Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
212 results about "Key server" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
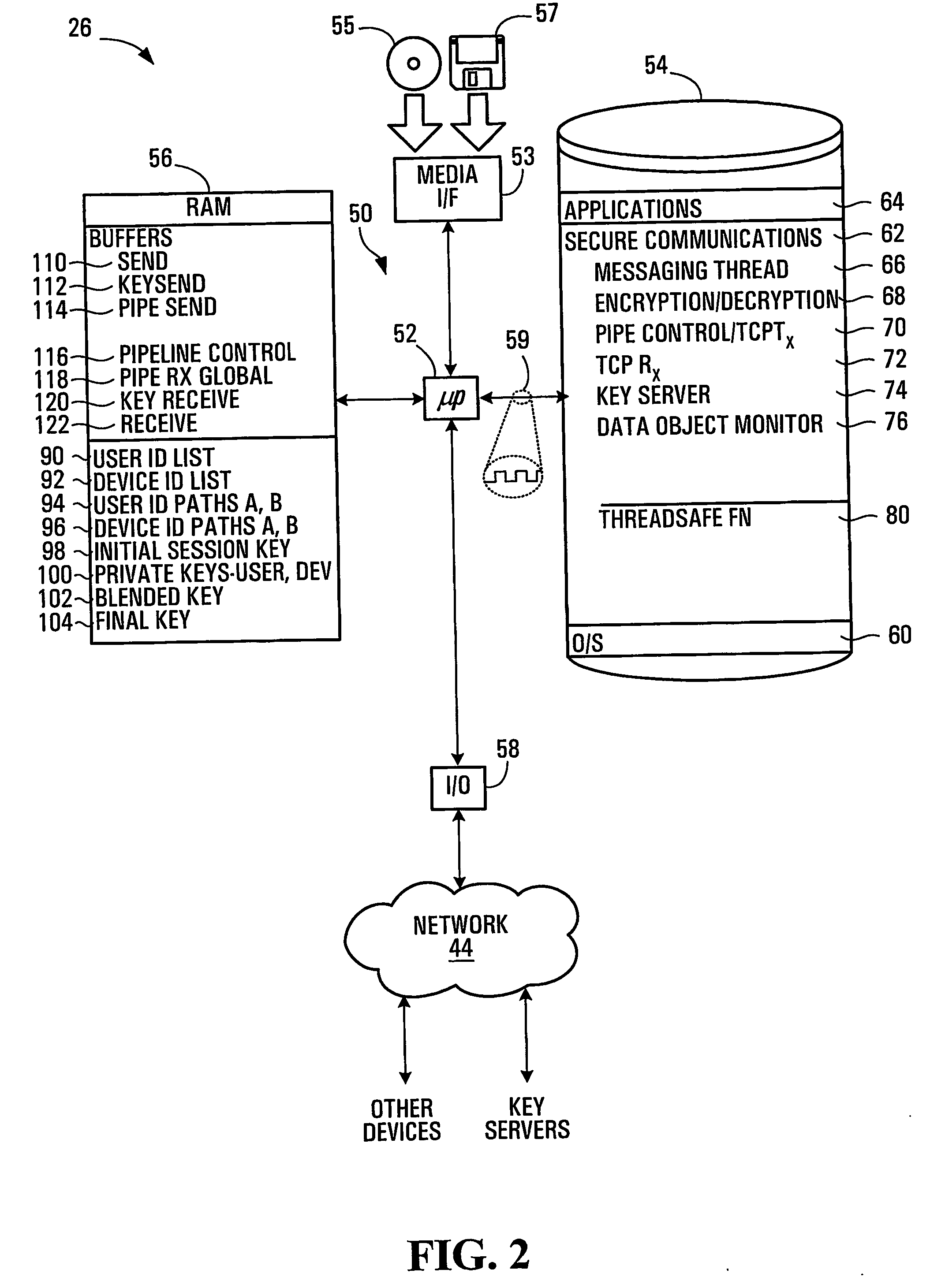
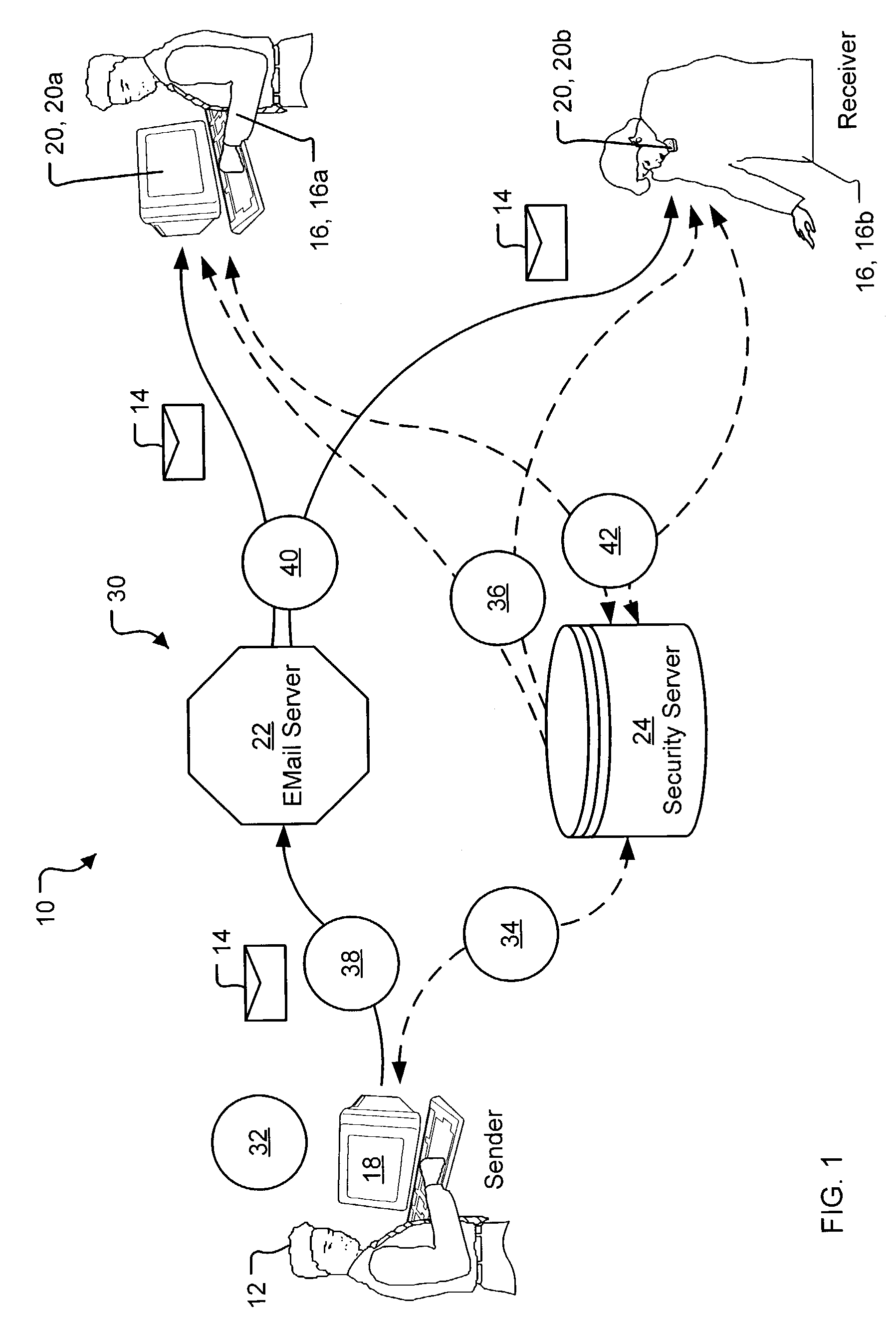
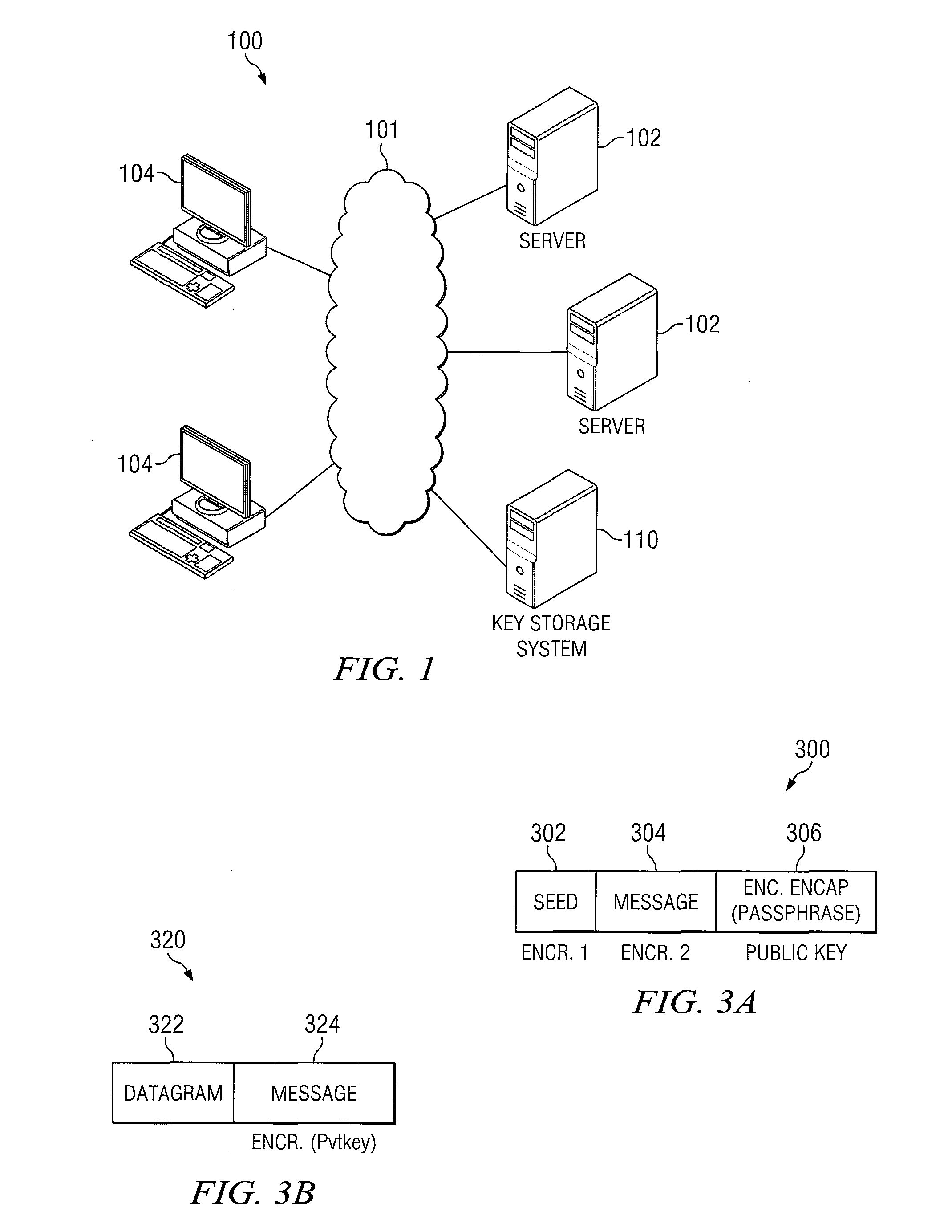
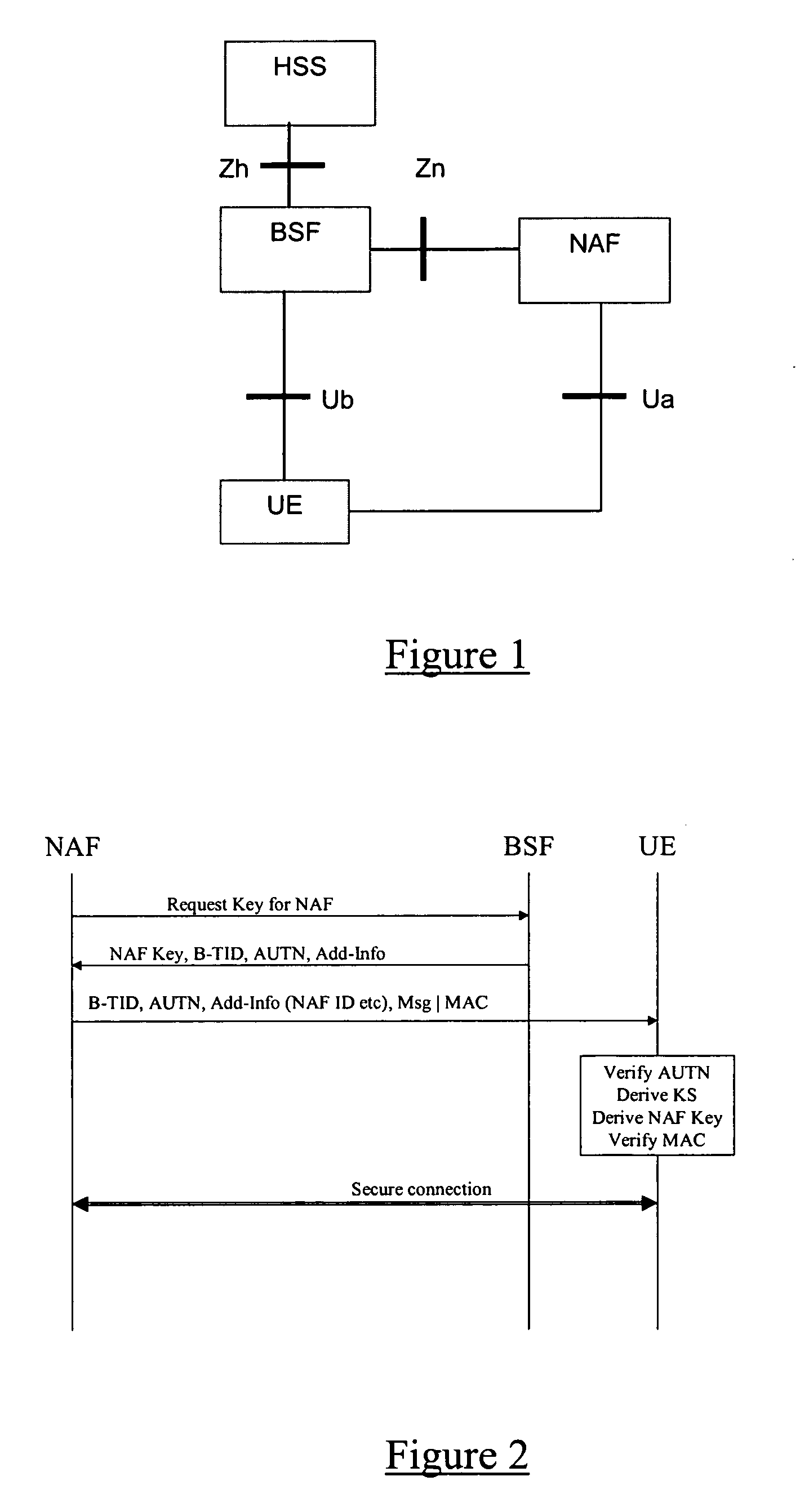
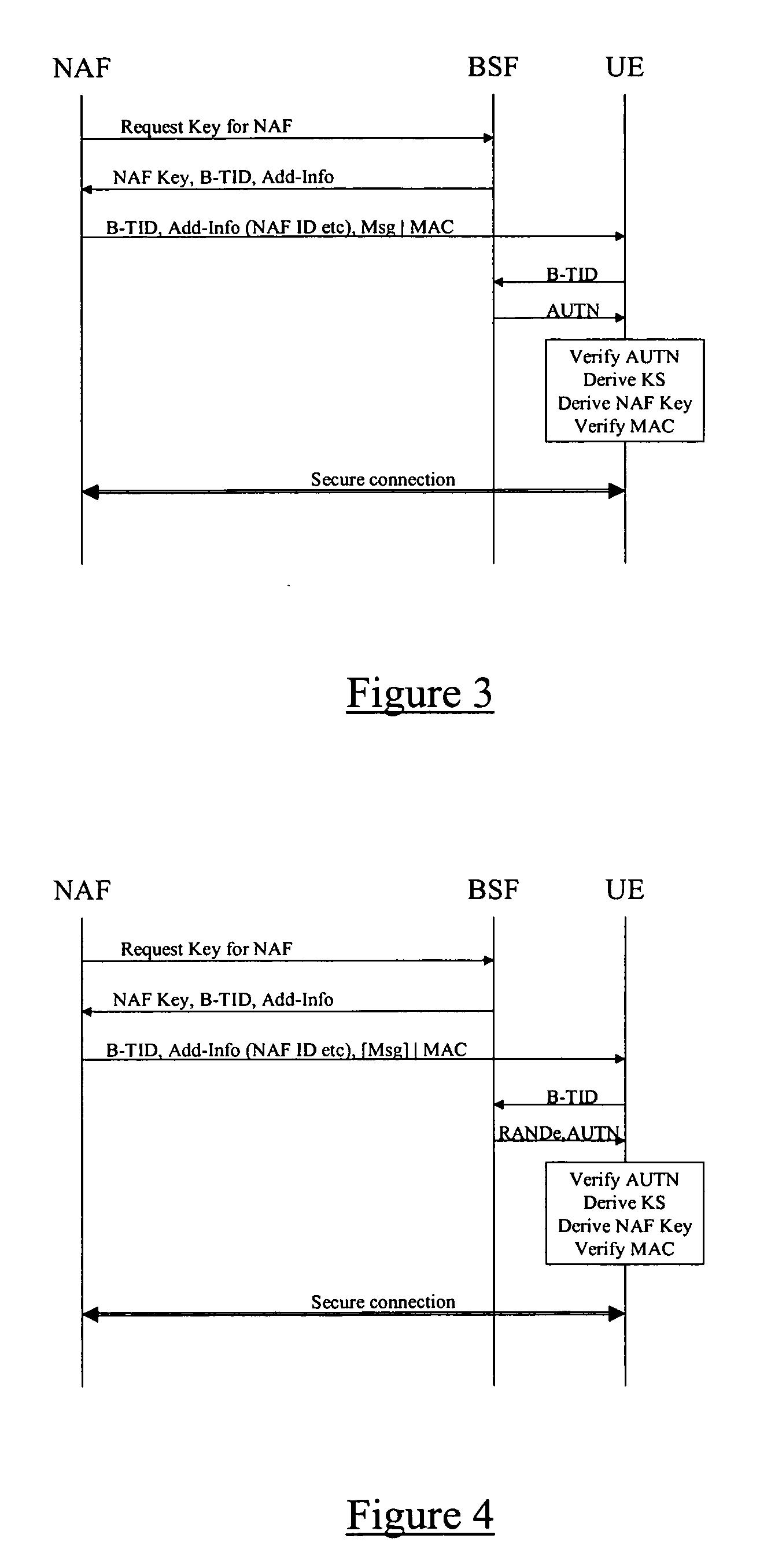
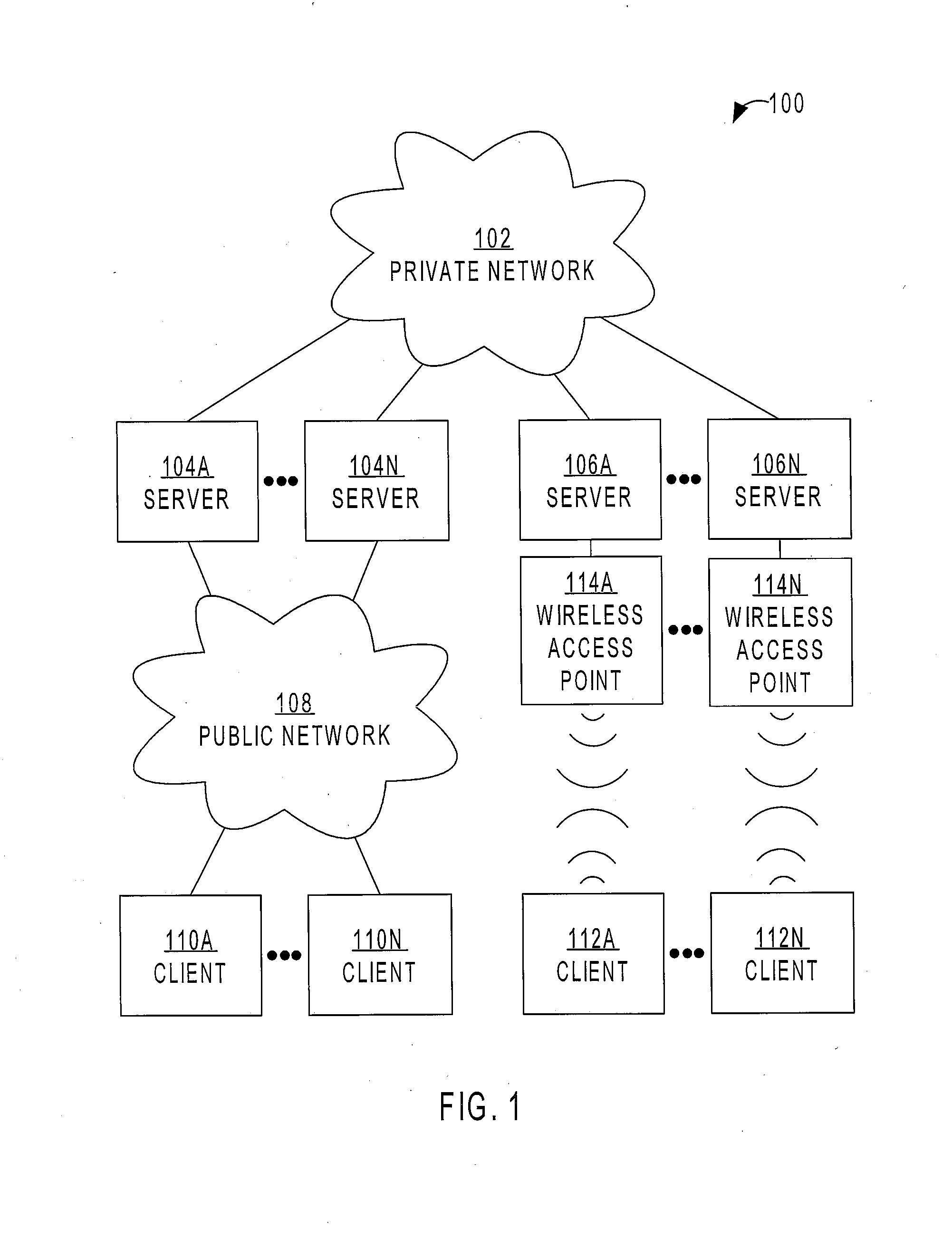
In computer security, a key server is a computer that receives and then serves existing cryptographic keys to users or other programs. The users' programs can be working on the same network as the key server or on another networked computer.
Encryption-Based Data Access Management
ActiveUS20140164774A1Key distribution for secure communicationSynchronising transmission/receiving encryption devicesKey serverData access
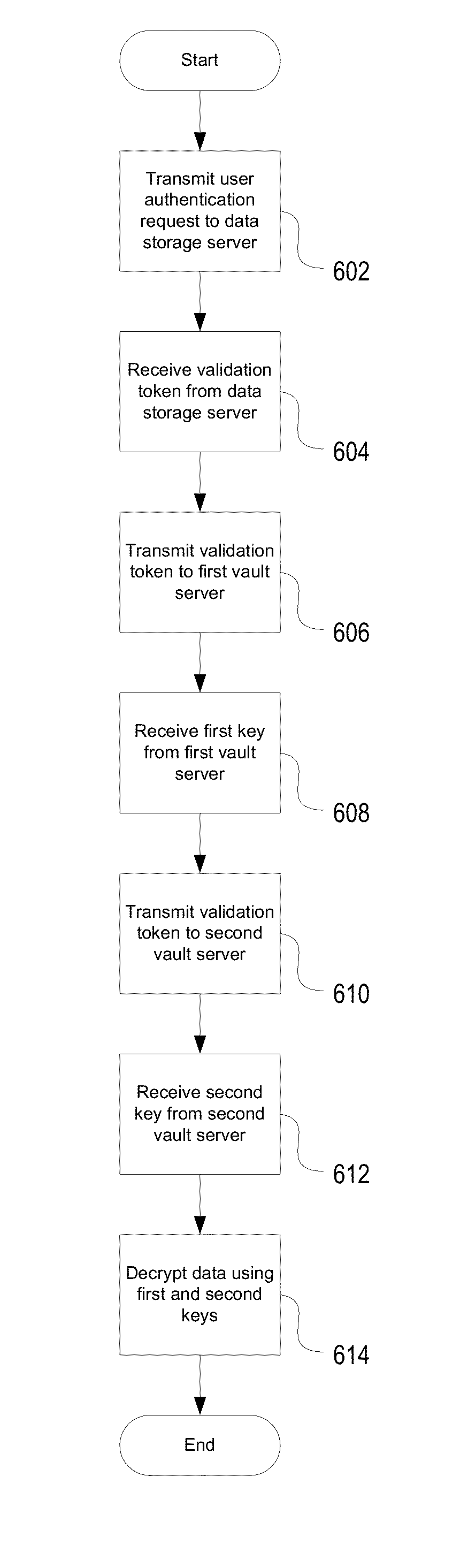
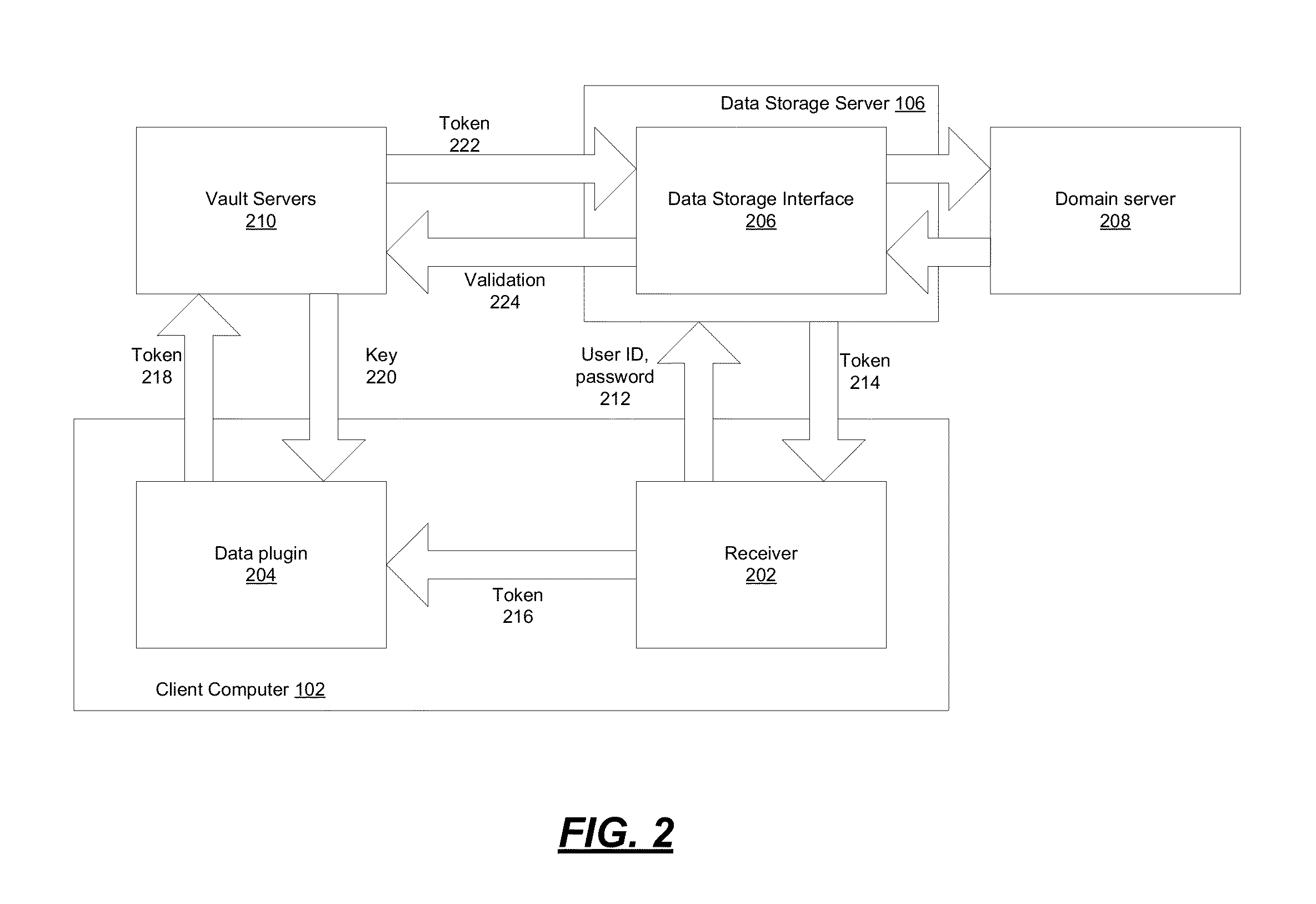
Encryption-based data access management may include a variety of processes. In one example, a device may transmit a user authentication request for decrypting encrypted data to a data storage server storing the encrypted data. The computing device may then receive a validation token associated with the user's authentication request, the validation token indicating that the user is authenticated to a domain. Subsequently, the computing device may transmit the validation token to a first key server different from the data storage server. Then, in response to transmitting the validation token the computing device may receive, from the first key server, a key required for decrypting the encrypted data. The device may then decrypt at least a portion of the encrypted data using the key.
