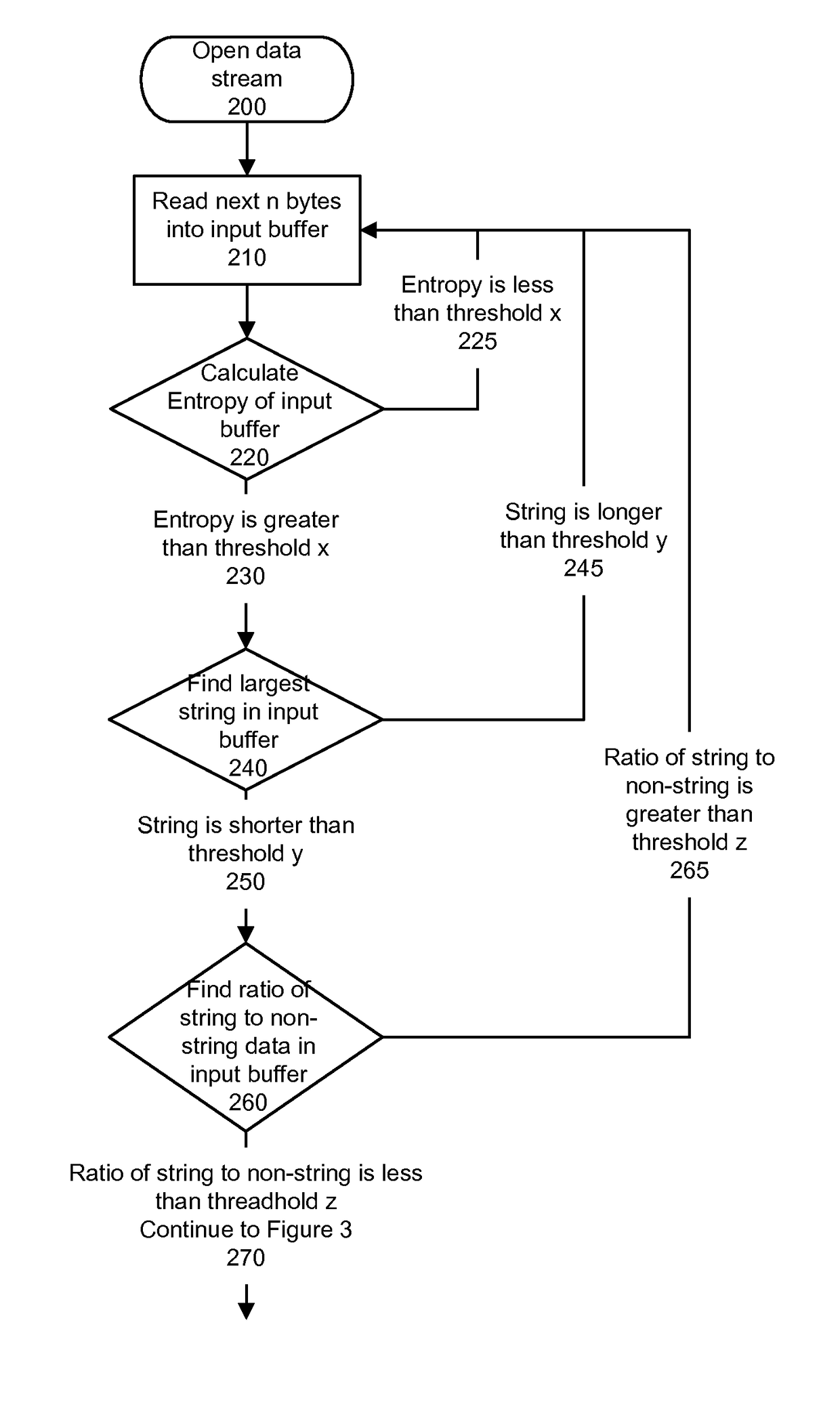
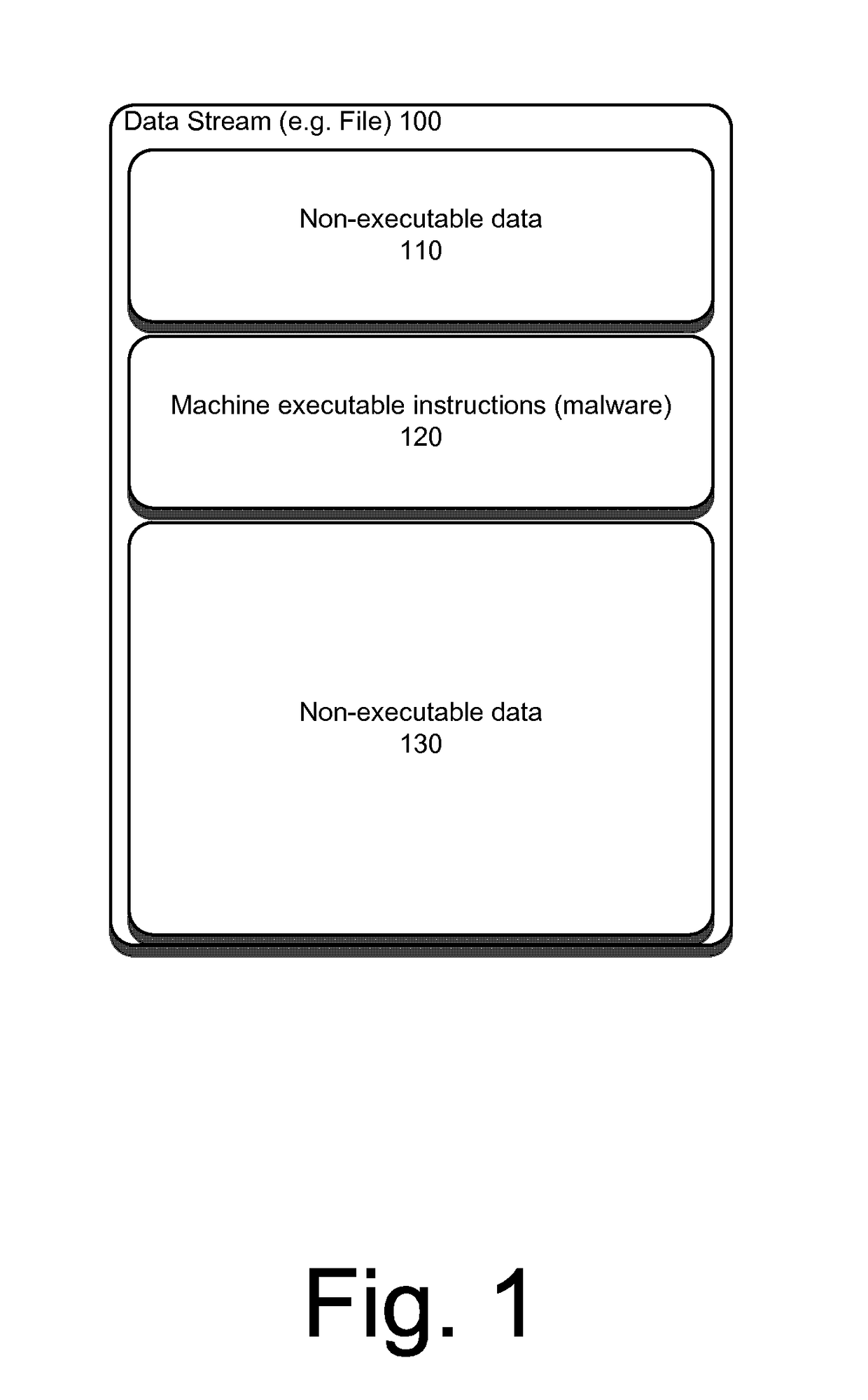
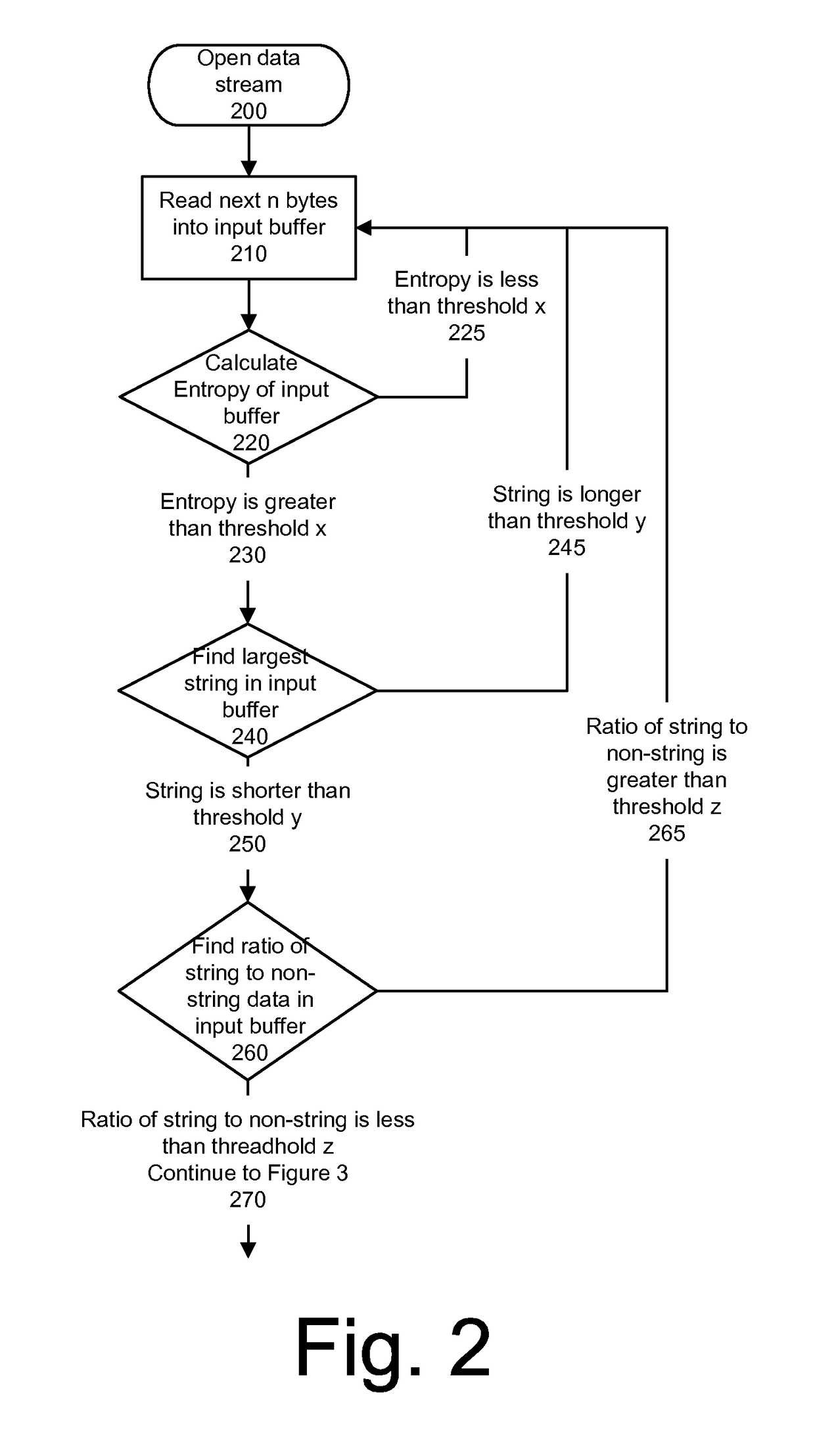
System and method for detecting executable machine instructions in a data stream
ActiveUS20140237600A1Effective presenceReliable identificationMemory loss protectionError detection/correctionData streamAlgorithm
Detecting executable machine instructions in a data is accomplished by accessing a plurality of values representing data contained within a memory of a computer system and performing pre-processing on the plurality of values to produce a candidate data subset. The pre-processing may include determining whether the plurality of values meets (a) a randomness condition, (b) a length condition, and / or (c) a string ratio condition. The candidate data subset is inspected for computer instructions, characteristics of the computer instructions are determined, and a predetermined action taken based on the characteristics of the computer instructions.
Owner:GOOGLE LLC
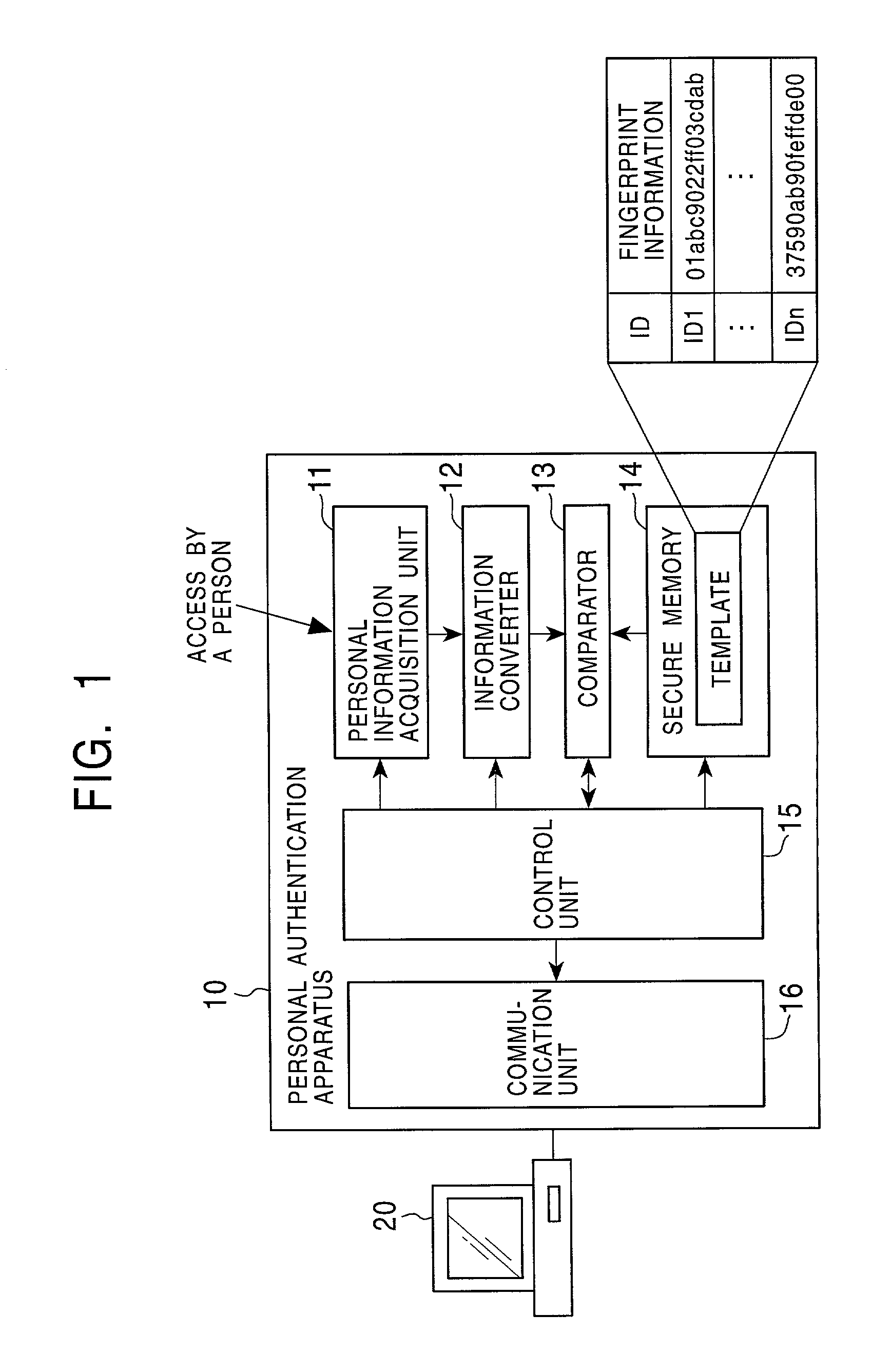
Biometric identification method and system
InactiveUS20010025342A1Reliable identificationDigital data processing detailsUser identity/authority verificationBiometric dataBiometric system
Owner:NEC CORP
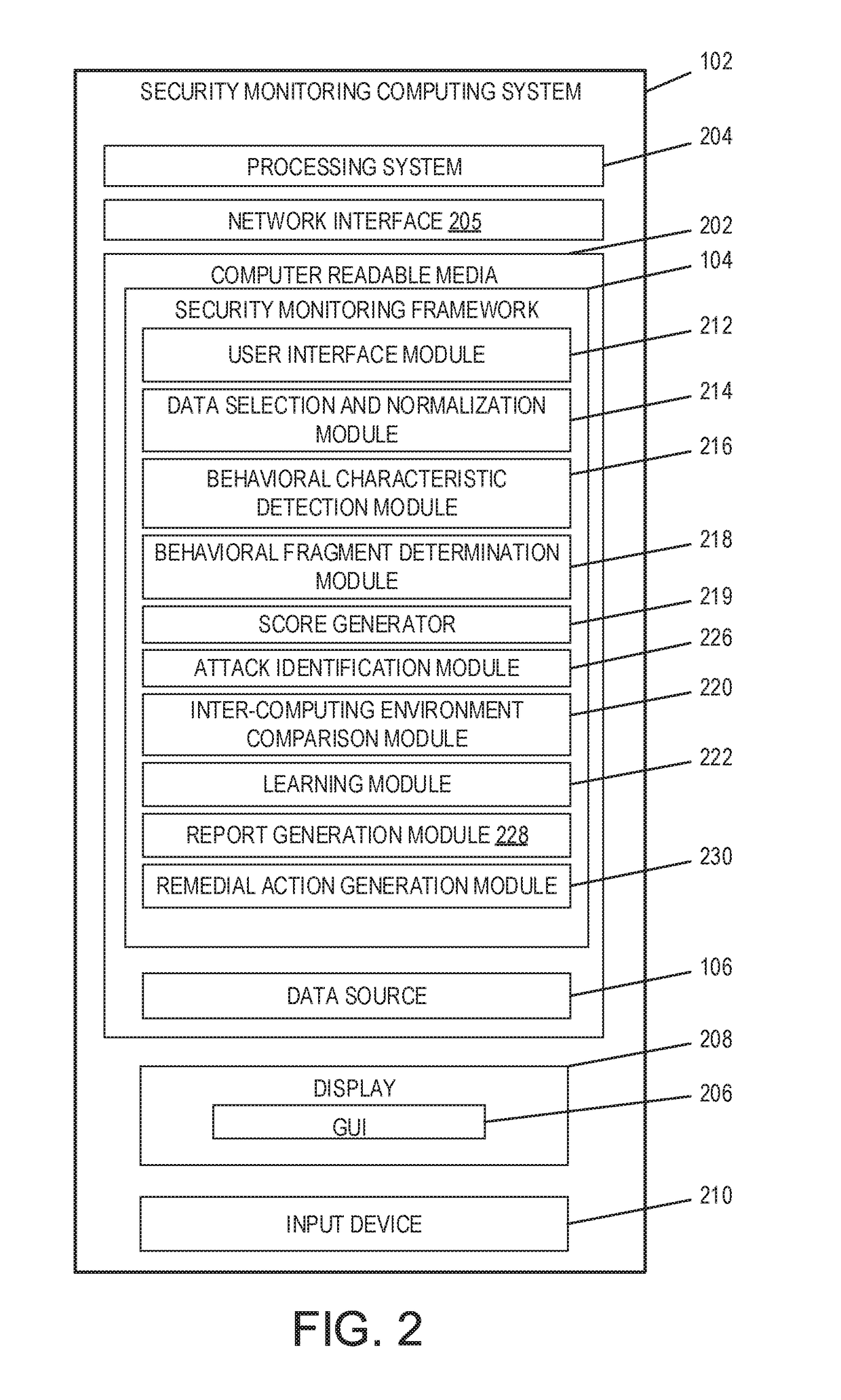
Analytic-based security with learning adaptability
ActiveUS10104102B1High attackReliable identificationMachine learningTransmissionRemedial actionSecurity monitoring
An analytics-based security monitoring system is adapted to receive data, such as in the form of event logs, from one or more network devices transferred through a computing environment, detect a plurality of behavioral characteristics from the received event logs, identify behavioral fragments composed of related behavioral characteristics, and identify an attack by correlating the behavioral fragments against patterns of known malicious attacks. The analytics-based security monitoring system may then perform a learning process to enhance further detection of attacks and perform one or more remedial actions when an attack is identified.
