Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49 results about "Atomic data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
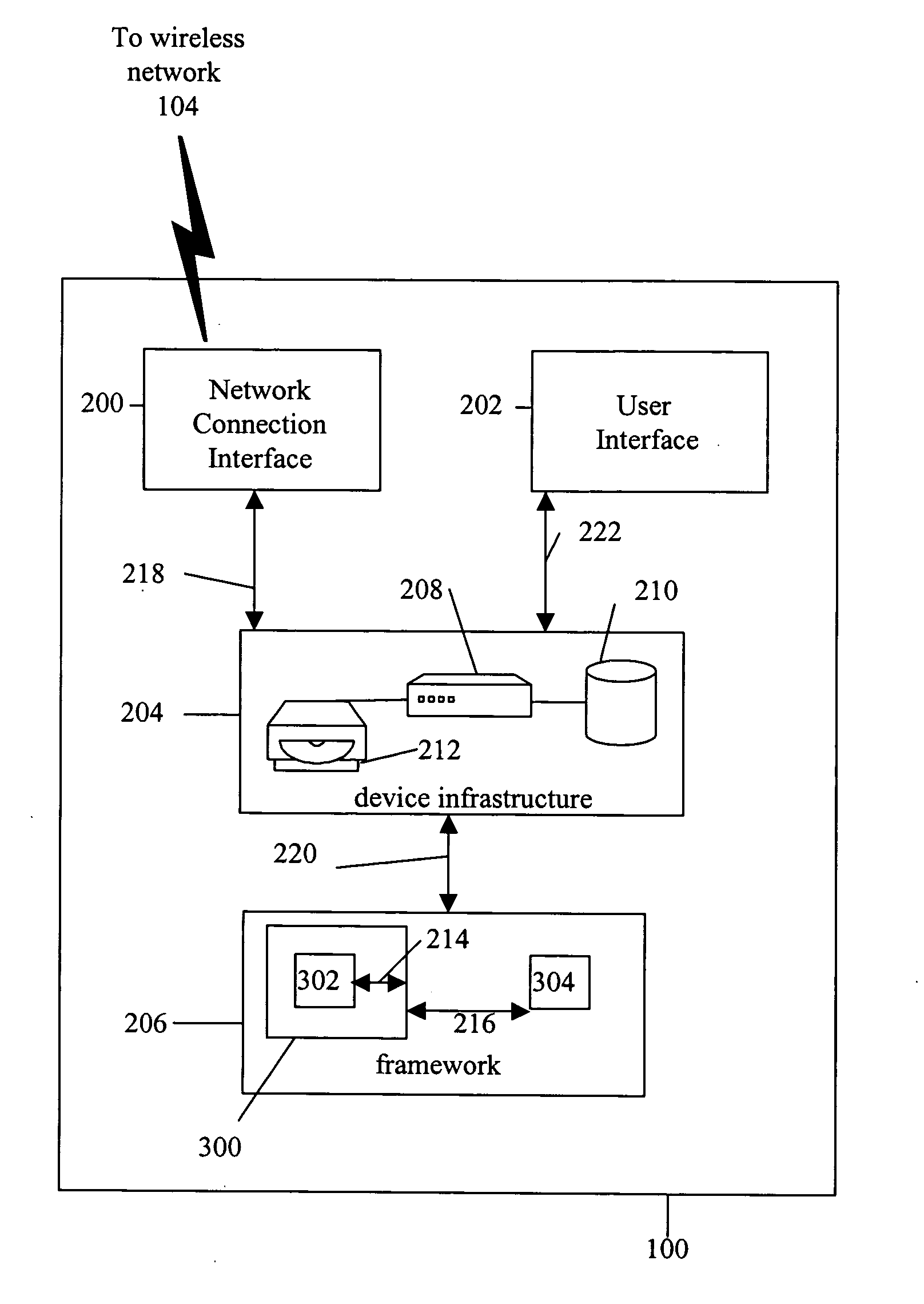
