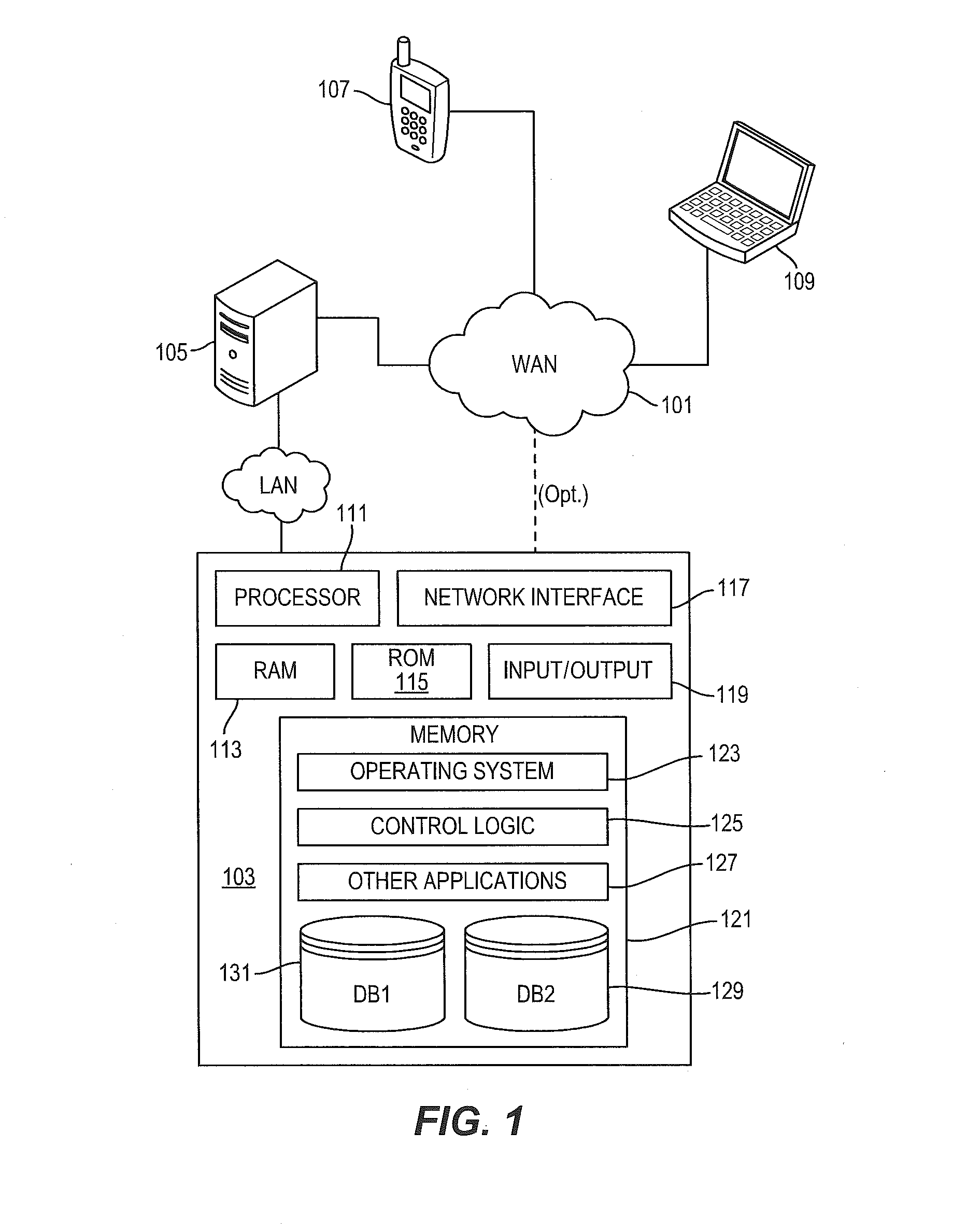
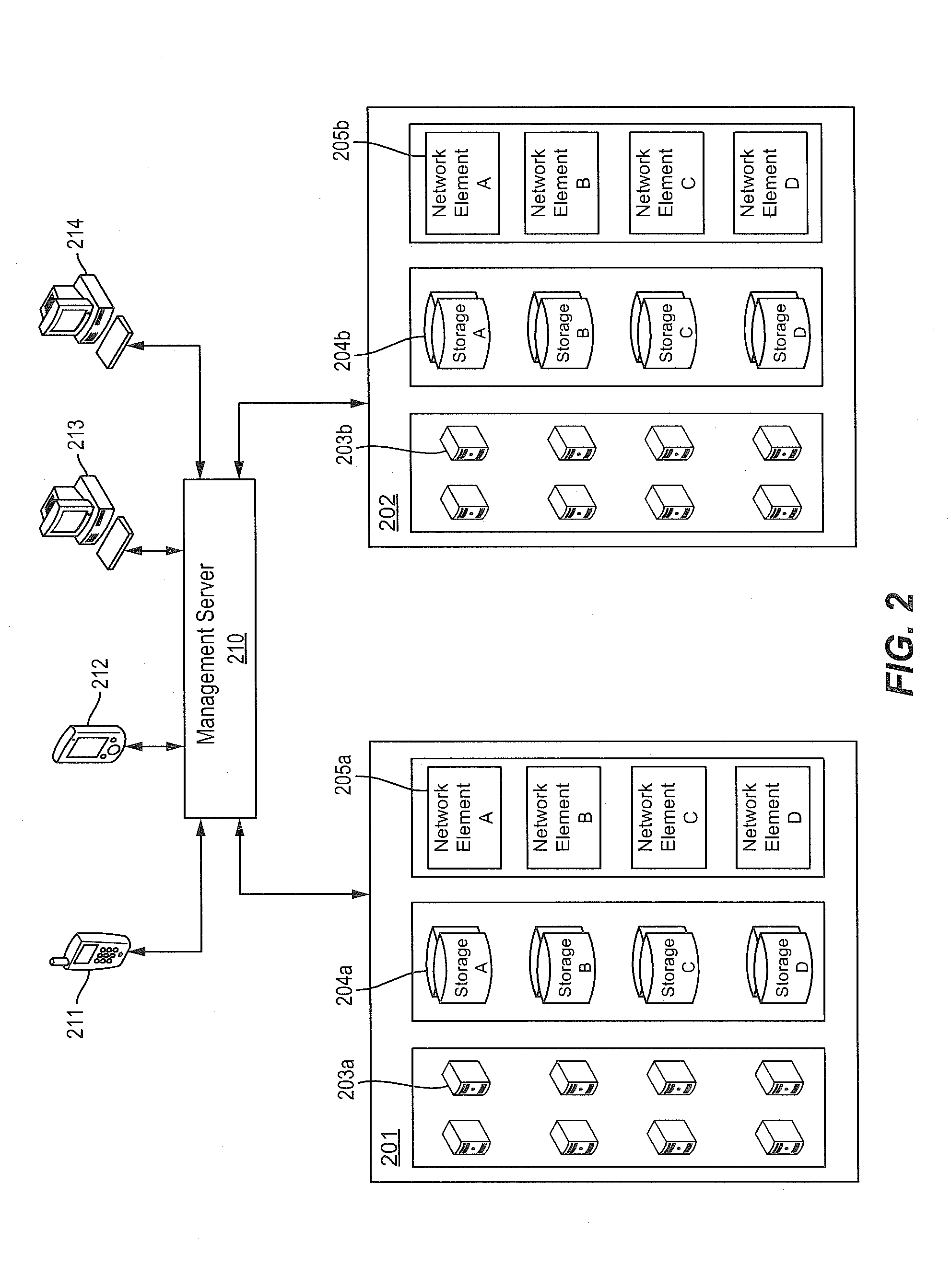
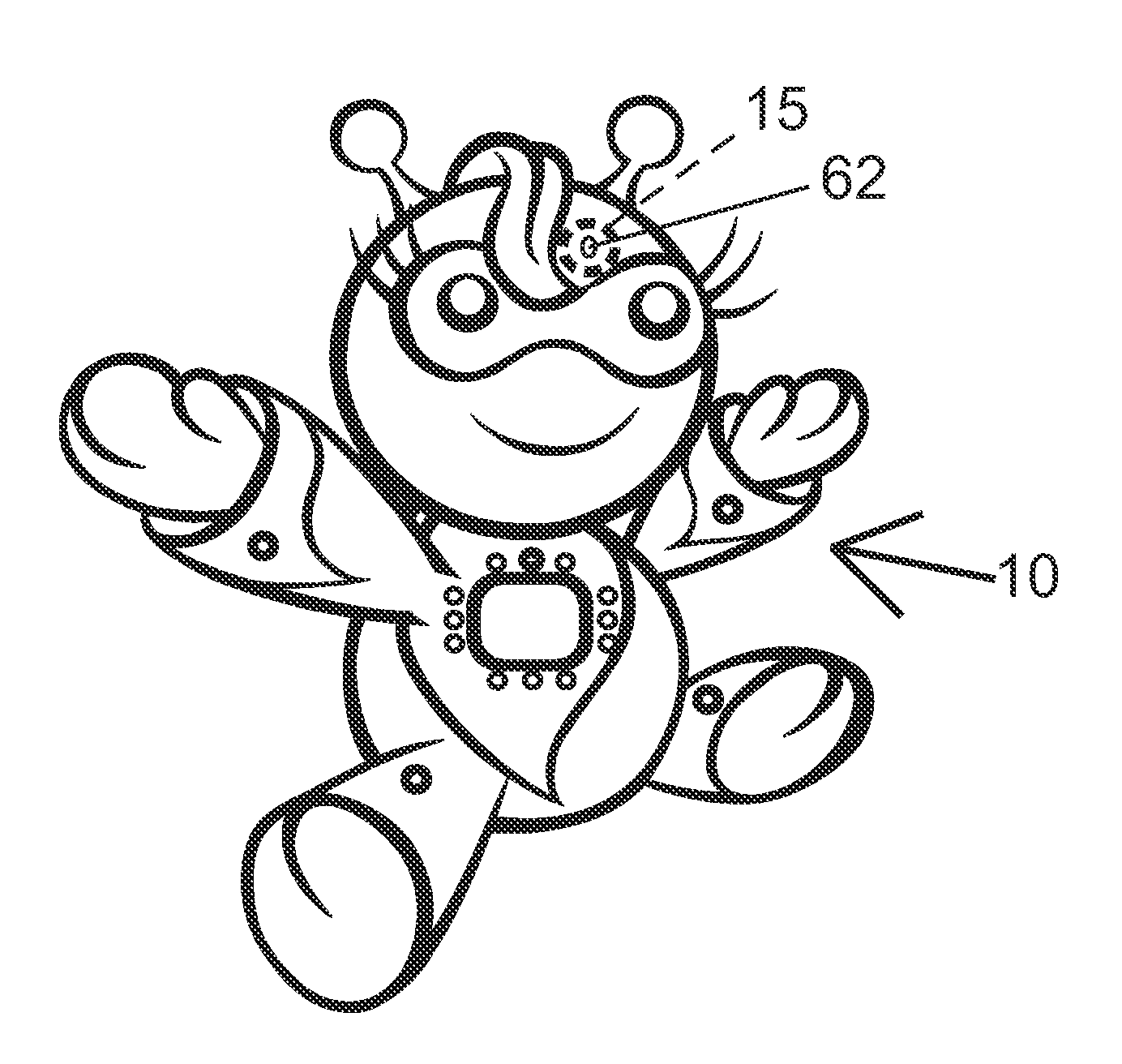Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
184 results about "App store" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An app store (or app marketplace) is a type of digital distribution platform for computer software called Applications, often in a mobile context. Apps provide a specific set of functions which, by definition, do not include the running of the computer itself. Complex software designed for use on a personal computer, for example, may have a related app designed for use on a mobile device. Today apps are normally designed to run on a specific operating system—such as the contemporary iOS, macOS, Windows or Android—but in the past mobile carriers had their own portals for apps and related media content.
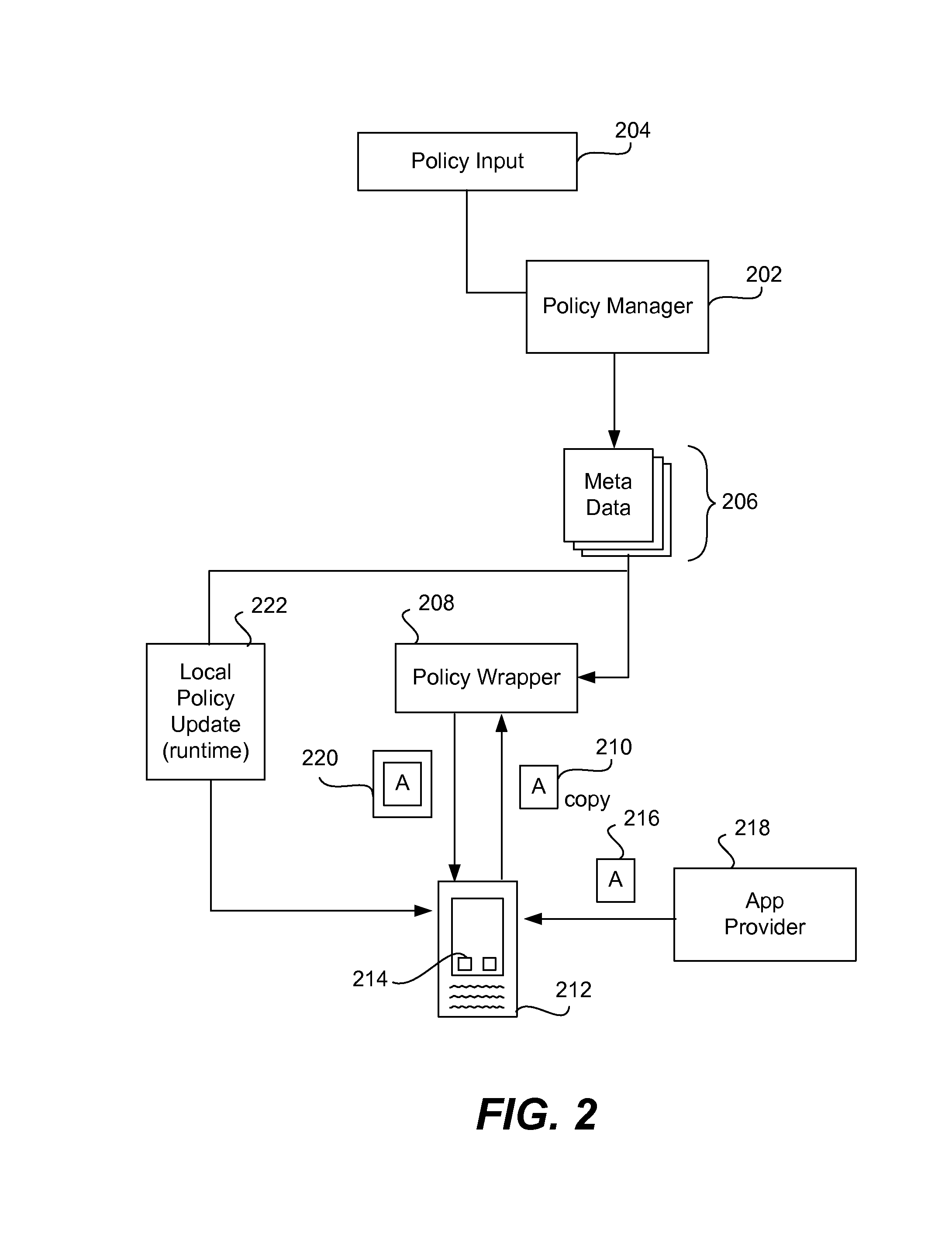
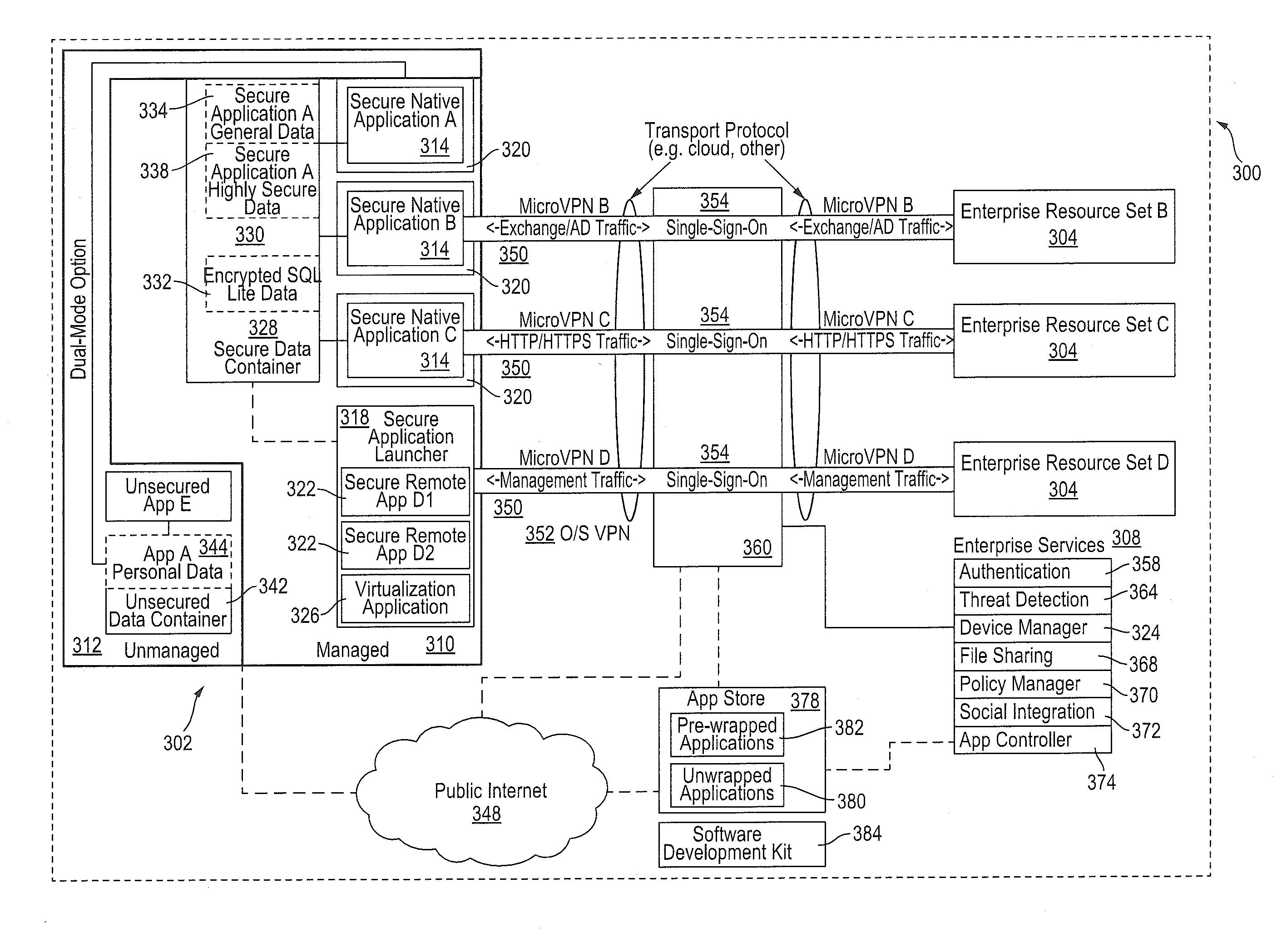
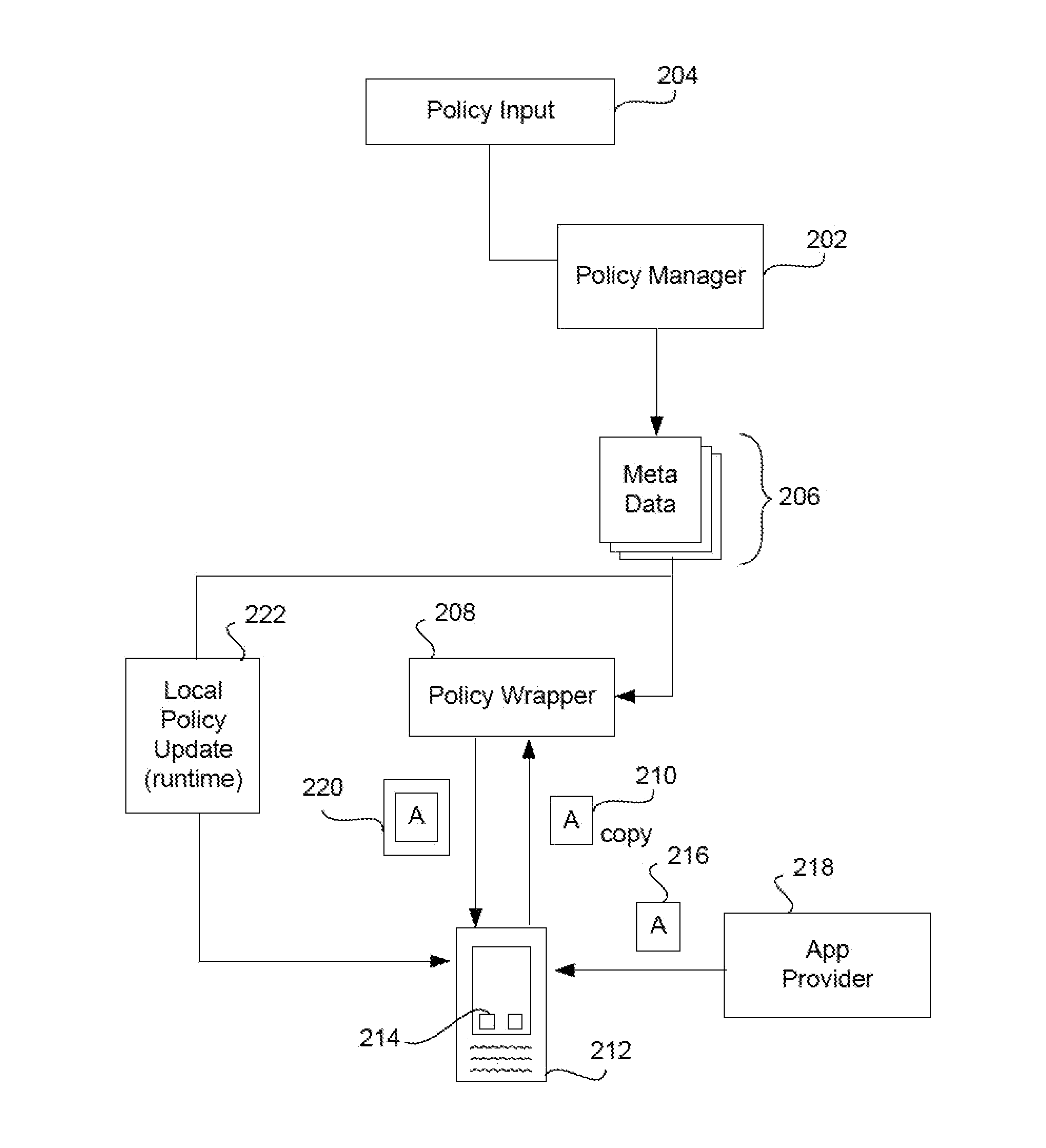
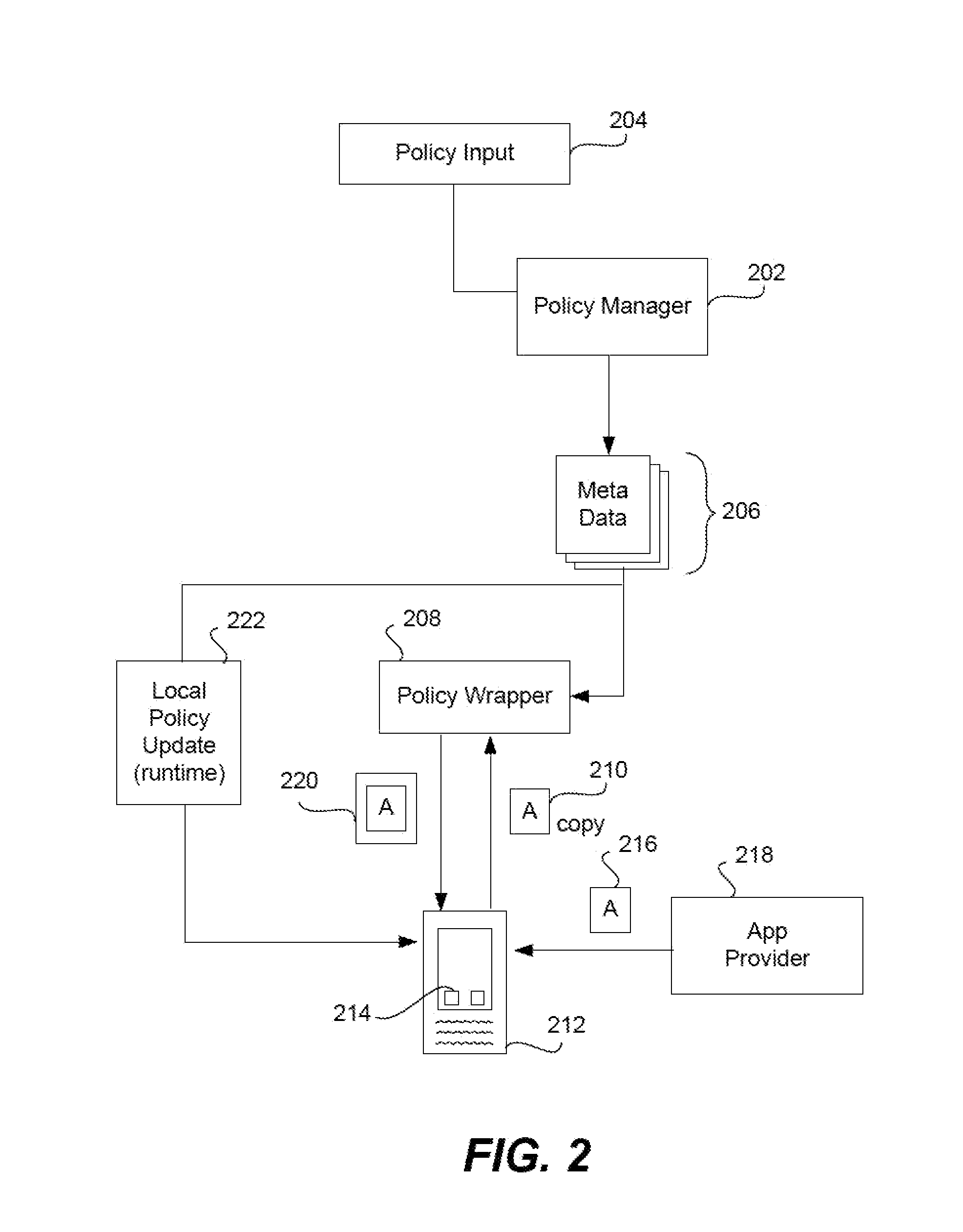
Policy-Based Application Management
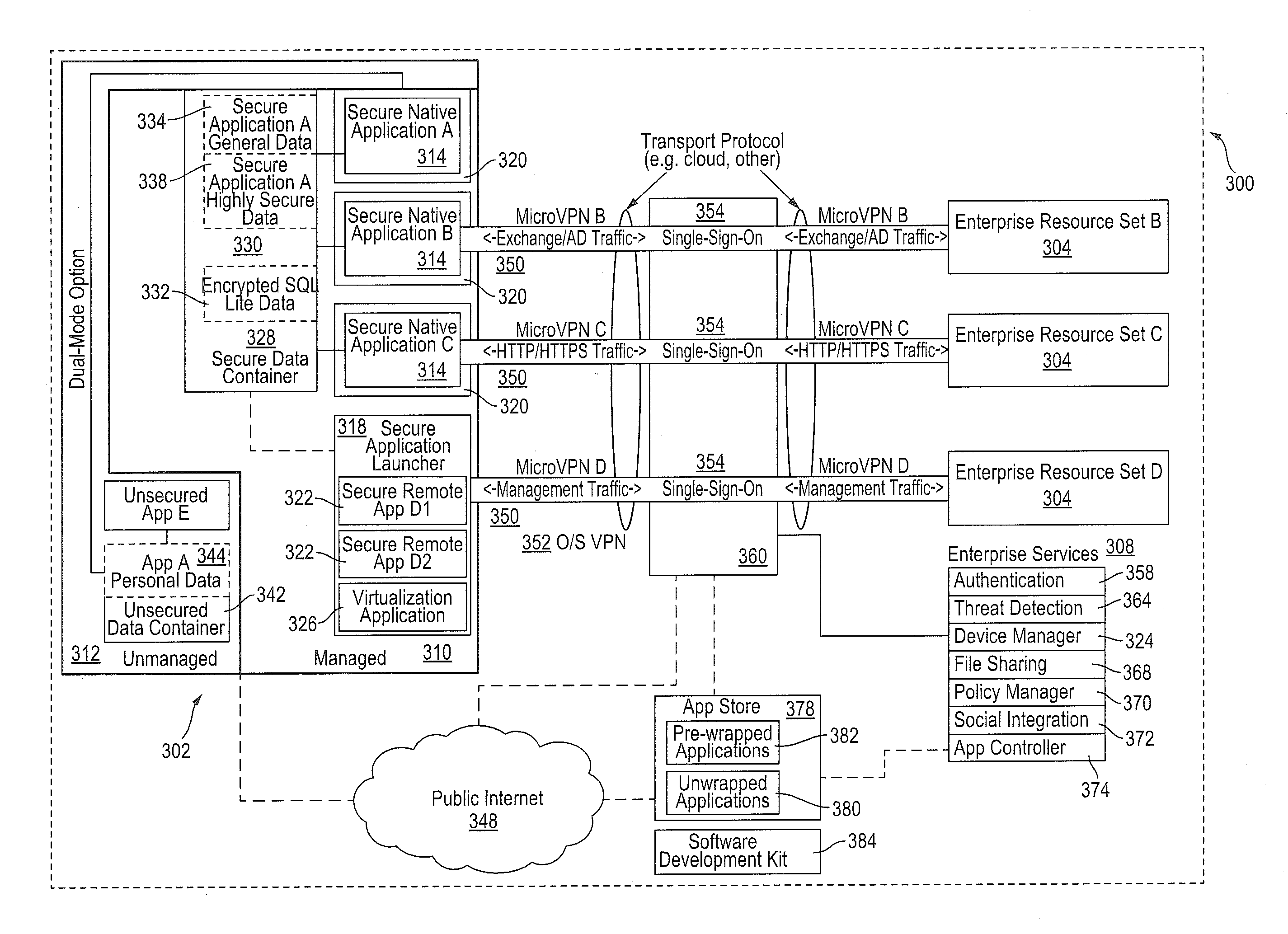
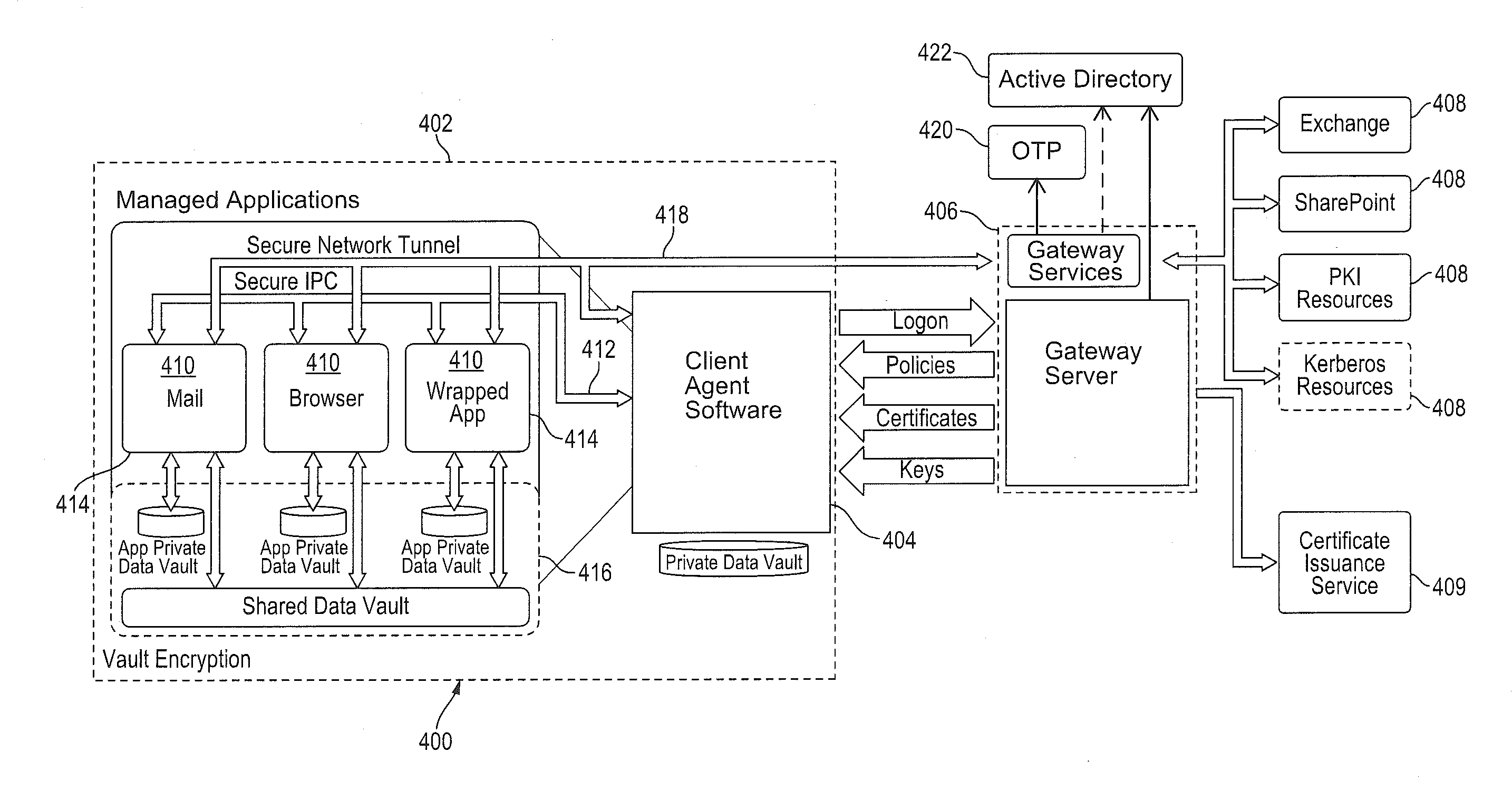
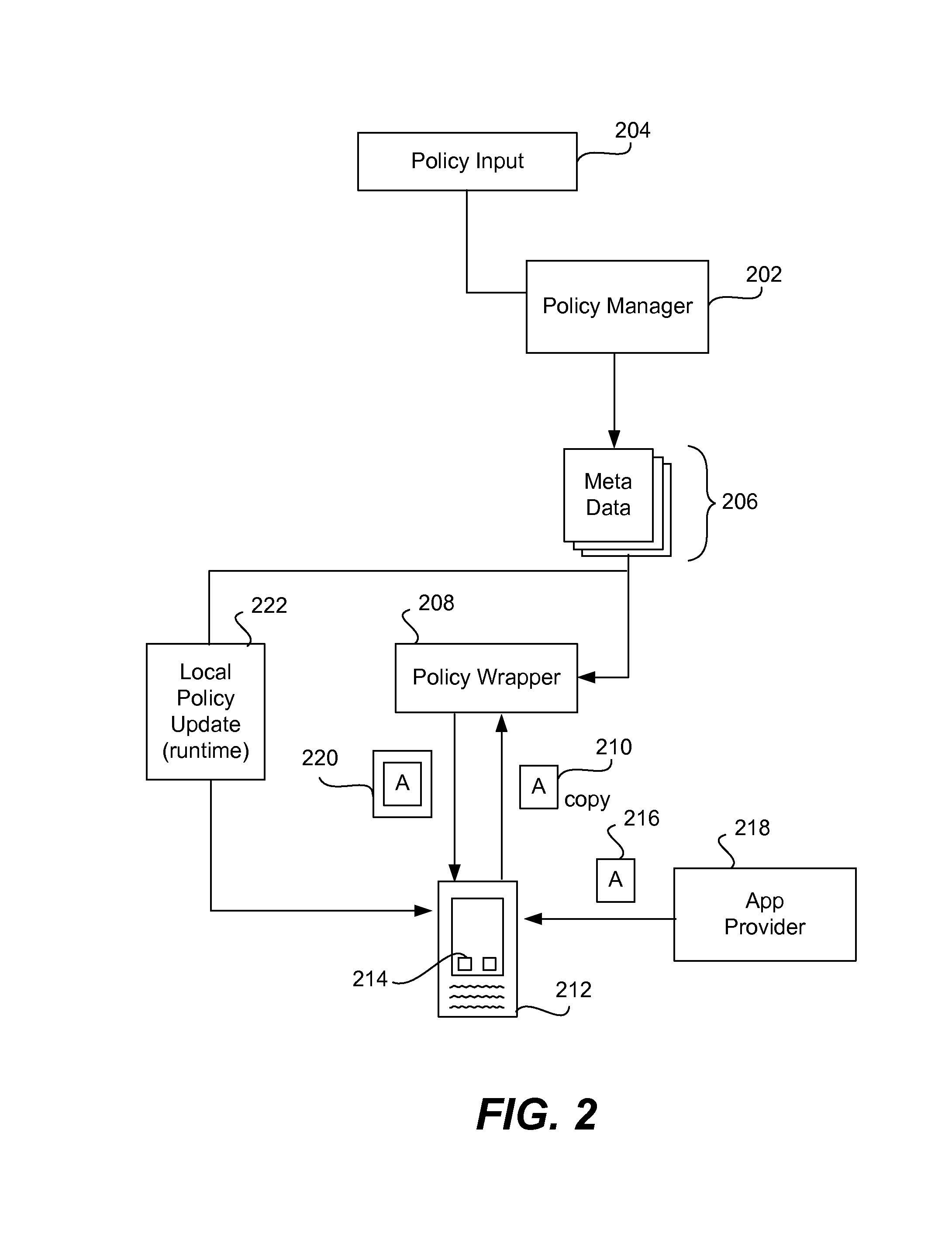
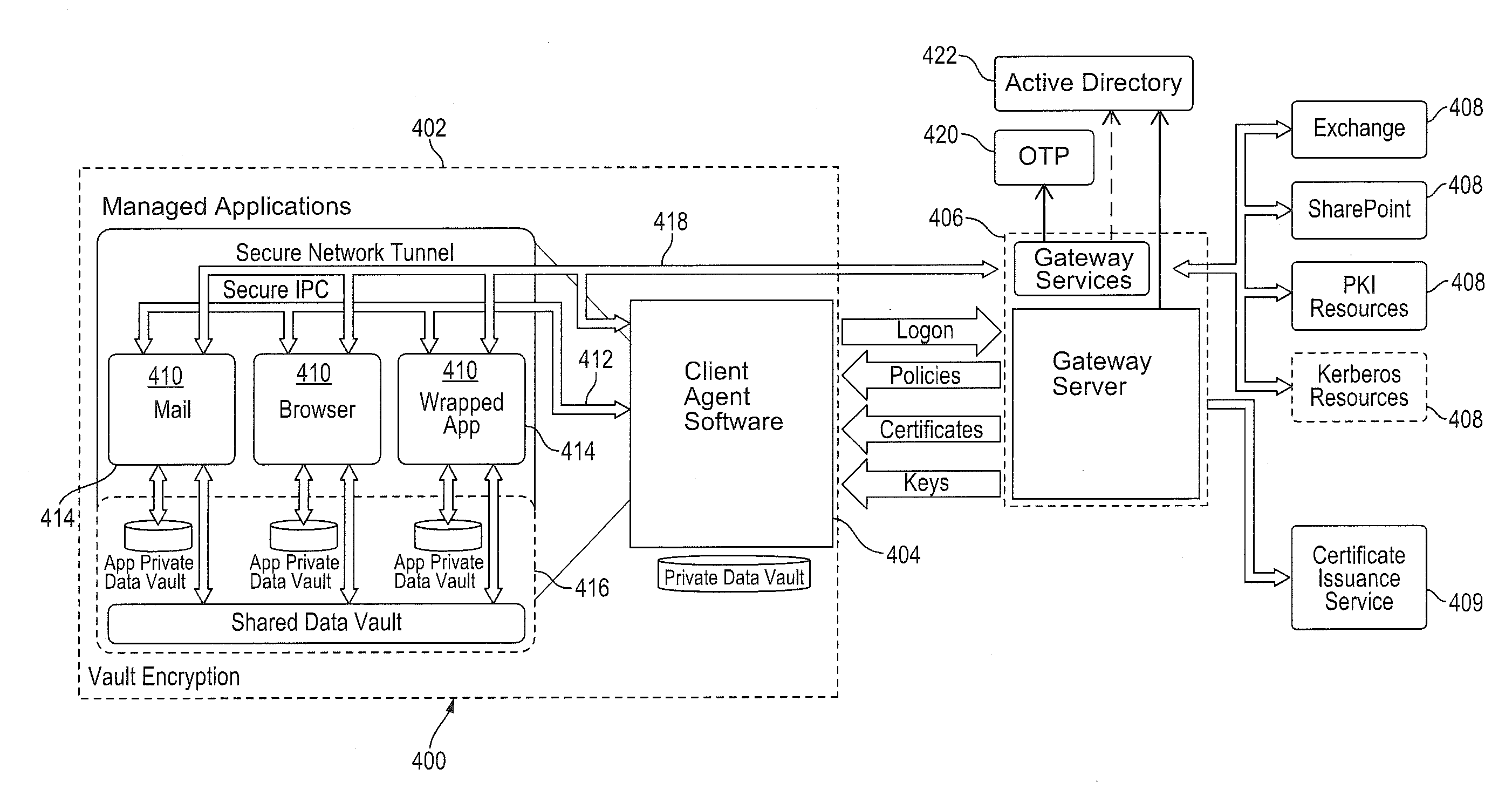
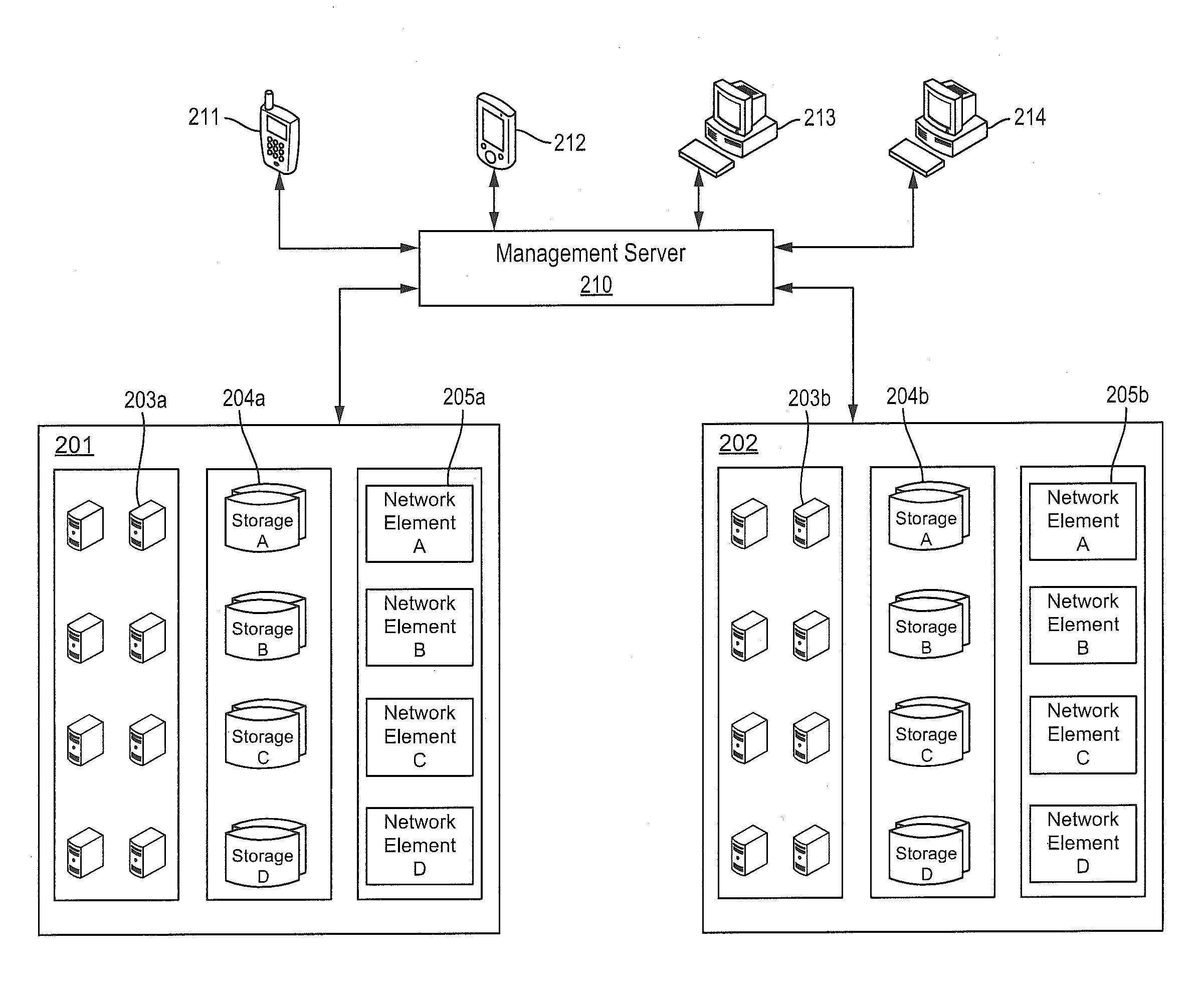
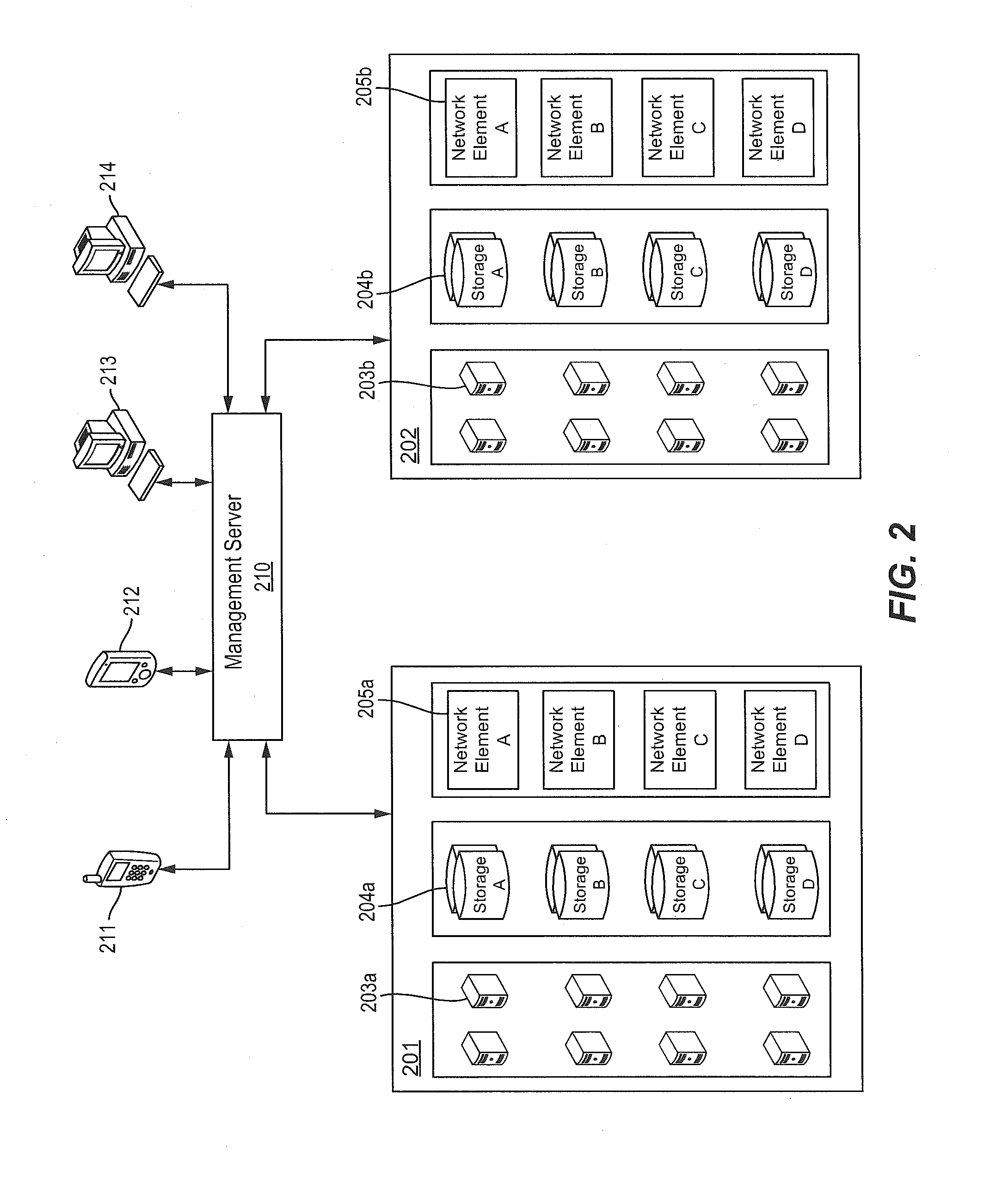
