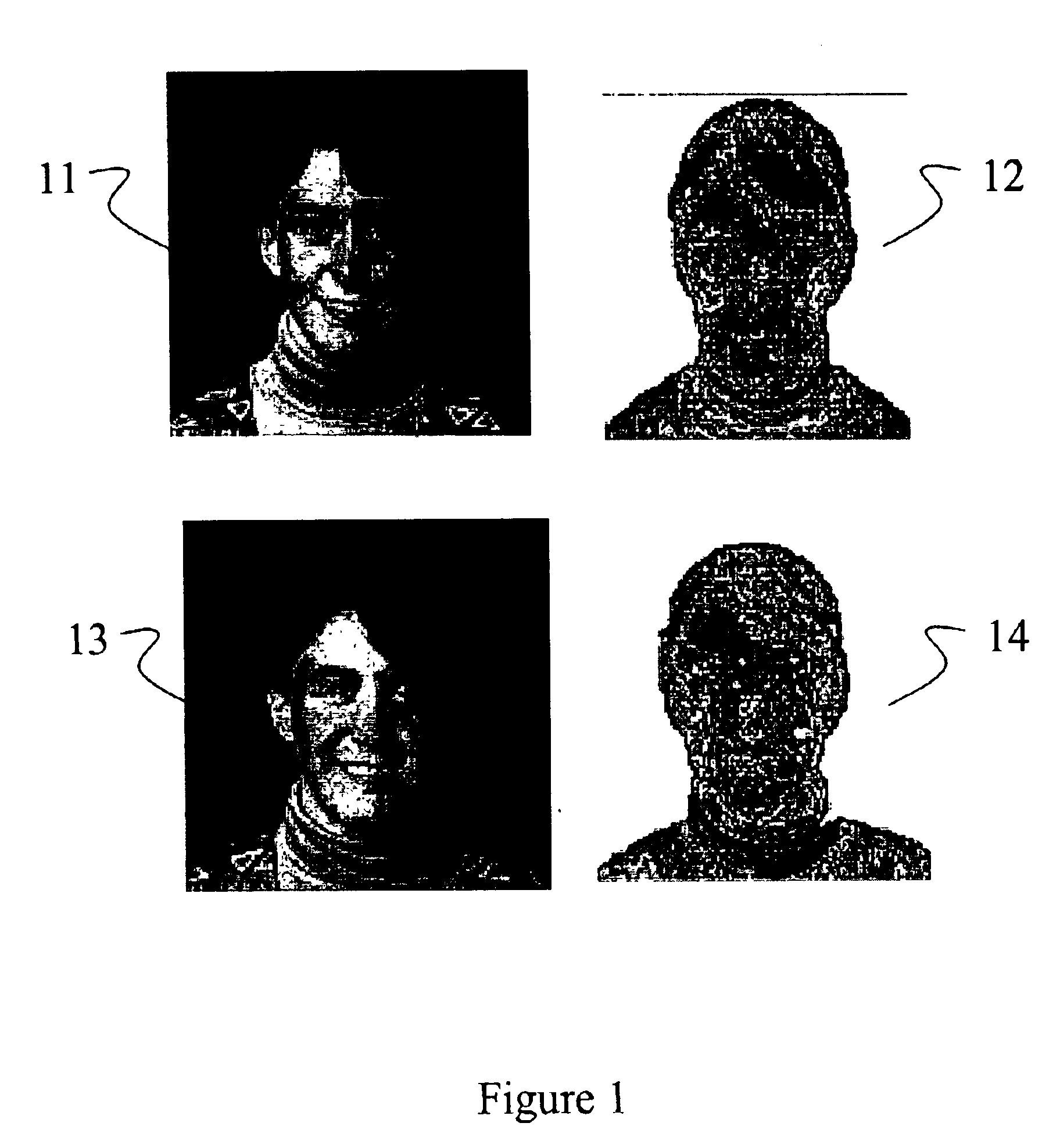
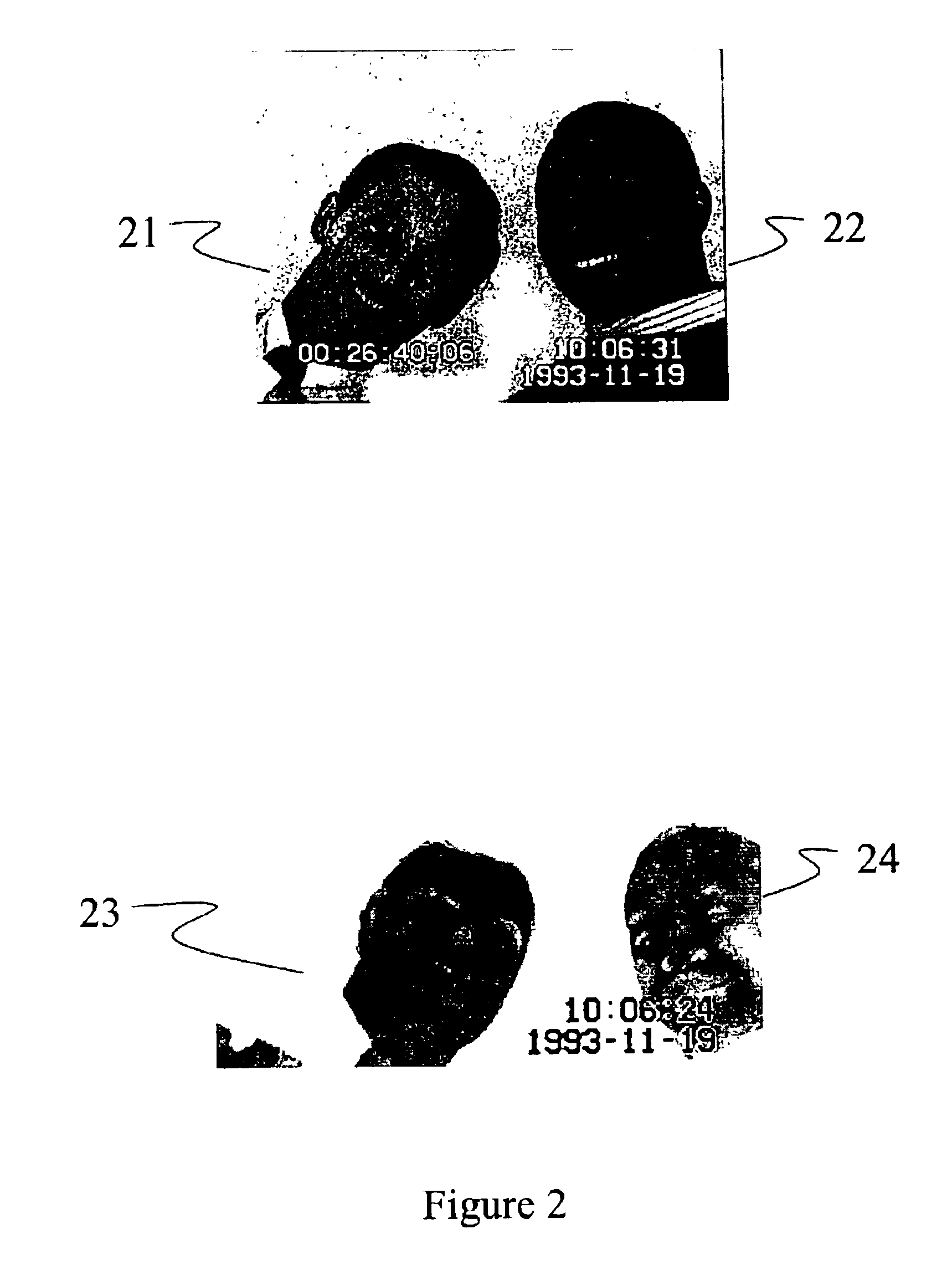
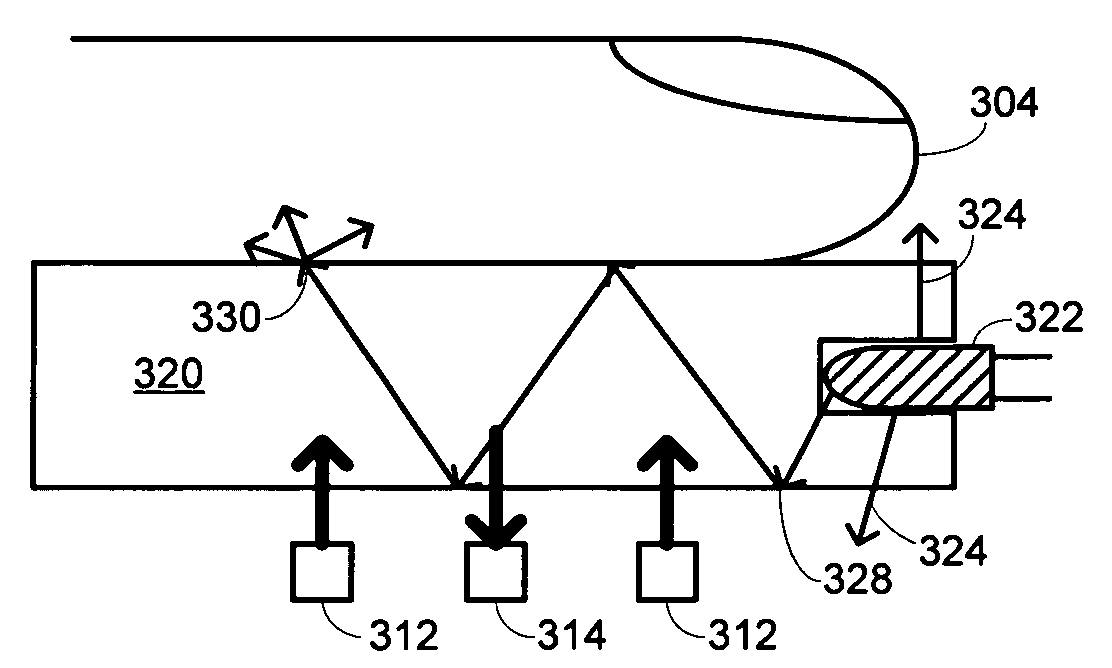
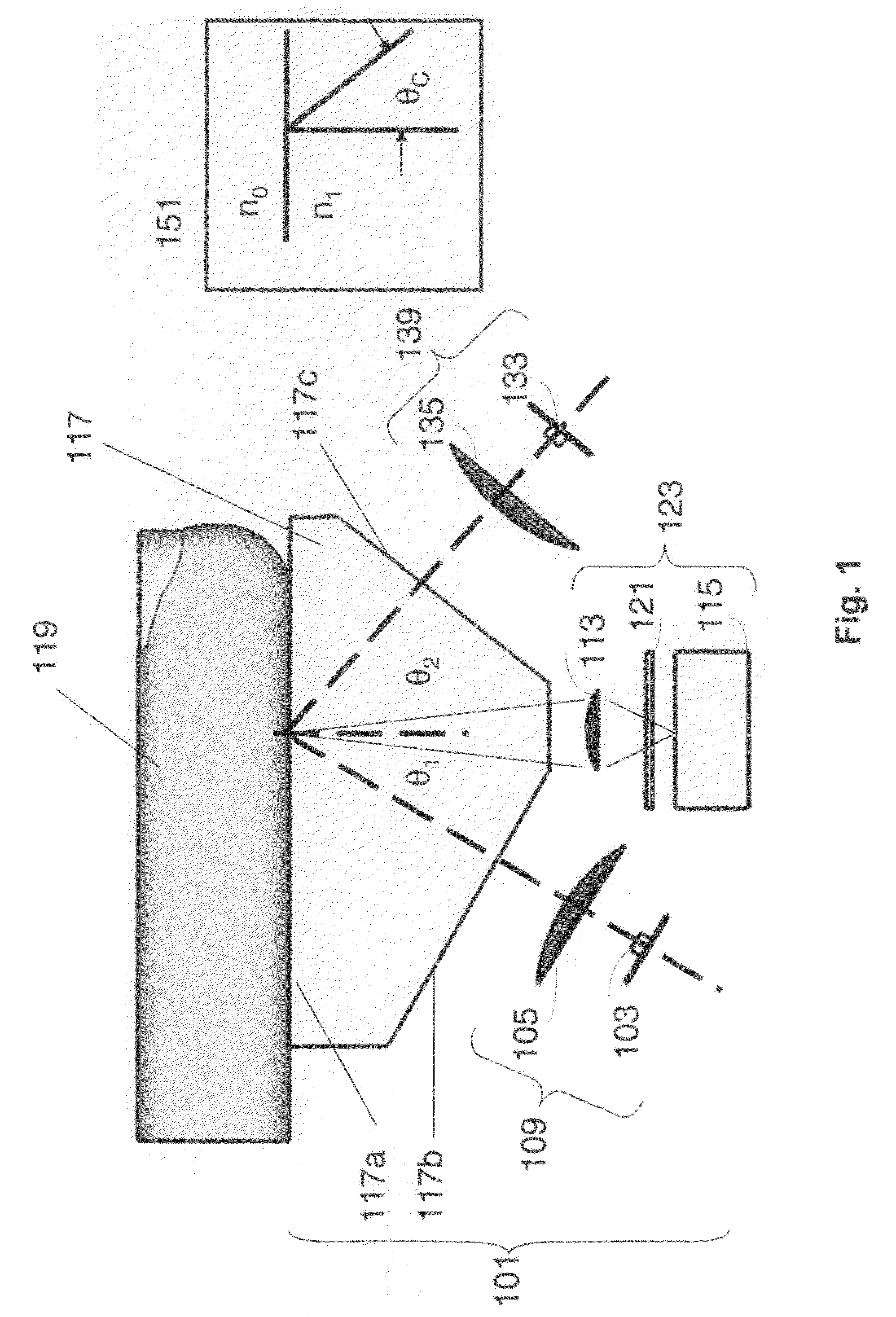
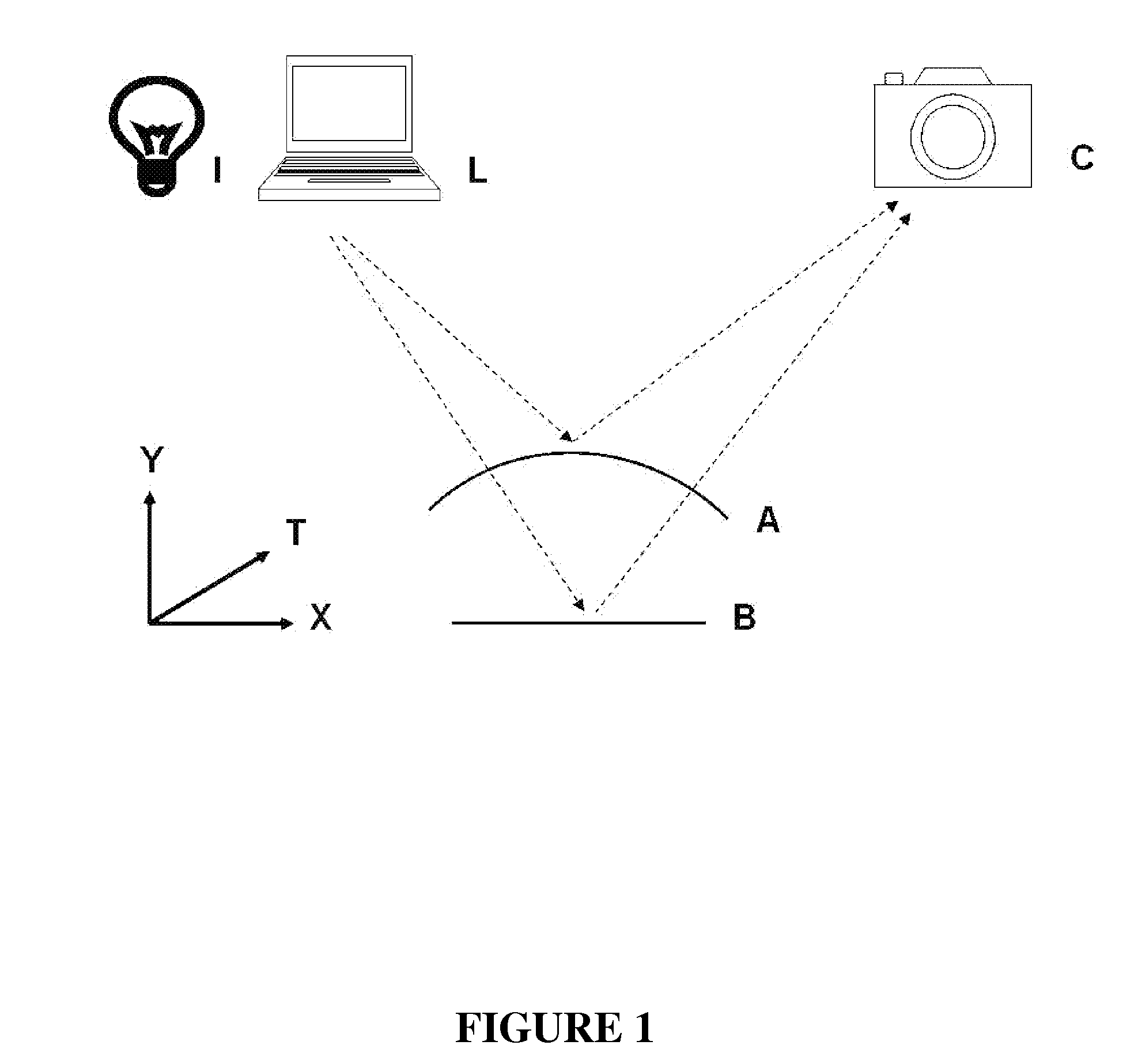
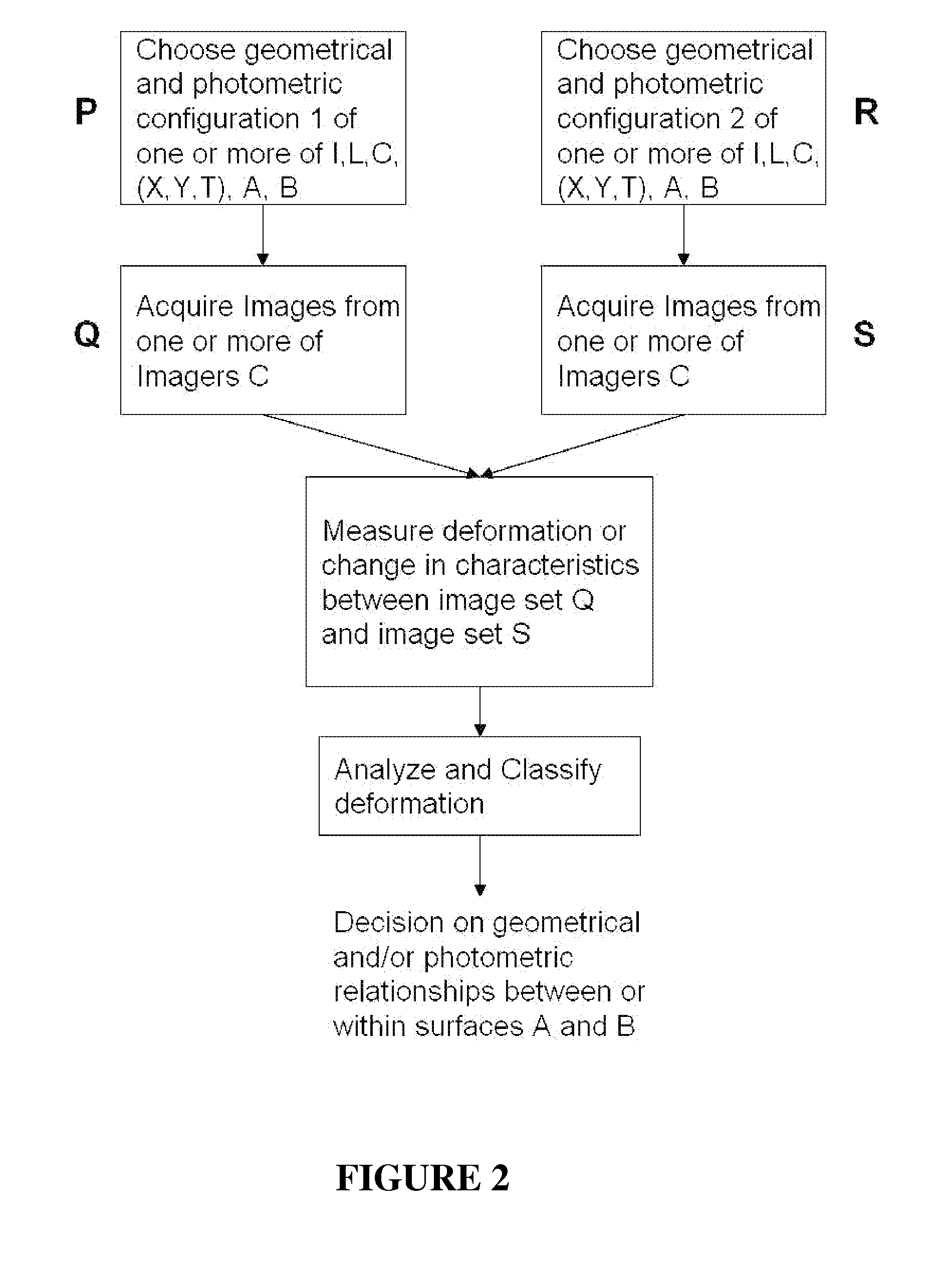
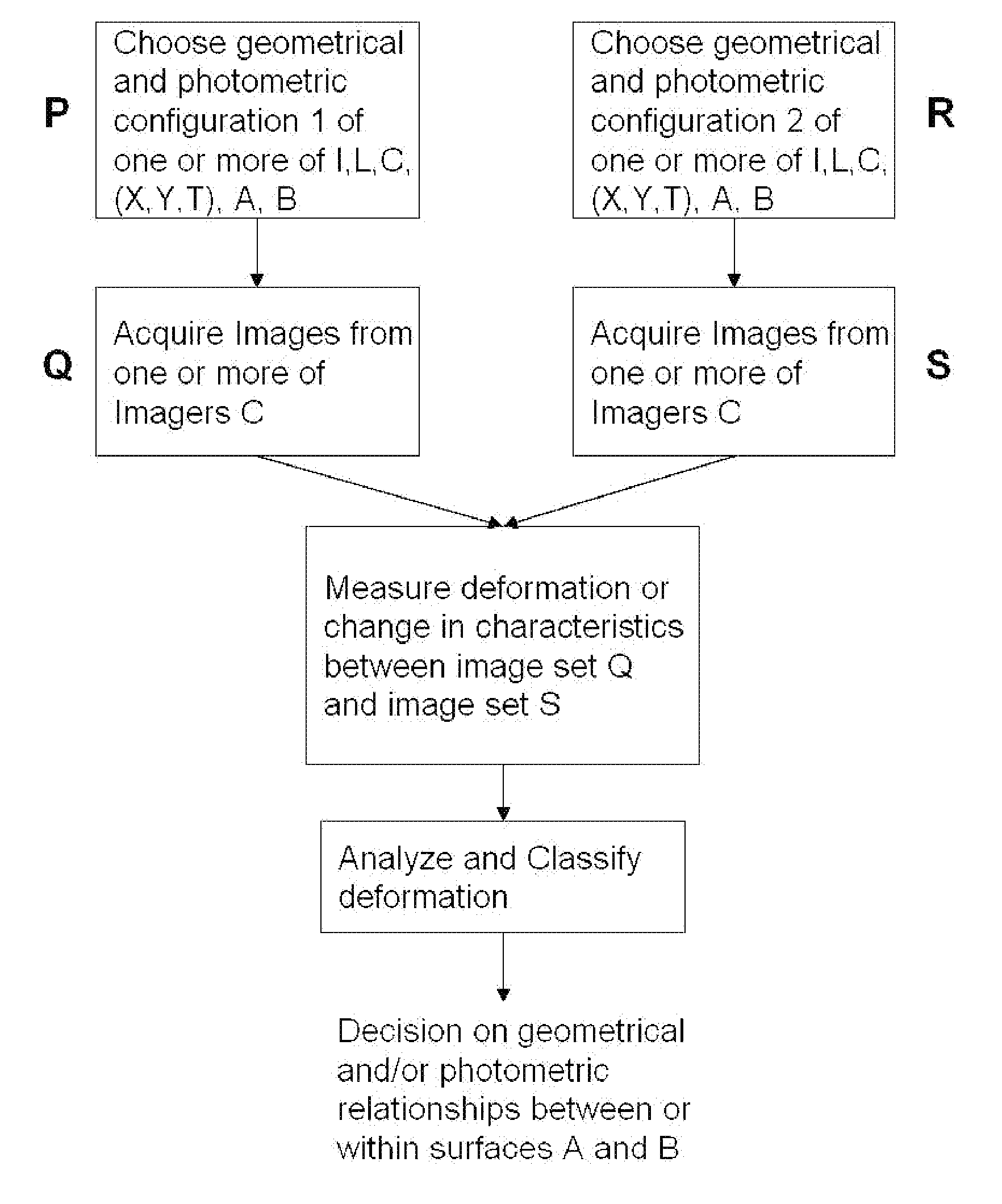
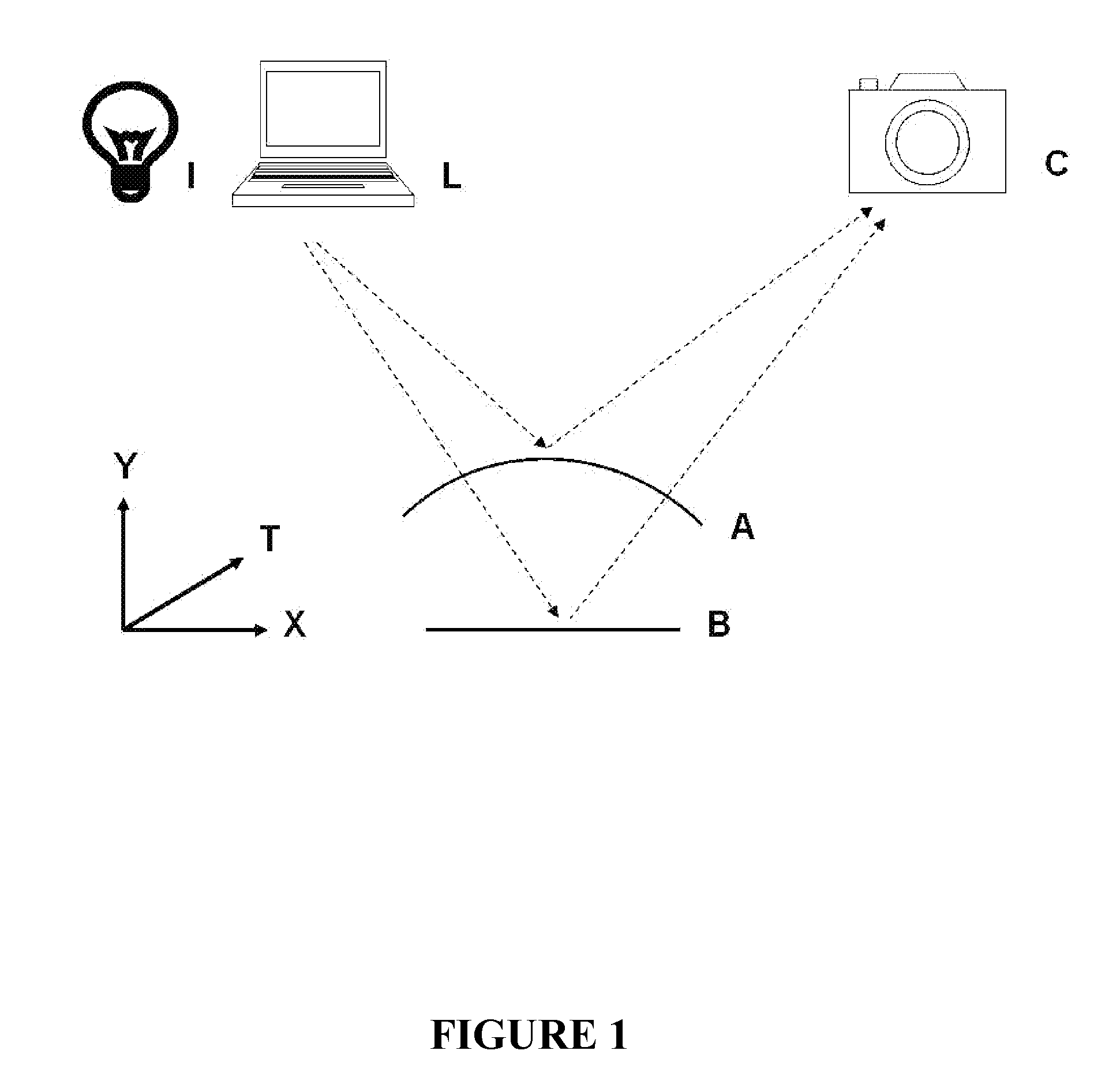
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
2774results about "Spoof detection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
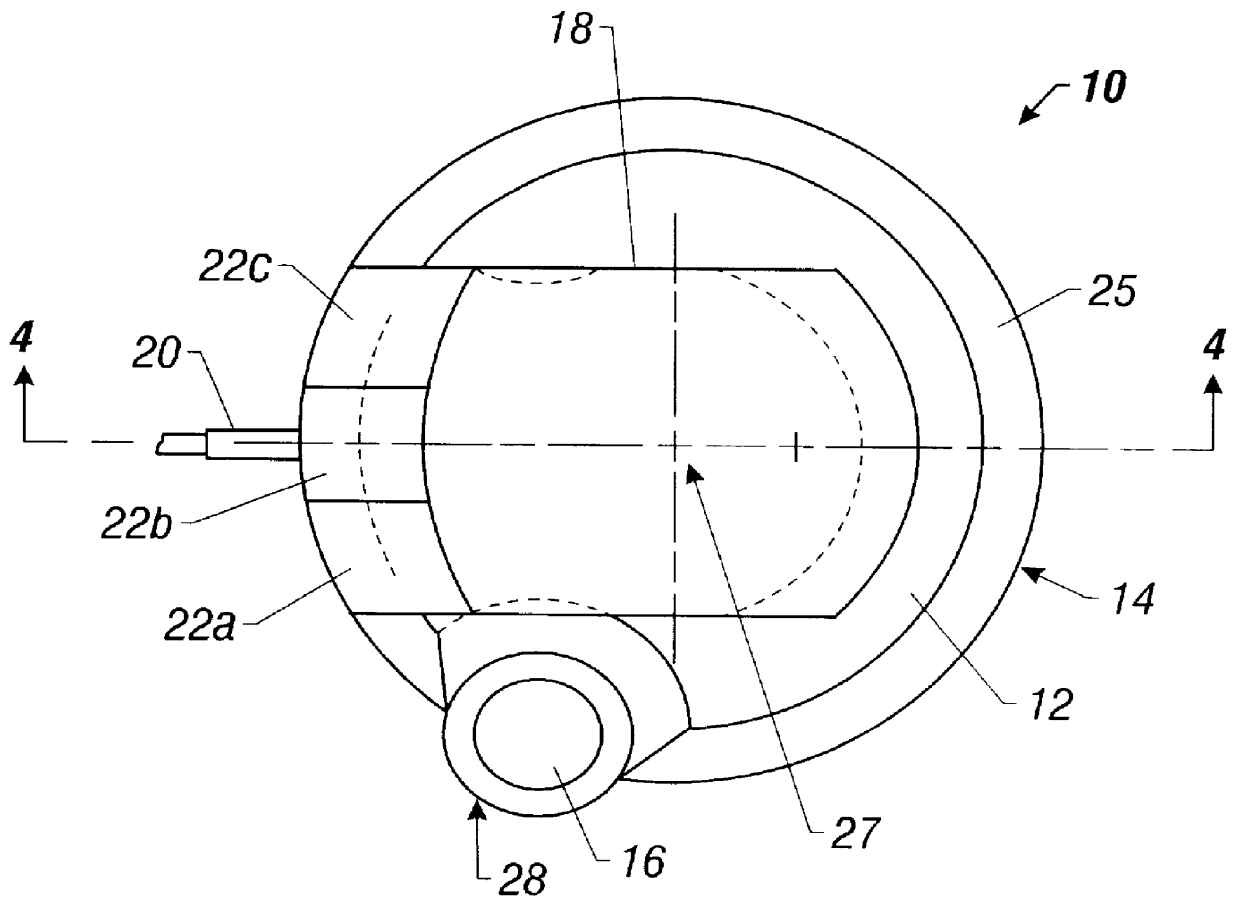
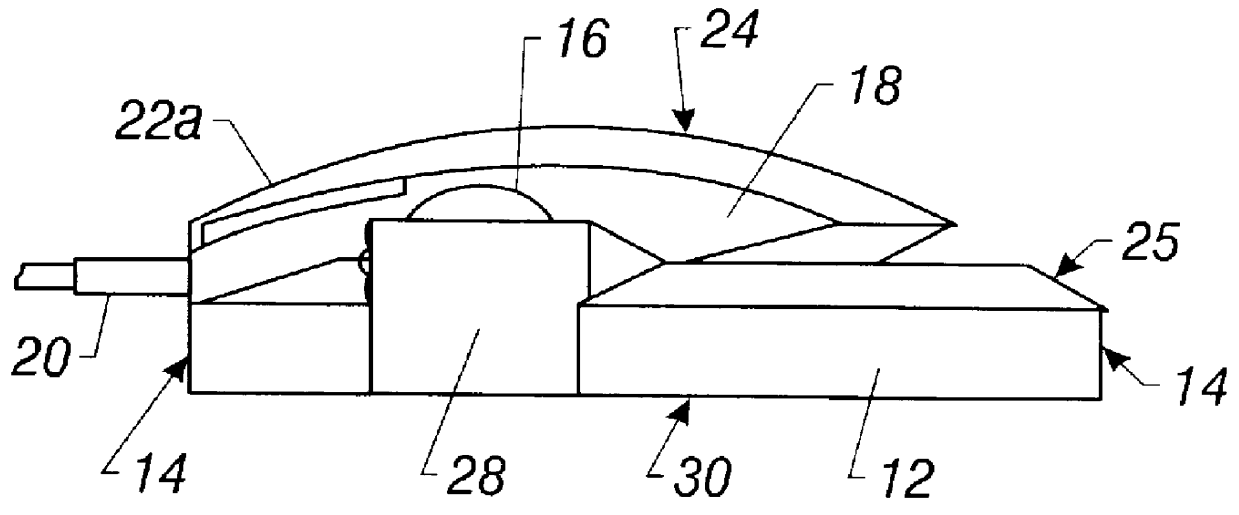
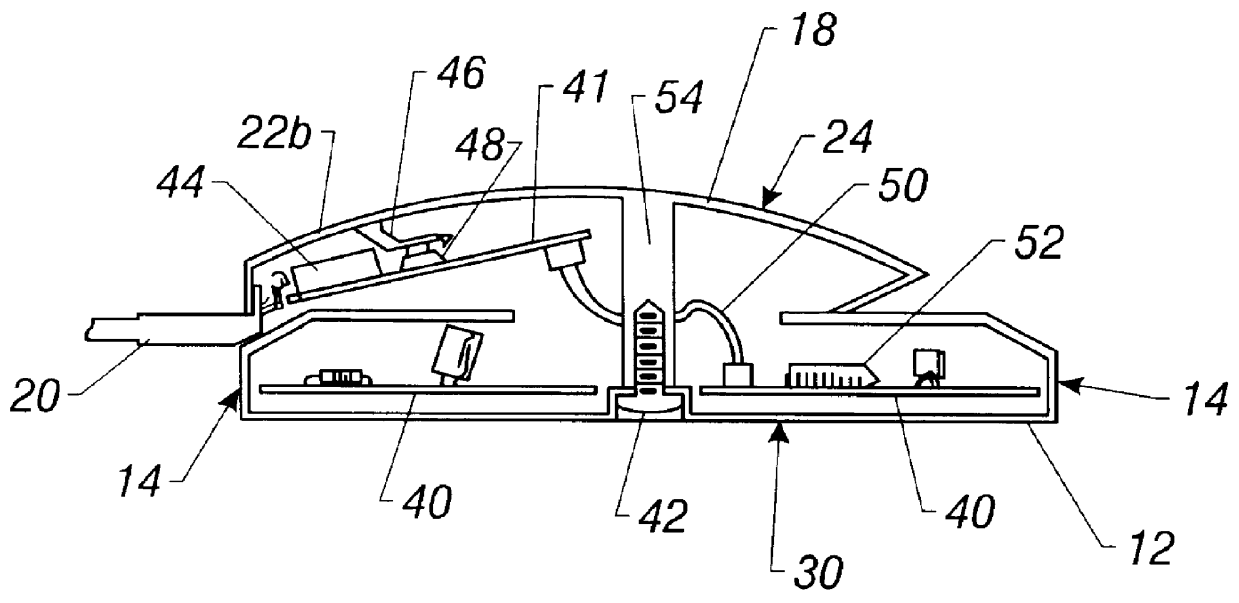
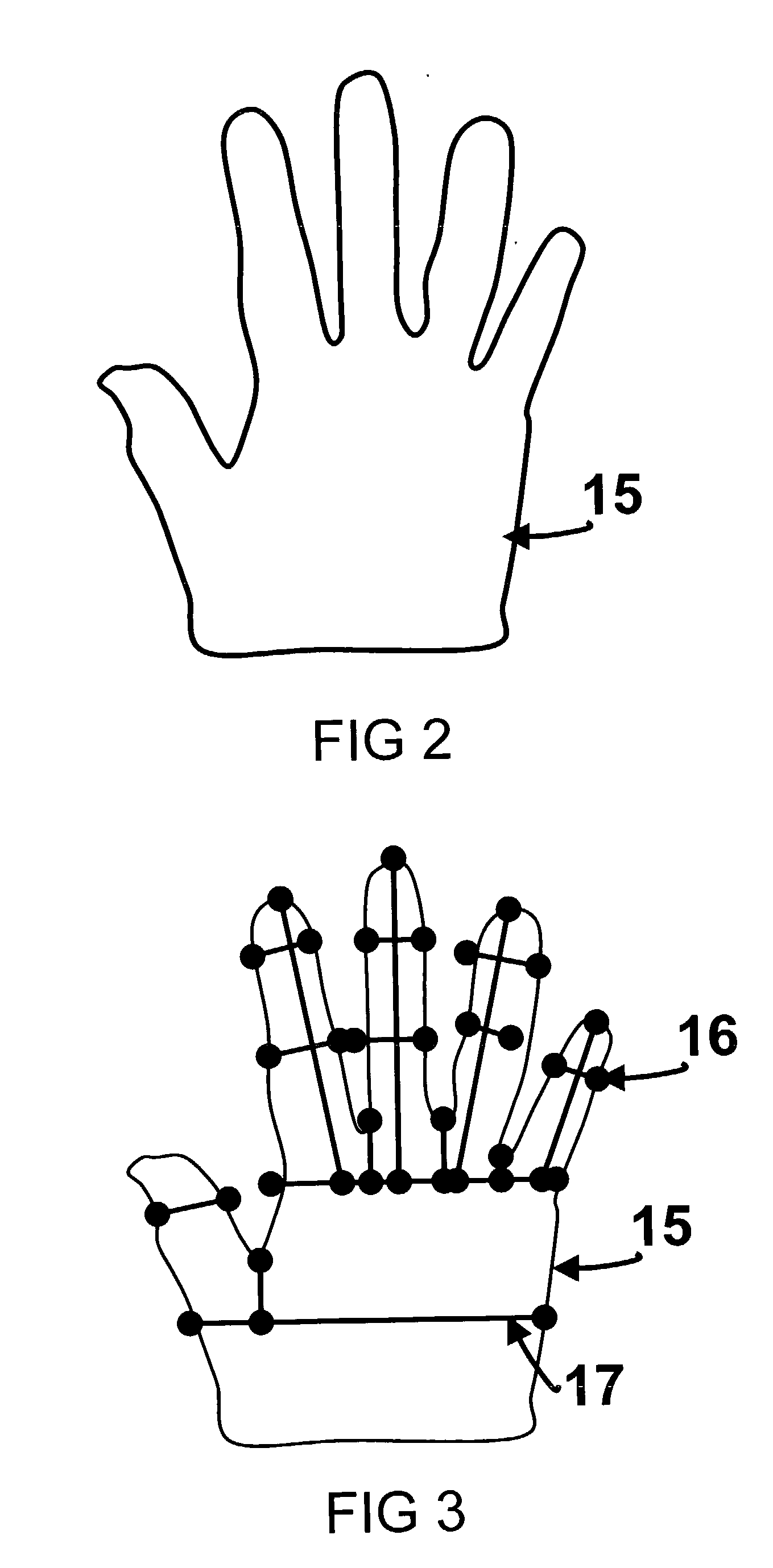
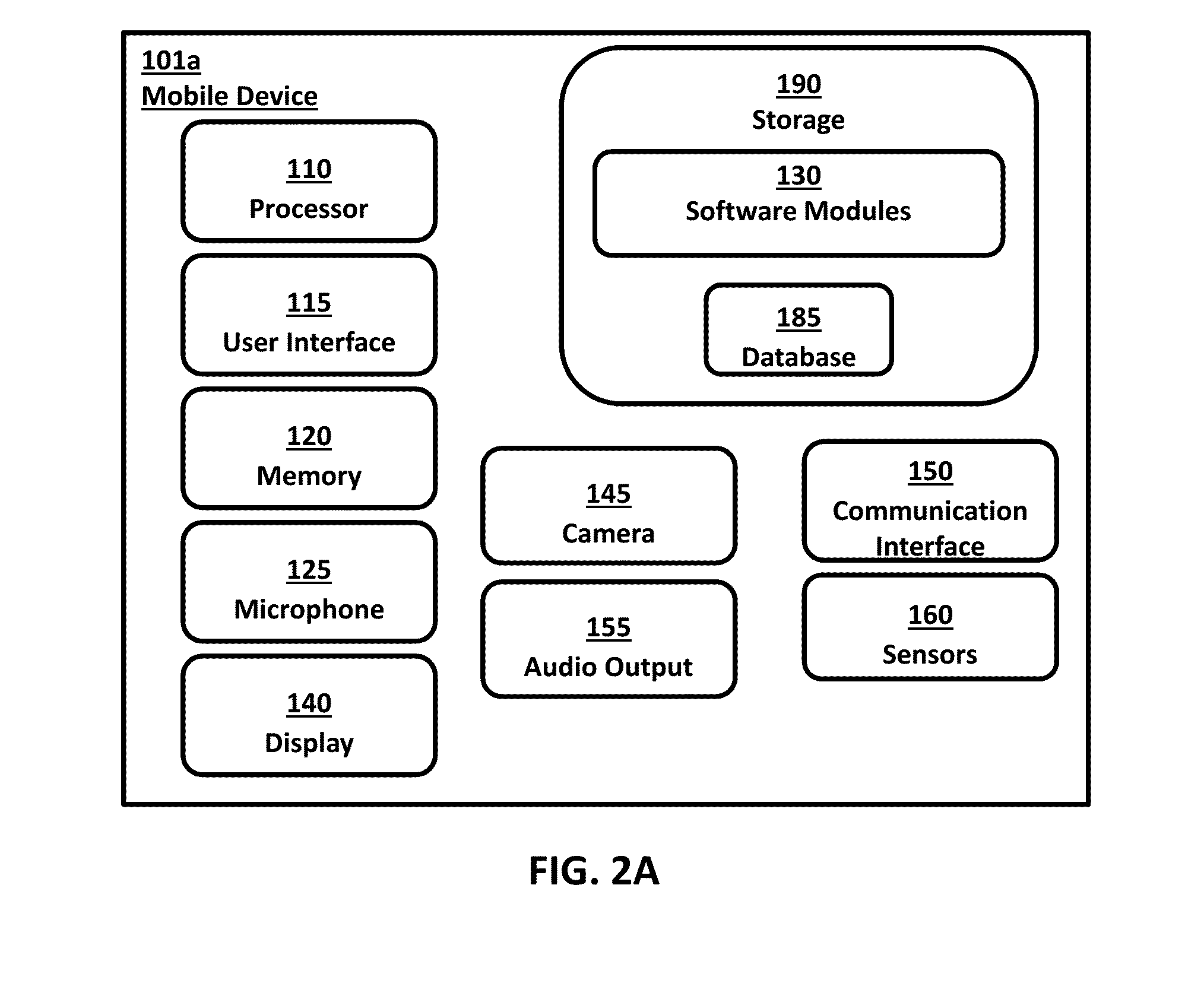
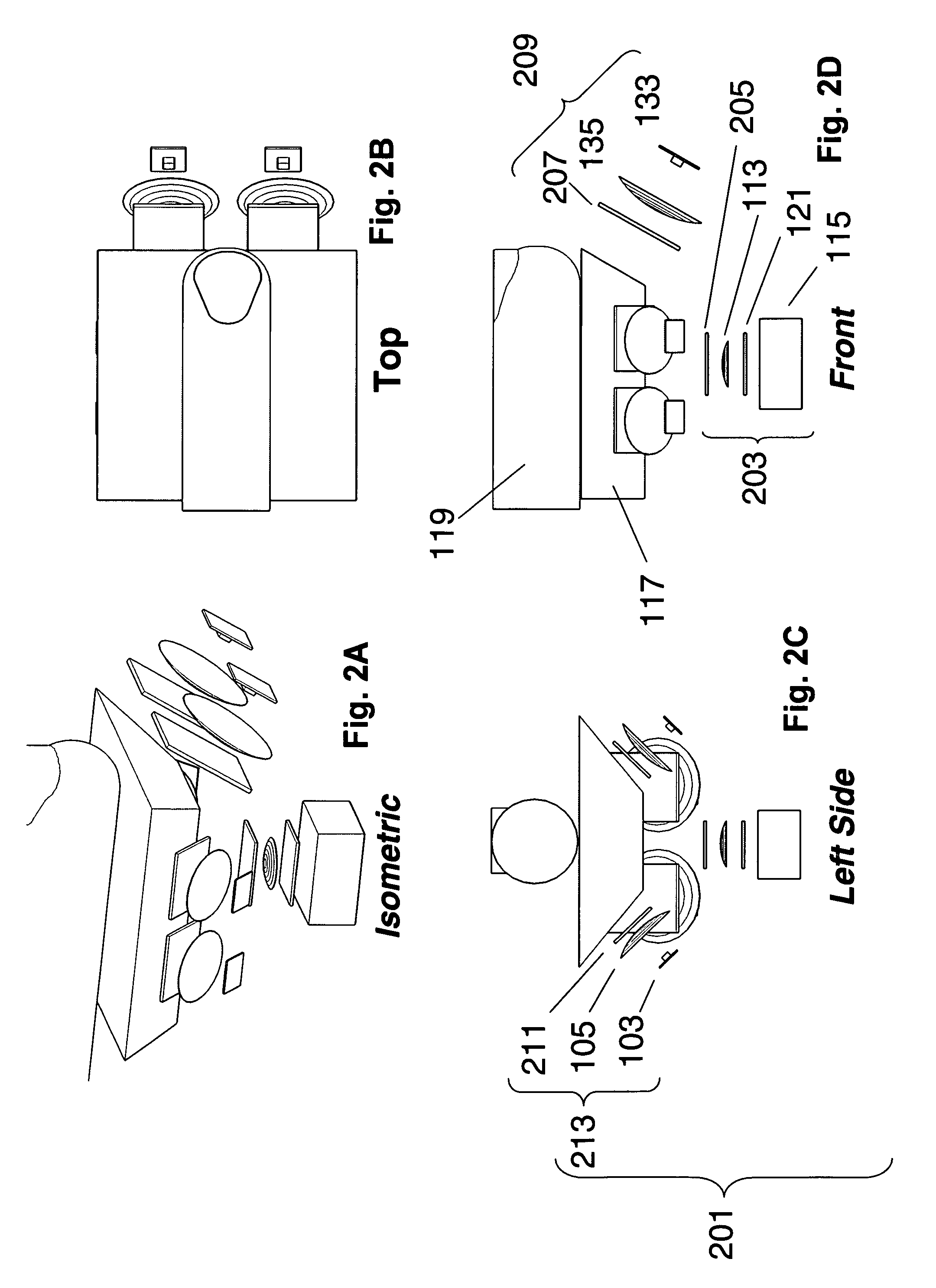
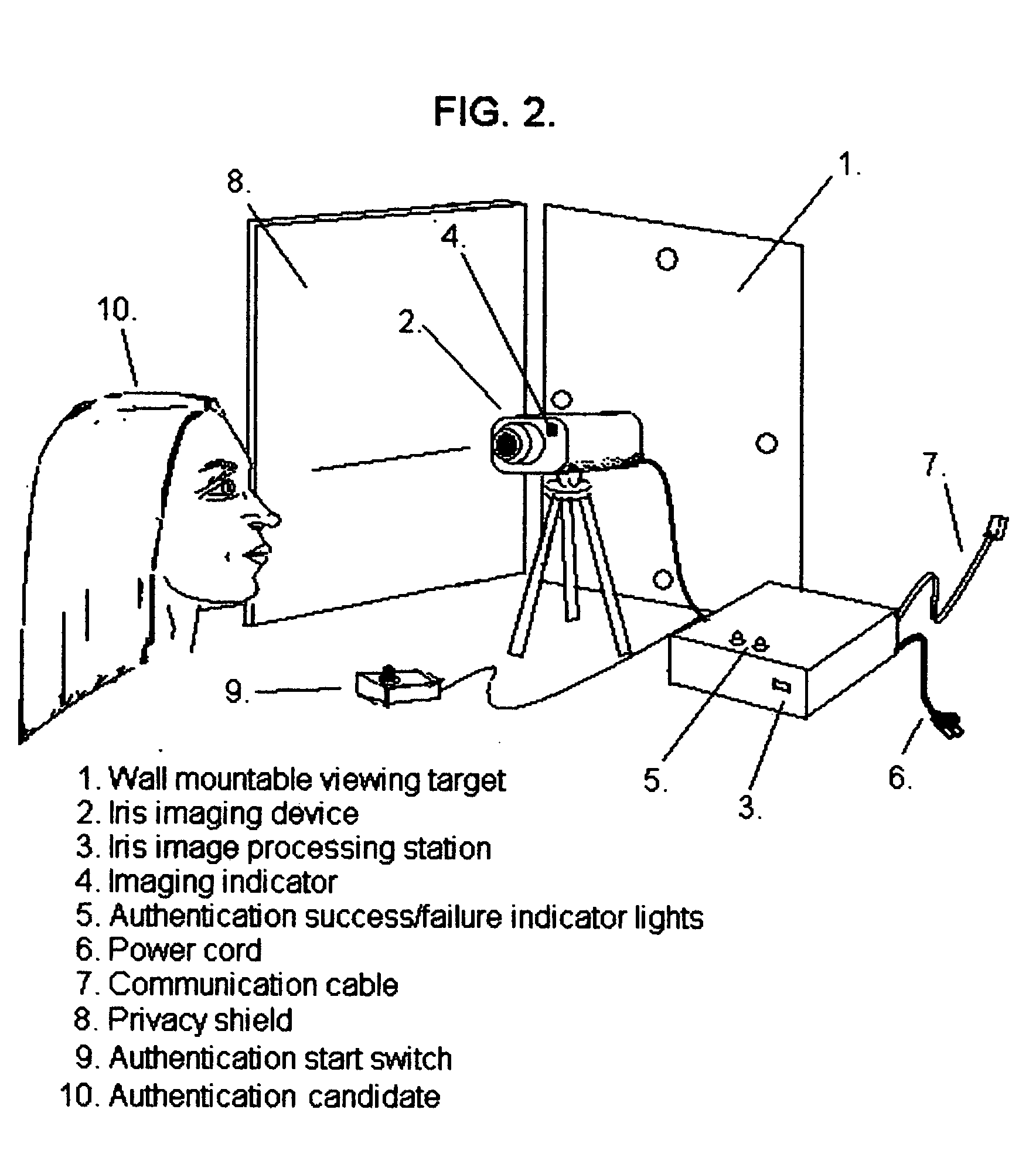
Pointing device with biometric sensor
InactiveUS6148094ACathode-ray tube indicatorsInternal/peripheral component protectionComputerized systemPointing device
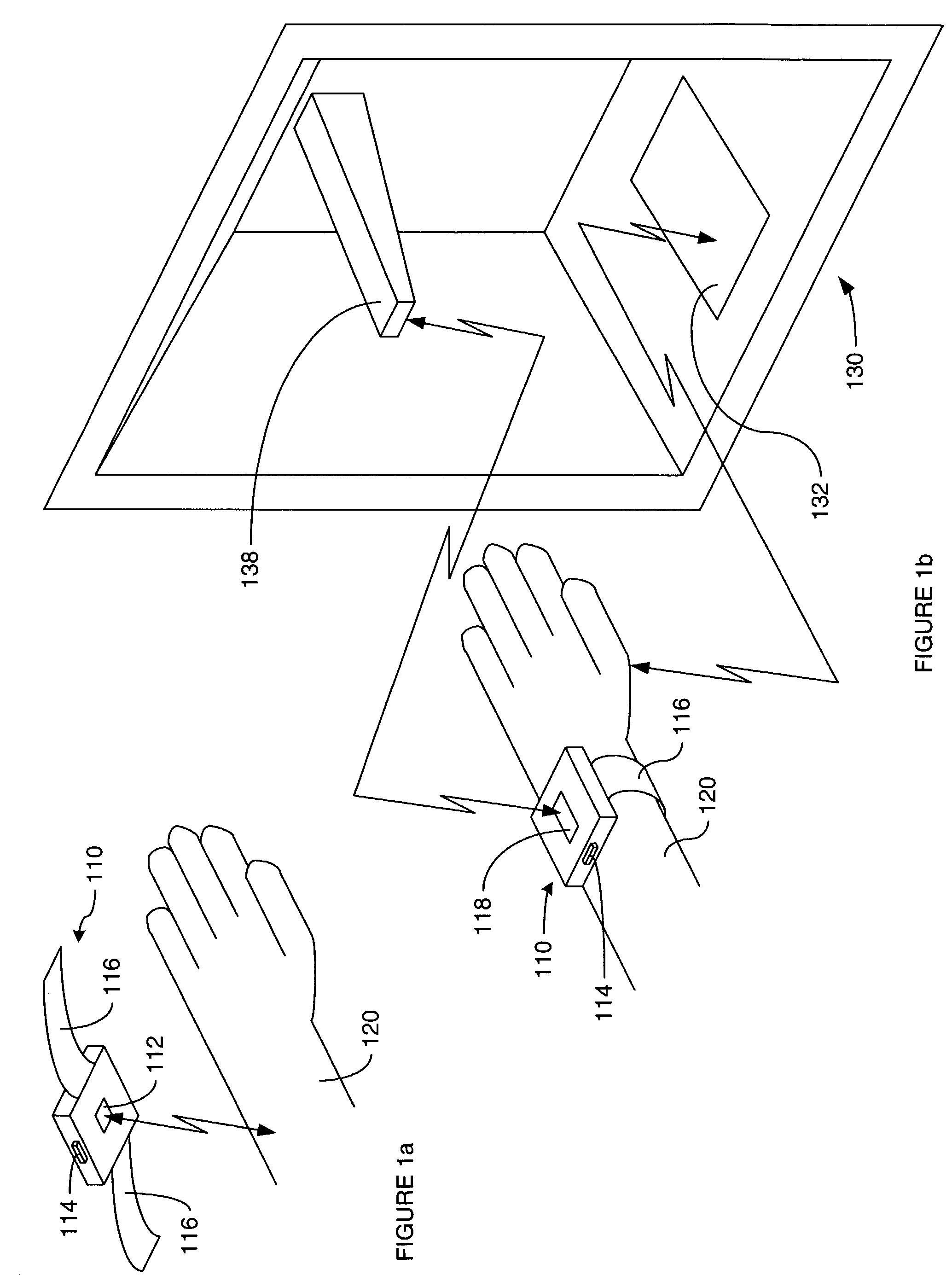
A pointing device incorporates a biometric sensor at a location such that when operating the pointing device in a normal manner, a user's hand rests naturally in a position to place a finger of the user's hand in proximity to and readable by the biometric sensor. In one embodiment, a computer trackball pointing device includes a fingerprint sensor which is equally well suitable for use by either a right-handed or a left-handed user. Along with positional information from a position sensor and user selection information from at least one user-depressable button, the pointing device also conveys to an attached computer system information associated with the user's identity detected by the fingerprint sensor. Such a pointing device is well suited to both transparent verification as well as continuous verification, for if a user removes his or her hand from the natural position when using the device, the user's fingerprint will no longer be detectable by the fingerprint sensor, and the computer system to which the pointing device is attached can be alerted as to the need to re-authenticate any additional attempts at using the pointing device.
Owner:DALTON PATRICK ENTERPRISES
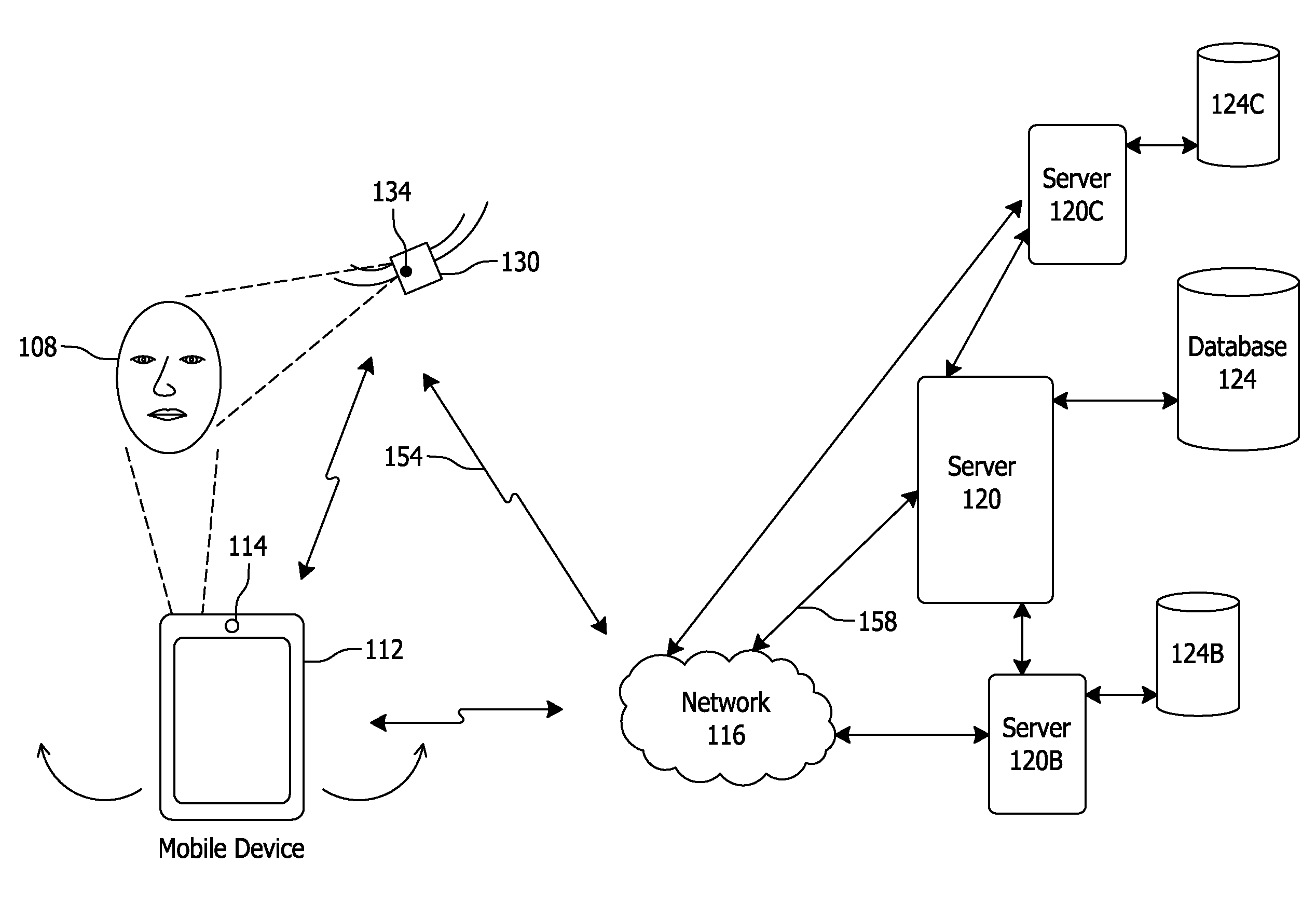
Facial Recognition Authentication System Including Path Parameters
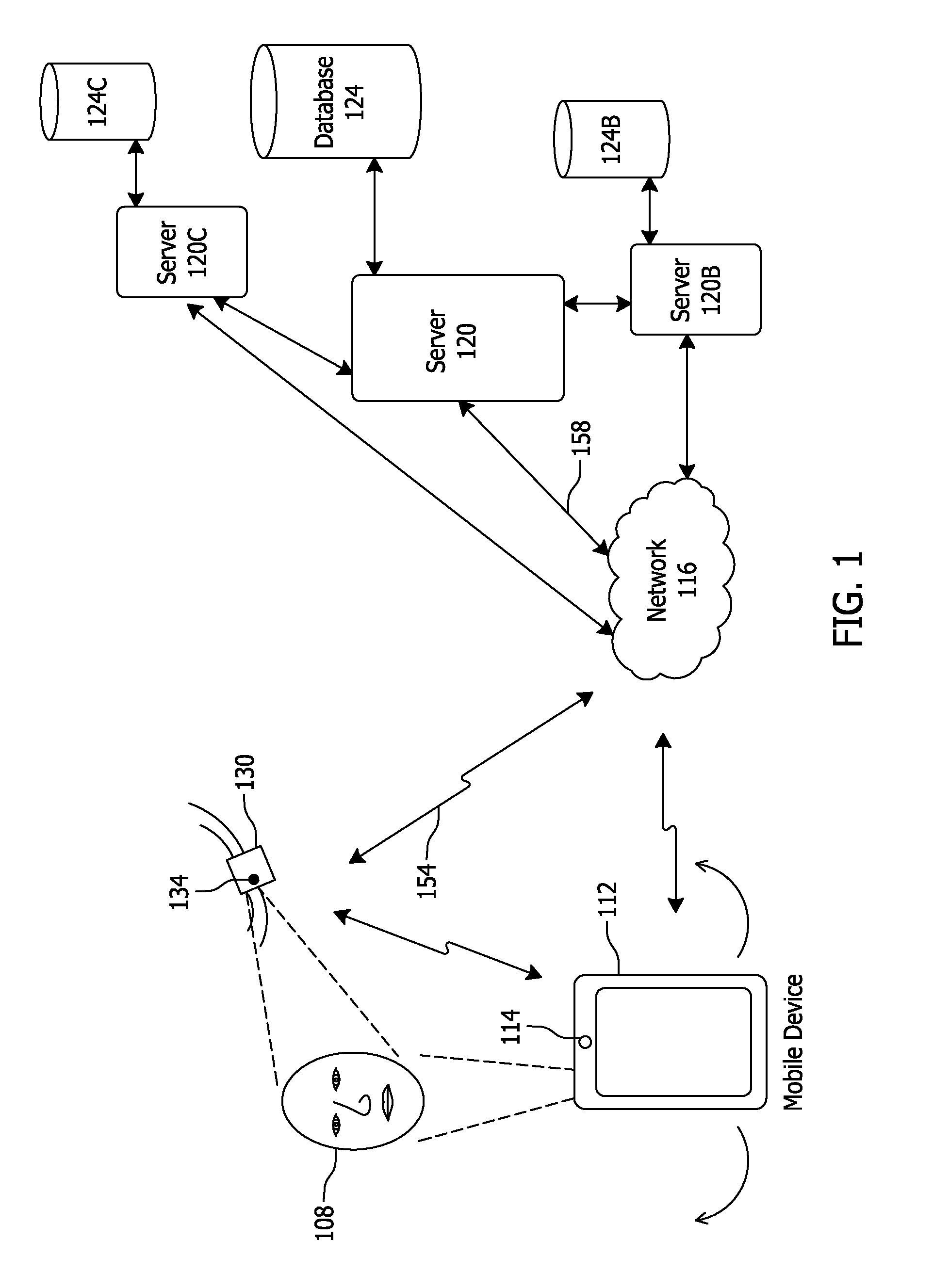
