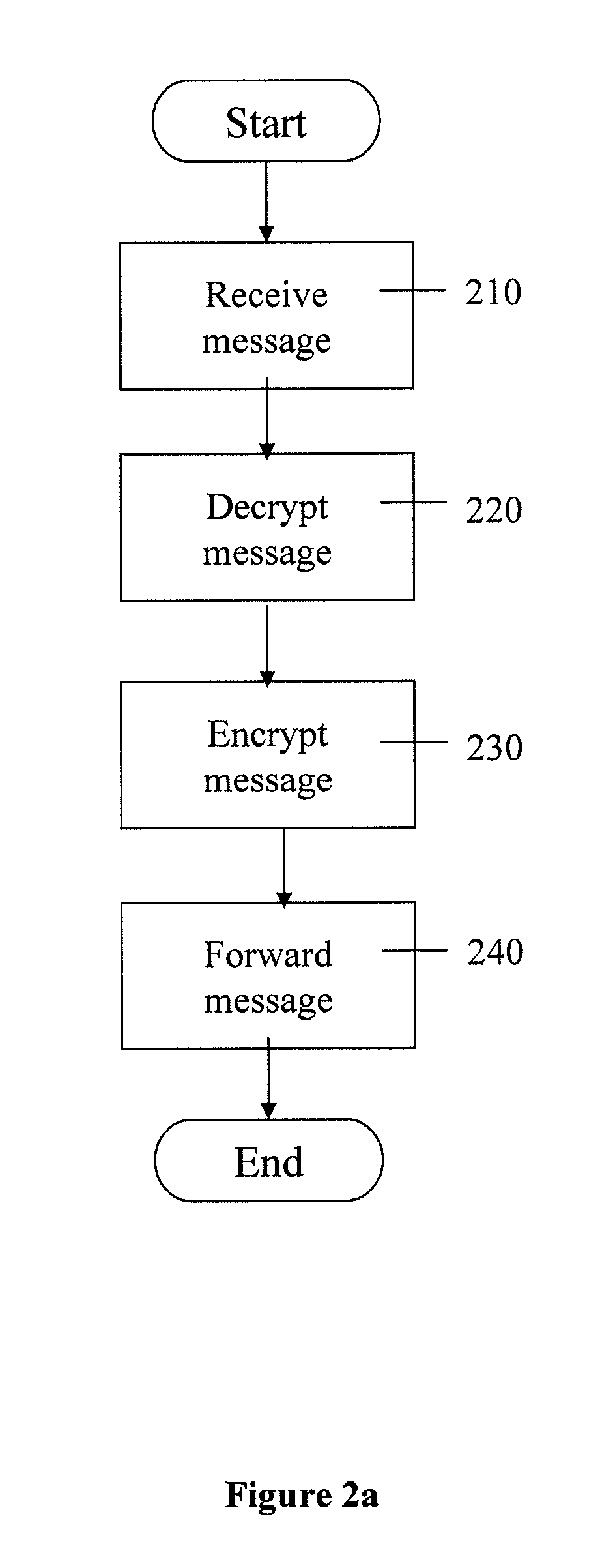
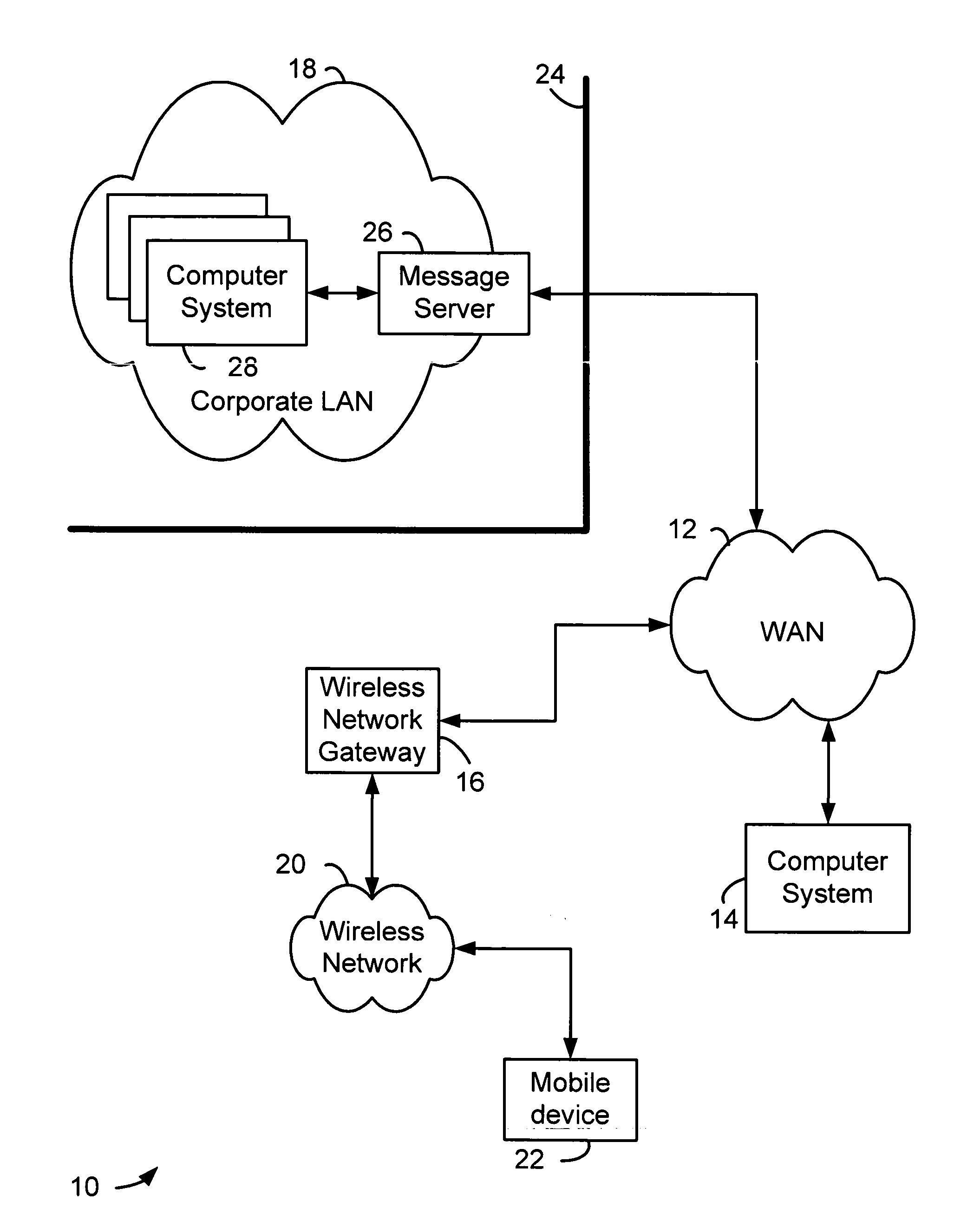
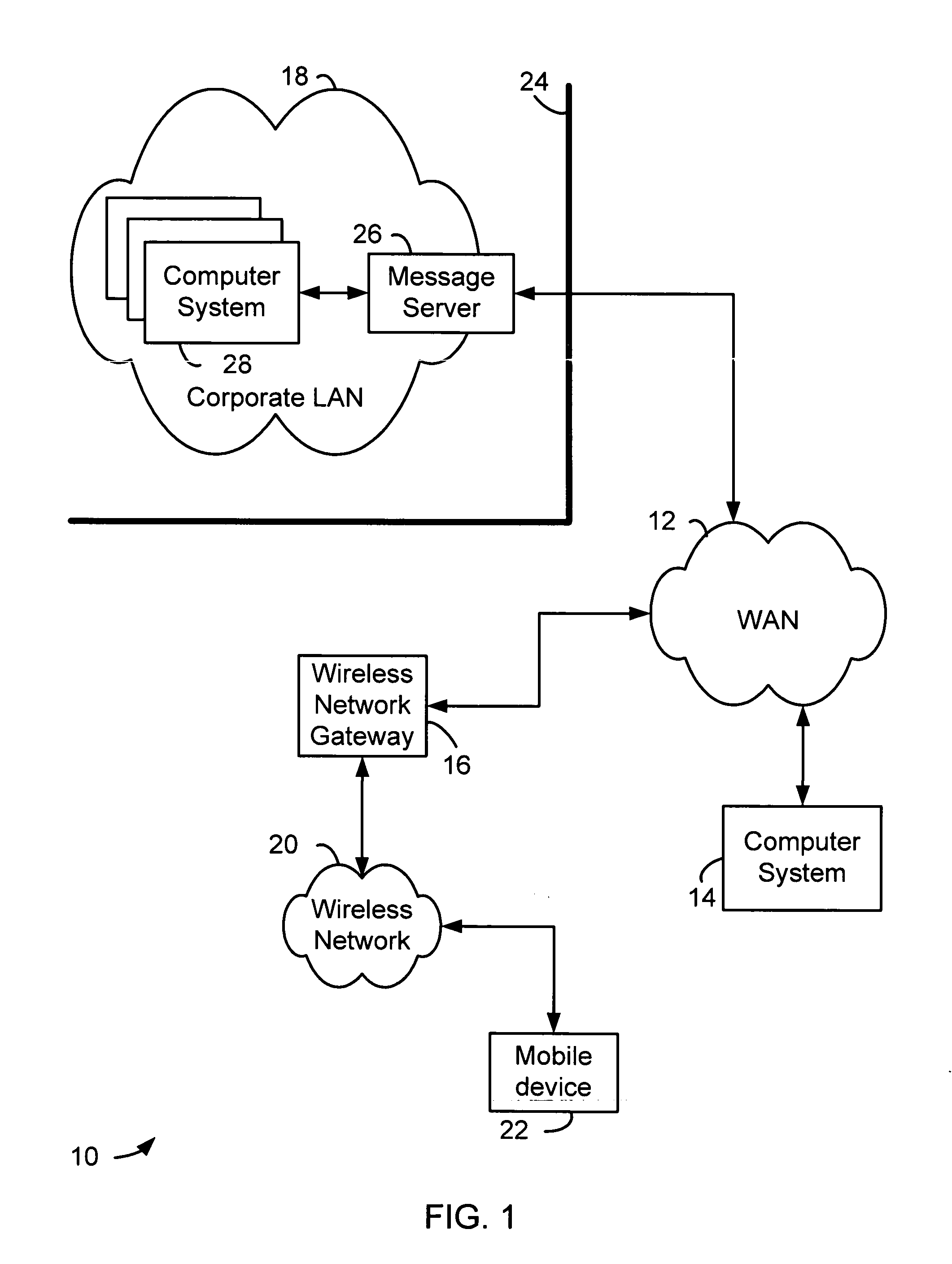
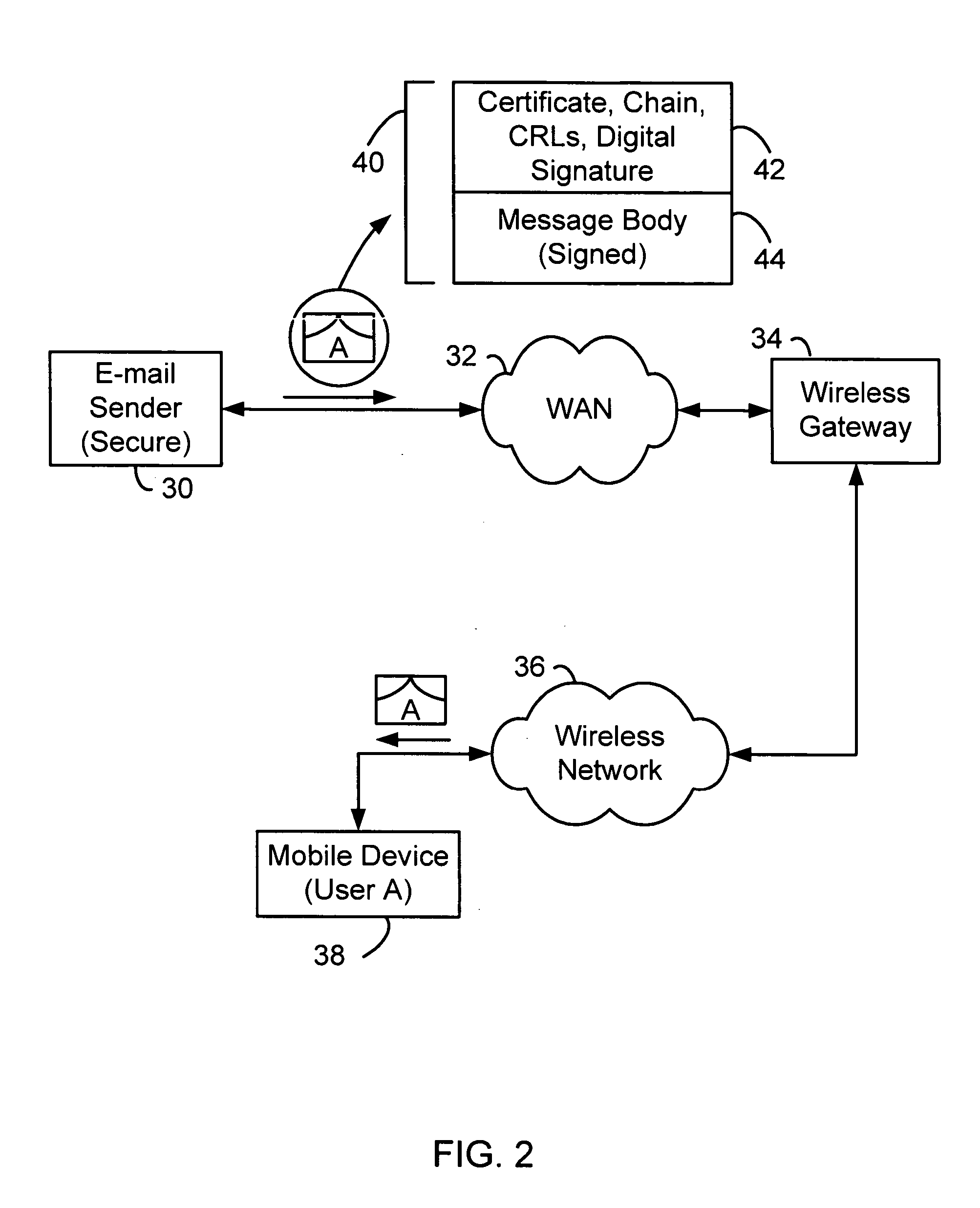
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
123 results about "Secure messaging" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
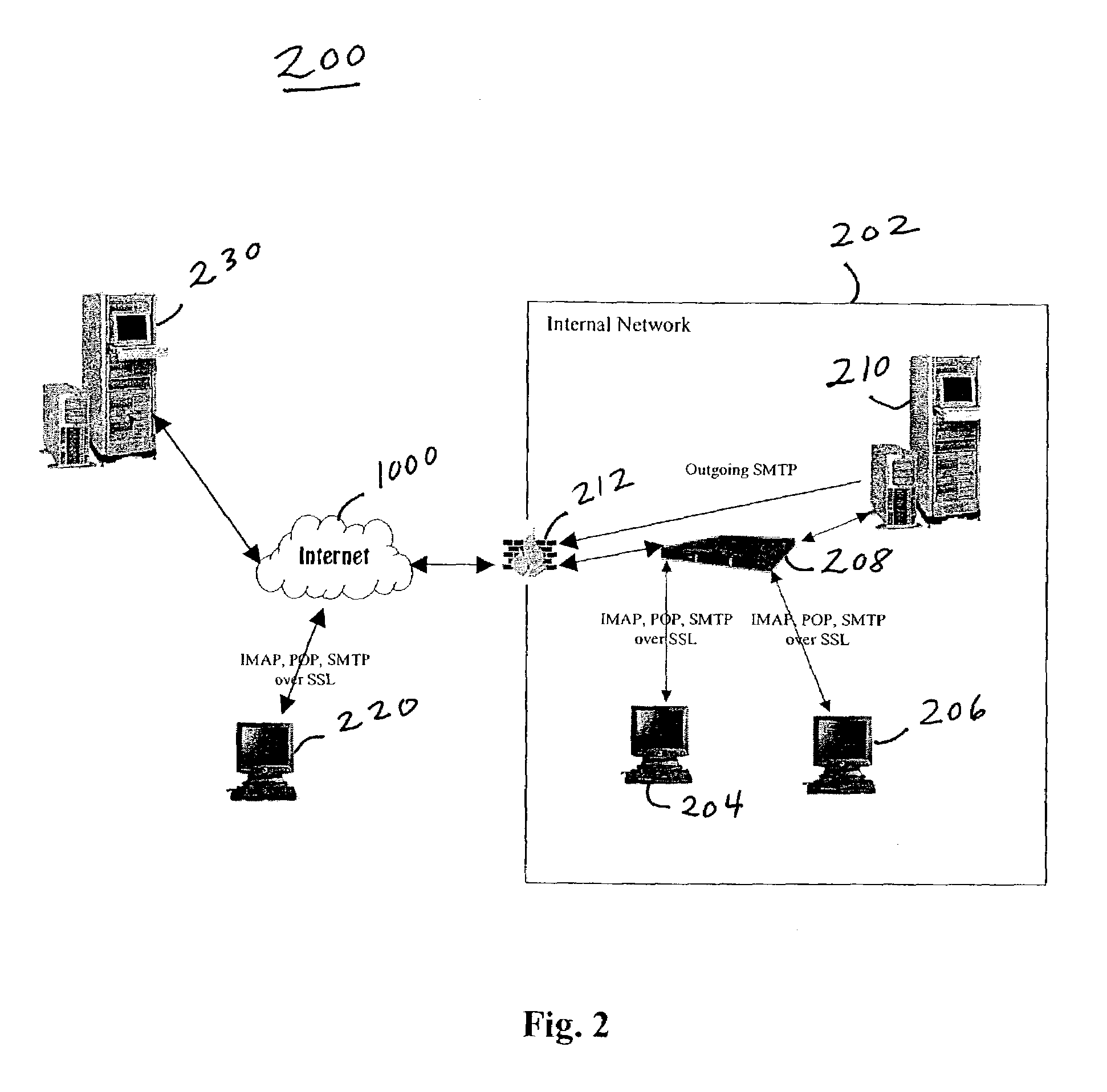
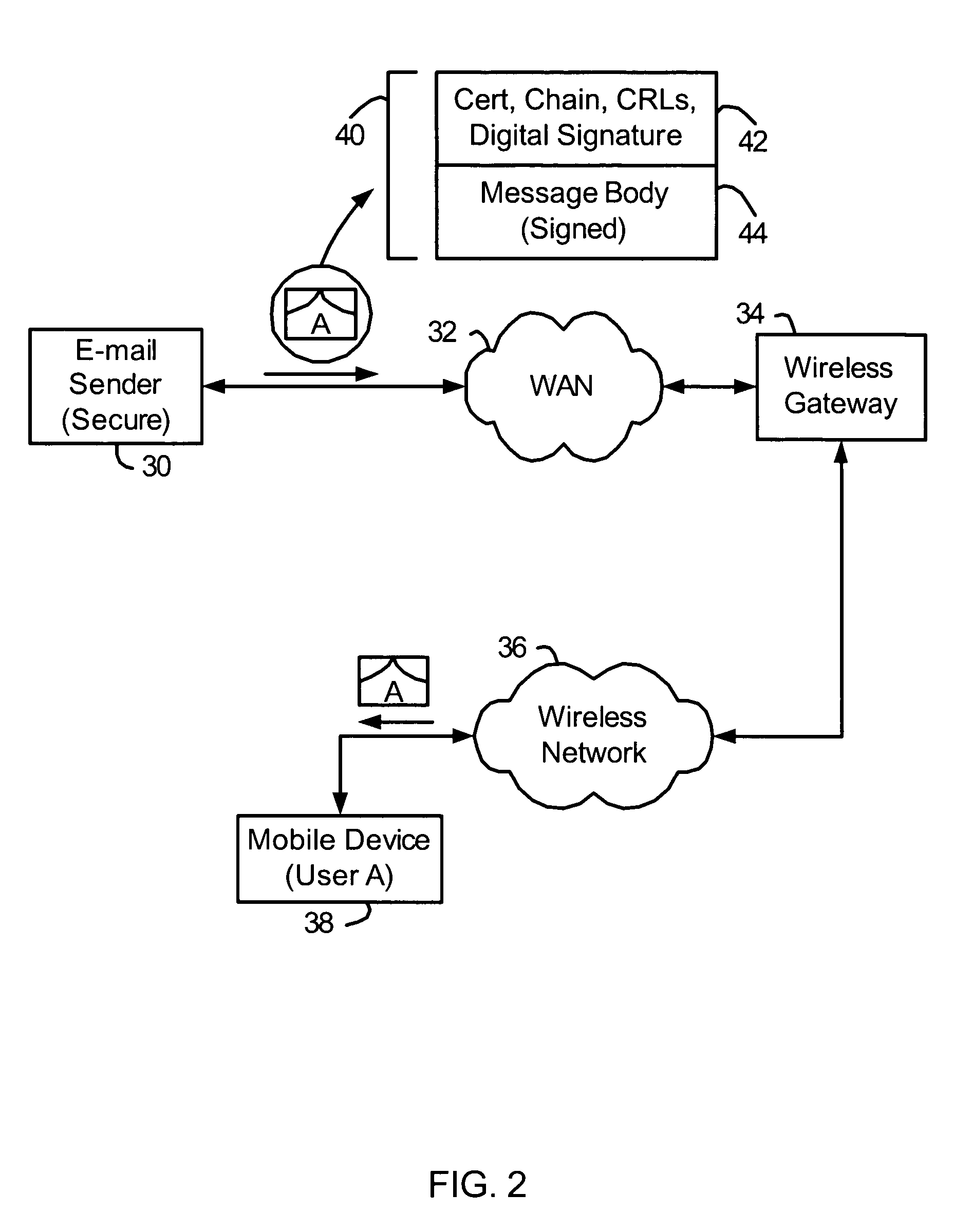
Secure messaging is a server-based approach to protect sensitive data when sent beyond the corporate borders and provides compliance with industry regulations such as HIPAA, GLBA and SOX. Advantages over classical secure e-mail are that confidential and authenticated exchanges can be started immediately by any internet user worldwide since there is no requirement to install any software nor to obtain or to distribute cryptographic keys beforehand. Secure messages provide non-repudiation as the recipients (similar to online banking) are personally identified and transactions are logged by the secure email platform.
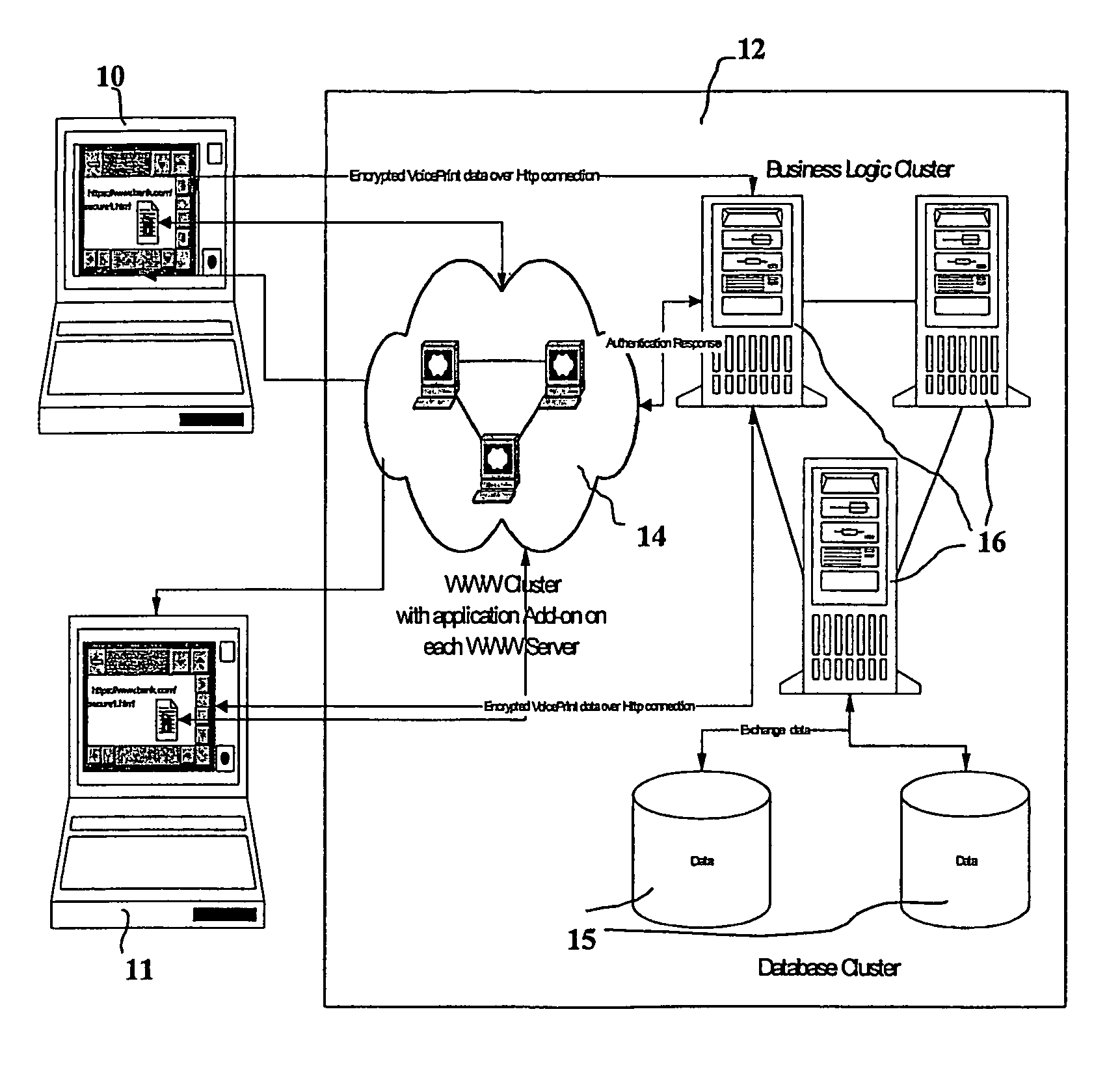
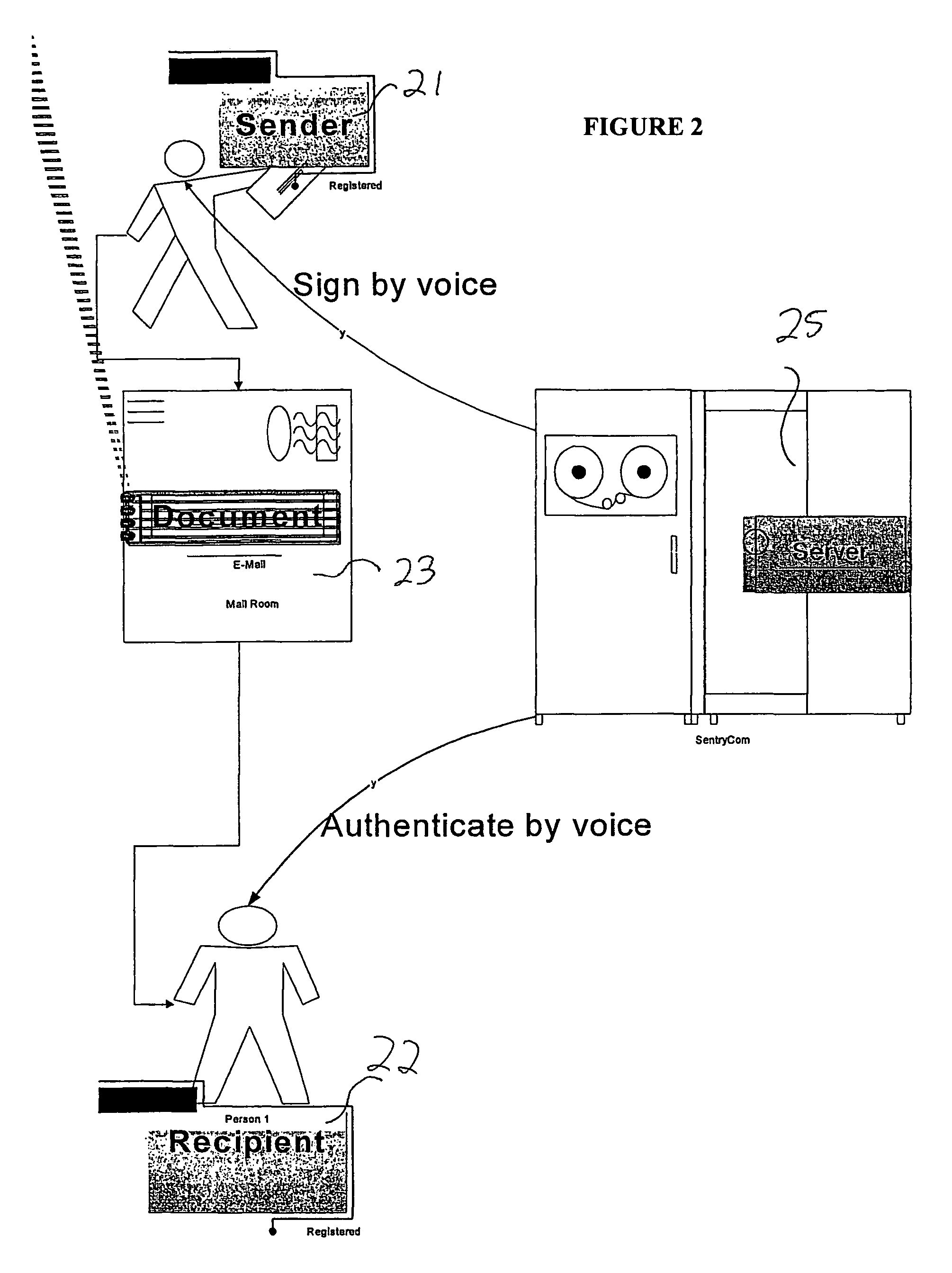
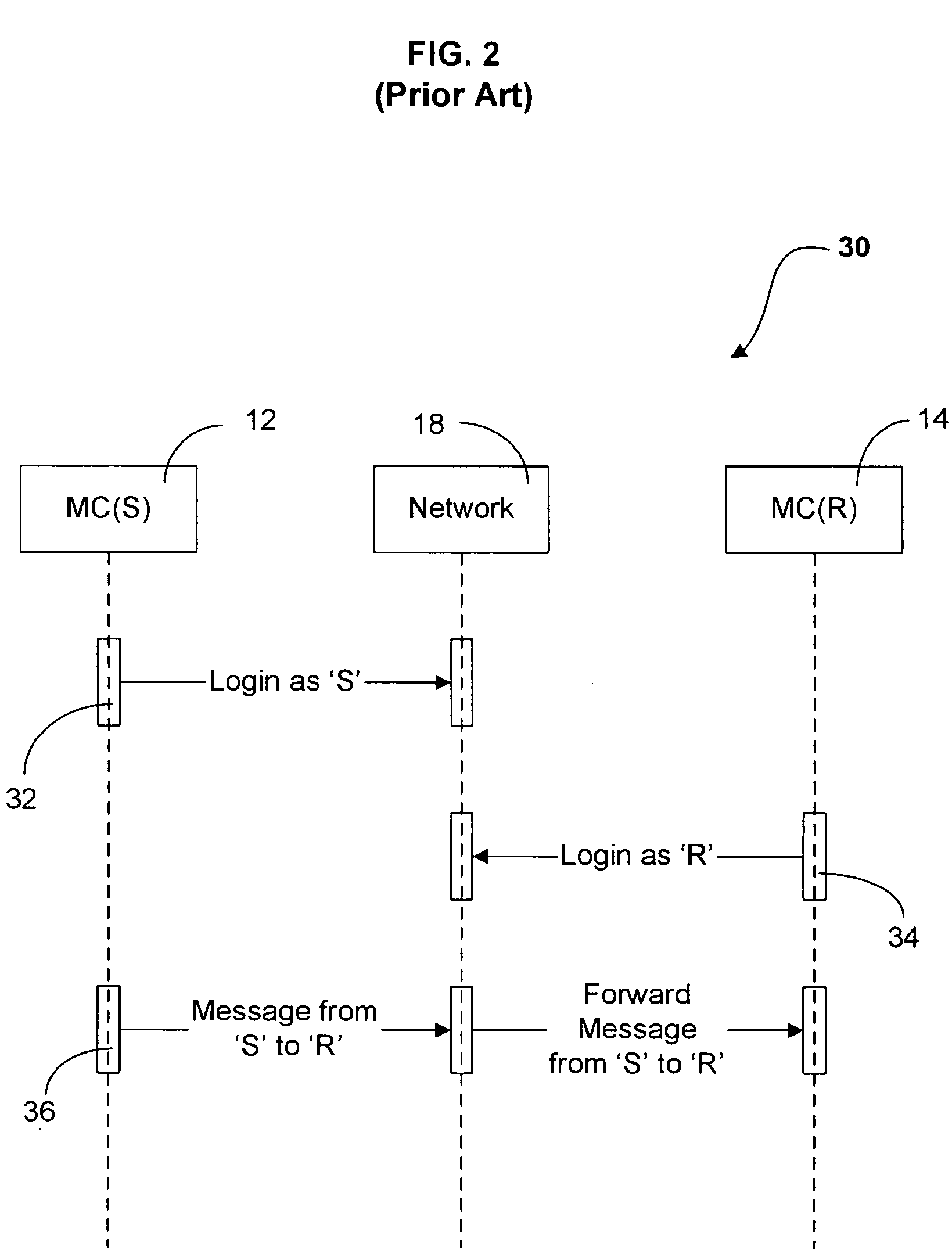
Biometric-based system and method for enabling authentication of electronic messages sent over a network
InactiveUS7689832B2Digital data processing detailsUser identity/authority verificationReal time validationData authenticity
A network based mechanism for real time verification and authentication of data and user identities. The present invention enables a method whereby biometric elements, such as voice prints, are utilized to enhance the Public Key Infrastructure as a means to decrypt data and verify data authenticity, such that the user's private key is authenticated remotely on a one-time basis. The present invention comprises an authentication server (25) with various software modules that enable authentication of user identity, secure user access to data, digital signatures, secure messaging and secure online transactions.
