Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
187results about How to "Prevent fraudulent use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
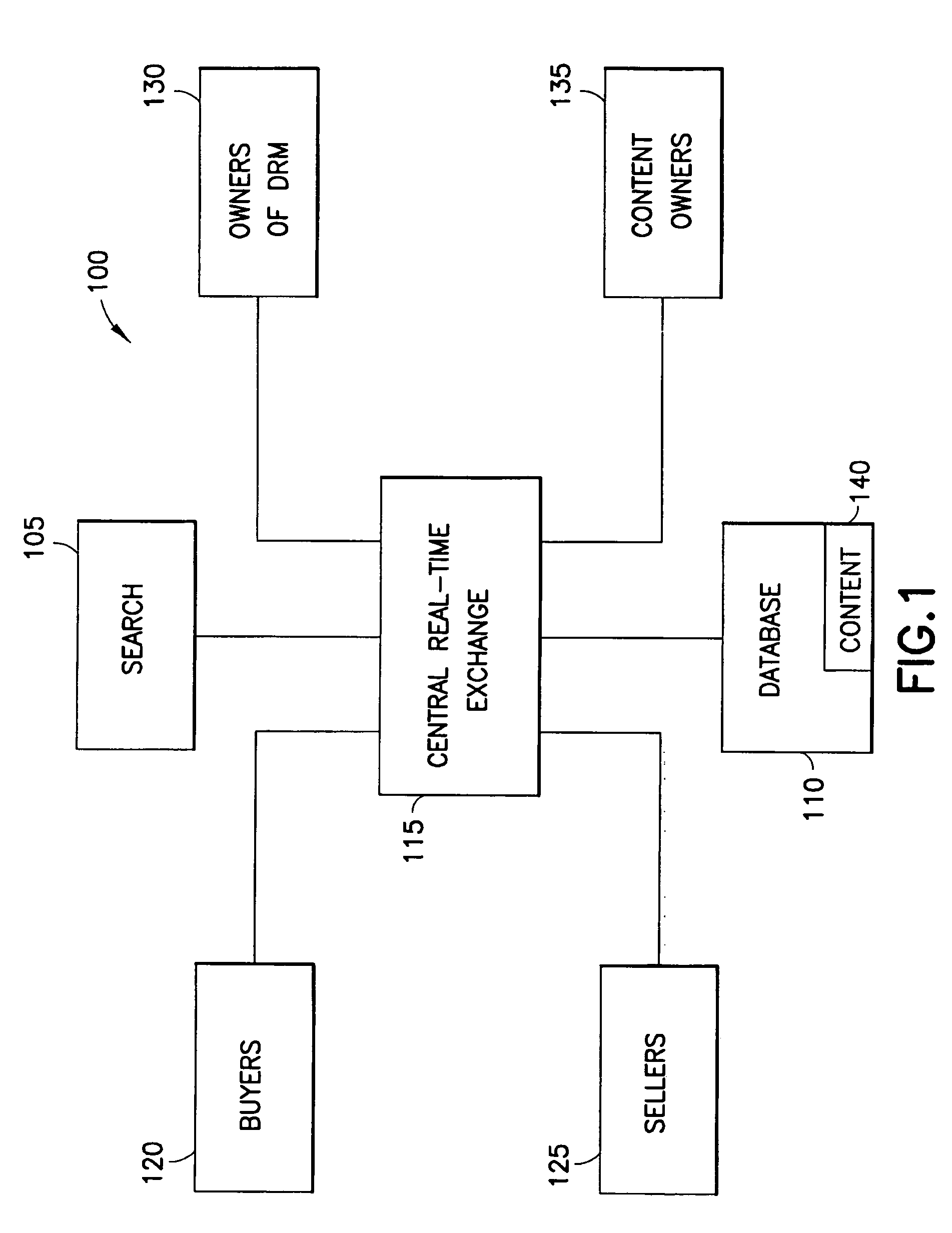
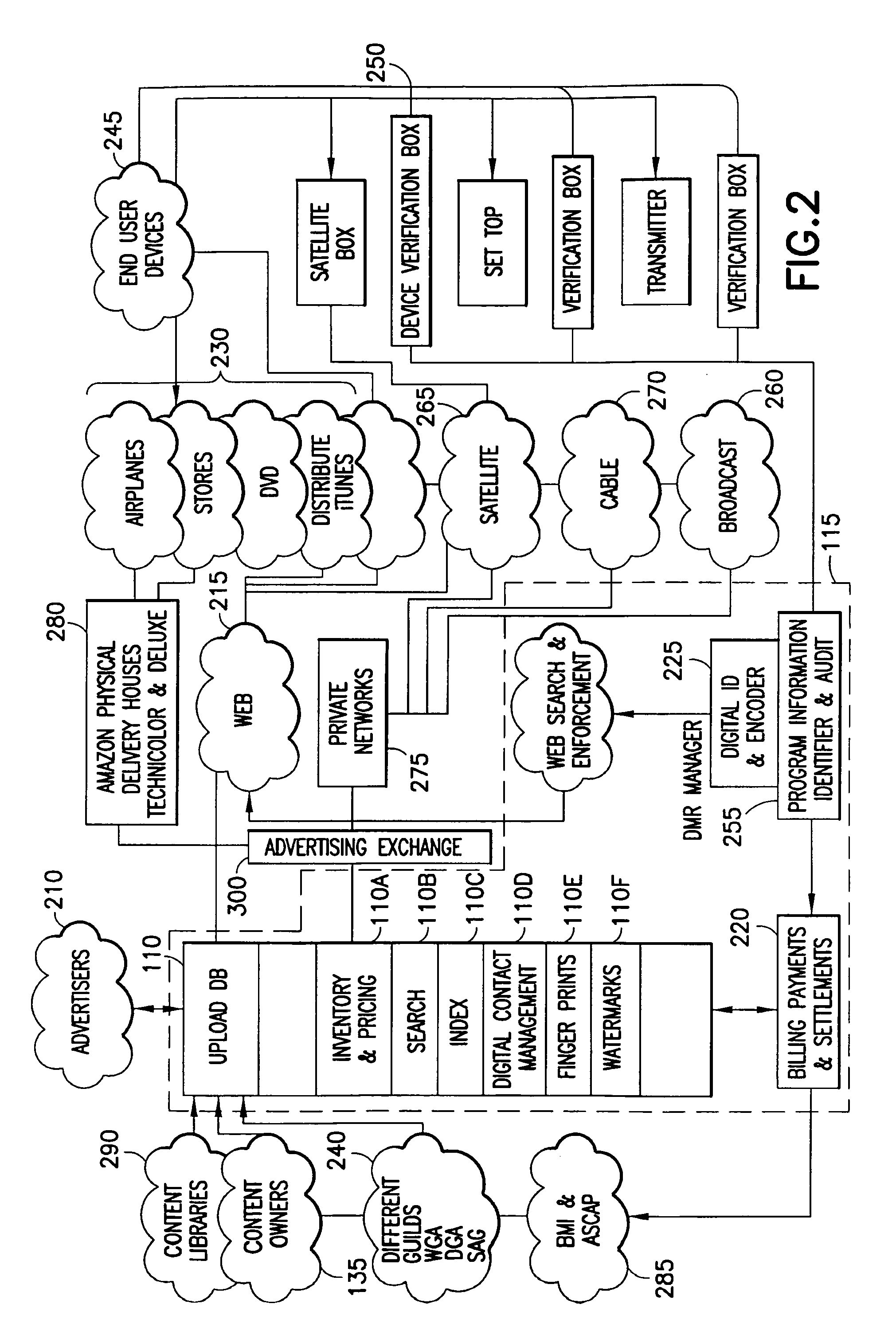
Digital rights management and data license management
InactiveUS20080228578A1Surpasses efficiencySurpasses convenience factorAdvertisementsDigital computer detailsDigital contentWeb service
A system and method for the exchanging, distributing and managing digital content, along with providing users with the ability to sell and transfer digital rights of products or services purchased from other users, wherein the system and method are used to manage synchronization and the use of applications, web services and media in combination with different digital rights management (DRM) solutions to authenticate and authorize such transactions.
Owner:ALEX MASHINSKY FAMILY TRUST +1
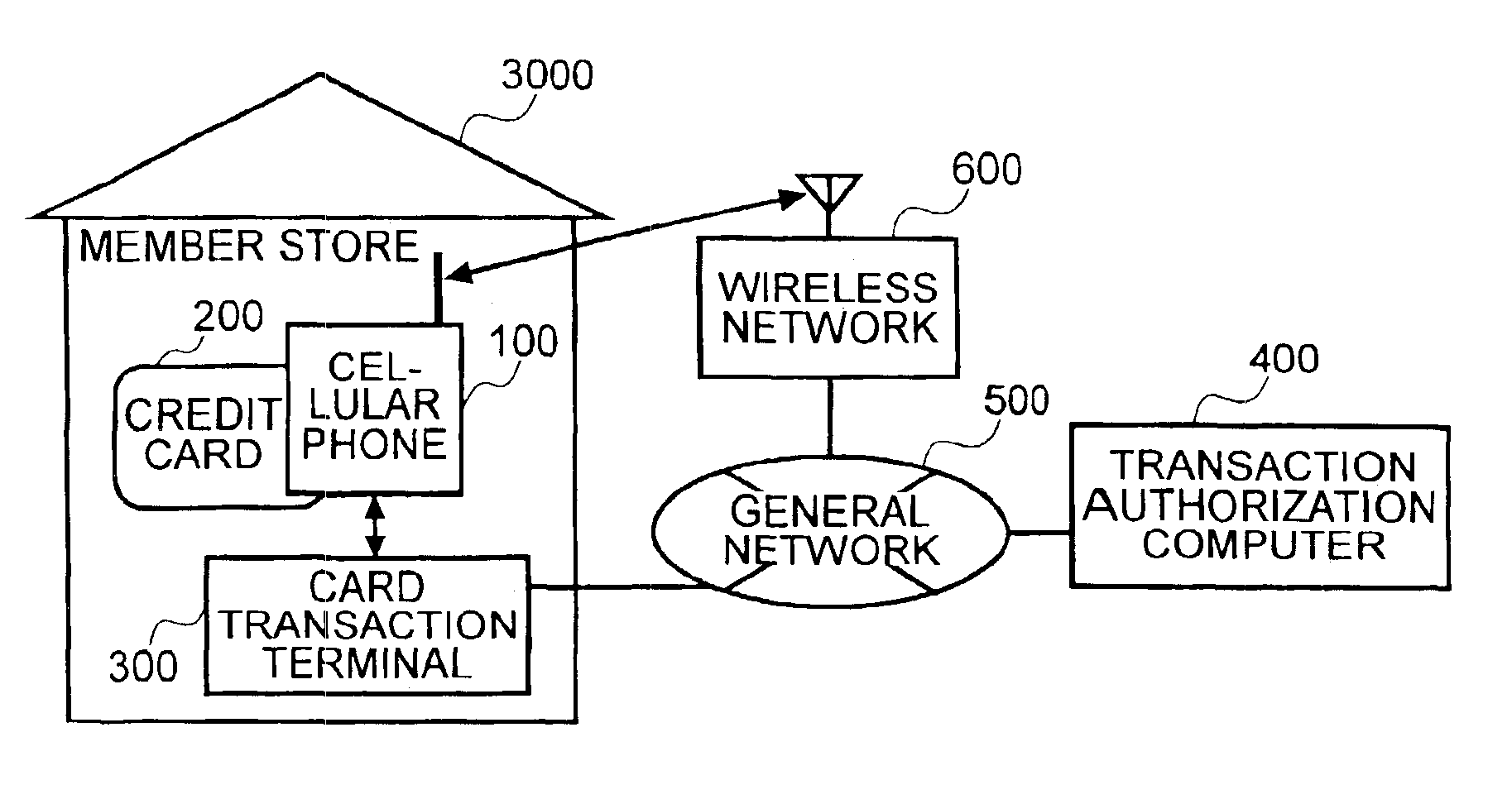
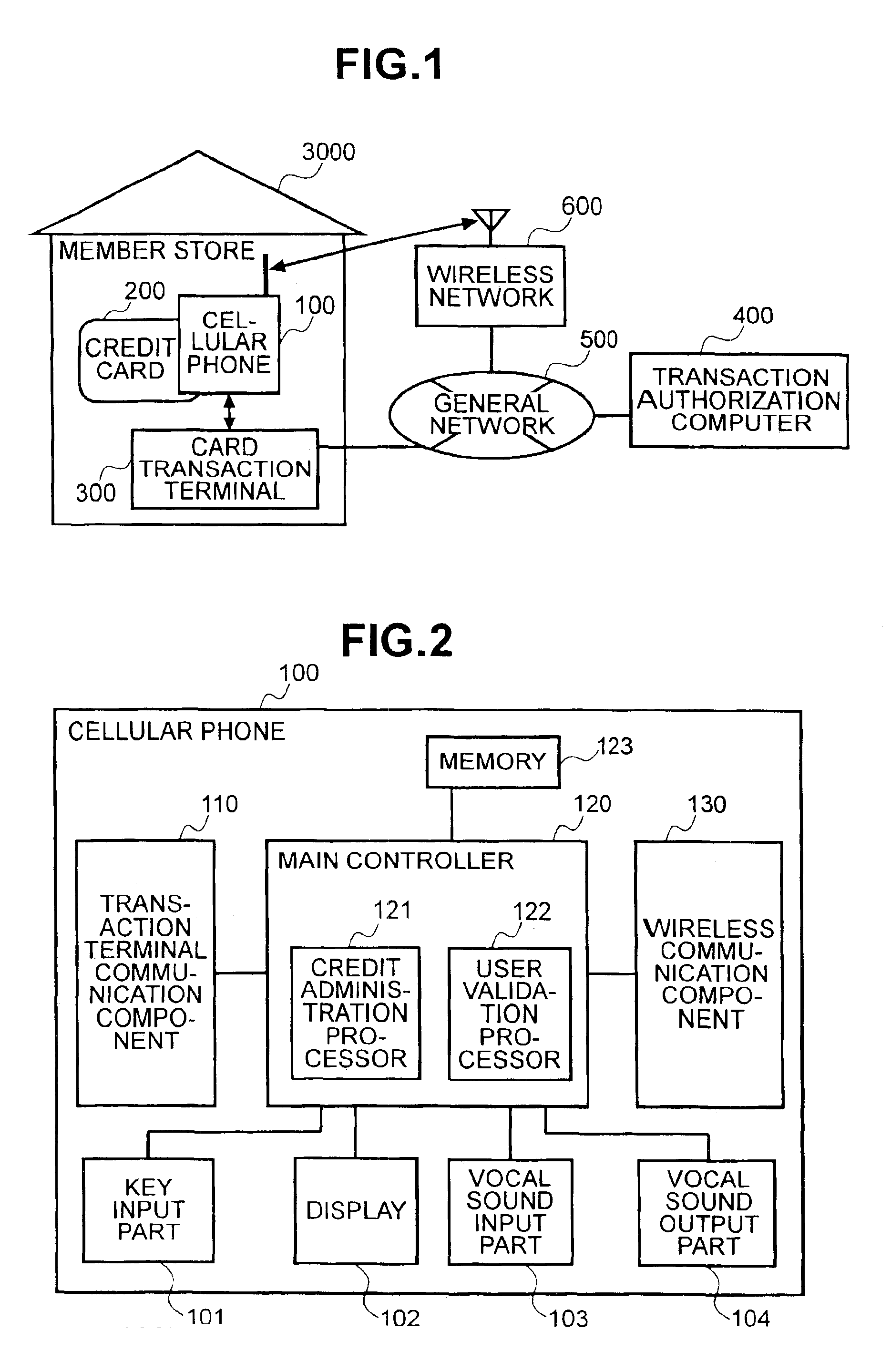
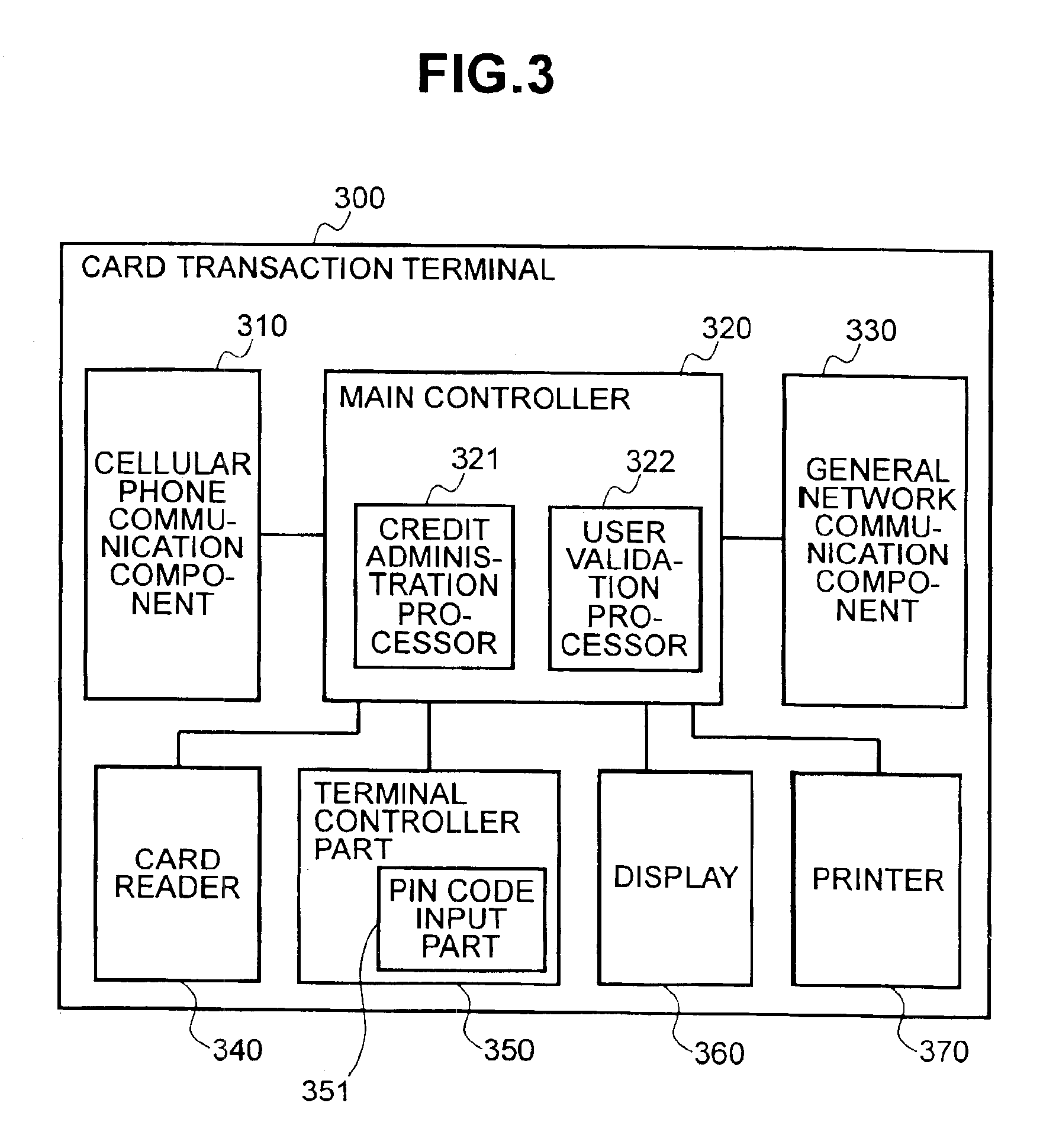
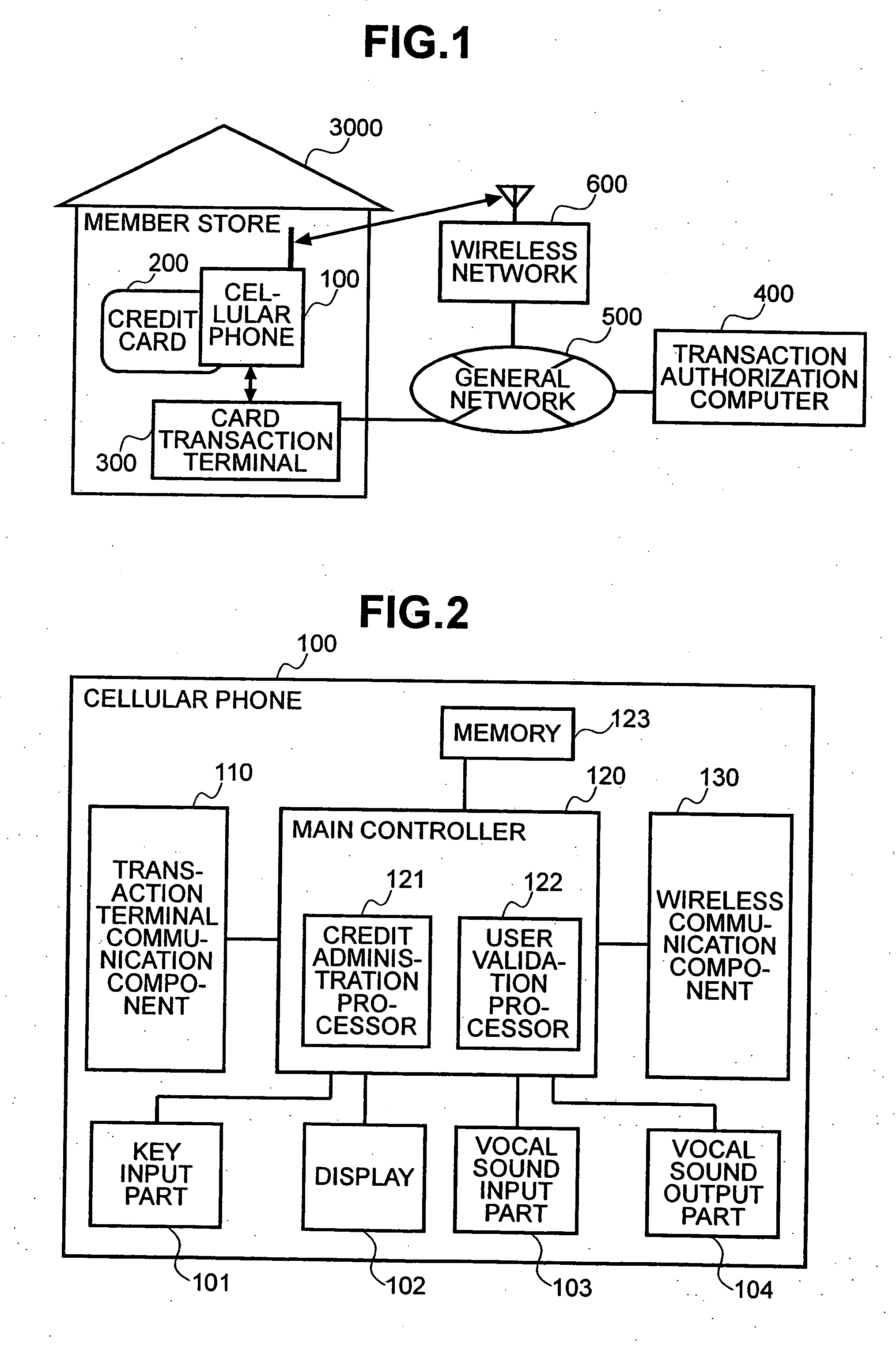
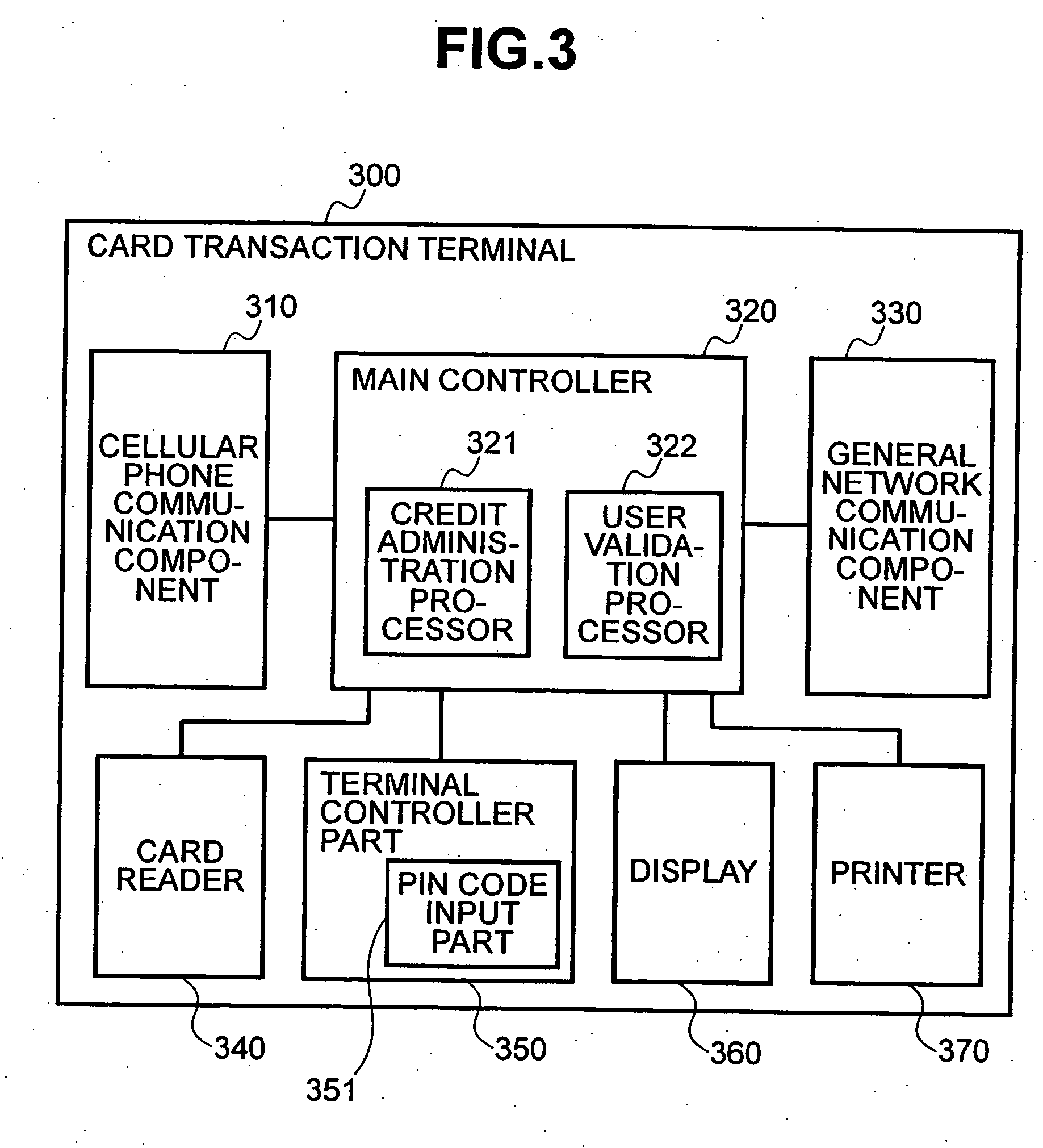
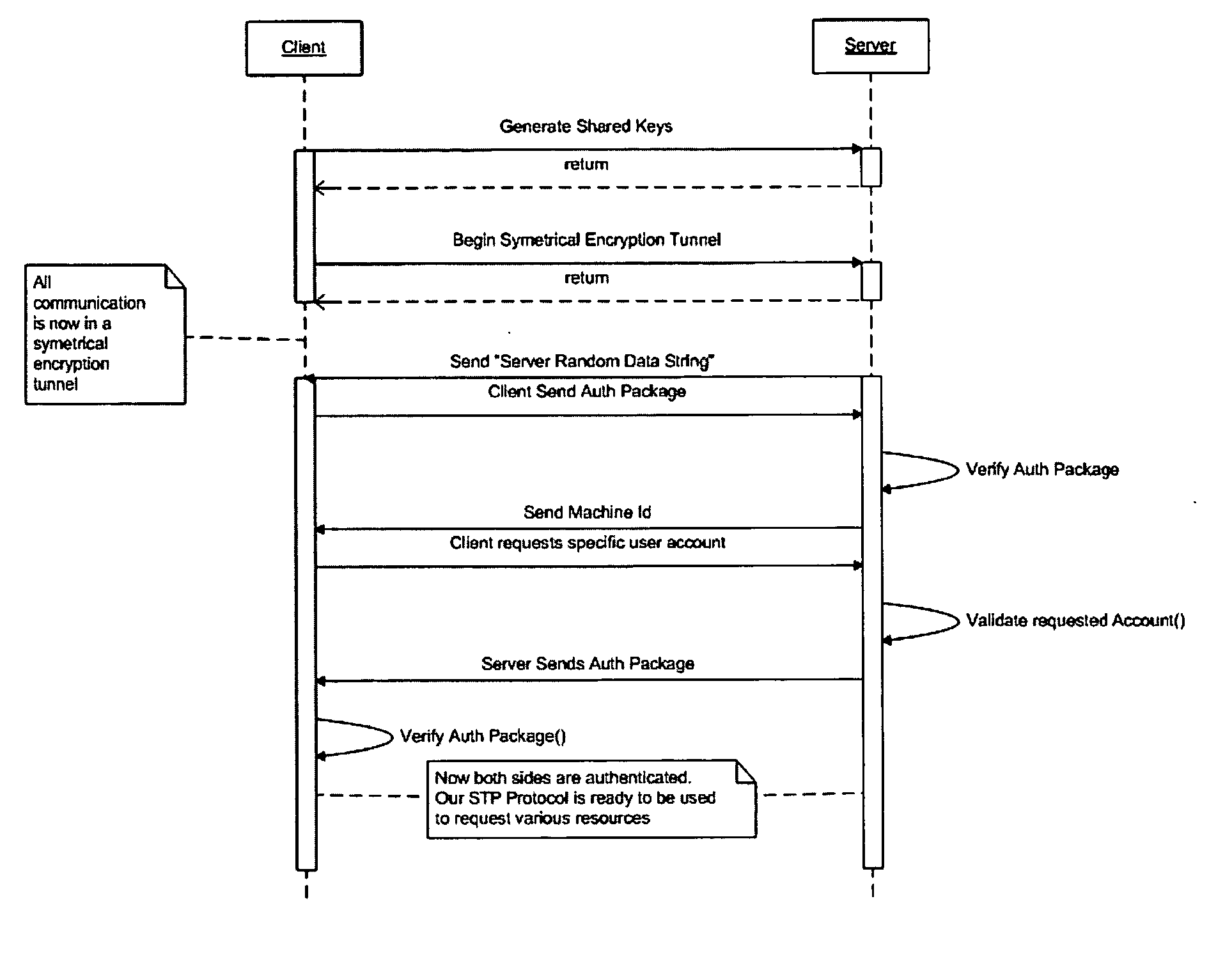
Method and system to prevent fraudulent payment in credit/debit card transactions, and terminals therefor
InactiveUS6913194B2Transaction can be blockedEliminate dangerBuying/selling/leasing transactionsVerifying markings correctnessUser verificationComputer terminal
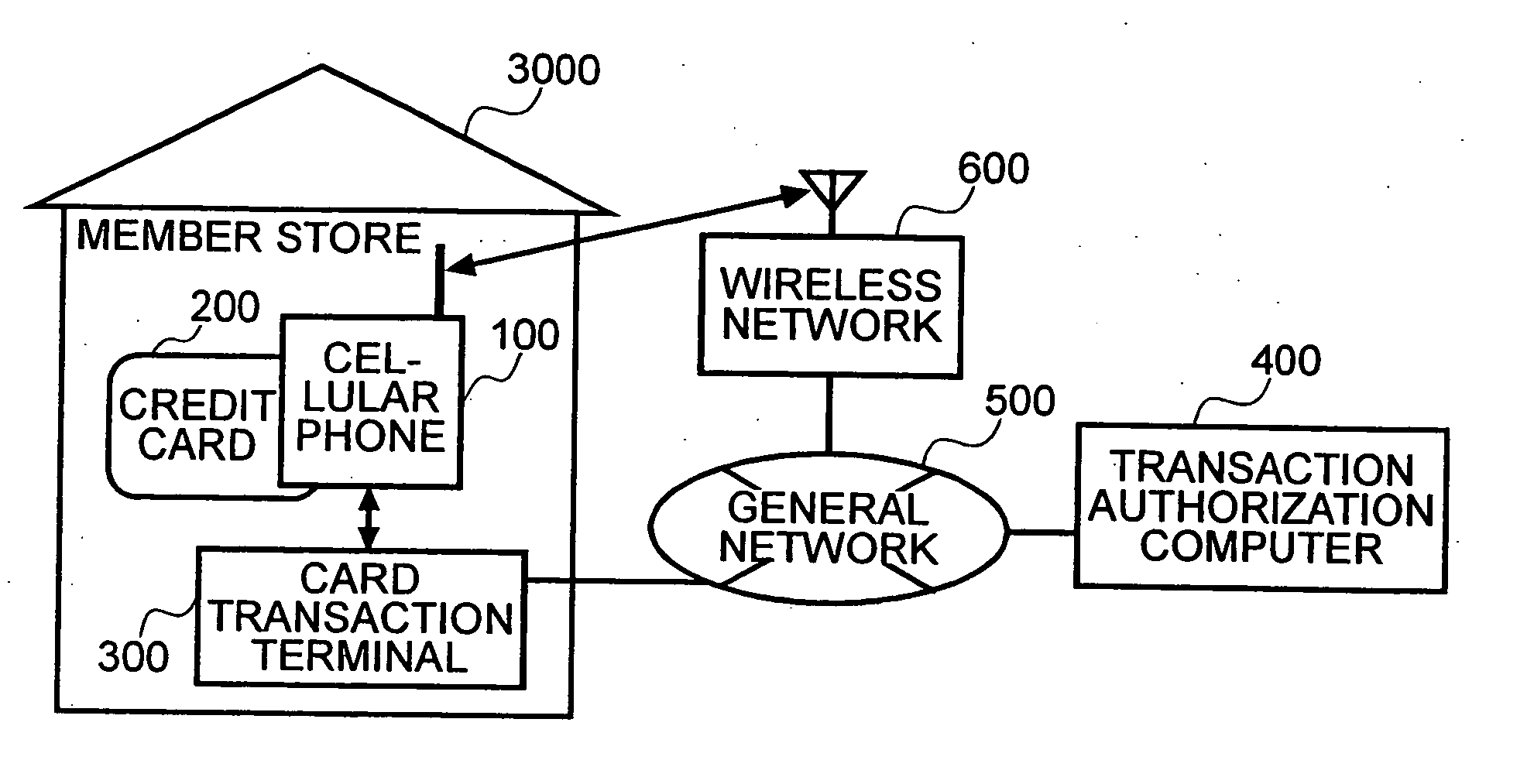
The present invention enables secure, valid card payments in credit transactions to be performed, preventing fraudulent card use even in cases of loss or theft of a card or of information theft. During a transaction authorization process using a transaction terminal disposed in a credit transaction member store and connected with a host computer, user validation or credit administration is carried out by using a portable communication terminal to input to the host computer identity information which has been previously registered in the portable communication terminal and / or location information for the portable communication terminal.
