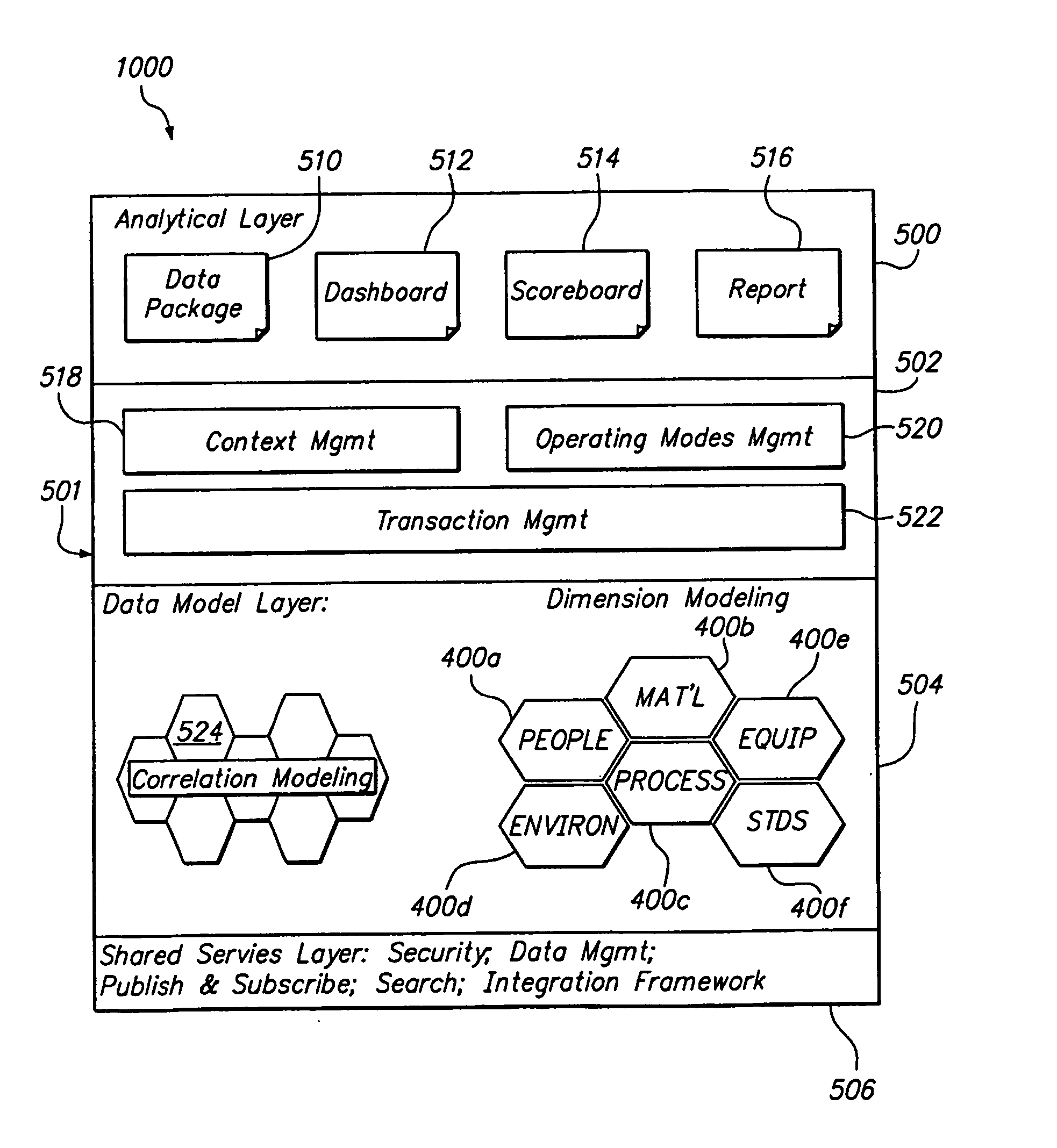
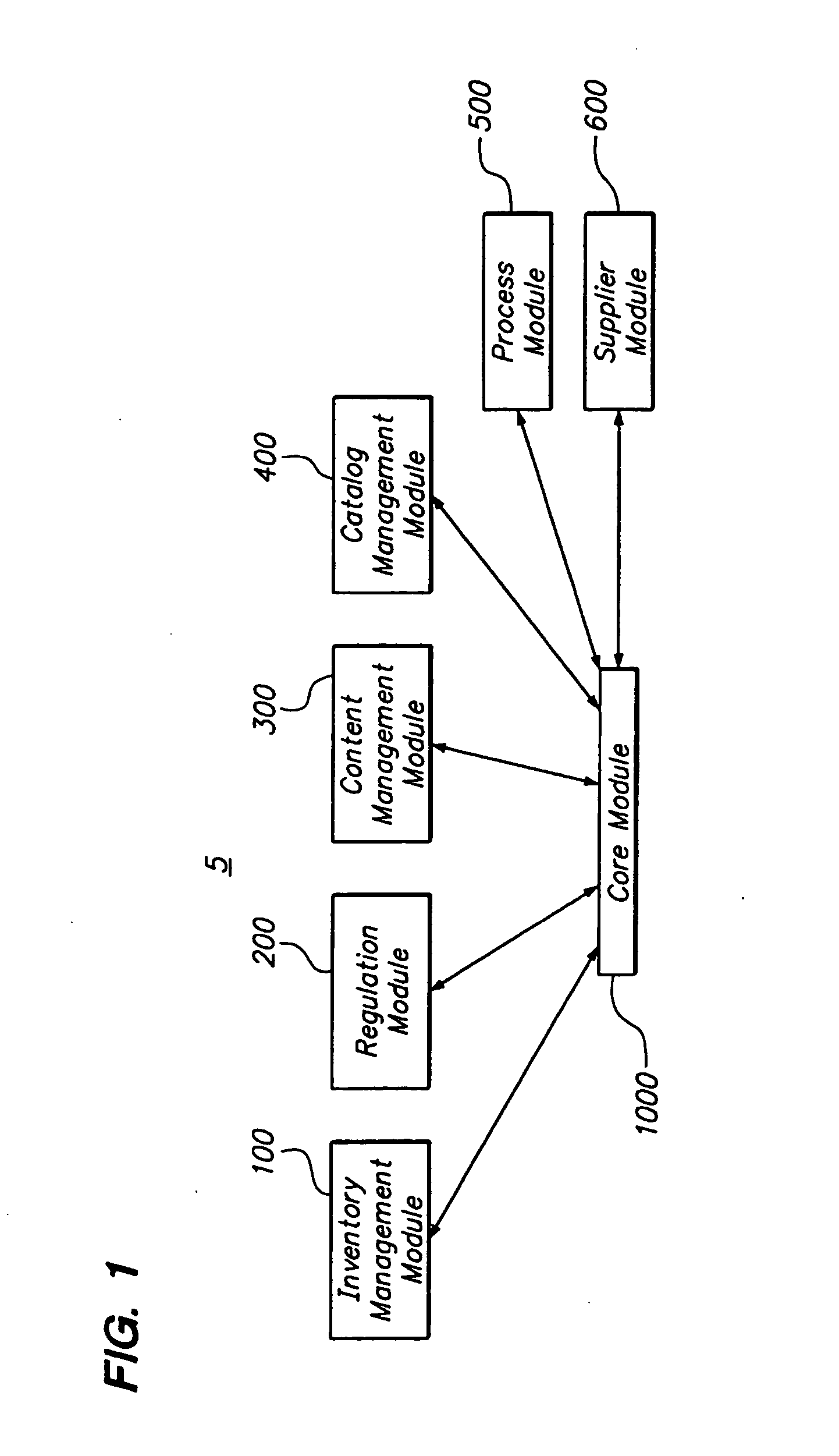
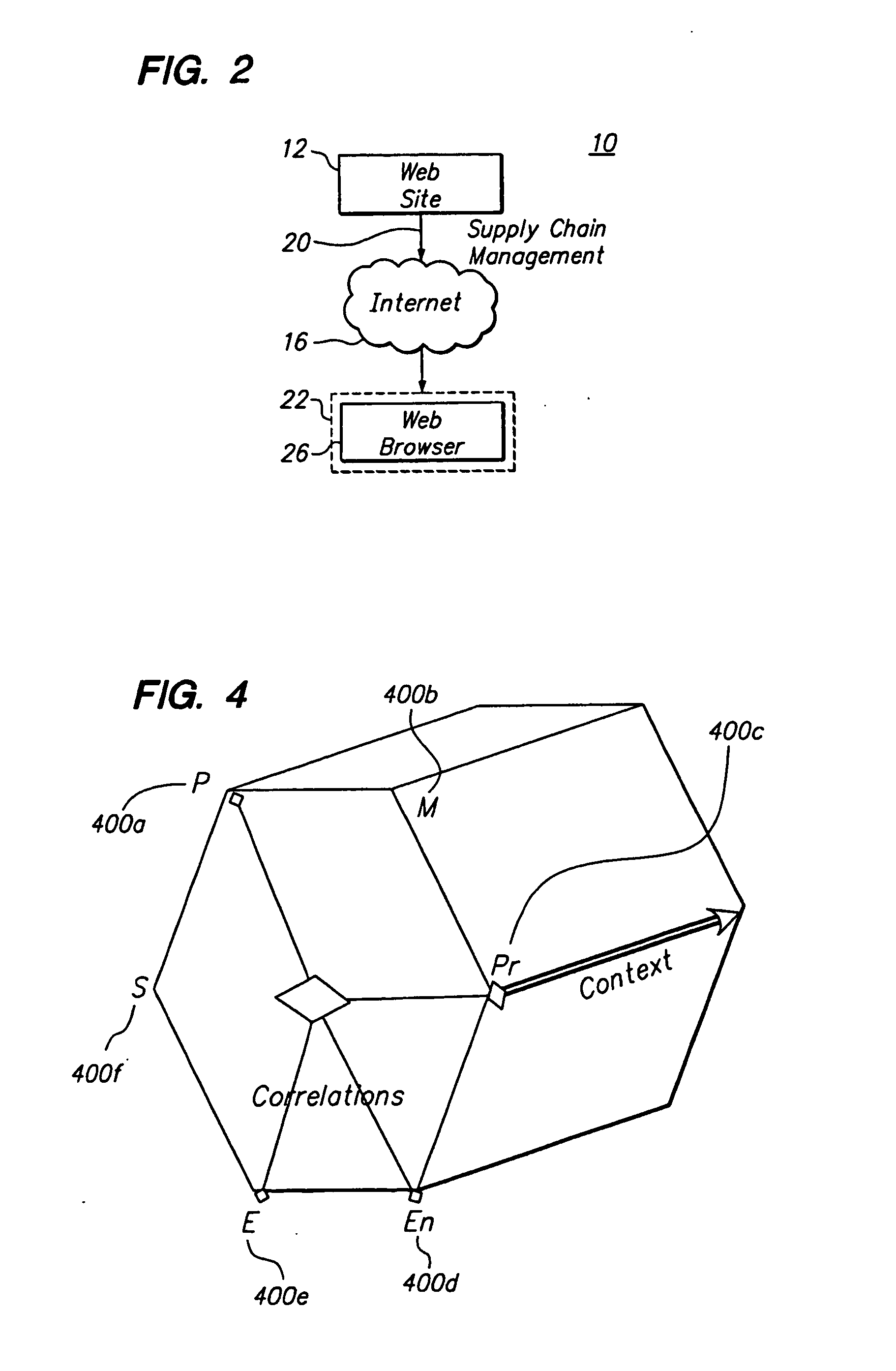
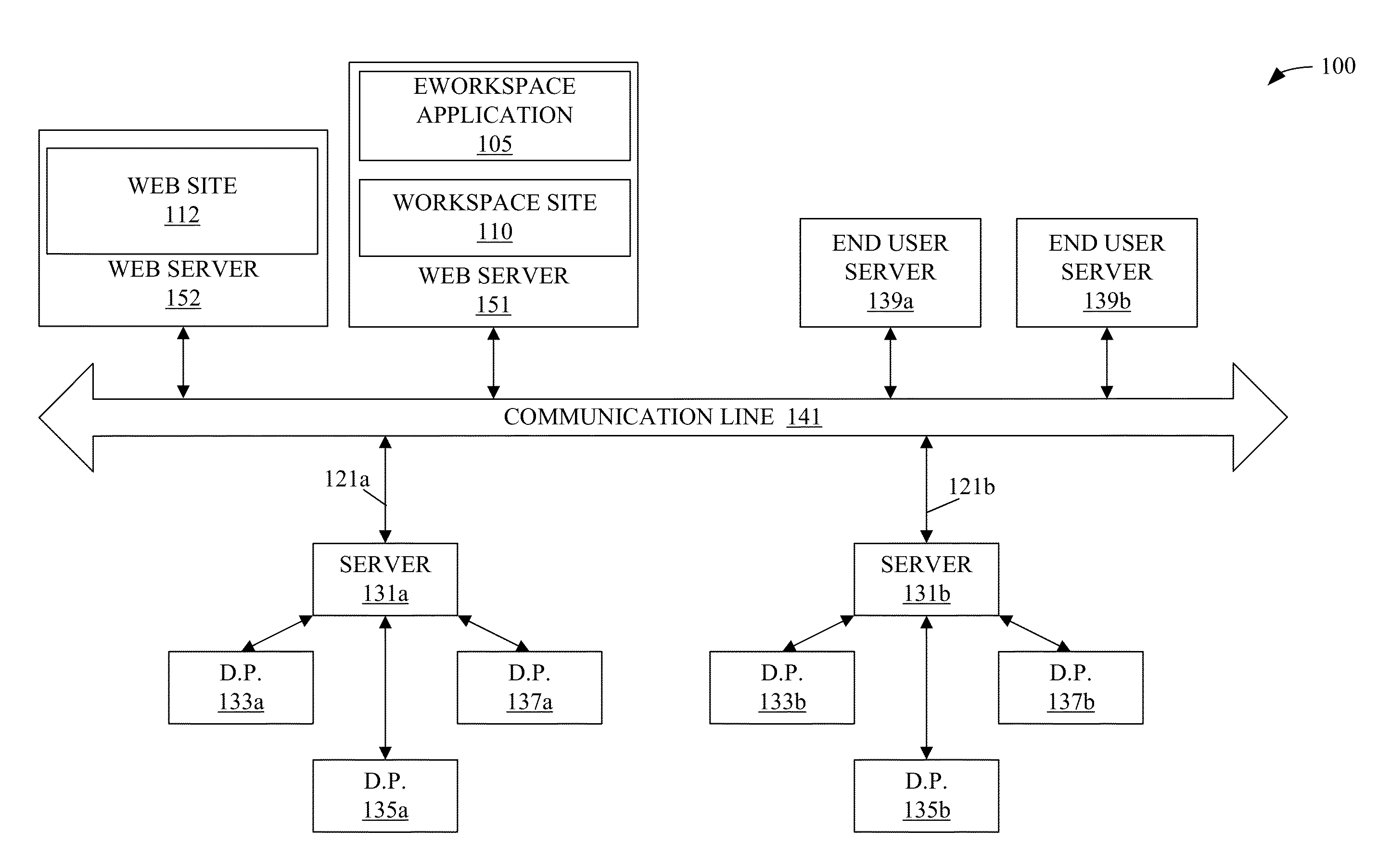
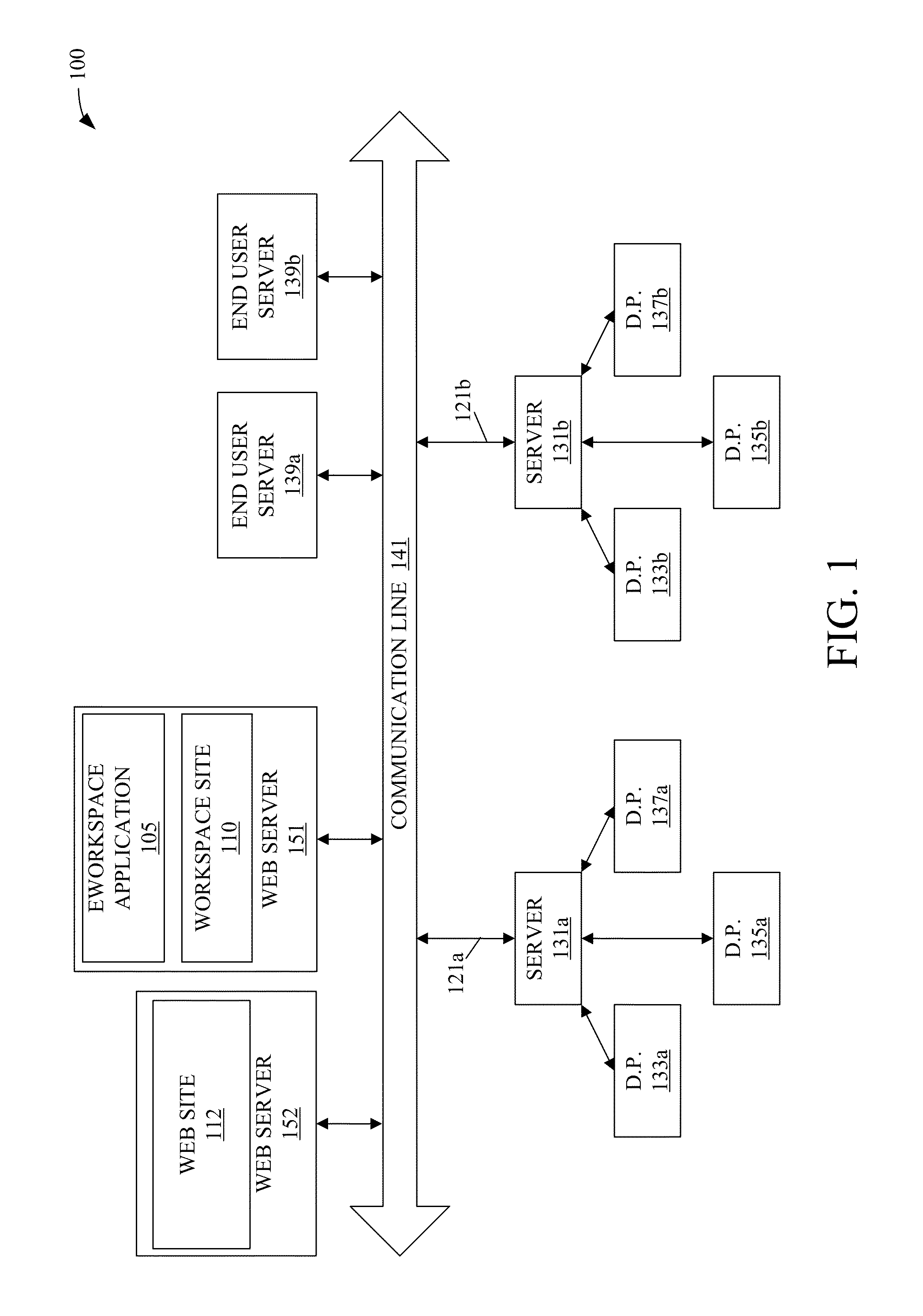
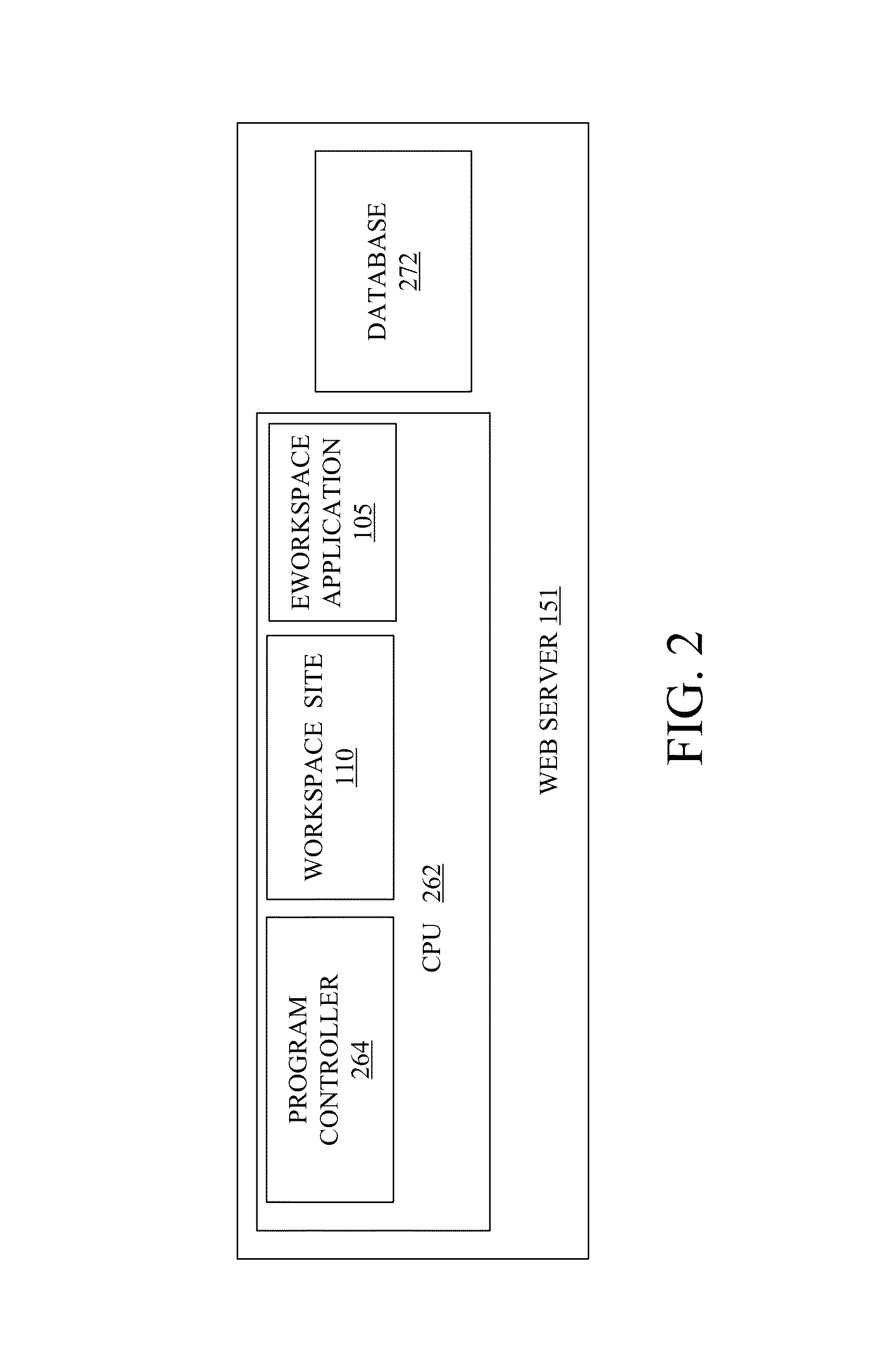
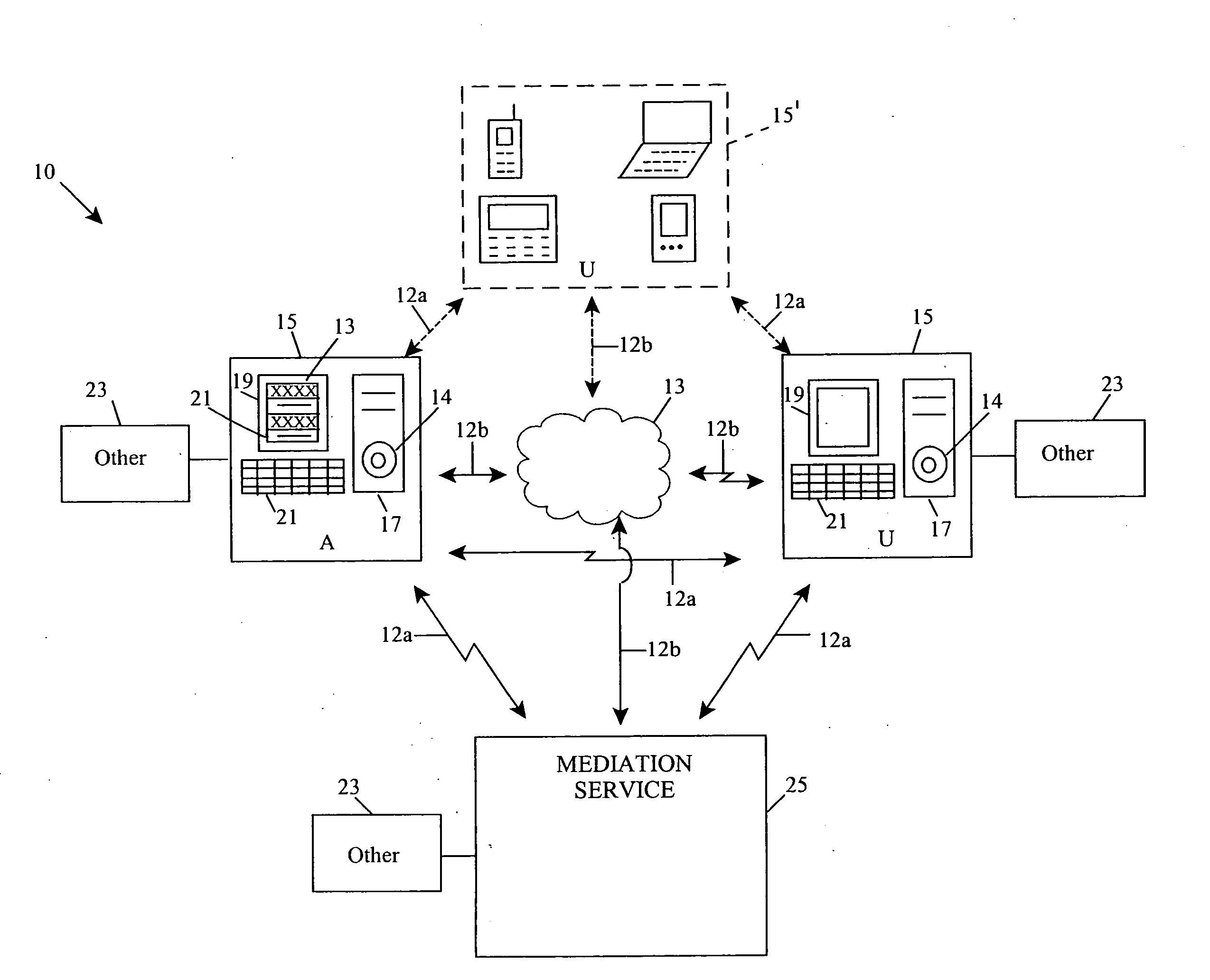
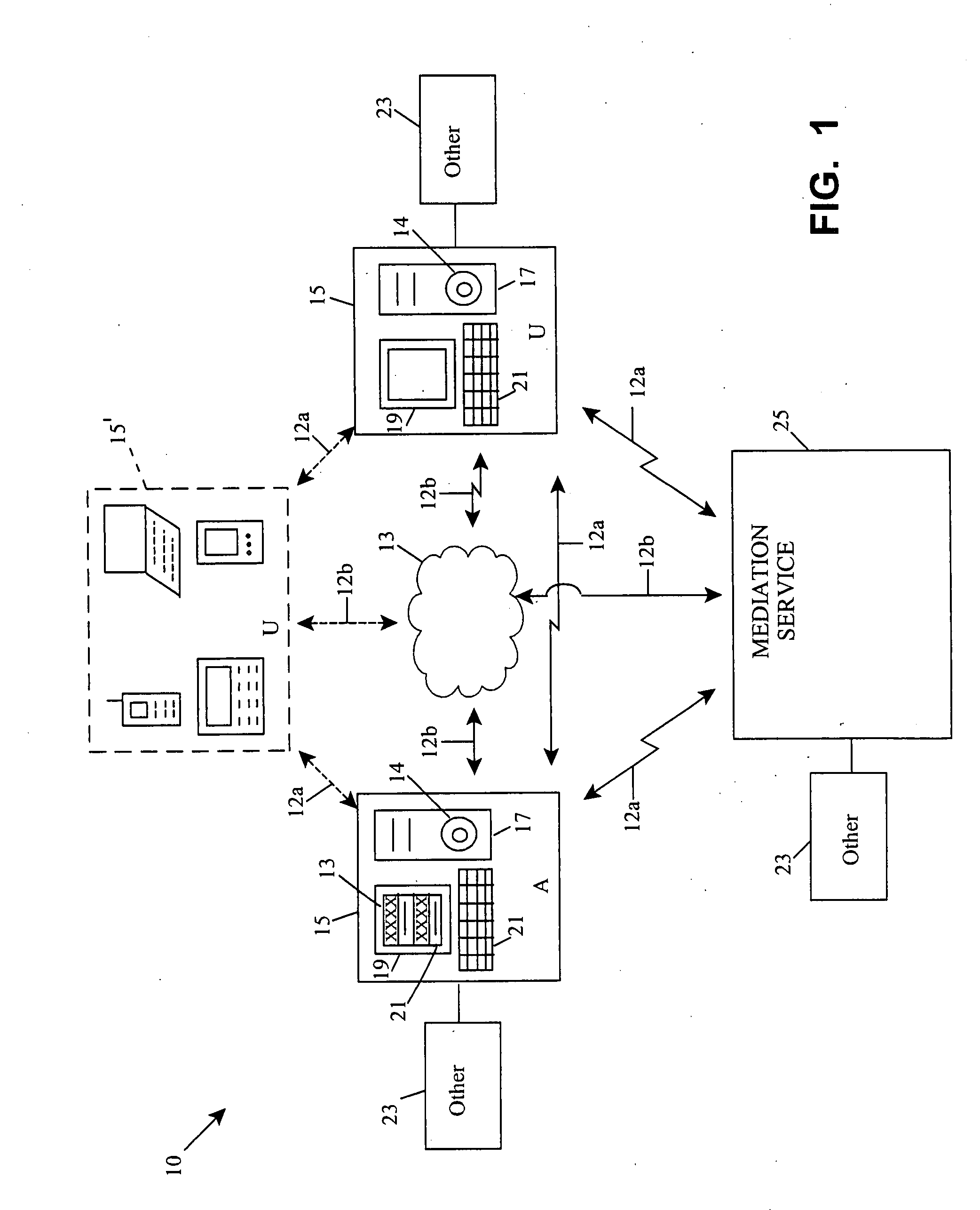
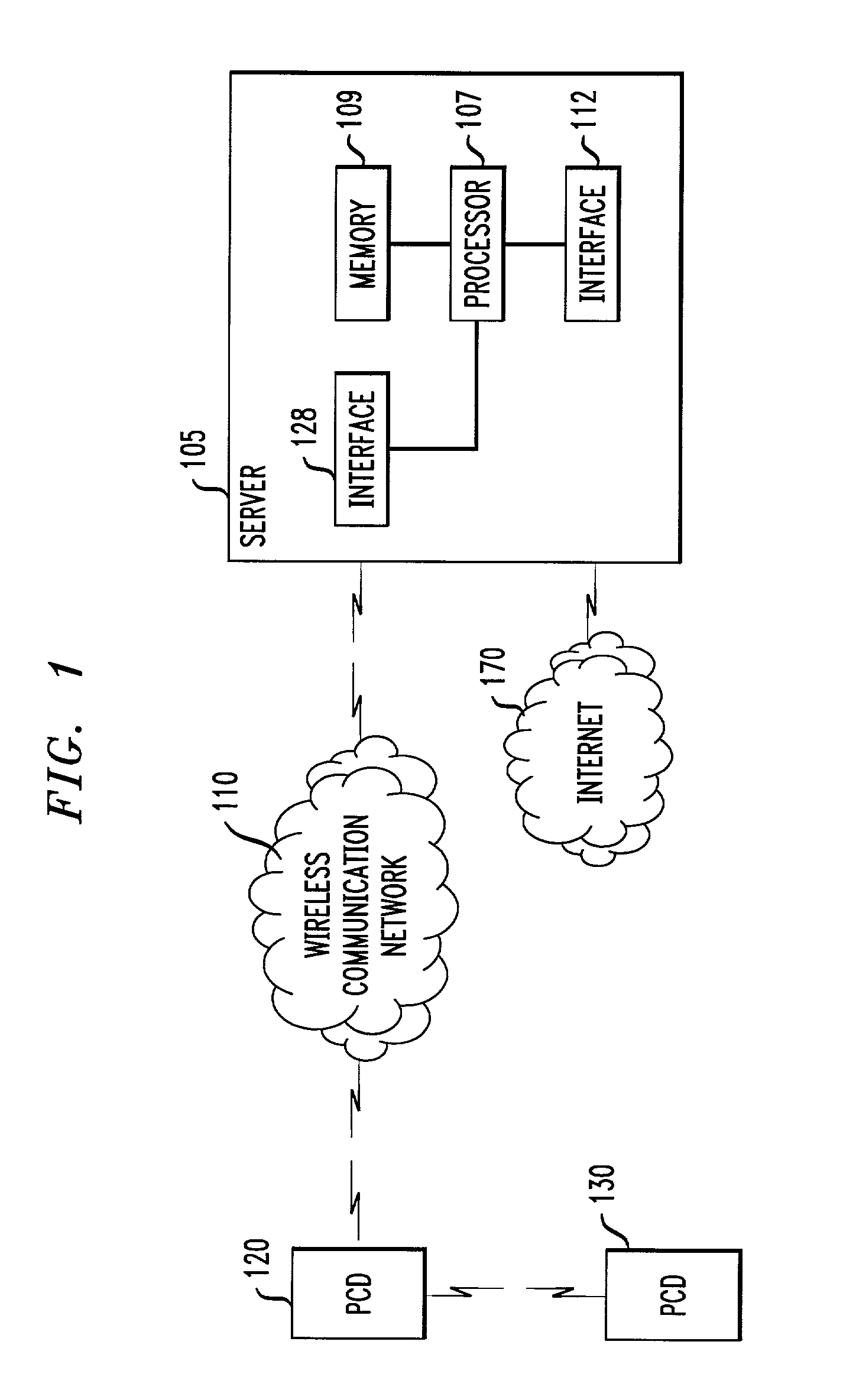
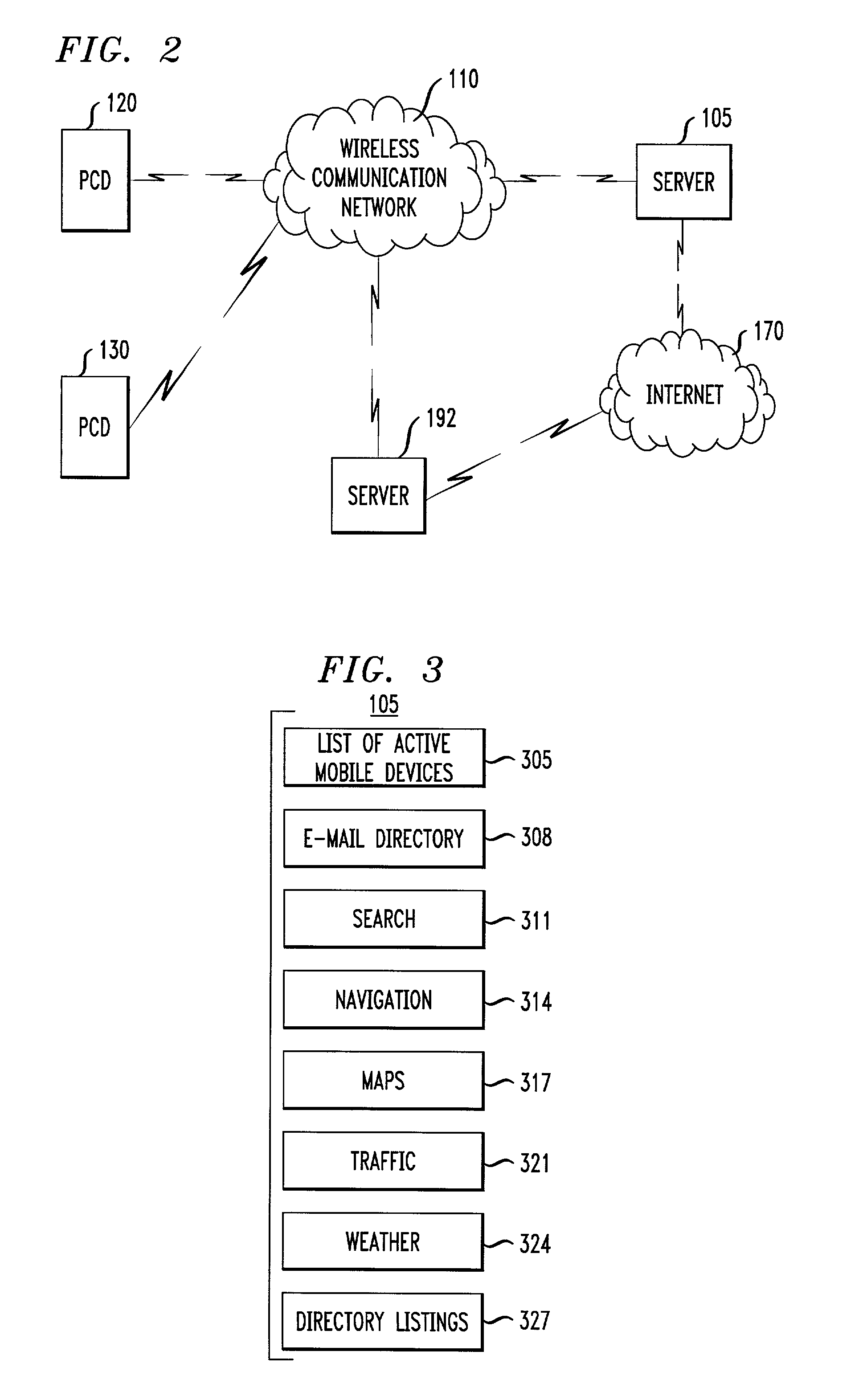
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
774 results about "User role" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
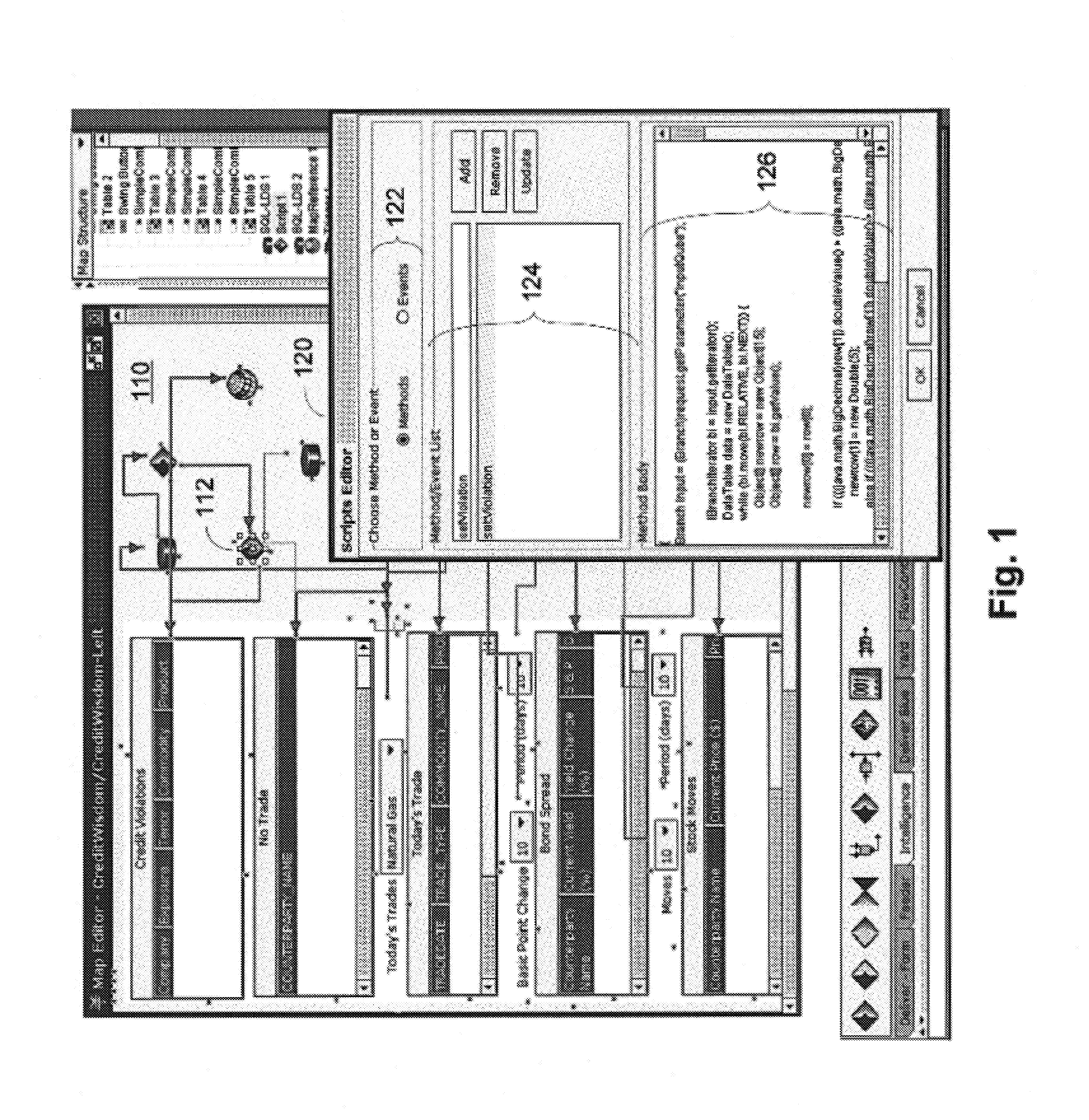
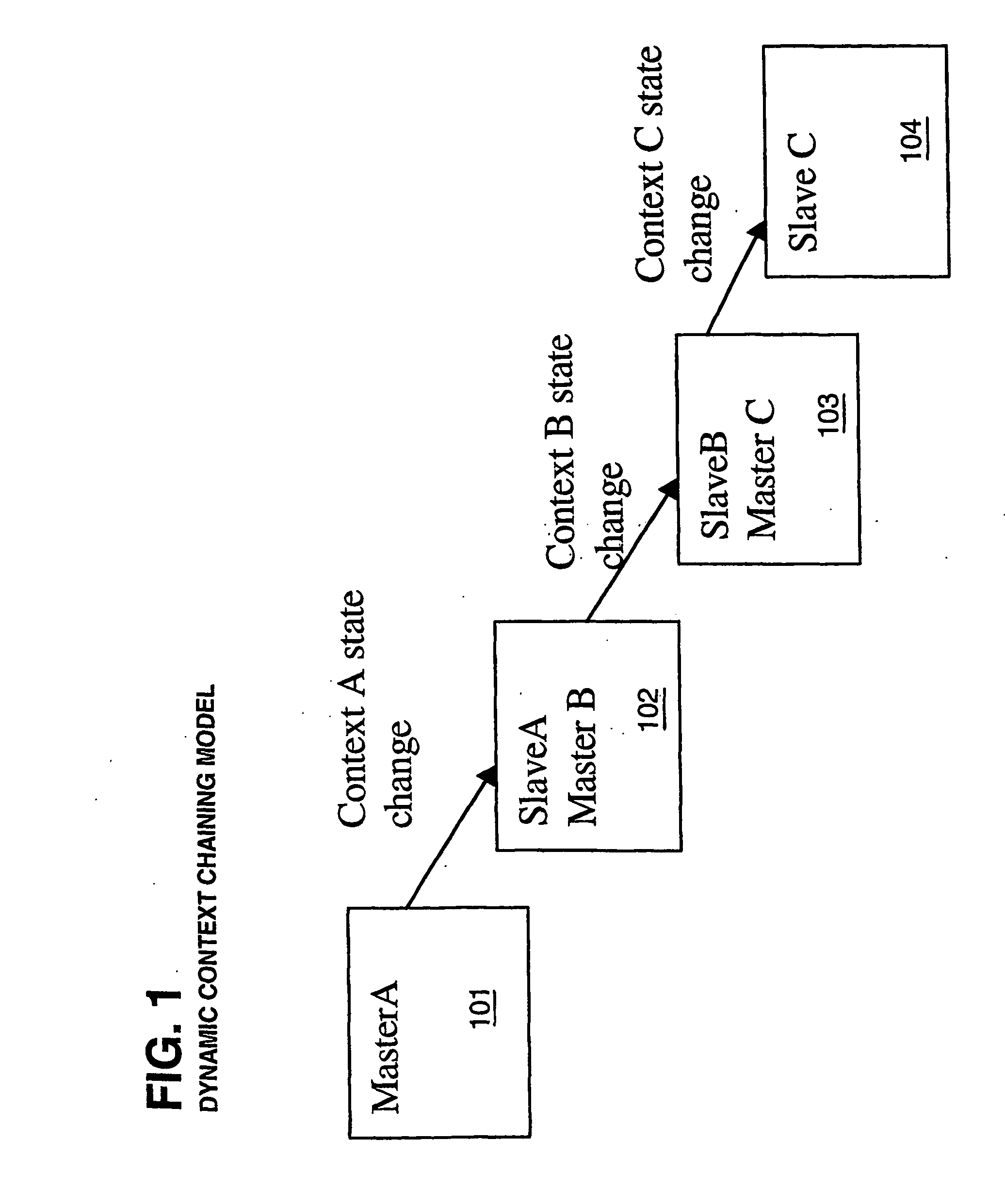
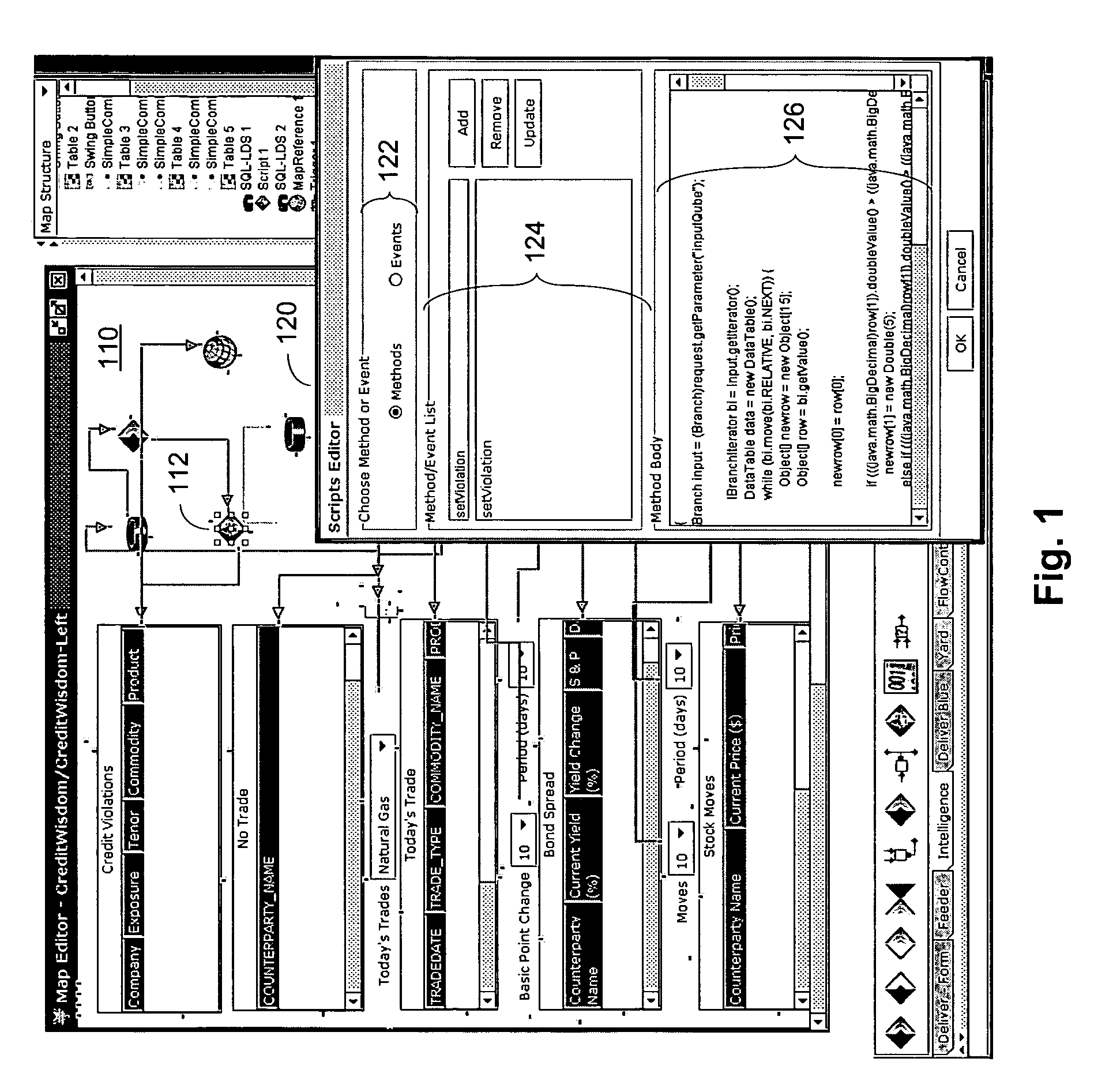
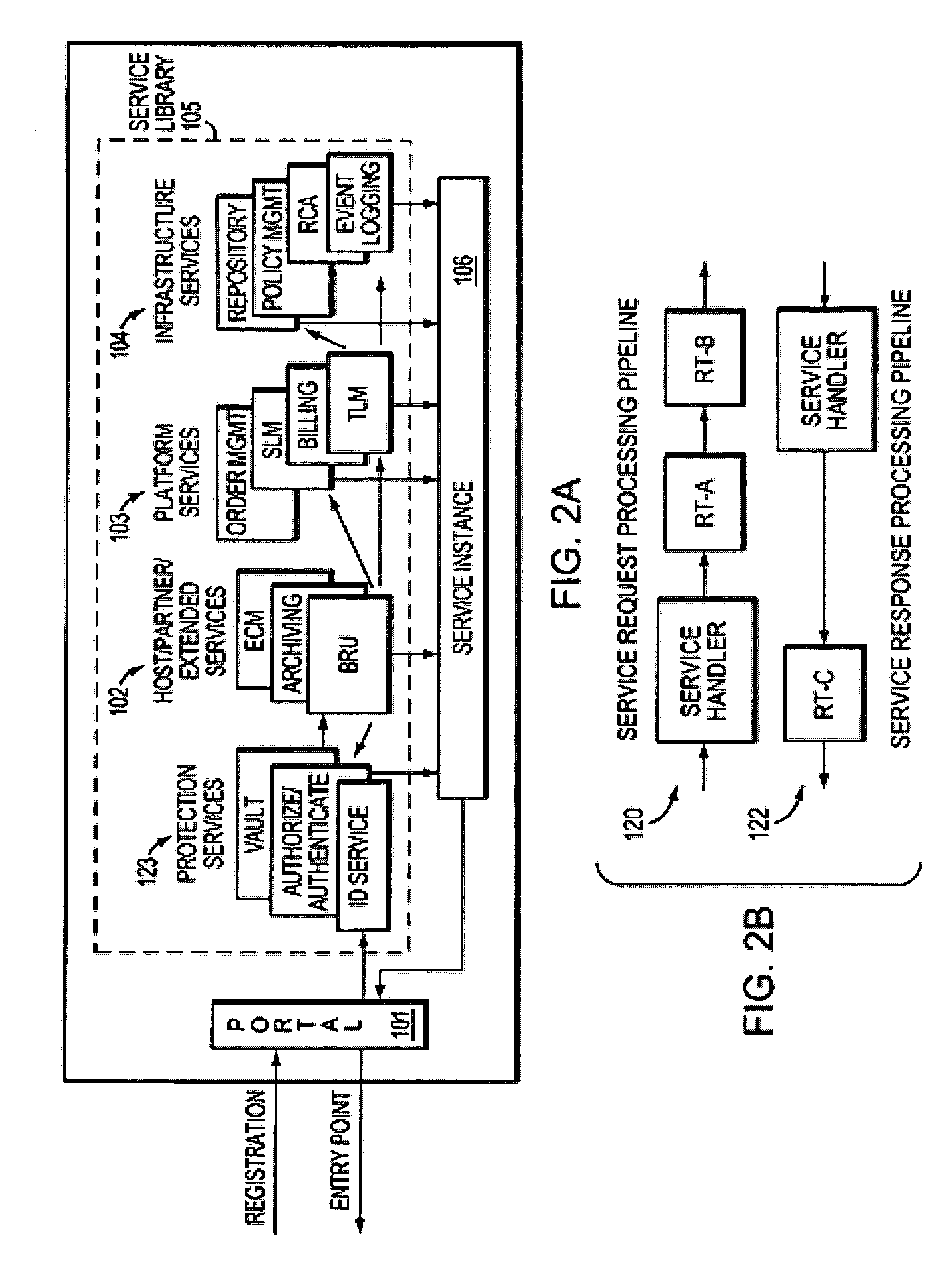
User roles are predefined categories that can be assigned to form users based on their job title or some other criteria. User roles can be used to present customized views of a form to different types of users, display different sections in a view, or calculate the default value of a field or control.
