Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
52results about How to "Transaction can be blocked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
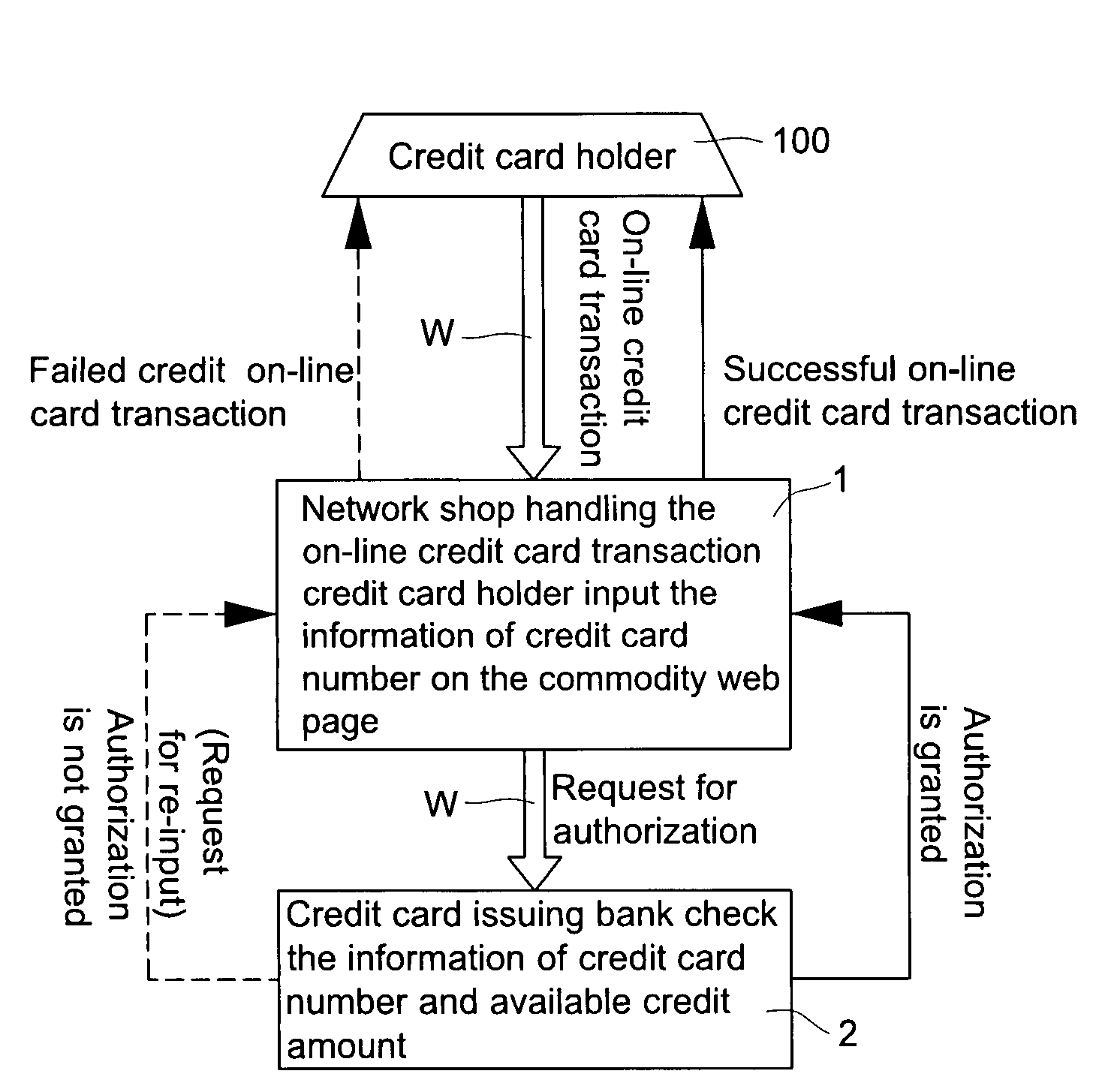
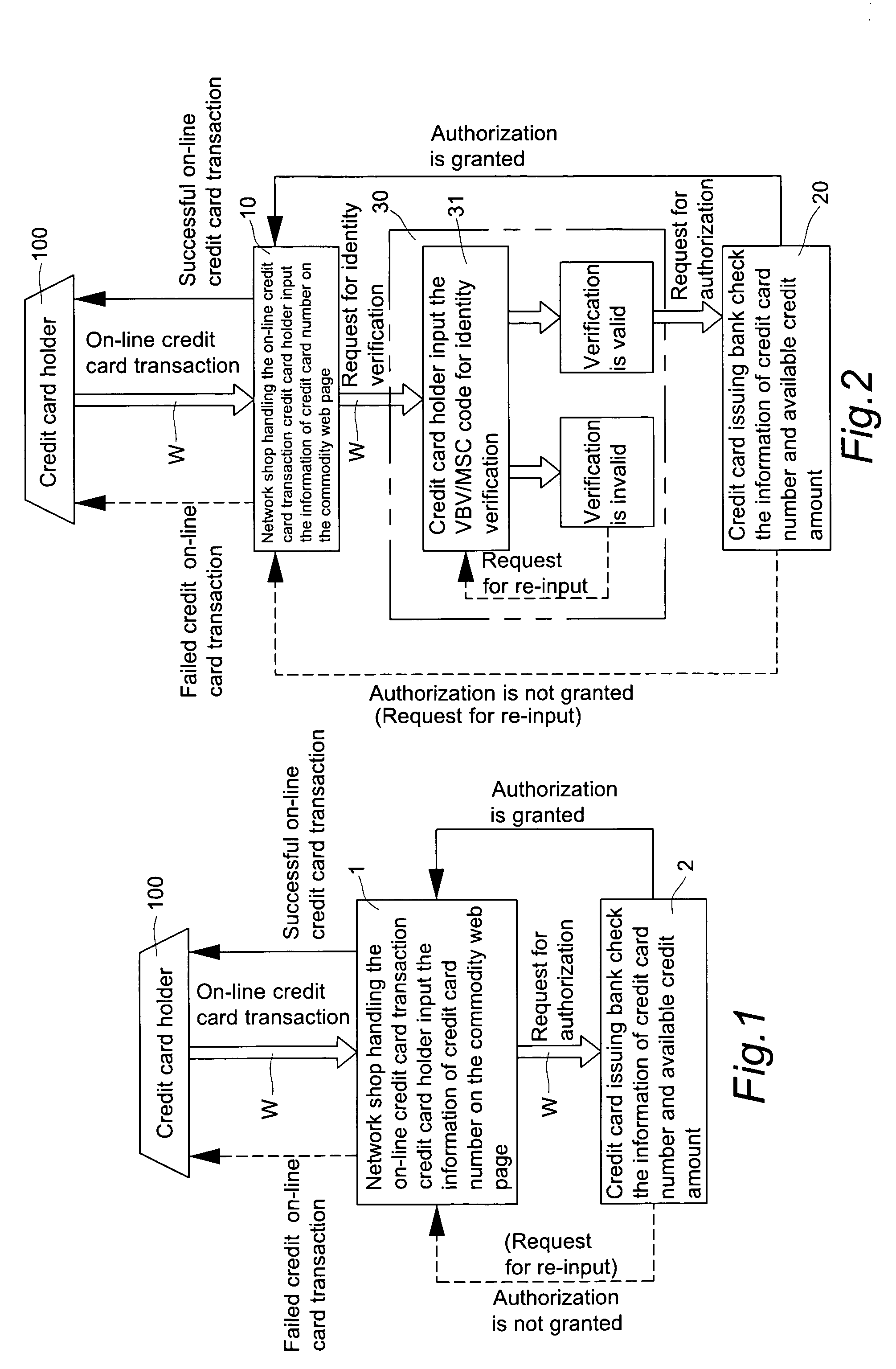
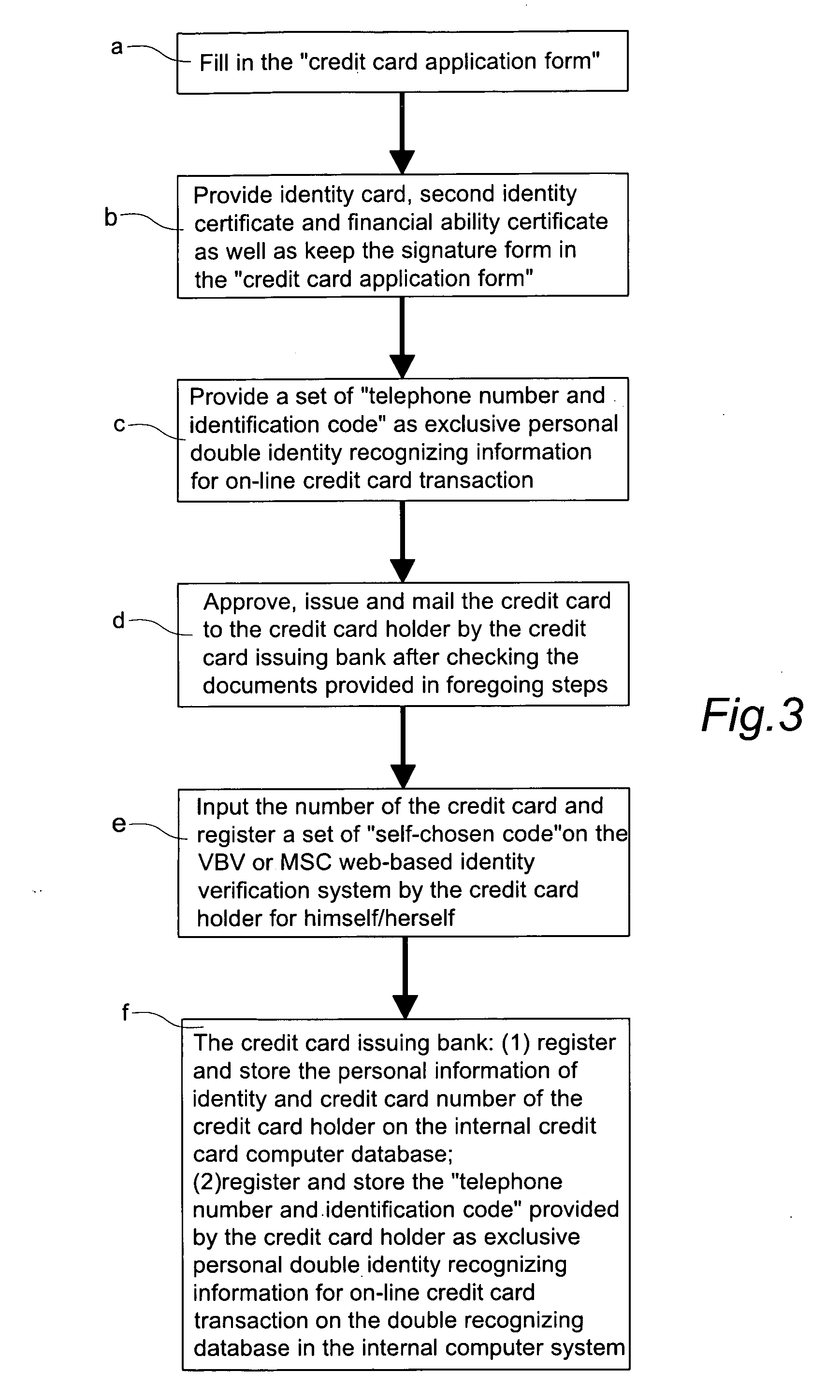
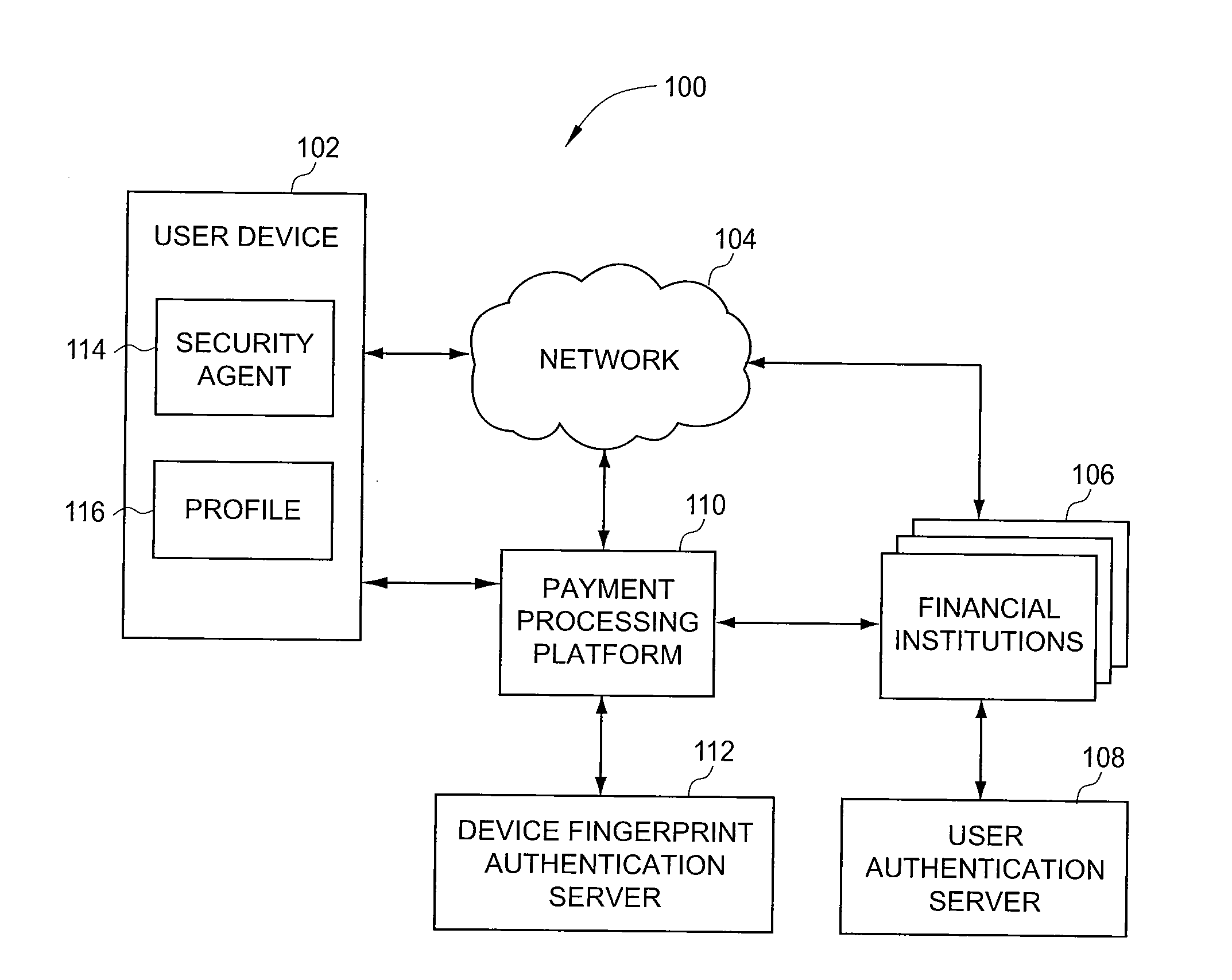
Double recognizing method by means of telephone number and identification code for online credit card transactions over the internet
The present invention relates to a “double recognizing method by means of telephone number and identification code for online credit card transactions over the internet,” in which the credit card holder not only registers a “self-chosen code” by himself / herself for VBV (Verified By VISA) or MSC (MasterCard SecureCode) network identity verification but also registers another set of “telephone number and identification code” by himself / herself for serving as an exclusive personal double identity recognizing information for online credit card transactions. The credit card issuing bank registers and stores the set of “telephone number and identification code” on a double recognizing database after checking truth of the related identity certificate provided by the credit card holder. When the credit card issuing bank handles the online credit card transaction of the credit card holder over the network, the credit card issuing bank not only proceeds the check on the “self-chosen code” used in the original VBV or MSC verification system but also performs the double check on the “telephone number and identification code” used in the telecommunications transceiving processor platform of the internal credit card double recognizing computer system, for example by sending out a short message to the credit card holder for requesting him / her to immediately reply by another short message to his / her “telephone number and identification code.”