Owner:MAXELL HLDG LTD
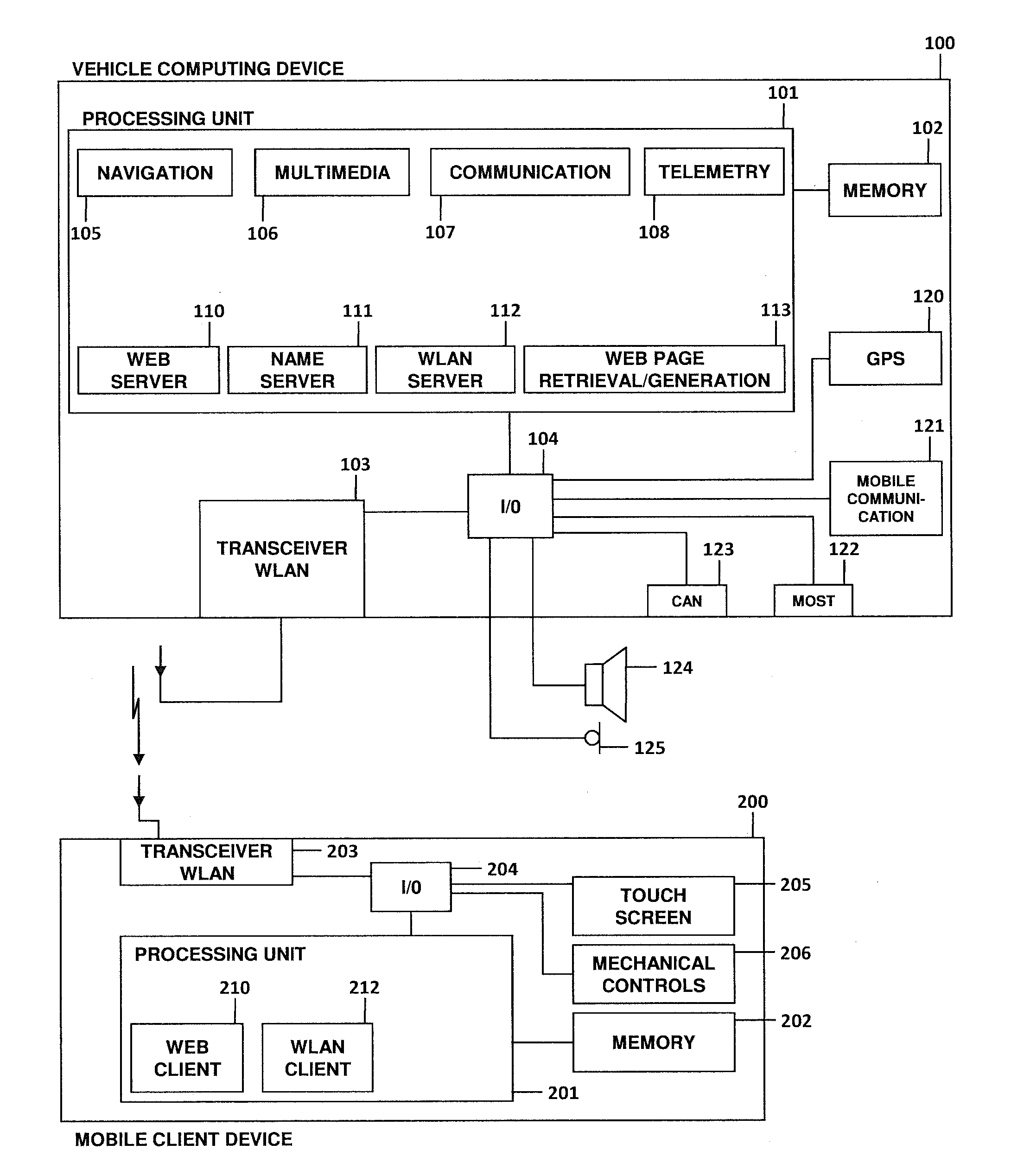
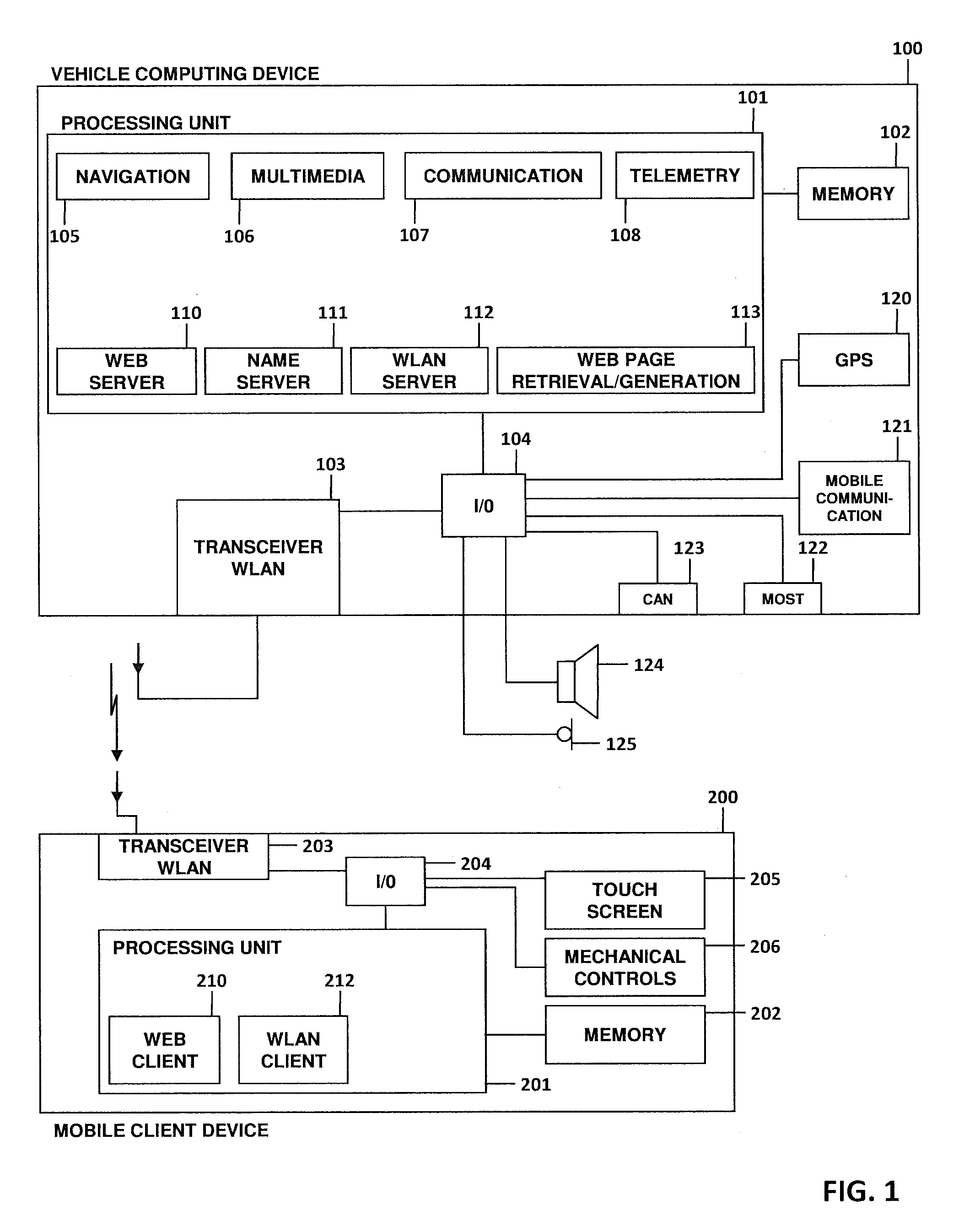
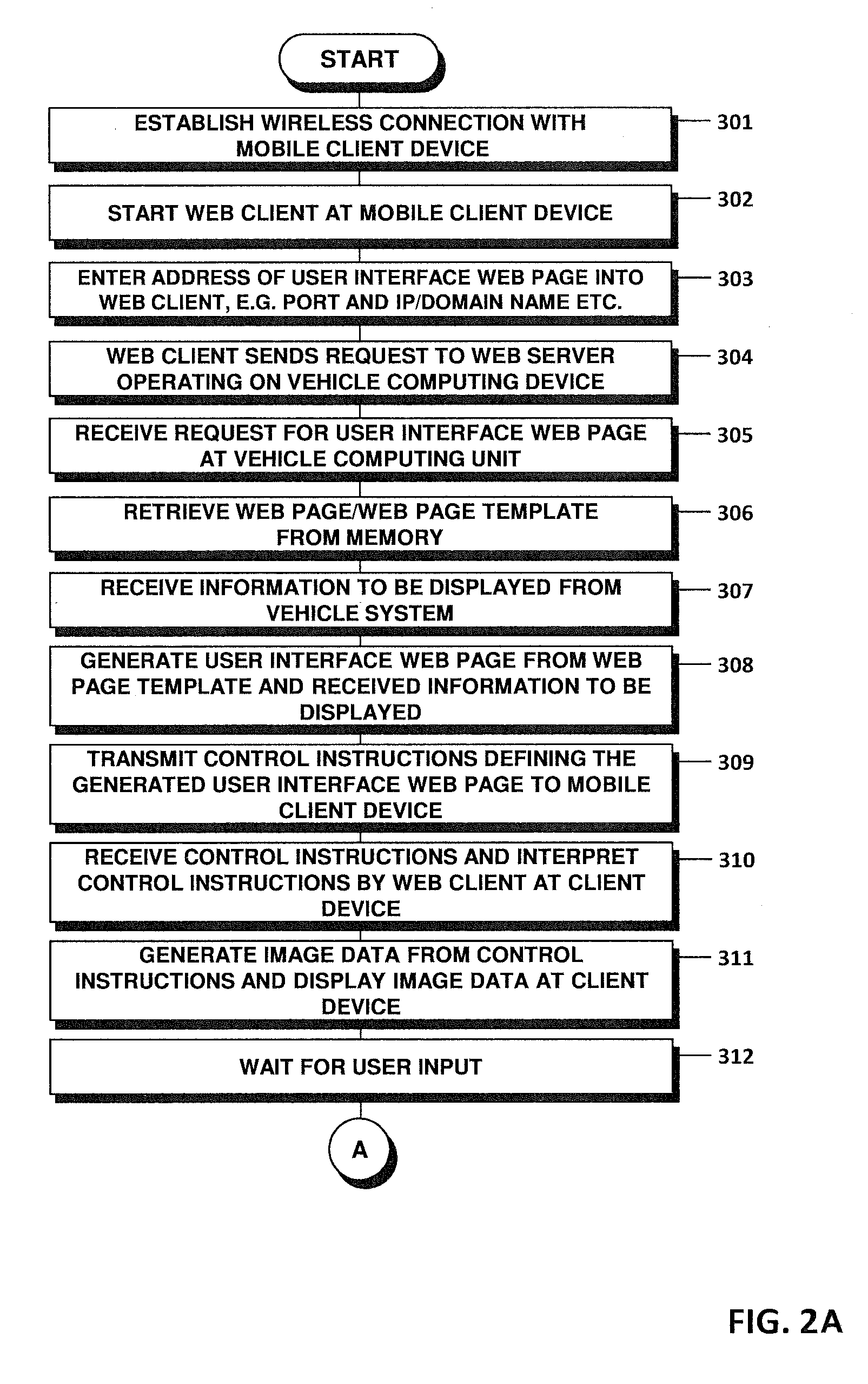
User interface for a vehicle system
ActiveUS20120065815A1Free up spaceReduce riskDashboard fitting arrangementsDigital data processing detailsGraphicsWireless data
A vehicle computing device and a method of providing a user interface to a vehicle system to control at least one function of the vehicle system are provided. The vehicle computing device communicates with a mobile client device over a wireless data connection. At the vehicle computing device, control instructions are provided. The control instructions comprise instructions for displaying at least one graphical control element at the client device to control the at least one function of the vehicle system. The vehicle computing device can be configured to transmit the control instructions to the client device over the wireless data connection.
Owner:HARMAN BECKER AUTOMOTIVE SYST
Dual transaction authorization system and method
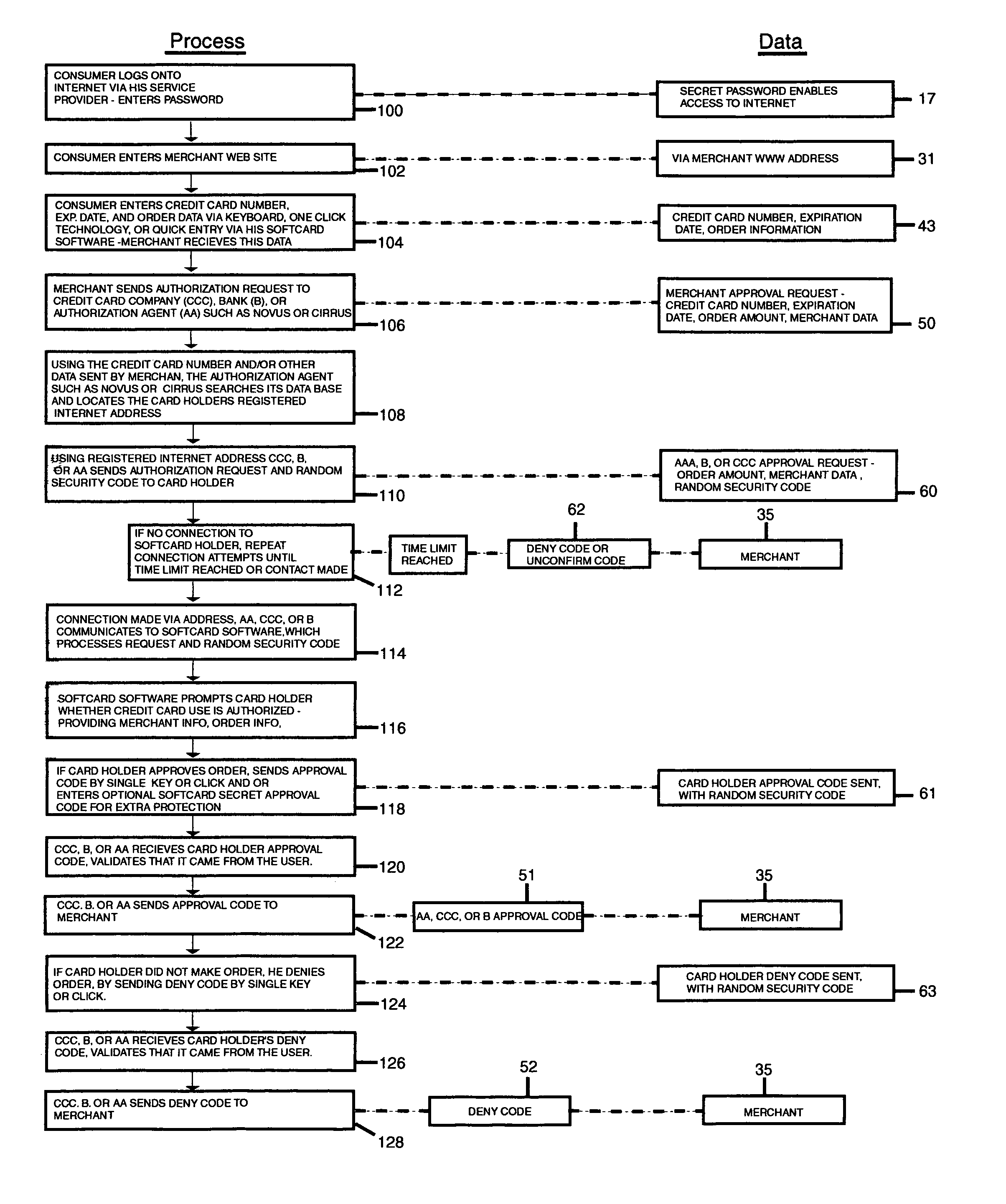
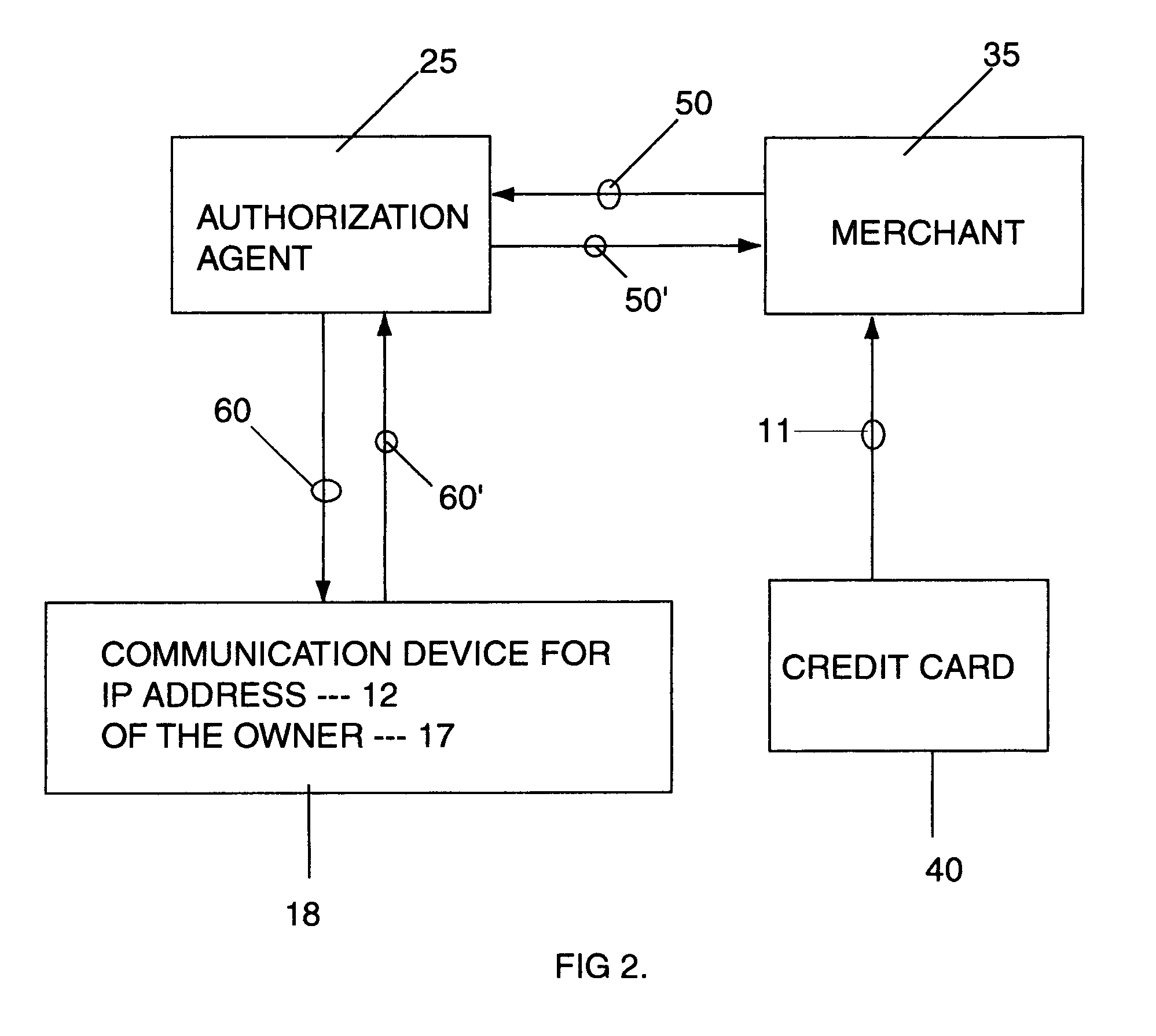
A general feature of the present invention is to provide a dual authorizing system and method to prevent fraudulent use of credit cards and E-signature. To do so, a third party verifier is provided to ensure that the rightful owner of the credit card or E-signature approves of the transaction before the purchase is completed between the merchant and the credit card user. This is accomplished by linking the owner's Internet address or addresses or other communication device address to the credit card number, and storing this information with the third party verifier, such as an Authorization agent. Once the card is used to make a purchase, the Authorization agent is notified of the purchase. The Authorization agent then pulls the corresponding Internet address or communication address for the credit card number, then sends an approval request message to the owner at the owner's Internet address or communication device. This way, only the owner who had previously registered the credit card number with the Authorization agent is notified of the pending purchase and can approve or deny the purchase and, thereby preventing unauthorized user from making purchase using the owner's credit card.
Owner:KLOOR HARRY THOMAS
Method and system to prevent fraudulent payment in credit/debit card transactions, and terminals therefor
InactiveUS20050242173A1Transaction can be blockedEliminate dangerBuying/selling/leasing transactionsVerifying markings correctnessUser verificationComputer terminal
The present invention enables secure, valid card payments in credit transactions to be performed, preventing fraudulent card use even in cases of loss or theft of a card or of information theft. During a transaction authorization process using a transaction terminal disposed in a credit transaction member store and connected with a host computer, user validation or credit administration is carried out by using a portable communication terminal to input to the host computer identity information which has been previously registered in the portable communication terminal and / or location information for the portable communication terminal.