Owner:SENTRYCOM
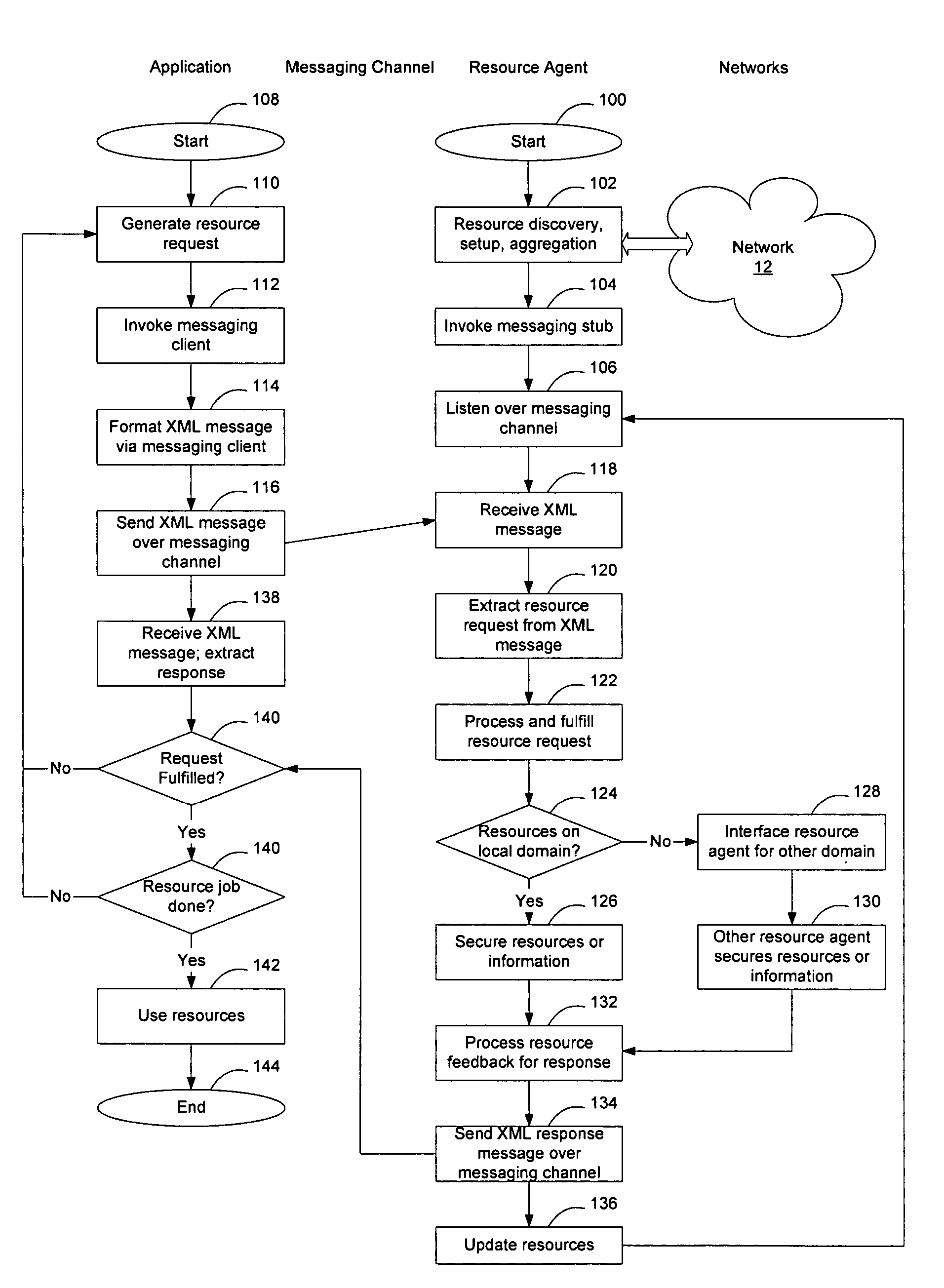
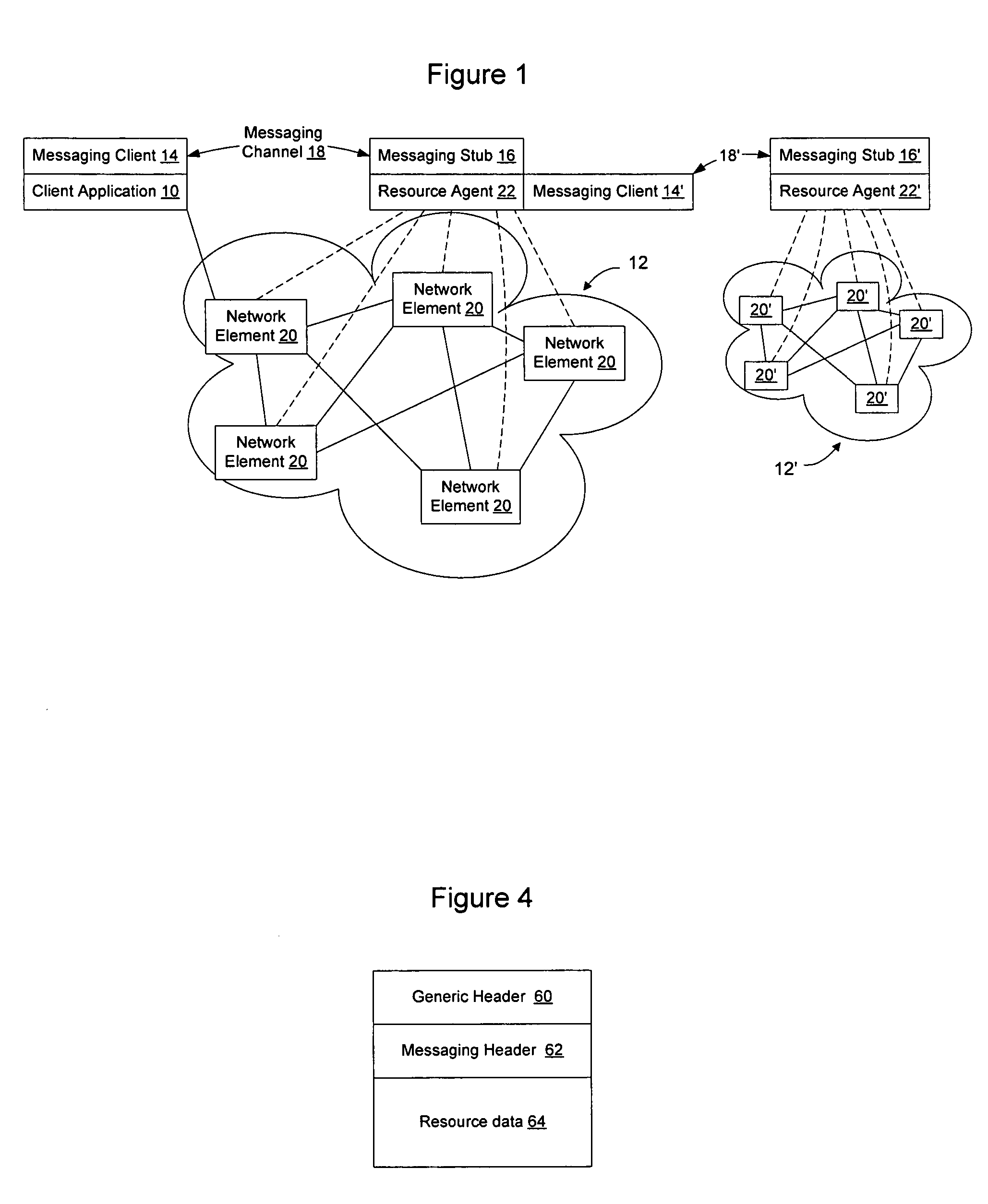
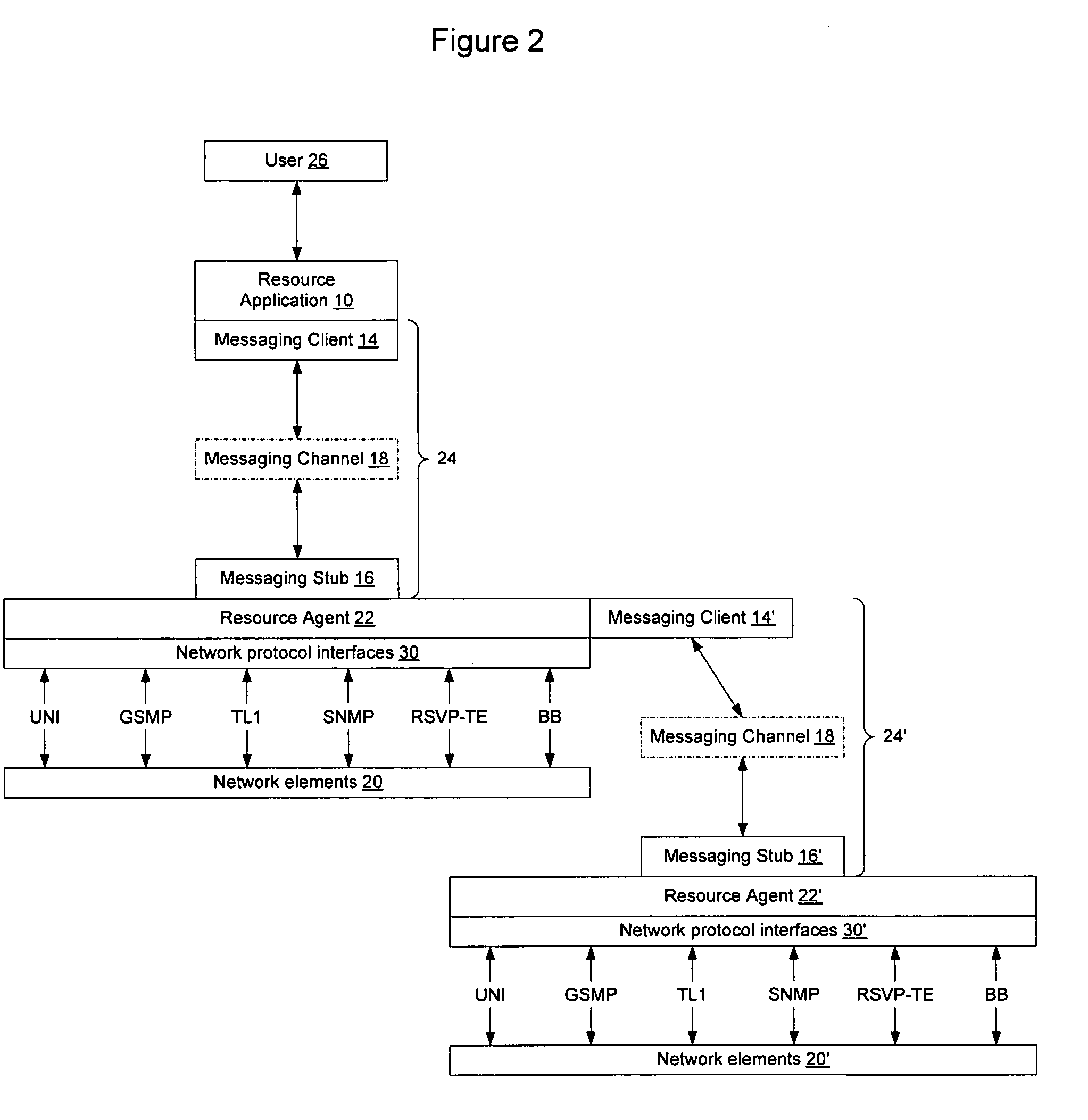
Extensible resource messaging between user applications and network elements in a communication network
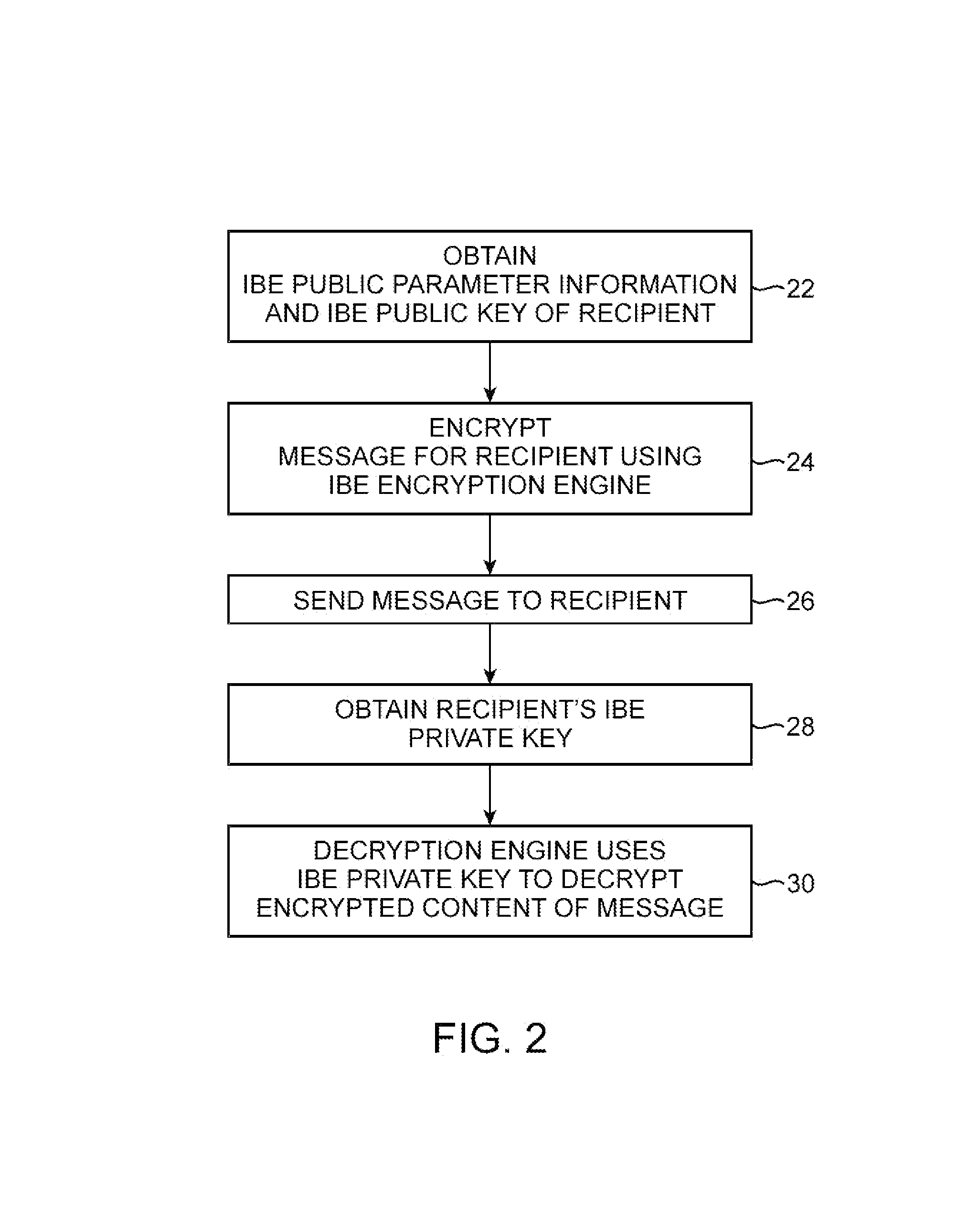
InactiveUS20060075042A1Easily use new network resourceAvoid resourcesMultiple digital computer combinationsTransmissionXML schemaMessage passing
Extensible resource messaging in a communication network is provided through creation of a flexible, extensible, and secure messaging environment. A client-server architecture may be implemented in which user applications employ messaging clients to send resource requests for network information, allocation and other operations and receive resource responses, and in which network elements, through resource agents, may use messaging servers to accept resource requests and return resource responses. Resource agents in different network domains may interact through the messaging environment and work together to fulfill resource requests. An XML-based messaging mechanism may be built with a defined message format that can provide flexible message contexts. Network resource semantics may be specified using XML schemas so that network resources are expressed as resource-specific XML elements and network updates can be implemented by updating the XML resource schemas. Secure enhancements may be realized by secure transport, message verification and other means.
Owner:NORTEL NETWORKS LTD
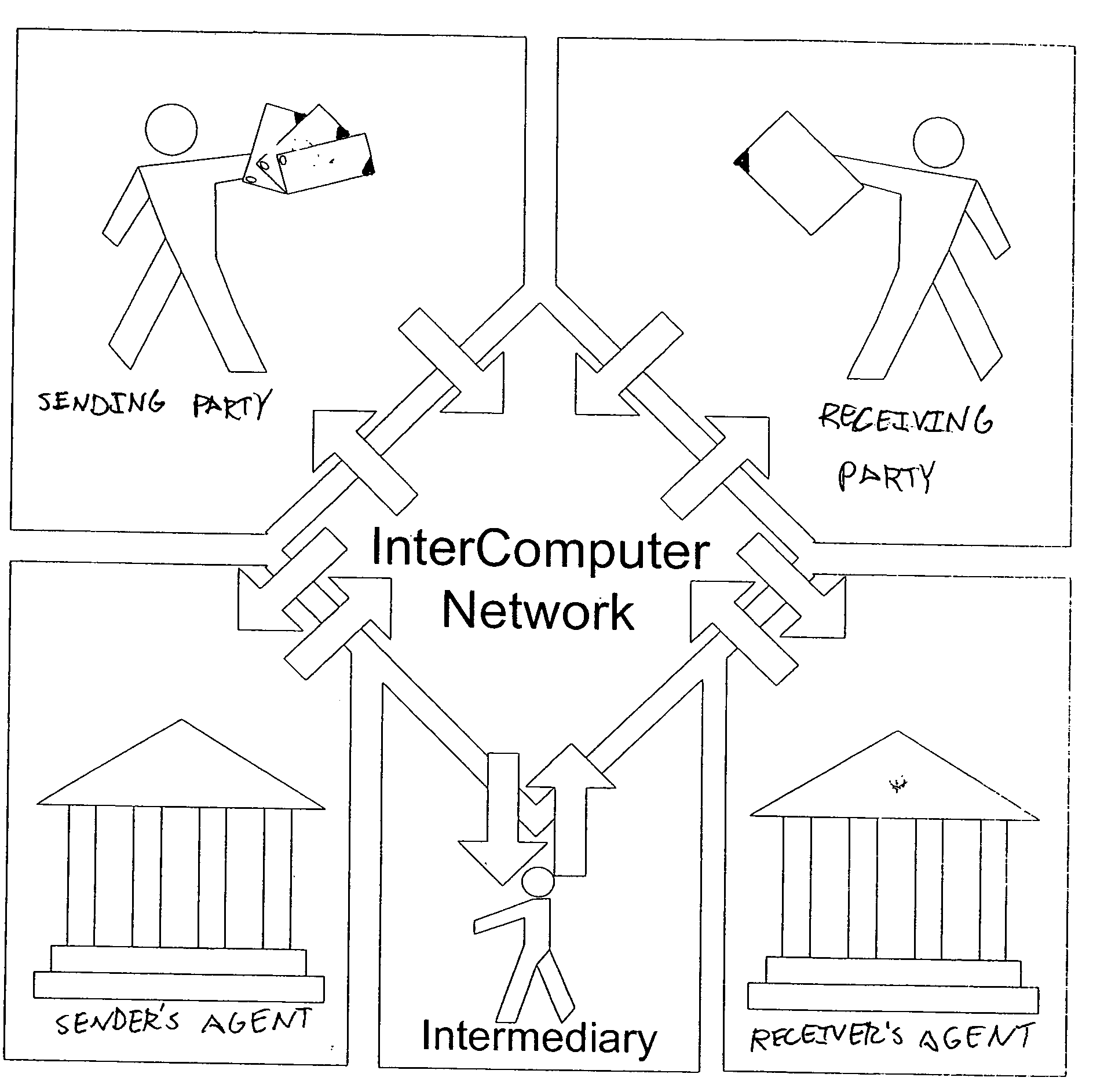
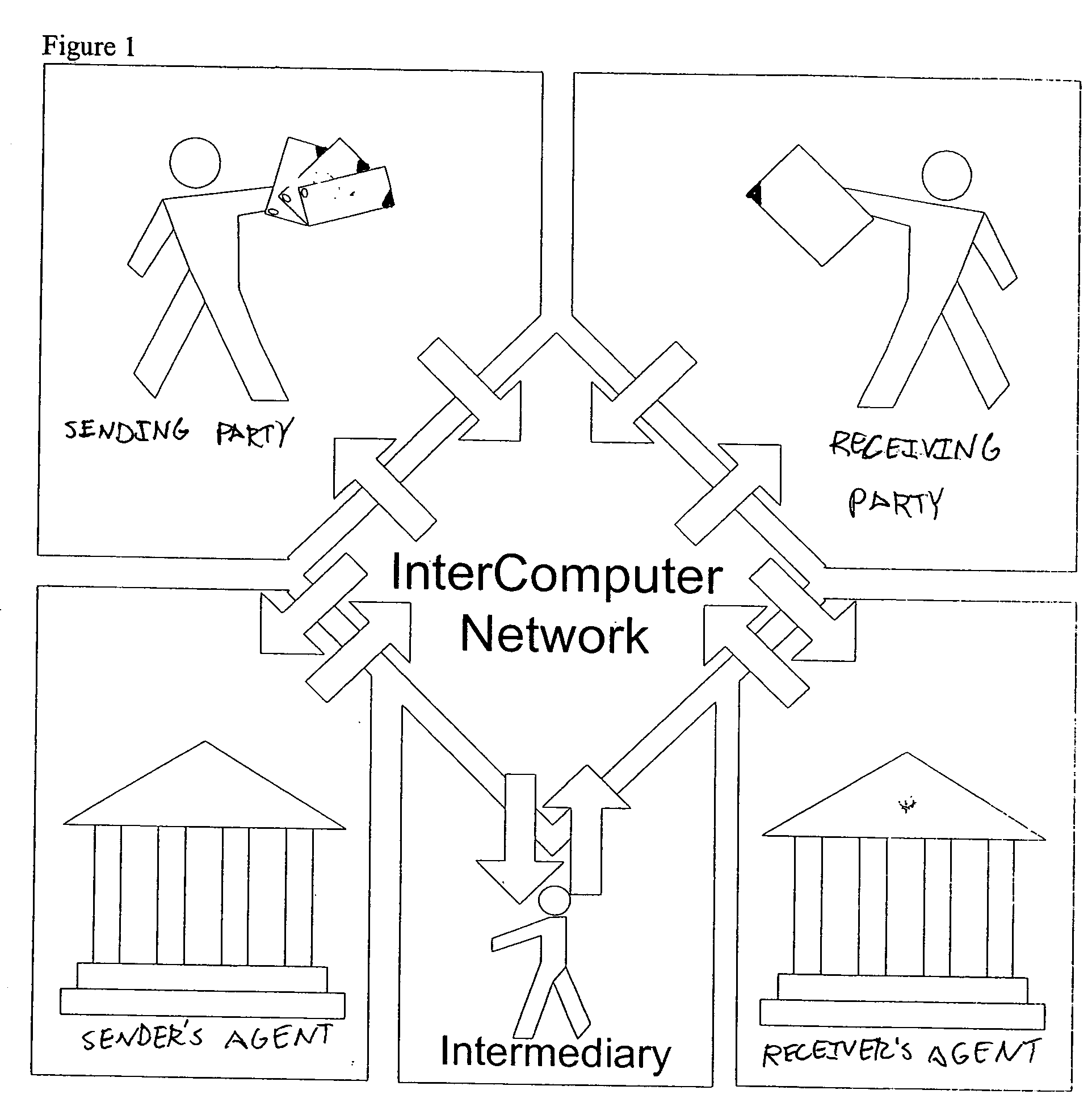
Secure messaging system
InactiveUS20050257045A1Guaranteed smooth progressUser identity/authority verificationPayment circuitsTransfer systemDocumentation
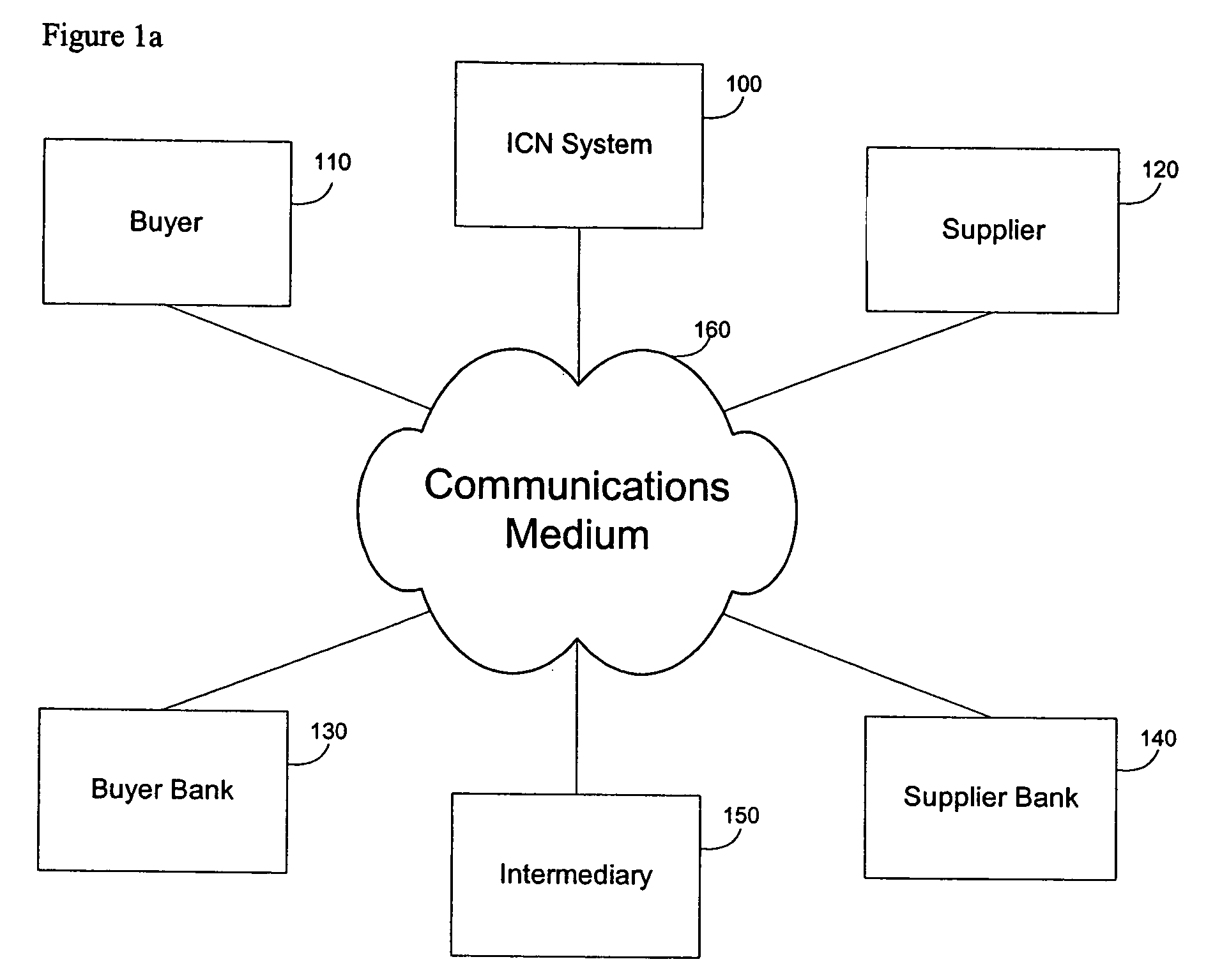
A method for secure data transactions over a computer network is described. In one embodiment, the act of generating at the first party a document, which authorizes the data transaction to proceed is performed. In one embodiment, the document content is signed using a computer network with audit-level encryption digital certificates. In one embodiment, a signed digital message (and / or document) is sent from the first party to the network transfer system electronically, and can be authenticated via the ICN certificate authorities to demonstrate the authorities of the signer of the signed document in assent to the transaction. In one embodiment, a copy of the signed digital document can be stored in a database associated with the transfer network system. In one embodiment, the system uses rules (patterns) of exchange agreed upon within and between organizations. These rules enable the exchange to progress smoothly and drive systematically the attention of participants to demands and problems etc. as a given transaction goes along.
Owner:INTERCOMP CORP
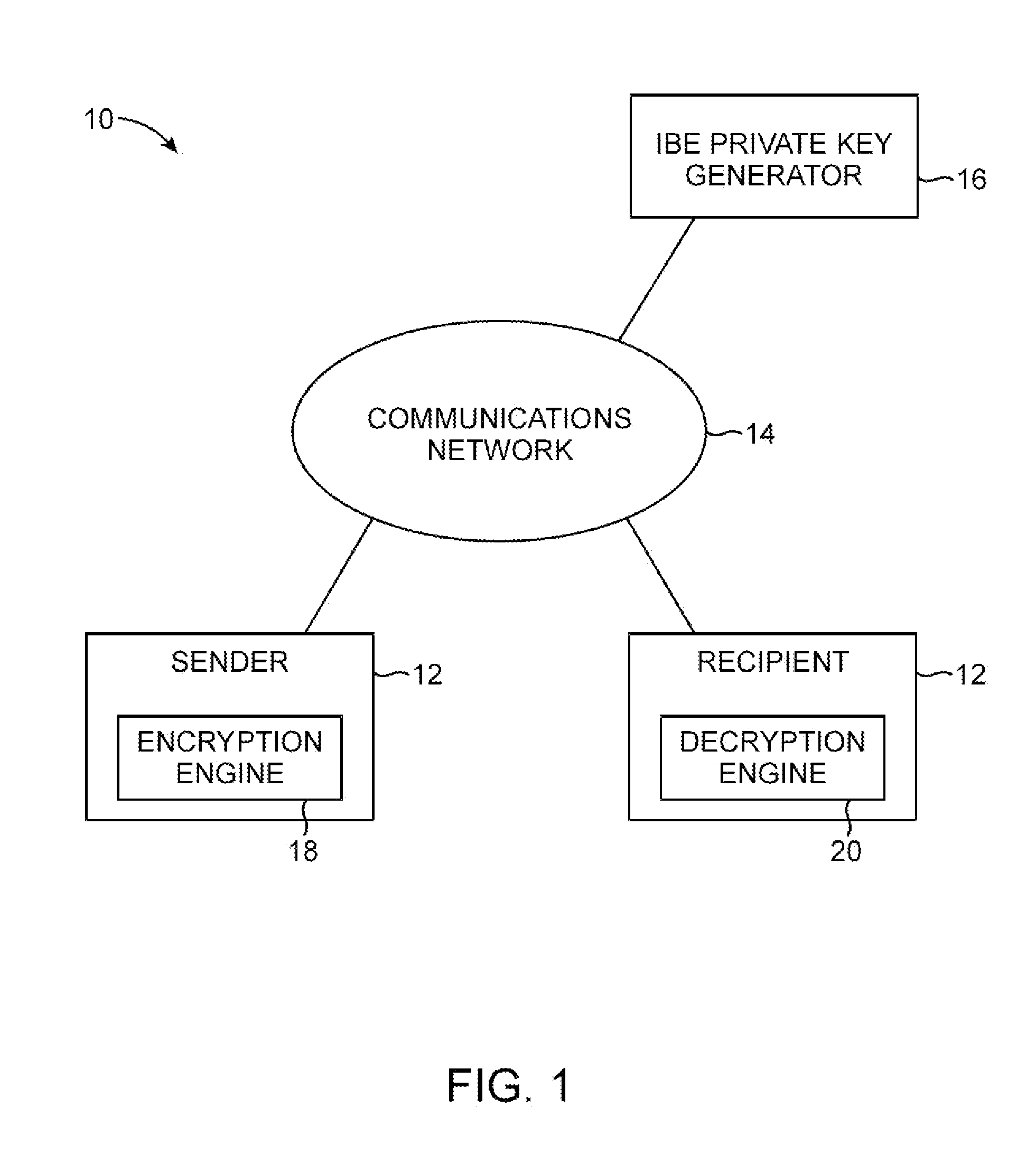
Secure message system with remote decryption service
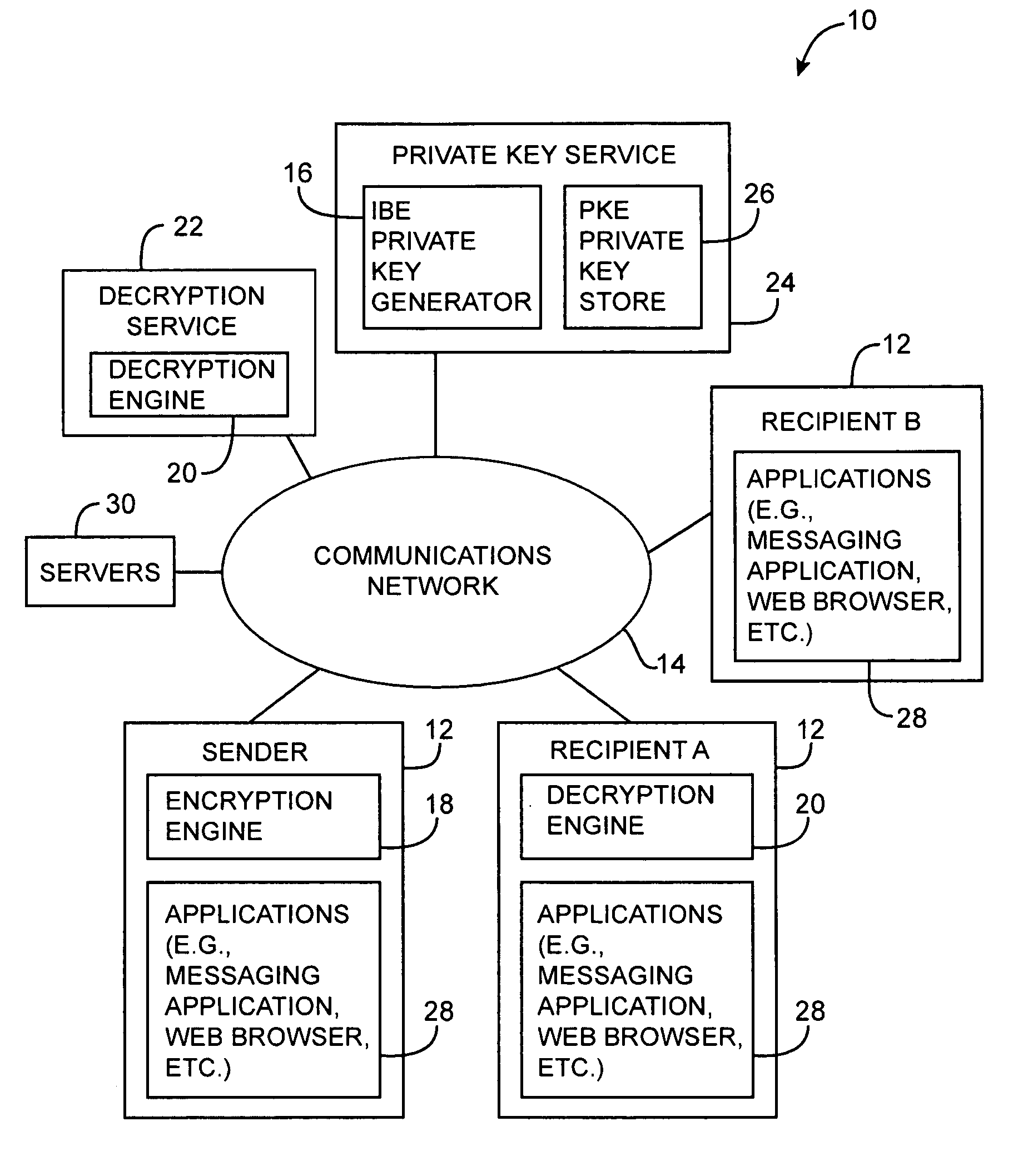
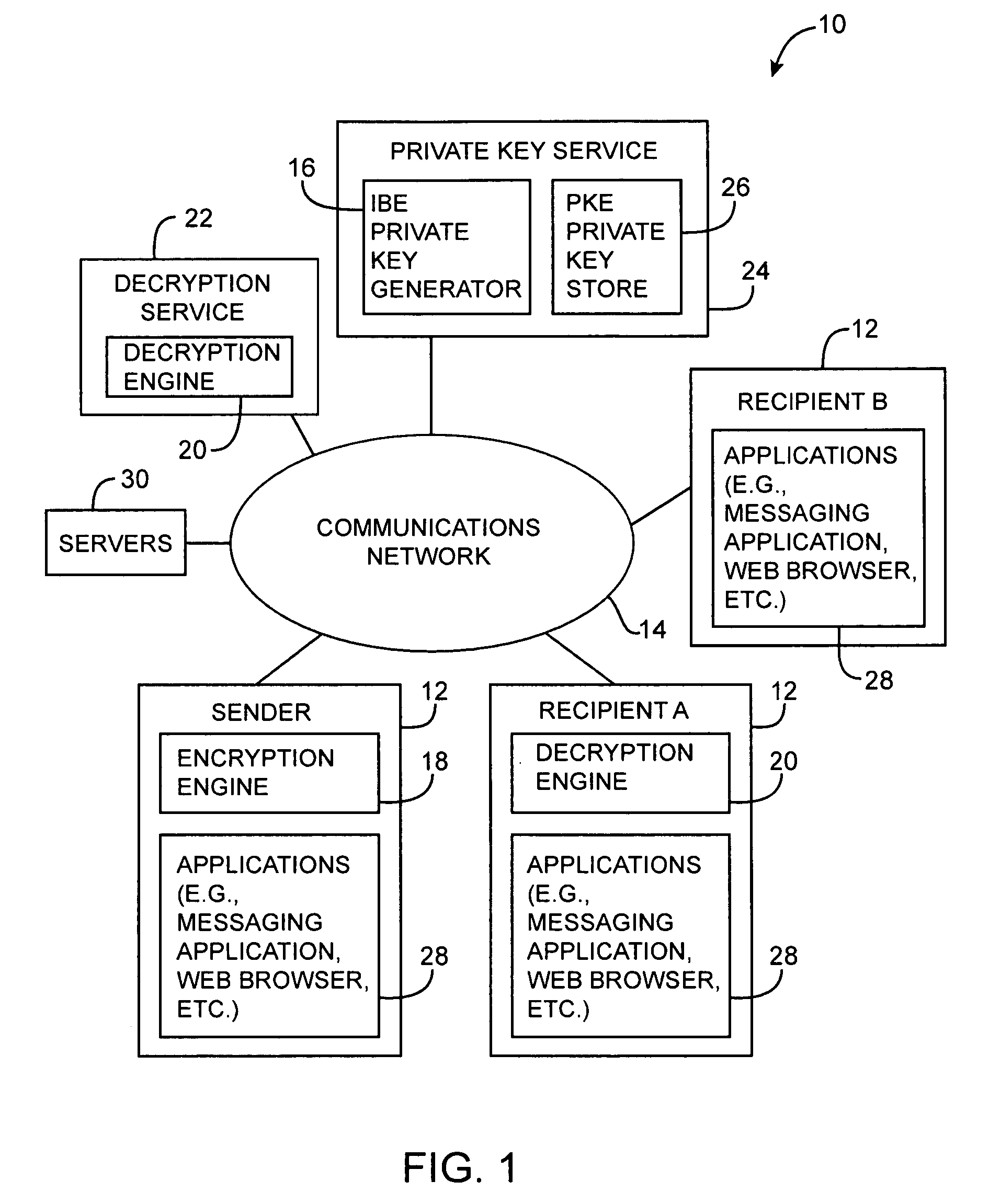
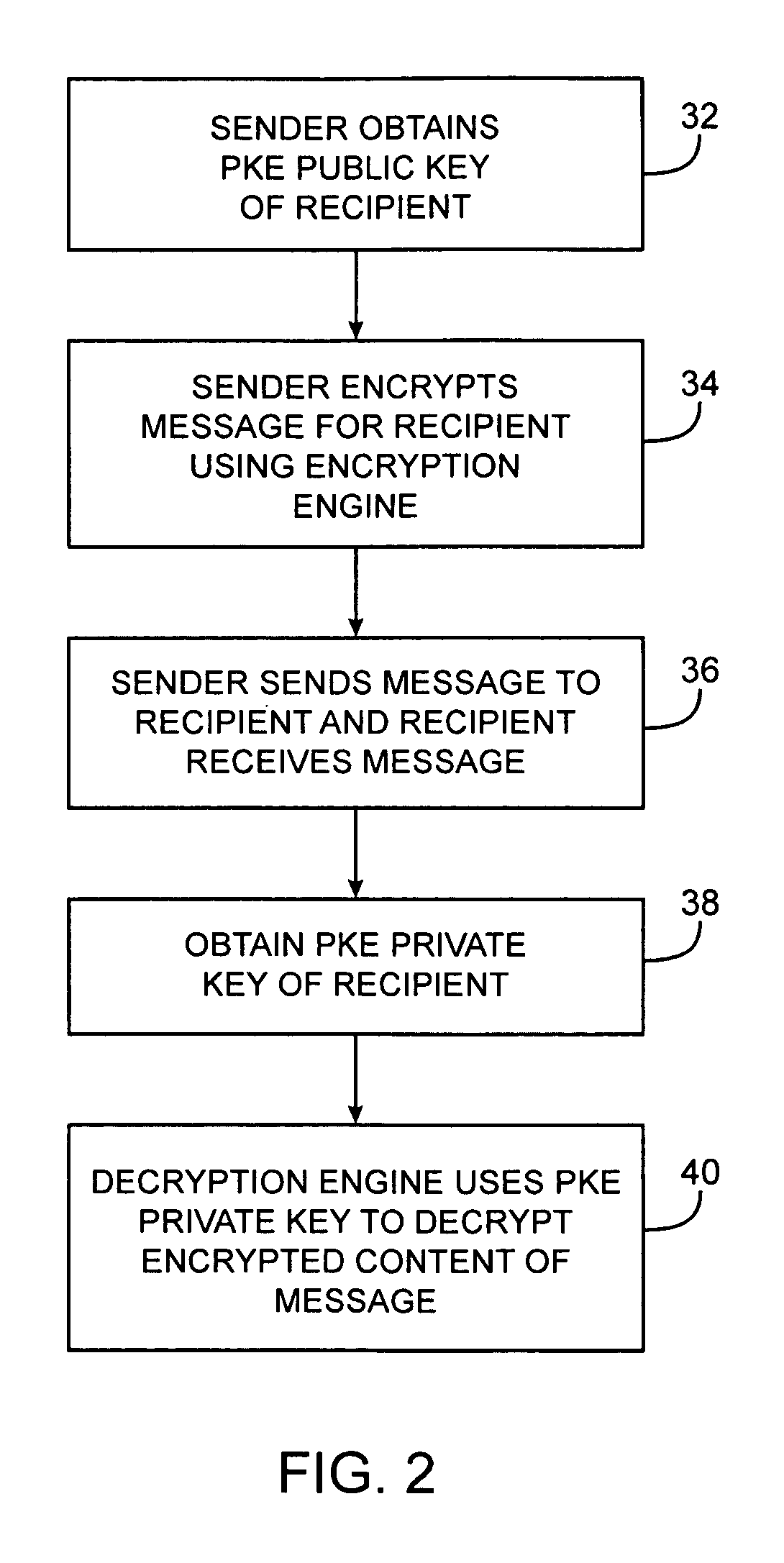
ActiveUS20050071632A1Reduce visual clutterKey distribution for secure communicationPublic key for secure communicationPasswordSecure messaging
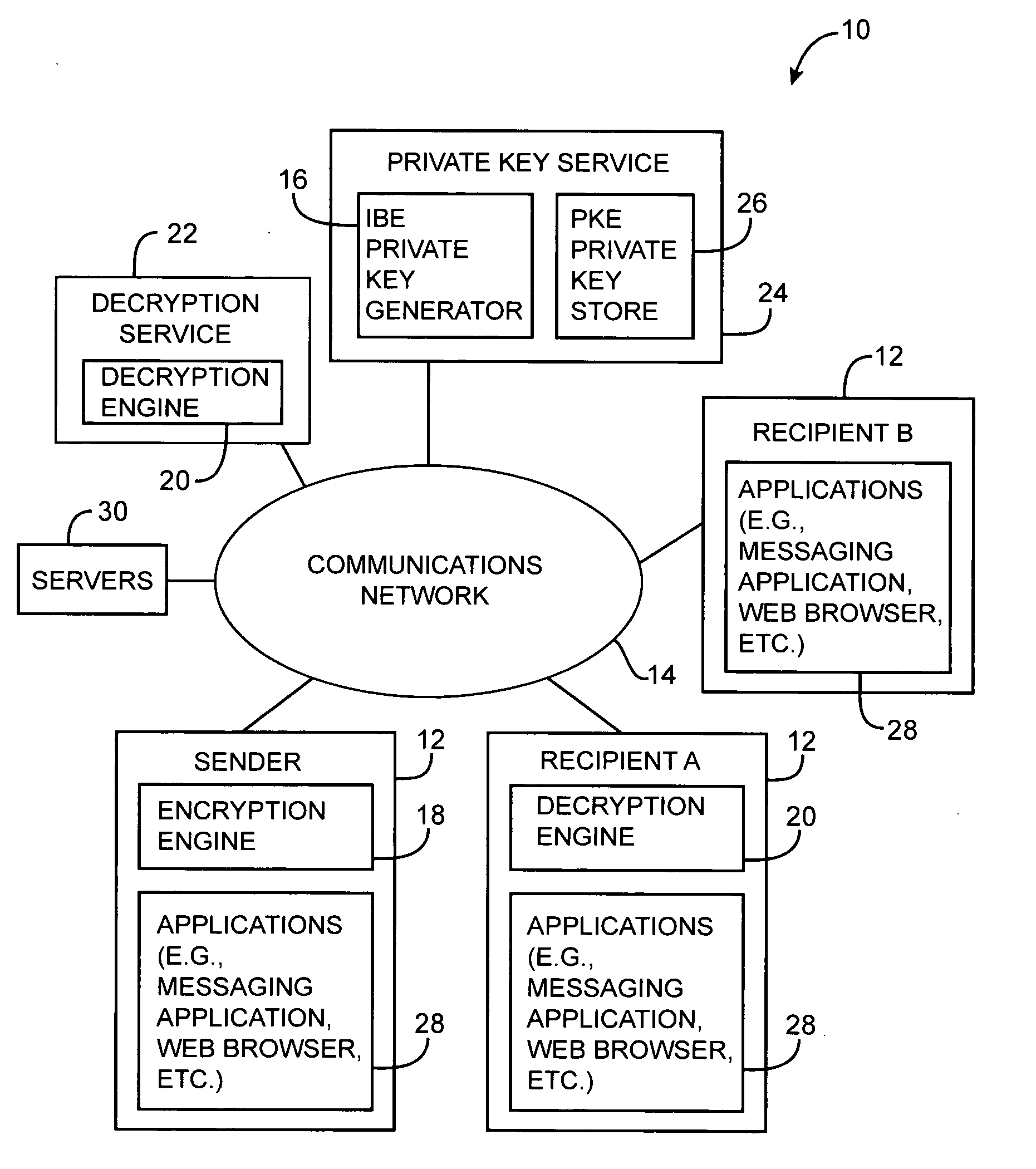
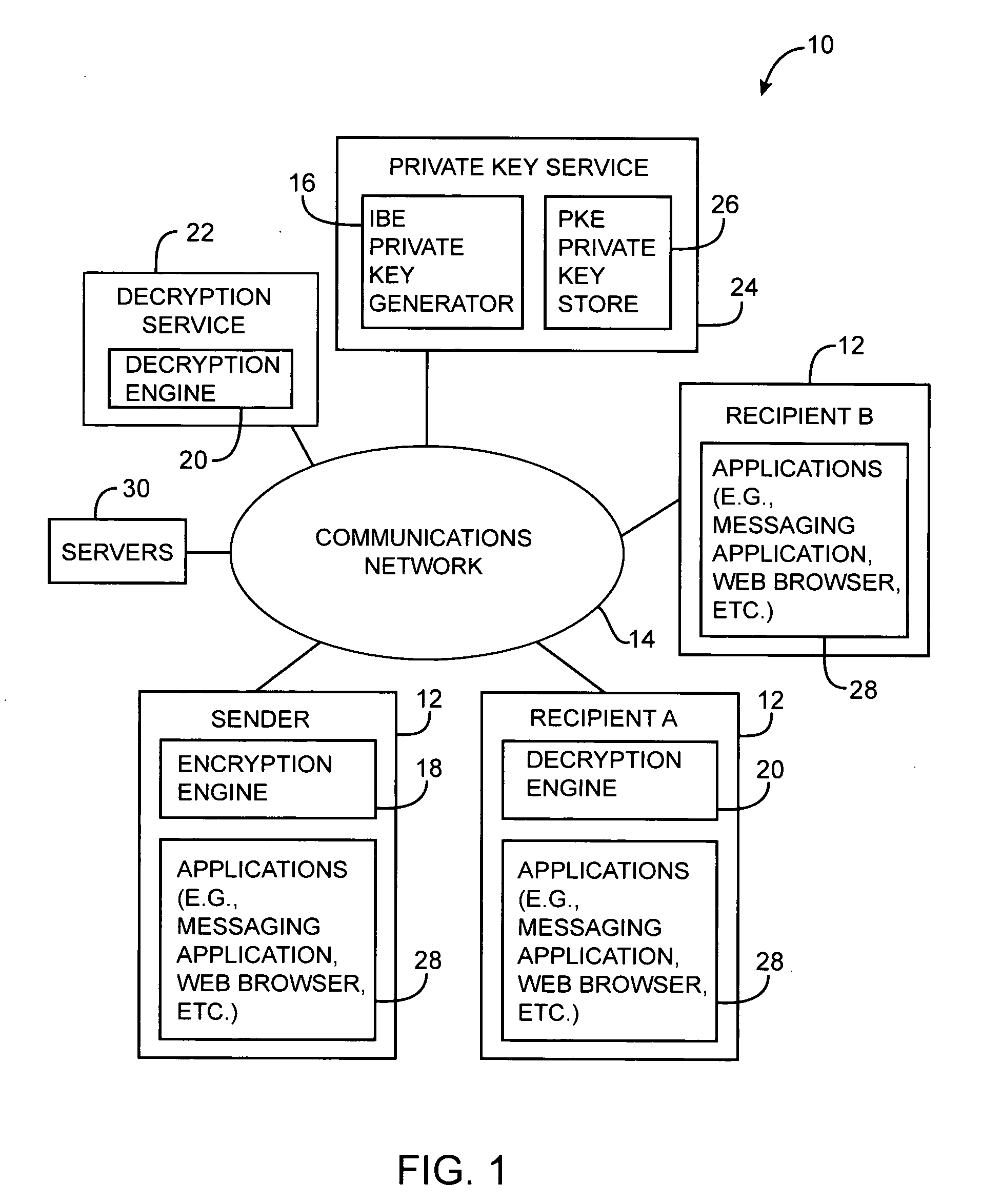
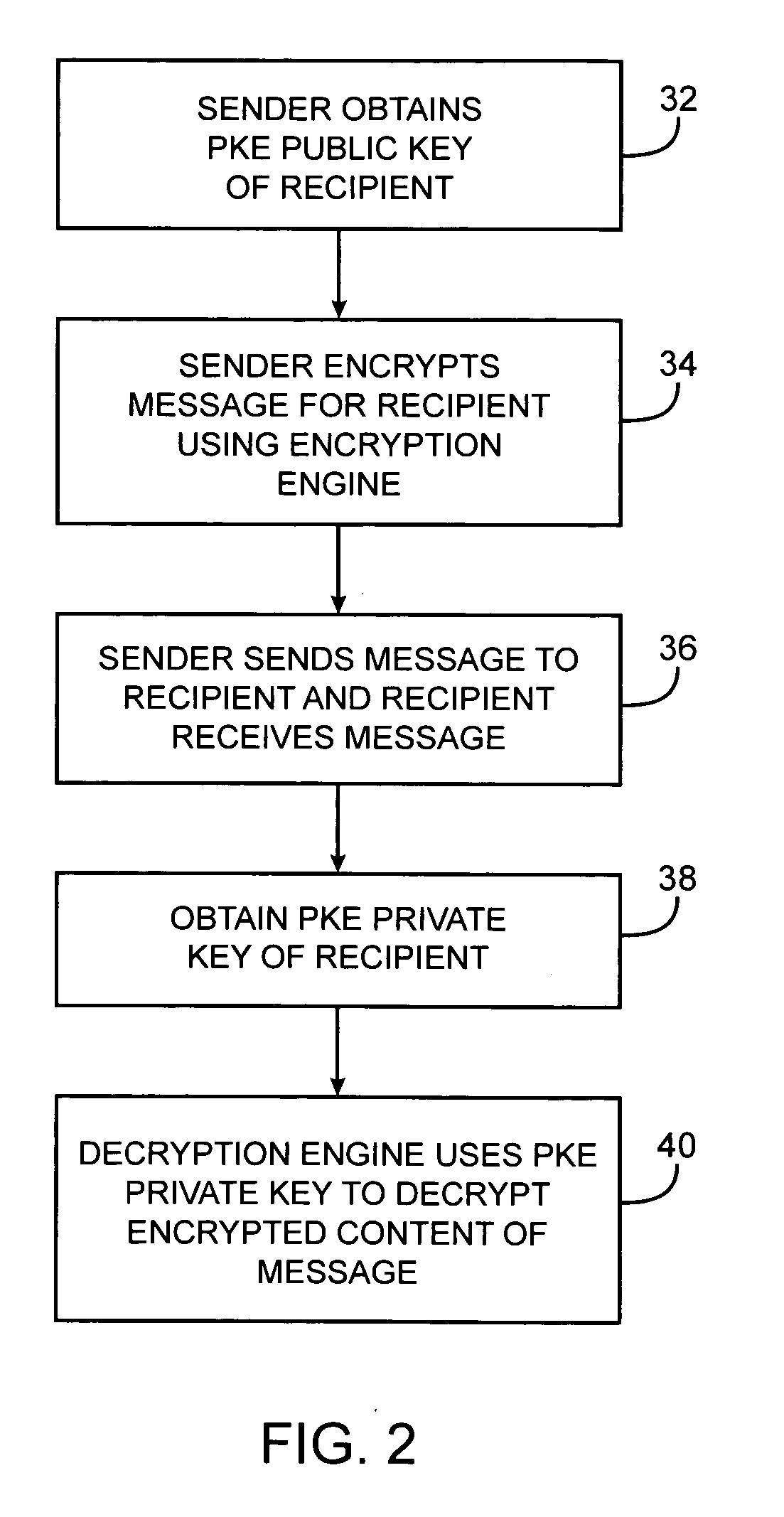
Systems and methods for secure messaging are provided. A sender may encrypt content and send the encrypted content to a recipient over a communications network. The encrypted content may be decrypted for the recipient using a remote decryption service. Encrypted message content may be placed into a markup language form. Encrypted content may be incorporated into the form as a hidden form element. Form elements for collecting recipient credential information such as username and password information may also be incorporated into the form. At the recipient, the recipient may use the form to provide recipient credential information to the remote decryption service. The recipient may also use the form to upload the encrypted content from the form to the decryption service. The decryption service may provide the recipient with access to a decrypted version of the uploaded content over the communications network.
