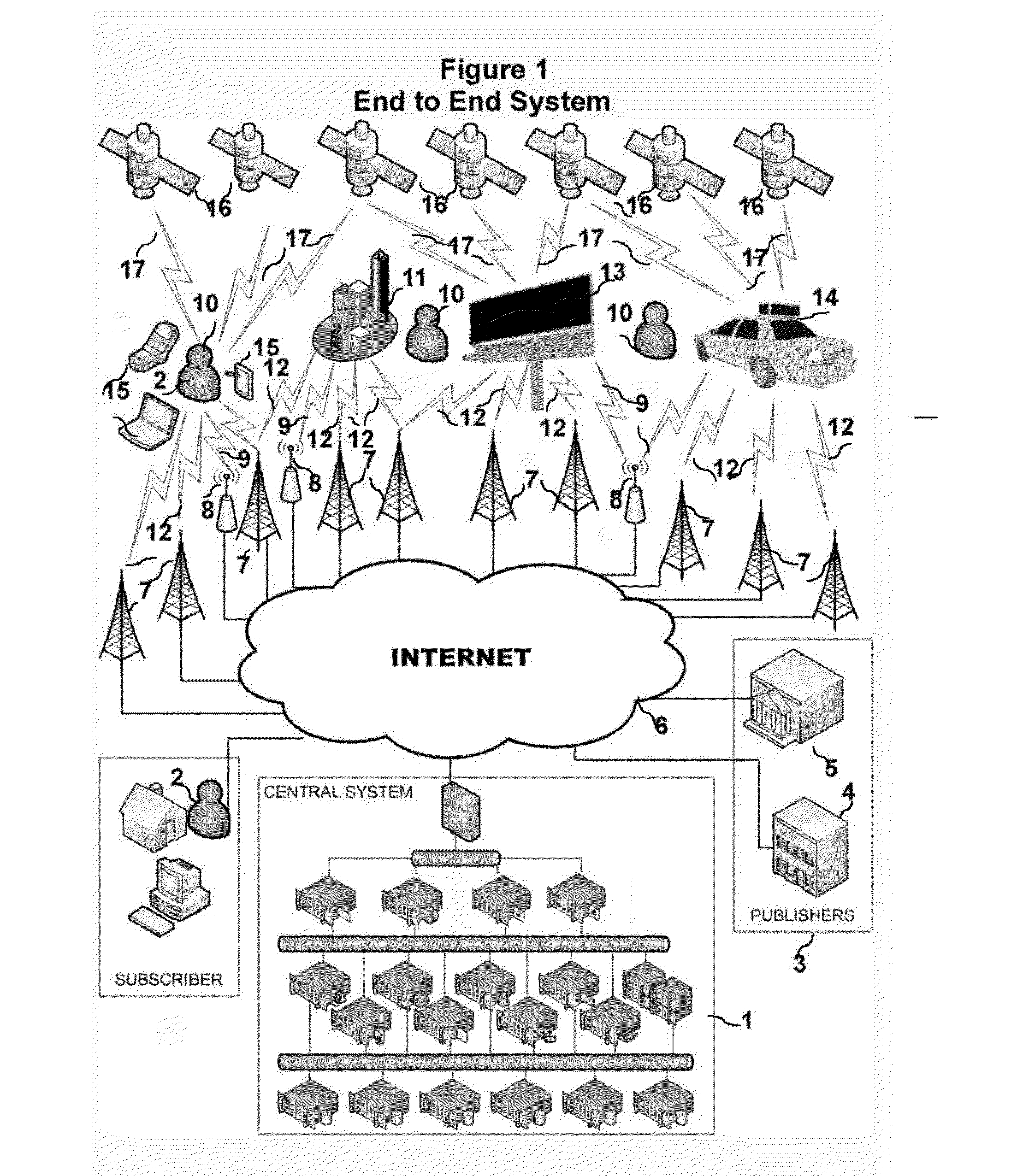
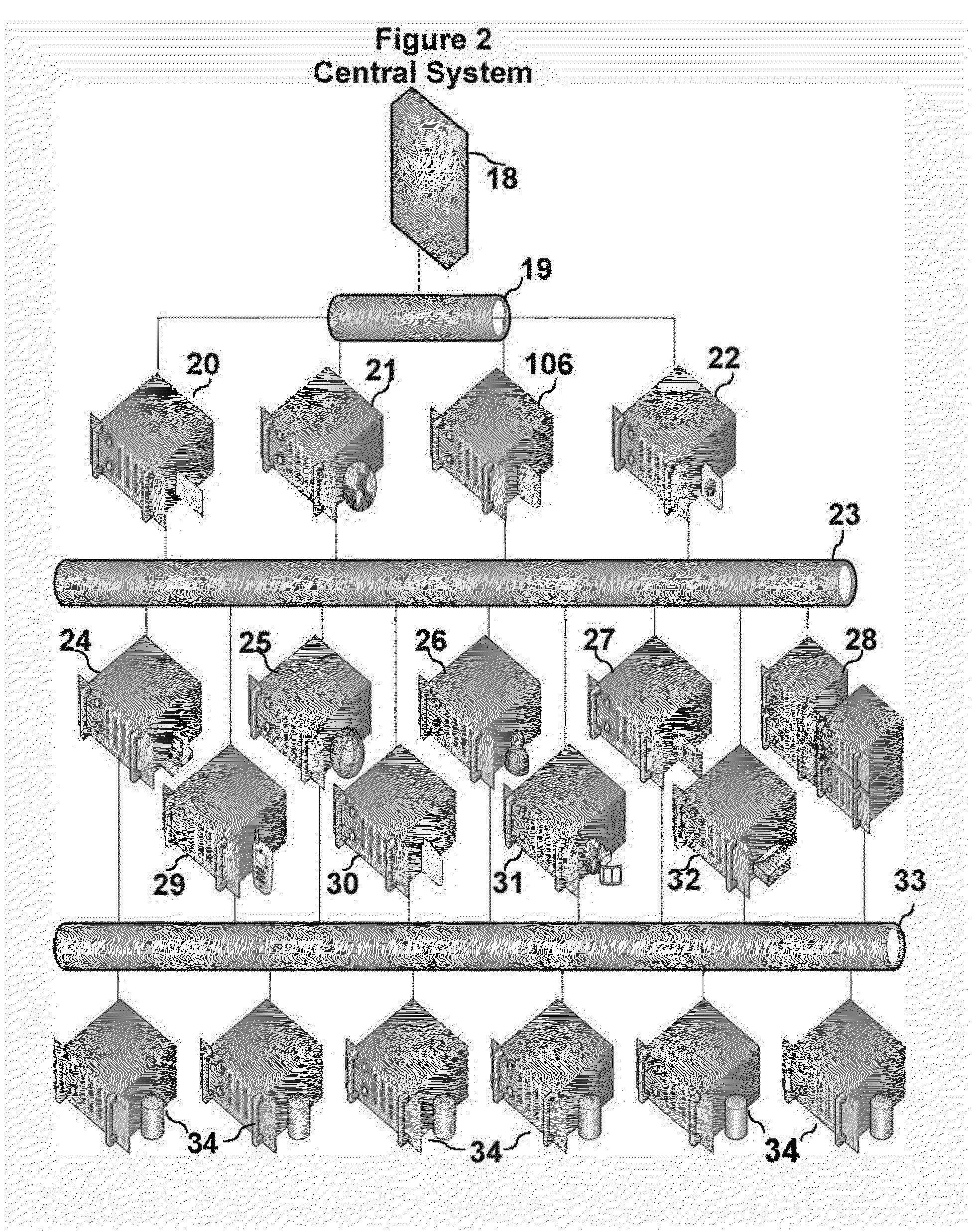
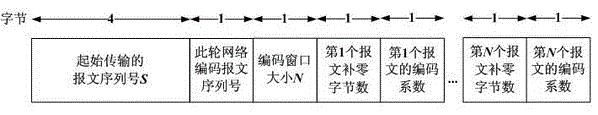
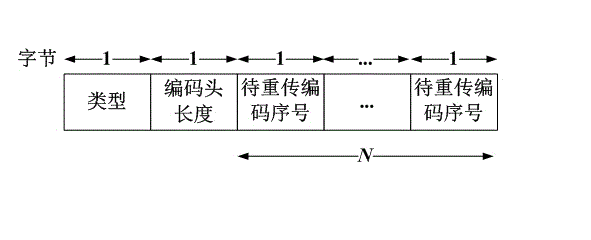
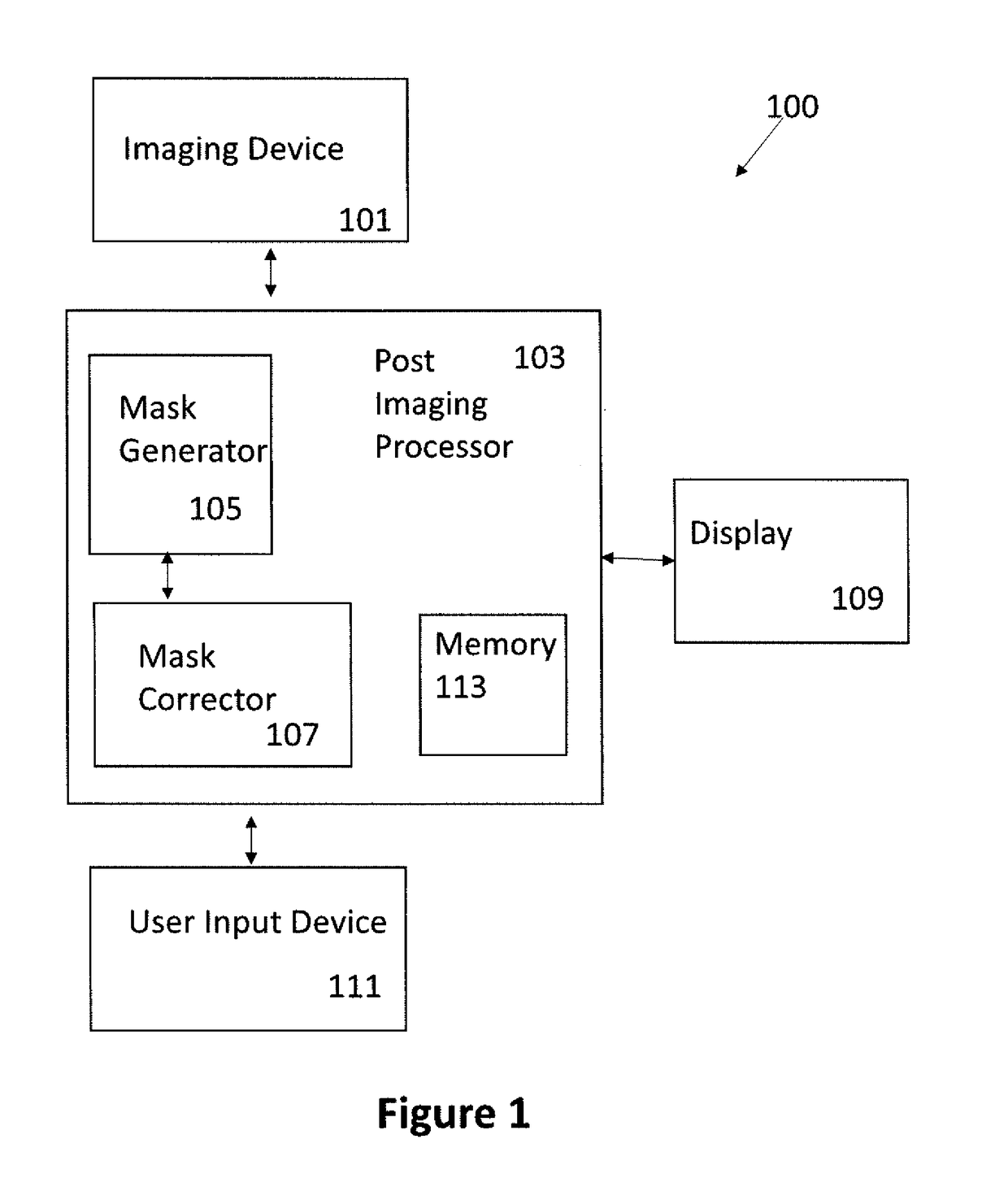
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
51 results about "End to end system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
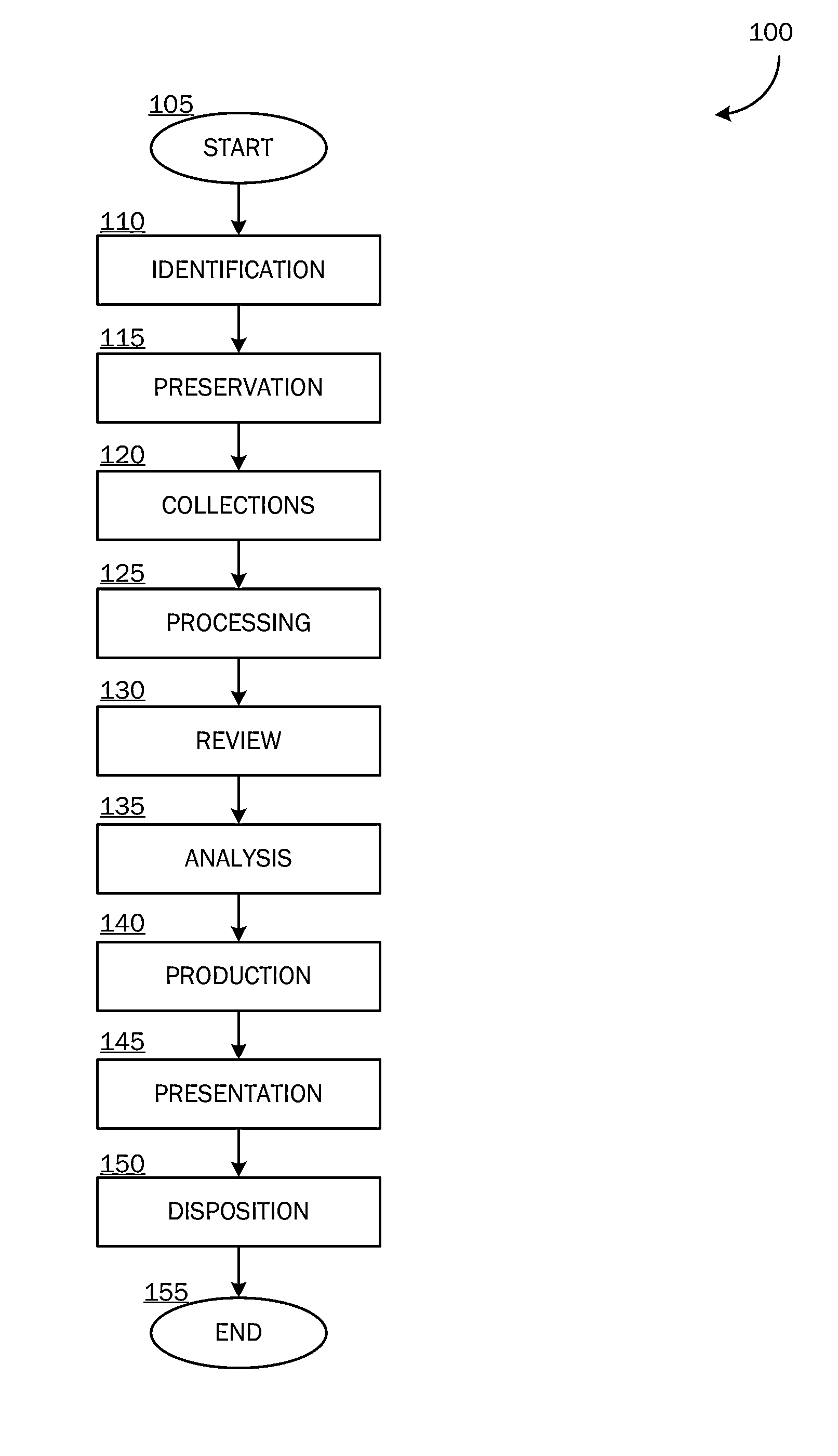
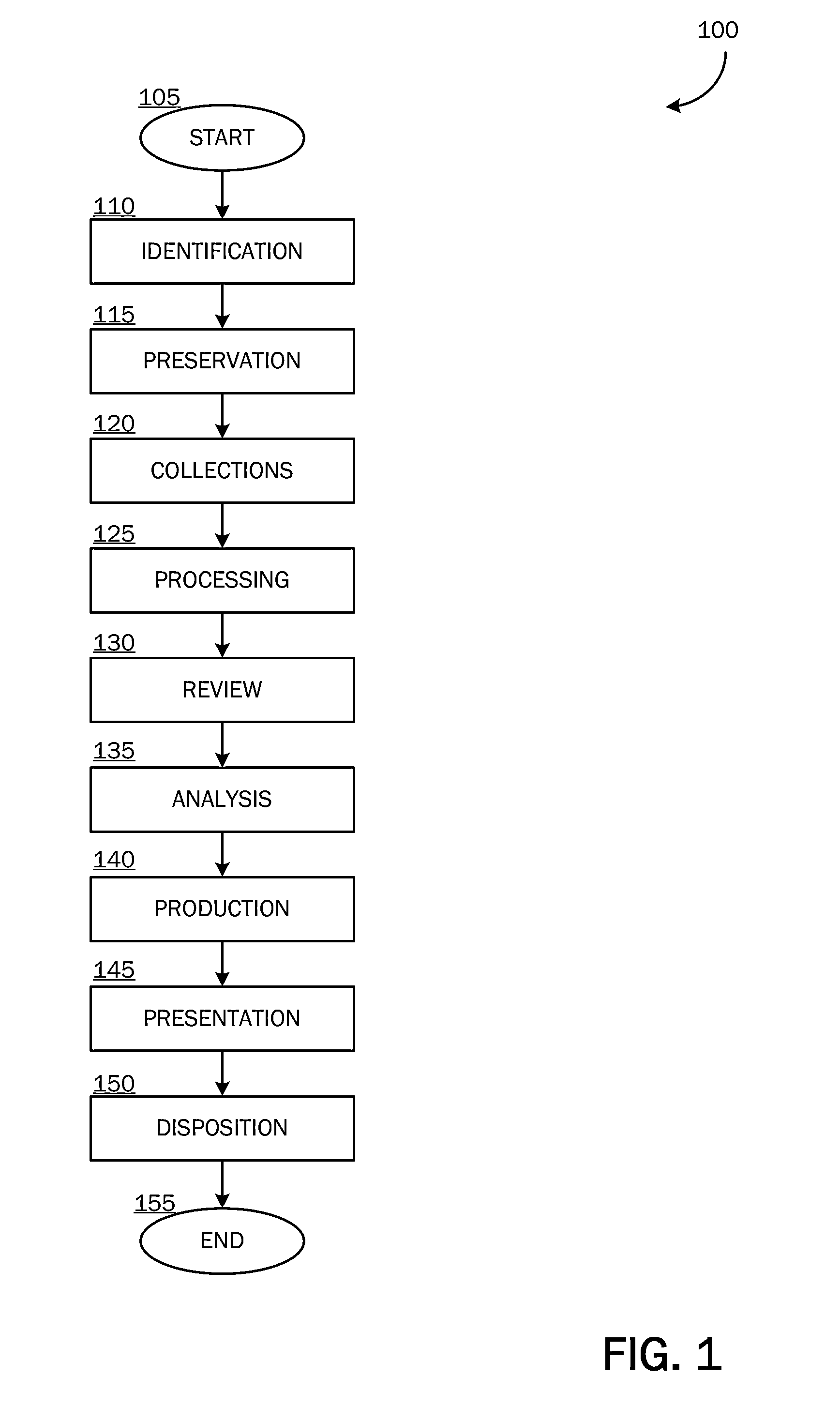
End-to-end testing is a methodology used to test whether the flow of an application is performing as designed from start to finish. The purpose of carrying out end-to-end tests is to identify system dependencies and to ensure that the right information is passed between various system components and systems.
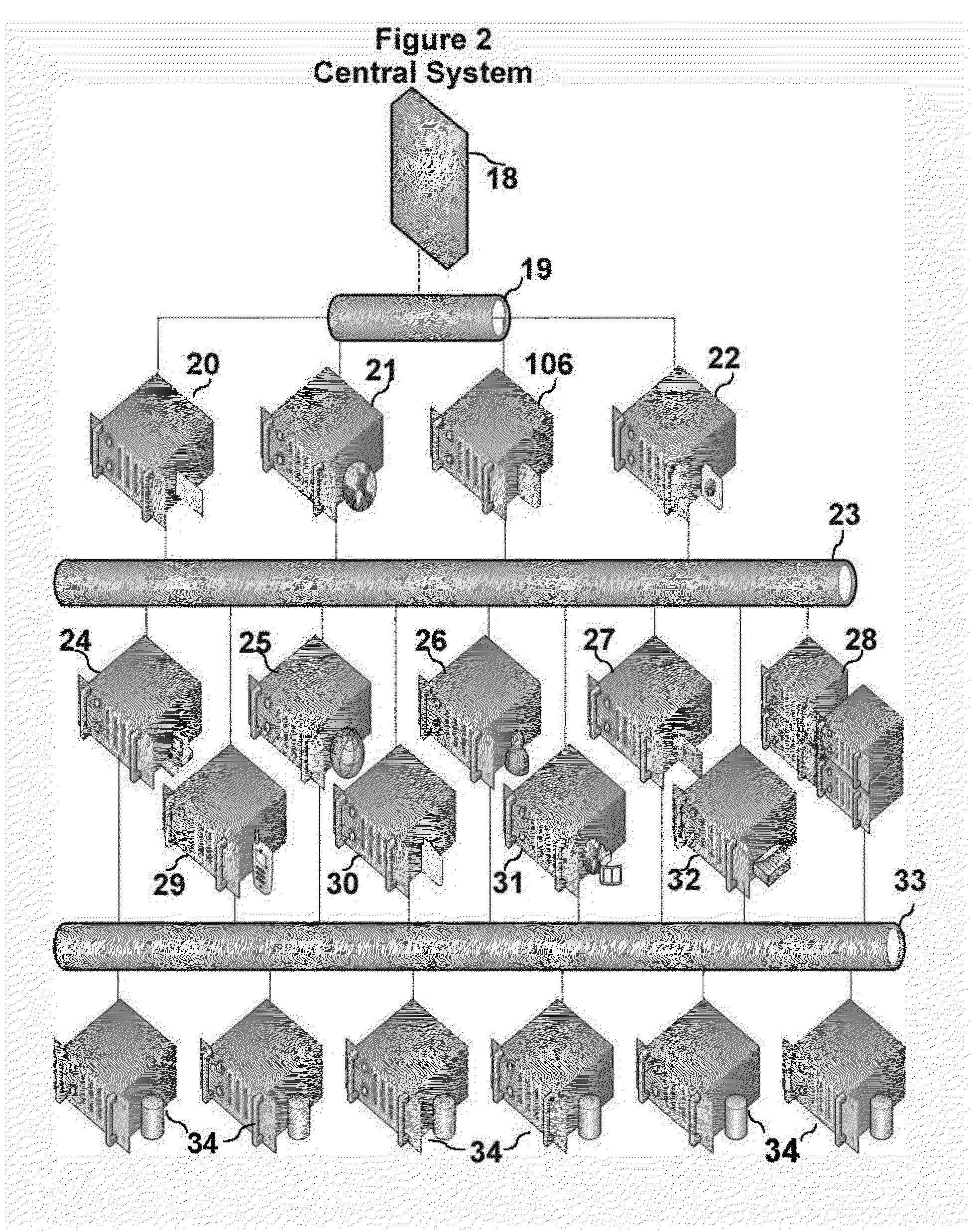
System and method for cloud based delivery and display of content on mobile devices
InactiveUS20130067035A1Multiple digital computer combinationsMobile application execution environmentsMobile appsCloud base
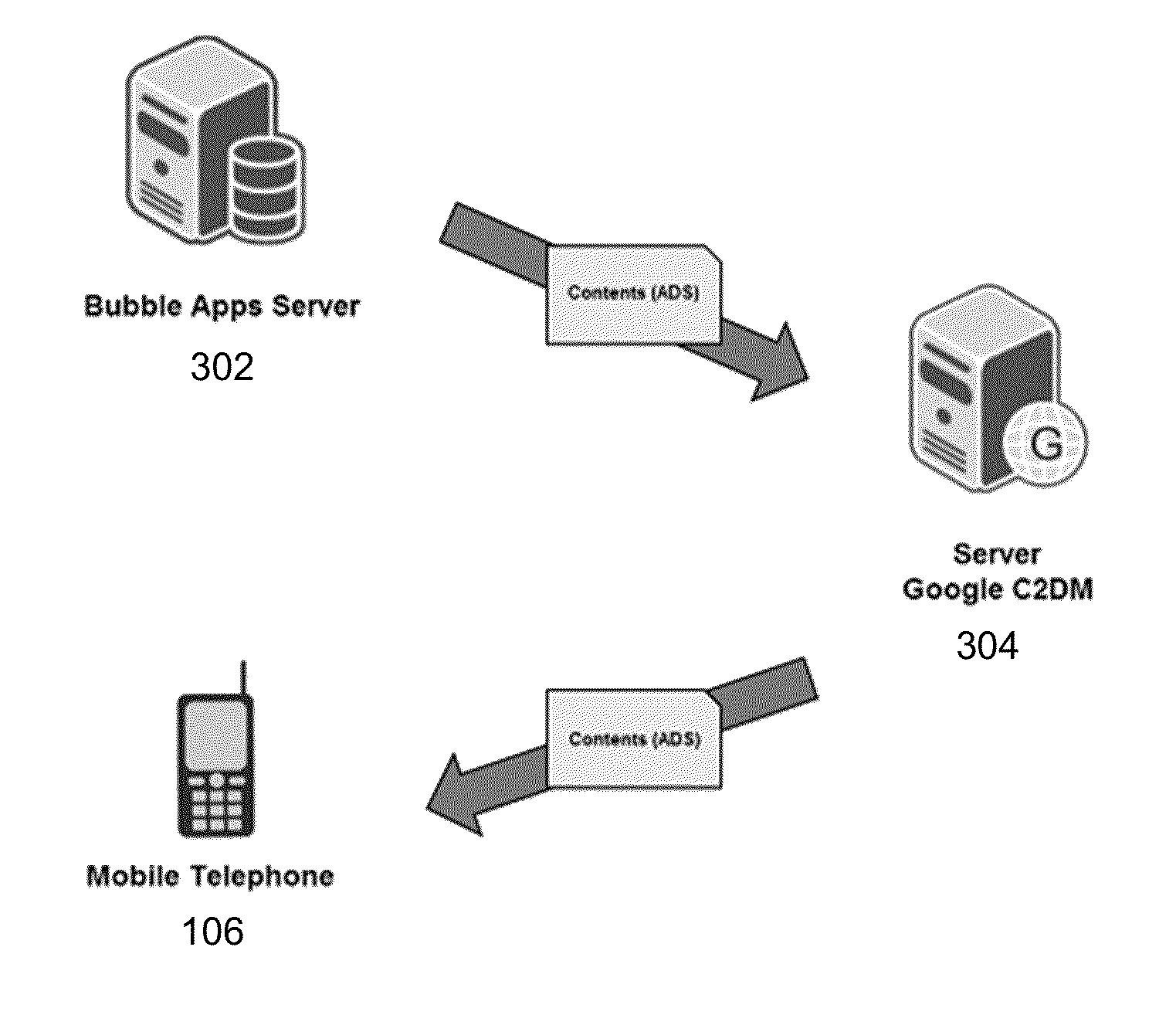
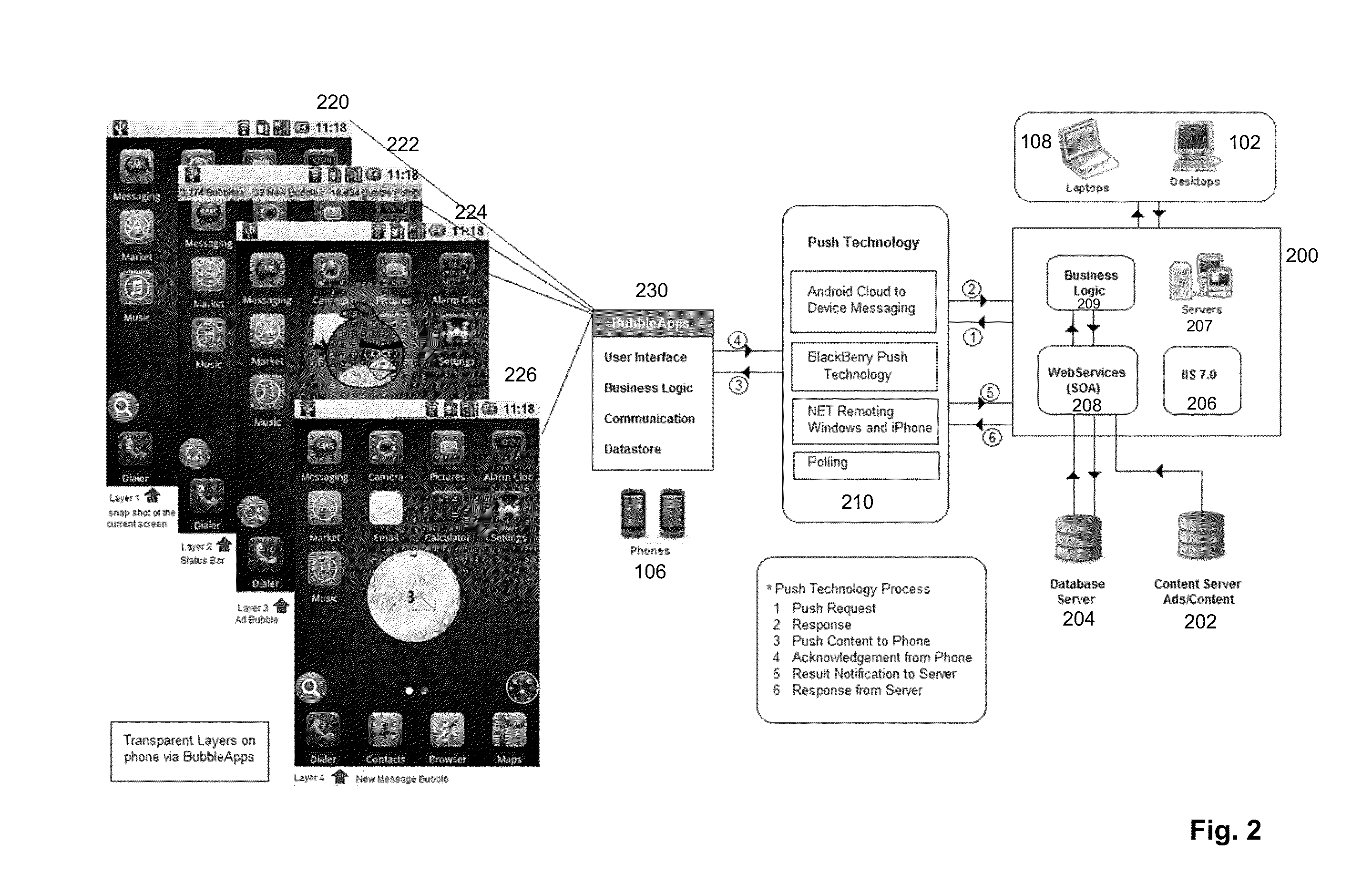
An end to end system and method for cloud based delivery of content and floating display of the content on a mobile device is presented. The system and method presented are suitable to delivery of any type of mobile content but are particularly adapted for delivery and distribution of mobile advertising, coupons and other promotional material. The mobile device is arranged to receive content from a content server via the cloud and display the content in a real time, non-intrusive floating bubble over the mobile devices currently active screen layer on the devices graphical display. The floating bubbles are simulated through the acquisition of a screen shot of a currently active mobile app, overlaying a bubble over the screen shot, and then presenting the composite image in a series of frames to simulate motion of the bubble ad over the previously top layer screen. As the bubble is presented on the screen, the mobile device reacts to the user's touch such that if the user touches a floating bubble a variety of choices may be presented, including full screen display of the bubble advertisement or content, sharing the content with friends through social networking or email, or calling or contacting the advertiser. If the user touches elsewhere the mobile device reverts to the previously active app. The system is further arranged to provide that the delivered content be targeted to users through a variety of features including user selection of content they wish to receive, user location, time of day, weather, past interest history and / or a combination of those criteria.