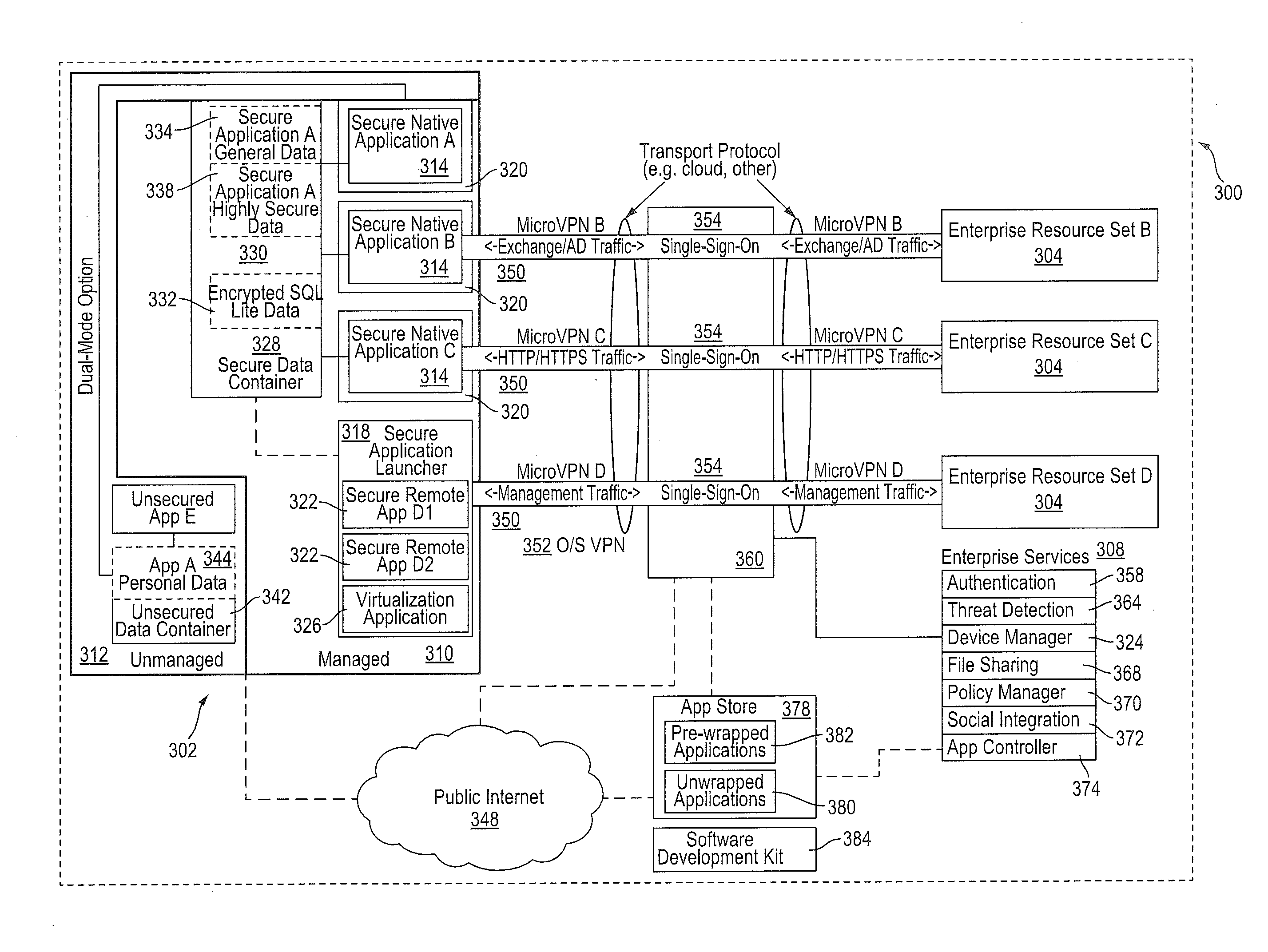
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Policy-Based Application Management
ActiveUS20140032691A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
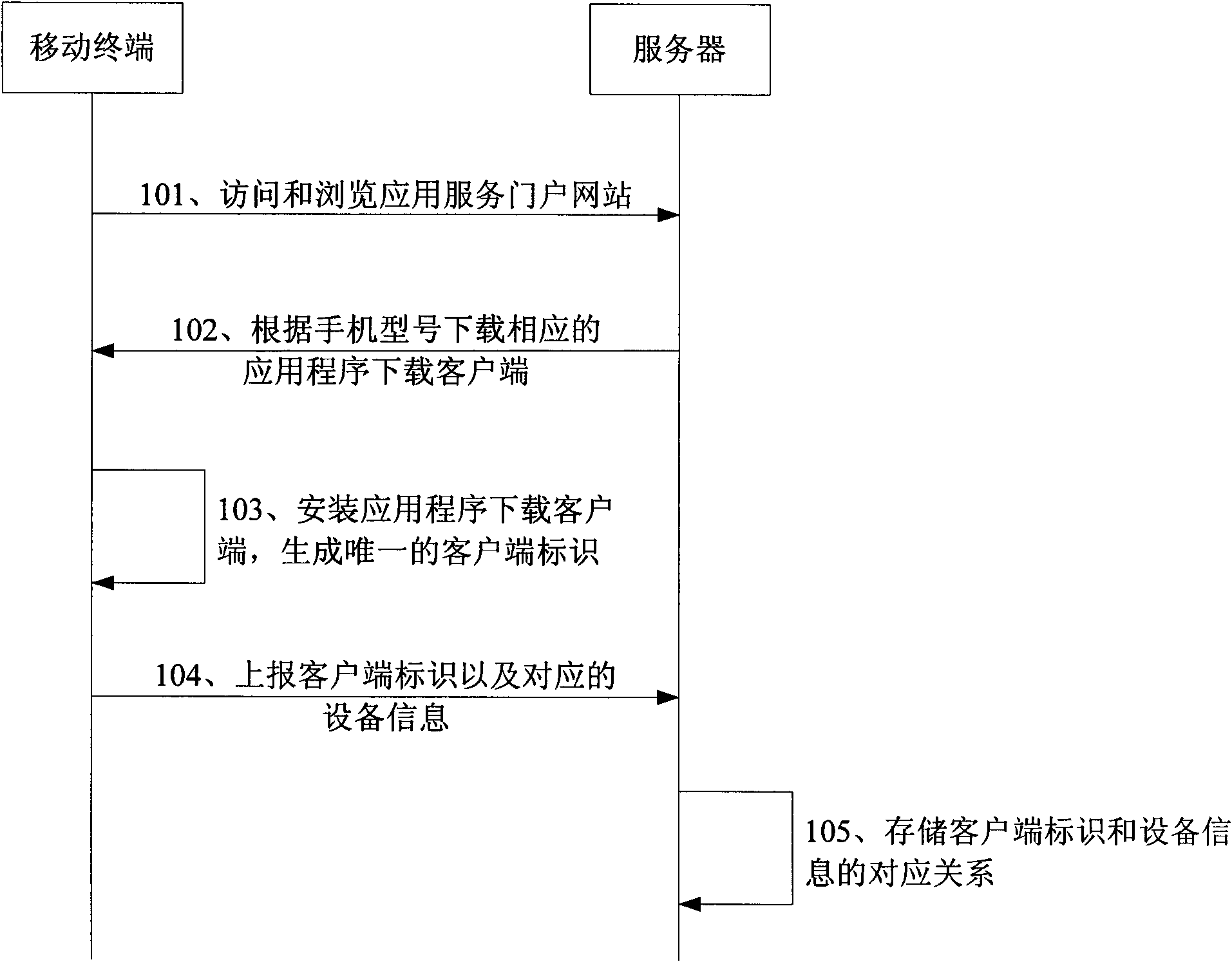
Method for providing mobile terminal application program, and server and mobile terminal
InactiveCN101959179ADownload automaticallyWireless network protocolsSecurity arrangementApp storeTerminal equipment
The invention discloses a method for providing a mobile terminal application program. The method comprises the following steps of: receiving a request for accessing an application program shop sent by an application program downloading client of a mobile terminal, wherein the request for accessing the application program shop carries a client identifier uniquely identifying the mobile terminal; and acquiring corresponding mobile terminal equipment information according to the client identifier and providing an application program list related to equipment information. When the application program downloading client of the mobile terminal downloads an application program, a proper application program is determined according to the corresponding equipment information of the client identifier of the mobile terminal, so that a client can automatically download the application program suitable for the machine type and operation system.