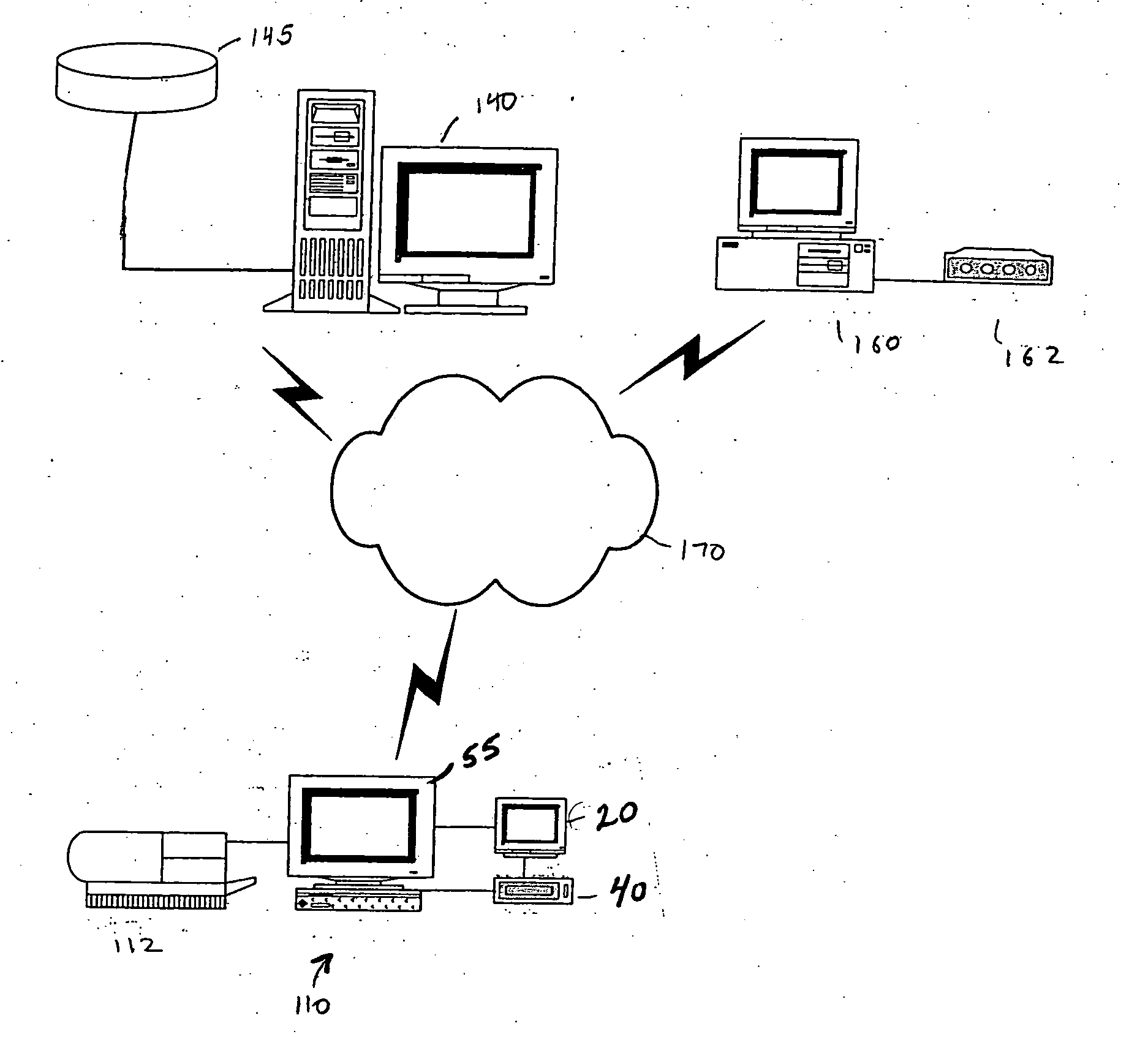
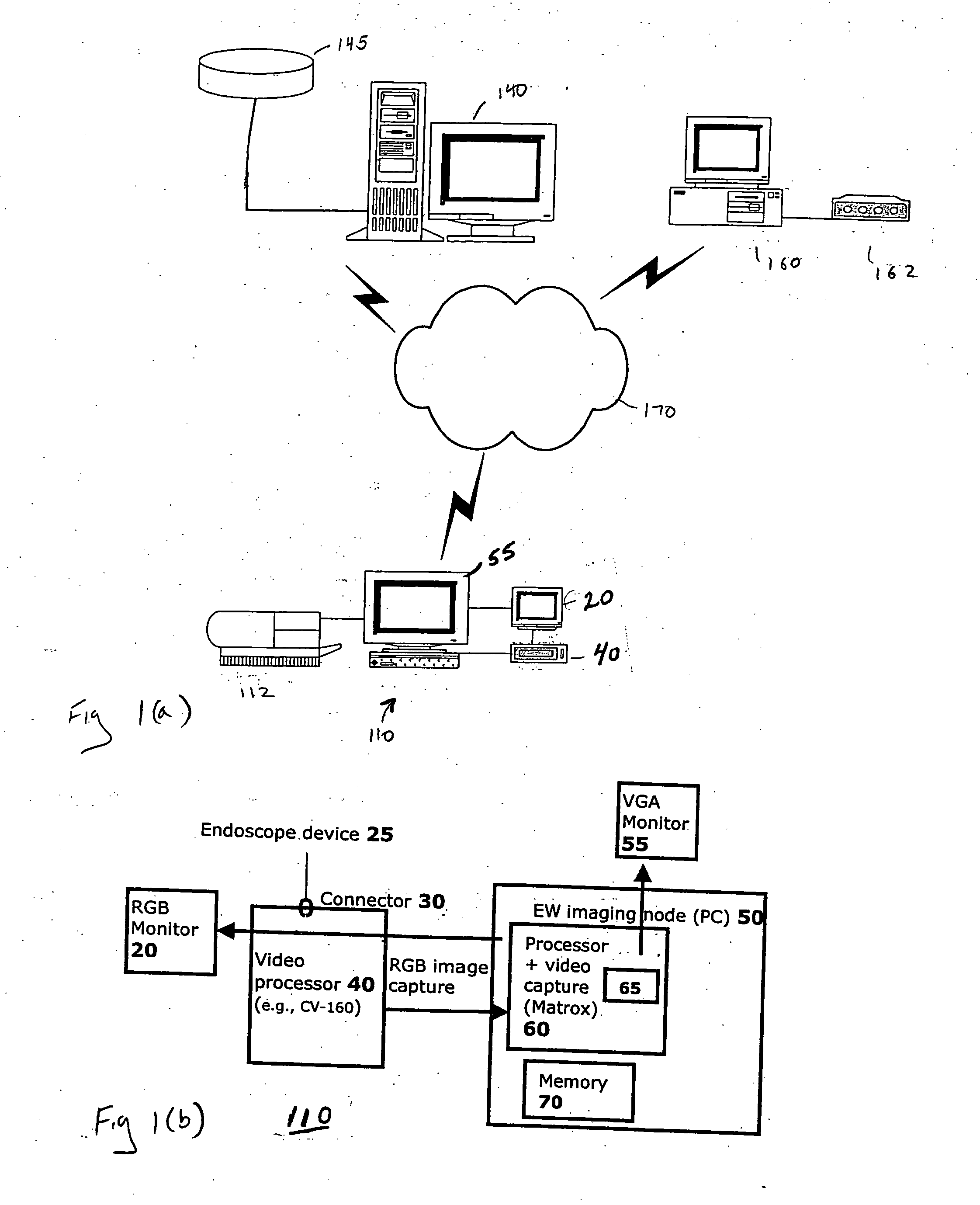
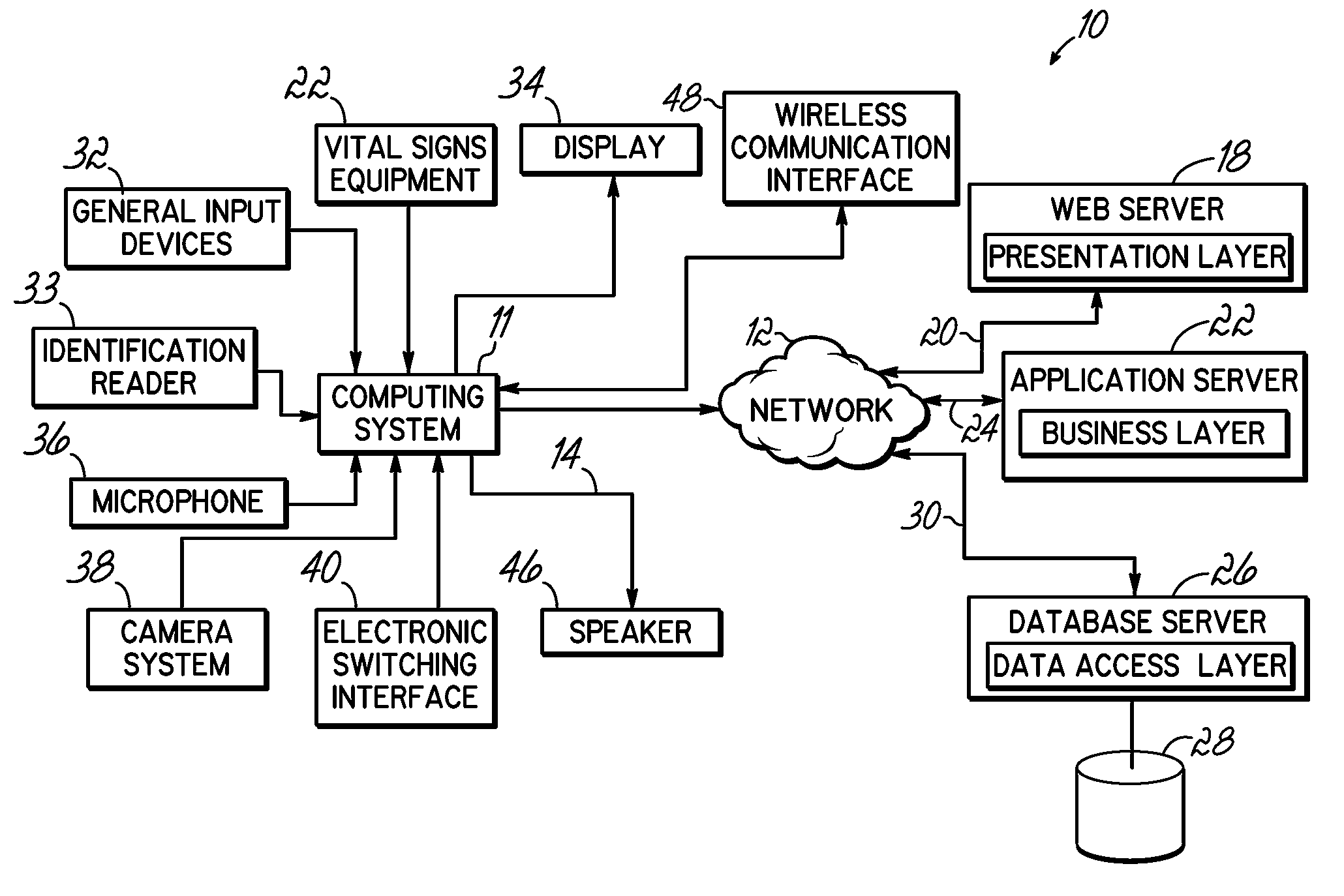
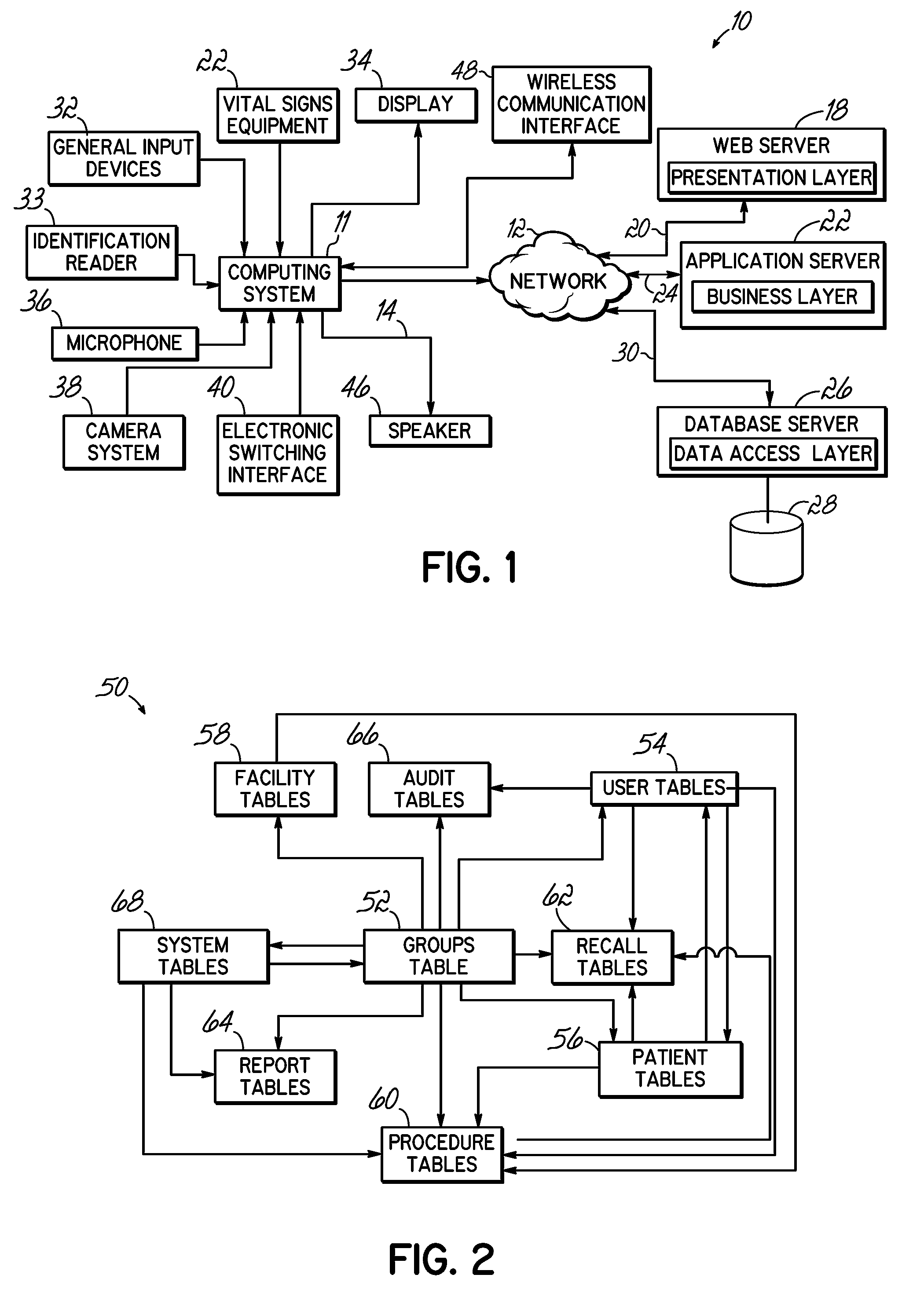
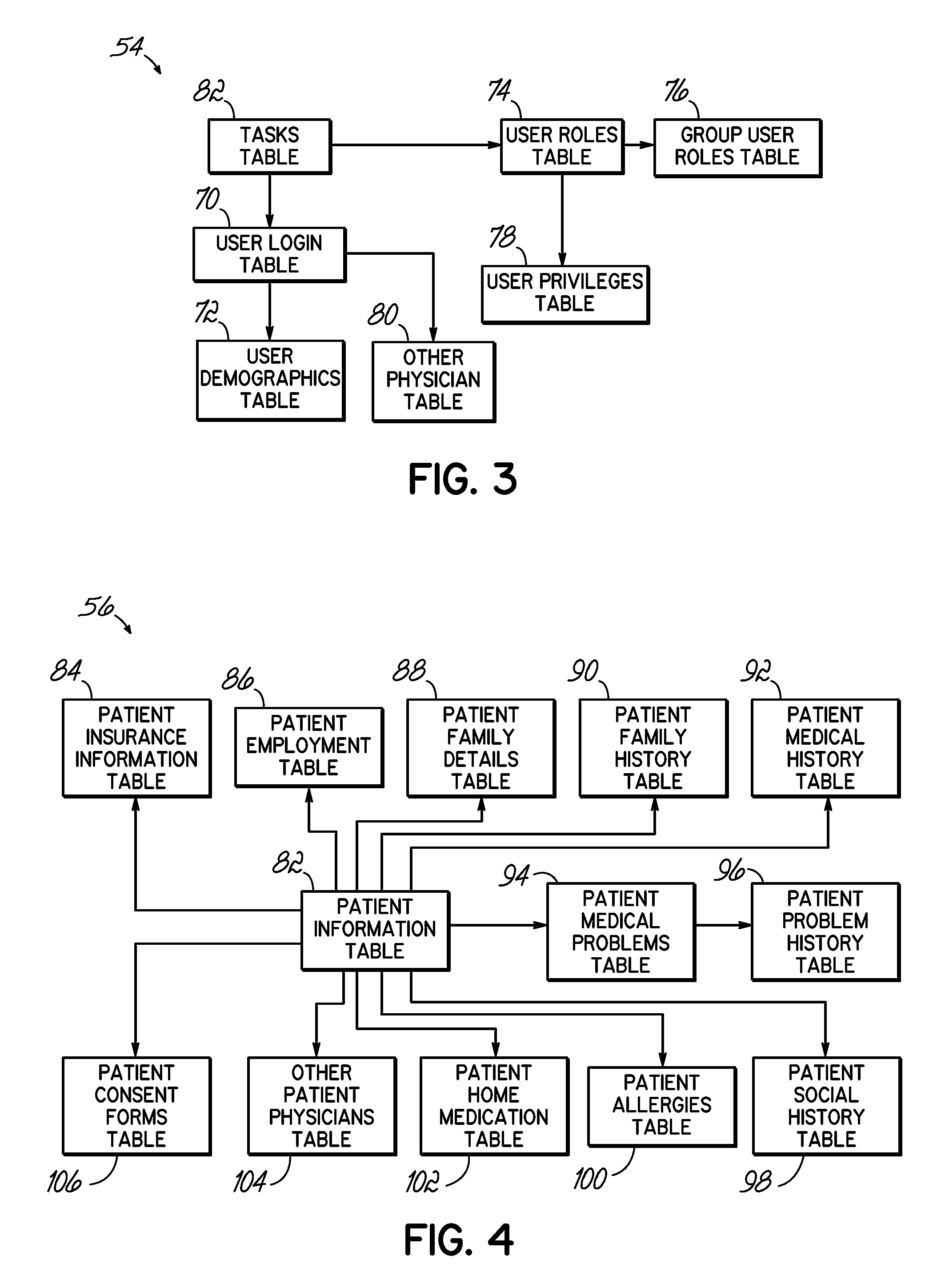
System and method for managing an endoscopic lab
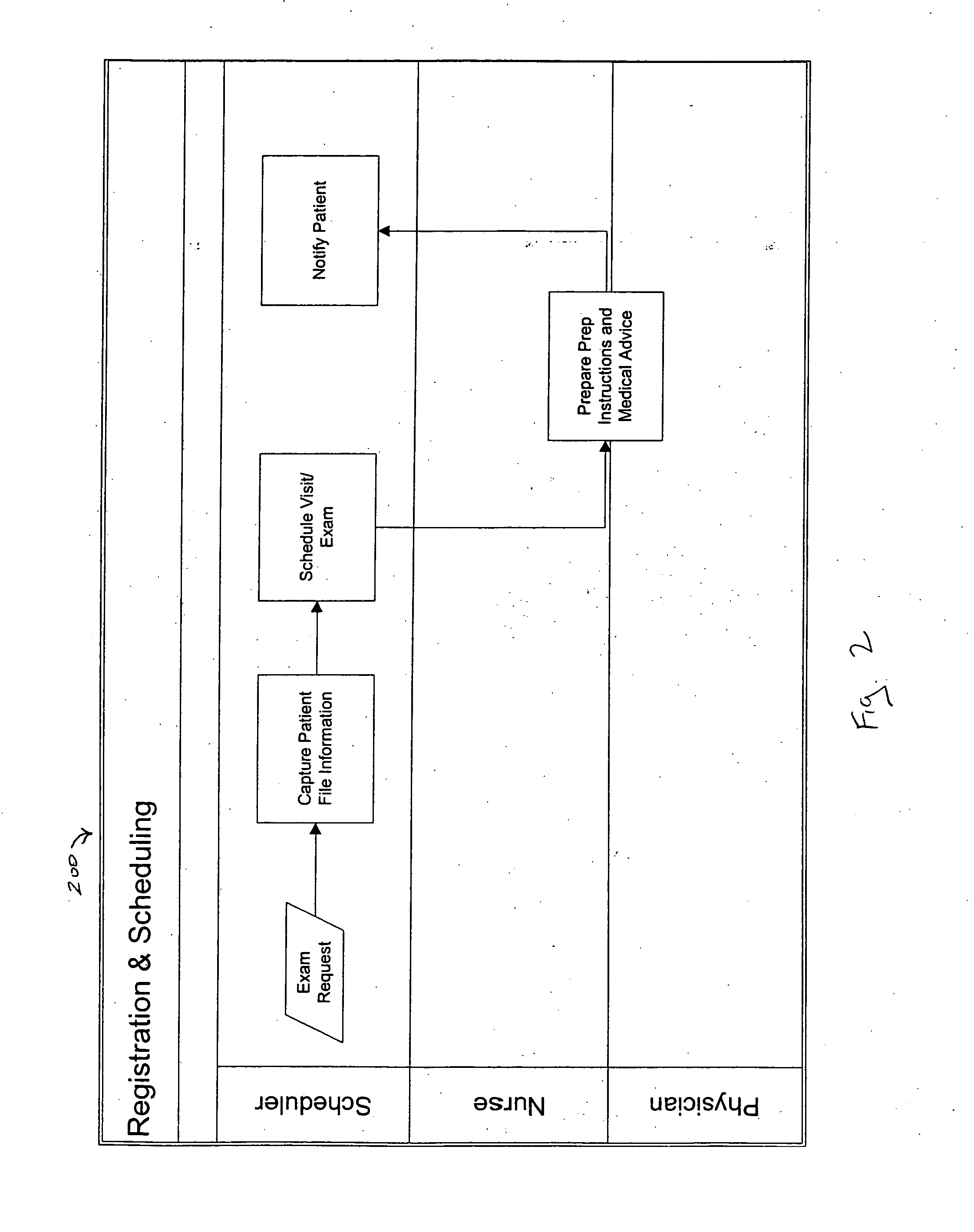
A system designed to support and manage the workflow for all user roles pertaining to an endoscopic laboratory, from registration and scheduling of patient information through pre-procedure, procedure and post-procedure phases of an endoscopic examination, including support for the entry, by various users associated with an endoscopic laboratory, of information and data including the processing and storage of endoscopic images captured during an endoscopic exam of a patient, for association with a patient record stored in a database, and including the entry of procedure notes and generation of reports that include the stored images, all via an integrated user interface.
