Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
429results about How to "Reduce vulnerability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
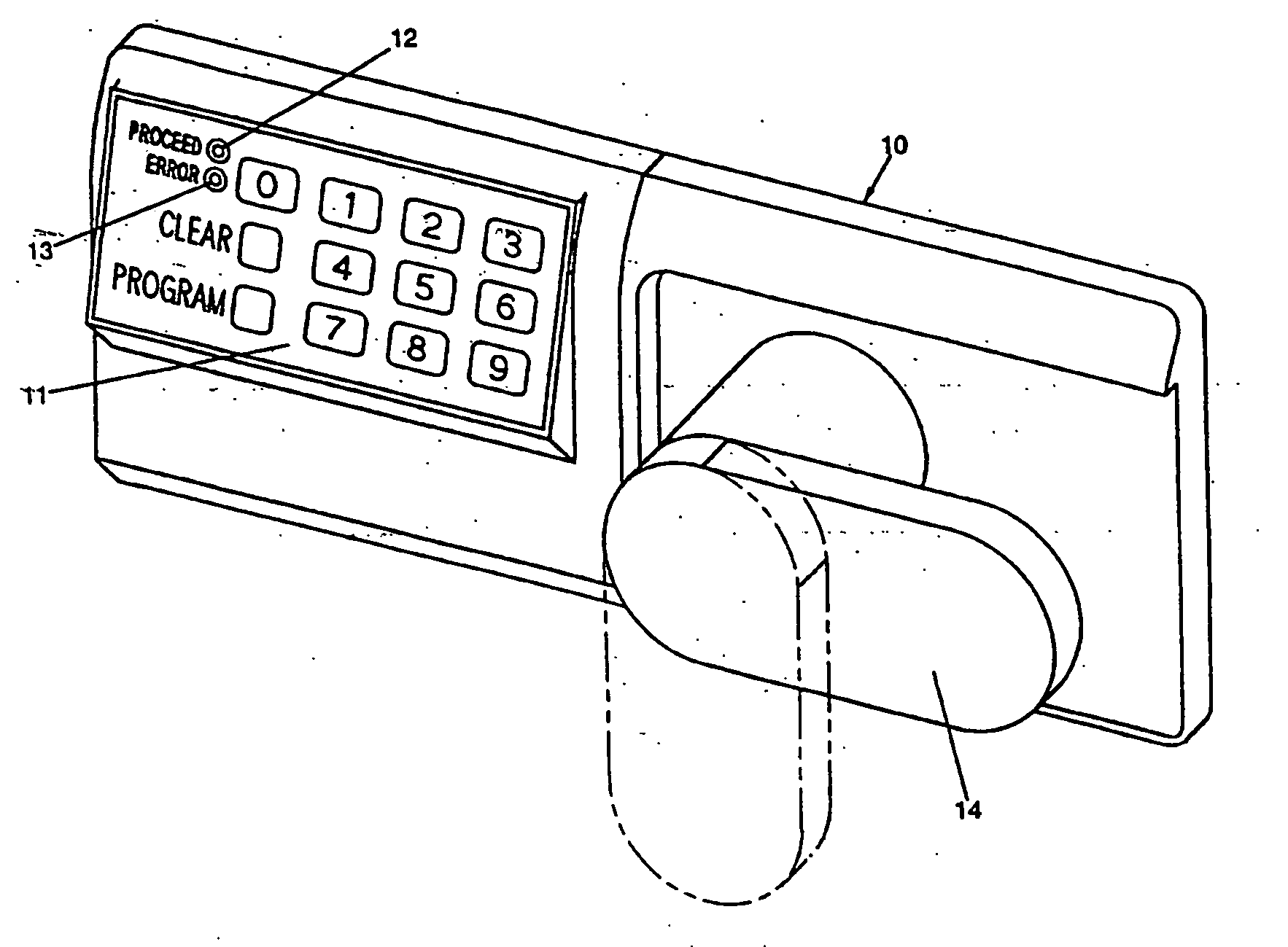
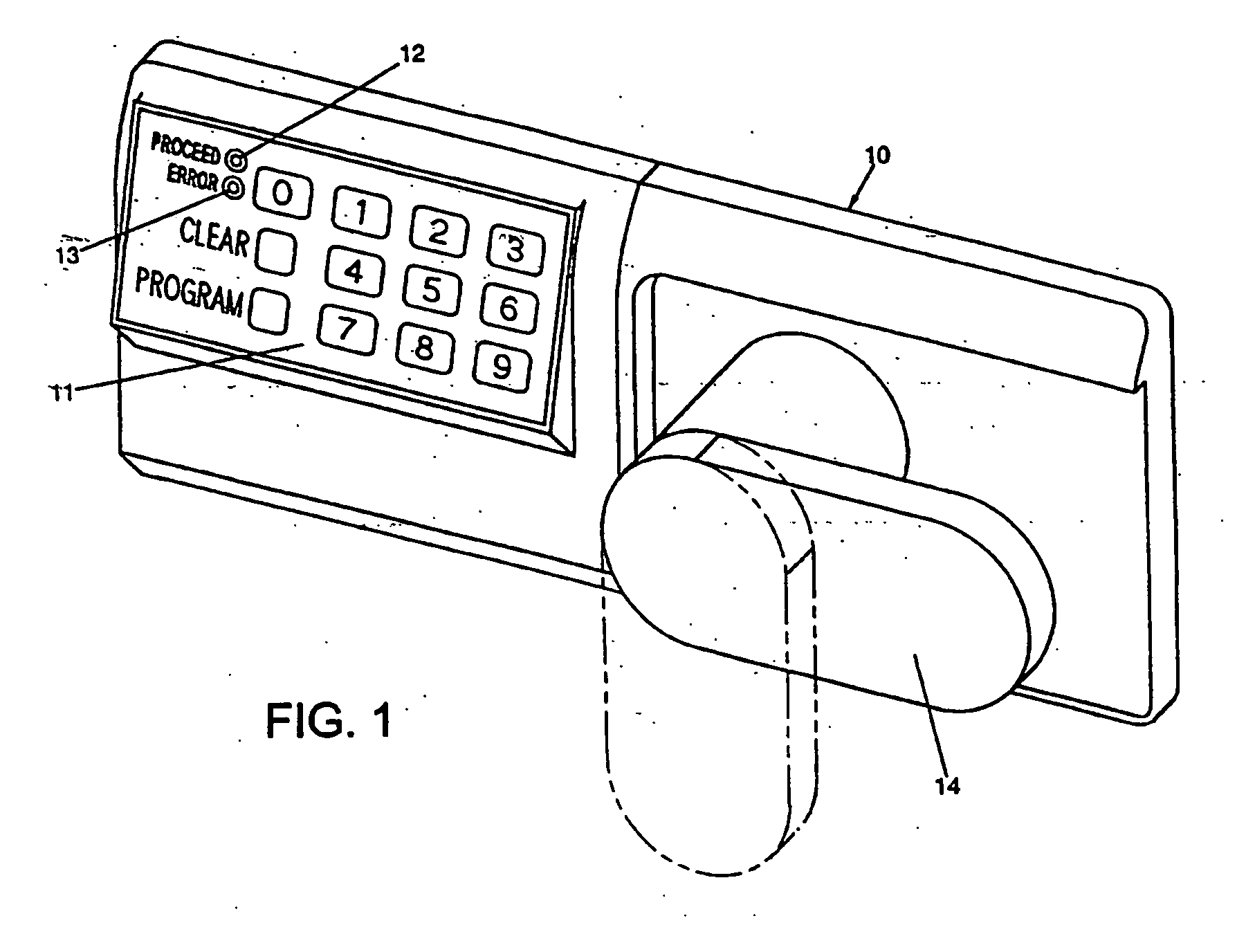
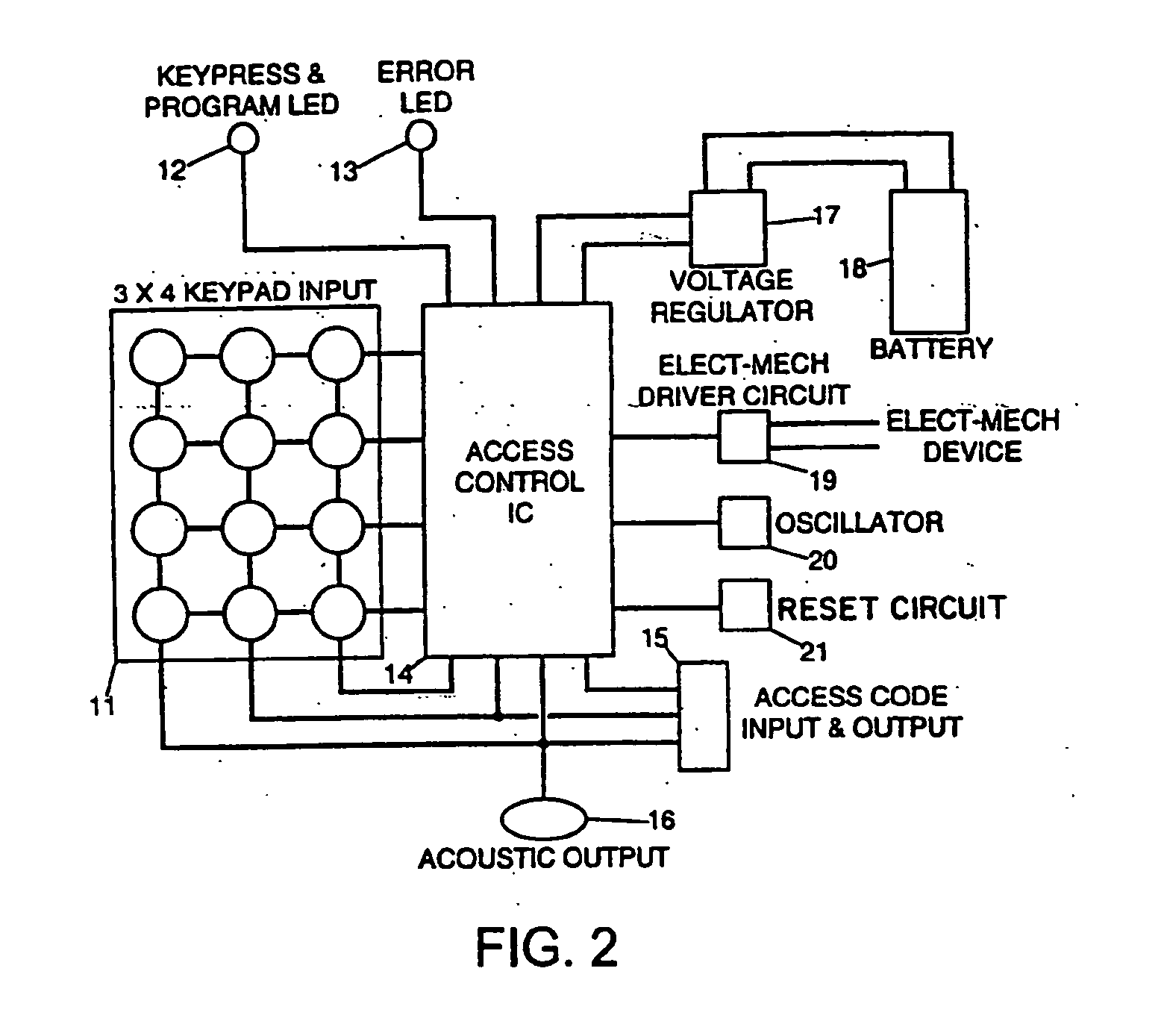
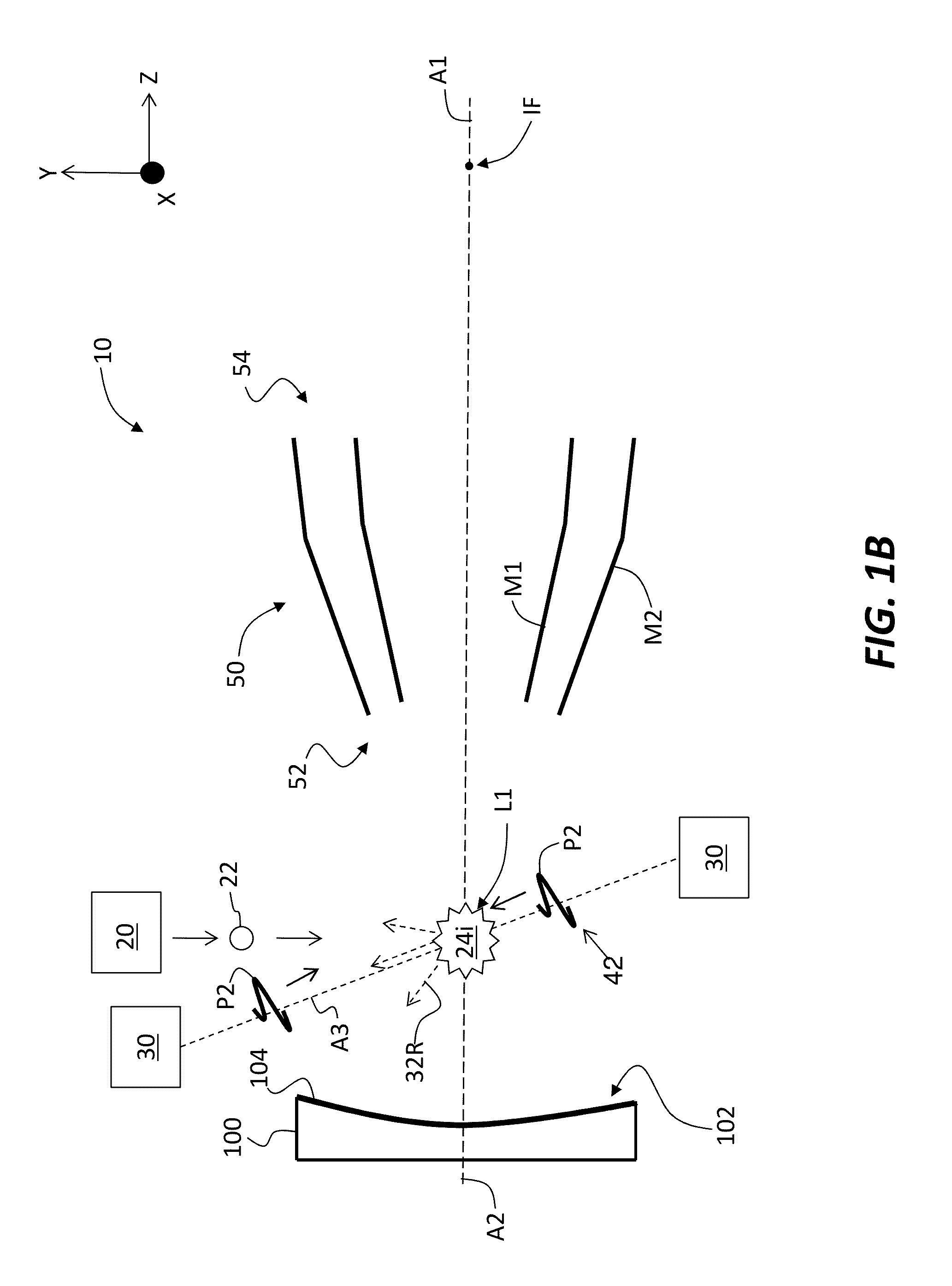
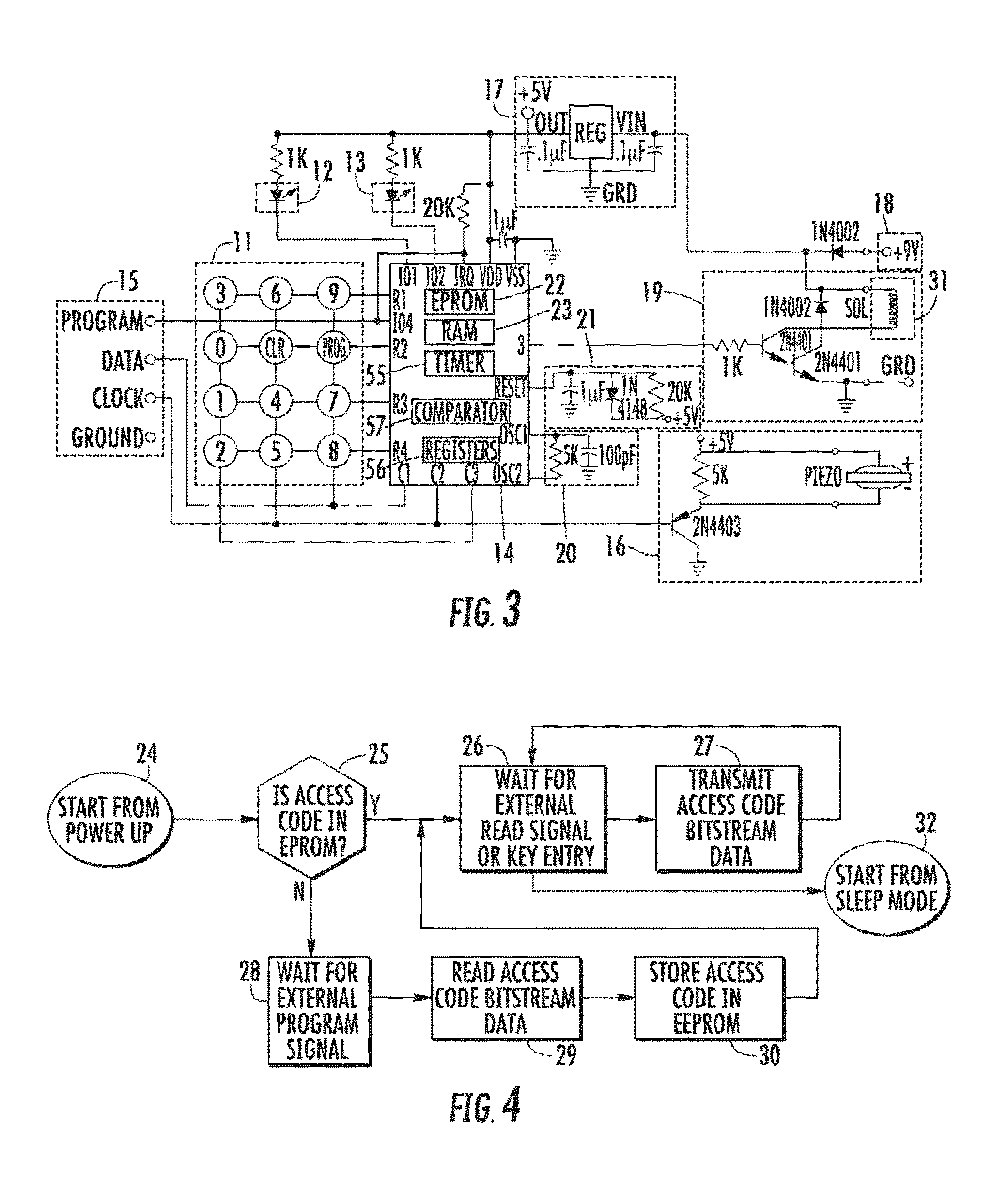
Network Communication System With Improved Security
ActiveUS20120174218A1Effectively shut downEffectively shut down the targets internet connection capabilityMemory loss protectionError detection/correctionPathPingSoftware engineering
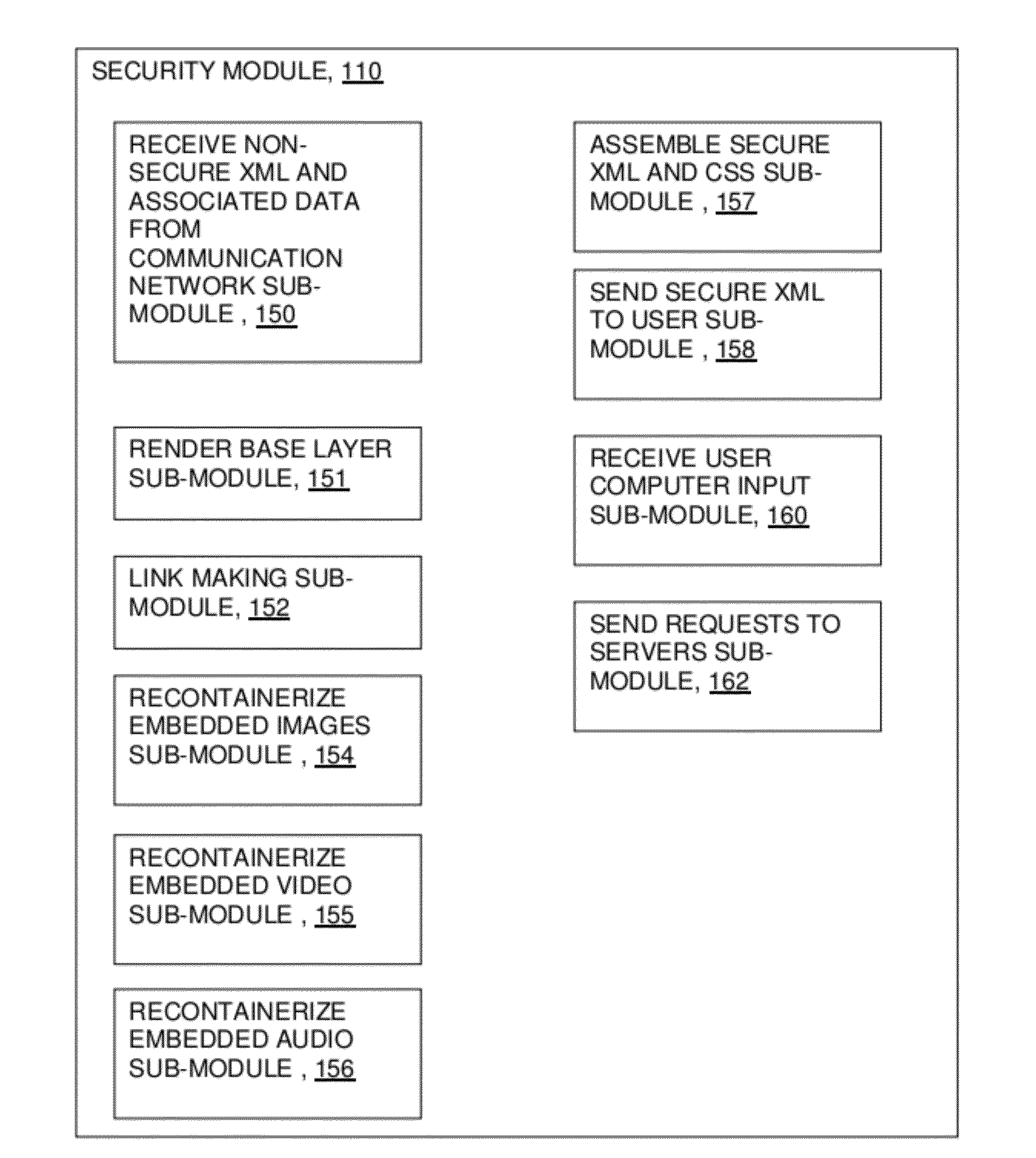
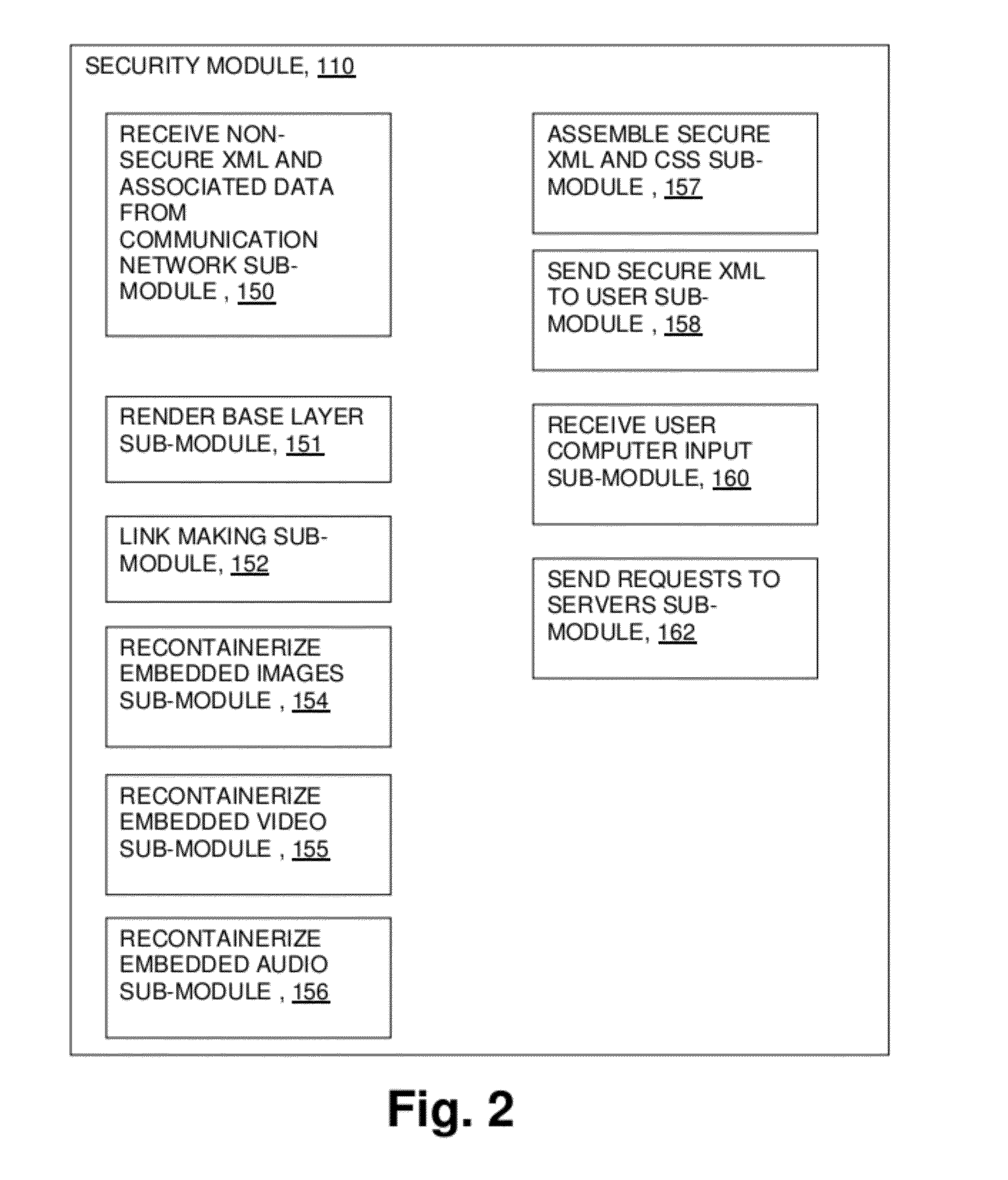
A computer network communication method and system wherein software rendering software is interposed in the data communication path between a browser running on a user computer and the internet data sources (for example, internet-accessible server computers) that the user browser wants to receive information from. The software rendering application gets data from internet data sources, but this data may contain malware. To provide enhanced security, the software rendering application renders this data to form a new browser readable code set (for example, an xml page with CSS layers), and this new and safe browser readable code set is sent along to the browser on the user computer for appropriate presentation to the user. As part of the rendering process, dedicated and distinct virtual machines may be used to render certain portion of the data, such as executable code. These virtual machines may be watched, and quickly destroyed if it is detected that they have encountered some type of malware.