Owner:MICRO FOCUS LLC
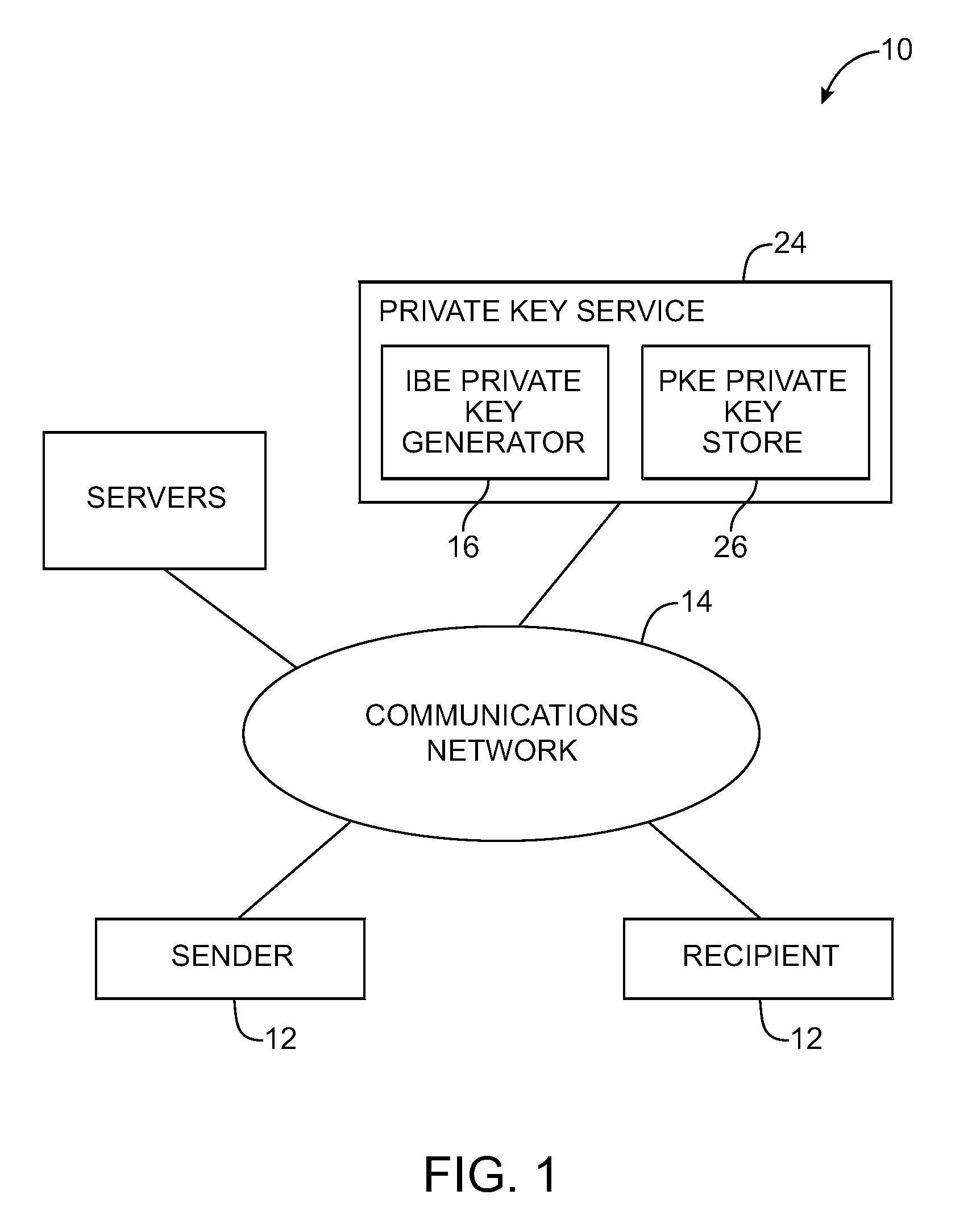
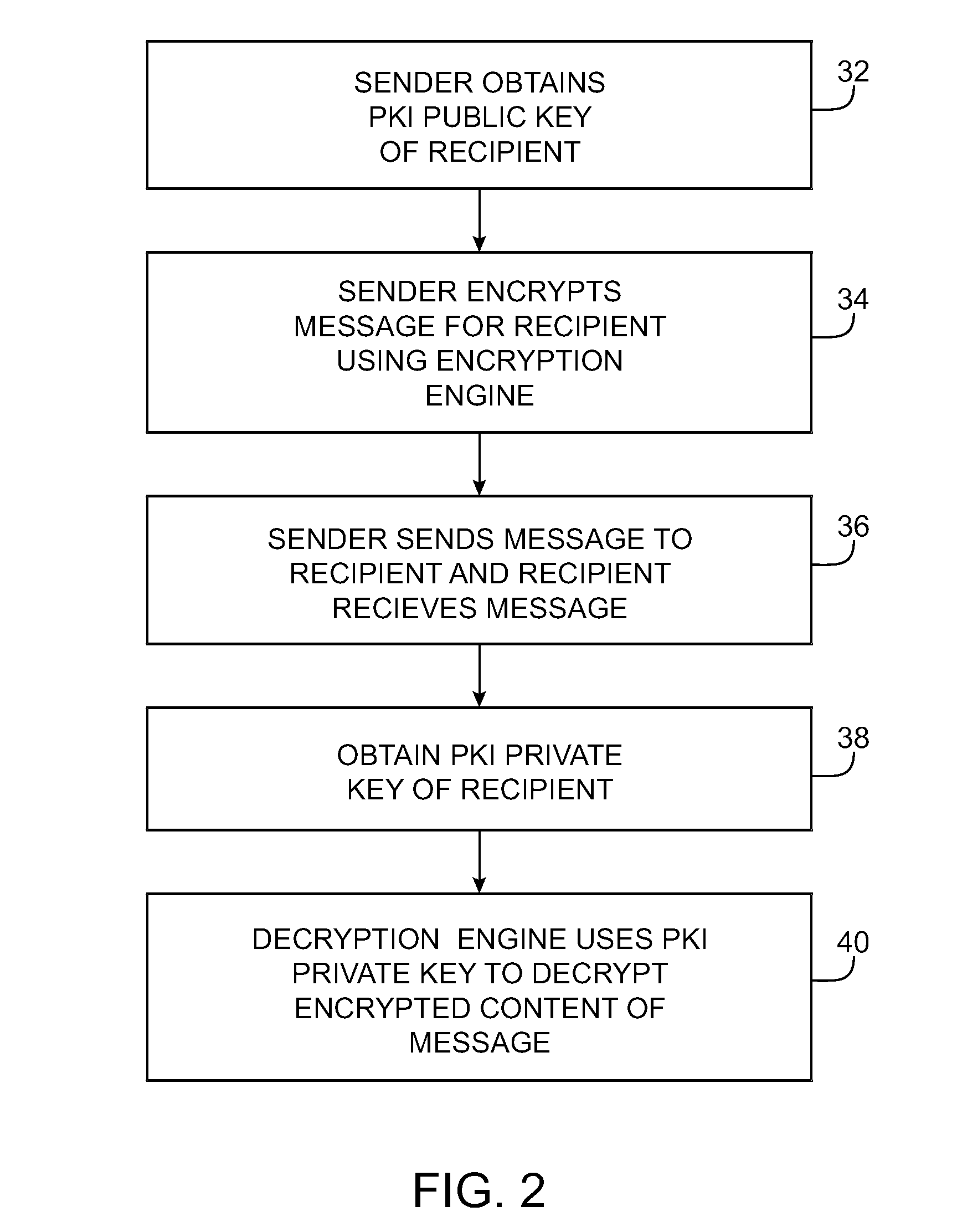
Secure messaging systems
A system is provided that uses cryptographic techniques to support secure messaging between senders and recipients. A sender may encrypt a message for a recipient using the recipient's public key. The sender may send the encrypted message to the message address of a given recipient. A server may be used to decrypt the encrypted message for the recipient, so that the recipient need not install a decryption engine on the recipient's equipment.
Owner:MICRO FOCUS LLC
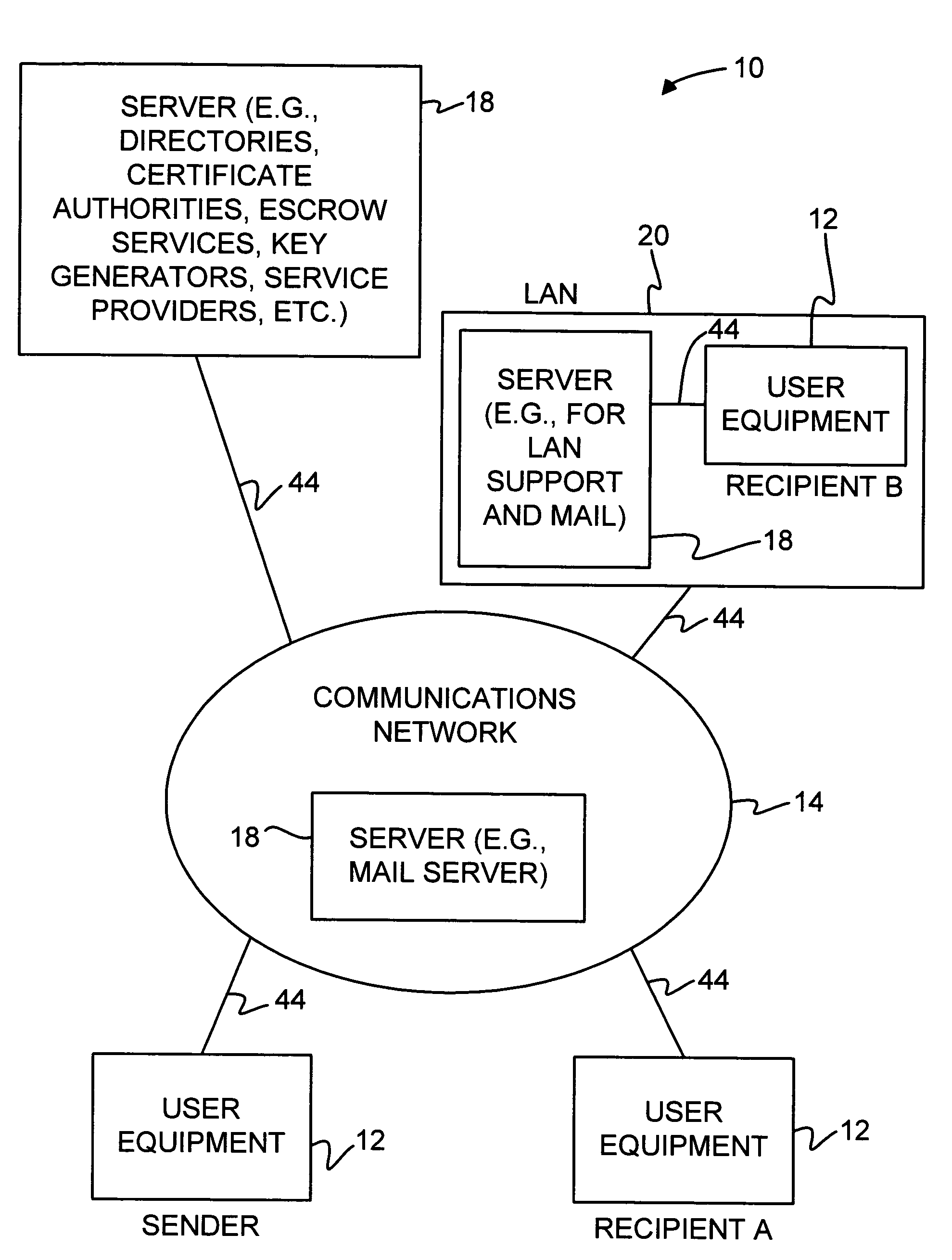
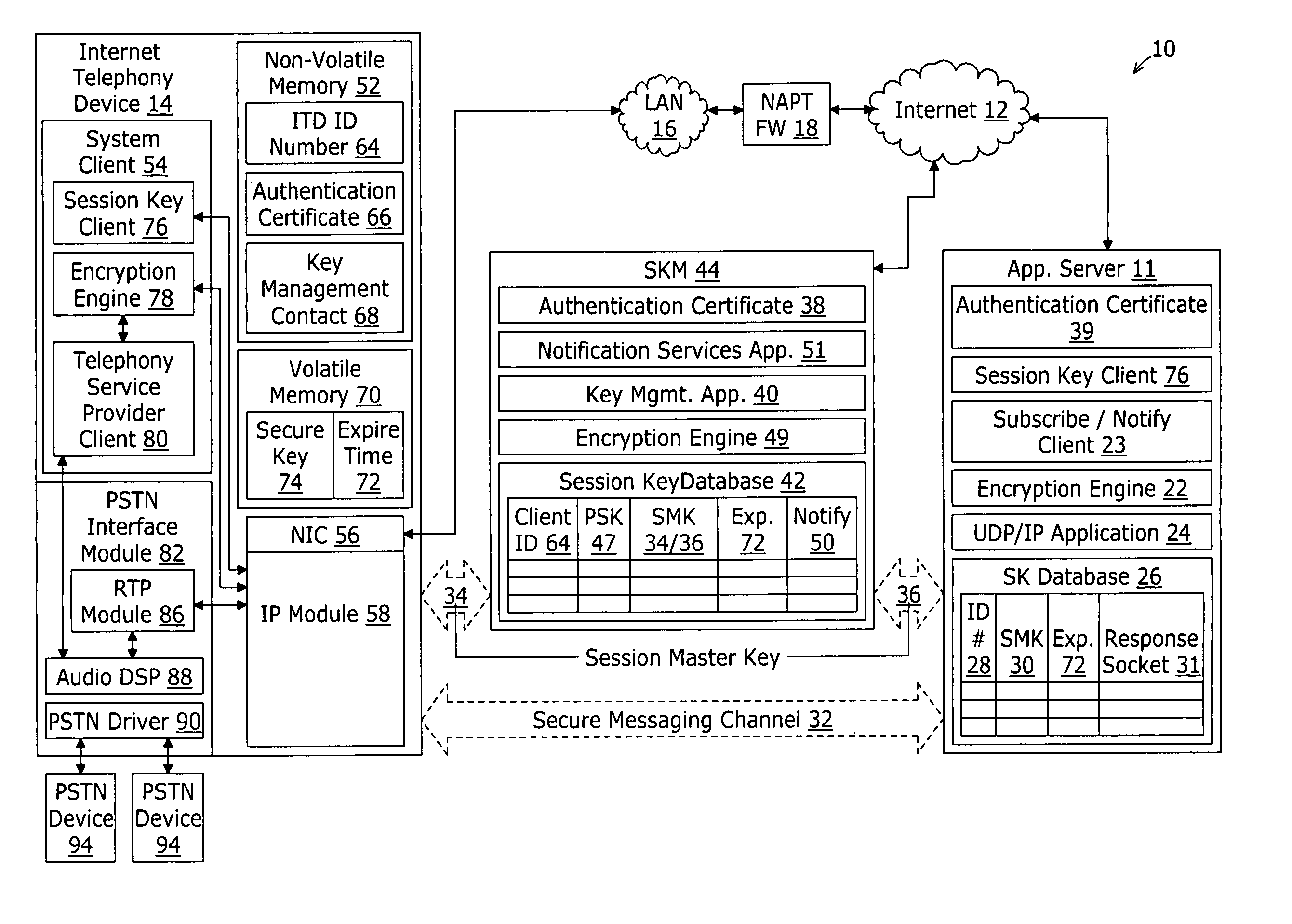
System and method for secure messaging with network address translation firewall traversal
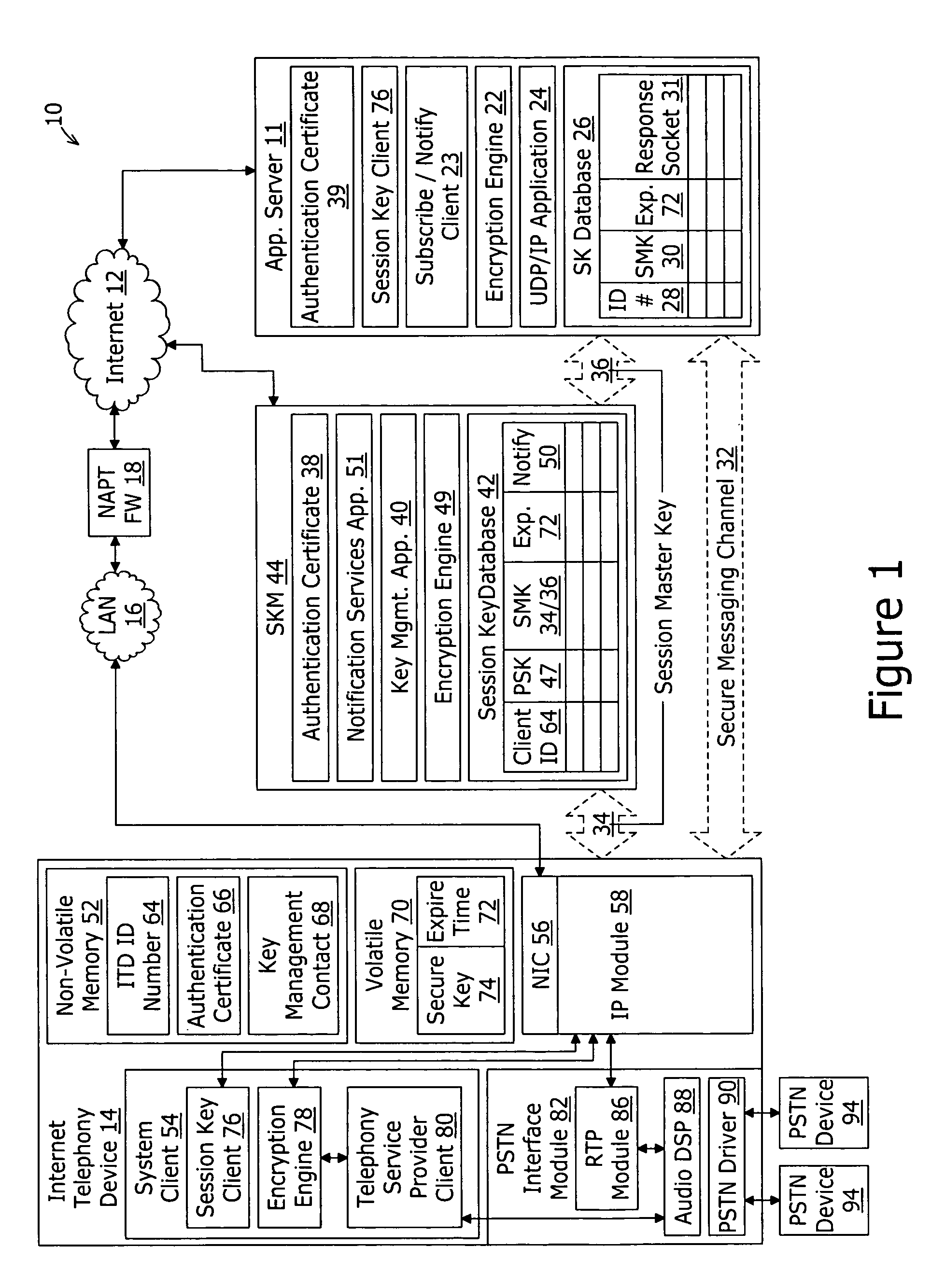
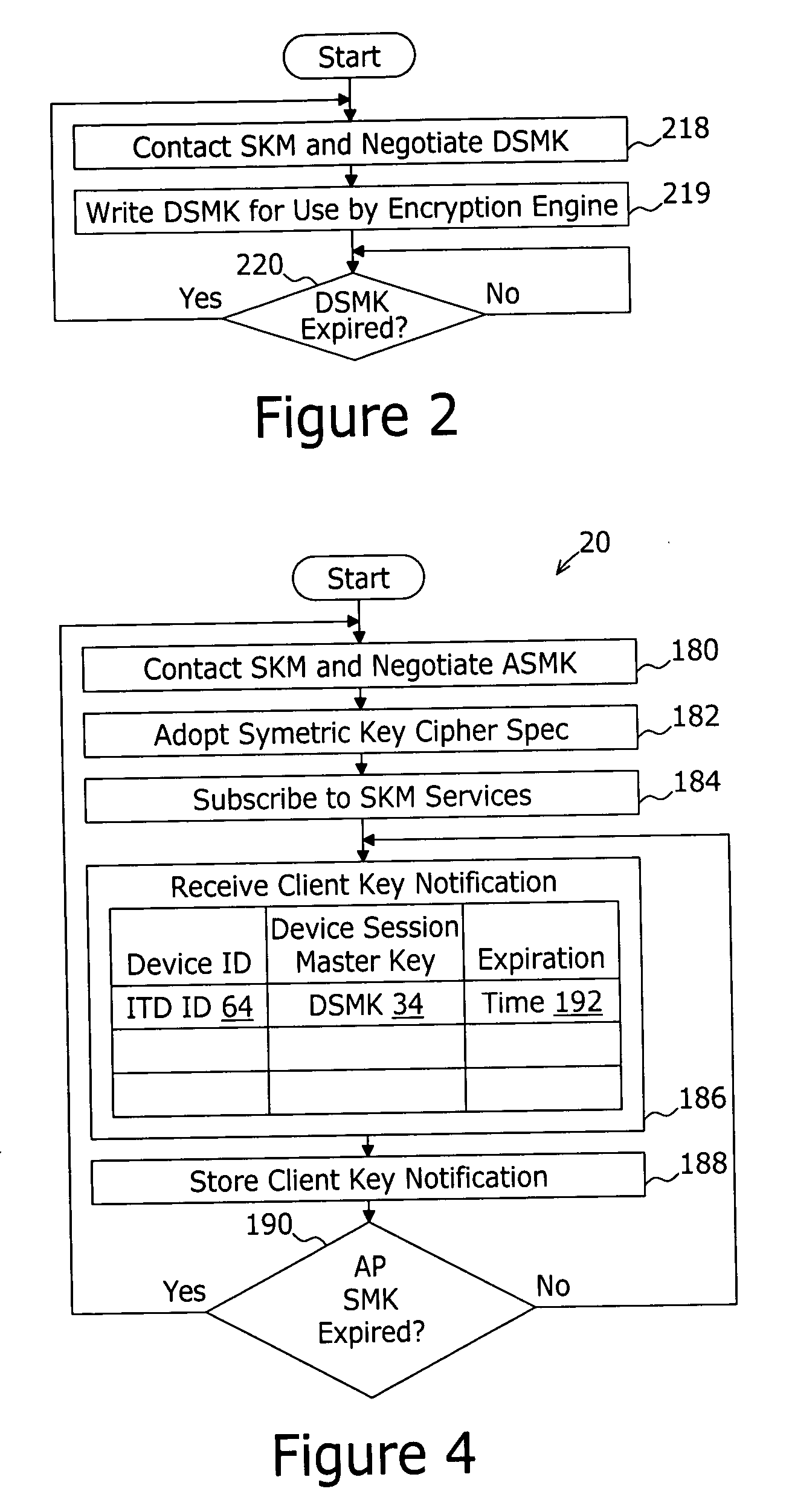
InactiveUS20060274899A1Key distribution for secure communicationSecure communicationApplication server
A system for securing communications between a client and an application server comprises a session key management server and the application server. The system enables network address translation firewall traversal. The session key management server comprises a key management application, a session key database, and a notification services application. The key management application receives a first transport layer security connection request from the client and negotiates a device session master key with the client as part of the transport layer security exchange. The session key database is coupled to the key management application for storing the device session master key in conjunction with an identification of the client. The notification services application coupled to the session key database and provides a notification message to subscribing application servers. The notification message comprises the device session master key in conjunction with an identification of the client.
Owner:INNOMEDIA PTE
System and method for secure electronic communication in a partially keyless environment
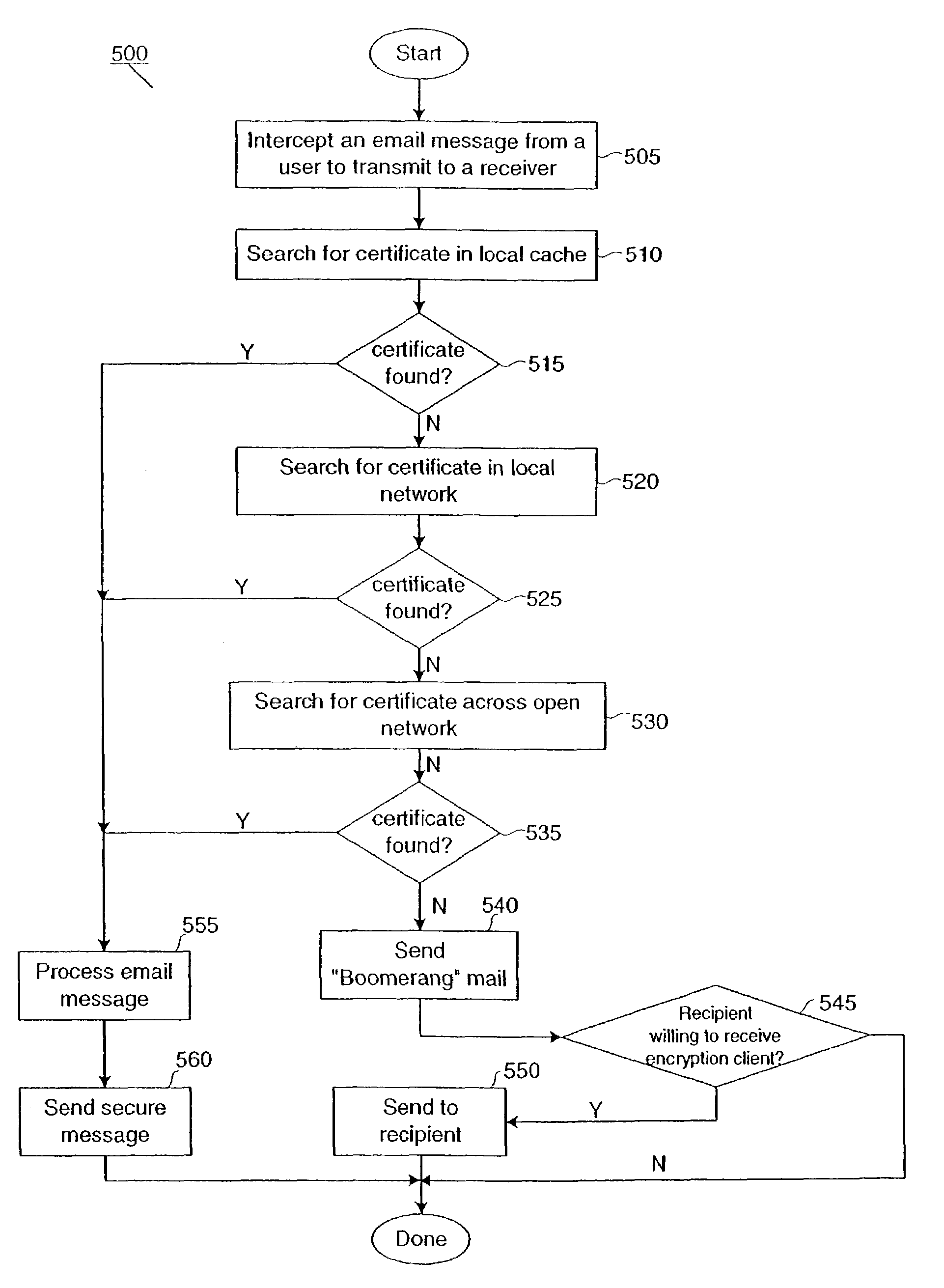
InactiveUS7640427B2Reduce the burden onImprove securityPublic key for secure communicationMultiple digital computer combinationsDigital identityPlaintext
This present invention provides users with secure transparent electronic communication, allowing them to send and receive encrypted and / or signed messages with little or no user involvement. In various embodiments, the present invention provides a user with e-mail security via automated hierarchical techniques for transparently sending and receiving secure messages, and lowers the burden on administrators. Such a system can also manage cryptographic keys and certificates for the users, and creates such keys and certificates for the users when necessary. A server according to the present invention can intercept unsecured messages from a user, automatically transform those messages into secured messages, and transmit those secure messages to the intended recipients. The server can also automatically transform messages after the recipient sends a digital identity to the server and downloads the software necessary for transforming the secured messages back into readable messages (i.e., from ciphertext into plaintext). The server can further intercept an unsecured message from a user, search for a digital identity of the intended recipient, secure the unsecured message upon finding such a digital identity, and transparently send the secured message to the intended recipient.