Owner:BUBBLE ADS
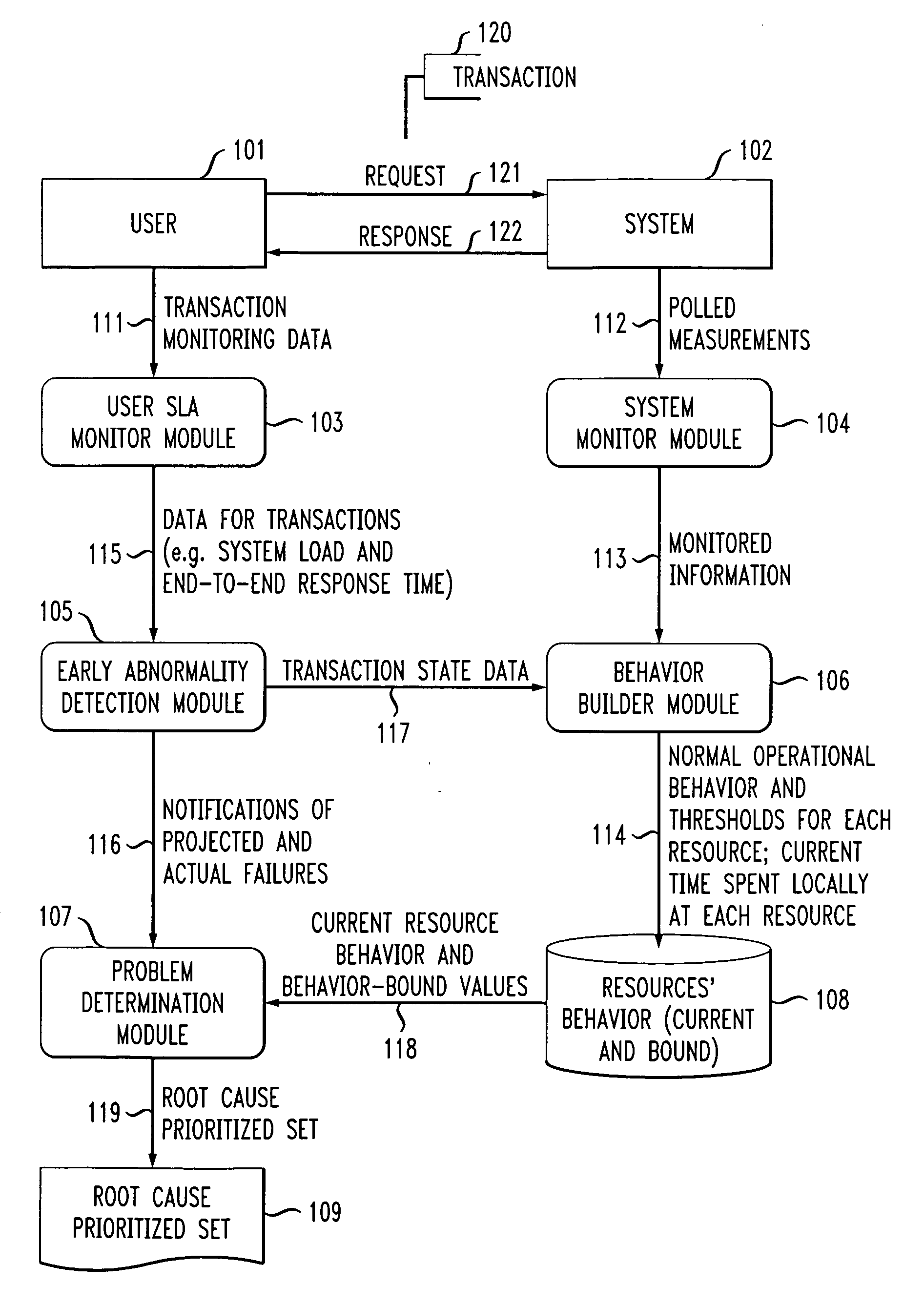
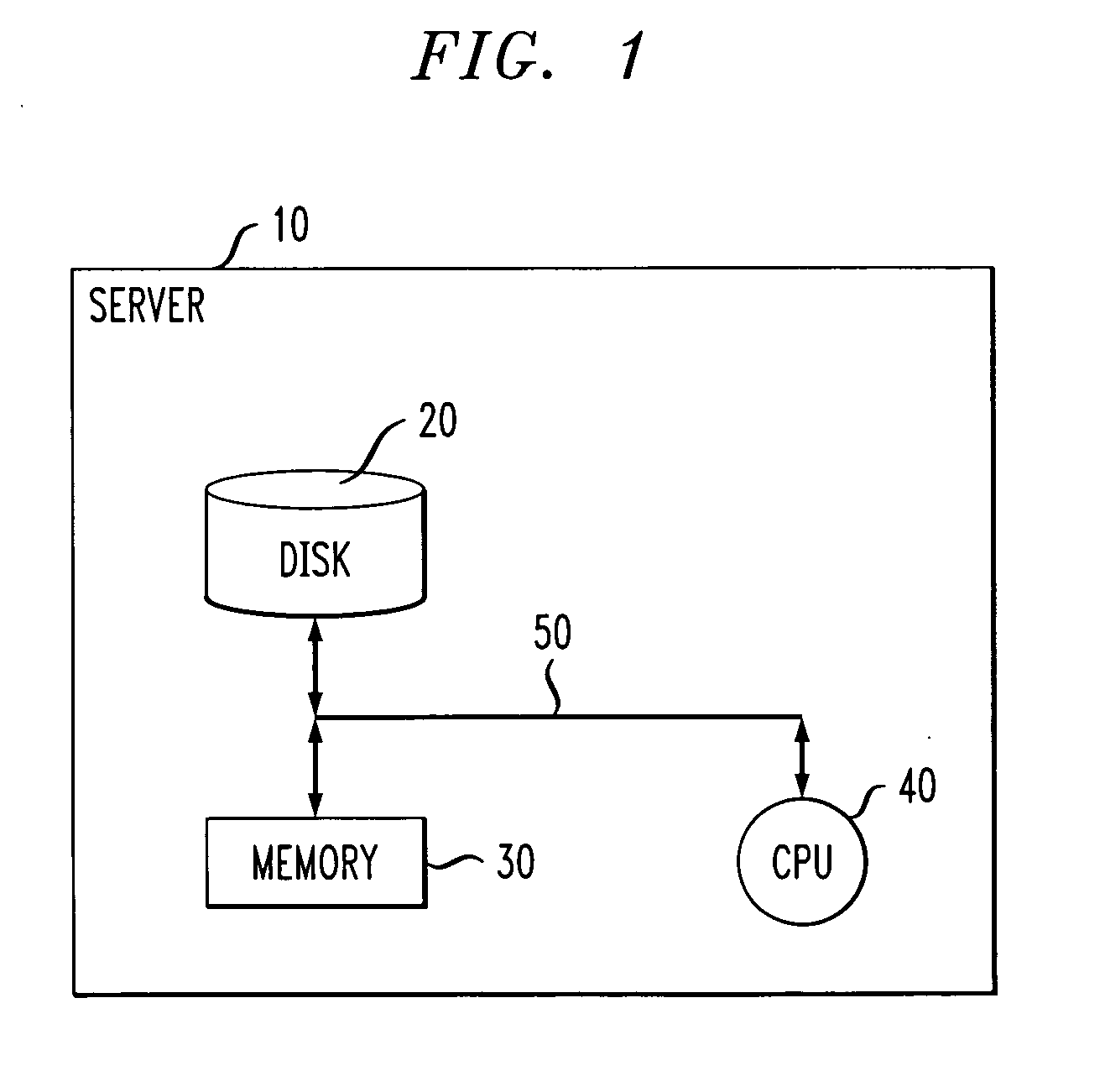
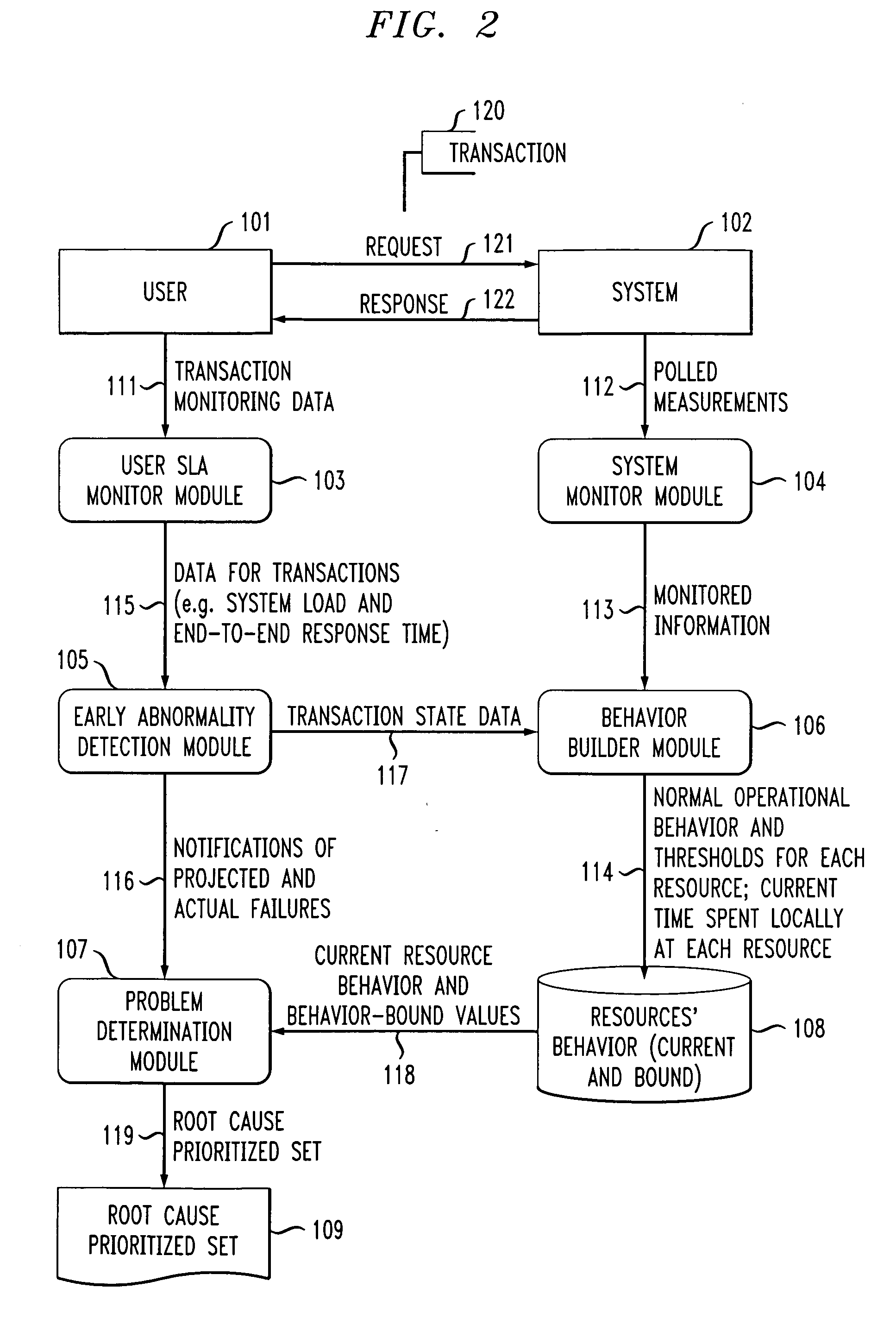
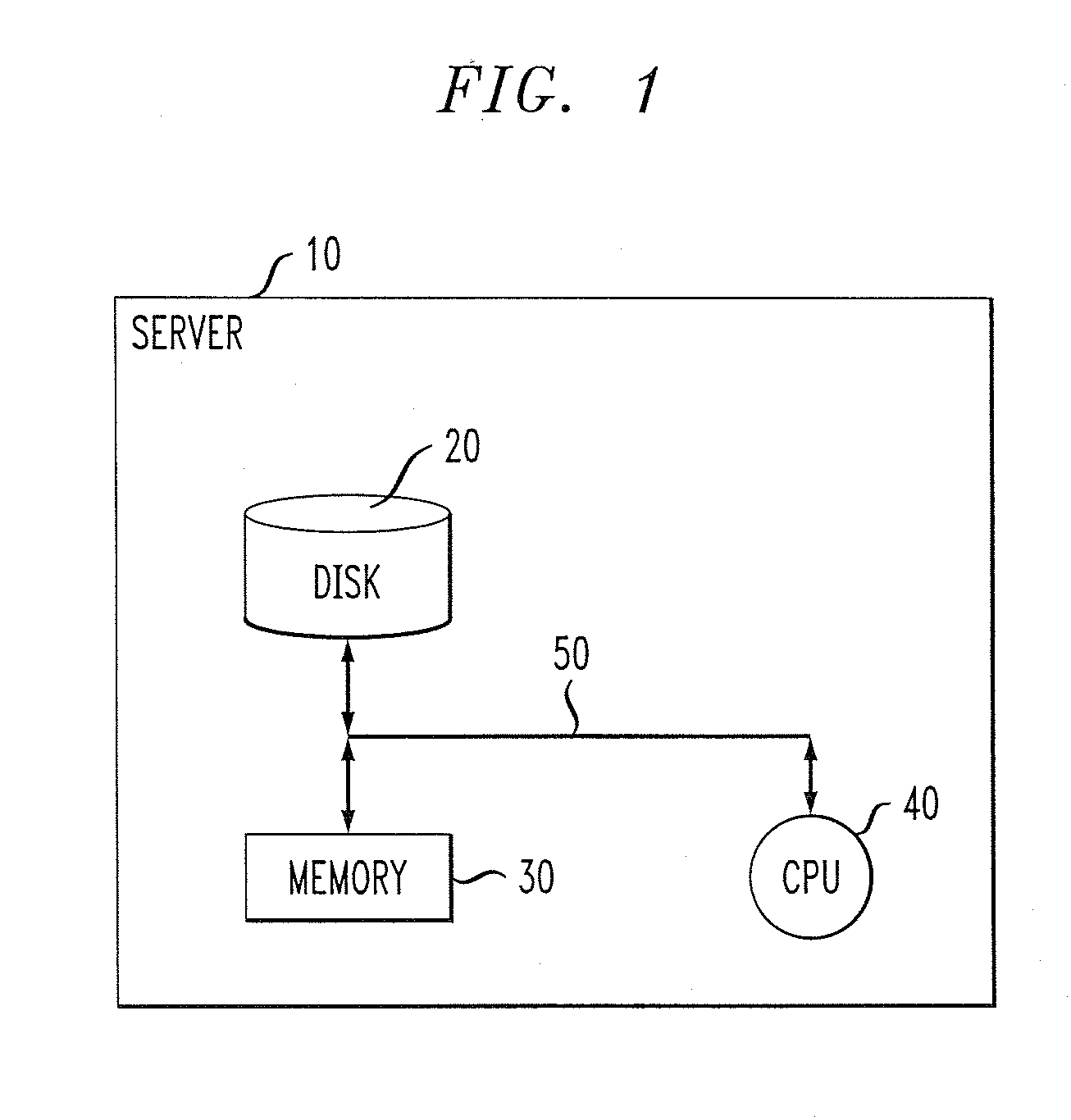
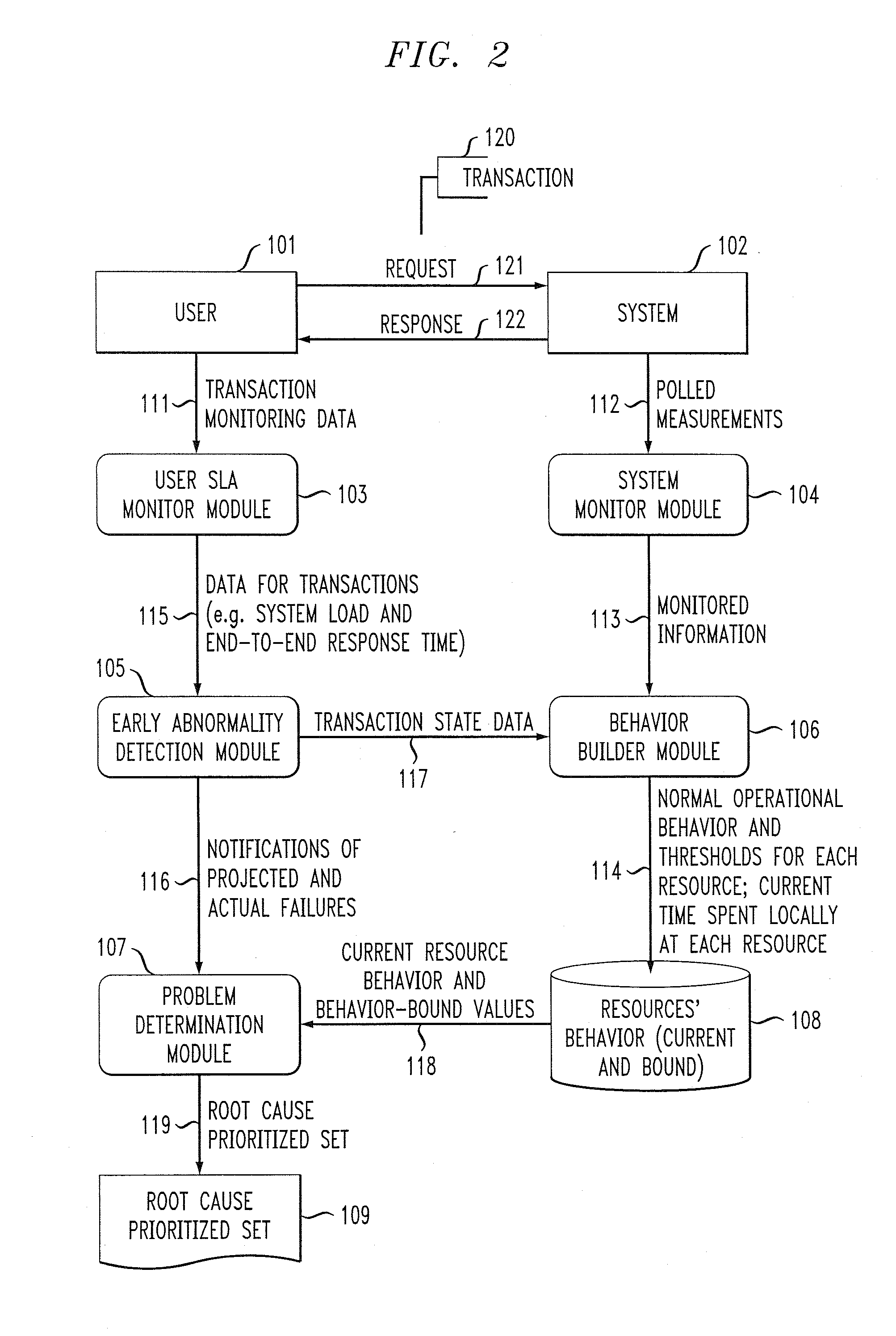
Performance degradation root cause prediction in a distributed computing system
InactiveUS20070271219A1Efficient and effective root cause predictionAvoid inaccuraciesMultiprogramming arrangementsReliability/availability analysisEnd systemEnd to end system
A method of identifying at least one resource in a distributed computing system which is a potential root cause of performance degradation of the system includes the steps of: computing operational bounds for the system and operational bounds for at least one resource in the system; comparing current end-to-end system performance with the operational bounds for the system; when the current end-to-end system performance is outside of the operational bounds for the system, comparing current performance of the at least one resource in the system with the operational bounds for the at least one resource; and generating at least one output identifying the at least one resource in the system which is a potential root cause of performance degradation of the system.
Owner:IBM CORP
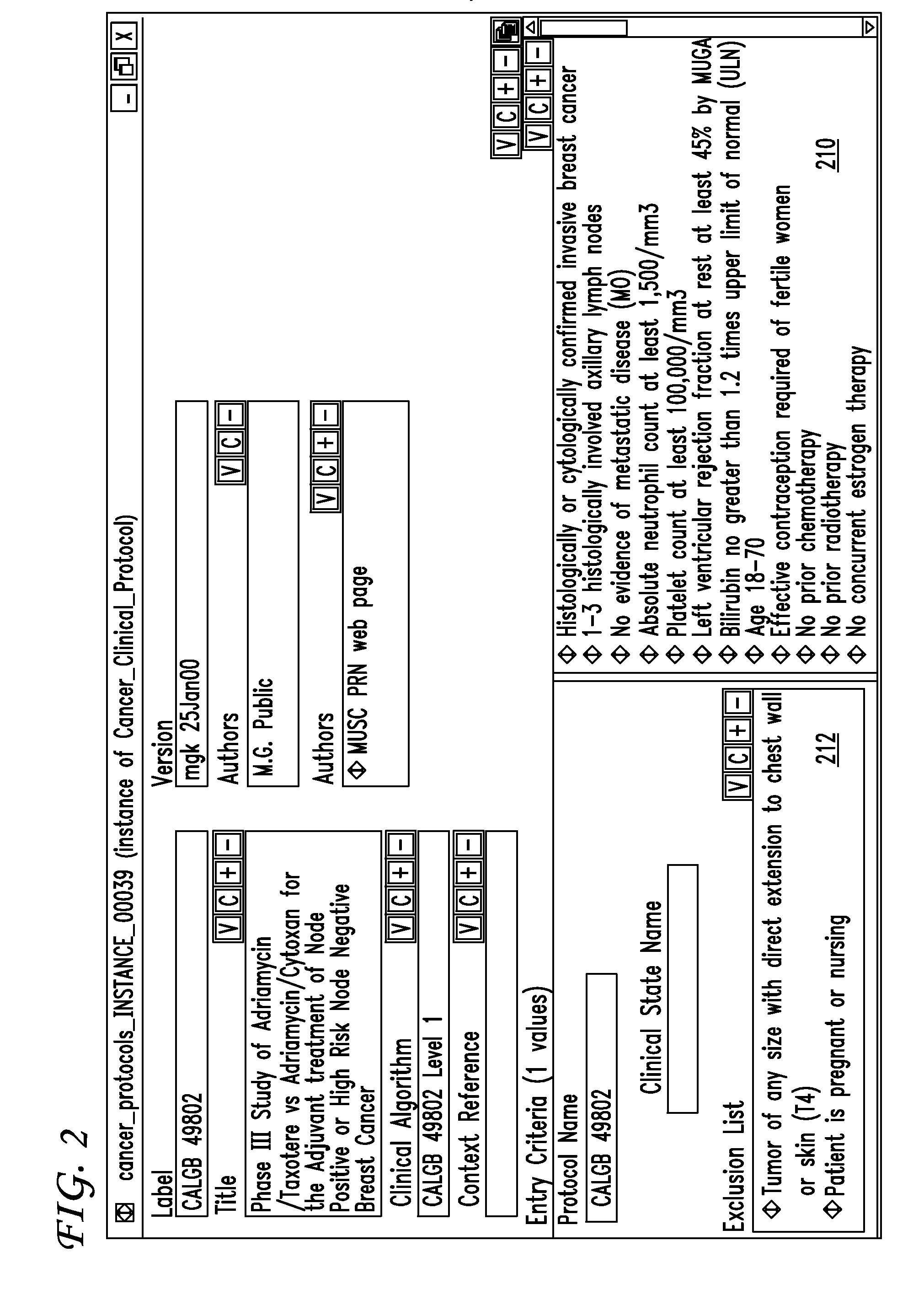
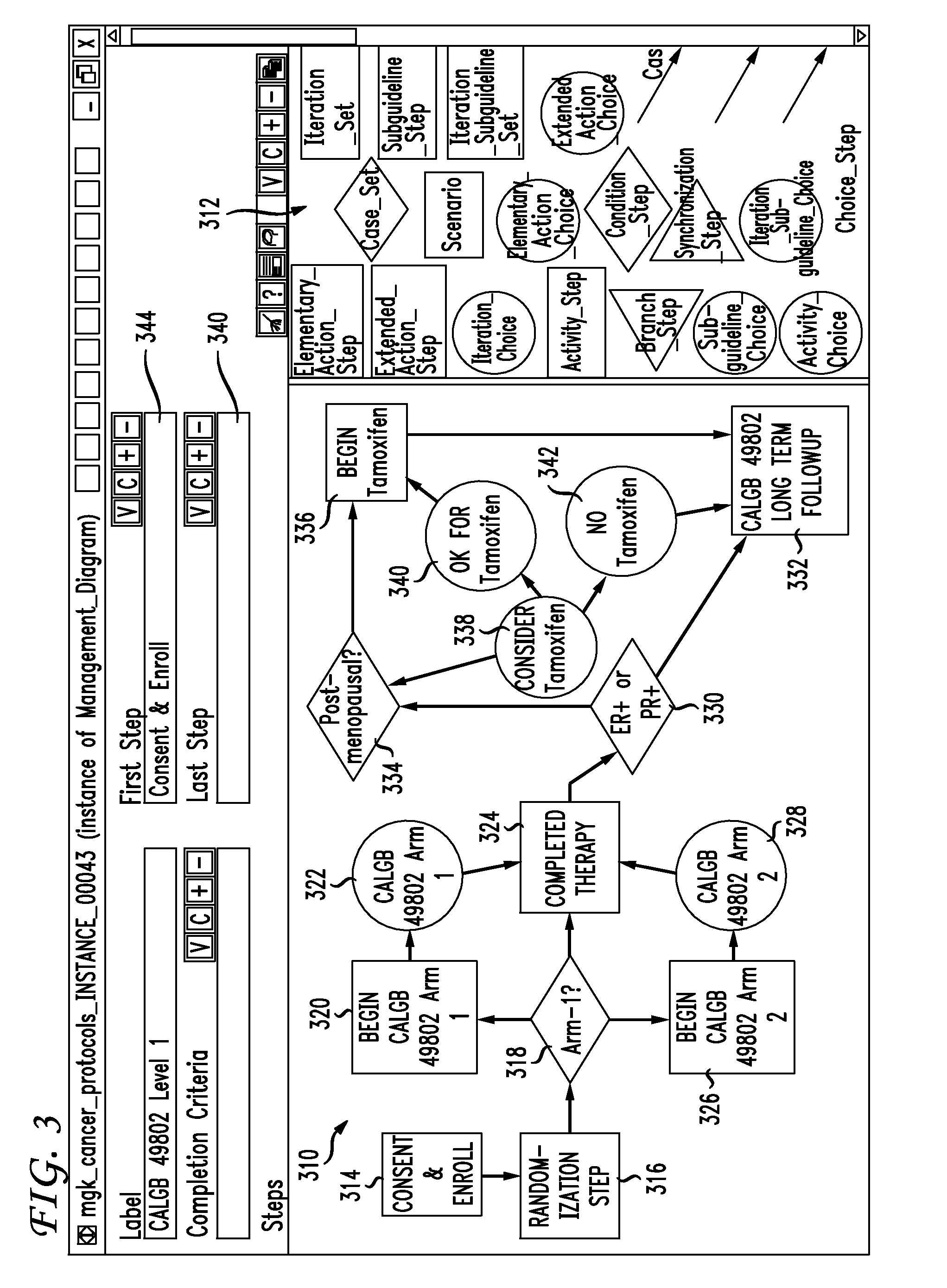
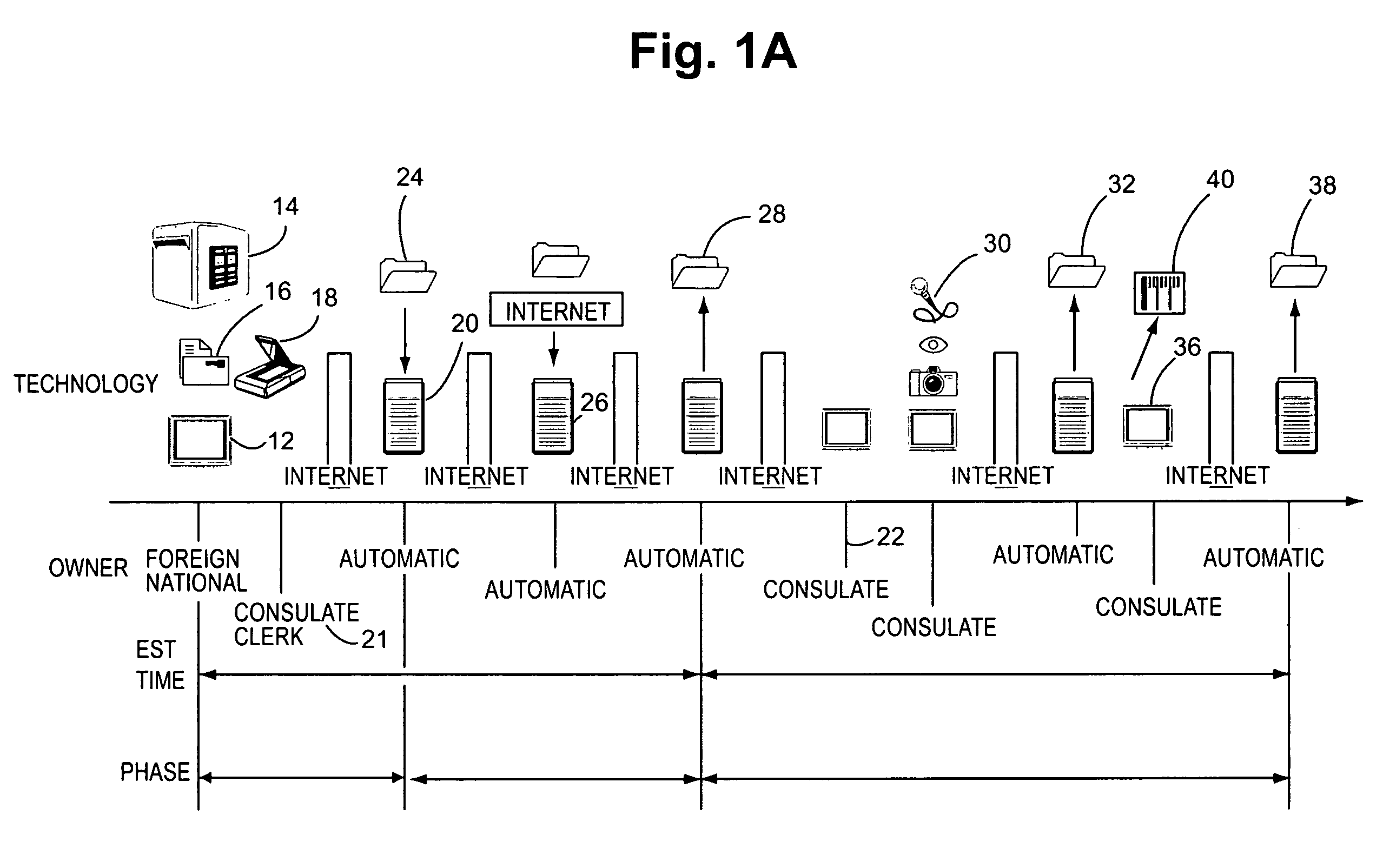
Clinical trials management system and method
InactiveUS20090313048A1Digital data processing detailsDrug and medicationsPatient managementEnd to end system
Clinical trials are defined, managed and evaluated according to an overall end-to-end system. The central authority creates protocol meta-models and makes them available to clinical trial protocol designers. Each meta-model includes a short list of preliminary patient eligibility attributes which are appropriate for a particular disease category. The protocol designer chooses the appropriate meta-model, and encodes the clinical trial protocol, including eligibility and patient workflow, within the selected meta-model. The resulting protocol database is stored together with databases of other protocols in a library of protocol databases. Sponsors and individual clinical sites have controlled access to the protocols. Study sites make reference to the pertinent protocol databases to which they have access in the protocol database library in order to perform patient eligibility screening. Once a patient is enrolled into a study, the protocol database indicates to the clinician what tasks are to be performed at each patient visit. These tasks can include both patient management tasks and data management tasks. The workflow graph advantageously also instructs the proper time for the clinician to obtain a patient's informed consent. The system reports patient progress to study sponsors, who can then monitor the progress of the trial, and to a central authority which can then generate performance metrics. Advantageously, a common controlled medical terminology database is used by all components of the system.