Owner:LIN CHUNG YU
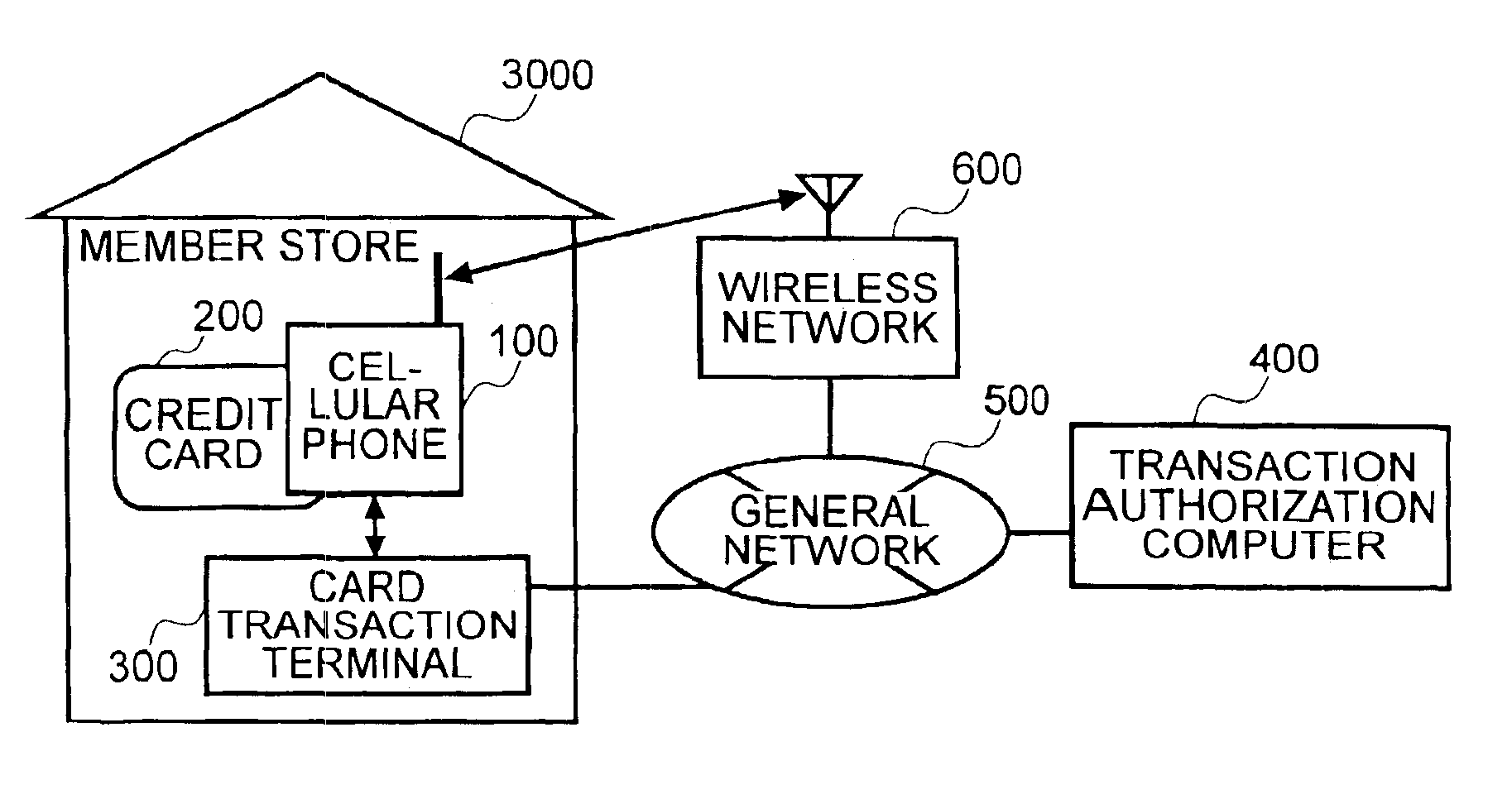
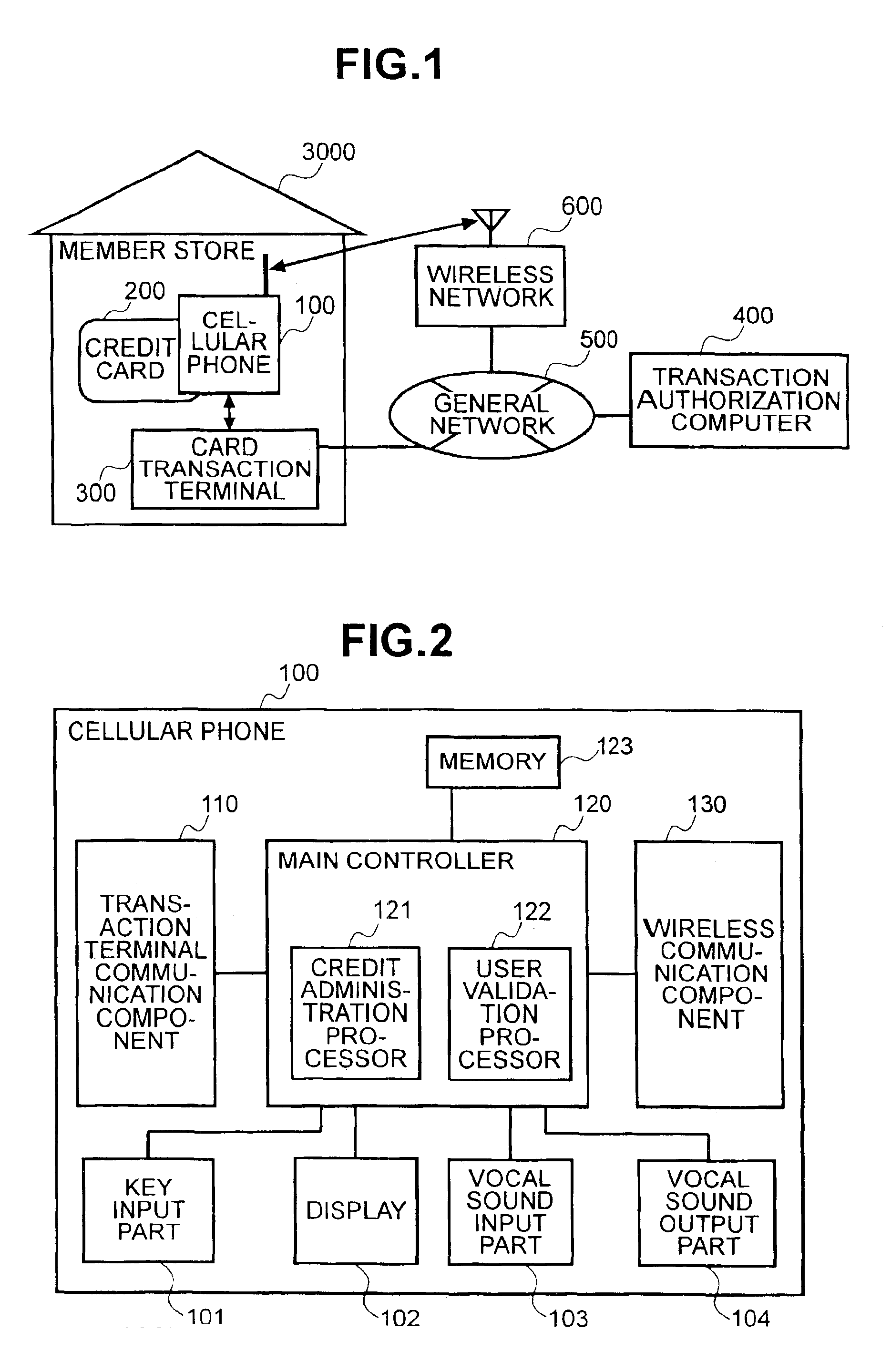
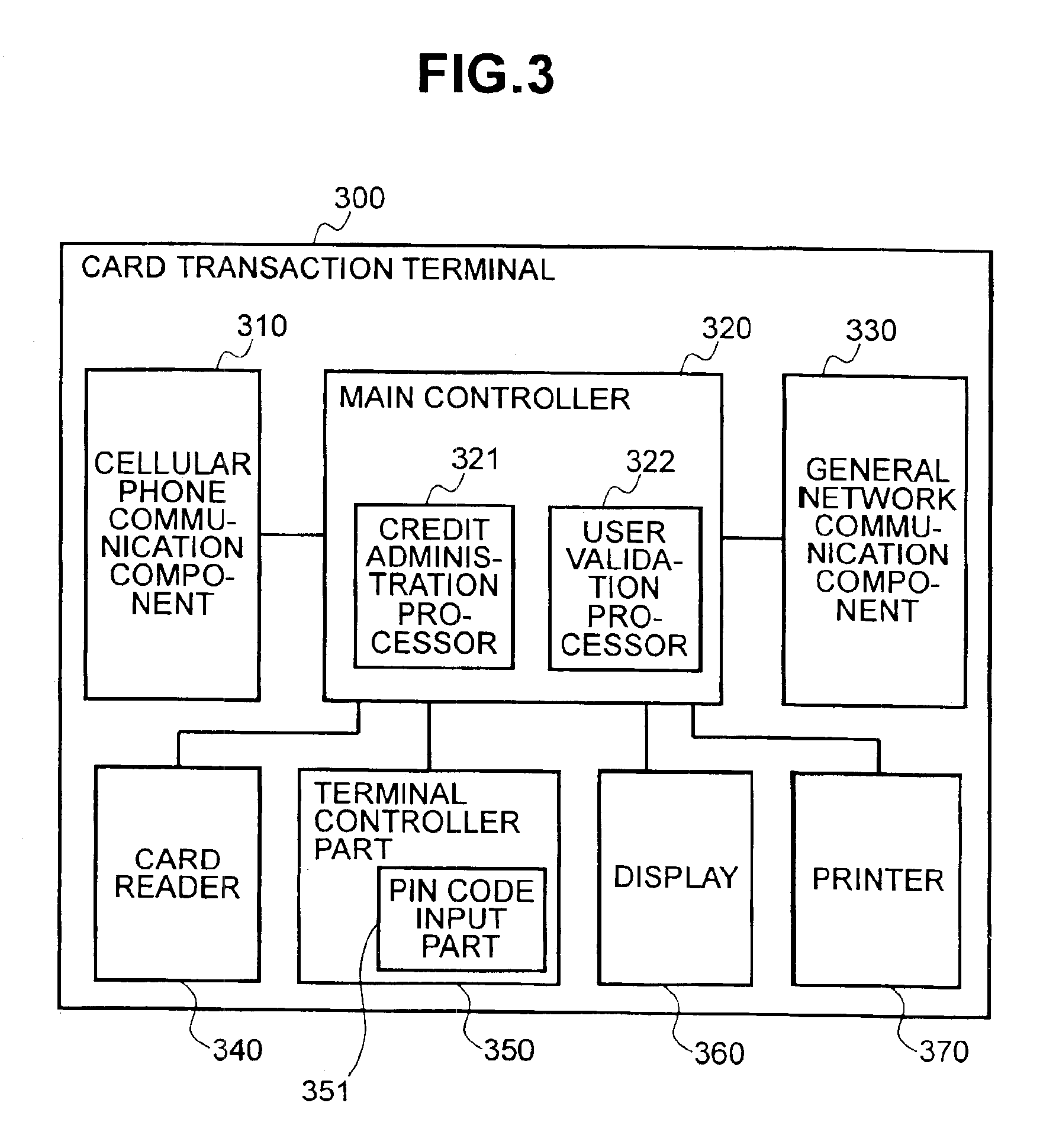
Method and system to prevent fraudulent payment in credit/debit card transactions, and terminals therefor
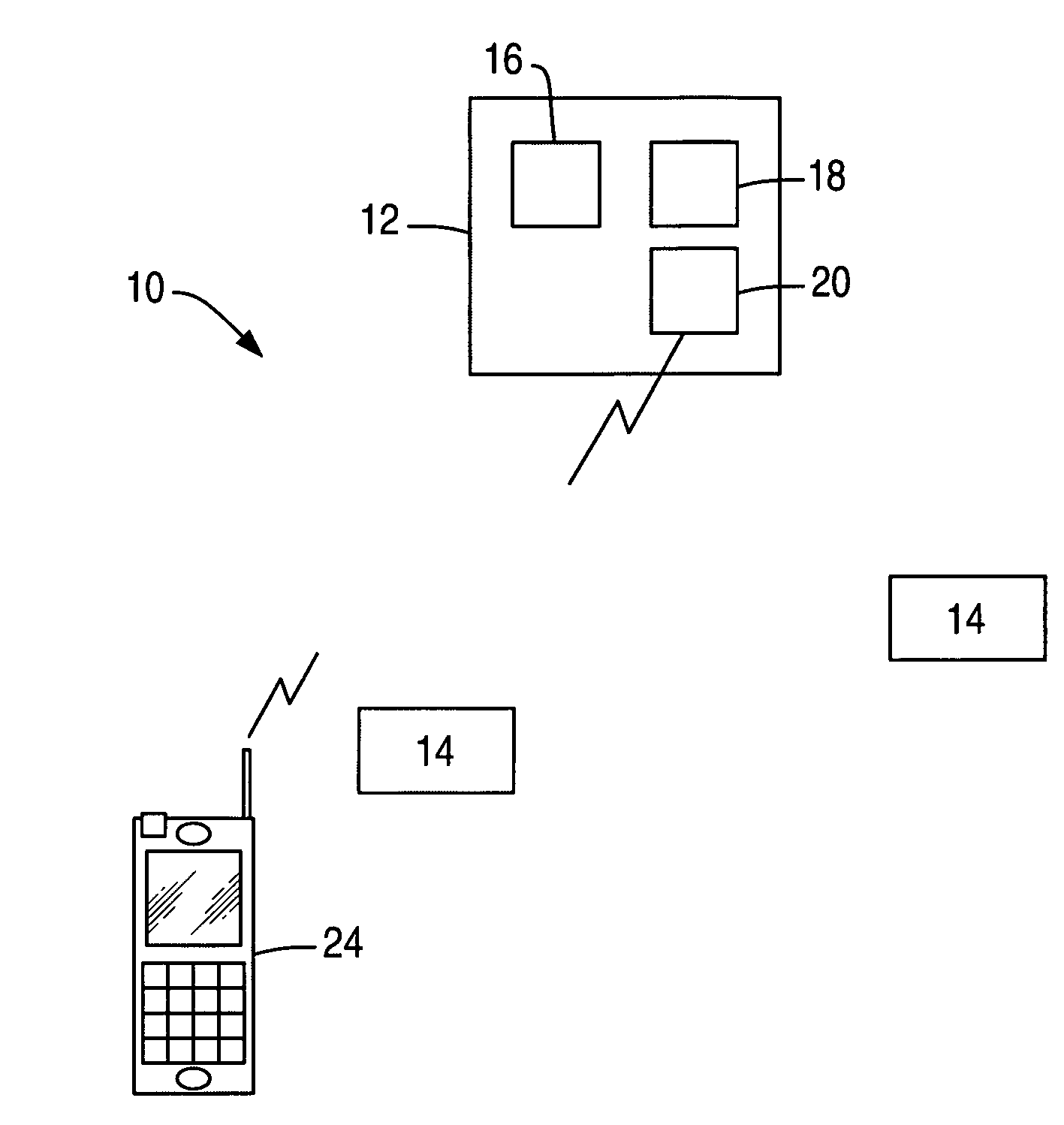
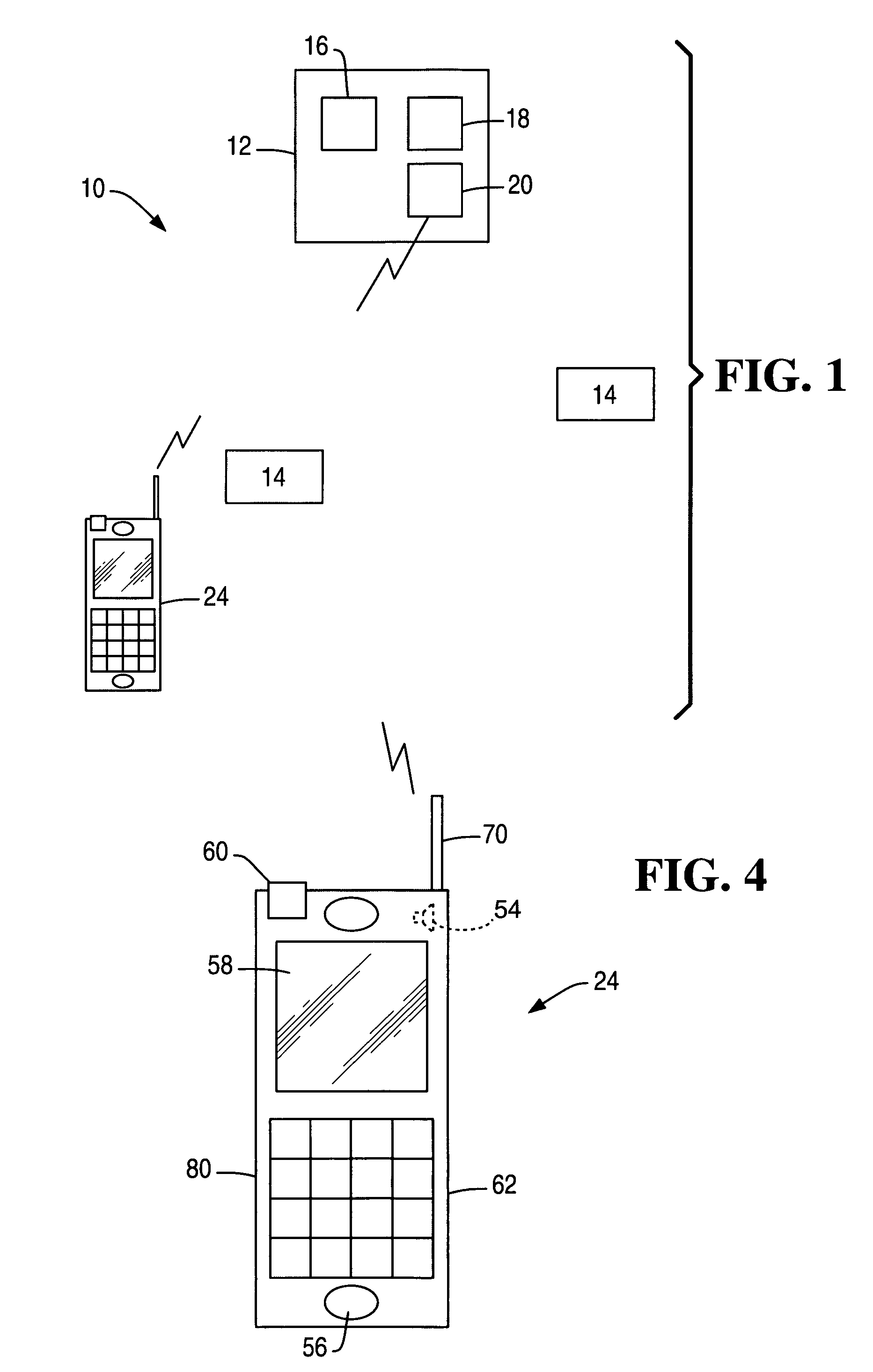
InactiveUS6913194B2Transaction can be blockedEliminate dangerBuying/selling/leasing transactionsVerifying markings correctnessUser verificationComputer terminal
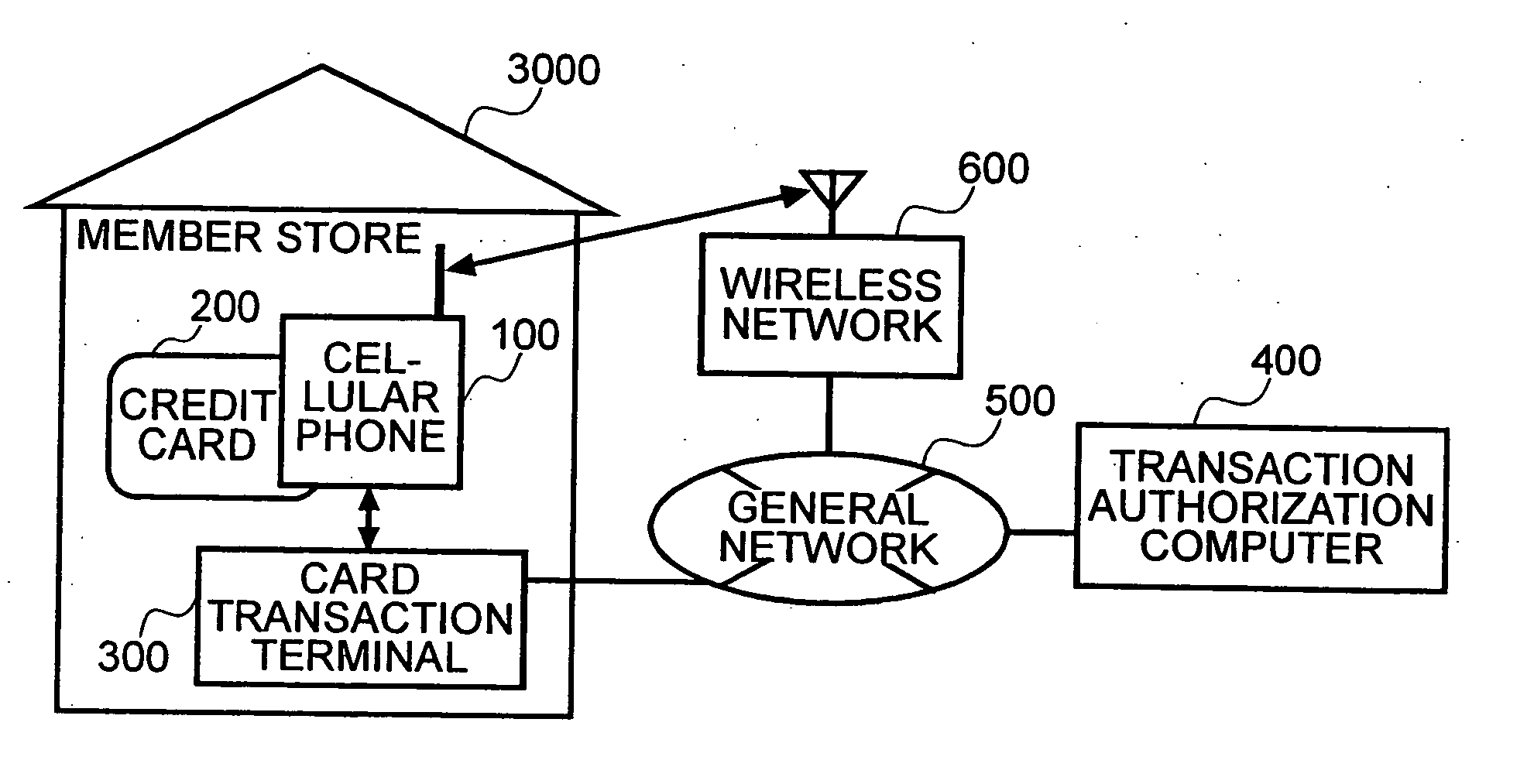
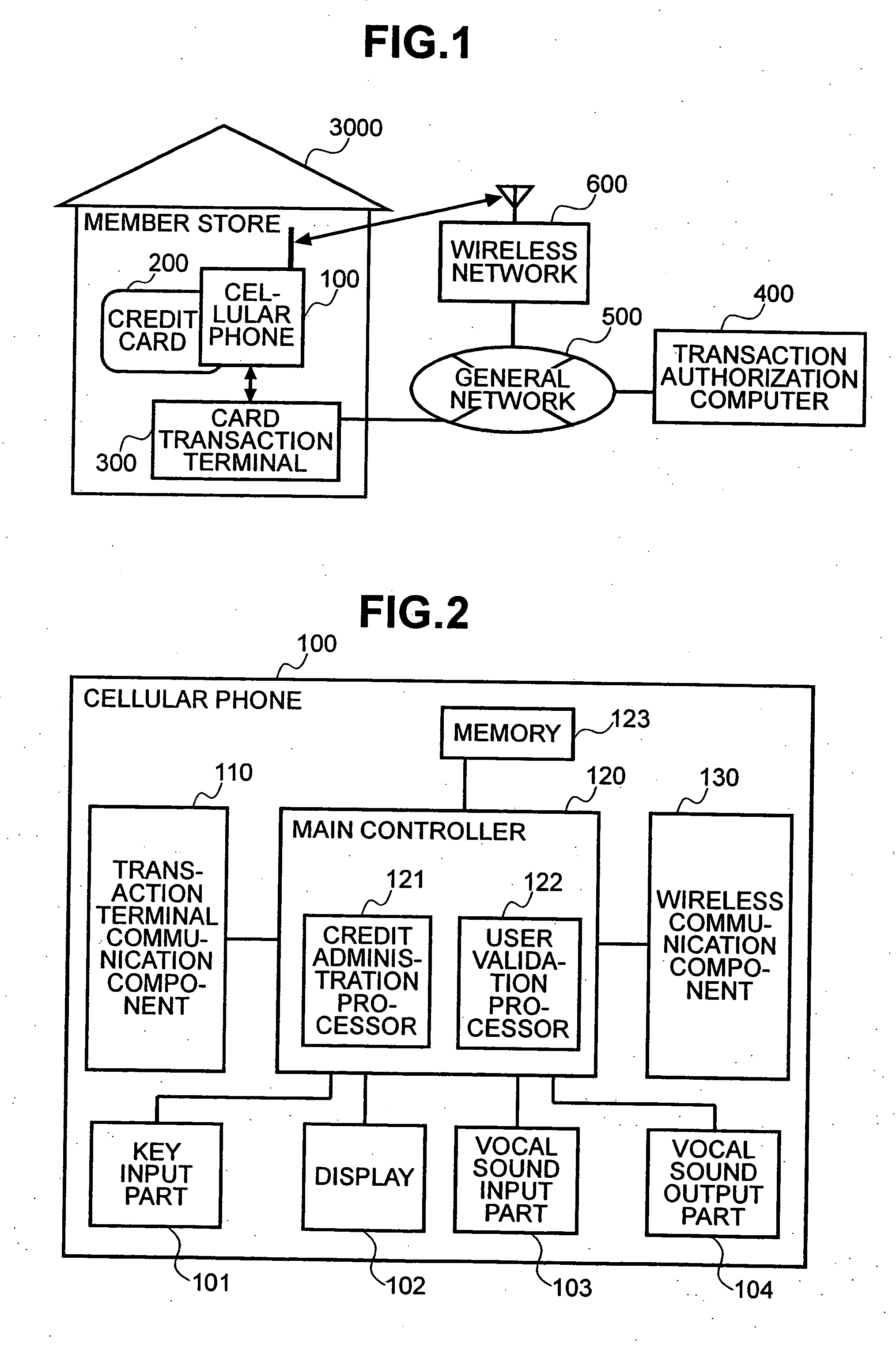
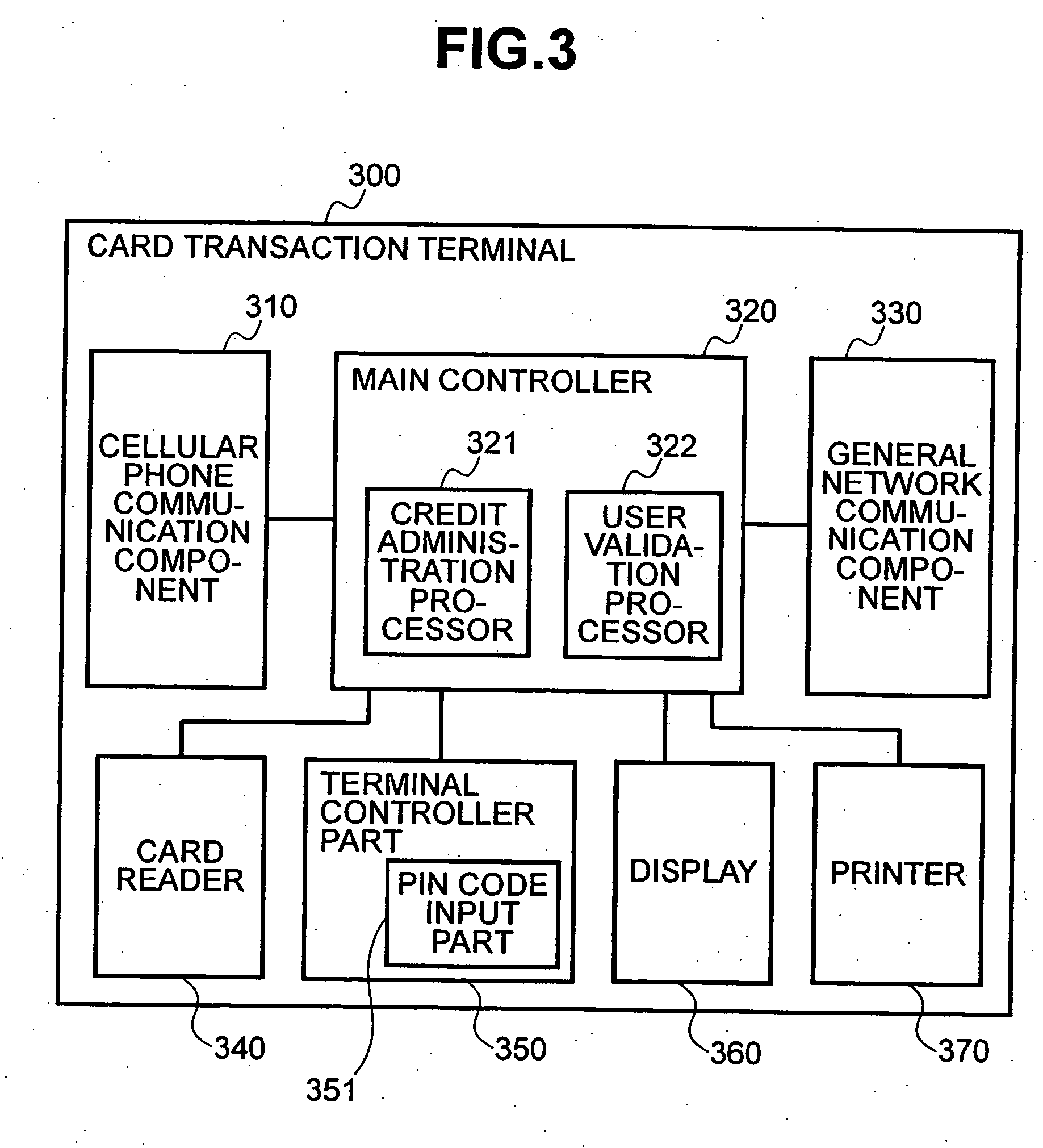
The present invention enables secure, valid card payments in credit transactions to be performed, preventing fraudulent card use even in cases of loss or theft of a card or of information theft. During a transaction authorization process using a transaction terminal disposed in a credit transaction member store and connected with a host computer, user validation or credit administration is carried out by using a portable communication terminal to input to the host computer identity information which has been previously registered in the portable communication terminal and / or location information for the portable communication terminal.