Owner:CITRIX SYST INC
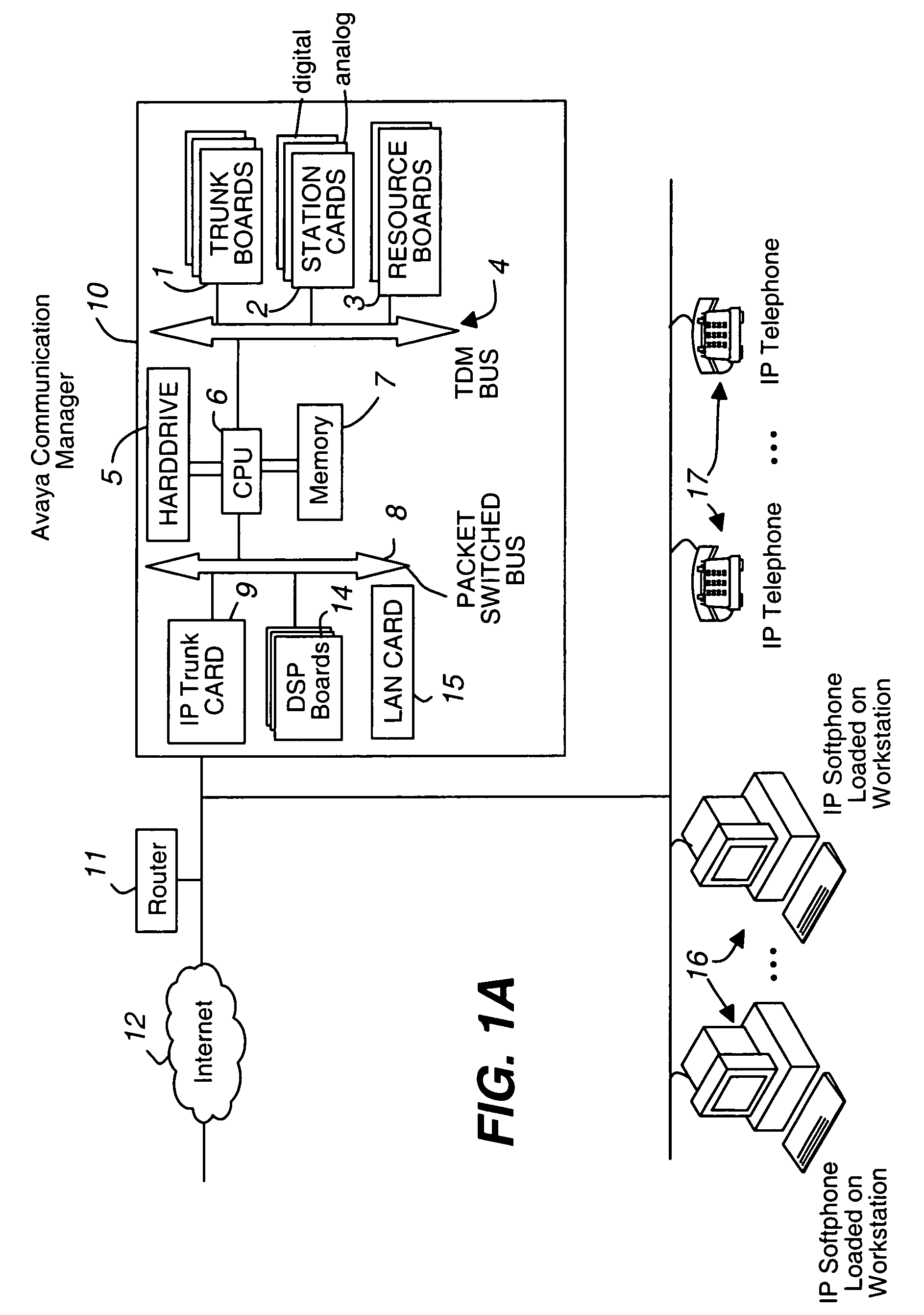
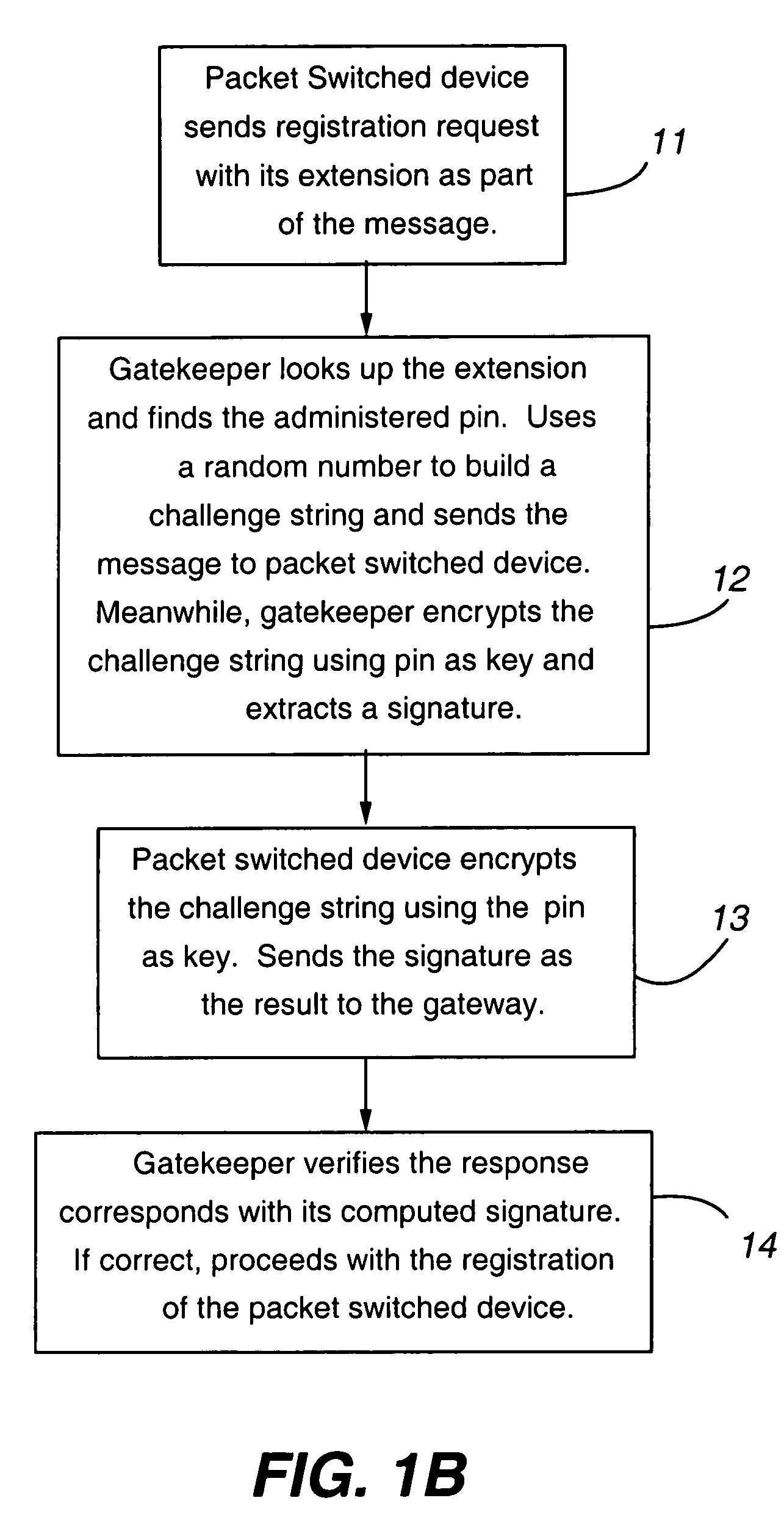
Key server for securing IP telephony registration, control, and maintenance
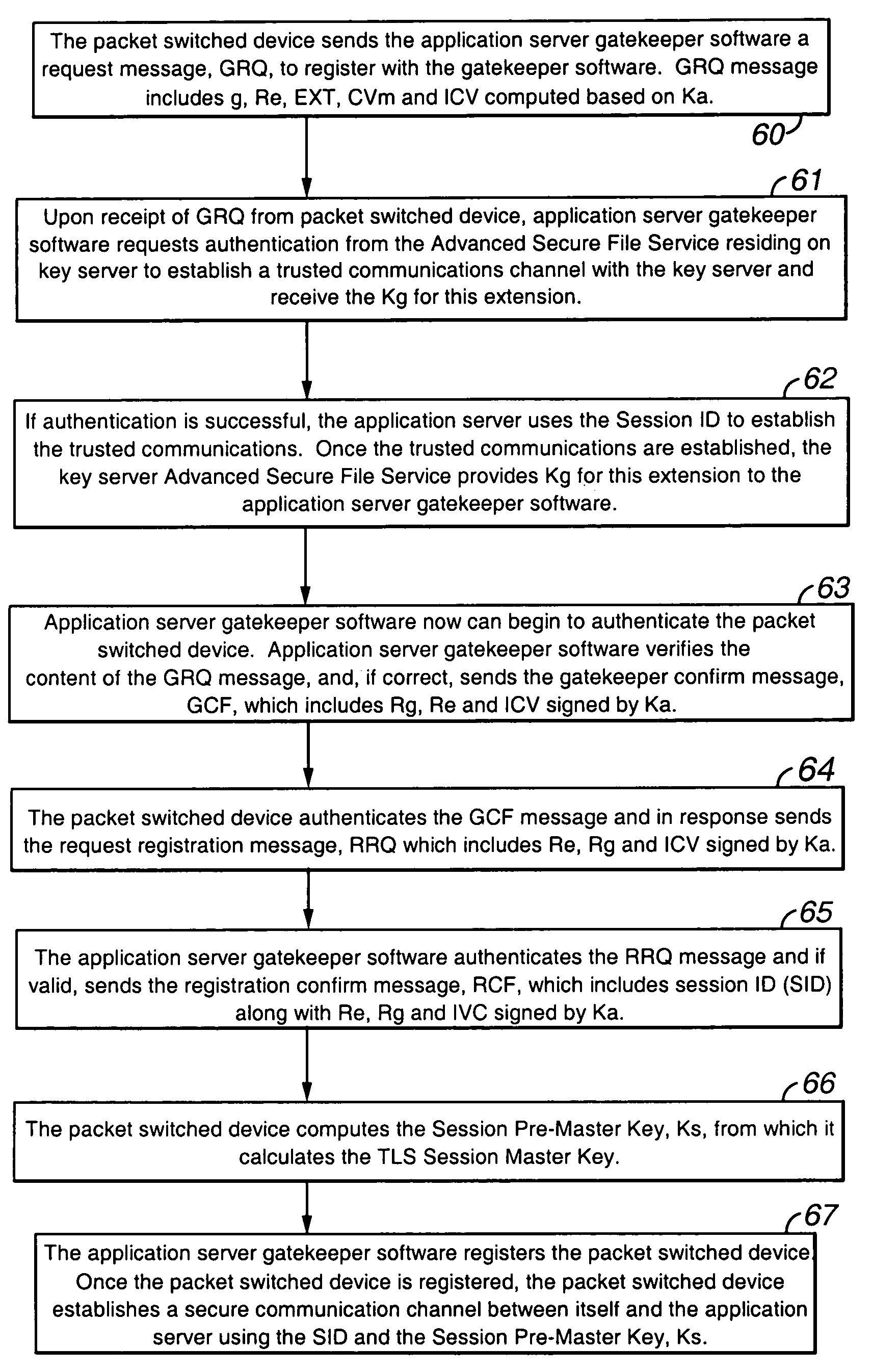
A packet-switched communications device in an enterprise network is provided. The packet-switched communications device has a corresponding unique identifier, such as an address or extension. The device includes a processor operable to (a) establish a secure communications session with a key generating agent in the enterprise network; (b) provide, to the key generating agent through the session, the unique identifier of the communications device; and (c) receive, from the key generating agent through the session, a secret key and a key identifier. An application server authenticates the packet switched device using the secret key. After authentication is successful, secure communications is established between the packet switched device and the application server.
Owner:AVAYA INC
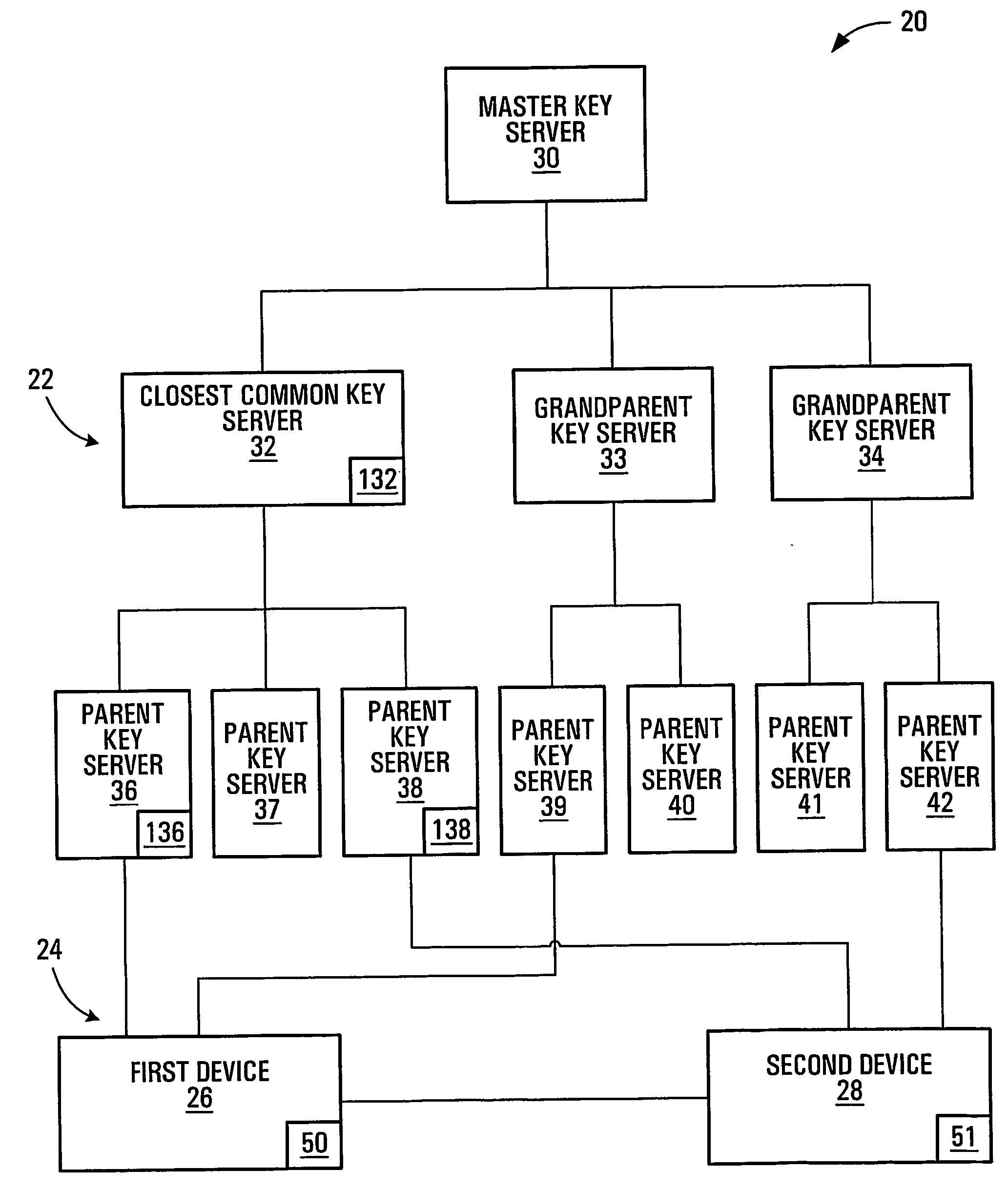
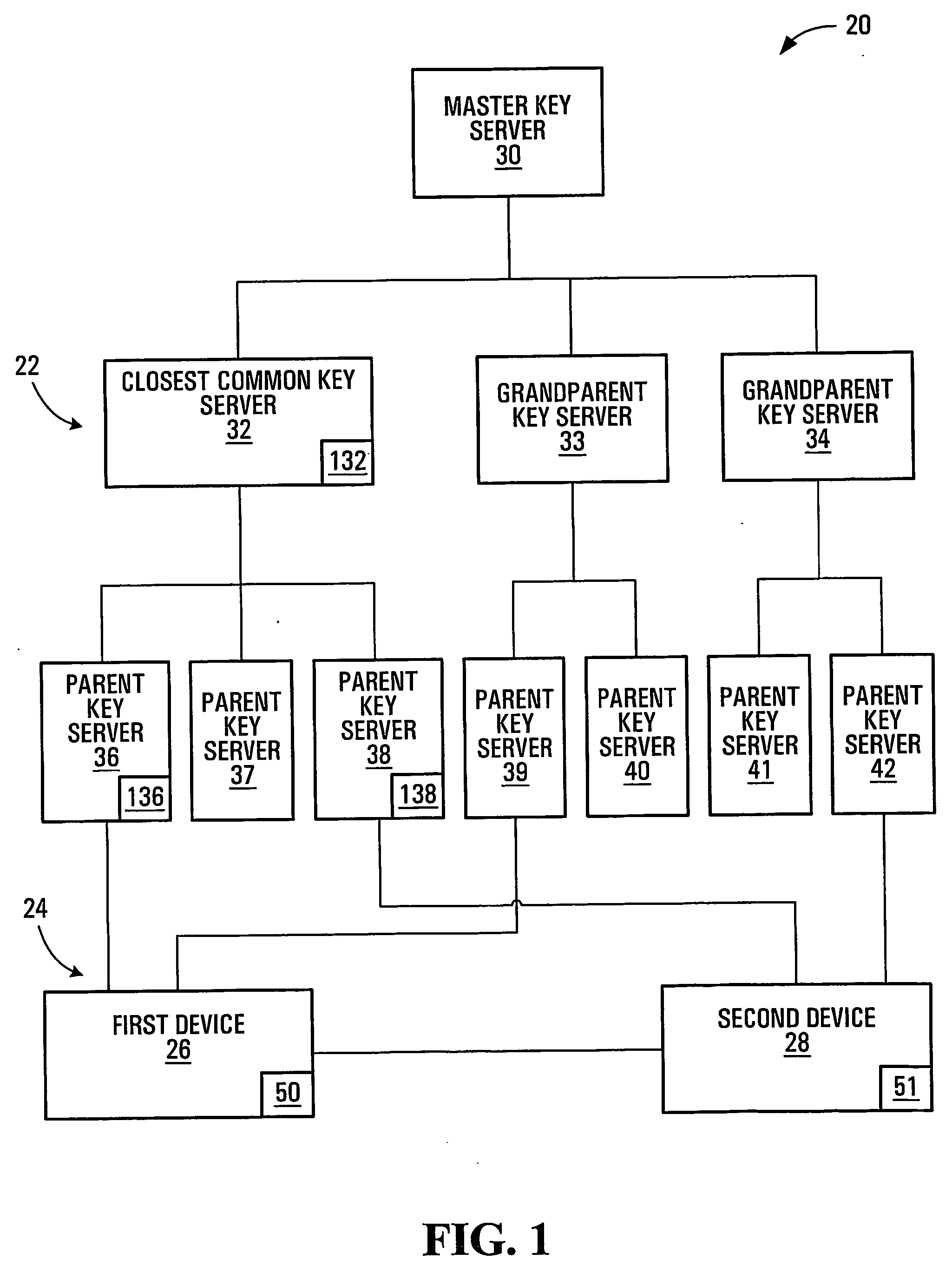
Session key distribution methods using a hierarchy of key servers
InactiveUS20050125684A1Facilitates secure communicationFacilitate communicationKey distribution for secure communicationPublic key for secure communicationSecure communicationKey server
Methods, apparatuses, media and signals for facilitating secure communication between a first device and a second device are disclosed. One method includes automatically identifying a common key server potentially accessible by both the first and second devices, and obtaining a secure private key from the common key server, for use in encrypting communications between the first and second devices. Identifying may include identifying as the common key server, a key server at an intersection of a first communication path defined between a first key server having a previously established relationship with the first device and a master key server, and a second communication path defined between a second key server having a previously established relationship with the second device and the master key server. Obtaining may include obtaining a plurality of private keys and blending the keys to produce a final private session key.
Owner:SCHMIDT COLIN MARTIN
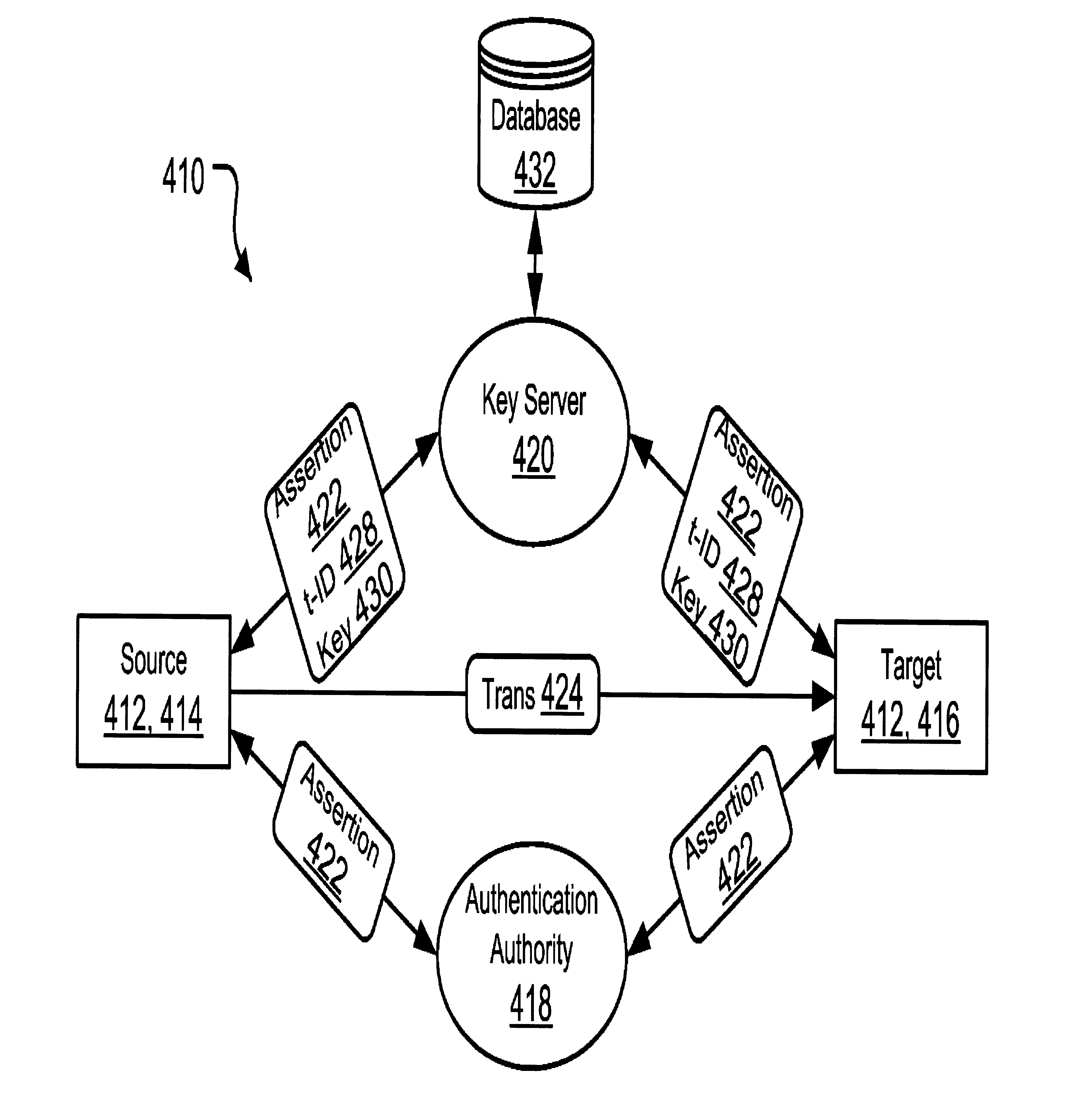
Implementing nonrepudiation and audit using authentication assertions and key servers
InactiveUS7376835B2Providing serviceMultiple level of strengthKey distribution for secure communicationUser identity/authority verificationKey serverCommunications system
A communication system (410) wherewith sources (414) and targets (416) employ a key server (420) to exchange transactions (424). A first request to the key server includes a source assertion (422) from an authentication authority (418), and optionally a key (430). The key server provides a transaction ID (428), and the key if not already provided, in reply to this request. The key server stores the transaction ID and source assertion. The source encrypts the transaction and sends it with the transaction ID to the targets. A second request to the key server includes a target assertion and the transaction ID. The key server provides the key in reply to this request. The key server also stores the target assertion in association with the transaction ID. The respective assertions then establish the source and targets of the transaction in a manner that cannot plausibly be repudiated.
Owner:PROOFPOINT INC
Delivery and storage system for secured content library
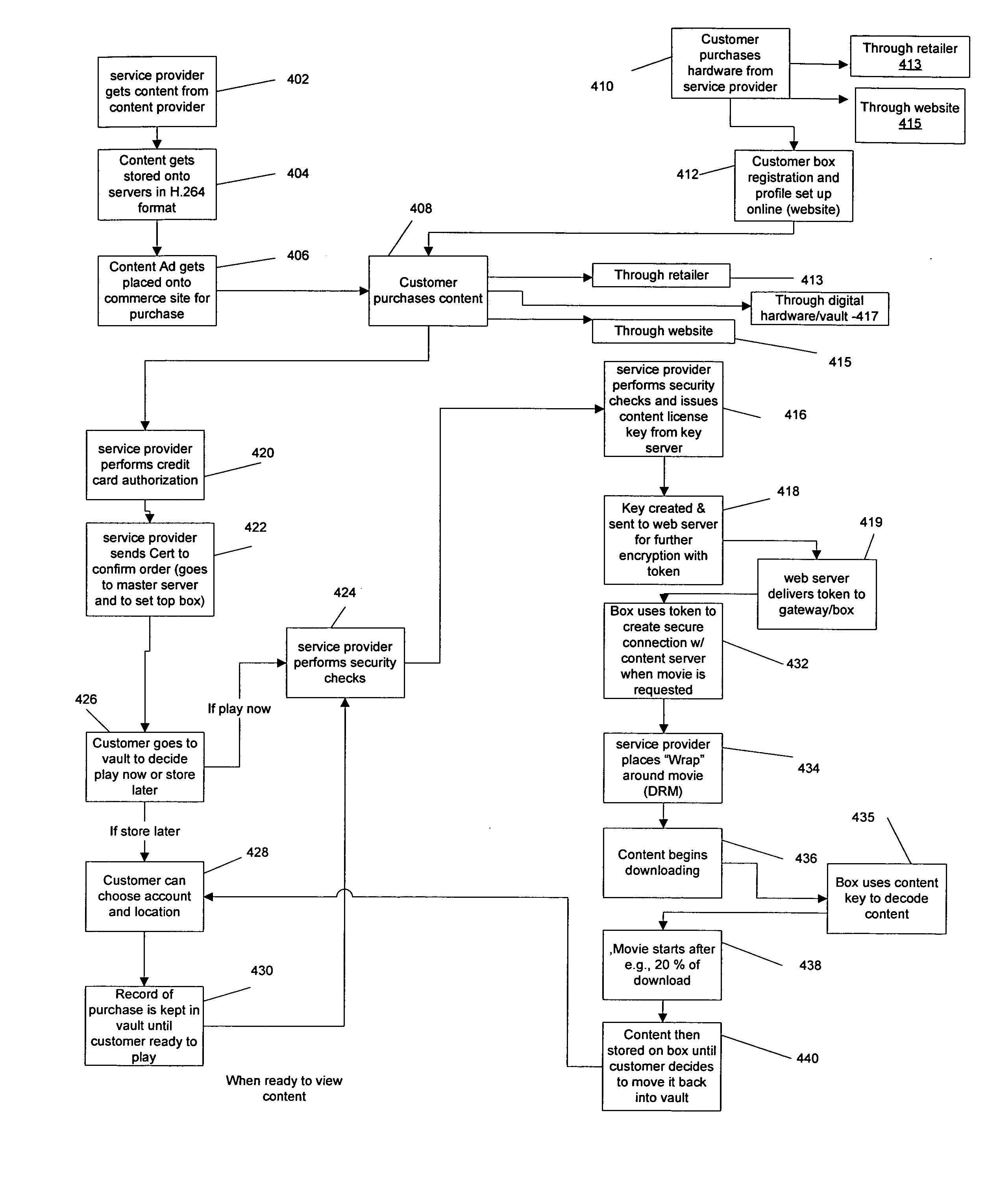
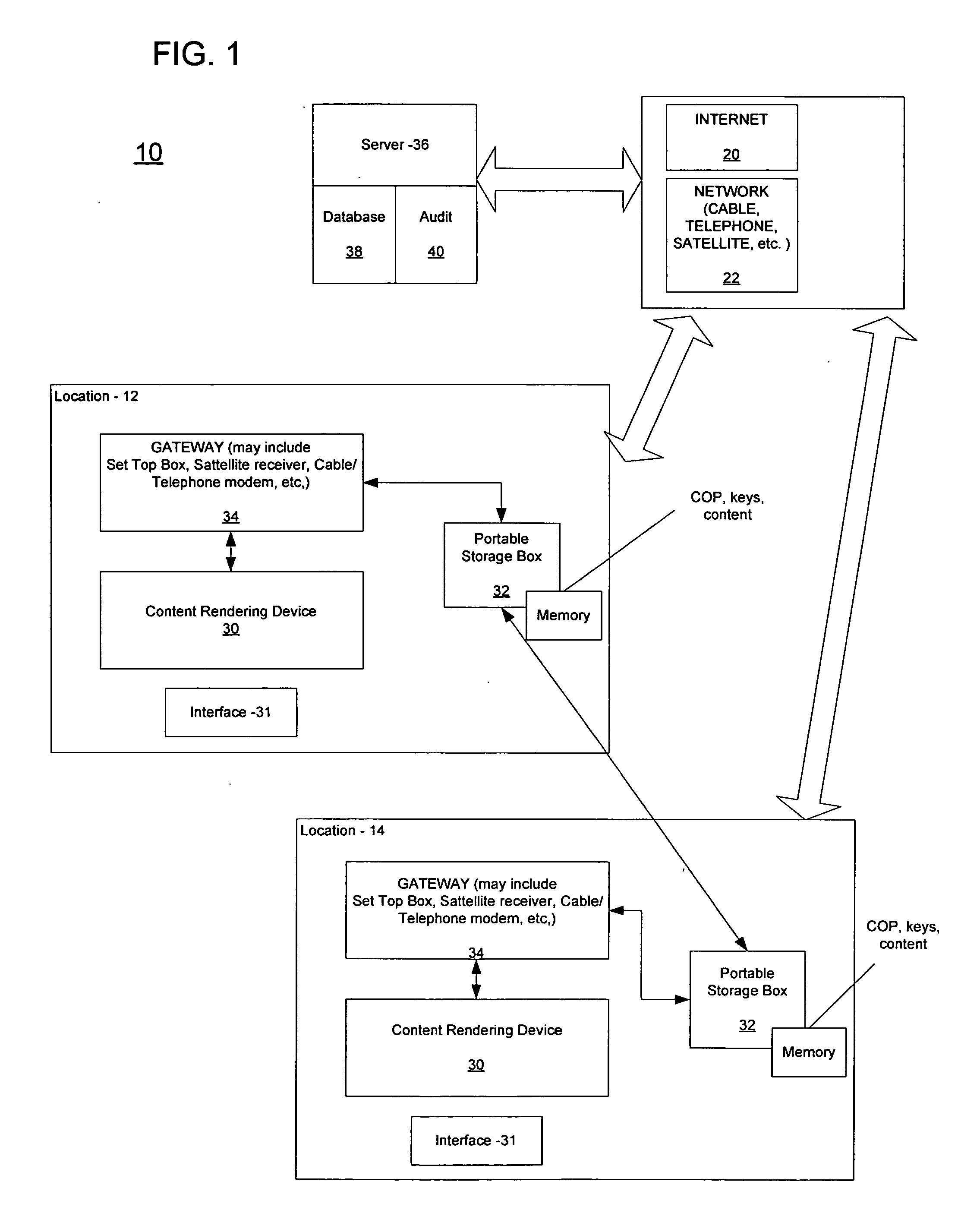
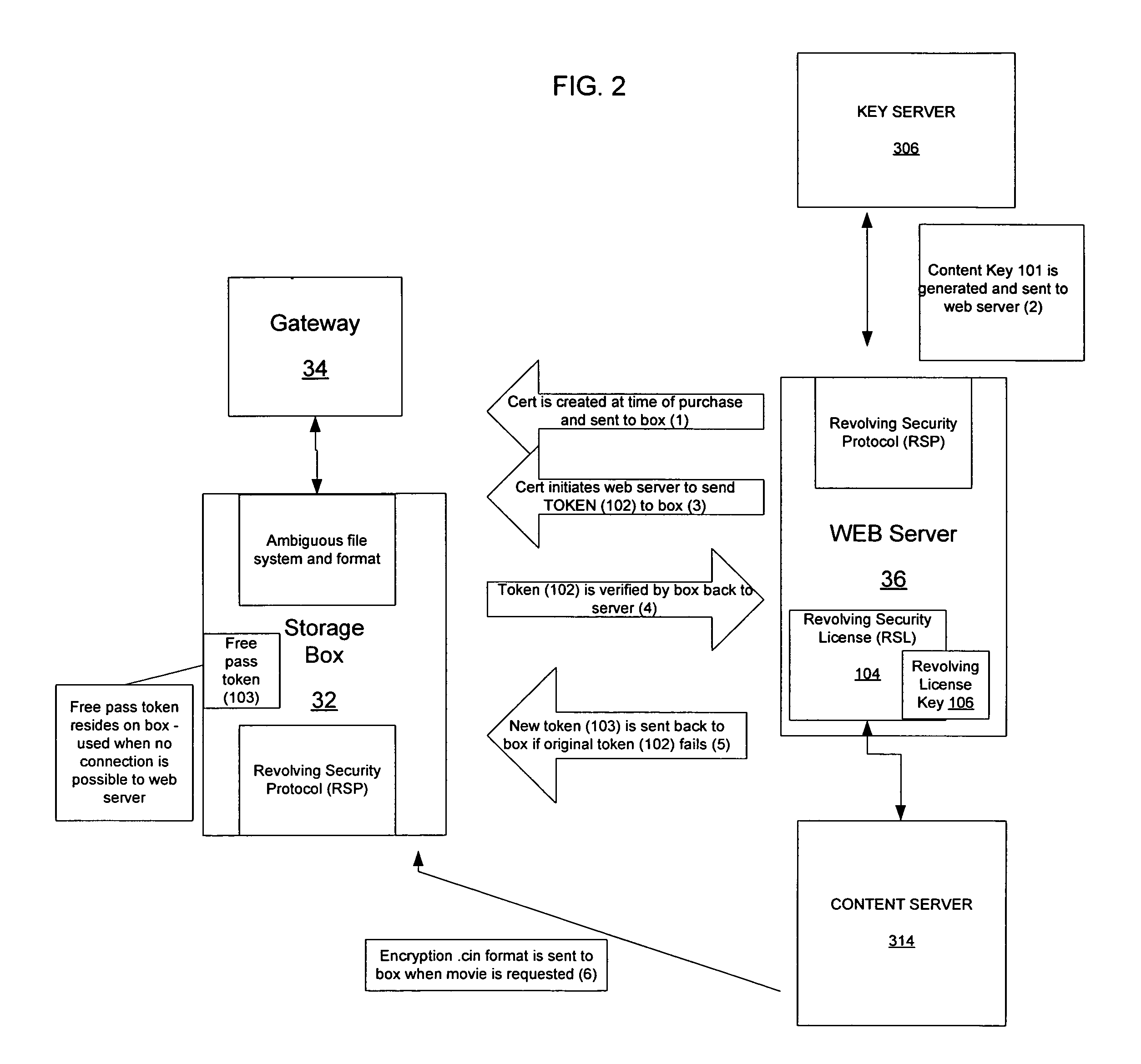
A system for maintaining a secure content library includes a server, which manages requests for copyrighted content and encrypts the content using a key server, which generates unique keys and associates the keys with the copyrighted content to create a token. A gateway receives the token and interacts with the server over a network. A client storage box interacts with the gateway to decode the token in accordance with a security protocol and sends a content key back to the server to enable the content to be downloaded and decoded, the storage box including memory for storing downloaded content. The client storage box has a use key that is updated by the server after a predetermined number of accesses to the content to enable further accessing of the content.
Owner:VCINEMA
Security server system
InactiveUS7325127B2Raise security concernsHigh degreeData switching networksSecuring communicationKey serverMessage Title
A security server system and method permitting participants acting as the source or destinations for a message or a conversation with multiple messages to securely communicate the messages. The messages have a message header and a message content. A message router connects the participants via a network and delivers the message between the participants based on the message header. A key server creates, stores, and releases conversation keys that the participants use to protect the message content of the message.