Owner:MAXELL HLDG LTD
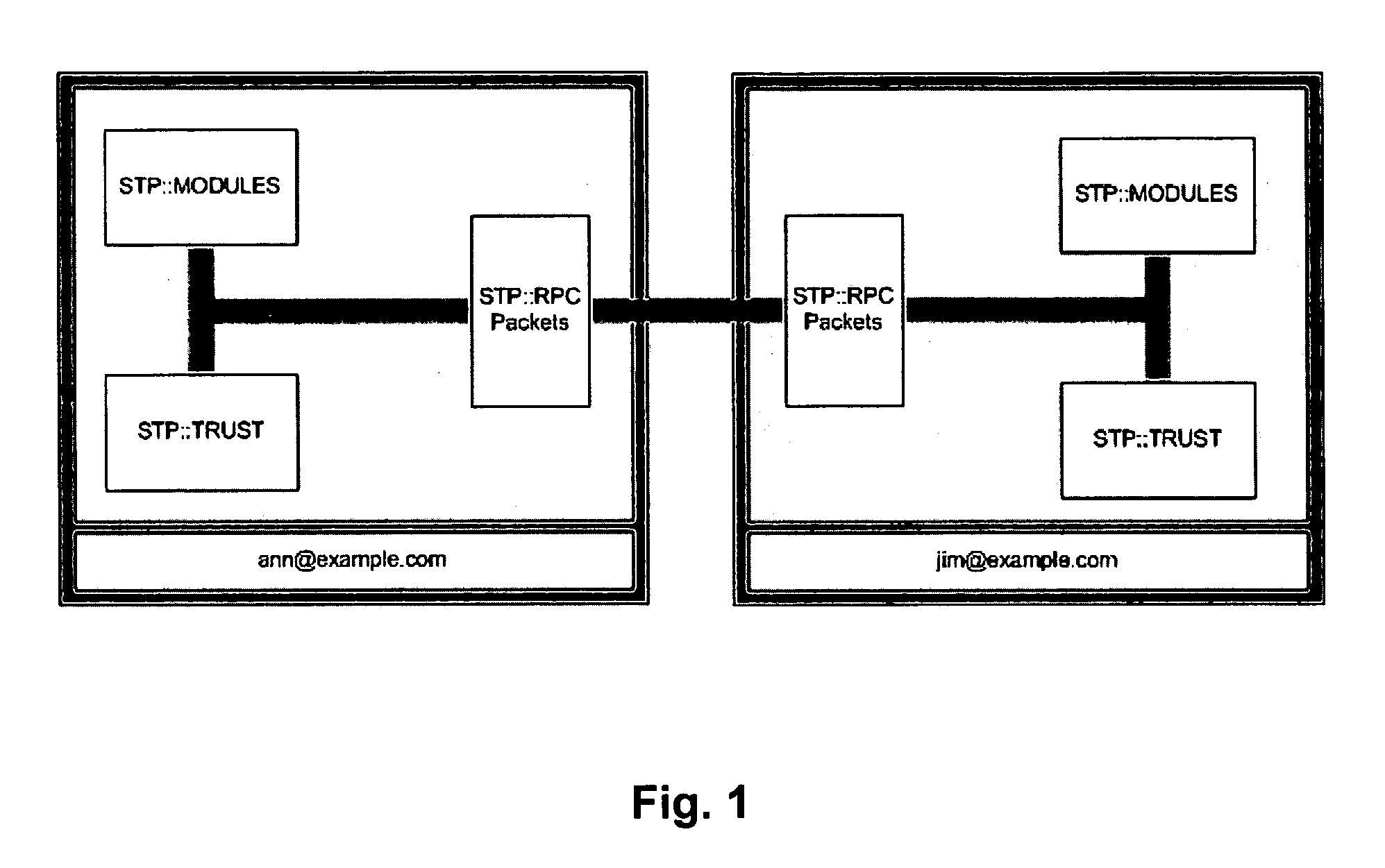
Method of providing secure access to computer resources
InactiveUS20070101400A1Easy accessLow level of trustDigital data processing detailsUser identity/authority verificationComputer resourcesTrusted authority
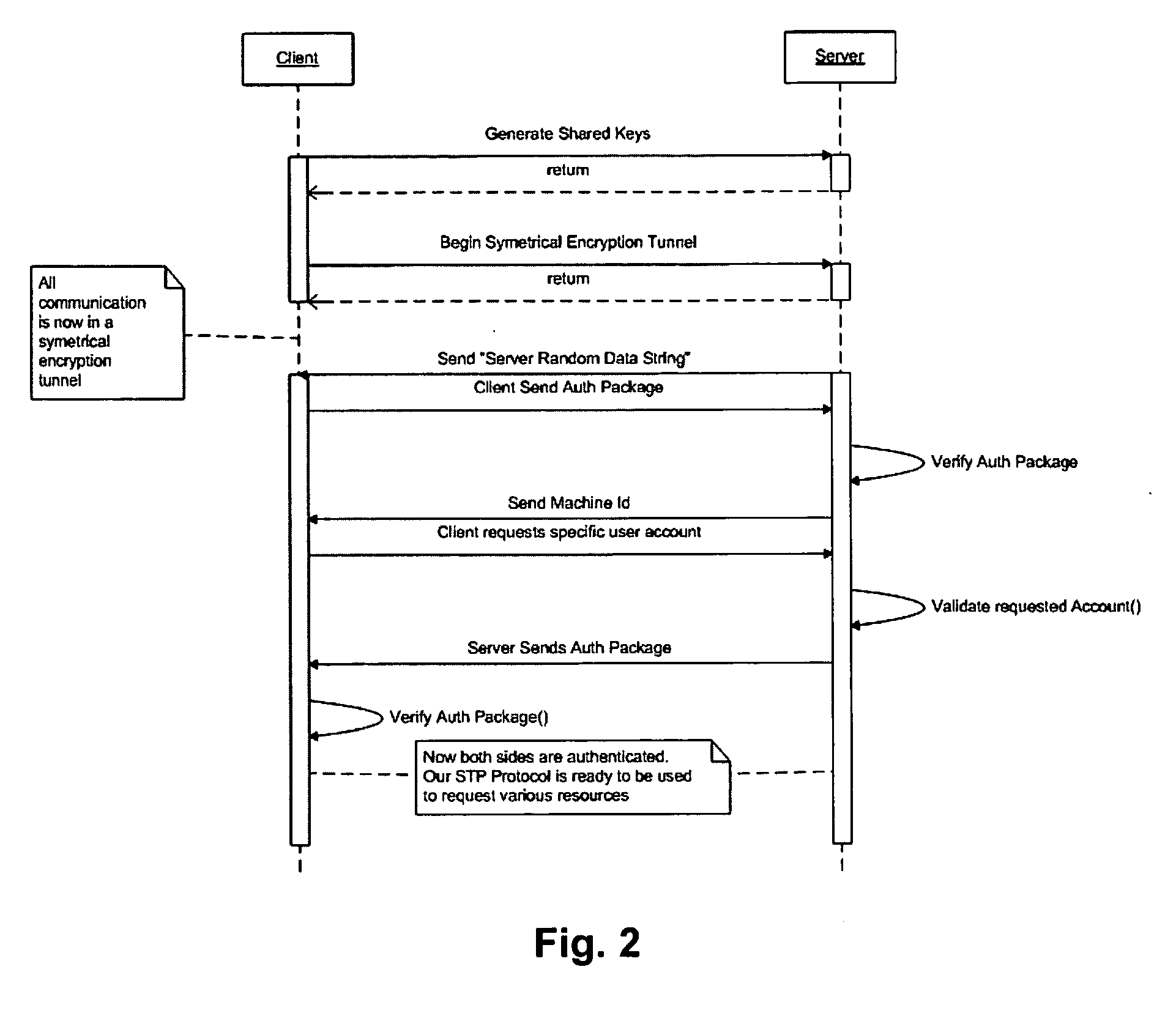
A method of providing varying levels of secure access to computer resources. A certificate is used to identify a particular data requester and the certificate is authenticated using asymmetrical encryption techniques, such as public-private key pairs. One or more trust authorities may be consulted to ascribe a trust level to the certificate, which is an indication of the veracity of the identity of the data requester. Individual system users may set differing levels of access to a number of shared system resources for a particular data requester. The authenticated and verified data requester is then provided with the pre-set level of access to the desired shared resource. The level of access to a particular shared system resource therefore depends upon the user the data is being accessed through, the authenticated identity of the data requester, and their ascribed trust level. The shared resource may comprise data and / or an application module that is accessed or executed through a secure symmetric encryption tunnel.
Owner:OVERCOW CORP
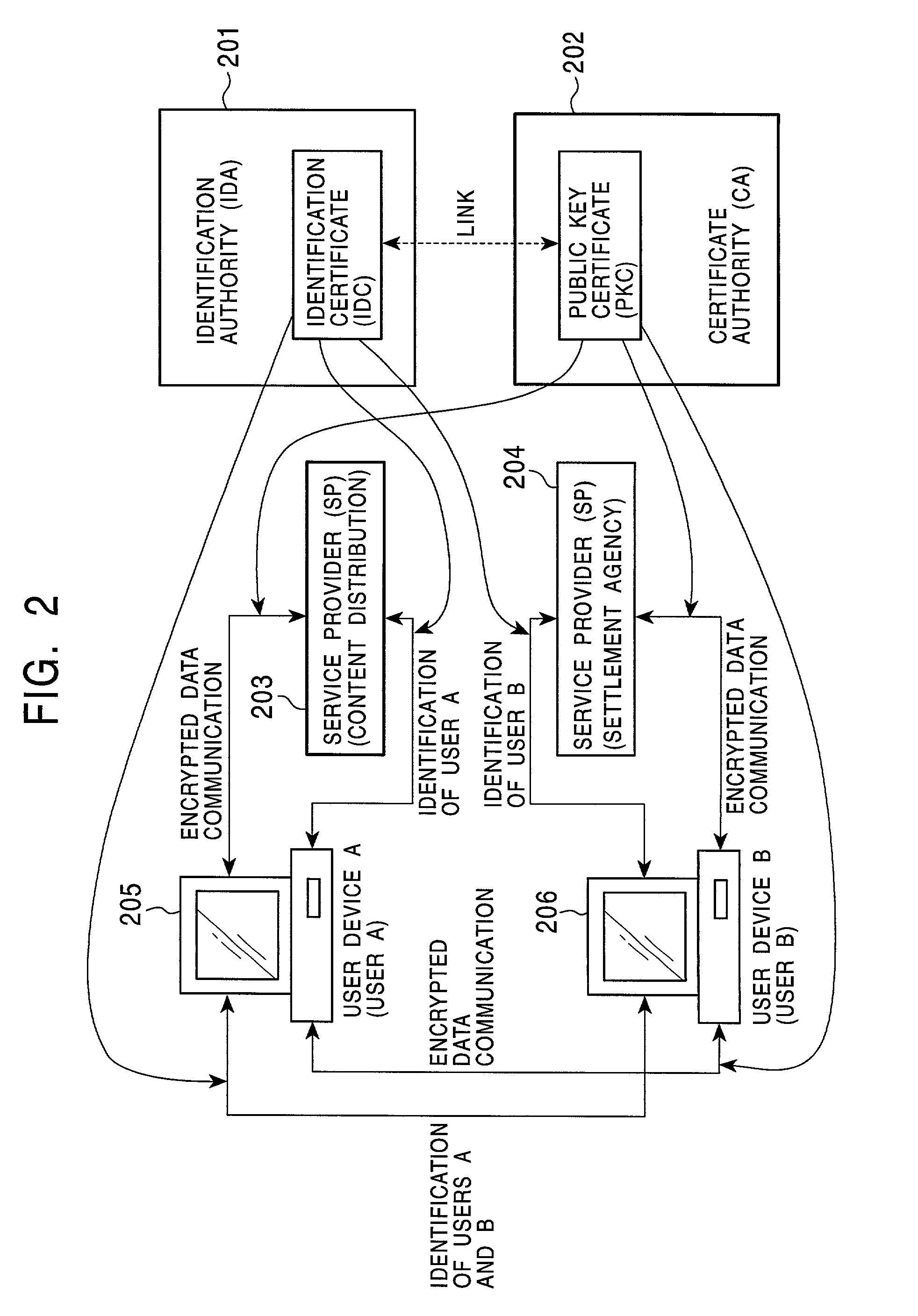
Content distribution system, content distribution method, information processing apparatus, and program providing medium
InactiveUS20050207578A1Improve reliabilityReliable fashionDigital data processing detailsUser identity/authority verificationInformation processingContent distribution
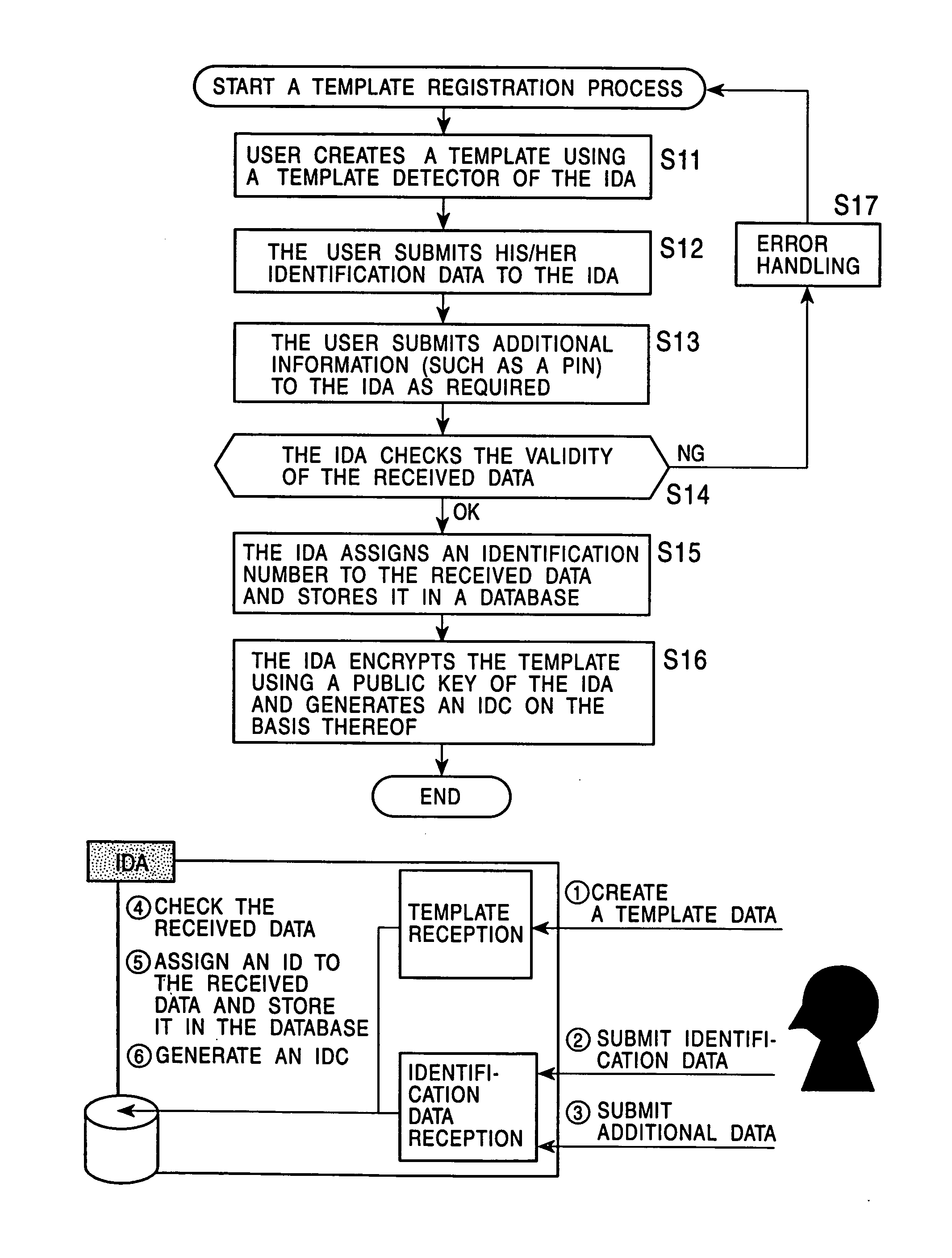
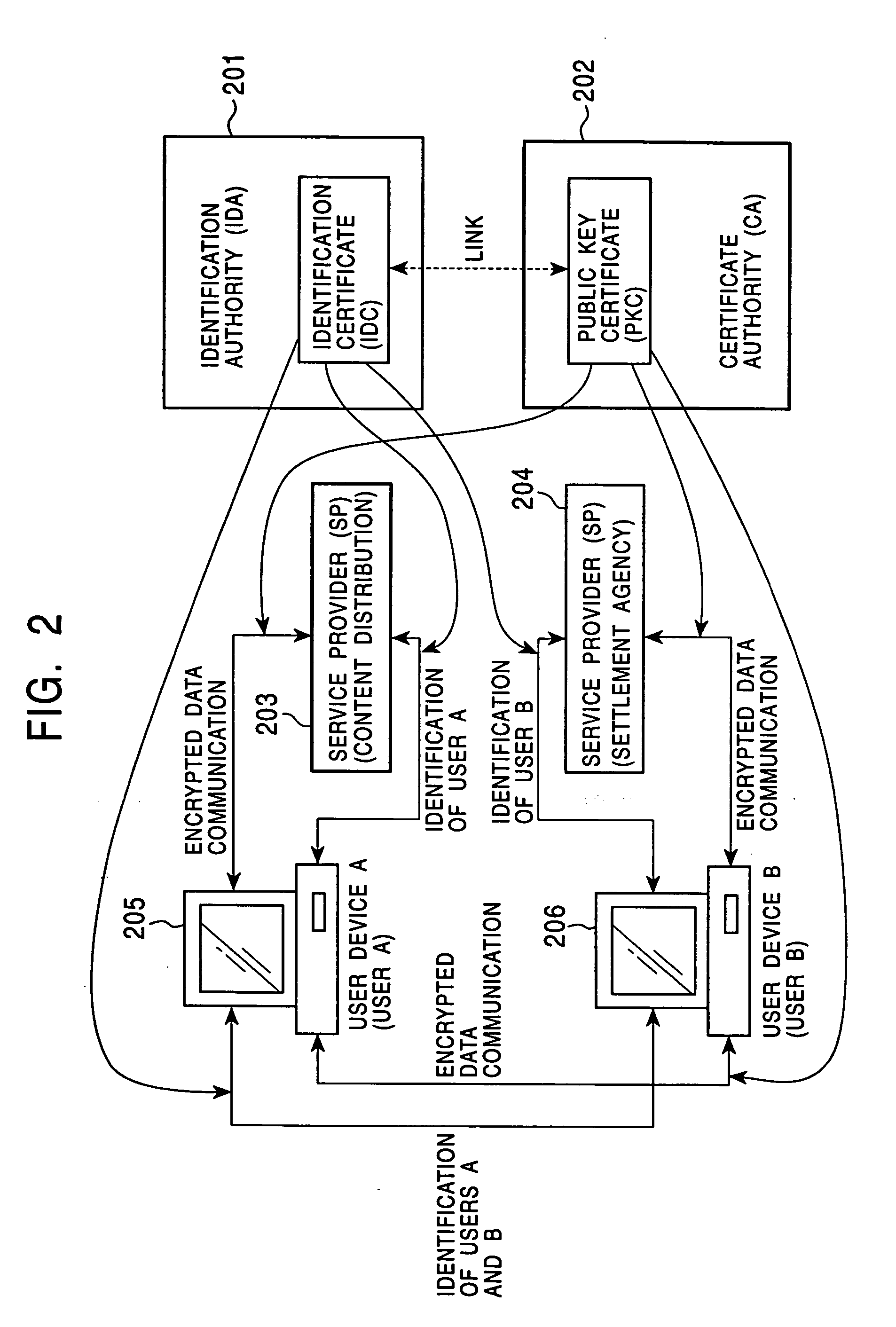
A content distribution is performed by a secure container including a content encrypted by a content key and container information set for a content transaction. The container information includes a person identification certificate identifiers list. Usage control status information including the list is generated and stored in a device during a secondary distribution among user devices after a primary distribution of the content. In the distribution among the user devices, identifying an identification certificate in reference to the list and performing a person authentication based on the identification certificate allows each of the user devices to use the transmitted content, when the authentication is affirmative.
Owner:SONY CORP
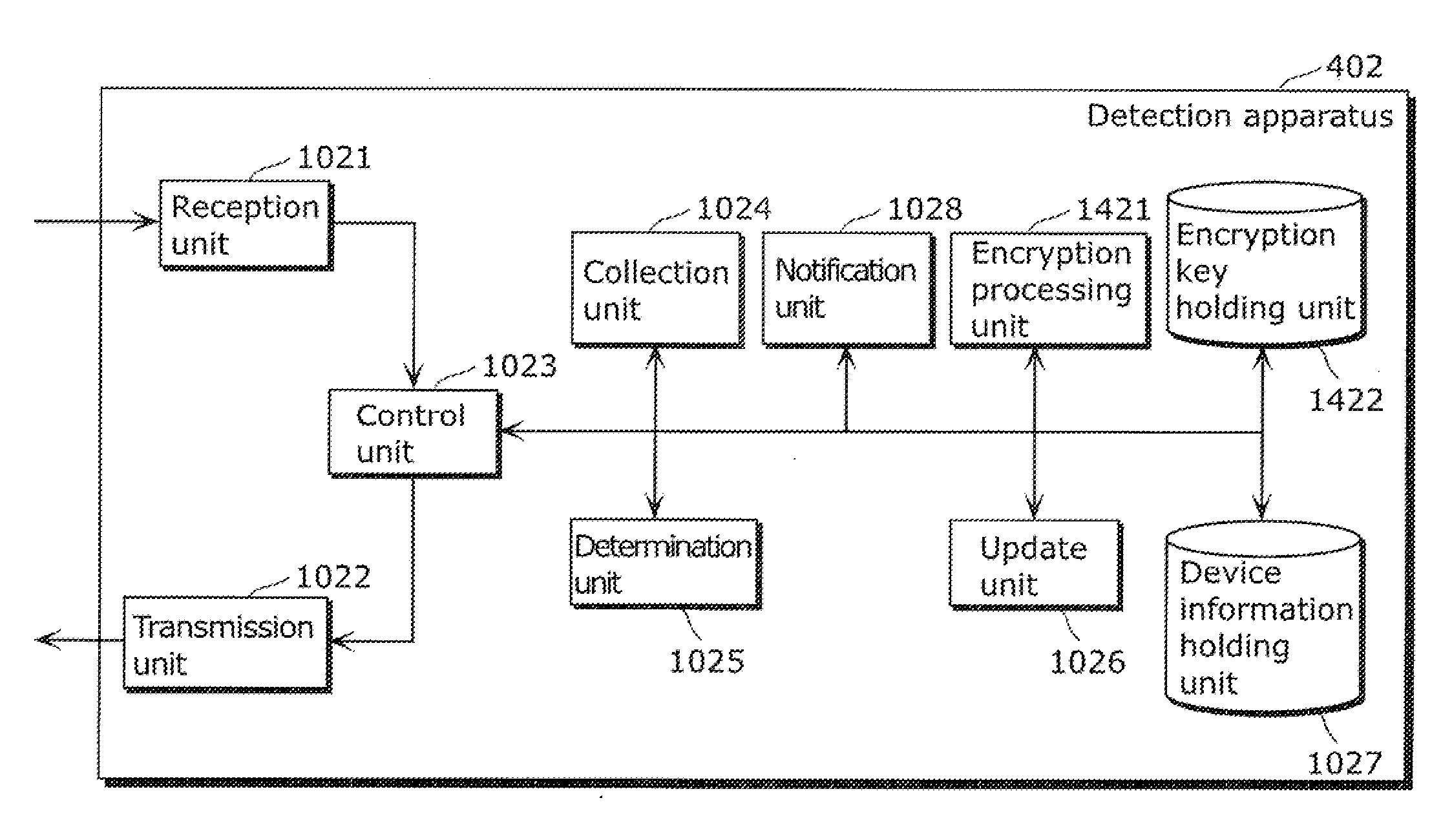
Detection apparatus and detection system
A detection apparatus (102) connected to a device in a residence and an electricity meter (100) indicating an amount of electric power consumed by the device in the residence, the detection apparatus (102) including: a reception unit (1021) which receives the amount of electric power from the electricity meter (100); a collection unit (1024) which collects usage status of the device; a device information holding unit (1027) which holds device information including the usage status of the device and electric power consumption of the device corresponding to the usage status; and a determination unit (1025) which determines whether or not the electricity meter (100) is tampered, by comparing an estimated electric power consumption amount with the amount of electric power received by the reception unit (1021), the estimated electric power consumption amount being estimated from the usage status of the device by using the device information, in which the determination unit (1025) determines that the electricity meter (100) is tampered, when a difference between the estimated electric power consumption amount and the amount of electric power received by the reception unit (1021) is equal to or more than a predetermined threshold.
