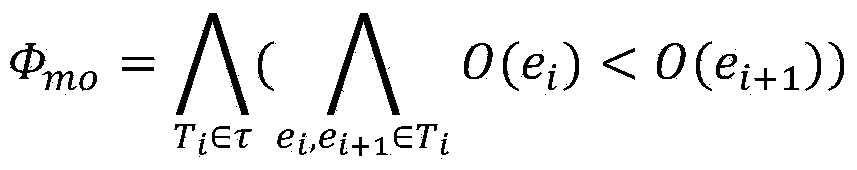Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
322 results about "Occurrence data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
The Occurrence Data is a raw and machine-readable dataset that is intended to be read, analyzed and interpreted by software and analytics tools.
Augmented reality systems and methods for user health analysis
ActiveUS20170323485A1Input/output for user-computer interactionMechanical apparatusData criteriaWavefront
Augmented reality systems and methods for user health analysis. Methods for user health analysis may include collecting data for an initial prediction model and continuing to collect additional data based on one or more data criteria. The methods may further include updating the initial prediction model based on the additional data to produce a revised prediction model or causing an intervention to occur based on the additional data. The data may be collected by a display system including one or more sensors configured to collect user-specific data and a display device configured to present virtual content to a user. The display device may be configured to output light with variable wavefront divergence.
Owner:MAGIC LEAP
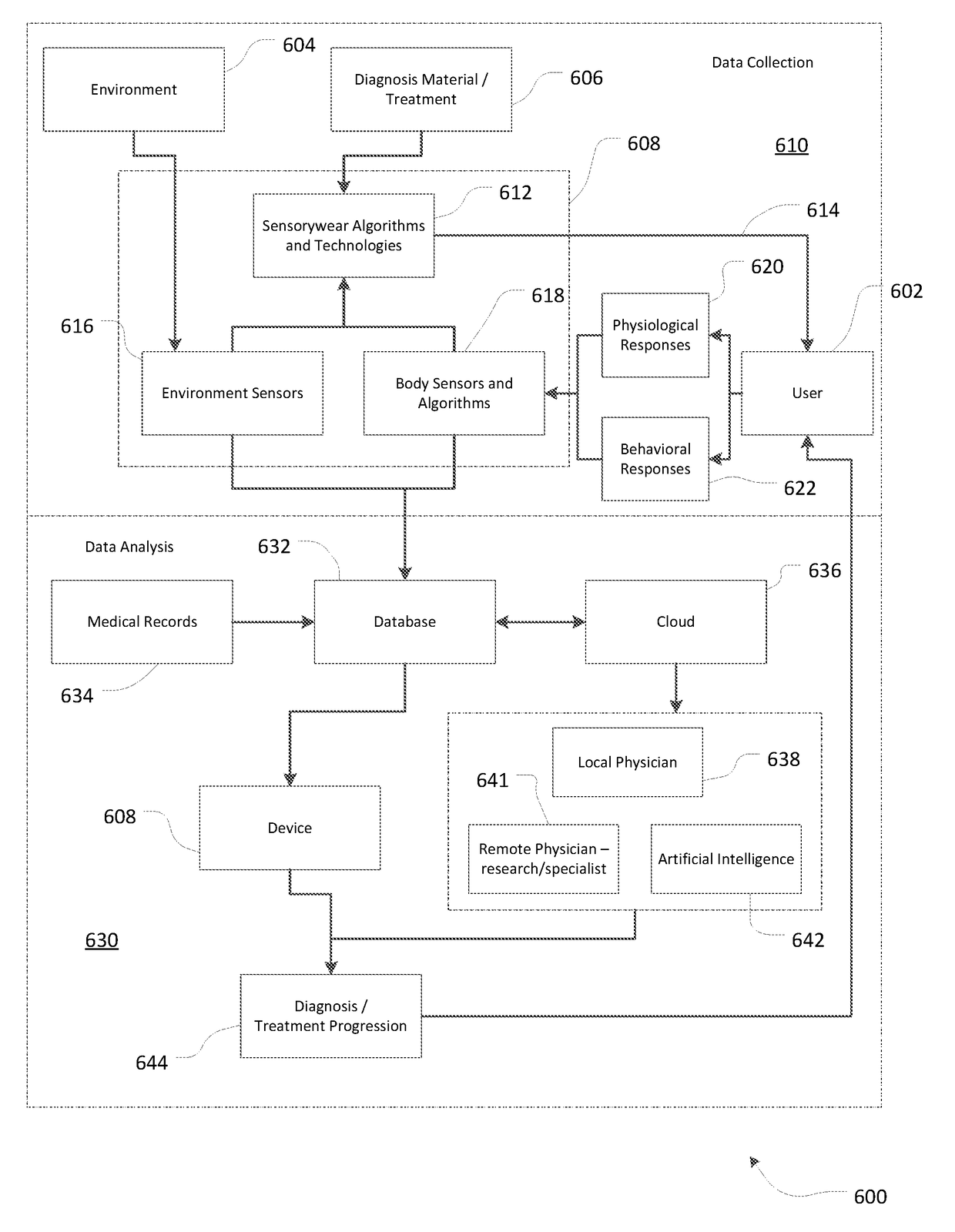
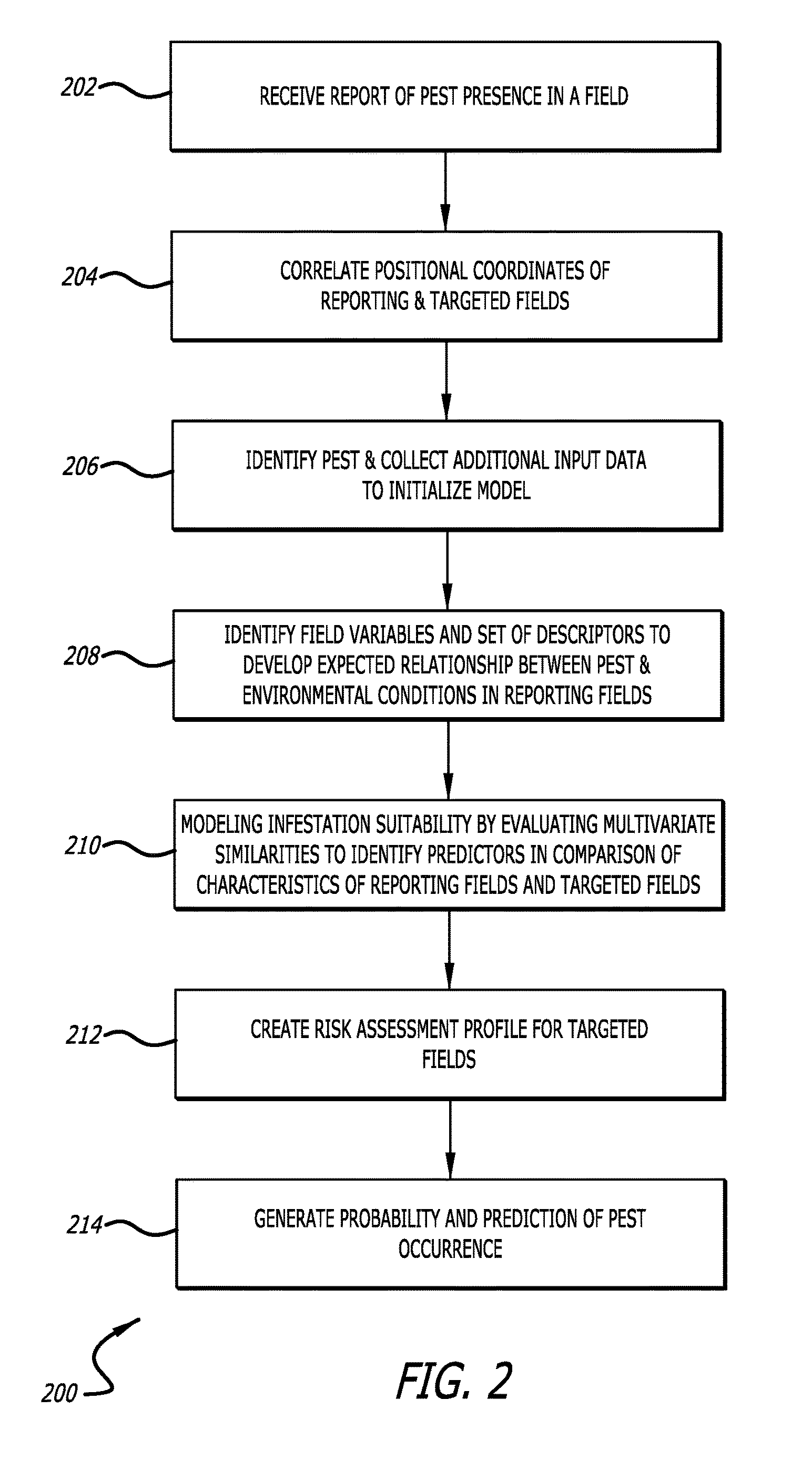
Pest occurrence risk assessment and prediction in neighboring fields, crops and soils using crowd-sourced occurrence data
ActiveUS9563852B1Improve rendering capabilitiesClimate change adaptationForecastingOccurrence dataCrop management
A pest and disease modeling framework for precision agriculture applies weather information, pest biological characteristics, and crop management data to anonymous crowd-sourced observations of pest presence for a reporting field. A risk assessment profile of pest occurrence for targeted fields in proximity to reporting fields is modeled to generate field-specific measures for pest management of pest infestation. The pest and disease modeling framework matches and filters weather and crop information in infested and pest-free fields based on the anonymous, crowd-sourced reporting of an existing pest presence, by evaluating similarities in pest-relevant data. Fields that are similar to infested fields have the highest risk of infestation, and the modeling framework provides output data in the form of a prediction of pest occurrence based on the risk assessment profile.
Owner:DTN LLC
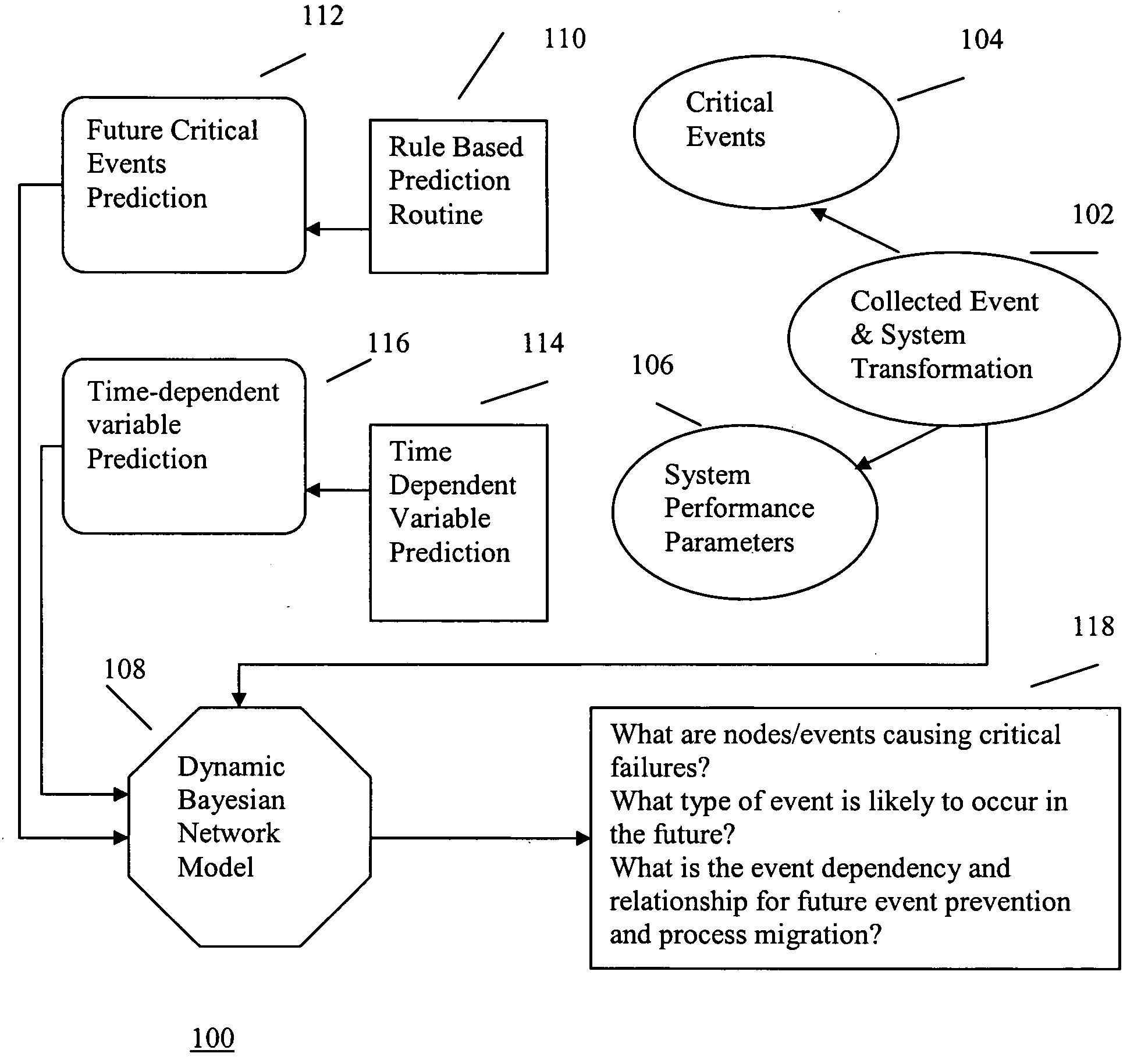
Hybrid method for event prediction and system control
InactiveUS20050114739A1Data processing applicationsDigital computer detailsComputer clusterHybrid approach
A hybrid method of predicting the occurrence of future critical events in a computer cluster having a series of nodes records system performance parameters and the occurrence of past critical events. A data filter filters the logged to data to eliminate redundancies and decrease the data storage requirements of the system. Time-series models and rule based classification schemes are used to associate various system parameters with the past occurrence of critical events and predict the occurrence of future critical events. Ongoing processing jobs are migrated to nodes for which no critical events are predicted and future jobs are routed to more robust nodes.
Owner:GLOBALFOUNDRIES INC
Error model formation
ActiveUS20050210017A1Appreciated and well received by many usersDry-dockingDigital data information retrievalOccurrence dataData mining
In a method of forming a target error model to facilitate correcting or suggesting corrections to misspelled input text related to a target data collection, a source query log containing user queries to at least one source data collection is provided. Next, target relational data is generated based on the source query log including corrective substring suggestions that relate to the target data collection and corresponding misspelled substrings extracted from the source query log. A target error model is then built using the target relational data. The target error model includes target statistical occurrence data for the substrings of the target relational data derived from the source query log. Finally, the target error model is stored on a computer readable medium. Additional embodiments of the invention are directed to a system configured to implement the method.
