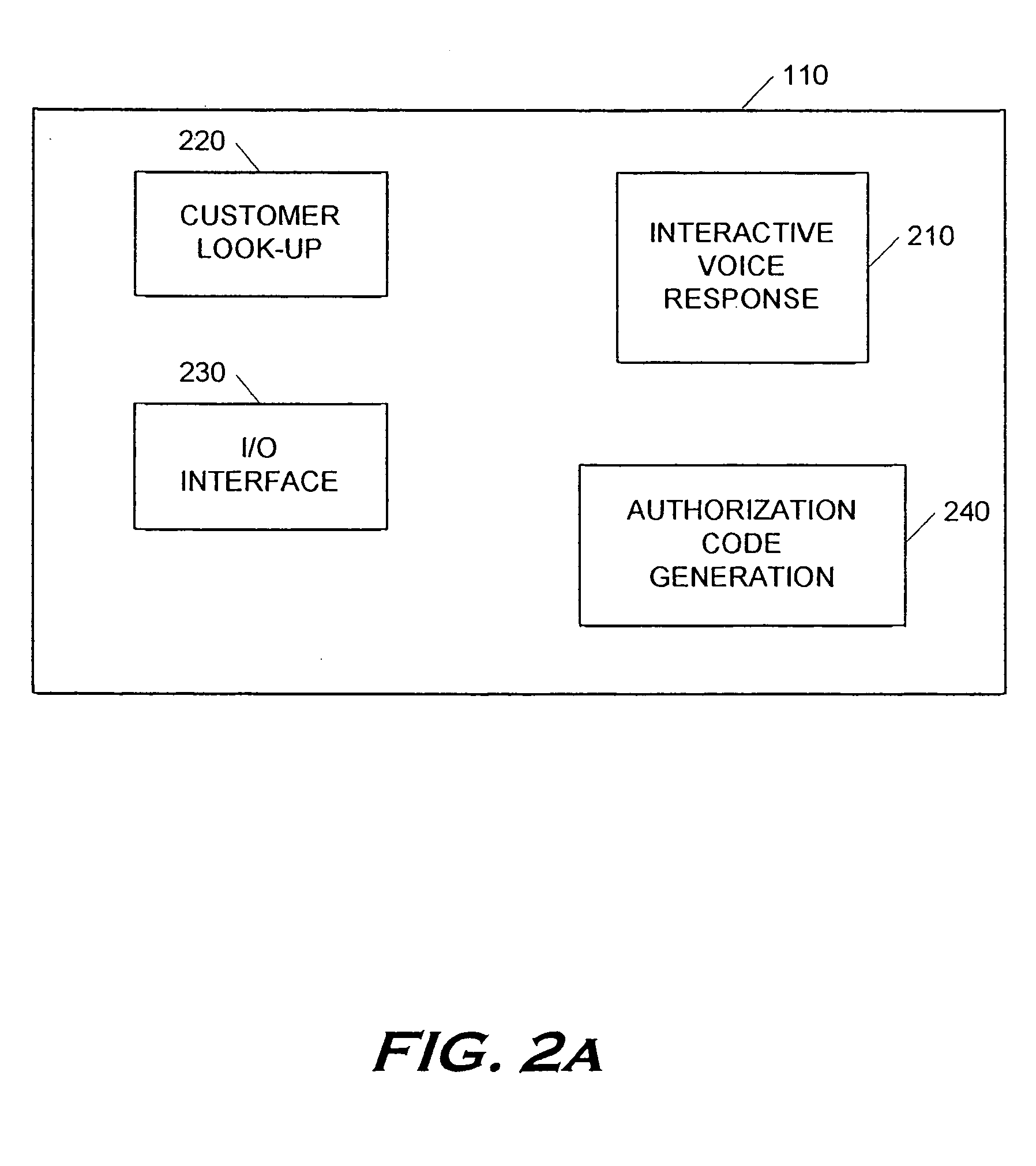
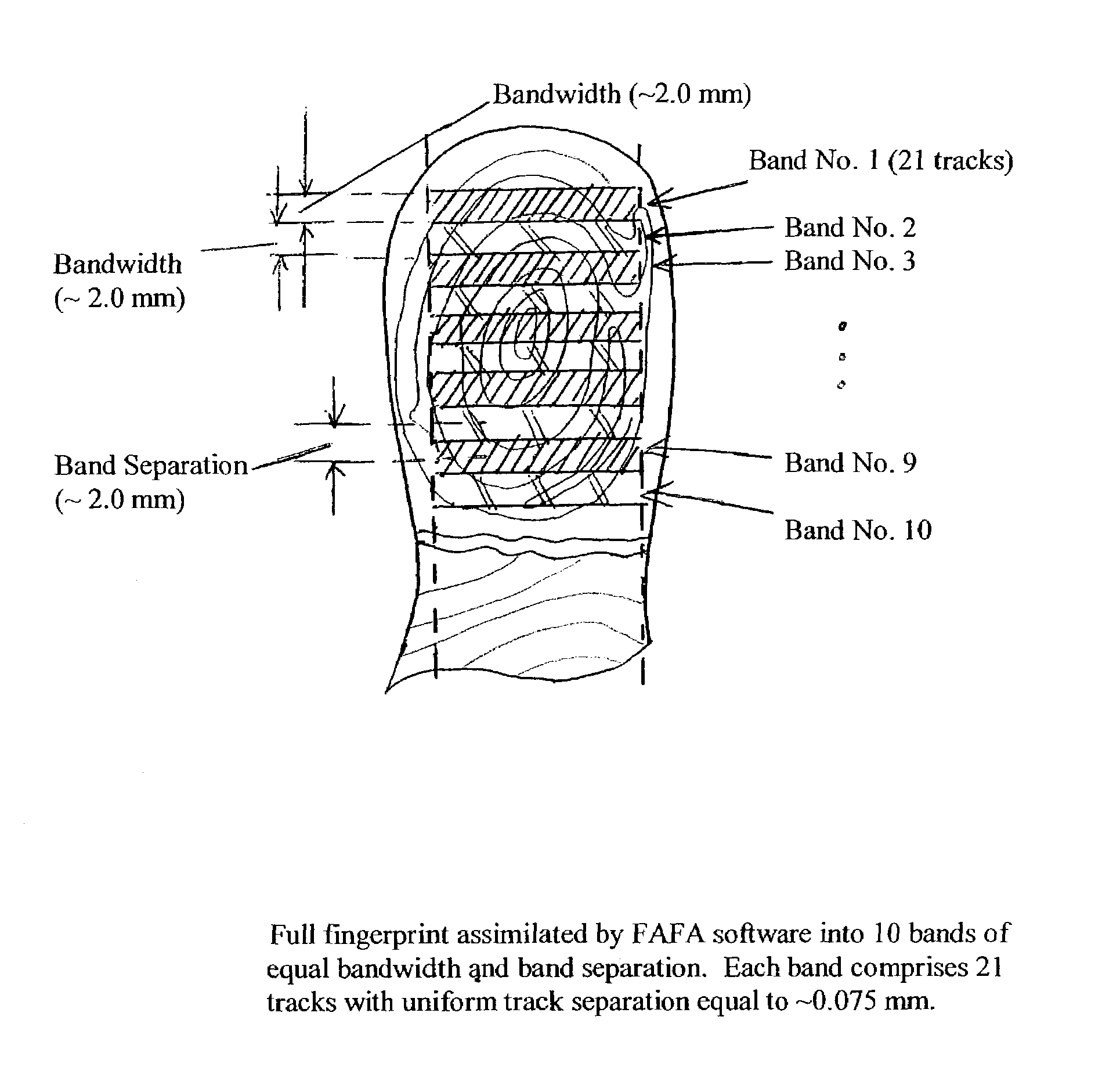
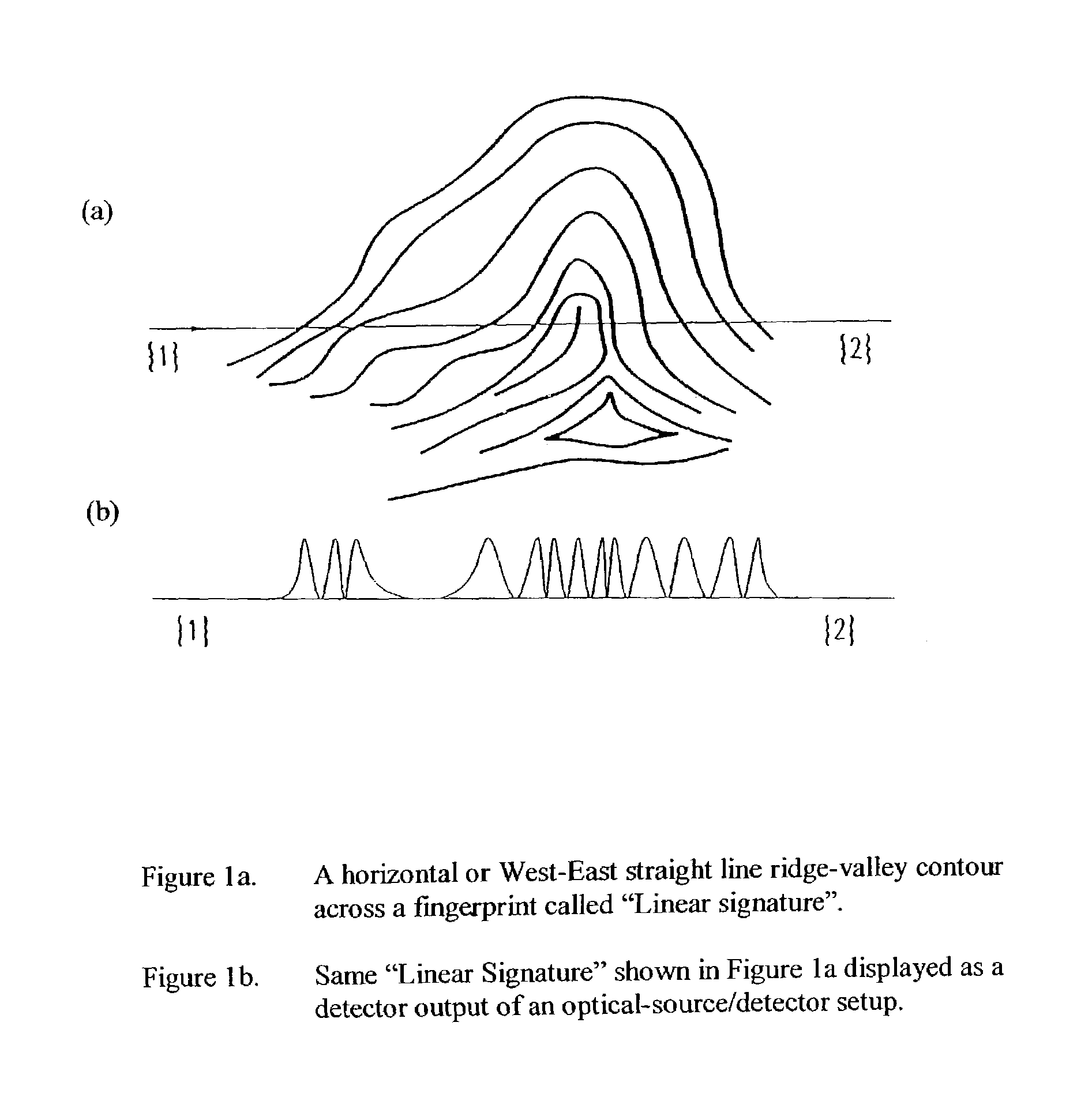
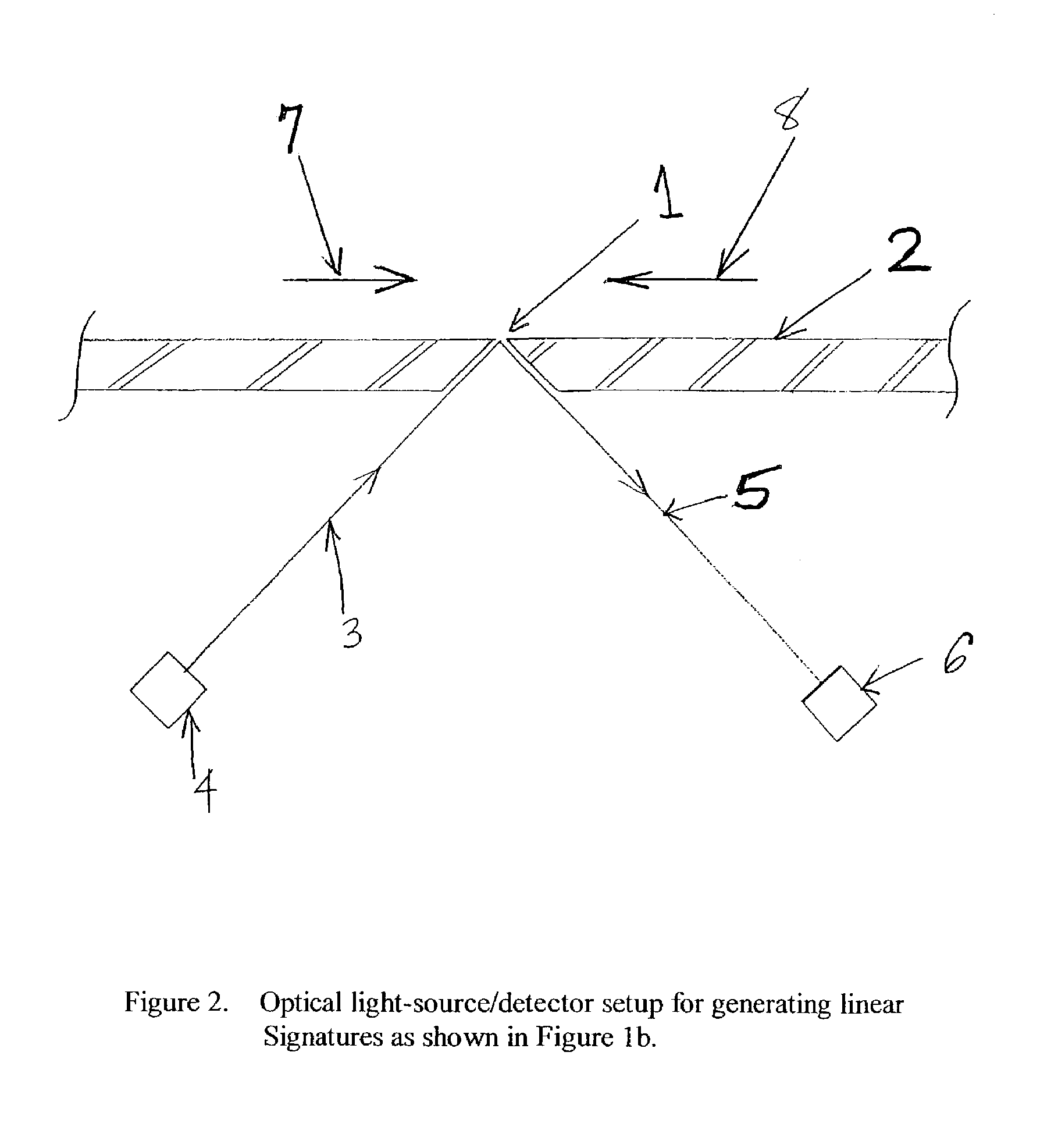
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1151 results about "Biometrics" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Biometrics is the technical term for body measurements and calculations. It refers to metrics related to human characteristics. Biometrics authentication (or realistic authentication) is used in computer science as a form of identification and access control. It is also used to identify individuals in groups that are under surveillance.
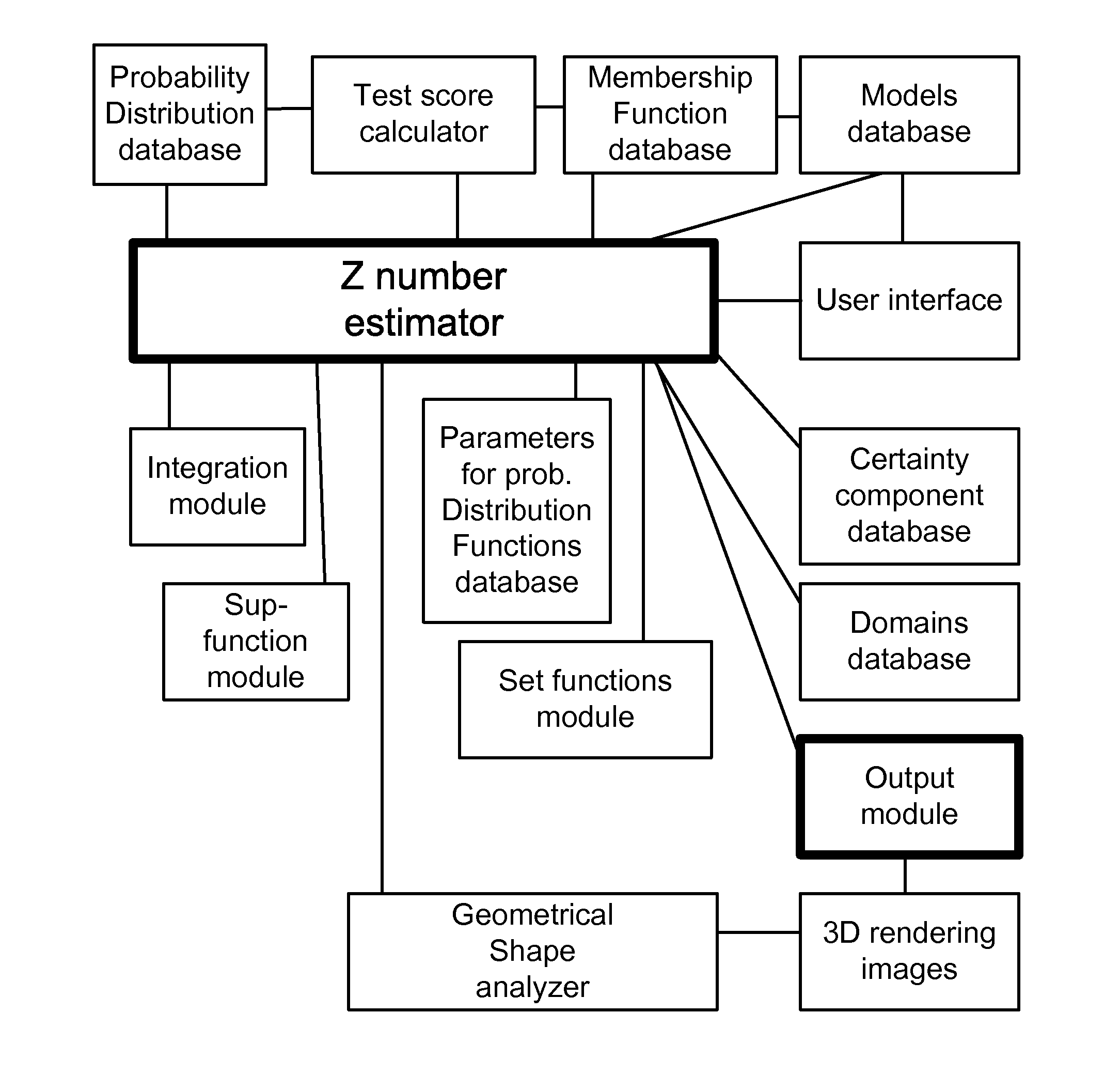
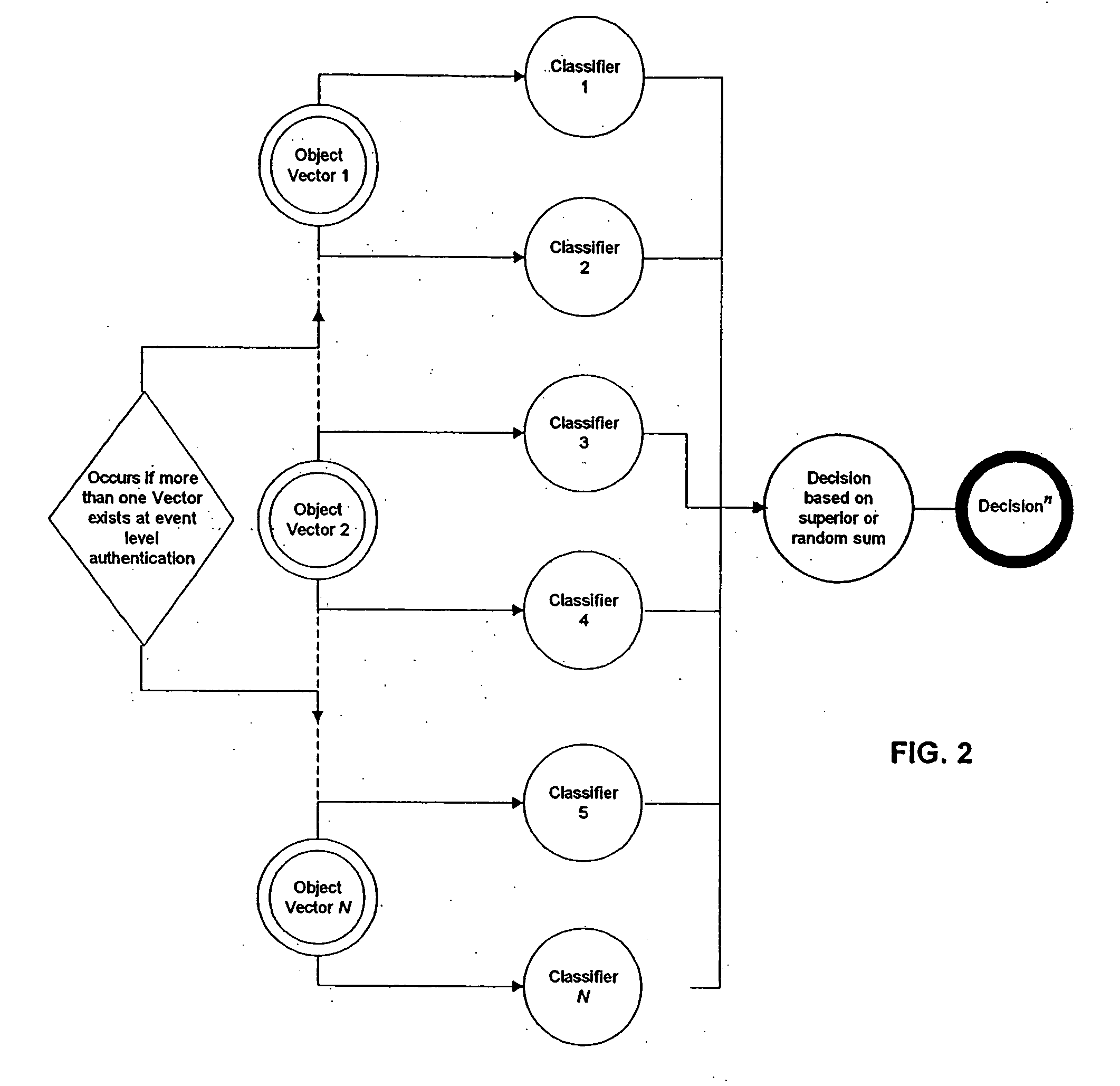
Application of Z-Webs and Z-factors to Analytics, Search Engine, Learning, Recognition, Natural Language, and Other Utilities
Here, we introduce Z-webs, including Z-factors and Z-nodes, for the understanding of relationships between objects, subjects, abstract ideas, concepts, or the like, including face, car, images, people, emotions, mood, text, natural language, voice, music, video, locations, formulas, facts, historical data, landmarks, personalities, ownership, family, friends, love, happiness, social behavior, voting behavior, and the like, to be used for many applications in our life, including on the search engine, analytics, Big Data processing, natural language processing, economy forecasting, face recognition, dealing with reliability and certainty, medical diagnosis, pattern recognition, object recognition, biometrics, security analysis, risk analysis, fraud detection, satellite image analysis, machine generated data analysis, machine learning, training samples, extracting data or patterns (from the video, images, and the like), editing video or images, and the like. Z-factors include reliability factor, confidence factor, expertise factor, bias factor, and the like, which is associated with each Z-node in the Z-web.
Owner:Z ADVANCED COMPUTING
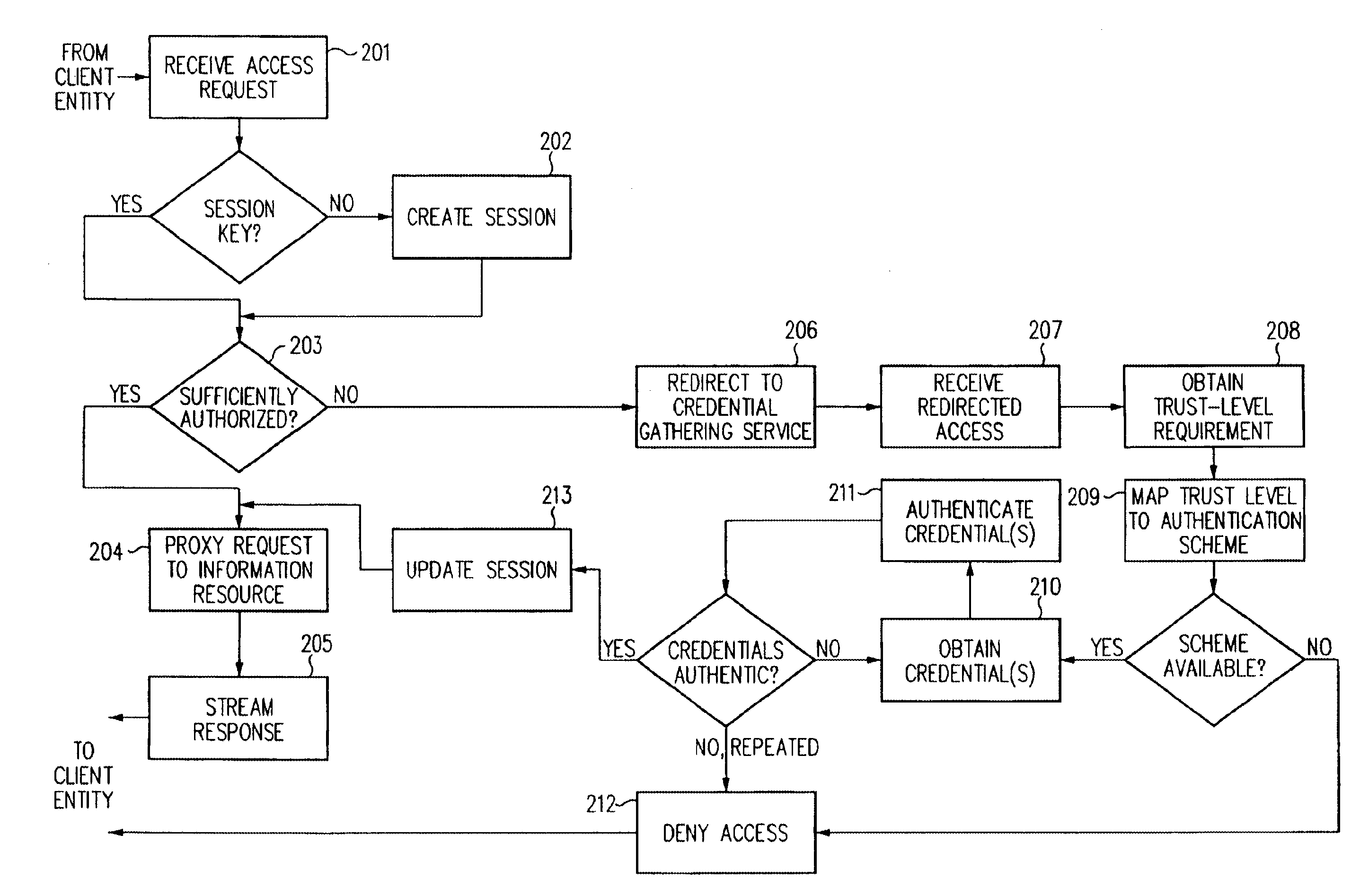
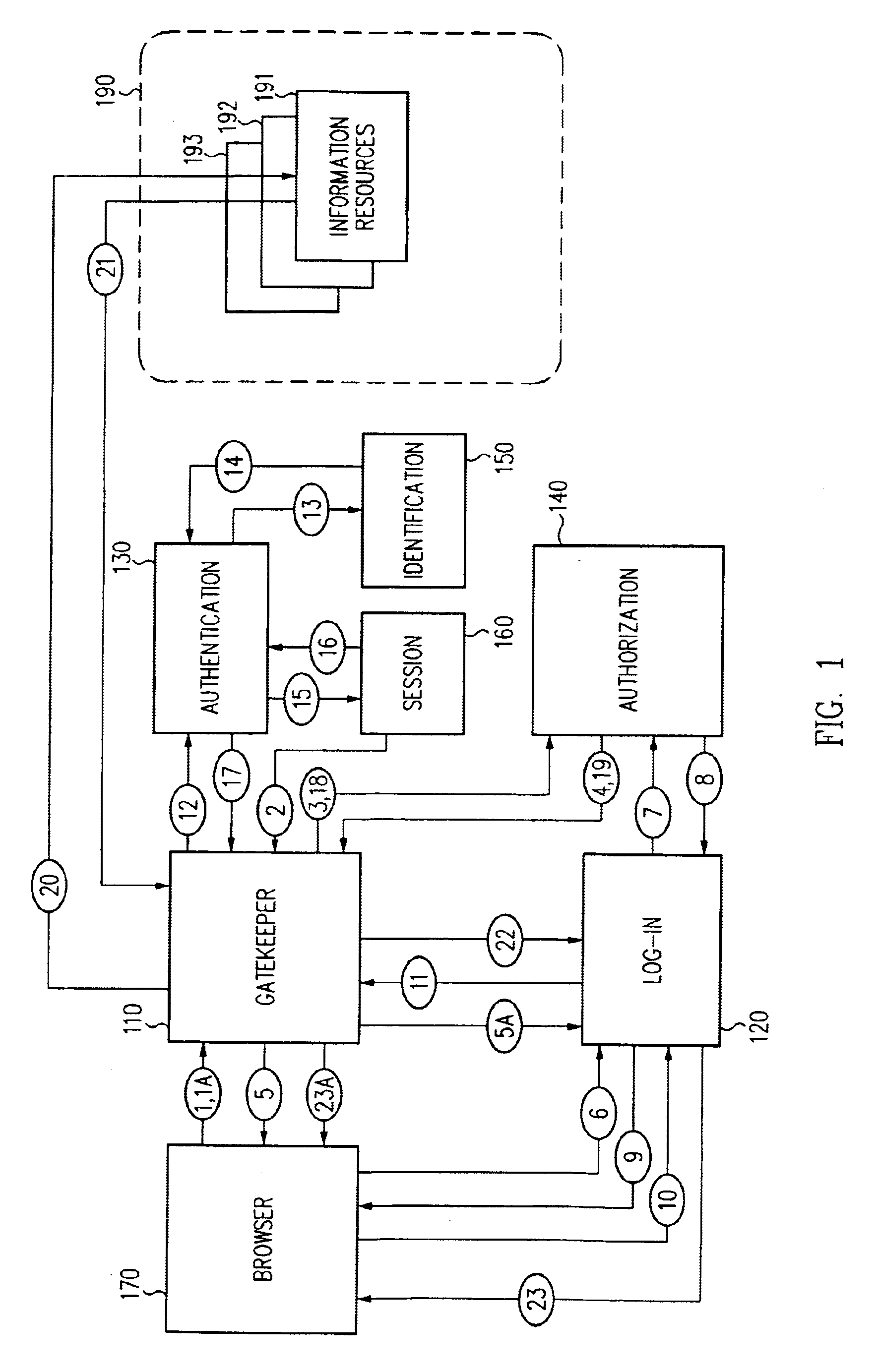
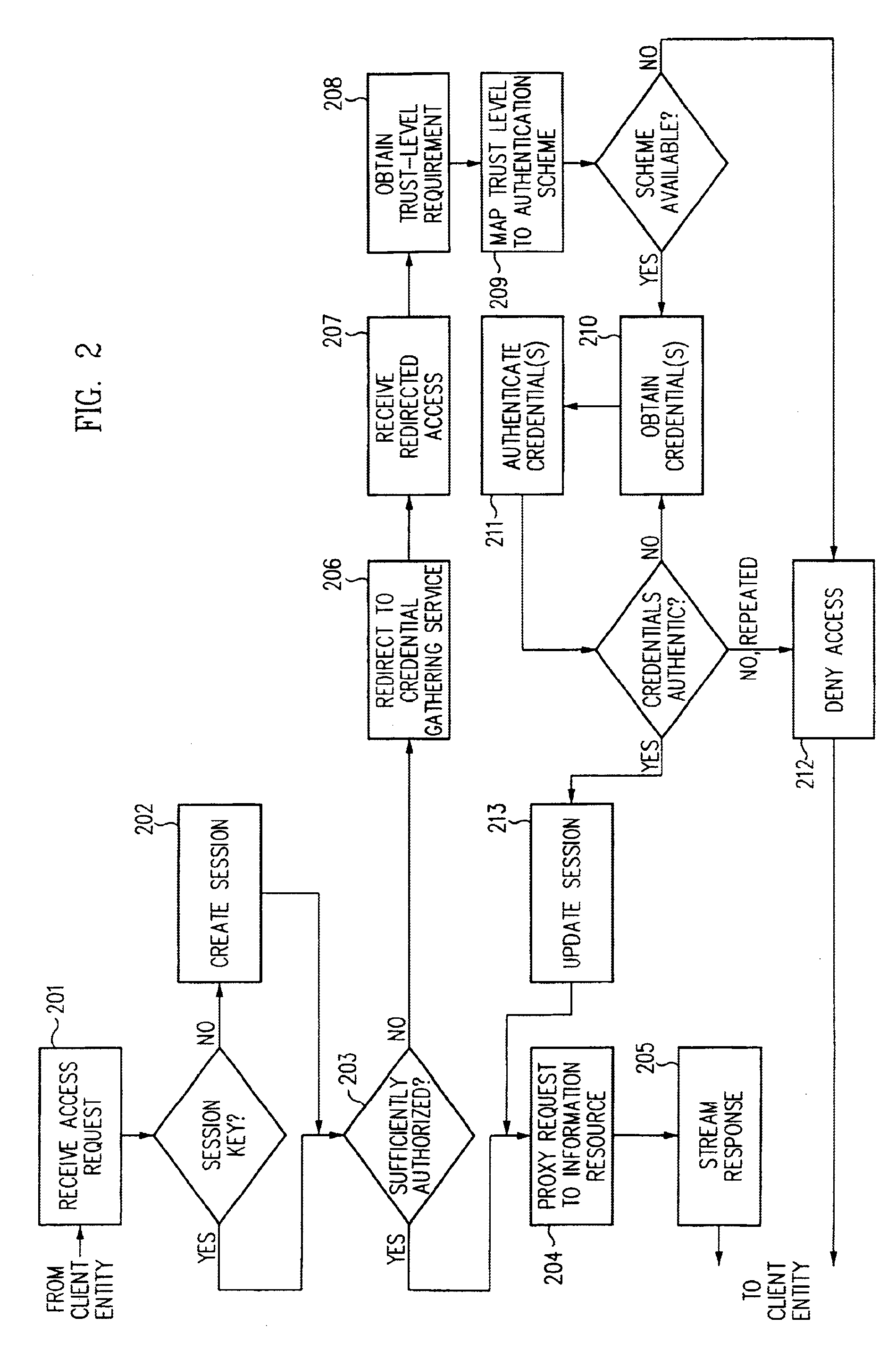
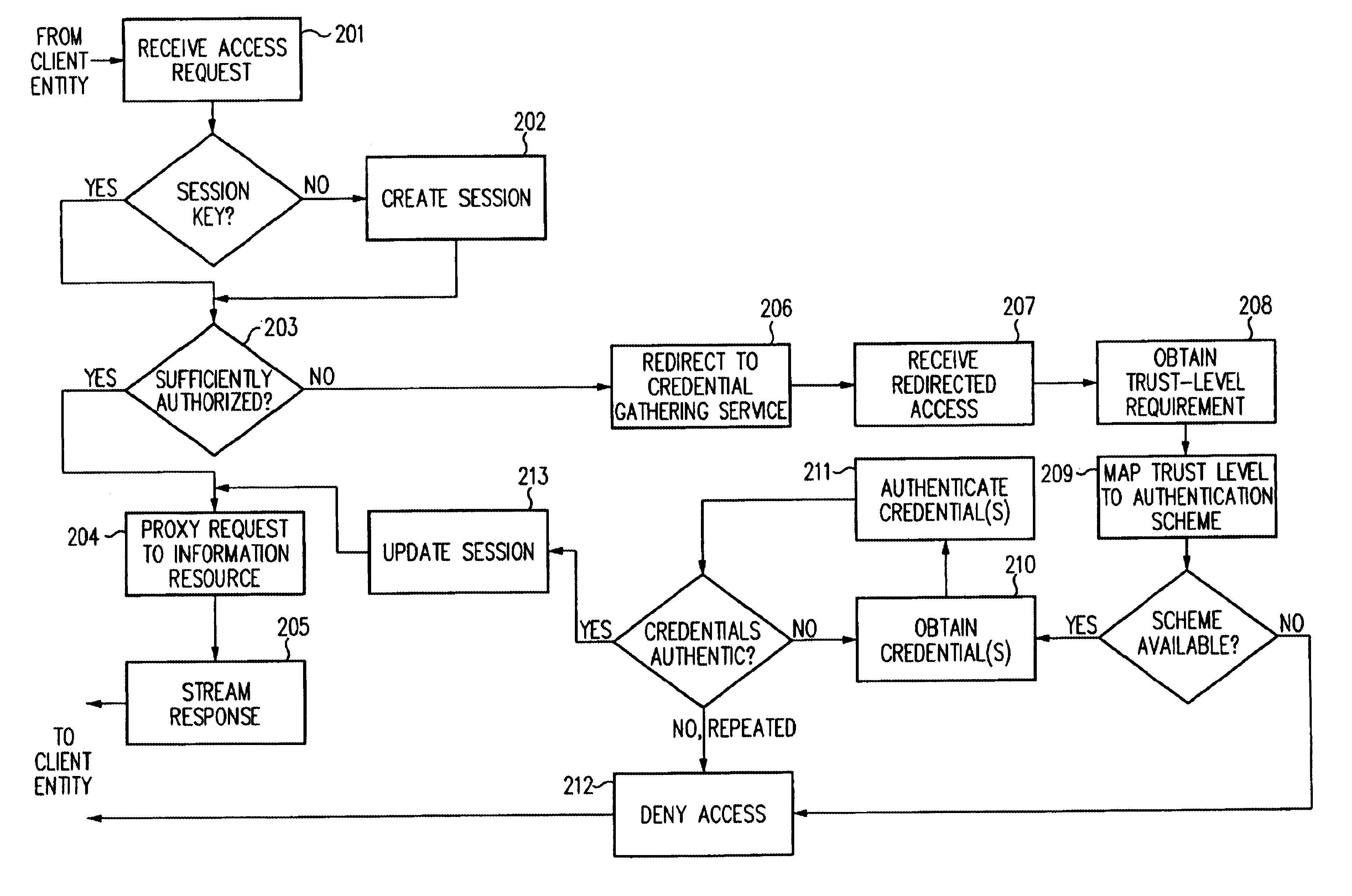
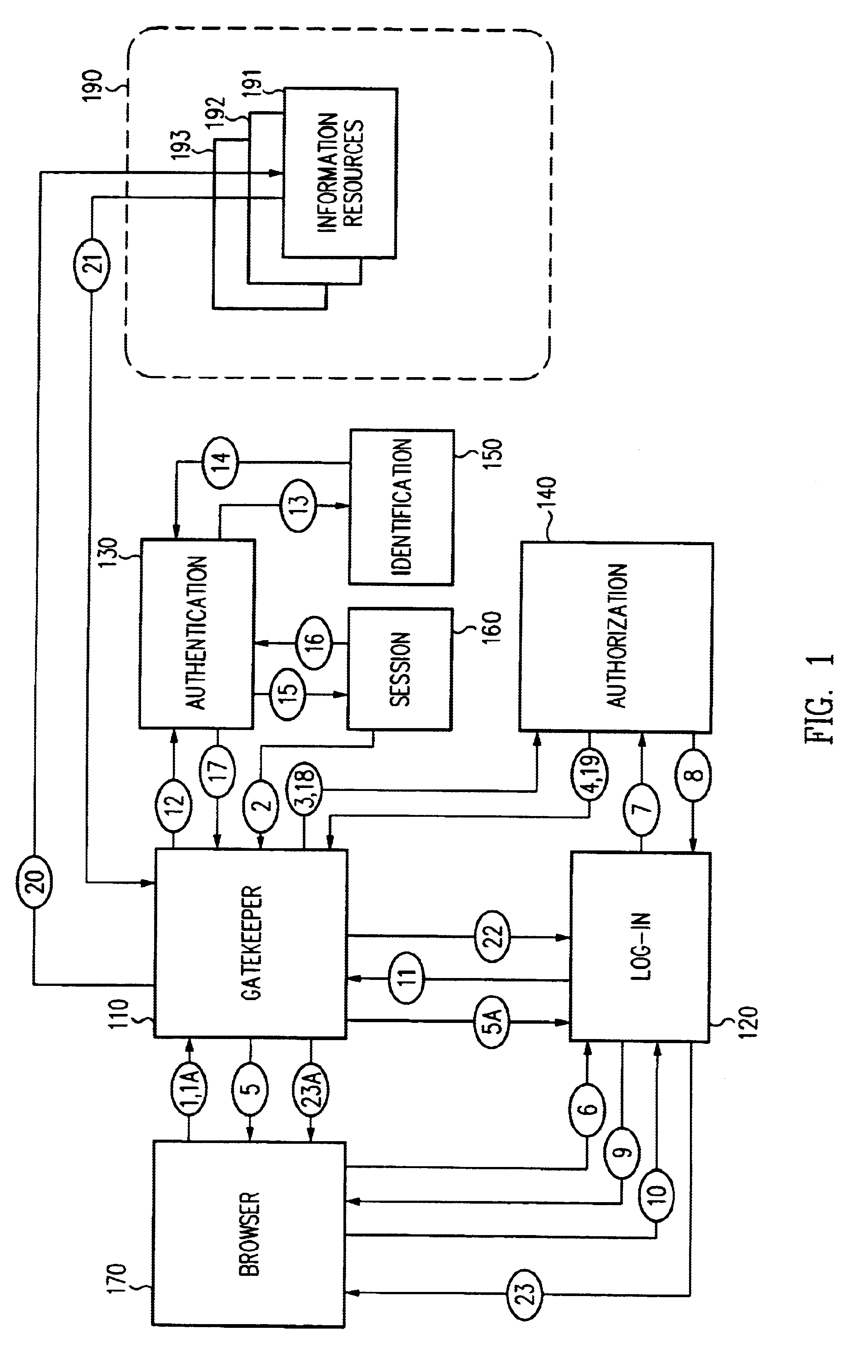
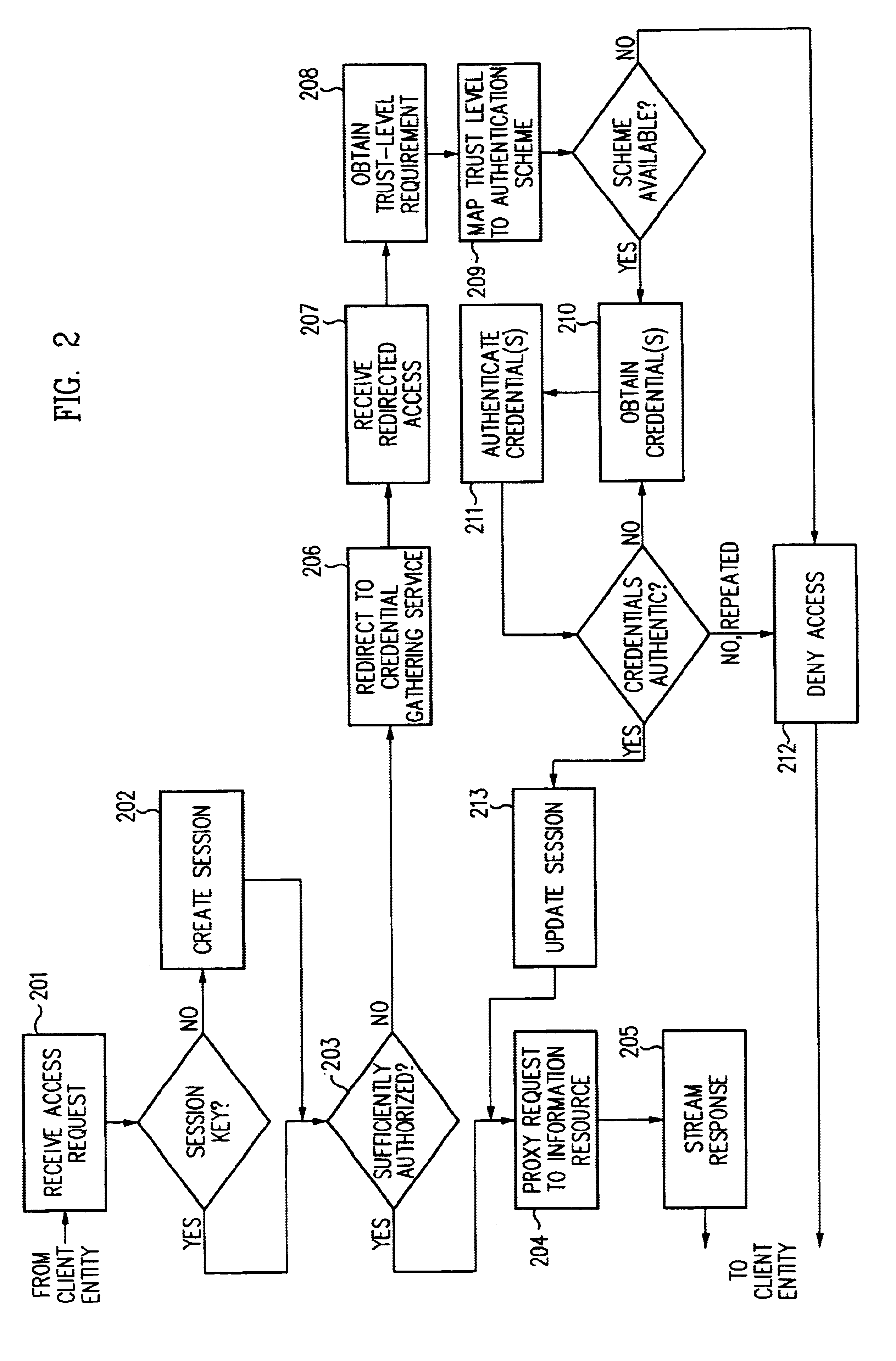
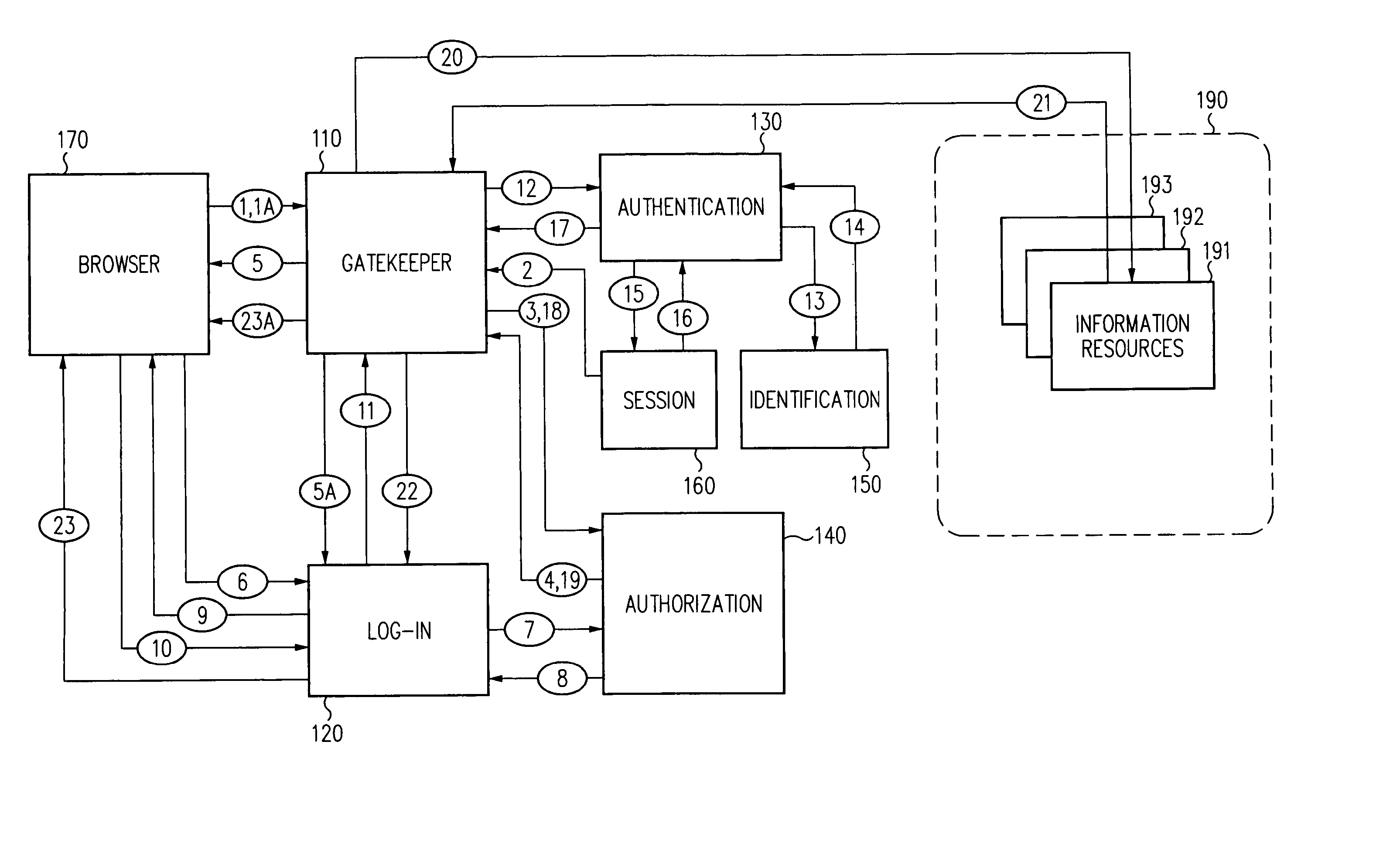
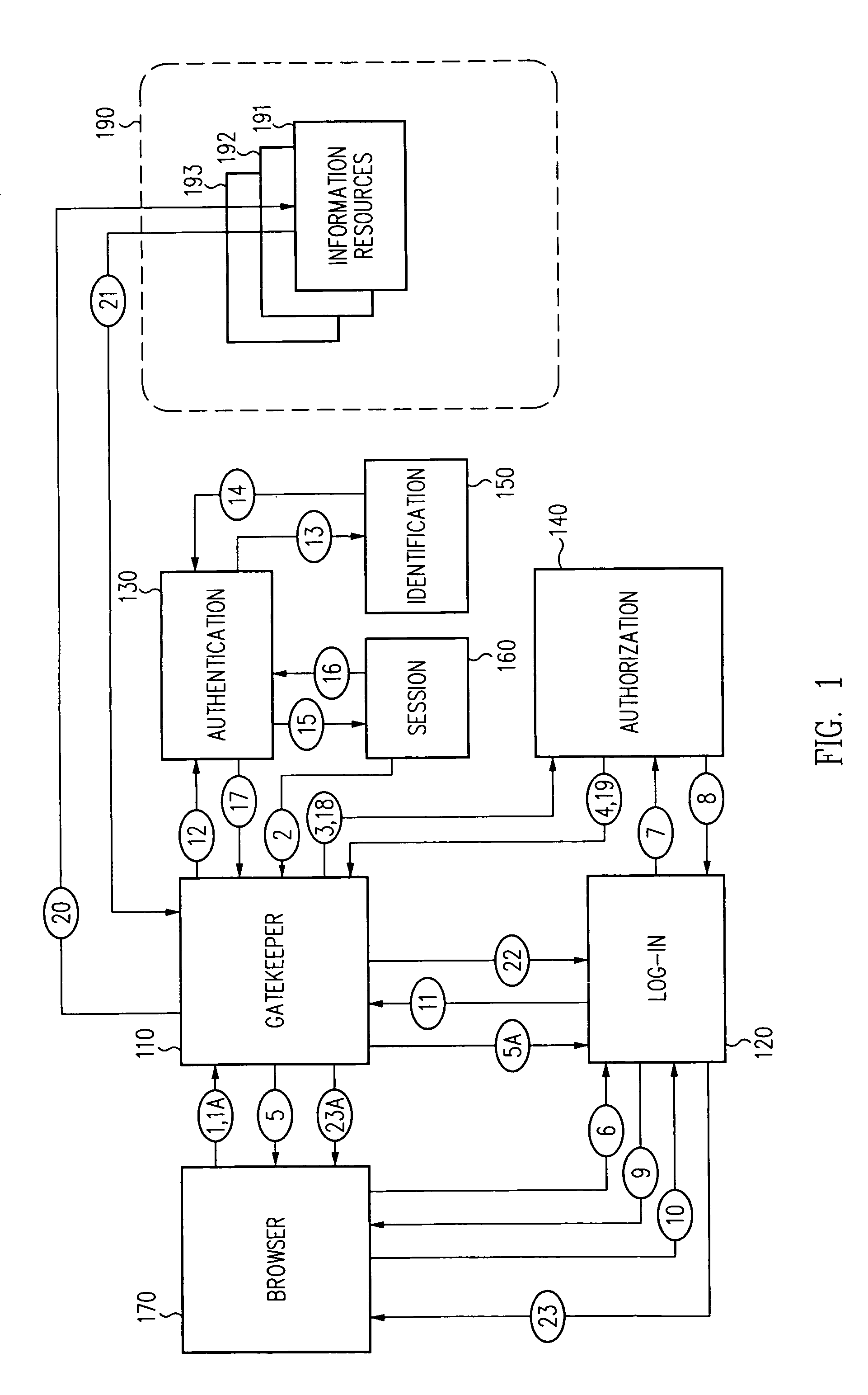
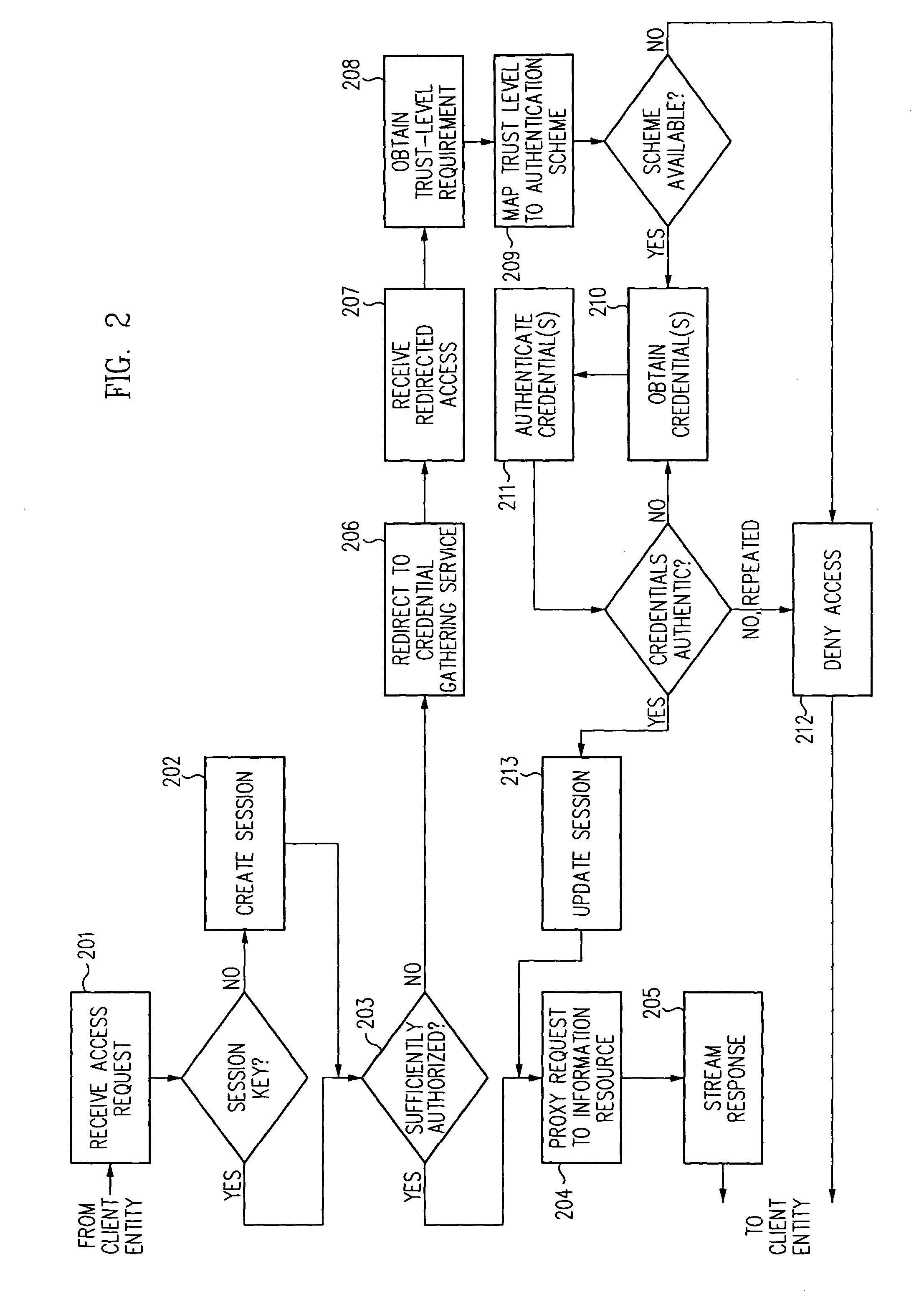
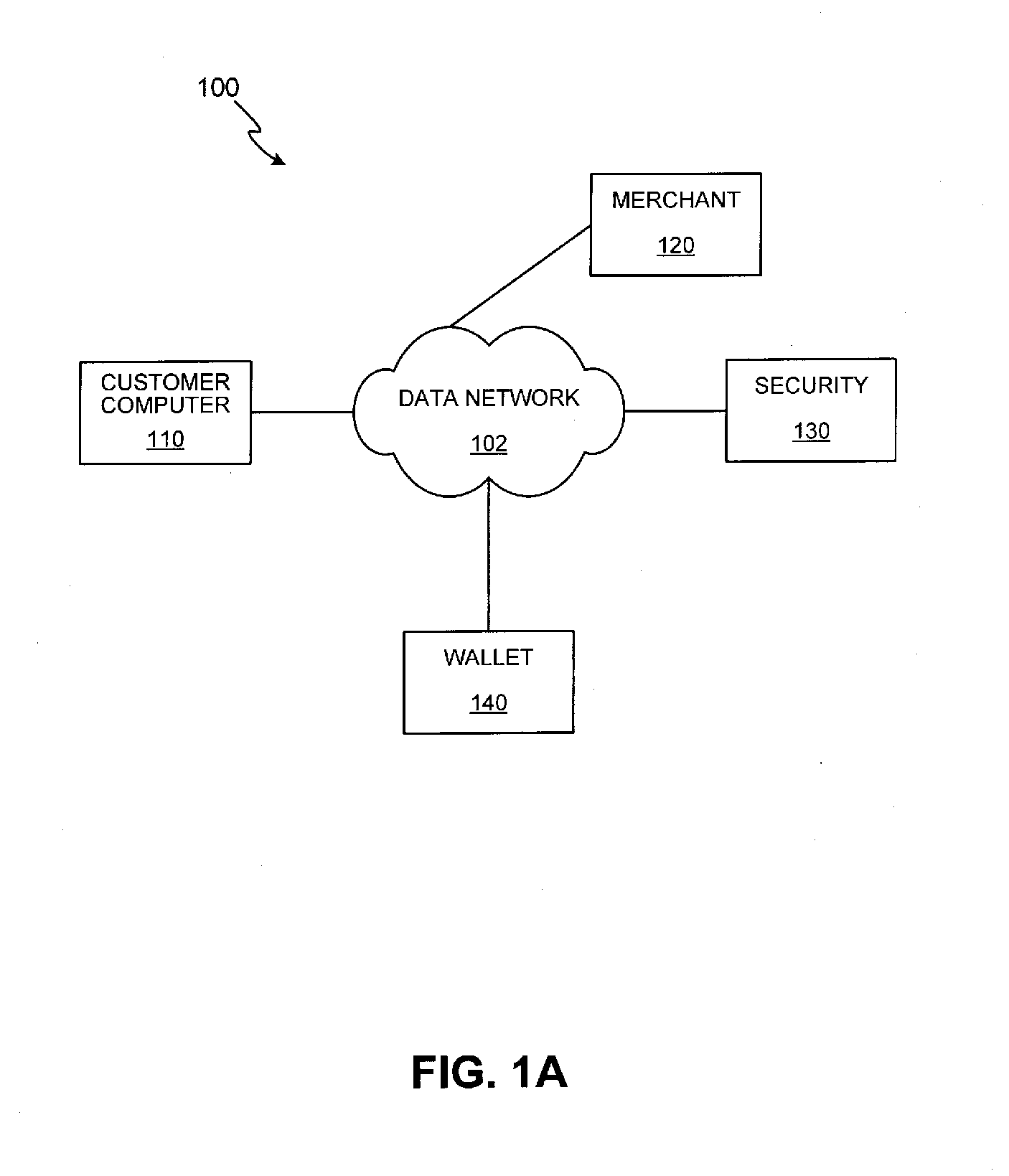
Single sign-on framework with trust-level mapping to authentication requirements
InactiveUS6892307B1Digital data processing detailsUser identity/authority verificationPasswordInformation resource
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels and a log-on service obtains credentials for an entity commensurate with the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:ORACLE INT CORP
Access management system and method employing secure credentials
InactiveUS6668322B1Digital data processing detailsUser identity/authority verificationInformation resourceTrust level
A security architecture has been developed in which a single sign-on is provided. Session credentials are used to maintain continuity of a persistent session across multiple accesses to one or more information resources, and in some embodiments, across credential level changes. Session credentials are secured, e.g., as a cryptographically secured session token, such that they may be inspected by a wide variety of entities or applications to verify an authenticated trust level, yet may not be prepared or altered except by a trusted authentication service. Some embodiments of the present invention associate trust level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are associated with trust levels, and in some embodiments, with environmental parameters. For example, in one configuration, a login