Owner:MAXELL HLDG LTD
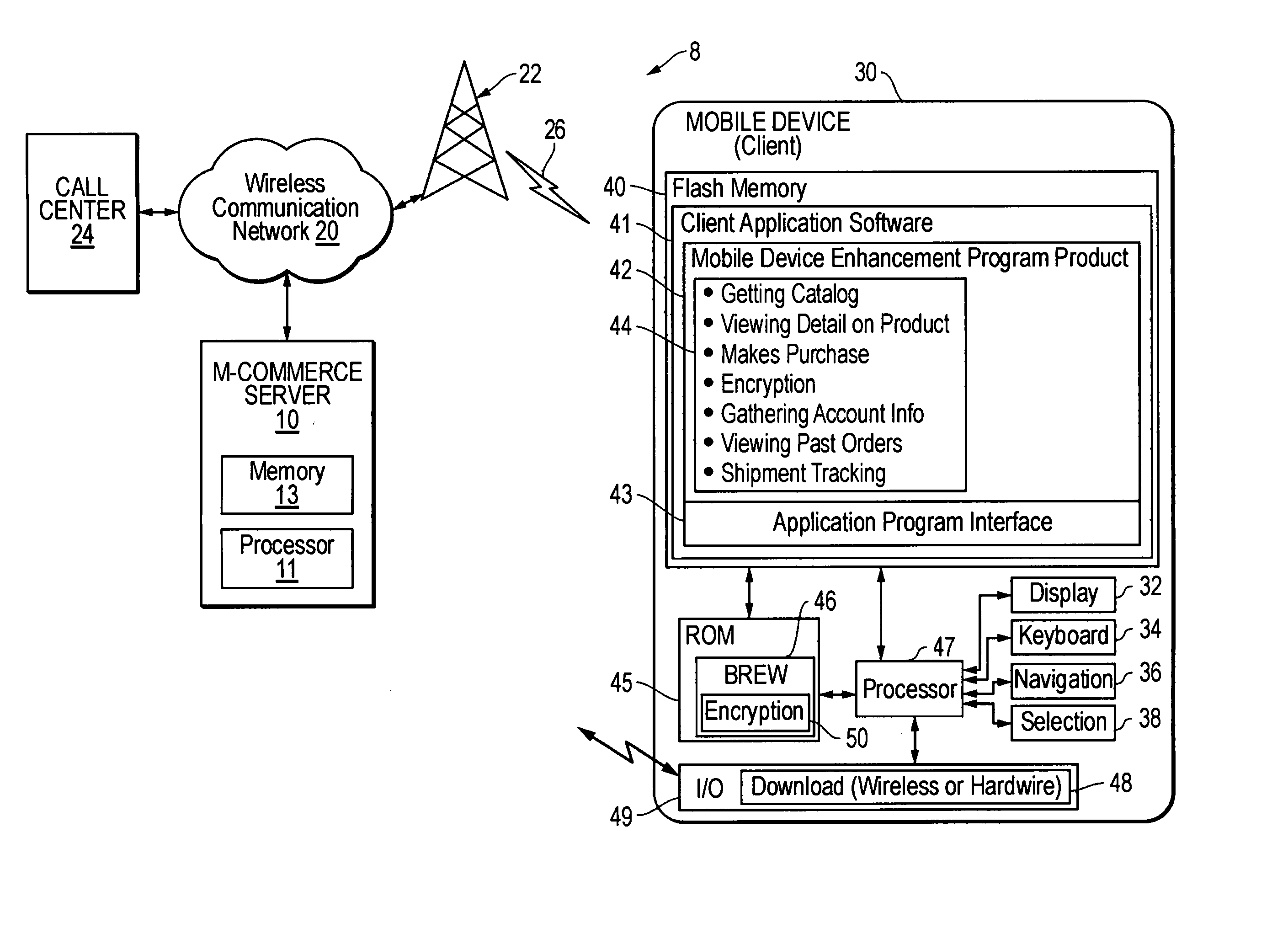
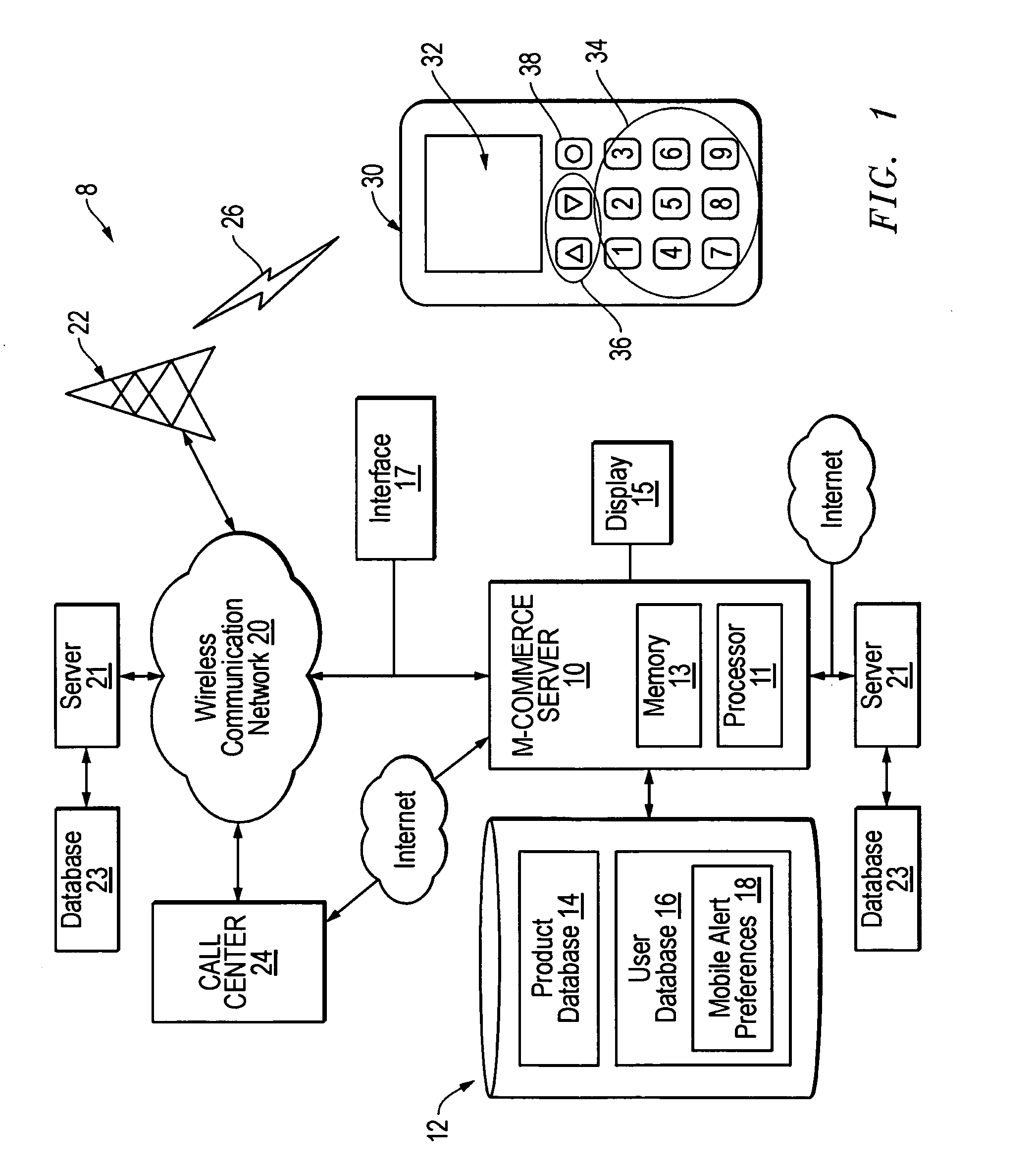
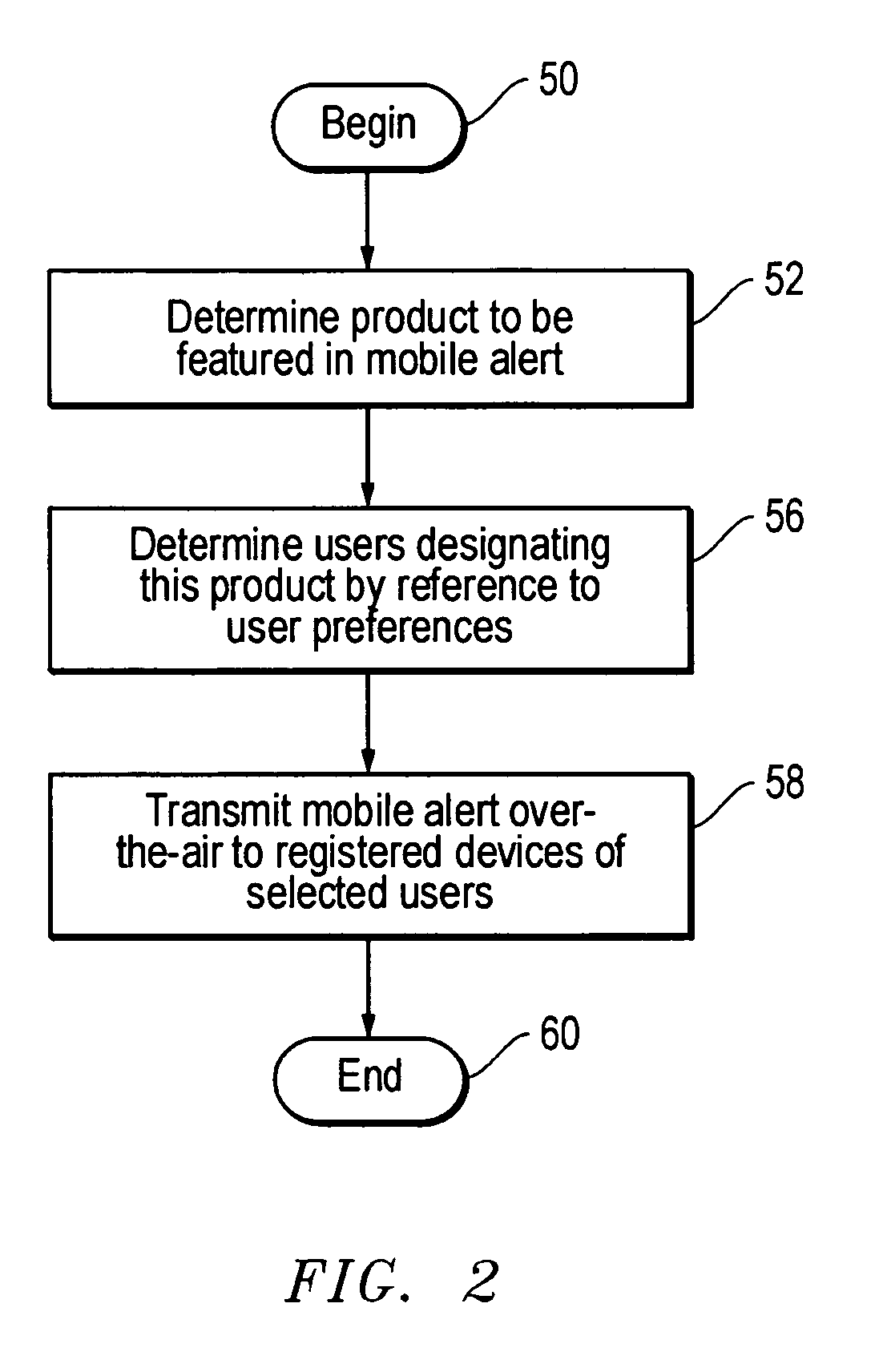
Method, system and program product for communicating e-commerce content over-the-air to mobile devices
InactiveUS20050131837A1Easy to optimizeFacilitating wireless mobile e-commerceConnection managementData switching by path configurationGraphicsService information
Product or service information in the form of selected wireless e-commerce content is transmitted from a server to a mobile device, such as mobile telephone or personal digital assistant. The e-commerce content is transmitted either in response to an explicit user request for communication of the e-commerce content, or, in the alternative, is “pushed” to the mobile device as permitted by a user but in the absence of a specific request. The e-commerce content received at the mobile device is presented to a user by the mobile device in textual or graphical format in conjunction with an indication of a communication needed to consummate an e-commerce transaction. If the user desires to purchase the good or service represented by the e-commerce content, the user initiates the communication indicated by the e-commerce content.
Owner:OVERSTOCK COM
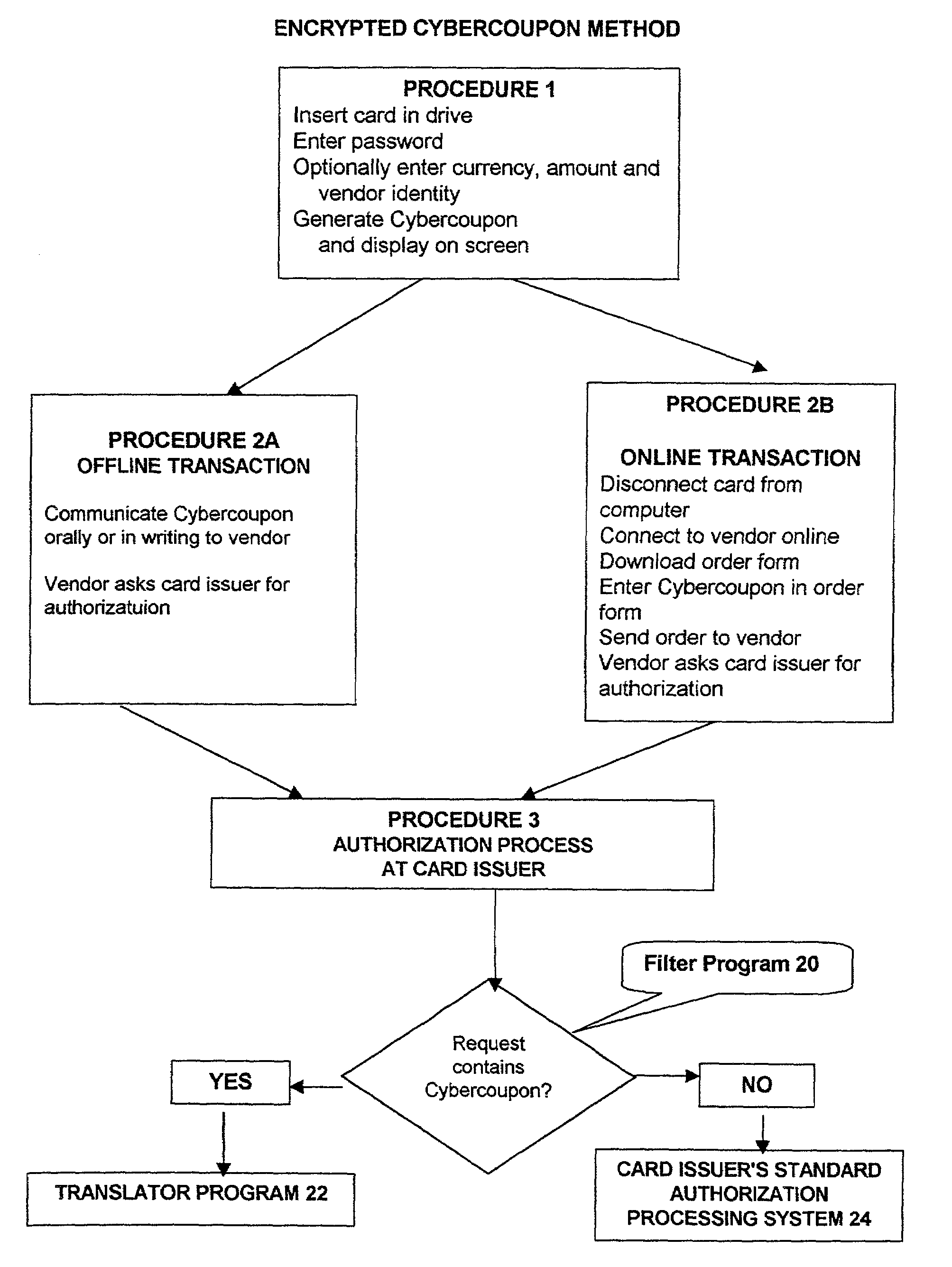
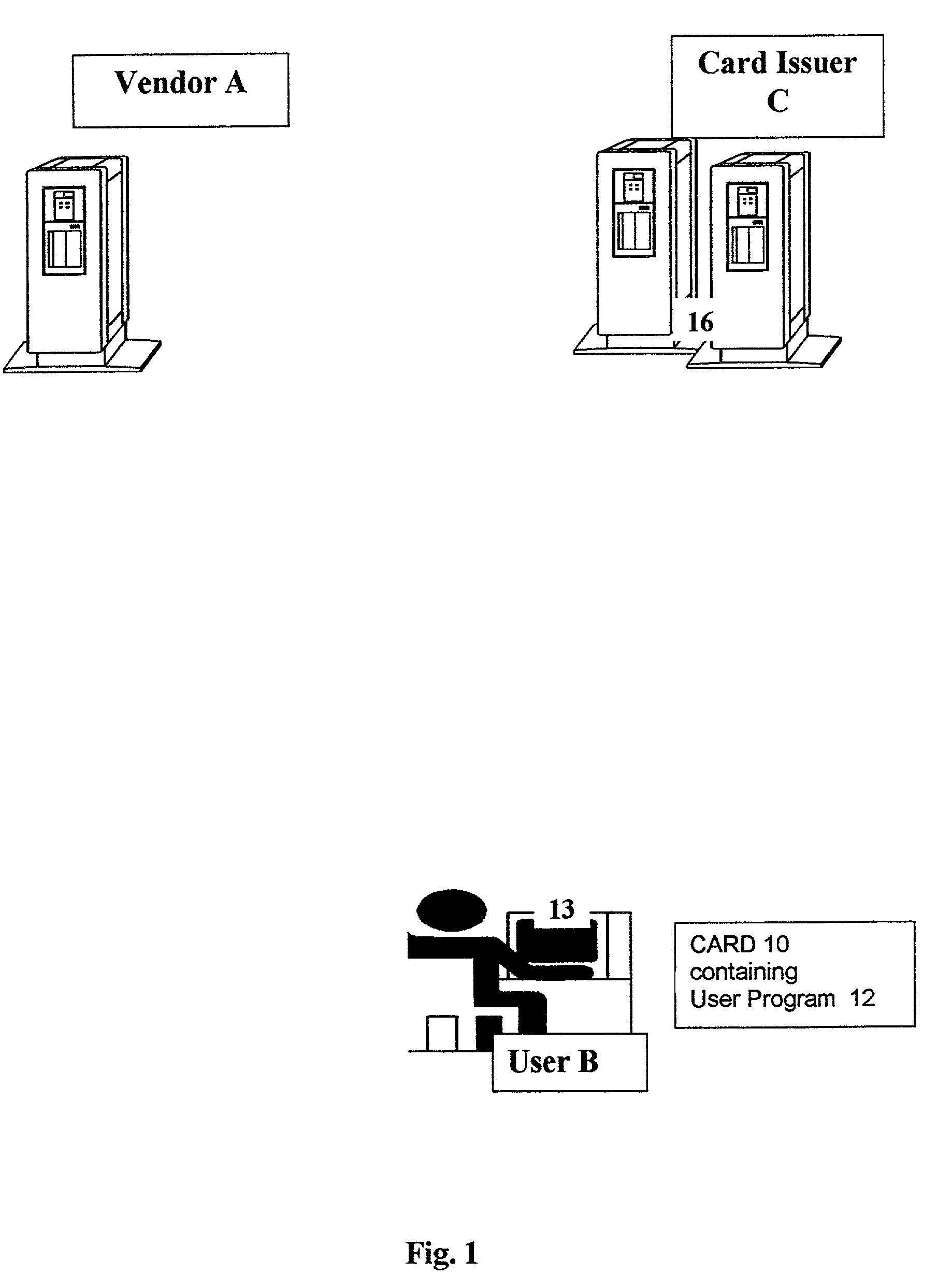
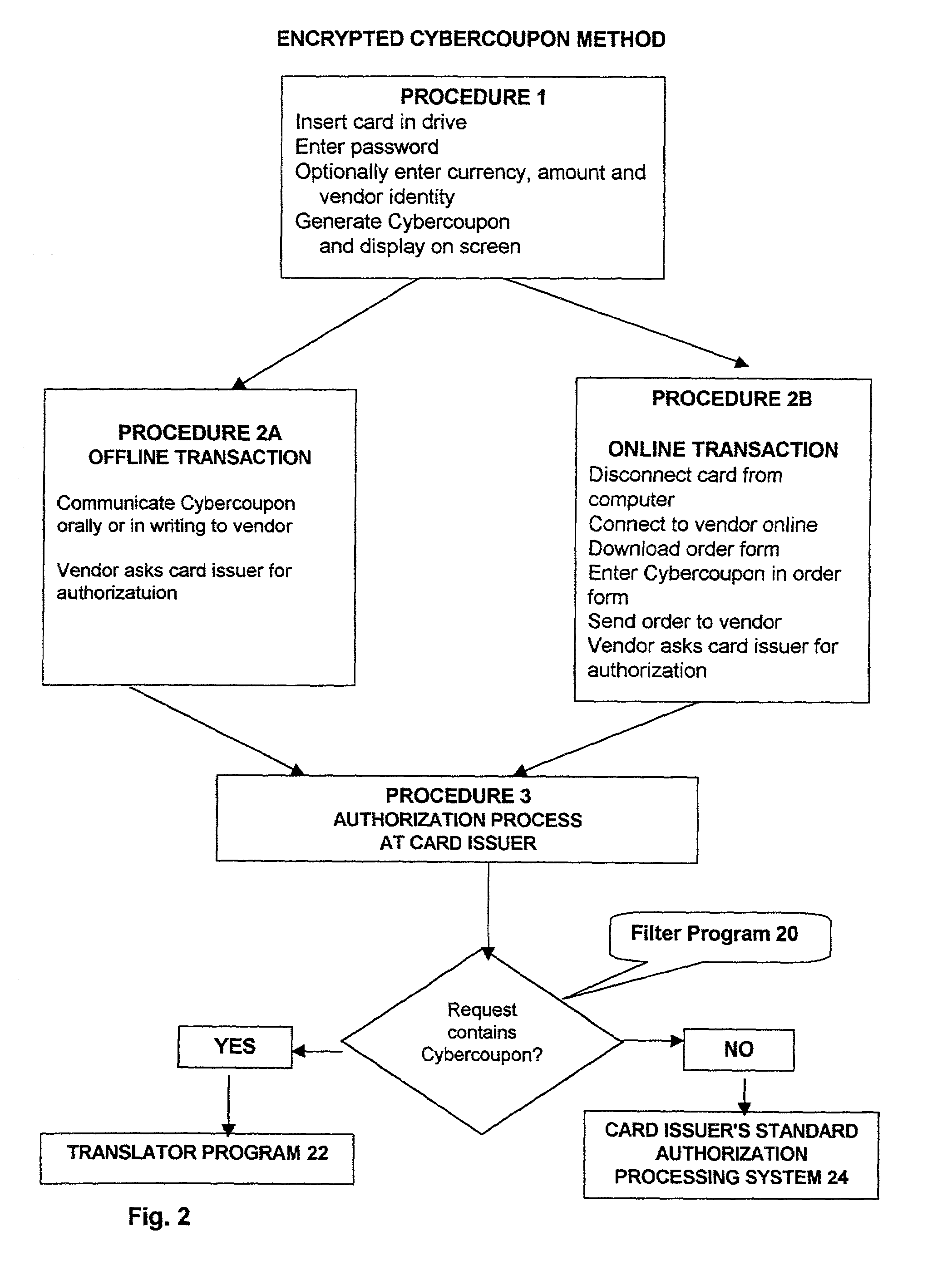
Method for preventing fraudulent use of credit cards and credit card information, and for preventing unauthorized access to restricted physical and virtual sites
InactiveUS7003501B2Preventing fraudulent card transactionOvercome disadvantagesPublic key for secure communicationSecret communicationComputer hardwareCredit card
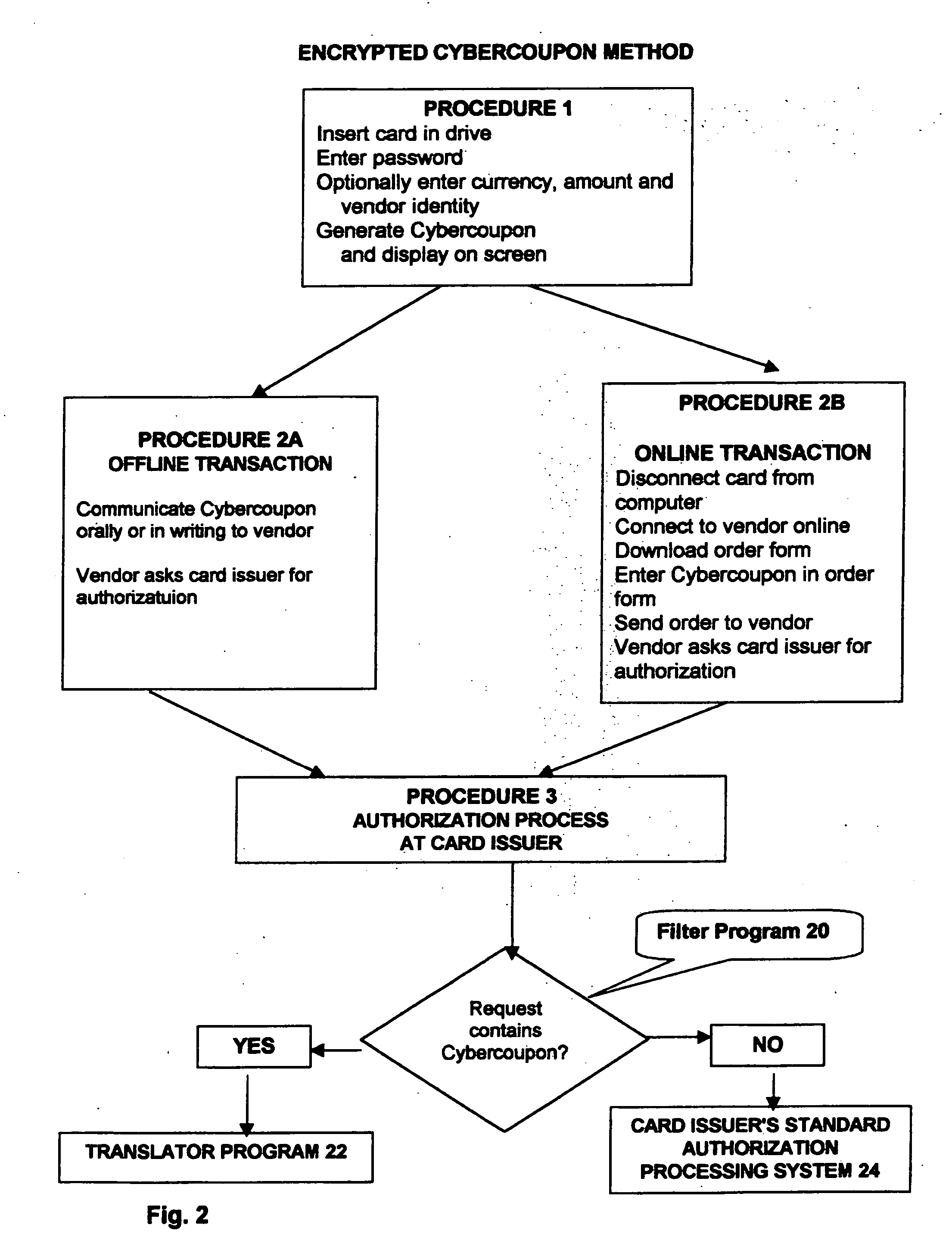
A method and a system for enabling secure authentication of a user in a computerized card access transaction. A card, identified by an identification number is issued to the user, containing software for generating a surrogate number referred to as a Cybercoupon for use in place of the regular card number. Online intrusion is avoided and the system is rendered portable for use on any computer equipped with a compatible operating system, by avoiding storage of any part of the system on the user's computer, placing the entire system instead on the card itself. The card contains advertising which appears on the user's computer screen. The card is protected by a password. If an incorrect password is entered more than a preset number of times, an “alert” Cybercoupon is generated containing a code advising the card issuer that an irregular attempt has been made to access the card.