Owner:CA TECH INC
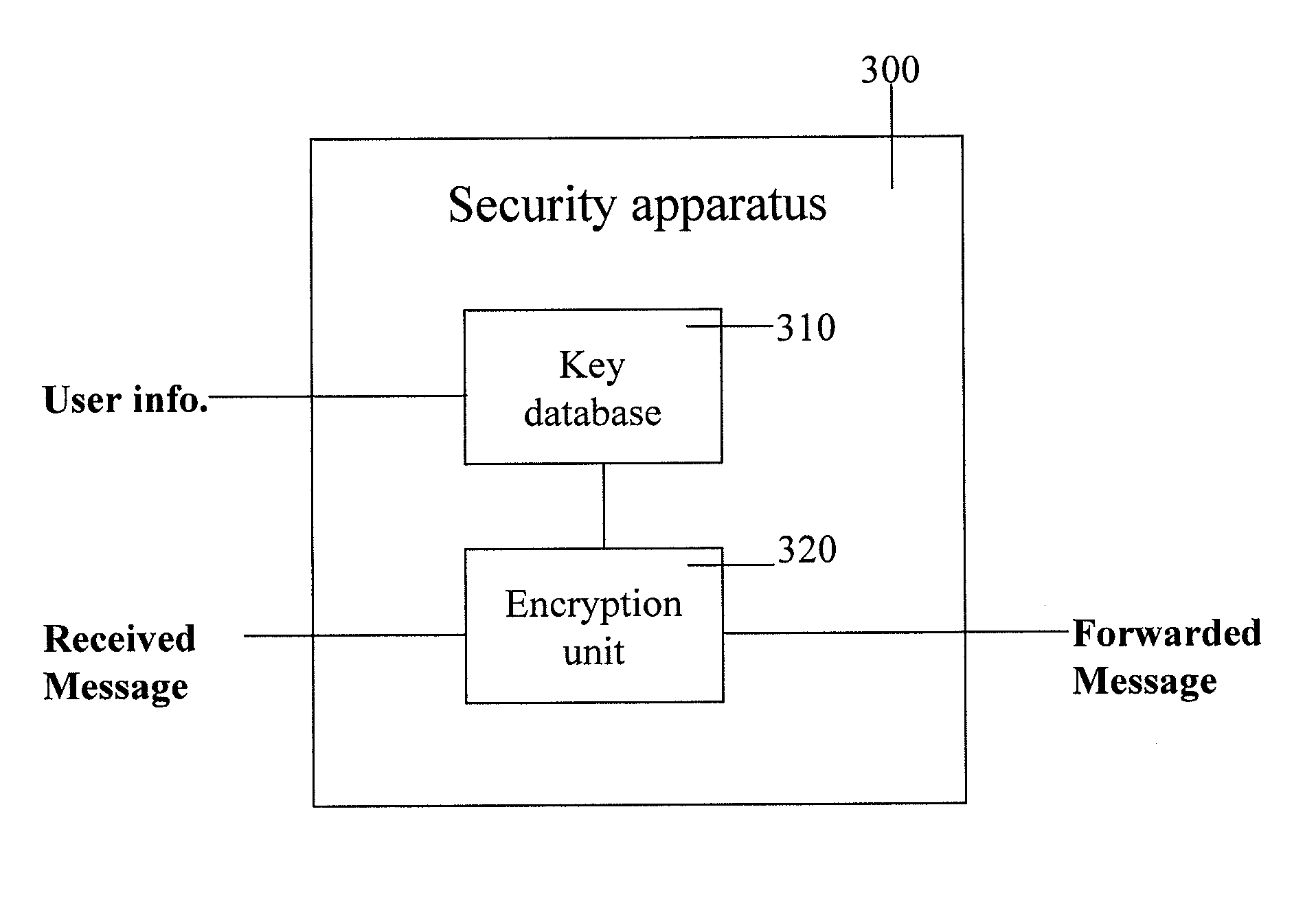
Secure messaging system and method
InactiveUS20090077649A1Improve the level ofIncrease opportunitiesComputer security arrangementsMultiple digital computer combinationsSecure messagingInternet privacy
A system and method for secure data communication between users when logged on to a central server through a network. The system permits subscribers to the system to create associations with non-subscribers which permits those non-subscribers to access the system to send and receive secure data communication to the subscriber that created the association with the non-subscriber.
Owner:SOFT TRUST
Method and apparatus for secure messaging
InactiveUS20070269041A1Easy to useLow costPublic key for secure communicationSecret communicationSecure messagingComputer science
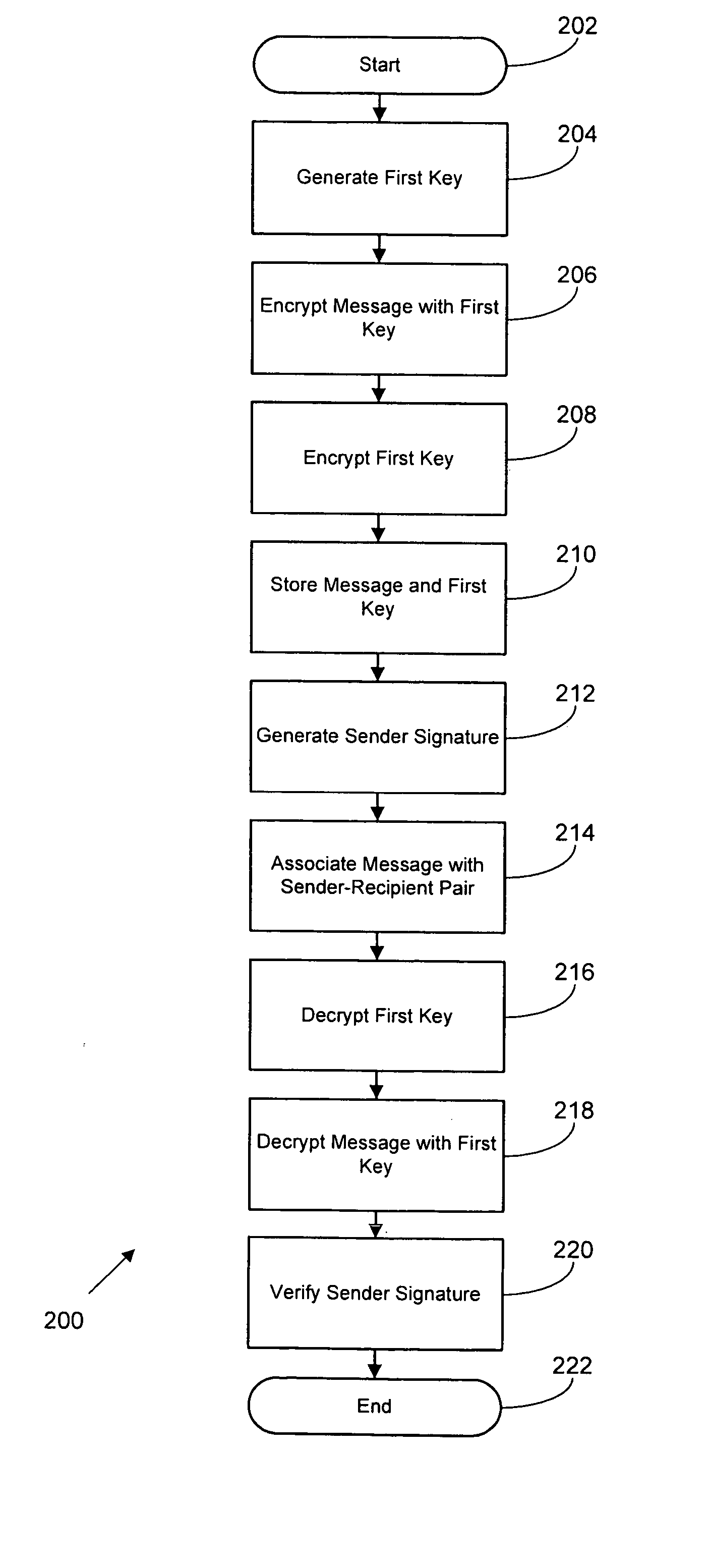
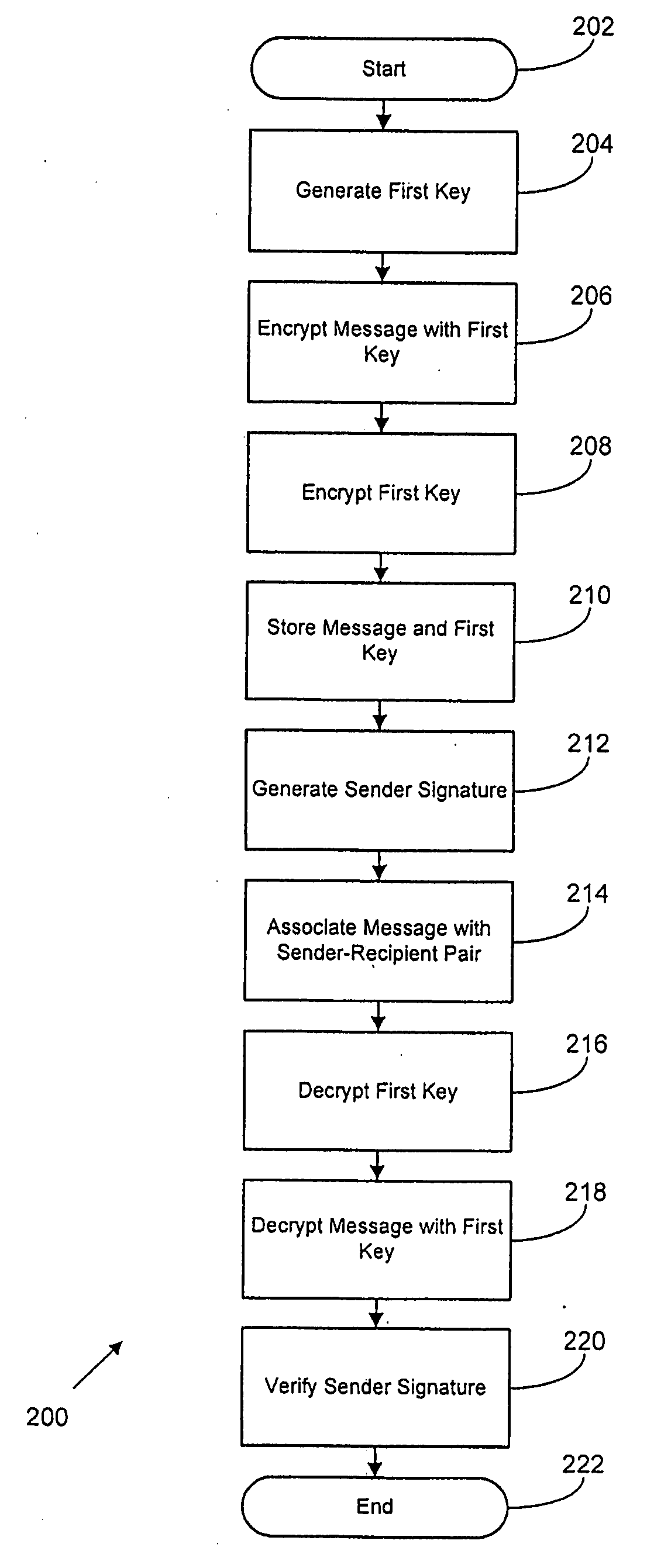
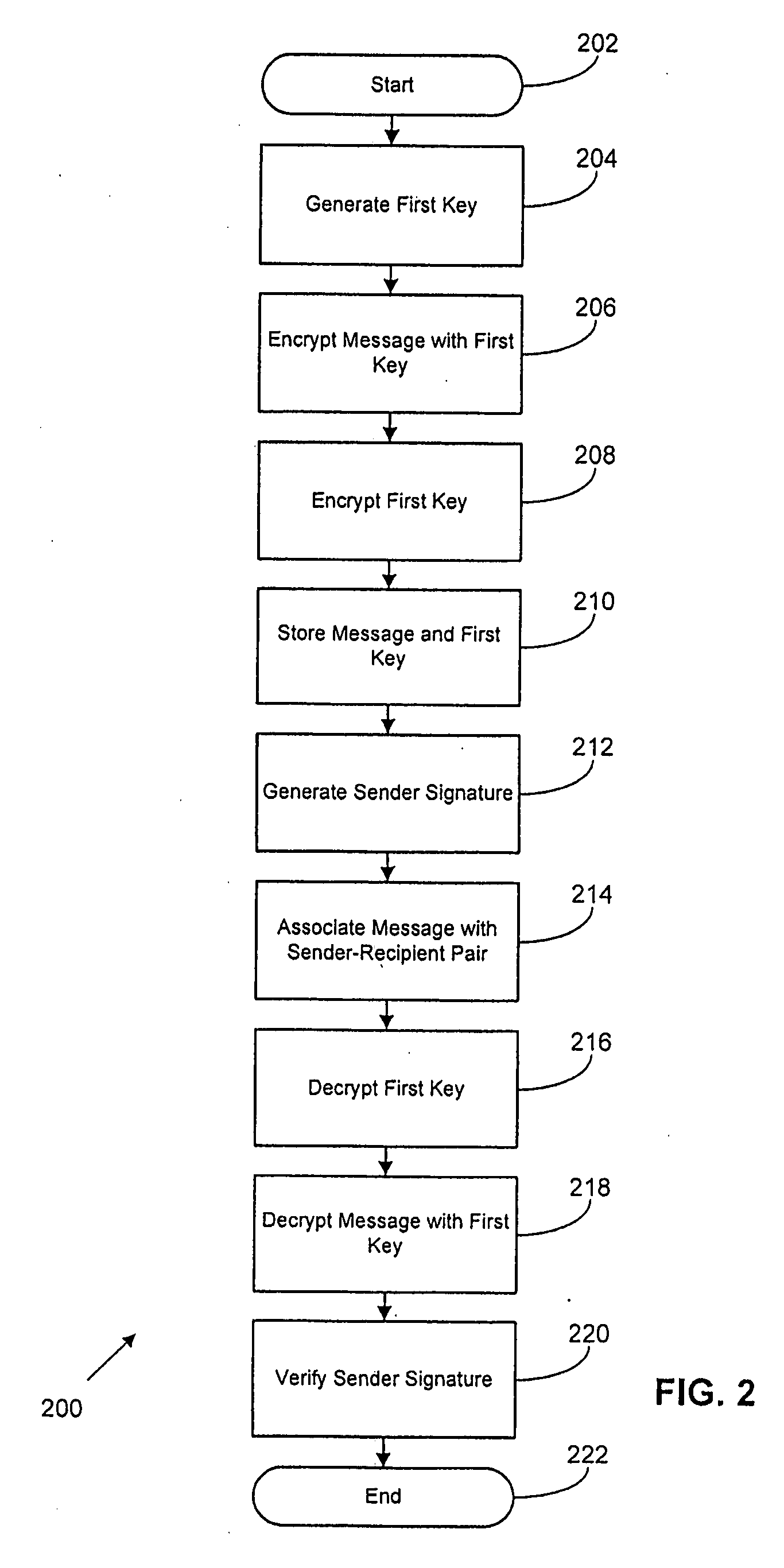
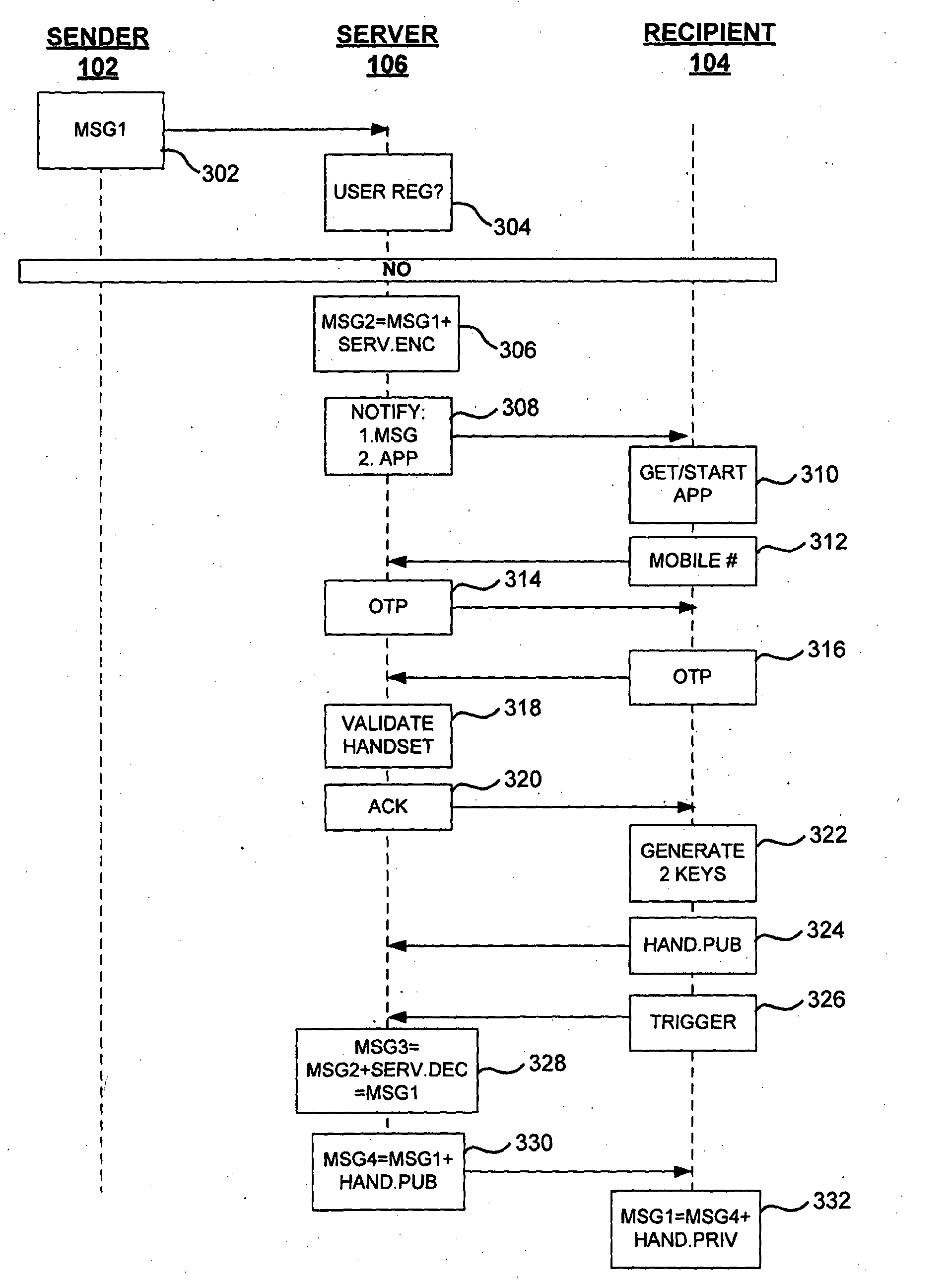
Methods and systems for secure messaging are disclosed. One method includes generating a first key associated with the sender. The method further includes encrypting a message from the sender to the recipient using the first key. The method also includes encrypting the first key with a second key. The method includes storing the encrypted message and the encrypted first key at a message server accessible to individuals including the sender and the recipient. The method includes associating the encrypted message with a sender and a recipient. The method also includes decrypting the encrypted first key using a key related to the second key, and decrypting the encrypted message using the first key. In the method, the message is encrypted on the message server at least while not accessed by the sender or recipient.
Owner:BHATNAGAR RAJAT +3
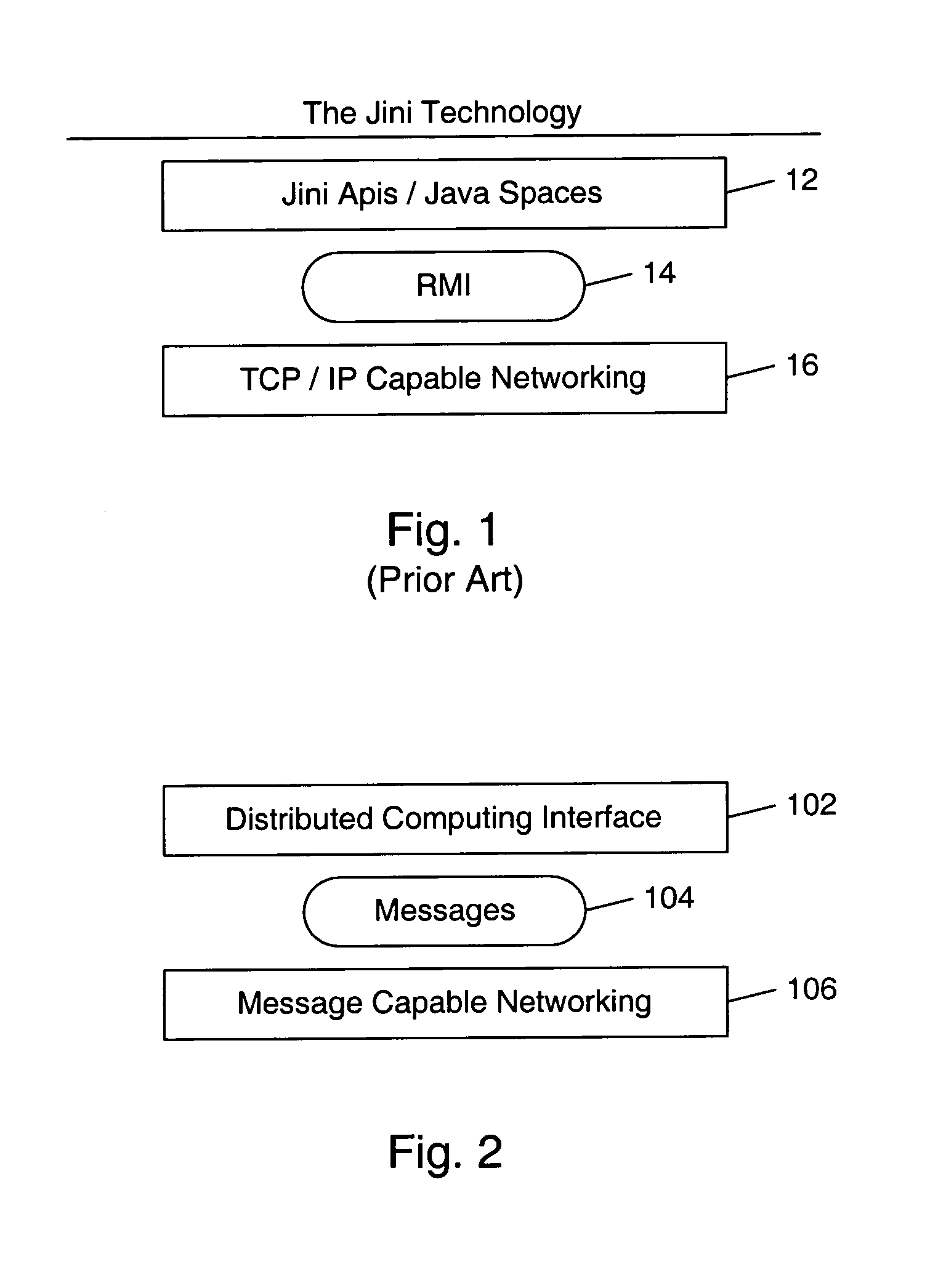
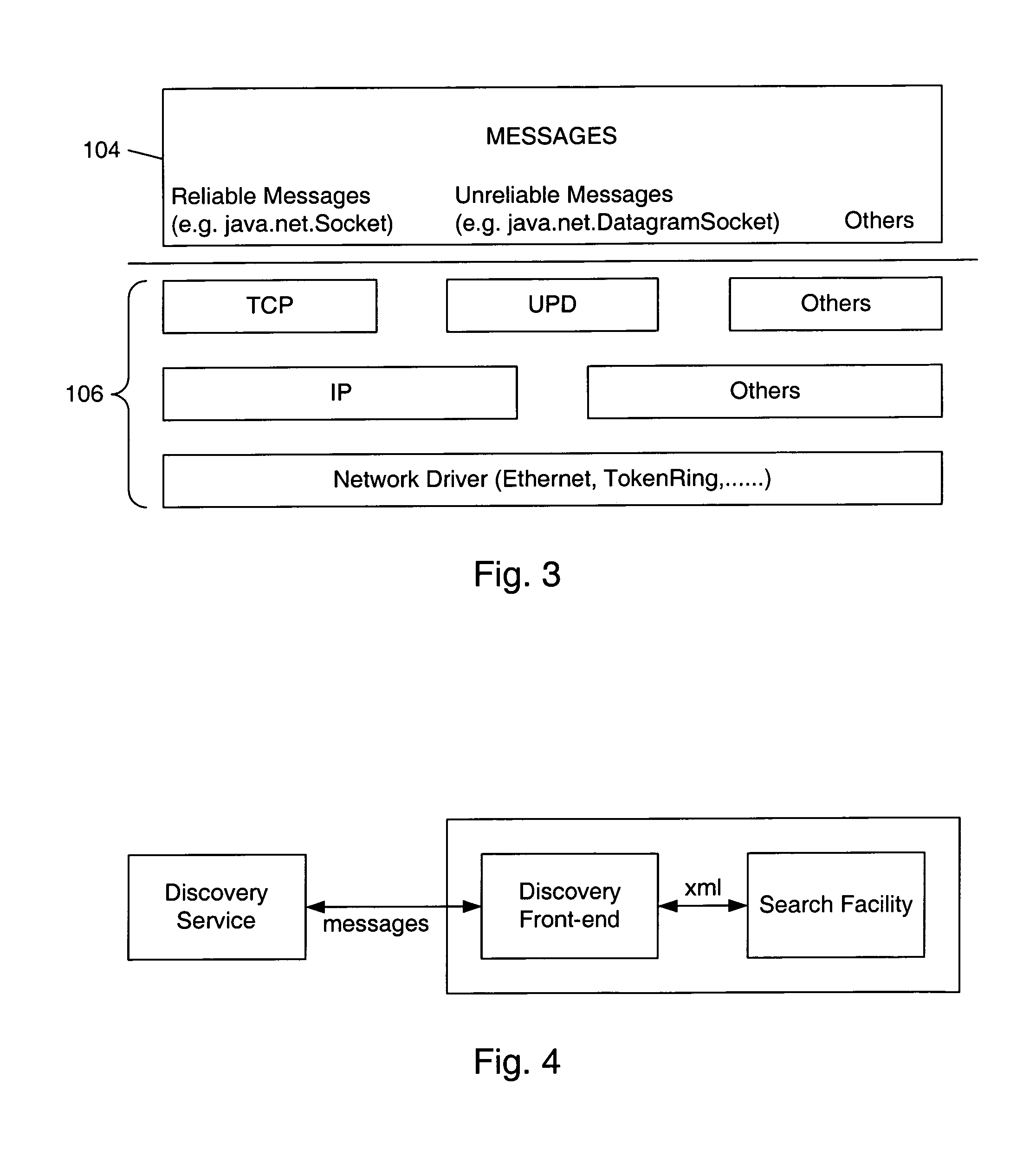
Remote method invocation with secure messaging in a distributed computing environment
ActiveUS7243356B1Interprogram communicationDigital computer detailsDistributed Computing EnvironmentClient-side
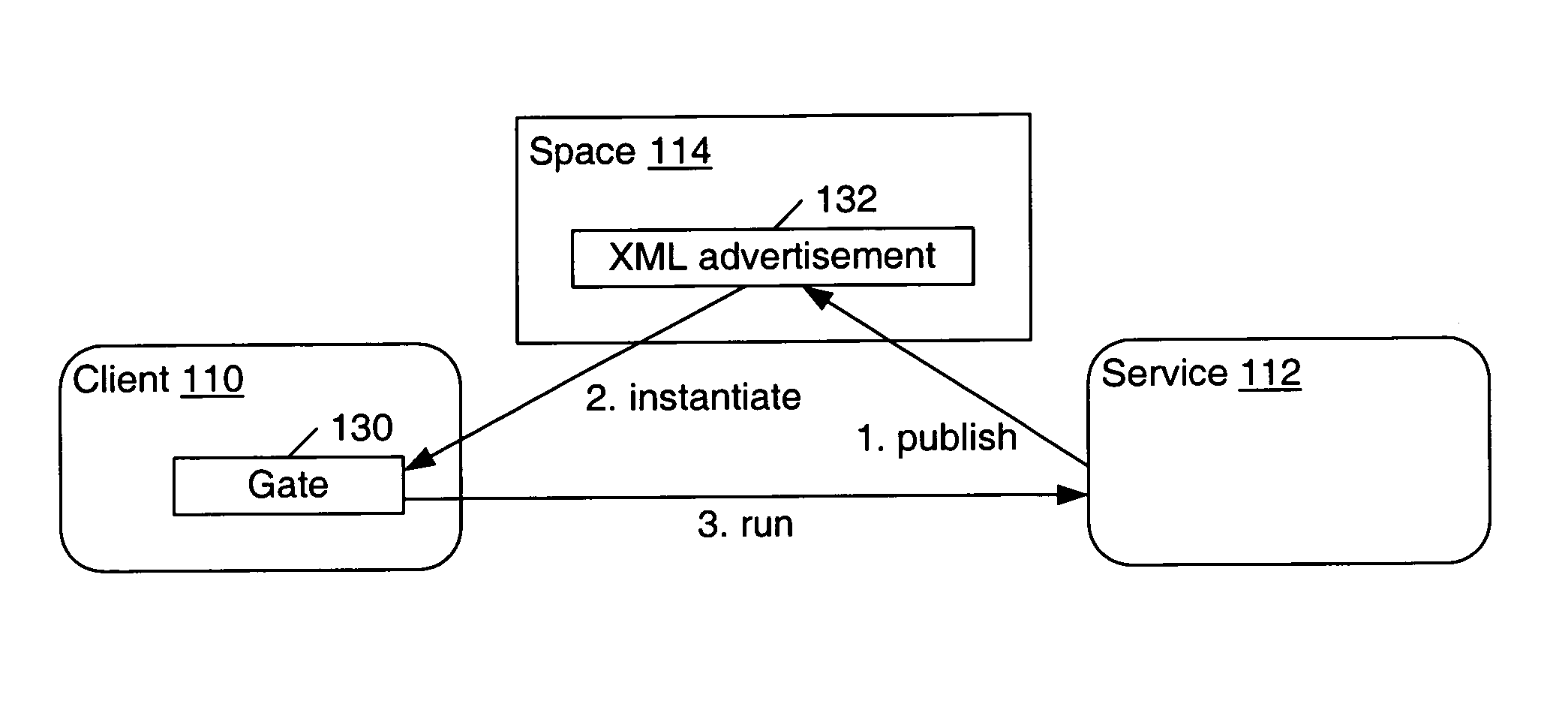
A secure interface between clients and services in a distributed computing environment is described. Method gates may provide an interface to remotely invoke functions of a service. A method gate may be generated from an advertisement that may include definitions for one or more messages for remotely invoking functions of the service. A client may generate messages containing representations of method calls. The service may invoke functions that correspond to the set of messages. A method gate on the service may unmarshal the message and invoke the function. The client may receive the results of the function directly. Alternatively, the results may be stored, an advertisement to the results may be provided, and a gate may be generated to access the results. Message gates may perform the sending and receiving of the messages between the client and service. In one embodiment, functions of the service may be computer programming language (e.g. Java) methods. In one embodiment, a message including a representation of a method call may be generated when no actual method call was made. In one embodiment, a method call may be transformed into messages that may be sent to the service; the service may not know that the messages were generated from a method call. In one embodiment, a service may transform messages requesting functions into method calls; the client may not know that the service is invoking methods to perform the functions. A credential may be embedded in messages and used for message authentication on the service.
Owner:ORACLE INT CORP
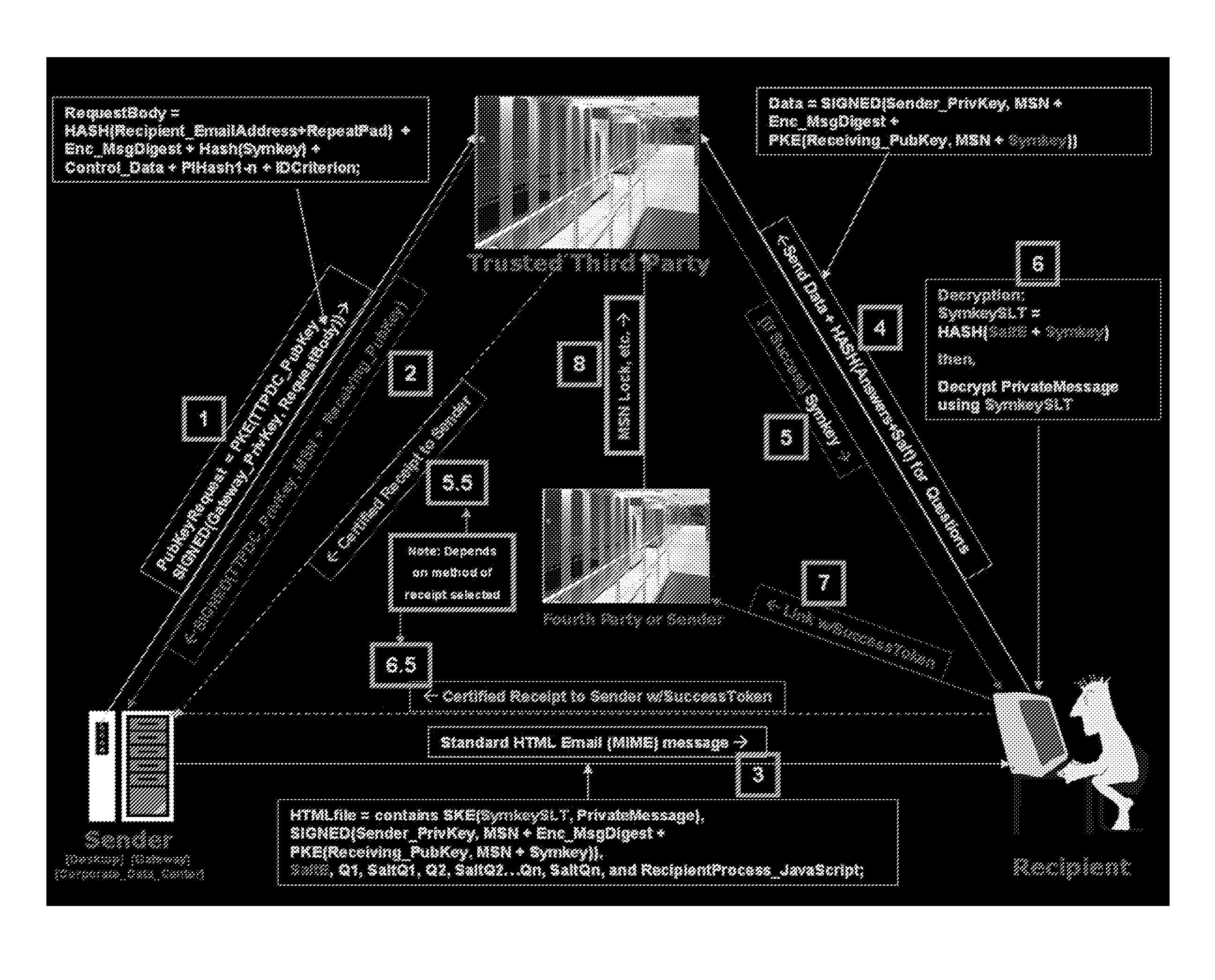
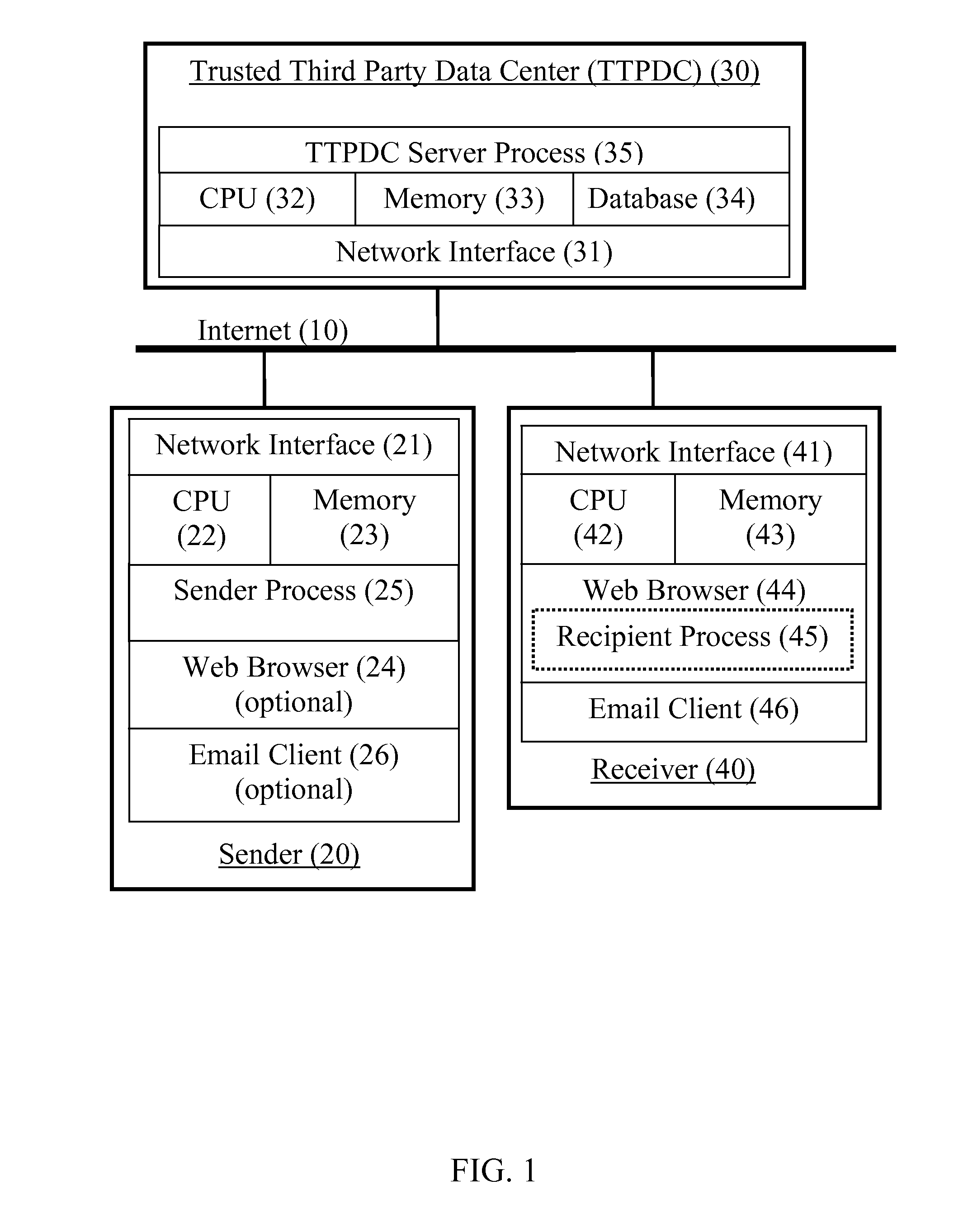
Secure messaging using a trusted third party
A system and method to send a secure message from a sender to a recipient using strong encryption protocols without the need for the recipient to create a public / private key pair and by using a third party to appropriately identify the recipient without revealing actual identification information to the third party. Upon successful identification, the third party is able to provide a recipient with information that enables recipient to create and use the actual decryption key without revealing the actual decryption key to the third party.
