Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
739 results about "Enterprise application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
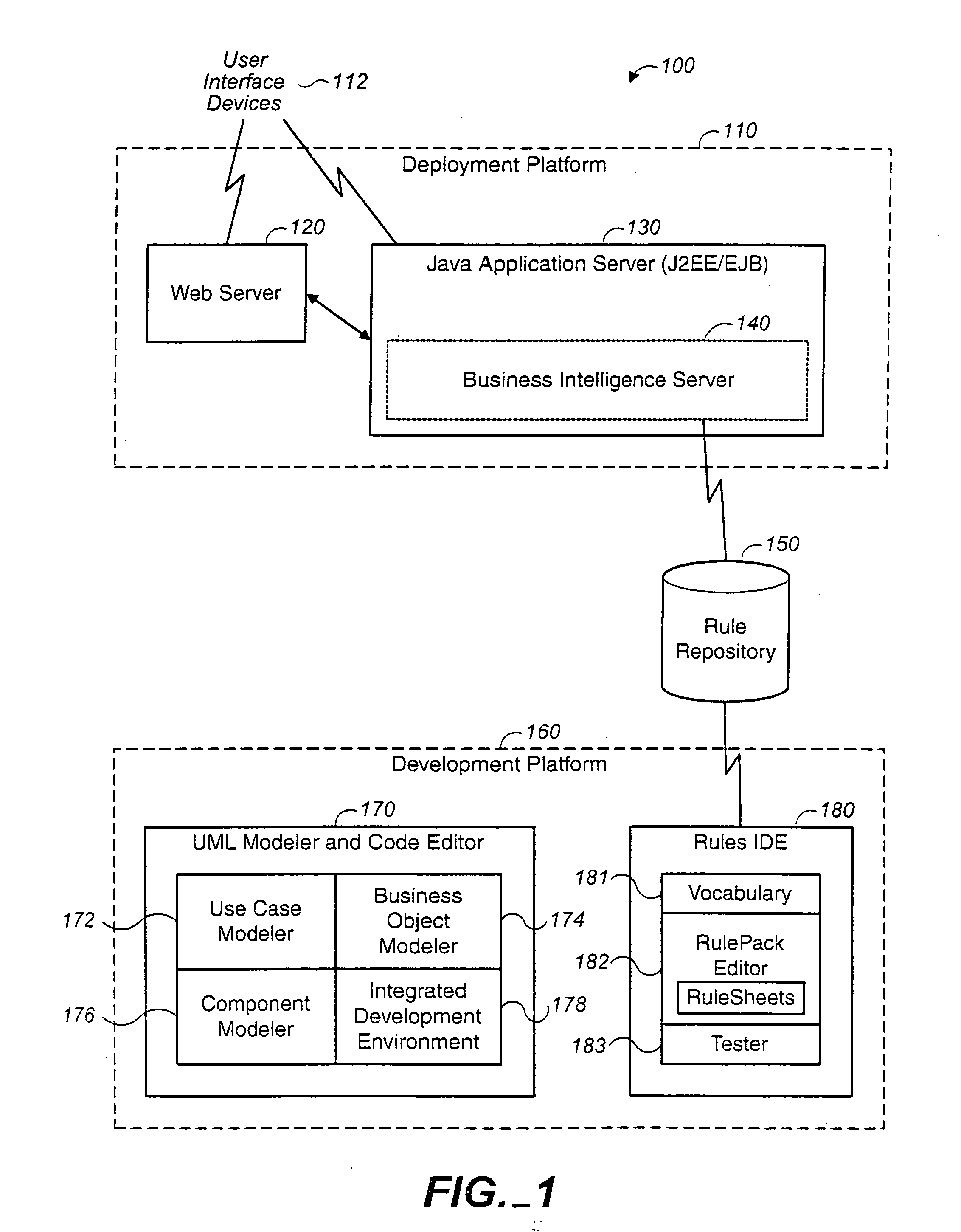
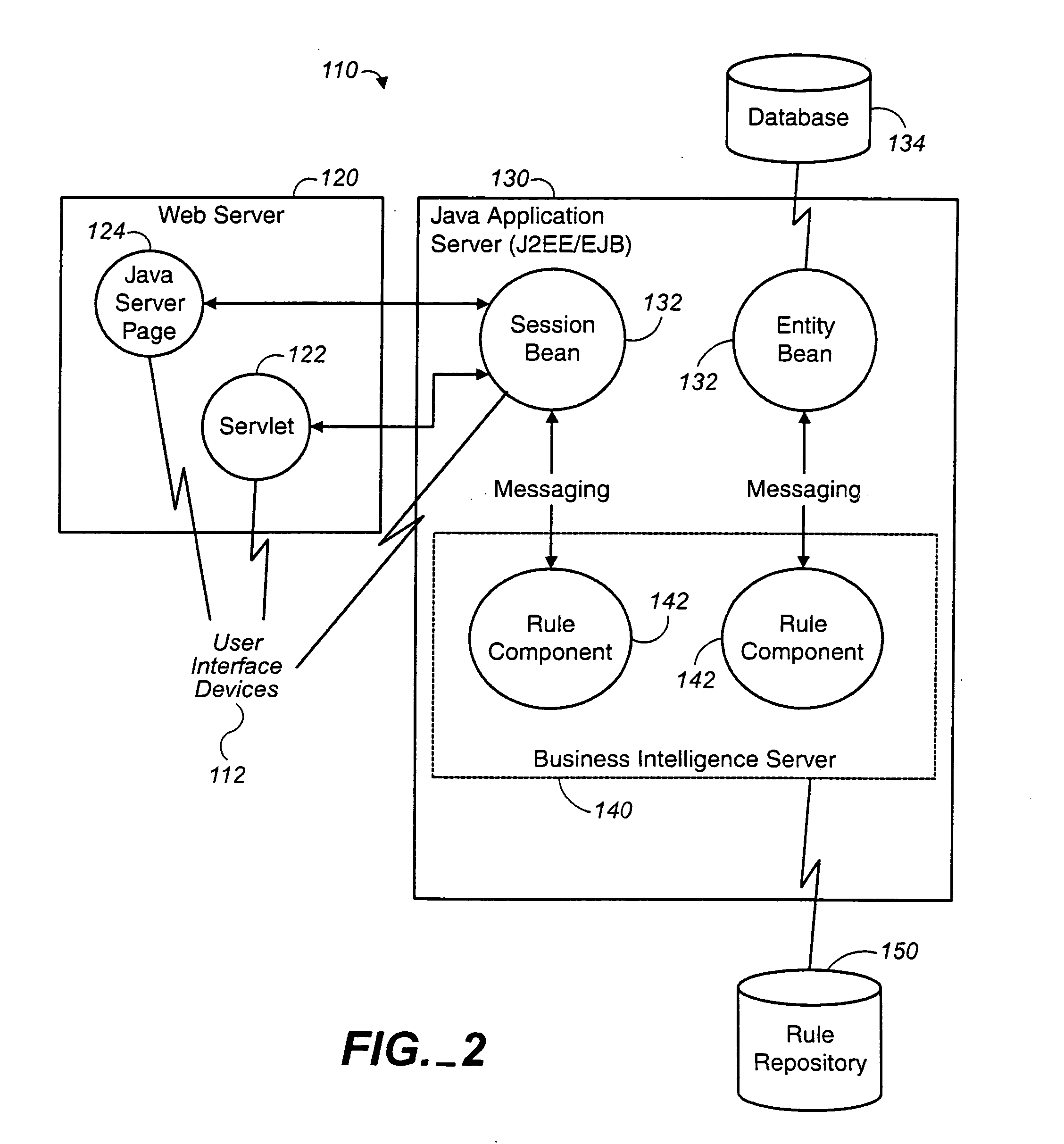
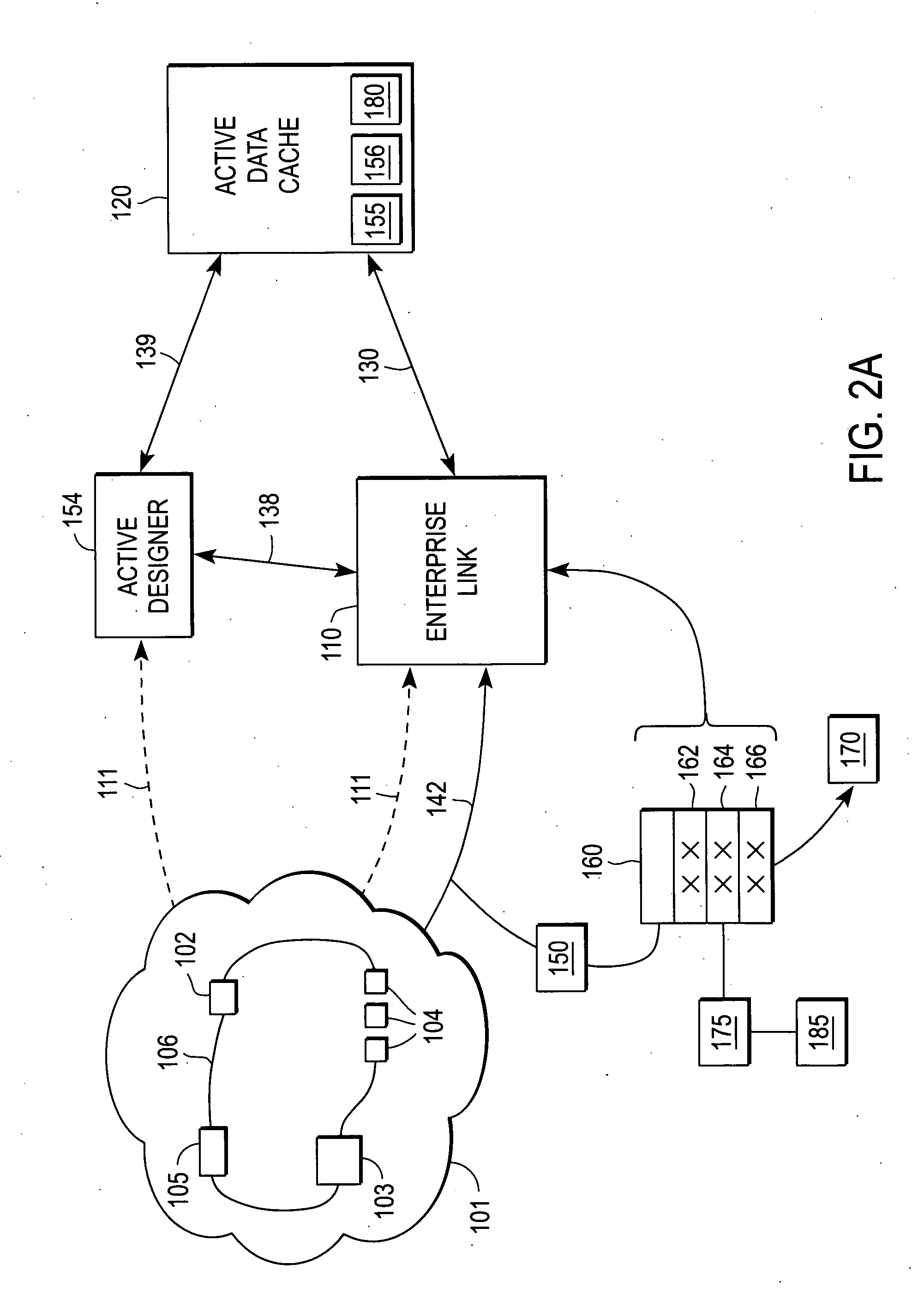
Policy-Based Application Management
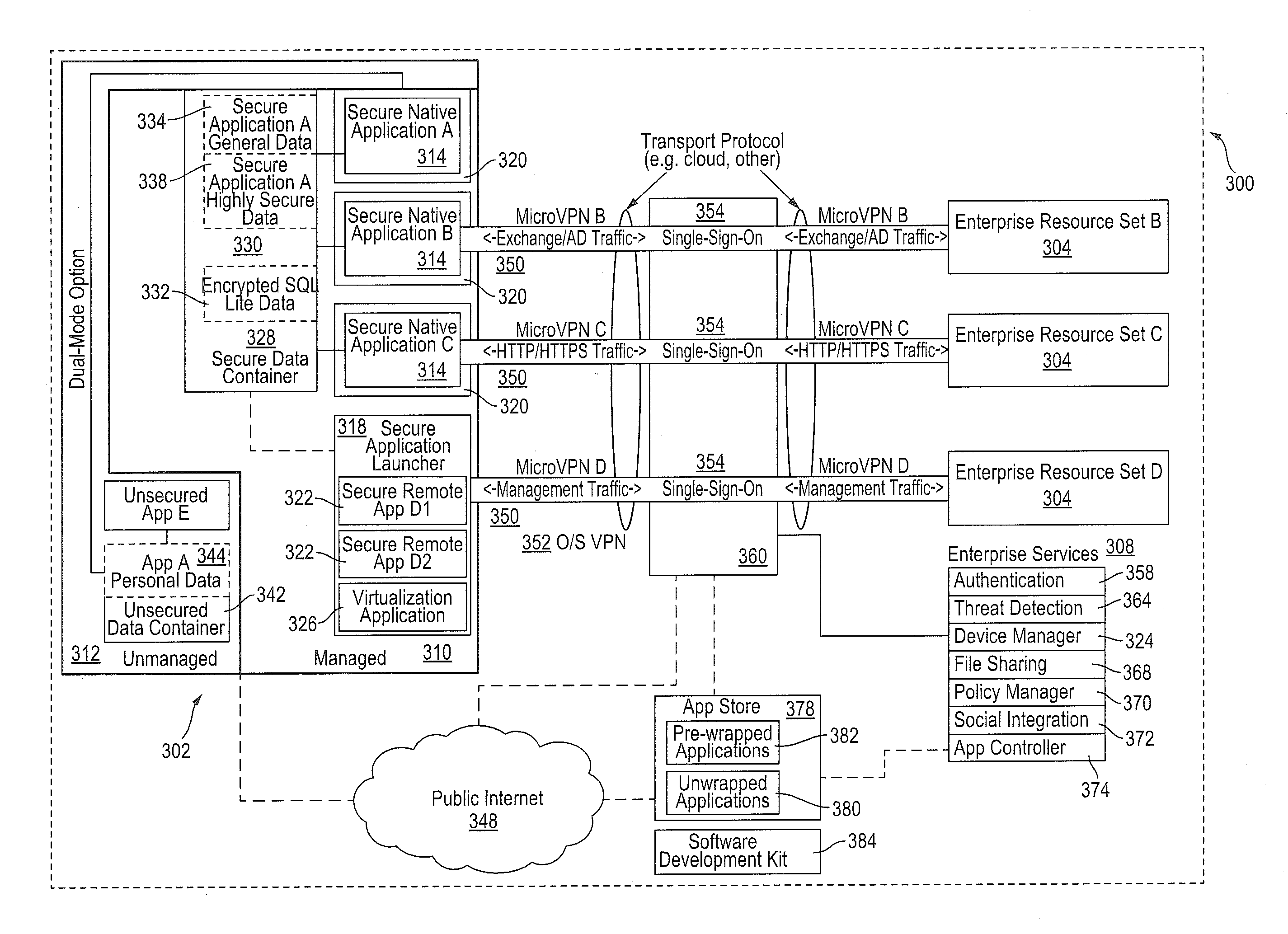
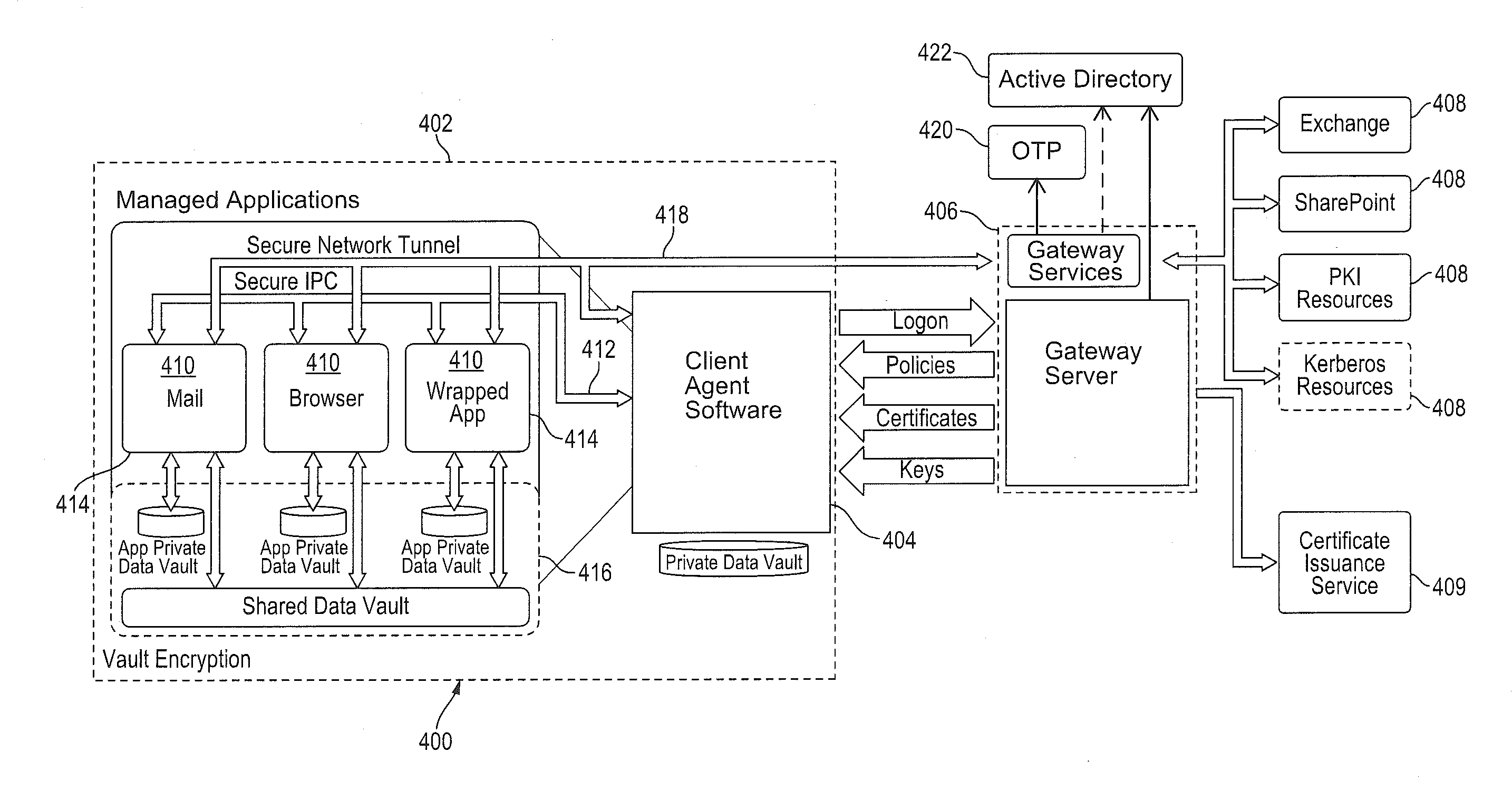
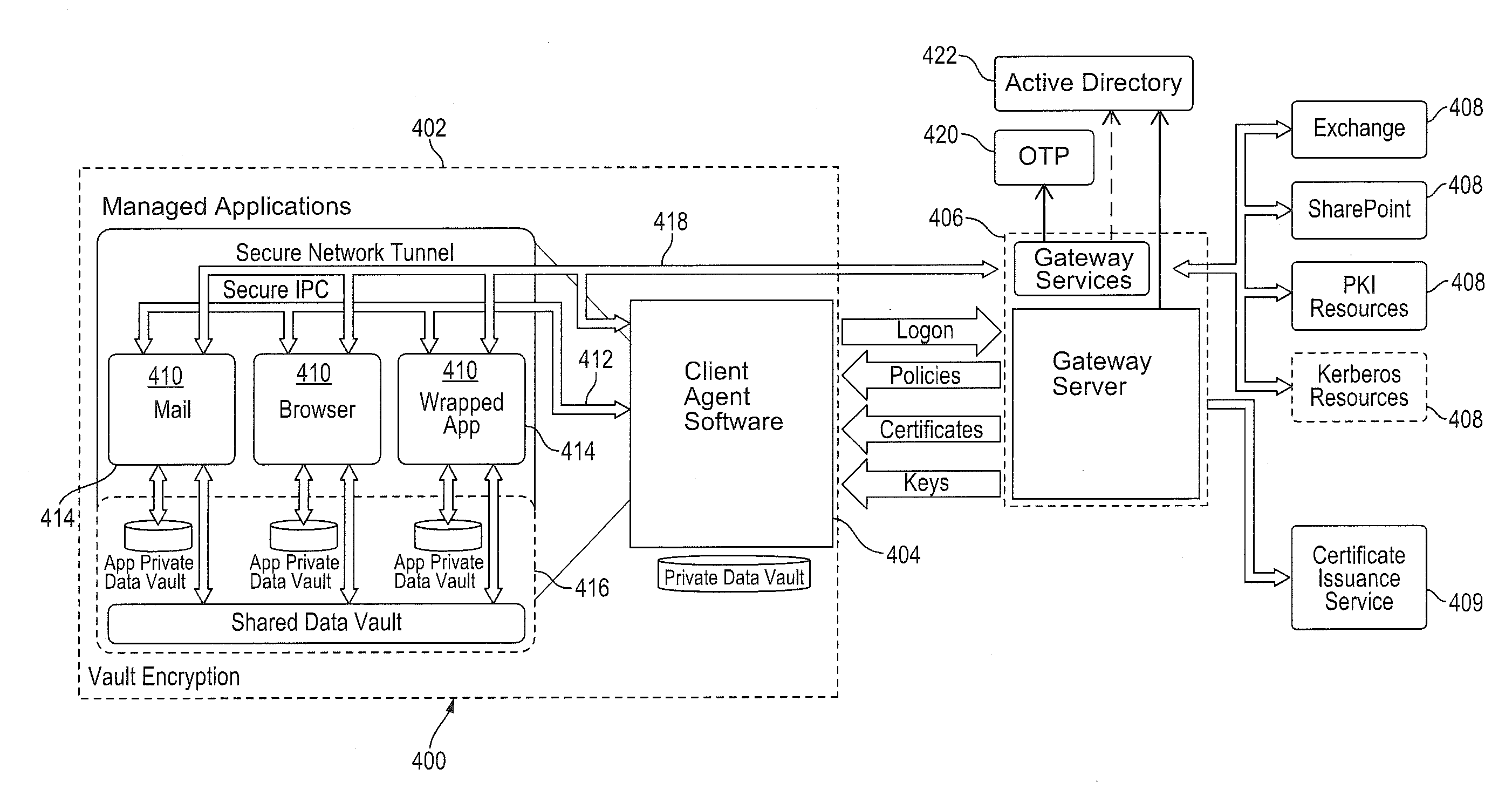
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Policy-Based Application Management
ActiveUS20140032691A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
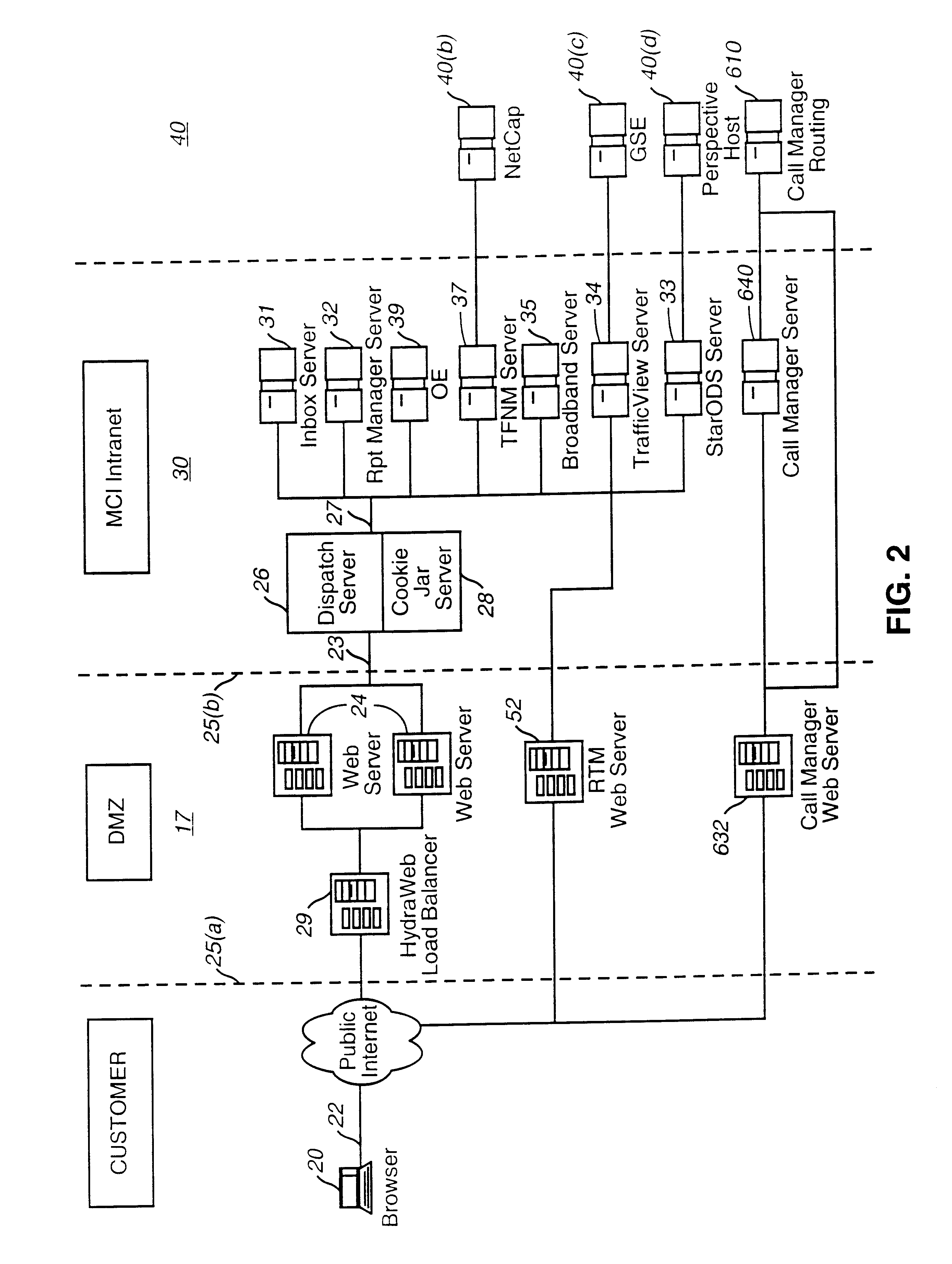
Integrated customer web station for web based call management
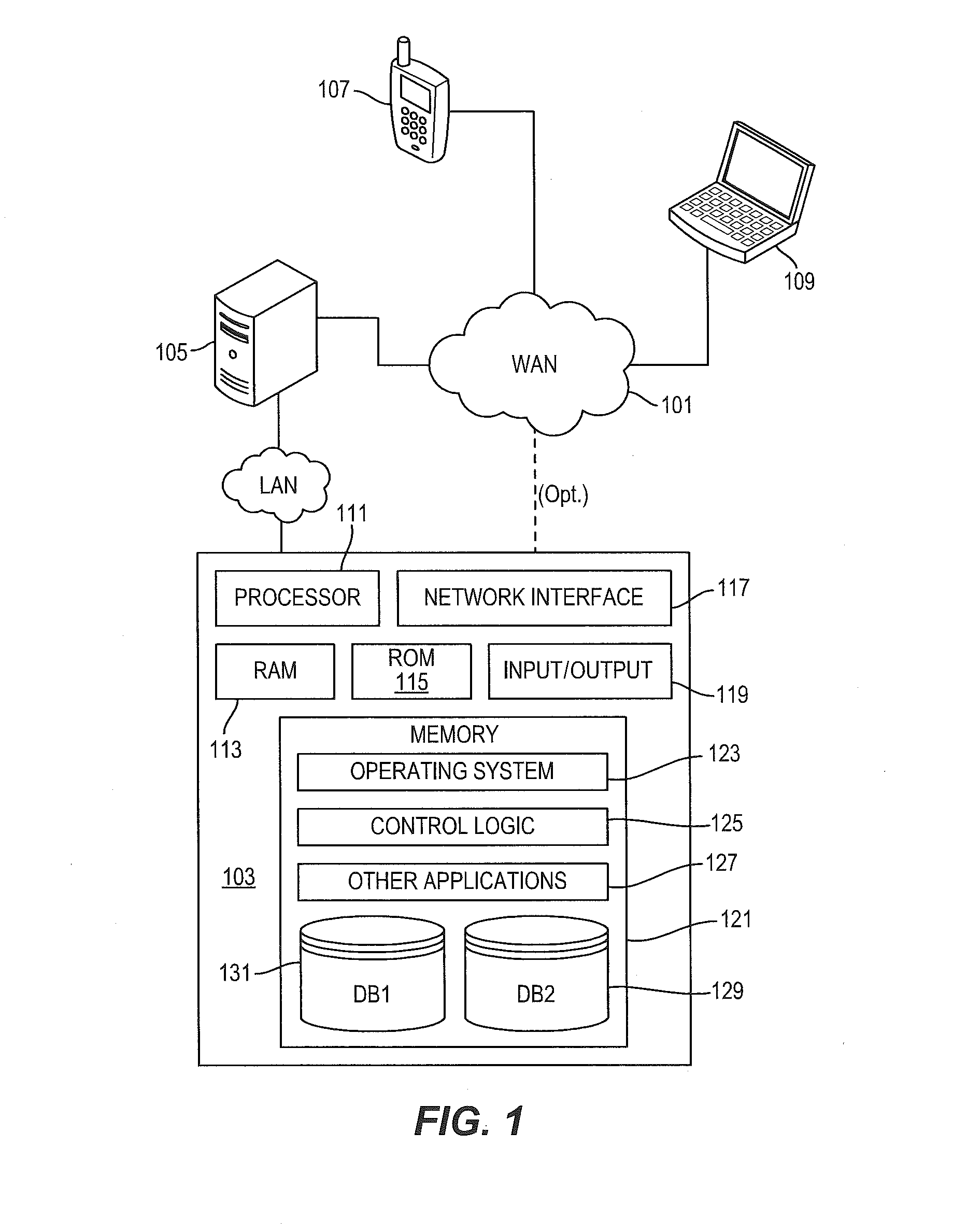
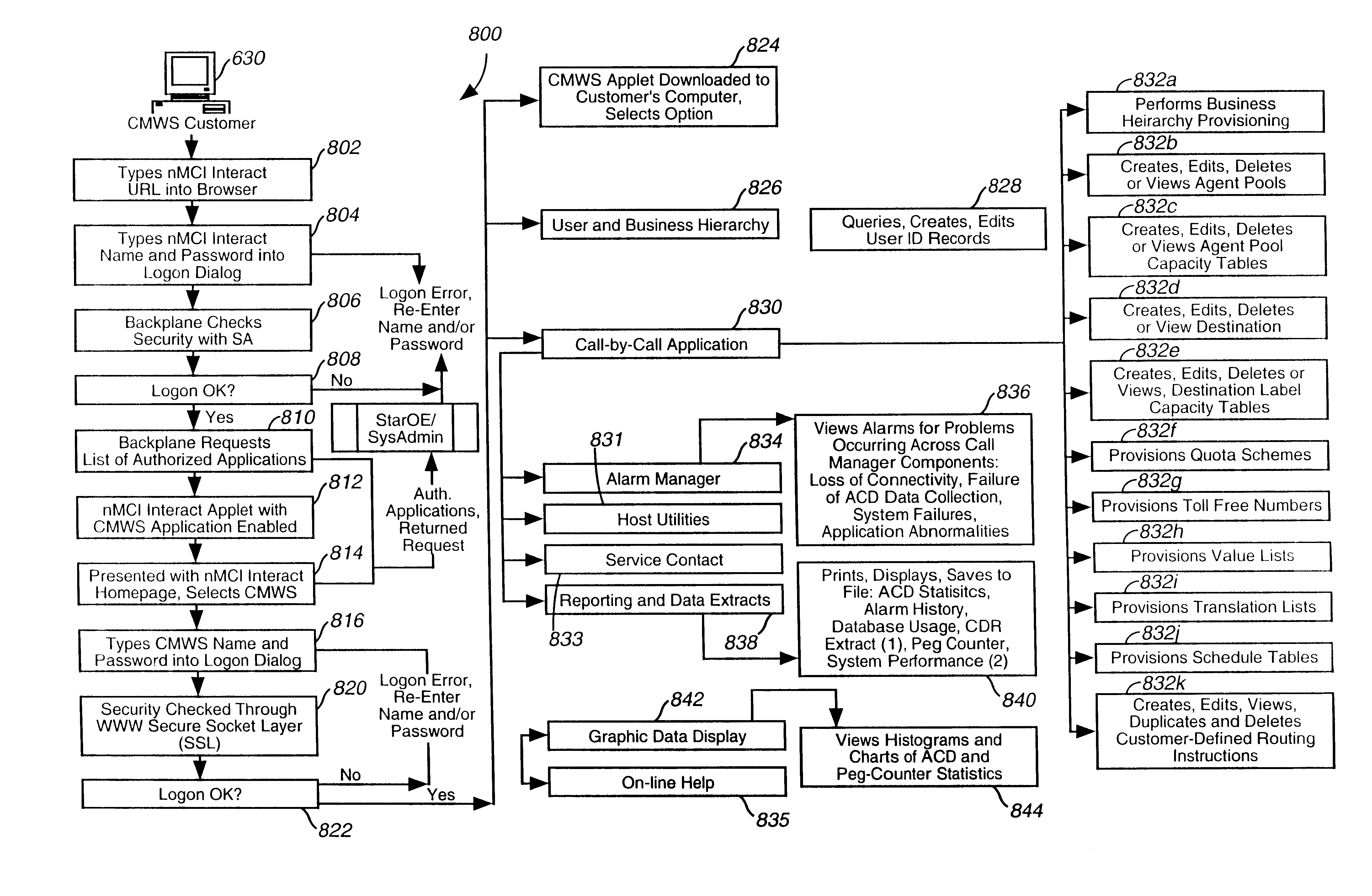
A Web-based call routing management workstation application which allows authorized customers to control toll free routing and monitor call center status. An architecture including one or more web servers located in a firewalled demilitarized zone (DMZ) as communications medium between the customer workstations at the customer sites and the enterprise back-end applications providing the call routing management services, provides a secure infrastructure for accessing the enterprise applications via the otherwise insecure public Internet. The present invention enables creation and management of call by call routing rules by a customer with a workstation having an Internet access and a supported Web browser. The customized rules may be tested and / or debugged via the Web-enabled workstation, using a debugger / tester which runs the routing rules under a simulated environment. In addition, customers may provision hierarchies for their business; create, modify or delete agent pools; manipulate capacity tables; and define quota schemes, value lists and schedule tables, all at the customer site via the Web-enabled workstation. The present invention also enables the customers to view near real-time displays of call center ACD statistics and peg counts based on routing rules, as well as, run provisioning and statistical reports on provisioning and statistical data and also to extract the data for further analysis. Additionally, the present invention supports foreign language and branding features on a graphical user interface. An infrastructure is provided which enables secure initiation, acquisition, and presentation of the call manager functionalities to customers from any computer workstation having a web browser and located anywhere in the world.