Owner:TOUCHPOINT PROJECTION SOLUTIONS LLC
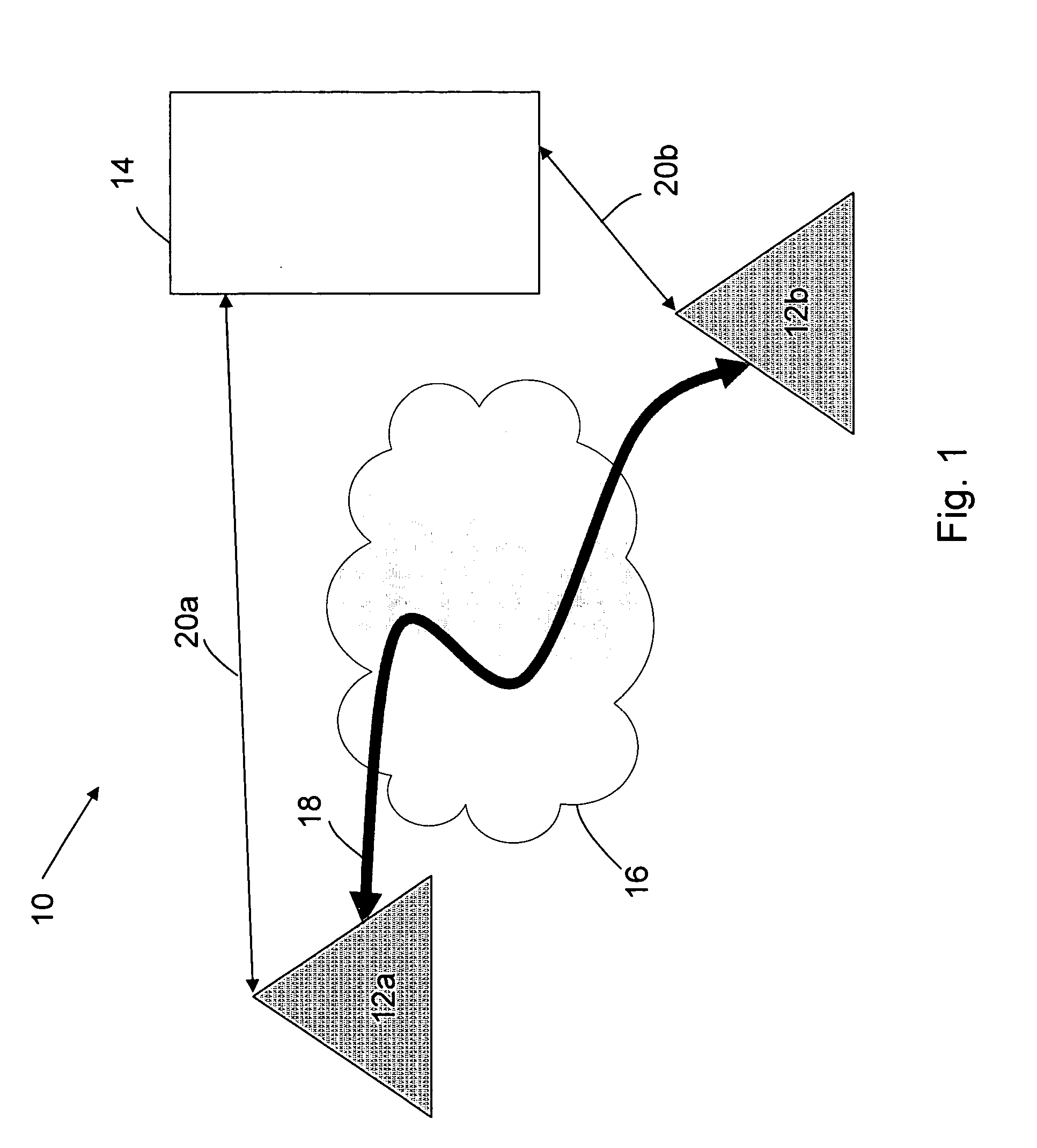
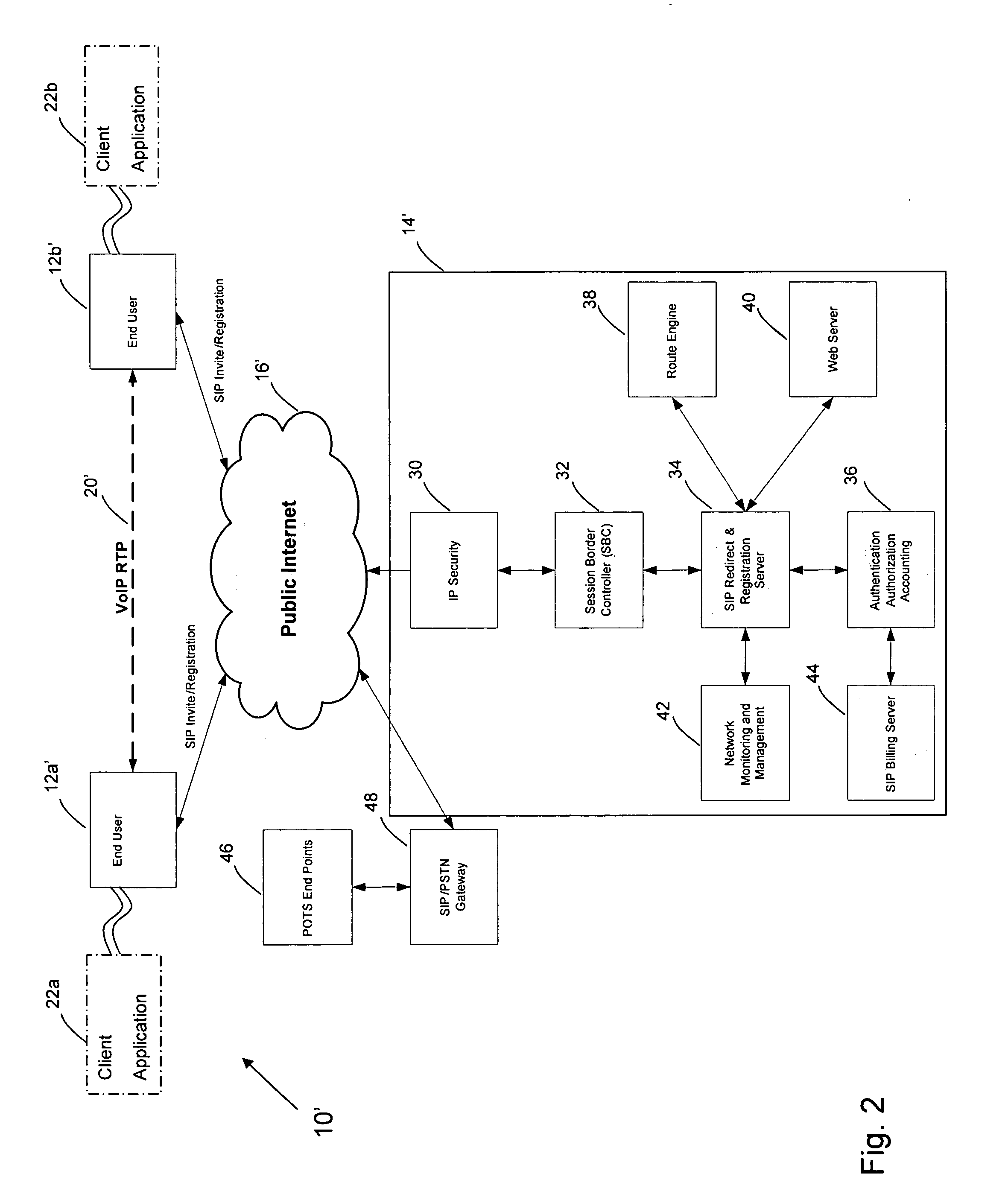
Distributed voice over internet protocol apparatus and systems
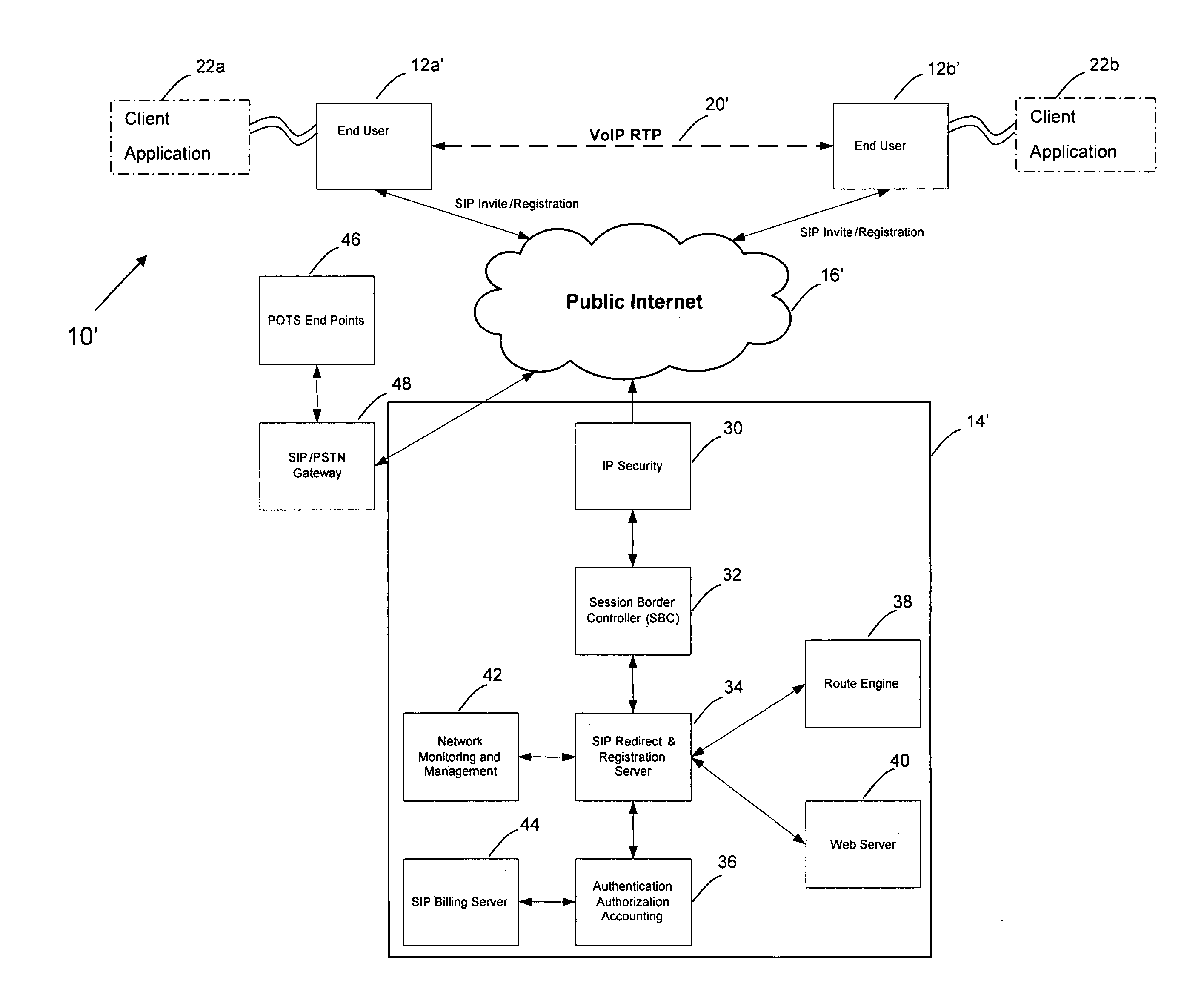
InactiveUS20070248077A1Low costIncreased economy of scaleMultiplex system selection arrangementsData switching by path configurationPublic networkClient-side
In one embodiment, the invention relates to a telephony system. In one embodiment of the invention, the system includes a first communication device adapted to interface with a client application, a second communication device, the second communication device adapted to exchange voice over internet protocol (VoIP) data with the first communication device, and a server comprising a route engine, wherein the route engine is adapted to exchange provisioning data with the client application such that VoIP packet data remains channeled through a public network such that it is separated from the server.
Owner:FUSION TELECOMM INT
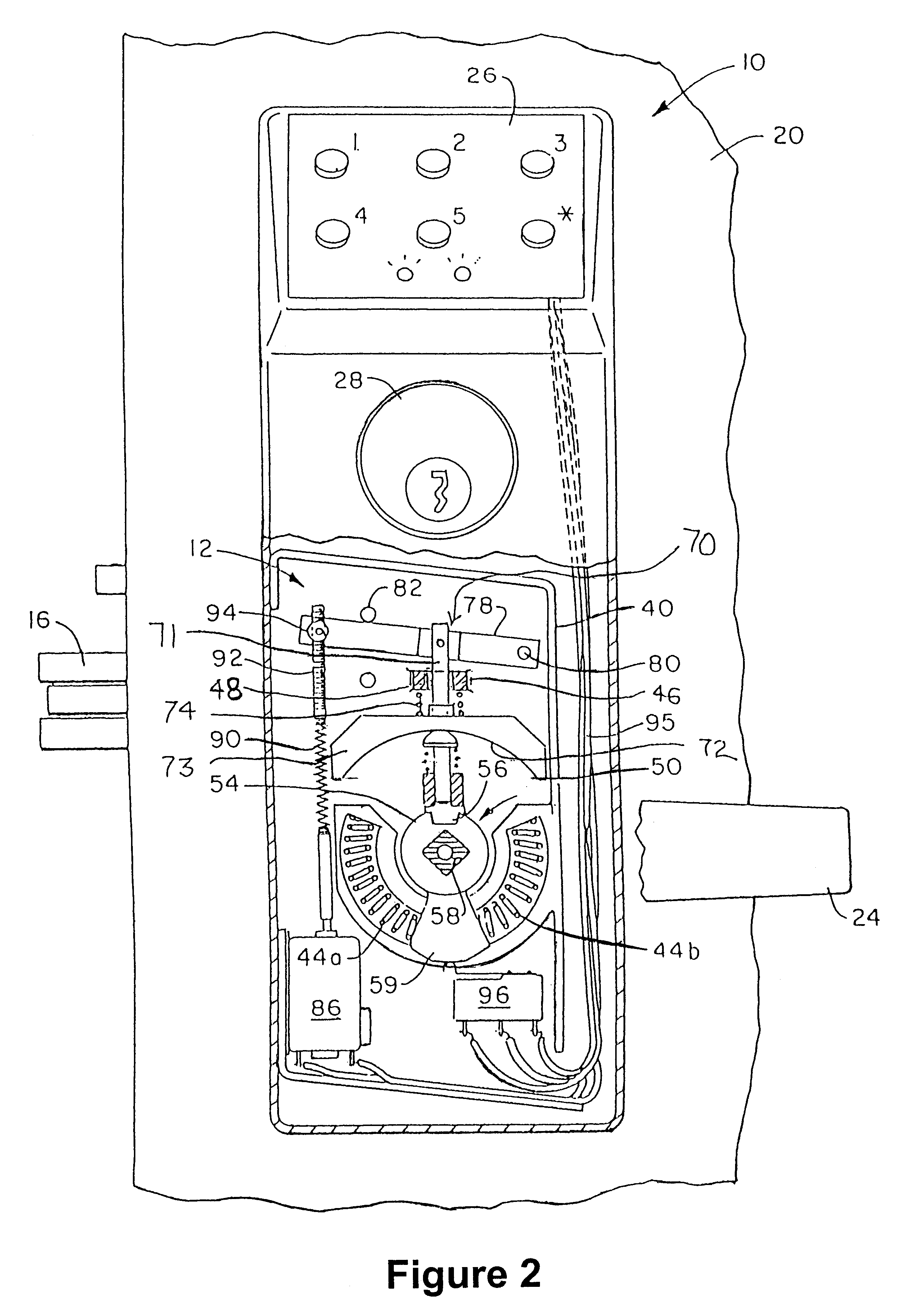
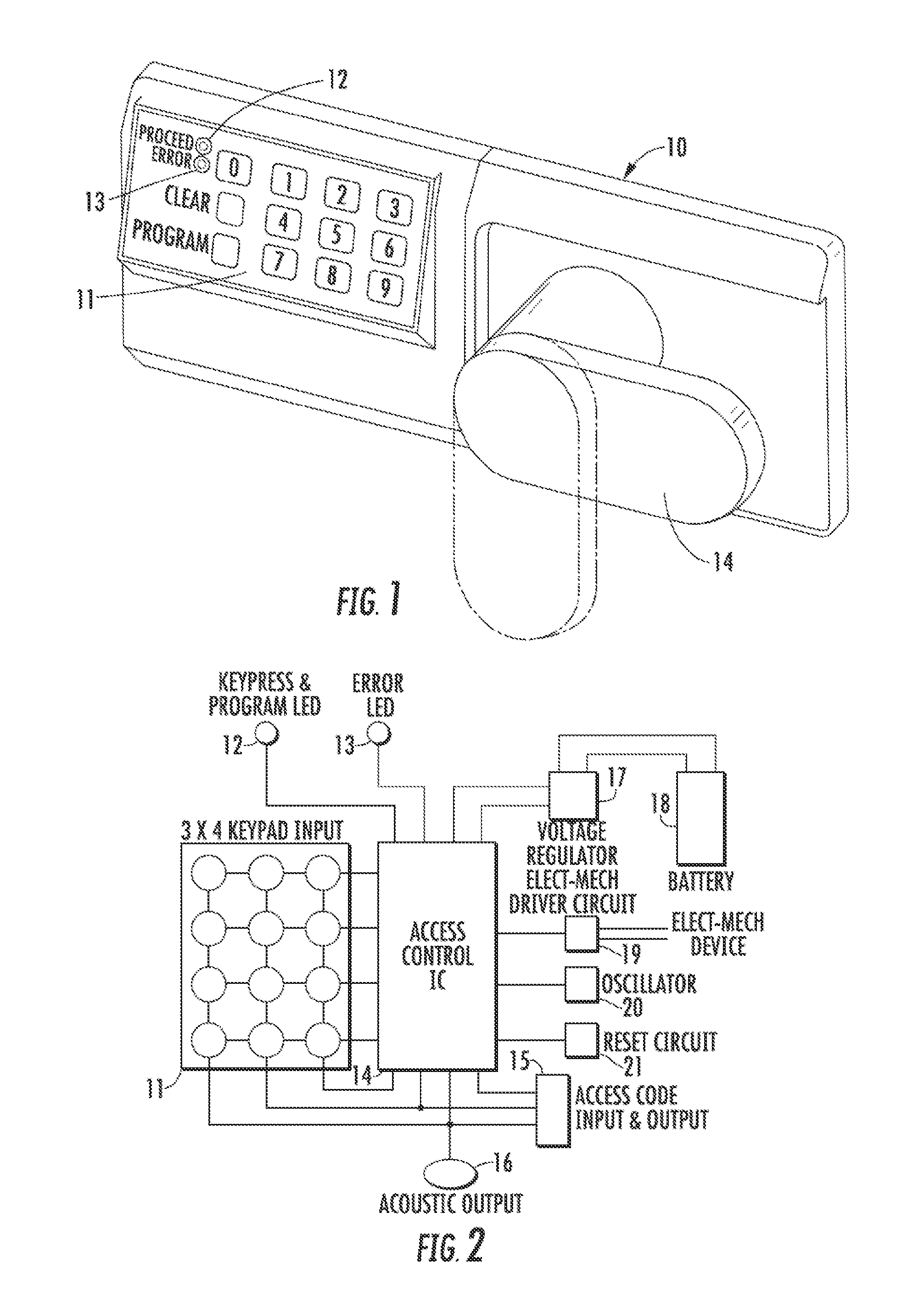
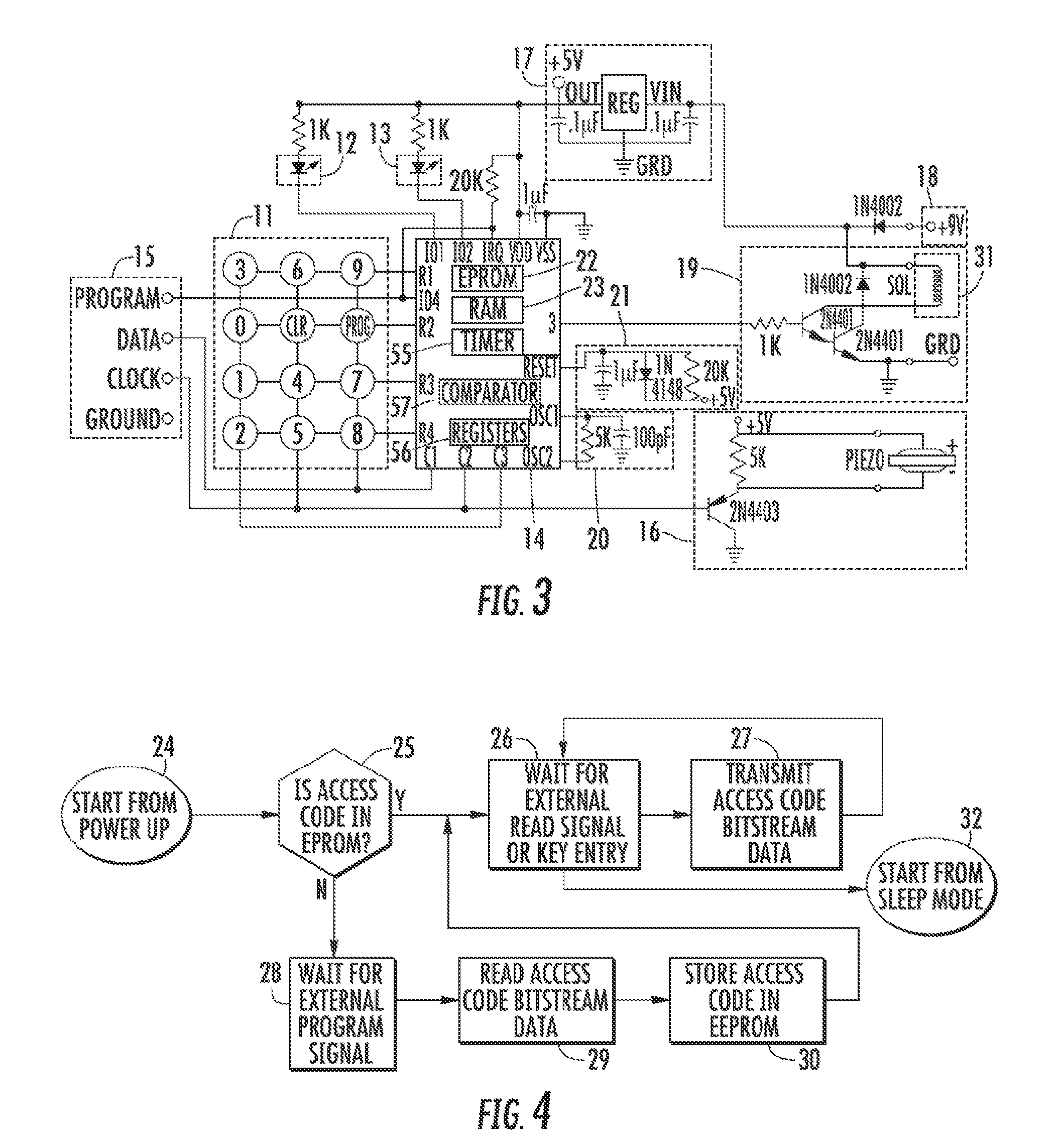
Clutch mechanism with moveable injector retainer wall for door lock system
InactiveUS6286347B1Efficient and reliable in operationEfficiently and effectively employAnti-theft cycle devicesAnti-theft devicesClutchInjector
A door lock system includes a clutch mechanism for a lockset and has particular applicability in conjunction with lever handles. Two coupling assemblies are selectively rotatably coupled by a coupling pin. One coupling assembly is rotatably coupled to the lockset actuator. The other coupling assembly is rotatably coupled to the exterior door handle. A drive assembly includes a motor and employs an injector which has a movable arcuate shoulder and which selectively controls the position of the coupling pin to provide for the locking and unlocking functions.
Owner:HARROW PRODS
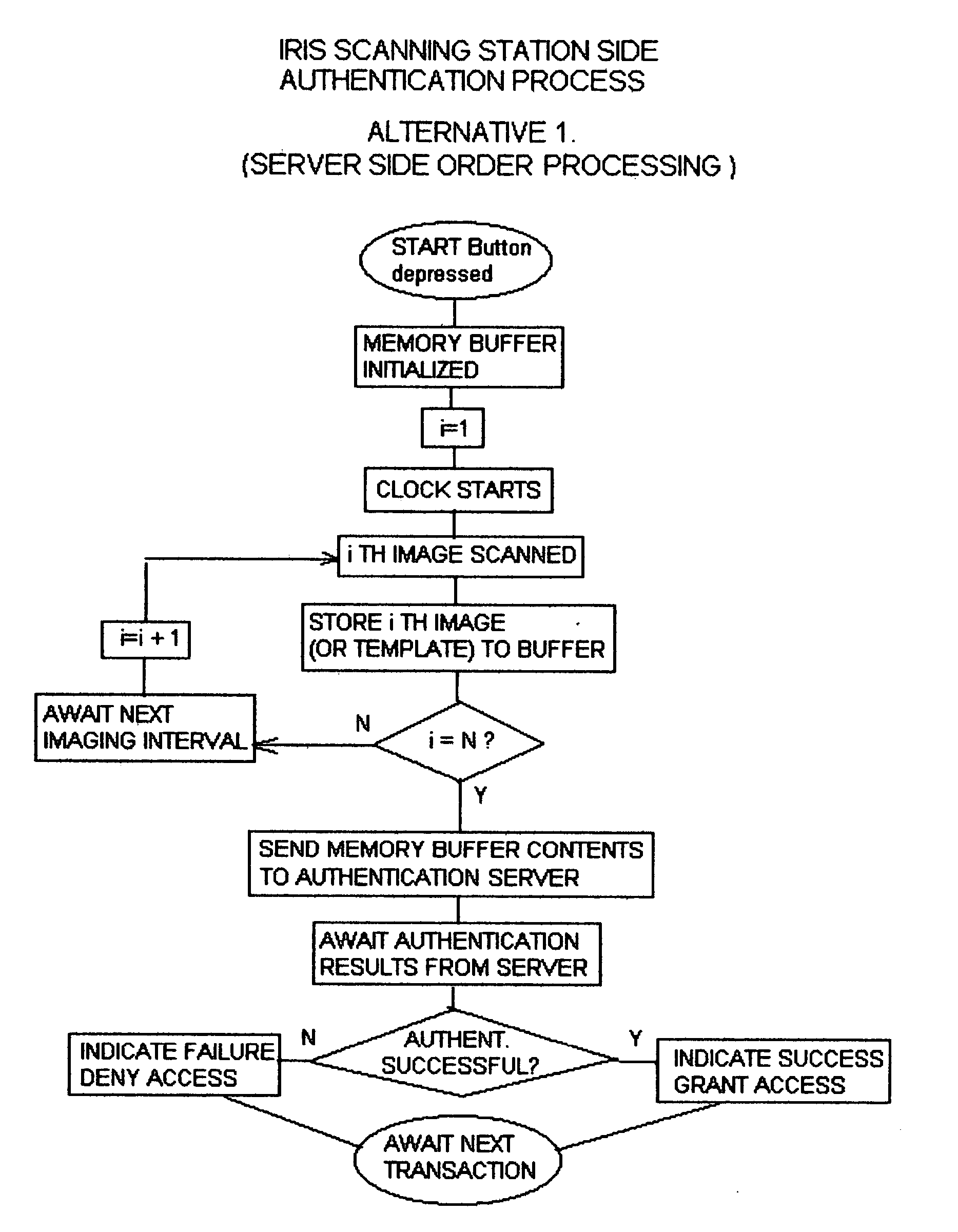
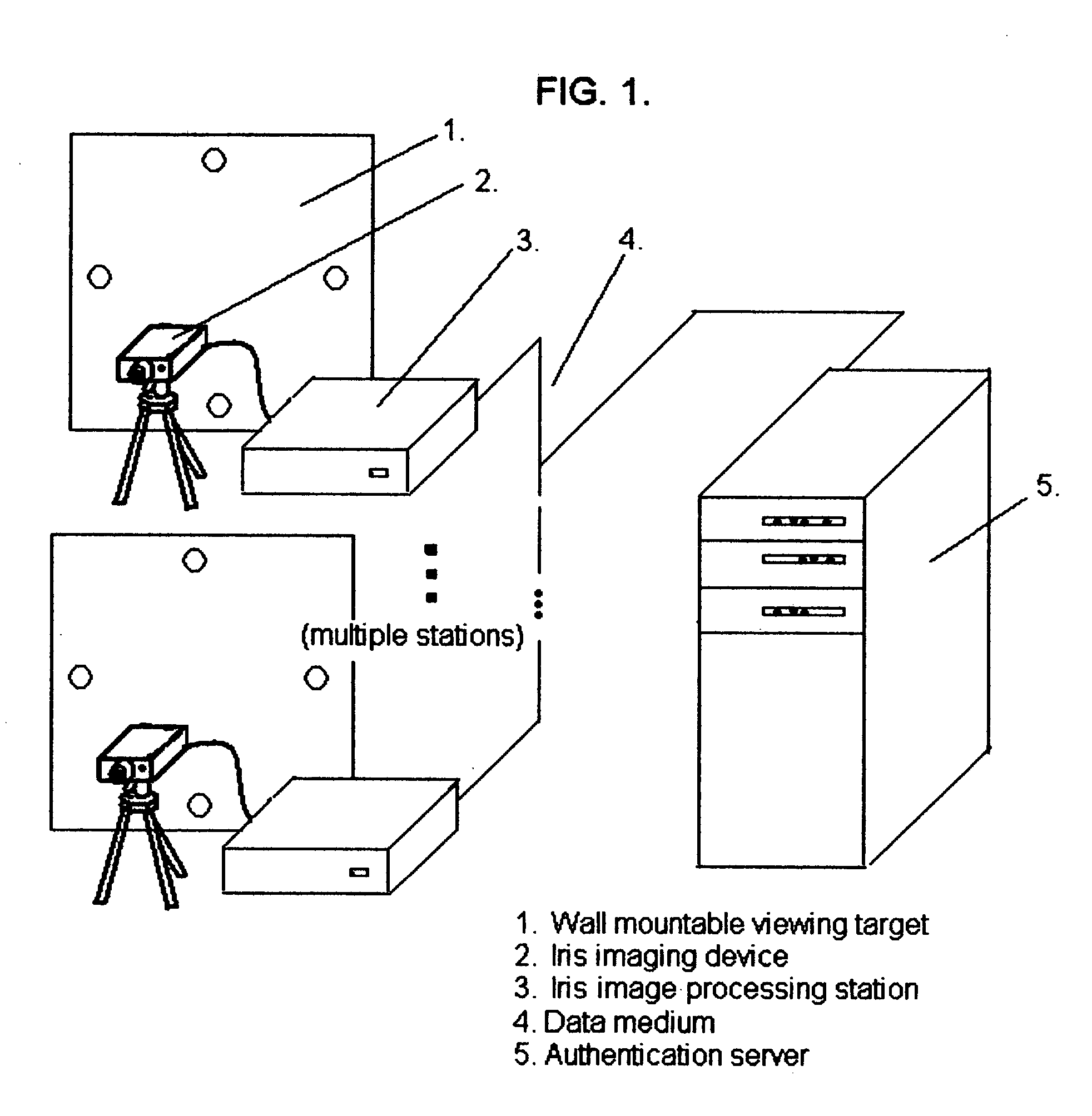
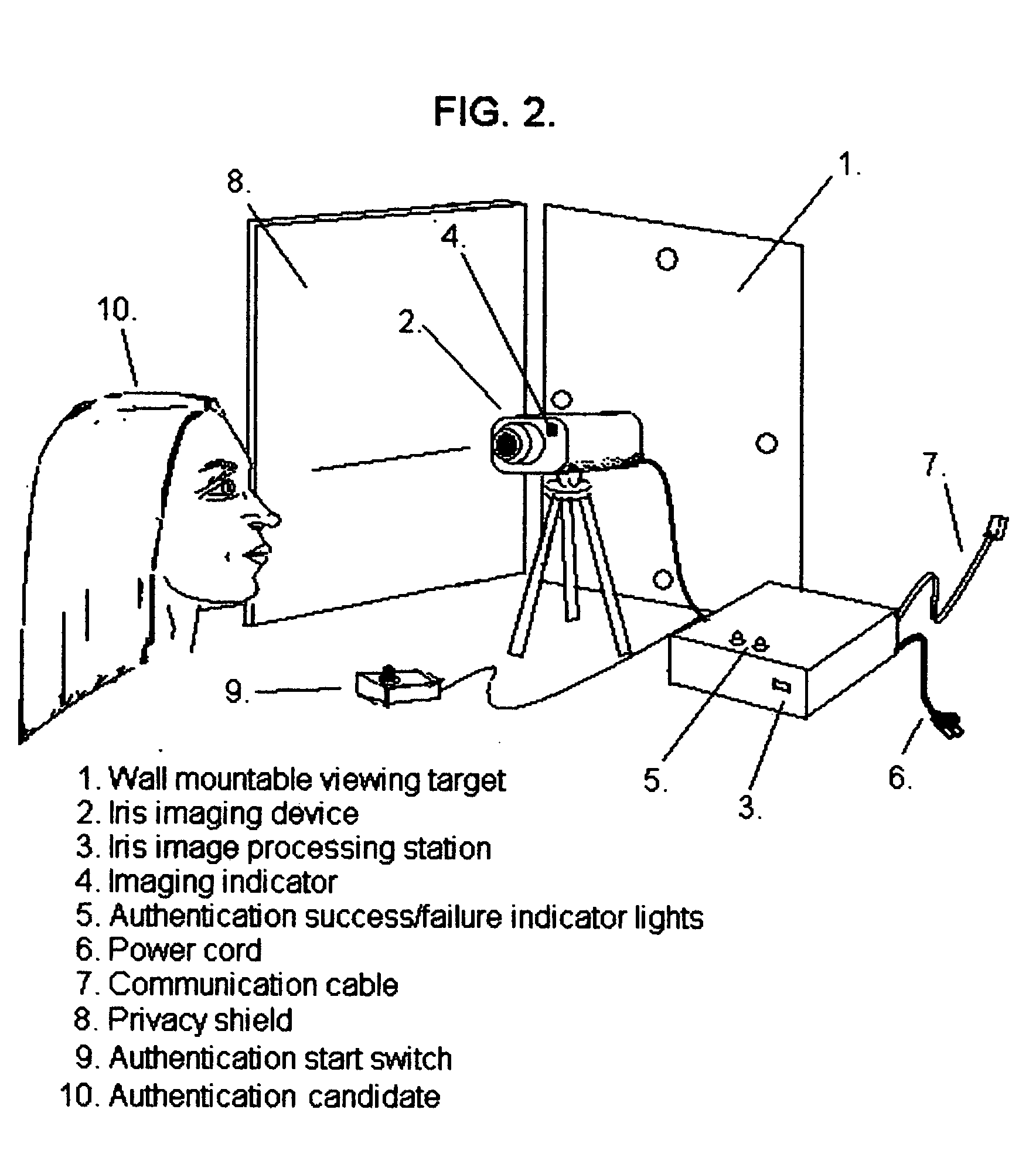
Technique using eye position and state of closure for increasing the effectiveness of iris recognition authentication systems
InactiveUS20050129286A1Increase in sizeSupport repeatabilitySpoof detectionEye stateInternet privacy
The invention, which is an embodiment of what the inventor calls, “Active Behavior Enhanced Iris Recognition Authentication”, employs a sequential iris imaging process where the authenticating party directs his or her gaze in specific directions, or closes their eyes for each image, so that an “eye state order” can be used to improve authentication security. Authentication security is strengthened based upon the reduced likelihood that a potential intruder would 1.) know what the correct sequence of eye states (i.e. up, down, left, right, camera view and closed) were associated with the control authentication template; 2.) be able to successfully “hack” the authentication server in order to gain access to the iris image information and also the eye state order information which would be required in order to fully compromise the authentication system. The technique embodied by the invention represents an overlay of a known, ordered sequence, over the iris recognition authentication process itself.