ActiveUS20160063235A1Improve securityAuthorization may be expandedDigital data processing detailsMultiple digital computer combinationsInternet privacyAuthentication system
Systems and methods for enrolling and authenticating a user in an authentication system via a user's camera of camera equipped mobile device include capturing and storing enrollment biometric information from at least one first image of the user taken via the camera of the mobile device, capturing authentication biometric information from at least one second image of the user, capturing, during imaging of the at least one second image, path parameters via at least one movement detecting sensor indicating an authentication movement of the mobile device, comparing the authentication biometric information to the stored enrollment biometric information, and comparing the authentication movement of the mobile device to an expected movement of the mobile device to determine whether the authentication movement sufficiently corresponds to the expected movement.
Owner:FACETEC INC
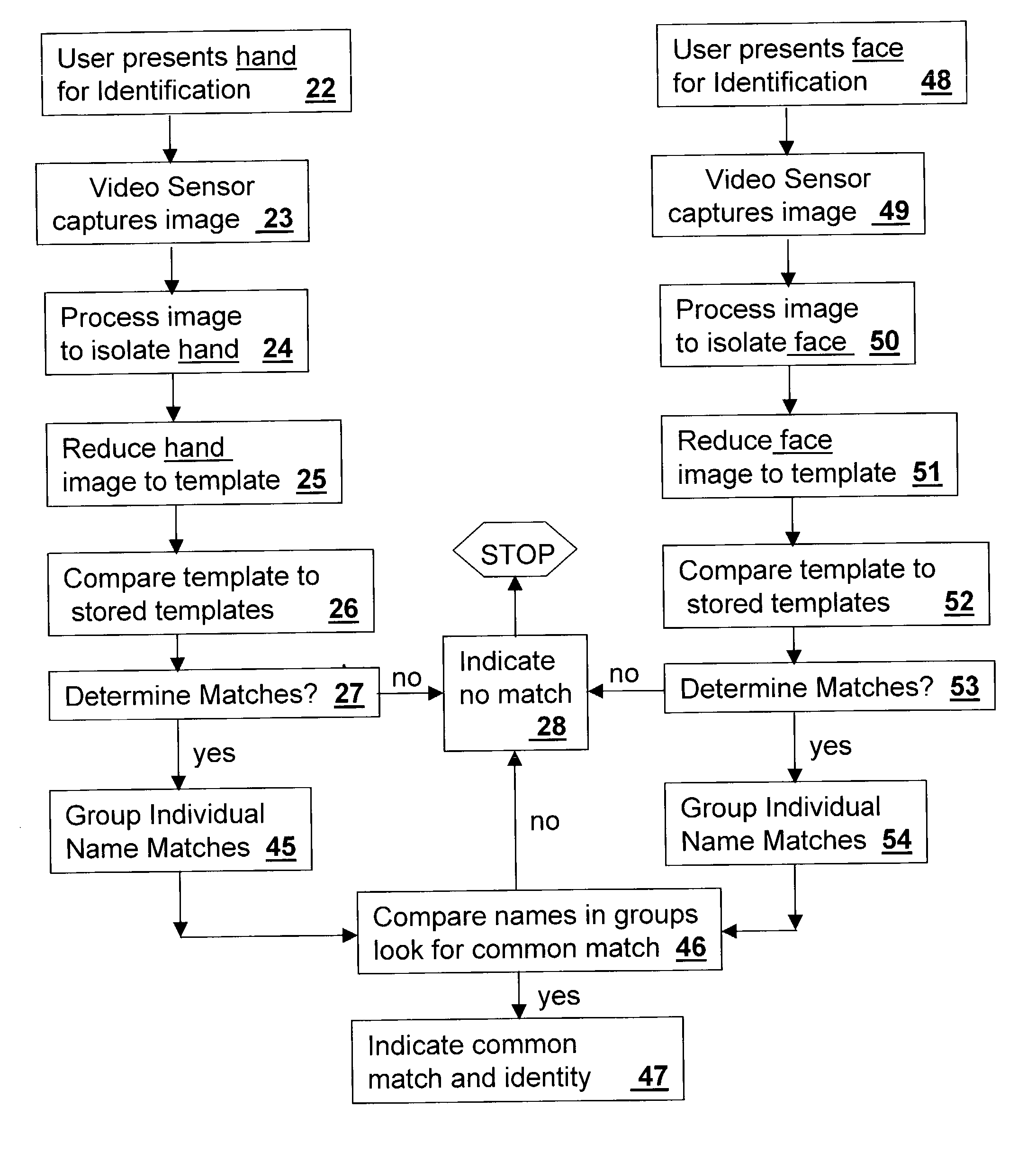
Method and apparatus for contactless hand recognition
A method and apparatus is provided for Contactless Hand Recognition (CHR) for positive identification of cooperative individuals seeking access to physical, logical, or informational systems. Contactless Hand Recognition (CHR) is based on a novel technique and apparatus that rapidly and contactlessly captures a livescan hand geometry video image with a visible wavelength, infrared, or thermal camera of a person desiring access, then reduces the image to a template, compares the livescan template to a reference template, and determines if there is a match. Contactless Hand Recognition (CHR) is a significant advancement over current state-of-the-art hand recognition systems because authentication is done contactlessly while on the move, and at a distance, while simultaneously verifying liveness. It can also be combined with a personal knowledge process to include the use of a Personnel Identification Number (PIN), a secret contactless sign (SCS), or unique hand / finger position biometrics known only to the user. The CHR invention offers the possibility for users to have a rapid, fully contactless three-factor system of authentication based on contactless tokens, biometrics, and personal knowledge identification signs.