Owner:HUAWEI TECH CO LTD
Policy-Based Application Management
ActiveUS20140033271A1Digital data protectionInternal/peripheral component protectionVirtualizationApp store
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
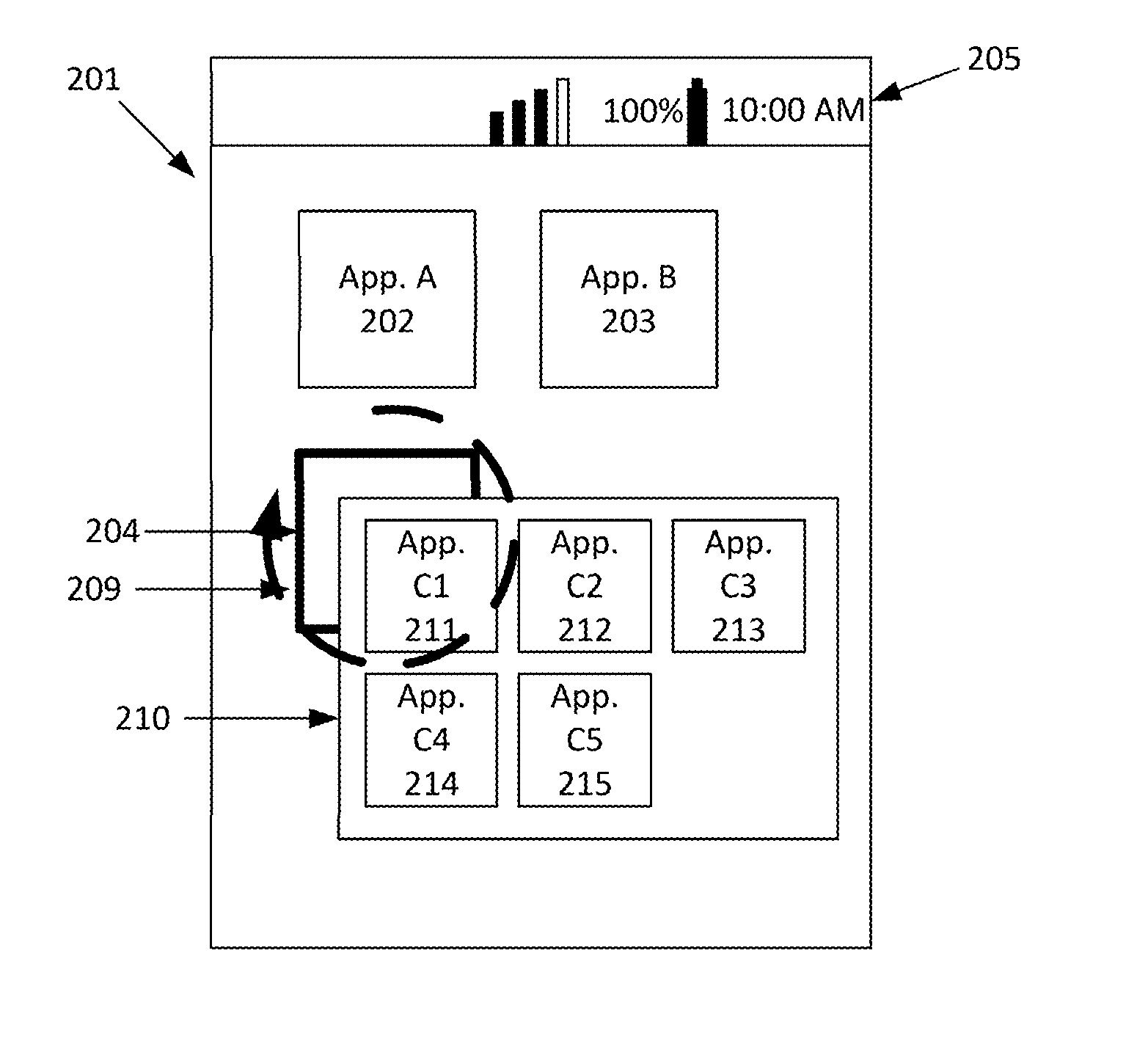
Securing and managing apps on a device
ActiveUS20120210443A1Preventing the app from malicious behavior on the deviceDigital data processing detailsAnalogue secracy/subscription systemsTablet computerOperational system
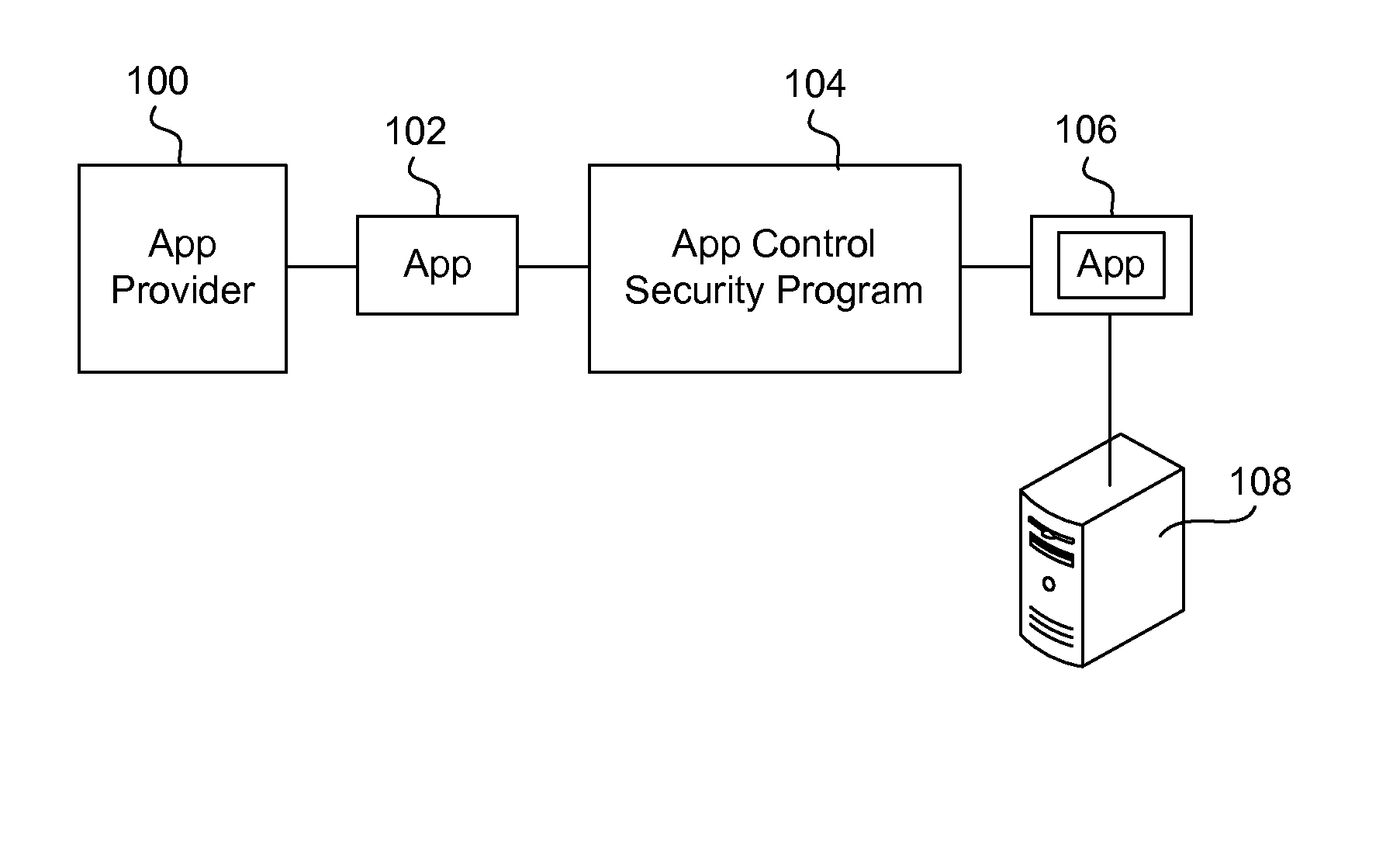
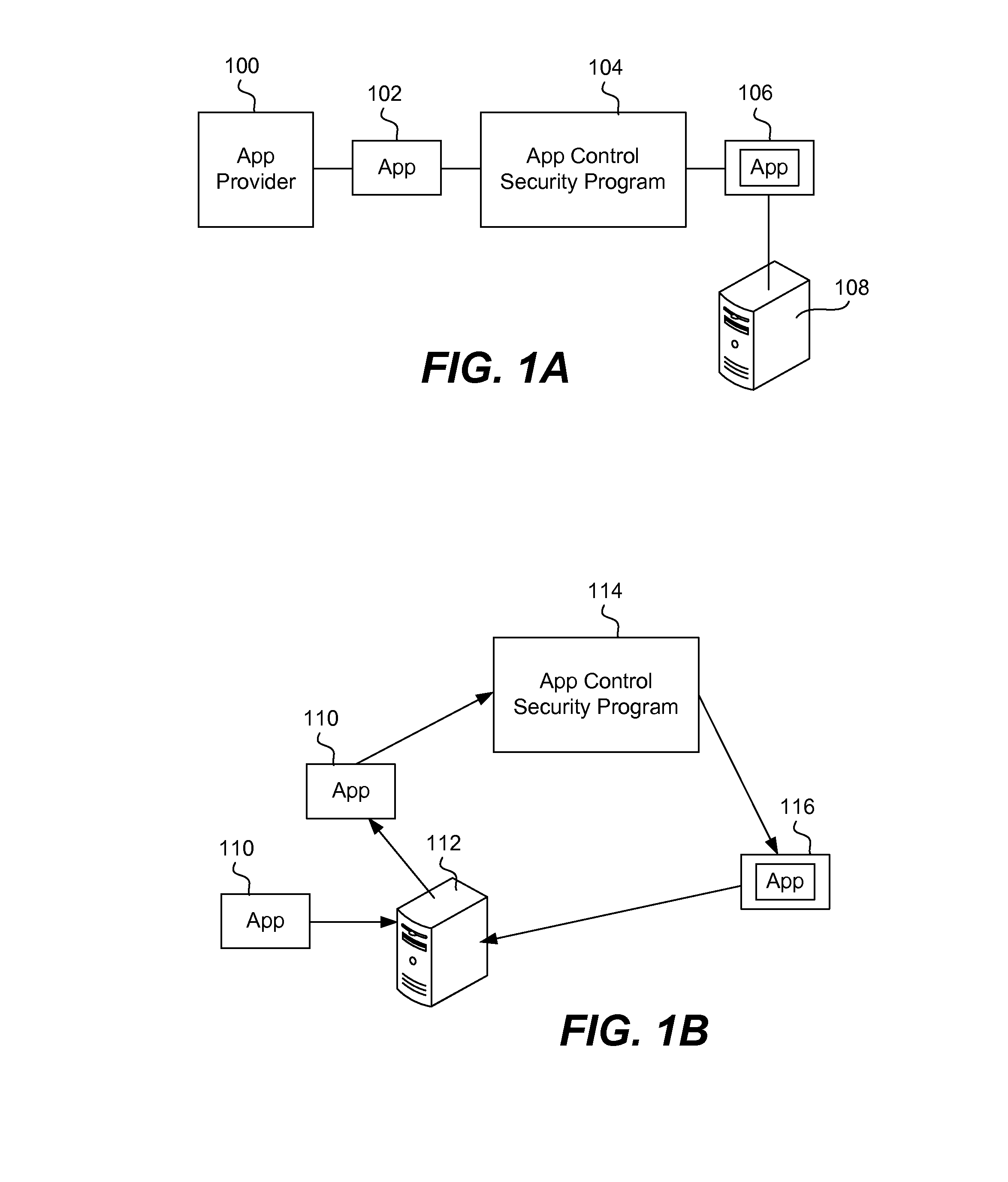
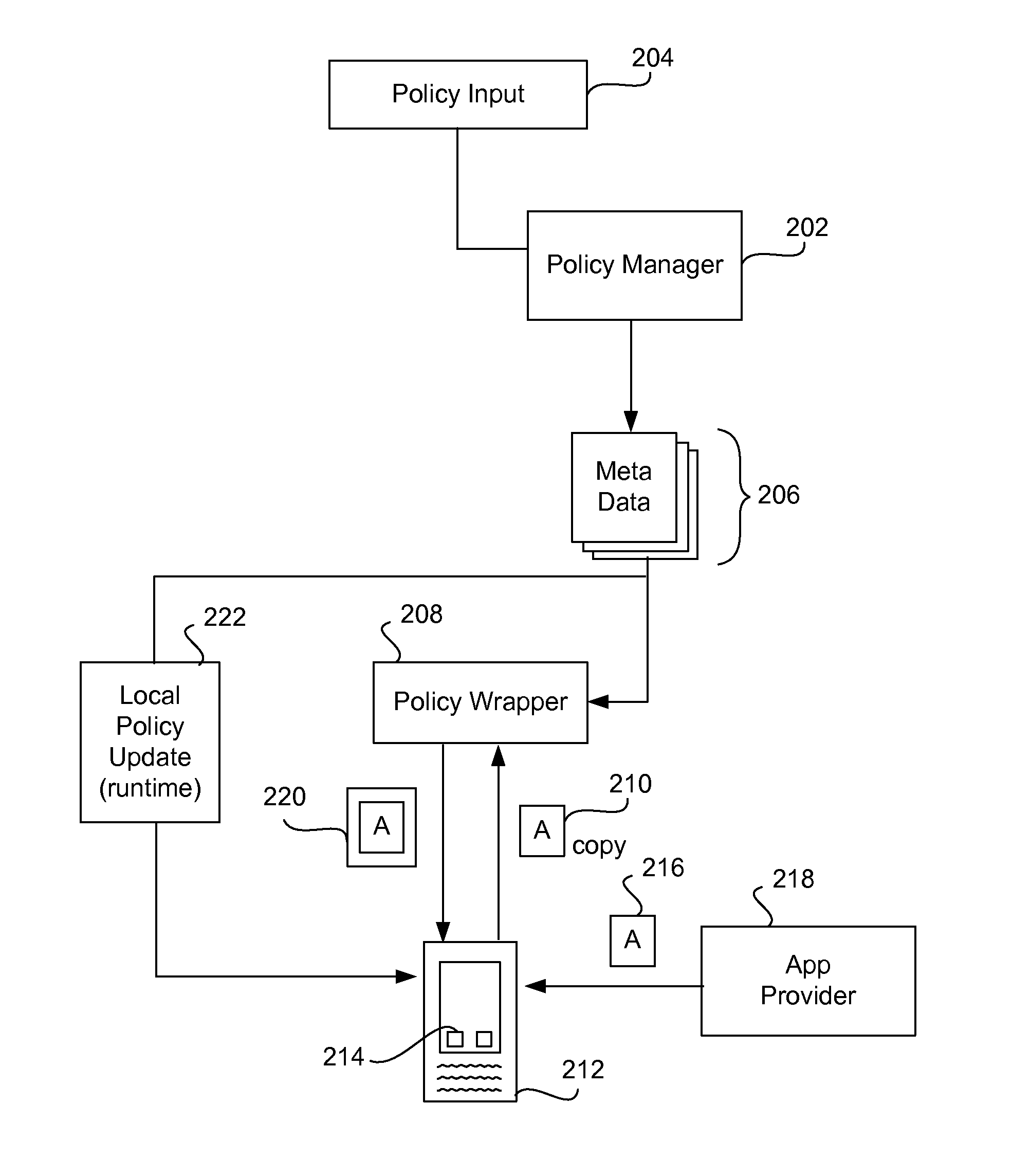
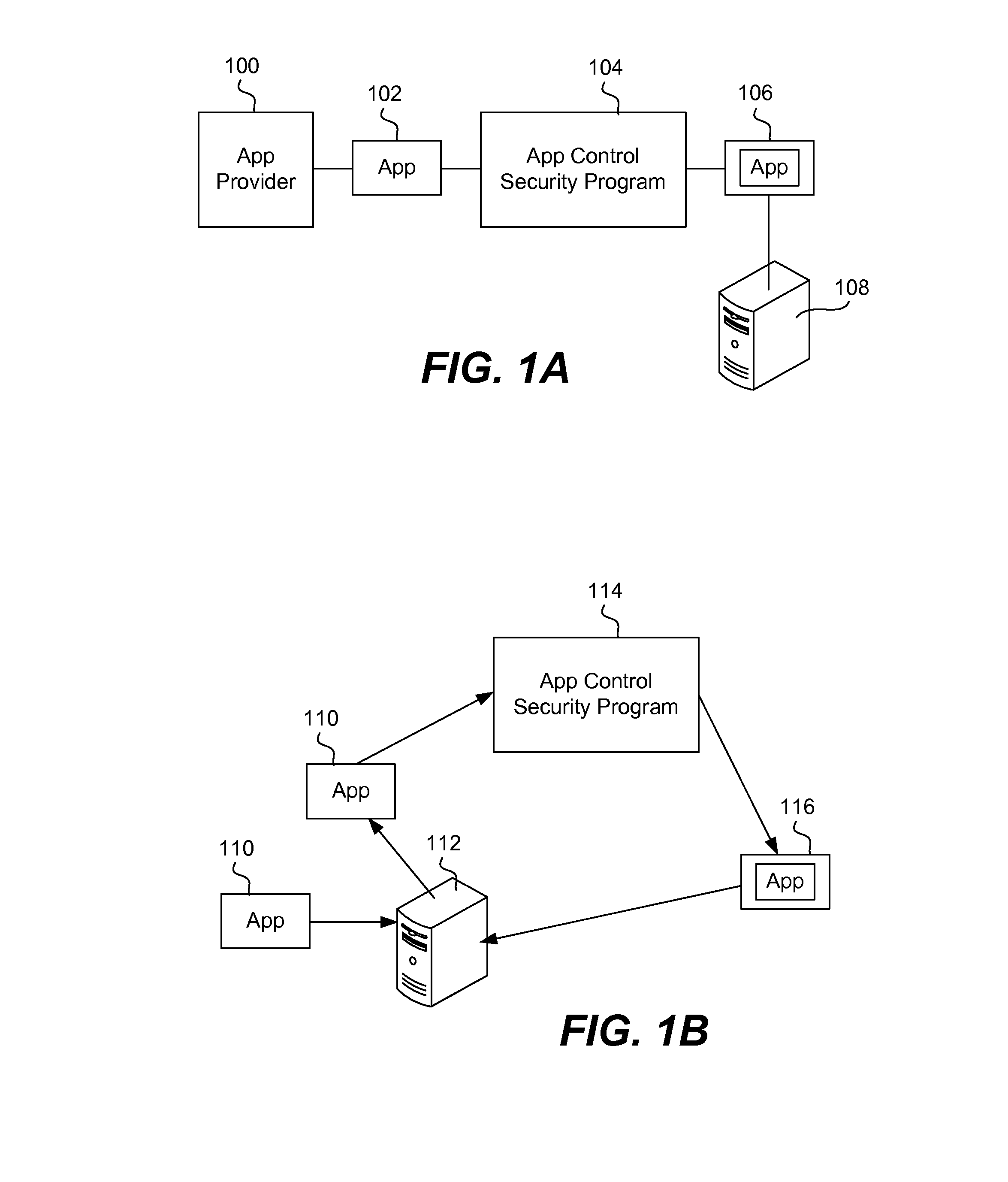
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smartphone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. An app provider, such as an employer or a cellphone provider, can secure its apps before consumers download an app from their app store or marketplace. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. Core object code of the app is obtained and the digital signature is removed. App object code is substituted with security program object code, thereby creating a security-wrapped app. The security-wrapped app is prepared for execution on the device and is re-signed with a new key.