Owner:OLYMPUS AMERICA +1
Role-oriented development environment
ActiveUS7590972B2Data processing applicationsSpecial data processing applicationsPower userHuman–computer interaction
This invention relates to a business application development and execution environment that recognizes and supports various development and user roles. Aspects of the method and system are adapted to builders, assemblers, power users and end users.
Owner:BACKSTOP SOLUTIONS GRP
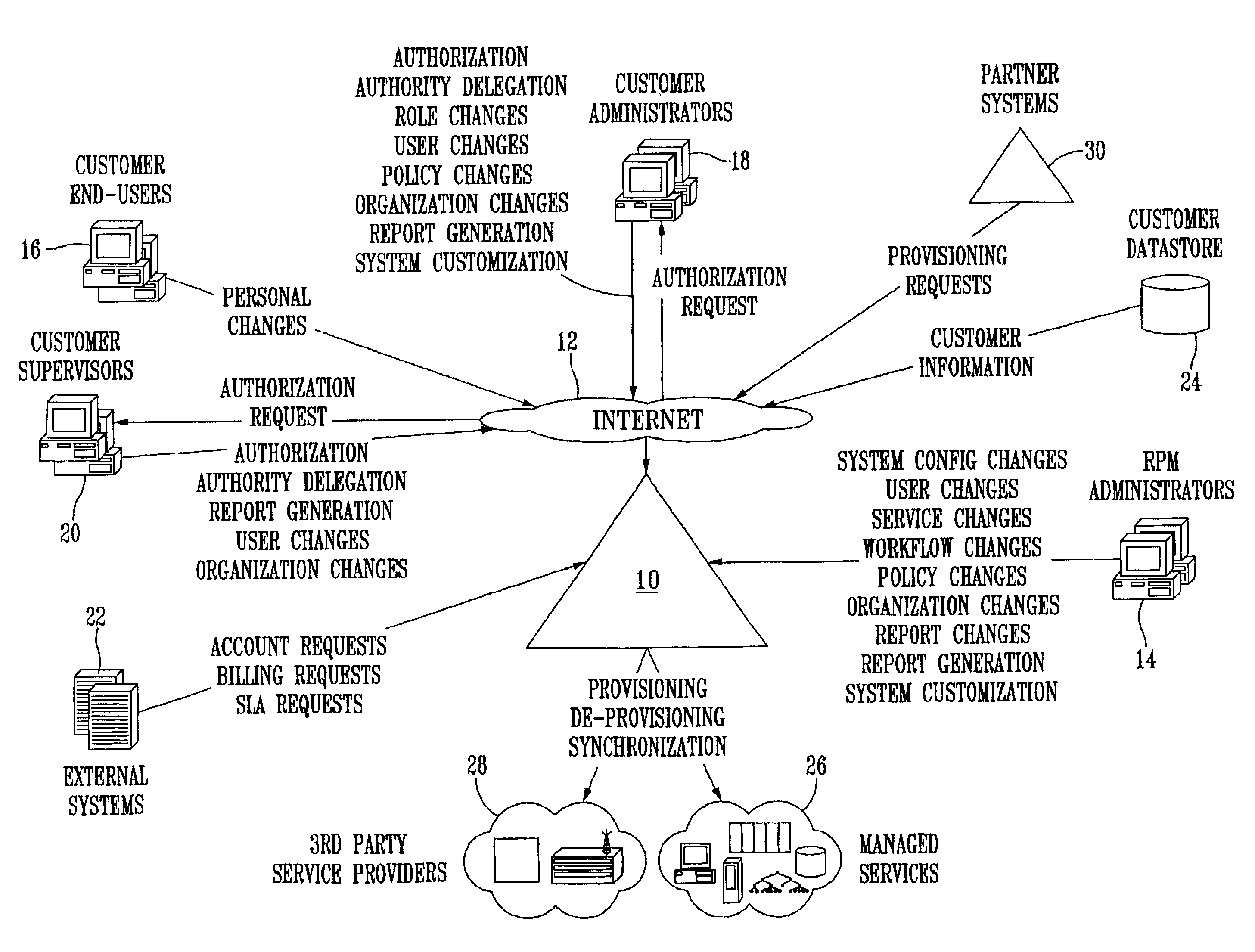
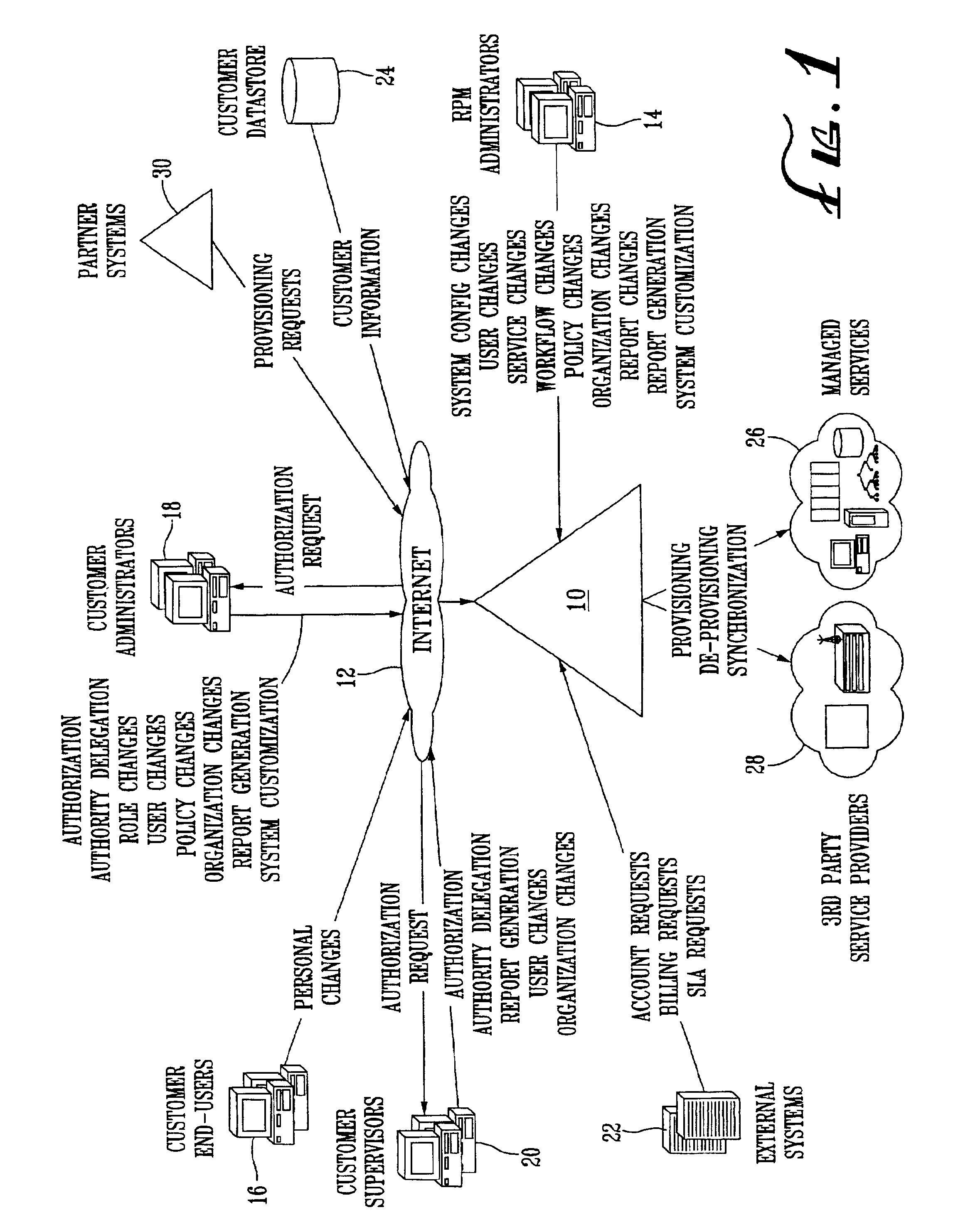
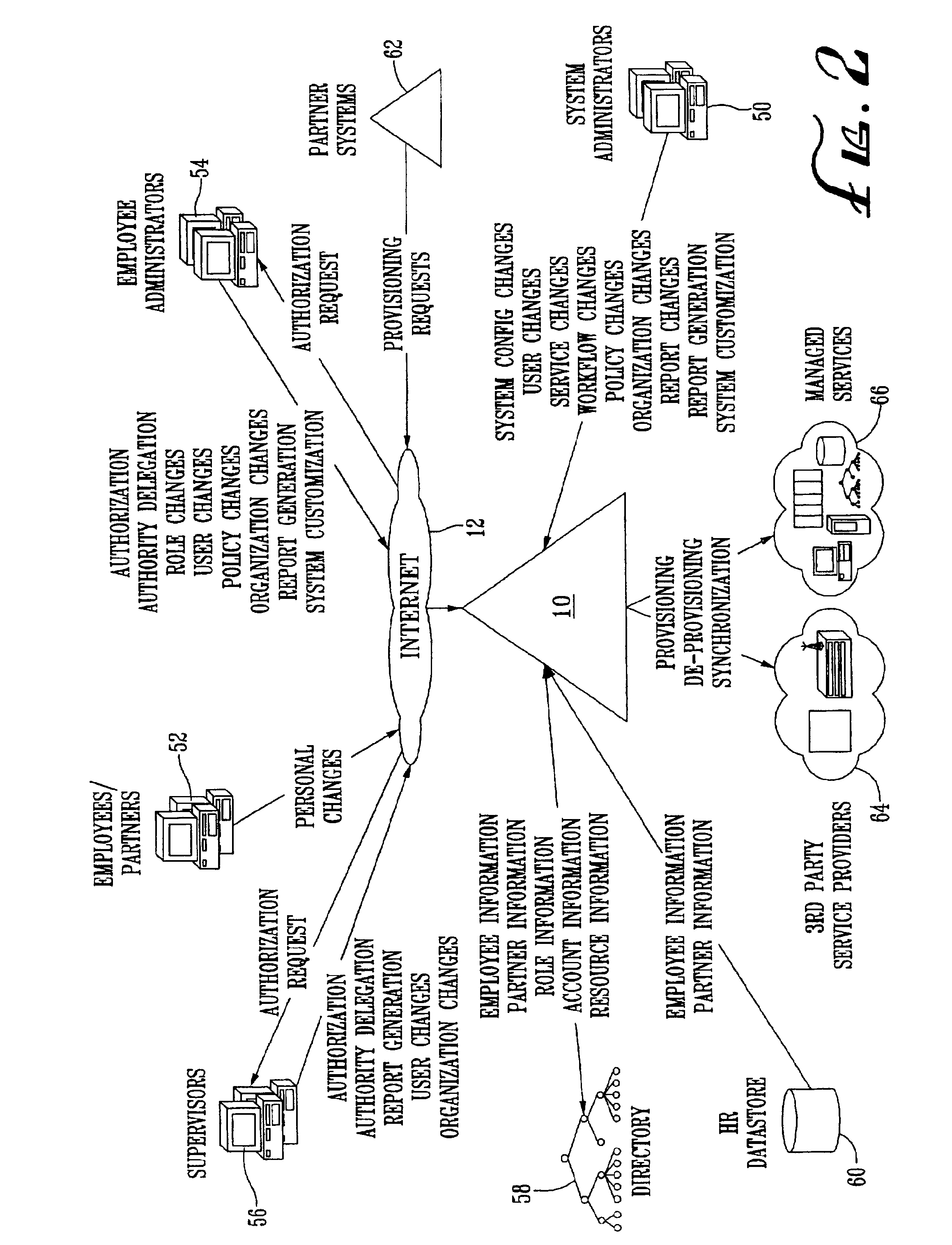
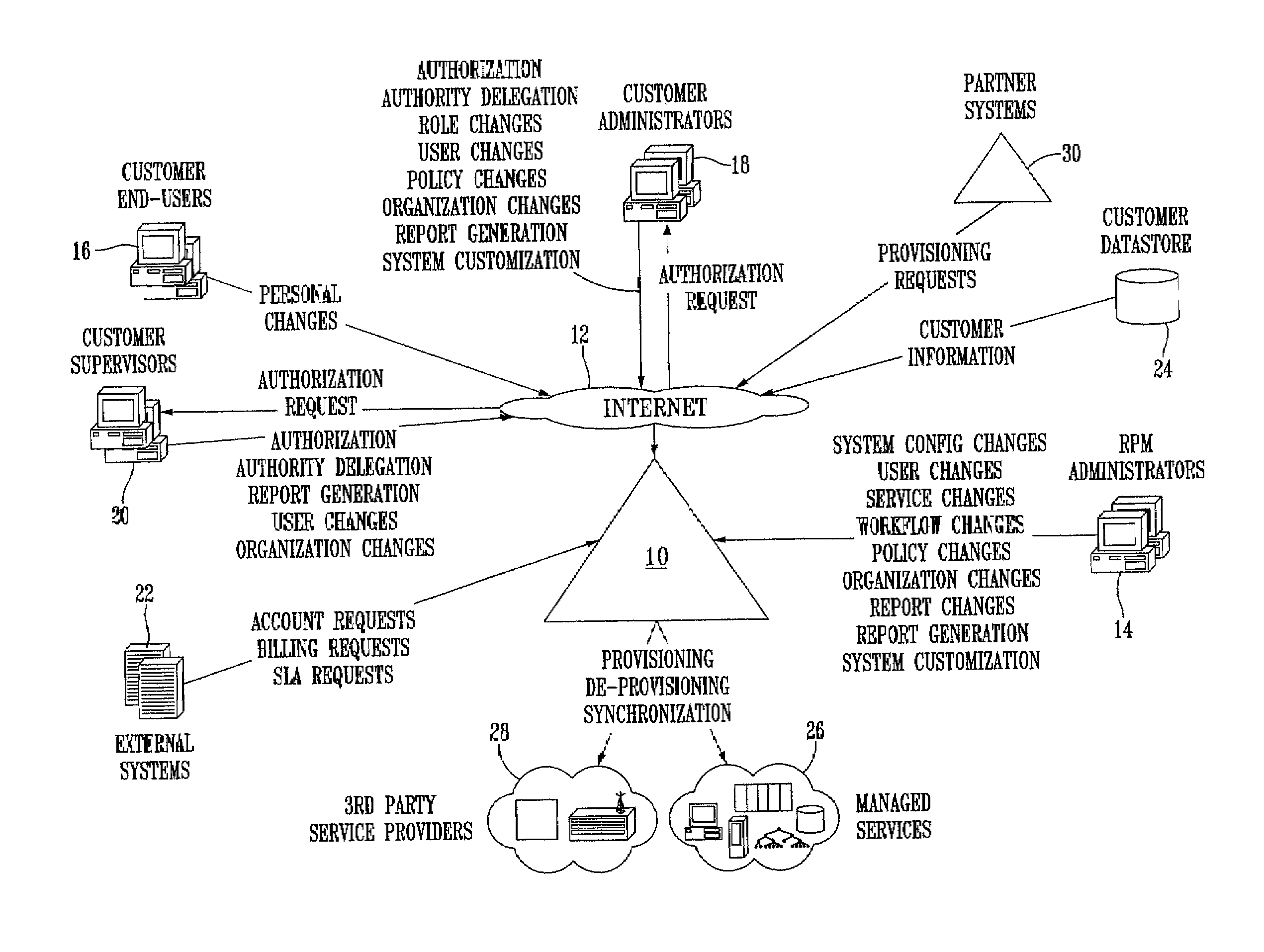
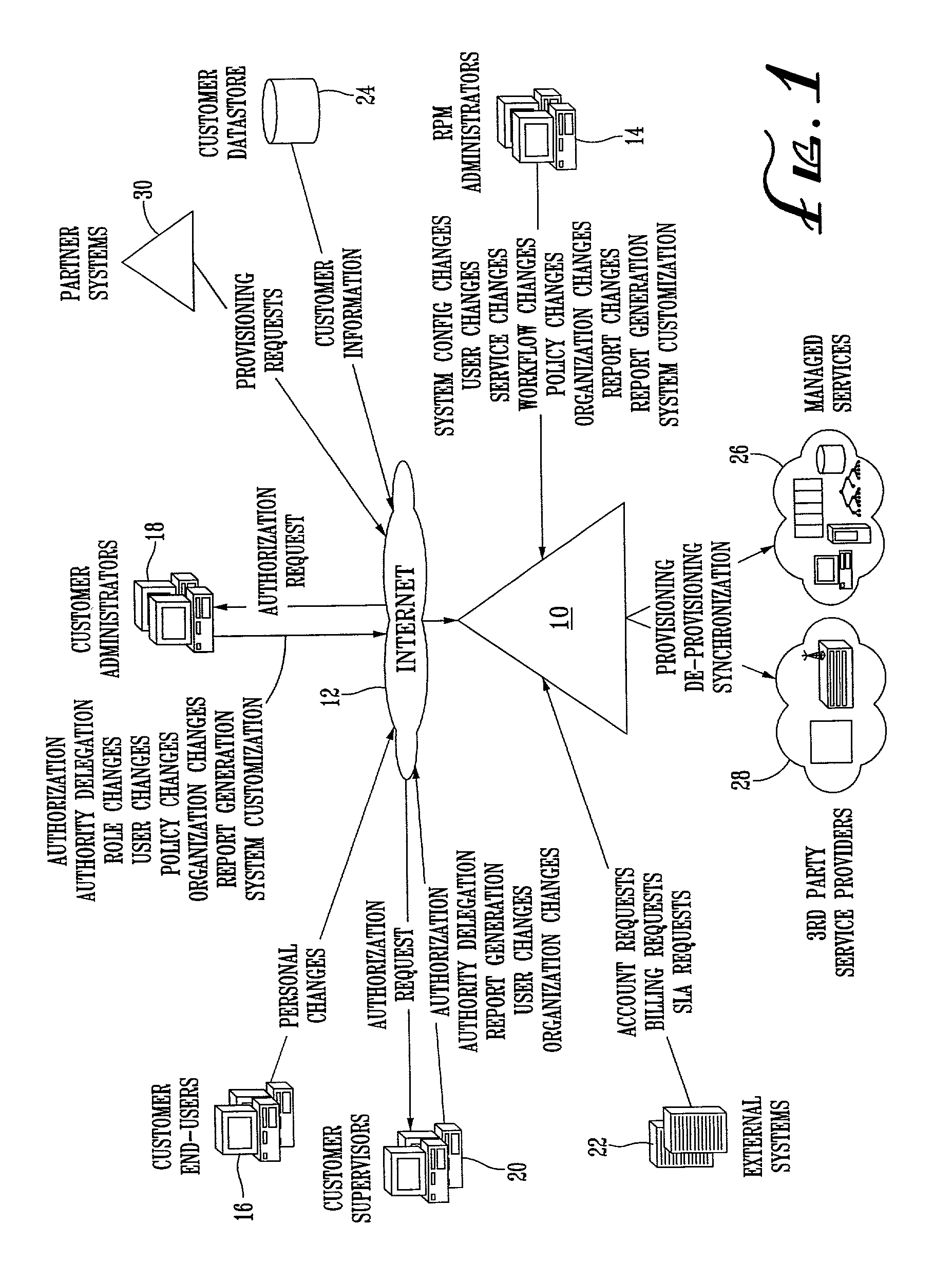
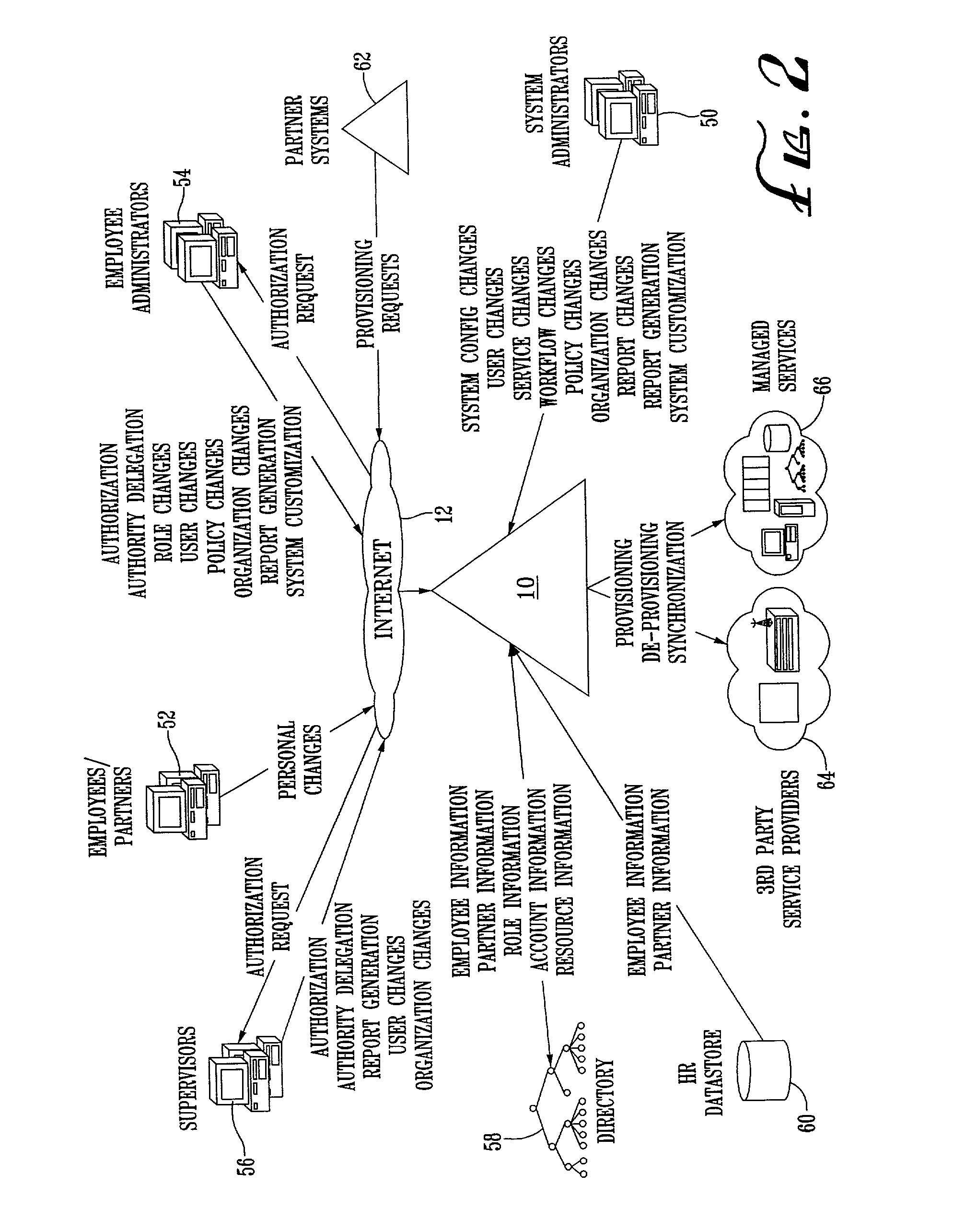
System and method for provisioning resources to users based on policies, roles, organizational information, and attributes
InactiveUS6947989B2Reducing and minimizing numberDigital data processing detailsSpecial service for subscribersResource basedApplication software
A method for provisioning users with resources is disclosed. The method includes the steps of establishing a set of attributes, organizational information, and user roles, and defining a plurality of resource provisioning policies based on selected attributes and user roles. The method also includes the steps of receiving attribute information, organizational information, and user role information for a particular user or resource, determining which resource access policies are applicable to the user based on the received user role information and attribute information, and provisioning the user with resources based on the applicable resource access policies. The resources to be provisioned include “hard” resources, such as telephones, computers, personal digital assistants, desks, chairs and the like, as well as “soft” resources. such as e-mail and voice mail accounts, application programs, databases, files, folders, the like.
Owner:IBM CORP
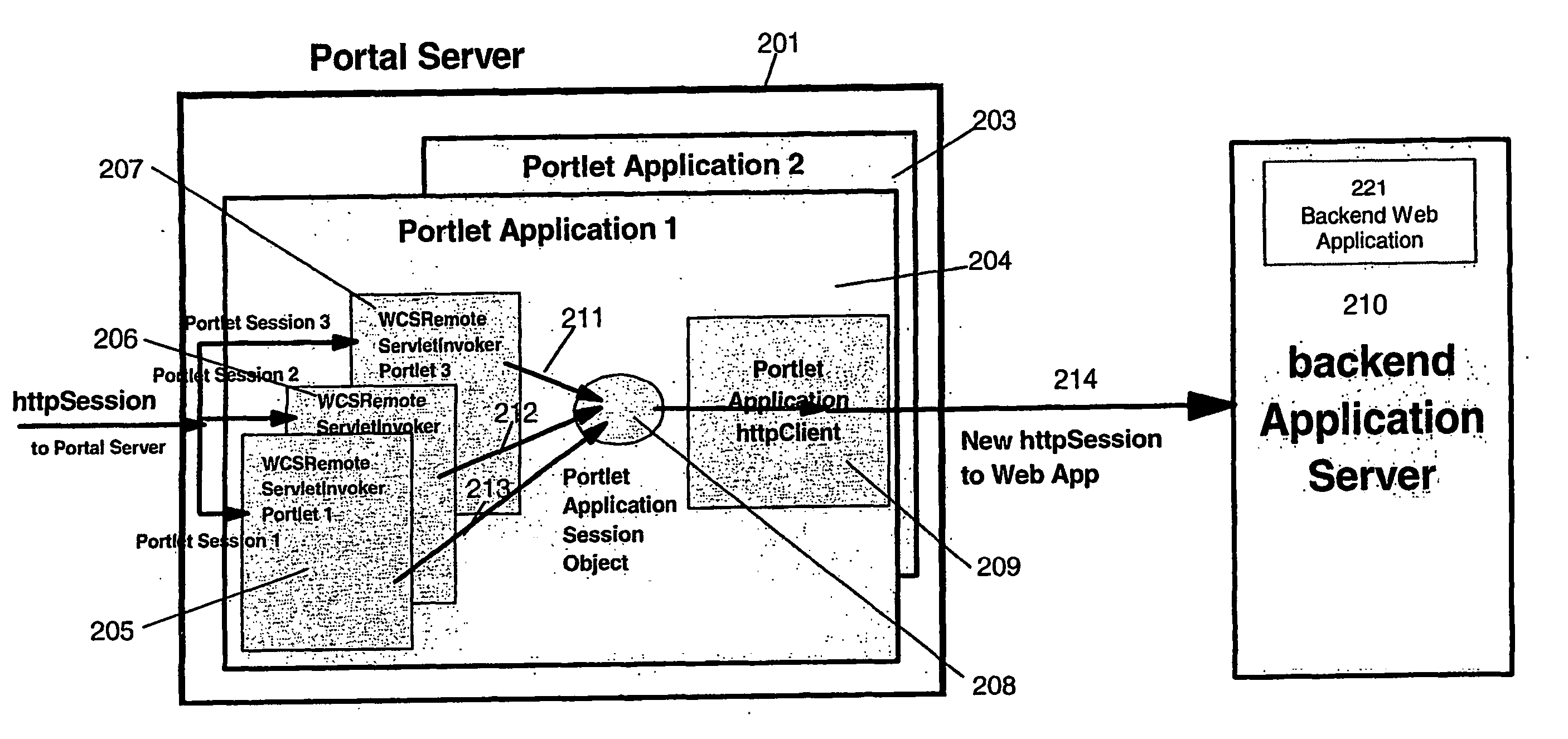
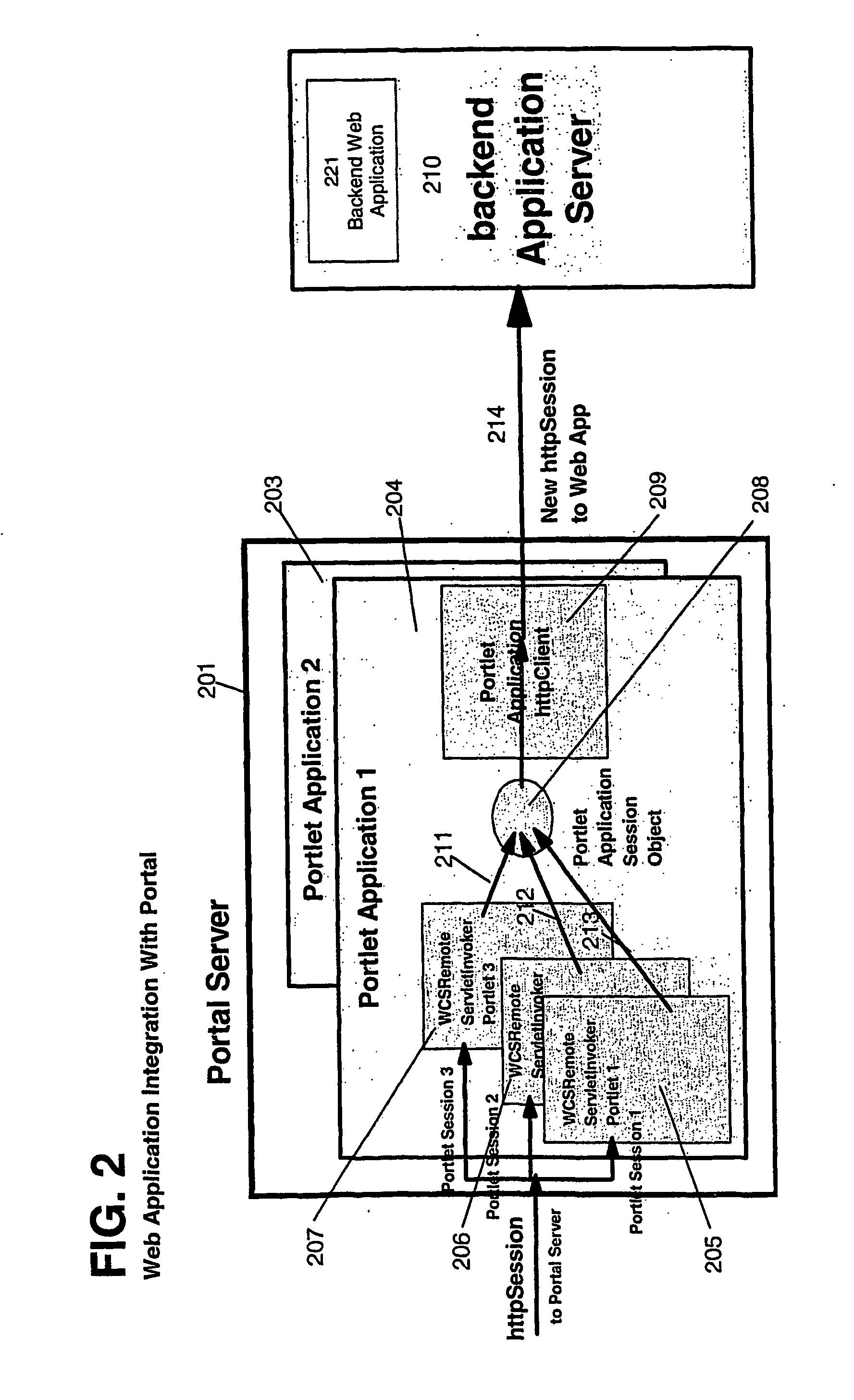
Method and apparatus for using business rules or user roles for selecting portlets in a web portal
InactiveUS20060235935A1Improve the level ofDigital data protectionMultiple digital computer combinationsPortletApplication software
An embodiment of the invention includes means to select portal resources (portlets, page and page groups) as displayed to a user based on pluggable rules engine; a rules database; and a portlet application aggregation engine which applies rules to select and display selected portlets, pages and page groups to a user.