service obtains login credentials for an entity commensurate with the trust level requirement(s) of an information resource (or information resources) to be accessed and with environment parameters that affect the sufficiency of a given credential type. Once login credentials have been obtained for an entity and have been authenticated to a given trust level, session credentials are issued and access is granted to information resources for which the trust level is sufficient. Advantageously, by using the session credentials access is granted without the need for further login credentials and authentication. In some configurations, session credentials evidencing an insufficient trust level may be remedied by a session continuity preserving upgrade of login credential.
Owner:ORACLE INT CORP
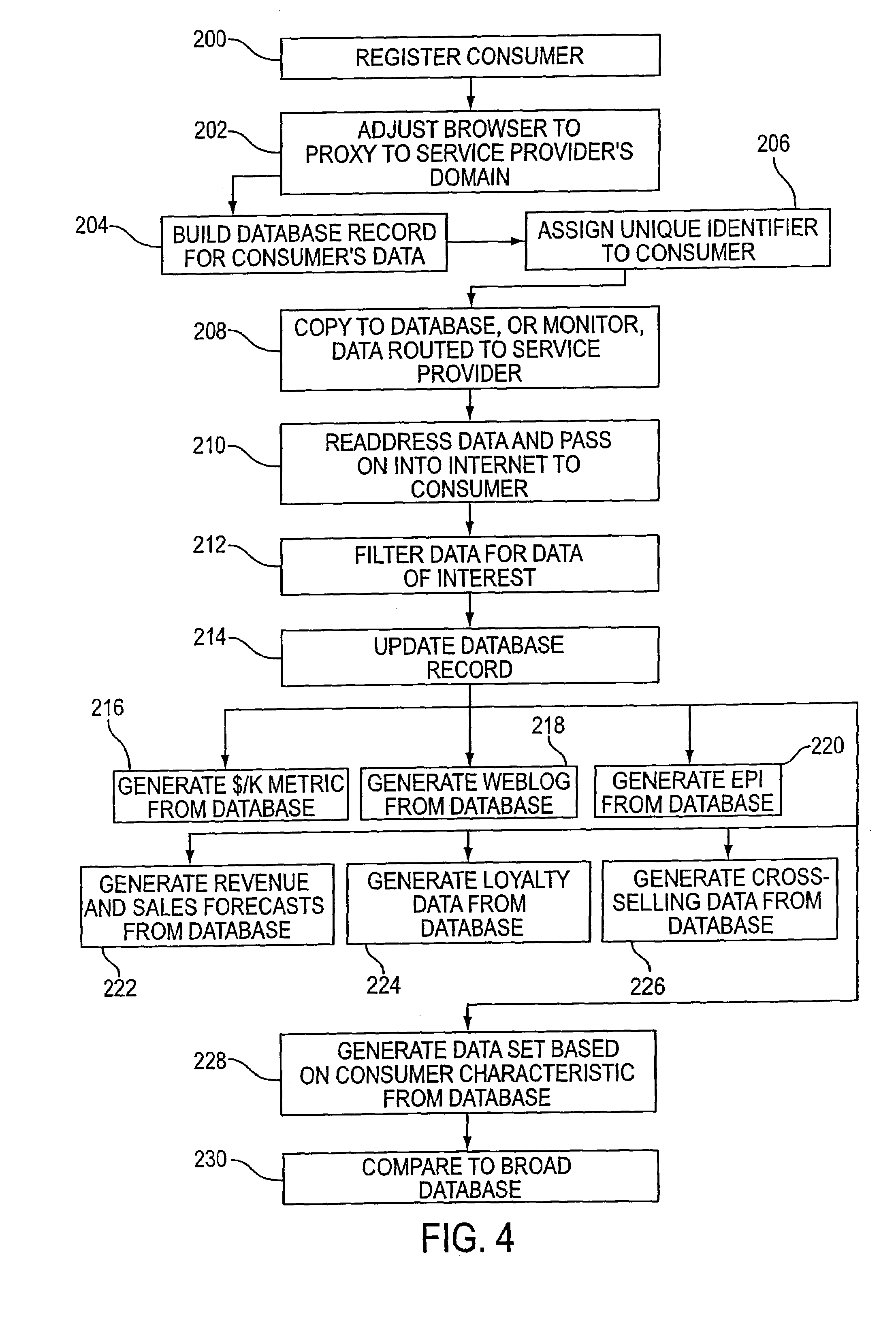
Systems and methods for user identification, user demographic reporting and collecting usage data usage biometrics
InactiveUS7260837B2Digital data information retrievalDigital data processing detailsData setDatabase server
Several ways of identifying users and collecting demographic information and market information are disclosed, including branding a browser with a unique identification in each user request, identifying a user by his key strokes or mouse clicks, gathering demographic information using multiple data sets and by monitoring network traffic. Additionally, user requested content is distinguished from other, non-user content, and the performance of a server can be monitor and analyzed from a client a client perspective. Further, an Internet user's Internet data is routed to a known domain on the Internet, from which it is routed on to the intended recipient. The domain includes proxy servers which proxy the user's data requests to the domain, and database servers, which filter and build a database of the user's Internet usage. Particular data concerning certain behaviors of interest, such as purchasing data, is filtered into the database, and can form the basis for numerous market measures.
Owner:COMSCORE
Multi-user remote health monitoring system with biometrics support
InactiveUS20030229514A2Easy to identifyData processing applicationsPerson identificationPharmacyPublic place
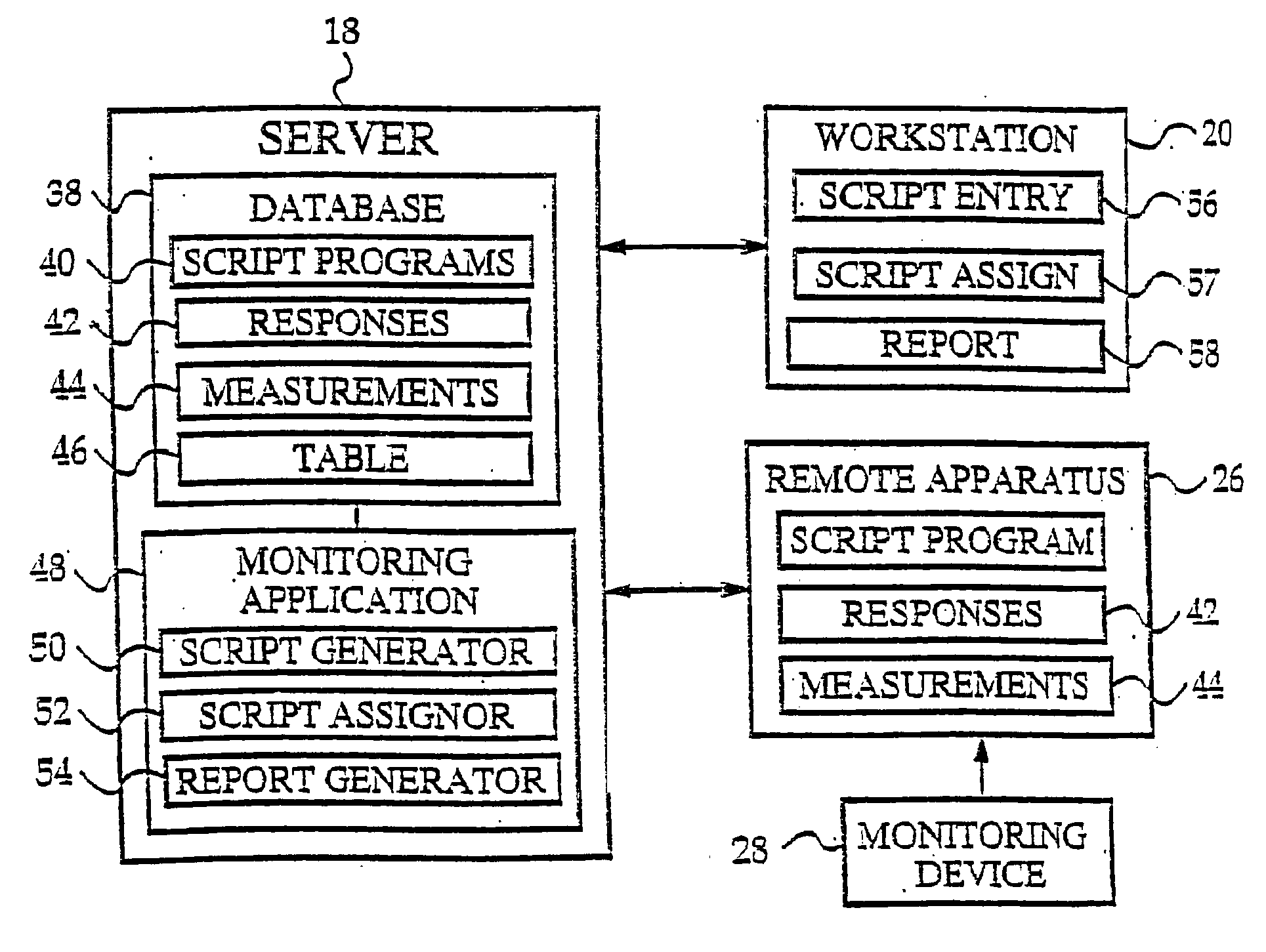
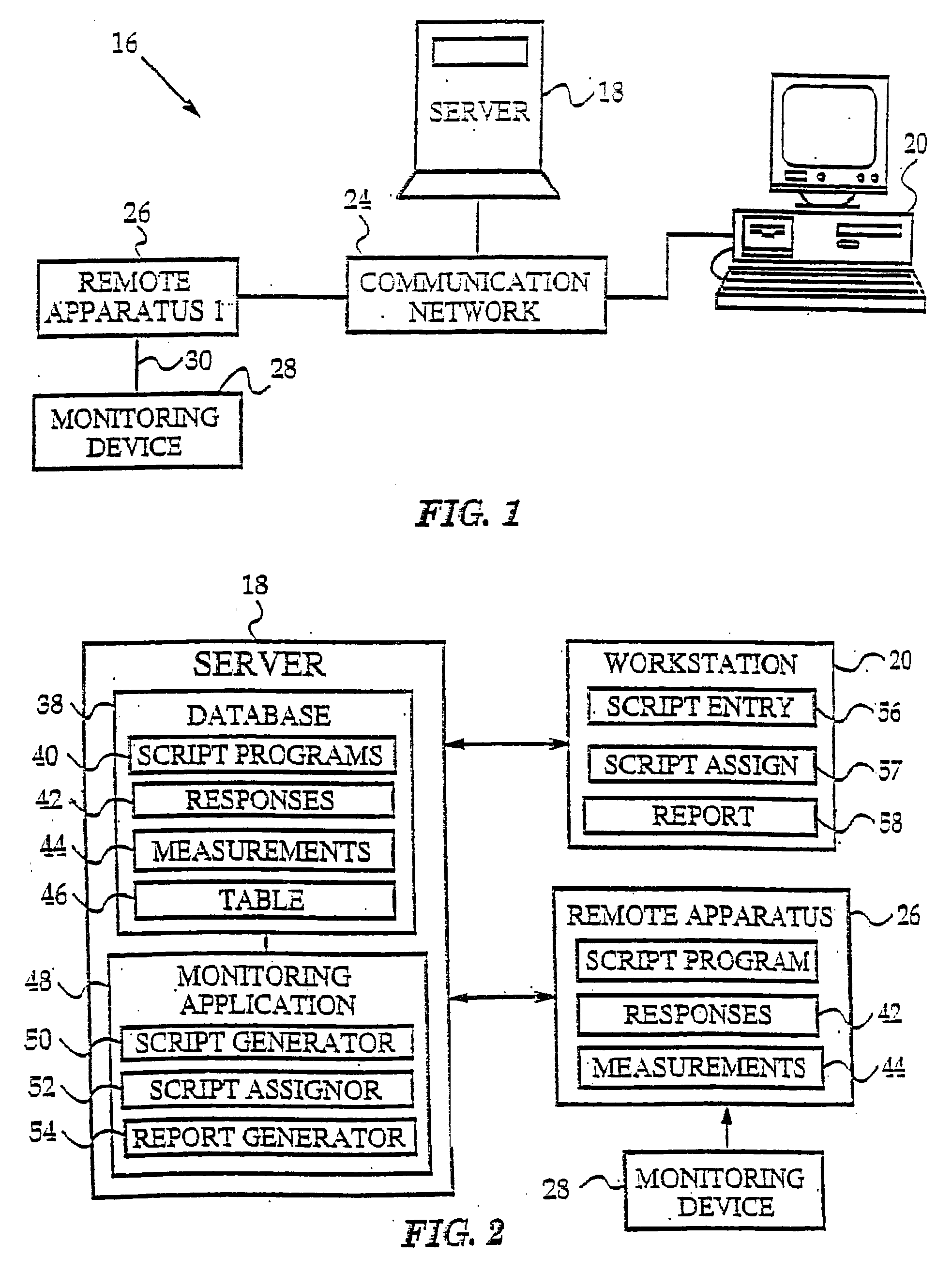
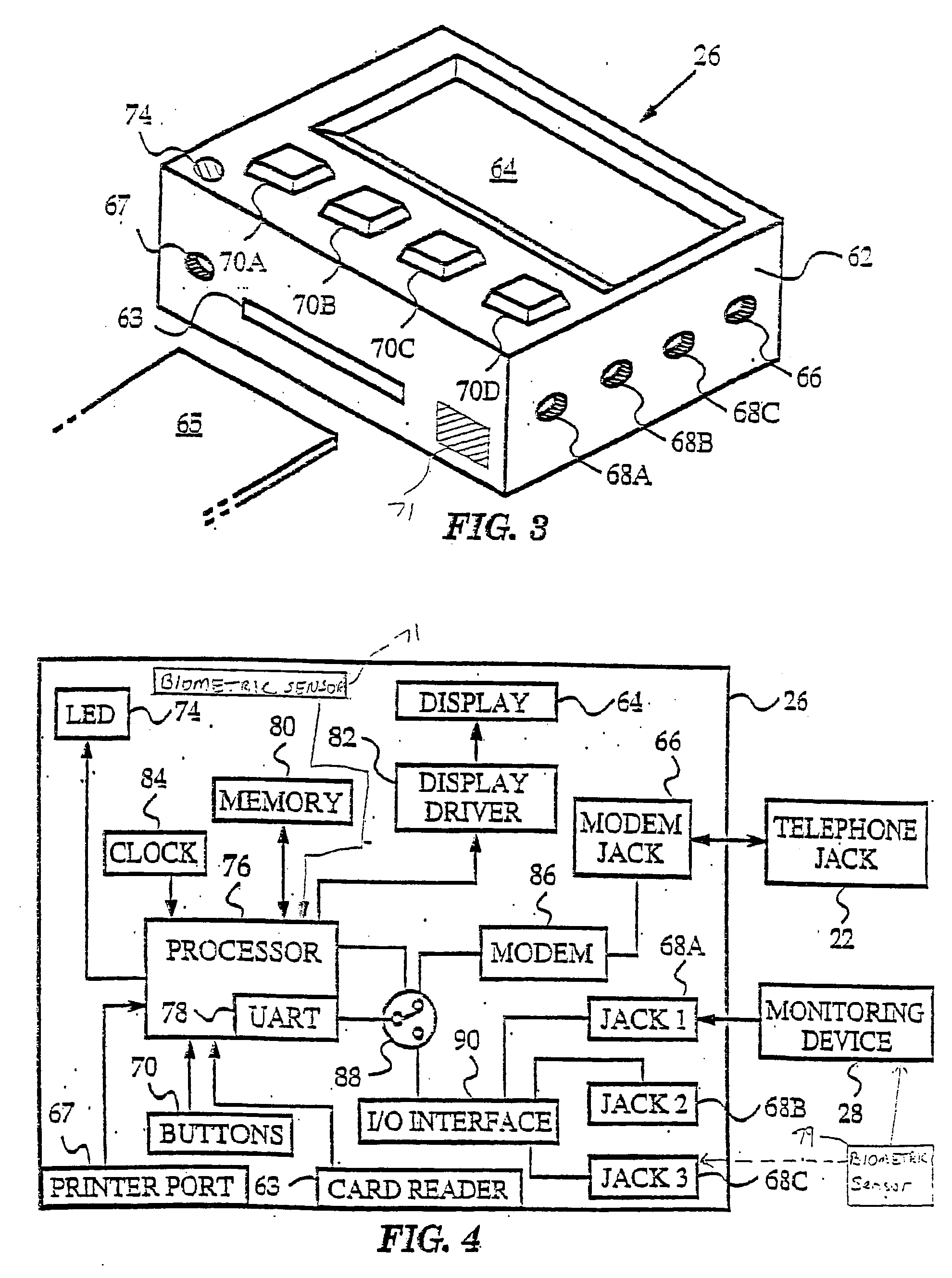
Abstract of the Disclosure The invention presents a networked system for identifying an individual, communicating information to the individual, and remotely monitoring the individual. The system includes a remotely programmable apparatus that occasionally connects to a server via a communication network such as the Internet. The remotely programmable apparatus interacts with the individual in accordance with a script program received from the server Among other capabilities, the script program may instruct the remotely programmable apparatus to identify the individual, to communicate information to the individual, to communicate queries to the individual, to receive responses to the queries, and to transmit information identifying the individual and the responses from the remotely programmable apparatus to the server. Information identifying the individual may be obtained via a biometrics sensor, a data card, a remote monitoring device, or the interception of data from a separate information system. The information identifying the individual may be used by either or both the server system and remotely programmable apparatus for security, customization and other purposes. As the present invention has multi-user capabilities, it can be used in a public place, such as a pharmacy or health care clinic. The multi-user capabilities also allow collection and tracking of user data for the healthcare industry.