Owner:MICROSOFT TECH LICENSING LLC
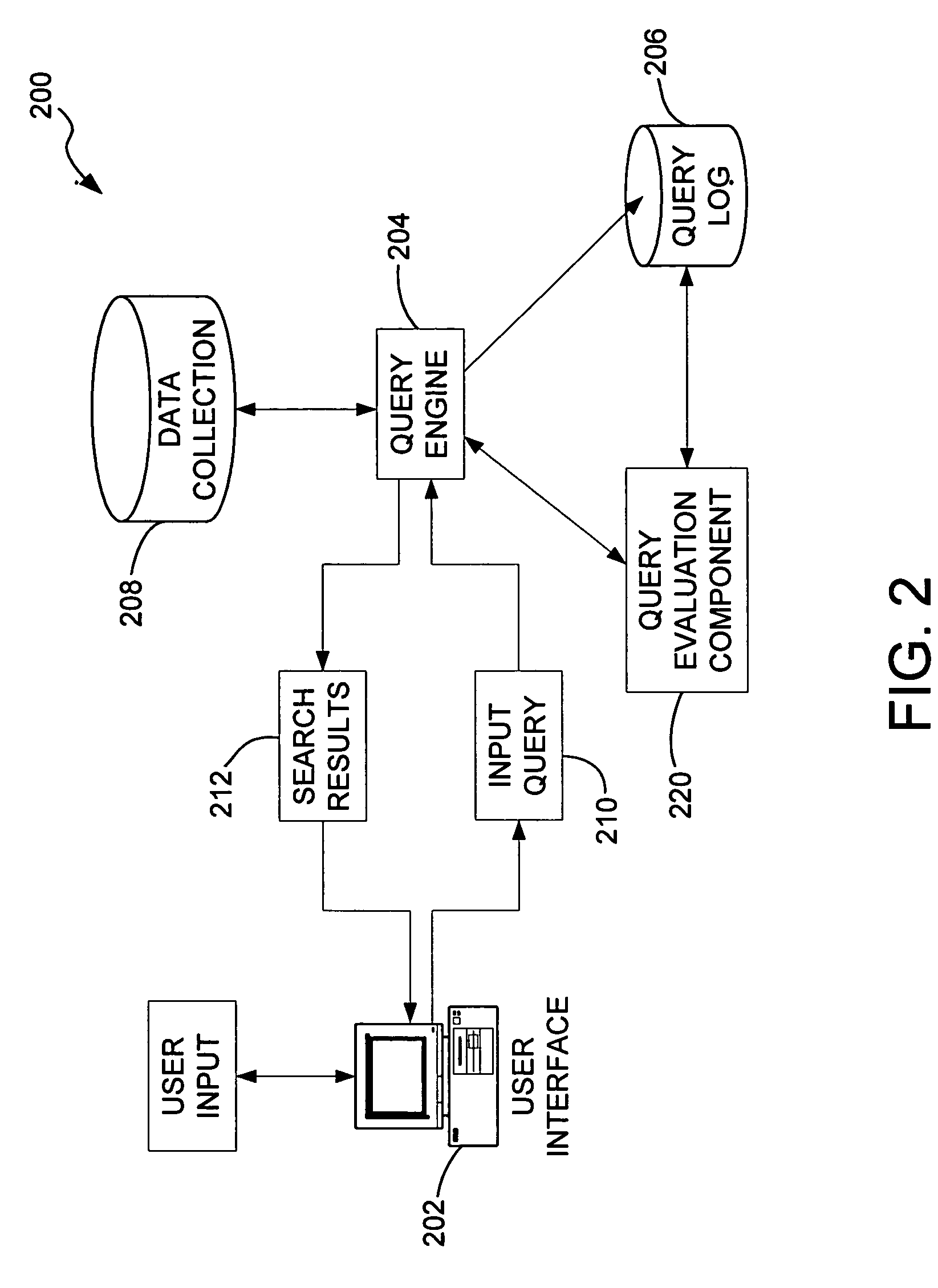
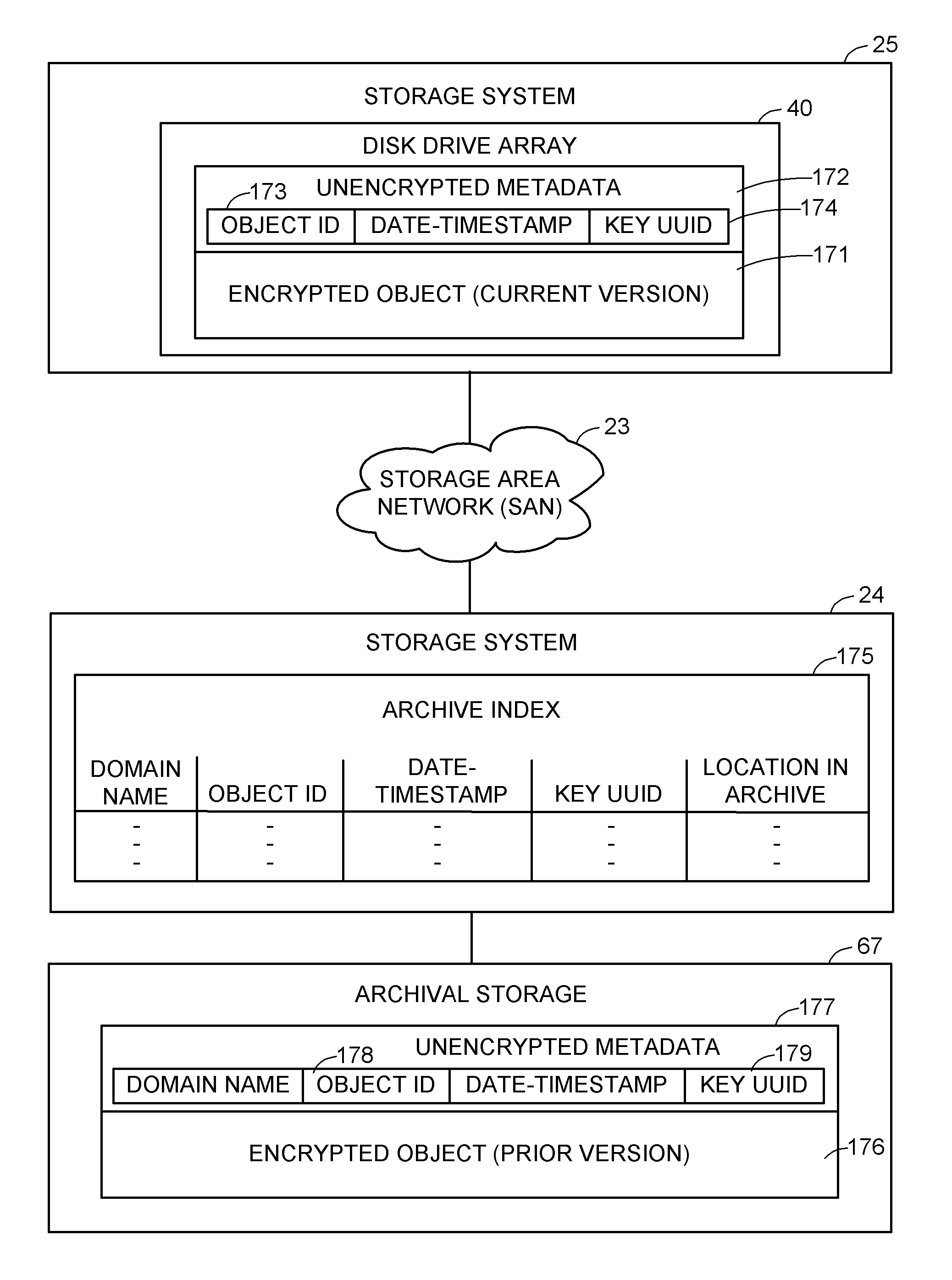
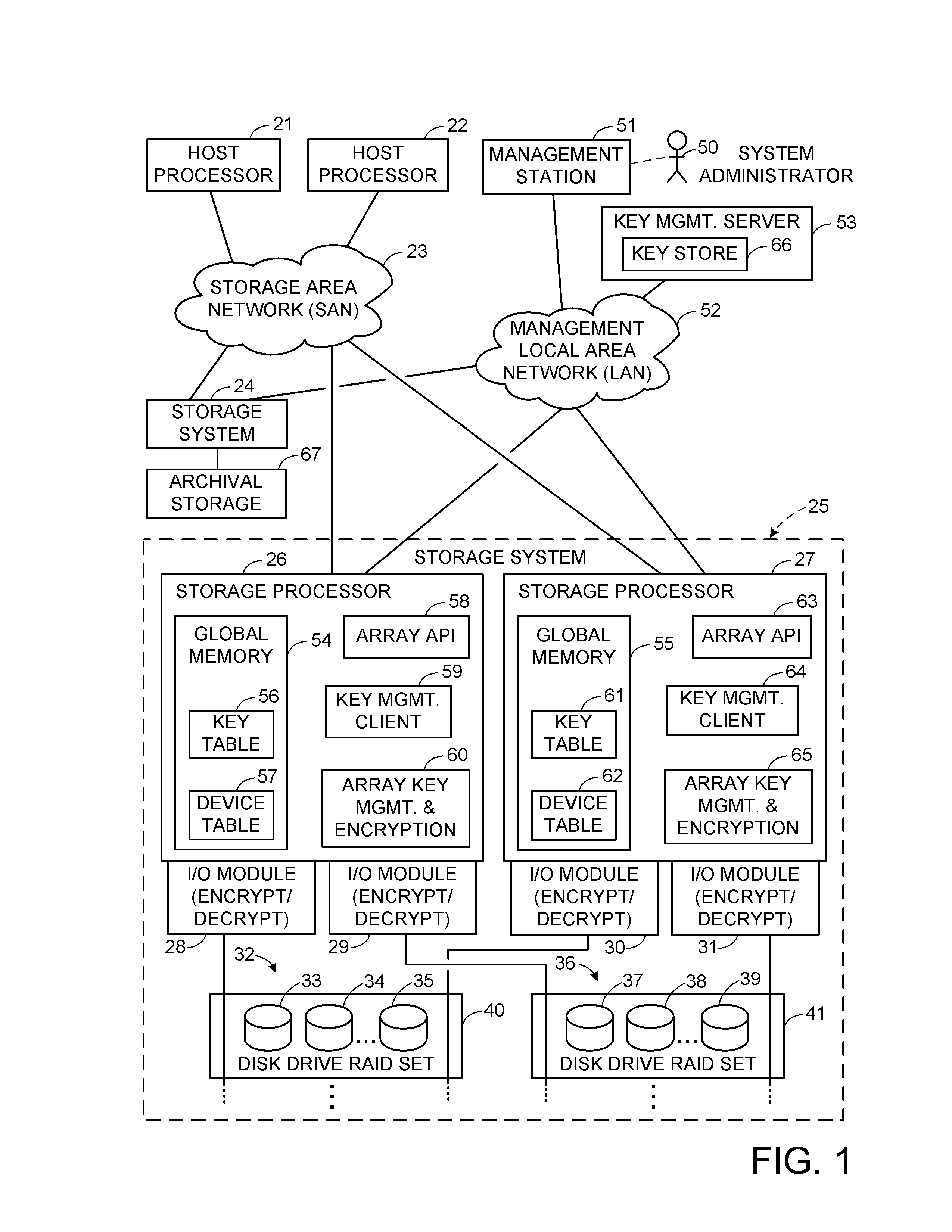
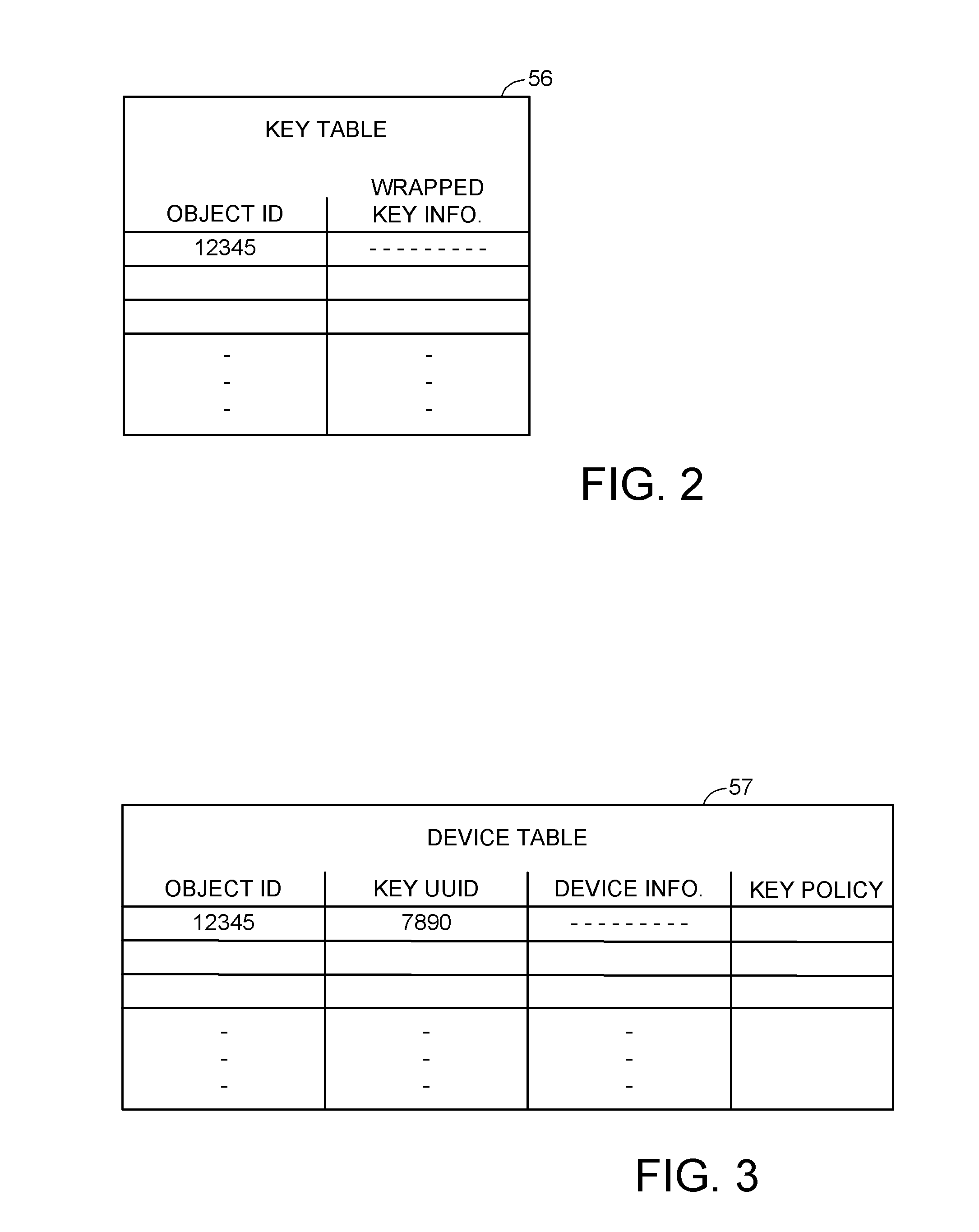
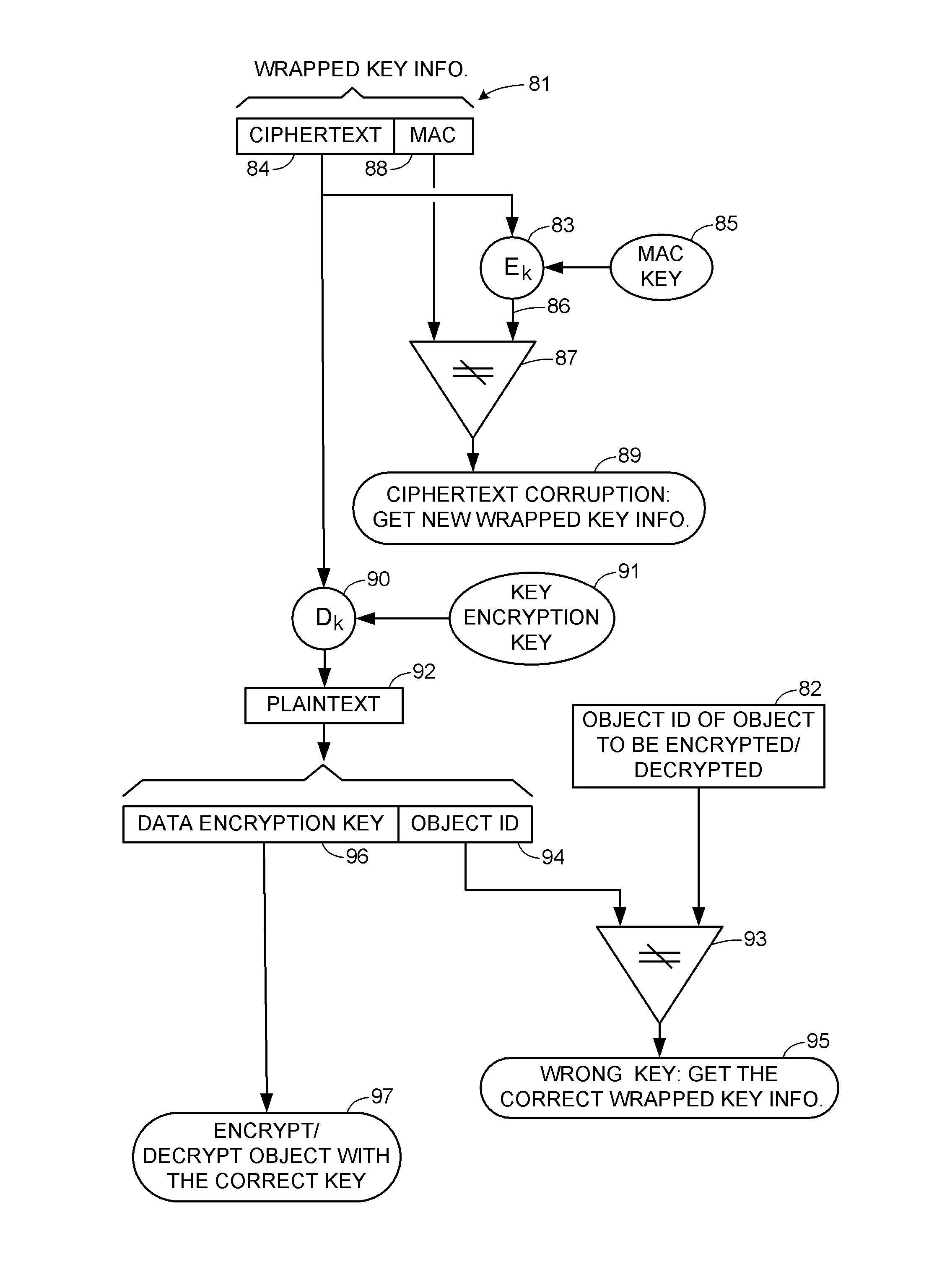
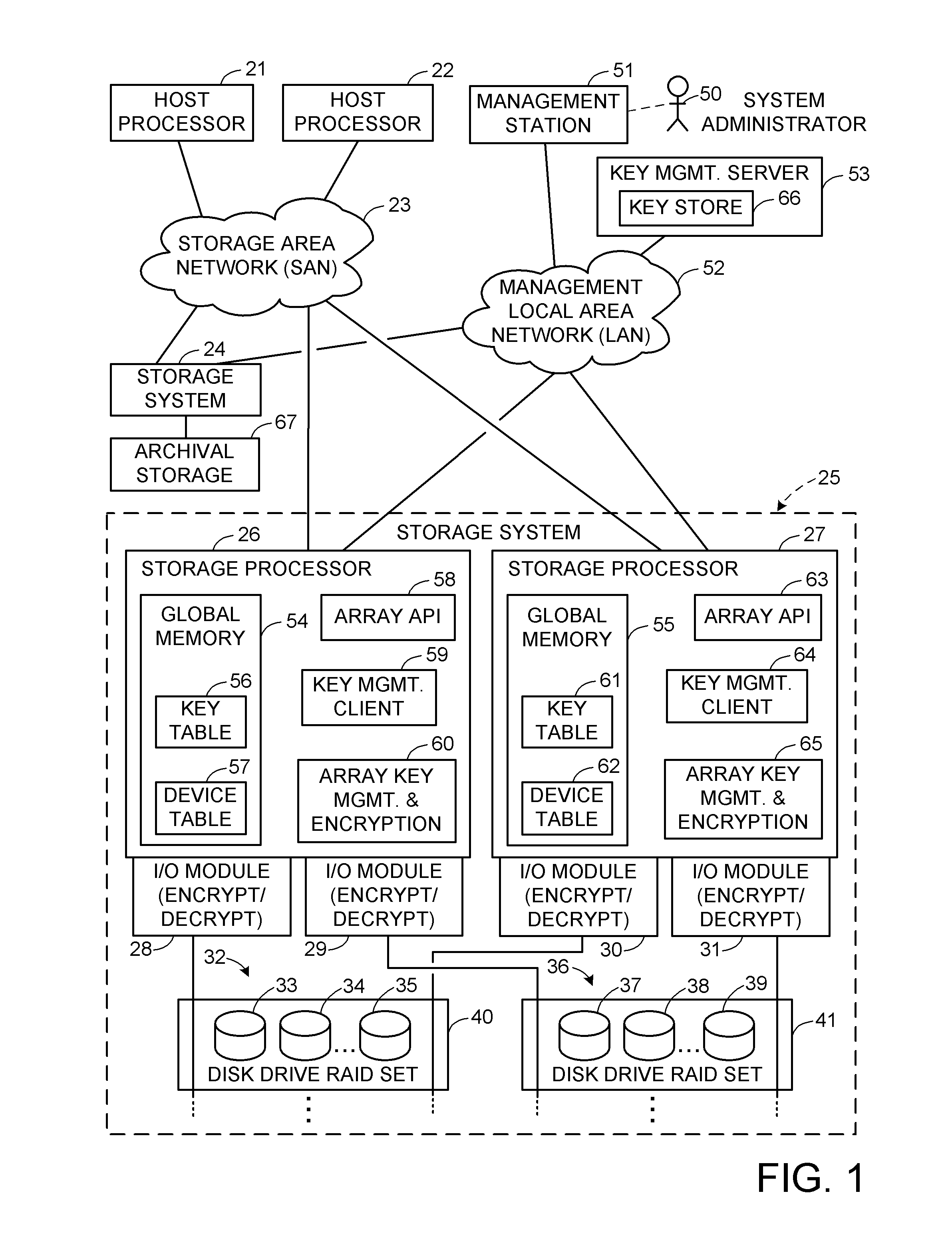
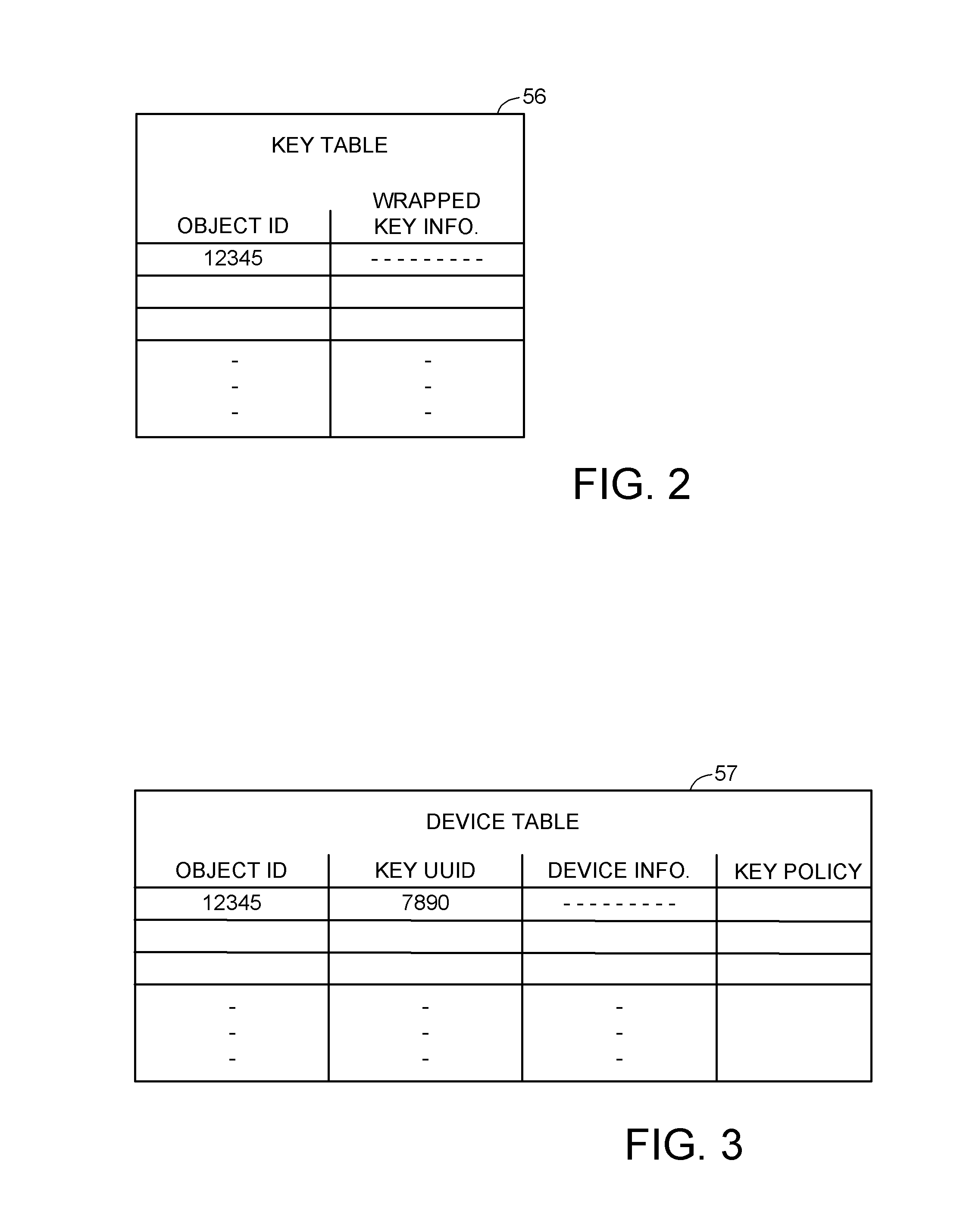
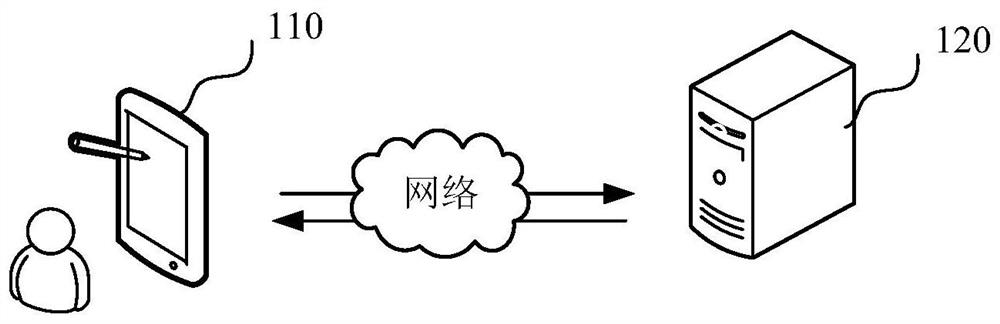
Encryption key recovery in the event of storage management failure
ActiveUS8588425B1Key distribution for secure communicationUser identity/authority verificationData processing systemOccurrence data
A data processing system stores encrypted data. Object identifiers are assigned to storage objects, and data encryption keys are assigned to the storage objects. When performing an operation upon a storage object, data encryption key failure may occur due to a corrupt or incorrect key. In this case, a copy of the data encryption key is fetched from a key server. It is possible for the association of the object identifiers with the data encryption keys to become lost or confused, so that the key server may fail to provide the correct key for a specified object identifier. Therefore, an absolute key identifier that is unique across the key server namespace also is stored in association with the object identifier in the storage system and in the key store of the key server, and the absolute key identifier is used as a failsafe for recovery of encrypted data.
Owner:EMC IP HLDG CO LLC
Systems, devices, and/or methods for managing sample selection bias
ActiveUS8291069B1Digital computer detailsAmplitude-modulated carrier systemsSelection biasOccurrence data
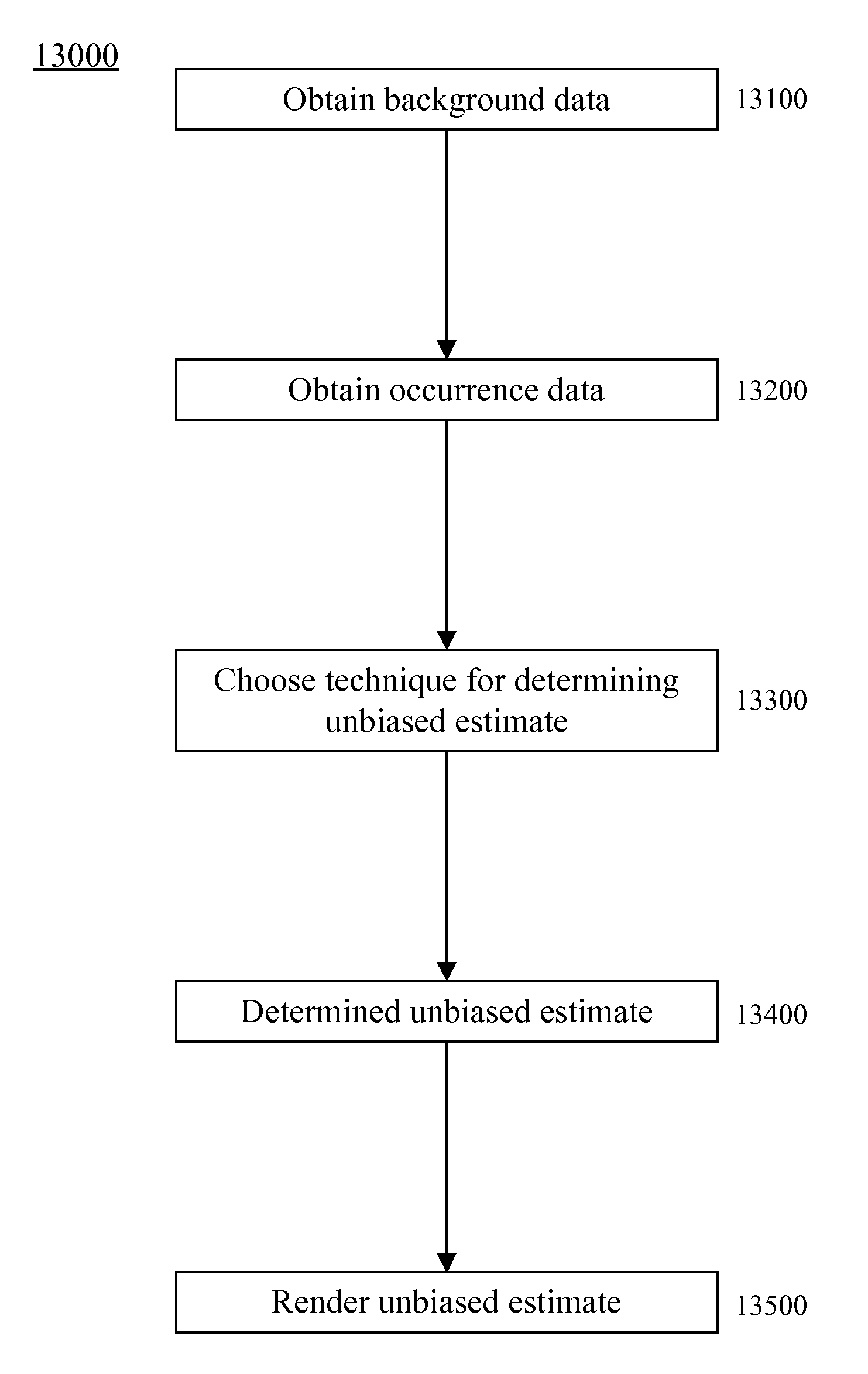
A method for managing sample selection bias is disclosed. Embodiments of the method can include automatically determining an unbiased estimate of a distribution from occurrence data via a special purpose processor. The occurrence data that is utilized in determining the estimate may have an occurrence data sample selection bias that is substantially equivalent to a background data sample selection bias associated with background data. Additionally, the occurrence data may be related to the background data, and the background data may be chosen with the background data sample selection bias. Furthermore, the occurrence data may represent a physically-measurable variable associated with one or more physical and tangible objects or substances.
Owner:NUANCE COMM INC
Data recovery method
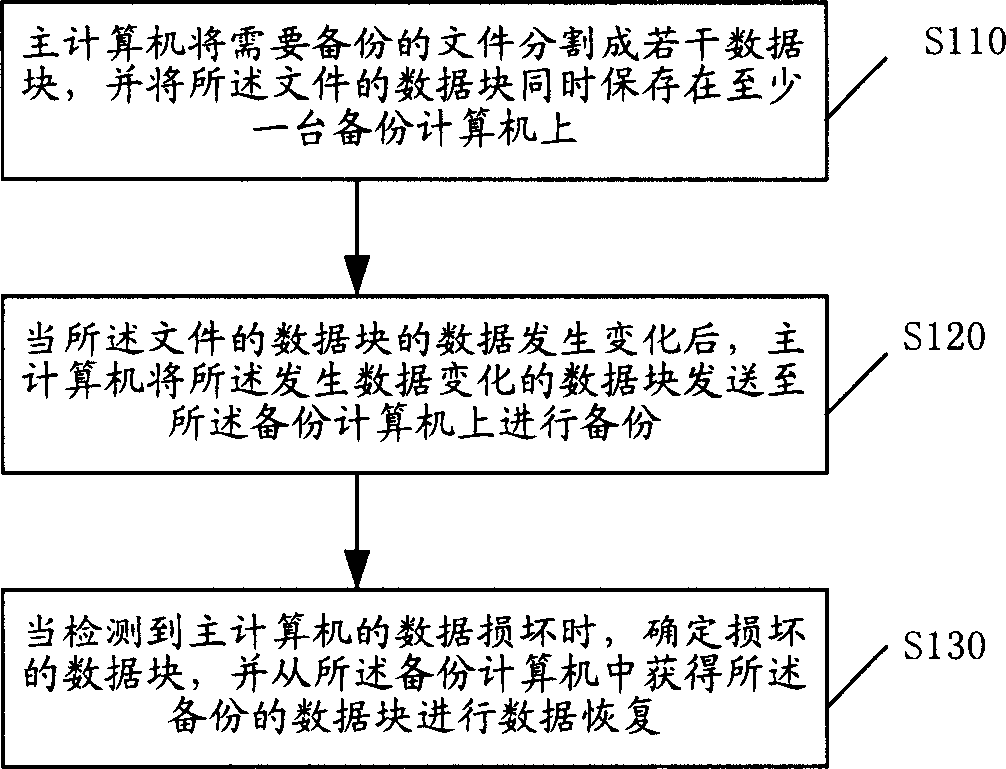
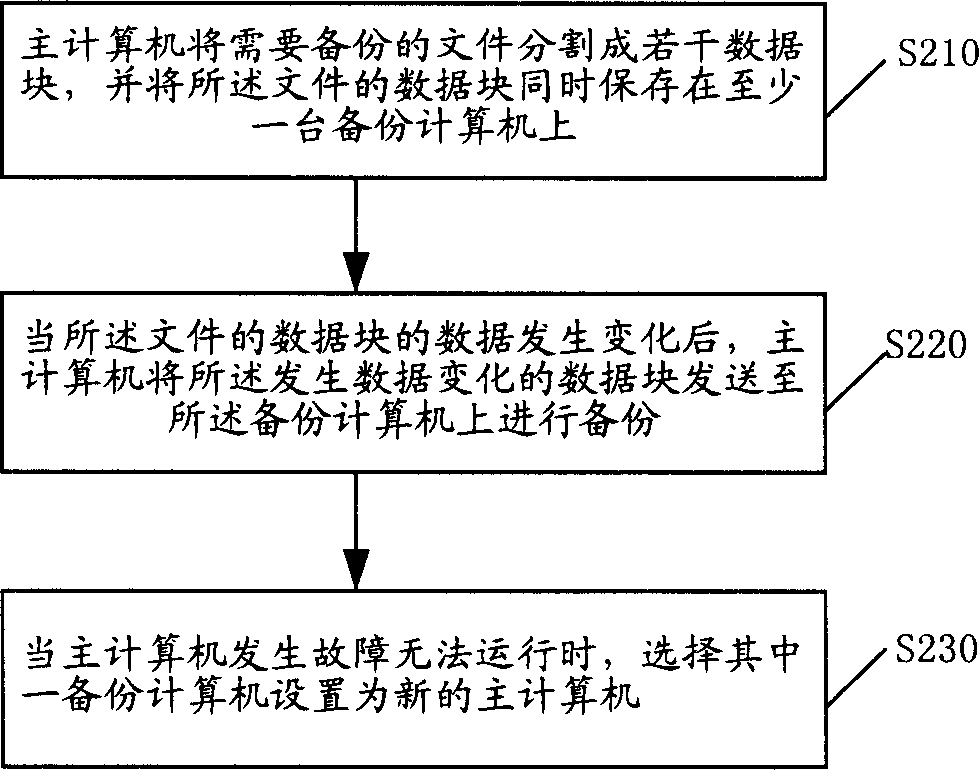
ActiveCN1801107ALittle impact on processing powerSmall recovery overheadRedundant operation error correctionRecovery methodData Corruption
The invention discloses a data restoring method within duplicating course and restoring course, which comprises the following steps: (1) the main computer divides the duplicated file into several data blocks through computer, which stores the data block on at least one duplicating computer; (2) when the relative file data changes, the main computer sends the data block of changed data on the duplicated computer; (3) when the detected data of main computer is damaged, it affirms the damaged data block and acquires the duplicated data block in the duplicated computer to restore the data; when the accident stops the operation, the main computer selects one duplicated computer as new main computer to finish system conversion. The invention can accomplish the data duplicating and restoring without stopping business, which minimizes the data damage scope and restoring cost to reach the neglect degree.