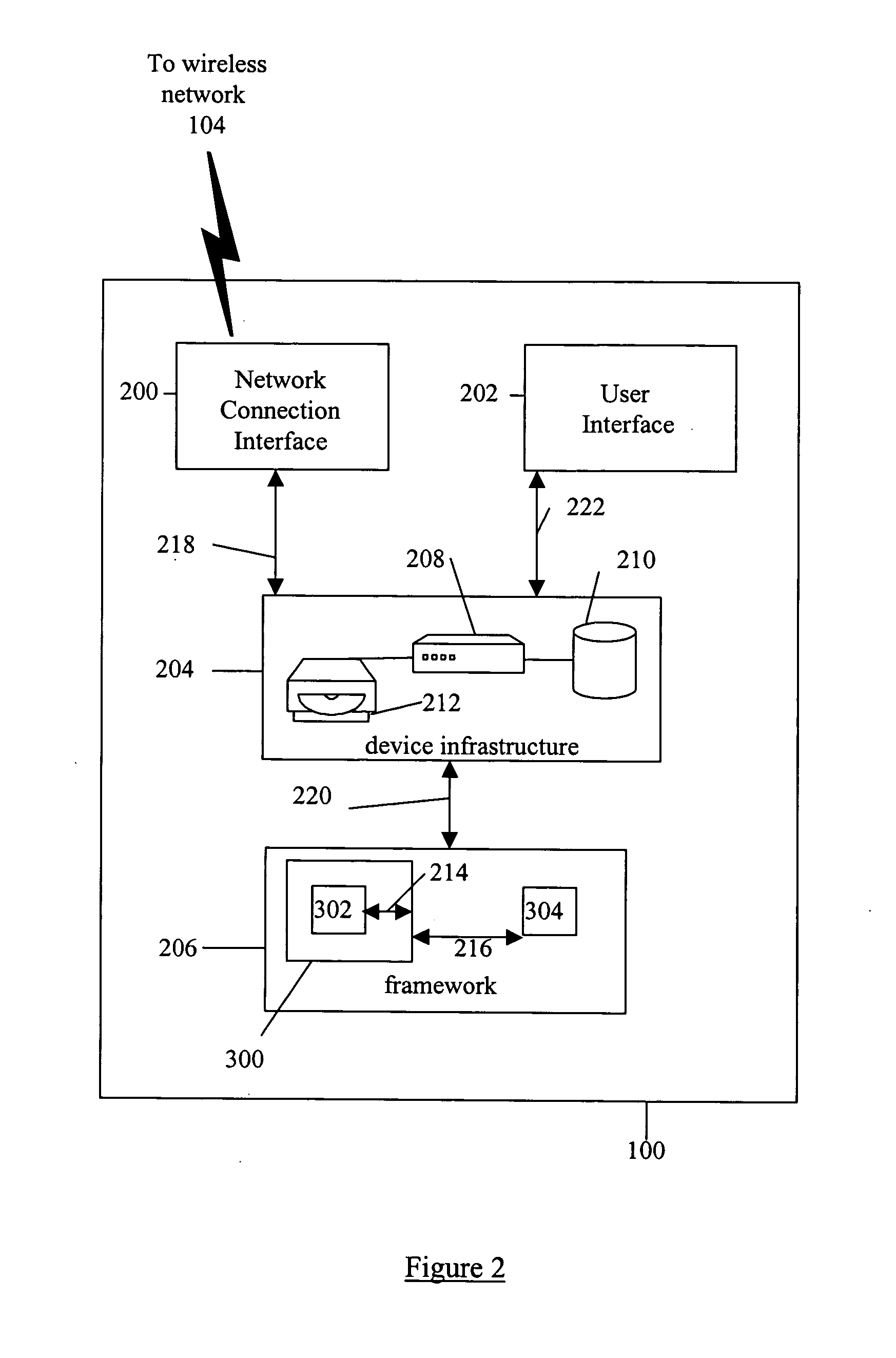
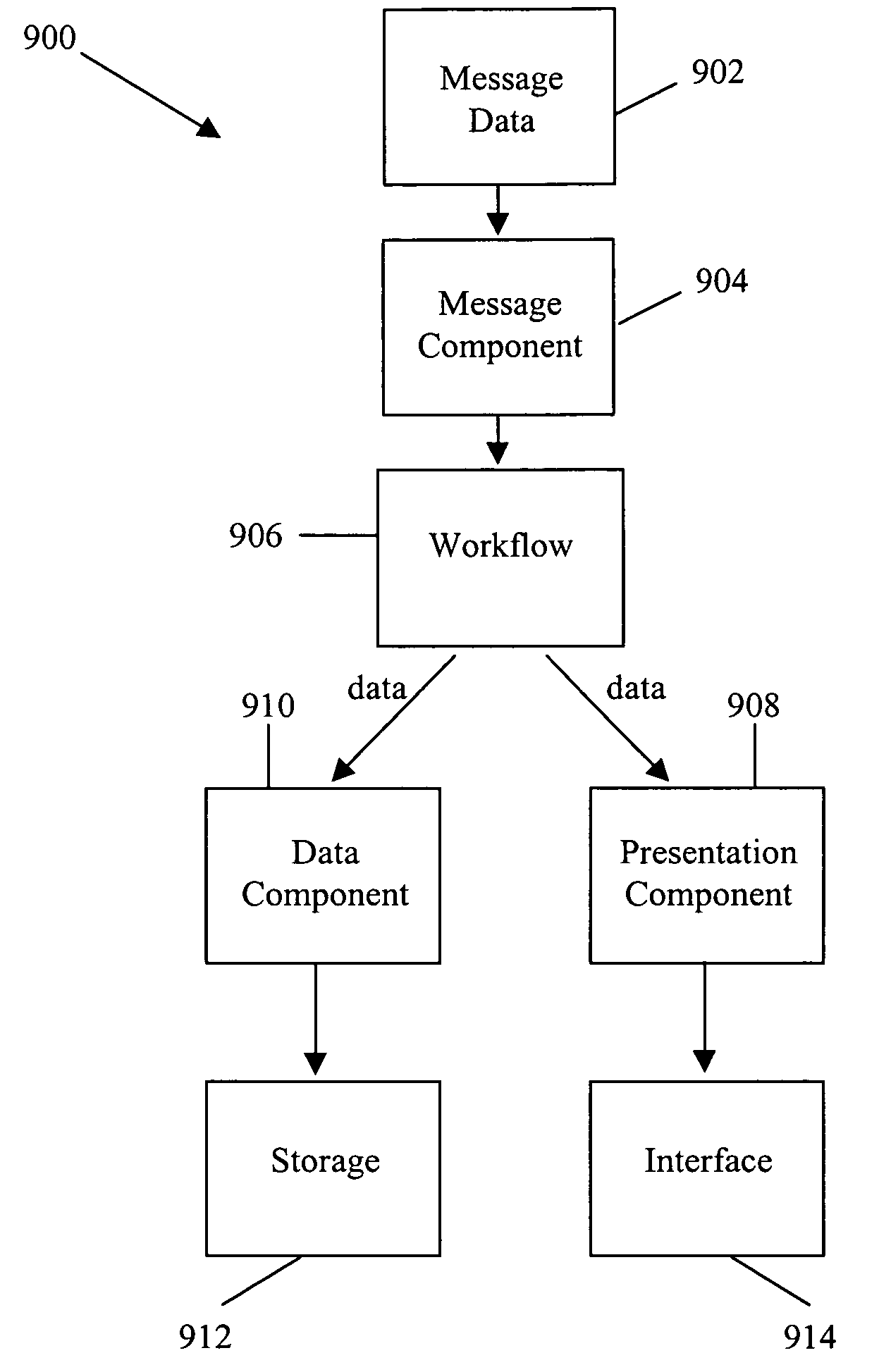