Owner:FIREEYE SECURITY HLDG US LLC +1
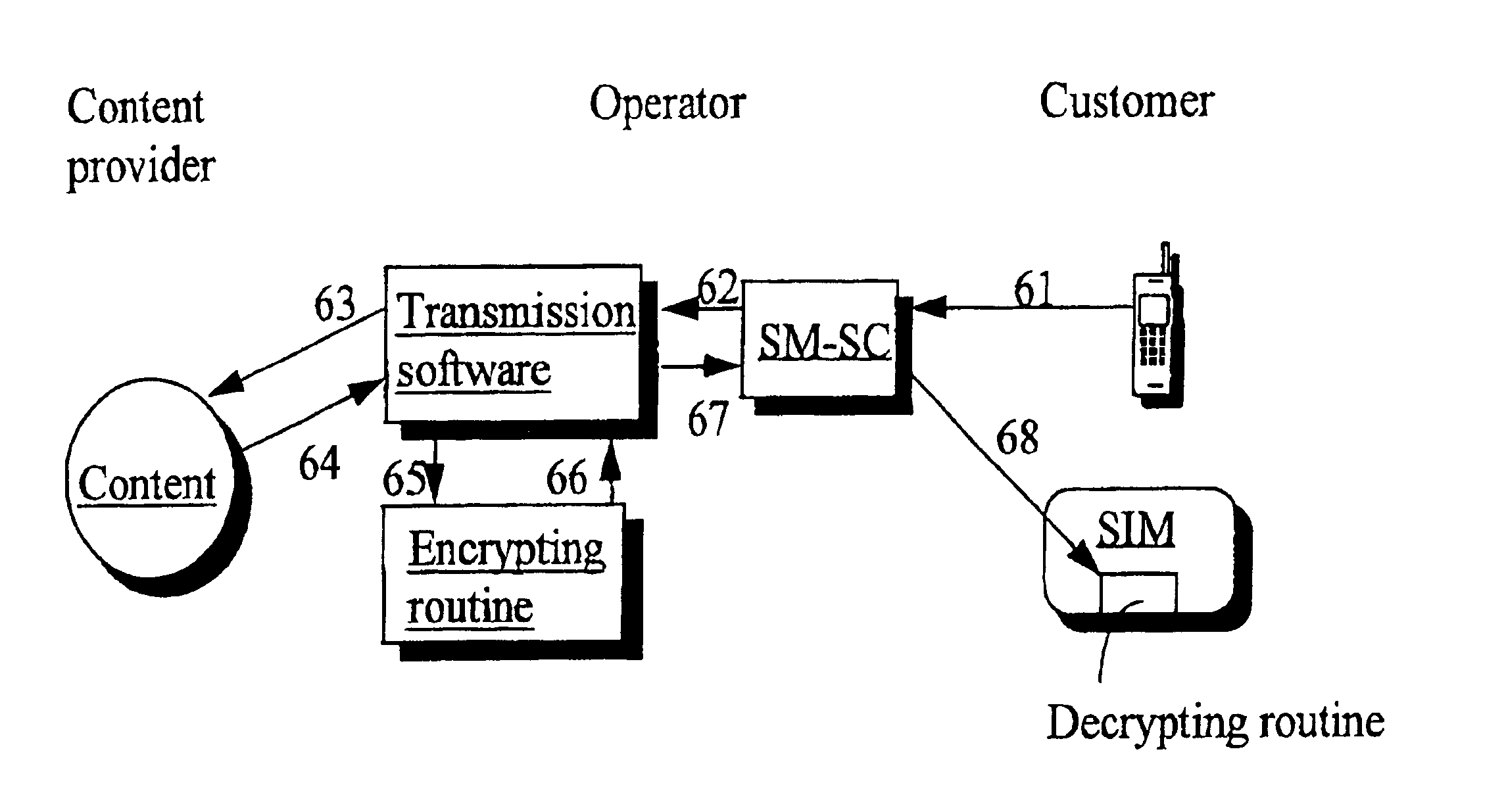
Method and system for the processing of messages in a telecommunication system
InactiveUS6925568B1Reliable identificationSynchronising transmission/receiving encryption devicesUnauthorized memory use protectionMobile stationGeographic area
A method and system for encrypting, in a telecommunication system, outgoing message traffic between mobile stations operating in accordance with current mobile communication standards and / or between a mobile station and a service provider, and for decrypting incoming message traffic, includes directing encrypted messages to and receiving encrypted messages from only those members of a limited closed receiver group that are located in a given geographic area.
Owner:SONERA
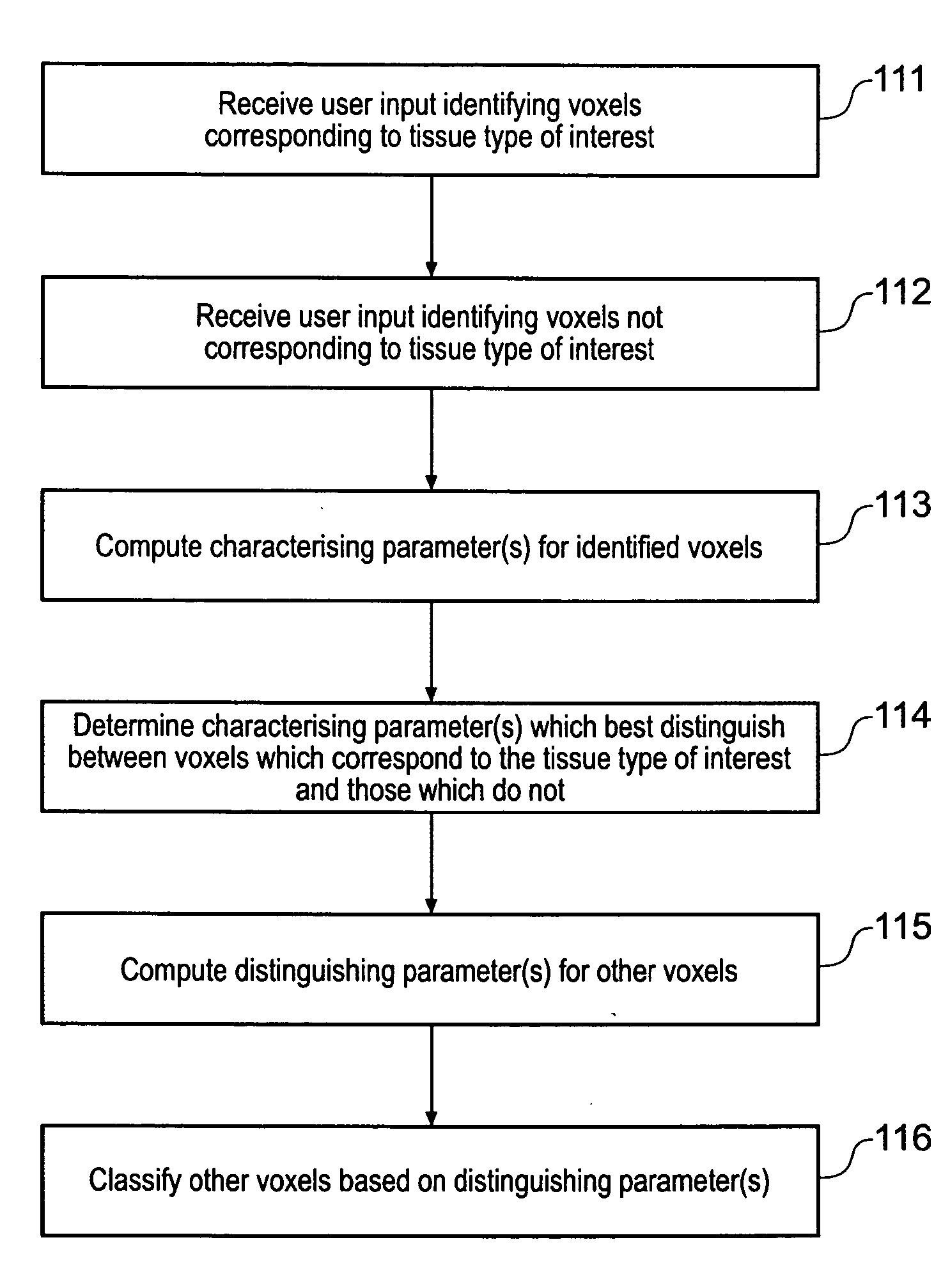
Displaying image data using automatic presets
InactiveUS20050017972A1Easy and intuitiveAccurate classificationUltrasonic/sonic/infrasonic diagnosticsImage enhancementPattern recognitionVoxel
A computer automated method that applies supervised pattern recognition to classify whether voxels in a medical image data set correspond to a tissue type of interest is described. The method comprises a user identifying examples of voxels which correspond to the tissue type of interest and examples of voxels which do not. Characterizing parameters, such as voxel value, local averages and local standard deviations of voxel value are then computed for the identified example voxels. From these characterizing parameters, one or more distinguishing parameters are identified. The distinguishing parameter are those parameters having values which depend on whether or not the voxel with which they are associated corresponds to the tissue type of interest. The distinguishing parameters are then computed for other voxels in the medical image data set, and these voxels are classified on the basis of the value of their distinguishing parameters. The approach allows tissue types which differ only slightly to be distinguished according to a user's wishes.
Owner:VOXAR
System and method for detecting executable machine instructions in a data stream
ActiveUS10019573B2Effective presenceReliable identificationPlatform integrity maintainanceData streamAlgorithm
Detecting executable machine instructions in a data stream is accomplished by accessing a plurality of values representing data contained within a memory of a computer system and performing pre-processing on the plurality of values to produce a candidate data subset. The pre-processing may include determining whether the plurality of values meets (a) a randomness condition, (b) a length condition, and / or (c) a string ratio condition. The candidate data subset is inspected for computer instructions, characteristics of the computer instructions are determined, and a predetermined action is taken based on the characteristics of the computer instructions.