Owner:VERIZON PATENT & LICENSING INC
Secure container for protecting enterprise data on a mobile device
ActiveUS20140006347A1Digital data information retrievalDecompilation/disassemblyDocumentation procedureApplication server
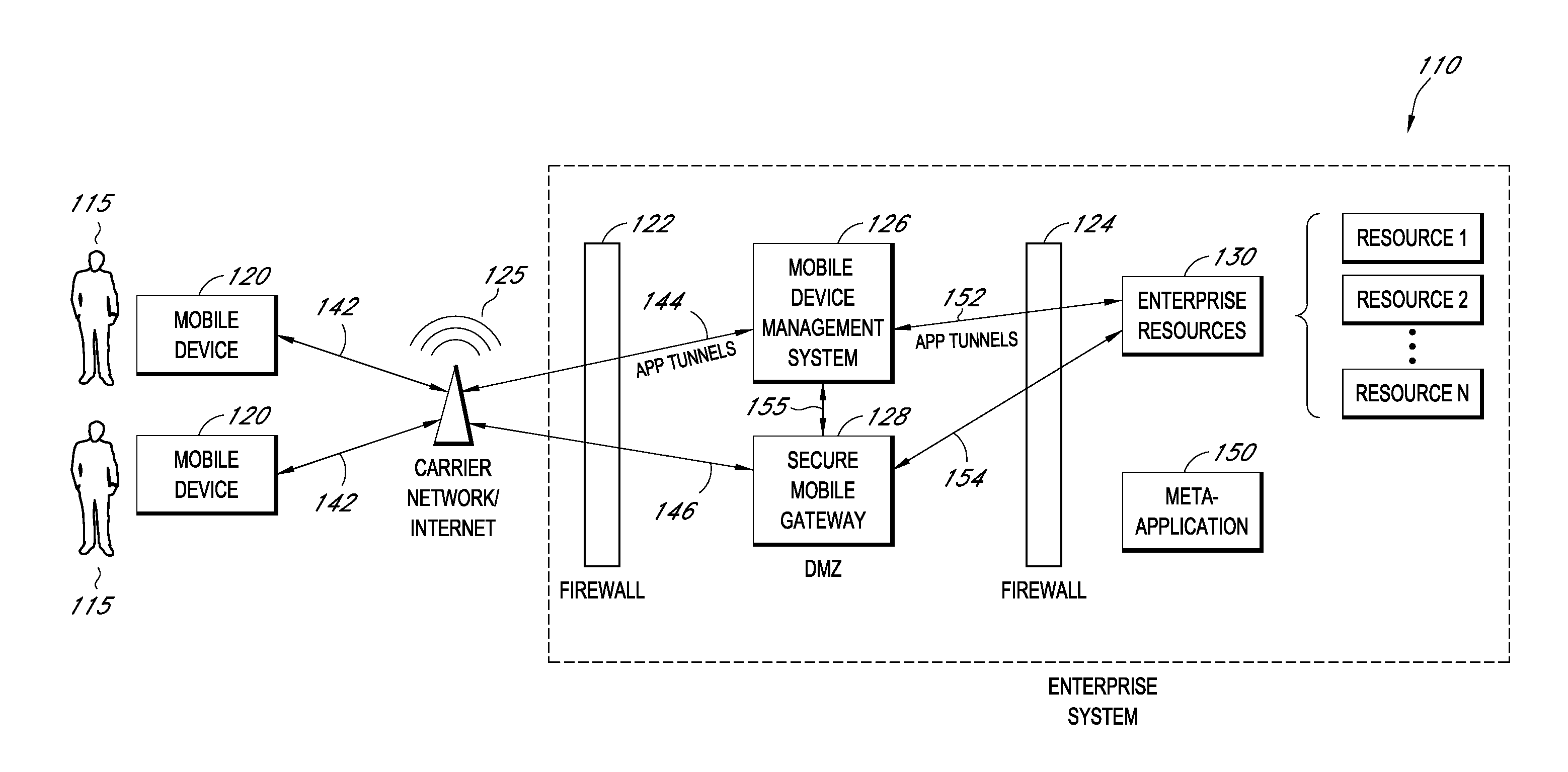
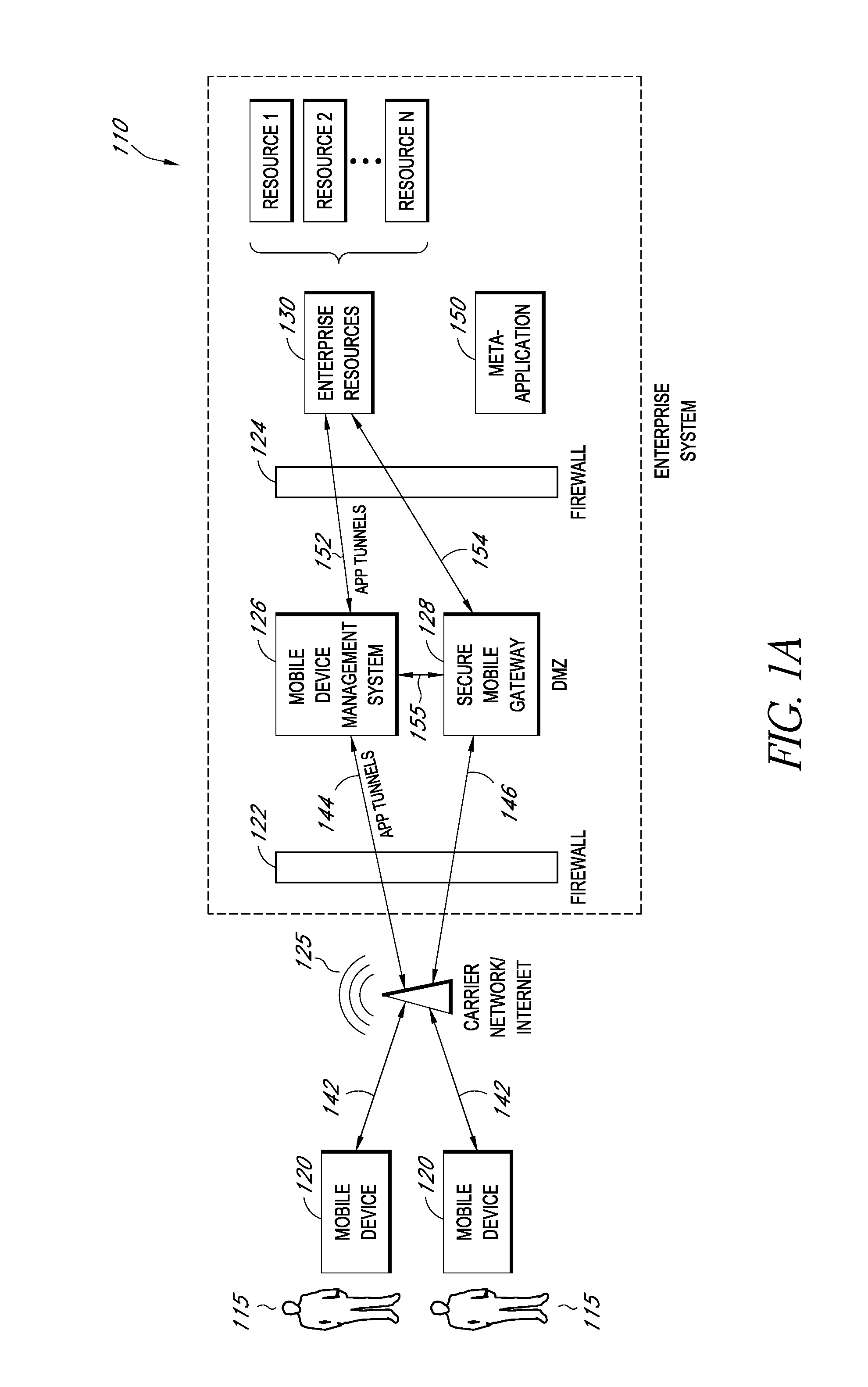
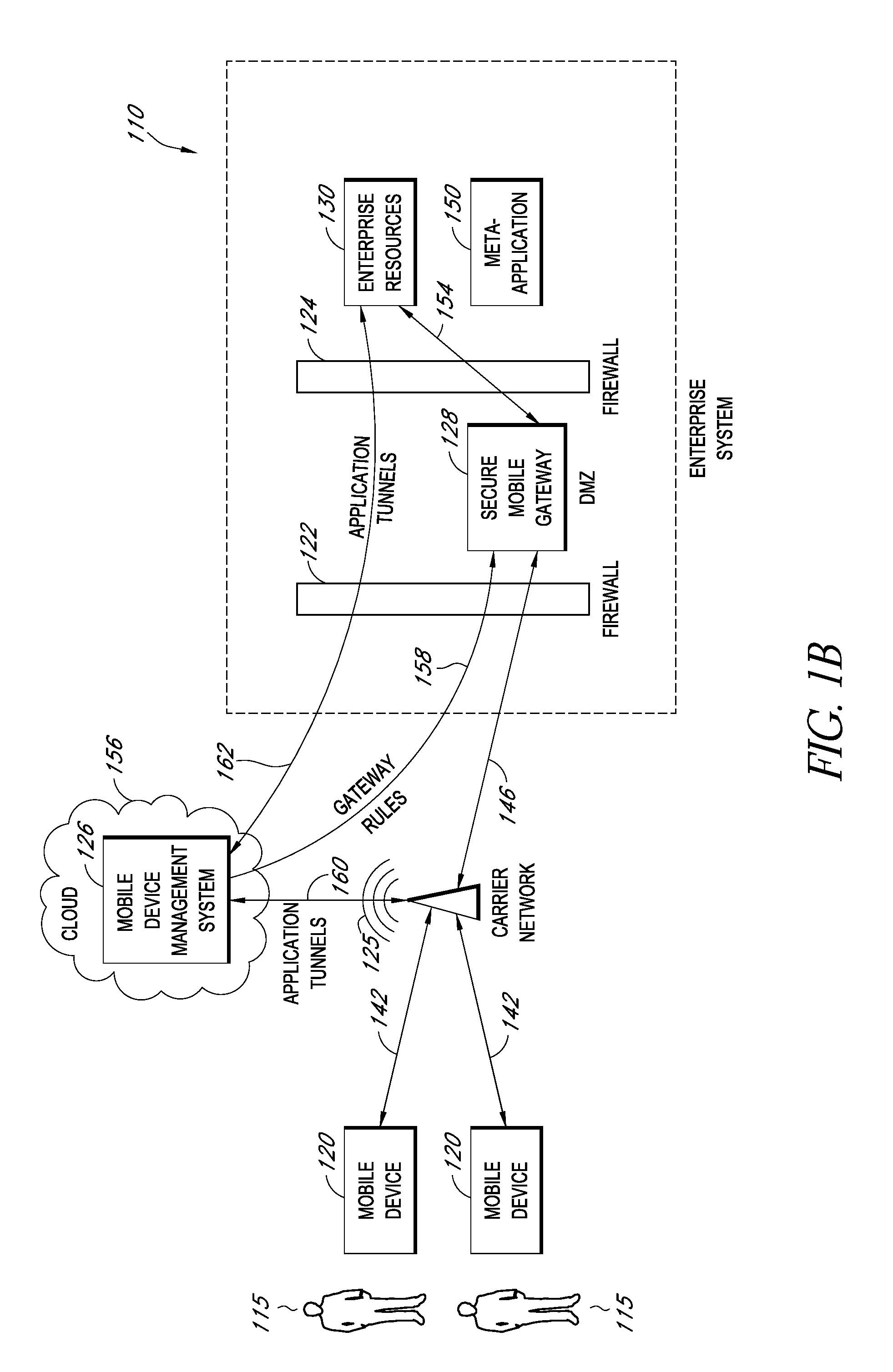
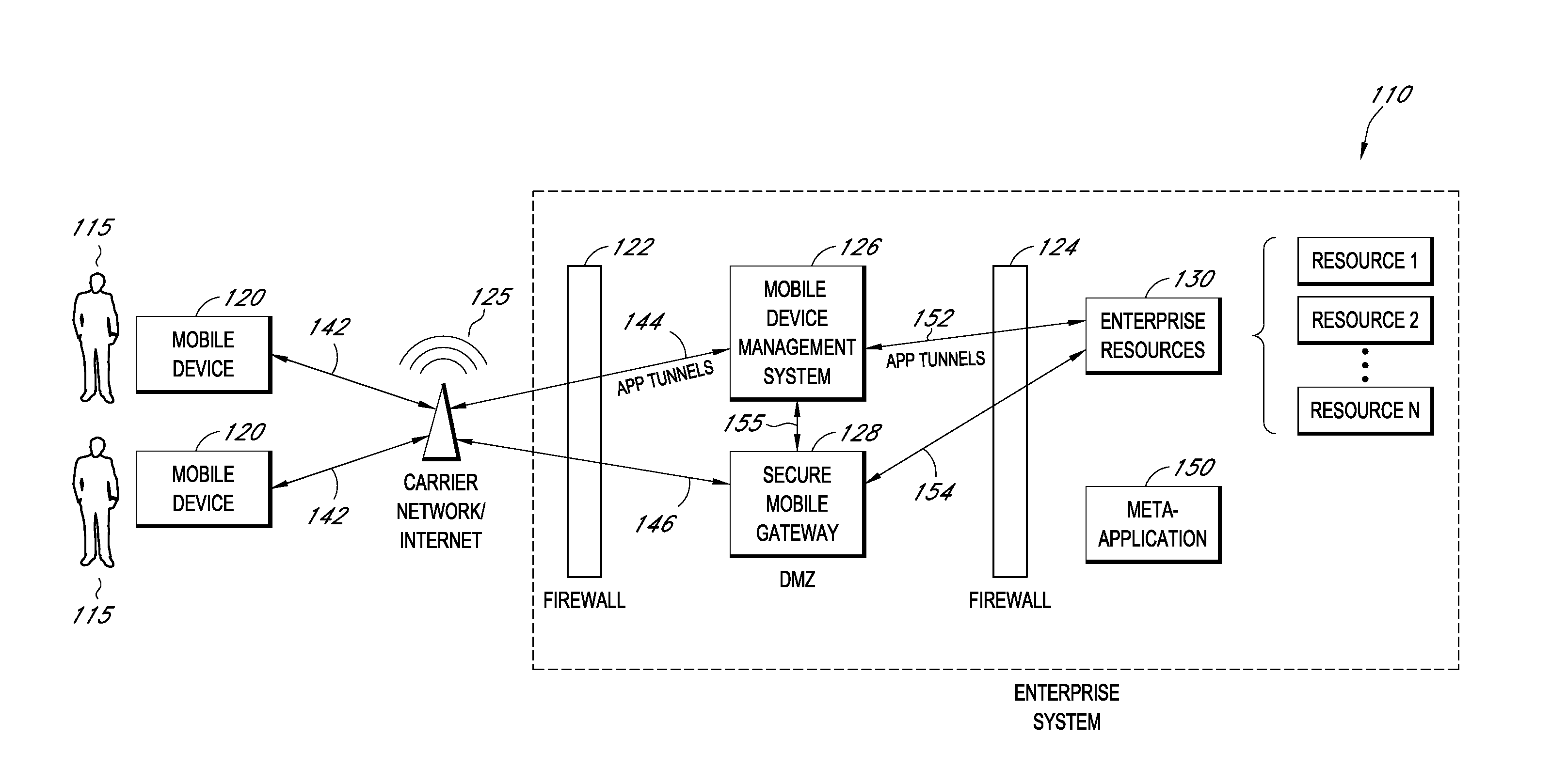
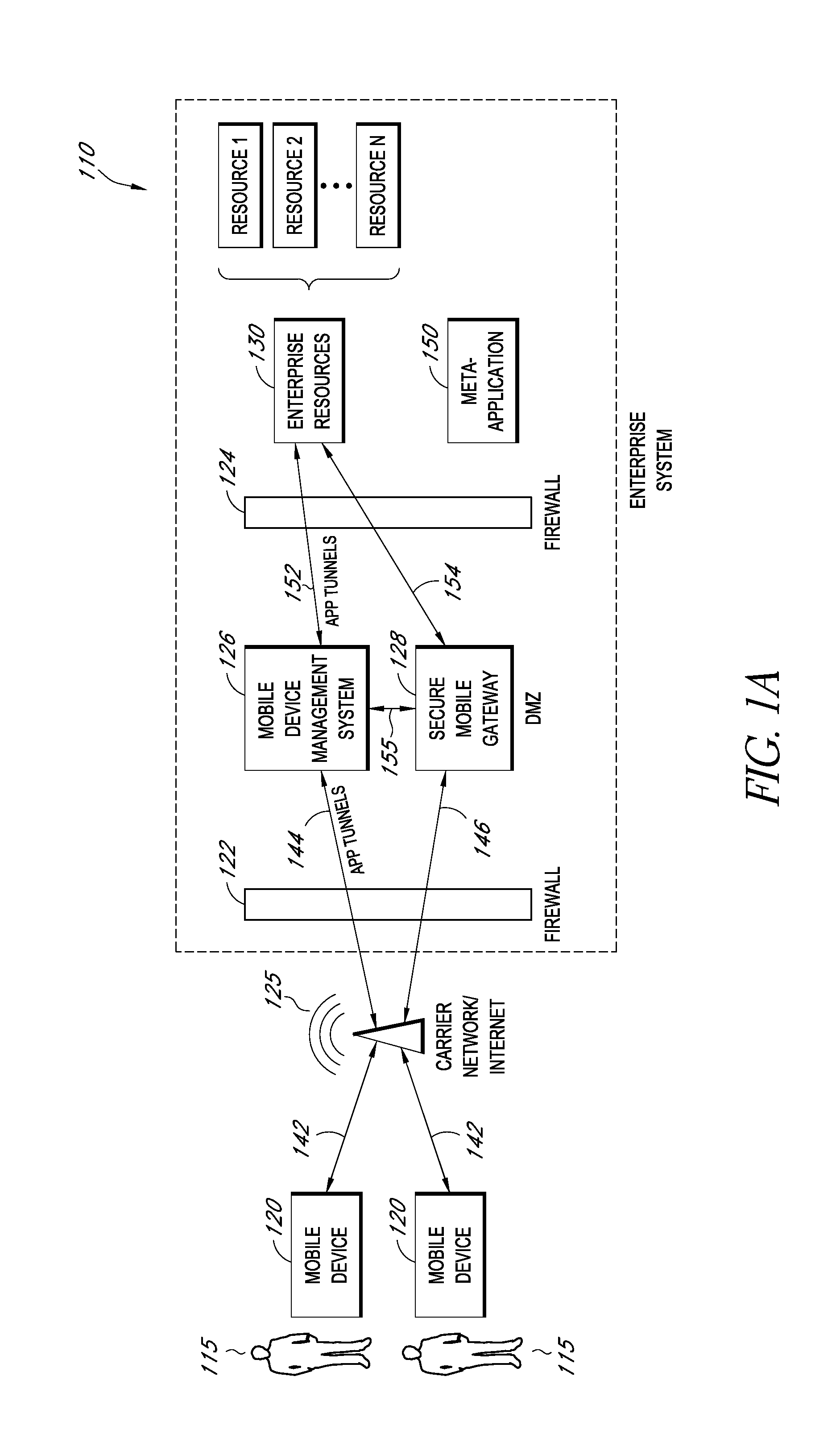
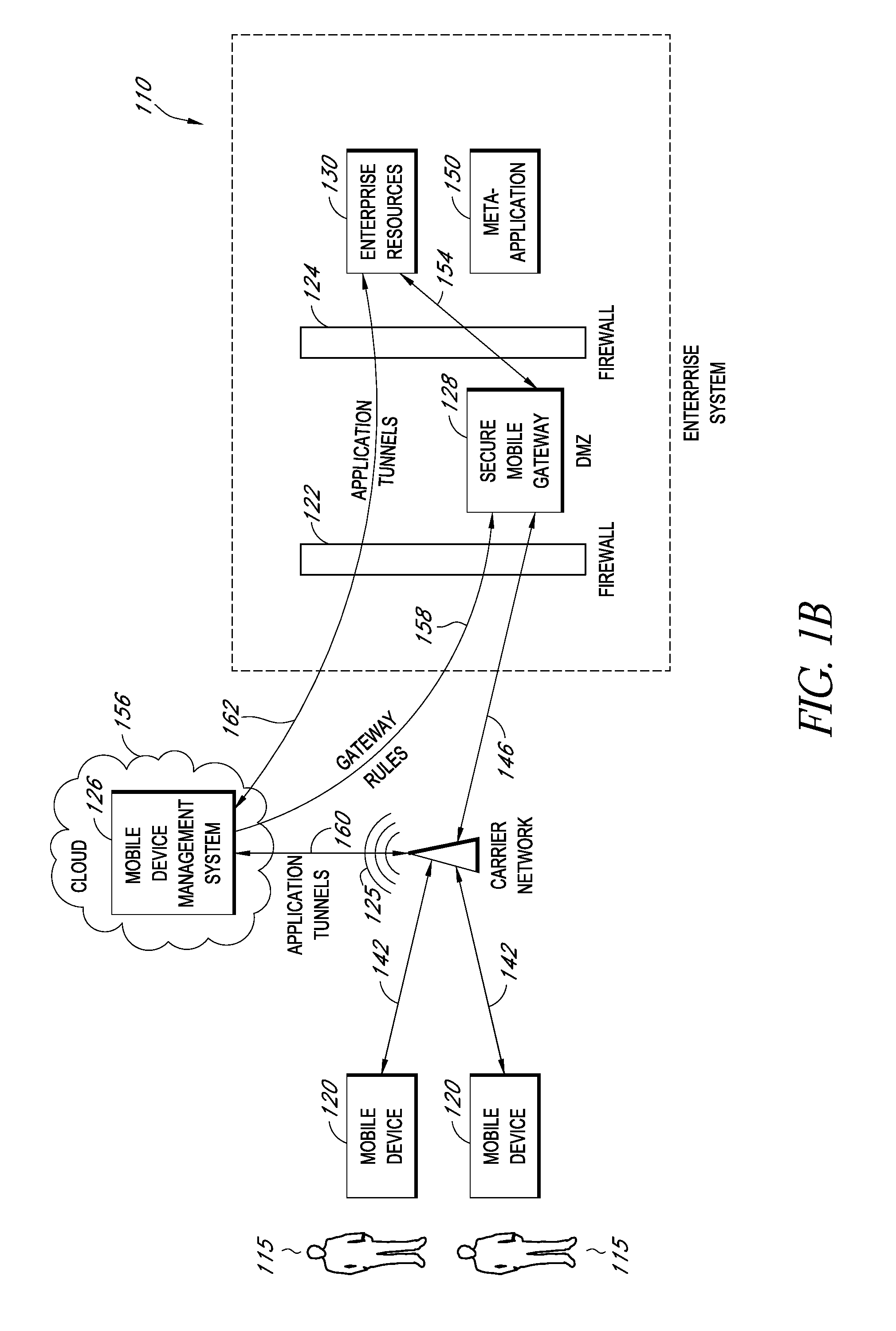
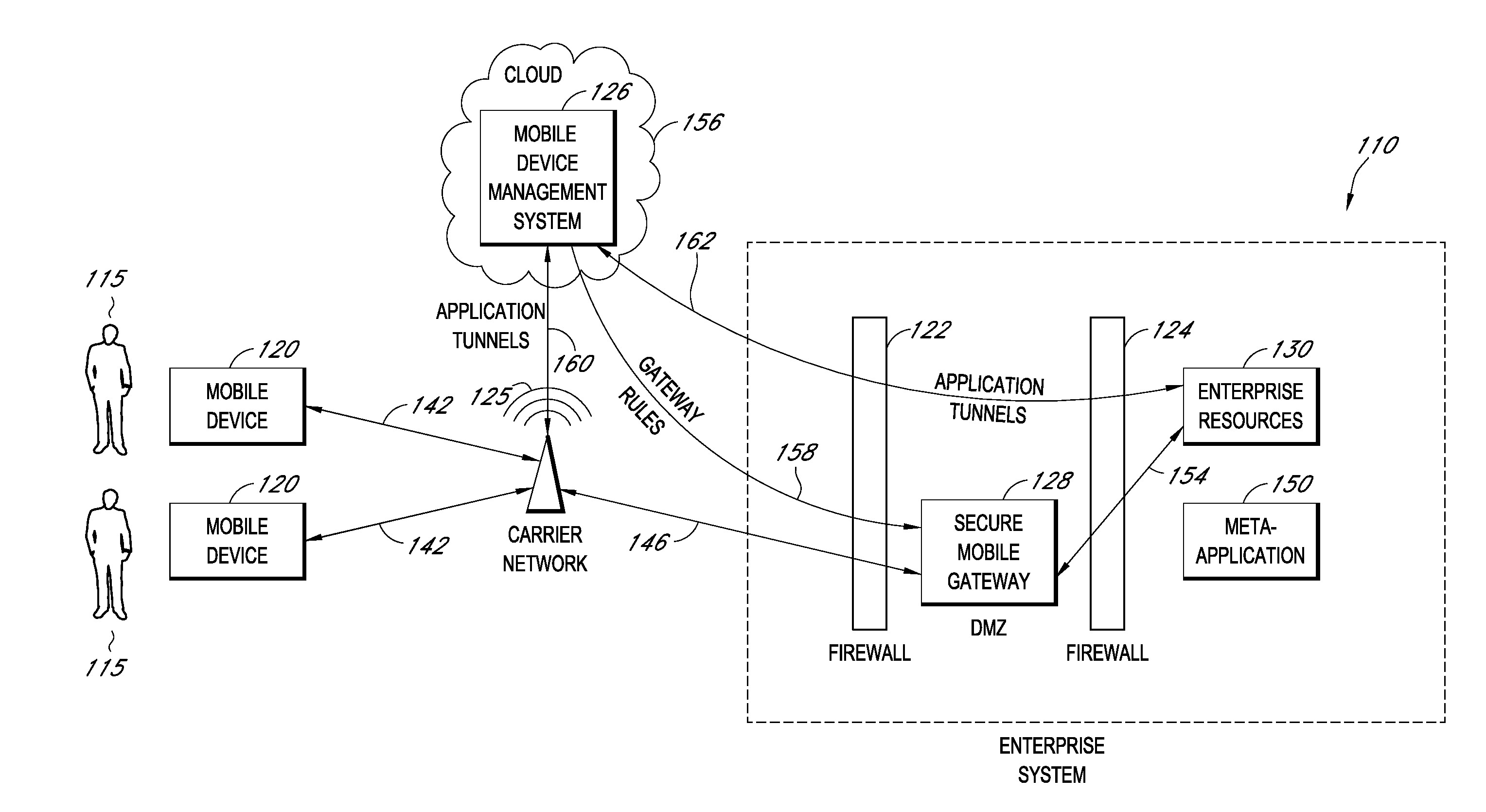
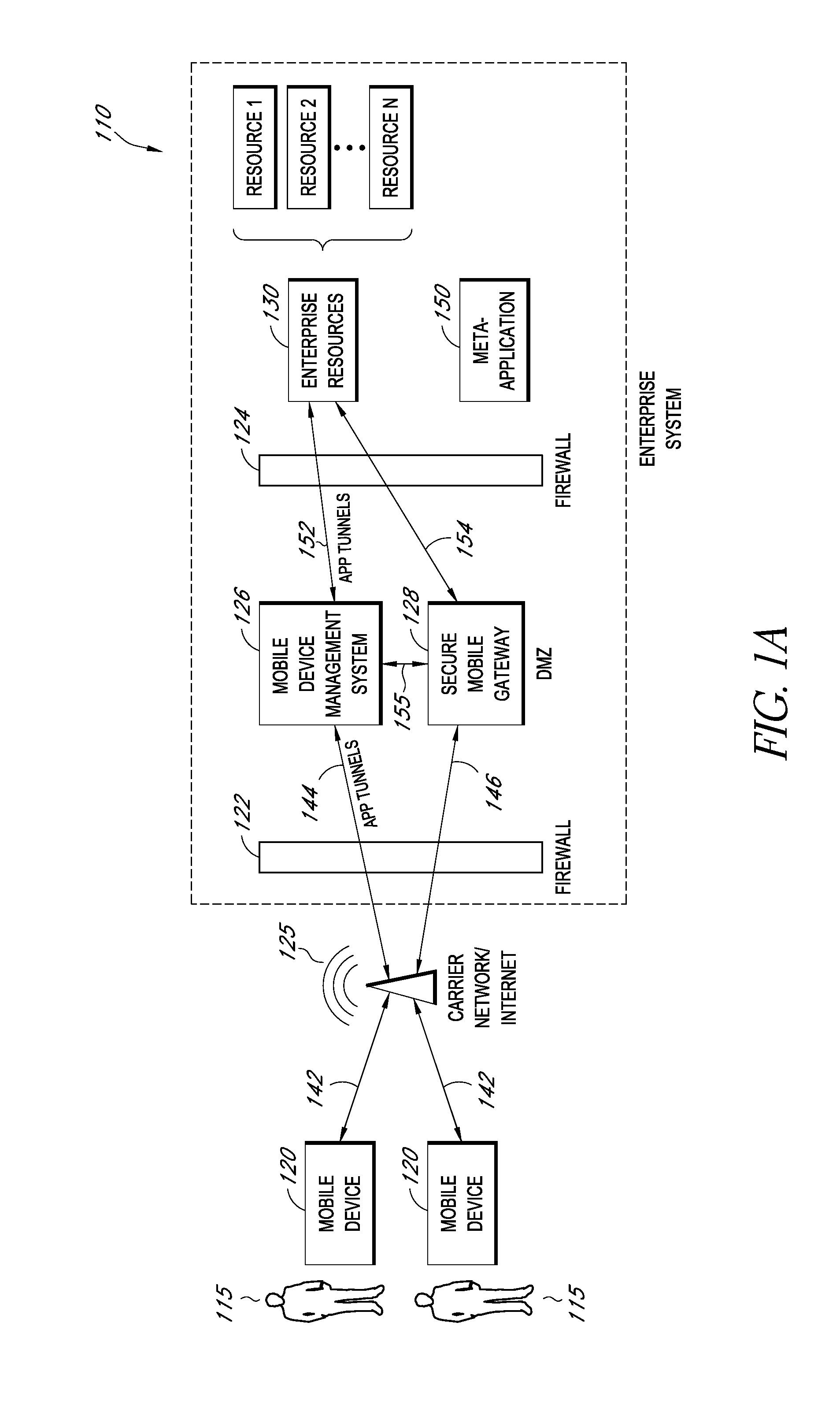
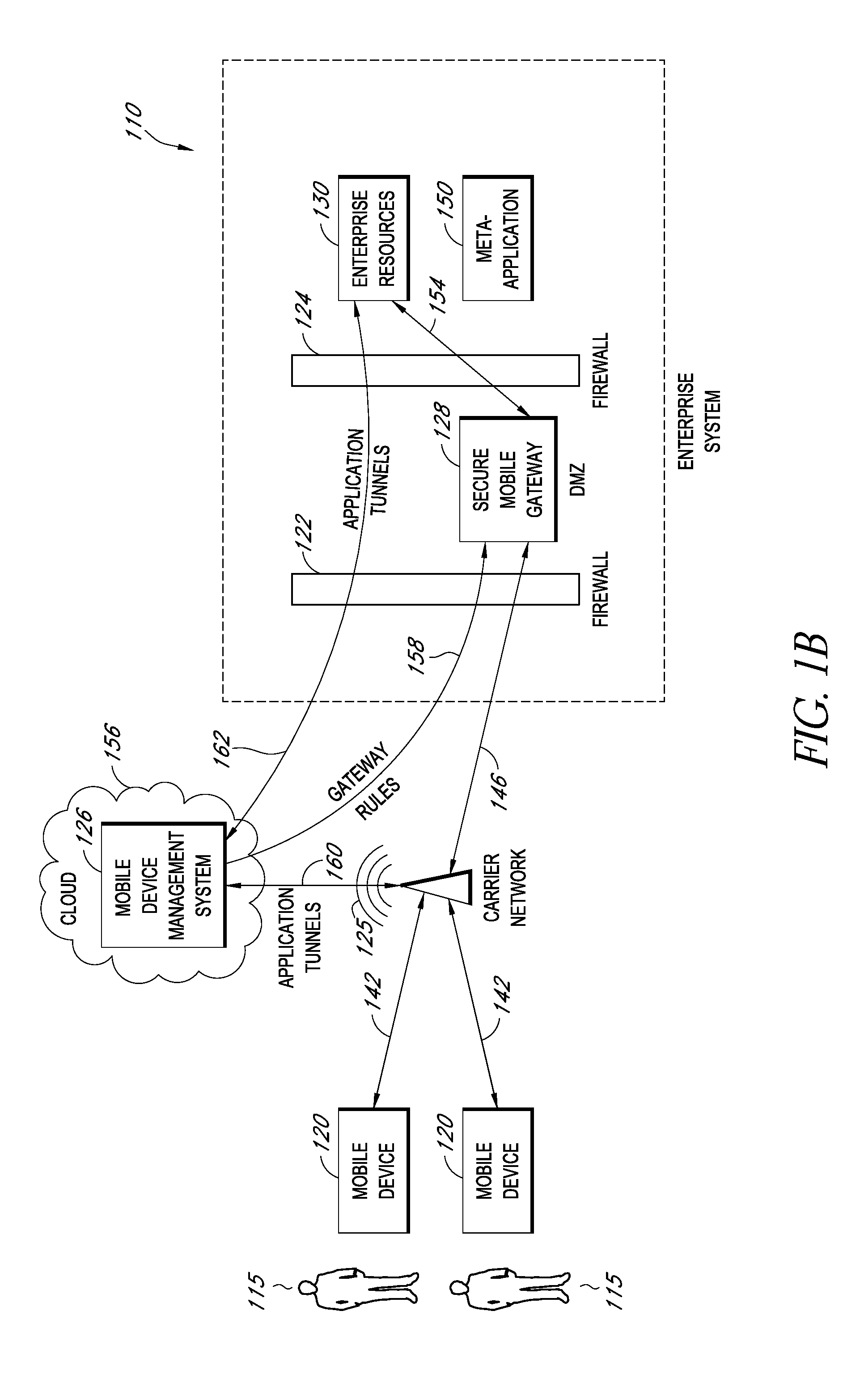
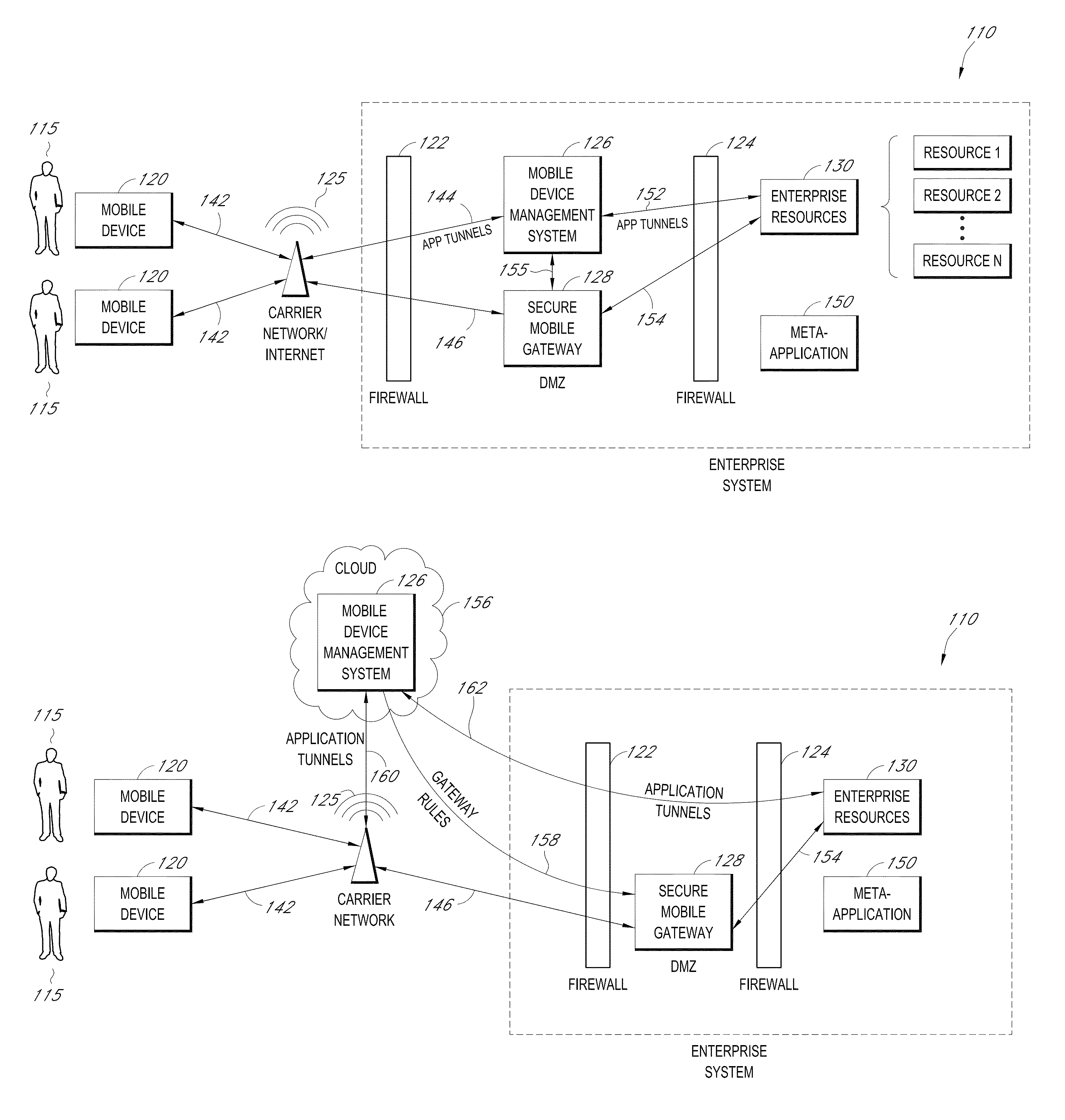
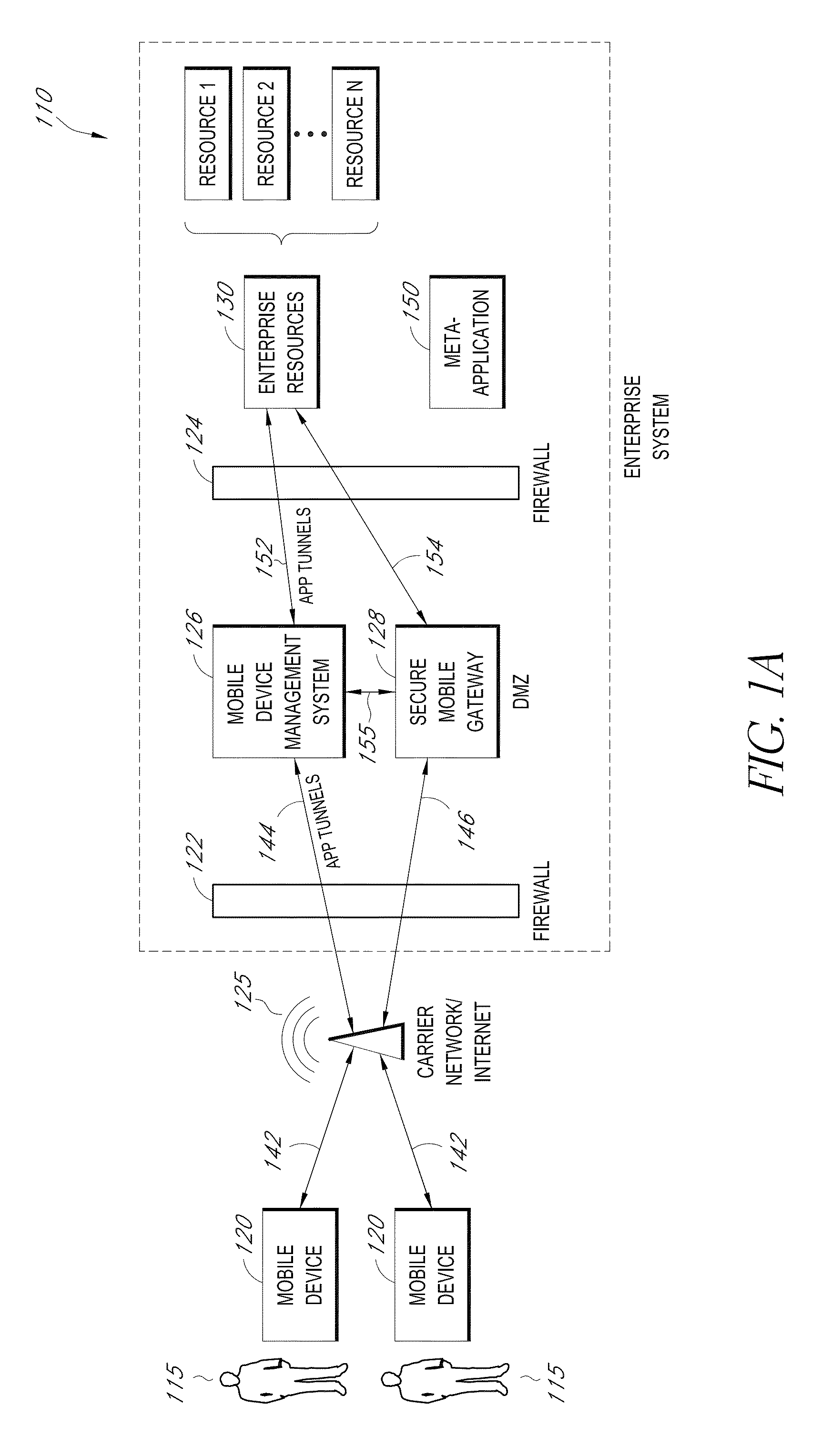
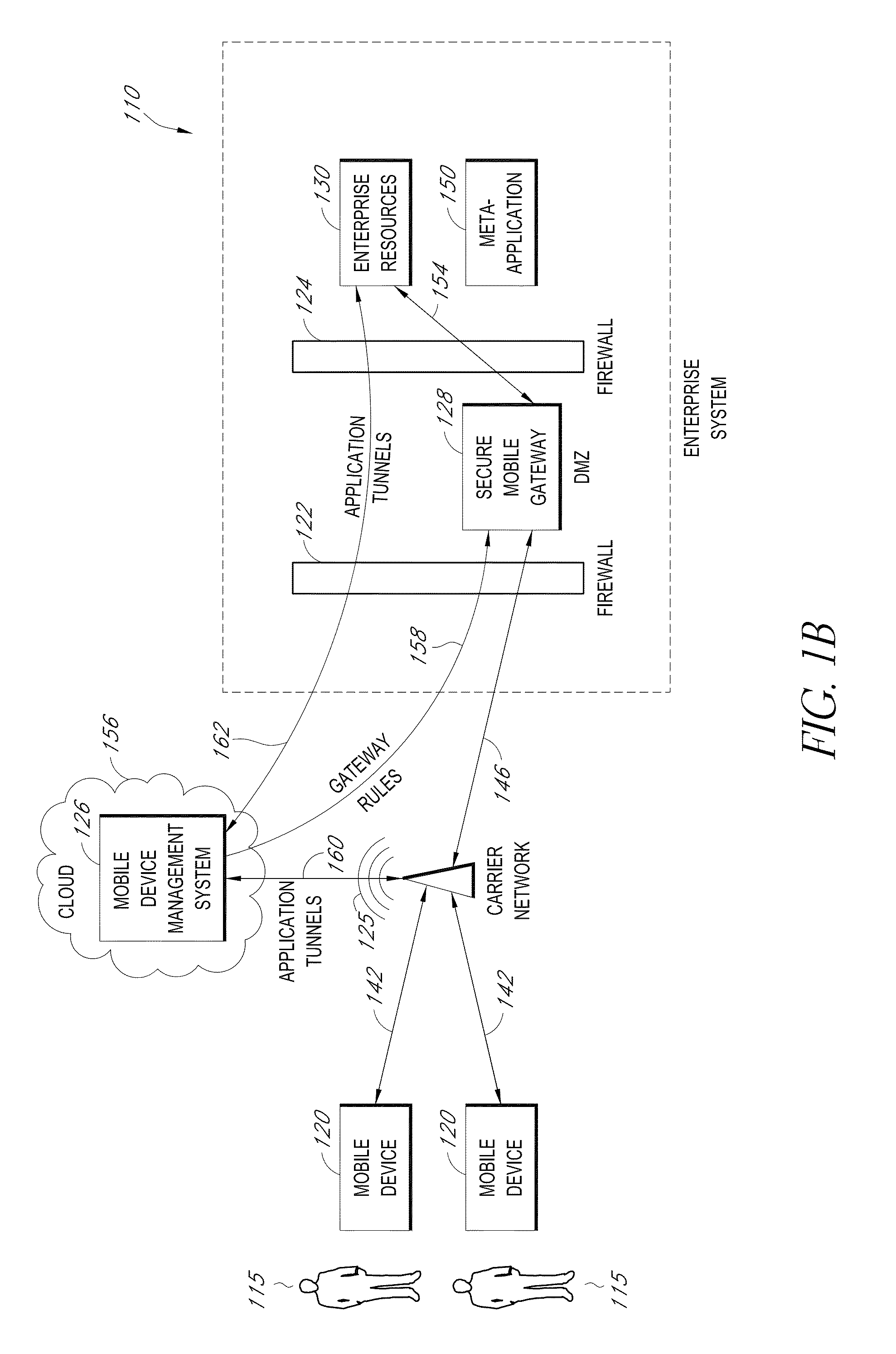
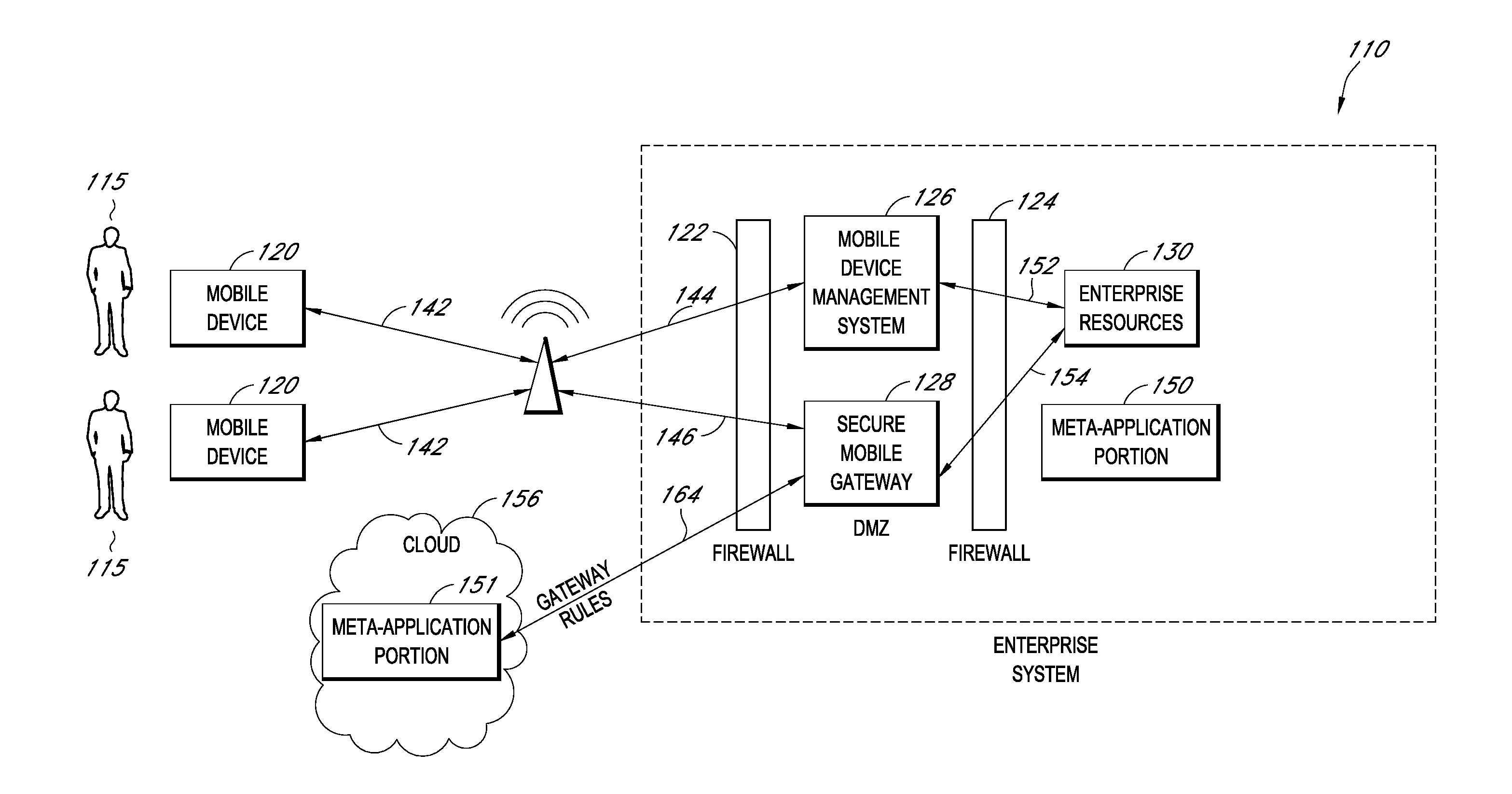
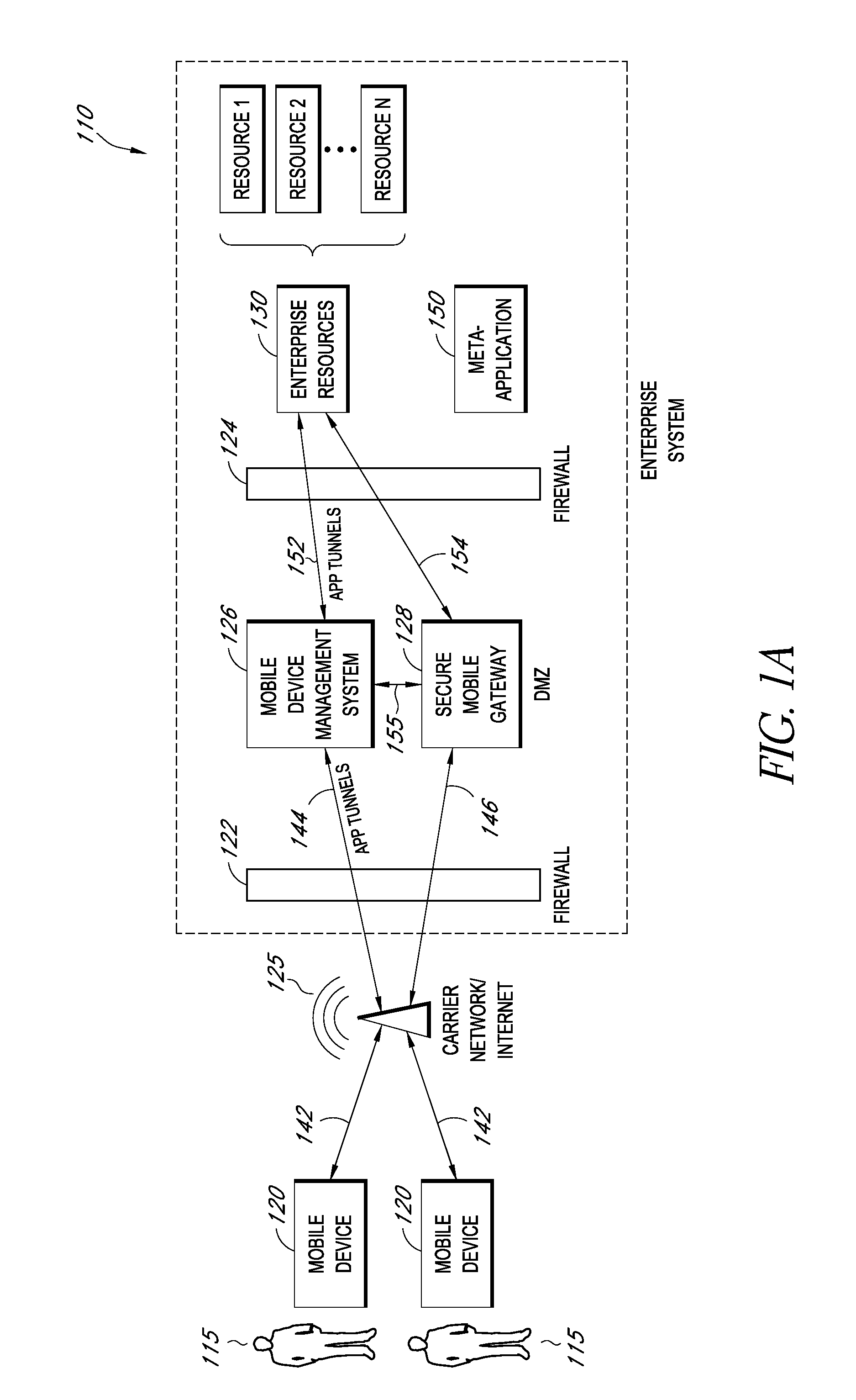
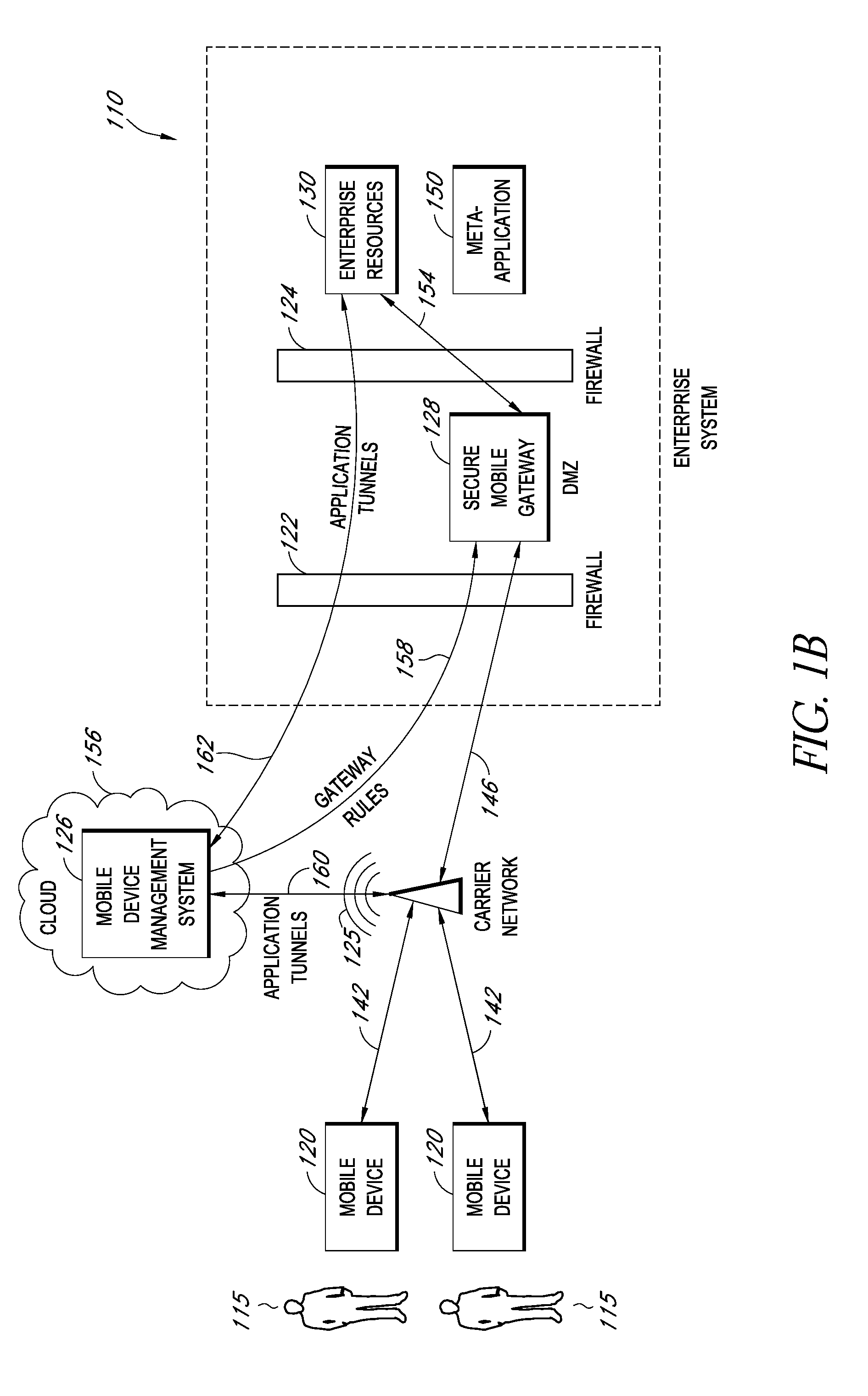
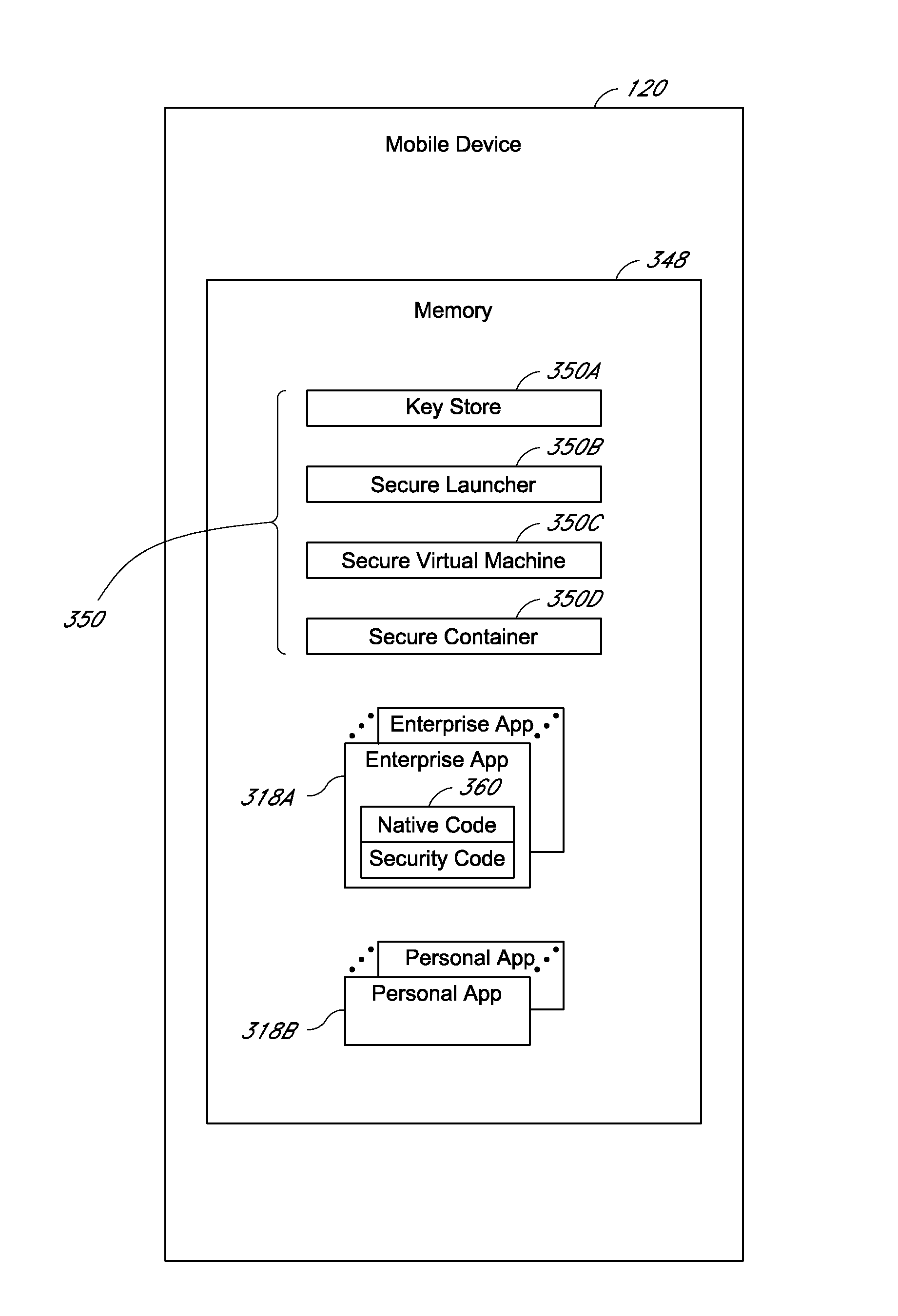
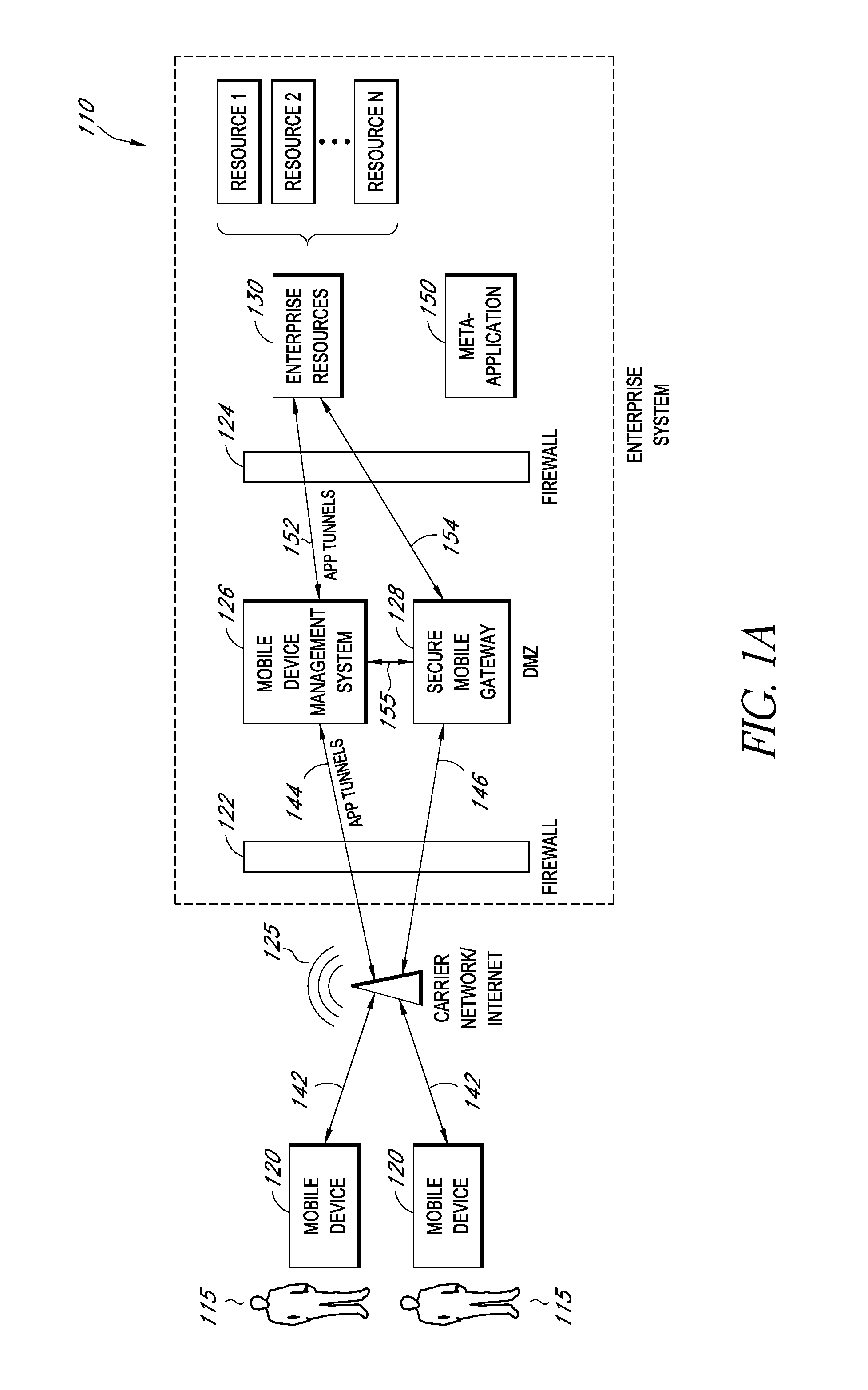
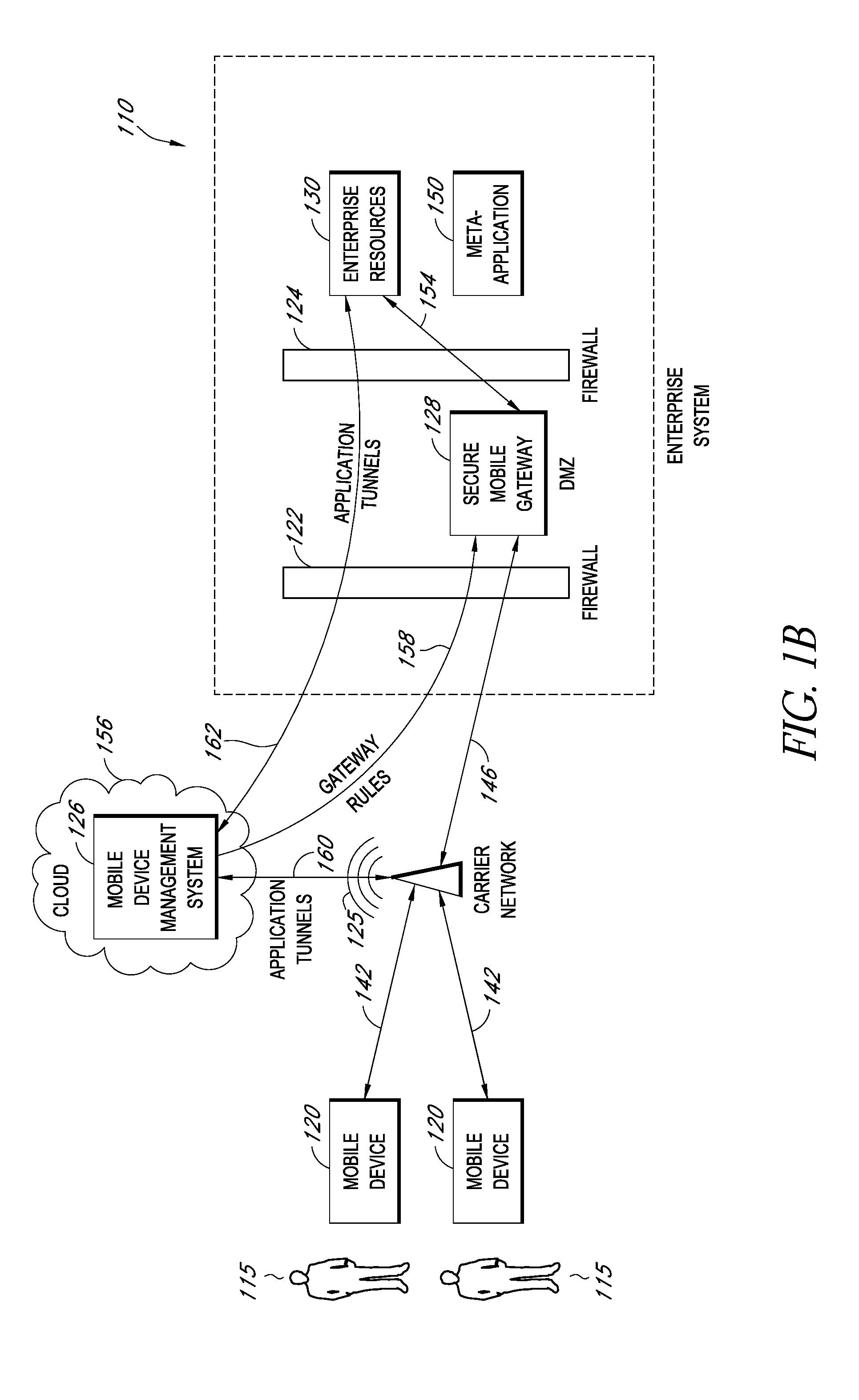
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
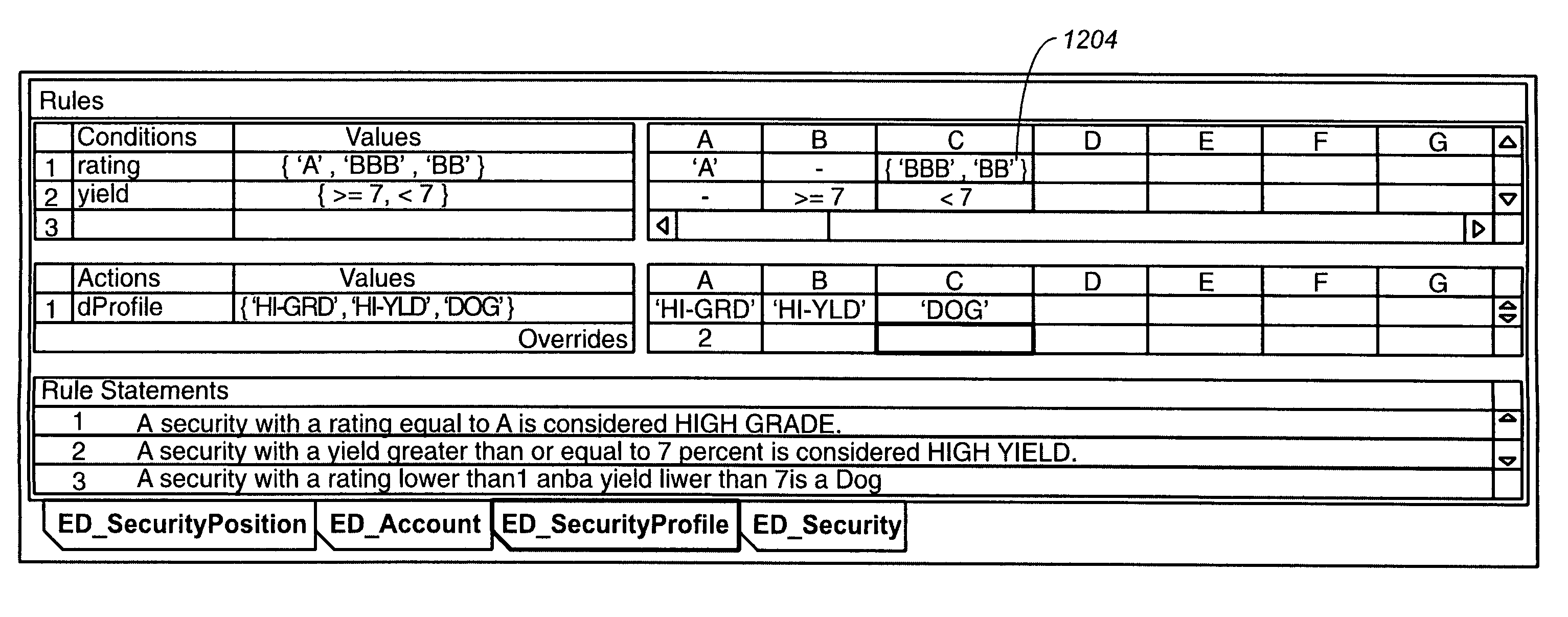