Owner:HEKIMIAN CHRISTOPHER DAVID
Secure web site authentication using web site characteristics, secure user credentials and private browser
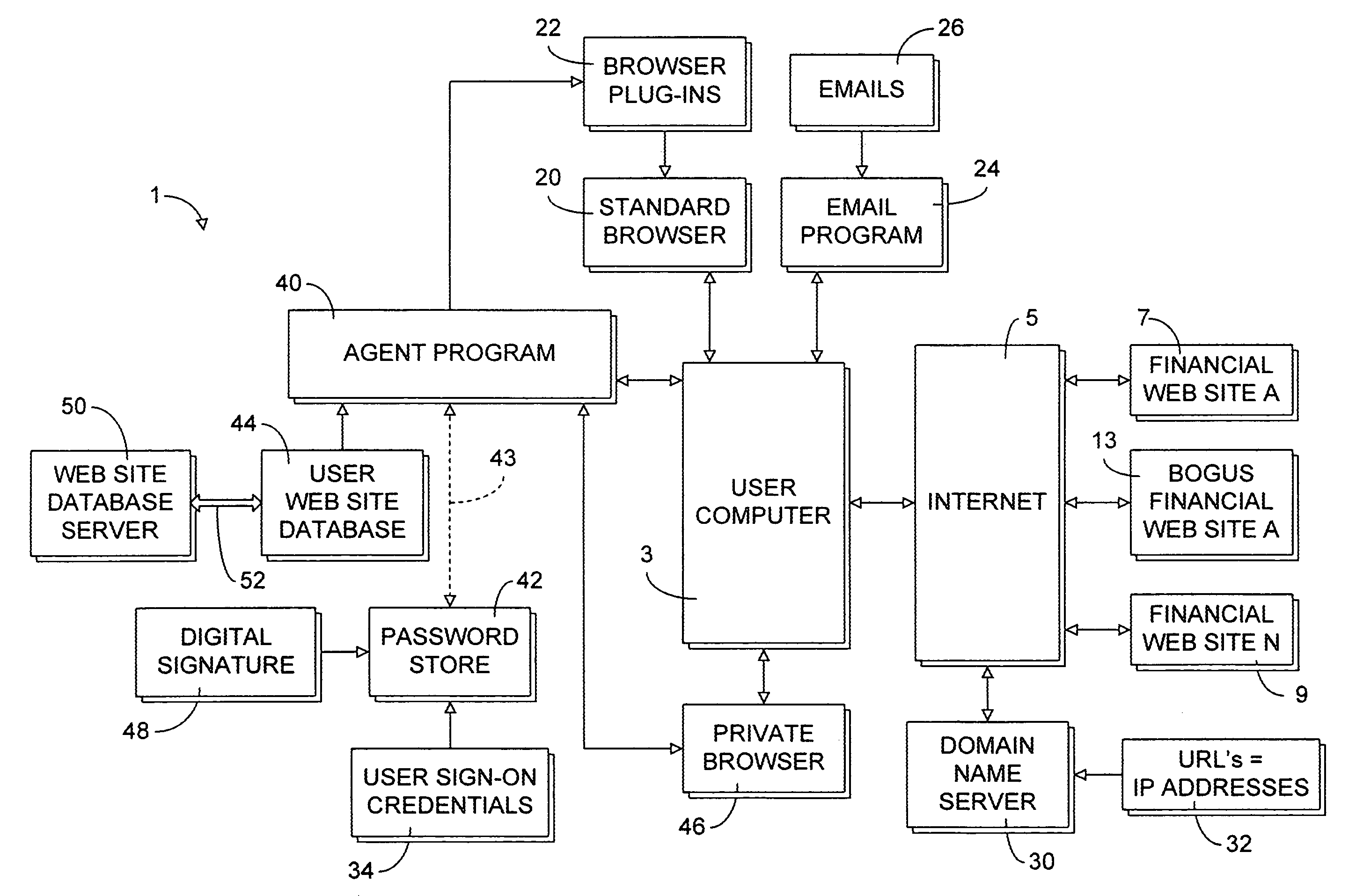
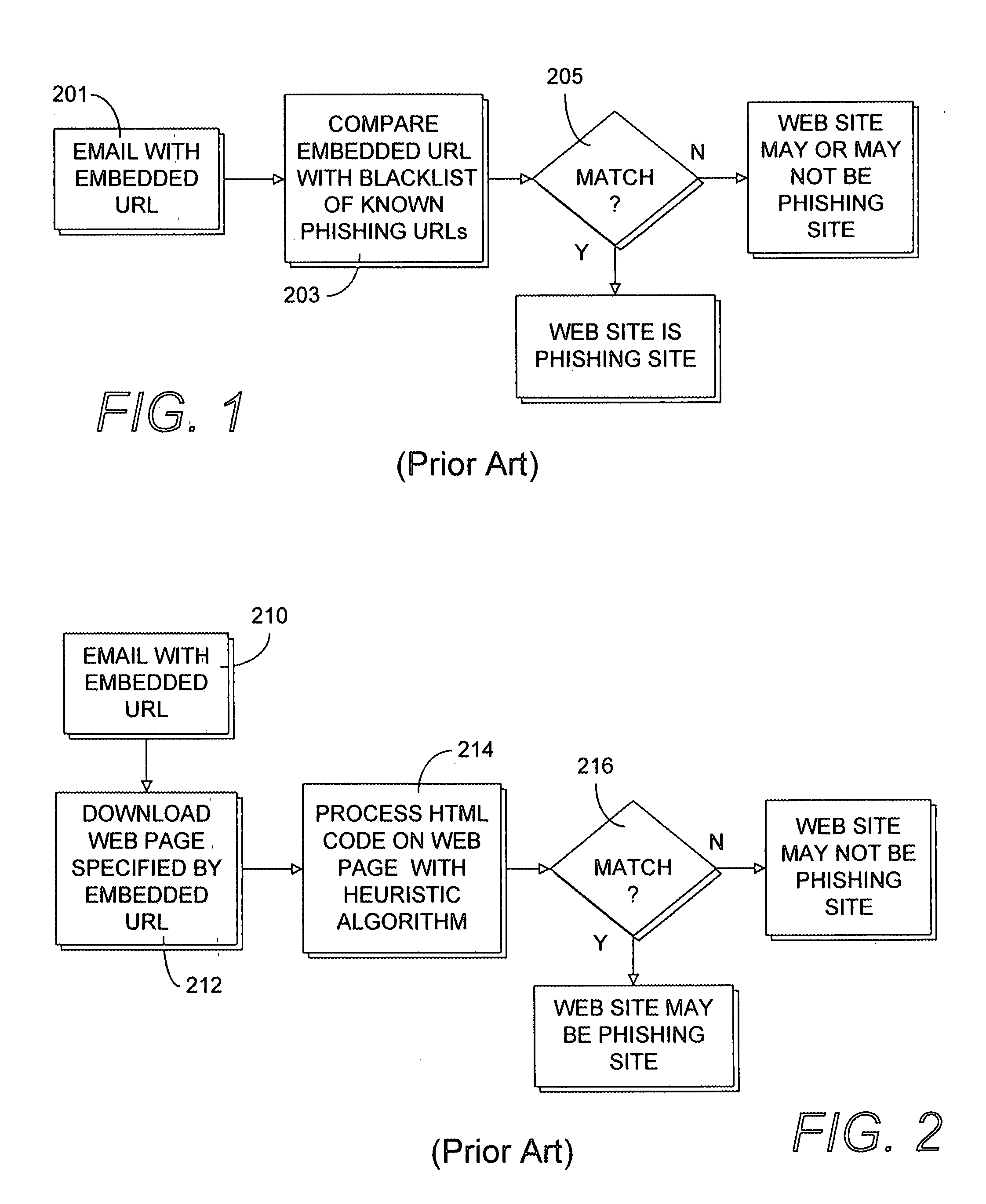
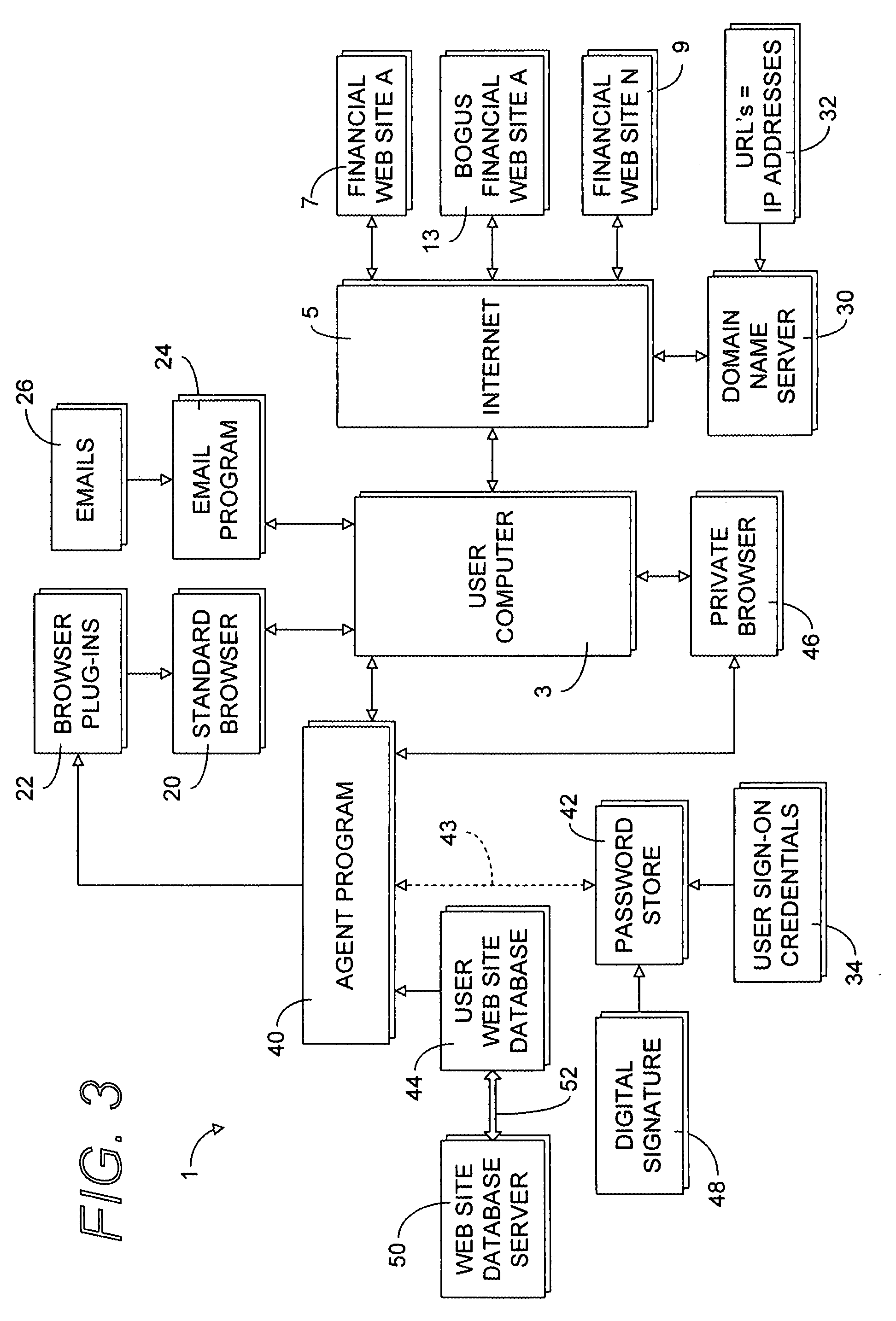
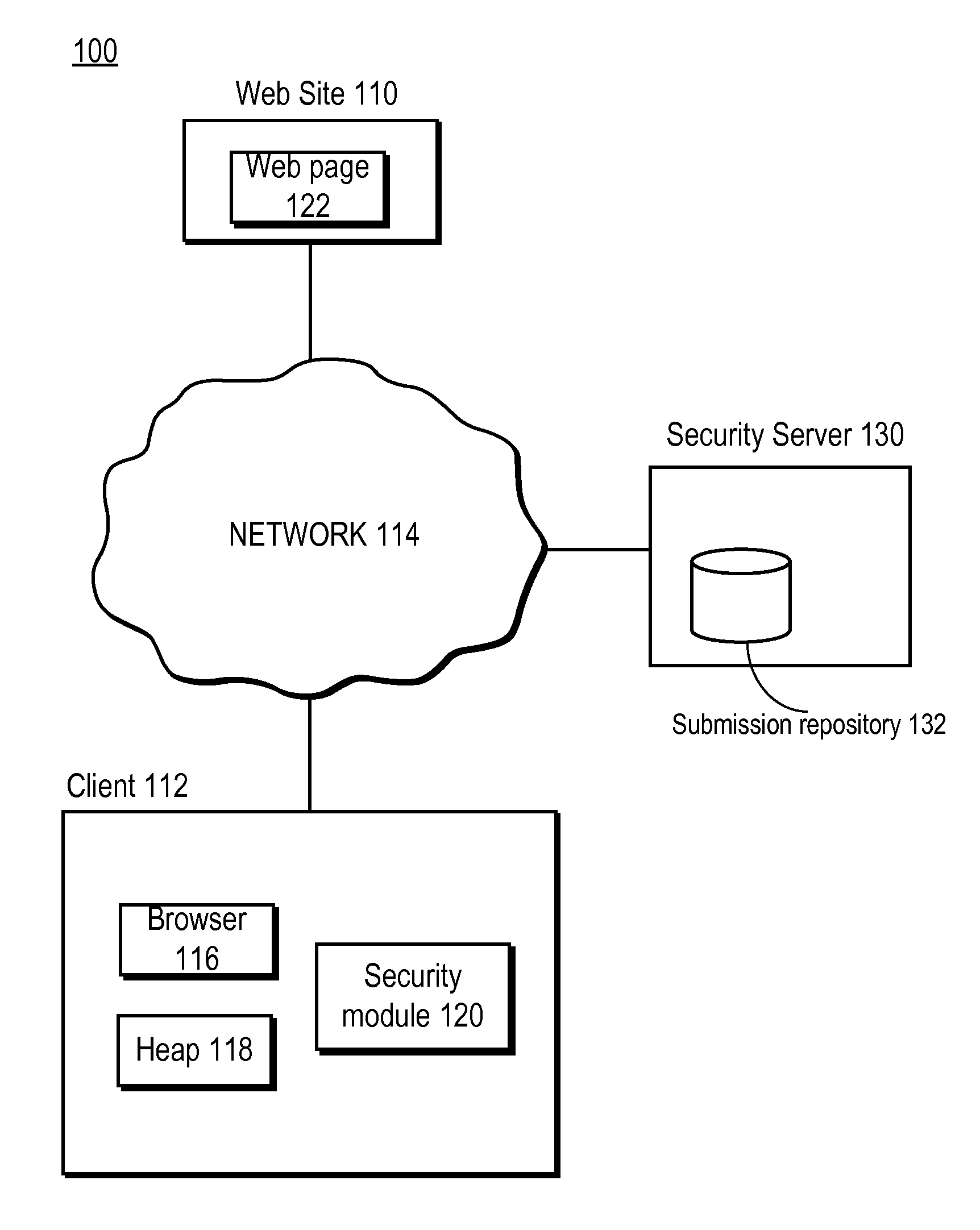
ActiveUS20080028444A1Overcome deficienciesImprove approachDigital data information retrievalMemory loss protectionWeb siteIp address
A secure authentication process detects and prevents phishing and pharming attacks for specific web sites. The process is based on a dedicated secure hardware store for user sign-in credentials, a database of information about specific web sites, and a private secure browser. All user web activity is monitored by an agent program. The agent program checks to make sure that user attempts to send any sign-in credentials stored in secure hardware store of user sign-in credentials, to any web site accessed by the user, is allowed only if the IP address of the web site accessed by the user matches at least one of the IP addresses stored web site database associated with the sign-in credential the user is attempting to send. The process also detects mismatches between a URL and the actual IP address of the web site associated with the URL.
Owner:AURA SUB LLC +1
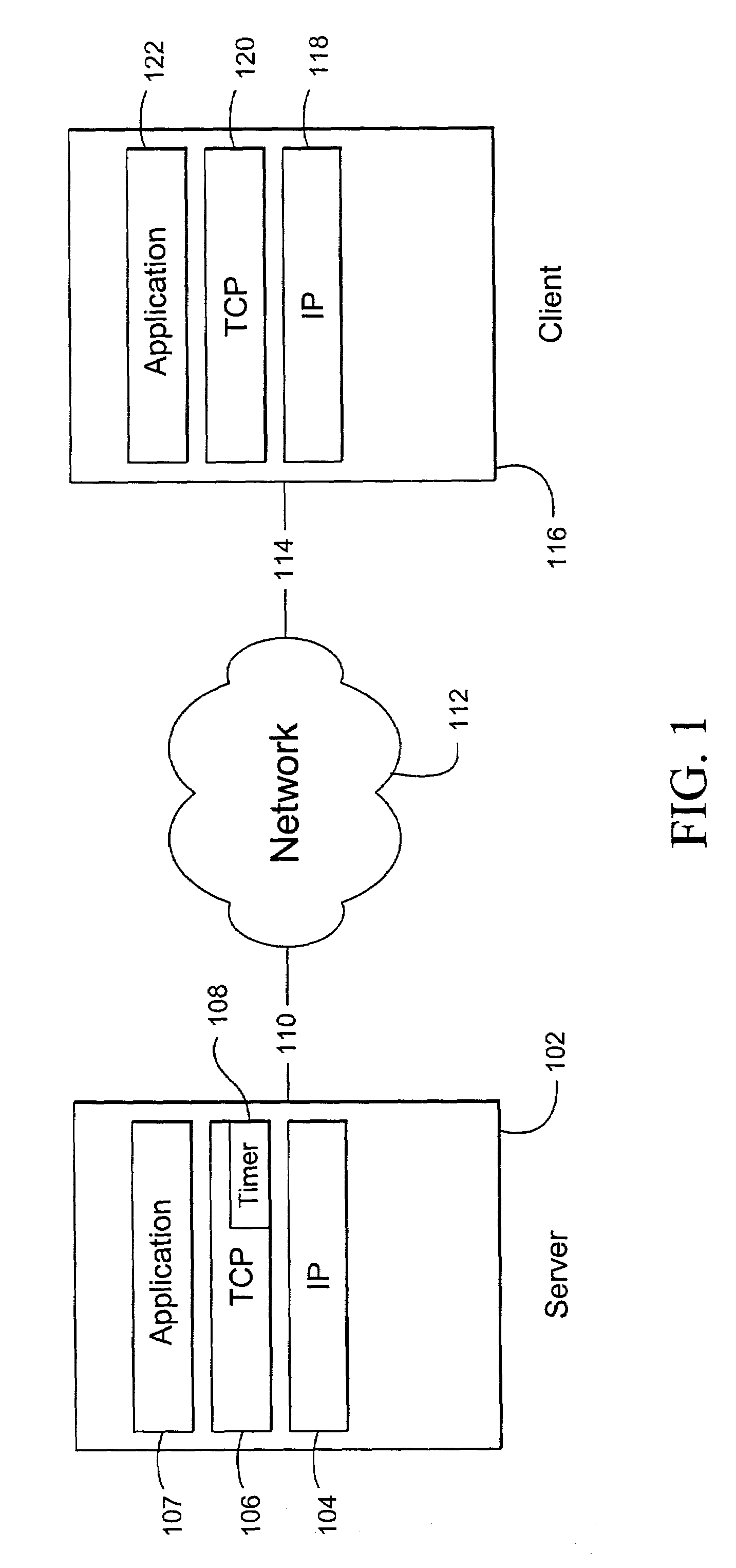
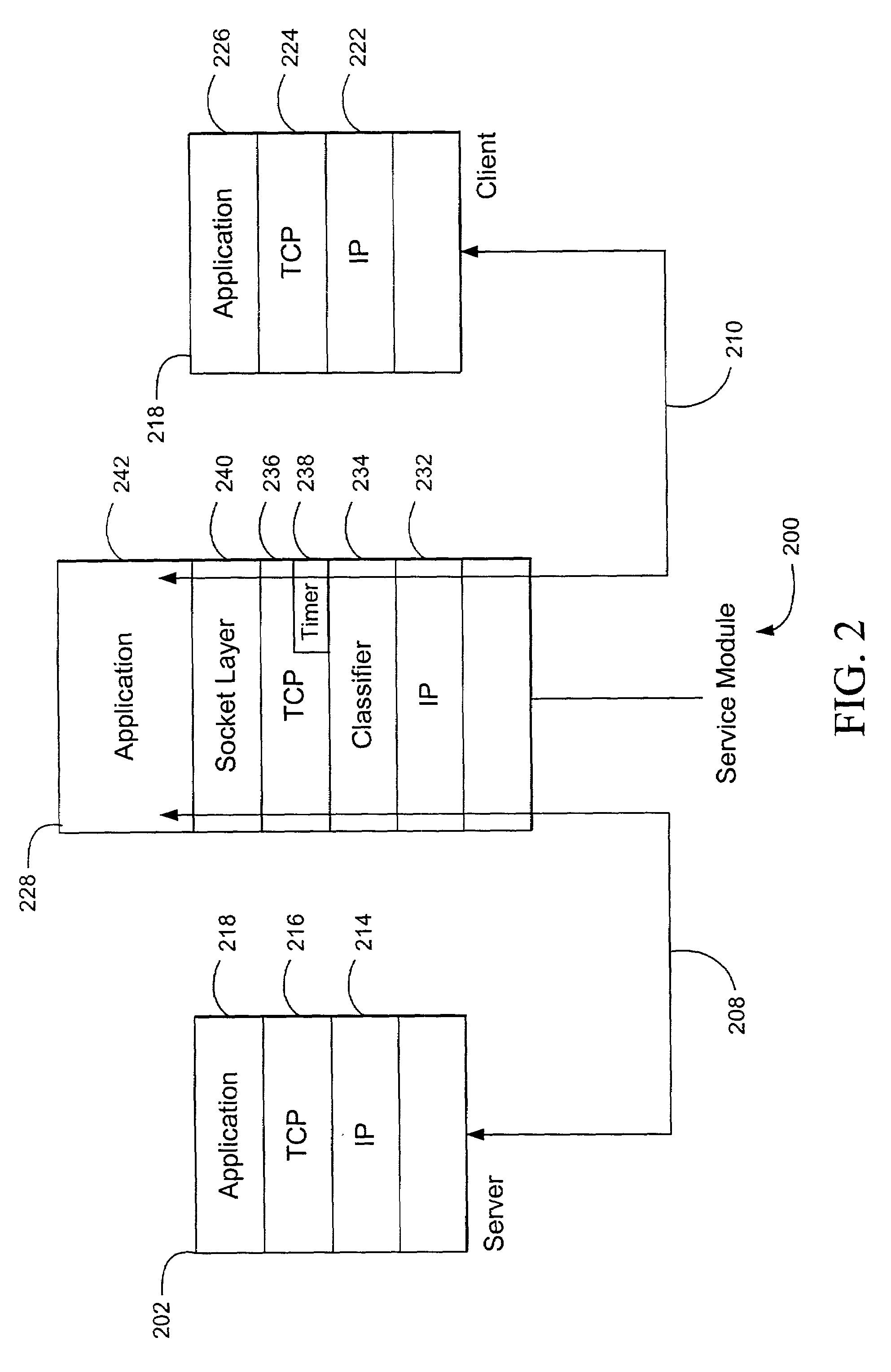
Data transport acceleration and management within a network communication system
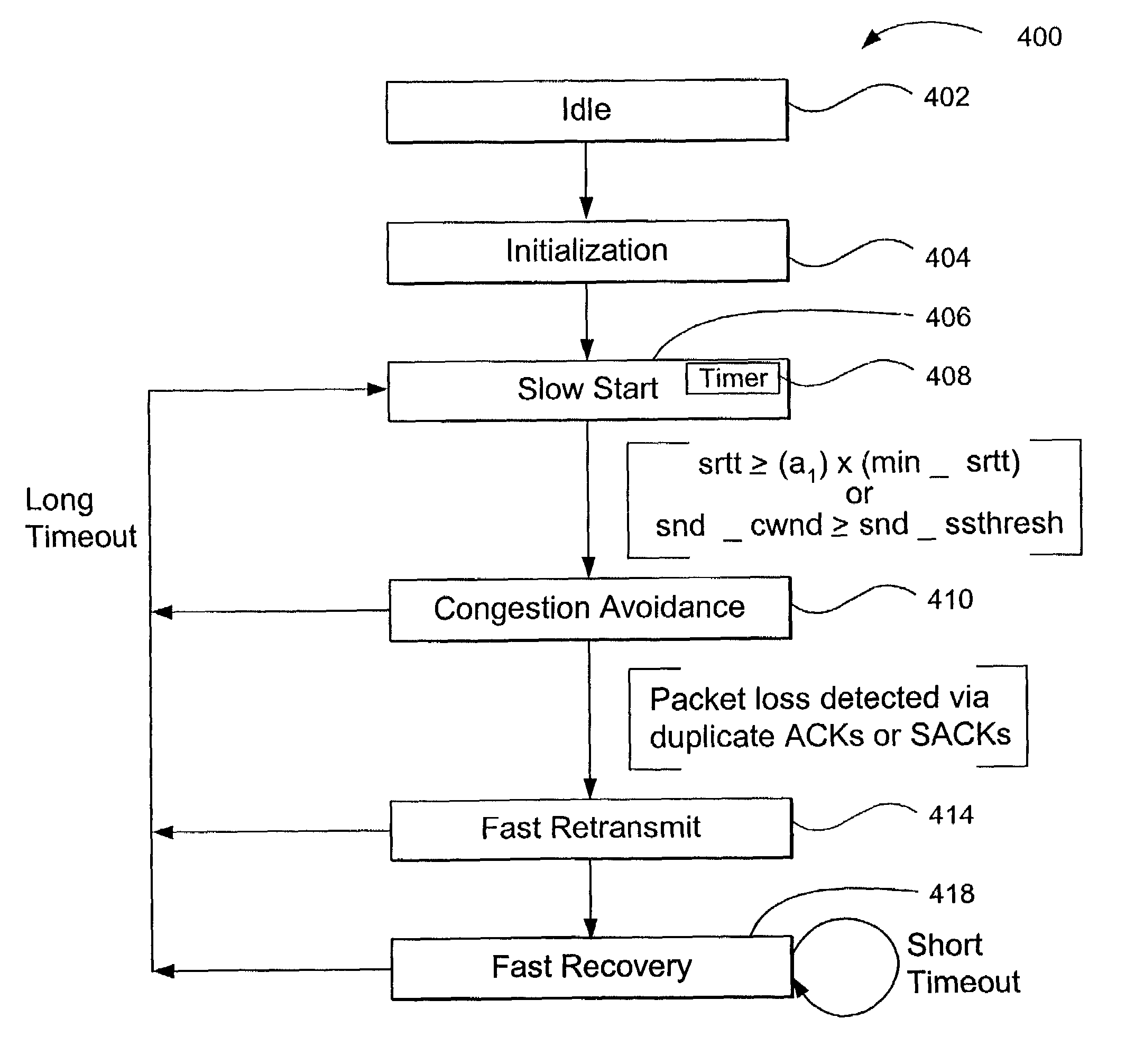
ActiveUS7099273B2Good estimateReduce and eliminate bursty transmission of dataEnergy efficient ICTError prevention/detection by using return channelCongestion windowPacket loss
Improved data transport and management within a network communication system may be achieved by utilizing a transmit timer incorporated within the sender device and exploiting host-level statistics for a plurality of connections between a sender and receiver. The period of the transmit timer may be periodically adjusted based on a ratio of the smoothed round-trip time and the smoothed congestion window, thereby reducing or eliminating bursty data transmission commonly associated with conventional TCP architectures. For applications having a plurality of connections between a sender and a receiver that share a common channel, such as web applications, the congestion window and smoothed round trip time estimates for all active connections may be used to initialize new connections and allocate bandwidth among existing connections. This aspect of the present invention may reduce the destructive interference that may occur as different connections compete with one another to maximize the bandwidth of each connection without regard to other connections serving the same application. Error recovery may also be improved by incorporating a short timer and a long timer that are configured to reduce the size of the congestion window and the corresponding transmission rate in response to a second packet loss with a predefined time period in order to increase resilience to random packet loss.
Owner:OPTIMORPHIX INC
Hybrid wireless network for data collection and distribution
ActiveUS7327705B2Minimize susceptibilityEasy to transportNetwork topologiesData switching by path configurationTelecommunicationsWireless transmission
An electronic data transport system includes a mobile access point and a carrier for moving the mobile access point over a surface and / or water route. The mobile access point includes a communications module for wirelessly transmitting data to and receiving data from one or more client devices when the client device is in proximity to the mobile access point.