Owner:THE RIGHT PROBLEM
Automobile security defence alarm system with face identification and wireless communication function
InactiveUS20060261931A1Easy to helpReduce operating loadElectric signal transmission systemsImage analysisTelecommunicationsAutomobile safety
An automobile alarm system includes: (1) a face identification and discrimination system, which consists of low-light, visible light, infrared light, and thermo-luminescence camera and / or digital camera device for photograph of inside and outside of automobiles, and face identification and discrimination hardware and software system for testing whether a mask or facial adornments or whether his / her face is directed at the camera; (2) redundancy device and / or redundancy function modules, anti-interference system for communication and anti-destructive detection system; (3) a automobile status recorder, which can record the statuses on the inside and outside of the automobile before, during and after an emergent event picked up by the camera; (4) a multi-functional burglar, anti-destructive and anti-hijacking alarm for automobiles, which can transmit a radio image to a remote equipment for reporting an incident. This invention can also be used for every supervision systems.
Owner:CHENG ZIYI
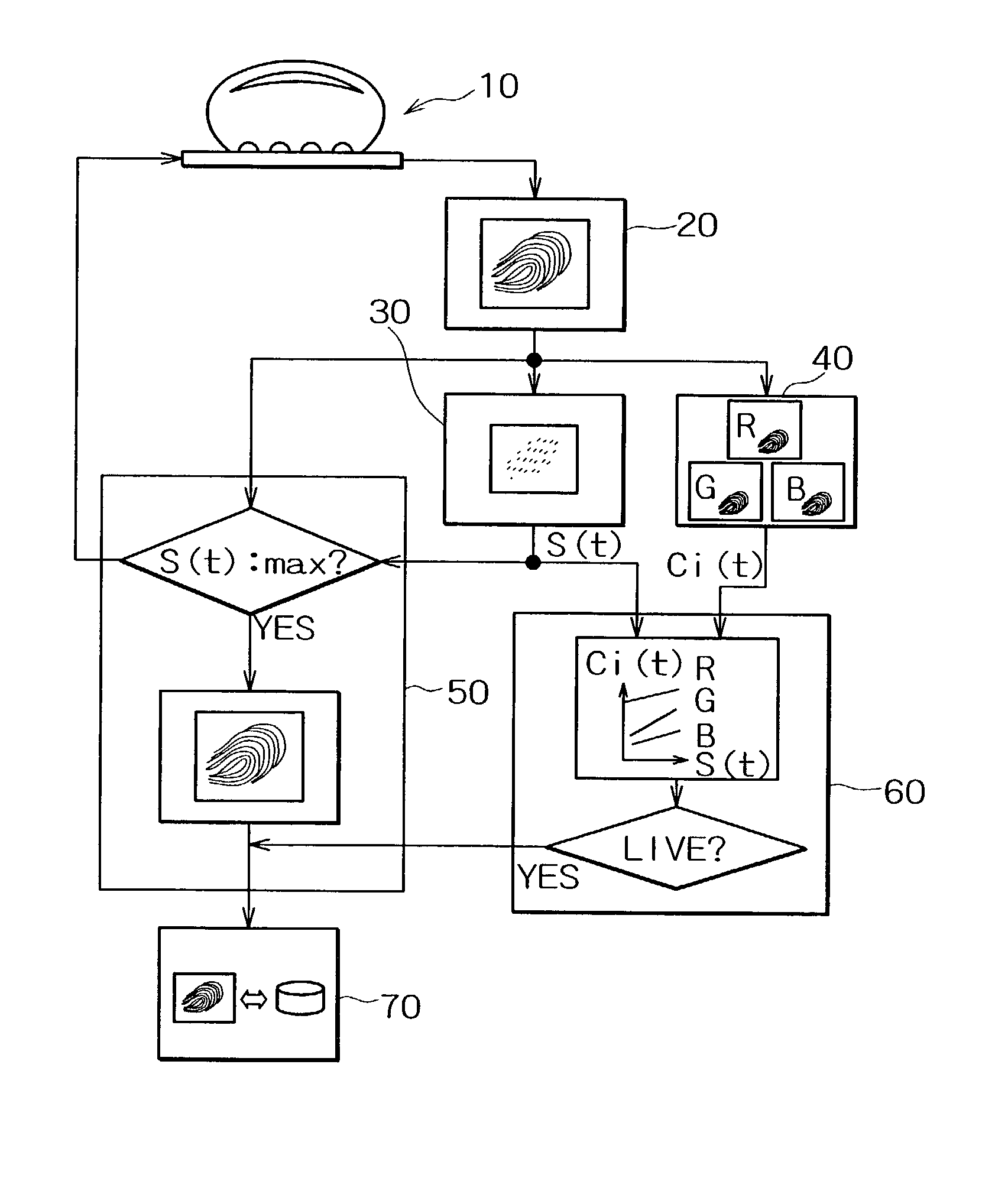
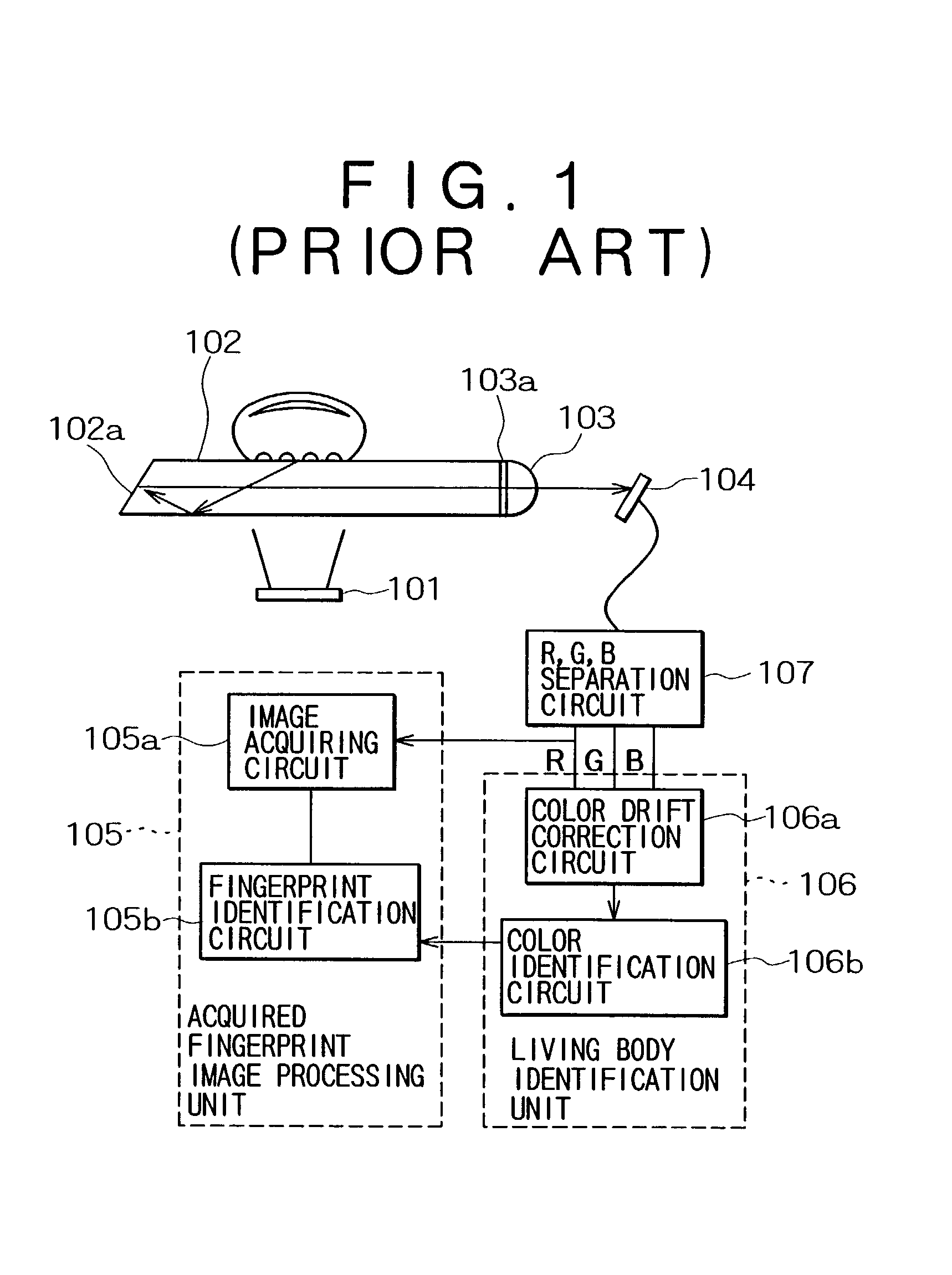
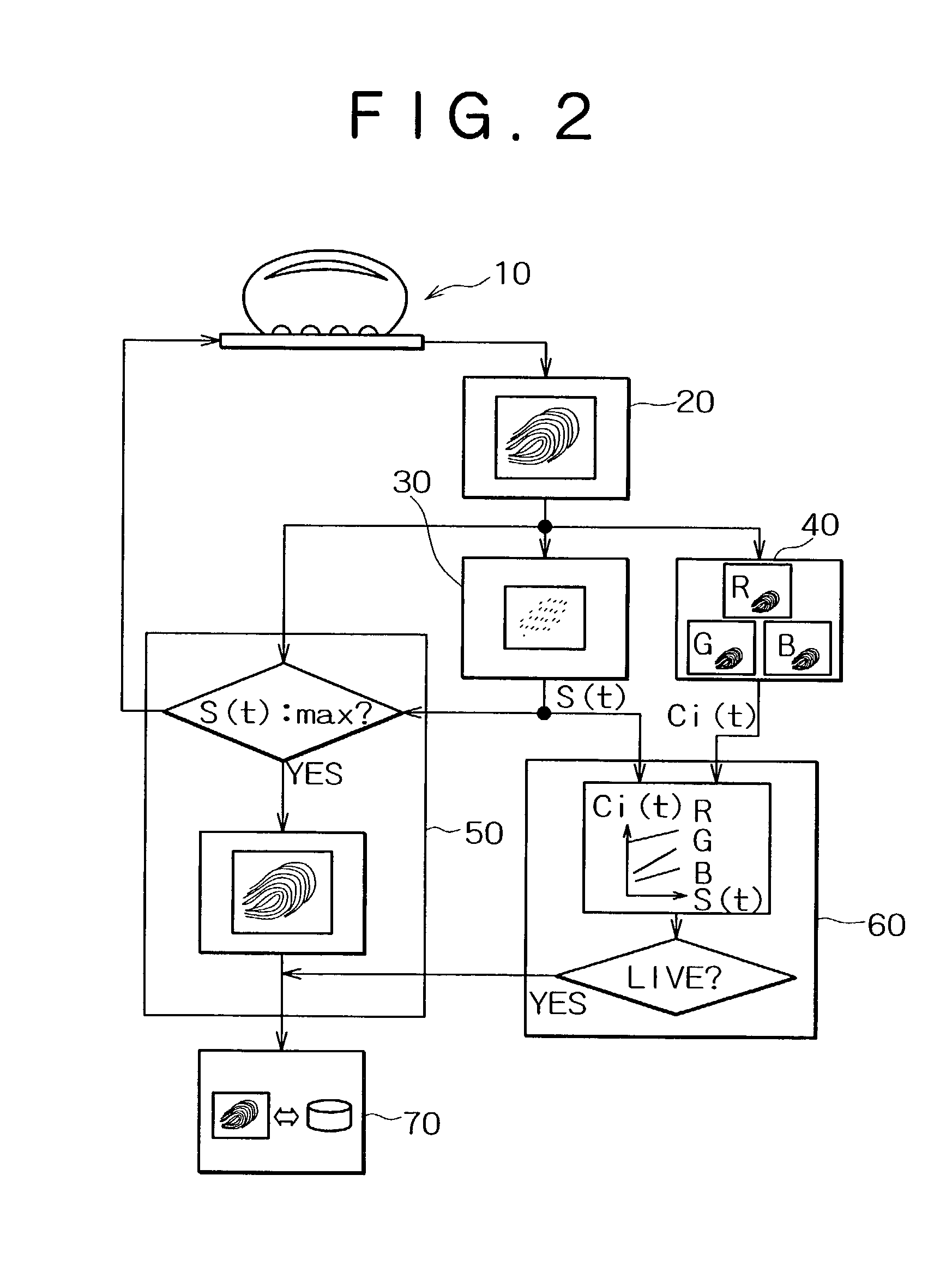
Fingerprint image input device and living body identification method using fingerprint image
InactiveUS20030044051A1Improve reliabilityElectric signal transmission systemsImage analysisPattern recognitionColor image
A color image sensor sequentially acquires a plurality of fingerprint images when a finger is pressed against the detector surface. A color information extraction unit detects the finger color in synchronization with the input of the plurality of fingerprint images. An areal information extraction unit detects a physical quantity representing the pressure applied by the finger to the color image sensor when the plurality of fingerprint images are acquired, particularly, the quantity related with the area of the finger in contact with the detector surface. A living body identification unit determines whether the finger is a live or dead one by the analysis of correlation between the physical quantity and the finger color. According to this configuration, even if the finger color does not change much, it is possible to distinguish living bodies from dead ones if there is a sufficient correlation with information such as the area of the fingerprint that reflects the finger pressure. The thickness of the fingerprint input unit is approximately 1-2 mm, determined by the sum of the thickness of the planar light source and that of the color image sensor.
Owner:VISTA PEAK VENTURES LLC
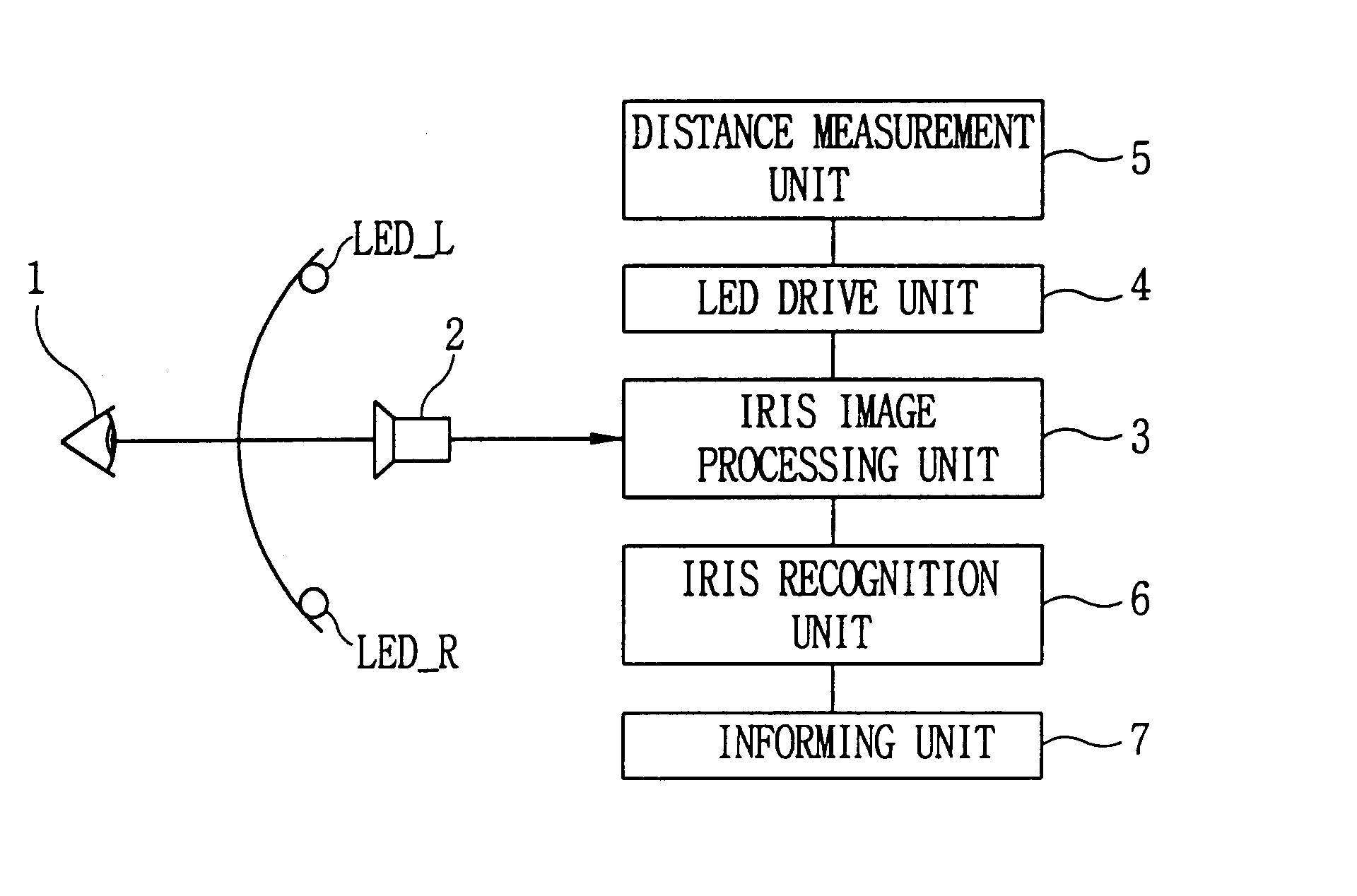
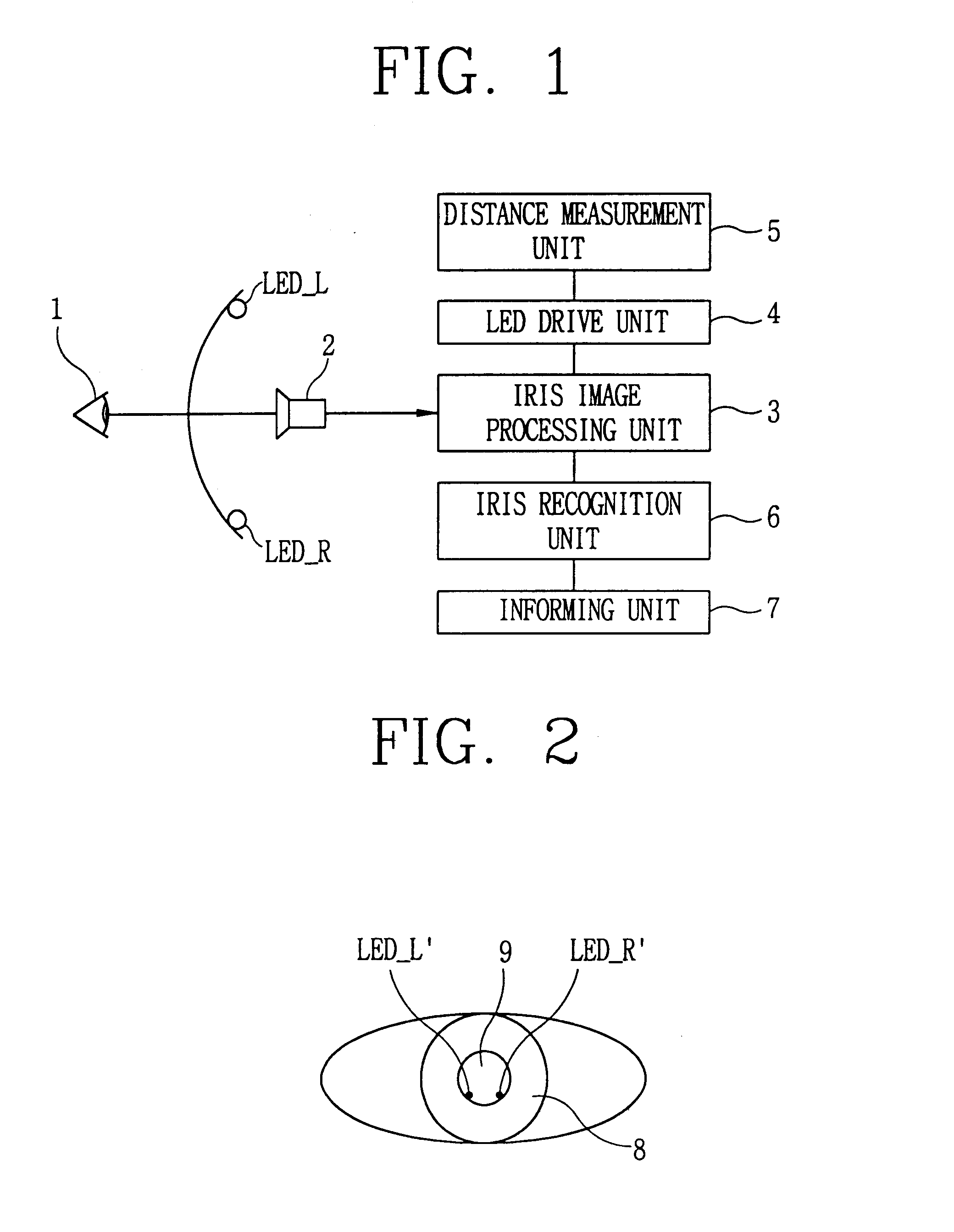
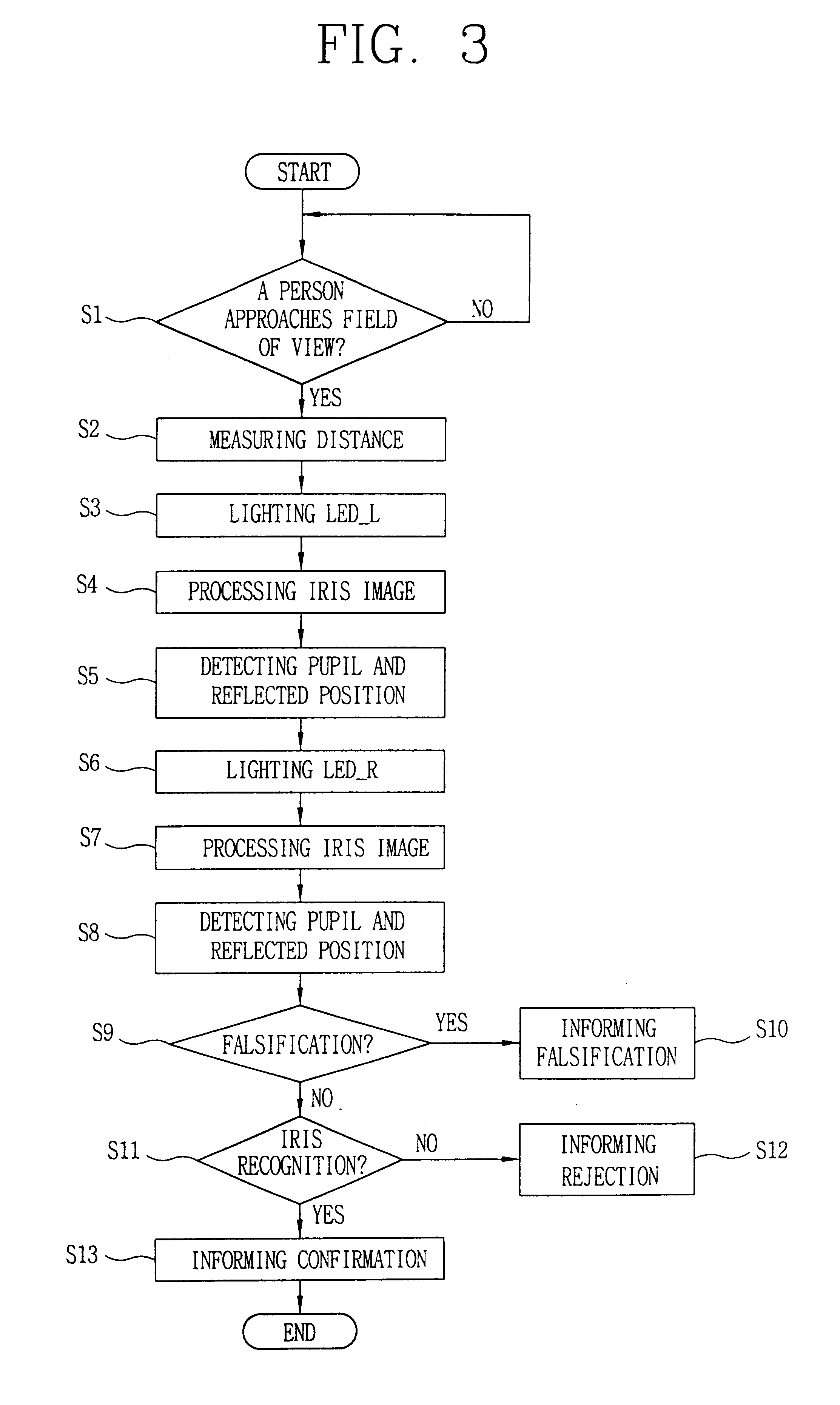
Falsification discrimination method for iris recognition system
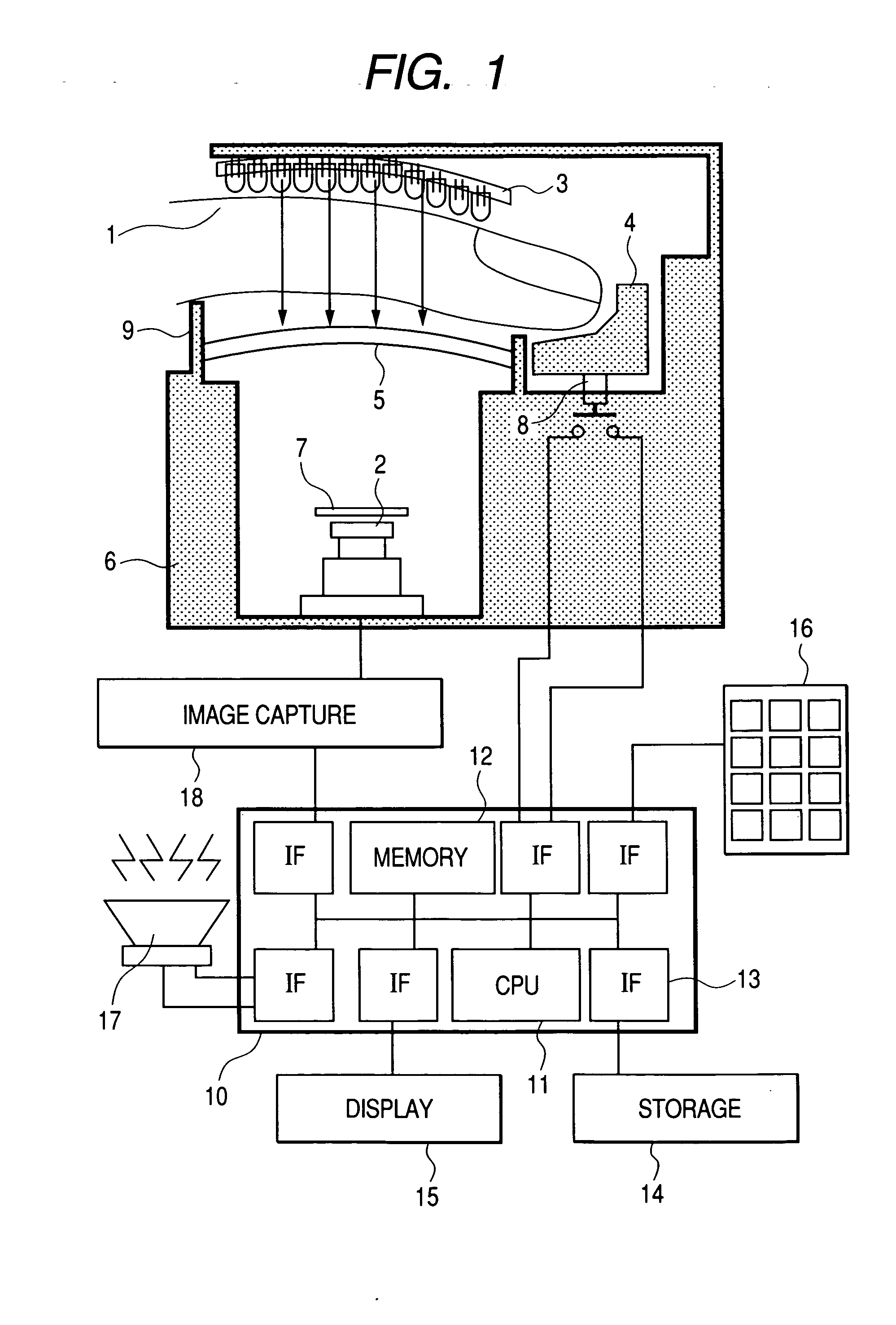
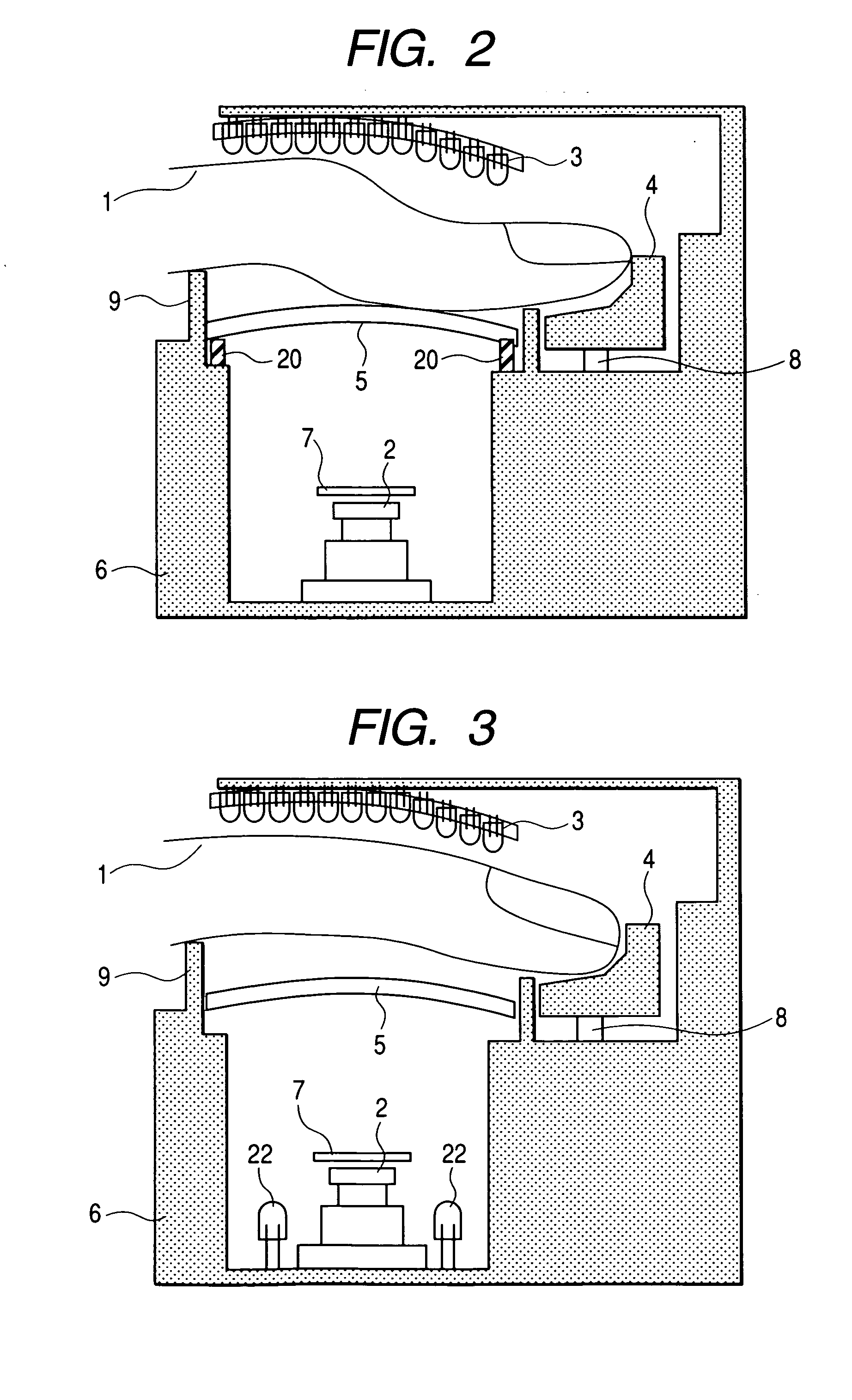
The present invention relates to a technique for checking if the reflected image of a light emitting diode for lighting is detected in the image of an iris and determining whether the iris is a living one in order to prevent an illegal intrusion using a simulacrum such as a photograph or dynamic image. The object of the present invention is achieved by a first step of imaging an eye of the user when the user approaches the field of view, processing the image signal, and capturing the image of the iris and pupil, a second step of selectively lighting LEDs for lighting installed on the both sides of a camera while imaging the eye of the user and detecting the reflected image of a corresponding LED in the image of the iris and pupil, a third step of determining that the iris is a falsification and informing the system of the fact if the reflect image of a the corresponding light emitting diode is not detected in the above steps, and determining that the iris is really recognized if detected, and a fourth step of performing a recognition of an iris image signal using a database if the iris is proven to be really recognized and determining whether the image is data registered in the database.