Owner:PROOFPOINT INC
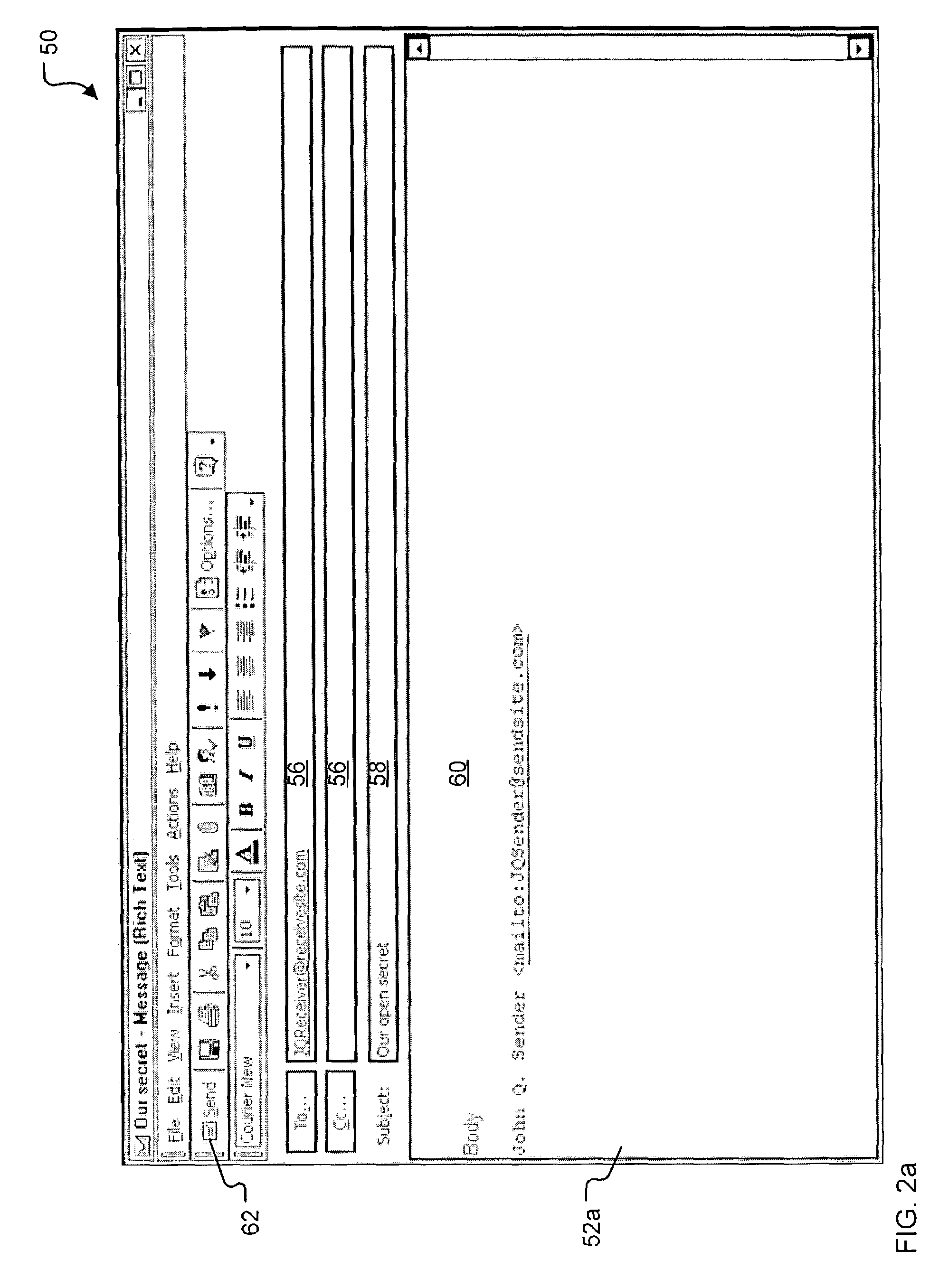
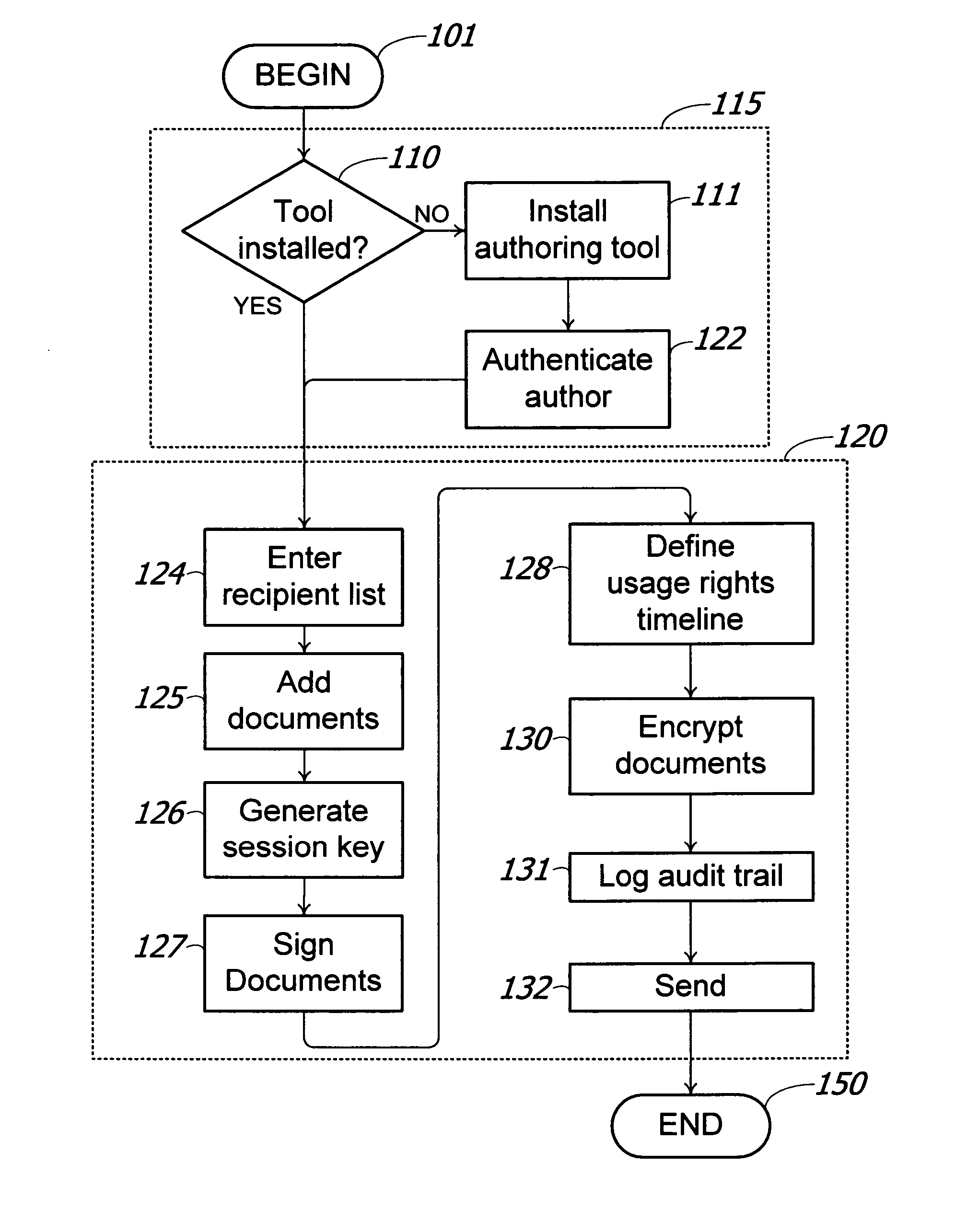
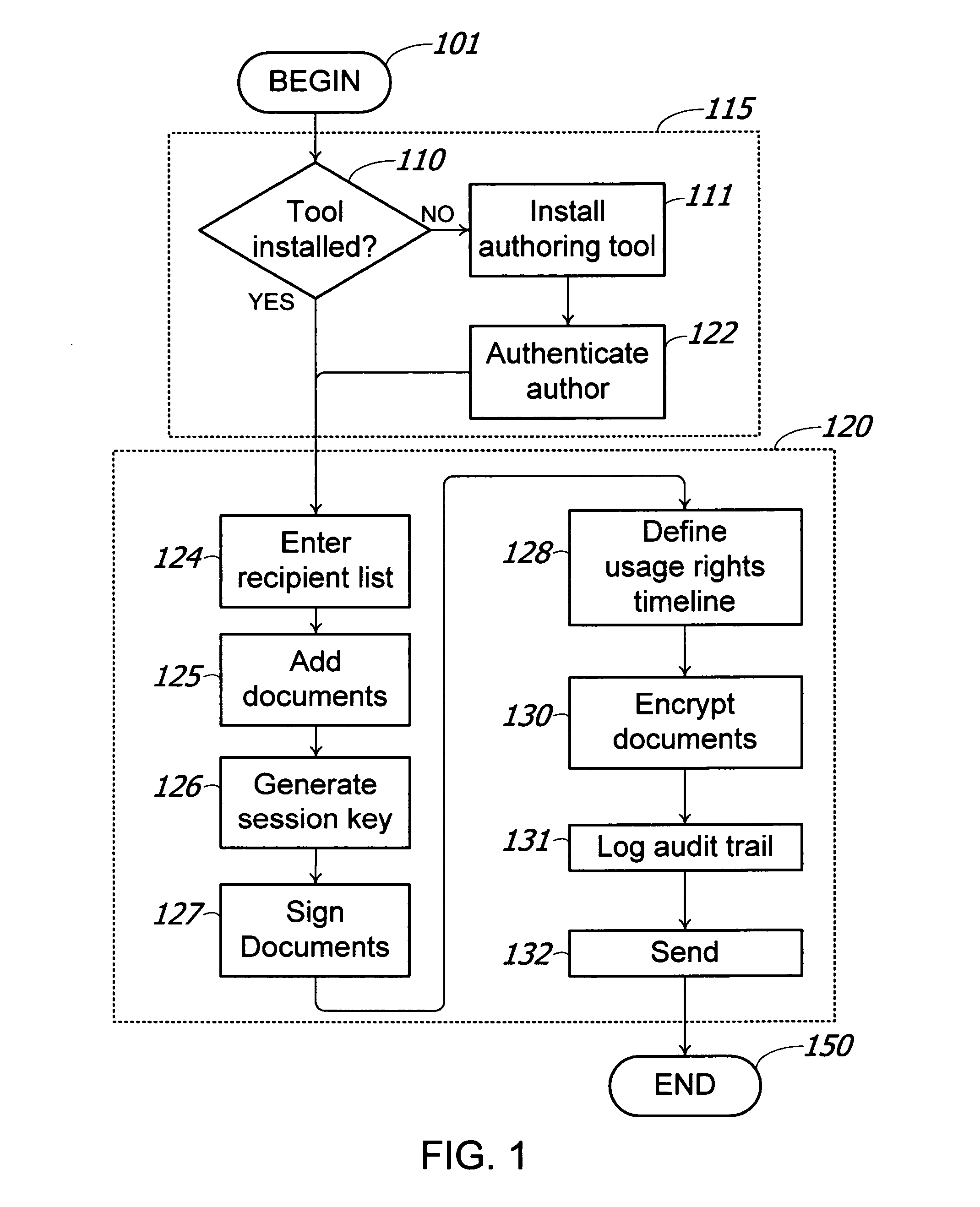
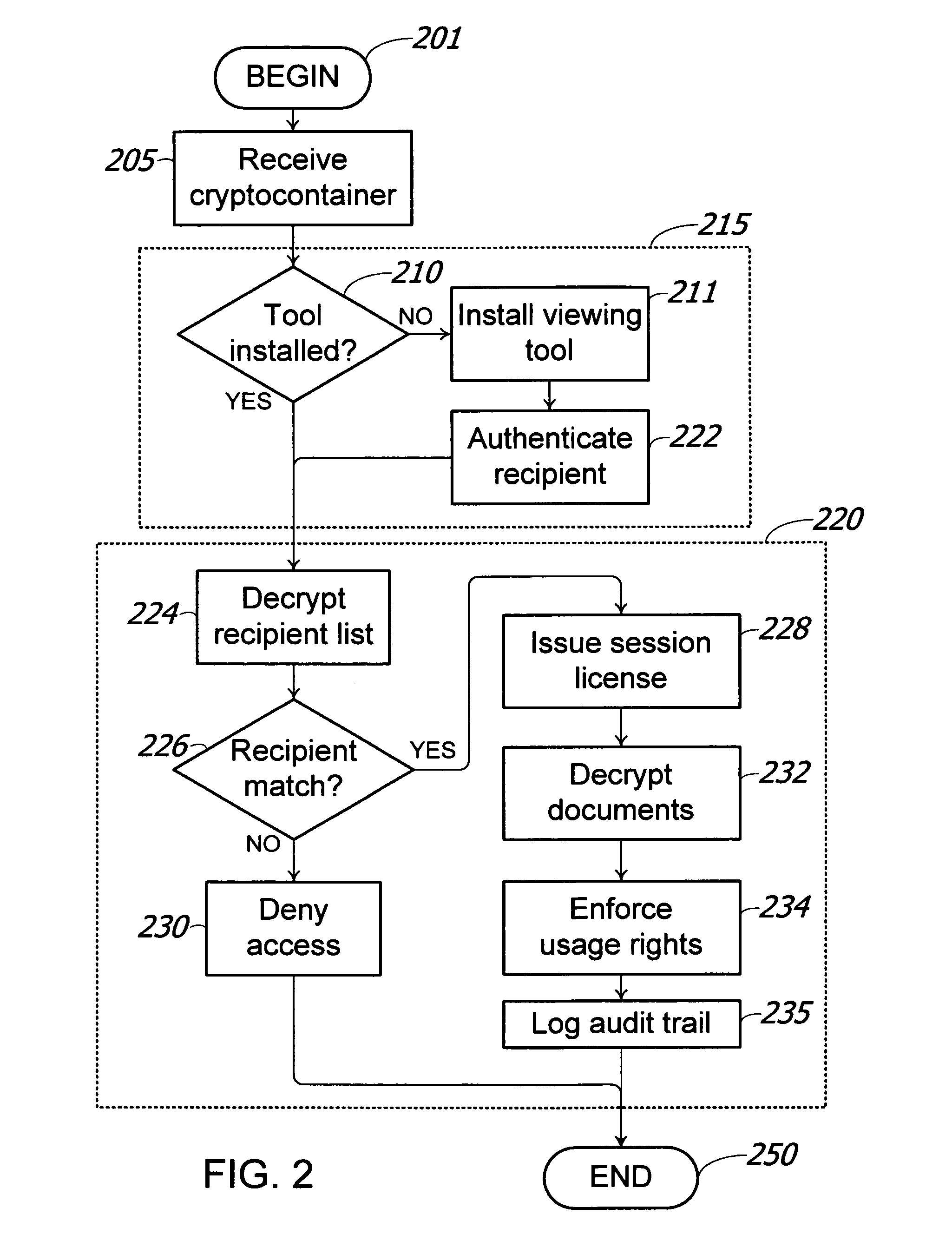
Method and system for digital rights management of documents
InactiveUS20070074270A1Widespread and transparent useDigital data processing detailsPublic key for secure communicationKey serverElectronic document
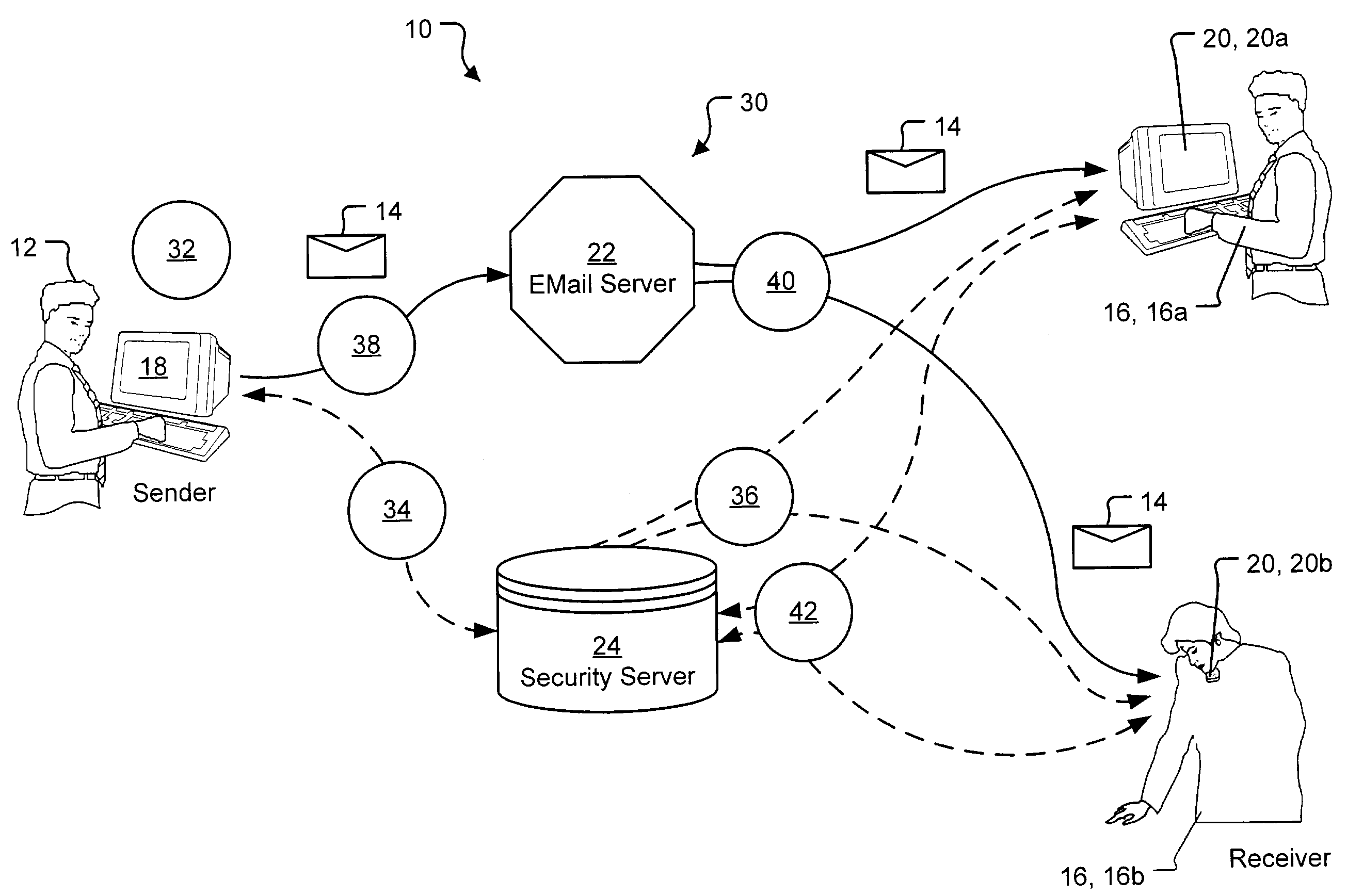
A method and system for transmission of digital content via e-mail with point of use digital rights management is disclosed. The secured access rights to the digital content may be customized for individual recipients by the sender, and may evolve over time. The access rights are enforced according to a time-dependent scheme. A key server is used to arbitrate session keys for the encrypted content, eliminating the requirement to exchange public keys prior to transmission of the digital content. During the entire process of transmitting and receiving e-mail messages and documents, the exchange of cryptographic keys remains totally transparent to the users of the system. Additionally, electronic documents may be digitally signed with authentication of the signature.
Owner:KEYAVI DATA CORP
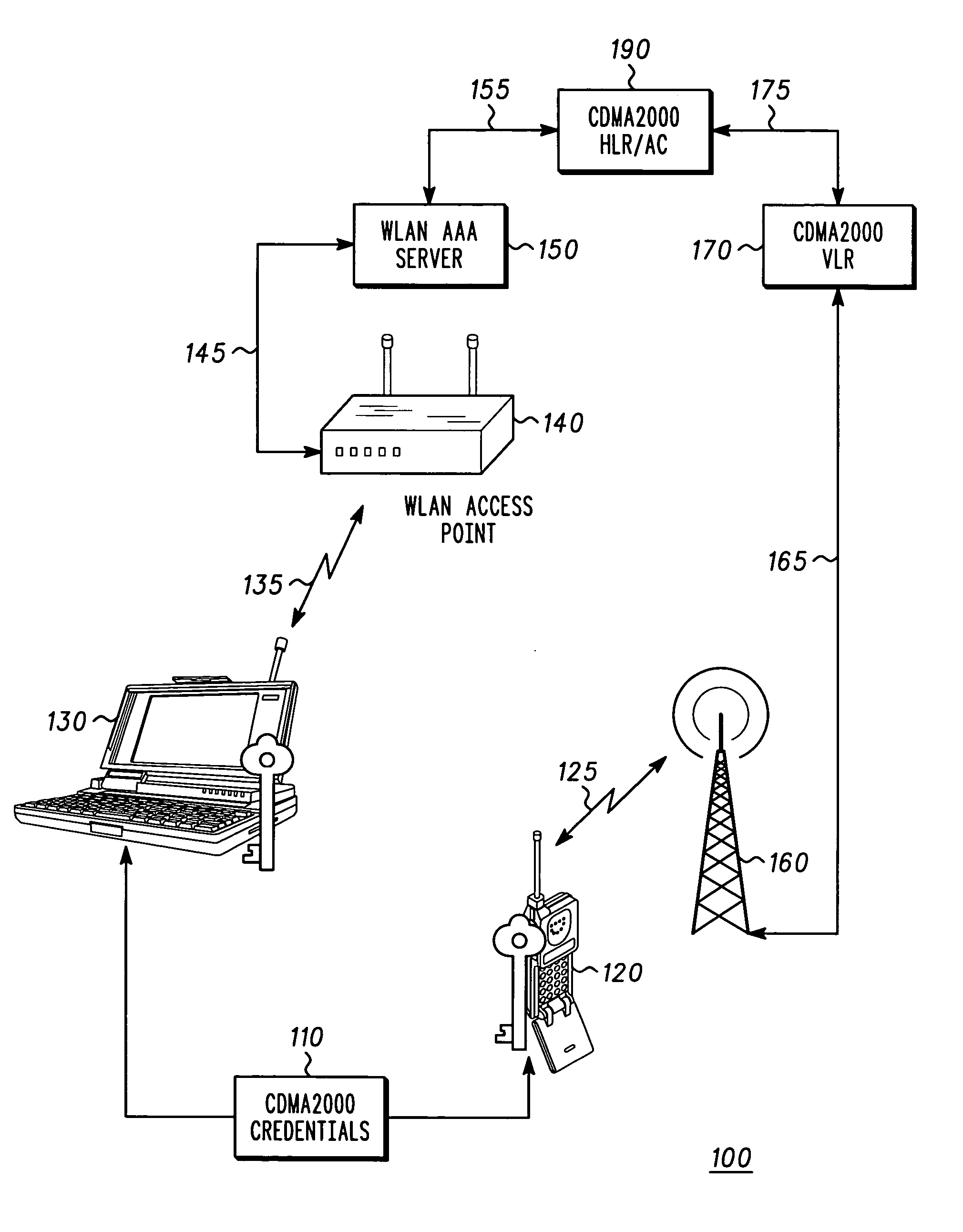
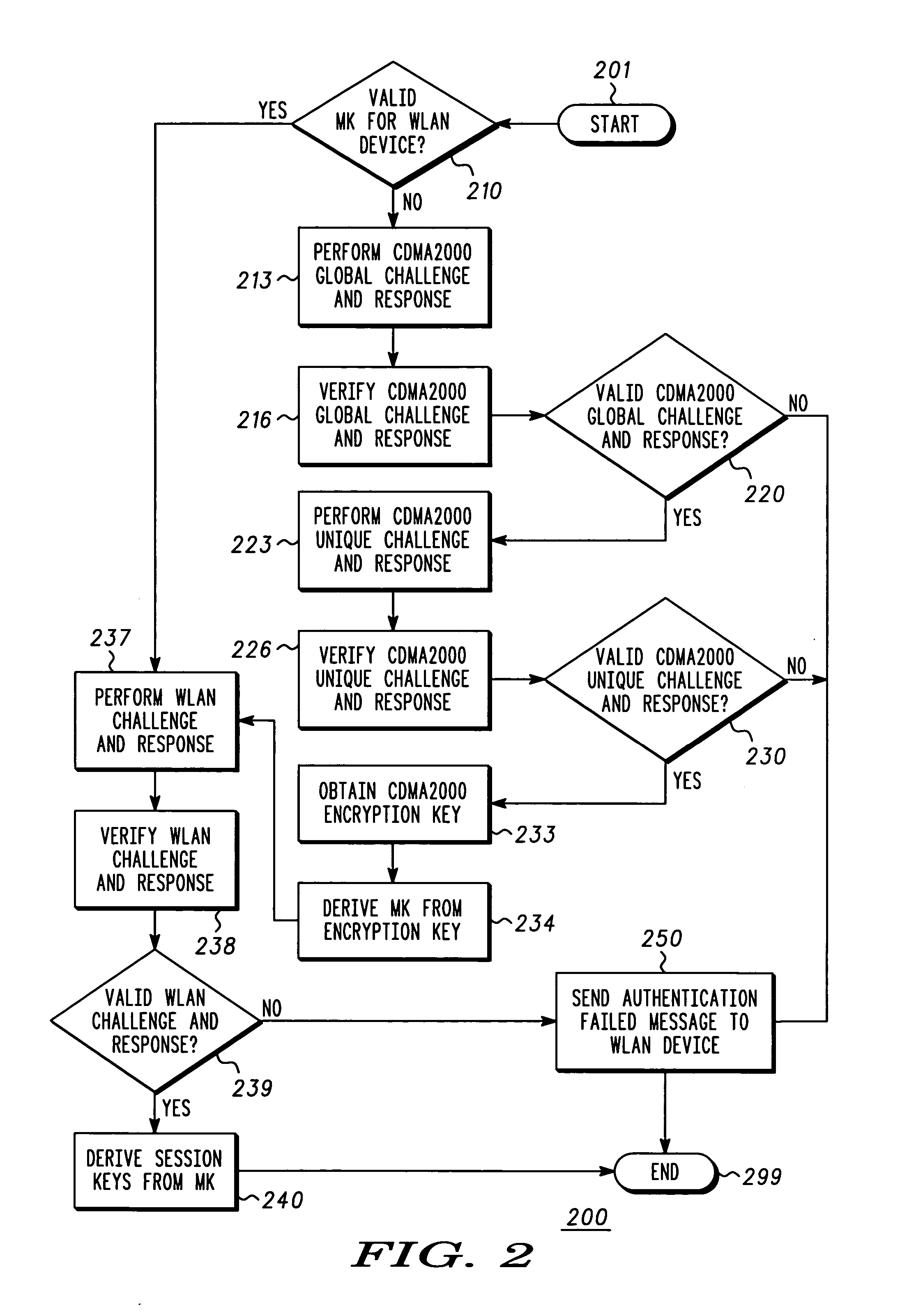
System, method and devices for authentication in a wireless local area network (WLAN)
A system (100) for authentication in a wireless local area network (WLAN) includes a CDMA2000 authentication center (190) for authenticating CDMA2000 credentials (110), a WLAN authentication server (150) for using the CDMA2000 credentials to authenticate WLAN devices holding CDMA2000 credentials, and at least one WLAN device (130) holding CDMA2000 credentials. The WLAN server (150) performs a CDMA2000 global challenge and response (213) and a CDMA2000 unique challenge and response (223) with a WLAN device to obtain a CDMA2000 encryption key (233). The WLAN server (150) derives a master key from the CDMA2000 encryption key (234) and uses the master key to perform a WLAN challenge and response (237) with the WLAN device (130) and then derives session keys from the master key (240). The session keys protect communications between the WLAN access point (140) and the WLAN device (130).
Owner:MOTOROLA INC
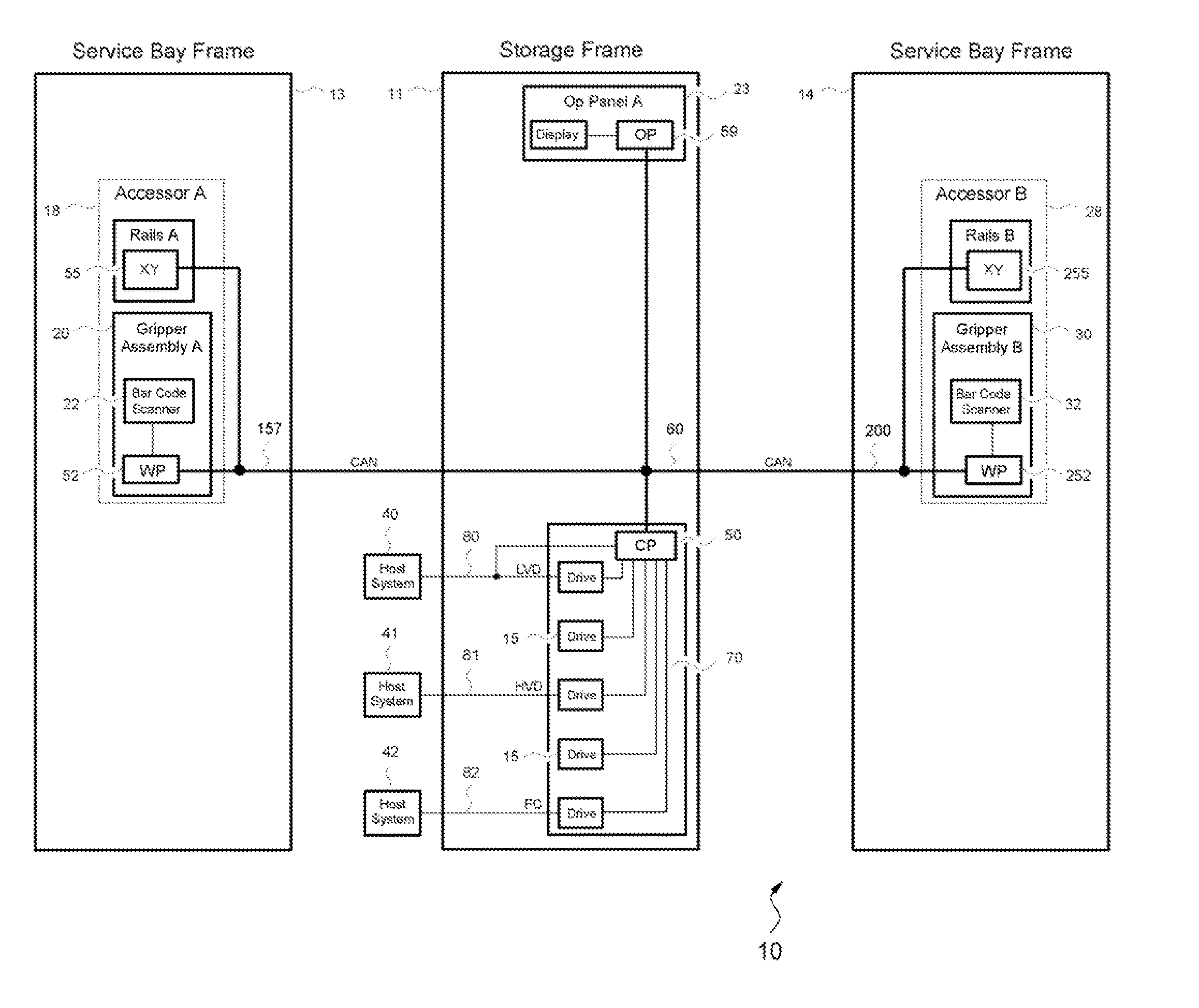
Selective encryption of data stored on removable media in an automated data storage library
In an automated data storage library, selective encryption for data stored or to be stored on removable media is provided. One or more encryption policies are established, each policy including a level of encryption one or more encryption keys and the identity of one or more data cartridges. The encryption policies are stored in a policy table and the encryption keys are stored in a secure key server. A host requests access to a specified data cartridge and the cartridge is transported from a storage shelf in the library to a storage drive. Based on the identity of the specified cartridge the corresponding encryption policy is selected from the table and the appropriate encryption key is obtained from the key server. The storage drive encrypts data in accordance with the key and stores the data on the media within the specified data cartridge.
