Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
743 results about "Data domain" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In data management and database analysis, a Data Domain refers to all the values which a data element may contain. The rule for determining the domain boundary may be as simple as a data type with an enumerated list of values.
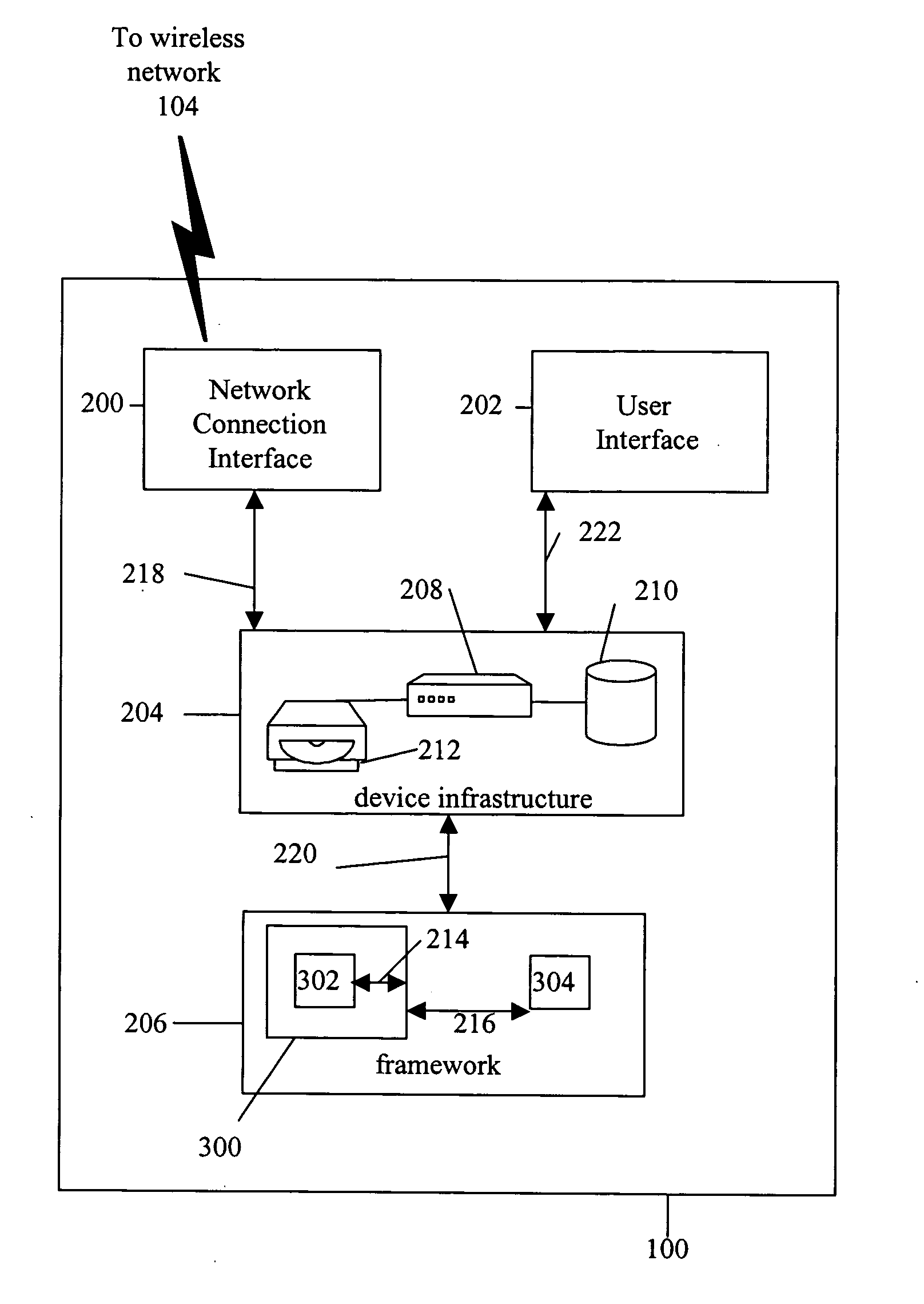
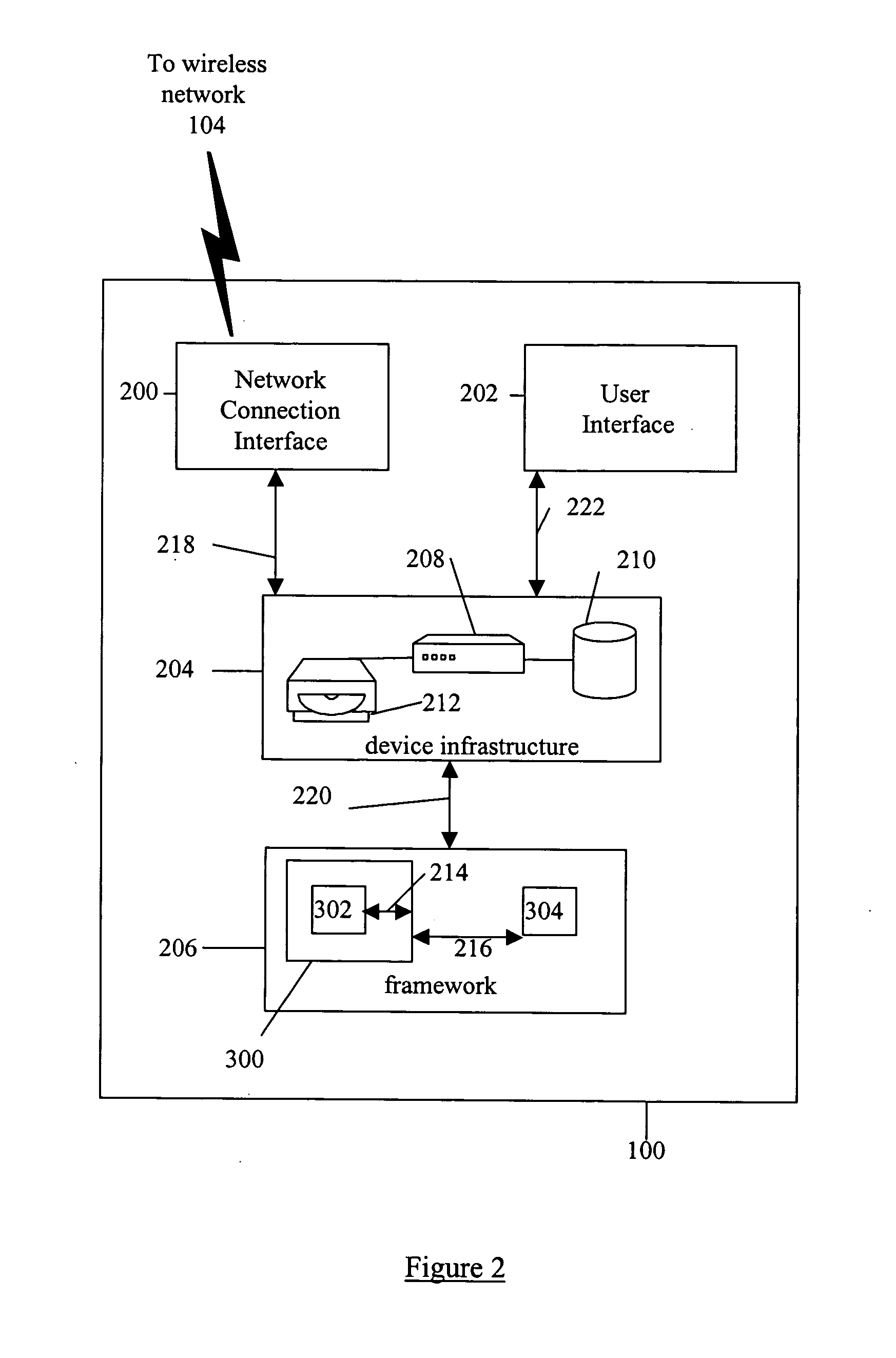
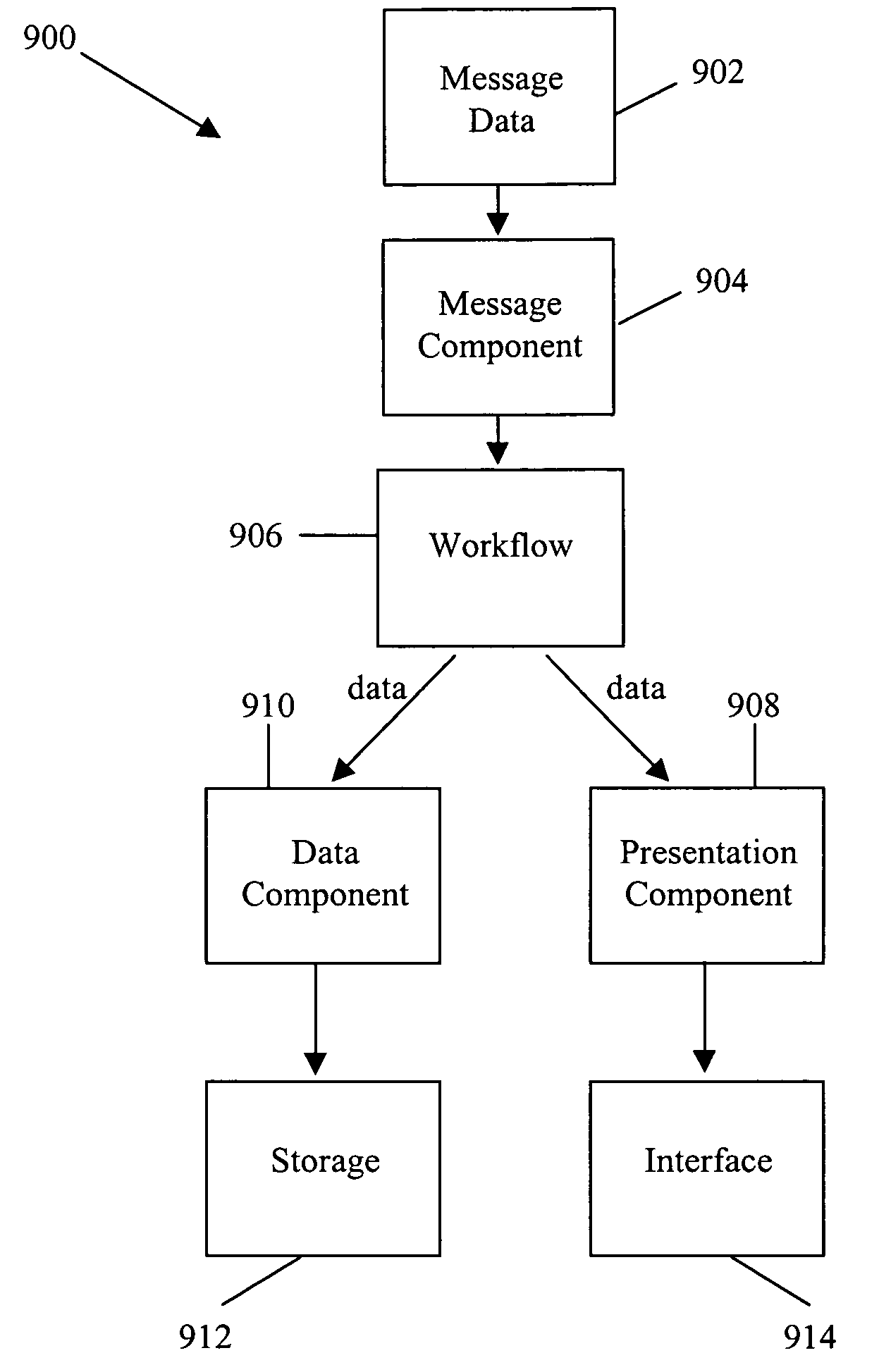
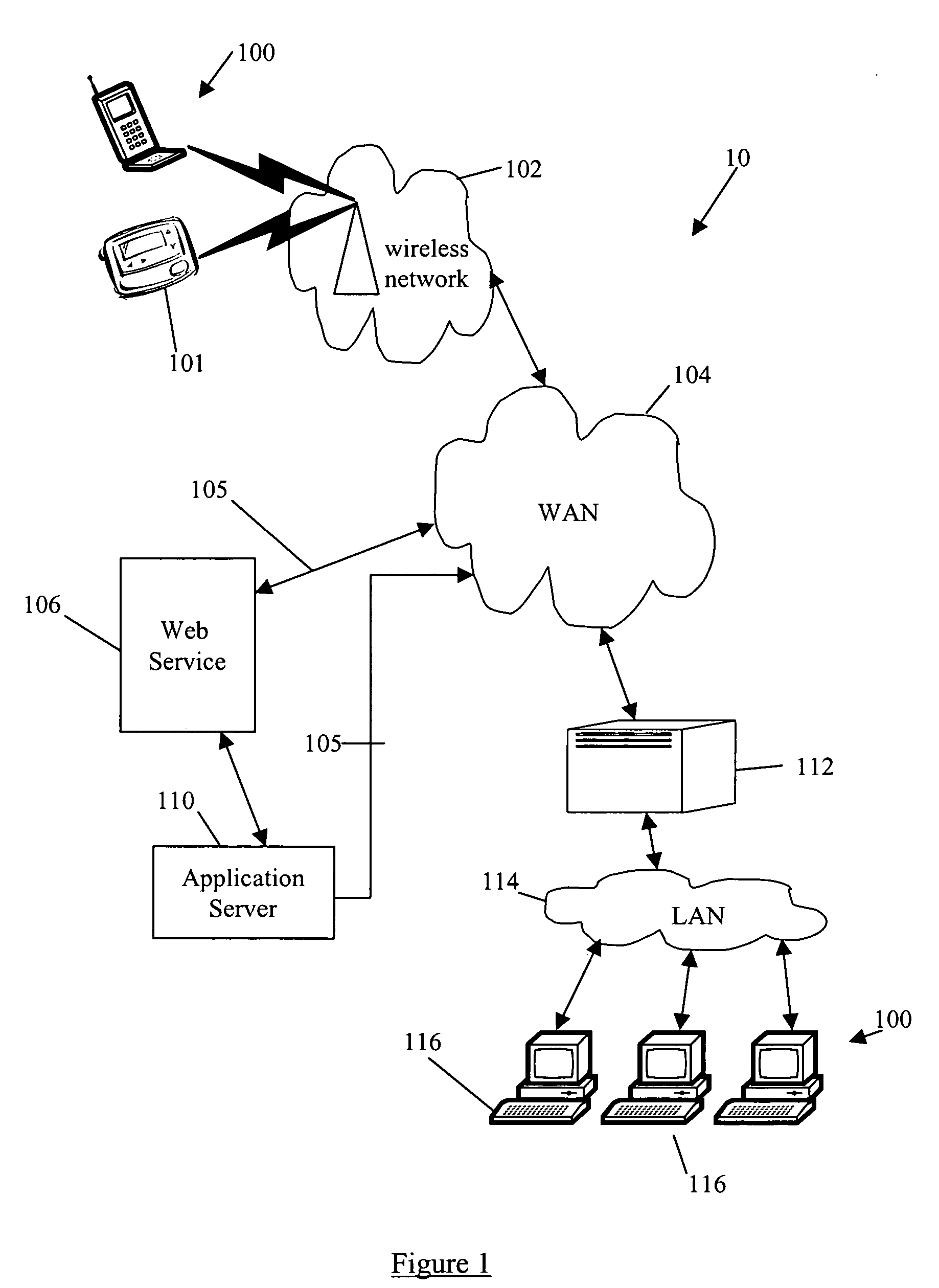
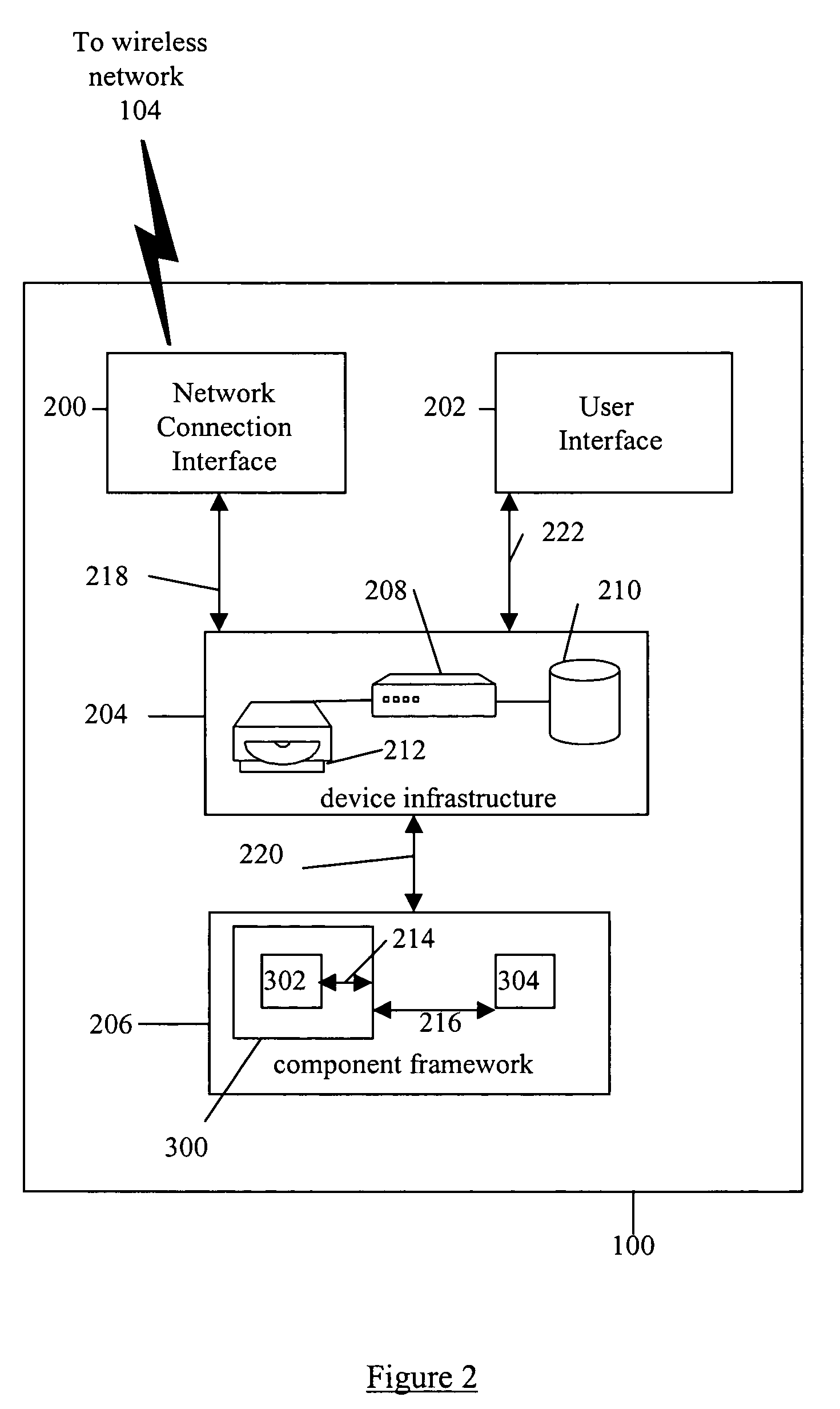
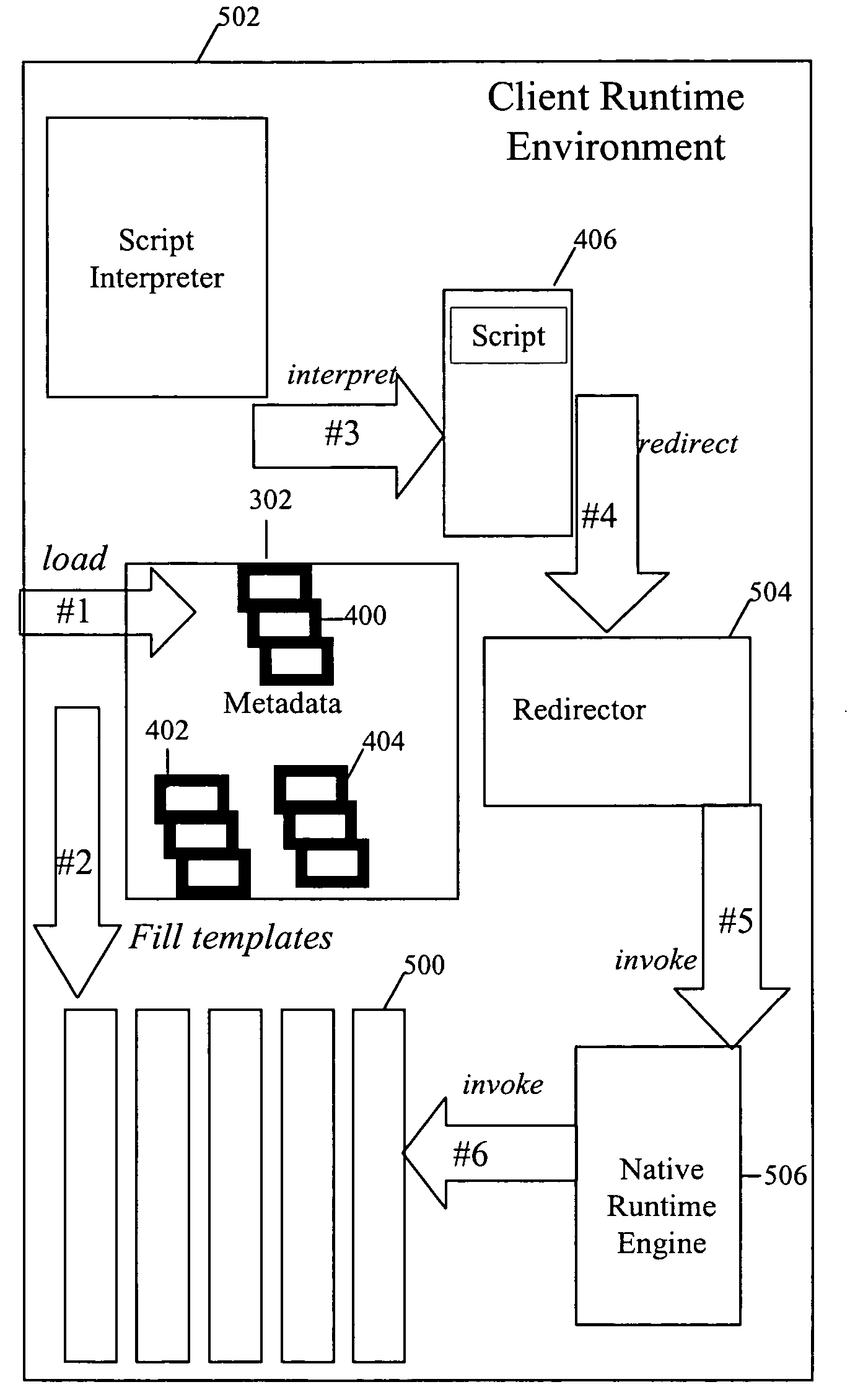
System and method for building wireless applications with intelligent mapping between user interface and data components
ActiveUS20050057560A1Reduce complexitySimplify development workDigital computer detailsMultiprogramming arrangementsData domainBasic service
A system and method is described for effective management of a User Interface (UI) of a wireless device by implementing direct mapping between the application data domain and UI screens and controls. The device has an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application, including a series of linked screen and data component definitions, and their interactions can simplify the development effort and reduce resource allocation. The data domain for this category of applications is defined using the atomic data component definitions. The communication between a device user interface and data components is defined using atomic screen component definitions. Both screen and data component definitions are described in metadata using a structured definition language such as XML. The relationships between the screen and data component definitions are embedded in the XML definitions in the form of screen / data mappings. Typically, rendered screens for display are derived from some underlying data component and screens controls affected by user events impact the current state (or data representation) of the application Changes to the application domain data are automatically synchronized with the user interface, and user-entered data is automatically reflected in the application domain data. The primary mechanism behind this synchronization is the mapping of screens and data. This mechanism enables creation of dynamic and interactive screens. All changes to the data component can be immediately reflected on the screen and vice versa. This model allows building effective wireless applications based on server-to-device notifications. The data updates asynchronously pushed from the server are instantaneously reflected at the UI screen.
