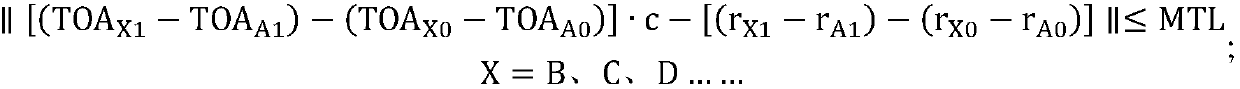Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
115 results about "Anti spoofing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Antispoofing, which is sometimes spelled anti-spoofing, is sometimes implemented by Internet Service Providers (ISPs) on behalf of their customers.
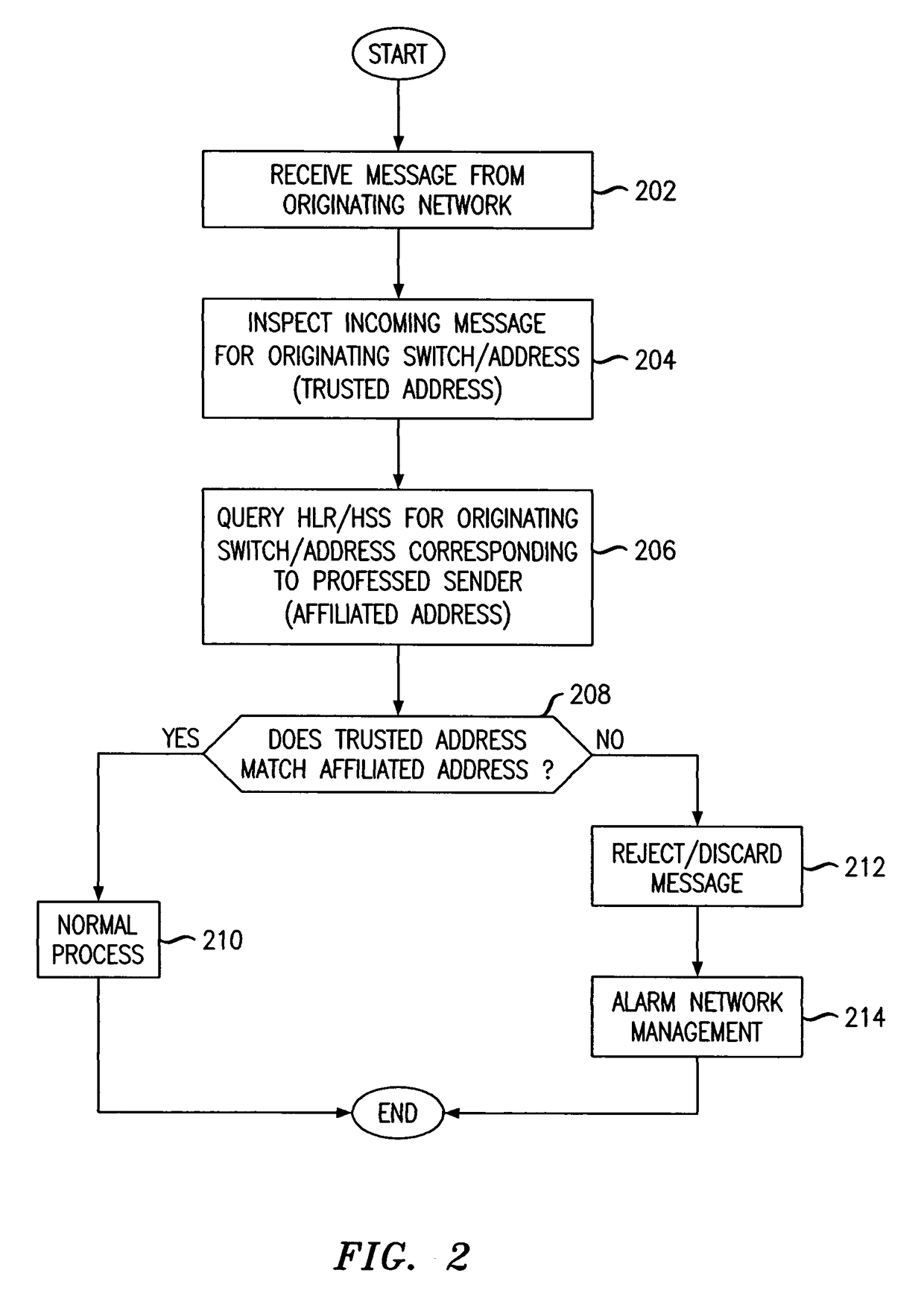
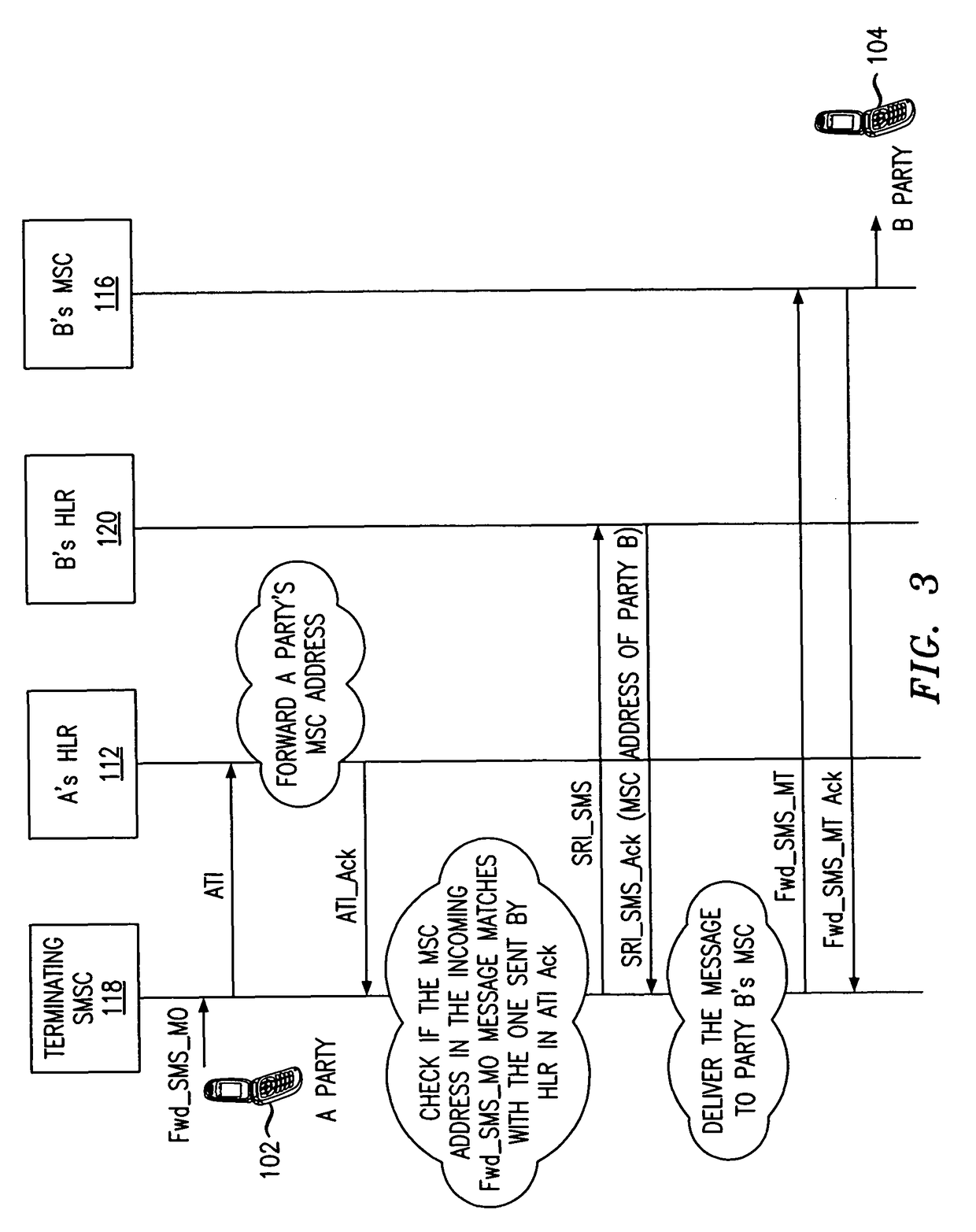
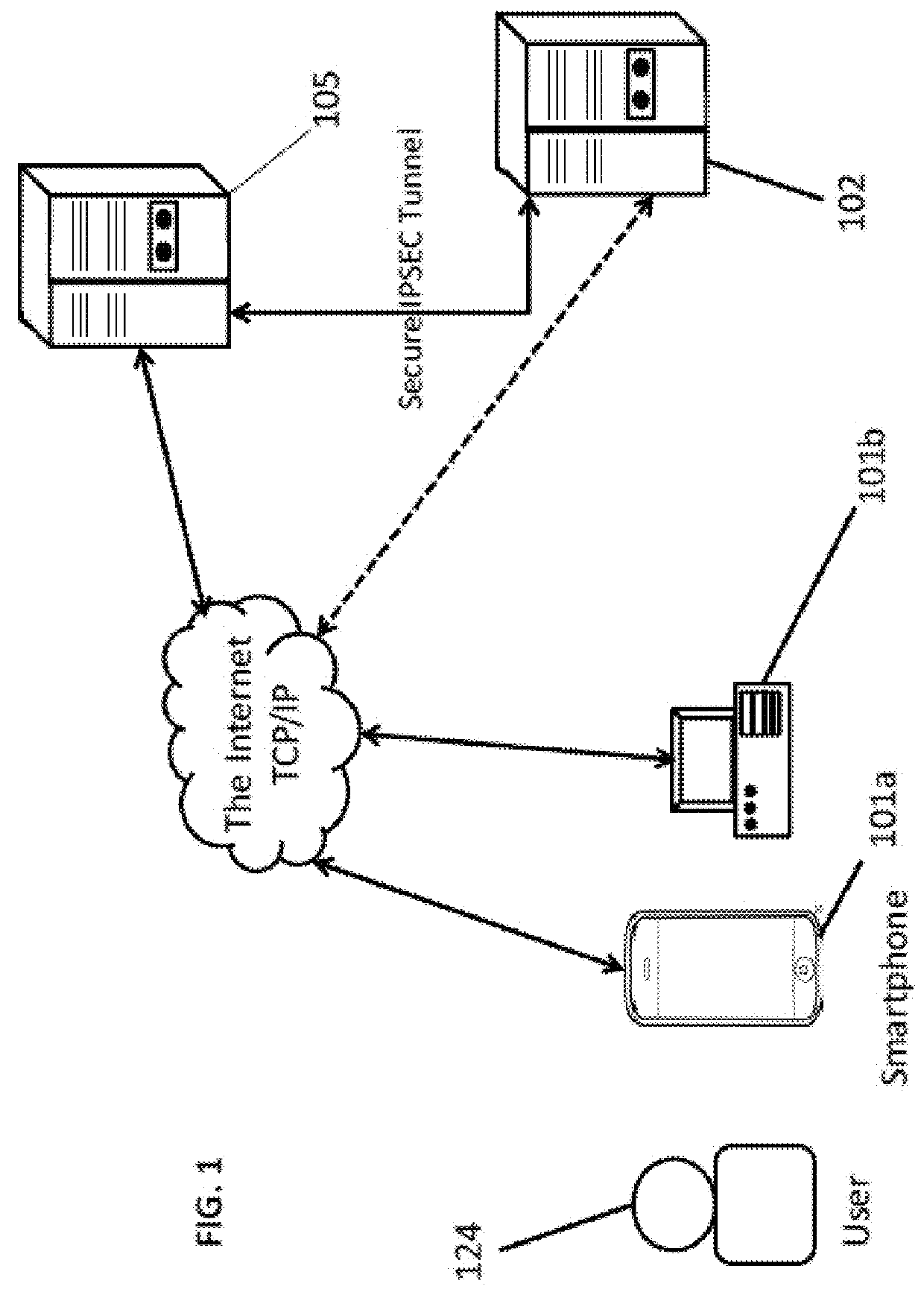
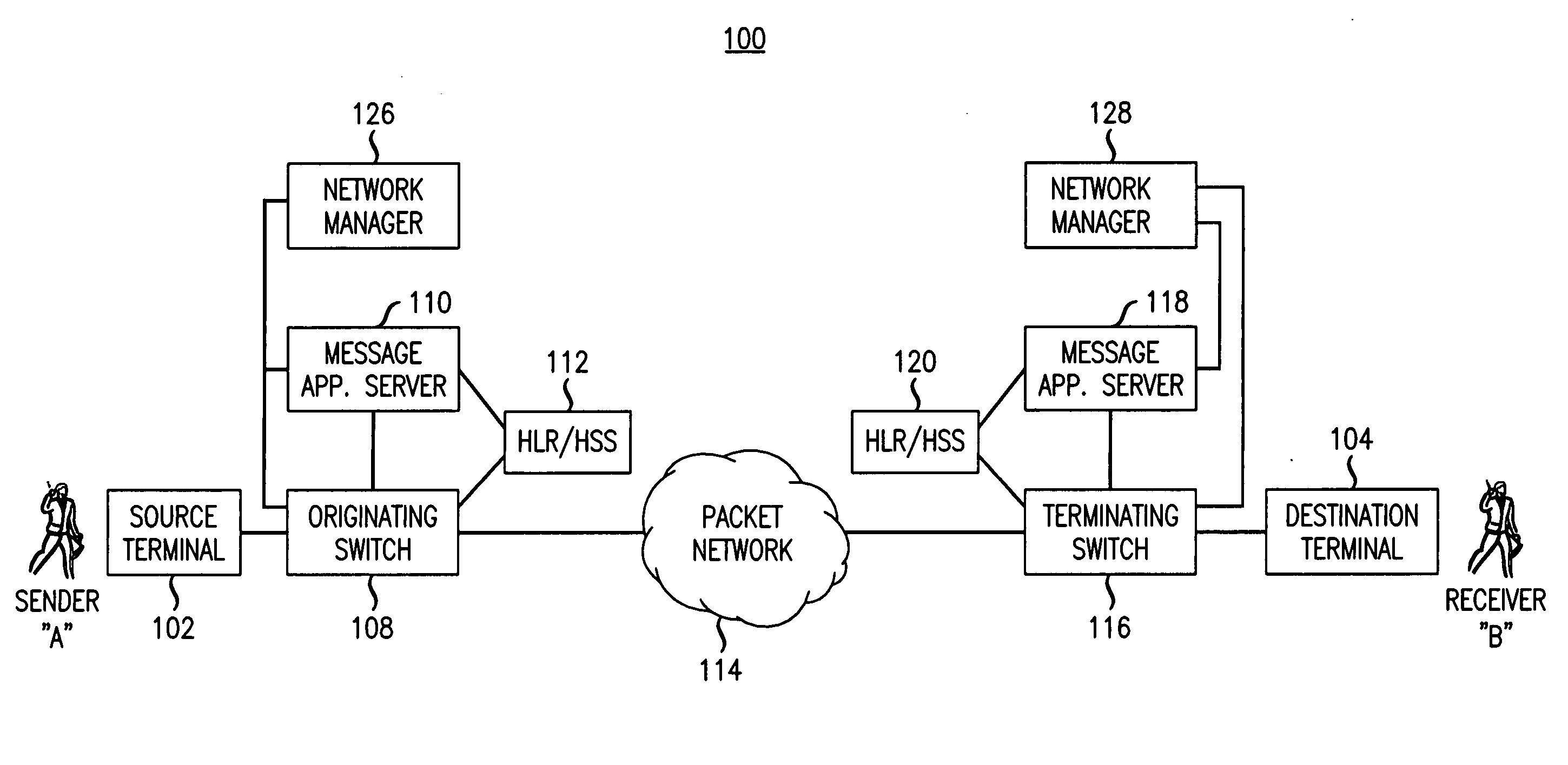
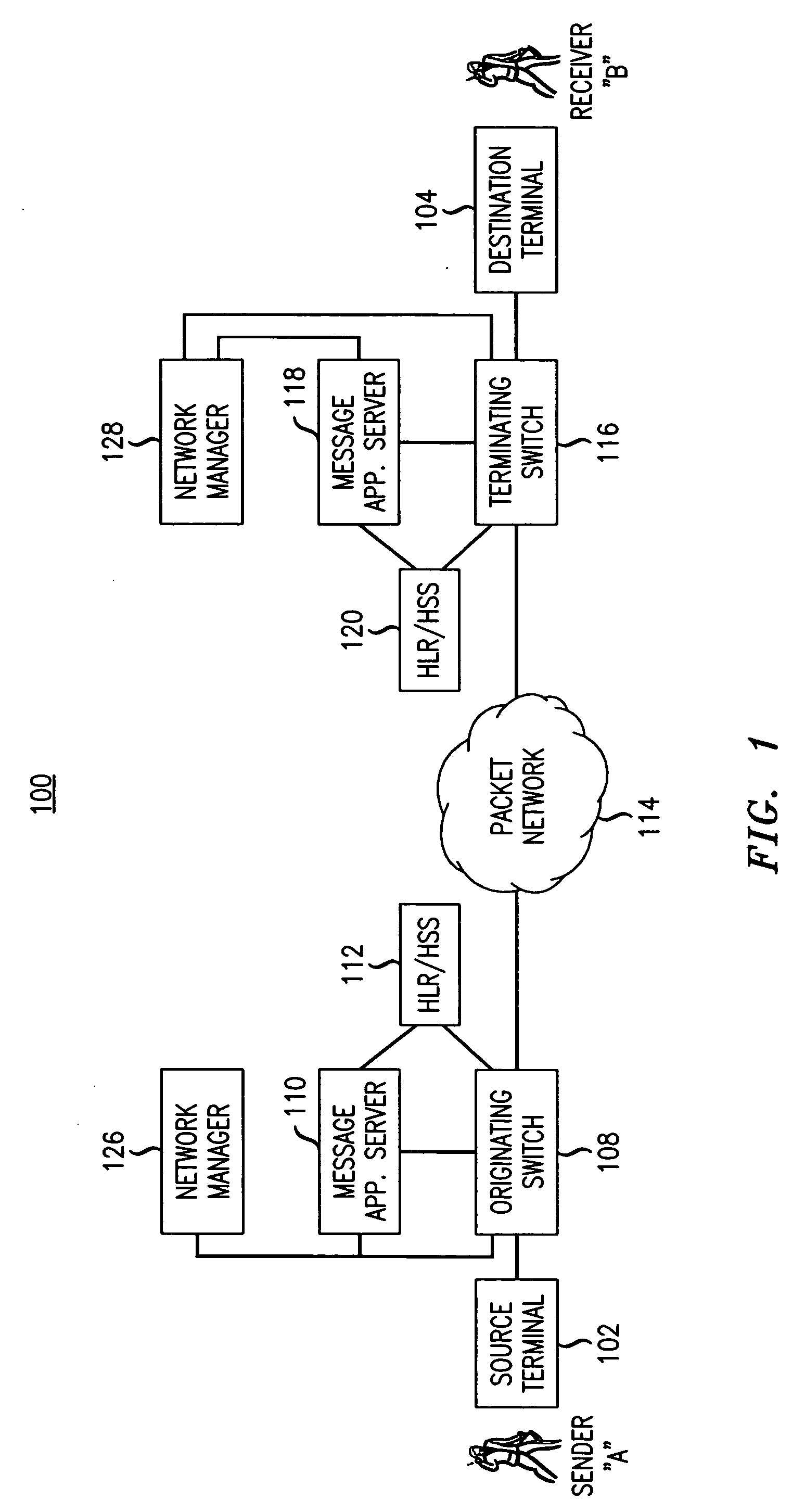
Message spoofing detection via validation of originating switch
Owner:ALCATEL LUCENT SAS
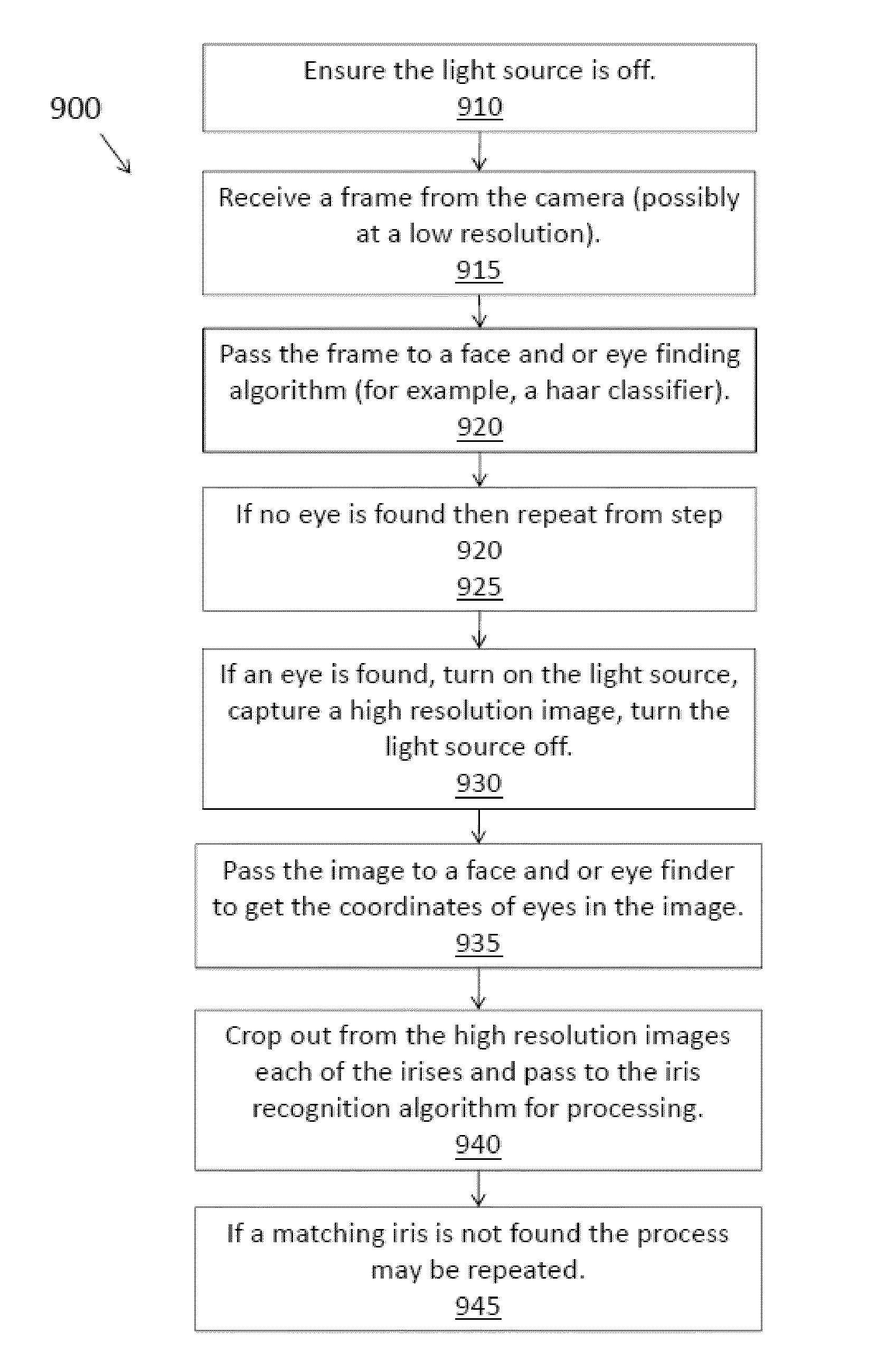
Systems and methods for performing iris identification and verification using mobile devices
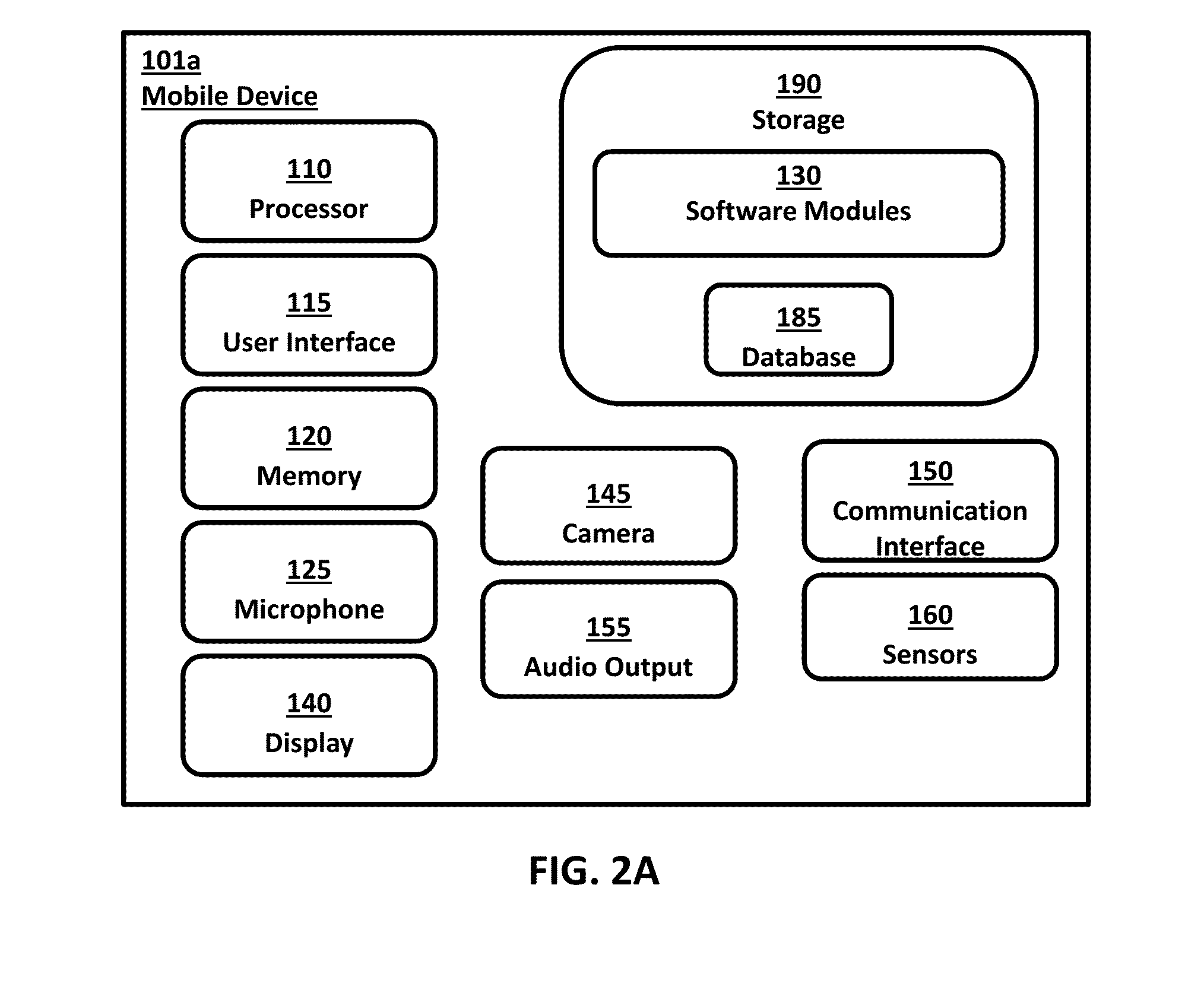
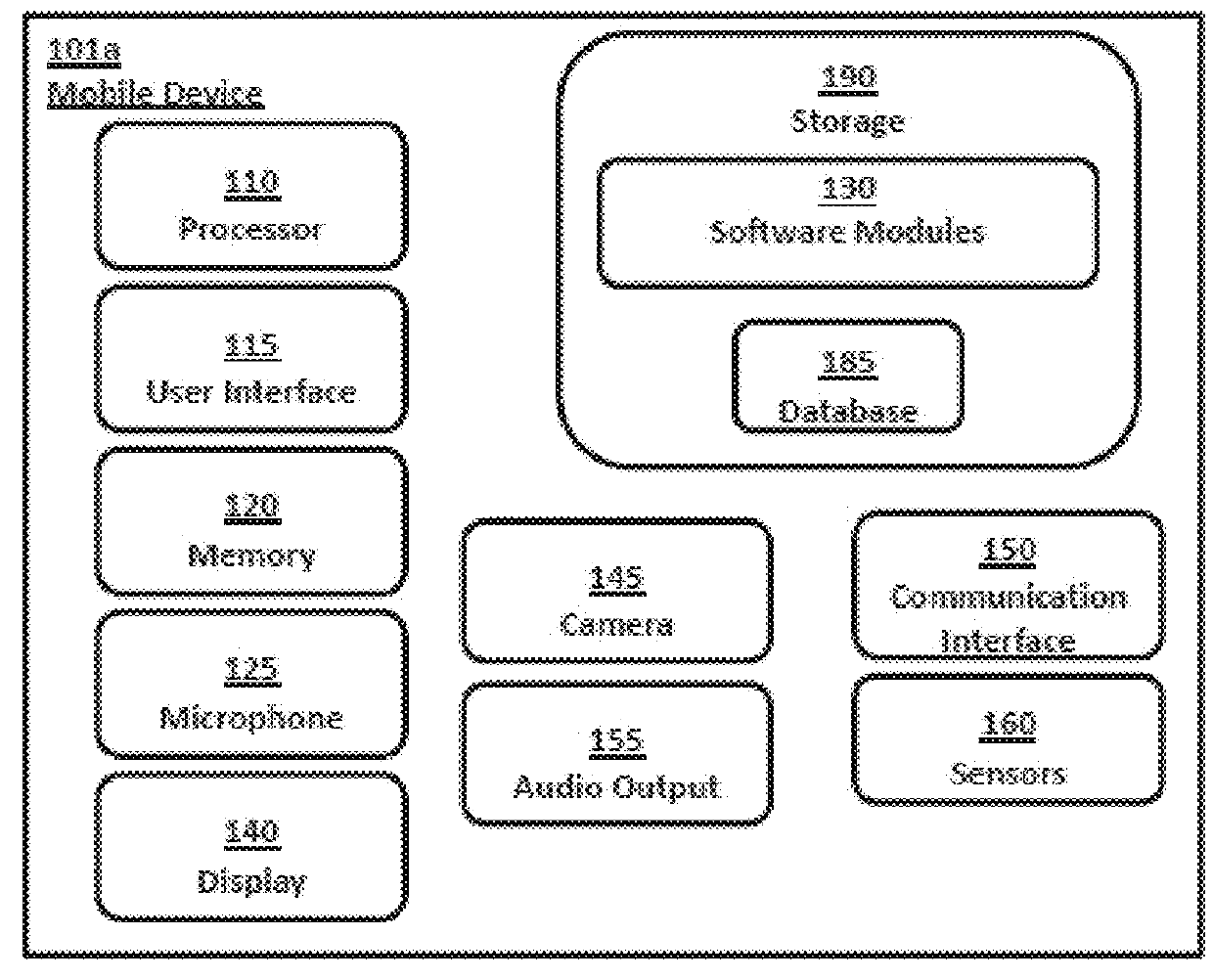
Technologies are presented herein in support of a system and method for performing iris identification and verification using mobile devices. Embodiments of the present invention concern a method for authenticating a user with a mobile device that includes steps for capturing imagery of a user's face, analyzing the imagery to identify the portion of the image depicting the user's eyes and segmenting the eye image to isolate the iris image data and encoding the iris image data in iris template. The present