Owner:PANASONIC INTELLECTUAL PROPERTY MANAGEMENT CO LTD
Mbms acknowledgements on rach
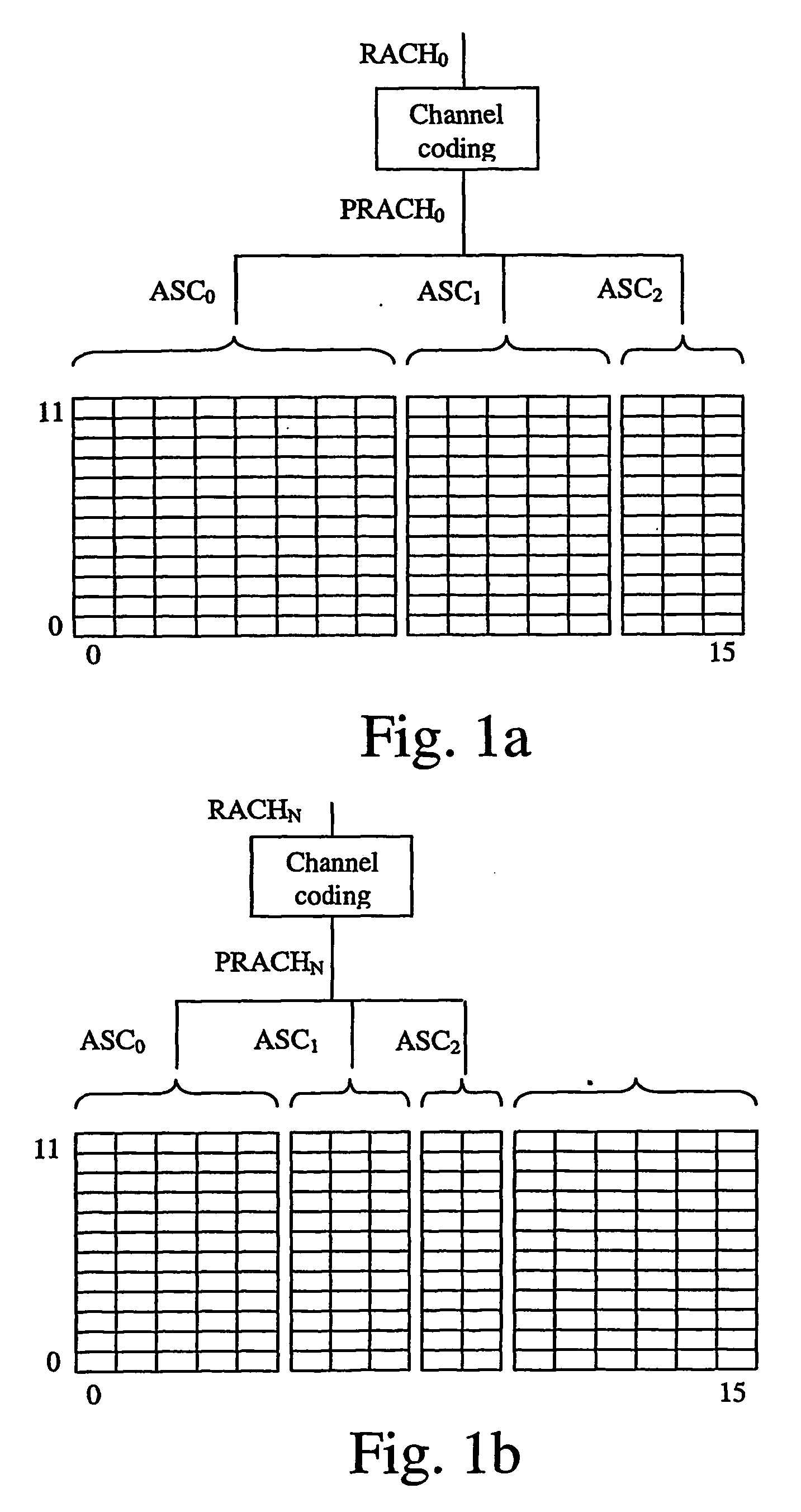
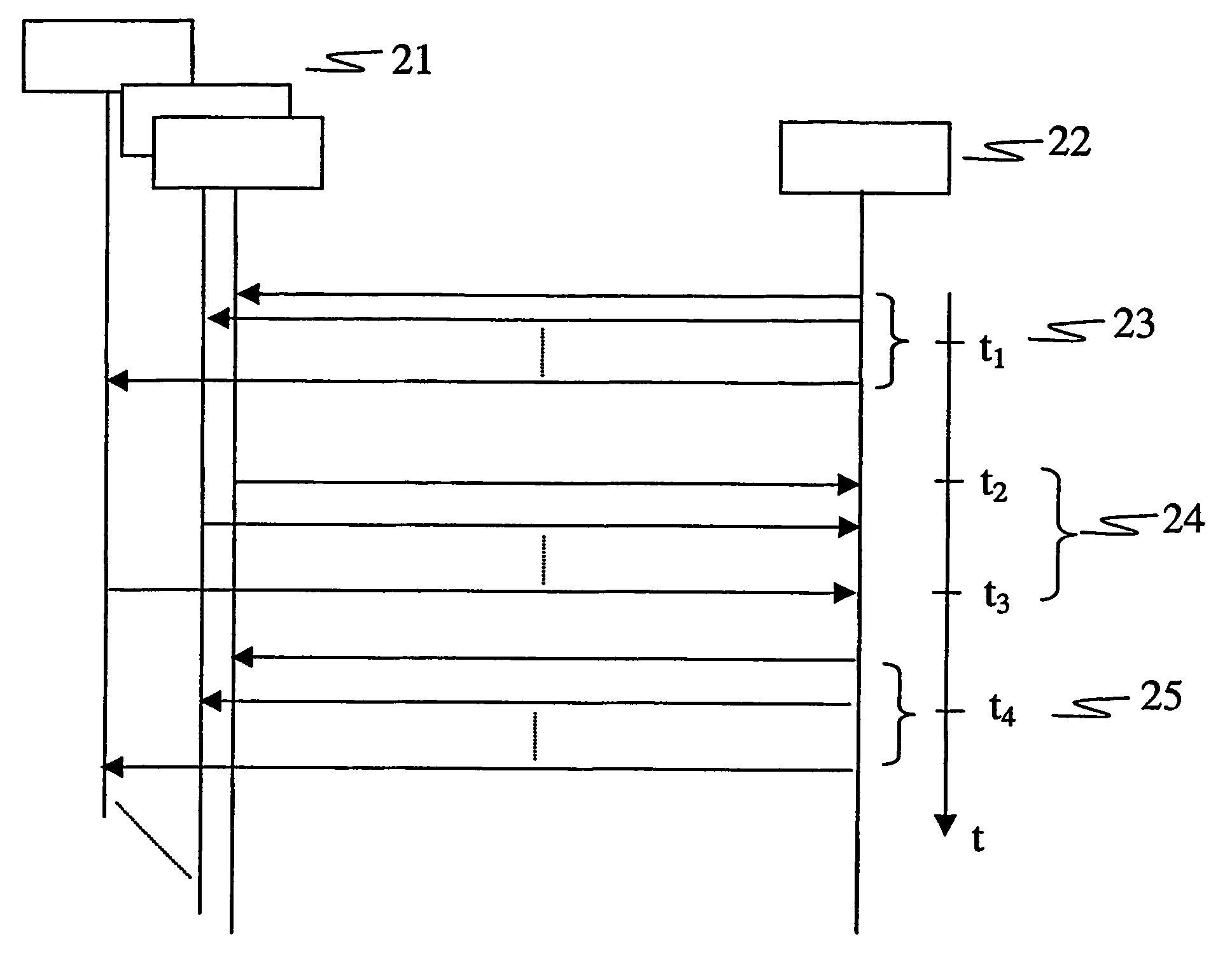
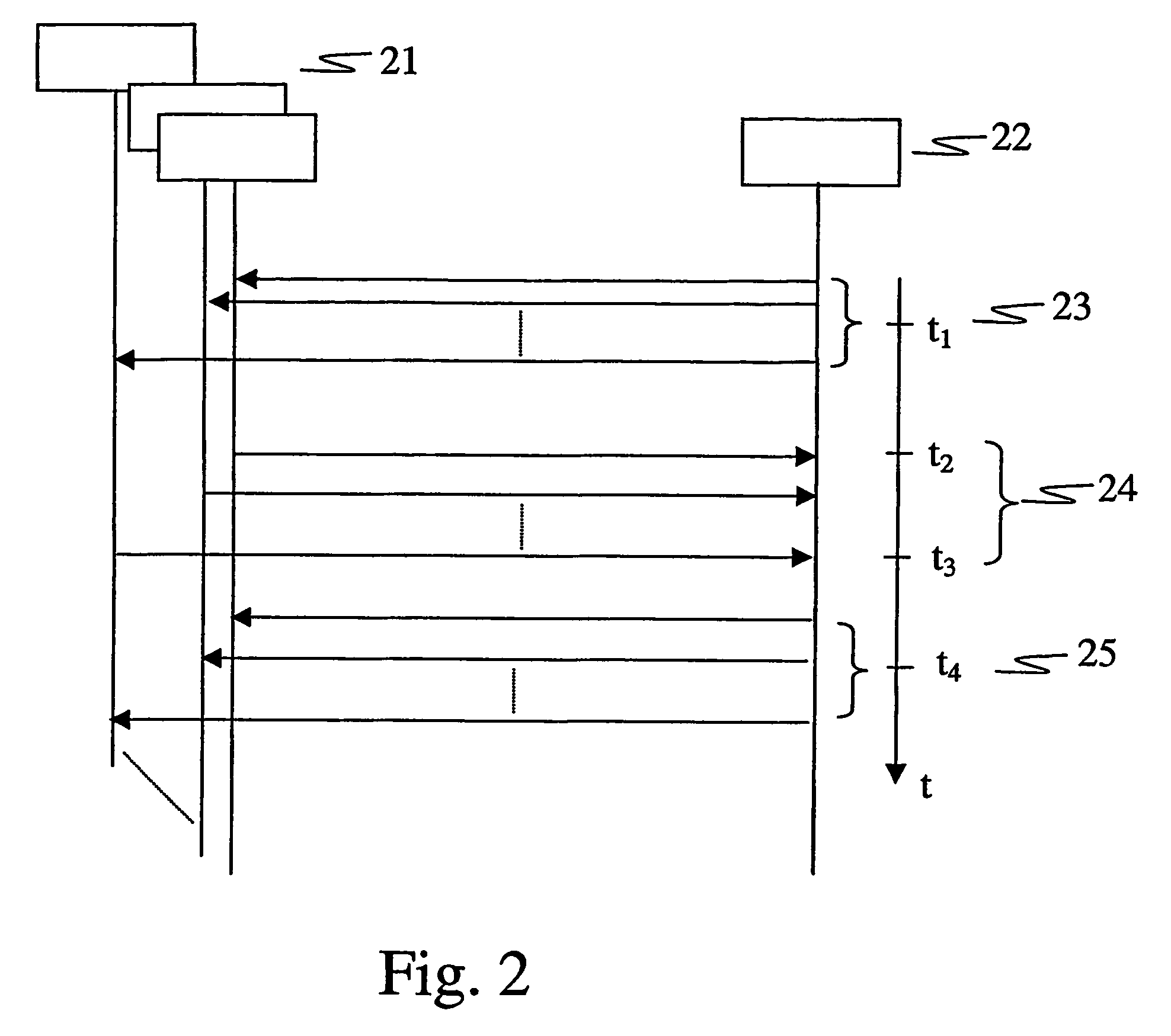
ActiveUS20070071025A1Avoid collisionLimited amountSpecial service provision for substationError prevention/detection by using return channelTelecommunicationsMulticast communication
The present invention relates to multicast communication systems and in particular to the implementation of a random access uplink channel, which can be used, e.g., for transmission of acknowledgement messages for received data. In order to prevent frequent collisions on said channel, the transmission of acknowledgement messages is spread at least over time or, additionally, with regard to another distinguishing channel property, e.g. a RACH sub-channel or RACH-signature.
Owner:TELEFON AB LM ERICSSON (PUBL)
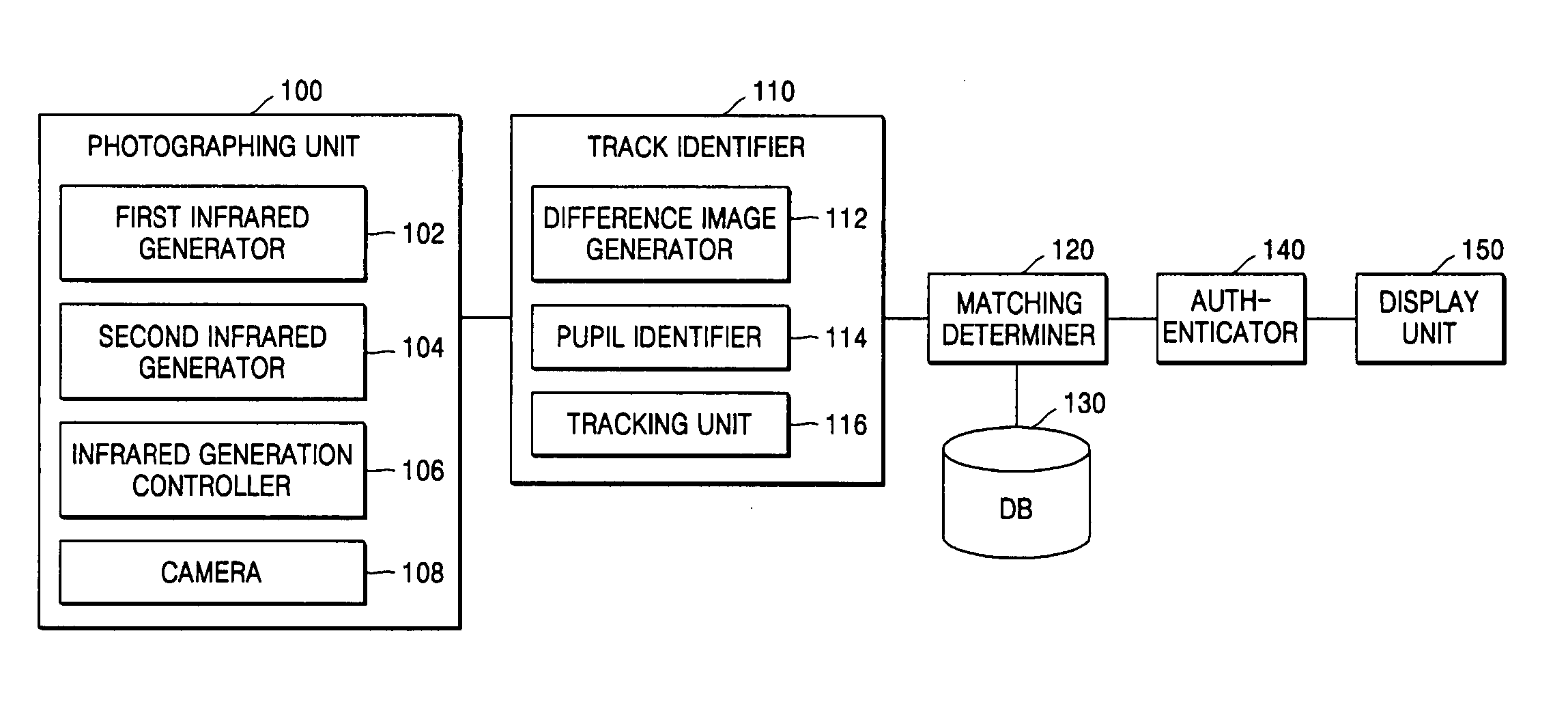
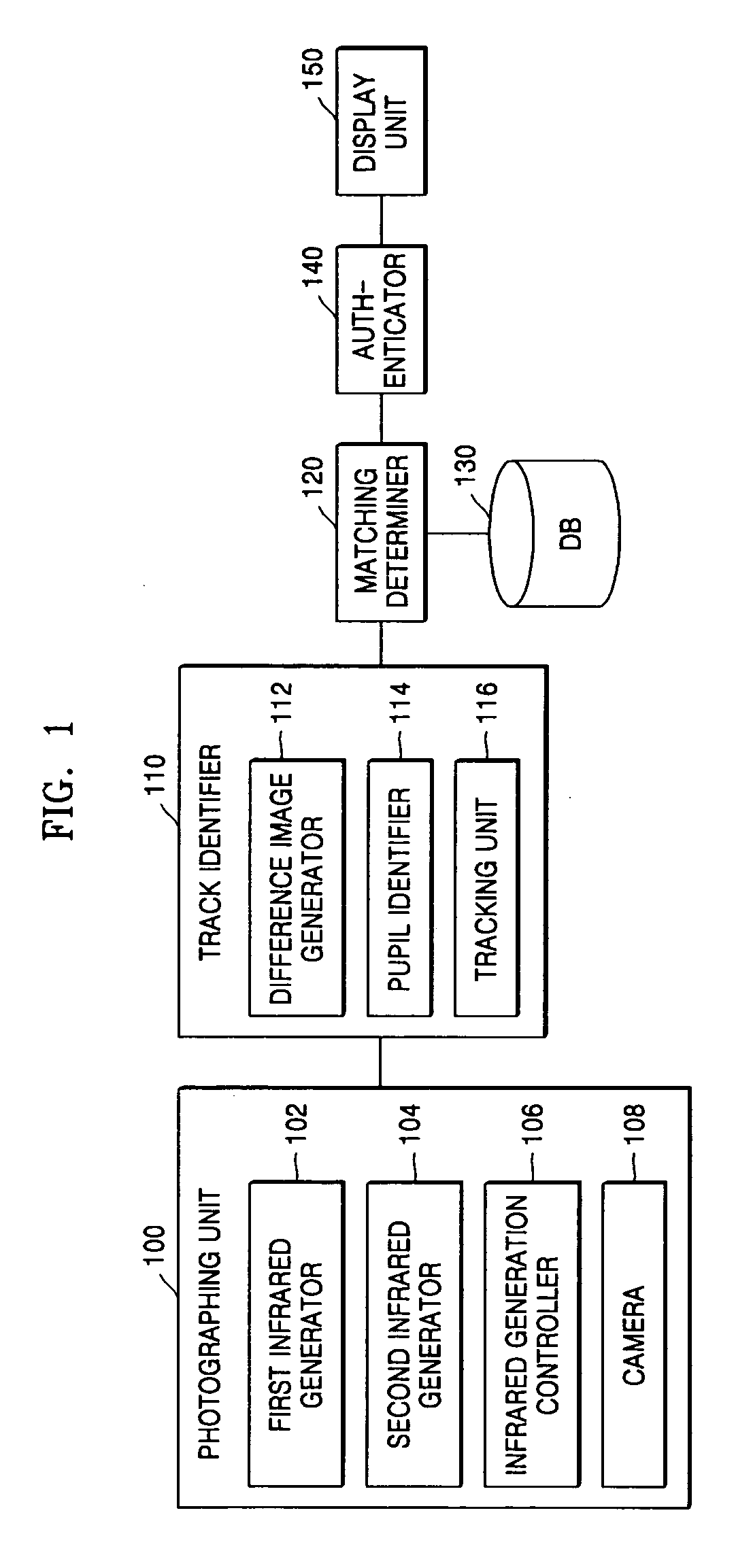
Line-of-sight-based authentication apparatus and method
A line-of-sight-based authentication apparatus and method are provided. In the method, a first image is generated by photographing the eyes of a person using first lighting generated on the same axis as a photographing axis of a camera and a second image is generated by photographing the eyes of the person using second lighting generated on a different axis from the photographing axis. Eye movements are tracked based on the first image and the second image and a track of the eye movements is identified. Then, it is determined if the identified track is the same as a track previously stored for authentication purposes.
Owner:SAMSUNG ELECTRONICS CO LTD
System for securing personal cards
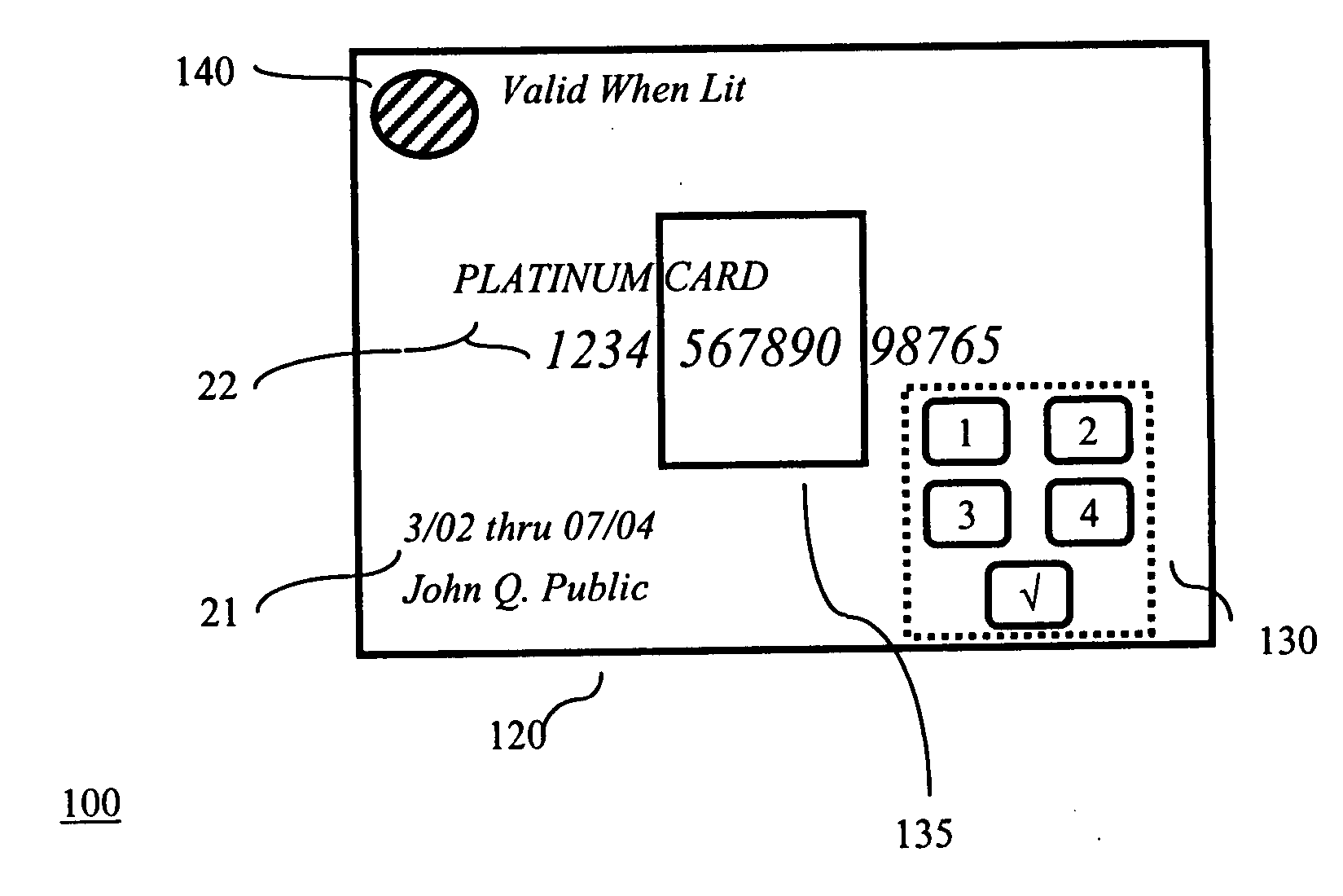
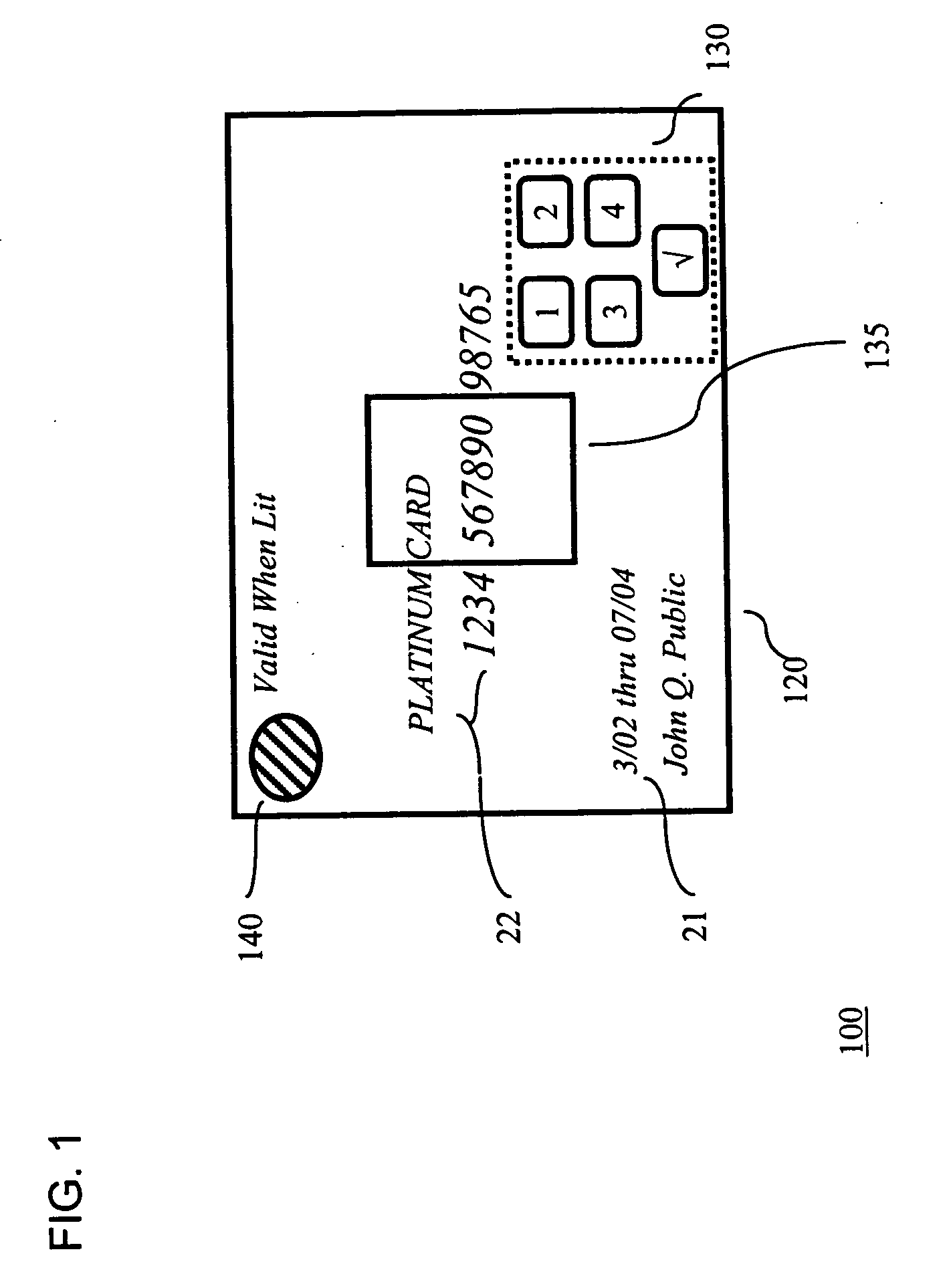
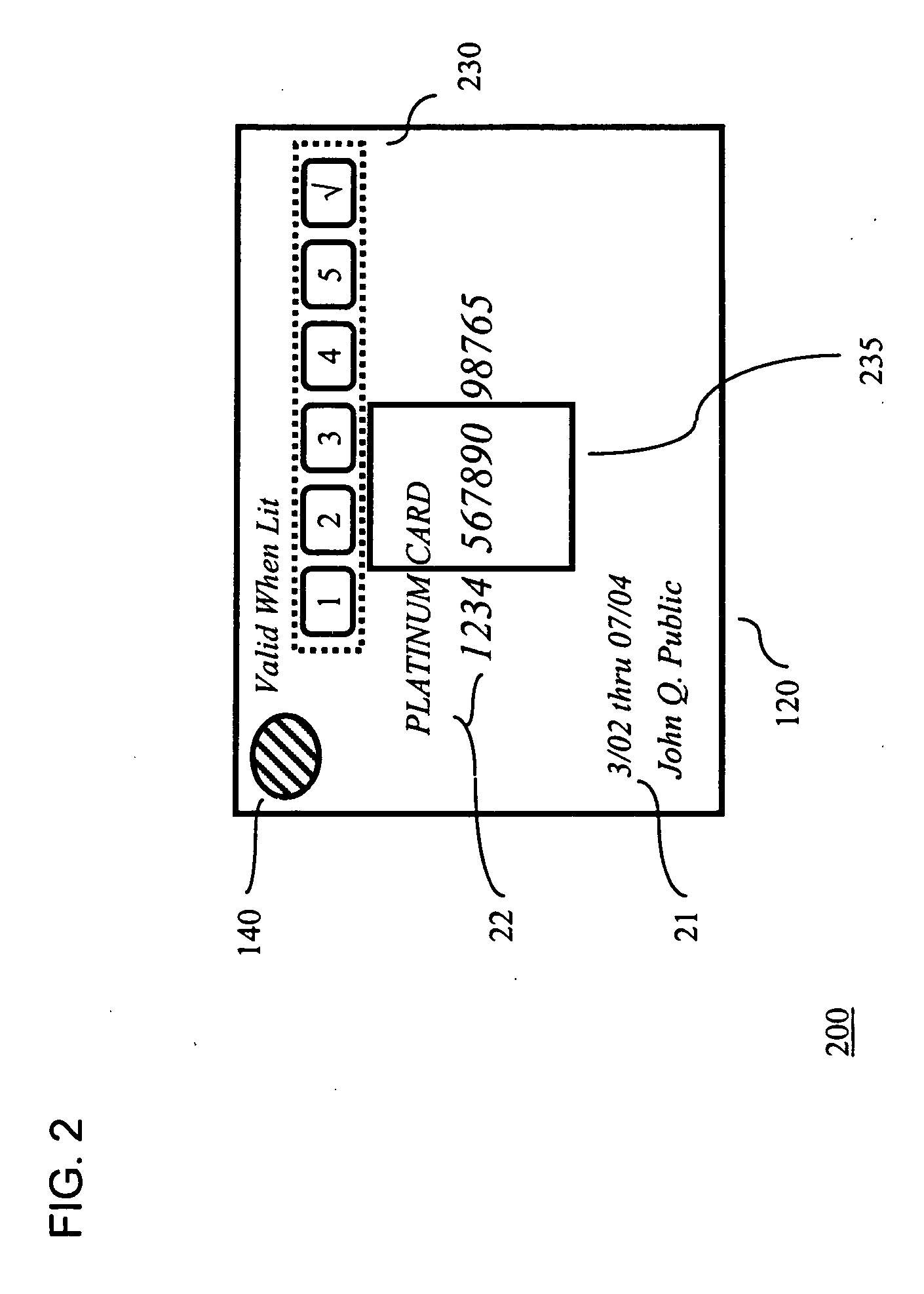
InactiveUS20050211785A1Easy authenticationConvenient verificationSensing record carriersRecord carriers used with machinesCredit cardPersonal identification number
A credit card comprises a plastic layer, a processor, and a keypad. The keypad provides the ability to input a code (e.g., a personal identification number (PIN) code) to the processor as a part of validating the transaction. Illustratively, the entry of a valid PIN code may cause the processor to trigger an alerting device as an indicator to the merchant that the holder of the credit card is authorized for its use.
Owner:T INK INC
Content distribution system, content distribution method, information processing apparatus, and program providing medium
InactiveUS7484246B2Reliable fashionWarranty periodDigital data processing detailsUser identity/authority verificationInformation processingUser device
A content distribution is performed by a secure container including a content encrypted by a content key and container information set for a content transaction. The container information includes a person identification certificate identifiers list. Usage control status information including the list is generated and stored in a device during a secondary distribution among user devices after a primary distribution of the content. In the distribution among the user devices, identifying an identification certificate in reference to the list and performing a person authentication based on the identification certificate allows each of the user devices to use the transmitted content, when the authentication is affirmative.