Owner:BLUE CEDAR NETWORKS INC
Policy-Based Application Management
InactiveUS20140032733A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
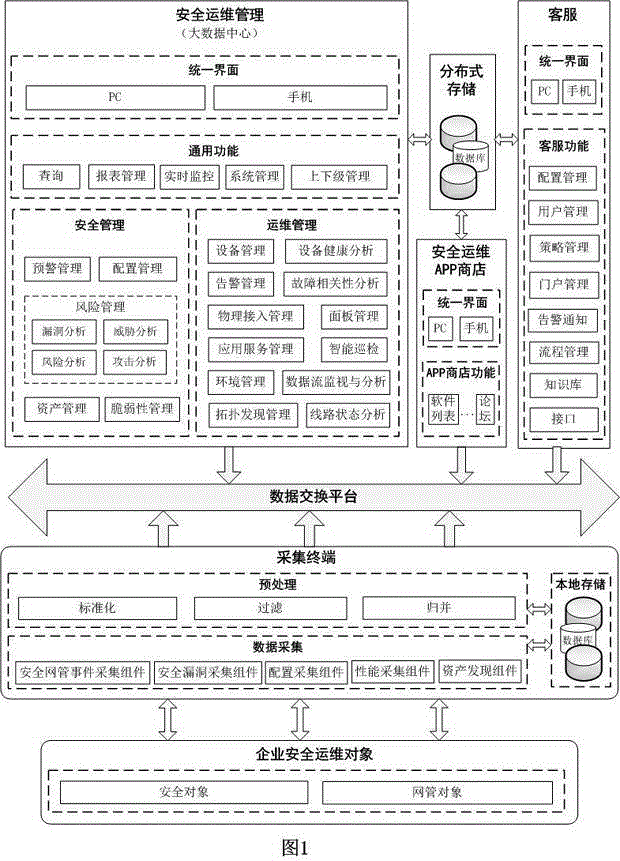
Distributed information security operation and maintenance management platform based on massive data
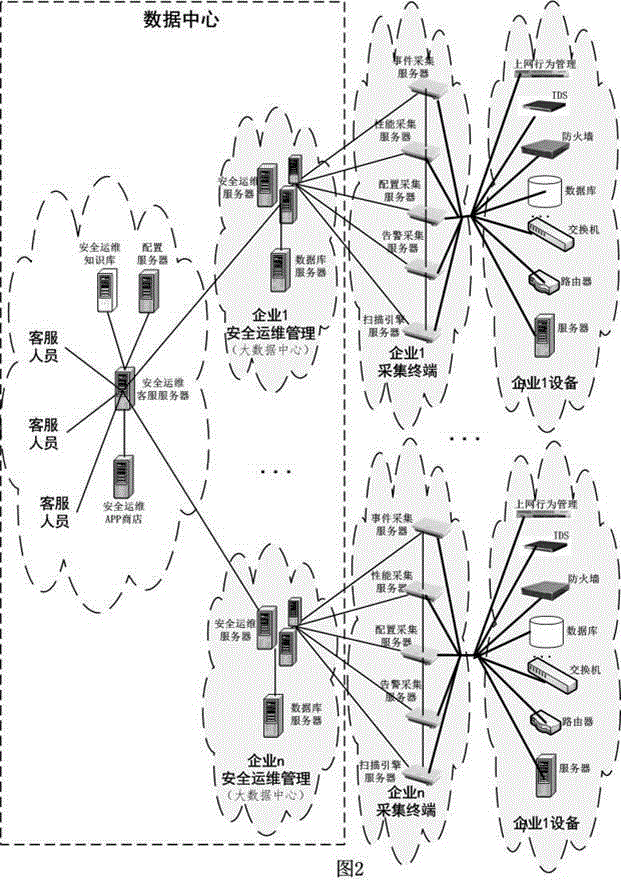
The invention discloses a distributed information security operation and maintenance management platform based on massive data. The distributed information security operation and maintenance management platform supports a single-user mode and a multi-user mode and comprises a customer service module, a security operation and maintenance management module, an acquisition terminal module, a distributed storage module and a security operation and maintenance APP store module. In the multi-user mode, the security operation and maintenance management module of each enterprise is autonomous; and one customer service module can simultaneously provide security operation and maintenance management services for a plurality of enterprises. APPs provided by the security operation and maintenance APP store on the platform include those cooperating with various information security operation and maintenance service providers together; and the distributed information security operation and maintenance management platform is convenient for users to use and can help the enterprises to rapidly position and solve problems.
Owner:NANJING LIANCHENG TECH DEV
Policy-Based Application Management
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
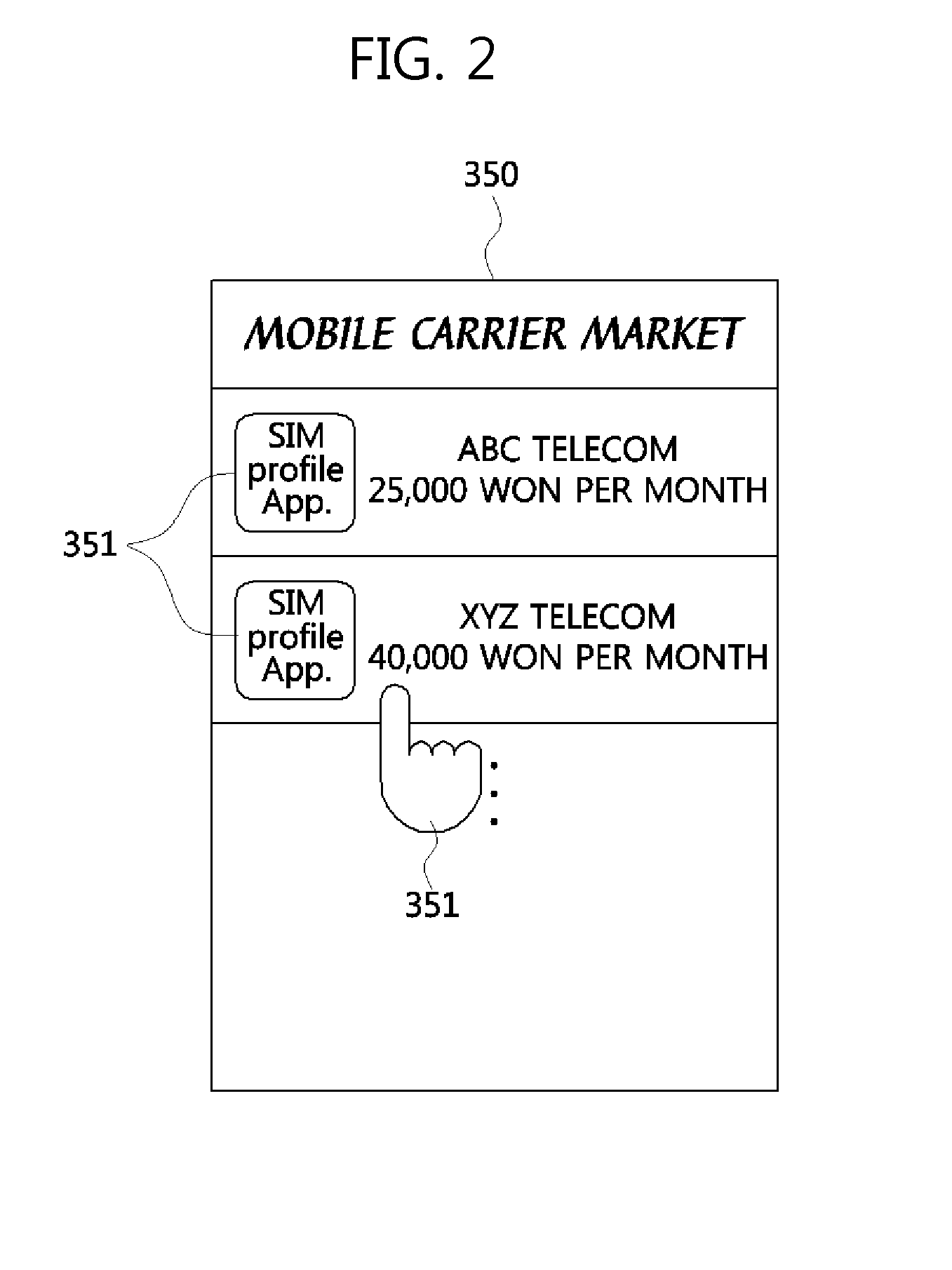
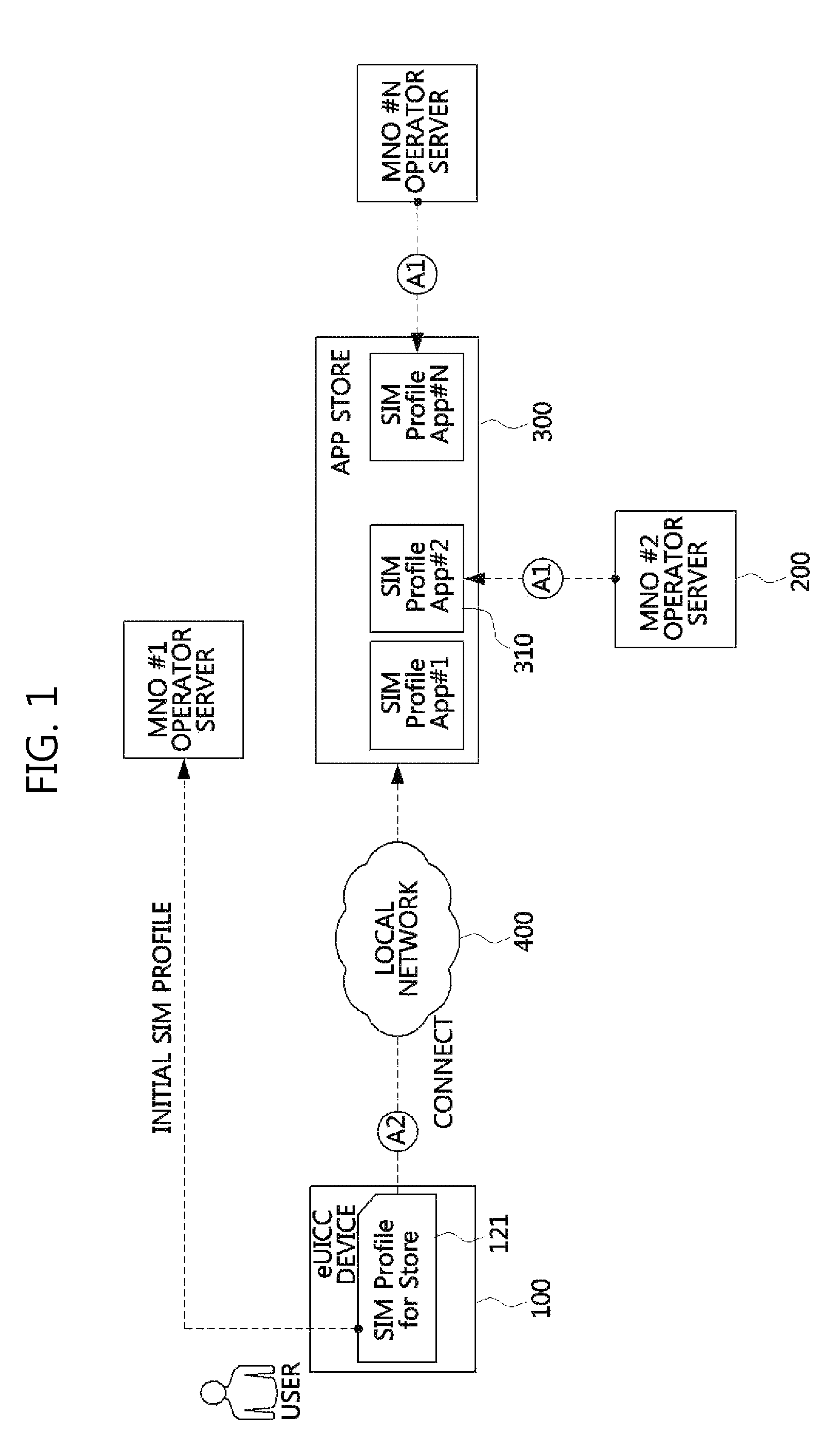
Method for providing sim profile in euicc environment and devices therefor
ActiveUS20140031012A1Unauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareApp store
There are provided a method of providing a SIM profile, and an eUICC device. The method of providing the SIM profile includes downloading a SIM profile application selected by a user who uses the eUICC device from an app store, executing and installing the SIM profile application in the eUICC device, accessing of the eUICC device having the SIM profile application installed therein to an operator server, and authenticating the eUICC device based on SIM profile information corresponding to the SIM profile application. The eUICC device includes a network connection unit configured to access the app store via a local network, a SIM profile storage configured to store the SIM profile application, and an authentication requesting unit configured to access the operator server based on the SIM profile information.
Owner:SAMSUNG ELECTRONICS CO LTD
Policy-Based Application Management
ActiveUS20140032758A1Digital computer detailsInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Securing and managing apps on a device
ActiveUS8549656B2Preventing the app from malicious behavior on the deviceDigital data processing detailsAnalogue secracy/subscription systemsTablet computerOperational system
Apps are secured or security-wrapped either before they are downloaded onto a device, such as a smartphone or tablet device, or after they are downloaded but before they are allowed to access the device operating system and cause any potential damage to the device. An app provider, such as an employer or a cellphone provider, can secure its apps before consumers download an app from their app store or marketplace. The app is secured before it is allowed to access the operating system of the device, thereby preventing the app from malicious behavior. Core object code of the app is obtained and the digital signature is removed. App object code is substituted with security program object code, thereby creating a security-wrapped app. The security-wrapped app is prepared for execution on the device and is re-signed with a new key.
Owner:BLUE CEDAR NETWORKS INC
Policy-Based Application Management
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
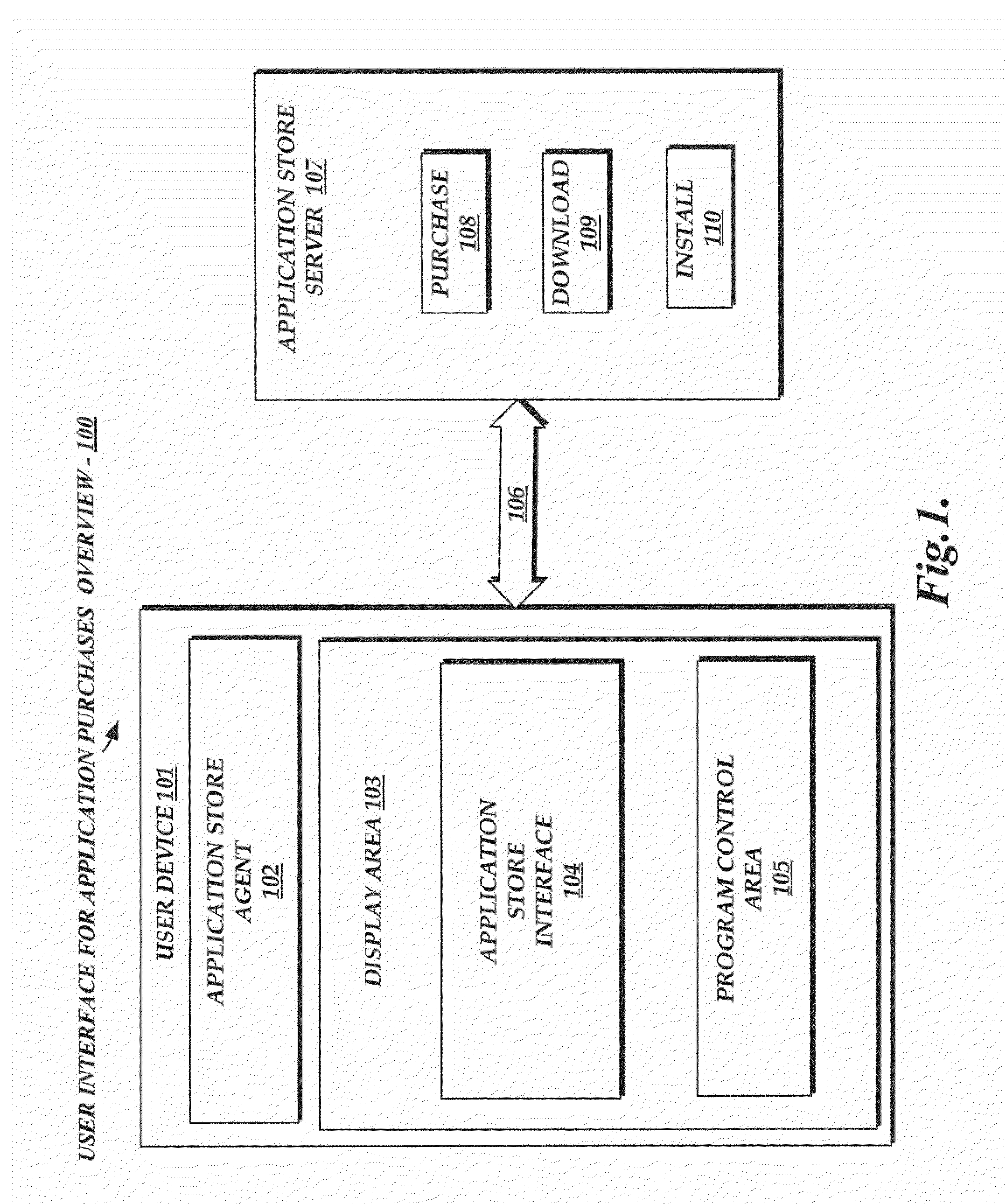
User interface for application transfers
InactiveUS20120096386A1Good lookingAltering its appearanceCommerceInput/output processes for data processingUser deviceApp store
Methods, systems and machine readable tangible storage media that provide a user interface to an application store. In one embodiment, an icon representing an application being transferred to a user device appears to fly across the display area during the download and installation of the application before landing on a dock or other program control area from which the application can subsequently be launched. The user device synchronizes the flight of the icon with the progress of the download and installation by tracking the progress in communication with the server from which the application was transferred. The appearance of flight can be both vertical and horizontal and the icon bounces after the download and installation is complete conveying to the user that the application is ready to launch. The appearances of the locations from which the icon begins and ends its journey are changed to enhance the simulation of flight. Other embodiments are also described.