Business rules user interface for development of adaptable enterprise applications
ActiveUS7020869B2Reduce complexityMinimization requirementsTechnology managementVisual/graphical programmingApplication softwareDisplay list
Methods and apparatus, including computer program products, for interacting with a user to define business rules in a declarative manner. The invention operates to display a rule set as an editable list of conditions and an editable list of actions, the conditions and actions being linked to each other by the combination of an editable list of if-values and an editable list of then-values, wherein if-values and then-values are explicitly linked to each other, conditions and if-values are explicitly linked to each other, and then-values and actions are explicitly linked to each other in the displayed lists.
Owner:PROGRESS SOFTWARE
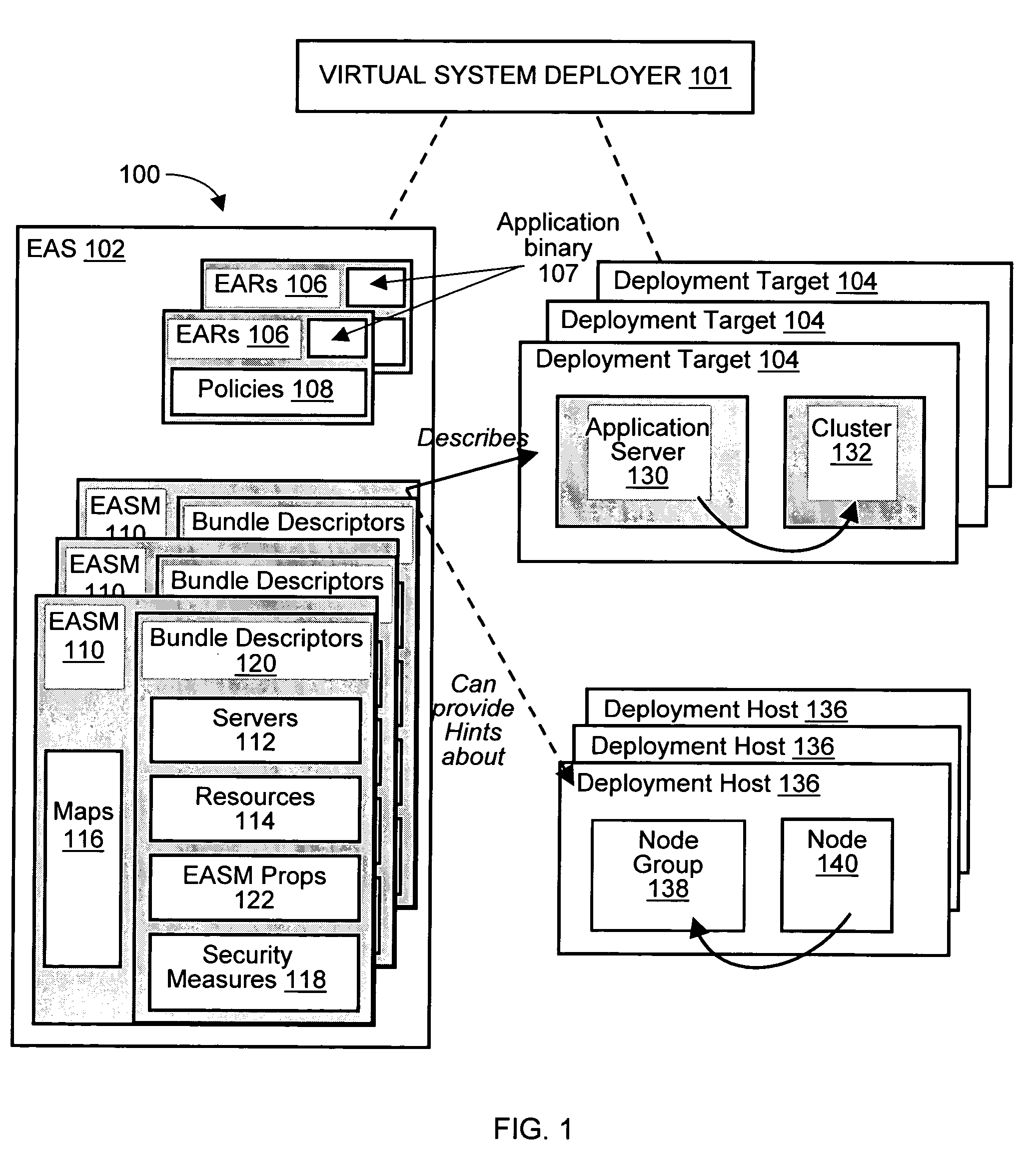
Deploying an application software on a virtual deployment target
InactiveUS20050289538A1Program loading/initiatingMemory systemsApplication program softwareRelevant information
Methods and arrangements to propagate application software to a virtual deployment target are contemplated. More specifically, a user may create multiple virtual deployment targets in a software system such as WebSphere™ and deploy applications to multiple the virtual deployment targets without having to manually fit policy-driven applications into each virtual deployment target. Embodiments are particularly advantageous when the application software is a business solution that needs to be deployed multiple times such as during the development and testing of the business solution. For example, application software of a business solution typically includes a group of applications designed to cooperatively function as a single entity. An application bundle such as an Enterprise Application Solution (EAS) file describes the application software and includes pertinent information about the application software, application configuration data, and runtime configuration data to implement the business solution. Then, the application bundle can be deployed automatically or substantially automatically.