Owner:SONY CORP
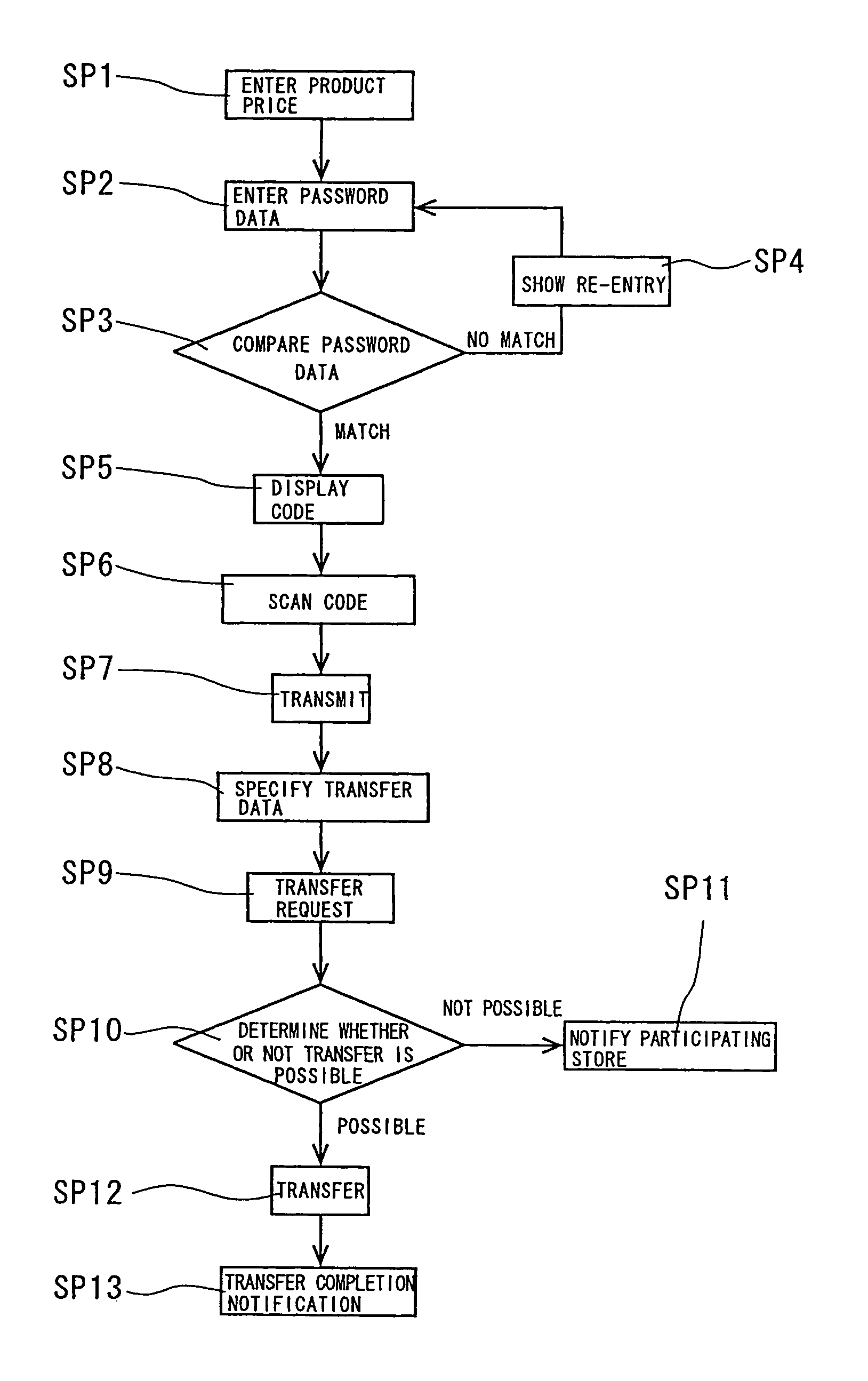
Mobile telephone
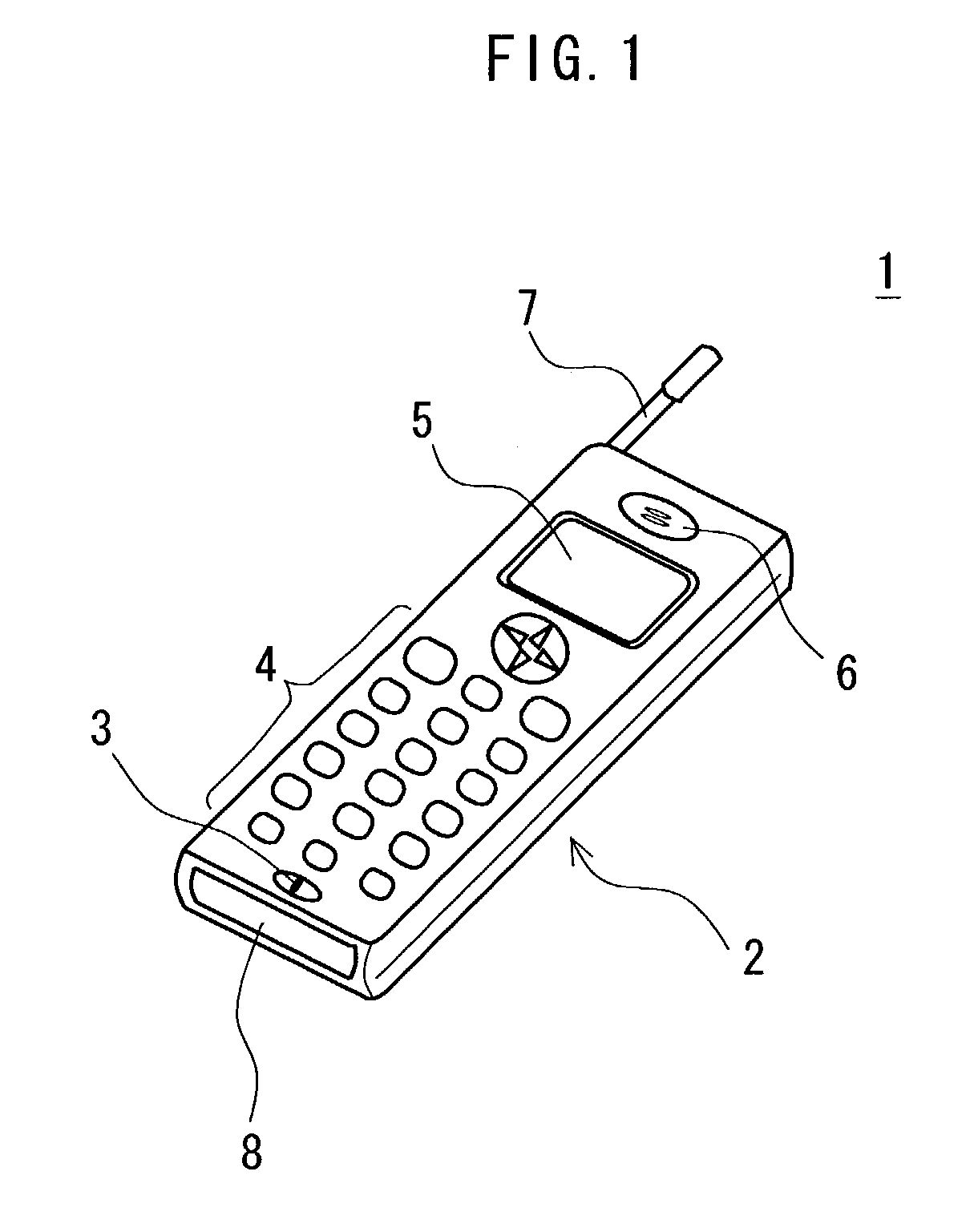
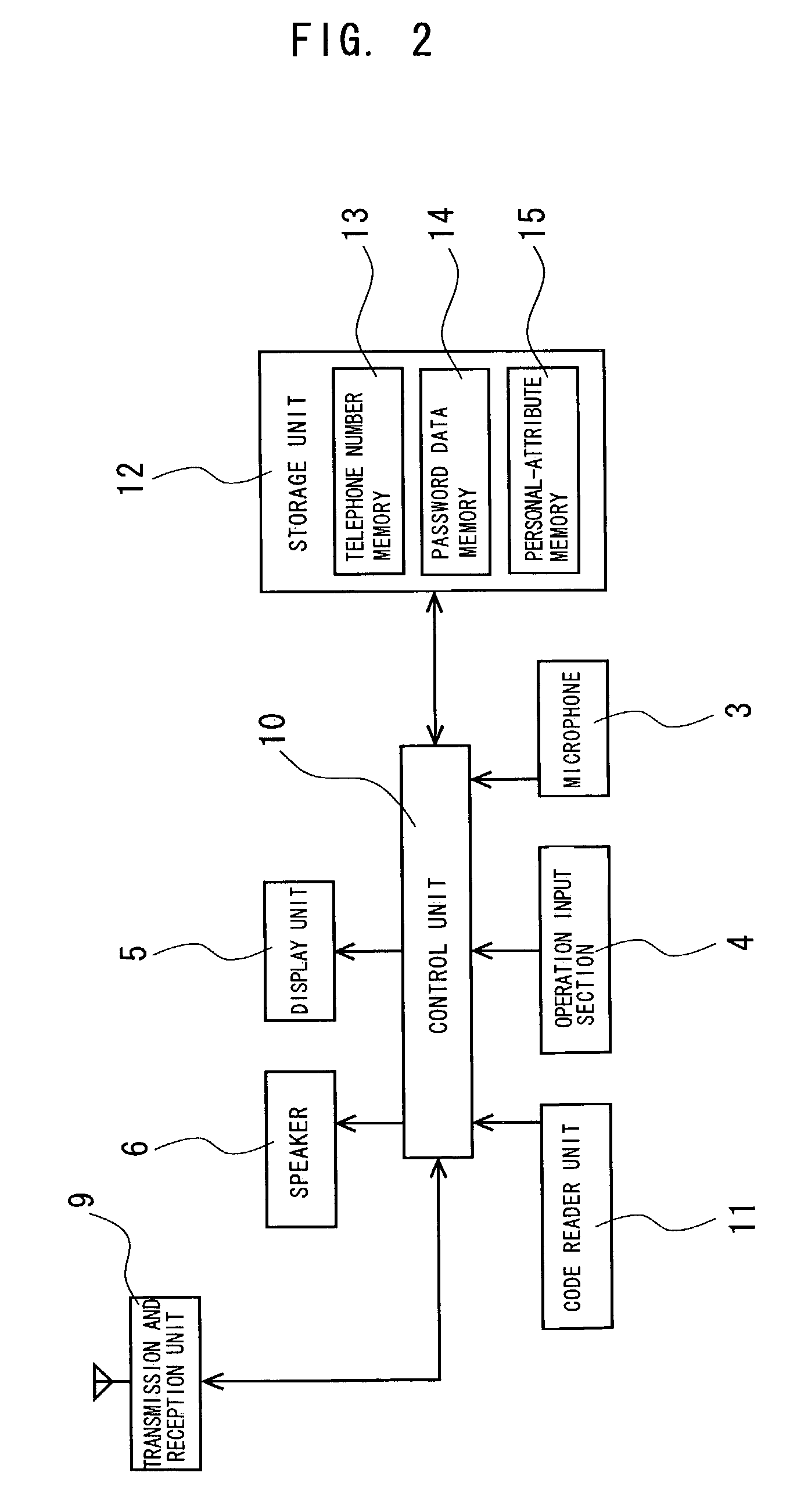
InactiveUS7363252B2Prevent fraudulent useFraudulent use of the mobile telephone apparatus can be preventedFinanceNetwork traffic/resource managementPasswordData memory
A portable telephone including a transmission and reception unit, a control unit, a speaker, a display unit, a code reader unit, an operation input section, a microphone and a storage unit. The storage unit includes a telephone number memory, a password-data memory, and a personal-attribute memory. A buyer scans a code, in which product information is encoded, using the code reader unit, and enters password data via the operation input section. The control unit performs a comparison of the entered password data and password data previously stored in the password-data memory. After the comparison, the transmission and reception unit transmits via an antenna the product information, the telephone number stored in the telephone number memory, and personal-attribute data stored in the personal-attribute memory to a mobile telephone company. The transmitted information is used in settlement of the sales amount.
Owner:FUJIMOTO TAKASHI
Recording system, playback system, key distribution server, recording device, recording medium device, playback device, recording method, and playback method
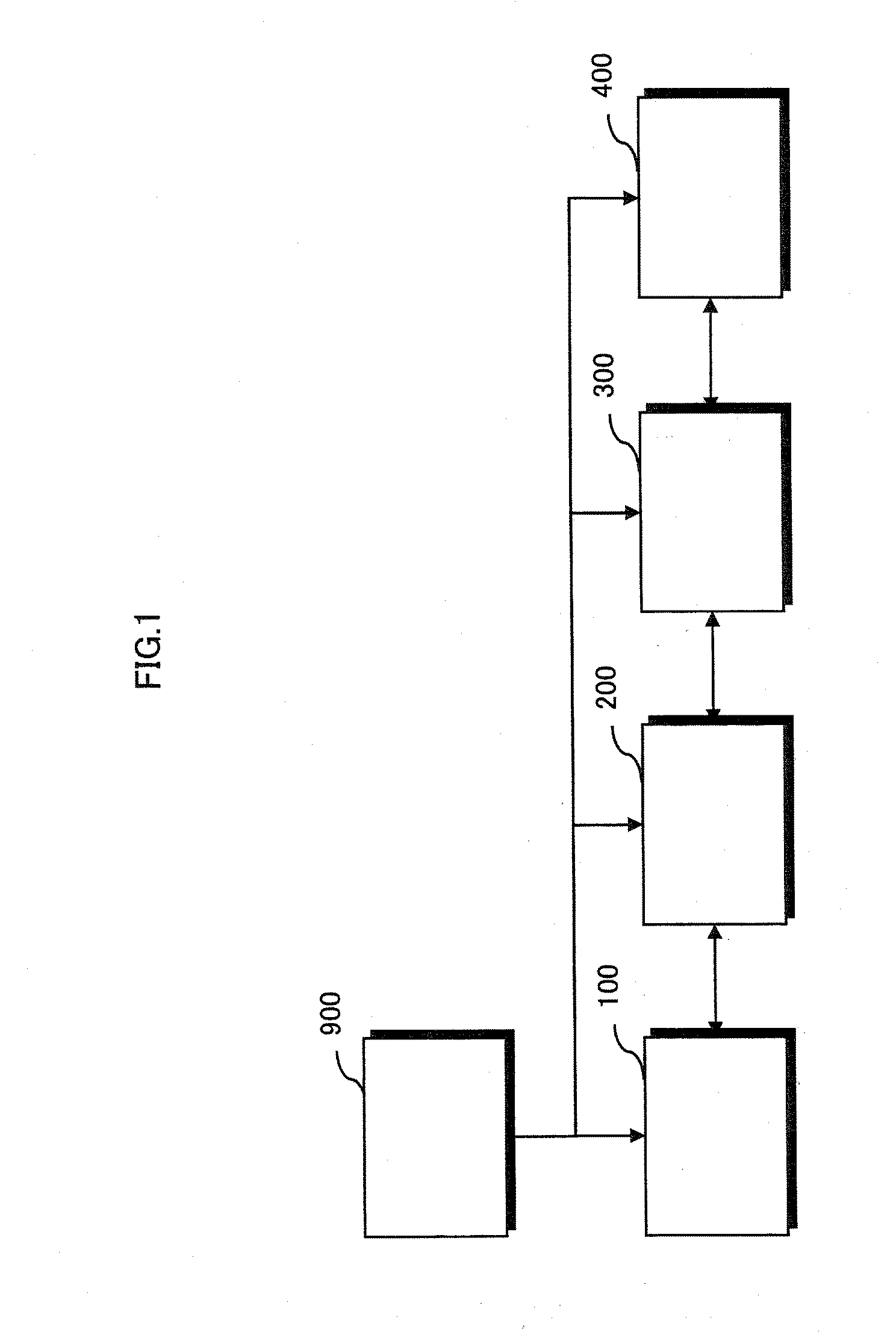
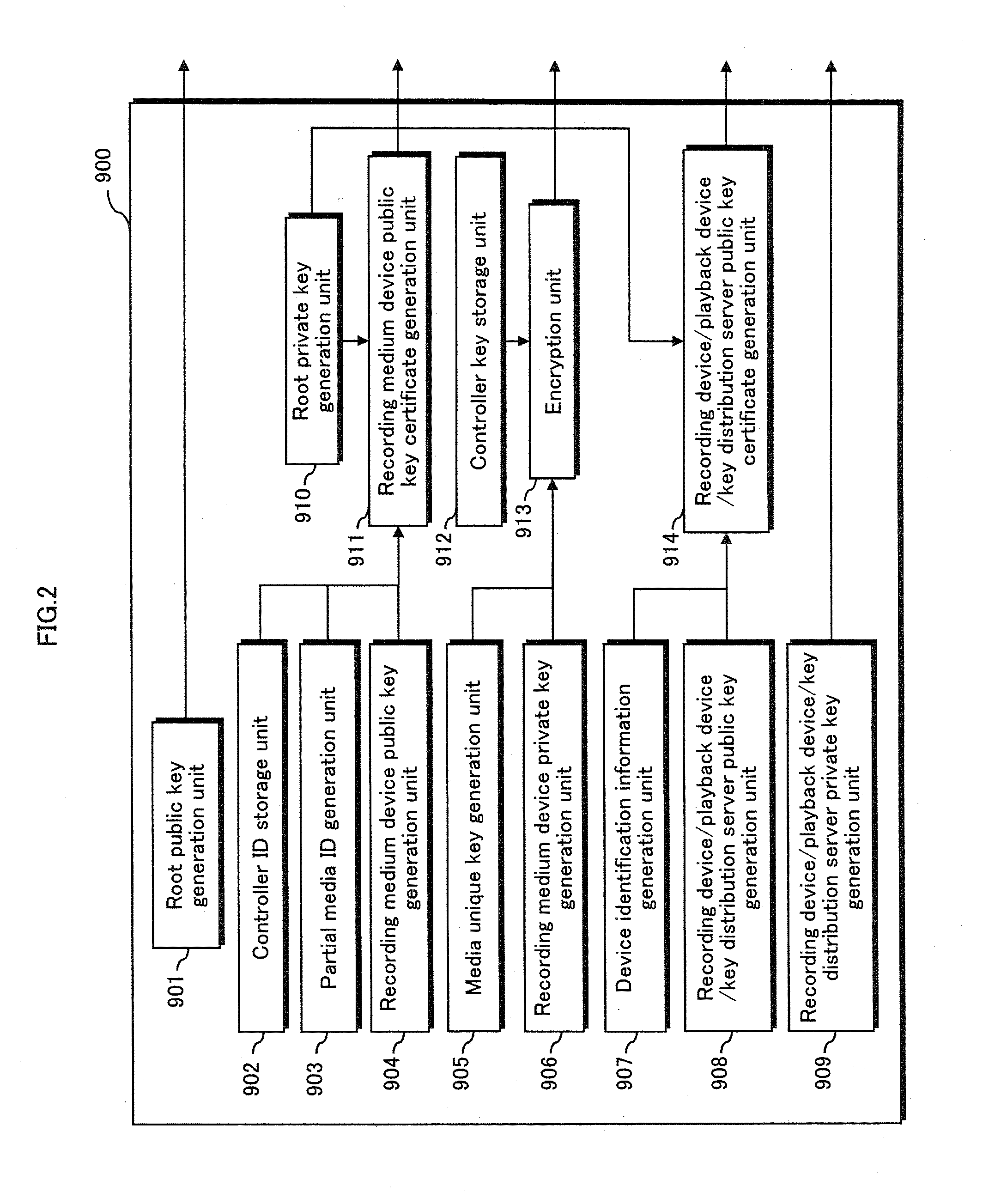
InactiveUS20110222691A1Prevent fraudulent useKey distribution for secure communicationDigital data protectionComputer hardwareDigital content
To protect rights of a copyright owner of digital content, technology is required to prevent digital content on a recording medium from being copied onto another recording medium and played back. A key distribution server securely receives a media unique key from a recording medium device, generates a first title key different for each content, encrypts the generated first title key with the media unique key, encrypts the content with the first title key, and transmits the encrypted first title key to the recording medium device and the encrypted content to the recording device. The recording device securely receives the encrypted content from the key distribution server and the first title key and a second title key from the recording medium device, decrypts the encrypted content with the first title key, encrypts the decrypted content with the second title key, and transmits the encrypted content to the recording medium device.
Owner:PANASONIC CORP
MBMS acknowledgements on RACH