Owner:HEALTH HERO NETWORK
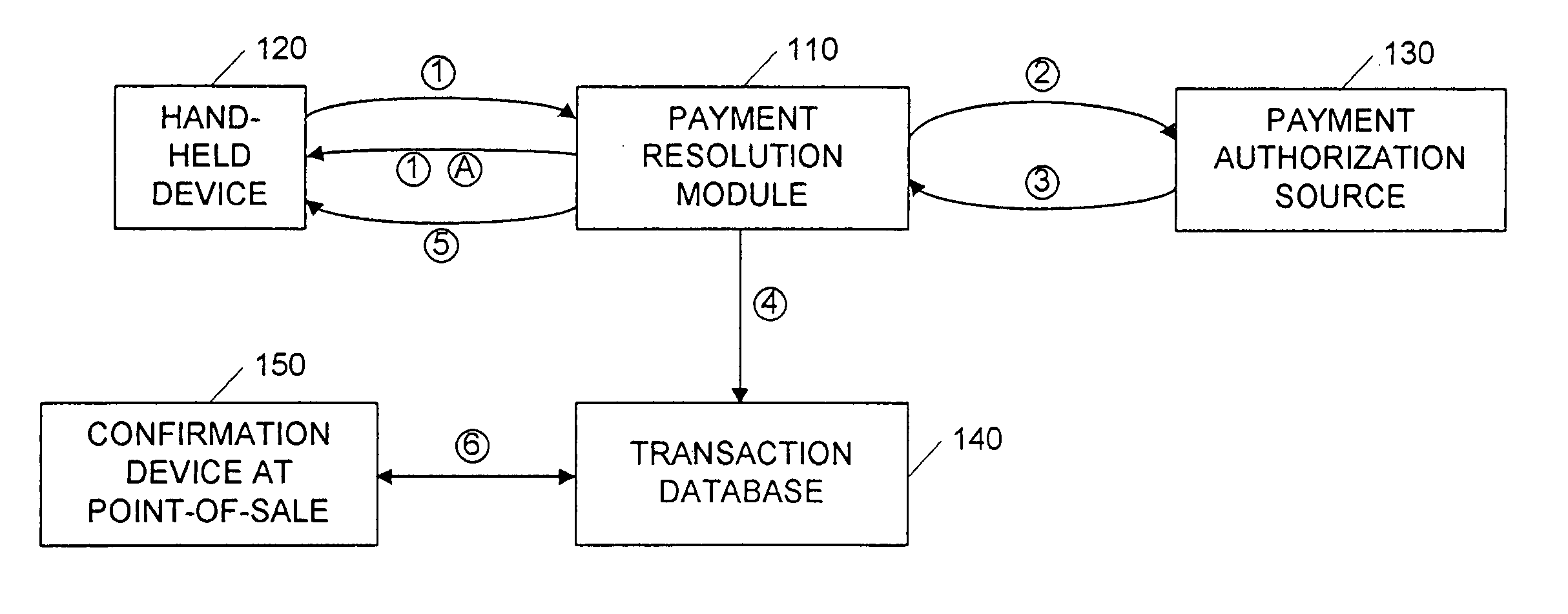
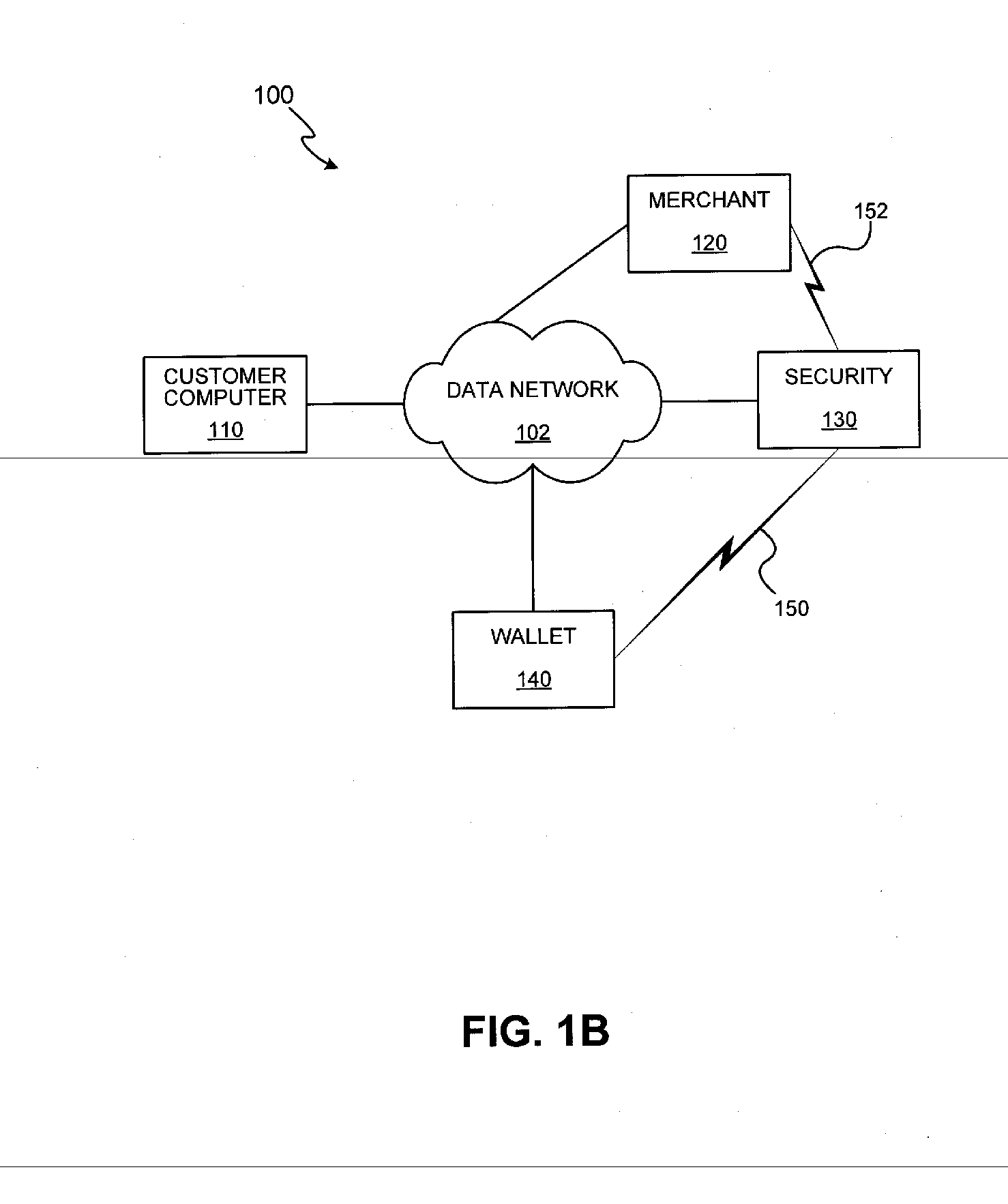
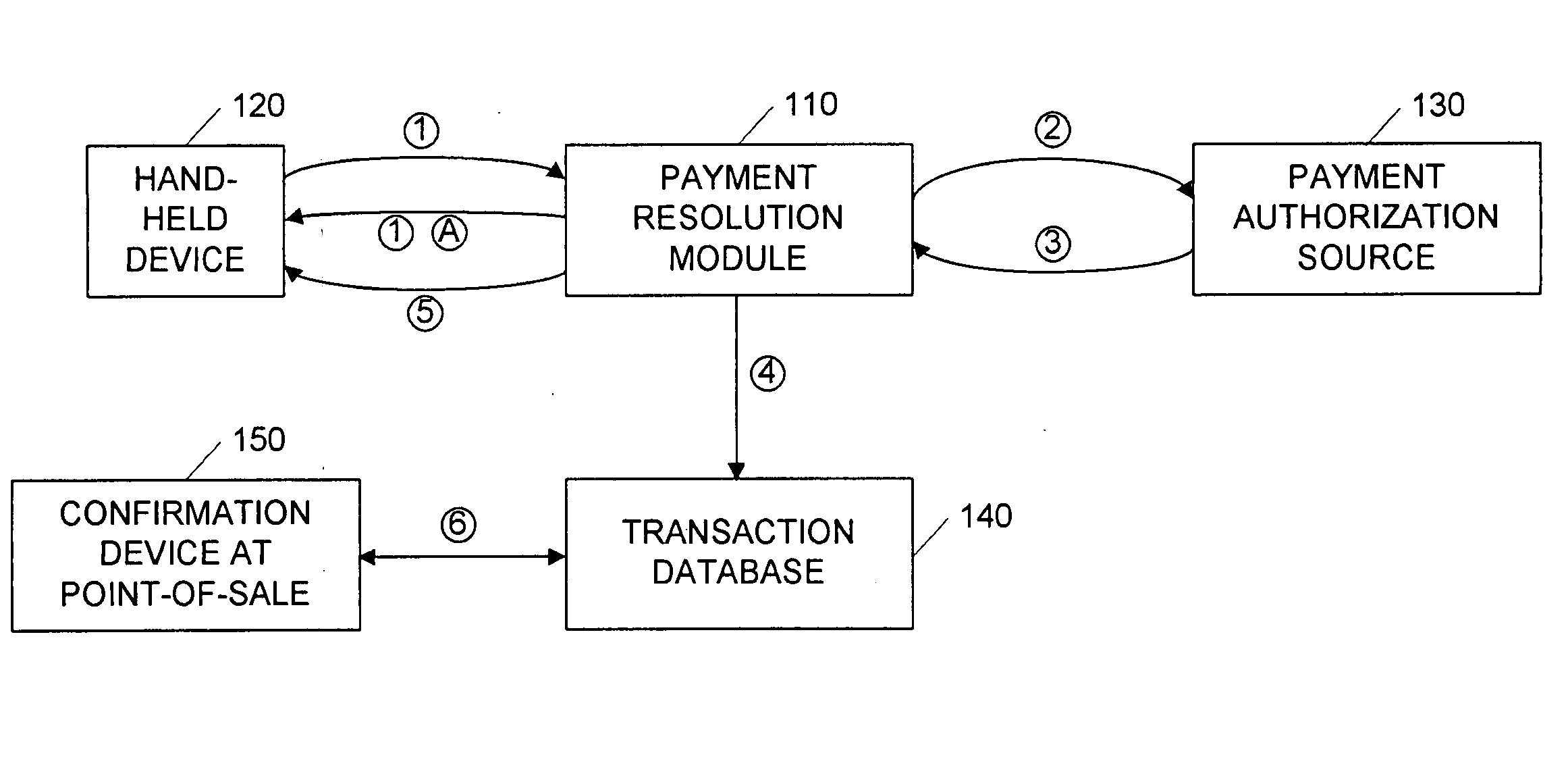
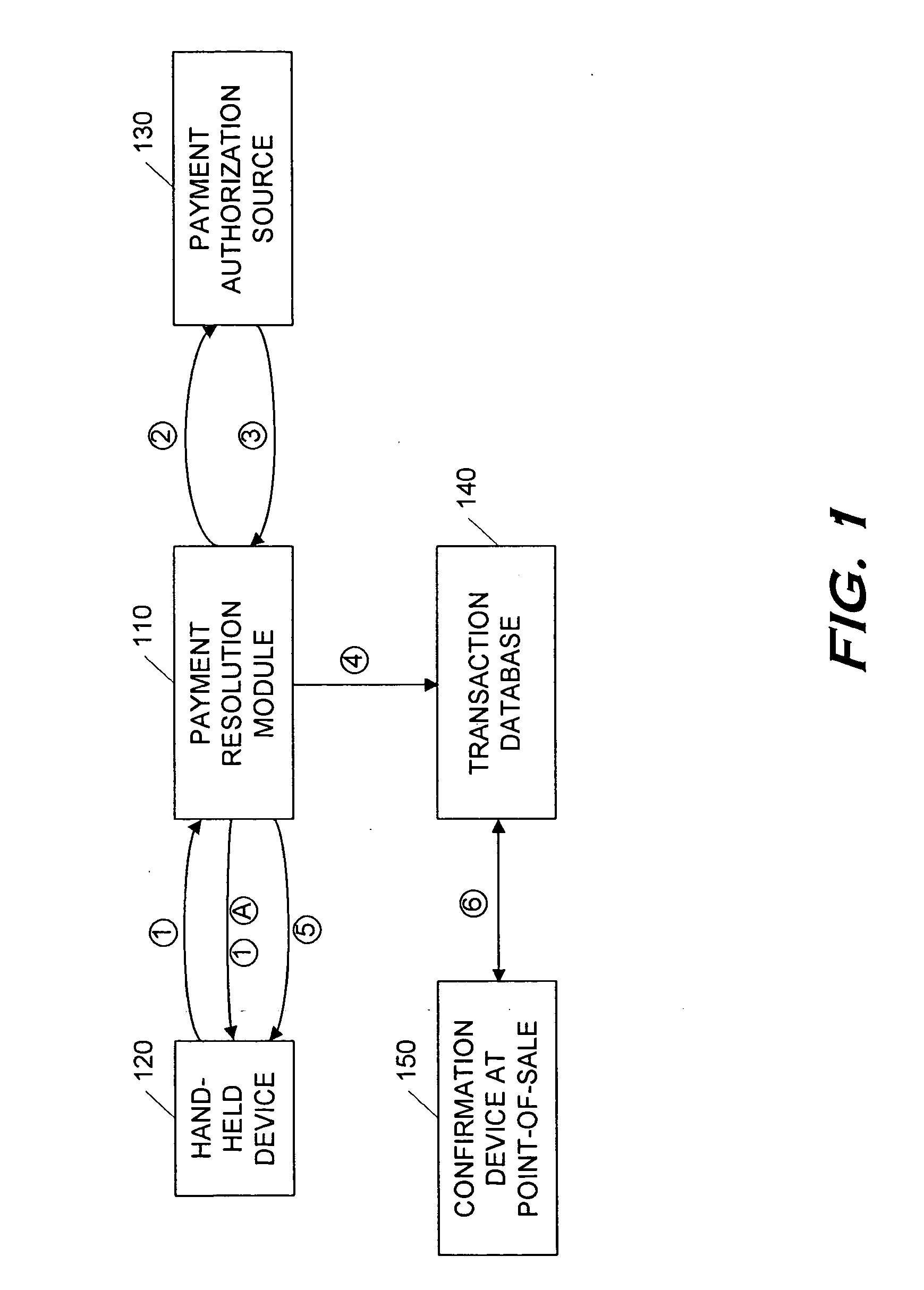
Secure money transfer between hand-held devices
A payment resolution module is configured to communicate with hand-held devices (such as mobile phones, PDA's, or computers) to allow secure transfer of funds between financial accounts associated with each of the hand-held devices. A user of a paying device may be identified as the owner of the device either by having the option to enter a personal identification code, or by using a biometric to identify himself, for example. Accordingly, only an authorized user of the hand-held device may use the hand-held device to transfer funds. A user of the recipient device may be identified by an identification code or a telephone number, for example, which is associated with a recipient financial account. After the payment resolution module receives authorization for a payment request to the recipient account, a payment transfer module transmits the requested amount from a payment source associated with the identified owner of the paying device to the recipient account.
Owner:XILIDEV
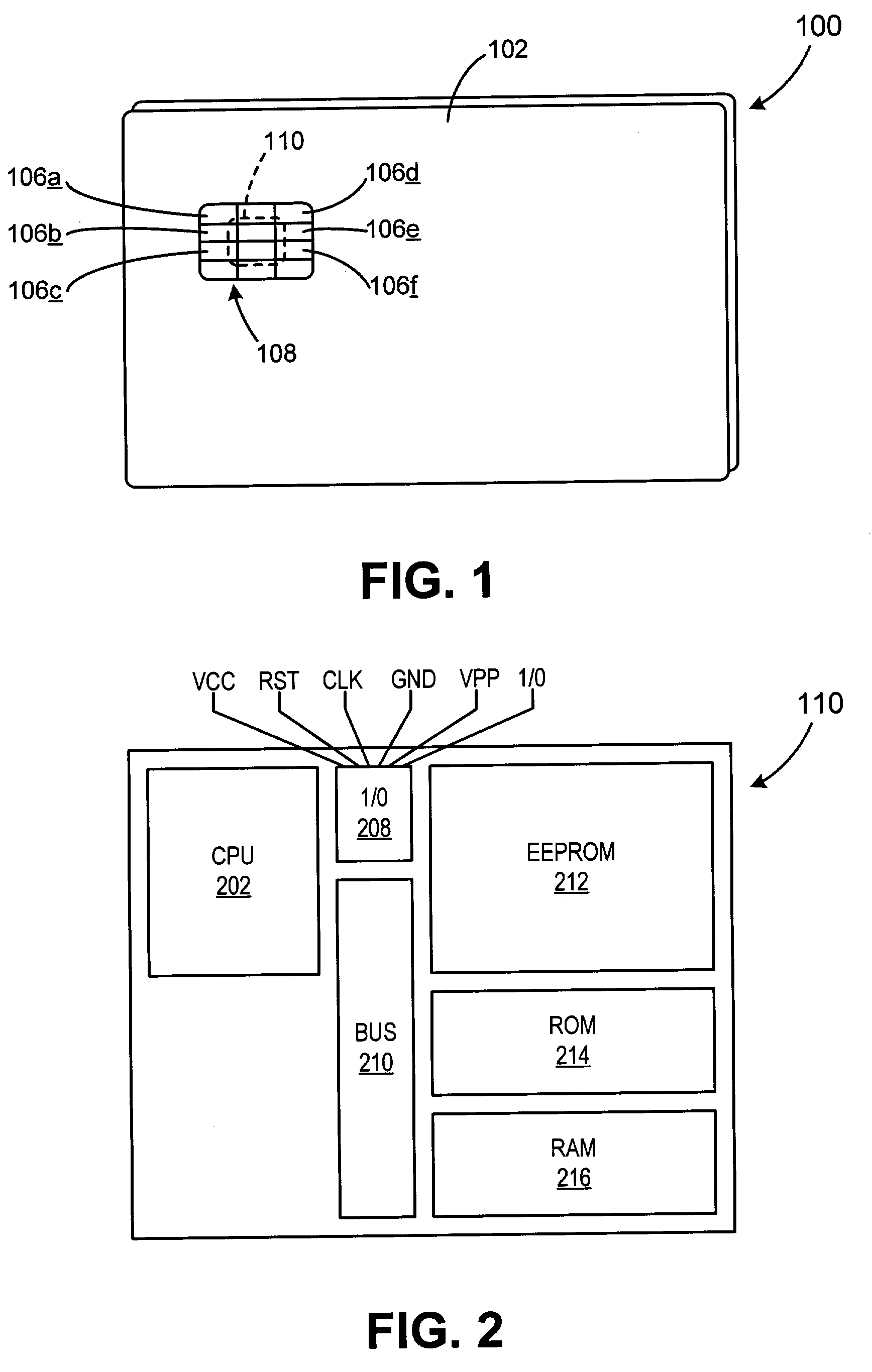
Method for authenticating an individual by use of fingerprint data
InactiveUS7136514B1Simple methodElectric signal transmission systemsImage analysisFast Fourier transformBiometrics
A method for authenticating an individual by use of fingerprint data that involves two different broad steps. The first step is to obtain a biometrics fingerprint signature template (“BFST”) for an individual in an enrollment process by selecting a plurality of bands for the BFST and obtaining a plurality of tracks corresponding to each of the plurality of bands by use of an enrollment frame of a selected finger of the individual, wherein the plurality of bands are spatially referenced to the enrollment frame and can be spatially referenced to a reference barrier. The second step is to authenticate (or not) a candidate finger against one or more BFST in an authentication process in which a swipe direction and an access code for the individual are selected, a plurality of candidate tracks are obtained from the candidate finger through use of the reference barrier in an authentication unit so that each of the plurality of candidate tracks is spatially referenced so as to be within a corresponding one of the plurality of bands, calculating a similarity index for each of the plurality of candidate tracks and each of the plurality of tracks for the band to which the candidate track corresponds by use of a Fast Fourier-transform fingerprint algorithm, and multiplying each maximum similarity index obtained for each of the plurality of candidate tracks to obtain a match index which indicates a match if it exceeds a preselected threshold.
Owner:WONG JACOB Y
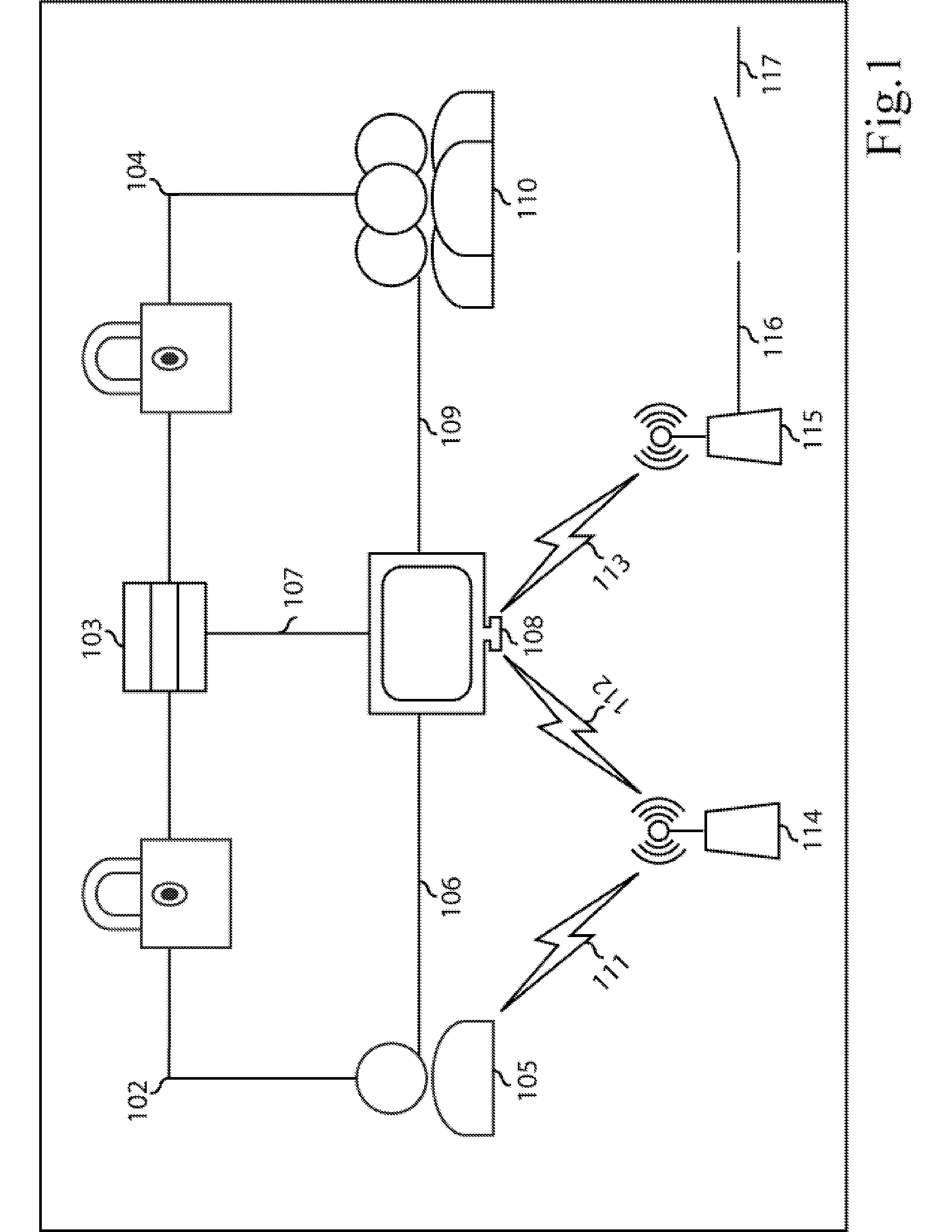
System and method for driver reaction impairment vehicle exclusion via systematic measurement for assurance of reaction time
InactiveUS20110304465A1Prevents DUI without social stigmaAlarmsDriver input parametersDriver/operatorMotor skill
A system and method for measuring impairment in an operator and stopping an impaired operator from operating a vehicle. The method empirically measures an operator's cognitive and motor skills requisite for safely operating a motorized vehicle and verifies the person's identity. The invention includes three interlocking major subsystems. The first subsystem provides generalized impairment measurement unit. The second subsystem interfaces with the impairment measurement unit and a vehicle ignition system and ensures the vehicle does not start if the operator is impaired. The third system determines whether the person blowing into a drug and alcohol analyzer connected to the first system is that person by detecting a various biometric. If the operator is not impaired and their identity is verified the vehicle ignition is enabled. If the operator is indeed impaired beyond a level requisite to safely operate the vehicle the ignition is disabled.
Owner:BOULT TERRANCE E +1
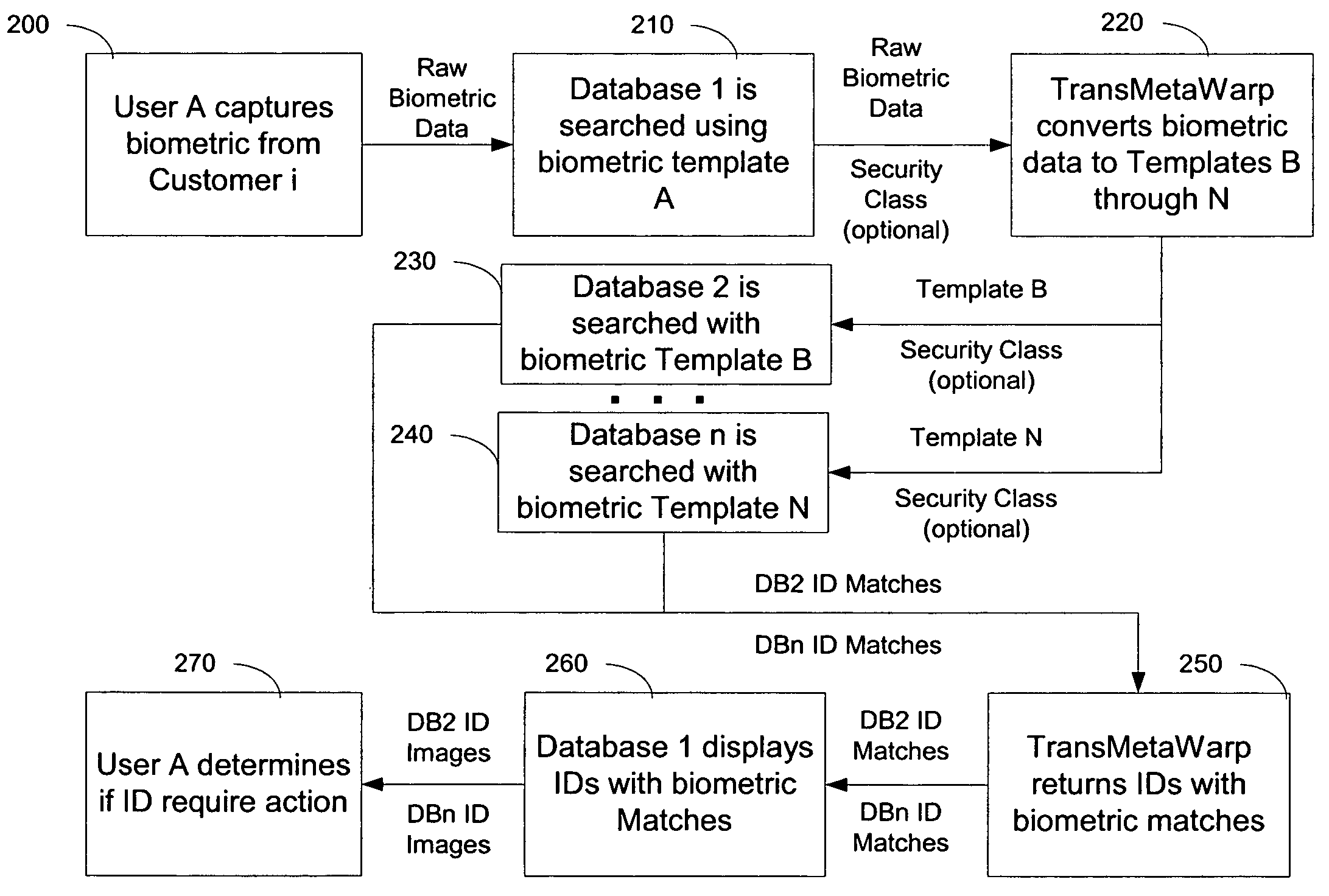
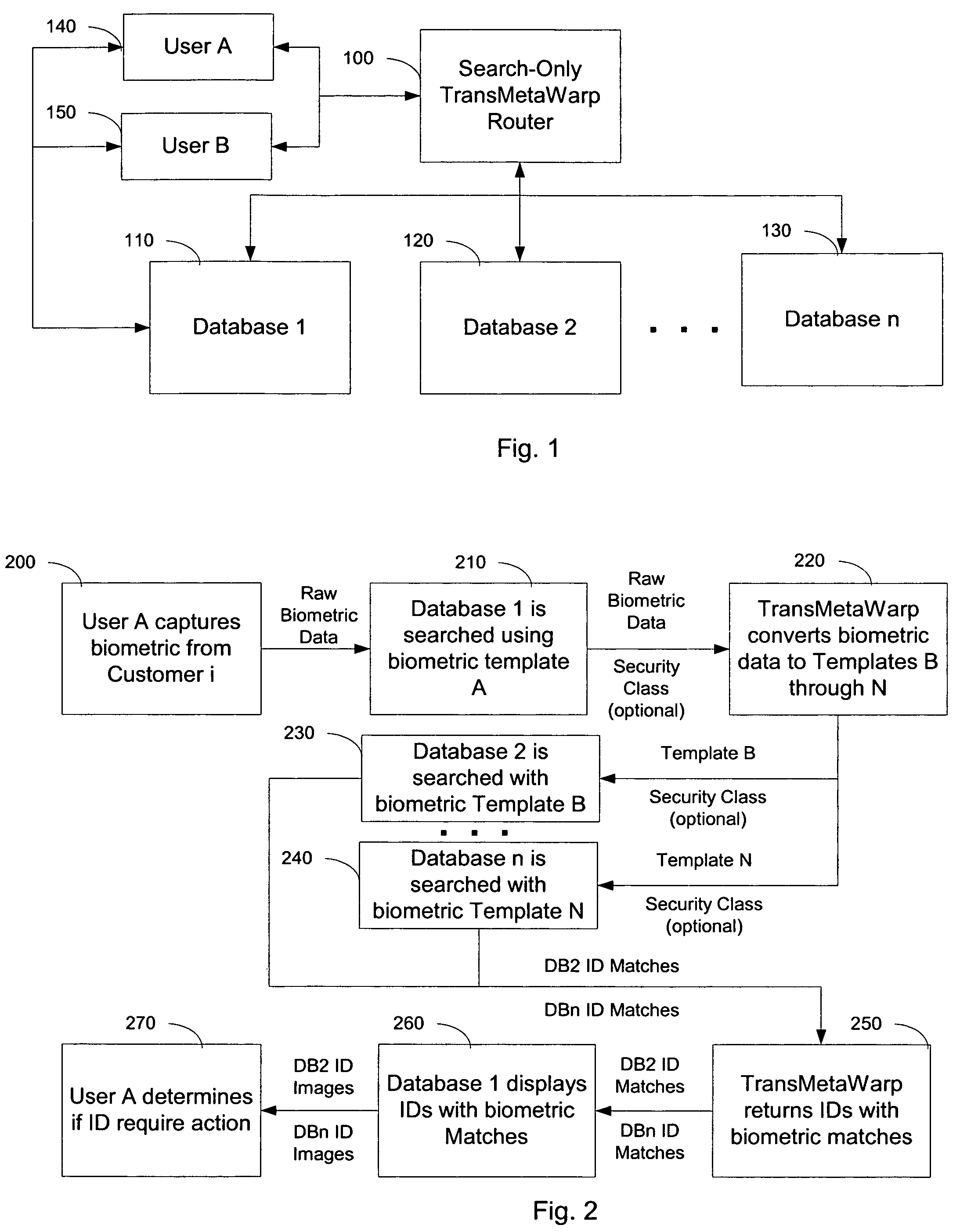
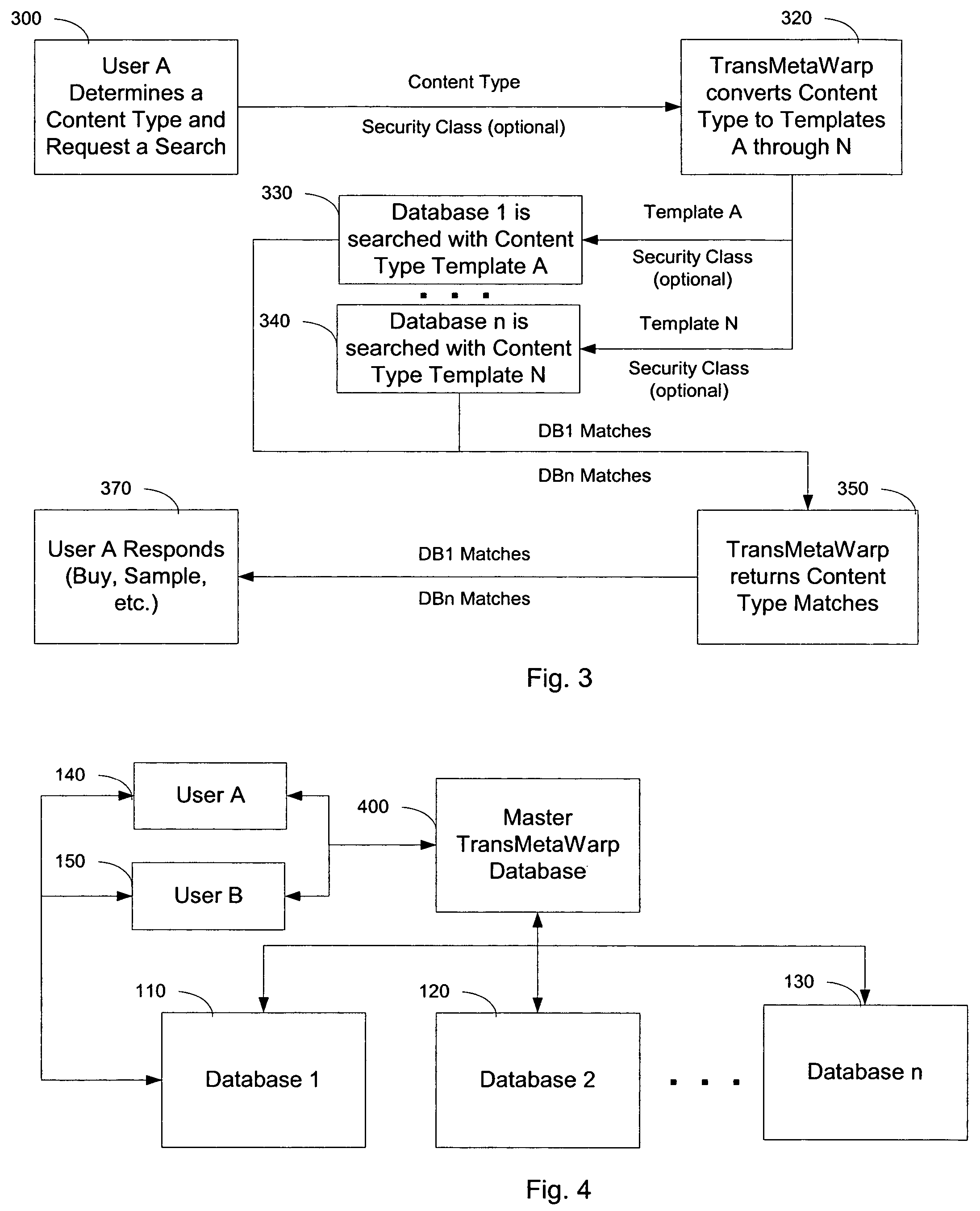
Integrating and enhancing searching of media content and biometric databases
ActiveUS7606790B2Increase incomeReduce identityData processing applicationsDigital data information retrievalInternet privacyBiometrics
The digital era is creating problems with identity and content theft. The solutions require searching different databases containing similar data. The novel method demonstrates how to search these different databases for similar information via TransMetaWarp routers and / or databases. Embodiments provide different balances of security and privacy issues, such as search-only TransMetaWarp routers and master TransMetaWarp databases. The system is applicable to biometrics for identity cards, such as drivers' licenses, as well as metadata, such as content title, creator information, and tour information, or content identification for entertainment content.