Owner:IRIS ID INC
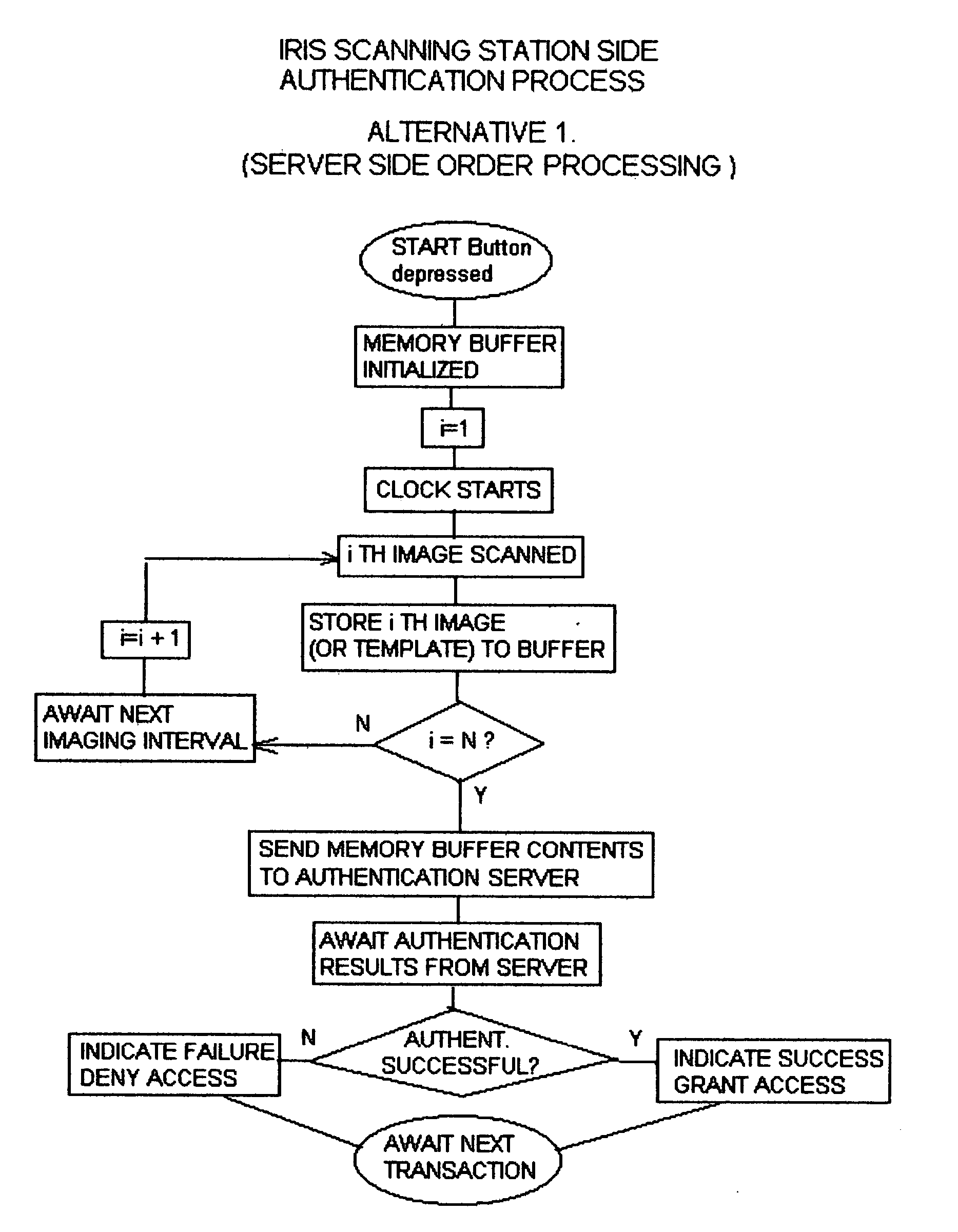
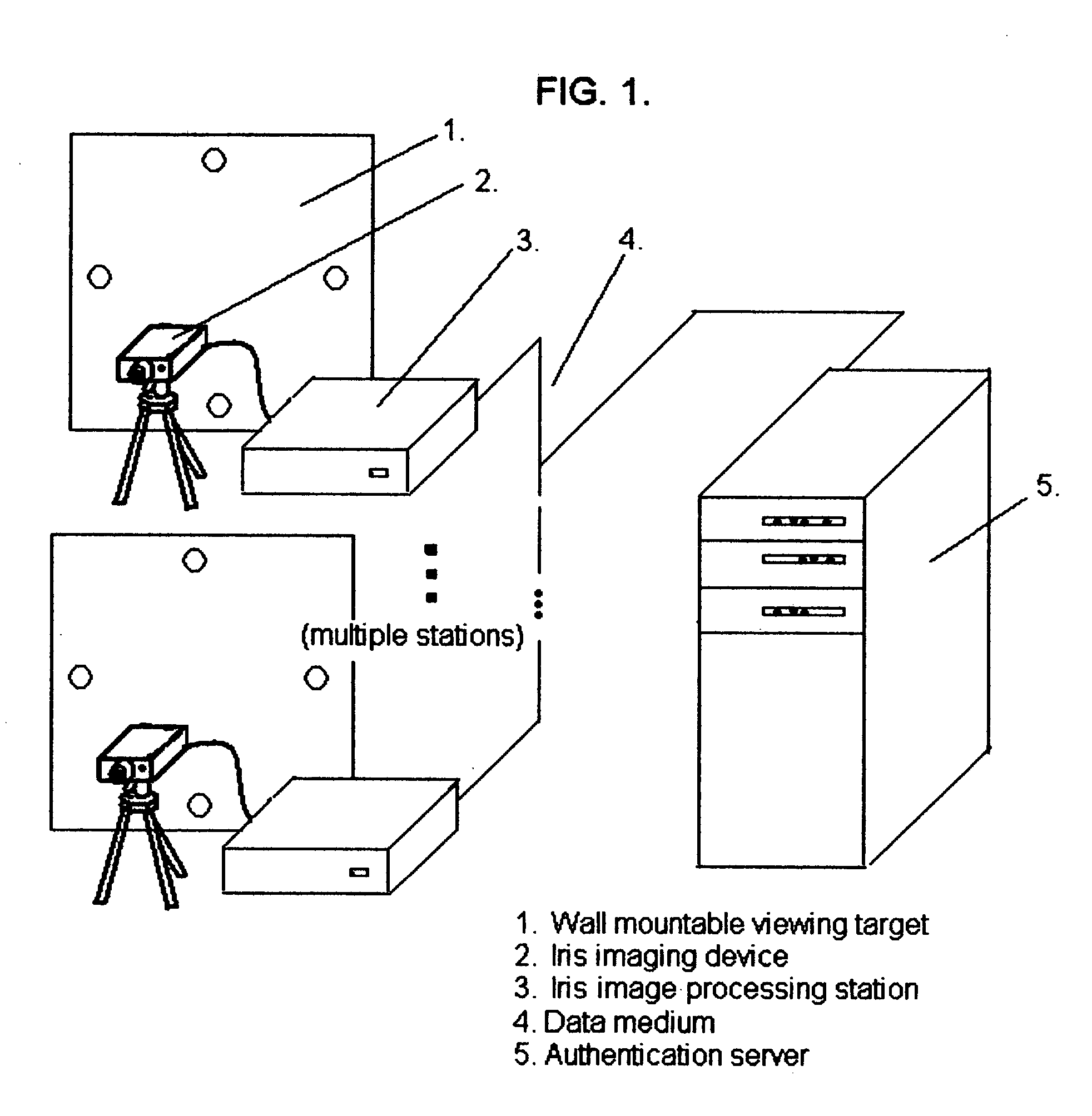
Systems and methods for performing iris identification and verification using mobile devices
Technologies are presented herein in support of a system and method for performing iris identification and verification using mobile devices. Embodiments of the present invention concern a method for authenticating a user with a mobile device that includes steps for capturing imagery of a user's face, analyzing the imagery to identify the portion of the image depicting the user's eyes and segmenting the eye image to isolate the iris image data and encoding the iris image data in iris template. The present disclosure further describes authenticating the user based on the encoded iris template and additional techniques for preventing erroneous authentication caused by spoofing. In some examples, the anti-spoofing techniques may include capturing one or more images of a user's eyes and analyzing the captured images for indications of liveness based on reflection characteristics depicted in the imagery.
Owner:VERIDIUM IP LTD
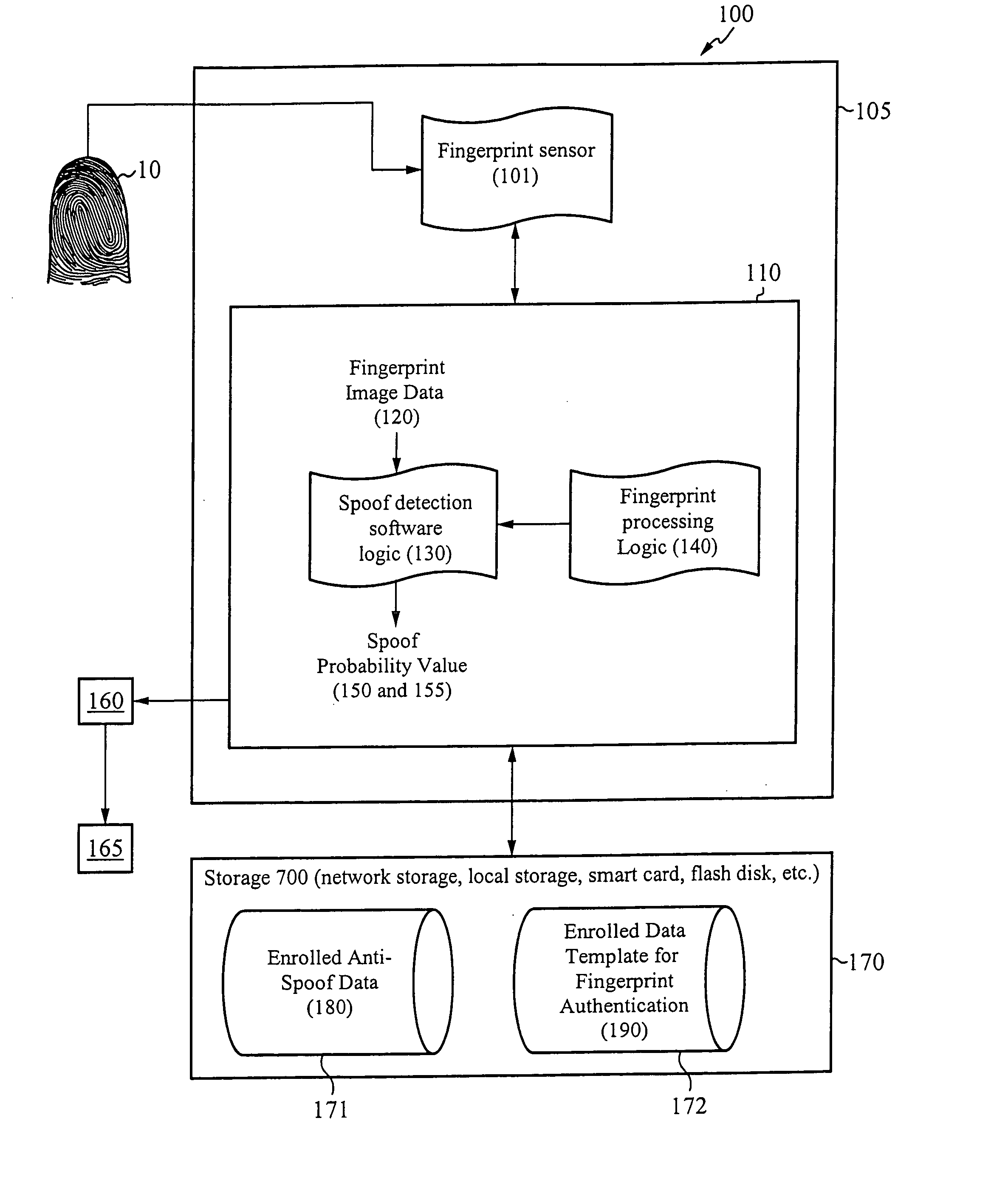
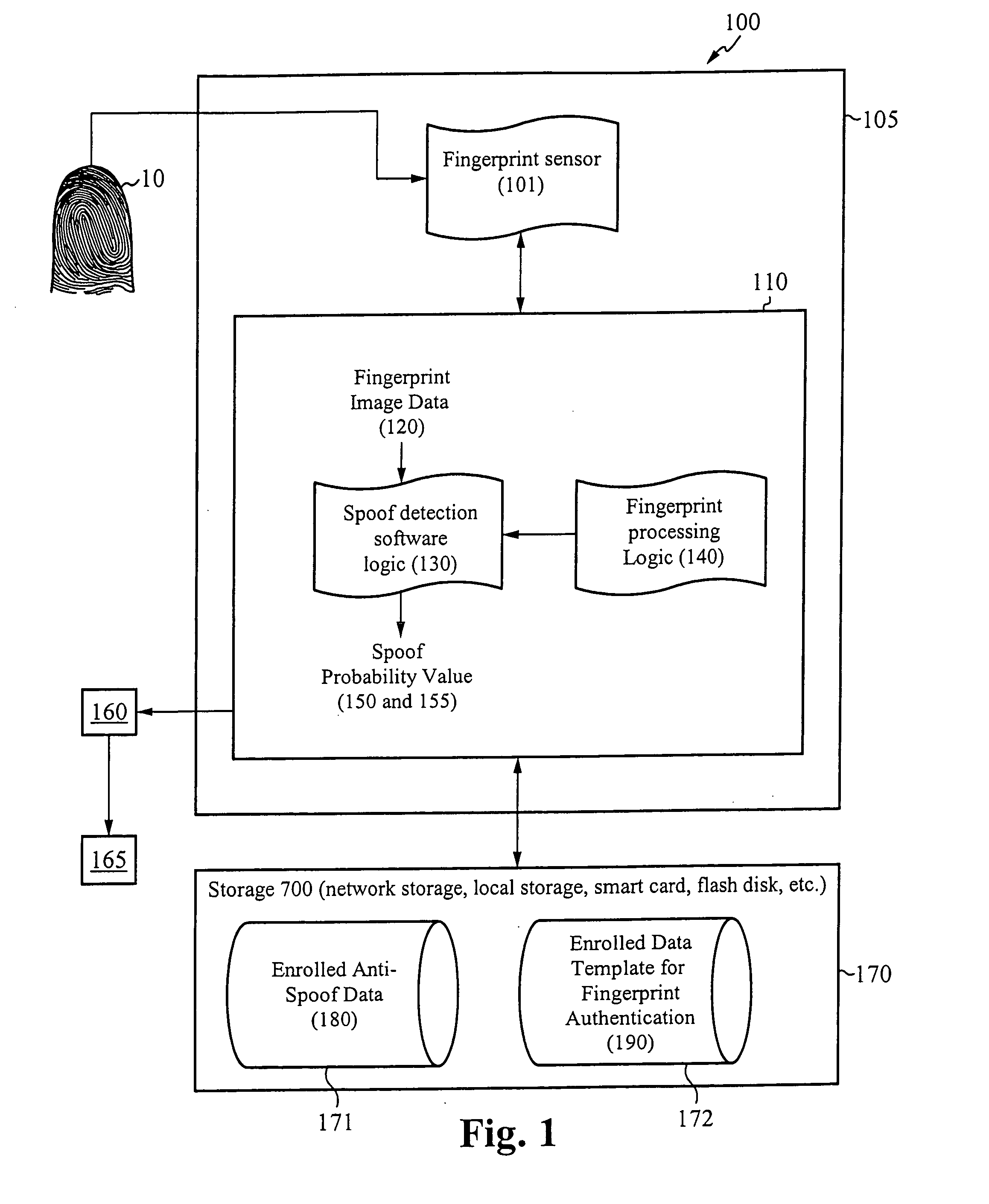
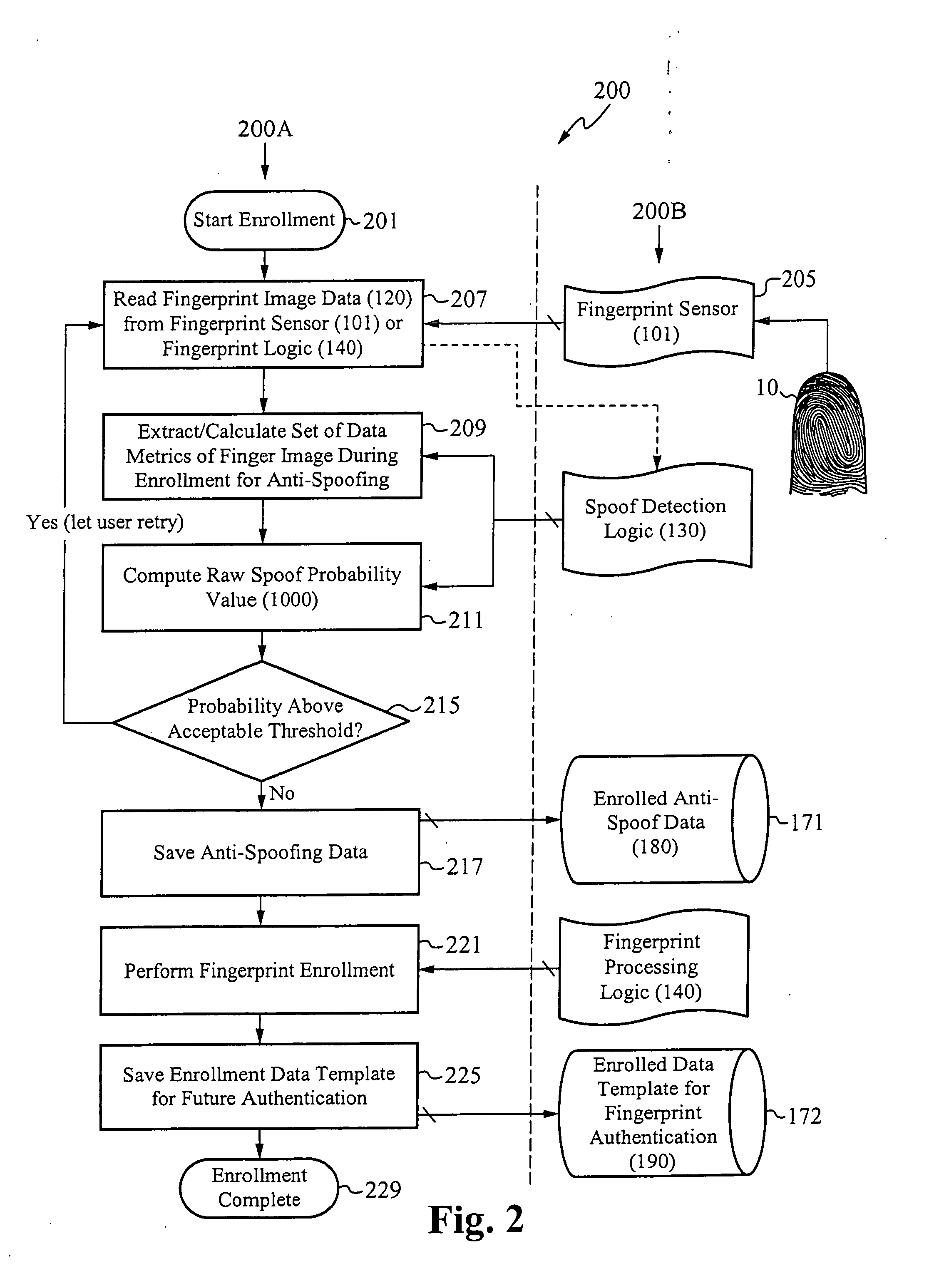
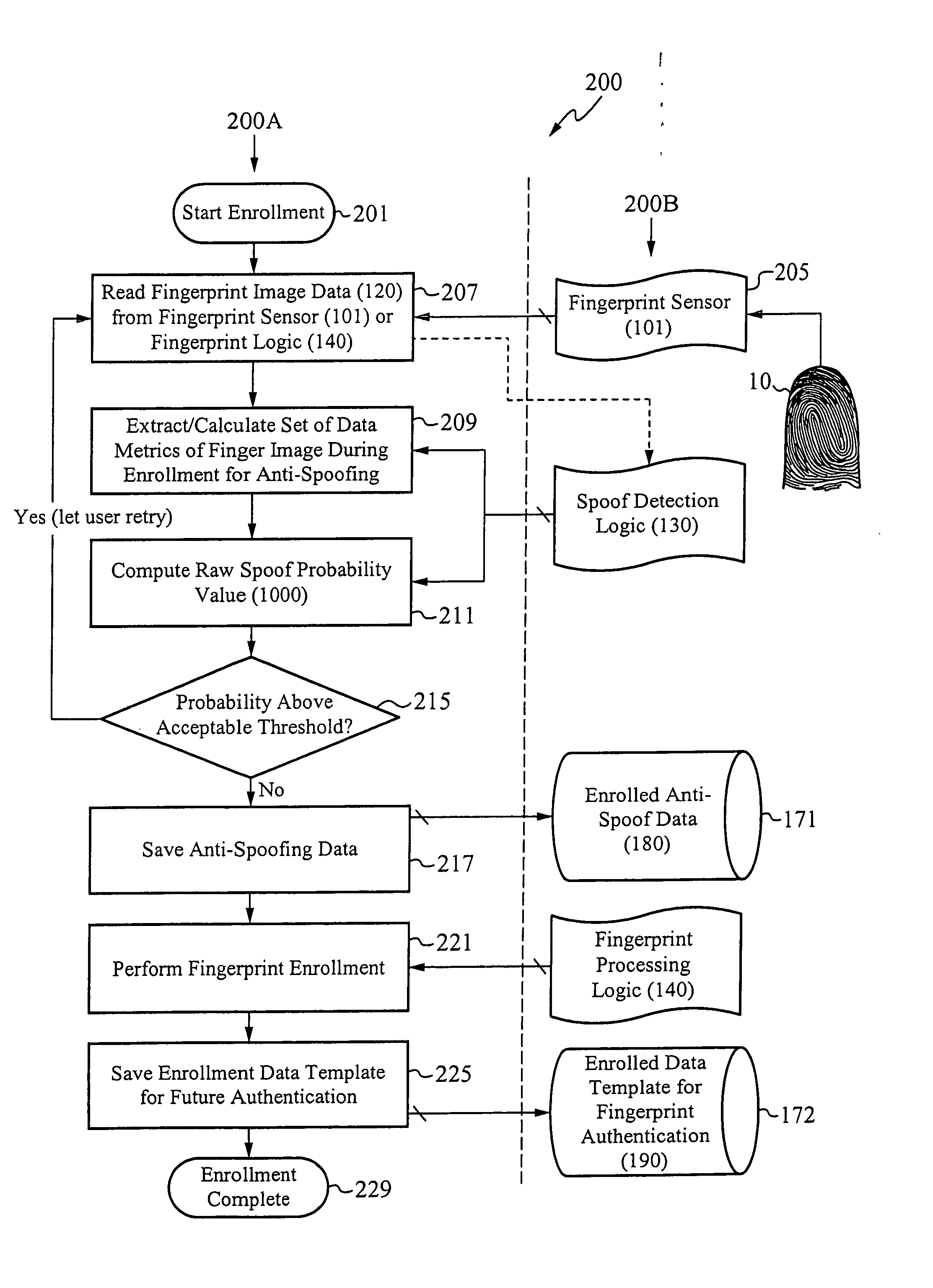
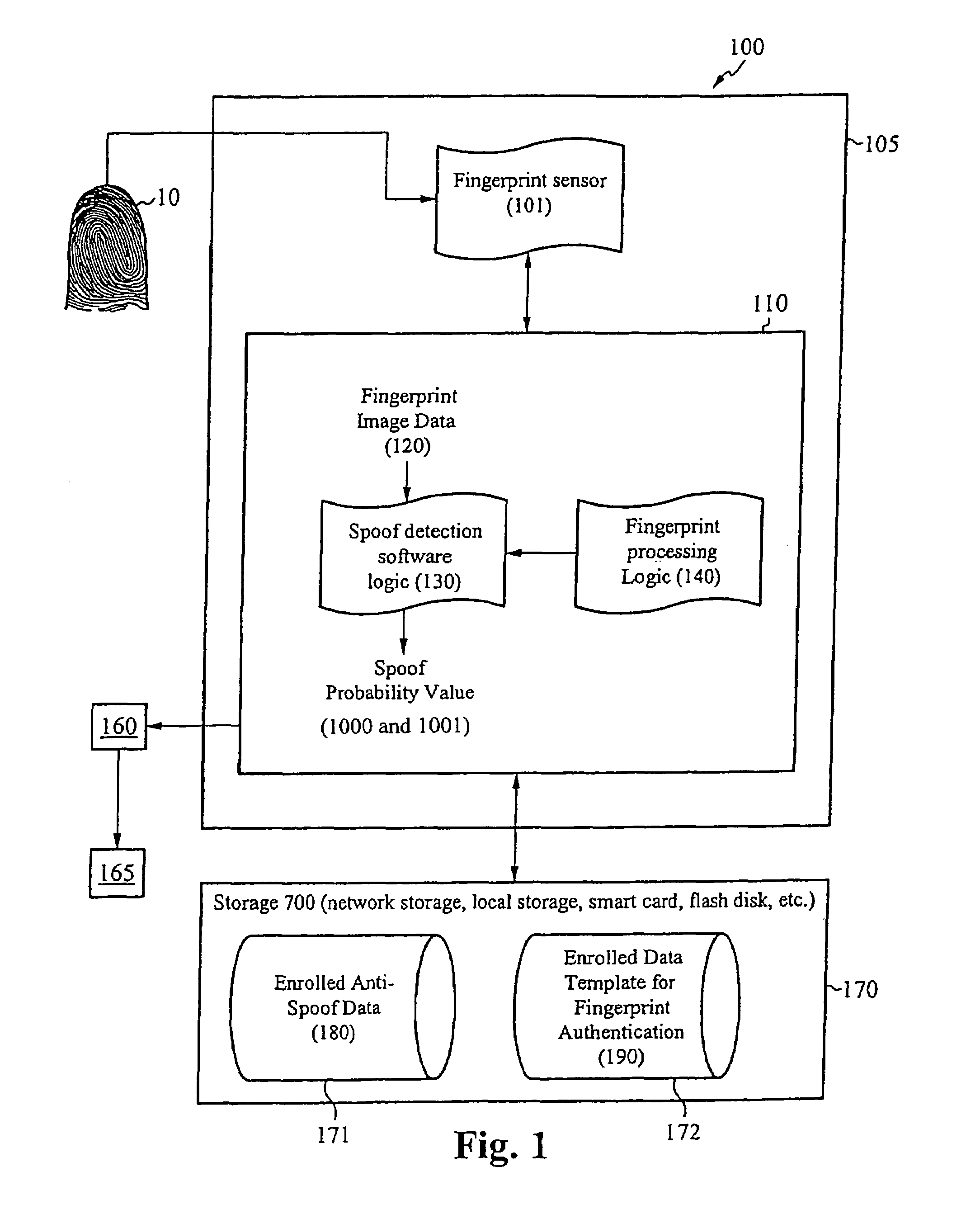
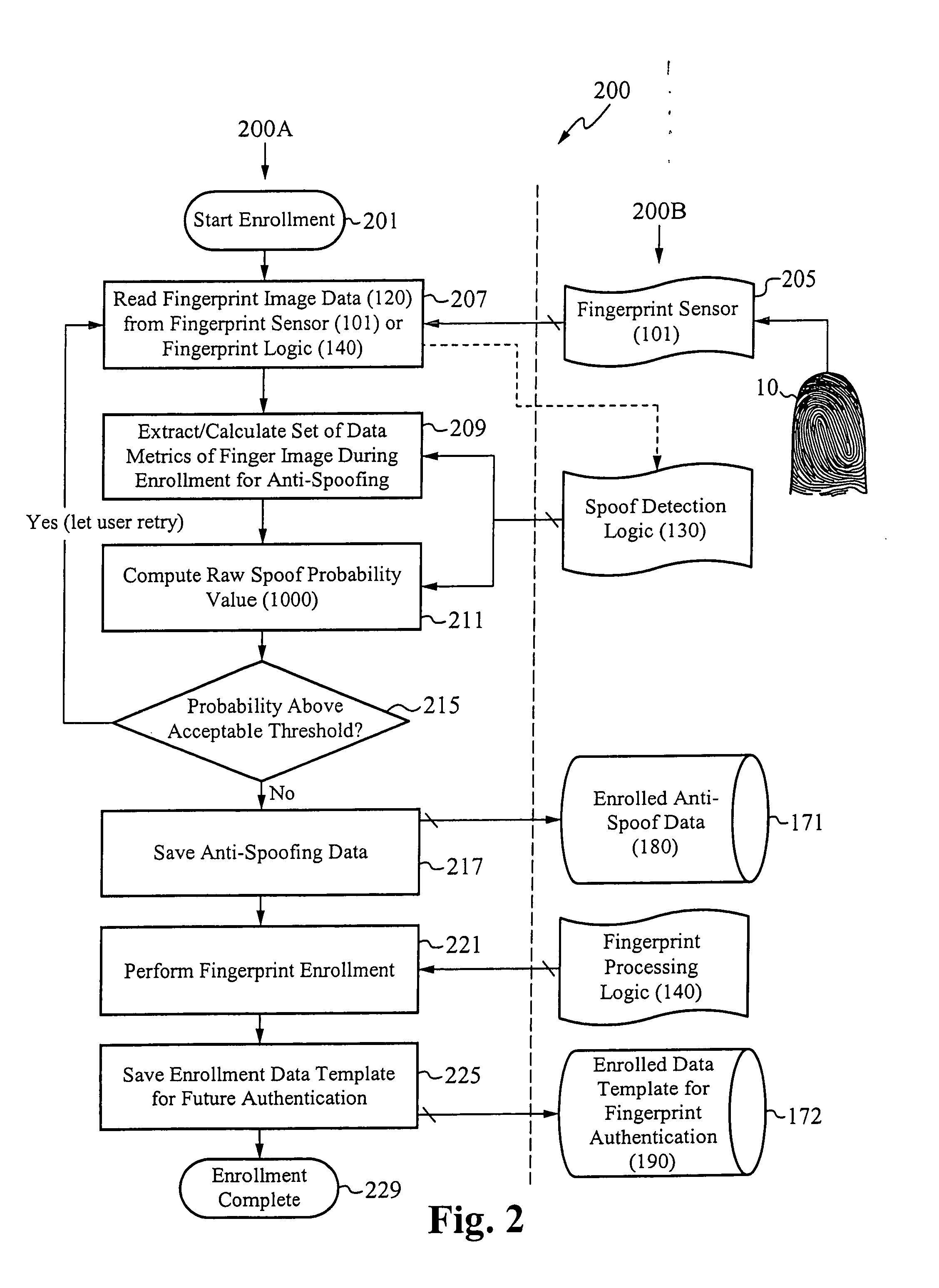
System for and method of securing fingerprint biometric systems against fake-finger spoofing
ActiveUS20070014443A1Easy to predictElectric signal transmission systemsImage analysisPattern recognitionGray level
A biometric secured system grants a user access to a host system by classifying a fingerprint used to verify or authorize the user to the system as real or fake. The classification is based on a probability that fingerprint image data corresponds to characteristics that reliably identify the finger as real. The system includes a fingerprint sensor for capturing fingerprint image data coupled to a spoof detection module. In one embodiment, the spoof detection module is programmed to determine spoof probability based on a combination of metrics that include, among other metrics, pixel gray level average and the variance of pixels corresponding to a fingerprint ridge, pixel gray level average and the variance of pixels corresponding to a fingerprint valley, density of sweat pores, and density of sweat streaks, to name a few metrics.