disclosure further describes authenticating the user based on the encoded iris template and additional techniques for preventing erroneous authentication caused by spoofing. In some examples, the anti-spoofing techniques may include capturing one or more images of a user's eyes and analyzing the captured images for indications of liveness based on reflection characteristics depicted in the imagery.
Owner:VERIDIUM IP LTD
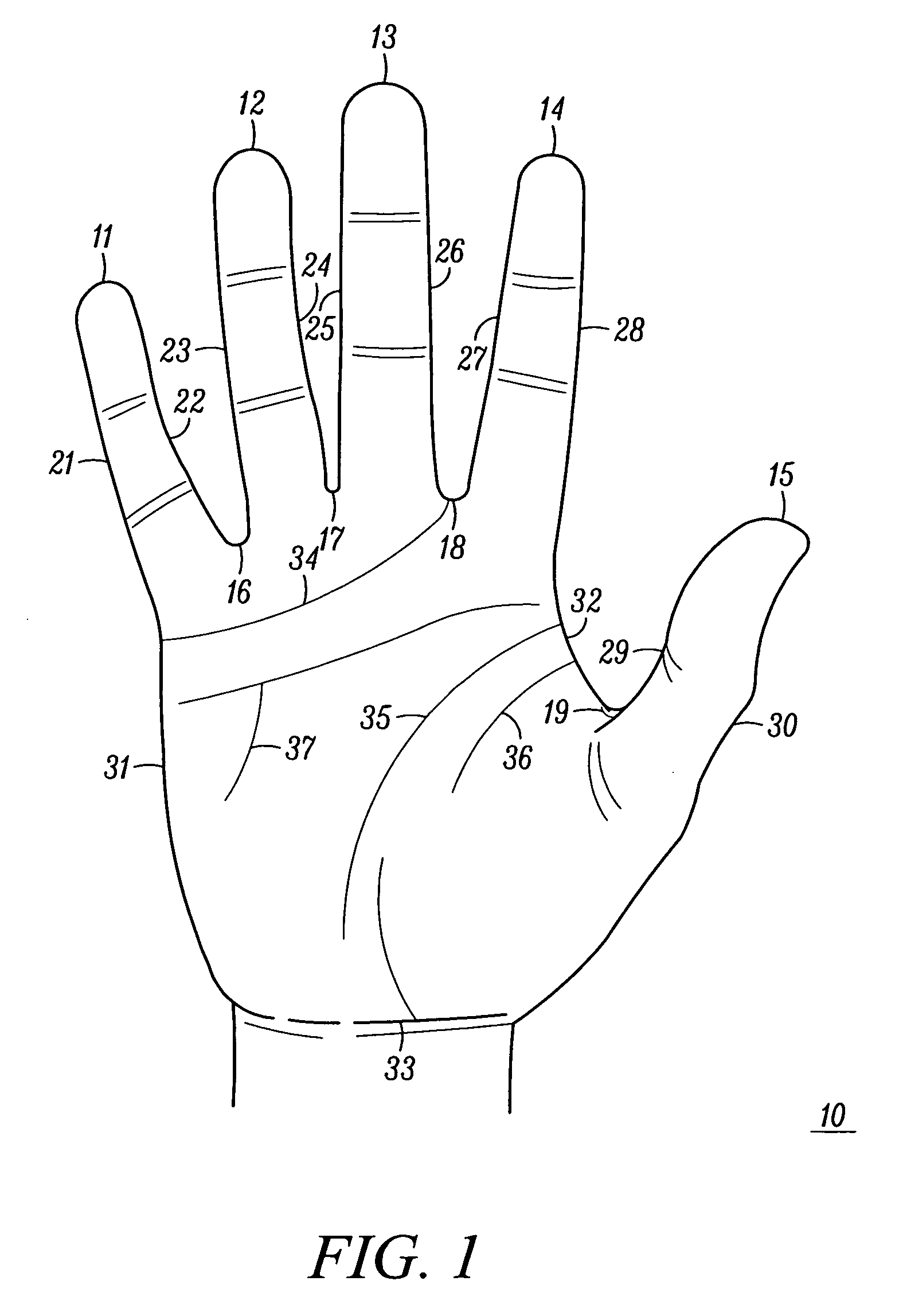
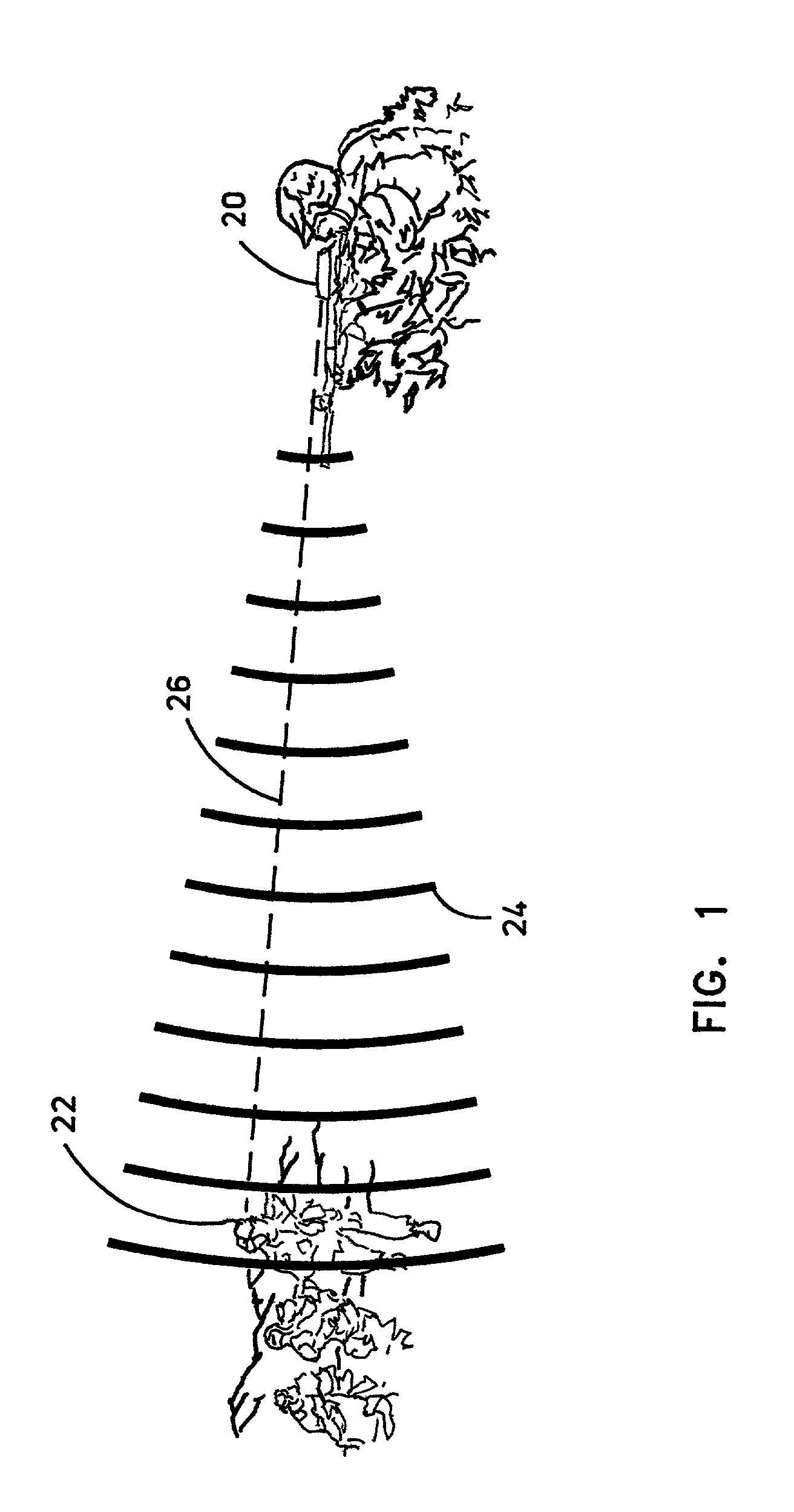
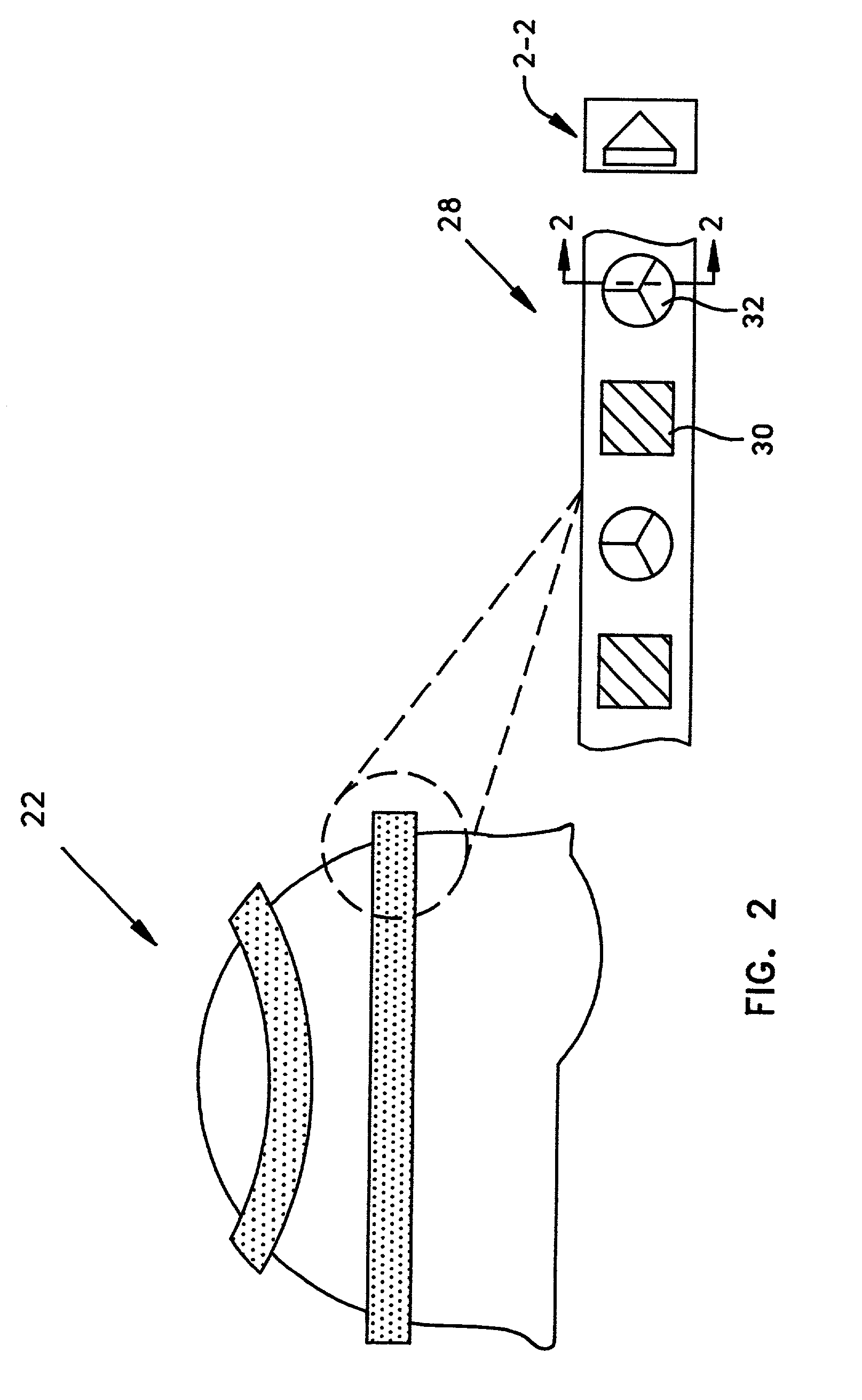
Recognition method using hand biometrics with anti-counterfeiting
ActiveUS20080002860A1Programme controlElectric signal transmission systemsPattern recognitionAnti spoofing
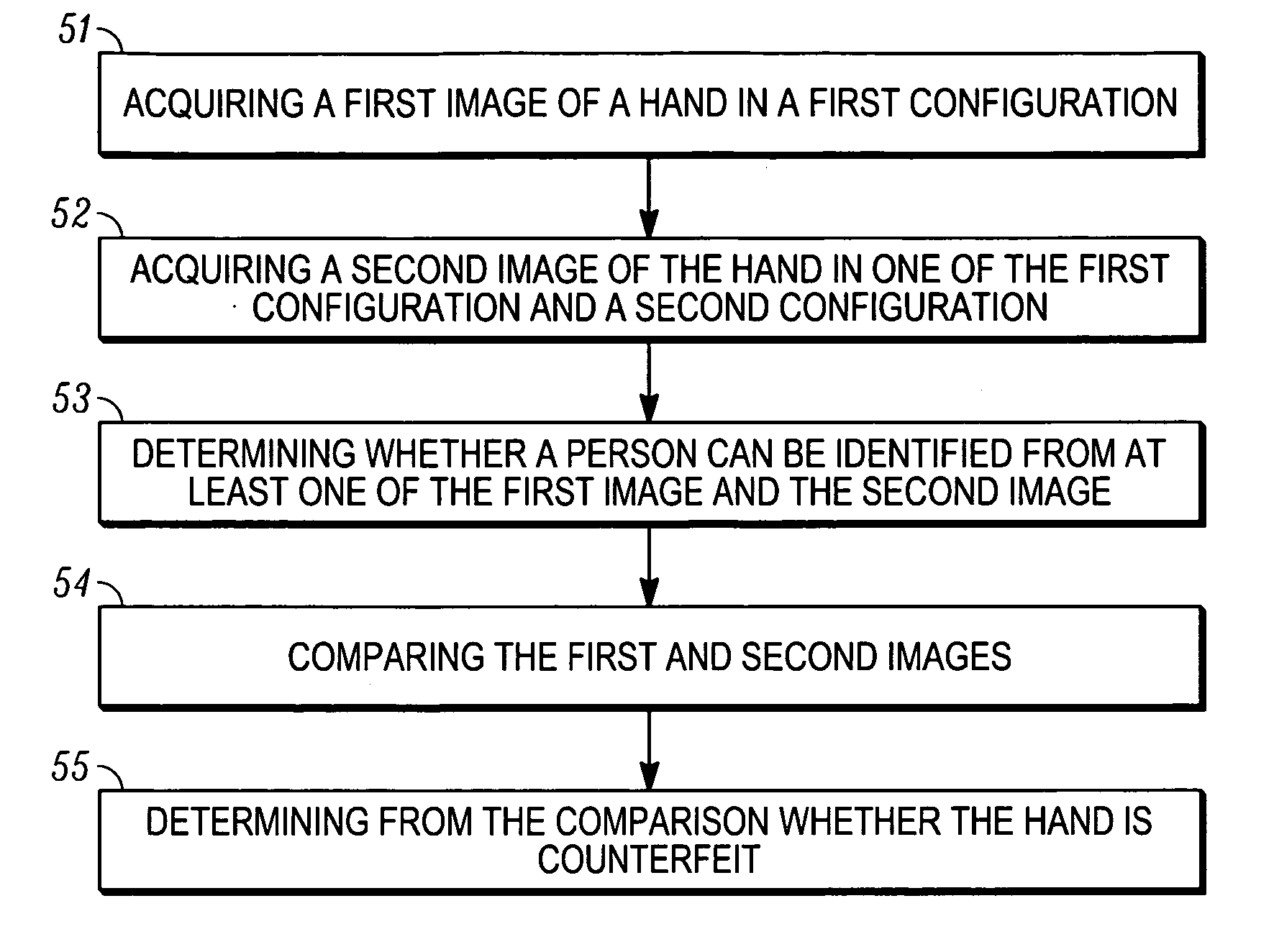
A method is provided for identifying and verifying a person using hand biometrics with an anti-spoofing measure. The method comprises acquiring (51) a first image (10) of a hand in a first configuration, acquiring (52) a second image (30, 40) of the hand in one of the first and a second configuration for comparison with the first image (10), determining (52) whether a person can be identified from at least one of the first image (10) and the second image (30, 40), and determining (55) from a comparison of the second image (30, 40) with the first image (10) whether the hand is a counterfeit.