Owner:DIGIMARC CORP
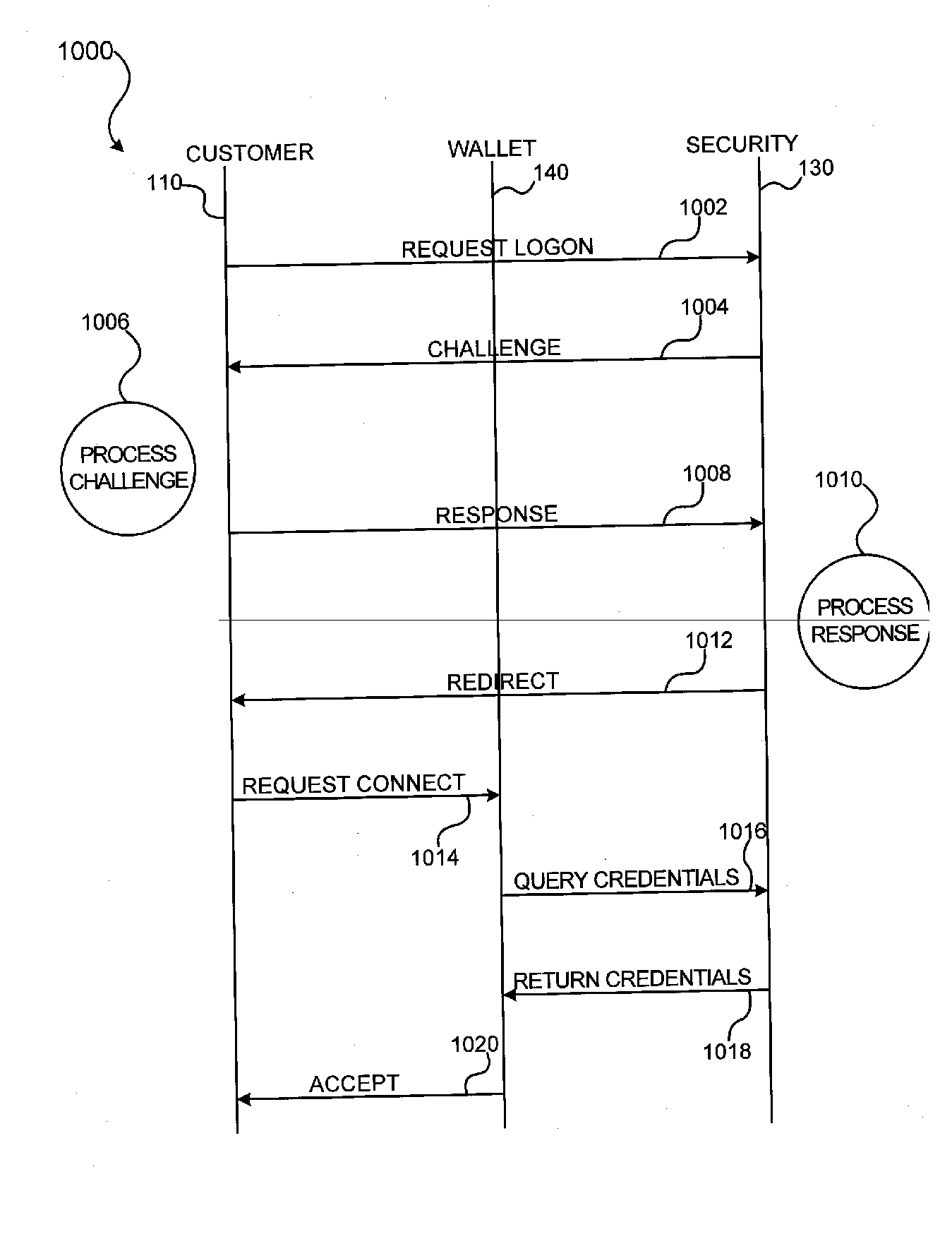
Log-on service providing credential level change without loss of session continuity
InactiveUS20040210771A1Digital data processing detailsUser identity/authority verificationInformation resourcePassword
A security architecture has been developed in which a single sign-on is provided for multiple information resources. Rather than specifying a single authentication scheme for all information resources, the security architecture associates trust-level requirements with information resources. Authentication schemes (e.g., those based on passwords, certificates, biometric techniques, smart cards, etc.) are employed depending on the trust-level requirement(s) of an information resource (or information resources) to be accessed. Once credentials have been obtained for an entity and the entity has been authenticated to a given trust level, access is granted, without the need for further credentials and authentication, to information resources for which the authenticated trust level is sufficient.
Owner:SUN MICROSYSTEMS INC
Tokenless identification system for authorization of electronic transactions and electronic transmissions
InactiveUS7152045B2Eliminate riskEnhances fraud resistanceCredit registering devices actuationDigital data processing detailsElectronic transmissionComputerized system
A tokenless identification system and method for authorization of transactions and transmissions. The tokenless system and method are principally based on a correlative comparison of a unique biometrics sample, such as a finger print or voice recording, gathered directly from the person of an unknown user, with an authenticated biometrics sample of the same type obtained and stored previously. It can be networked to act as a full or partial intermediary between other independent computer systems, or may be the sole computer systems carrying out all necessary executions. It further contemplates the use of a private code that is returned to the user after the identification has been complete, authenticating and indicating to the user that the computer system was accessed. The identification system and method of additionally include emergency notification to permit an authorized user to alert authorities an access attempt is coerced.
Owner:EXCEL INNOVATIONS +1
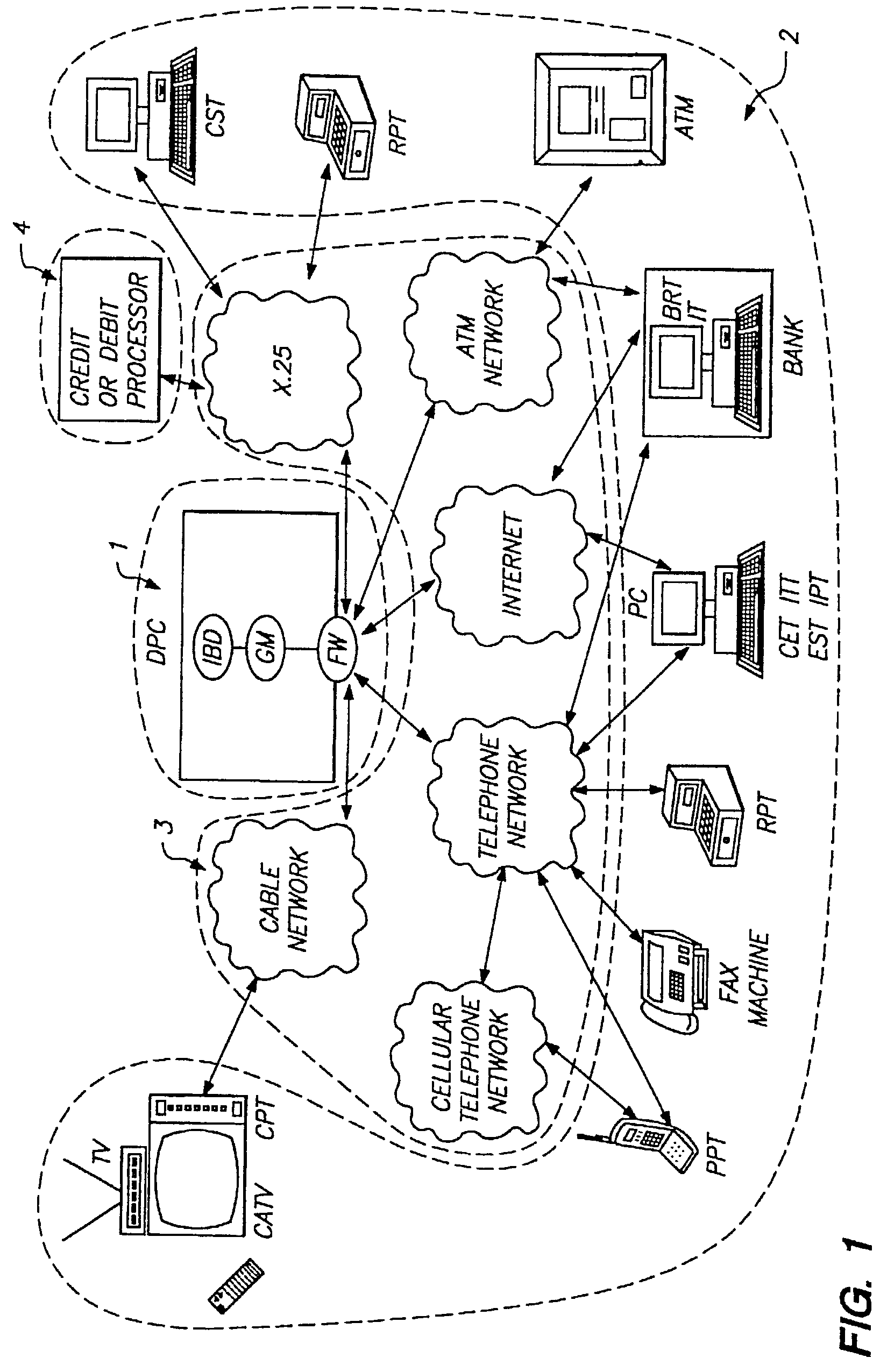
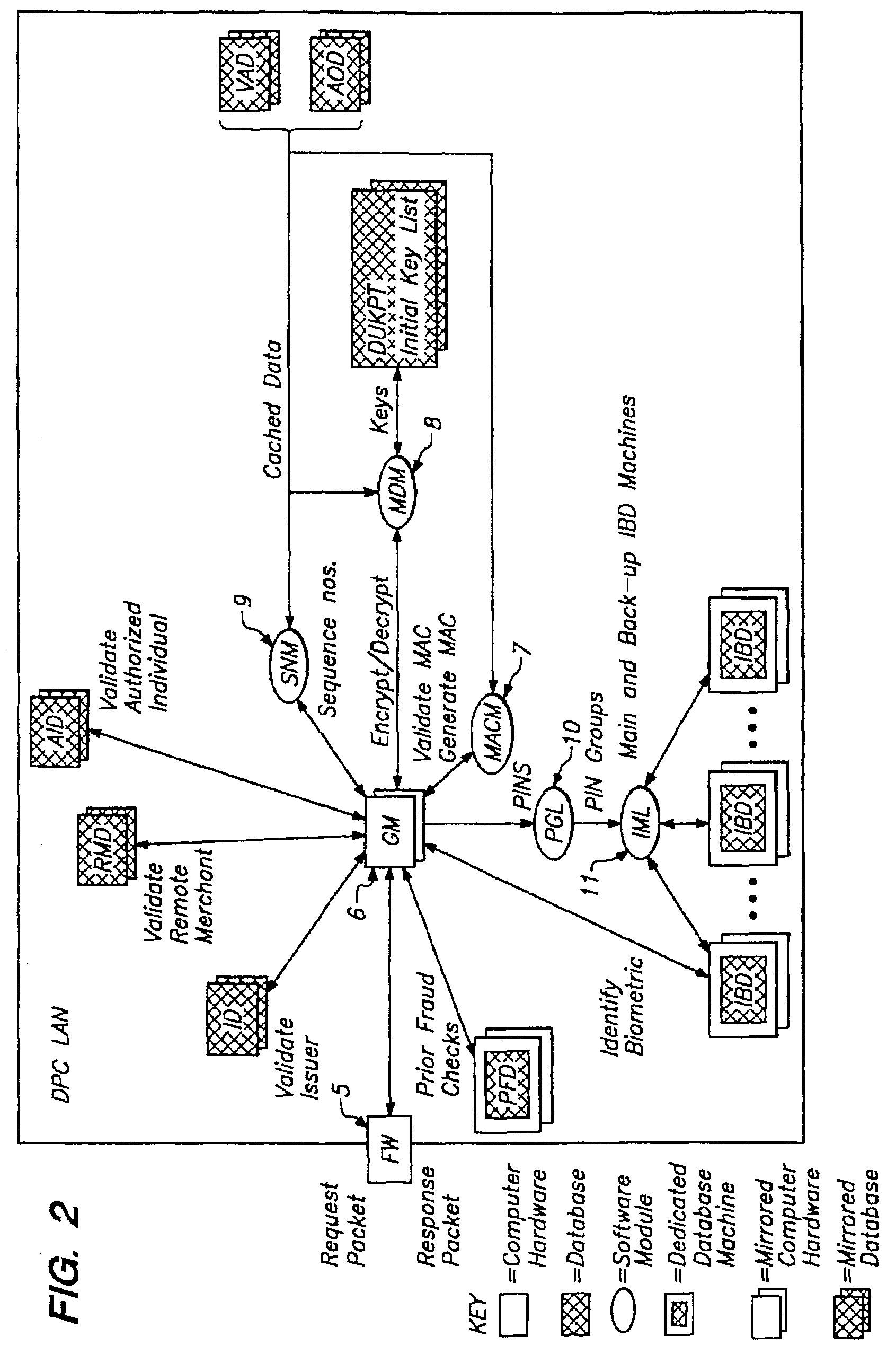
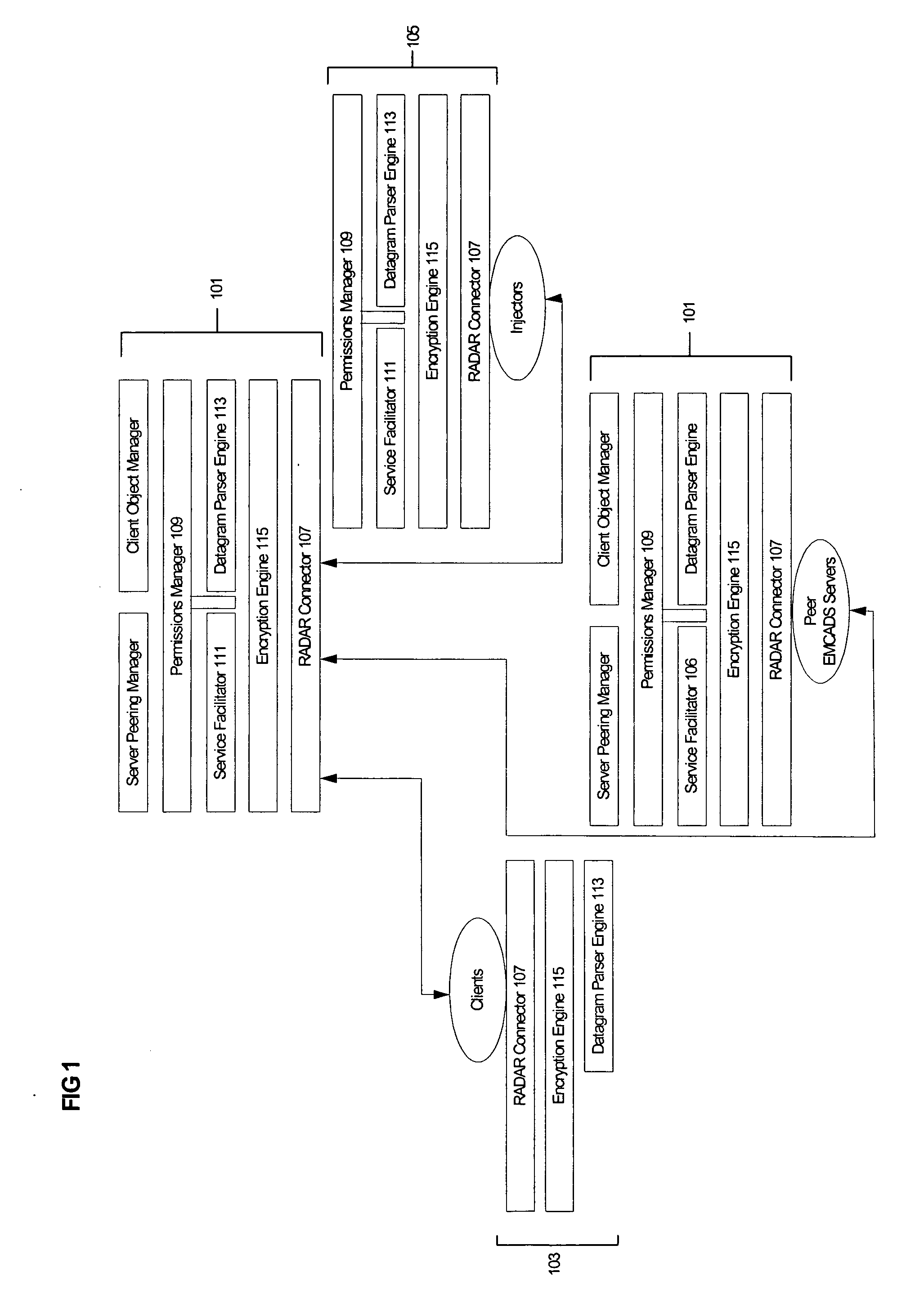
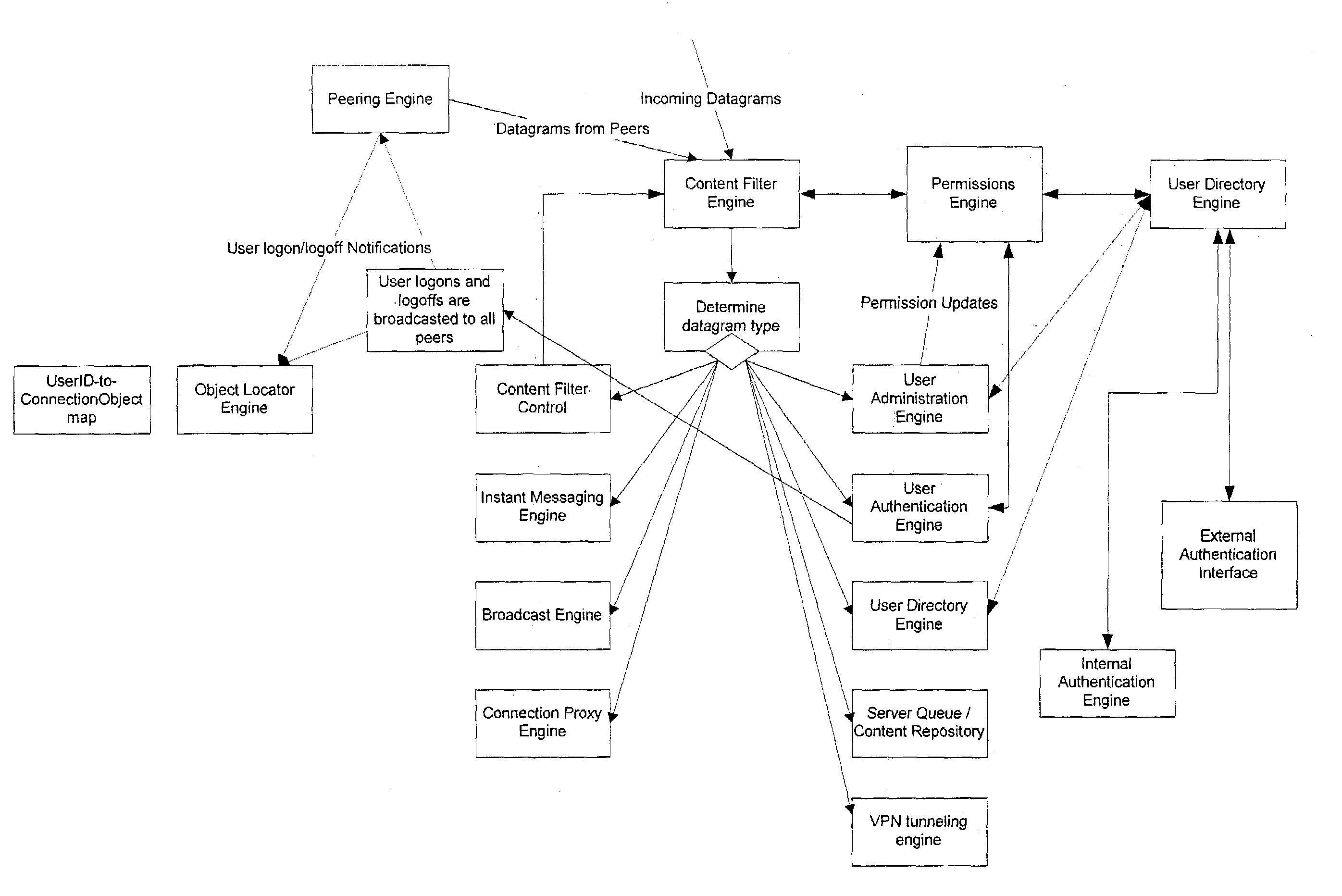
Pervasive, user-centric network security enabled by dynamic datagram switch and an on-demand authentication and encryption scheme through mobile intelligent data carriers
InactiveUS20040221163A1Improve reliabilityIncrease flexibilityKey distribution for secure communicationUnauthorised/fraudulent call preventionNetwork connectionEngineering
Methods and systems are provided for improving access control, administrative monitoring, reliability, as well as flexibility of data transmission and remote application sharing over a network. Secure, stable network connections and efficient network transactions among multiple users are supported by an open and distributed client-server architecture. A datagram schema is adapted to enable dynamic datagram switching in support of a multitude of applications and network services. Mobile intelligent data carriers are provided that allow for the implementation of an authentication and encryption scheme. The intelligent data carriers are adapted to target deliver applications to authorized users, thereby achieving access control to not only data but also applications. The authentication and encryption scheme in one embodiment is based on physical or performance biometrics. The methods and systems of this disclosure may be advantageously deployed in an enterprise network environment to support a wide spectrum of business, research, and administrative operations.
Owner:GIRITECH APS
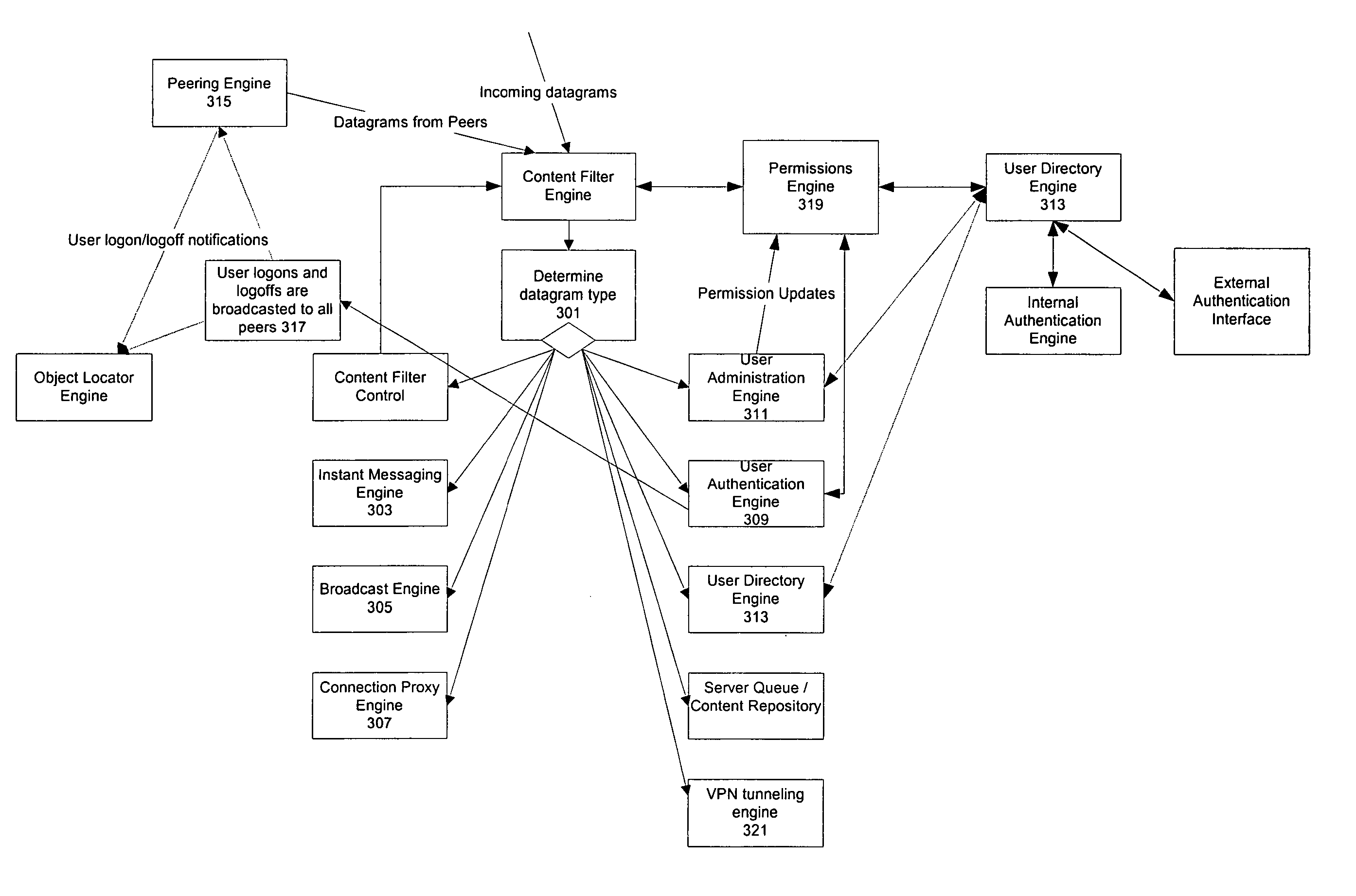
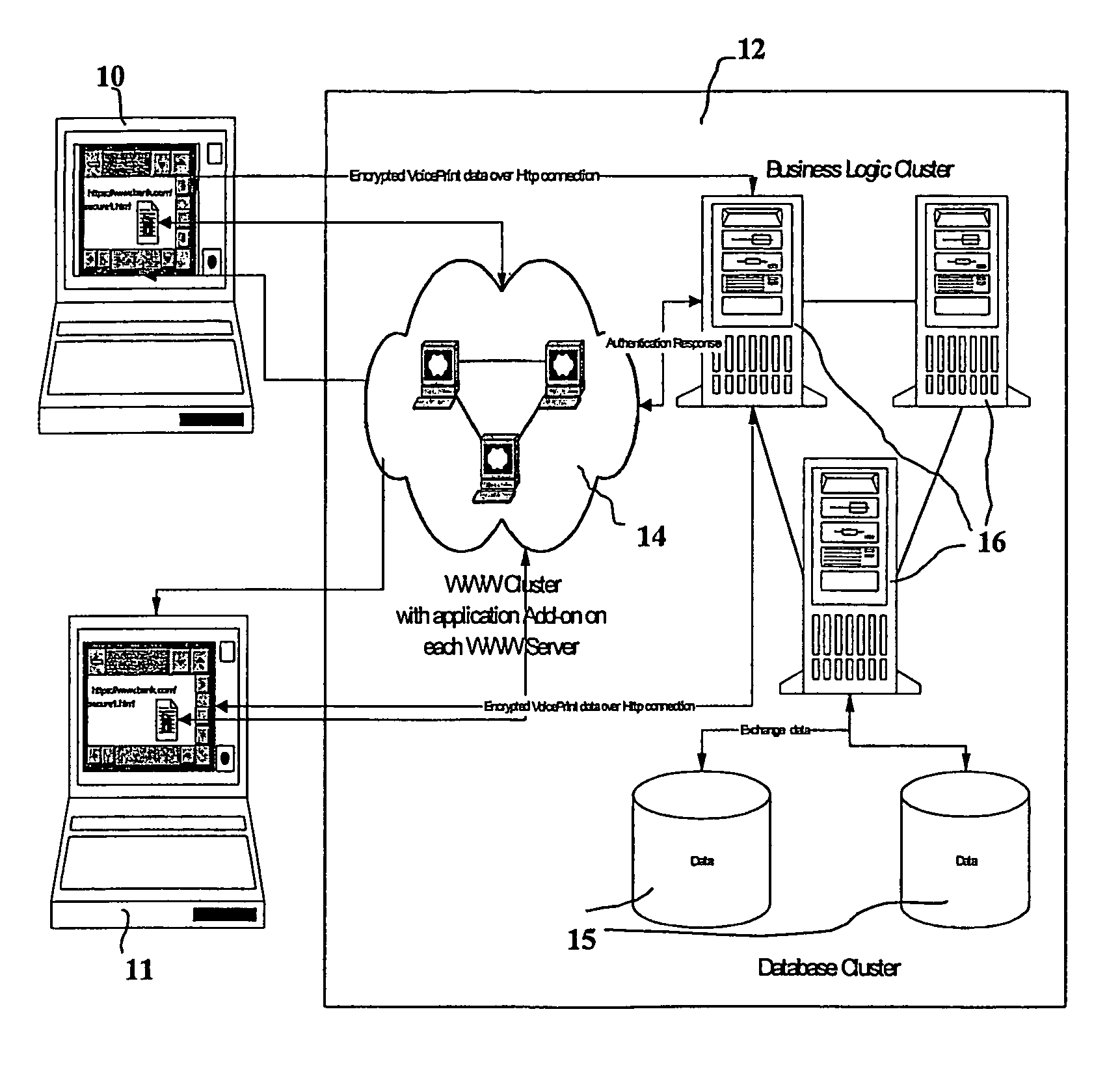
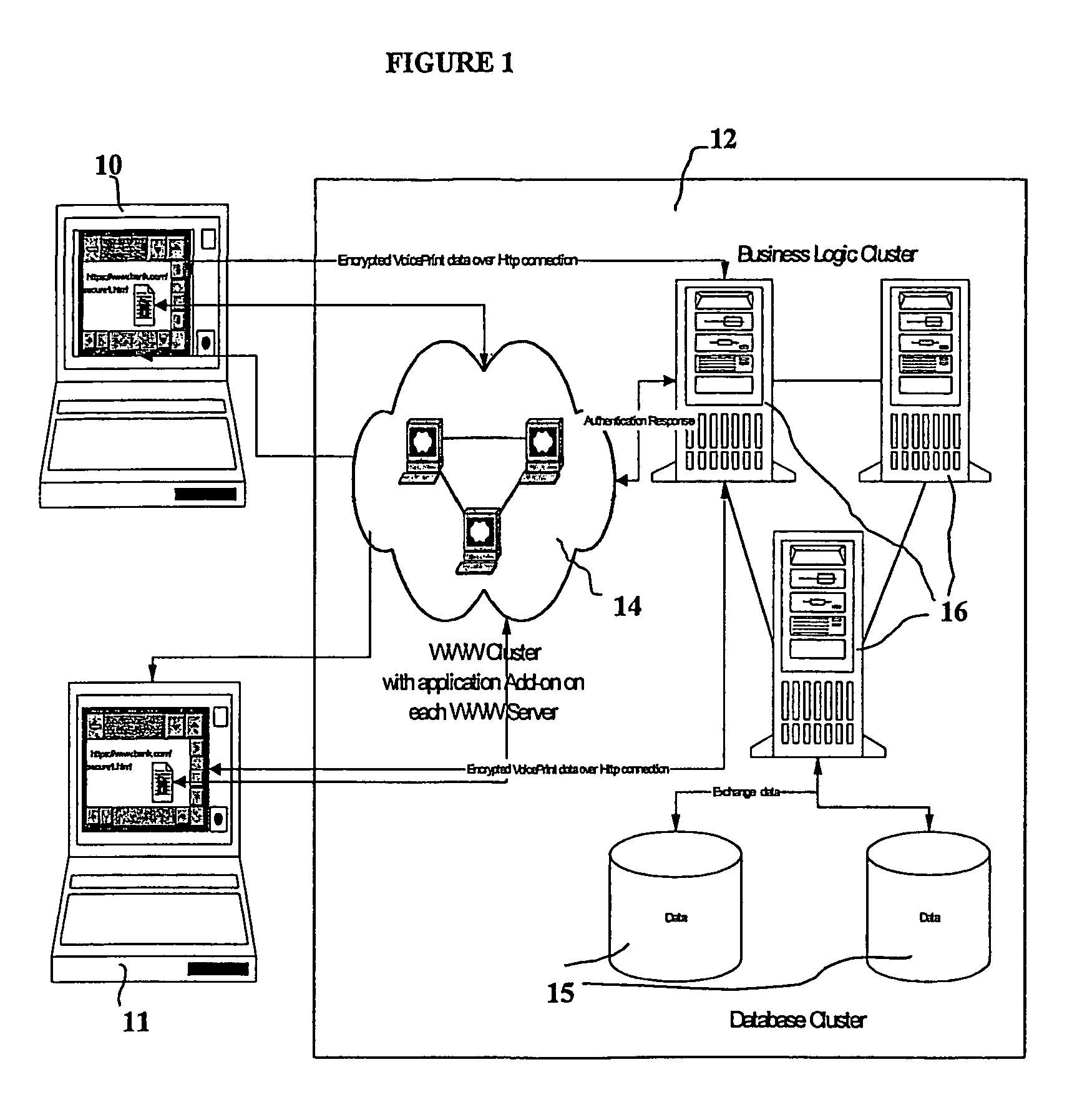
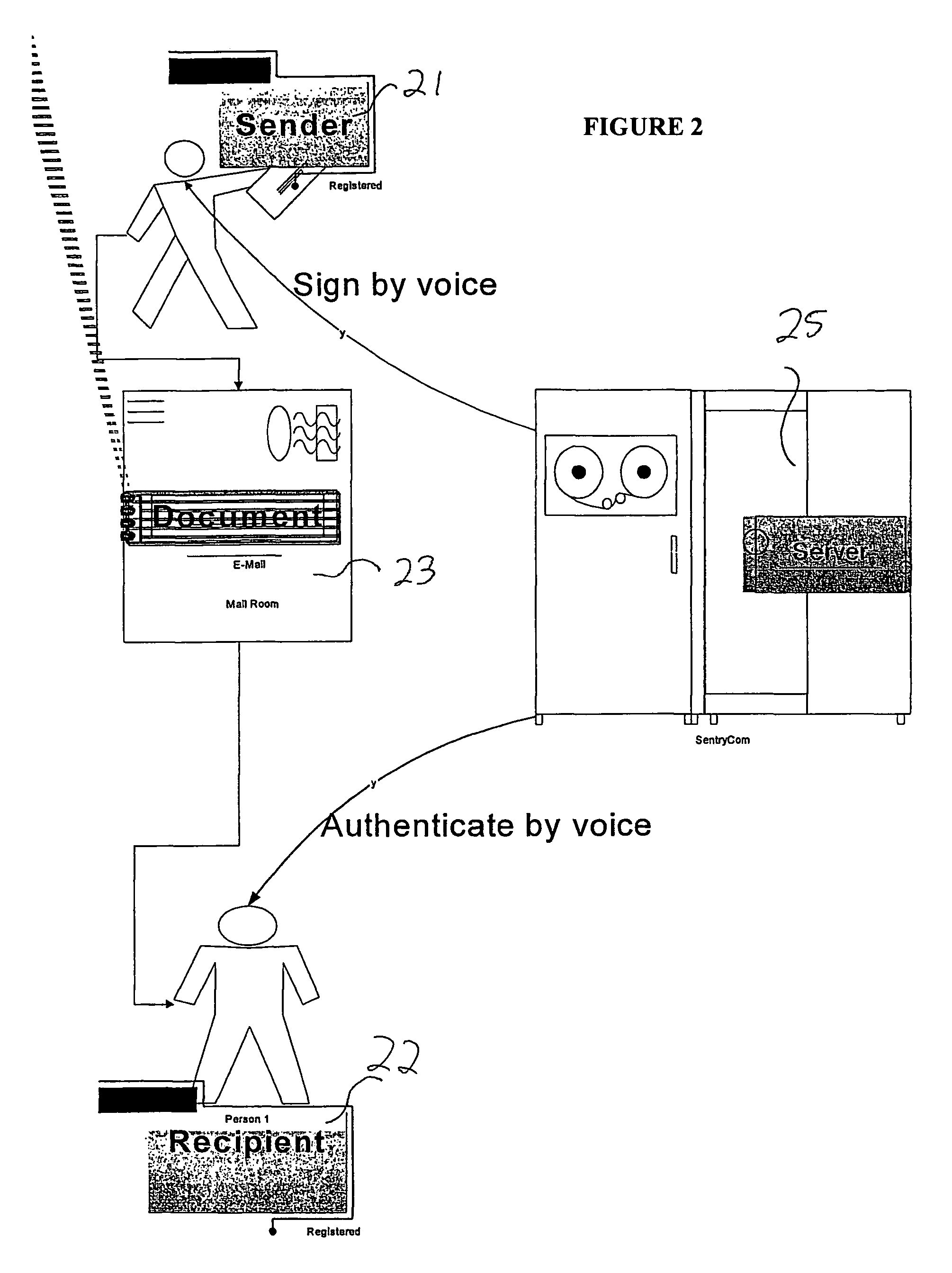
Biometric-based system and method for enabling authentication of electronic messages sent over a network
InactiveUS7689832B2Digital data processing detailsUser identity/authority verificationReal time validationData authenticity
A network based mechanism for real time verification and authentication of data and user identities. The present invention enables a method whereby biometric elements, such as voice prints, are utilized to enhance the Public Key Infrastructure as a means to decrypt data and verify data authenticity, such that the user's private key is authenticated remotely on a one-time basis. The present invention comprises an authentication server (25) with various software modules that enable authentication of user identity, secure user access to data, digital signatures, secure messaging and secure online transactions.