Owner:OSTROFF MAURICE
Method and system to prevent fraudulent payment in credit/debit card transactions, and terminals therefor
InactiveUS20050242173A1Transaction can be blockedEliminate dangerBuying/selling/leasing transactionsVerifying markings correctnessUser verificationComputer terminal
The present invention enables secure, valid card payments in credit transactions to be performed, preventing fraudulent card use even in cases of loss or theft of a card or of information theft. During a transaction authorization process using a transaction terminal disposed in a credit transaction member store and connected with a host computer, user validation or credit administration is carried out by using a portable communication terminal to input to the host computer identity information which has been previously registered in the portable communication terminal and / or location information for the portable communication terminal.
Owner:MAXELL HLDG LTD
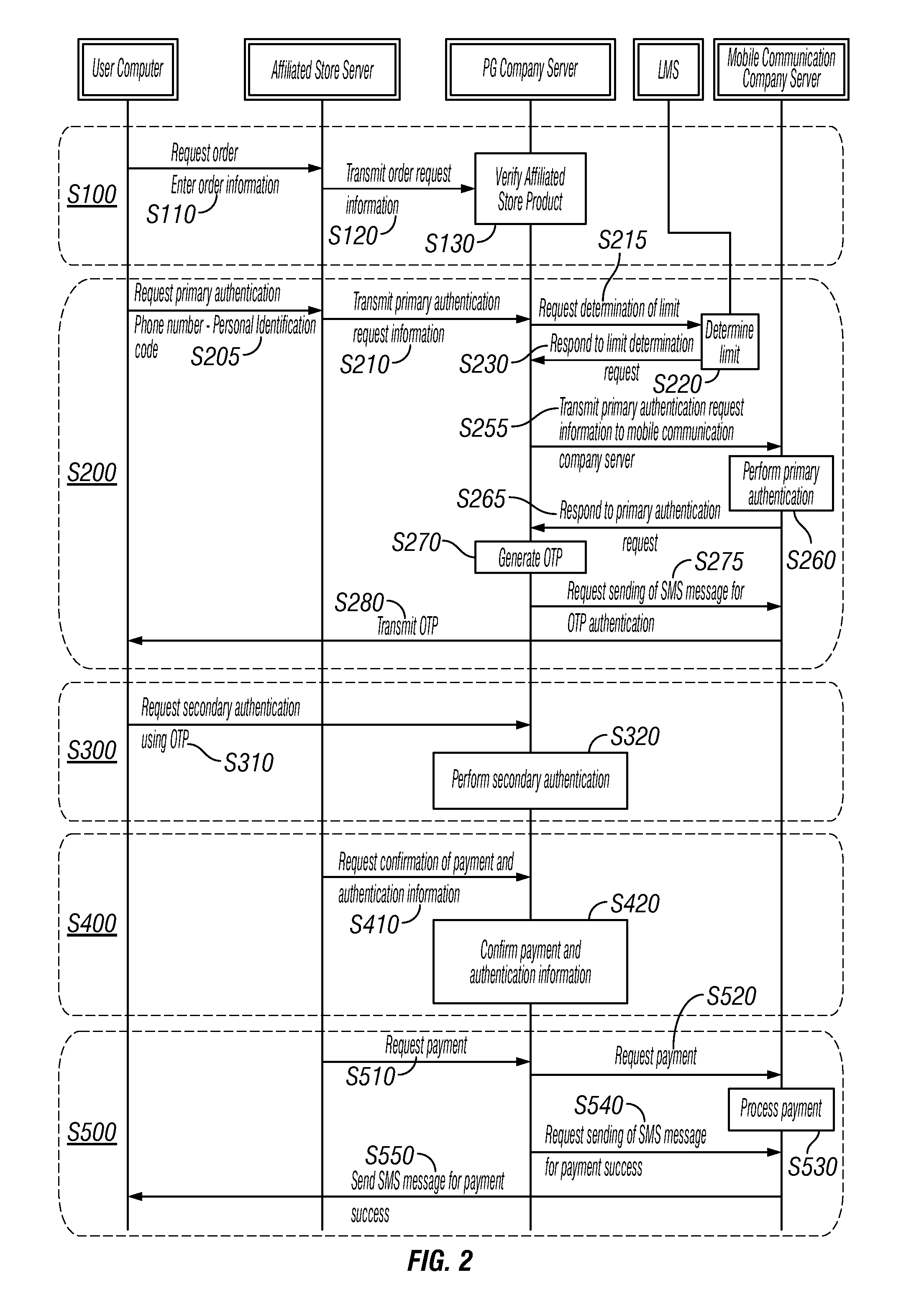
Multi-Step Authentication-Based Electronic Payment Method Using Mobile Terminal
ActiveUS20110082767A1Improve securityImprove user convenienceFinanceDigital data processing detailsPaymentComputer terminal
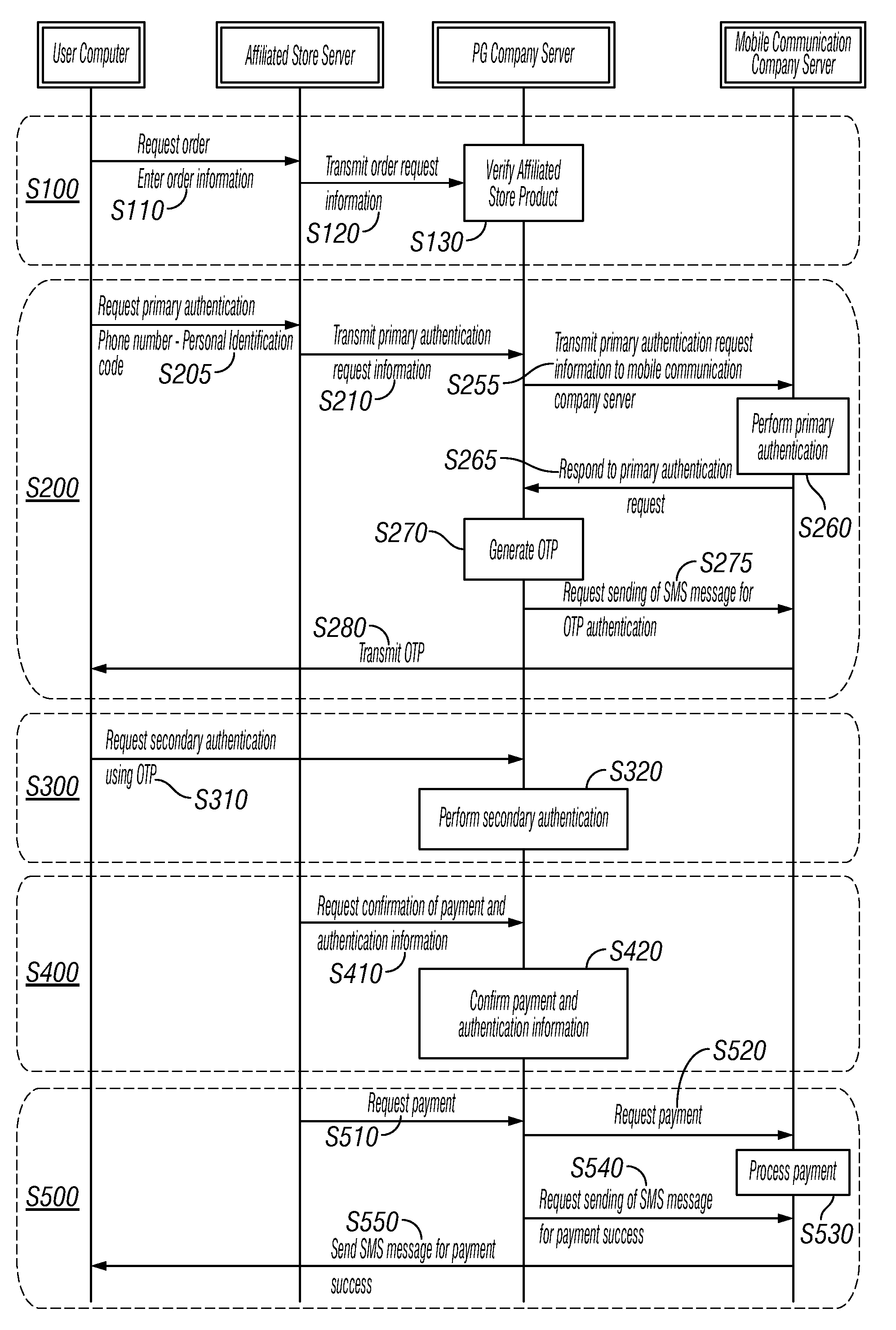
Disclosed herein is a multi-step authentication-based electronic payment method using a mobile terminal. Order request information of a product is sequentially transmitted to an affiliated store server and a PG company server, and the product and a relevant affiliated store are verified. A mobile communication company server primarily authenticates the user, and the PG company server generates an OTP. The OTP is transmitted to allow the PG company server to secondarily authenticate the user using the OTP. The affiliated store server requests the PG company server to confirm information about a payment for the product and to information about authentication of the user, and the PG company server confirms payment and authentication information. The affiliated store server requests the PG company server to process payment for the product, the PG company server requests the mobile communication company server to process payment, and the mobile communication company server processes requested payment.