Owner:MEDIDATA SOLUTIONS
Systems and methods for producing biochar-based products
An end-to-end system / process for producing advantageous end products from a raw biomass feedstock is provided. The process includes steps for enhancing biomaterial feedstock, biochar generation and end-product fabrication. The method steps may be employed in selecting, treating and handling biomass materials and their additive inputs to tailor their end performance. Each operative step in the process may be employed to enhance the overall effectiveness of biochar generation and use. Charring furnace design and operational parameters are provided that generate desirable biochar material for various applications, including specifically fabrication of ultra-capacitor electrodes and electric battery components.
Owner:CARBONCHARGE TECH LLC
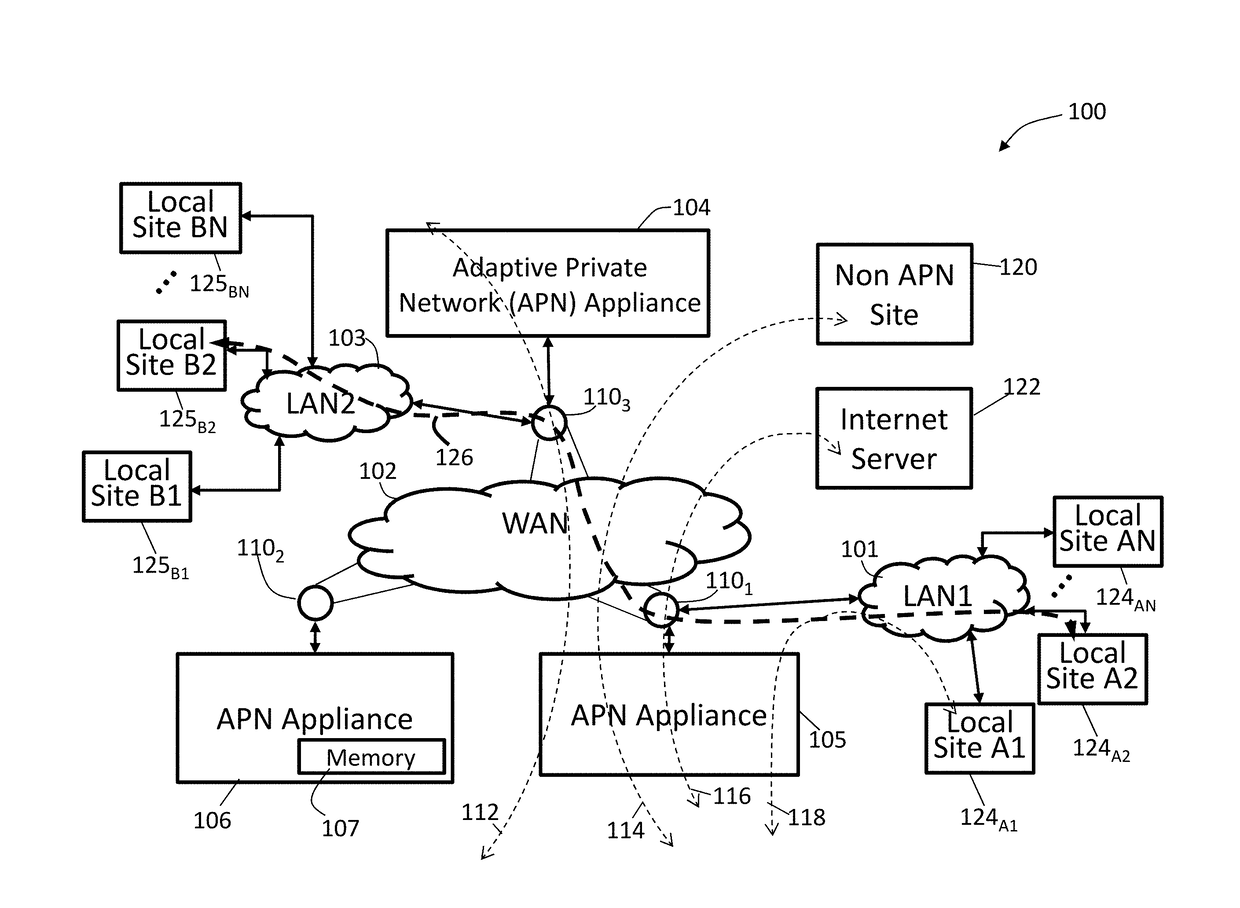
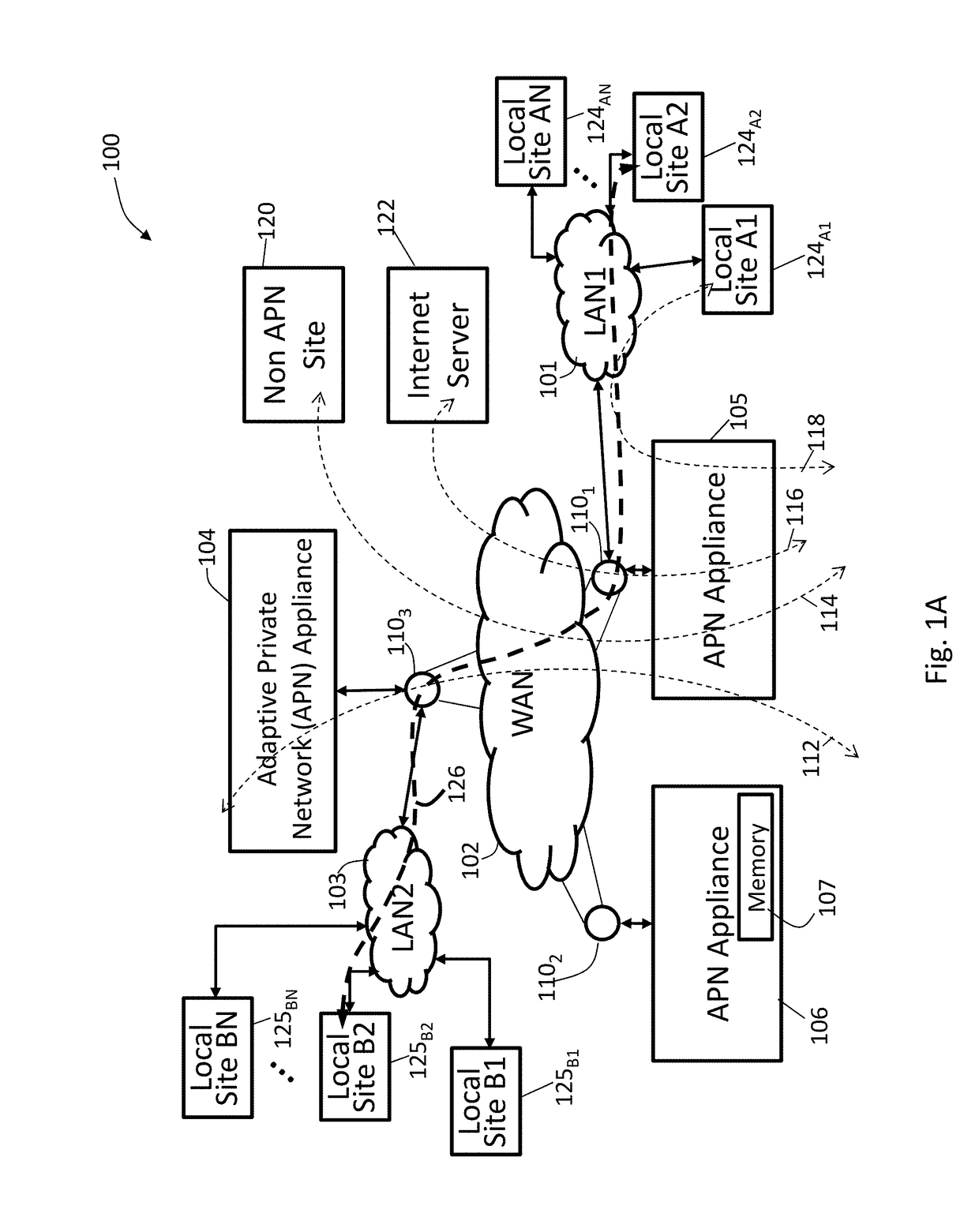
Methods and apparatus for accessing dynamic routing information from networks coupled to a wide area network (WAN) to determine optimized end-to-end routing paths
ActiveUS20170207963A1Accurate and cost techniqueReduce outage timeSubstation equipmentData switching networksRouting tablePrivate network
Techniques are described which apply a method for including a routing stack to provide a timely way to dynamically learn about route changes for an end to end system in the context of an adaptive private network (APN). By allowing learned routes to be assigned different services based on filtering rules, the APN can efficiently manage traffic through the WAN. Techniques for learning routes and to advertise the learned routes in different networks are also described. Upon an APN route change being detected in the APN, a route table is updated with the APN route change, wherein the route table contains routes in a local area network (LAN) and routes in a wide area network (WAN). The APN route change is selected from the route table and configured to a protocol for the LAN. The selected APN route change is advertised in the protocol to local routers in the LAN.
Owner:TALARI NETWORKS
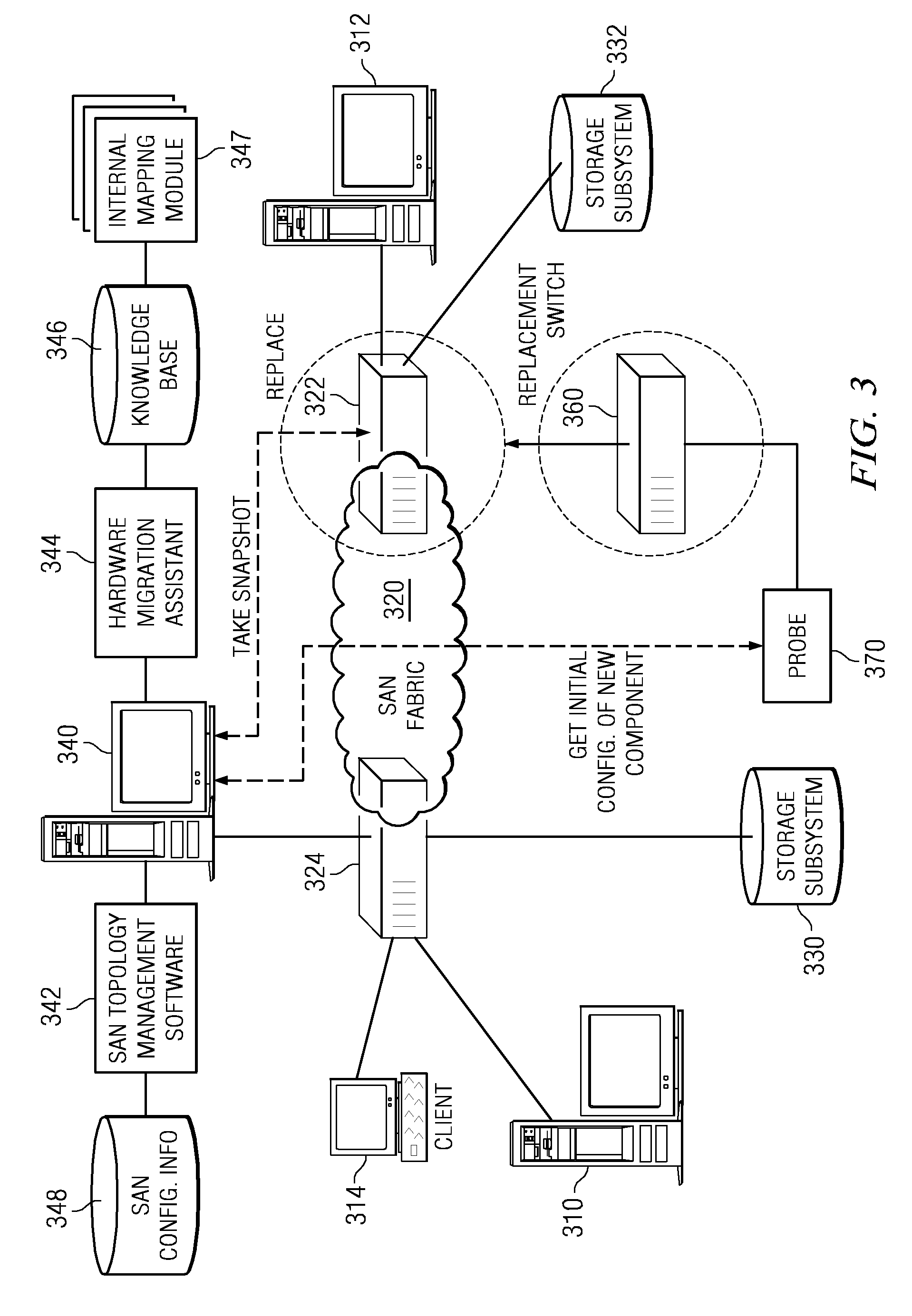
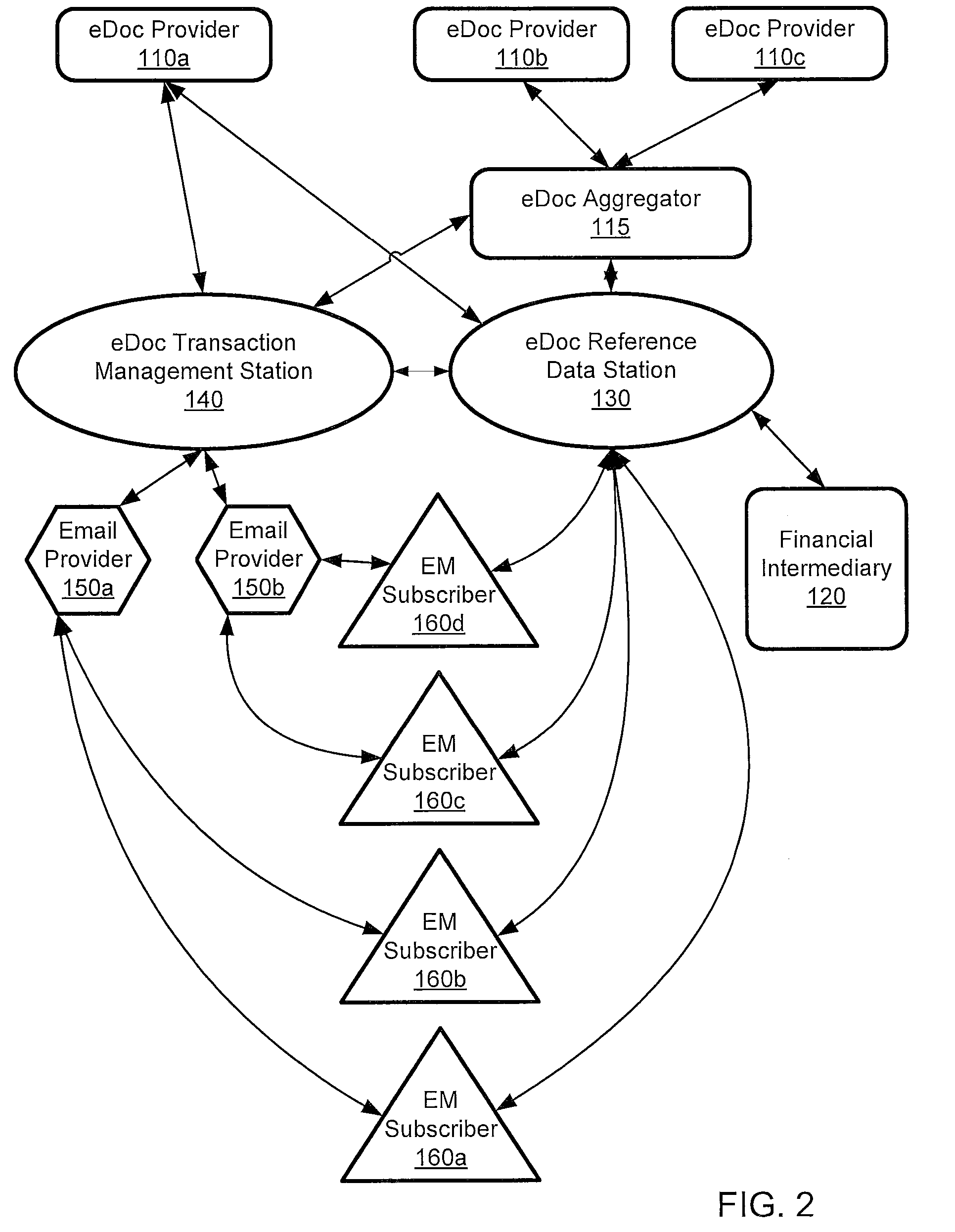
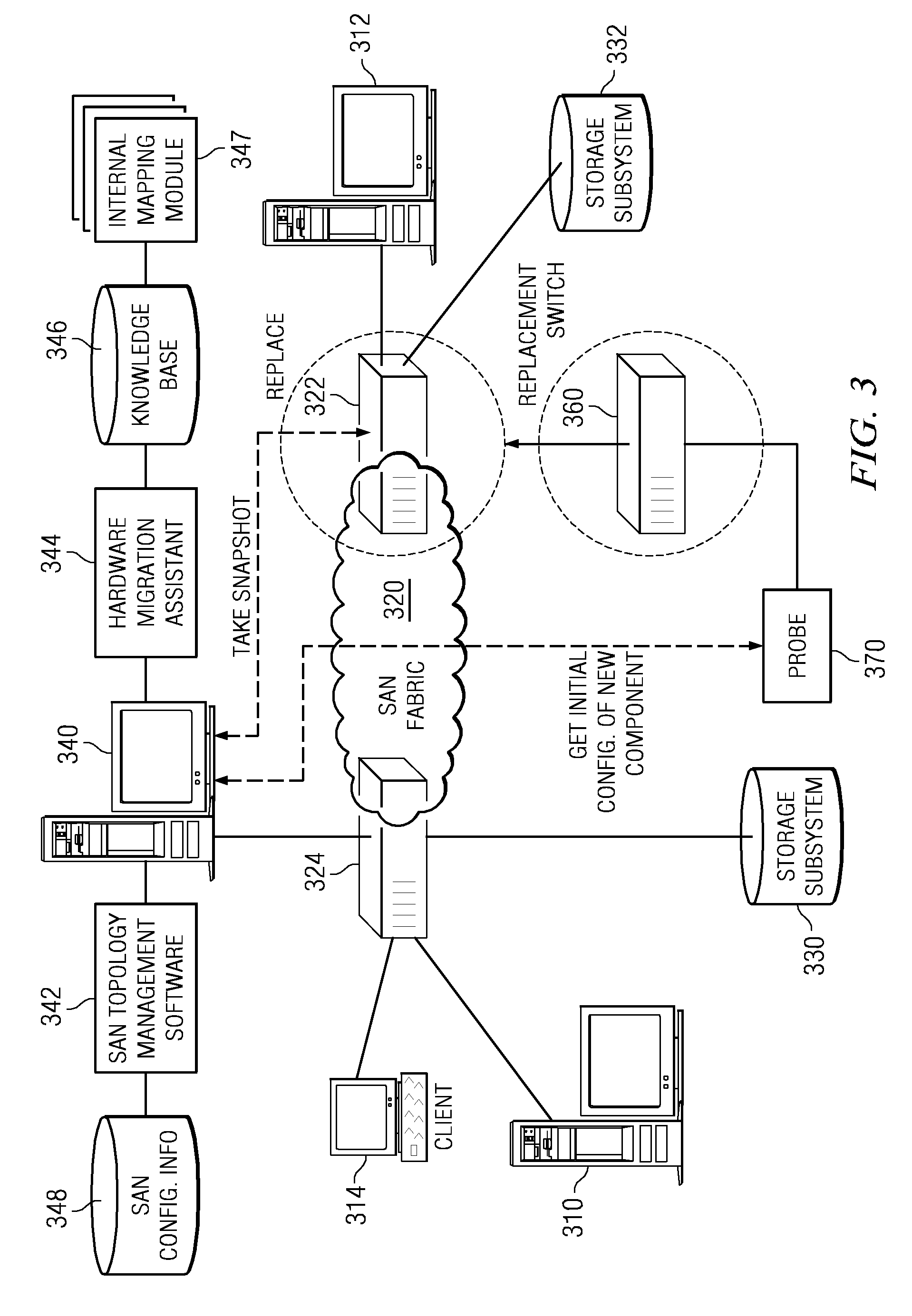
System and Method for Enabling Storage Area Network Component Migration
InactiveUS20090177878A1Simplify migration stepFew sourceDigital computer detailsData resettingComponent MigrationStorage area network
A system and method for enabling storage area network (SAN) component migration are provided. An end-to-end systems management console, referred to as the hardware migration assistant, is provided to simplify the migration steps for a SAN administrator to replace key SAN components. The hardware migration assistant provides a single interface suitable for stepping the SAN administrator through the reconfiguring task faster and with fewer sources of error than the known distributed manual process. The hardware migration assistant of the illustrative embodiments provides an interface through which a user may specify a type of SAN component that is being replaced and identifies the particular SAN components that are being replaced. The hardware migration assistant provides a knowledge base for guiding the user through the replacement operation and the reconfiguring of the SAN components, including the new SAN components, based on the previous configuration of the replaced components.