Owner:SENTRYCOM
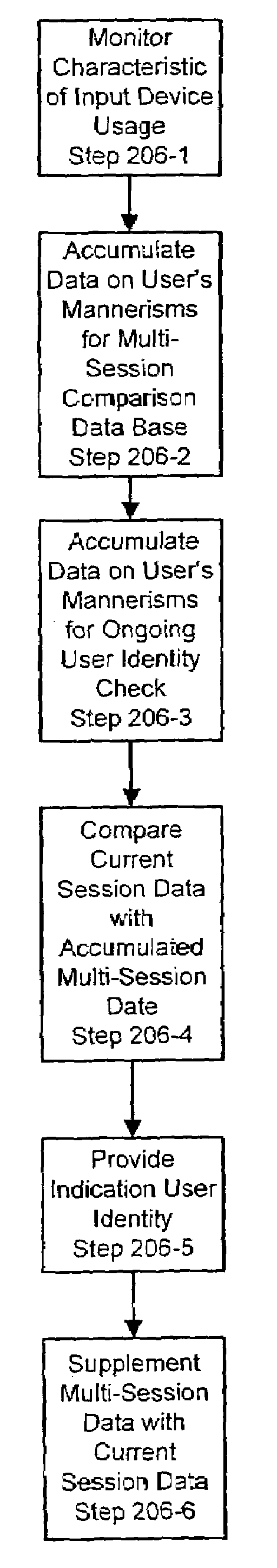
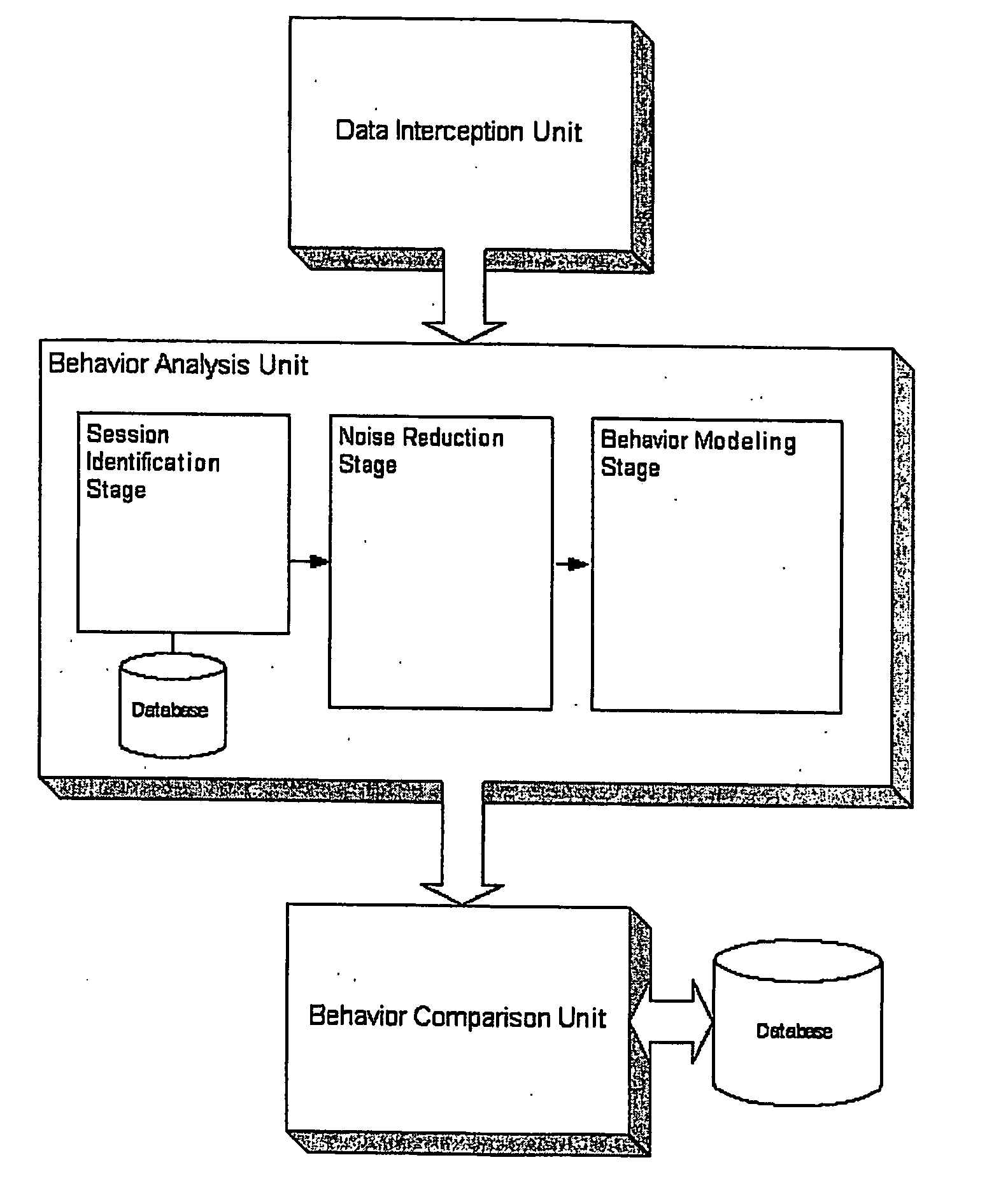
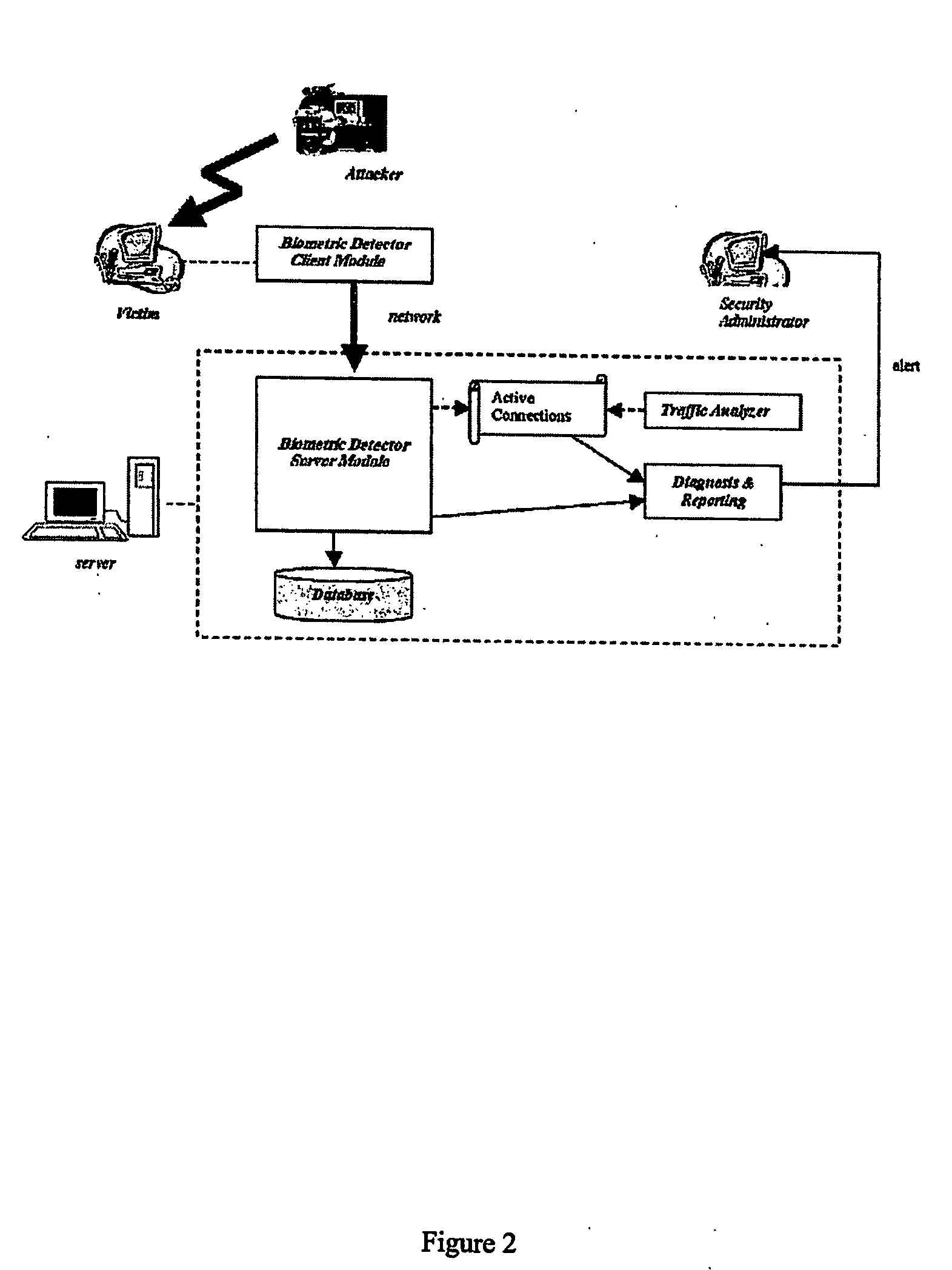
System and method for determining a computer user profile from a motion-based input device
ActiveUS20060224898A1Reduce noiseDigital data authenticationSecret communicationComputer usersBiometrics
The present invention provides a system and methods for computer user profiling based on behavioral biometrics. The approach consists of establishing distinctive profiles for computer users based on how they use a motion-based input device such as, but not limited to, a mouse and / or a keyboard. The profiles computed in the present invention are more accurate than those obtained through the traditional statistical profiling techniques, since they are based on distinctive biological characteristics of users.
Owner:PLURILOCK SECURITY SOLUTIONS INC
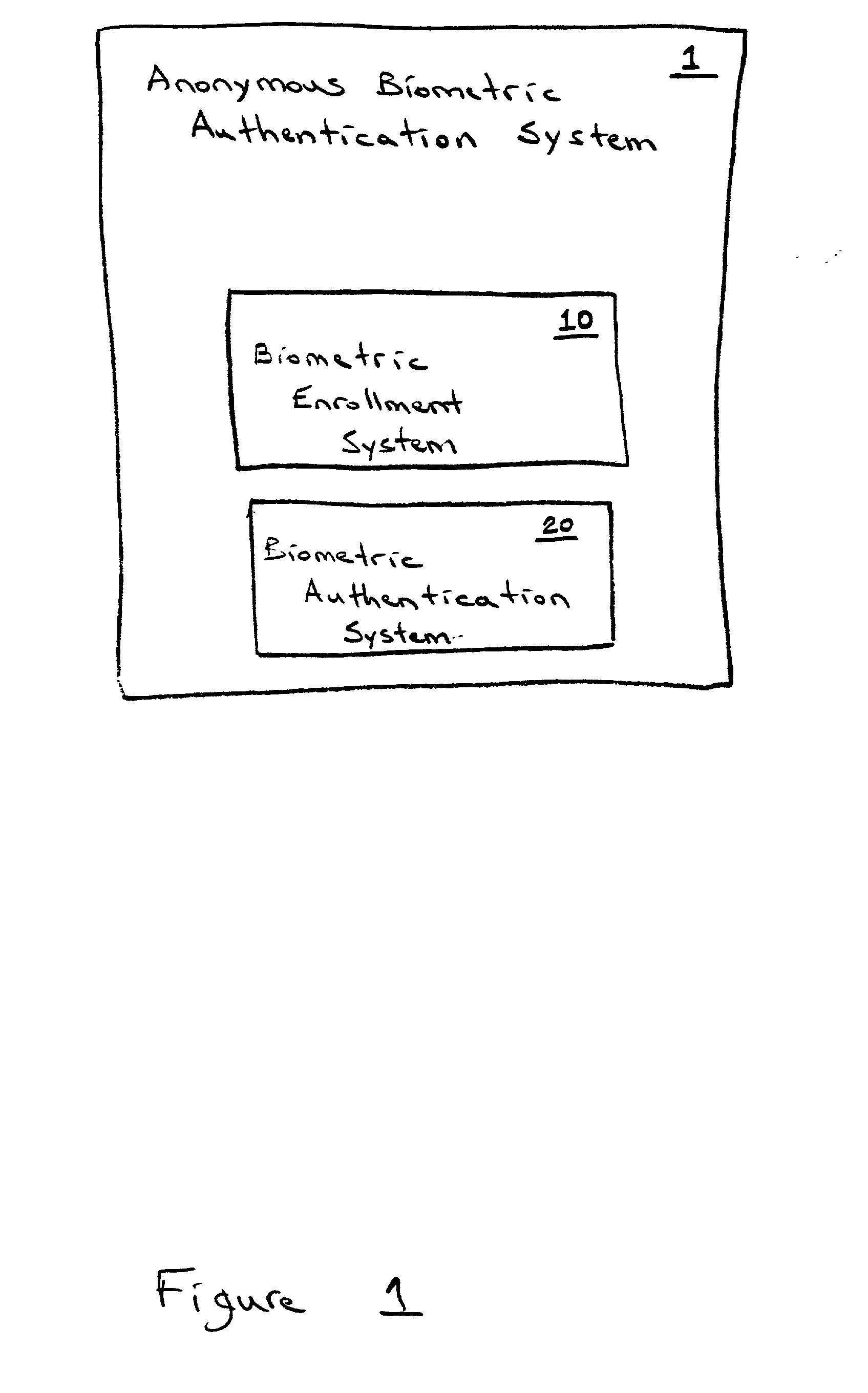
Anonymous biometric authentication
InactiveUS20020112177A1Digital data processing detailsUser identity/authority verificationInternet privacyAnonymous authentication
The use of an anonymous biometric authentication system and method that use biometrics to anonymously authenticate an individual and grant certain privileges based on the anonymous authentication is provided. The system and method permit enrollment of an individual by submission of a first biometric and associated identity documents or credentials to an enrollment authority. The enrollment authority verifies the identity of the identity of the individual submitting the biometric using the credentials which are then returned to the individual or discarded. The first biometric is stored in a database for later retrieval in anonymously authenticating an individual seeking to exercise certain privileges. No other personal identity information is stored along with the biometric during the enrollment process. When an individual later seeks to exercise certain privileges, they must submit a second biometric that is compared to the stored biometrics in the database in order to anonymously authenticate the identity of the individual as having access to such privileges. No other personal information is captured, collected, or solicited during the authentication process. Privileges are granted to an individual based on the comparison of the later captured biometric to the stored biometrics in the database. Alternatively, the anonymous biometric authentication system can be designed to avoid repeat offenders by capturing a biometric of an individual seeking to exercise a privilege and denying the privilege if the captured biometric is matched to a biometric stored in a database containing the biometrics of previous offenders. Preferably, the system and method include capture and storage of a powerful biometric identifier based on the iris of the eye which uniquely identifies the individual that has submitted the biometric. Anonymous biometric authentication allows verification of the identity of an individual seeking certain privileges while at the same time protecting the privacy of personal information about the individual.
Owner:IRIDIAN TECH
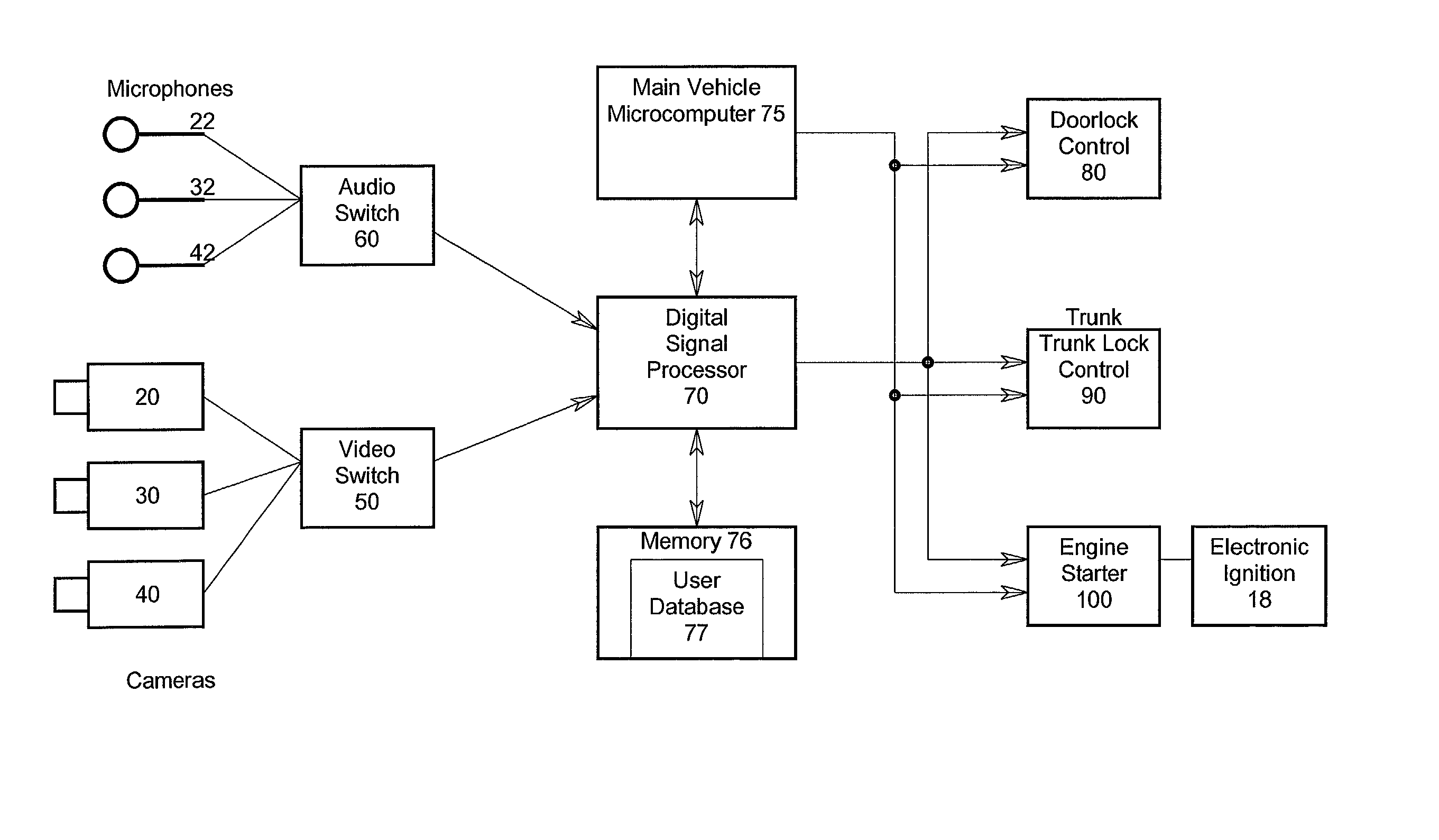
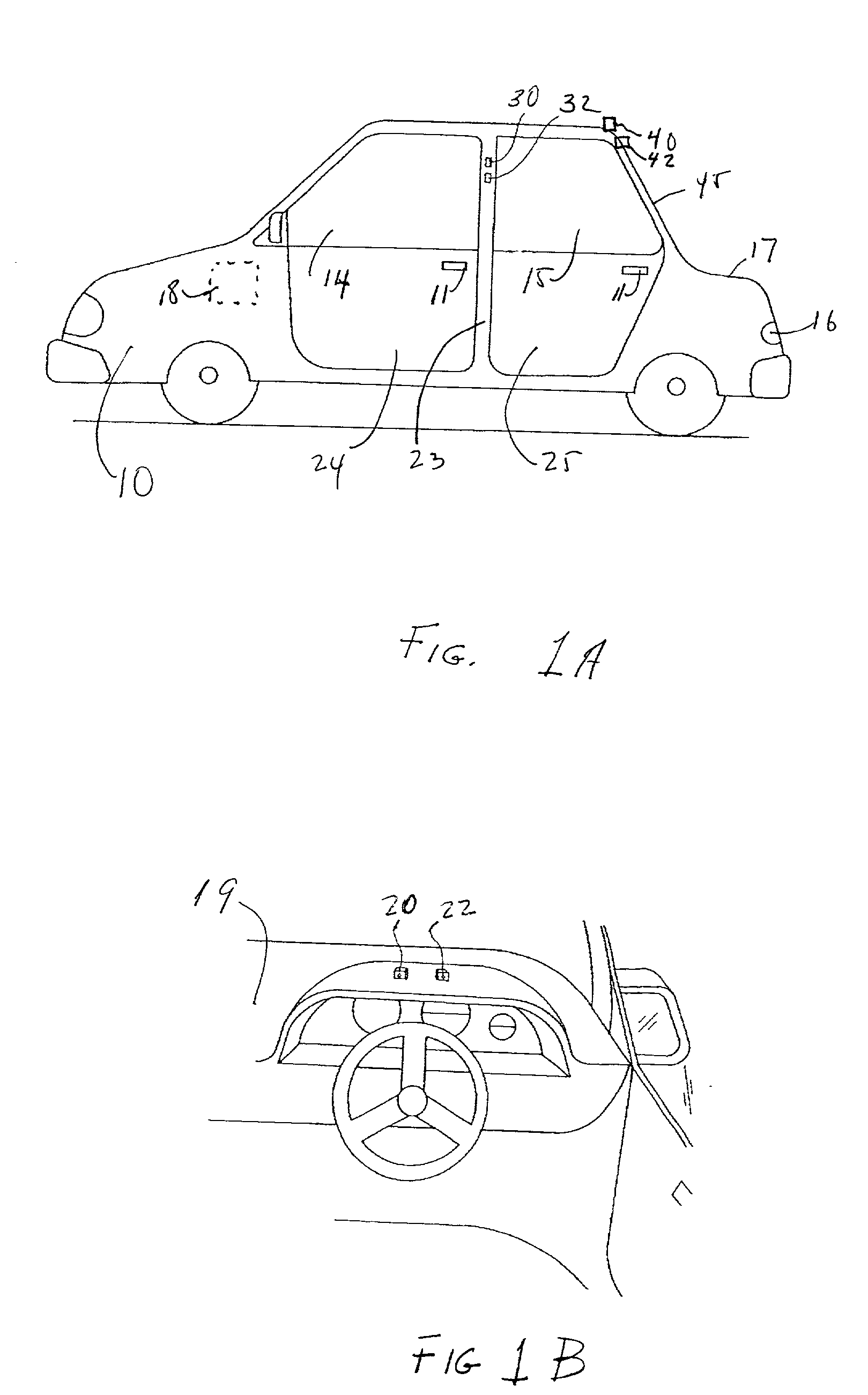
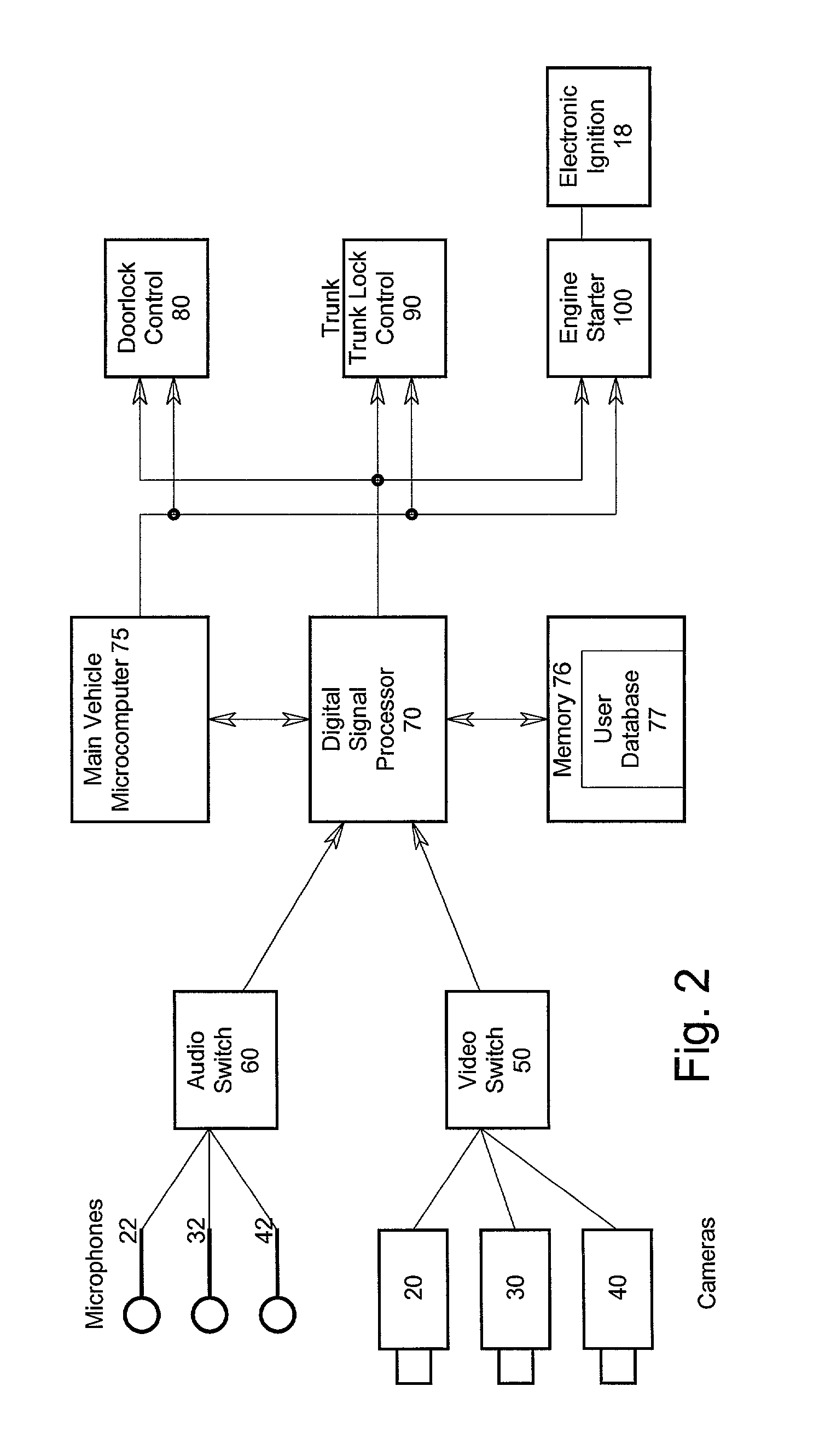
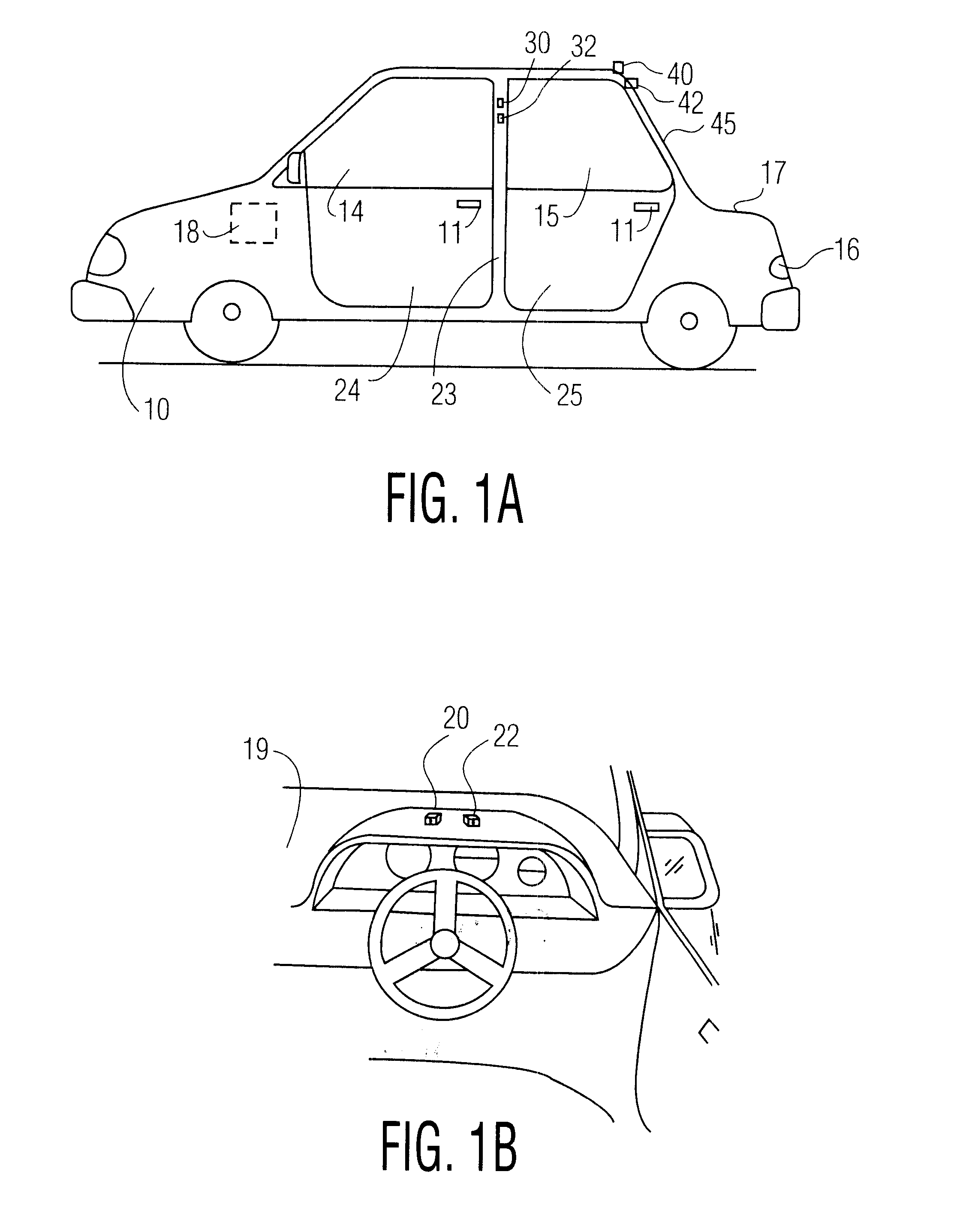
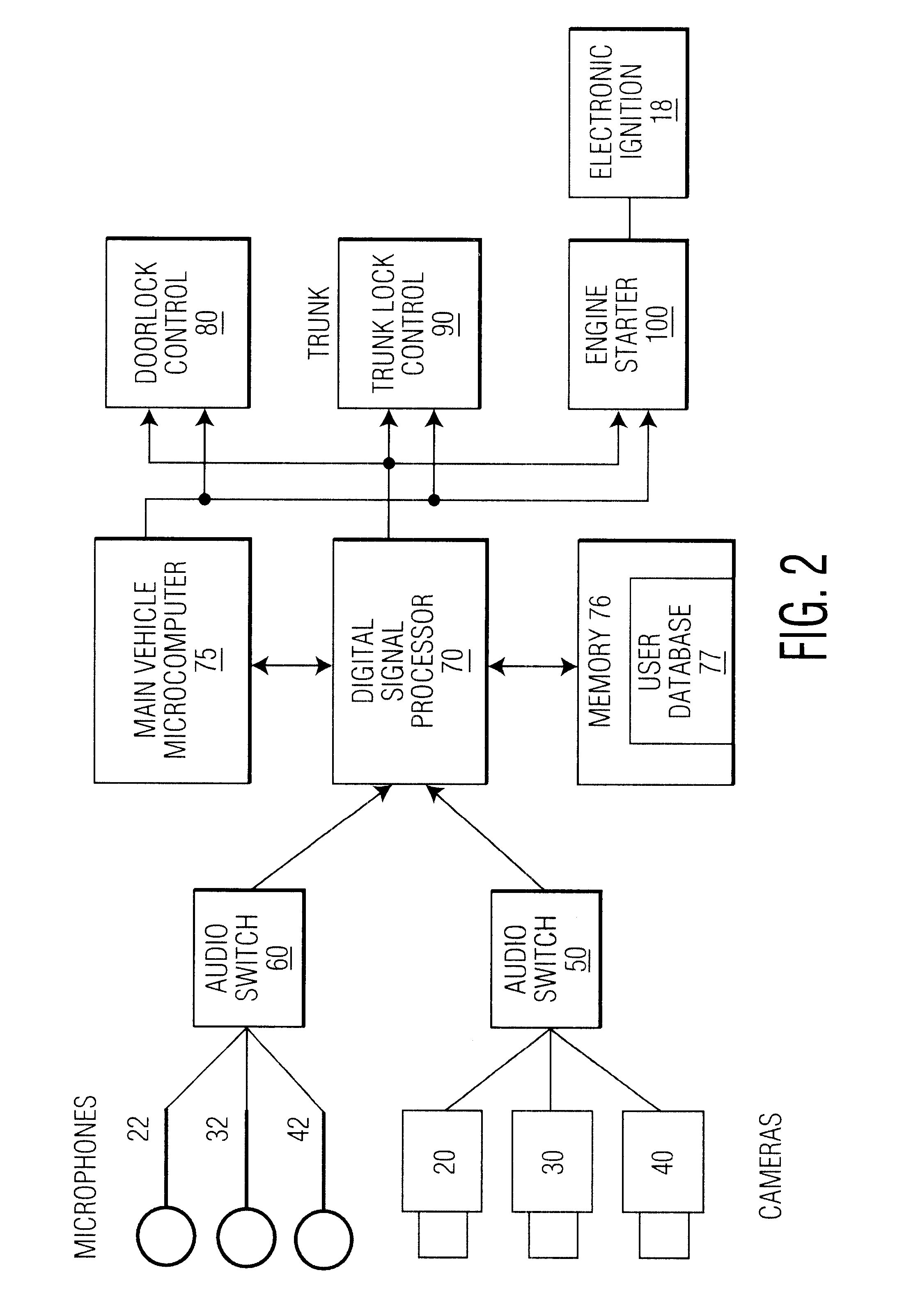
Automatic access to an automobile via biometrics
InactiveUS20020152010A1Digital data processing detailsAnti-theft devicesHuman–computer interactionBiometrics
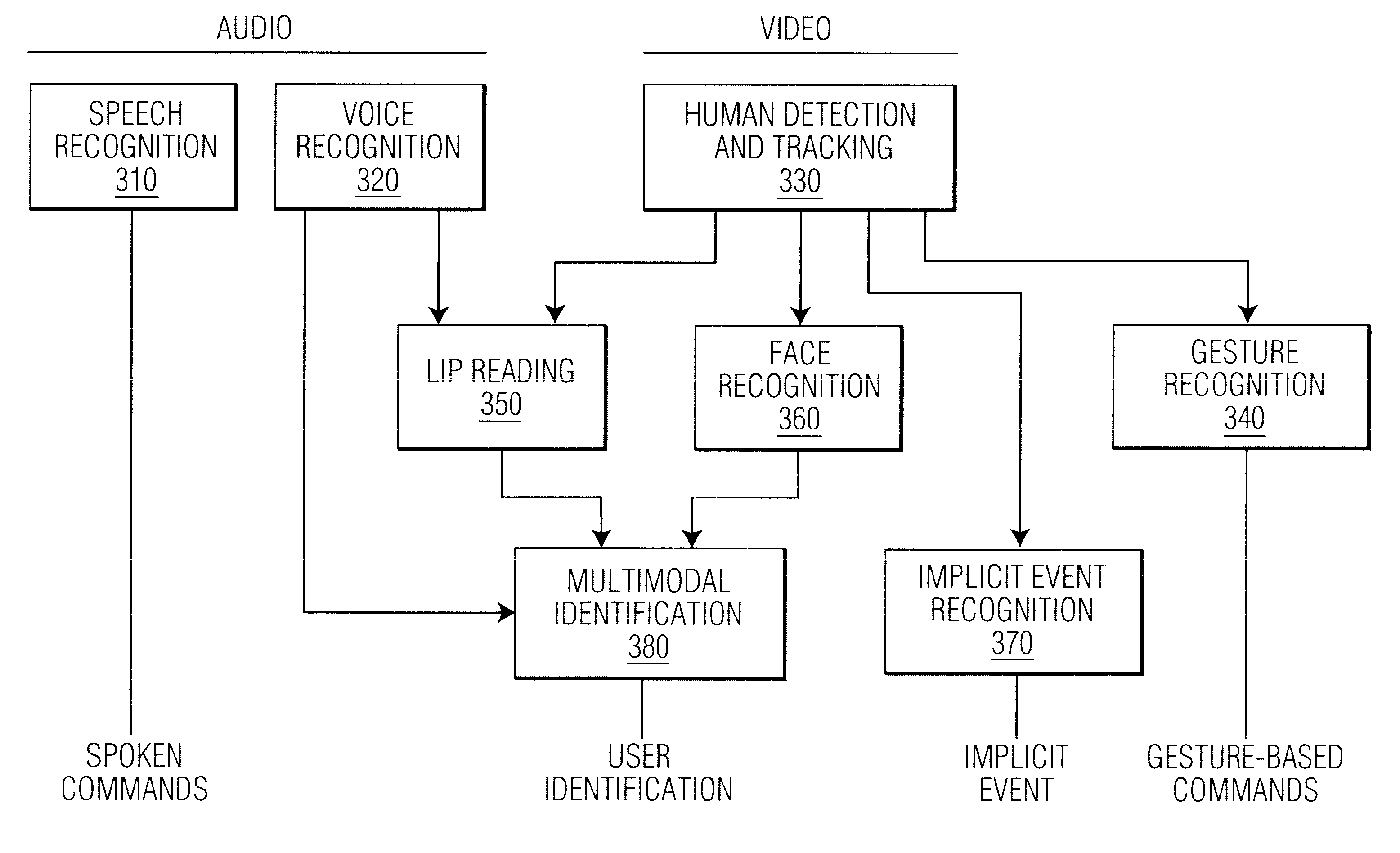
A system and method for identifying persons who are authorized to activate one or more vehicle mechanisms uses both an implicit identification of a face and an explicit identification of speech or a gesture. This system and method enables identification to be performed where a single identification is otherwise unable to perform the identification for some reason and improves the reliability and accuracy of an identification so that only authorized persons can activate the vehicle mechanisms. Vehicle mechanisms that can be activated using this multimodal identification system and method include, for example, automatic locks, automatic windows, a trunk lock, a vehicle engine, outdoor or interior lights, and a vehicle alarm.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Pervasive, user-centric network security enabled by dynamic datagram switch and an on-demand authentication and encryption scheme through mobile intelligent data carriers