Owner:DANAL
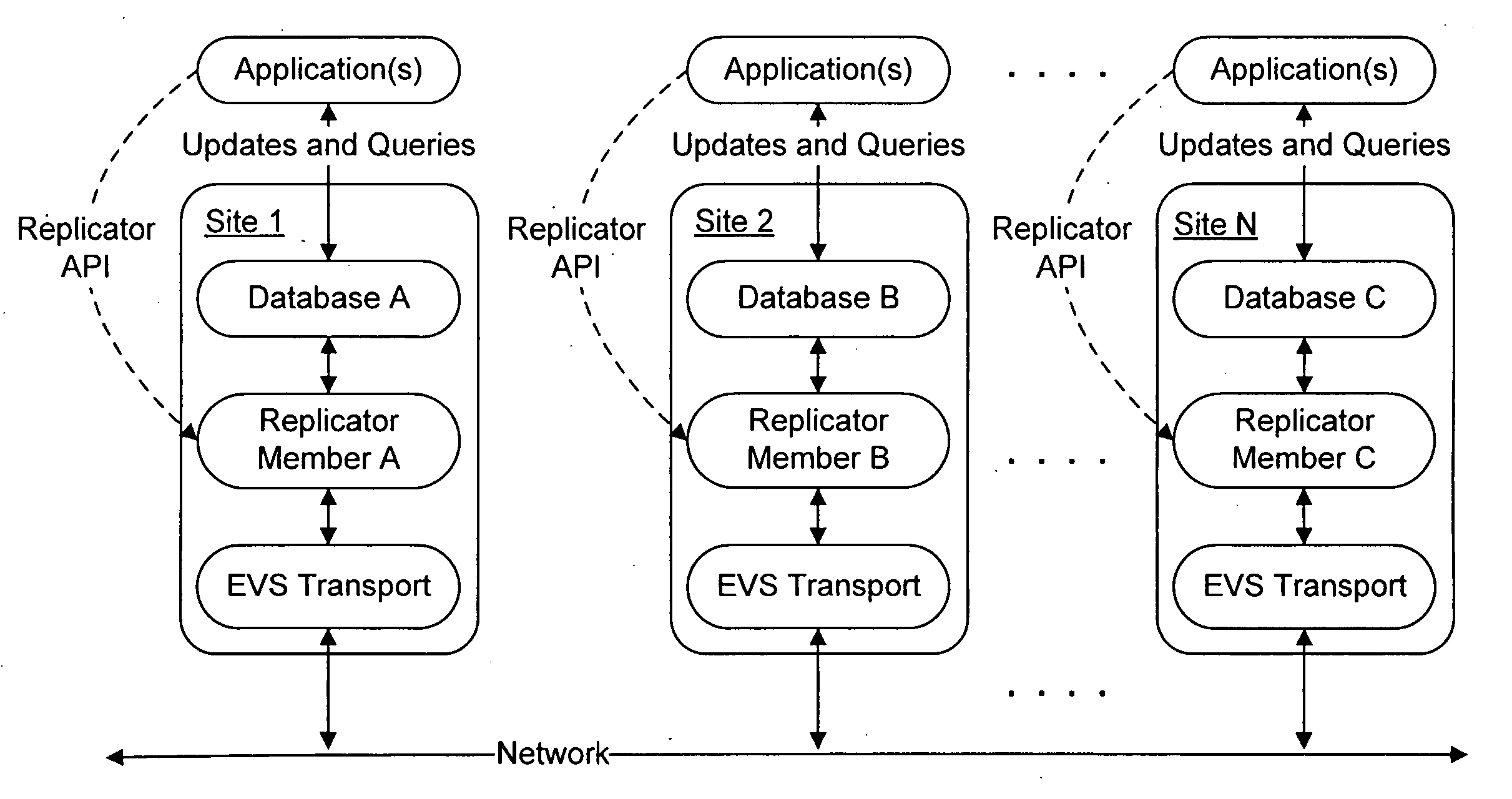
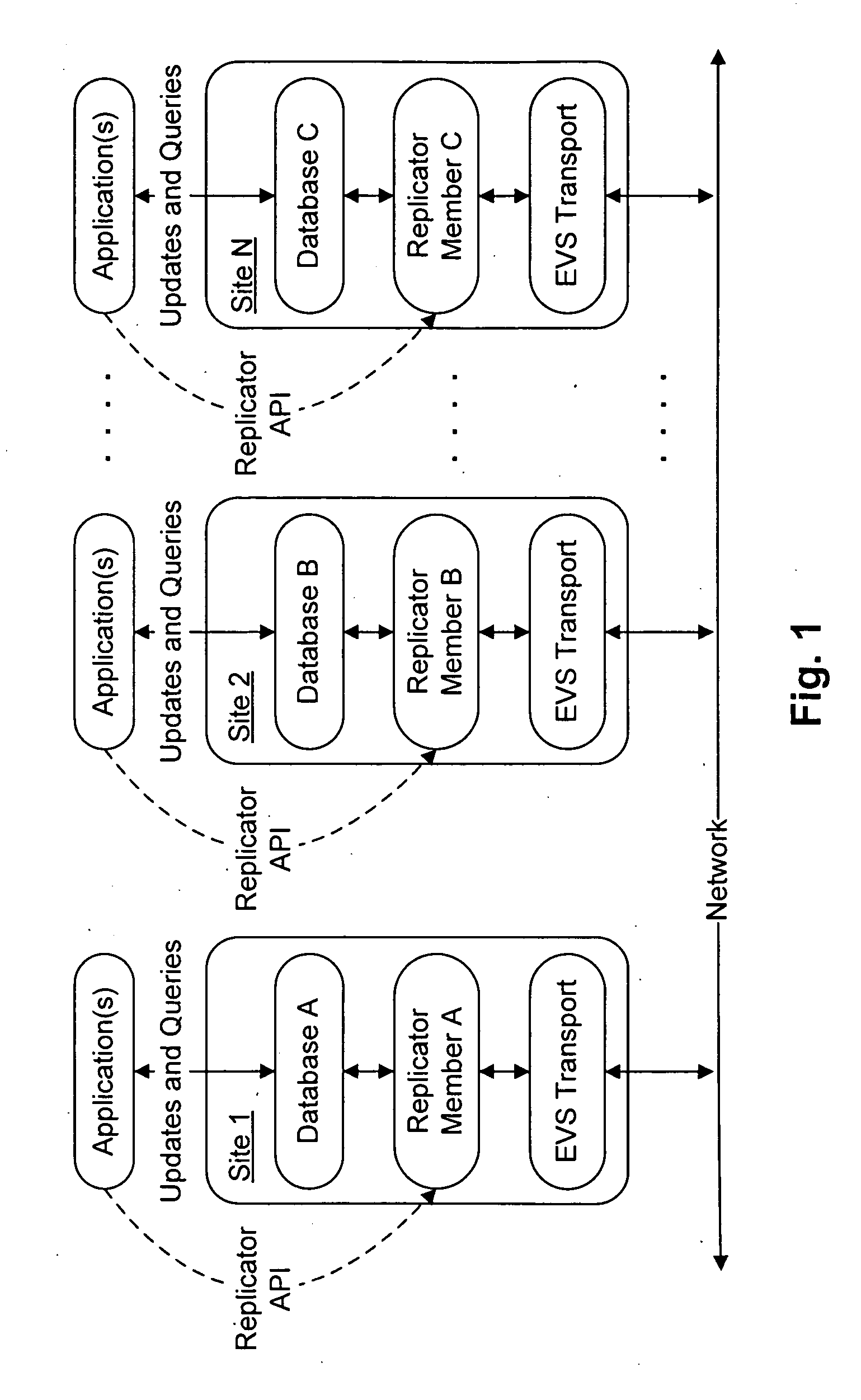
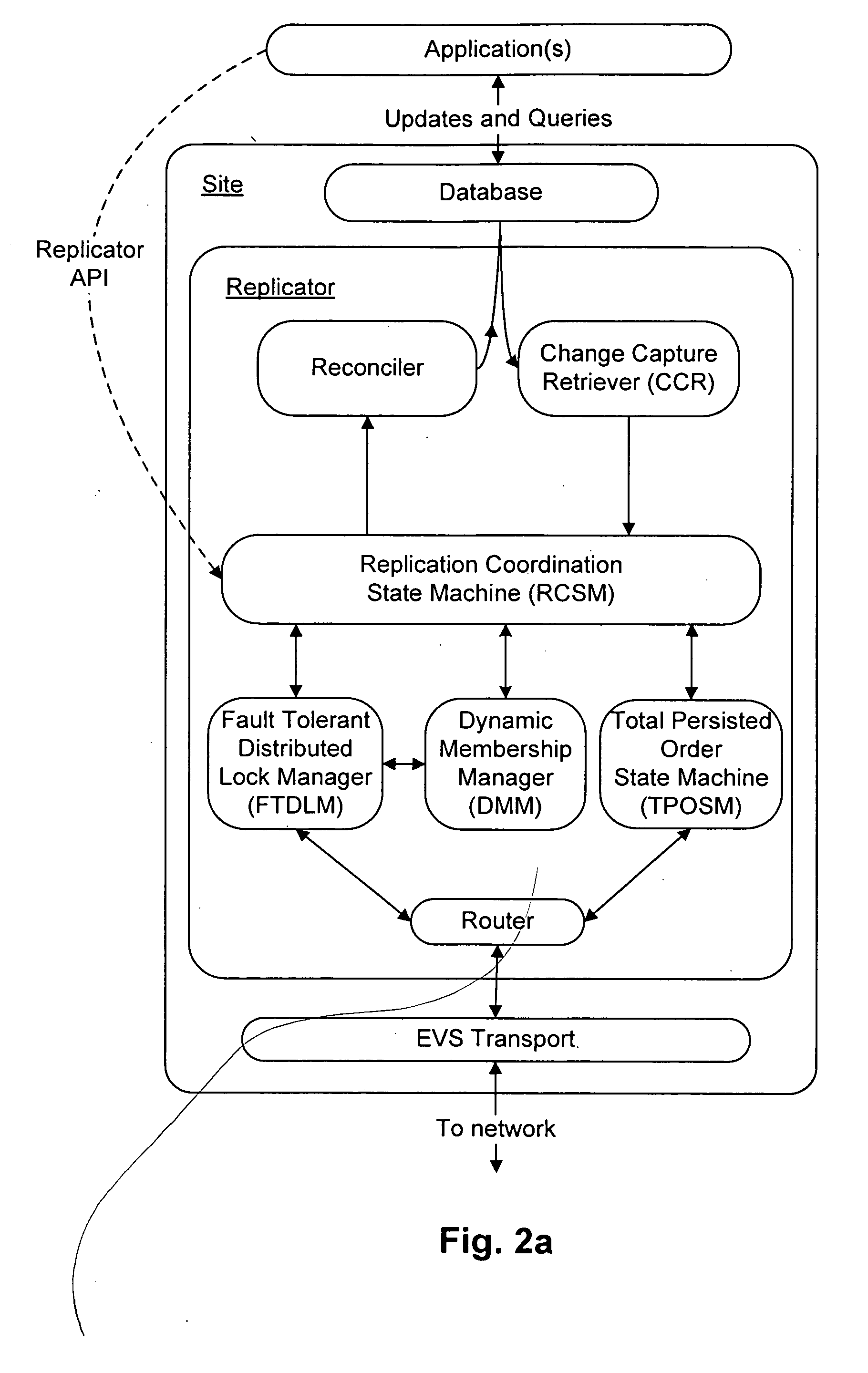
Dynamic membership management in a distributed system
ActiveUS20060235889A1Resolve differencesAvoid actionDigital data information retrievalDigital data processing detailsDistributed computingManagement system
Transactional database replication techniques are disclosed that do not require altering of the database management system implementation. A replicator module includes a dynamic membership manager, which is configured to manage the persistent membership of a coordination group. The persistent membership can be, for example, a durable set of sites that can replicate changes amongst themselves. Changes from sites not in the persistent membership are discarded. The set of recovered members is a subset of the persistent membership. The persistent membership changes incrementally by either removing or adding members. Failed members may still be part of the persistent membership. The dynamic membership manager module manages the modification of the persistent membership, initialization of replicas, and propagation of membership information.
Owner:PROGRESS SOFTWARE
Apparatus and method for secure credit card processing infrastructure
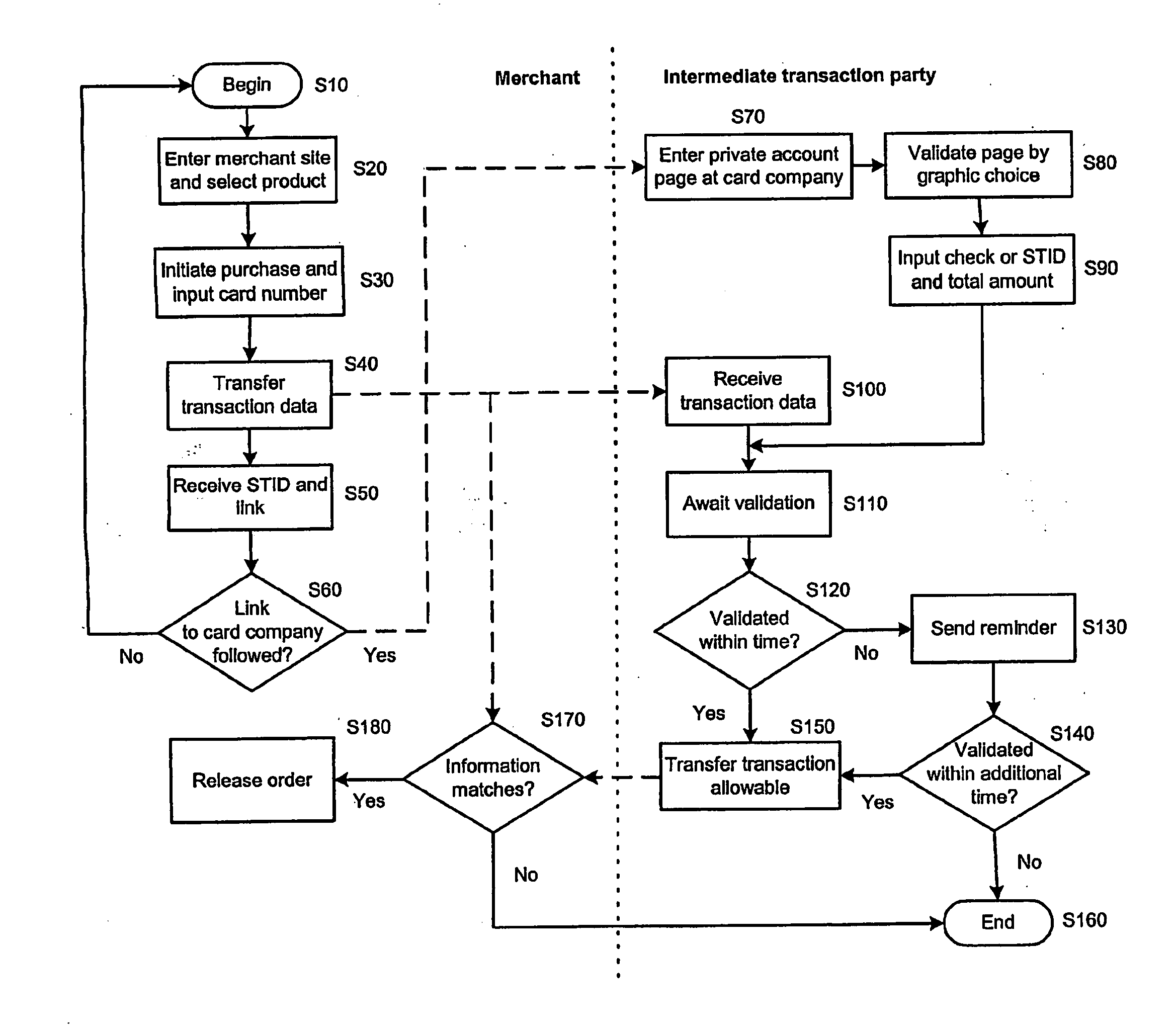
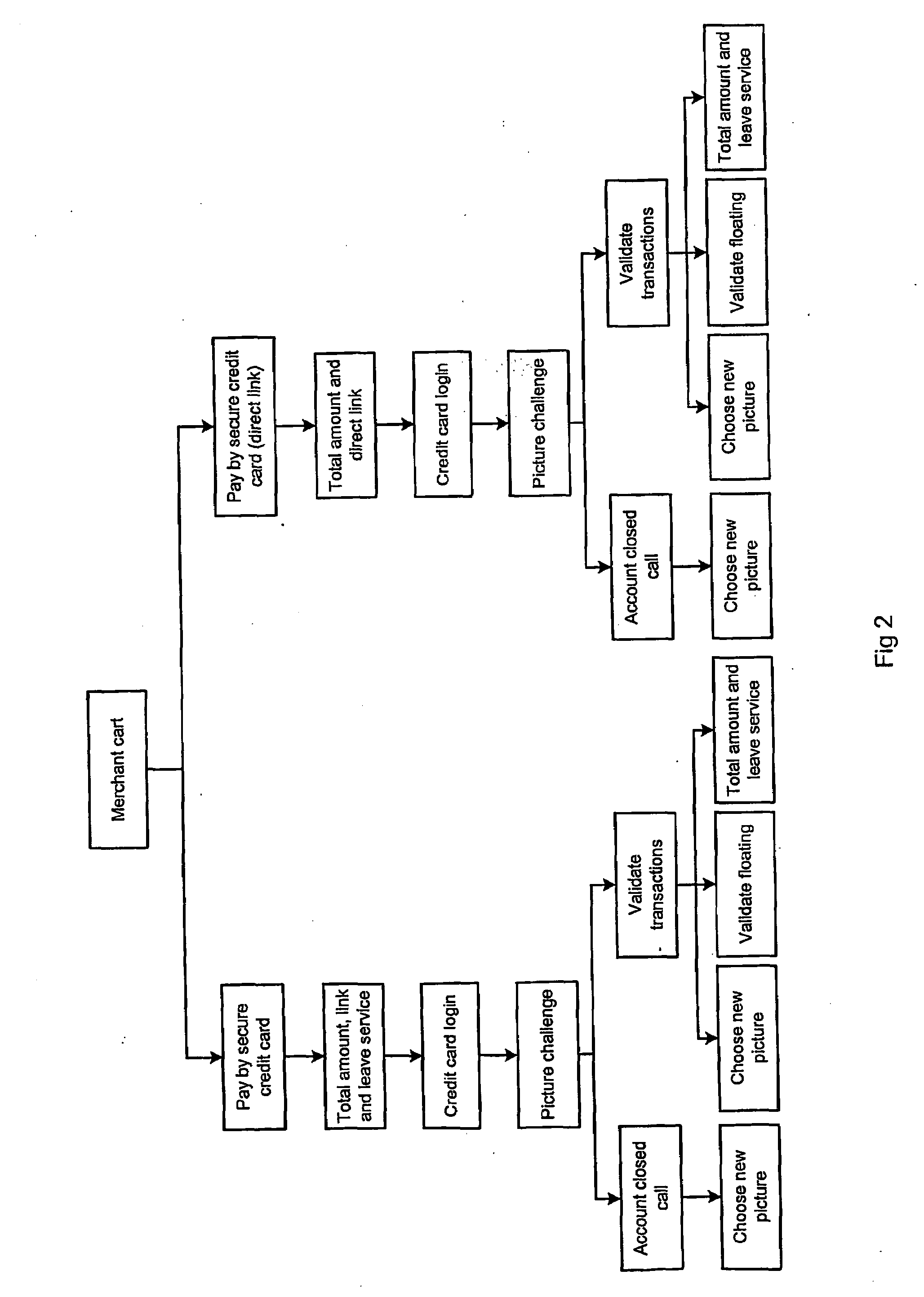
InactiveUS20090132413A1Good Privacy-aImprove securityFinanceDigital data processing detailsCode moduleCredit card
The present invention relates to an apparatus and a method for secure value transactions between a customer and a merchant in a computerised environment being part of a global interconnecting network, such as the Internet. The method is adapted for utilising existing credit card processing infrastructure and includes the steps of: the customer obtaining a password, such as a PIN, from an intermediate transaction party and validating a server of the intermediate transaction party, the merchant having installed a code module function on its web-based service that generates a transaction identification number, and redirecting or presenting the customer with a link to the intermediate transaction party. The present invention is characterised by the intermediate transaction party presenting the customer with a password-protected account page to validate a purchase either by marking a correct validation or inputting the transaction identification number and amount.
Owner:RUNTIME
Method and system for preventing fraudulent use of credit cards and credit card information, and for preventing unauthorized access to restricted physical and virtual sites
InactiveUS20060190412A1Preventing fraudulent card transactionOvercome disadvantagesLock-out/secrecy provisionPayment circuitsCredit cardInternet privacy
A method and system for preventing fraudulent card transactions and unauthorized access to computers and physical and virtual sites online and offline whether or not involving payment. A physical card, identified by a unique identification number (ID) is issued to the user. The method provides a system of password-protected, single-use, disposable Cybercoupons for secure, authenticated on-line credit transactions, each of the Cybercoupons comprising a personal user identification number (ID) modified by combination with a one-time Cybercode selected from a number of numeric or alphanumeric codes allocated by a credit supplier.
Owner:OSTROFF MAURICE
Multi-step authentication-based electronic payment method using mobile terminal
ActiveUS8180686B2Improve securityConvenient electronic paymentsFinanceDigital data processing detailsPaymentAuthentication information
Disclosed herein is a multi-step authentication-based electronic payment method using a mobile terminal. Order request information of a product is sequentially transmitted to an affiliated store server and a PG company server, and the product and a relevant affiliated store are verified. A mobile communication company server primarily authenticates the user, and the PG company server generates an OTP. The OTP is transmitted to allow the PG company server to secondarily authenticate the user using the OTP. The affiliated store server requests the PG company server to confirm information about a payment for the product and information about authentication of the user, and the PG company server confirms payment and authentication information. The affiliated store server requests the PG company server to process payment for the product, the PG company server requests the mobile communication company server to process payment, and the mobile communication company server processes requested payment.
Owner:DANAL
Multilevel Authentication
ActiveUS20130067551A1Authentication be reduced eliminatedDisadvantages can be reduced eliminatedDigital data processing detailsUser identity/authority verificationInternet privacyUser input
In an exemplary embodiment, a system includes a memory operable to store a user account identifier associated with a user account and a mobile device identifier associated with a mobile device. The memory is also operable to store a first user credential and a second user credential, the second user credential, wherein the second user credential comprises user input data captured by a sensor. The system includes a network interface operable to receive a request to authenticate a requesting user. The system also includes a processor operable to determine information included in the request to facilitate authentication of the requesting user and whether the information included in the request matches the information associated with the user account. The processor is further operable to authenticate the requesting user if the request is associated with the user account and information included in the request matches the information associated with the user account.
Owner:BANK OF AMERICA CORP
Offline to online payment
InactiveUS20120078789A1Accelerating transactionTransaction can be blockedFinanceProtocol authorisationTelephonyOnline payment
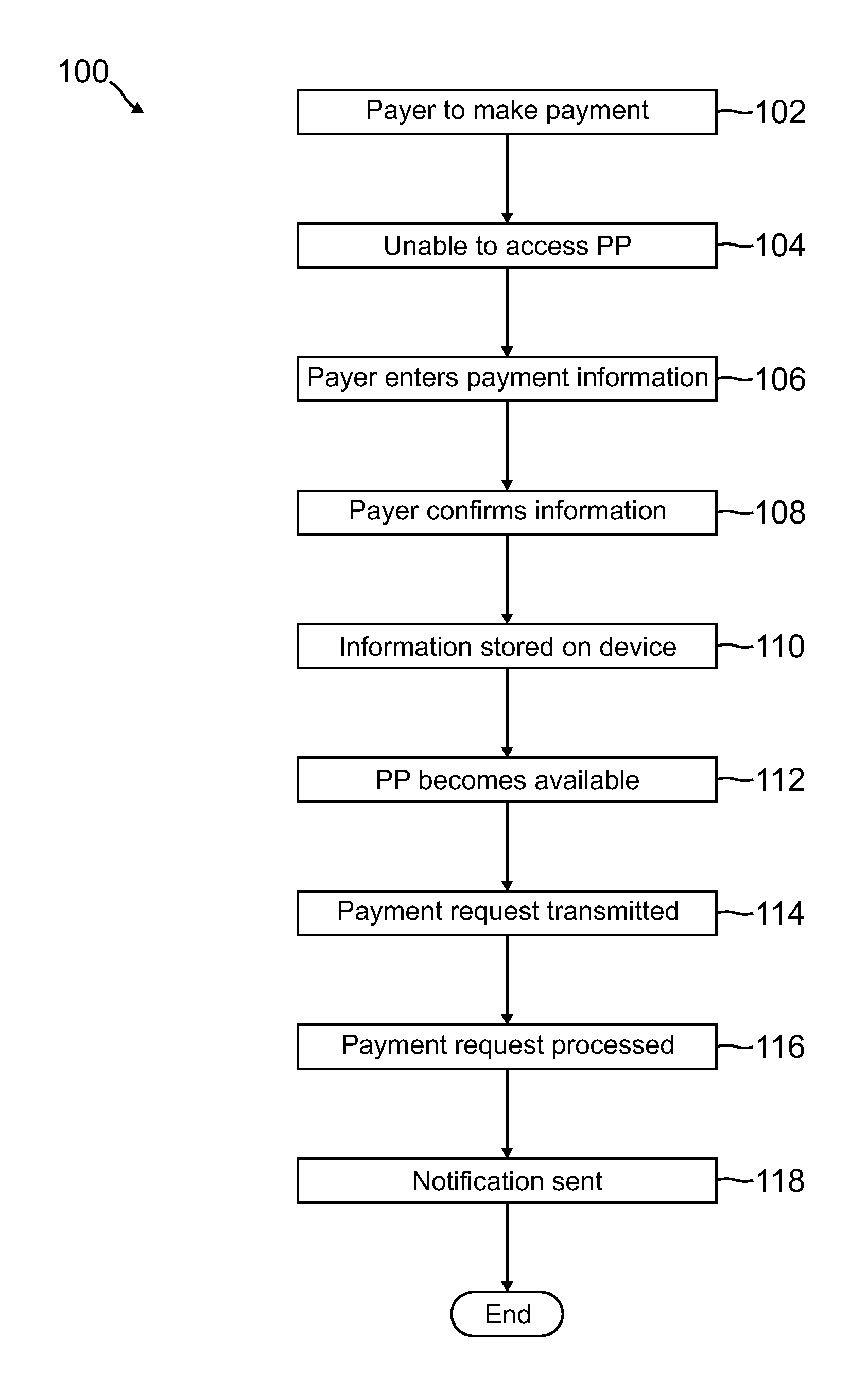
A payer submits a payment request when there has been no connection established with an online payment provider. The payment request is stored on the payer's device, such as a phone, and is transmitted to the payment provider when a connection is established. The payer can submit a plurality of offline payment requests, all of which can be transmitted and processed when received by the payment provider.