Owner:上海洲信信息技术有限公司
Efficient storage mechanism for representing term occurrence in unstructured text documents
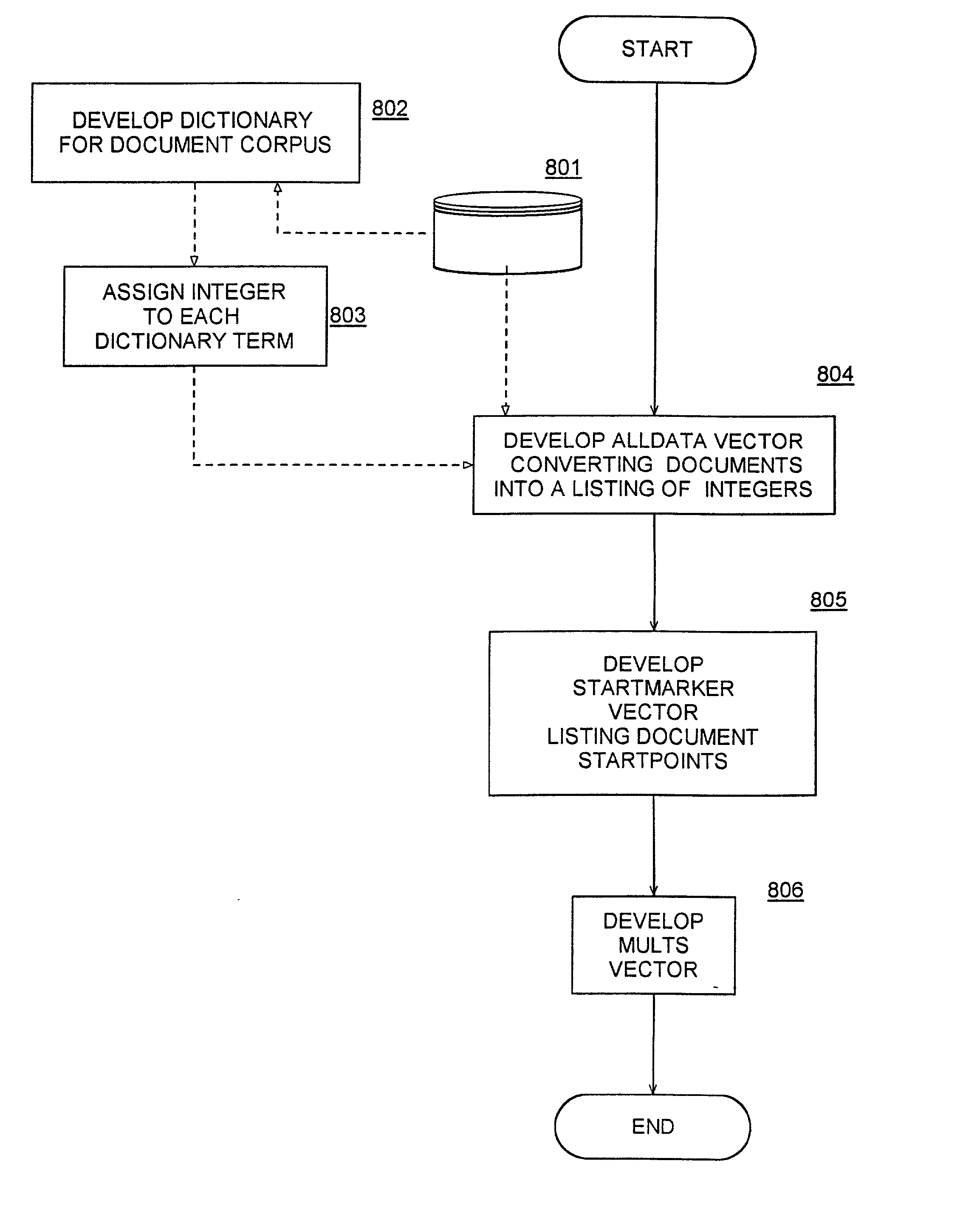
InactiveUS20020165884A1Digital computer detailsSpecial data processing applicationsOccurrence dataDocument preparation
A method and structure converts a document corpus containing an ordered plurality of documents into a compact representation in memory of occurrence data, where the representation is to be based on a dictionary previously developed for the document corpus and where each term in the dictionary has associated therewith a corresponding unique integer. The method includes developing a first vector for the entire document corpus, the first vector being a sequential listing of the unique integers such that each document in the document corpus is sequentially represented in the listing according to the occurrence in the document of the corresponding dictionary terms. A second vector is also developed for the entire document corpus and indicates the location of each of the document's representation in the first vector.
Owner:IBM CORP
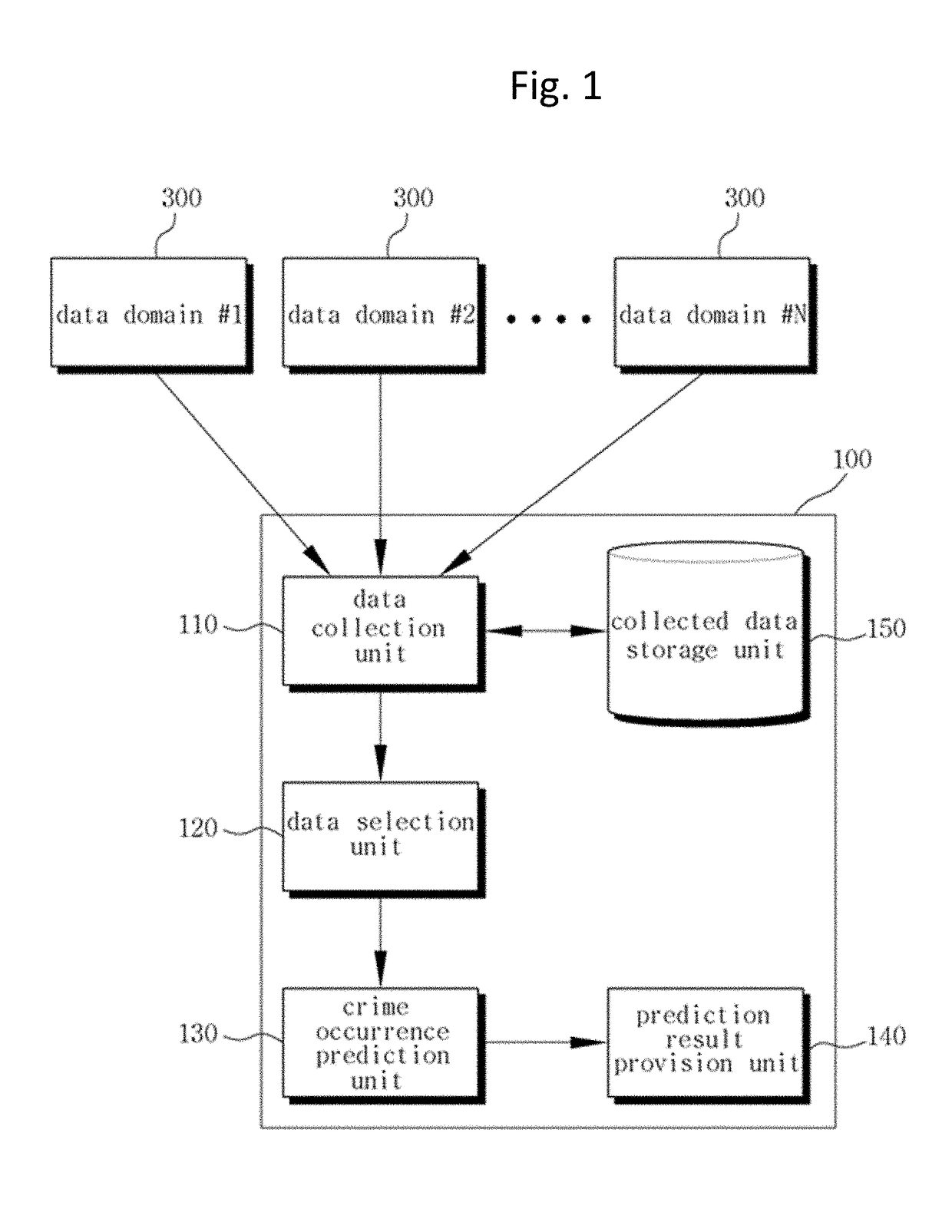
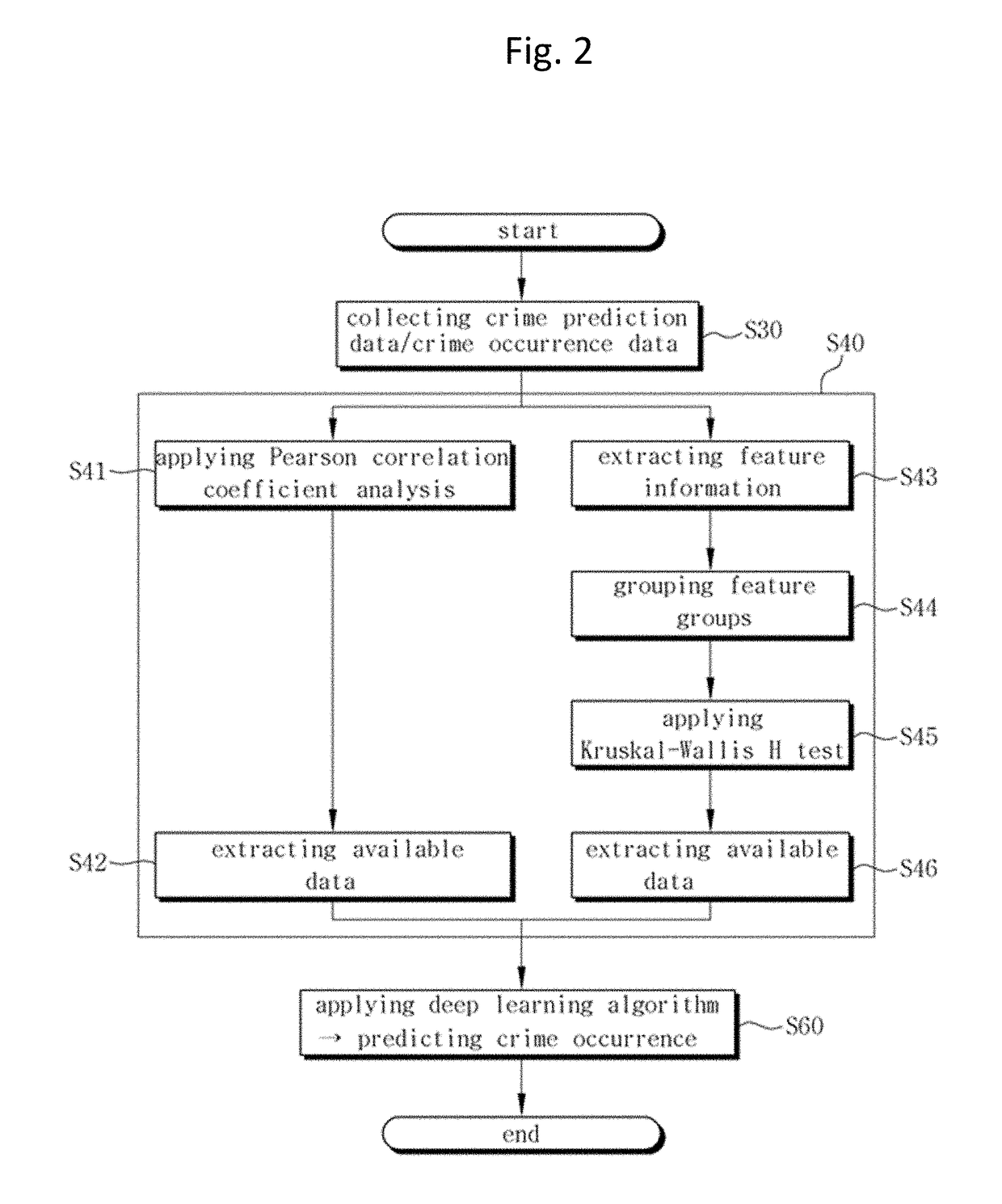
Method of predicting crime occurrence in prediction target region using big data
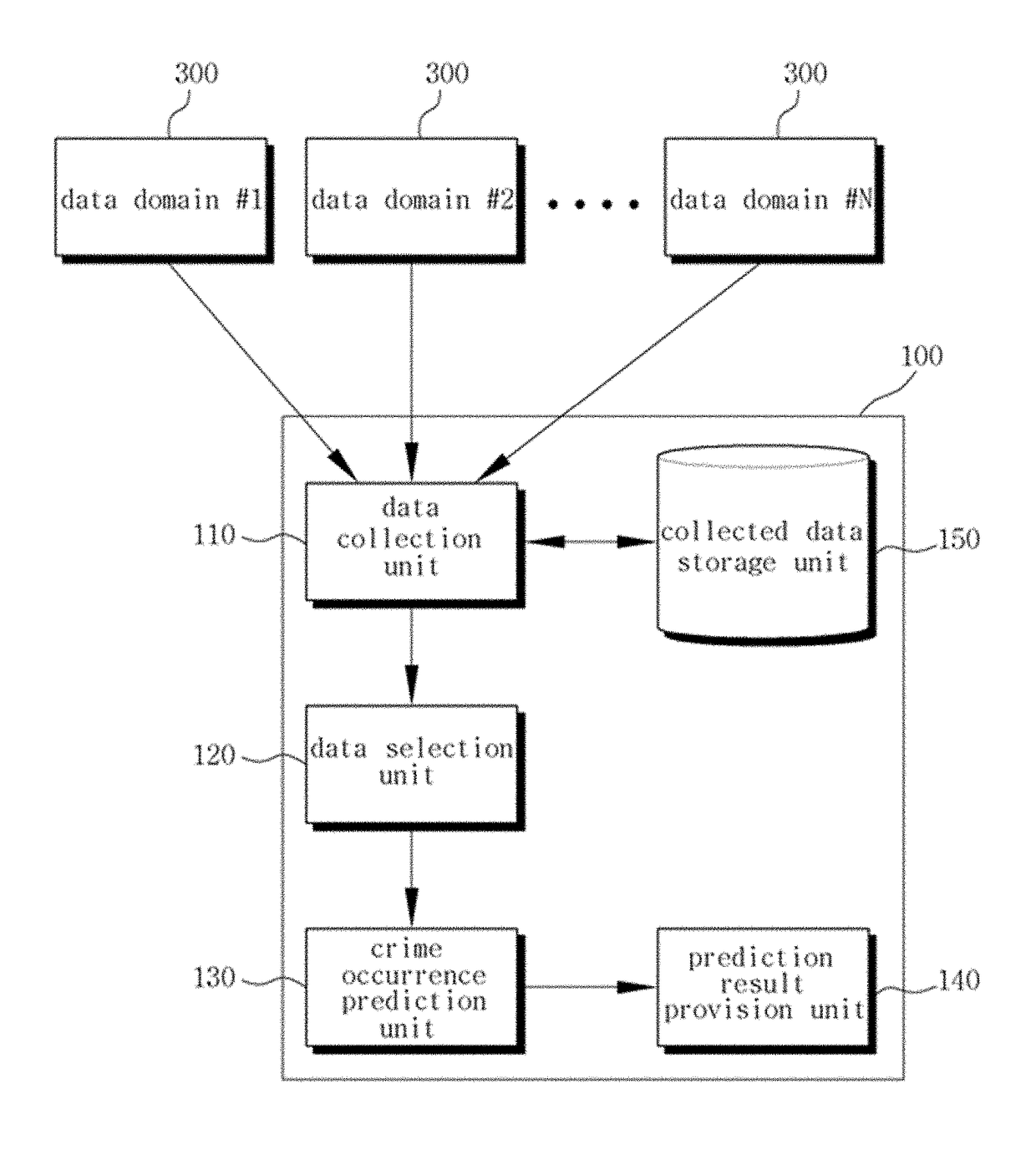
InactiveUS20180053110A1Accurate predictionBiological neural network modelsForecastingOccurrence dataData domain
Disclosed is a method of predicting crime occurrence in a prediction target region using big data, the method including: collecting crime prediction data of the prediction target region from a plurality of data domains; collecting crime occurrence data of crime that occurred in the prediction target region during a preset period of time from a crime occurrence record domain; analyzing the crime prediction data and the crime occurrence data of each of the data domains according to a statistical analysis, and extracting meaningful data of the crime prediction data as available data by each of the data domains; and predicting crime occurrence by applying the available data to a pre-registered deep learning algorithm, wherein the available data is classified into a plurality of data groups according to a data type, and the deep learning algorithm includes: a first deep neural network; a second deep neural network; and an output.
Owner:THE CATHOLIC UNIV OF KOREA IND ACADEMIC COOPERATION FOUND
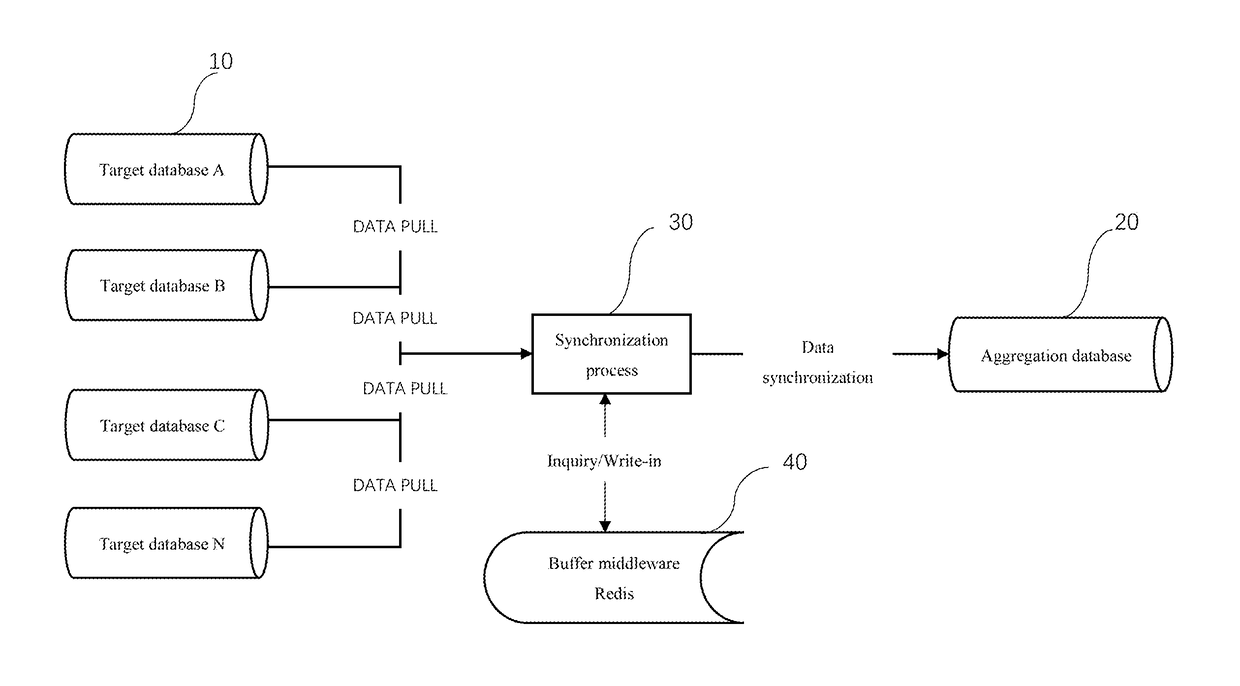
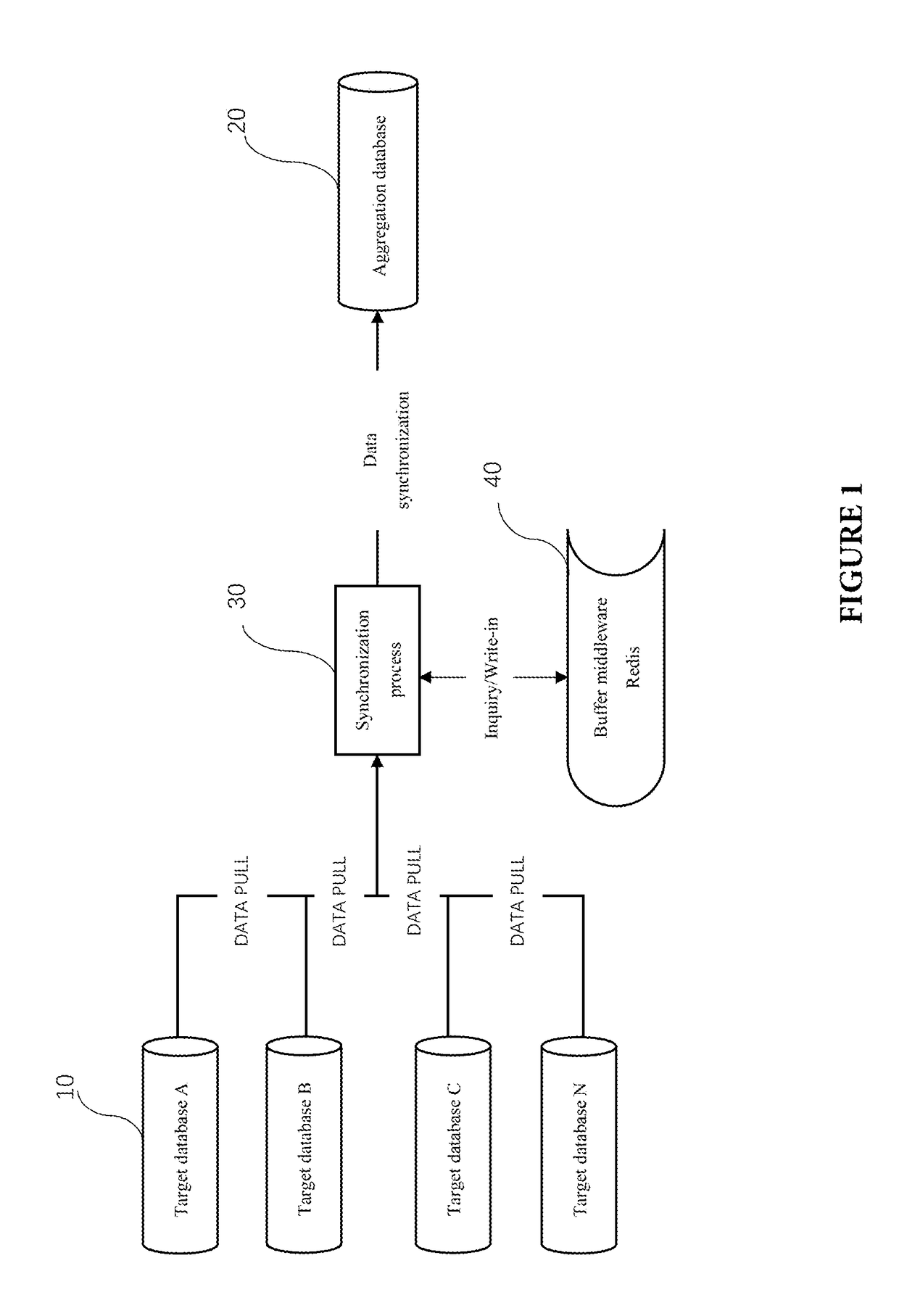
Redis-based database data aggregation and synchronization method
ActiveUS20180260435A1Easy to createDatabase updatingSpecial data processing applicationsData aggregatorPrimary Key
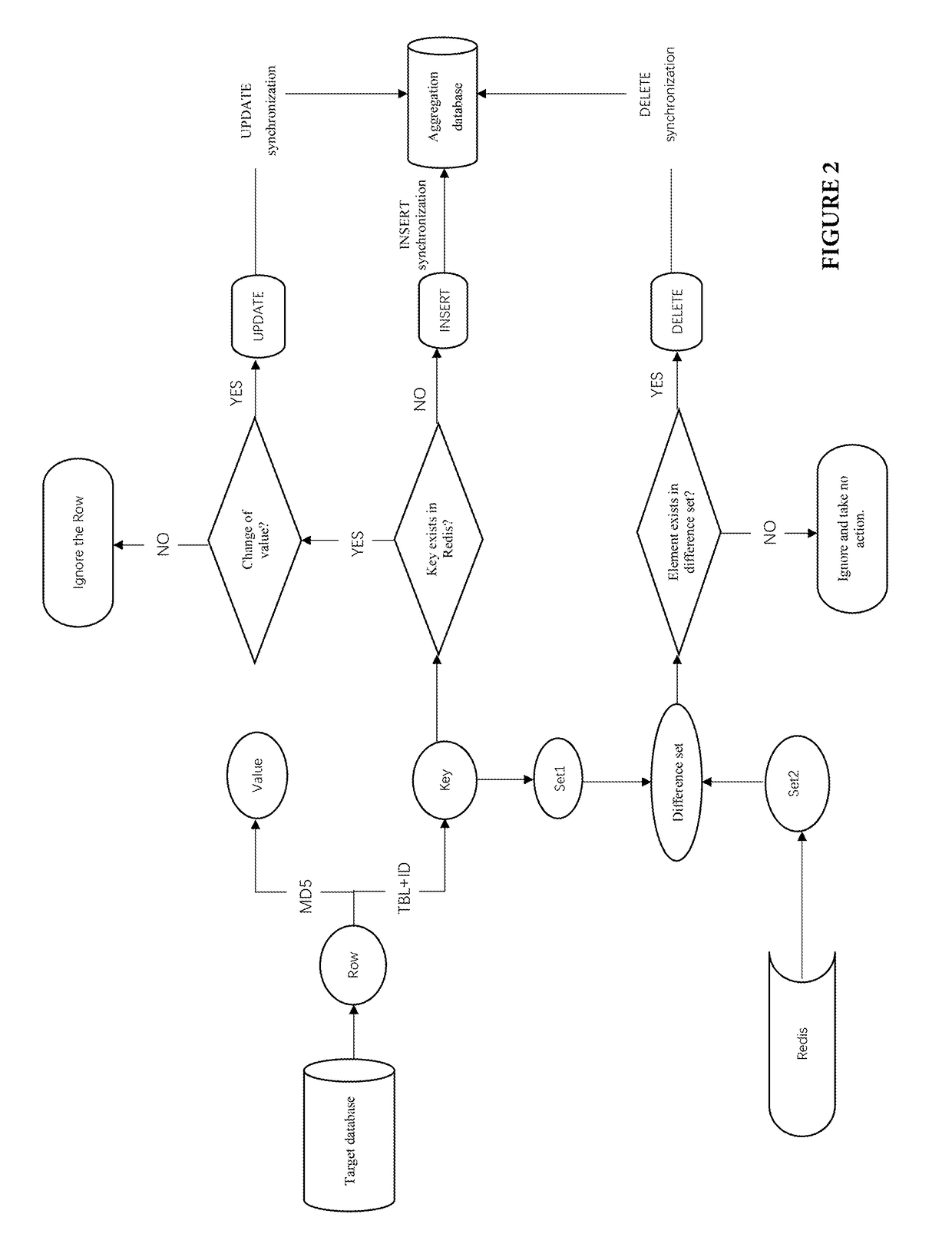
In a Redis-based database data aggregation and synchronization method, a synchronization program scans data of a table of a target database, calculates and stores a Key and a Value of each row into a Redis, while writing the row into an aggregation database. When there is a change of data in the table of the target database, the synchronization program re-calculates a new Key and a new Value of each row in the target database and inquires whether a key same as the new Key exists in the Redis to update the data in the aggregation database, and then perform a difference set calculation for the data after the synchronization of the primary key set of the table of the target database and the corresponding primary key set of the table of the aggregation database, and delete the data from the aggregation database by determining whether or an element exists in the difference set.