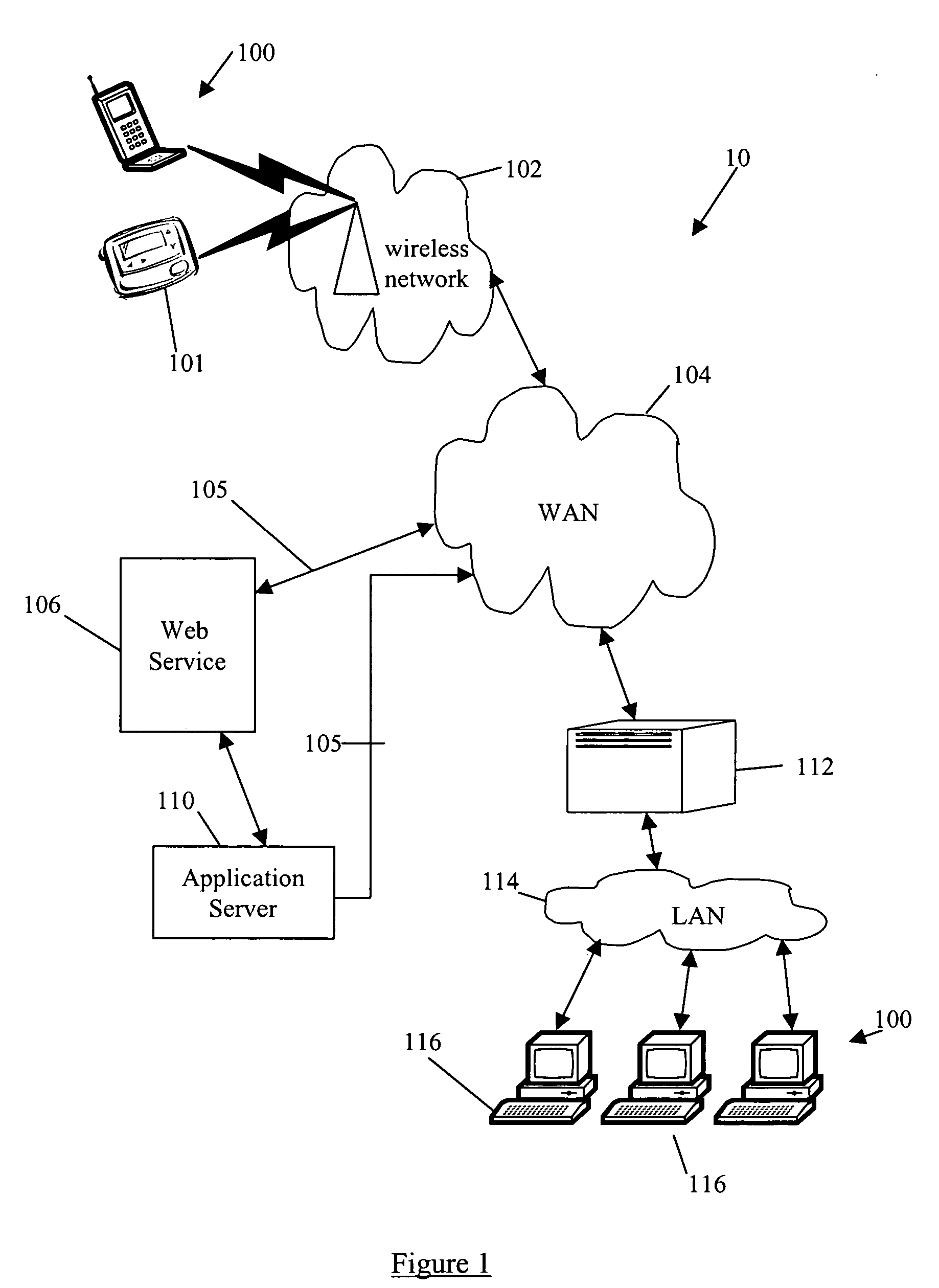
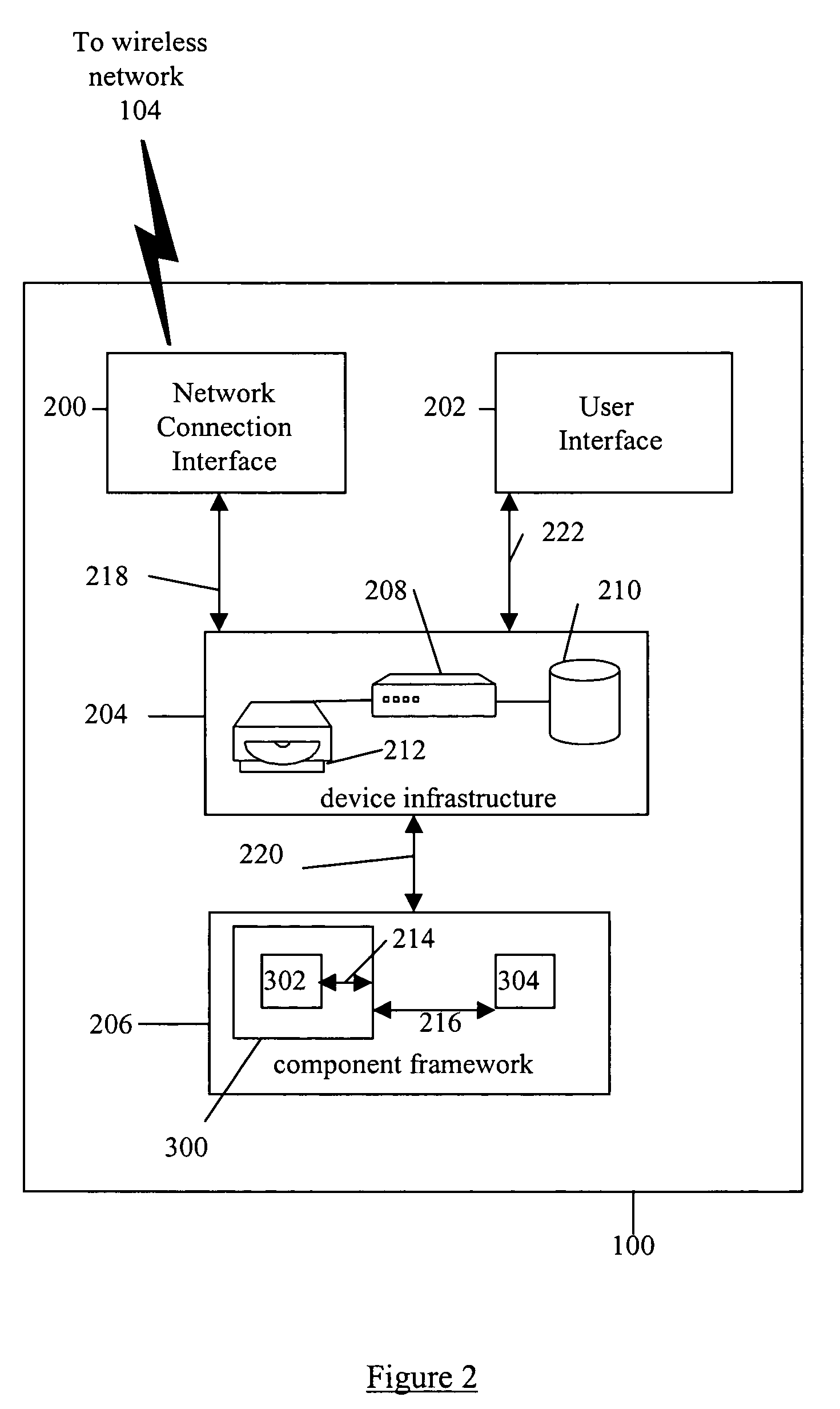