Owner:MASSACHUSETTS INST OF TECH
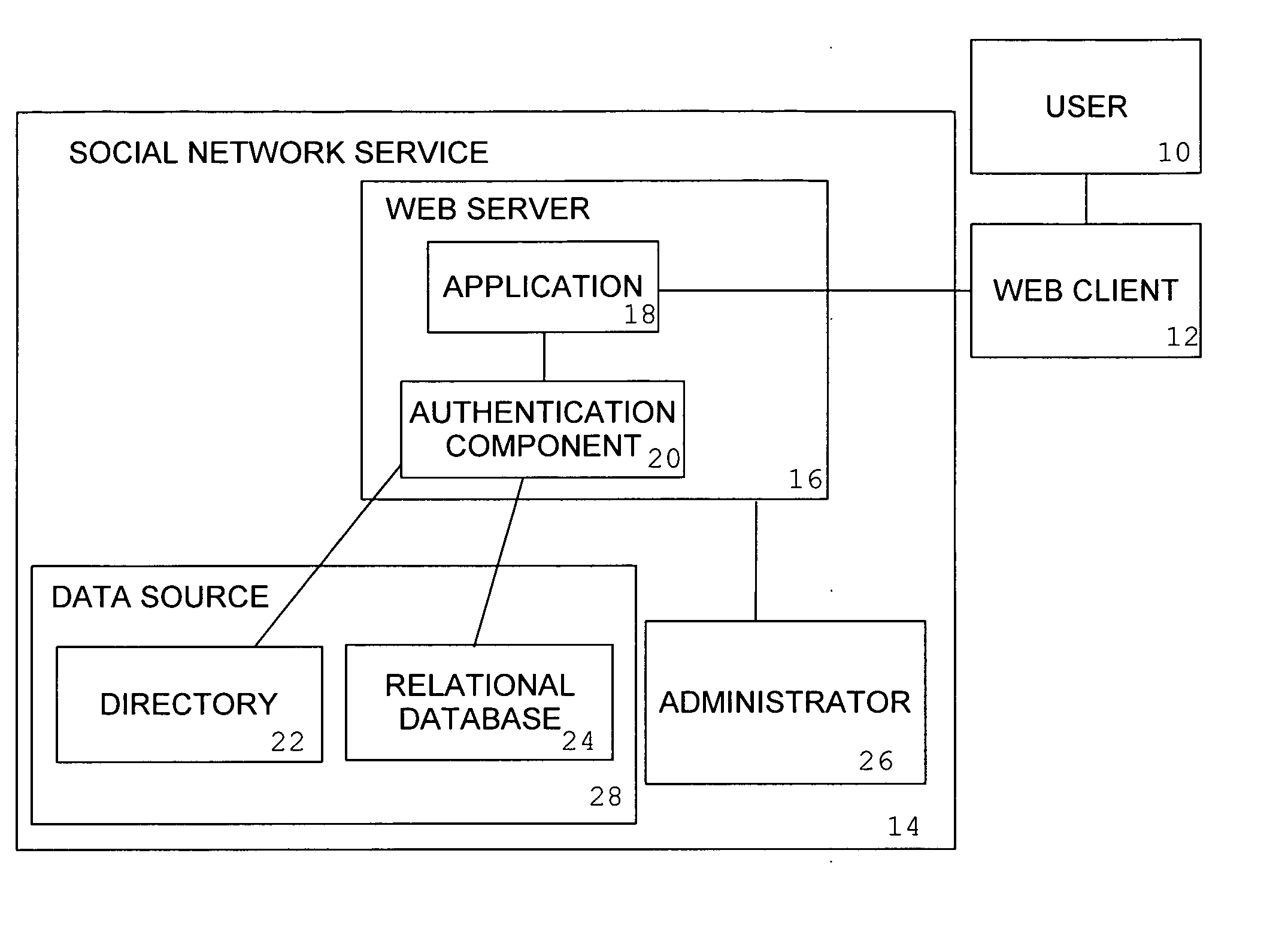
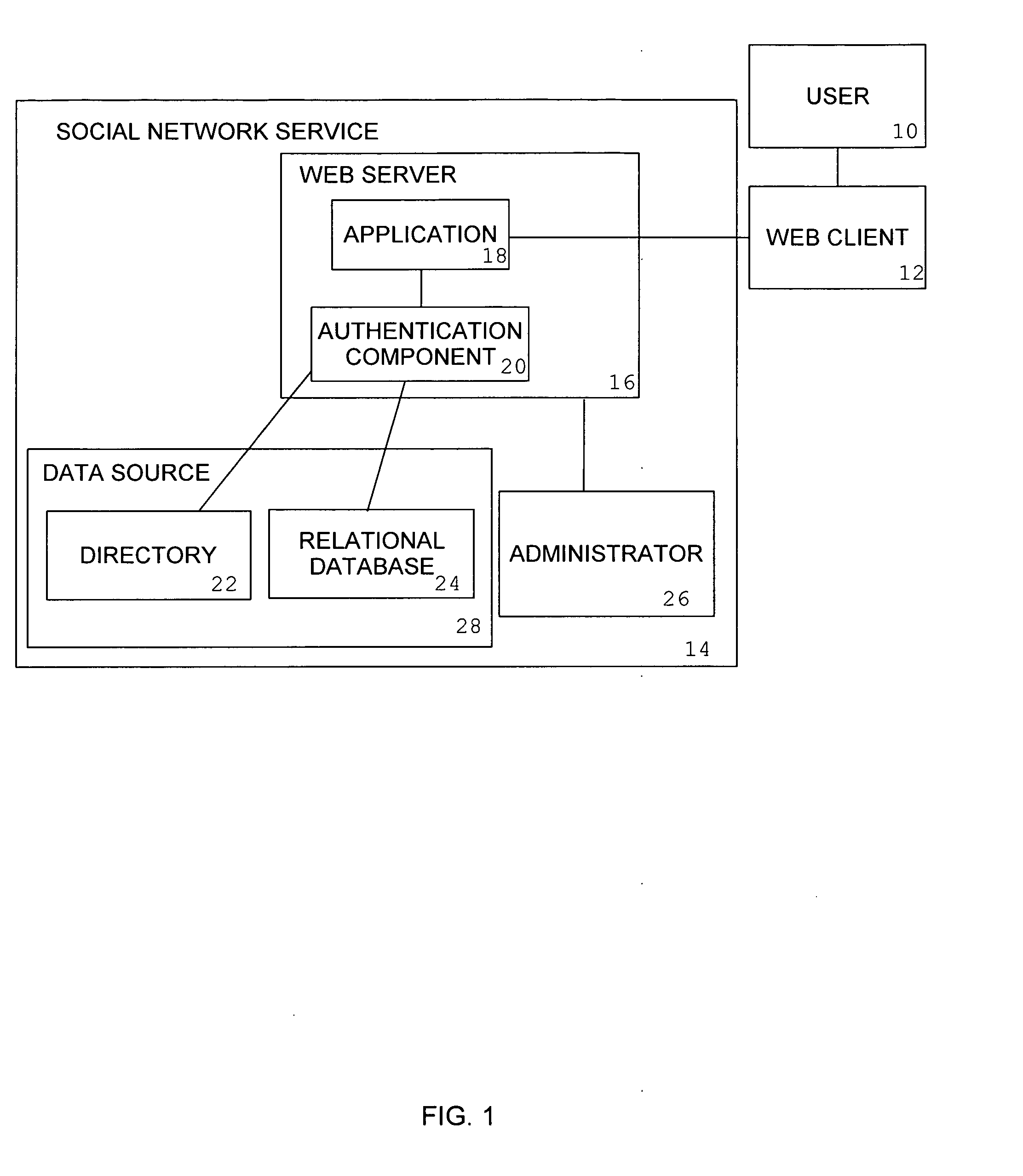
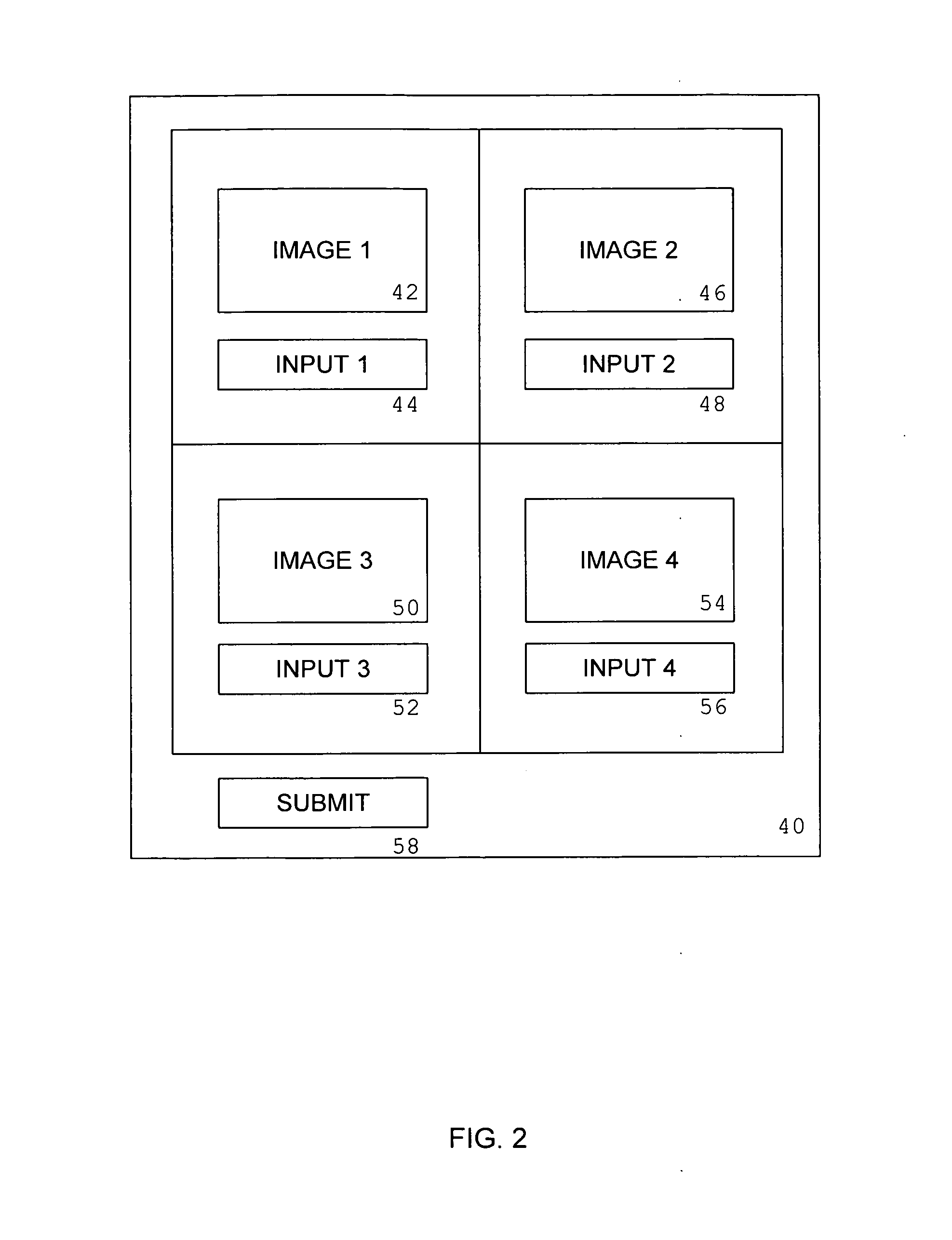
System and method for authentication in a social network service
InactiveUS20080148366A1Reduce vulnerabilityDigital data processing detailsMultiple digital computer combinationsInformation processingSocial network service
An information processing system for providing a social network service to clients on a computer network is augmented with the ability to authenticate users by their ability to recognize digital photograph images of other users of the system with whom the user being authenticated has an affiliation, in which the user being authenticated will be presented with a set of photographs and will be required to correctly supply to the system the names of the individuals represented in those photographs.
Owner:WAHL MARK FREDERICK
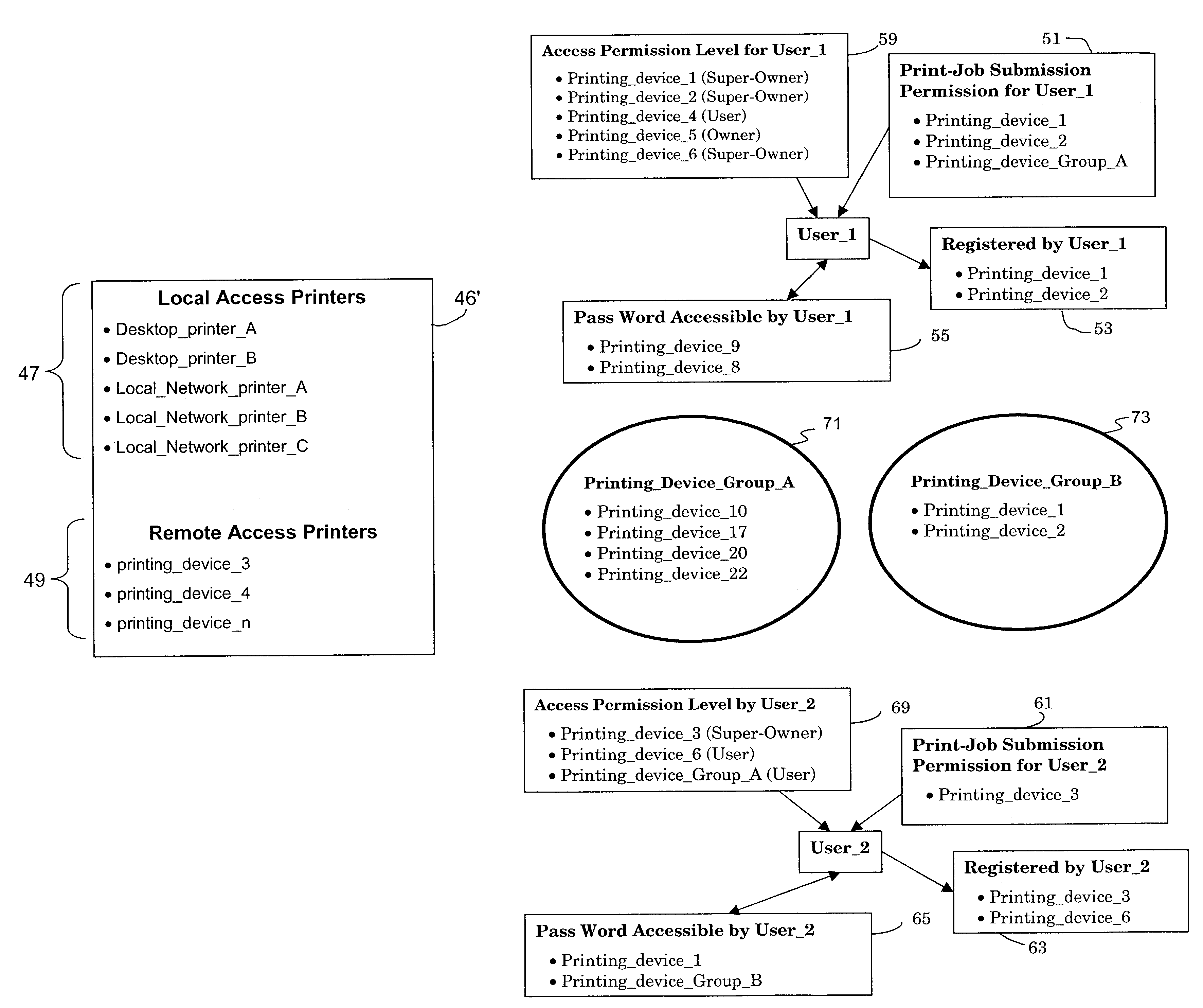
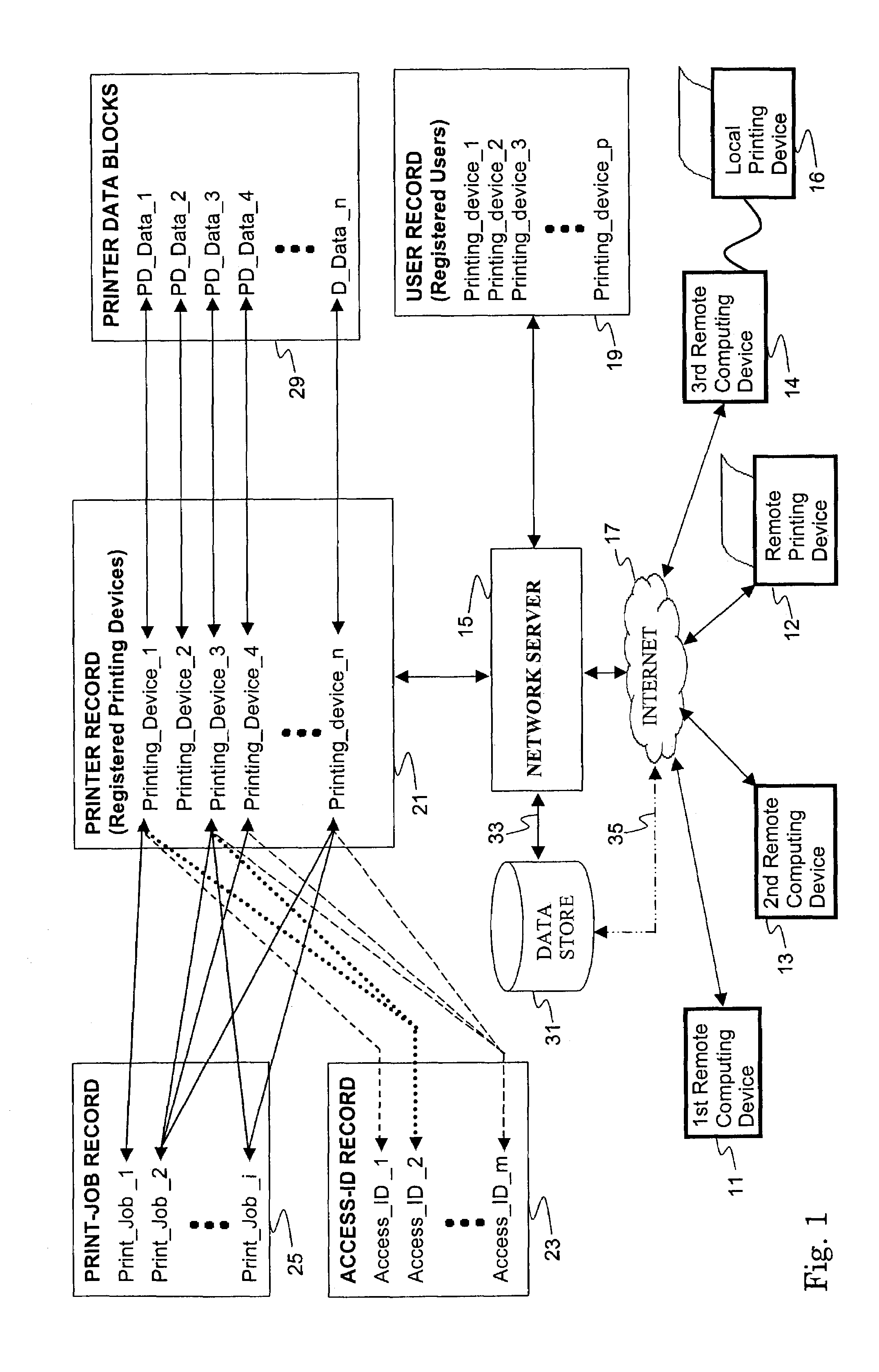
Document sharing service for network printing
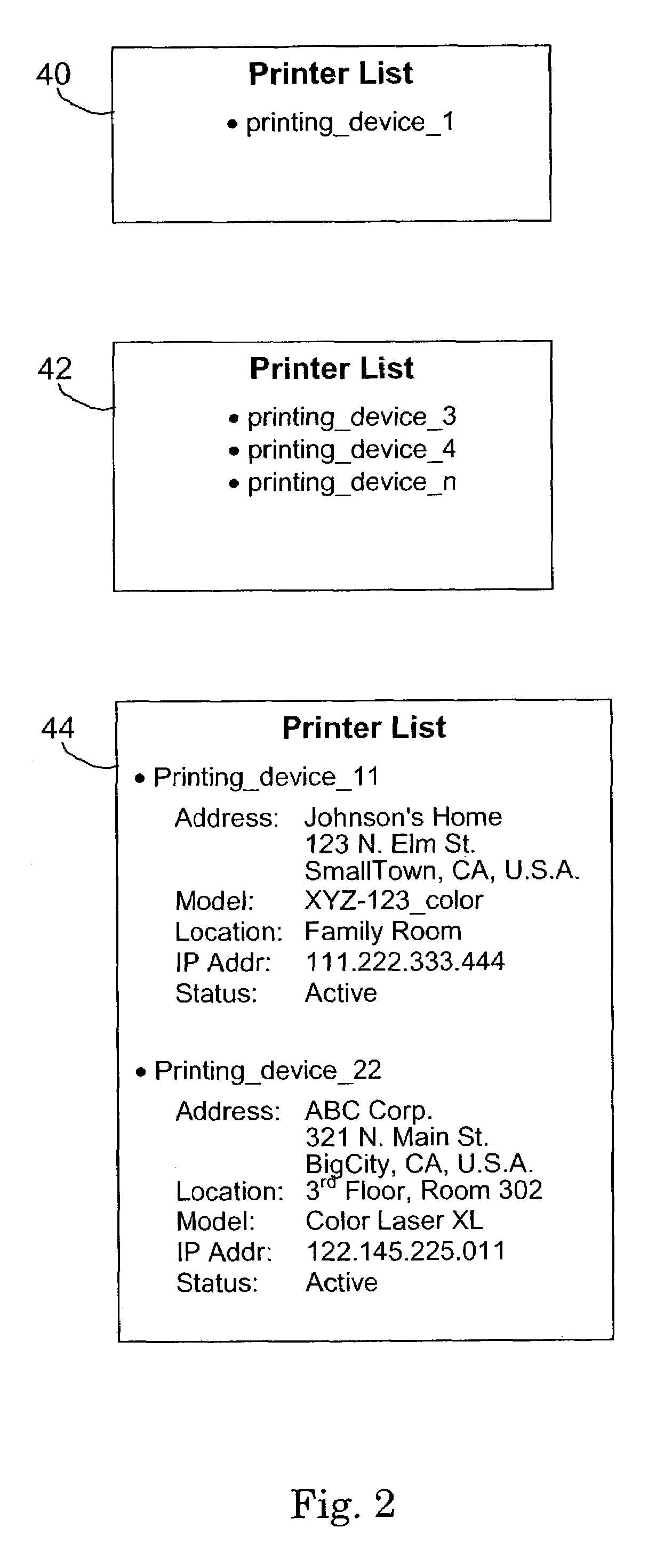
ActiveUS7359076B2Direct accessReduce vulnerabilityData processing applicationsComputer security arrangementsWeb pageAccess management
An internet accessible server permits access management to remote printing devices by remote users. Only users having printing access to a target remote printing device may submit a print job for printing on the target remote printing device. Users having printing access permission are further divided into owner status and user status. Owner status user of a remote printing device may grant or revoke the printing permission of non-owner status users. At least one owner status user is designated a super-owner, and can grant and revoke the owner status of other users. The super-owner user may relinquish its super-owner status to any other user. After submitting a print job for a target printing device, the print job is stored in a storage space on the Internet and is transferred to the target printing device only when the target printing device itself downloads the print job using standard internet protocols similar to those used in the downloading of a web page.
Owner:SEIKO EPSON CORP
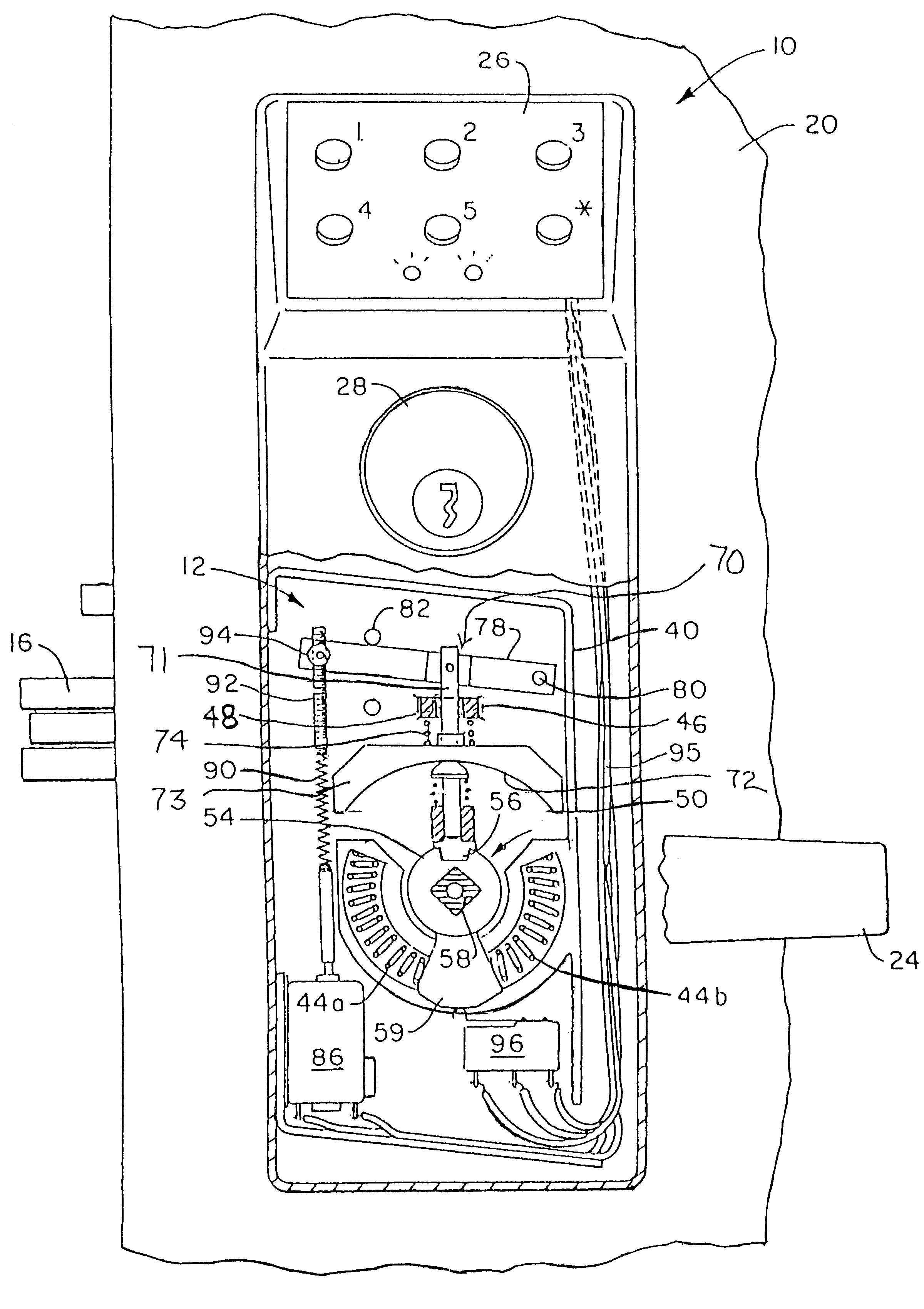
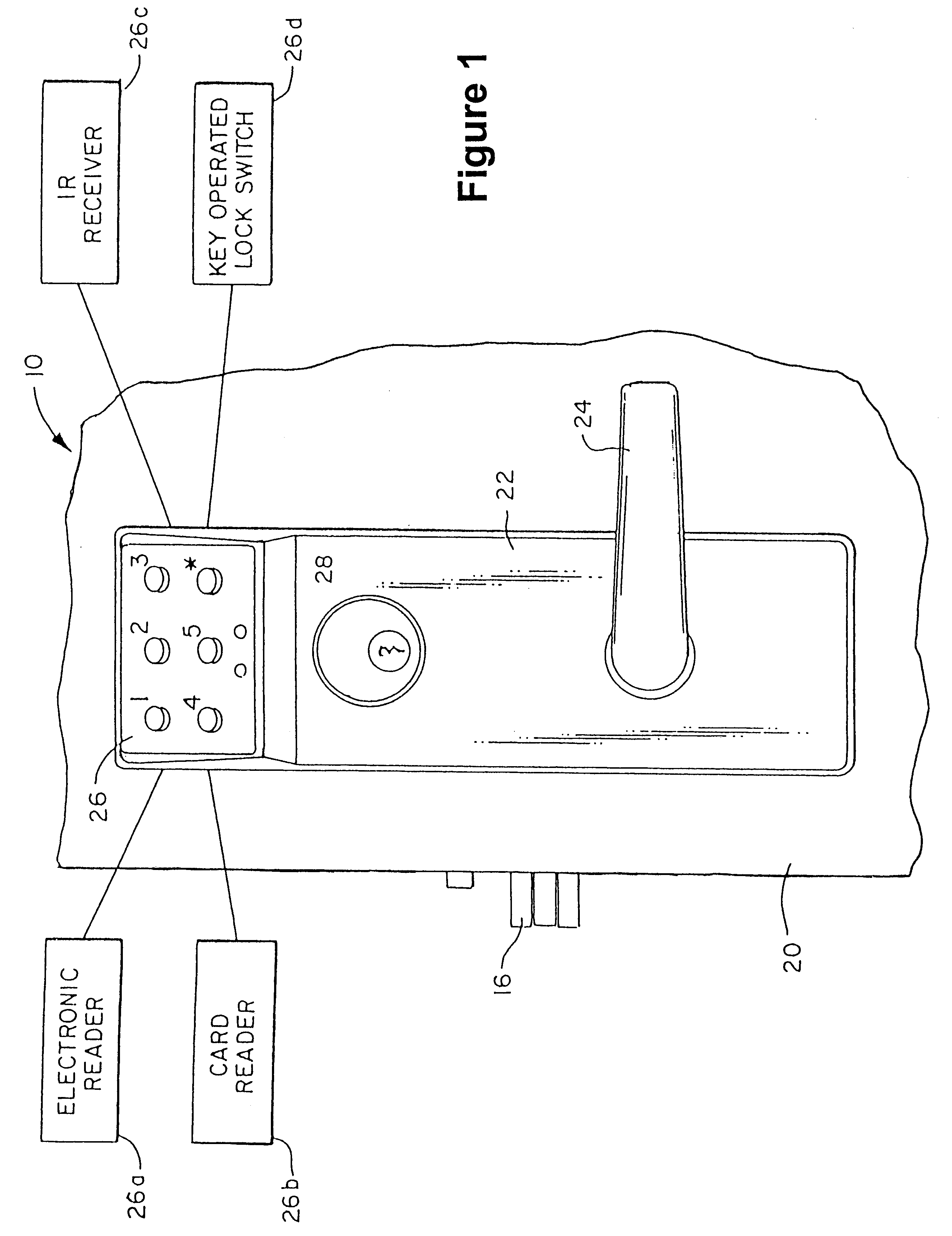
Method for Controlling and Recording the Security of an Enclosure
InactiveUS20120011367A1Easy to manufactureGuaranteed uptimeProgramme controlDigital data processing detailsElectronic accessEvent data
A method for controlling and recording the security of an enclosure is disclosed. A mobile electronic control device, such as an electronic key, is used to access or otherwise control the operations of a field device, such as an appliance, power tool, shipping container, and the like. In a control event in which the mobile control device interacts with the field device via wired or wireless communications, the control device obtains the current location and the field device ID. The communications between the mobile control device and the field device may be secured with encryption. The location information is used by the mobile control device to determine whether the field device should be accessed or enabled. Alternatively, the location information may be stored separately in a location sensing device, and the control event data recorded by the key and the location information recorded by the location sensing device are later combined when they are downloaded into a management system for auditing. Moreover, an electronic access control device is disclosed comprising two microprocessors.