Owner:APPLE INC
Method and system for tracking user performance
InactiveUS20050033619A1Easy to useDigital data processing detailsCash registersTask completionSkill sets
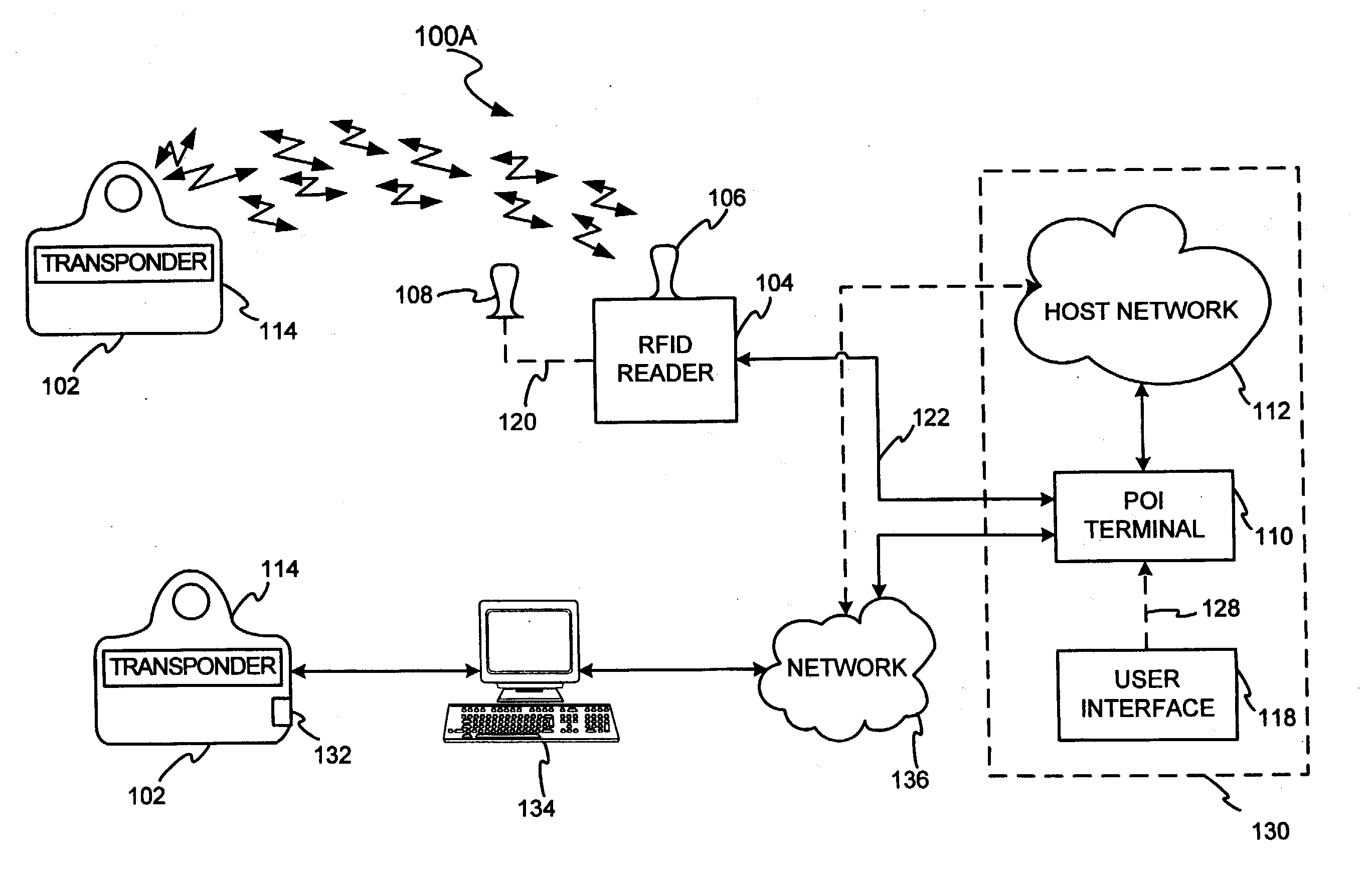
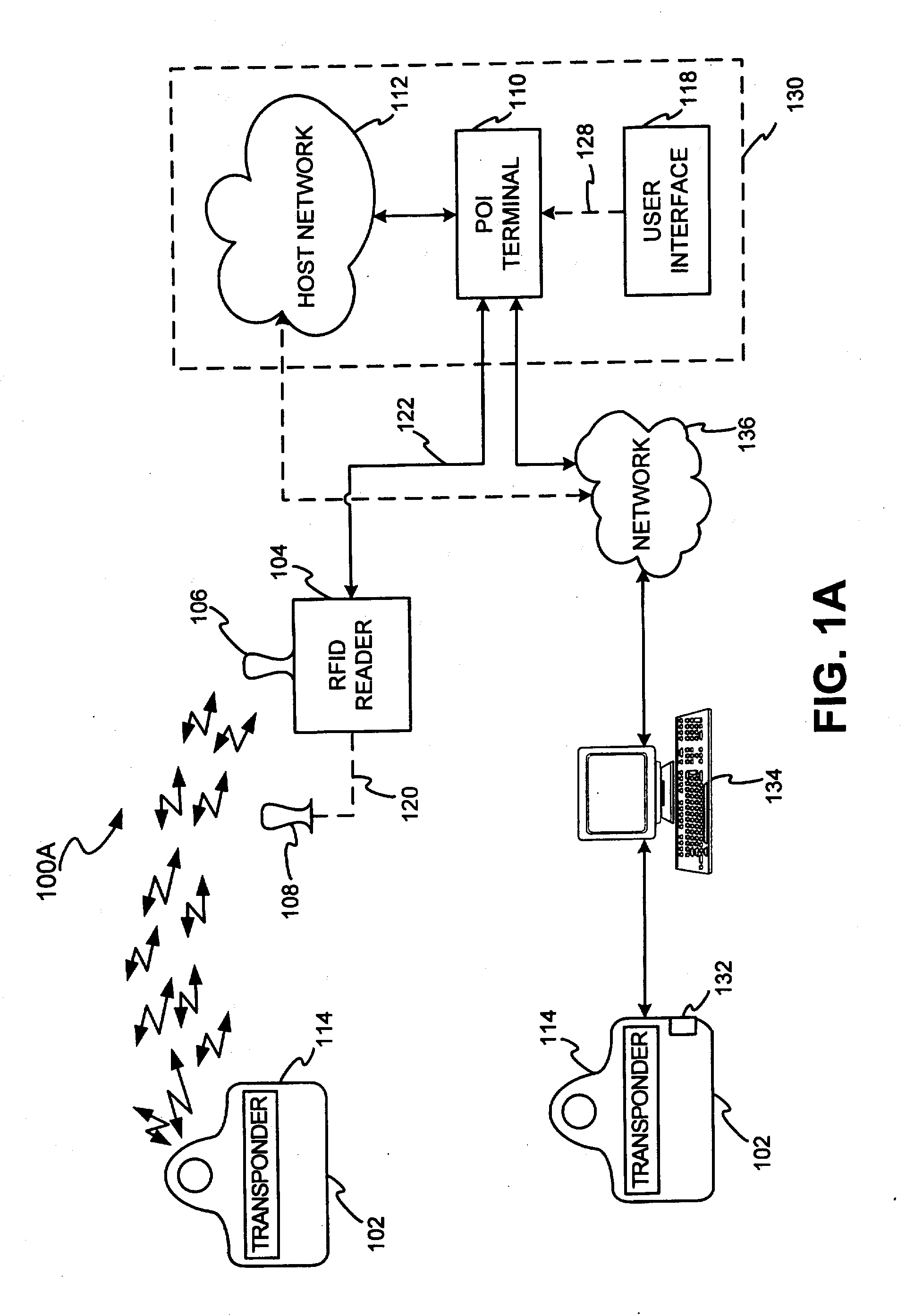
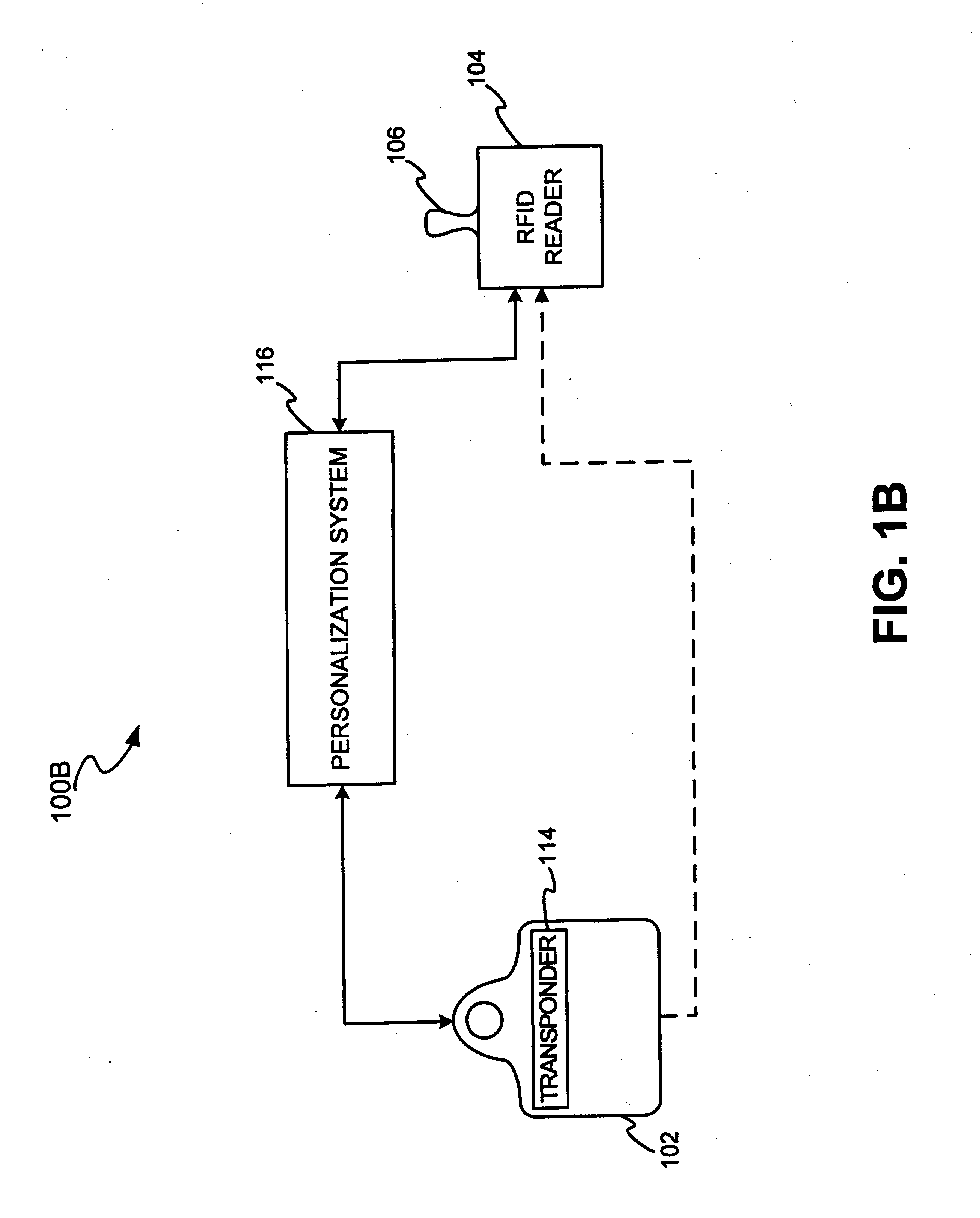
A system and method for using RFID technology to track resource performance and task completion is disclosed. In one exemplary embodiment, a fob and an RFID reader may engage in mutual authentication. Where the RFID reader and the fob successfully mutually authenticate, the fob may transmit to the RFID reader information identifying the resource”s performance tracking account to which the fob is associated. The RFID reader may receive and forward the information to facilitate performance tracking. In one exemplary embodiment, the RFID reader may forward the information to a point of interaction terminal for transaction completion. In another exemplary embodiment, the fob completes tasks via a computer interface. In still another exemplary embodiment, the fob resource and / or a manager access to a resource engine, wherein the resource engine may be used to automatically grade, track, score, and assign resources based on resource skills and skill sets.
Owner:LIBERTY PEAK VENTURES LLC
Dual band biometric identification system
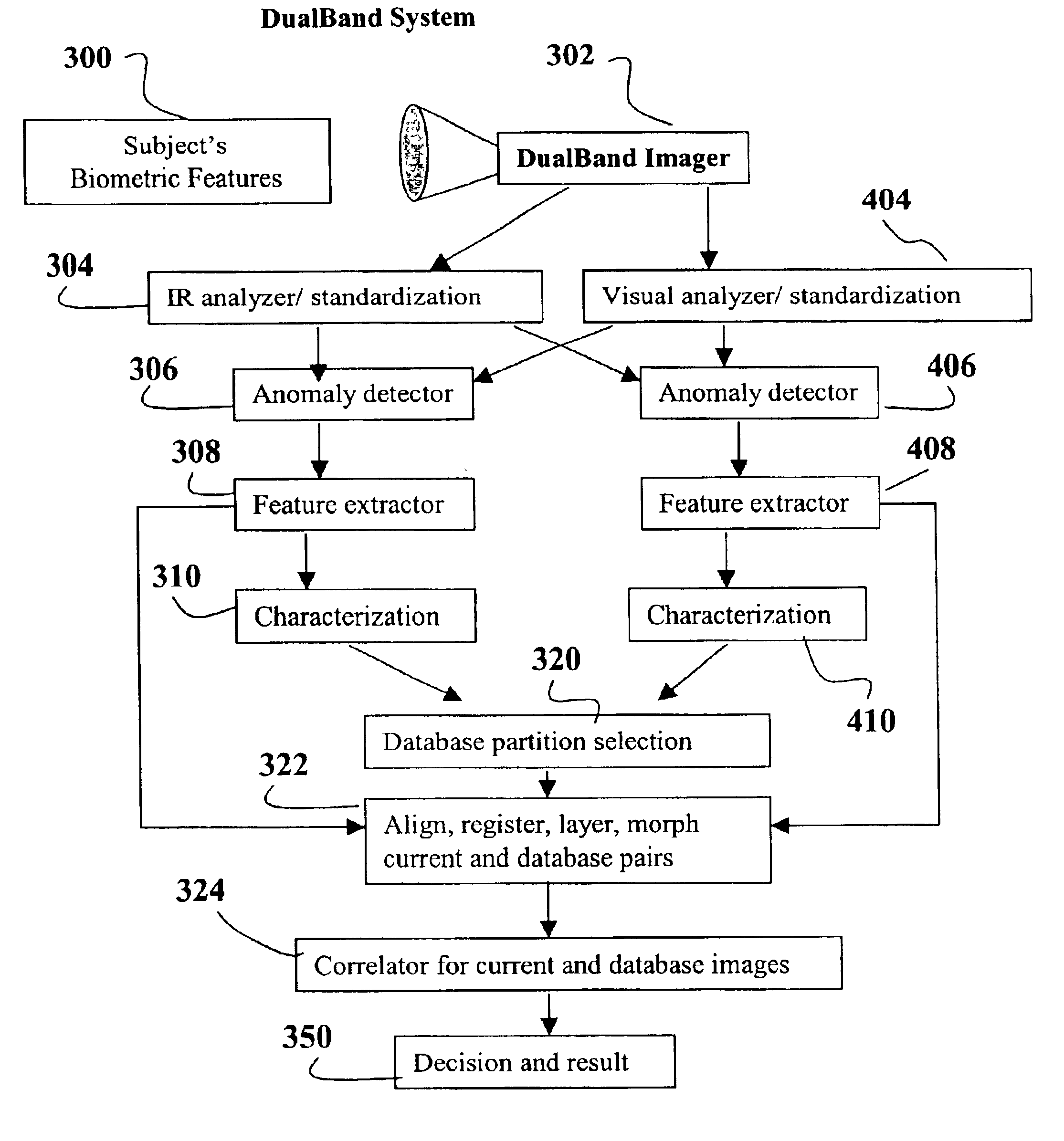
InactiveUS6920236B2Improve accuracyRaise the possibilitySpoof detectionSubcutaneous biometric featuresVirtual cameraVisual perception
Owner:MIKOS
Hygienic biometric sensors
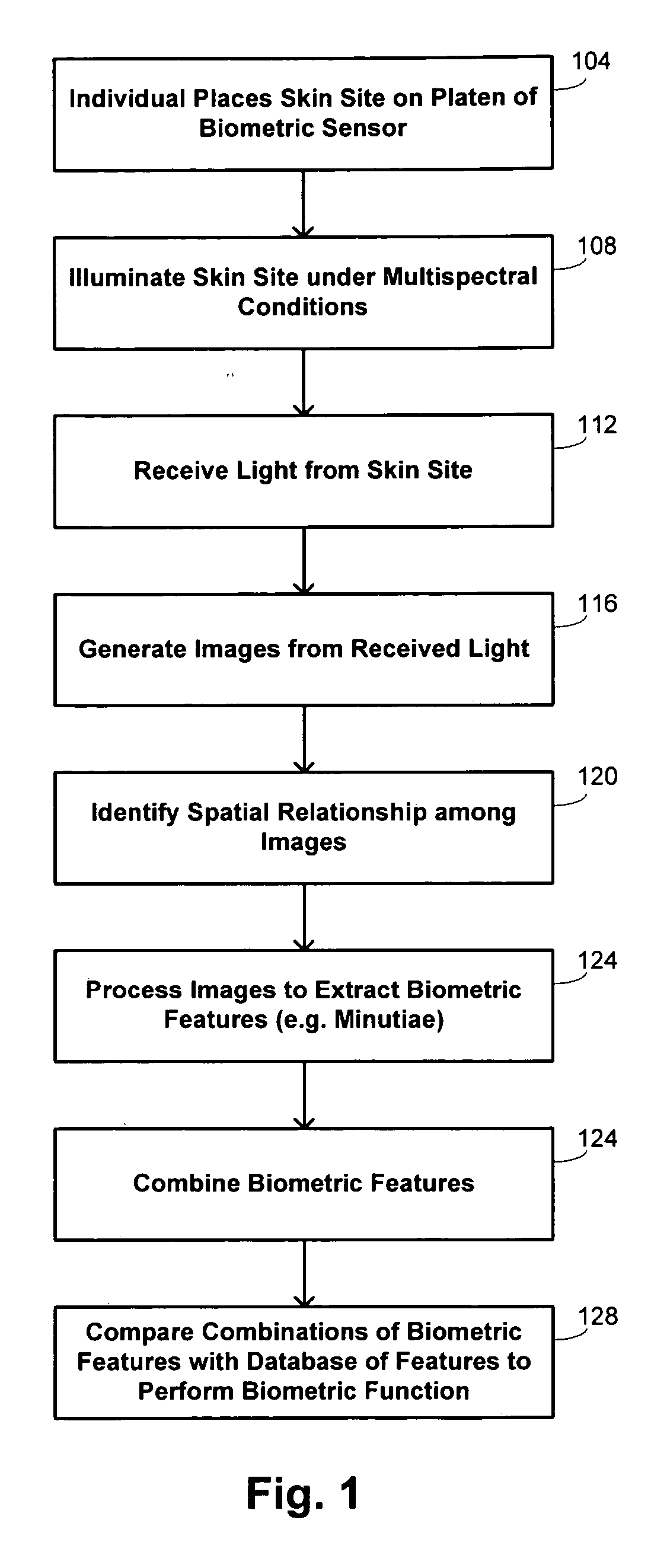
Methods and systems for performing a biometric measurement on an individual are disclosed. A containment film is disposed between a skin site of the individual and a platen. Light is directed through the containment film to the skin site to illuminate the skin site under multiple distinct optical conditions. Light scattered from the skin site is received for the multiple optical conditions. A multispectral image of the skin site is derived from the received light. A biometric function is performed with the derived multispectral image.
Owner:HID GLOBAL CORP
System for and method of securing fingerprint biometric systems against fake-finger spoofing
ActiveUS7505613B2Easy to predictElectric signal transmission systemsImage analysisPattern recognitionGray level
A biometric secured system grants a user access to a host system by classifying a fingerprint used to verify or authorize the user to the system as real or fake. The classification is based on a probability that fingerprint image data corresponds to characteristics that reliably identify the finger as real. The system includes a fingerprint sensor for capturing fingerprint image data coupled to a spoof detection module. In one embodiment, the spoof detection module is programmed to determine spoof probability based on a combination of metrics that include, among other metrics, pixel gray level average and the variance of pixels corresponding to a fingerprint ridge, pixel gray level average and the variance of pixels corresponding to a fingerprint valley, density of sweat pores, and density of sweat streaks, to name a few metrics.
Owner:APPLE INC
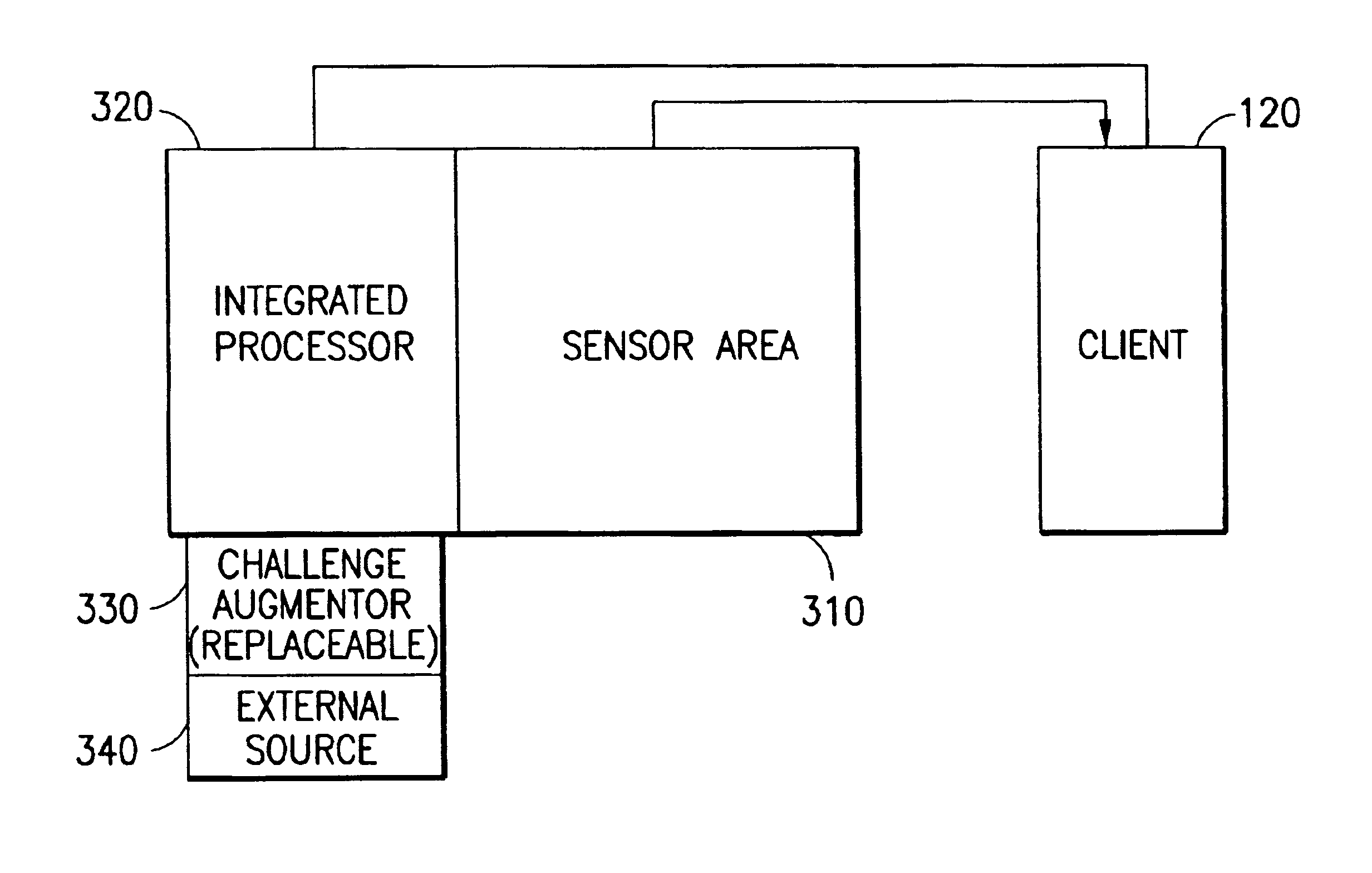
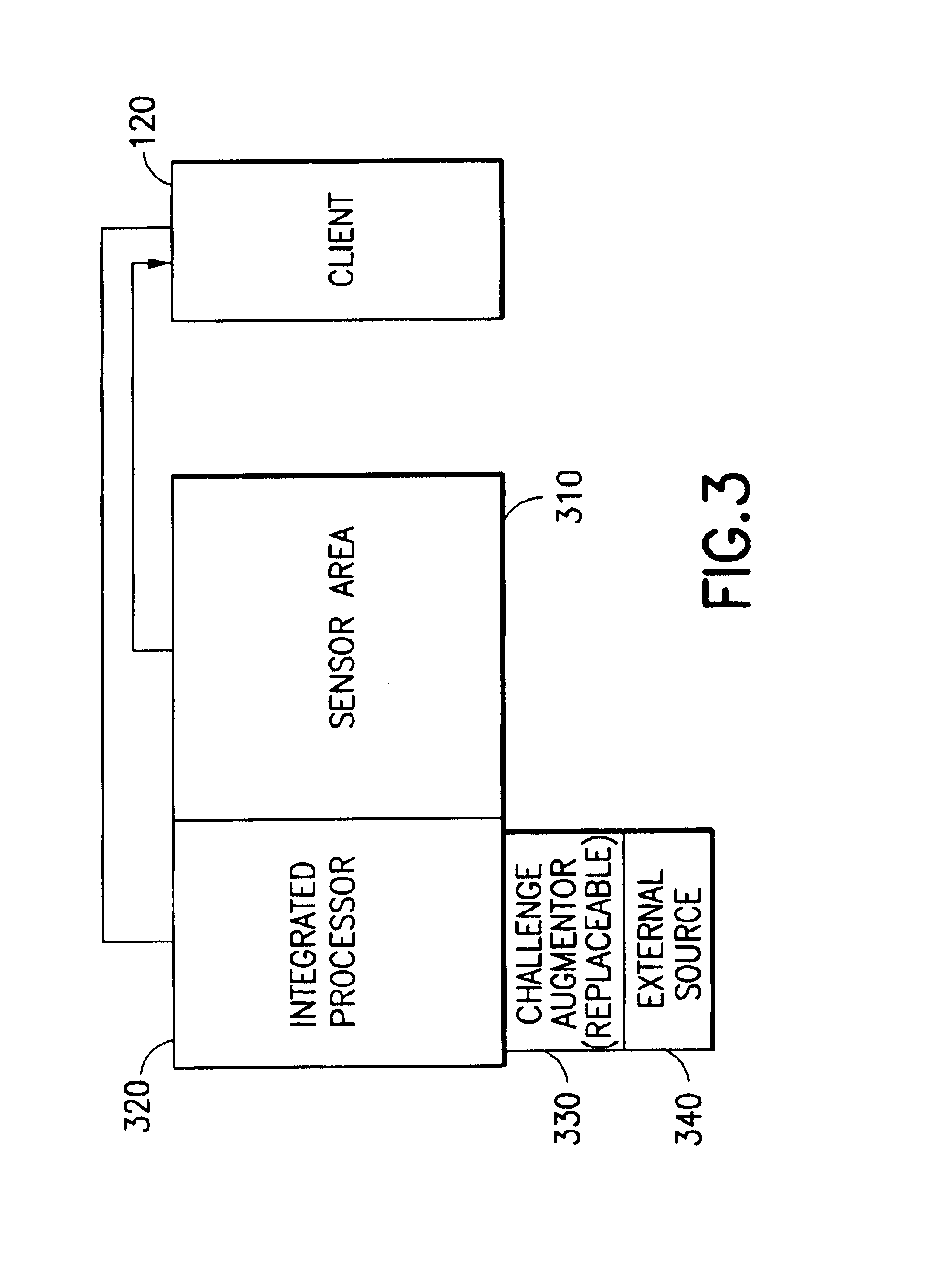
System and method for liveness authentication using an augmented challenge/response scheme
InactiveUS6851051B1Opportunities decreaseEasy to modifyUser identity/authority verificationDigital data authenticationLivenessMedical imaging
An integrated signal sensor with processing power to augment a challenge from server and compute the response is proposed to guarantee that the sensed signal is live and not stored. The sensor-processor computes the response to the augmented challenge based on the signal charactersitics of the sensed signal and then transmits both the signal and the response. The host or the server can verify the response to authenticate liveness of the input image / signal and reject it if the response is different. Areas of application include automated biometrics and remote medical imaging.
Owner:LENOVO PC INT
Personal identification device and method
ActiveUS20050047632A1Recognition capability decreaseLow costImage analysisPerson identificationFinger vein recognitionLight-adapted
A personal identification device and method prevent the reduction in the finger vein recognition rate which otherwise occur due to erroneous insertion of a finger by a user not accustomed to operation or insertion of a false finger at low cost. The device includes an imager picking up an image of a finger vein pattern, a light source emitting light adapted to be transmitted through the finger, an image operating unit matches the image, guides indicating the position of picking up the finger image, a detector detecting the contact between the finger and the guides, another light source radiating light reflected from the thick of the finger, a switch which is depressed by the forward end of the finger, a further light source emitting light transmitted through the forward end of the finger, and a light-sensor receiving the light from the further light source through the finger.
Owner:HITACHI LTD
Apparatus and method for the identification of fake fingerprints
InactiveUS20100113952A1Easy to identifyLow cost productionResistance/reactance/impedenceDiagnostic recording/measuringLivenessElectric signal
An apparatus for identifying fake fingerprints has electrodes disposed along a platen surface of a fingerprint scanner and whether or not the skin of one or more fingers presented to the surface are real and alive is determined in accordance with analysis of electrical signals received from the electrodes. Electronics of the apparatus determines one or more liveness parameter(s) in accordance with signals received from electrodes. Information from an image of the fingerprint may be used to select which electrode signals to use for liveness detection. To further confirm the presence of a live finger(s), additional liveness parameter(s) of the pulse and / or temperature may also be sensed. The skin may be one of in contact with the platen of the fingerprint scanner, separated from direct contact with the platen's electrodes by an insulating layer or a pad, or not in physical contact with the platen or a pad thereupon.
Owner:CROSS MATCH TECH
Technique using eye position and state of closure for increasing the effectiveness of iris recognition authentication systems
InactiveUS20050129286A1Increase in sizeSupport repeatabilitySpoof detectionEye stateInternet privacy
The invention, which is an embodiment of what the inventor calls, “Active Behavior Enhanced Iris Recognition Authentication”, employs a sequential iris imaging process where the authenticating party directs his or her gaze in specific directions, or closes their eyes for each image, so that an “eye state order” can be used to improve authentication security. Authentication security is strengthened based upon the reduced likelihood that a potential intruder would 1.) know what the correct sequence of eye states (i.e. up, down, left, right, camera view and closed) were associated with the control authentication template; 2.) be able to successfully “hack” the authentication server in order to gain access to the iris image information and also the eye state order information which would be required in order to fully compromise the authentication system. The technique embodied by the invention represents an overlay of a known, ordered sequence, over the iris recognition authentication process itself.