Owner:GOOGLE TECH HLDG LLC
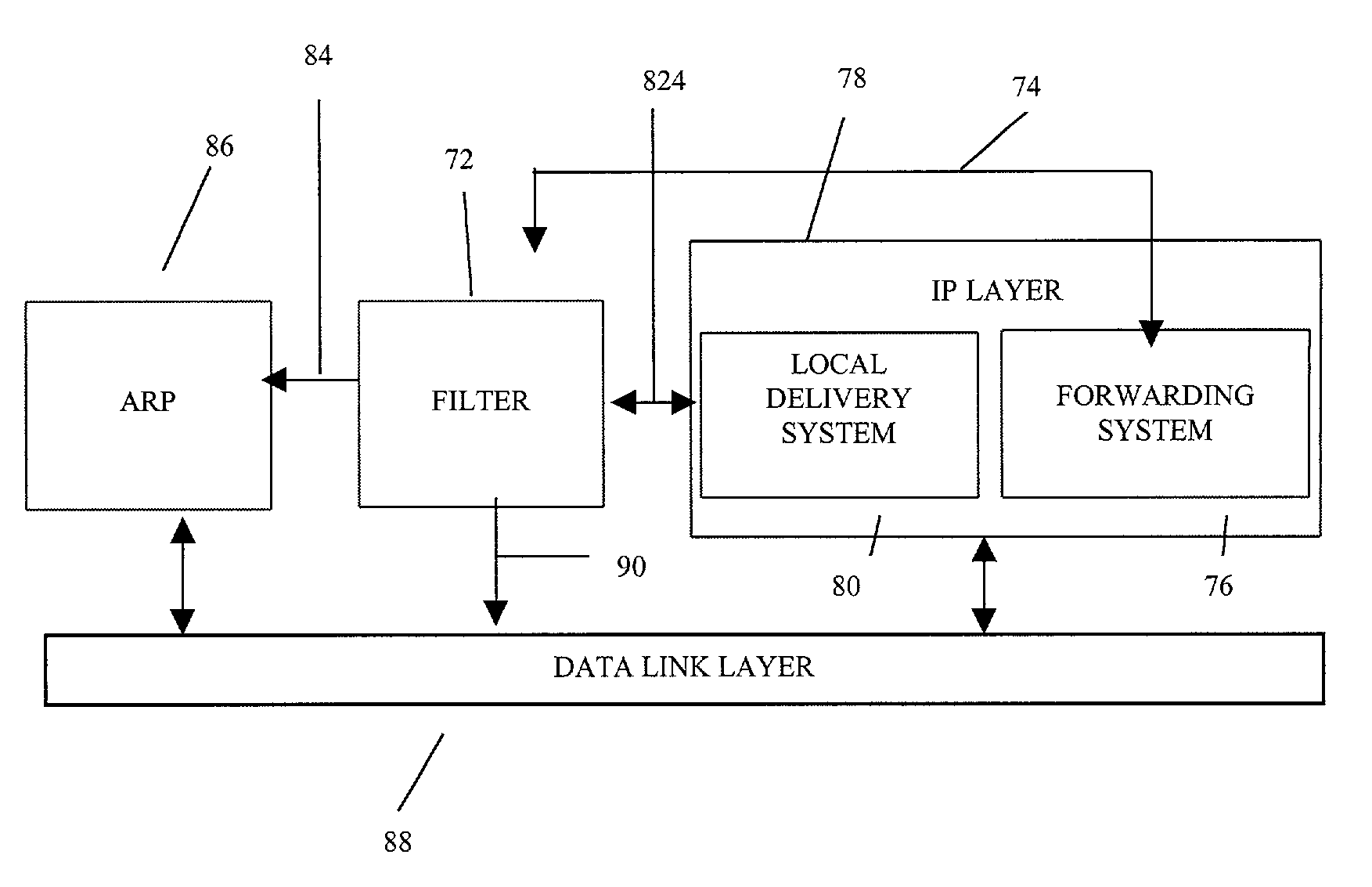
Method and system for filtering spoofed packets in a network
ActiveUS7360245B1Prevent counterfeitingMemory loss protectionError detection/correctionAnti spoofingPrivate network
A method and system is disclosed for preventing an address spoofing based attack from a private network. The private network has at least one host and at least one router connected therein for transporting at least one packet. An anti-spoofing filter is implemented in each interface of every router. When a packet is received on the interface, the filter determines whether the packet is address spoofed by comparing its source physical address derived from the received packet with expected physical address derived from interface IP address, a subnet mask of the interface, an ARP cache of the interface and a list of physical addresses of neighboring routers formed a priori If the packet is determined to be address spoofed, the received packet is discarded by the filter on the interface.
Owner:MICRO FOCUS SOFTWARE INC
Hybrid multi-sensor biometric identification device
ActiveUS20090166411A1Expand the marketCharacter and pattern recognitionDiagnostic recording/measuringProximity sensorAnti spoofing
An improved fingerprint sensing device is provided with multiple sensing apparatus, two or more of which operating on different sensing principles. For example, a capacitive sensor may be integrally formed with an optical sensor on a single substrate. Ideally, the multiple sensing apparatus are disposed such that they may sense nearly identical portions of a fingerprint simultaneously. A primary sensor may be employed to establish the identity of a user based on a fingerprint, while a secondary sensor may be employed to establish that the fingerprint is part of a live human (anti-spoofing). Integrated light sources may be provided to drive an optical sensor. The light sources may also provide visual cues for usage, and enhance the aesthetics of the device.
Owner:APPLE INC
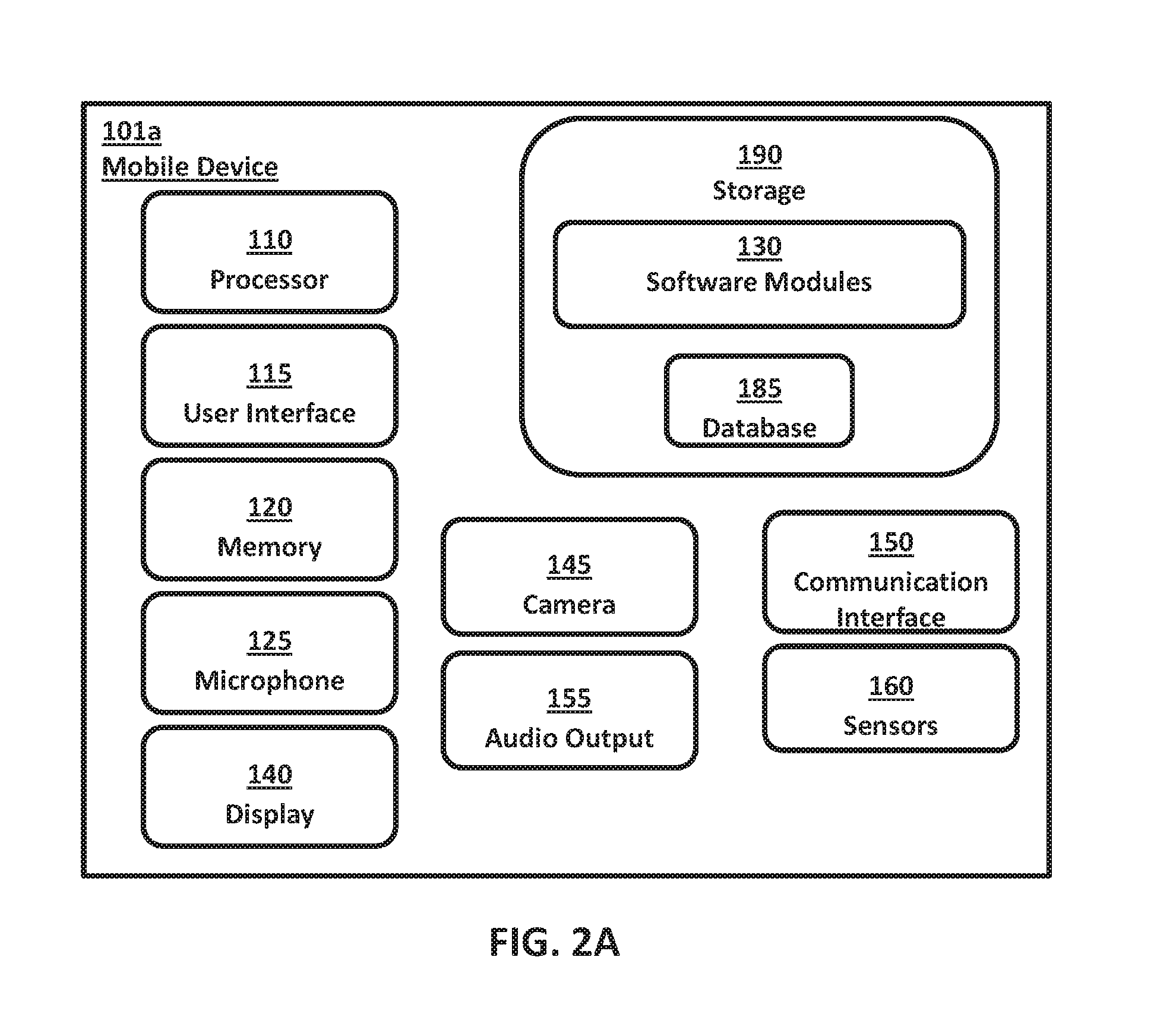
Systems and methods for performing fingerprint based user authentication using imagery captured using mobile devices
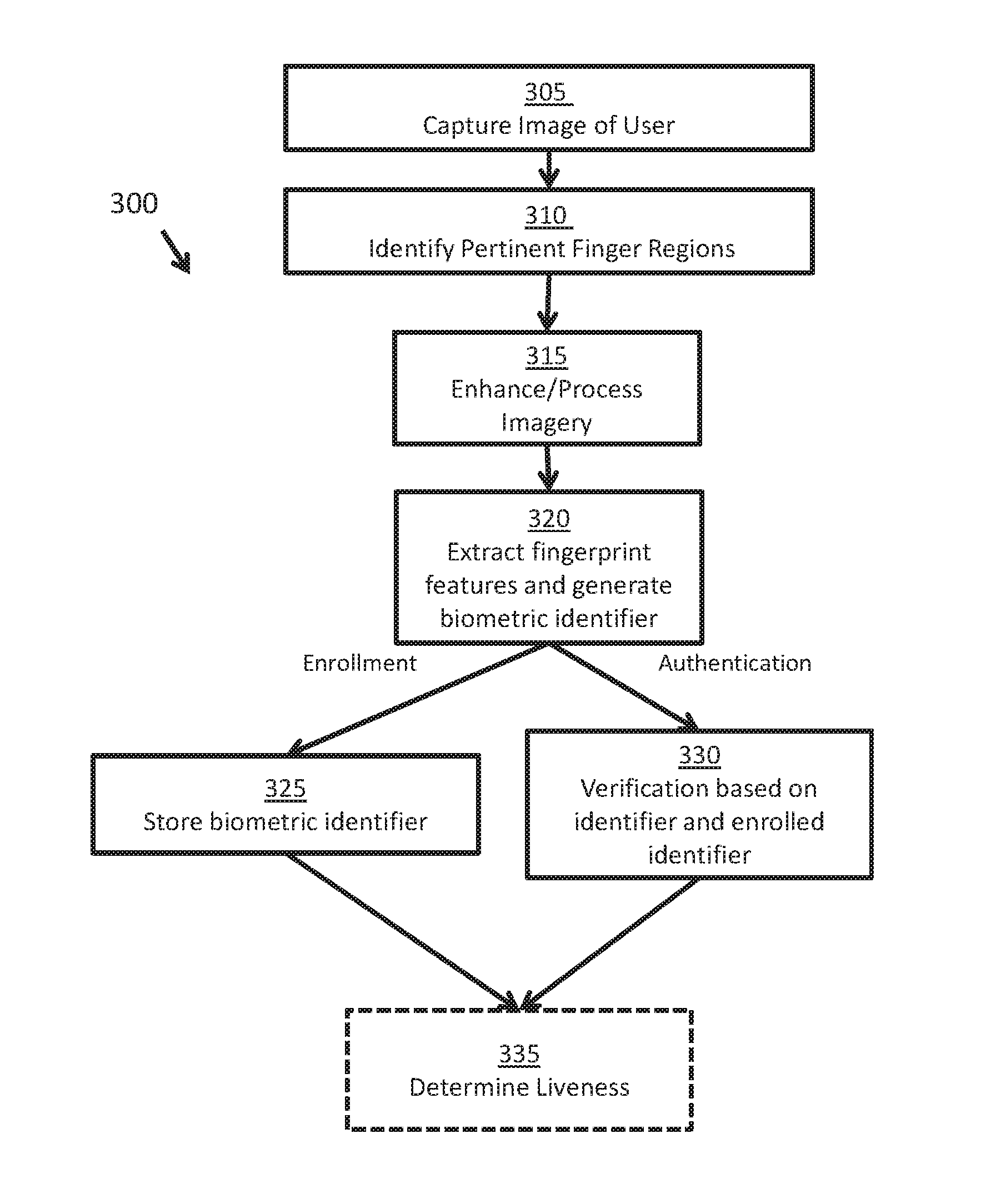
Technologies are presented herein in support of a system and method for performing fingerprint recognition. Embodiments of the present invention concern a system and method for capturing a user's biometric features and generating an identifier characterizing the user's biometric features using a mobile device such as a smartphone. The biometric identifier is generated using imagery captured of a plurality of fingers of a user for the purposes of authenticating / identifying the user according to the captured biometrics and determining the user's liveness. The present disclosure also describes additional techniques for preventing erroneous authentication caused by spoofing. In some examples, the anti-spoofing techniques may include capturing one or more images of a user's fingers and analyzing the captured images for indications of liveness.
Owner:VERIDIUM IP LTD
Message spoofing detection via validation of originating switch
ActiveUS20080026778A1Digital data authenticationRadio/inductive link selection arrangementsAnti spoofingComputer security
Owner:ALCATEL LUCENT SAS
Systems and methods for performing fingerprint based user authentication using imagery captured using mobile devices
Technologies are presented herein in support of a system and method for performing fingerprint recognition. Embodiments of the present invention concern a system and method for capturing a user's biometric features and generating an identifier characterizing the user's biometric features using a mobile device such as a smartphone. The biometric identifier is generated using imagery captured of a plurality of fingers of a user for the purposes of authenticating / identifying the user according to the captured biometrics and determining the user's liveness. The present disclosure also describes additional techniques for preventing erroneous authentication caused by spoofing. In some examples, the anti-spoofing techniques may include capturing one or more images of a user's fingers and analyzing the captured images for indications of liveness.
Owner:VERIDIUM IP LTD
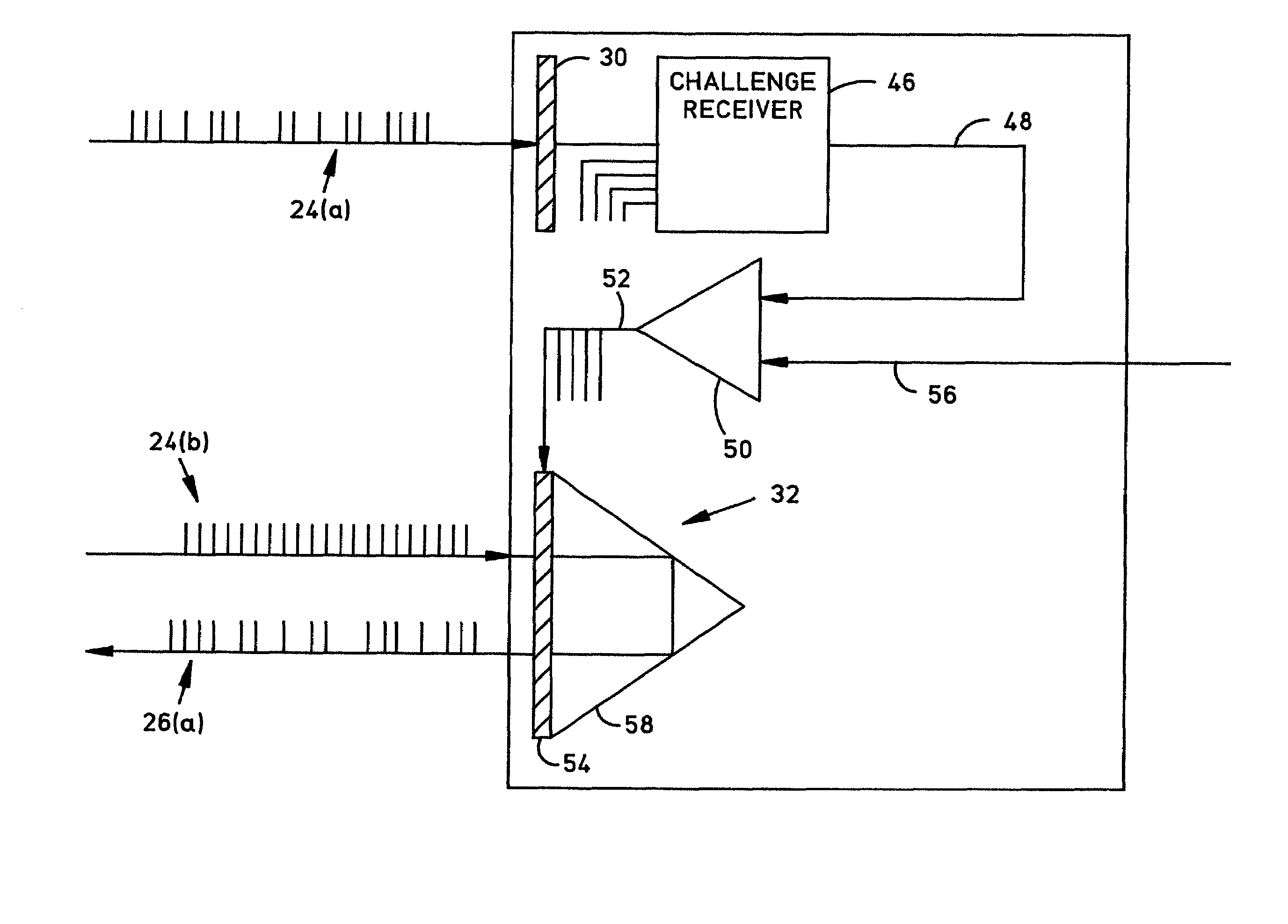
Secure covert combat identification friend-or-foe (IFF) system for the dismounted soldier
ActiveUS7308202B2Minimize opportunityReduce usageAiming meansElectromagnetic transmissionInfraredAnti spoofing
A combat IFF system, for use in a combat exercise or on the battlefield, including a helmet-mounted passive IFF response unit and a weapon-mounted IFF interrogatory unit for each soldier. Infrared (IR) signals are employed for both challenge and response. The IR response signal is a very narrowly-targeted reflection of the relatively narrow IR transmit signal, thereby minimizing interception opportunities. The transmit and response signals are encoded in a transaction that cannot be compromised even when either or both signals are intercepted and decoded by the enemy. The combat IFF system includes biometric anti-spoofing features that prevent any use by an enemy in possession of captured units. Military radio-frequency (RF) spectrum is not required so there are no bandwidth limitations on simultaneous IFF transactions in the battlefield. A combat IFF transaction is completed in milliseconds.
Owner:CUBIC DEFENSE SYST
Systems and methods for performing fingerprint based user authentication using imagery captured using mobile devices
Technologies are presented herein in support of a system and method for performing fingerprint recognition. Embodiments of the present invention concern a system and method for capturing a user's biometric features and generating an identifier characterizing the user's biometric features using a mobile device such as a smartphone. The biometric identifier is generated using imagery captured of a plurality of fingers of a user for the purposes of authenticating / identifying the user according to the captured biometrics and determining the user's liveness. The present disclosure also describes additional techniques for preventing erroneous authentication caused by spoofing. In some examples, the anti-spoofing techniques may include capturing one or more images of a user's fingers and analyzing the captured images for indications of liveness.