Owner:MOLBASE SHANGHAI BIOTECH CO LTD
Data race detection and evidence generation method based on multithreaded program constraint building
ActiveCN104077144ANo overheadSoftware testing/debuggingSpecific program execution arrangementsFirst-order logicOccurrence data
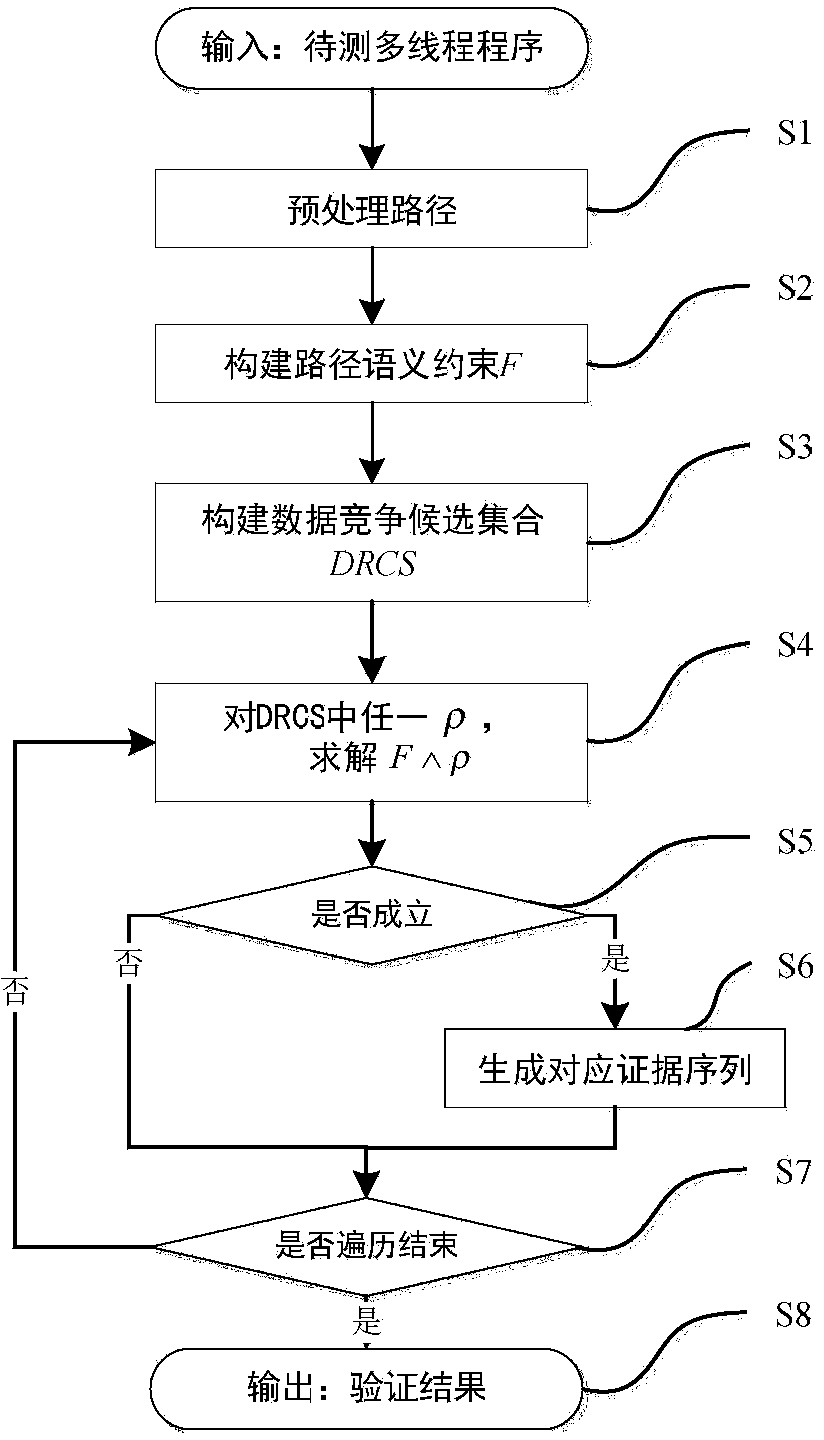
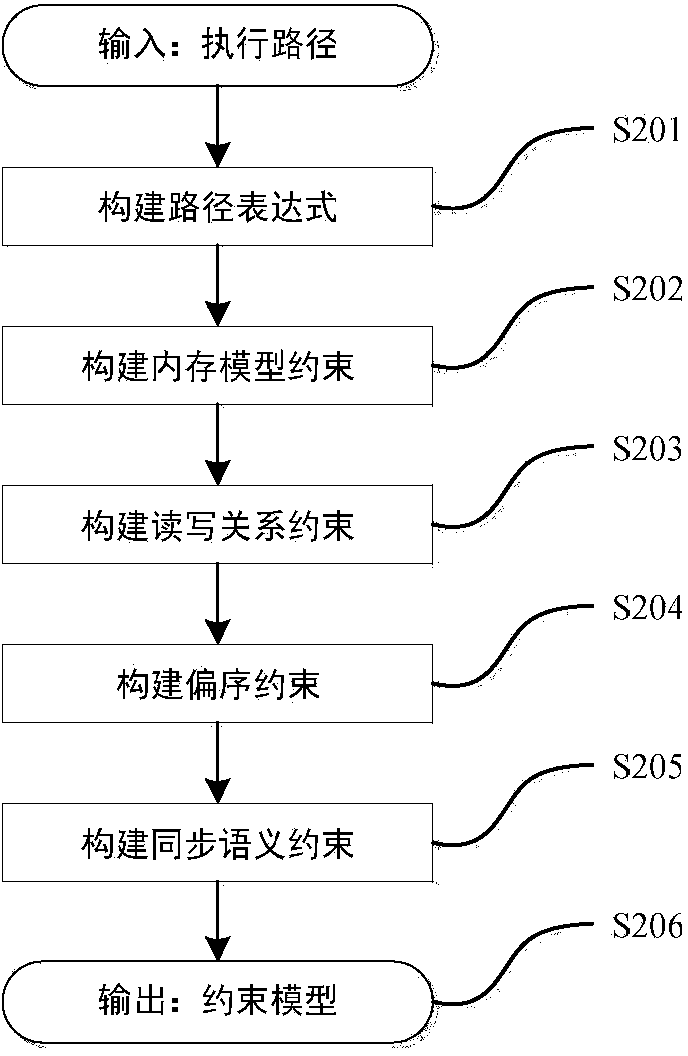
The invention provides a data race detection and evidence generation method based on multithreaded program constraint building. The data race detection problem is converted into a constraint solving problem by building a constraint expression according to the multithreaded program semanteme, a constraint solver is used for detecting possible data races and program execution paths triggering the data races are generated; the data race detection and evidence generation method comprises the steps of firstly, carrying out the instrumentation of the detected program, executing the program and obtaining an execution path, secondly, converting the execution path into a quantifier-free first-order logic expression covering all feasible thread interleaving according to the multithreaded program execution semanteme, thirdly, building a data race candidate set according to the sequential relationship of statements when a data race happens and generating candidate conditions for races, and finally, traversing the candidate set to determine whether the data race exists, and if so, generating a corresponding evidence sequence. The method is capable of finding out all data races in once operation without misinformation; for each data race, the evidence sequence indicating the trigger process of the data race is generated.
Owner:XI AN JIAOTONG UNIV
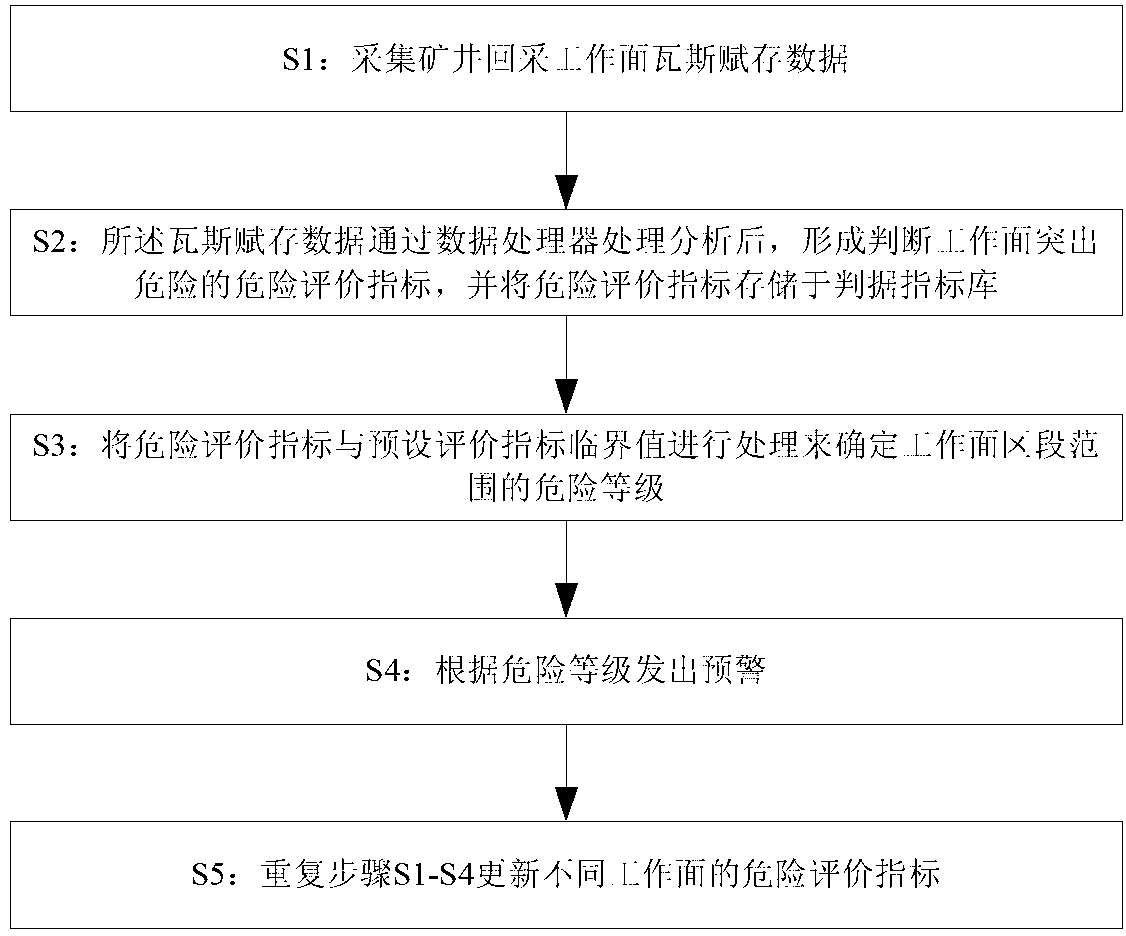
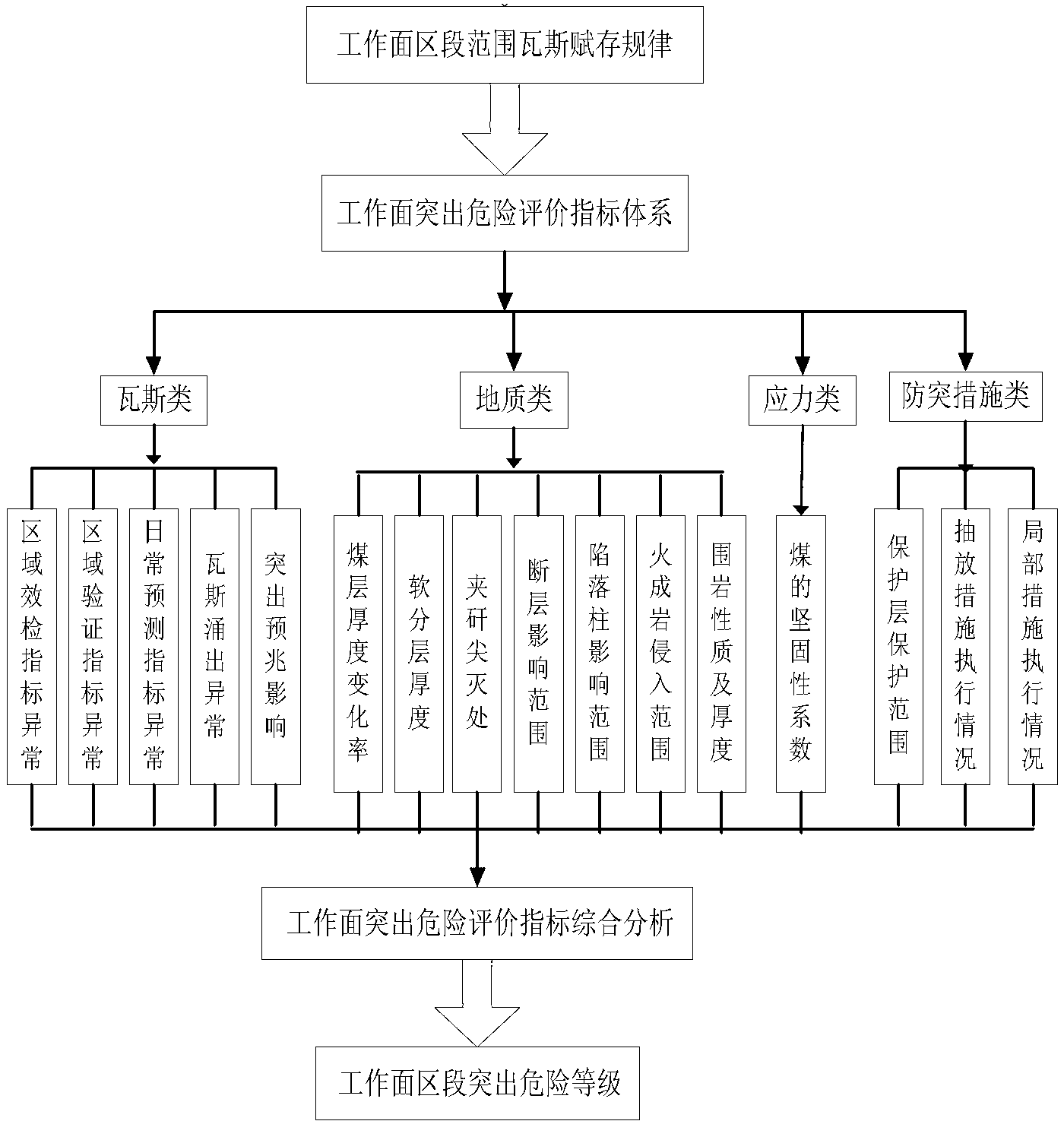
Working surface outburst risk evaluation index system analysis method
ActiveCN102705010AEnsure safe productionReasonably formulatedMining devicesRisk levelEvaluation result
The invention discloses a working surface outburst risk evaluation index system analysis method, which comprises the following steps of: acquiring gas occurrence data of a mine stope face; comprehensively analyzing the data to form risk evaluation indexes for judging working surface outburst risk, and storing the risk evaluation indexes in a criterion index library; processing the risk evaluation indexes and preset evaluation index critical values to determine the risk level of a working surface region range; and pre-warning according to the risk level. According to the method, working surface outburst risk dynamic evaluation indexes are classified into a gas index, a geology index, a stress index and an outburst prevention measure index on the basis of researching the gas occurrence rule of the mine stope face, so that the change rule of each evaluation index is grasped in time and analyzed intelligently, a working surface outburst evaluation result is formed comprehensively, outburst risk pre-warning of different levels is generated automatically, and real-time change update of each evaluation index can be predicted along with outburst; and the blindness of outburst prevention work is reduced, outburst prevention engineering cost is saved, and safe production of a mine is ensured.
Owner:CHINA COAL TECH ENG GRP CHONGQING RES INST
Method and computer program product for testing a software application
InactiveUS20070168967A1Error detection/correctionDigital computer detailsReal time analysisData loss
A method and computer program product for testing a software application program. Randomized input is provided into a logging facility and automated testing of the logging facility is performed in a multi-processing environment. Self-verification of data retrieved from the logging facility is performed to ensure no data loss occurs due to external system events or failures driven by a test tool. Real-time analysis of results received is performed by the test tool based on the randomized input into the logging facility. First failure data is captured and self-verification of results of a data recovery operation of the logging facility is performed in a disaster recovery scenario.
Owner:IBM CORP
DMA latency compensation with scaling line buffer
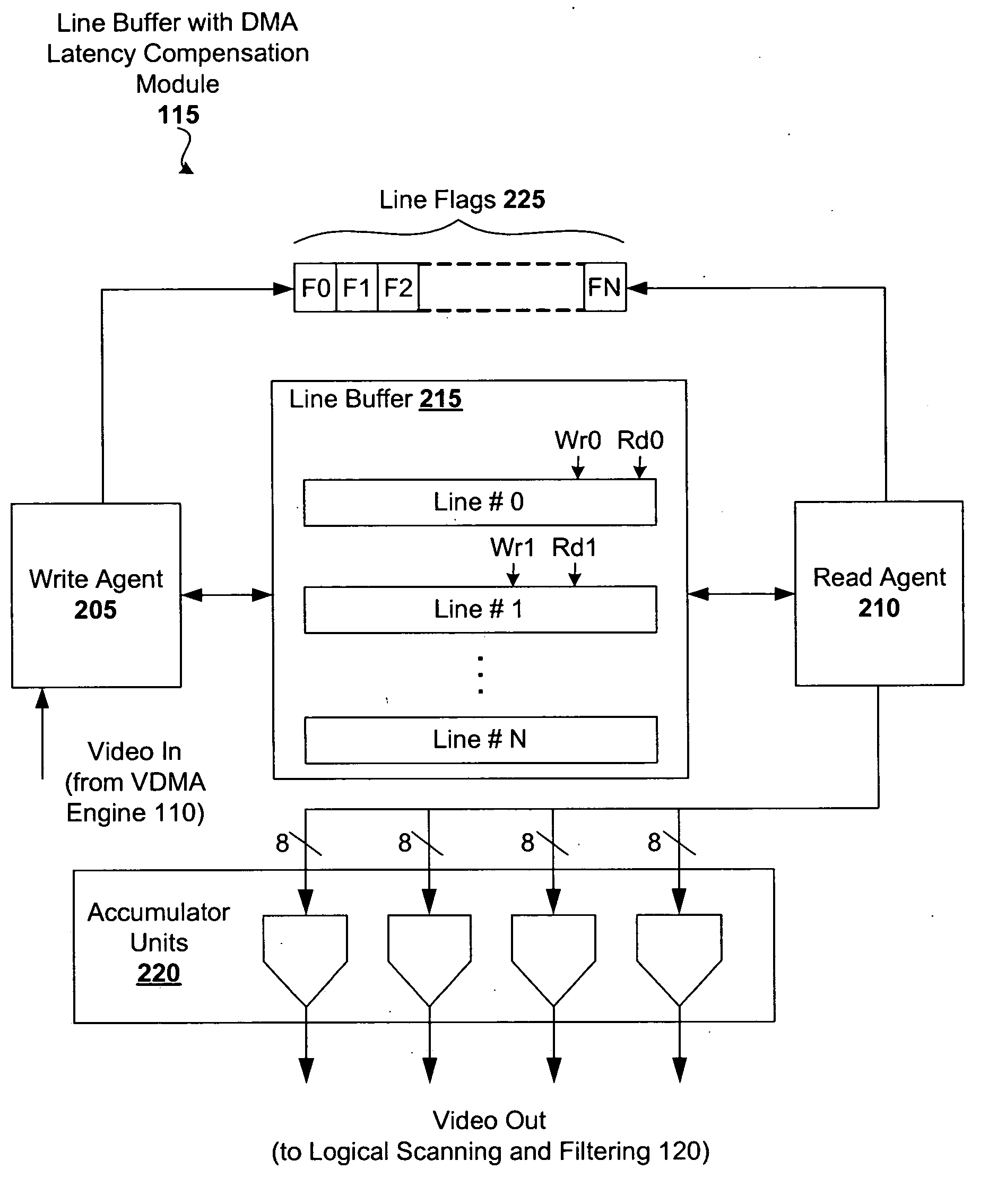
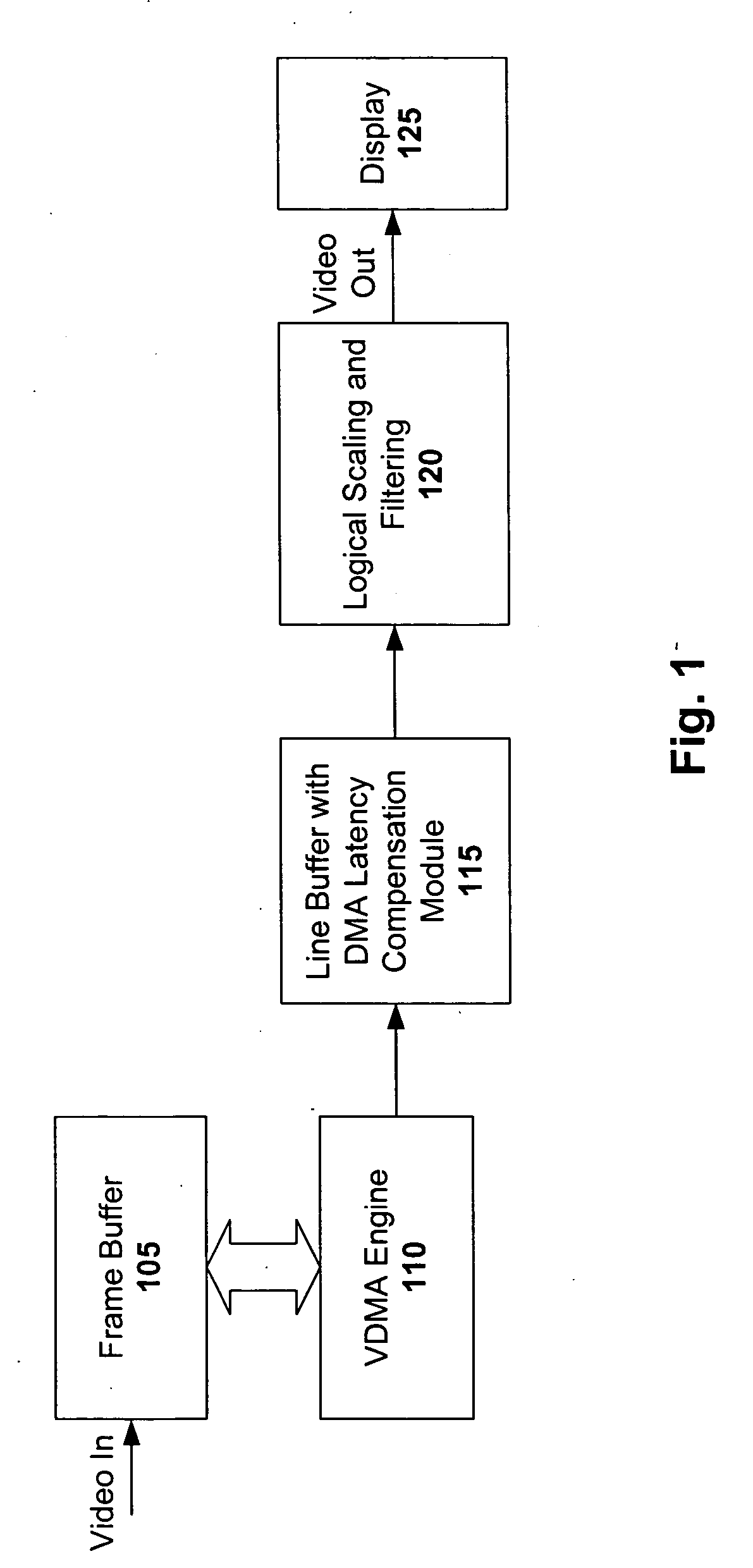
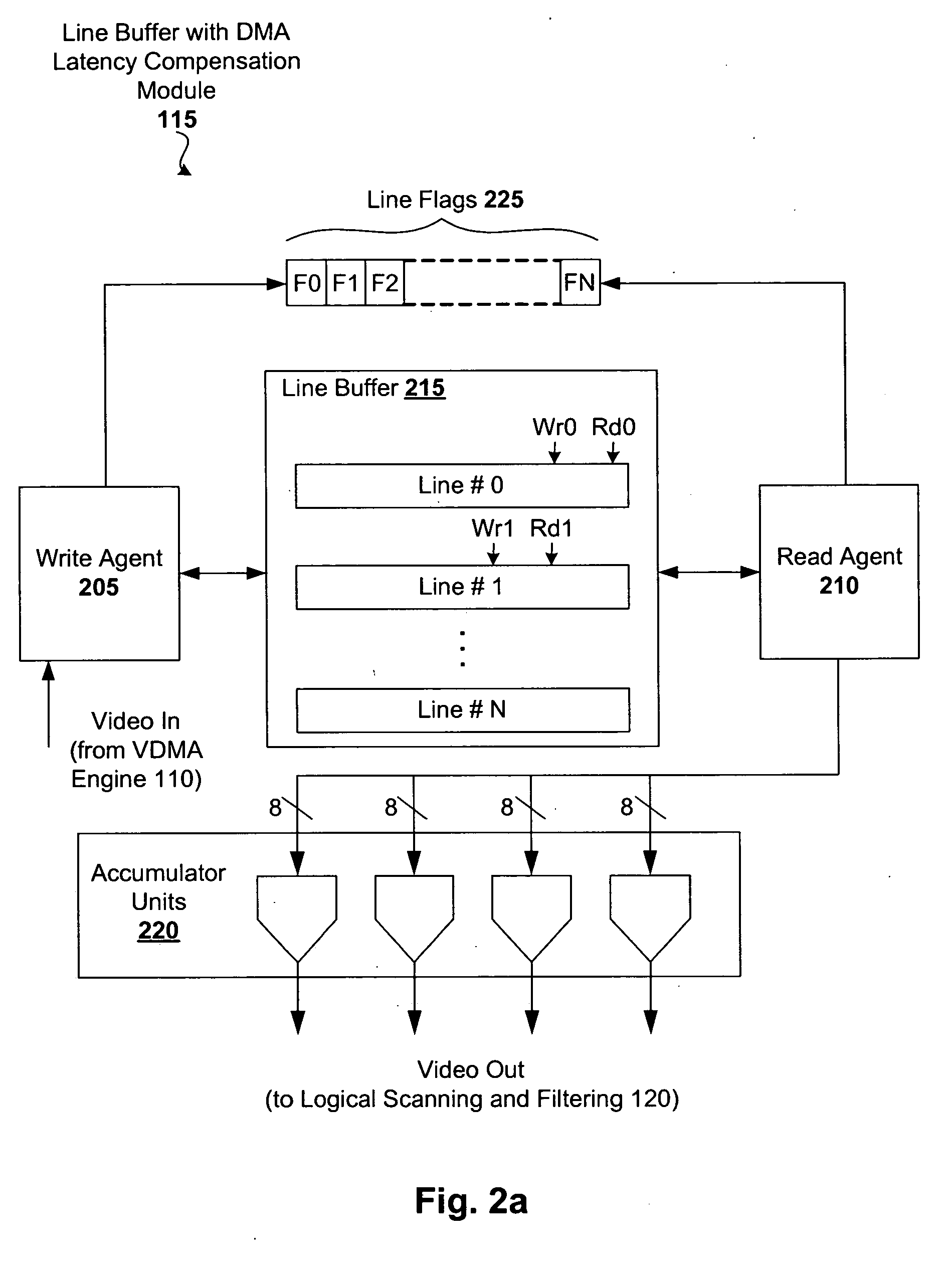
InactiveUS20060125835A1Easy transferAlleviate shortagesCathode-ray tube indicatorsOccurrence dataVideo processing
A video processing system configured with DMA latency compensation is disclosed. This compensation helps minimize or otherwise mitigate shortages of data to the display, thereby improving the quality of displayed video. A relatively small line buffer is used to stage data for video processing. Should an underflow of data occur (where the buffer reading process is ahead of the buffer writing process), data is read from the previous line buffer. This not only prevents shortages of data to the display, but also provides data that is more likely to be relevant to the actual scene being displayed (as compared to random data).