Owner:IBM CORP
System and method for communicating with a key management system
ActiveUS8667267B1Digital data processing detailsUser identity/authority verificationKey serverBlock match
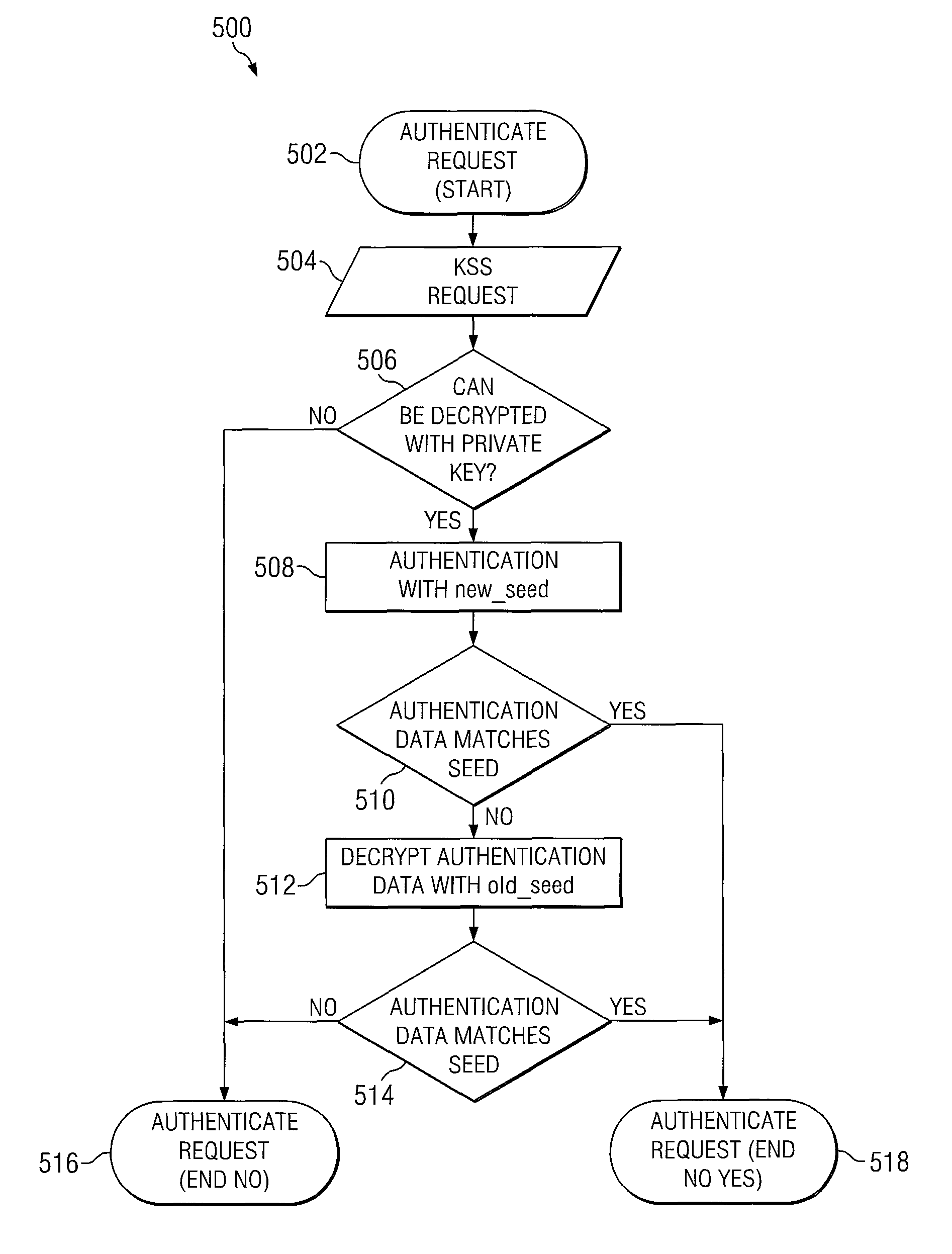
A method for providing authenticated access to an encrypted file system includes generating a first seed; providing a request for a key to a key server, the request including at least a first seed block having a first encryption, a message block having a second encryption, and an encryption encapsulation block having a third encryption, the encryption encapsulation block including information for decrypting the message block; at the key server, decrypting the encryption encapsulation block and using the information therein to decrypt the at least a first seed block and the message block; and authenticating the message if the first seed in the at least a first seed block matches a first predetermined seed.
Owner:CLOUDERA
Rekeying in secure mobile multicast communications
InactiveUS20070143600A1Easy to calculateReduce the impactKey distribution for secure communicationKey serverGroup controller
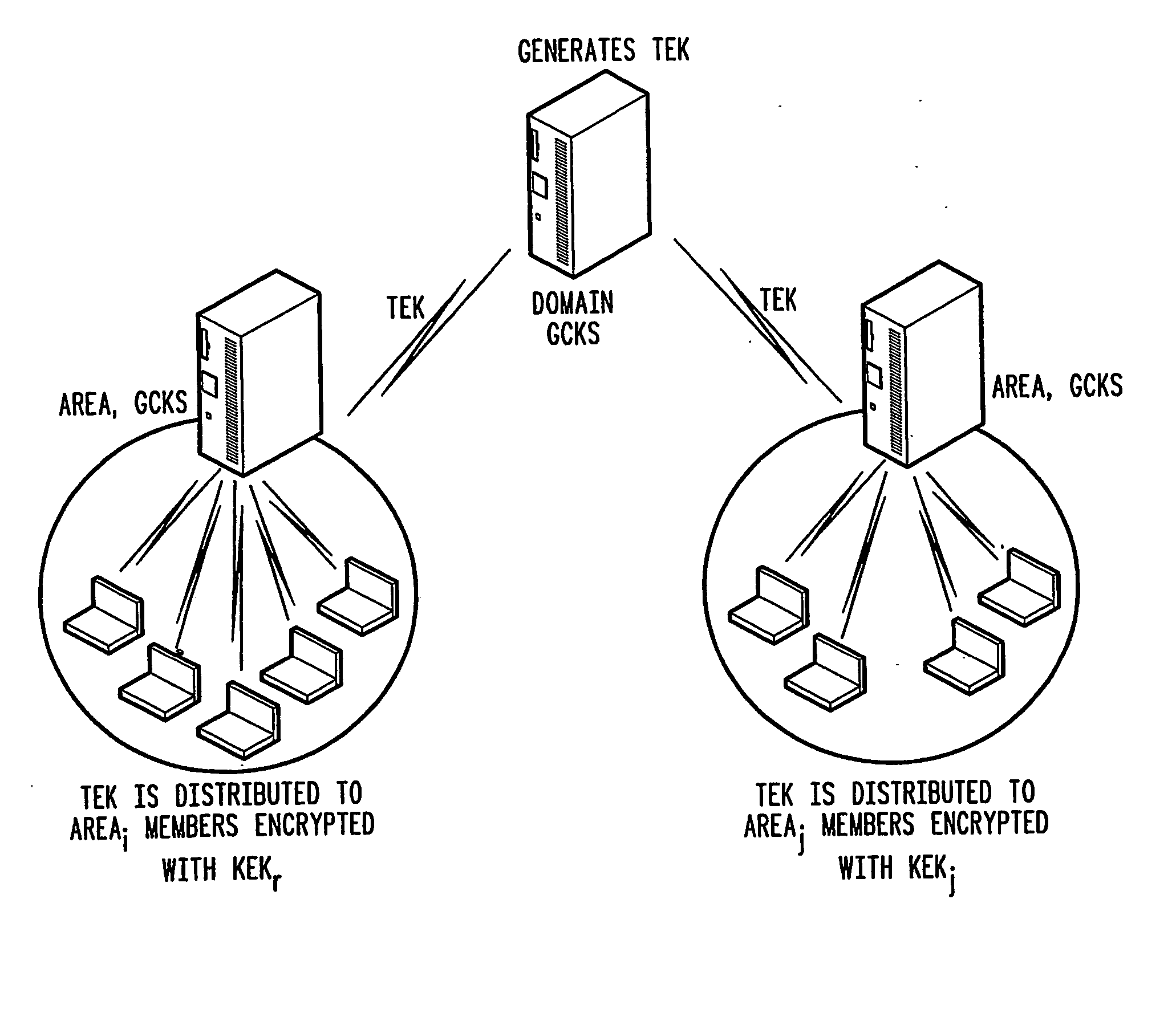
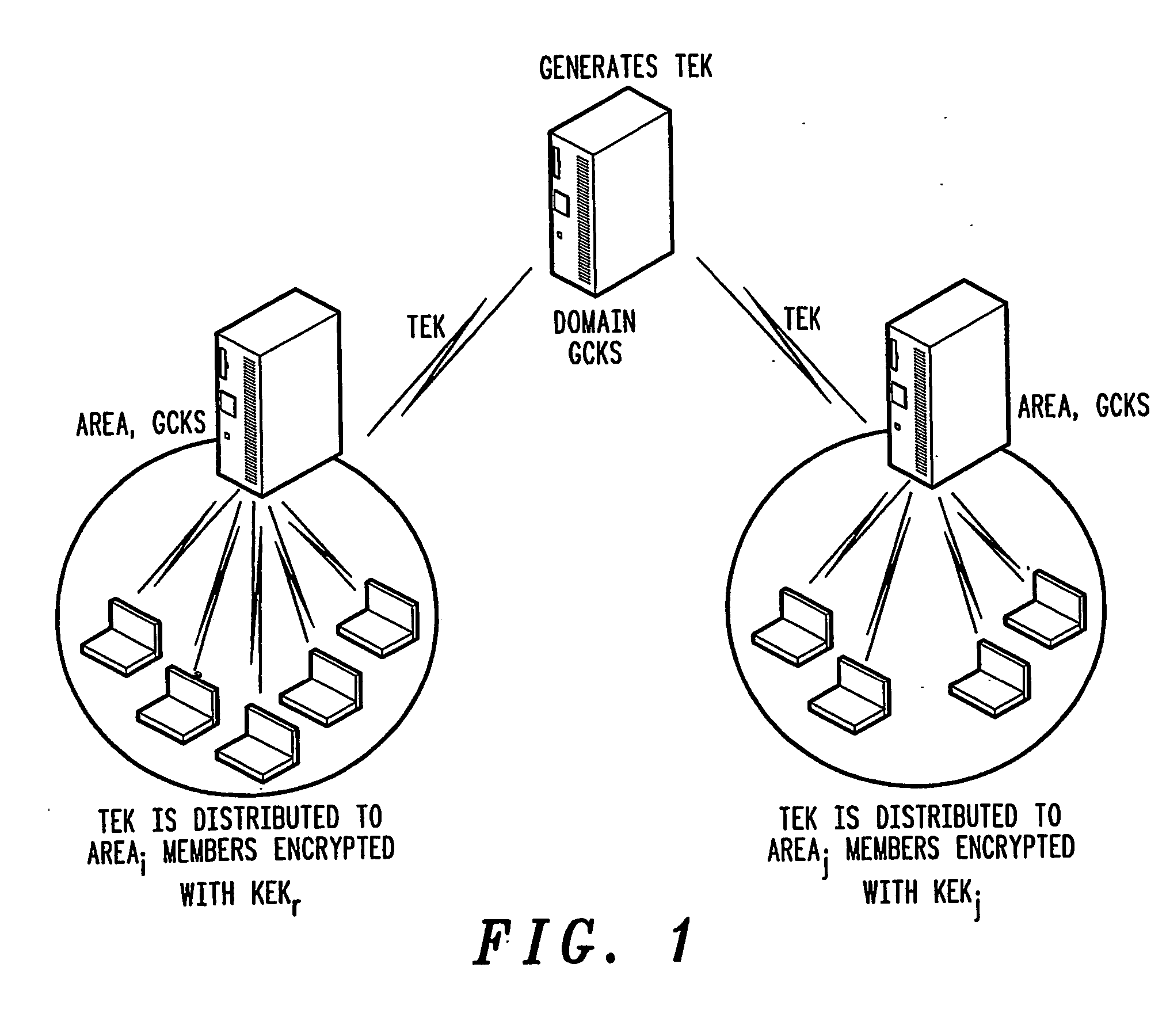
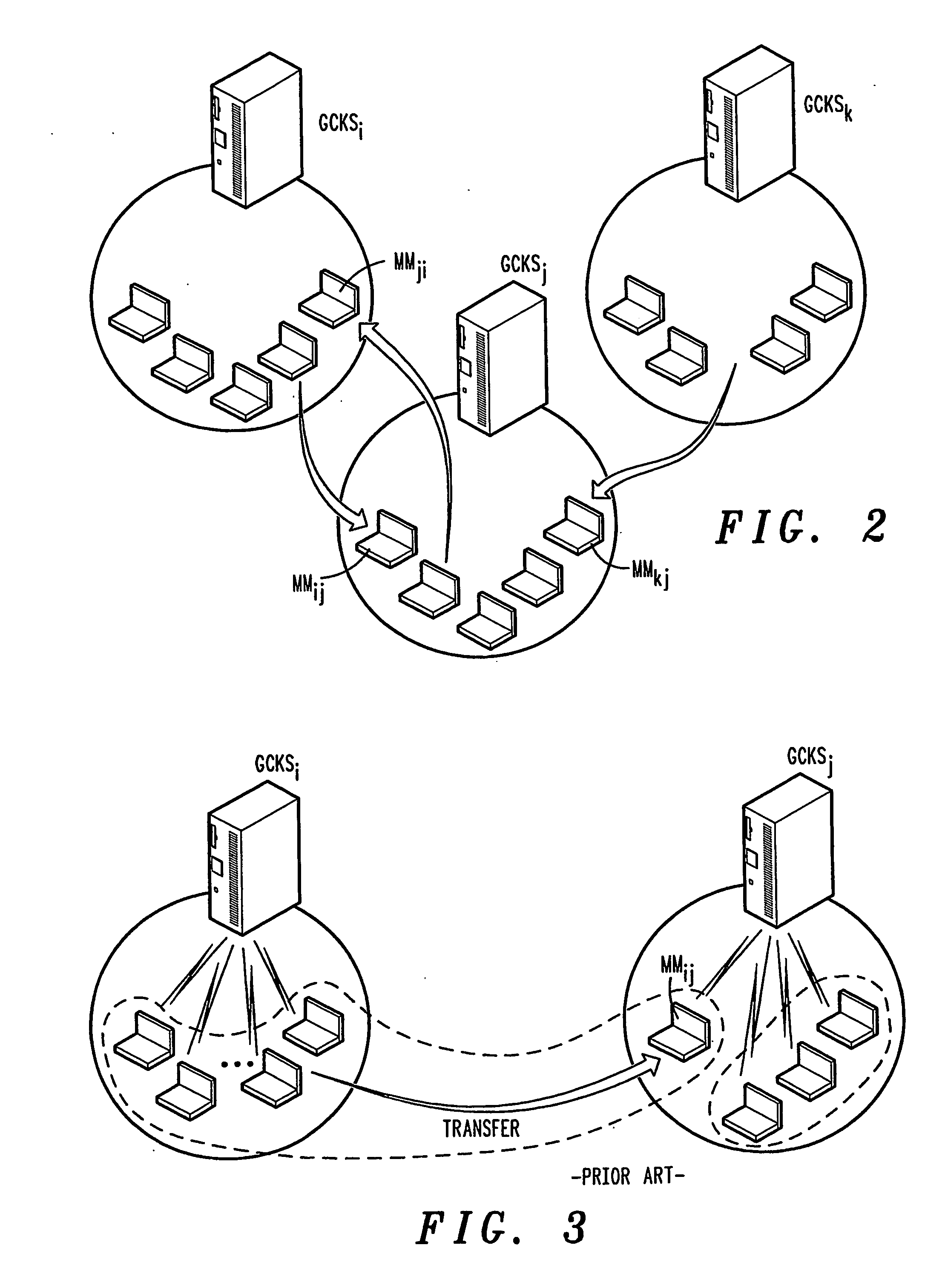
A method of inter-area rekeying of encryption keys in secure mobile muiticast communications, in which a Domain Group Controller Key Server (Domain GCKS) distributes Traffic Encryption Keys (TEK) to a plurality of local Group Controller Key Servers (local GCKS), and said local Group Controller Key Servers forward said Traffic Encryption Keys, encrypted using Key Encryption Keys (KEKi, KEKj) that are specific to the respective local Group Controller Key Server (local GCKSi, GCKSj), to group members, said local Group Controller Key Servers (GCKSi, GCKSj) constituting Extra Key Owner Lists (EKOLi, EKOLj) for group key management areas (areai, areaj) that distinguish group members (MMi, MMj) possessing Key Encryption Keys (KEKi, KEKj) and situated in the corresponding group key management area (areai, areaj) from group members (MMij) possessing Key Encryption Keys (KEKi) that were situated in the corresponding group key management area (areai) but are visiting another area (areaj).
Owner:MOTOROLA INC
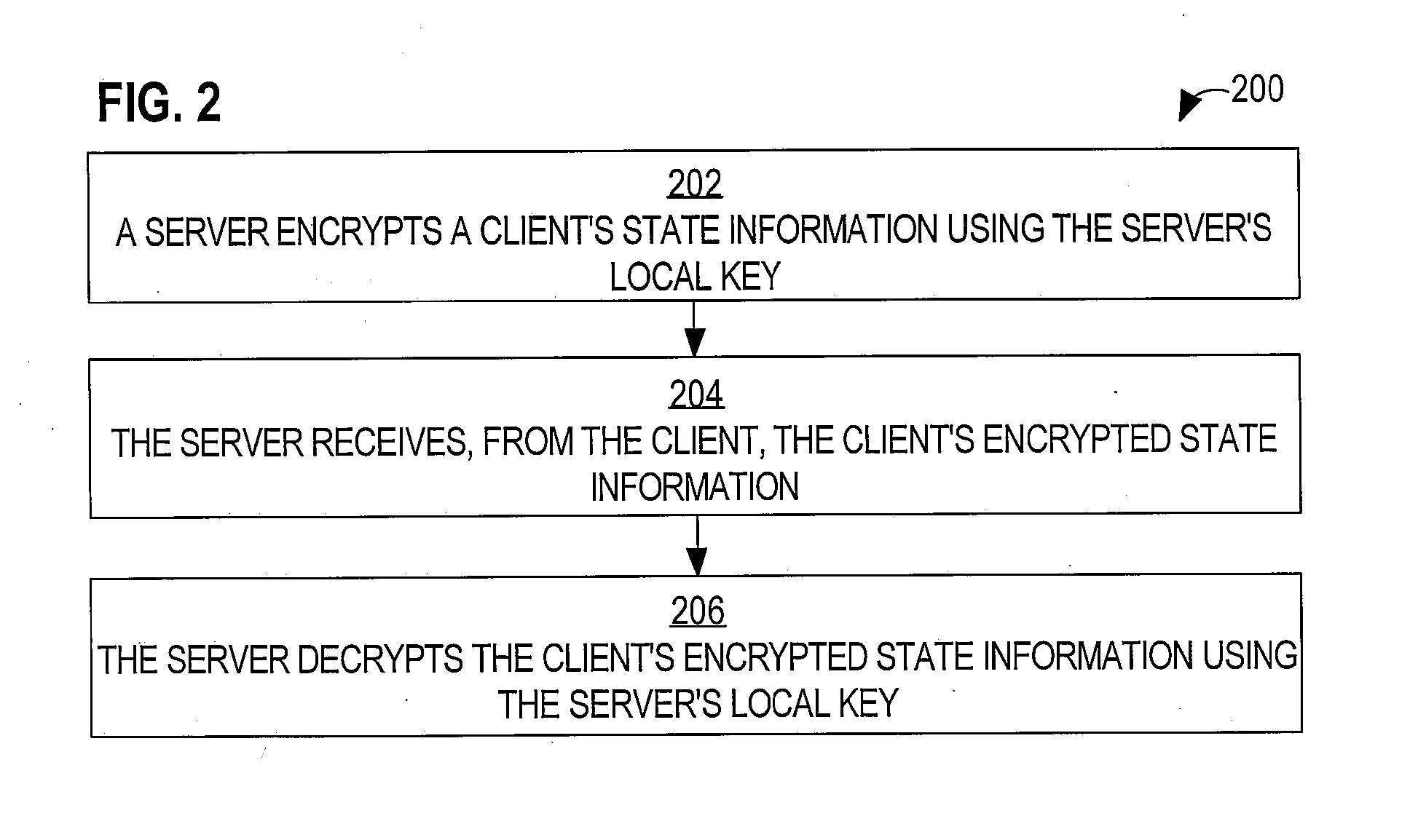
Enabling stateless server-based pre-shared secrets
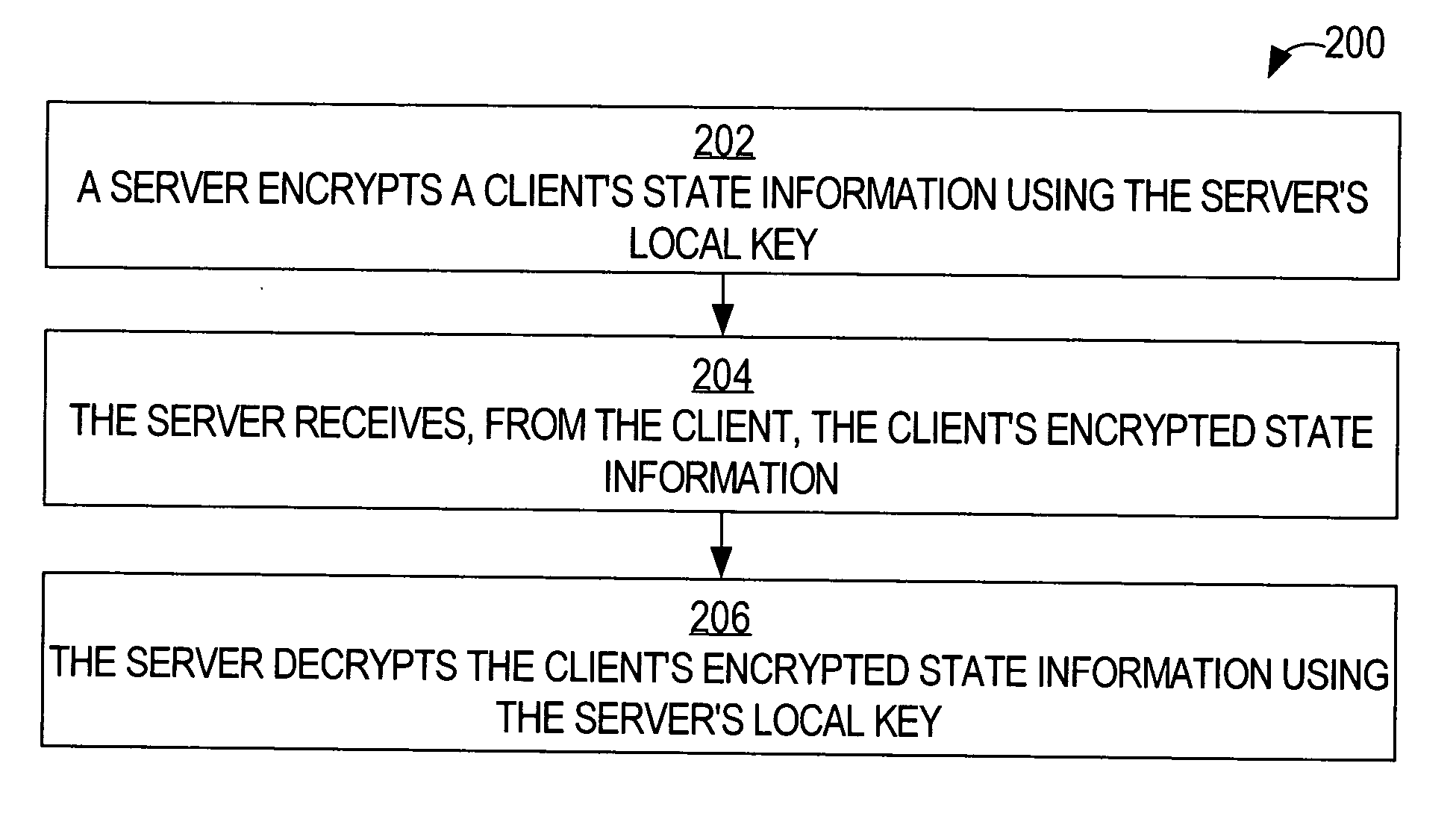
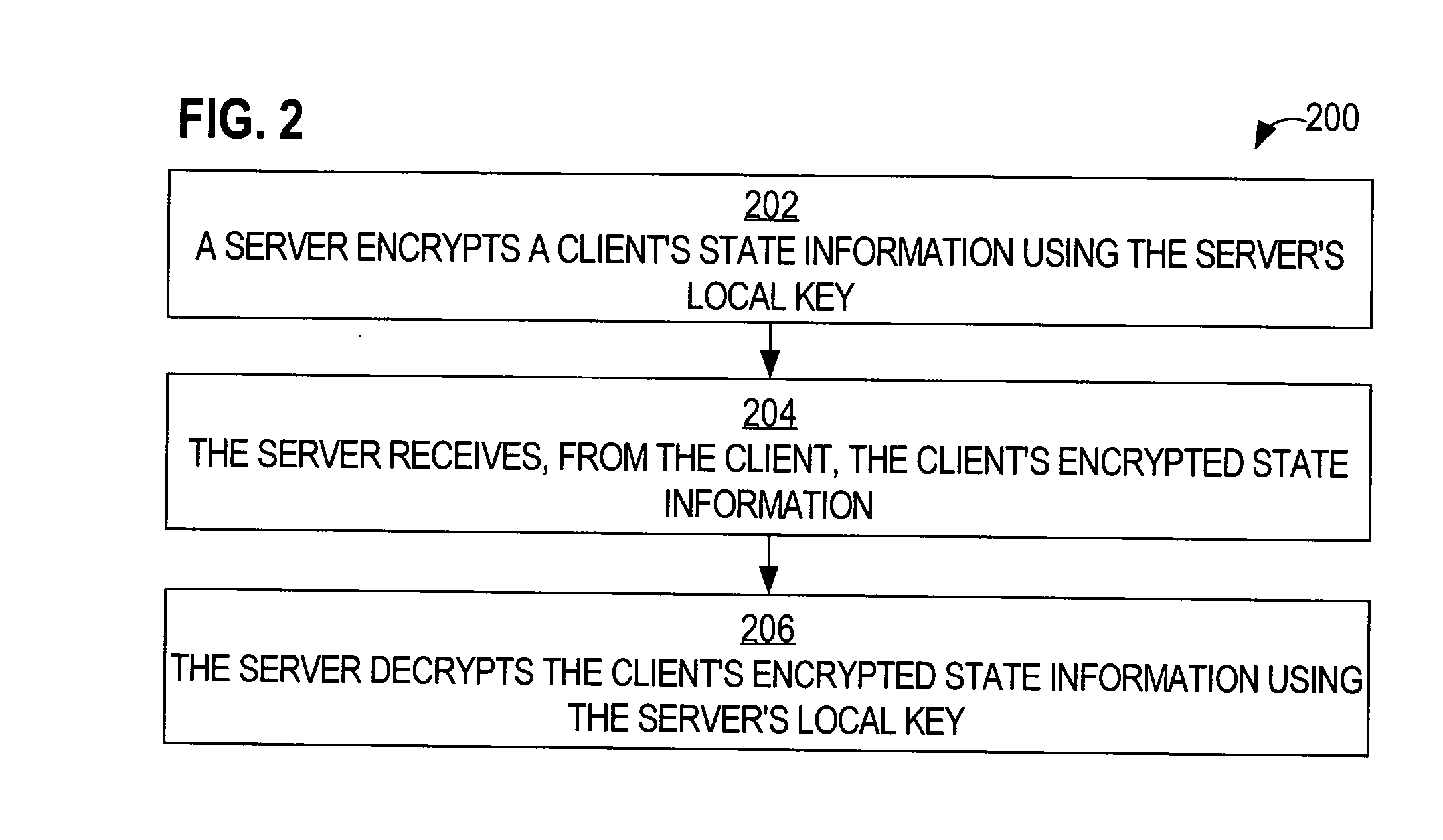
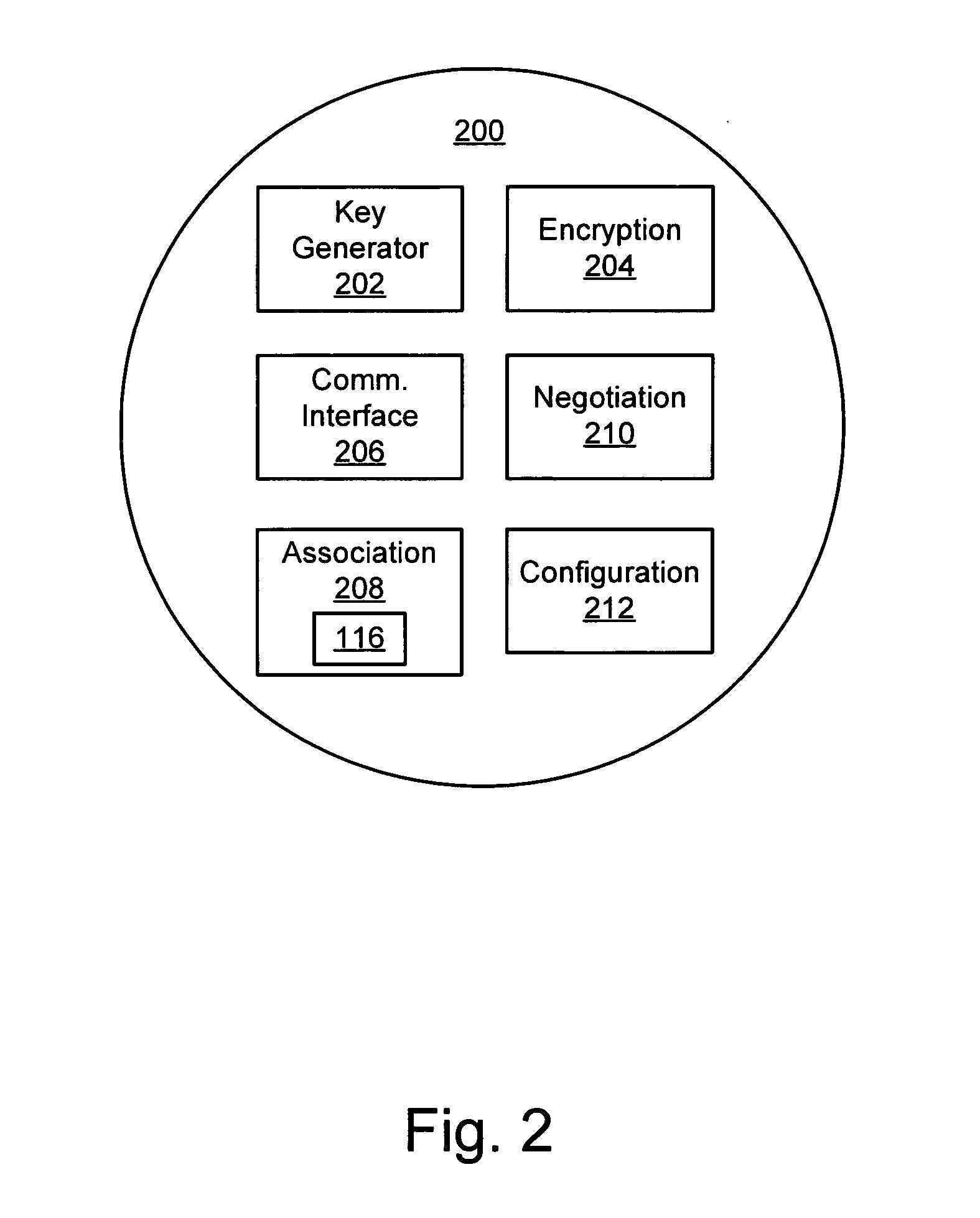
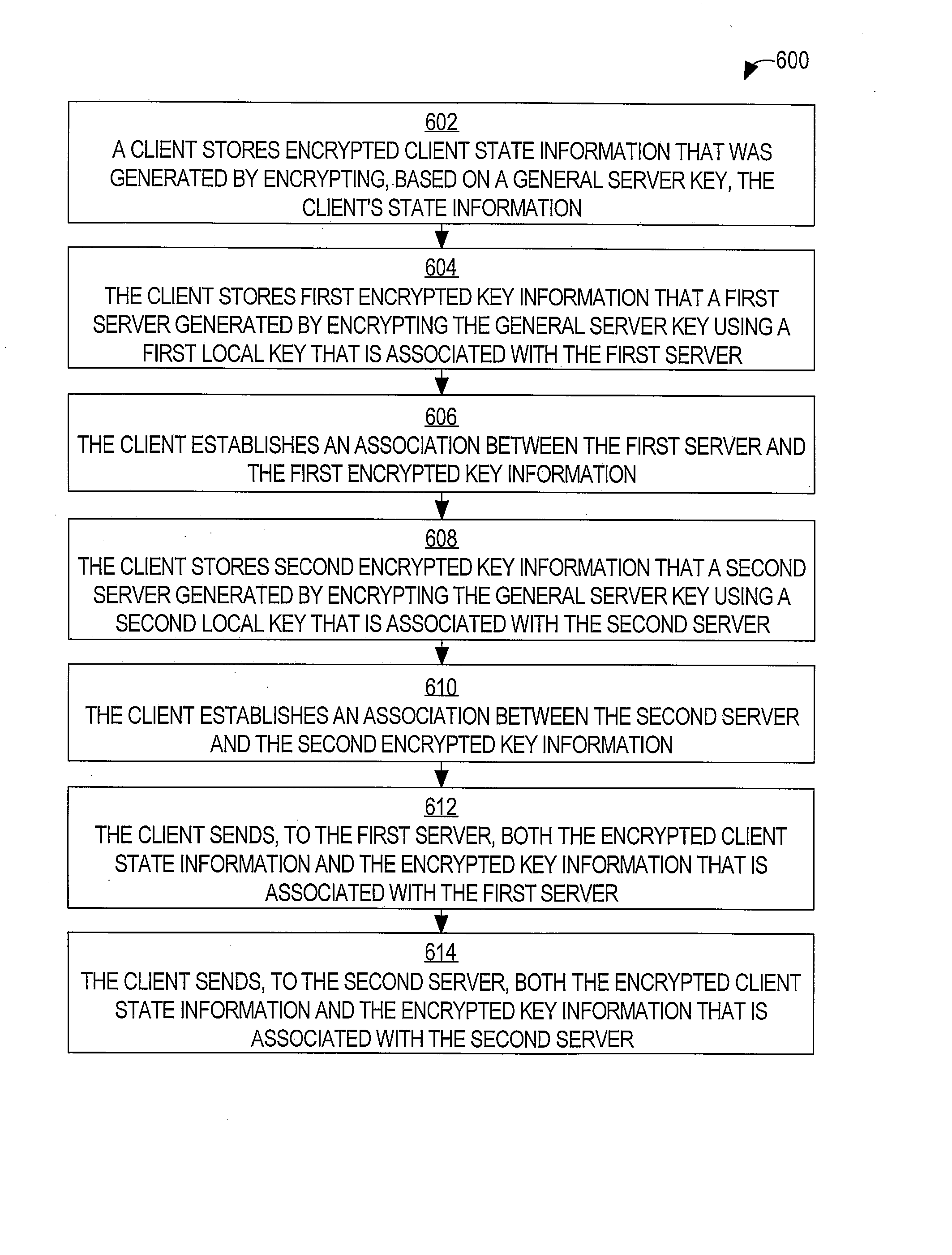
ActiveUS20050154873A1Reduce usageDigital data processing detailsUser identity/authority verificationKey serverClient-side
A method is disclosed for enabling stateless server-based pre-shared secrets. Based on a local key that is not known to a client, a server encrypts the client's state information. The client's state information may include, for example, the client's authentication credentials, the client's authorization characteristics, and a shared secret key that the client uses to derive session keys. By any of a variety of mechanisms, the encrypted client state information is provided to the client. The server may free memory that stored the client's state information. When the server needs the client's state information, the client sends, to the server, the encrypted state information that the client stored. The server decrypts the client state information using the local key. Because each client stores that client's own state information in encrypted form, the server does not need to store any client's state information permanently.