Owner:IBM CORP
Systems and methods for managing the development and manufacturing of a drug
InactiveUS20070192715A1Easy to optimizeManagement complexityComputer-assisted medical data acquisitionTechnology managementGraphicsChemical reaction
Graphical user interfaces, computer readable media, and computer systems for monitoring a chemical process. An administration module sets a plurality of user preferences associated with the chemical process. A people management module defines a user role in the chemical process. An organization module defines an organizational structure of an organization that runs the chemical process. An equipment module defines equipment used in the chemical process. A material module controls a chemical used in the chemical process. A process module defines a chemical reaction in the chemical process.
Owner:ORACLE INT CORP
Web-based collaborative framework
InactiveUS8561153B2Digital data processing detailsNatural language data processingWeb siteNetwork communication
Embodiments of the present disclosure provide systems and methods for facilitating network communications. Briefly described, one embodiment of the system, among others, includes a server-based application configured to produce web pages for a web site in accordance with input received from a user; and an interface to the server-based application receiving selections of features which are available to be added to the web site in response to user prompts and to set access rights on which features are to be available to different roles of users. Other systems and methods are also provided.
Owner:AT&T INTPROP I L P
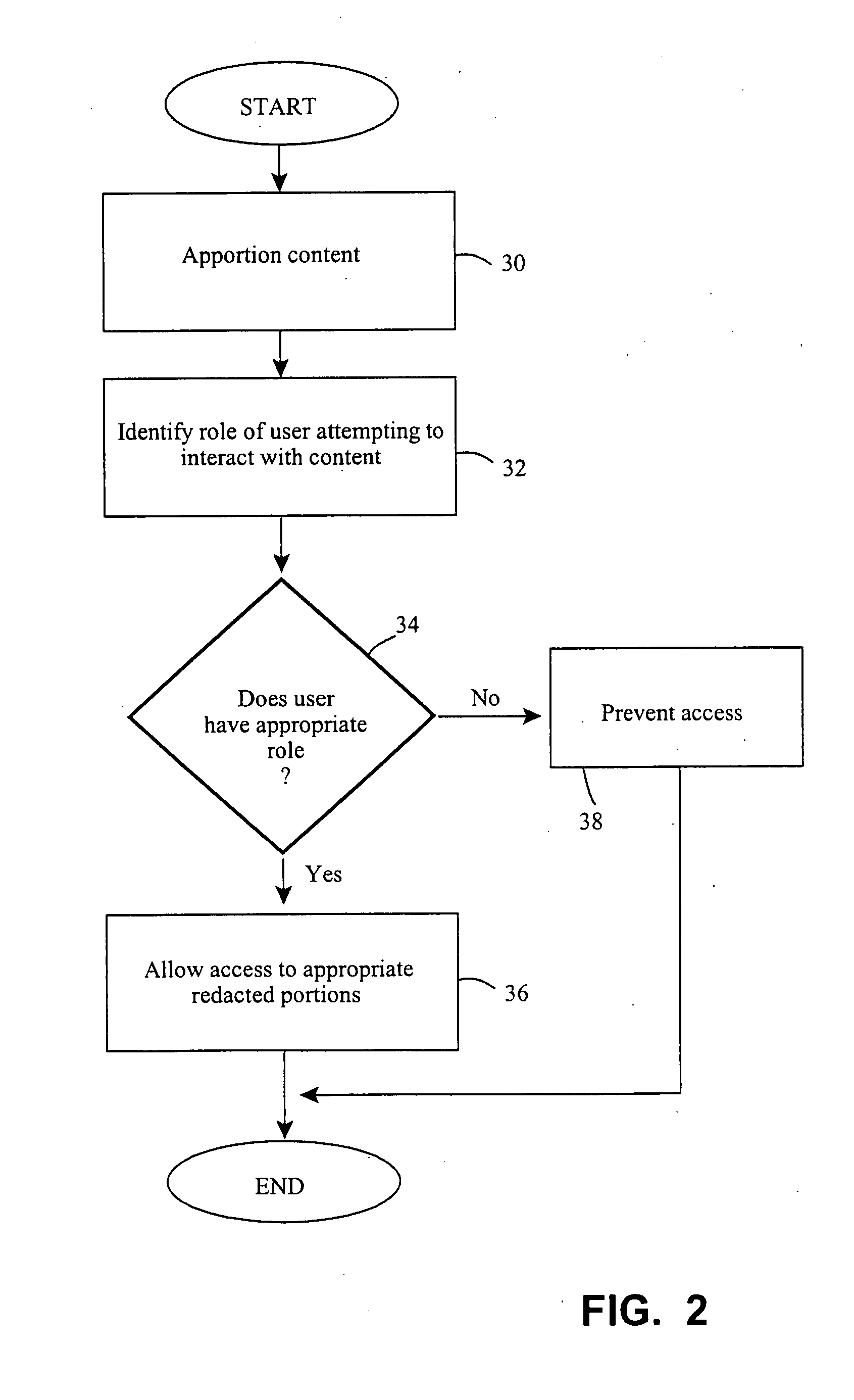
Role-based access control for redacted content
InactiveUS20090025063A1Digital data processing detailsComputer security arrangementsMedia access controlUser interface
Apparatus and methods are described for accessing redacted material based on user roles. An author designates portions of content as to-be-redacted. The author establishes various users roles able to access it and defines attributes or time constraints affecting the viewing / using. Upon electronically saving the content, the to-be-redacted portion is encrypted. An intermediary, such as a keytable service, mediates access between later users and the content. Upon identification of a