Owner:IBM CORP
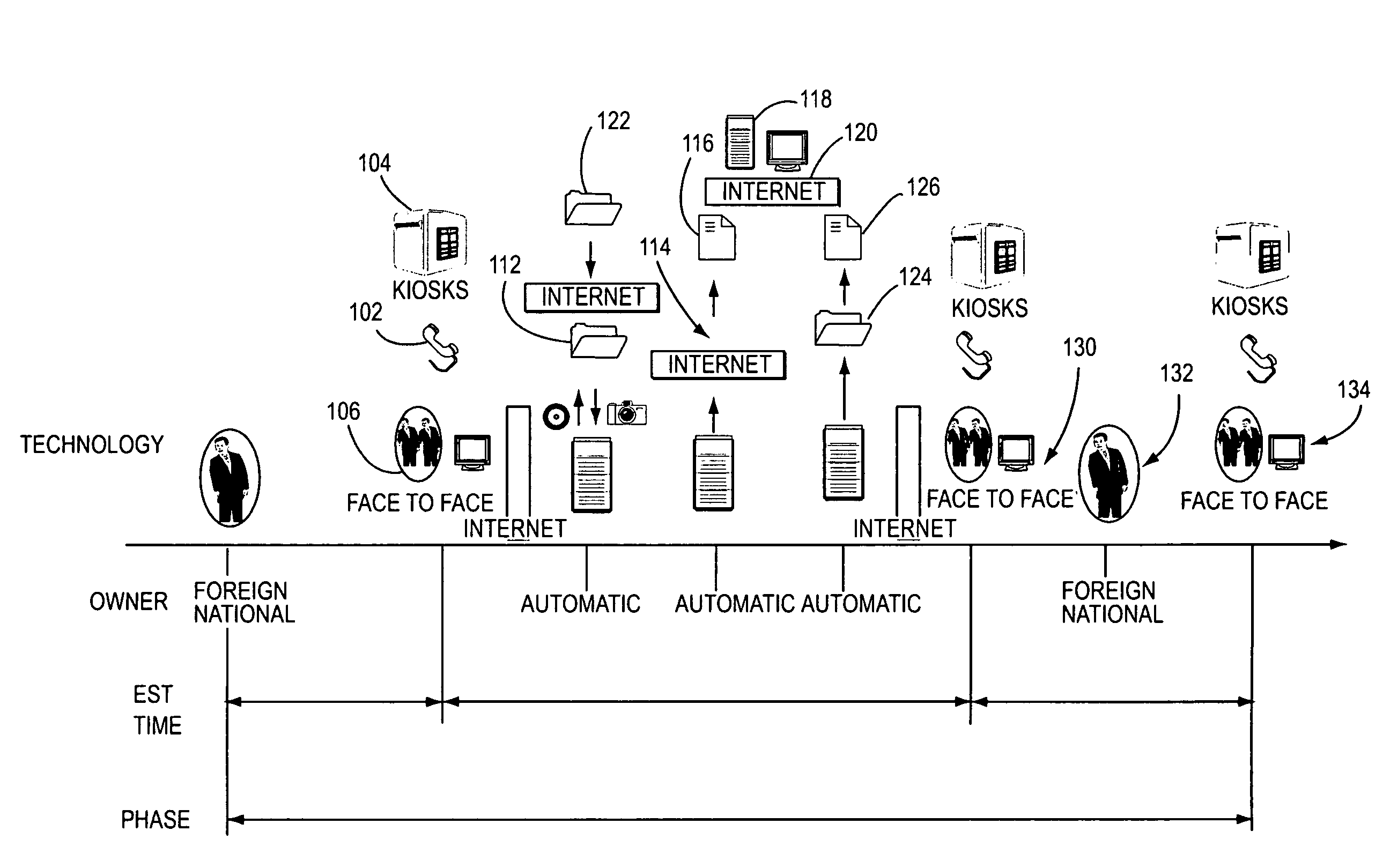
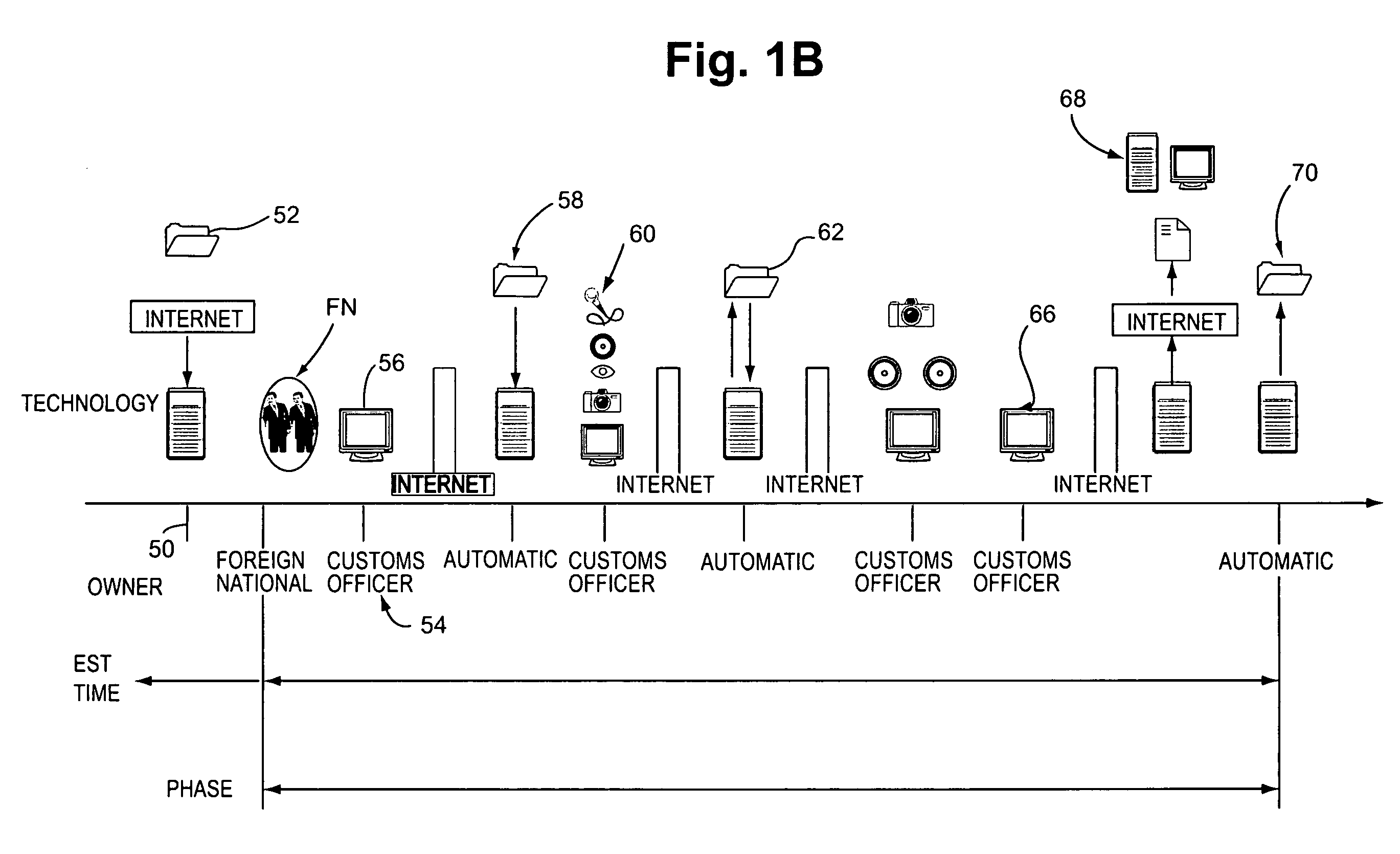
Intelligent controlled entry-exit system
InactiveUS7173532B2Electric signal transmission systemsMultiple keys/algorithms usageEnd to end systemM-government
The present invention is to an integrated end-to-end system and process composed of numerous application systems and subsystems (applicable in total or in subparts) which enables parties (such as businesses, buildings, prisons, governments, etc.) to acquire information (biometric and textual) regarding an applicant requesting entry, verify the acquired information—checking it against defined (e.g., government enforcement agencies) offender lists, and utilizing the acquired information at defined points in the process to track individuals. Further, the system preferably includes mandatory, scheduled check-ins to ensure compliance with the visitation requirements during the stay by the party in the sponsoring facility, country, business, etc.
Owner:XEGESIS
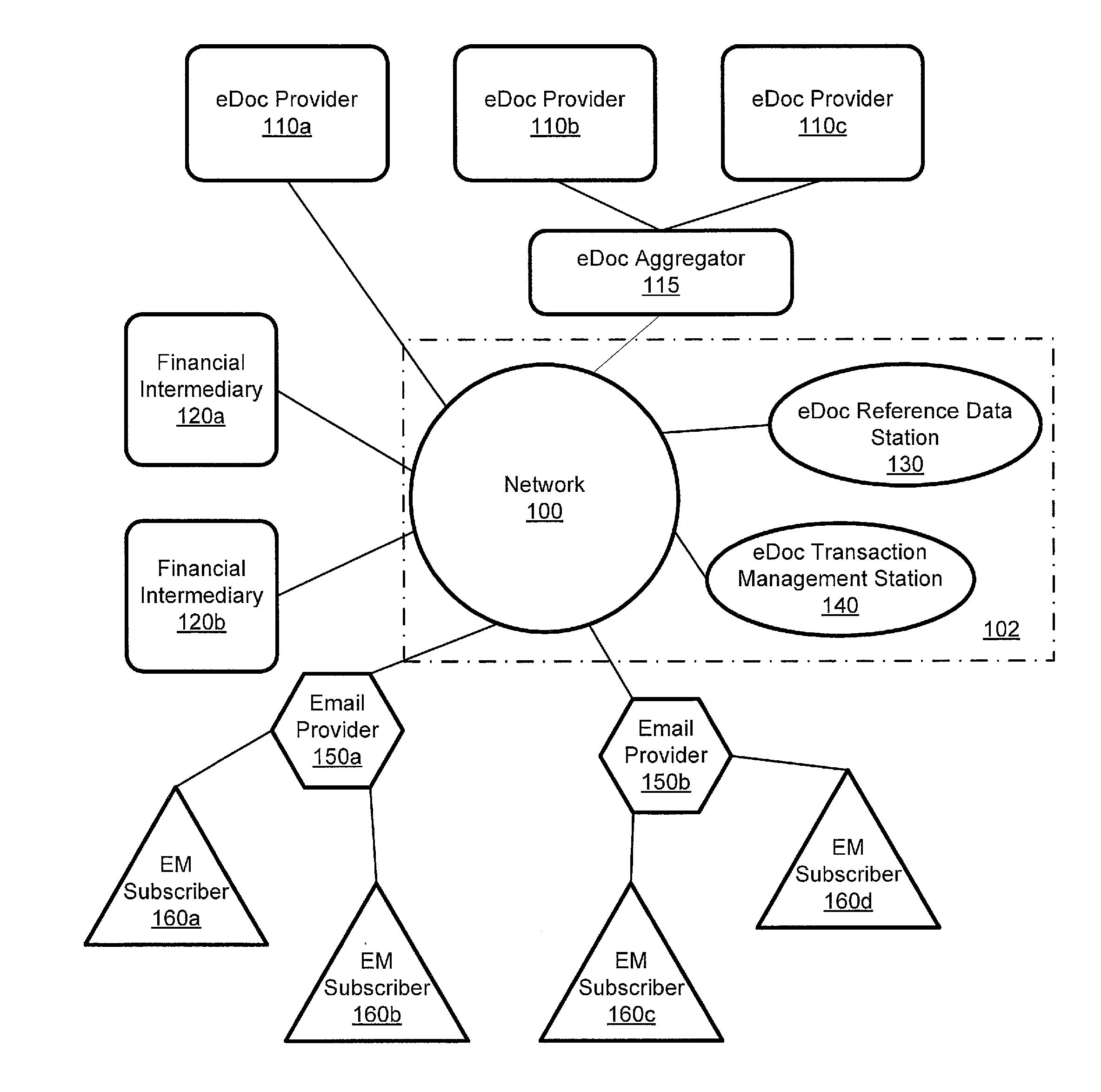
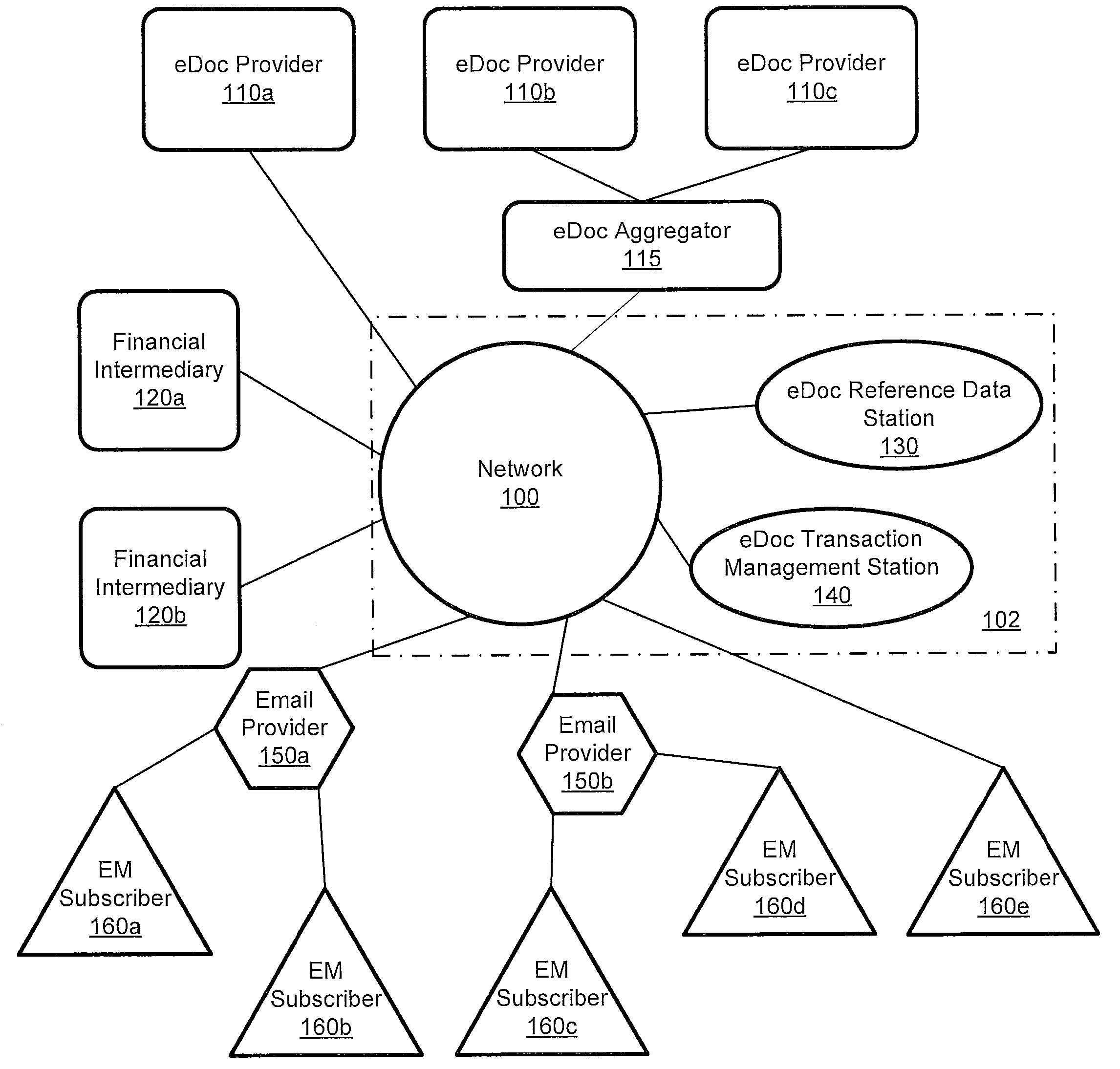
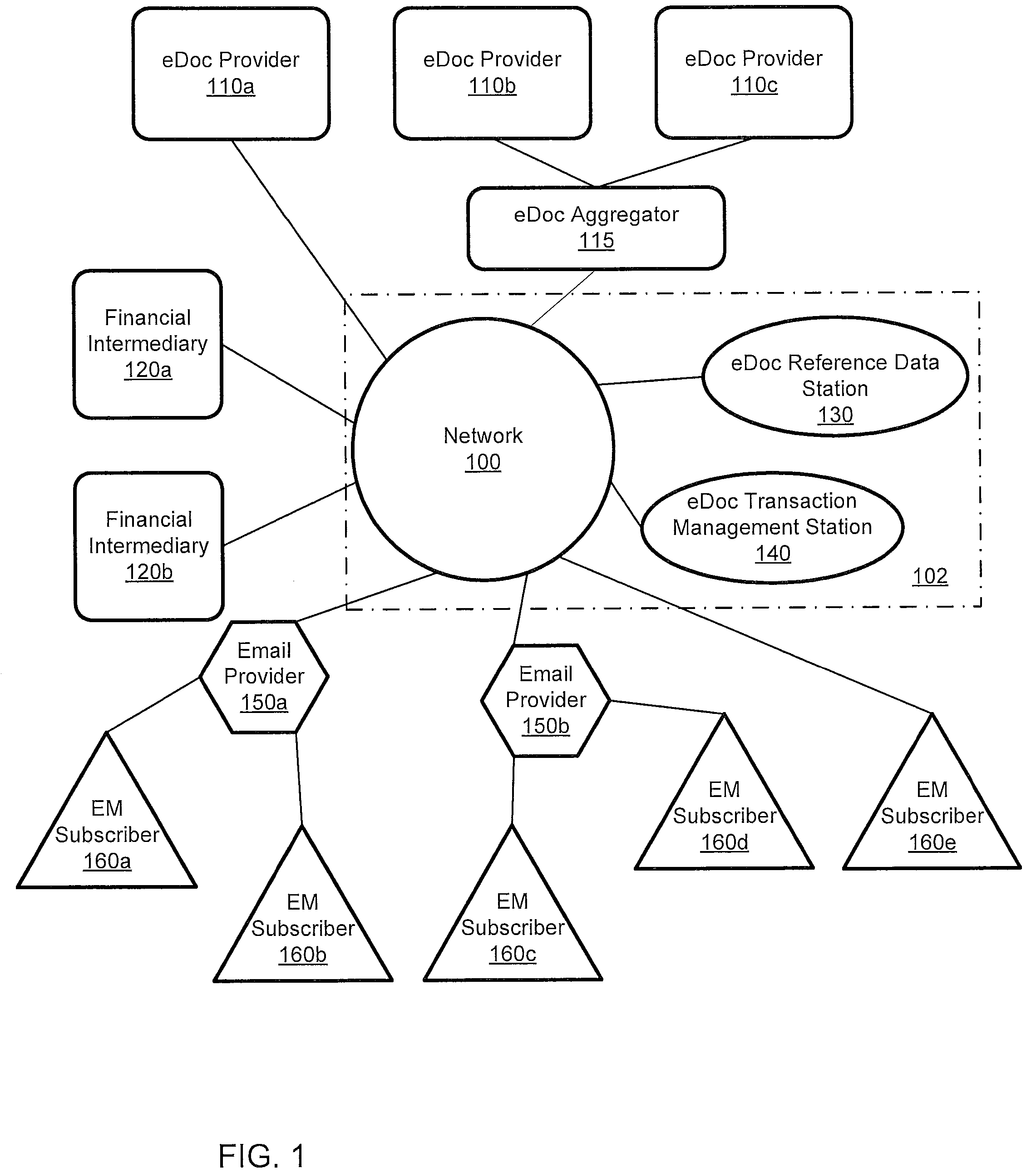
System for management and processing of electronic vendor mail
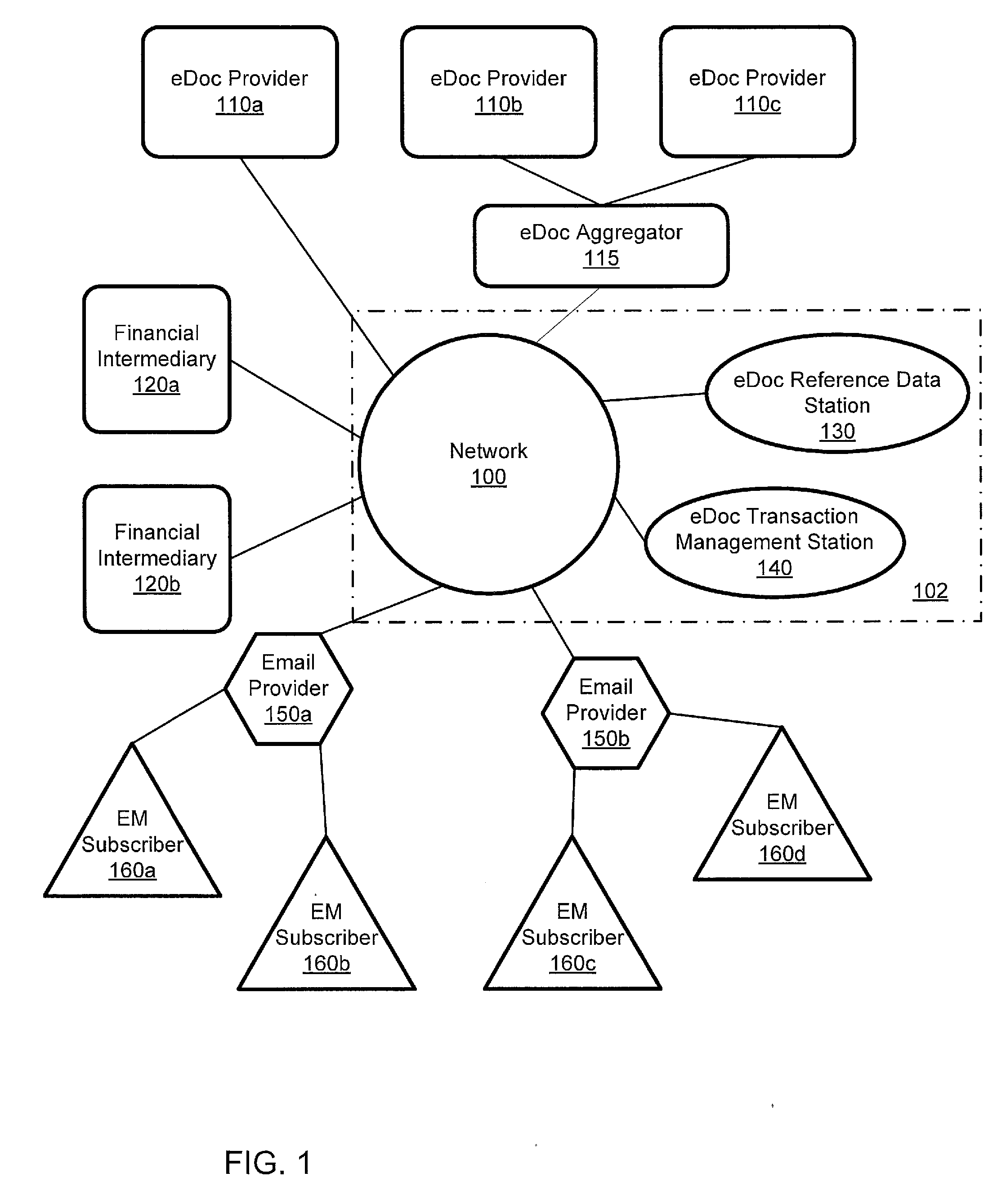
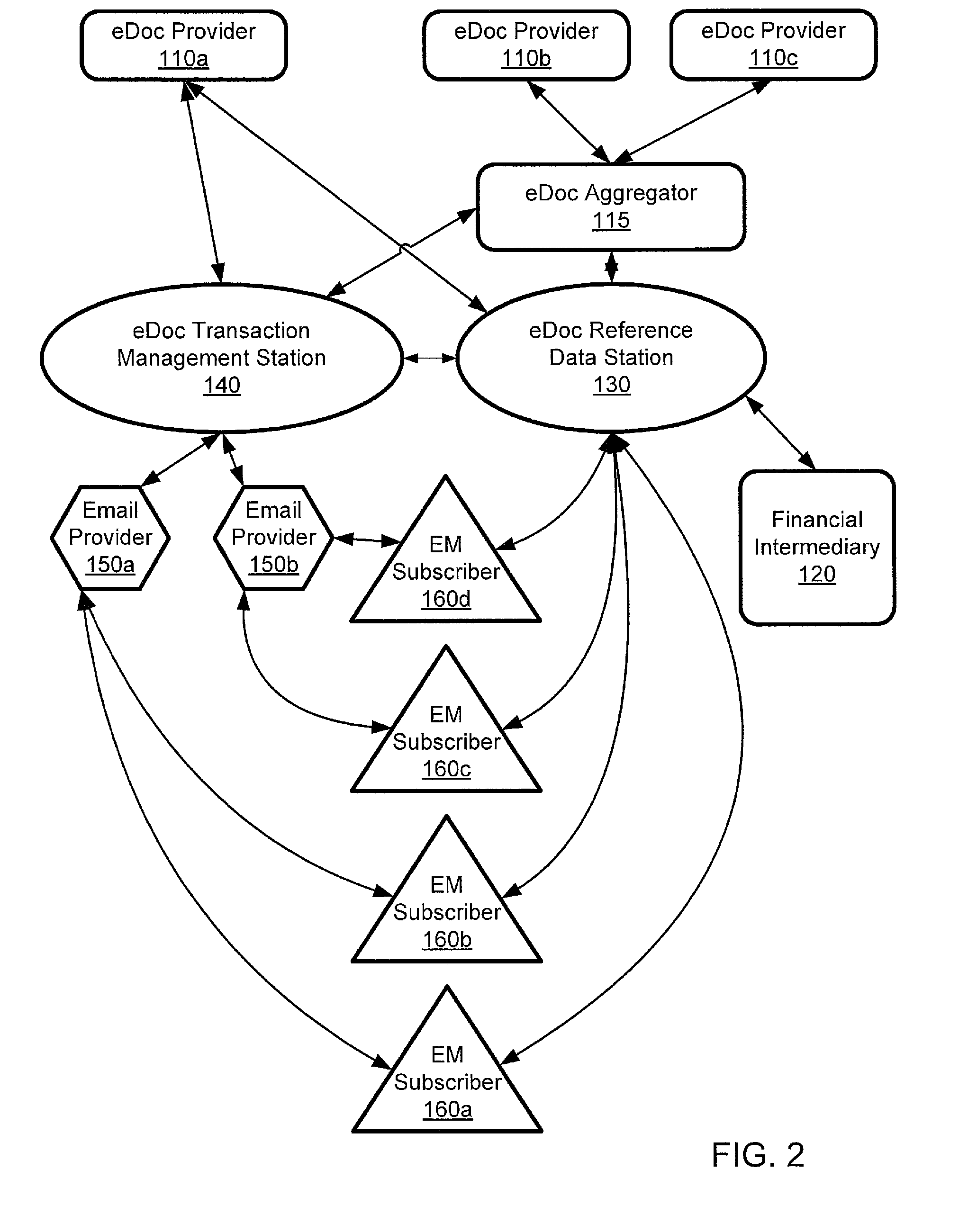
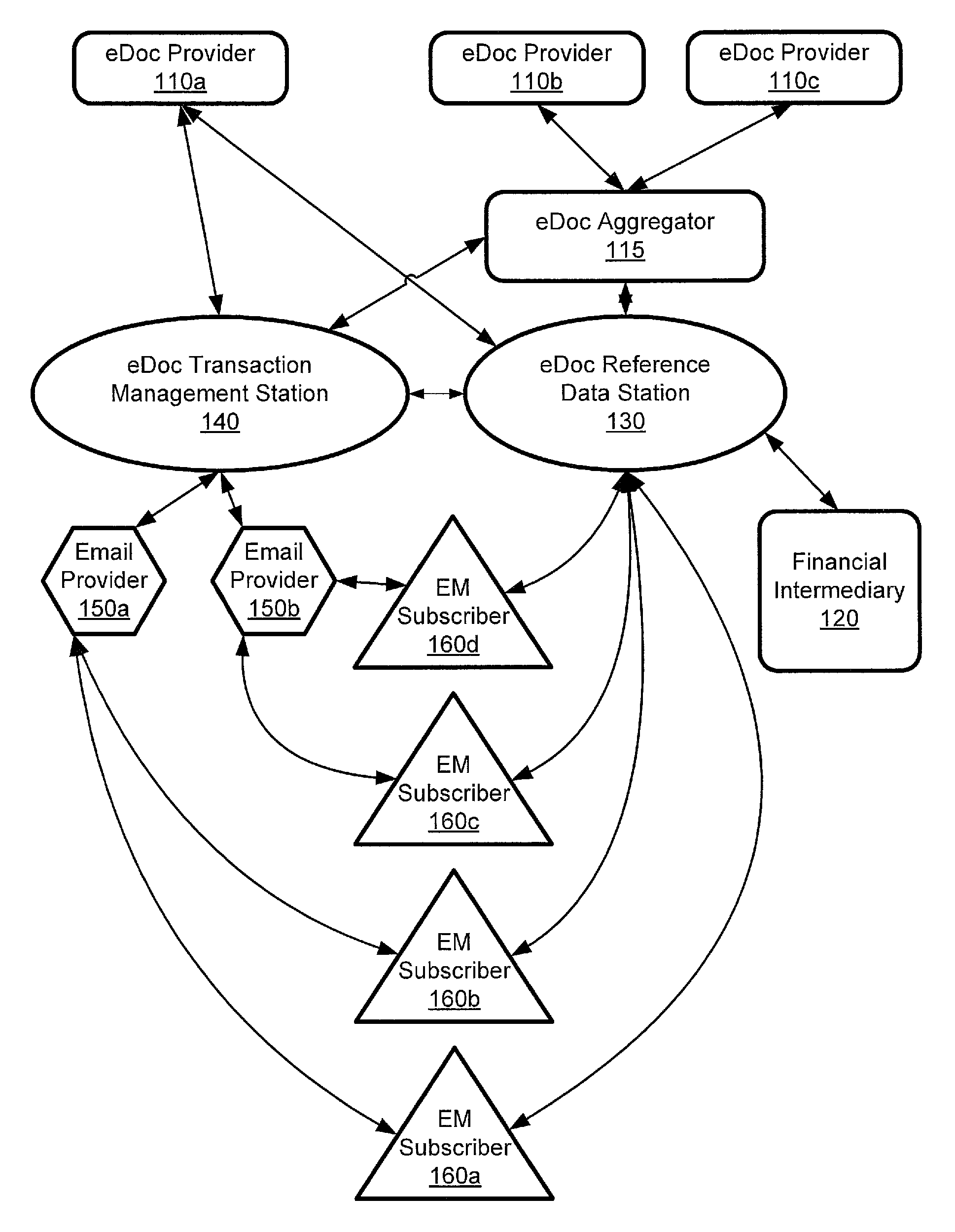
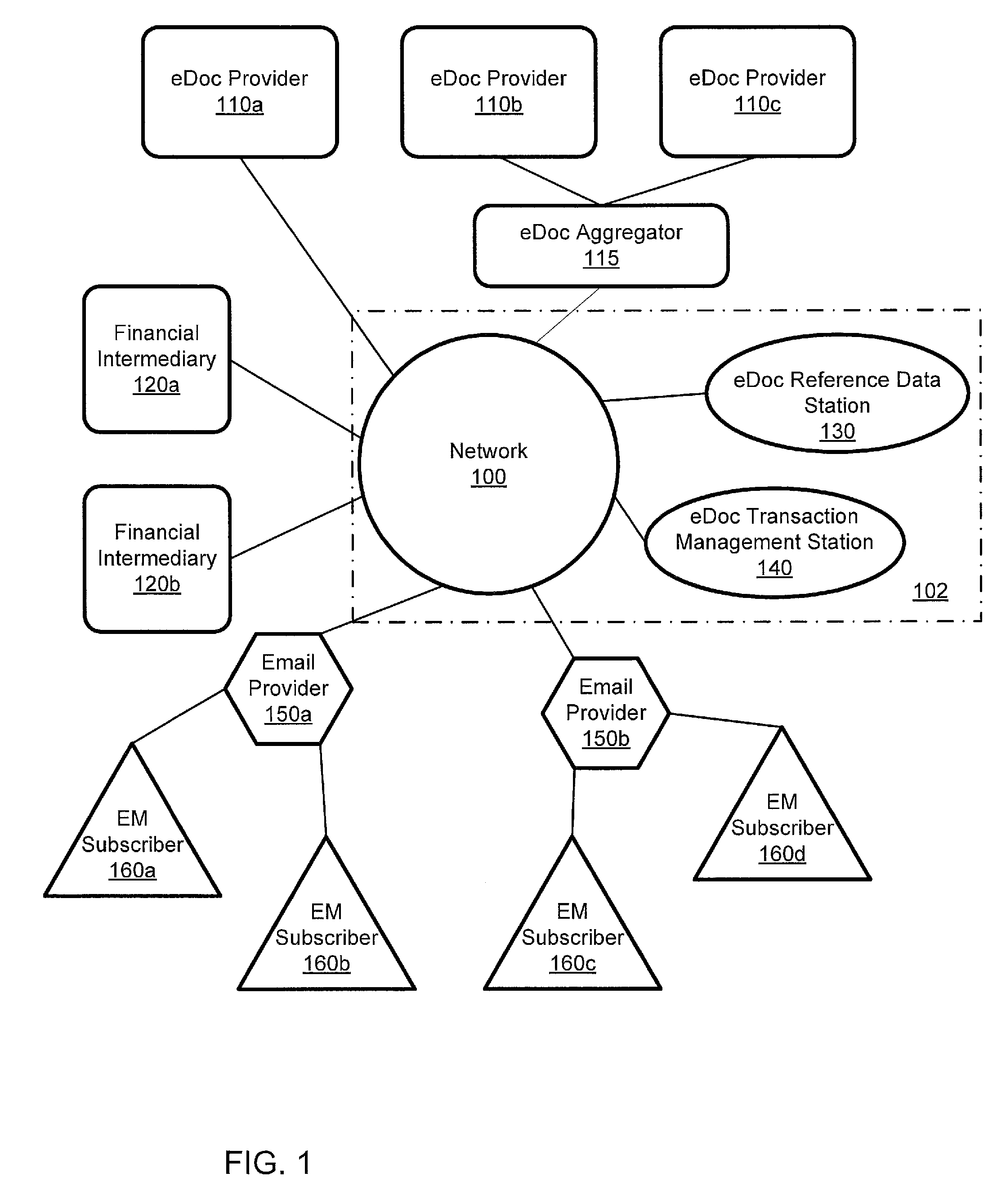
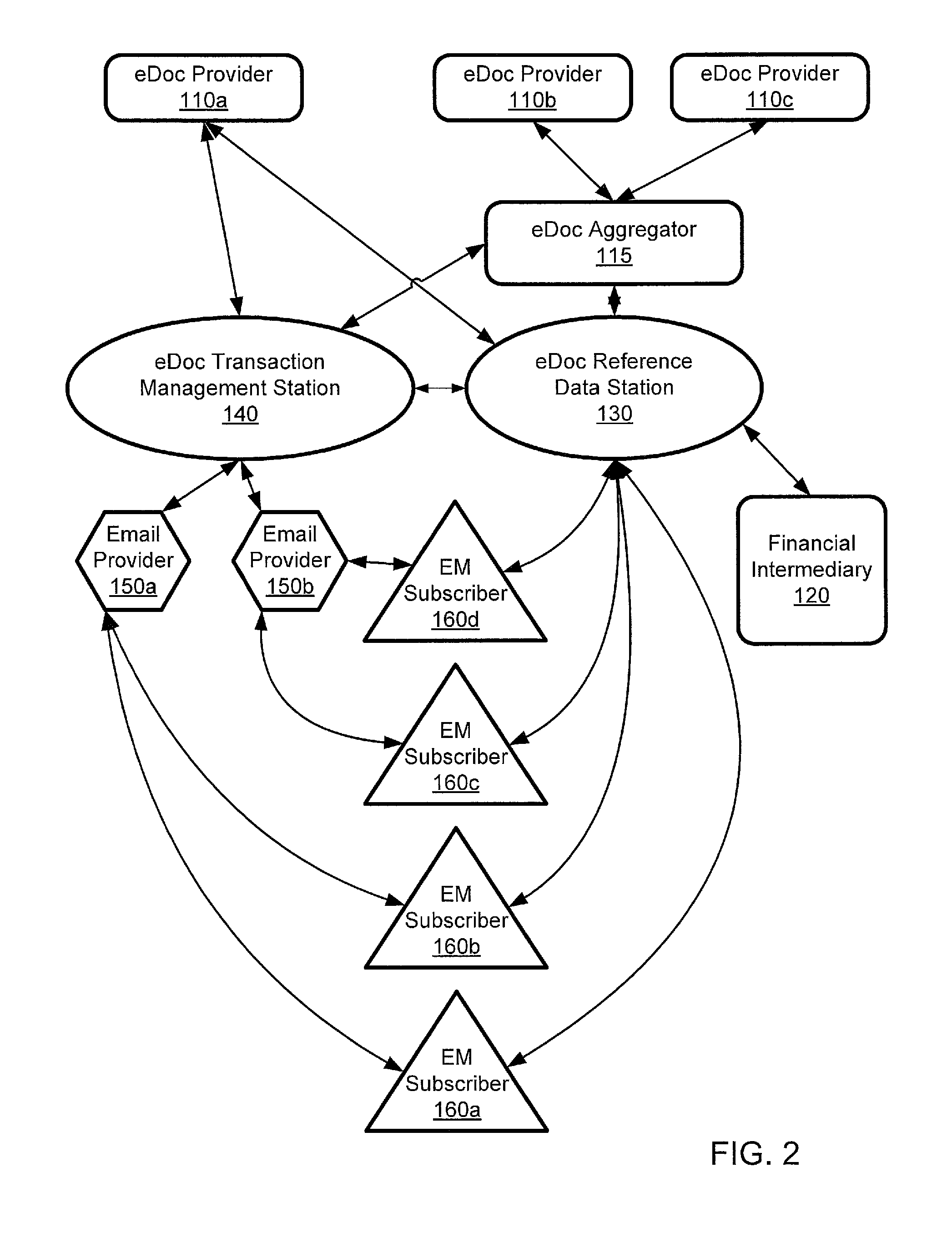
ActiveUS20110035581A1Multiple digital computer combinationsOffice automationElectronic documentEnd to end system
A computer-implemented system processes secure electronic documents from one or more content providers in accordance with subscriber instructions has a processor and modules operative within the processor. A monitoring module obtains a provider GUID, a subscriber GUID, and a transaction ID from public metadata associated with a transaction received from a particular content provider. A determination module determines any designees of the subscriber and contact information one or more of the subscriber and any designees. A transaction module distributes a transaction addressed to at least one of the subscriber and any designees. Each distributed transaction includes data that is used for management, tracking, and alerting. Also described is a station for constructing transactions for distribution to subscribers through such a system. An end-to-end system and method are described.