ActiveUS7876771B2Avoid collisionLimited amountSpecial service provision for substationError prevention/detection by using return channelCommunications systemMulticast communication
The present invention relates to multicast communication systems and in particular to the implementation of a random access uplink channel, which can be used, e.g., for transmission of acknowledgement messages for received data. In order to prevent frequent collisions on said channel, the transmission of acknowledgement messages is spread at least over time or, additionally, with regard to another distinguishing channel property, e.g. a RACH sub-channel or RACH-signature.
Owner:TELEFON AB LM ERICSSON (PUBL)
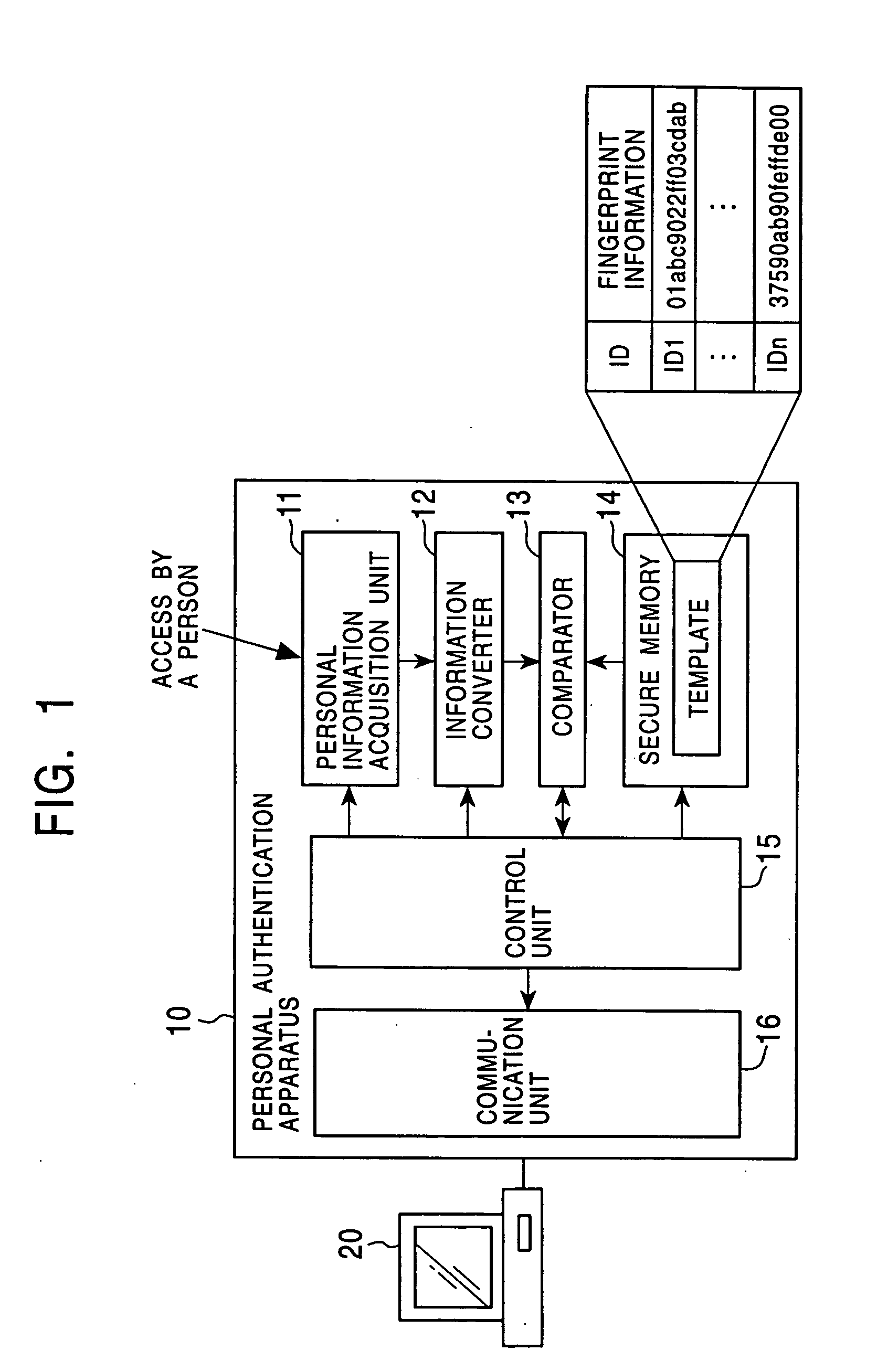
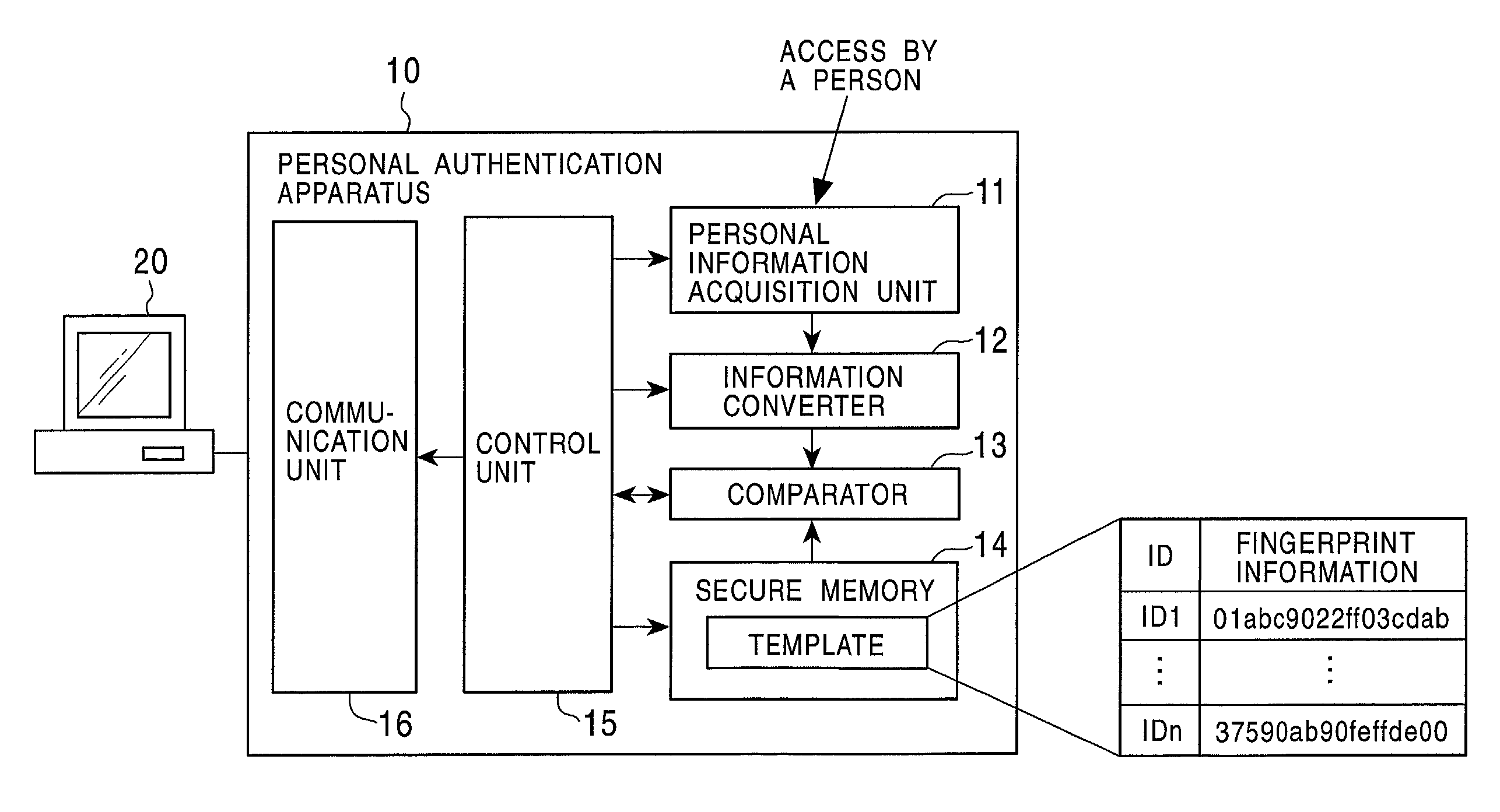
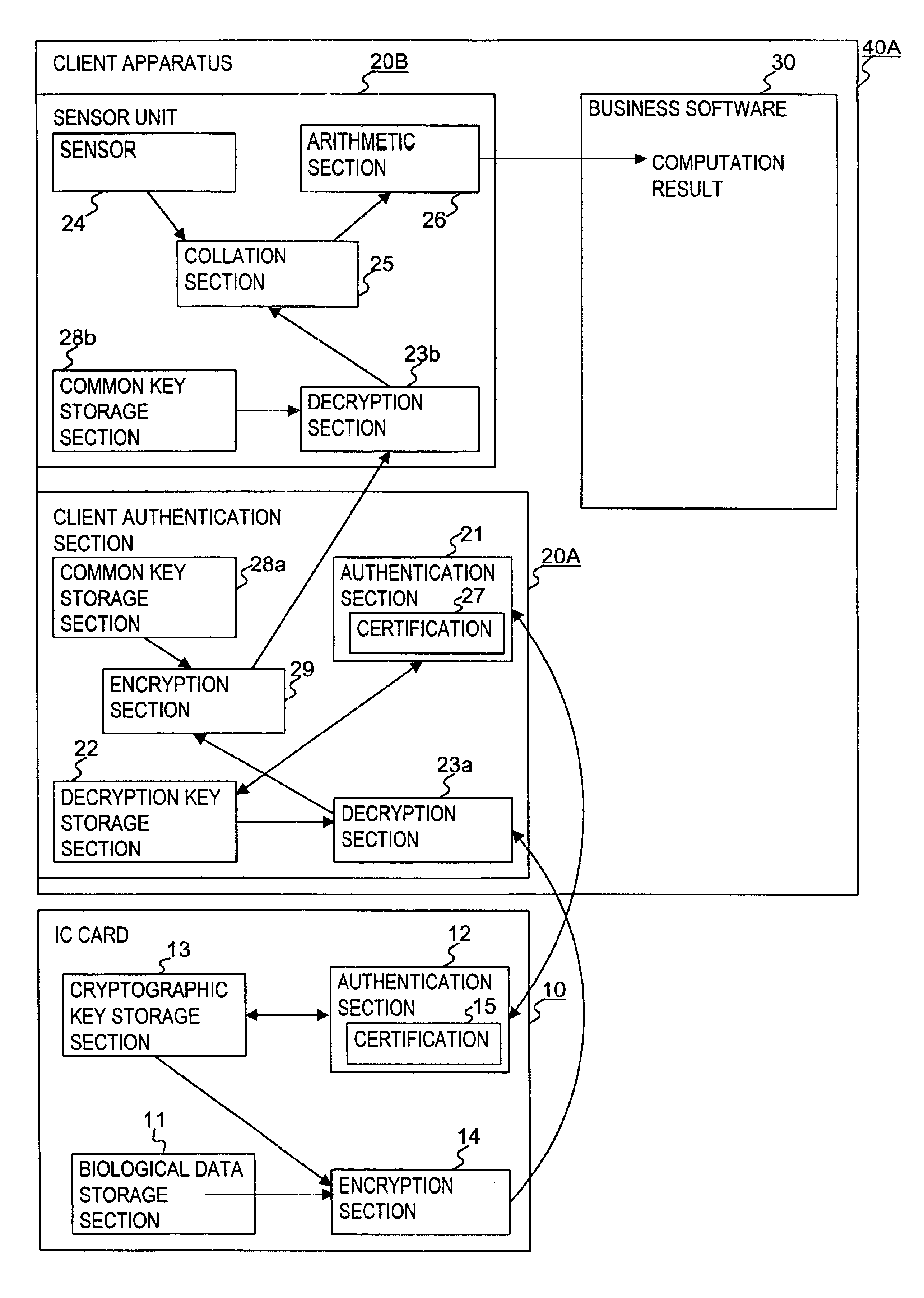
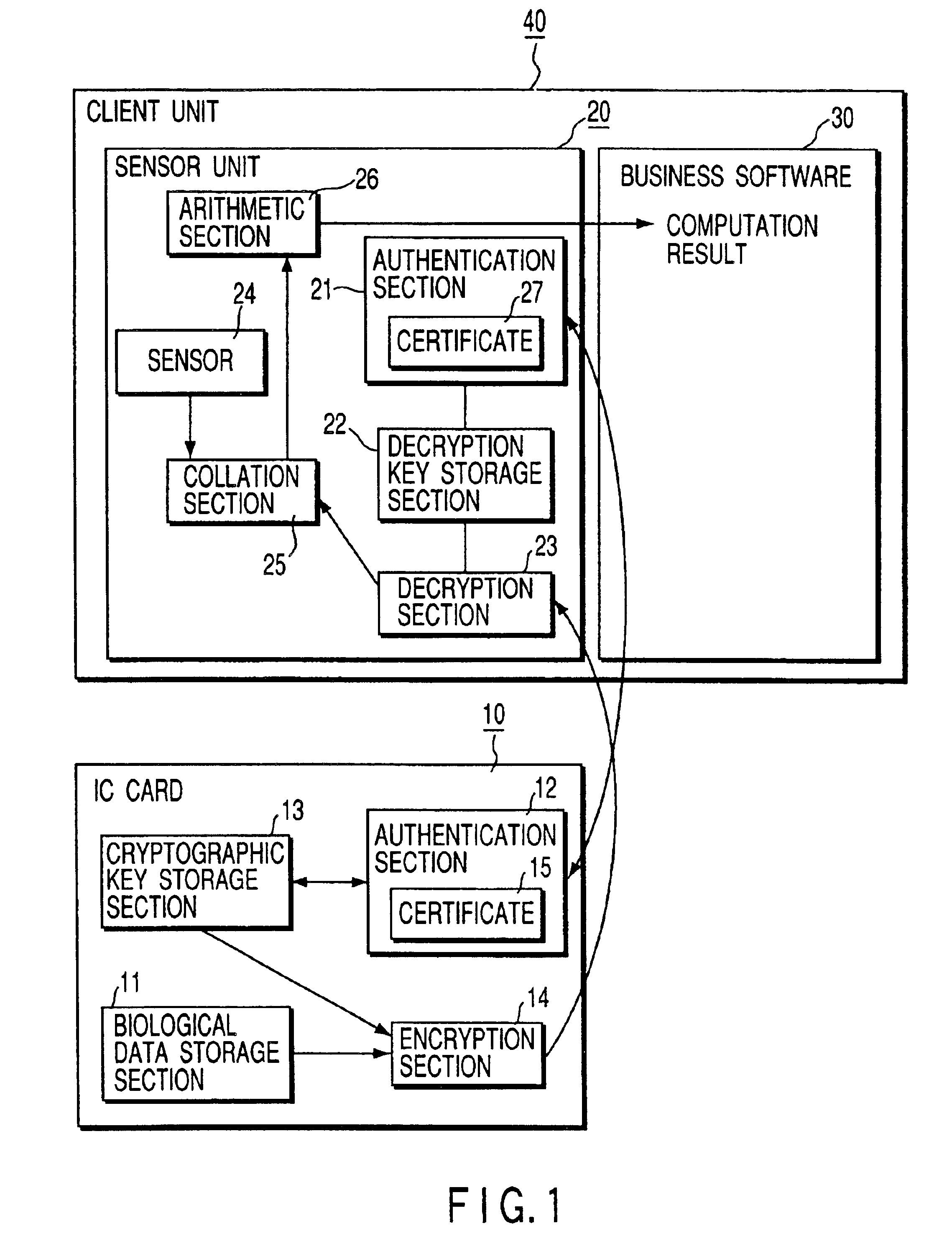
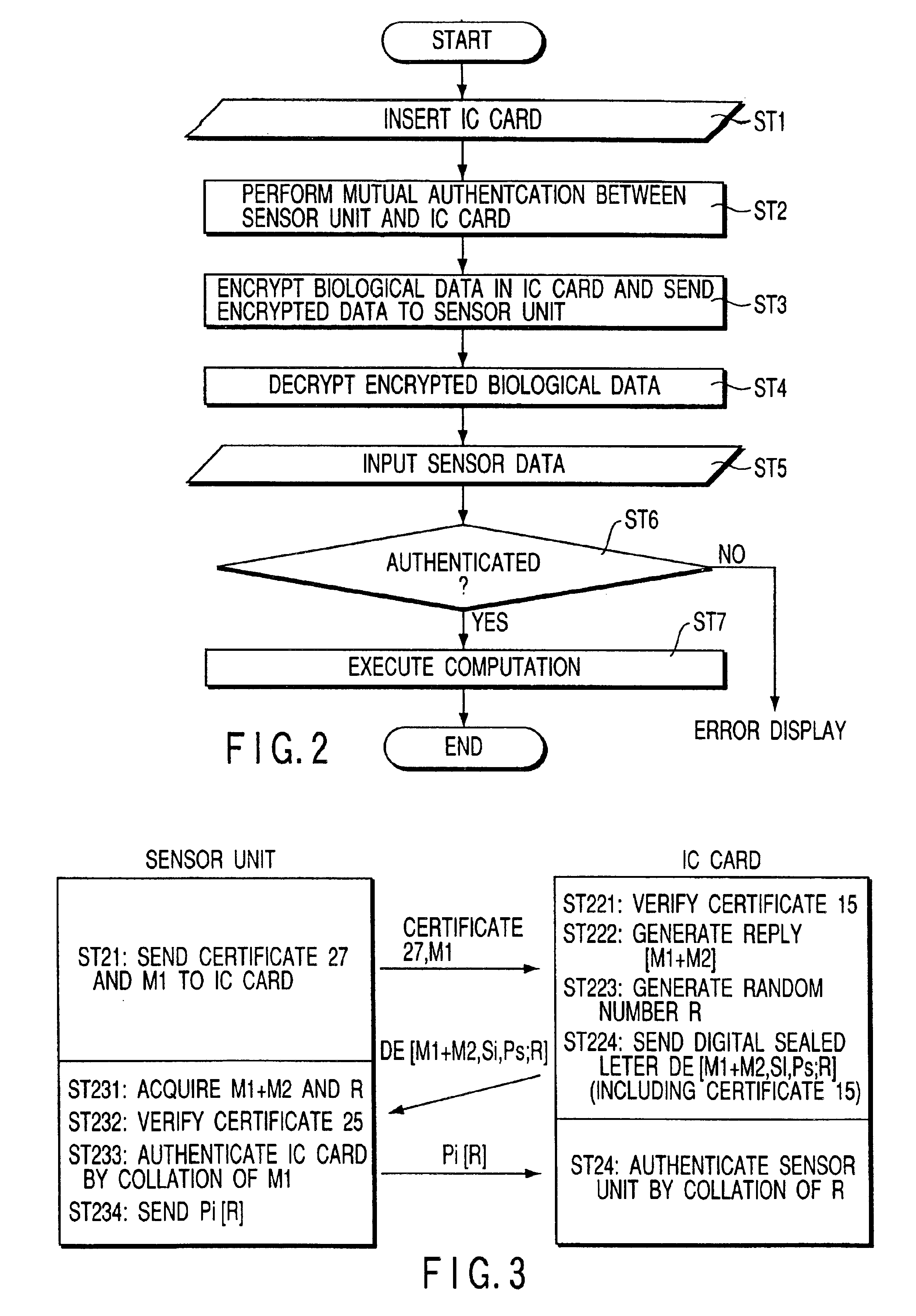
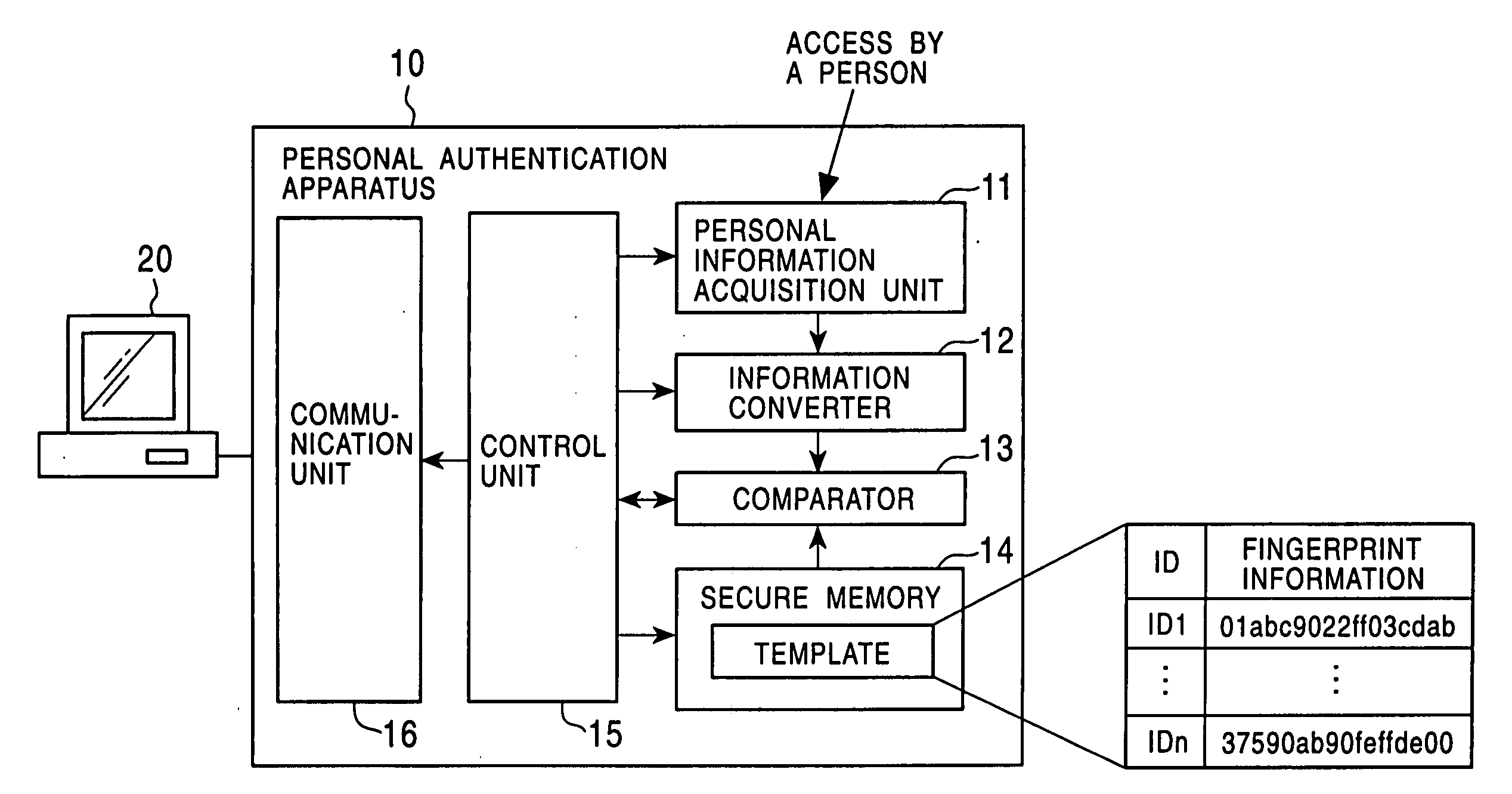
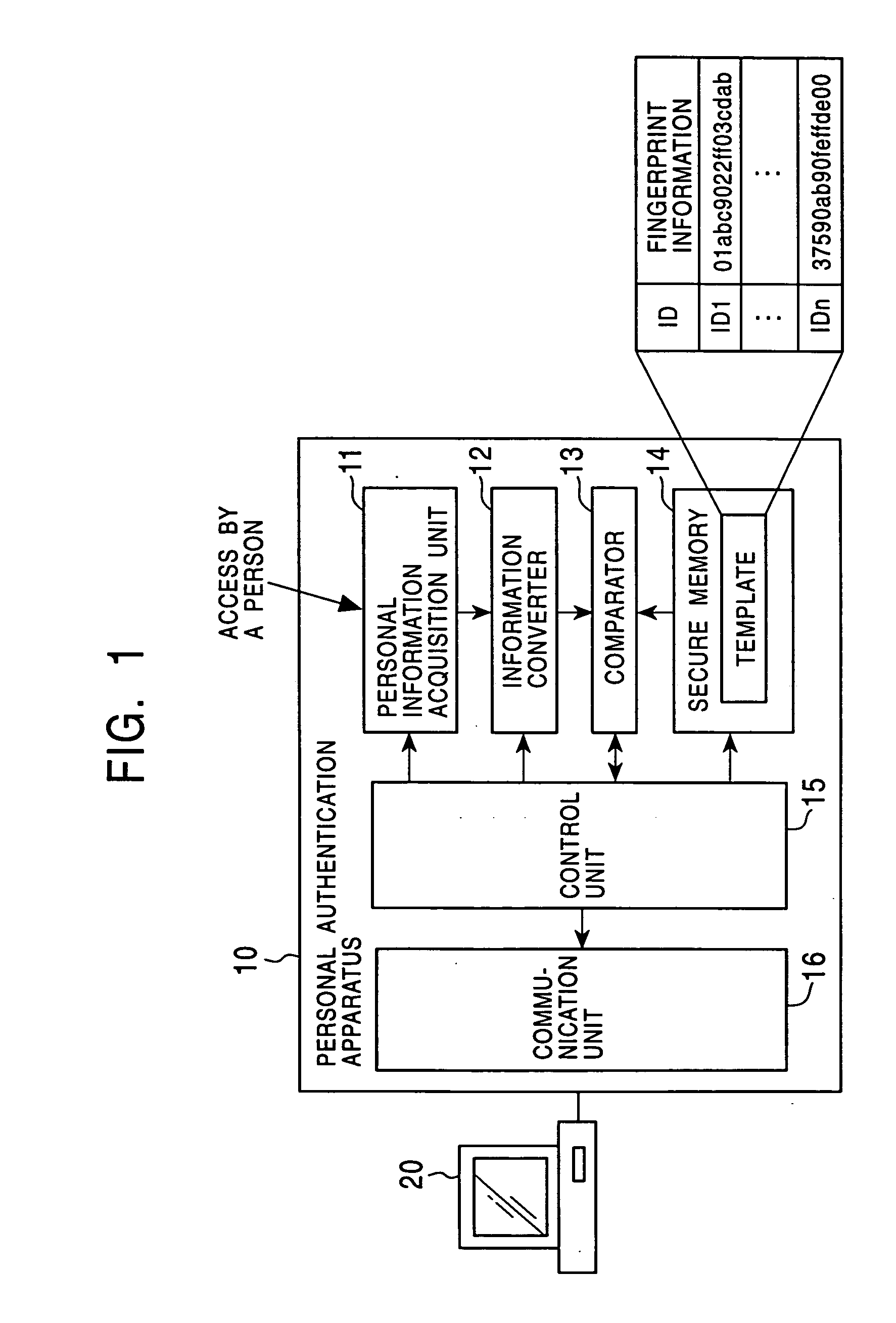
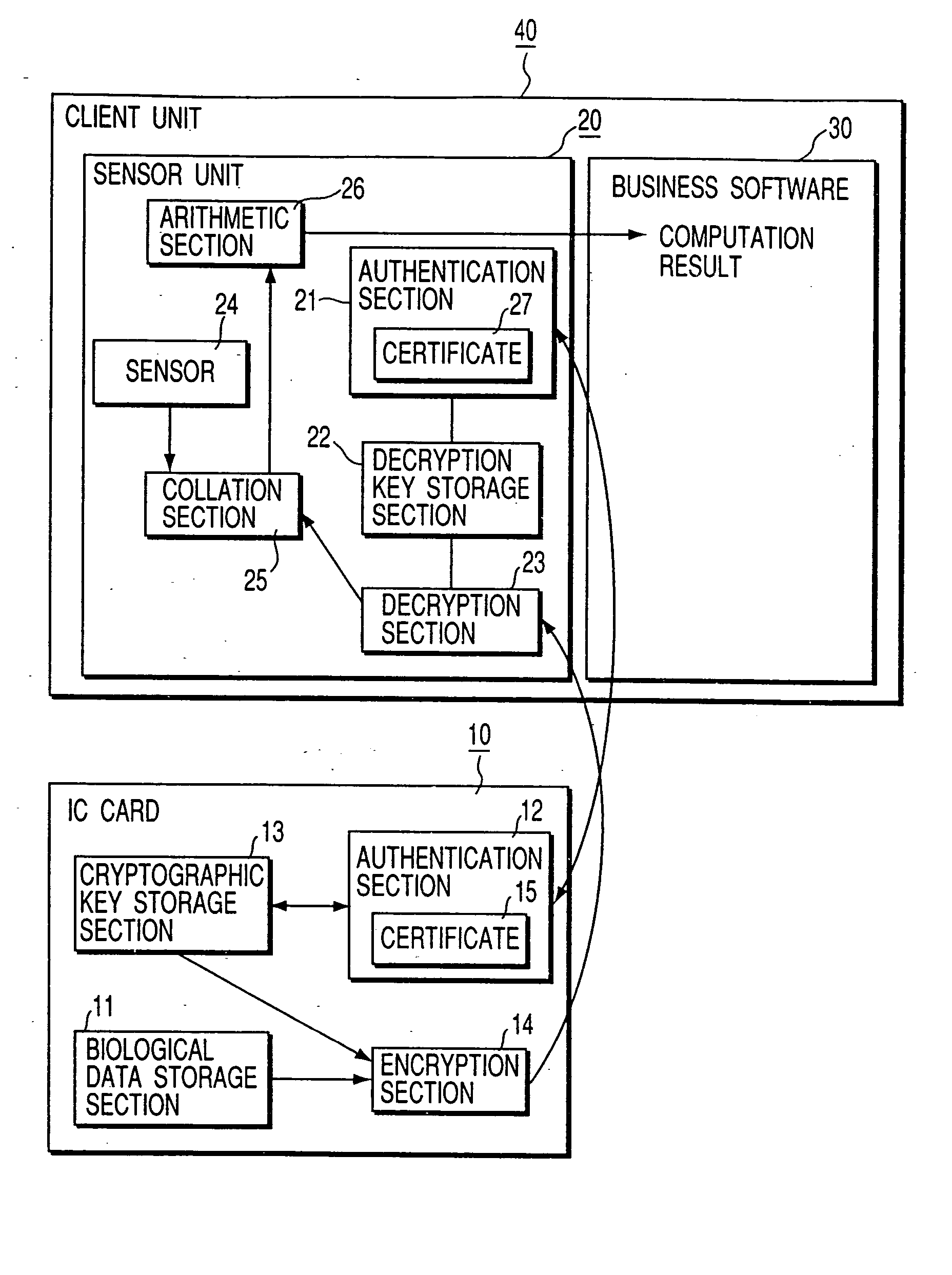
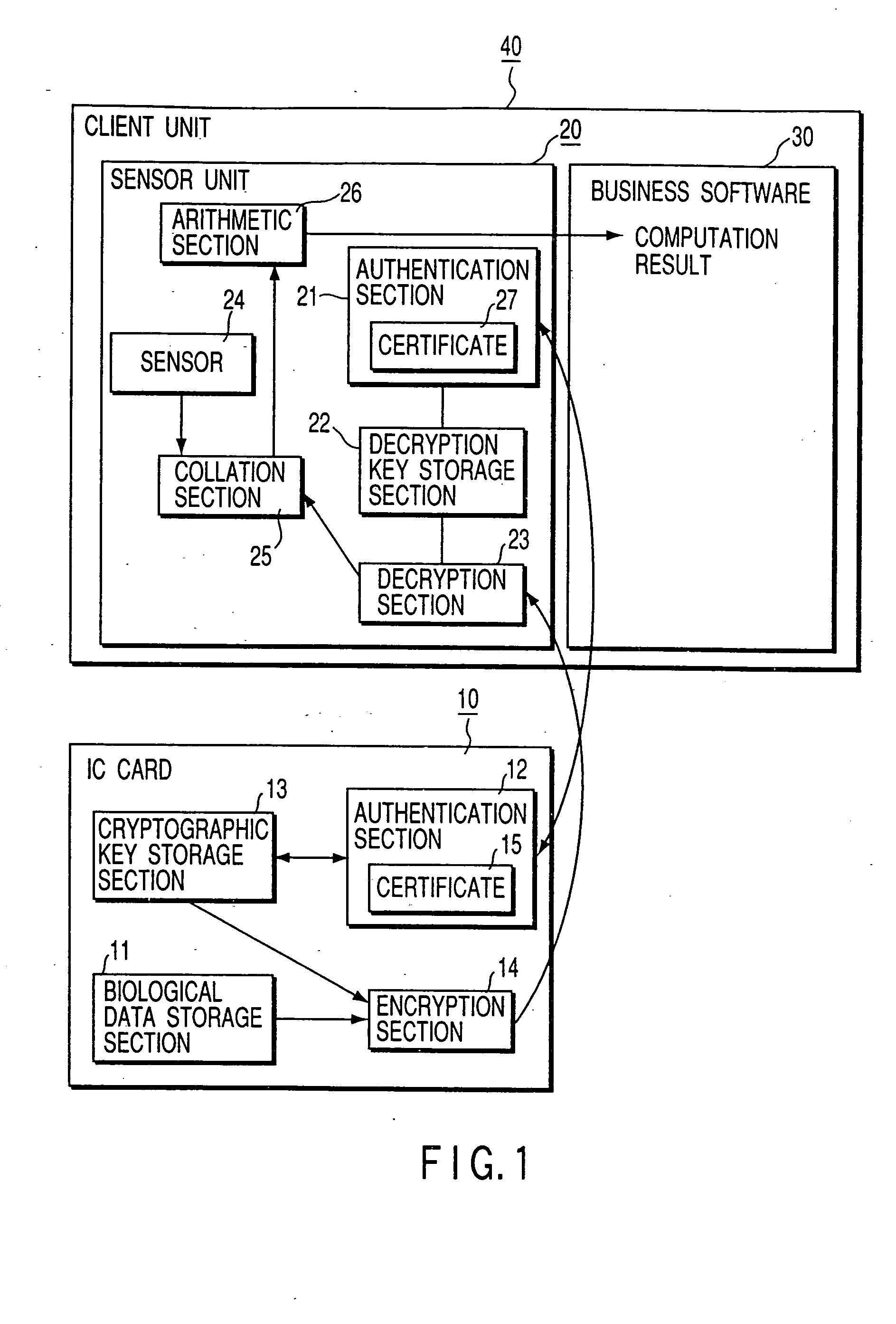
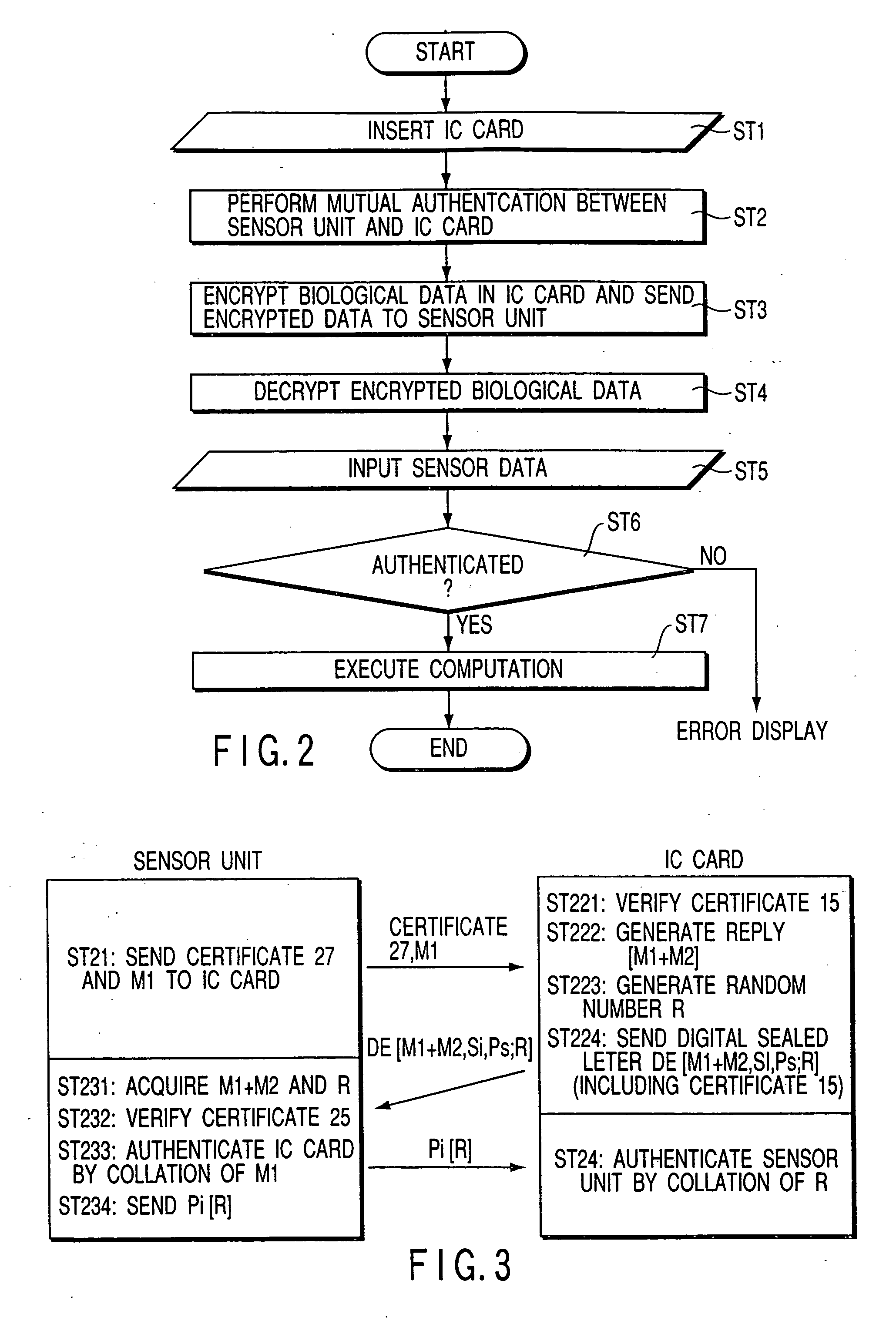
Personal authentication system and portable unit and storage medium used therefor
InactiveUS6910131B1Prevent fraudulent useUser identity/authority verificationCo-operative working arrangementsComputer hardwareCiphertext
Owner:KK TOSHIBA
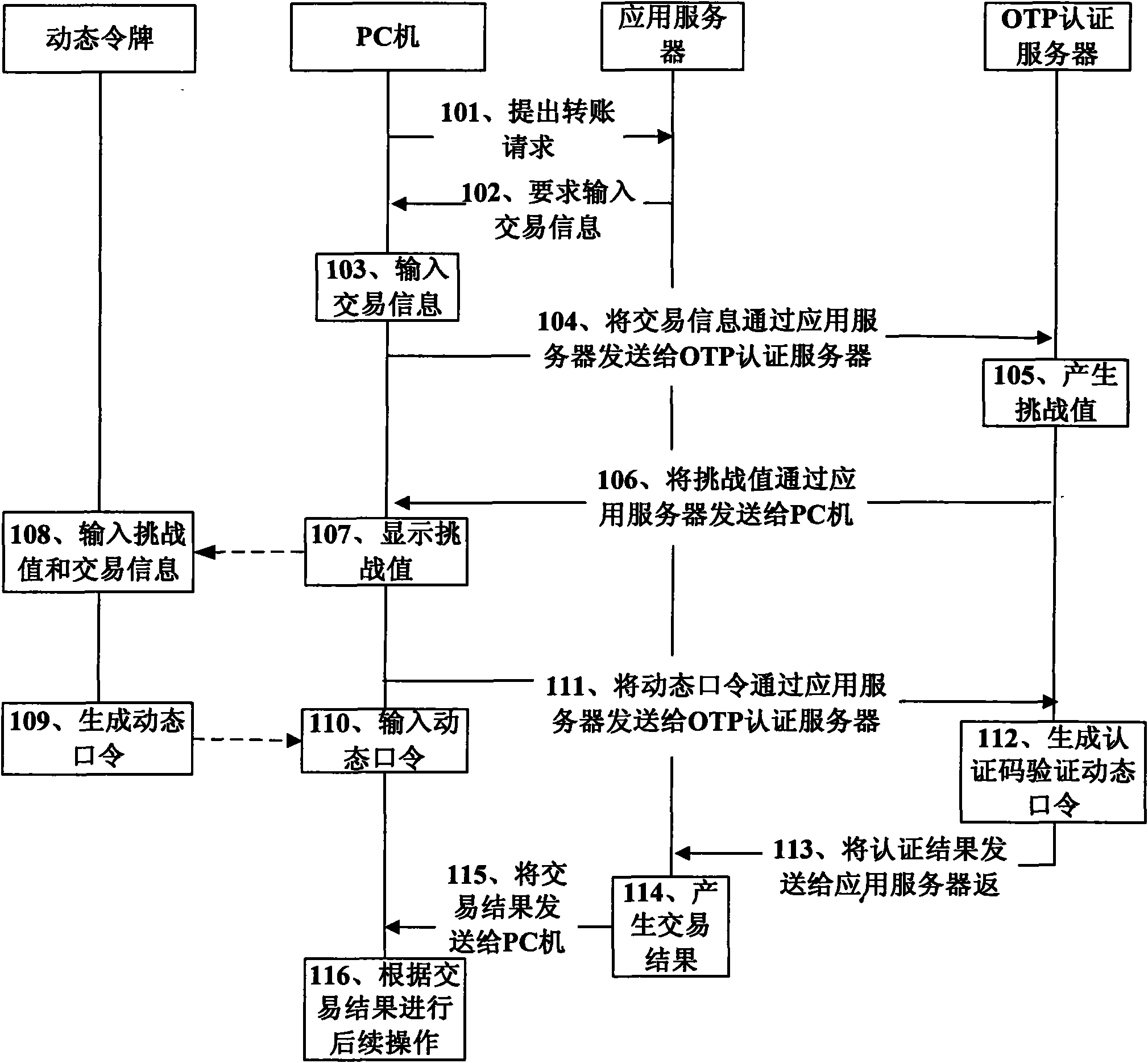
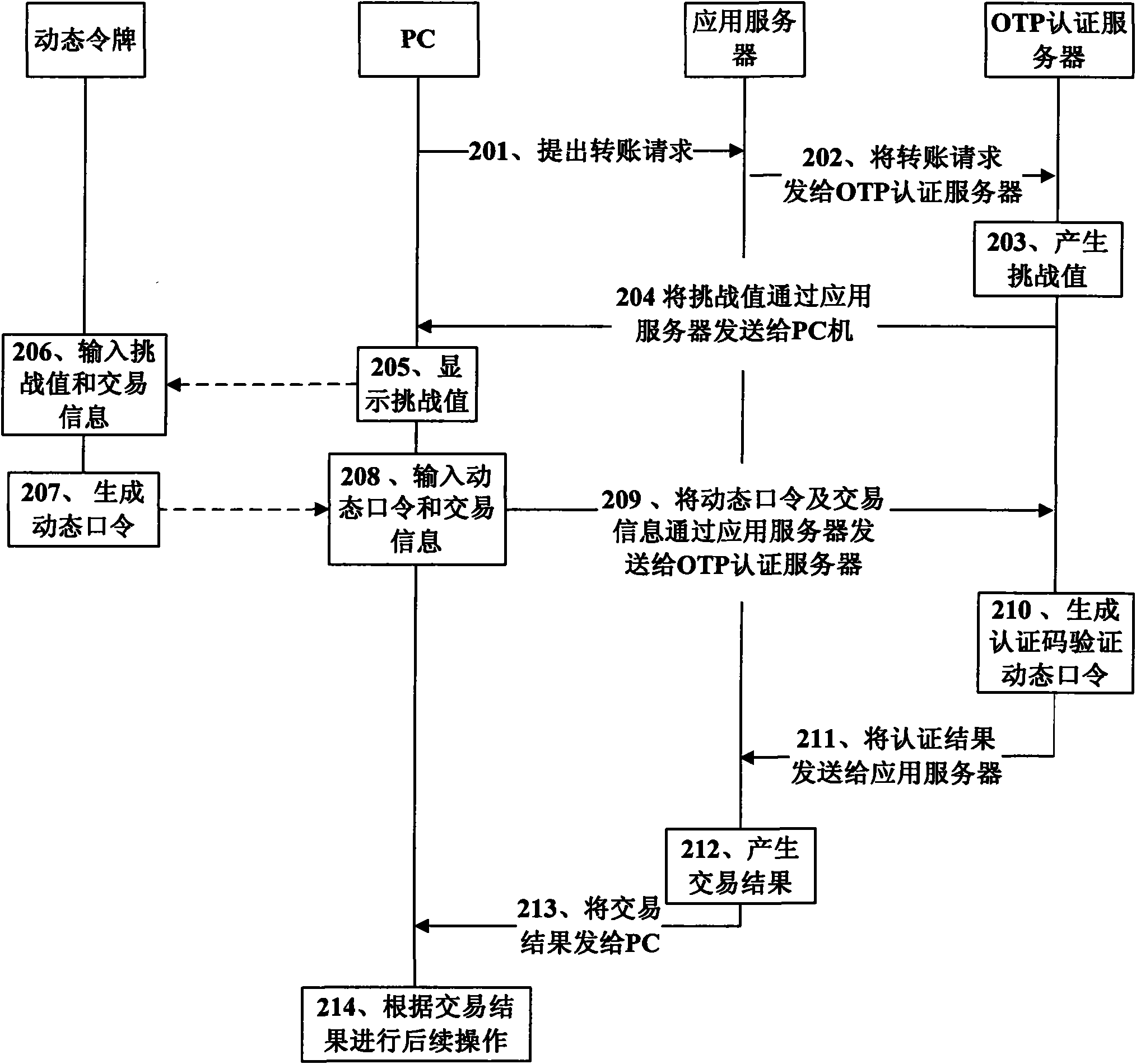
Method and system for enhancing security of network transactions
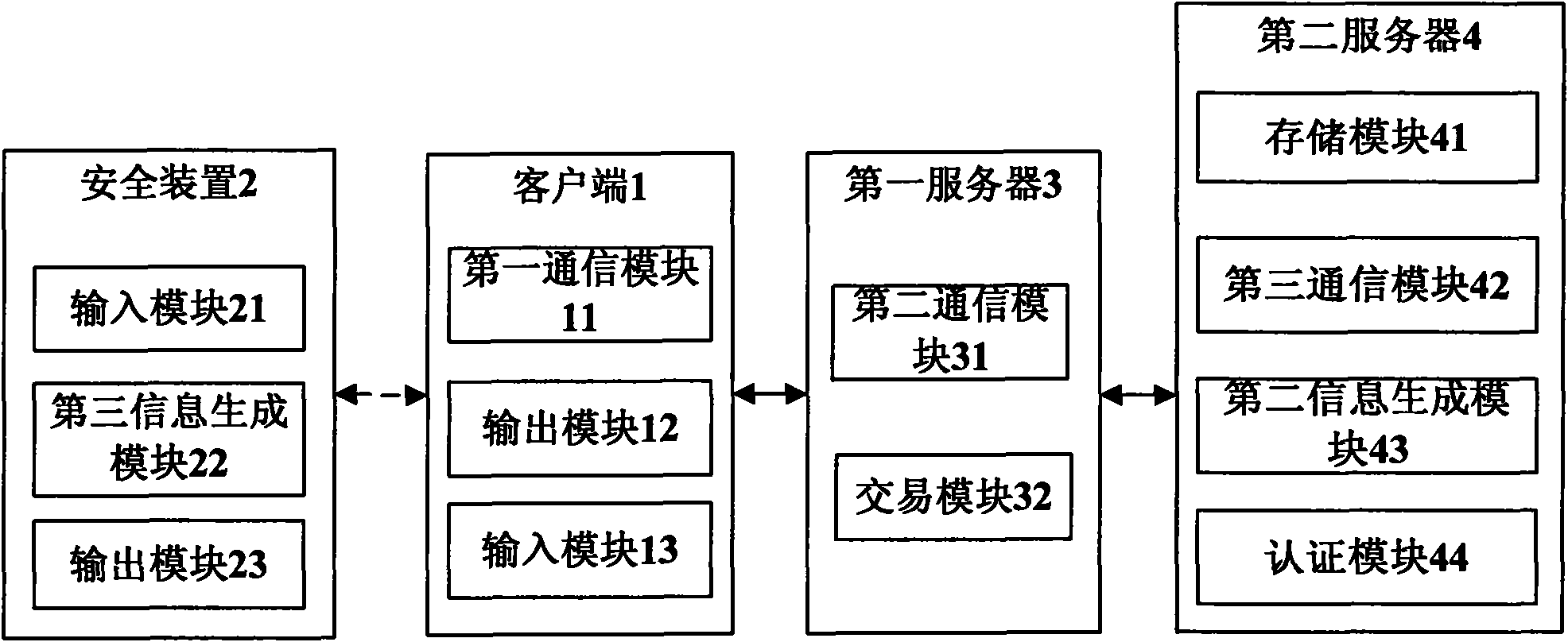
The invention discloses a method and a system for enhancing the security of network transactions, belonging to the field of information security. The method comprises the following steps: a client sends a service request to a first server, the first server sends first information to a second server, the second server generates second information, and the second information is returned to the client by the first server so as to be supplied to a user; a security device receives the first information and the second information input by the user and generates third information for the user; the client receives the third information input by the user, the first server sends the third information to the second server, when the second server receives the third information, the second server generates an authentication code by utilizing the same method that the security device generates the third information, the second server compares the authentication code with the third information for authentication and returns results to the first server, and the first server executes transactions when the authentication is success and returns the transaction result to the client. The system comprises the client, the security device, the first server and the second server. The invention greatly enhances the security in the transaction process.