Owner:CISCO TECH INC
Method and apparatus for obtaining routing information on demand in a virtual private network
InactiveUS7590074B1Overcomes drawbackData switching by path configurationGroup controllerRouting table
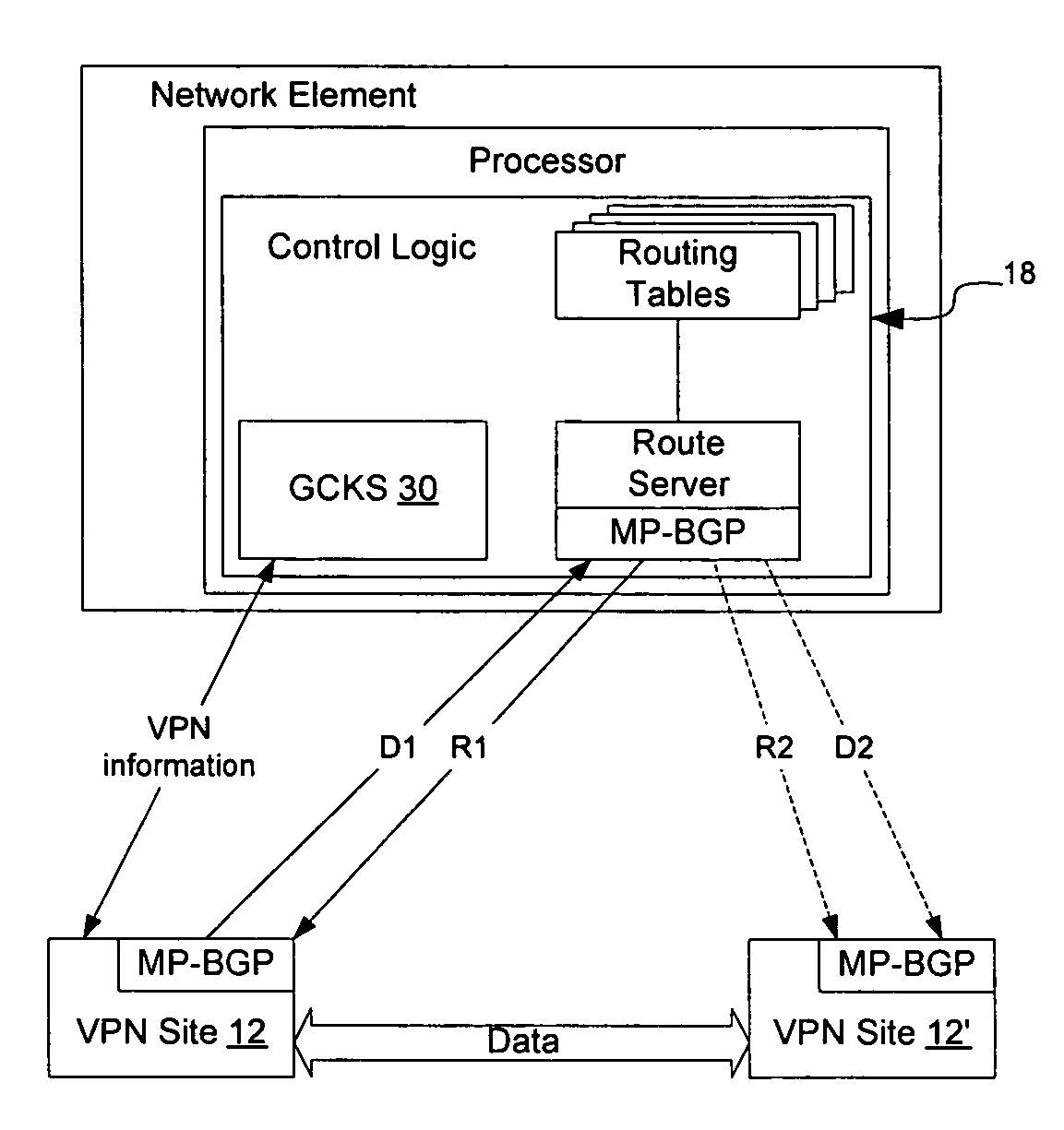
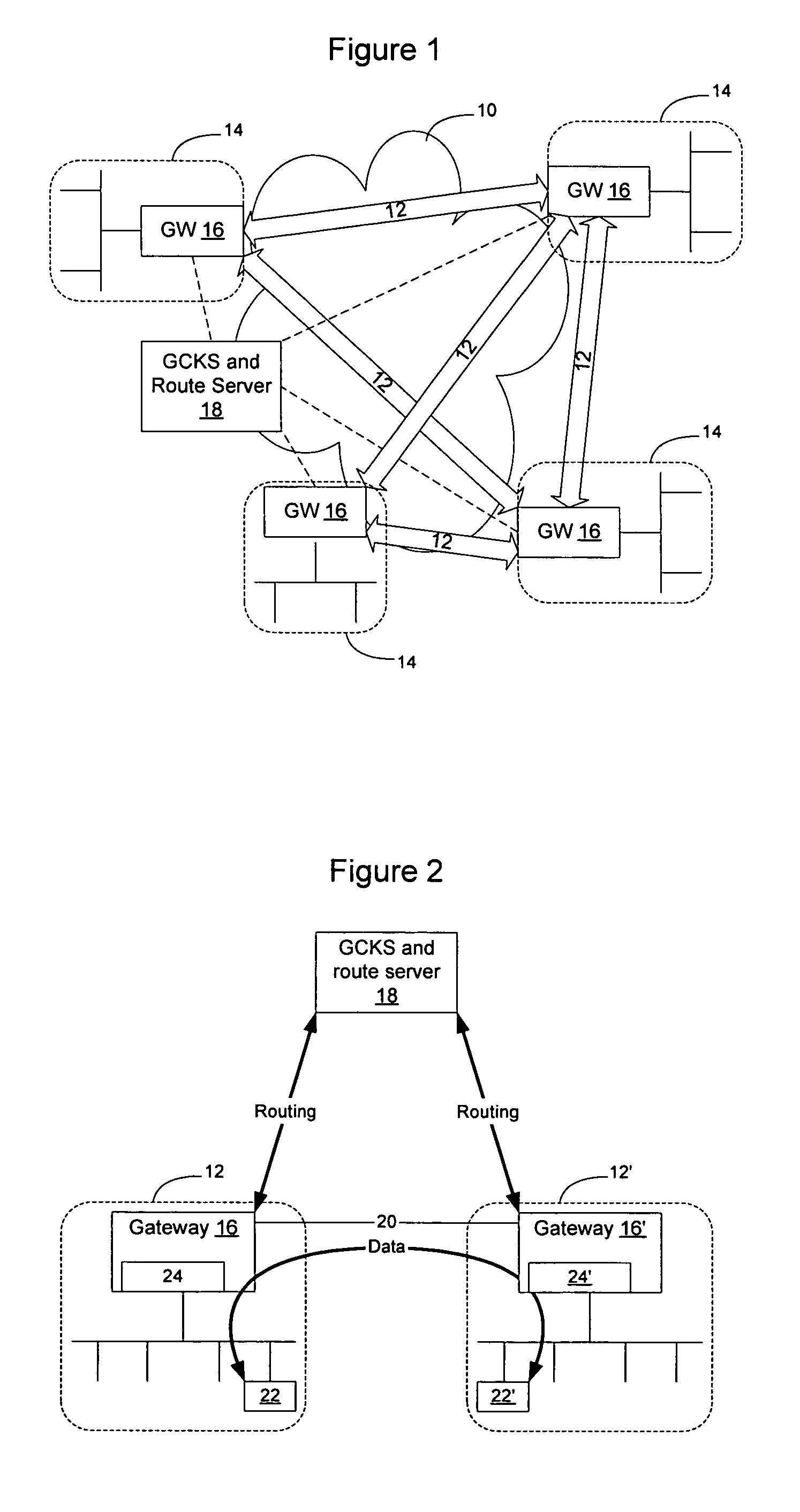
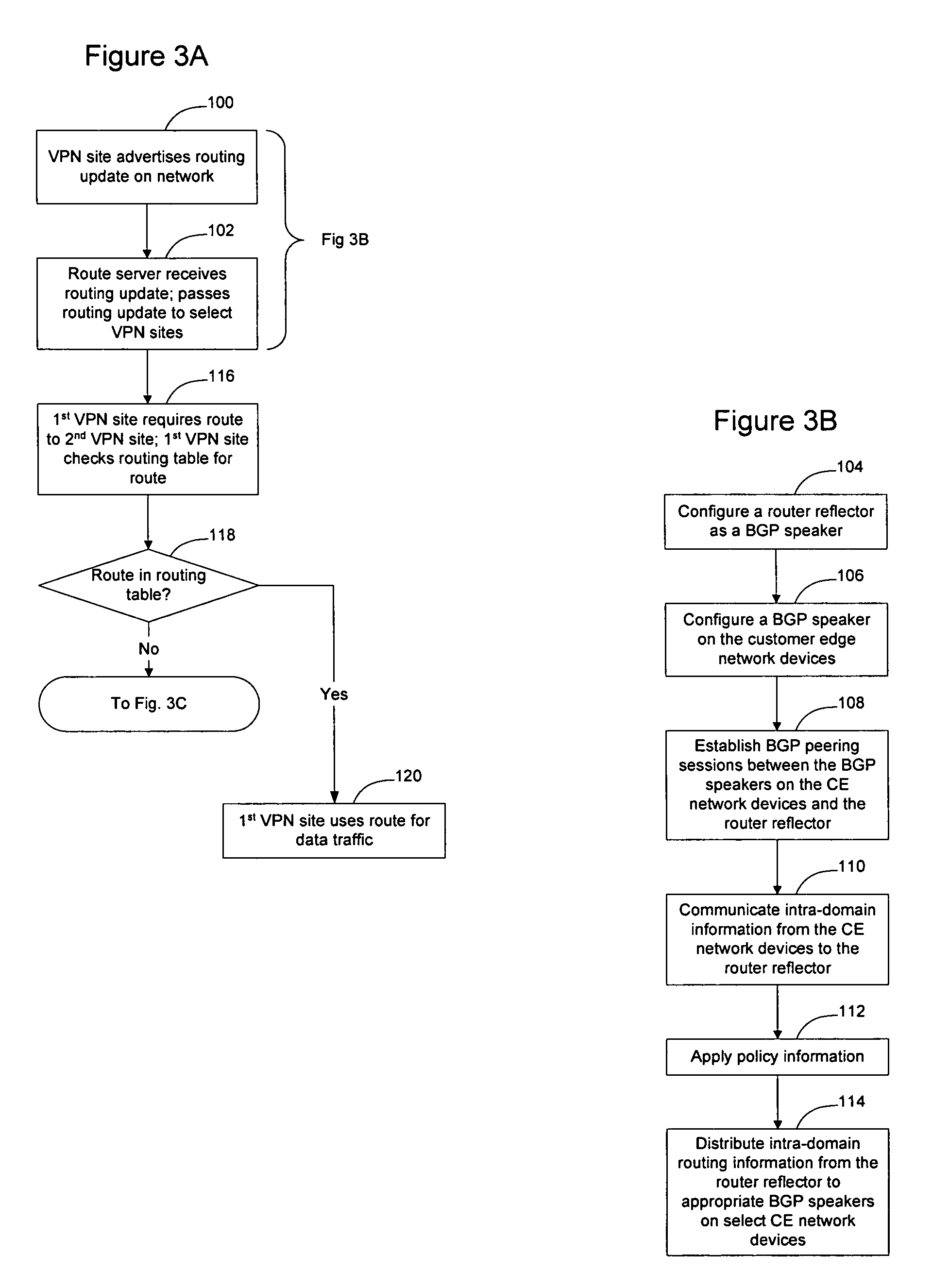
Routing information may be provided to VPN sites on demand to allow smaller VPN sites with smaller routing tables to communicate directly with other VPN sites. This allows the meshed VPN architecture to scale to a size larger than where each VPN site is required to store routing information for all other VPN sites. A route server is instantiated on the network, optionally in connection with a Group Controller Key Server, to manage distribution of routes on the network and to provide routes to VPN sites on demand. As routes are learned by the VPN sites they are advertised to the route server, which selectively advertises the routes to other VPN sites depending on the per-site preferences. When a VPN site needs routing information to communicate with another VPN site, the network element will check its routing table for the route, and if the route is not available, will obtain the route on-demand from the route server.
Owner:RPX CLEARINGHOUSE
Method and apparatus for establishing a security association
ActiveUS20070086591A1Reduce decreaseKey distribution for secure communicationUser identity/authority verificationKey serverSecurity association
A method for establishing a security association between a client and a service node for the purpose of pushing information from the service node to the client, where the client and a key server share a base secret. The method comprises sending a request for generation and provision of a service key from the service node to a key server, the request identifying the client and the service node, generating a service key at the key server using the identities of the client and the service node, the base secret, and additional information, and sending the service key to the service node together with said additional information, forwarding said additional information from the service node to the client, and at the client, generating said service key using the received additional information and the base key. A similar approach may be used to provide p2p key management.
Owner:TELEFON AB LM ERICSSON (PUBL)
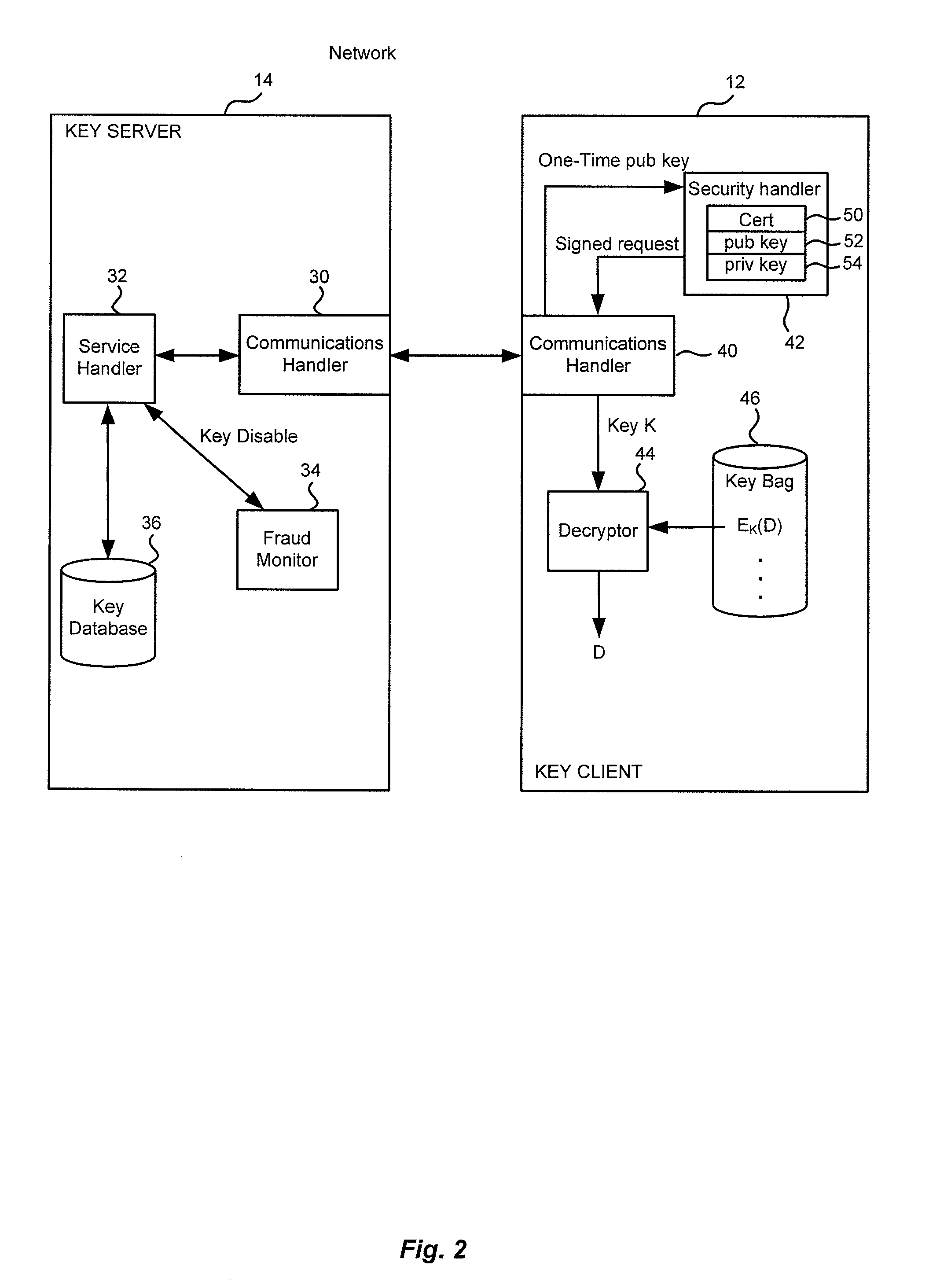
Method and apparatus for cryptographic key storage wherein key servers are authenticated by possession and secure distribution of stored keys
InactiveUS20100172504A1Key distribution for secure communicationPublic key for secure communicationKey serverKey storage
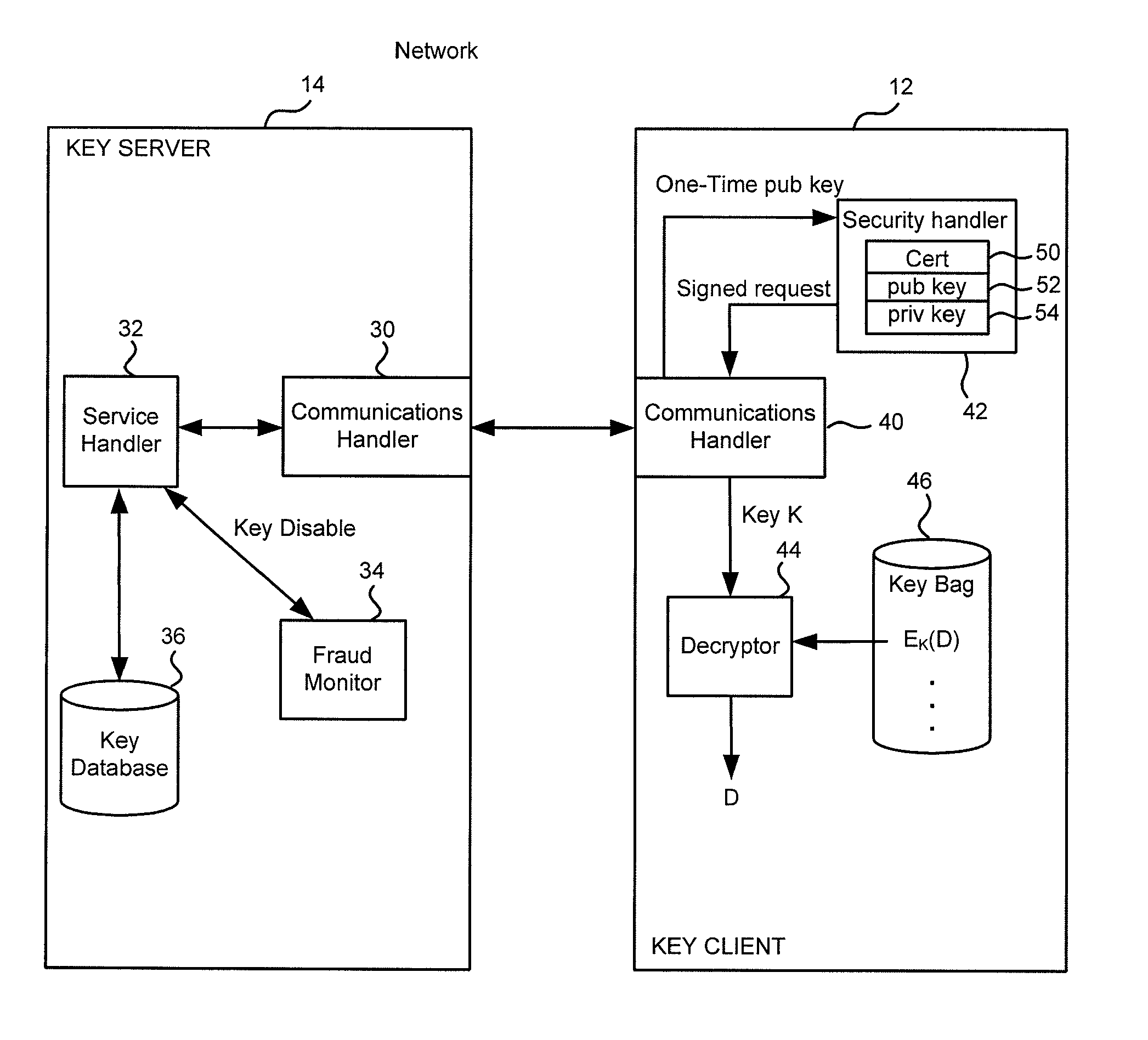
A key management system includes secured data stored on a first system secured by a control key stored securely on a key server. The secured data is secured against attacks such as unauthorized use, modification or access, where authorization to access the secured data is determined by knowledge of an access private key of an access key pair. When an authorized user is to access the secured data, the first system generates a request to the key server, signed with the access private key, wherein the request is for a decryption control key and the request includes a one-time public key of a key pair generated by the first system for the request. The first system can decrypt the decryption control key from the response, using a one-time private key. The first system can then decrypt the secured data with the decryption control key remaining secured in transport.
Owner:CA TECH INC
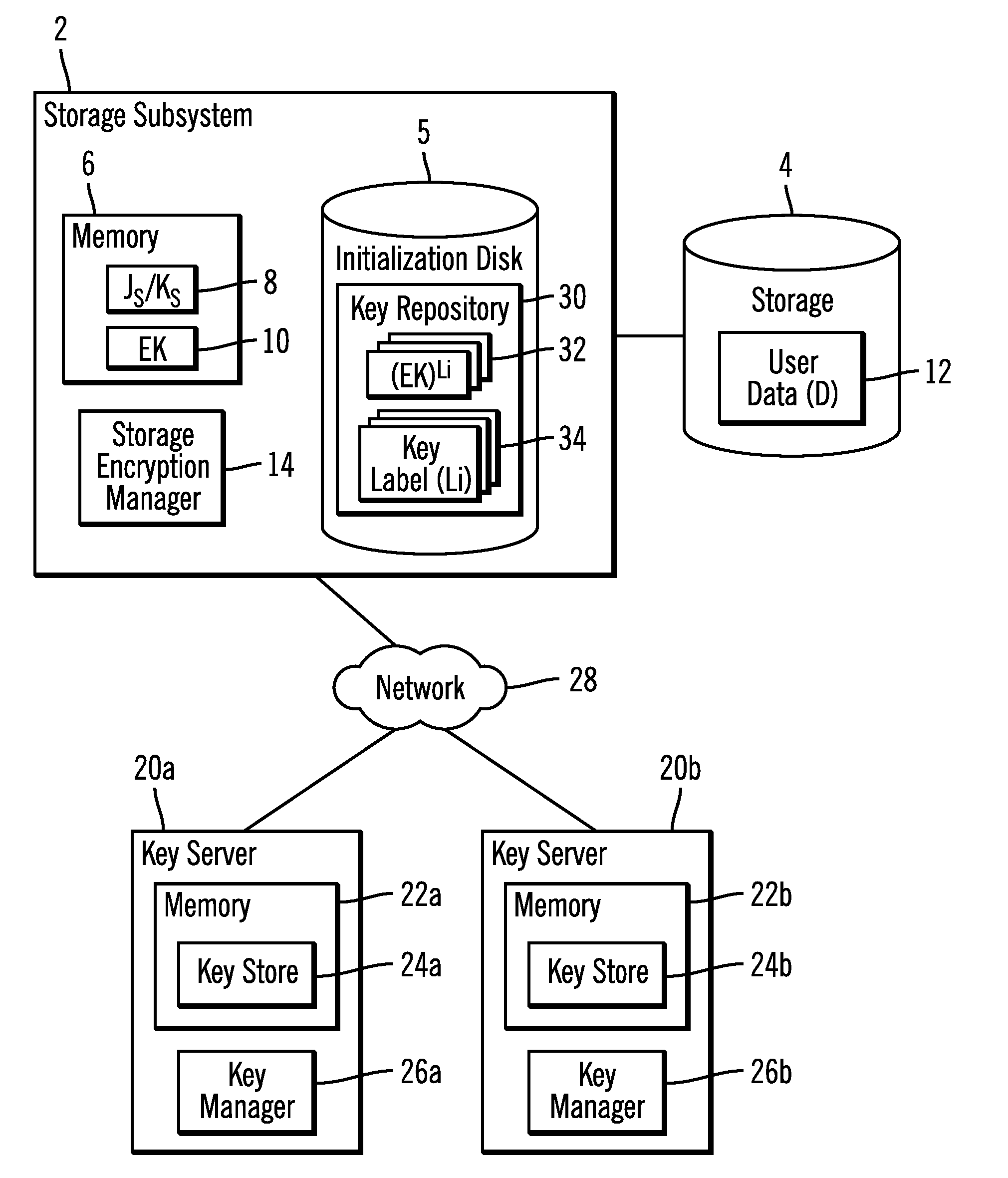
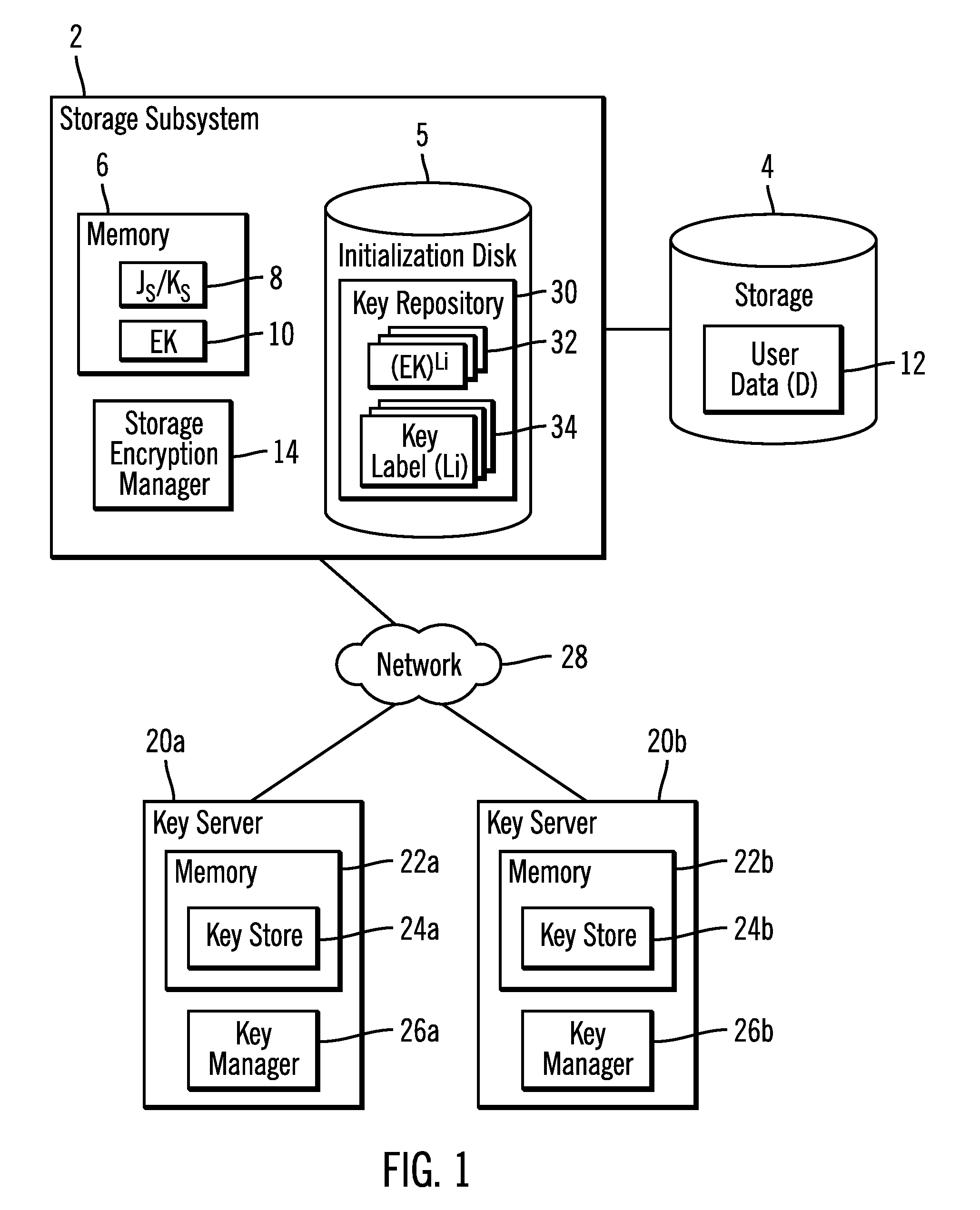
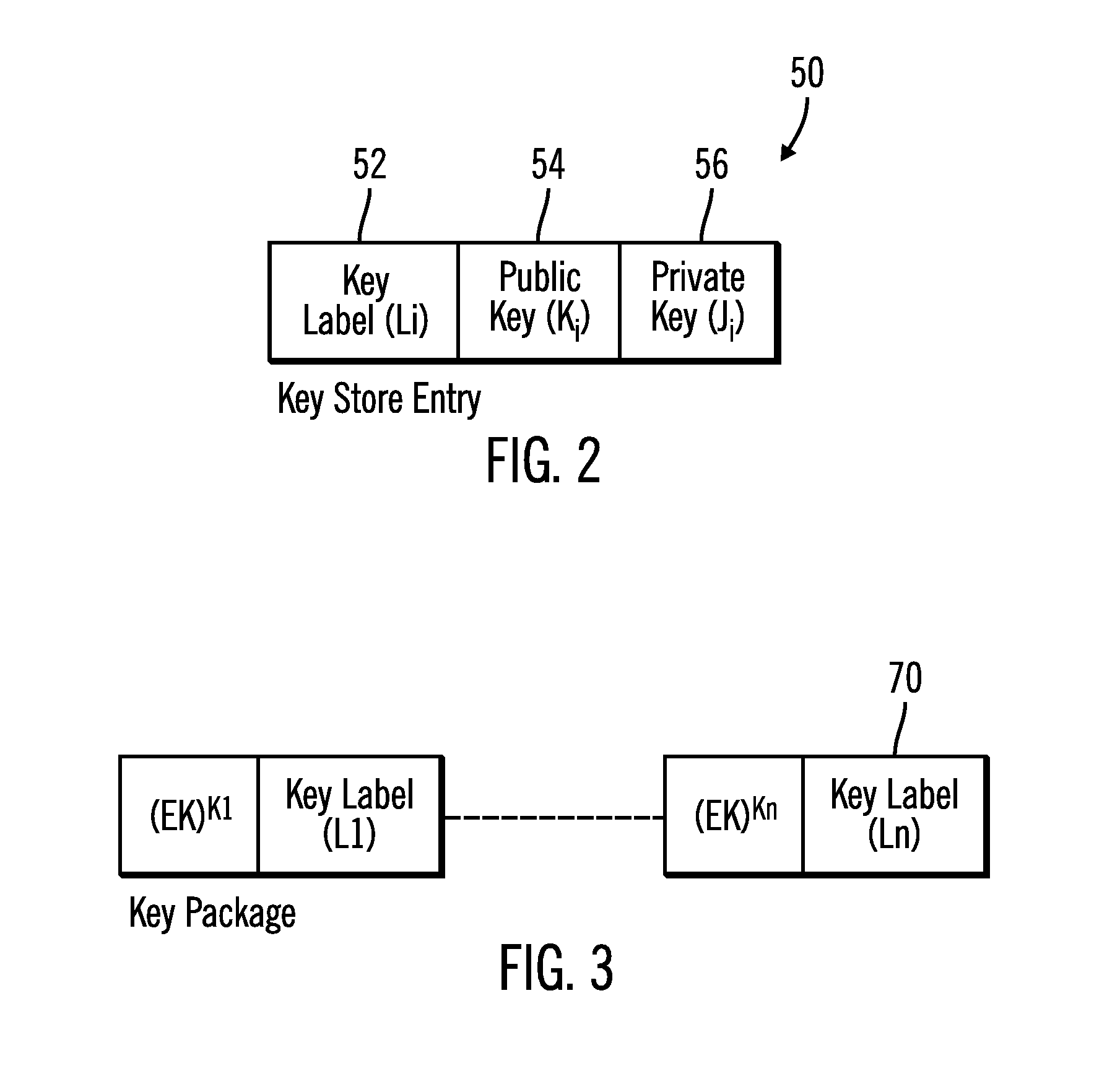
Redundant key server encryption environment
Provided are a computer program product, system and method for a redundant key server encryption environment. A key server transmits public keys associated with the key server and at least one device to at least one remote key server. The key server receives from the at least one remote key server public keys associated with the at least one remote key server. The key server receives a request for an encryption key from a requesting device comprising one of the at least one device and generates the encryption key for use by the requesting device to unlock a storage. The key server generates a first wrapped encryption key by encrypting the encryption key with a requesting device public key associated with the requesting device. The key server generates a second wrapped encryption key by encrypting the encryption key with a public key associated with the key server. At least one additional wrapped encryption key is generated for each of the at least one remote key server by encrypting the encryption key with the at least one public key provided by the at least one remote key server. The key server transmits the first, second and the at least one additional wrapped encryption key to the requesting device.