Owner:GOOGLE LLC
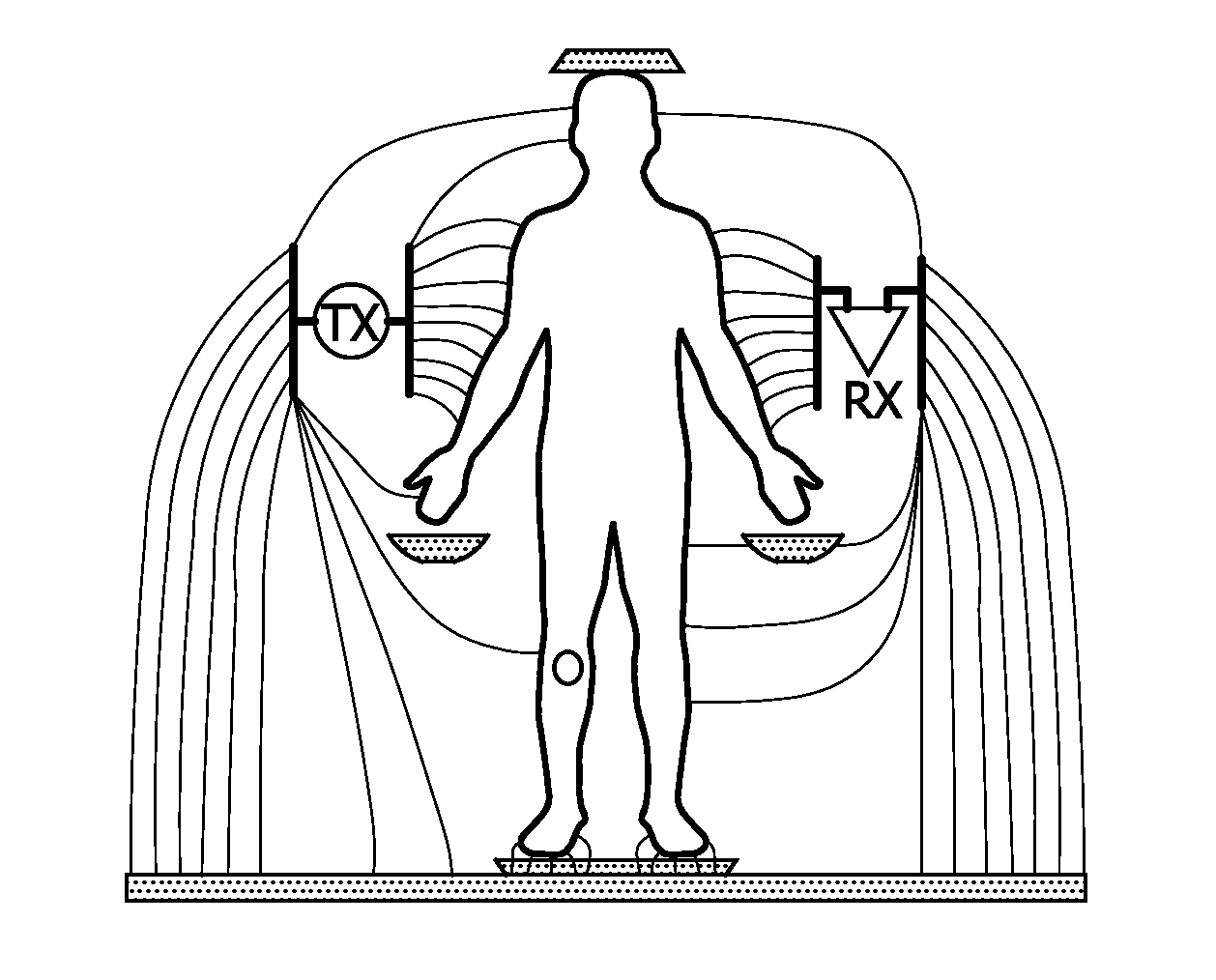
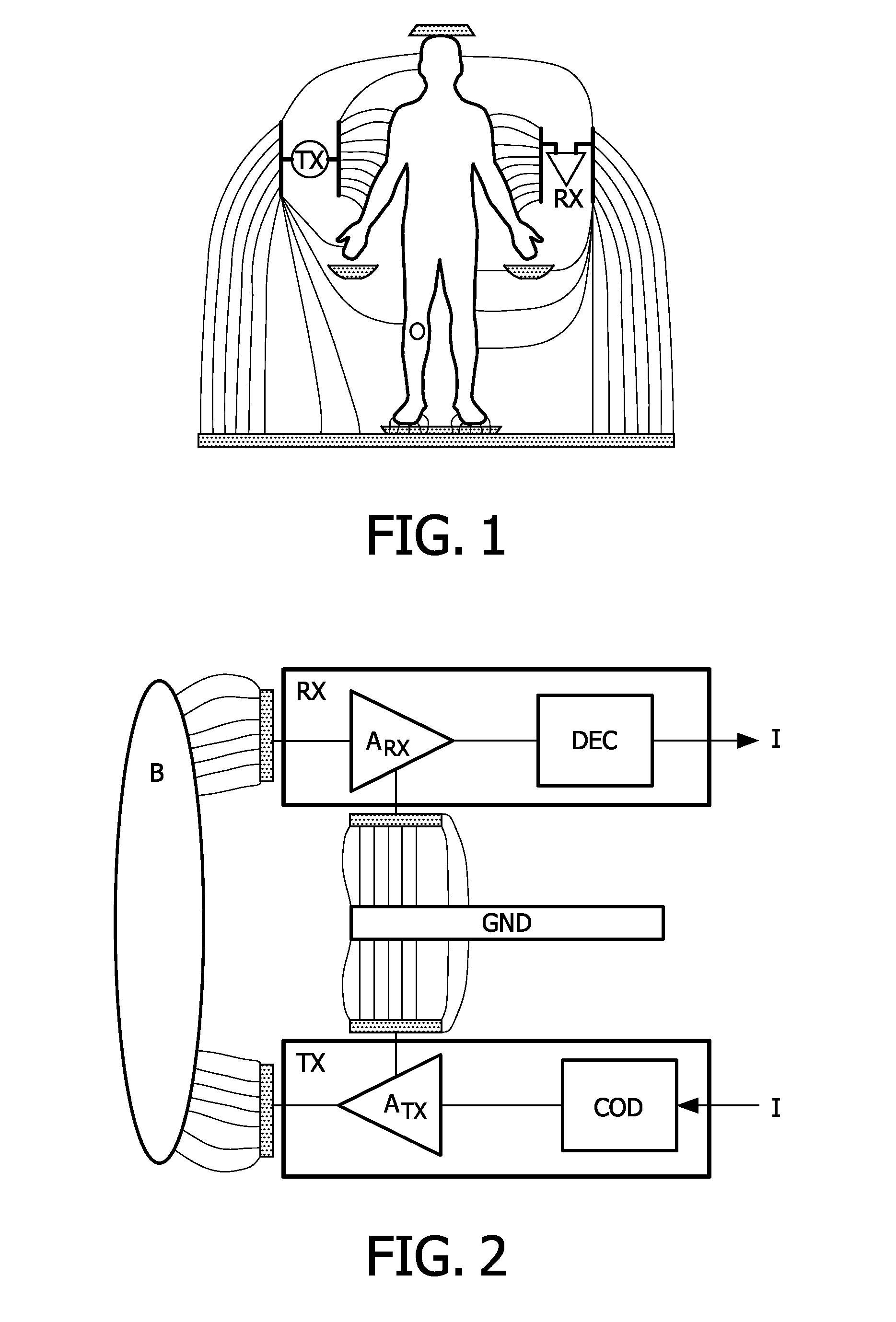
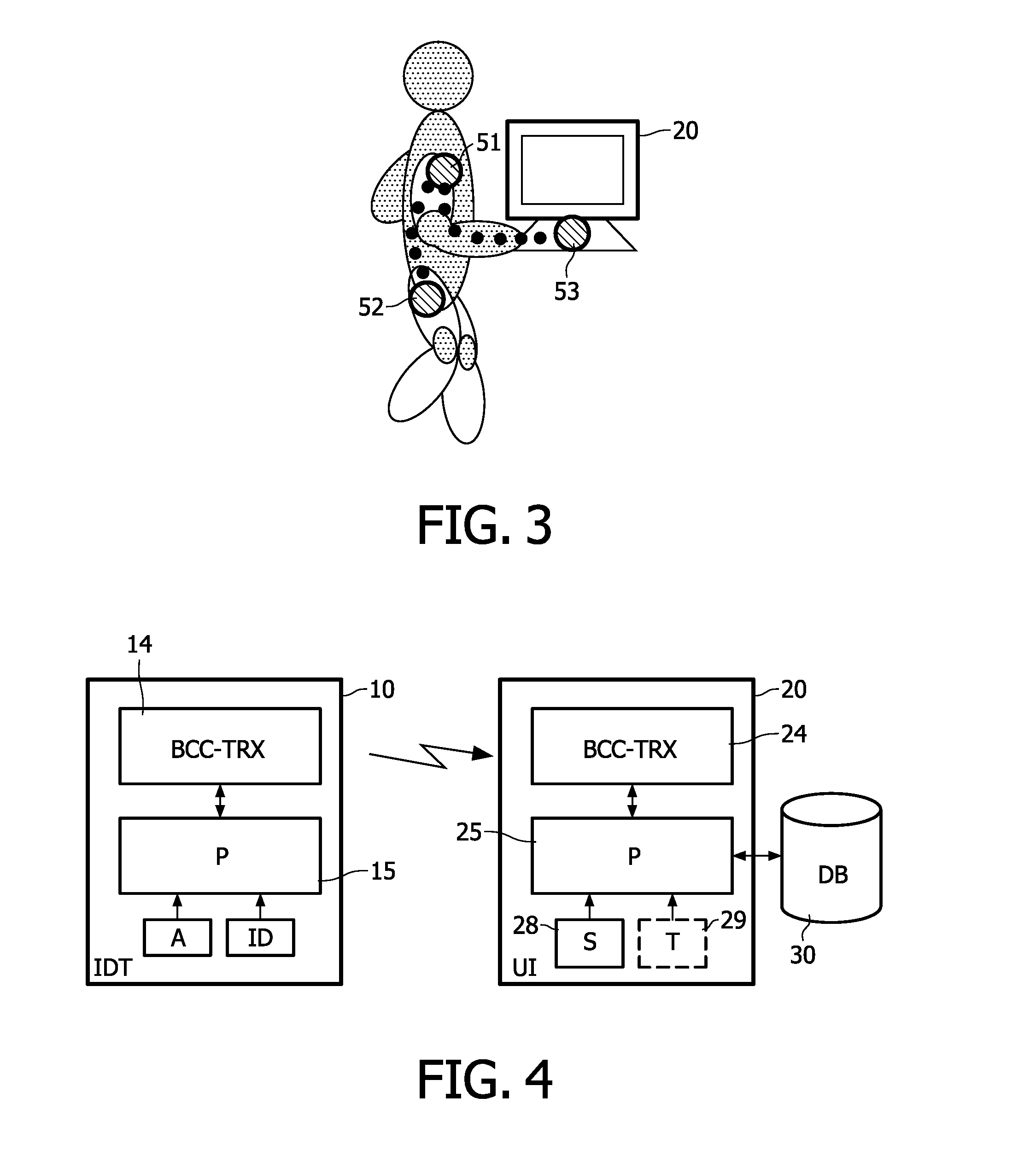
User identification based on body-coupled communication
InactiveUS20110227856A1Reliable user identificationEasy accessUser identity/authority verificationNear-field systems using receiversIdentification deviceUser interface
A secure identification system is proposed in which a user gets access through an identification device or badge or tag (51) worn on his / her body, which applies the techniques of body coupled communication (BCC) to create a kind of aura around the user. An identification (ID) is communicated to a user interface of the secure identification system through BCC communication, and the user is authenticated by the system through an authentication procedure checking the identity of the user on the basis of an assumed secure BCC communication of the ID.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
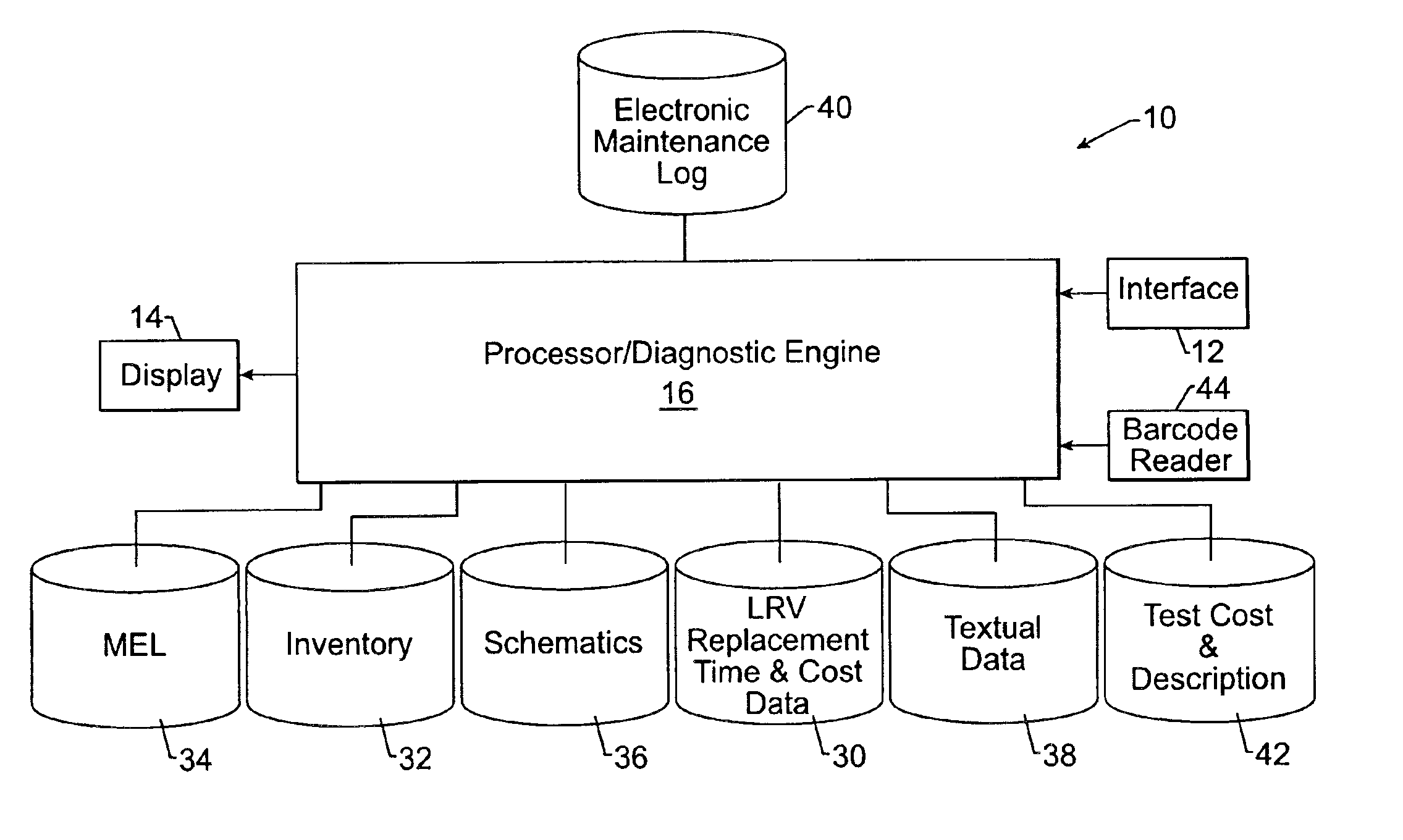
Diagnostic system and method
InactiveUS6868319B2Shorten the timeMaintaining and improving reliability of maintenanceVehicle testingRegistering/indicating working of vehiclesDisplay deviceProcessing element
A diagnostic system and method are provided that include an interface for receiving input relating to observed symptoms indicative of one or more failed components, a processing element for correlating the input relating to the observed symptoms with at least one suspect component that is capable of causing the observed symptoms upon failure, and a display for presenting information relating to the suspect components. The processing element correlates the input relating to the observed symptoms with the suspect components in accordance with a diagnostic model constructed based upon systemic information, experiential information and factual information. The processing element generally presents the suspect components in a listing prioritized based upon the relative likelihood that the respective suspect components caused the observed symptoms. Additionally, the processing element can present a prioritized listing of tests that can be conducted to refine the identification and prioritization of the suspect components.
Owner:THE BOEING CO
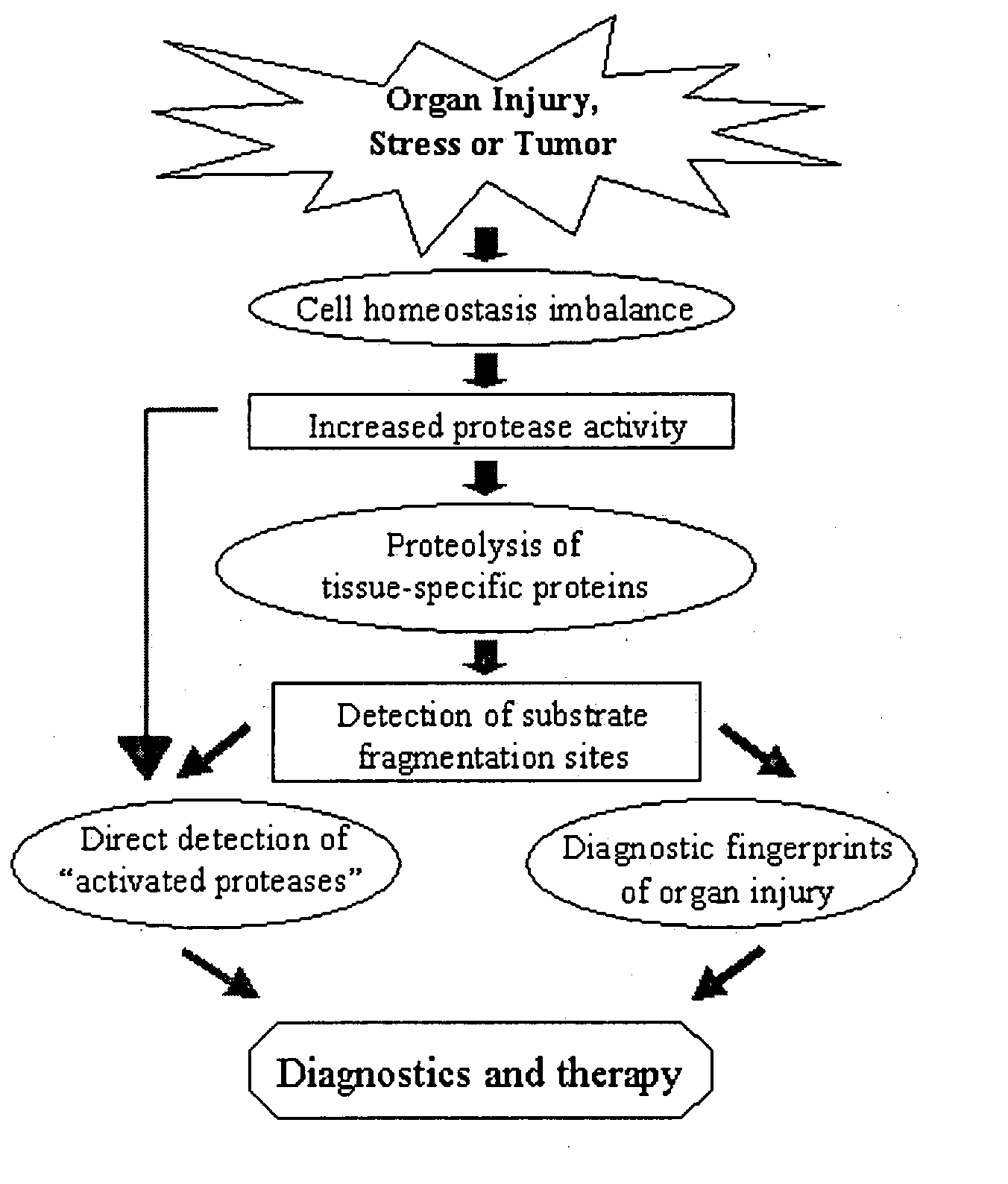
Proteolytic markers as diagnostic biomarkers for cancer, organ injury and muscle rehabilitation/exercise overtraining
ActiveUS20050260697A1Reliable detectionReliable identificationMicrobiological testing/measurementBiological testingOvertrainingMedicine
The present invention identifies biomarkers that are diagnostic of nerve cell injury, organ injury, and / or neuronal disorders. Detection of different biomarkers of the invention are also diagnostic of the degree of severity of nerve injury, the cell(s) involved in the injury, and the subcellular localization of the injury.