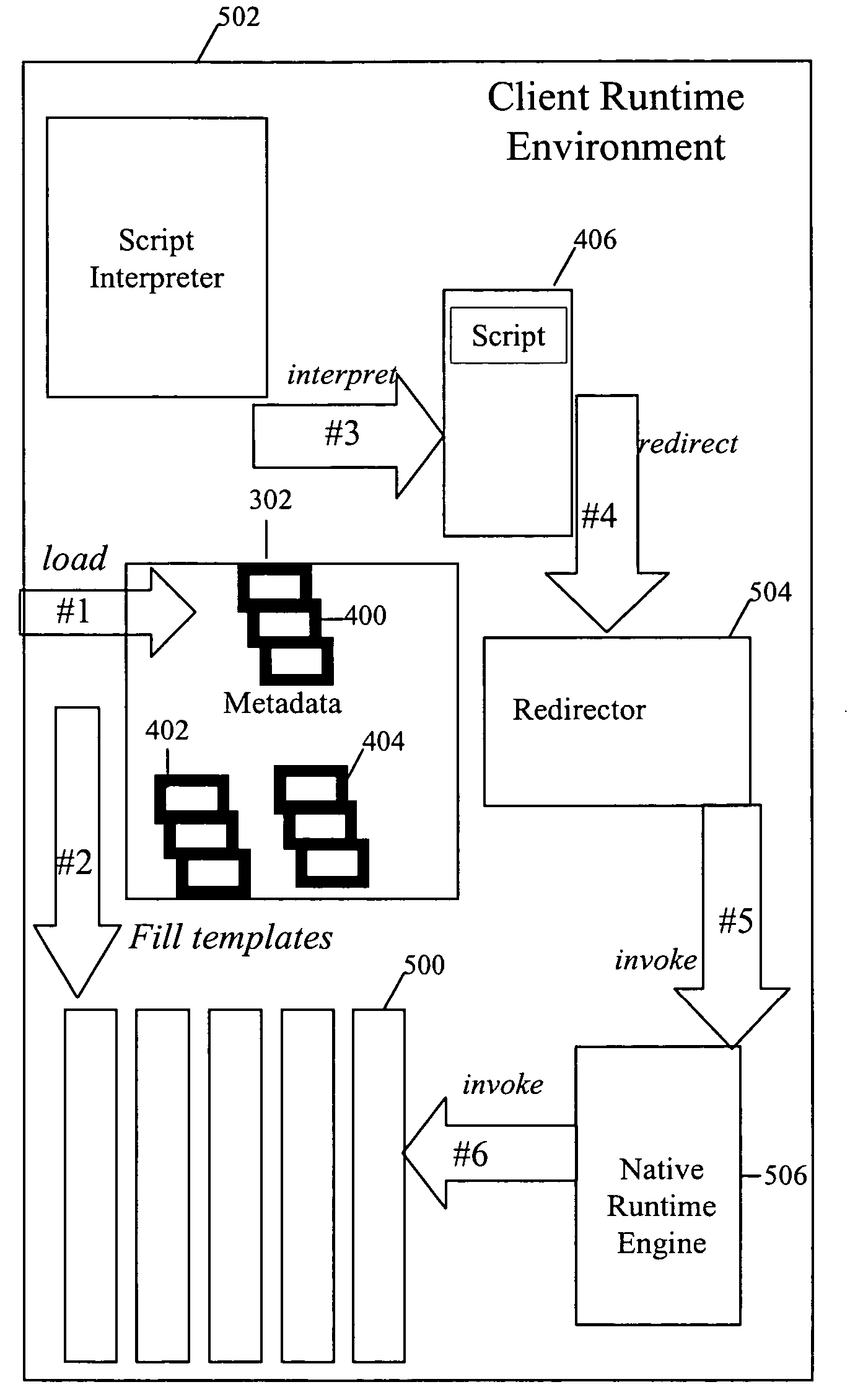
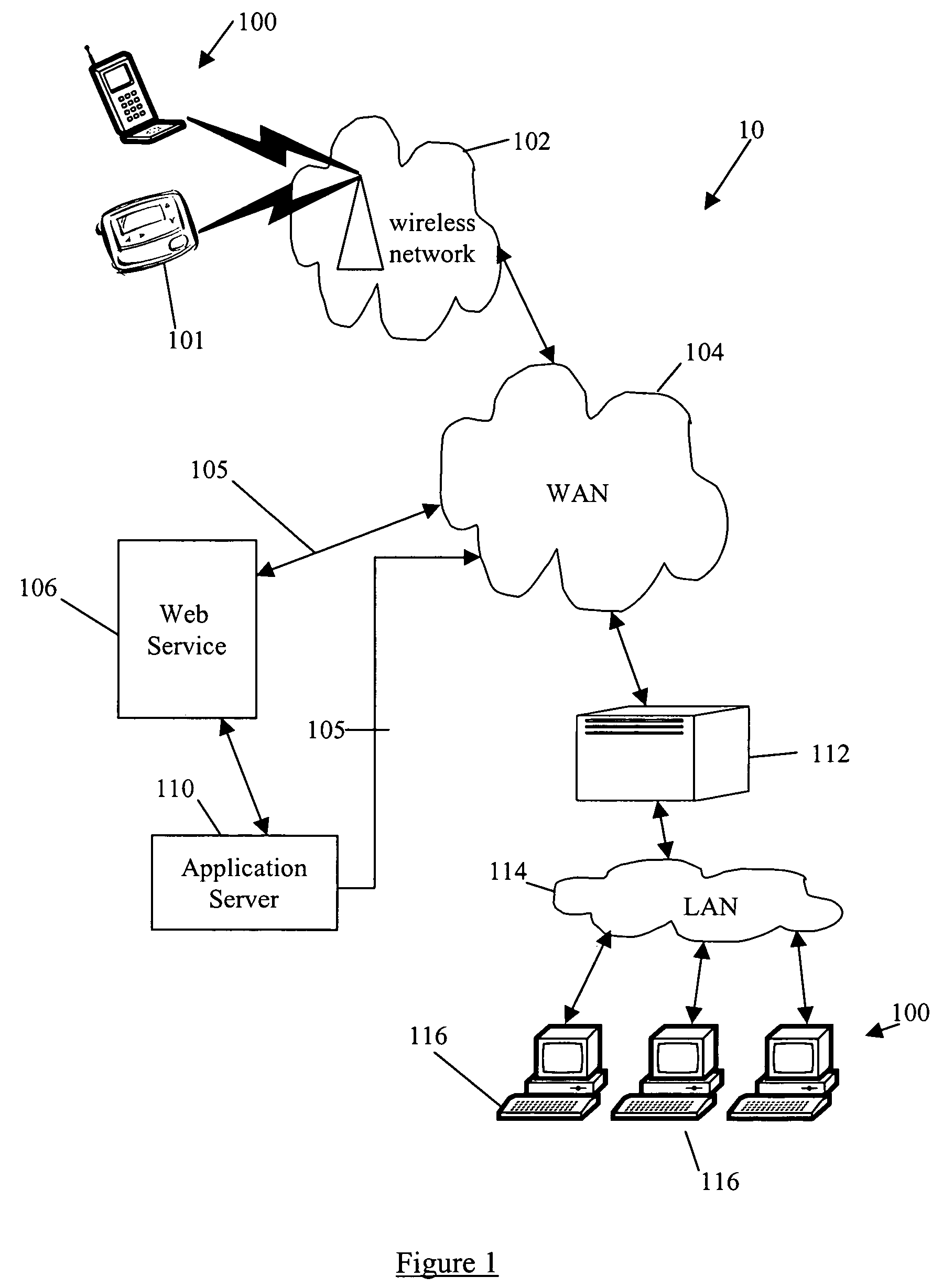