Owner:APPLE INC
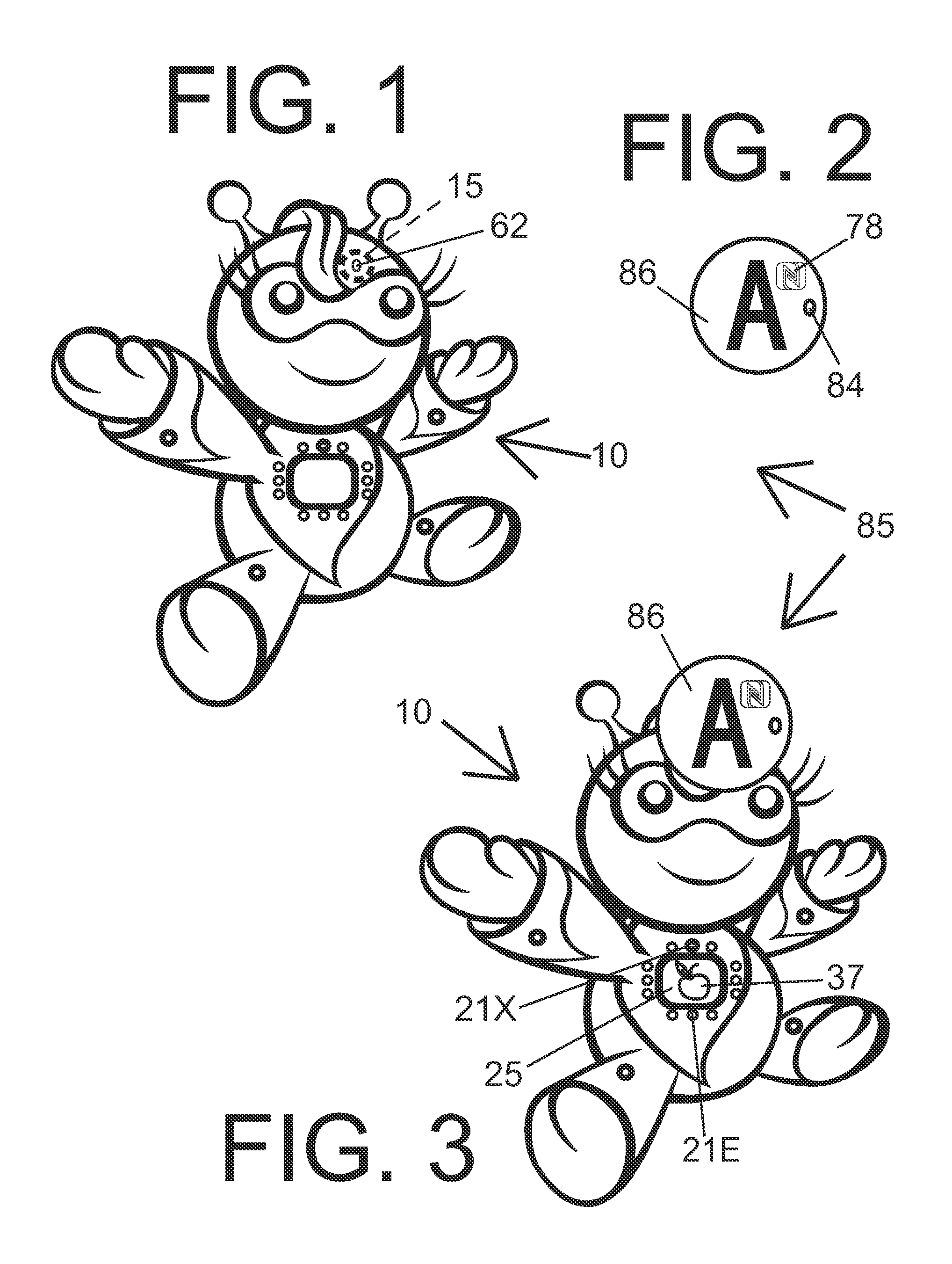
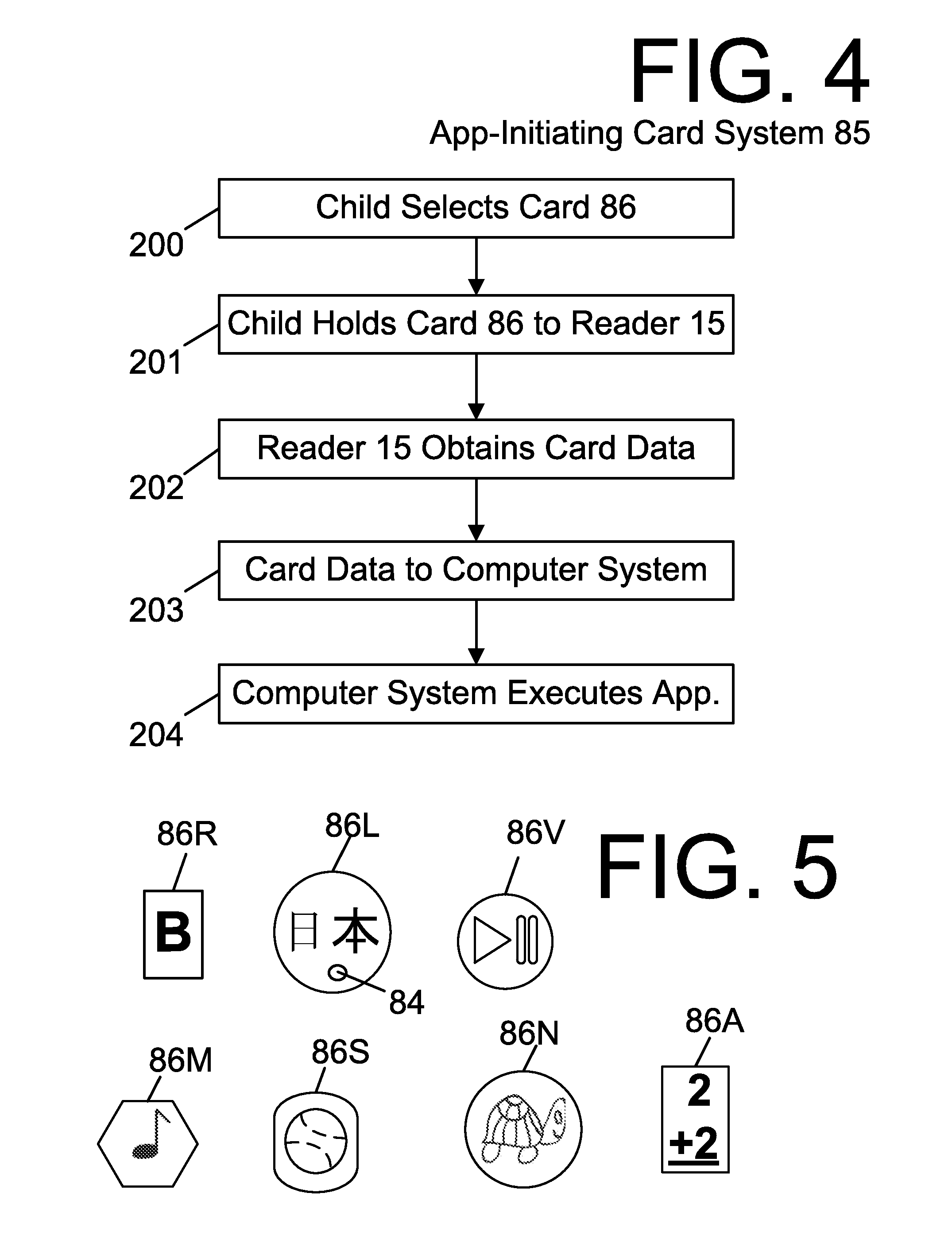
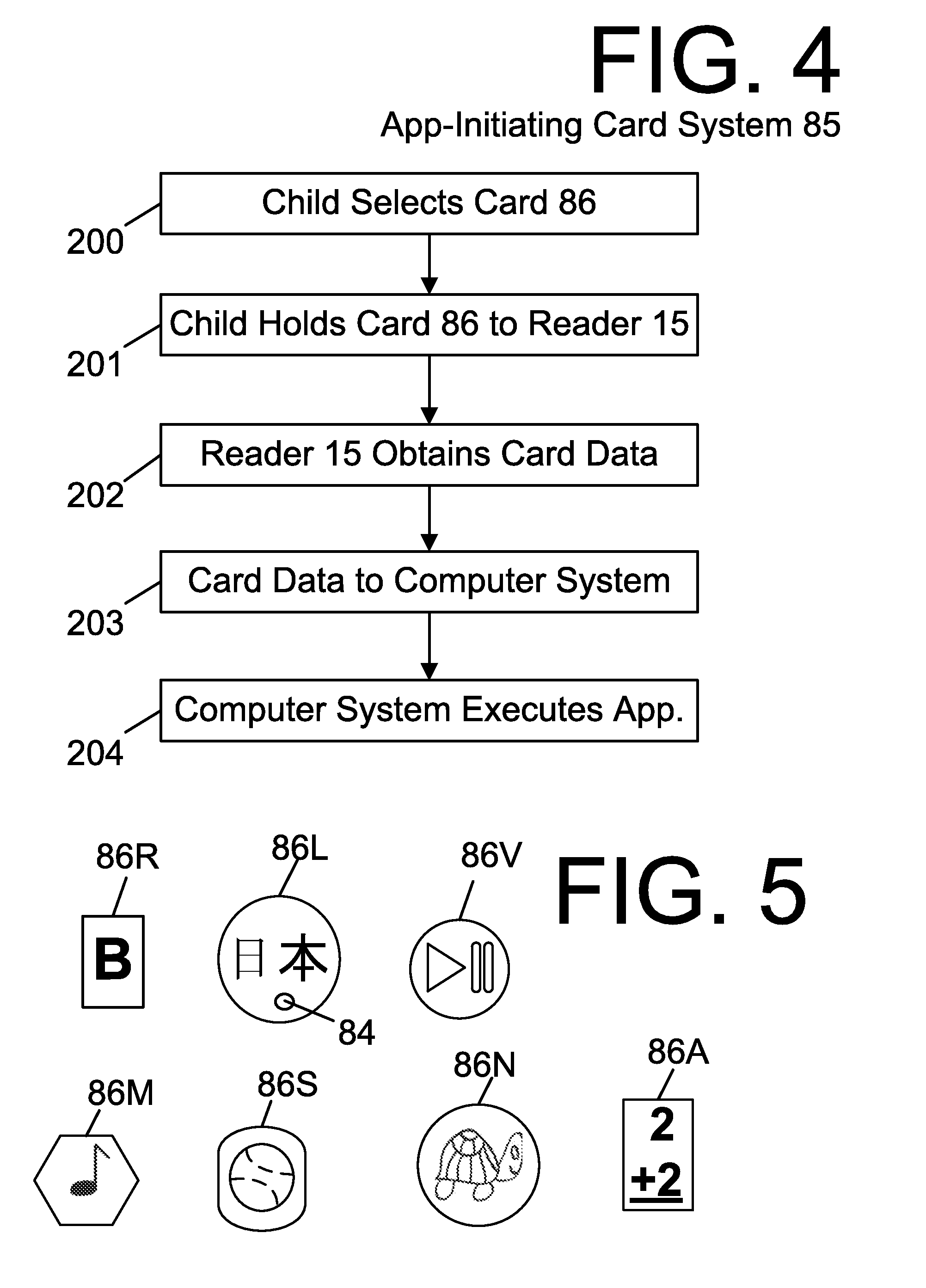
Doll Companion Integrating Child Self-Directed Execution of Applications with Cell Phone Communication, Education, Entertainment, Alert and Monitoring Systems
ActiveUS20120295510A1Easily expandableEasily modifiableNear-field transmissionDollsSmall Island Developing StatesApp store
The presented cell phone-enabled doll companion allows a child novel ways to self-select and self-execute applications while requiring no intervention or supervision from the parent. Further, it provides learning, entertainment and safety by integrating cell phone communication, education, entertainment, alert and monitoring systems. While providing a convenient means of communication between the child and parent, the system allows surveillance of a child's real-time environment, GPS monitoring and SIDS / health monitoring. The functionality and the physical elements of the system are programmable through installation of applications downloadable from an application store. Various options for parental access to a configuration interface to modify settings and download applications are provided, including via a cell phone, a website, customer service call center and / or the doll companion touch screen.
Owner:LEARNING SQUARED INC
Policy-based application management
ActiveCN104838630ADigital data protectionInternal/peripheral component protectionVirtualizationDual mode
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Automatic web presence feature deployment
InactiveUS20130204746A1Easy to install automaticallyEasy to collectBuying/selling/leasing transactionsResourcesApp storeMultimedia
An app store provides a searchable catalog of selectable elements representing programs that provide capabilities for enabling the online presence of a customer, and automatically installs such programs and enables such web presence-enabling capabilities upon selection by the customer of the selectable element.
Owner:ENDURANCE INTERNATIONAL GROUP
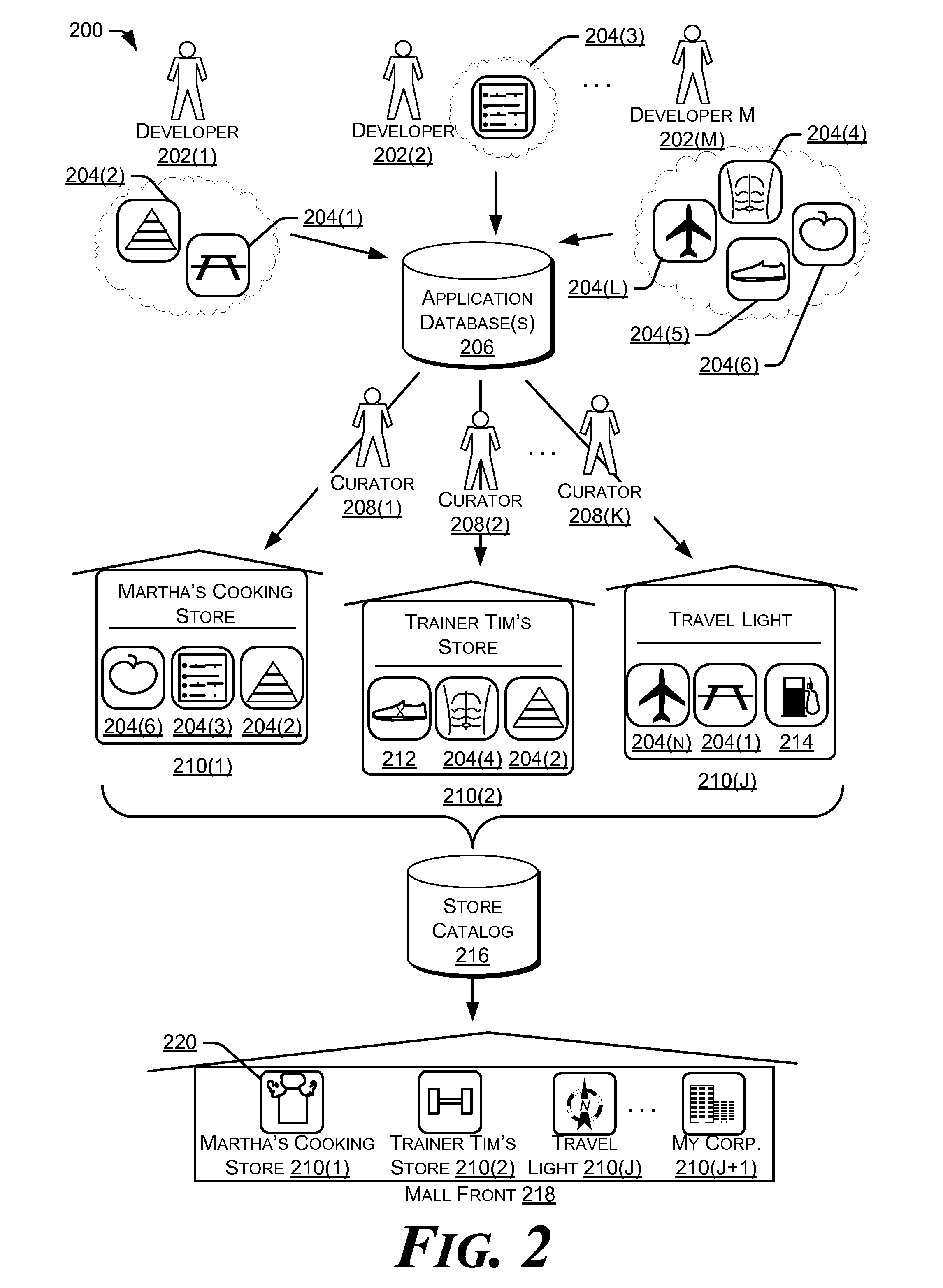
Curated Application Store
InactiveUS20120072312A1Find quicklyBuying/selling/leasing transactionsApp storeMultiple applications
A curated application store is a virtual storefront that includes applications provisioned from one or more application databases. For example, a curator may browse through an application database to find notable applications based on his or her expertise in a certain area and then provision the notable applications from the application database for inclusion in an application store curated by the curator. Accordingly, users browsing for applications pertaining to the area of expertise of the curator may shop for the applications from within a virtual application mall which includes a collection of curated application stores such as the application store curated by the curator. In return, the curator of the store may receive a revenue share from the purchases made within his or her application store.