Owner:VERIDIUM IP LTD
Automatic dependent surveillance system secure ADS-S
InactiveUS7876259B2Analogue computers for vehiclesAnalogue computers for trafficSystem capacityFrequency spectrum
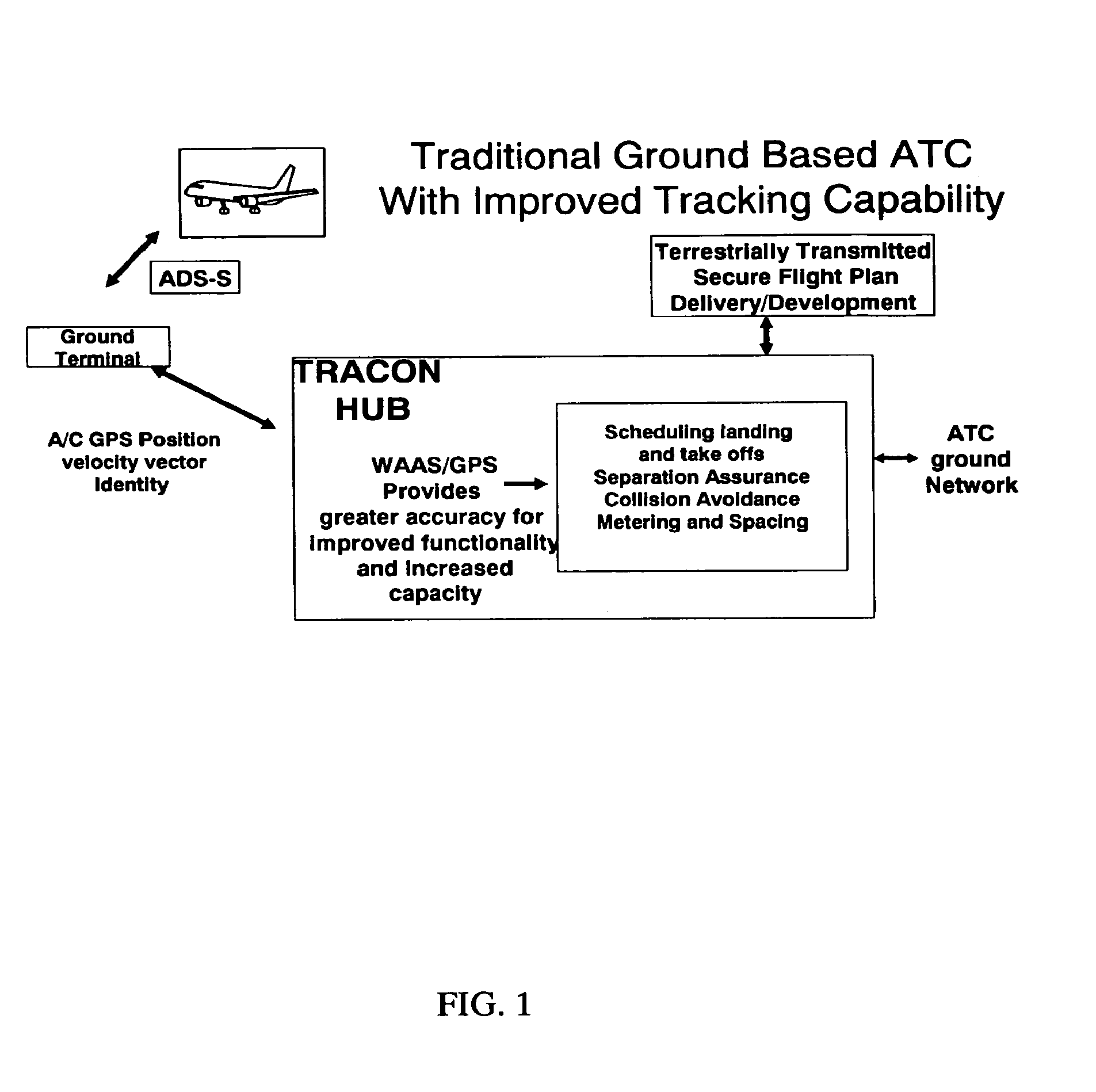
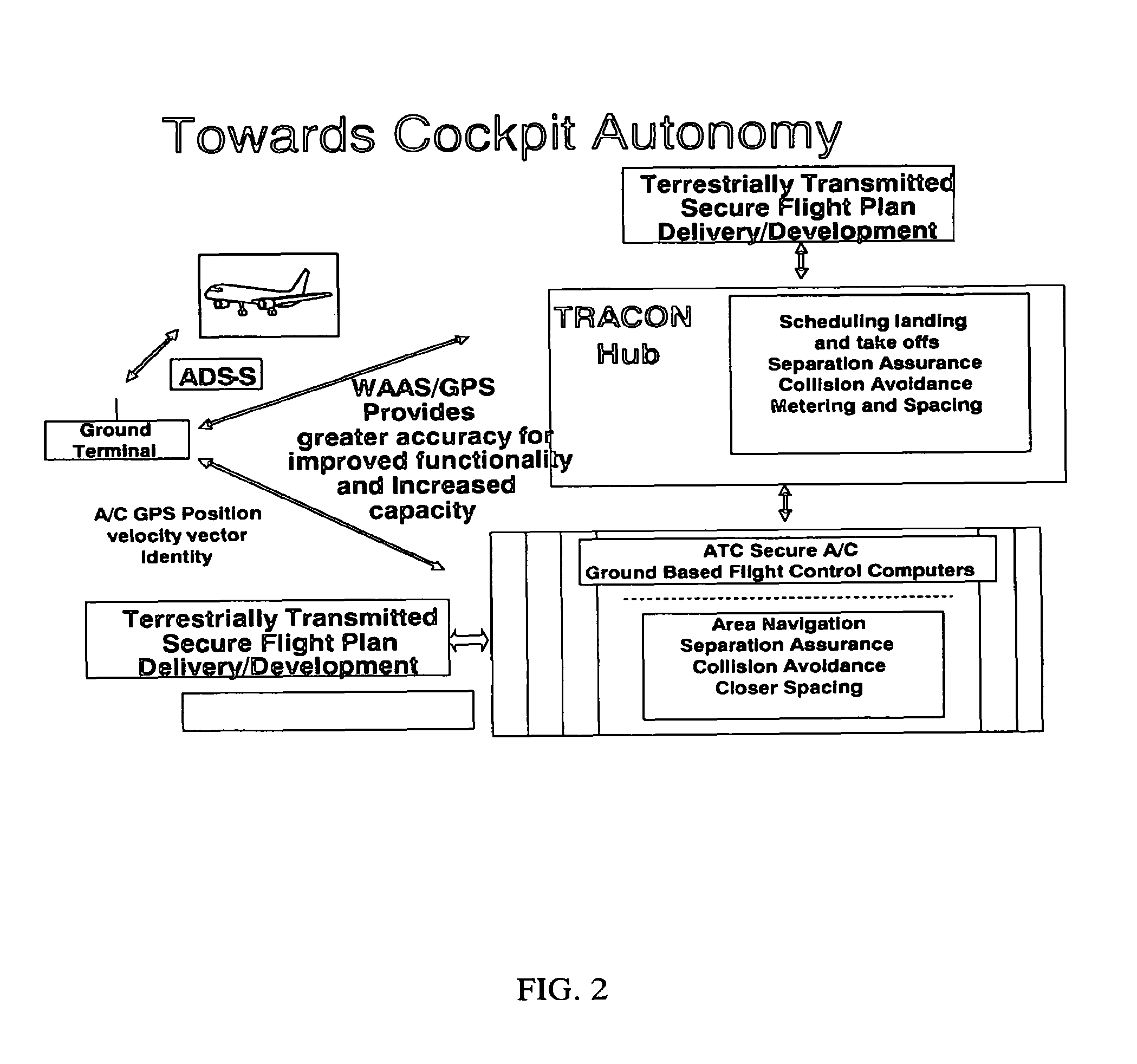
An air traffic control automatic dependent, WAAS / GPS based, surveillance system (ADS), for operation in the TRACON airspace. The system provides encryption protection against unauthorized reading of ADS messages and unauthorized position tracking of aircraft using multilateration techniques. Each aircraft has its own encryption and long PN codes per TRACON and transmit power is controlled to protect against unauthorized ranging on the ADS-S aircraft transmission. The encryption and PN codes can be changed dynamically. Several options which account for available bandwidth, burst data rates, frequency spectrum allocations, relative cost to implement, complexity of operation, degree of protection against unauthorized users, system capacity, bits per aircraft reply message and mutual interference avoidance techniques between ADS-S, ADS-B Enroute and Mode S / ATCRBS TRACON are disclosed. ADS messages are only transmitted as replies to ATC ground terminal interrogations (no squittering). Derivative surveillance backup systems provide an anti-spoofing capability.
Owner:SCHUCHMAN LEONARD
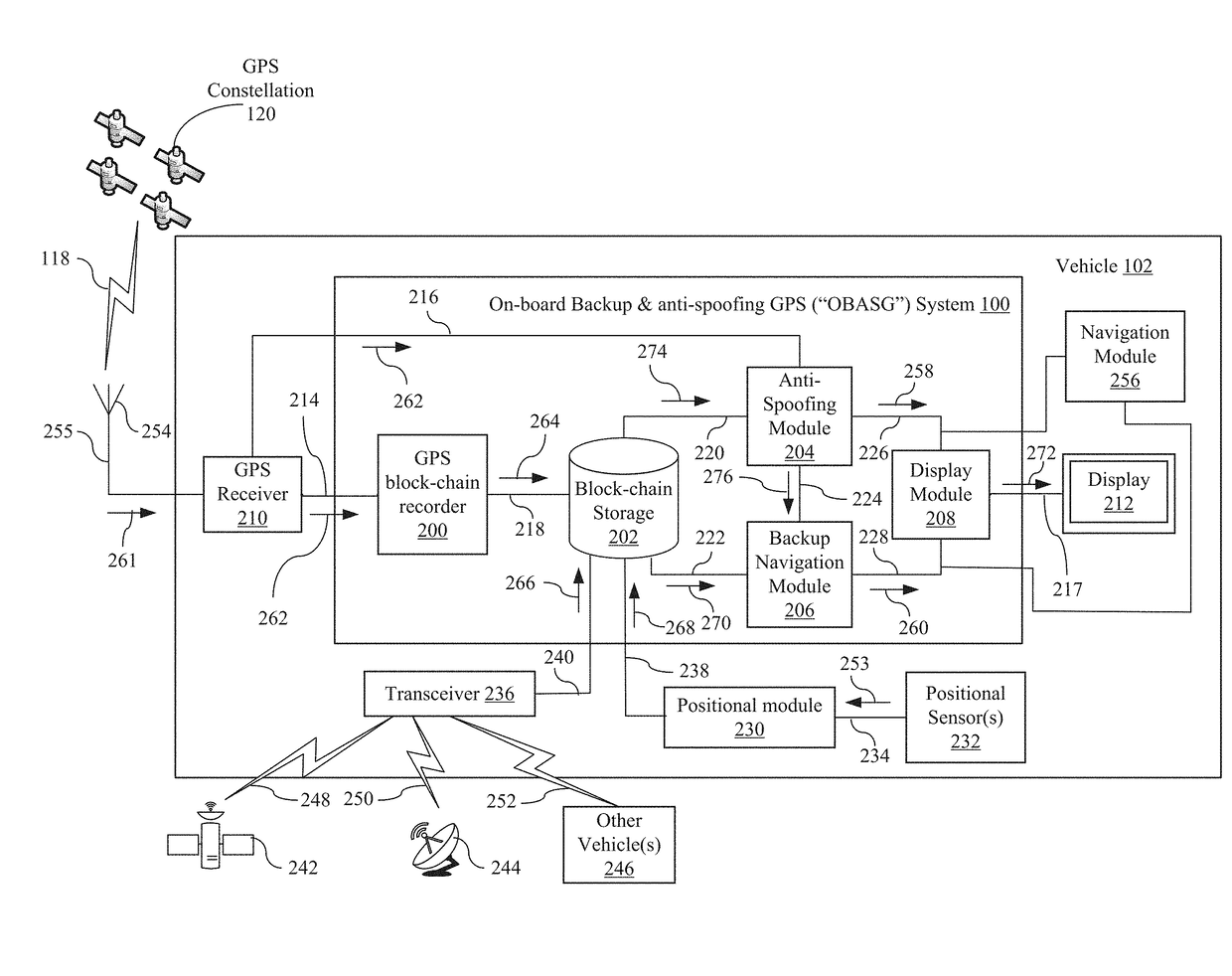
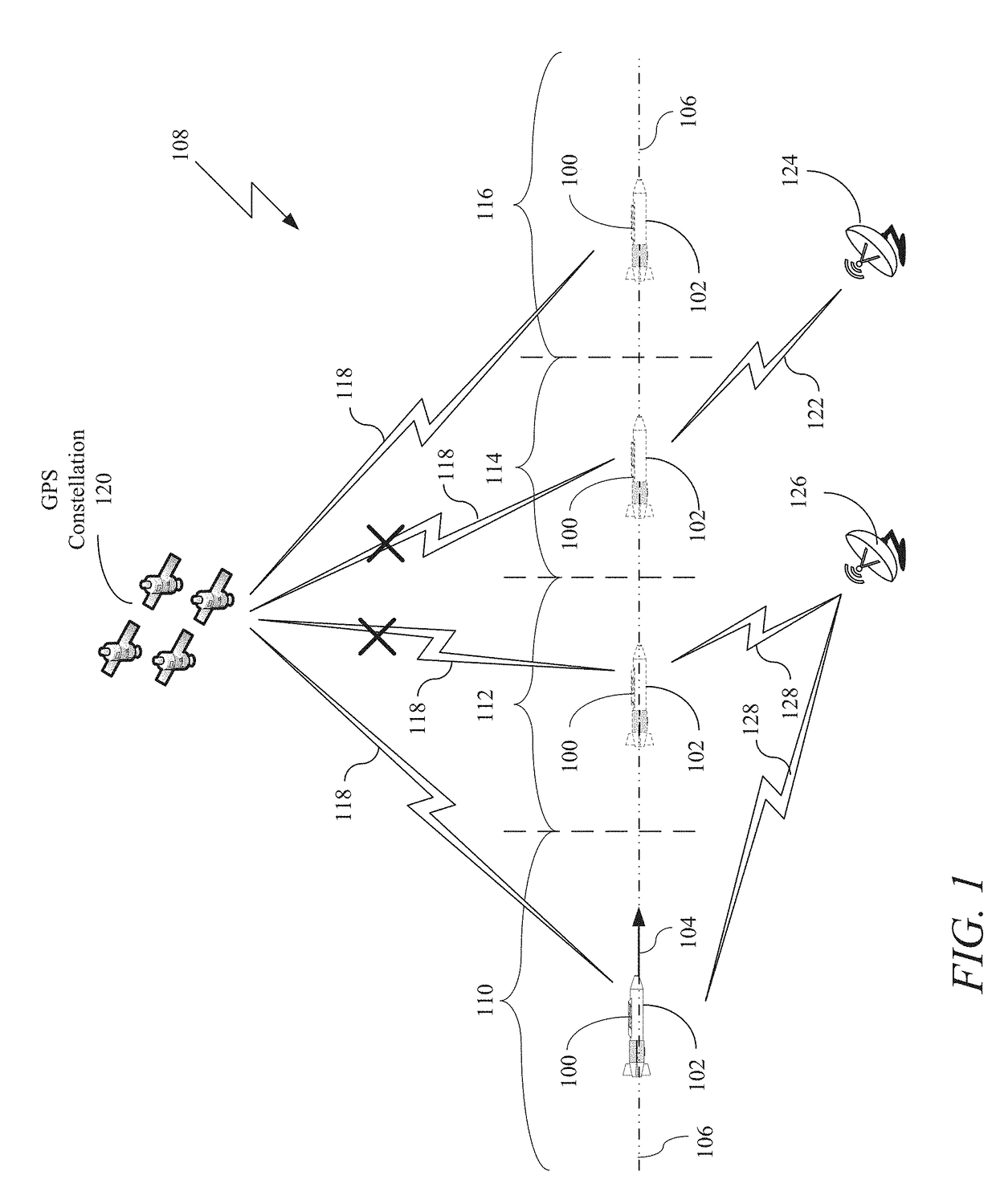
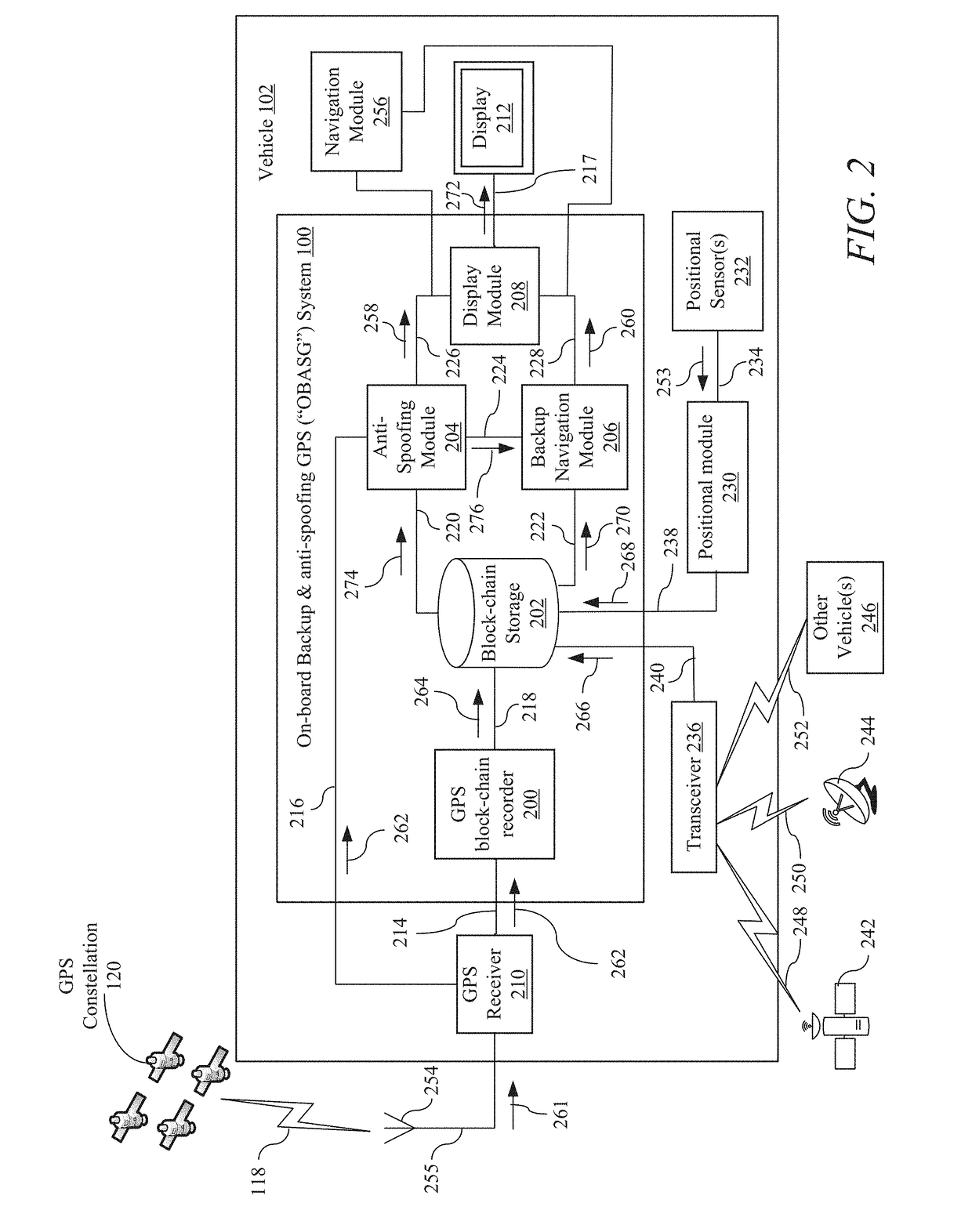
On-board backup and Anti-spoofing GPS system
Disclosed is an on-board backup and anti-spoofing GPS (“OBASG”) system for navigating a vehicle through an environment with a GPS receiver. The GPS receiver is configured to receive GPS signals within the environment where the GPS signals may suffer a GPS outage or are unreliable within the environment. In general, the OBASG includes a GPS block-chain recorder, a block-chain storage module, an anti-spoofing module, and a backup navigation module.
Owner:THE BOEING CO
Anti-spoofing system and methods useful in conjunction therewith
An anti-spoofing system operative for repulsing spoofing attacks in which an impostor presents a spoofed image of a registered end user, the system comprising a plurality of spoof artifact identifiers including a processor configured for identifying a respective plurality of spoofed image artifacts in each of a stream of incoming images and a decision maker including a processor configured to determine an individual image in the stream is authentic only if a function of artifacts identified therein is less than a threshold criterion.
Owner:ISITYOU
Countercheck method for automatically identifying speaker aiming to voice deception
ActiveCN105139857ACountermeasures work wellEnhanced confrontation abilitySpeech analysisCosine similaritySupport vector machine
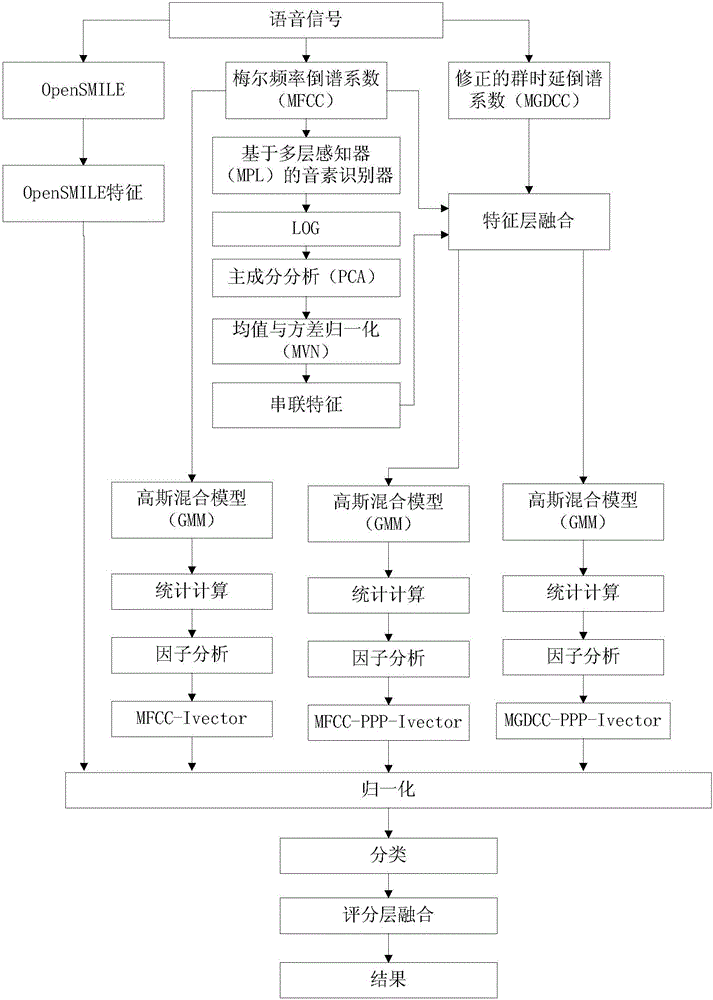
The invention provides a countercheck method for automatically identifying a speaker aiming to voice deception, which is a voice anti-spoofing technology based on a method combining various features and a plurality of sub-systems. According to the invention, the serial features of the posterior probability of a phoneme in the phonological level and the MFCC features of voice level or MFDCC features of phase level are combined, thus the performance of the system is significantly enhanced. By combining the provided i-vector sub-system and OpenSMILE (open Speech and Music Interpretation by Large Space Extraction criterion containing voice and rhythmic information, the final presentation of the system is further enhanced. To a back-end model, the development datum are used; and under the situation of knowing deceptive attacks, a two-level support vector machine has better performance compared with one-level cosine similarity or PLDA evaluations, while the one-level evaluation approach has better robustness under the situation without seeing the test datum and knowing the deceptive conditions.