Owner:IBM CORP
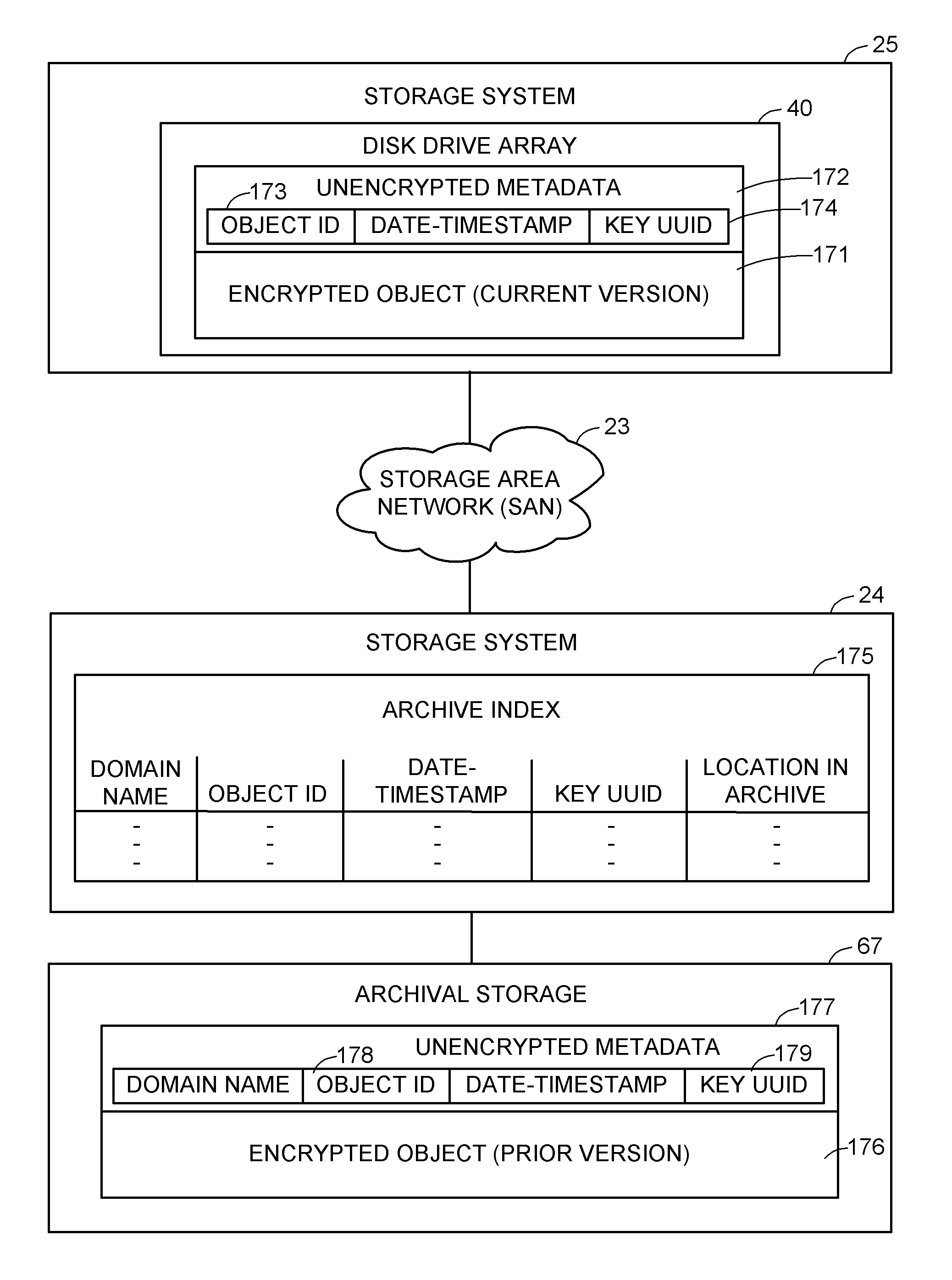
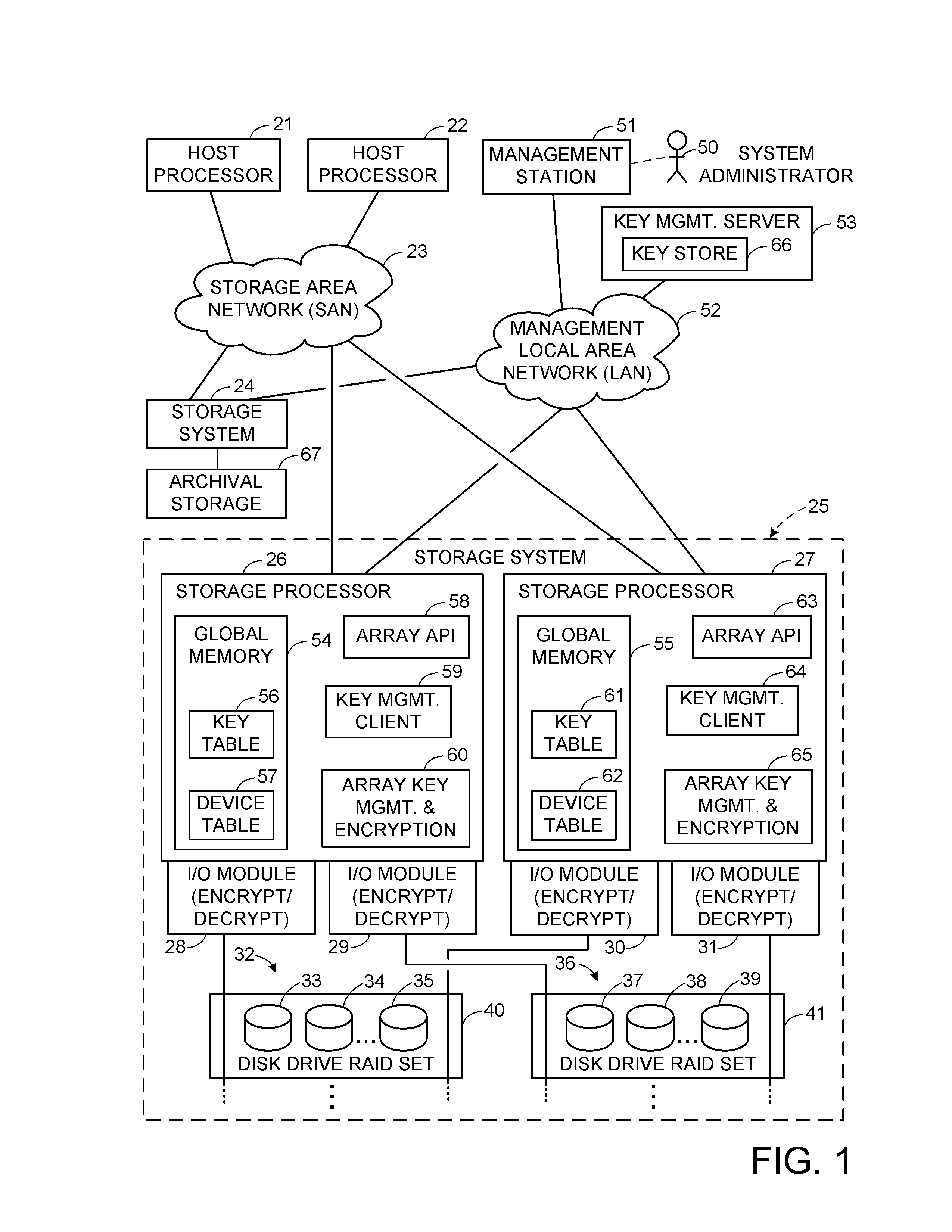
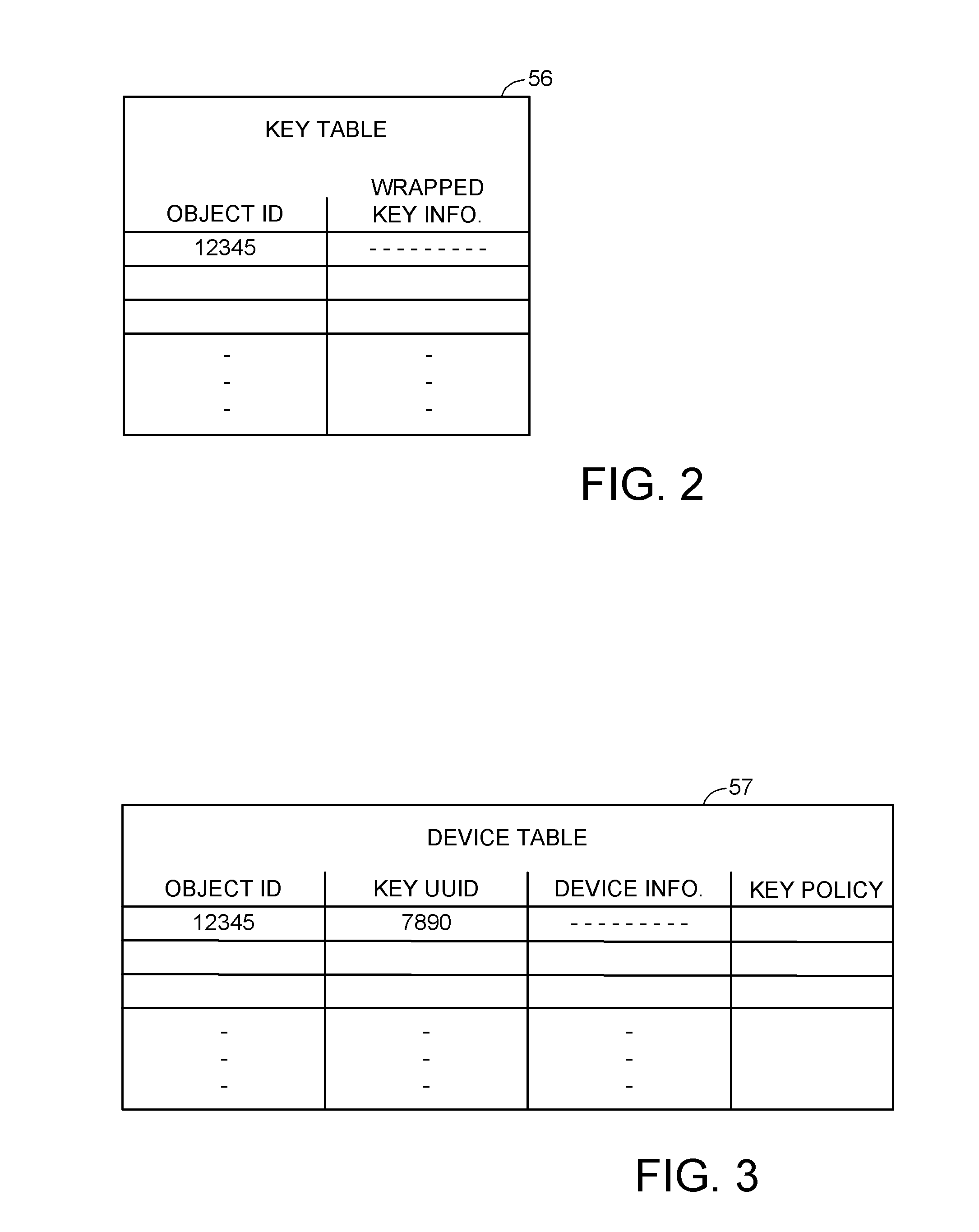
Encryption key recovery in the event of storage management failure
ActiveUS8588425B1Key distribution for secure communicationUser identity/authority verificationData processing systemOccurrence data
A data processing system stores encrypted data. Object identifiers are assigned to storage objects, and data encryption keys are assigned to the storage objects. When performing an operation upon a storage object, data encryption key failure may occur due to a corrupt or incorrect key. In this case, a copy of the data encryption key is fetched from a key server. It is possible for the association of the object identifiers with the data encryption keys to become lost or confused, so that the key server may fail to provide the correct key for a specified object identifier. Therefore, an absolute key identifier that is unique across the key server namespace also is stored in association with the object identifier in the storage system and in the key store of the key server, and the absolute key identifier is used as a failsafe for recovery of encrypted data.
Owner:EMC IP HLDG CO LLC
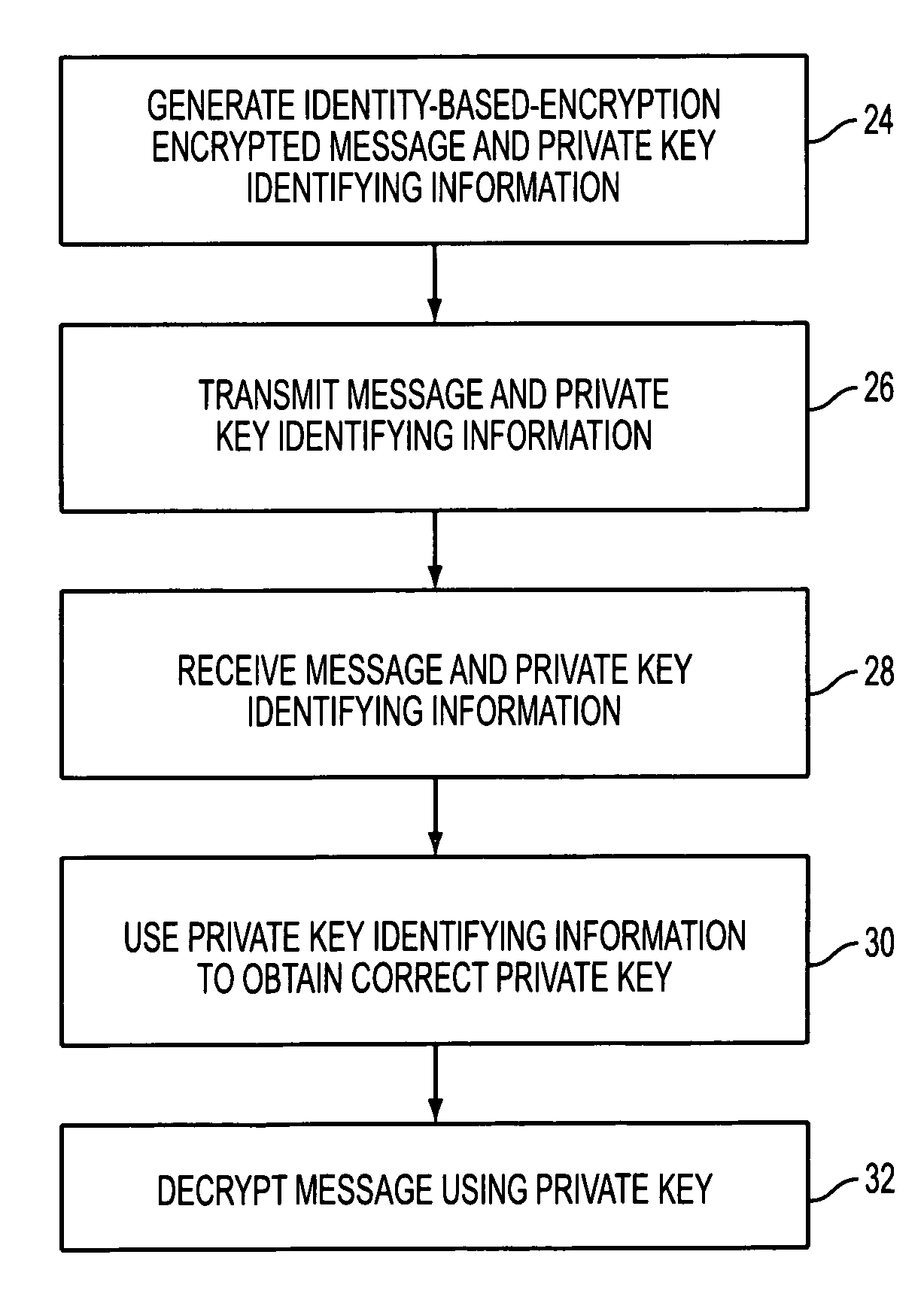
Identity-based-encryption messaging system
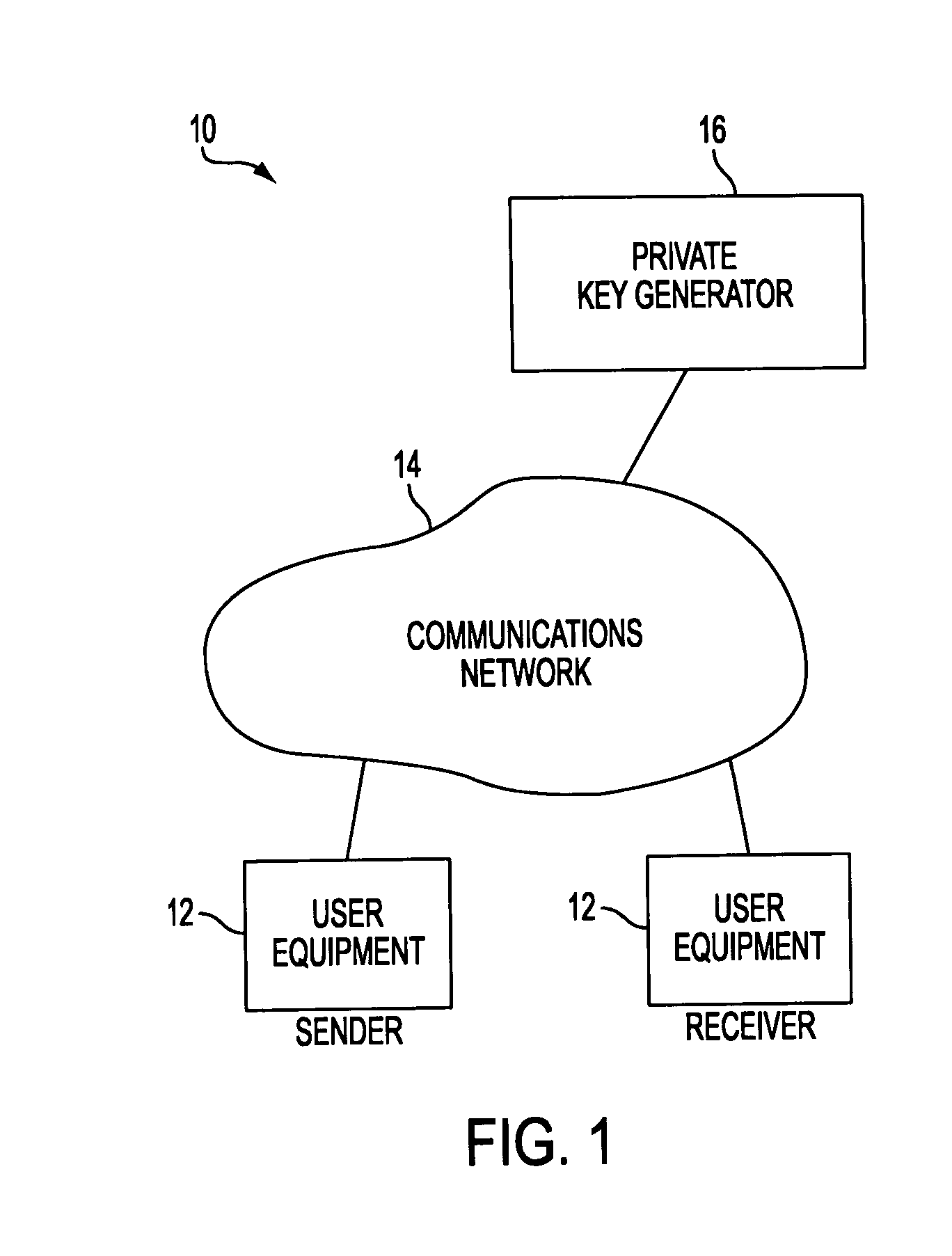
InactiveUS7571321B2Reduce decreaseKey distribution for secure communicationDigital data processing detailsSecure communicationKey generator
A system is provided that uses identity-based encryption to support secure communications between senders and recipients over a communications network. Private key generators are used to provide public parameter information. Senders encrypt messages for recipients using public keys based on recipient identities and using the public parameter information as inputs to an identity-based encryption algorithm. Recipients use private keys to decrypt the messages. There may be multiple private key generators in the system and a given recipient may have multiple private keys. Senders can include private key identifying information in the messages they send to recipients. The private key identifying information may be used by the recipients to determine which of their private keys to use in decrypting a message. Recipients may obtain the correct private key to use to decrypt a message from a local database of private keys or from an appropriate private key server.
Owner:MICRO FOCUS LLC
Apparatus, system, and method for transparent end-to-end security of storage data in a client-server environment
InactiveUS20060126850A1Transparent end-to-end security of storage dataKey distribution for secure communicationSecret communicationComputer hardwareKey server
The present invention includes one or more clients in communication with a server. The client desires to send a storage construct to the server for storage. The client negotiates a transmission key with the server. The client generates a storage key associated specifically with the storage construct. The client encrypts the storage construct using the storage key and encrypts the storage key using the transmission key. The encrypted storage construct and encrypted storage key are sent to the server. The server decrypts the storage key using the transmission key. The server stores the storage construct on a storage device separate from a storage device storing the storage key. Preferably, any changes to the storage construct location, the storage key location, or the storage construct name are tracked and proper modifications are made to an association relating the location of the storage construct and the location for the corresponding storage key.
Owner:IBM CORP
Enabling stateless server-based pre-shared secrets
ActiveUS20070288743A1Reduce usageMultiple keys/algorithms usageMultiple digital computer combinationsKey serverClient-side
A method is disclosed for enabling stateless server-based pre-shared secrets. Based on a local key that is not known to a client, a server encrypts the client's state information. The client's state information may include, for example, the client's authentication credentials, the client's authorization characteristics, and a shared secret key that the client uses to derive session keys. By any of a variety of mechanisms, the encrypted client state information is provided to the client. The server may free memory that stored the client's state information. When the server needs the client's state information, the client sends, to the server, the encrypted state information that the client stored. The server decrypts the client state information using the local key. Because each client stores that client's own state information in encrypted form, the server does not need to store any client's state information permanently.
Owner:CISCO TECH INC
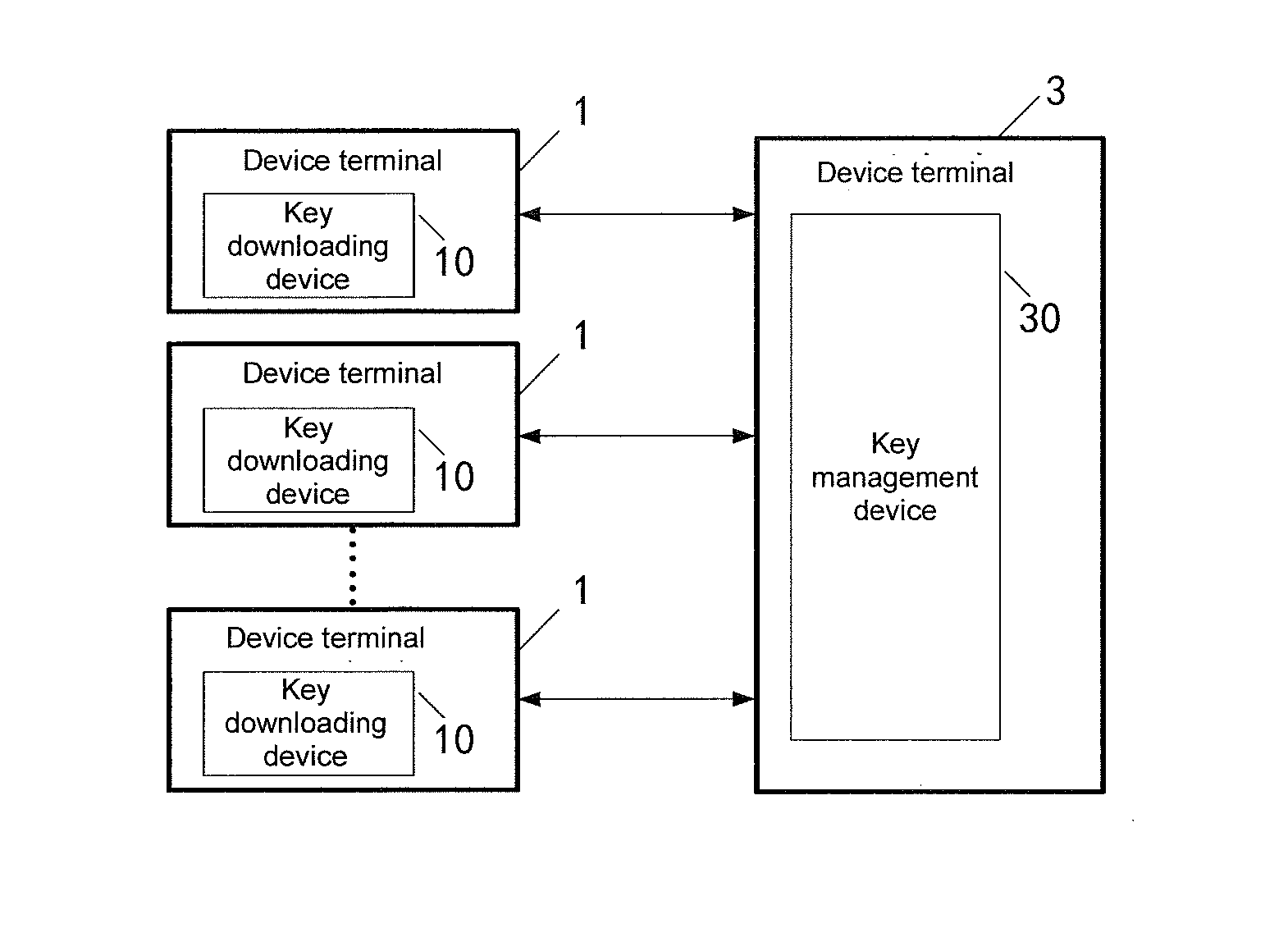
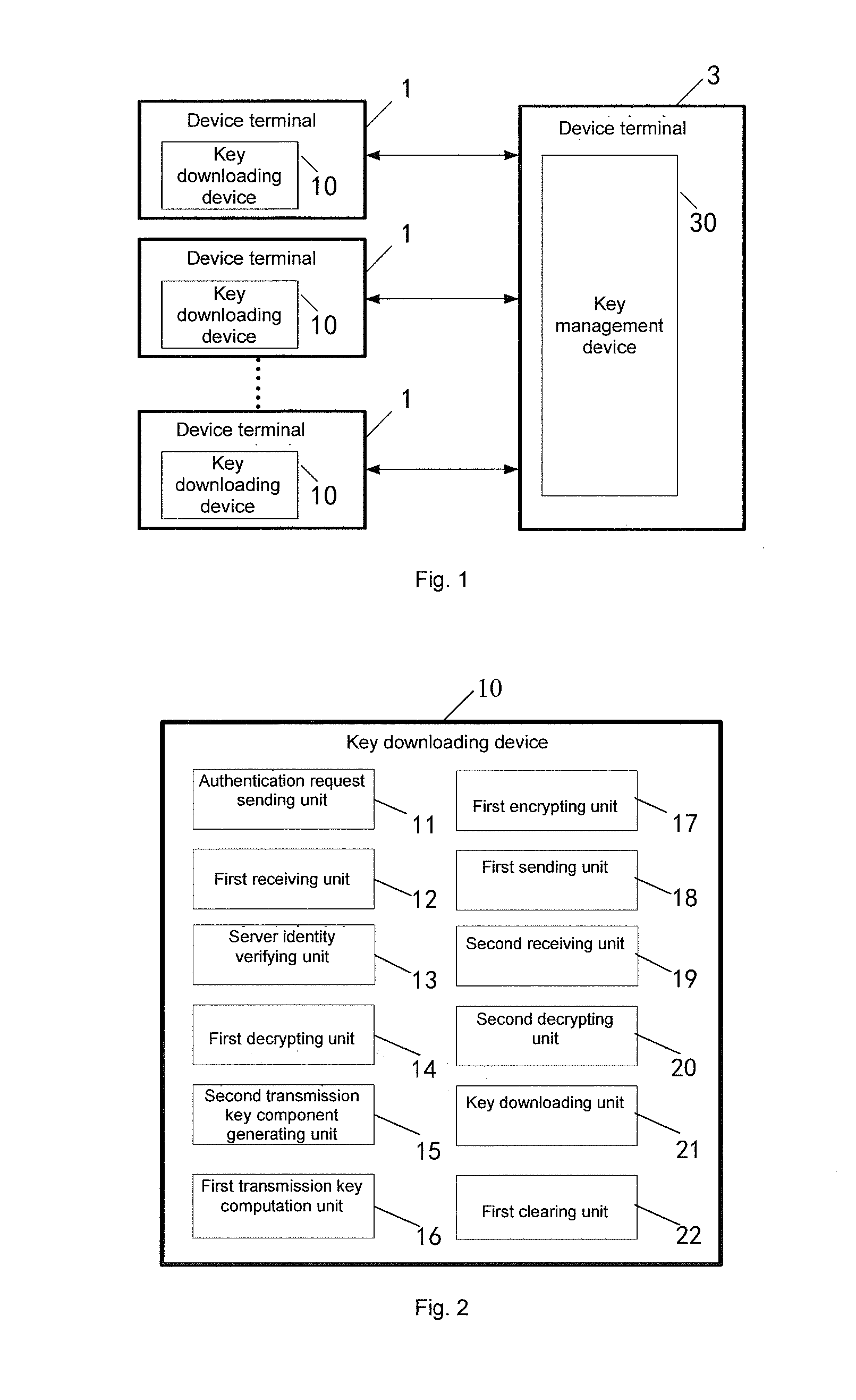
Key downloading method, management method, downloading management method, device and system
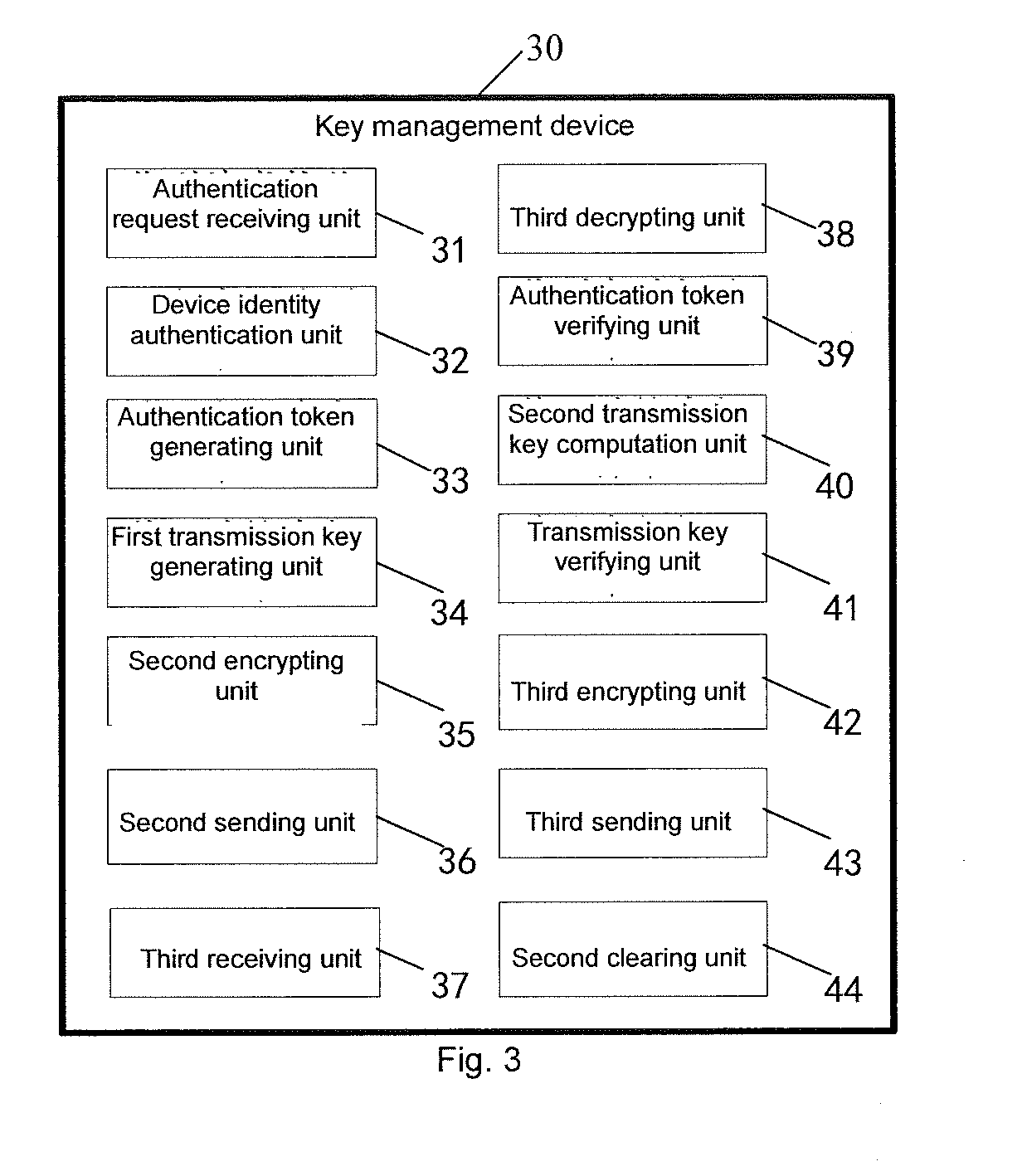
ActiveUS20160028548A1Preventing situationPublic key for secure communicationUser identity/authority verificationKey serverDigital signature
Disclosed is a key download and management method, comprising: a device end authenticating the validity of an RKS server by checking the digital signature of a public key of an operating certificate of the RKS server; the RKS server generating an authentication token (AT); after being encrypted with a device identity authentication public key of the device end, returning a ciphertext to the device end; after being decrypted by the device end with a device identity authentication private key thereof, encrypting the ciphertext with the public key of the operating certificate and then returning same to a key server; after being decrypted with a private key of the operating certificate, the key server contrasting whether the decrypted authentication token (AT) is the same as the generated authentication token (AT); and if so, indicating that the POS terminal of a device is valid, thereby realizing bidirectional identity authentication.