Owner:MICRO ENHANCED TECH
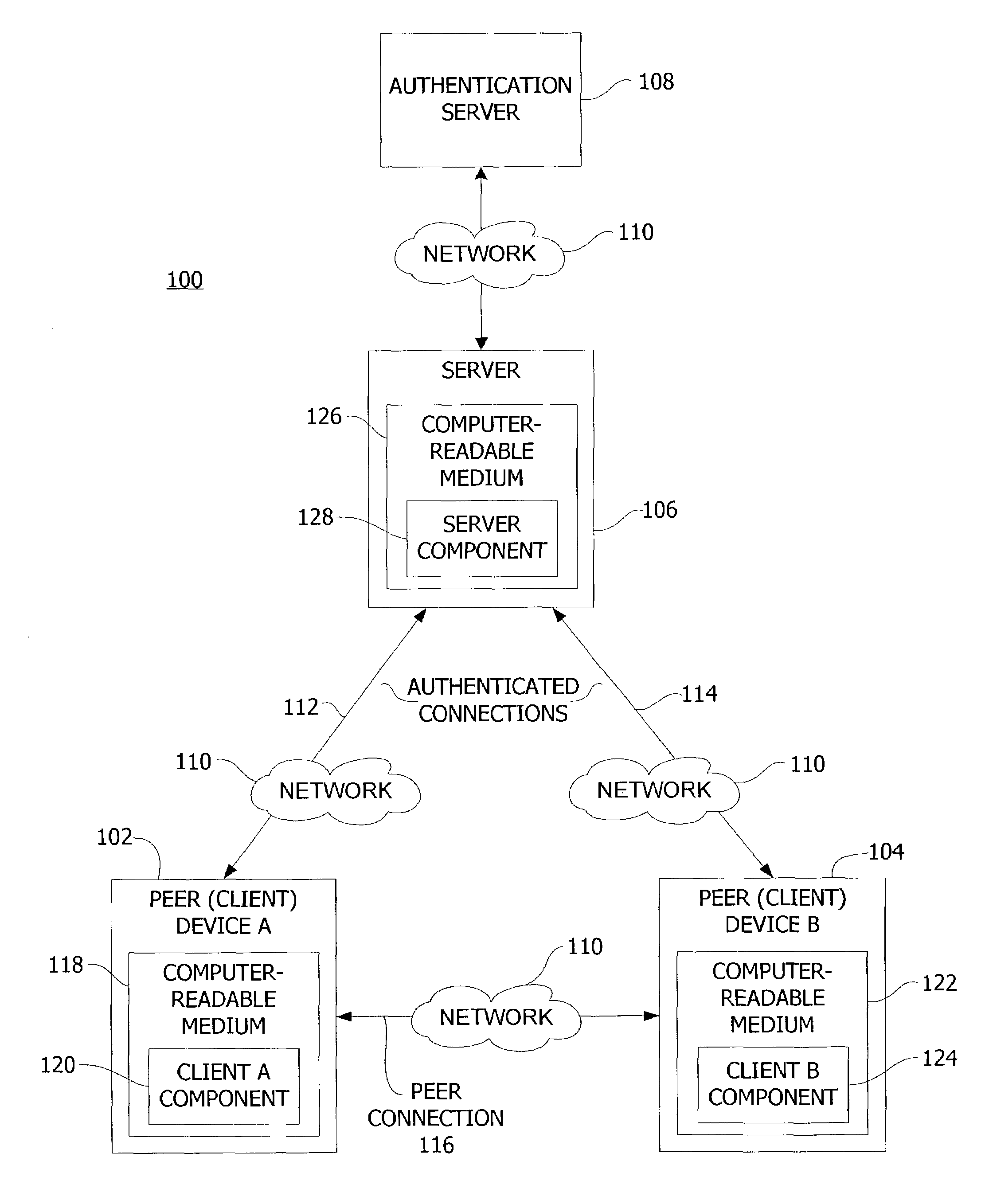
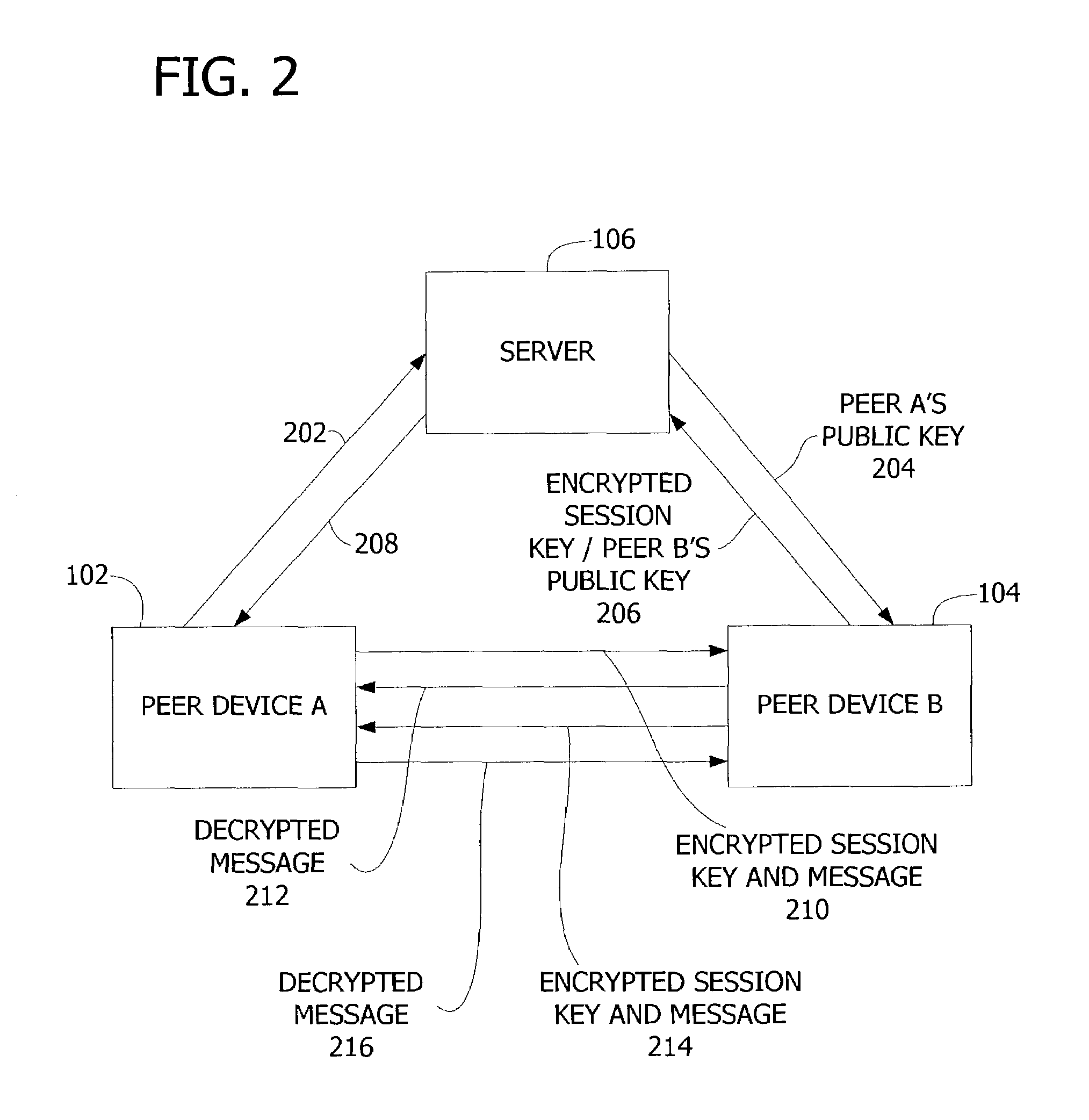
Authenticating peer-to-peer connections
InactiveUS7386878B2Potential vulnerabilityReduce vulnerabilityKey distribution for secure communicationDigital data processing detailsPlaintextData transmission
Systems and methods employing authenticated connections to a central server to establish and authenticate a peer-to-peer connection between peer devices. The invention circumvents the potential vulnerability of clear-text transmission of secrets through a series of encrypted data transfers. A secret key is encrypted and then transmitted from one peer device to another using authenticated connections to the server. The secret key is then used to transmit encrypted data over a peer connection between the peer devices for the purpose of authenticating the peer devices on each end of the connection.
Owner:MICROSOFT TECH LICENSING LLC
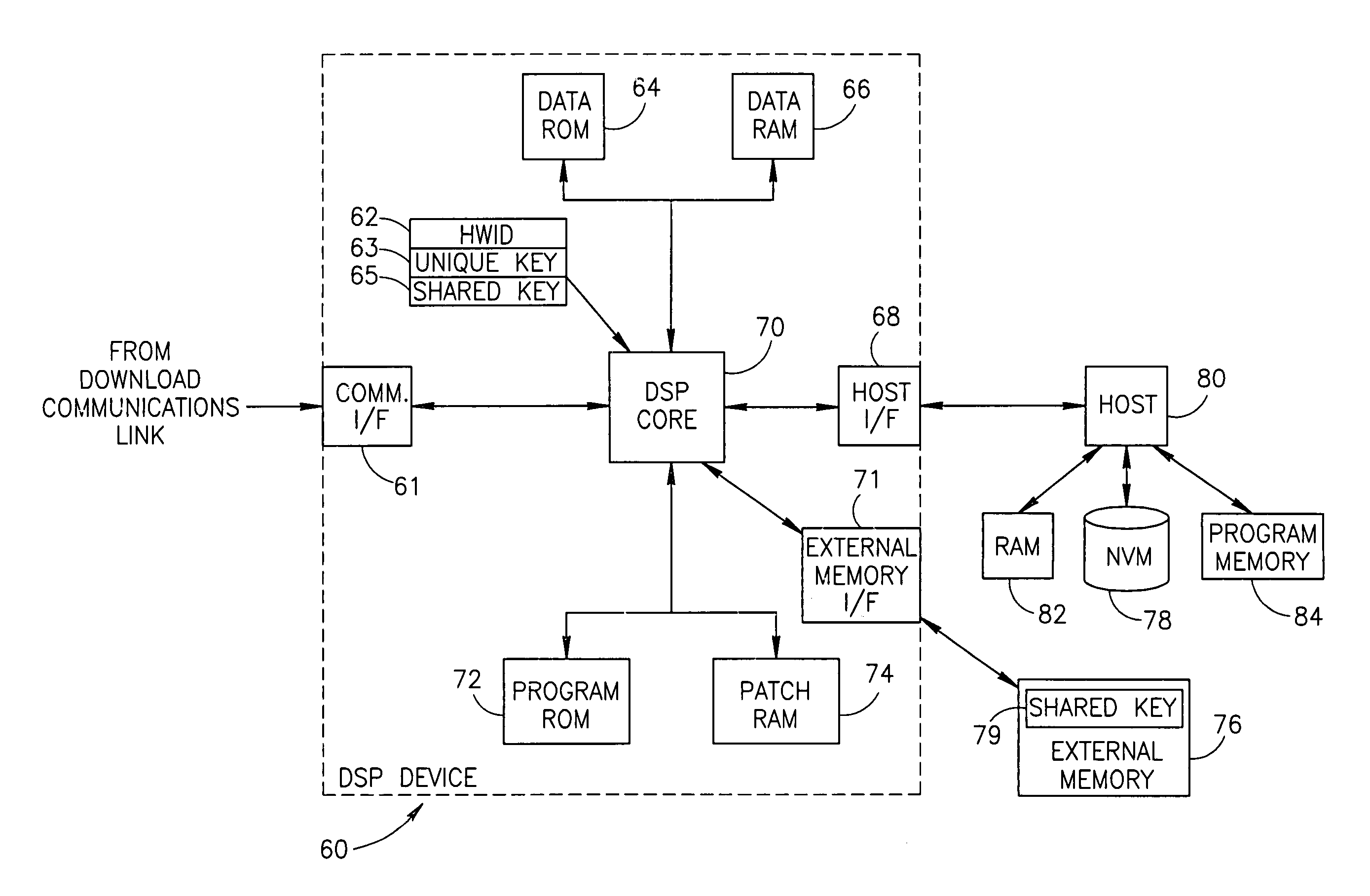
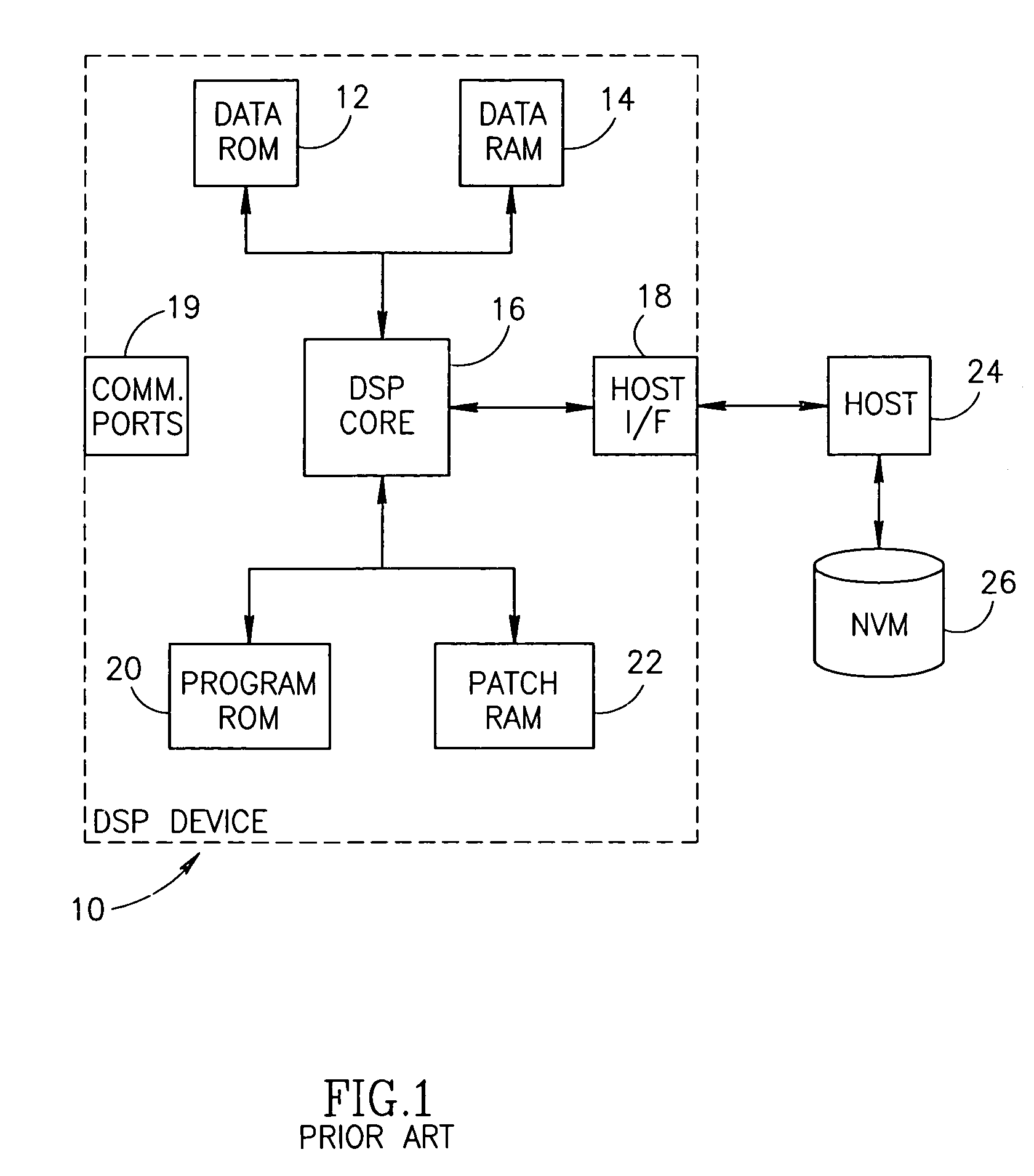
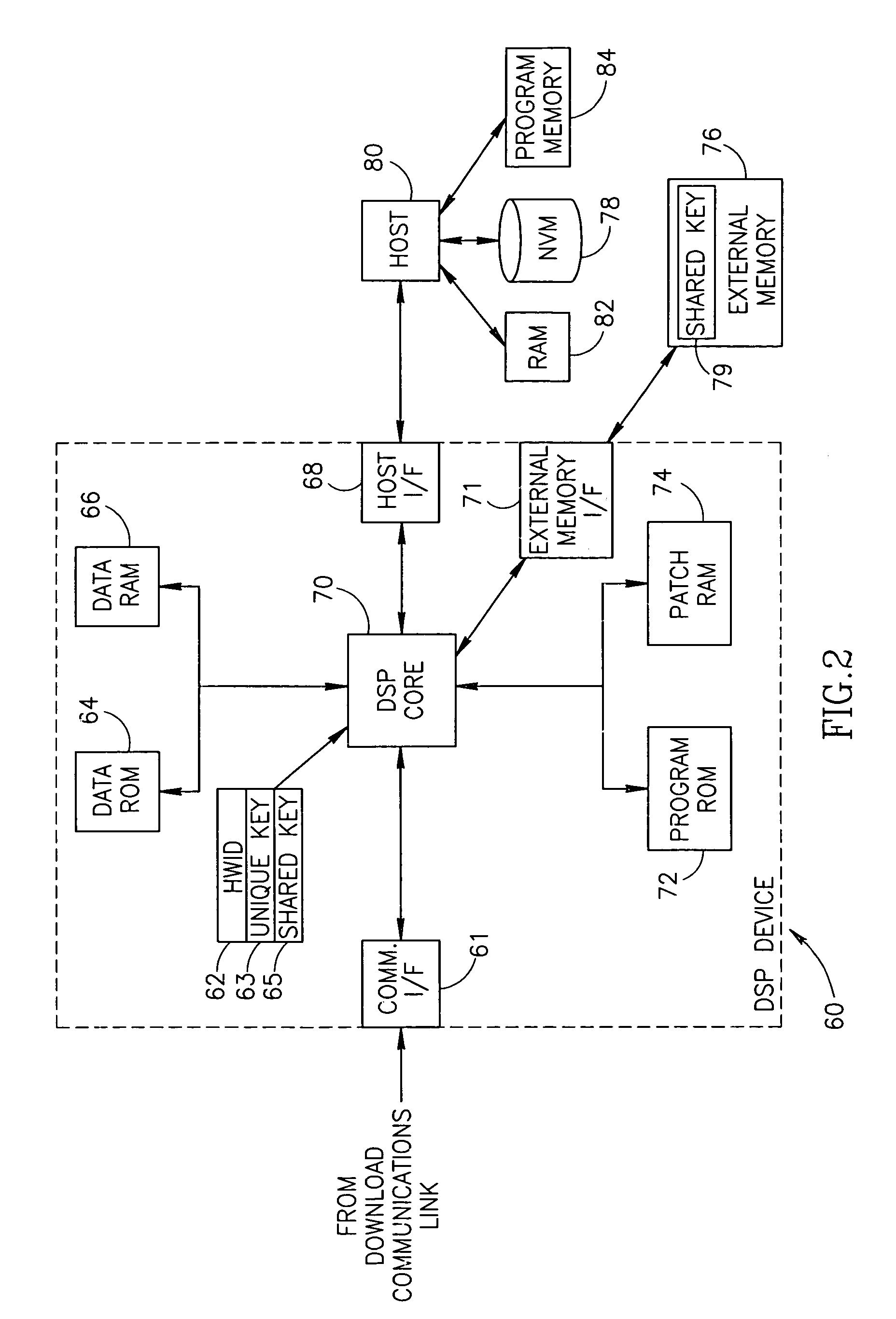
Apparatus for and method of securely downloading and installing a program patch in a processing device
InactiveUS6970565B1Reduce vulnerabilityNone of methods is secureSecret communicationPlatform integrity maintainanceSatellite radioTelecommunications link
A novel and useful apparatus for and method of securely downloading and installing a patch program in a processing device. Each processing device is assigned a unique key embedded therein during manufacture and has knowledge of a shared key. The program patch is encrypted using the shared key and transmitted over a communication link, such as a satellite radio link, to each device. The patch is decrypted using the shared key and re-encrypted using the unique key known only to the device itself. The re-encrypted patch program is stored in nonvolatile memory and upon reset of the device, the encrypted patch contents are read out of the nonvolatile memory, decrypted using the unique key and loaded into patch memory for execution by the processing device.
Owner:SIRIUS XM RADIO INC
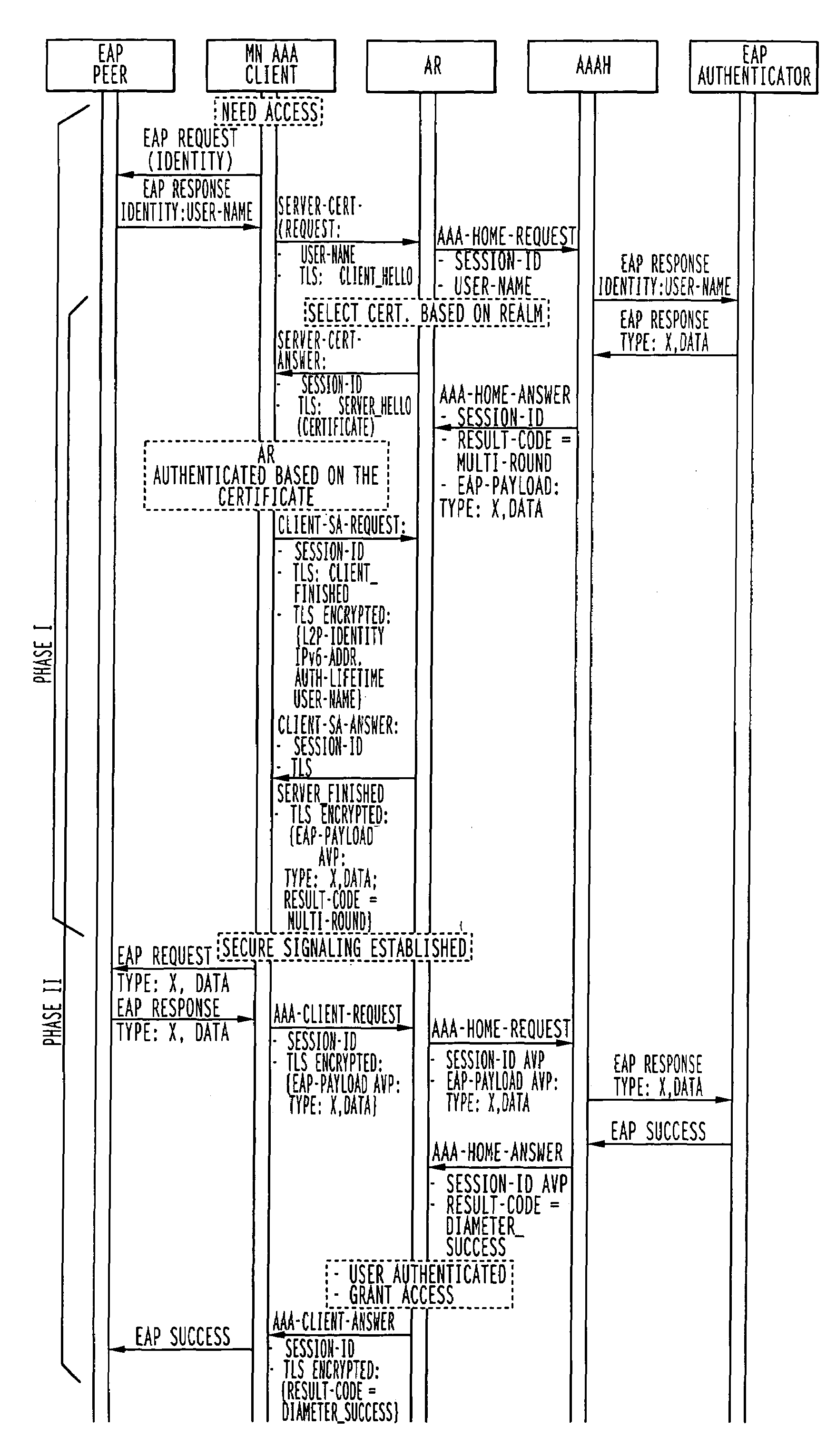
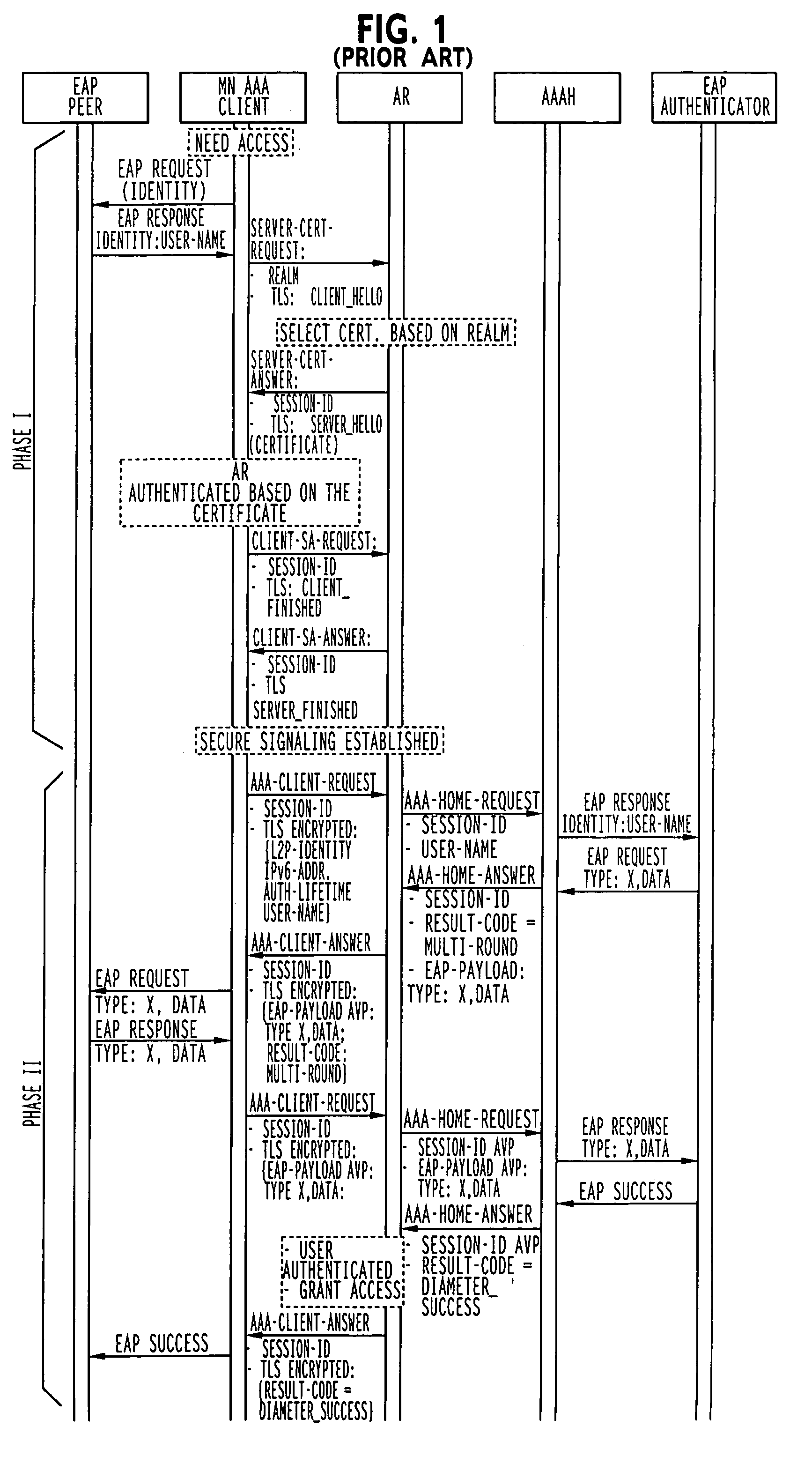
Faster authentication with parallel message processing
InactiveUS7458095B2Fast authenticationLower Level RequirementsMemory loss protectionDigital data processing detailsCommunications systemMessage processing
The invention is a method of connecting user equipment to at least one network, a communication system, and a user equipment. In a communication system comprising at least one network, including network entities which provide connectivity to user equipment, a method of connecting the user equipment to the at least one network in accordance with the invention includes establishing a secure tunnel which provides connection between the user equipment and one of the network entities; and authenticating the user equipment with another of the network entities; and wherein the authenticating of the user equipment with the another of the network entities occurs at least partially simultaneously with the establishing of the secure tunnel.