Owner:MICRONAS
Encryption key recovery in the event of storage management failure
ActiveUS9571278B1Key distribution for secure communicationUser identity/authority verificationData processing systemOccurrence data
A data processing system stores encrypted data. Object identifiers are assigned to storage objects, and data encryption keys are assigned to the storage objects. When performing an operation upon a storage object, data encryption key failure may occur due to a corrupt or incorrect key. In this case, a copy of the data encryption key is fetched from a key server. It is possible for the association of the object identifiers with the data encryption keys to become lost or confused, so that the key server may fail to provide the correct key for a specified object identifier. Therefore, an absolute key identifier that is unique across the key server namespace also is stored in association with the object identifier in the storage system and in the key store of the key server, and the absolute key identifier is used as a failsafe for recovery of encrypted data.
Owner:EMC IP HLDG CO LLC
Image data processing method and device, computer equipment and storage medium
PendingCN111897579AAvoid CatonImprove processing efficiencyImage memory managementConcurrent instruction executionData packOccurrence data
The invention relates to an image data processing method, which comprises the steps of obtaining image data of N to-be-processed images, and the image data of each to-be-processed image comprising C parts of image channel data; storing the image data into C storage areas of a local memory, wherein N storage units in each storage area store one piece of image channel data of N to-be-processed images respectively; when a data reading instruction occurs, determining a historical address according to a current address carried by the data reading instruction, thereby reading target image channel data from a local memory based on the storage address; arranging the read target image channel data in the form of a two-dimensional matrix, enabling the data corresponding to the same channel to be inthe same matrix row, and enabling the data corresponding to the same to-be-processed image in the adjacent matrix rows to be distributed in two adjacent matrix columns; and sequentially transmitting each column of data arranged in a two-dimensional matrix form to the pulsation array according to a time sequence for operation to obtain an operation result. By adopting the method, the data processing efficiency can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
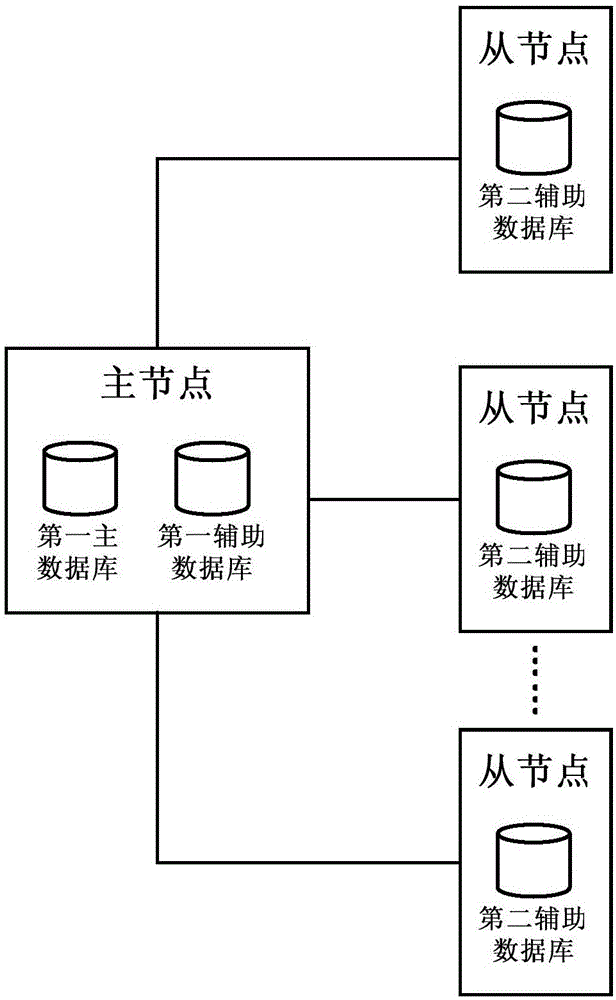
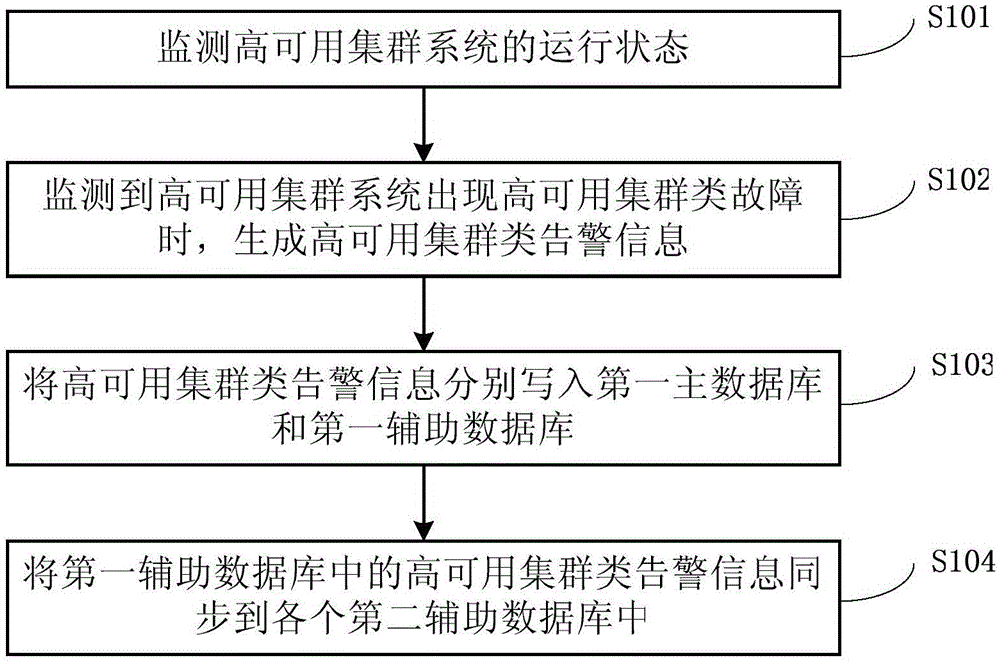
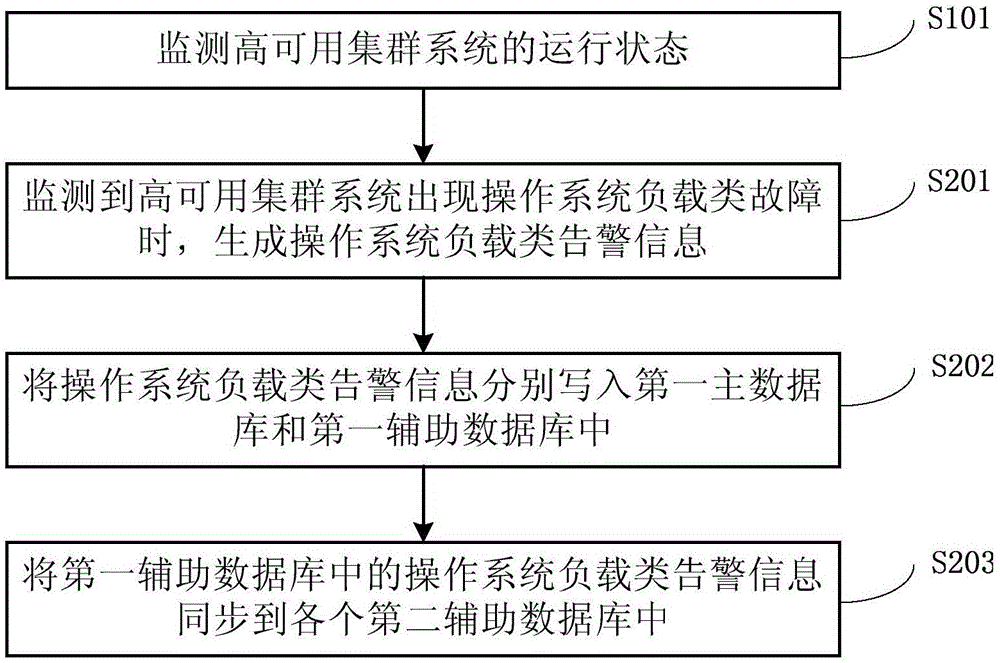
HAC system, warning method based on HAC system and warning system based on HAC system
ActiveCN105138441AGuaranteed uptimeImprove system performanceInput/output to record carriersHardware monitoringData miningDatabase connection
The invention provides an HAC (High Availability Cluster) system, a warning method based on the HAC system and a warning system based on the HAC system. When the HAC system, the warning method and the HAC system are used, warning information is simultaneously stored in a first main database and a first auxiliary database of a master node and second auxiliary databases of each slave node. Under the condition that a database connection fault does not occur, the warning information stored in each database is consistent. The warning information can be obtained from the database of the currently accessed node no matter whether the node currently accessed by a user is a master node or a slave node. Even when the database of the master node or the slave node fails, the user can also obtain the warning information from the second auxiliary databases of any one slave node, so that corresponding dealing measures can be taken in time according to the obtained warning information; the normal operation of the HAC system is ensured; the loss since the dealing measures are not taken in time is effectively avoided; and the system performance of the HAC system is greatly improved.
Owner:CHINA STANDARD SOFTWARE
Format-preserving data desensitization method
InactiveCN105426445AAvoid loading errorsEnsure safetySpecial data processing applicationsProcess mechanismChinese characters
The invention discloses a format-preserving data desensitization method, which relates to a data desensitization method, in particular to a format-preserving data processing method. The method aims to solve the problems that data accuracy is seriously affected since data missing happens when a traditional protection method of client sensitive data carries out a data association operation, an algorithm is easy in cracking since the adopted algorithm is too simple and no effective historical data processing mechanism is provided after a key is exposed. A GB2312 Chinese character set is divided into 72 isometric unit intervals on the basis of the coding structure of the GB2312 Chinese character set within a range of B0A0, and the code distribution of each unit interval is the same. The method comprises the coding structure of the GB2312 Chinese character set, a GBK (Guo-Biao Kuozhan) isometric encryption algorithm, a GBK isometric decryption algorithm, a number scrambling algorithm and a number descrambling algorithm. The method belongs to the field of computer software.
Owner:TIANJIN JIANING KUNXIANG TECH CO LTD
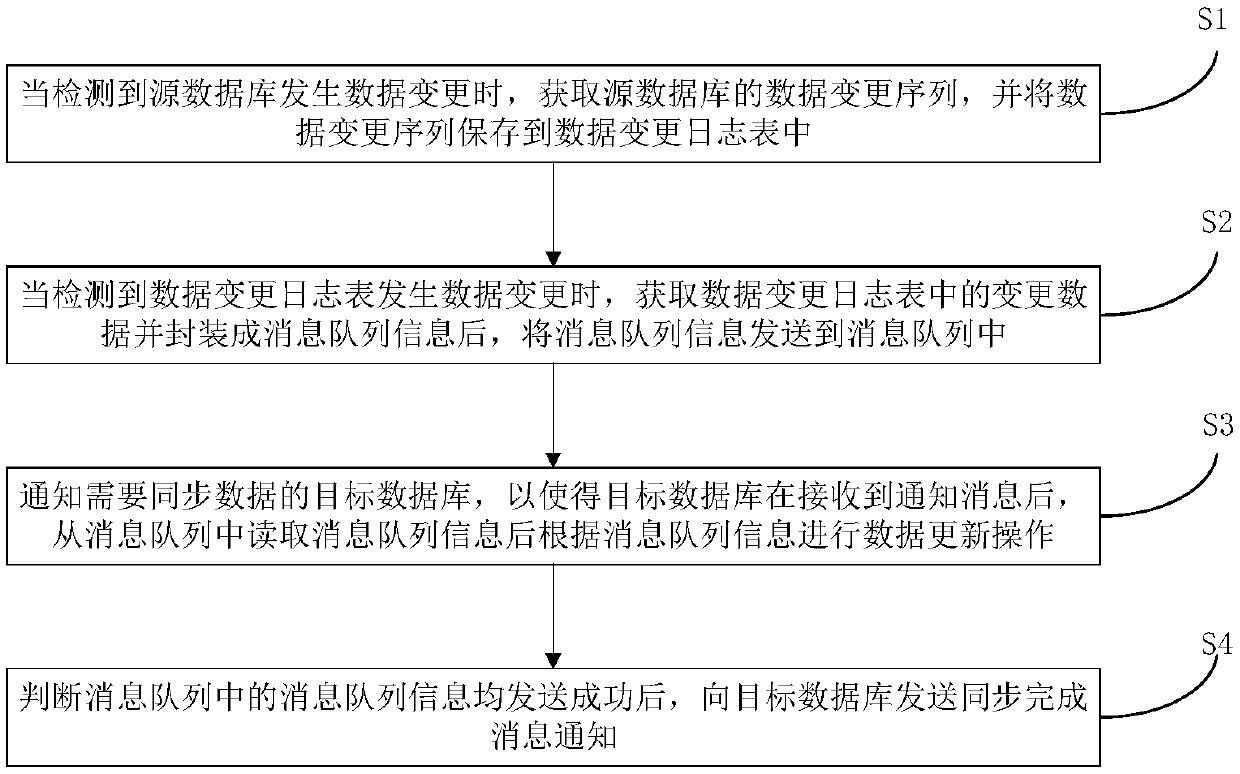
Data real-time synchronization method and system
InactiveCN109582731AReduce development difficultySynchronization is simpleInterprogram communicationDatabase distribution/replicationData synchronizationMessage queue
The invention discloses a real-time data synchronization method and system, and the method comprises the steps: obtaining a data change sequence of a source database when detecting that the source database has data change, and storing the data change sequence in a data change log table; When it is detected that the data change occurs in the data change log table, obtaining change data in the datachange log table, packaging the change data into message queue information, and sending the message queue information to a message queue; Informing a target database needing to synchronize data, so that after receiving the notification message, the target database reads the message queue information from the message queue and then performs data updating operation according to the message queue information; And after judging that the message queue information in the message queue is successfully sent, sending a synchronization completion message notification to the target database. The synchronization mode is simple, program development difficulty is low, synchronization efficiency is high, data synchronization can be carried out in time, the period is short, and the method can be widely applied to the software technology industry.
Owner:恒峰信息技术有限公司
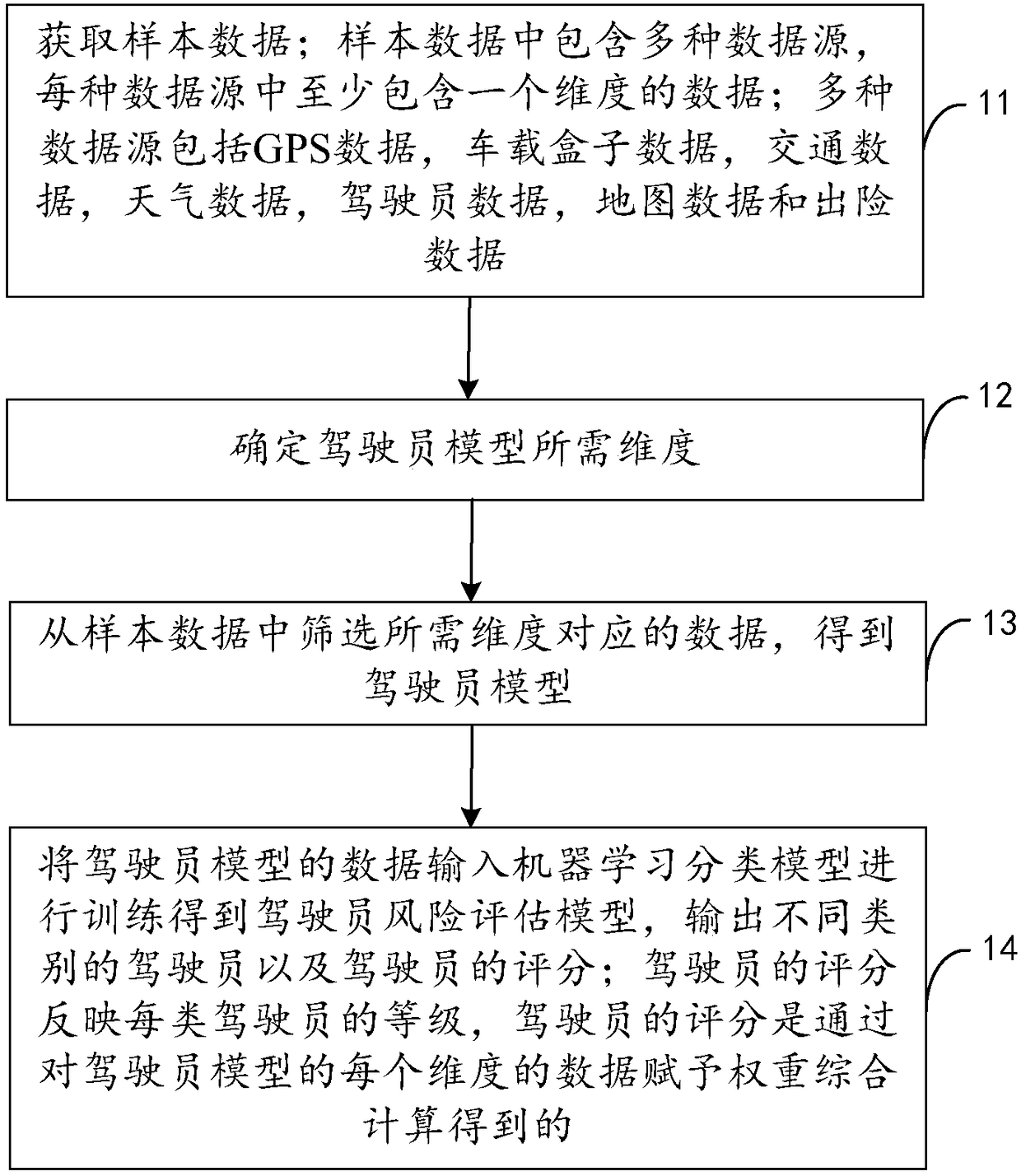
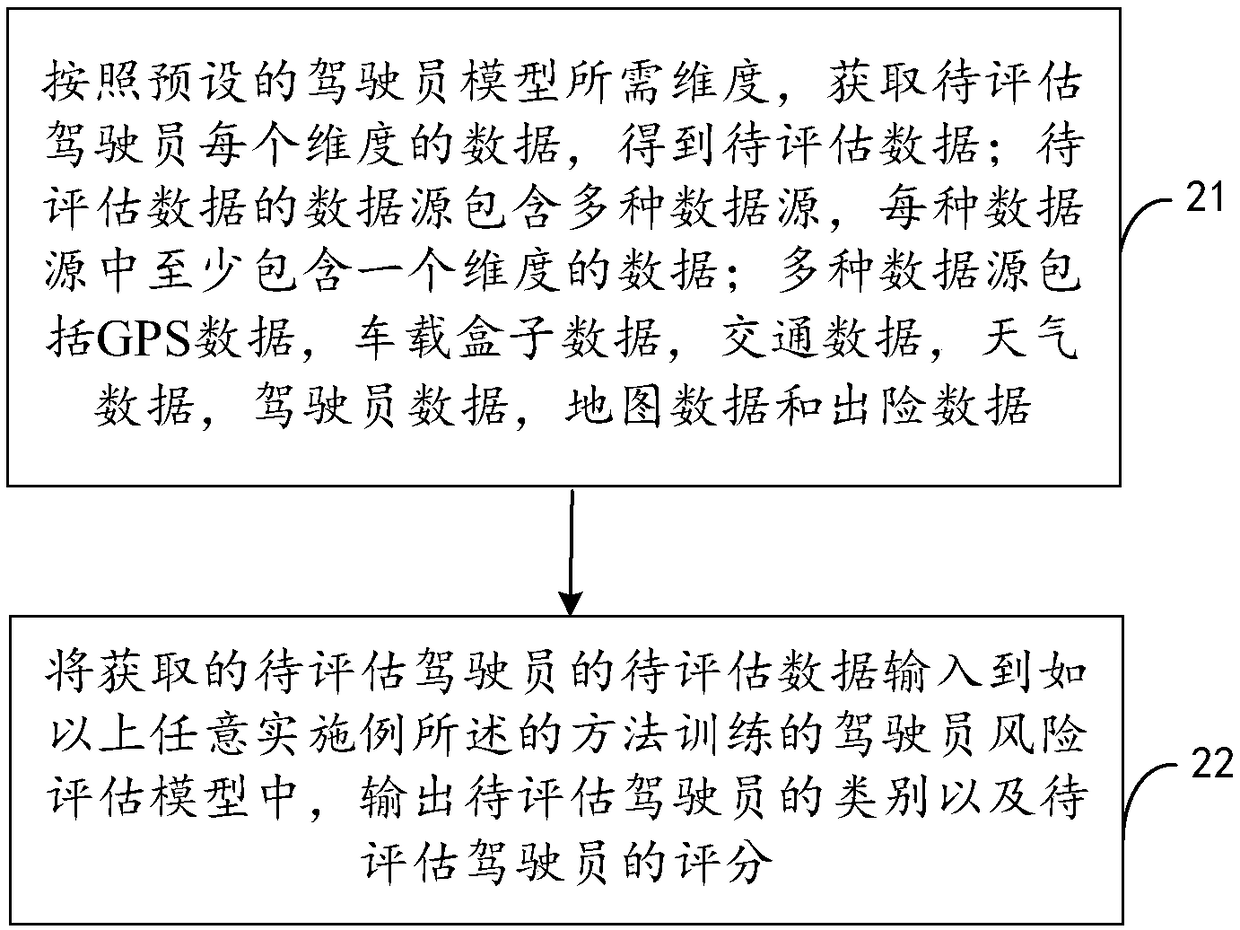
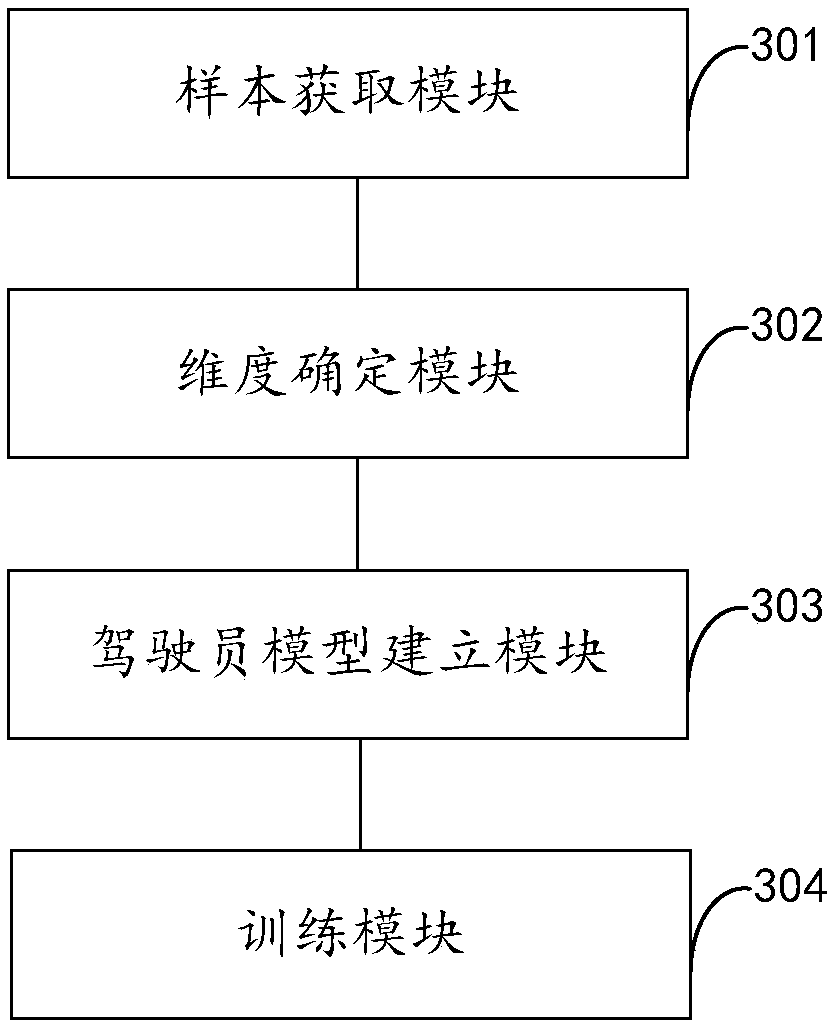
Driver risk assessment model training method and device and risk assessment method and device
The invention relates to a driver risk assessment model training method and device and a risk assessment method and device. According to the invention, data corresponding to dimensions required by a driver model is obtained from various data resources, wherein the data sources comprise GPS data, vehicle-mounted box data, traffic data, weather data, driver data, map data and insurance accident occurrence data, the data sources are very rich, the data for assessment is more comprehensive based on the data sources, and the driver type and score outputted by a trained machine learning classification model can reflect the level of each type of drivers. In addition, the data sources comprise the insurance accident occurrence data, the driver score is comprehensively calculated by giving a weightto the data of each dimension of the driver model, so that the obtained driver type and score are more accurate, and the vehicle insurance price set according to the model is more accurate.
