Transparent trust chain constructing system based on virtual machine architecture
A virtual machine and trust chain technology, applied in computer security devices, software emulation/interpretation/simulation, instruments, etc., can solve problems such as a large number of system vulnerabilities, inability to support application layer integrity measurement and authentication, and opaque operating systems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
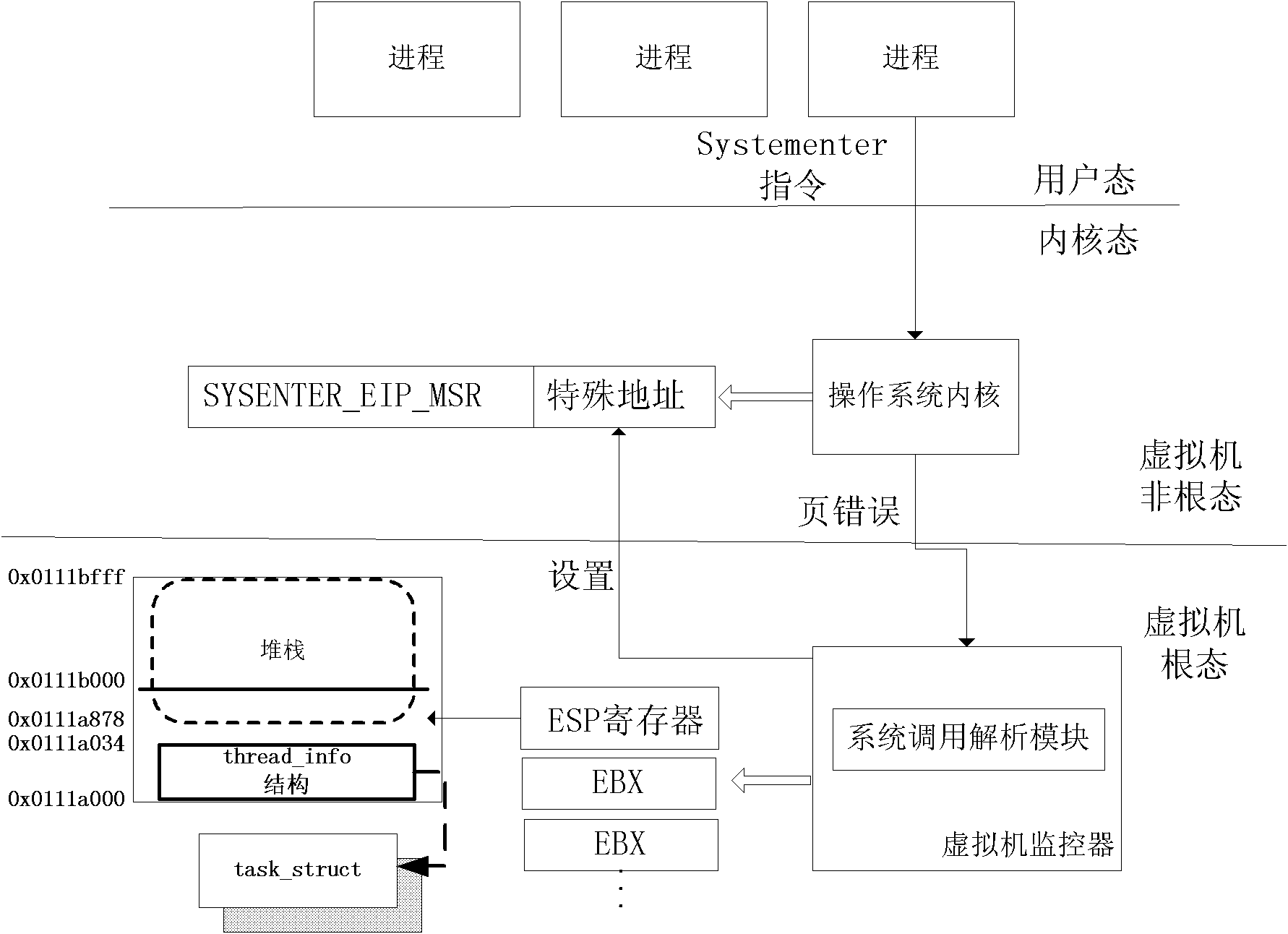
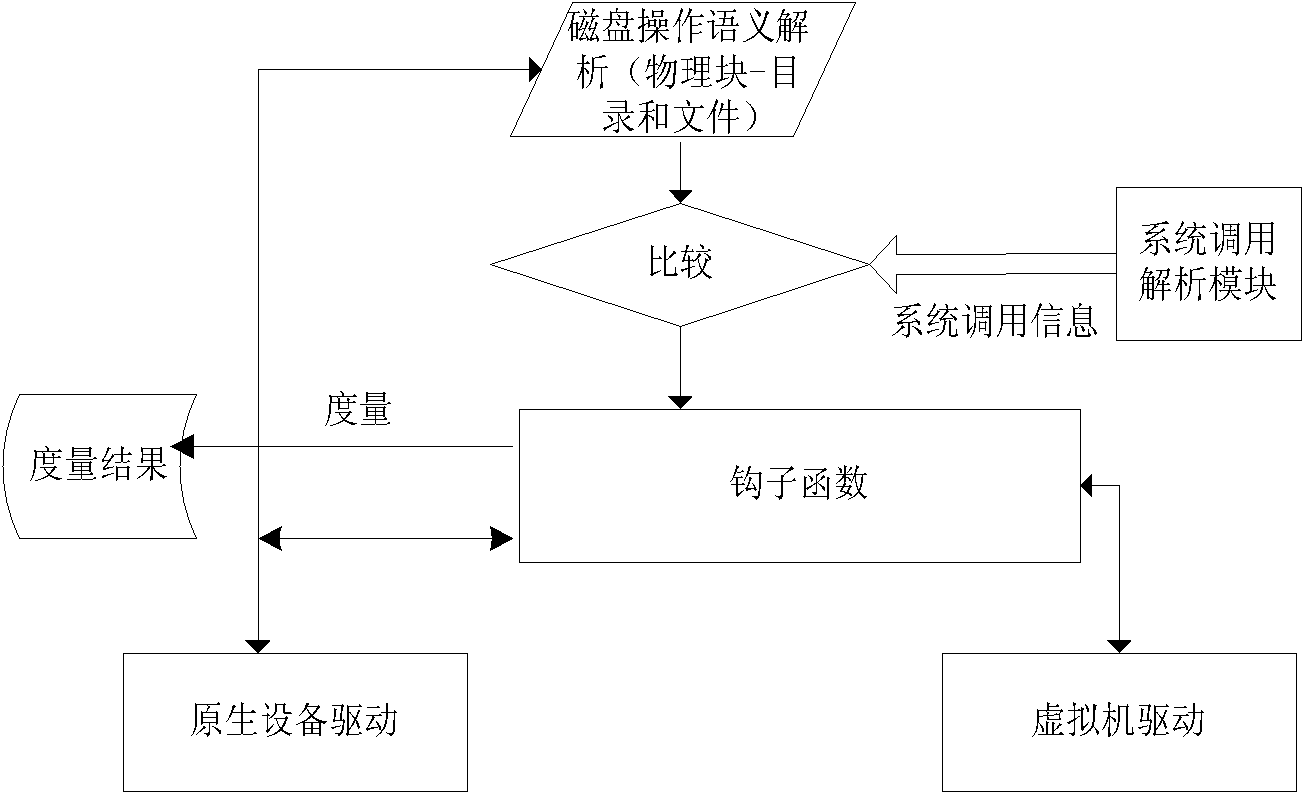
[0017] In order to make the features and advantages of the present invention more clearly understood, below in conjunction with accompanying drawing, describe in detail as follows: figure 1 Describes the schematic diagram of the system structure of the present invention and illustrates the realization of relevant functions in the form of modules. The host (hardware) needs to have the Trusted Platform Module (TPM) specification conforming to the Trusted Computing Group (Trusted Computing Group, TCG) or China Trusted Computing Group. A security chip of the cryptographic module (TCM) specification, and a processor supporting hardware virtualization technology (hardware-assisted virtualization processor); a virtual machine monitor is set on top of the hardware, which has a security chip driver module and a disk operation analysis and measurement module And system call parsing module.
[0018] The virtual machine monitor in the present invention refers to a virtual machine monitor ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com