Owner:HEKIMIAN CHRISTOPHER DAVID
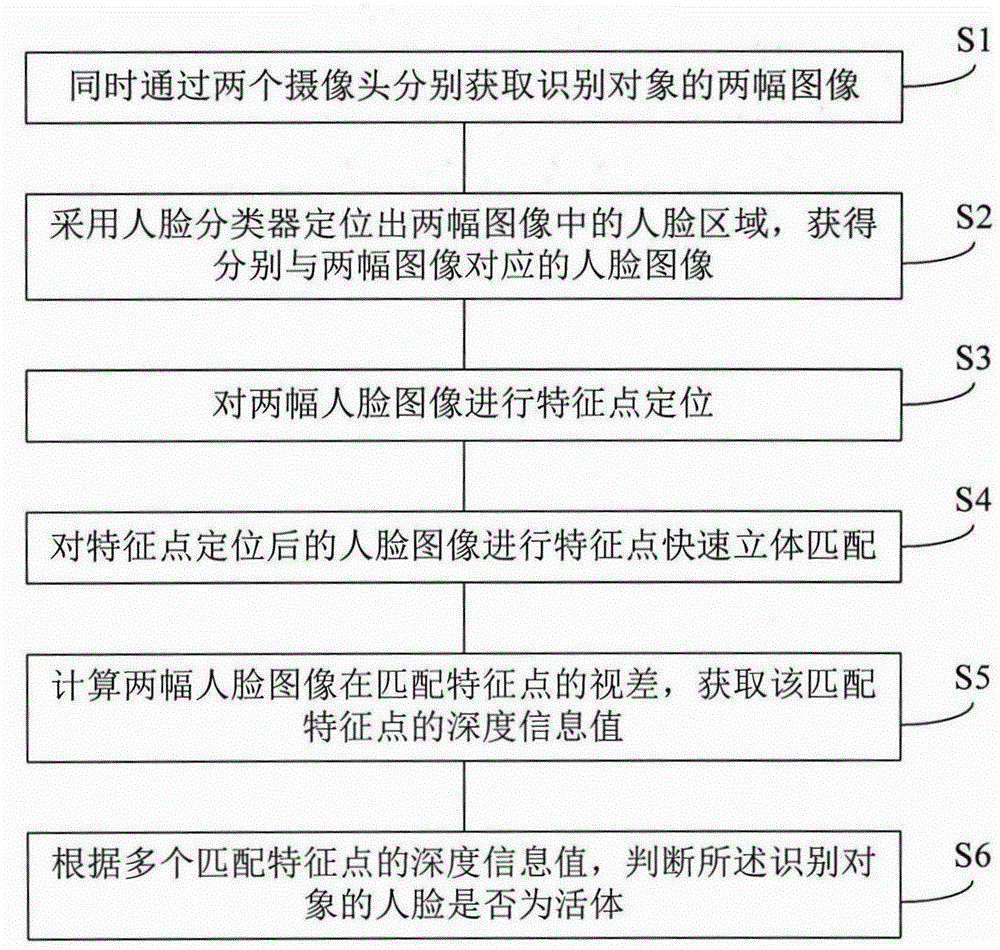
Face living body detection method and system
The present invention discloses a face in-vivo detection method and system. The face in-vivo detection method comprises the steps of: simultaneously and respectively acquiring two images of an identification object by two cameras; positioning face regions in the two images by adopting a face classifier so as to acquire face images which respectively correspond to the two images; carrying out feature point positioning on the two face images; carrying out feature point rapid stereo matching on the face images subjected to feature point positioning; calculating parallax errors of the two face image at match feature points and acquiring depth information values of the match feature points; and according to the depth information values of a plurality of match feature points, judging whether the face of the identification object is a living body. According to the present invention, excessive cooperation of a user is not required; safety is high; hidden performance is high; attitude adaptability is high; the application range is wide; a matching speed is high; and user experience is good.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI +1
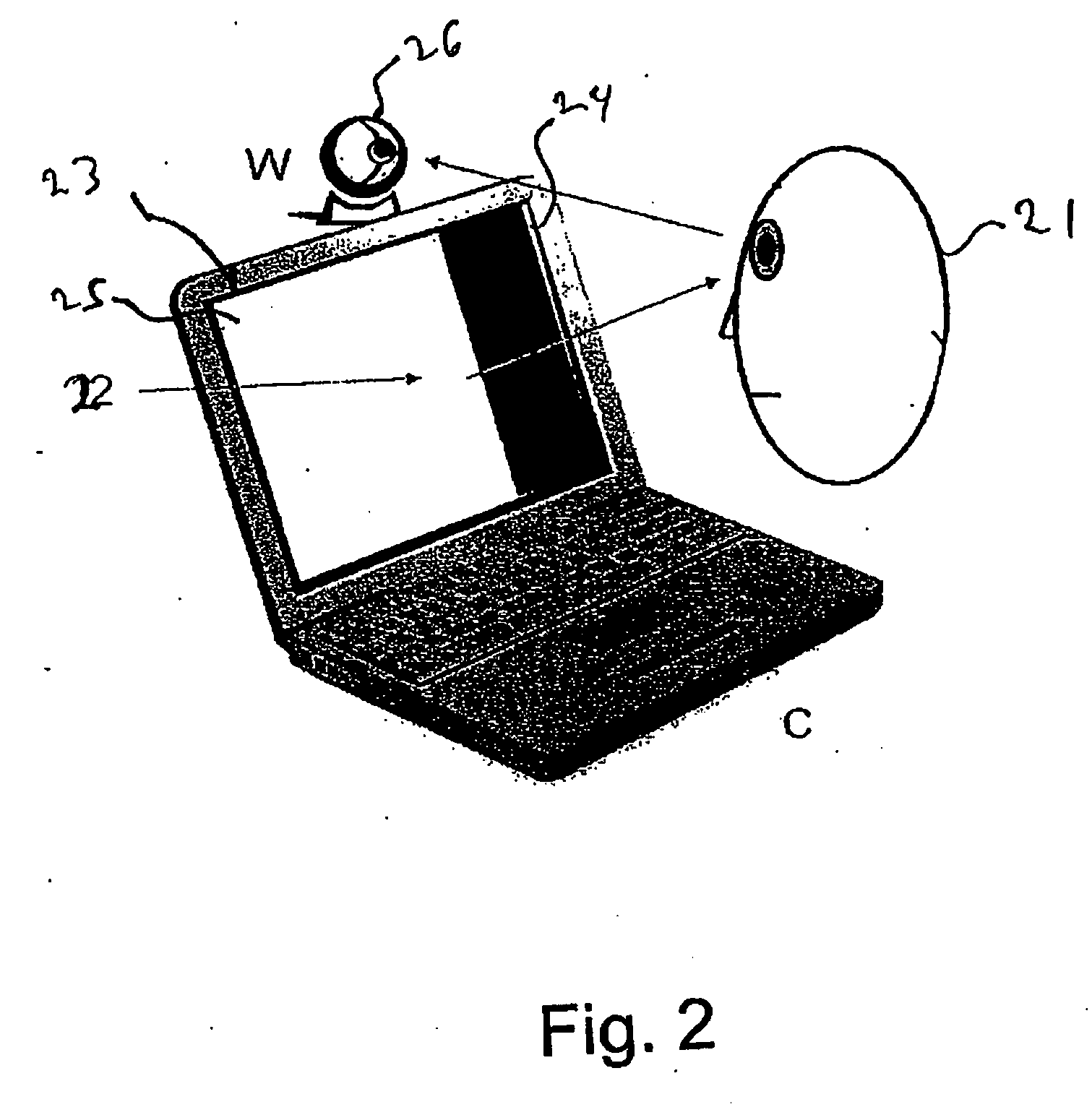
Method and apparatus for authentication utilizing iris
InactiveUS20050270386A1Easy to getLevel of qualityTelevision system detailsImage analysisComputer graphics (images)Authentication
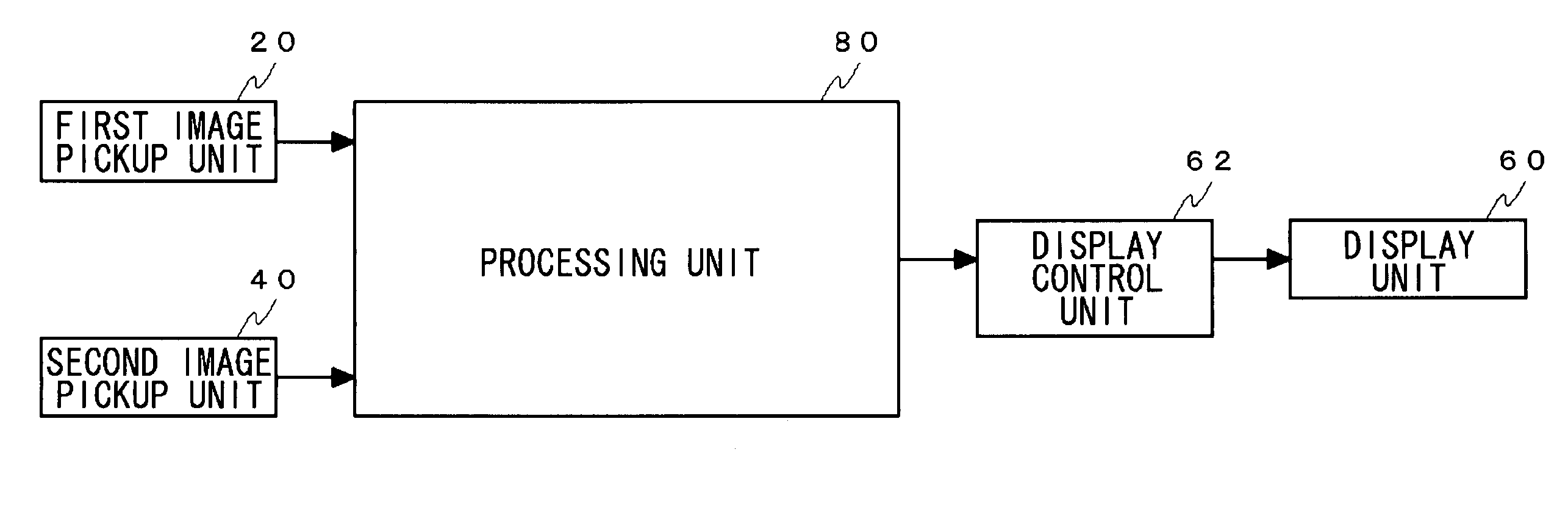
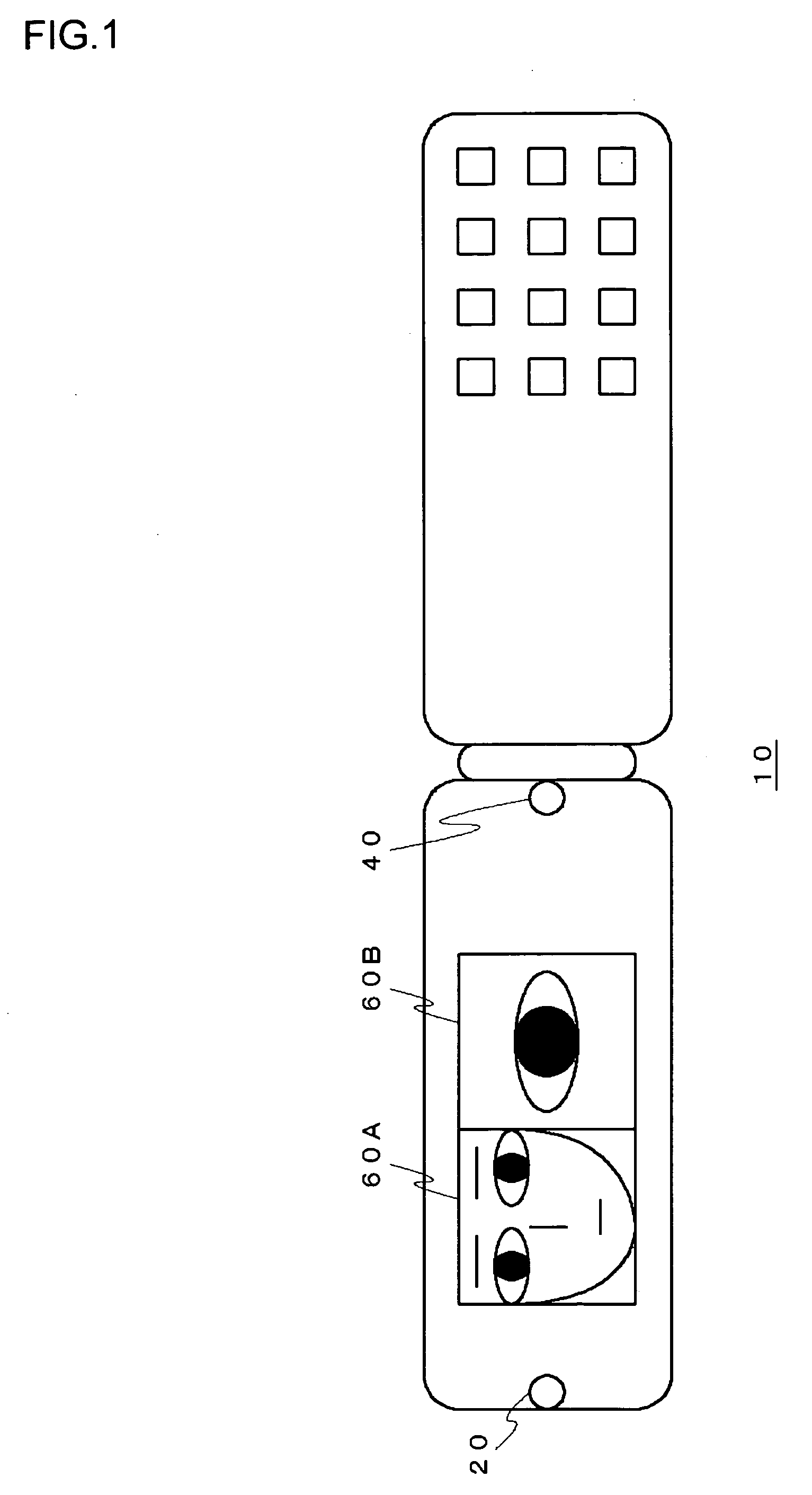
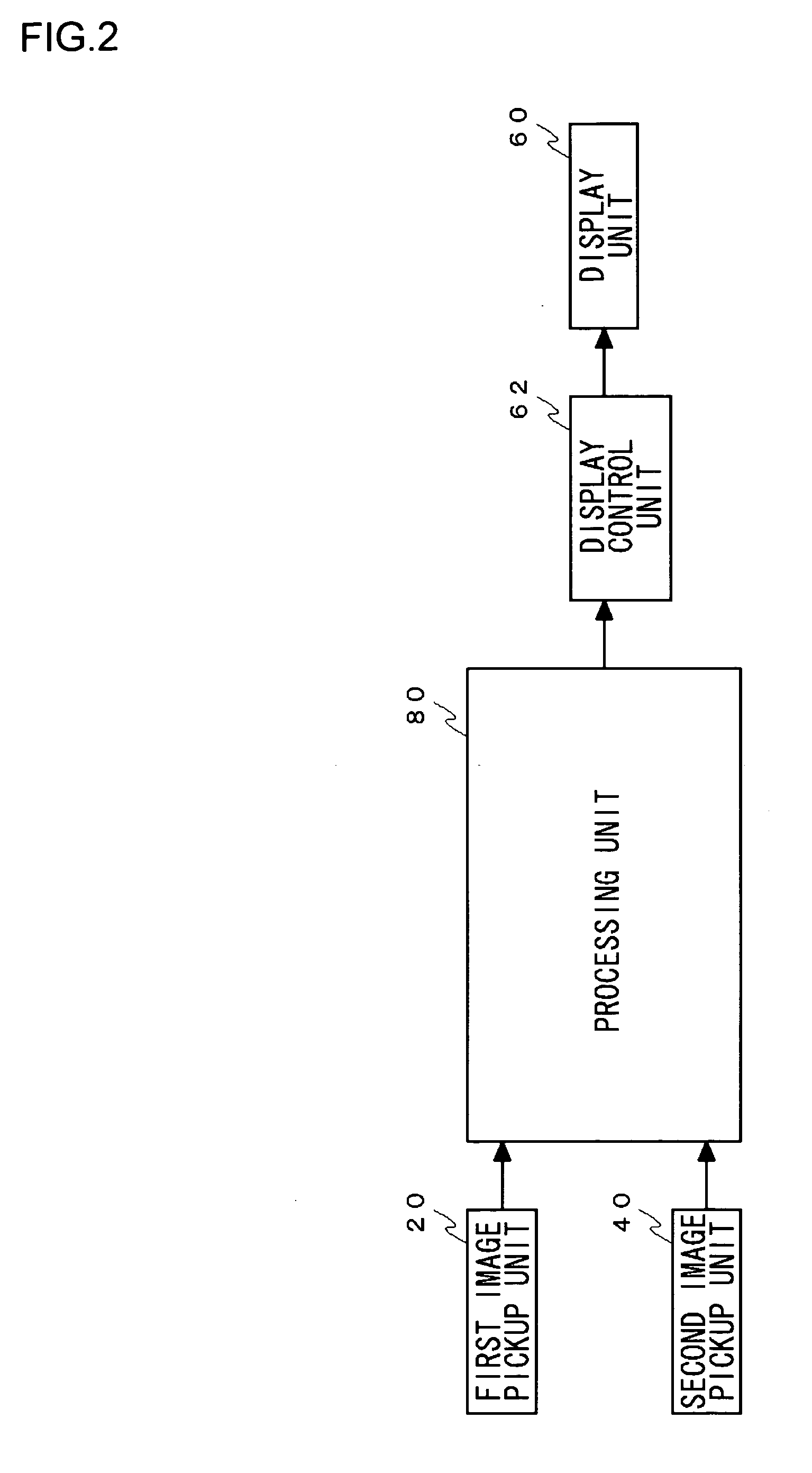
A first image pickup unit mainly captures the image of whole face. A second image pickup unit mainly captures an image of iris in an eye. A display unit simultaneously displays both an image picked up by the first image pickup unit and an image picked up by the second image pickup unit on divided display regions, and naturally prompts a user to operate in such manner as to include himself / herself within an image pickup range. When the user moves his / her face or an authentication apparatus upon seeing this display, a relative position or direction of the iris and the image pickup device can be set to a desired state.
Owner:SANYO ELECTRIC CO LTD
Person identification using ocular biometrics with liveness detection
ActiveUS20130336547A1Person identificationAcquiring/recognising eyesAnatomical structuresOcular biometrics
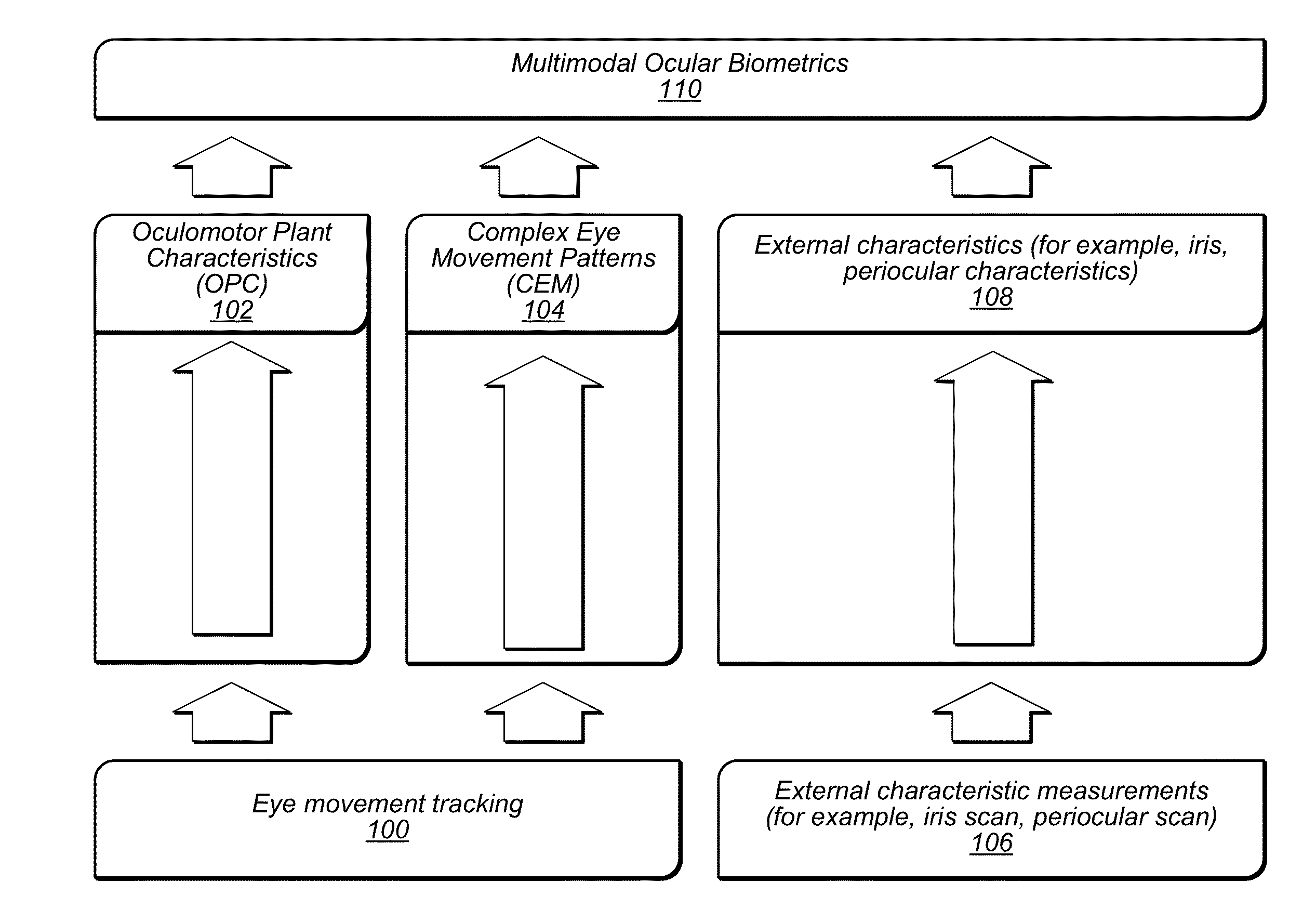
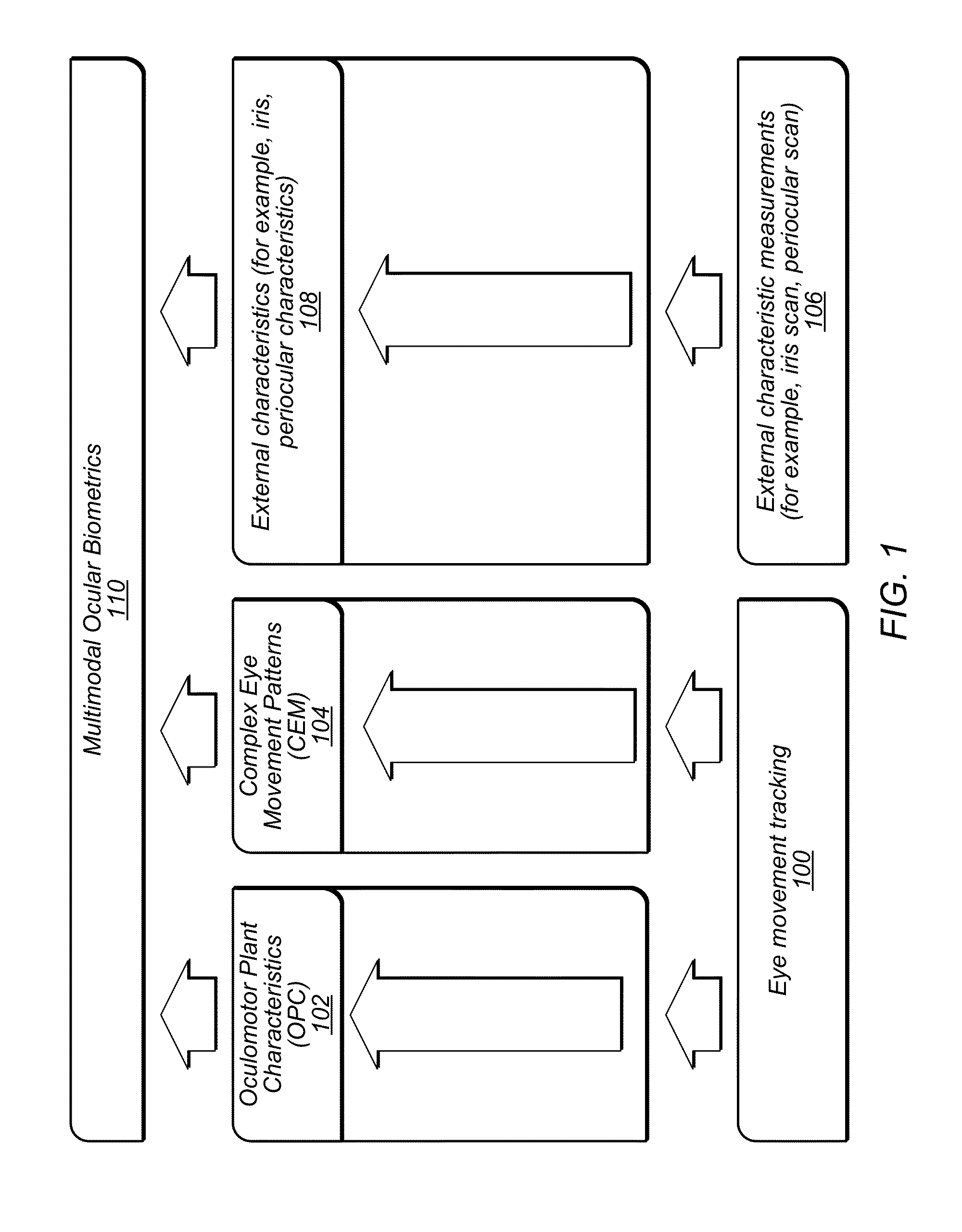
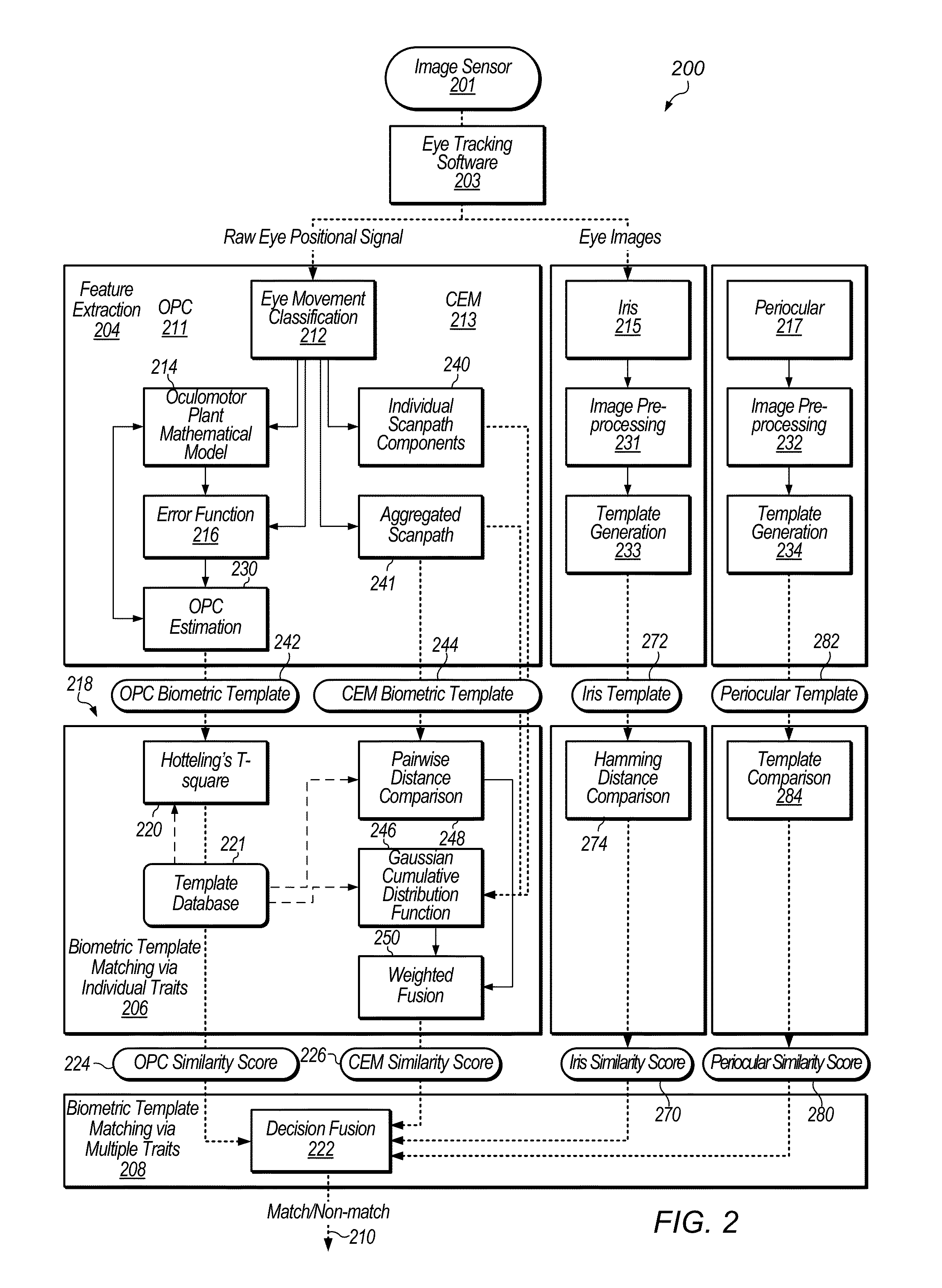
A method of assessing the identity of a person by one or more of: internal non-visible anatomical structure of an eye represented by the Oculomotor Plant Characteristics (OPC), brain performance represented by the Complex Eye Movement patterns (CEM), iris patterns, and periocular information. In some embodiments, a method of making a biometric assessment includes measuring eye movement of a subject, making an assessment of whether the subject is alive based on the measured eye movement, and assessing a person's identity based at least in part on the assessment of whether the subject is alive. In some embodiments, a method of making a biometric assessment includes measuring eye movement of a subject, assessing characteristics from the measured eye movement, and assessing a state of the subject based on the assessed characteristics.
Owner:TEXAS STATE UNIVERSITY
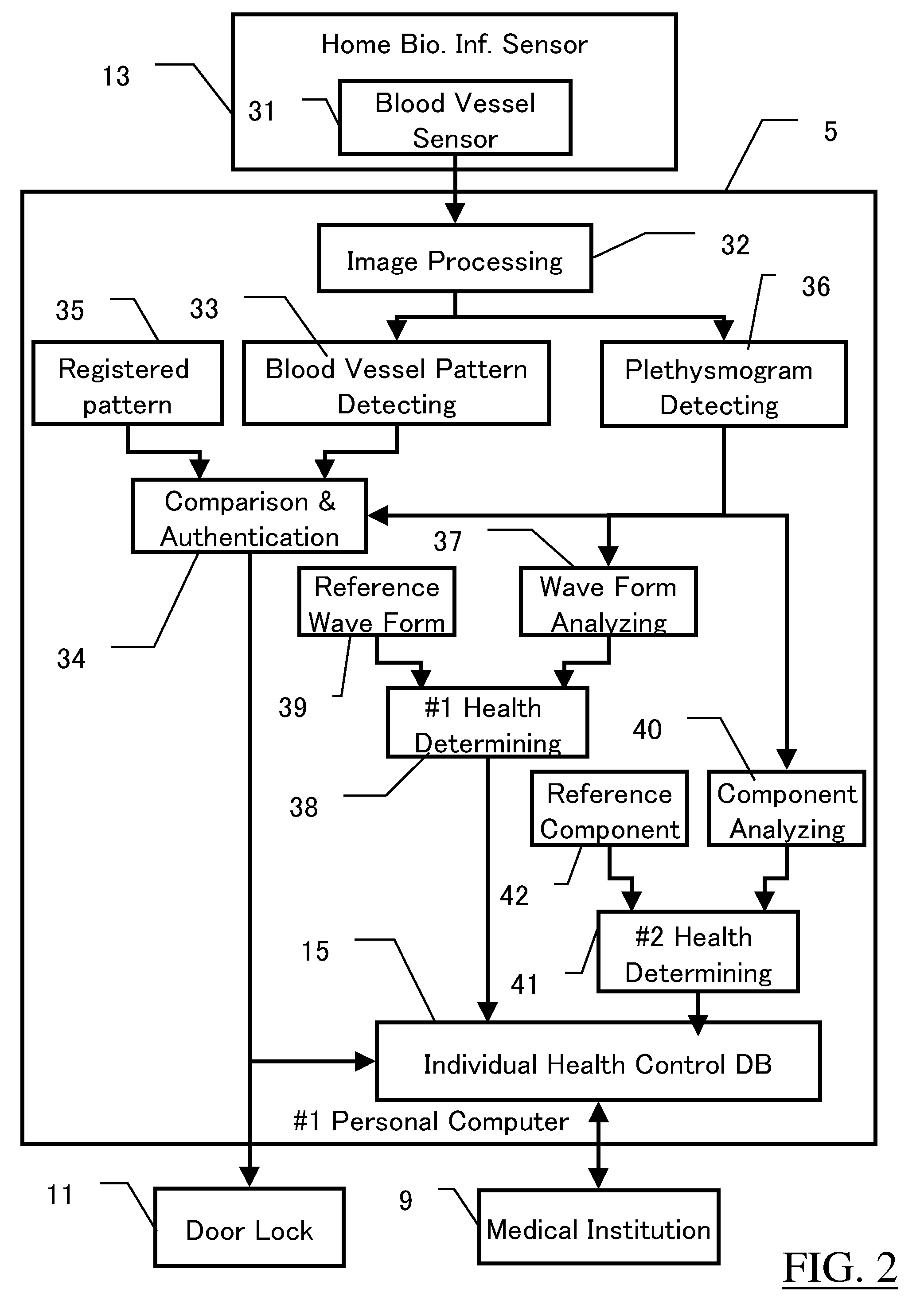
Biometrics System, Biologic Information Storage, and Portable Device
ActiveUS20070177771A1Improve securityPrevent forgeryPerson identificationDigital data authenticationSystems managementBank account
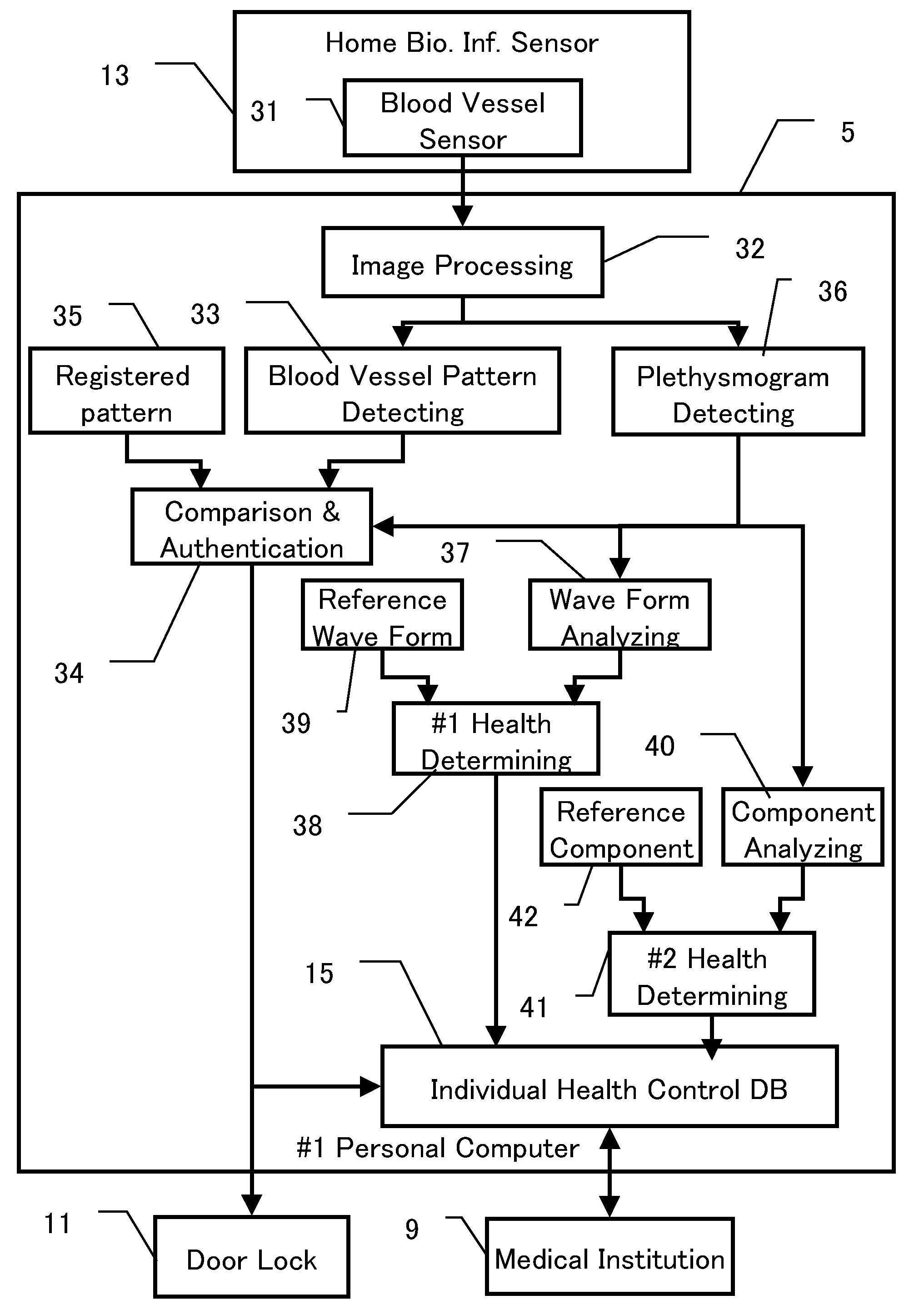
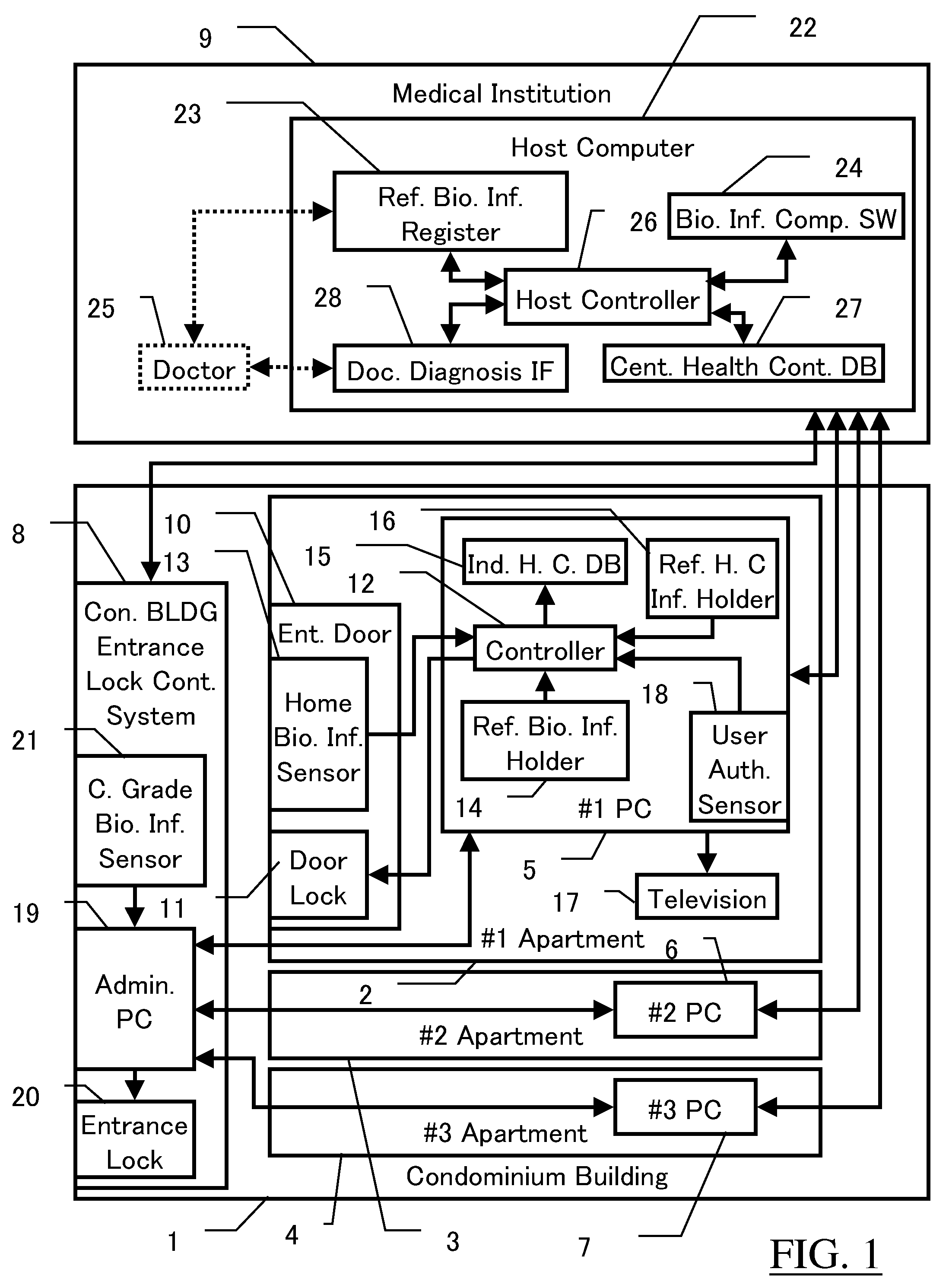
In a biometrics system for a building entrance unlocking or a bank account authentication, reference information registered under administration by the system is transmitted to a room or mobile-phone for private storage, with the original reference information deleted from the system. Biologic information gotten upon authentication is transmitted through wireless system to the room or mobile-phone for comparison with the reference, the result being returned to the system. Or, the reference is tentatively sent back to the system for comparison with the gotten biologic information. The biologic information sent to mobile-phone also includes health control information for storage and display. Mobile-phone also can receive blood pressure information at a waiting lounge of medical institution though wireless local communication even if the main power shut down. The communication between the biometrics system and the mobile-phone is encrypted. The system includes sensor unit and protection unit, the abnormality thereof being separately checked.