Owner:SUN YAT SEN UNIV +1
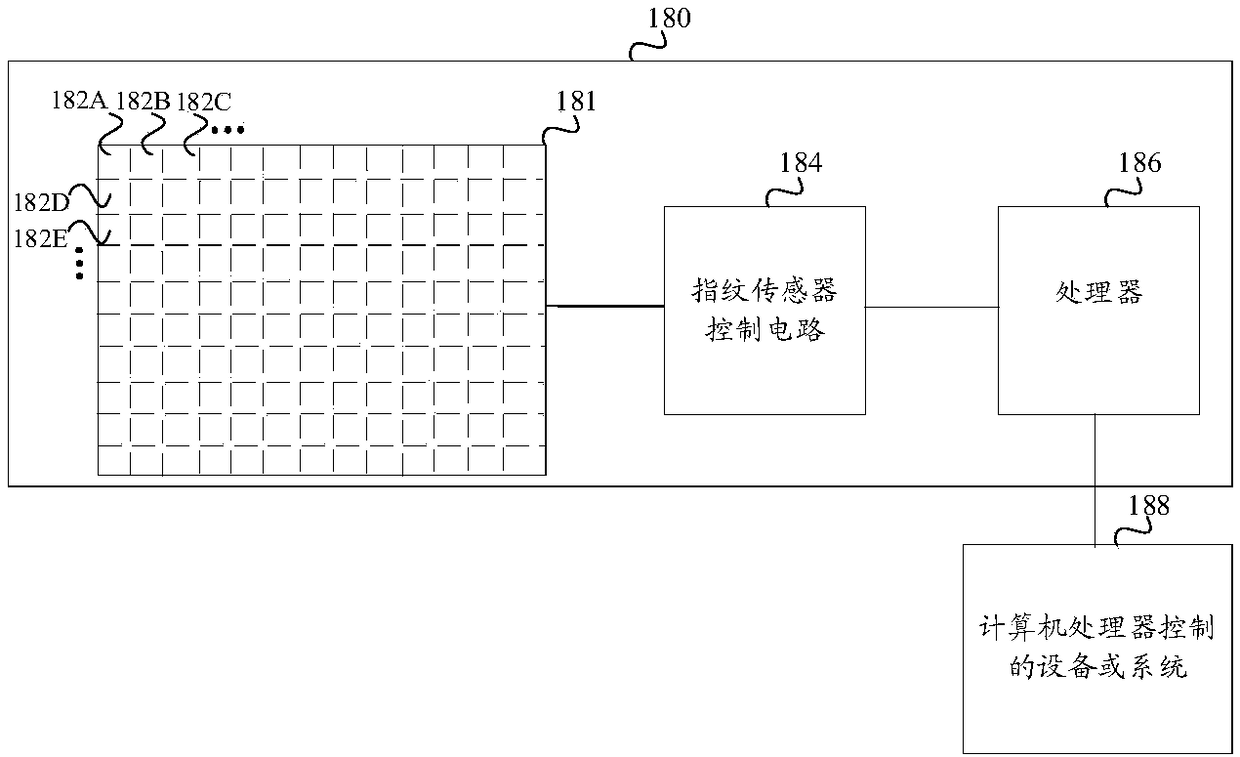
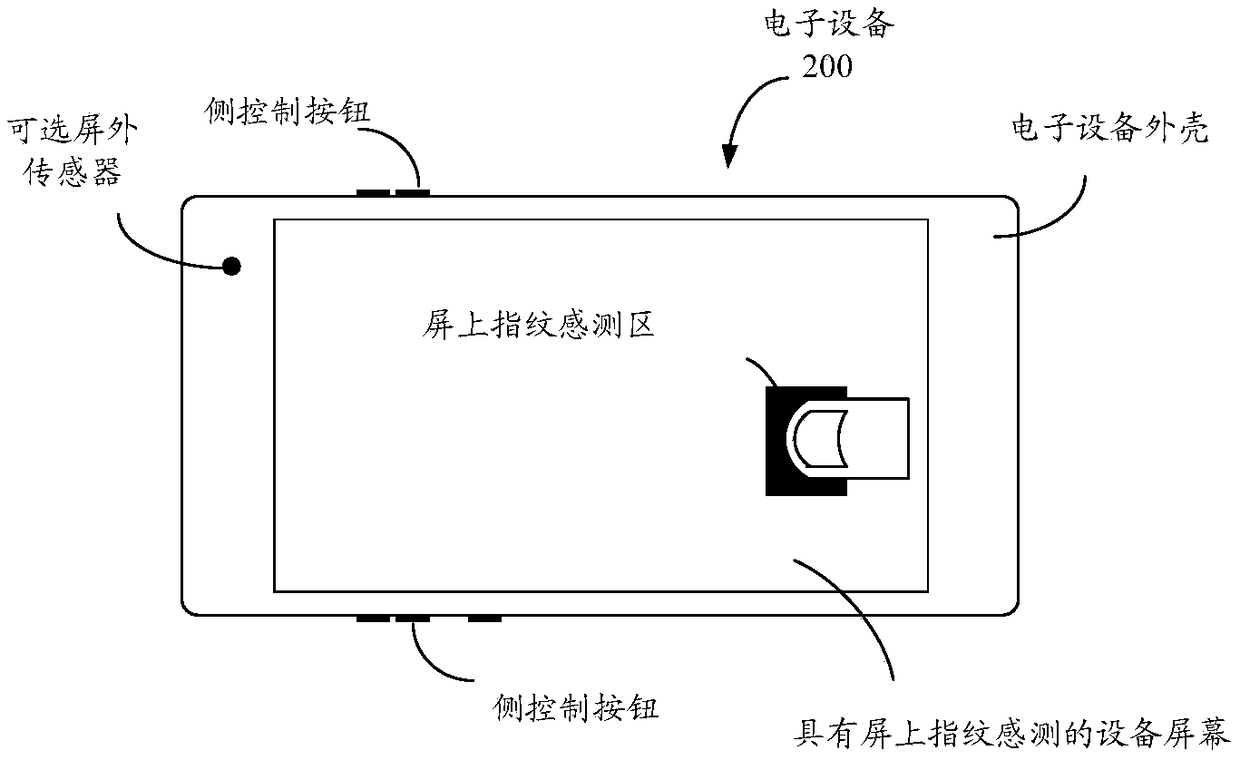
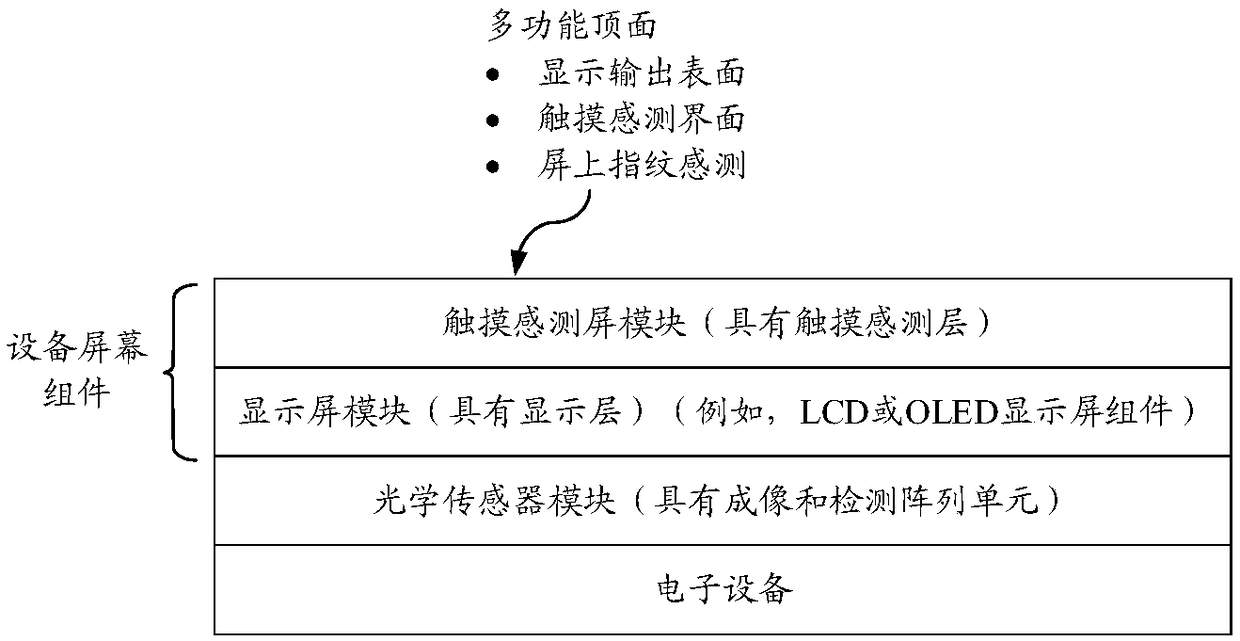
Anti-spoofing sensing for rejecting fake fingerprint patterns in under-screen optical sensor module for on-screen fingerprint sensing
Devices and optical sensor modules are provided for provide on-screen optical sensing of fingerprints by using a under-LCD or OLED screen optical sensor module that captures and detects returned lightand anti-spoofing sensing for rejecting fake fingerprint models based on capacitive sensing or optical sensing.
Owner:SHENZHEN GOODIX TECH CO LTD
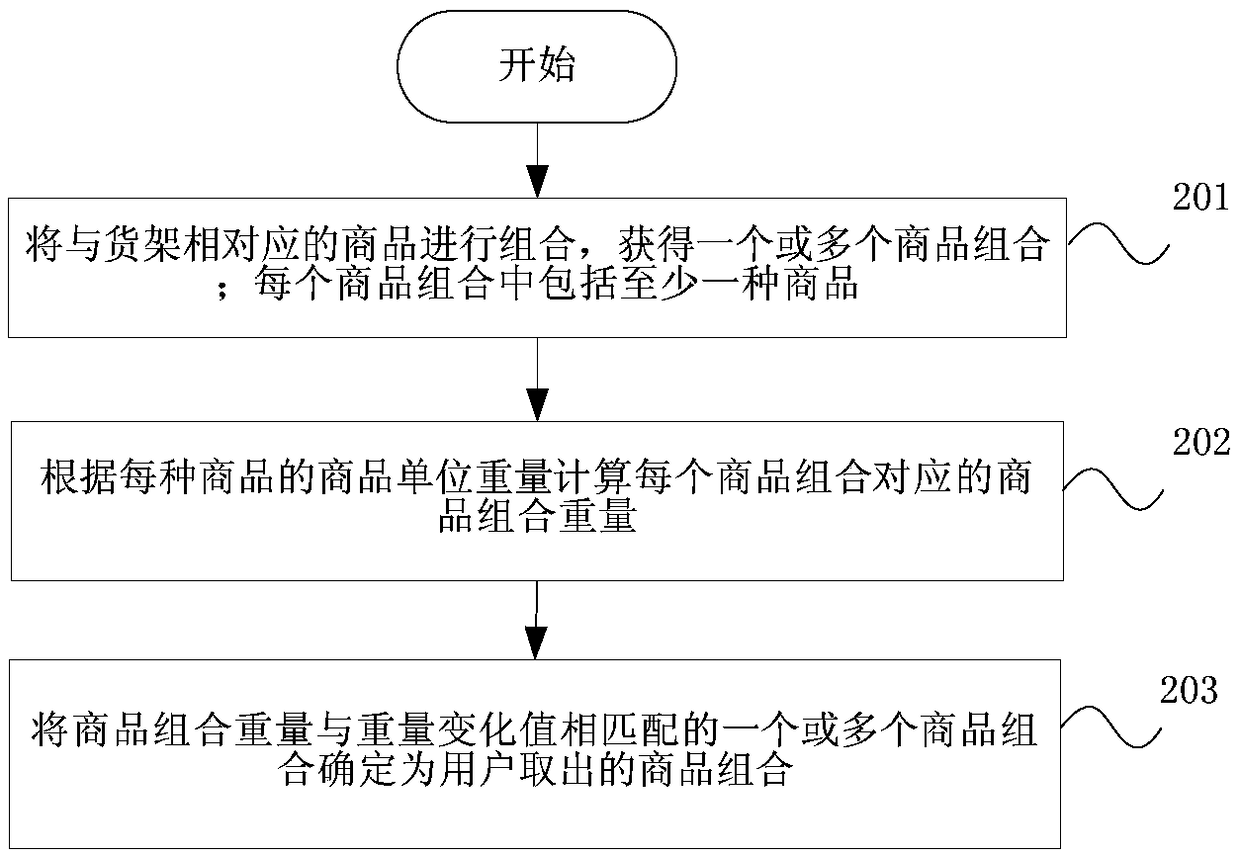
Identification method and device for shopping goods and vending machine
ActiveCN108875664ALow costEasy to identifyCoin-freed apparatus detailsCharacter and pattern recognitionAnti spoofingWeight change
The invention provides an identification method and device for shopping goods and a vending machine, and relates to the technical field of the vending machine. The method comprises the following stepsof: determining the weight change value of a shelf in which the weight changes and determining a goods combination taken by a user when a door closing signal of the vending machine is received; obtaining a goods result to be identified based on an identification result of a monitoring image corresponding to the shelf, and determining the goods shopped by the user according to the to-be-recognizedgoods result if the goods combination is matched with the to-be-identified goods result. According to the identification method and device and the vending machine, it is not necessary to attach labels or other operations to the goods, the cost of the goods is not increased, and the replenishment is convenient; the double verification is carried out on the goods information shopped by the user through the combination of a camera device and a weighing device, so that the abnormality of the goods can be accurately identified, the anti-spoofing capability is effectively improved, and the reliability of the transaction is enhanced; the brand-new sale form of the goods is realized, and the experience of the user can be improved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
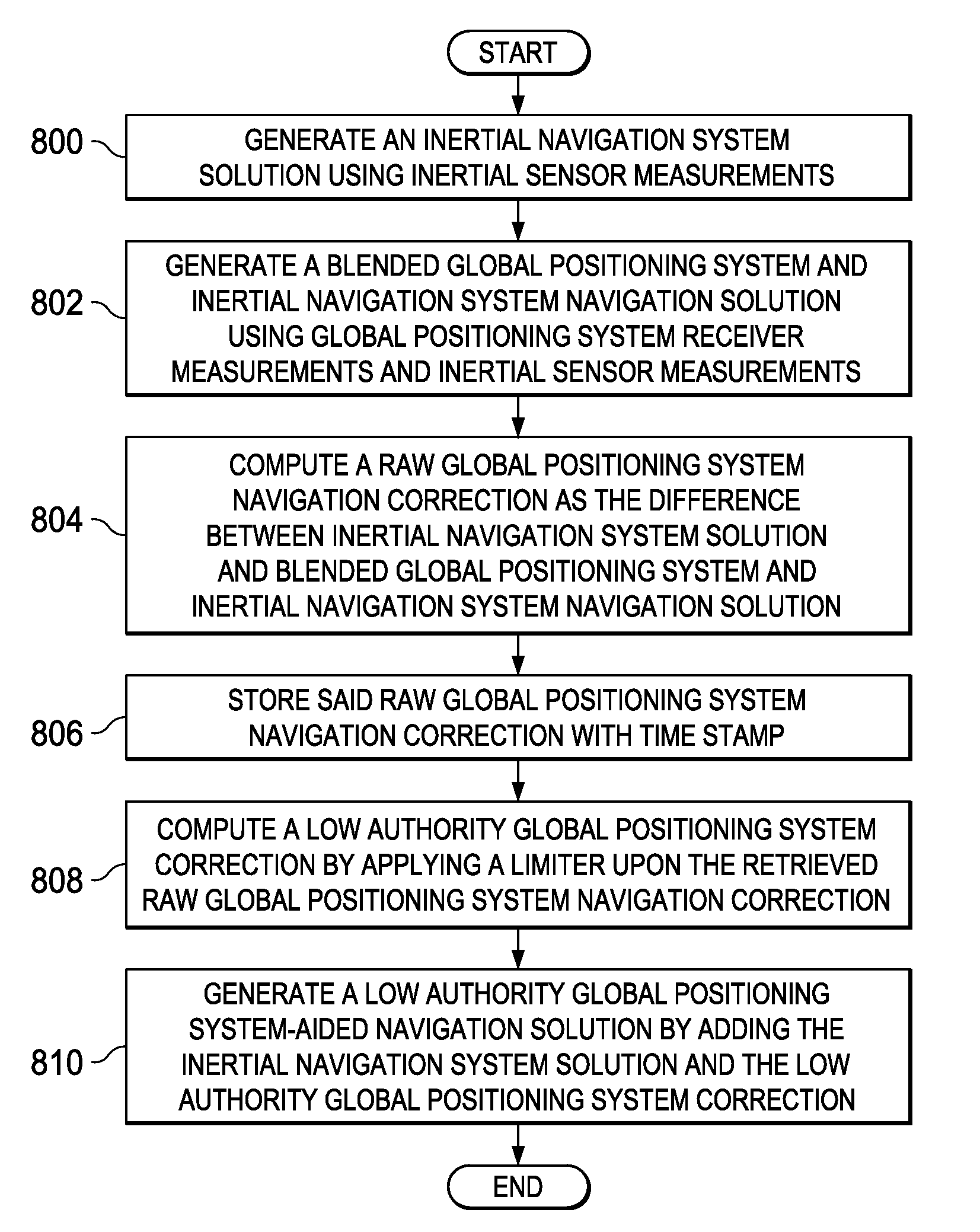
Low authority GPS aiding of navigation system for Anti-spoofing
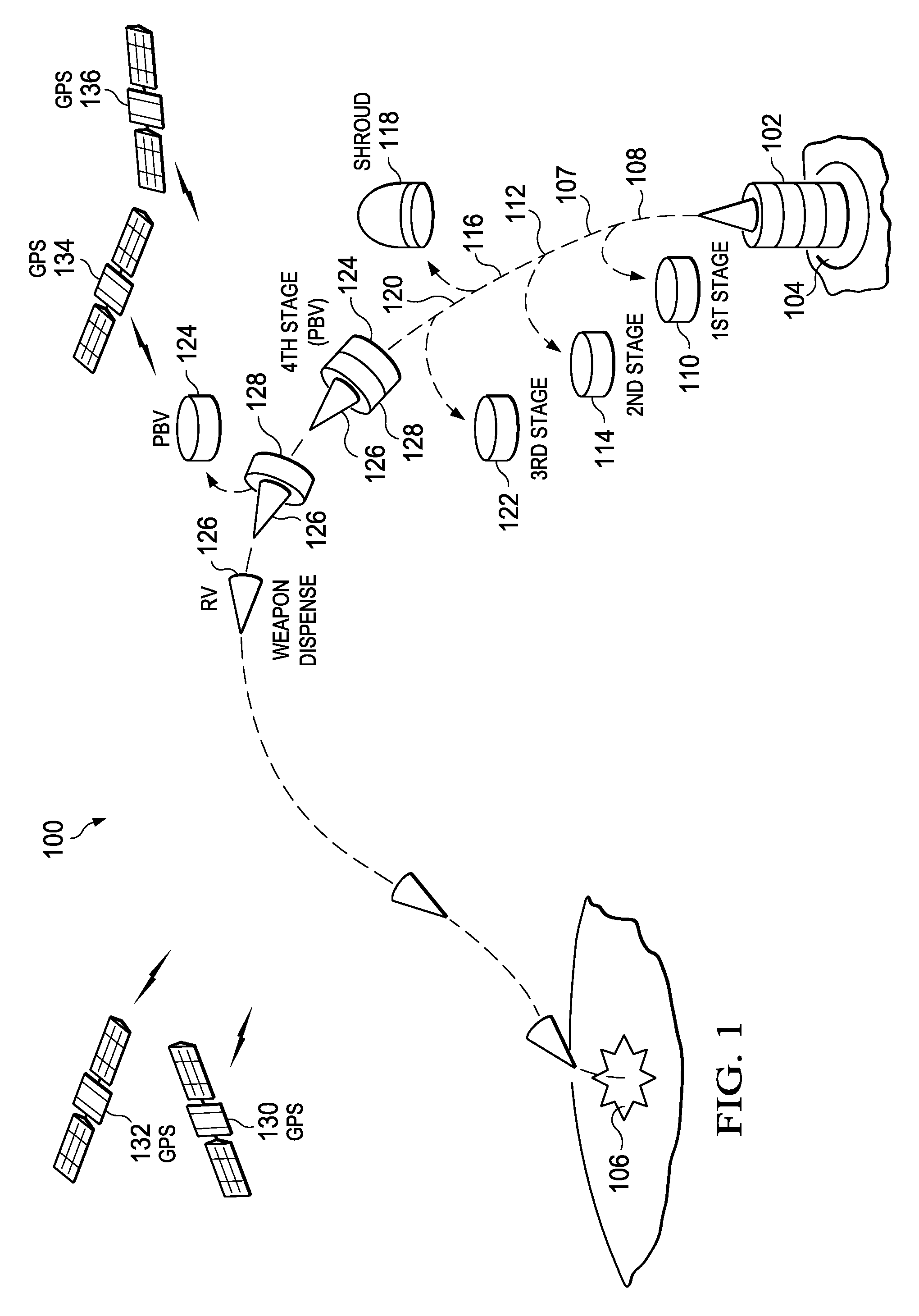
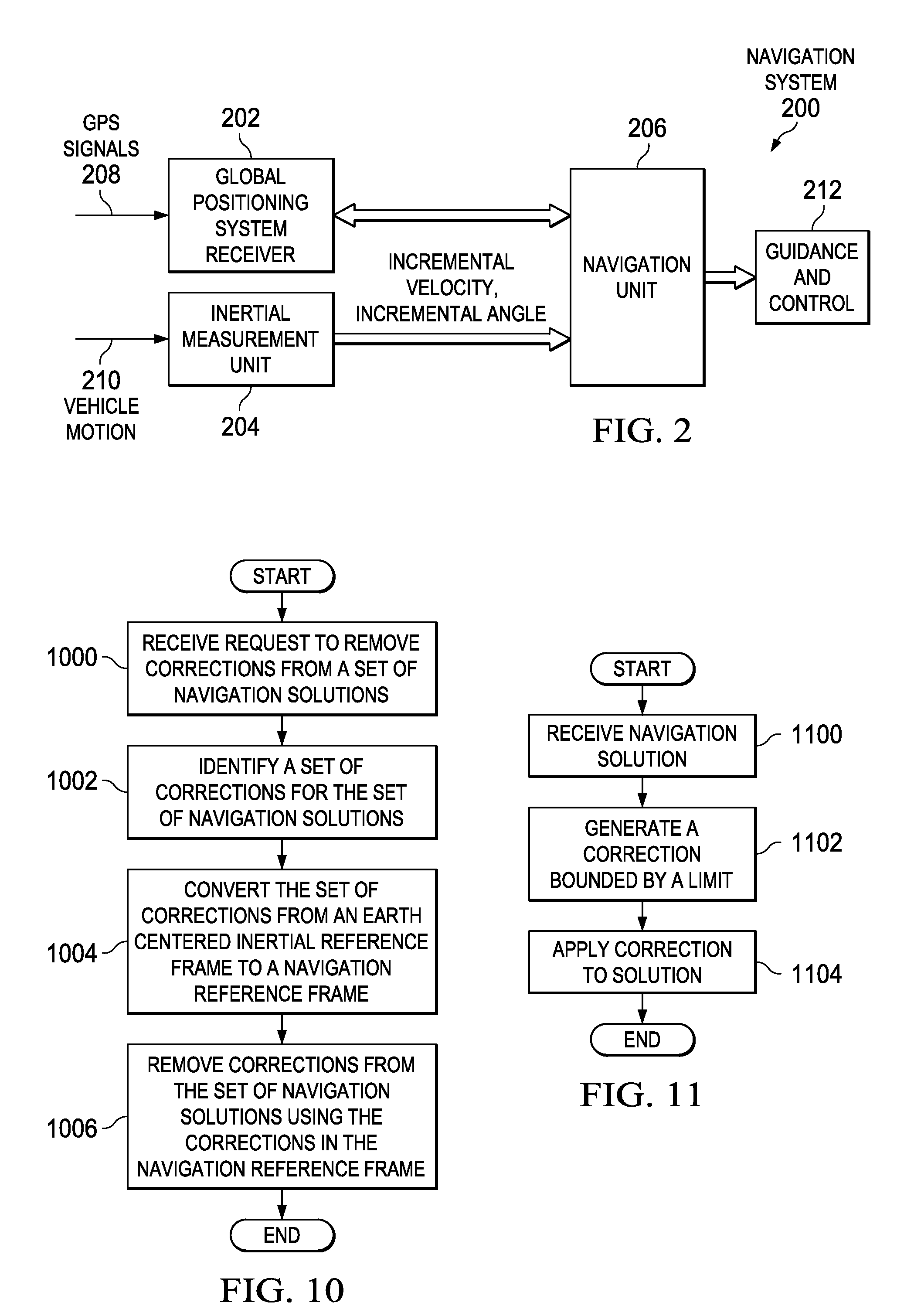
InactiveUS20090254278A1Position fixationNavigation by speed/acceleration measurementsAnti spoofingNavigation system
A method and apparatus for generating navigation solutions. A global positioning system based navigation solution unit; an inertial navigation solution unit; a correction unit, a limiter, and an adding unit. The global positioning system based navigation solution unit is capable of generating a first navigation solution. The inertial navigation solution unit is capable of generating a second navigation solution. The correction unit is capable of generating a raw correction. The limiter is capable of selectively modifying the raw correction to fall within a selected range of corrections to form a correction. The adding unit is capable of adding the correction to the second navigation solution to form a navigation solution.