Owner:BEIJING AUTOMOBILE RES GENERAL INST +1
Method and system for data packet queue recovery
ActiveUS20120110163A1Avoid and minimize and recover from effectAccelerates data deliveryHybrid transportMultiple digital computer combinationsOccurrence dataNetwork packet
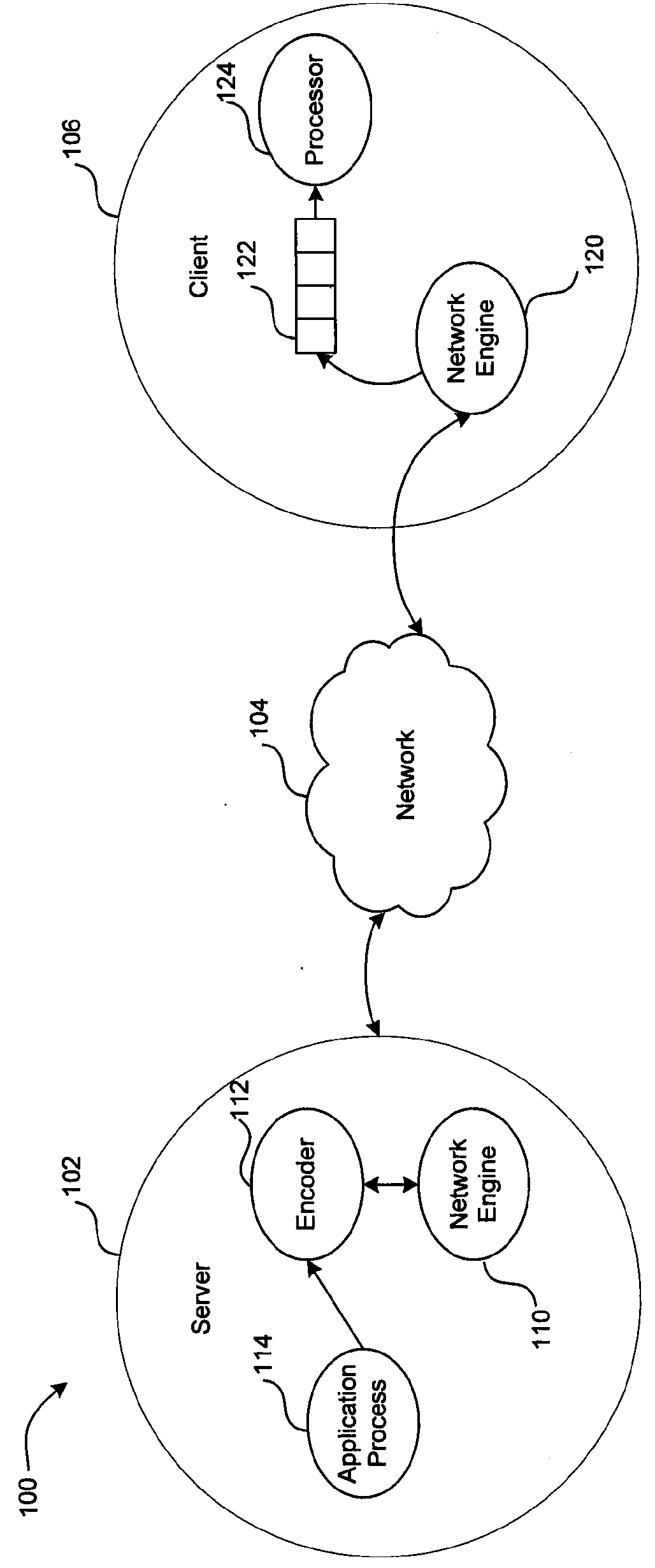
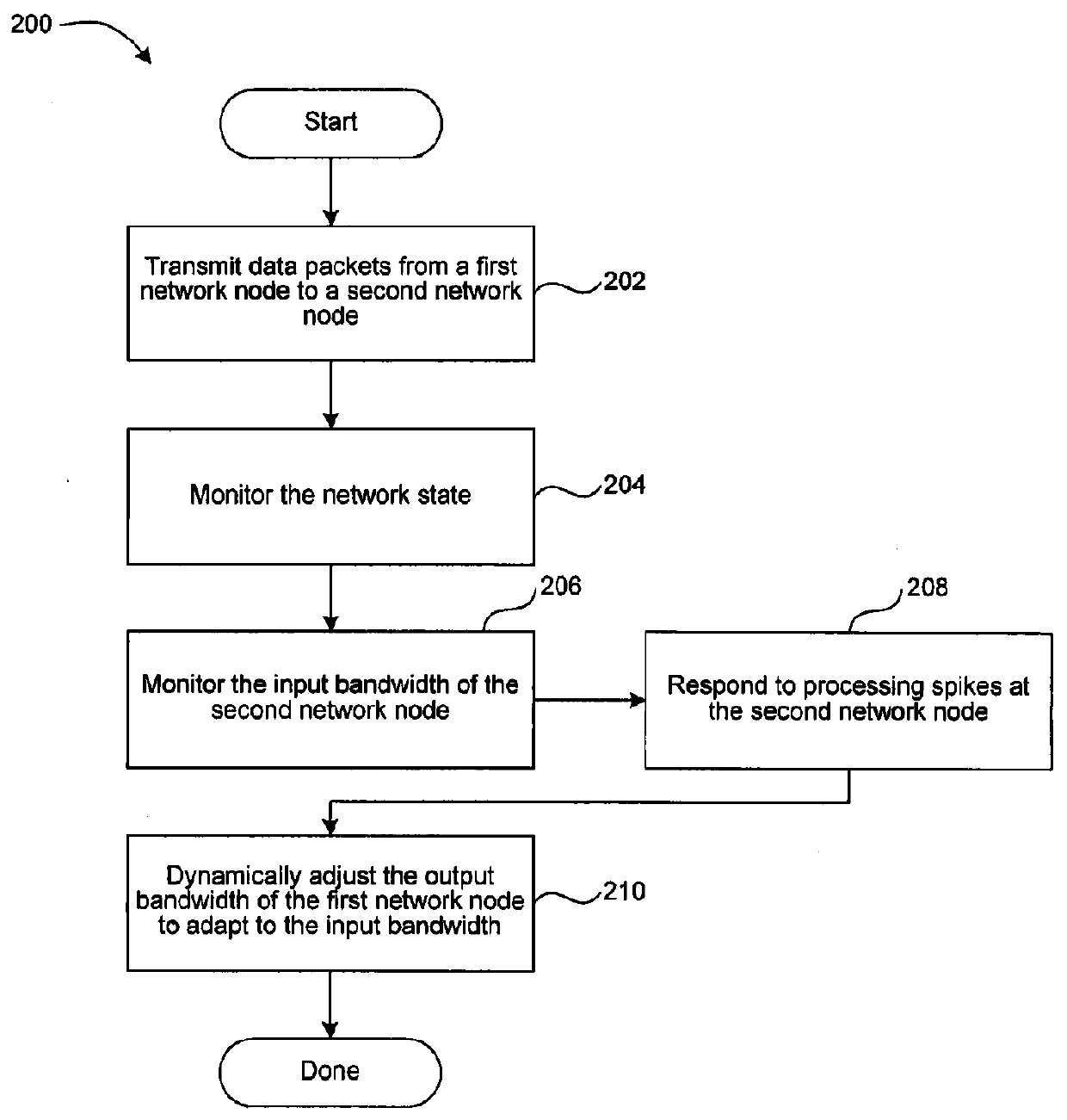
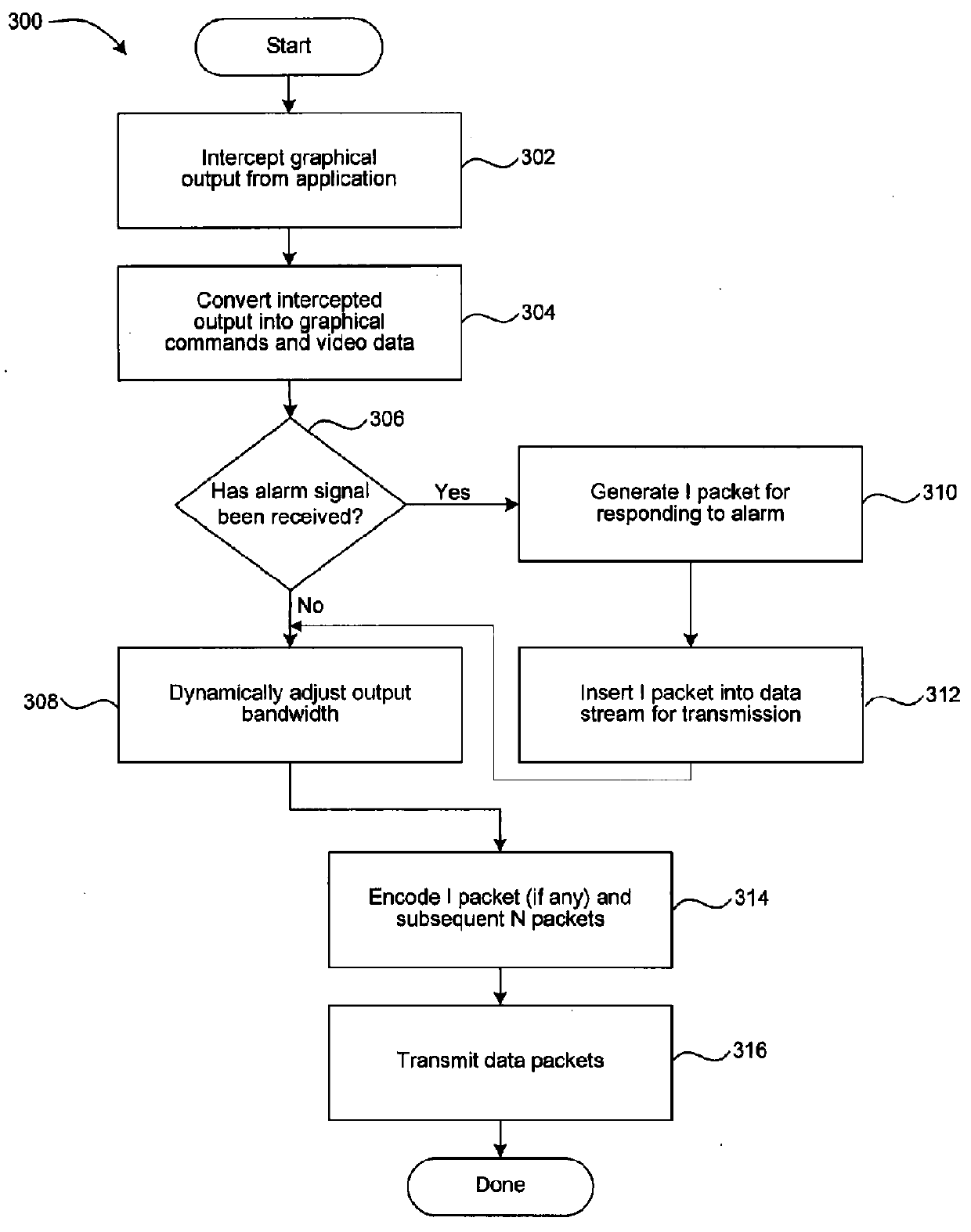
Resource-aware dynamic bandwidth control uses information about current network state and receiver performance to avoid, minimize and / or recover from the effects of network spikes and data processing spikes. Linear models may be used to estimate a time required to process data packets in a data processing queue, and are thus useful to determine whether a data processing spike is occurring. When a data processing spike occurs, an alarm may be sent from a client to a server notifying the server that the client must drop packets. In response, the server can encode and transmit an independent packet suitable for replacing the queued data packets which can then be dropped by the client and the independent packet present to the processor instead.
Owner:AMAZON TECH INC +11
Fault-tolerance method for high-reliability disk array
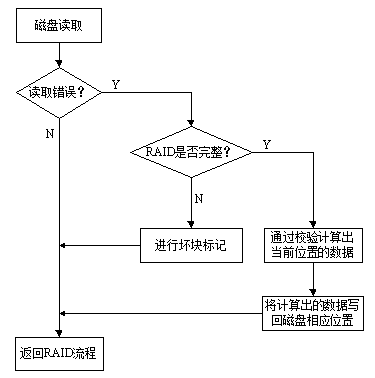
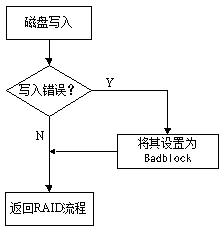
ActiveCN103309775AReduce the frequency of cullingExtended service lifeRedundant hardware error correctionOccurrence dataDisk array
The invention discloses a fault-tolerance method for a high-reliability disk array. The fault-tolerance method comprises the following steps: when a data write error occurs, confirming storage space of a disk in which data with the write error is, and carrying out bad block marking on the storage space; when a data read error occurs, judging if the disk array is complete, if so, working out current position data by checking, writing the data in a corresponding position of the disk, and otherwise, carrying out bad block marking on the storage space with the data read error; and when a next write operation is carried out, carrying out the write operation on the storage space subjected to bad block marking, if the storage space is successfully written and the subsequent read operation is also successful, removing a bad block mark of the storage space, and on the contrary, remaining the bad block mark. According to the fault-tolerance method, the technical problems that only bad block information of read-write errors is recorded and bad blocks are not repaired in a disk array system and the disk array system is limited by a fault-tolerance range in the prior art are solved; and the fault-tolerance method is in particular suitable for occasions with low data accuracy requirements.
Owner:SUZHOU KEDA TECH
Method to optimize effective page number to real page number translation path from page table entries match resumption of execution stream
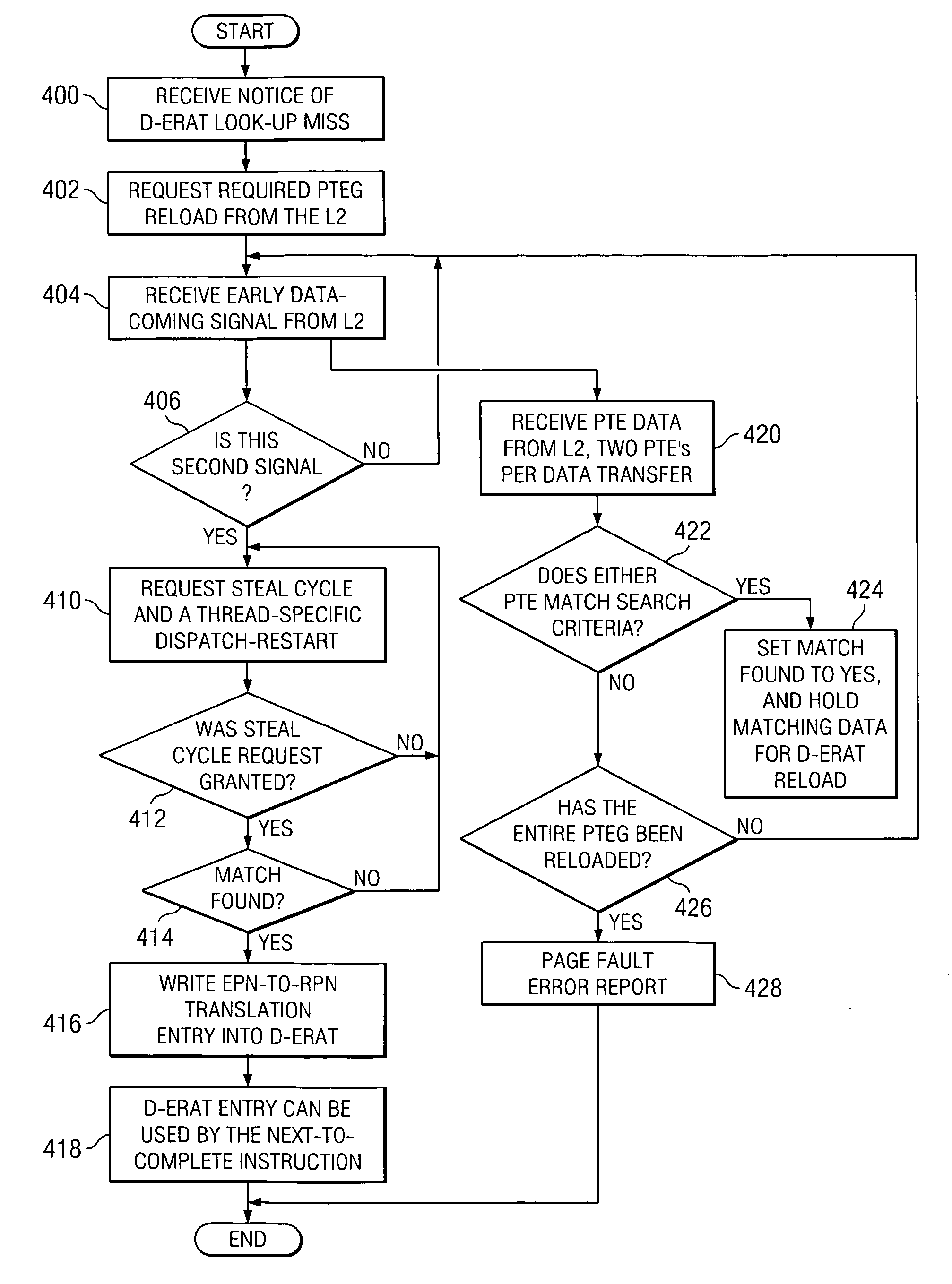
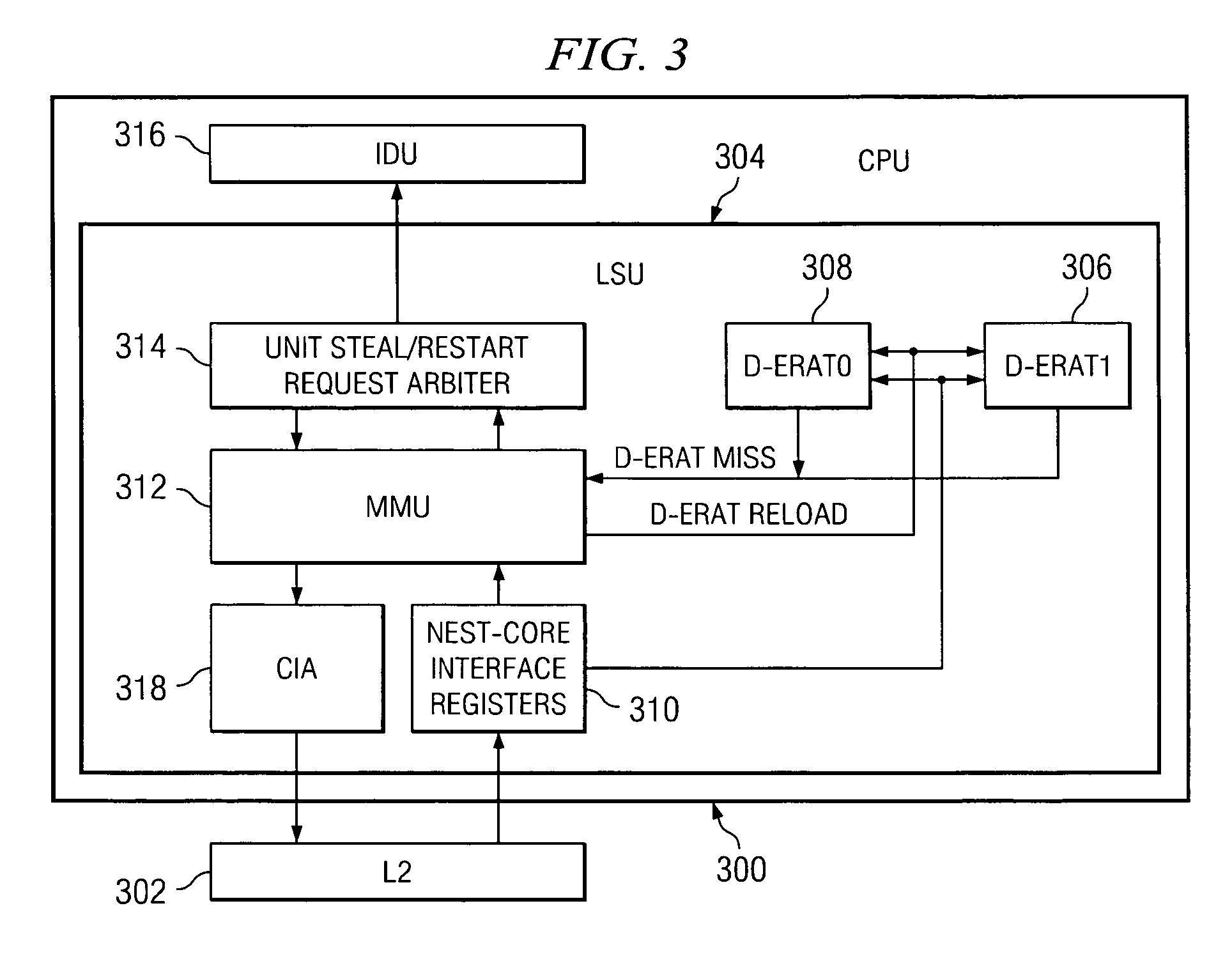
ActiveUS7350051B2Memory architecture accessing/allocationMemory adressing/allocation/relocationArray data structureOccurrence data
A method, system and computer program product for optimizing EPN to RPN translation when a data miss occurs. The method, system and computer program product take advantage of the high-likelihood of finding the matching PTE in the first half of the PTEG and utilize early data-coming signals from the L2 cache to prime the data-flow pipe to the D-ERAT arrays and requesting a joint steal cycle for executing the write into the D-ERAT and a restart request for re-dispatching the next-to-complete instruction.