Owner:COOK DAVID P +1
Secure message system with remote decryption service
ActiveUS7266847B2Reduce visual clutterKey distribution for secure communicationPublic key for secure communicationPasswordComputer science
Owner:MICRO FOCUS LLC
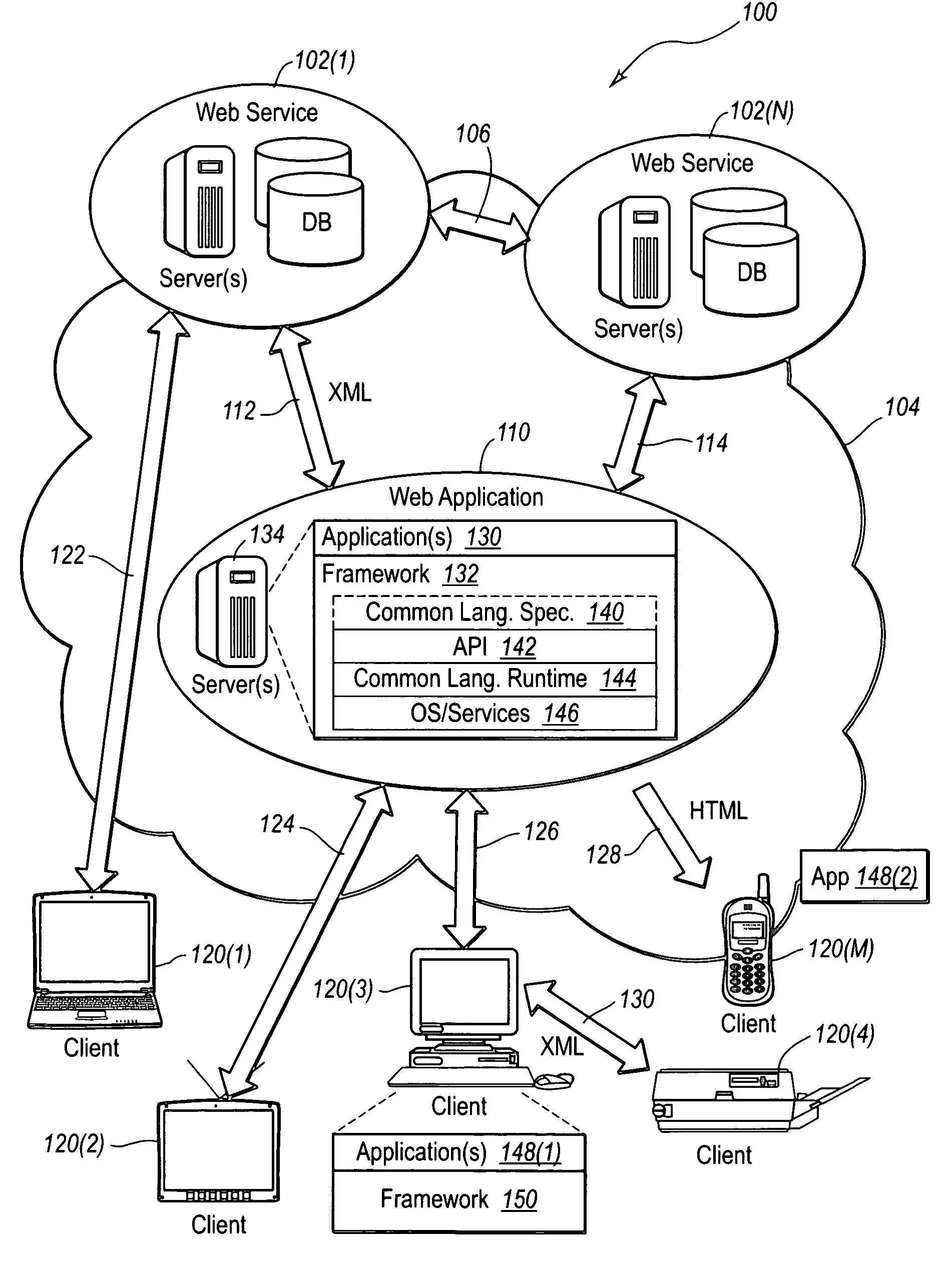
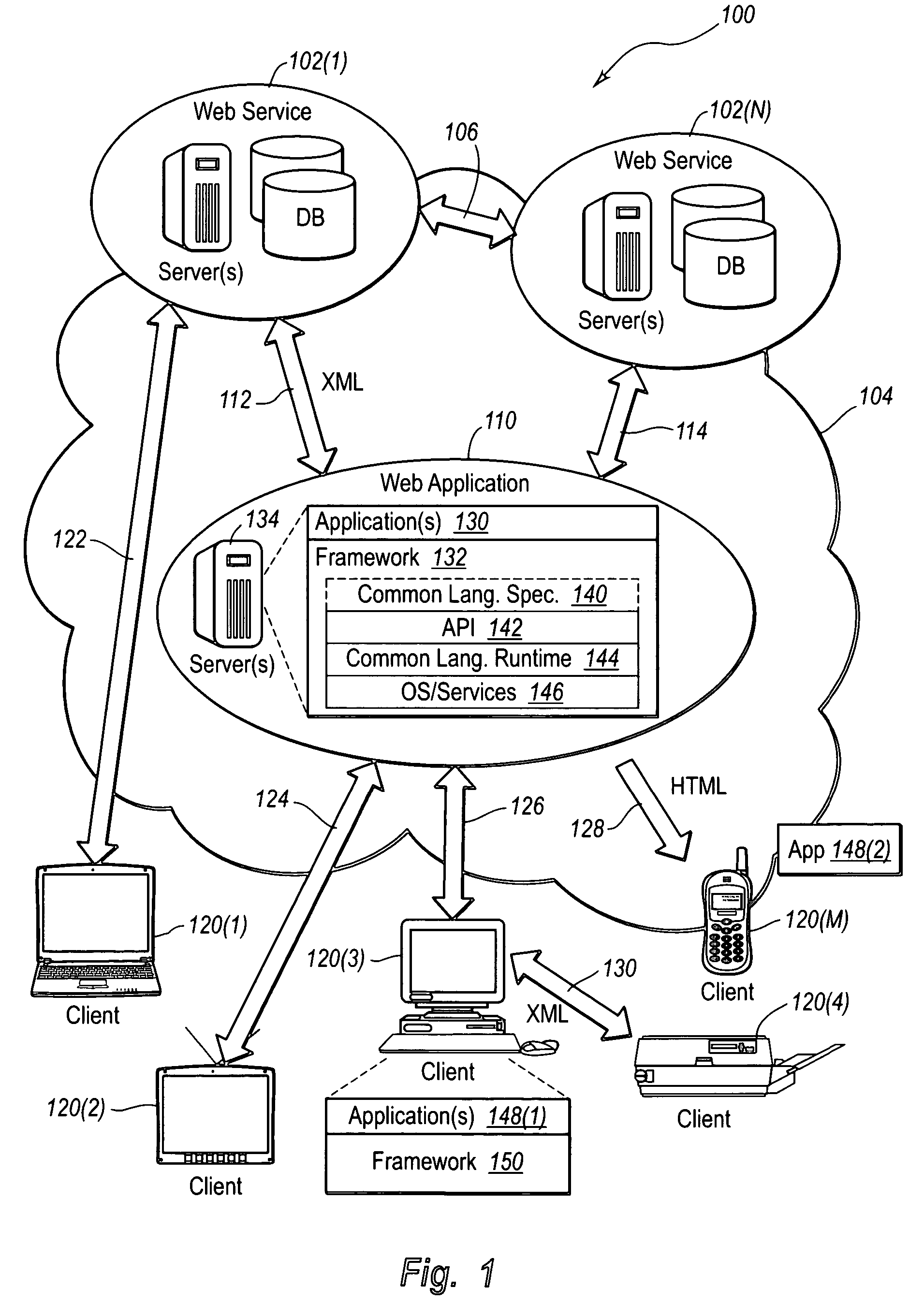
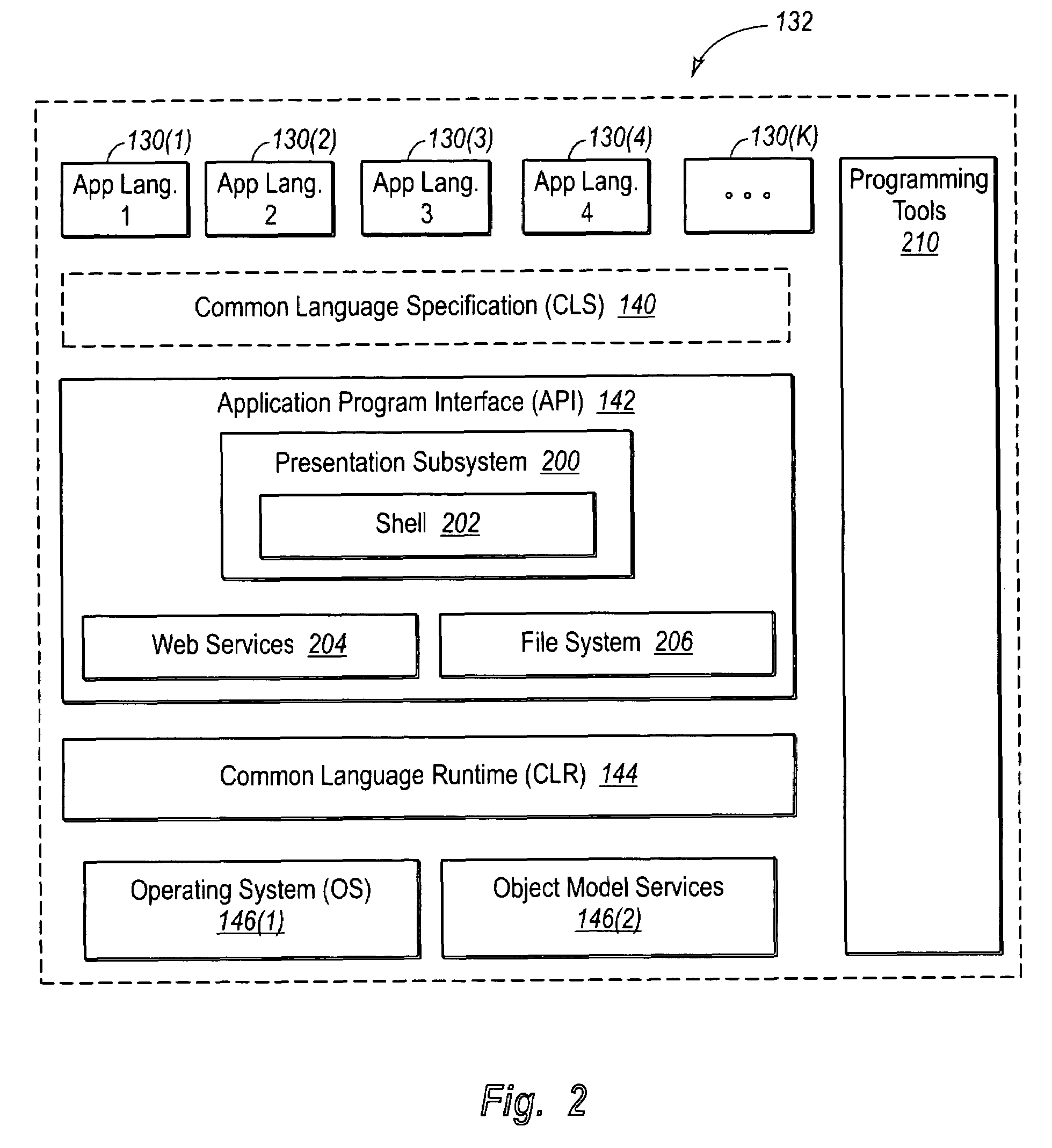
Interface infrastructure for creating and interacting with web services
InactiveUS7512957B2Improve efficiencyImprove performanceMultiple digital computer combinationsProgram controlReliable messagingExtensibility
A web services namespace pertains to an infrastructure for enabling creation of a wide variety of applications. The infrastructure provides a foundation for building message-based applications of various scale and complexity. The infrastructure or framework provides APIs for basic messaging, secure messaging, reliable messaging and transacted messaging. In some embodiments, the associated APIs are factored into a hierarchy of namespaces in a manner that balances utility, usability, extensibility and versionability.
Owner:MICROSOFT TECH LICENSING LLC
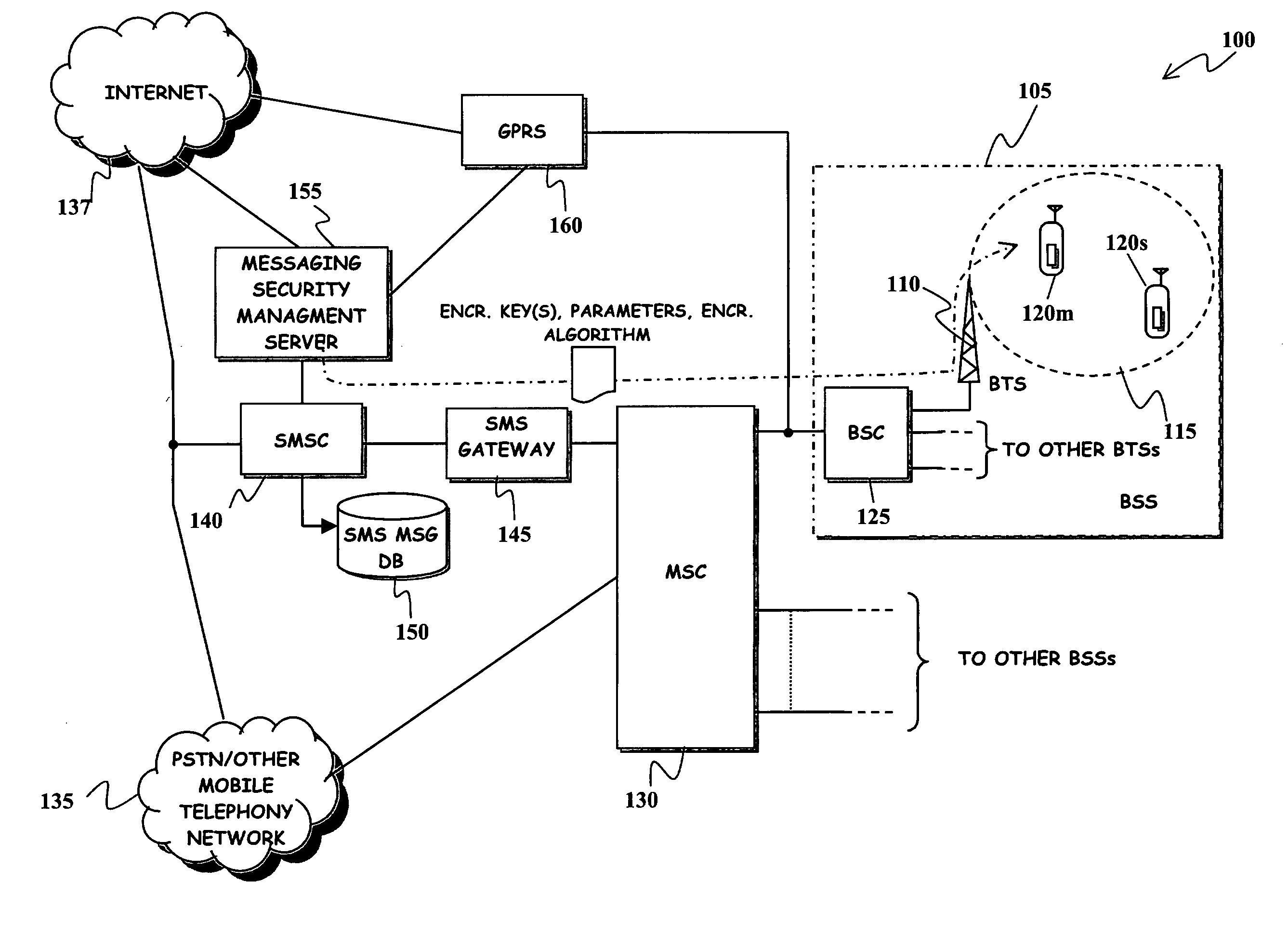
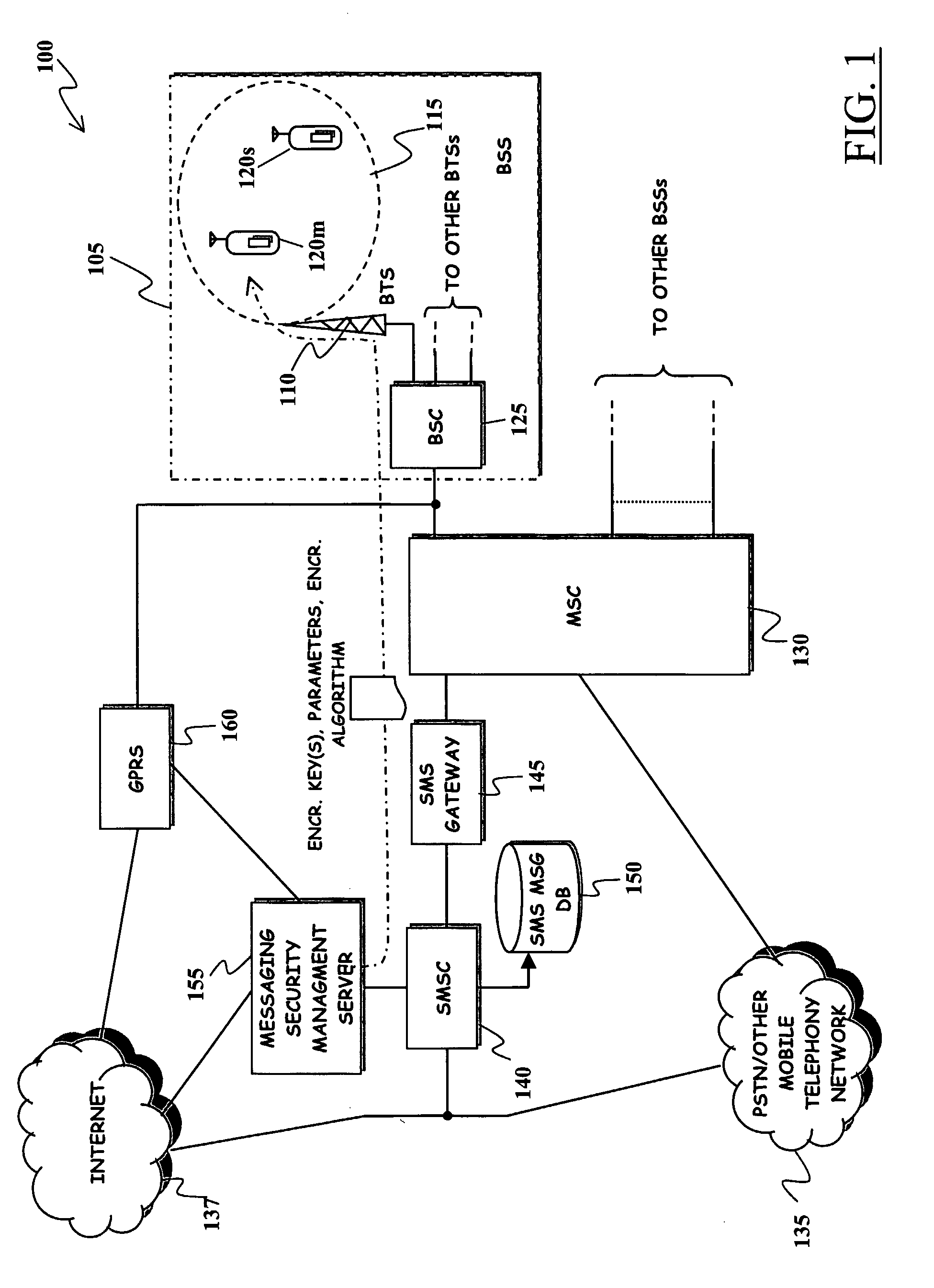
Method and System for Improving Robustness of Secure Messaging in a Mobile Communications Network
ActiveUS20080292101A1Increase flexibilityImprove robustnessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsComputer hardwareEnd to end security
A mobile communications network has mobile communications capabilities and supports a secure messaging service, such as an SMS messaging service, that allows a message sender and at least one message receiver (at least one among the message sender and the message receiver being a user of the mobile communications network) to exchange messages encrypted by means of a cryptographic process performed by the message sender, so as to obtain an encrypted message that can be decrypted by a corresponding cryptographic process performed by the intended message receiver. End-to-end security of the exchanged message is thus achieved. A cryptographic algorithm, exploited by the user of the mobile communications network for performing the cryptographic process, is modified by exploiting the mobile communications capabilities of the mobile communications network. Robustness and reliability over time of the end-to-end security messaging is improved.
Owner:TELECOM ITALIA SPA
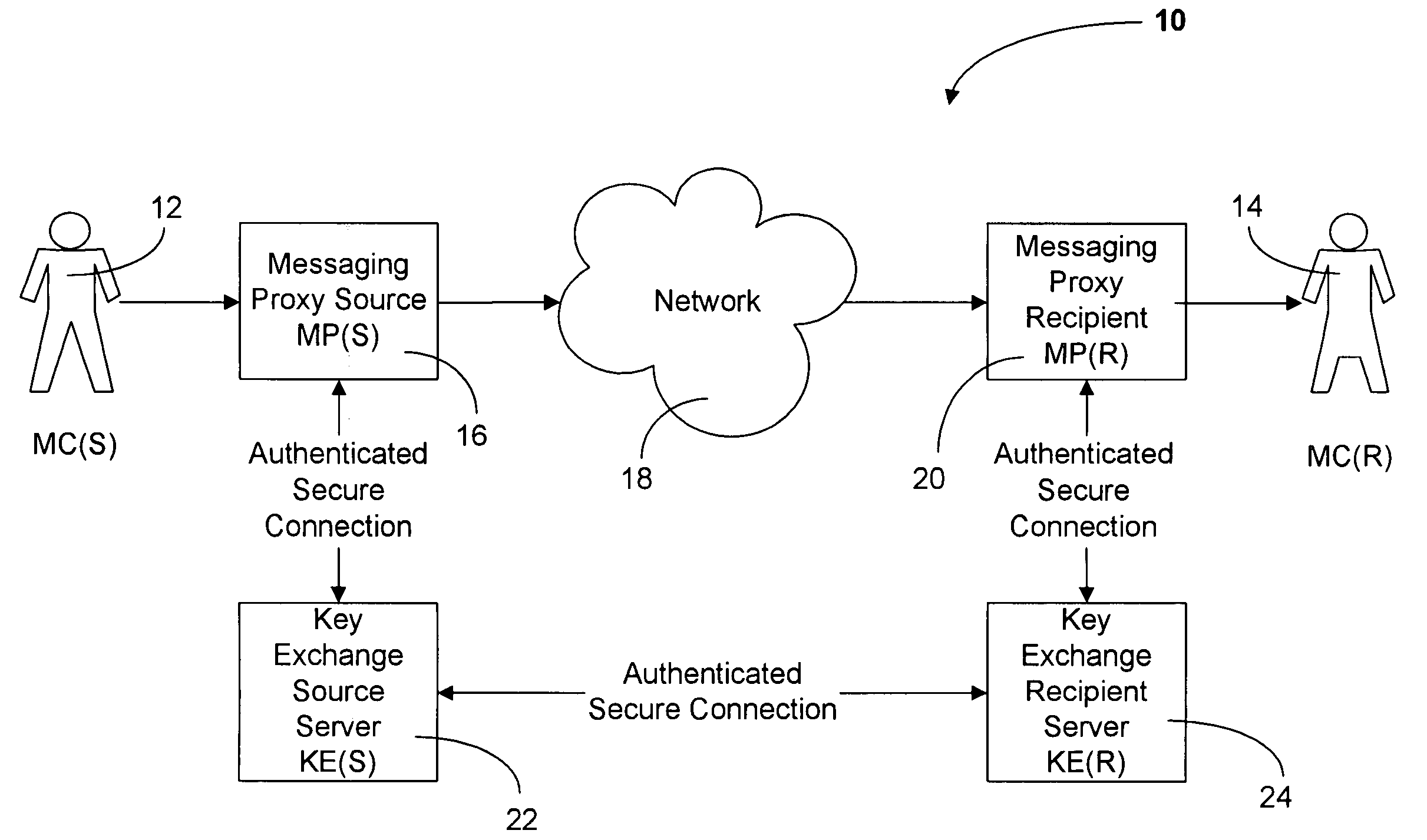
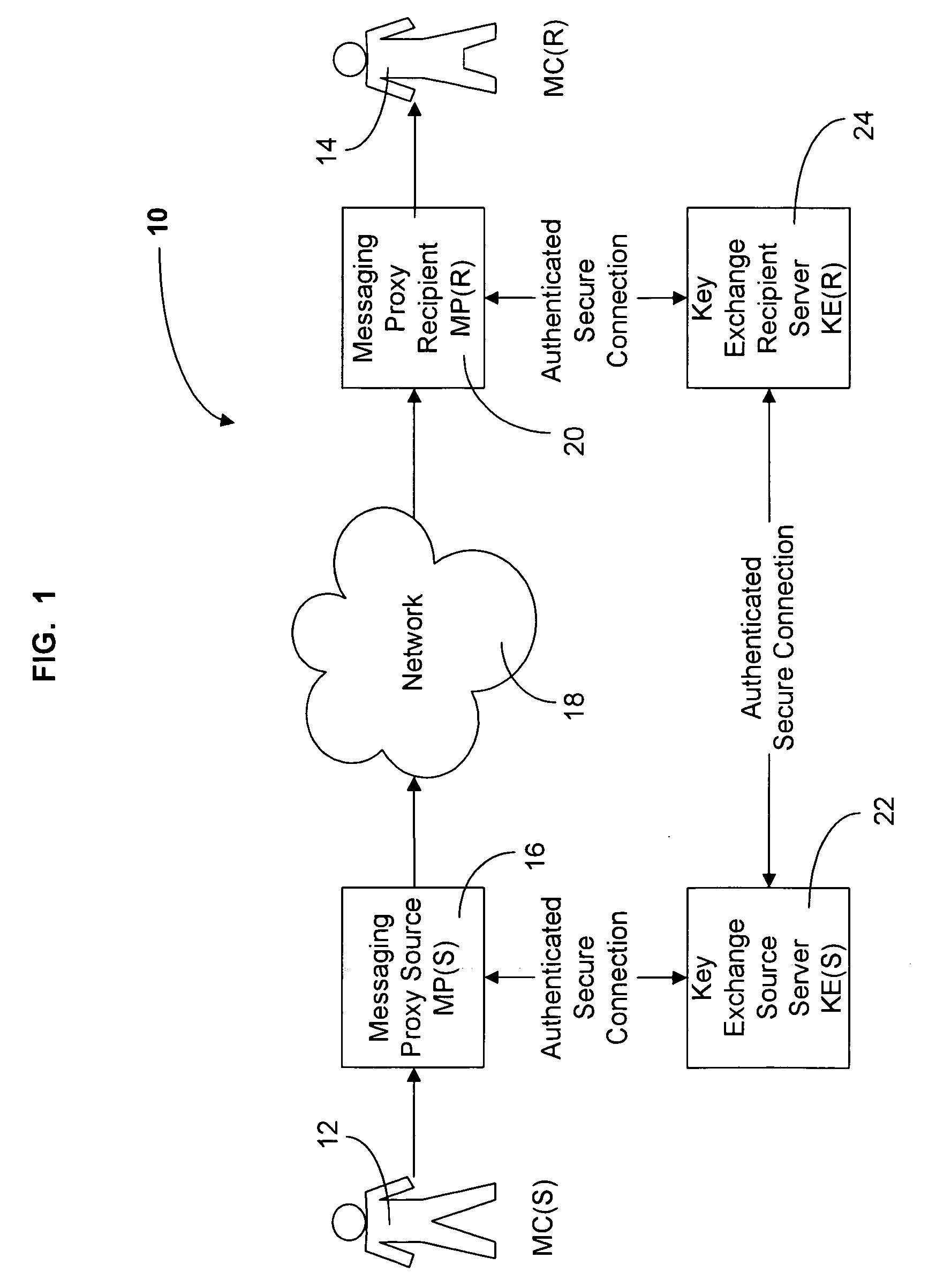
Method and system for sending secure messages over an unsecured network
InactiveUS20050182937A1Key distribution for secure communicationUser identity/authority verificationKey exchangeMessage delivery
The present invention is directed to a system and method for providing the secure exchange of messages utilizing an existing unsecured messaging network such as the Internet. A messaging proxy is provided between a sender of a message and the unsecured messaging network. In sending a secure message, the messaging proxy contacts a key exchange server via an authenticated secure connection. The messaging proxy generates a key with which to encrypt the message. The key is sent via an authenticated secure connection to a messaging proxy of a recipient. If the sender receives an acknowledgement of the recipient receiving the key, the message is encrypted and sent via the unsecured messaging network. The recipient then uses the key to decrypt the message. Should the recipient not have a proxy in place to receive encrypted messages and a corresponding key exchange server, the message is sent unencrypted.
Owner:BEDI HARMEET SINGH
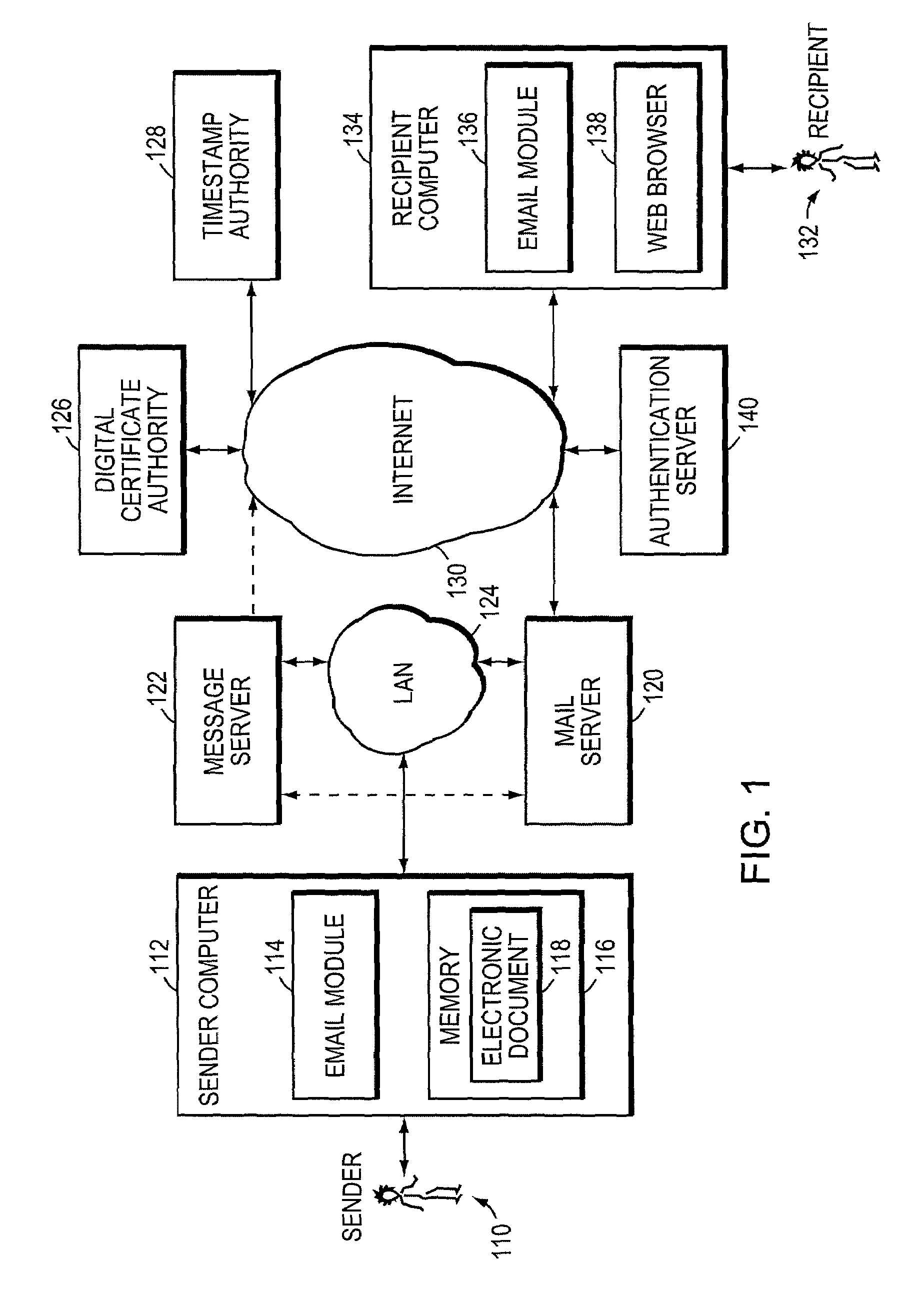
Electronically verified digital signature and document delivery system and method
InactiveUS7082538B2Low costReduce complexityPublic key for secure communicationUser identity/authority verificationWeb serviceNetwork service
The secure messaging system of the invention encrypts an electronic document using a symmetric key and transmits the encrypted document and related message parameters to a recipient whose identity is then authenticated by a web server. The web server dynamically regenerates the symmetric key from a hidden key and from the message parameters accompanying the encrypted document, and thus avoids having to maintain a central repository of encrypted documents as required by typical “post and pick-up” encrypted messaging systems. Further, an audit trail produced while practicing the invention provides timestamped message digest data for a plurality of time intervals, where the message digests for adjacent time intervals are computationally linked together. The audit trail effectively enables timestamped message digest data to verify not only the existence of a document during a first time interval, but also to verify the existence of documents encountered in a prior time interval.
Owner:UPLAND SOFTWARE INC
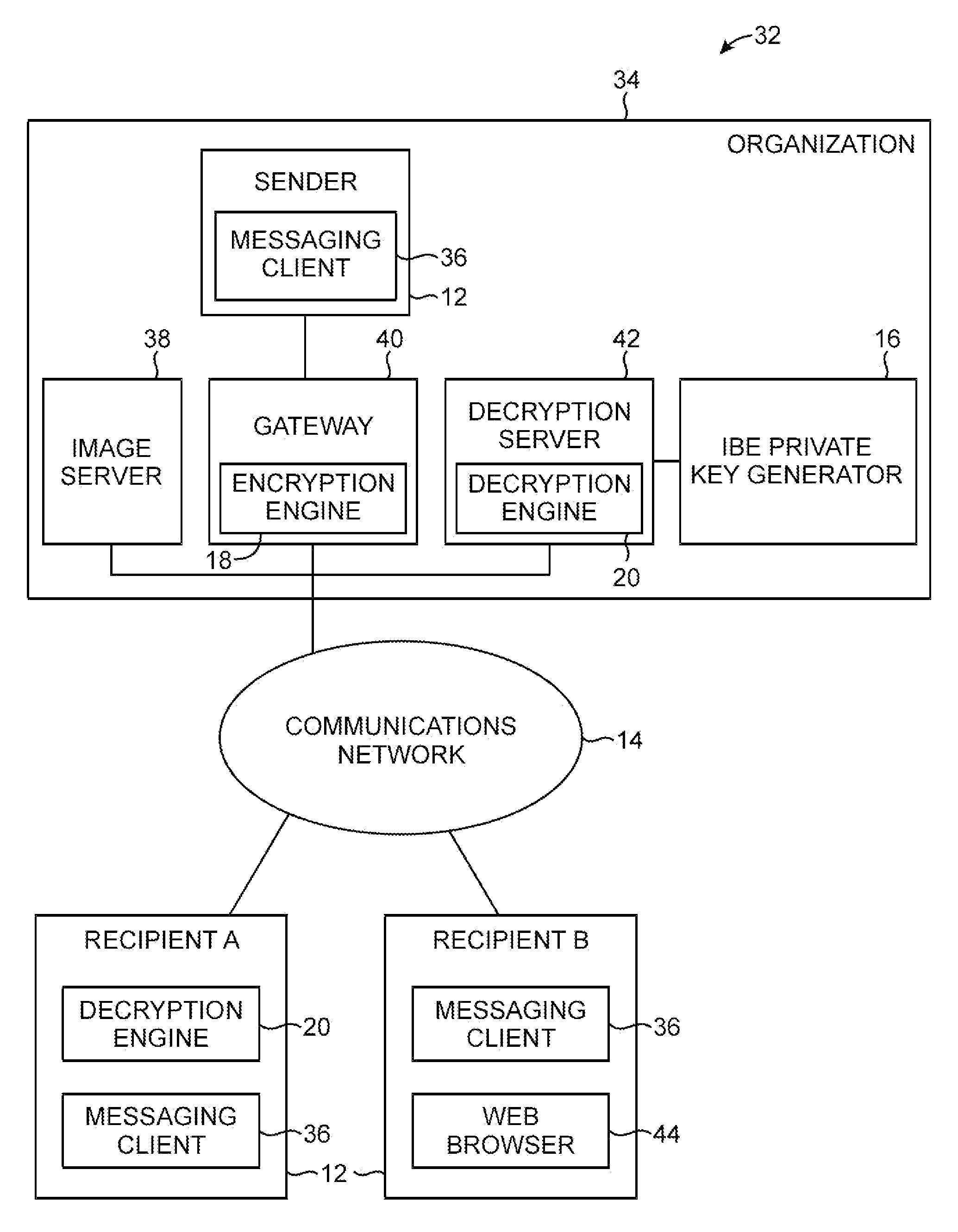
Secure messaging system with personalization information
ActiveUS8145718B1Digital data processing detailsUser identity/authority verificationPersonalizationImage reference
Personalization images are included in email messages to combat phishing attacks in which an attacker attempts to trick a user into divulging sensitive information over the Internet. When a recipient of an email message receives a message, the recipient can visually inspect the personalization image in the message. If the personalization image is missing or if the personalization image is not valid, the email recipient is alerted to the possibility of a phishing attack. Email message content may be encrypted. A gateway associated with an email message sender may be used to perform encryption operations on the message content. The gateway may create an html version of the email by placing the encrypted message content in an html wrapper. An image reference corresponding to the personalization image may be embedded in the html version of the message.