Owner:FEITIAN TECHNOLOGIES
Pre-control of a program in an additional chip card of a terminal
InactiveUS6925560B1Prevent fraudulent useUnauthorised/fraudulent call preventionEavesdropping prevention circuitsTelecommunications networkComputer terminal
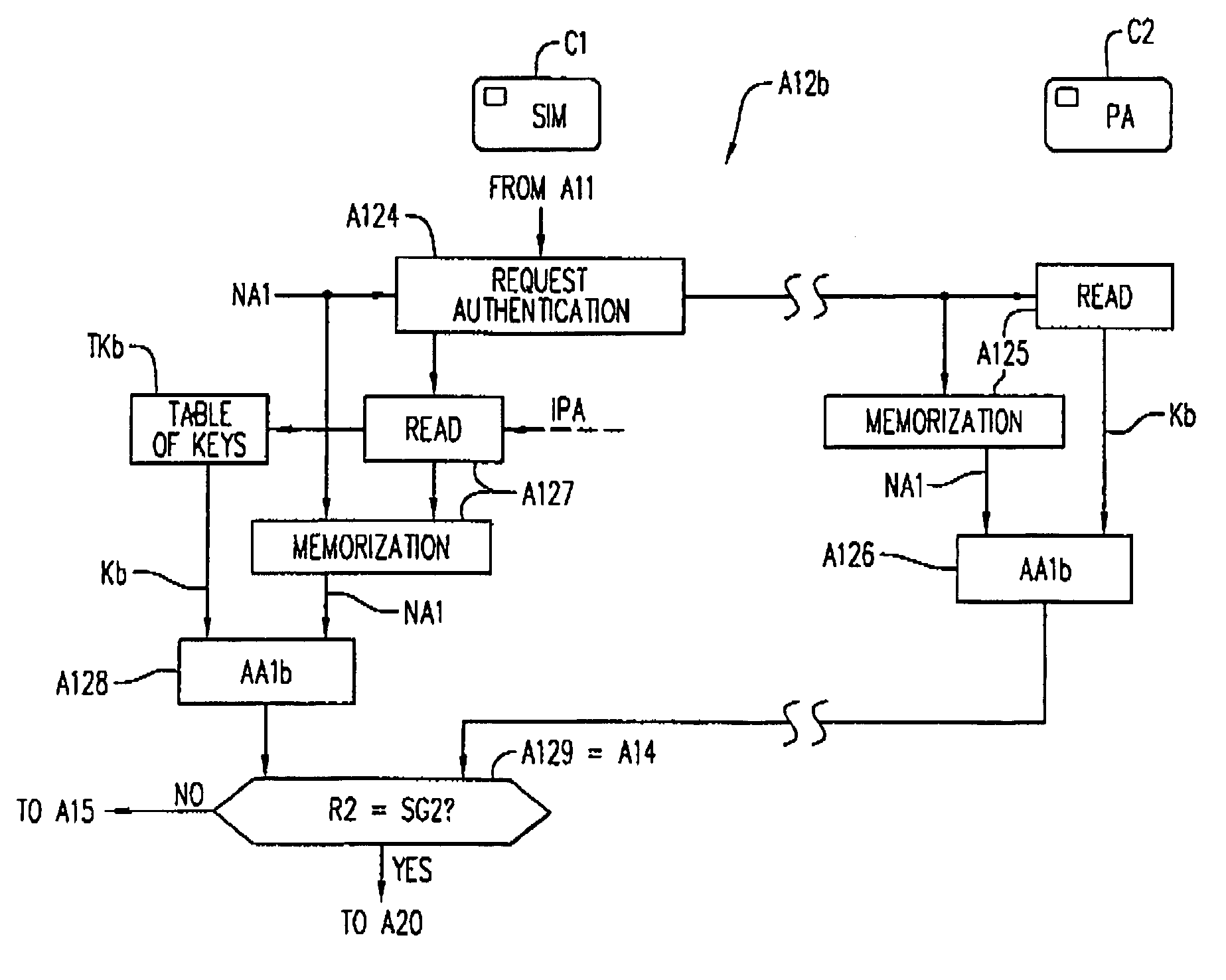
Prior to the execution of a program contained in a second chip card inserted in a terminal such as a mobile radio telephone terminal, in addition to a first chip card containing data and connected to a telecommunication network to which the terminal is linked, one of the cards is authenticated by the other, or the two cards are authenticated mutually. This double authentication ensures the authenticity of the program for its overall execution in the terminal and the origin of the second card, distributed through conventional channels, for the network operator.
Owner:GEMPLU
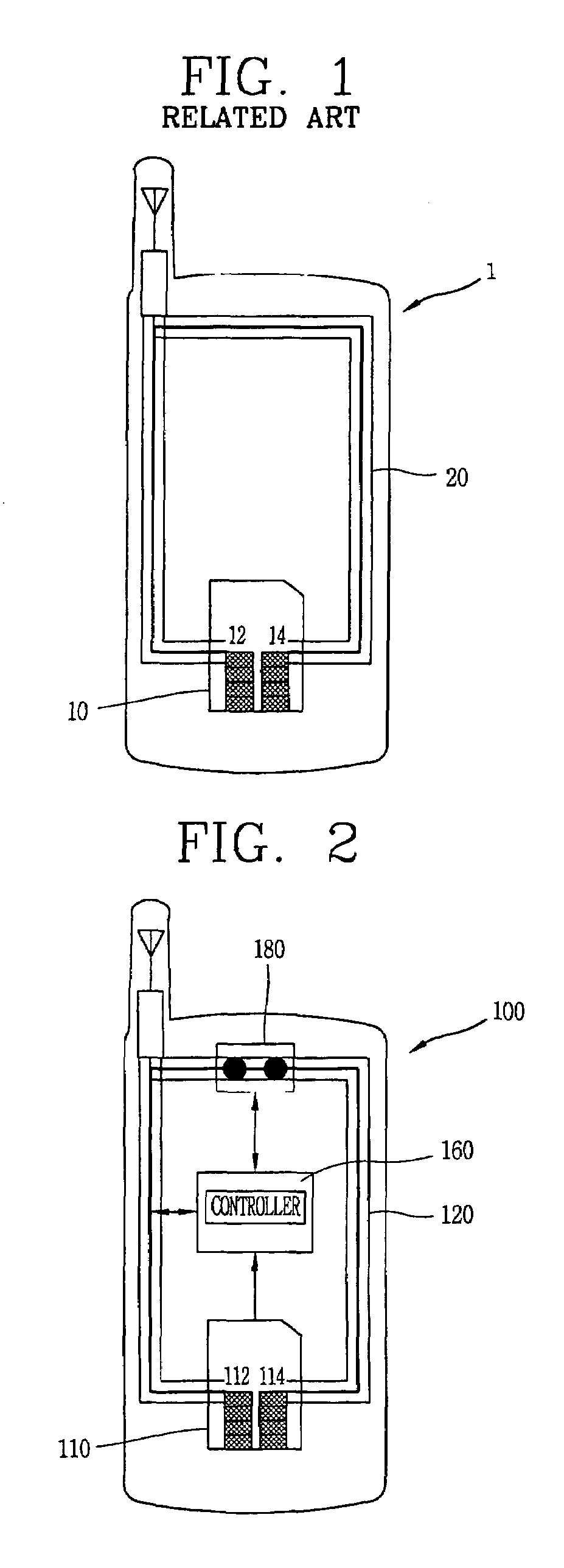
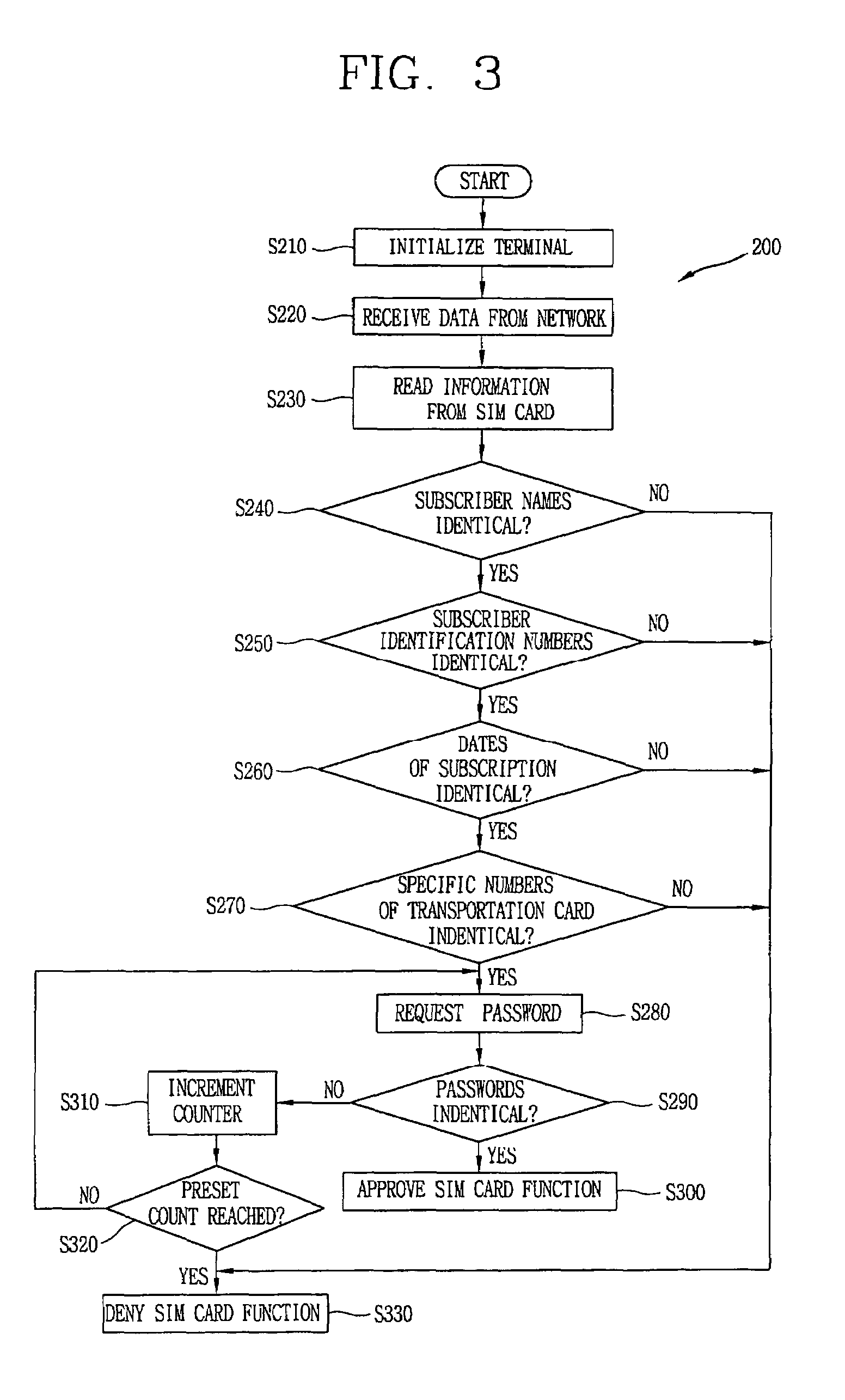
Apparatus and method for controlling use of a SIM card of a mobile terminal
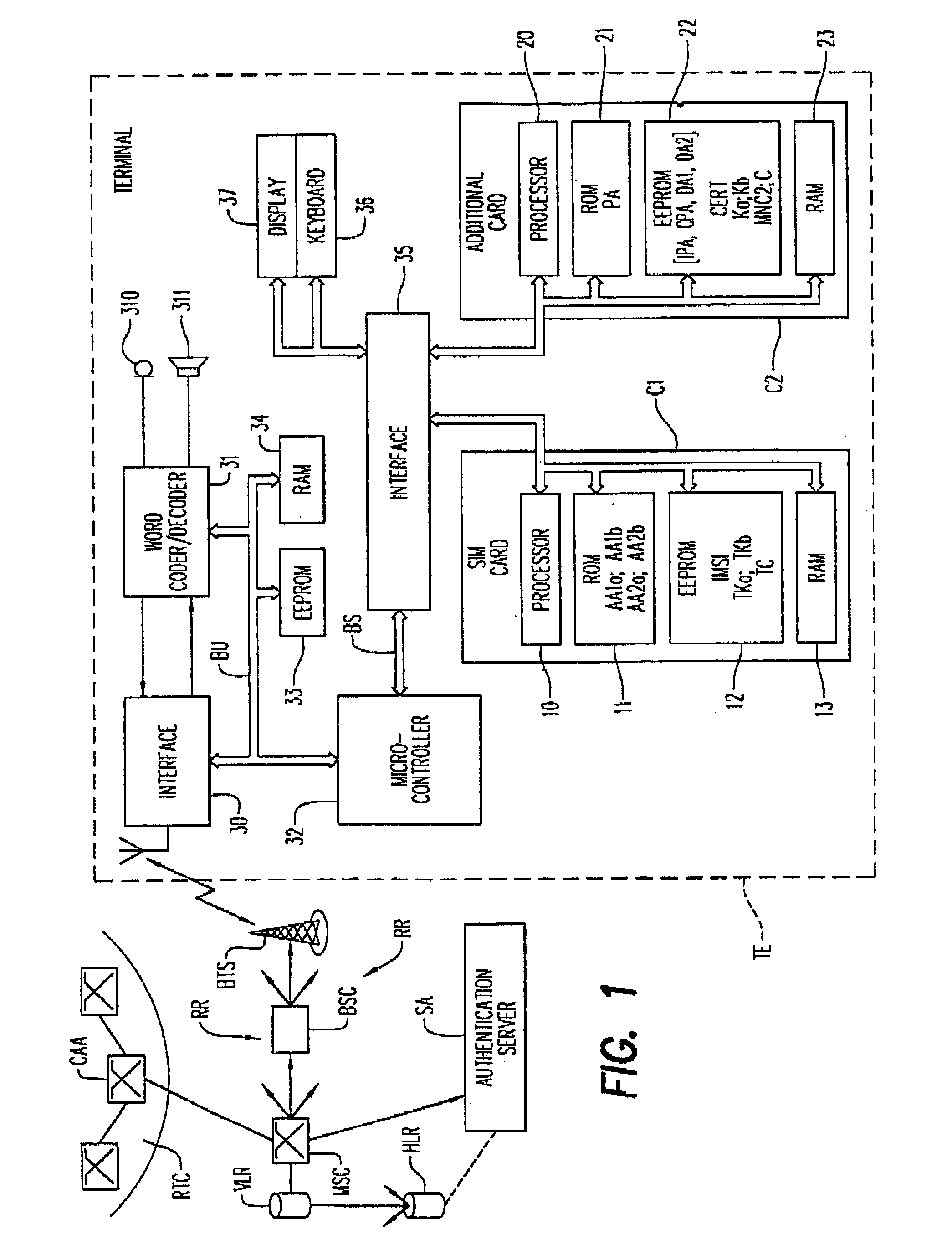
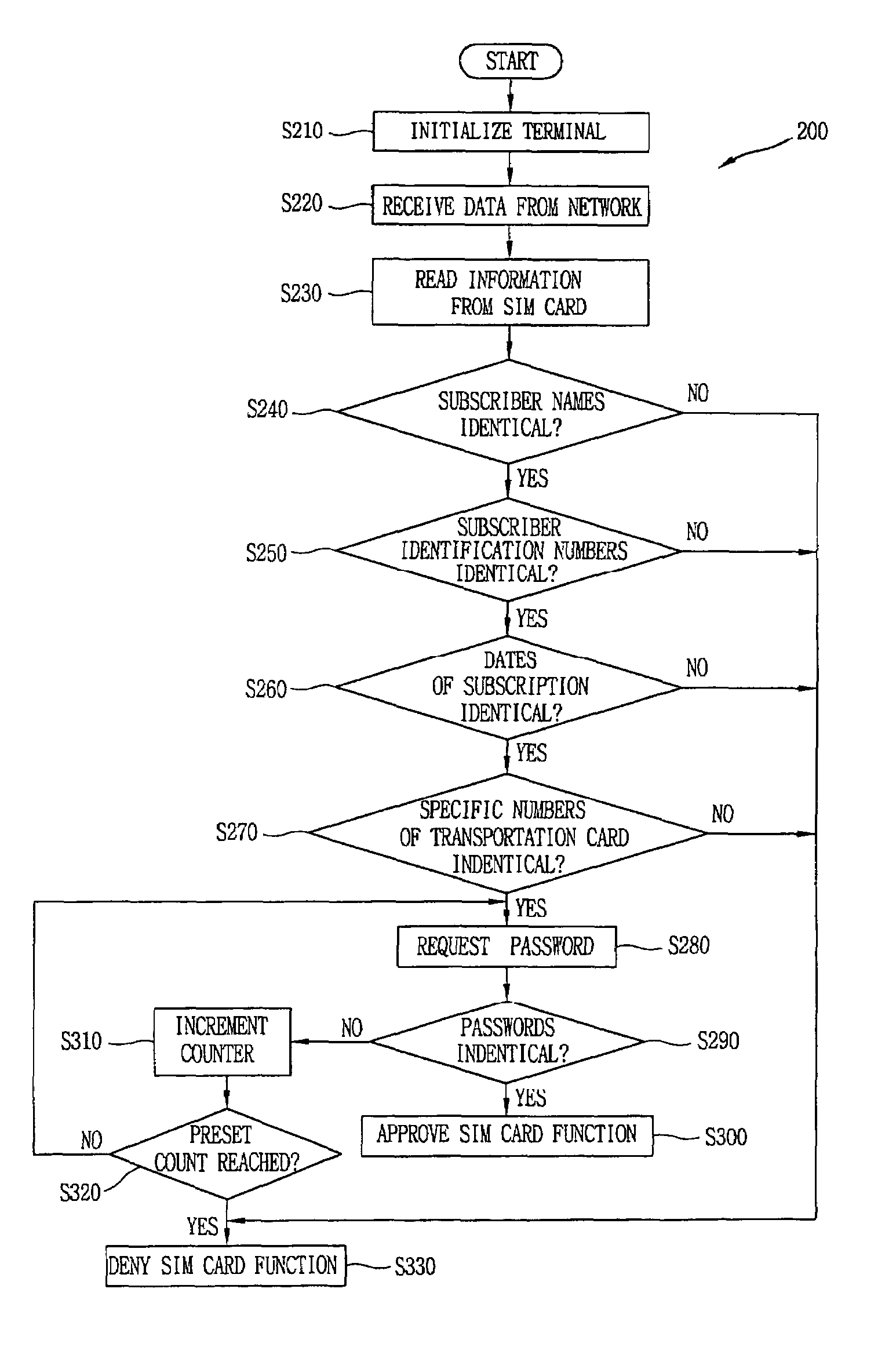
InactiveUS7689251B2Unauthorized use can be preventedUnauthorized useCo-operative working arrangementsNear-field systems using receiversControl signalComputer terminal
An apparatus and a method for controlling the use of a SIM card mounted in a mobile terminal by employing a fraud technology includes comparing data related to the SIM card received from a network to information read from the SIM card in the terminal as part of a terminal initialization process and generating a control signal to cause an RF antenna switch to open or close an RF antenna loop structure in order to disable or enable a requested SIM card function. The data received form the network and the information read from the SIM card in the terminal include subscriber information and transportation card information that allow a determination of whether a user requesting a SIM card function is the subscriber entitled to access the function. If the data received form the network and the information read from the SIM card are identical, the requested SIM card function is approved. If the data received from the network and the information read form the SIM card are not identical, the requested SIM card function is not approved. Optional password protection of SIM card functions may also be provided.