InactiveUS7103772B2Improve reliabilityIncrease flexibilityKey distribution for secure communicationPublic key for secure communicationNetwork connectionApplication software
Owner:GIRITECH APS
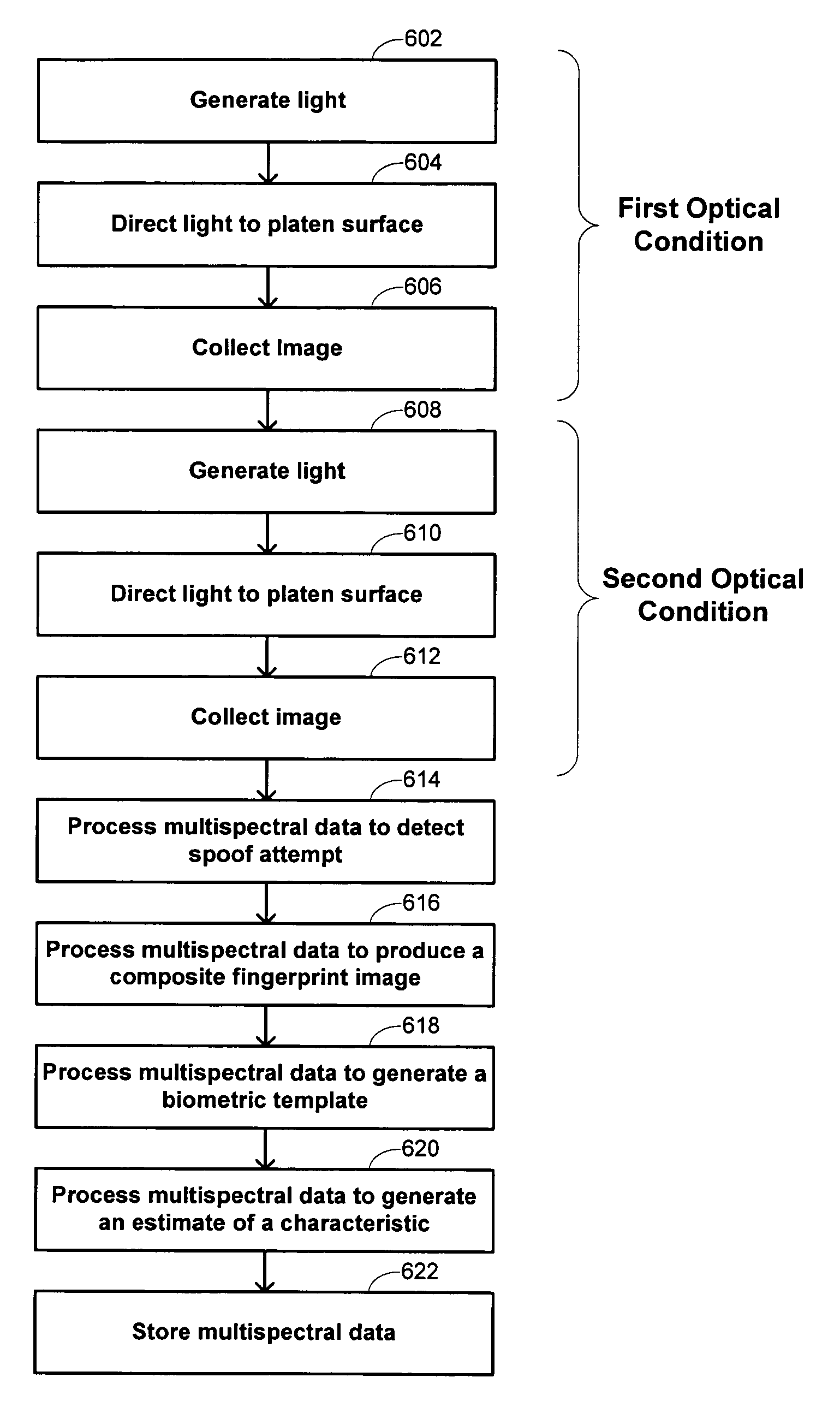
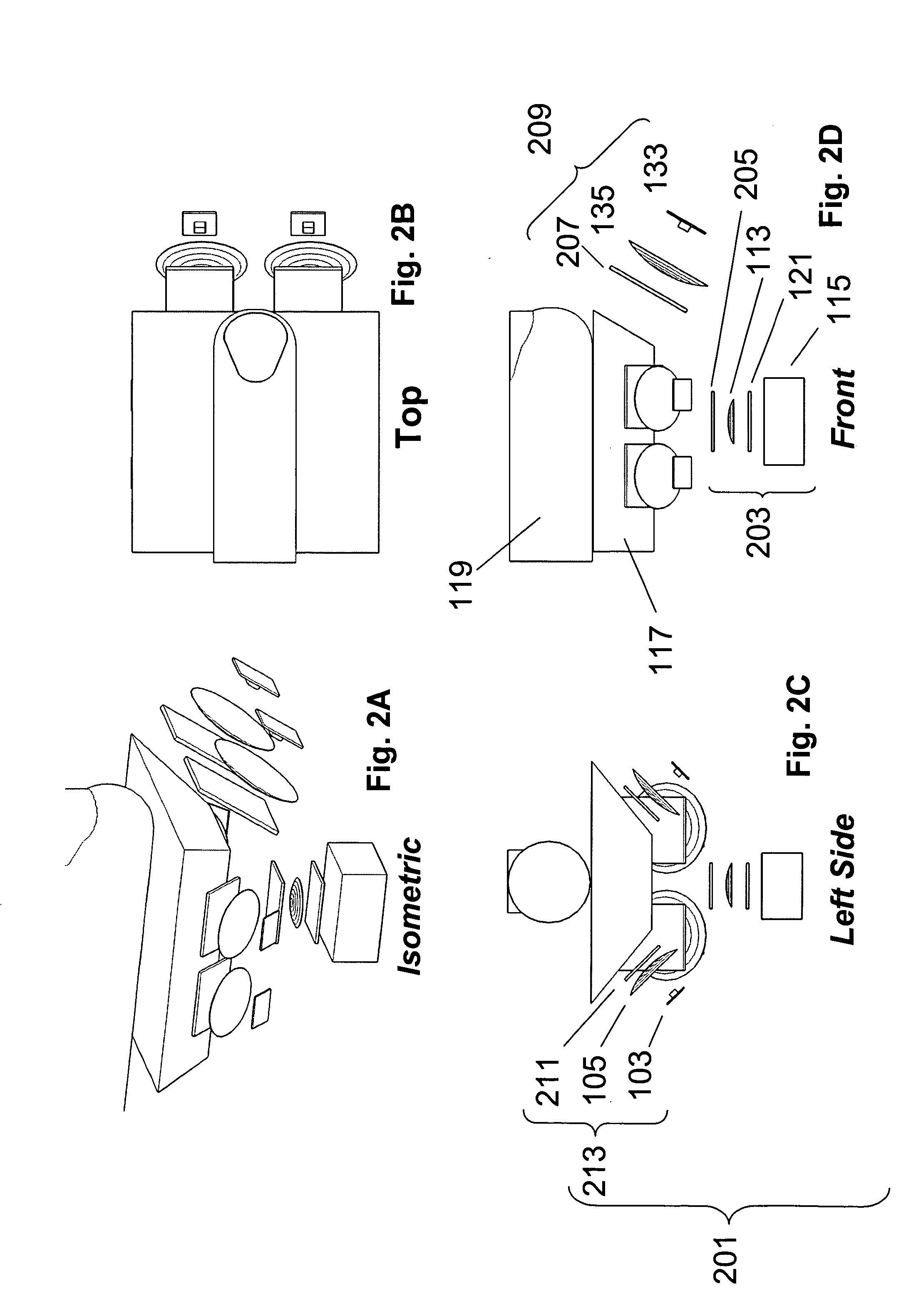
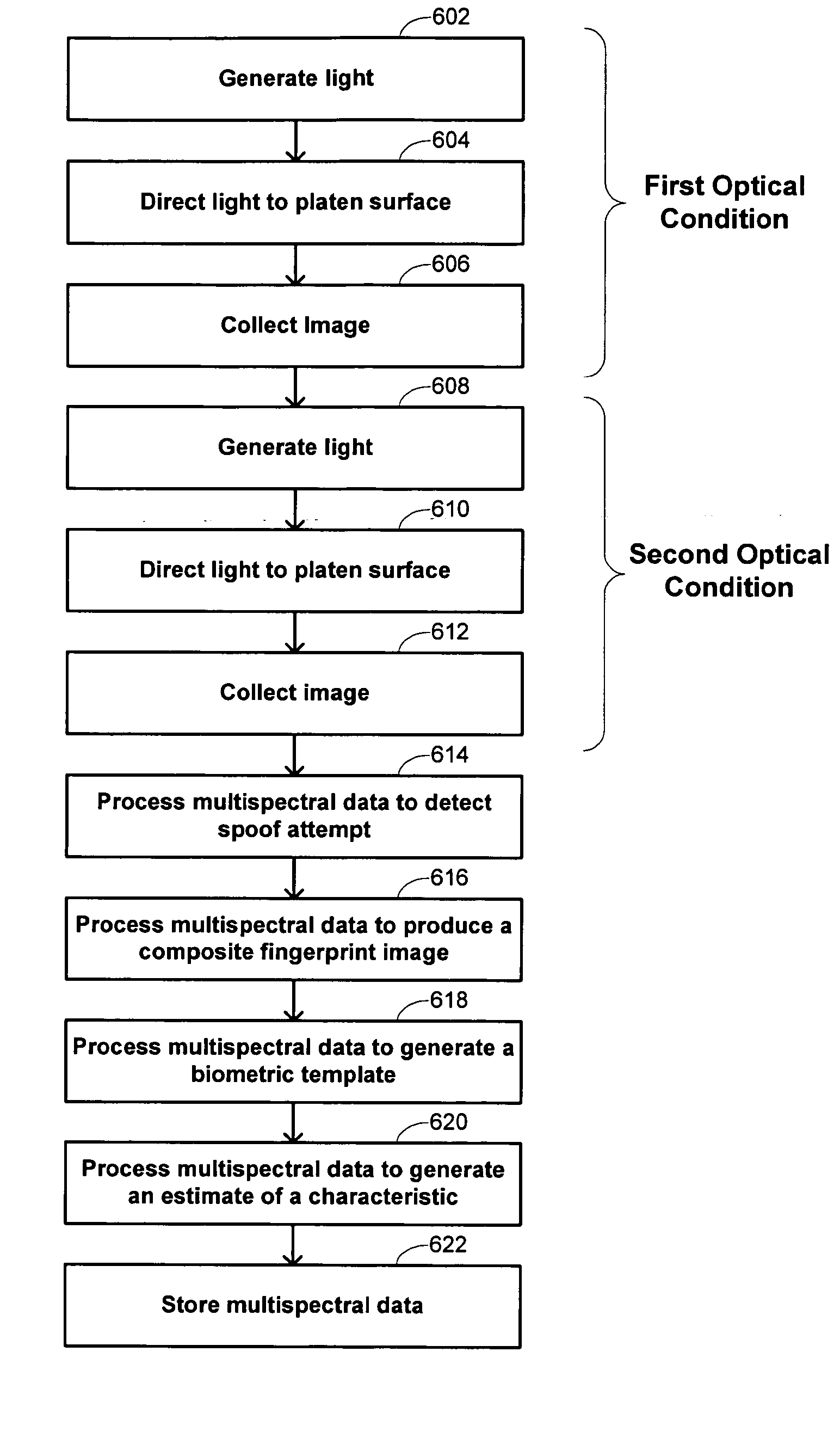
Multispectral imaging biometrics
Methods and systems are provided for performing a biometric measurement on an individual. A purported skin site of the individual is illuminated under a plurality of distinct optical conditions during a single illumination session. Light scattered beneath a surface of the purported skin site is received separately for each of the plurality of distinct optical conditions. A multispectral image of the purported skin site is derived from the received light. A biometric function is performed with the derived multispectral image.
Owner:HID GLOBAL CORP
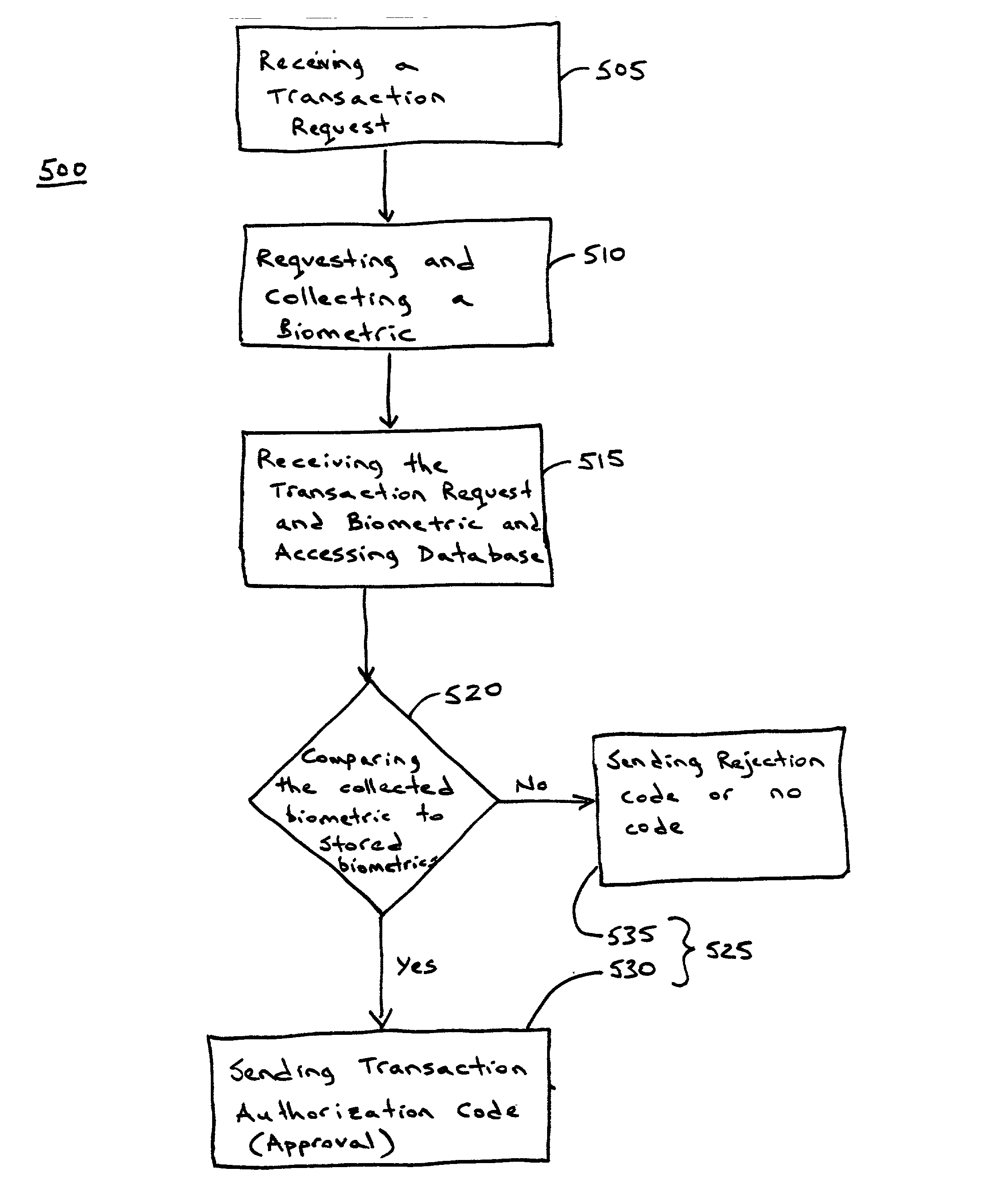
Methods and apparatus for conducting electronic transactions using biometrics
InactiveUS20050187883A1Improve reliabilityConfidenceDigital data processing detailsAnalogue secracy/subscription systemsBiometricsComputer science
A system and method for facilitating electronic transactions using a biometric are disclosed. The system for facilitating electronic transactions using a biometric comprises a smartcard-reader transaction system. The method comprises determining if a transaction violates an established rule, such as a preset spending limit. The method also comprises notifying a user to proffer a biometric sample in order to verify the identity of said user, and detecting a proffered biometric at a sensor to obtain a proffered biometric sample. The method additionally comprises verifying the proffered biometric sample and authorizing a transaction to continue upon verification of the proffered biometric sample.
Owner:LIBERTY PEAK VENTURES LLC
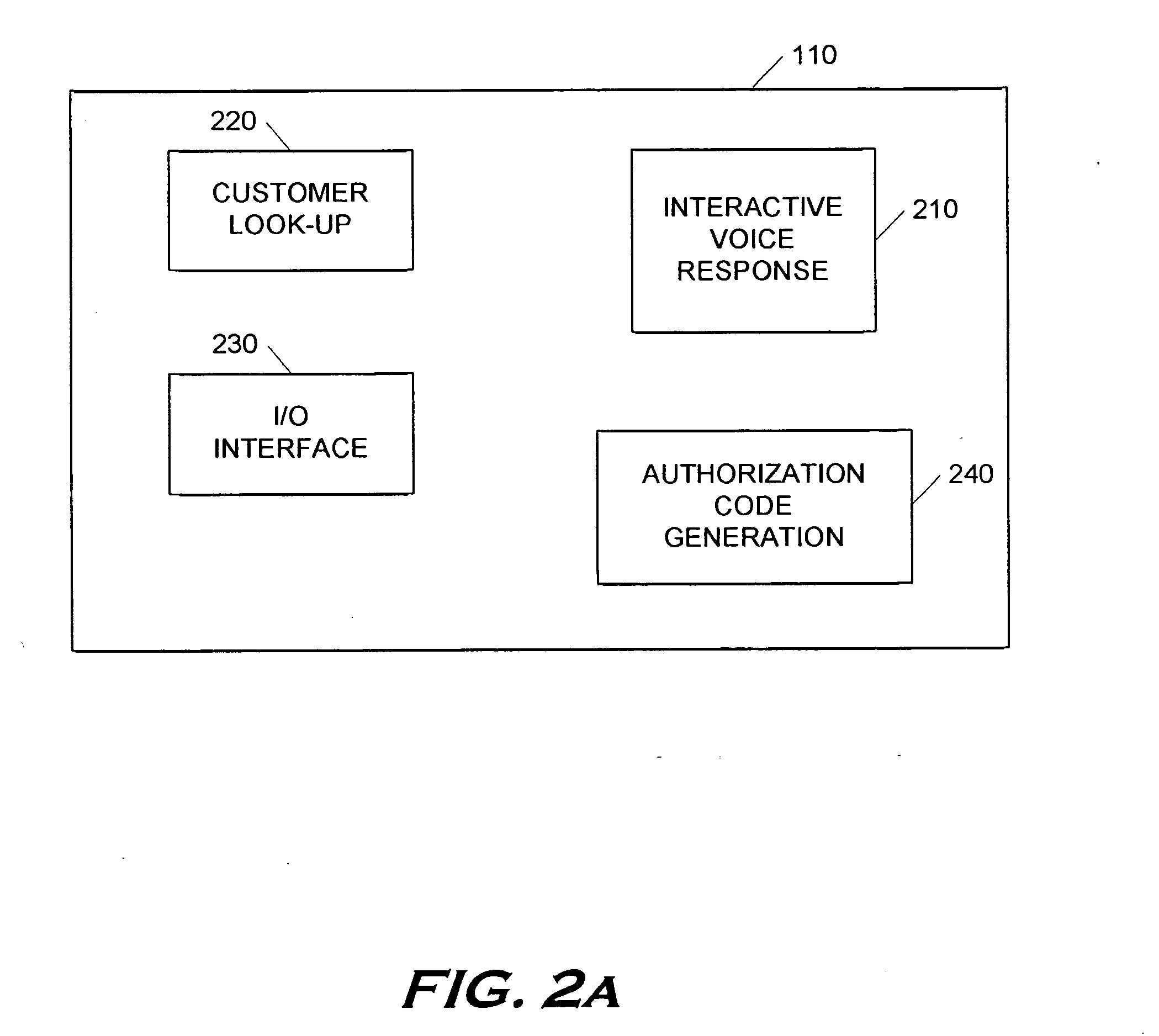
Point-of-sale billing via hand-held devices
InactiveUS20050109838A1Reduce fraudComplete banking machinesFinancePaymentPersonal identification number
A payment resolution module is configured to communicate with hand-held devices (such as mobile phones, PDA's, or computers) to allow purchase of products using the hand-held devices, without requiring the user of the hand-held device to enter payment information for each transaction. The user of the hand-held device may be identified as the owner of the device either by having the option to enter a personal identification code, or by using a biometric to identify himself, for example. Accordingly, only an authorized user of the hand-held device may use the hand-held device to purchase products. After the payment resolution module receives authorization for payment, an authorization code is transmitted to the mobile device. The user may be required to present the authorization code at the point of sale, such as by entering the code into a computing device at the point-of-sale, prior to completion of the transaction.
Owner:XILIDEV
Method and system for protecting personal information infringement using division of authentication process and biometric authentication
InactiveUS20190384934A1Eliminate chancePreventing situationKey distribution for secure communicationUser identity/authority verificationComputer terminalBiometrics
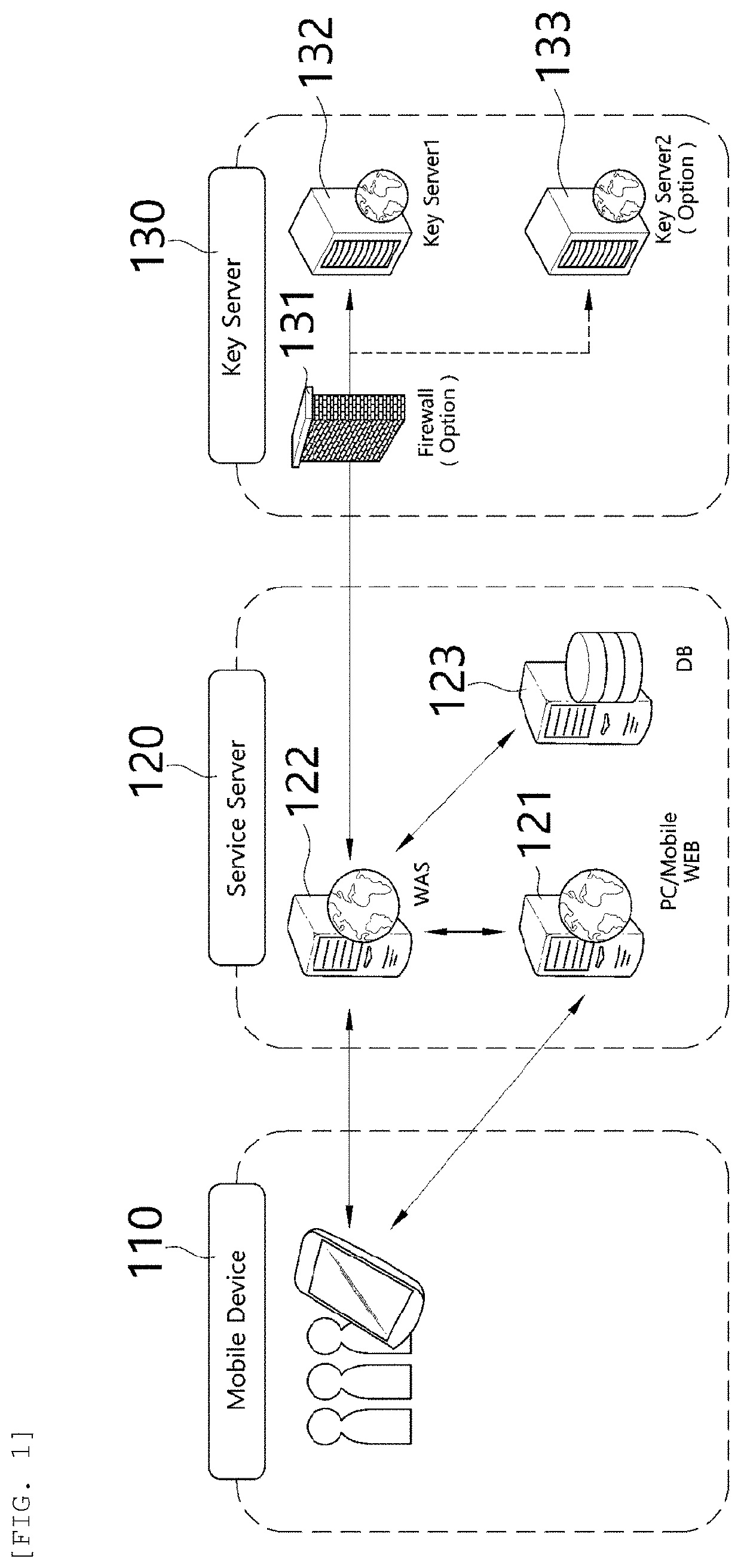
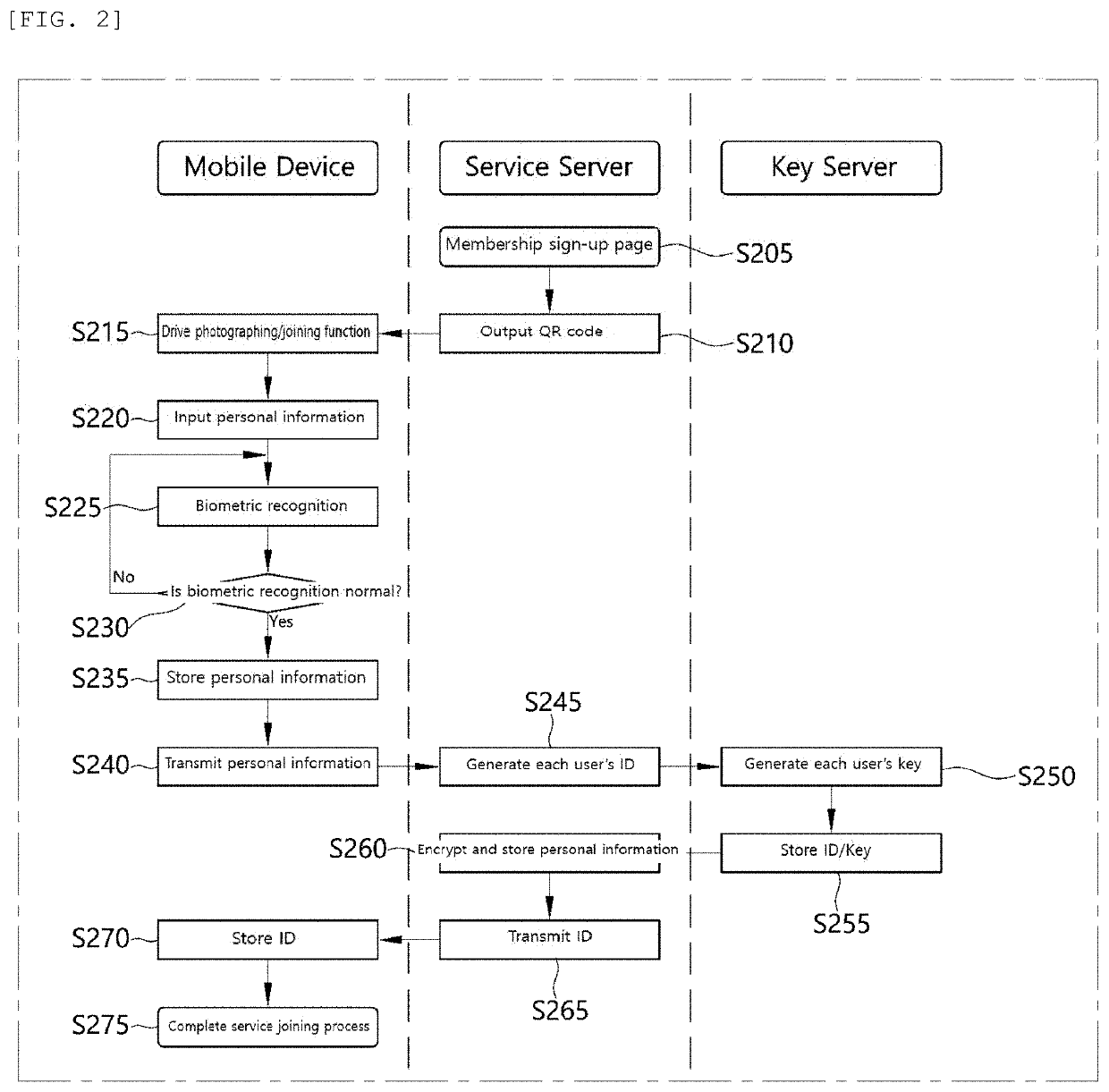
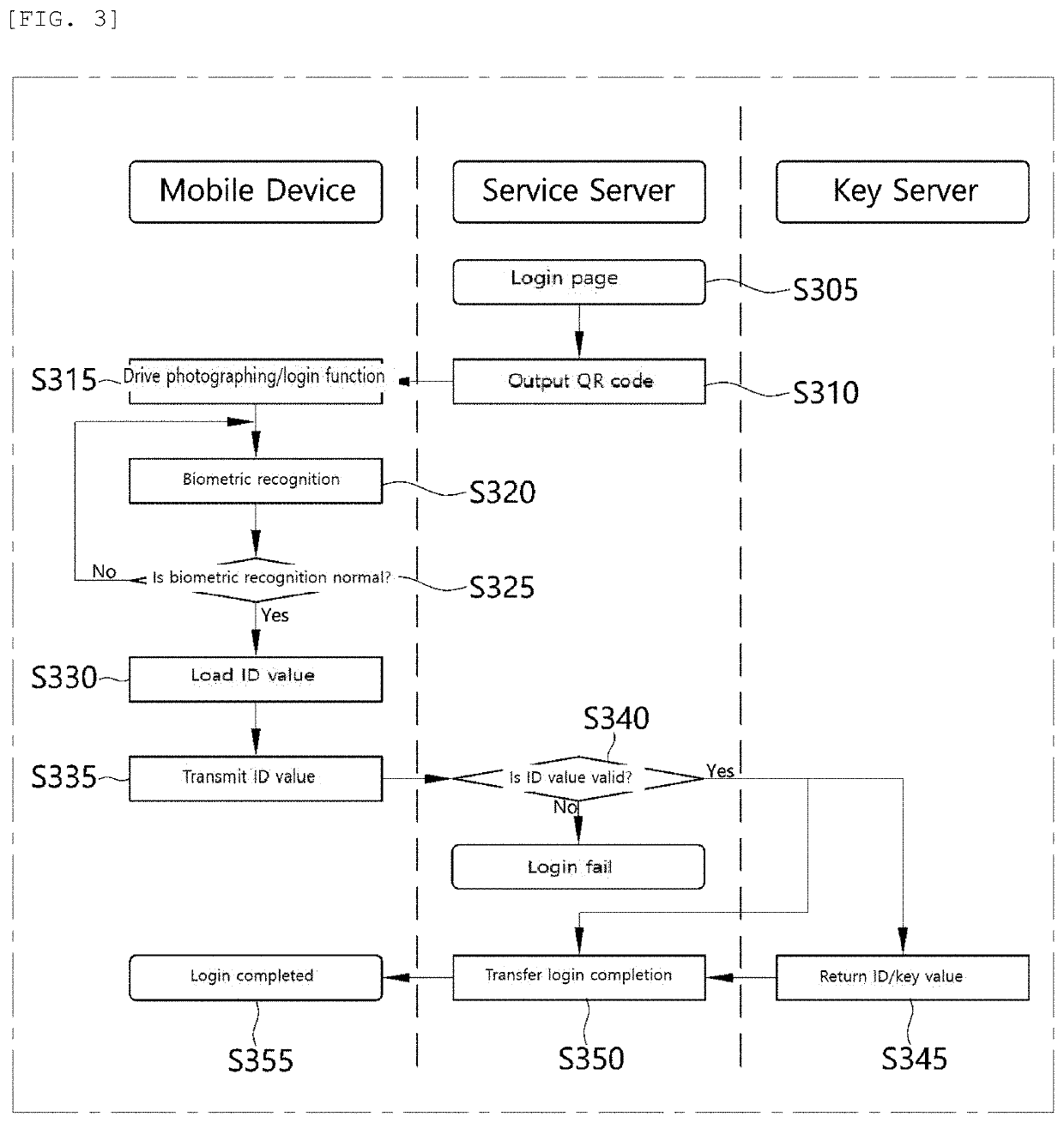
A personal information infringement protection system, includes: a portable terminal having an application installed therein to photograph a QR code and recognize biometrics; a service server for storing the encrypted personal information, and generating an ID of a user and transmitting the ID to the portable terminal to be stored therein or informing the portable terminal of login completion when the ID received from the portable terminal is a valid ID; and a key server for generating a key value for encryption and decryption of the personal information, classifying and storing the key value by user, and providing the key value to the service server.