Owner:THE AIR FORCE THE US SEC
Hybrid multi-sensor biometric identification device
ActiveUS8073204B2Expand the marketElectric signal transmission systemsDigital data processing detailsProximity sensorAnti spoofing
Owner:APPLE INC
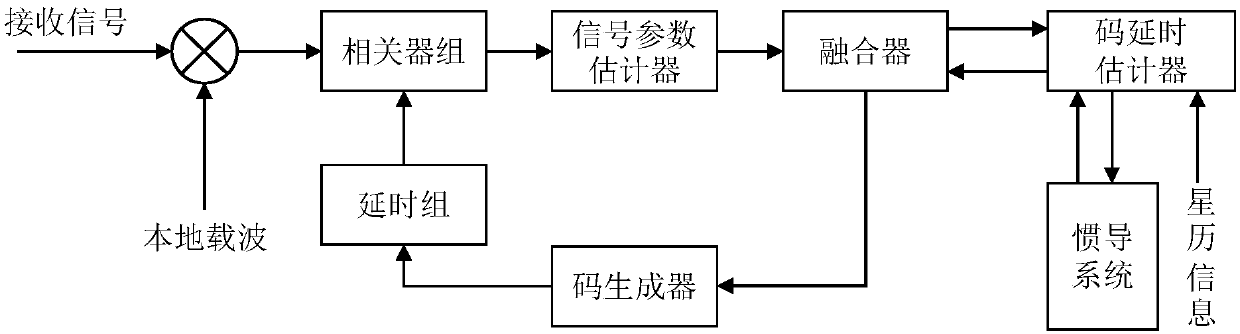
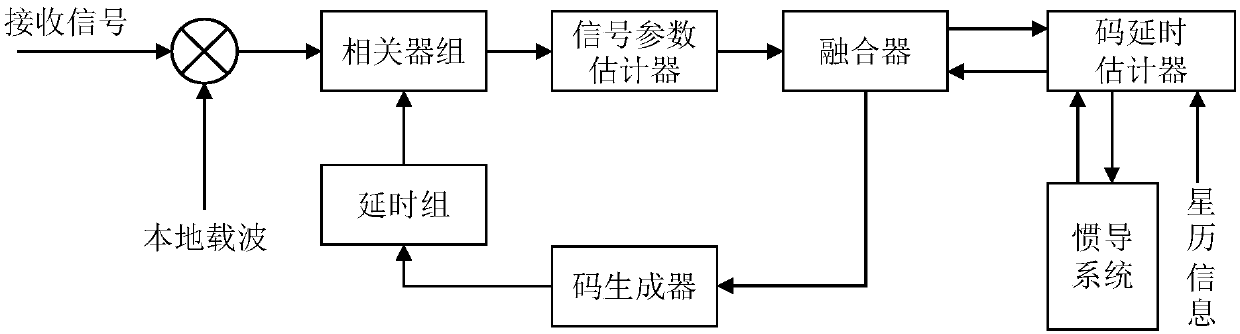
GNSS (global navigation satellite system) anti-spoofing loop tracking method based on inertial information aiding and parameter estimation
ActiveCN106772455AGuaranteed accuracyGuaranteed stabilitySatellite radio beaconingAnti spoofingAlgorithm
The invention provides a GNSS (global navigation satellite system) anti-spoofing loop tracking method based on inertial information aiding and parameter estimation. The GNSS anti-spoofing loop tracking method comprises the following steps of performing exploring study on the application of a signal estimation algorithm in an anti-spoofing field; utilizing a signal estimation algorithm to estimate a similar GNSS signal, identifying by aiding with the inertial information, and integrating the information to distinguish a spoofing signal and a true signal. The signal estimation algorithm is aided by the inertial navigation information, so as to propose a new tracking loop structure, thereby realizing double advantages of more reference for the tracking loop, and relative independence of the GNSS and an inertial navigation system. The GNSS anti-spoofing loop tracking method has the advantages that one set of complete anti-spoofing plan integrating signal estimation and detection, spoofing signal inhibition and true signal tracking is realized, and the spoofing interference can be inhibited to ensure the accuracy and stability of a receiver in working.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
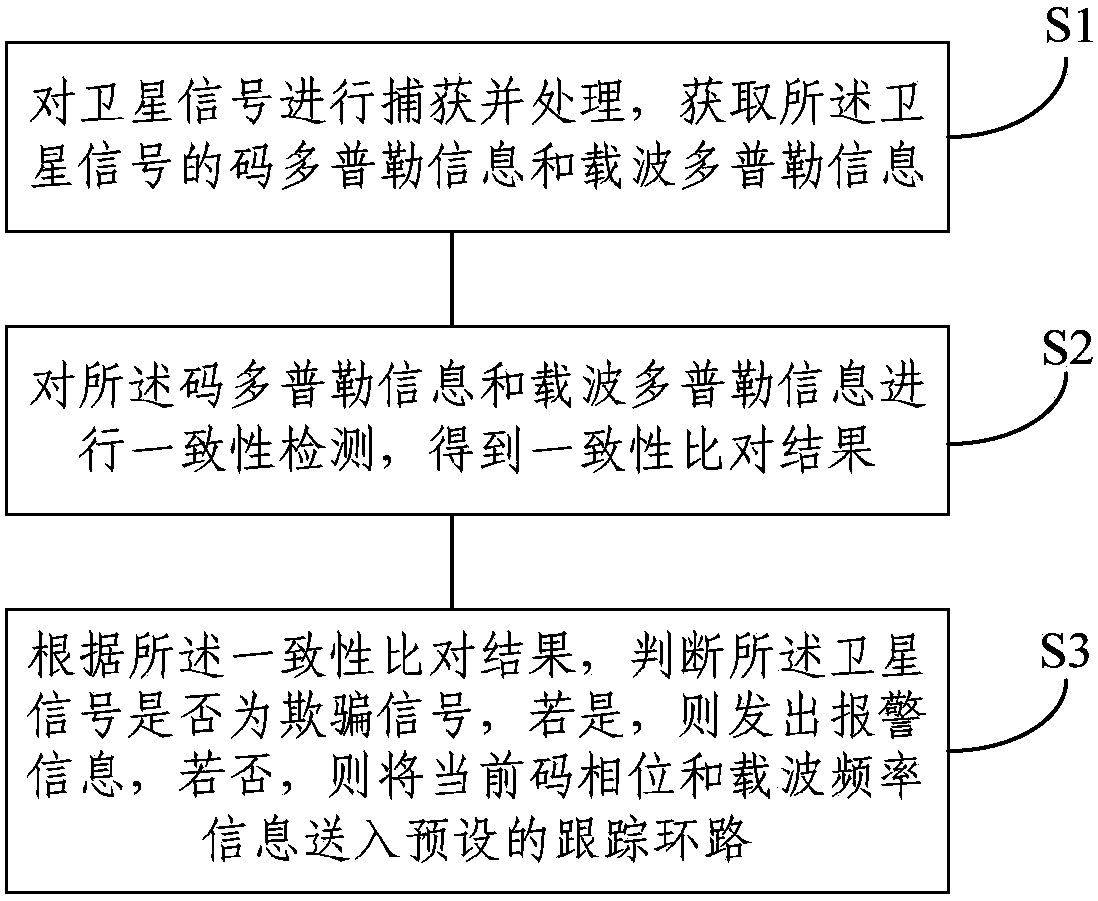
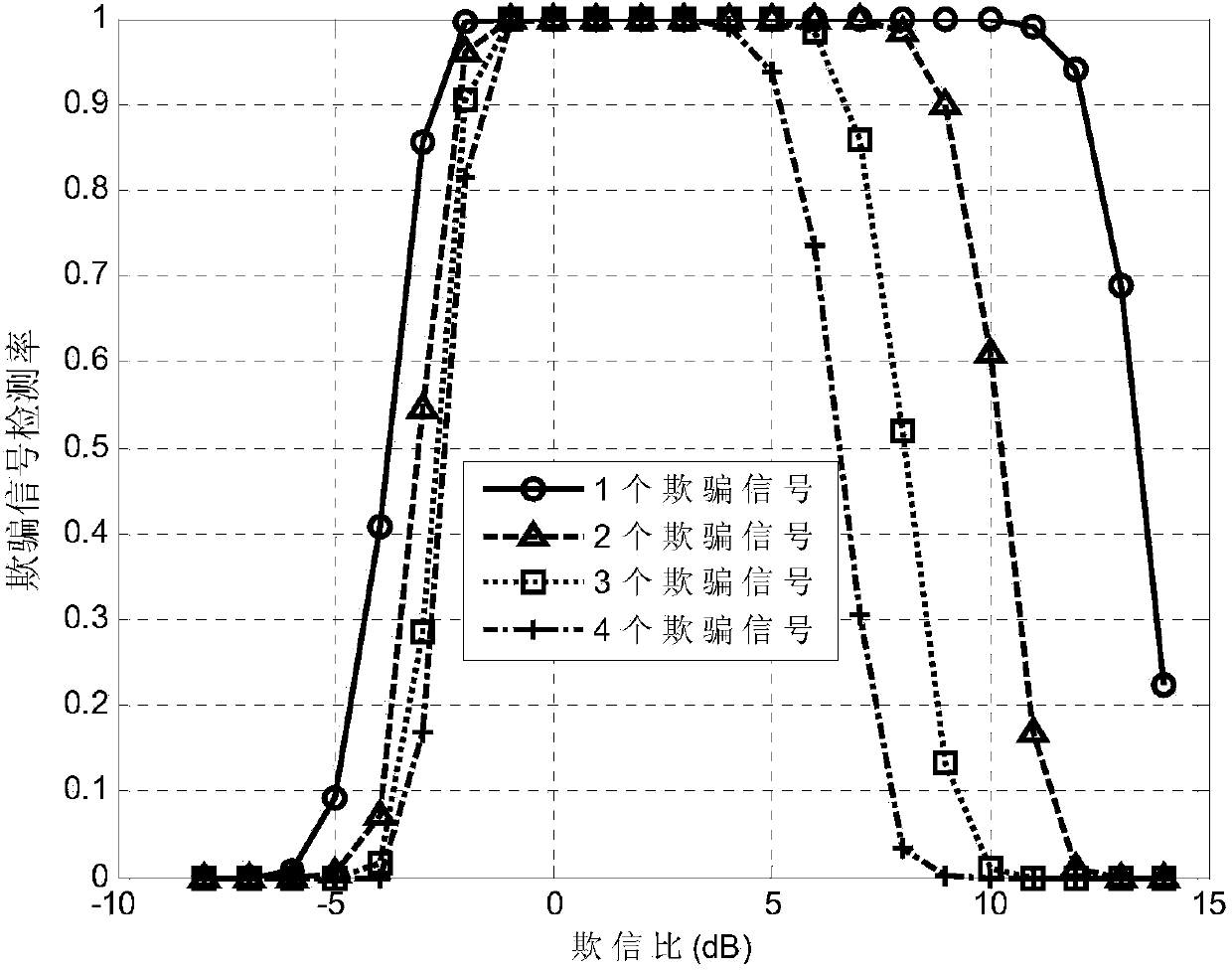
Anti-spoofing-attack method and system applied to satellite navigation system
ActiveCN104155663AWith spoofing signal suppression functionStrong anti-spoofing abilitySatellite radio beaconingAnti spoofingSignal Repression
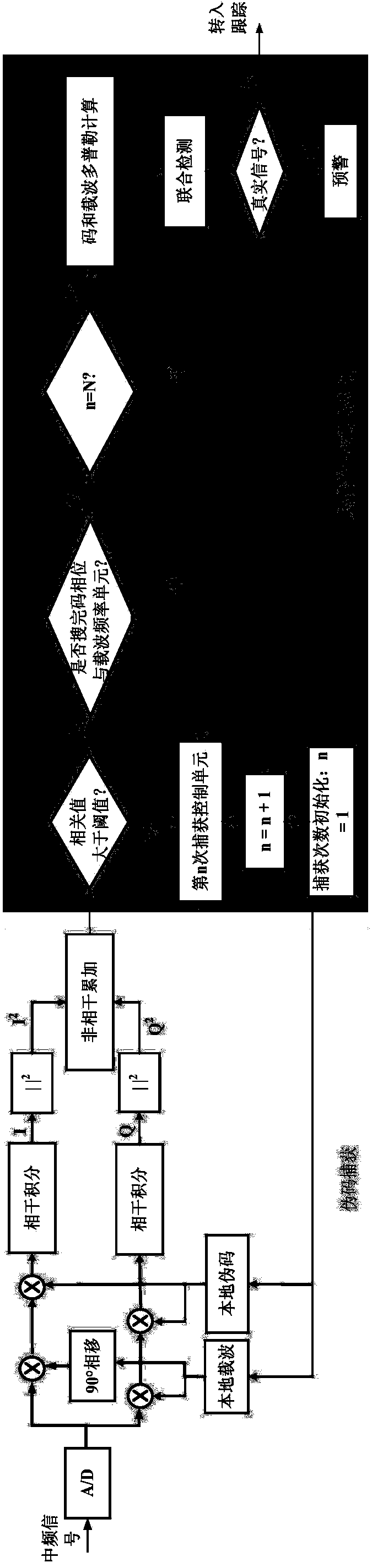
The invention discloses an anti-spoofing-attack method and system applied to a satellite navigation system. The method comprises the following steps: S1) capturing and processing satellite signals, and obtaining code Doppler information and carrier wave Doppler information of the satellite signals; S2) carrying out consistency detection on the code Doppler information and the carrier wave Doppler information to obtain a consistency comparison result; and S3) judging whether the satellite signals are spoofing signals, sending alarm information if the satellite signals are spoofing signals, and sending current code phase position and carrier wave frequency information to a preset tracking loop if the satellite signals are not spoofing signals. The method and system in the invention not only can judge whether the spoofing signals exist in the received signals, but also can judge which signals are the spoofing signals and which signals are real signals, that is, the second layer can be reached; and the method and system have spoofing signal suppression function and also have strong anti-spoofing capability.
Owner:TSINGHUA UNIV
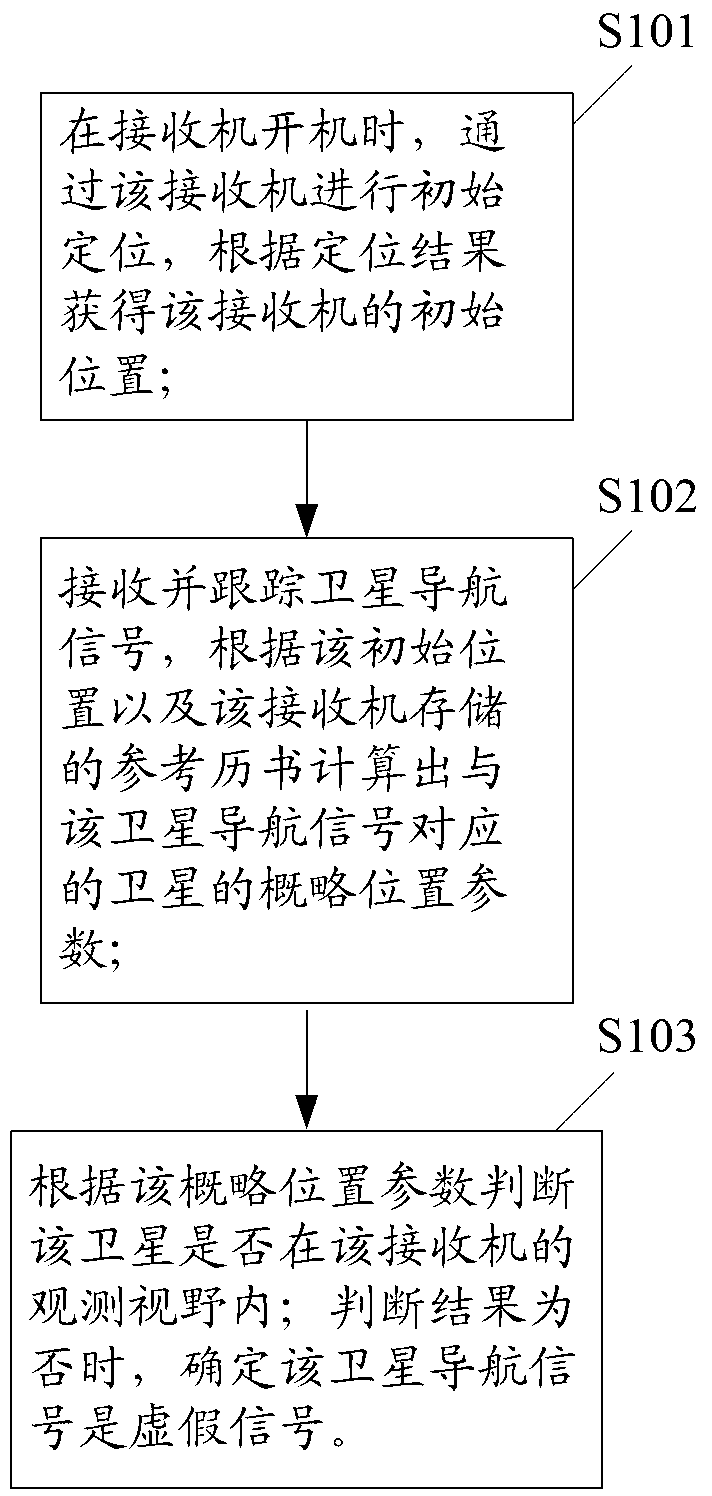
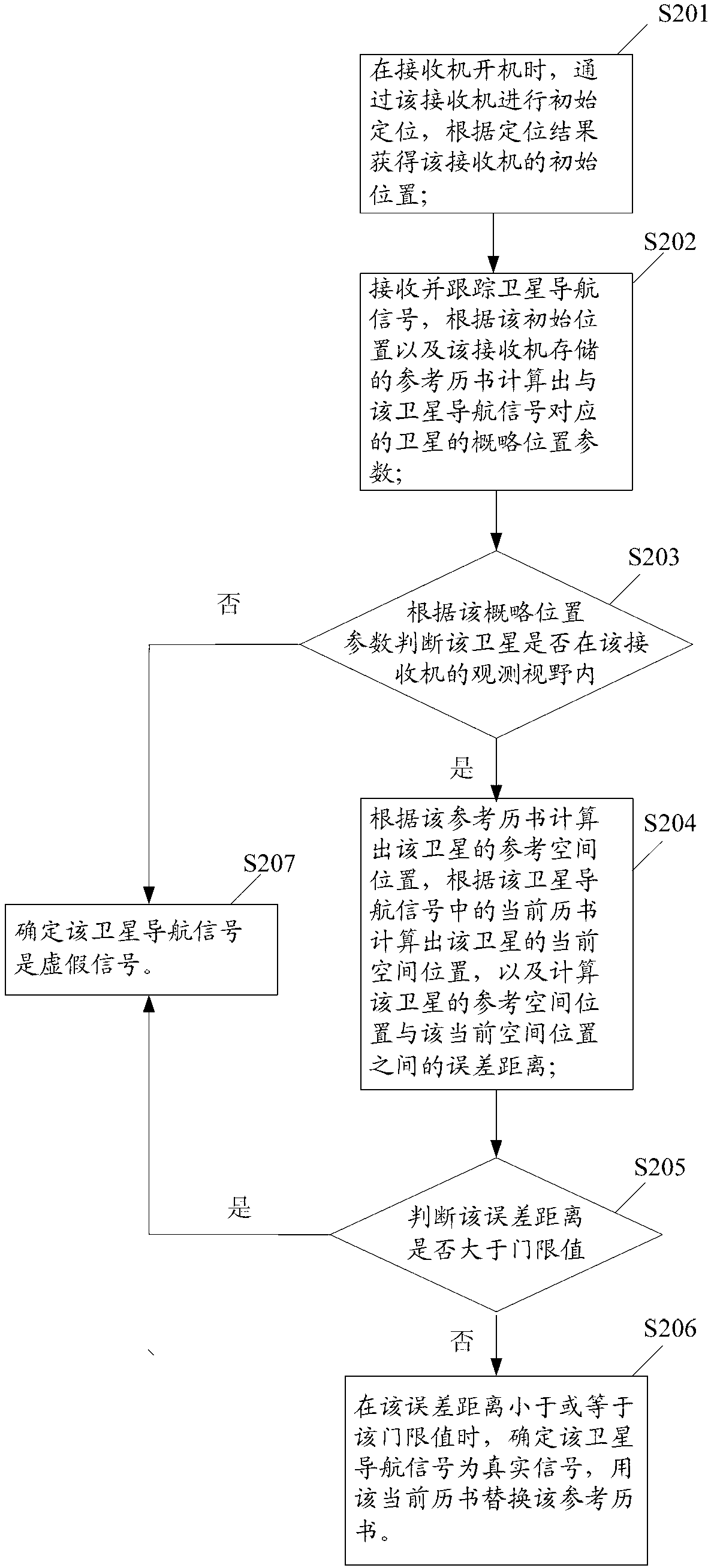
False detection method of satellite navigation signals and satellite navigation positioning receiver
ActiveCN103105615AEnhanced anti-spoofing capabilitiesImplementation method is flexibleSatellite radio beaconingAcquisition timeAnti spoofing
The invention discloses a false detection method of a satellite navigation signals. The false detection method of the satellite navigation signals can record the acquisition time of a current ephemeris by recording the updating time of a reference ephemeris, and calculates the time interval between the acquisition time of the current ephemeris and the updating time of the reference ephemeris so as to judge whether the time interval conforms to the updated frequency value of a broadcast ephemeris, thus achieving the false detection of the satellite navigation signals. The invention further discloses a satellite navigation positioning receiver. By means of the above-mentioned ways, anti-spoofing ability of the receiver is reinforced. In addition, the false detection method of the satellite navigation signals and the satellite navigation positioning receiver have the advantages that low cost is achieved, expansibility is strong and the like.