Owner:ECO MAIL DEV
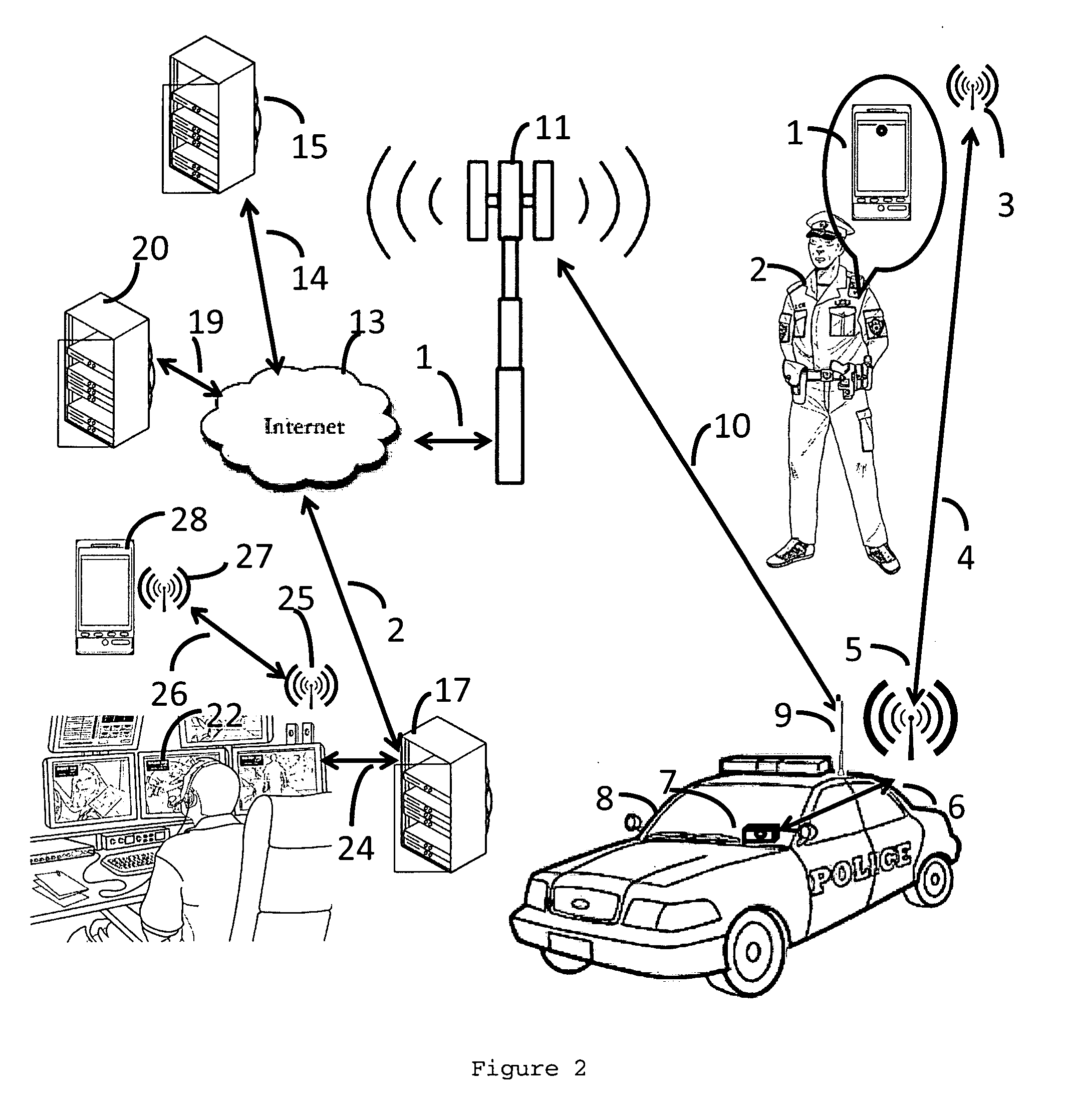
Law enforcement real time digital information chain of custody assurance system and method
InactiveUS20160119667A1Reduce storageReduce the amount requiredTelevision system detailsColor television signals processingEnd to end systemChain of custody
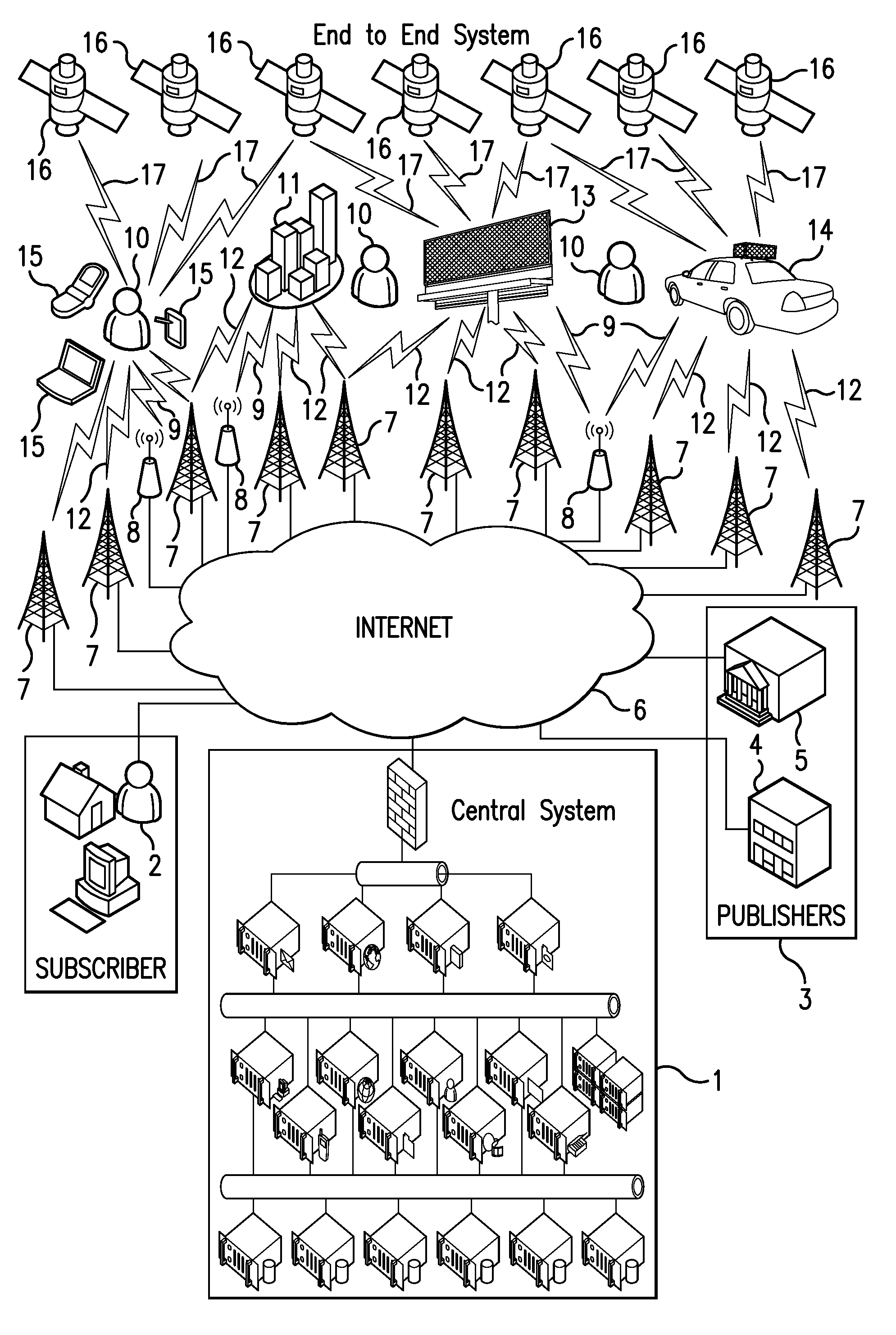
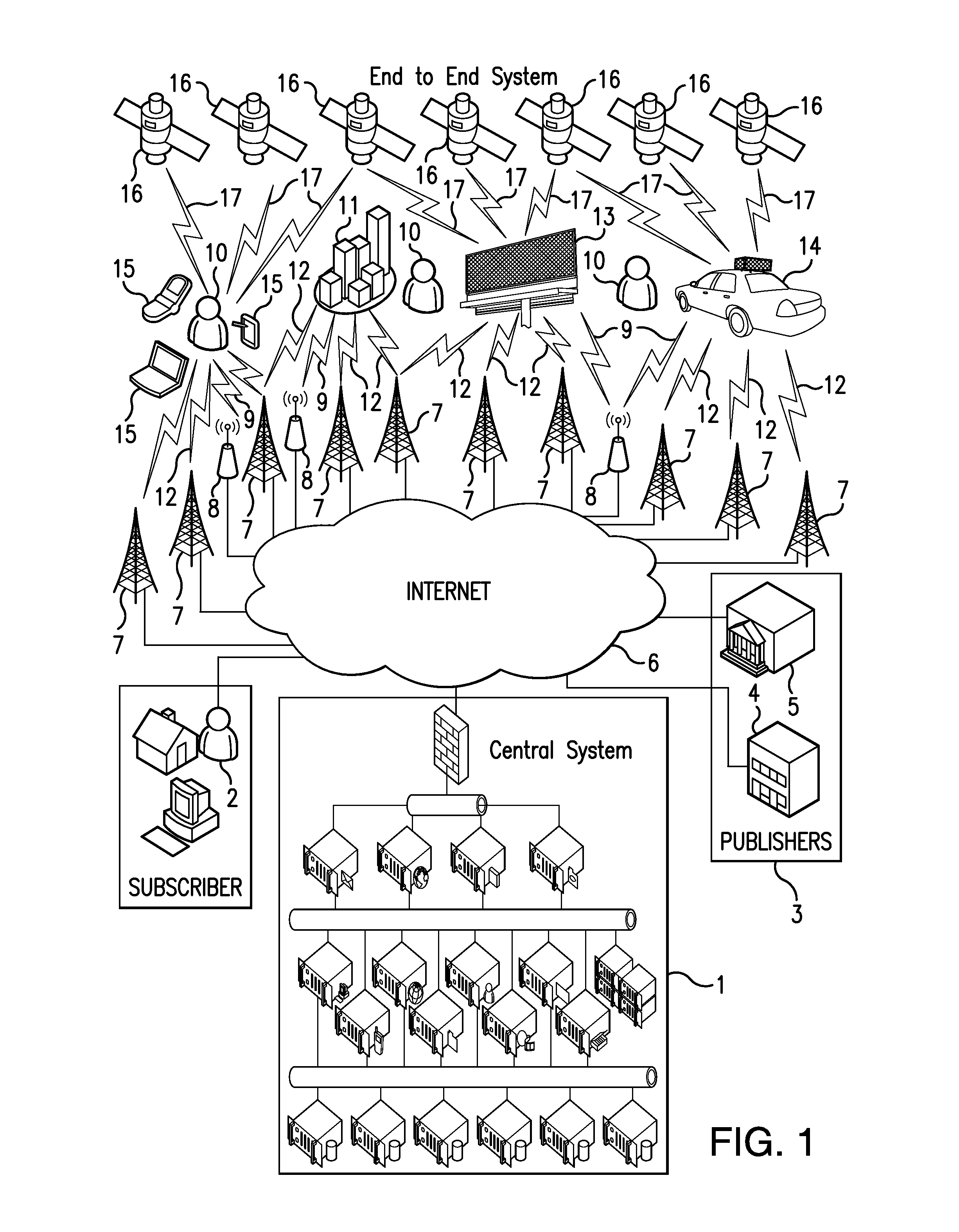
The invention disclosed relates to the end to end system, the methods and apparatuses for delivering real time HD video and audio content using a secure chain of custody method over the ubiquitous cellular network and providing a solution for the lone worker in hazardous environments.
Owner:LAYSON JR HOYT MAC +1
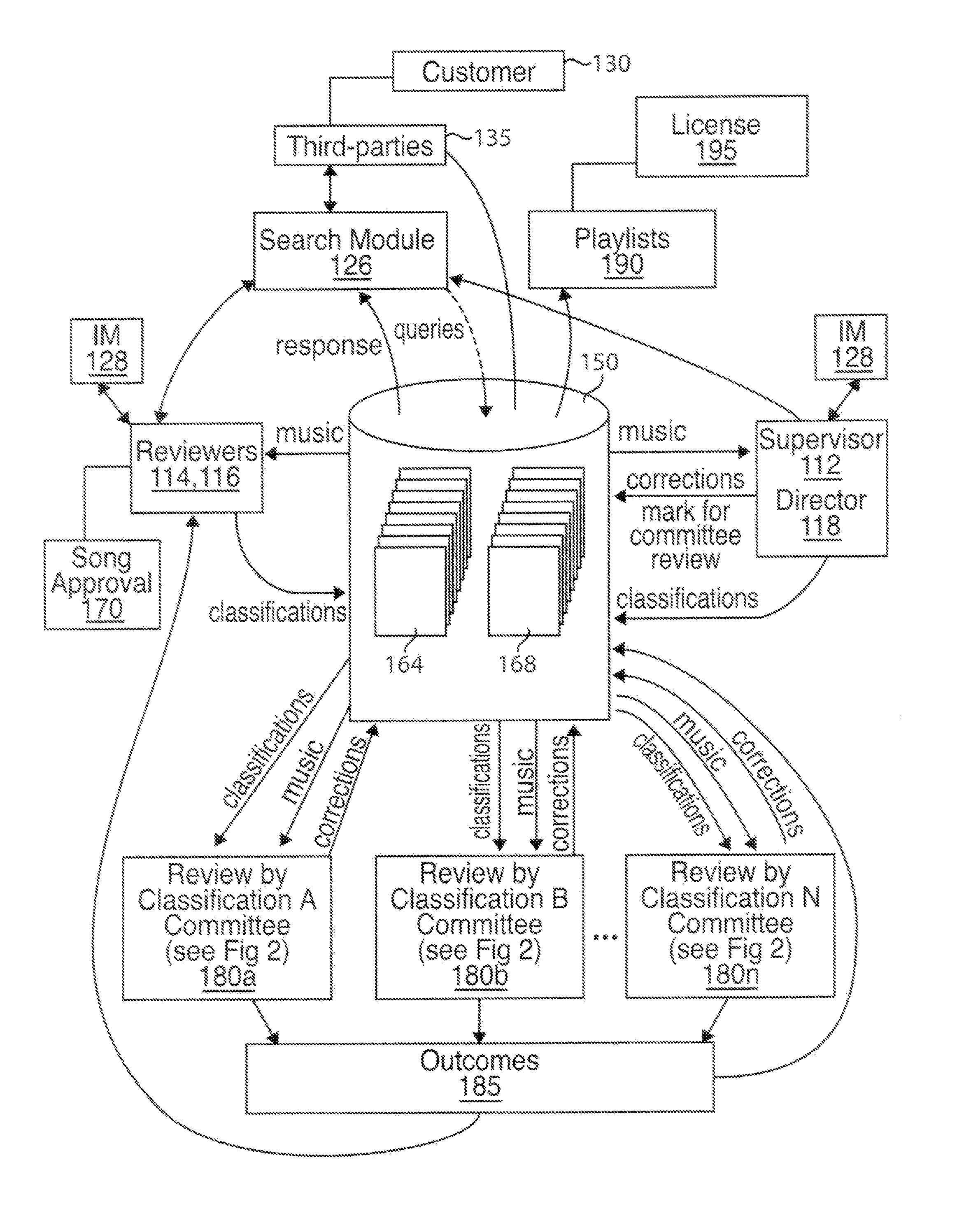
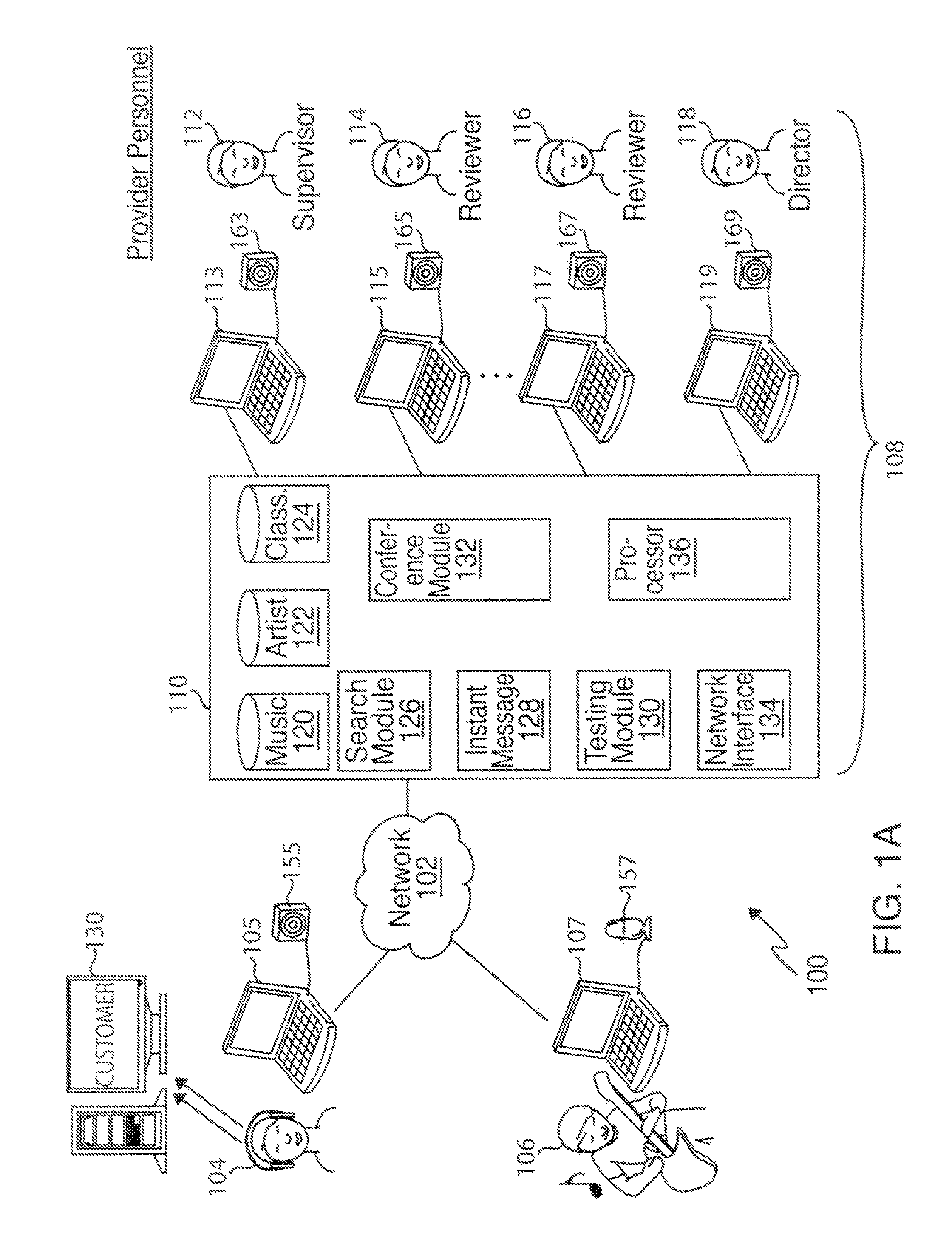
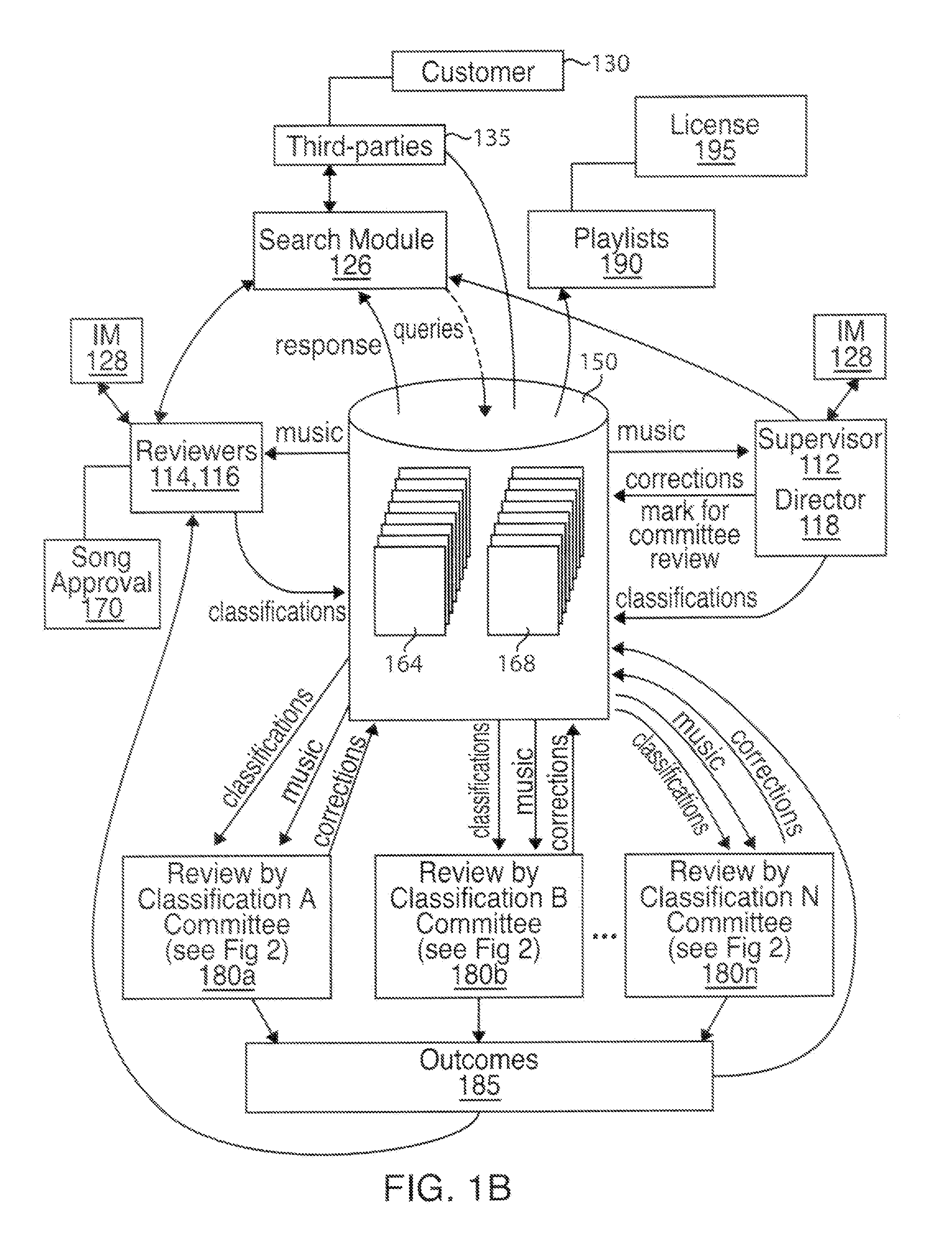
Method and System for Gathering and Pseudo-Objectively Classifying Copyrightable Material to be Licensed Through a Provider Network
InactiveUS20120030230A1Good choiceInput/output for user-computer interactionDigital data processing detailsThird partyGuideline
Disclosed is a method and system for gathering and pseudo-objectively classifying copyrightable material so as to facilitate identification of selected copyrightable material for licensing through a provider network. More particularly, disclosed is an end-to-end system and method that facilitates the licensing or sale of an author's copyrighted work(s) to third parties through a database of copyrighted works accessible to such users, such database being searchable based on certain predetermined criteria to allow the buyer / licensee to efficiently search for the desired genre or style of artwork for a given purpose. Also disclosed is a system and method of providing users with customized content lists (such as musical playlists, visual artwork lists, or textual copylists) based on subjective criteria that are objectivized using predetermined quality control guidelines.