Owner:PAYPAL INC
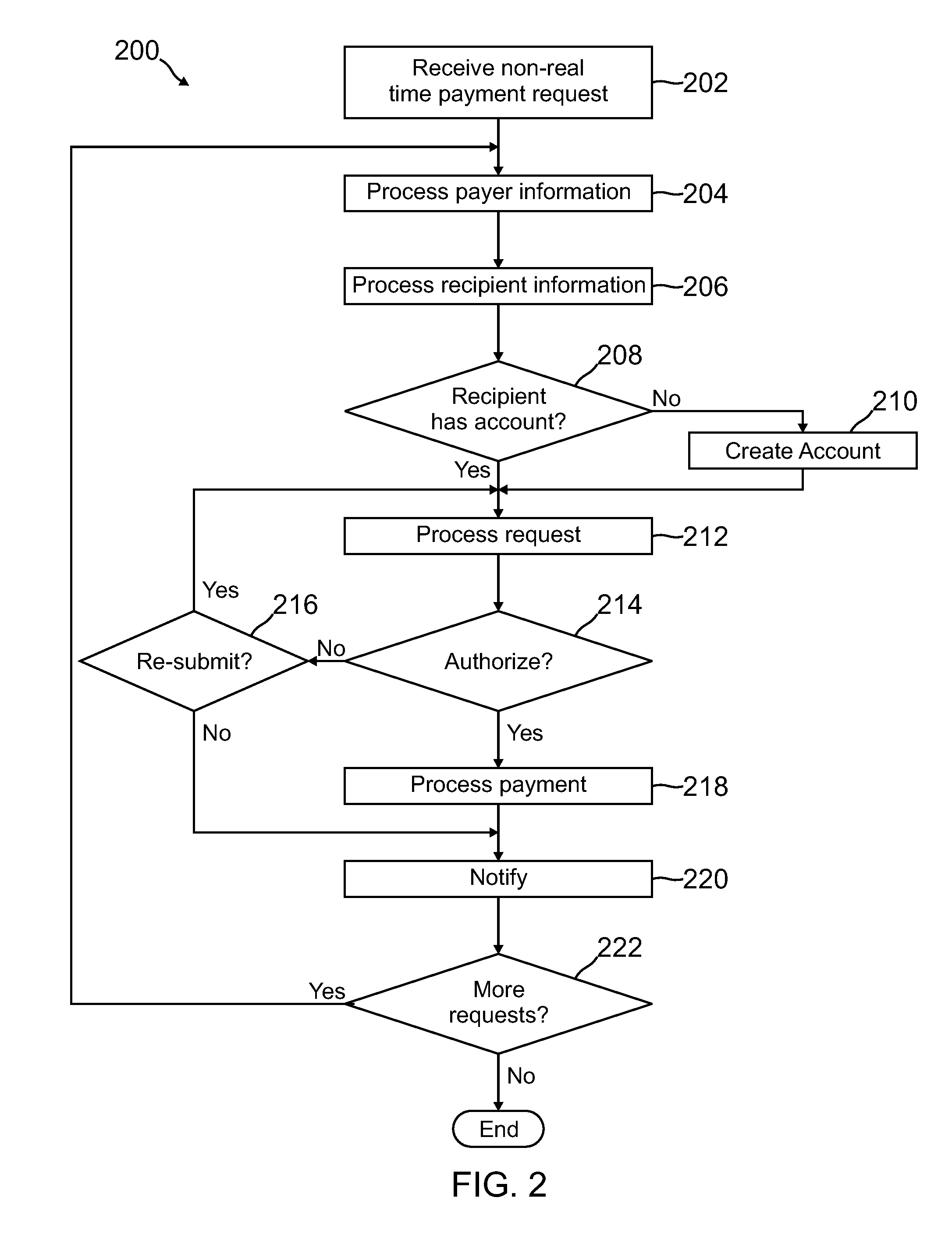
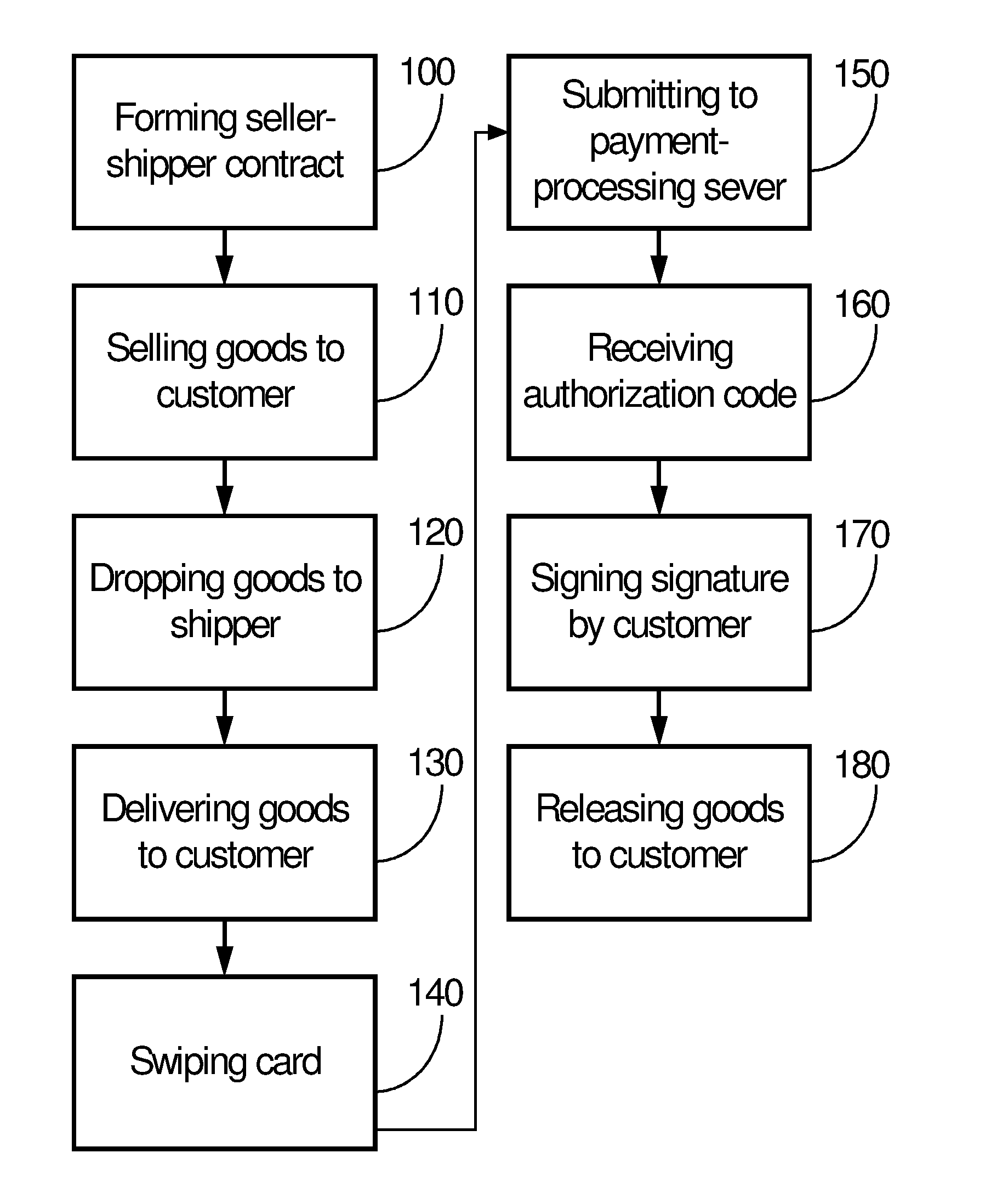
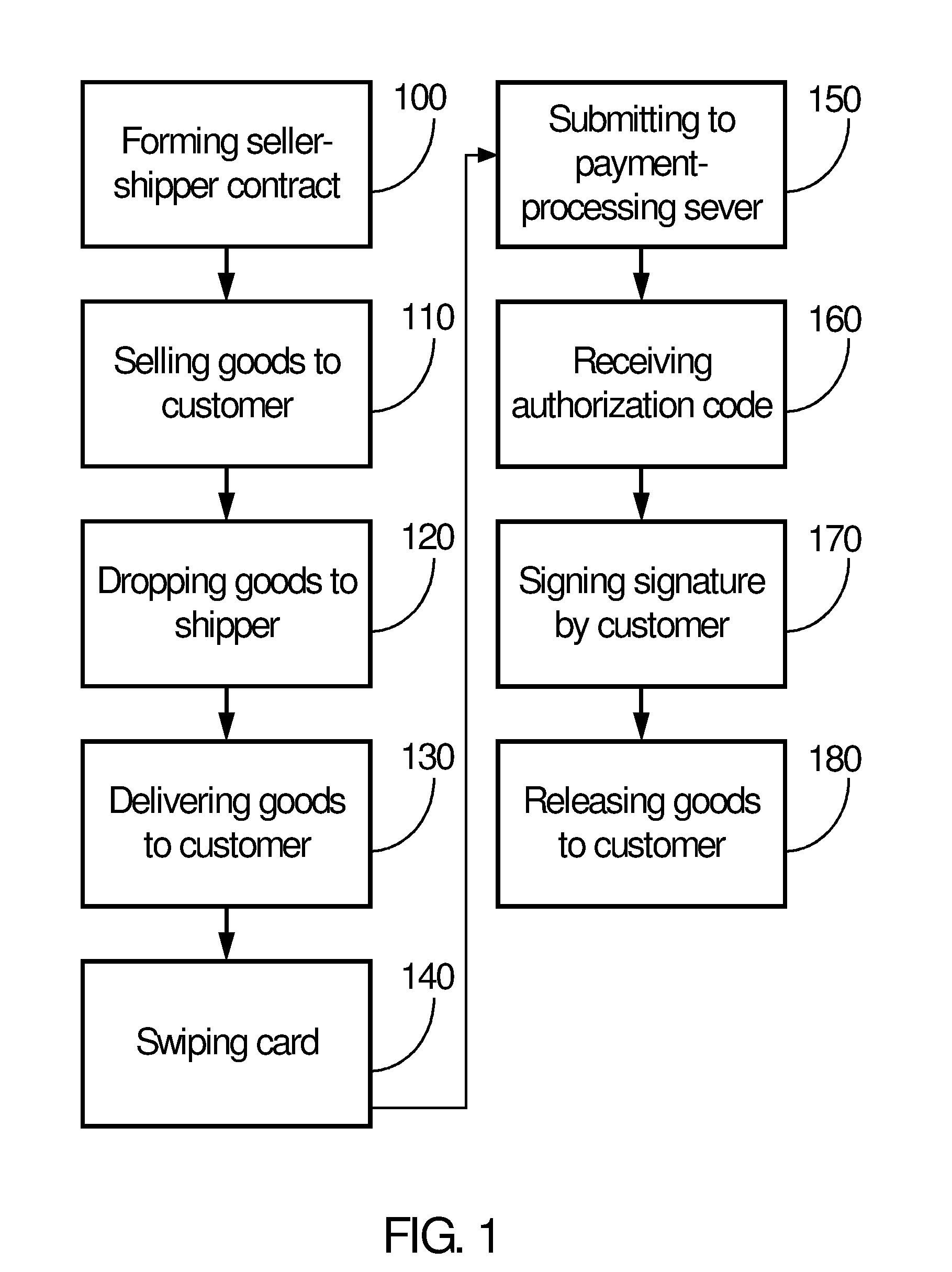
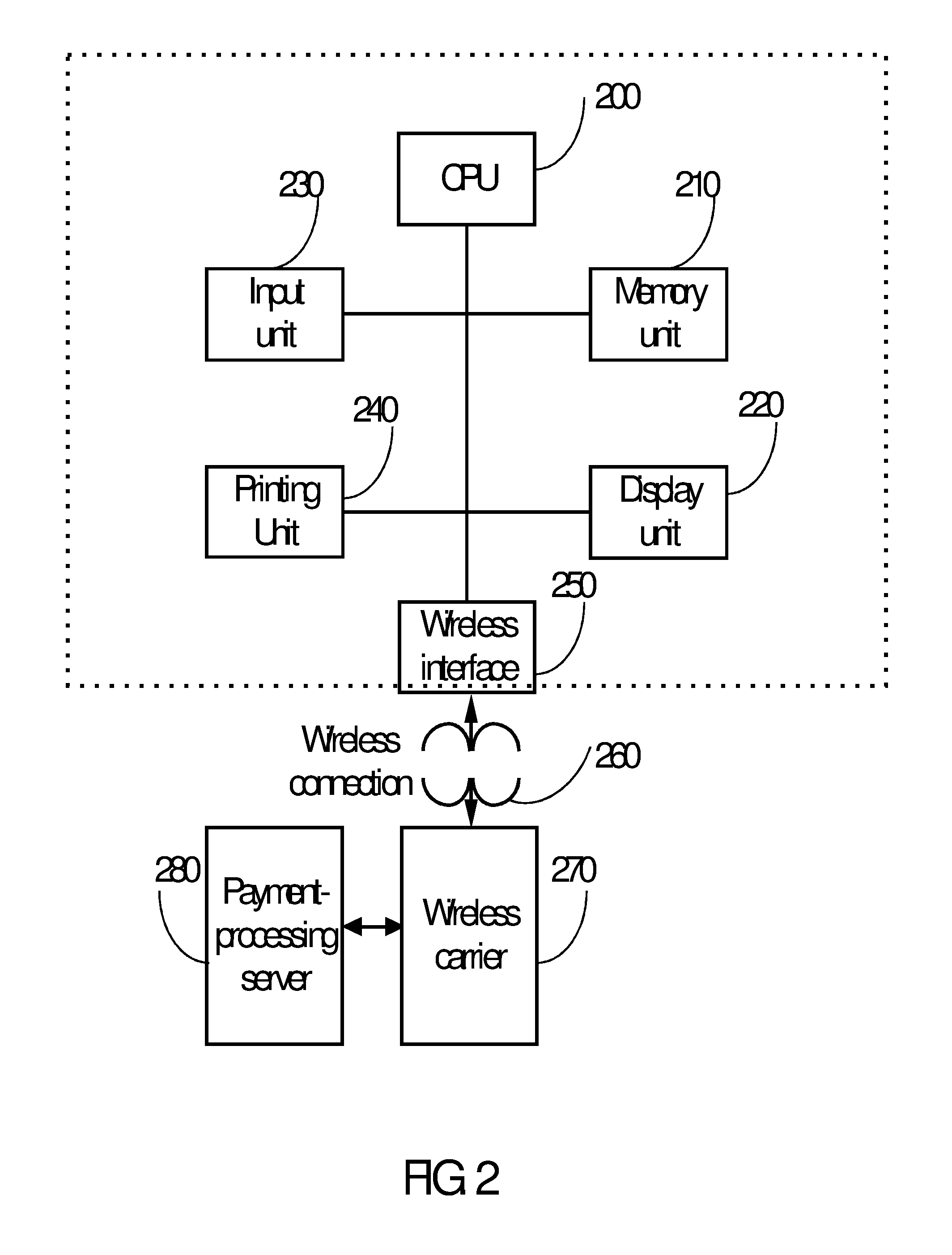
Method of processing credit payments at delivery
InactiveUS20060004658A1Lower costConvenient methodAcutation objectsFinanceHand held devicesDebit card
A method of processing signature-required payment using a handheld device with a wireless access capability is disclosed. When a consumer buys goods from a seller, the seller and consumer agree on the amount of payment and acceptable payment species. The delivery person of the shipper who delivers the goods on behalf of the seller processes the payment using customer's credit / debit card and a cellular phone or handheld device at the door of the customer. Upon approval of the payment, the delivery person releases the goods to the customer.
Owner:HYPERCOM CORP
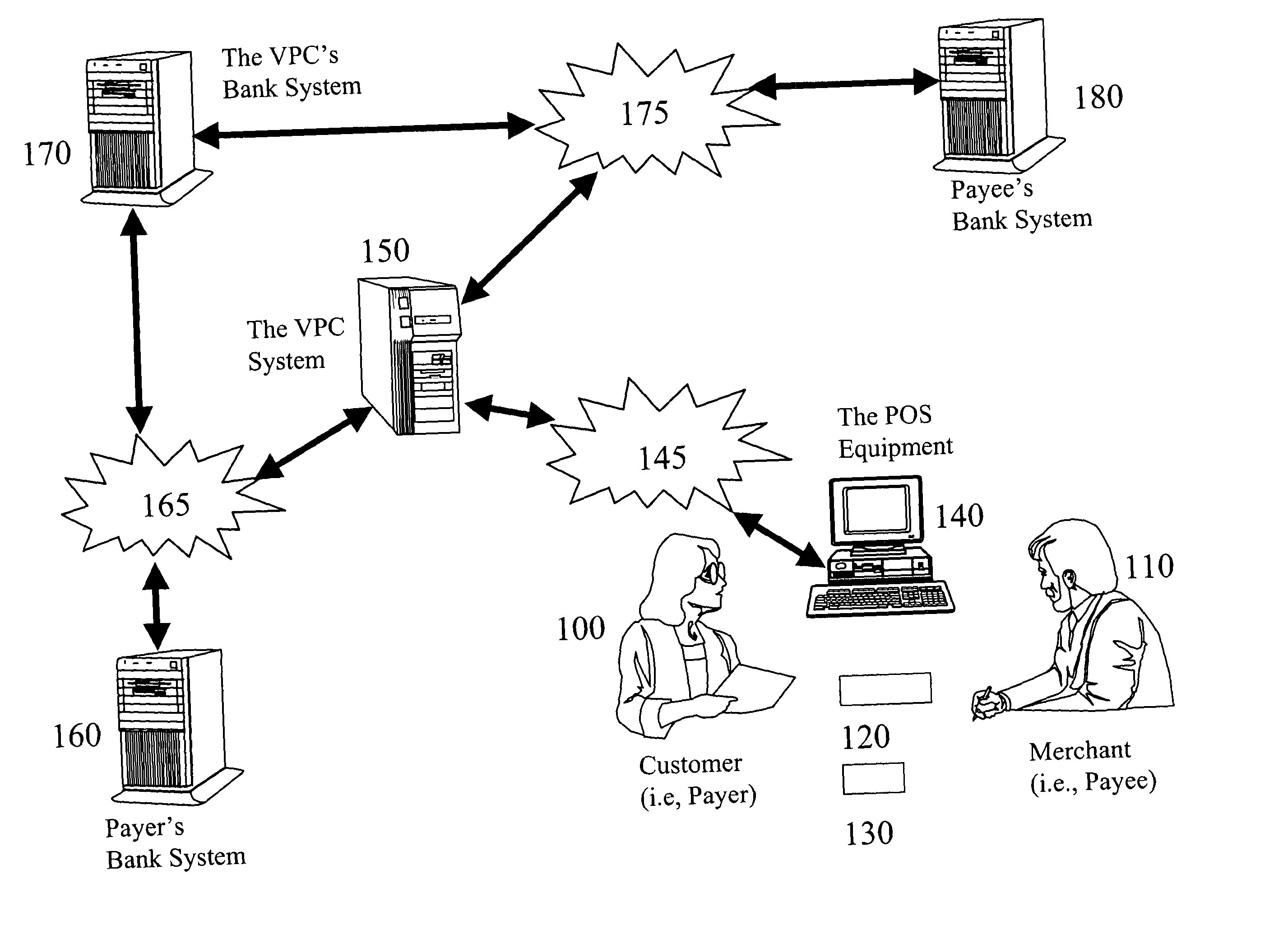
Anti-fraud POS transaction system
InactiveUS20040138955A1Reducing resultant financial lossReduce fraudPayment circuitsPoint-of-sale network systemsPayment transactionDebit card
Anti-fraud measures are provided for a point-of-sale transaction using various consumer-oriented financial instruments such as credit cards, debit cards, and checks. Through a network, the payer is authenticated by a machine-readable official identification document and the availability of funds is verified by the payer's financial institution before the transaction is completed and the funds are immediately secured during the transaction. The entire transaction is securely verified and maintained in such a way that no party has a chance to alter any part of the transaction.
Owner:SONG YUH SHEN +3
Systems and methods for controlling payment processing
ActiveUS20110184857A1Avoid overdraft feeAvoid declined transactionFinancePayment architecturePayment transactionFinancial transaction
A computer-implemented method for generating a financial product that is configured to be used for one or more payment transactions. The method includes receiving a selection of a plurality of core accounts for providing financial backing for the financial product, and generating the financial product based on one or more control parameters that define use restrictions for the financial product.
Owner:VERIENT
Method and apparatus for verifying a financial instrument
InactiveUS20060026097A1Transaction can be blockedFinanceBilling/invoicingVerification systemPhysical address
An apparatus and method for verifying a customer's legitimacy to use a payment instrument based on access to financial account information provided by the instrument issuer is disclosed. A seller accepts details about goods and services to be delivered, and information about a payment instrument to be used in a purchase by a customer. More specifically, a merchant accepts information about a financial account from the customer including the account's billing address and the account's telephone number associated with the billing address. The merchant obtains a verified billing address from the financial institution holding the financial account by using an address verification system (AVS) and a verified physical address by performing a reverse telephone number query against a reverse telephone number database. The merchant then compares the verified billing address to the verified physical address. For further security the merchant can call either the telephone number provided by the customer or the numbers obtained from the reverse look up or AVS. The number may be called with an interactive voice system and ask questions about the transaction to verify that the customer has indeed made the transaction. Regardless of whether the telephone number provided by the “customer” is at the billing address or not, if a person commits fraud they gave a phone number where they can be reached and that phone number provides a link to the frauder which makes it easier to locate and prosecute them. Just the presence of such a link will deter some frauders.