Owner:NL GIKEN
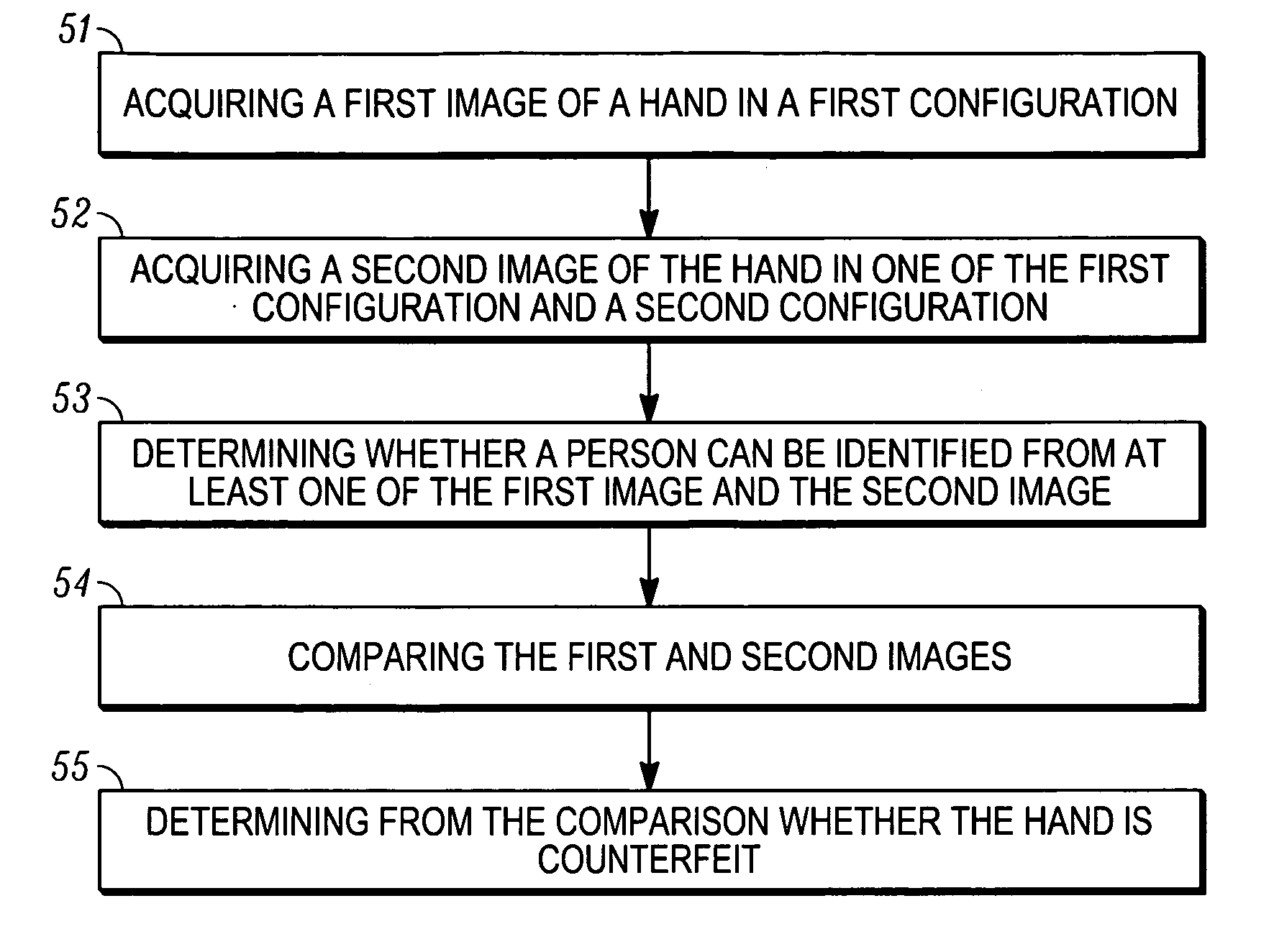
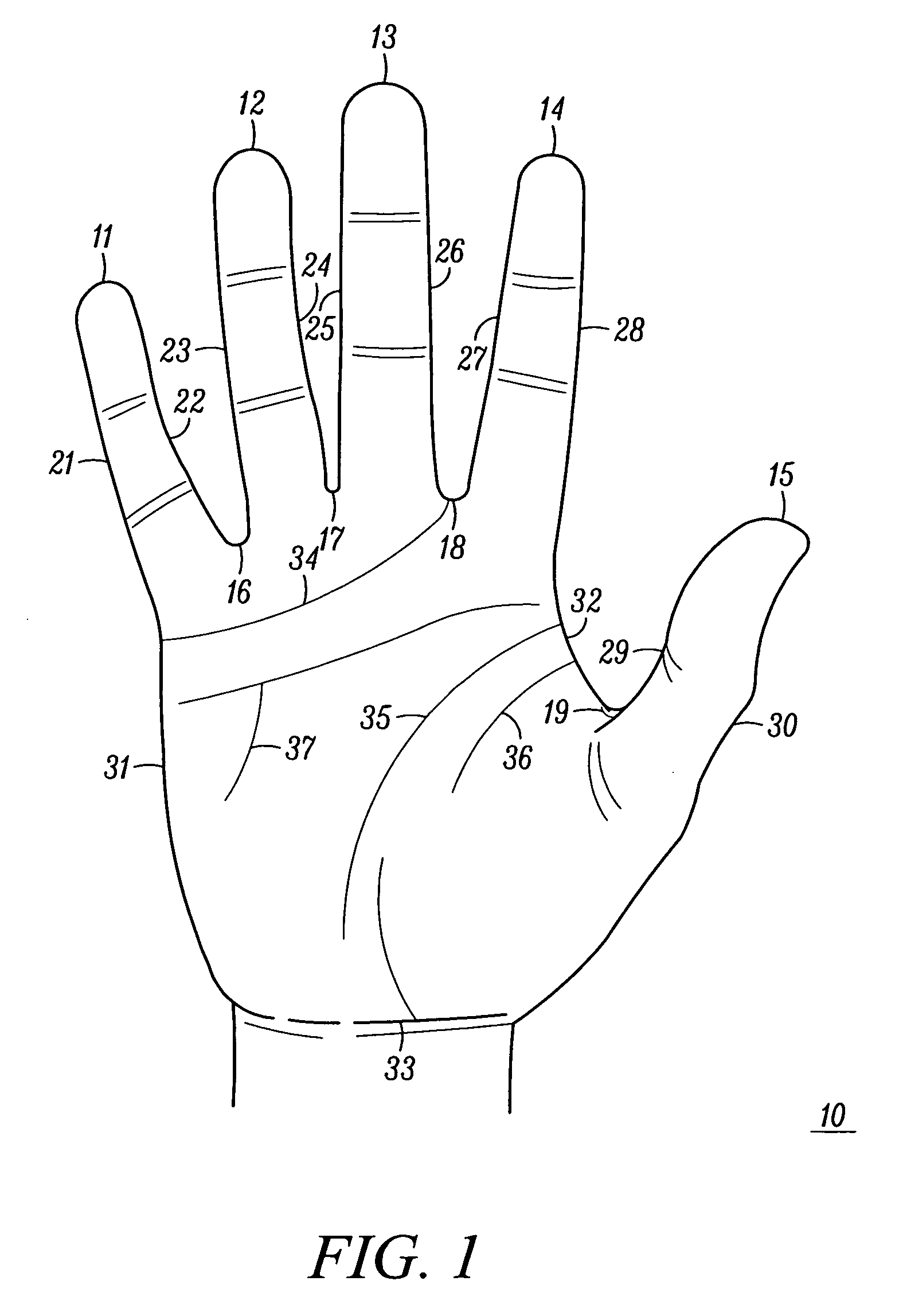
Recognition method using hand biometrics with anti-counterfeiting
ActiveUS20080002860A1Programme controlElectric signal transmission systemsPattern recognitionAnti spoofing
A method is provided for identifying and verifying a person using hand biometrics with an anti-spoofing measure. The method comprises acquiring (51) a first image (10) of a hand in a first configuration, acquiring (52) a second image (30, 40) of the hand in one of the first and a second configuration for comparison with the first image (10), determining (52) whether a person can be identified from at least one of the first image (10) and the second image (30, 40), and determining (55) from a comparison of the second image (30, 40) with the first image (10) whether the hand is a counterfeit.
Owner:GOOGLE TECH HLDG LLC
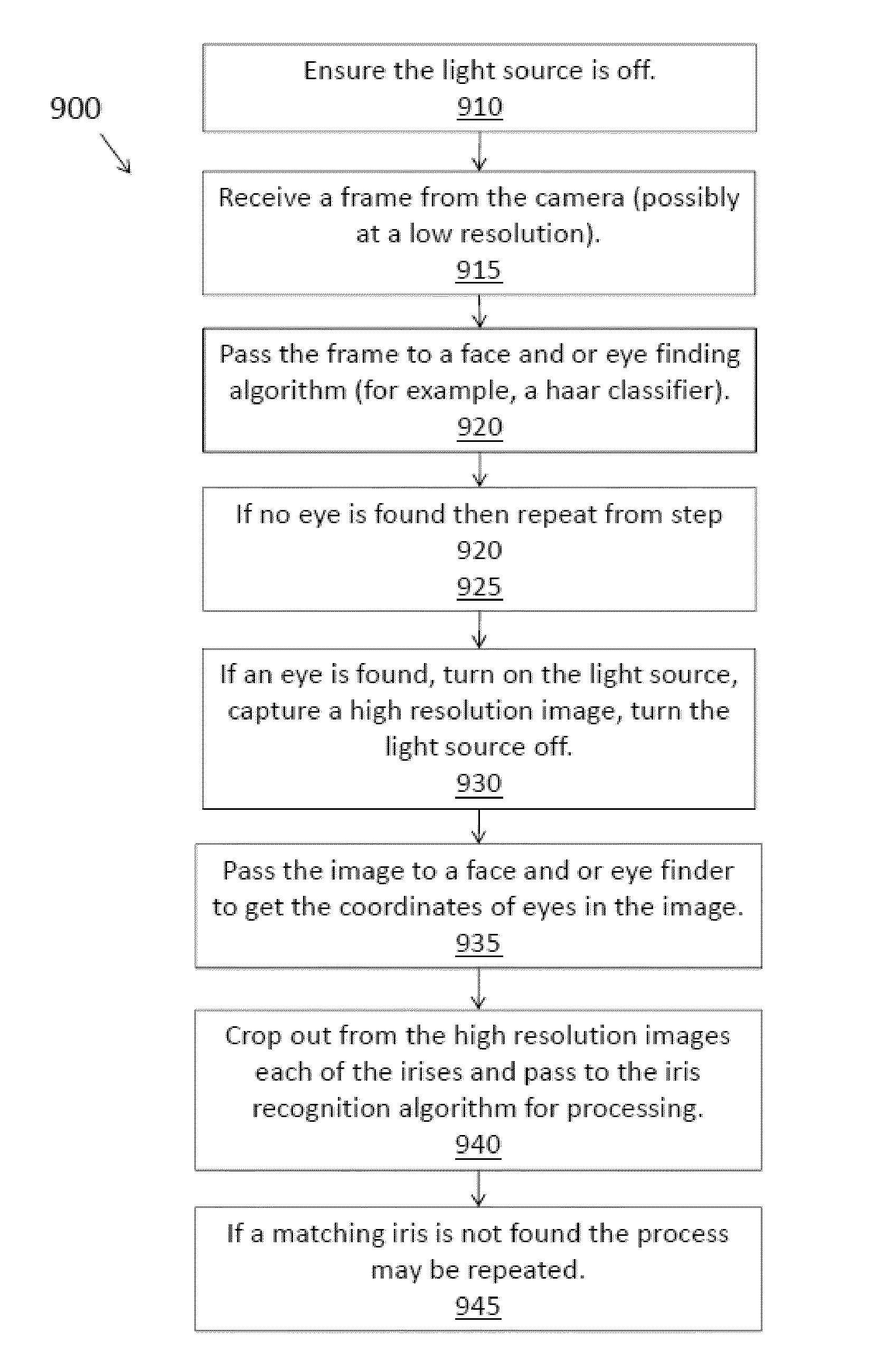
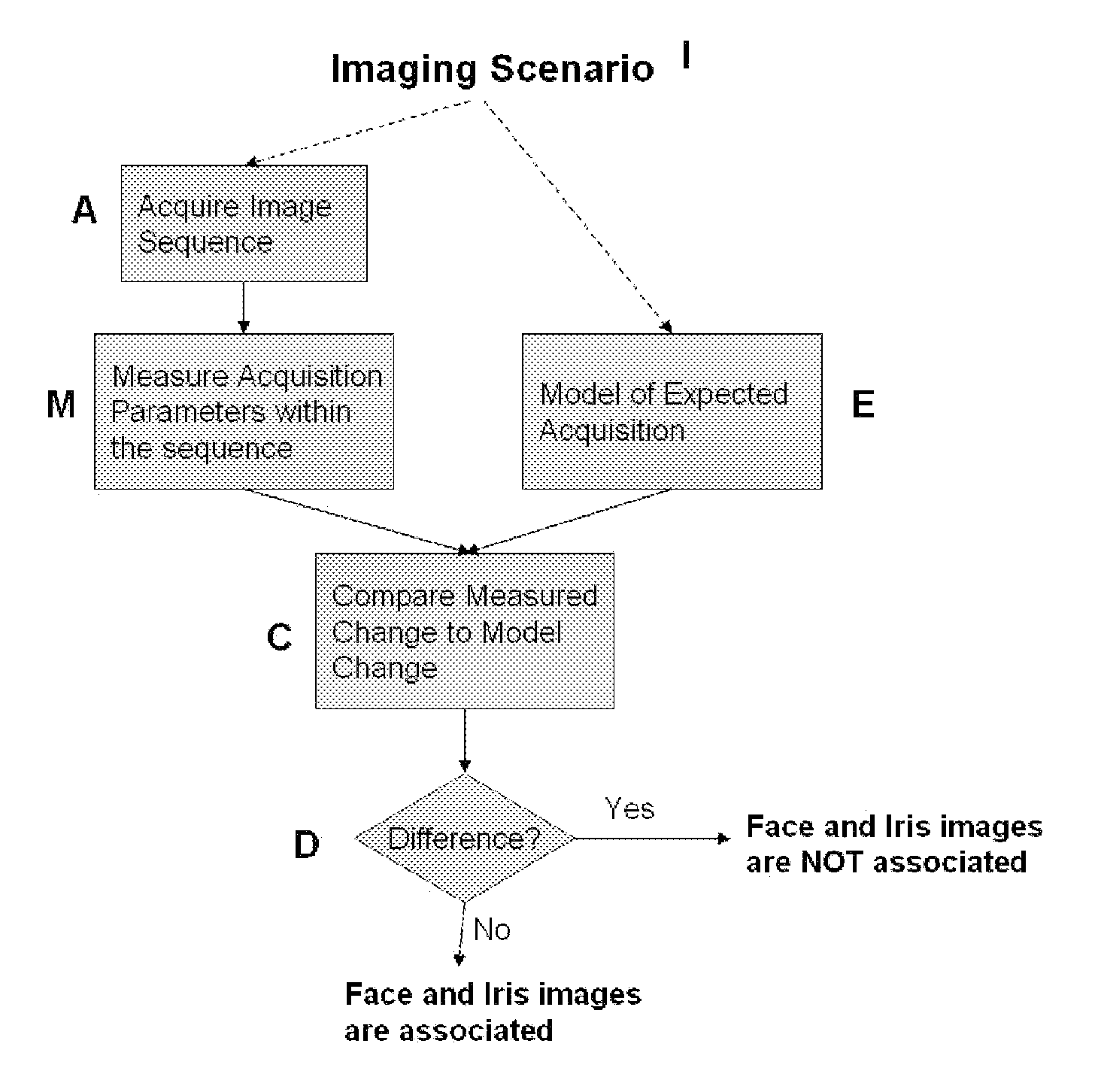
Methods for performing biometric recognition of a human eye and corroboration of same
A method of biometric recognition is provided. Multiple images of the face or other non-iris image and iris of an individual are acquired. If the multiple images are determined to form an expected sequence of images, the face and iris images are associated together. A single camera preferably acquires both the iris and face images by changing at least one of the zoom, position, or dynamic range of the camera. The dynamic range can be adjusted by at least one of adjusting the gain settings of the camera, adjusting the exposure time, and / or adjusting the illuminator brightness. The expected sequence determination can be made by determining if the accumulated motion vectors of the multiple images is consistent with an expected set of motion vectors and / or ensuring that the iris remains in the field of view of all of the multiple images.
Owner:EYELOCK
Apparatus and methods for detecting the presence of a human eye
Owner:GLOBAL RAINMAKERS INC PUERTO RICO CORP +1
Method, Apparatus, and Computer-Readable Recording Medium for Authenticating a User
InactiveUS20140165187A1Security vulnerability can be overcomeImprove the authentication success rateDigital data processing detailsUnauthorized memory use protectionPattern recognitionPattern matching
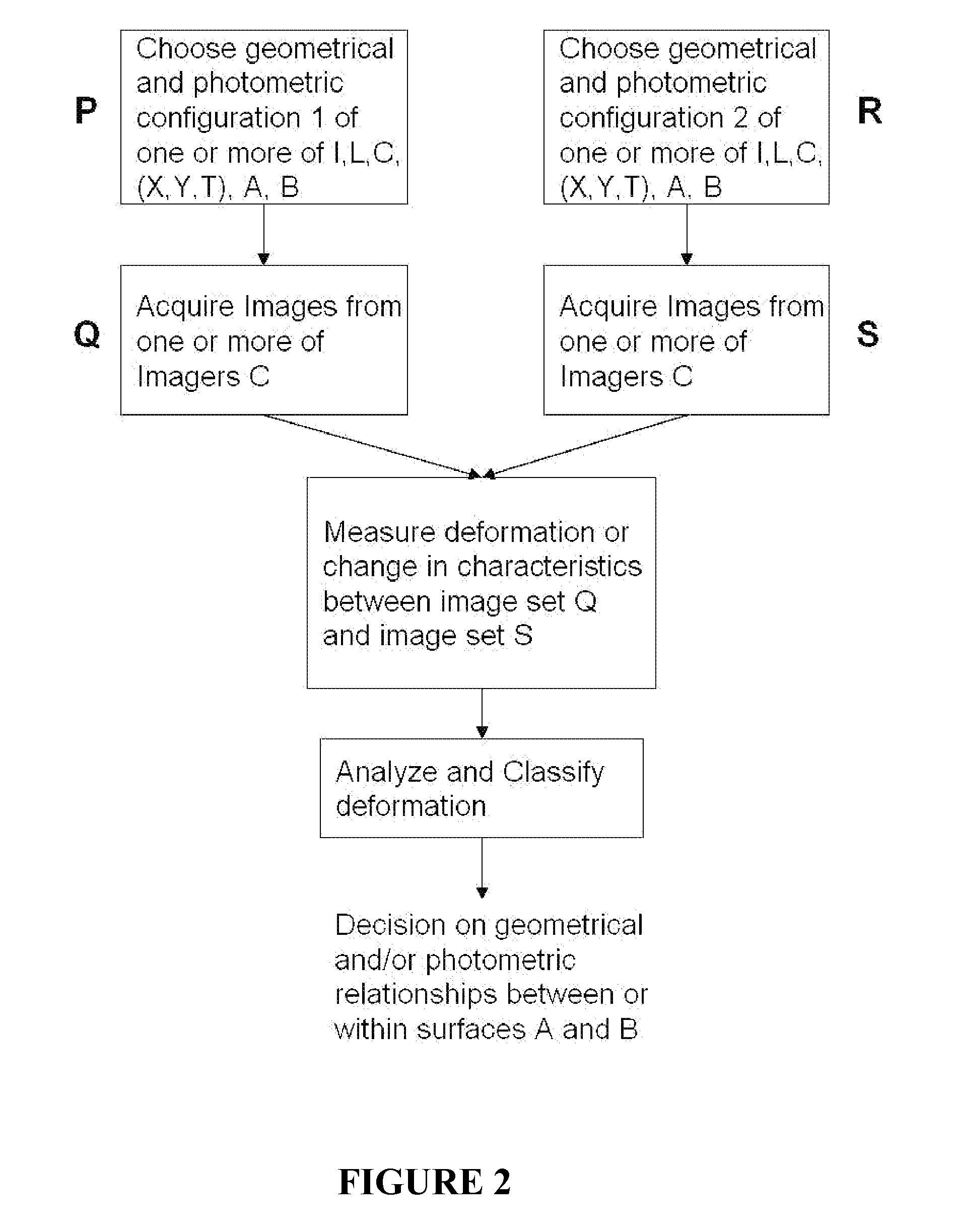
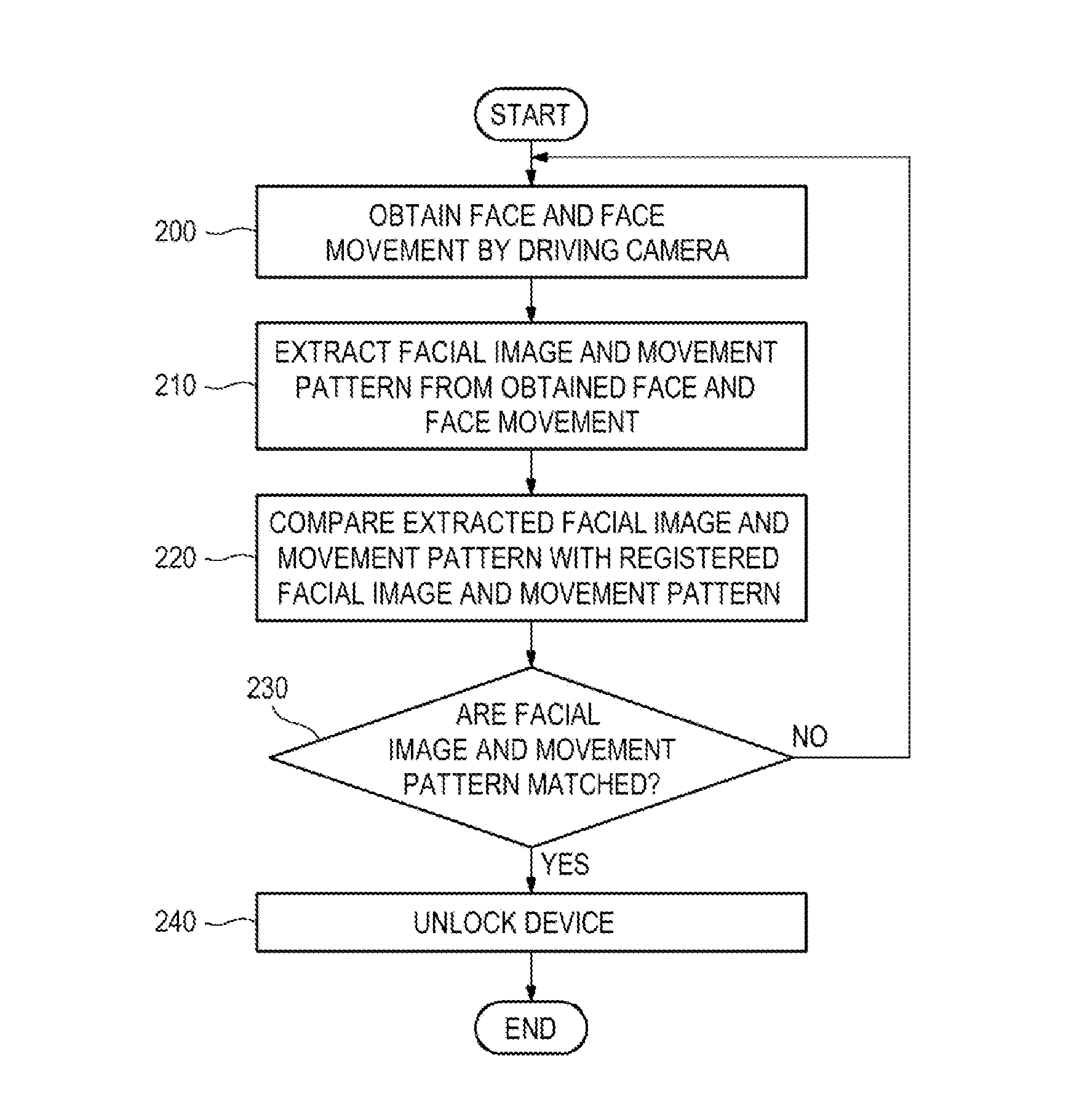
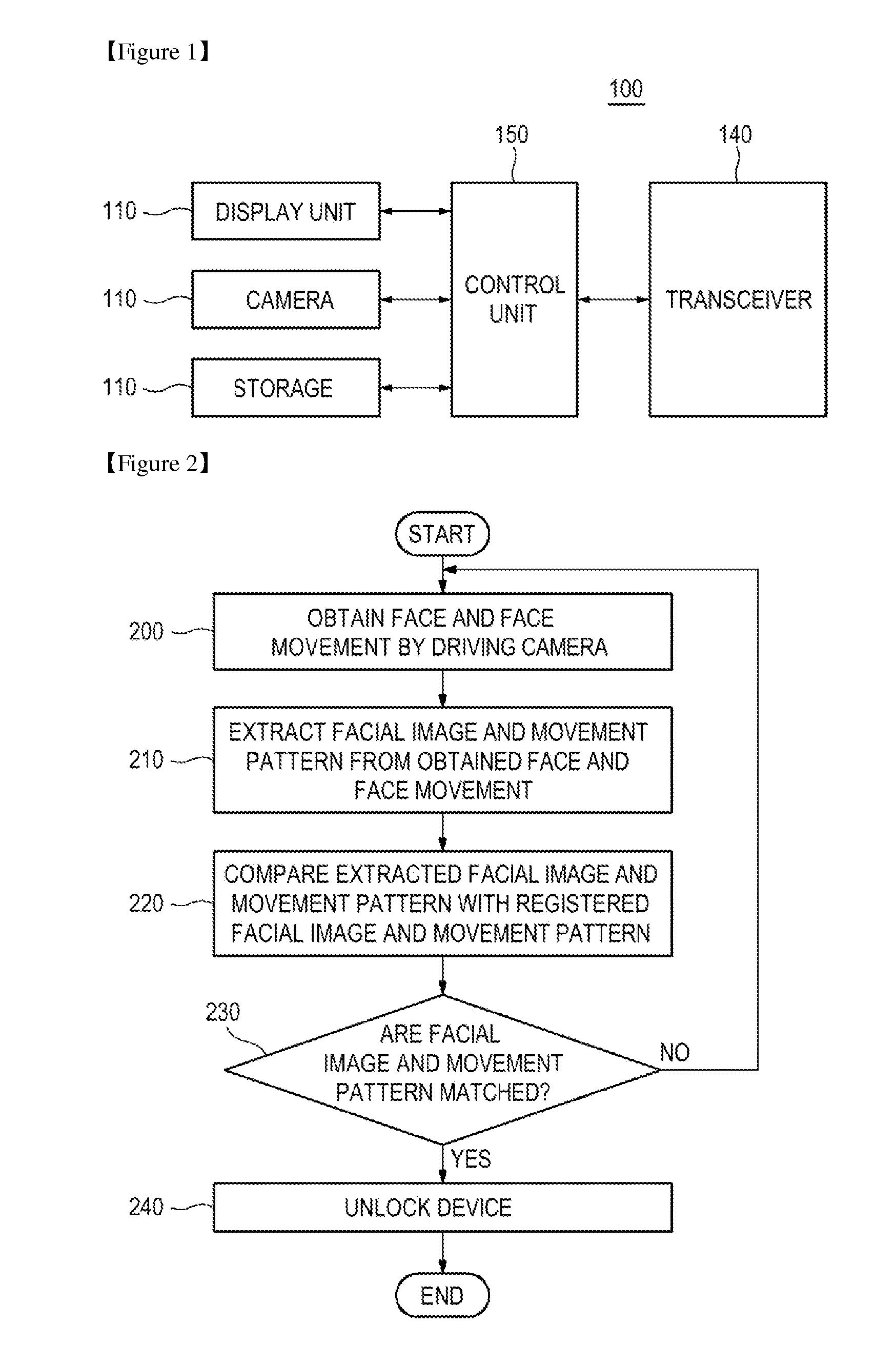
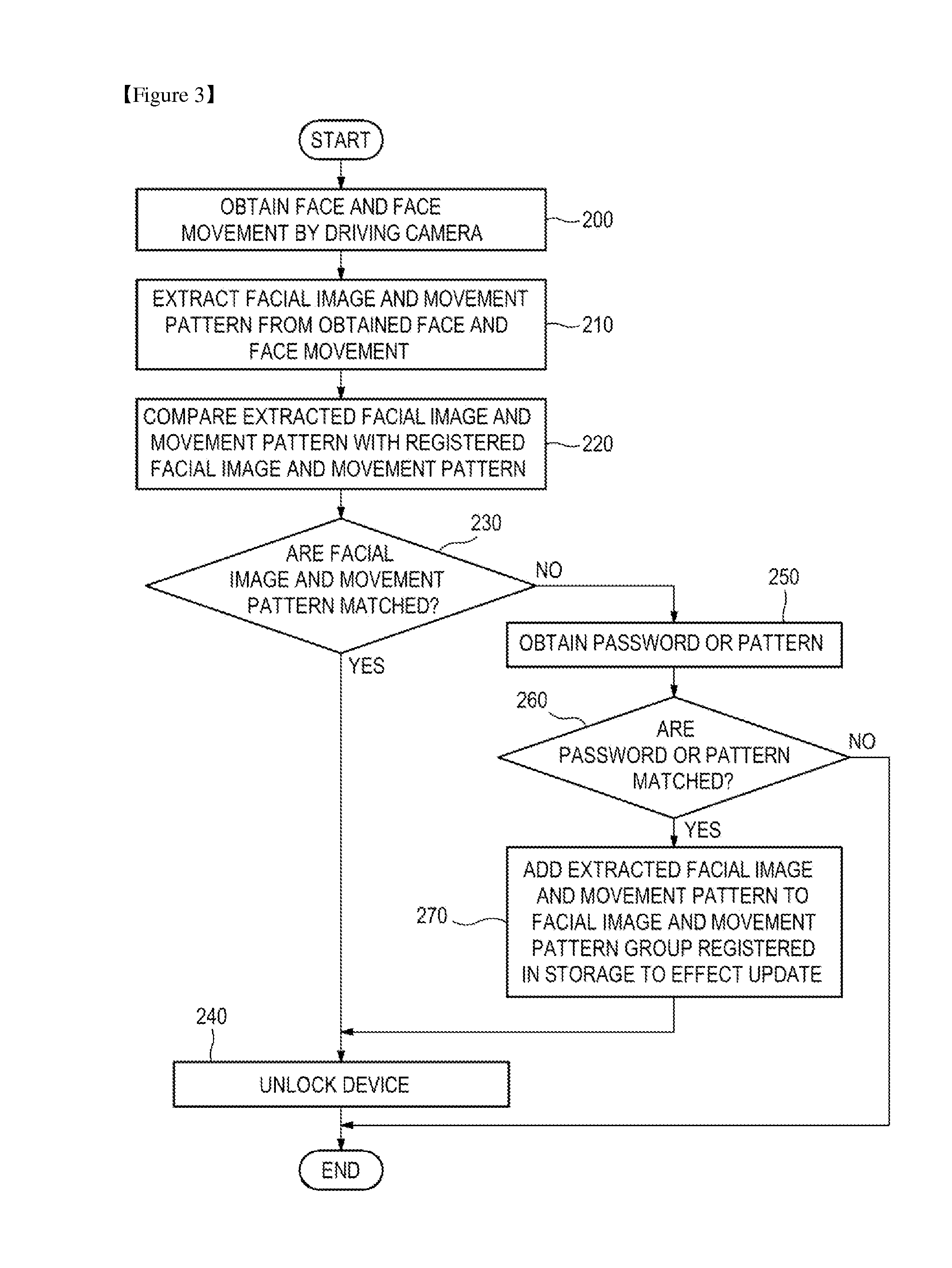
Provided are a method, apparatus, and computer-readable recording medium for authenticating a user. The user authentication method includes obtaining an image including a face and a face movement by driving a camera to extract feature information on a facial image and a movement pattern from the obtained image, and comparing the extracted feature information on the facial image with feature information on a facial image registered in a storage and, when the extracted feature information matches the registered feature information, comparing the extracted movement pattern with a movement pattern registered in the storage and, when the extracted movement pattern matches the registered movement pattern, unlocking a device.