Owner:RENOMEDIA CO LTD
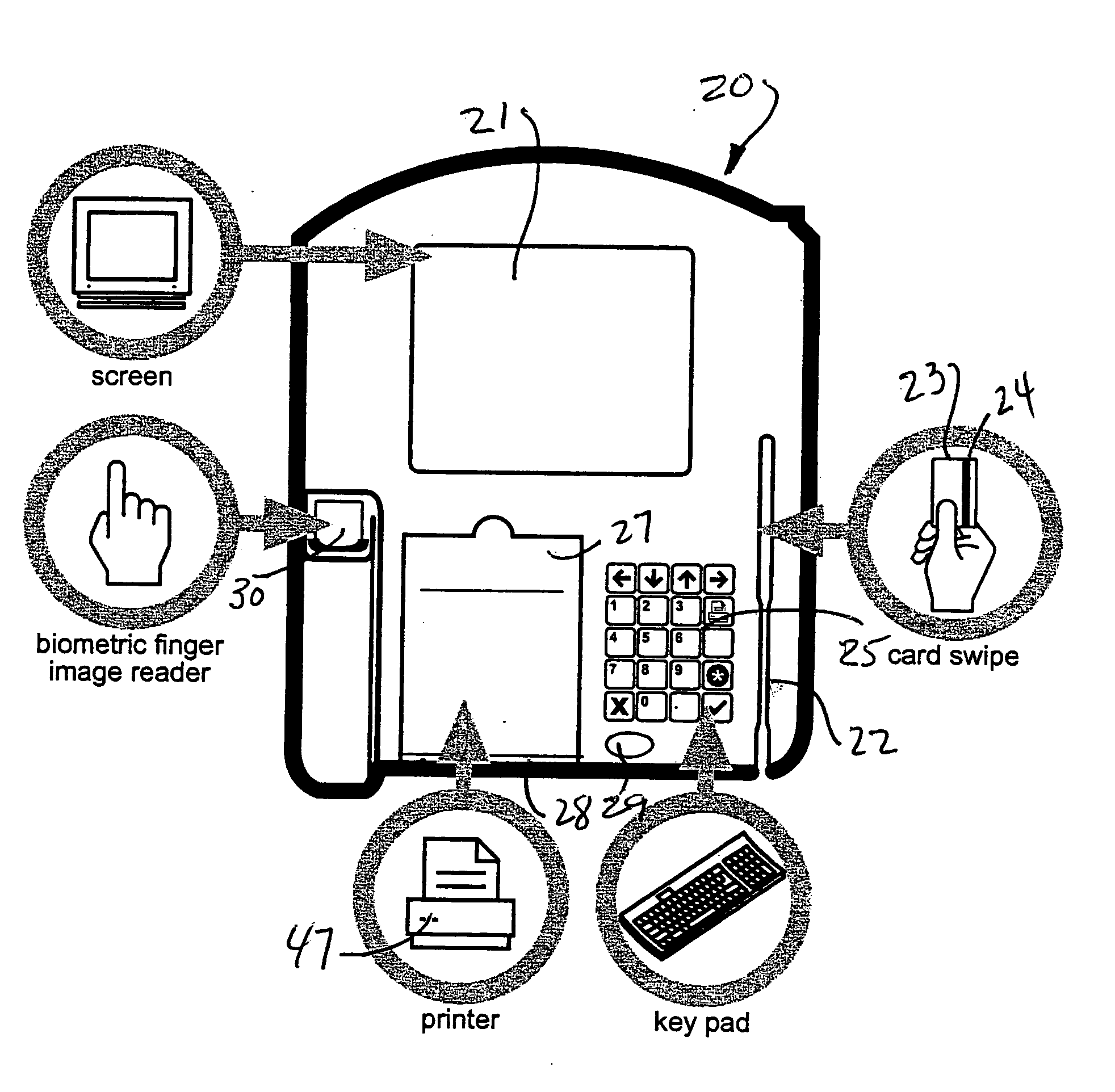
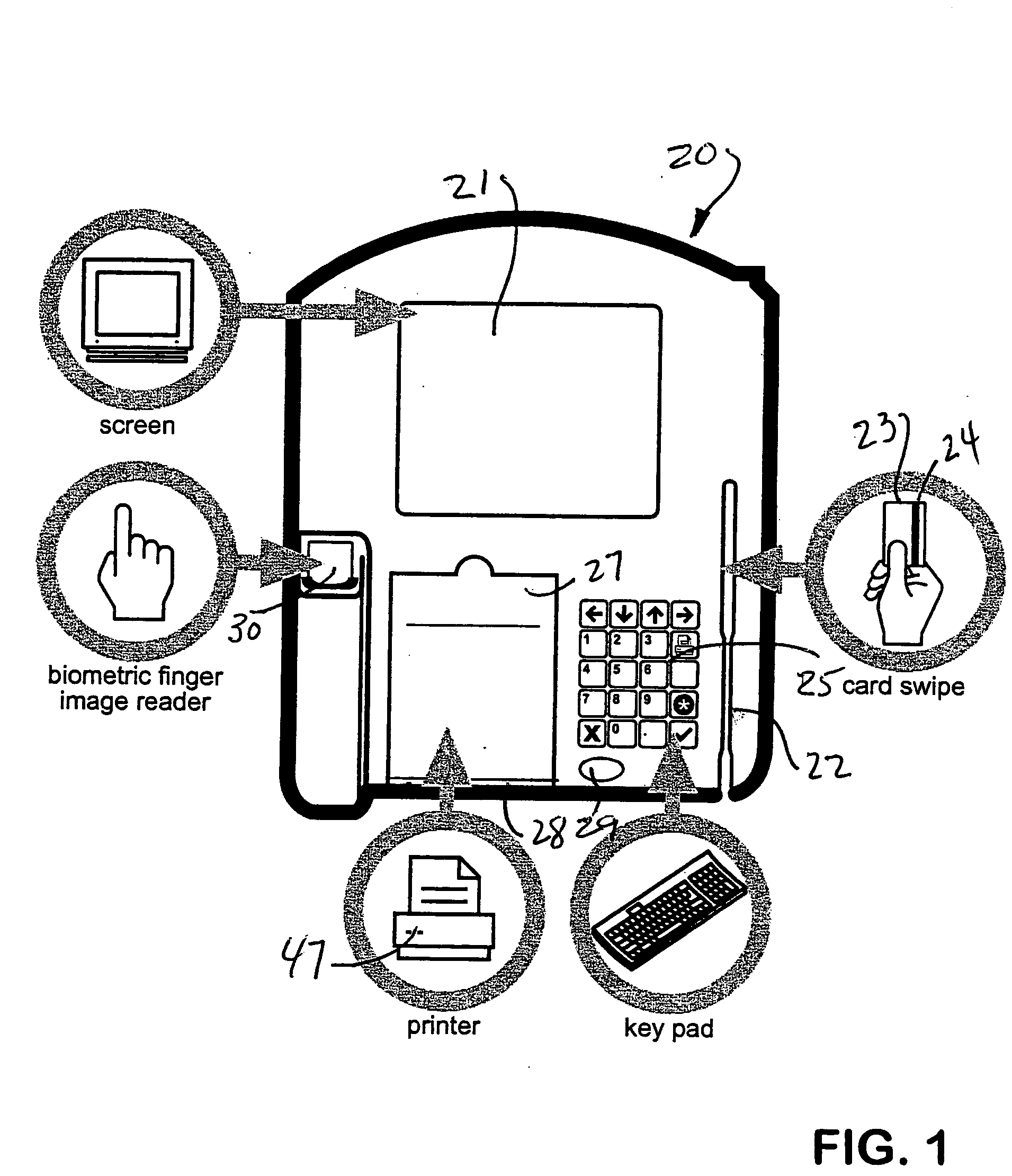
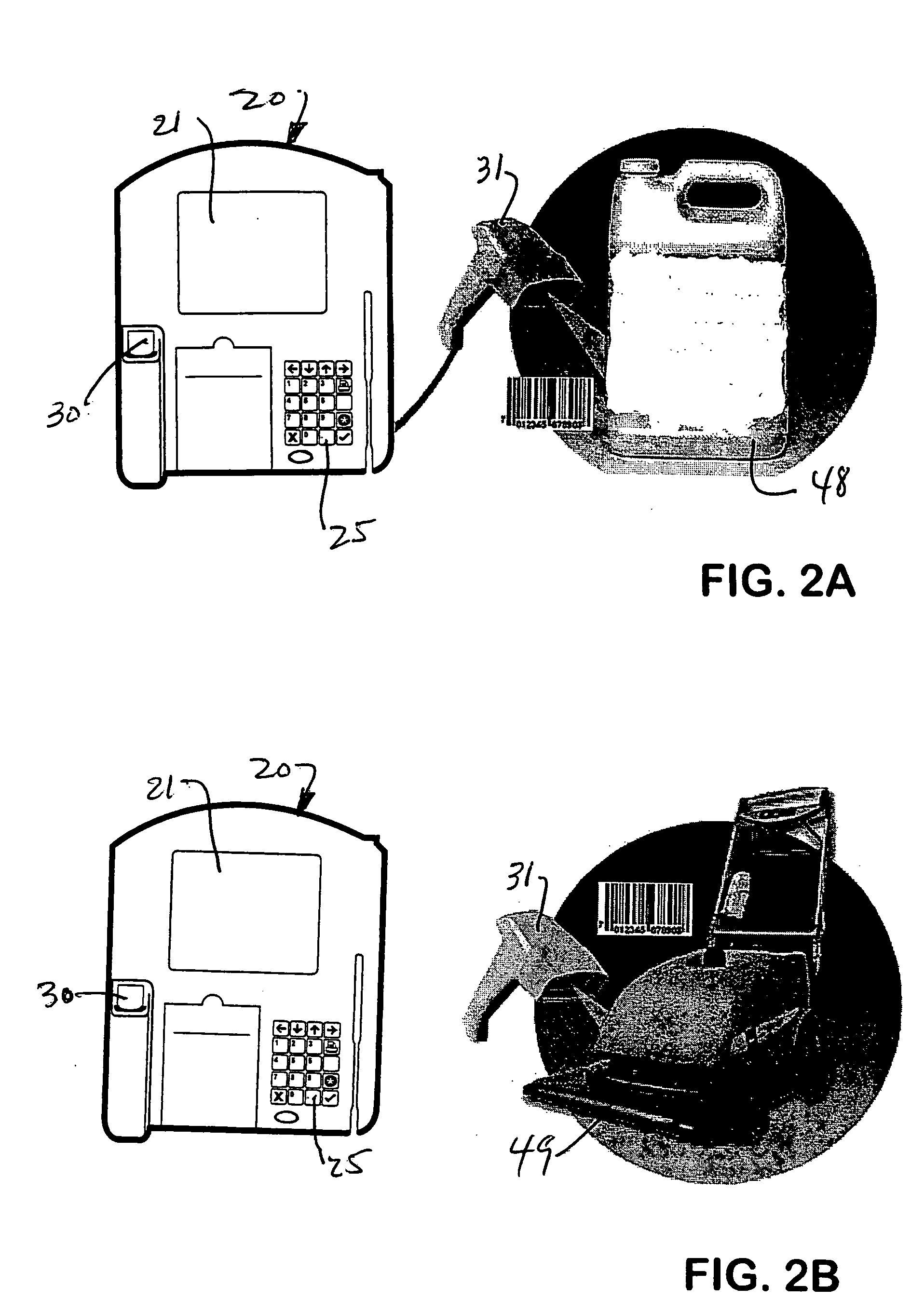
Biometric multi-purpose terminal, payroll and work management system and related methods
InactiveUS20050109836A1Efficient use ofAssist in managementRegistering/indicating time of eventsFinancePersonal identification numberBank account
Employees gain access to a payroll and work management system by authentication at a multi-purpose terminal with a bankcard encoded with a unique account number and a personal identification number (PIN). The terminal may then be used to check-in and checkout of work, to receive new work instructions or assignments, to review payroll details, to print a payroll stub, to execute financial transactions, to print a receipt of financial transactions or to review or to upload the results of work quality audits. The invention also includes systems and methods that utilize such multi-purpose terminals to calculate the payroll and deductions for each employee and to issue electronic fund transfers from the employer's bank account to deposit the net pay in a bank account associated with each employee's bankcard so that the pay is immediately accessible by each employee, such as by withdrawal of cash at an ATM or by purchases at a point of sale. Electronic payrolls may be processed and employee's accounts credited with pay on a daily basis, or on any preset period of time, including hourly.
Owner:AMERICAN EPS
Automatic access to an automobile via biometrics
InactiveUS6498970B2Digital data processing detailsAnti-theft devicesHuman–computer interactionBiometrics
A system and method for identifying persons who are authorized to activate one or more vehicle mechanisms uses both an implicit identification of a face and an explicit identification of speech or a gesture. This system and method enables identification to be performed where a single identification is otherwise unable to perform the identification for some reason and improves the reliability and accuracy of an identification so that only authorized persons can activate the vehicle mechanisms. Vehicle mechanisms that can be activated using this multimodal identification system and method include, for example, automatic locks, automatic windows, a trunk lock, a vehicle engine, outdoor or interior lights, and a vehicle alarm.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Biometric safeguard method with a smartcard
InactiveUS20060016877A1Security is importantDigital data processing detailsPayment architectureSmart cardFinancial transaction
A method for facilitating biometric security in a smartcard-reader transaction system is provided. The method includes determining if a transaction violates an established rule, such as a preset spending limit. The method also includes notifying a user to proffer a biometric sample in order to verify the identity of said user, and detecting a proffered biometric at a sensor to obtain a proffered biometric sample. The method additionally comprises verifying the proffered biometric sample and authorizing a transaction to continue upon verification of the proffered biometric sample.
Owner:LIBERTY PEAK VENTURES LLC
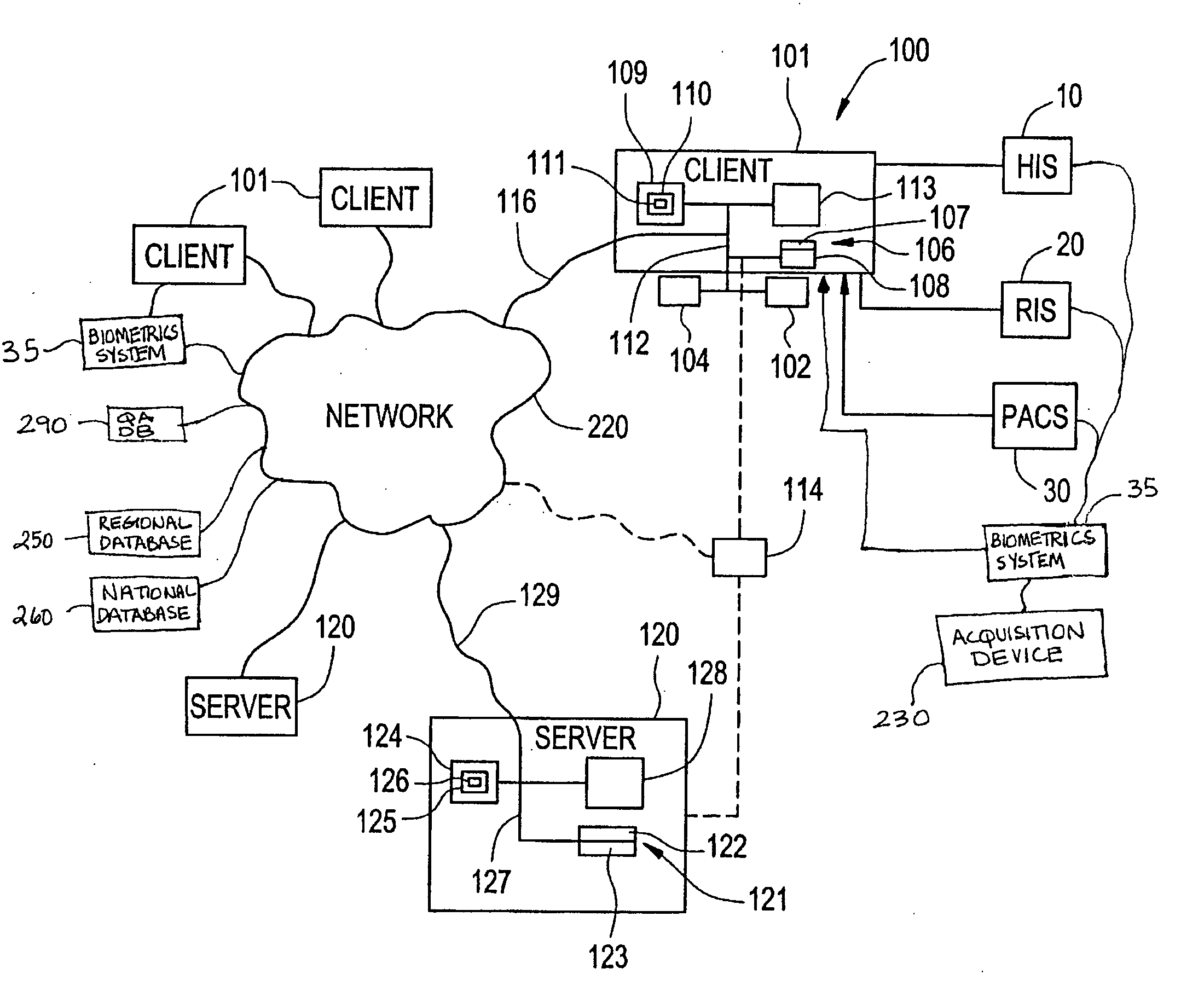
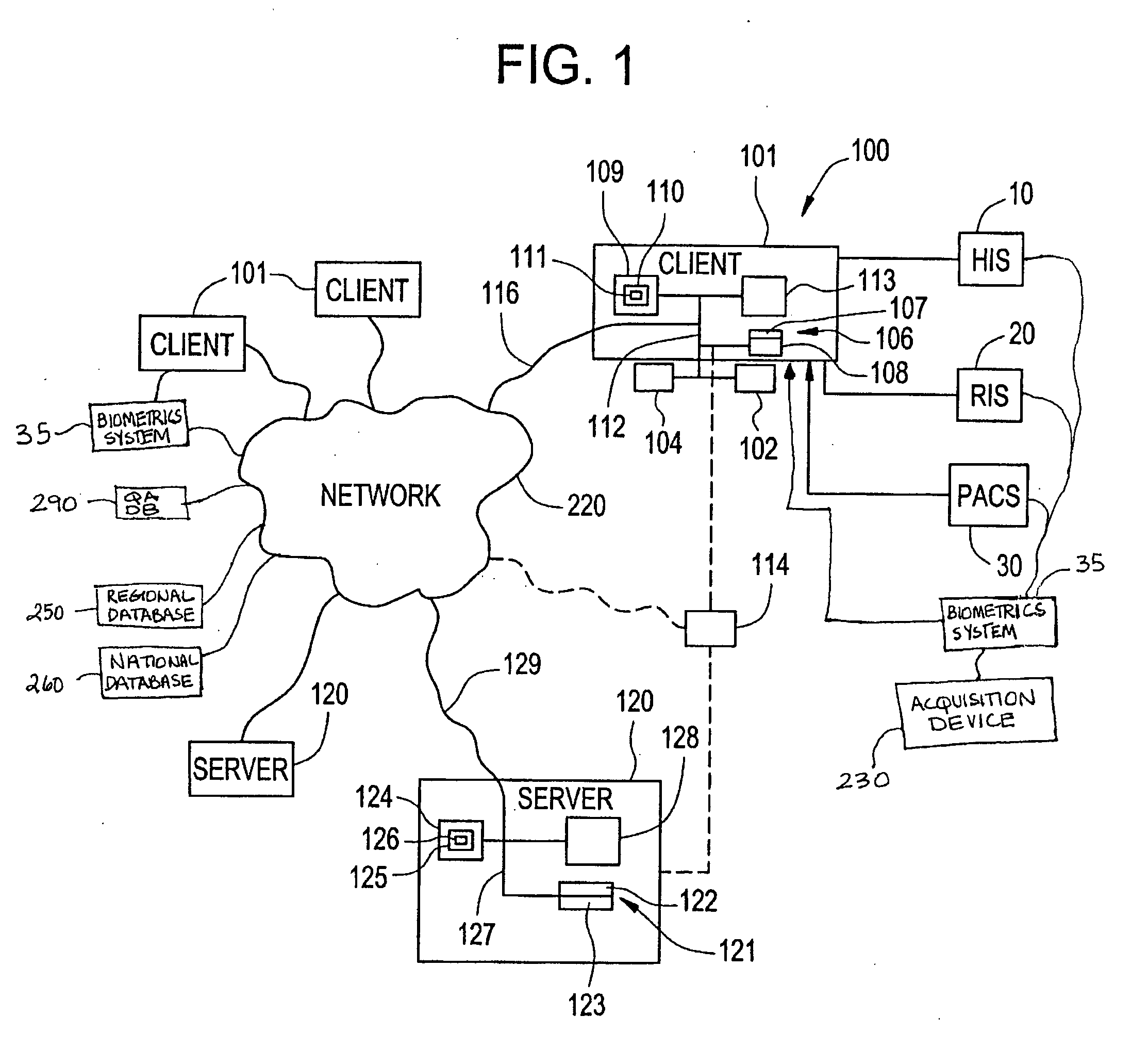
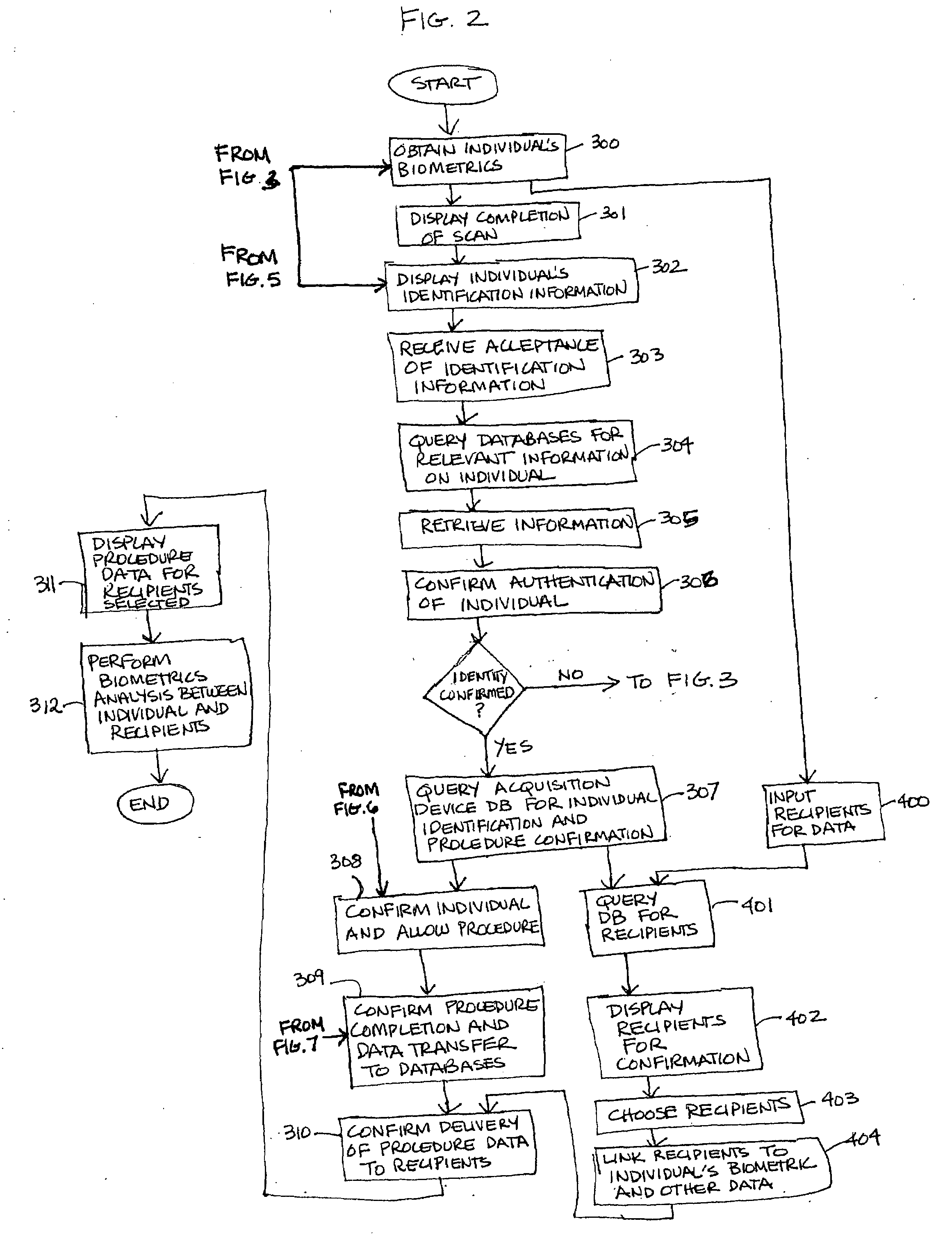
Apparatus and method for utilizing biometrics in medical applications
ActiveUS20070258626A1Avoid mistakesAvoid accessDigital data processing detailsDrug and medicationsPharmacyBiometrics
In the present invention, the user will sign onto a system, utilizing a biometrics authentication or identification procedure. Once authentication and identification takes place, local, regional, and centralized medical databases can be automatically queried using the identification-specific biometrics signature. All data intrinsic to the medical procedure or examination being performed will be automatically tagged and downloaded into that specific patient's electronic medical database. At the same time, that patient's medical database is queried to provide all historical data relevant to the medical examination or procedure being performed to assist with planning, protocol, and analysis of the data being collected. The biometrics authentication can be performed at patient intake, at an imaging device, at a pharmacy, or in the operating room, to ensure that the personnel and the patient are correctly identified before any procedure is performed or drug administered.
Owner:IMPRIVATA
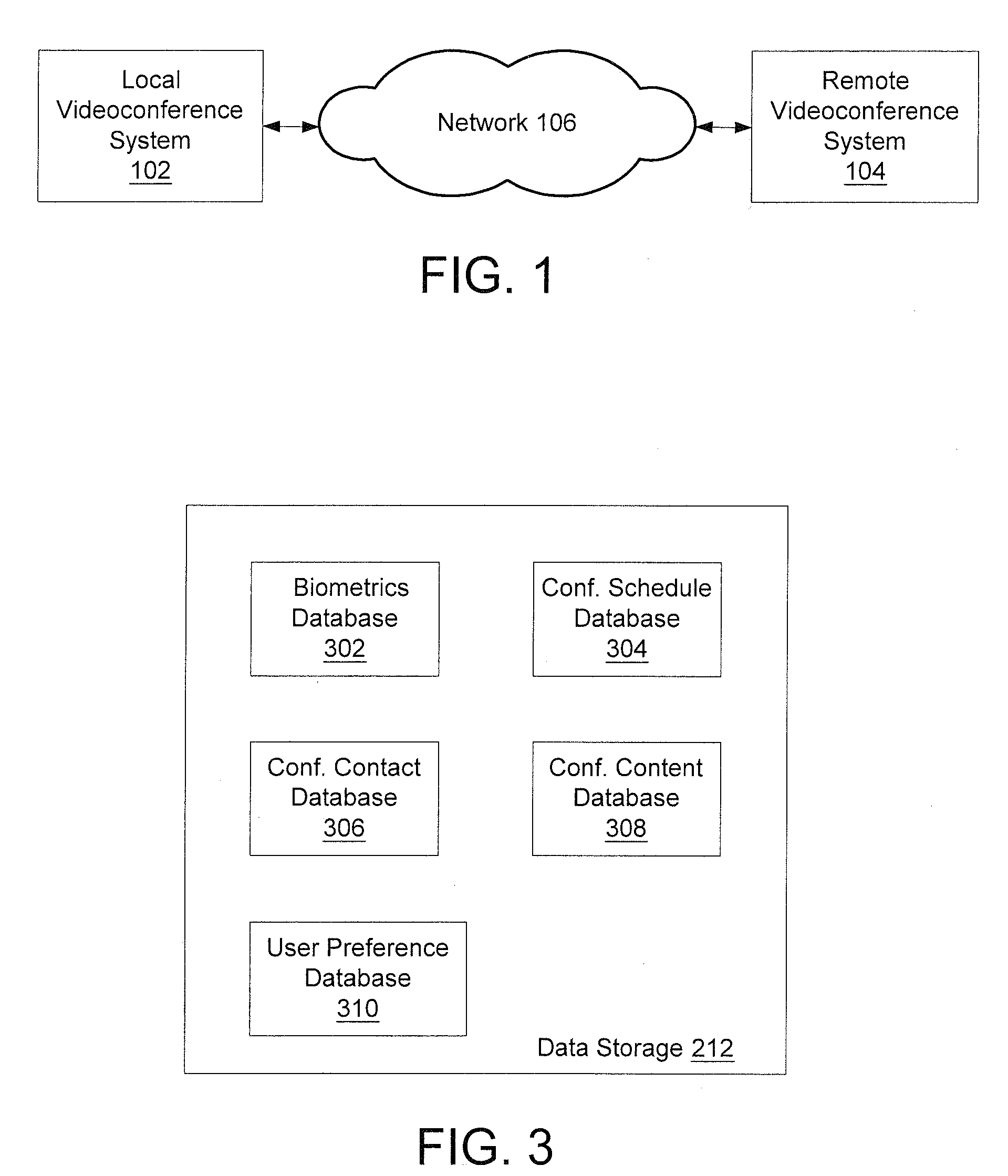
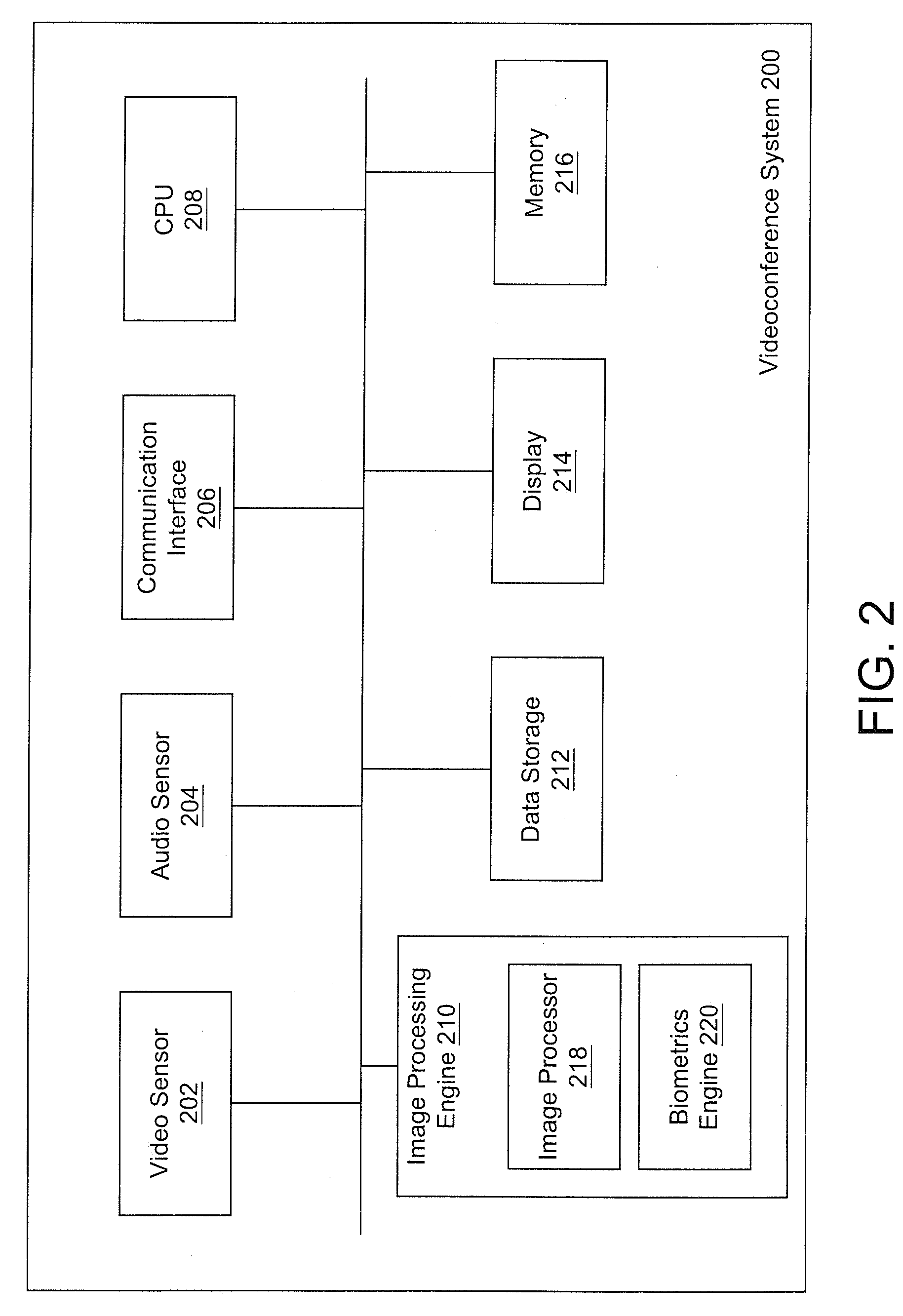
System and method for using biometrics technology in conferencing
ActiveUS20060259755A1Easy accessDigital computer detailsCharacter and pattern recognitionVideo sensorsHuman–computer interaction
A system and method are provided which utilize biometrics technology in a conference environment. A biometrics engine detects facial images of a user, generates biometrics of the detected facial images, and compares the generated biometrics with biometrics information of authorized users. If a match is found, then the user is authorized and is automatically logged into the conference network. Once logged in, conferences may be automatically established, the user may be tracked by at least one video sensor, user preferences may be automatically set, and / or conference content may be easily accessed and shared with remote conference participants.
Owner:HEWLETT PACKARD DEV CO LP
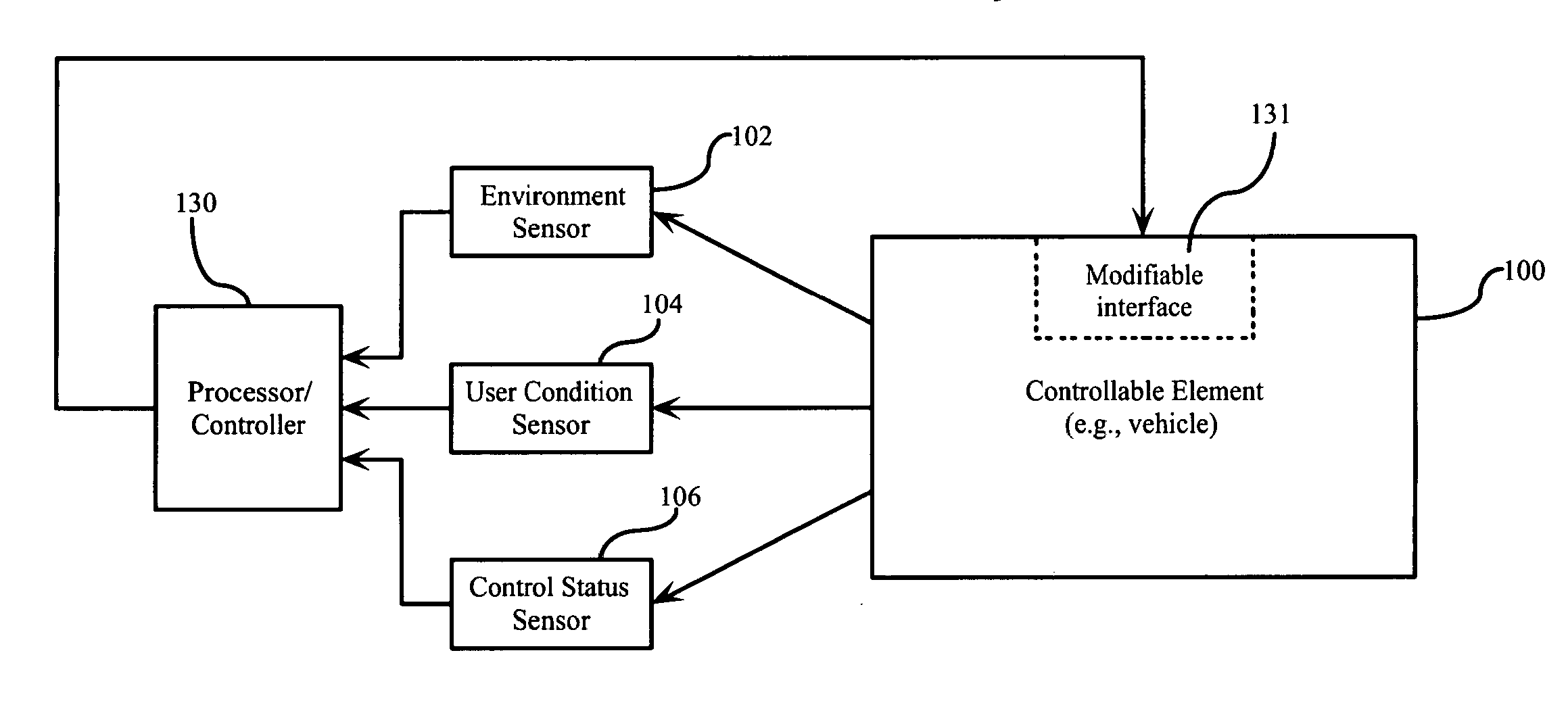
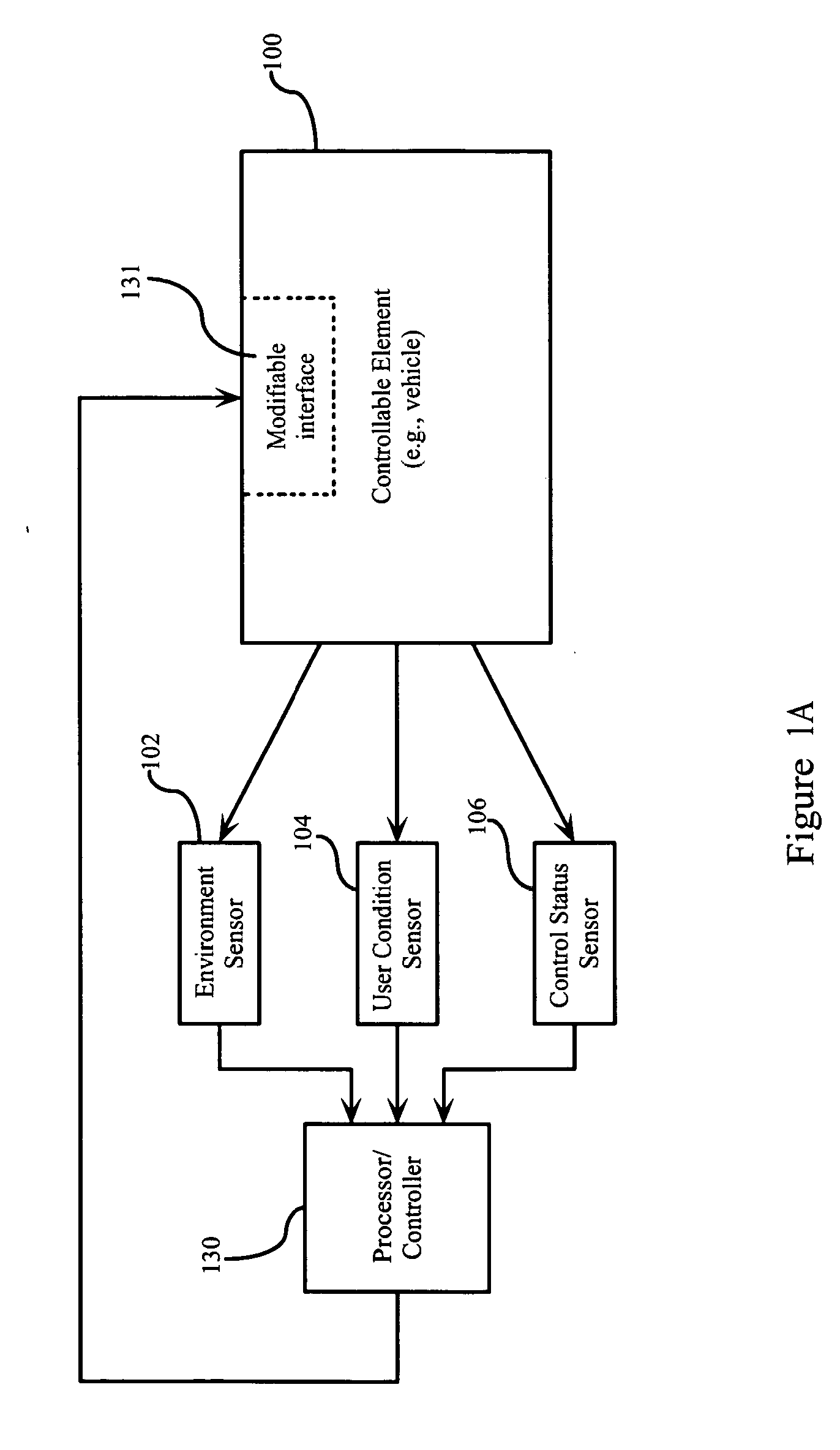
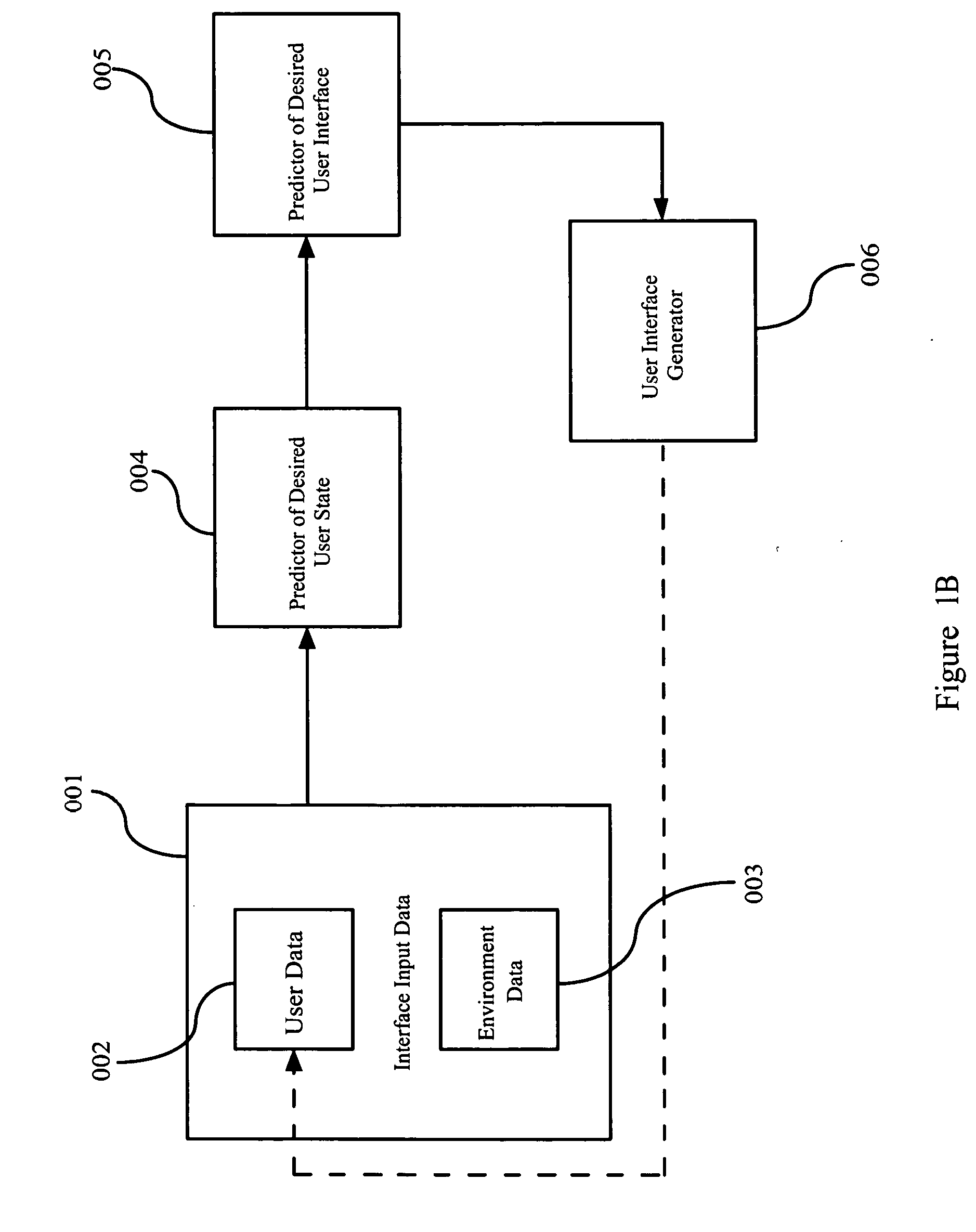
Predictive user modeling in user interface design
Dynamic modification of user interfaces is disclosed, based upon identification of the current state of the user and the sensing of a particular situation in which the user is involved and / or environment in which the user is situated. In particular, emotional and mental states of a user are identified and these states are taken into consideration when creating and / or adapting an interface to be used by the user. The interface is modified / created automatically based on identified user biometrics, that is, measured physical properties of the user.