role of a user attempting to interact with the content, and matching the role to one of the author-established roles, the encrypted redacted portion is decrypted. In this manner, users gain access to content based only on their role. The surrounding events are also loggable, traceable, and verifiable. A monitored connection between the user and the content, as well as various user interface options, are other noteworthy features. Computer program products and computing network interaction are also defined.
Owner:NOVELL INTPROP HLDG
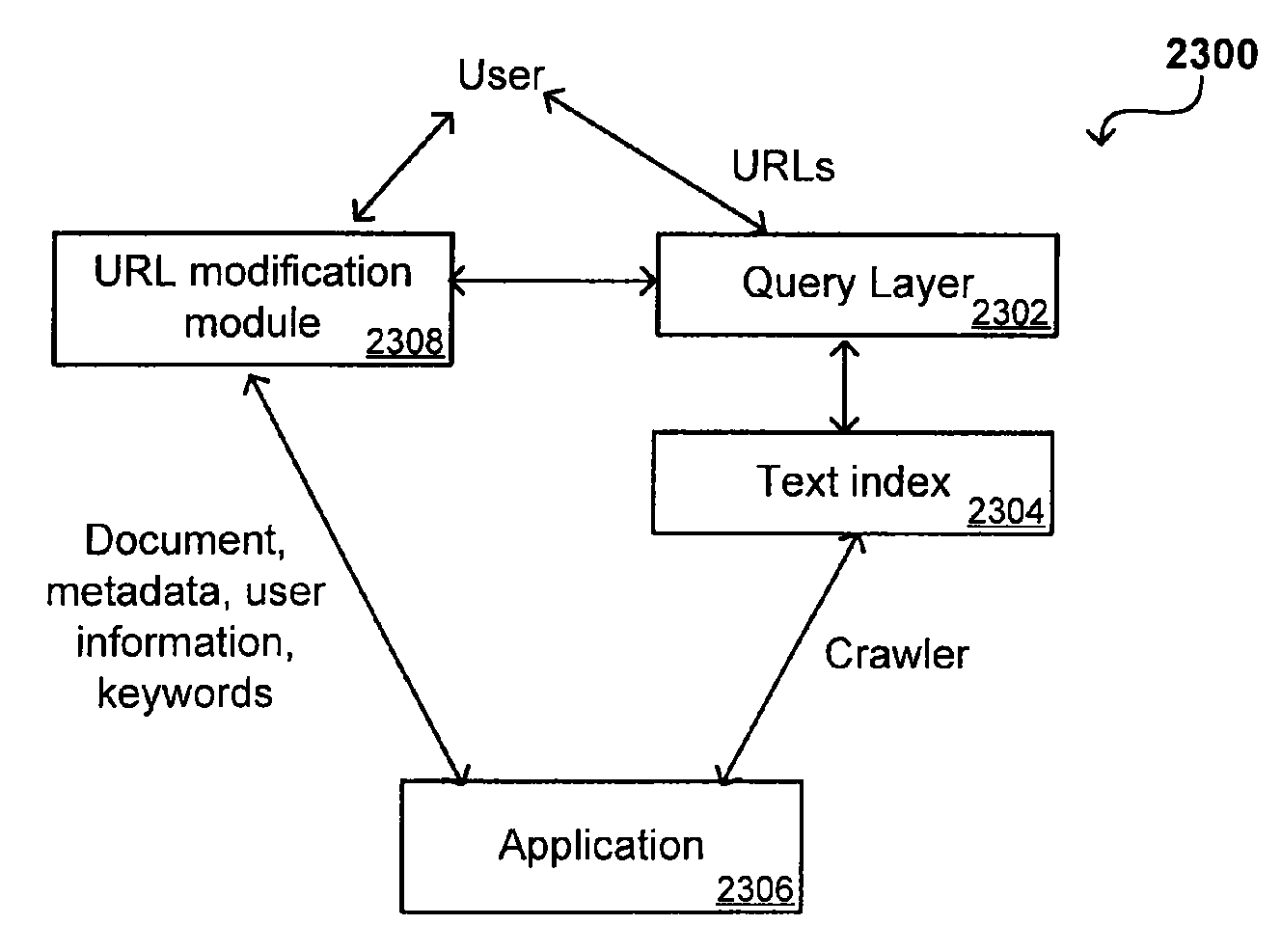
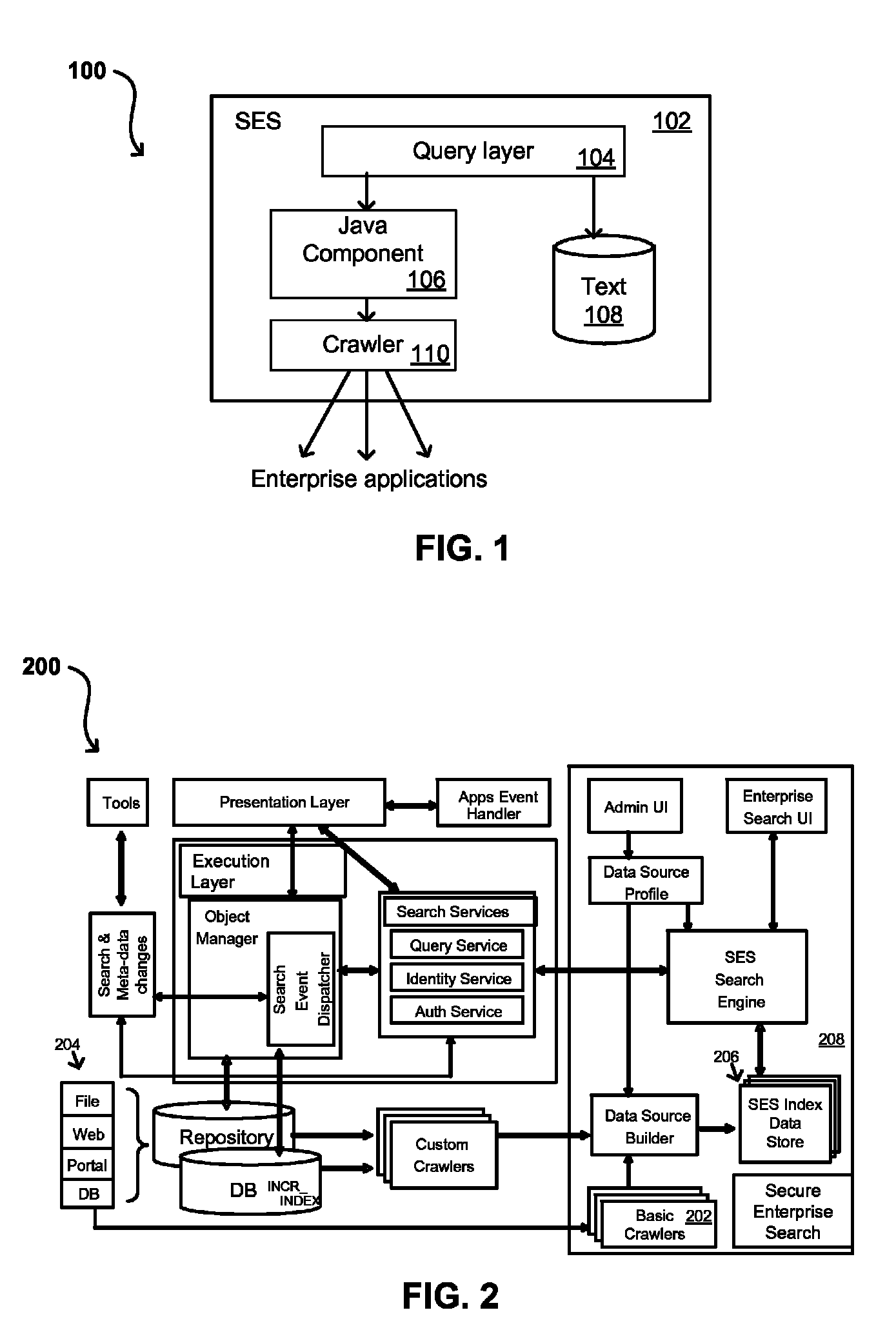
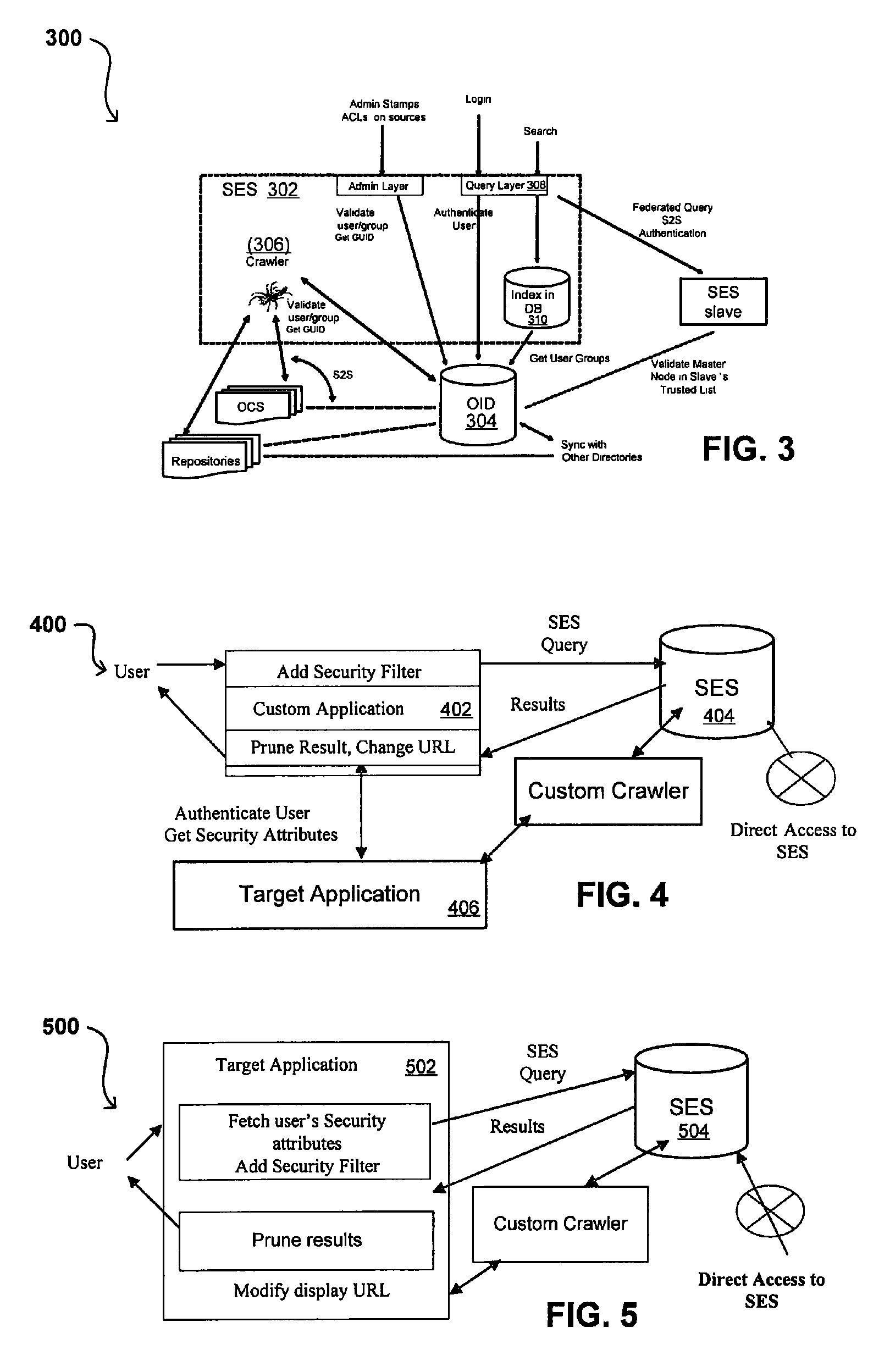
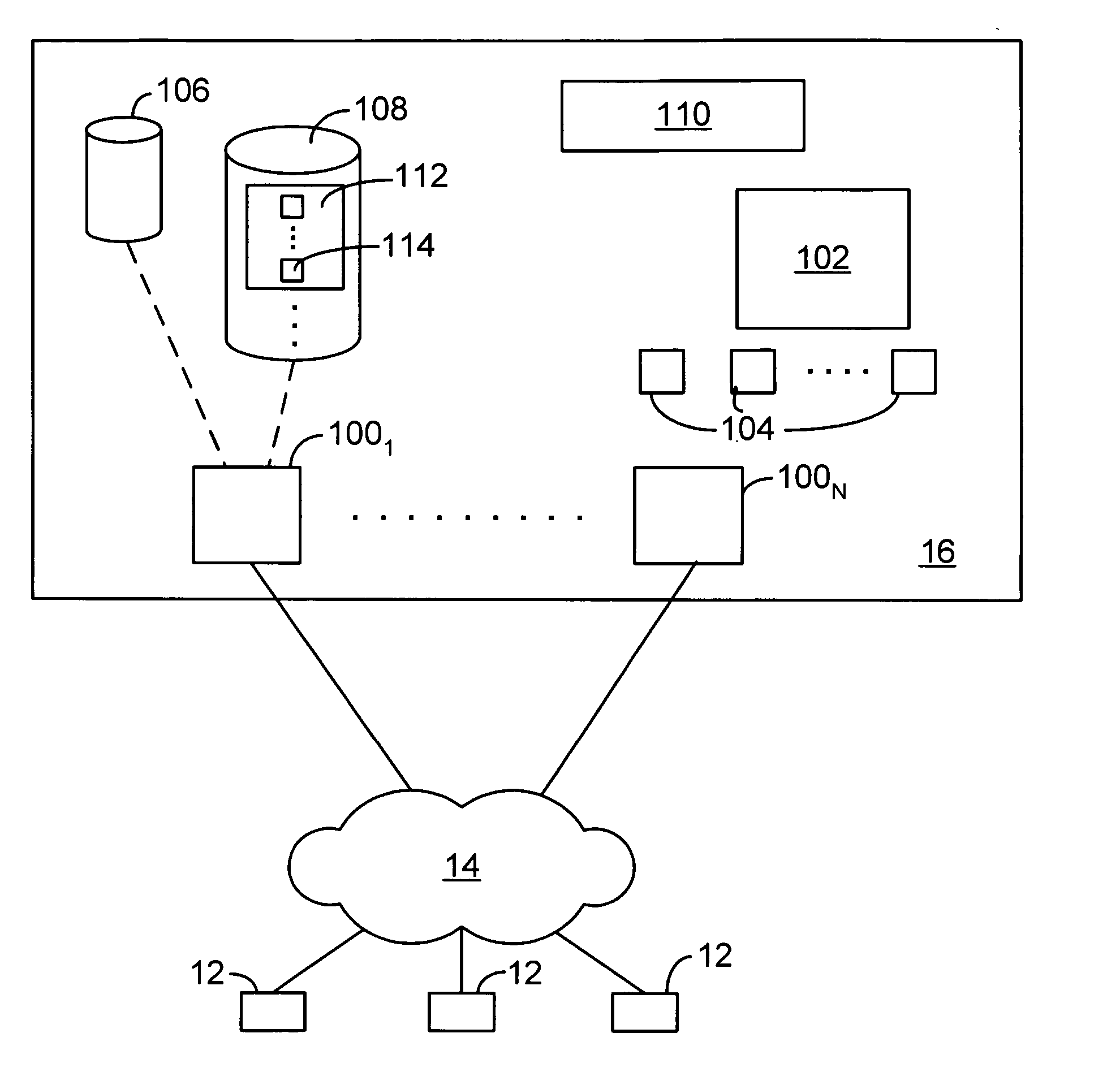
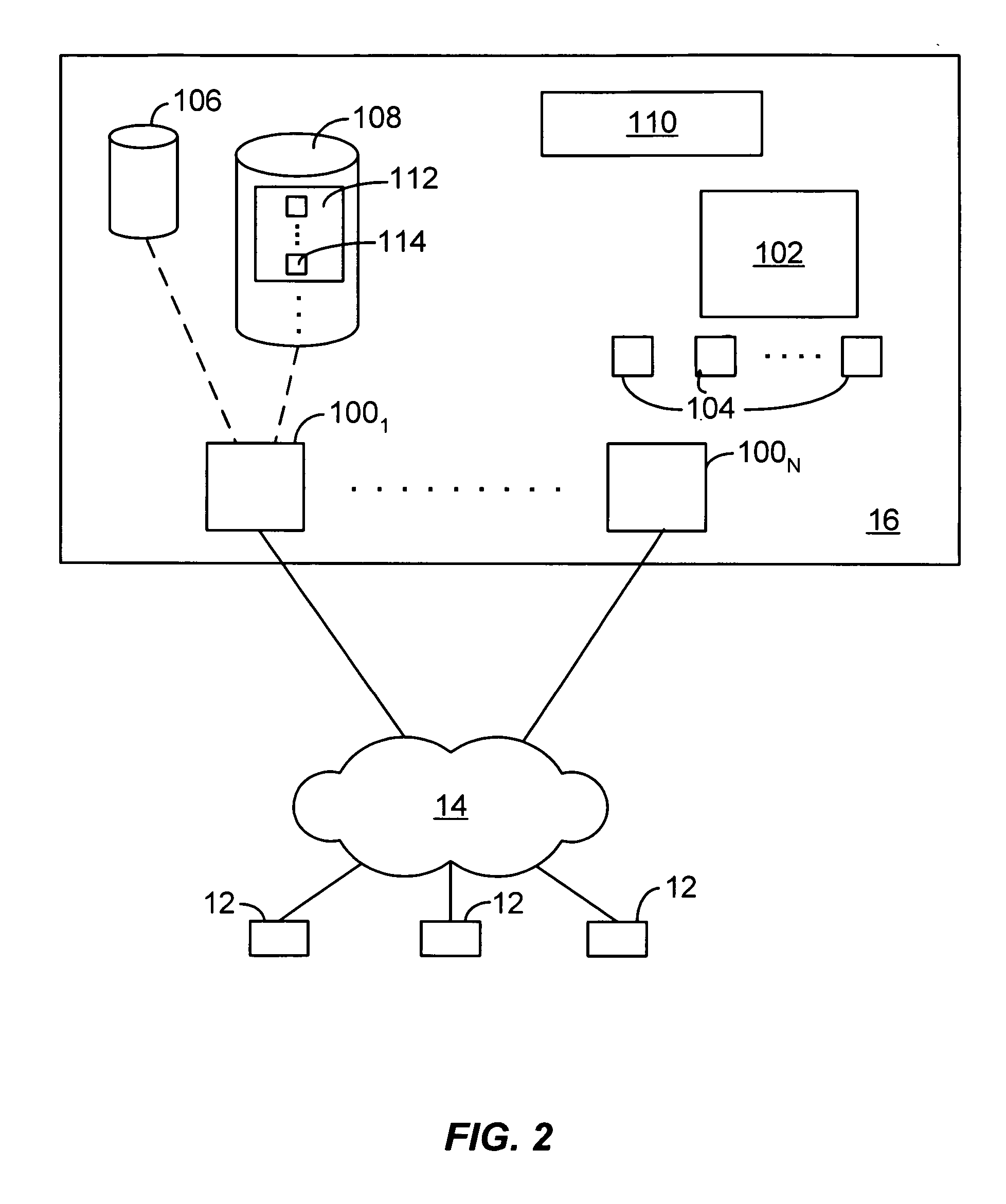
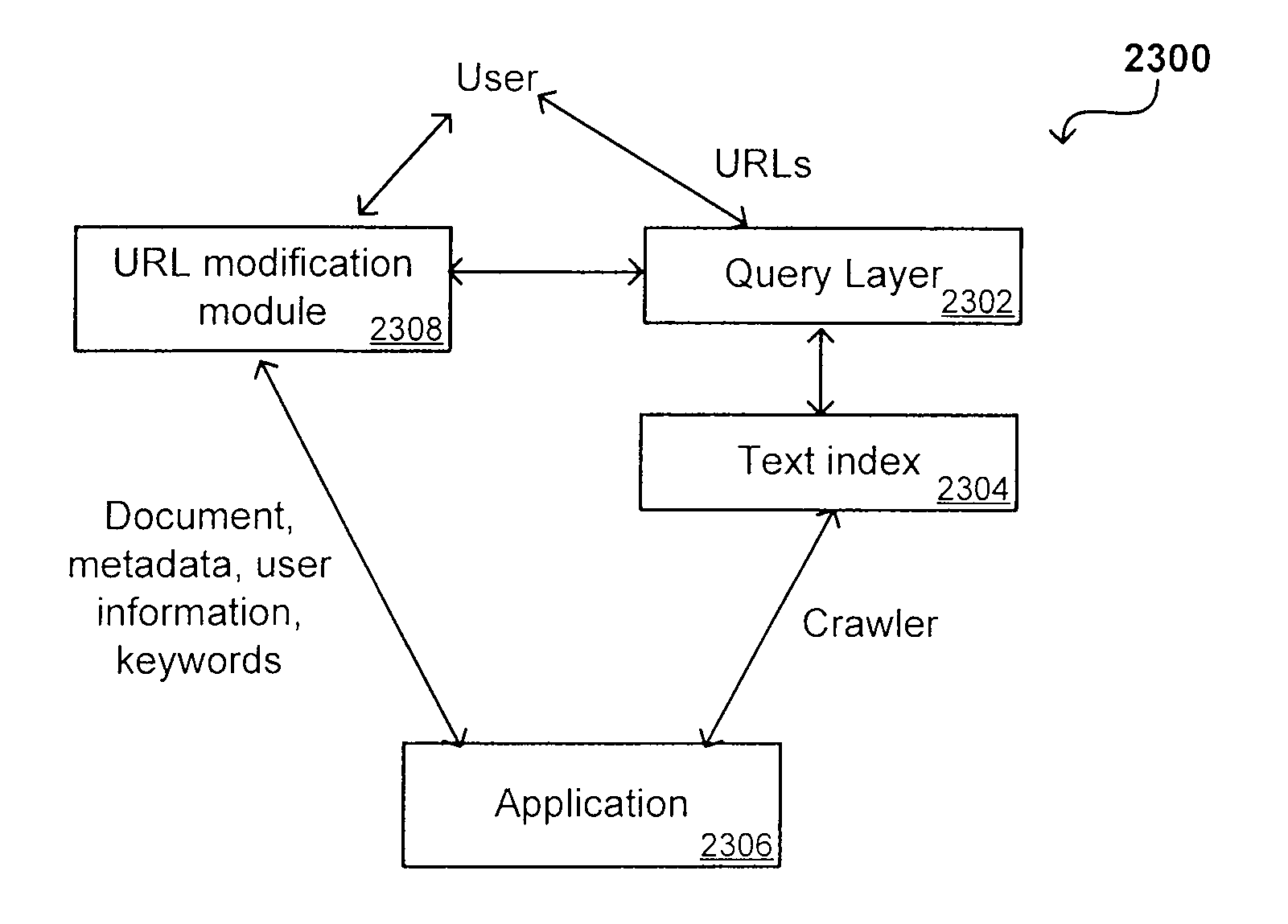
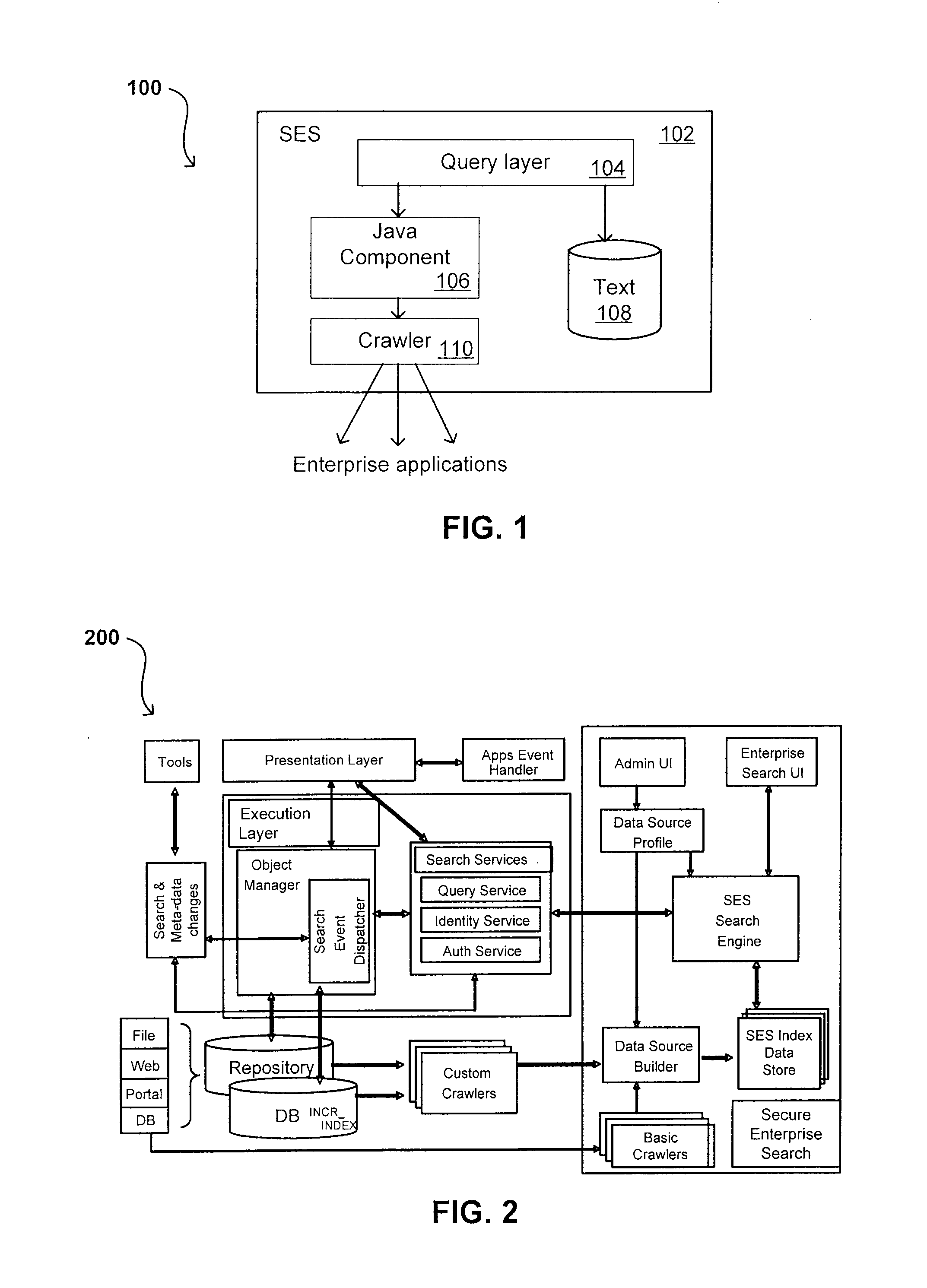
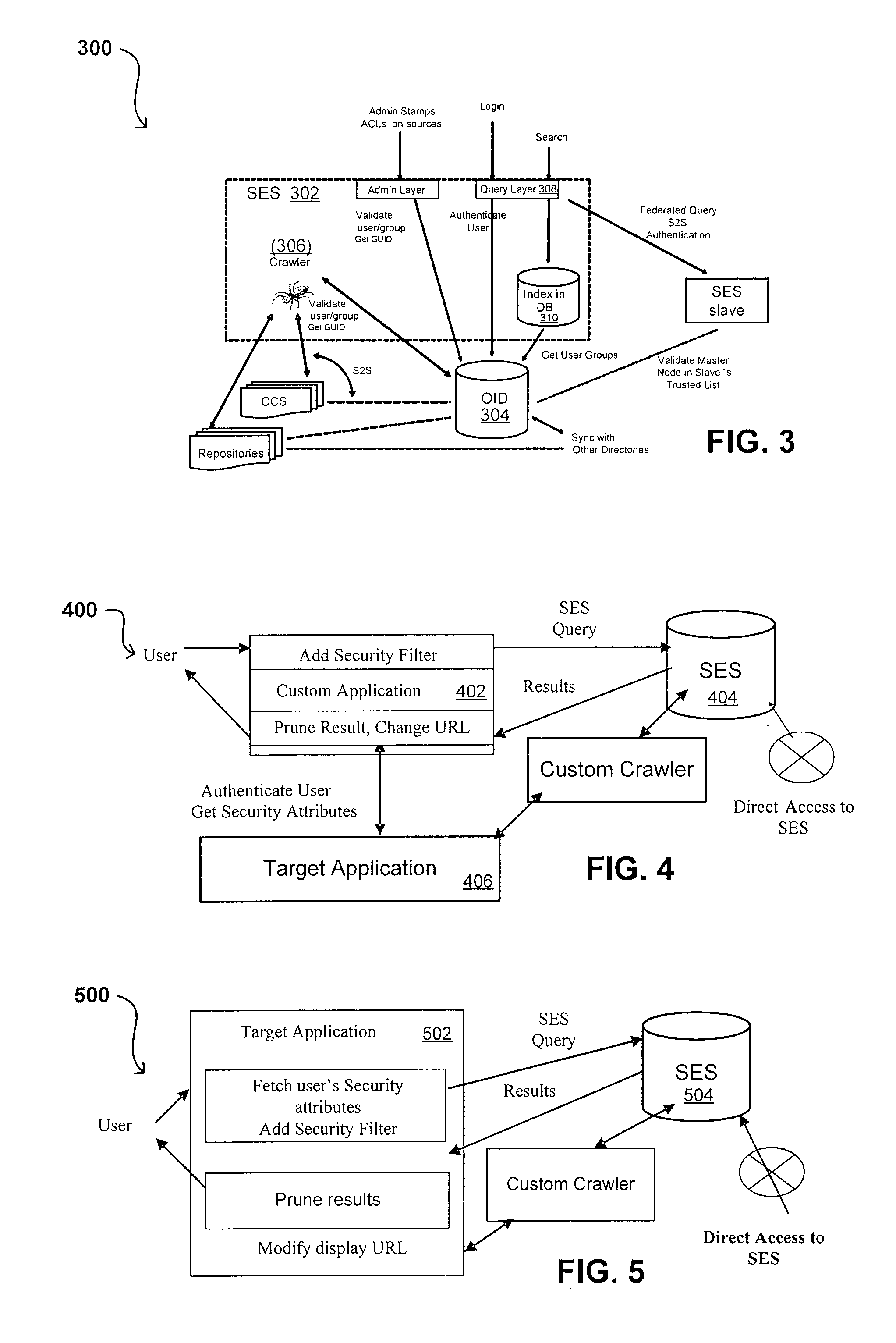
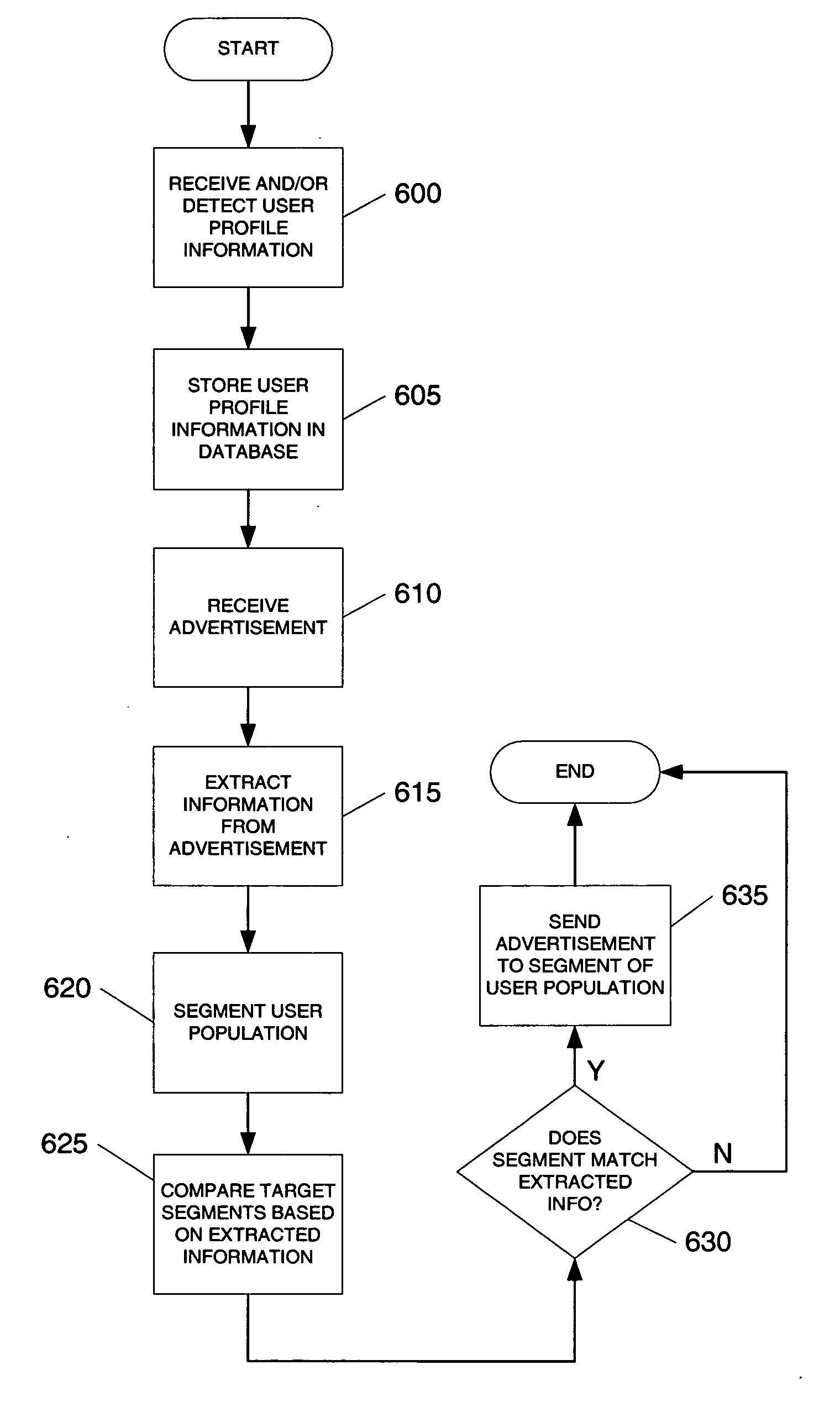
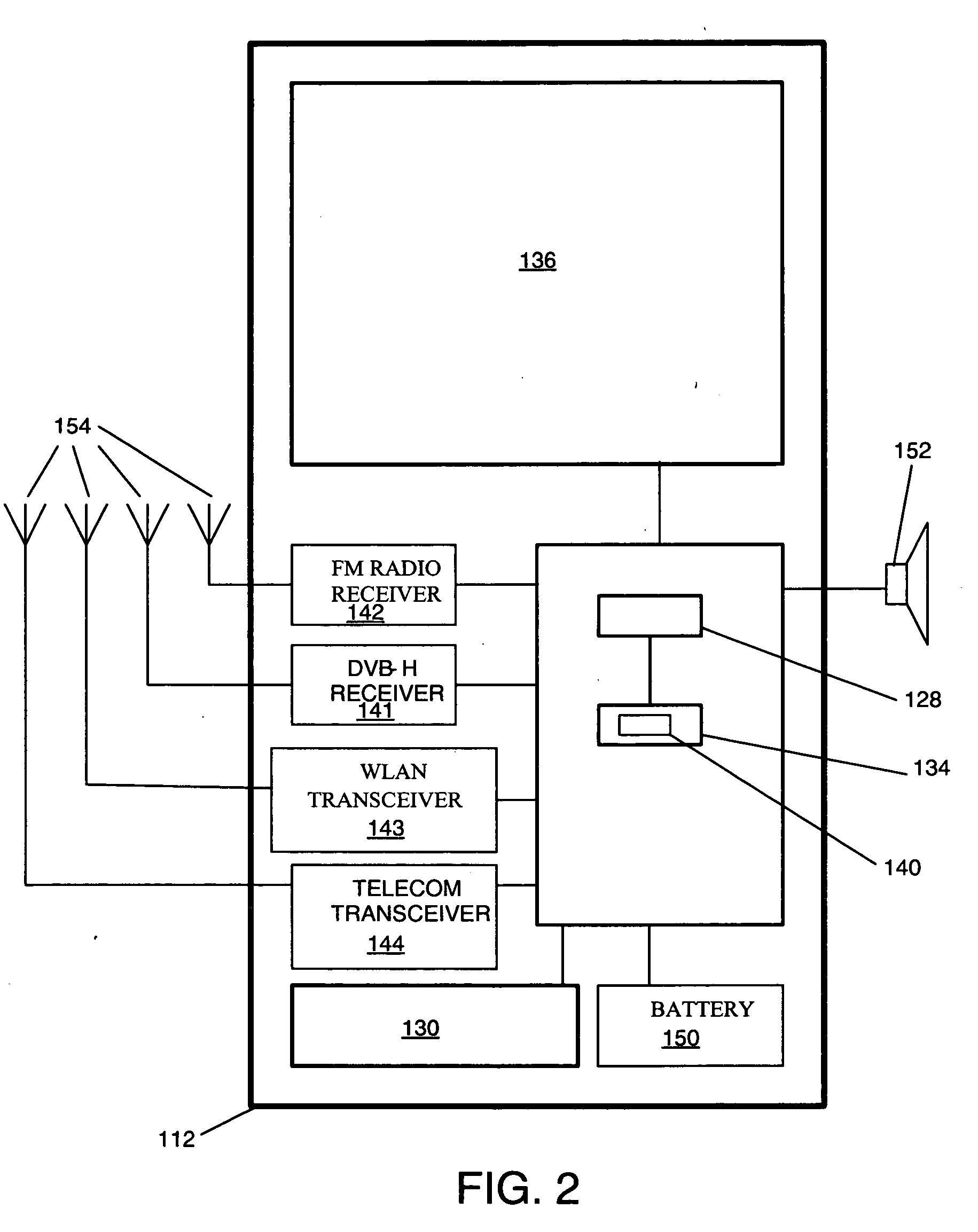
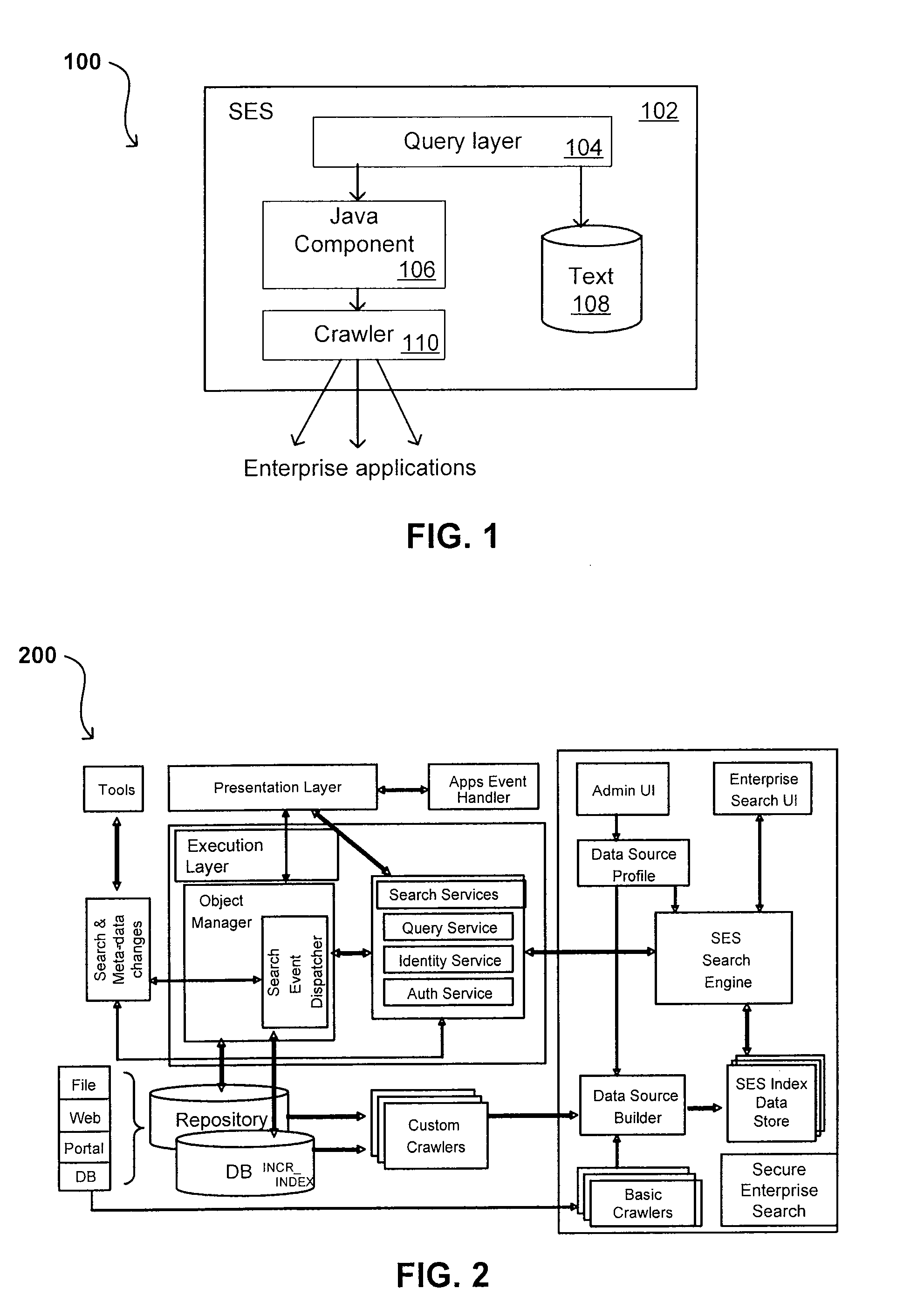
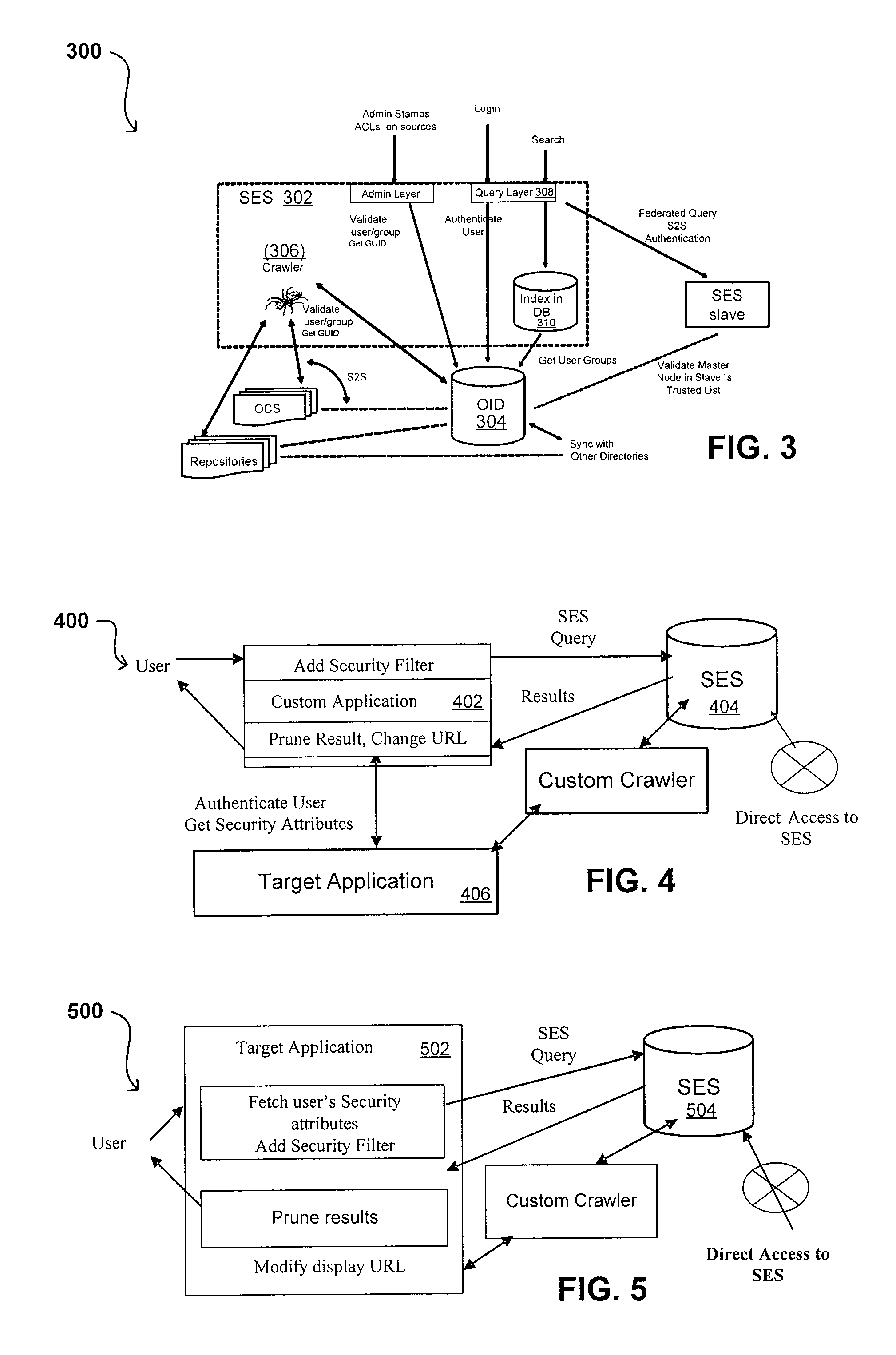
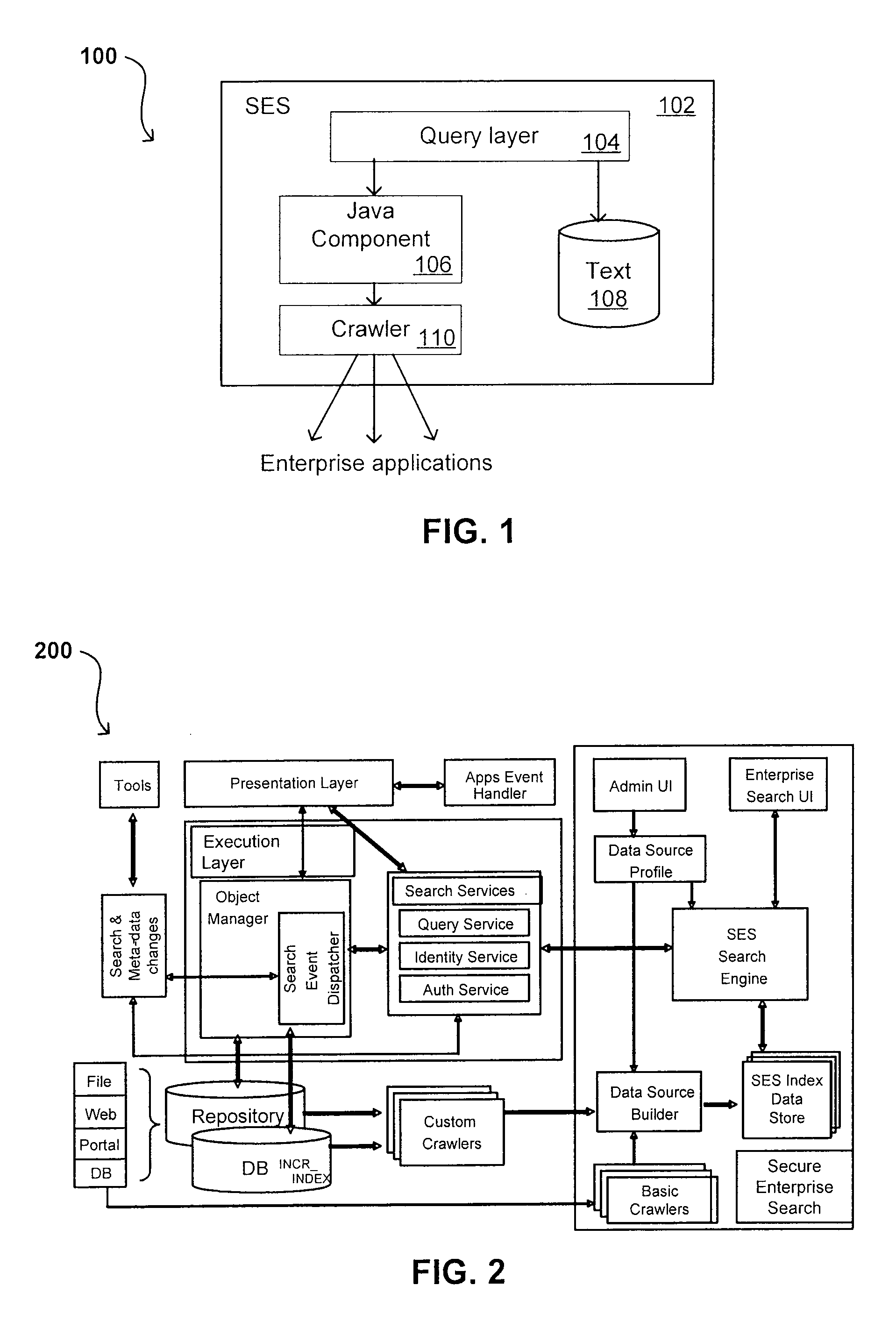
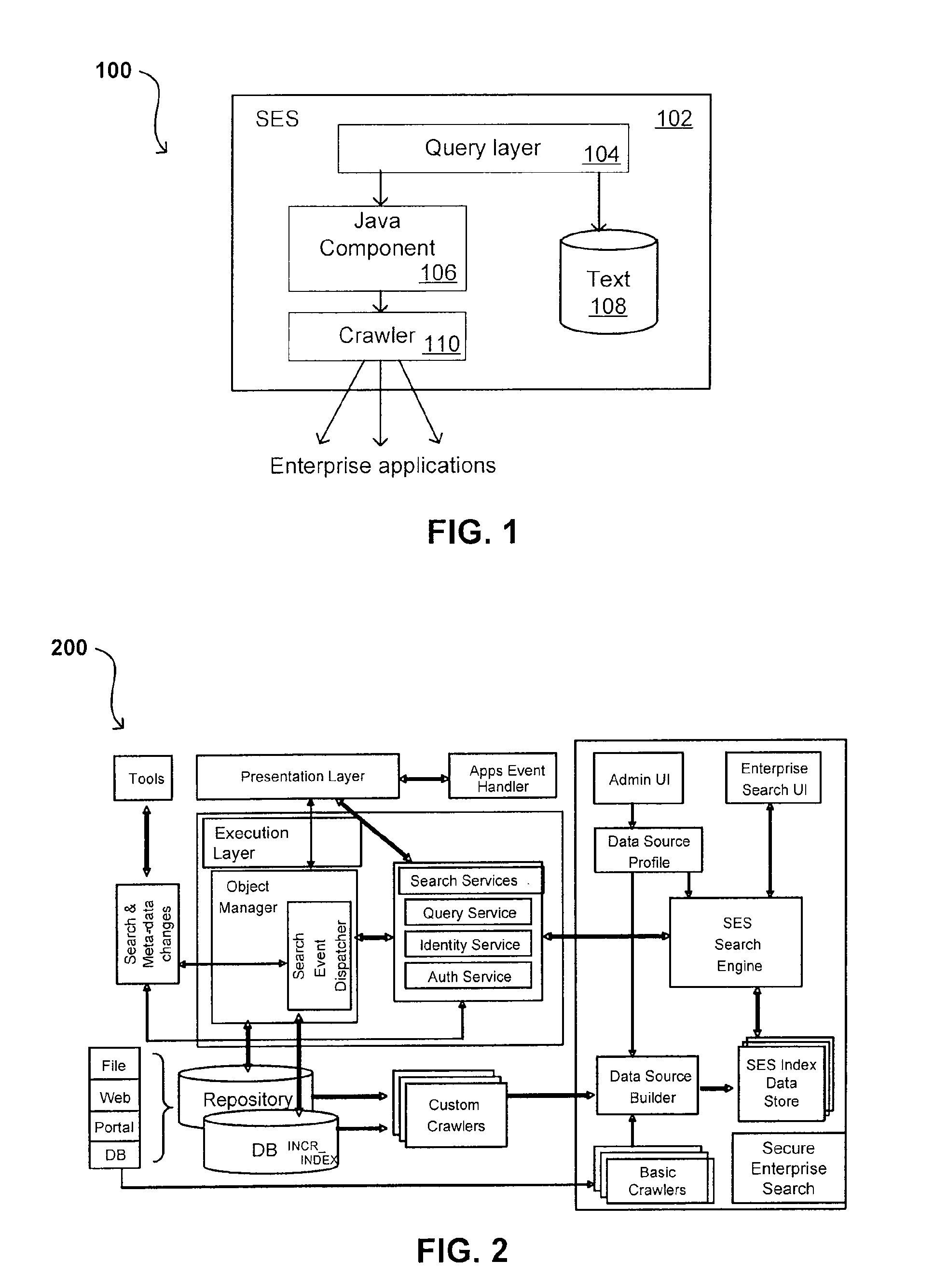
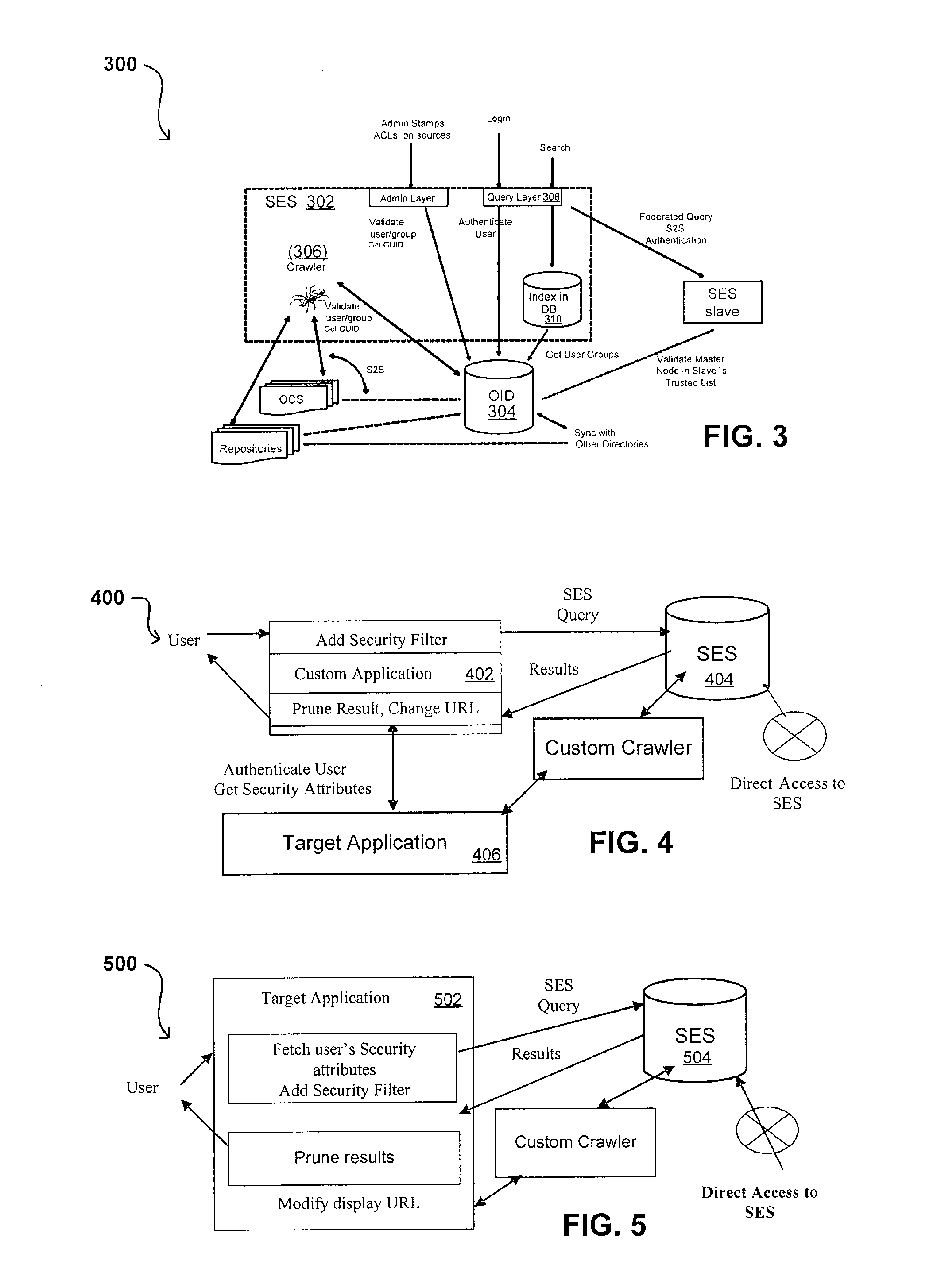
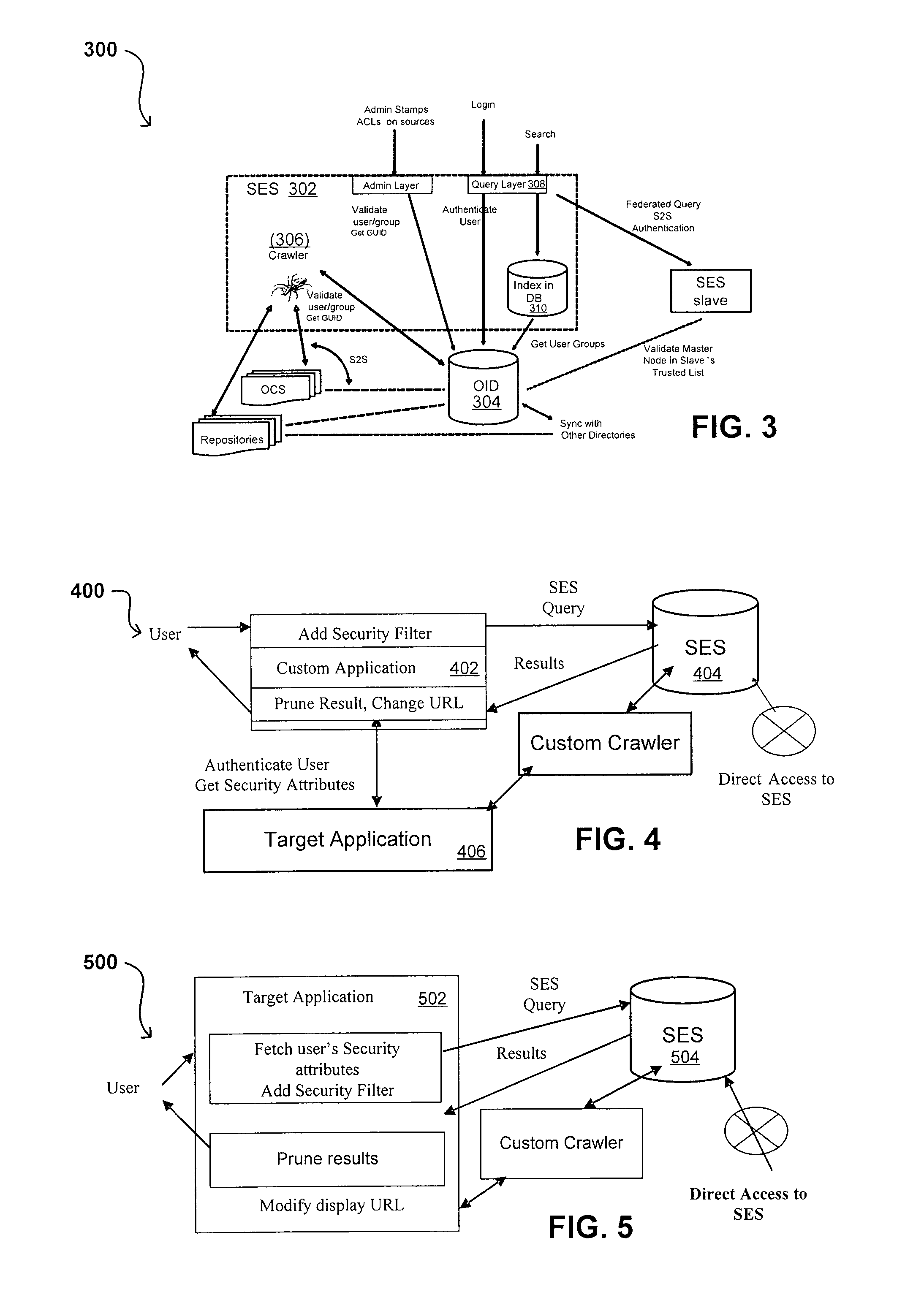
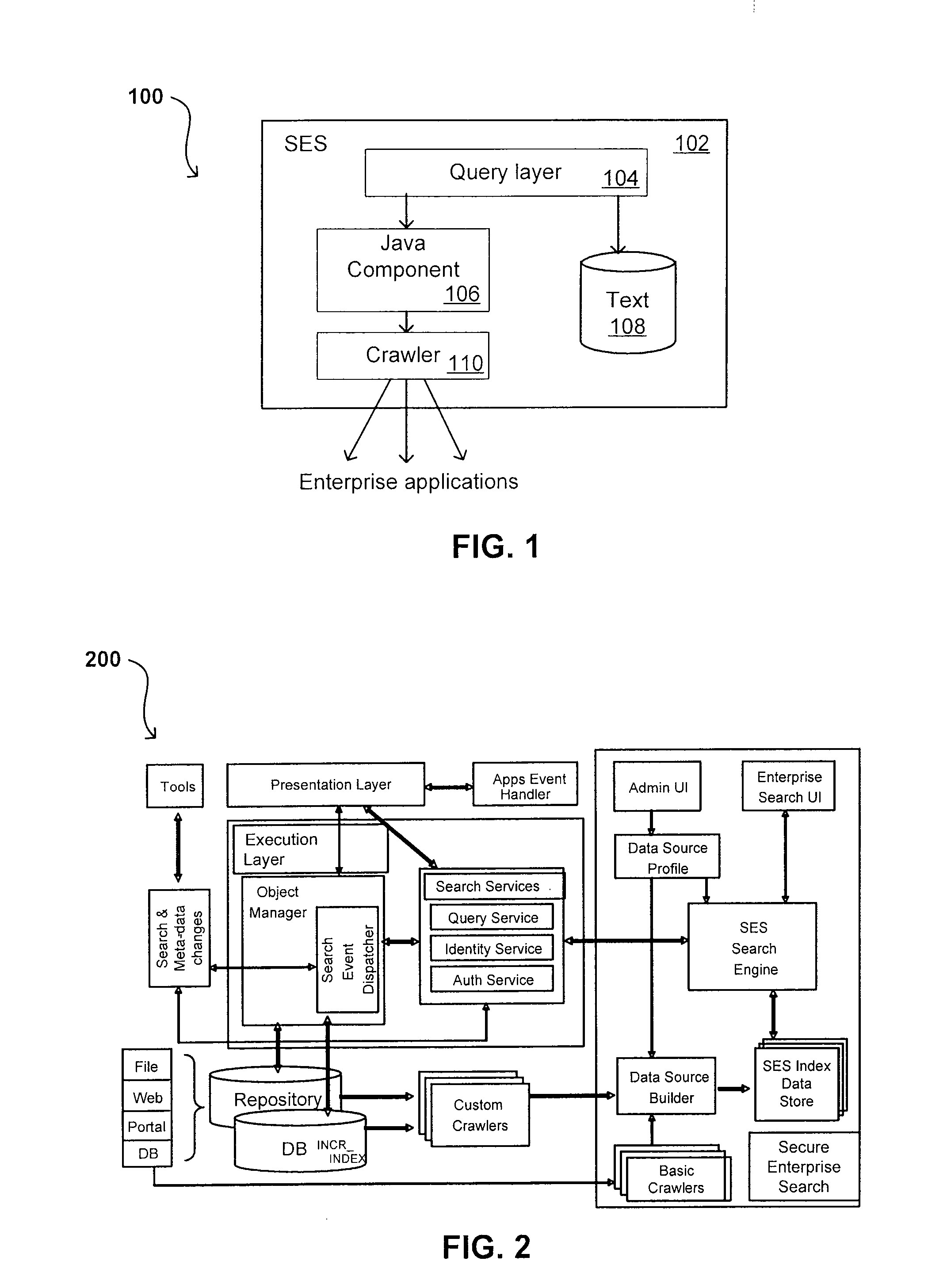
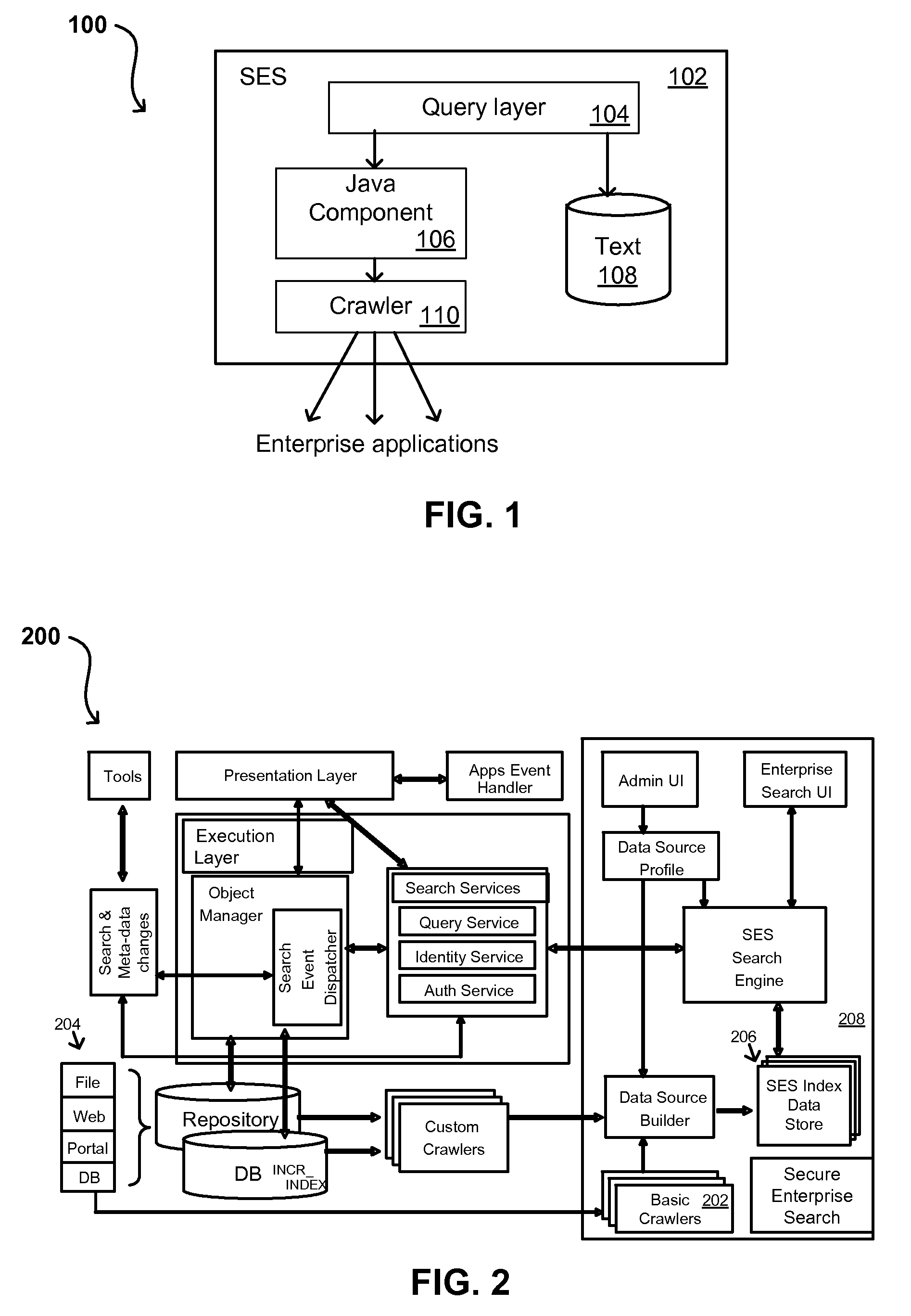
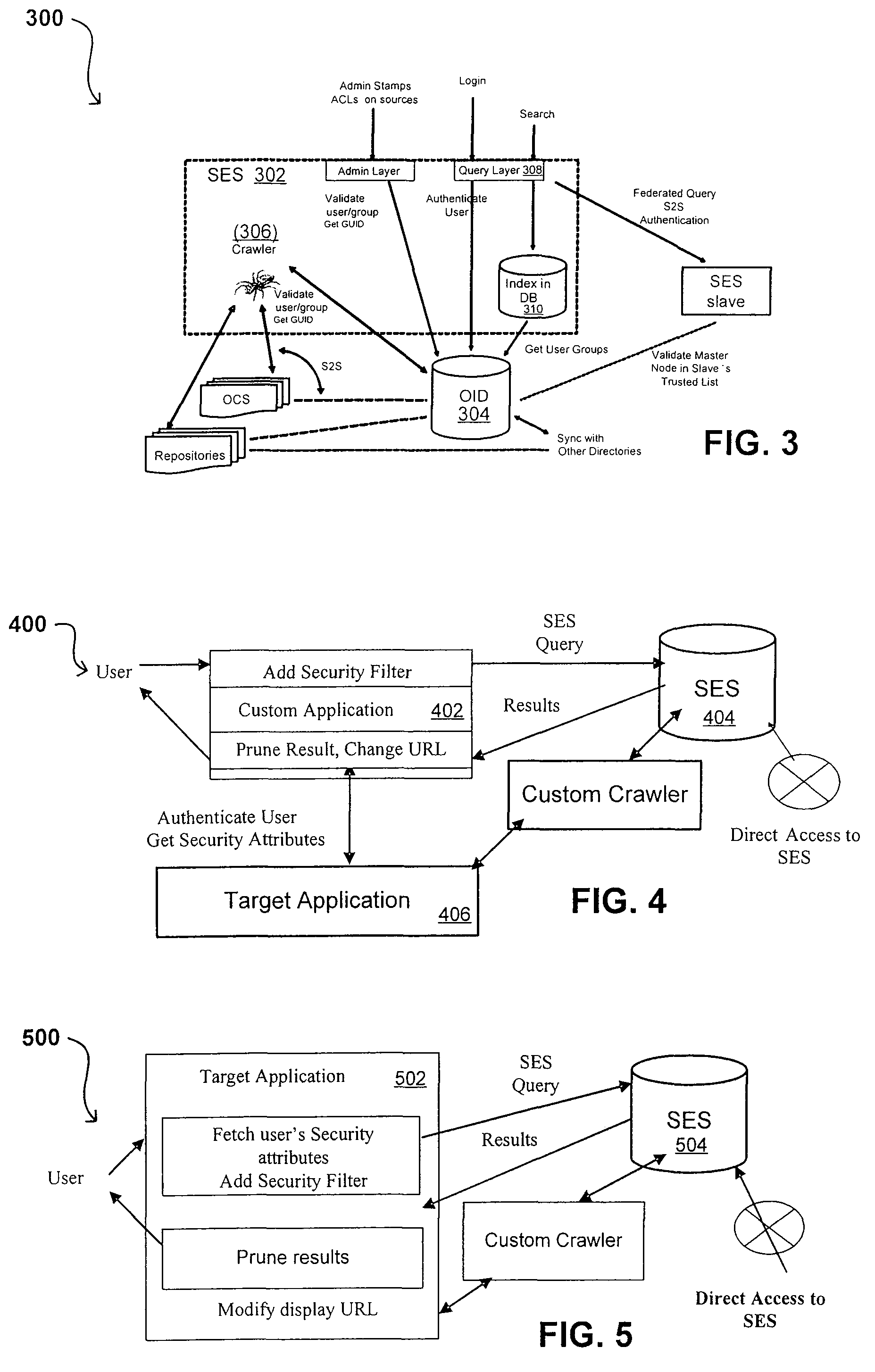
Search hit URL modification for secure application integration
ActiveUS8707451B2Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsExtensible architectureThe Internet
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Methods and systems for optimizing text searches over structured data in a multi-tenant environment
ActiveUS20070130137A1Increased its relevancyHandy search resultsDatabase queryingNatural language data processingApplication softwareUser role
Search systems and methods for searching structured data and enhancing the relevancy of search results provided to a requesting user or application. Enhanced search results are provided by searching a cache of a users most recently used items to eliminate or reduce search indexing latency. Also, more relevant search results are provided by re-ranking results based on use history, data security models and / or hierarchical user role models. Further, enhanced search results are provided by including user information in the search index.