Owner:GOOGLE TECH HLDG LLC
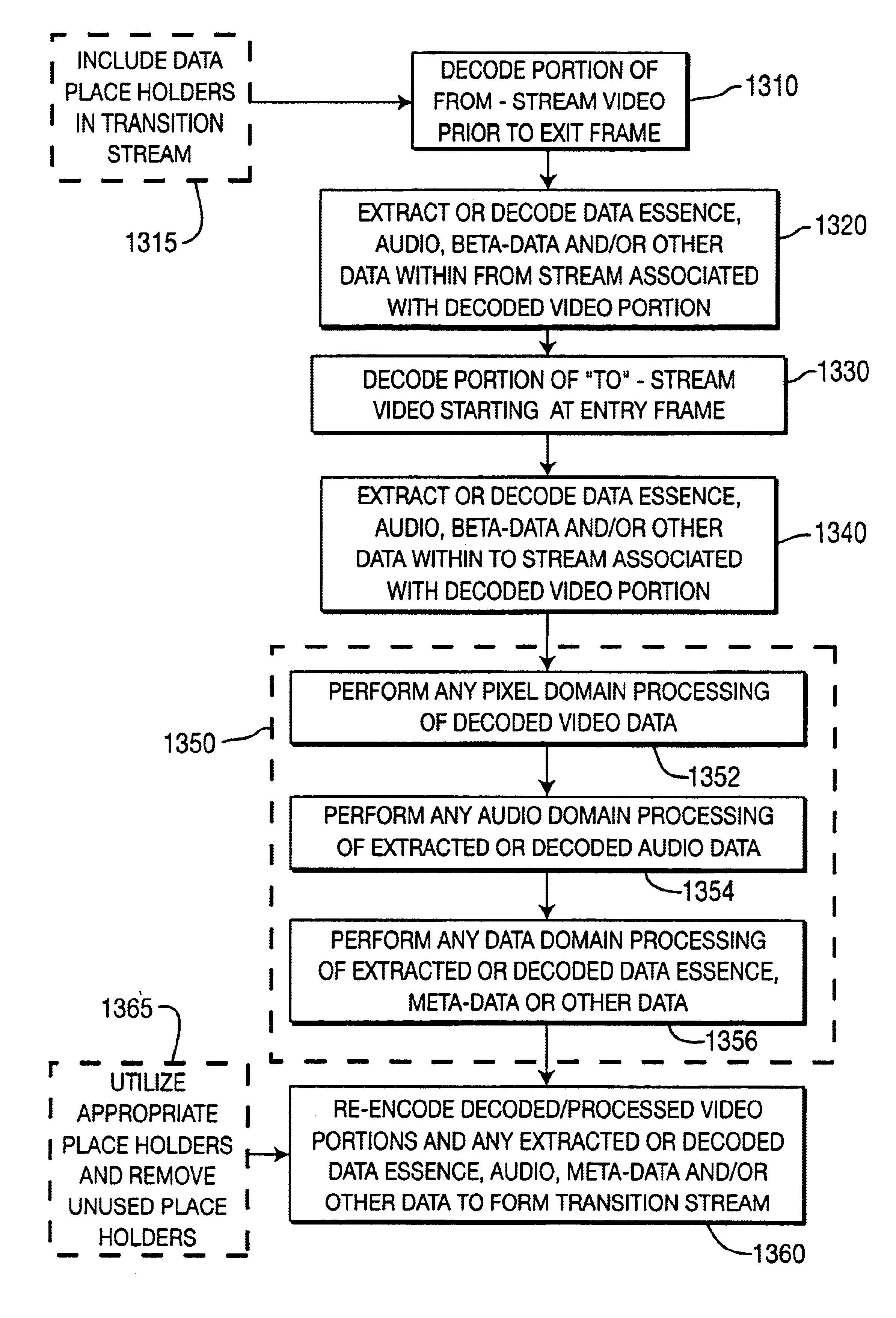
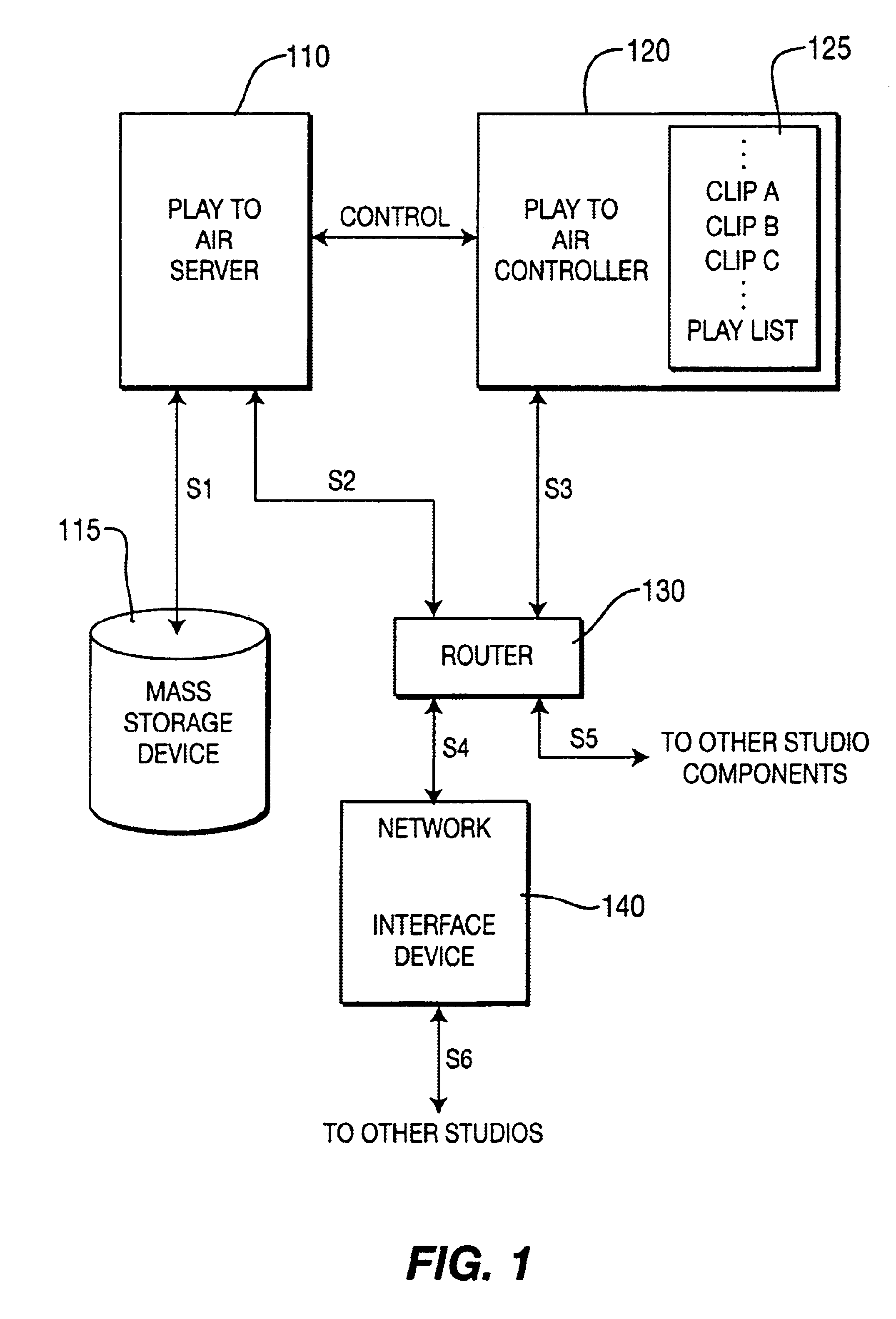
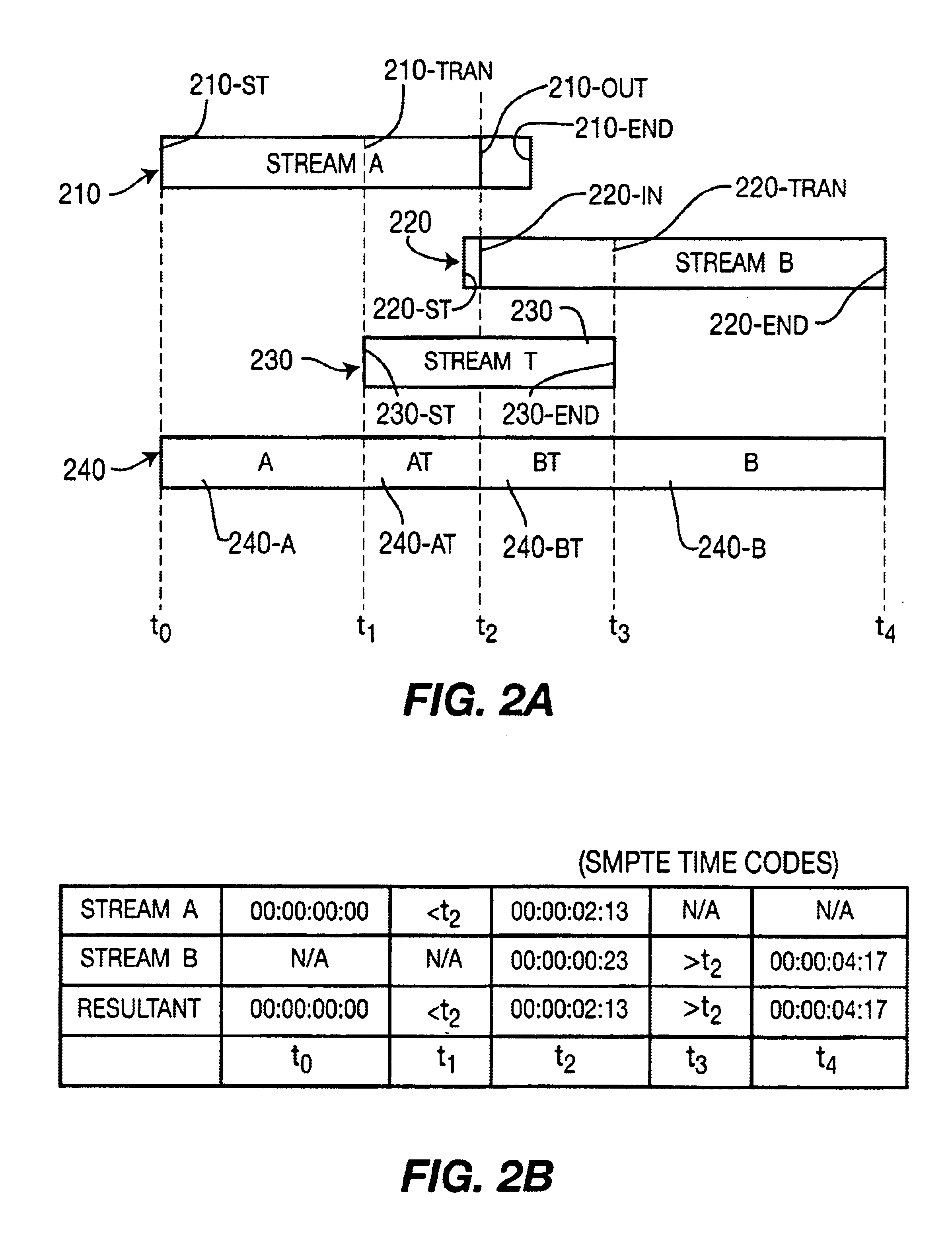
Method for generating and processing transition streams
InactiveUS6909743B1Television system detailsPulse modulation television signal transmissionAlgorithmData domain
A method for generating a transition stream and processing video, audio or other data within the transition stream using, respectively, pixel domain processing, audio domain processing or other data domain processing.
Owner:MEDIATEK INC
Method and device for wireless subframe resource allocation
ActiveUS20110194523A1Improve featuresTransmission path divisionSignal allocationRadio access technologyCommunications system
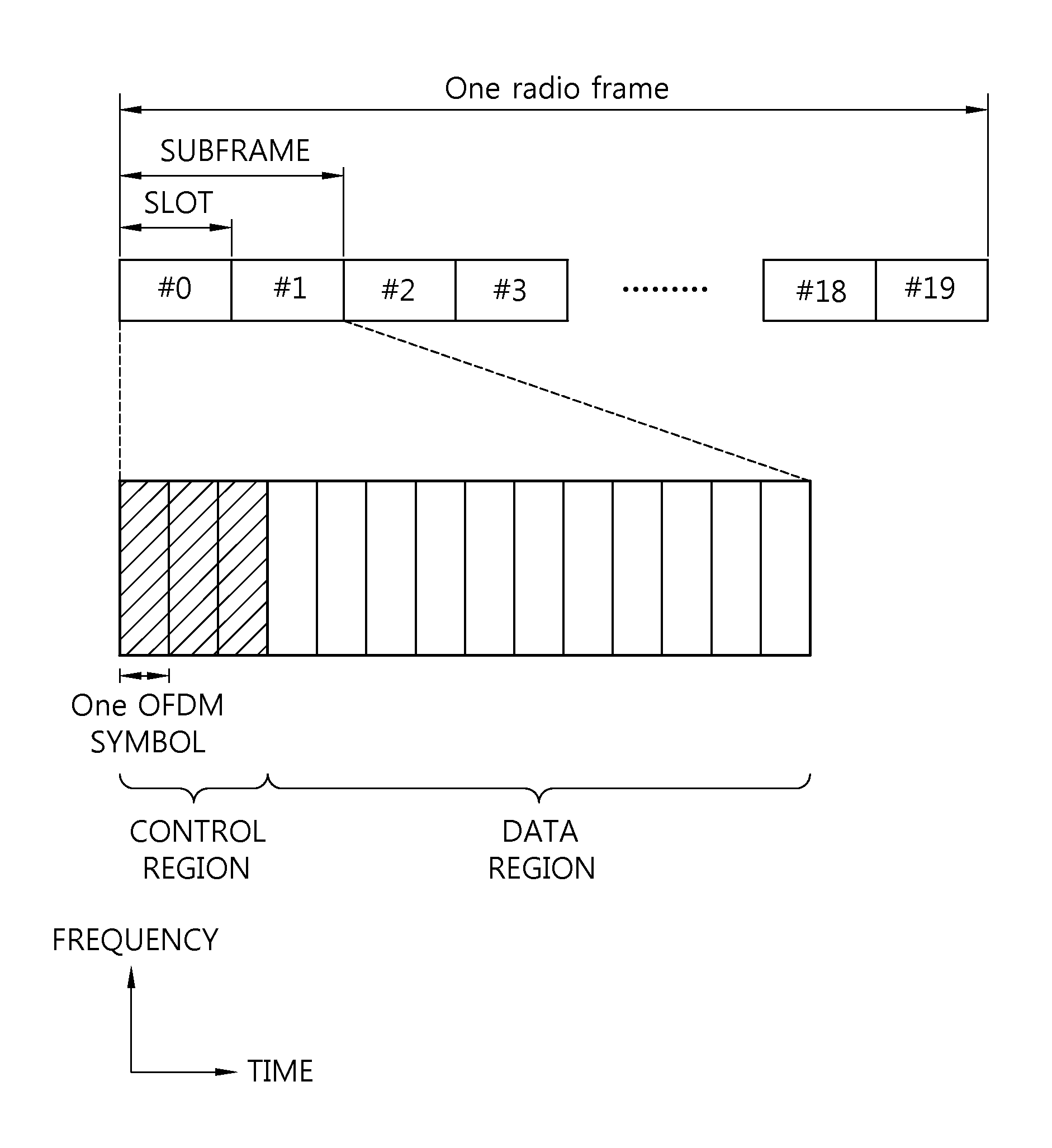
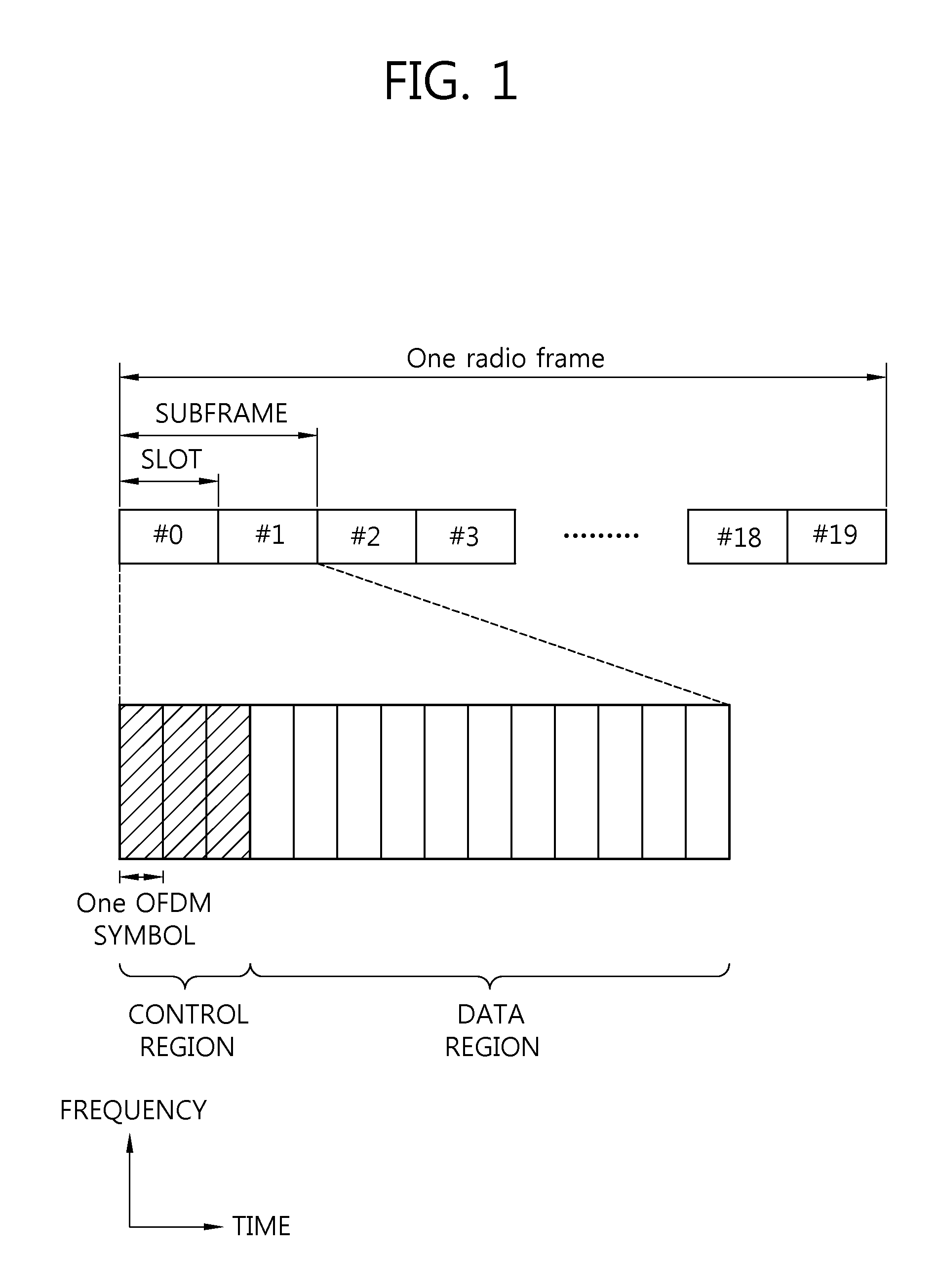
The method for wireless resource subframe allocation comprises the following steps: allocation of the control channel based on the first RAT (Radio Access Technology) of the first control domain, which includes the OFDM symbol of the first number from the sub-frame containing multiple OFDM symbols and multiple subcarriers in the frequency domain; allocation of the control channel based on the second RAT of the second control domain including the OFDM symbol of the second number which follows said first control domain; and the allocation of a data channel in the data domain which includes the OFDM symbols positioned outside said first control domain and second control domain. This invention provides a sub-frame structure which is compatible with existing wireless communication systems. This method allows the continued use of existing control channel systems or base signal structures. The method is also capable of supporting advanced features.
Owner:LG ELECTRONICS INC
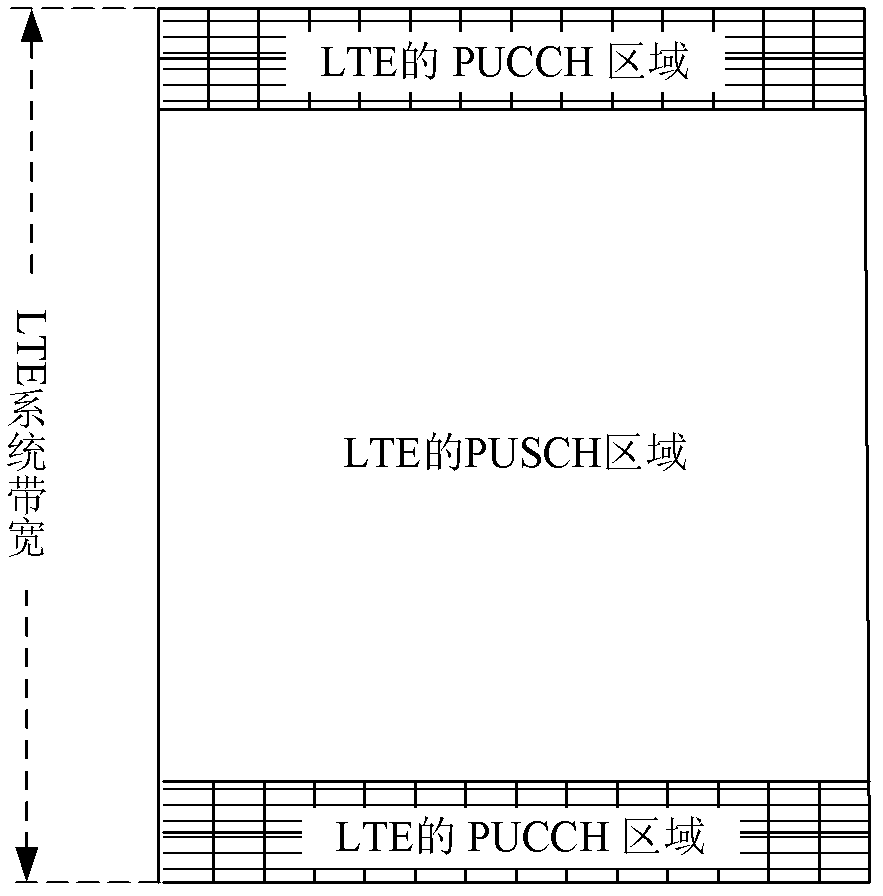
Downlink transmission method and device thereof
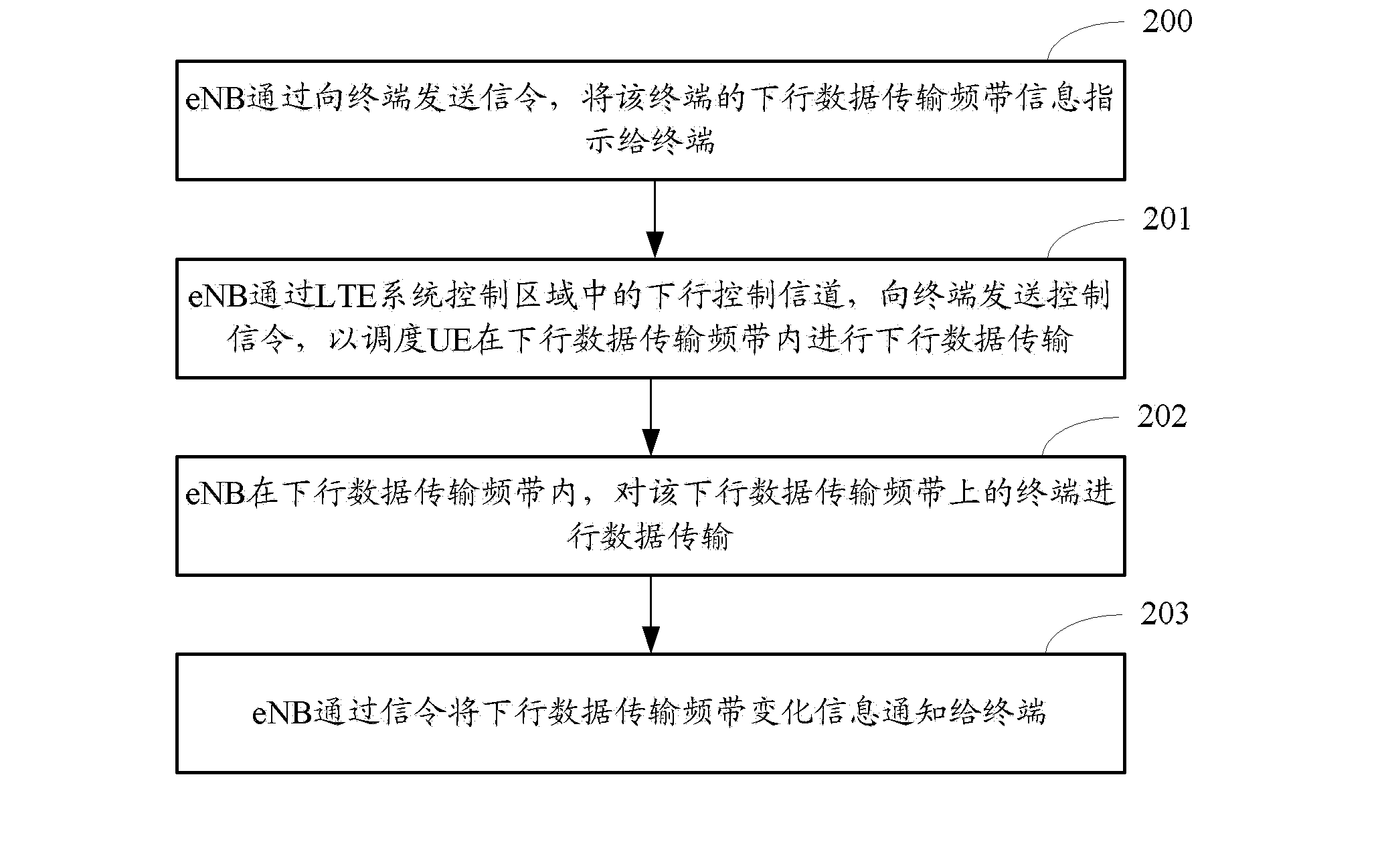
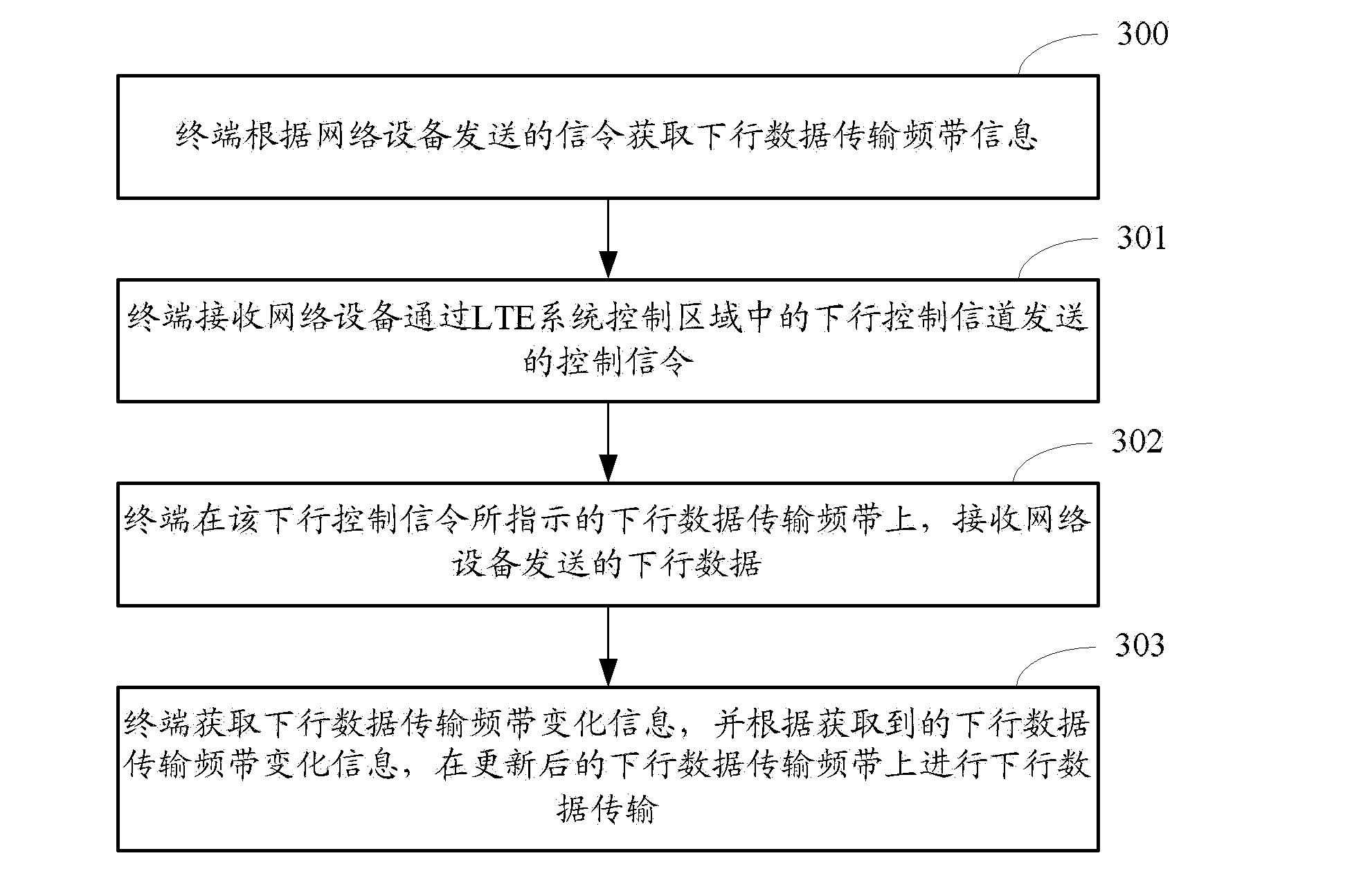
ActiveCN103220796ASave bandwidthReduce the impactWireless communicationControl signalControl channel
The invention discloses a downlink transmission method and a device thereof. The method is applied to an LTE system, at least one downlink data transmission band is configured in a data field of a downlink system working band of the downlink data transmission band, and the band width of the downlink data transmission band is smaller than the band width occupied by a control channel area of the LTE system. The method comprises the steps of enabling a network device to control the downlink control channel in the control area through the LTE system to sending a control signaling to a terminal, and scheduling the terminal to transmit downlink data in the downlink data transmission band; and enabling the network device to carry out data transmission on the terminal on the downlink data transmission band. The downlink transmission method can reduce the data transmission band width of the terminal and consider compactness of the control channel while reducing cost of the terminal.