Owner:META PLATFORMS INC
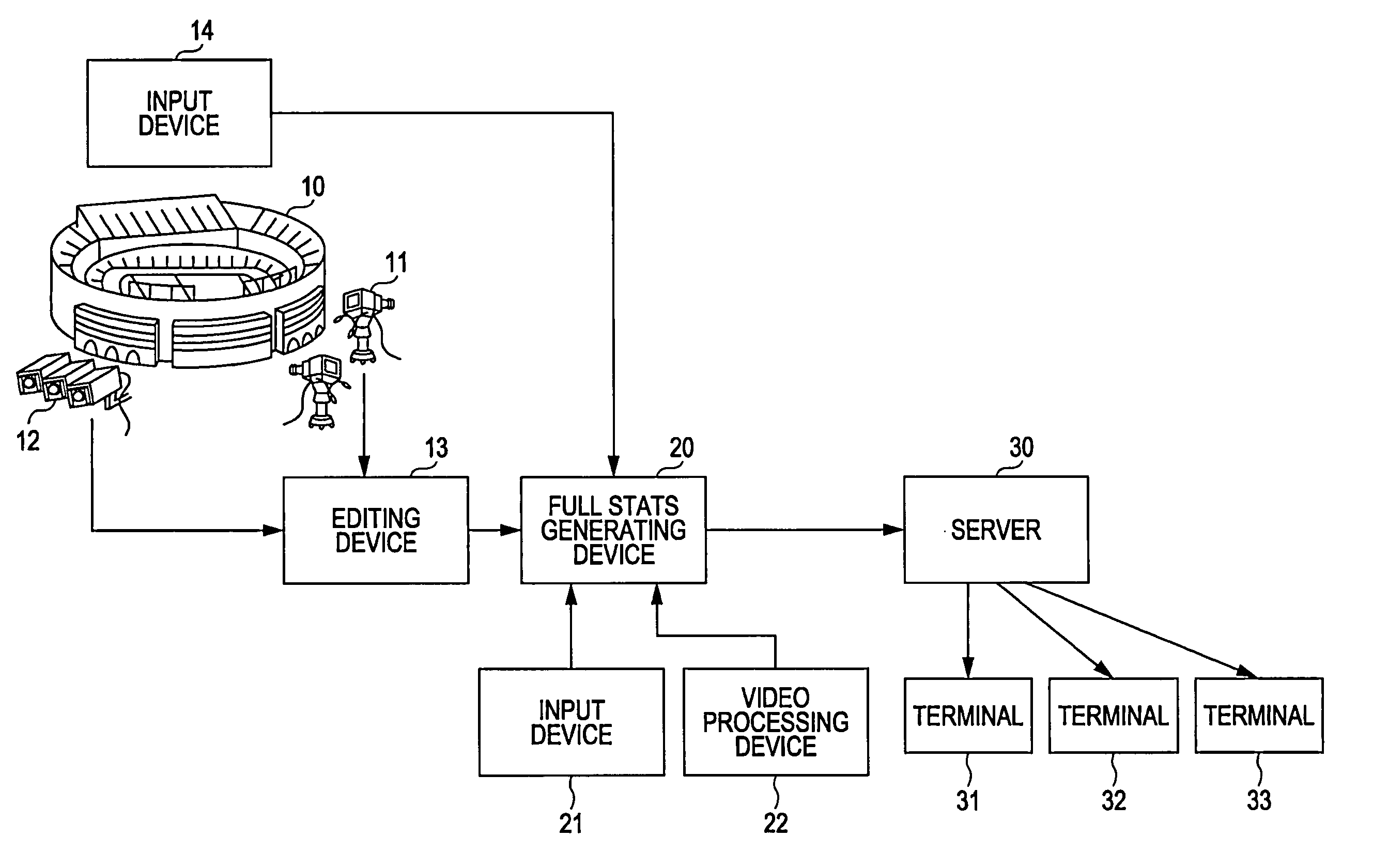
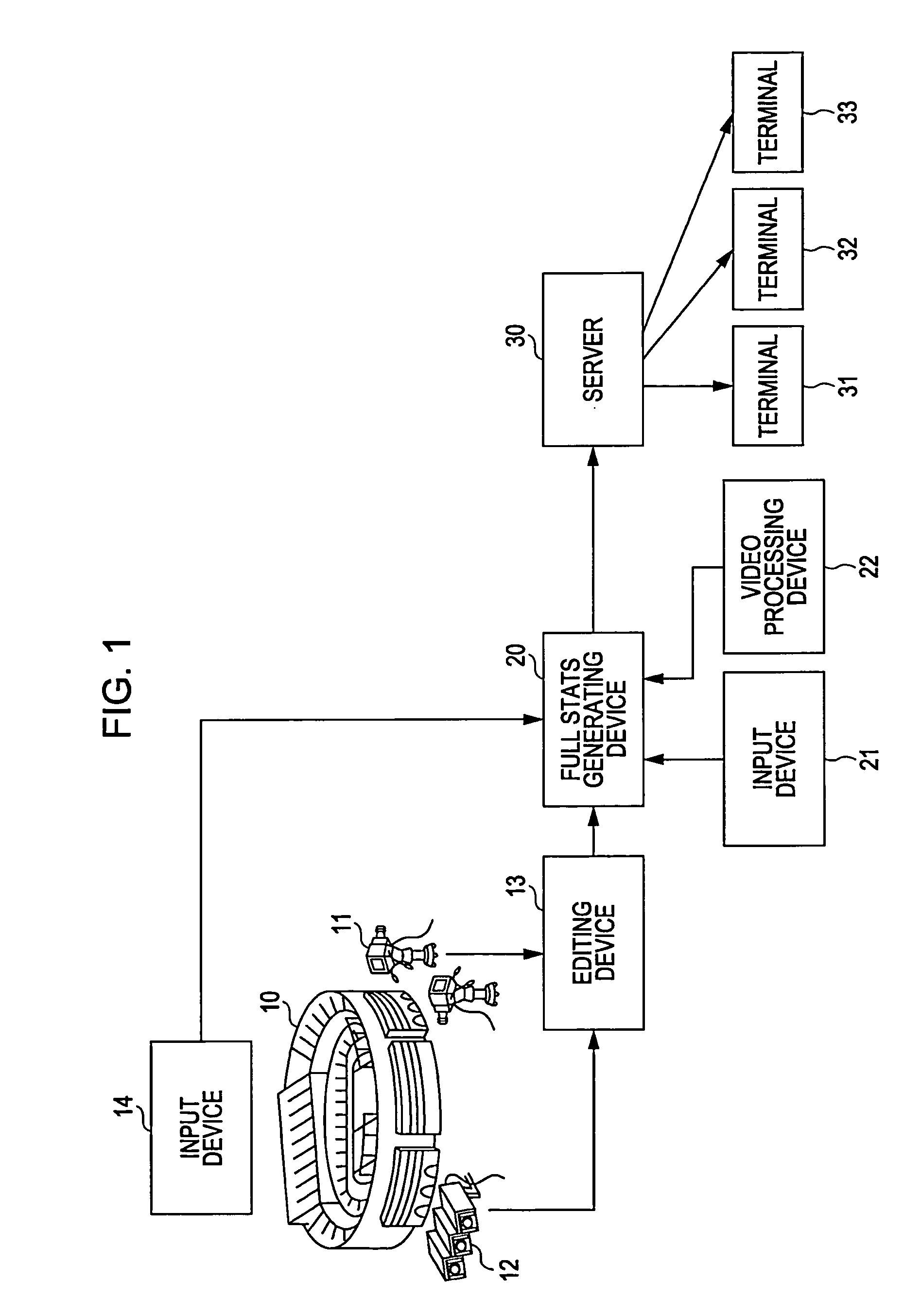
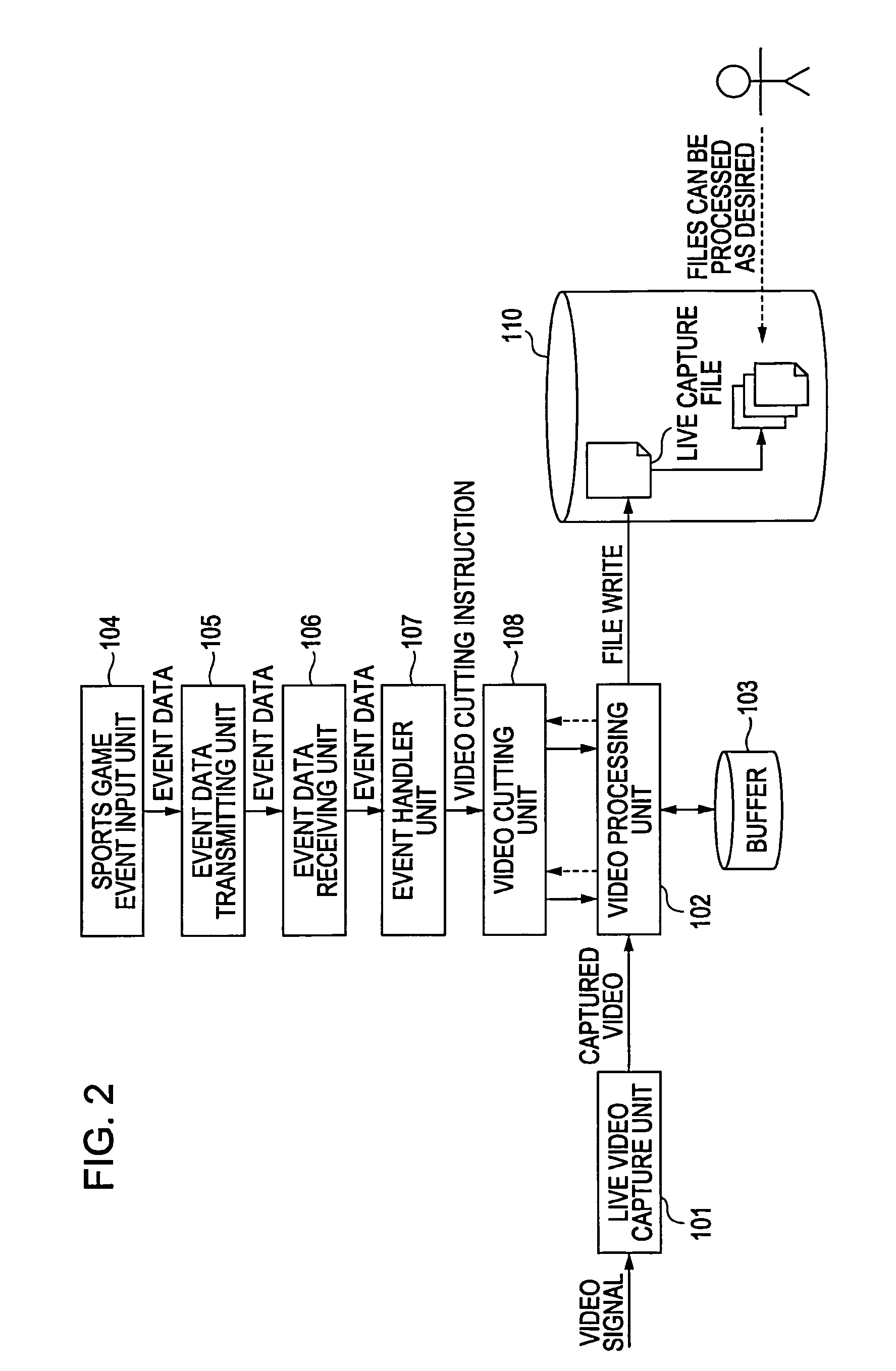
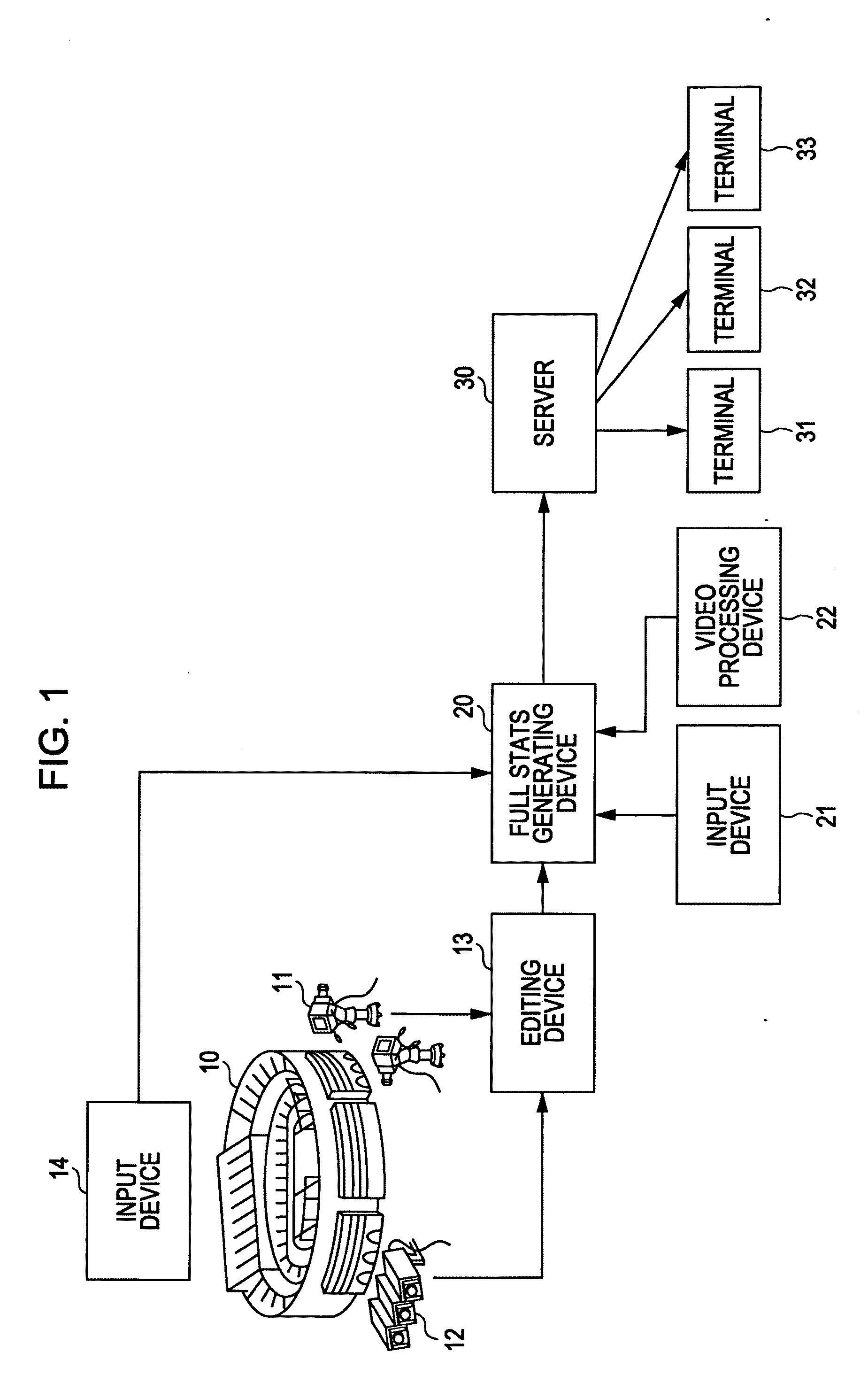
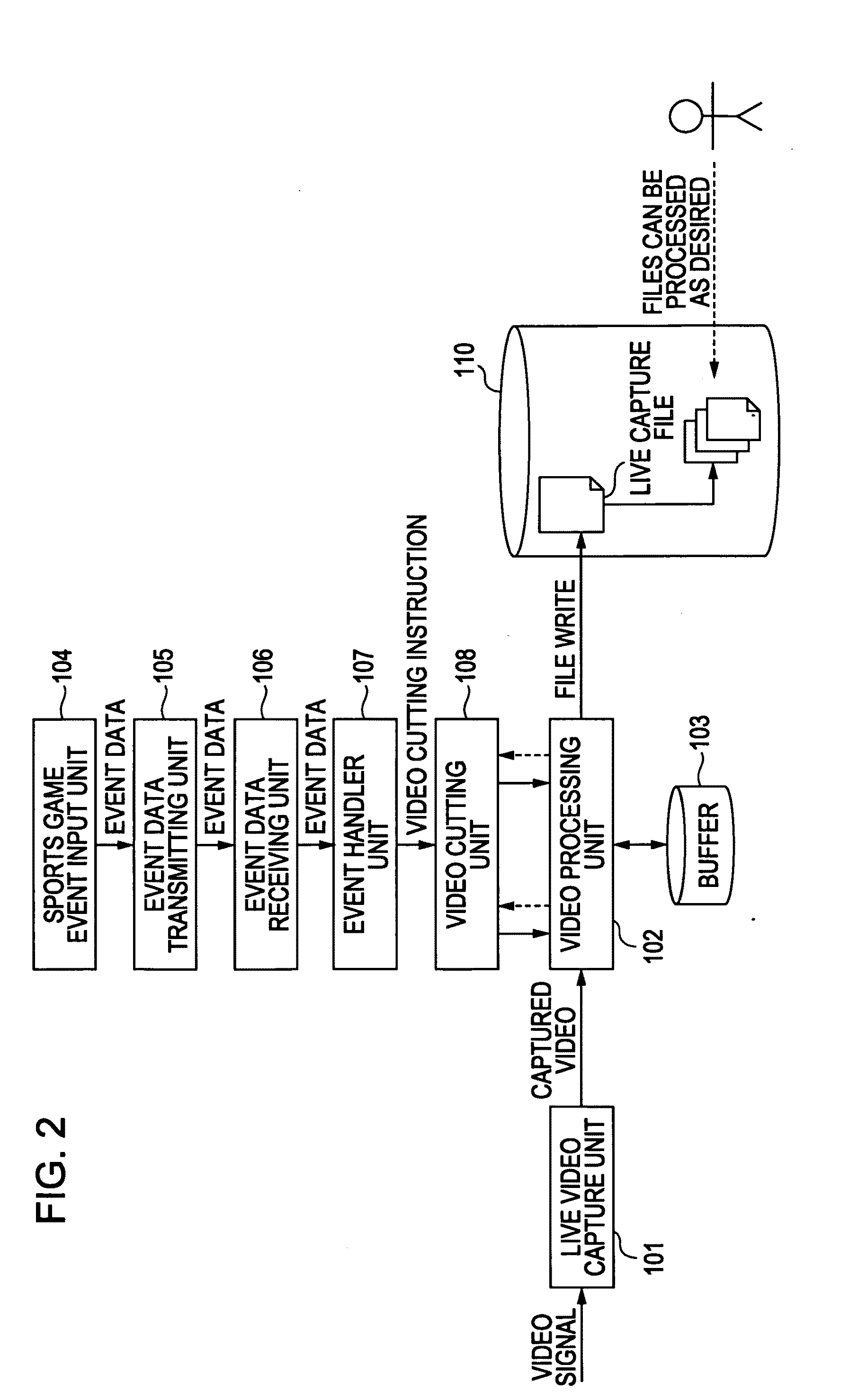
Video processing device, video processing method, and program
InactiveUS8988528B2Easy retrievalTelevision system detailsElectronic editing digitised analogue information signalsOccurrence dataComputer graphics (images)
A video processing device includes a video obtaining unit configured to obtain video data by capturing video of a specific area, a video accumulating unit configured to accumulate the video data obtained by the video obtaining unit, a data input unit configured to input event occurrence data indicating an event that has occurred in a video image corresponding to the video data obtained by the video obtaining unit and object specifying data for specifying an object relating to the event, and an addition processing unit configured to add the event occurrence data and object specifying data input by the data input unit to the video data accumulated in the video accumulating unit using a predetermined format through provision of link data for linking the video data to the event occurrence data and the object specifying data.
Owner:SONY CORP
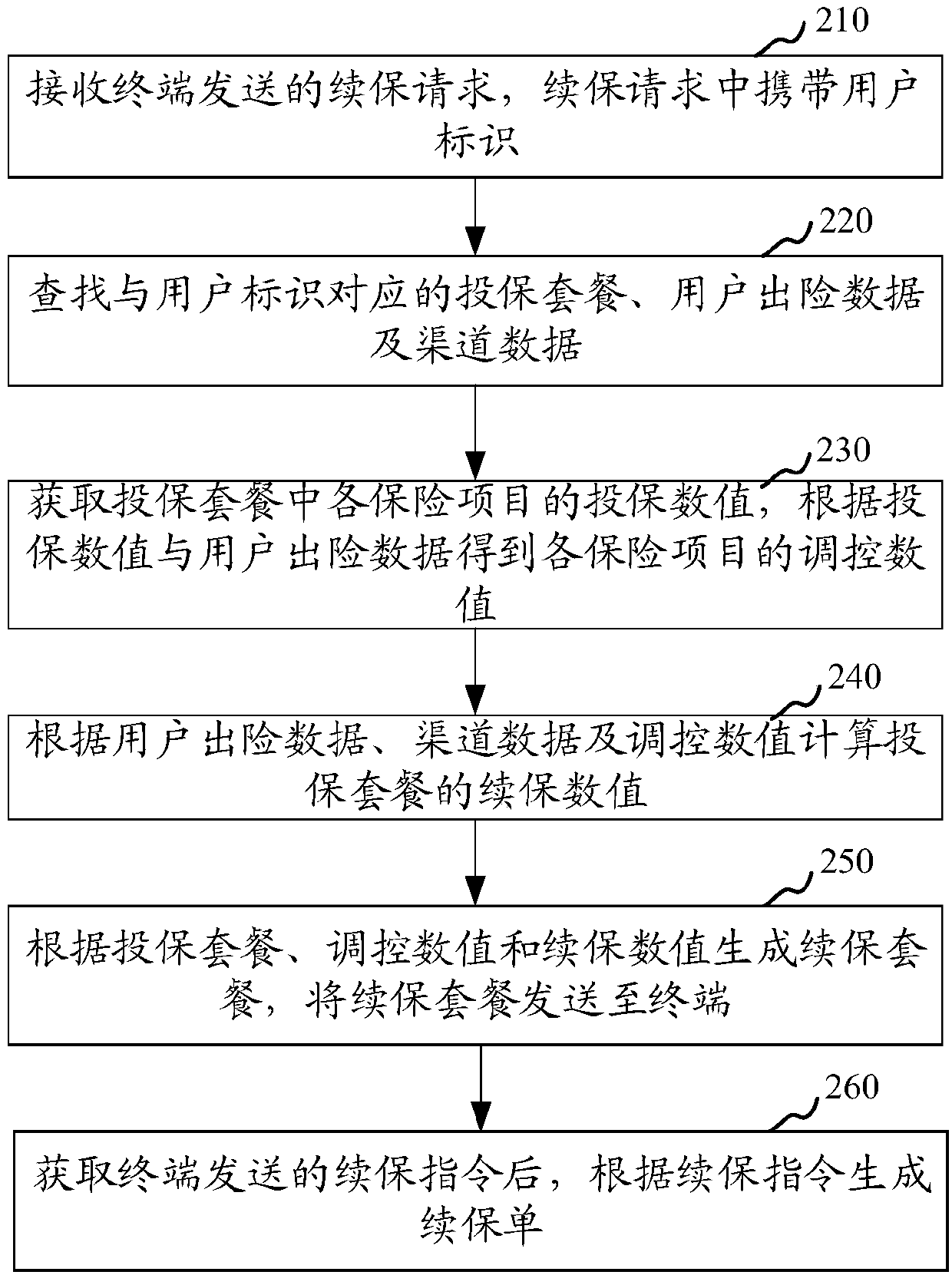
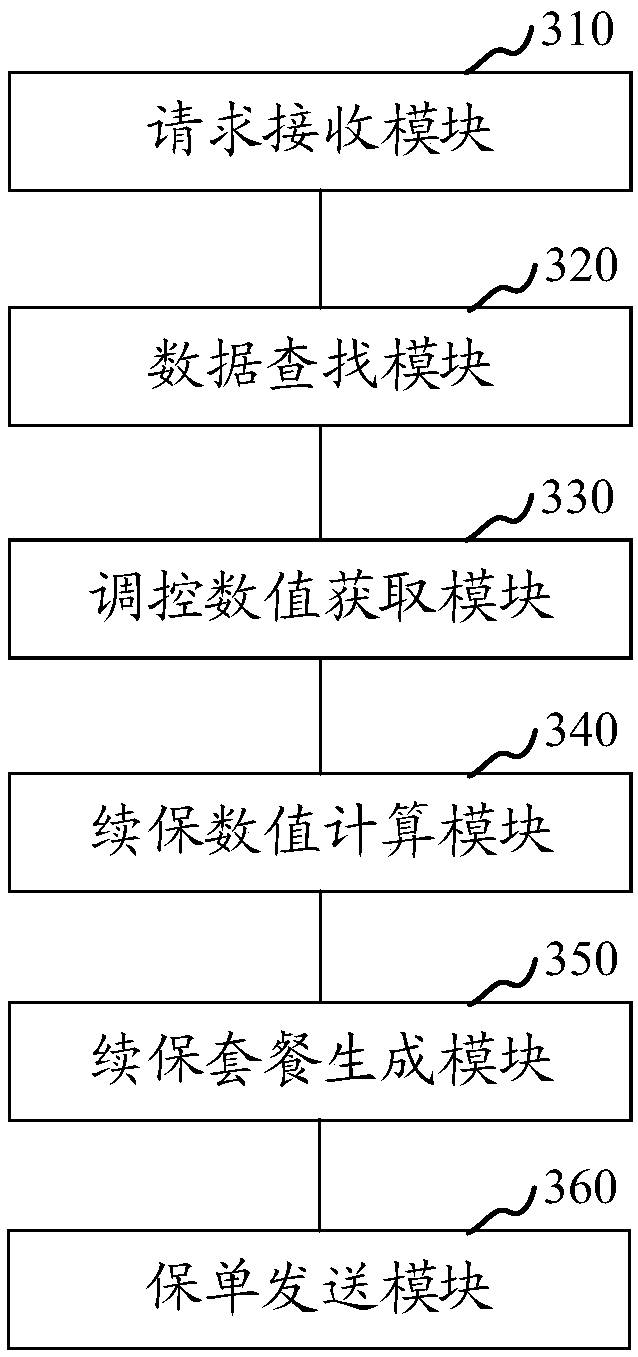
Insurance renewal processing method and apparatus, computer device and storage medium
The invention relates to an insurance renewal processing method and apparatus, a computer device and a storage medium. The method includes the steps of receiving an insurance renewal request sent by aterminal, the insurance renewable request carrying a user identifier; searching for an insurance package, user loss occurrence data and channel data corresponding to the user identifier; obtaining aninsurance value of each insurance item in the insurance package, and obtaining a regulation value of each insurance item according to the insurance value and the user loss occurrence data; calculating a insurance renewal value of the insurance package based on the user loss occurrence data, the channel data and the regulation value; generating an insurance renewal package based on the insurance package, the regulation value and the insurance renewal value, and sending the insurance renewal package to the terminal; and after acquiring an insurance renewal instruction sent by the terminal, generating an insurance renewal policy according to the insurance renewal instruction. The insurance renewal processing method and apparatus, the computer device and the storage medium can effectively improve the processing efficiency of the insurance renewal.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
Remote programming of radio preset stations over a network
InactiveUS20030083028A1Broadcast services for monitoring/identification/recognitionTransmissionGraphicsComputer network
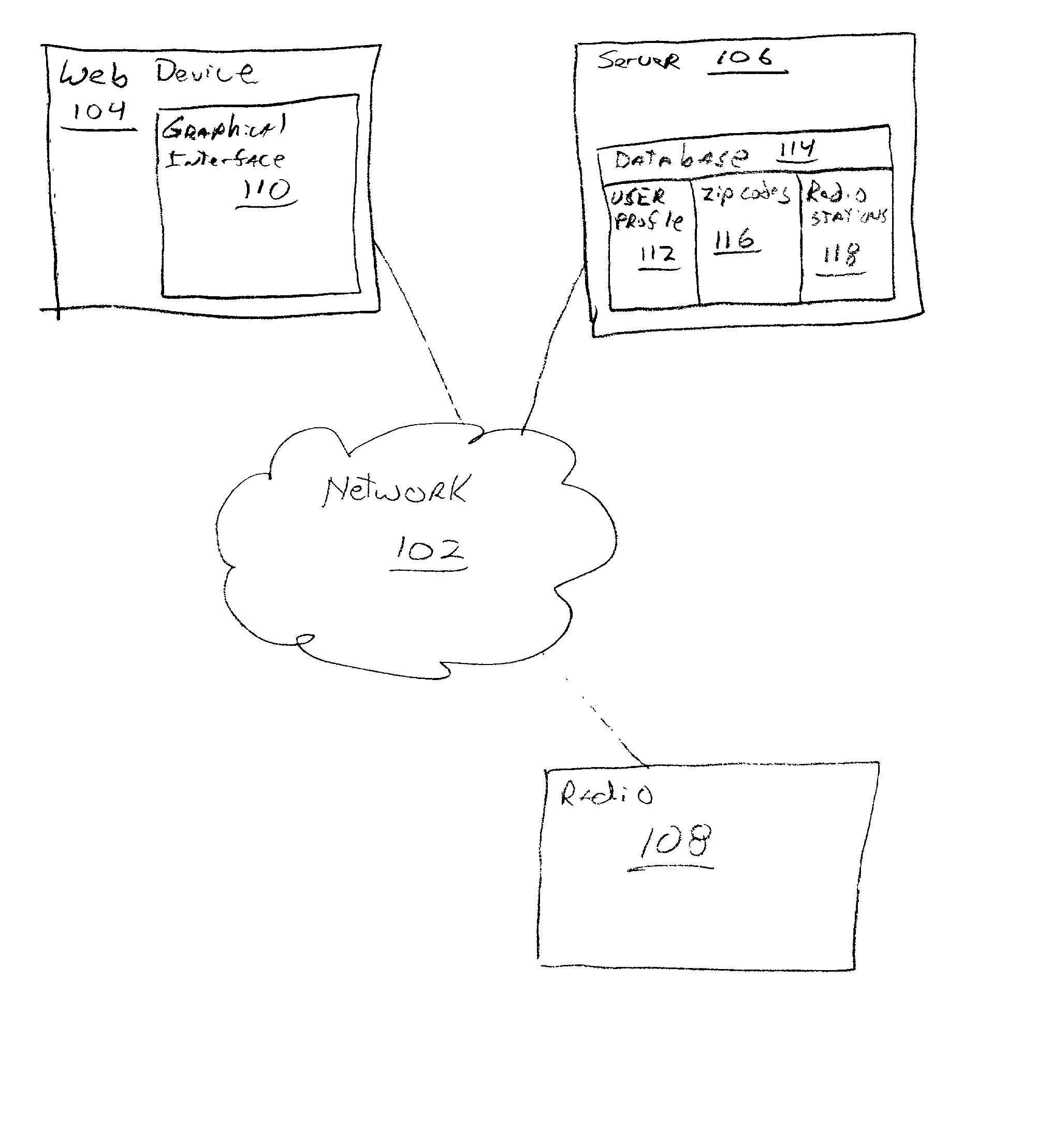
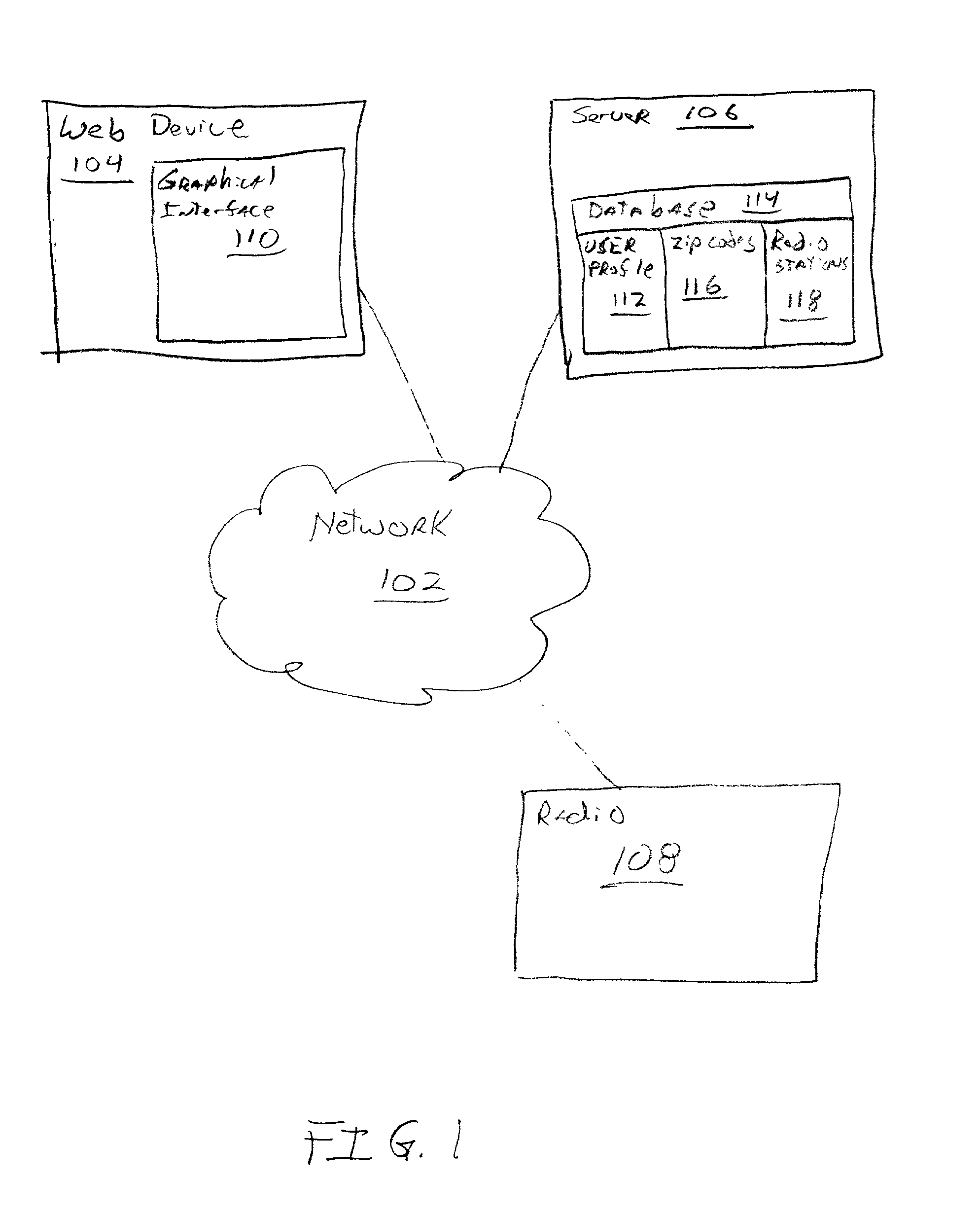
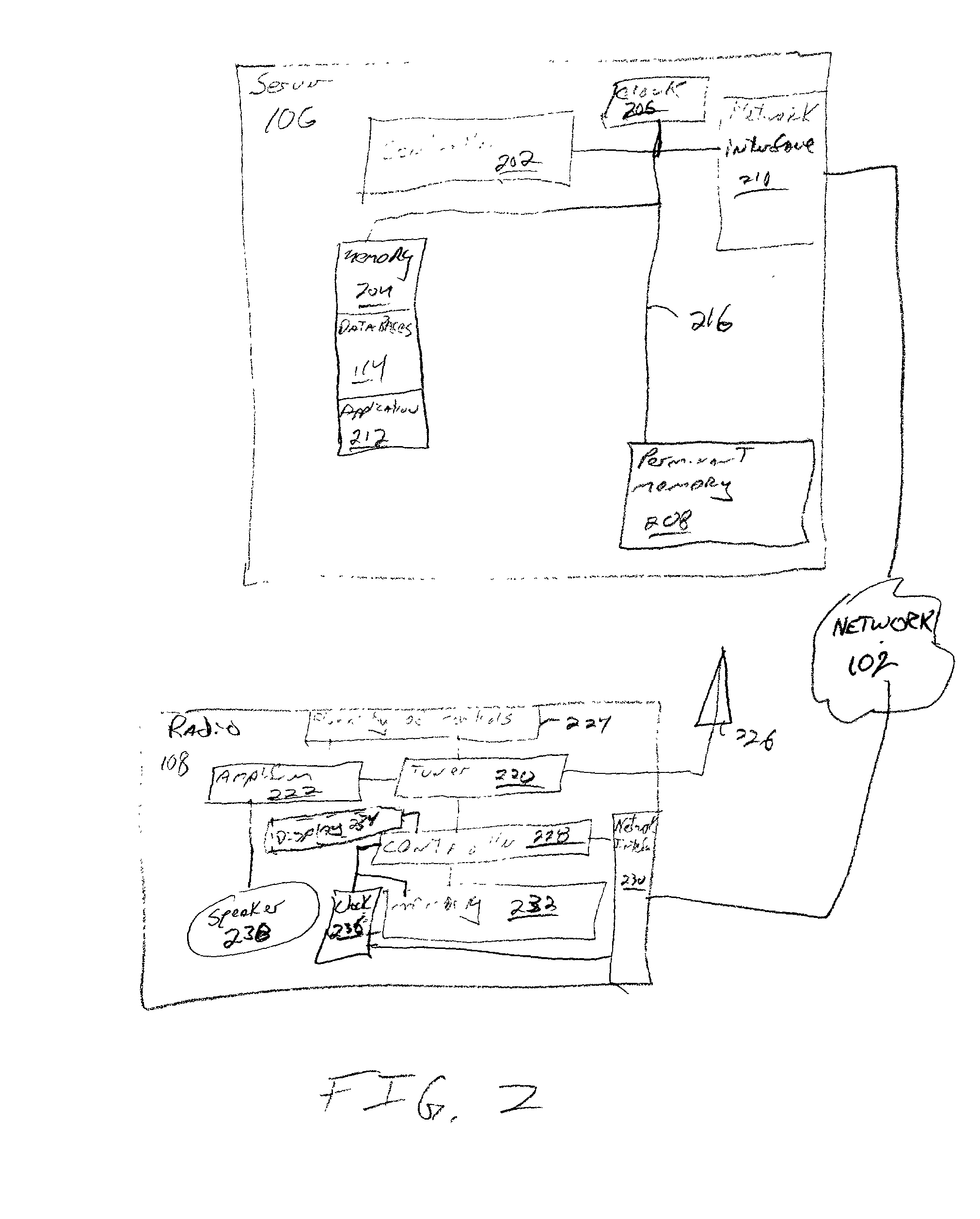
The invention may be broadly conceptualized as an approach in which the configuration of a radio (108) occurs by a user entering data into a graphical interface (110), the data is stored in a user profile (112) at a server (106) and also downloaded to the radio (108).