Owner:PIECE FUTURE PTE LTD
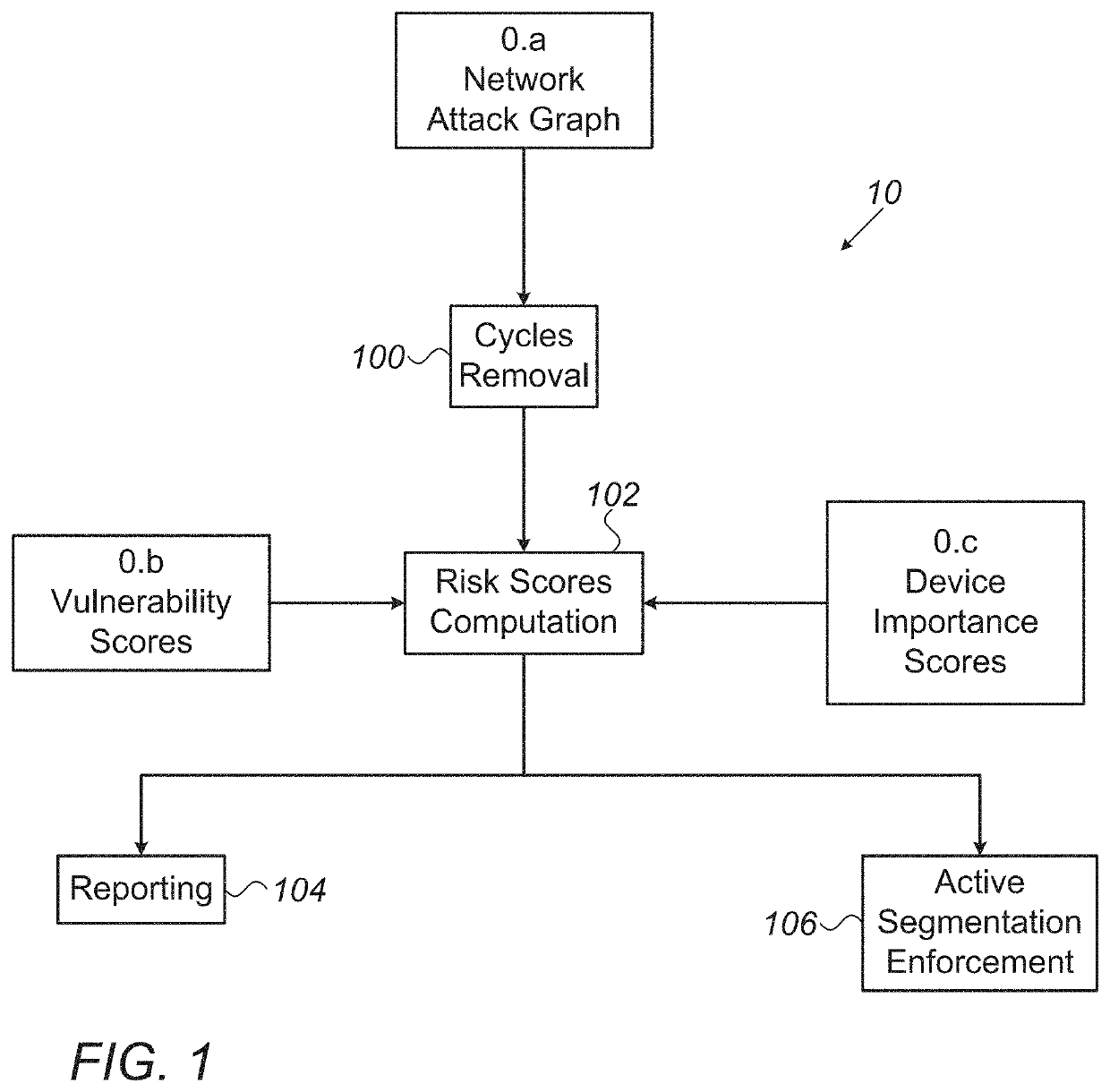
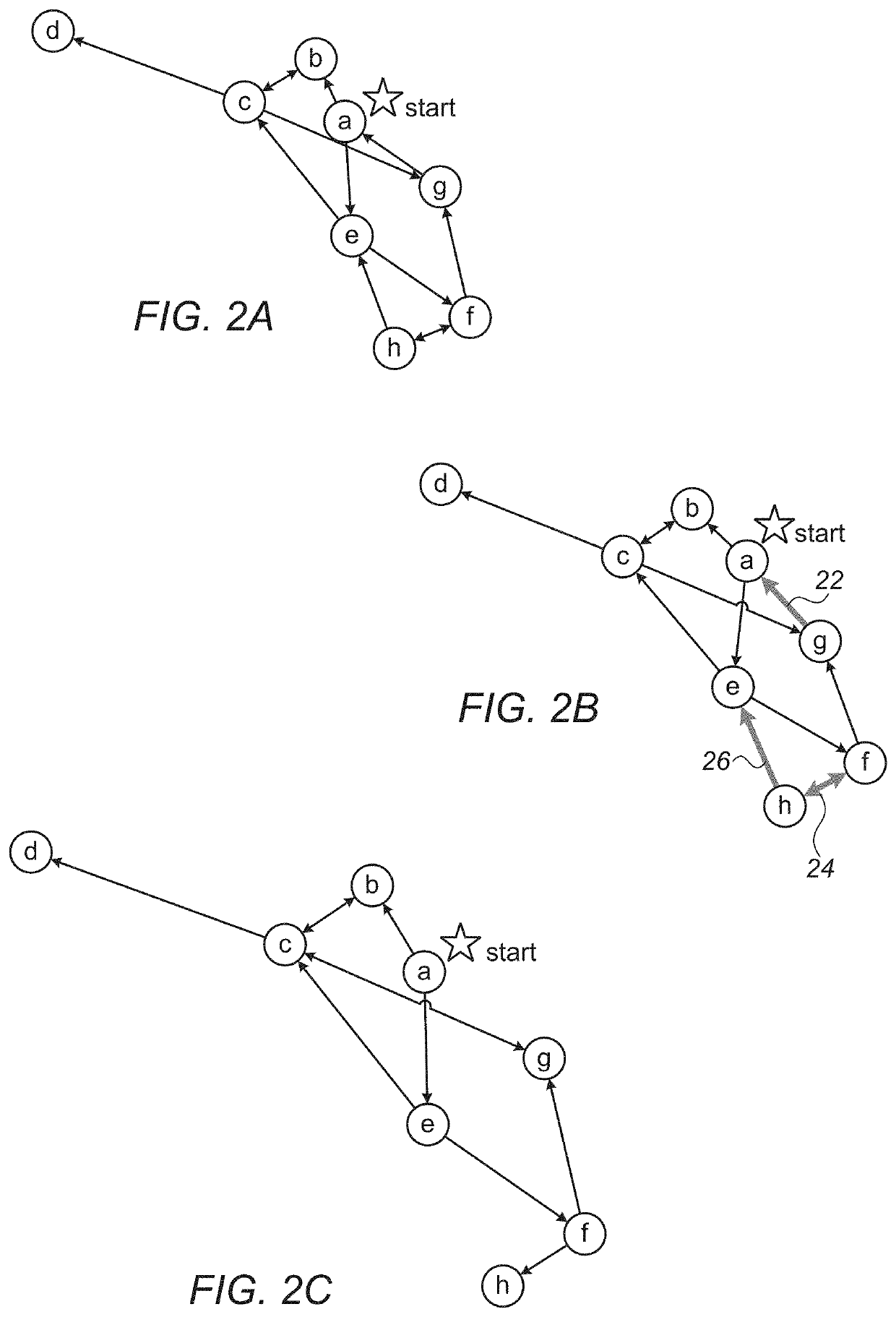
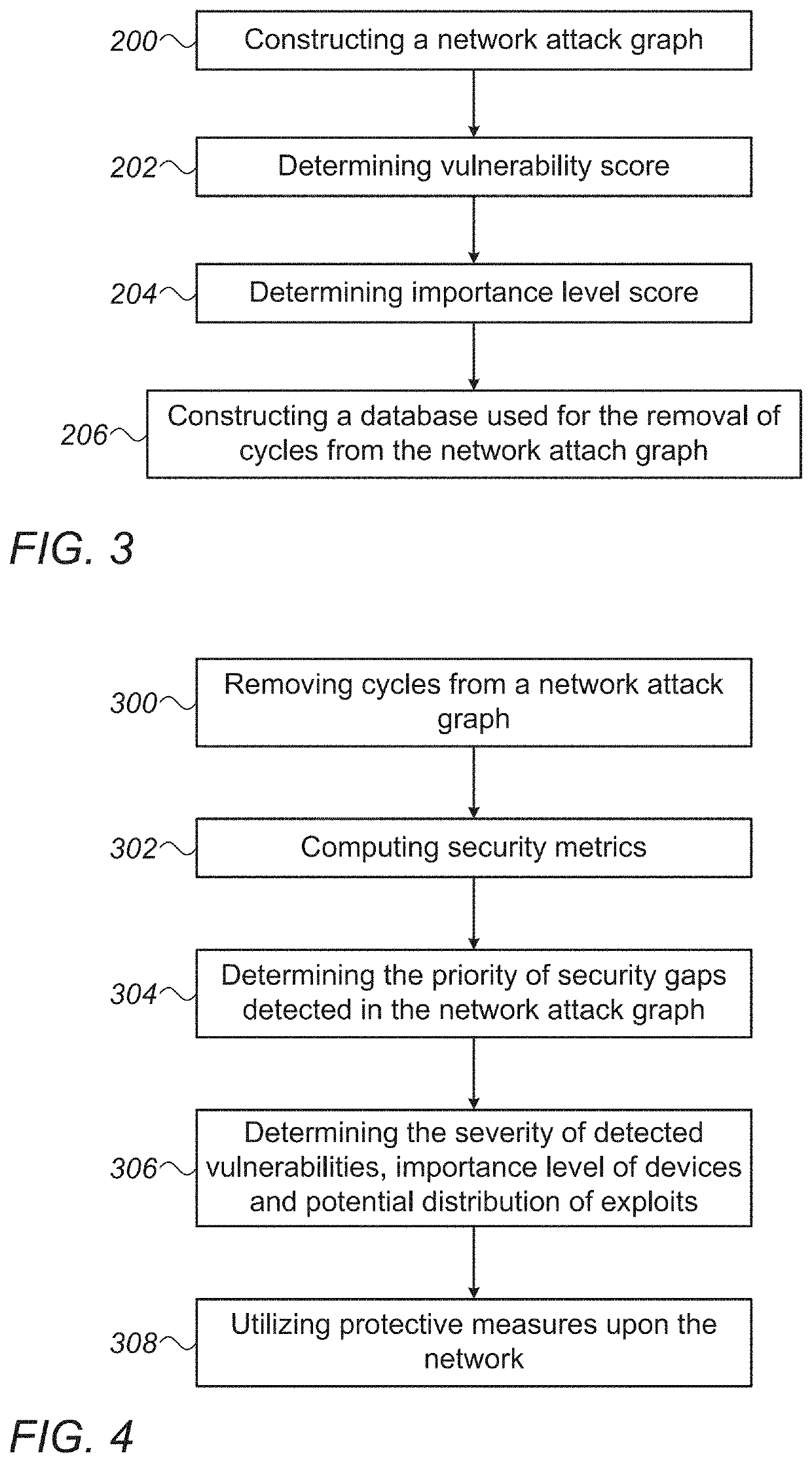
Operational Network Risk Mitigation System And Method
InactiveUS20210288995A1Reduce stepsAutomated network segmentationComputer security arrangementsData switching networksEngineeringContext data
A computer network risk mitigation system includes a computerized platform configured to utilize gathered contextual data regarding cyber-risk metrics in an operational technology network. The computerized platform is configured to conduct network configuration changes in accordance with the gathered contextual data in order to mitigate cyber-security threats. Methods for refining a network attack graph and for utilizing risk score evaluation are also described.
Owner:OTORIO LTD
Electronic access control device
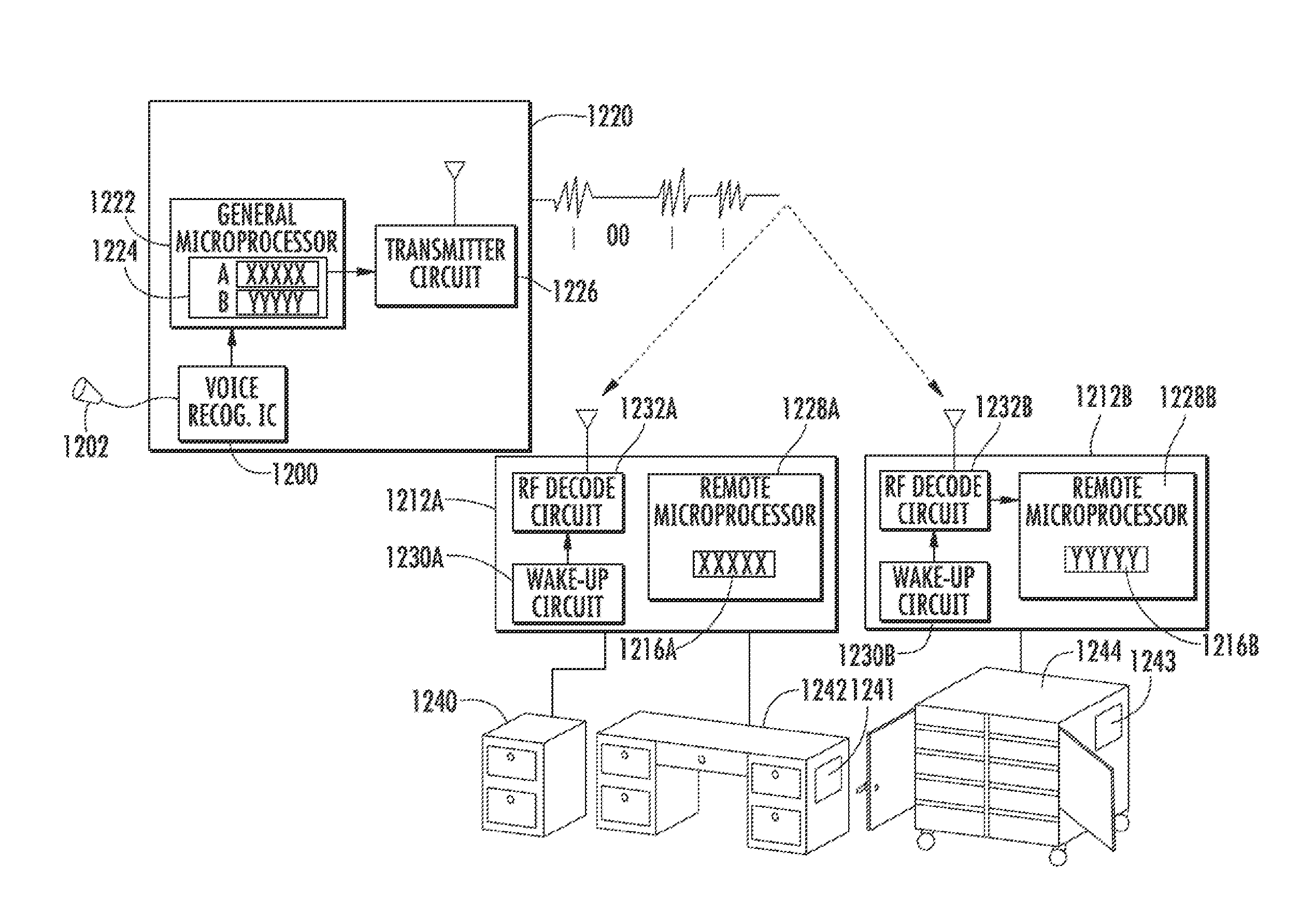
InactiveUS20050212656A1Easy to manufactureGuaranteed uptimeElectric signal transmission systemsAnti-theft cycle devicesElectronic accessMicroprocessor
An electronic access control device is disclosed comprising two microprocessors. The first microprocessor receives a wirelessly transmitted that is compared to a stored access code. If those two codes match, the first microprocessor transmits a special communication code to the second microprocessor. The second microprocessor opens the lock if the transmitted communication code matches a stored communication code.
Owner:O S SECURITY
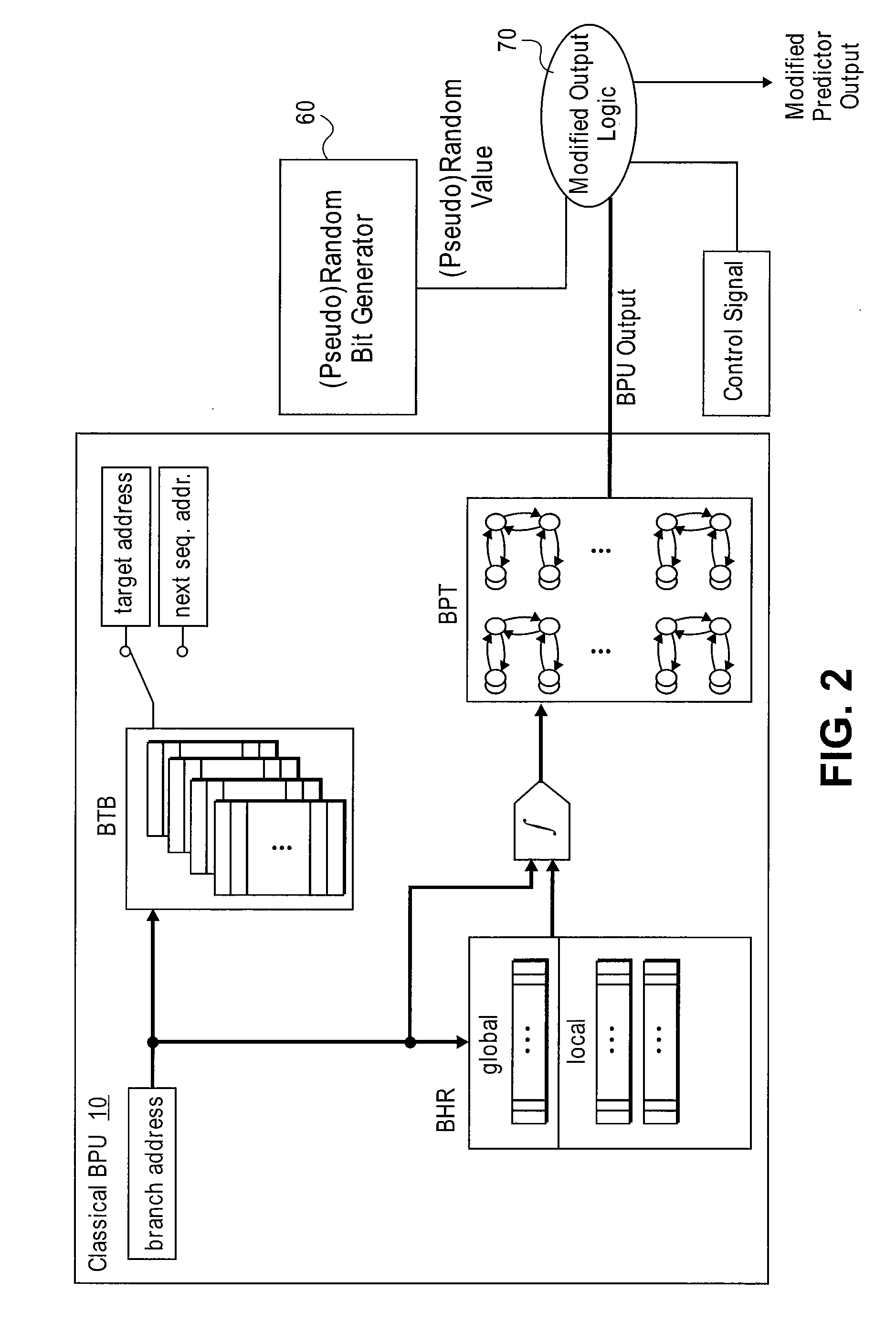
Systems and methods for providing security for computer systems
ActiveUS20080052499A1Reduce and eliminate vulnerabilityReduce vulnerabilityRandom number generatorsDigital computer detailsCountermeasureComputerized system
Hardware and / or software countermeasures are provided to reduce or eliminate vulnerabilities due to the observable and / or predictable states and state transitions of microprocessor components such as instruction cache, data cache, branch prediction unit(s), branch target buffer(s) and other components. For example, for branch prediction units, various hardware and / or software countermeasures are provided to reduce vulnerabilities in the branch prediction unit (BPU) and to protect against the security vulnerabilities due the observable and / or predictable states and state transitions during BPU operations.
Owner:KOC PH D CETIN KAYA
Apparatus and method for secure credit card processing infrastructure
InactiveUS20090132413A1Good Privacy-aImprove securityFinanceDigital data processing detailsCode moduleCredit card
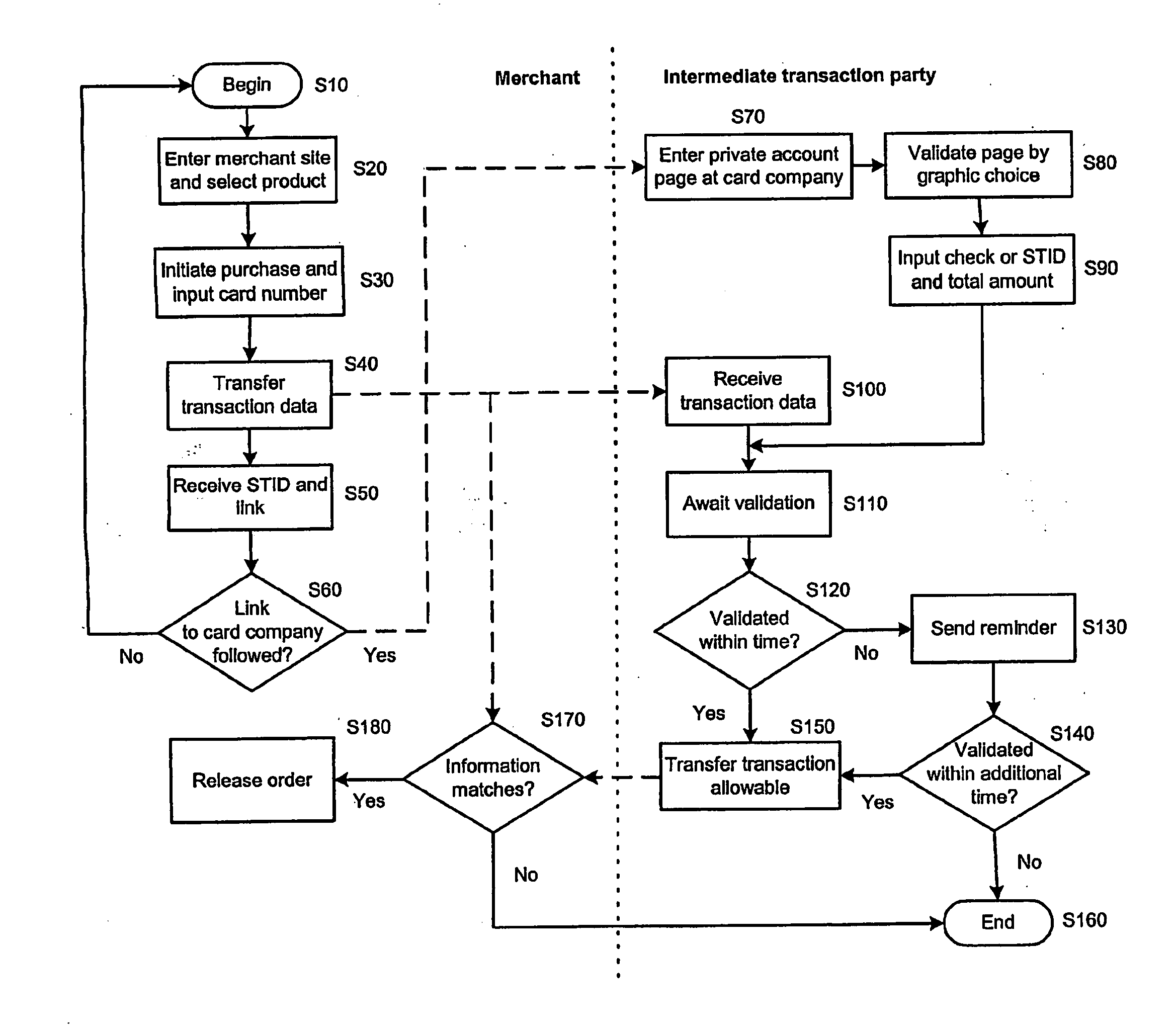
The present invention relates to an apparatus and a method for secure value transactions between a customer and a merchant in a computerised environment being part of a global interconnecting network, such as the Internet. The method is adapted for utilising existing credit card processing infrastructure and includes the steps of: the customer obtaining a password, such as a PIN, from an intermediate transaction party and validating a server of the intermediate transaction party, the merchant having installed a code module function on its web-based service that generates a transaction identification number, and redirecting or presenting the customer with a link to the intermediate transaction party. The present invention is characterised by the intermediate transaction party presenting the customer with a password-protected account page to validate a purchase either by marking a correct validation or inputting the transaction identification number and amount.
Owner:RUNTIME
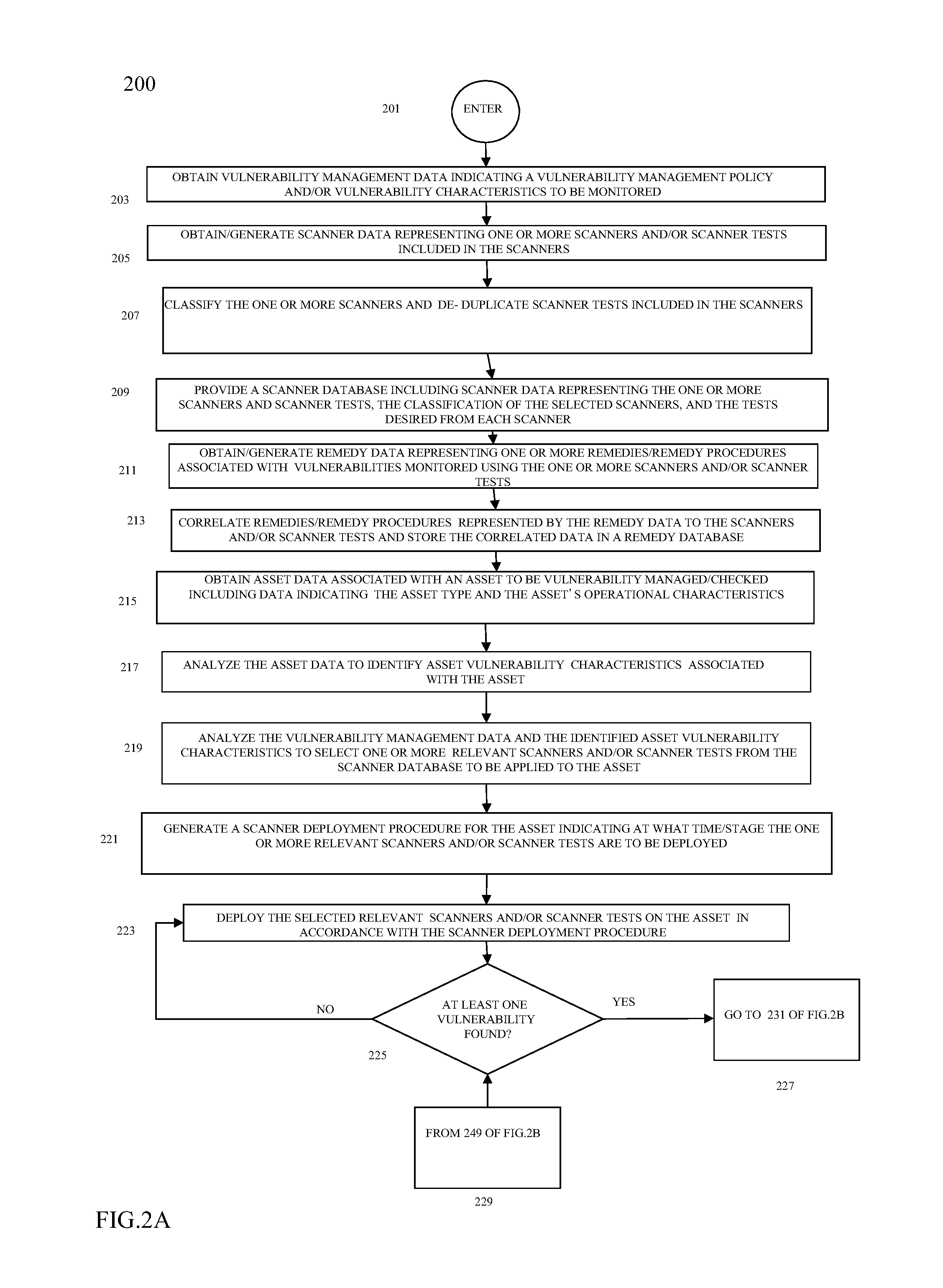
Method and system for dynamic and comprehensive vulnerability management
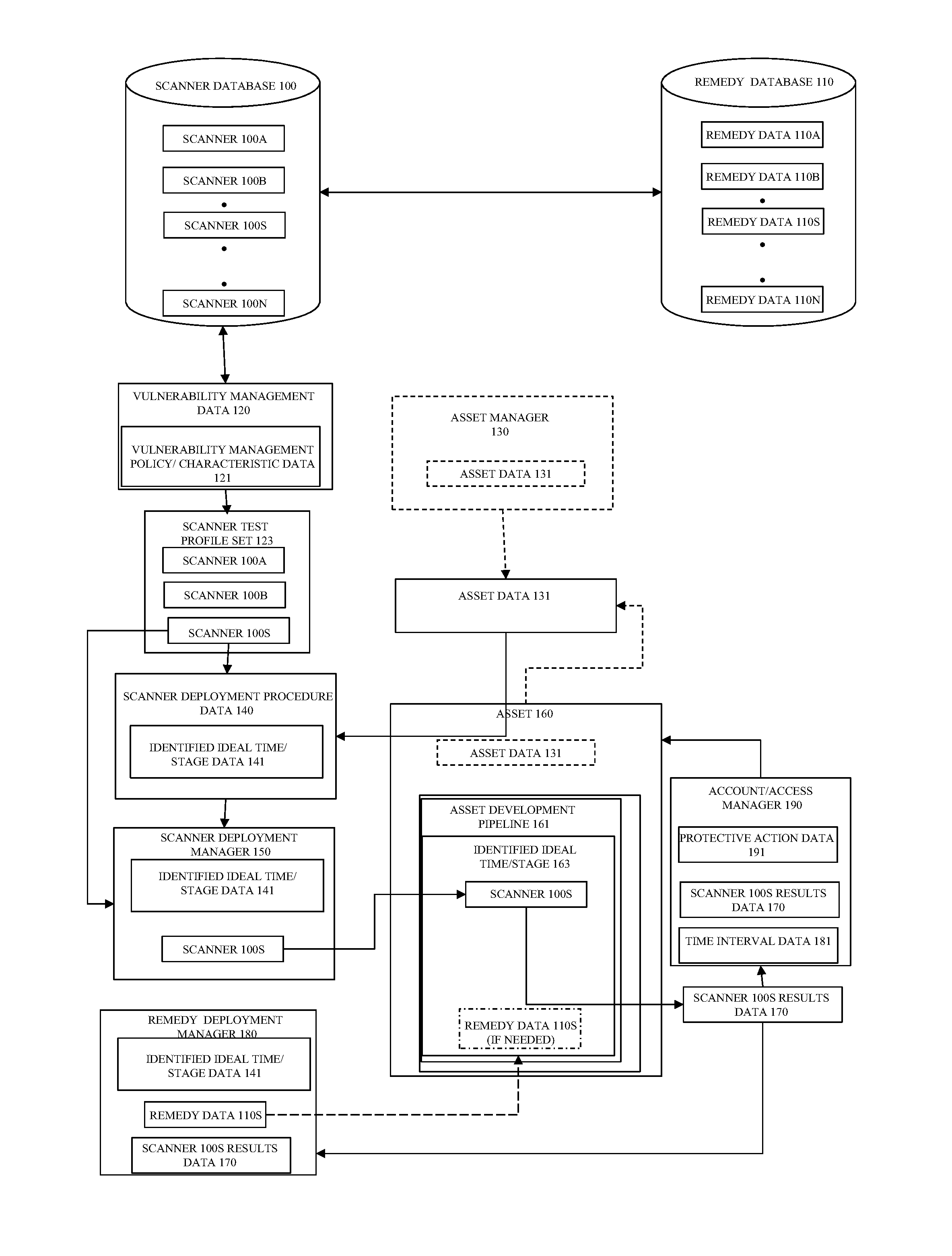
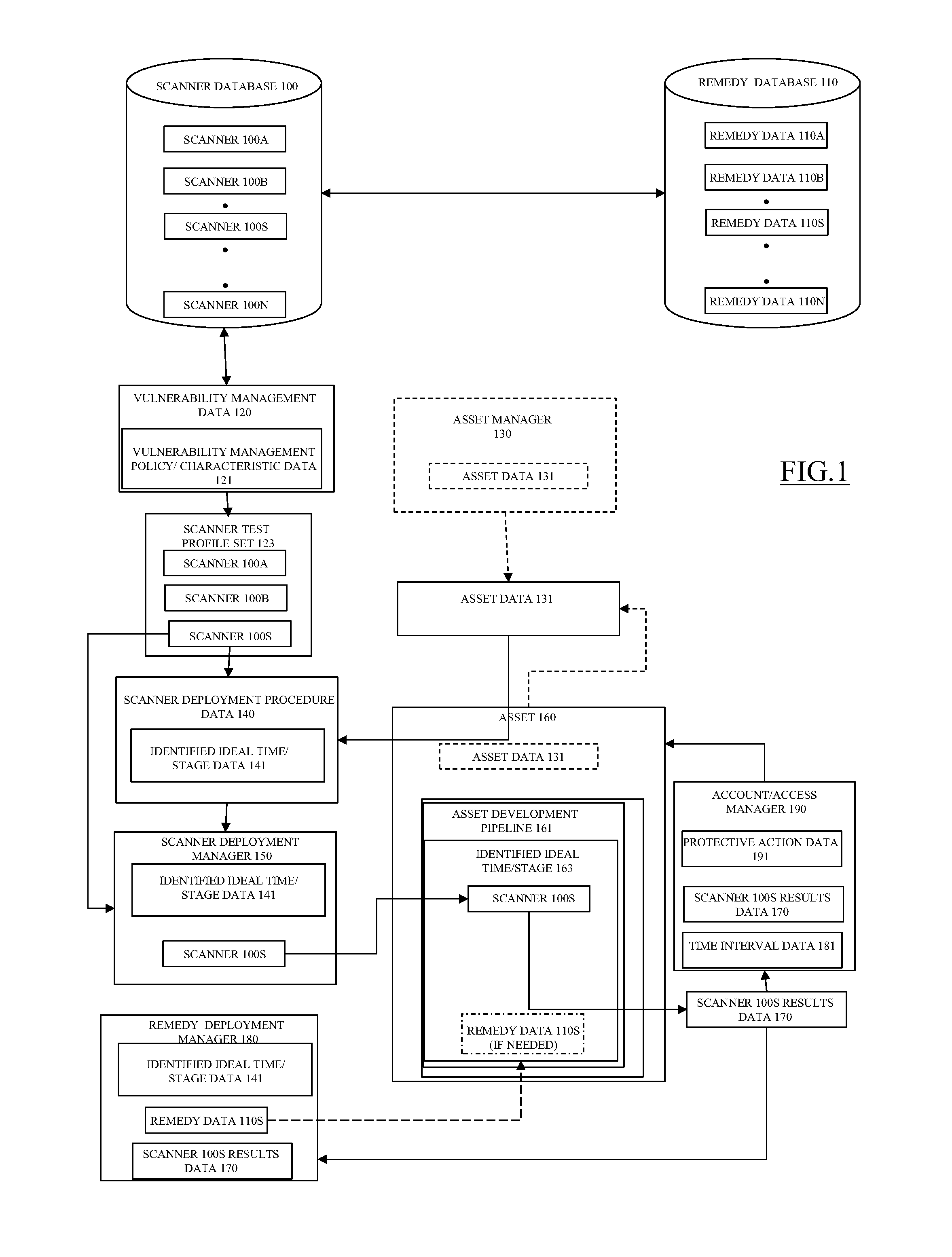
ActiveUS20150106939A1Reduce vulnerabilityMemory loss protectionError detection/correctionVulnerability managementRemedial action
One or more relevant scanners used to identify asset vulnerabilities are identified, obtained, and logically arranged for deployment on an asset in accordance with a vulnerability management policy and a scanner deployment policy such that the relevant scanners are deployed at, or before, a determined ideal time to minimize the resources necessary to correct the vulnerabilities, if found. The relevant scanners are then automatically deployed in accordance with the scanner deployment policy and, if a vulnerability is identified, one or more associated remedies or remedy procedures are applied to the asset. At least one of the one or more relevant scanners are then re-deployed on the asset to determine if the identified vulnerability has been corrected and, if the vulnerability is not corrected at, or before, a defined time, protective measures are automatically taken.