Owner:DATANG MOBILE COMM EQUIP CO LTD
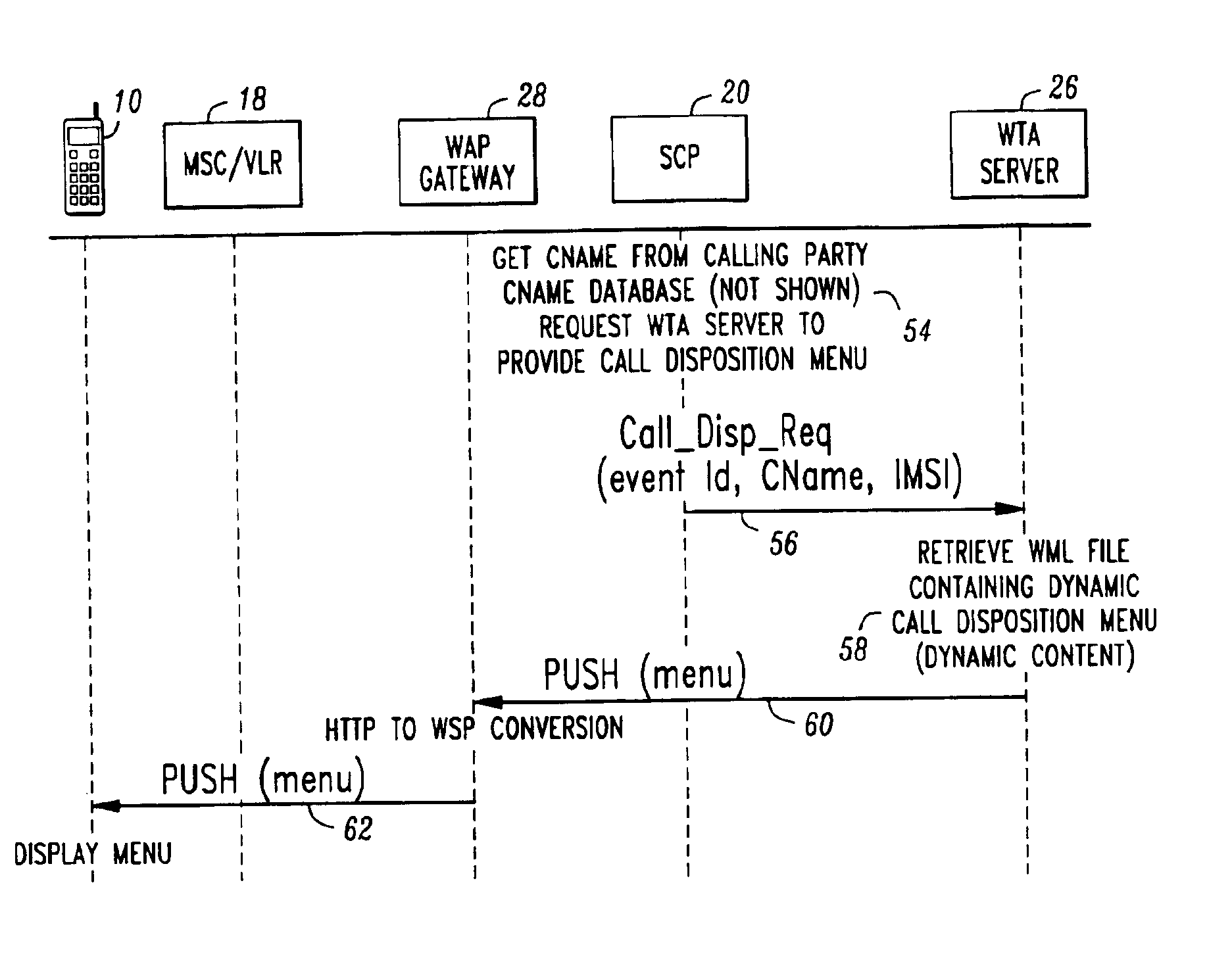
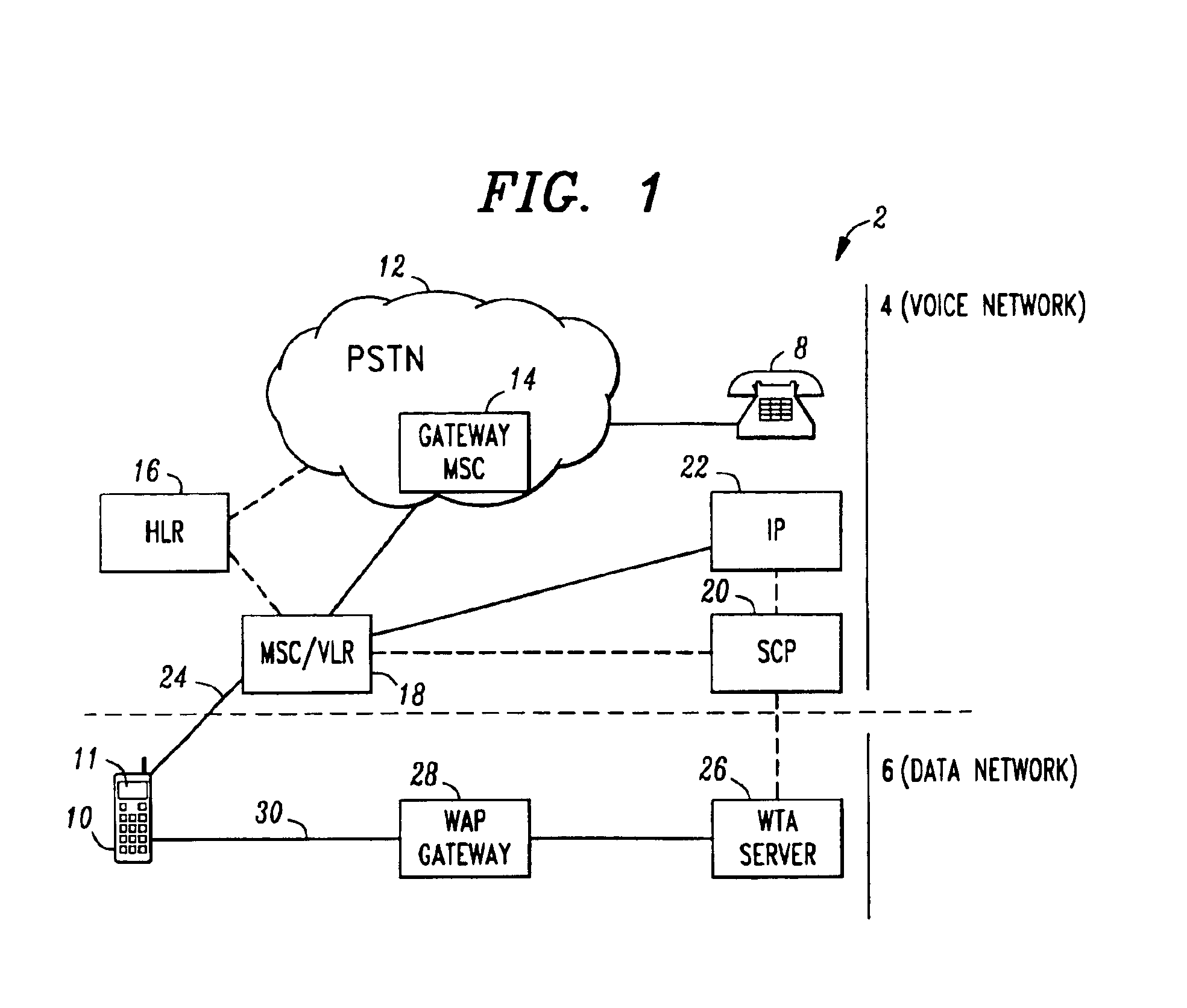
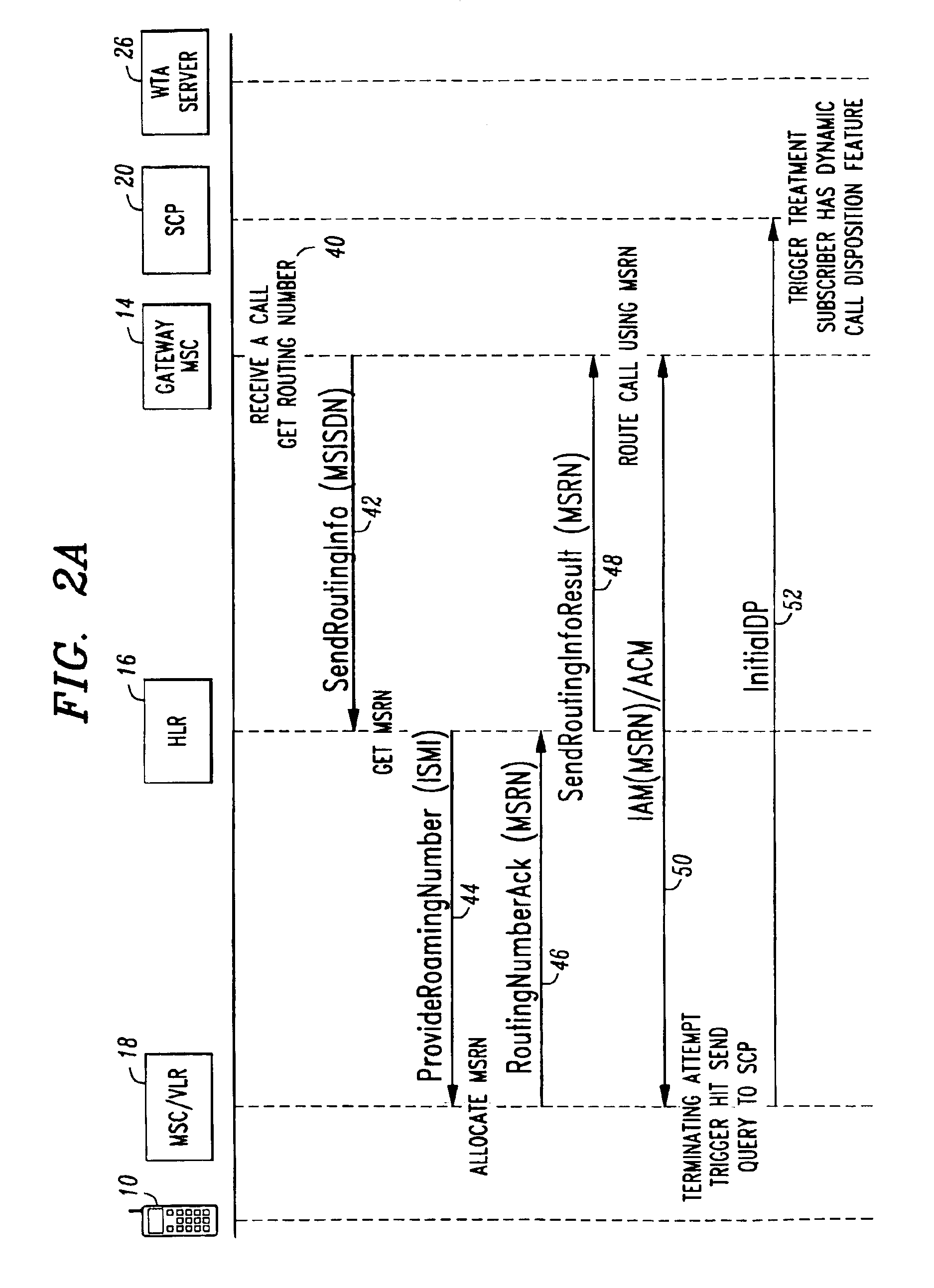
System and method for providing dynamic call disposition service to wireless terminals
InactiveUS6882838B1Telephone data network interconnectionsSpecial service for subscribersTelecommunicationsData domain
A system and method for providing dynamic call disposition service to a wireless terminal that may be occupied or unoccupied. In response to a call to the wireless terminal in a voice domain, call disposition options are provided to the wireless terminal in a data domain. A call disposition action is then taken according to an option selection made at the wireless terminal as part of a cooperative effort between resources in the voice and data domains.
Owner:LUCENT TECH INC +1
System and method for building component applications using metadata defined mapping between message and data domains
ActiveUS20050198100A1Reduce complexitySimplify development workMultiple digital computer combinationsProgram loading/initiatingData domainBasic service
It is desirable to drive down the complexity involved in developing the wireless application by reducing the need to do any explicit coding, as well as reducing device resources utilized by the application when provisioned. Having an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application as a series if application components, and their interactions, can simplify the development effort and reduce resource allocation. The wireless application is described as a set of components. The data domain for this category of applications is defined using atomic data components. The communication between the device and a server is defined using atomic message components. Both message and data components are described in metadata using a structured definition language such as XML. The relationships between the message and data components are embedded in the XML definitions in the form of message / data mappings. Typically, outgoing messages are derived from some underlying data component and incoming messages affect the current state (or data representation) of the application. It is therefore apparent that the metadata defined mapping relationship is preferable between the expression of data and message components.
Owner:MALIKIE INNOVATIONS LTD
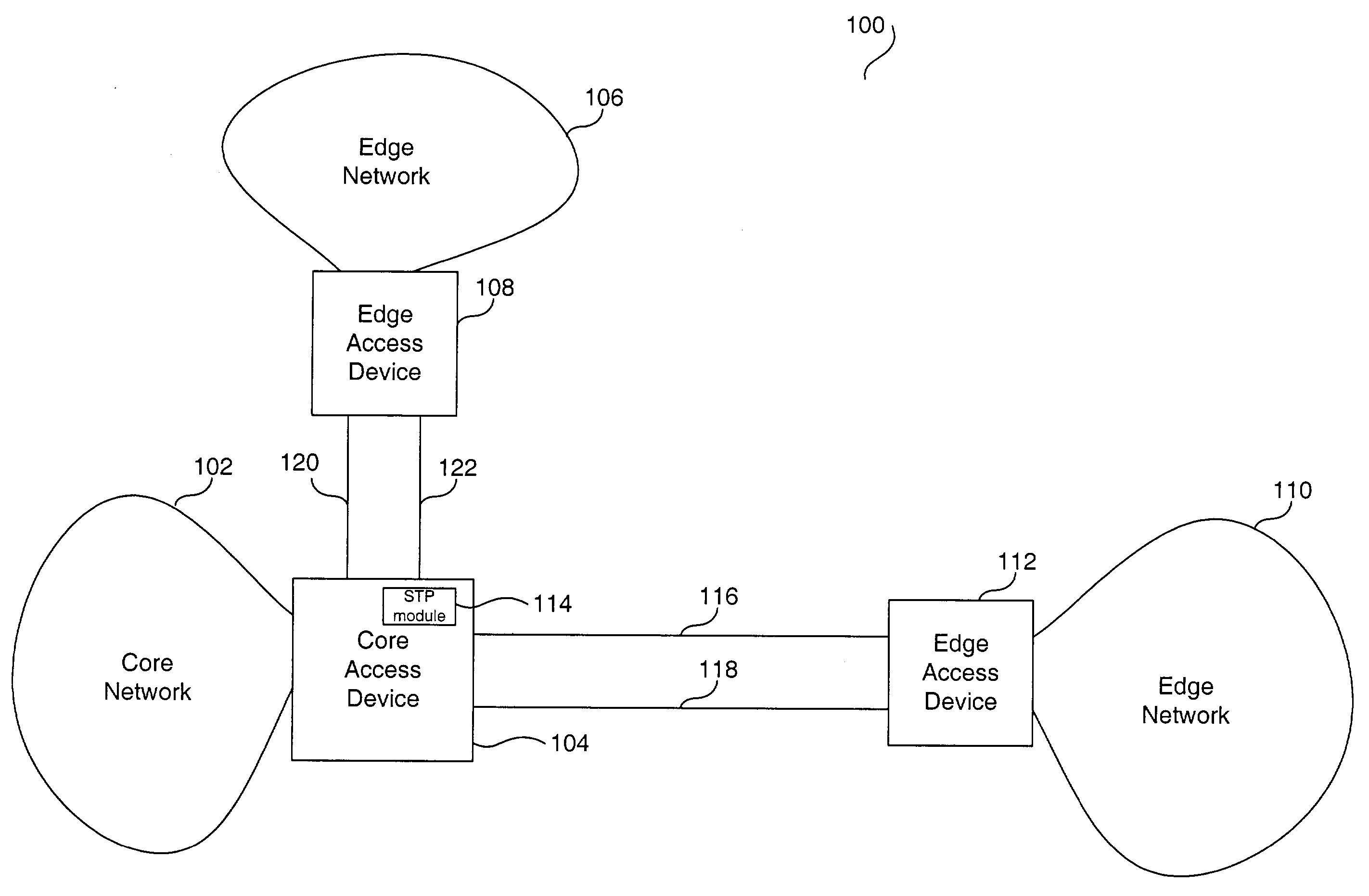
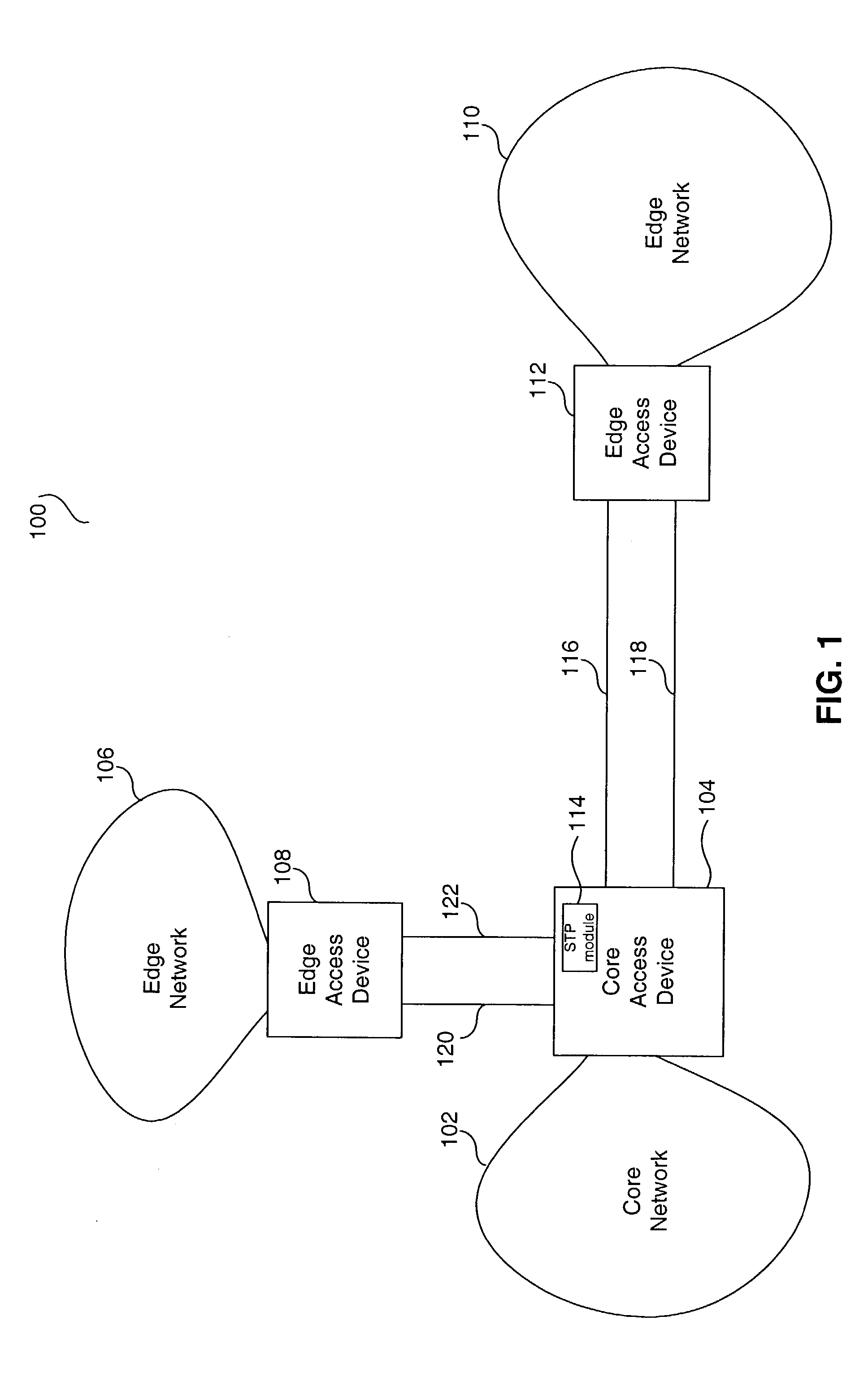
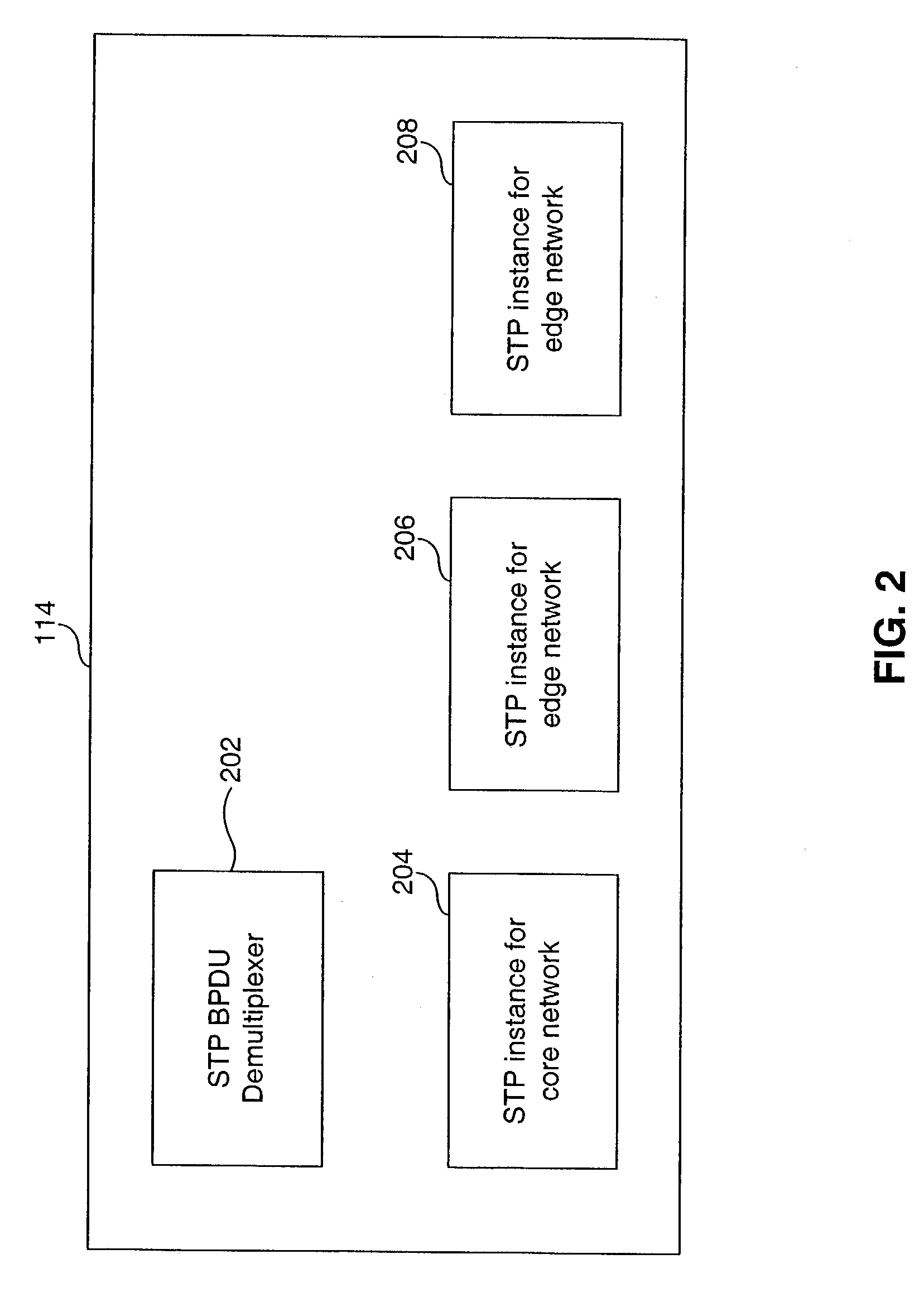
System and method for multiple spanning tree protocol domains in a virtual local area network
InactiveUS20050013260A1Modifies its behaviorStar/tree networksNetworks interconnectionVirtual LANData domain
A system and method that modifies the behavior of the IEEE 802.1D STP standard to thereby decouple the one data domain from the one control domain involves managing multiple spanning tree protocol (STP) instances in a virtual local area network (VLAN). The method includes the step of assigning a unique set of ports within the VLAN to each of the multiple STP instances. Then, each of the multiple STP instances are managed to keep each of the multiple STP instances separate. Finally, when a topology change is detected in one of the multiple STP instances, entries that have been learned on the unique set of ports assigned to the STP protocol instance where the topology change is detected are fast-aged or transitioned from one state to another.