Owner:IBM CORP
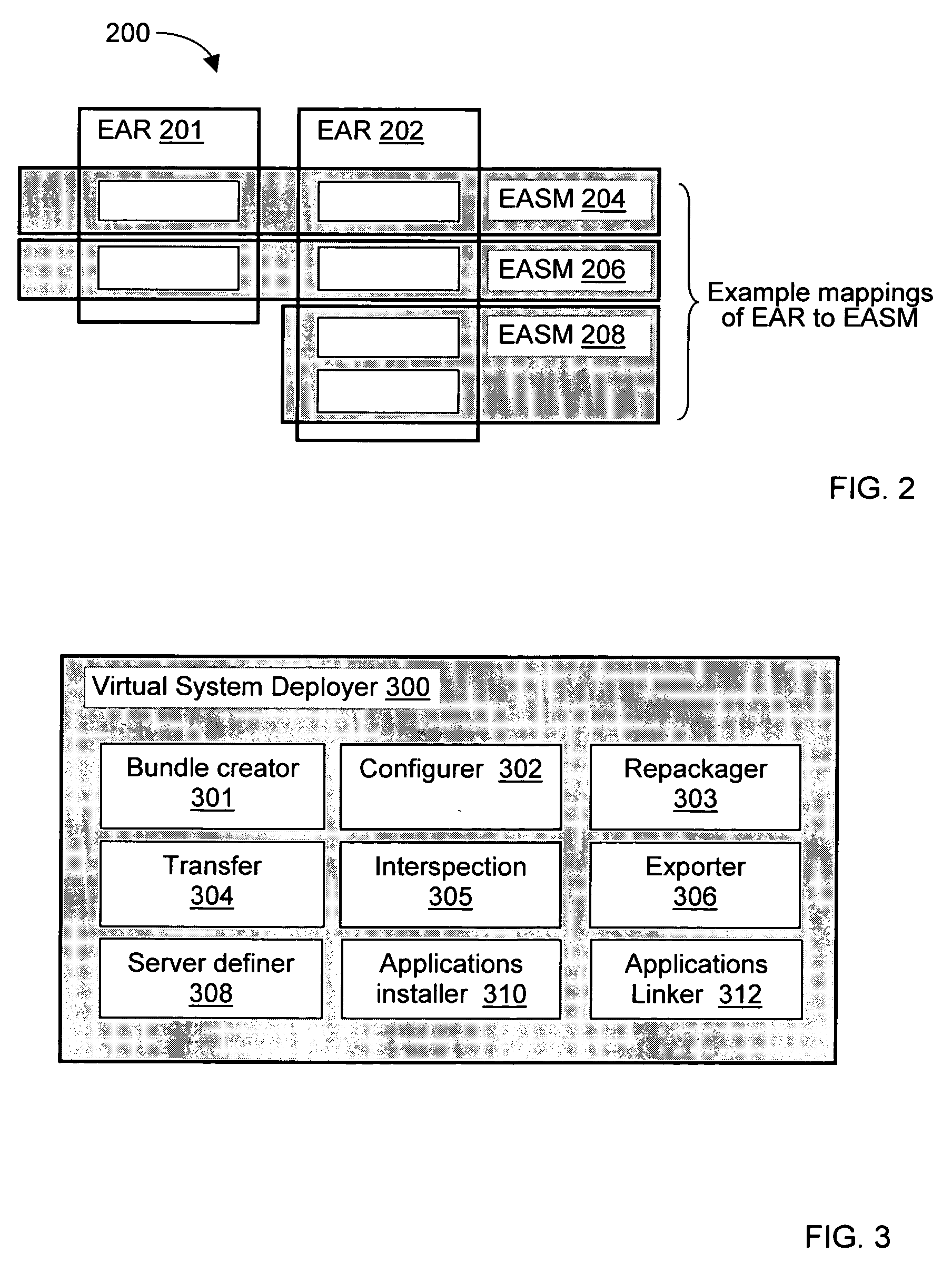
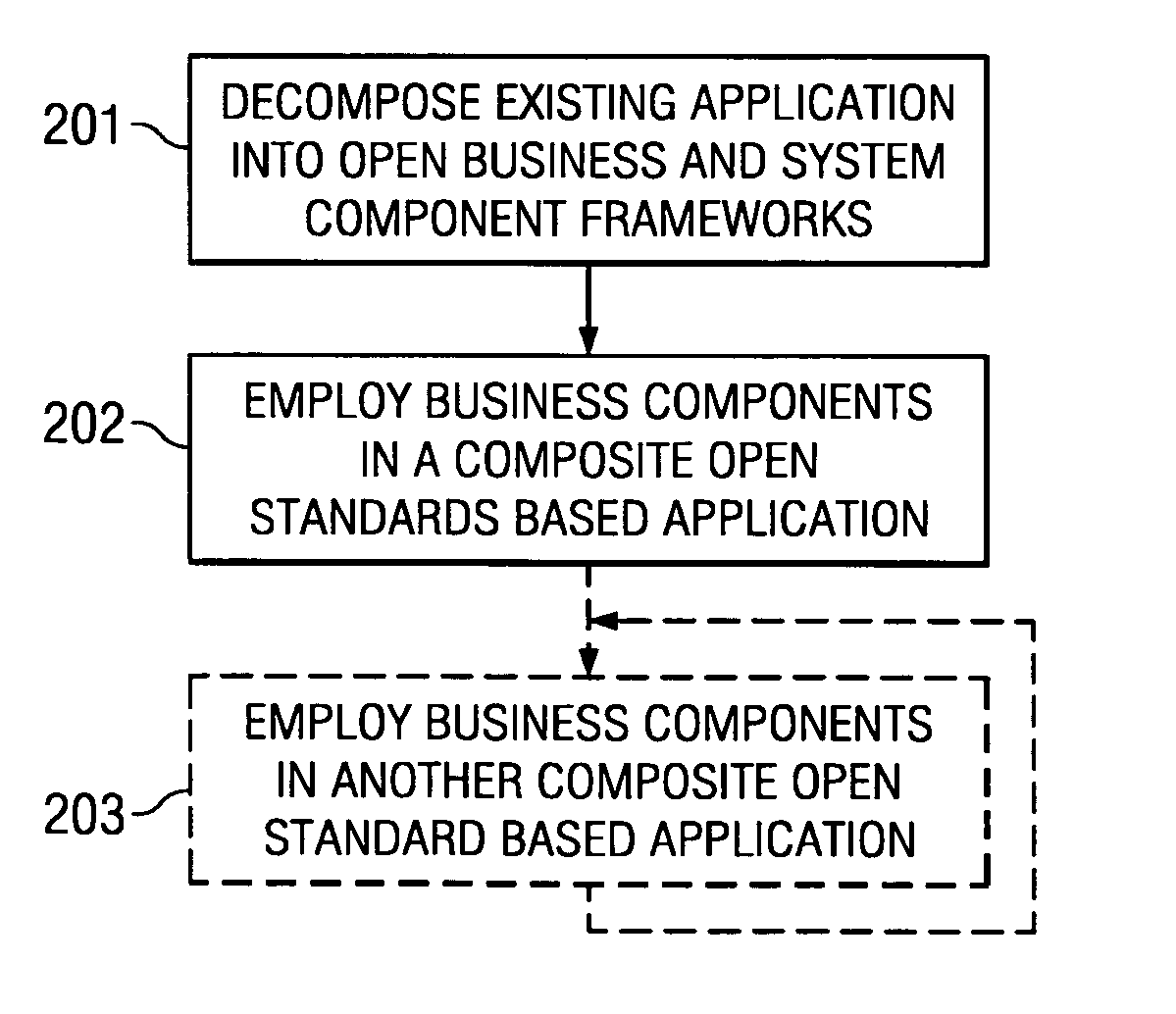
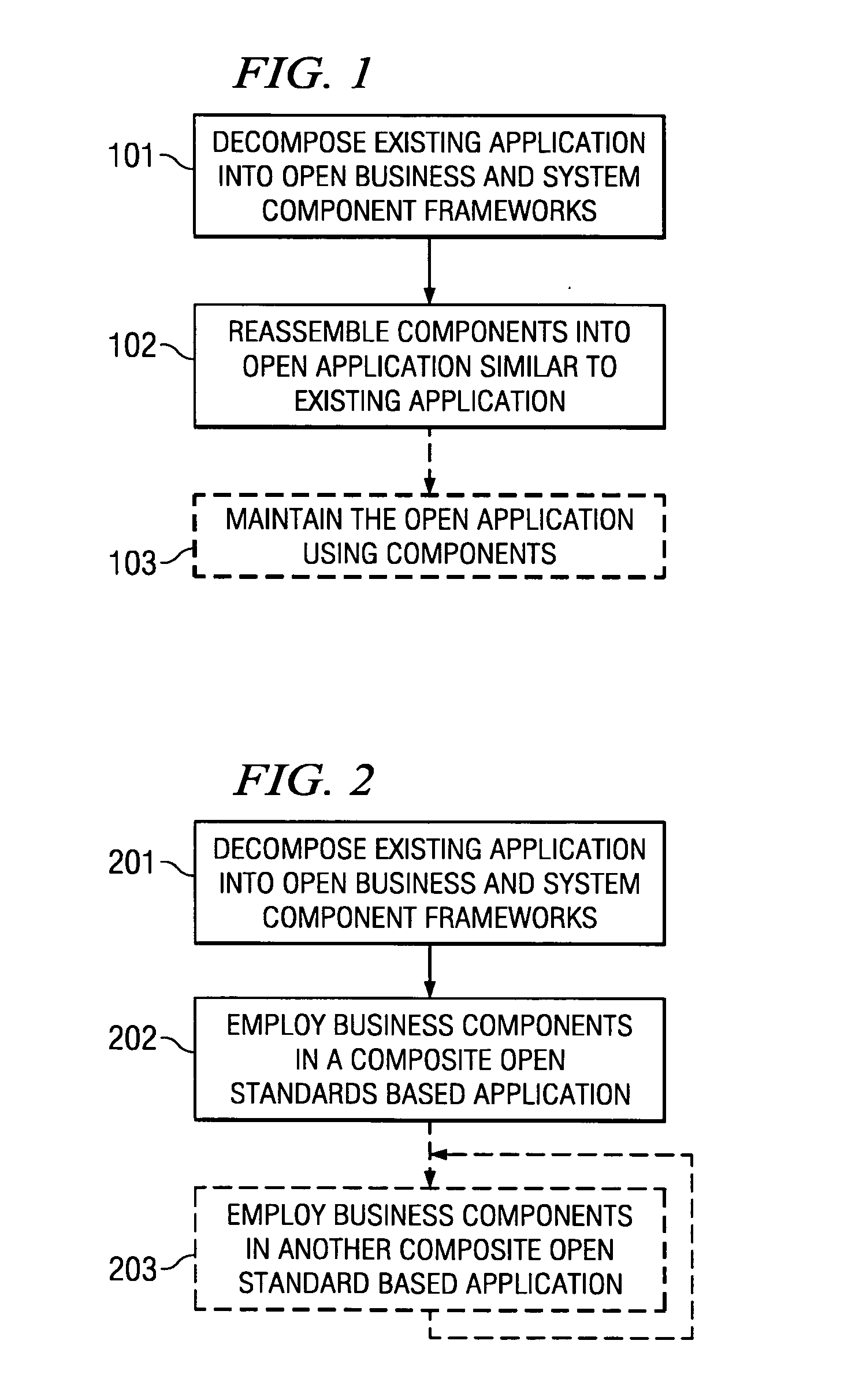
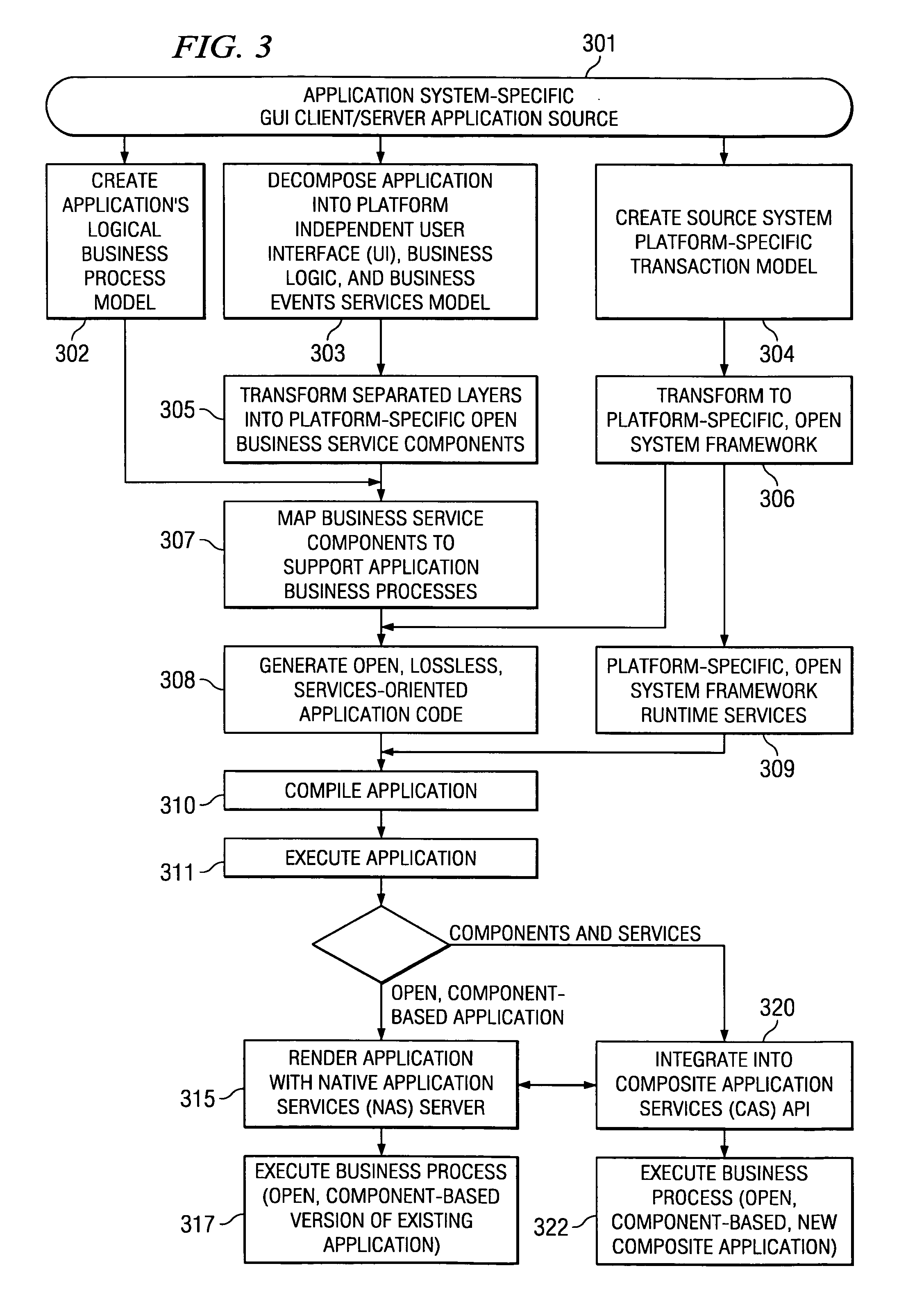
Systems and methods for modeling and generating reusable application component frameworks, and automated assembly of service-oriented applications from existing applications
InactiveUS20050144226A1Effective and meaningful supportLower barrierSoftware maintainance/managementMultiple digital computer combinationsService oriented applicationsBusiness process
Embodiments of systems and methods model and generate open reusable, business components for Service Oriented Architectures (SOAs) from existing client / server applications. Applications are decomposed into business component frameworks with separate user interface, business logic, and event management layers to enable service-oriented development of new enterprise applications. Such layers are re-assembled through an open standards-based, Native Application Services (NAS) to render similar or near identical transactional functionality within a new application on an open platform, without breaking former production code, and without requiring a change in an end-user's business processes and / or user experience. In addition, the same separated layers may form re-usable business components at any desired level of granularity for re-use in external composite applications through industry-standard interfaces, regardless of usage, context, or complexity in the former Client / Server application.
Owner:SAP AG
Controlling mobile device access to enterprise resources
ActiveUS20140007183A1Decompilation/disassemblyDigital data protectionApplication serverEnterprise resource planning
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Content driven process routing for integrated enterprise applications
InactiveUS20070255781A1Facilitates routing of application processMultiple digital computer combinationsTransmissionUser profileBusiness process
In one embodiment, an application integration system receives business application information and generates certain business flow and state information for the application, users based on the shared business content within the system. The content driven routing process facilitates the routing of application processes and user communication on the basis of the business content. The content-based routing process establishes integration connections on demand among users and or applications based on the business content utilized by their respective applications. Content data is encapsulated within a content table that consists of a number of tags that describe various parameters related to the content, such as user profiles, application that use the content, and data types within the content, so that it can be properly routed within the hub and processed by the integrated applications. The routing process of the collaboration hub routes the content or task to the appropriate user in the system and provides the hooks to invoke the appropriate application or otherwise process the content.
Owner:BAYHUB
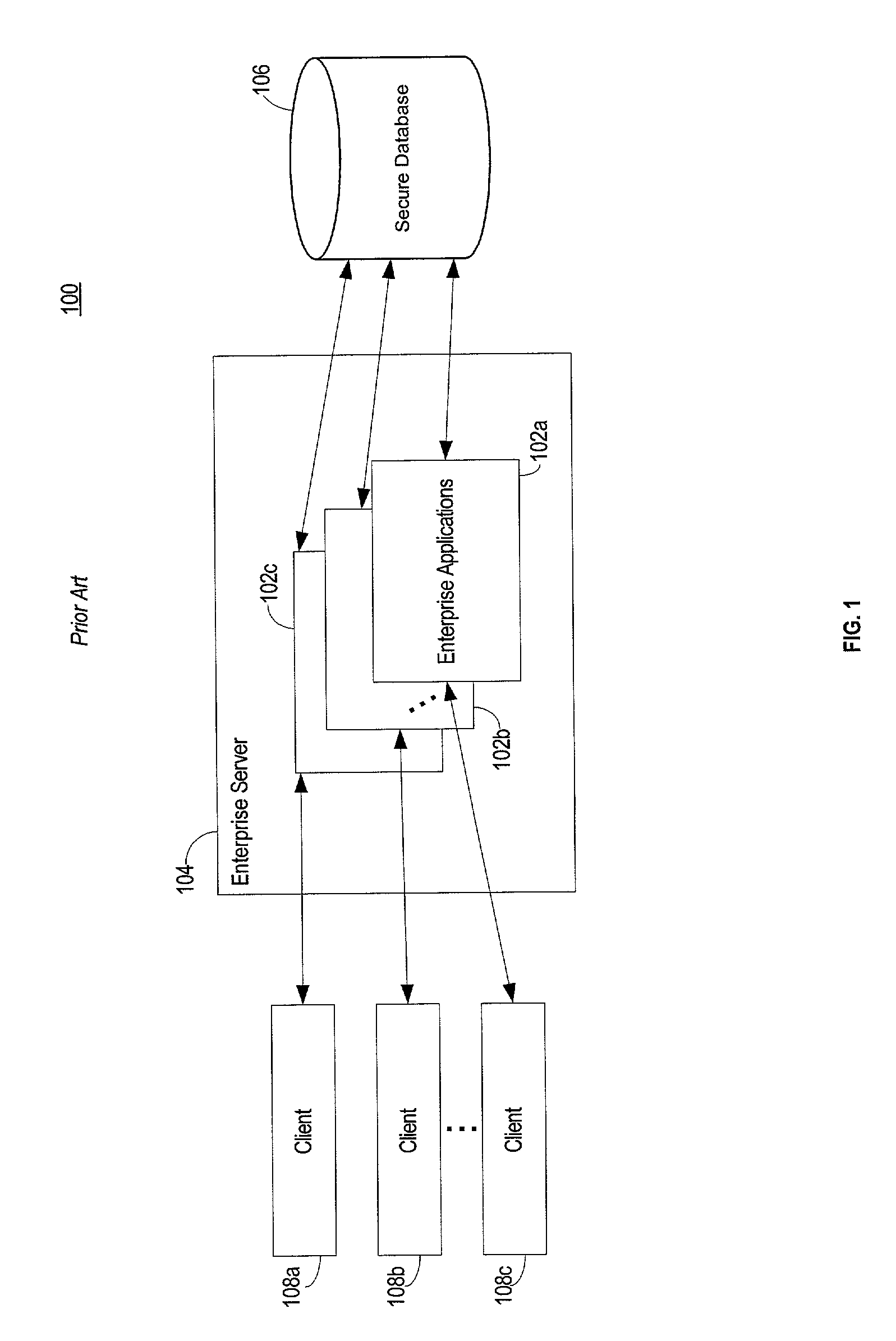
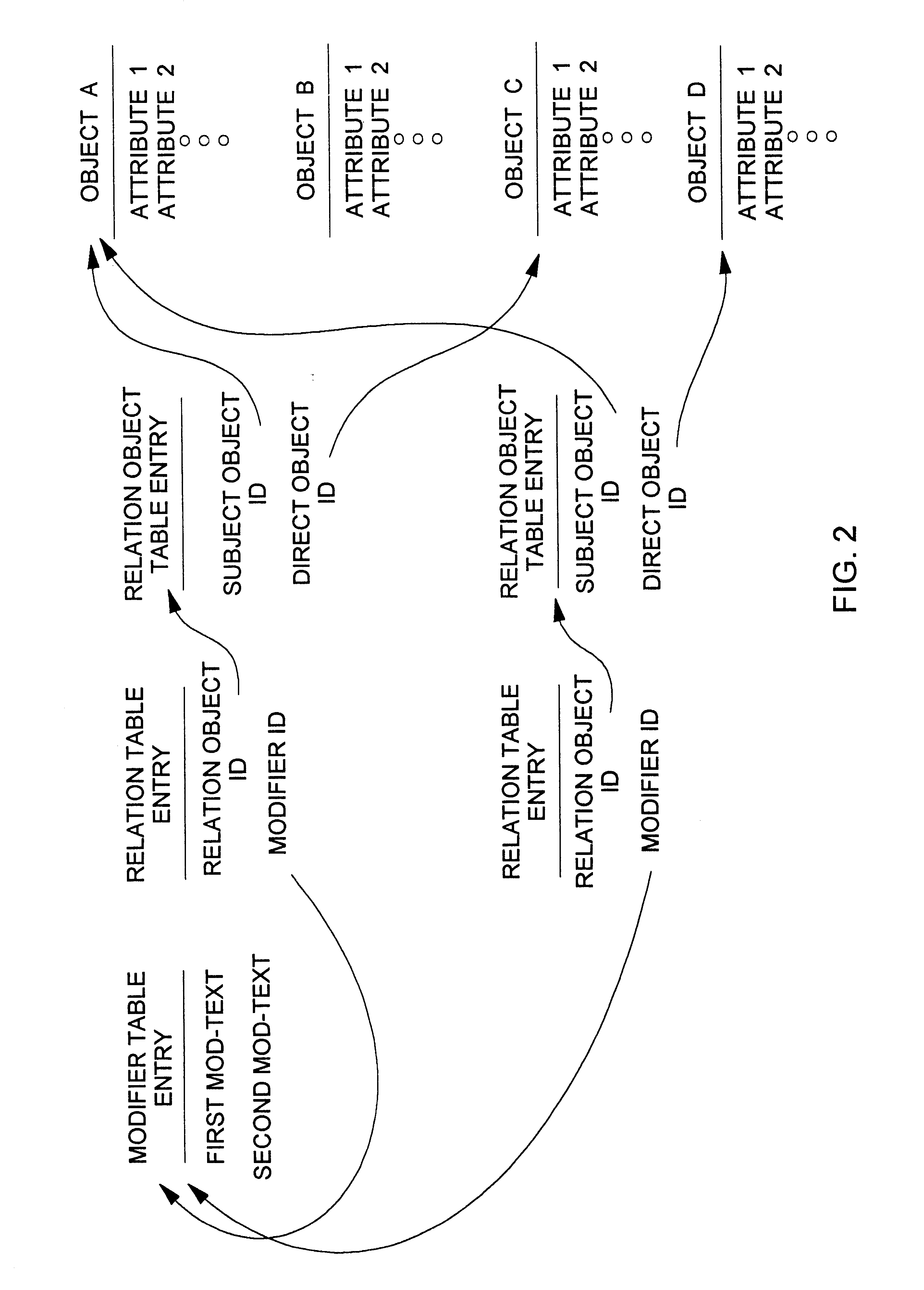
Database query handler supporting querying of textual annotations of relations between data objects
InactiveUS6618732B1EffectivelySave storage spaceData processing applicationsDigital data processing detailsDatabase queryCustomer relationship management
An improved command handler (and database system utilizing the improved command handler) interfaces to a datastore storing item data for a plurality of items and bi-directional modifier data, corresponding to a relation between at least one first item and at least one second item, that represents first text characterizing semantics of a relationship of the at least one first item to the at least one second item, and represents second text characterizing semantics of a relationship of the at least one second item to the at least one first item. The command handler operates, in response to receiving a first-type query command that specifies at least one given item, to access the datastore to identify i) at least one related item that is related to the given item, and identify ii) either the first text or the second text characterizing semantics of the relation between the given item and the at least one related item. The command hander returns i) data corresponding to the at least one related item; and ii) data corresponding to the identified first text and or second text characterizing semantics of the relation between the given item and the at least one related item. Preferably, the data returned in response to the first-type query command identifies the at least one related item. and identifies the first text or second text characterizing semantics of the relation between the given item and the at least one related item. In addition, the command handler preferably supports additional commands that retrieve from the datastore information related to specified objects, object types, and relations.The command handler (and database system) of the present invention may be used in a wide assortment of software applications, including enterprise applications (such as e-business applications, supply chain management applications, customer relationship management applications, decision support applications), the file system in operating systems, web browsers, e-mail applications and personal information management applications. Importantly, the command handler (and database system) provides an efficient mechanism to query the organization of the data elements (and the relationships therebetween) stored and accessed in such software applications, in a manner that efficient and readily adaptable to client-server database systems or other distributed database systems.
Owner:REVELINK
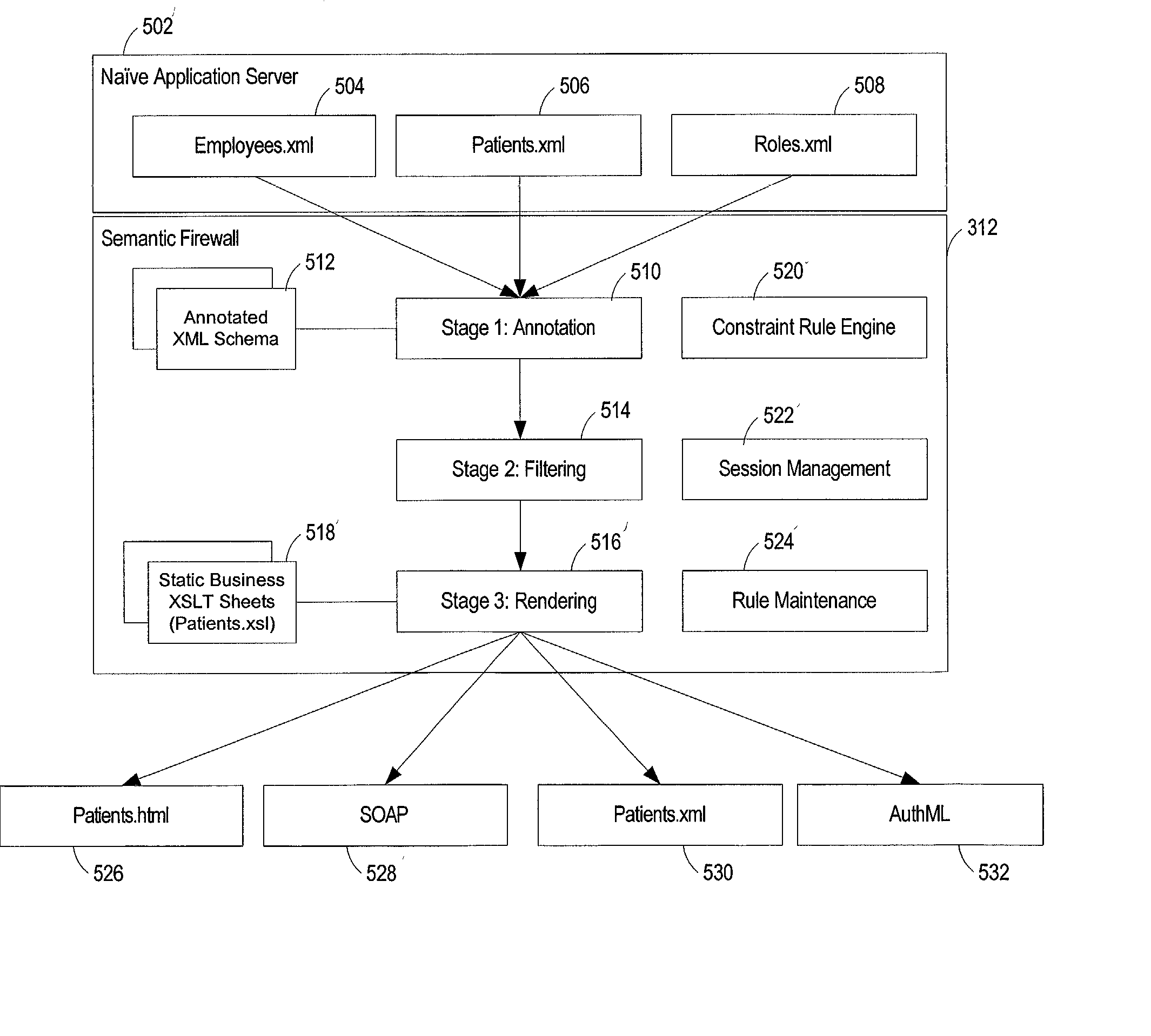
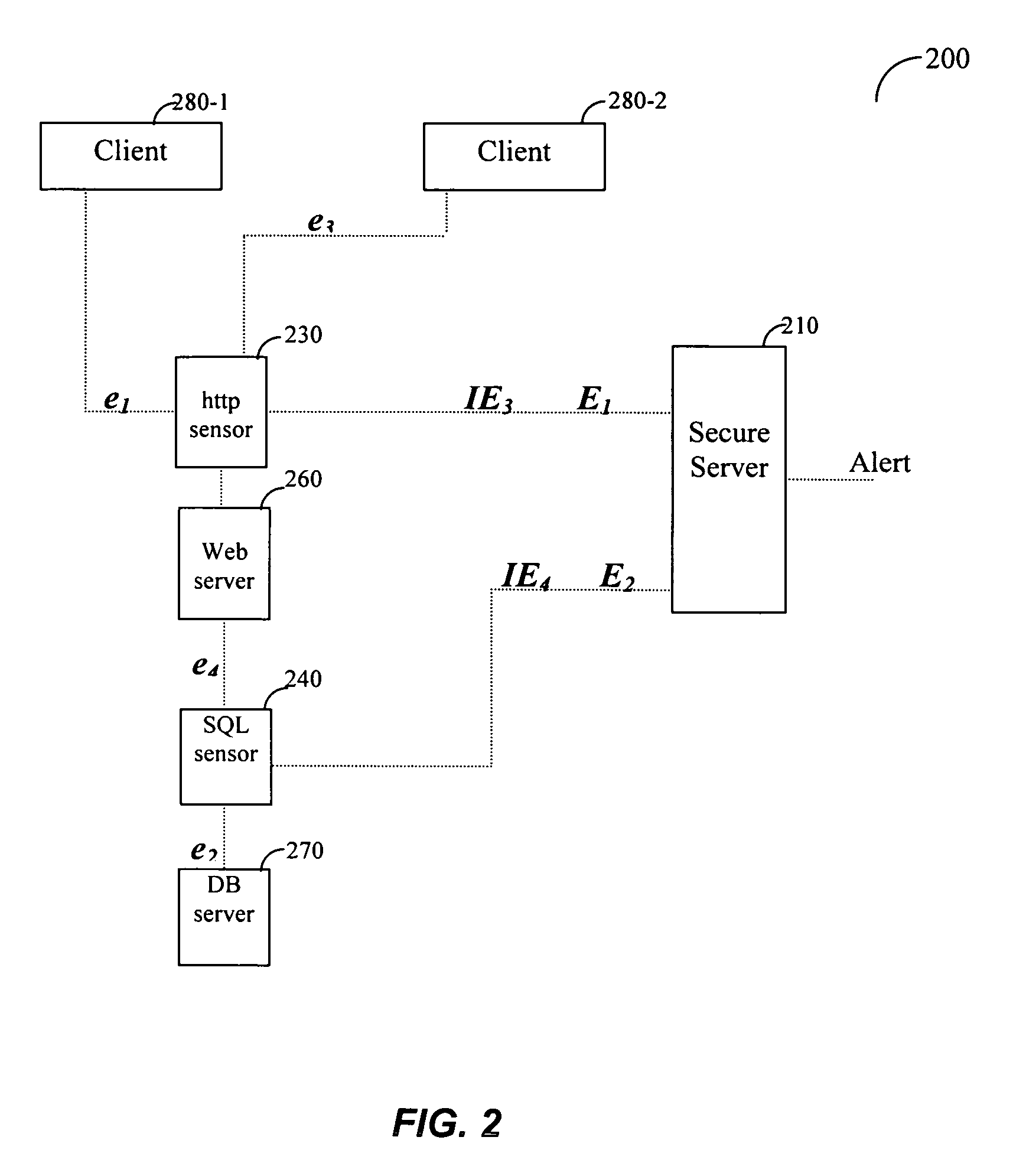
Layering enterprise application services using semantic firewalls
InactiveUS20020157023A1Digital data processing detailsMultiple digital computer combinationsApplication serverApplication software
A system for processing data requests from clients via a network is disclosed. The system has an application server coupled to a network, and a semantic firewall to pass and filter the content between the application server and the clients. The application server provides content from a database to the clients via the network, and the semantic firewall restricts access to a portion of the content for one or more clients.
Owner:SPHERE SOFTWARE CORP
Gateway for controlling mobile device access to enterprise resources
ActiveUS20140007214A1Decompilation/disassemblyDigital data processing detailsApplication serverResource based
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
System and method for using social networks to facilitate business processes
InactiveUS20060026033A1Improve effectivenessImprove efficiencyBuying/selling/leasing transactionsResourcesKnowledge managementBusiness process
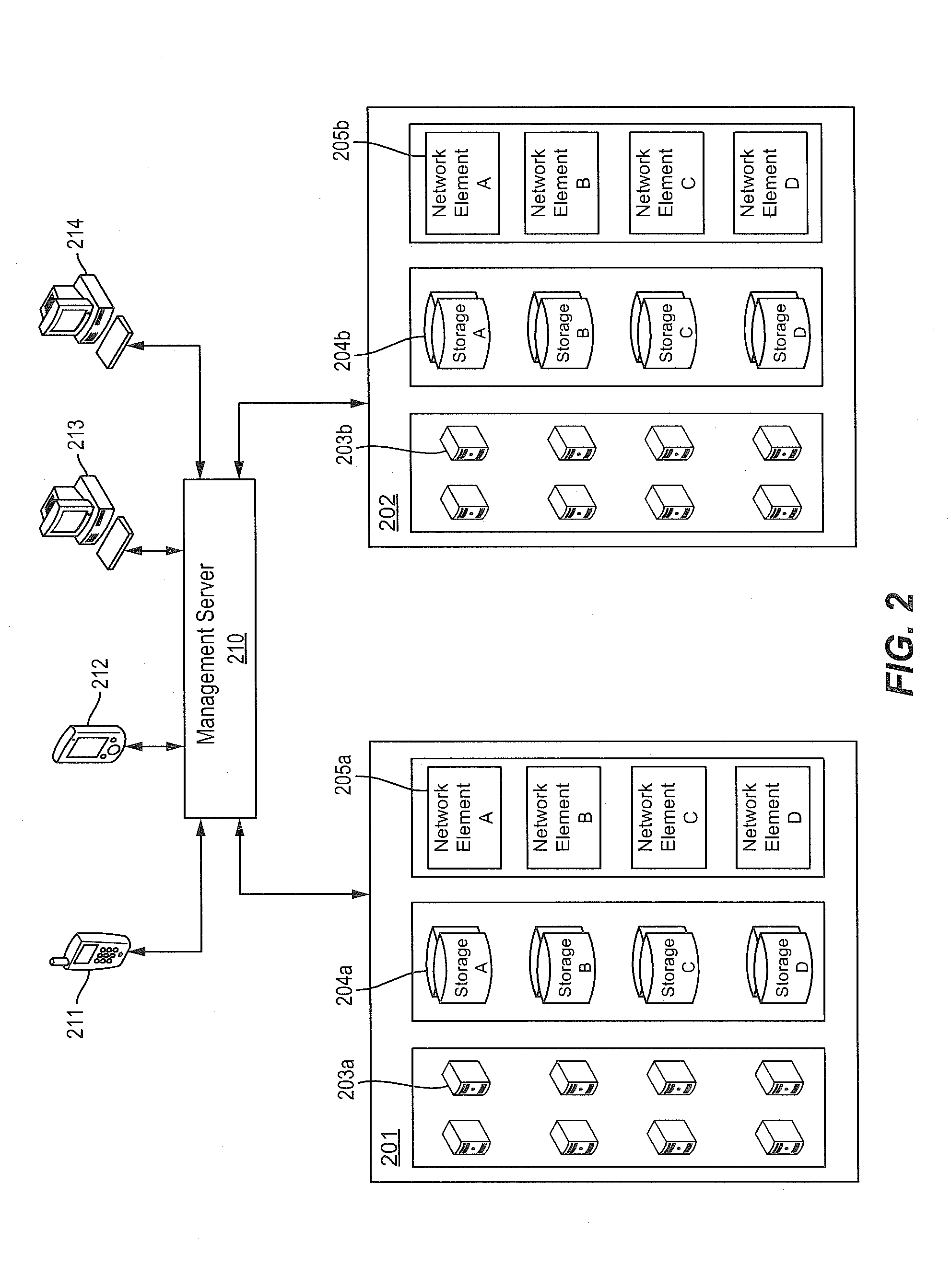
The present invention provides methods and systems for facilitating business processes in an enterprise application. The method according to one embodiment of the present invention comprises obtaining information regarding one or more entities and analyzing the information regarding the one or more entities to determine one or more paths between the one or more entities and one or more members of an enterprise. Information regarding the one or more entities is distributed to the one or more members of the enterprise where one or more paths exist between the one or more members of the enterprise and the one or more entities.