Owner:FUJIAN LANDI COMML TECH CO LTD
Method and apparatus for establishing a security association
InactiveUS20070086590A1Reduce decreaseKey distribution for secure communicationSecurity arrangementKey serverComputer network
A method for establishing a security association between a client and a service node for the purpose of pushing information from the service node to the client, where the client and a key server share a base secret. The method comprises sending a request for generation and provision of a service key from the service node to a key server, the request identifying the client and the service node, generating a service key at the key server using the identities of the client and the service node, the base secret, and additional information, and sending the service key to the service node together with said additional information, forwarding said additional information from the service node to the client, and at the client, generating said service key using the received additional information and the base key.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method, system and device for realizing multi-party communication security
InactiveUS20090271612A1Improve deployabilityImprove portabilityKey distribution for secure communicationUser identity/authority verificationCommunications securityKey server
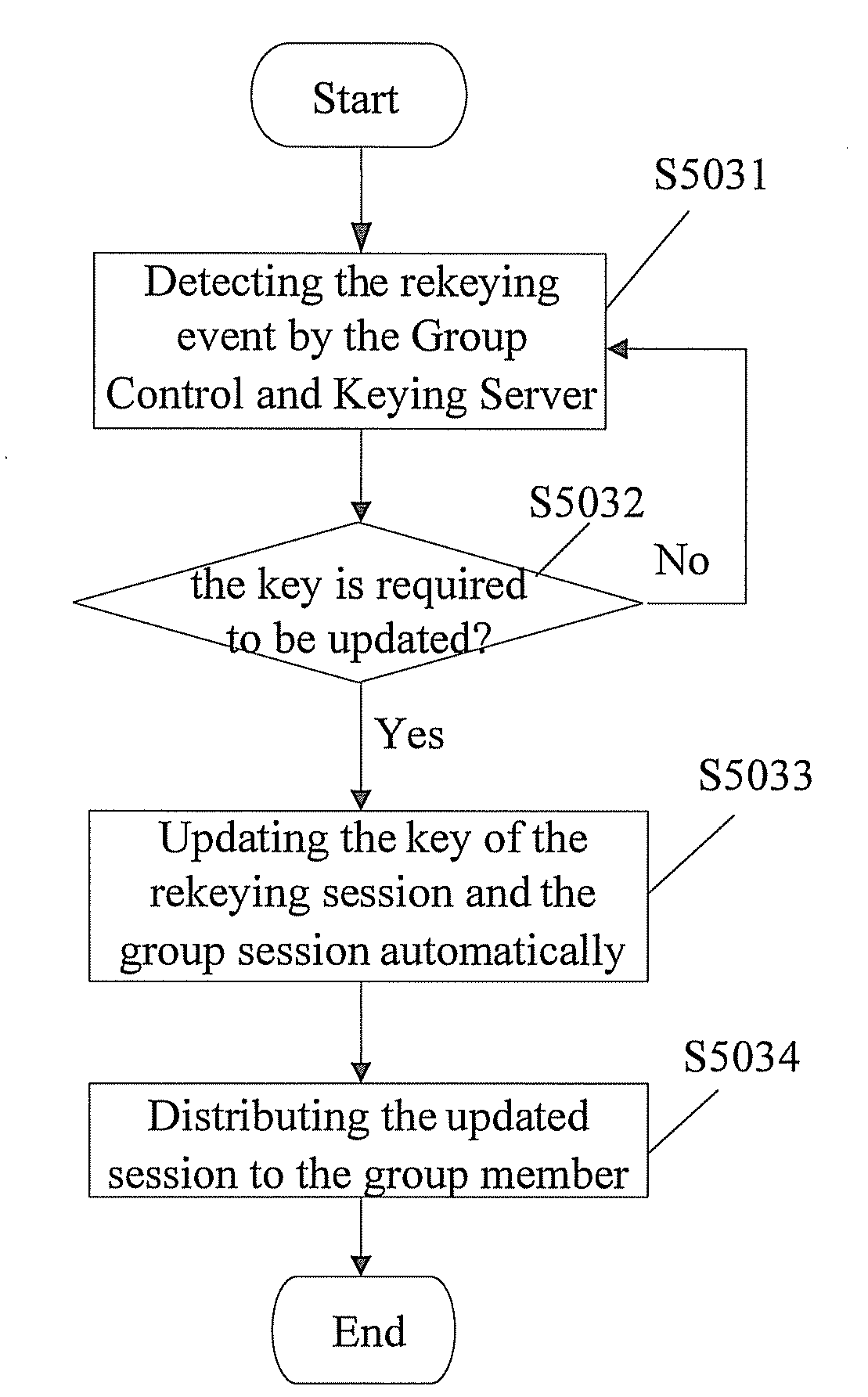
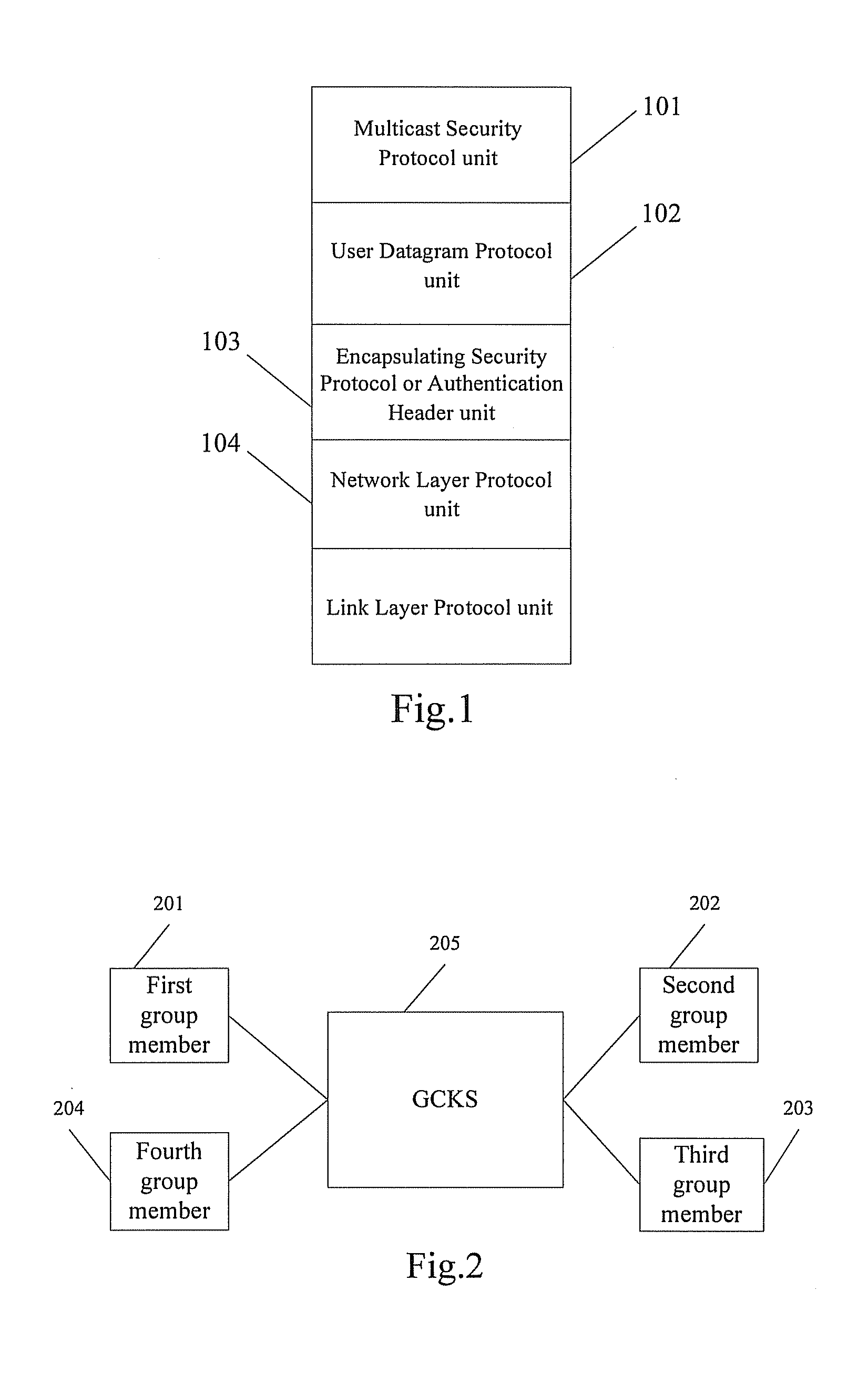
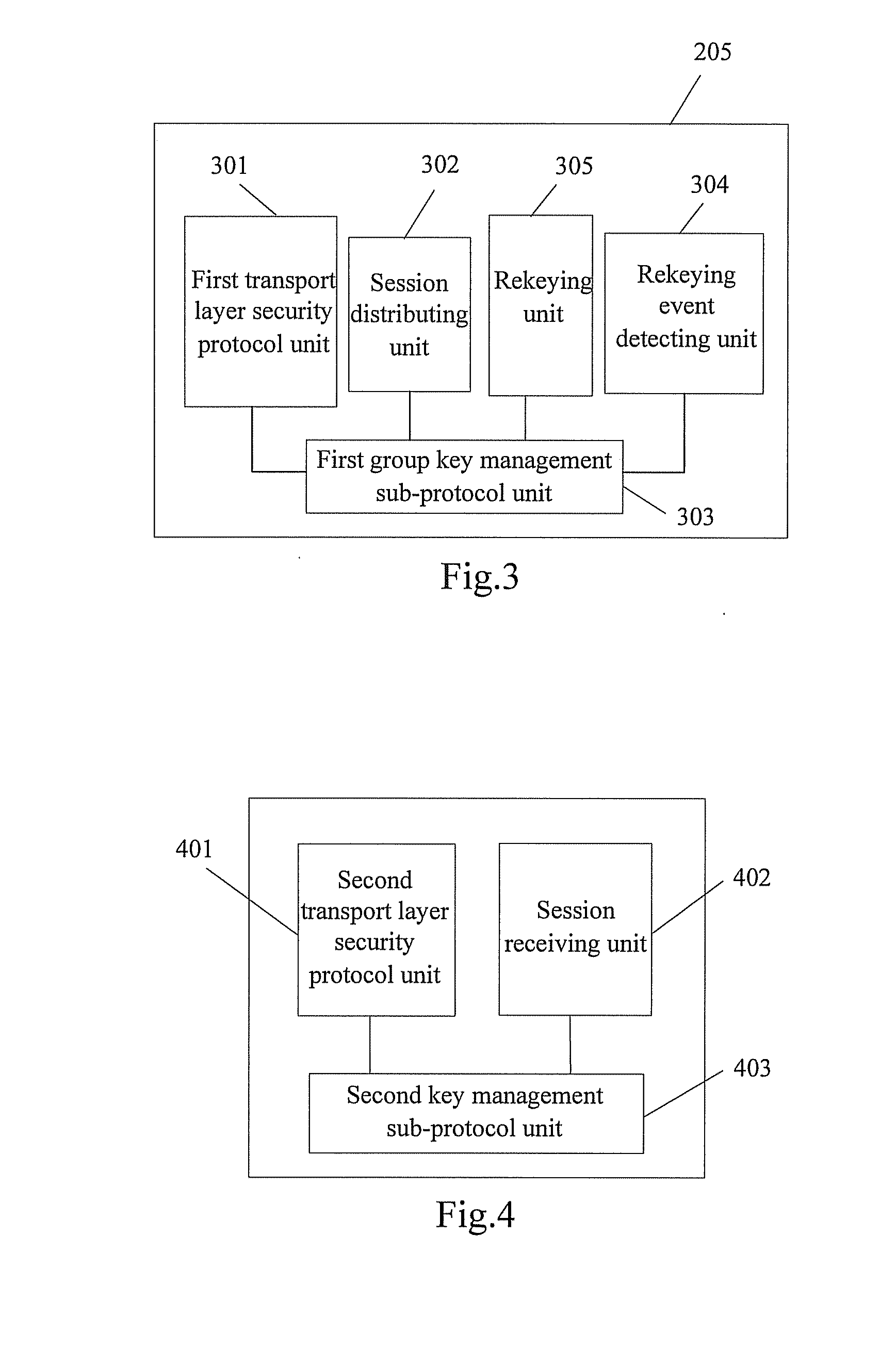
A method for realizing multi-party communication security includes: performing identification authentication and negotiating to create an initiation session through running the transport layer security protocol or datagram transport layer security protocol by a Group Control and Keying Server and a group member device; distributing a group session and a rekeying session to the group member device through running a group key management sub-protocol on the Group Control and Keying Server and the group member devices; rekeying through running the group key management sub-protocol on the Group Control and Keying Server and the group member devices, when a rekeying event is detected by the Group Control and Keying Server. A relevant multi-party communication security system and a device are further provided in the present invention.
Owner:HUAWEI TECH CO LTD
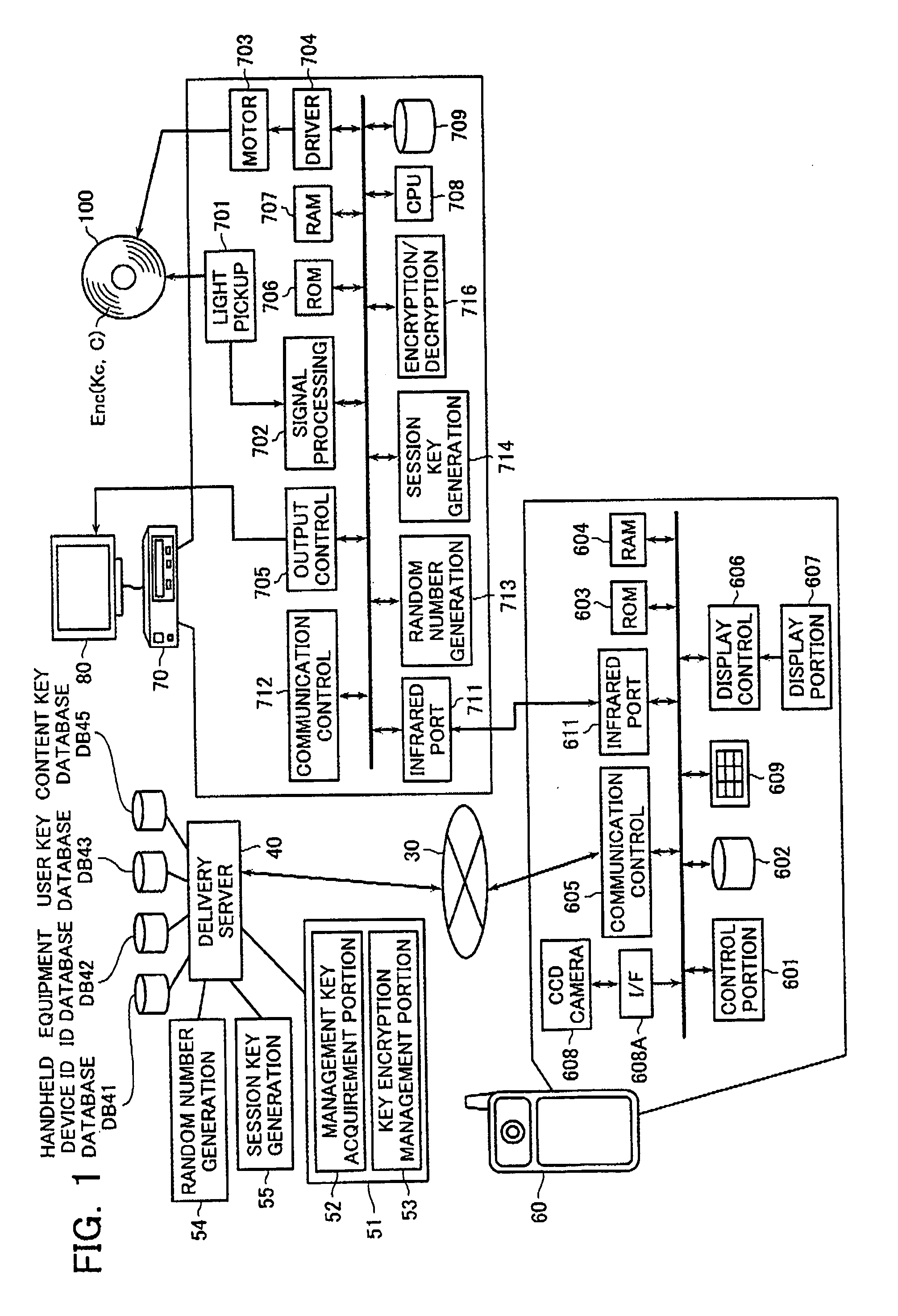
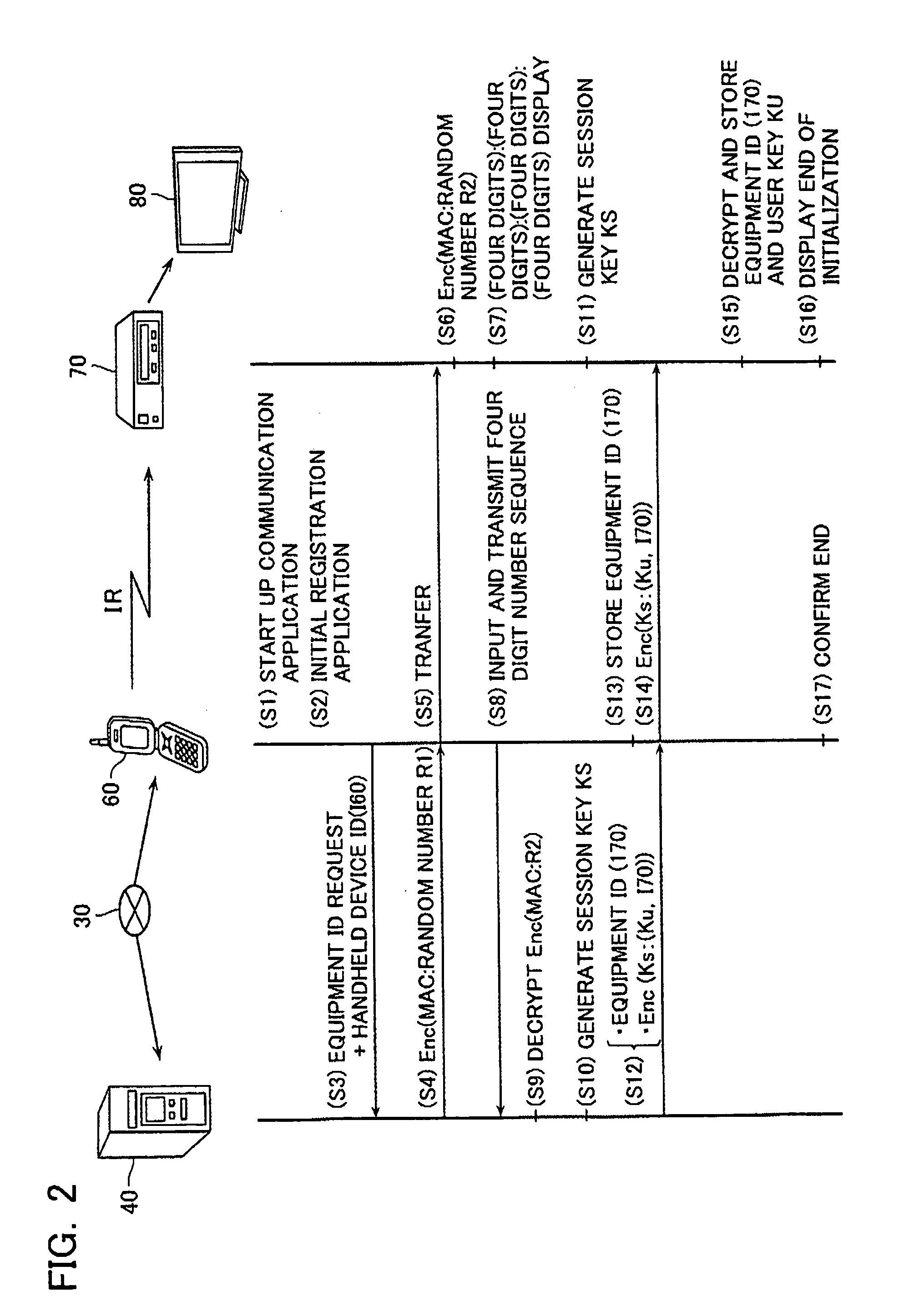
Content data delivery method and content data delivery system and handheld device for use therein
InactiveUS20070064936A1Record information storageRecording signal processingComputer hardwareKey server
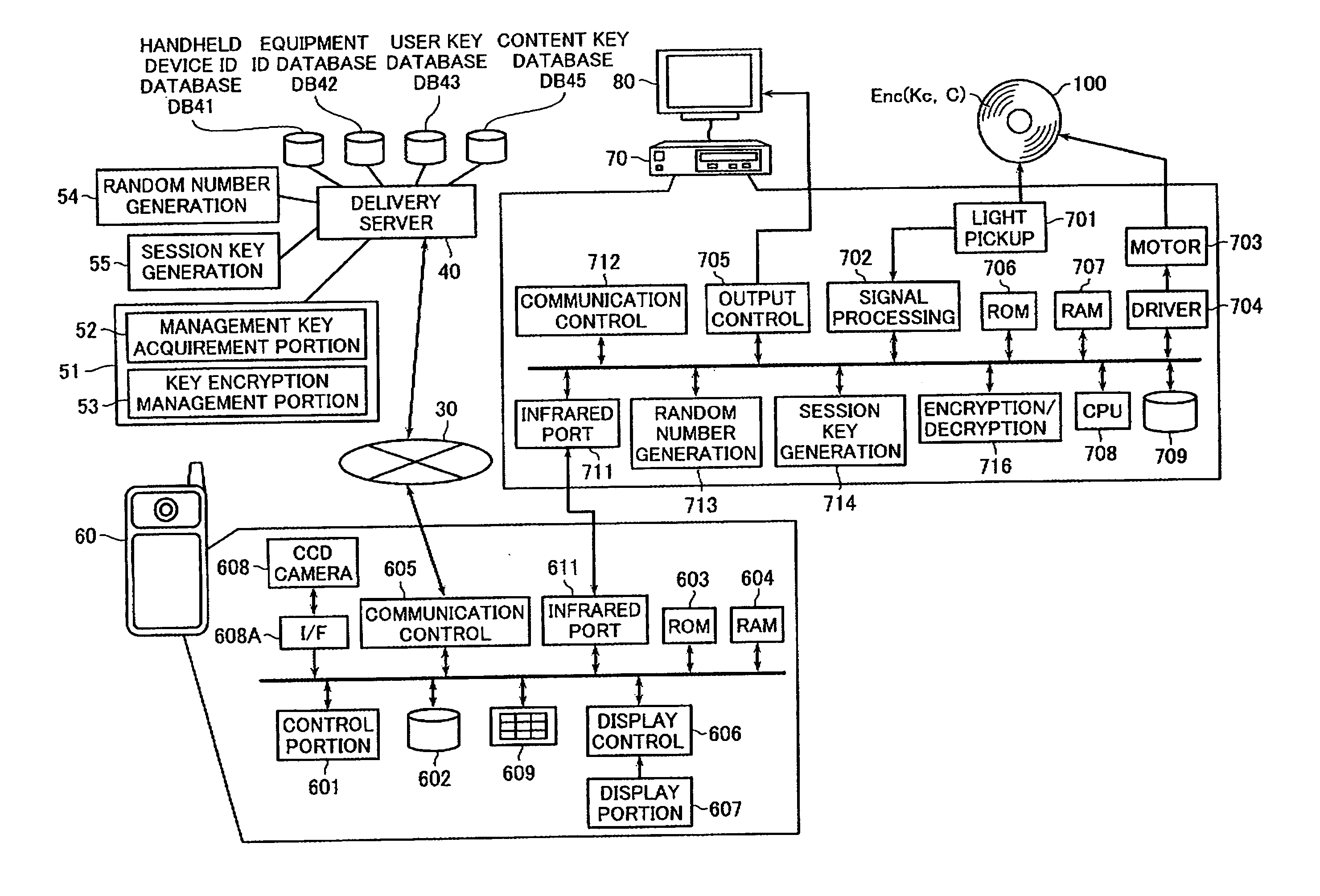
There is provided a content data delivery system including a playback equipment that is adapted to be able to decrypt a content data encrypted with a content key data and to play back the decrypted content data and that holds an equipment ID to identify itself; a handheld device that is adapted to be able to communicate data with the playback equipment and holds a handheld device ID to identify itself; and a server that delivers the content key data to the playback equipment via the handheld device. The server generates a first random number and transmits the first random number to the playback equipment via the handheld device. The playback equipment generates a second random number. The handheld device transmits to the server the equipment ID, handheld device ID, and second random number to provide a request for delivery of the content key data. The server and playback equipment use the first random number and second random number as a basis to generate a session key. The server uses the session key to encrypt the content key data and transmits the encrypted content key data to the playback equipment via the handheld device.