Owner:MICRO FOCUS LLC
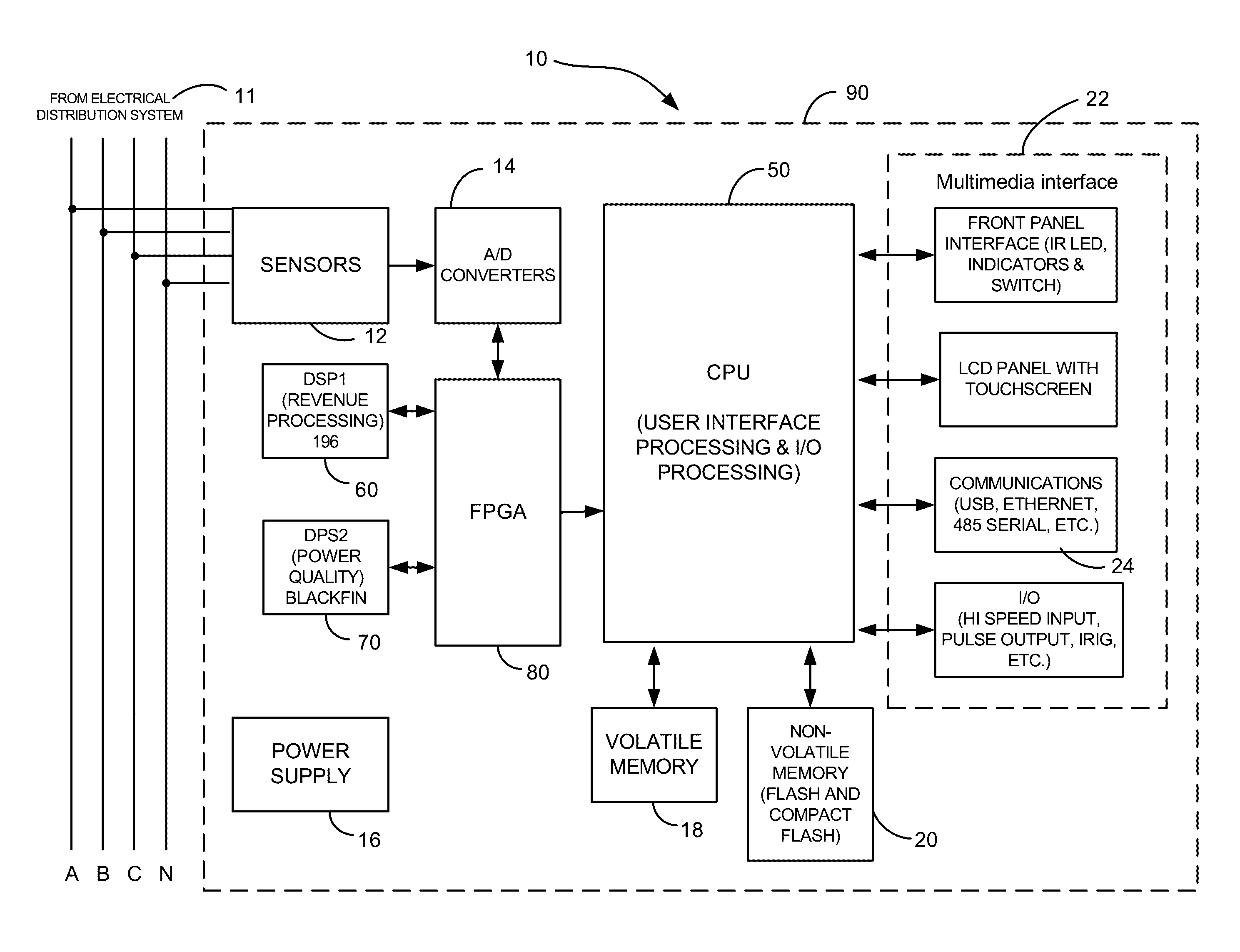
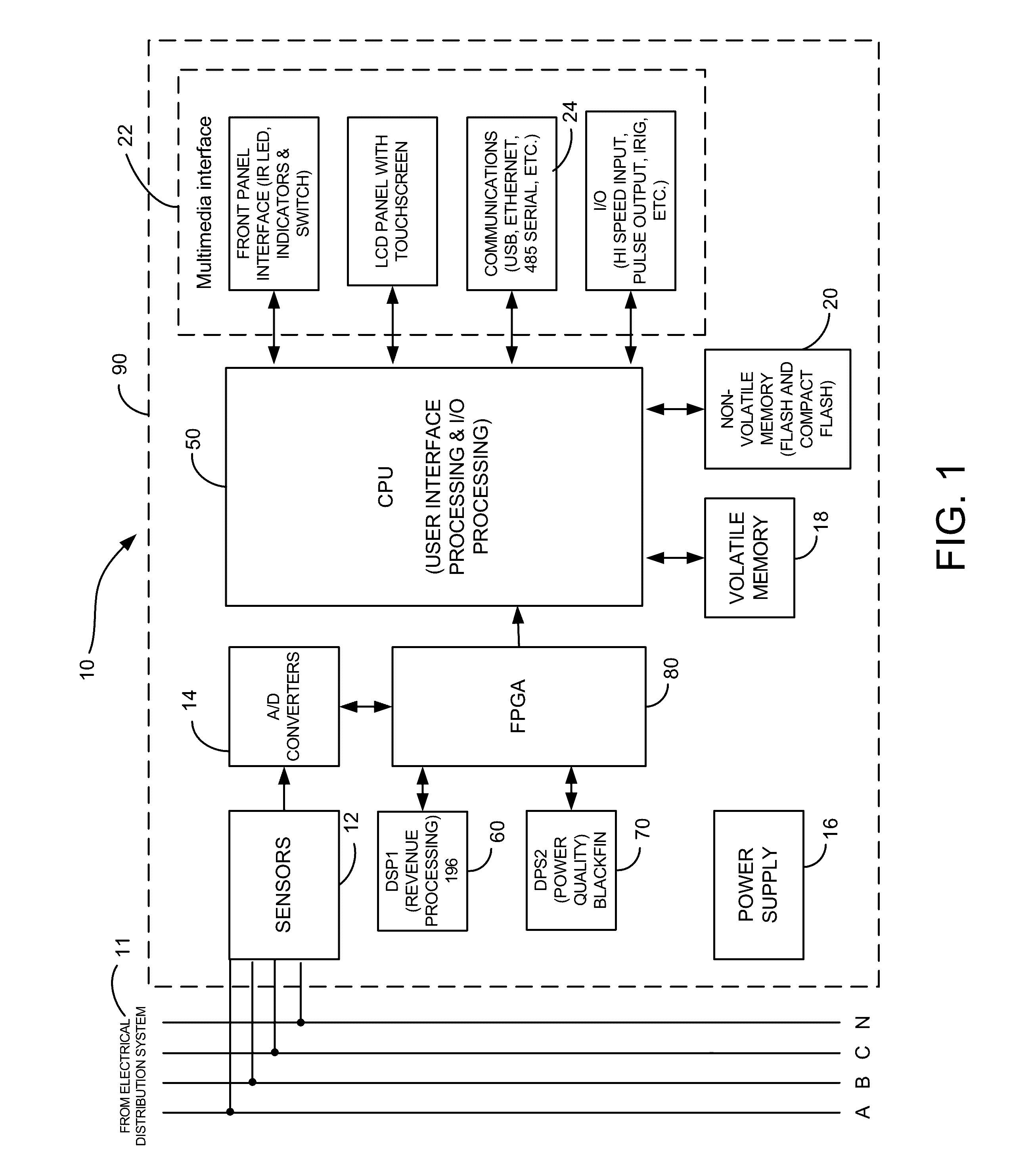
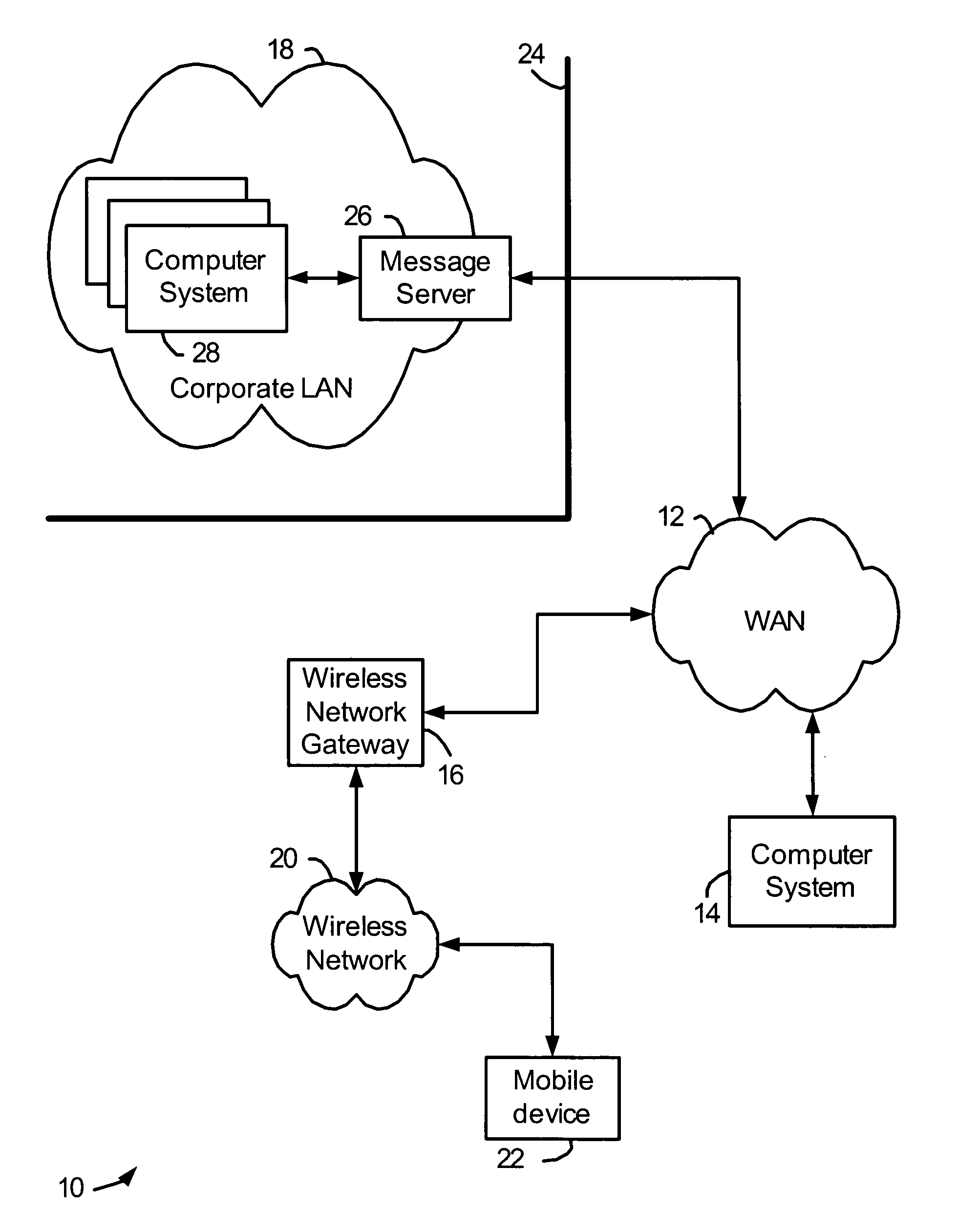
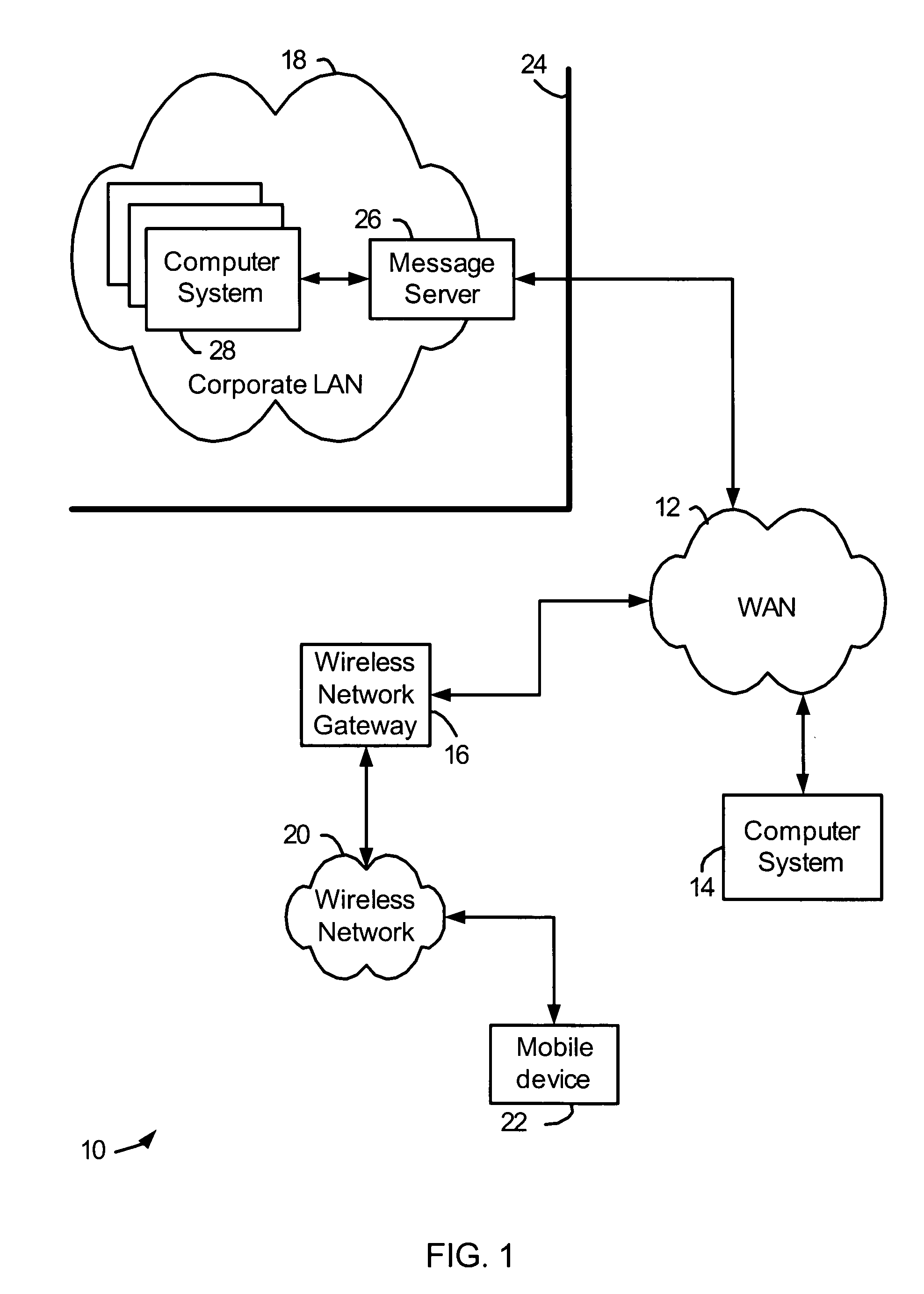
Intelligent electronic devices, systems and methods for communicating messages over a network
ActiveUS20160285872A1Data processing applicationsTariff metering apparatusDistribution systemElectric power quality
Intelligent electronic devices (IEDs), systems and methods for communicating messages over a network is provided. The IED of the present disclosure implements an alarm and notification message feature to send messages to a client or server when selected events occur regarding power usage and power quality for any metered point within a power distribution system. The IED of the present disclosure may be configured to monitor user-selected events according to user-selected settings stored in the IED. In one aspect of the present disclosure, the messages sent by the IED are emails. The IED of the present disclosure may be configured to encrypt the messages sent. The IED of the present disclosure may also be configured to send messages to a logging server via secure messaging.
Owner:ELECTRO INDUSTRIES GAUGE TECH
Techniques for managing secure communications
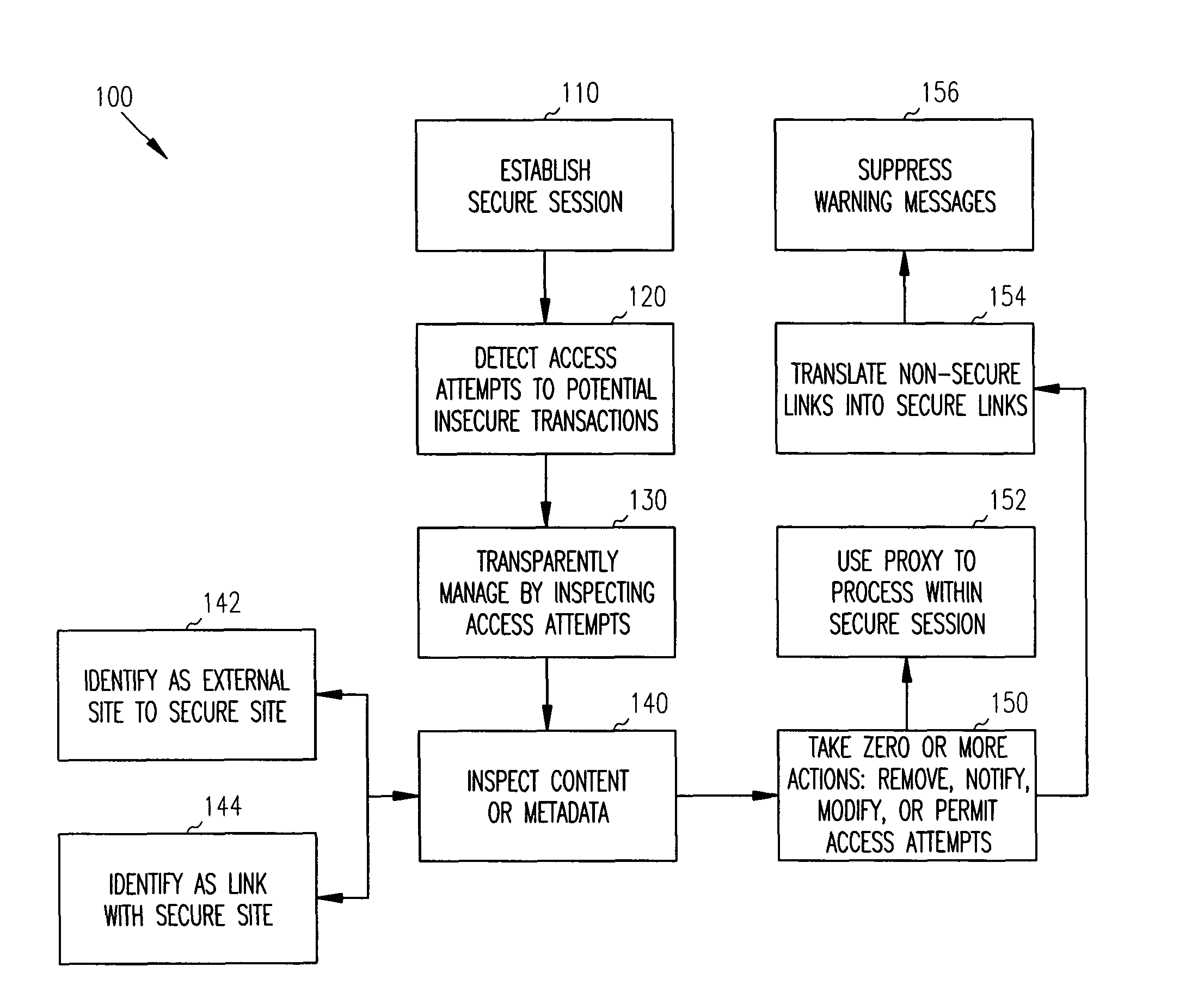
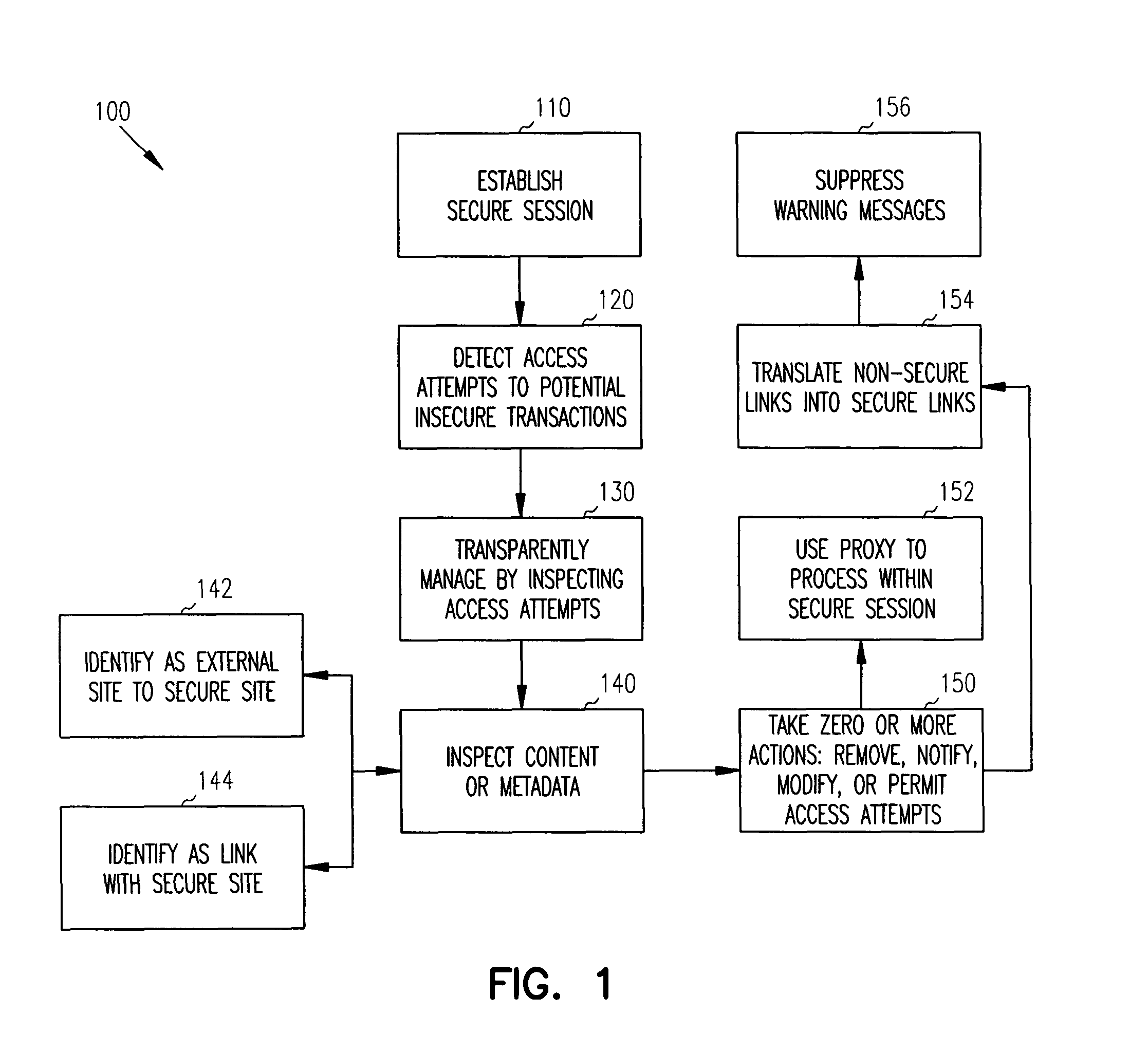
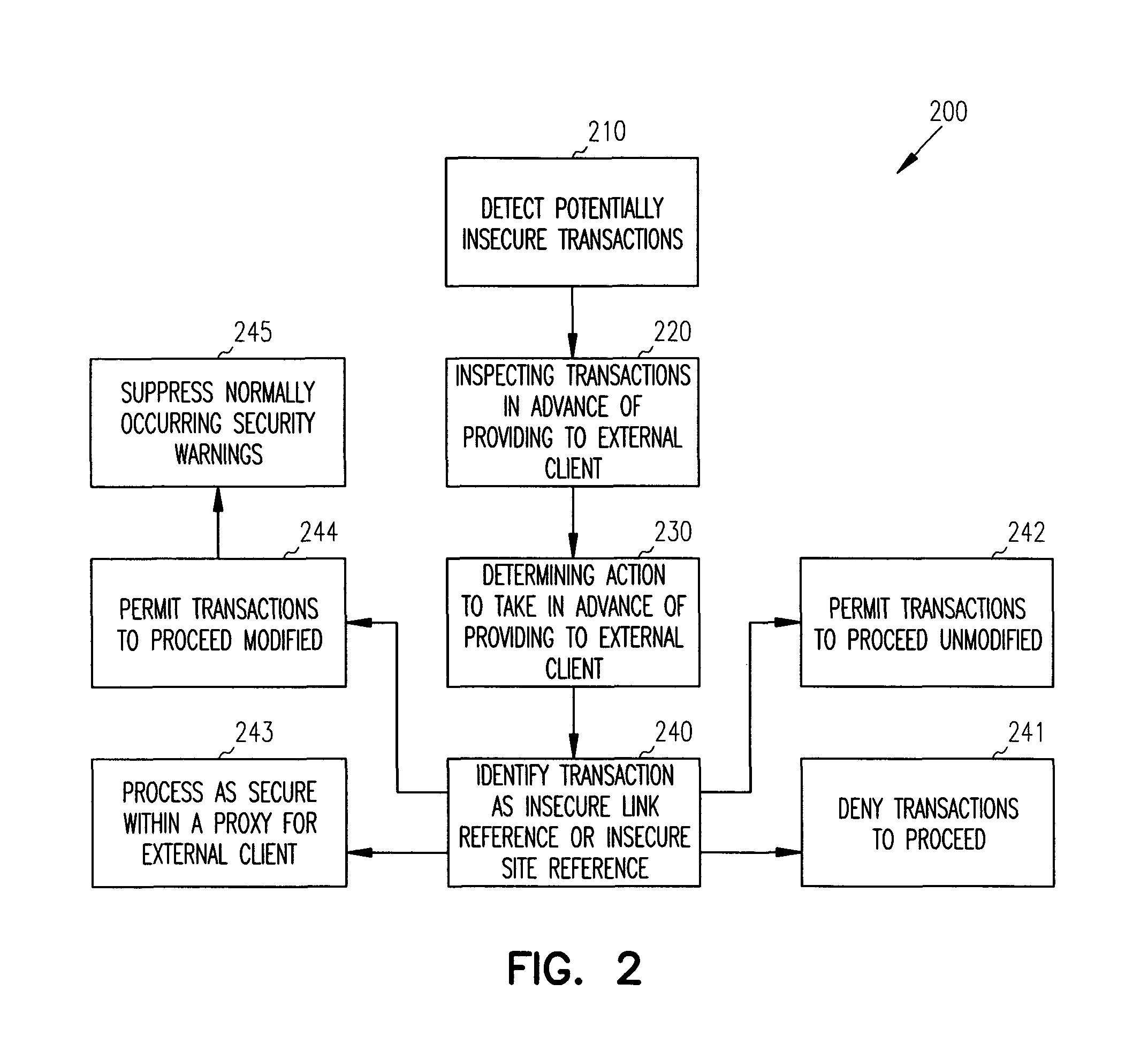
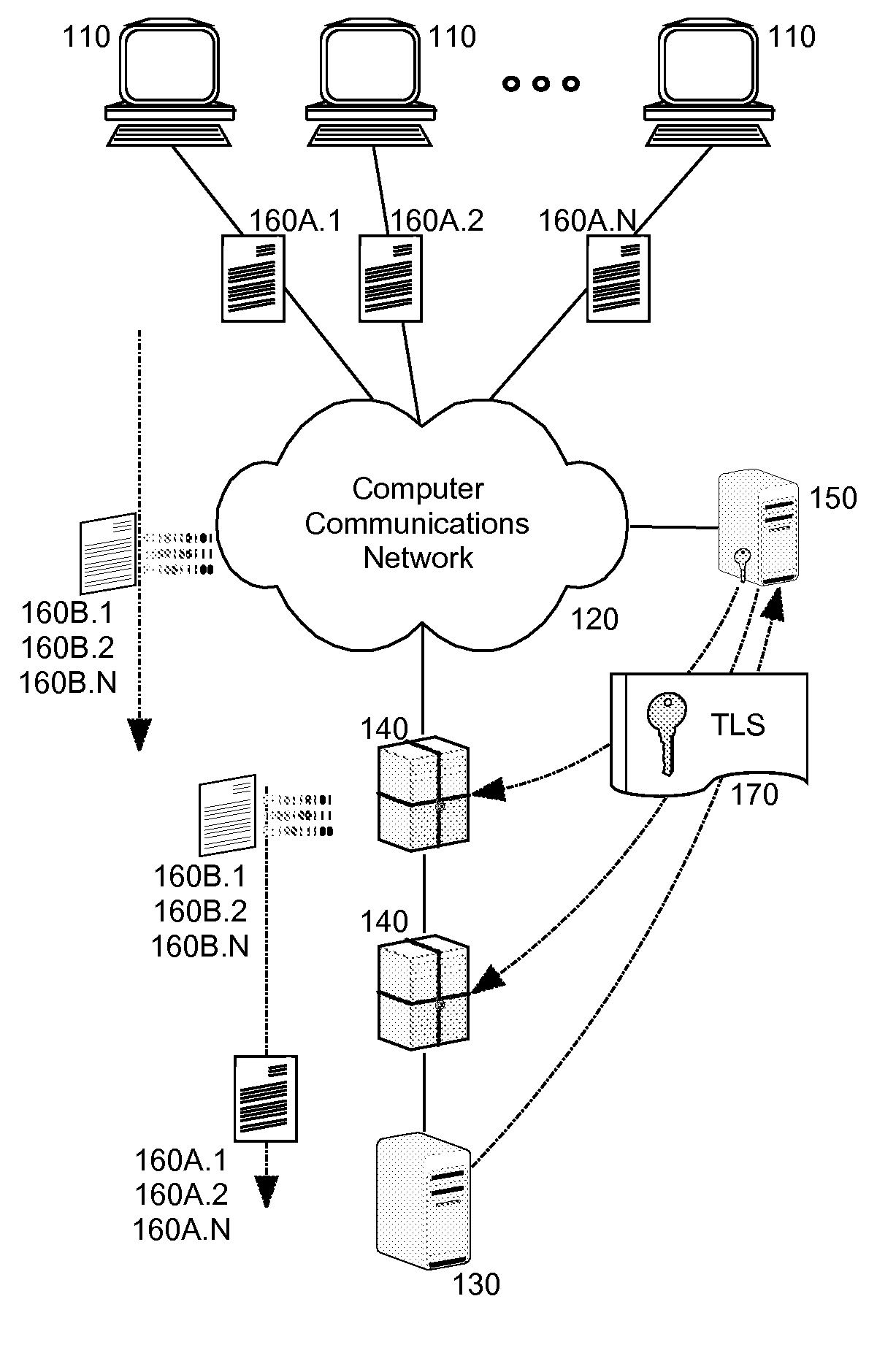
Methods and systems for managing secure communications are provided. An external client establishes secure communications with a secure site. During the secure session, the external client attempts to access potentially insecure references. These potentially insecure references are inspected before being made available to the external client. In some instances, the potentially insecure references are translated into secure references, which suppress normally occurring security warning messages that are issued to the external client. In other instances, the potentially insecure references are processed by a proxy on behalf of the external client and appear to the external client to occur within the secure session.
Owner:MICRO FOCUS SOFTWARE INC
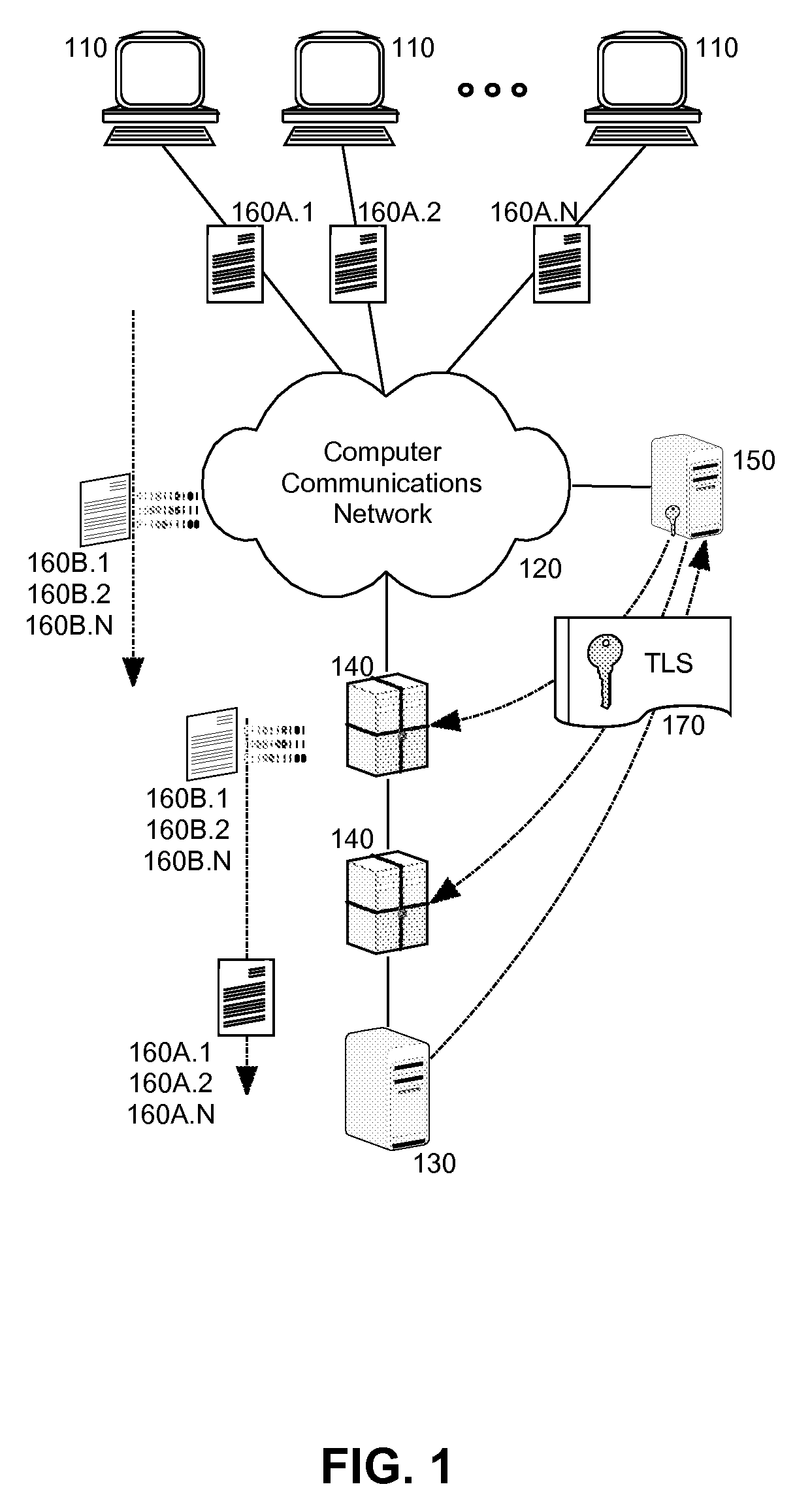
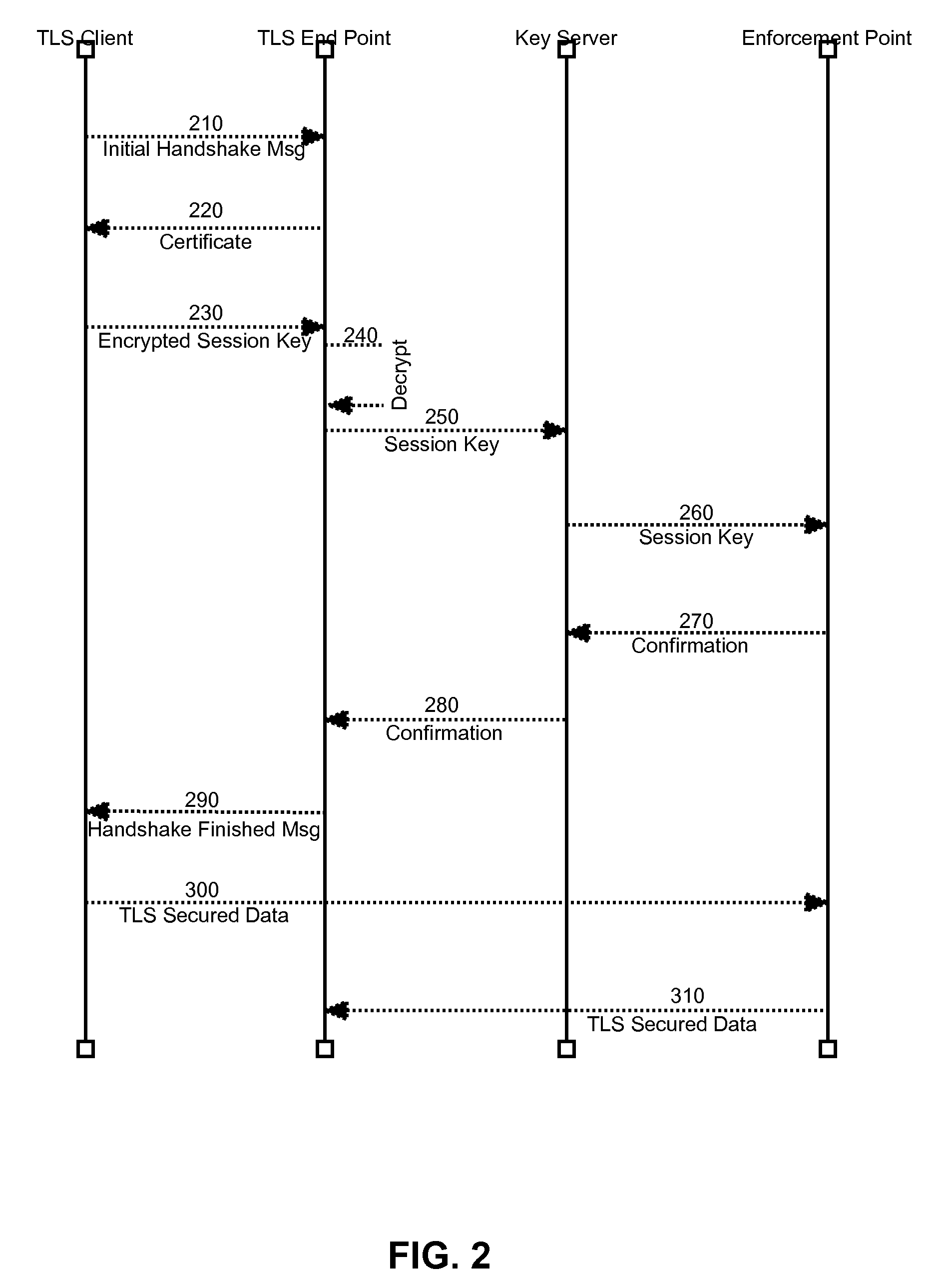
Secure sharing of transport layer security session keys with trusted enforcement points
InactiveUS20090025078A1Communication securityMultiple digital computer combinationsProgram controlSecure communicationOperability
Embodiments of the present invention address deficiencies of the art in respect to security enforcement point operability in a TLS secured communications path and provide a novel and non-obvious method, system and computer program product for the secure sharing of TLS session keys with trusted enforcement points. In one embodiment of the invention, a method for securely sharing TLS session keys with trusted enforcement points can be provided. The method can include conducting a TLS handshake with a TLS client to extract and decrypt a session key for a TLS session with the TLS client traversing at least one security enforcement point. The method further can include providing the session key to a communicatively coupled key server for distribution to the at least one security enforcement point. Finally, the method can include engaging in secure communications with the TLS client over the TLS session.