Owner:JIANGSU COMPASS NAVIGATION & COMM TECH CO LTD
Global navigation satellite system (GNSS) signal receiver spoofing signal parameter estimating method
ActiveCN109188469AReduce the probability of losing lockImprove stabilitySatellite radio beaconingKaiman filterPhase difference
The invention provides a global navigation satellite system (GNSS) receiver spoofing signal parameter estimating method. The GNSS receiver spoofing signal parameter estimating method comprises the steps that (1) a digital intermediate-frequency signal from a GNSS receiver antenna and two paths of sinusoidal / cosine signals, with the 90-degree phase difference, locally generated according to the Doppler frequency output by a carrier wave NCO are input into frequency mixers; and (2) output results of the two branch frequency mixers and C / A codes of locally generated different code phases are input into a multichannel correlator to be subjected to correlation operation, and output signals operated by the multichannel correlator become real baseband signals only containing navigation data information. According to the GNSS receiver spoofing signal parameter estimating method, by extending iterative state estimation of a Kalman filter, signal energy of GNSS signals and spoofing signals, thecode interval between the GNSS signals and a final spoofing position as well as the code interval between the spoofing signals and the final spoofing position are calculated in real time, and thus theanti-jamming ability and anti-spoofing ability of a GNSS receiver are improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Systems and methods for performing iris identification and verification using mobile devices
Technologies are presented herein in support of a system and method for performing iris identification and verification using mobile devices. Embodiments of the present invention concern a method for authenticating a user with a mobile device that includes steps for capturing imagery of a user's face, analyzing the imagery to identify the portion of the image depicting the user's eyes and segmenting the eye image to isolate the iris image data and encoding the iris image data in iris template. The present disclosure further describes authenticating the user based on the encoded iris template and additional techniques for preventing erroneous authentication caused by spoofing. In some examples, the anti-spoofing techniques may include capturing one or more images of a user's eyes and analyzing the captured images for indications of liveness based on reflection characteristics depicted in the imagery.
Owner:VERIDIUM IP LTD
Systems and methods for performing fingerprint based user authentication using imagery captured using mobile devices
Technologies are presented herein in support of a system and method for performing fingerprint recognition. Embodiments of the present invention concern a system and method for capturing a user's biometric features and generating an identifier characterizing the user's biometric features using a mobile device such as a smartphone. The biometric identifier is generated using imagery captured of a plurality of fingers of a user for the purposes of authenticating / identifying the user according to the captured biometrics and determining the user's liveness. The present disclosure also describes additional techniques for preventing erroneous authentication caused by spoofing. In some examples, the anti-spoofing techniques may include capturing one or more images of a user's fingers and analyzing the captured images for indications of liveness.
Owner:VERIDIUM IP LTD
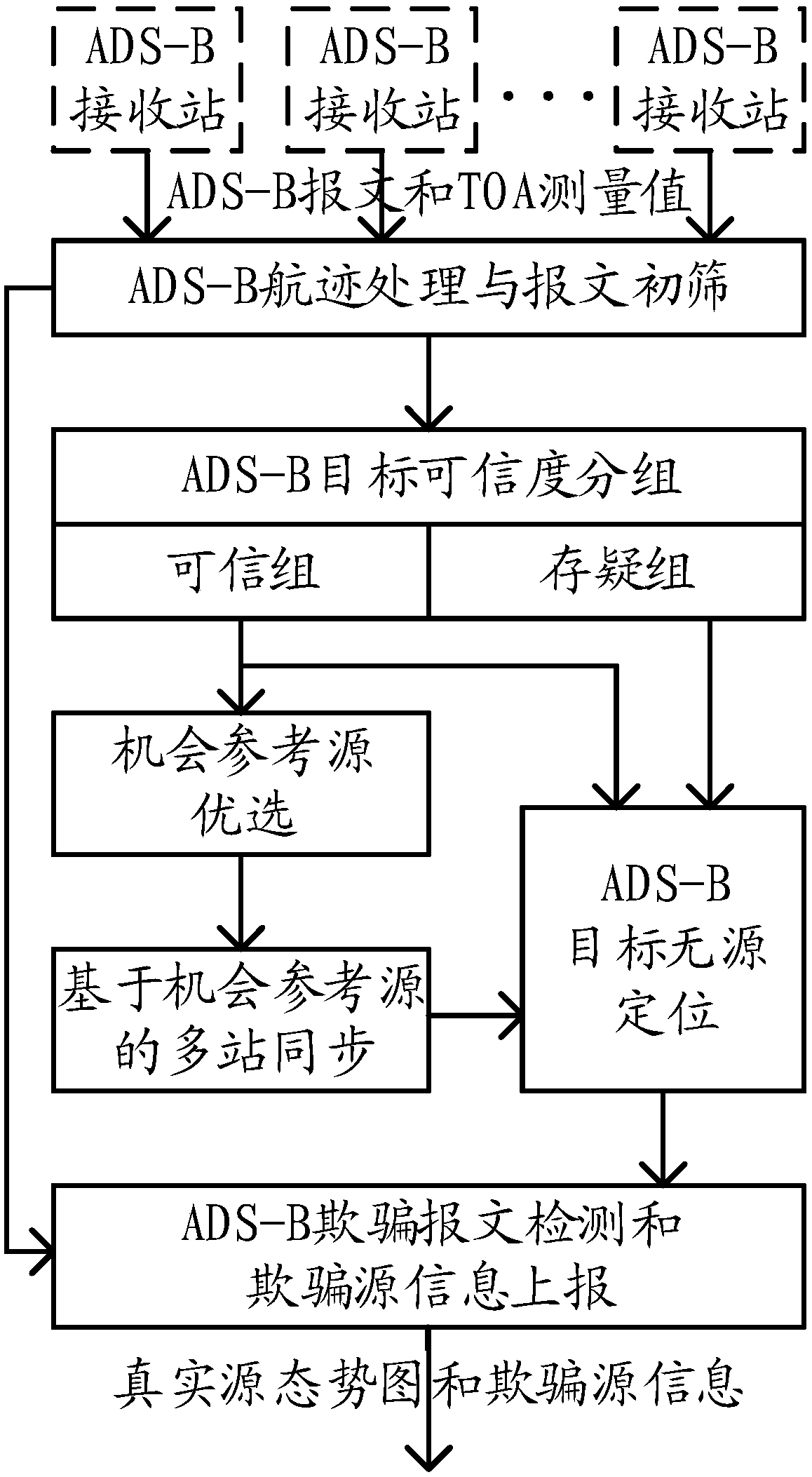
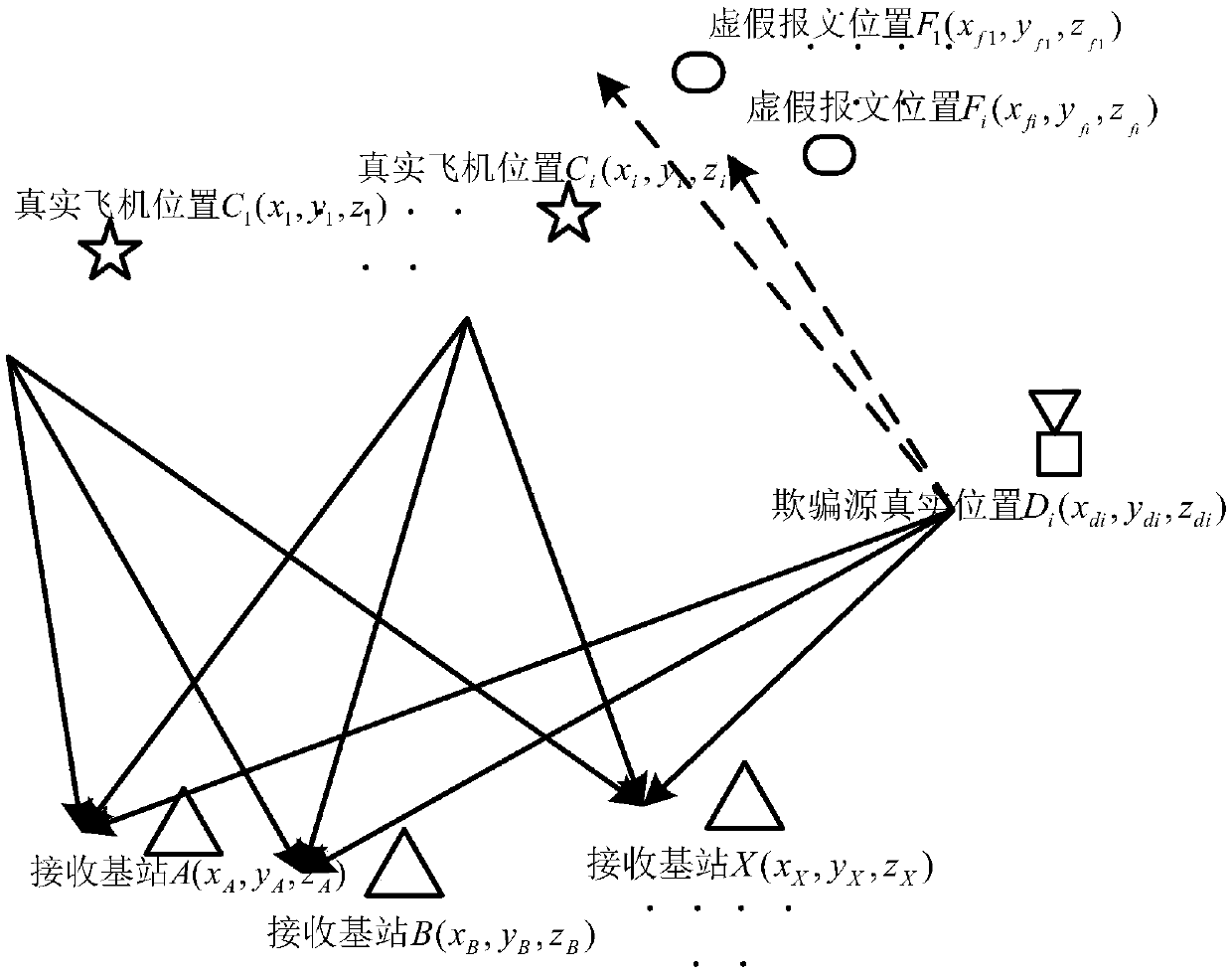
Method for realizing distributed ADS-B passive positioning anti-spoofing function on basis of opportunity reference sources
ActiveCN109541538AImprove reliabilityAlleviate heavy dependencePosition fixationHigh level techniquesMulti siteAnti spoofing
The invention relates to a method for realizing a distributed ADS-B passive positioning anti-spoofing function on basis of opportunity reference sources. The method comprises the following steps of: (1) carrying out track processing by an ADS-B system and eliminating interference information and screening wrong messages; (2) carrying out relative position goodness fit verification by the ADS-B system; (3) selecting an opportunity reference source suitable for multi-site synchronization and high in local arrival time TOA measurement accuracy from a trusted group; (4) calculating a local arrivaltime TOA synchronization correction value of each station by using position information in messages of the opportunity reference source and position information of each station; (5) carrying out passive positioning on ADS-B target sources through an arrival time difference; and (6) detecting and reporting spoofing ADS-B source. By adoption of the method, the functions of spoofing ADS-B message detection and spoofing source positioning can be realized at the same time through receiving ADS-B signals by a plurality of ADS-B receivers; and the method has the characteristics of being good in detection performance and low in system and realizing spoofing source positioning.
Owner:EAST CHINA UNIV OF SCI & TECH +1
Systems and methods for performing fingerprint based user authentication using imagery captured using mobile devices
Technologies are presented herein in support of a system and method for performing fingerprint recognition. Embodiments of the present invention concern a system and method for capturing a user's biometric features and generating an identifier characterizing the user's biometric features using a mobile device such as a smartphone. The biometric identifier is generated using imagery captured of a plurality of fingers of a user for the purposes of authenticating / identifying the user according to the captured biometrics and determining the user's liveness. The present disclosure also describes additional techniques for preventing erroneous authentication caused by spoofing. In some examples, the anti-spoofing techniques may include capturing one or more images of a user's fingers and analyzing the captured images for indications of liveness.
Owner:VERIDIUM IP LTD
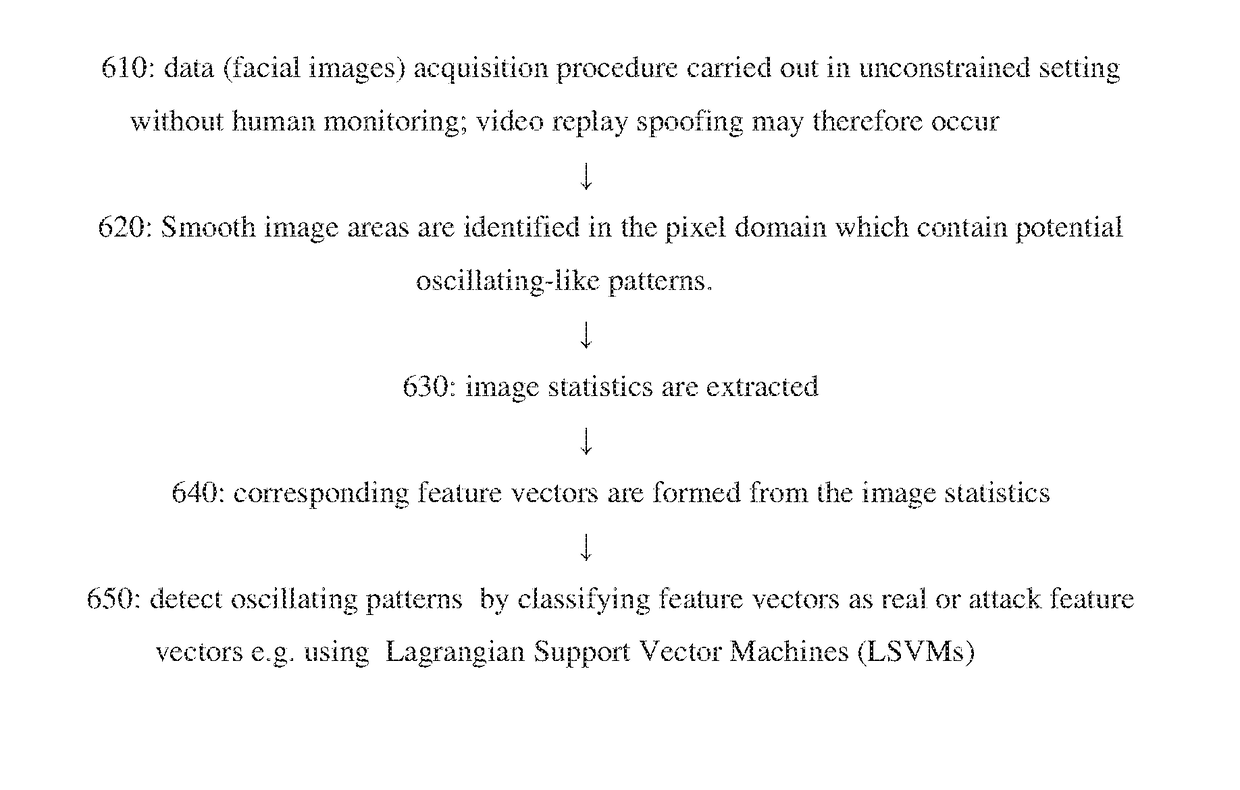
Mobile data communication using biometric encryption
InactiveUS20160100314A1Improve robustnessProtect dataUser identity/authority verificationDigital data protectionMobile appsFeature vector
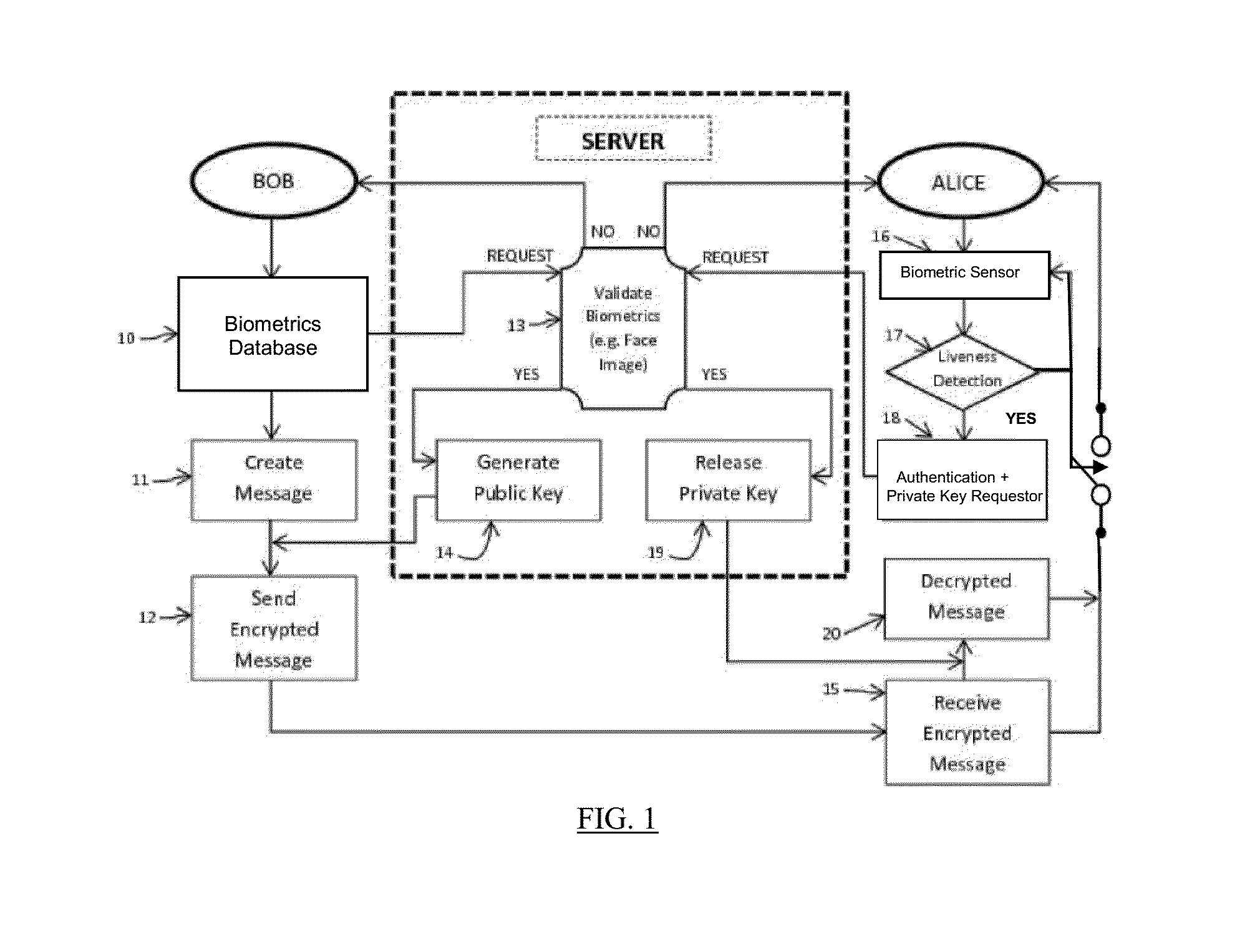
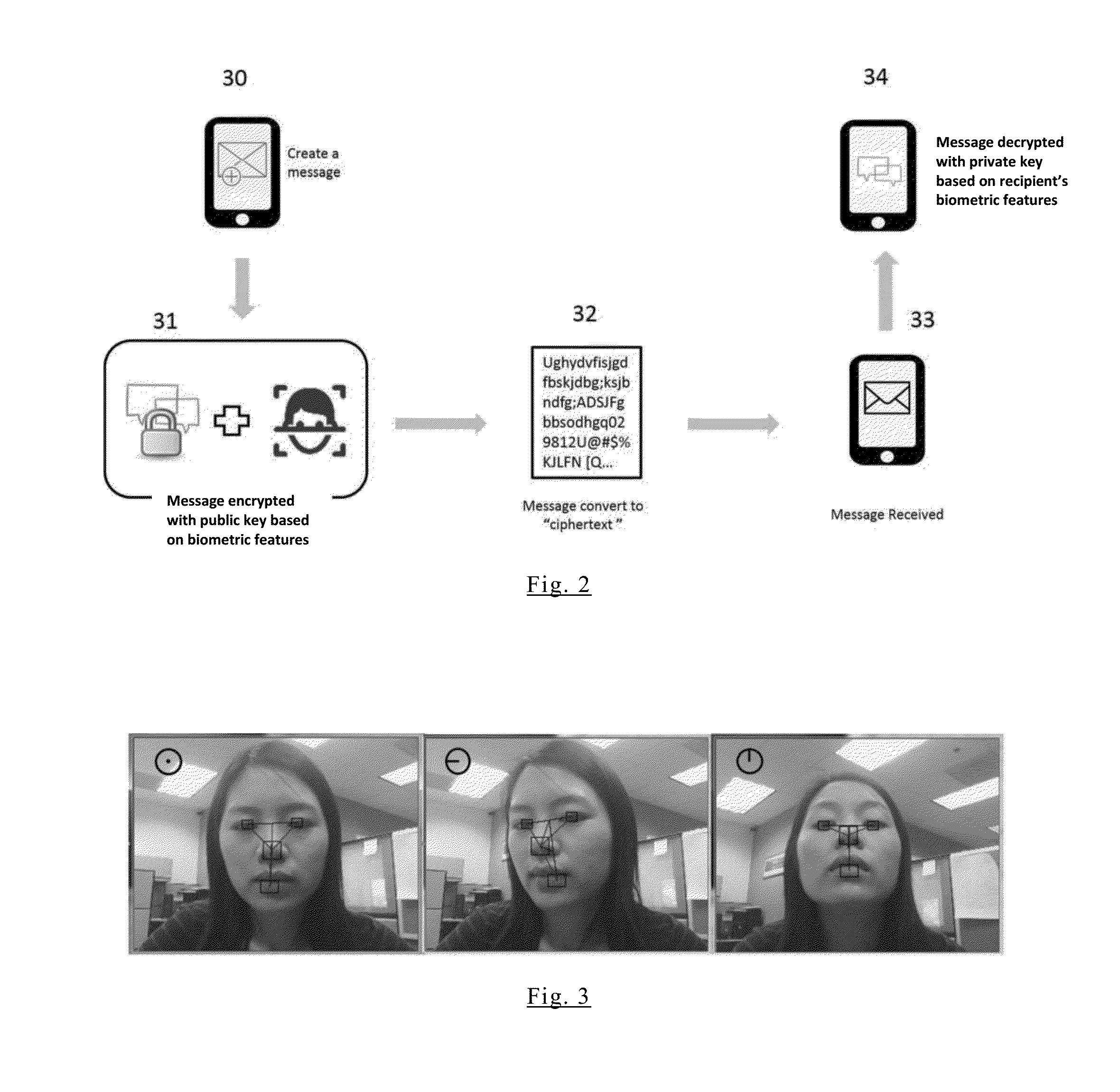
A mobile App using biometric encryption and decryption for privacy and security having both authentication and recognition functions. It utilizes the built-in camera of the mobile device to provide facial images for authentication purposes. It further includes a secured data communication system for conveniently sending and receiving data on the mobile devices. The secured data communication system also utilizes biometric encryption and decryption technology for granting permissions to access the data communication system. The biometric encryption is implemented by using a selective biometric feature and optimized biometric feature detection and tracking methods. Different biometric feature authentication methods are optimized for use on various mobile platforms, such as, Android, iOS, Windows and others. Data encryption and decryption are achieved by using selected biometric feature vectors as cryptographic keys. The biometric data encryption system further includes liveness detection module with anti-spoofing features to ensure the encryption and decryption processes only accept biometric features from a live person conveniently without the user's intervention. Alternative authentication method is provided if the biometric feature authentication module fails to recognize the valid user, or fails in the liveness detection module in order to maintain privacy and security of the data in the mobile device.