Owner:MICROSOFT TECH LICENSING LLC
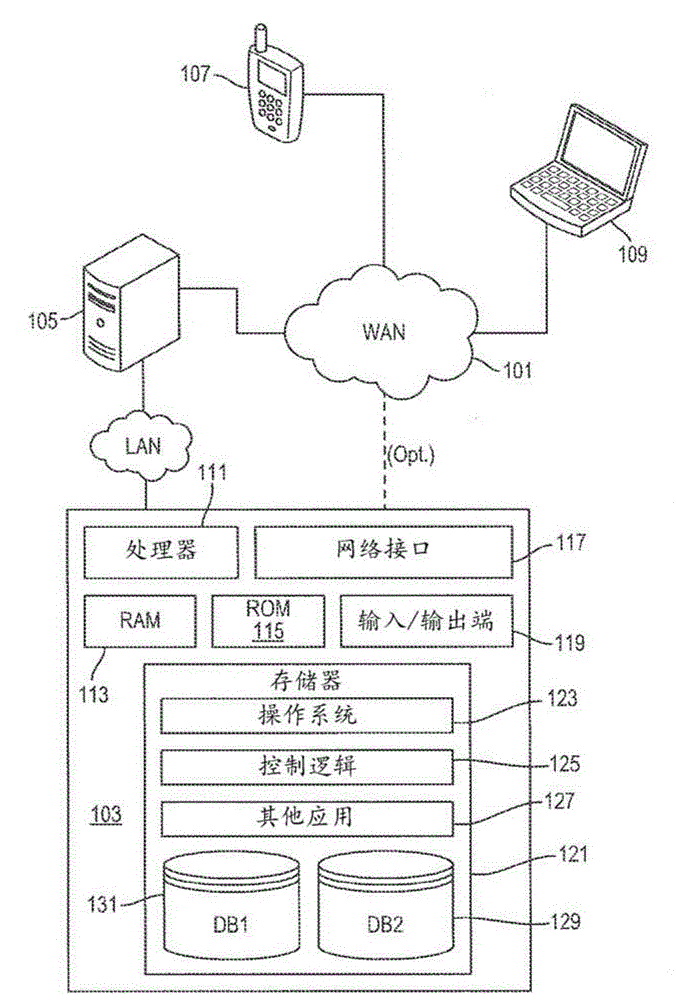
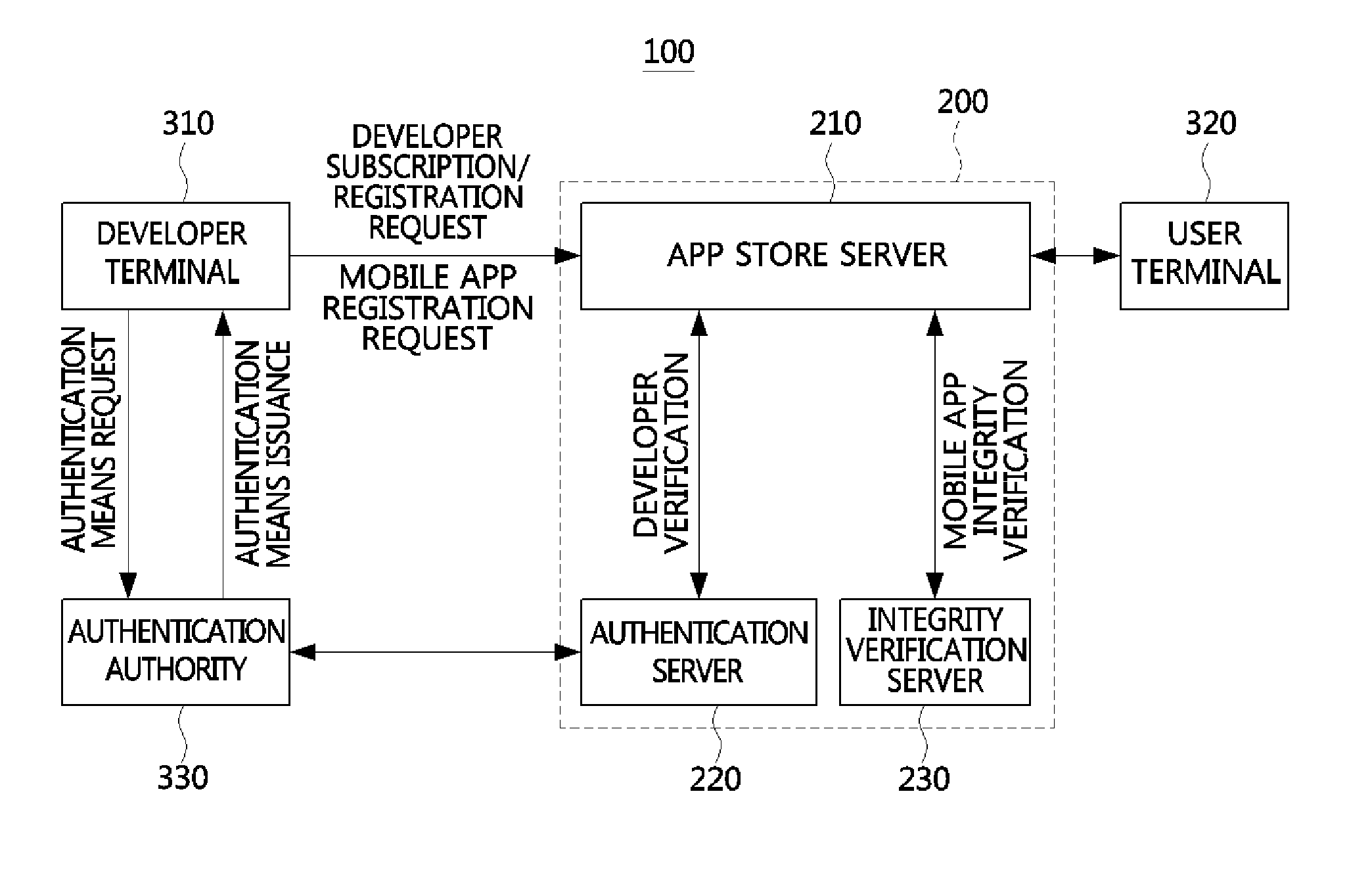
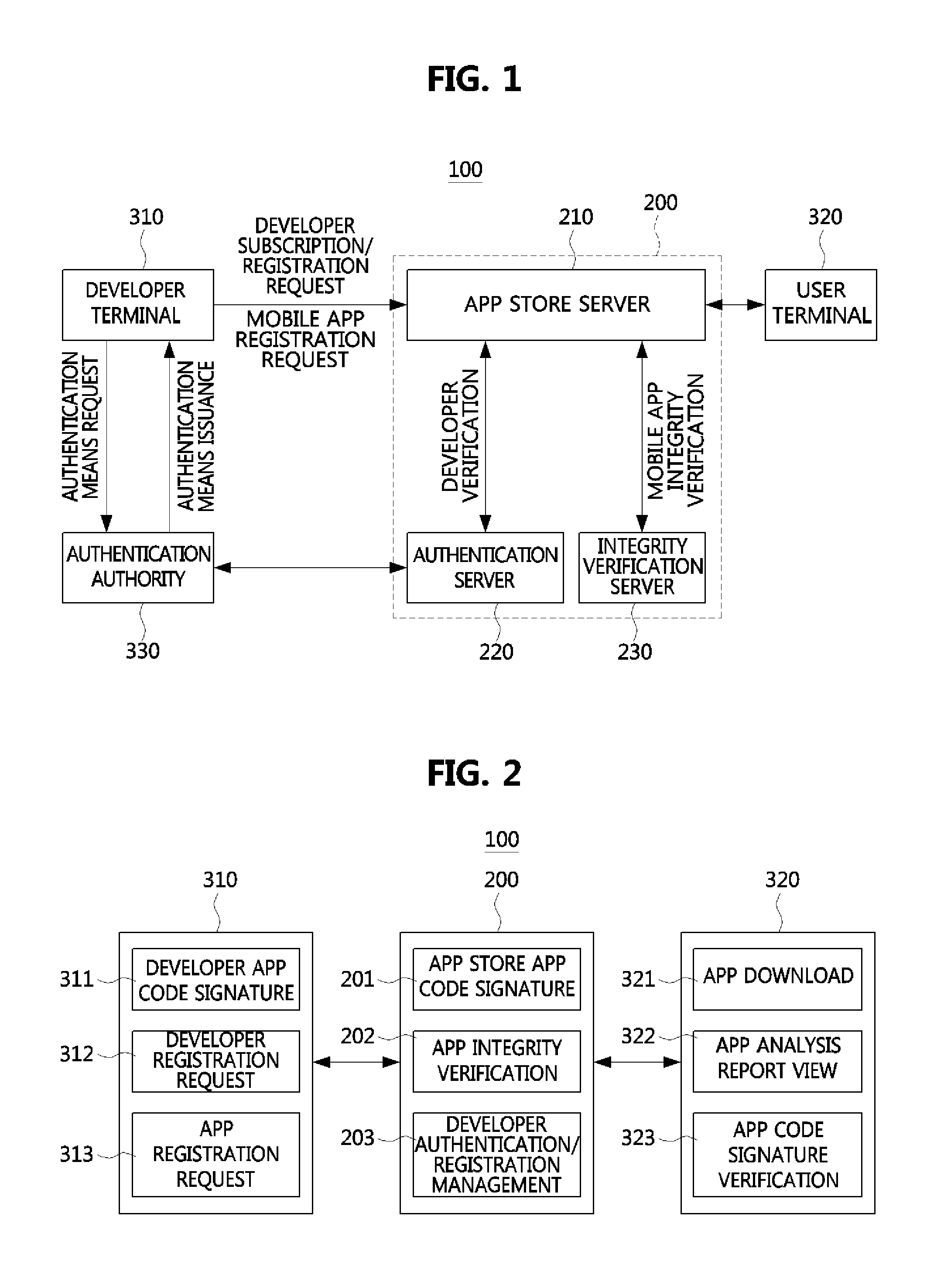
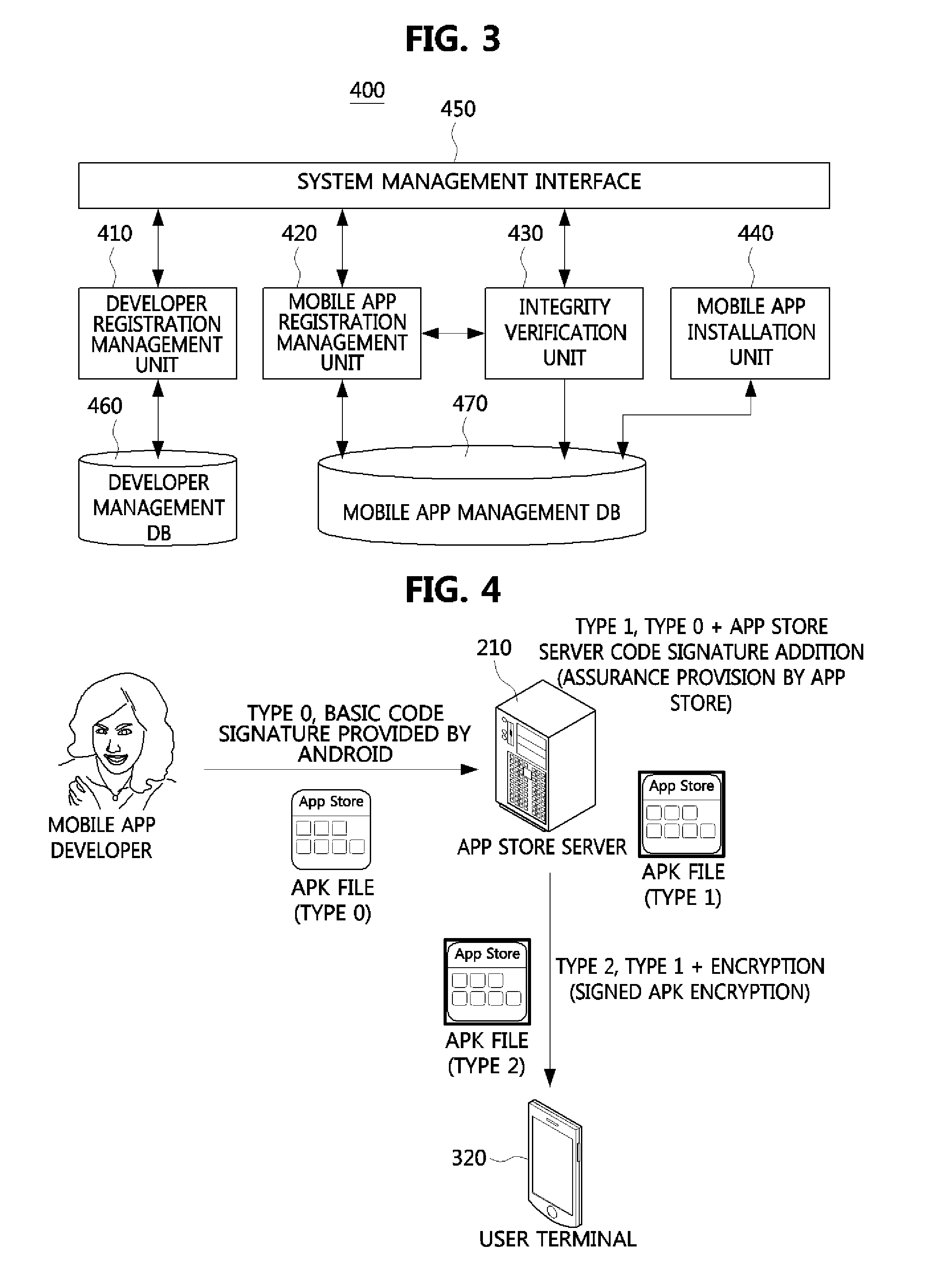
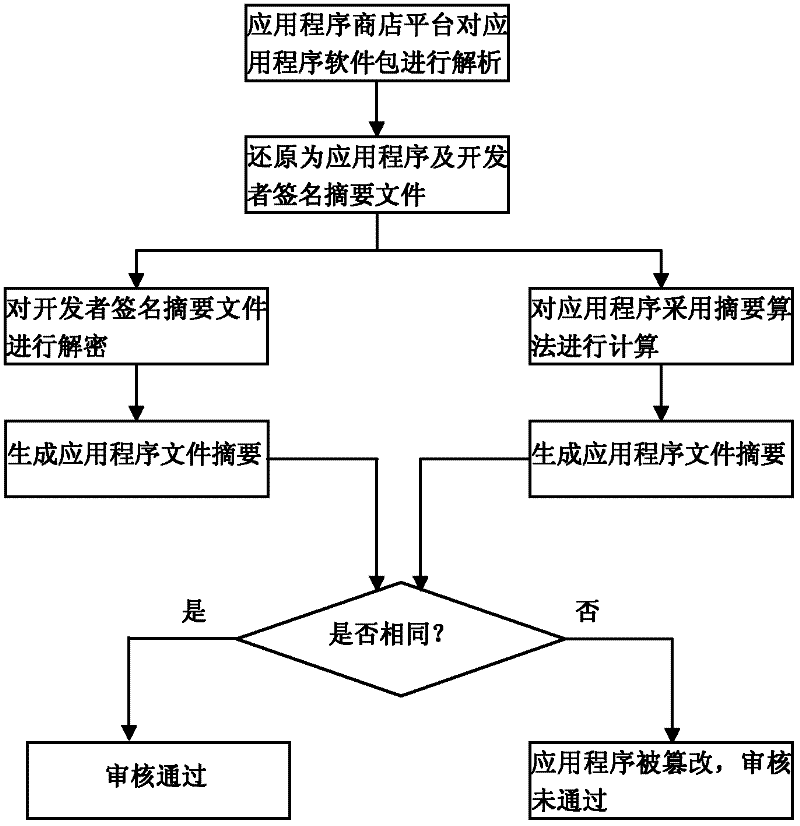
Method for assuring integrity of mobile applications and apparatus using the method
InactiveUS20140150096A1Memory loss protectionError detection/correctionApplication program softwareMobile apps
An apparatus for assuring integrity of a mobile application or application software (app) includes a developer registration management unit configured to authenticate a mobile app developer based on an authentication means in response to a subscription and registration request of the mobile app developer, and an integrity verification unit configured to verify whether the mobile app has the integrity by unpackaging the mobile app uploaded to an app store server in a packaged state and determine whether to write a code signature of the app store server to the mobile app based on an integrity verification result. Thus, a secure mobile ecosystem can be constructed.
Owner:ELECTRONICS & TELECOMM RES INST
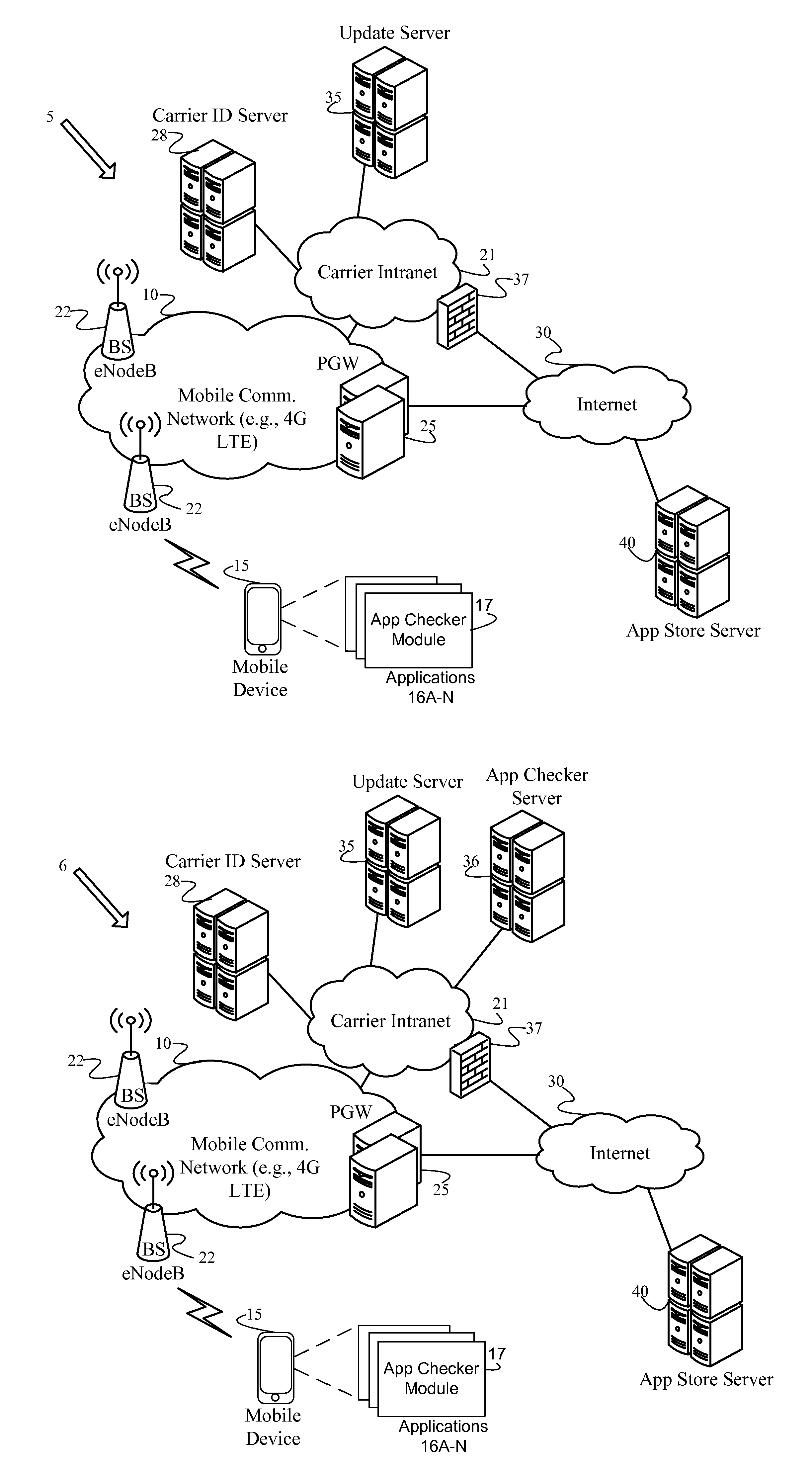
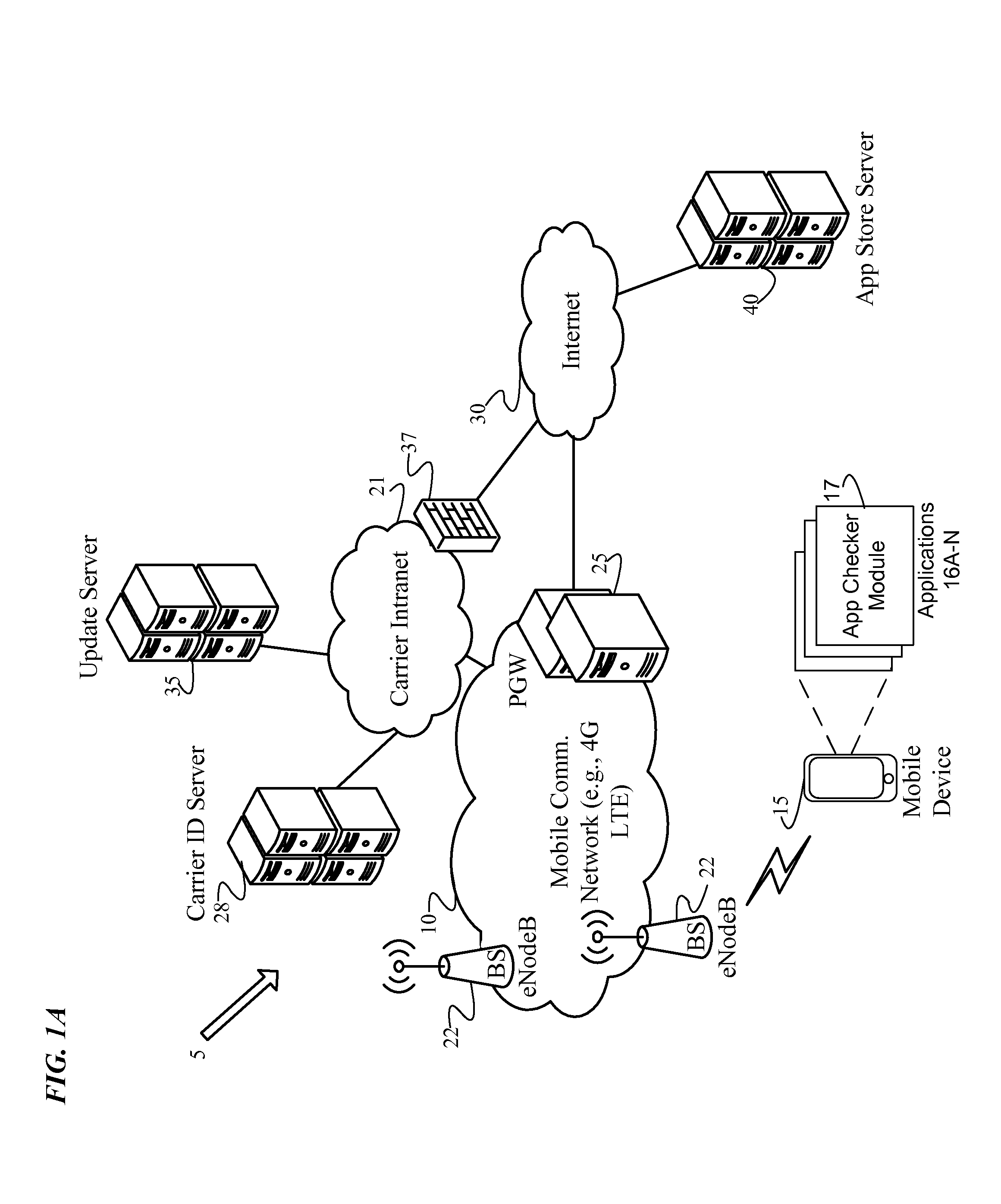
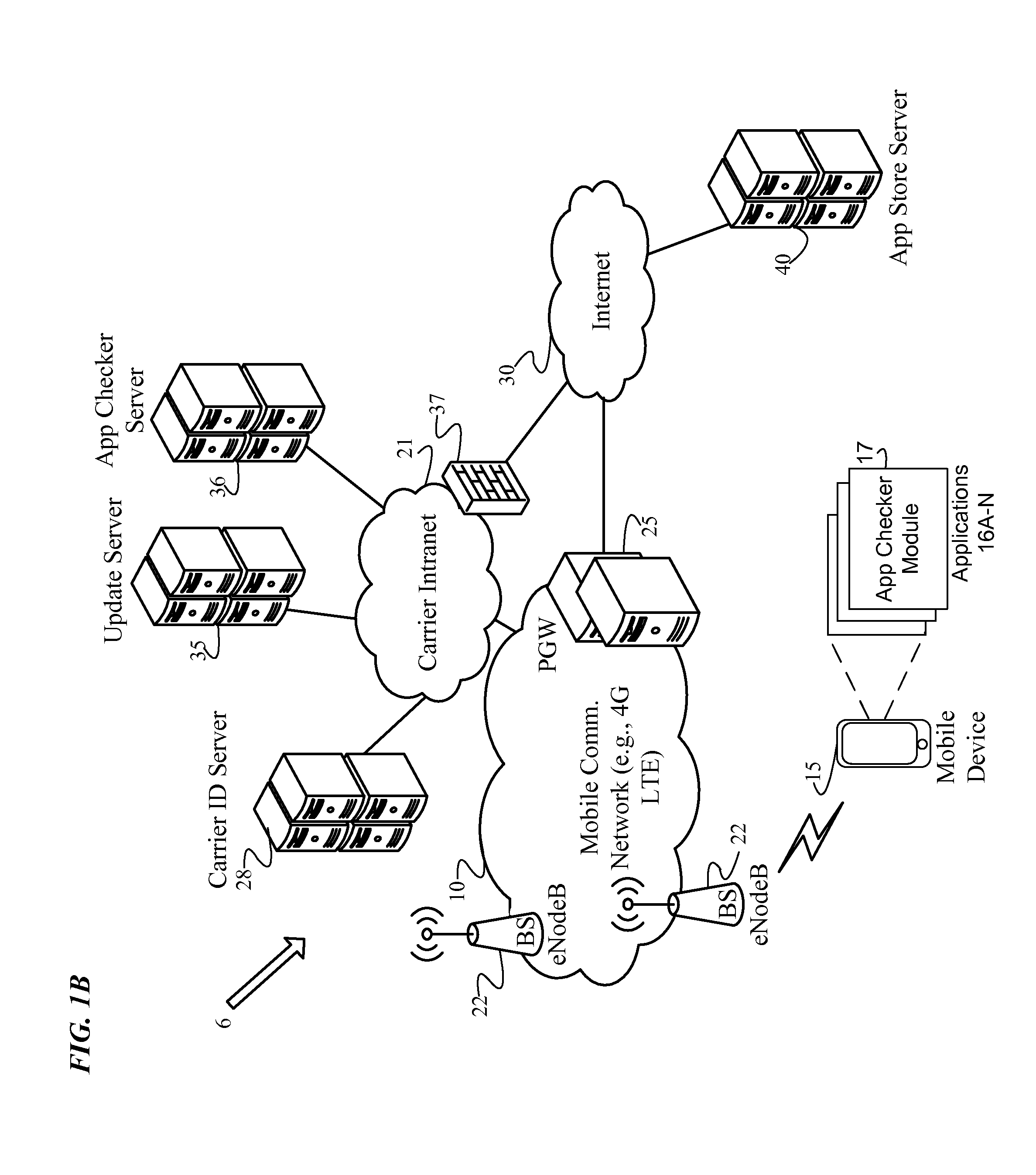
Identification and isolation of incompatible applications during a platform update
An Application (“App”) Checker identifies and isolates incompatible applications on a mobile device during a software platform update. After receiving a target platform version number from an Update Server, the App Checker generates a list of installed applications on the mobile device. Next, the App Checker sends a request to an App Store Server or Update Server for an application catalog of applications compatible with the target platform version. Upon receiving the application catalog indicating compatibility status of applications relative to the target platform version, the App Checker iteratively compares the installed application list with the application catalog to identify whether or not each installed application is compatible with the target platform. The App Checker then populates an application quarantine or removal database to identify each incompatible application to isolate incompatible applications, and quarantines or removes the incompatible applications. Finally, the mobile device is upgraded to the target platform version.