Owner:AVAGO TECH INT SALES PTE LTD
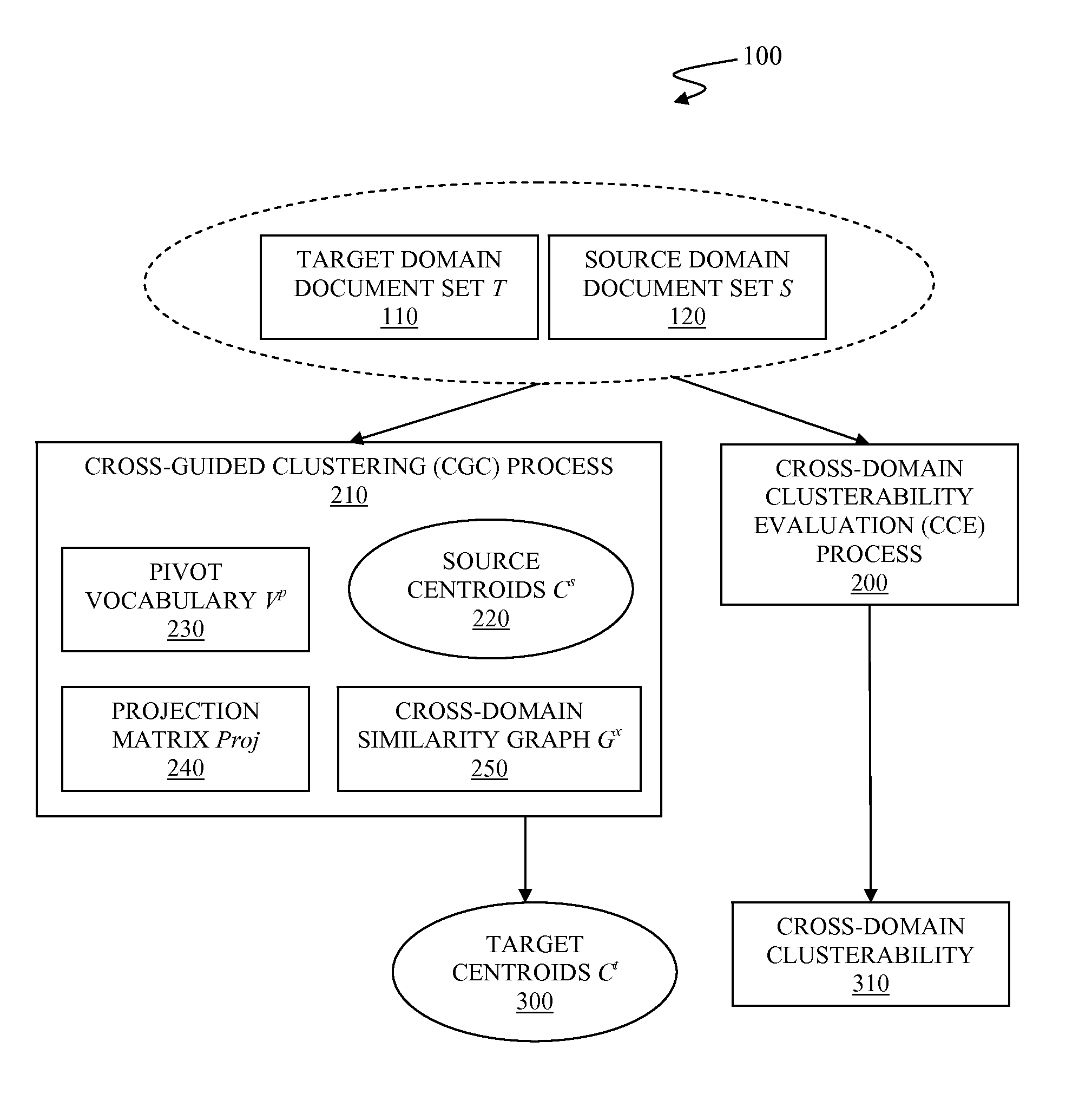
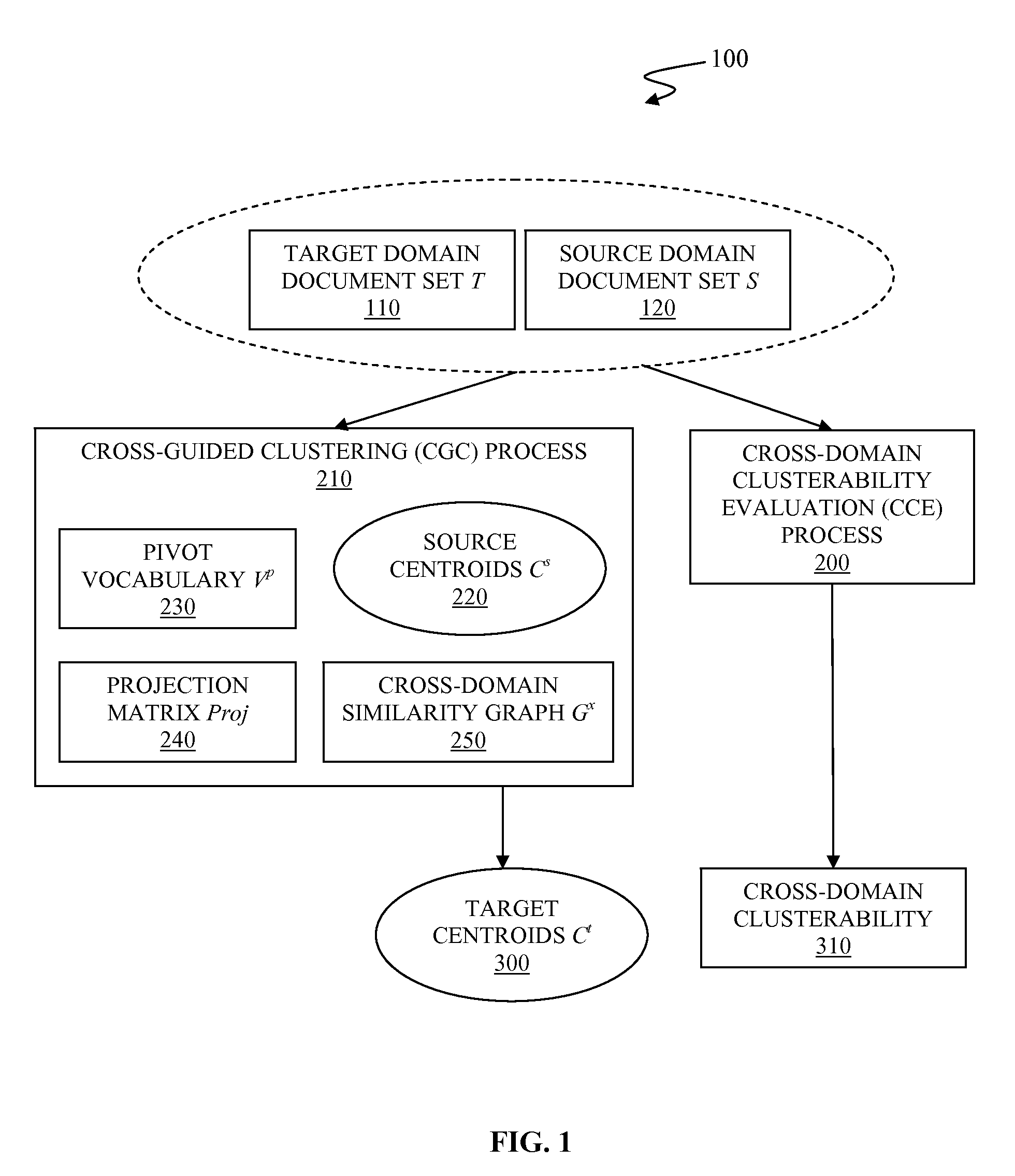
Cross-domain clusterability evaluation for cross-guided data clustering based on alignment between data domains
A system and associated method for evaluating cross-domain clusterability upon a target domain and a source domain. The cross-domain clusterability is calculated as a linear combination of a target clusterability and a source-target pair matchability, by use of a trade-off parameter that determines relative contribution of the target clusterability and the source-target pair matchability. The target clusterability quantifies how clusterable the target domain is. The source-target pair matchability is calculated as an average of a target-side matchability and a source-side matchability, which quantifies how well target centroids of the target domain are aligned with the source centroids and how well source centroids of the source domain are aligned with the target centroids, respectively.
Owner:KYNDRYL INC
Extended multi line address driving
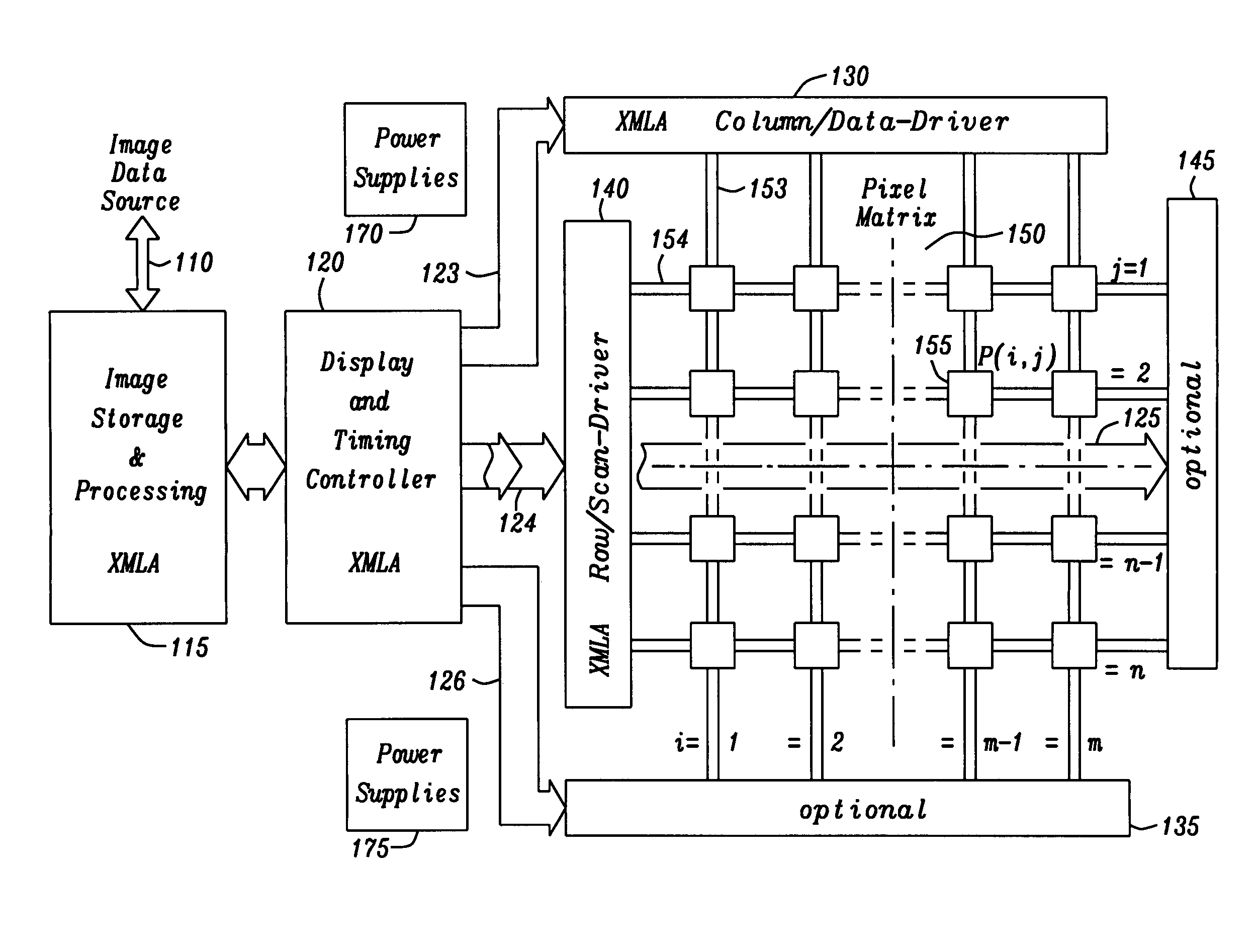
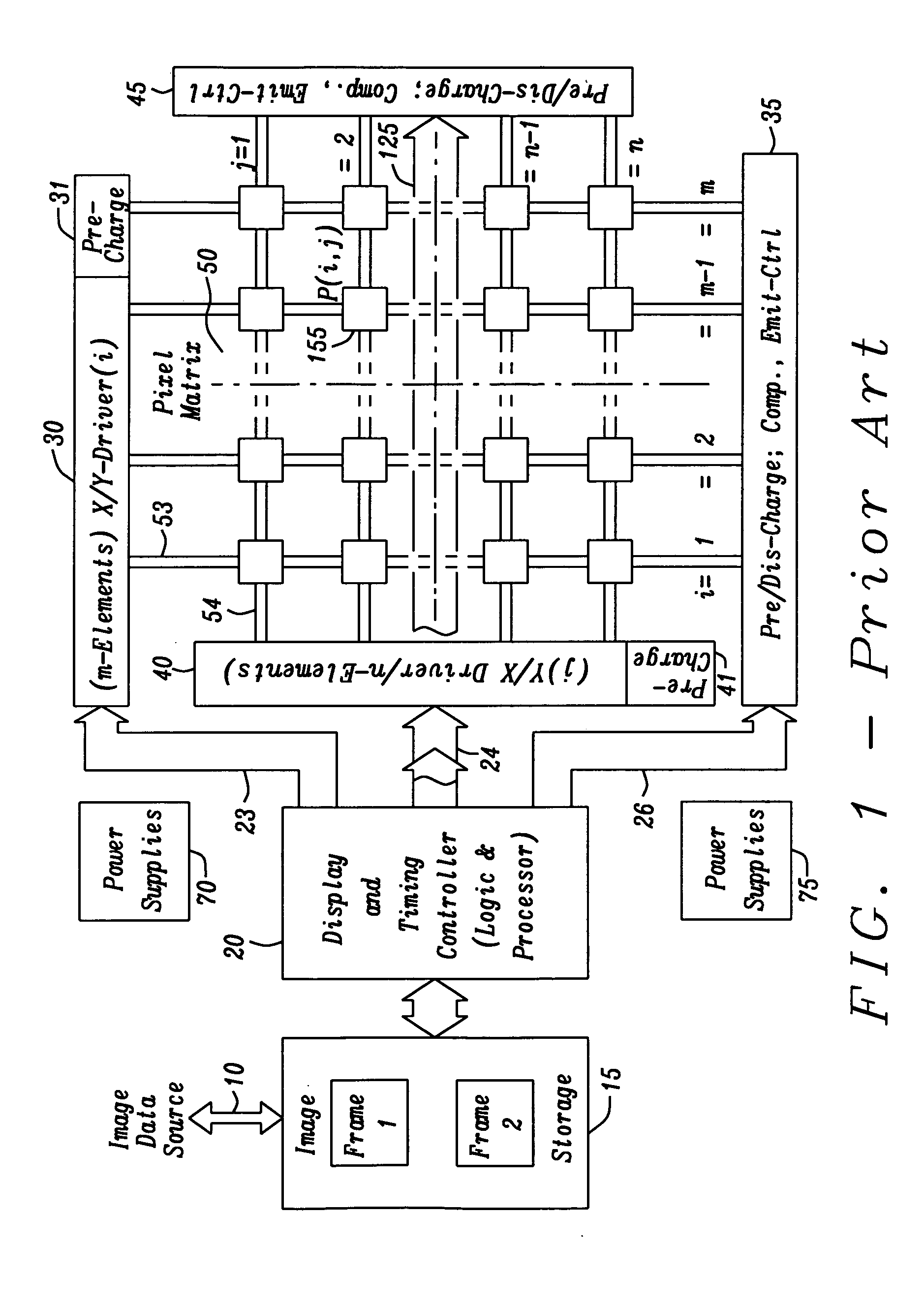
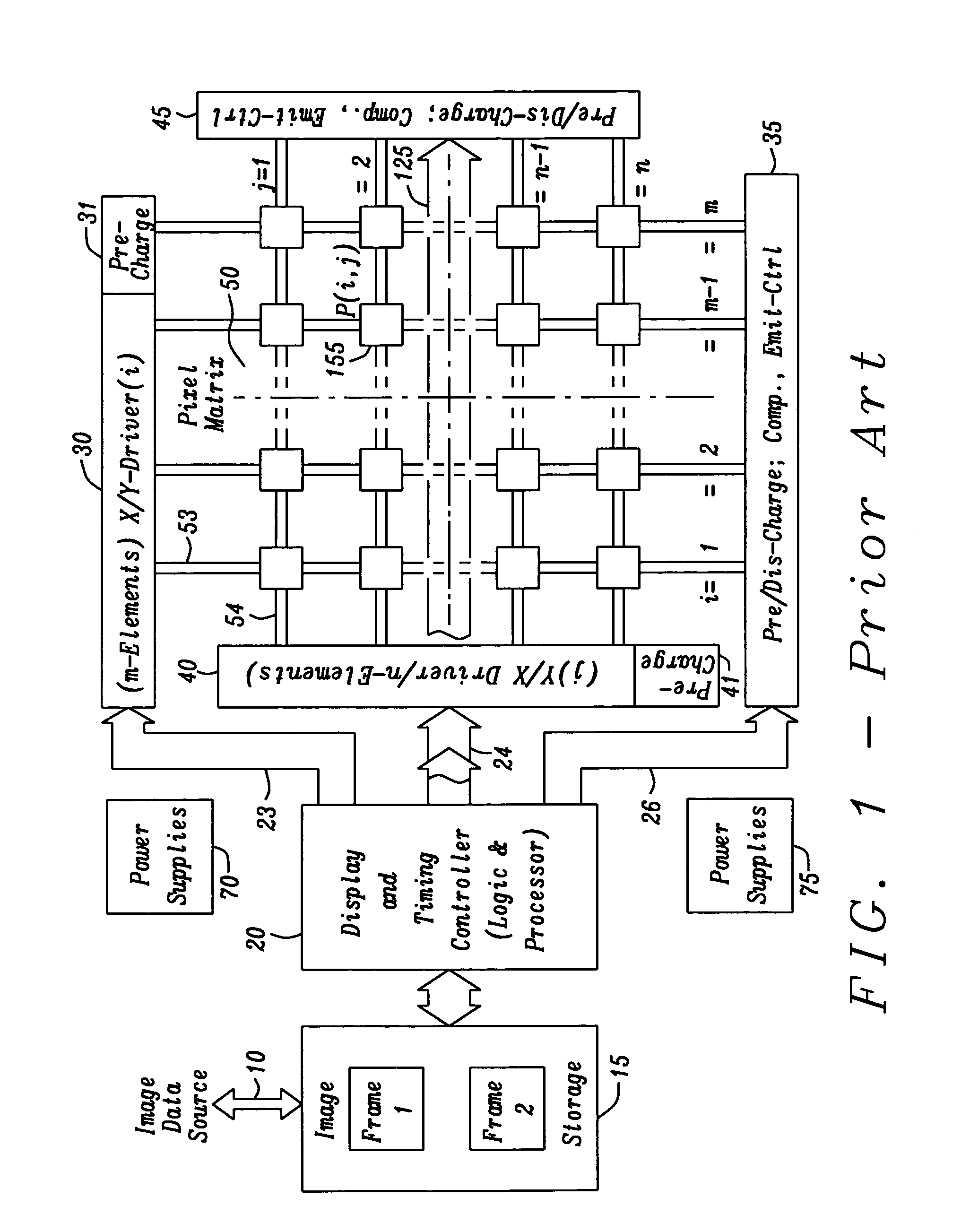
InactiveUS20100295861A1Reduce complexityCathode-ray tube indicatorsInput/output processes for data processingData domainDisplay device
A circuit for a flat panel display includes an image storage block, a display and timing controller block, an image pixel matrix containing a multitude of row and column arranged pixel elements, also one or more controlled row and column driver blocks, and a pixel display operation employing the extended multi line addressing (XMLA) operation. That XMLA operation comprises a decomposition of image data by analyzing image data from at least two lines from the image data but employing as many lines of the image data as possible according to a certain ‘best match’ criterion directly expanding these operations over their ‘widest possible range’ of lines using that ‘best match’ criterion to find within multiple lines common parts of contents, then separating these common parts into a multi line and the residual parts into a single line data domain thus allowing for a separate display of those data domains.
Owner:DIALOG SEMICONDUCTOR GMBH
Method and apparatus for transmitting data in a wireless communication system
ActiveUS20140161088A1Avoid wastingEfficient data communicationPower managementSignal allocationTime domainCommunications system
Provided are a method and apparatus for transmitting data in a wireless communication system. The method comprises the steps of: setting up a frame including both a control domain for transmitting scheduling information to a first terminal and a data domain for transmitting first data to the first terminal; and transmitting, to a second terminal, second data in the control domain. The frame comprises a plurality of orthogonal frequency division multiplexing (OFDM) symbols in a time domain. The control domain consists of a first number N (where N is any natural number equal to or less than 4) of OFDM symbols in the frame. The data domain consists of OFDM symbols other than a number N of OFDM symbols in the frame. The second data has a predetermined bit size.
Owner:LG ELECTRONICS INC
System, Network, Device and Stacked Spectrum Method for Implementing Spectrum Sharing of Multiple Contiguous and Non-Contiguous Spectrum Bands Utilizing Universal Wireless Access Gateways to Enable Dynamic Security and Bandwidth Policy Management
InactiveUS20180376006A1Improve rendering capabilitiesQuality improvementService provisioningInterconnection arrangementsFrequency spectrumAir interface
A system and method in various embodiments implements a virtual spectrum band stacking technique facilitating spectrum sharing by converting and combining spectrum bands consisting of several different RF channels, common air interfaces, and radio channel protocols in the radio frequency channel domain to form IP Virtual Radio Channels (IP-VRCs) in the packet data domain. This virtual spectrum stacking technique combines the transmissions of contiguous and non-contiguous RF channels with differing physical layers into IP-VRCs. This technique enables simultaneous parallel high-speed wireless transmission; virtual radio channel hopping for enhanced security; and customized security schemes for different IP-VRC Groups. The deployment of the combination of IP-VRC Groups; Universal “Small Cell” Base Stations; and Universal Wireless End-Point Devices allows the aggregation of all available spectrum bands for use within a building environment. Some benefits of this deployment include expansion of spectrum utilization, service quality, security, applications and transmission throughput for wireless end-point devices.
Owner:INCNETWORKS
Vehicle-mounted CAN bus network abnormity detection method and system
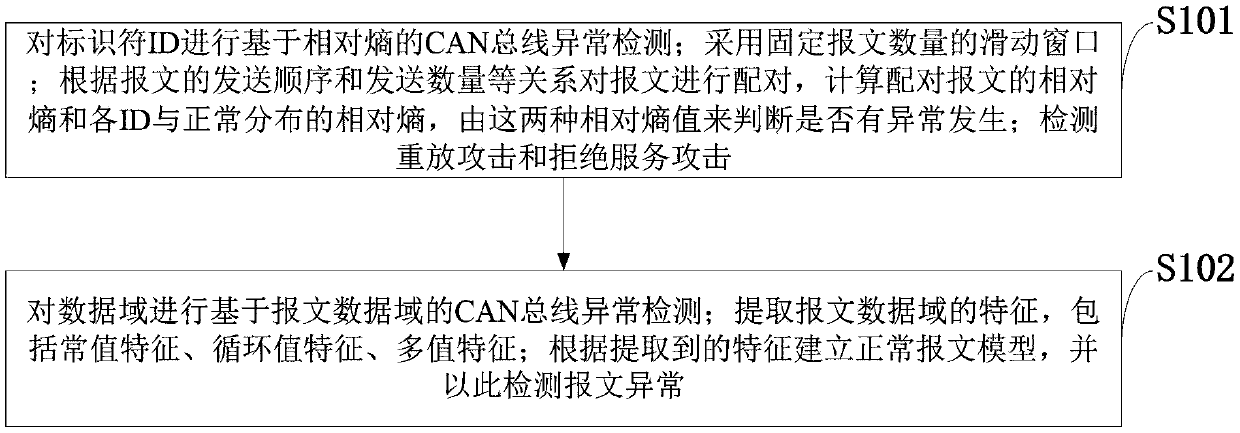
ActiveCN110275508ANo need to change the structureAvoid the influence of relative entropyProgramme controlElectric testing/monitoringAnomaly detectionSlide window
The invention, which belongs to the technical field of vehicle-mounted network, discloses a vehicle-mounted CAN bus network abnormity detection method and system. CAN bus abnormity detection based on a relative entropy is performed on an identifier ID; a sliding window with a fixed message number is employed; messages are paired based on a relationship between a message sensing sequence and a sending number, relative entropies of the paired messages and relative entropies of all IDs and normal distribution are calculated, and whether abnormity occurs is determined based on the two kinds of relative entropies; a replay attack and a denial of service attack are detected; CAN bus network abnormity detection based on a message data domain is performed on a data domain; features, including a constant value feature, a cyclic value feature, and a multi-value feature, of the message data domain are extracted; and a normal message model is established based on the extracted features and the message abnormity is detected. Therefore, the replay attack, the denial of service attack, the tampering attack and the forgery attack can be detected effectively and efficiently; more abnormal information is provided; and thus subsequent protection can be performed well.