Owner:INTUIT INC
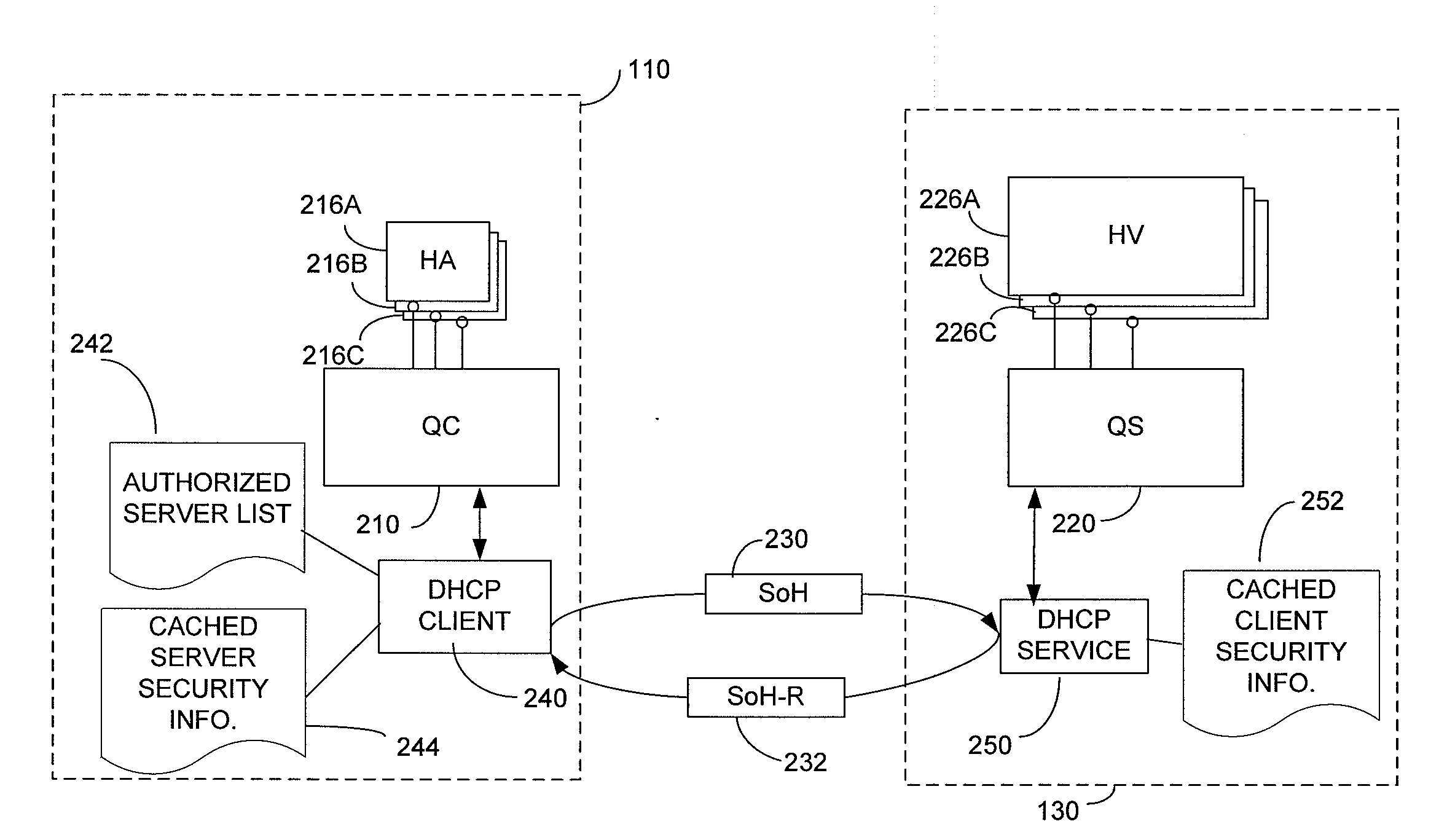
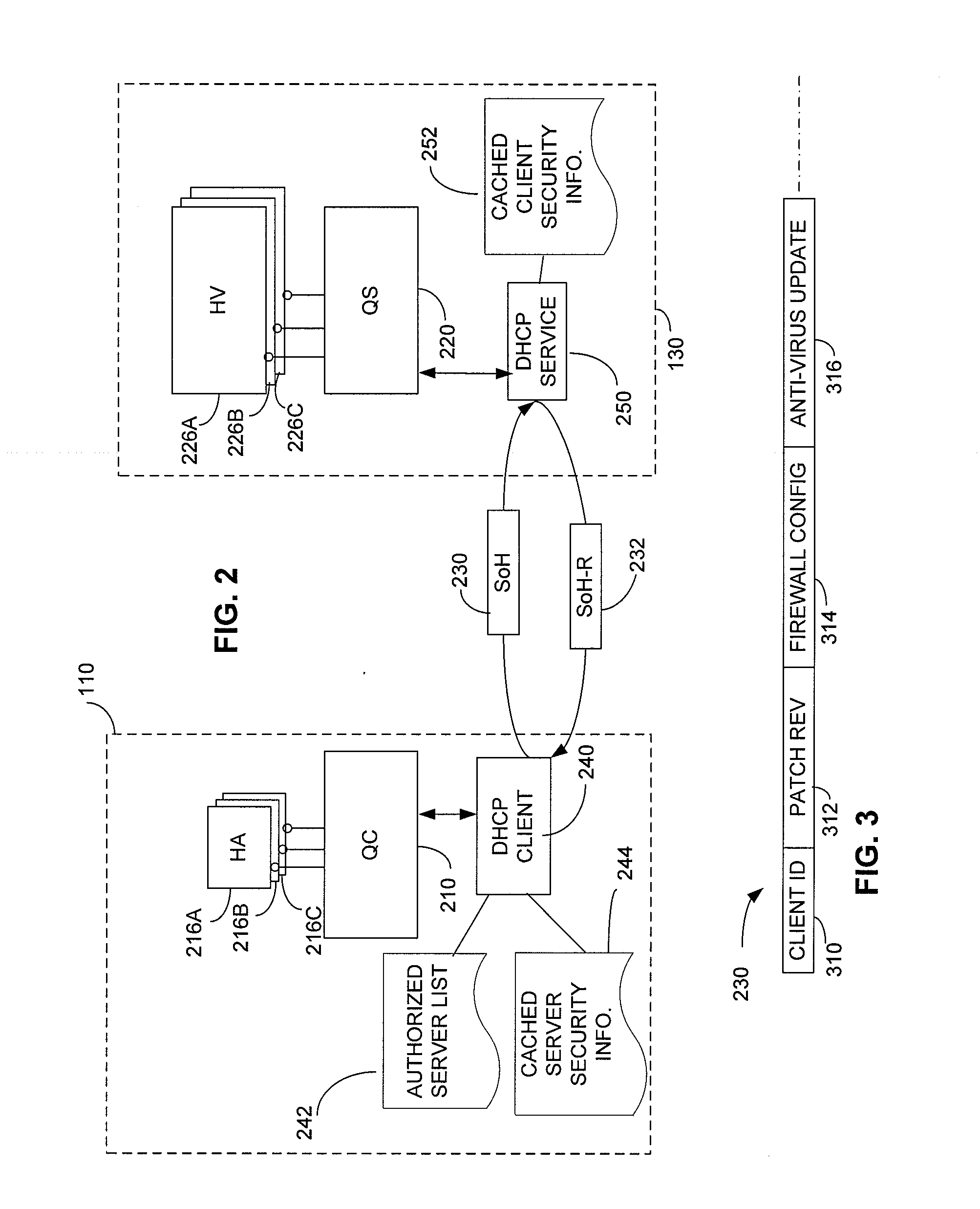
Secure network address provisioning
ActiveUS20100017597A1Reduce vulnerabilityAvoid problemsTransmissionConfidentialityNetwork addressing
A network in which a client receives a network credential, such as a valid network address, following an exchange of messages with a credential server that includes security information. The security information may validate the credential, avoiding rogue devices inadvertently or maliciously distributing credential information that can interfere with clients attempting to connect to the network or with the network itself. If obtaining a network credential requires an exchange of information about the configuration of the client that could reveal security vulnerabilities, the security information may be used to ensure the confidentiality of that configuration information. The security information may be incorporated into messages according to a known protocol, such as by incorporating it into options fields of DHCP messages.
Owner:MICROSOFT TECH LICENSING LLC
Method for Controlling and Recording the Security of an Enclosure
InactiveUS20110289123A1Easily manufactureReliable in operationProgramme controlDigital data processing detailsMobile electronicsManagement system
A method for controlling and recording the security of an enclosure is disclosed. A mobile electronic control device, such as an electronic key, is used to access or otherwise control the operations of a field device, such as an appliance, power tool, shipping container, and the like. In a control event in which the mobile control device interacts with the field device via wired or wireless communications, the control device obtains the current location and the field device ID. The communications between the mobile control device and the field device may be secured with encryption. The location information is used by the mobile control device to determine whether the field device should be accessed or enabled. Alternatively, the location information may be stored separately in a location sensing device, and the control event data recorded by the key and the location information recorded by the location sensing device are later combined when they are downloaded into a management system for auditing. Moreover, an electronic access control device is disclosed comprising two microprocessors.
Owner:MICRO ENHANCED TECH
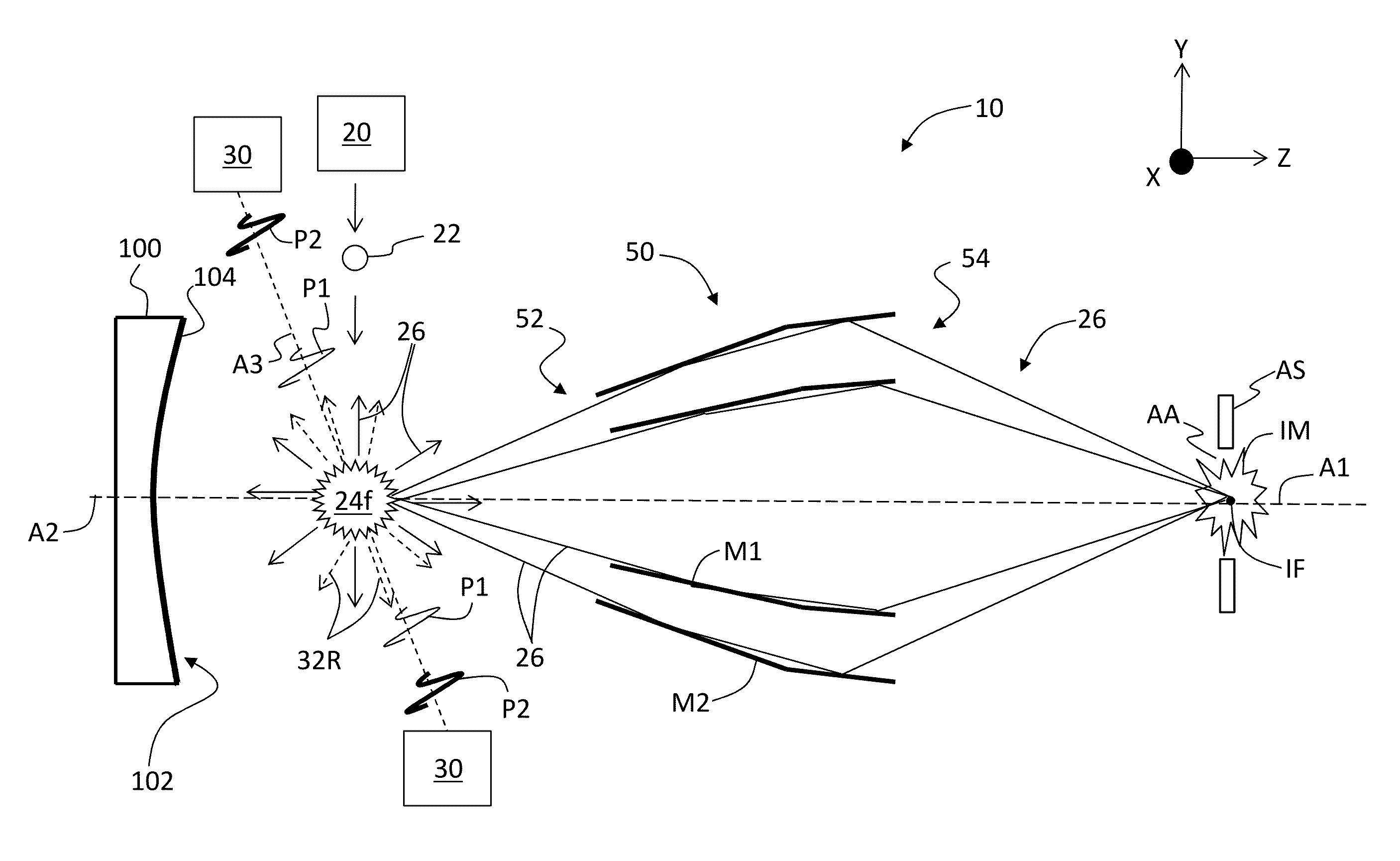
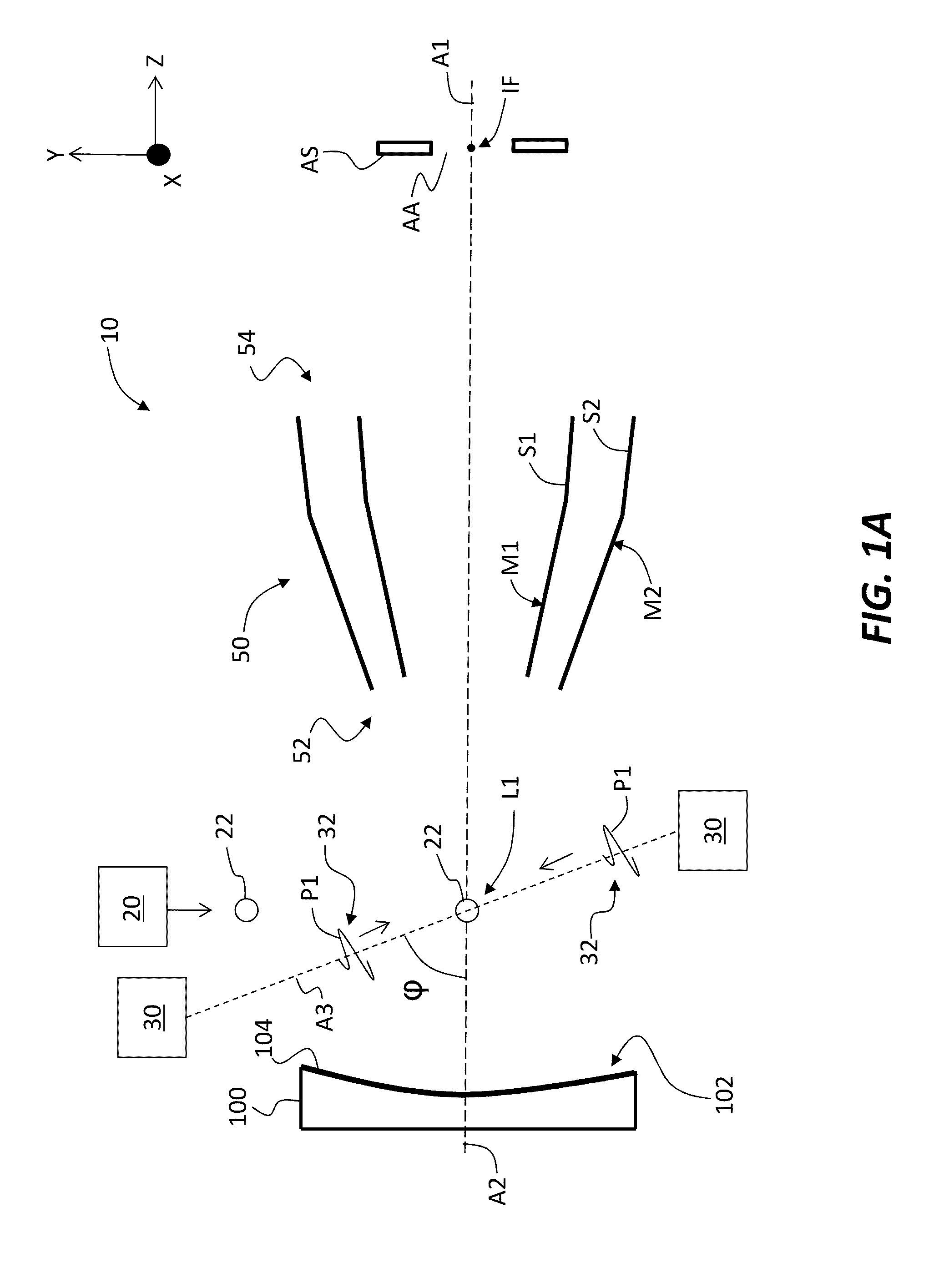
Source-collector modules for EUV lithography employing a GIC mirror and a LPP source
ActiveUS20130207004A1Maximize collectionConvenient amountRadiation pyrometryRadiation/particle handlingGratingLithographic artist
Source-collector modules for use with EUV lithography systems are disclosed, wherein the source-collector modules employ a laser-produced plasma EUV radiation source and a grazing-incidence collector. The EUV radiation source is generated by first forming an under-dense plasma, and then irradiating the under-dense plasma with infrared radiation of sufficient intensity to create a final EUV-emitting plasma. The grazing incidence collector can include a grating configured to prevent infrared radiation from reaching the intermediate focus. Use of debris mitigation devices preserves the longevity of operation of the source-collector modules.
Owner:MEDIA LARIO SRL
Collecting malware samples via unauthorized download protection
ActiveUS8353033B1Prevents malware installationPrevents executionMemory loss protectionError detection/correctionComputer hardwareApplication software
A hook is set for one or more downloading functions. Subsequently, code is executed within an application process. Responsive to the executed code calling one of the hooked functions to download code, a return address of the called function is examined. If the return address is within a memory area not marked executable, the code is permitted to be downloaded and the downloaded code is submitted to a security server for analysis.
Owner:NORTONLIFELOCK INC
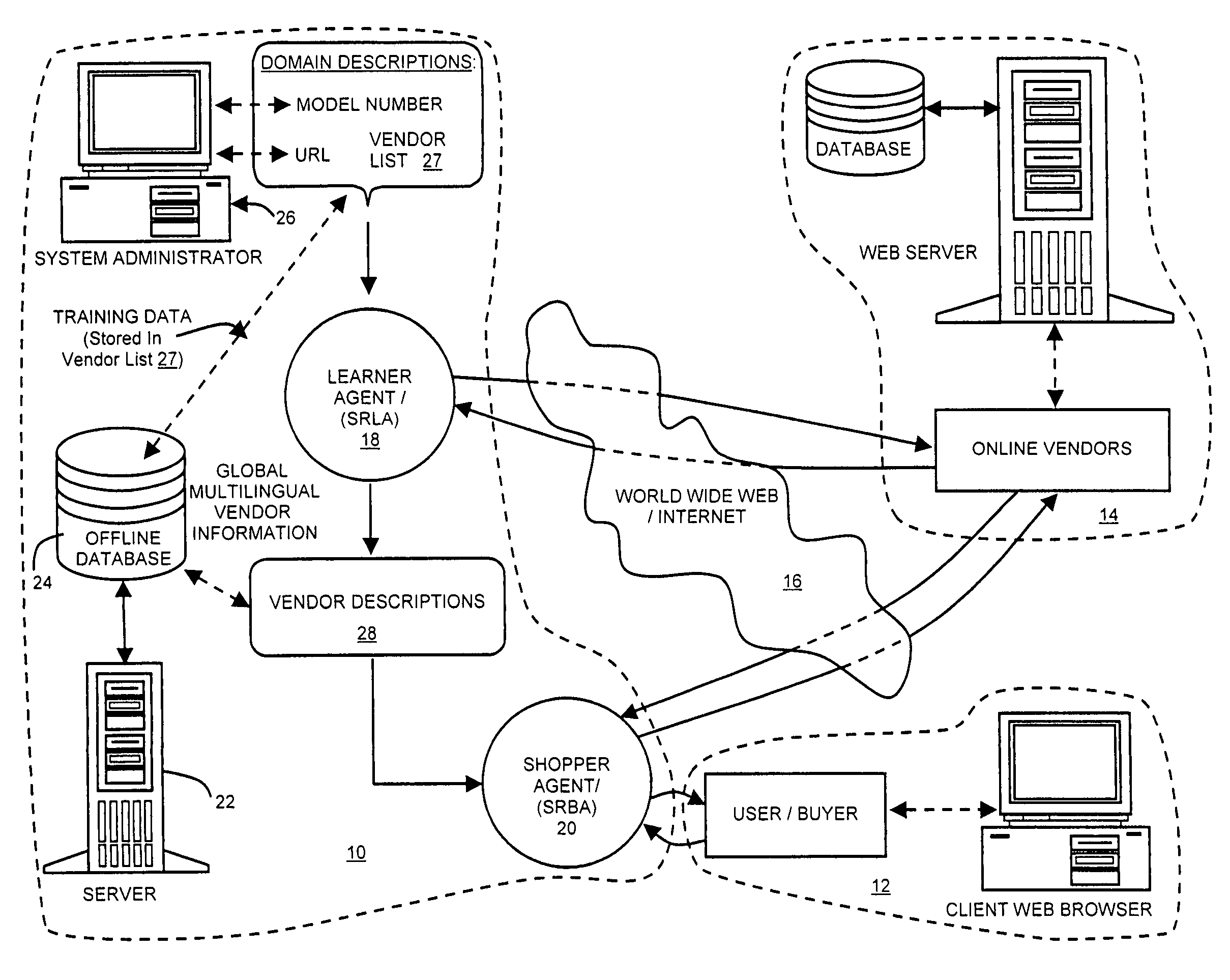
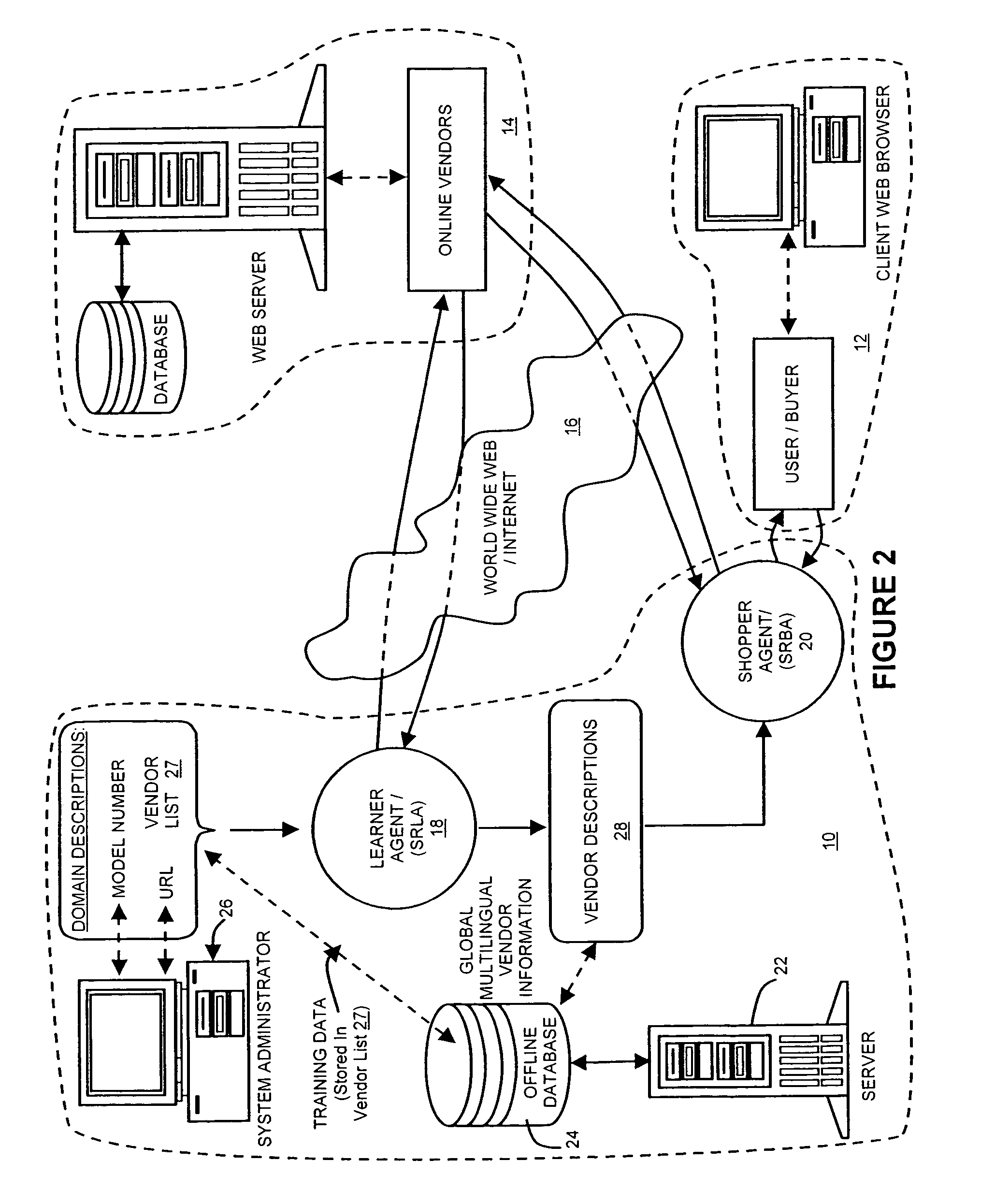
Online intelligent multilingual comparison-shop agents for wireless networks
ActiveUS7536323B2Accurate identificationImprove compatibilitySpecial data processing applicationsMarketingWireless handheld devicesUniform resource locator
A method and system for real-time online search processing over inter-connected computer networks of search requests received from wireless handheld clients, in which a server communicates with a wireless handheld client using an XML-like protocol, and an offline database information is maintained for a plurality of vendor sites from the inter-connected computer networks. The information includes URLs, search form URLS, description of domains, and vendor descriptions which include generalized rules about how product information is organized on each of the vendor sites. A product keyword request from the wireless handheld device client is processed using the information maintained in the offline database. Real-time price and product information are extracted from identified ones of the plurality of vendor sites in a native language of the site; and the extracted price and product information are communicated to the user through the server.