Owner:LG ELECTRONICS INC
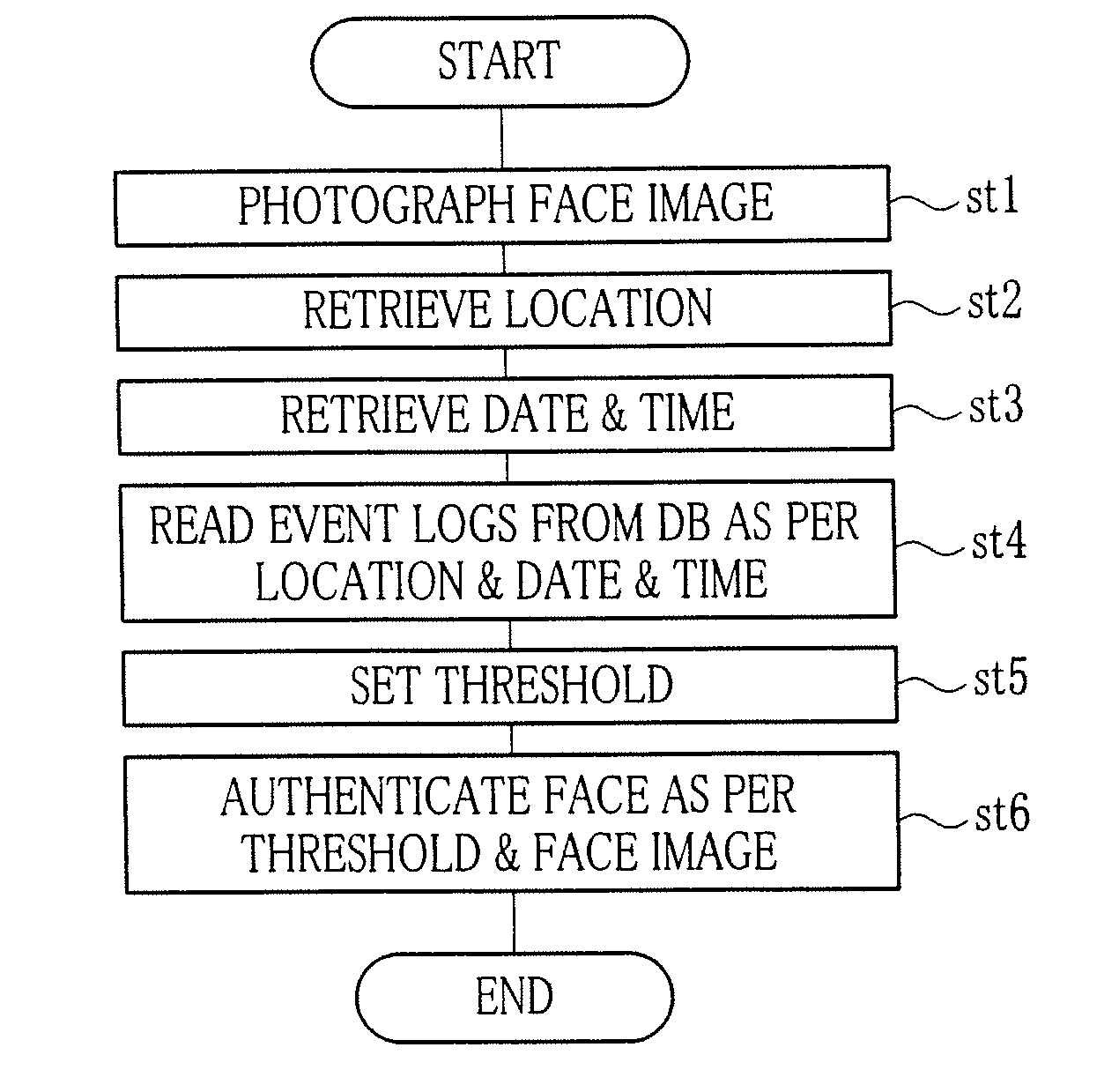
Authenticator and authentication method
InactiveUS20100245042A1Prevent fraudulent useVerify reliabilityProgramme controlElectric signal transmission systemsTelephone callCellular telephone
An authenticator authenticates a person at a cellular telephone according to a registered given user biometrically, in which a predetermined threshold is used in comparison with degree of matching between face images. A location information retriever retrieves information of a first location of the cellular telephone upon retrieval of the person's face image, and a second location of the cellular telephone after detecting the first location at a predetermined time. A movement detector detects whether travel of the cellular telephone occurs upon retrieval of the person's face image according to the first and second locations. A log database unit stores information of the travel from the movement detector. A threshold determining unit determines the threshold according to the information of the travel in relation to one or more earlier event logs of authentication.
Owner:FUJIFILM CORP
Content distribution system, content distribution method, information processing apparatus, and program providing medium
InactiveUS20050234828A1Reliable fashionWarranty periodDigital data processing detailsUser identity/authority verificationInformation processingContent distribution
A content distribution is performed by a secure container including a content encrypted by a content key and container information set for a content transaction. The container information includes a person identification certificate identifiers list. Usage control status information including the list is generated and stored in a device during a secondary distribution among user devices after a primary distribution of the content. In the distribution among the user devices, identifying an identification certificate in reference to the list and performing a person authentication based on the identification certificate allows each of the user devices to use the transmitted content, when the authentication is affirmative.
Owner:SONY CORP
Secure point of sale presentation of a barcode at an information handling system display
ActiveUS20140263623A1Reduce disadvantagesReduce problemsSensing record carriersRecord carriers used with machinesDisplay deviceHandling system
Unauthorized copying of a transaction barcode is prevented by including a sensed condition or other publicly-accessible data with the transaction barcode for use as a comparison with the publicly accessible data determined at a barcode reader. If the sensed condition included in the transaction barcode indicates that the transaction barcode was generated for a different transaction, then the barcode reader invalidates the transaction. For instance, if the barcode was generated too distant in time, position, or sequential transactions, then the barcode reader invalidates the transaction barcode as an unauthorized copy of a transaction barcode generated for a different transaction.
Owner:DELL PROD LP
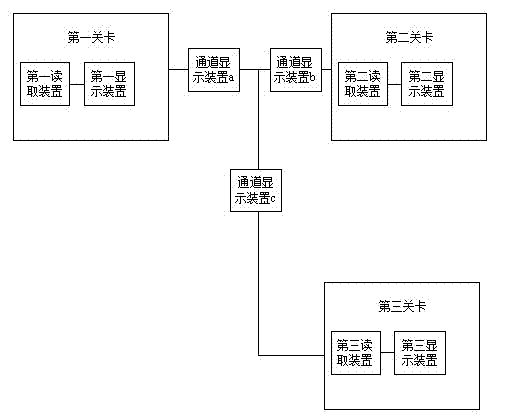
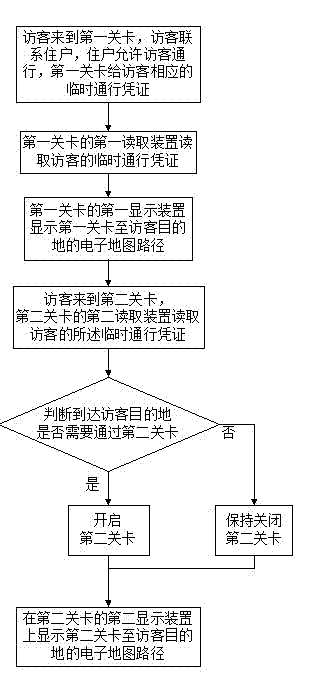
Visitor coming control guide method and system
InactiveCN103198545AExtension of timeIncrease traffic speedIndividual entry/exit registersDisplay deviceComputer science
The invention discloses a visitor coming control guide method and system. The method comprises the following steps of: after a first reading device of a first gate reads a temporary passport of a visitor, displaying an electronic map path between the first gate and a destination of the visitor on a first display device of the first gate; when the visitor reaches a second gate, reading the temporary passport of the visitor by a second reading device of the second gate, and judging whether the visitor needs to pass through the second gate in order to reach the destination of the visitor; if so, opening the second gate; and otherwise, keeping closing of the second gate, and displaying an electronic map path between the second gate and the destination of the visitor on a second display device of the second gate. According to the method, the safety of other regions is ensured, the destination reaching time of the visitor is shortened, and the passing speed of a whole district is accelerated; the situation of using of a false certificate is avoided, and the passing of the gates by using certificates of other people is prevented; and a resident can check visitor information in real time, and can remotely authorize the visitor.
Owner:SHENZHEN WONGLONG INTELLIGENT TECH
Secure storage systems and methods
ActiveUS20190333304A1Provide limited provisionsPrevent fraudulent useKey distribution for secure communicationMultiple keys/algorithms usageCryptographic protocolChain of custody
Secure storage platforms and their application in secure temporary property storage applications are disclosed and comprise: secure locker systems; secure locker systems comprising emergency access; secure locker systems comprising collapsible lockable compartments; secure storage systems comprising chain of custody management, recording and authentication; redirected delivery including post-delivery redirected delivery, en route delivery and dispatch delivery services comprising chain of custody services; and secure property claim check and car valet systems. A secure storage platform uses a secure protocol to establish challenge code and verification code generators to provide short lived single use access authentication codes to enable secure access and custody management of secured and stored property.
Owner:BINBOX INC
Personal authentication system and portable unit and storage medium used therefor
InactiveUS20050055557A1Prevent fraudulent useUser identity/authority verificationCo-operative working arrangementsComputer hardwareCiphertext
When a personal authentication is to be executed, the encryption section of an IC card encrypts biological data and supplies the obtained ciphertext to a sensor unit. When the decryption section of the sensor unit obtains biological data by decrypting the ciphertext, a collation section collates the biological data with input biological measurement data, thereby authenticating personal identification.
Owner:KK TOSHIBA
System for securing personal cards
InactiveUS7347382B2Cost-effectiveMinimally affects existing merchant transactionsSensing record carriersRecord carriers used with machinesCredit cardComputer hardware
A credit card comprises a plastic layer, a processor, and a keypad. The keypad provides the ability to input a code (e.g., a personal identification number (PIN) code) to the processor as a part of validating the transaction. Illustratively, the entry of a valid PIN code may cause the processor to trigger an alerting device as an indicator to the merchant that the holder of the credit card is authorized for its use.
Owner:T INK INC
Two-dimensional code, coding system and method of two-dimensional code
InactiveCN102243714AEasy to useImprove securityDigital data authenticationTransmissionProgramming languageTerminal equipment
The invention discloses a two-dimensional code, a coding system and method of the two-dimensional code. The coding method includes the steps of, a user's terminal device representing a user's ID through a first region of the two-dimensional code, and representing a user's cipher through a second region of the two-dimensional code; a client computer receiving the two-dimensional code sent from the user's terminal device, decoding ID and cipher corresponding to the two-dimensional code, and sending the decoded ID and cipher to a management server; the management server examining the consistency of the ID and cipher and the data stored in a database, and sending the examining results to the client computer; and the client computer receives the examination result sent from the management server. User's ID and cipher can be set in a two-dimensional code, which improving safety. A two-dimensional code with a simple structure can represent encryption of a given user's ID, checks ID cipher logged on a server, thereby ensuring user's information safety.
Owner:TRUE SOFTWARE LTD
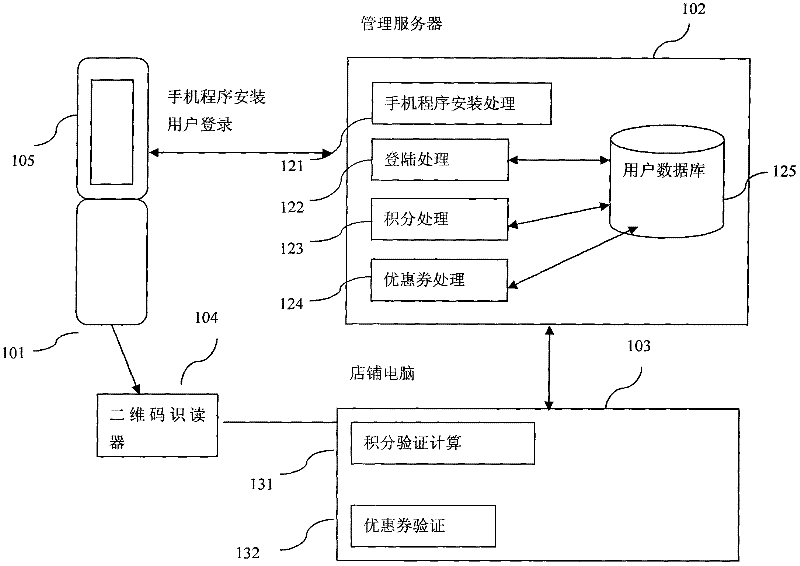
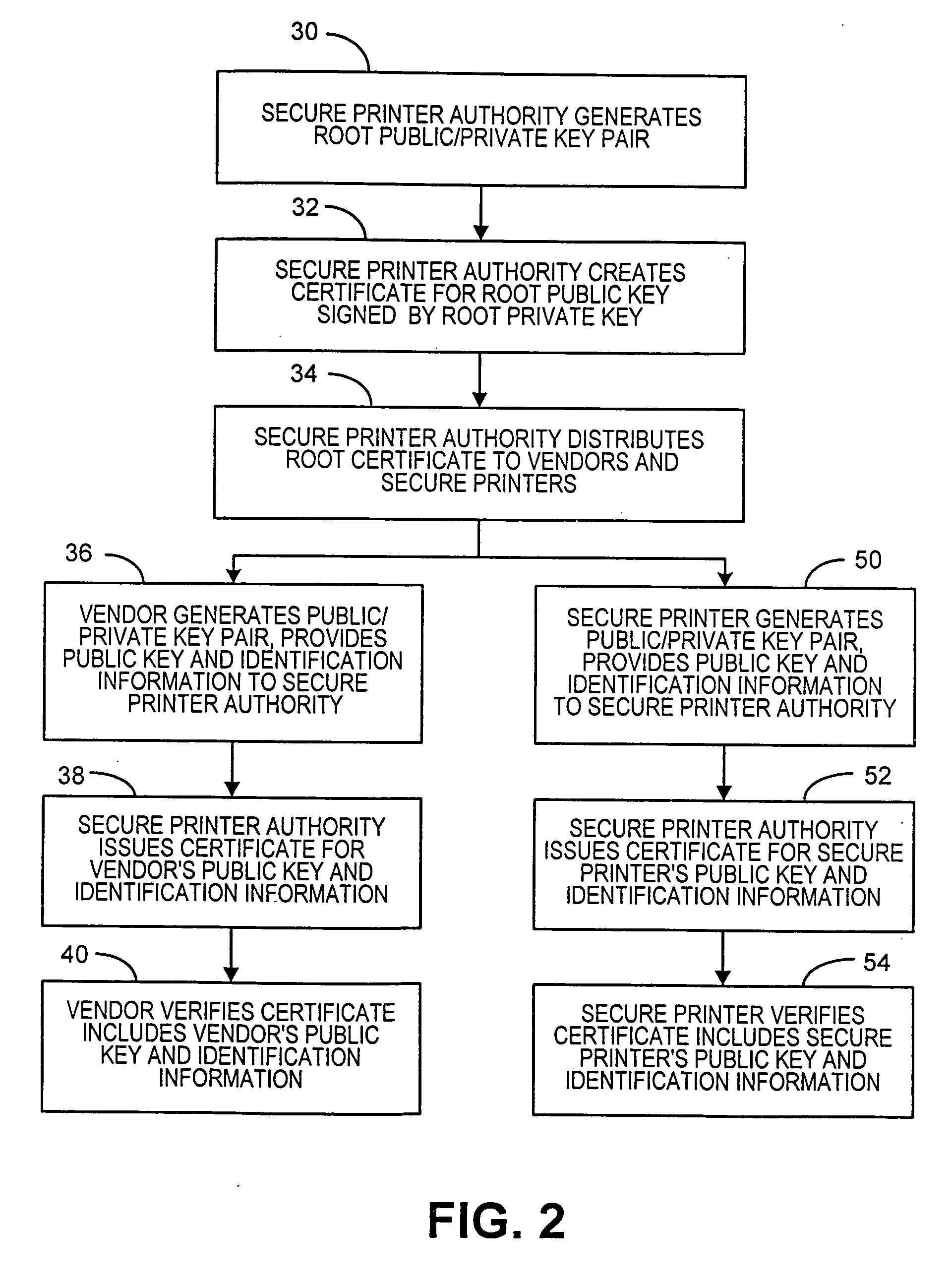
Method and system for printing transaction documents using a multi-vendor secure printer under control of a printer authority
InactiveUS20060064580A1Improve securityBlock valueUser identity/authority verificationComputer security arrangementsComputer printingPaper document
A low-cost, network based, secure printer that can provide multiple vendors with independent protected access, as authorized by a secure printer authority, is provided. The secure printer authority issues certificates for each secure printer and authorized vendor. Each certificate includes a public key and identification for the respective secure printer or vendor. The certificates are utilized during generation of a secret session key that preferably can be utilized only once to print the requested document. The secret session key is used by the vendor to encrypt the document, and used by the printer to decrypt the document. Since the secret session key is preferably valid for only a single document, printing of the document can only occur once, thereby preventing any fraudulent printing of the document. Additionally, only vendors authorized by the secure printer authority will have the ability to establish session keys with the printer.
Owner:PITNEY BOWES INC
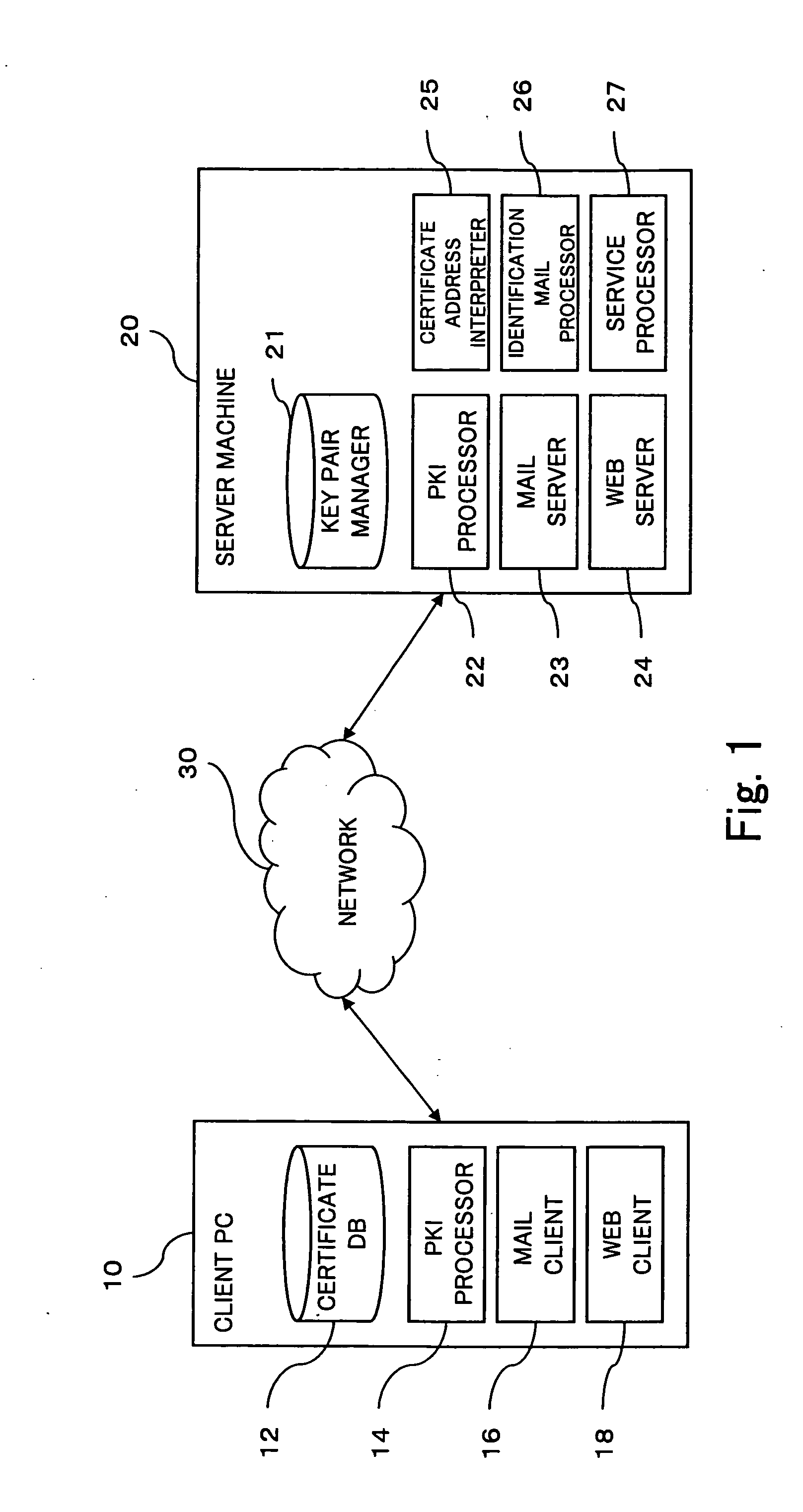
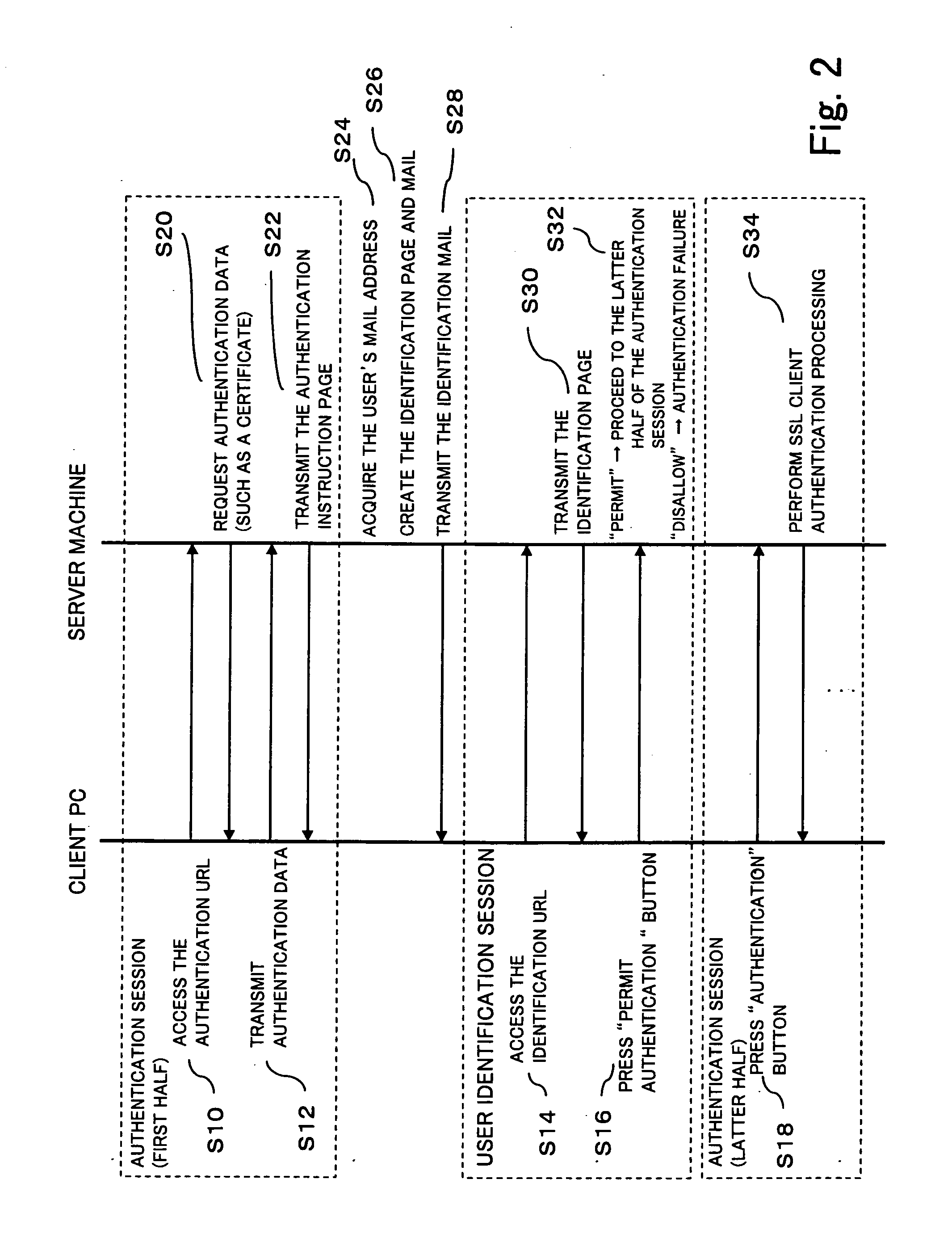
Server with authentication function, and authentication method
InactiveUS20060200854A1Prevent fraudulent useDigital data processing detailsUser identity/authority verificationDigital signatureInternet privacy
A server for authenticating a user has a receiving unit, an identification mail transmitting unit and an authentication control section. The receiving unit receives an authentication request from the user. The identification mail transmitting unit transmits an identification mail to the user. The identification mail identifies whether or not the user is a legitimate user. The authentication control section determines that the authentication request is unsuccessful regardless of whether or not a digital signature on the authentication request is valid, when the identification mail identifies that the user is not the legitimate user.
Owner:FUJIFILM BUSINESS INNOVATION CORP
System and Method for Location-Based Transaction
InactiveUS20180204204A1Convenient transactionPrevent fraudulent useNear-field transmissionRegistering/indicating working of vehiclesPaymentMobile device
A system and method for using at least location information to facilitate a transaction is provided. In one embodiment of the present invention, a mobile application operating on a mobile device is used to determine a location of the mobile device. Location information is then provided to a host device, where it is used to identify a second party. Information on the second party, including transactions offered, is then provided to the first party (e.g., via the mobile device, an intermediate device, and / or a device operated and / or owned by the second party). The first party can then interact with the mobile application to select or confirm at least one of the offered transactions. If the transaction is a purchase of goods / services, then a linked payment method may be charged. If the transaction is financial, then the first party may have to further provide authentication data (e.g., a PIN).
Owner:KEY 2 MOBILE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com