Owner:MUSIC DEALERS
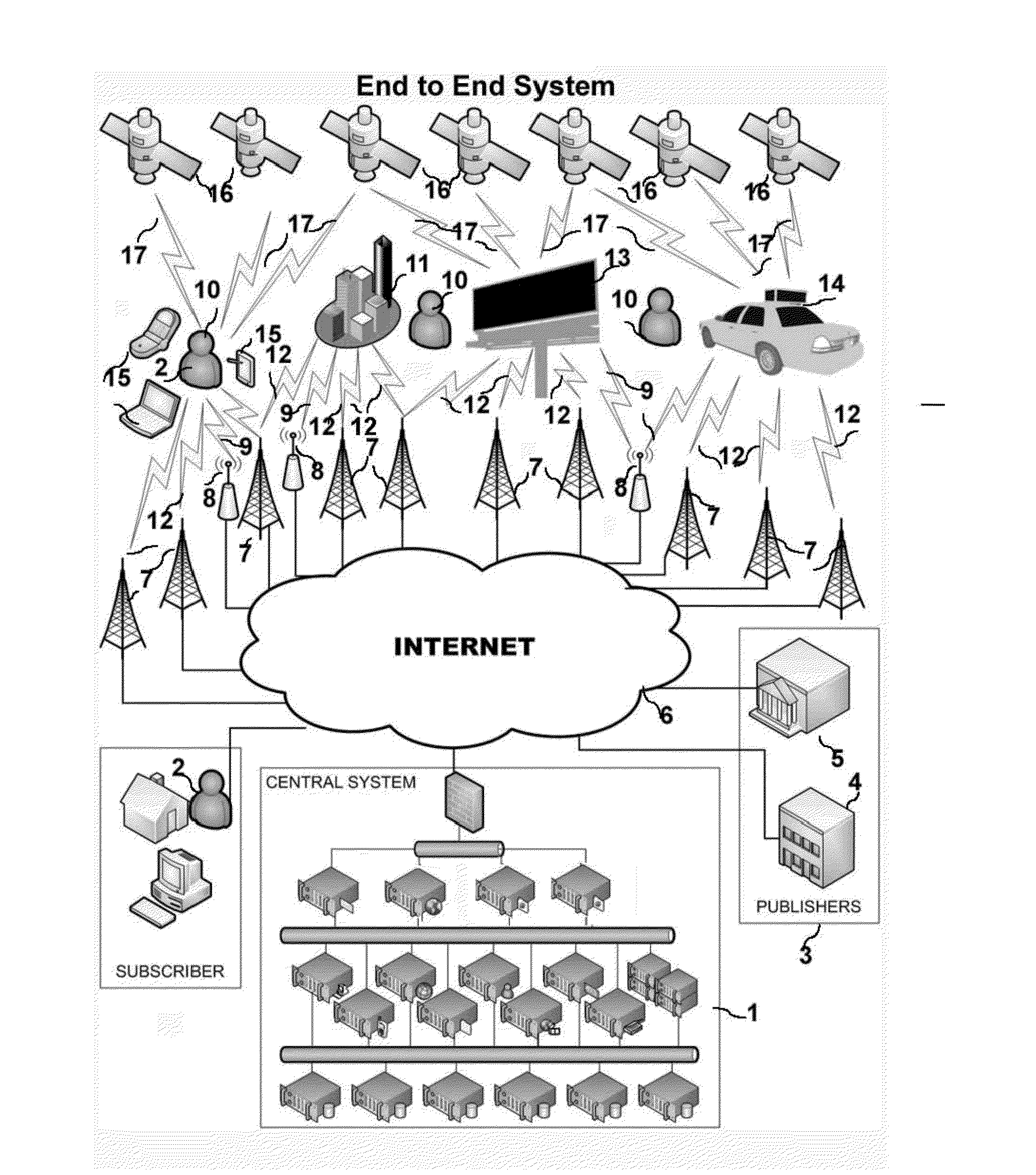
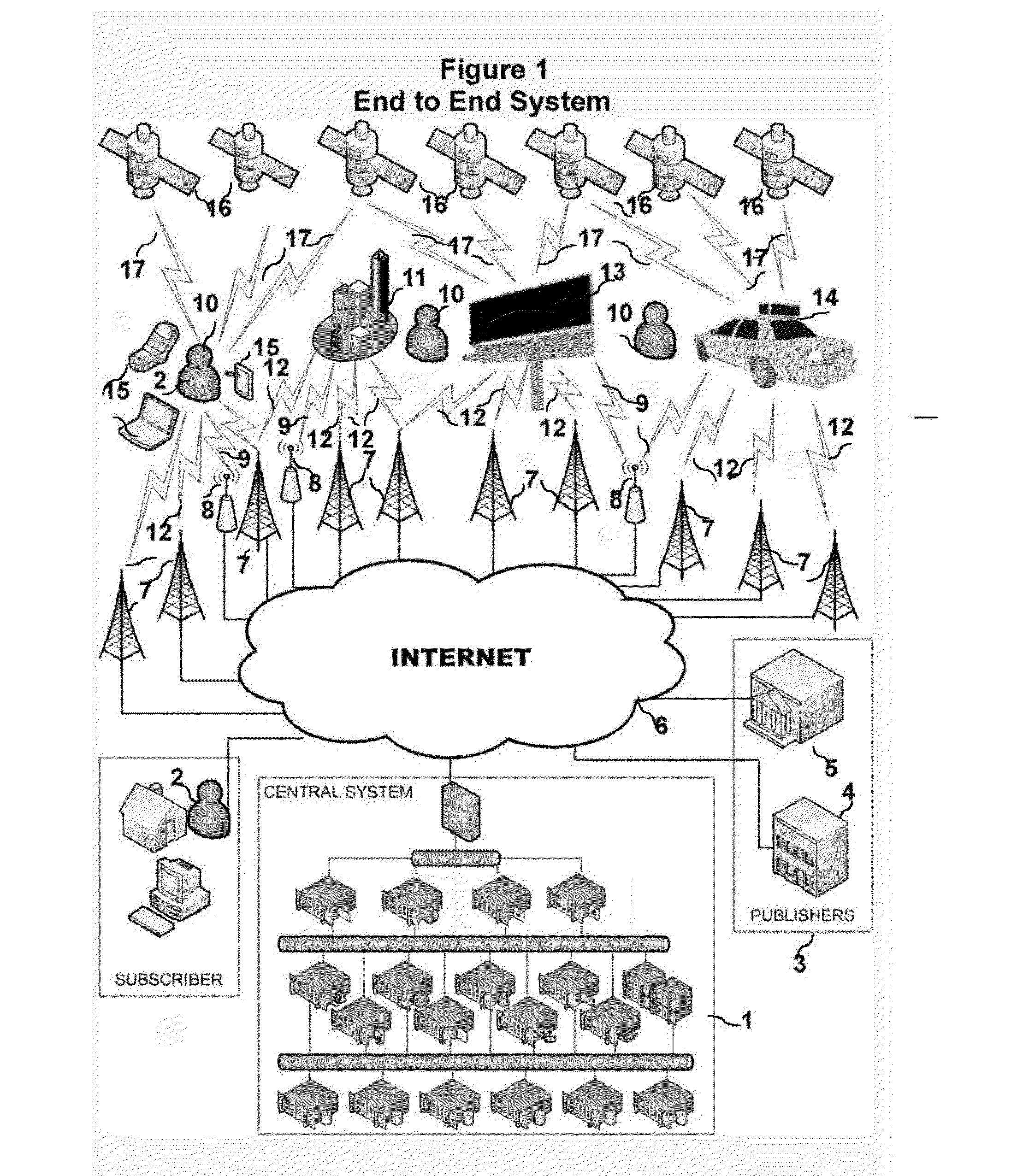
Head Mounted Portable Wireless Display Device For Location Derived Messaging
InactiveUS20150109186A1Low noise and stabilityImprove stabilityCathode-ray tube indicatorsLocation information based serviceEnd to end systemDisplay device
The invention disclosed relates to a head mounted portable wireless display device which is part of the end to end system, the methods and apparatuses for delivering message content from publishers to recipients, such recipients being comprised of subscribers and non subscribers, based on the geospatial location of the recipients using a plurality of devices, stationary and mobile, to deliver geospatial location relevant message content to the recipients with dynamic display devices and a means to provide publishers with data and statistics related to recipient observation of message content.
Owner:LAYSON JR HOYT MAC
An image semantic segmentation method based on local region conditional random field model
InactiveCN109285162AReduce time complexityReduce calculationImage enhancementImage analysisRegion selectionConditional random field
The invention relates to an image semantic segmentation method based on a local area conditional random field model. A full convolution neural network structure of the invention extracts input picturefeatures and obtains a rough segmentation result. The region selection structure filters the edge of the segmentation result map, and selects the segmentation result as the largest circumscribed rectangle of the pedestrian, bicycle and motor vehicle parts. The local region conditional random field model establishes the conditional random field model in the rectangular region and refines the segmentation result of the rectangular region. The invention effectively combines the advantages of the precision of the conditional random field model with the advantages of the speed of the full convolution neural network. The computational method of the conditional random field model is optimized so that the time complexity of the model is greatly reduced. The segmentation accuracy of the traditional full convolution neural network is improved. The application of probability graph model and full convolution neural network is designed as an end-to-end system.
Owner:HANGZHOU DIANZI UNIV
Head Mounted Portable Wireless Display Device For Location Derived Messaging
InactiveUS20160154239A9Improvement in angular random walkAccurate displayCathode-ray tube indicatorsLocation information based serviceEnd to end systemDisplay device
The invention disclosed relates to a head mounted portable wireless display device which is part of the end to end system, the methods and apparatuses for delivering message content from publishers to recipients, such recipients being comprised of subscribers and non subscribers, based on the geospatial location of the recipients using a plurality of devices, stationary and mobile, to deliver geospatial location relevant message content to the recipients with dynamic display devices and a means to provide publishers with data and statistics related to recipient observation of message content.
Owner:LAYSON JR HOYT MAC
Method for improving end-to-end wireless transmission control protocol (TCP) linear network coding
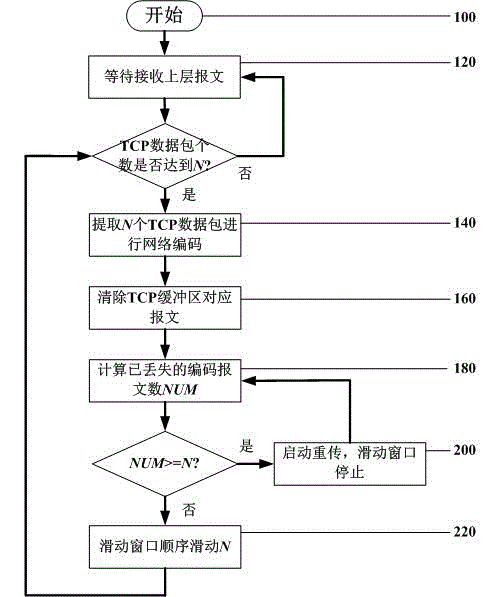
InactiveCN103152359AImprove throughputReduce coding complexityError prevention/detection by using return channelPacket lossWireless transmission
The invention provides a method for improving end-to-end wireless transmission control protocol (TCP) linear network coding. Particularly, the method comprises the following steps of: (1) optimizing a network coding head frame design on a network coding layer, so that required parameters of coding and decoding are comprehensively considered, the length of a network coding head is shortened, and the complexity of the network coding head is reduced; (2) according to the condition of wireless network packet loss, designing reasonable sliding windows and coding windows, and optimizing so that the sizes of the sliding windows and the coding windows are equal; (3) determining piggyback information content to be network coding message sequence expected to be received next time; and (4) amending a message loss retransmission mechanism, and starting retransmission when the accumulated packet loss number of coding messages achieves the number of sliding windows. Through the operation, the complexity of network coding can be reduced, and the network coding efficiency and the TCP throughput of an end-to-end system are improved.
Owner:SHANGHAI QIANLONG INFORMATION TECH CO LTD
Method and apparatus for automatic generation of system test libraries
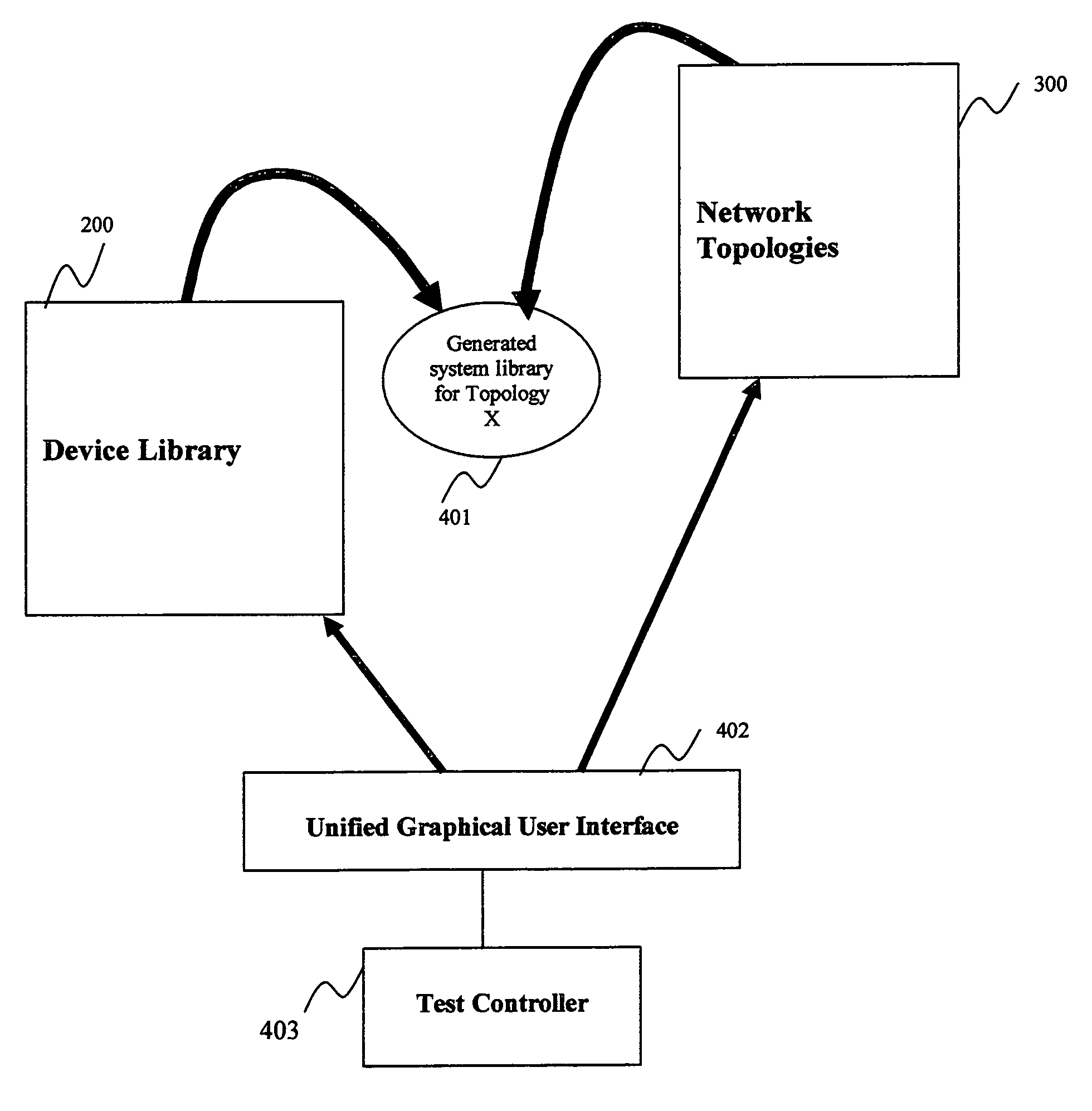
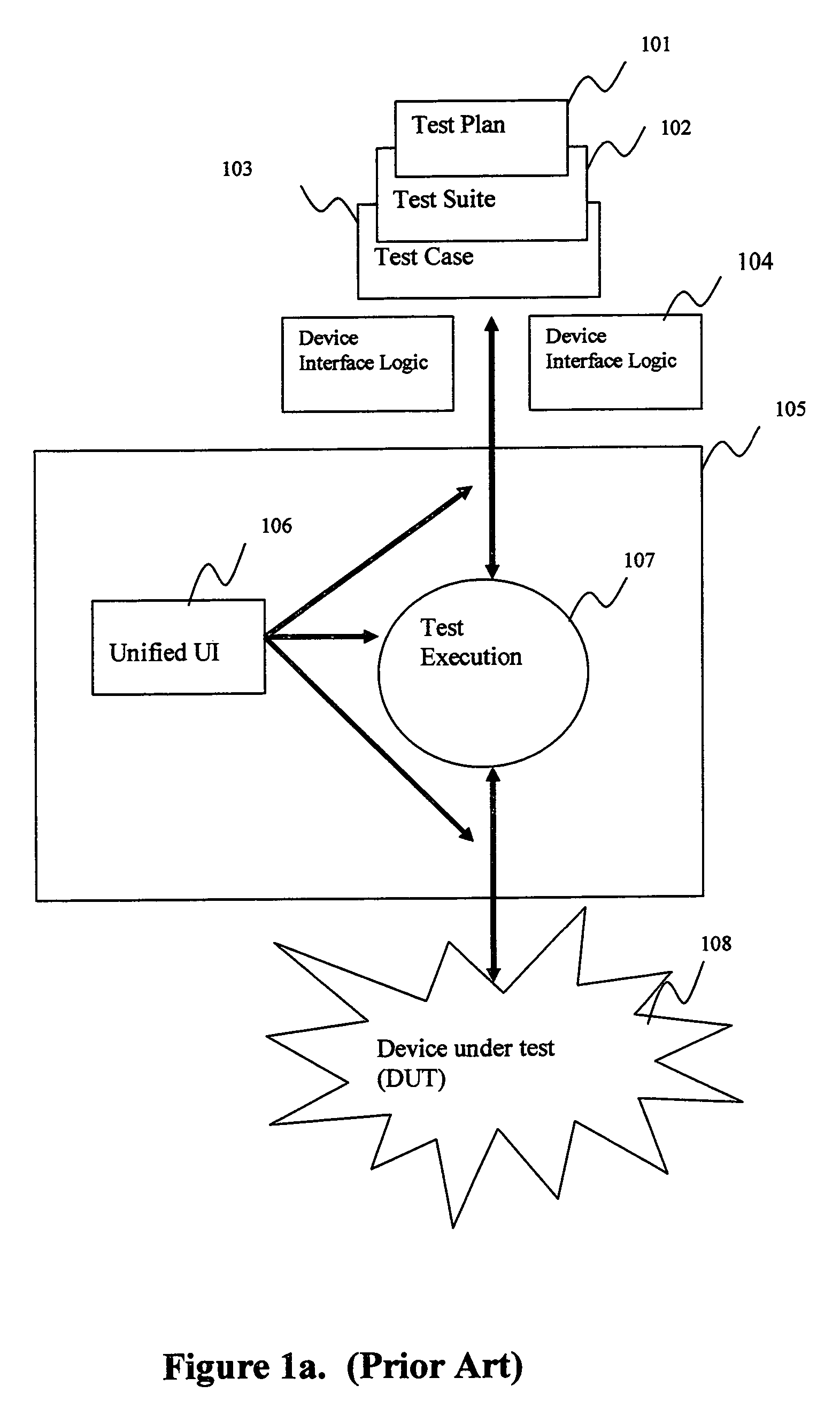
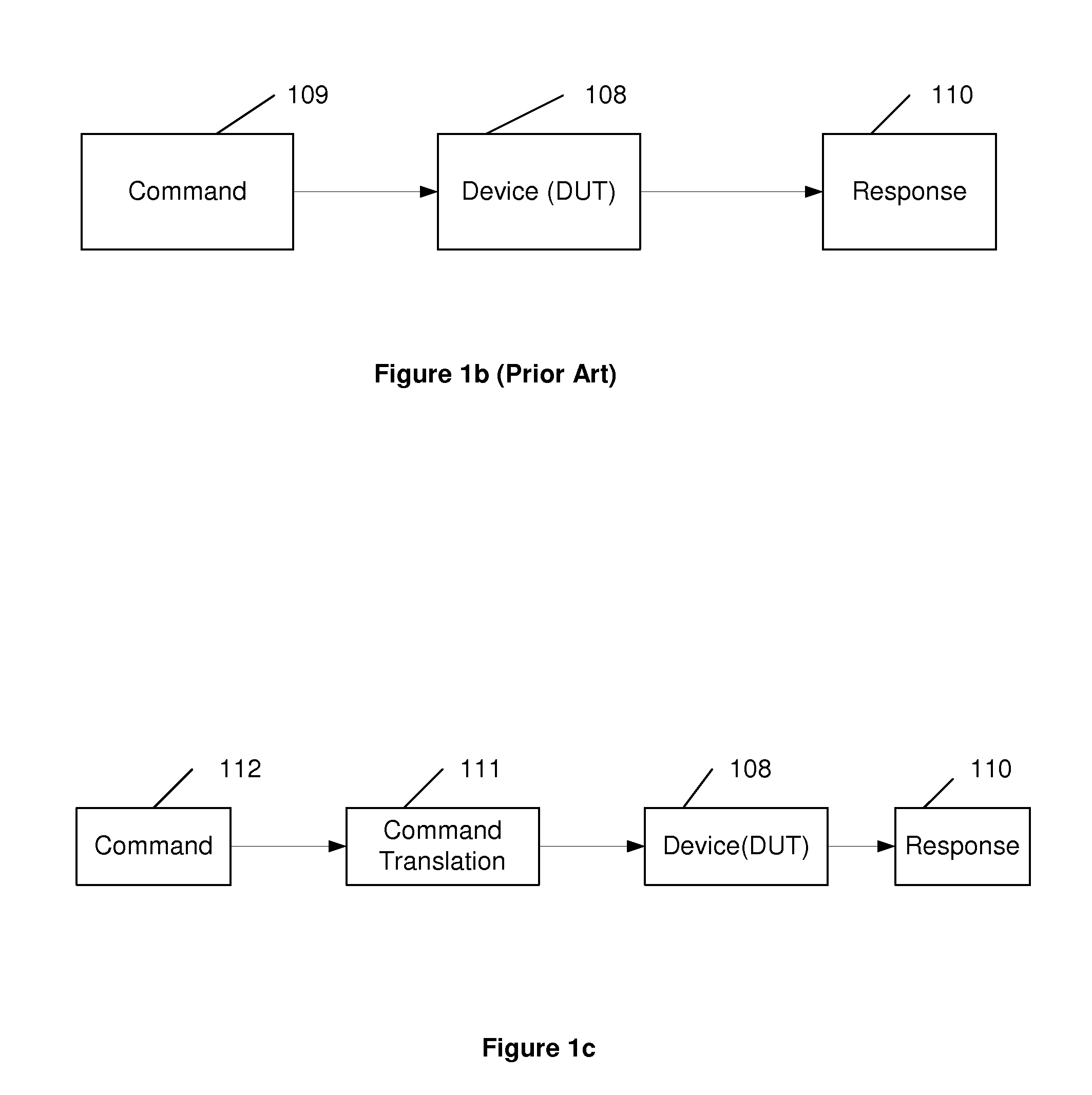
InactiveUS7496815B2Electronic circuit testingError detection/correctionComputer hardwareSystem testing
An apparatus and associated methodology are provided to generate system test libraries for solution testing involving heterogeneous devices from different vendors. A unified user interface employs received information to execute the tests based on provided device and network topology libraries, generating the system library to perform the required end-to-end system testing. The unified user interface and the library generation mechanism provide a layer of abstraction avoiding complexities of the system configuration commands native to disparate devices.
Owner:SAPPHIRE INFOTECH
Location derived messaging system
InactiveUS8606865B2Reduce the amount requiredPositive confirmation of consumer viewingMultiple digital computer combinationsAutomatic exchangesEnd to end systemGeographic space
The invention disclosed relates to the end to end system, the methods and apparatuses for delivering message content from publishers to recipients, such recipients being comprised of subscribers and non subscribers, based on the geospatial location of the recipients using a plurality of devices, stationary and mobile, to deliver geospatial location relevant message content to the recipients with dynamic display devices and a means to provide publishers with data and statistics related to recipient observation of message content.
Owner:LAYSON JR HOYT M
System for detecting whether coronary angiography has complete occlusion lesion or not based on deep learning
ActiveCN110490863AFocus on lesion characteristicsSolve misjudgmentImage enhancementImage analysisSystems designEnd to end system
The invention discloses a system for detecting whether coronary angiography has a complete occlusion lesion or not based on deep learning. A deep learning recurrent neural network is used for analyzing an overall video, a GPU (graphics processing unit) is used for accelerating calculation to obtain a detection result, the calculation delay is small, and the real-time problem of detection is solved. The system comprises a video input module, a convolutional neural network module, a coding and decoding attention module and a classification module. Particularly, the encoding and decoding attention module and the supervision algorithm thereof provided by the invention are used for generating a proper attention weight to improve the detection accuracy. The end-to-end system design achieves automation of the coronary artery complete occlusion detection process, and complex intermediate steps are not needed. Compared with other systems for detecting whether the complete occlusion lesion exists or not, the whole video instead of a single image is analyzed, the situation of misjudgment caused by the single image is reduced, and the accuracy of existence judgment of the complete occlusion lesion is remarkably improved.