Owner:VERIZON PATENT & LICENSING INC
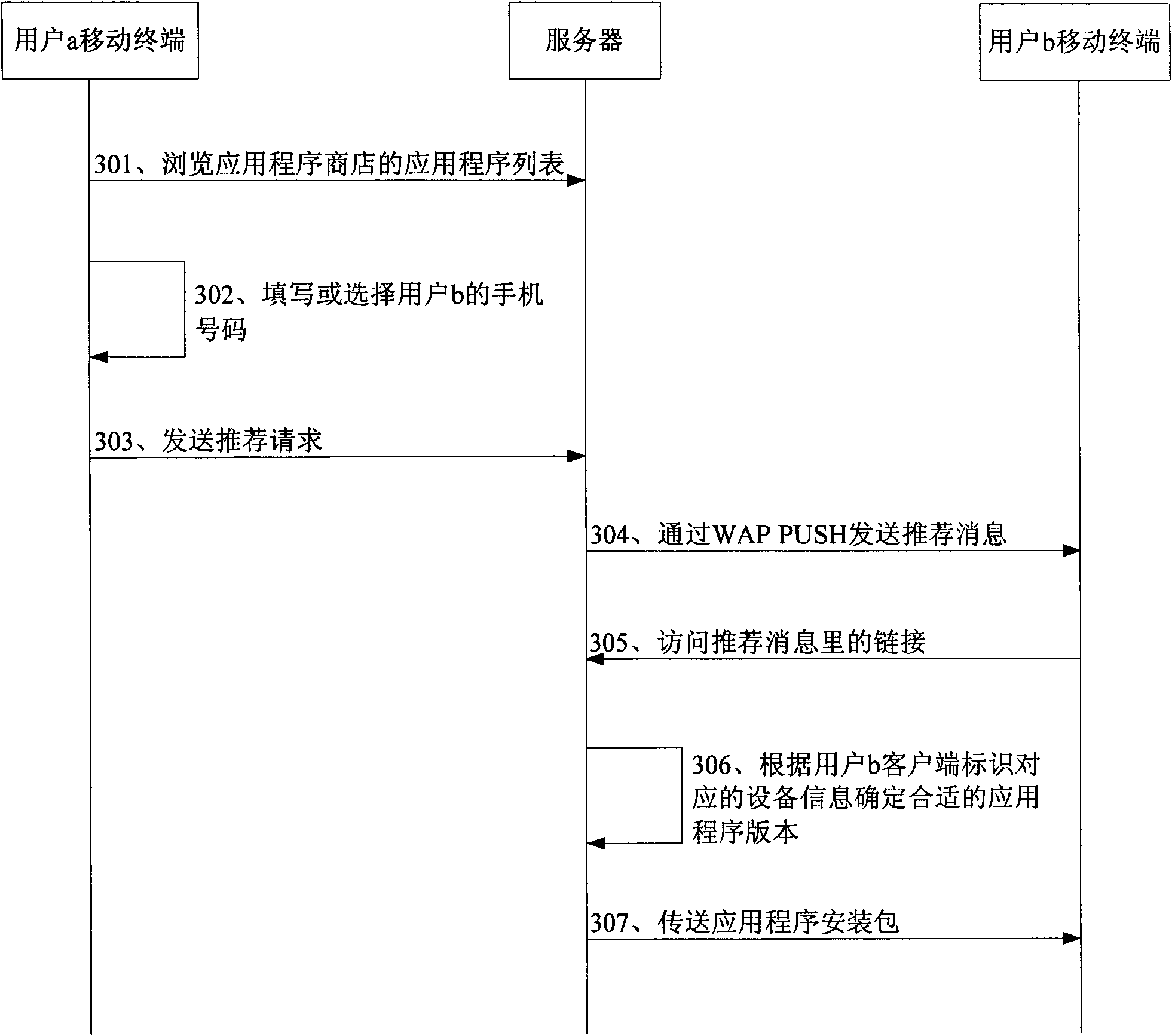
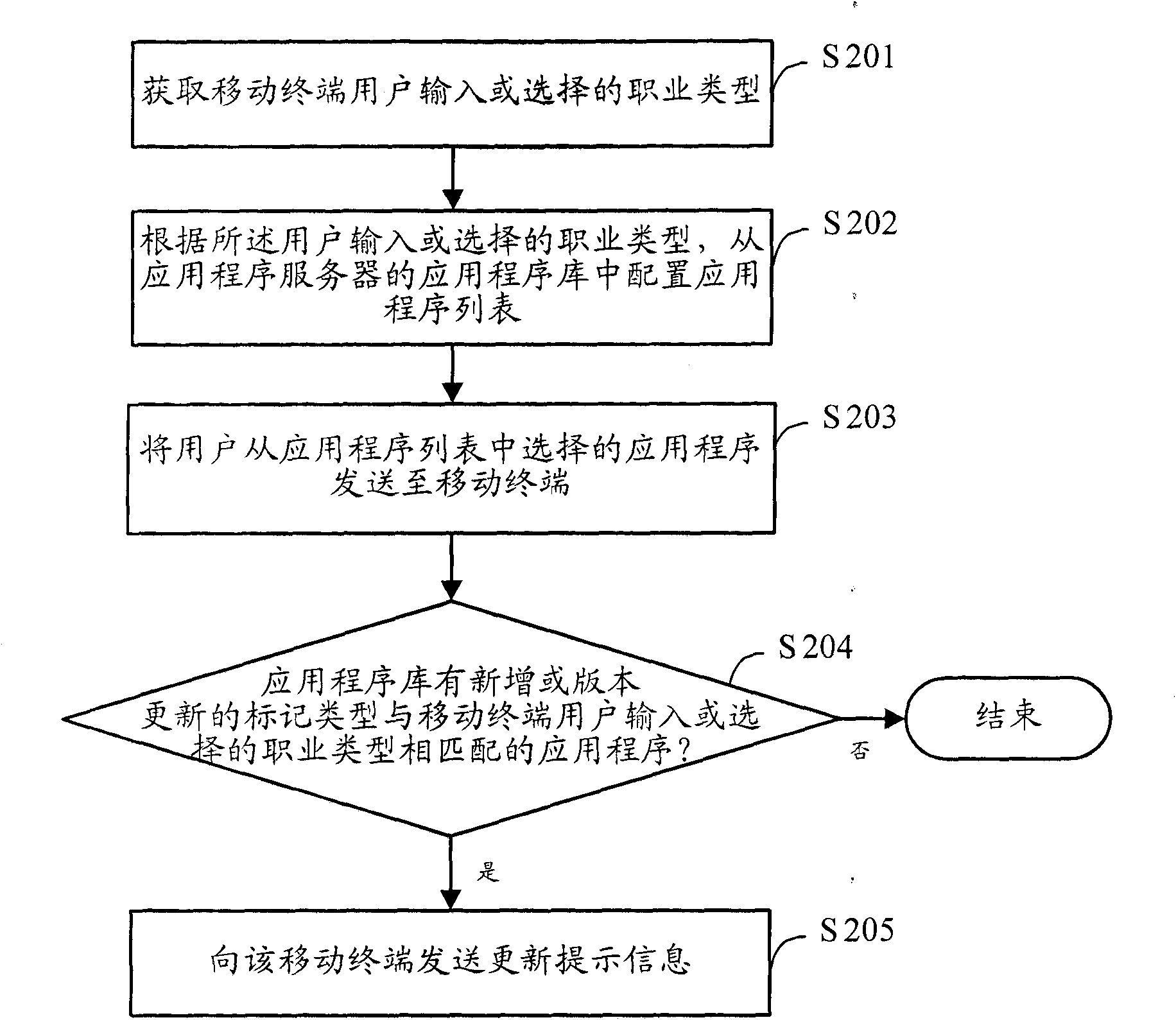
Method for pushing application program and application program server
InactiveCN101848230AShorten the timeImprove the efficiency of downloading applicationsTransmissionApplication serverUser input
The embodiment of the invention discloses a method for pushing an application program, which comprises the following steps of: acquiring a vocation type input or selected by a mobile terminal user; collocating an application program list in an application program library of an application program server according to the vocation type input or selected by the user; and sending the application program selected from the application program list by the user to a mobile terminal. Correspondingly, the embodiment of the invention also discloses the application program server. According to the embodiment of the invention, the application program server automatically collocates the application program related with the vocation type by receiving the vocation type input or selected by the mobile terminal user, provides a plurality of selectable application program downloads for the mobile terminal user, and sends the application program downloads to the mobile terminal in a form of an application program packet so as to save the time of searching the application program in an application program store by the user and improve the efficiency of downloading the application program.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
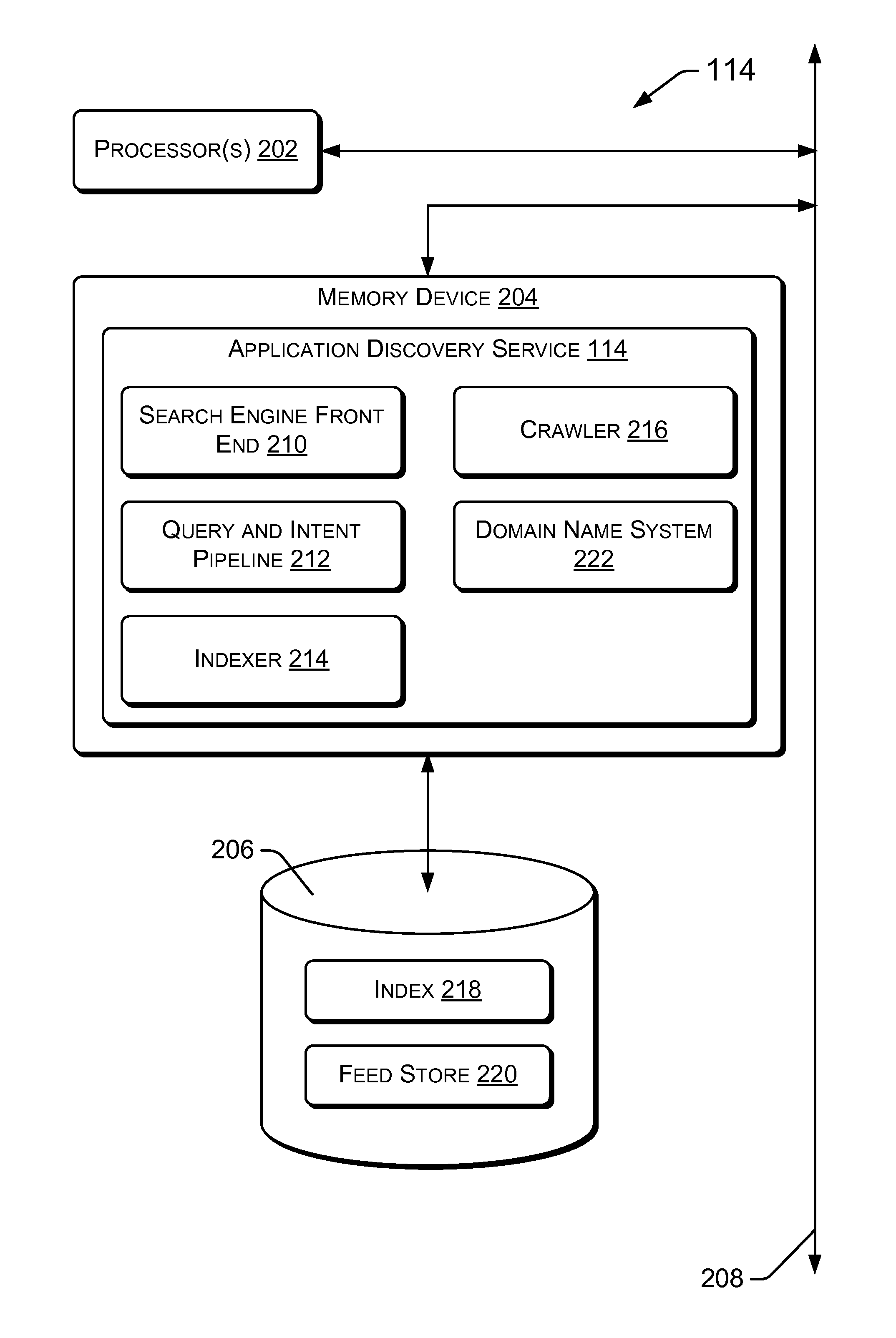
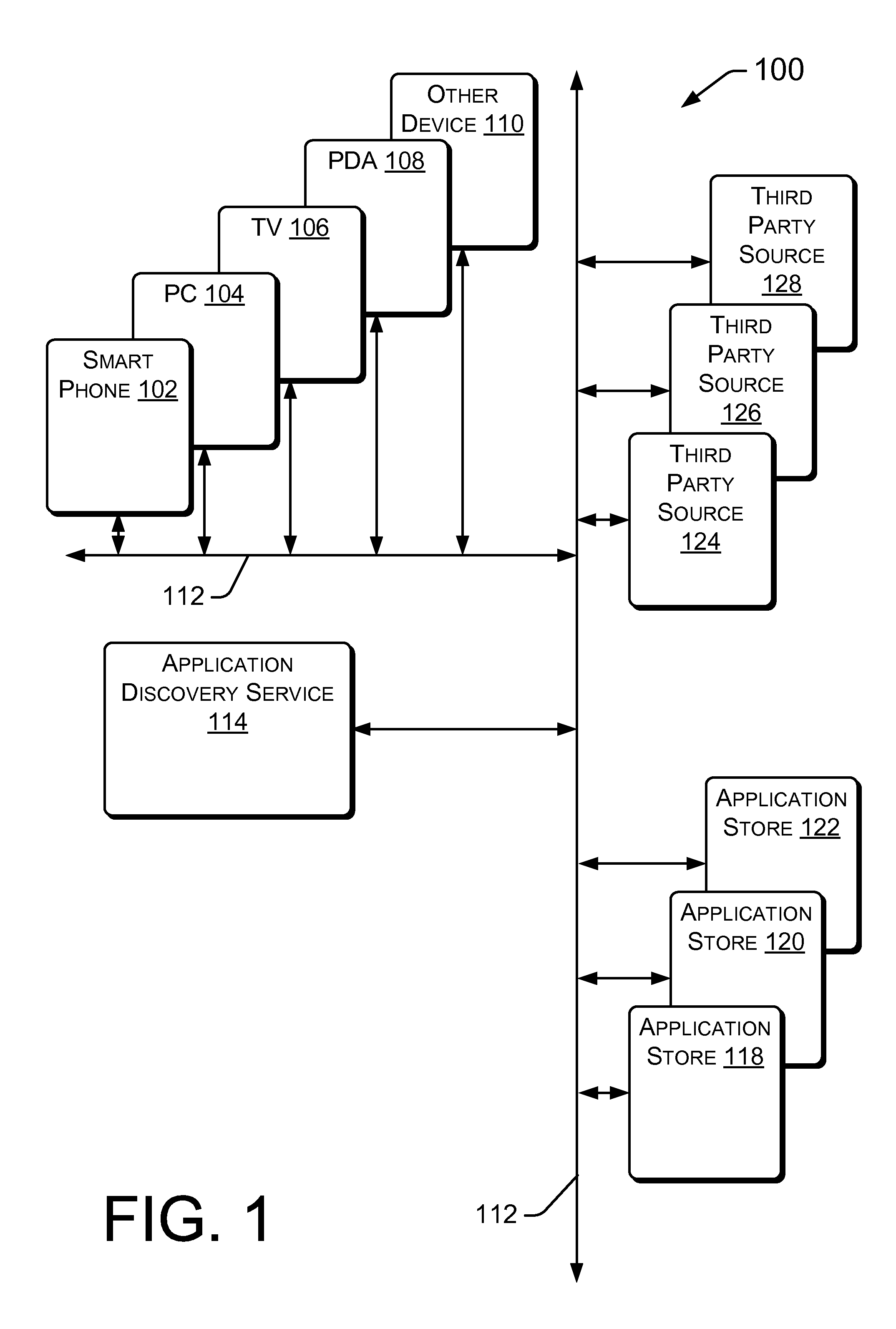
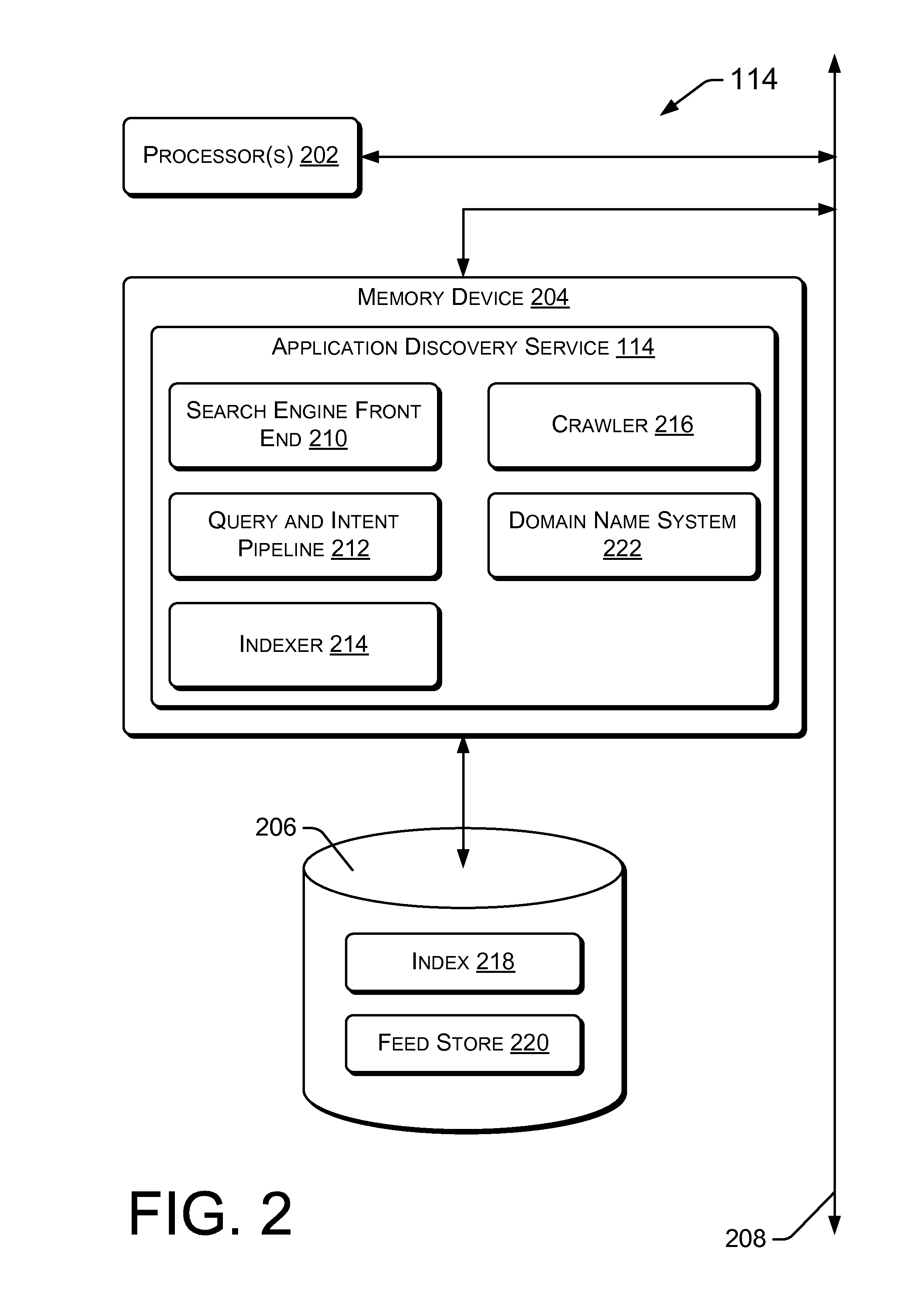
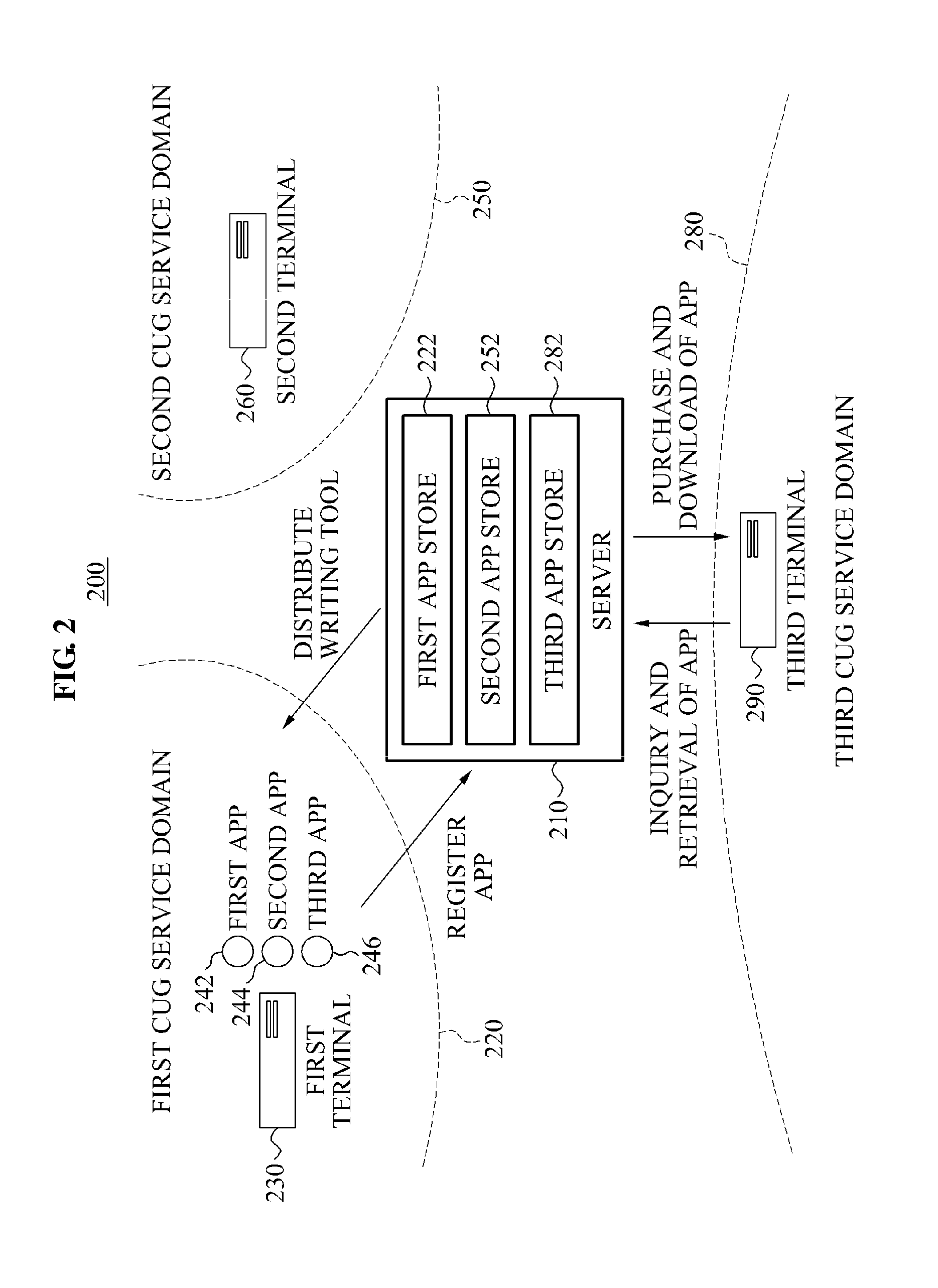
Unified Application Discovery across Application Stores
InactiveUS20120124028A1Well formedDigital data processing detailsSpecial data processing applicationsWeb siteApp store
Techniques for discovery of applications across a plurality of application stores are described herein. The discovery may be in response to a query and intent process, which may be initiated by a search query. The search query may reveal user intent to discover an application by operation of a search engine. The user intent may be matched with indexed application content. The application content may be obtained by operation of a discovery and indexing process. A crawler may discover and crawl a plurality of application stores. Additionally or alternatively, a feed store may receive direct feeds of application information and links to download locations from a plurality of application stores. Both the discovered data and direct feeds may be sent to an indexer, to create and maintain an index. Search results pages may be returned to provide users with information, links to developer websites and links to download pages from a plurality of application stores.