Owner:IBM CORP
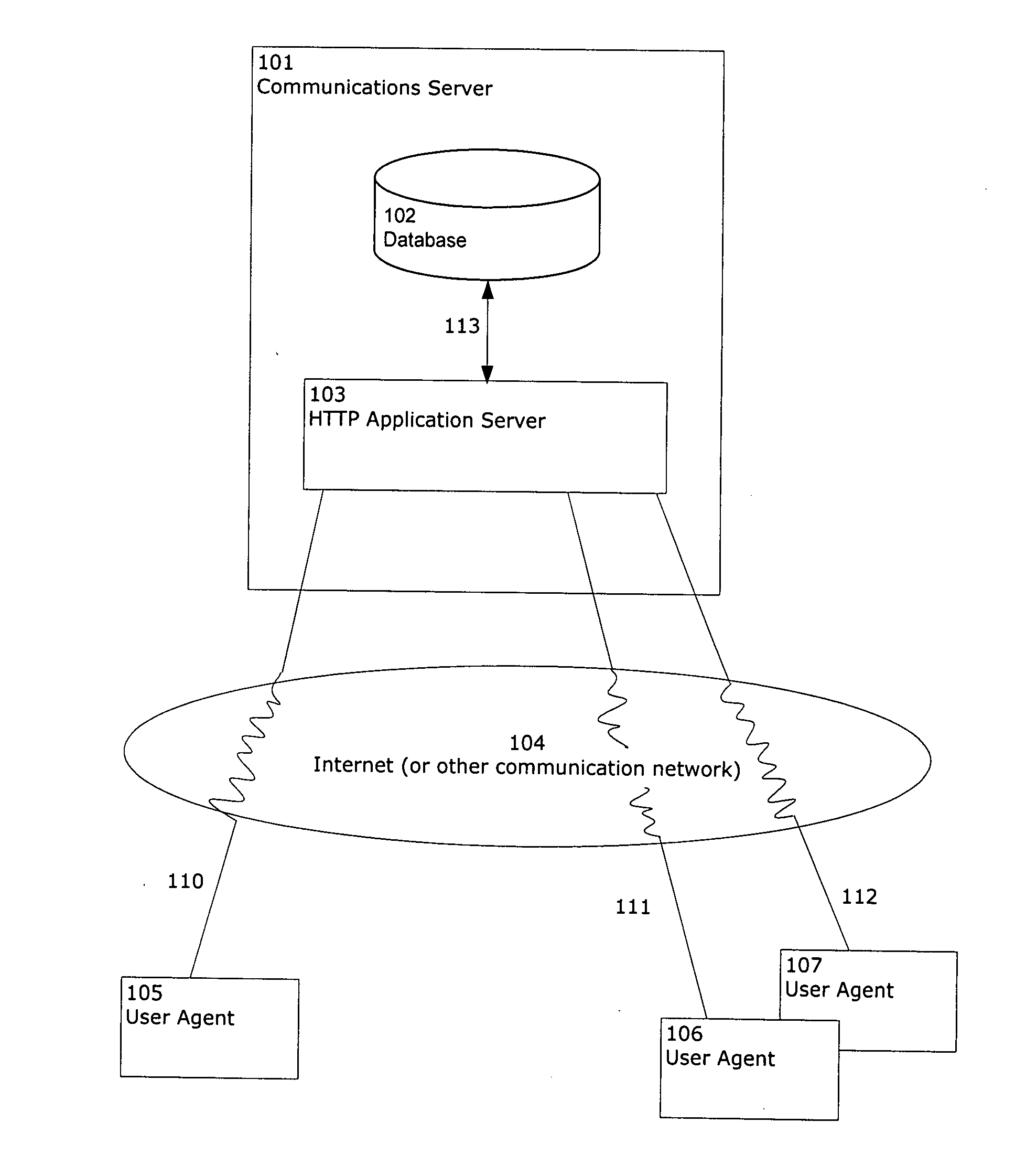
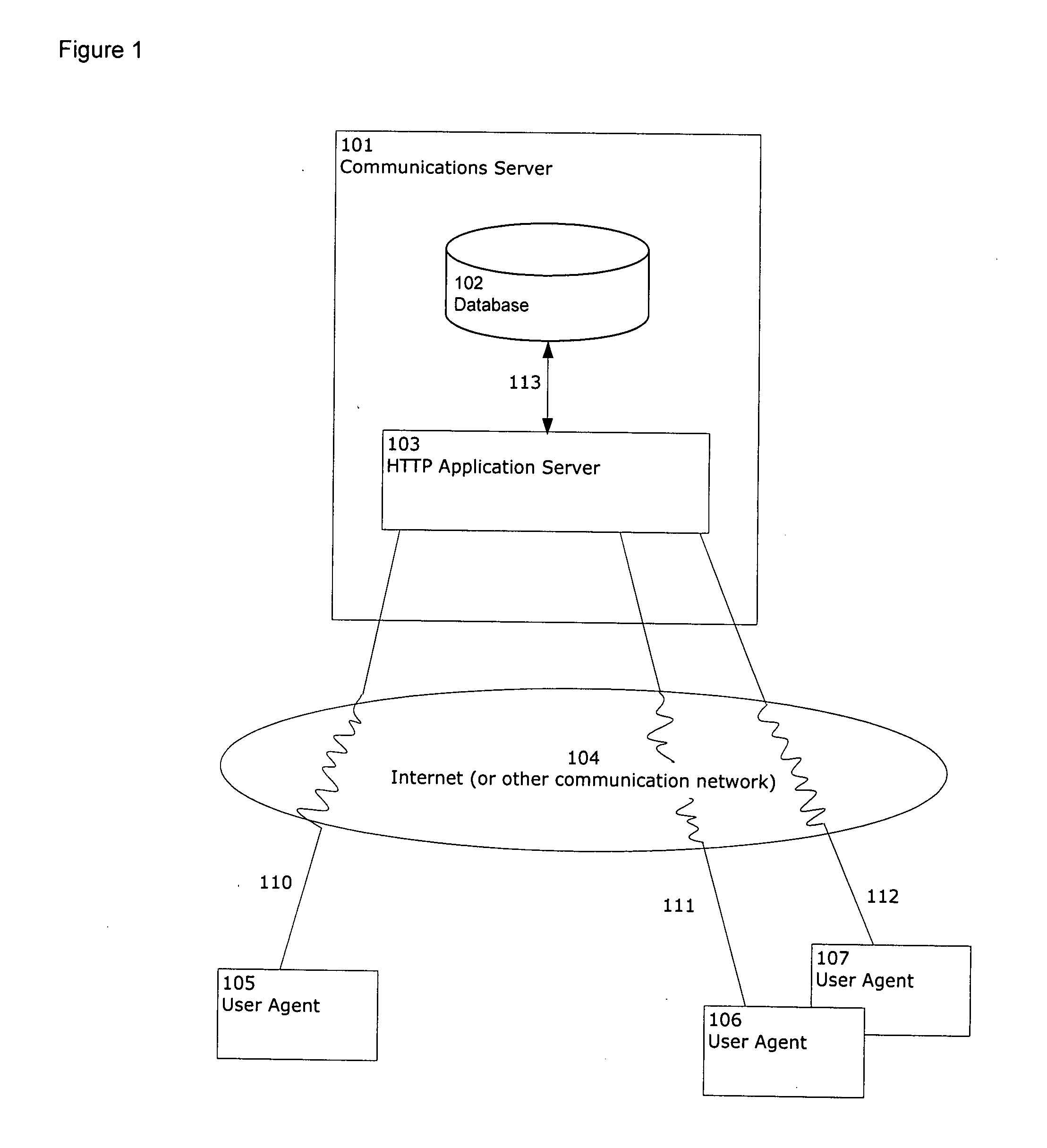
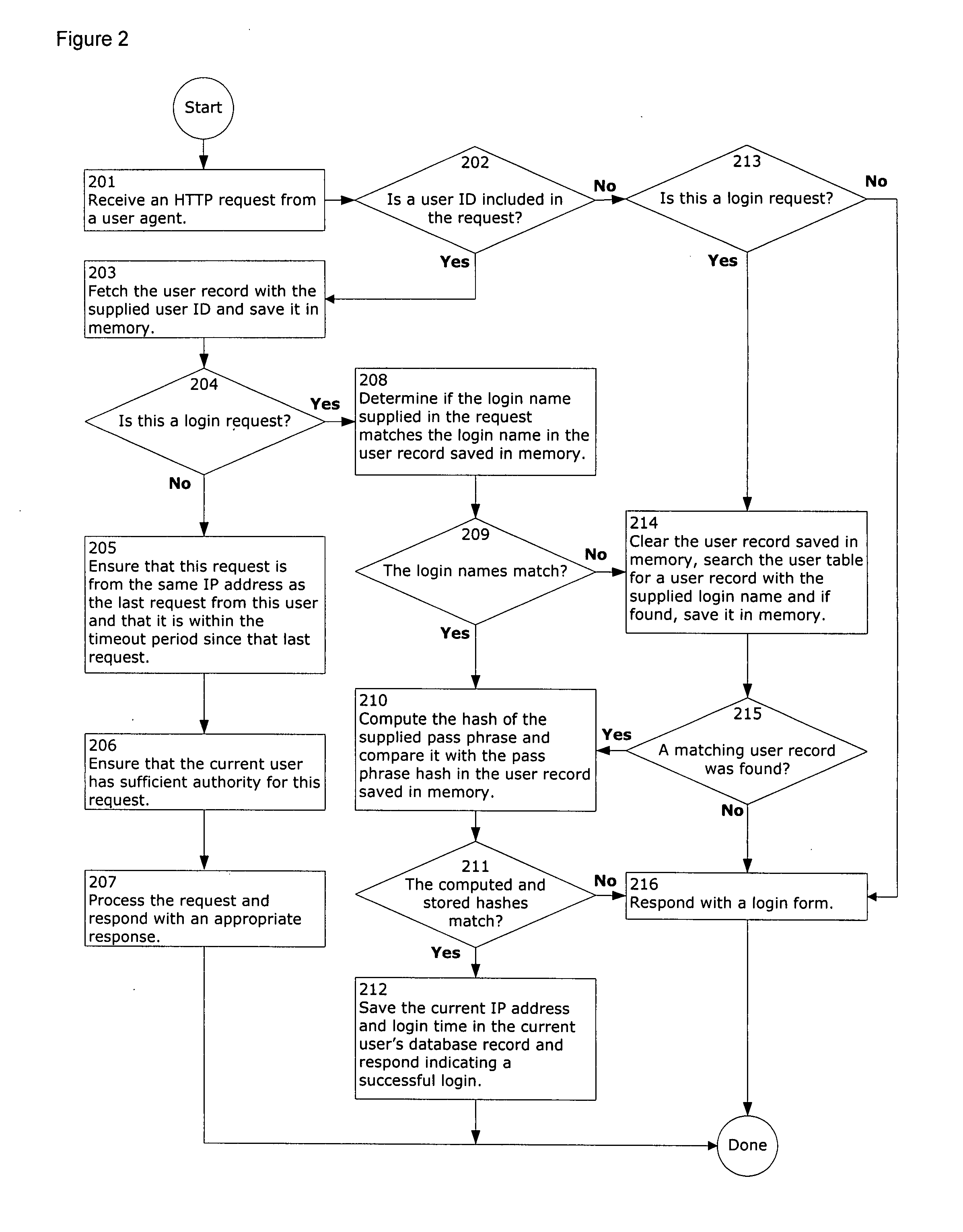
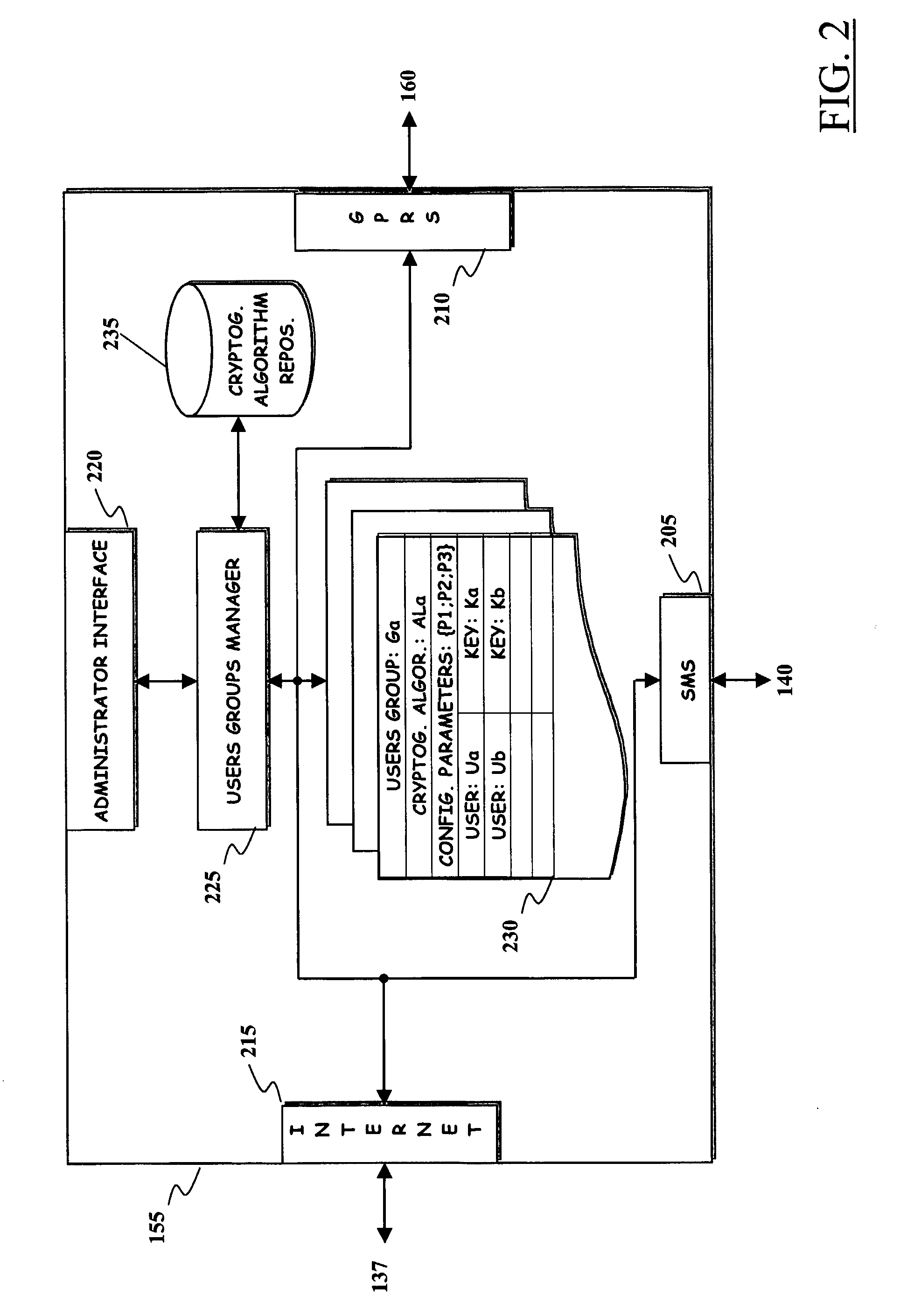
System and method of accessing keys for secure messaging
ActiveUS20050038991A1User identity/authority verificationNetwork topologiesMobile deviceSecure messaging
Methods and systems for handling on an electronic device a secure message to be sent to a recipient. Data is accessed about a security key associated with the recipient. The received data is used to perform a validity check related to sending a secure message to the recipient. The validity check may uncover an issue that exists with sending a secure message to the recipient. A reason is determined for the validity check issue and is provided to the mobile device's user.
Owner:MALIKIE INNOVATIONS LTD
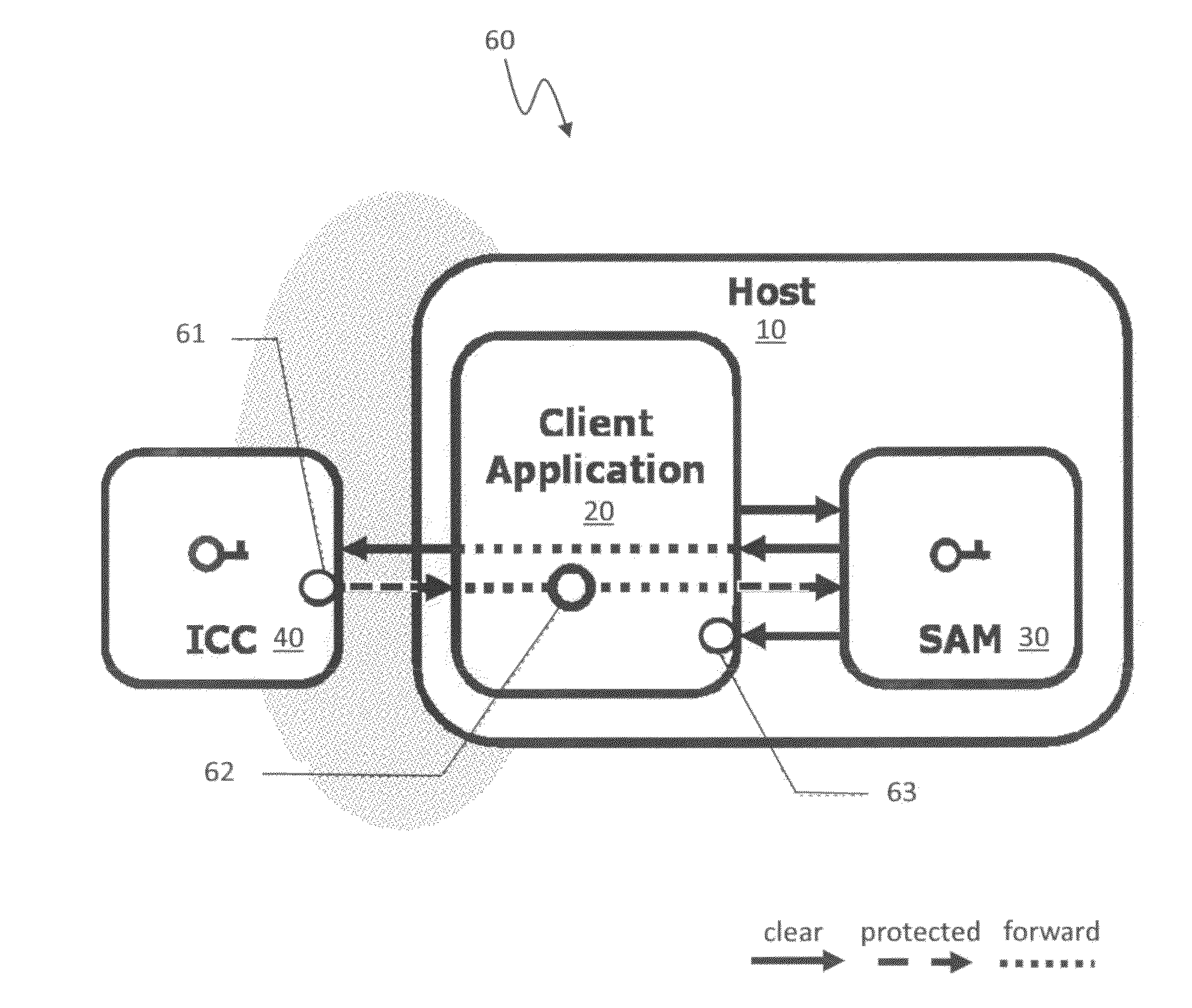
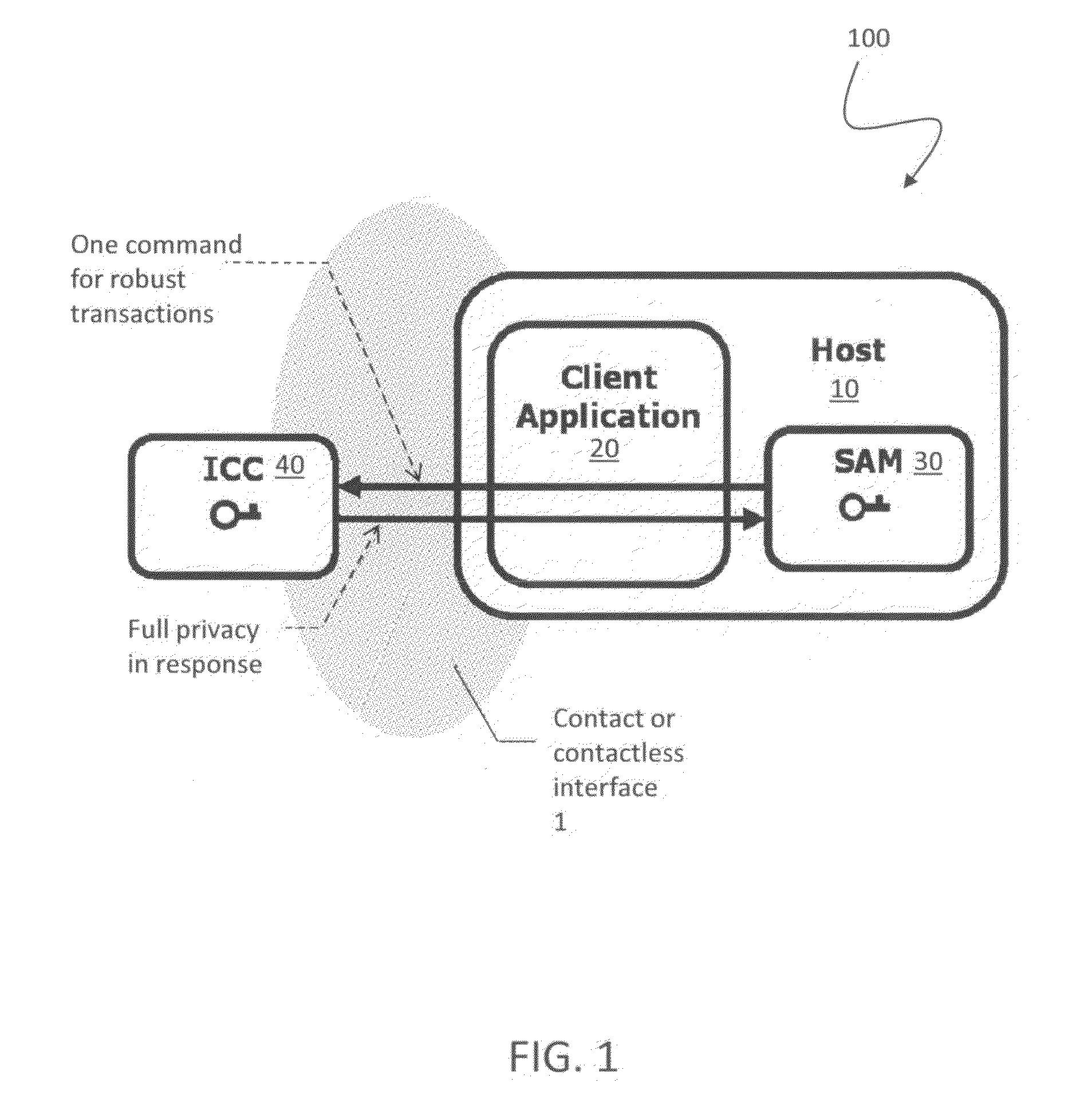
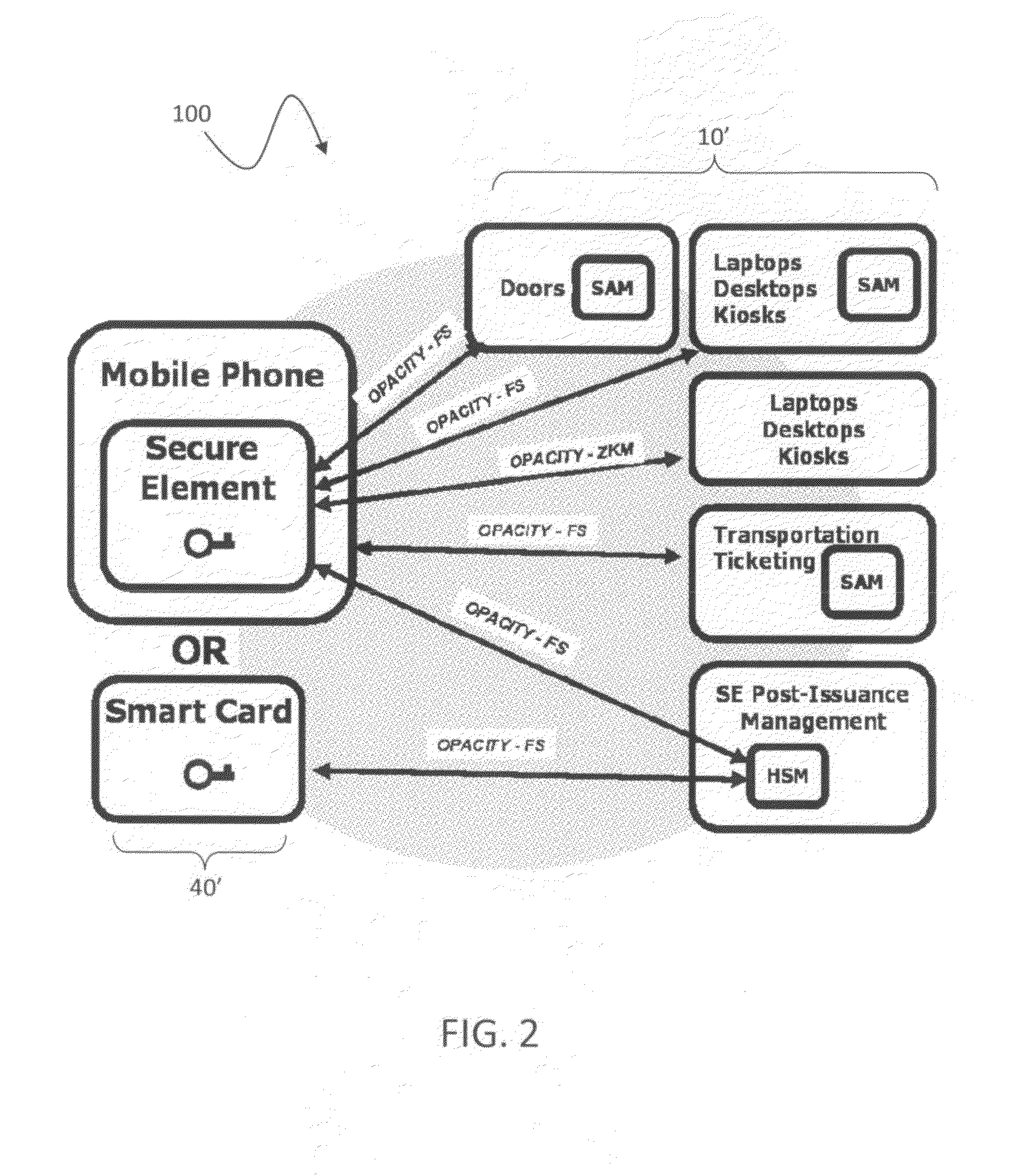
Open protocol for authentication and key establishment with privacy
ActiveUS20120144193A1Public key for secure communicationUser identity/authority verificationSmart cardPhysical access
A suite of efficient authentication and key establishment protocols for securing contact or contactless interfaces between communicating systems. The protocols may be used in secure physical access, logical access and / or transportation applications, among other implementations. The system authenticates a mobile device such as a smart card and / or mobile phone equipped with a secure element presented to one or more host terminals and establishes shared secure messaging keys to protect communications between the device and terminal. Secure messaging provides an end-to-end protected path of digital documents or transactions through the interface. The protocols provide that the device does not reveal identification information to entities different from a trusted host. The terminal may be a contactless reader at a door for controlling physical access, a desktop, laptop or kiosk for controlling logical access, and / or an access point for obtaining an encrypted digital ticket from an authenticated mobile device used for transit applications.
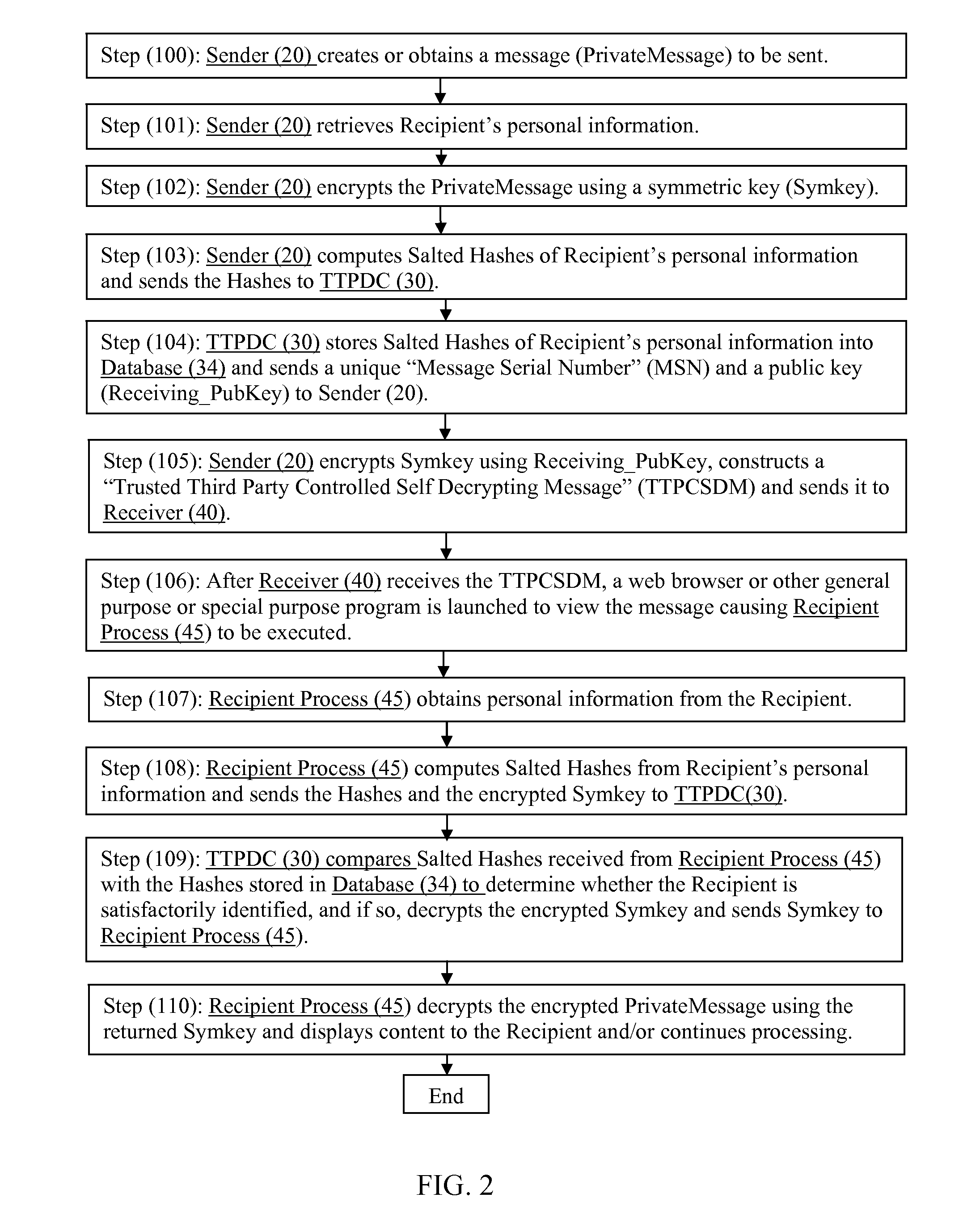
Owner:ASSA ABLOY AB
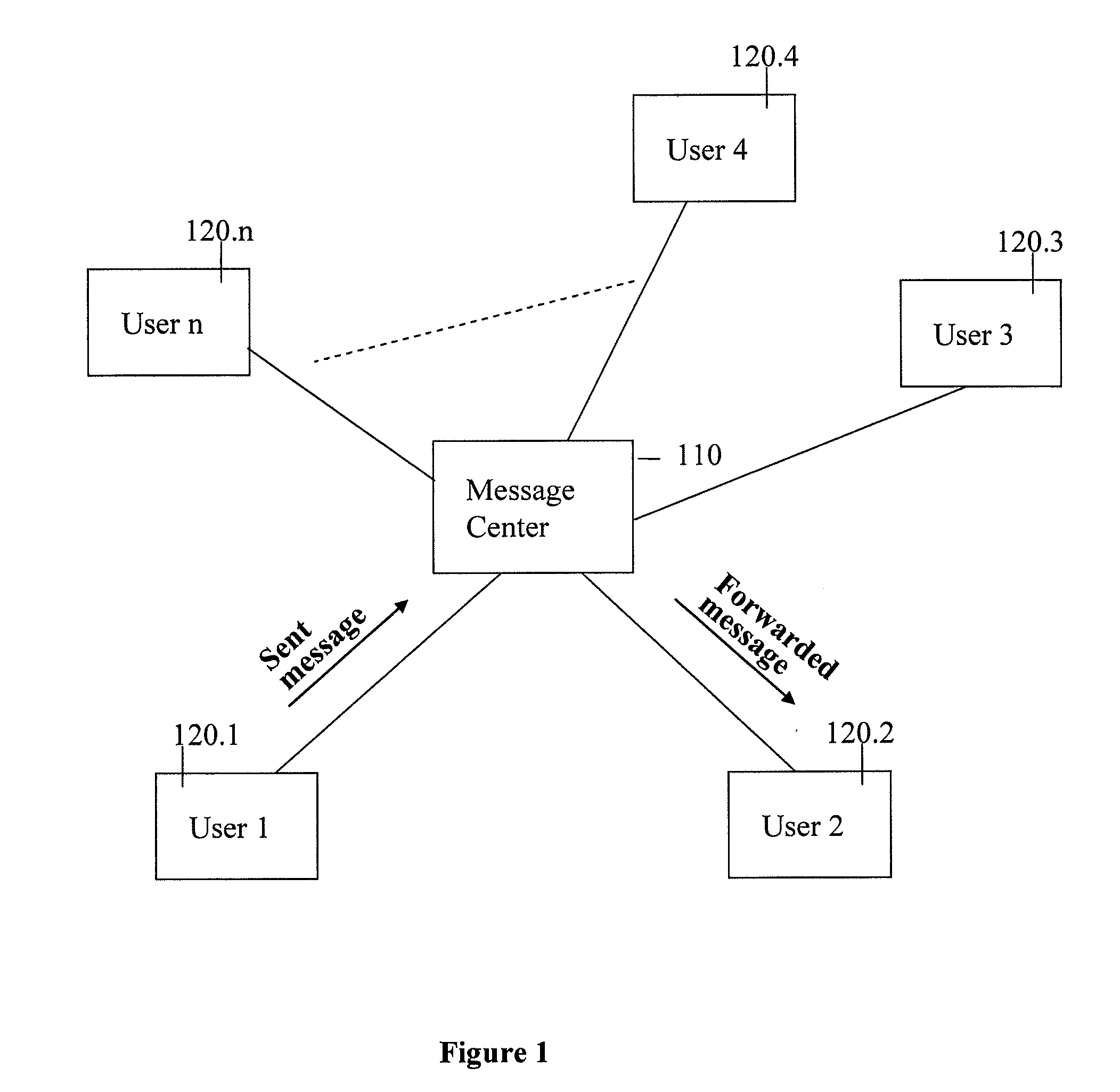
Secure messaging
InactiveUS20080123850A1Easy to useLow costData switching networksSecuring communicationSecure messaging
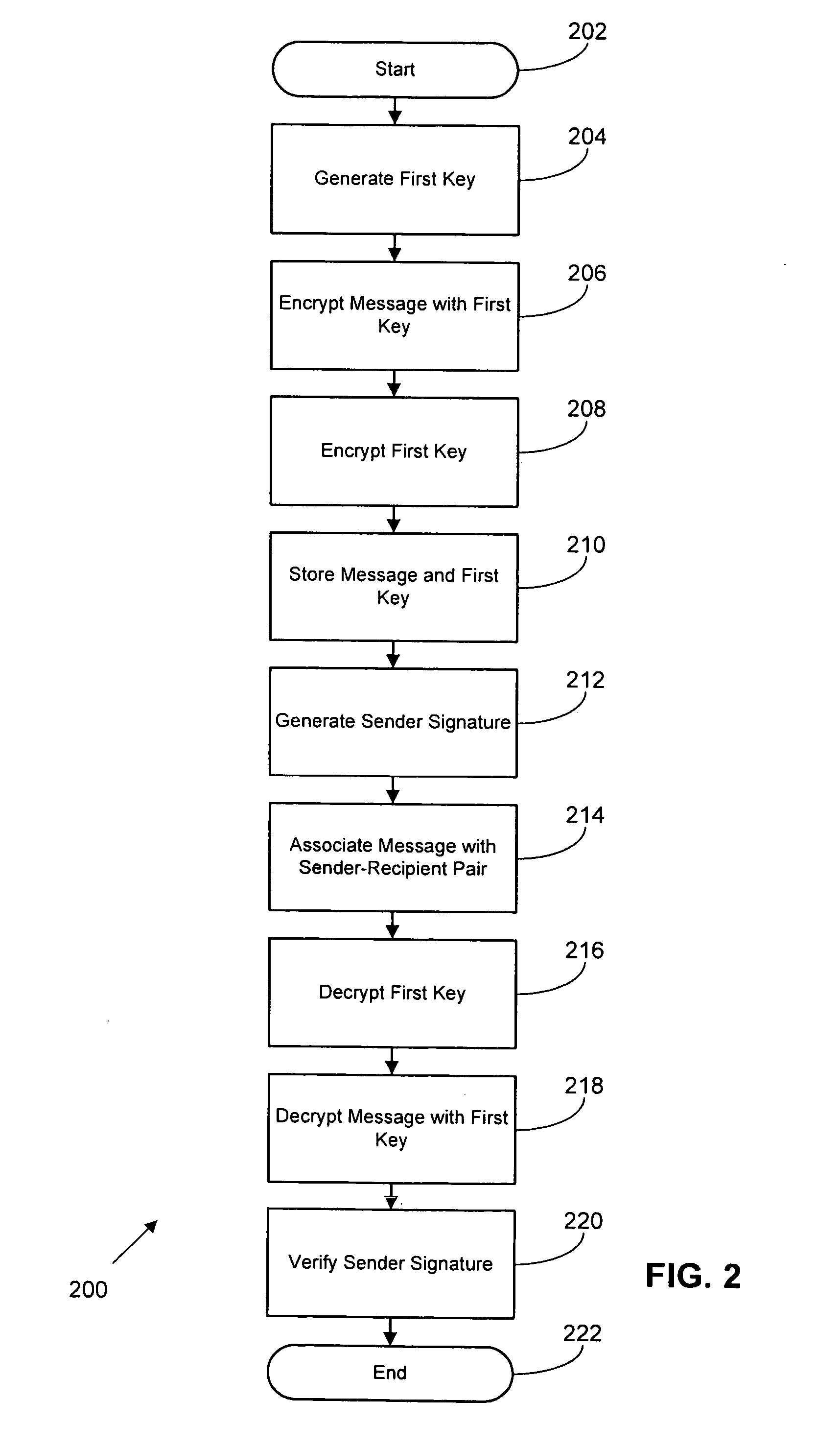
Methods, systems, and computer readable media for secure messaging. One method includes generating a first key associated with the sender. The method further includes encrypting a message from the sender to the recipient using the first key. The method also includes encrypting the first key with a second key. The method includes storing the encrypted message and the encrypted first key at a message server accessible to individuals including the sender and the recipient. The method includes associating the encrypted message with a sender and a recipient. The method also includes decrypting the encrypted first key using a key related to the second key, and decrypting the encrypted message using the first key.