Owner:北京红云智胜科技有限公司 +1
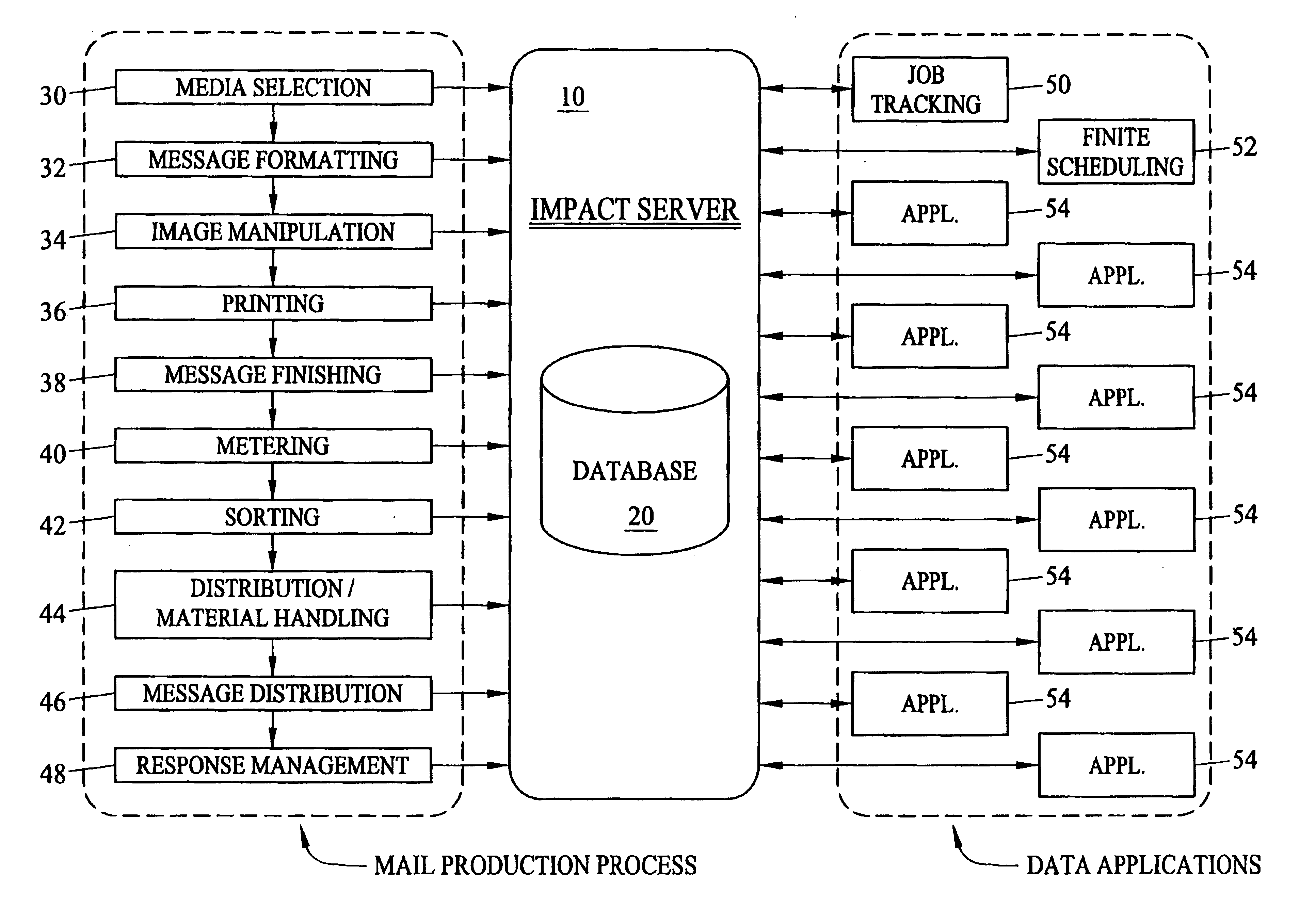
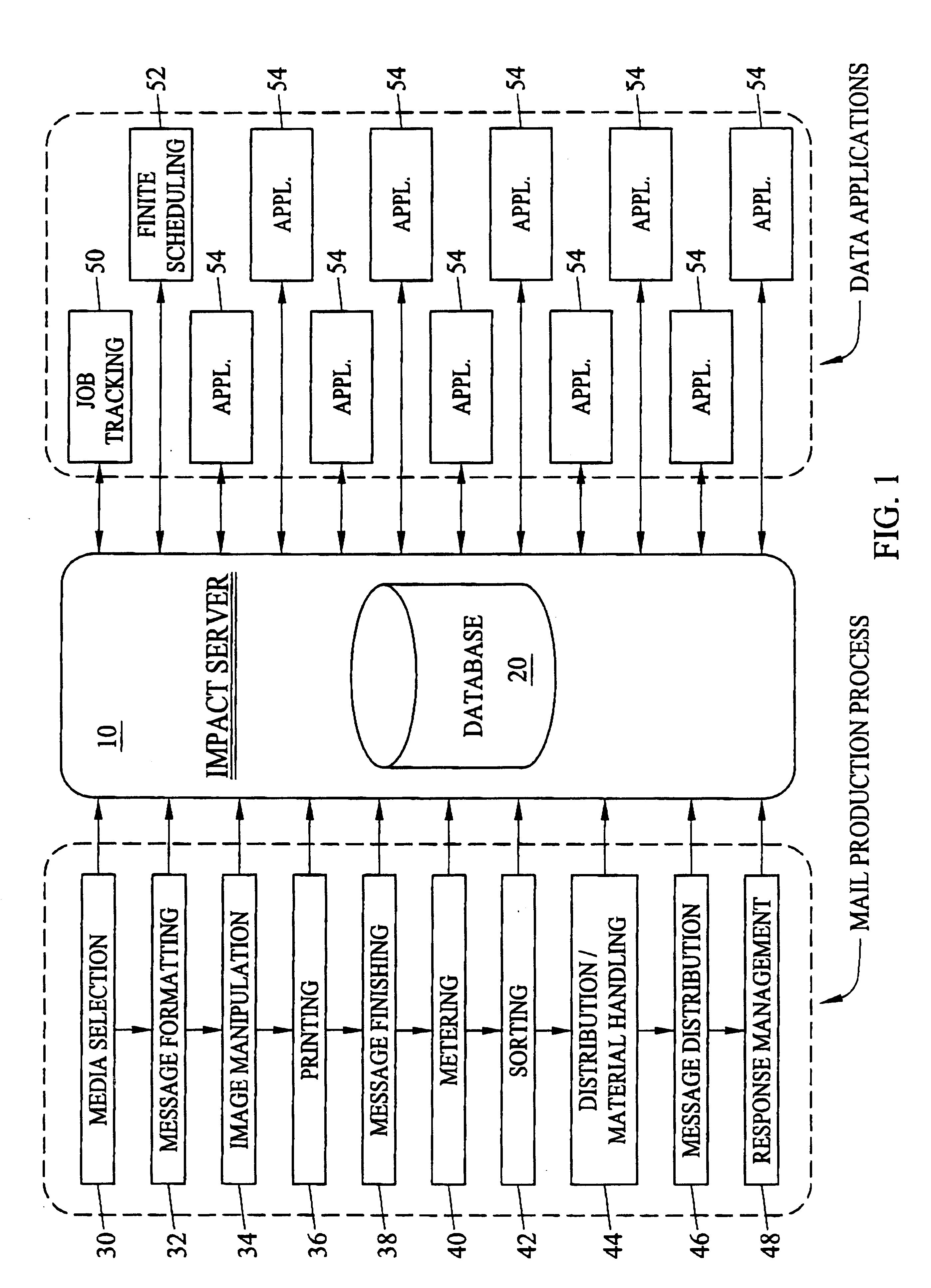
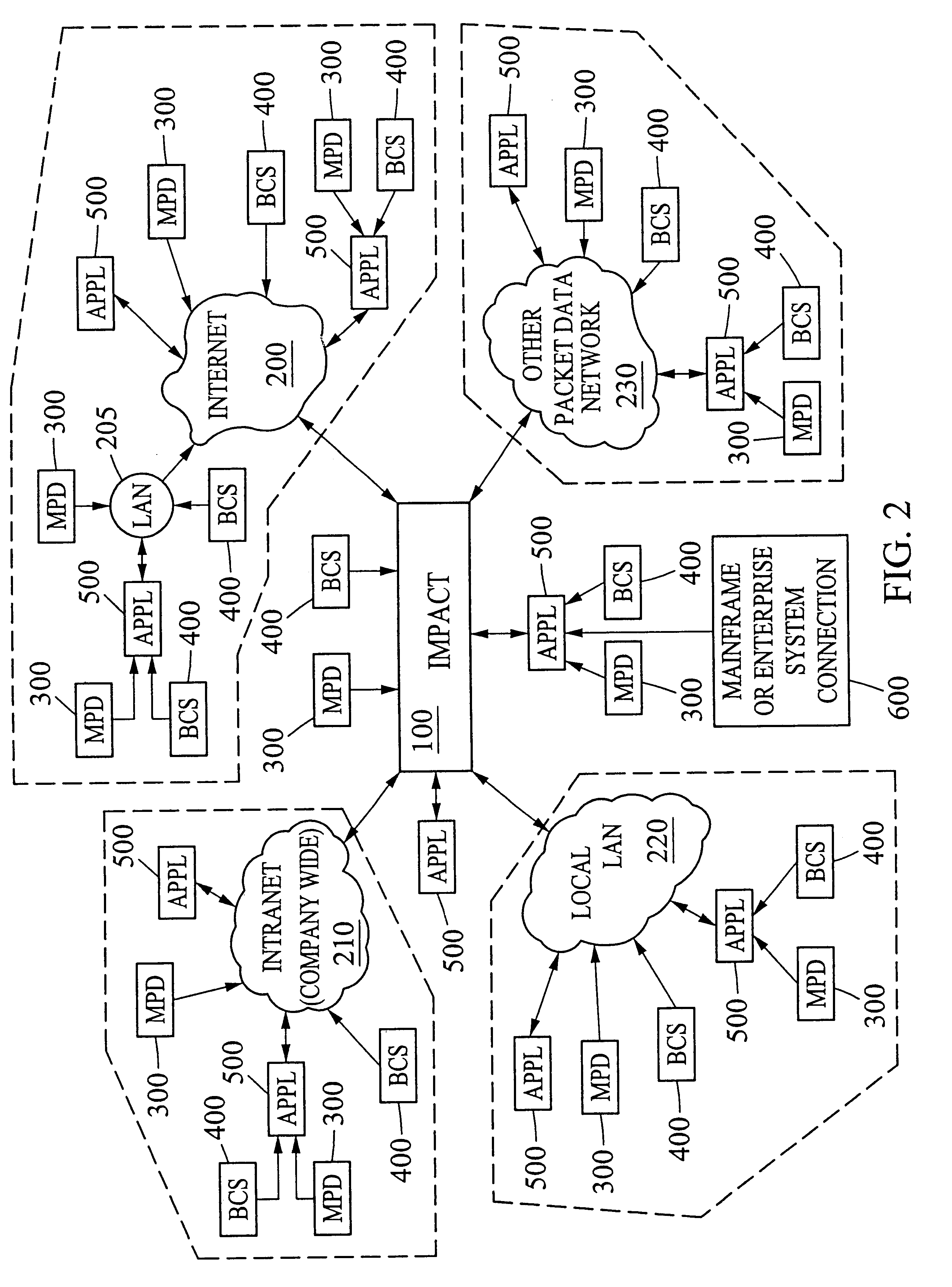
Tracking system, method and computer program product for document processing
InactiveUS6901412B2Improve performanceImprove efficiencyCharacter and pattern recognitionOffice automationEnd to end systemApplication software
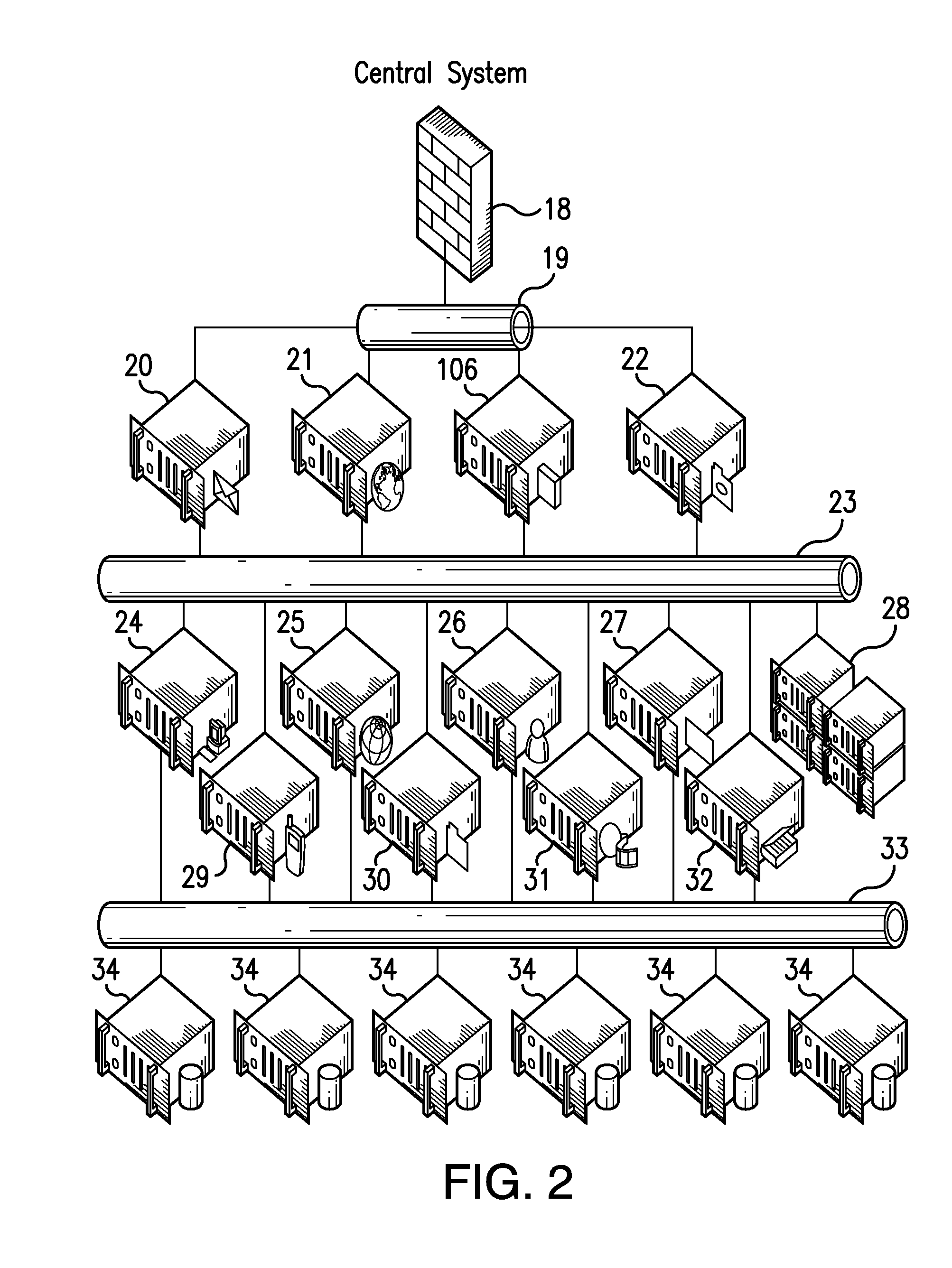
An integrated computer system architecture for tracking of job data in a document processing environment including an infrastructure built on processes, hardware, software and interfaces designed to monitor and control mail processing and data collection through a variety of manual and machine processes in real-time. Computers, networks, web-based applications, databases and scanners are used to interface and integrate traditional mail processing equipment with customized software. The invention integrates the entire mail production process to form and establish a complete end-to-end system. A job tracking scheme is detailed illustrating a particular data mining application.
Owner:BELL & HOWELL CO
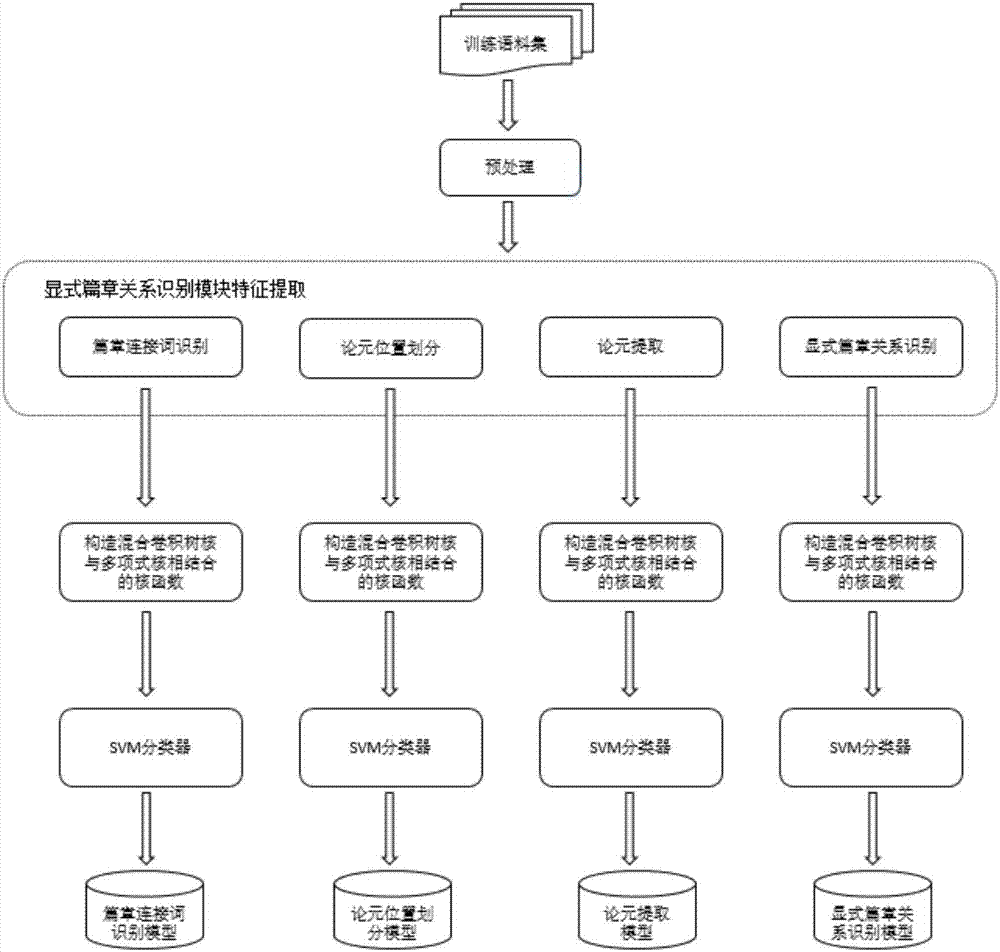
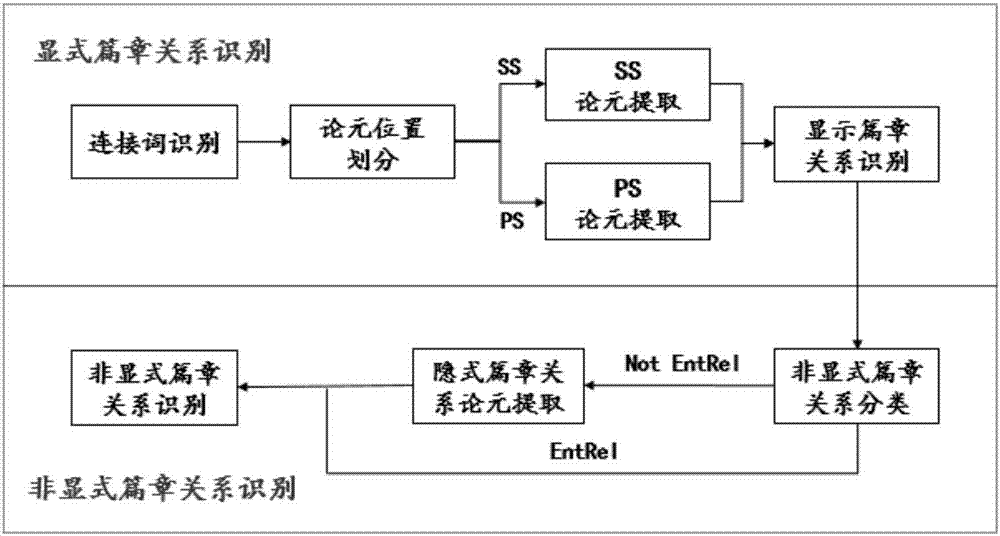
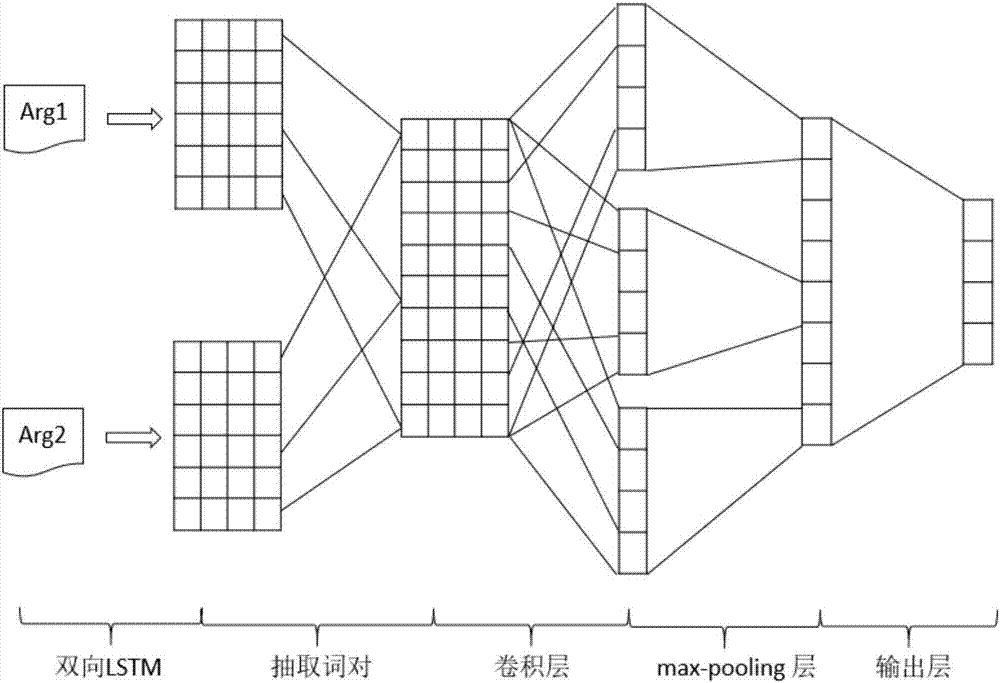
Automatic end-to-end English text structure analysis method based on pipeline mode
ActiveCN107273358AArgument Divide Subtask BoostingHigh precisionSemantic analysisCharacter and pattern recognitionAlgorithmEnd to end system
The invention relates to an automatic end-to-end English text structure analysis method based on a pipeline mode and belongs to the technical field of natural language processing applications. According to the method, the explicit text relation is identified, for the shortcoming of characteristic vectorization performed by adopting a word bag model in a traditional method, a characteristic representation and calculation method based on combination of a hybrid convolutional tree kernel and a polynomial kernel is proposed, and syntax characteristics and flat characteristics are divided and ruled. The characteristic vector dimensionality can be greatly reduced, and detailed information in expression characteristics can be fully expressed. Furthermore, for the problem that deeper semantics cannot be mined based on linguistic characteristics and the traditional method brings sparse data and semantic gaps during identification of non-explicit text relation, a non-explicit text relation identification model based on deep learning is provided by analyzing the identification characteristics of the non-explicit text relation in detail and applying the advantages of word pair characteristics. Compared with the prior art, the precision of a whole end-to-end system is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
System and Method for Improved In-Browser Notification
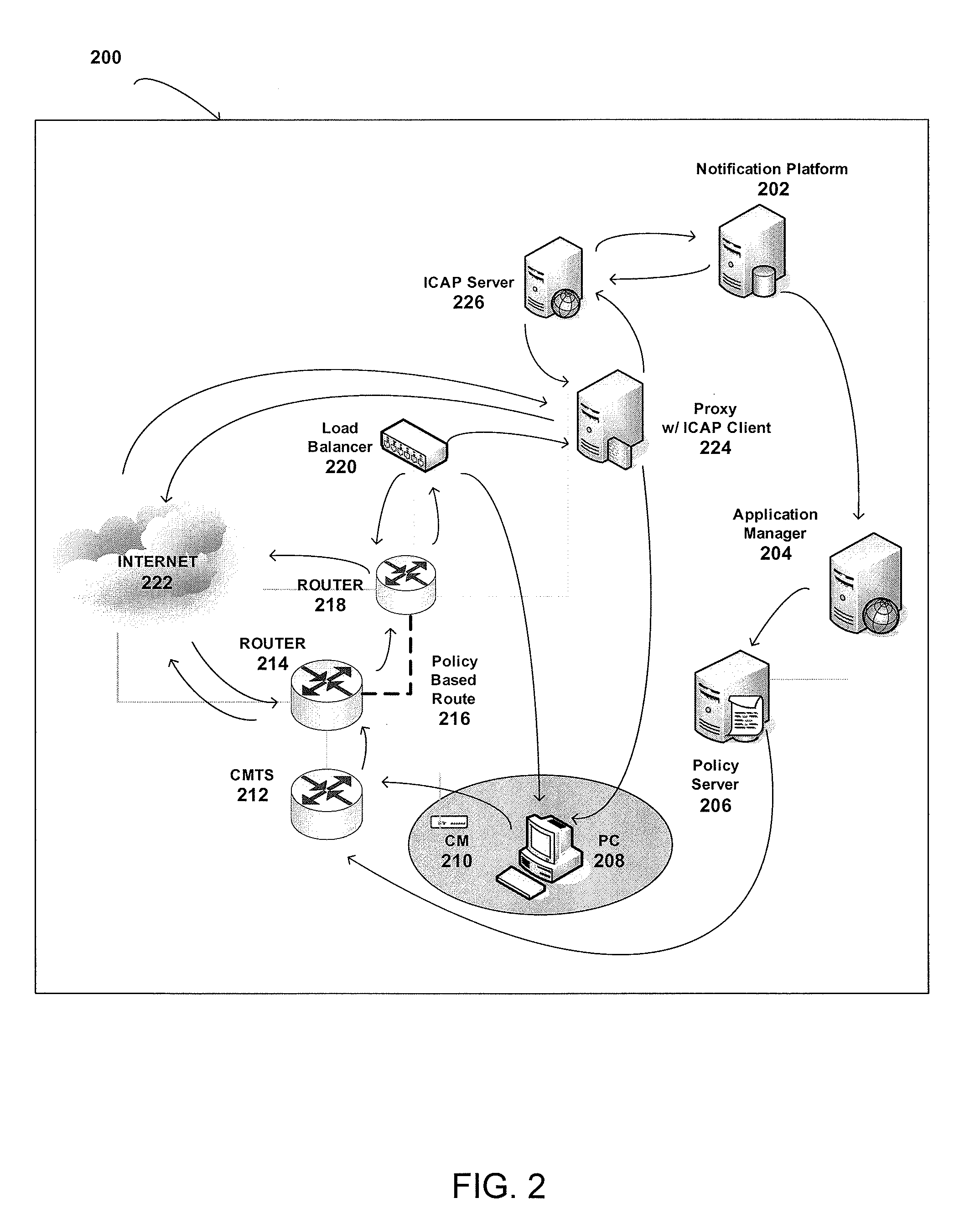
ActiveUS20100325217A1Multiple digital computer combinationsData switching networksTraffic capacityInternet content
Systems and methods for sending / receiving improved in-browser notification messages are provided. The notification messages are overlaid on HTTP traffic on port 80 for IP addresses provisioned to receive the notification messages from various sources, including weather, emergency broadcast, and police stations. A load balancer within the end-to-end system allows HTTP traffic on port 80 to be forked from non HTTP traffic on port 80 to selectively insert notification messages. The notifications are inserted by an internet content adoption protocol (ICAP) server in communication with other devices within the system.
Owner:COMCAST CABLE COMM LLC
System for management and processing of electronic vendor mail
ActiveUS8443185B2Office automationBuying/selling/leasing transactionsElectronic documentEnd to end system
A computer-implemented system processes secure electronic documents from one or more content providers in accordance with subscriber instructions has a processor and modules operative within the processor. A monitoring module obtains a provider GUID, a subscriber GUID, and a transaction ID from public metadata associated with a transaction received from a particular content provider. A determination module determines any designees of the subscriber and contact information one or more of the subscriber and any designees. A transaction module distributes a transaction addressed to at least one of the subscriber and any designees. Each distributed transaction includes data that is used for management, tracking, and alerting. Also described is a station for constructing transactions for distribution to subscribers through such a system. An end-to-end system and method are described.