Owner:WASHINGTON SOFTWARE INC
System and method of anti-spoofing notification based on cell-phone message contents
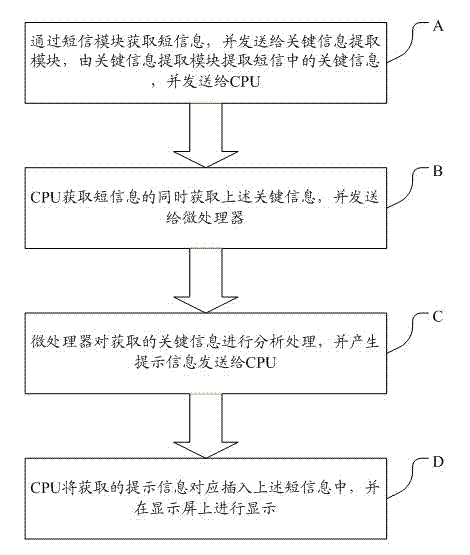
InactiveCN103179246AReminder is intuitive and clearPrevent being cheatedSubstation equipmentAnti spoofingComputer science
Owner:SHENZHEN GIONEE COMM EQUIP
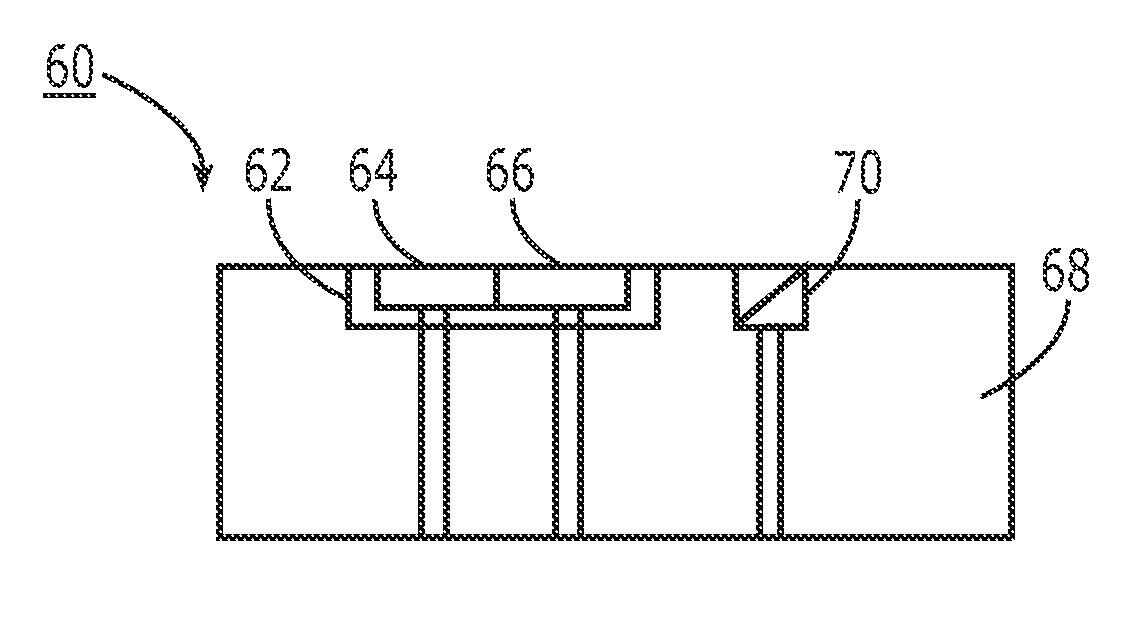
Metabolism- or Biochemical-Based Anti-Spoofing Biometrics Devices, Systems, and Methods
InactiveUS20080226137A1Highly secureHighly spoofing-resistantMagnetic measurementsDiagnostics using lightAnti spoofingIdentification device
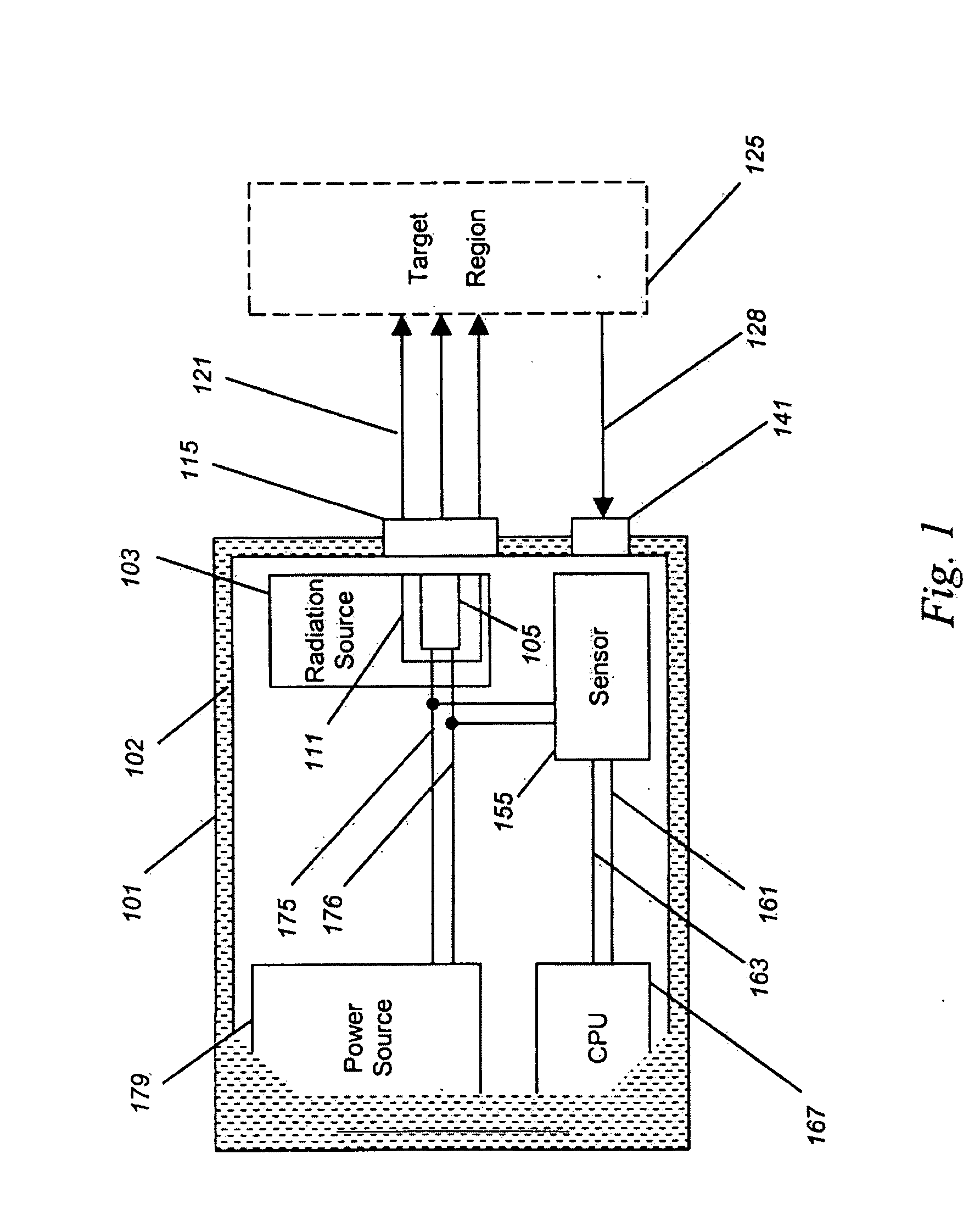
A biometric device for detecting biological tissue based upon ratiometric measurements of metabolic and / or biochemical intermediates is provided in which a radiation source (103) is electromagnetically coupled to a target region (125). A radiation sensor (155) receives emission signals (128) from the target region as a result of emitted radiation (121) interacting with the target region. A CPU (167) receives a signal from the sensor, and provides a biometric output signal based upon the presence of live, healthy tissue versus sham or dead tissue. Optionally, a conventional, non-metabolism, non-biochemical-based biometric sensor can be incorporated into the present invention, and the biometric output signal is then a result of both the metabolism- and / or biochemical based and non-metabolism non-biochemical-based biometric determinations. A method of performing this biometric analysis is also described.
Owner:J FITNESS LLC
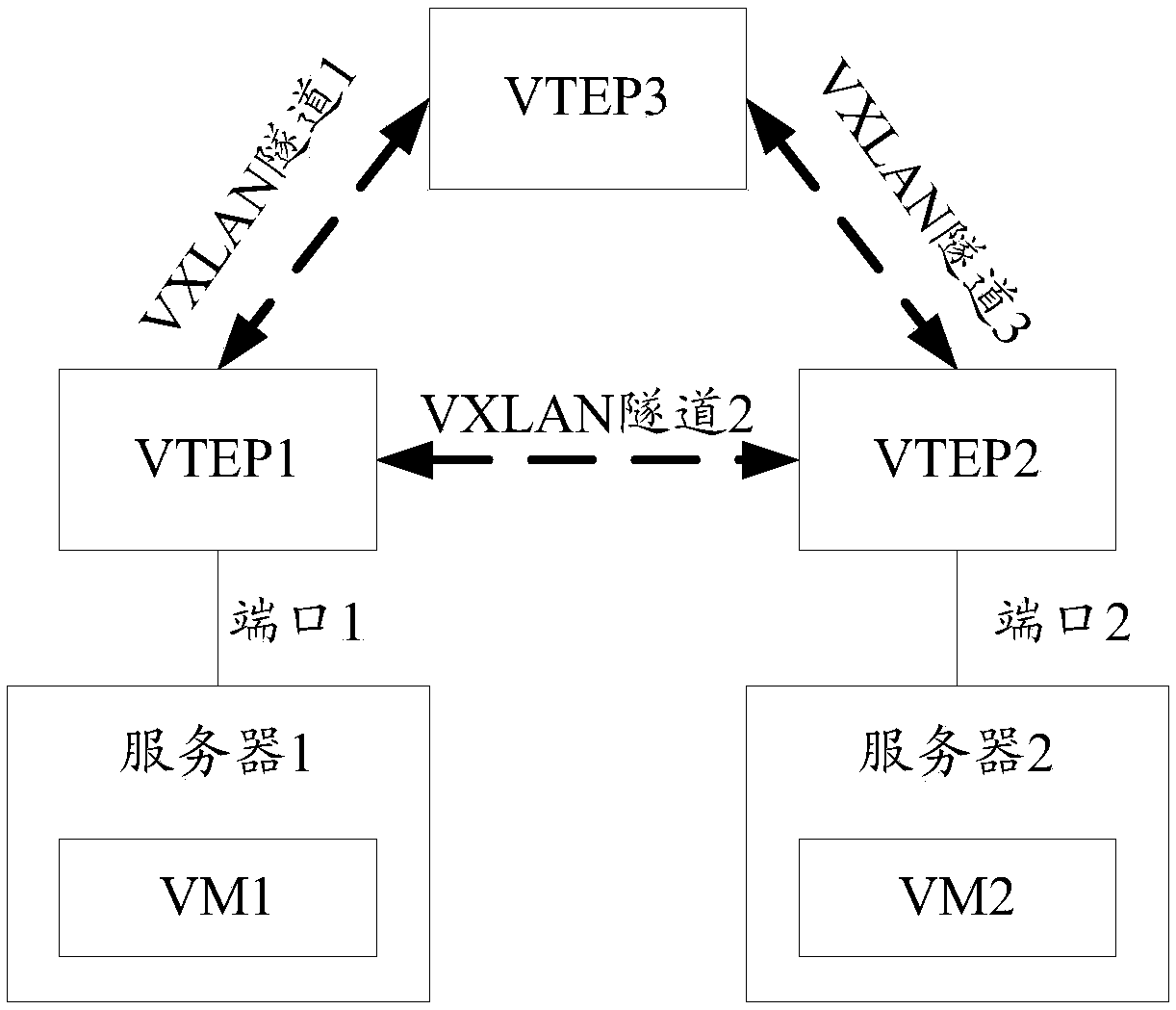
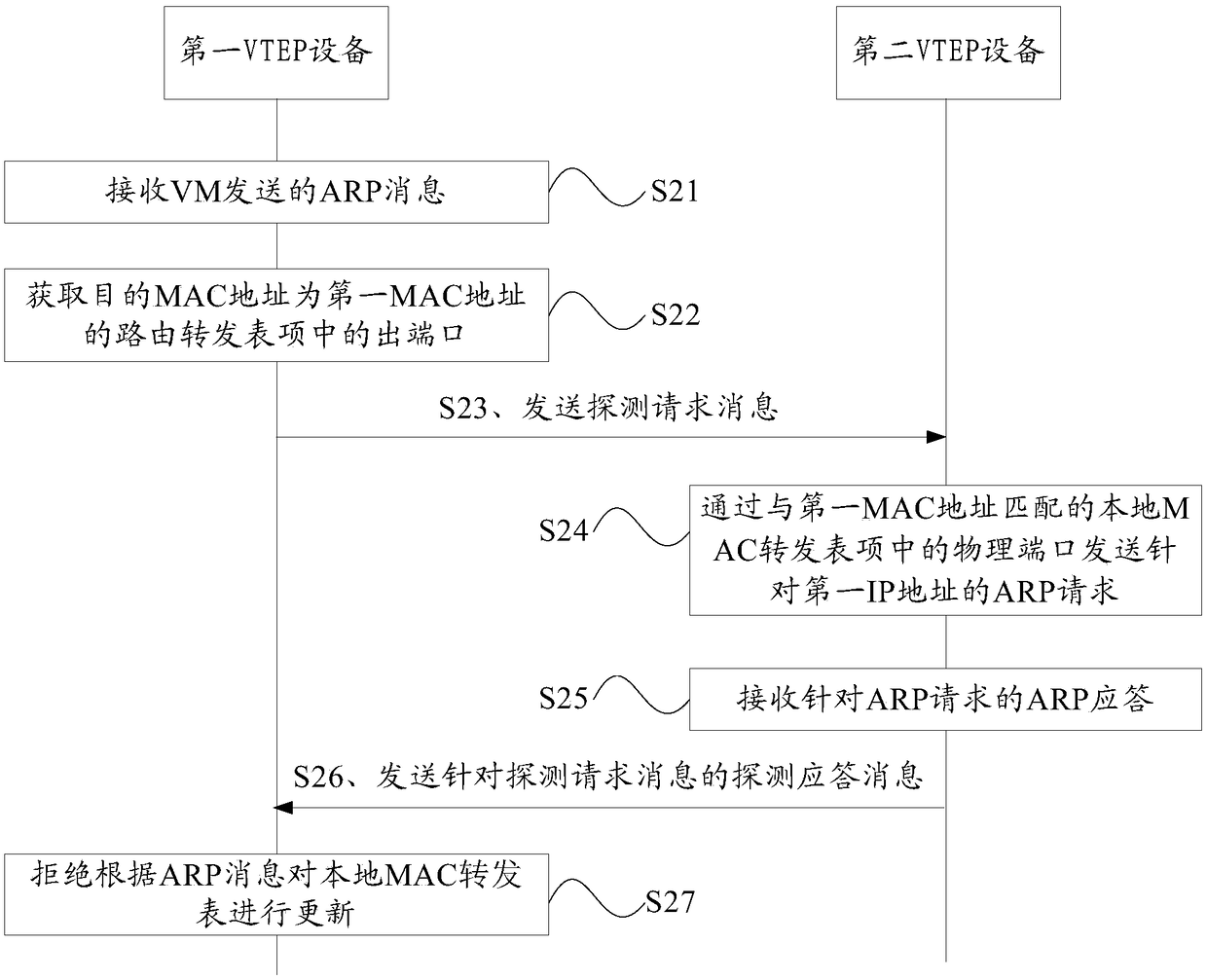
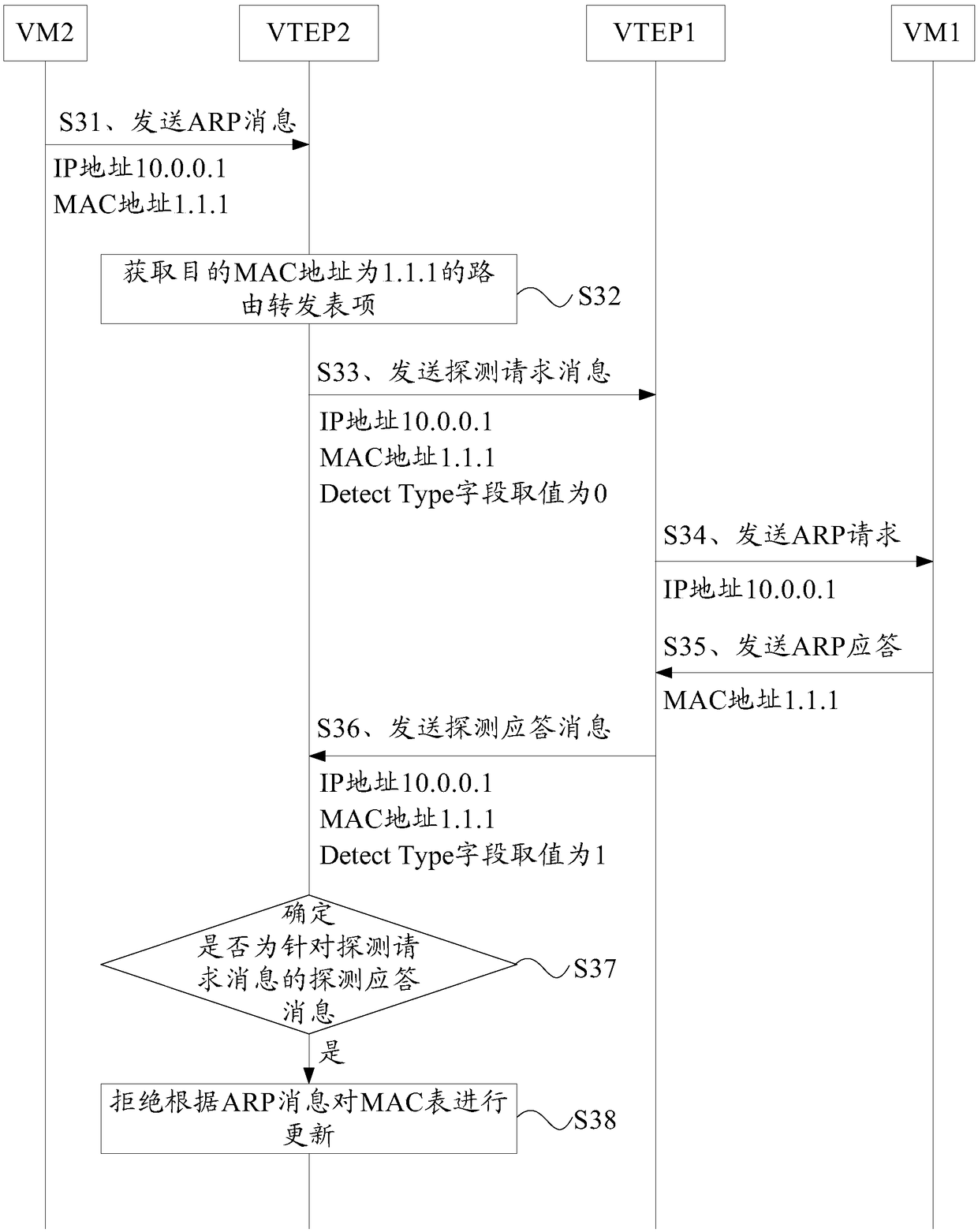
A method and apparatus for anti-spoofing in a VXLAN
The present application provides a method and apparatus for preventing spoofing in a VXLAN, which relate to the field of communication technology and are used to solve the problem that a part of VETPin the prior art cannot recognize spoofing, thereby forwarding data to an attacker. The method comprises the following steps of: receiving an ARP message sent by a virtual machine VM. The ARP messagecarries a first IP address and a first MAC address. Obtaining an outbound port in a forwarding table entry whose destination MAC address is a first MAC address; sending a probe request message to thesecond VTEP device. The second VTEP device is a VTEP device connected with an outlet port in a forwarding table item. The probe request message is used for instructing the second VTEP device to send an ARP request for the first IP address through the physical port in the local MAC forwarding table entry matching the first MAC address; upon receiving the probe response message for the probe requestmessage sent by the second VTEP device, the local MAC forwarding table is refused to be updated according to the ARP message. This application is intended to prevent spoofing in VXLANs.
Owner:MAIPU COMM TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com