Owner:CHEMTRON RES
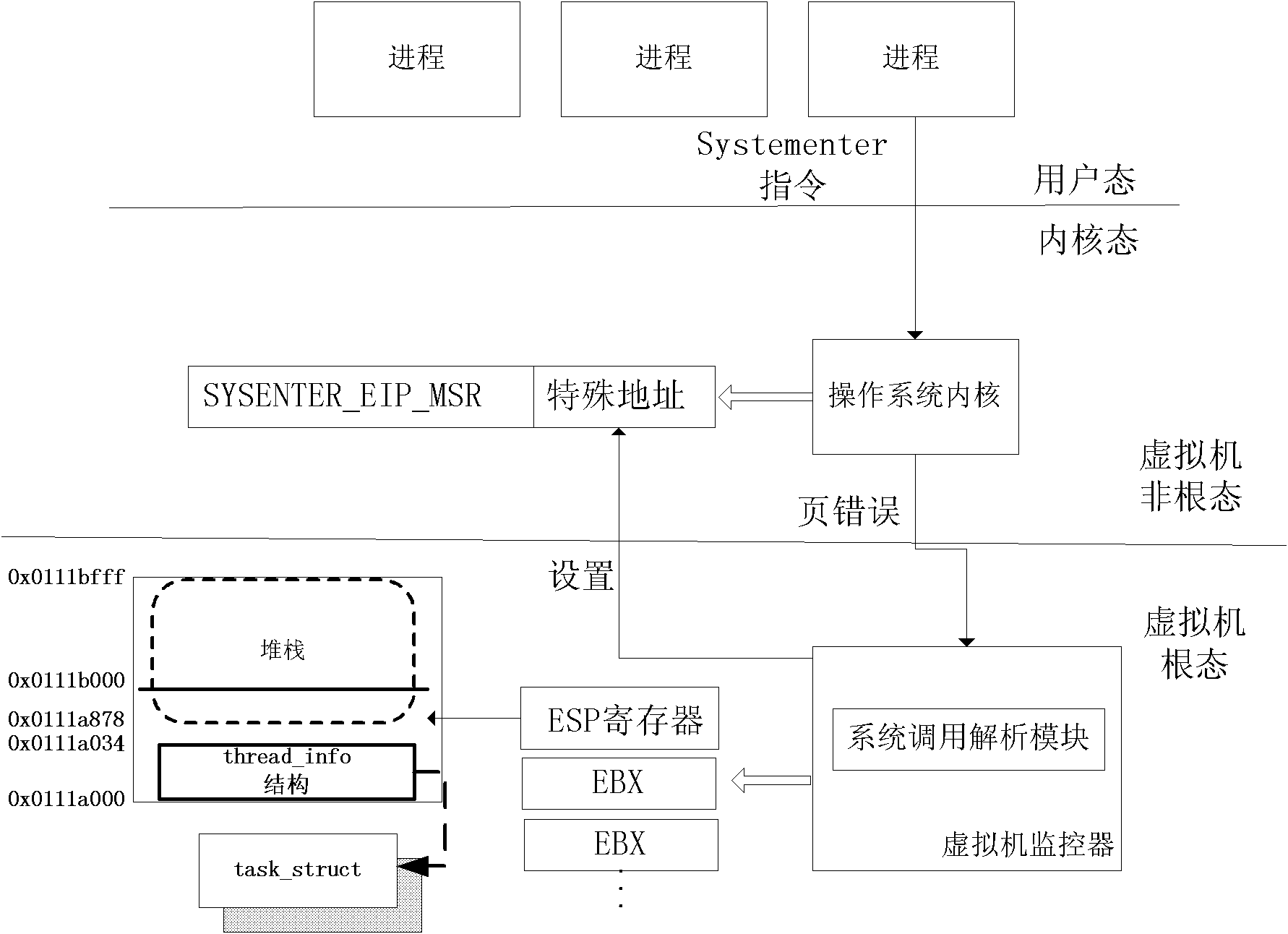
Transparent trust chain constructing system based on virtual machine architecture
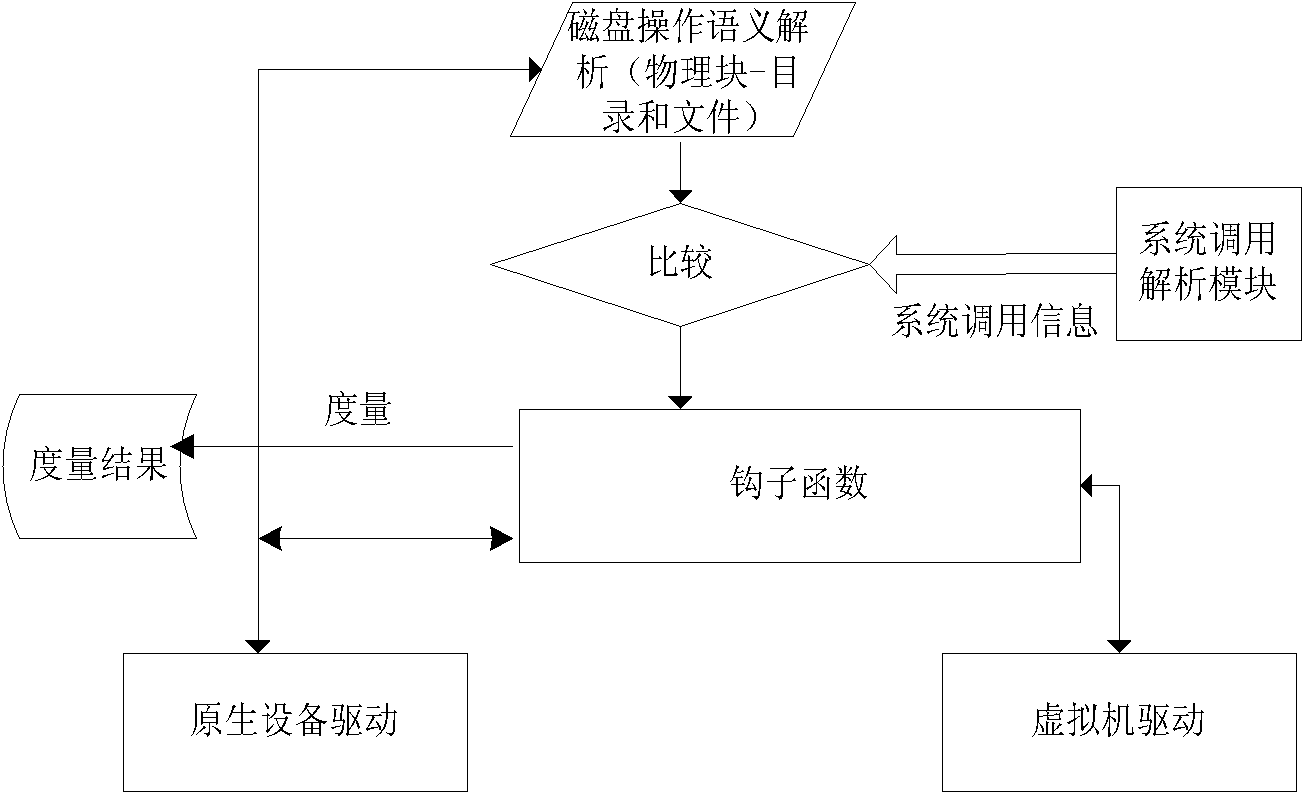
InactiveCN101866408AReduce the amount of codeReduce vulnerabilityPlatform integrity maintainanceSoftware simulation/interpretation/emulationOperational systemSemantics
The invention discloses a transparent trust chain constructing system based on virtual machine architecture. The system is provided with a virtual machine monitor on the mainframe, the virtual machine monitor comprises a safety chip drive module, a system call analysis module and a disk analysis measurement module. The invention measures the operation system and the executable code loaded after the operation system is started in the virtual machine monitor, without any modification of the existing operation system and the application program. The invention can obtain low-level operation semantic information, such as the system call and the disk access, of the operation system in the client machine, analyzes the operation semantics of the client machine operation system, and controls the operation of the client operation system on the disk to realize the transparent measurement. The technology can be used in the distributed cooperation environment, and provide transparent trust chain and integrity certification for the operation system. The invention can protect the existing property of the user and enable the existing operation system to support the process level TCG trust chain without any modification.
Owner:HUAZHONG UNIV OF SCI & TECH
System and method for reducing the vulnerability of a computer network to virus threats
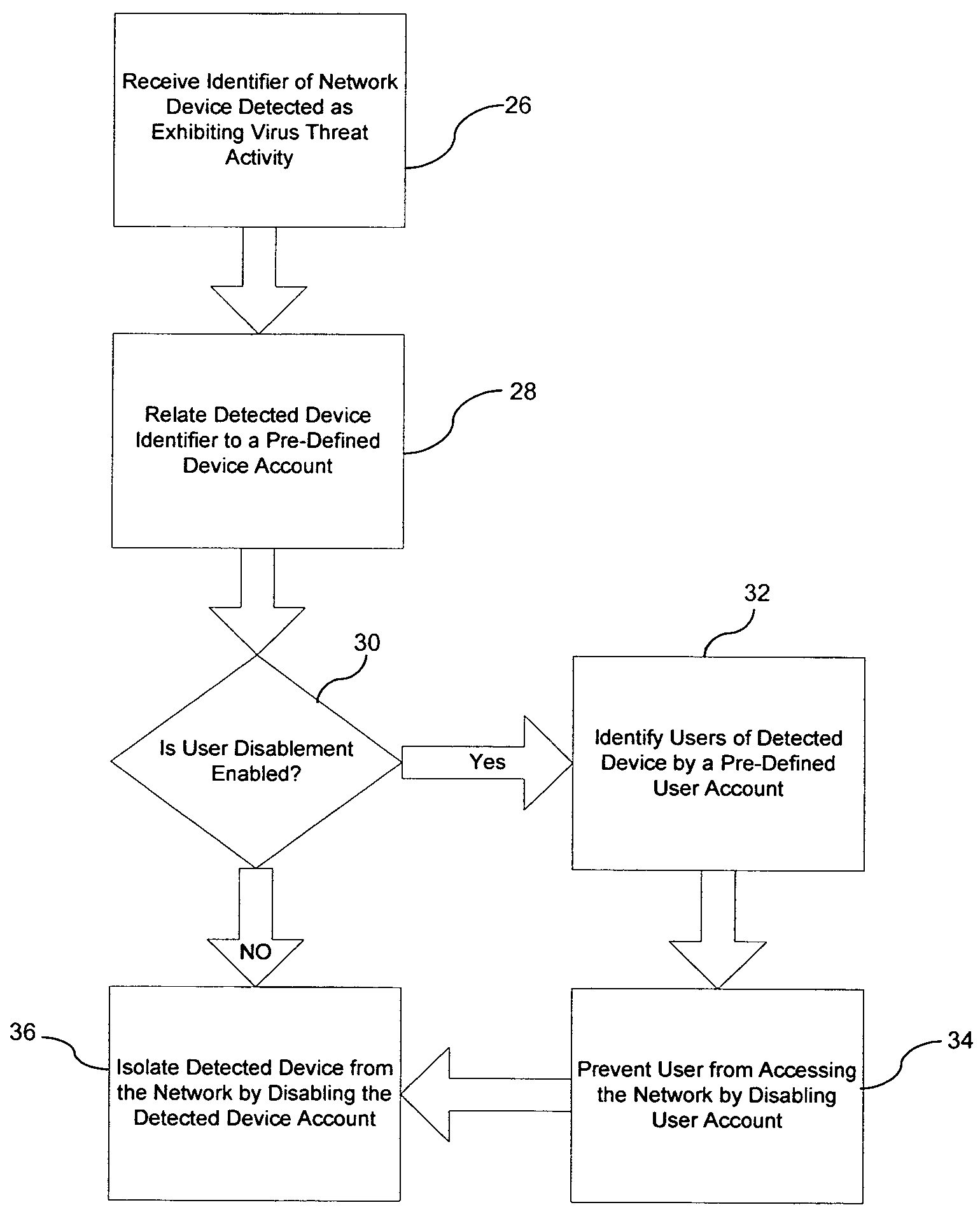
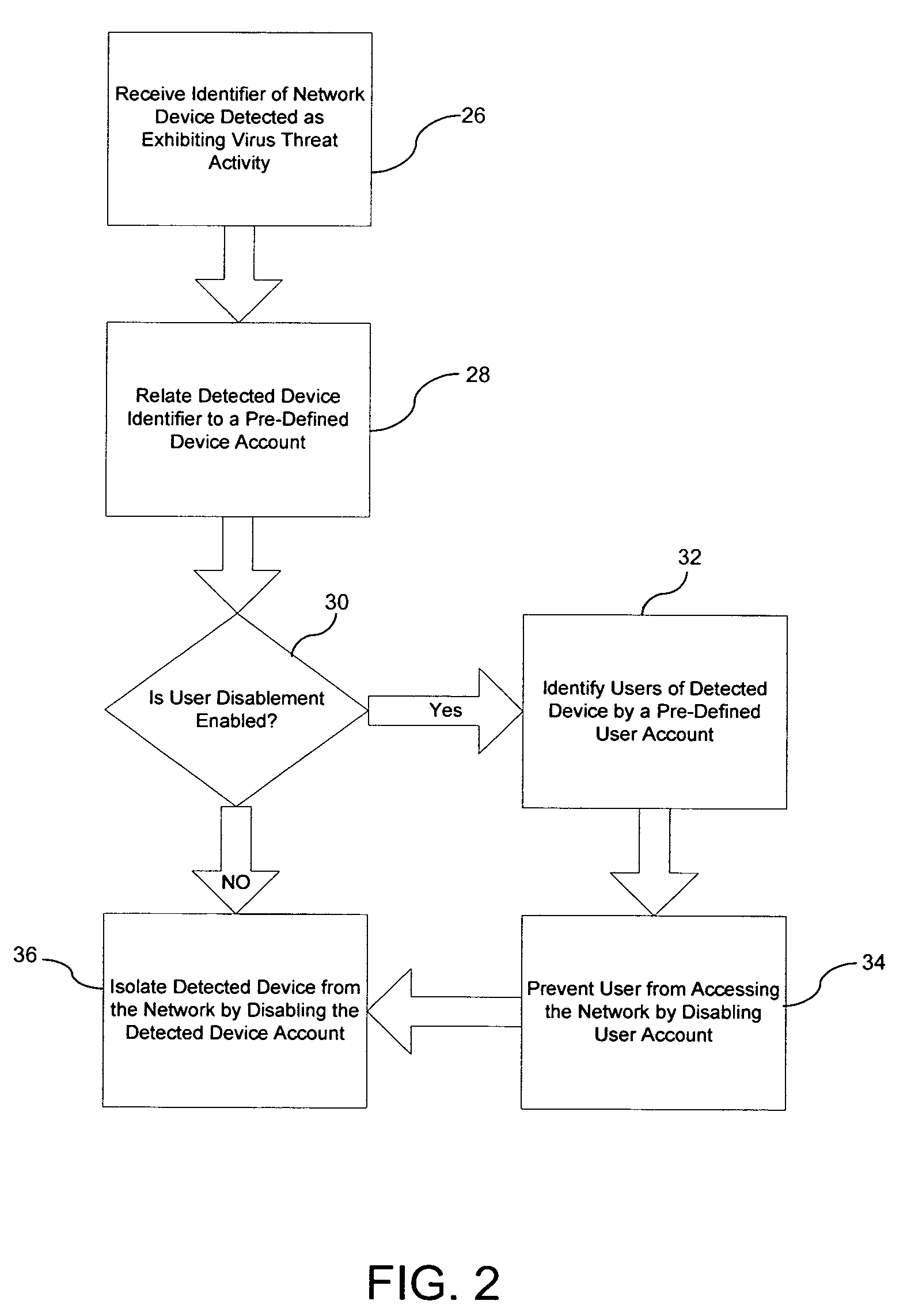
ActiveUS7571483B1Avoid infectionReduce vulnerabilityMemory loss protectionError detection/correctionNetwork isolationVirus
A method for reducing vulnerability of a computer network to a detected virus threat includes receiving an identifier of a network device detected as a source of virus activity. The method also includes relating the identifier to a predetermined account of the detected device and then automatically disabling the device account. Accordingly, the detected device is isolated from the network to prevent infection of the network by the detected device.
Owner:LOCKHEED MARTIN CORP
Distributed monitoring and control system
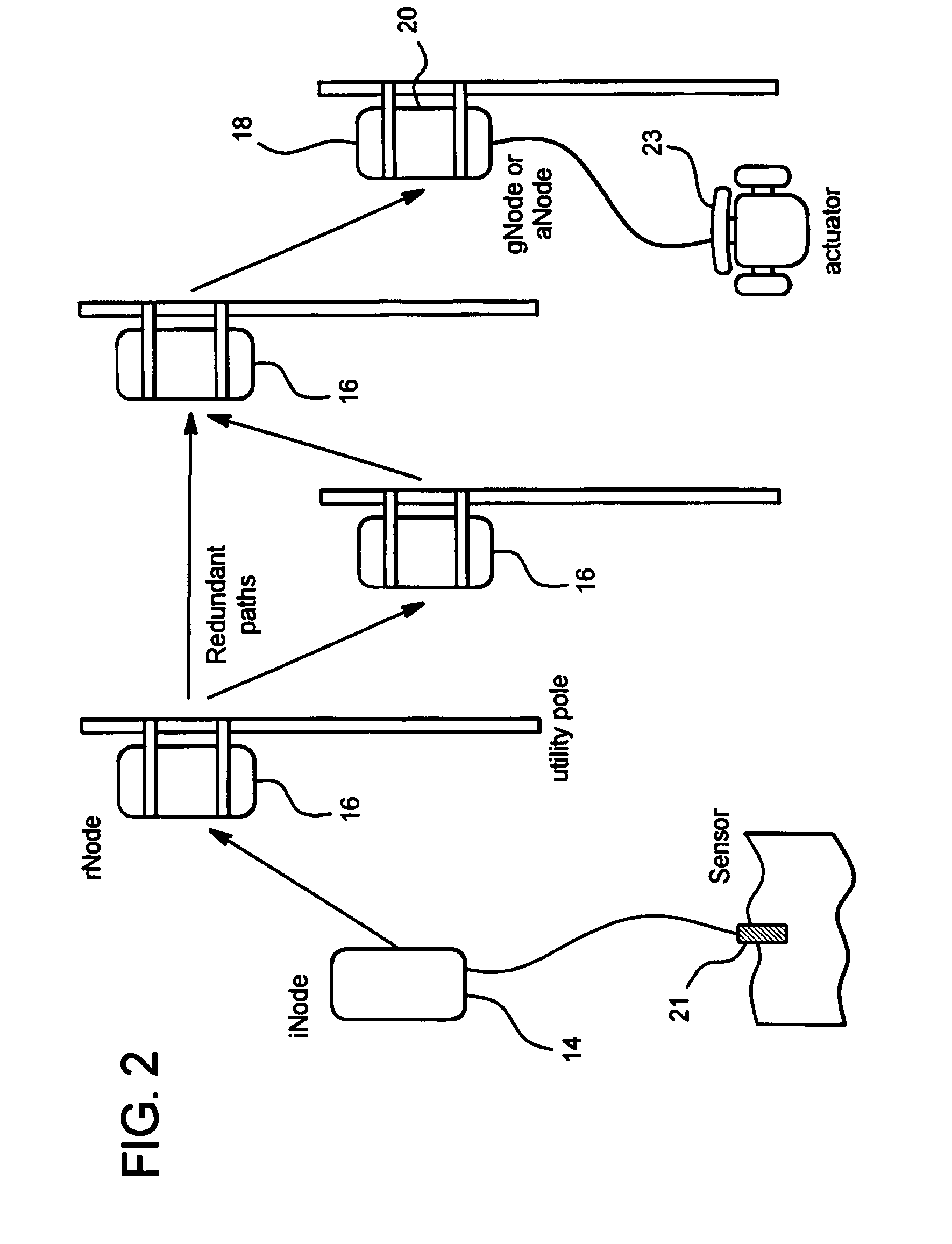
ActiveUS7792126B1Reduce generationImprove system robustnessMultiplex system selection arrangementsSoil drainageTransceiverReal-time computing
A distributed monitoring and control system includes a plurality of nodes forming a redundant communication network. Each of the nodes includes a processor, a memory and a transceiver. At least one of the nodes includes a sensor for acquiring information. At least one of the nodes includes an actuator. At least one of the processors is programmed with a control algorithm to receive information acquired from the sensors, calculate a control command and communicate the control command to the actuators for execution.
Owner:EMNET INC +1
Techniques for optimizing orientation of models for three-dimensional printing
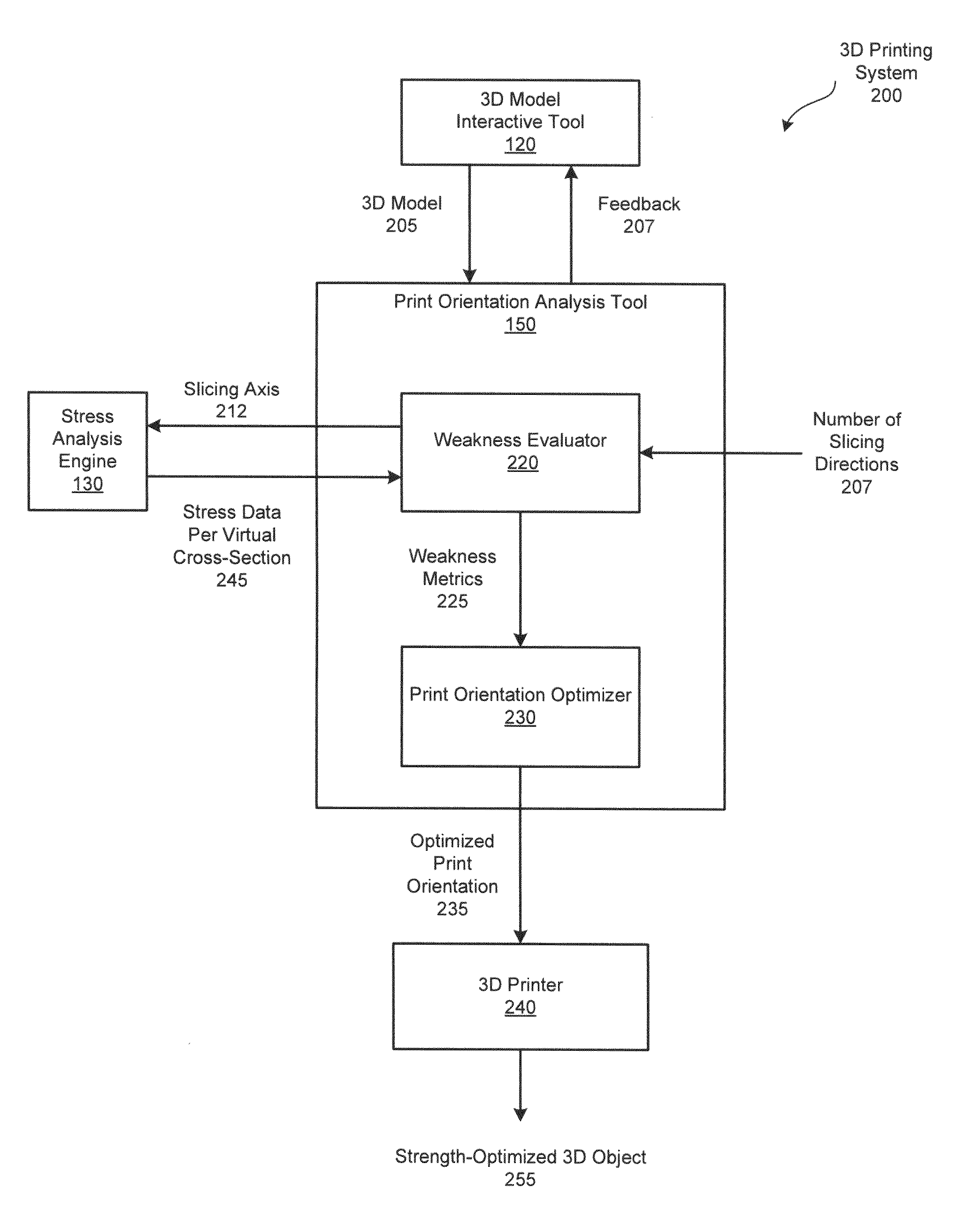
ActiveUS20150154321A1Automatically and efficiently mitigate undesirable weaknessReduce vulnerabilityProgramme controlAdditive manufacturing apparatusComputer graphics (images)Structural stress
In one embodiment of the present invention, a print orientation tool efficiently determines an orientation of a three-dimensional (3D) model such that, when 3D printed, the structural integrity of the resulting 3D object is optimized. In operation, the print orientation tool configures a stress analysis engine to slice the 3D model into two-dimensional (2D) cross-sections. The stress analysis engine then compute structural stresses associated with the 2D cross-sections. The print orientation tool translates the structural stresses to weakness metrics. Subsequently, the print orientation tool evaluates the orientations of the cross-sections in conjunction with the corresponding weakness metrics to select a printing orientation that minimizes weaknesses in the 3D model. Advantageously, by aligning the 3D model to the print bed based on the optimized printing orientation, the user mitigates weaknesses in the corresponding 3D object attributable to the 3D printing manufacturing process.
Owner:AUTODESK INC
Method for Controlling and Recording the Security of an Enclosure
InactiveUS20110276609A1Easy to manufactureGuaranteed uptimeProgramme controlDigital data processing detailsElectronic accessEvent data
A method for controlling and recording the security of an enclosure is disclosed. A mobile electronic control device, such as an electronic key, is used to access or otherwise control the operations of a field device, such as an appliance, power tool, shipping container, and the like. In a control event in which the mobile control device interacts with the field device via wired or wireless communications, the control device obtains the current location and the field device ID. The communications between the mobile control device and the field device may be secured with encryption. The location information is used by the mobile control device to determine whether the field device should be accessed or enabled. Alternatively, the location information may be stored separately in a location sensing device, and the control event data recorded by the key and the location information recorded by the location sensing device are later combined when they are downloaded into a management system for auditing. Moreover, an electronic access control device is disclosed comprising two microprocessors.
Owner:MICRO ENHANCED TECH
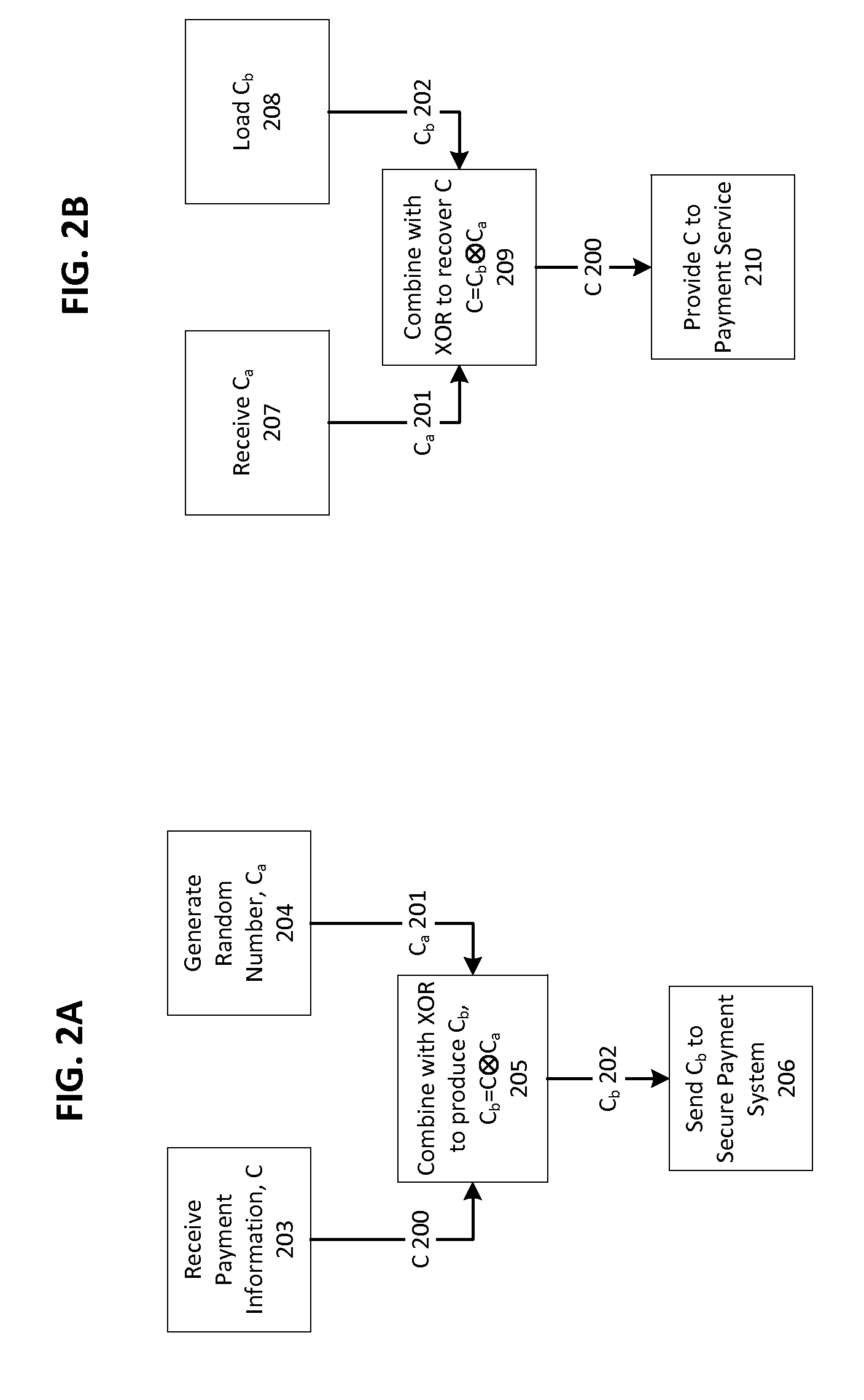
Securely Storing and Using Sensitive Information for Making Payments Using a Wallet Application
ActiveUS20150310436A1Reduce vulnerabilityFinanceProtocol authorisationFinancial transactionMobile device
A payment system implemented on a mobile device authorizes and processes transactions. The mobile device generates a public-private key pair and receives payment information. The private key and the payment information are split into a local and a remote fragment. The public key, a private key fragment, and a payment information fragment are sent to a secure payment system, and the other fragments are stored on the mobile device. When a transaction is received by the mobile device to authorize, the mobile device sends a payment fragment to the secure payment system and receives a private key fragment from the secure payment system. The mobile device authorizes the transaction using the private key, recovered from the private key fragments. The secure payment system verifies the transaction using the public key and processes the transaction using the recovered payment information. Additional techniques to process transactions using data splitting are disclosed.
Owner:MINKASU
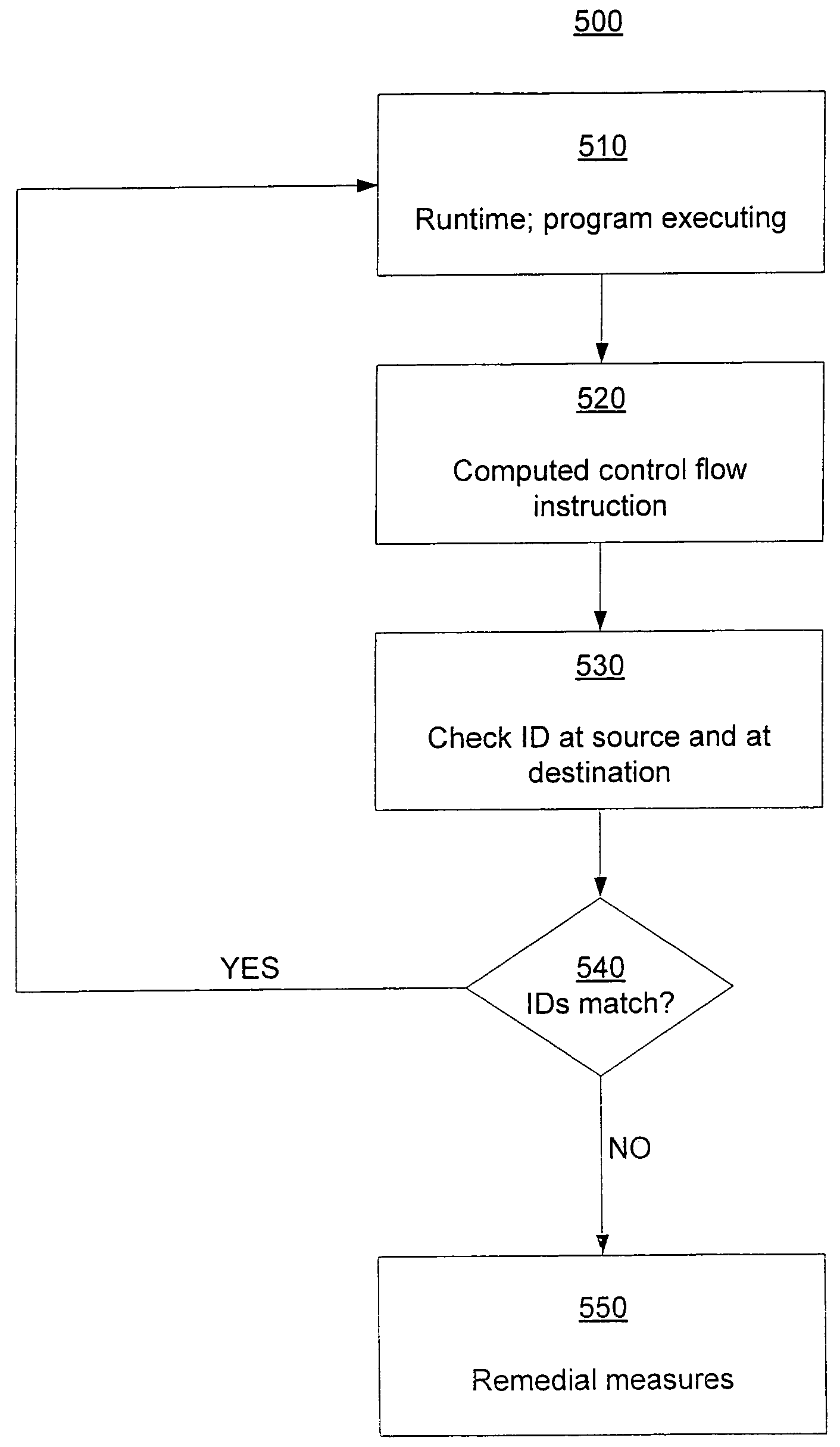
Software security based on control flow integrity
InactiveUS7577992B2Reduce vulnerabilityAvoid successionMemory loss protectionUnauthorized memory use protectionSecurity MeasureSoftware engineering
Software control flow integrity is provided by embedding identifying bit patterns at computed control flow instruction sources and destinations. The sources and destinations of computed control flow instructions are determined with reference to a control flow graph. The identifying bit patterns are compared during software execution, and a match between a source and a respective destination ensures control flow consistent with the control flow graph. Security measures are implemented when the comparison results in a mismatch, indicating that control flow has deviated from the anticipated course.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com