Owner:ECO MAIL DEV
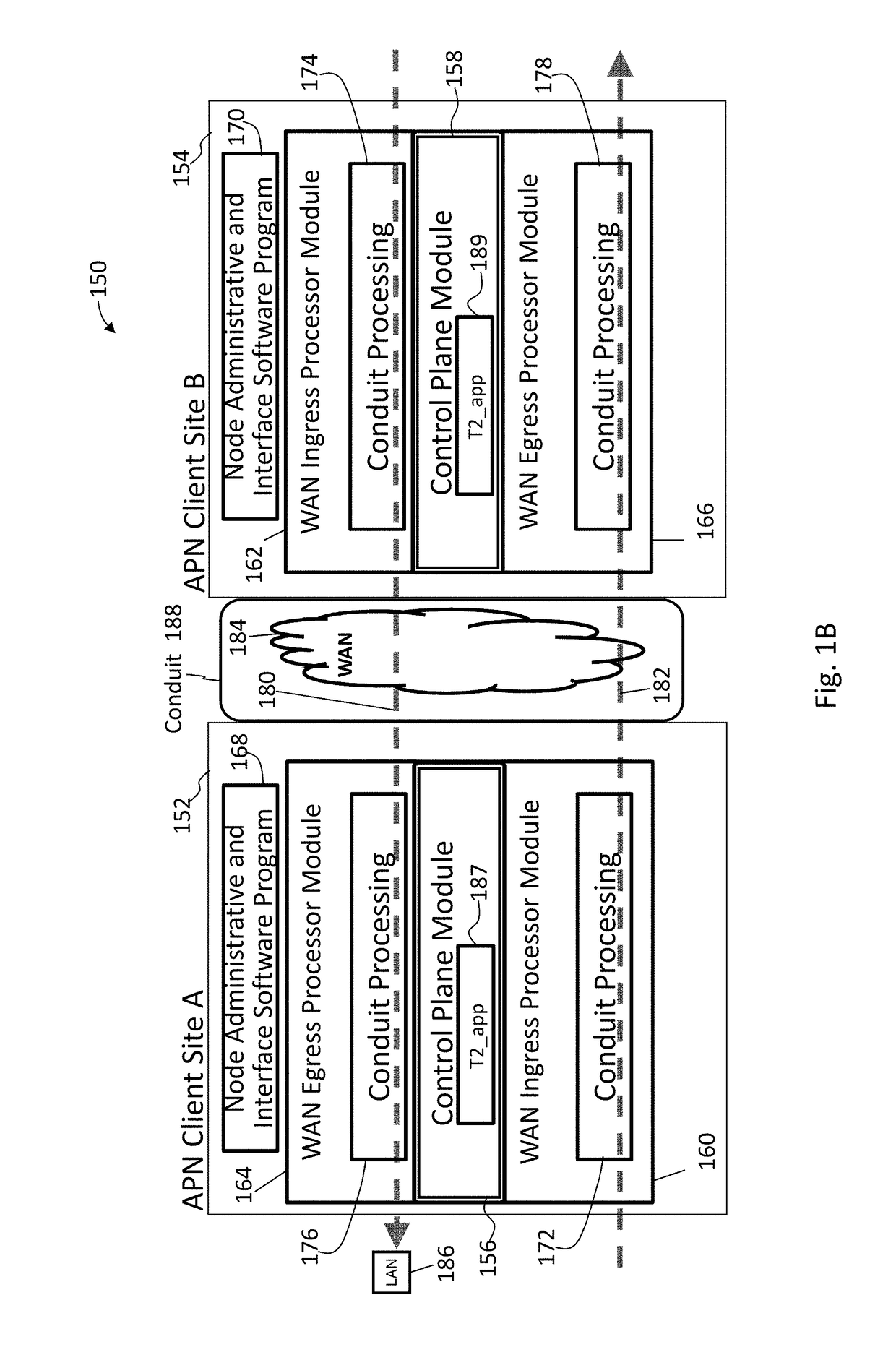
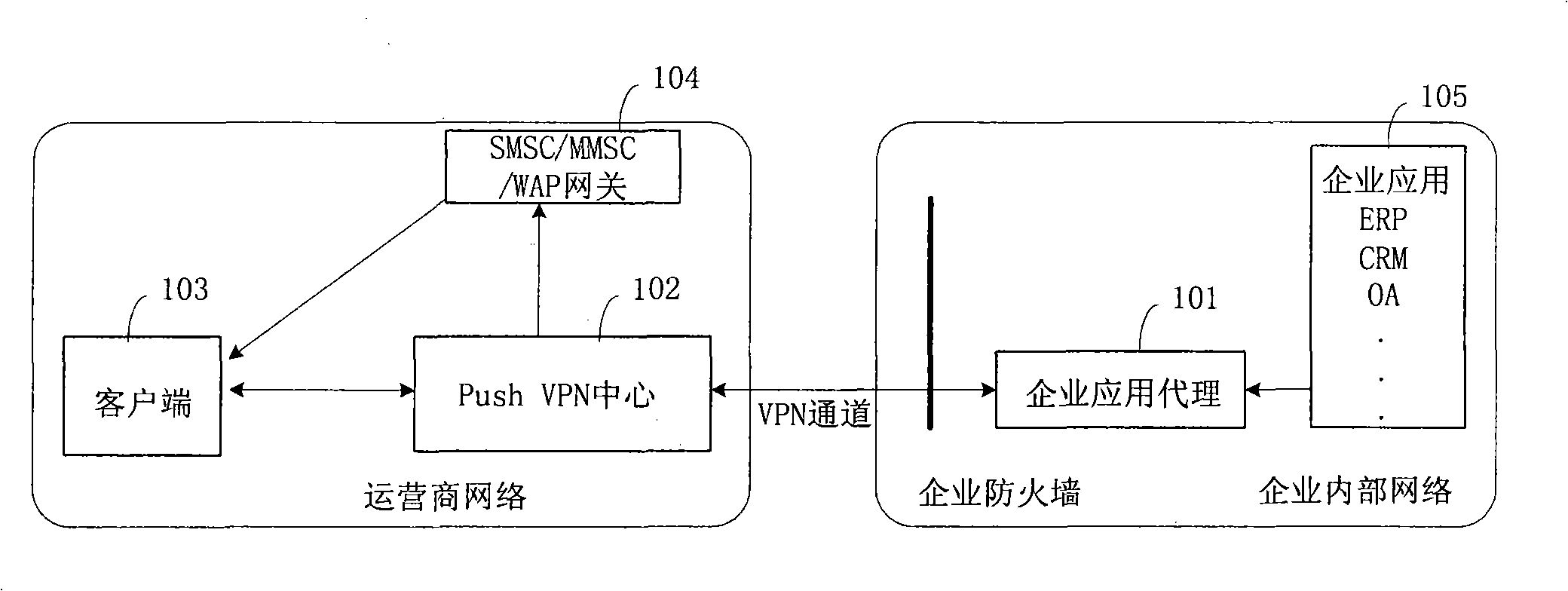
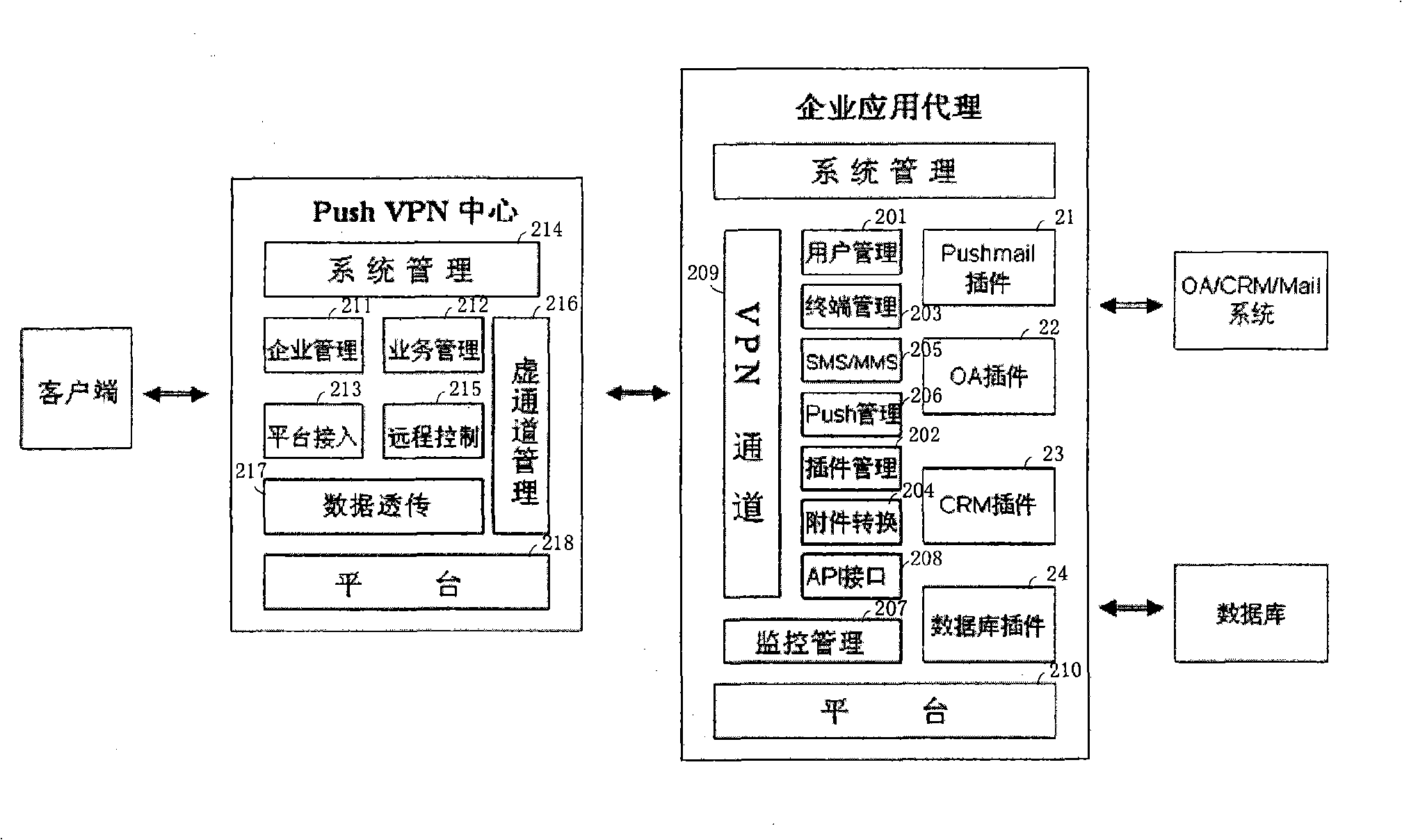
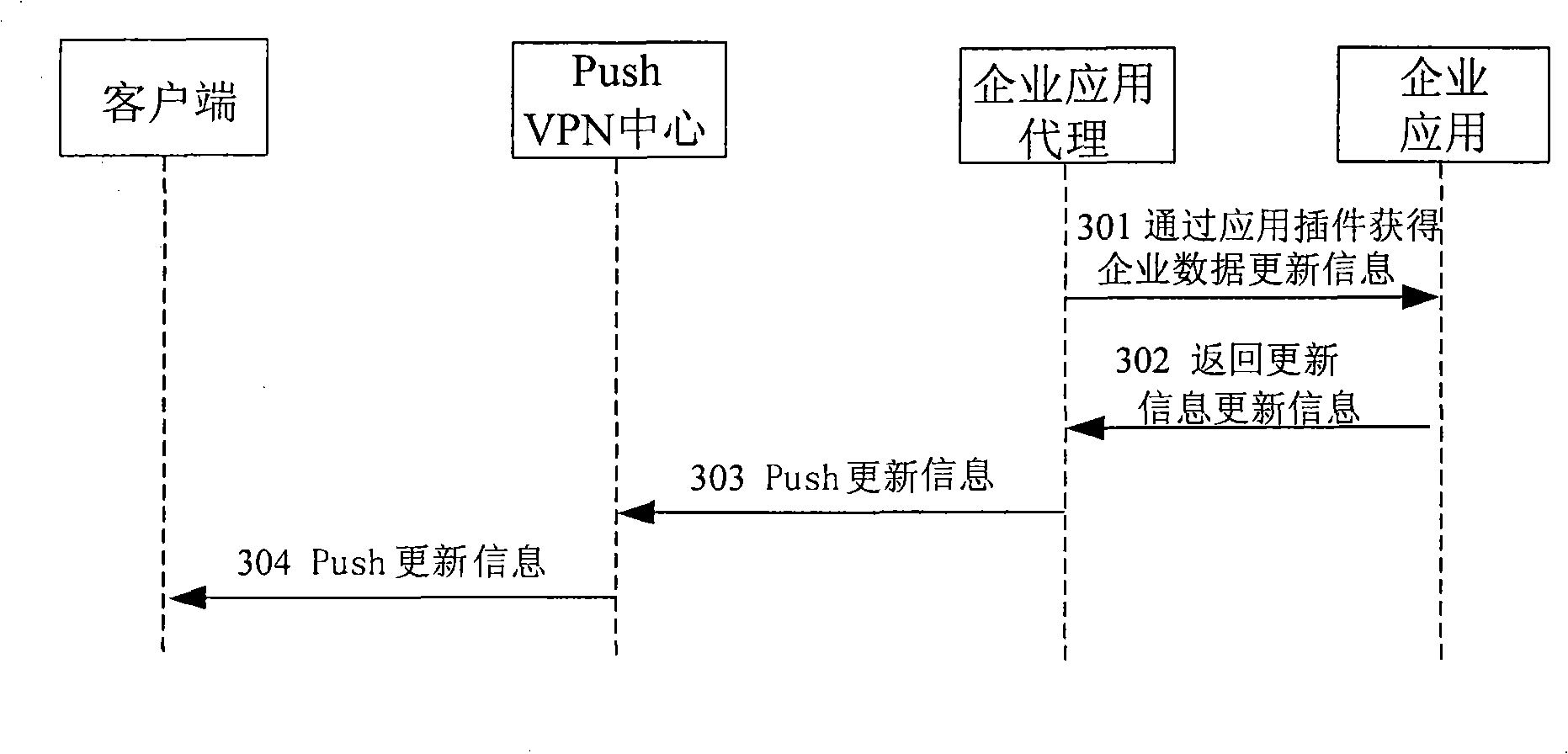
End-to-end system for implementing enterprise application data real time propelling movement and method thereof
ActiveCN101409939AReal-time interactionNetwork topologiesMessaging/mailboxes/announcementsPrivate networkBusiness enterprise
The invention discloses an end-to-end system for realizing real-time push of enterprise application data and a method thereof. An enterprise application proxy device is arranged in an enterprise in-house network, and a push virtual private network (Push VPN) central device is arranged in an operator network; the enterprise application proxy device is used for obtaining internal information of an enterprise application system, performing format conversion processing on the obtained internal information, and pushing the push message Push of the updated information to the Push VPN central device; and the Push VPN central device is used for receiving the push message sent by the enterprise application proxy device by a VPN channel and sending the push message to a user terminal client side by the operator network. The method solves the disadvantage in the present traditional enterprise information mobile schemes, causes a user to be able to automatically and timely push the change of the enterprise in-house data to a user mobile phone terminal without intervention; meanwhile, the mobile phone terminal can also interact with the enterprise in-house data in a real-time manner.
Owner:CHINA TELECOM CORP LTD
Performance Degradation Root Cause Prediction in a Distributed Computing System
InactiveUS20080177698A1Efficient and effective root cause predictionAvoid inaccuraciesDigital data processing detailsReliability/availability analysisEnd systemEnd to end system
A method of identifying at least one resource in a distributed computing system which is a potential root cause of performance degradation of the system includes the steps of: computing operational bounds for the system and operational bounds for at least one resource in the system; comparing current end-to-end system performance with the operational bounds for the system; when the current end-to-end system performance is outside of the operational bounds for the system, comparing current performance of the at least one resource in the system with the operational bounds for the at least one resource; and generating at least one output identifying the at least one resource in the system which is a potential root cause of performance degradation of the system.
Owner:IBM CORP
Teired key communication system and method in support of controlled vendor message processing
ActiveUS8787581B2Key distribution for secure communicationDigital data protectionElectronic documentCommunications system
A computer-implemented system processes secure electronic documents from one or more content providers in accordance with subscriber instructions has a processor and modules operative within the processor. A monitoring module obtains a provider GUID, a subscriber GUID, and a transaction ID from public metadata associated with a transaction received from a particular content provider. A determination module determines any designees of the subscriber and contact information one or more of the subscriber and any designees. A transaction module distributes a transaction addressed to at least one of the subscriber and any designees. Each distributed transaction includes data that is used for management, tracking, and alerting. Also described is a station for constructing transactions for distribution to subscribers through such a system, and management of local-advertising to users of such a system. An end-to-end system and method are described.
Owner:ECO MAIL DEV
Enabling storage area network component migration
InactiveUS8341251B2Simplify migration stepAvoid excessive errorDigital computer detailsData resettingComponent MigrationStorage area network
Enabling storage area network (SAN) component migration are provided. An end-to-end systems management console, referred to as the hardware migration assistant, is provided to simplify the migration steps for a SAN administrator to replace key SAN components. The hardware migration assistant provides a single interface suitable for stepping the SAN administrator through the reconfiguring task faster and with fewer sources of error than the known distributed manual process. The hardware migration assistant of the illustrative embodiments provides an interface through which a user may specify a type of SAN component that is being replaced and identifies the particular SAN components that are being replaced. The hardware migration assistant provides a knowledge base for guiding the user through the replacement operation and the reconfiguring of the SAN components, including the new SAN components, based on the previous configuration of the replaced components.
Owner:INT BUSINESS MASCH CORP
Systems and methods for an integrated system for visualizing, simulating, modifying and 3D printing 3D objects
ActiveUS20180144516A1Accurate representationReduce data volumeImage enhancementReconstruction from projectionEnd to end systemEngineering
Methods and systems for visualizing, simulating, modifying and / or 3D printing objects are provided. The system is an end-to-end system that can take as input 3D objects and allow for various levels of user intervention to produce the desired results.
Owner:3D SYST INC
Web-based general Internet product data comparison test method and apparatus
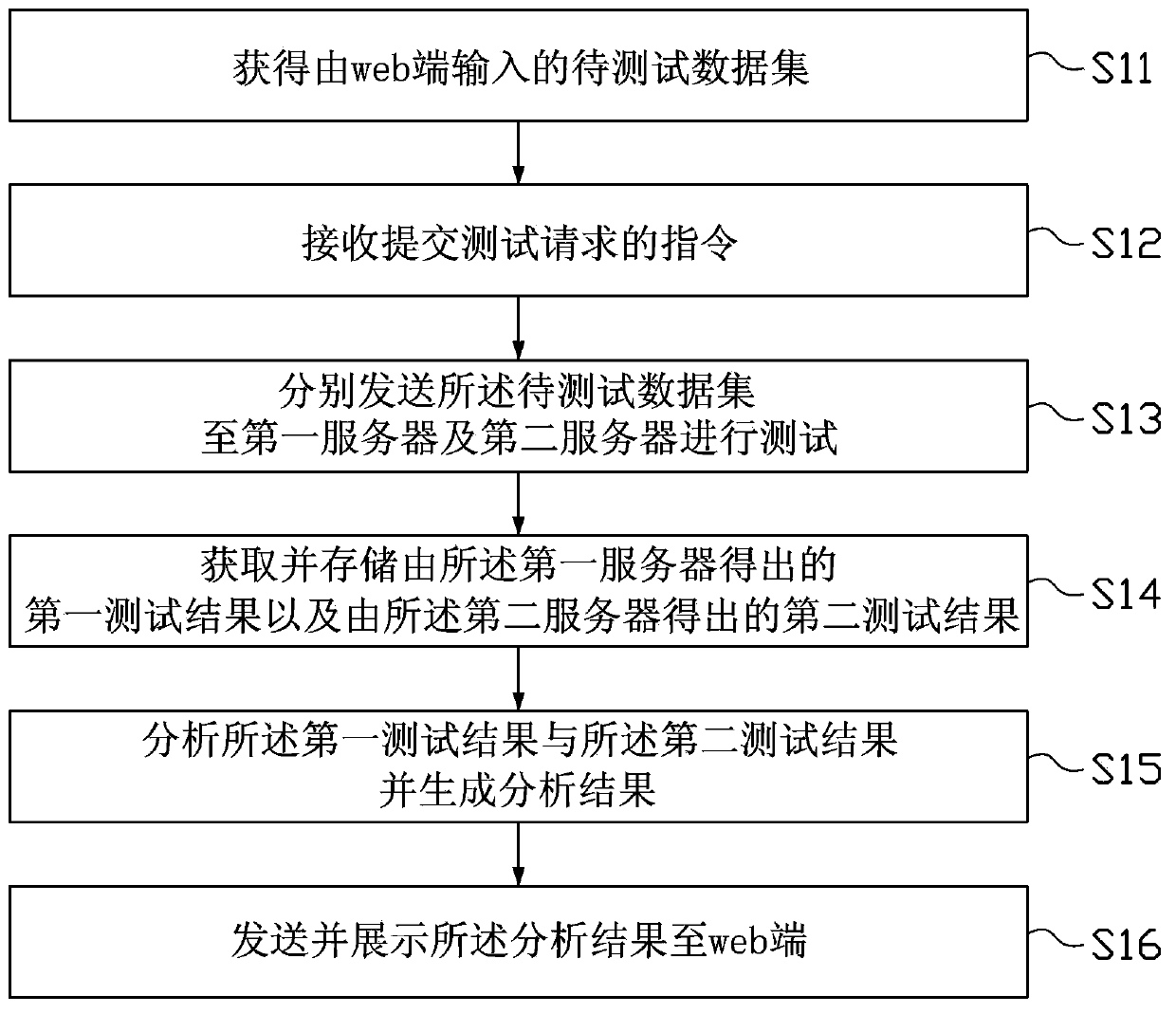
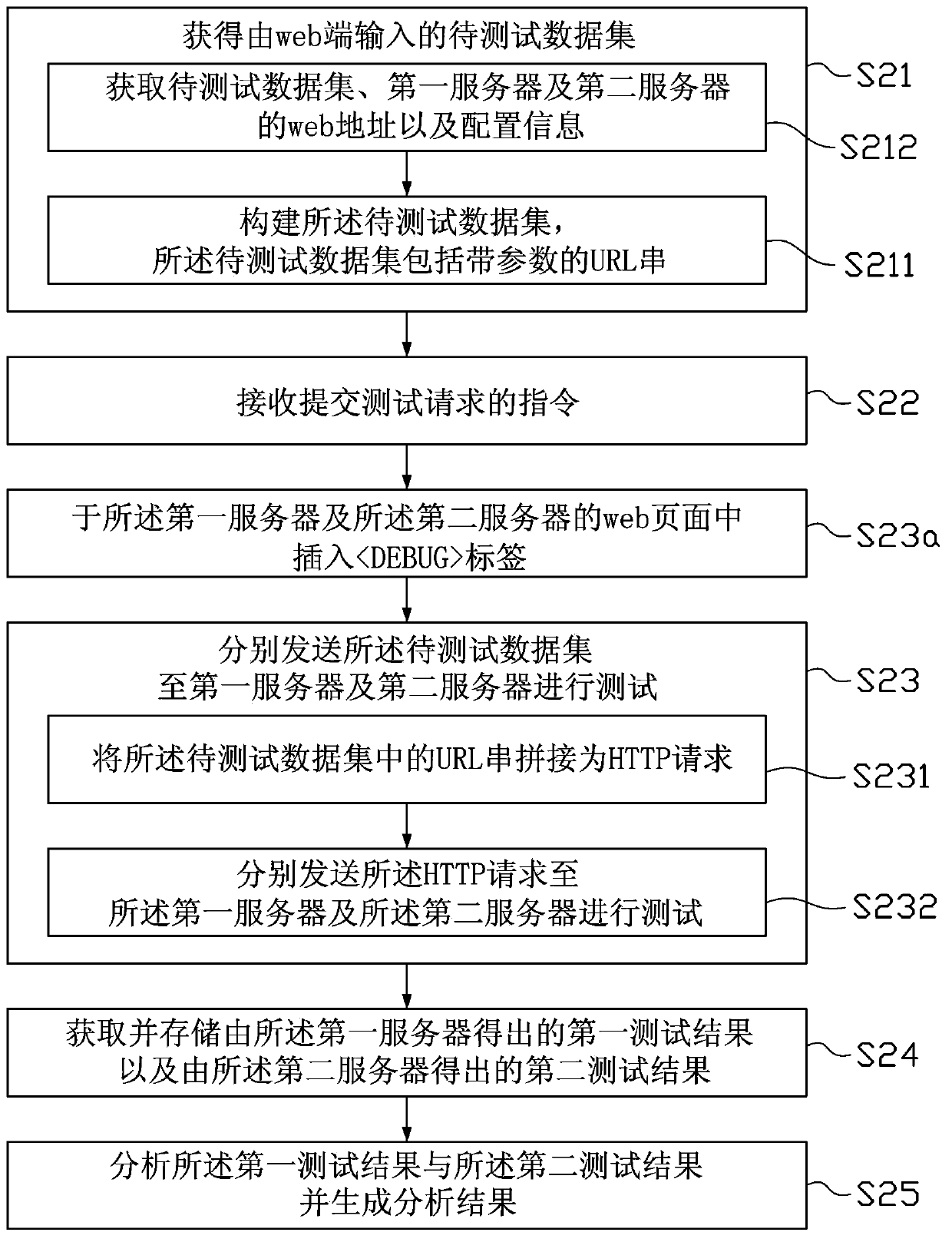
The invention provides a web-based general Internet product data comparison test method and a web-based general Internet product data comparison test apparatus. The web-based general Internet product data comparison test method comprises the following steps that: a data set to be tested inputted by a web end is obtained; an instruction for submitting a test request is received; the data set to be tested is transmitted to a first server and a second server respectively so as to be tested; first test results acquired by the first server and second test results acquired by the second server are obtained and saved; and the first test results and the second test results are analyzed, and analysis results are generated; and the analysis results are transmitted to and displayed at the web end. With the web-based general Internet product data comparison test method of the invention adopted, end-to-end system test can be realized; batched data sets to be tested can be quickly tested; differences between two servers of the same system can be quickly found and summarized; result comparison and analysis can be performed; time consumption can be decreased; easiness in use can be realized; and manpower can be saved.
Owner:SHENZHEN SHI JI GUANG SU INFORMATION TECH
Technical electronic discovery action model
ActiveUS8645401B2Database queryingDigital data processing detailsElectronic discoveryEnd to end system
Owner:COX COMMUNICATIONS
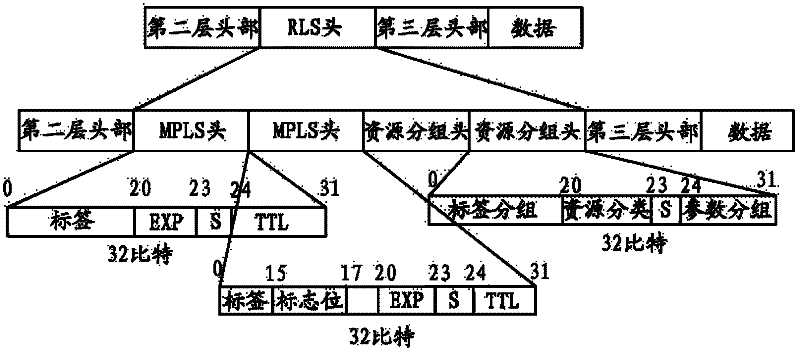
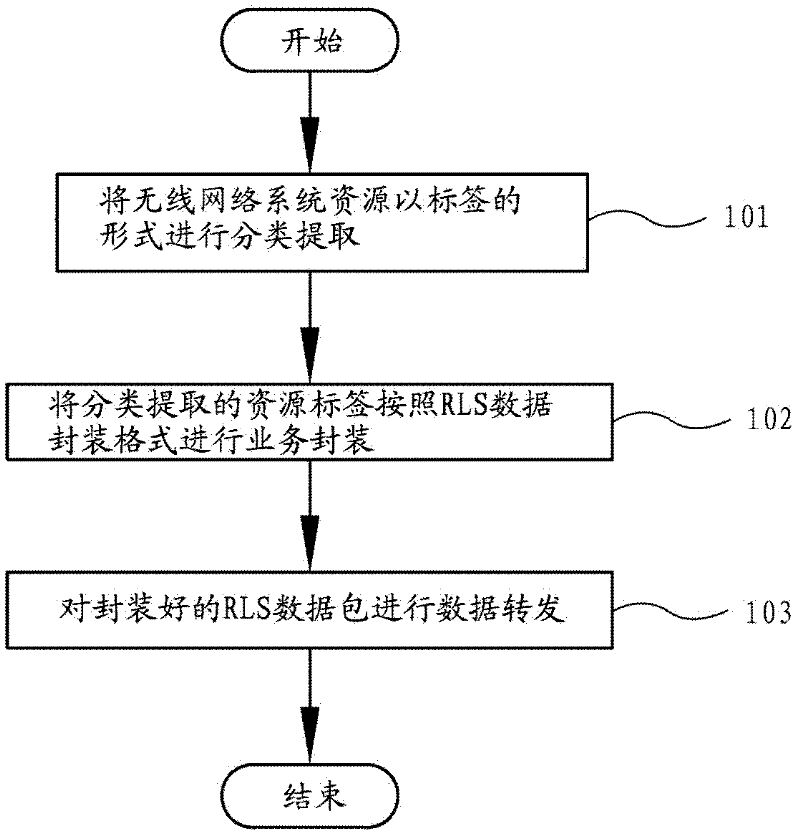
Wireless network system resource label switch method
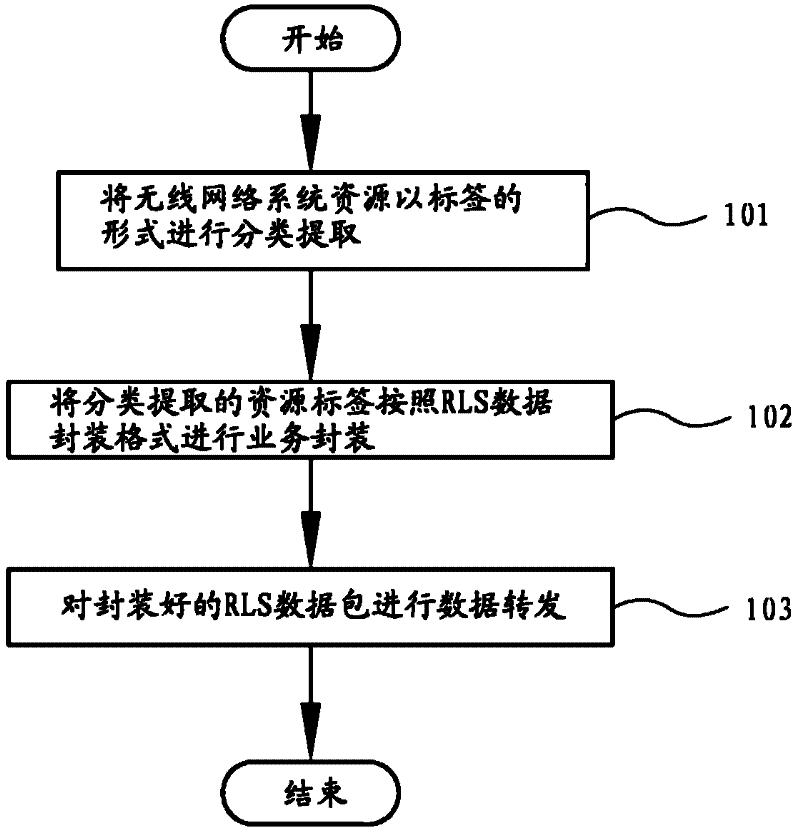
InactiveCN102244896AImprove performance parametersKnow quickly and accuratelyNetwork traffic/resource managementInformation sharingEnd to end system
The invention provides a wireless network system resource label switch method. The method comprises the following steps of: classifying and extracting the wireless network system resources in the label manner; performing service packaging on the classified and extracted resource labels according to a resource label switch data packaging format; and performing data forwarding on the packaged resource label switch data packets, wherein the resource label switch data packaging format is a resource label switch shim inserted between a header part of a data link layer and a header part of a network layer; the resource label switch shim comprises one or more multi-protocol label switch headers and one or more resource packet headers; and the classified and extracted resource labels are packaged in the one or more resource packet headers. The wireless network system resources can be divided into three types of resource classification labels, namely a wireless network end system, an access point and a wireless network channel system. According to the method disclosed by the invention, wireless network end-to-end system resource information can be shared; and the end system can be used for improving network system performance parameters according to the shared information by adopting an independent or cooperative strategy.
Owner:BEIJING INFORMATION SCI & TECH UNIV
Systems and Methods for Producing Biochar-Based Products
ActiveUS20170040083A1Electrode thermal treatmentElectrode melt handlingEnd to end systemProcess engineering
An end-to-end system / process for producing advantageous end products from a raw biomass feedstock is provided. The process includes steps for enhancing biomaterial feedstock, biochar generation and end-product fabrication. The method steps may be employed in selecting, treating and handling biomass materials and their additive inputs to tailor their end performance. Each operative step in the process may be employed to enhance the overall effectiveness of biochar generation and use. Charring furnace design and operational parameters are provided that generate desirable biochar material for various applications, including specifically fabrication of ultra-capacitor electrodes and electric battery components.
Owner:CARBONCHARGE TECH LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com