Owner:MICROSOFT TECH LICENSING LLC
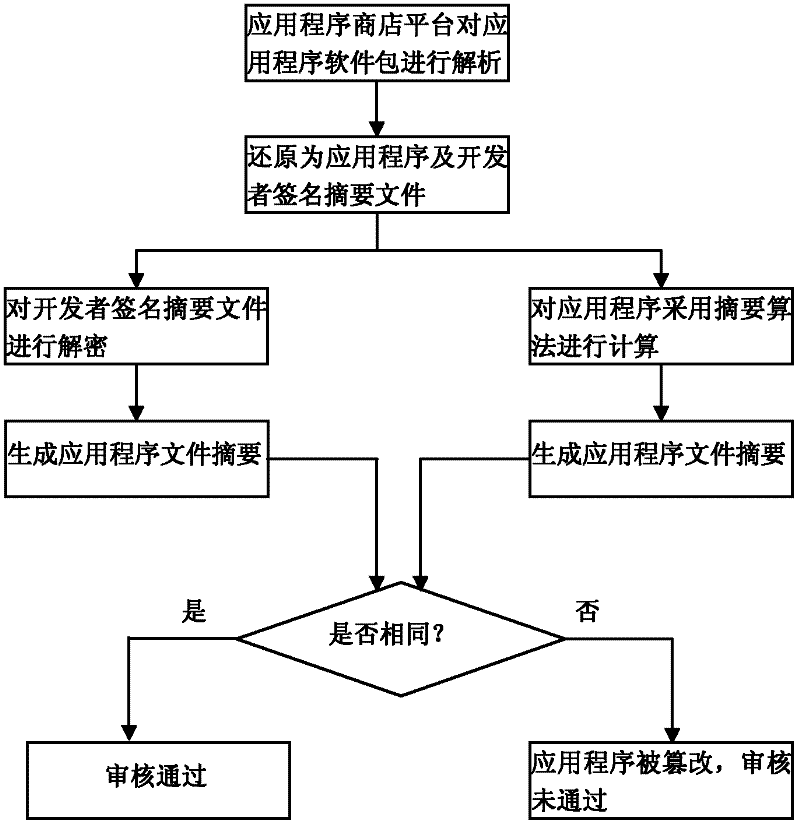
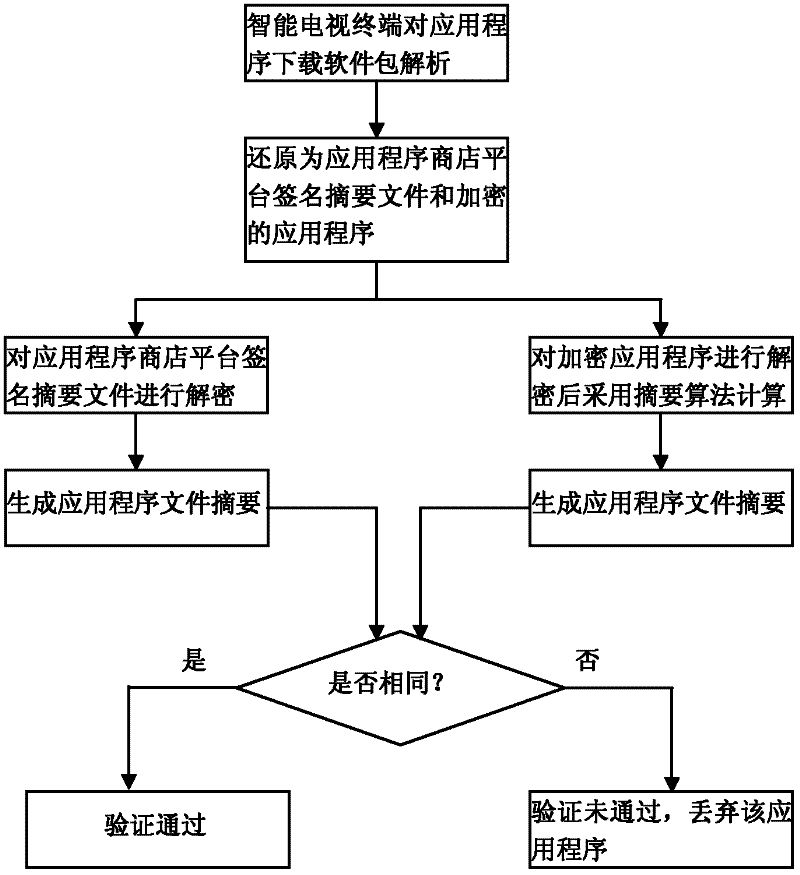
Security control method of intelligent television application program
ActiveCN102546604AGuaranteed legalityEnsure safetyUser identity/authority verificationSelective content distributionNetwork connectionApp store
The invention relates to software security control technology and discloses a security control method of intelligent television application programs, wherein the security of application software is monitored from a plurality of levels, thereby ensuring the security of application software downloaded and installed in an intelligent television terminal. The key points of the technical scheme are summarized as that an application program developer signs for the first time when packing and uploading the application program to an application program store platform; signature of the second time is performed after the application program store platform verifies the application program; the intelligent television terminal hands over a public key of the intelligent television terminal to the platform through a network connection platform, the software is encrypted using the public key at the platform and transmitted to the intelligent television terminal, the intelligent television terminal performs security verification to the application program, and the application program is installed after the verification is accepted. Legitimacy and security of application of the application program is ensured with such method, and such method is applicable for security control of the application software.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
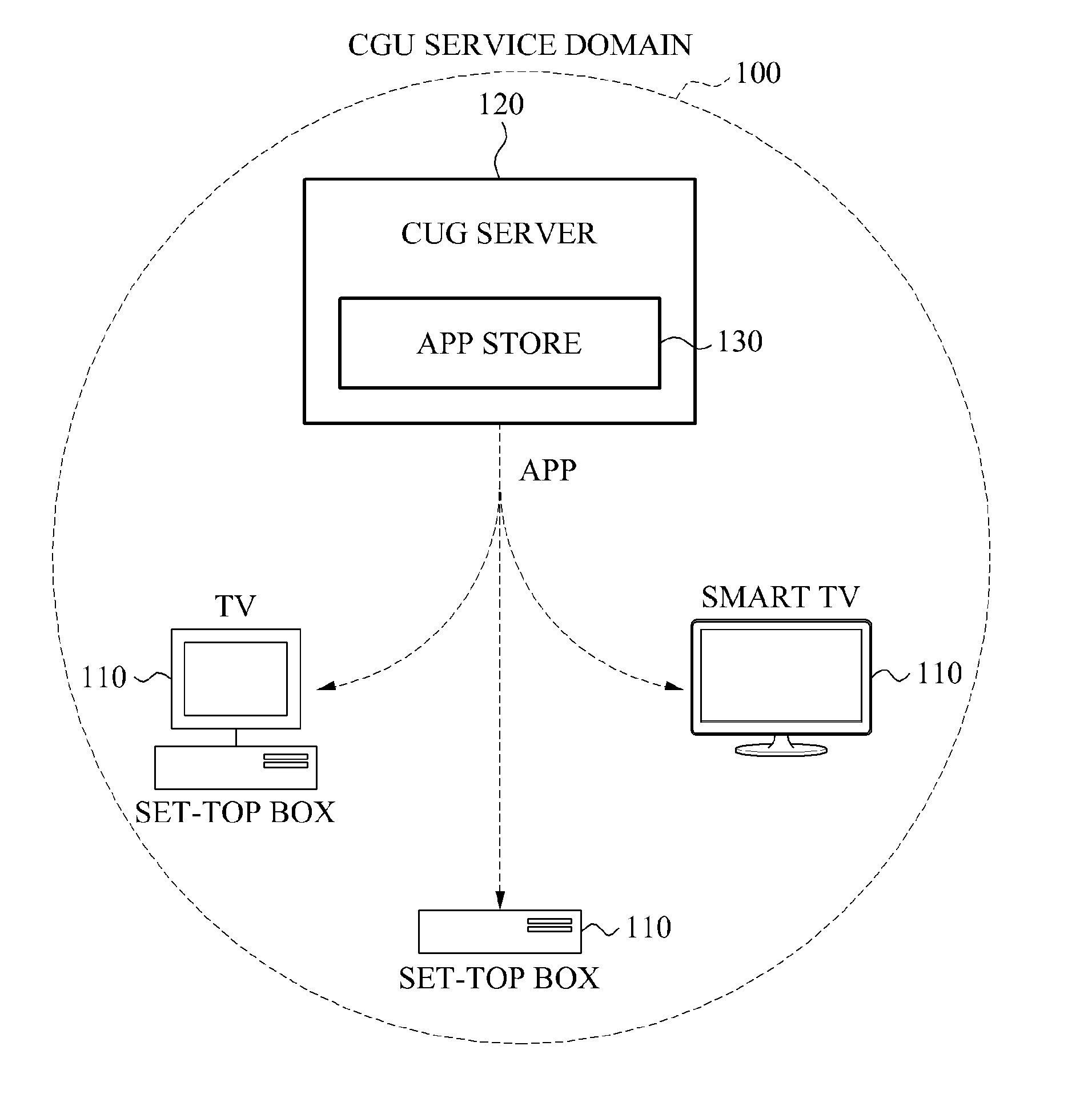
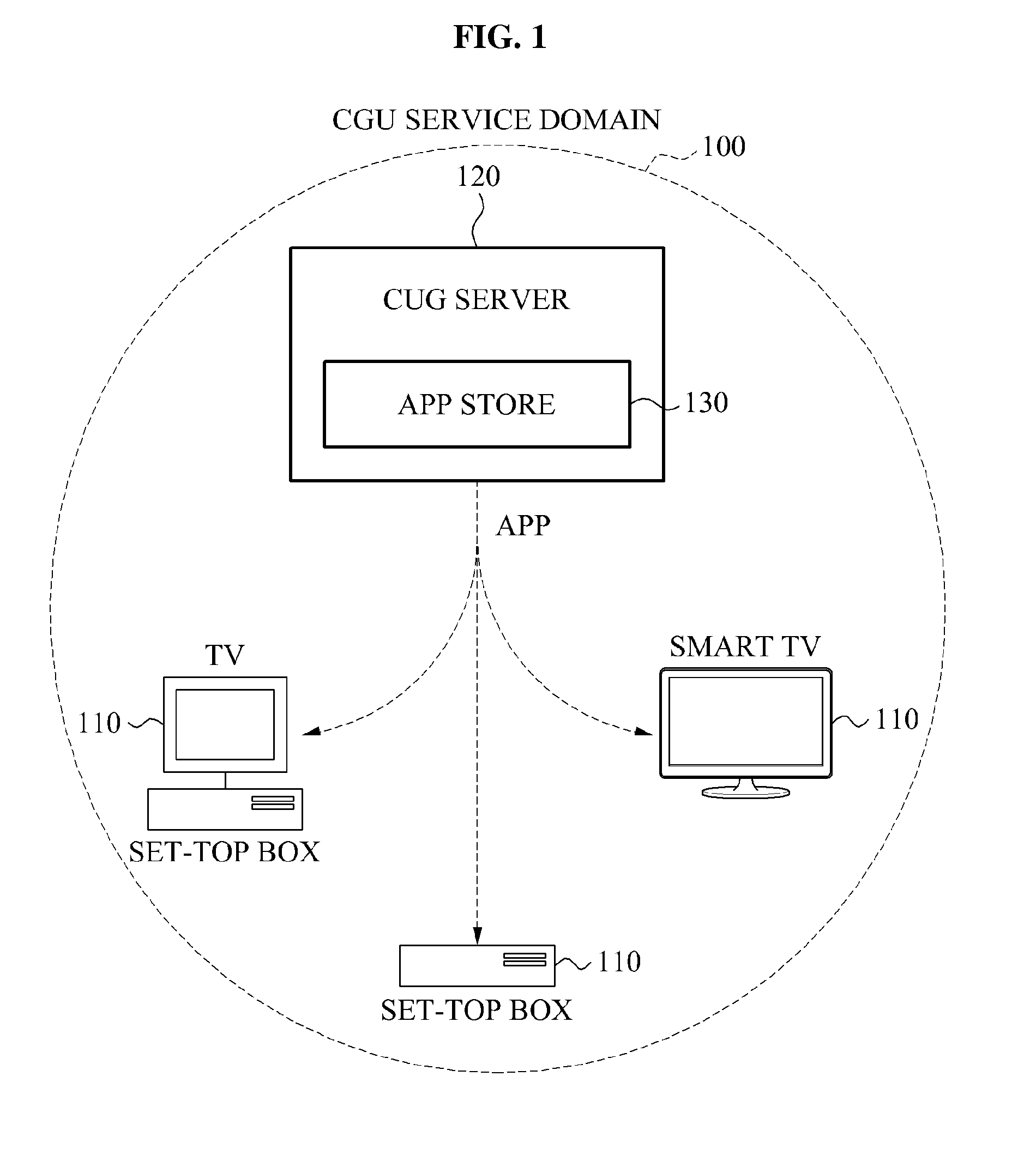
Apparatus for providing service linking closed user groups based on smart television and smart set-top box
InactiveUS20130091053A1Increase profitFinanceMultiple digital computer combinationsApp storeSet top box
Provided is an apparatus for providing a service that links closed user groups (CUGs) based on a smart TV and a smart set-top box. A server may provide at least one application (app) store: The app store may register apps provided by developers, and may provide the registered apps to users of a CUG. The app retriever may provide a result of inquiry and retrieval performed with respect to apps registered in the at least one app store, to a terminal that performs the inquiry and retrieval. The terminal distributed for a predetermined CUG service may use apps associated with varied CUG services through the server.
Owner:HANWHA SOLUTION & CONSULTING
Policy-Based Application Management
Improved techniques for managing enterprise applications on mobile devices are described herein. Each enterprise mobile application running on the mobile device has an associated policy through which it interacts with its environment. The policy selectively blocks or allows activities involving the enterprise application in accordance with rules established by the enterprise. Together, the enterprise applications running on the mobile device form a set of managed applications. Managed applications are typically allowed to exchange data with other managed applications, but are blocked from exchanging data with other applications, such as the user's own personal applications. Policies may be defined to manage data sharing, mobile resource management, application specific information, networking and data access solutions, device cloud and transfer, dual mode application software, enterprise app store access, and virtualized application and resources, among other things.
Owner:CITRIX SYST INC
Method for providing SIM profile in eUICC environment and devices therefor
There are provided a method of providing a SIM profile, and an eUICC device. The method of providing the SIM profile includes downloading a SIM profile application selected by a user who uses the eUICC device from an app store, executing and installing the SIM profile application in the eUICC device, accessing of the eUICC device having the SIM profile application installed therein to an operator server, and authenticating the eUICC device based on SIM profile information corresponding to the SIM profile application. The eUICC device includes a network connection unit configured to access the app store via a local network, a SIM profile storage configured to store the SIM profile application, and an authentication requesting unit configured to access the operator server based on the SIM profile information.
Owner:SAMSUNG ELECTRONICS CO LTD
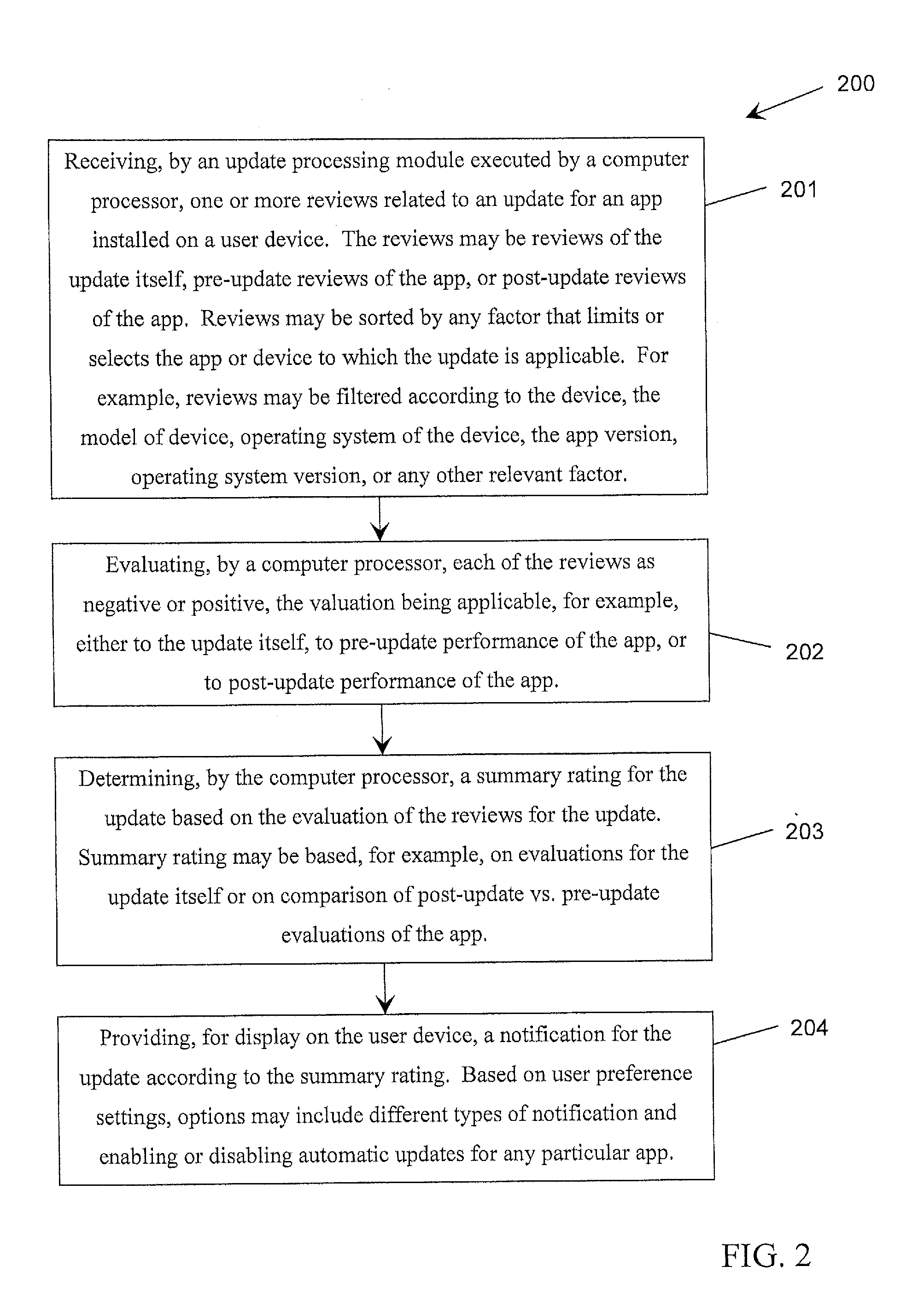
App store update notification and warning system
ActiveUS20160179498A1Software testing/debuggingProgram loading/initiatingTablet computerOperational system
A system for maintaining and upgrading hardware device functioning provides processes to select and install updates for software (e.g., applications or apps) on the hardware device. A notification system provides information for discretion and control over the selection of software updates to be applied to consumer mobile devices according to the particular characteristics of the device, e.g., the model of device, the specific operating system of the device, and software applications installed on the device. The notification system may be integral with app stores on mobile devices and tablets, and may also be applicable to the Internet of Things. A notification may take the form, for example, of a warning or recommendation associated with an update for an app on the user device and may enable the user to make an informed decision beforehand about whether or not to install a particular update on the user device.
Owner:PAYPAL INC
Method and device for implementing personalized user interface
ActiveCN102662679AThe actual needs meetImprove user experienceSubstation equipmentSpecific program execution arrangementsPersonalizationApp store
The invention discloses a method and a device for implementing a personalized user interface. The method includes: acquiring the type of a user; and acquiring column names and column contents according to the user type, and displaying the column names and the column contents on the user interface of a client side. By the aid of the technical scheme, the problems of low use ratio and poor use experience of users due to great differences between an application recommendation interface of a mobile phone application store client side and practical demands of the users in the prior art are solved, and the user interface of the client side can be dynamically changed according to various factors so that practical demands of the users are more effectively met, and use experience of the users is improved.
Owner:BEIJING QIHOO TECH CO LTD
Network linker for secure execution of unsecured apps on a device
InactiveUS20130205415A1Digital data processing detailsAnalogue secracy/subscription systemsDigital signatureApp store
An app is made secure using an app wrapping security technique and a network linker that creates an executable binary file of the wrapped app that does not use custom dynamic libraries. The network linker includes a client-side linker component and a server-side linker component. When the app is created and the developer decides to have it security wrapped, an extra parameter is inserted in the client-side linker component for invoking the network linker of the present invention. If a call is being made from app security wrapping code, then the invocation resolves to normal system libraries and the call is not shimmed. Once all the symbols have been resolved on the server-side linker, the executable binary is transmitted back to the client-side linker component where it is digitally signed by the app developer and put in a suitable form for uploading to an app store or marketplace.
Owner:BLUE CEDAR NETWORKS INC
Automatic discovery and retrieveal of interoperable applications
ActiveUS20160162270A1Platform integrity maintainanceProgram loading/initiatingApp storeApplication software
The disclosed implementations provide a seamless mechanism for end users to discover and try out new and / or updated applications. An application store may determine alternative applications to a frequently used first application on the client device that are similar to the first application. It may provide installation packages to the client device that installs the applications in a manner that associates the alternative applications with the first application. A notice may be generated by the client device that indicates the applications have been installed and / or that the data generated by the first application has been imported into the alternative applications. A selection of a user interface element may launch one of the alternative applications. Data generated by the first application may be displayed according to the user interface of the alternative application.
Owner:GOOGLE LLC
Doll companion integrating child self-directed execution of applications with cell phone communication, education, entertainment, alert and monitoring systems
ActiveUS9126122B2Easily expandableEasily modifiableNear-field transmissionDollsSmall Island Developing StatesApp store
The presented cell phone-enabled doll companion allows a child novel ways to self-select and self-execute applications while requiring no intervention or supervision from the parent. Further, it provides learning, entertainment and safety by integrating cell phone communication, education, entertainment, alert and monitoring systems. While providing a convenient means of communication between the child and parent, the system allows surveillance of a child's real-time environment, GPS monitoring and SIDS / health monitoring. The functionality and the physical elements of the system are programmable through installation of applications downloadable from an application store. Various options for parental access to a configuration interface to modify settings and download applications are provided, including via a cell phone, a website, customer service call center and / or the doll companion touch screen.
Owner:LEARNING SQUARED INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com