Owner:BHATNAGAR RAJAT +3
Subscription management service for secure messaging system
InactiveUS7685414B1Key distribution for secure communicationPublic key for secure communicationInternet privacyService provision
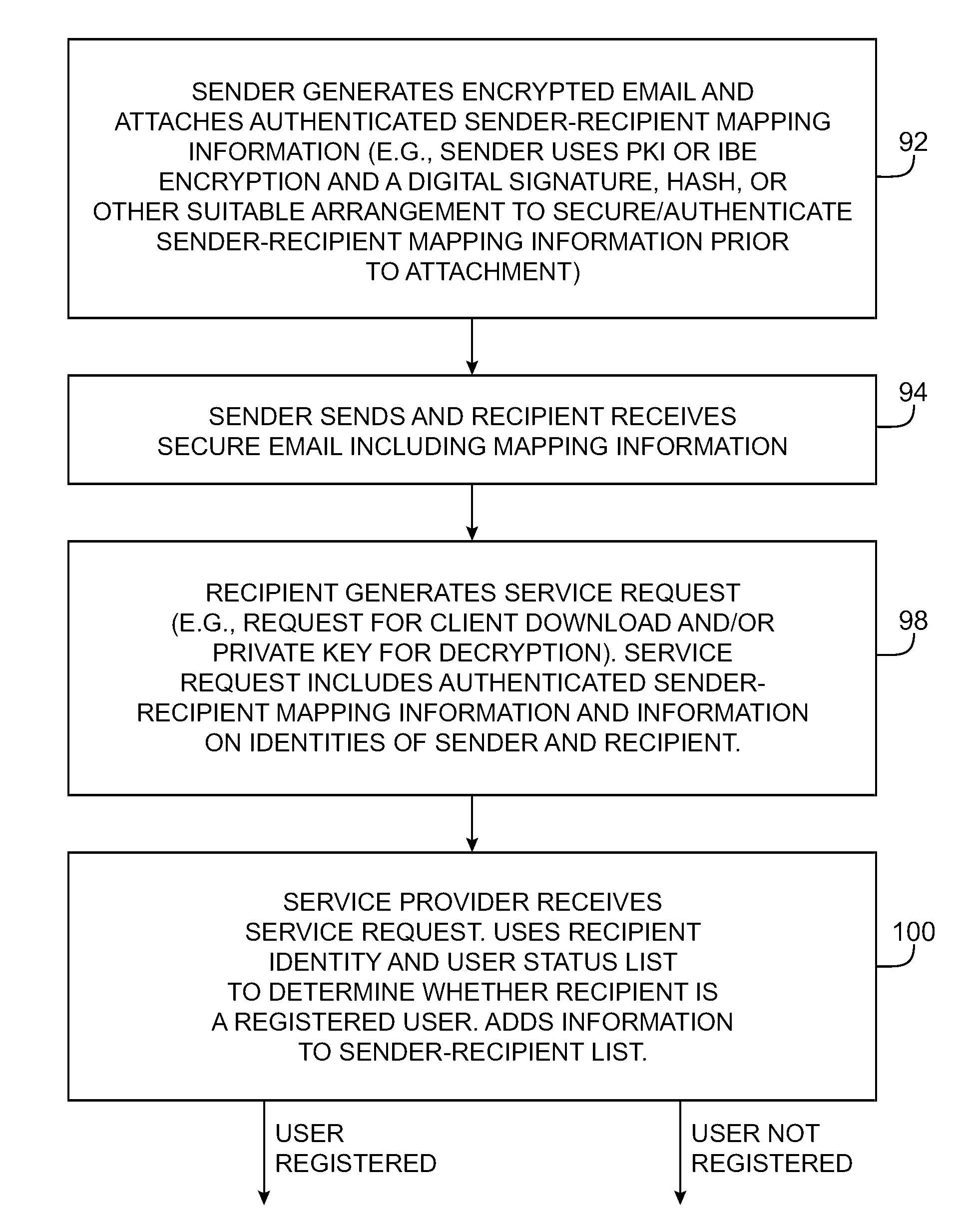
Systems and methods for secure messaging are provided. A sender may encrypt an email message for a recipient. The email message may contain authenticated sender-recipient mapping information. When a recipient requests a client software download or private key from a service provider, the service provider can verify the authenticity of the sender-recipient mapping information. This assures the service provider that the recipient has received a communication from the sender and allows the service provider to provide services to the recipient based on the status of the sender. If the sender is a member of an organization that is a direct customer of the service provider, the service provider may satisfy the recipient's service request.
Owner:MICRO FOCUS LLC
Method and apparatus for secure messaging
InactiveUS20090257593A1Multiple keys/algorithms usageSecret communicationComputer hardwareStore and forward
A network-based method for secure messaging is performed by: receiving a message sent by a sender to a recipient with a store-and-forward protocol, at a network location. The received message is decrypted at the network location with the sender's encryption key. Then the decrypted message is encrypted at the network location with the recipient's encryption key, and forwarded from the network location for delivery to the recipient.
Owner:COMVERSE
System and method of indicating the strength of encryption
ActiveUS20050039004A1Data switching by path configurationPlatform integrity maintainanceTrust levelSecure messaging
A method and system are provided for secure messaging on mobile computing devices. The method and system provide for an indication of a security trust level associated with a security method used with an electronic message.
Owner:MALIKIE INNOVATIONS LTD
Secure messaging
ActiveUS20130275758A1Improve the level ofReduce consumptionKey distribution for secure communicationUser identity/authority verificationPrivate communicationOff the shelf
Given the rise in popularity of communicating personal, private, sensitive, or vital peer-to-peer or peer-to-group information over insecure text messaging infrastructure, it would be highly desirable to provide a lightweight solution that enables the exchange of information in a secure manner. The non-limiting technology herein provides systems and methods for the exchange of cryptographic material that can be used to encipher message-oriented communications between at least two peer devices. Once the cryptographic material is exchanged between cooperating peers, this lightweight solution can be used by common off the shelf hardware such as smartphones, tablets, feature phones, or special purpose machine to machine devices for private communications, such as command and control, location services, etc. using insecure voice or data communication paths, such as SMS.
Owner:GLOBAL INTEGRITY INC
Secure messaging
ActiveUS20140310514A1Key distribution for secure communicationDigital data authenticationTransmitterSecure messaging
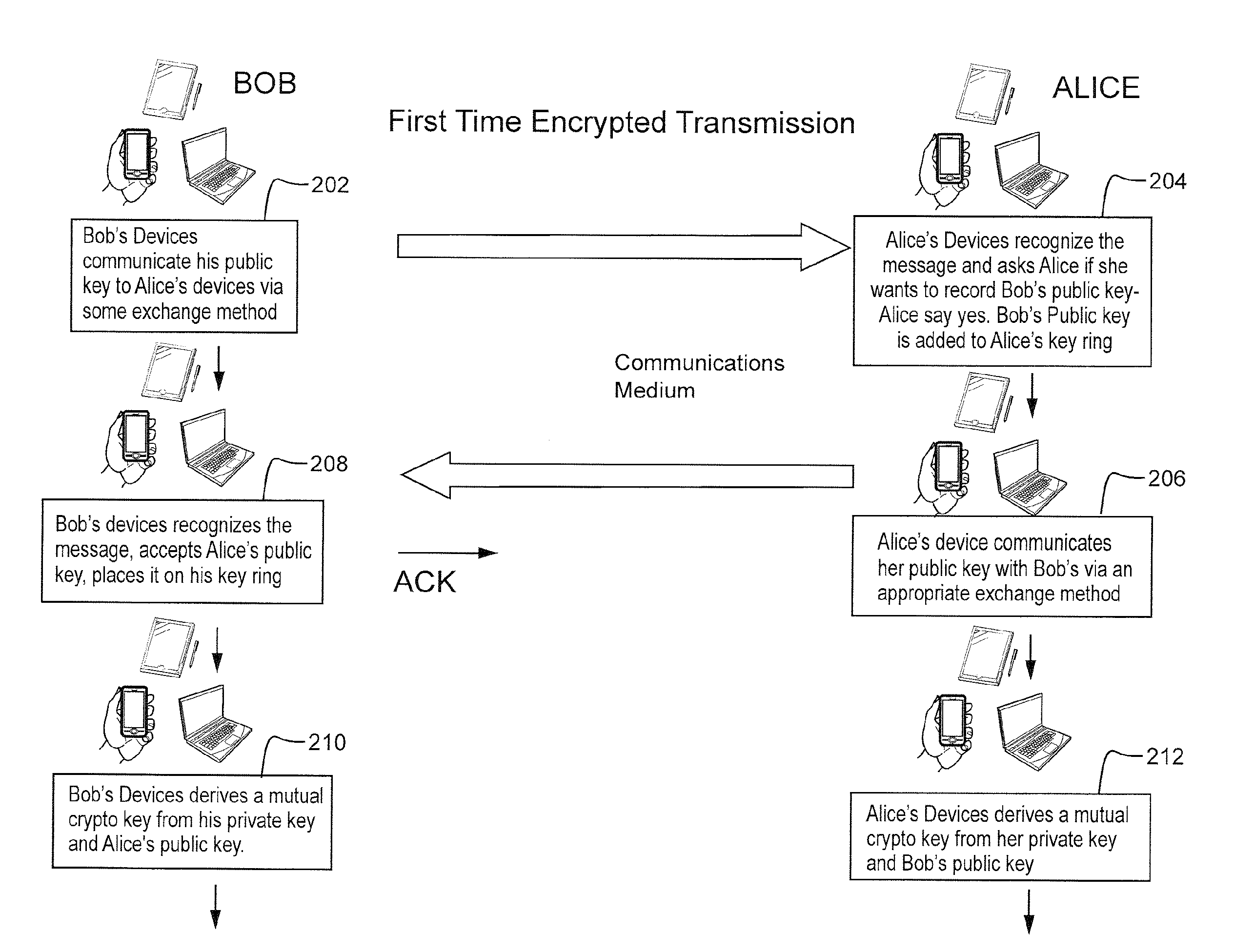
A method for transmitting an encrypted message from a messaging server (106) to a handset (104) comprising the steps of receiving, at the messaging server (106) and from a sender computer (102), a message to be sent to the handset (104) and a handset identifier associated with the handset and determining that the handset is not registered with the messaging server (106) by determining that the handset identifier does not have an associated handset encryption key stored at the messaging server. The handset (104) is registered by sending a notification to the handset requesting registration, receiving back a handset encryption key associated with the handset identifier; and storing the handset encryption key against the handset identifier at the messaging server which is to be used to encrypt the received message before sending. Prior to registering the handset (104), intermediate encryption of the message may be employed to create an intermediate encrypted message to be stored at the messaging server.
Owner:SOPRANO DESIGN PTY LTD
User authentication
ActiveUS20140250512A1Digital data processing detailsMultiple digital computer combinationsUser authenticationMessage authentication code
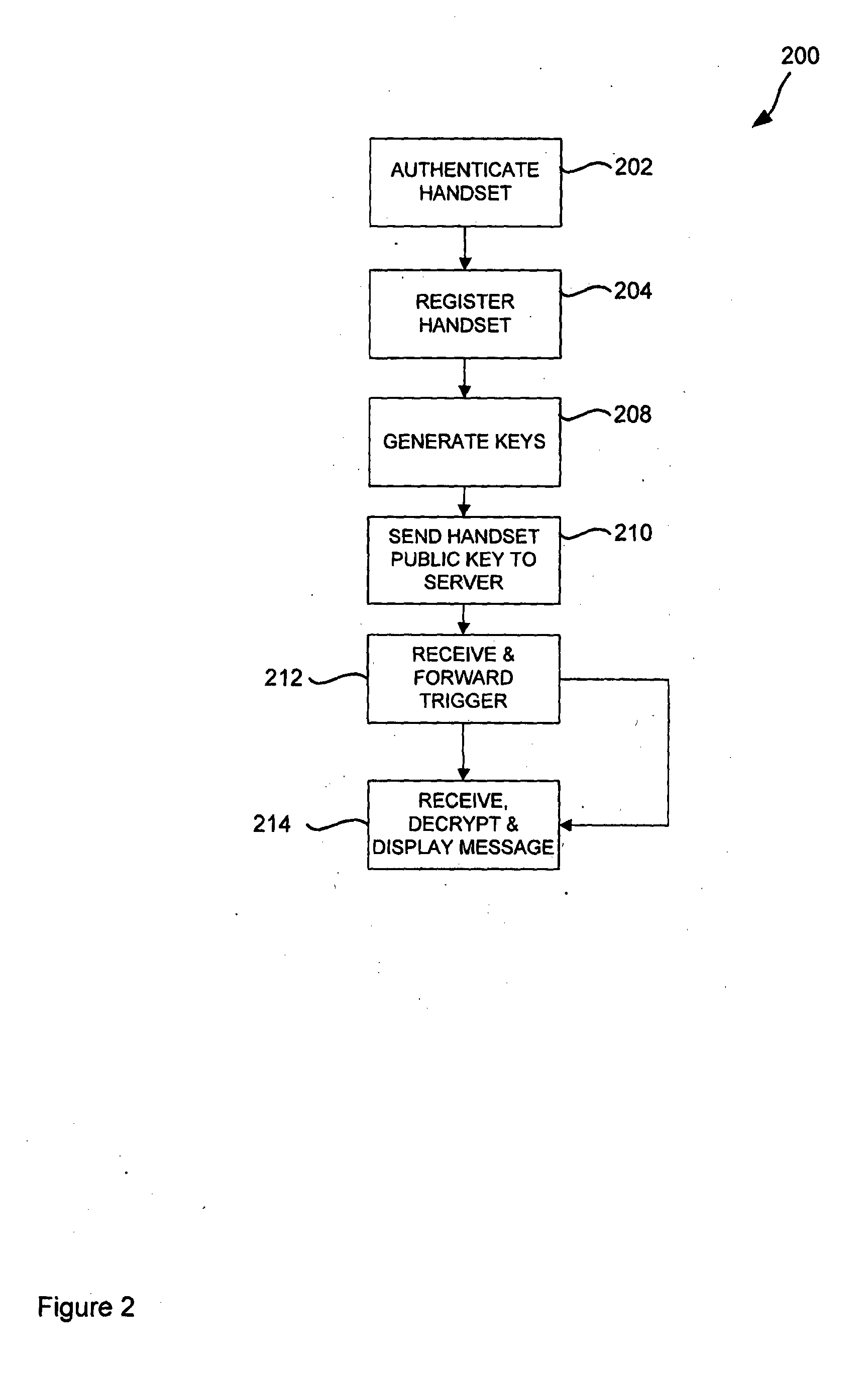
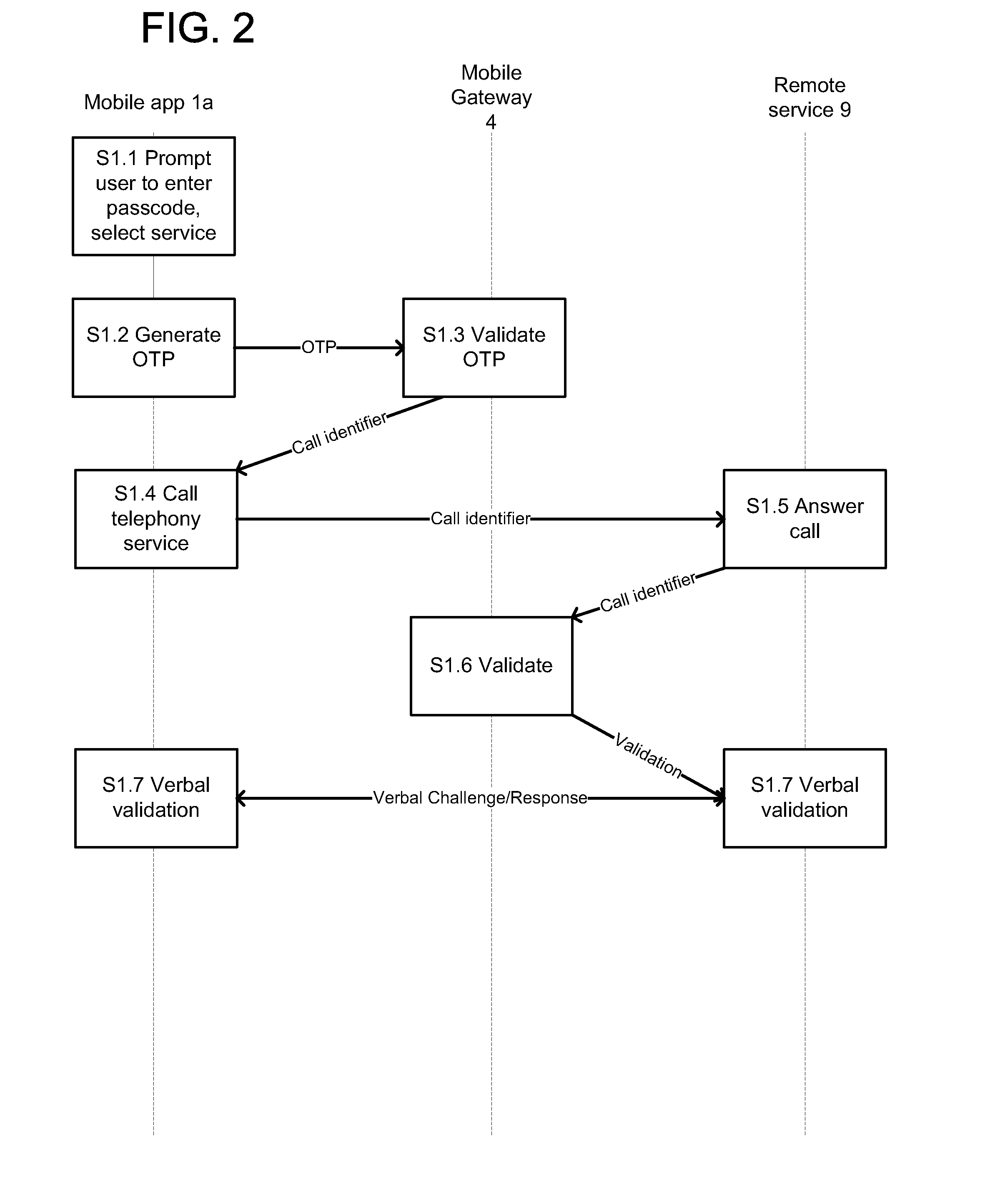
User Authentication A mobile user authentication application is operable to perform one or more of the following operations: •authenticate a user in a voice call to a telephony service, by passing an authentication code to the telephony service within the voice call [FIGS. 2, 2c]; •validate a user instruction during a secure messaging session [FIG. 3]; and •authenticate a user at a physical local service by obtaining a challenge code at that local service, validating the challenge code with a remote authentication service, obtain a confirmation code from the authentication service and presenting the confirmation code for validation at the local service [FIGS. 4, 4a and 4b].
Owner:BARCLAYS EXECUTION SERVICES LTD
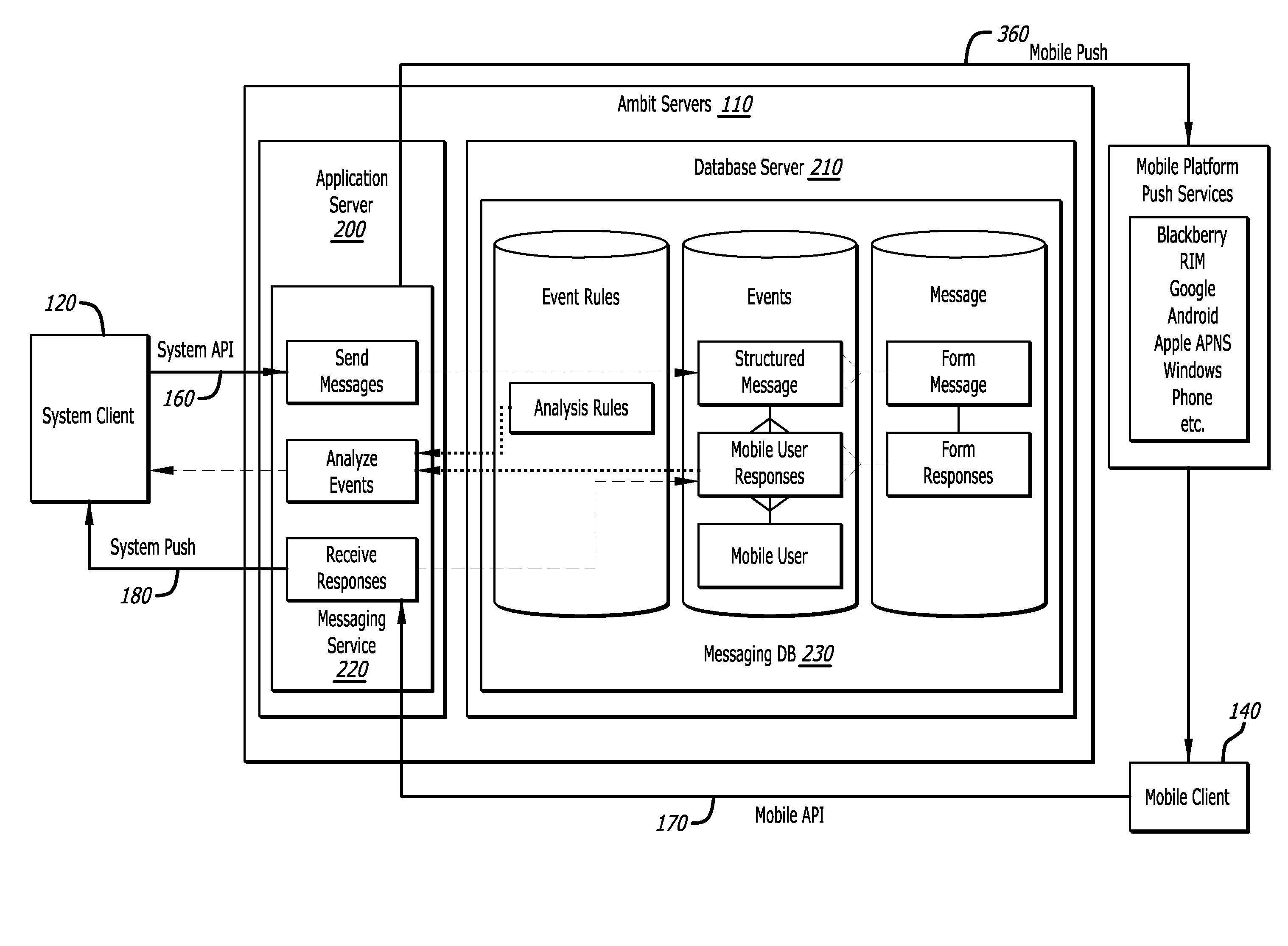
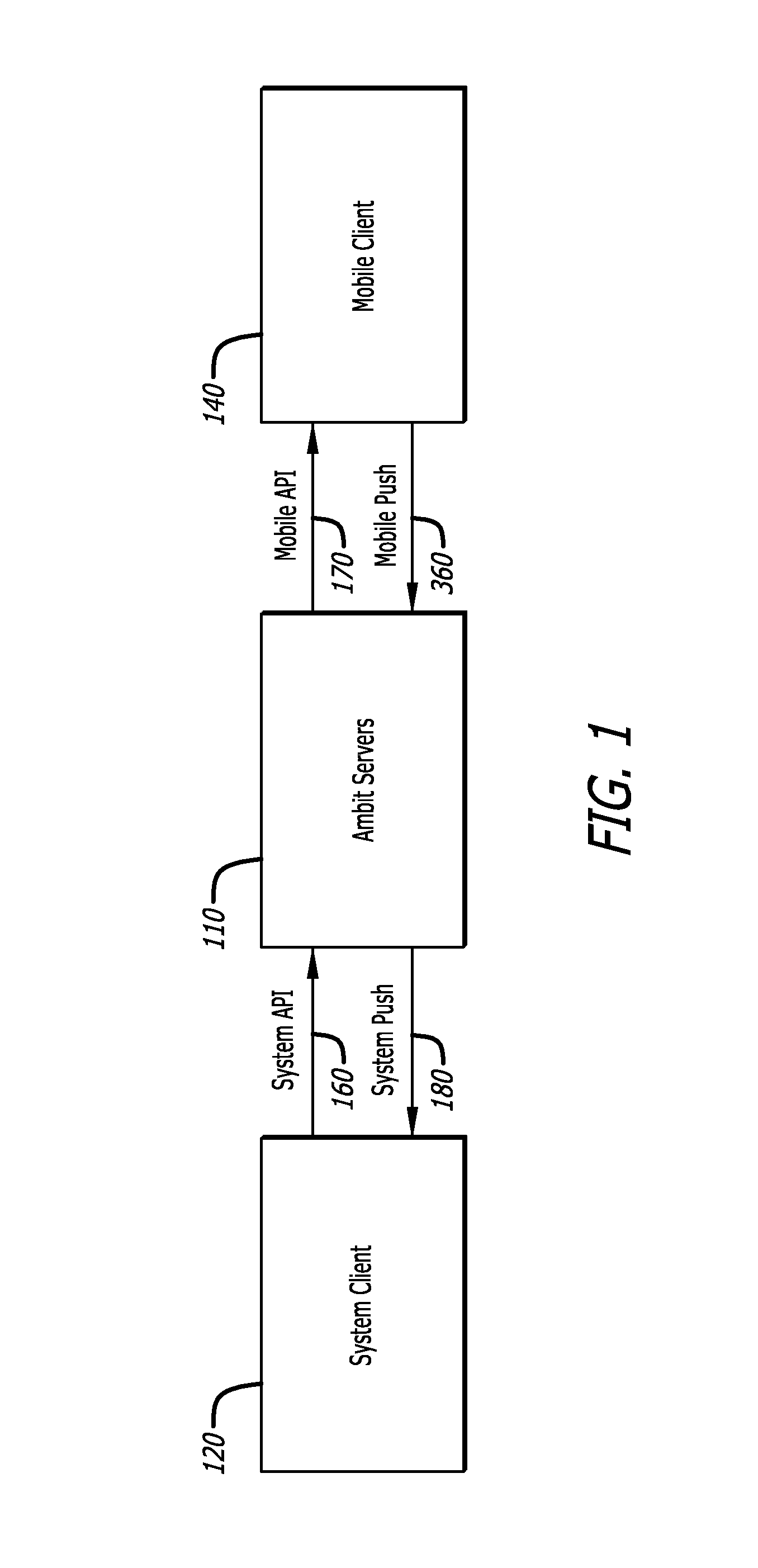
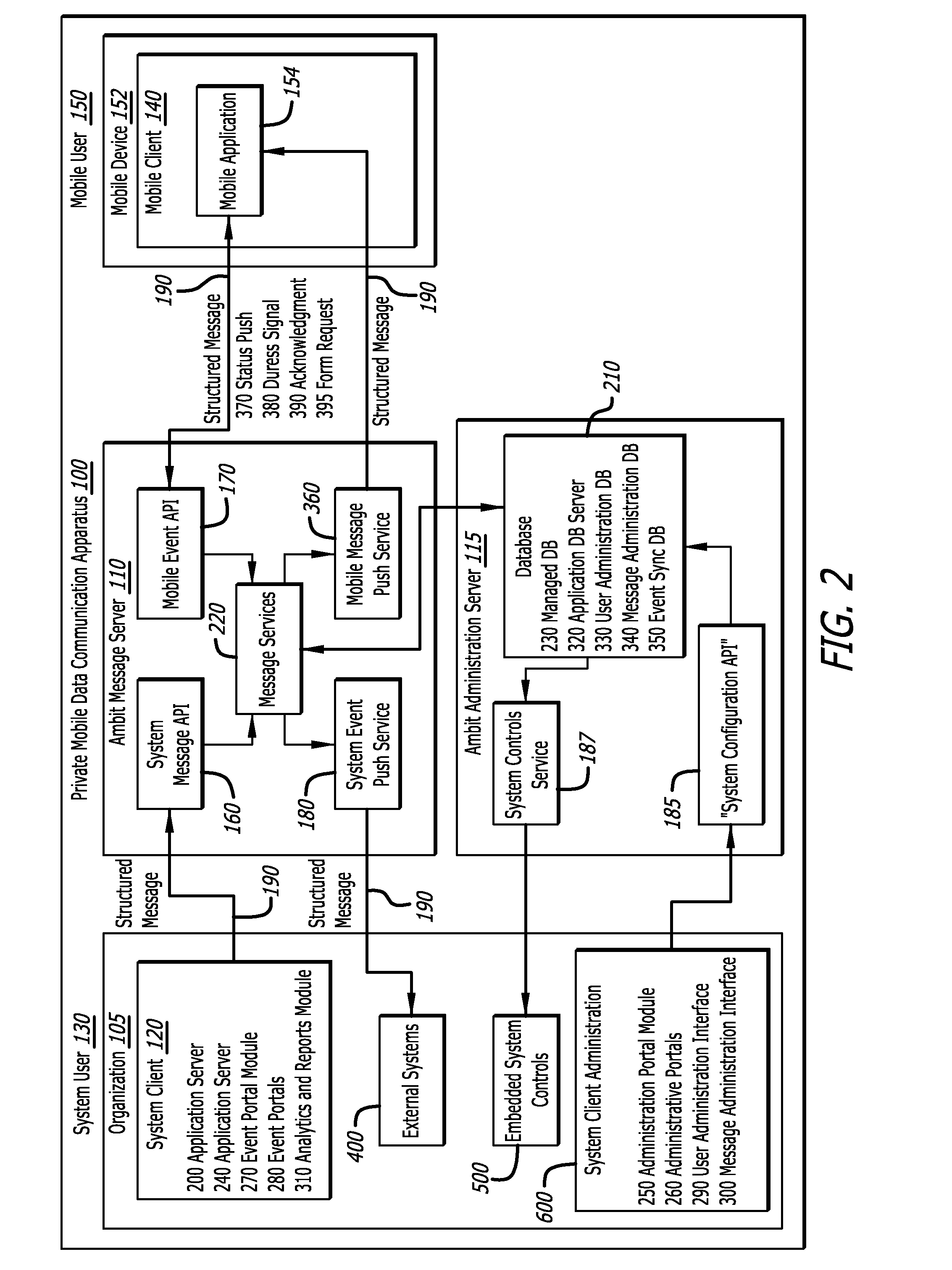
Private mobile messaging and data communications apparatus and method of managing organizational messaging
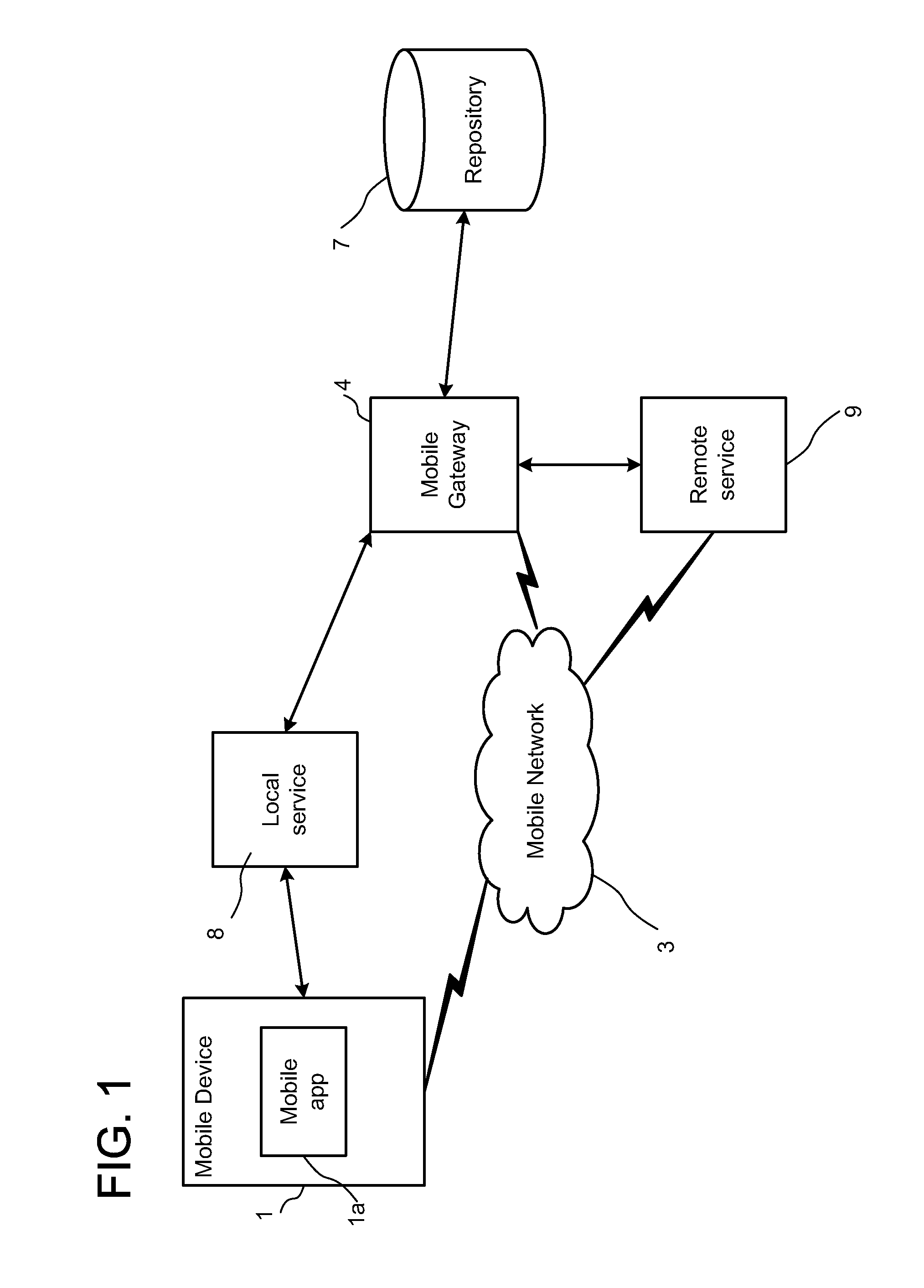
ActiveUS20120047214A1Simple structureEmergency connection handlingMultiple digital computer combinationsData streamApplication software
A private mobile data communications apparatus and methods of managing organizational data flow and coordinate a secure messaging infrastructure allow organizations to communicate with and monitor one or more mobile users each having at least one mobile device with which they communicate. The apparatus includes a server component, system client, a mobile client, and multiple application programming interface modules configured to manage information flow and correspond with external systems as needed.
Owner:HEYHQ INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com