Owner:UNIV OF FLORIDA RES FOUNDATION INC +1
Dual mode transmitter/receiver and decoder for RF transponder units
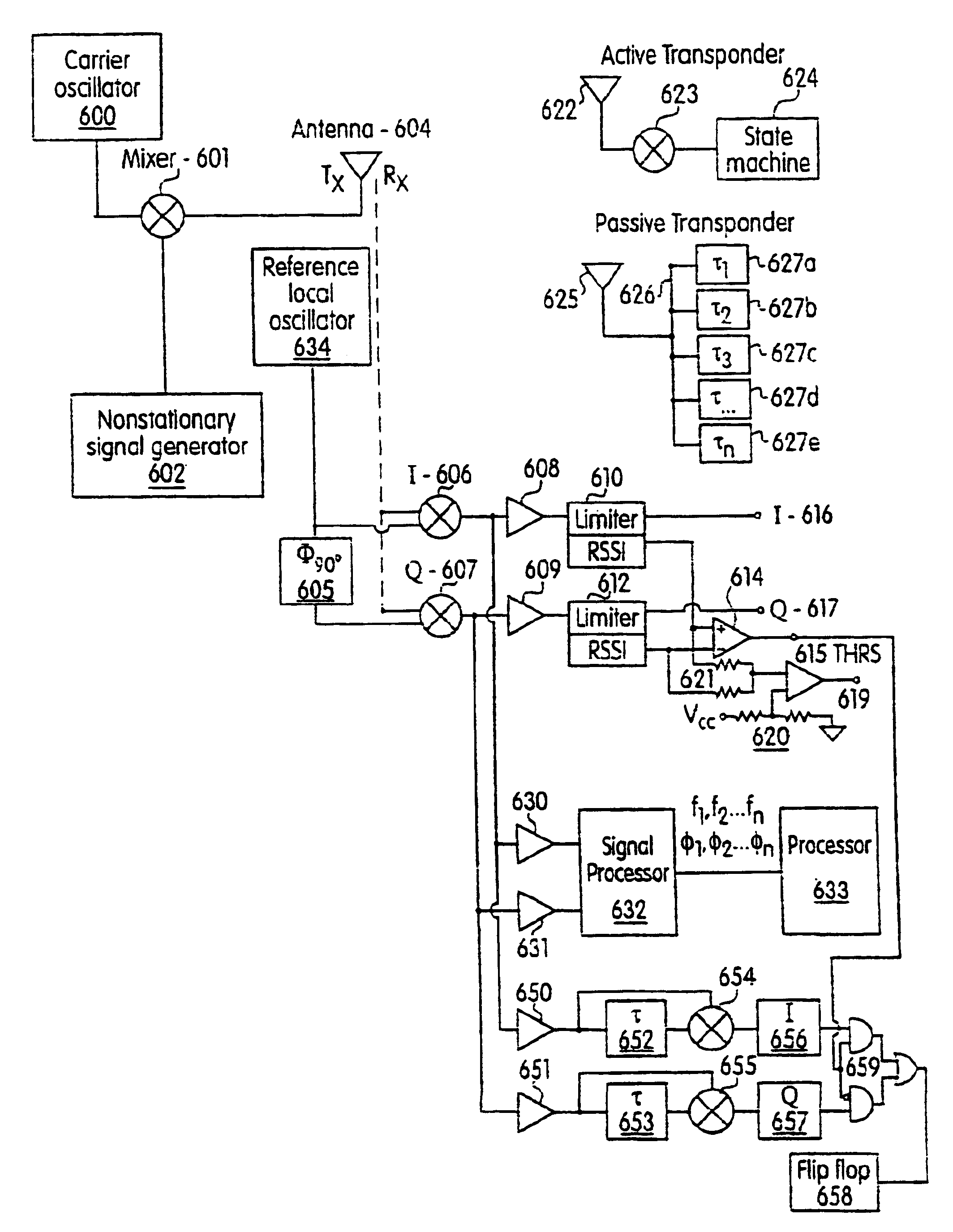
InactiveUS6950009B1Enhanced informationReduce riskImpedence networksMemory record carrier reading problemsEnvironmental effectEngineering
An enhanced backscatter RF-ID tag reader system and multiprotocol RF tag reader system is provided. In a multiprotocol mode, the system emits a non-stationary interrogation signal, and decodes a phase modulated backscatter signal by detecting a stronger phase component from quadrature phase representations or determining phase transition edges in a phase of a received signal. The RF tag reader system predicts or follows the phase of the backscatter signal, thereby avoiding interference from nulls in the received signal waveform due to the non-stationary interrogation signal, relative movement or environmental effects. An acoustic RF-ID tag detection system detects the reradiated signal corresponding to respective transformation of a signal in the tag. Detection of either type of RF-ID tags therefore is possible, and the absence of any tag or absence of any valid tag also determined.
Owner:X CYTE
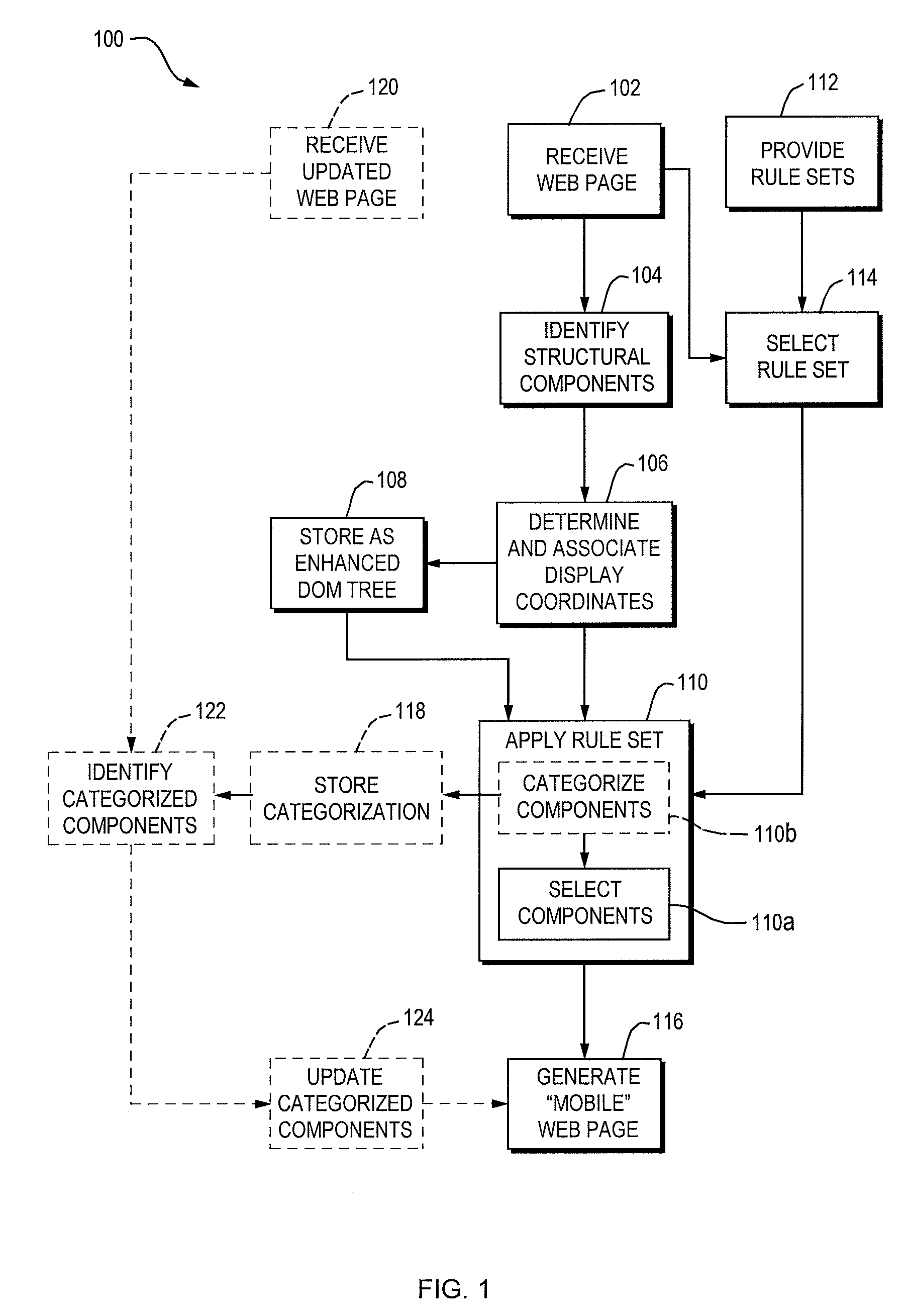
Displaying Content on a Mobile Device
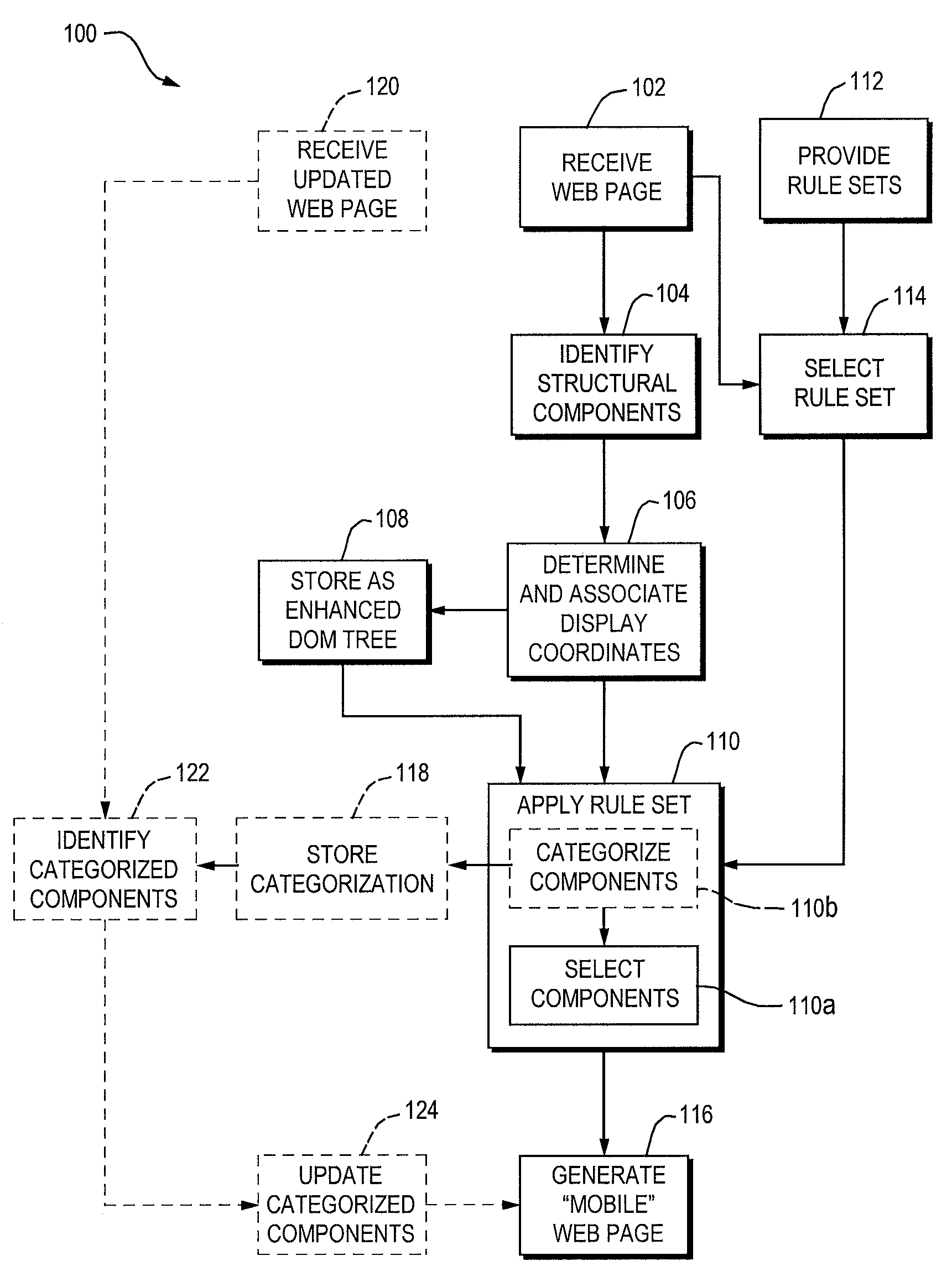
ActiveUS20090070413A1Improves automatic creationReduce screen sizeDigital data information retrievalNatural language data processingWeb pageSource code
A method for facilitating the rendering of a web page on a mobile device includes providing an enhanced DOM tree for the web page that includes web page components and their display coordinates. A rule set is applied to the DOM tree, thereby selecting components for display on the mobile device. A mobile-device-specific version of the source code is generated based on the selected components.