Owner:KK TOSHIBA
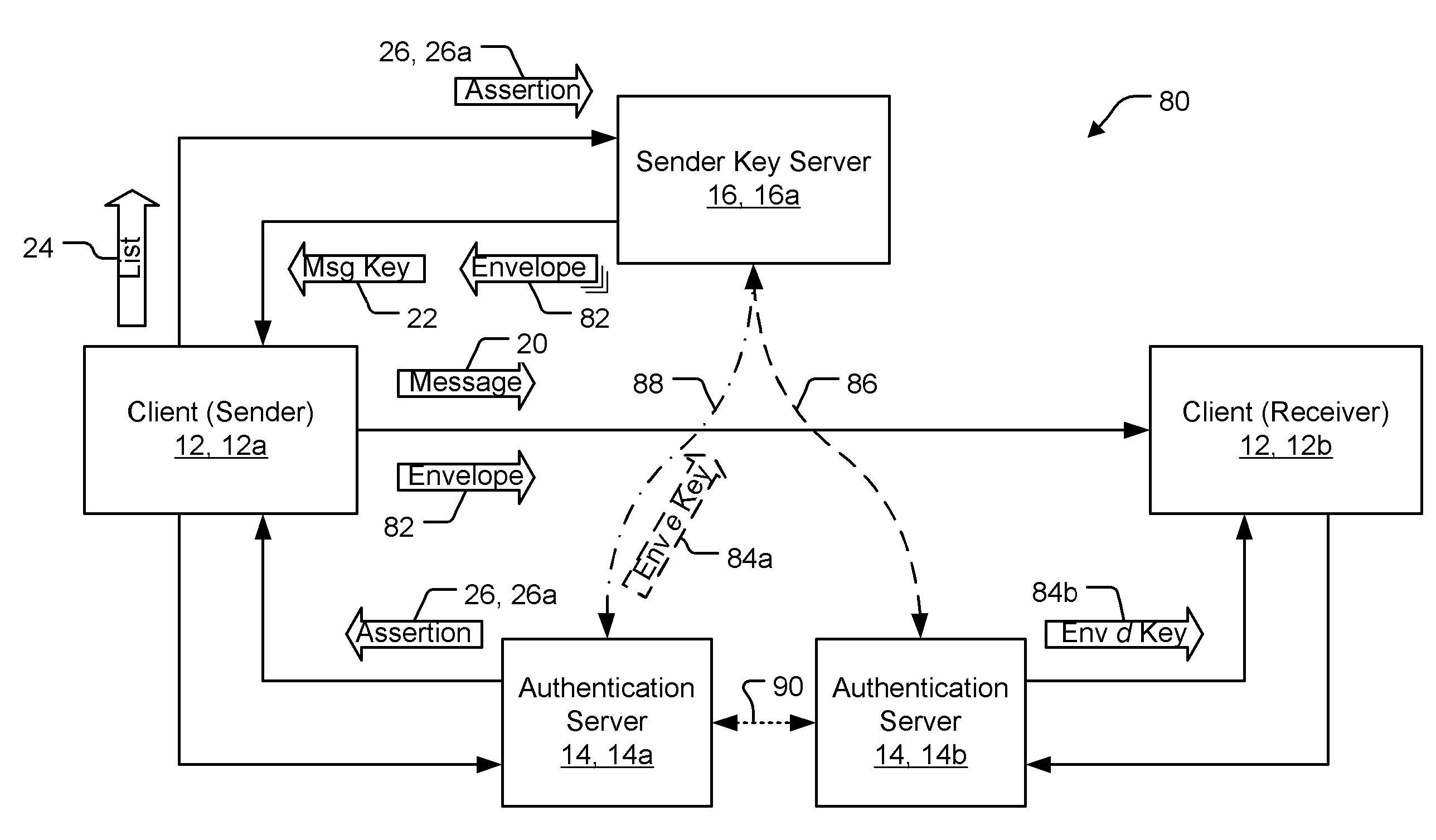
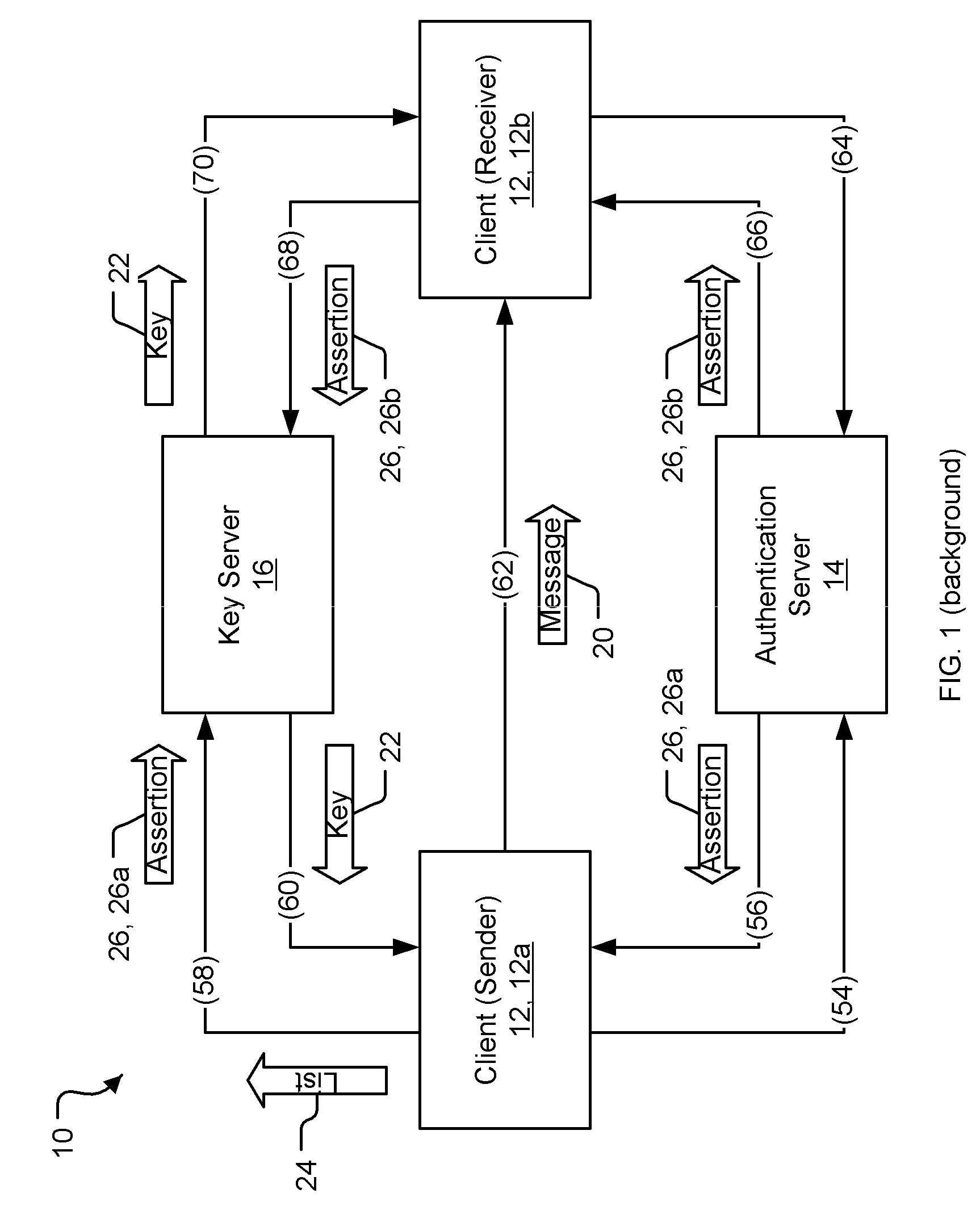
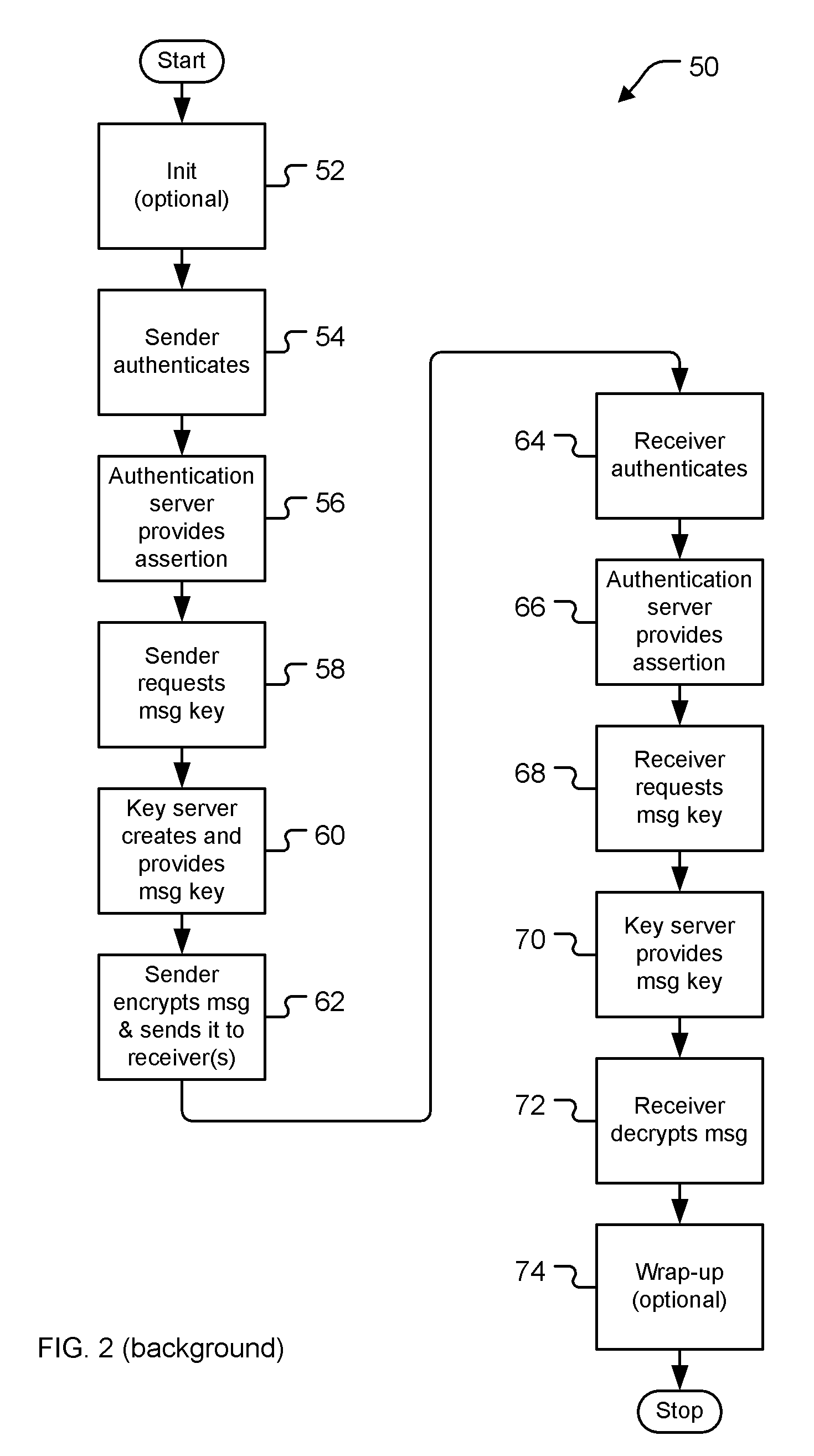
Mediated key exchange between source and target of communication
ActiveUS20060248336A1Easy to useGood encryptionDigital data processing detailsPublic key for secure communicationKey exchangeAuthentication server
A system for communicating a message securely between a sender and a receiver. The sender provides a key server with a string specifying the receiver. The key server obtains a message key and a particular envelope encryption key corresponding with a particular envelope decryption key, encrypts the message key with the envelope encryption key (creating the envelope), and provides the envelope to the sender-client. The sender-client encrypts the message with the message key and provides it and the envelope to the receiver. The receiver-client receives these and asks an authentication server for the envelope decryption key. The authentication server obtains the envelope decryption key and provides it to the receiver. The receiver then decrypts the envelope with the envelope decryption key, to get the message key, and decrypts the message.
Owner:PROOFPOINT INC
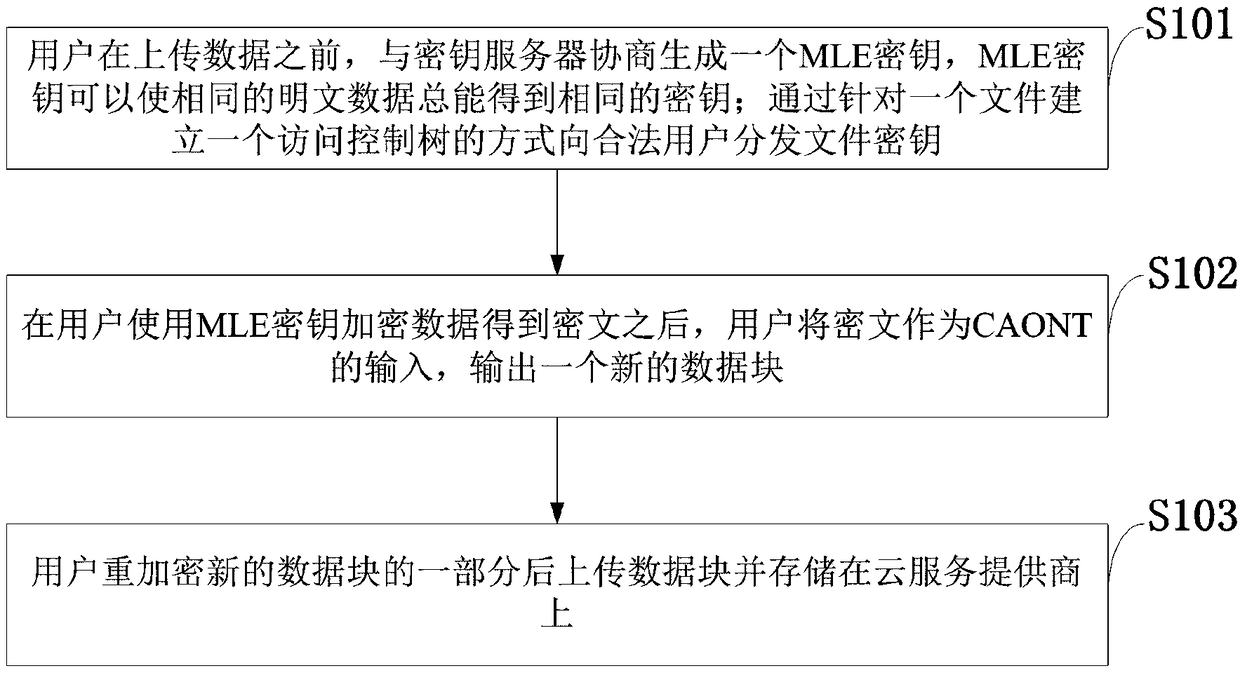
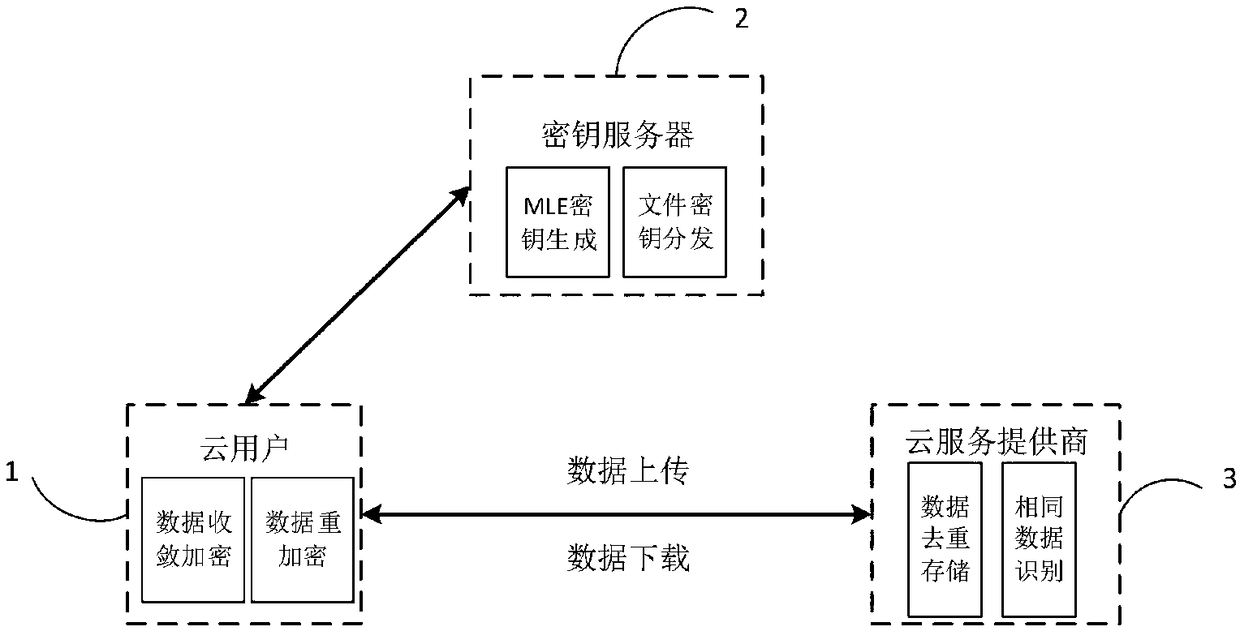
High-efficiency data re-encryption method and system supporting data deduplication and cloud storage system
ActiveCN109379182AReduce computational overheadPrivacy protectionKey distribution for secure communicationDigital data information retrievalCiphertextCloud storage system
The invention belongs to the technical field in which a protocol is taken as the characteristic, and discloses a high-efficiency data re-encryption method and system supporting data deduplication anda cloud storage system. Before a user uploads data, the user consults with a key server to generate an MLE key, and the MLE key enables the same clear-text data to always obtain the same key; in a mode of establishing one access control tree for one file, a file key is distributed to a valid user; after the user encrypts data to obtain ciphertext by using the MLE key, the user uses the ciphertextas an input of CAONT and a new data block is output; and after re-encrypting one part of the newly generated data block, the user uploads the data block and stores the data block at a cloud service provider. According to the invention, a rescinding user can be prevented from continuously accessing sensitive data of a data owner; and computation cost when the data owner carries out re-encryption can be greatly reduced. Experiments show that by adopting the high-efficiency data re-encryption method and system supporting data deduplication and the cloud storage system which are disclosed by the invention, computation cost when the data owner carries out re-encryption is greatly reduced.
Owner:XIDIAN UNIV
Systems and methods for establishing and using distributed key servers
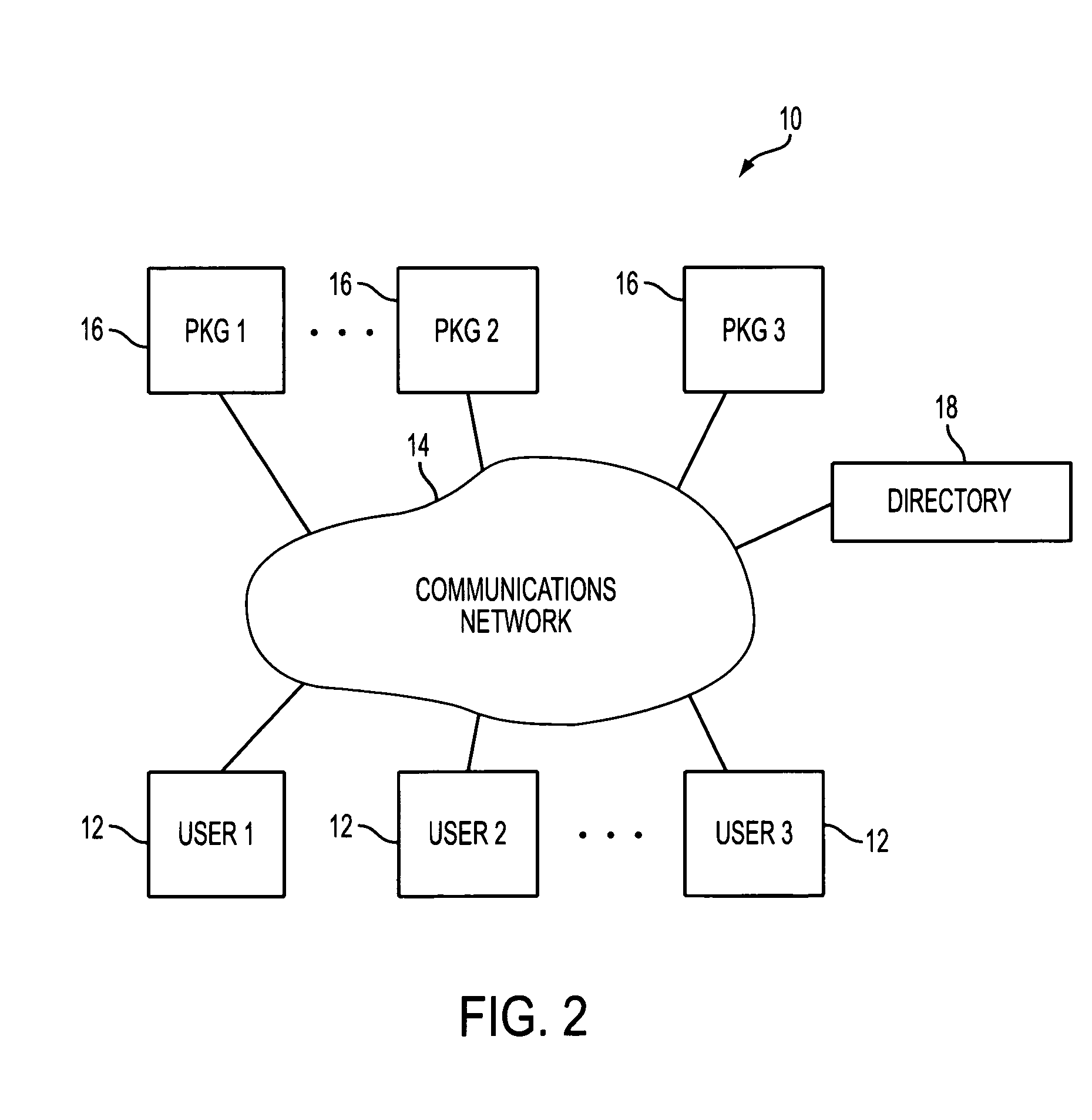
InactiveUS20150089231A1Improve efficiencyImprove robustnessKey distribution for secure communicationUser identity/authority verificationKey serverAuthorization
Systems and methods in which multiple key servers operate cooperatively to securely provide authorization codes to requesting devices. In one embodiment, a server cloud receives a device authorization code request and selects an “A server”. The “A server” requests authorization from one or more “B servers” and authorizes the “B servers” to respond. The “B servers” provide authorization to the “A server”, and may provide threshold key inputs to enable decryption of device authorization codes. The “A server” cannot provide the requested device authorization code without authorization from the “B server(s)”, and the “B server(s)” cannot provide the requested server authorization code and threshold inputs without a valid request from the “A server”. After the “A server” receives authorization from the “B server(s)”, it can provide the initially requested device authorization code to the requesting device.
Owner:TORUS VENTURES LLC
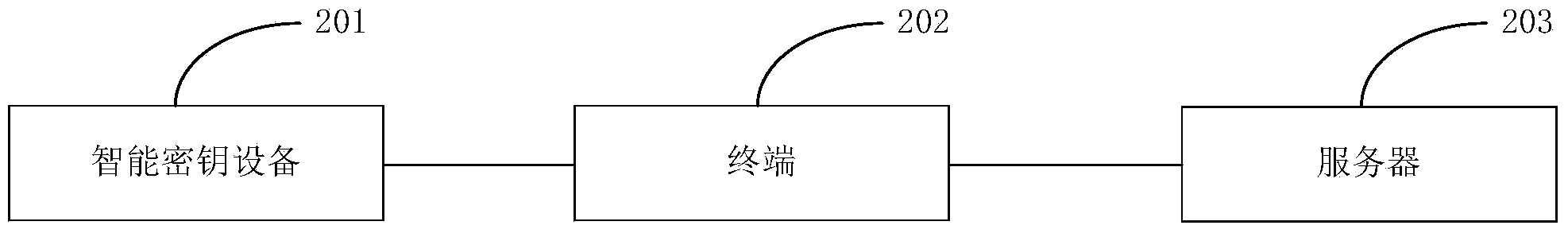
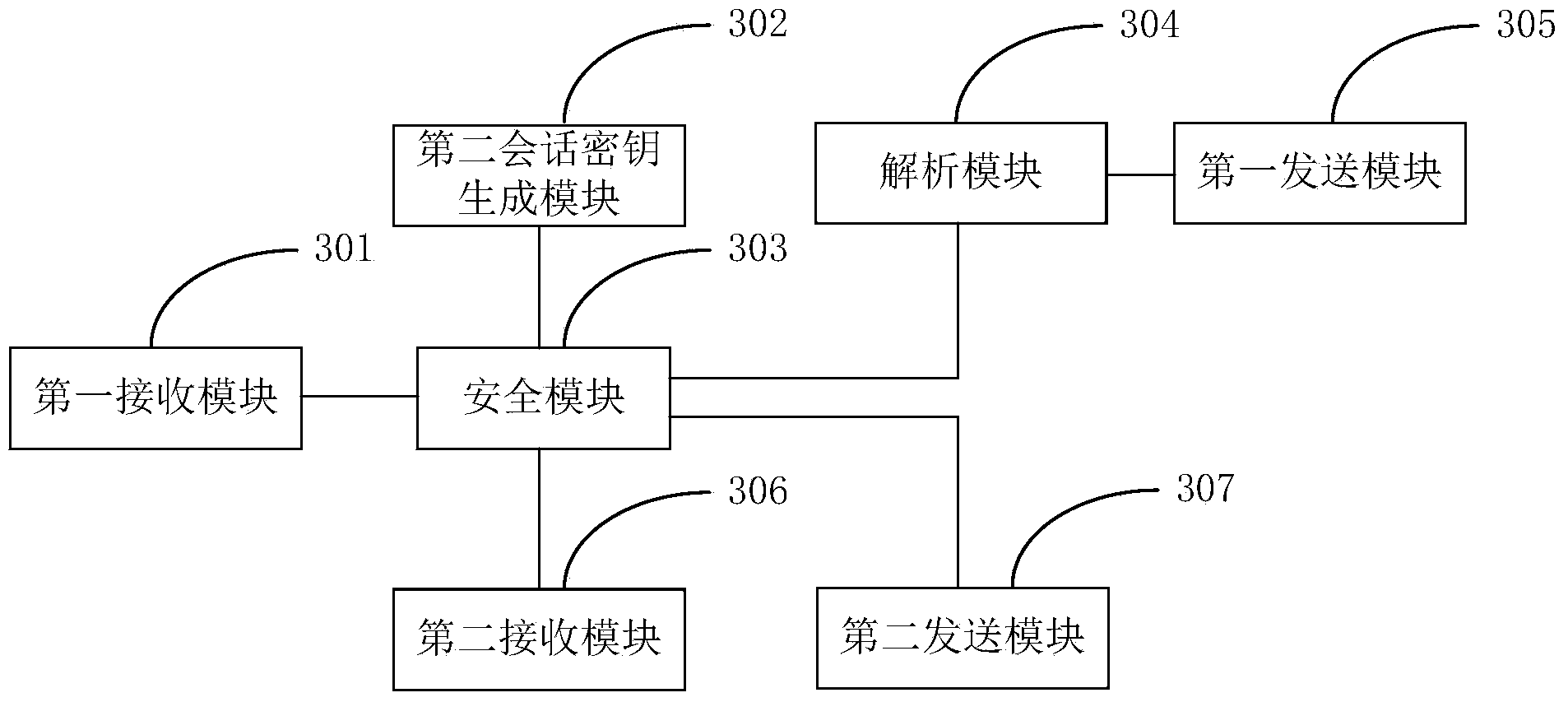
Information interaction method and system and smart key equipment
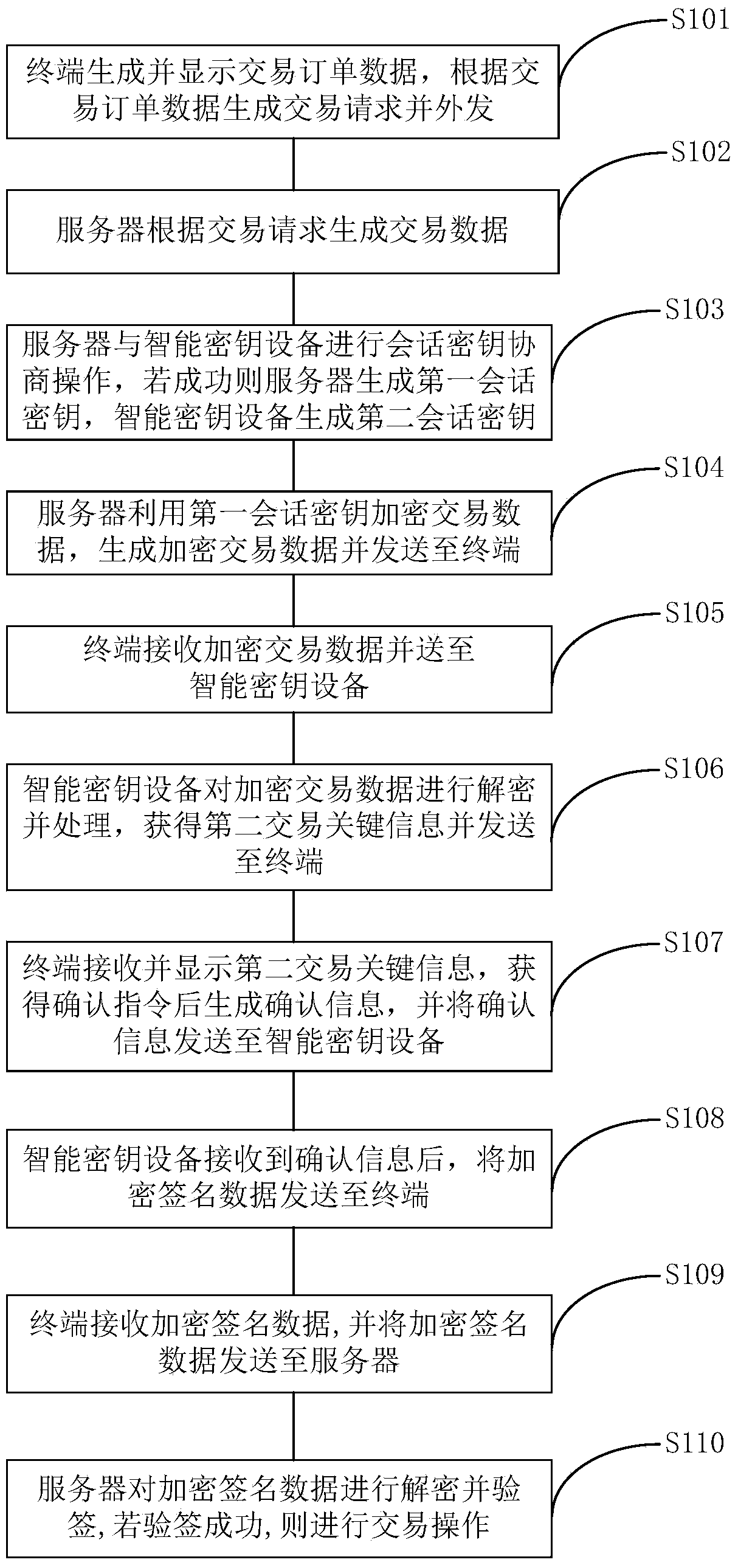
ActiveCN104243451AImprove portabilityReduce volumeFinanceUser identity/authority verificationTransaction dataComputer terminal
The invention provides an information interaction method and system and smart key equipment. The information interaction method comprises the steps that a terminal generates and displays transaction order data and generates and issues a transaction request; a server receives the transaction request and generates transaction data; the server and the smart key equipment conduct session key negotiation operation, and a first session key and a second session key are generated respectively; the server uses the first session key to encrypt the transaction data, generates the encrypted transaction data and sends the encrypted transaction data to the terminal; the terminal receives the encrypted transaction data and sends the encrypted transaction data to the smart key equipment; the smart key equipment uses the second session key for decryption to obtain the transaction data, processes the transaction data, obtains second transaction key information and sends the second transaction key information to the terminal; the terminal displays the second transaction key information, generates a confirmation information after obtaining confirmation instruction and sends the confirmation information to the smart key equipment; the smart key equipment sends encrypted signature data to the terminal, and the terminals receives the encrypted signature data and sends the encrypted signature data to the server; the server uses the first session key to decrypt the encrypted signature data, obtains the signature data and conducts attestation operation.
Owner:TENDYRON CORP
System and method for secure biometric identification
A system and method for secure biometric identification. The inventive system includes a mobile unit and a server. The mobile unit is adapted to receive biometric input and provide a first signal in response thereto. In the illustrative implementation, the mobile unit is a Personal Digital Assistant (PDA) and the biometric input is provided by a fingerprint sensor mounted thereon. A first transceiver is mounted on the PDA for transmitting the first signal and receiving a second signal in response thereto. The PDA is adapted to encrypt the first signal and decrypt the second signal. A secure device is mounted at the PDA. The secure device has two modes of operation: a first locked mode by which access thereto is prohibited and a second unlocked mode by which access thereto is enabled on receipt of the second signal. In the illustrative implementation, the secure device is an encrypted database for which the second signal is a decryption key. The server unit includes a second transceiver for receiving the first signal transmitted via the wireless link. The first and second transceivers are adapted to operate in accordance with the Bluetooth specification. The server is equipped with a system for authenticating the biometric data and providing the second signal in response thereto. The second signal is then communicated to the mobile unit where it is utilized to access the secure device, e.g., encrypted database.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
System and method for securely delivering installation keys to a production facility
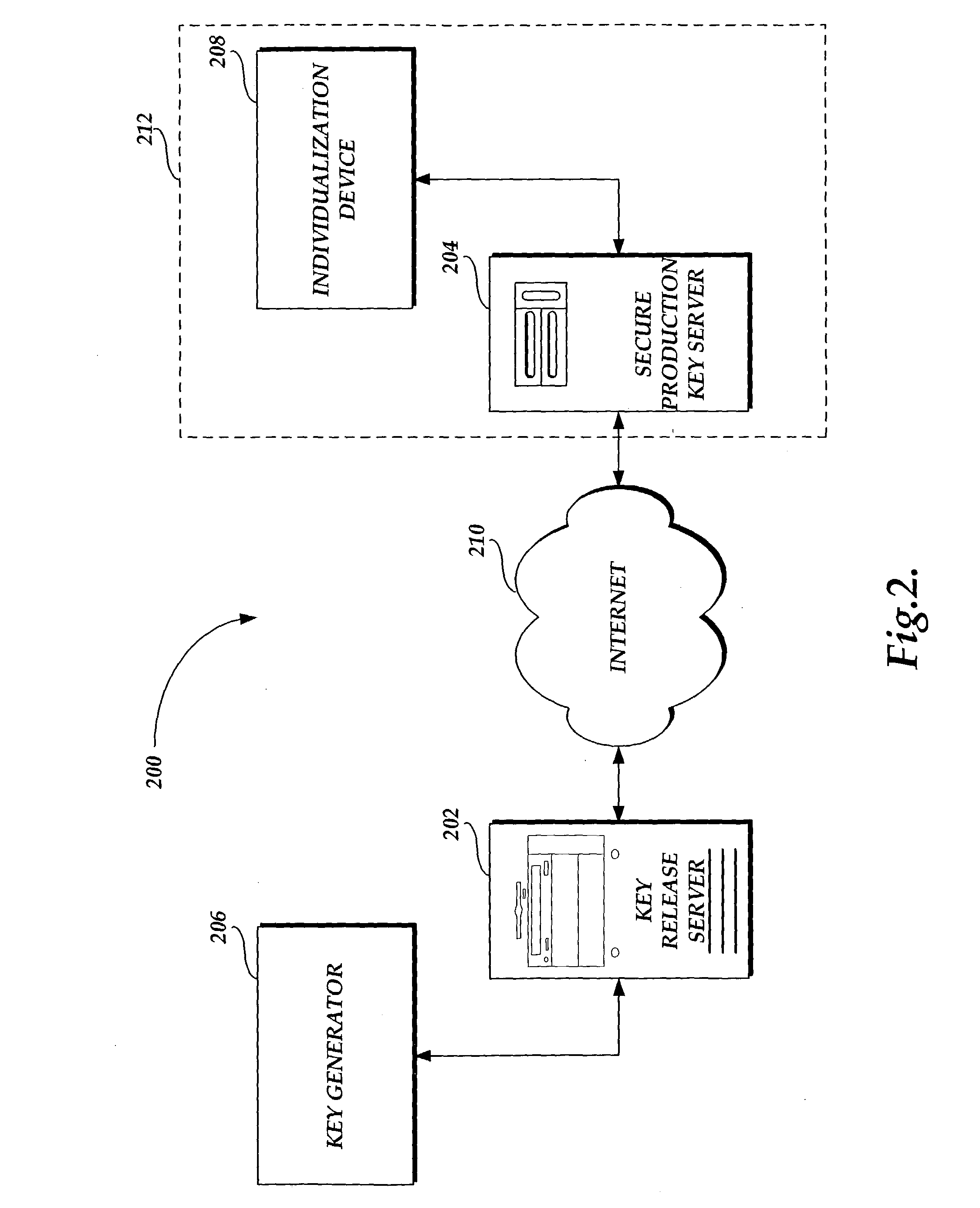
InactiveUS20050021962A1User identity/authority verificationUnauthorized memory use protectionPersonalizationKey server
A system and method for securely delivering installation keys from a key generator to an individualization device at a production facility is presented. Operators, using a production key server at the manufacturing facility, send a request to a key release server for a number of installation keys according to a production run. The key release server verifies the request, and if valid, returns the requested number of installation keys to the production key server in an encrypted format. The production key server then decrypts and delivers installation keys to the individualization device in a just-in-time fashion. The production key server includes various security devices including a hardware decryption device to decrypt the installation keys, a smart card reader for authenticating authorized operators, and a limiting switch to disable the production key server if it is tampered with.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com