Owner:XIDIAN UNIV
System and method for building component applications using metadata defined mapping between message and data domains
ActiveUS7698383B2Drive down the complexity involvedReduce resource utilizationDigital data processing detailsMultiprogramming arrangementsData domainBasic service
It is desirable to drive down the complexity involved in developing the wireless application by reducing the need to do any explicit coding, as well as reducing device resources utilized by the application when provisioned. Having an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application as a series if application components, and their interactions, can simplify the development effort and reduce resource allocation. The wireless application is described as a set of components. The data domain for this category of applications is defined using atomic data components. The communication between the device and a server is defined using atomic message components. Both message and data components are described in metadata using a structured definition language such as XML. The relationships between the message and data components are embedded in the XML definitions in the form of message / data mappings. Typically, outgoing messages are derived from some underlying data component and incoming messages affect the current state (or data representation) of the application. It is therefore apparent that the metadata defined mapping relationship is preferable between the expression of data and message components.
Owner:MALIKIE INNOVATIONS LTD
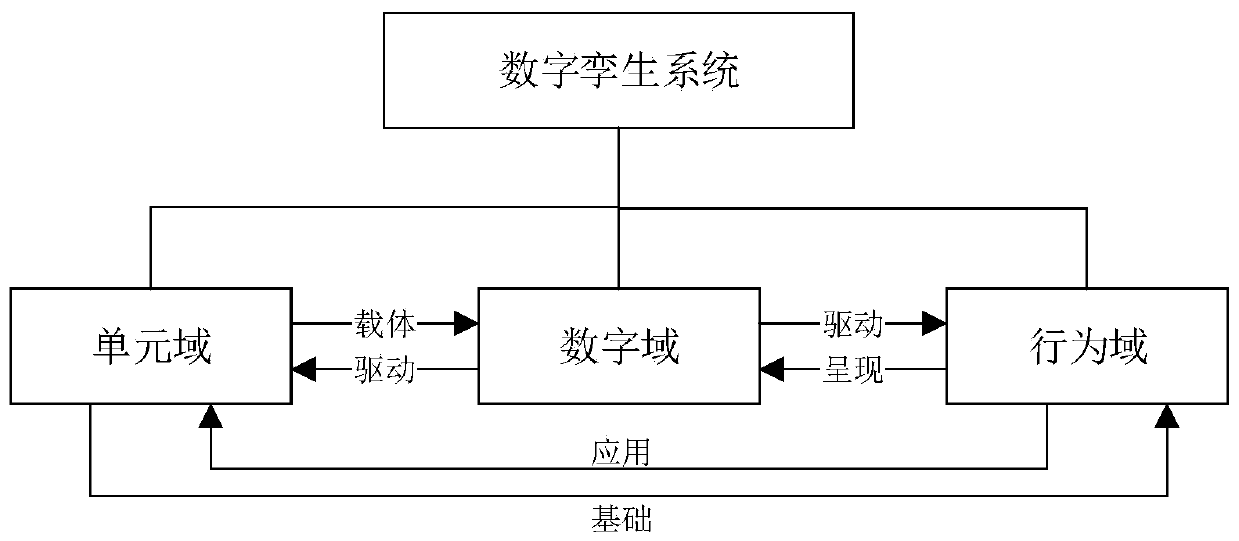
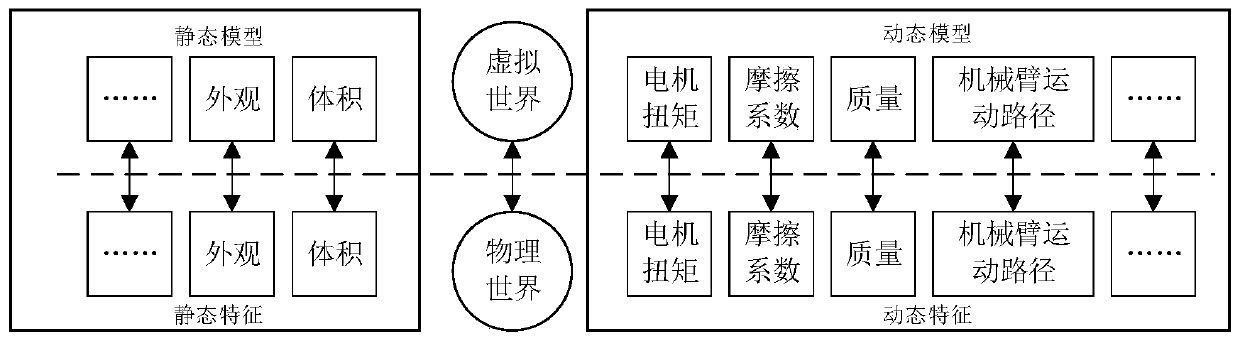
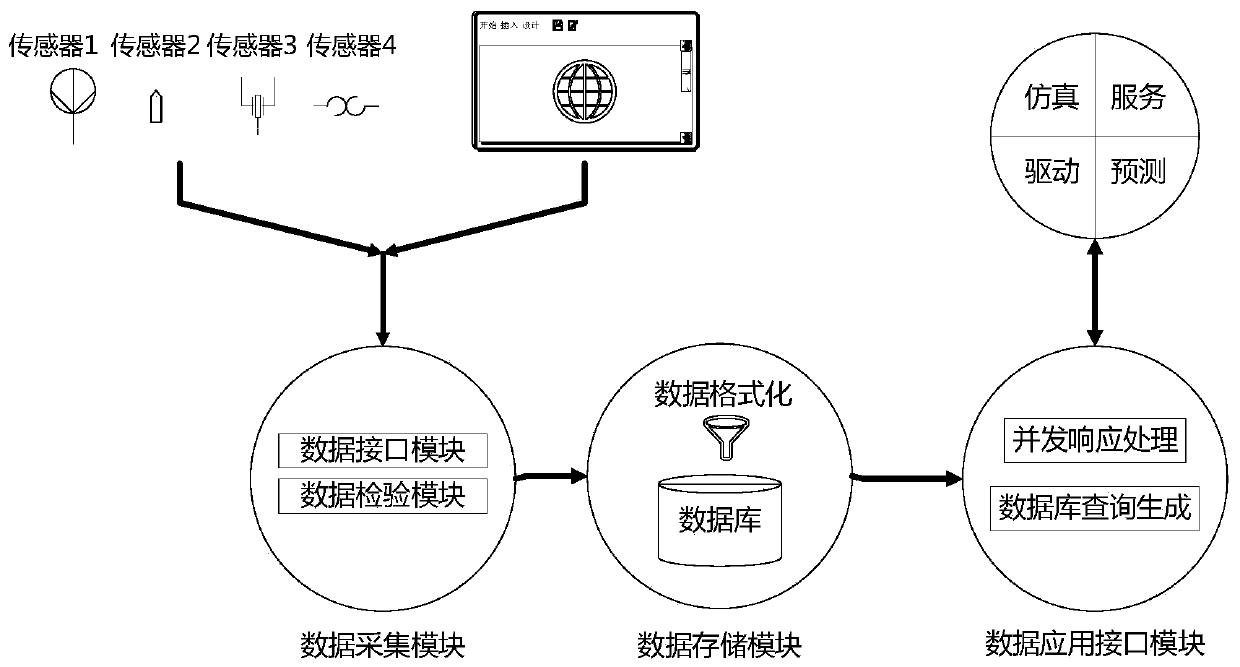
Digital twinning body for production line and construction method and application thereof
ActiveCN110399642AEasy for production managementTotal factory controlSpecial data processing applicationsProduction lineDynamic models
The invention discloses a digital twinning body for a production line and a construction method and application thereof, and the digital twinning body comprises: a unit domain which comprises a staticmodel and a dynamic model of physical equipment, provides a data carrier for a data domain, and provides a model basis for the implementation of a behavior domain; the data domain which is used for acquiring operation data of physical equipment and products and instruction data of the digital management system, performing format conversion and storage on the acquired data according to a unified data structure, and supporting a behavior domain to access the data; and the behavior domain which is used for defining semantic description of each behavior in the operation process of the productionline, and driving a model of the unit domain to operate synchronously with the physical world according to the data acquired by the data domain. The digital twinning body can be quickly deployed in areal production environment, and operations such as monitoring, simulation and prediction are carried out on production from different dimensions.
Owner:ZHEJIANG UNIV +1
Transmission method and device of uplink control signaling
ActiveCN102307082AGuaranteed to workError prevention/detection by using return channelWireless communicationTelecommunicationsControl signal
The invention discloses a transmission method and device of an uplink control signaling, aiming to realize the purpose that the terminal can transmit the uplink control signaling of the terminal in a cell of which the system bandwidth is larger than the bandwidth supported by the terminal through the uplink control signaling of an LTE (long term evolution) system transmission terminal, and the terminal can be guaranteed to work normally. The sending method of the uplink control signaling, which is provided by the invention, comprises the following steps: determining an uplink control signaling required to be sent of the terminal; and sending the uplink control signaling of the terminal by an uplink data domain of the LTE system or an uplink data domain and an uplink control domain of the LTE system.
Owner:DATANG MOBILE COMM EQUIP CO LTD
Zooming controller
InactiveUS6366303B1Cost effectiveIncrease speedInput/output processes for data processingProportional controlImage resolution
A method and device for accessing a broad data field having a fine resolution. The user selects a scale which can be varied. The scale controls a range within the data field. By moving the range to encompass different portions of the data field, the user can scan that portion of the data field. The present invention allows the user to simultaneously select the scale while moving the range over different portions of the data field. Thus, the user can "zoom in" and "zoom out" of different portions of the data field.In one embodiment of the present invention, a particular piece of data within the broad data field can be accessed. First, the scale is selectively varied, thereby controlling a range within the data field. Then, the range is moved to encompass portions of the data field in which the piece of data resides. Next, the scale is successively decreased while, simultaneously, points successively closer to the location are kept with the range. The scale is decreased (i.e., increasing the range's resolution) and the range is moved in this manner until the piece of data is actually accessed.
Owner:APPLE INC
Method for implementing dynamic update of Java program
InactiveCN101174217AGuaranteed to compile onceWill not interfere with each otherSpecific program execution arrangementsSoftware updateData field
The invention relates to a method for realizing dynamic update of Java program in the computer technical field, which comprises the following steps: firstly, modifying the class definitions that need dynamic update in the passive dynamic update program, and adding update support method for realizing judgment to the subobjects of the class objects one by one, wherein the parameter is class loader; secondly, modifying the update class definitions in the dynamic update program, and adding update method for realizing initialization to the variables under the update class objects, wherein, the input parameter is class loader and old object; thirdly, modifying part of the method invocation, data field memory, and object set of the updated program with the Java reflection to realize running recovery of the program; finally, adding update support method to the main class and adding update checkpoint in the main method circulation. The invention has the advantages of avoiding software update that needs halt, update and reboot and avoiding loss caused by halt.
Owner:SHANGHAI JIAO TONG UNIV
Executing method of multimode terminal network selection and multimode terminal
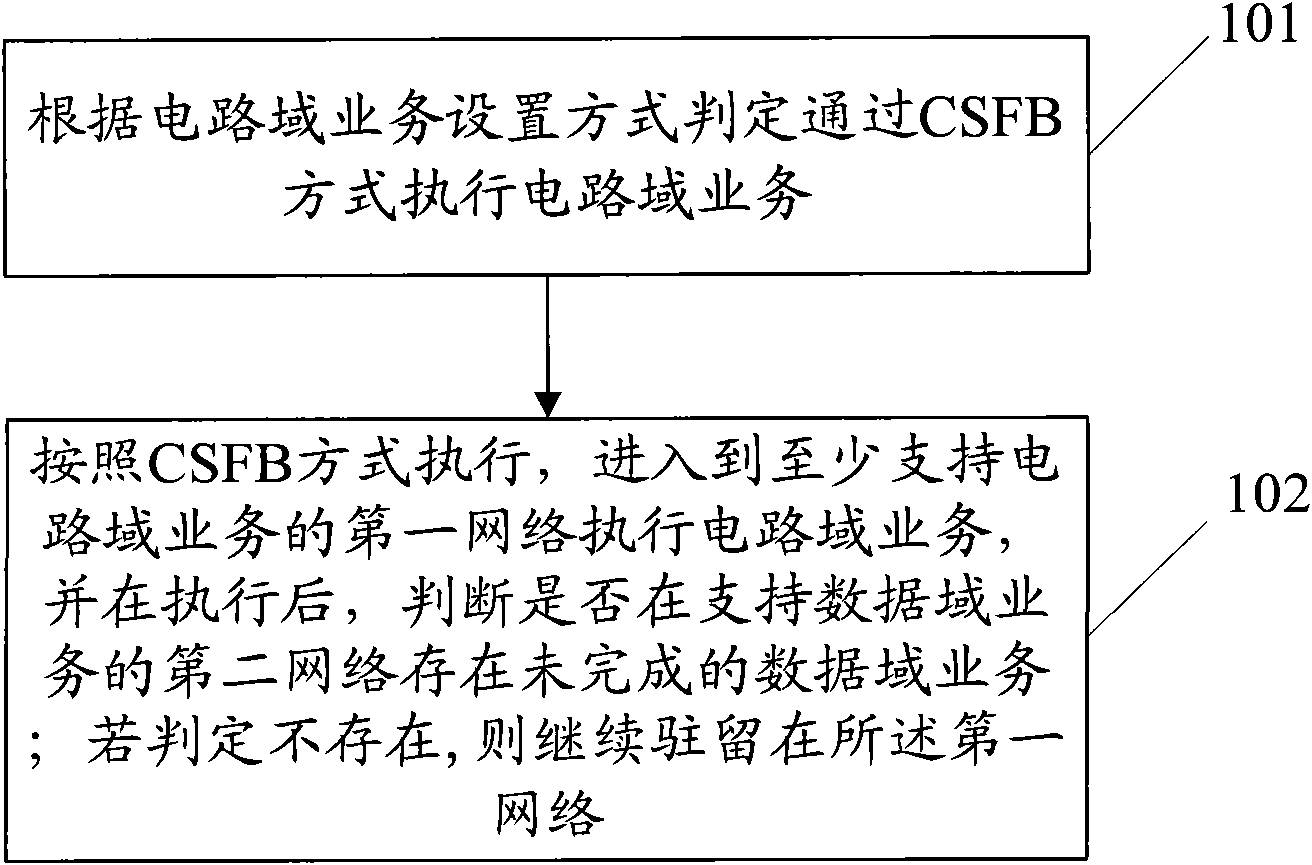
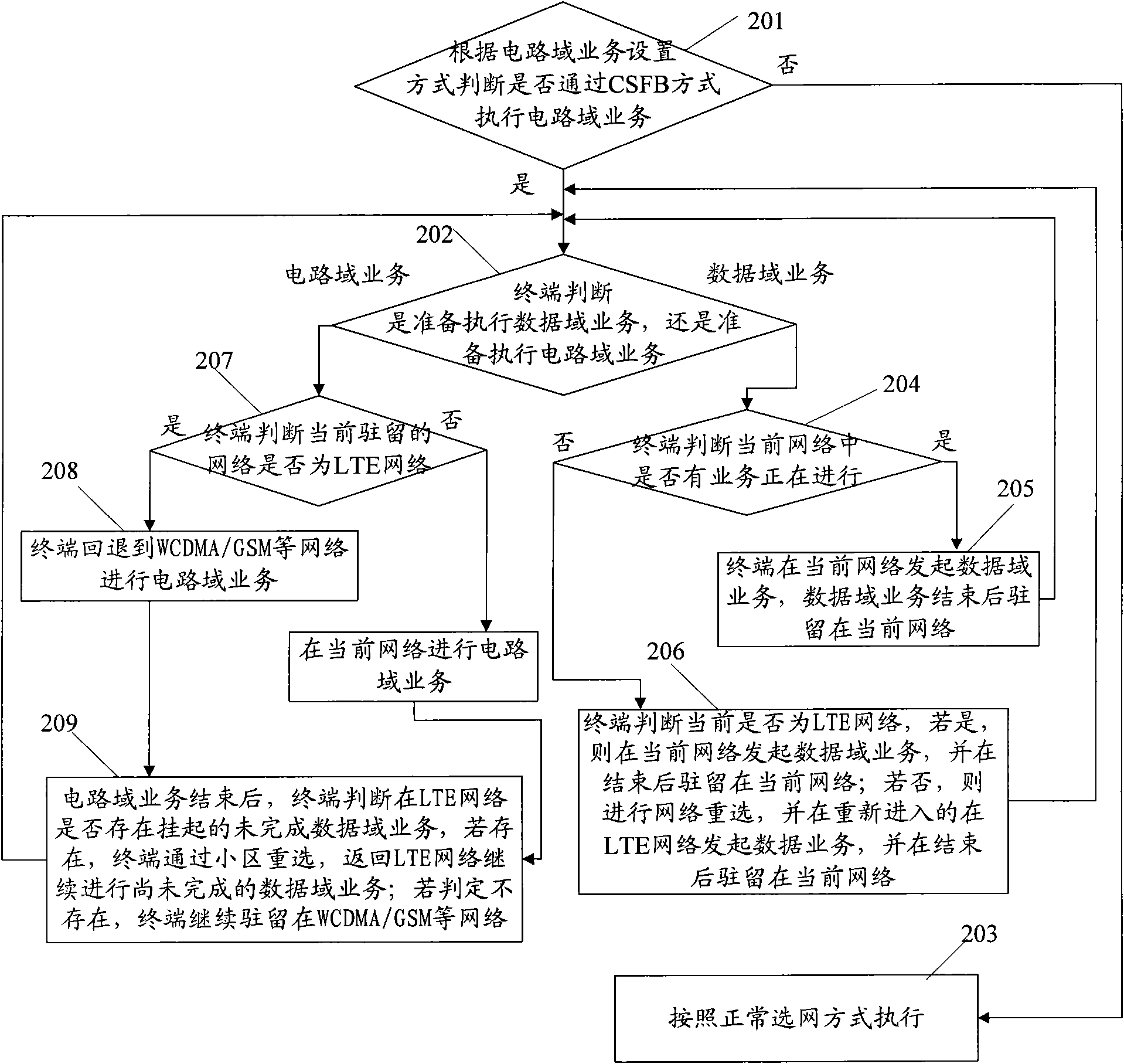
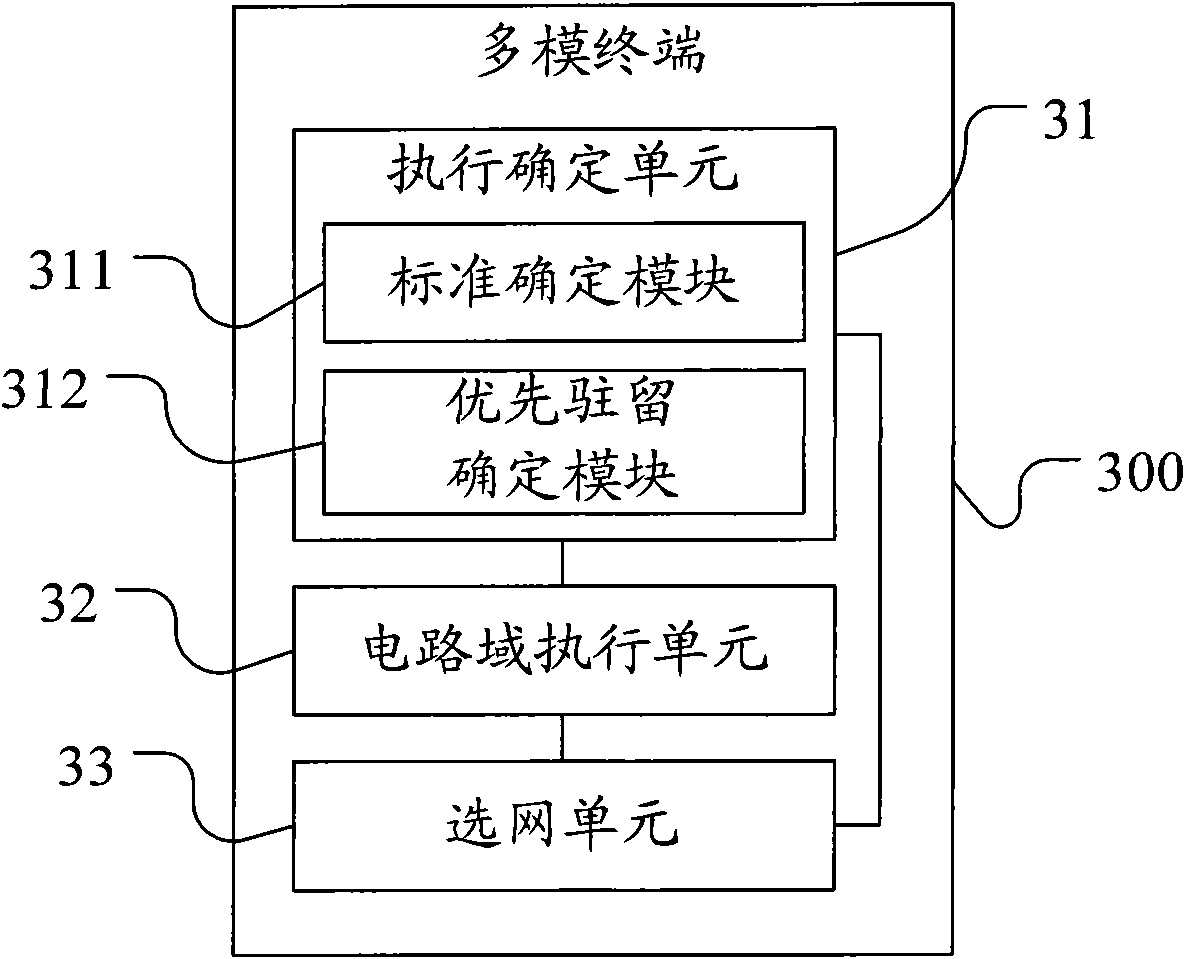
InactiveCN101835246AImprove experienceReduce switchingAssess restrictionData domainDistributed computing
The embodiment of the invention discloses an executing method of multimode terminal network selection and a multimode terminal, relating to the technical field of communication and solving the technical problem that the multimode terminal is frequently switched when a CSFB mode is adopted in the prior art. The method comprises the steps of: judging whether a circuit domain service is executed by the CSFB mode according to a circuit domain switch setting mode; if so, entering a first network executing circuit switch service, and judging whether a hung-up uncompleted data domain service exists in a second network after the circuit domain service is completely executed, wherein the first network at least supports the circuit domain service, and the second network supports the data domain service; and if the hung-up uncompleted data domain service exists in the second network, continuing to remain the first network. The embodiment of the invention is mainly applied to the terminal.