Owner:SALTON
Method for preventing read-disturb errors, memory control circuit unit and memory storage apparatus
ActiveUS20160011930A1Effectively prevent occurrenceAvoid mistakesRead-only memoriesNon-redundant fault processingOccurrence dataEngineering
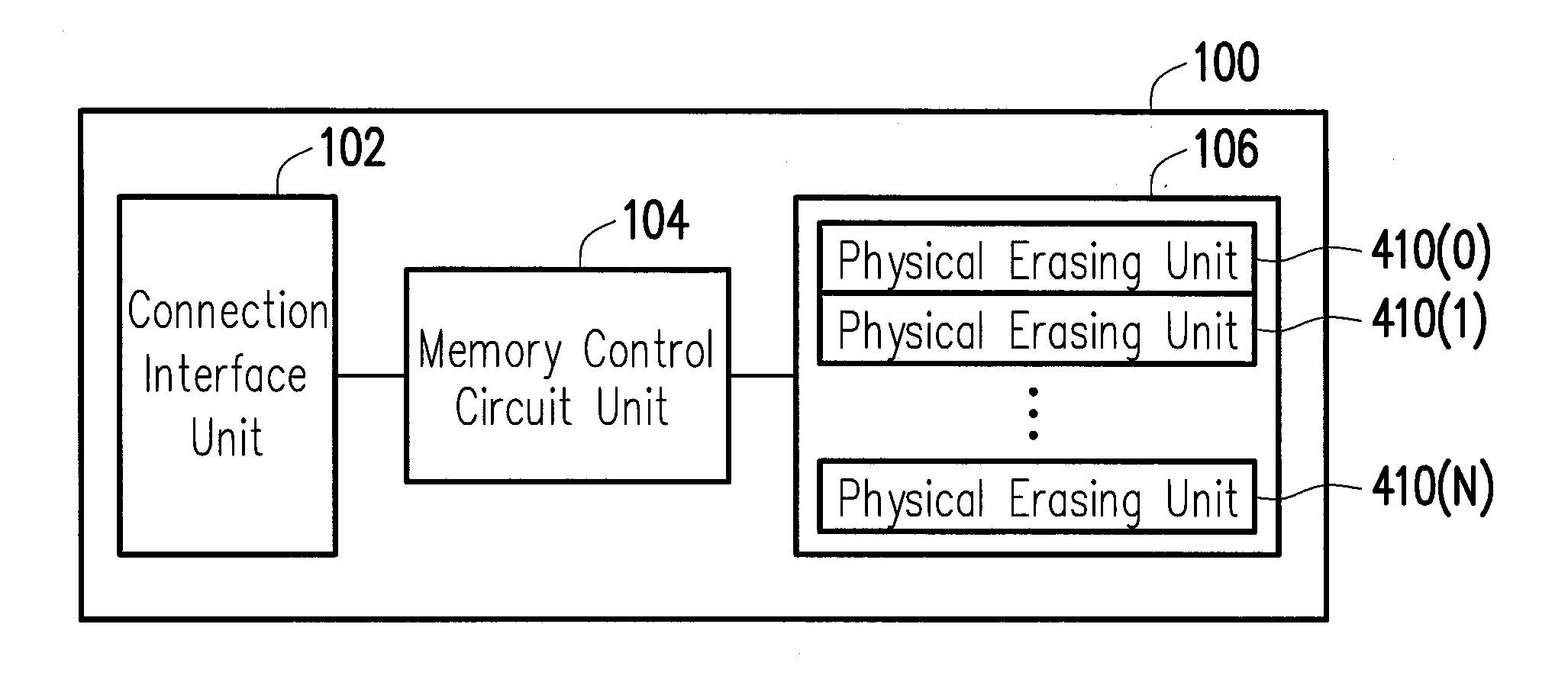
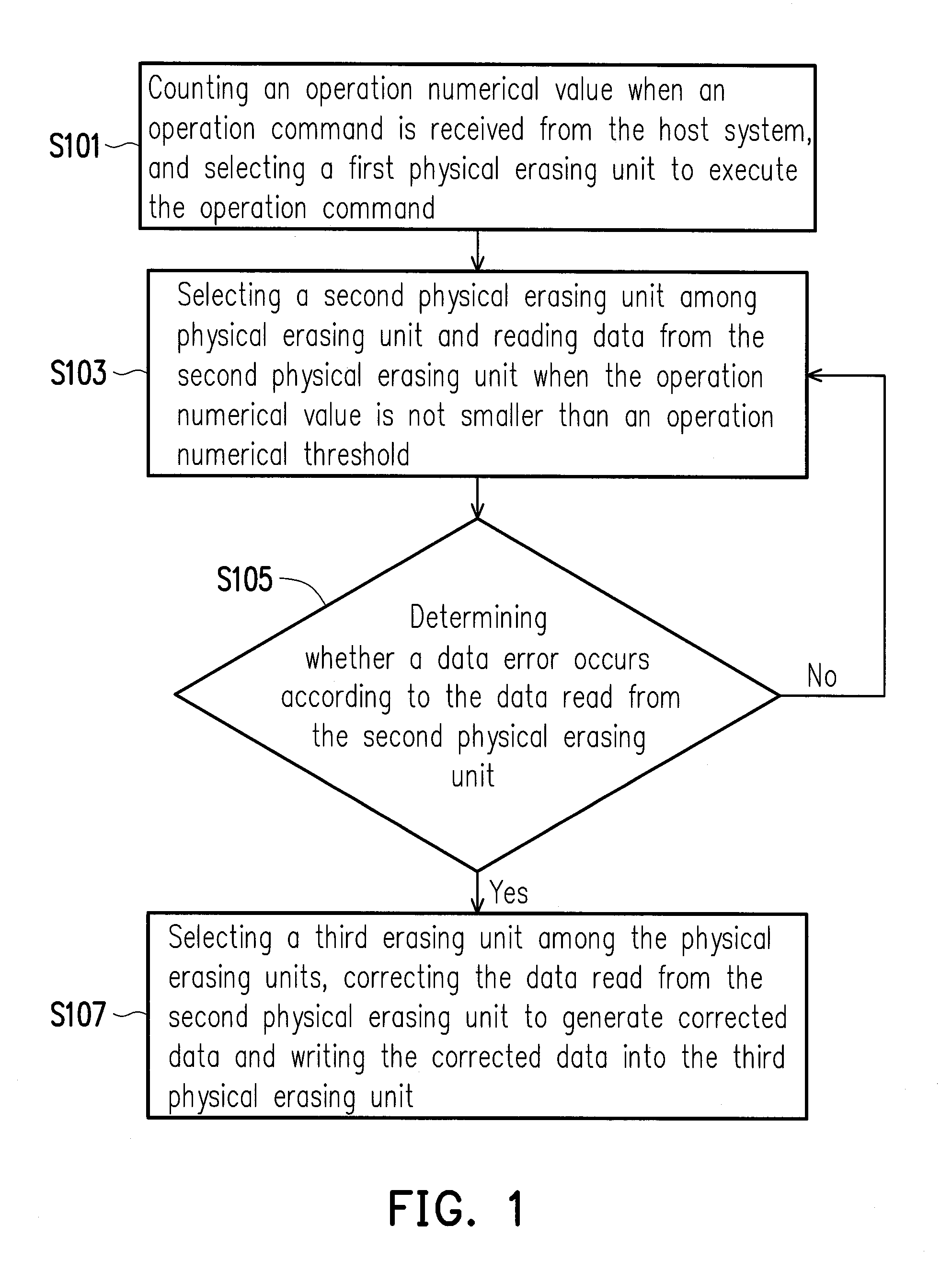
A method for preventing read-disturb errors, a memory storage apparatus and a memory control circuit unit are provided. The method includes counting an operation numerical value when receiving an operation command from the host system, wherein a first physical erasing unit is selected for executing the operation command. The method also includes selecting a second physical erasing unit and reading data from the second erasing unit. The method further includes determining whether a data error occurs at the second physical erasing unit according to the data read from the second physical erasing unit, and if the data error occurs, selecting a third physical erasing unit, correcting the data read from the second physical erasing unit to generate corrected data and writing the corrected data into the third physical erasing unit.
Owner:PHISON ELECTRONICS
Blockchain storage method supporting incremental updating of Internet of Things data
ActiveCN111949672AImplement incremental updatesReduce consumptionDatabase updatingDatabase distribution/replicationShardOccurrence data
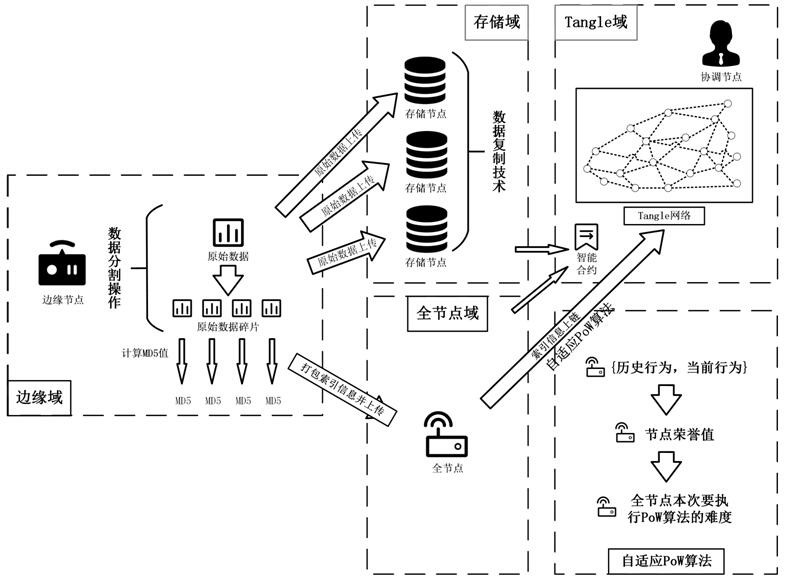
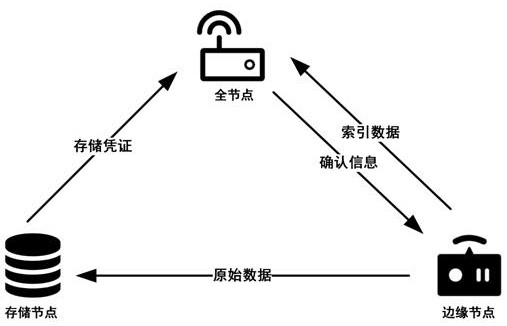
The invention discloses a blockchain storage method supporting incremental updating of Internet of Things data. The method comprises the following steps of partitioning data, calculating a MD5 value after the data is processed into fragmented data, and sending the processed MD5 value to a full node domain; calling the intelligent contract by all nodes, and executing an adaptive PoW algorithm to complete an uplink operation; transmitting the fragmented data to a storage domain for storage, and sending a storage certificate to a full node domain after the storage node successfully stores the fragmented data. In the data updating stage, the edge nodes compare MD5 values of the fragmented data before and after modification, the fragments with data change are screened out and uploaded, and waste of storage space is reduced. According to the invention, incremental updating of data is realized, and consumption of storage space in the data server is effectively reduced. In addition, the difficulty-adaptive PoW algorithm is utilized to improve the transaction efficiency of the blockchain network.
Owner:HANGZHOU DIANZI UNIV
Video processing device, video processing method, and program
ActiveUS20100194892A1Facilitate easy and high-quality display of videoTelevision system detailsElectronic editing digitised analogue information signalsOccurrence dataComputer graphics (images)
A video processing device includes a video accumulating unit configured to accumulate video data obtained by capturing video of a specific area, event occurrence data indicating an event that has occurred in a video image corresponding to the video data, and object specifying data for specifying an object relating to the event, a video processing unit configured to apply a predetermined effect to the video data accumulated in the video accumulating unit in accordance with the event occurrence data and the object specifying data that are added to the video data accumulated in the video accumulating unit to produce a modified video image, and a video output unit configured to output the modified video image to which the effect has been applied by the video processing unit.
Owner:SONY CORP
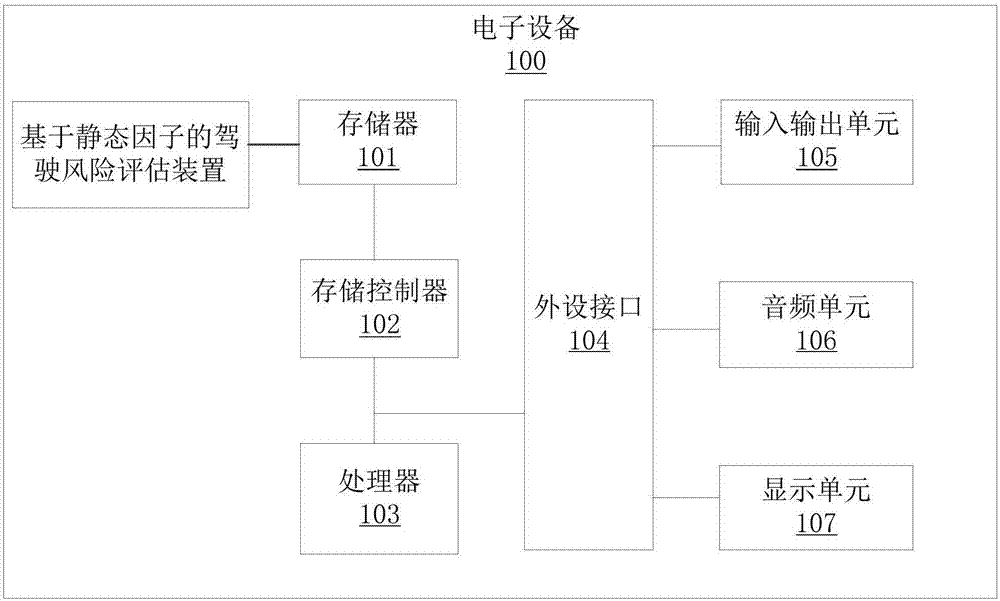
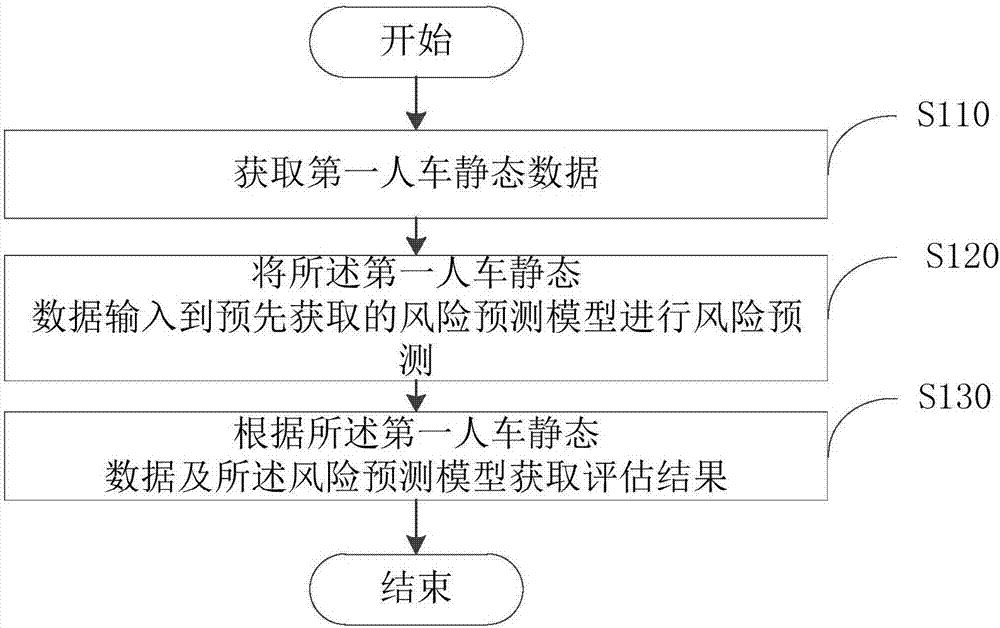
Driving risk evaluation method and device based on static state factor
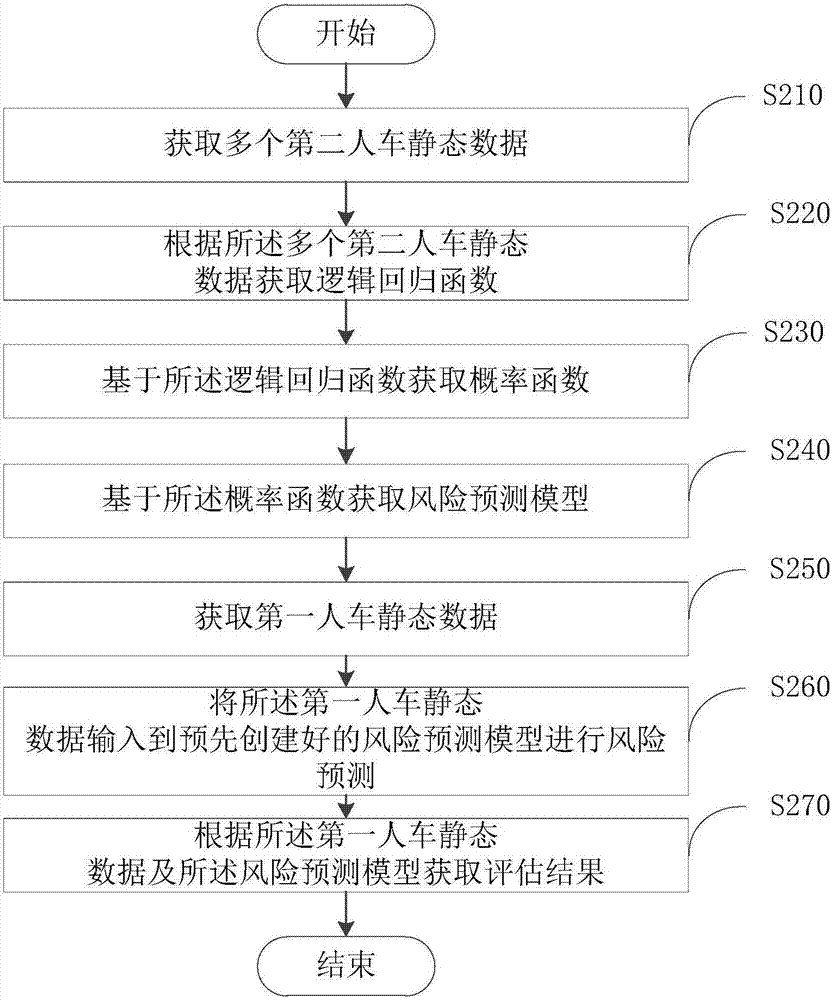
InactiveCN106980911AImprove accuracyReduce the comprehensive payout ratioFinanceForecastingEvaluation resultDriving risk
The invention provides a driving risk evaluation method and device based on a static state factor, and belongs to the field of risk prediction. The method comprises that first human-vehicle static state data including first vehicle-owner personal characteristic data, first vehicle physical parameter data and first insurance accident occurrence data is obtained; the first human-vehicle static state data is input to a pre-obtained risk prediction model to implement risk prediction; and an evaluation result is obtained according to the first human-vehicle static state data and the risk prediction model. An evaluation result is high in accuracy, insurance companies can identity and screen driving risks via data output, the integrated loss ratio is reduced, and a win-win effect is achieved; technical and data support is provided for innovative and different pricing of the auto insurance industry, and fairer and more reasonable commercial insurance price is provided for vehicle owners who drives safely.
Owner:南京人人保网络技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com