Owner:KAGI
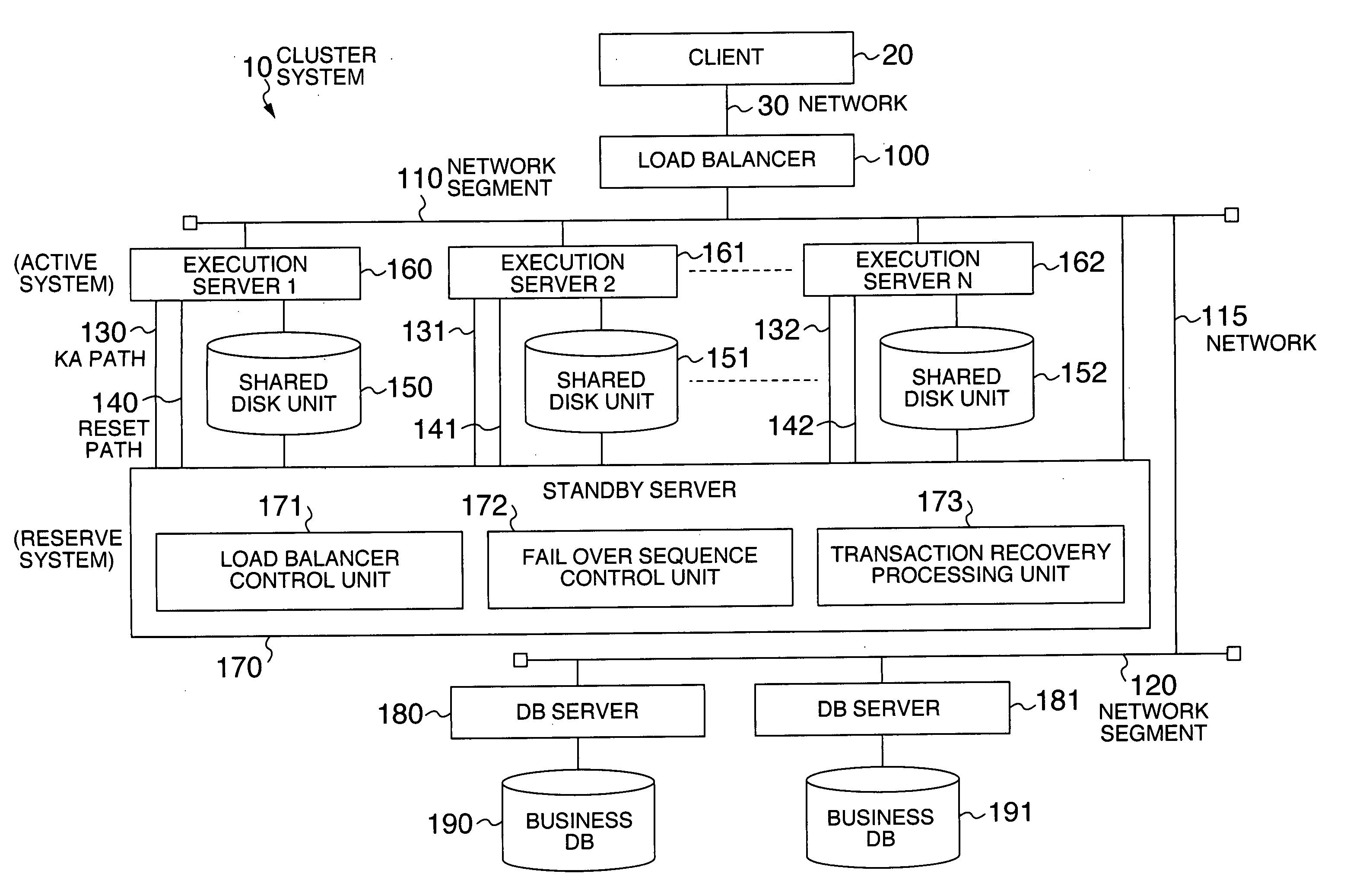
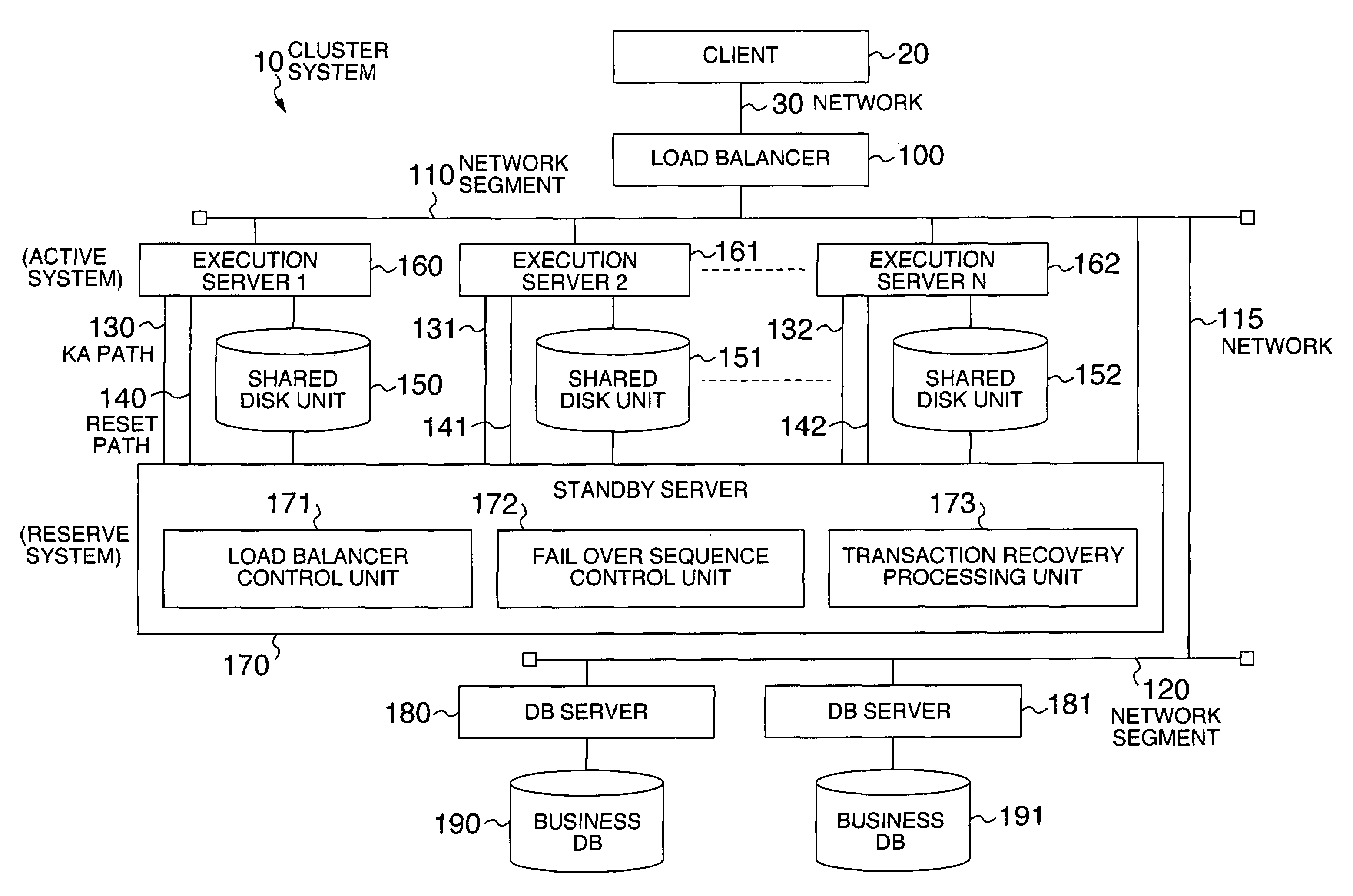
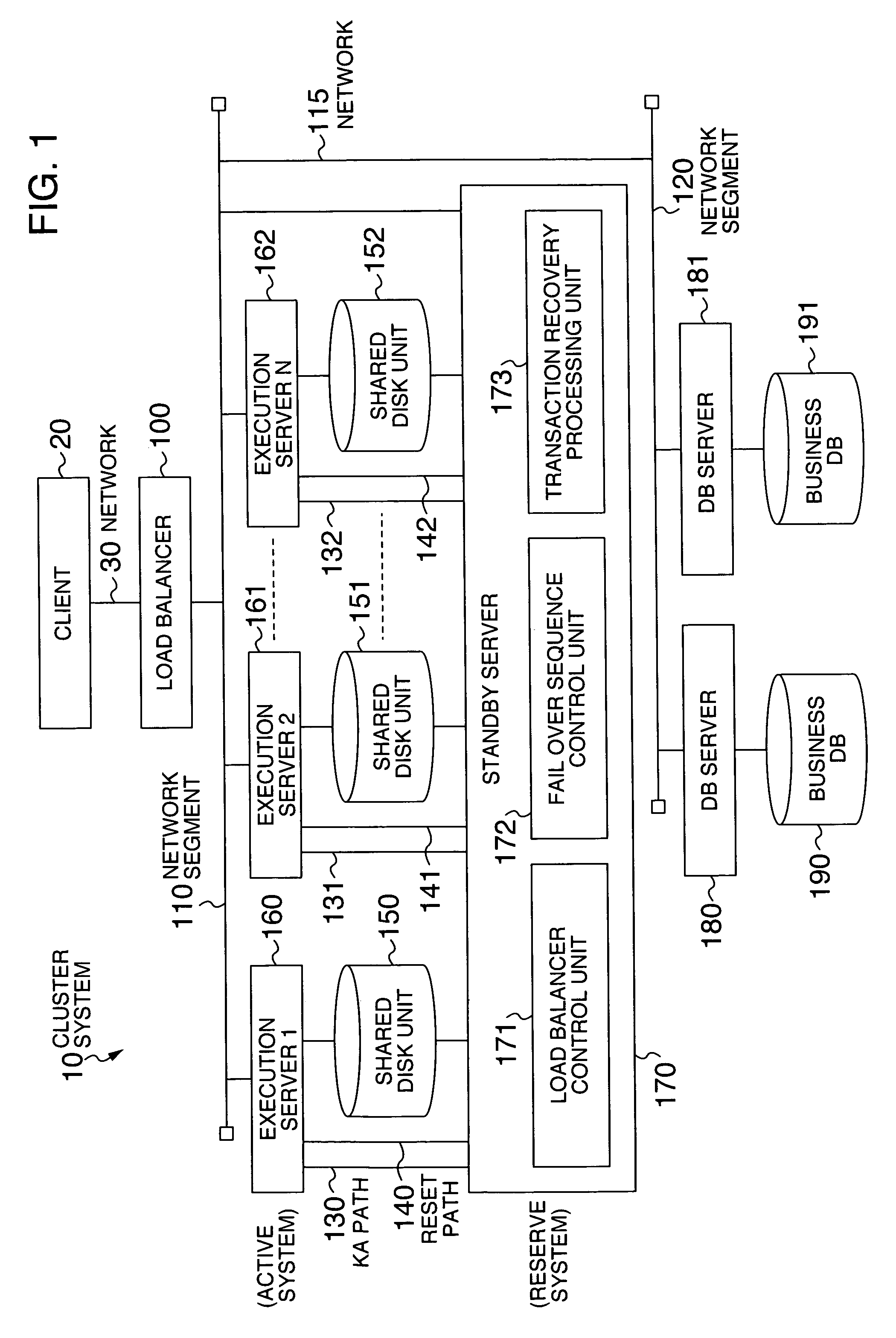
System and method for highly available data processing in cluster system
InactiveUS20050262381A1Short timeRestore consistencyRedundant operation error correctionRedundant hardware error correctionDouble faultIp address
Even if business processing is transaction, a standby-type cluster system copes with double faults in a short time while holding down the standby computer cost to the minimum. An execution server monitoring thread in a standby server periodically monitors an operation state of an execution server. Upon detecting time-out as a result of the monitoring, the thread resets the execution server, stops load balancing to an IP address of the execution server, recovers transaction of the execution server, and returns to monitoring of the operation state. If normality of the execution server is detected as the result of monitoring and an operation state in an execution server management table is “stop,” the thread starts the load balancing to the execution server and returns to the monitoring of the operation state.
Owner:HITACHI LTD
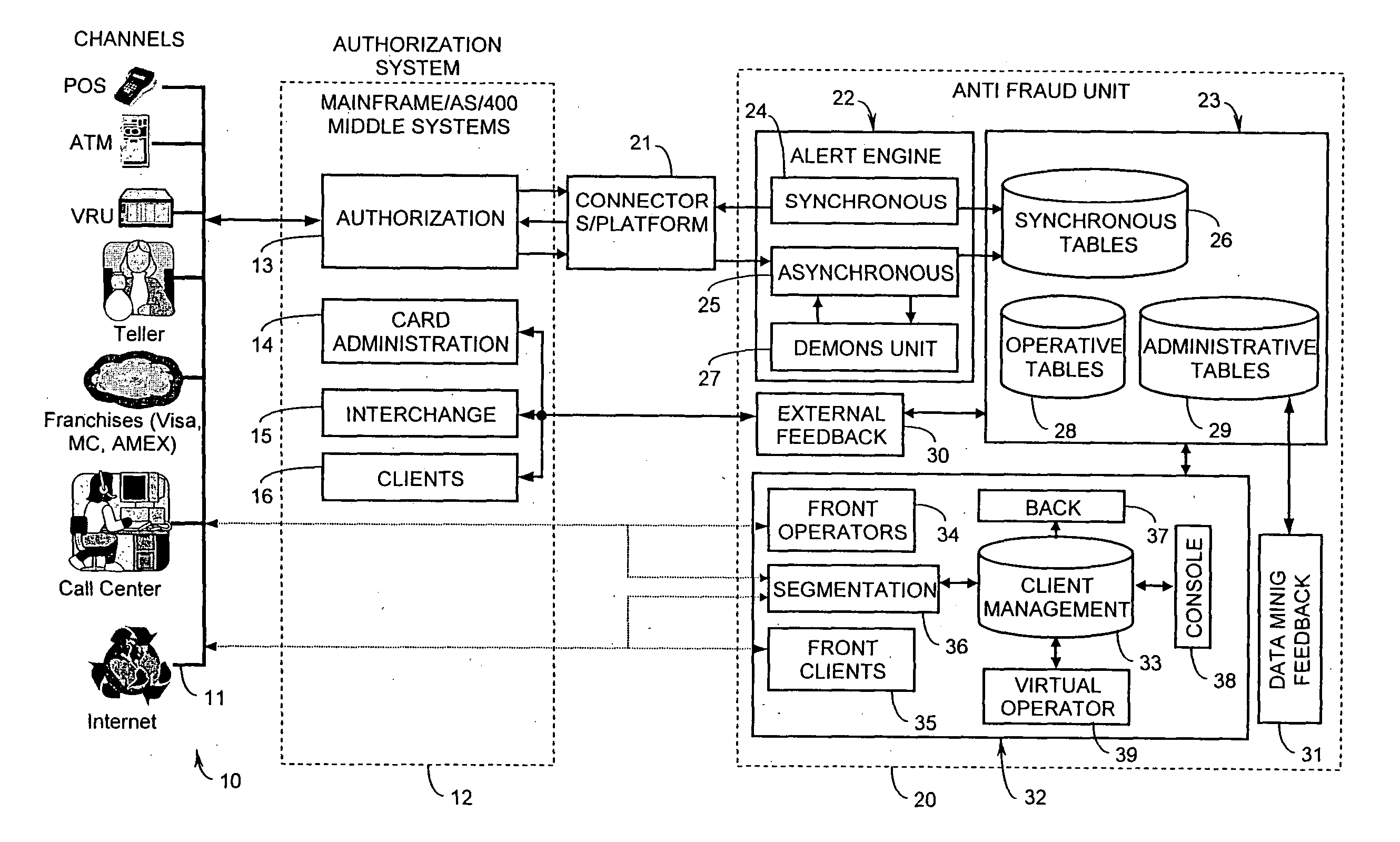
Method and system for determining whether a situation meets predetermined criteria upon occurrence of an event
InactiveUS20050027667A1Easy to handleMinimize the numberFinanceDigital data processing detailsCurrent thresholdContinuous parameter
A method and system for determining whether a situation is logically true or false upon occurrence of an event uses conditions associated with the situation in combination with current values of parameters related thereto to create and maintain a database of current thresholds each corresponding to respective limits which characterize the situation and at least one of which is a composite threshold that encapsulates multiple conditions that can be directly compared with a single parameter associated with an event. Responsive to an event, successive parameters associated with the event are compared with respective ones of the current thresholds until either there are no more thresholds to be compared or until it can be definitively established that the situation is logically true or false. Prior to processing a subsequent event, the current database thresholds are updated.
Owner:KROLL MENAHEM
Content usage management system method, and program providing medium therefor
InactiveUS8117128B2Transaction can be blockedAvoid distributingDiscounts/incentivesFinanceUser deviceComputer science
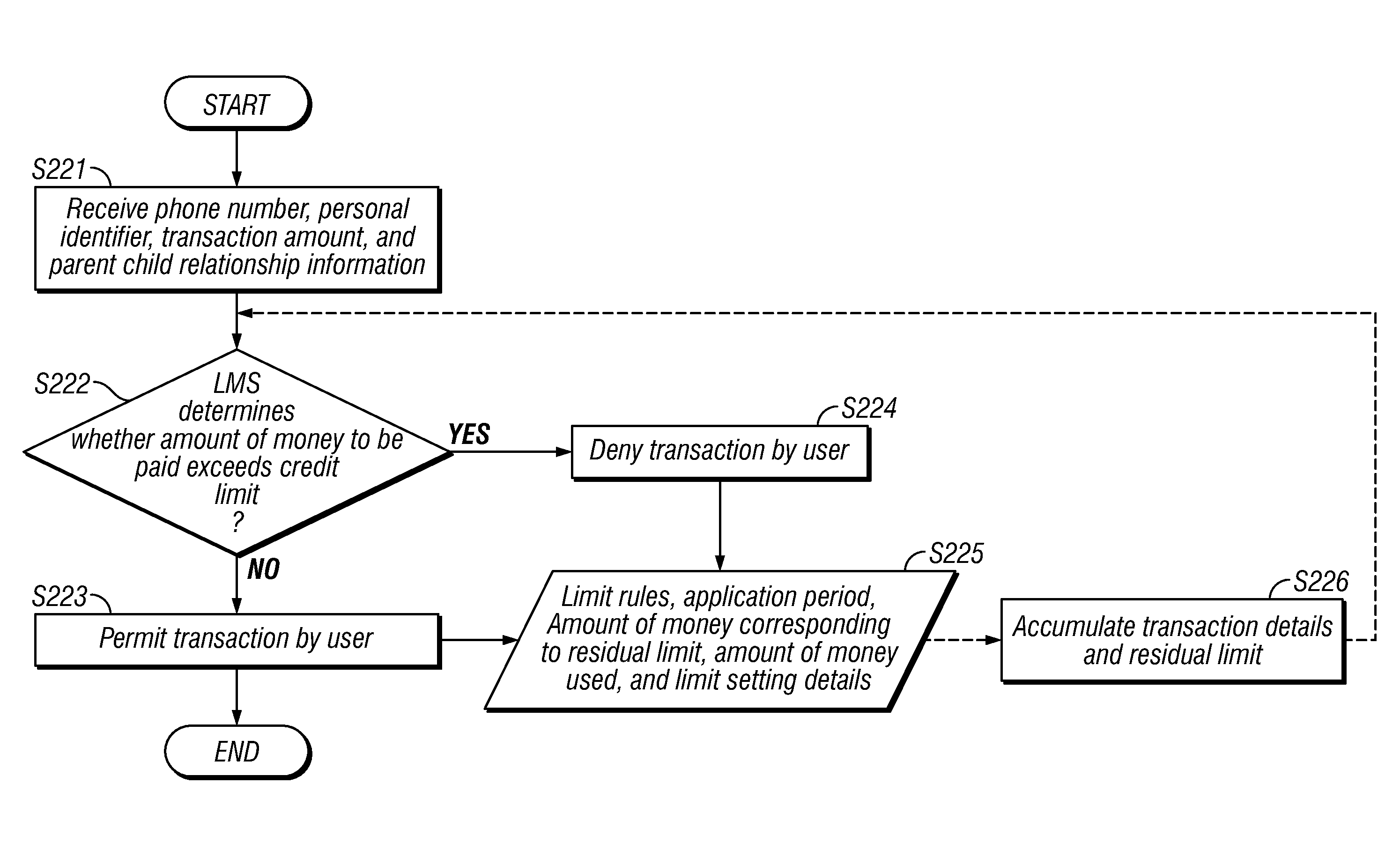
When the encrypted content is provided from a service provider to a user device, a usage log including information of the content usage fee is created in the user device. The created usage log is then sent to the service provider. The service provider compares the content usage fee in the received usage log with a predetermined threshold. If the content usage fee is found to exceed the predetermined threshold, the service provider requests a clearing center to inquire about the electronic money balance of the user. If it is determined that it seems difficult to collect money from the user, the transmission of a content key to the user is suspended. The clearing center also creates an issue log in which the effective period and an allowable amount of money spent by the user are set, and performs settlement processing only when the payment of the content usage fee has been made within the effective period.
Owner:SONY CORP
Method for securing card transaction by using mobile device
InactiveUS20080255981A1Reduce lossesTransaction can be blockedFinanceUser identity/authority verificationComputer hardwareMobile device
A method for securing card transaction by using mobile device is a method of personal card transaction added with a mechanism of mobile device so that it is capable of preventing the card from being embezzled and counterfeited effectively. Hence, it is possible for the card proprietor to place more trust in the safety of card transaction.
Owner:SHIU MING CHING
Self-service terminal
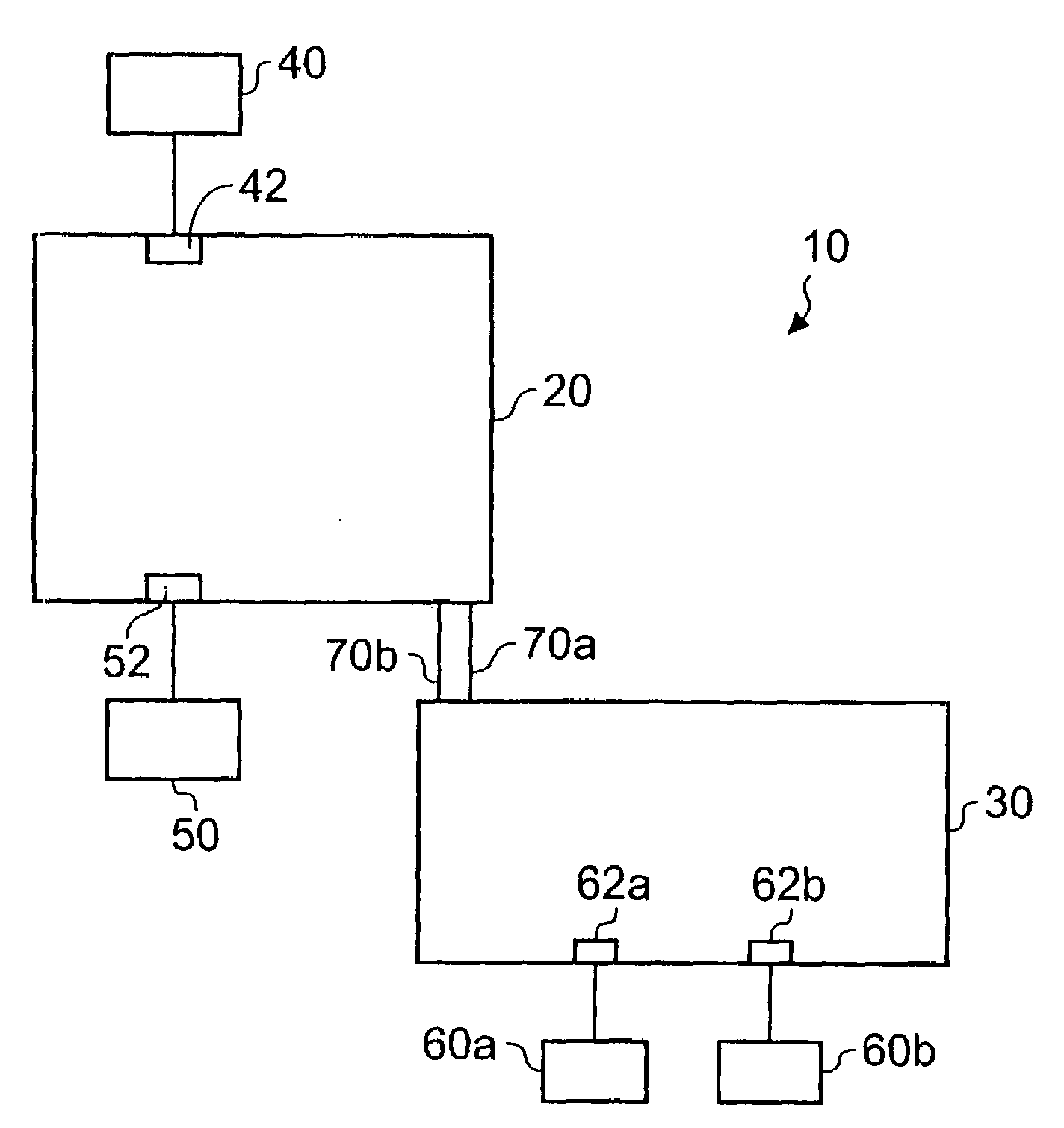
ActiveUS7637420B2Low costSimplified user interfaceComplete banking machinesFinanceRemote computerComputer terminal
A self-service terminal, such as an ATM (Automated Teller Machine). The ATM has a communication port for interfacing with a user's portable electronic device. The ATM is operable to receive a transaction authorization from the user's portable electronic device, to examine the transaction authorization, and to dispense an item to fulfil a requested transaction associated with the transaction authorization, without the terminal preparing an authorization request to a remote computer.