Owner:THE DUN & BRADSTREET CORPORATION
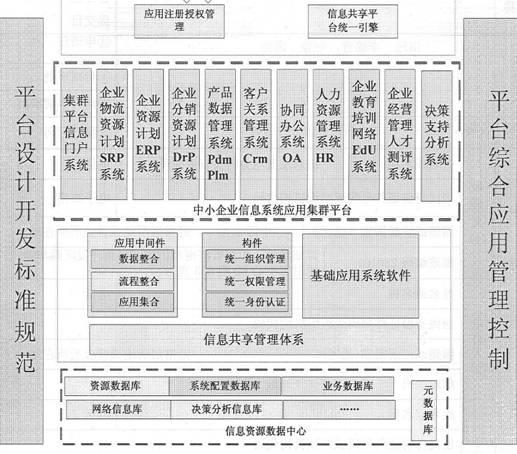
Informatization application cluster platform of small and medium enterprises
InactiveCN102324074ALow application costOptimal Management BottlenecksInstrumentsInformatizationCustomer relationship management
The invention discloses an informatization application cluster platform of small and medium enterprises. The informatization application cluster platform comprises a portal management system, an enterprise logistics supply chain resource planning management system, an enterprise resource planning management system, an enterprise distribution resource planning and supply chain management system, an enterprise customer relation management system, an enterprise collaborative working platform management system, an enterprise product data management and product life cycle management system, an enterprise human resource management system, an enterprise operating management talent assessment system, an enterprise educational training network platform integrated system and a decision supporting analysis system. The informatization application cluster platform of the small and medium enterprises has the advantages that: by real-time on-line application and management for a plurality of small and medium enterprises, the safety of the operation data of on-line enterprises can be guaranteed; the investment of economic and technical talents for the informatization application of the small and medium enterprises of China is greatly reduced; an enterprise management bottleneck is optimized; the information technology (IT) application cost of the enterprises is greatly saved; and the implementation of the informatization of the small and medium enterprises is simplified.
Owner:SHANDONG CENTONG TECH
Policy-Based Application Management
ActiveUS20140033271A1Digital data protectionInternal/peripheral component protectionVirtualizationApp store
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
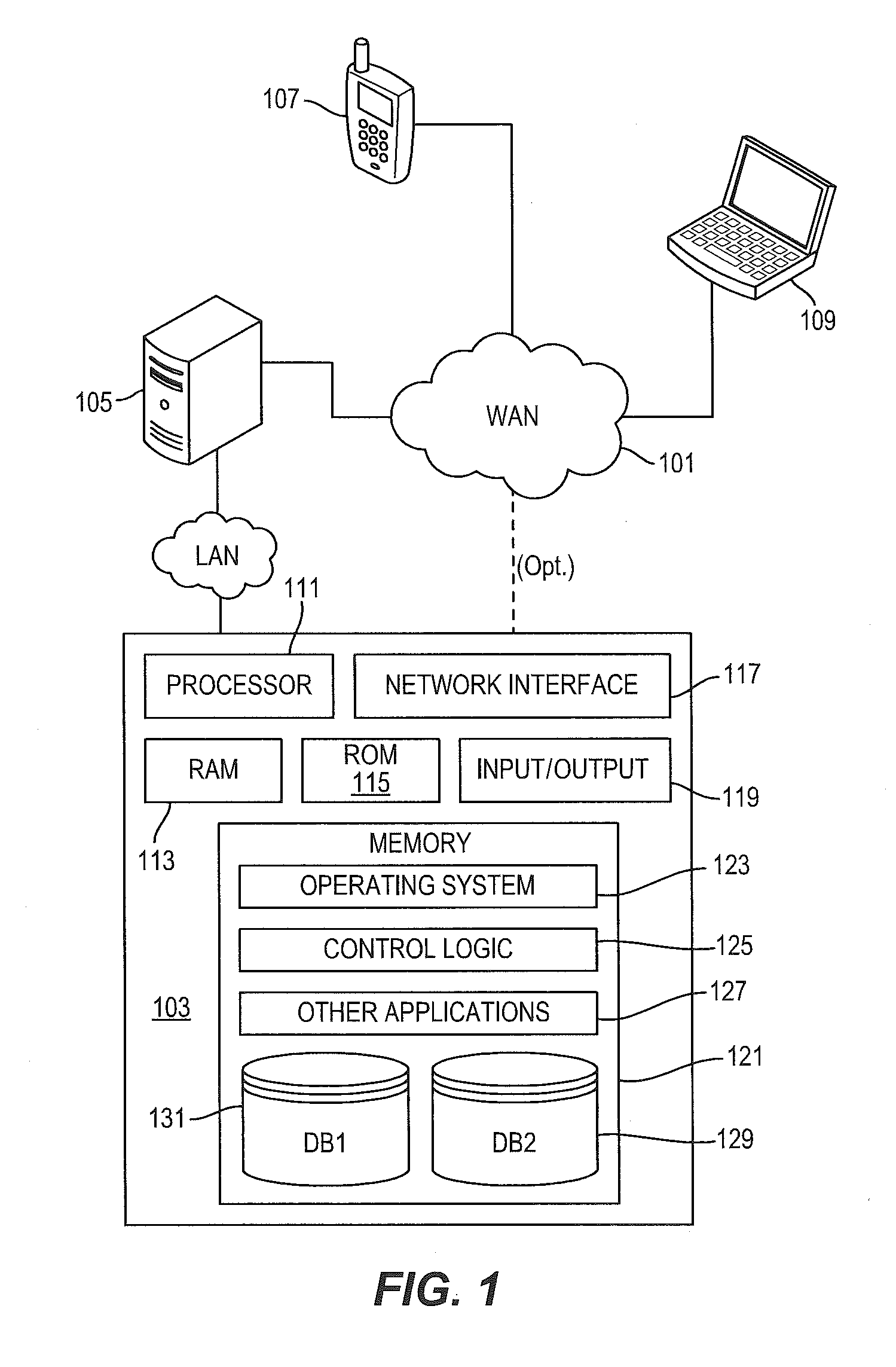
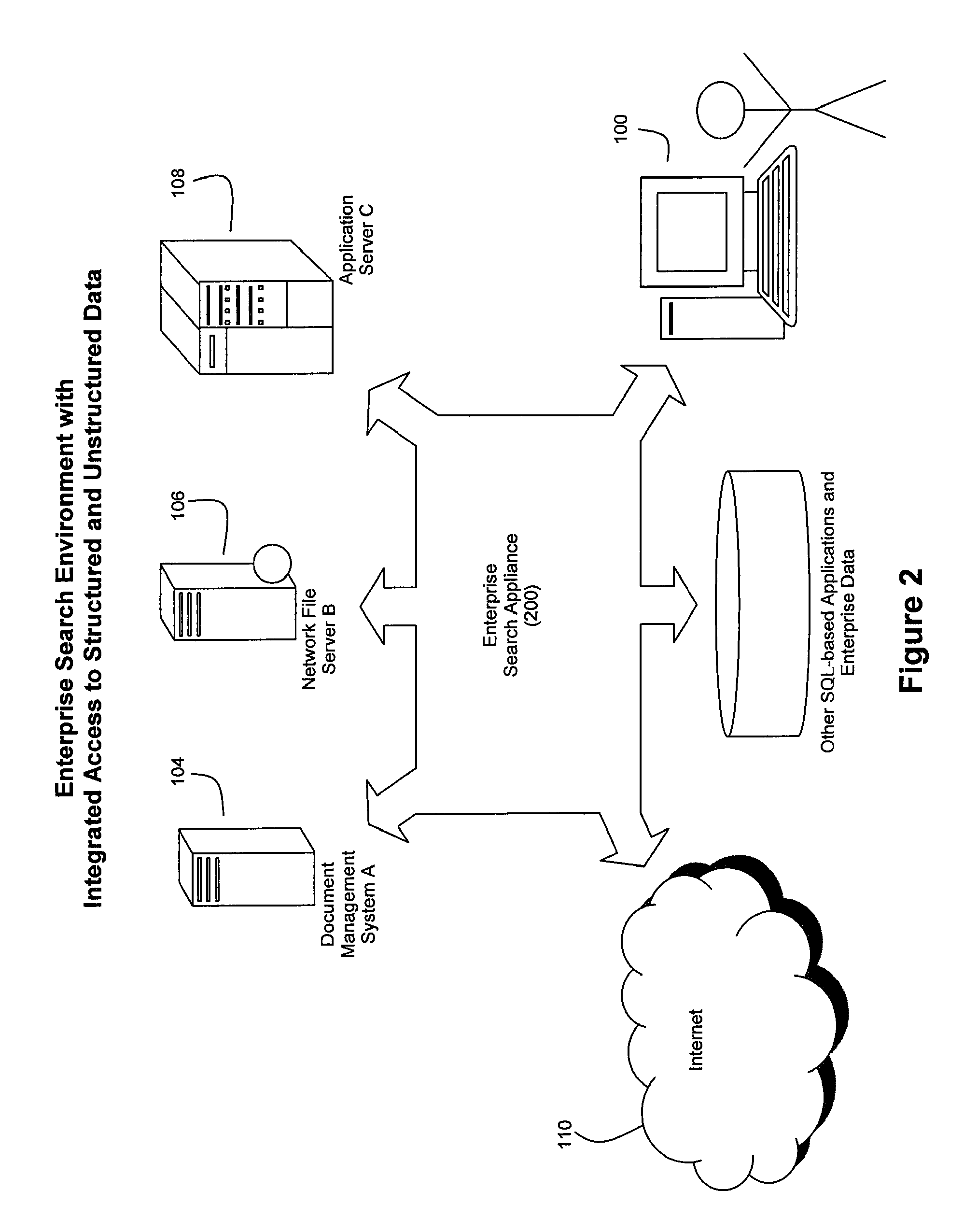
Method and System for High Performance Integration, Processing and Searching of Structured and Unstructured Data Using Coprocessors
ActiveUS20080114724A1Faster and more unified accessEffectively bifurcate query processingData processing applicationsDigital data processing detailsFull text searchRelational database
Disclosed herein is a method and system for integrating an enterprise's structured and unstructured data to provide users and enterprise applications with efficient and intelligent access to that data. Queries can be directed toward both an enterprise's structured and unstructured data using standardized database query formats such as SQL commands. A coprocessor can be used to hardware-accelerate data processing tasks (such as full-text searching) on unstructured data as necessary to handle a query. Furthermore, traditional relational database techniques can be used to access structured data stored by a relational database to determine which portions of the enterprise's unstructured data should be delivered to the coprocessor for hardware-accelerated data processing.
Owner:IP RESERVOIR
Secure mobile browser for protecting enterprise data
ActiveUS8869235B2Decompilation/disassemblyDigital data information retrievalDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
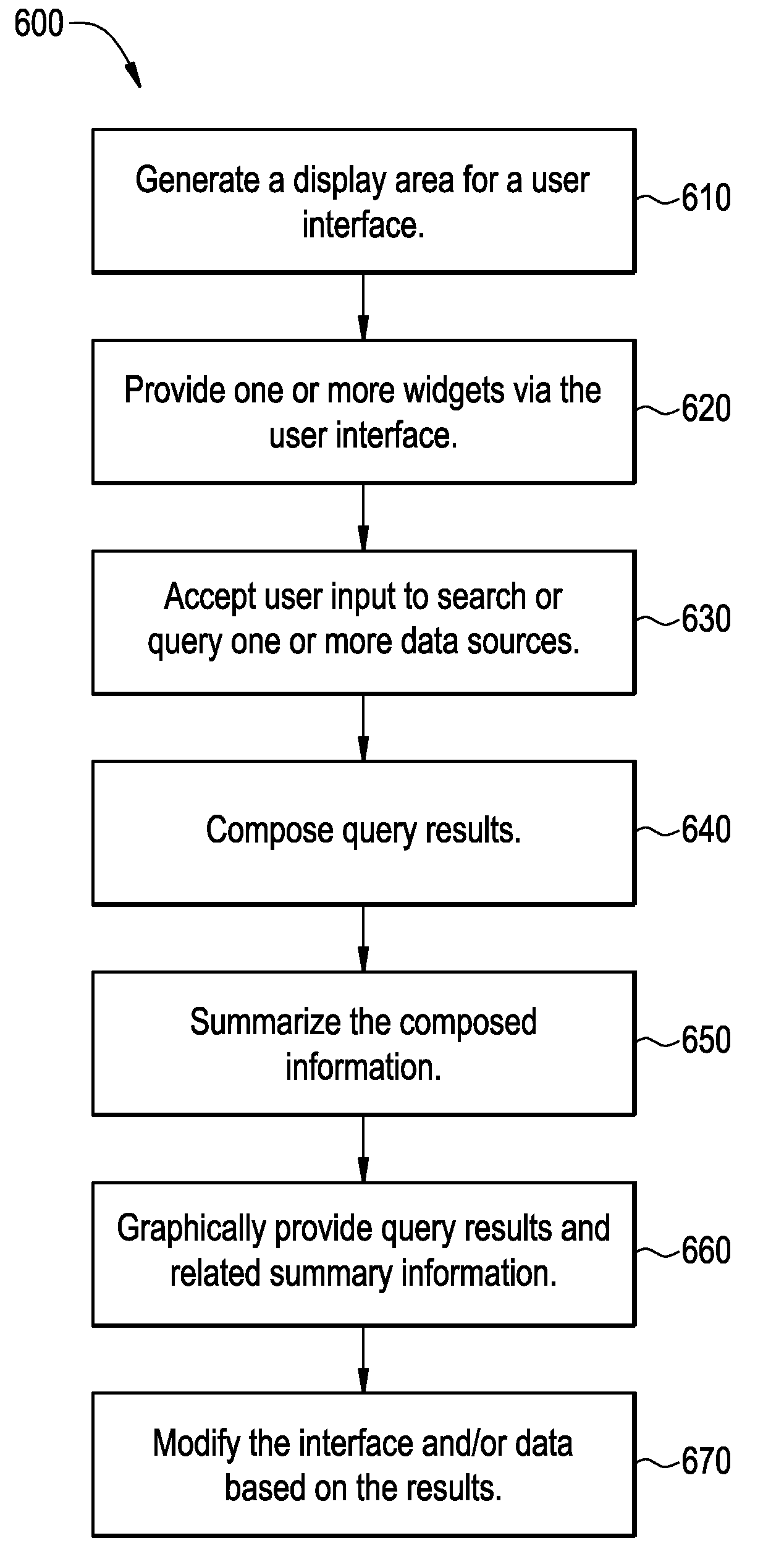
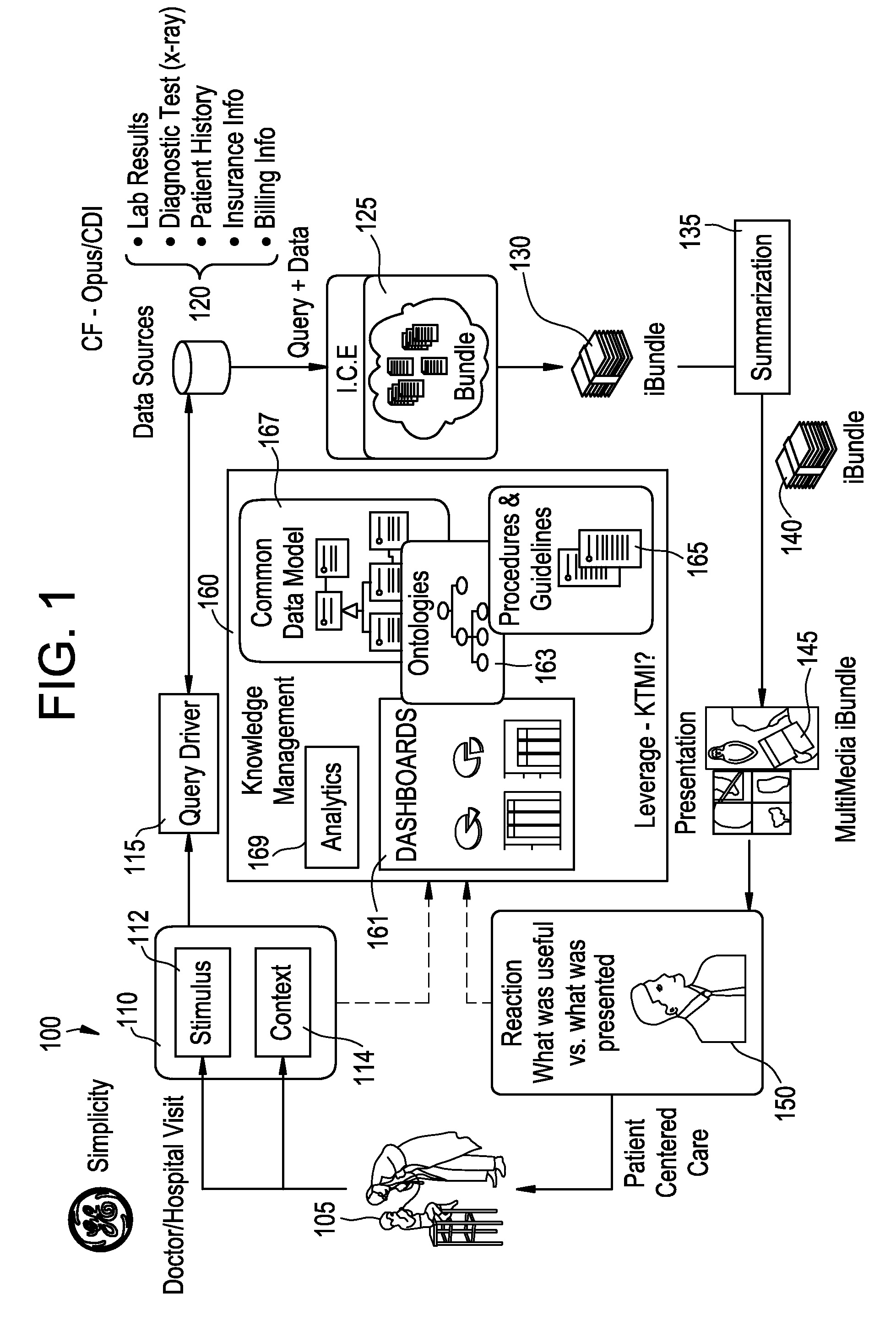
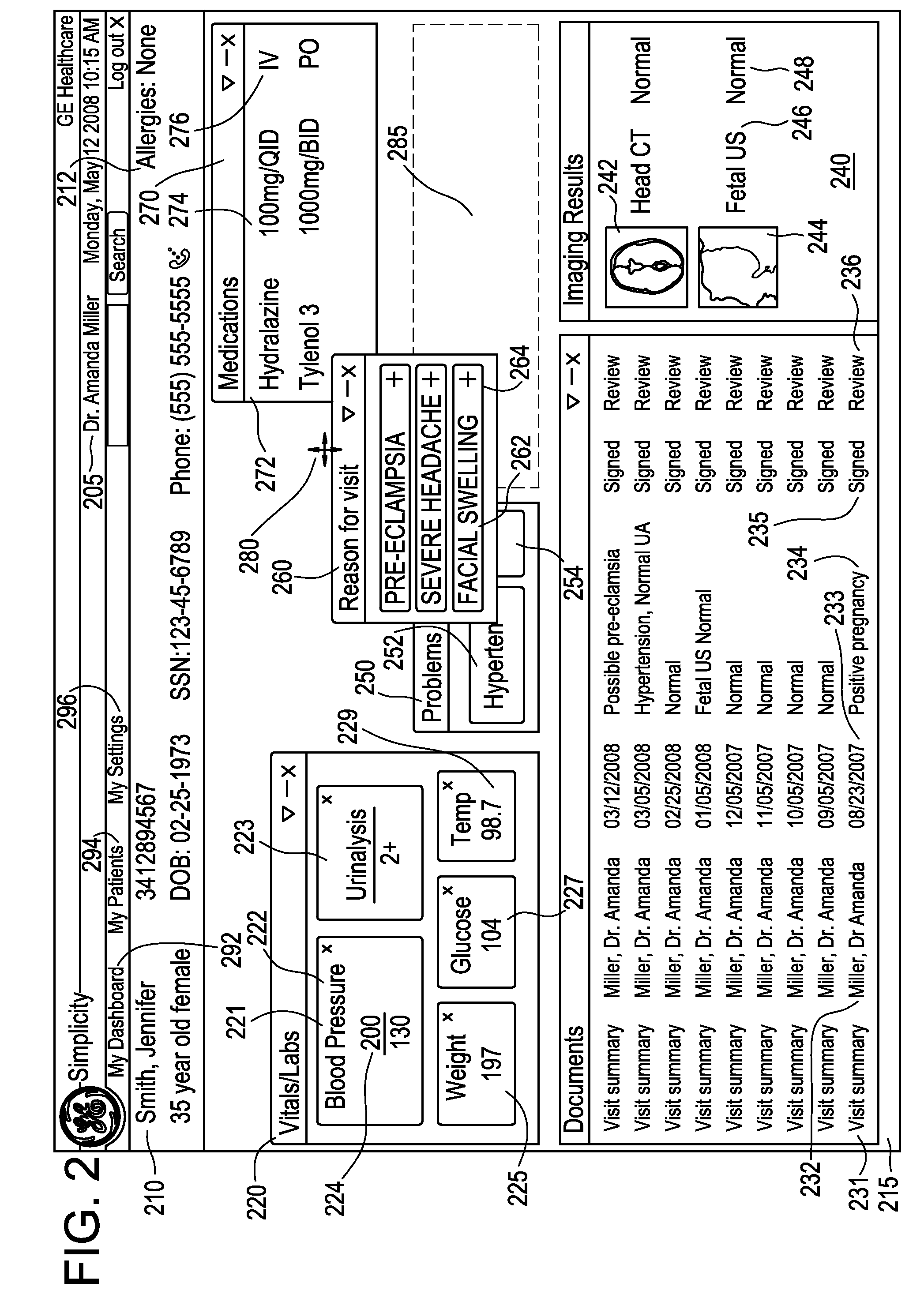
Adaptive user interface systems and methods for healthcare applications
InactiveUS20100131482A1Easy accessLocal control/monitoringDigital data processing detailsAdaptive user interfaceData source
Systems and methods for providing adaptive, work-centered healthcare services via an adaptive user interface are provided. An example adaptive user interface apparatus includes a plurality of widgets providing applications and / or data to a user based on a particular data context, the plurality of widgets responsive to input from the user. The apparatus also includes a query engine providing customized query results from a connectivity framework of data sources based on a user query and the particular data context. The apparatus further includes a user interface display area configurable by the user to position widget(s) and query engine access to enable the user to access, input, and search medical information across a healthcare enterprise. The user interface includes an adaptive, work-centered interface employing an ontology modeling approach to characterize the user's workspace based on workflow activities and computation mechanisms to support the user's workflow and access to enterprise applications and data.
Owner:GENERAL ELECTRIC CO
Business rules user interface for development of adaptable enterprise applications
InactiveUS20060129978A1Highly effectiveRobust and scalable deploymentTechnology managementVisual/graphical programmingDatabaseUser interface
Methods and apparatus, including computer program products, for interacting with a user to define business rules in a declarative manner. The invention operates to display a set of business rules as editable conditions and editable actions, the conditions and the actions being linked to each other by a combination of editable if-values and editable then-values.
Owner:PROGRESS SOFTWARE
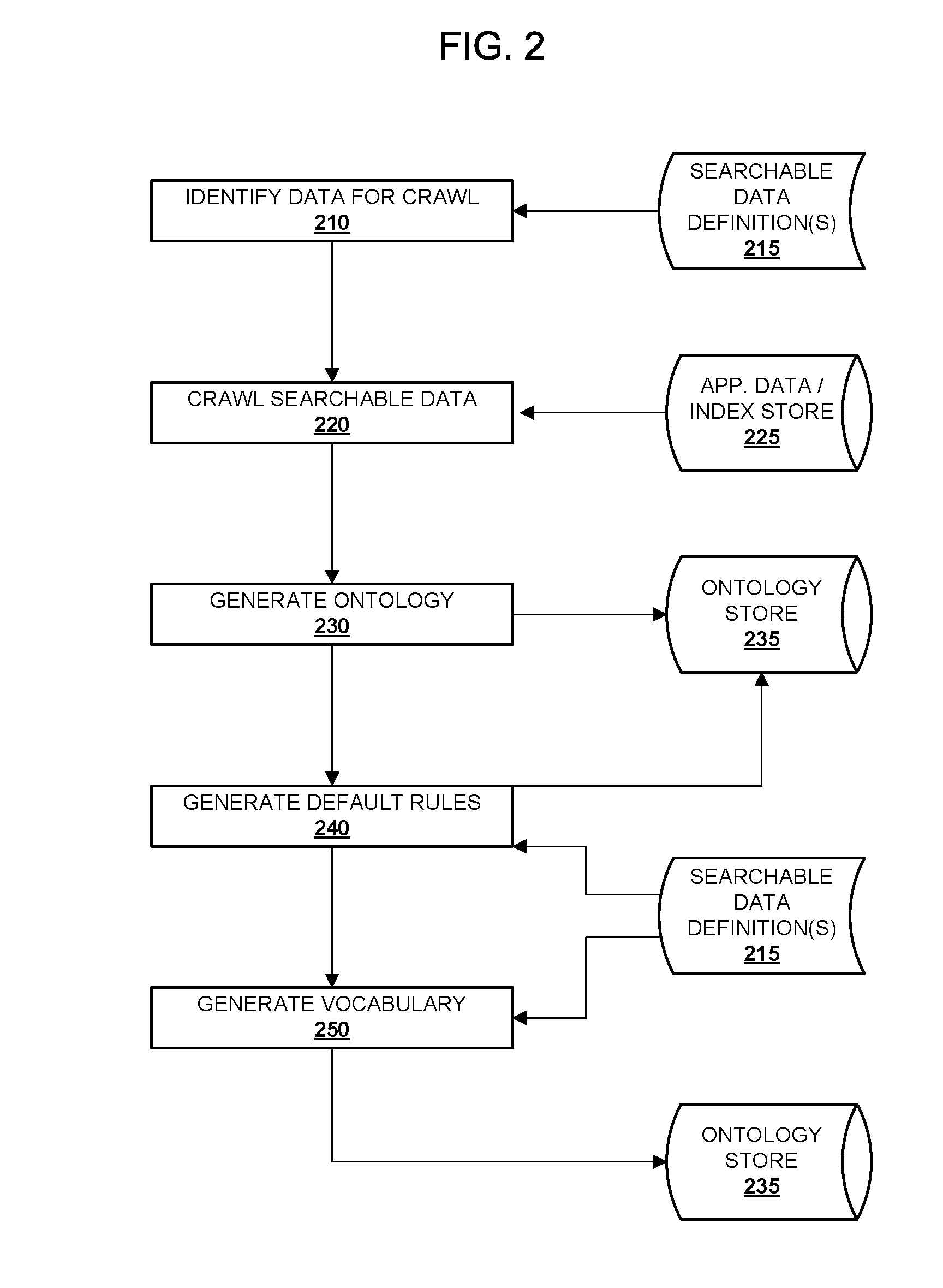
System and Method for Semantic Search in an Enterprise Application
ActiveUS20100070517A1Digital data information retrievalDigital data processing detailsSemantic searchSemantic information
Embodiments of the present invention provide techniques for searching enterprise data using semantic information associated with enterprise applications. One or more searchable data definitions that describe searchable data associated with one or more enterprise applications may identify semantic relationships among searchable data in the application. An ontology for the application that describes semantic relationships among data associated with the application may be generated from the searchable data definitions. The ontology may be used to execute search queries and provide search results that include or result from semantic relationships among the searched data.