Owner:INTEL CORP
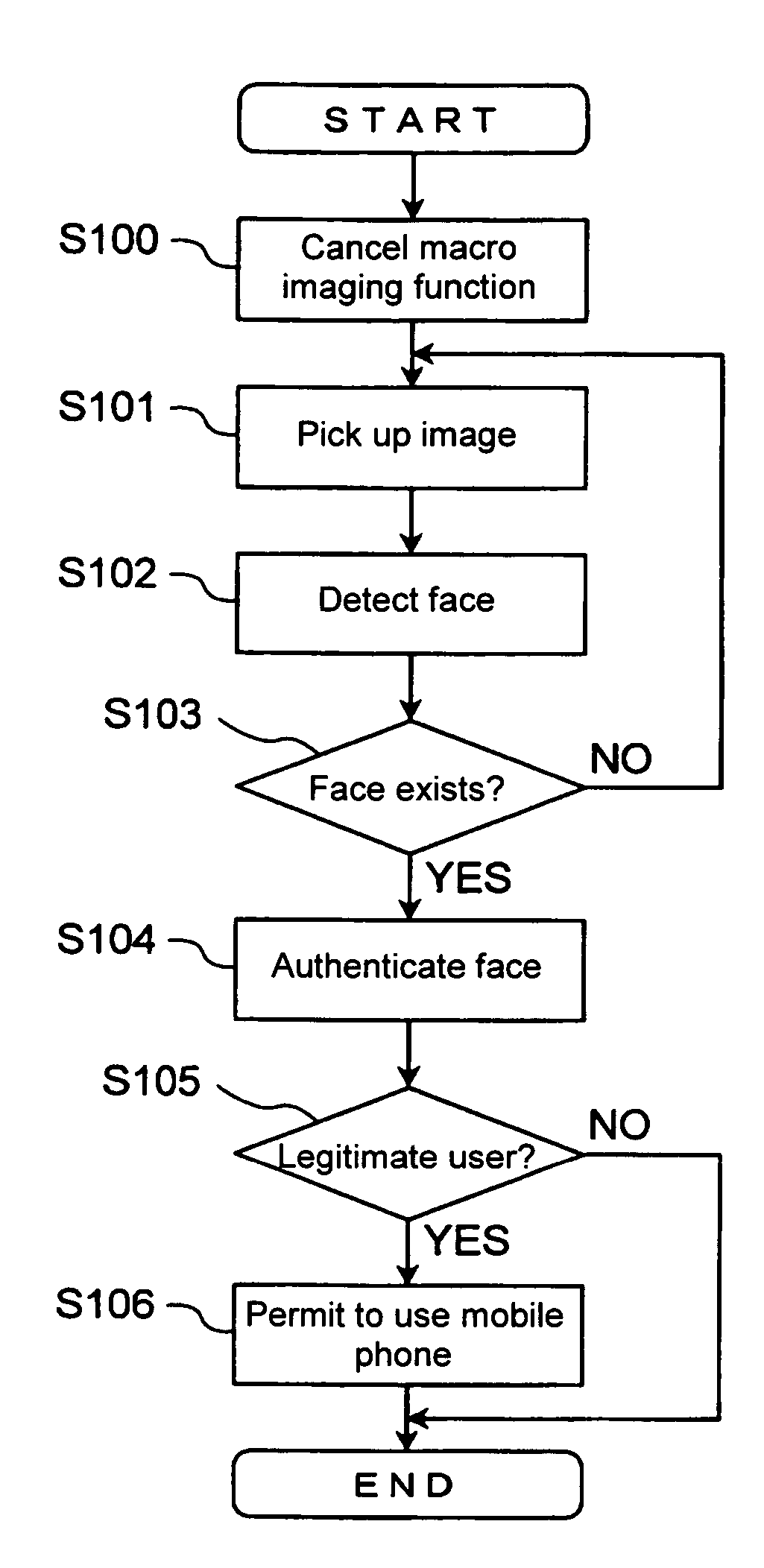
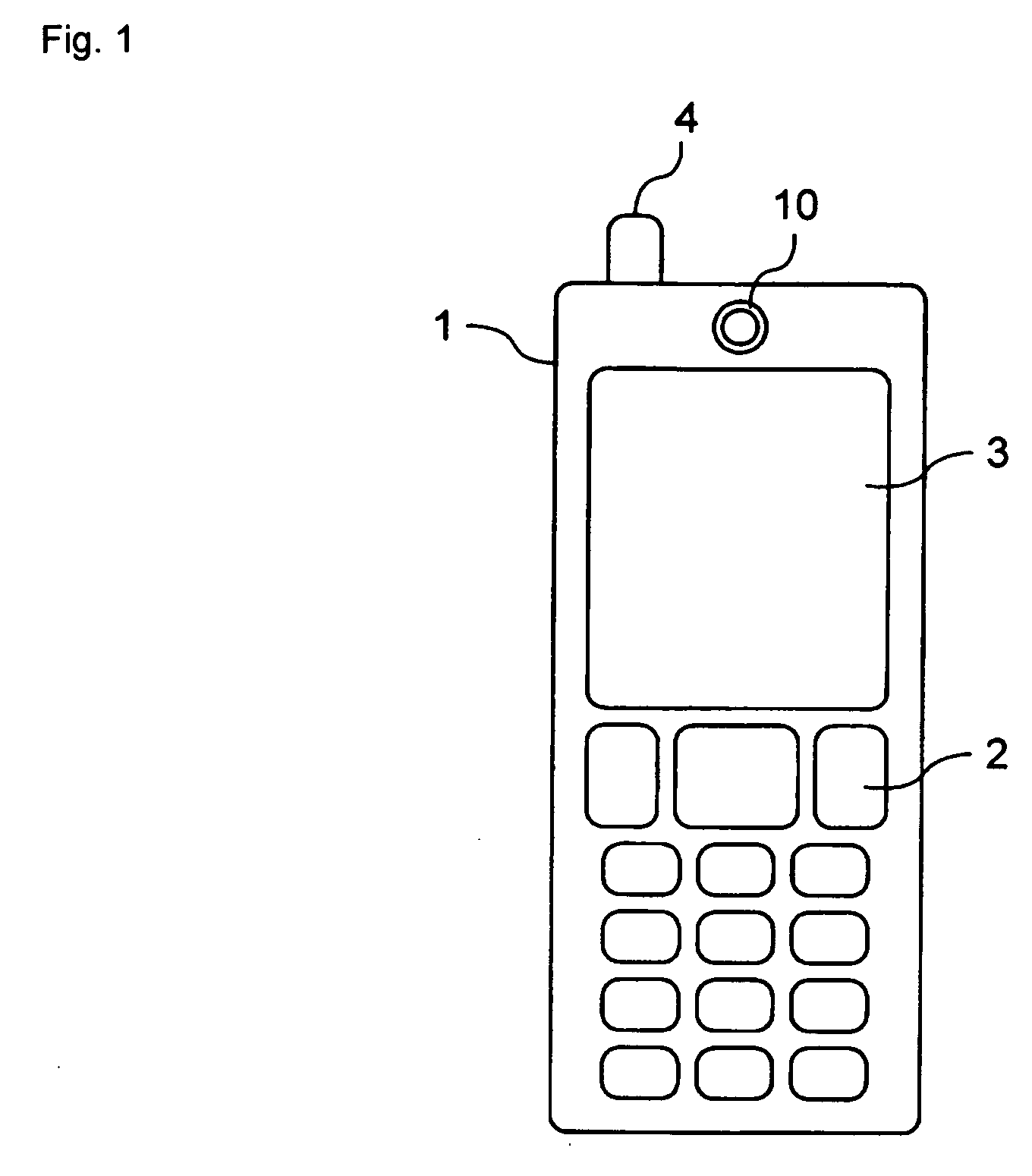
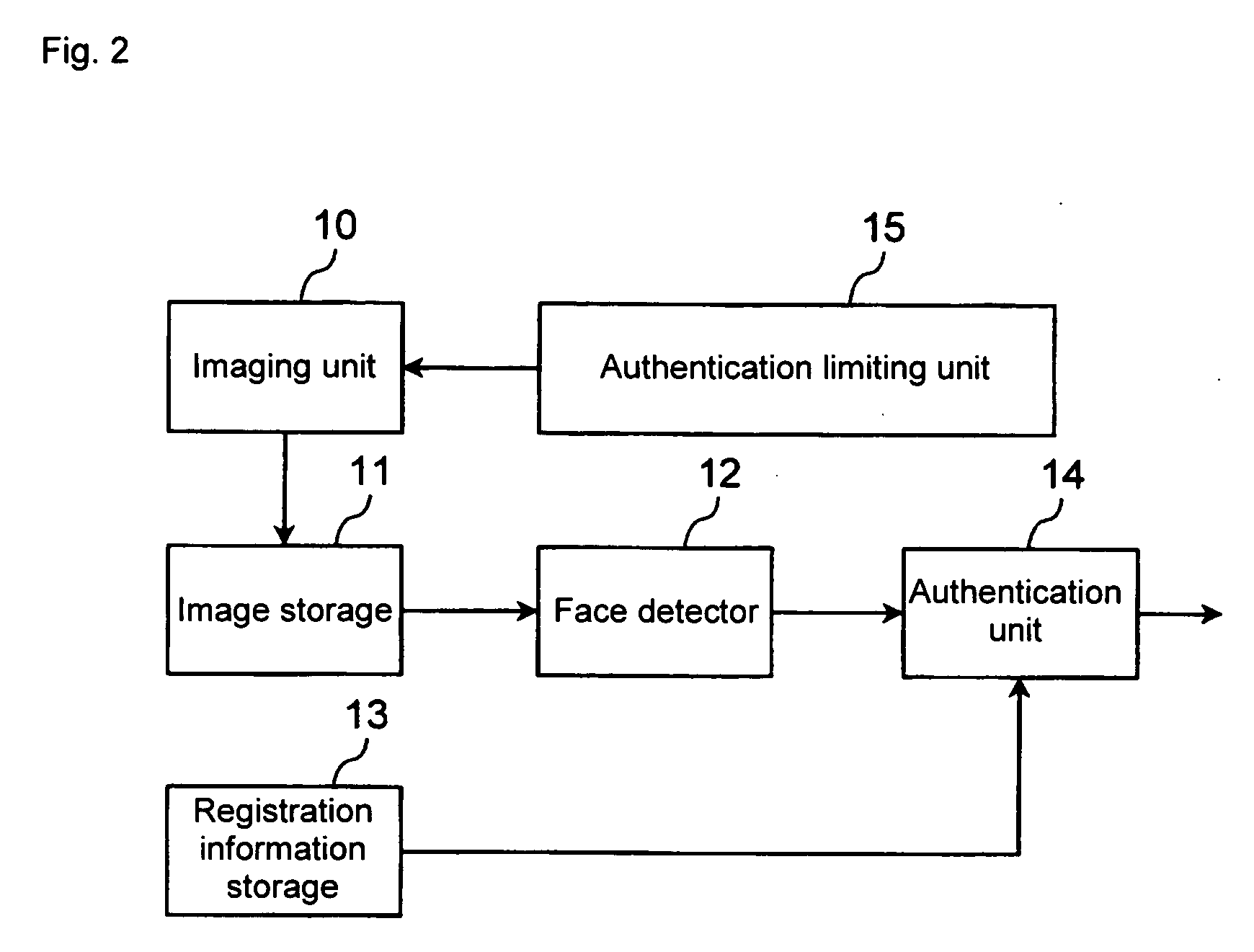
Authentication apparatus and portable terminal
ActiveUS20070113099A1Unauthorised/fraudulent call preventionDigital data processing detailsComputer hardwareUser authentication
An authentication apparatus includes an imaging device having at least one of a macro imaging function, an auto focusing function and a zoom imaging function, an authentication device for authenticating a user through a face image picked up by the imaging device, and an authentication limiting device for canceling the specified function of the imaging device in picking up an image for the user authentication.
Owner:ORMON CORP
Systems and methods for improved biometric feature definition
Methods and systems are provided for performing a biometric function. A purported skin site of an individual is illuminated under distinct optical conditions during a single illumination session for a fixed position of the purported skin site. Light from the purported skin site is received for each of the optical conditions. Images of the purported skin site are generated from the received light. The images are analyzed to identify a biometric feature as a characteristic in a portion of at least one of the images. The biometric function is implemented in accordance with an identification of the biometric feature.
Owner:HID GLOBAL CORP
Personal authentication method and apparatus sensing user vicinity
InactiveUS7356706B2Volume/mass flow measurementUser identity/authority verificationInternet privacyAuthentication
Owner:INTEL CORP
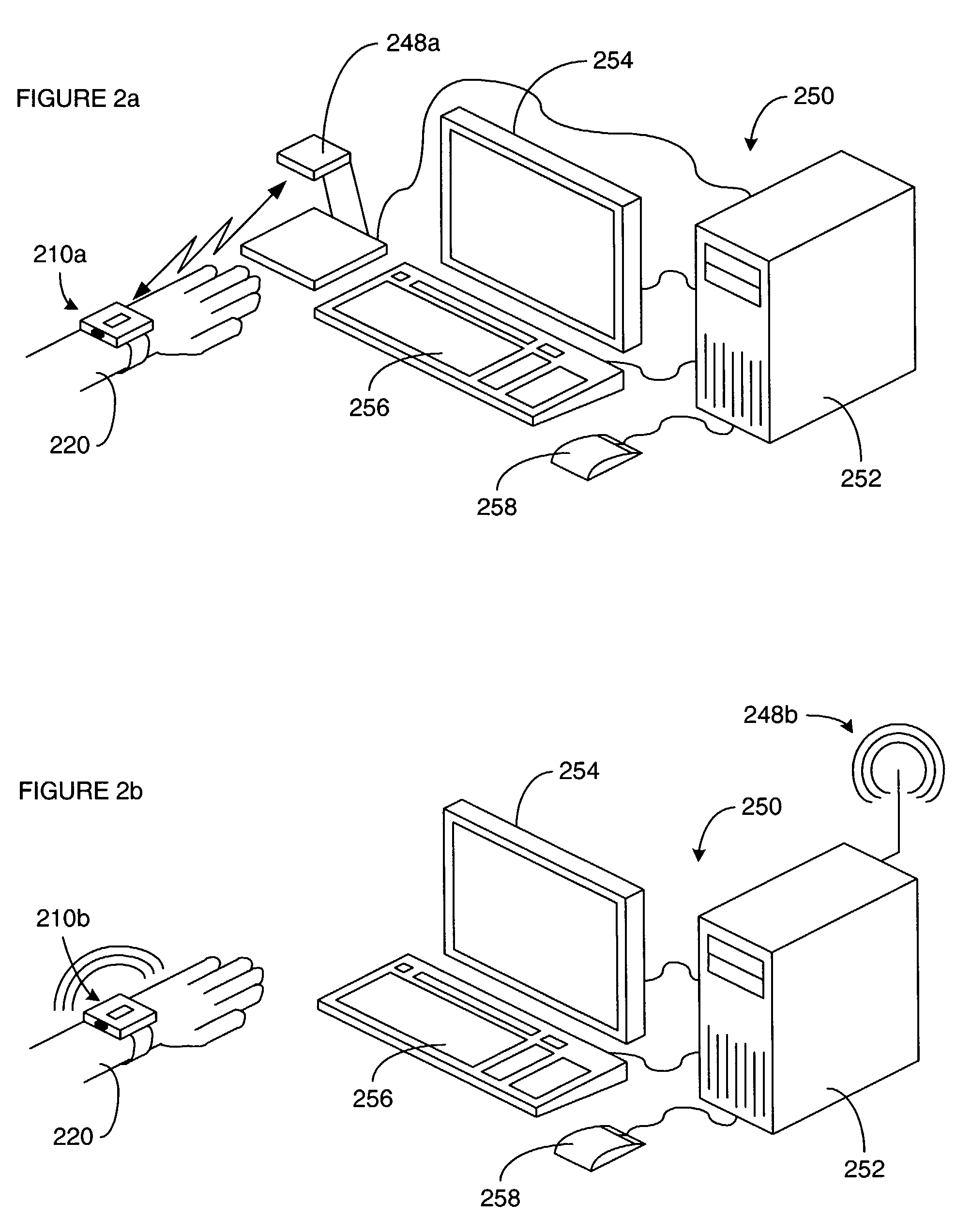
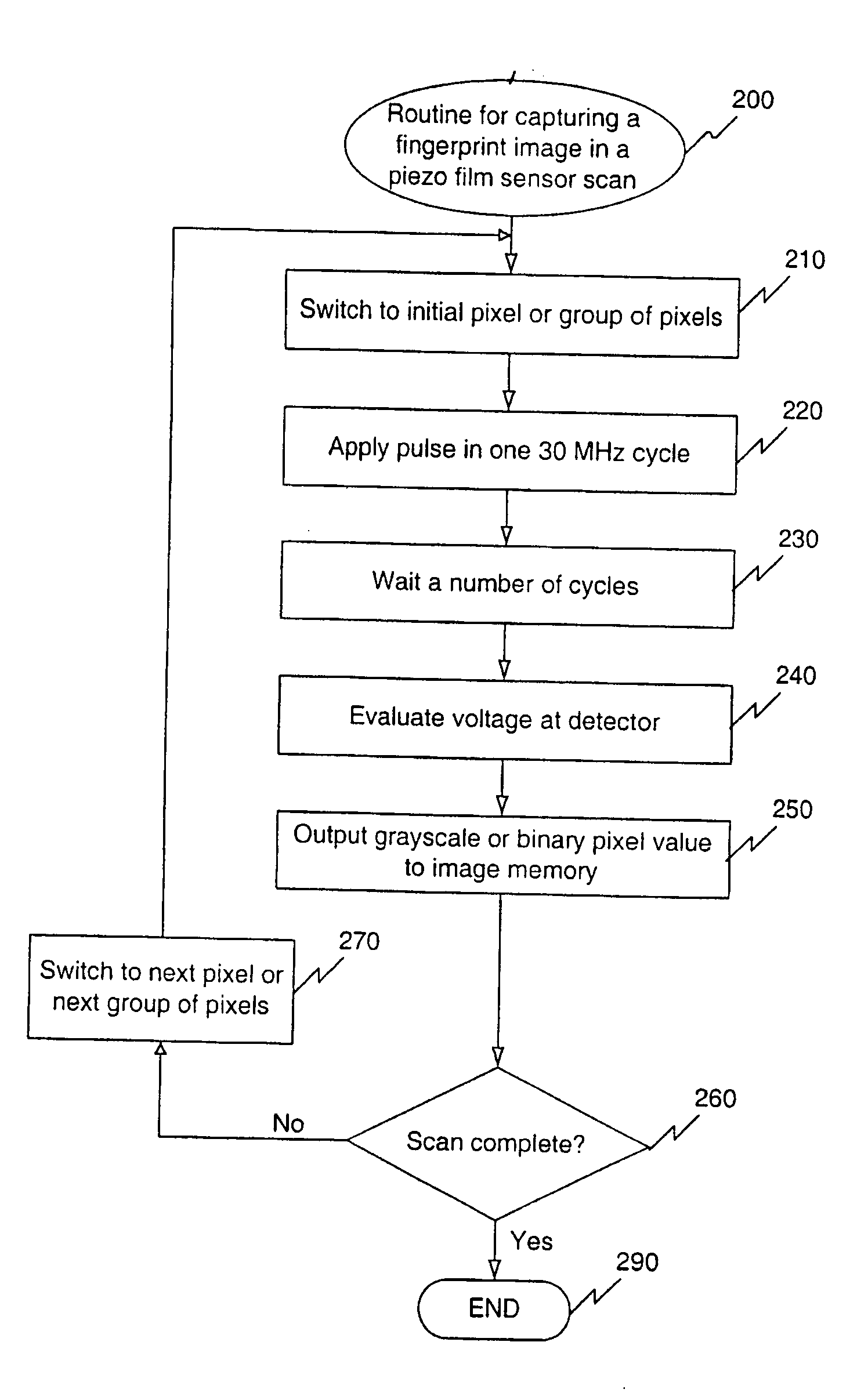
Biometric piezo scanner
InactiveUS20080175450A1Provide informationBlood flow measurement devicesPerson identificationSensor arrayElectrical conductor
A piezoelectric thin film sensor array is used to scan and capture biometric data, for example, a fingerprint image. In one embodiment, a multi-layer structure includes a PVDF layer in between two conductor grids arranged orthogonally to one another. Urethane can be added to one side where a finger is placed. A foam substrate can be used as a support. In one feature, the PVDF, and grids can be peeled off like a label for easy replacement. Multiplexers are switched to scan the sensor. A single pixel or a group of pixels can be detected and output to an image memory. The presence of a fingerprint ridge is detected by virtue of a ring-down oscillation that arises from reflection when an electric field is applied to the piezoelectric thin film sensor array at a pixel in contact with the fingerprint ridge. For example, such a ring-down value associated with a fingerprint ridge can be detected at about 150 ns. (or 5 cycles at 30 MHZ). Other reflections indicative of additional biometrics (e.g. from tissue, blood, bone, fingernail, etc.) can also be detected. A Doppler effect due to reflections from circulating blood can also be detected. Such a Doppler effect can provide further information about direction and speed of blood circulation. An instantaneous pyroelectric effect can also be detected to indicate a live finger presence.
Owner:SONAVATION INC
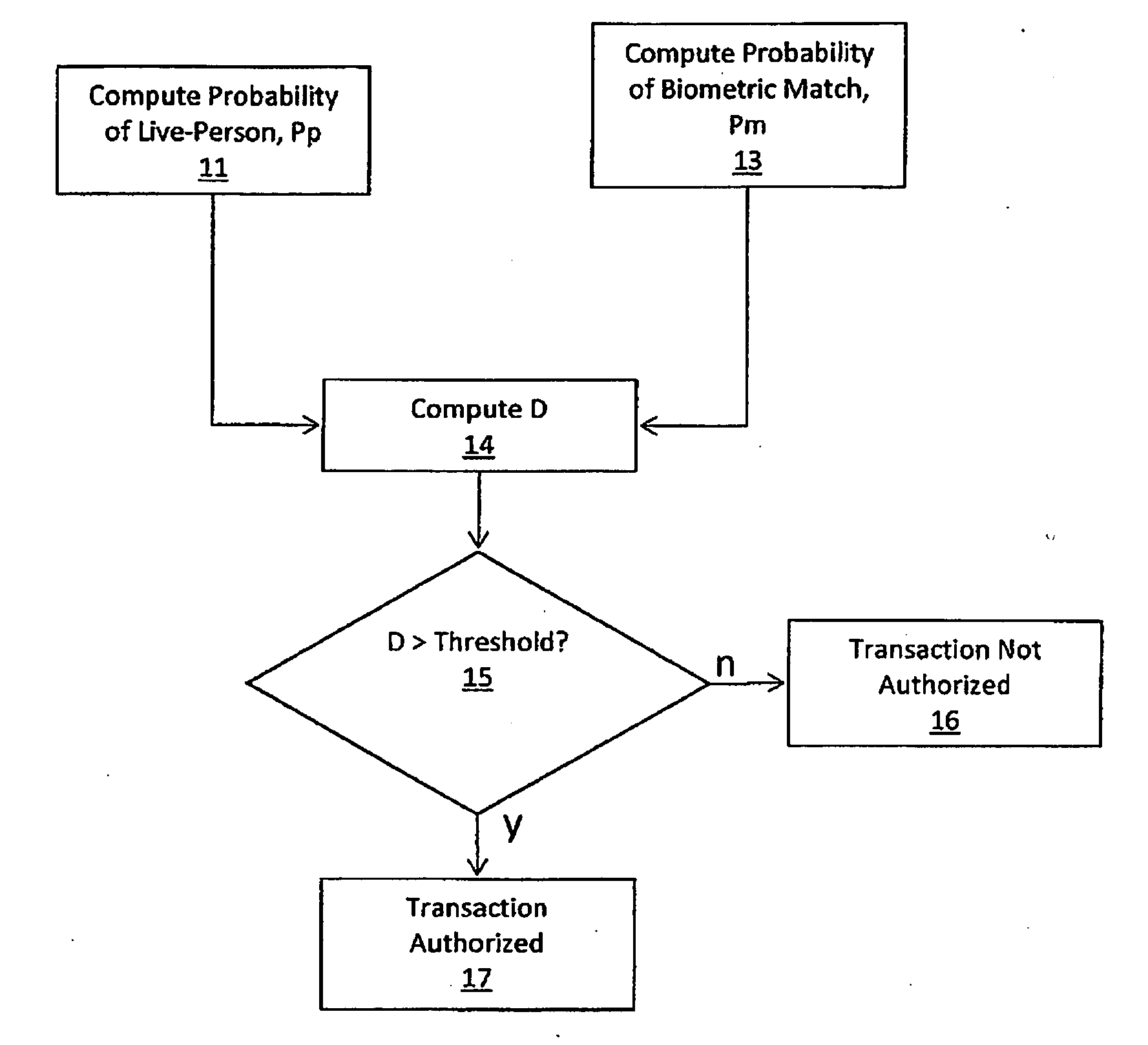
Fraud Resistant Biometric Financial Transaction System and Method
ActiveUS20100014720A1Out of controlReduce scrap rateElectric signal transmission systemsImage analysisLivenessBiometric data
A method and system for authenticating financial transactions is disclosed wherein biometric data is acquired from a person and the probability of liveness of the person and probability of a match between the person or token and known biometric or token information are calculated, preferably according to a formula D=P(p)*(K+P(m)), wherein K is a number between 0.1 and 100, and authenticating if the value of D exceeds a predetermined value.
Owner:EYELOCK
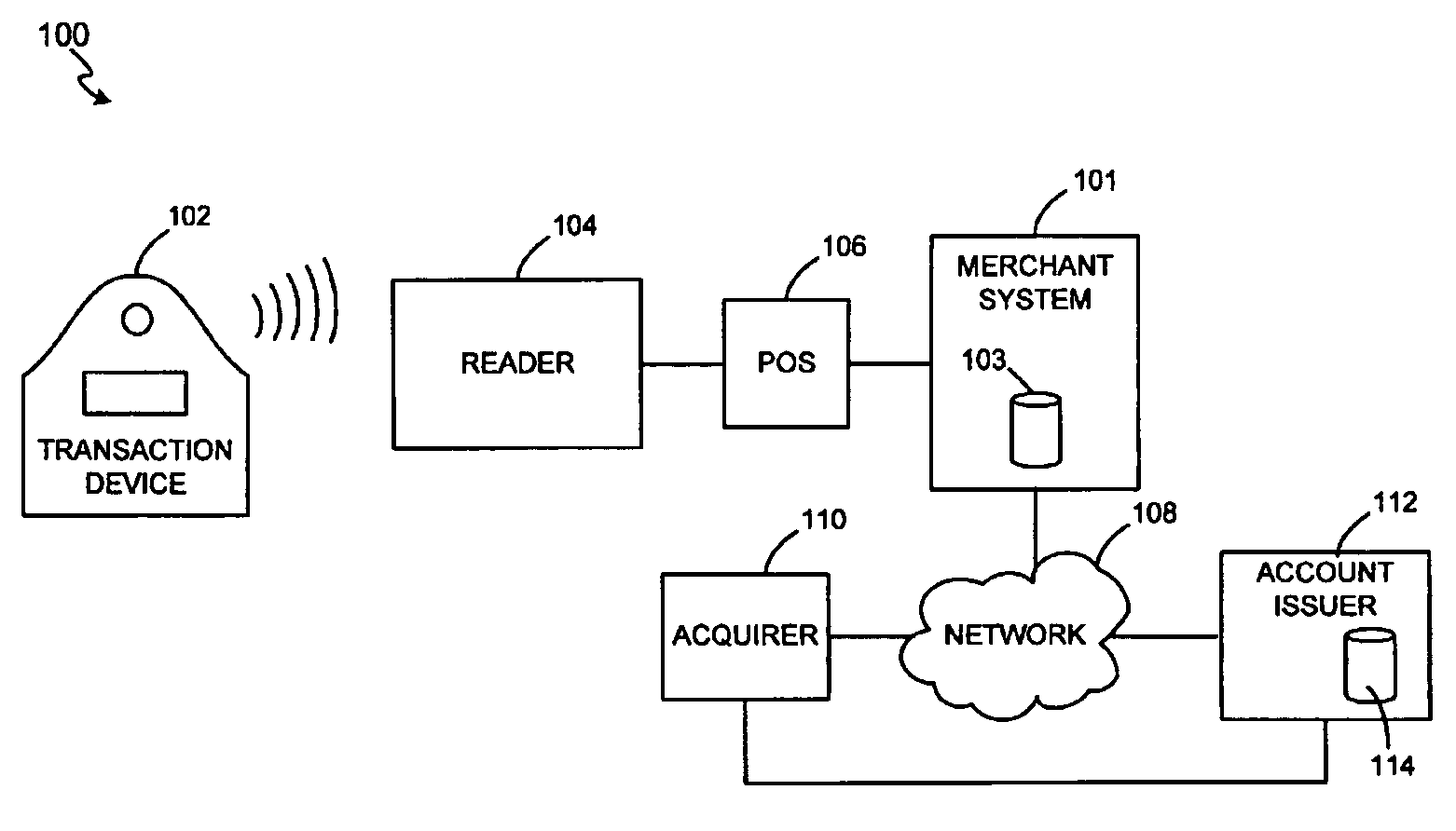
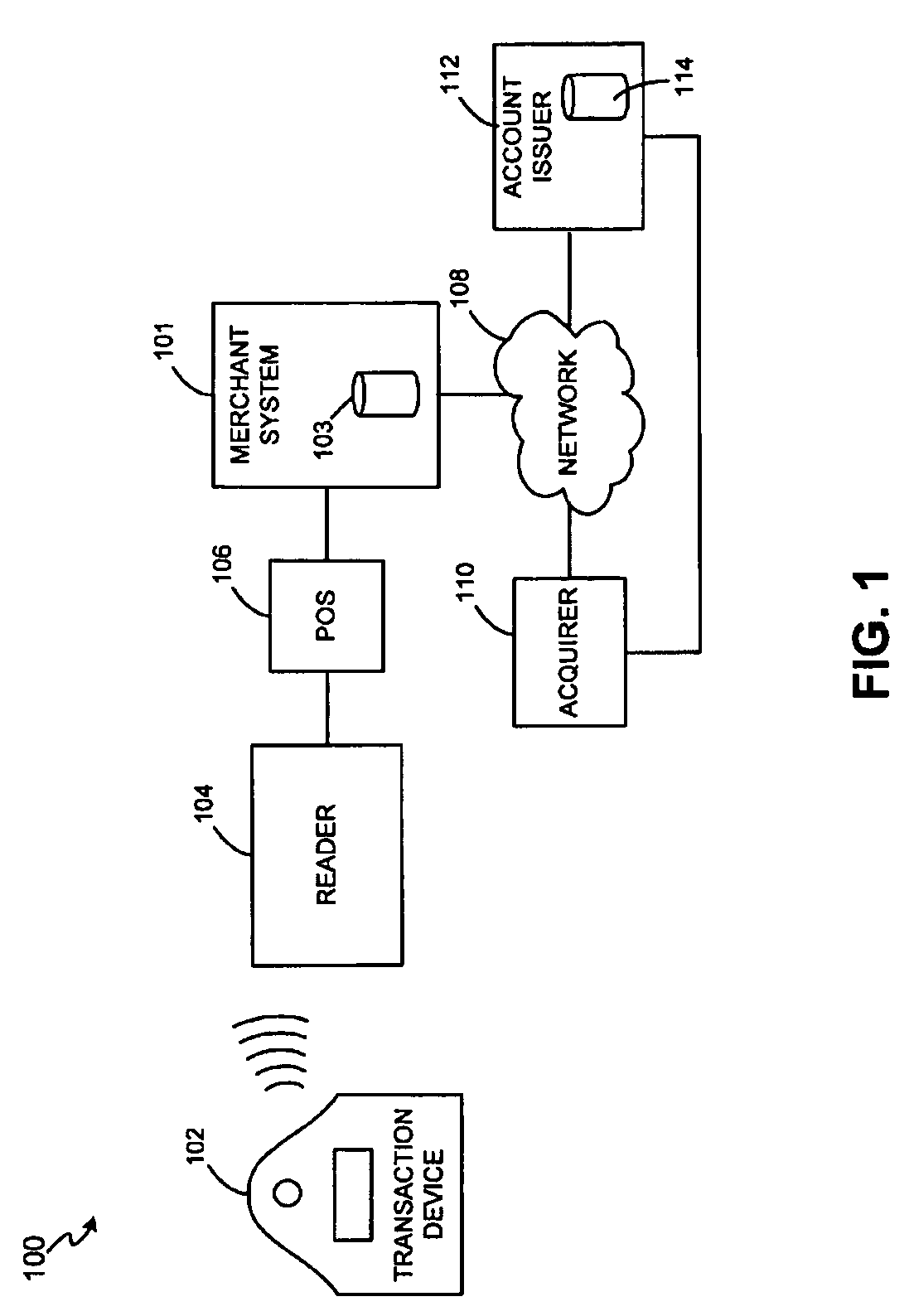
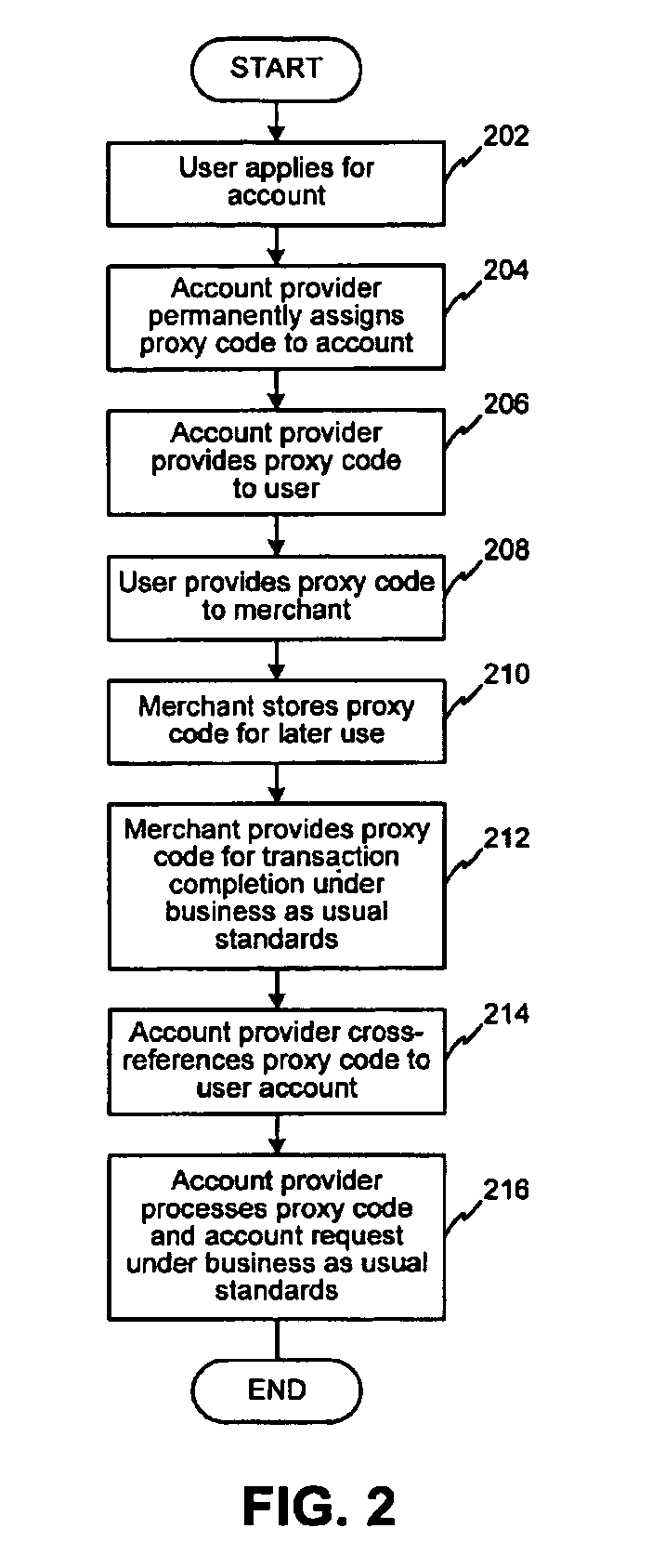
System and method for secure transactions manageable by a transaction account provider
InactiveUS7543738B1Cash registersIndividual entry/exit registersFinancial transactionTransaction account
Owner:LIBERTY PEAK VENTURES LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com