Owner:SALESFORCE COM INC
Search Hit URL Modification for Secure Application Integration
ActiveUS20070209080A1Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Advertising based on widgets
ActiveUS20080010133A1Improve segmentationImprove protectionCommerceSpecial data processing applicationsUser inputElectronic information
Electronic advertisements and other types of electronic information are distributed based on user profiles and in particular, collections of widgets. User profiles may be generated based on a combination of user entered information and information inferred or derived from user behavior and interaction patterns. The use and collection of various widgets may also be recorded by a user profile to determine a user's preferences and interests. An advertisement may be distributed by segmenting a user population according to user profile information and one or more attributes of the advertisement. Users may further interact with the widgets in a variety of ways including requesting additional information about the advertised product or service and / or requesting communications with an advertiser without compromising their privacy.
Owner:NOKIA TECHNOLOGLES OY
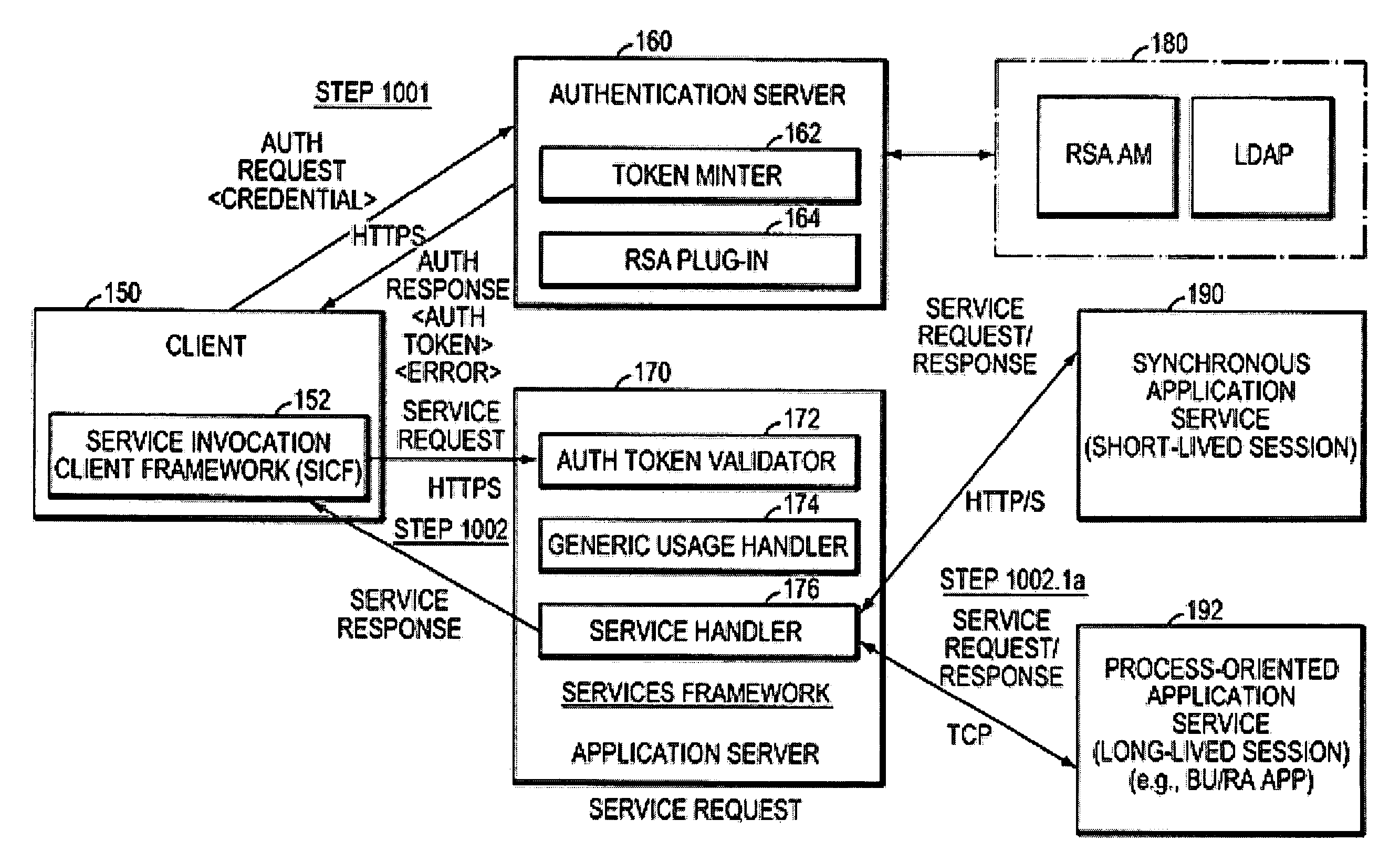
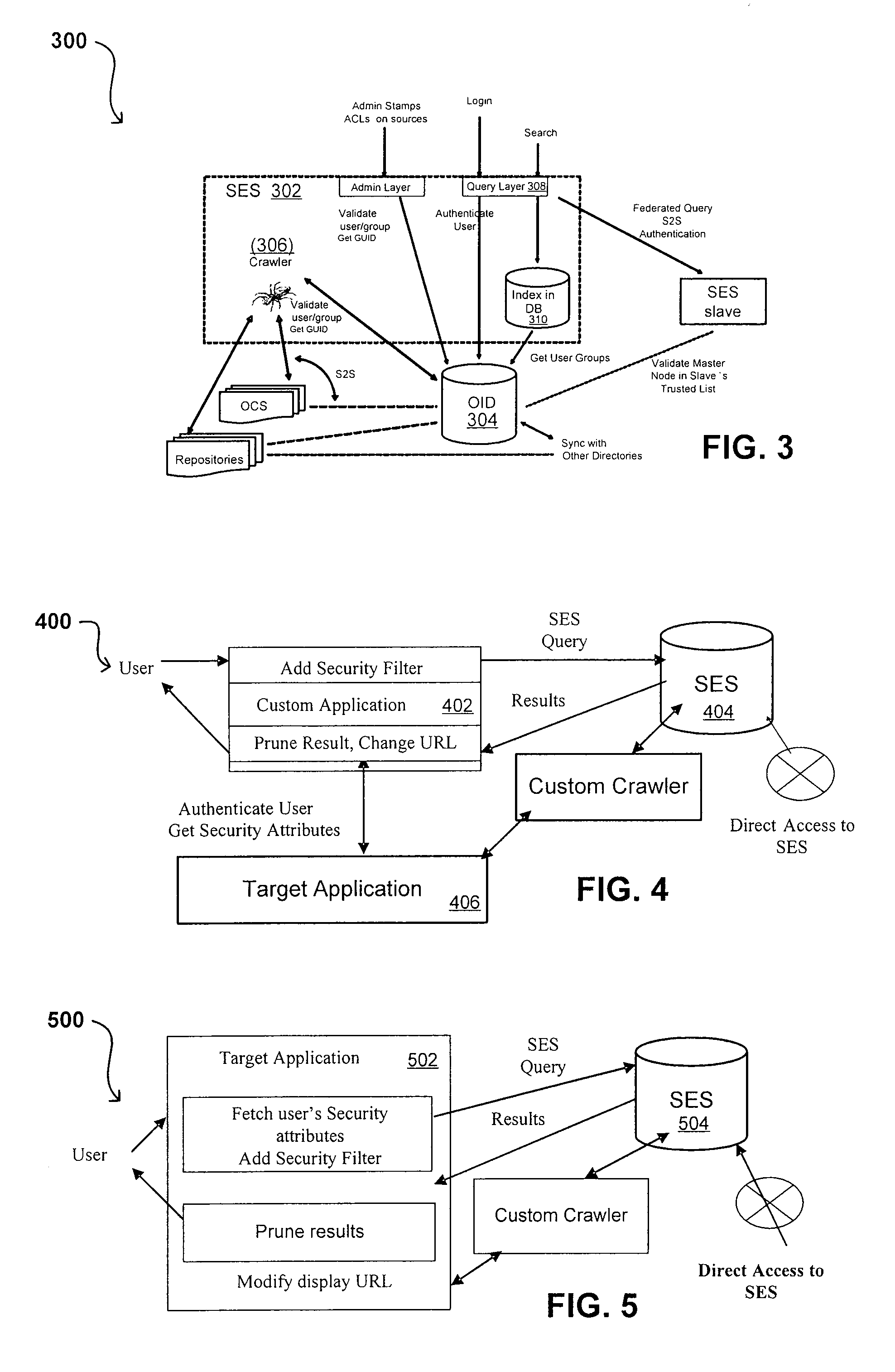
Flexible Authentication Framework
ActiveUS20070208744A1Limited lifetimeImprove performanceWeb data indexingDigital data authenticationThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
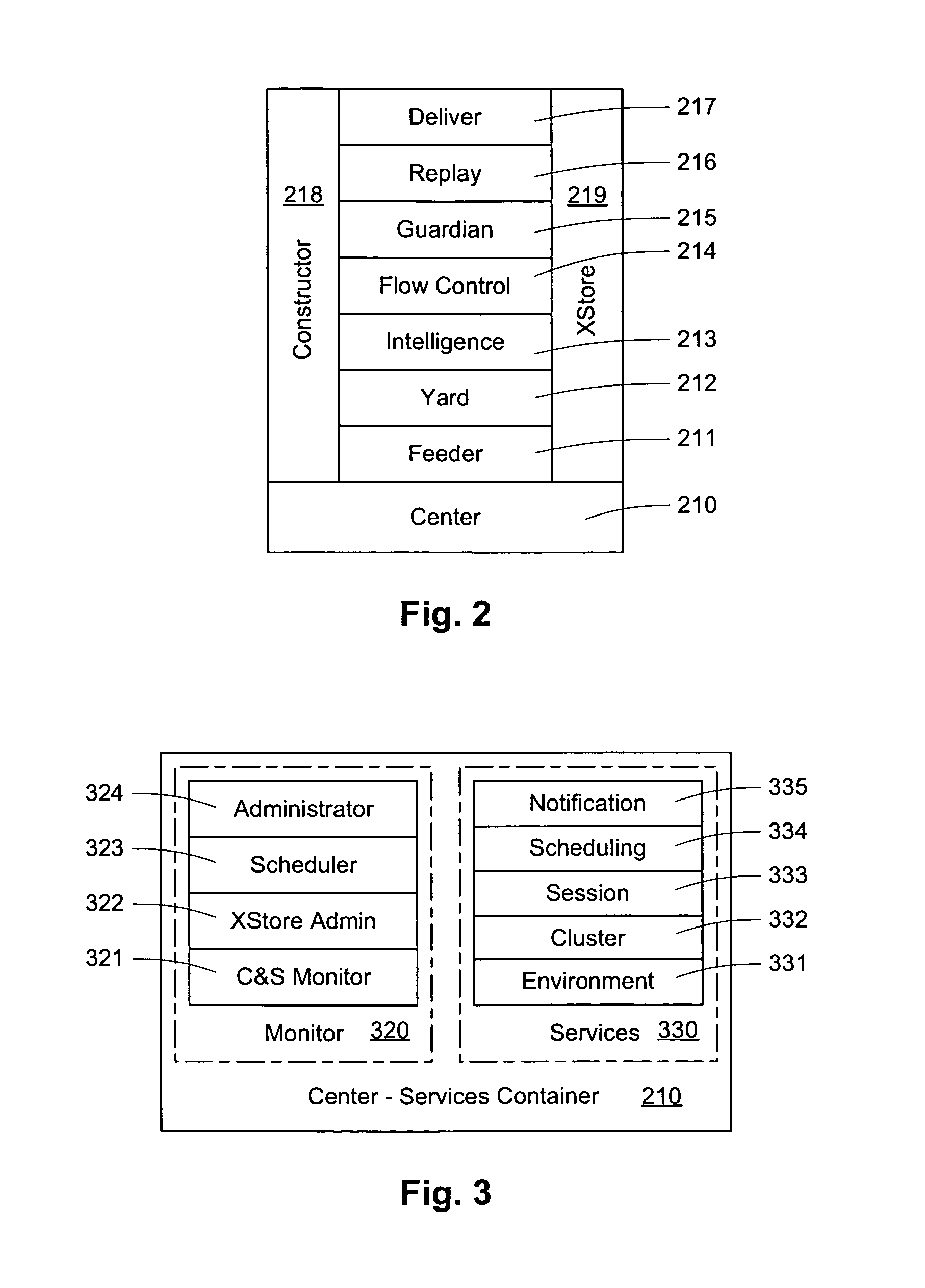
Computer implemented medical treatment management system
InactiveUS20100036676A1Limit user accessMedical report generationComputer-assisted treatment prescription/deliveryUser inputEndoscopic surgery
Owner:E MERGE HEALTH SOLUTIONS
Role-oriented development environment
ActiveUS20060095276A1Data processing applicationsSpecific program execution arrangementsPower userHuman–computer interaction
This invention relates to a business application development and execution environment that recognizes and supports various development and user roles. Aspects of the method and system are adapted to builders, assemblers, power users and end users.
Owner:BACKSTOP SOLUTIONS GRP
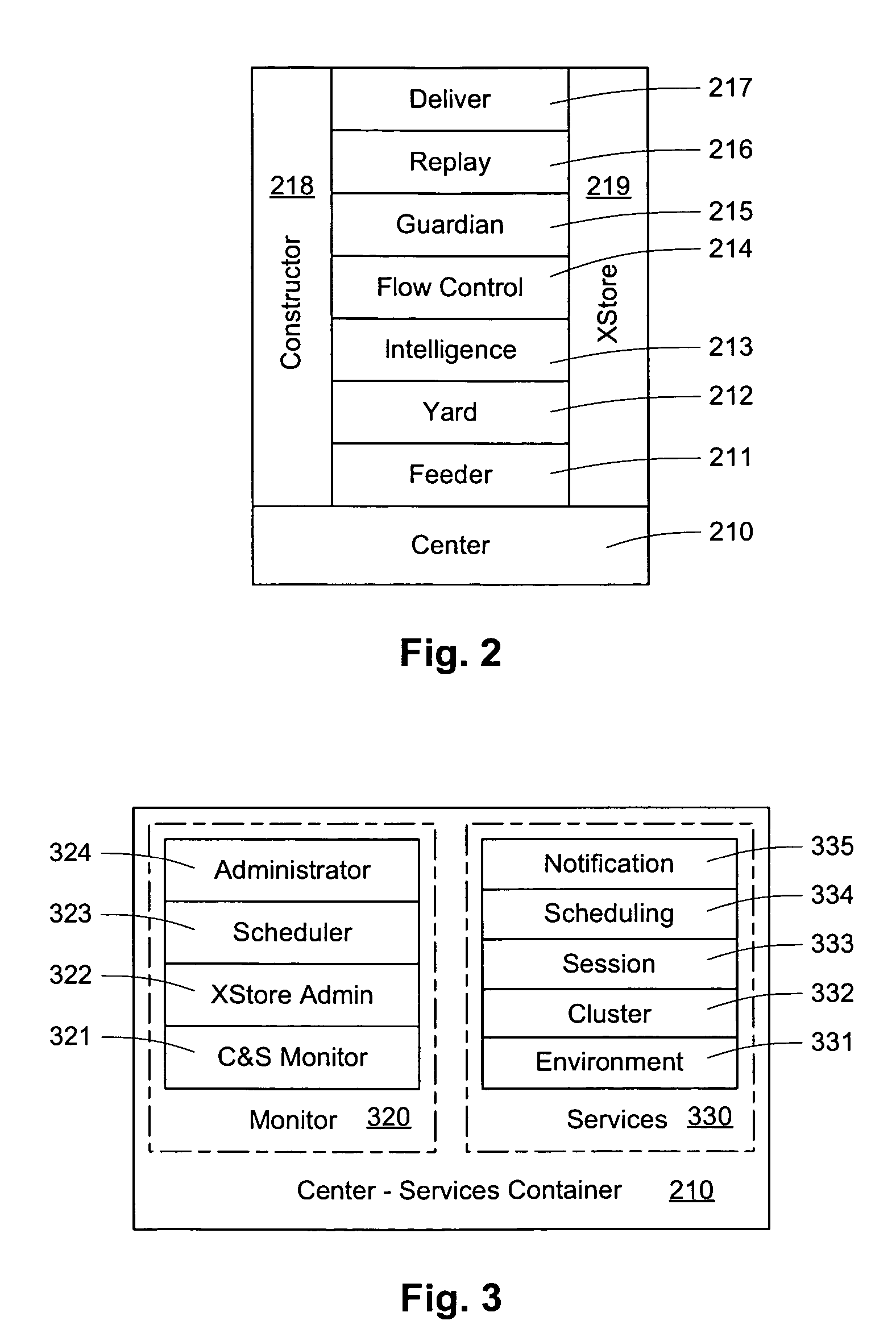
Tenant life cycle management for a software as a service platform
ActiveUS8291490B1Digital data processing detailsUnauthorized memory use protectionApplication specificApplication software
Managing user access to application-specific capabilities of a system includes maintaining data correlating application-specific capabilities for each of the applications of the system, where the application-specific capabilities of different applications are independent of each other. Managing user access also includes maintaining data correlating user identifiers with user roles, maintaining data correlating user roles with application-specific capabilities, and managing the data using a security module that accesses the data correlating application-specific capabilities, data correlating user identifiers, and the data correlating user roles. The system may have a plurality of tenants and wherein each of the tenants subscribes to one or more of the applications. Each of the users may correspond to a particular one of the tenants. Each tenant may subscribe to a particular set of applications / features.
Owner:EMC IP HLDG CO LLC
System and method for provisioning resources to users based on roles, organizational information, attributes and third-party information or authorizations
InactiveUS6985955B2Reducing and minimizing numberMultiple digital computer combinationsResourcesThird partyComputer science
A method for provisioning users with resources is disclosed. The method includes the steps of establishing a set of attributes, organizational information, and user roles and defining a plurality of resource provisioning policies based on selected attributes, organizational information, and user roles. The method also includes the steps of receiving attribute information and user role information for a particular user or resource, determining which resource provisioning policies are applicable to the user based on the received user role information, organizational information, and attribute information, seeking additional information or authorizations from third parties in accordance with the applicable resource provisioning policies, and provisioning the user with the resources specified by the applicable resource provisioning policies if all necessary additional information or authorizations have been received from the third parties.
Owner:IBM CORP
Method and system for enterprise network access control and management for government and corporate entities
InactiveUS20090254392A1Data processing applicationsComputer security arrangementsNetwork Access ControlIdentity management
A method, system, computer program product, and devices for enterprise network access control and management for Government and Corporate entities, including interagency identity management; connectors and controls; an interagency directory services transformation service; a user / duty position resolving service; role-based encryption key management; role-based business process modeling; and proximity-based access control enabled by user-role-track association.
Owner:ZANDER VAN S
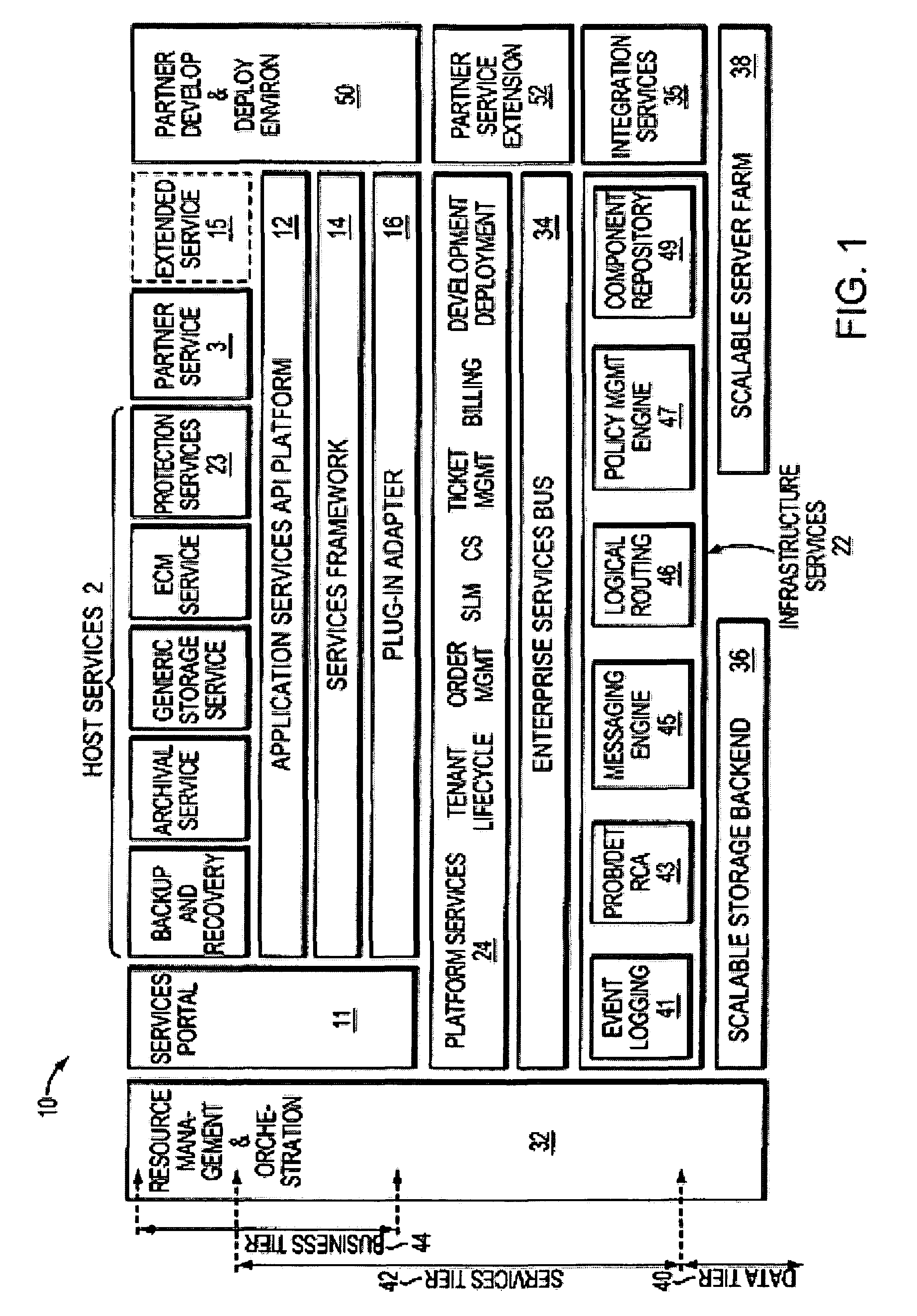
On-demand active role-based software provisioning
ActiveUS20050125509A1Avoid the needMultiple digital computer combinationsProgram loading/initiatingSoftware distributionSoftware license
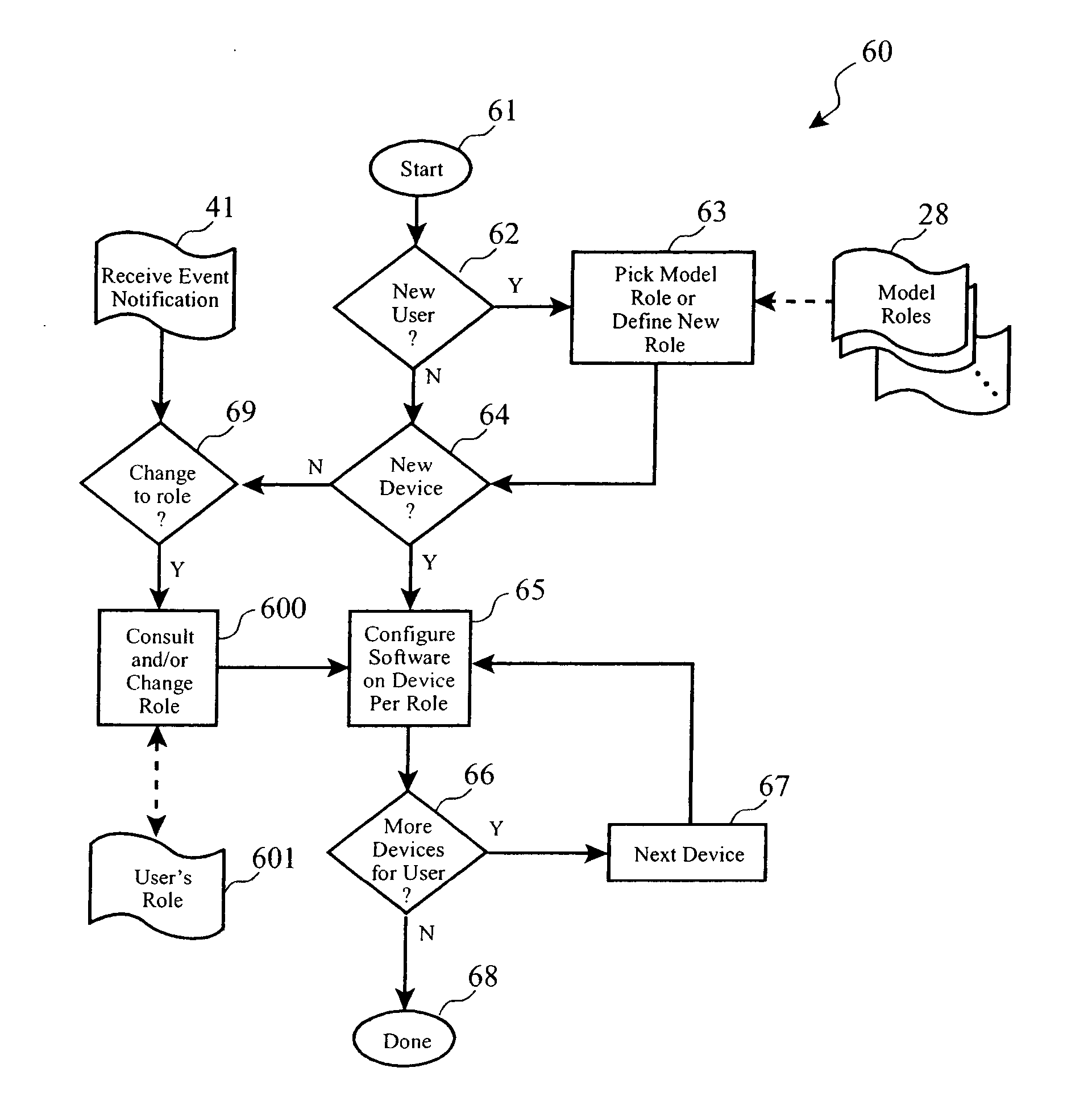
Automated software provisioning based upon a set of role definitions for a user of a configurable device such as a computer or personal digital assistant. The present invention may be realized as an enhancement or extension to currently available software distribution tools which are used to distribute software to remote and local machines, and to permit unattended software installation and maintenance. The invention provides role-based software provisioning which automatically distributes the appropriate software programs and updates to computers that are owned by users based on the role of each user, thereby avoiding the need for intensive manual efforts to determine which computers need what software. The invention may also be interfaced to a License Management system in order to accomplish automatic recovery of unused software licenses, and to obtain permission for installing new licenses, based on user role changes.