Owner:ORACLE INT CORP
Policy-Based Application Management
InactiveUS20140032733A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
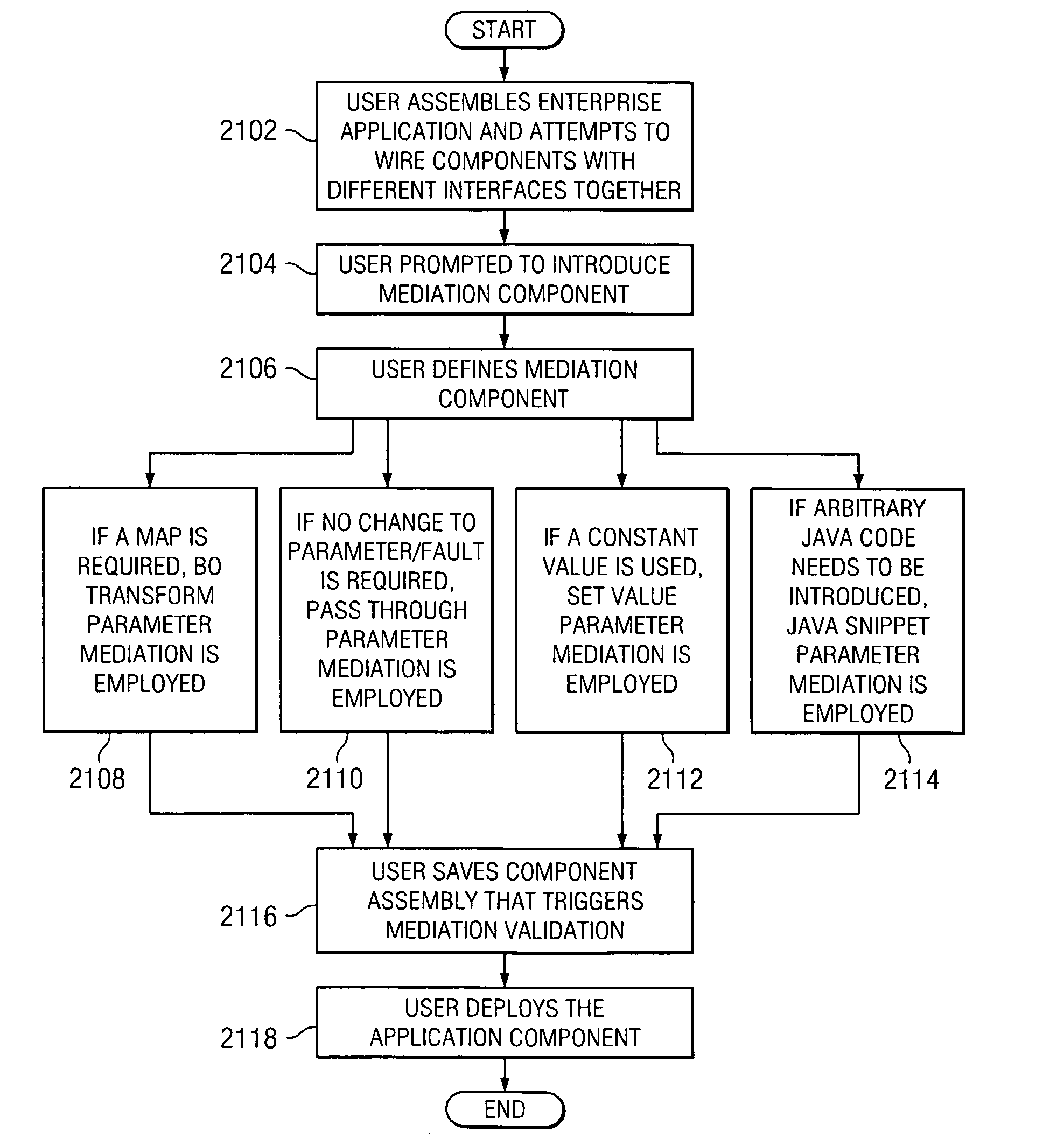
Generic framework for integrating components with different interfaces in an enterprise application intergration environment
ActiveUS20060265719A1Multiprogramming arrangementsSpecific program execution arrangementsEnterprise application integrationCommon framework
A method, system, and computer program code for integrating components with different interfaces in an enterprise application integration environment. When an enterprise application is assembled, a user may try to wire a component to another component in the enterprise. However, if the reference on the source component does not match the interface on the target component, the components cannot be wired together. In this situation, the user is prompted to introduce an interface mediation component between the source and target application components. The mediation component comprises an interface matching the reference on the source component and a reference matching the interface on the target component. The mediation component mediates the different interfaces at runtime by binding an operation in the source component to an operation in the target component, and performing a parameter mediation of parameters in the first operation to parameters in the second operation.
Owner:IBM CORP +1
Business intelligence system with interface that provides for immediate user action
InactiveUS20060089939A1Digital data information retrievalDigital data processing detailsGraphicsGraphical user interface
A business intelligence system includes a business activity monitor with a data cache to receive and store enterprise data integrated from a plurality of enterprise applications, the data cache being updated in real-time as the enterprise data changes. A computer coupled with the data cache runs a program that produces a graphical user interface on a display. The graphical user interface provides a user with a real-time report of the enterprise data and a page that allows the user to specify at least one action affecting operation of the enterprise. The page also including a button selection of which causes the computer to send a first message designating one or more selected actions to the BAM. In response, the BAM sends a second message to one or more of the enterprise applications to execute the one or more selected actions in real-time. It is emphasized that this abstract is provided to comply with the rules requiring an abstract that will allow a searcher or other reader to quickly ascertain the subject matter of the technical disclosure. It is submitted with the understanding that it will not be used to interpret or limit the scope or meaning of the claims.
Owner:ORACLE INT CORP
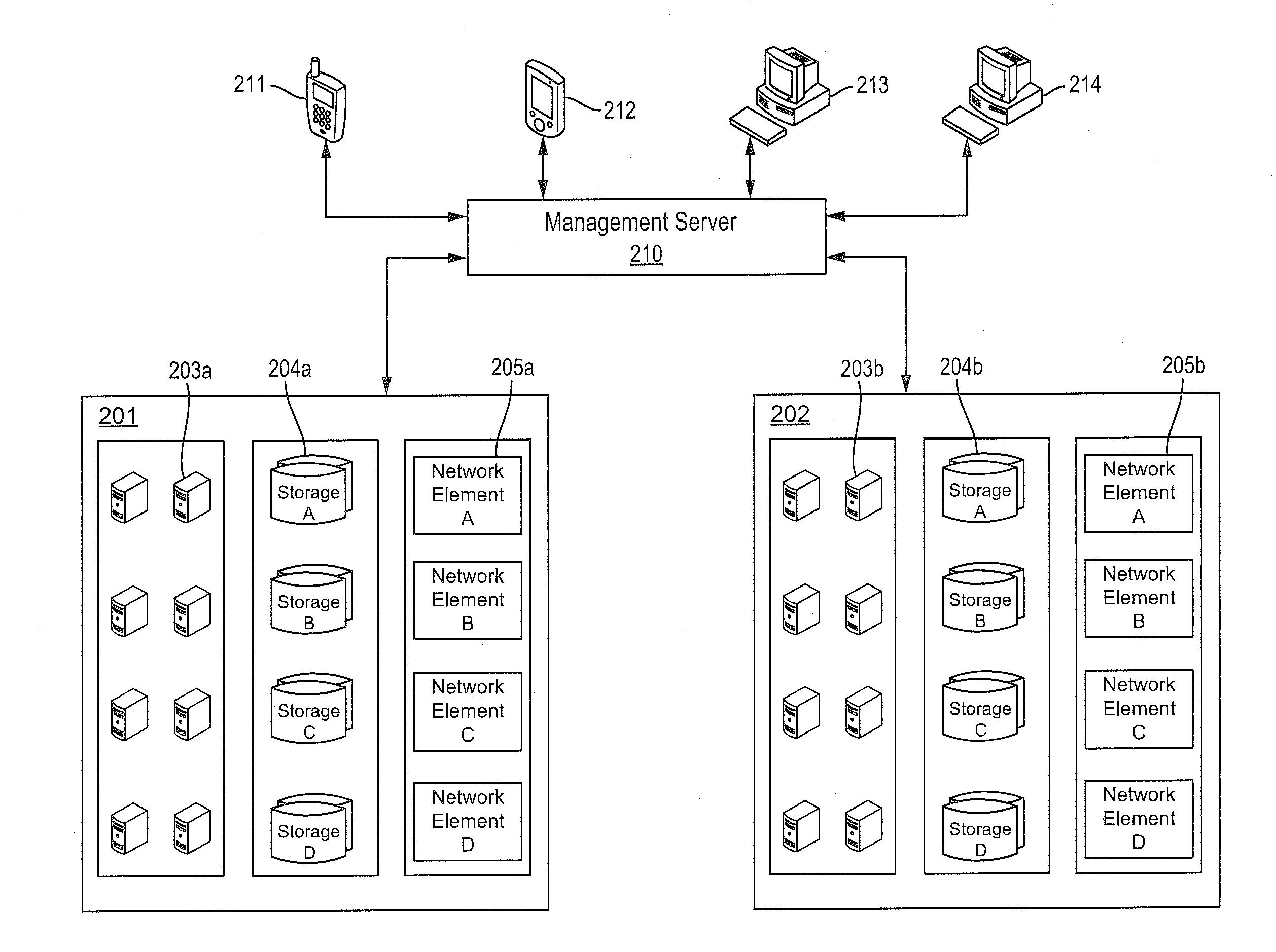
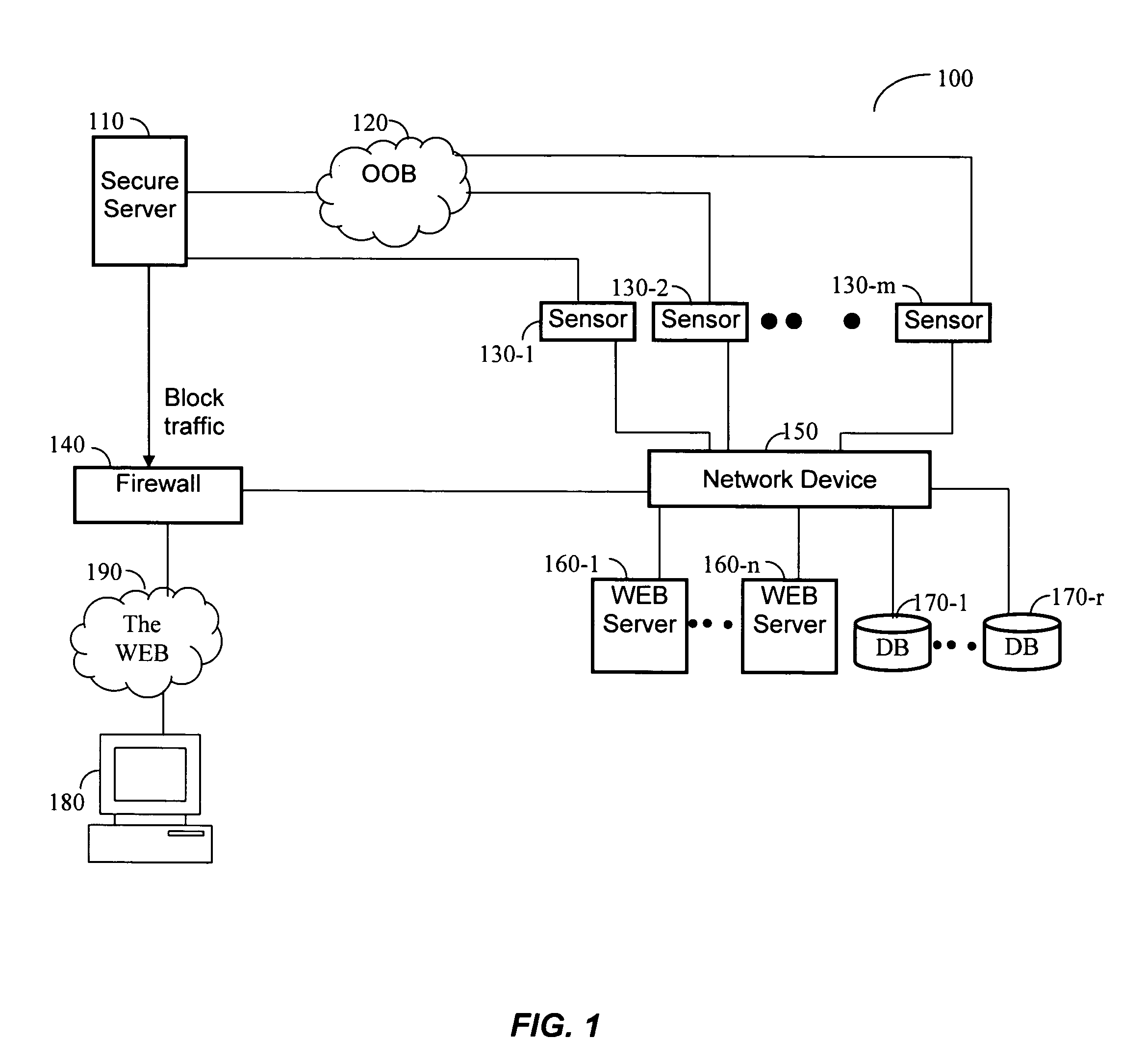
Dynamic learning method and adaptive normal behavior profile (NBP) architecture for providing fast protection of enterprise applications
ActiveUS20050120054A1Quick protectionDigital data information retrievalMemory loss protectionDynamic learningStudy methods
A dynamic learning method and an adaptive normal behavior profile (NBP) architecture for providing fast protection of enterprise applications are disclosed. The adaptive NBP architecture includes a plurality of profile items. Each profile item includes a plurality of profile properties holding the descriptive values of the respective item. An application-level security system can identify and prevent attacks targeted at enterprise applications by matching application events against at least a single profile item in the adaptive NBP.
Owner:IMPERVA
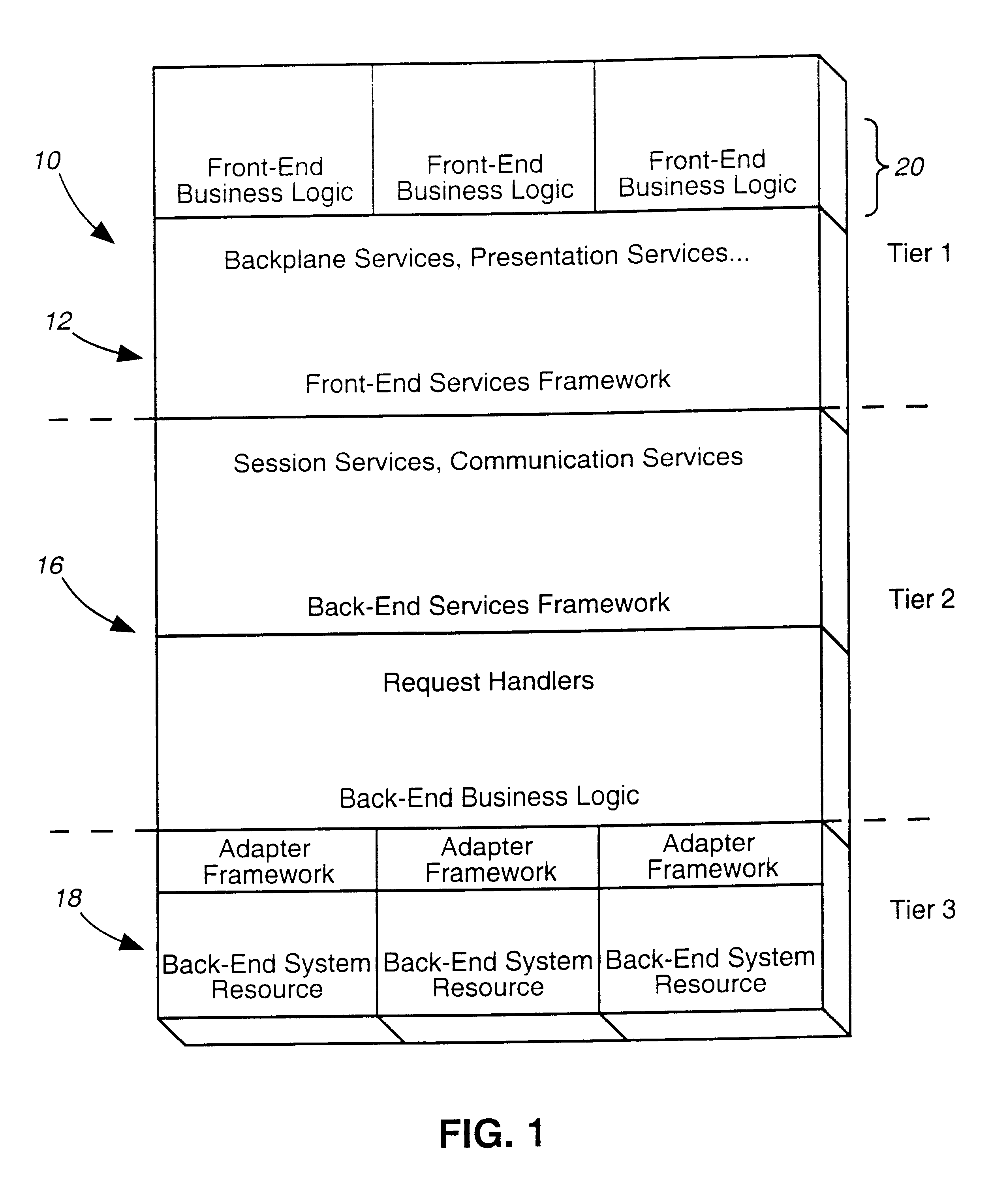
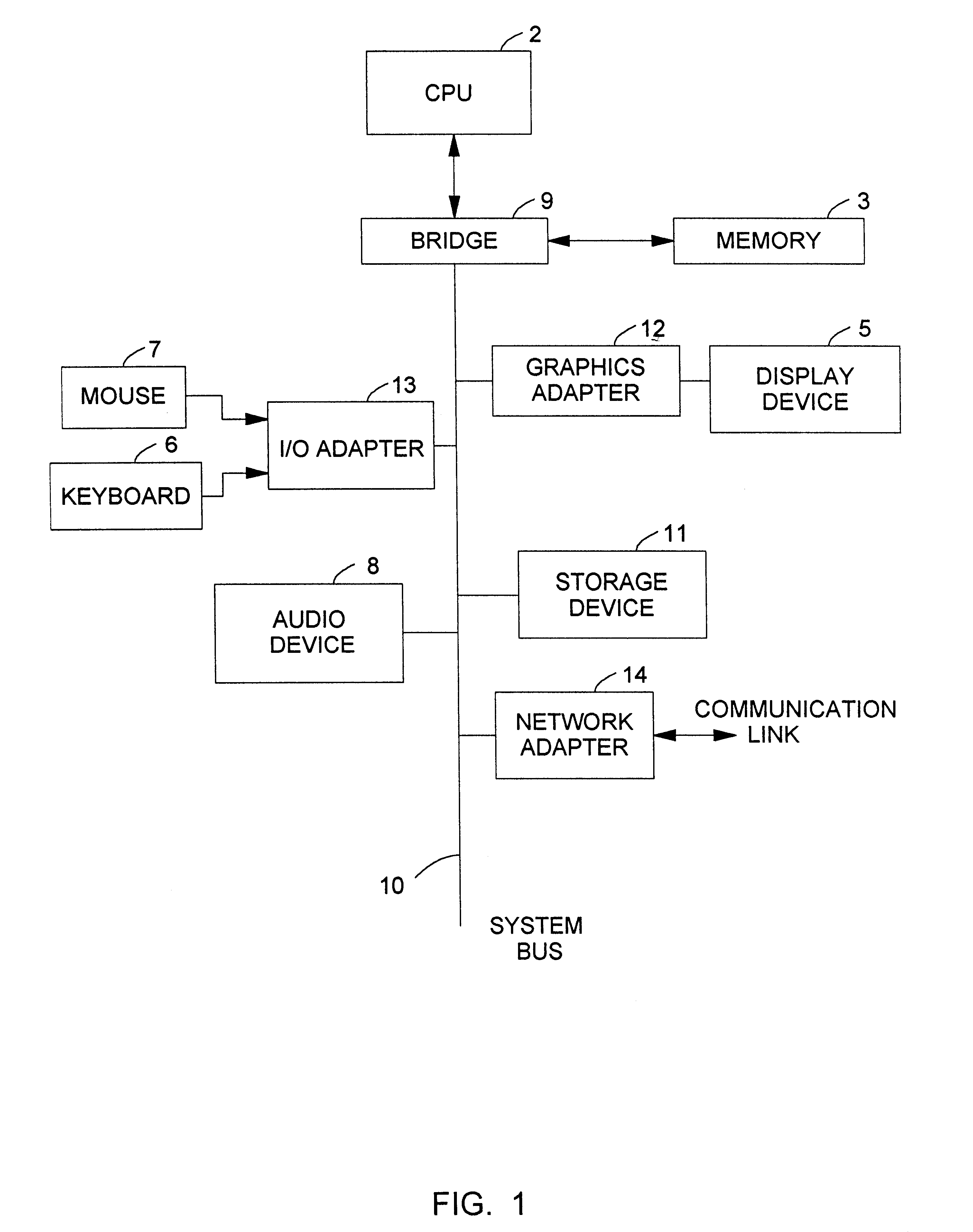
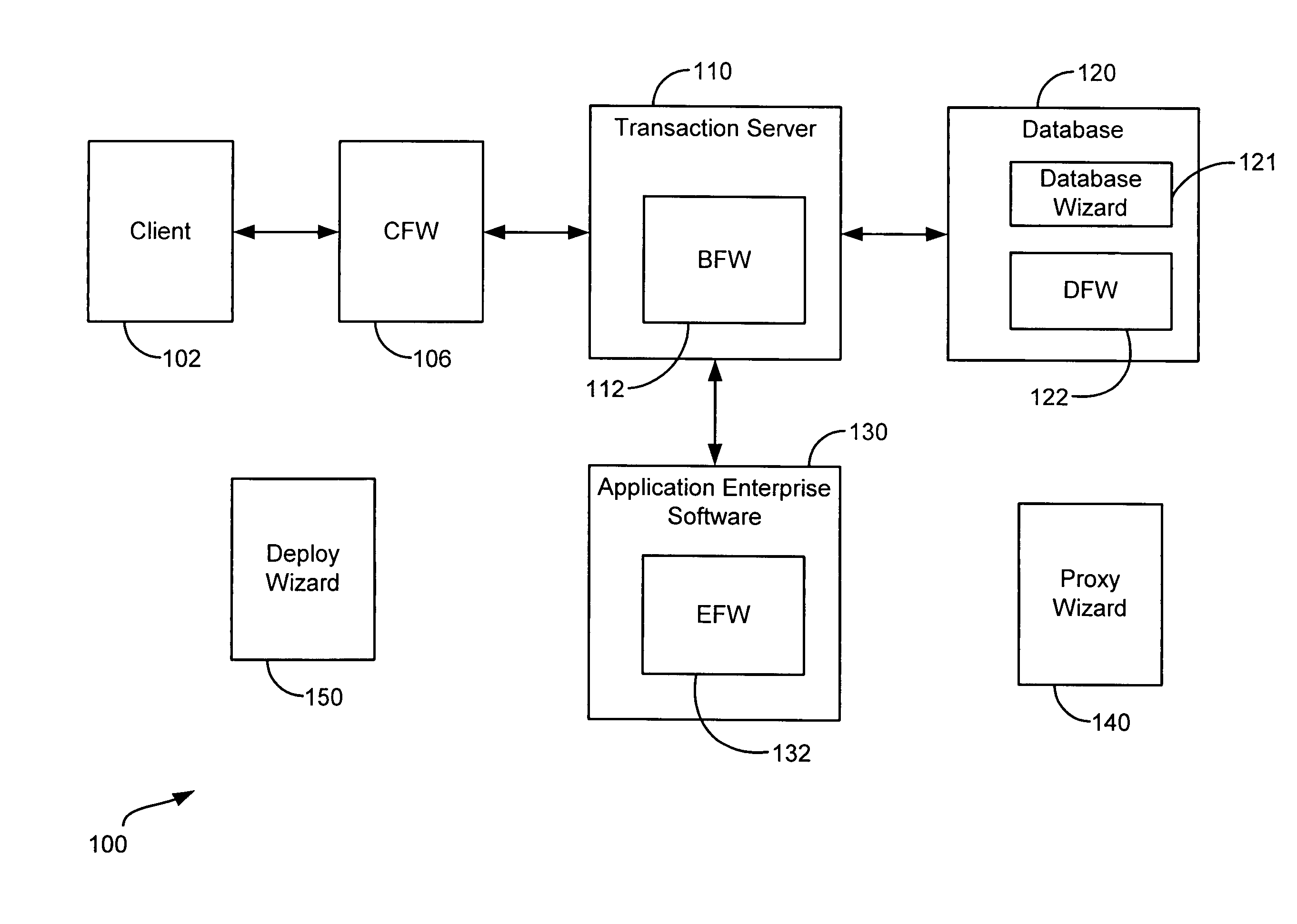
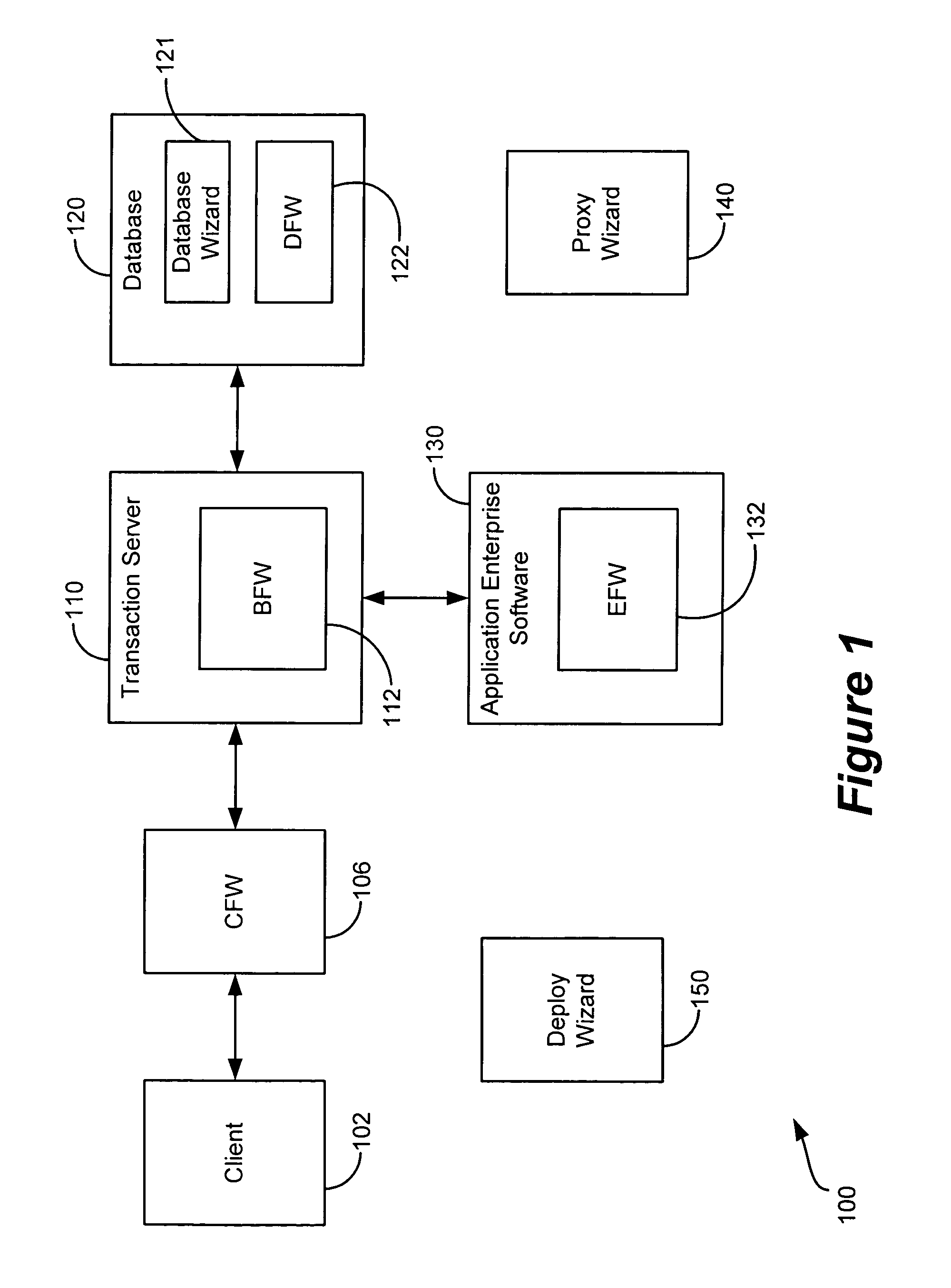
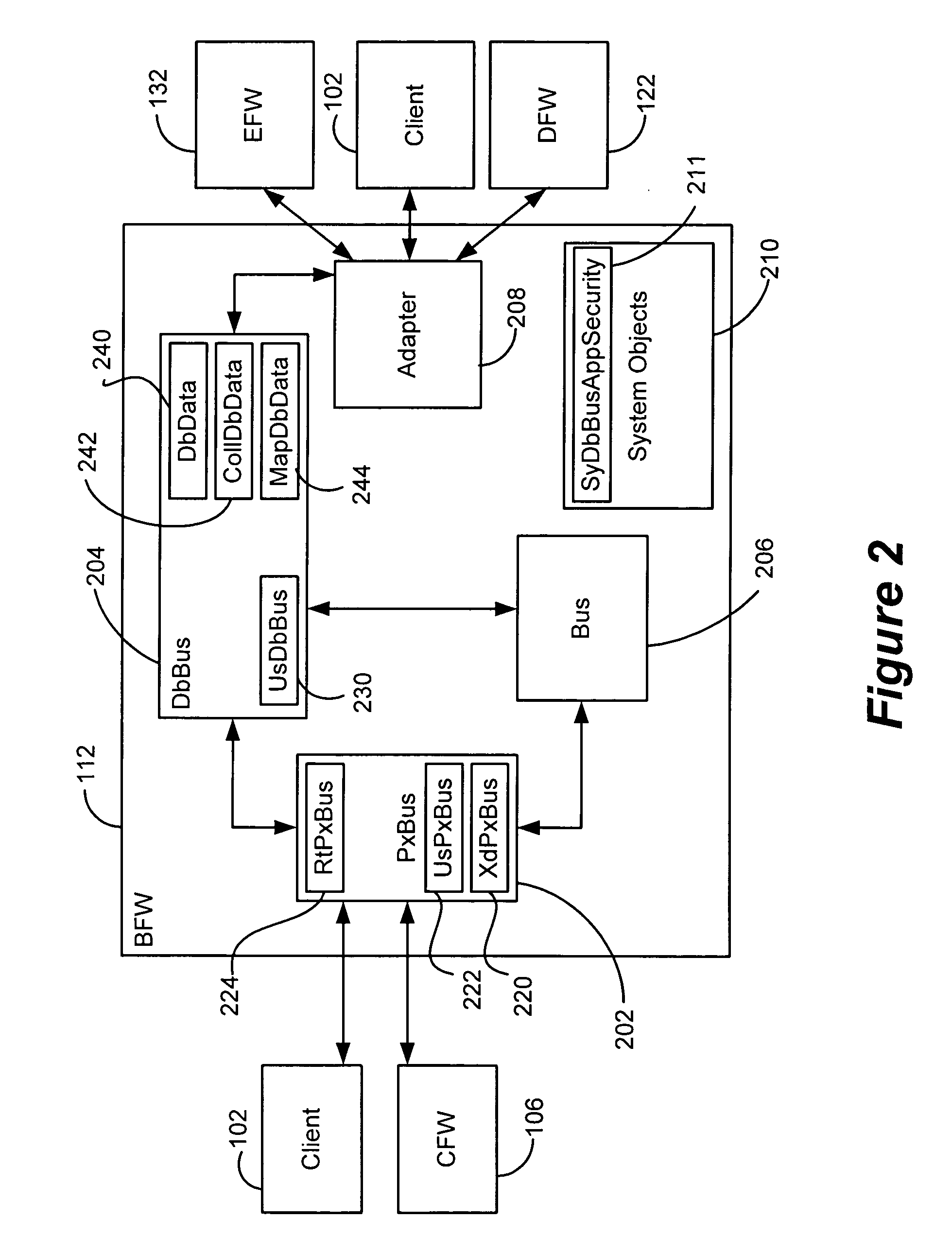
Generic framework for applying object-oriented models to multi-tiered enterprise applications
A system and method are provided for the structured, rapid development and deployment of software components that together, would constitute a robust multi-tiered enterprise software application. Four sub-components are provided for handling various aspects of the business objects. A client framework is used to interact with client users and client software processes. A database framework is used to handle data retention and search functions. An external framework is used to interact with software processes that are outside the gambit of the present system. Finally, a business framework is used to operate the business objects themselves. The business framework can be configured under the services of a transaction server.