Owner:HUAWEI DEVICE CO LTD
Advanced clustering method for material separation in dual energy ct
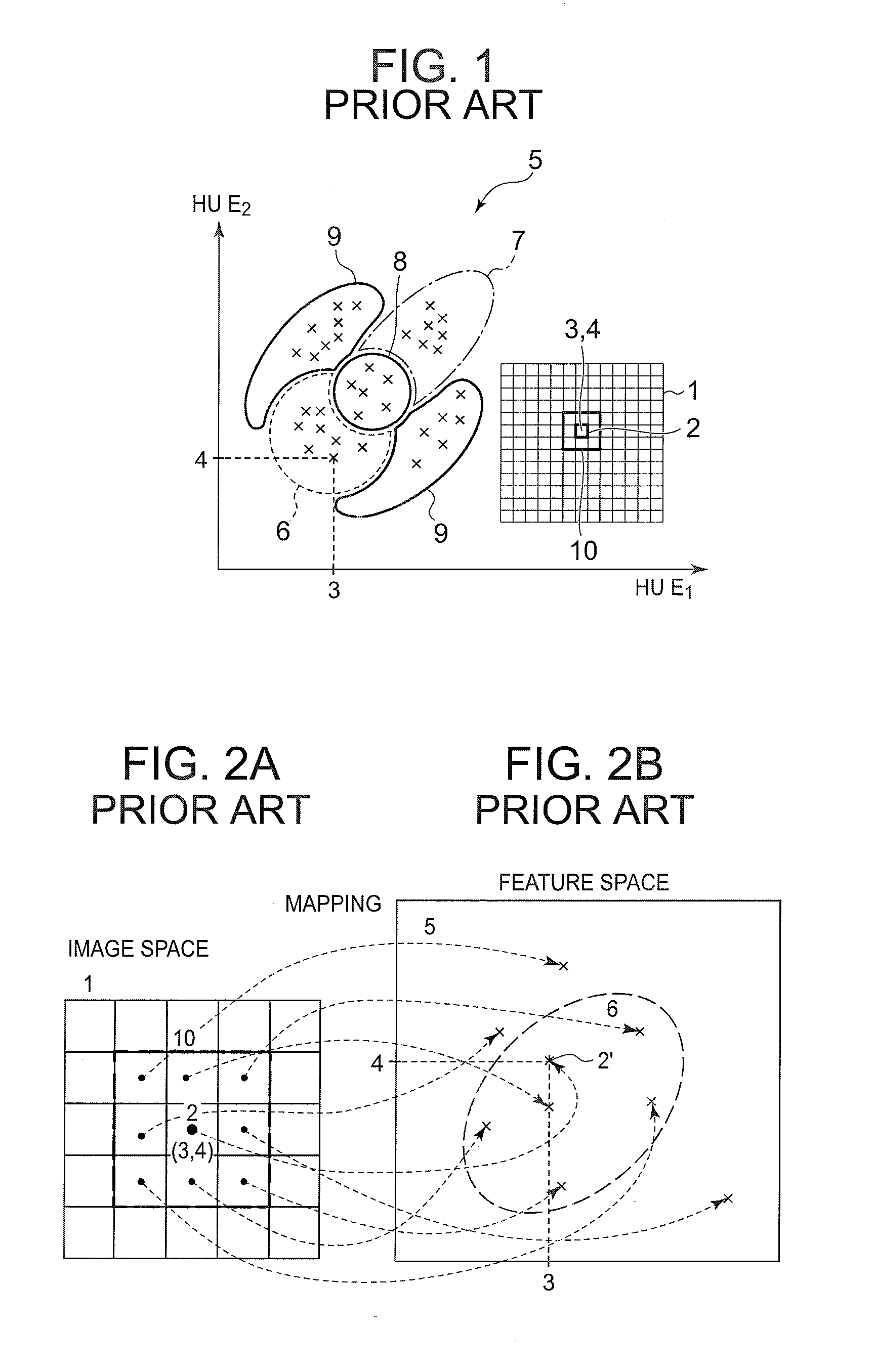
ActiveUS20100328313A1Reconstruction from projectionDrawing from basic elementsDecompositionData domain
Three or more materials are advantageously separated from dual energy data by using a material separation technique. To effectively separate material clusters, a density plot is introduced to automatically render cluster separations. Initially, the projection data optionally undergo data-domain dual energy decomposition. Then, the image data is plotted in a vector plot whose axes are the low HU values and the high HU values. For a given data point in the vector plot, a number of data points is counted within in a region of interest surrounding the given data point to generate a density plot where each point now represents a density level surrounding the data point. Thus, clustering of a certain material is visualized by a predetermined color assignment scheme. Furthermore, special image processing methods such as Gaussian decomposition are used to improve the accuracy of material separation. In addition, the HSL color model may be used for better visualization and to bring a new dimension in material separation display.
Owner:TOSHIBA MEDICAL SYST CORP
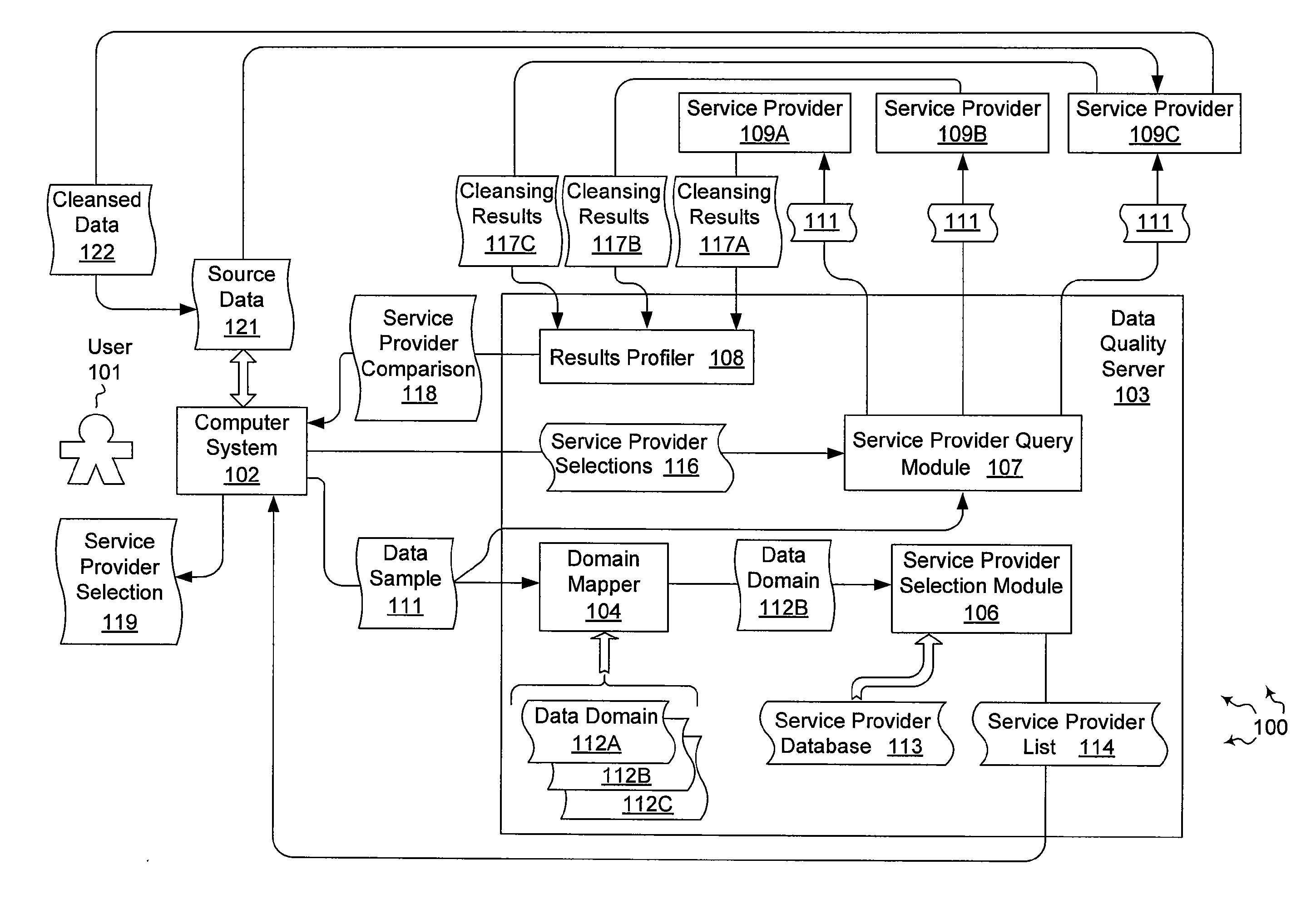
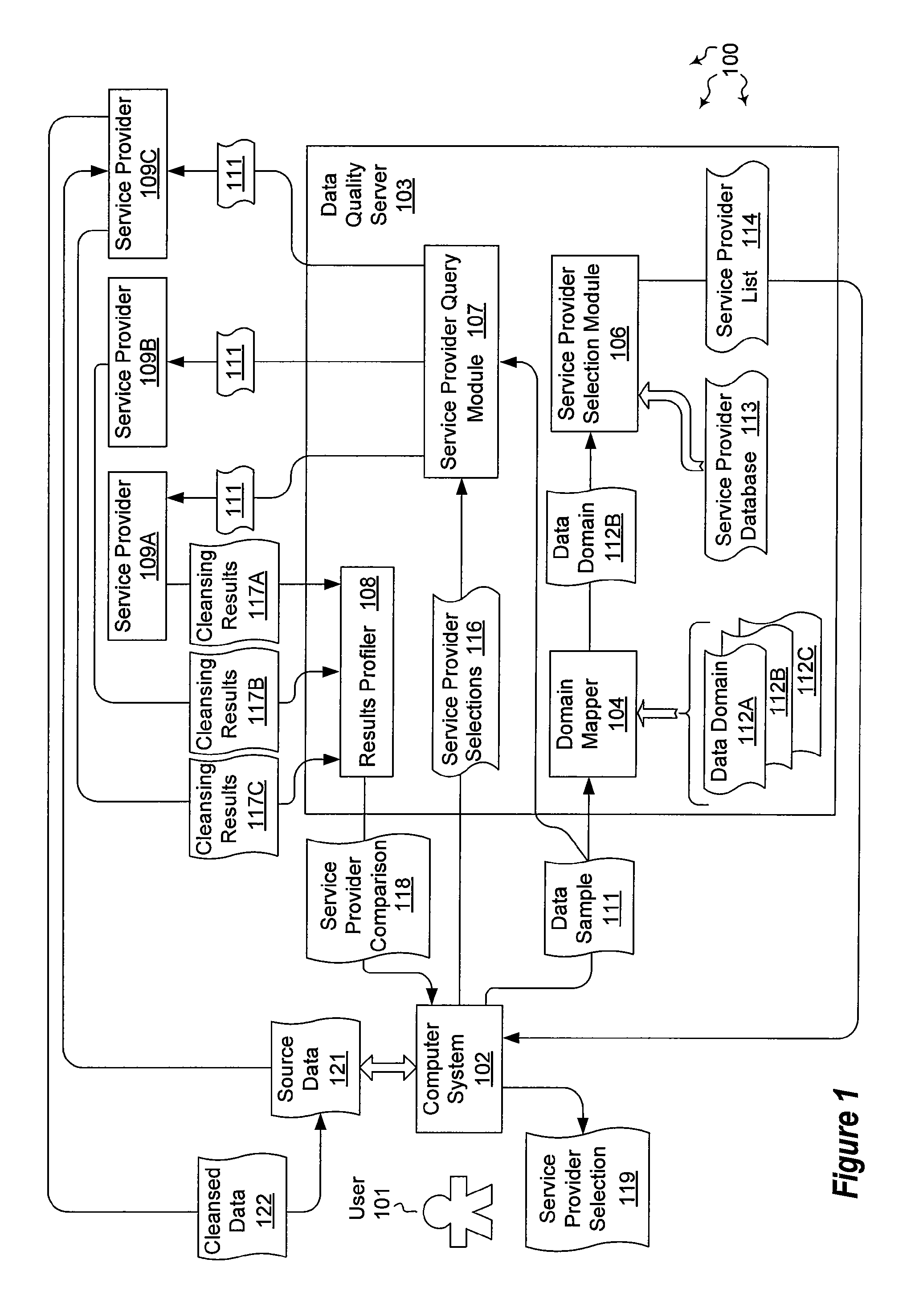
Comparing and selecting data cleansing service providers
The present invention extends to methods, systems, and computer program products for exploring and selecting data cleansing service providers. Embodiments of the invention permit a user to explore different data cleansing service providers and compare quality results from the different data cleansing service providers. Sample data is mapped to a specified data domain. A list of service providers, for cleansing data for the selected data domain, is provided to a user. The user selects a subset of service providers. The sample data is submitted to the subset of service providers, which return results including allegedly cleansed data. The results are profiled and a comparison of the subset of service providers is presented to the user. The user selects a service provider to use when cleansing further data.
Owner:MICROSOFT TECH LICENSING LLC
Advanced multi line addressing
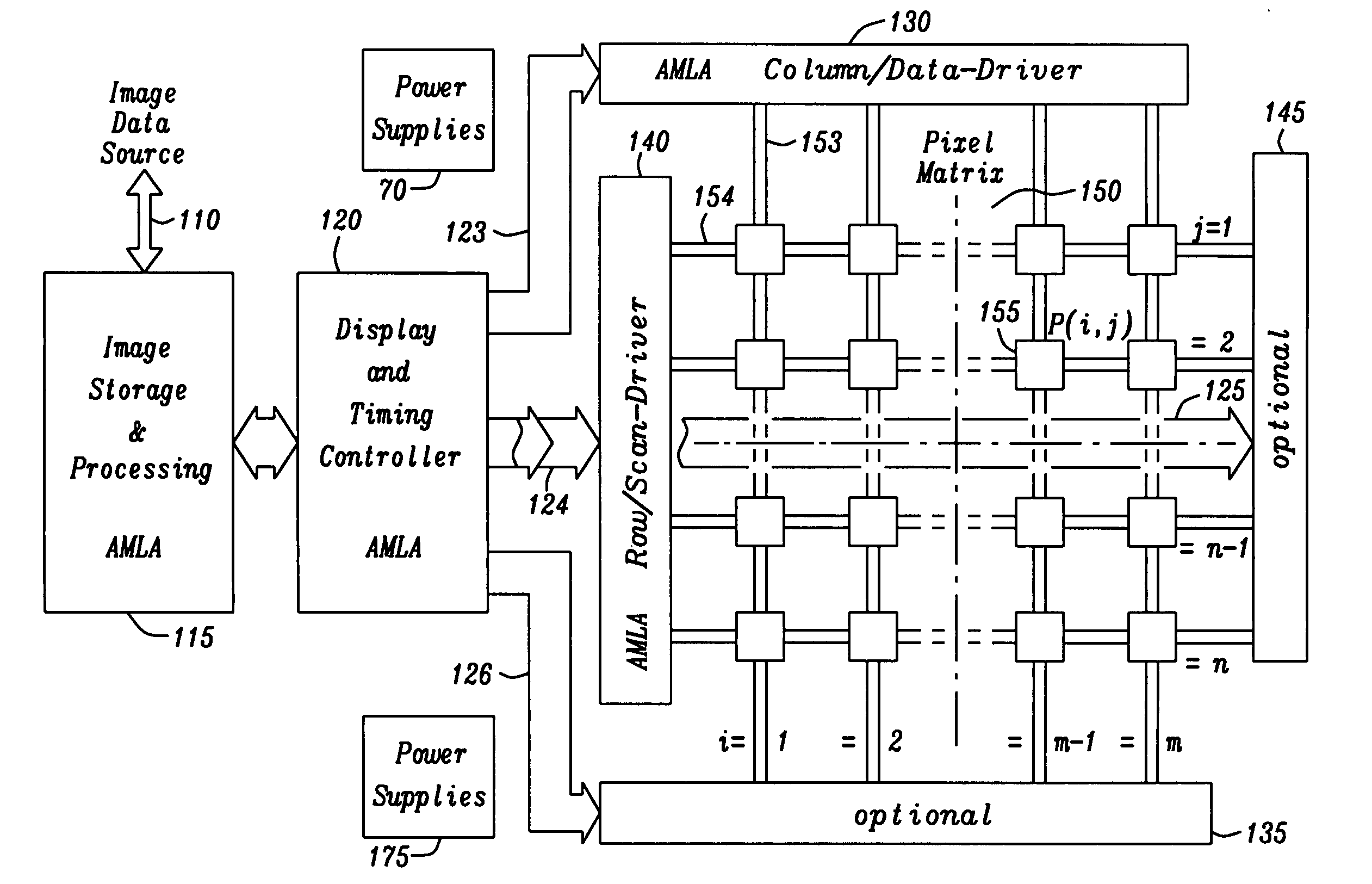
ActiveUS20100295760A1Reduce complexityReduce power consumptionTelevision system detailsTelevision system scanning detailsDisplay deviceData domain
A circuit for a flat panel display, capable of displaying images, is provided. The circuit includes an image storage and processing block for the images to be displayed, a display and timing controller block controlling the display operation, an image pixel matrix containing a multitude of rows and columns arranged pixel elements. The circuit also includes one or more controlled row driver blocks, one or more controlled column driver blocks, and a pixel display operation for displaying pixel elements employing an advanced multi line addressing operation applied to a row and / or column drive activated pixel element display operation. The advanced multi line addressing operation signifies that during every operating sequence a decomposition operation of image data is taking place by analyzing image data from multiple lines for common contents by pixel data comparison, separating common parts of the image data into a multi line data domain and residual parts of the image data into a single line data domain thus allowing for a display of these two data domains in separately activated pixel element display operations.
Owner:DIALOG SEMICONDUCTOR GMBH
Data source based application sandboxing
A computing device and a method for a computing device to control access to data stored on a data store of the device. An access component of the device having control over access to the data. The access component being operative to receive a request for data from a requesting component, identify an assigned access domain of the requesting component and an assigned data domain of the requested data and determine whether the requesting component is authorized to access the data by comparing the assigned access domain and the data domain with permissions specified in a security policy. If the assigned access domain is authorized to access the data domain, the access component may provide access to the requested data.
Owner:MALIKIE INNOVATIONS LTD
Adaptive intelligent integration detection method of radar range extension target
ActiveCN103544296AAdaptableAvoid mismatchWave based measurement systemsOther databases retrievalSupport vector machinePoor adaptive skills
The invention discloses an adaptive intelligent integration detection method of a radar range extension target and belongs to the radar signal processing field. The adaptive intelligent integration detection method of the radar range extension target aims at overcoming the defects that the existing range extension target statistical detection method is poor in adaptive capability to the clutter and target environment and the like under the condition of the unknown clutter background. According to the adaptive intelligent integration detection method of the radar range extension target, normalized processing is performed on a radar echo one-dimensional range profile, integration optimization is performed through data domain description characteristics of a clutter one-dimensional range profile, a detection method of the constant false alarm rate of a one-class support vector machine is established, a kernel function parameter is adjusted to ensure constant false alarm rate characteristics of the detection method, and a clutter database is updated according to a detection result; statistical modeling does not need to be performed on the clutter background; the detection method is suitable for the positive and negative sample quantity seriously asymmetrical radar target detection environment; the false alarm control capability is strong, the computation is less, the engineering implementation is convenient, and the popularization and application value is high.
Owner:NAVAL AERONAUTICAL UNIV
System And Method For Performing A Purchase Transaction With A Mobile Electronic Device
InactiveUS20150302374A1Shorten the timeDebit schemesPayment circuitsElectronic systemsFinancial transaction
An electronic system (1) is described to perform a purchase transaction of goods or services. The system includes a mobile electronic device (2) configured to receive (t3) a second message (MSG2) carrying an authorization data field (AUT_D) dicating a valid or invalid authorization to use an electronic money for performing the purchase transaction, configured to store the content of the authorization data field into a non-volatile memory (160) inside the mobile electronic device and configured to transmit (t5; t7′) a third message (MSG3; MSG4′) carrying an electronic money identification data field (EM_ID) for indicating data identifying the electronic money used for performing the purchase transaction and carrying the authorization data field (AUT_D; AUT_D′). The system further includes a transaction server (4) configured to transmit (t2) the second message (MSG2) carrying the authorization data field (AUT_D) and configured to receive (t10) a fifth message (MSG5) carrying the electronic money identification data field (EM_ID) and carrying a bill amount field (BL_AM) indicating a bill amount to be paid for the selected goods or services and transmit (t11) therefrom a sixth message (MSG6) carrying a settlement result field (RES_STL) for indicating if the value of the bill amount has been debited on the electronic money. The system further includes a Point-of-Sale device (6) configured to receive (t6; t8′) from the mobile electronic device the third message (MSG3; MSG4′) carrying the electronic money identification data field (EM_ID) and the authorization data field (AUT_D; AUT_D′) and transmit (t9) therefrom the fifth message (MSG5) carrying the electronic money identification data field and the bill amount field (BL_AM), in case of a valid value of the content of the authorization data field.
Owner:SARTOR ANDREA
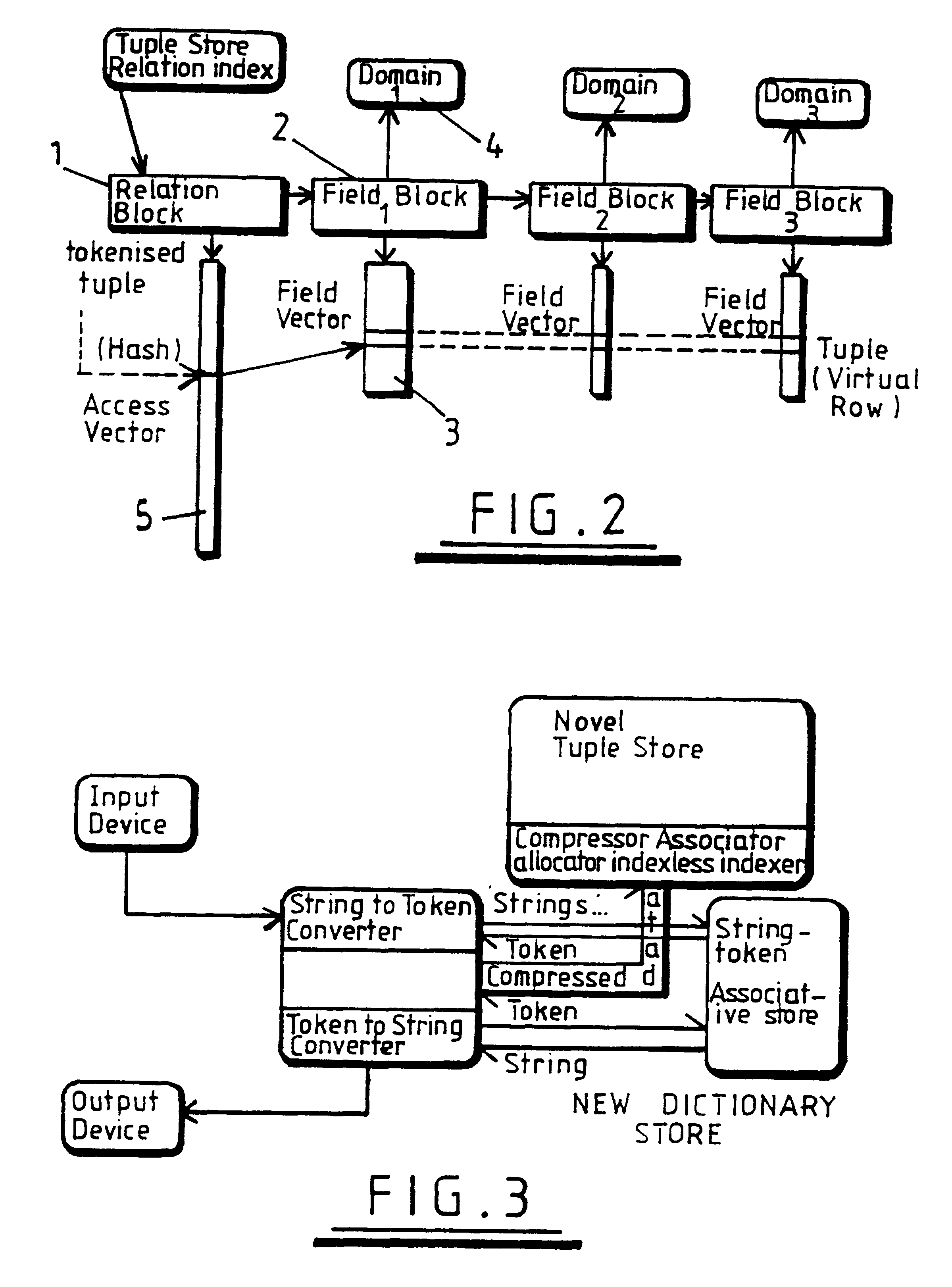
Databases
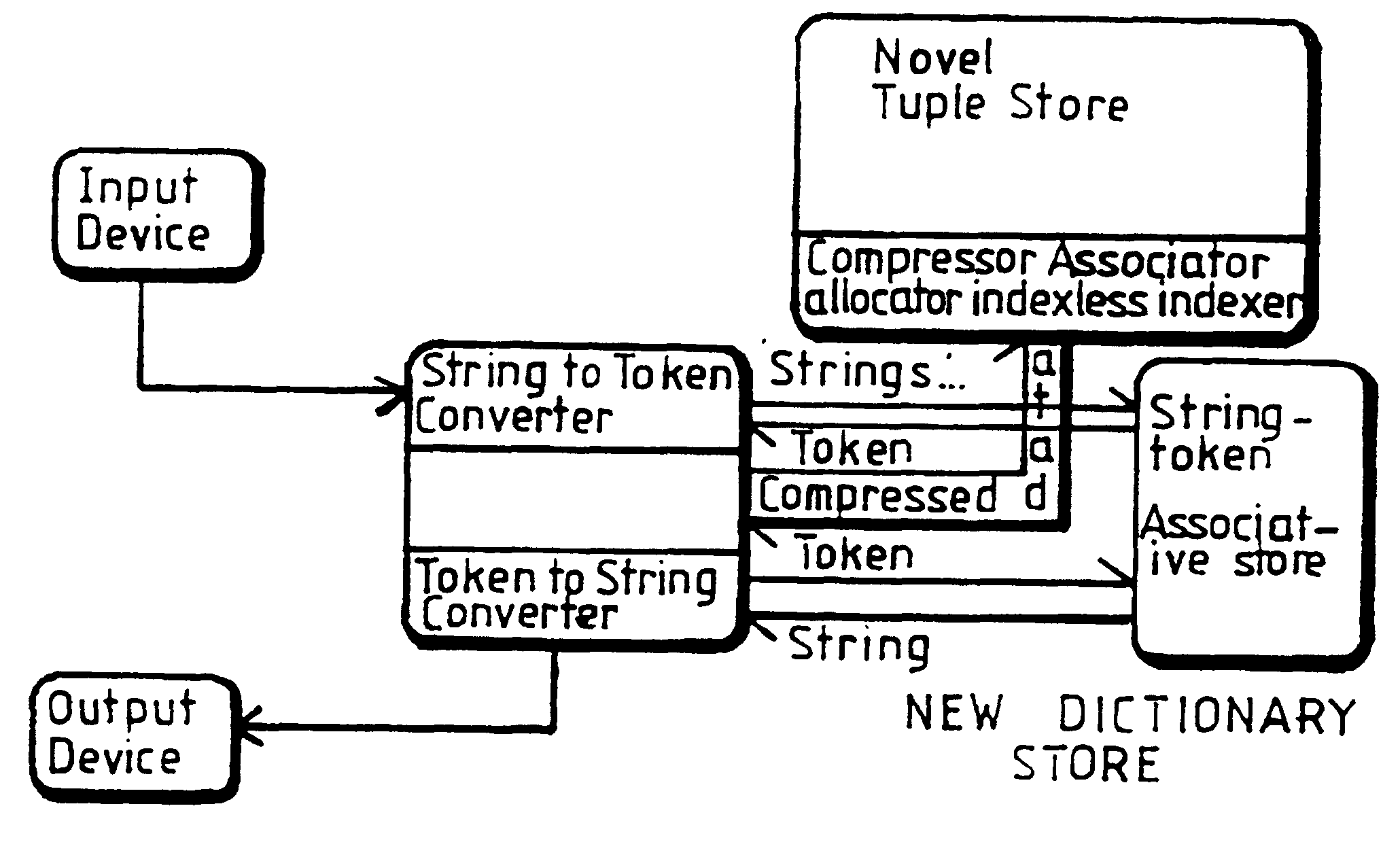
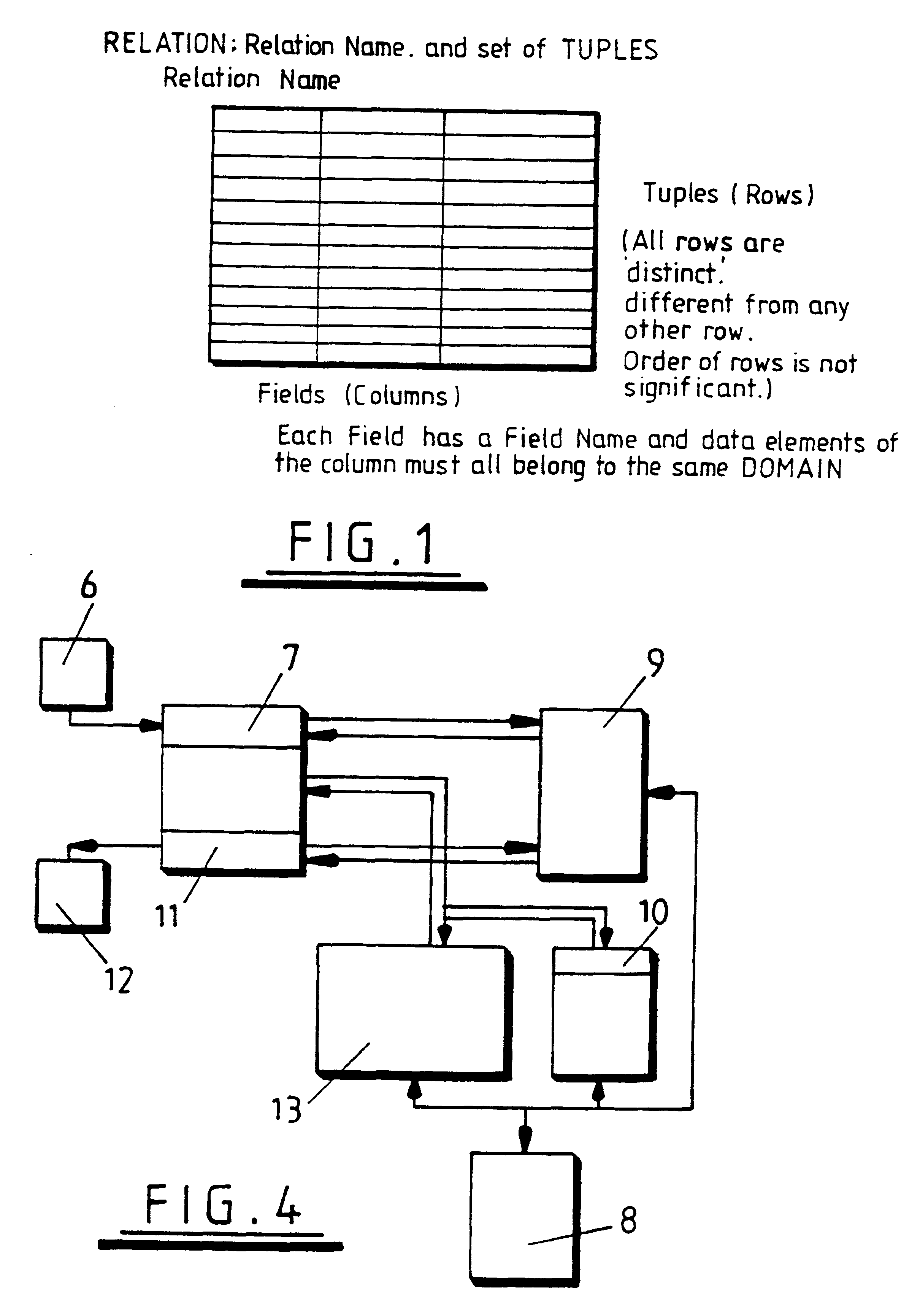
InactiveUS6169990B1Optimises compression ratioOptimises access speedData processing applicationsDigital data information retrievalTheoretical computer scienceData field
A computer database for storing information in tuple form wherein each tuple comprises fields with corresponding fields in the tuples constituting a column, generates for each data domain a domain dictionary which matches each distinct data value in that domain with a corresponding distinct token, and stores each domain dictionary. A tokenised store for each data field column is created. All of the tokens for a domain are initially of the same size being substantially the minimum size necessary to provide the required plurality of distinct tokens for initialize size of that domain. When further tuples are received for storage for each field of the tuple, the data value is compared in the corresponding domain dictionary. If no match is found, a new token within the existing token size is generated and added to the domain dictionary, but if all tokens within the existing token size are utilised a new token is generated having a size which is at least 1-bit wider than previously, such broadened token being entered into a new tokenised store for that column.