Owner:IBM CORP
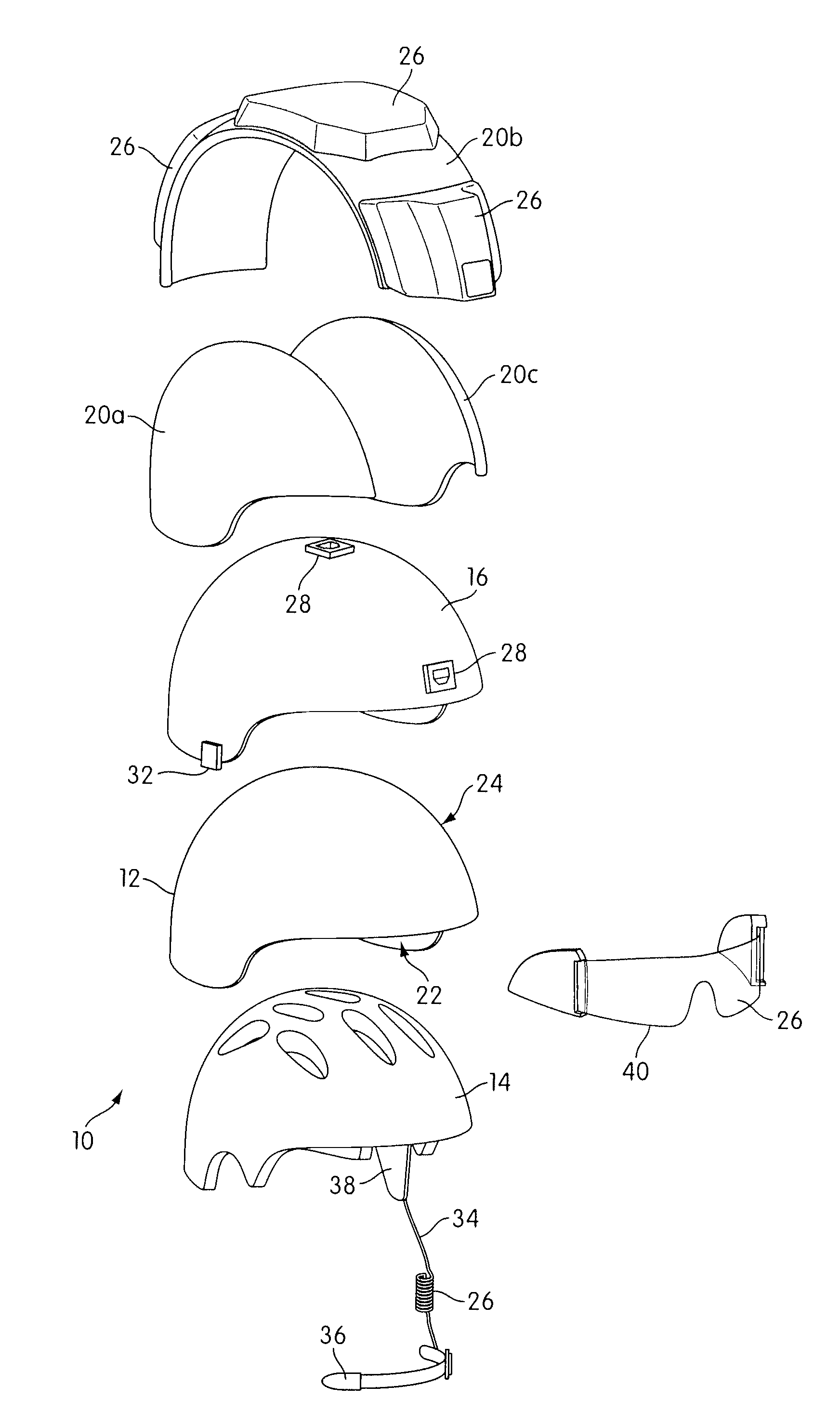
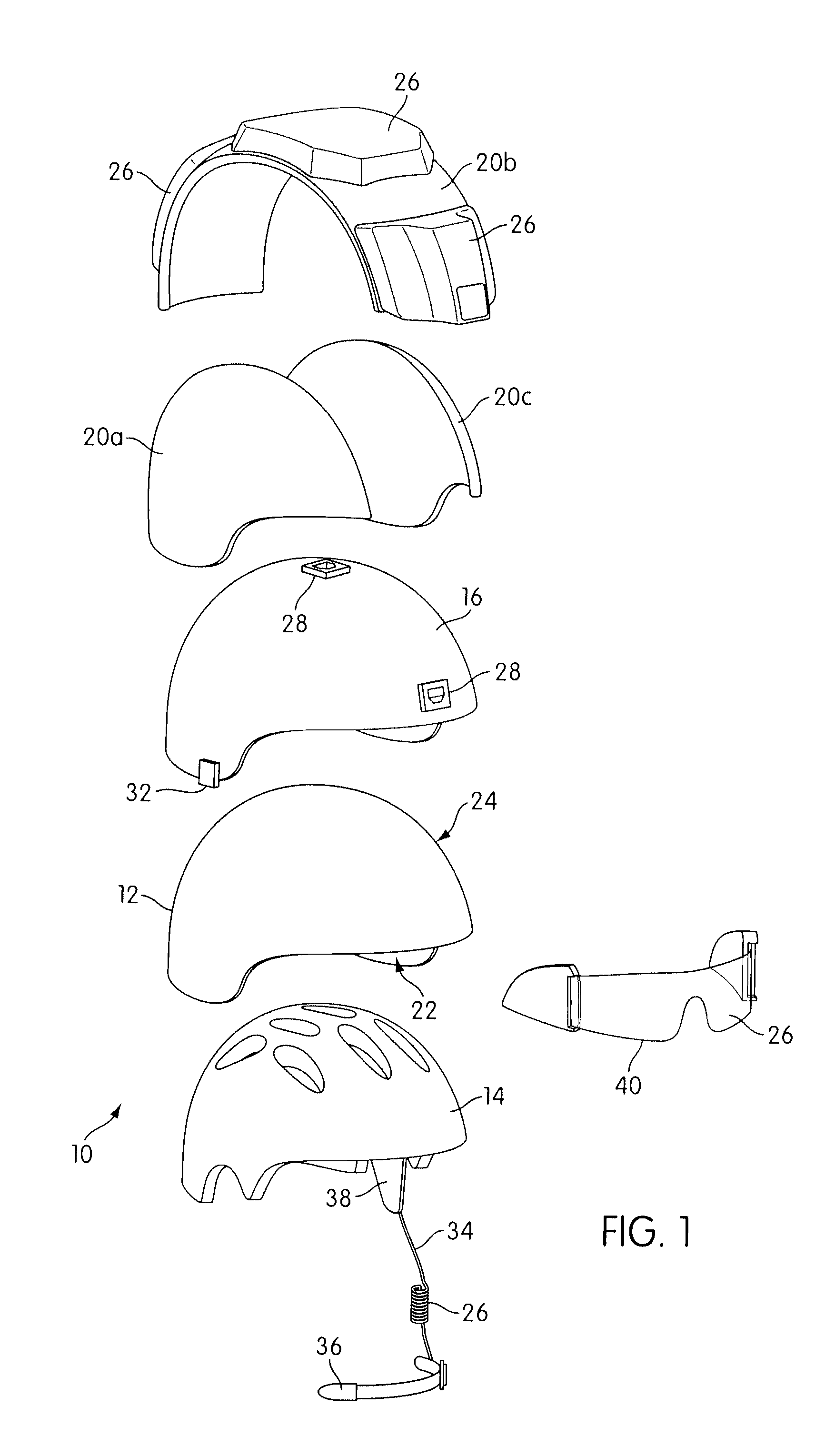
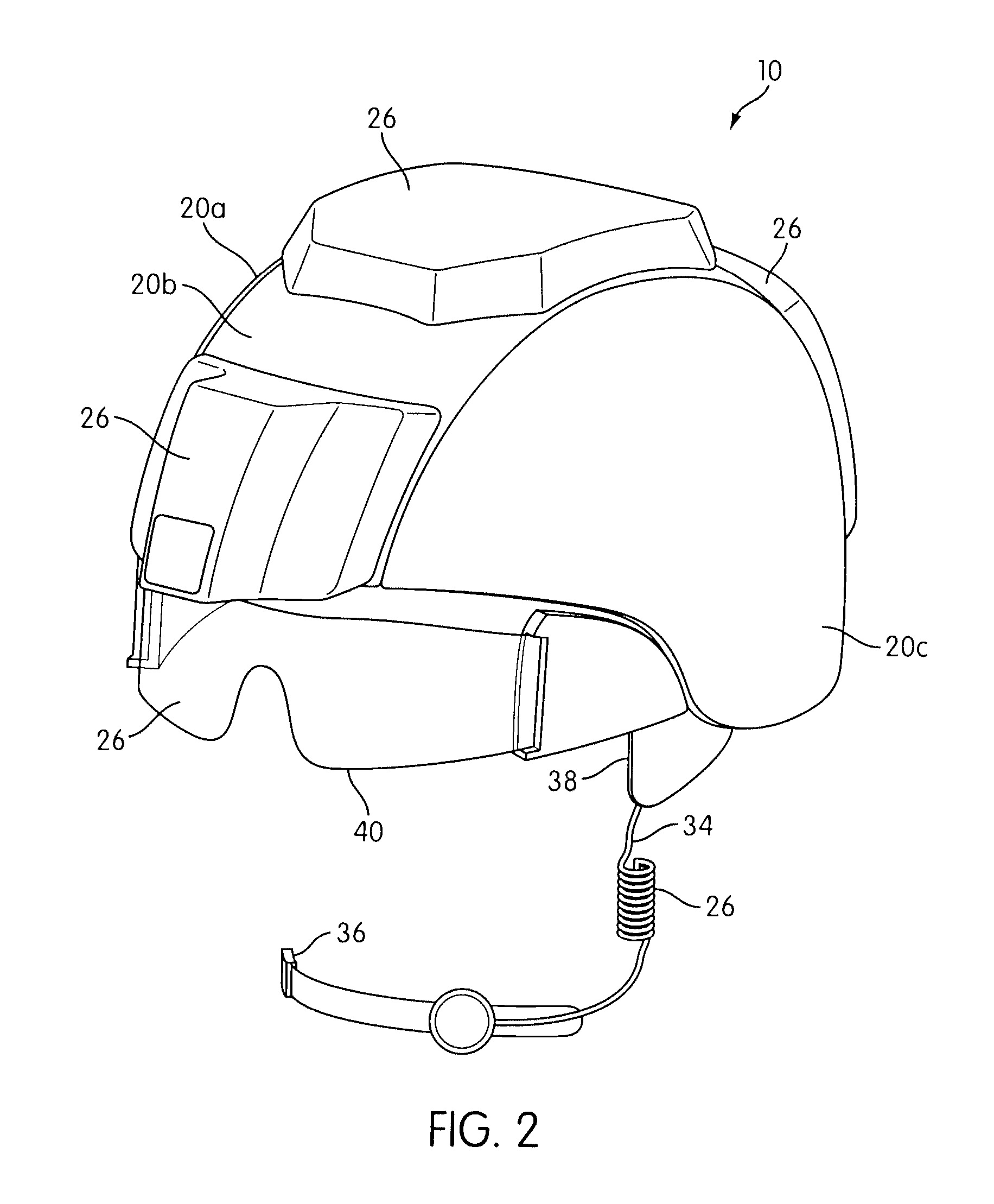
Customizable military helmet system
InactiveUS20110197327A1Easy to customizeImprove protectionVehicle seatsLayered productsInformation processingInformation transmission
A helmet system that enables a user of the helmet system to customize the helmet system according to personal taste, a task at hand, responsibilities within a tactical group (e.g., communications, command, etc.), and / or according to other parameters. The customization of the helmet system may include a customization of electronics modules carried on the helmet system that optionally provide communications, environment detection, health or biometrics monitoring, power, information transmission / reception, information processing, and / or other functionalities. The customization of the helmet system may include a customization of structural components that enable the user to balance the structural protection provided to the user against other considerations. The other considerations may include, for example, weight, form factor, comfort, and / or other considerations.
Owner:BAE SYSTEMS LAND & ARMAMENTS LP
System for preventing theft of articles from an enclosure
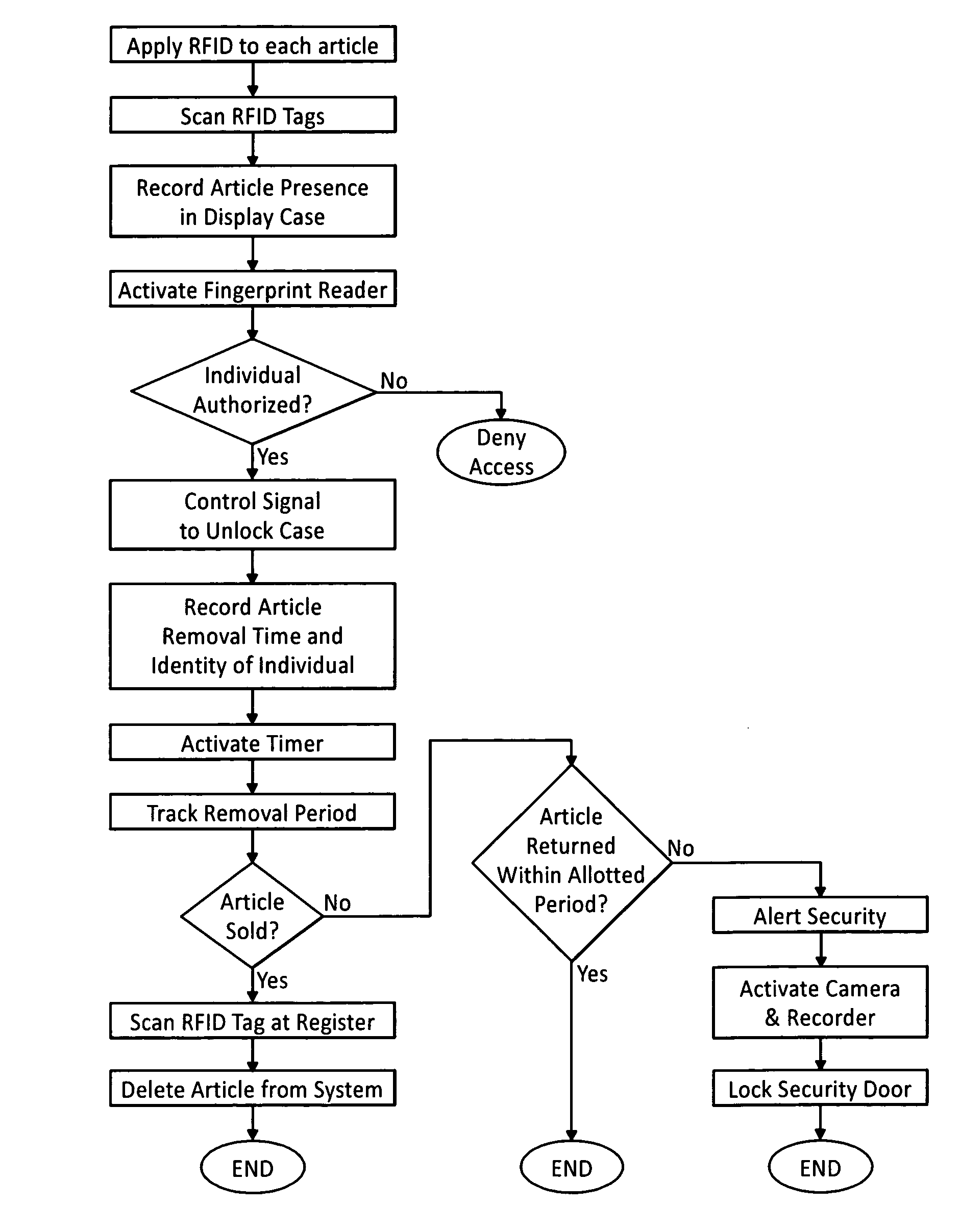
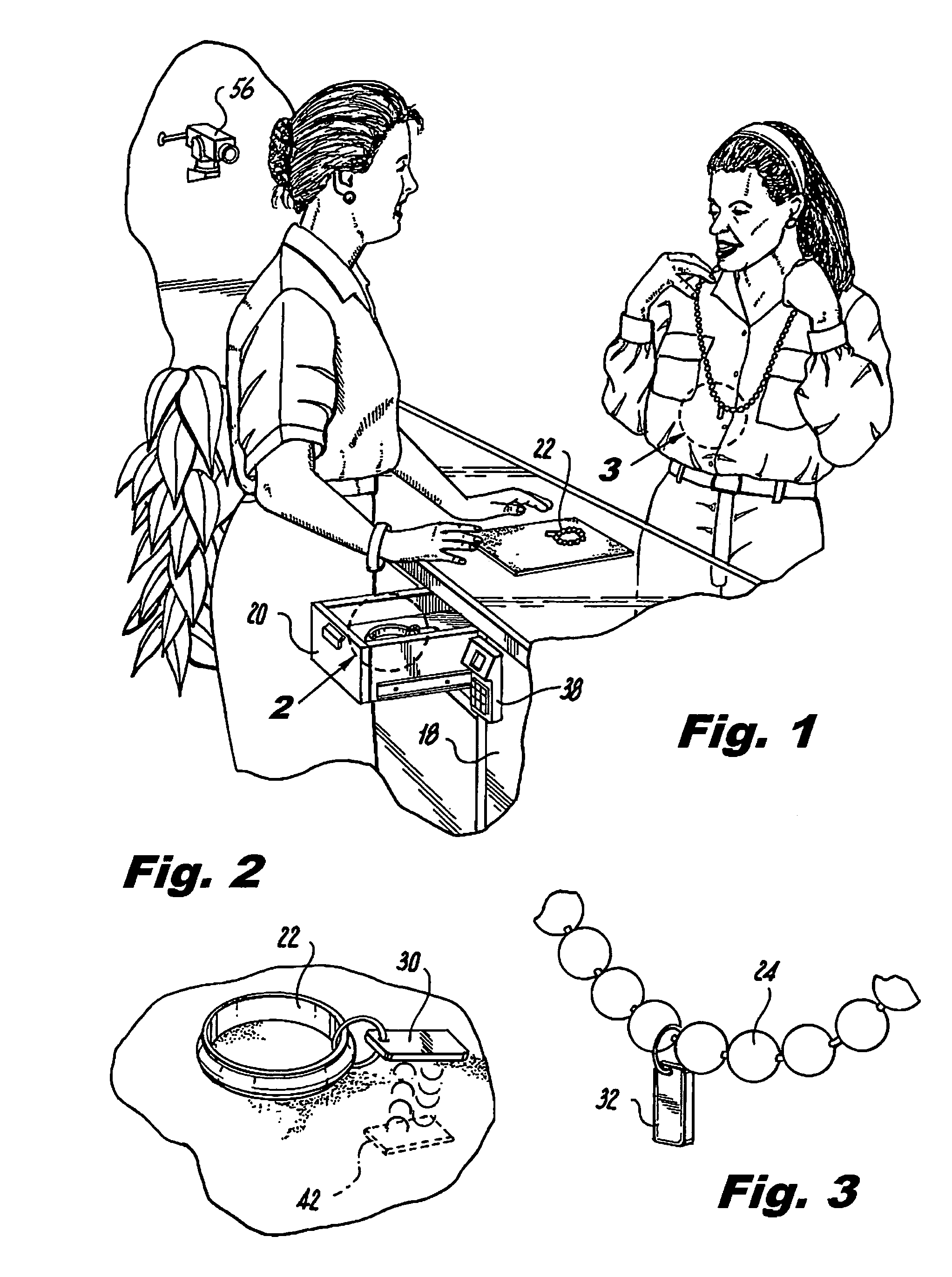
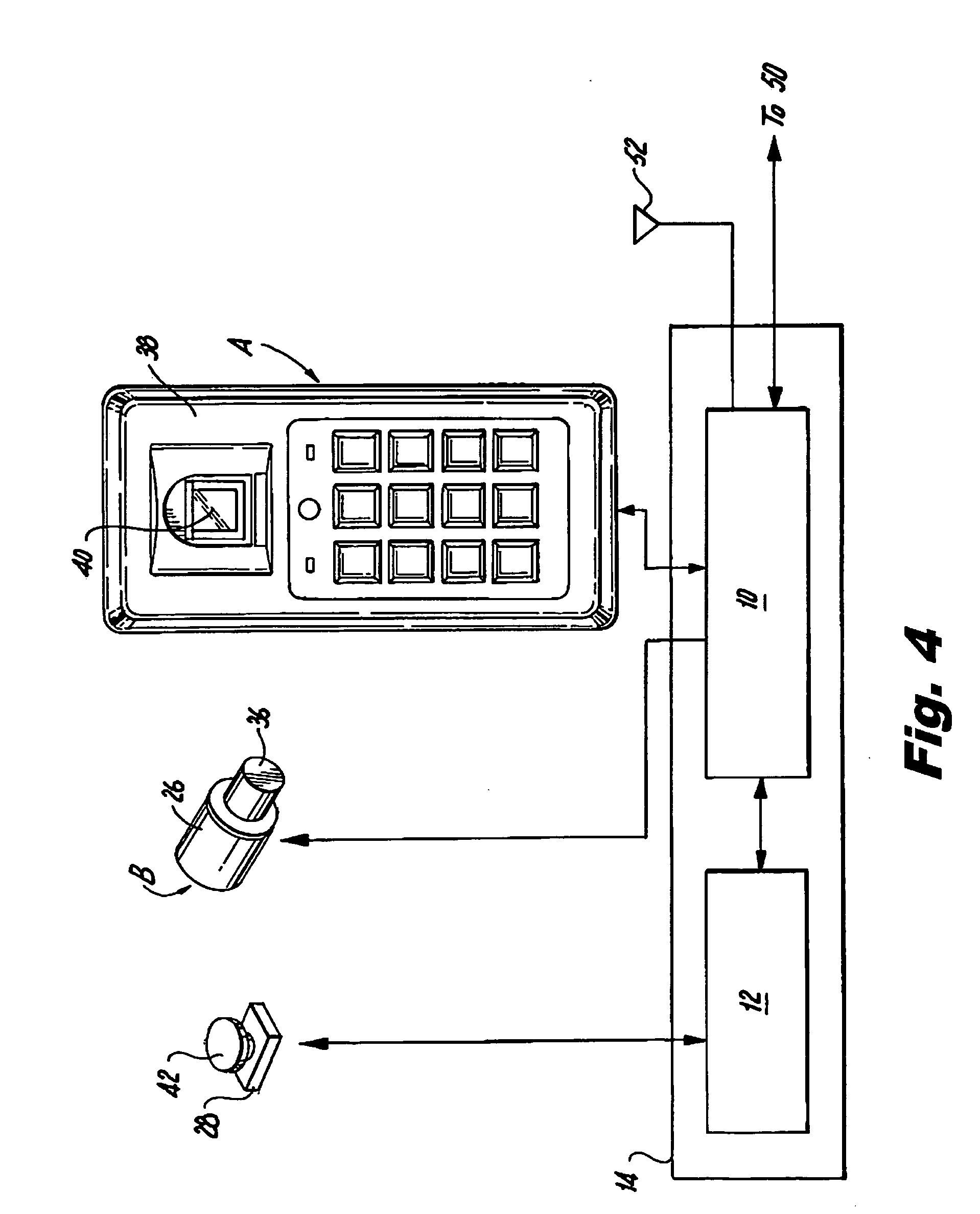
InactiveUS20090224875A1Prevent theftElectric signal transmission systemsImage analysisEngineeringClosed-circuit television camera
The security system prevents theft of articles from an enclosure having a lockable access opening. Using RFID technology, a transponder periodically scans the enclosed display area to interrogate RFID tags associated with each of the articles within the enclosure. Access to the enclosure is controlled by an electronically activated retrofit lock associated with the access opening. Biometric technology is used to identify an individual attempting to access the enclosure and to determine whether the identified individual is authorized to access the enclosure. If the individual is authorized, the identity of the authorized individual, the identity of an article removed from the enclosure, and the time that the article was removed from the enclosure are recorded. A POS / inventory control system notes the sale of the removed article. A security alert signal is generated if the removed article is not sold or returned to the enclosure within a given time period after the article was removed from the enclosure. Images of the area proximate the enclosure may be captured by a closed circuit video camera and stored.
Owner:VERSATILE SYST
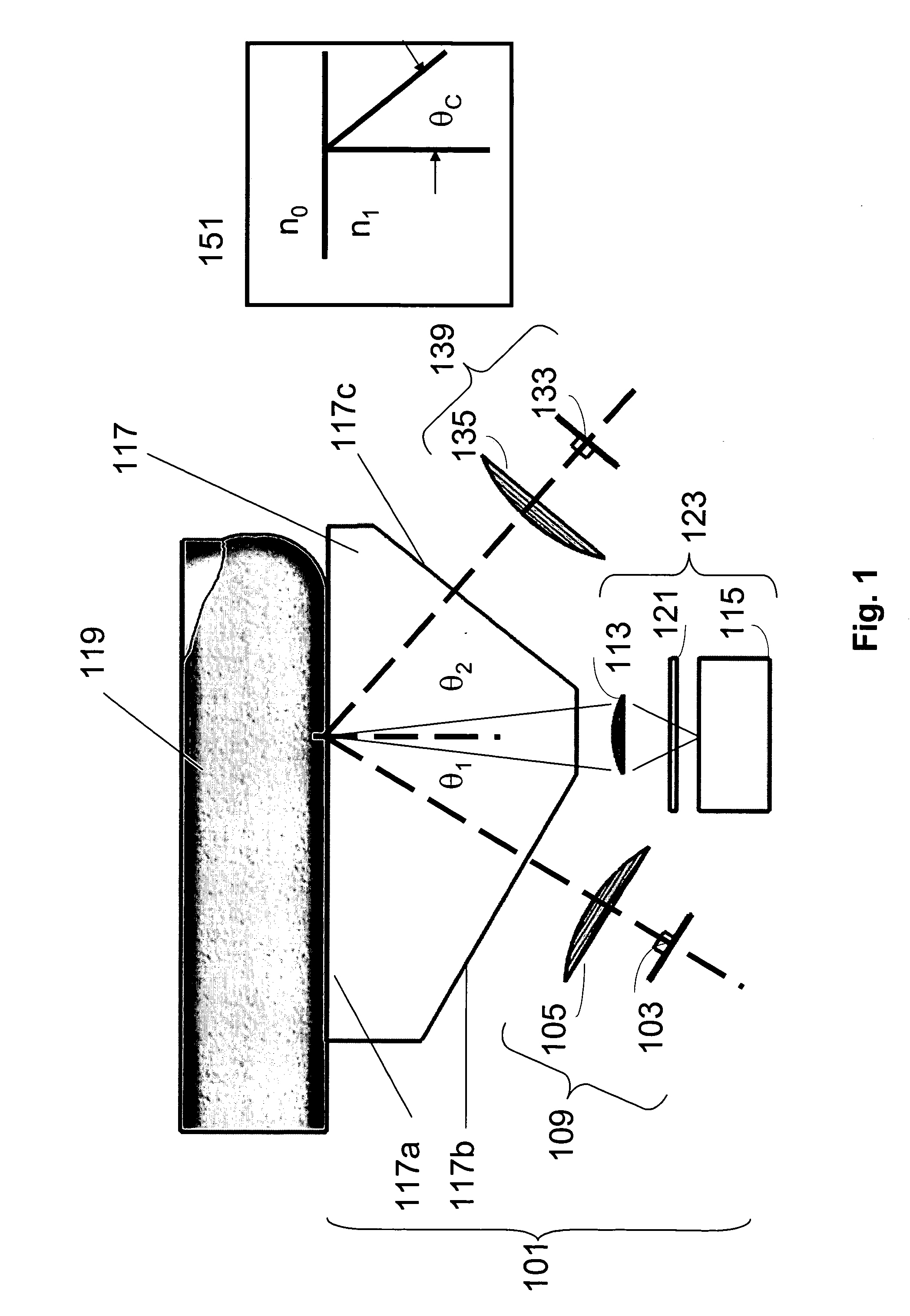
Multispectral biometric imaging
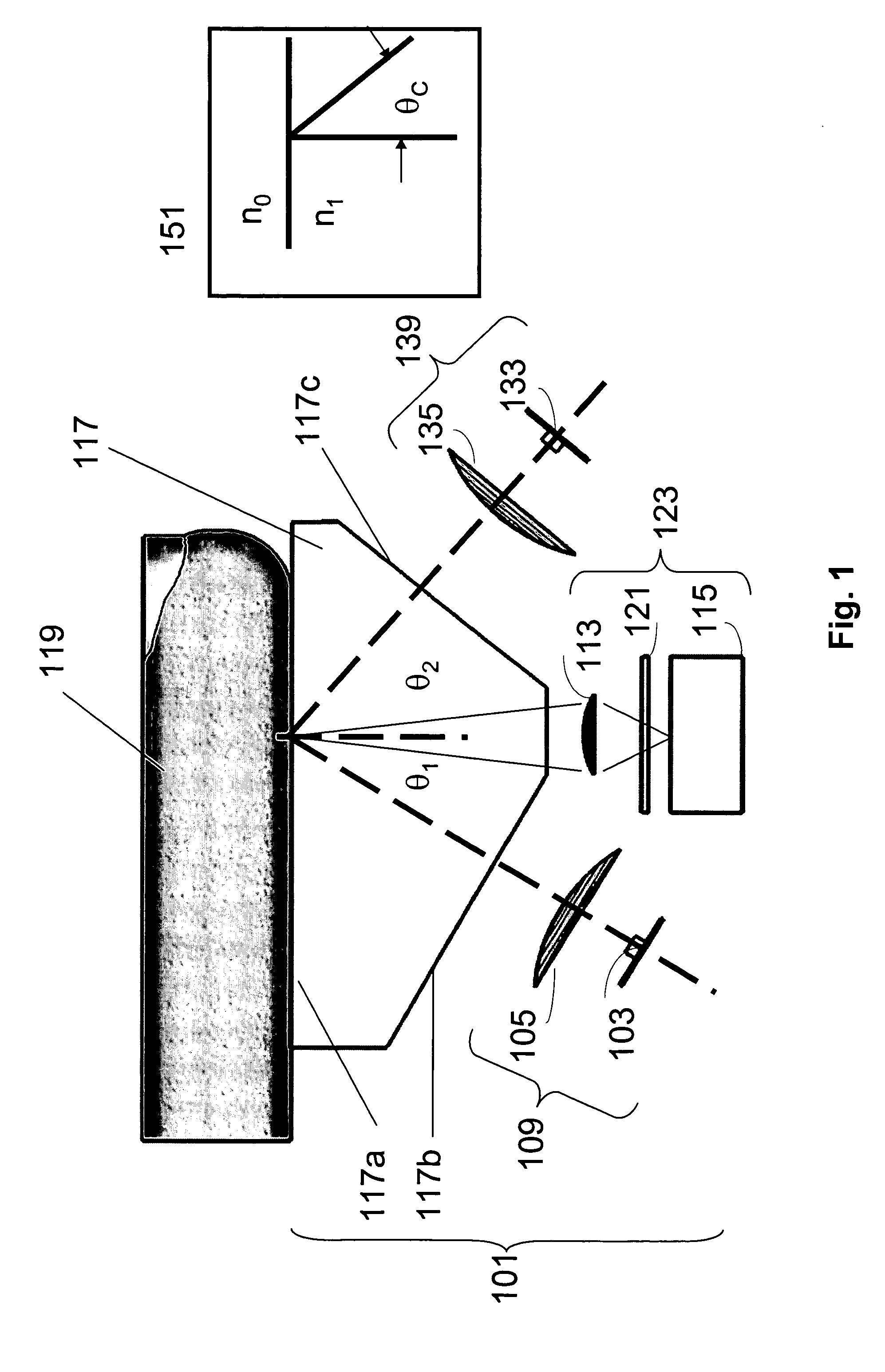
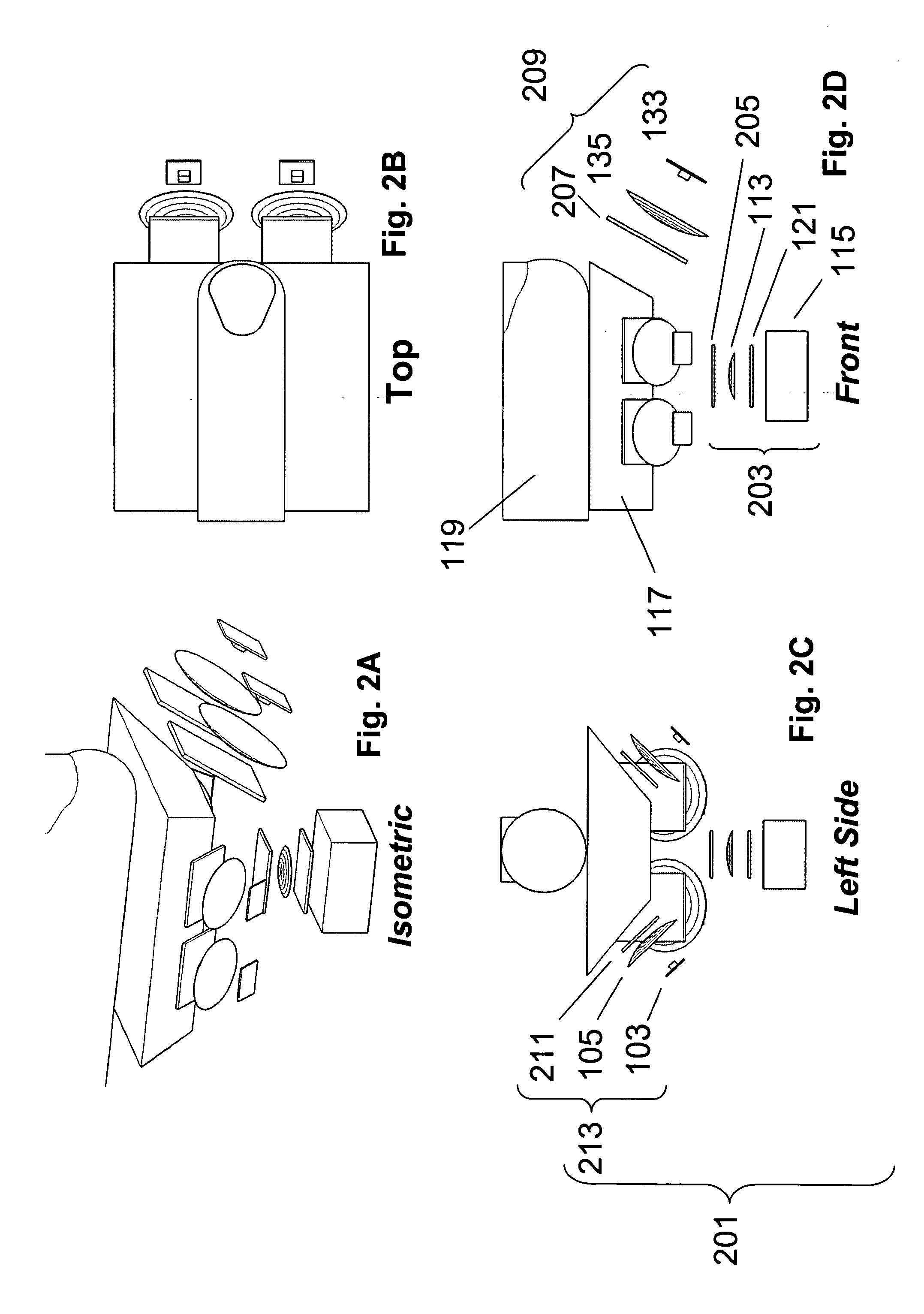
ActiveUS20050265586A1Programme controlElectric signal transmission systemsMultispectral imageBiometrics
Methods and systems are provided for performing a biometric measurement on an individual. A purported skin site of the individual disposed relative to a platen is illuminated under distinct optical conditions during a single illumination session. At least one of the optical conditions includes illuminating the purported skin site with light at an angle greater than a critical angle defined by an interface of the platen with an external environment. At least another of the distinct optical conditions includes illuminating the purported skin site with light at an angle less than the critical angle. Light scattered from the purported skin site is received separately for each of multiple optical conditions to derive a multispectral image of the purported skin site.
Owner:HID GLOBAL CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com