Owner:APPLE INC
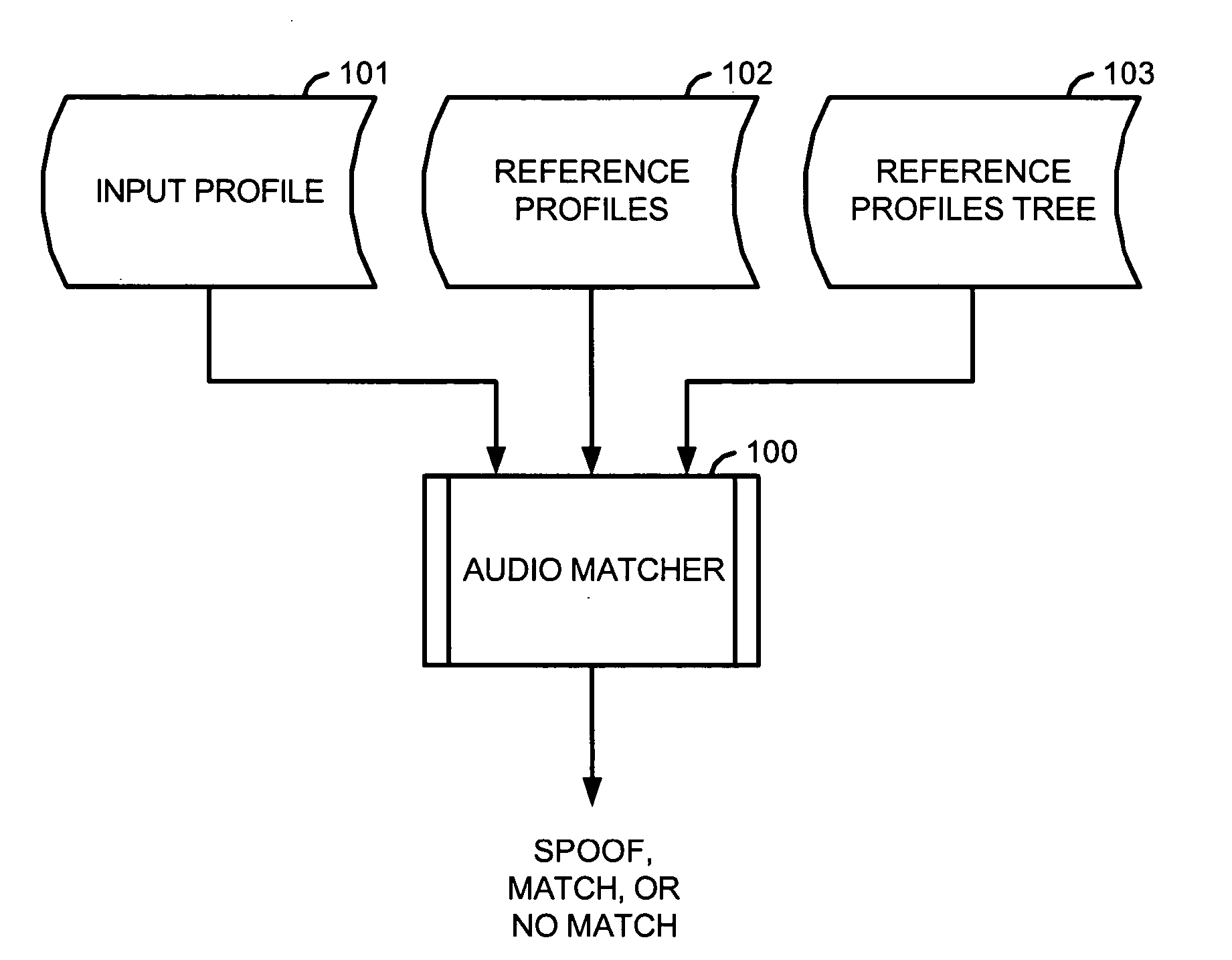
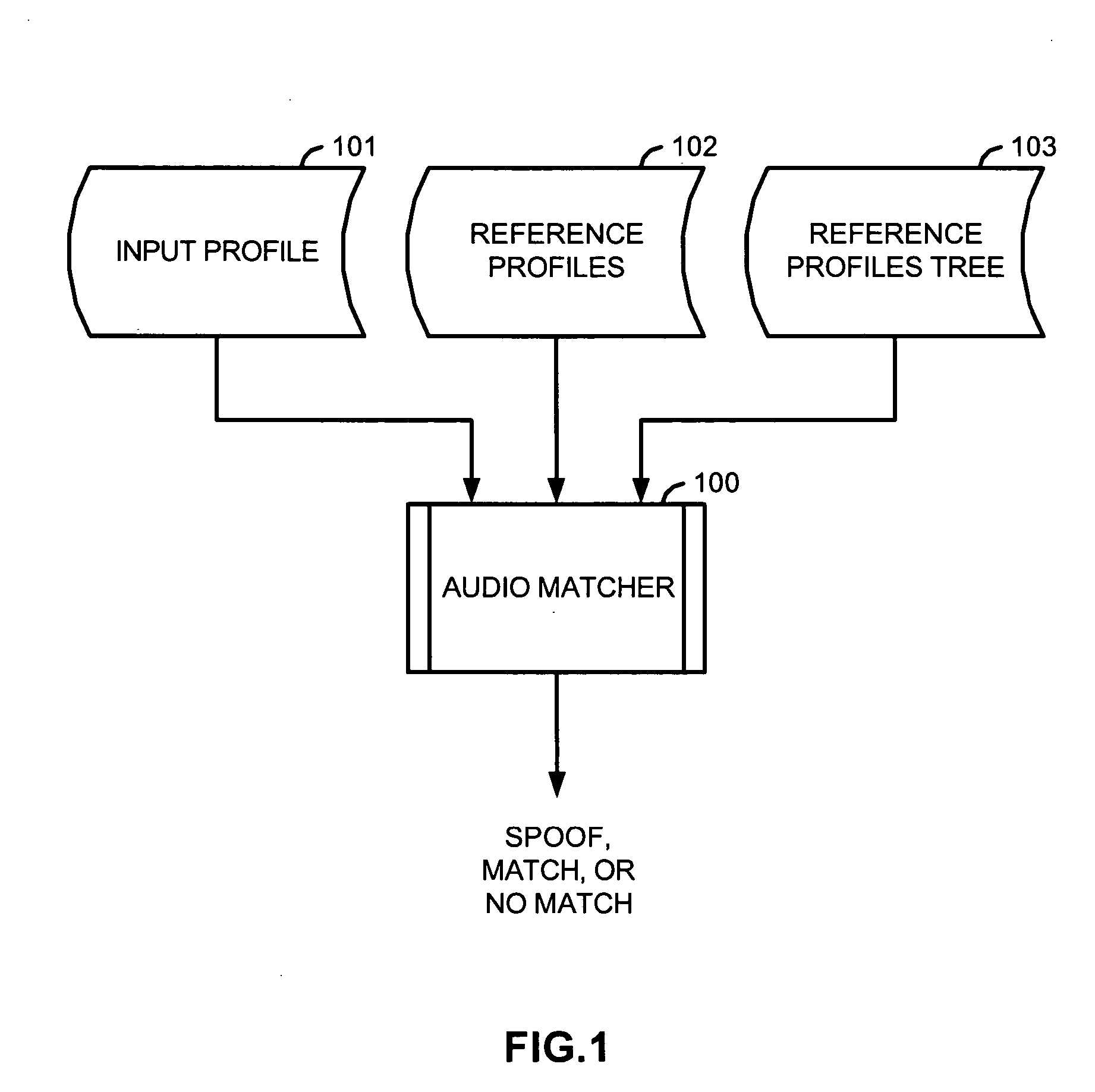
Identification of input files using reference files associated with nodes of a sparse binary tree
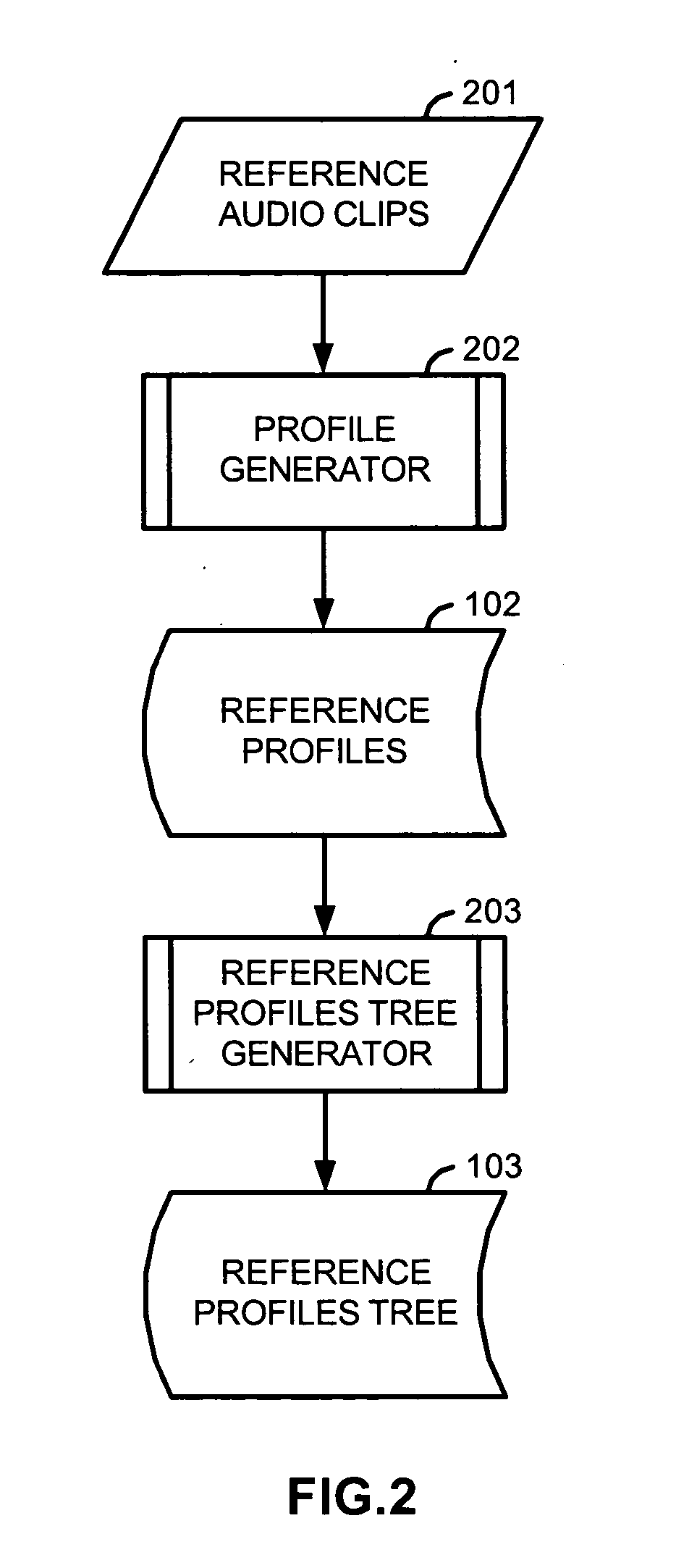
ActiveUS20050216433A1Reliable identificationMinimize data storage requirementElectrophonic musical instrumentsDigital data information retrievalBinary treeReference Document
An input profile is generated from an input audio file using a measurable attribute that was also used to generate reference profiles from reference audio files. The input profile is then subjected to a process that was also used to generate a reference profiles tree, which is structured as a sparse binary tree, from the reference profiles. As a result of the process, information of reference profiles having similar characteristics as the input profile, with respect to the measurable attribute, are retrieved from resulting nodes of the reference profiles tree. The input profile is then compared with this subset of the reference profiles, representing potential matches, to determine that either it matches one of the reference profiles, or that it is a spoof, or that it does not match any of the reference profiles.
Owner:ROVI SOLUTIONS CORP
System and method for utility usage, monitoring and management
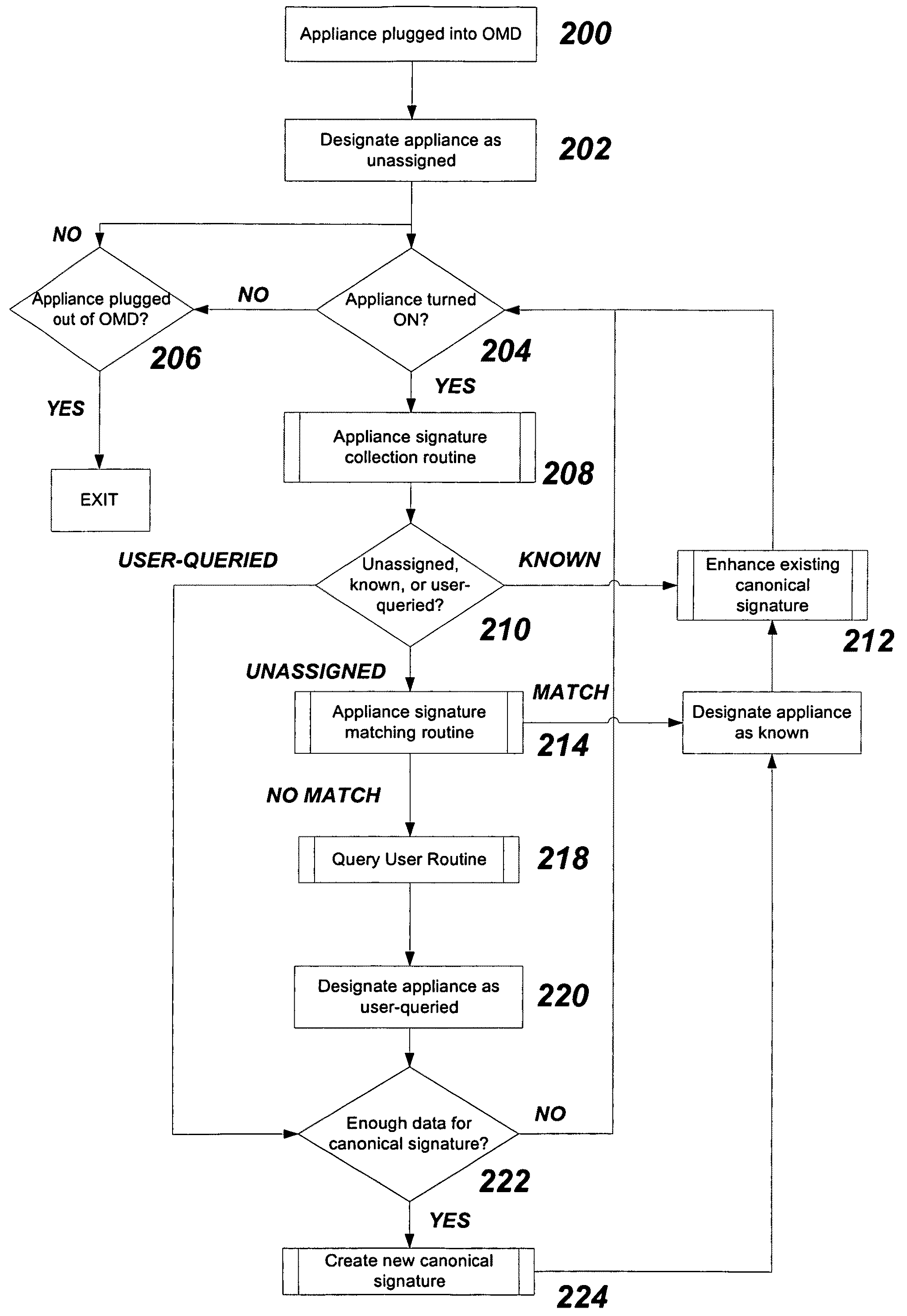
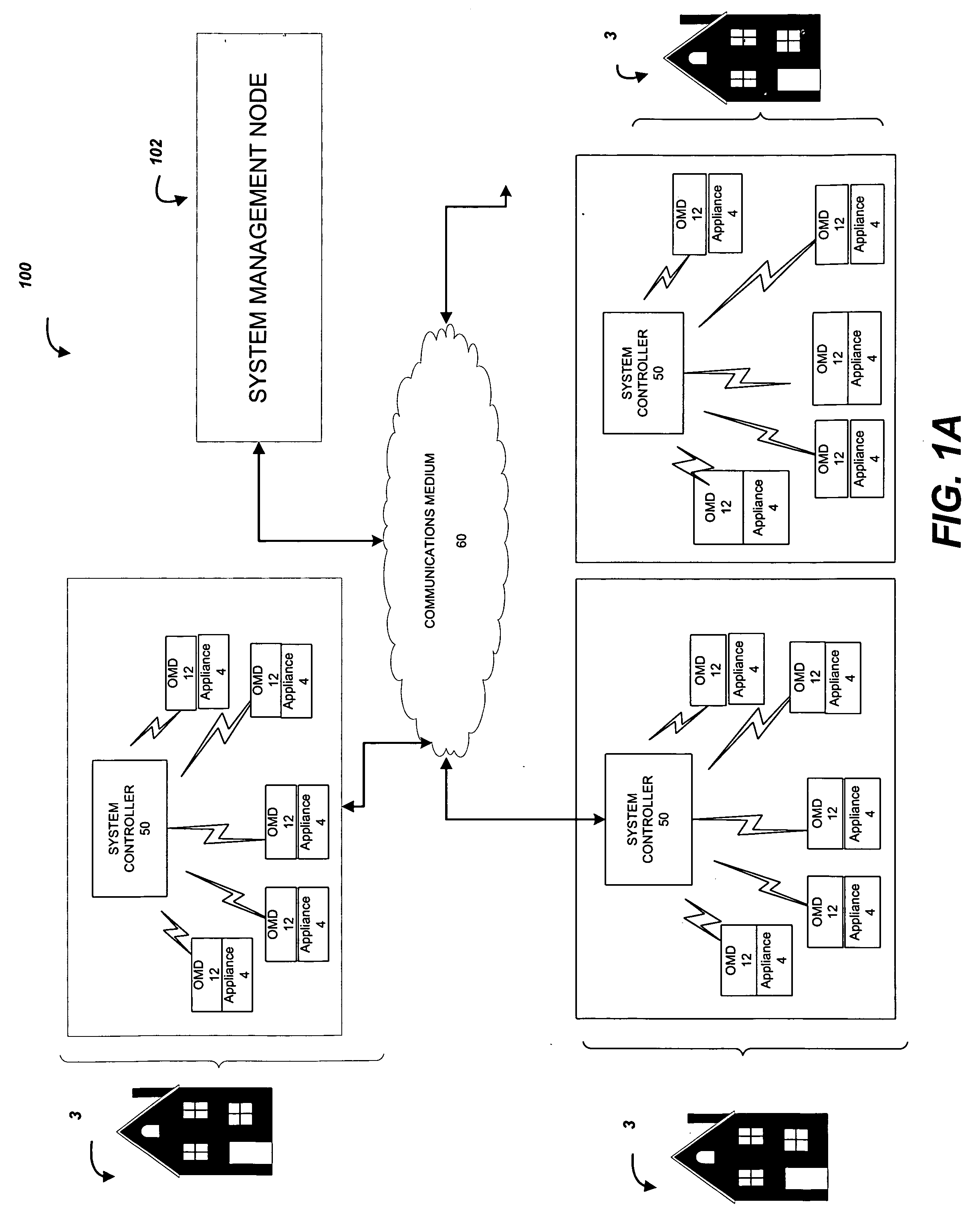
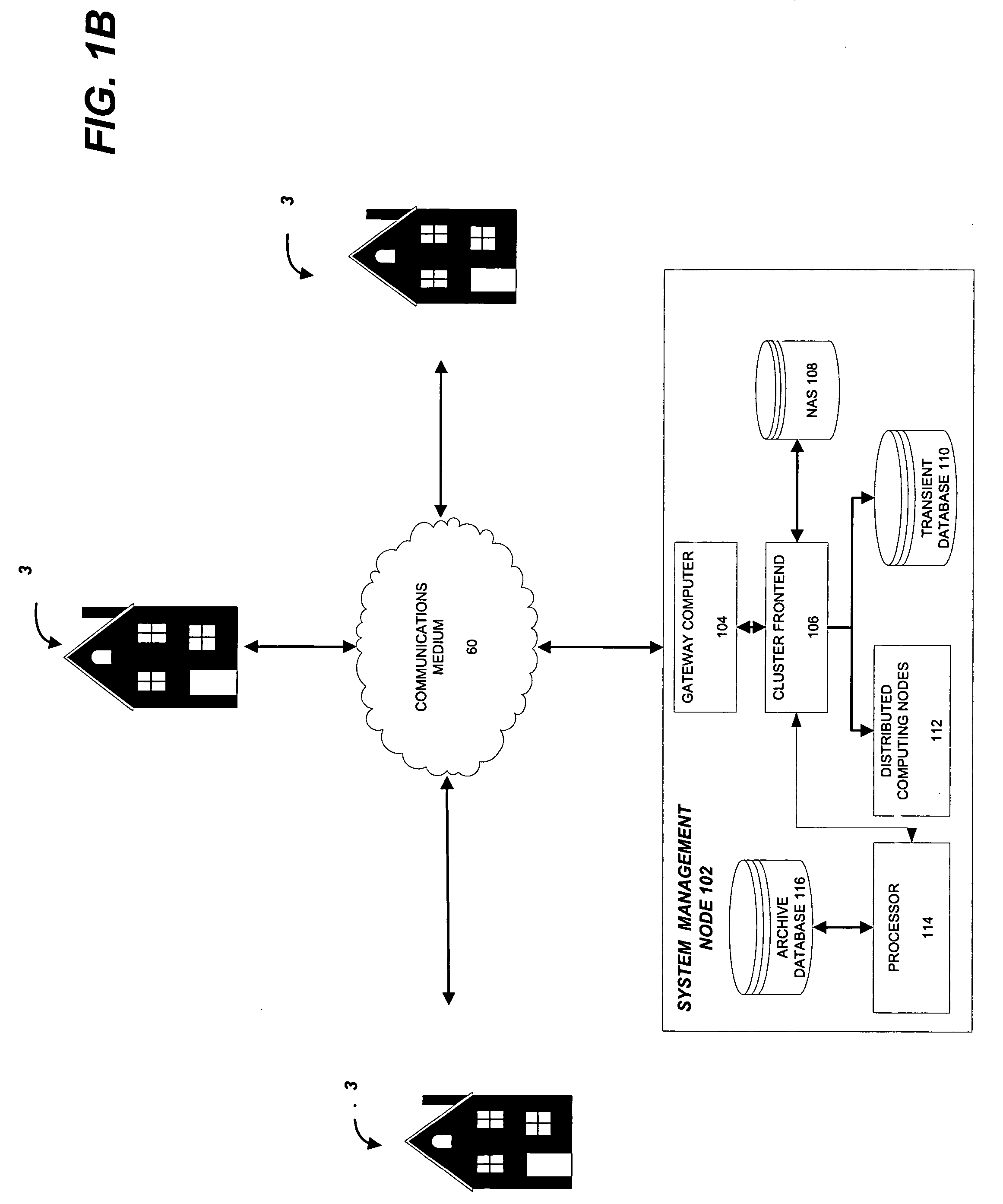
ActiveUS20100280978A1Reliable identificationManagement intelligencePower network operation systems integrationCircuit arrangementsEngineeringSystem controller
Systems and methods are provided for collecting waveform data for a plurality of appliances that may be found in a residential or commercial setting using multi-port outlet monitoring devices to obtain power consumption profiles that indicate power consumption on a per-appliance and / or per-location basis and / or per user basis. The plurality of appliances is reliably identified from the power consumption profiles. In accordance with a method embodiment, waveform data transmitted from an unknown appliance is independently metered via a multi-port monitoring device over an elapsed time period. The metered waveform data is wirelessly transmitted from the multi-port monitoring device to a co-located system controller which constructs an appliance signature. The process may be repeated to generate multiple appliance signatures. The one or more appliance signatures are compared to a database of pre-stored canonical signatures to determine if there is a match to identify the appliance.