Owner:NCR CORP
Paperless Coupon Transactions System
PendingUS20110225045A1Easily fabricatedEasy to be stolenFinanceDigital data authenticationInternet privacyFinancial transaction
Owner:SONG YUH SHEN +3
System and method for highly available data processing in cluster system
InactiveUS7401256B2Holding down cost of standbyAvoid stagnationRedundant operation error correctionRedundant hardware error correctionData processing systemDouble fault
Even if business processing is transaction, a standby-type cluster system copes with double faults in a short time while holding down the standby computer cost to the minimum. An execution server monitoring thread in a standby server periodically monitors an operation state of an execution server. Upon detecting time-out as a result of the monitoring, the thread resets the execution server, stops load balancing to an IP address of the execution server, recovers transaction of the execution server, and returns to monitoring of the operation state. If normality of the execution server is detected as the result of monitoring and an operation state in an execution server management table is “stop,” the thread starts the load balancing to the execution server and returns to the monitoring of the operation state.
Owner:HITACHI LTD
System and method for electronic transactions
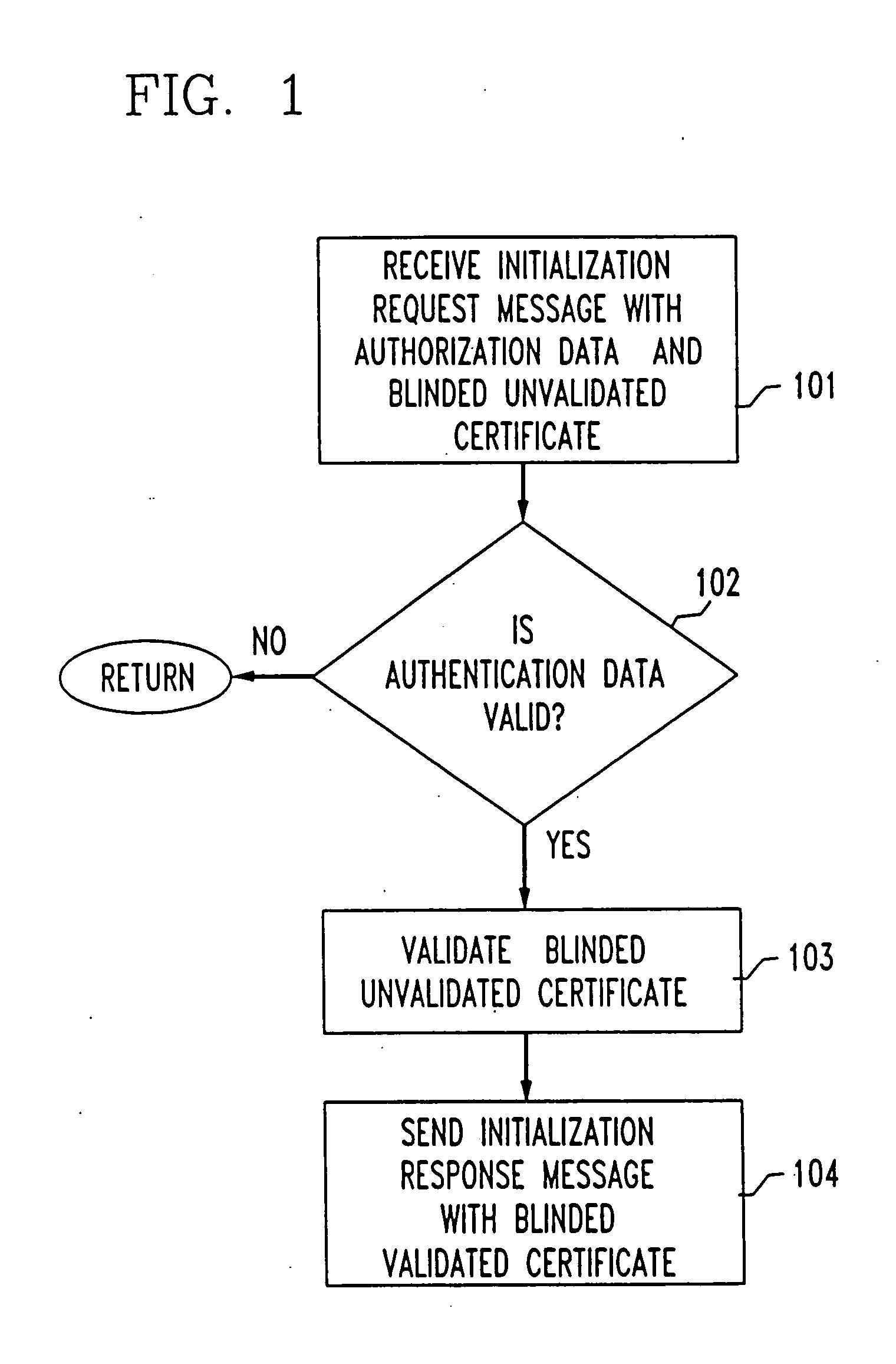
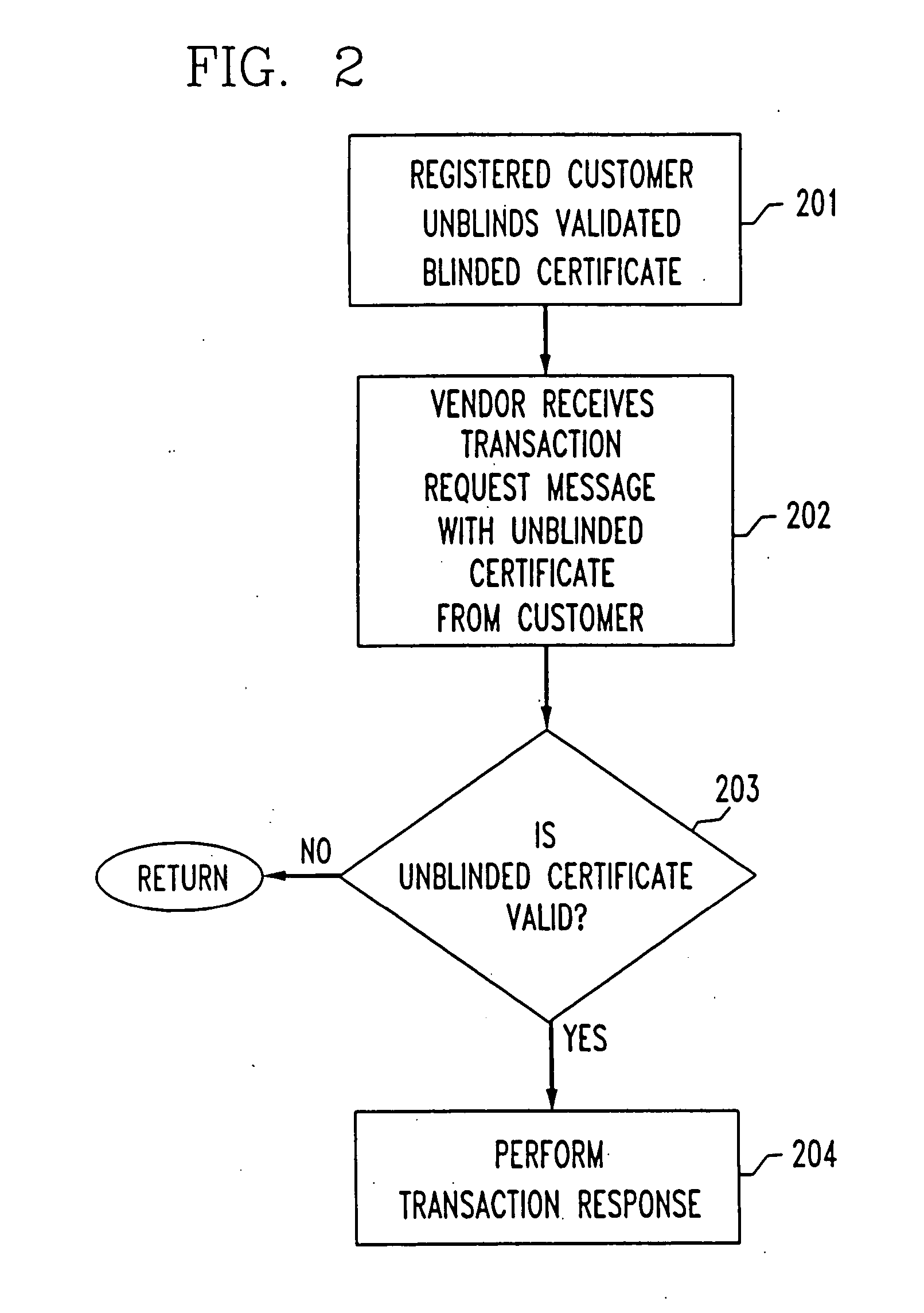
InactiveUS20060036480A1Enhance security and robustnessReliable correlationVoting apparatusError detection/correctionInternet privacyElectronic trading
A system and method for performing an electronic transaction, including registration, audit and trusted recovery features. A transaction request message is received from a registered user that includes an unblinded validated certificate, and a blinded unvalidated certificate. If the unblinded validated certificate is determined to be legitimate, then a transaction can be performed, and the blinded unvalidated certificate is validated to obtain a blinded, validated certificate that is sent to the user. An audit protocol can be used to further verify the legitimacy of the transaction request message, and a user can recover from a broken connection by replaying a protocol run.
Owner:GOLDSCHLAG DAVID M +2
Interconnecting initiator devices and recipient devices
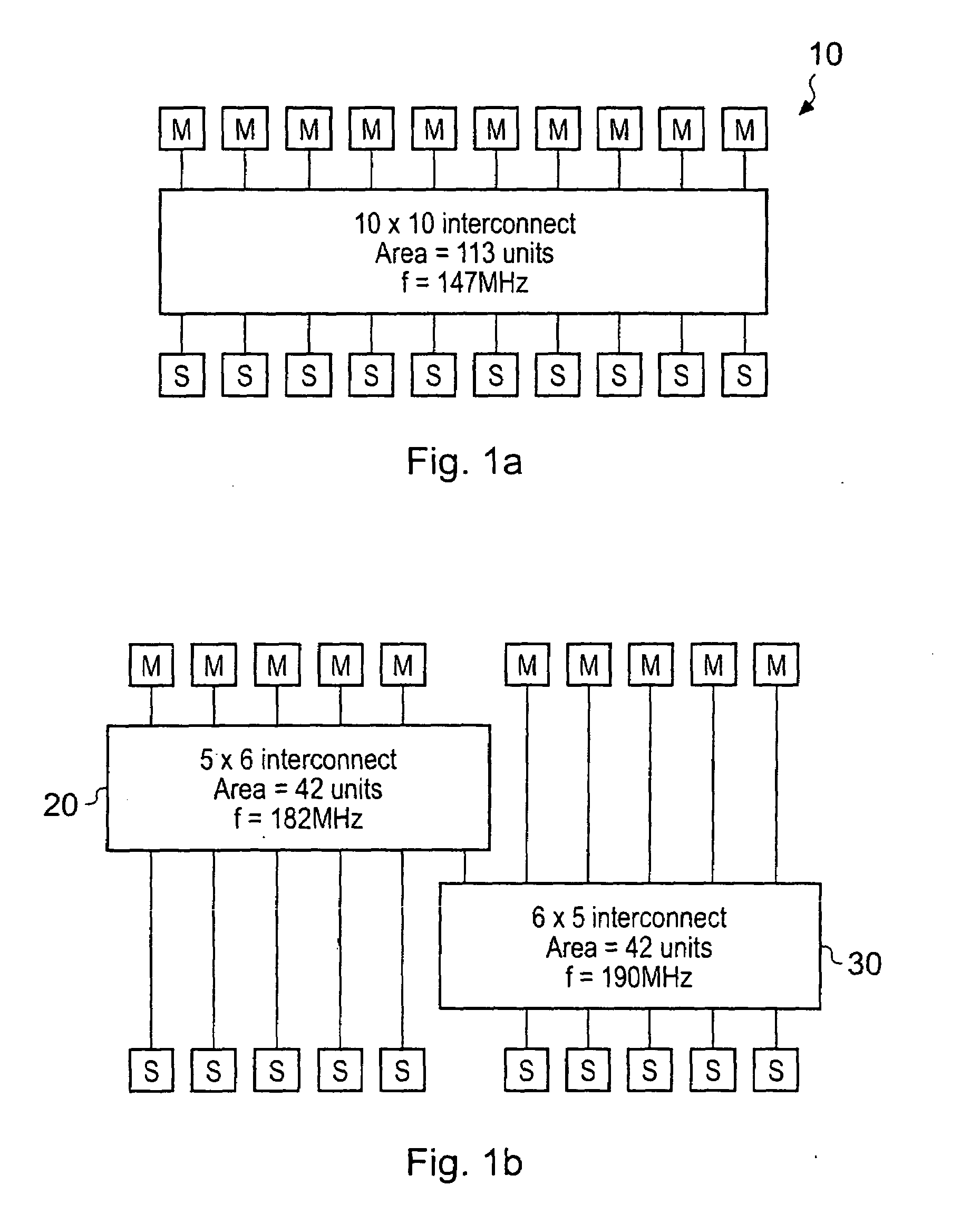
ActiveUS20080086572A1Increase the areaImprove performanceError preventionFrequency-division multiplex detailsDatapathData path
An interconnect block for a data processing apparatus, said interconnect block being operable to provide data routes via which one or more initiator devices may access one or more recipient devices, said interconnect block comprising: a first and a second portion; said first portion comprising at least one initiator port for communicating with one of said initiator devices, and at least one recipient port for communicating with one of said recipient devices; said second portion comprising at least two recipient ports for communicating with at least two recipient devices, said second portion being connected to said first portion via at least two parallel connecting routes, said at least two recipient ports being connectable to said at least two parallel connecting routes; wherein in response to a request received from one of said initiator devices at said first portion to perform a transaction accessing one of said at least two recipients in communication with said second portion, said interconnect block is operable to provide a data route between said initiator device and said recipient device via said at least two parallel connecting routes and to maintain said data route for the duration of said transaction.
Owner:ARM LTD
Systems and methods for controlling payment processing
ActiveUS20110184856A1Avoid overdraft feeAvoid declined transactionFinancePayment architecturePayment transactionProduct base
A computer-implemented method for generating a financial product that is configured to be used for one or more payment transactions. The method includes receiving a selection of a plurality of core accounts for providing financial backing for the financial product, and generating the financial product based on one or more control parameters that define use restrictions for the financial product.
Owner:VERIENT
Last-room-available search apparatus and method
InactiveUS20120089482A1Commercial viability can be improvedTransaction can be blockedReservationsBuying/selling/leasing transactionsThird partyQuality rating
A system and method for customer-oriented searching and purchasing of goods and services relies on a database having records corresponding to purveyors, products and services, and purchasers and maintained by a third party independent from all the foregoing. Searches may obtain information with or without cooperation of purveyors (vendors). Filtering before presentation to a user, according to specific needs or requirements eliminates inapplicable vendors, products, or services. Particularly, if quality rating, features, or actual availability is lacking, the system does not waste a user's time to evaluate. Deal-killer parameters and values punish vendors lacking disclosure. Rather than publish what the seller wants to advertise, the system retrieves for a user the information on items that meet criteria of, and according to their importance to, a user, especially deal-killer parameters.
Owner:PATEL NARENDRA
Multilevel authentication
ActiveUS9204298B2Authentication be reduced eliminatedDisadvantages can be reduced eliminatedDigital data processing detailsUser identity/authority verificationUser inputInternet privacy
In an exemplary embodiment, a system includes a memory operable to store a user account identifier associated with a user account and a mobile device identifier associated with a mobile device. The memory is also operable to store a first user credential and a second user credential, the second user credential, wherein the second user credential comprises user input data captured by a sensor. The system includes a network interface operable to receive a request to authenticate a requesting user. The system also includes a processor operable to determine information included in the request to facilitate authentication of the requesting user and whether the information included in the request matches the information associated with the user account. The processor is further operable to authenticate the requesting user if the request is associated with the user account and information included in the request matches the information associated with the user account.
Owner:BANK OF AMERICA CORP
Techniques to reduce contention windows
ActiveUS20160070747A1Improve concurrencyPreventing transactionDigital data information retrievalDigital data processing detailsDatabase
Embodiments of the present invention provide improved concurrency by reducing the time period (also referred to herein as a locking window or contention window) during which a record is locked. This provides the benefits of pessimistic locking schemes by preventing transaction due to concurrent updates, while also reducing the time during which a record is exclusively locked. This improves user experience and performance.
Owner:ORACLE INT CORP
Electronic transaction method using an electronic coupon
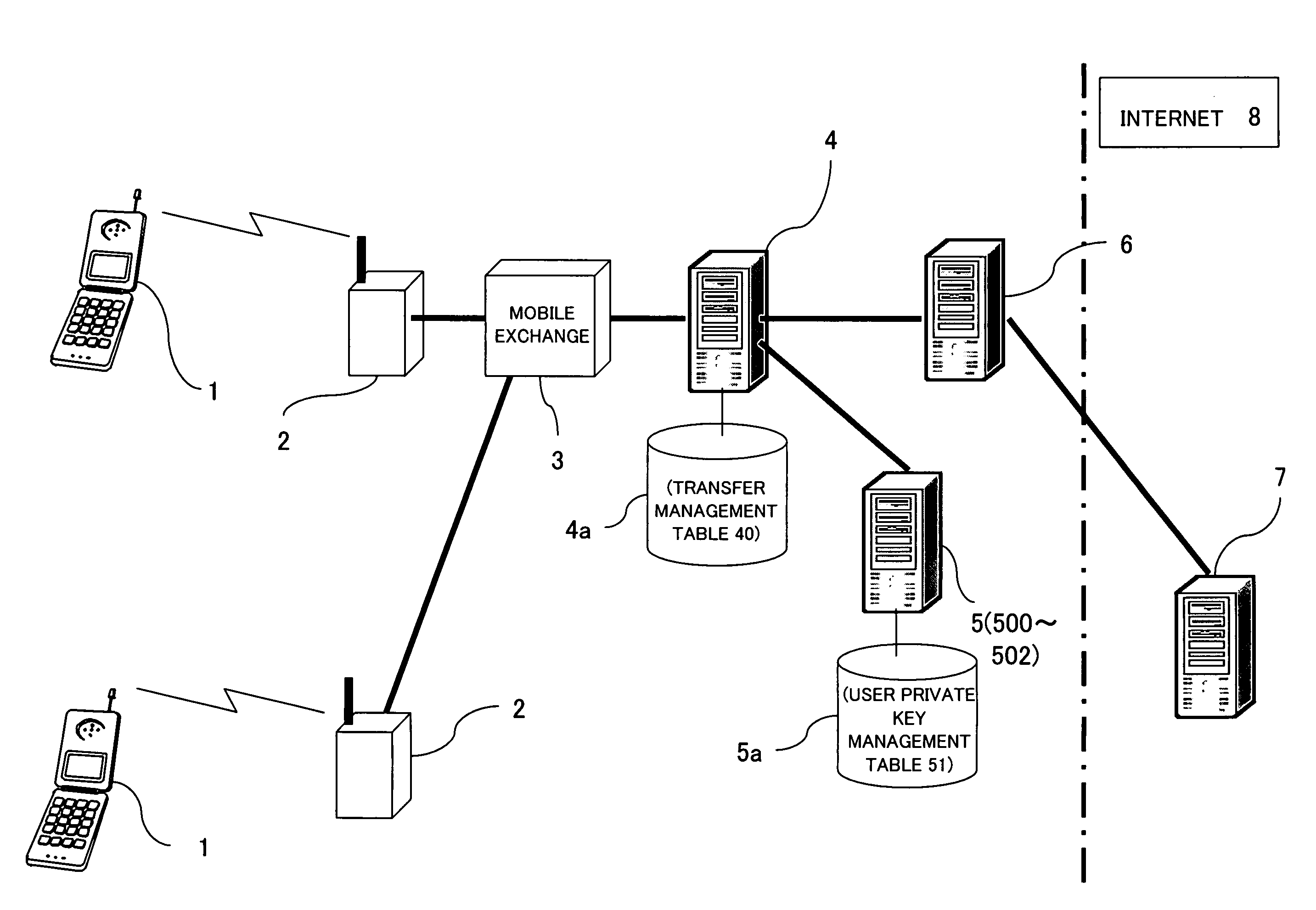
InactiveUS7979353B2Reduce the amount requiredImprove convenienceFinanceComputer security arrangementsThe InternetComputer science
In an electronic transaction on the Internet, an electronic coupon having pecuniary value information usable in the electronic transaction and owner identification information based on information characteristic of an information terminal is issued to the information terminal, the pecuniary value information and the owner identification information of the electronic coupon are recorded and managed as coupon management information in a transfer management memory, and the owner identification information in the transfer management memory is changed according to a transferee apparatus of the electronic coupon, whereby a settlement in the electronic transaction can be made simply and safely.
Owner:FUJITSU LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com