Owner:MARATHON PETROLEUM
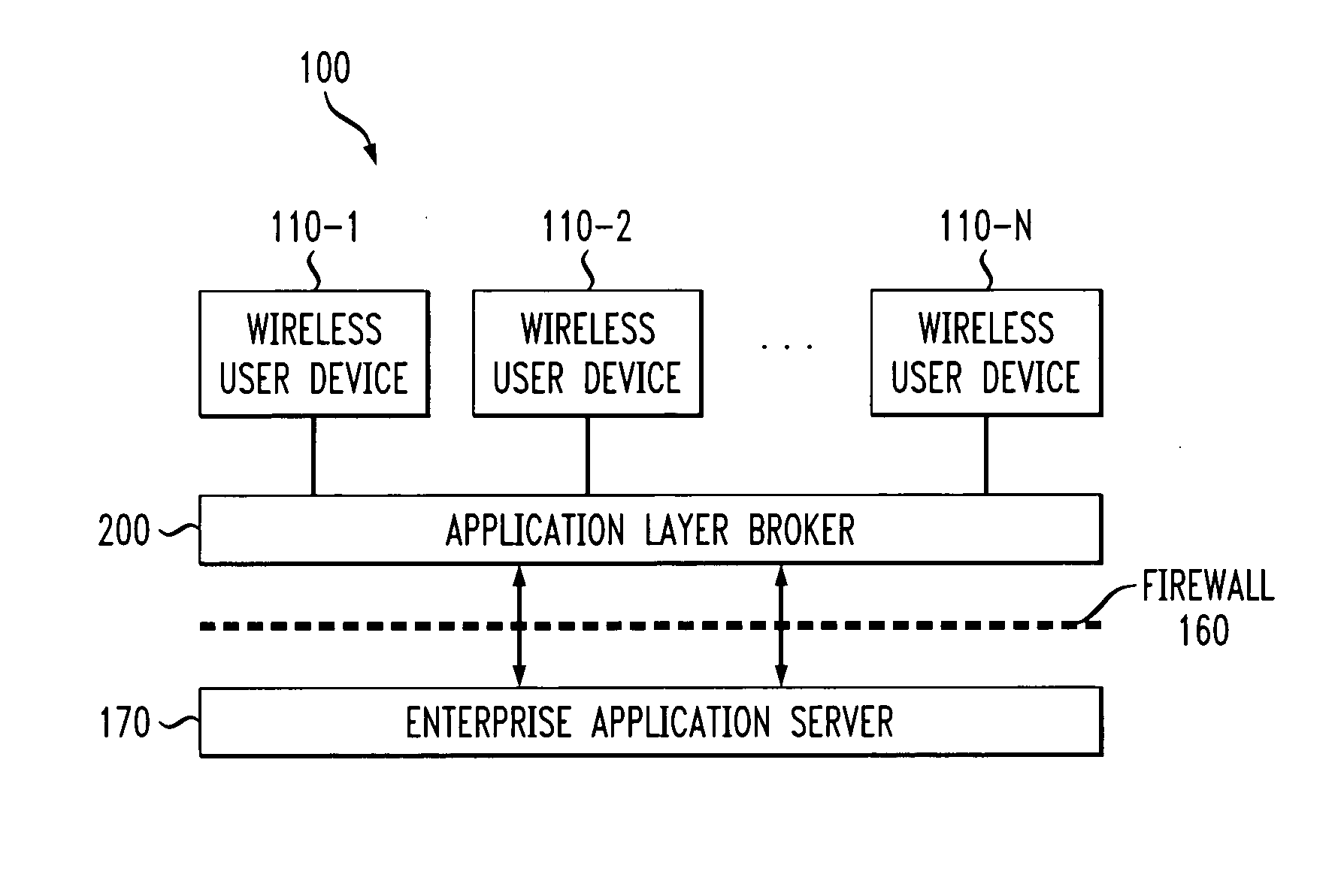
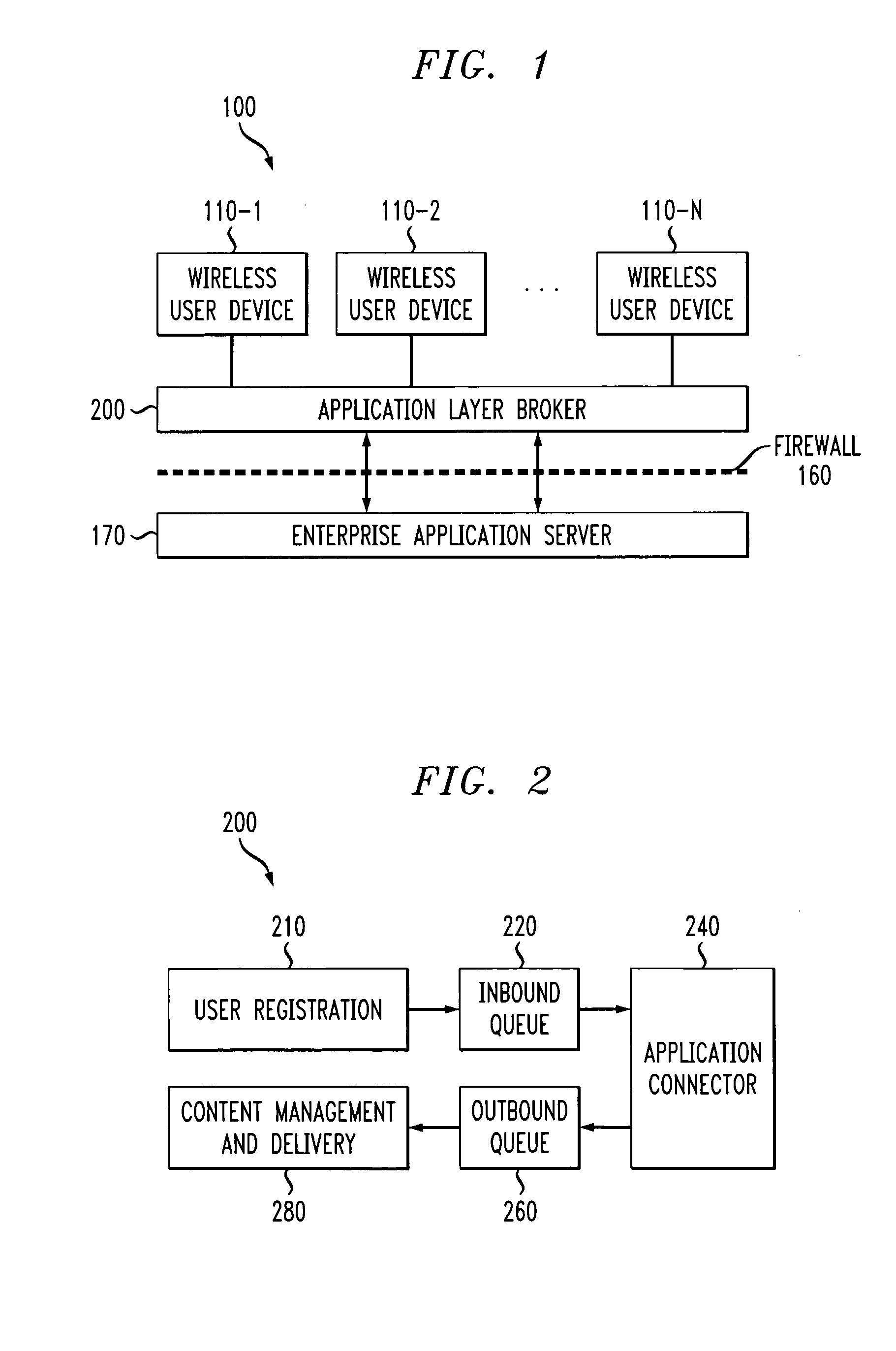
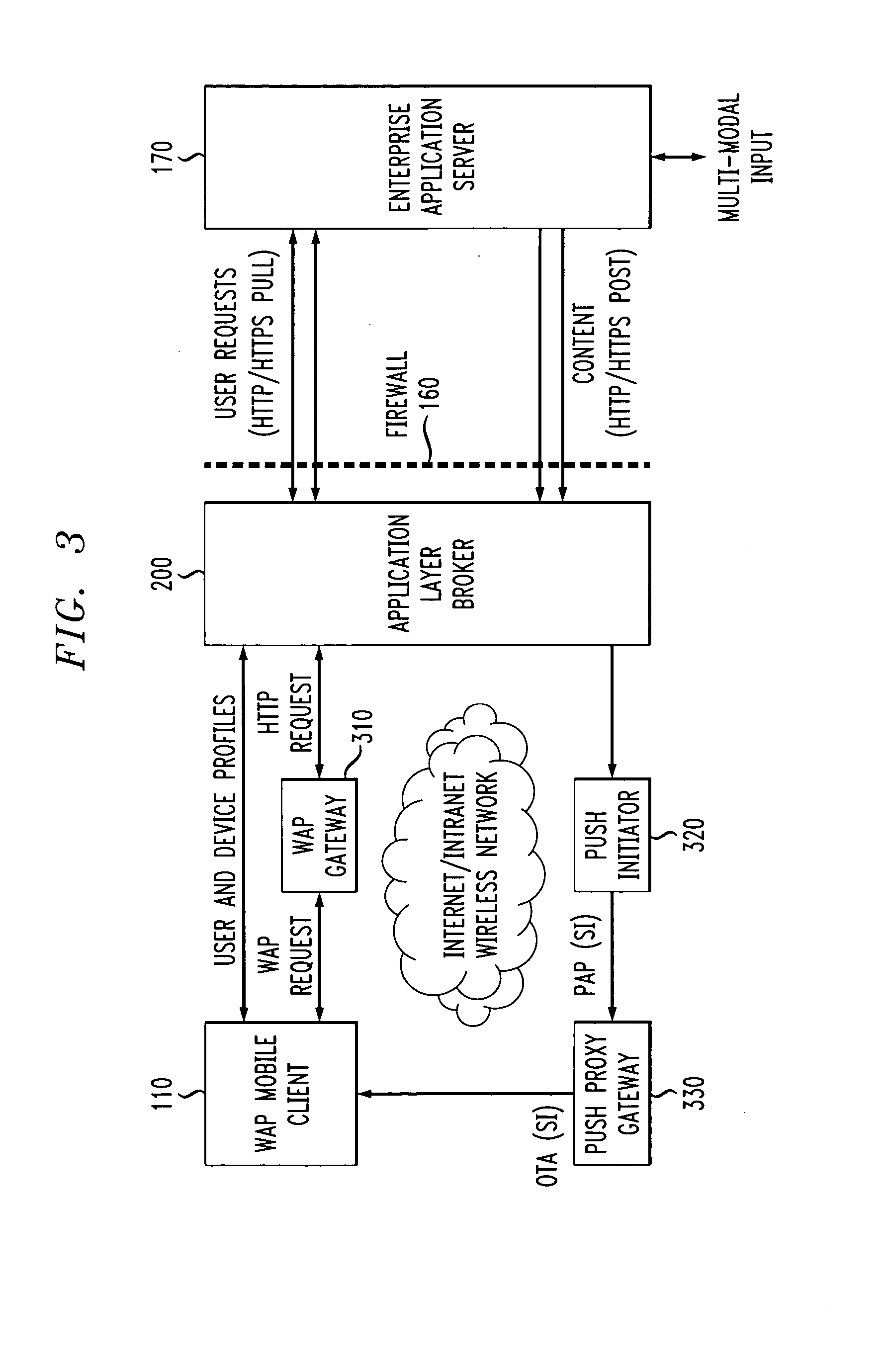
Method and apparatus for secure wireless delivery of converged services
ActiveUS20050071674A1Digital data processing detailsUnauthorized memory use protectionApplication serverService control
A method and apparatus are provided for the secure delivery of converged services to users of wireless devices in a wireless environment. An application layer broker is position between the user devices and the application server to provide an indirect coupling between the enterprise application server and the wireless user devices. The application layer broker links the wireless environment to the enterprise application server through an event triggered content delivery mechanism without providing a direct link between the wireless user device and the enterprise application server. Delivered content can only be accessed by the intended user and the authorized device. The application layer broker provides adaptation to various user devices and the various capabilities associated with each user device. Wireless devices can be upgraded independently from upgrades to the application server. The decoupling performed by the application layer broker separates the service control, such as user registration from the service delivery.
Owner:AVAYA INC
Secure mobile browser for protecting enterprise data
ActiveUS20140007182A1Decompilation/disassemblyDigital data protectionDocumentation procedureApplication server
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Policy-Based Application Management
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
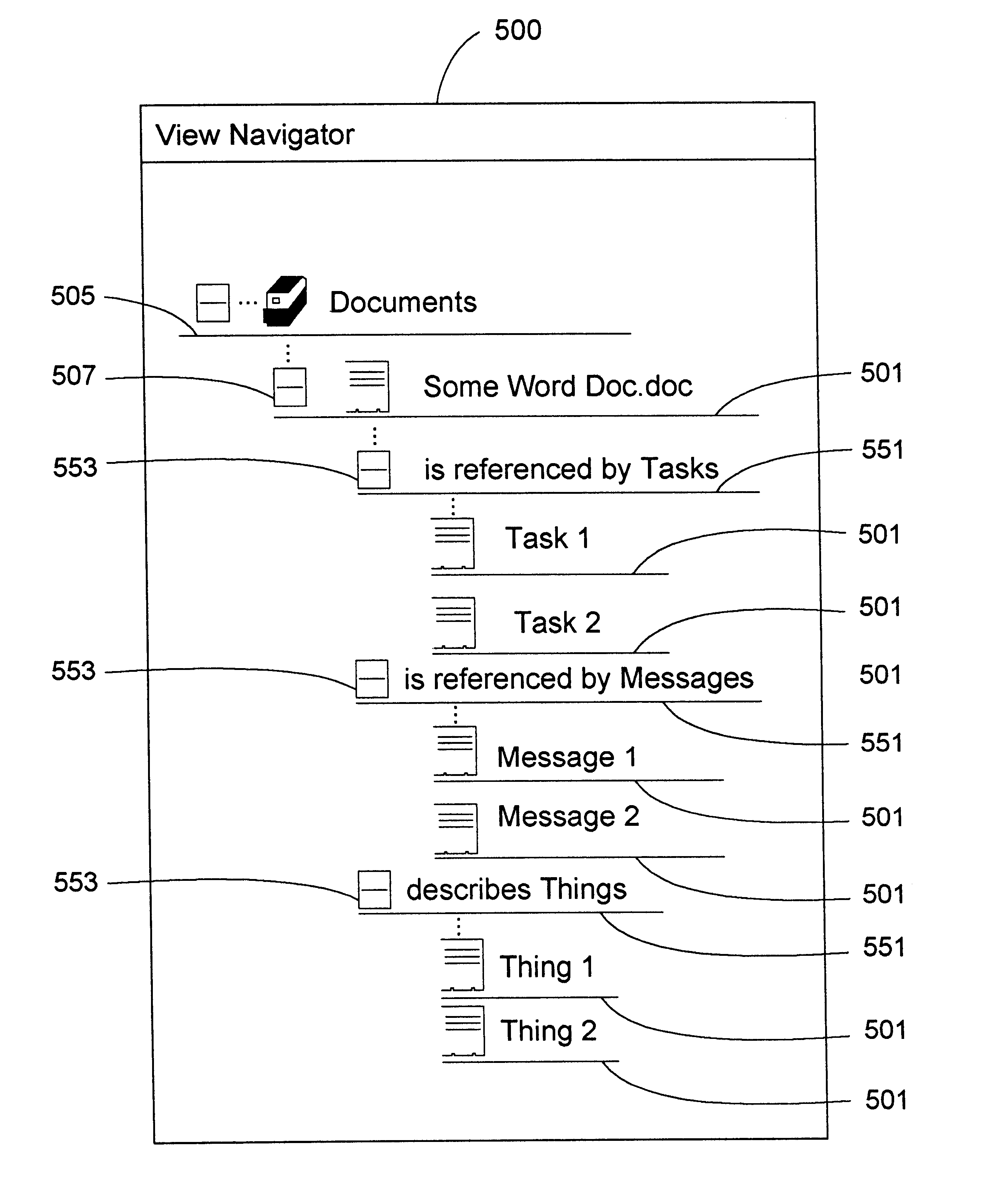
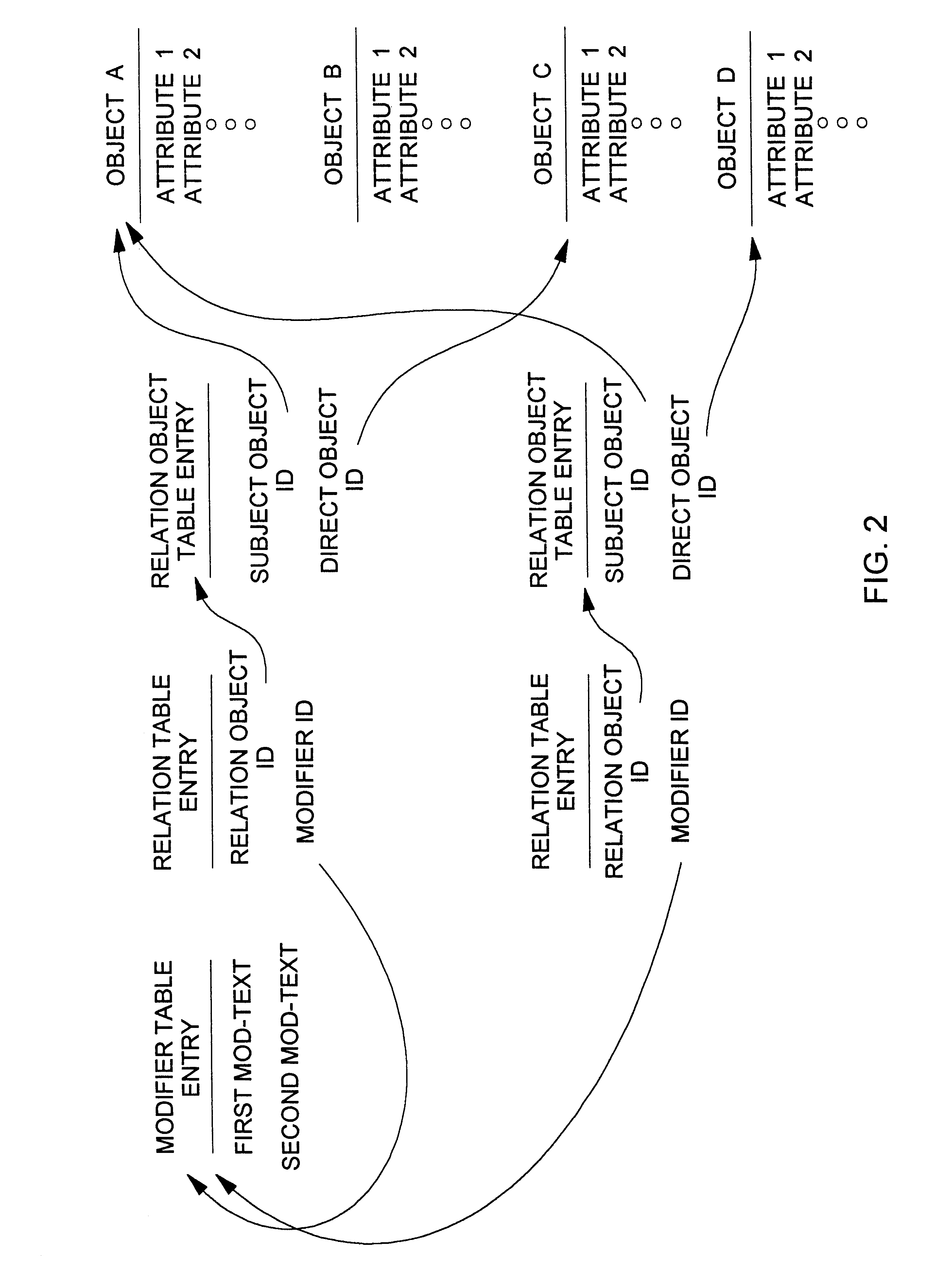
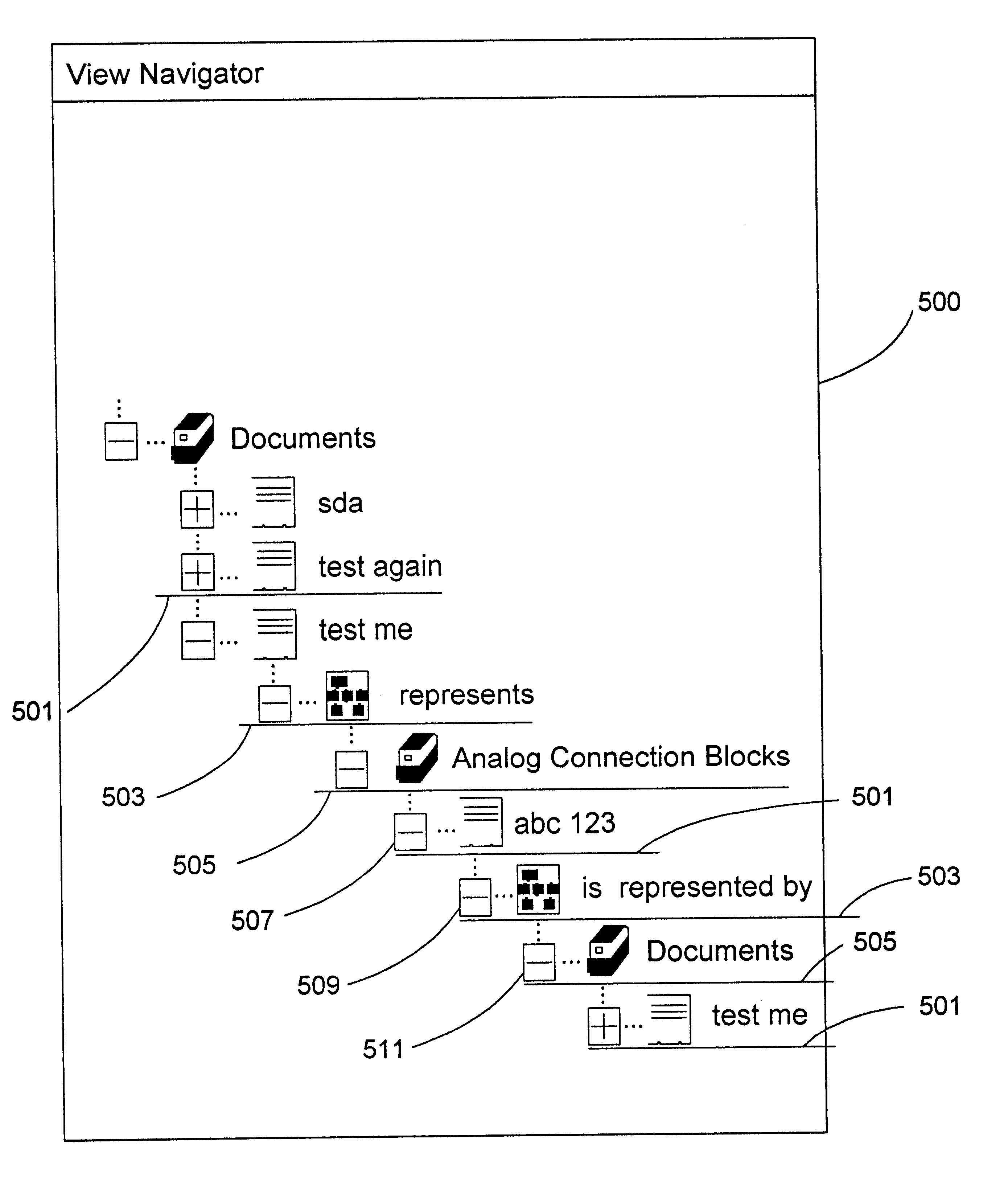
View navigation for creation, update and querying of data objects and textual annotations of relations between data objects
InactiveUS6618733B1EffectivelySave storage spaceData processing applicationsDigital data processing detailsCustomer relationship managementOperational system
A method (and corresponding database system) for displaying in a view window information characterizing semantics of relations between objects. For each given relation between at least one subject object and at least one direct object, bi-directional modifier data is stored that represents first text characterizing semantics of a relationship of the at least one first object to the at least one second object, and represents second text characterizing semantics of a relationship of the at least one second object to the at least one first object. In response to predetermined user input associated with an object node displayed in the view window, a set of relations whose at least one subject object or at least one direct object is associated with the object node is identified. For at least one relation in the set of relations, the view window is updated to include a second node comprising a graphical representation of: the first text of the given relation in the event that the given object is a subject object in the given relation, or the second text of the given relation in the event that the given object is a direct object in the given relation. The second node may be a relation node associated with a given relation, or a mixed node associated with a relation-type pair. In response to predetermined input with a second node, the second node may be expanded to identify and display one or more object nodes (identifying direct object(s) of relations derived from expansion of a subject object associated therewith or identifying subject object(s) of relations derived from expansion of a direct object associated therewith). Preferably, this expansion routine is recursive in nature.The method (and database system) of the present invention may be used in a wide assortment of software applications, including enterprise applications (such as e-business applications, supply chain management applications, customer relationship management applications, decision support applications), the file system in operating systems, web browsers, e-mail applications and personal information management applications. Importantly, the method (and database system) provides an easy, user friendly and efficient mechanism to define, view and query the organization of the data elements (and the relationships therebetween) stored and accessed in such software applications, in a manner that conveys the real-world meaning of such relationships.
Owner:REVELINK
Modifying pre-existing mobile applications to implement enterprise security policies
ActiveUS20140007048A1Decompilation/disassemblyDigital data protectionApplication serverCorporate security
A system is disclosed that includes components and features for enabling enterprise users to securely access enterprise resources (documents, data, application servers, etc.) using their mobile devices. An enterprise can use some or all components of the system to, for example, securely but flexibly implement a BYOD (bring your own device) policy in which users can run both personal applications and secure enterprise applications on their mobile devices. The system may, for example, implement policies for controlling mobile device accesses to enterprise resources based on device attributes (e.g., what mobile applications are installed), user attributes (e.g., the user's position or department), behavioral attributes, and other criteria. Client-side code installed on the mobile devices may further enhance security by, for example, creating a secure container for locally storing enterprise data, creating a secure execution environment for running enterprise applications, and / or creating secure application tunnels for communicating with the enterprise system.
Owner:CITRIX SYST INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com