Owner:THINKECO
Explosives detection using differential ion mobility spectrometry
InactiveUS20050133716A1Easy to separateHigh resolutionTime-of-flight spectrometersFuel testingOptical spectrometerPhysical chemistry
System for control of ion species behavior in a time-varying filter field of an ion mobility-based spectrometer to improve species identification for explosives detection.
Owner:DH TECH DEVMENT PTE
Rail vehicle identification and processing
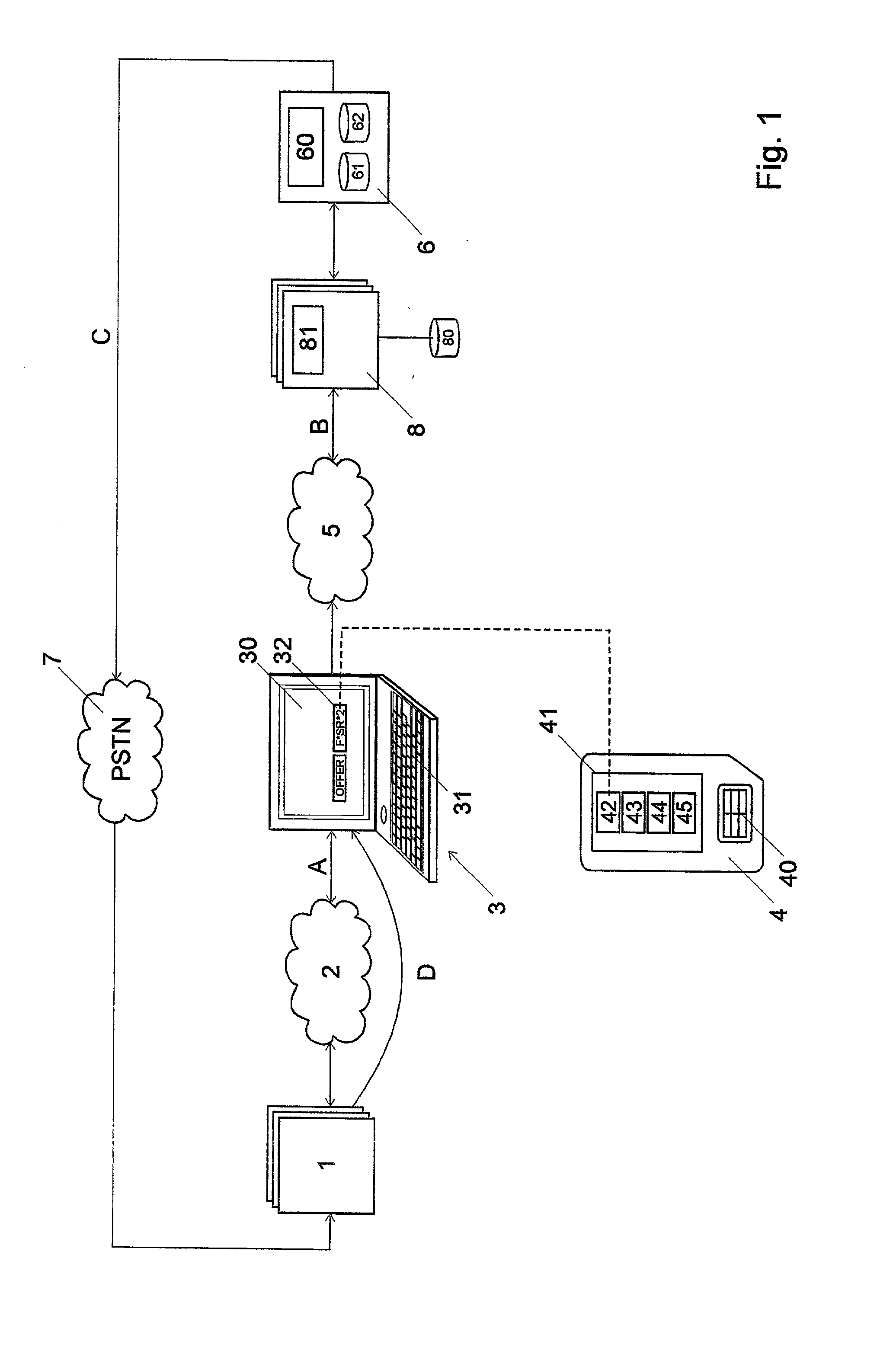
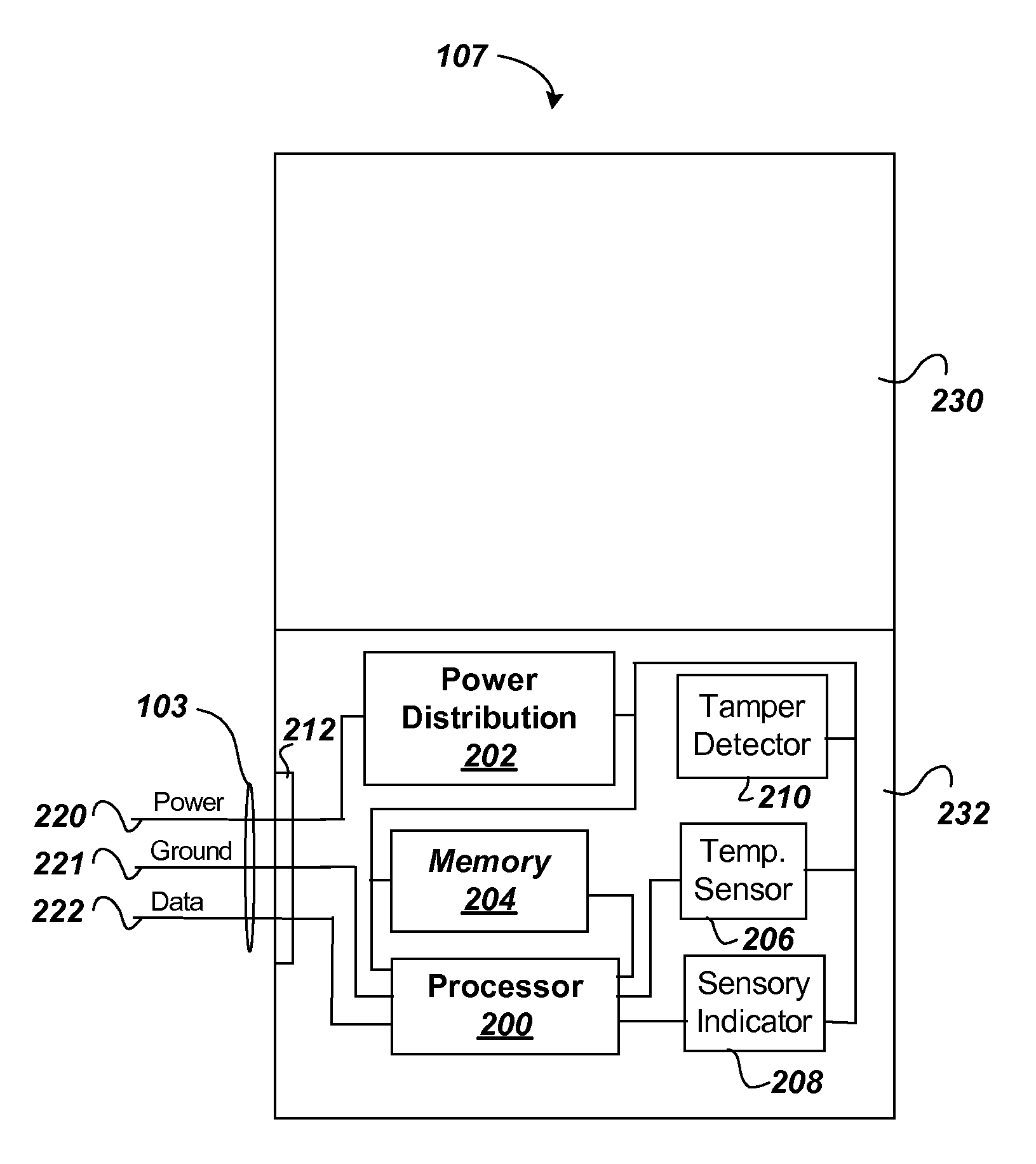
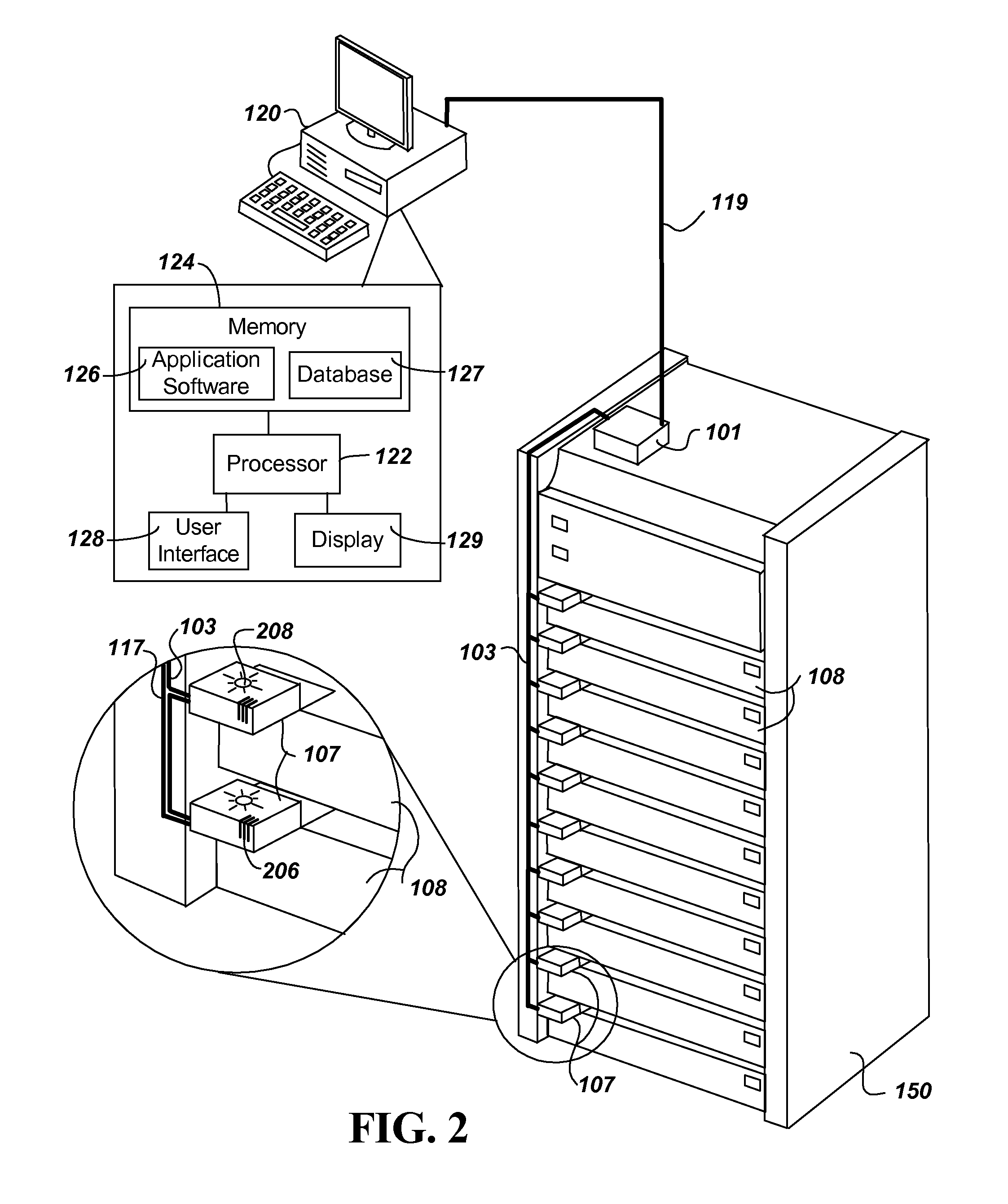
ActiveUS8140250B2Reliable identificationReliable distributionVehicle testingRegistering/indicating working of vehiclesUnsafe conditionVehicle identification
A solution for further automating the identification, processing, and / or routing of rail vehicles is provided. Each individual rail vehicle in a series of rail vehicles is identified and measurement data is acquired for the rail vehicle. The measurement data is analyzed and the rail vehicle is automatically routed based on the analysis. The rail vehicle can be routed to an outbound track based on a destination, to a maintenance shop for repair, and / or to a local track for repair and / or re-measurement. The solution can further incorporate expert systems and data mining to reduce the number of rail vehicles that are unnecessarily routed for repair and / or inadvertently allowed to pass with one or more unsafe conditions.
Owner:INT ELECTRONICS MACHINES
Marker device for X-ray, ultrasound and MR imaging
InactiveUS20060293581A1Sharp contrastEasily introduced into tissueUltrasonic/sonic/infrasonic diagnosticsPowder deliveryDiagnostic Radiology ModalityMicrosphere
An imaging marker comprised of glass and iron-containing aluminum microspheres in a gel matrix which shows uniformly good contrast with MR, US and X-Ray imaging. The marker is small and can be easily introduced into tissue through a 12-gauge biopsy needle. The concentration of glass microspheres and the size dictate the contrast for US imaging. The contrast seen in MRI resulting from susceptibility losses is dictated by the number of iron-containing aluminum microspheres; while the artifact of the marker also depends on its shape, orientation and echo time. By optimizing the size, iron concentration and gel binding, an implantable tissue marker is created which is clearly visible with all three imaging modalities.