Owner:DROPBOX
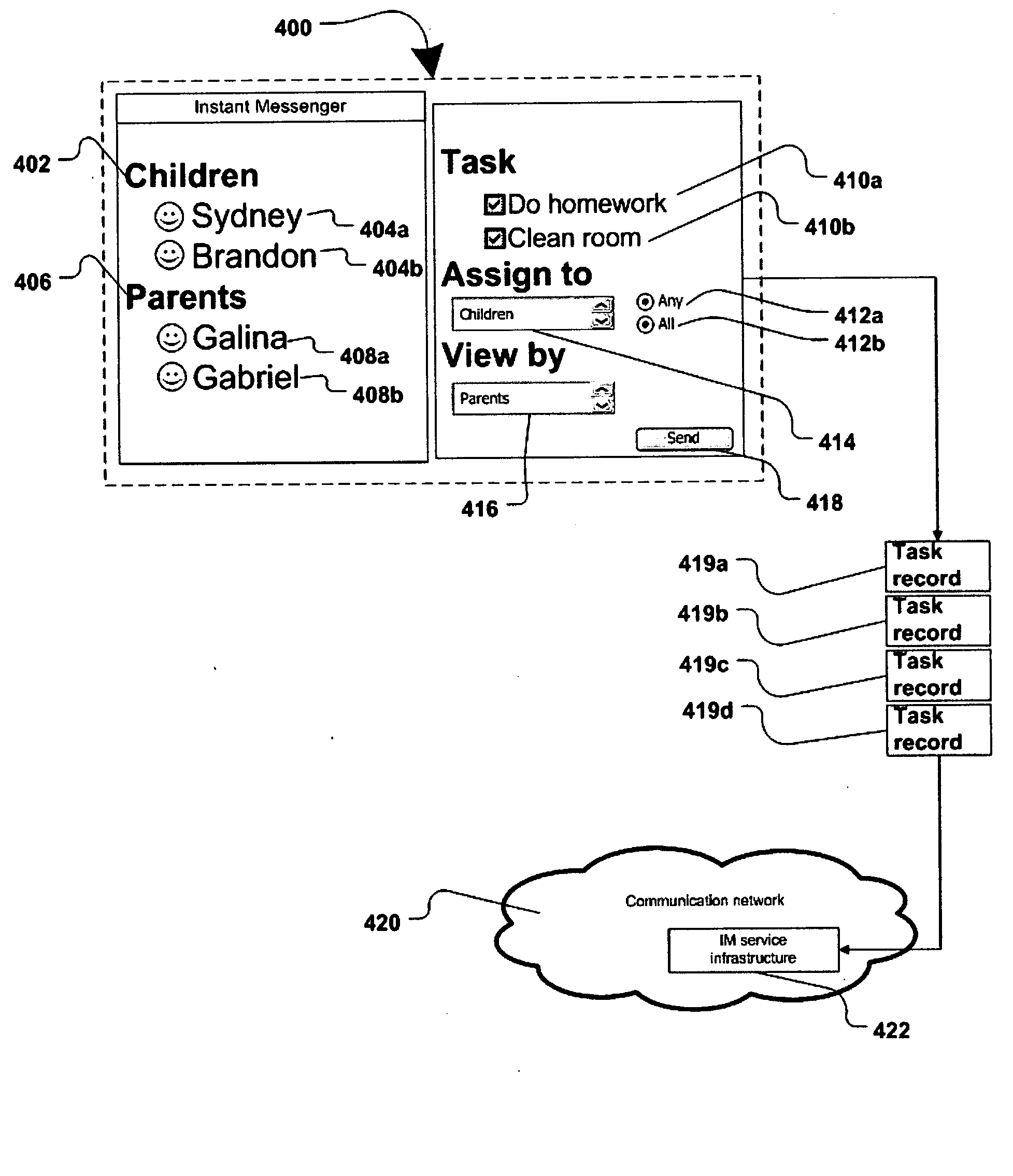
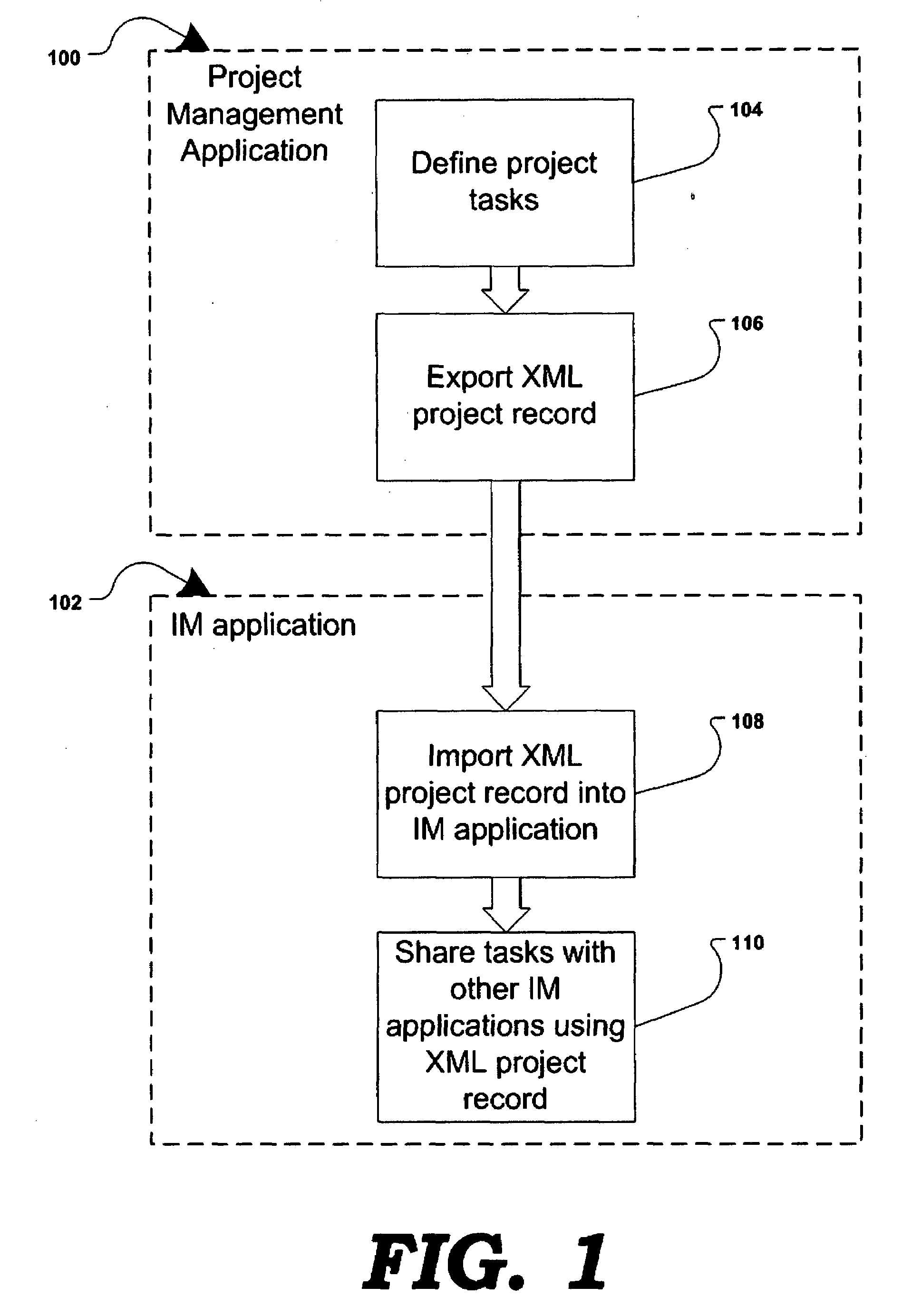
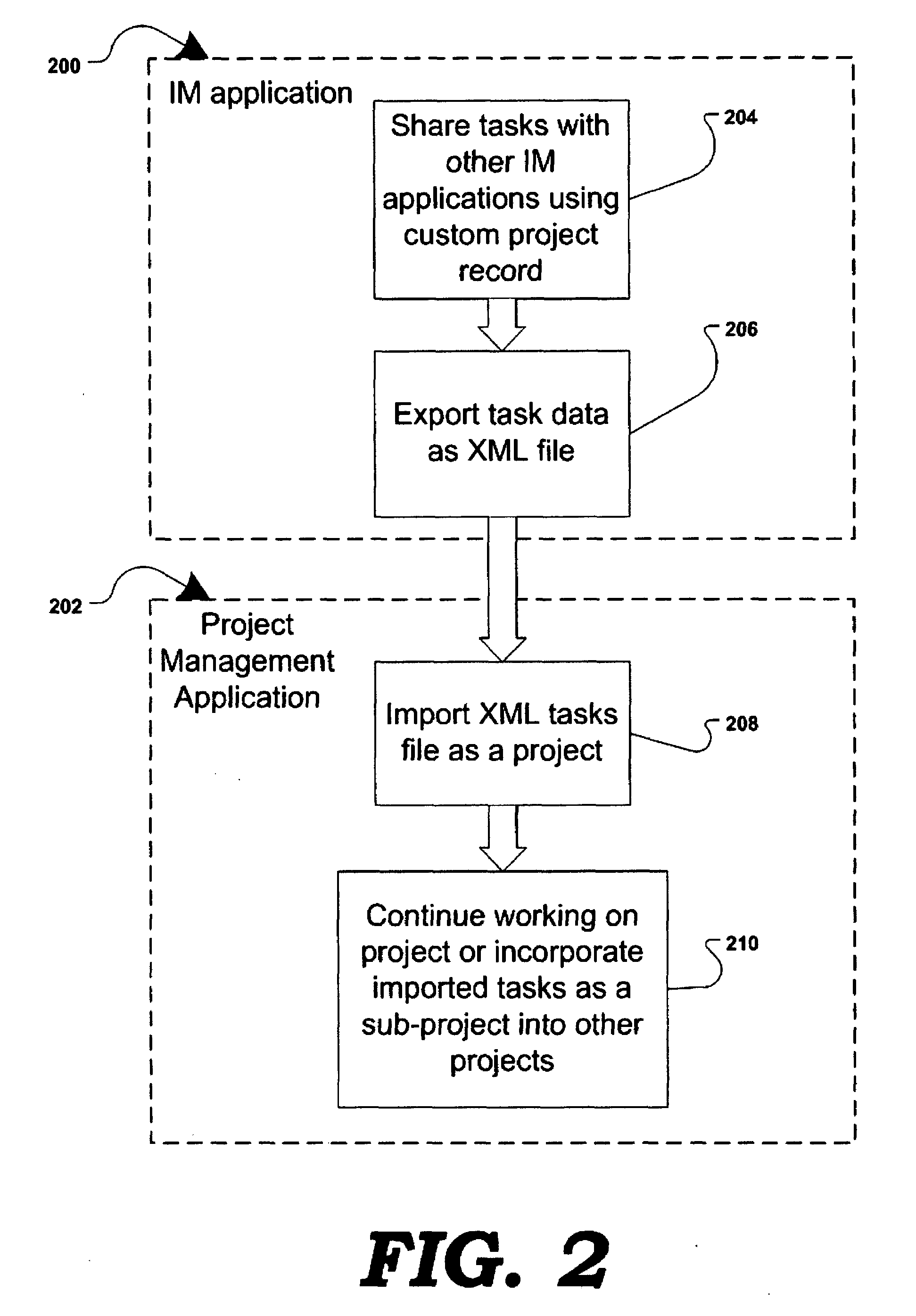
Method and system of project management and task collaboration over instant messenger
InactiveUS20080209417A1Multiprogramming arrangementsMultiple digital computer combinationsWork taskMilestone
Owner:JAKOBSON GABRIEL
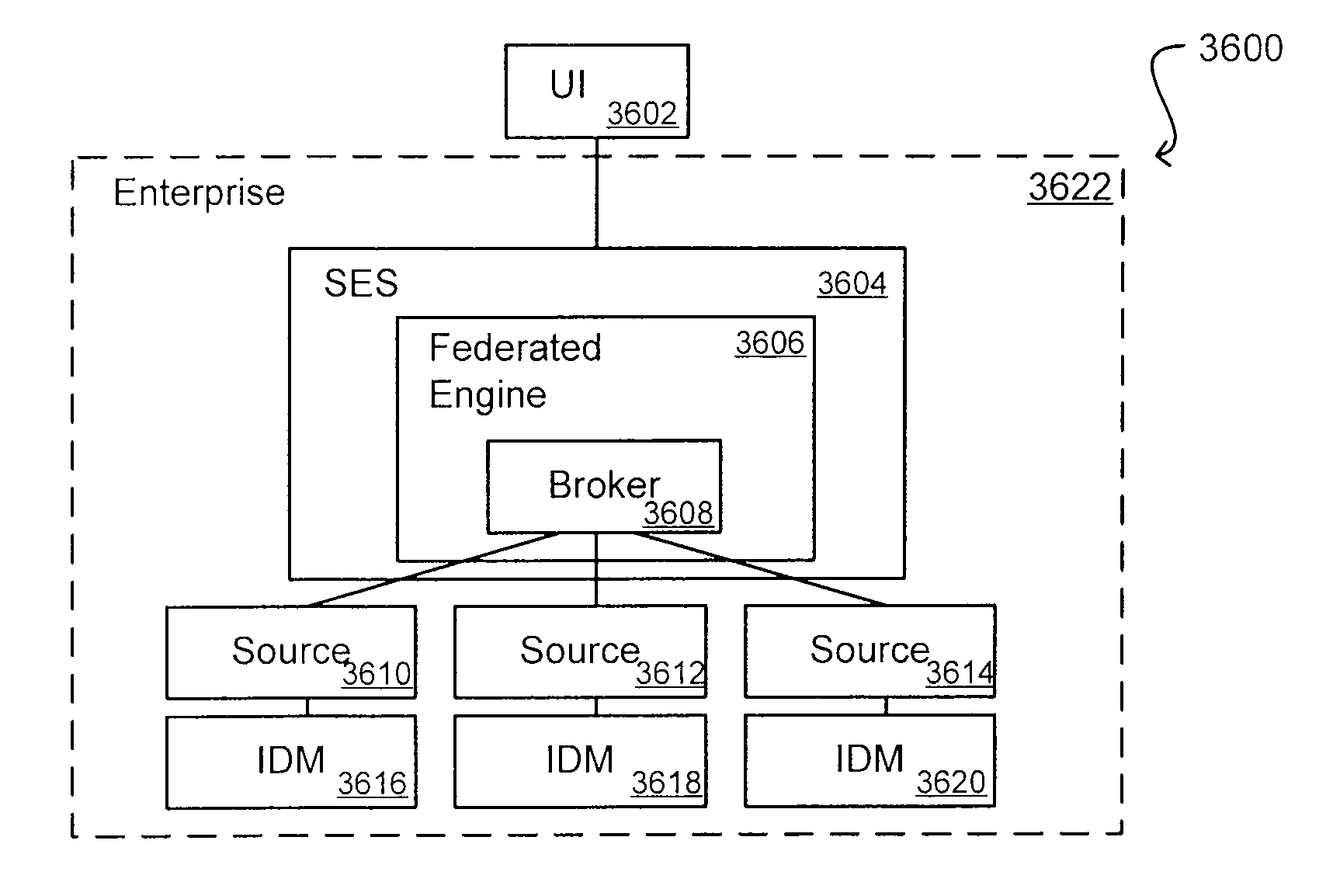
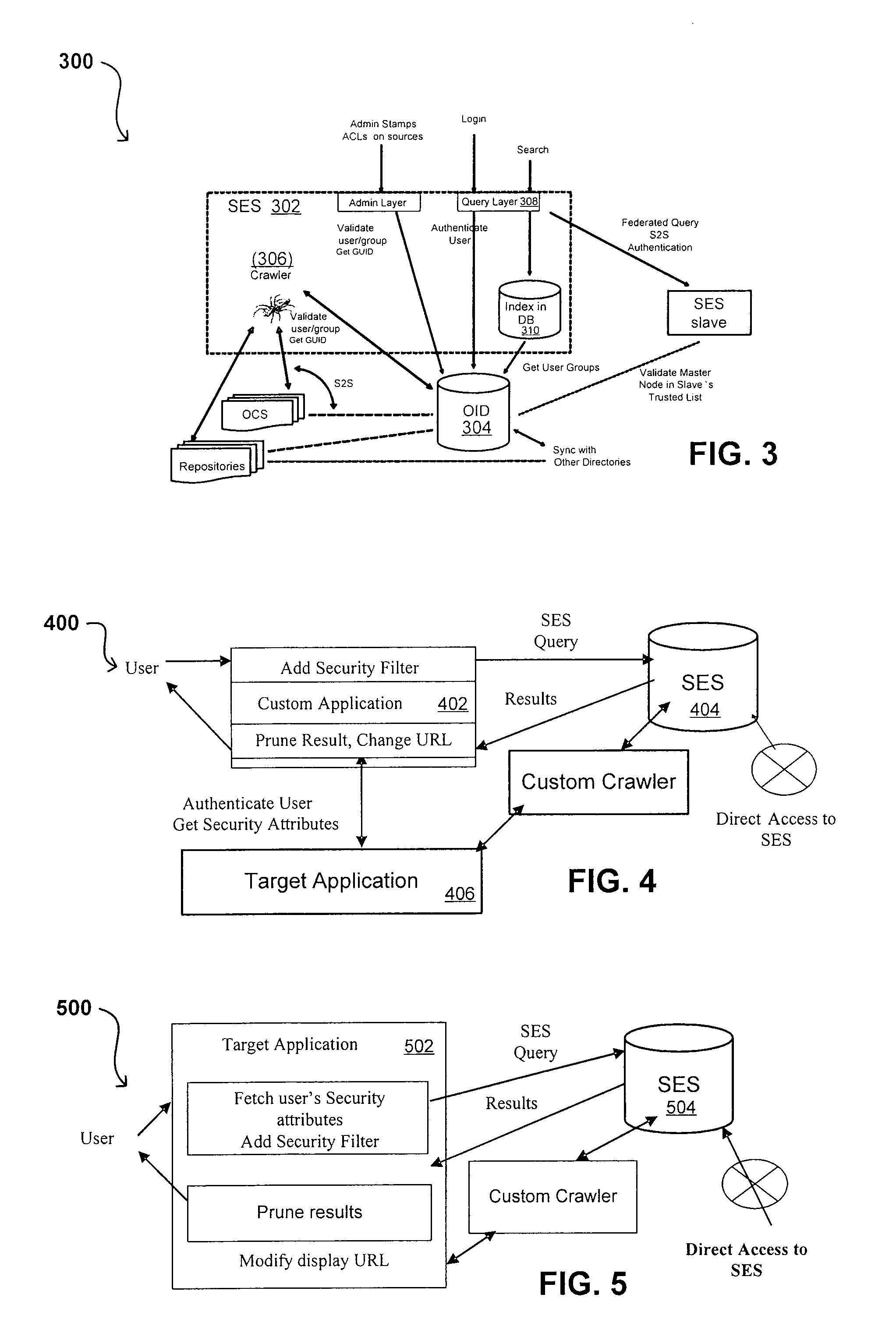
Propagating User Identities In A Secure Federated Search System
ActiveUS20070220268A1Limited lifetimeImprove performanceDigital data information retrievalDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
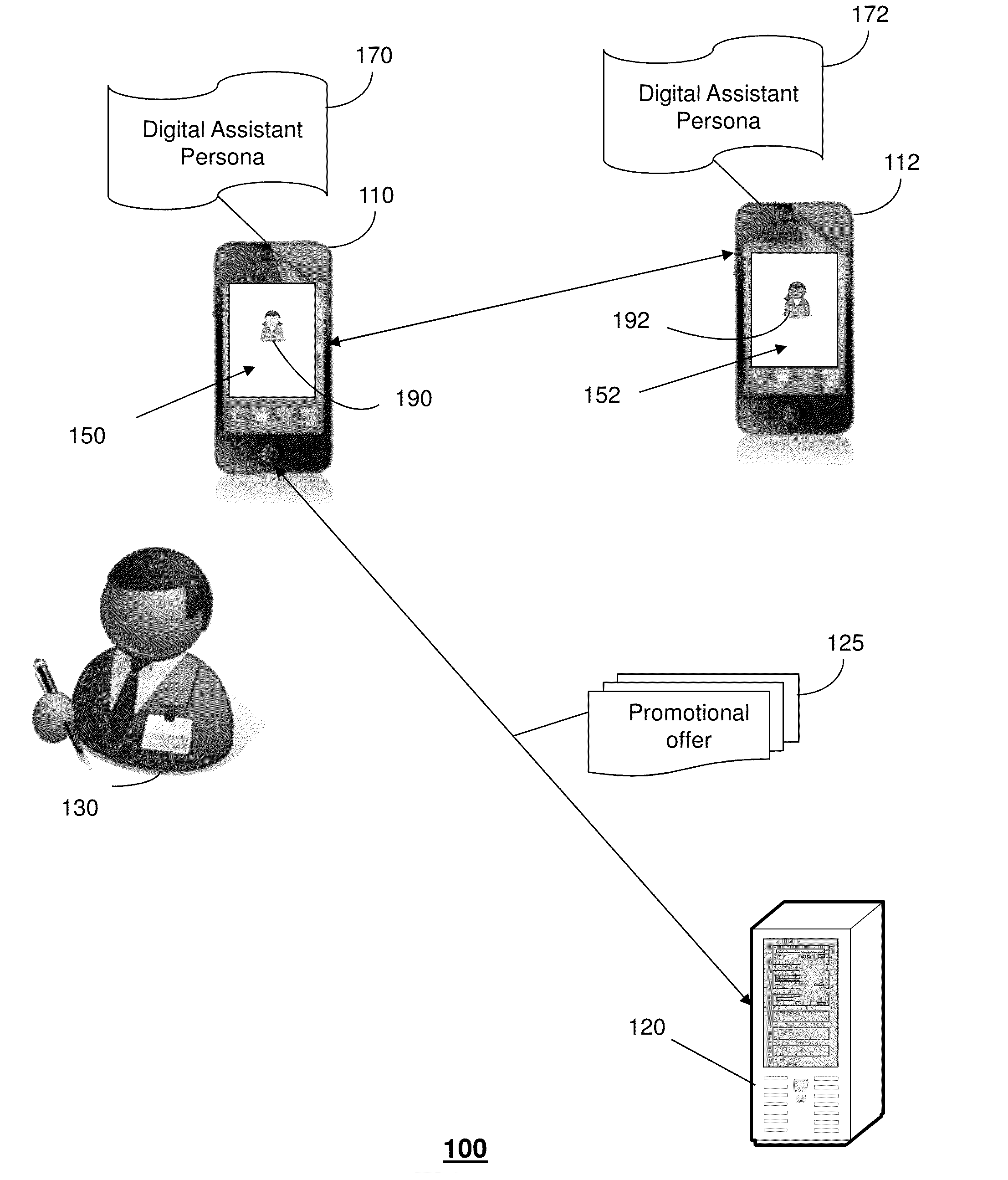
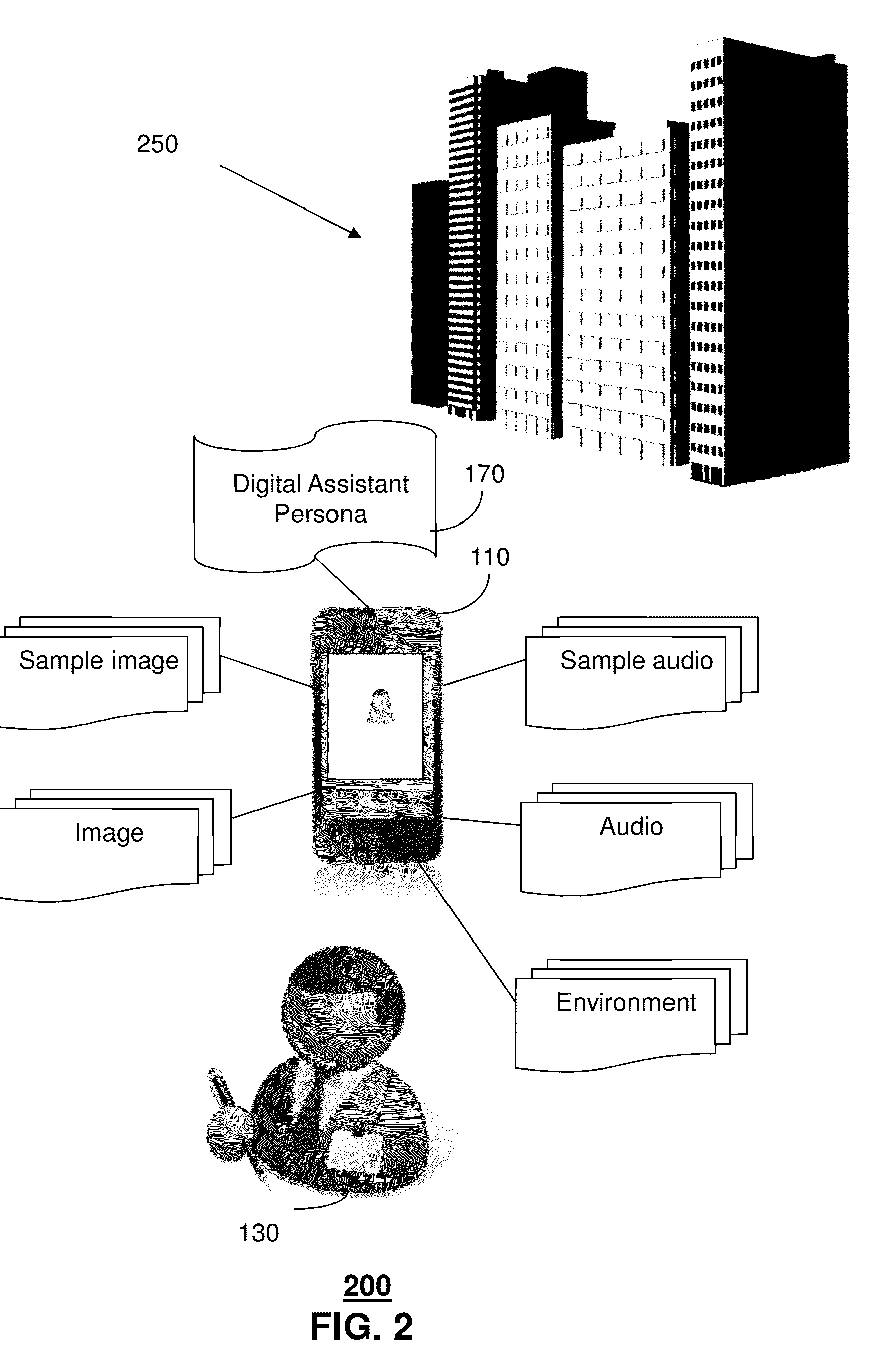
Method and apparatus for adjusting a digital assistant persona
A method that incorporates the subject disclosure may include, for example, providing a first digital assistant to engage in a first communication exchange with a user of the first communication device where the first digital assistant has a first digital assistant persona that controls information provided by the first digital assistant during communication exchanges, analyzing user input during the first communication exchange, and adjusting the first digital assistant persona based on one or more of the user persona, user deficiency, or promotional offers. Other embodiments are disclosed.
Owner:AT&T INTPROP I L P
Technique for effective organization and communication of information
InactiveUS8126960B2Easy to operateReduce the amount requiredData processing applicationsInformation formatElectronic informationUser profile
Owner:SILVER STATE INTELLECTUAL TECH
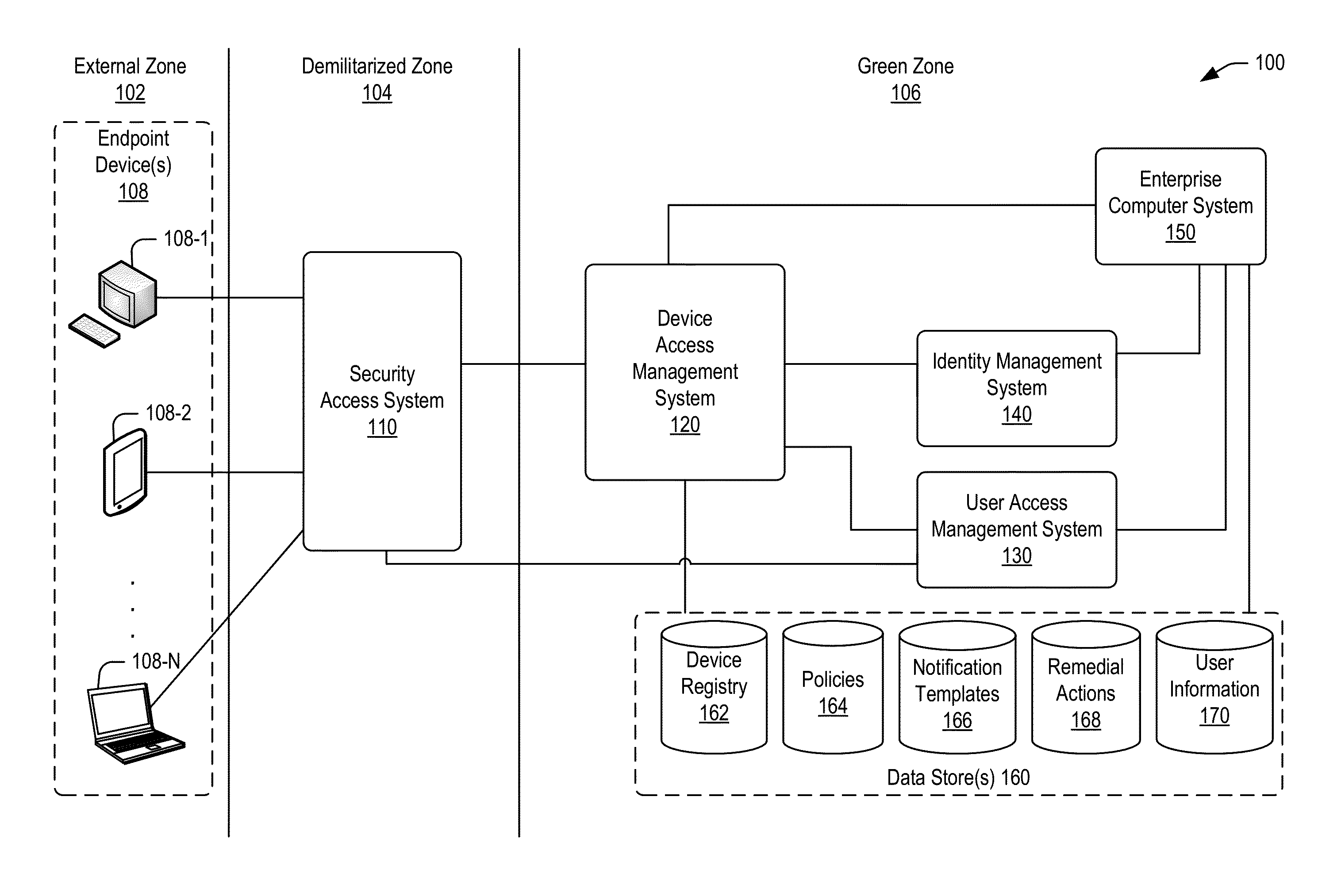
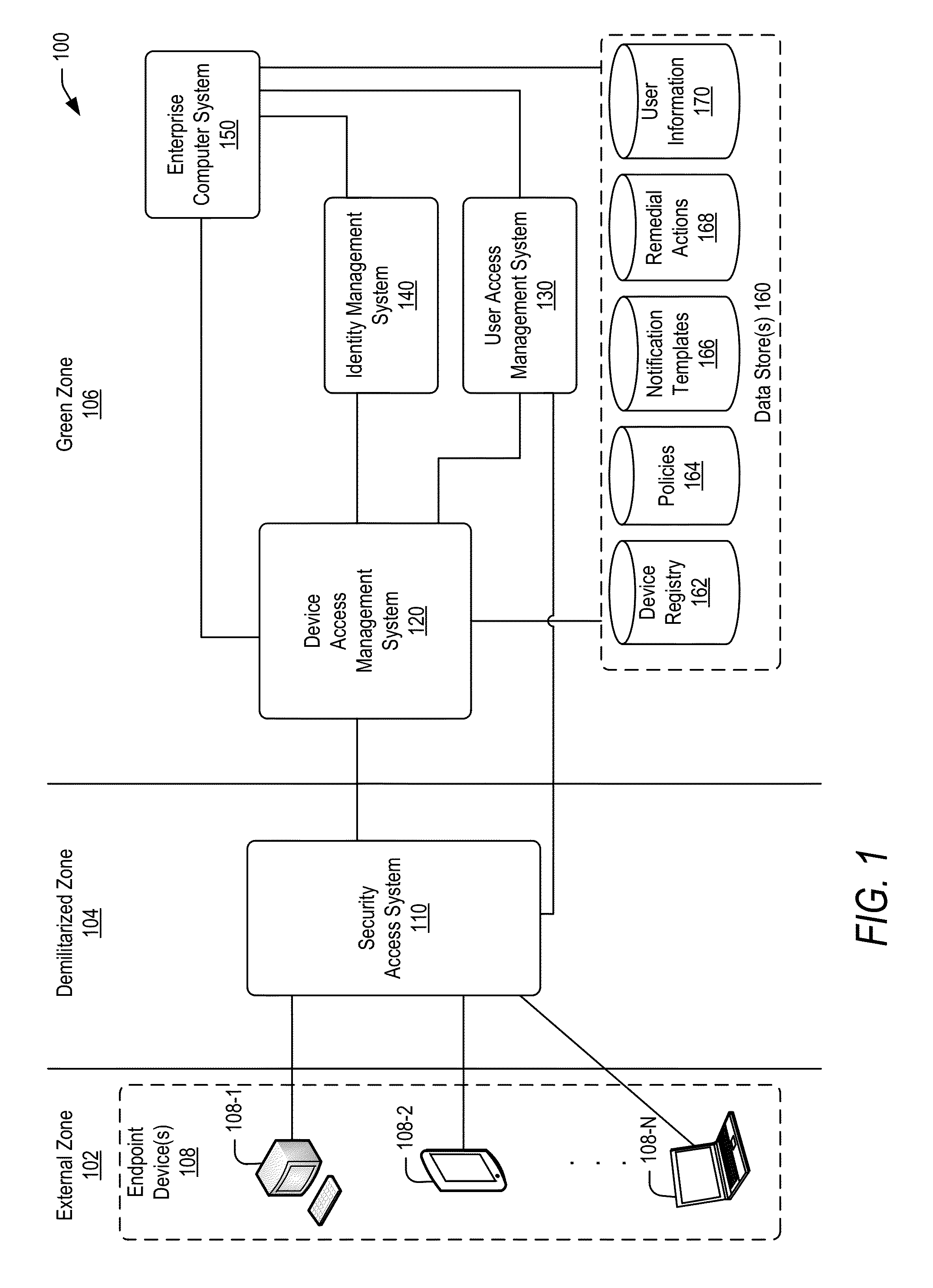
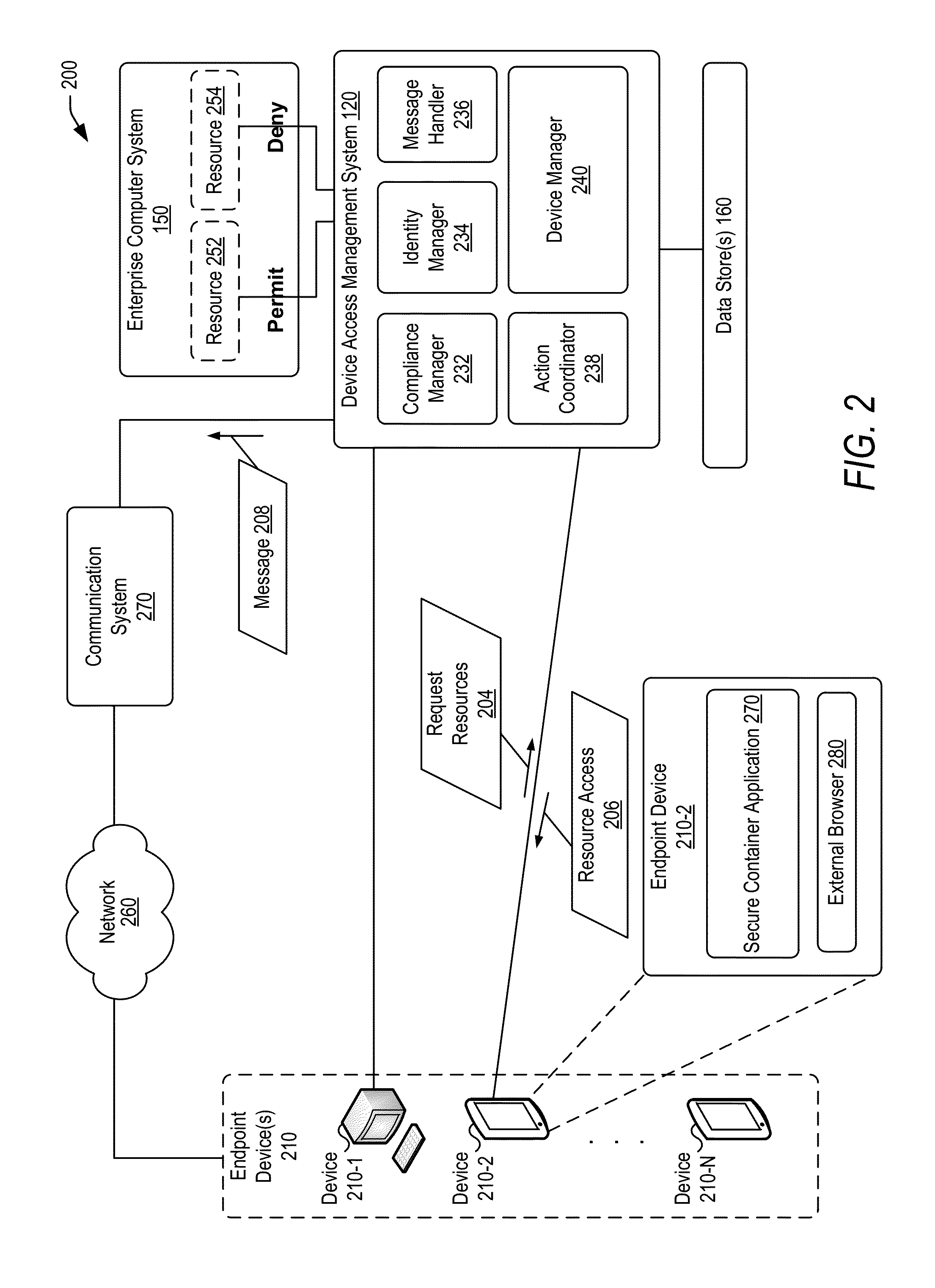
Policy-based compliance management and remediation of devices in an enterprise system
ActiveUS20160088021A1Reduce the burden onAvoid accessService provisioningVersion controlNon complianceEnterprise system
The present disclosure relates generally to managing compliance of remote devices that access an enterprise system. More particularly, techniques are disclosed for using a compliance policy to manage remediation of non-compliances of remote devices that access an enterprise system. A device access management system may be implemented to automate remediation of non-compliances of remote devices accessing an enterprise system. Remediation may be controlled based on different levels of non-compliance, each defined by one or more different non-compliances. In some embodiments, a level of non-compliance may be conditionally defined by one or more user roles for which non-compliance is assessed. Access to computing resources of an enterprise system may be controlled for a remote device based on compliance of the remote device. Access may be inhibited for those resources not permitted during a time period of a non-compliance.