Owner:STRATHCLYDE UNIV OF
Method of predicting crime occurrence in prediction target region using big data
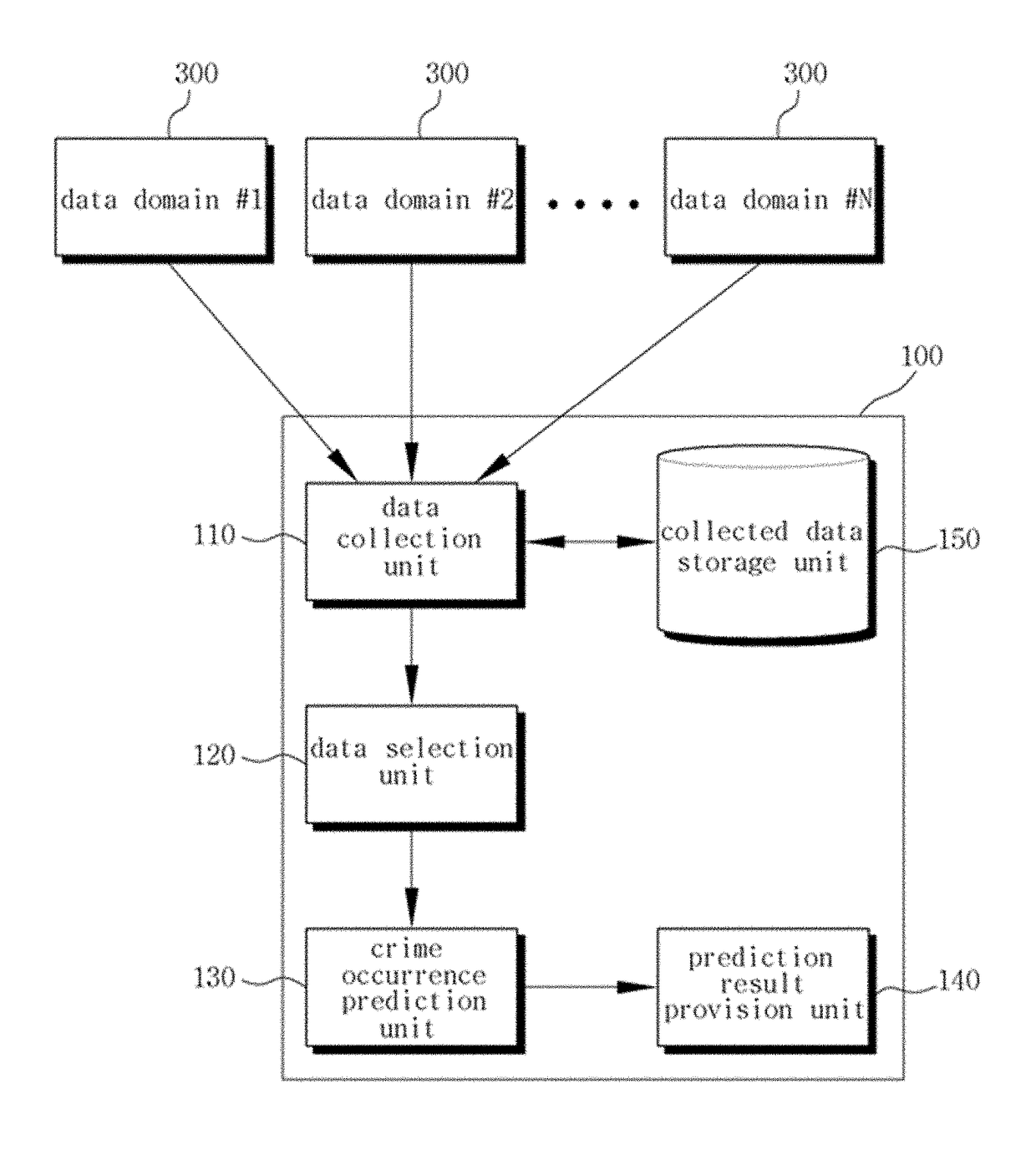
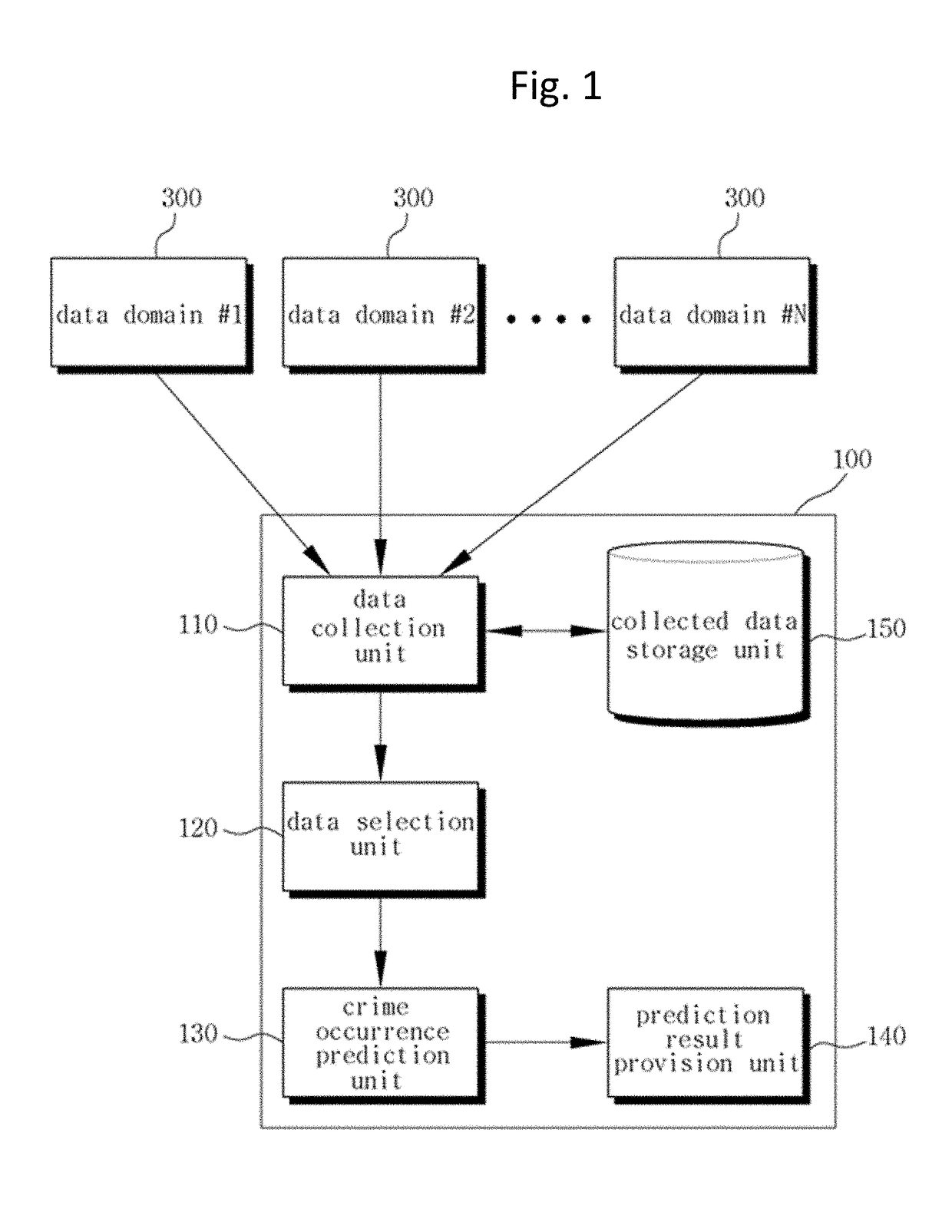
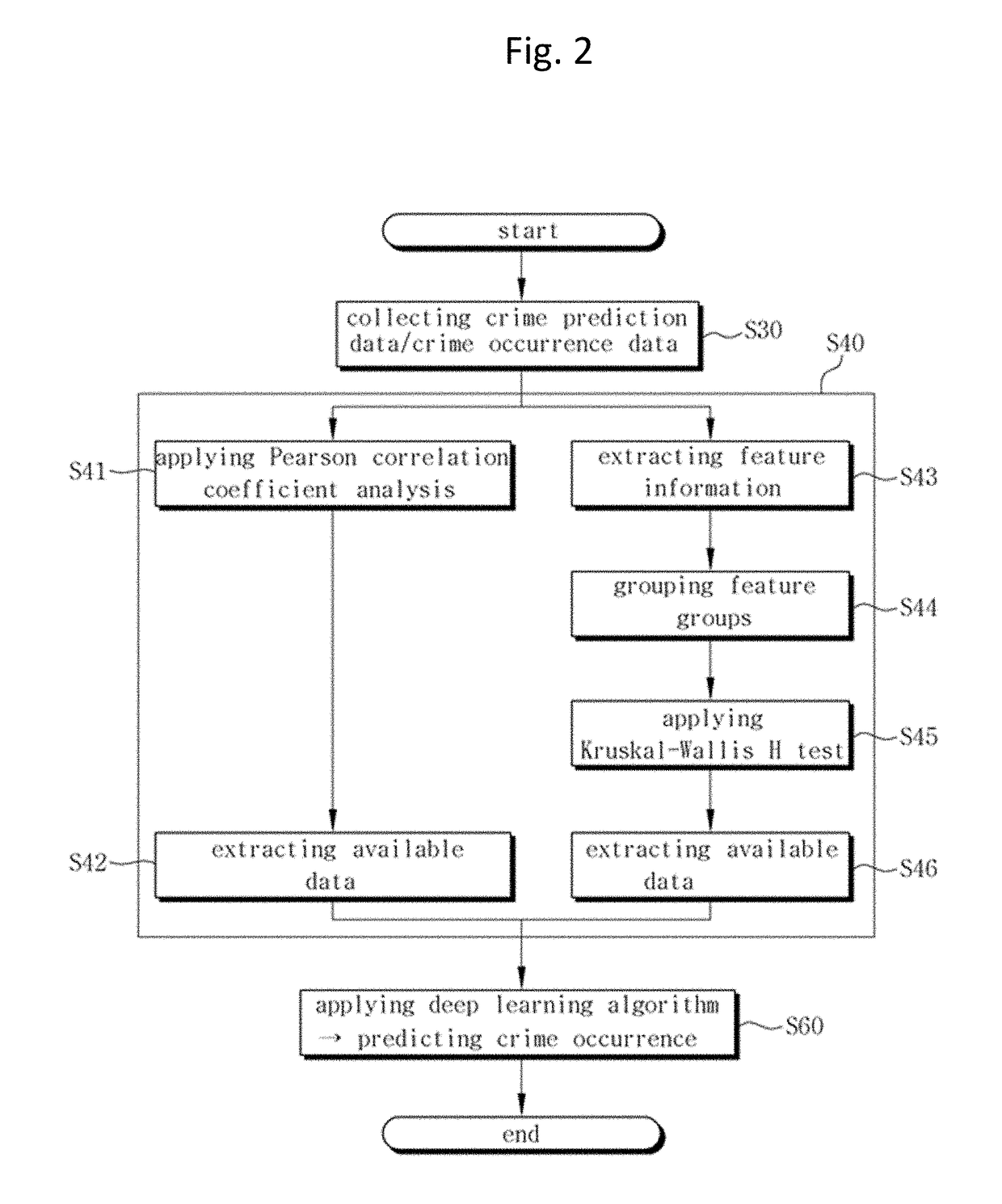
InactiveUS20180053110A1Accurate predictionBiological neural network modelsForecastingOccurrence dataData domain
Disclosed is a method of predicting crime occurrence in a prediction target region using big data, the method including: collecting crime prediction data of the prediction target region from a plurality of data domains; collecting crime occurrence data of crime that occurred in the prediction target region during a preset period of time from a crime occurrence record domain; analyzing the crime prediction data and the crime occurrence data of each of the data domains according to a statistical analysis, and extracting meaningful data of the crime prediction data as available data by each of the data domains; and predicting crime occurrence by applying the available data to a pre-registered deep learning algorithm, wherein the available data is classified into a plurality of data groups according to a data type, and the deep learning algorithm includes: a first deep neural network; a second deep neural network; and an output.
Owner:THE CATHOLIC UNIV OF KOREA IND ACADEMIC COOPERATION FOUND
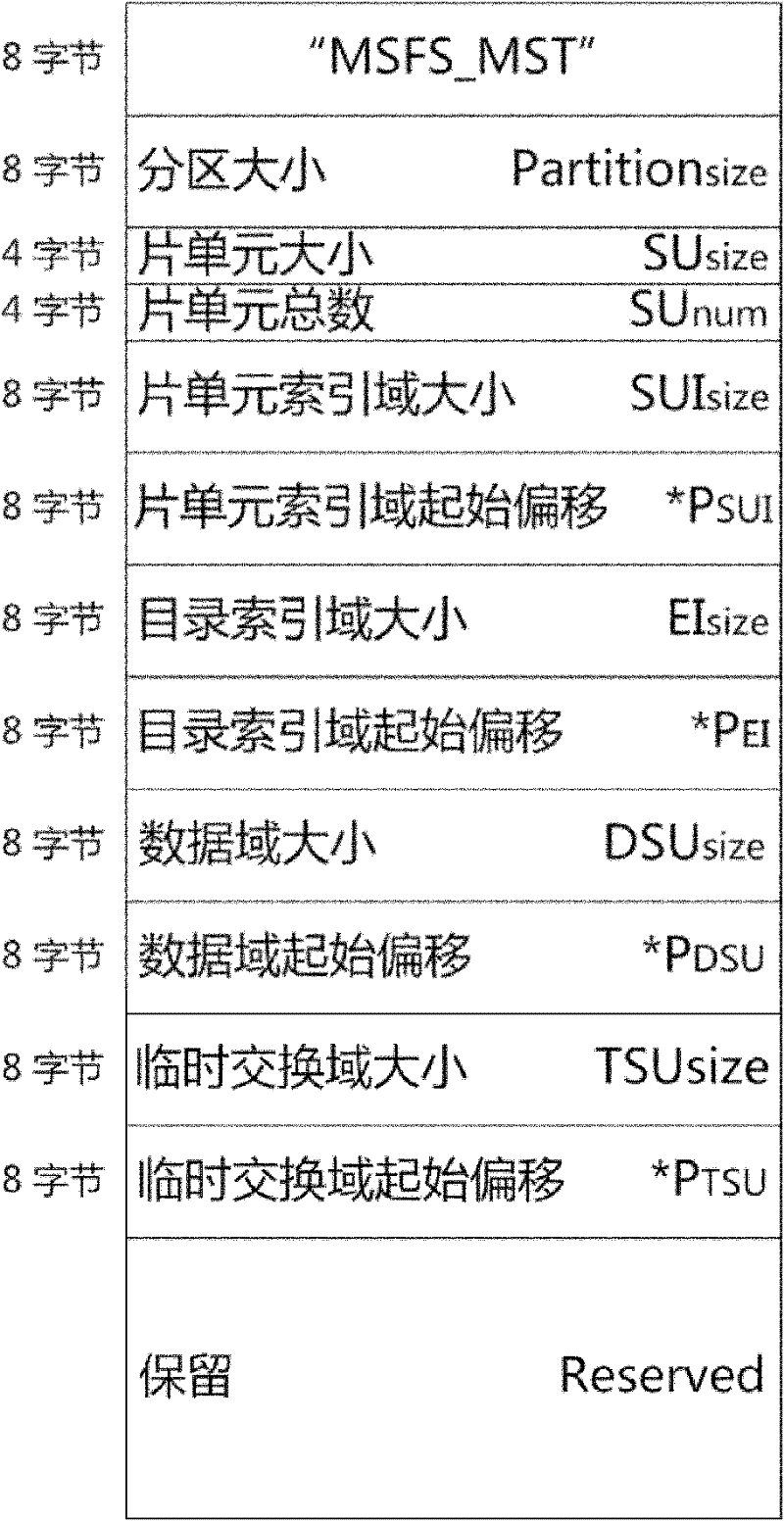
High-definition media-oriented embedded file storage structure and method
ActiveCN102682015AEasy to organize and manageReduce in quantitySpecial data processing applicationsFile systemData domain
The invention discloses a high-definition media-oriented embedded file storage structure and method. The storage structure comprises a label domain, a wafer unit indexing domain, a directory indexing domain, a data domain and a temporary switching domain, wherein the label domain is used for recording attribute information of a file system per se; the wafer unit indexing domain is used for indexing a minimum data unit in the file system and establishing a mapping relation with the data domain; the directory indexing domain is used for recording the attribute information of detailed files or directories; the data domain is used for storing corresponding actual data of the files and carrying out indexing management through the wafer unit indexing domain in the using process; and the temporary switching domain is used for storing certain temporary data which is generated for assisting search of a memory. Storage organization and management of files in an embedded system is realized by utilizing interaction relationship among the five domains. The high-definition media-oriented embedded file storage structure and method disclosed by the invention have the advantages of providing a storage structure with metadata and actual data separation and being capable of improving the stability and the reading-writing efficiency of the file system.