Owner:SUNNYBROOK & WOMENS COLLEGE HEALTH SCI CENT
Order method
InactiveUS20020111164A1Simple and reliable processEasy accessSpecial service for subscribersRadio/inductive link selection arrangementsOrder formComputer terminal
Order method comprising following steps: reproduction of the offer of a provider with electronic reproduction means of a personal terminal, selection of the offer through the user, execution in said personal terminal of an order program linked to the selected offer, with which order data can be entered, the order program using the order parameters transmitted with the offer, linking of said order data with user identification data stored in a personal identification module, transmission of an order message with said linked data to the provider.
Owner:SWISSCOM
Data center equipment location and monitoring system
InactiveUS20110084839A1Quickly and easily identifyReliable identificationMetering/charging/biilling arrangementsAccounting/billing servicesOperator interfaceData center
A data center equipment location system includes both hardware and software to provide for location, monitoring, security and identification of servers and other equipment in equipment racks. The system provides a wired alternative to the wireless RFID tag system by using electronic ID tags connected to each piece of equipment, each electronic ID tag connected directly by wires to a equipment rack controller on the equipment rack. The equipment rack controllers then link over a local area network to a central control computer. The central control computer provides an operator interface, and runs a software application program that communicates with the equipment rack controllers. The software application program of the central control computer stores IDs of the equipment rack controllers and each of its connected electronic ID tags in a database. The software application program in operation receives information from the electronic ID tags in real time enabling the central control computer to monitor the status, such as temperature and movement or tampering of each piece of equipment through its connected electronic ID tag. Further, the software application program can send a signal to an individual electronic ID tag to activate a sensory indicator to enable a technician(s) to locate a piece of equipment that is in need of repair or replacement.
Owner:ATTEND SYST
Equipment control apparatus, control method, and control program
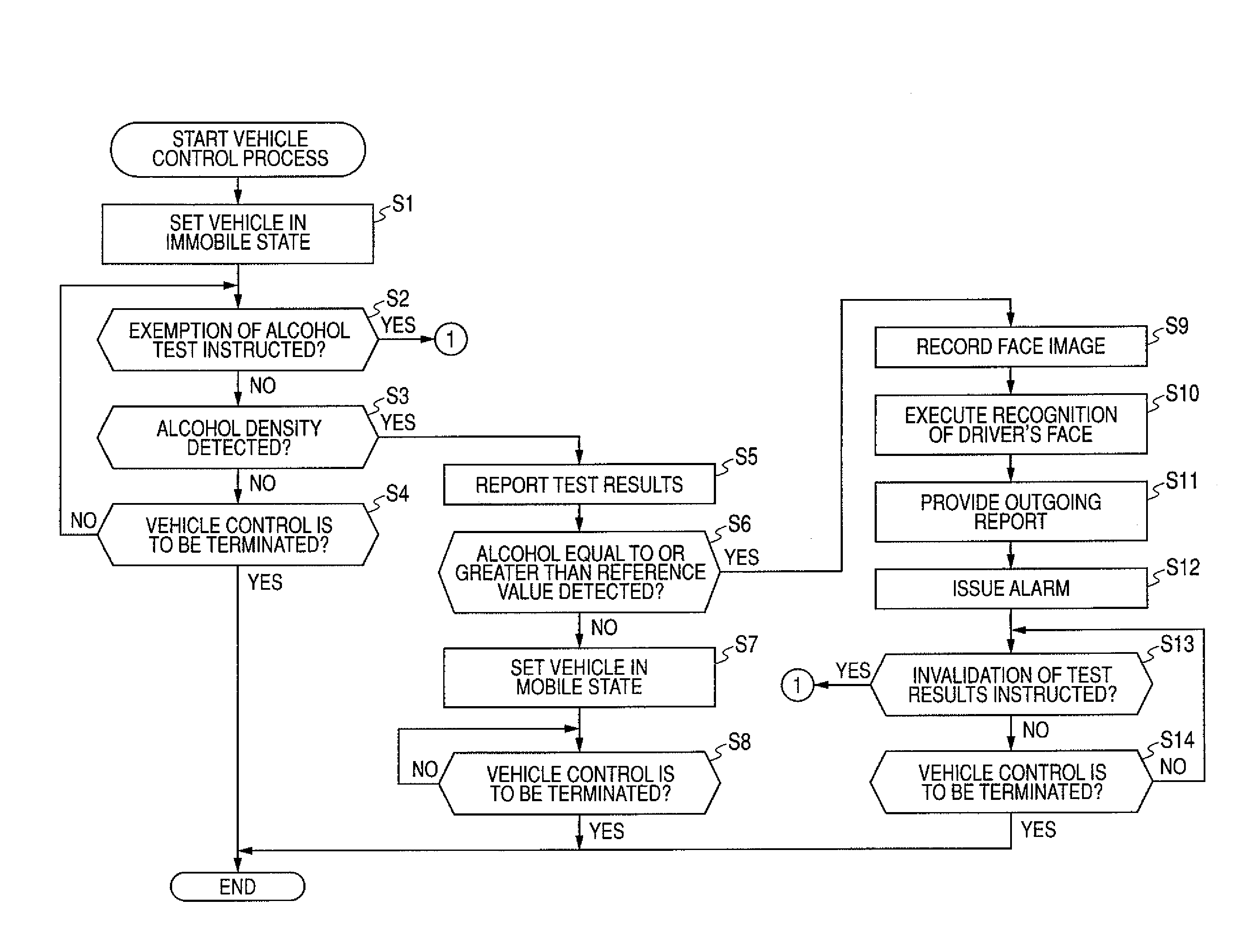
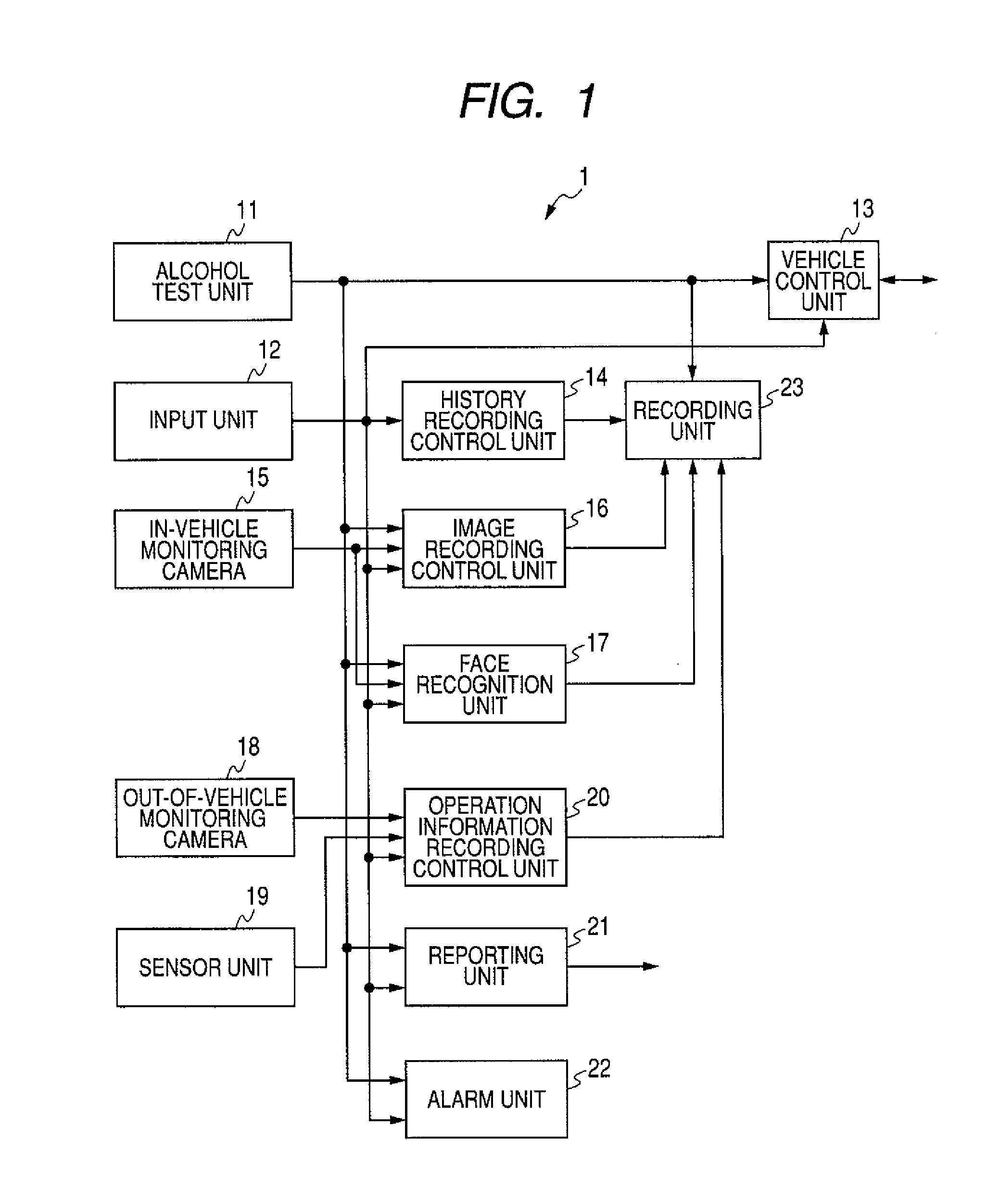
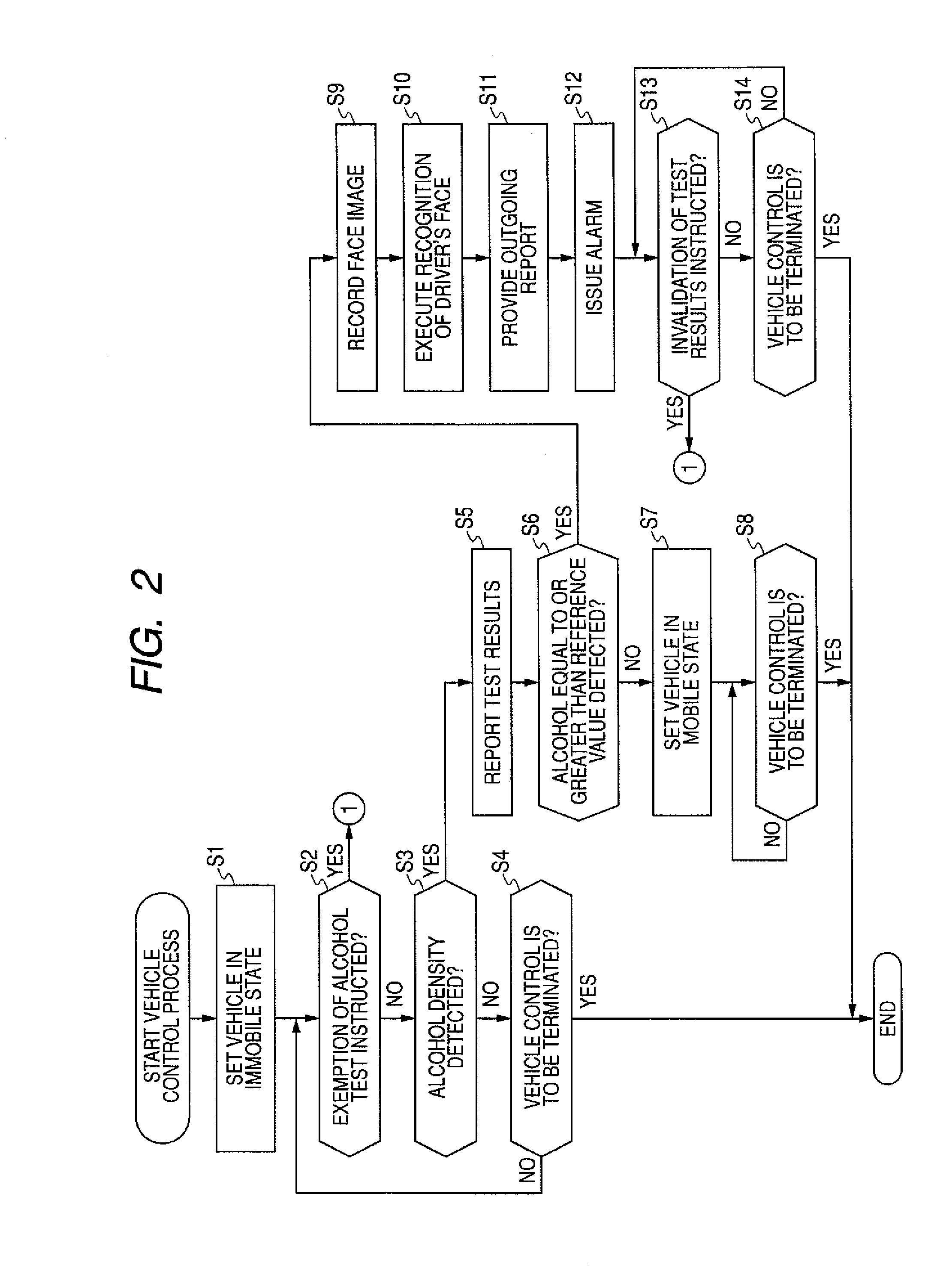
InactiveUS20090043409A1Avoid testingReliable identificationWithdrawing sample devicesAlarmsAlcoholDriver/operator
An alcohol density test can be avoided, but the alcohol density test is prevented from being easily avoided at the same time. A vehicle control unit sets a controlled vehicle in a mobile state when an alcohol density detected from the driver is determined to be lower than a predetermined threshold based on results of a test conducted using an alcohol test unit or when an instruction for exemption of the alcohol test is input through an input unit. When an instruction for exemption of the alcohol test is input, a history recording control unit records a history indicating that the alcohol density test has been exempted in a recording unit. The invention may be applied to a vehicle control apparatus for controlling a vehicle based on results of an alcohol density test conducted on the driver.