Owner:ORACLE INT CORP
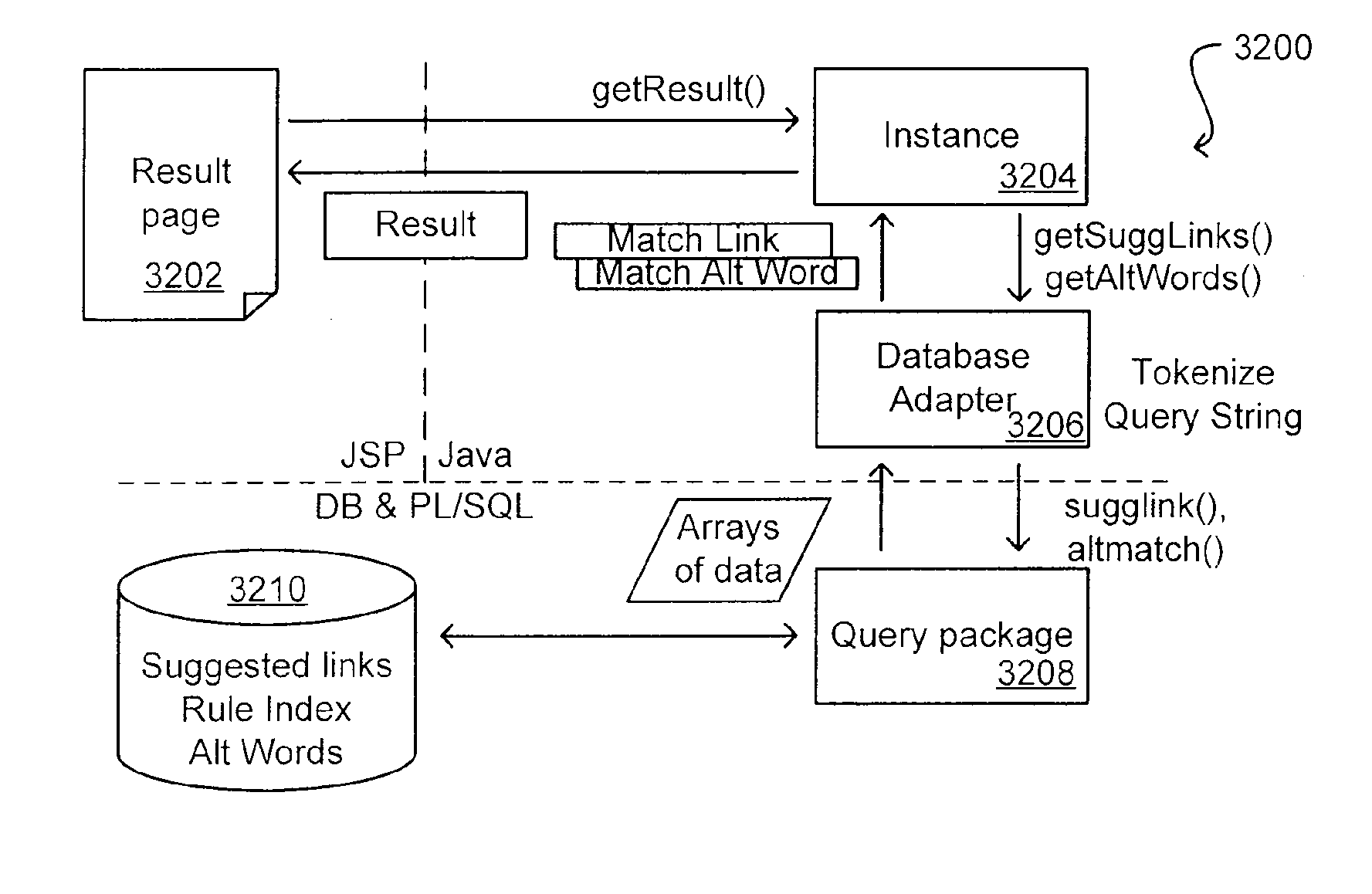
Method for Suggesting Web Links and Alternate Terms for Matching Search Queries
ActiveUS20070208714A1Limited lifetimeImprove performanceWeb data indexingComputer security arrangementsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
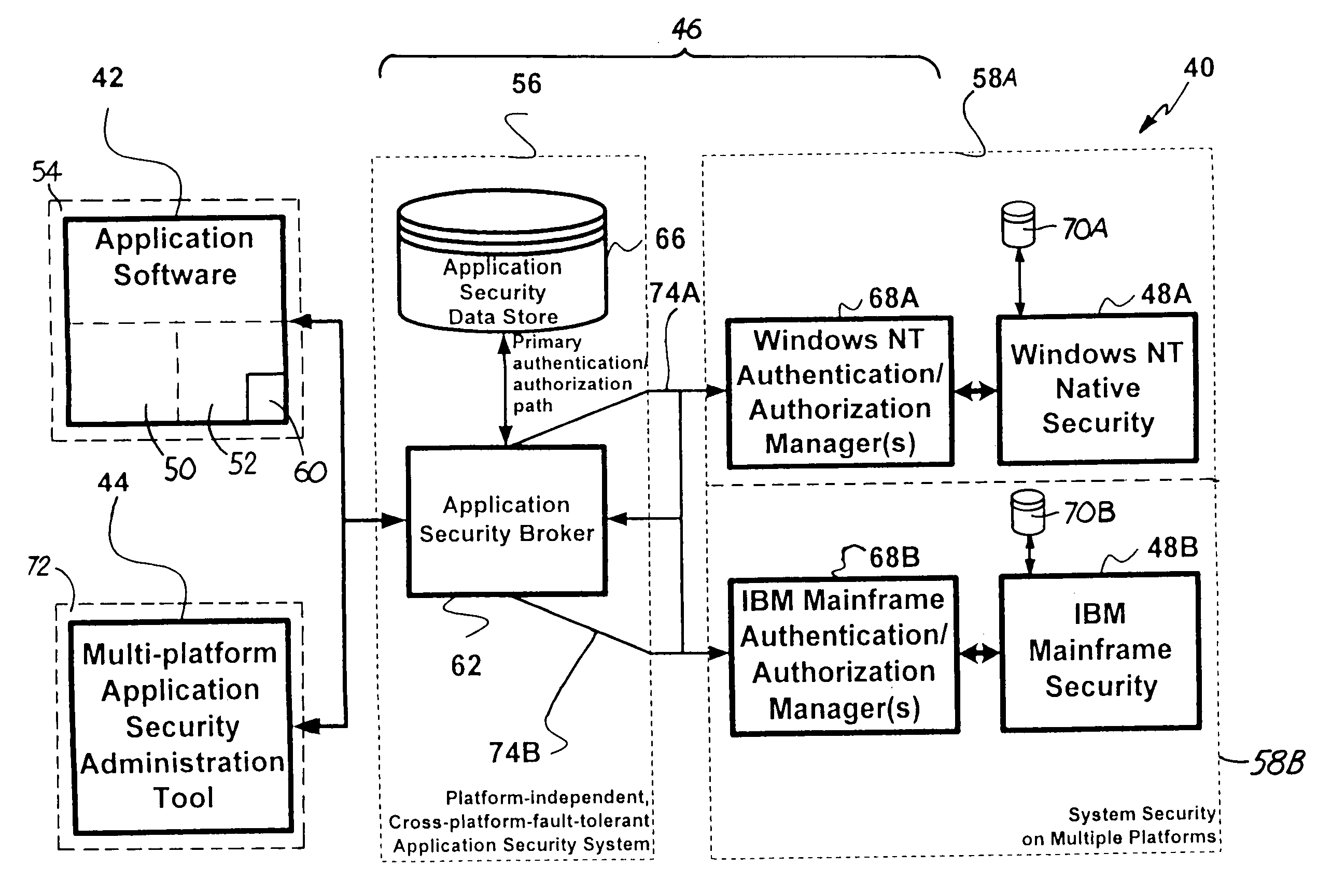
Computer security system
InactiveUS7131000B2Data processing applicationsDigital data processing detailsComputerized systemComputer security model
A computer system provides system-wide computer application security using role-based identifiers. The programmer identifies secured functions within a software application using a hierarchical identifier. The hierarchical identifiers are grouped together into privilege sets. The privilege sets and other hierarchical identifiers are grouped together into job functions, which are in turn grouped into larger subsets called user roles. These user roles are stored in a data store. User identifiers are created. Each user identifier is linked to one user role in the data store. A surrogate identifier is created to correspond to each user role and is stored in the data store. The surrogate identifiers are not disclosed to the users. A user is given permission to access secured functions within an application by retrieving a surrogate identifier from the data store, which shares the same user role as the user. Access rights are determined using the surrogate identifier to validate permissions on a security provider.
Owner:JOLLY SEVEN SERIES 70 OF ALLIED SECURITY TRUST I
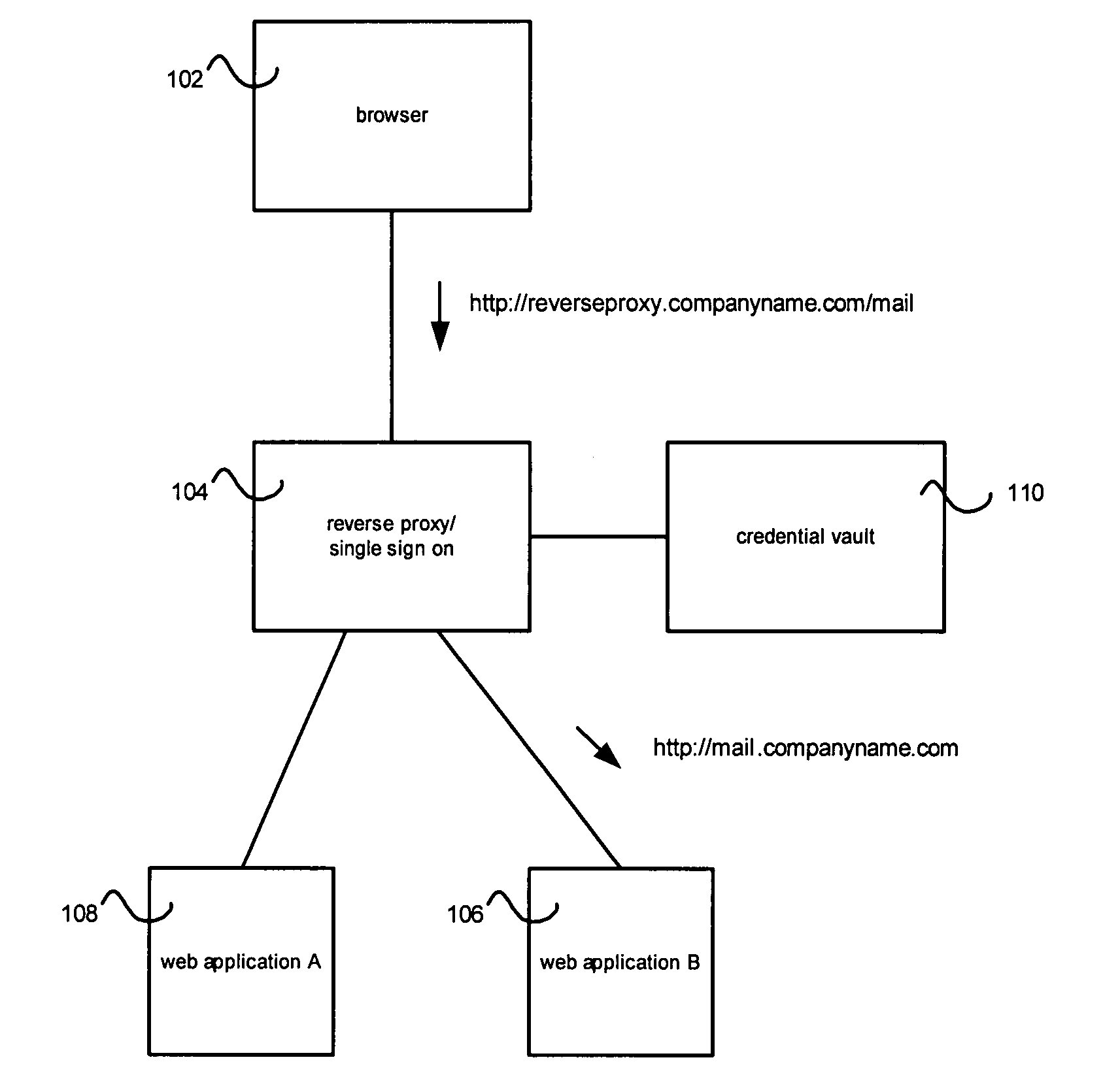
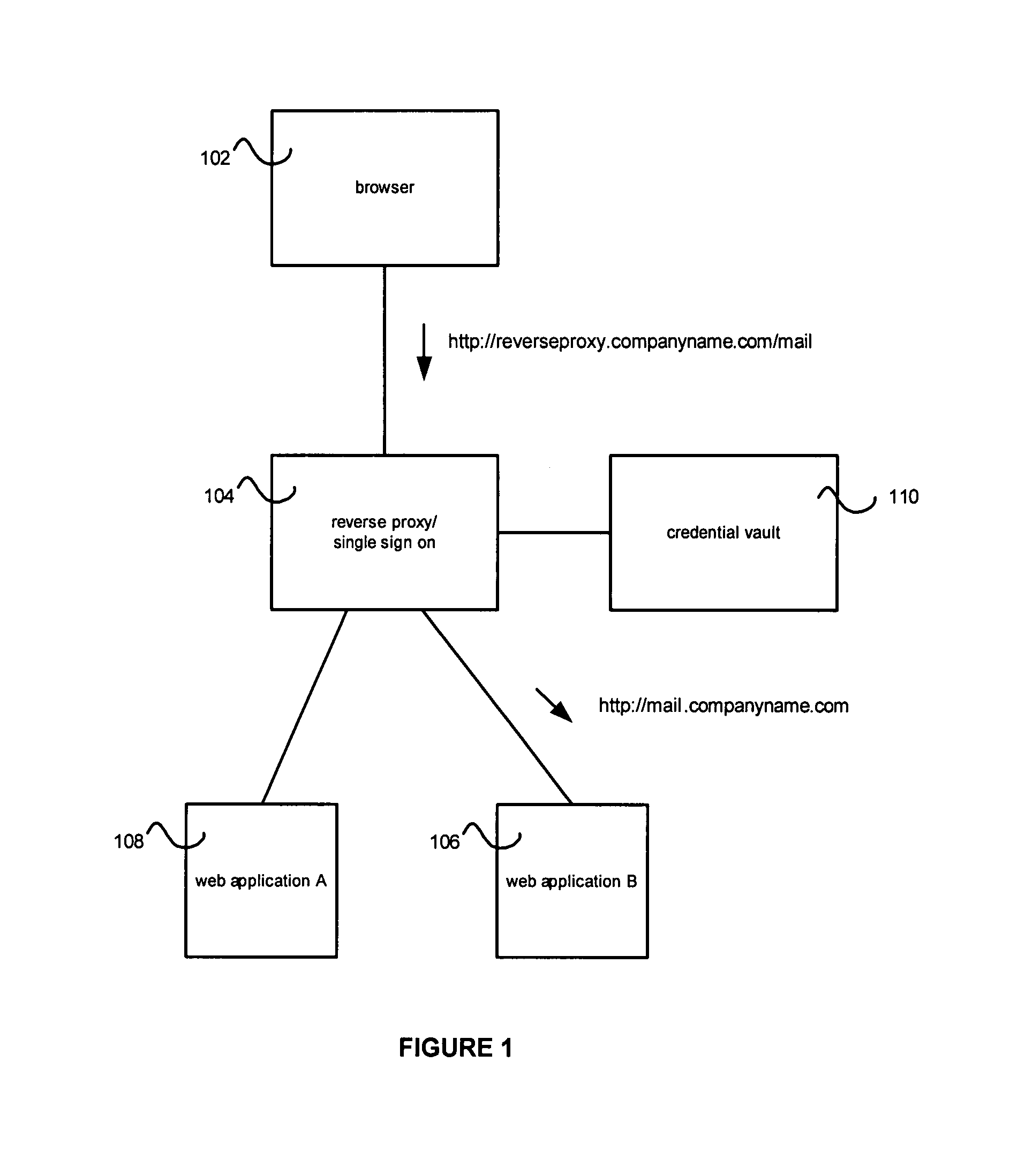
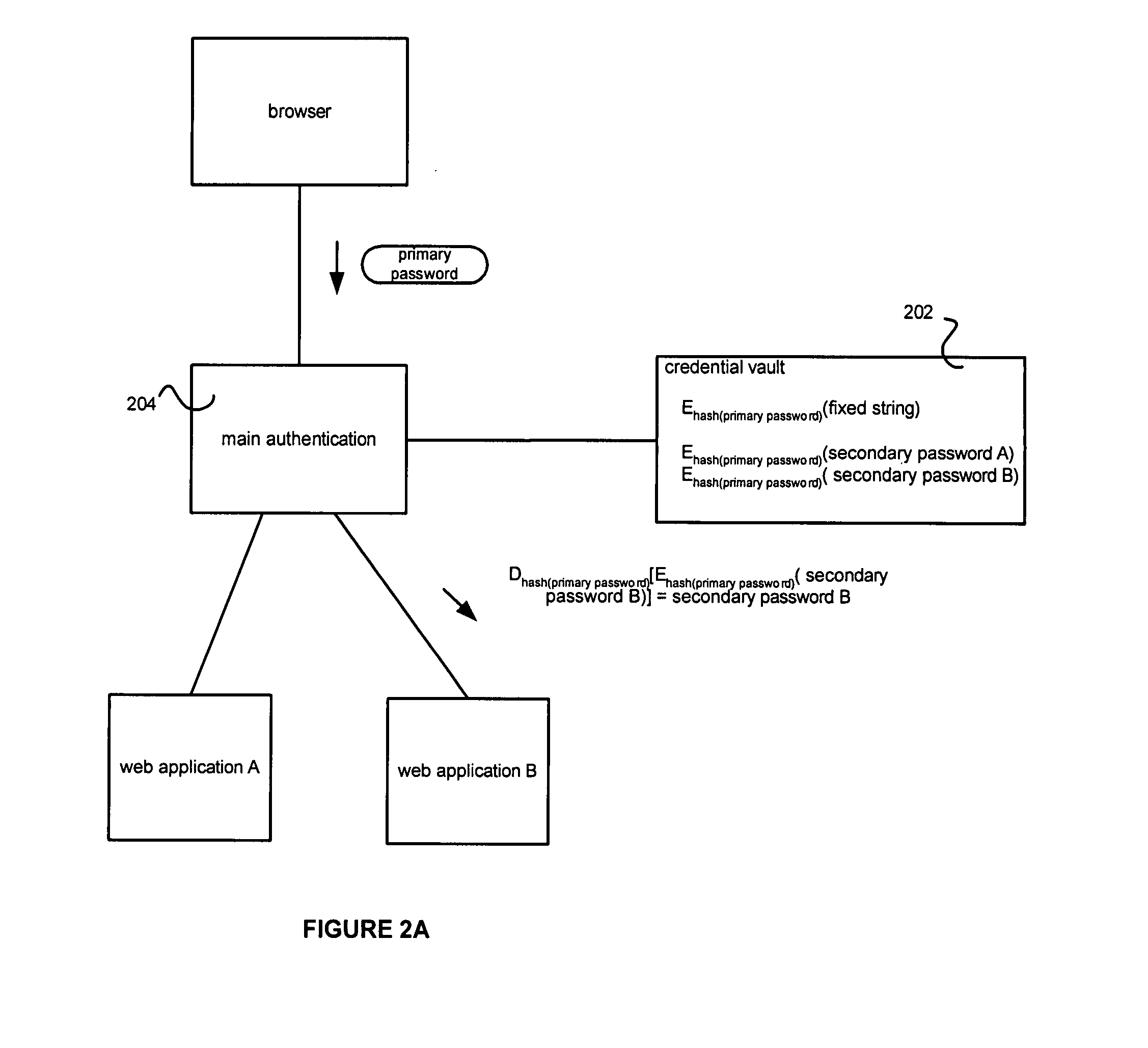
Credential vault encryption
InactiveUS20080077982A1Natural language data processingMultiple digital computer combinationsWeb applicationReverse proxy
Application role mappings can be maintained at a reverse proxy server. When a request for a web application is received at the reverse proxy servers, the proper user role for the web application can be determined at the reverse proxy server. The proper user role can be sent as part of a HTTP header to the web application. The web application can use the user role without doing an independent mapping of the user to a role.
Owner:ORACLE INT CORP
Flexible Authorization Model for Secure Search
InactiveUS20070214129A1Limited lifetimeImprove performanceWeb data indexingSpecial data processing applicationsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
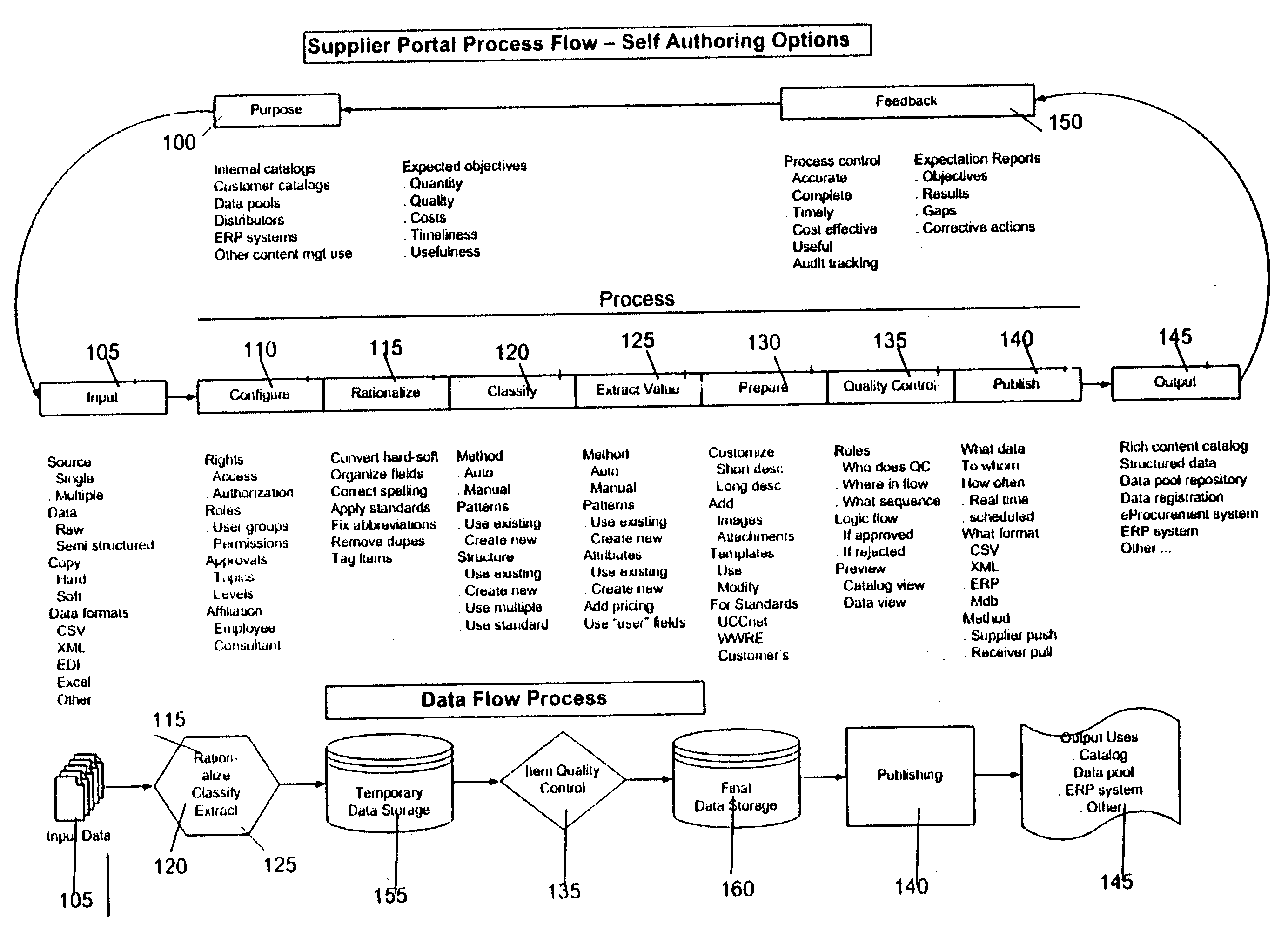
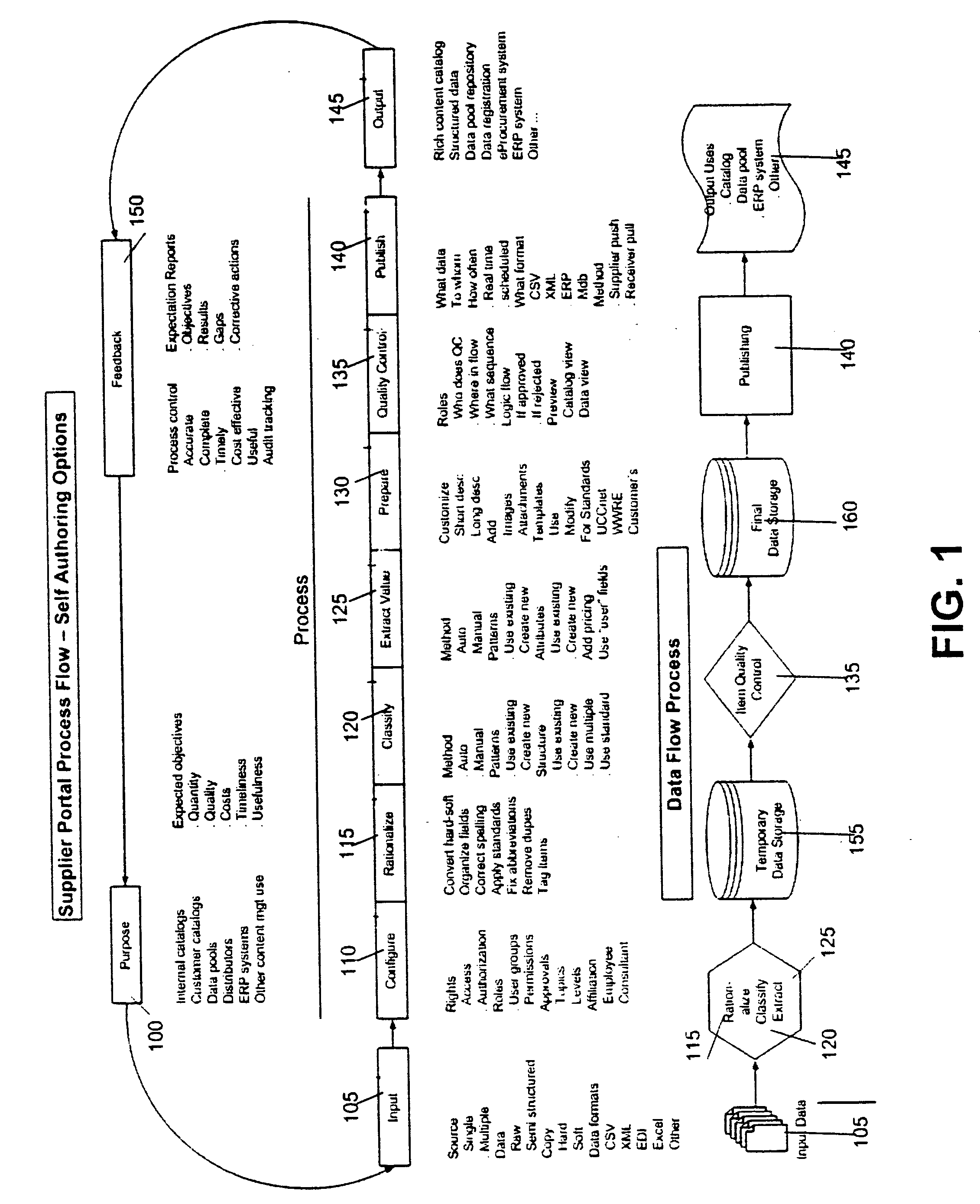
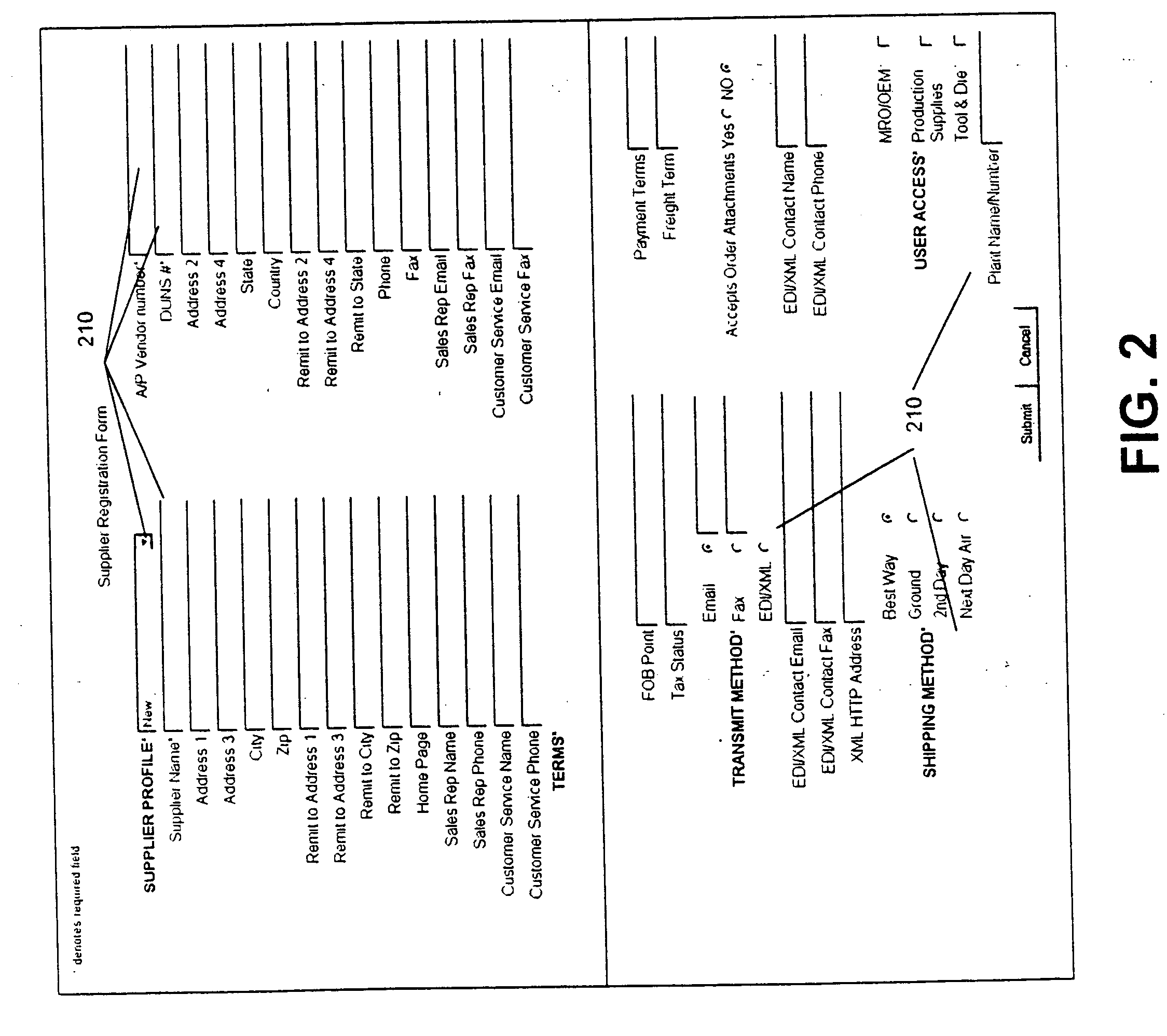
System and method for eCatalog supplier portal
InactiveUS20050251409A1Significant competitive advantageBig advantageSpecial data processing applicationsMarketingHand heldNetwork communication
A Supplier Portal is provided to allow a Supplier to self-author the business process elements (BPEs) of a business process (BP) to create, manage and publish rich-content for use in eCatalogs, Data Pools, Enterprise Resource Planning (ERP) systems, and other knowledge management situations. The resulting business process (BP) for content management incorporates the Supplier's business process (BP) model. At the business process (BP) level, self-authoring allows users to adapt business process elements (BPEs) such as workflows, approval rules and approver roles and permissions, event notification and metrics. At the activity level, self-authoring allows users to adapt business process elements (BPEs) such as user interaction templates, business process (BP) rules and user roles and permissions that relate to the input, configuration, rationalization, classification, value extraction, quality control, publication, and ongoing management of rich-content. The resulting published rich-content incorporates a supplier's unique way of doing business while adhering to the quality, integrity and consistency imposed by the Supplier Portal to achieve a seamless published rich-content such as an ecatalog. The Supplier Portal can be any and all of a hosted behind a firewall solution, accessible via a browser on at least one of a Personal Computer, hand held, or wireless / wired networked communication or standalone device.
Owner:EPLUS SYST
Suggested Content with Attribute Parameterization
ActiveUS20070208755A1Limited lifetimeImprove performanceDigital data processing detailsDigital data authenticationThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety or sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security attributes to be submitted at query time, for example, in order to provide real-time secure access to enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Document date as a ranking factor for crawling
ActiveUS7725465B2Limited lifetimeImprove performanceWeb data indexingDigital data processing detailsThe InternetExtensible architecture
A flexible and extensible architecture allows for secure searching across an enterprise. Such an architecture can provide a simple Internet-like search experience to users searching secure content inside (and outside) the enterprise. The architecture allows for the crawling and searching of a variety of sources across an enterprise, regardless of whether any of these sources conform to a conventional user role model. The architecture further allows for security, recency, or other attributes to be submitted at query time, for example, in order to re-rank query results from enterprise resources. The user query also can be transformed to provide for dynamic querying that provides for a more current result list than can be obtained for static queries.
Owner:ORACLE INT CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com