Owner:ZHENGZHOU SEANET TECH CO LTD
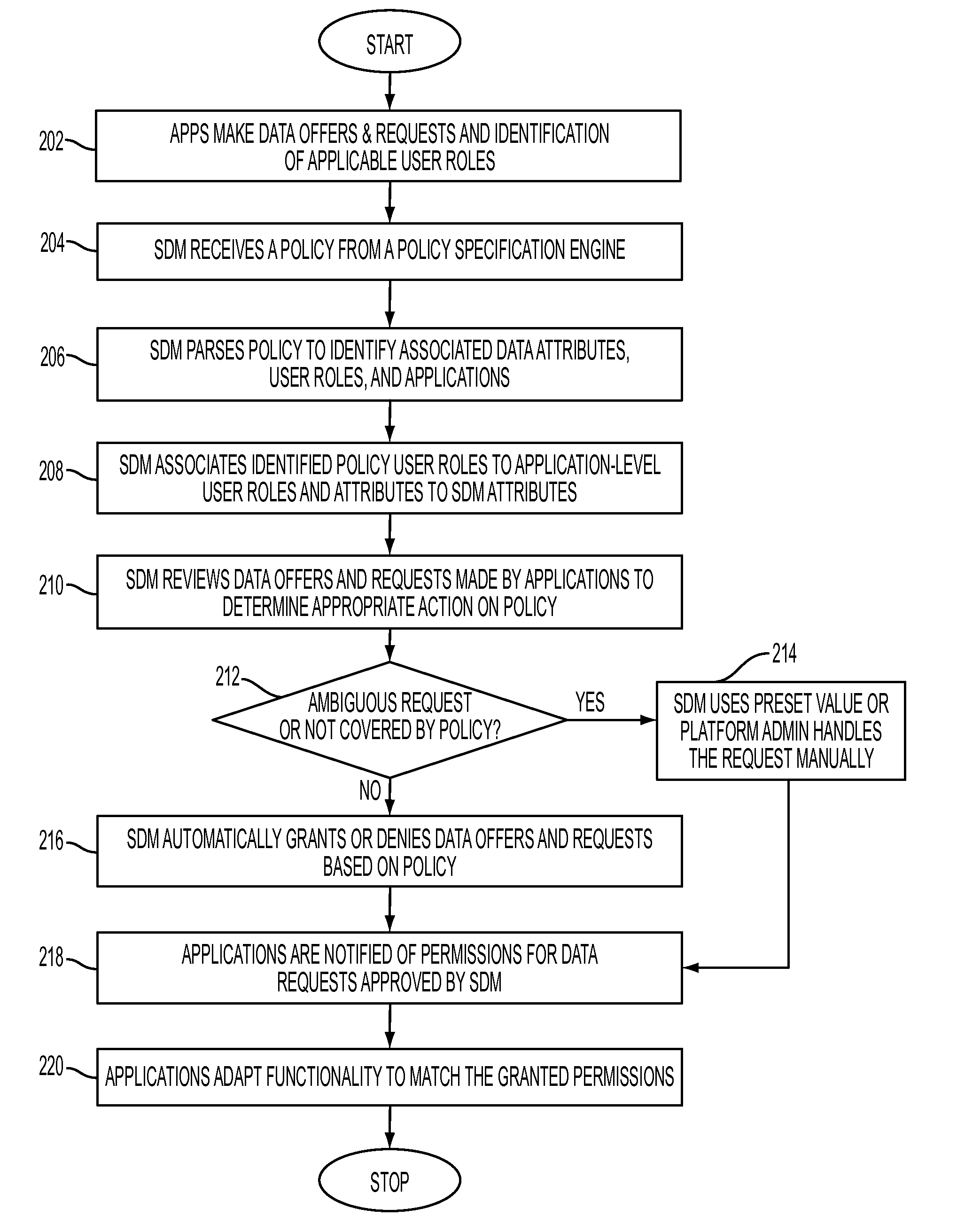
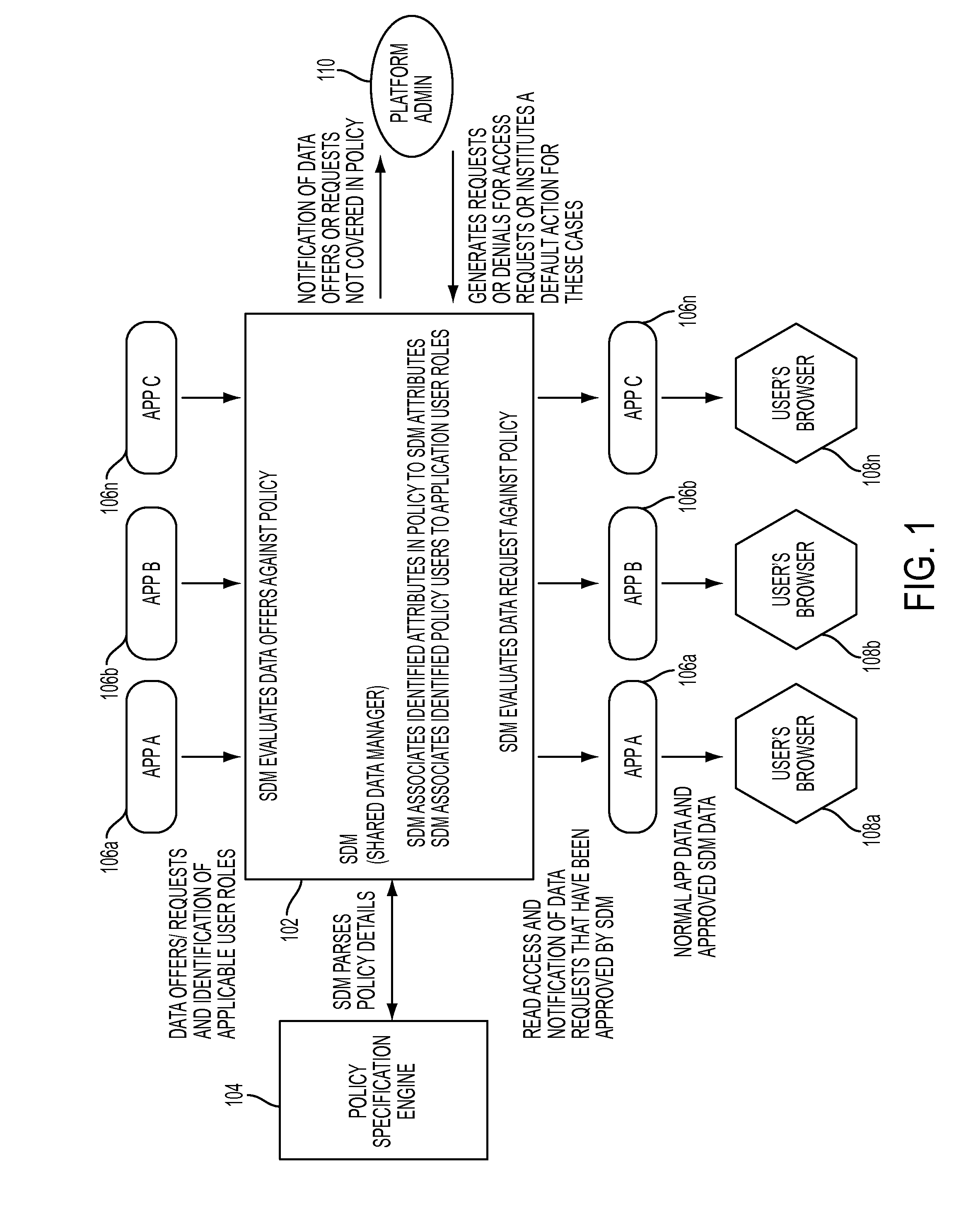
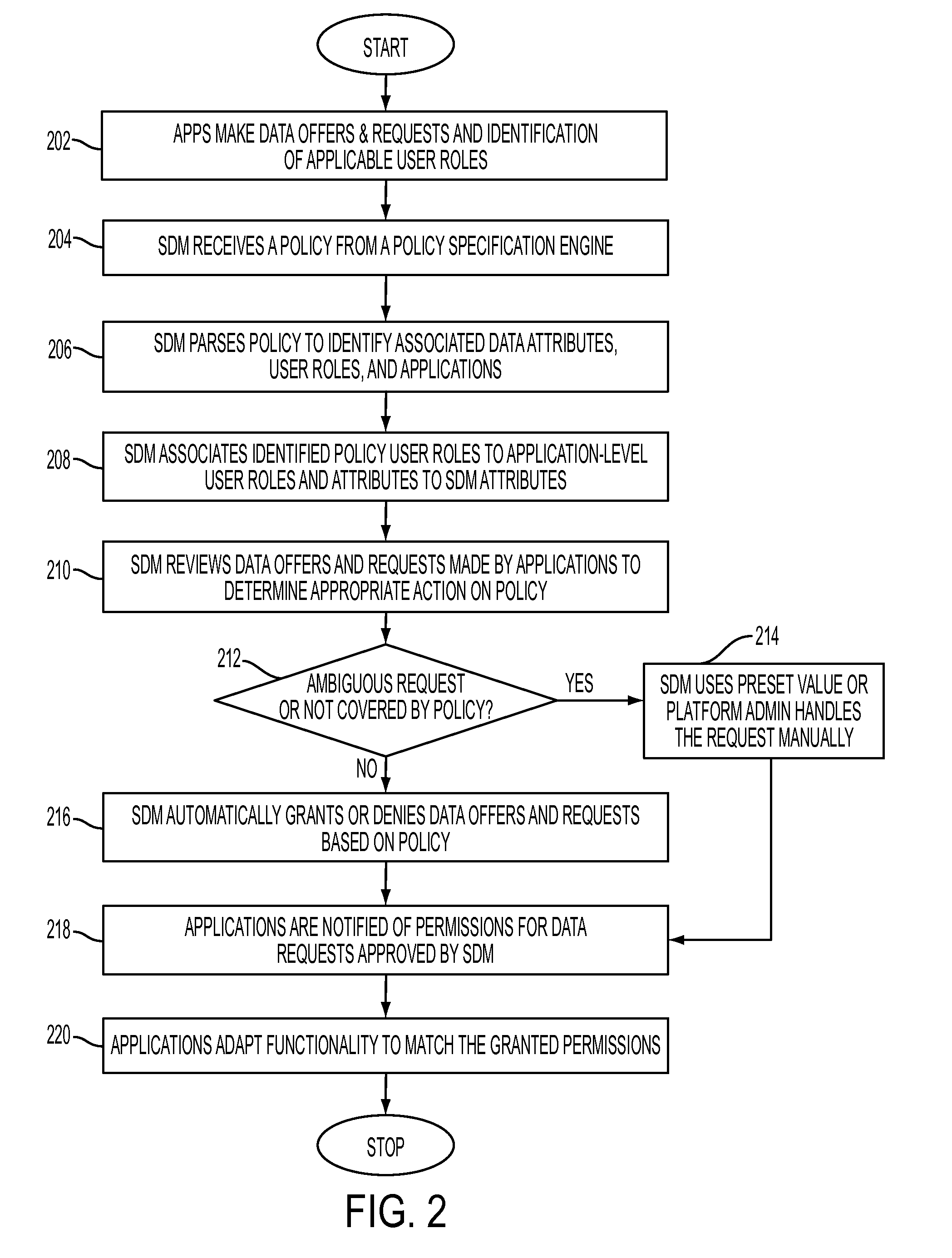
Enforcing data sharing policy through shared data management
InactiveUS8595798B2Digital data processing detailsAnalogue secracy/subscription systemsData accessData domain
Enforcing data sharing policy through shared data management, in one aspect, may include extracting data access rights from the one or more data policies based on a user role, data purpose, an object set and a constraint identification; extracting a data domain from the one or more data policies based on the data purpose and the object set; associating the data access rights and the data domain with data attributes of the shared data; automatically responding to application-based offers and requests for the shared data within a Software-as-a-Service platform based on the data access rights.
Owner:IBM CORP +1
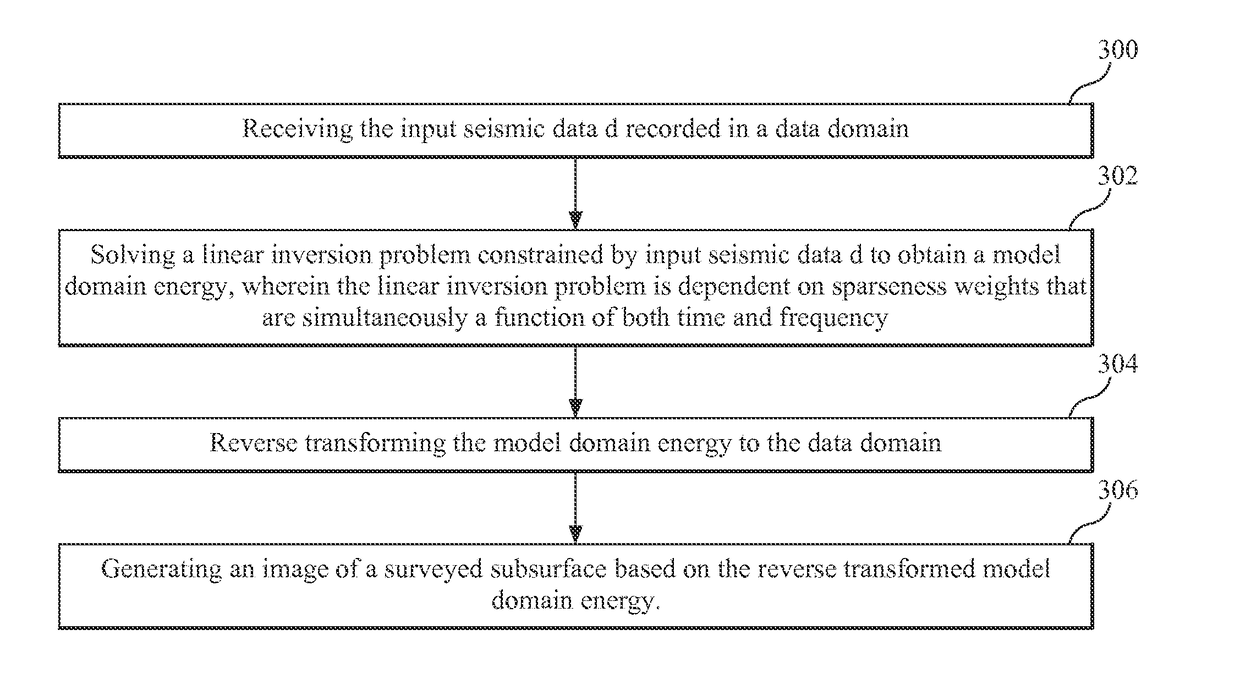
Device and method for weighted sparse inversion for seismic processing
Computing device, computer instructions and method for processing input seismic data d. The method includes receiving the input seismic data d recorded in a data domain, solving a linear inversion problem constrained by input seismic data d to obtain a model domain and its energy, wherein the linear inversion problem is dependent on sparseness weights that are simultaneously a function of both time and frequency, reverse transforming the model domain energy to the data domain, and generating an image of a surveyed subsurface based on the reverse transformed model domain energy.
Owner:CGG SERVICES SAS
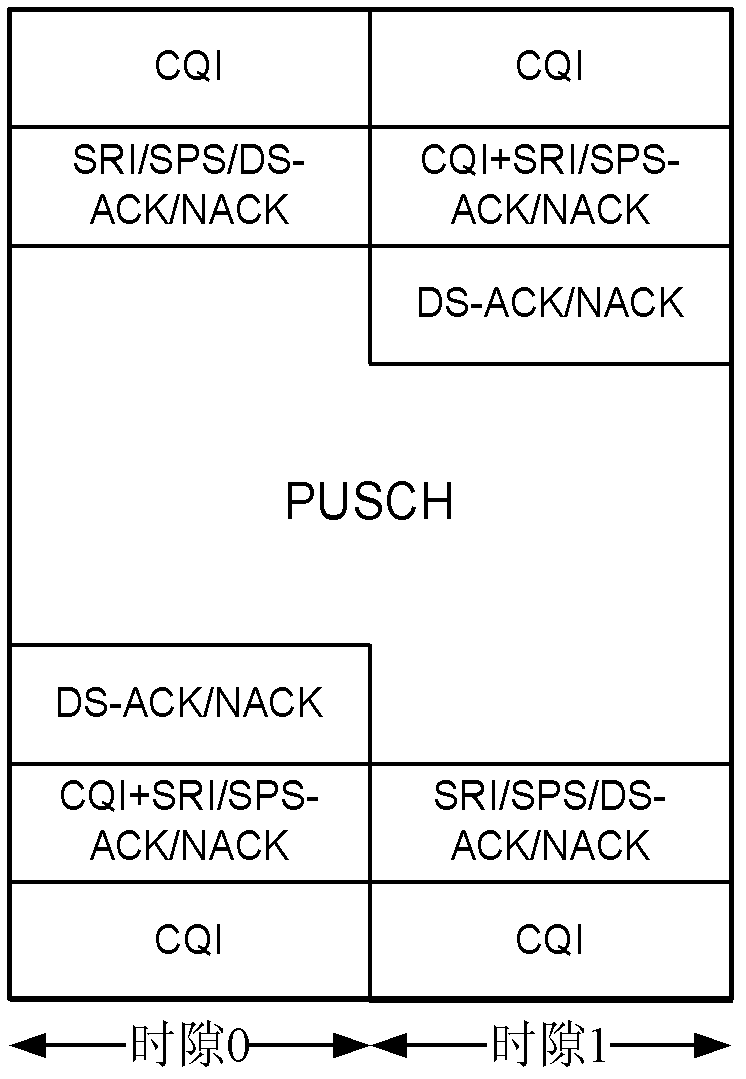
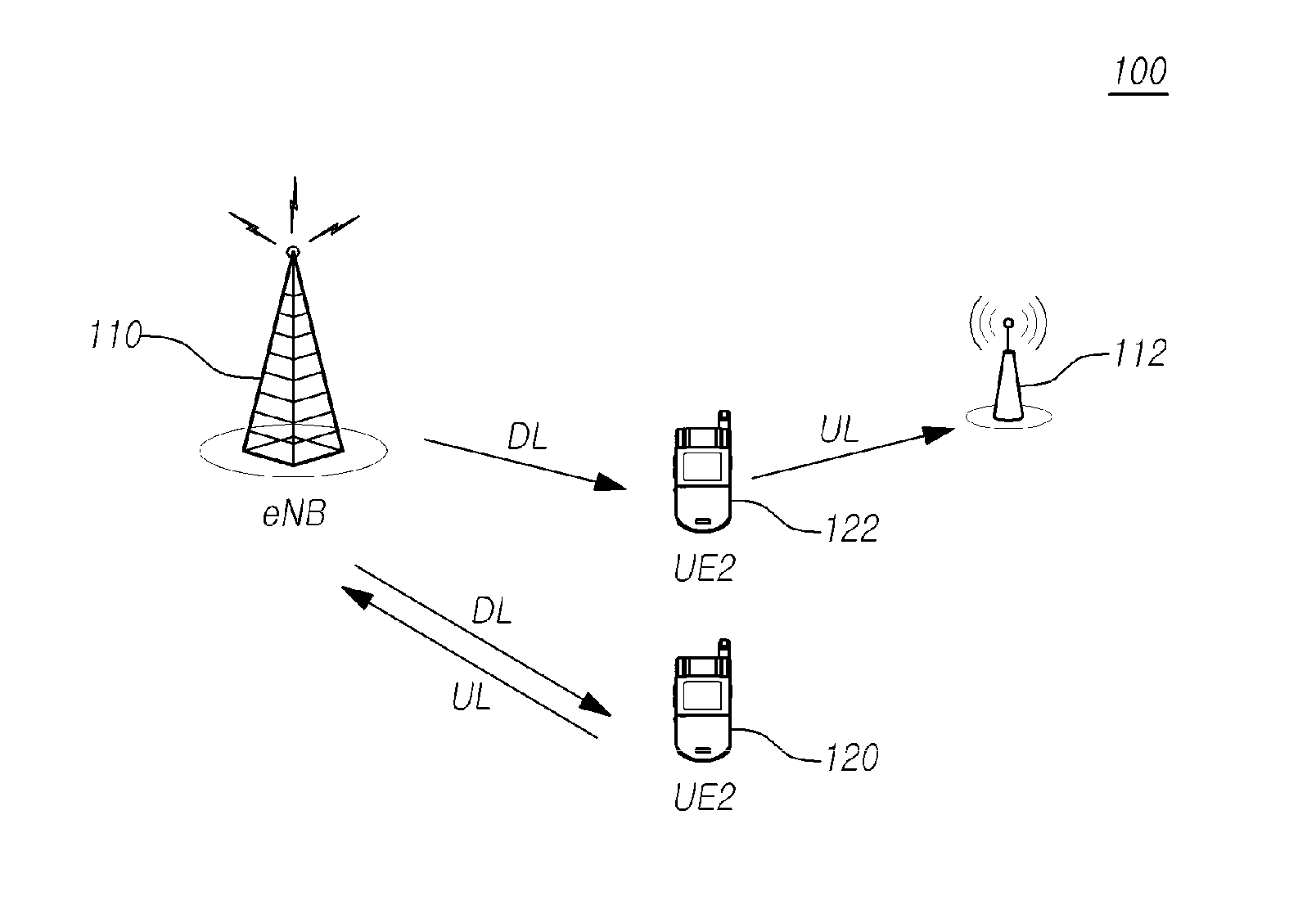
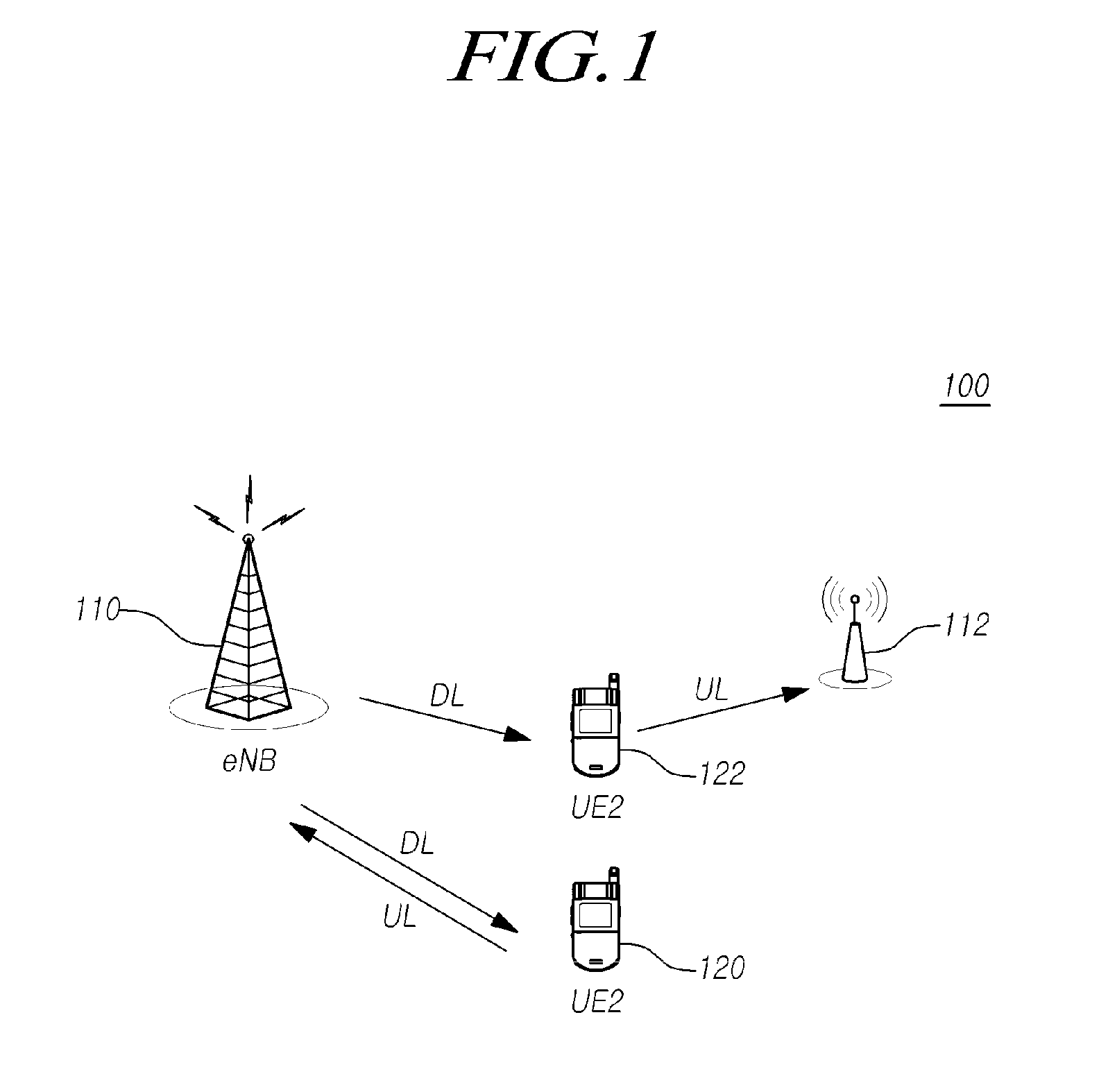
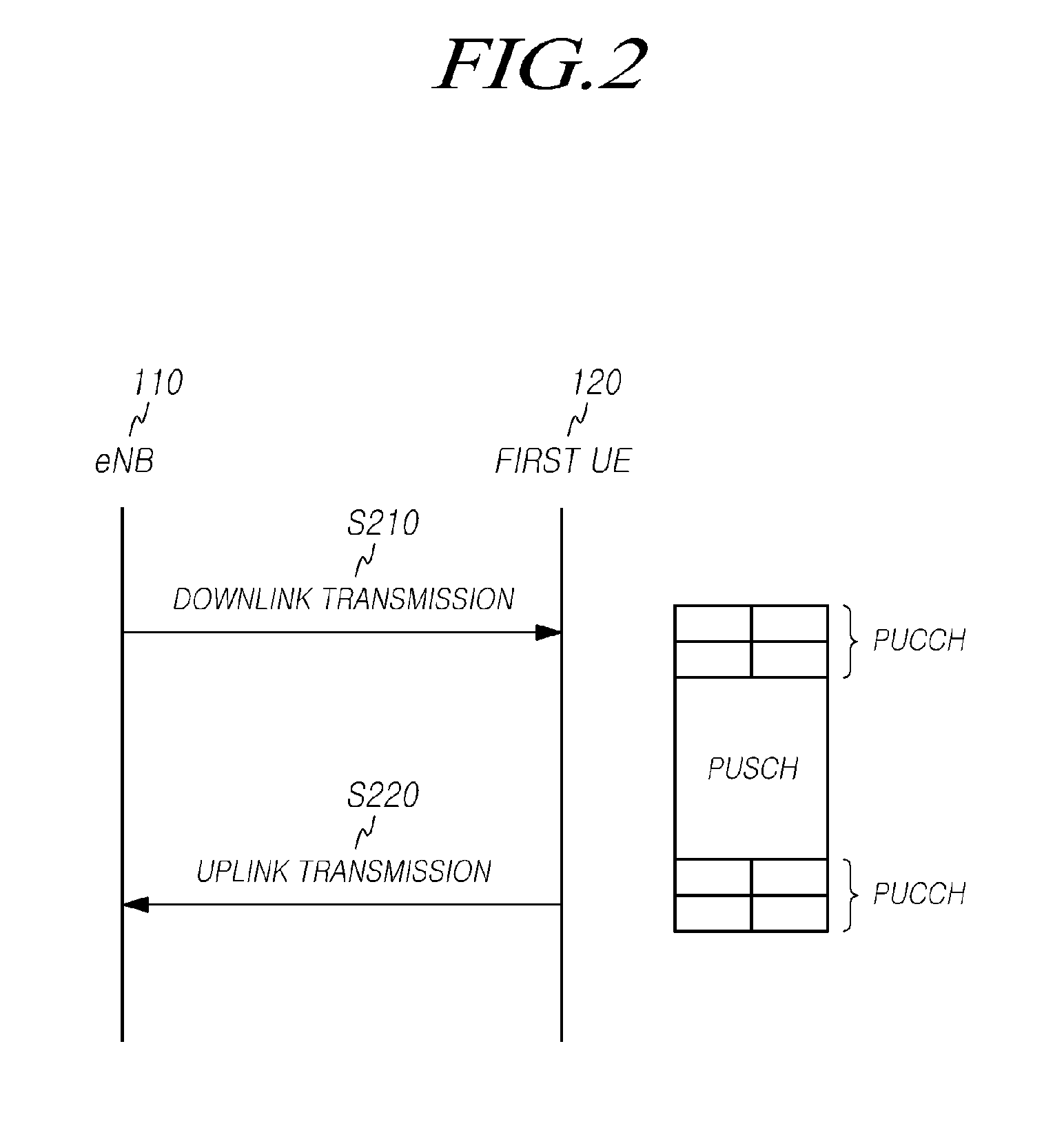
Method for transmitting control information on transmission points and corresponding transmission point, as well as method for mapping uplink control channel resource of terminal and corresponding terminal
ActiveUS20150208391A1Guaranteed normal transmissionError preventionSignal allocationTelecommunicationsData domain
The present disclosure relates to a method and apparatus for transmitting uplink control information for a terminal. That is, the method and apparatus may be provided for transmitting downlink control information through a downlink control channel which is introduced into a data domain and receiving control information. More particularly, a method and apparatus may be provided for mapping an uplink control channel resource for feeding back uplink HARQ ACK / NACK of the terminal for a downlink data channel through downlink scheduling information, which is transmitted via the downlink control channel.
Owner:KT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com