Owner:ORMON CORP
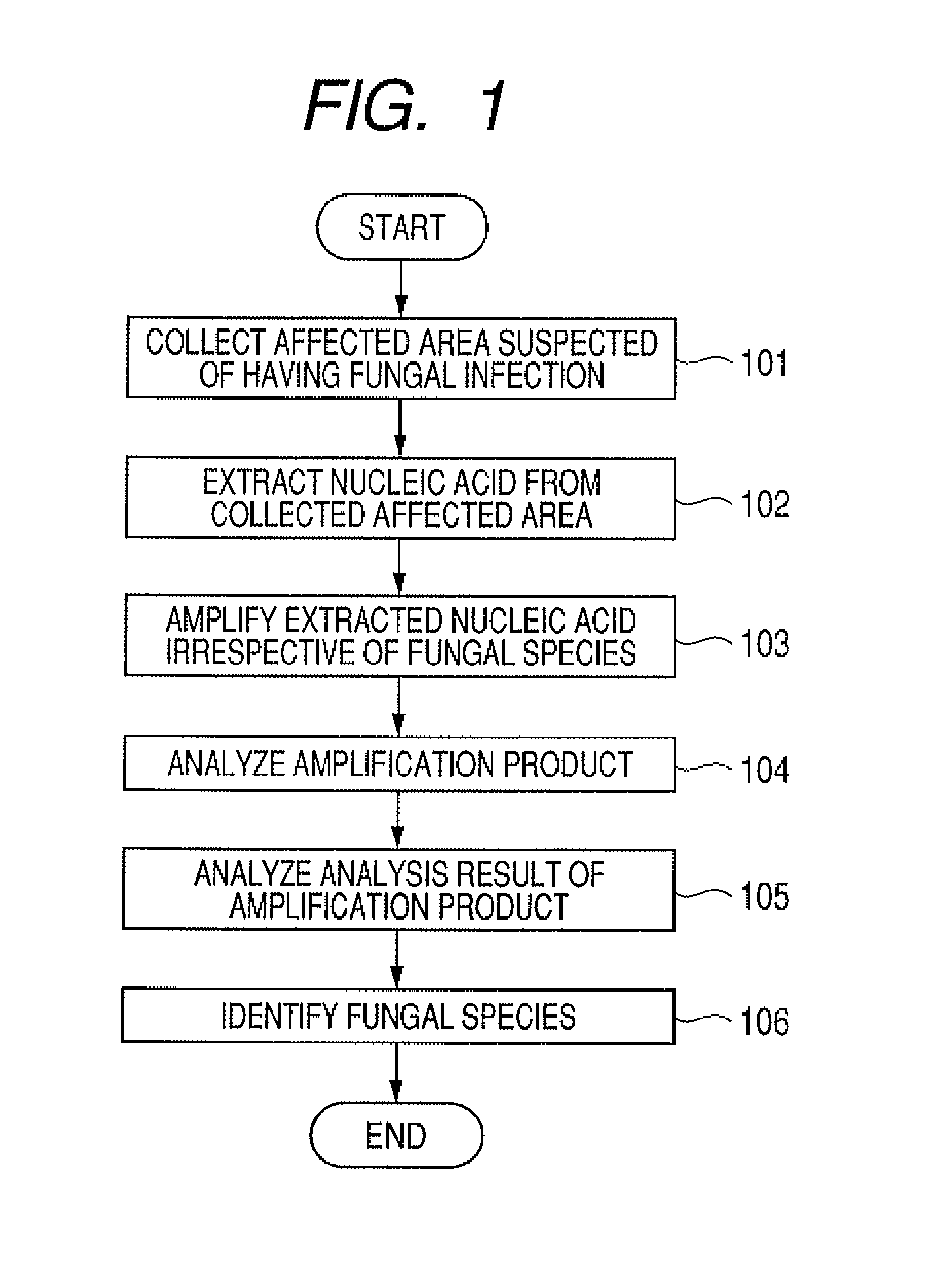
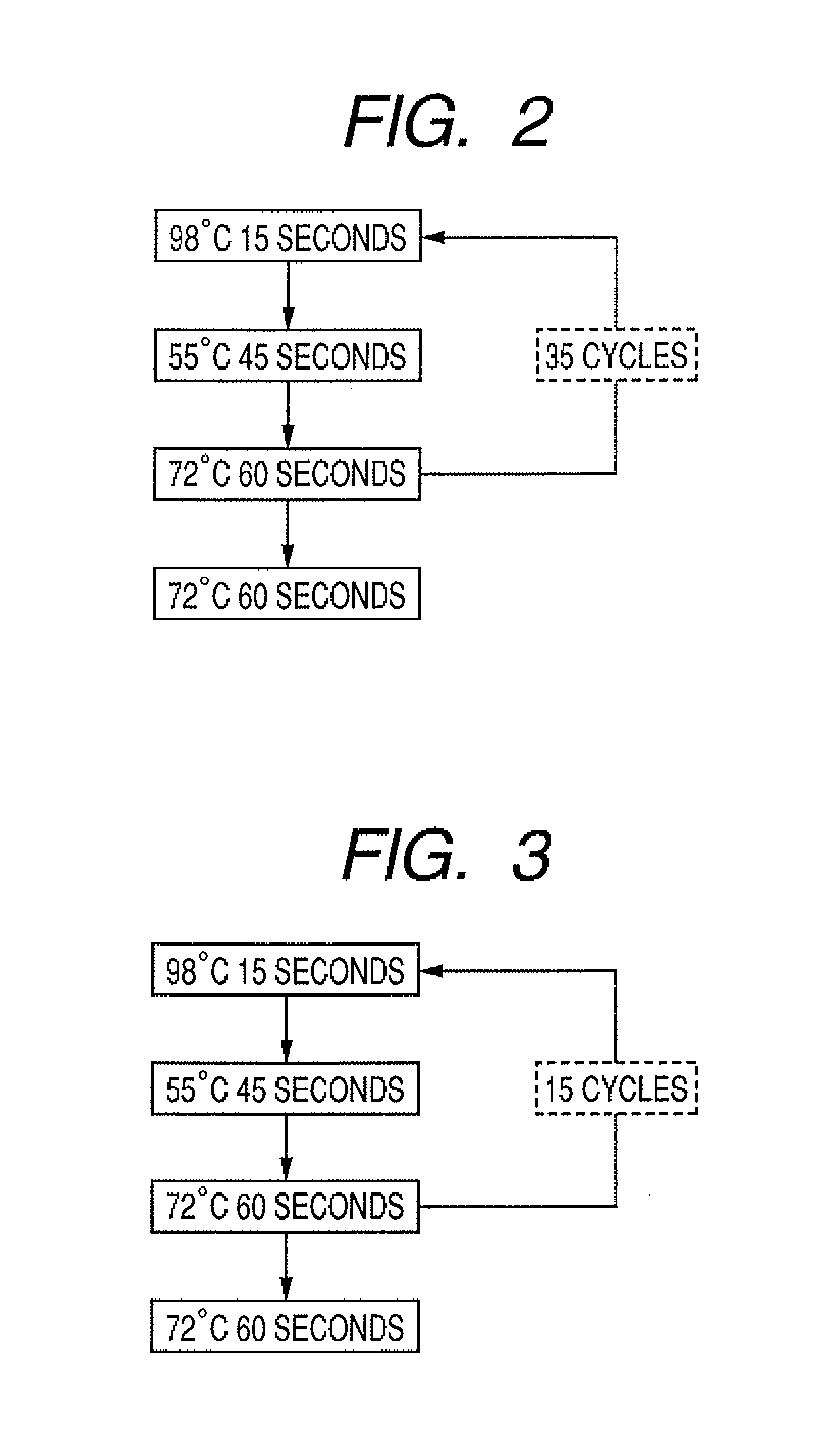
Probe set, probe carrier, and method for determining and identifying fungus
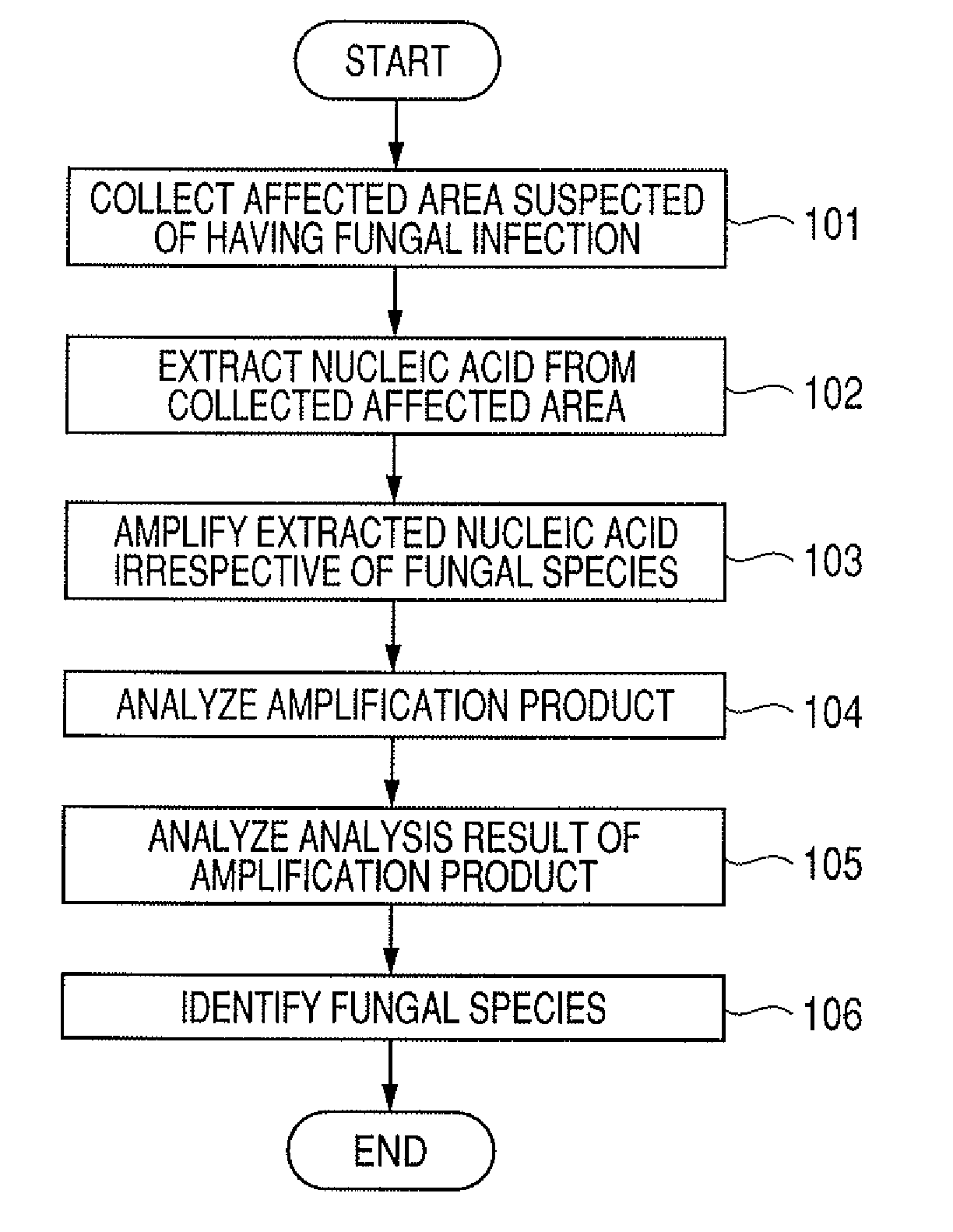
ActiveUS20090081666A1Reliable identificationMore performanceSugar derivativesMicrobiological testing/measurementHybridization probeBiotechnology
It is intended to provide a method for identifying a causative fungus of skin disease. The method includes: simultaneously performing amplification treatments under the same conditions using primers common to plural fungal species; then simultaneously performing hybridization procedures under the same conditions using probes respectively specific to fungi; and determining the presence or absence of each fungus from the hybridization intensity of each probe.
Owner:CANON KK
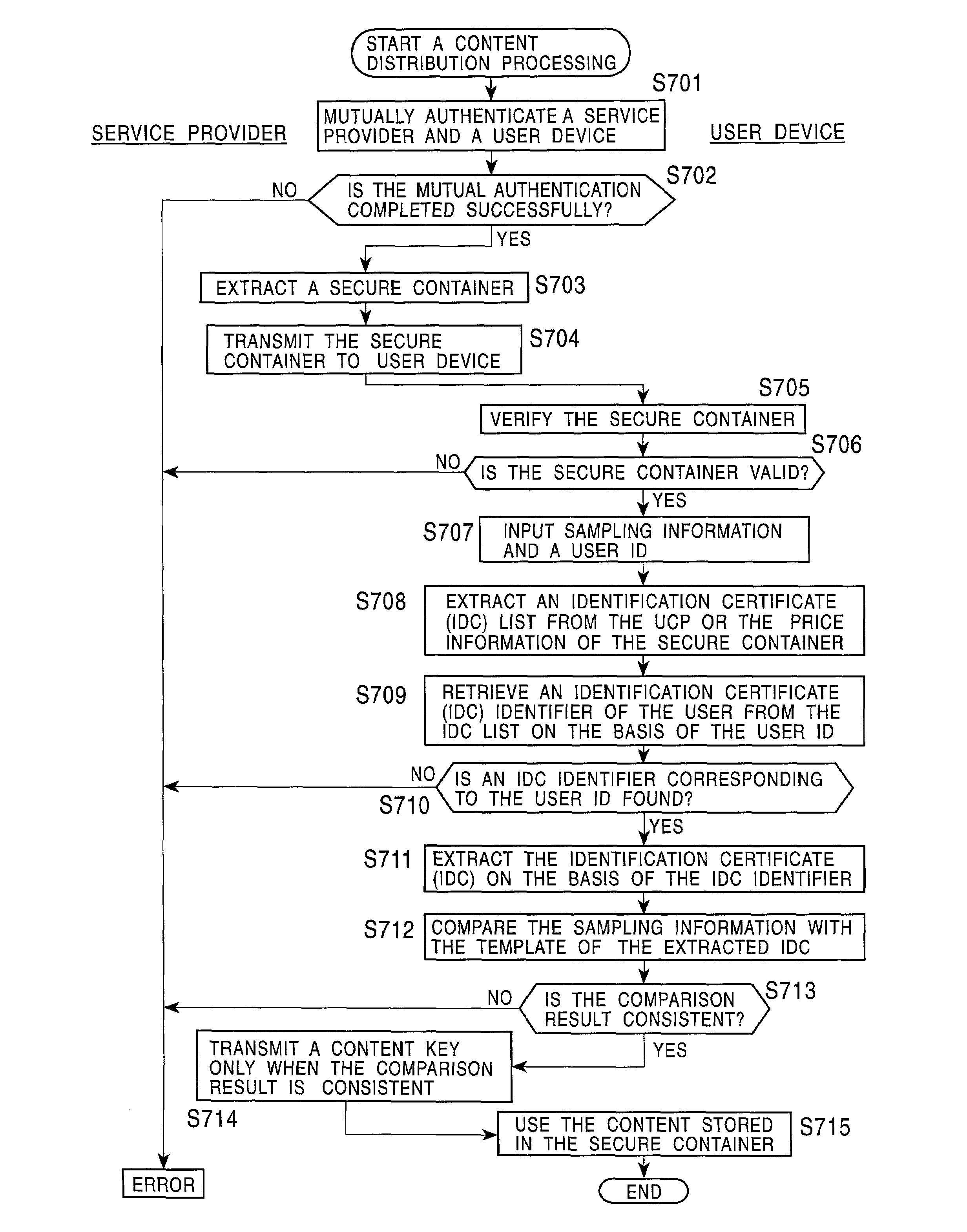
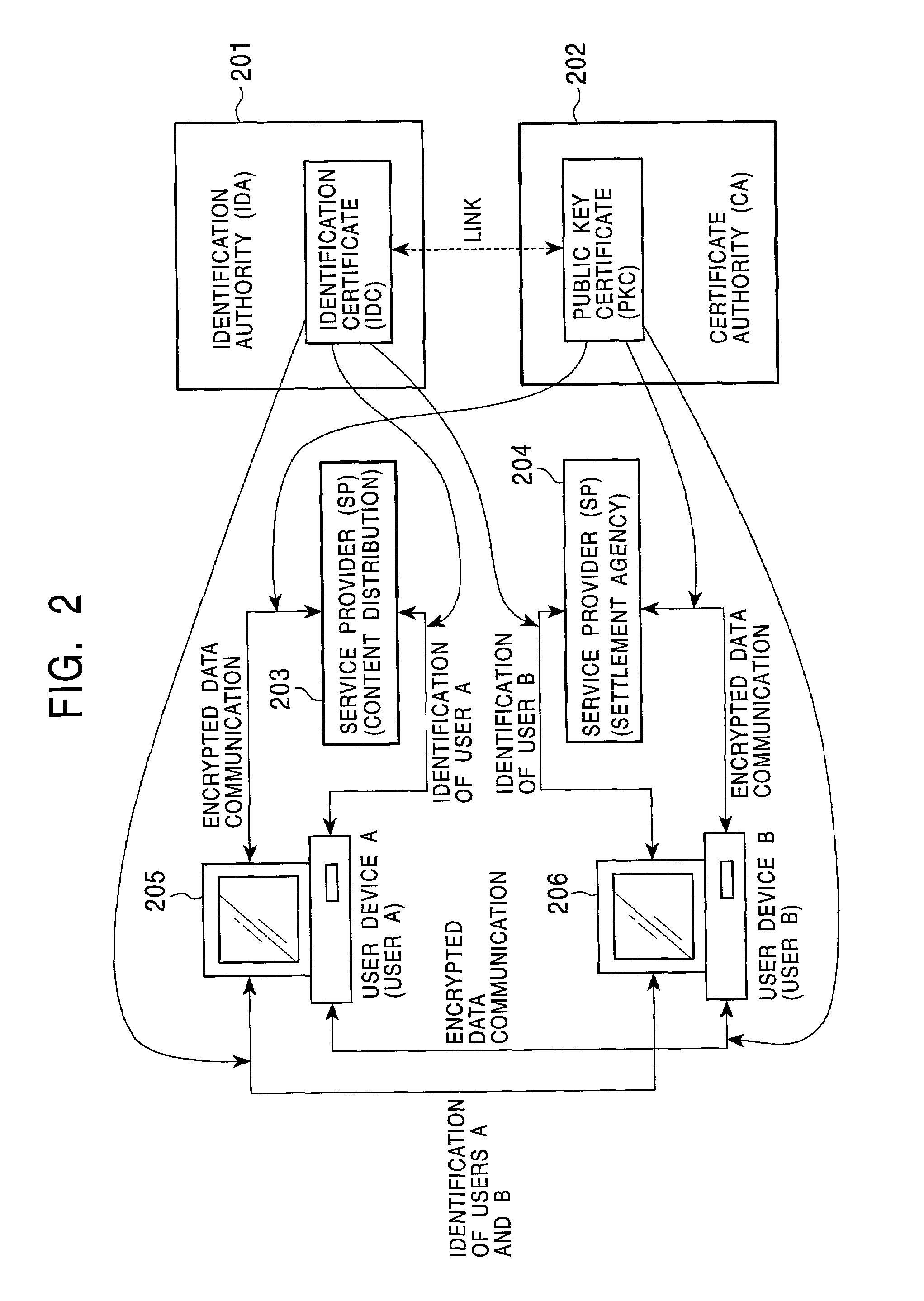
Content distribution system authenticating a user based on an identification certificate identified in a secure container
InactiveUS7310732B2Improve reliabilityWarranty periodKey distribution for secure communicationDigital data processing detailsContent distributionUser device
A content distribution system allowing user authentication to be performed to identify a user in content transaction, thereby permitting the content to be used. The content is distributed with a secure container. The secure container includes the content enciphered with a content key and container information in which the content transaction condition is set. The container information includes an identification certificate identifier list. An identification certificate contains a template serving as personal identification data of a user who is to receive the content and it is identified in accordance with the list. A service provider, a user device, or the like authenticates the user in accordance with the identified certificate, and then permits the content to be used.
Owner:SONY CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com