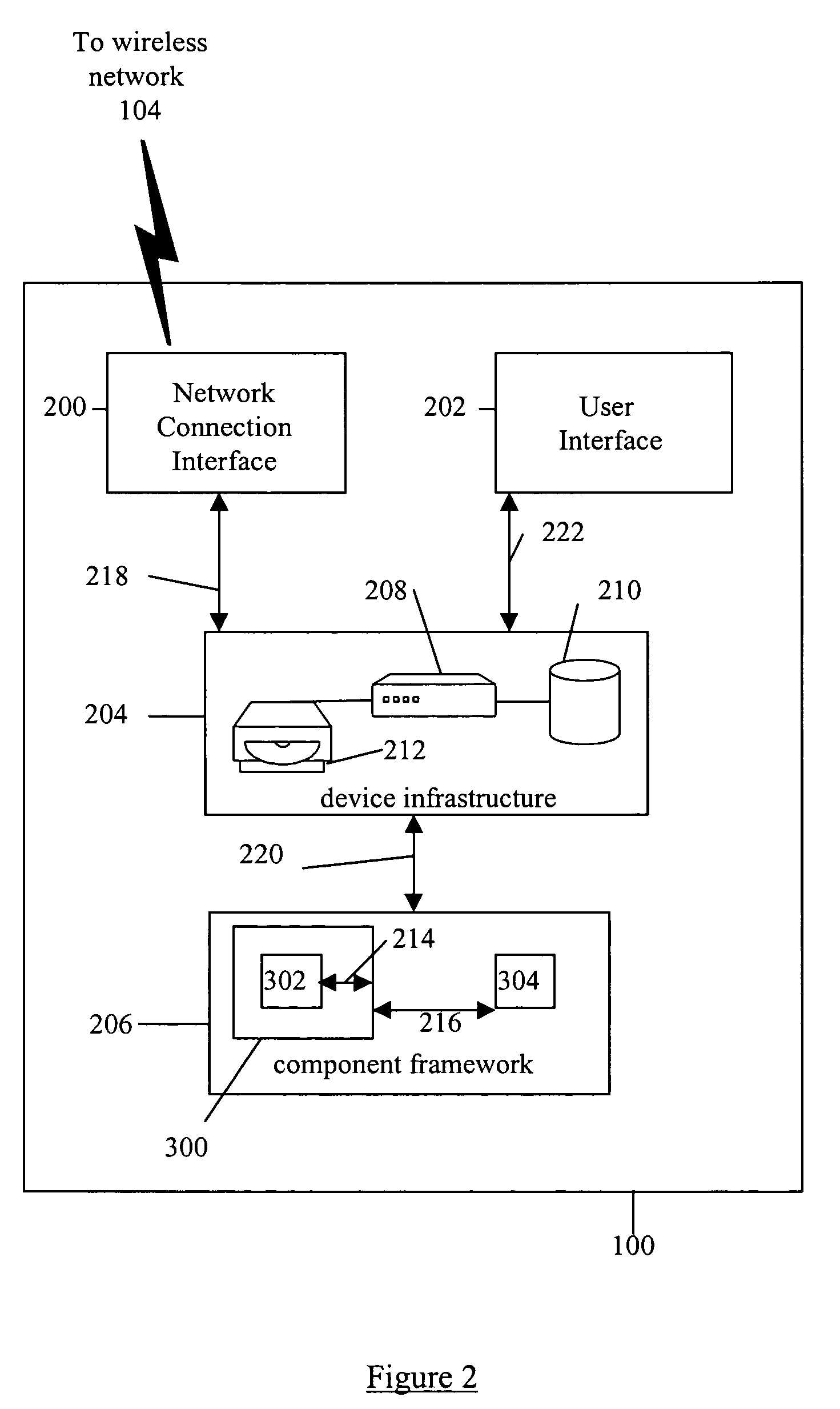
System and method for building wireless applications with intelligent mapping between user interface and data components
ActiveUS20050057560A1Reduce complexitySimplify development workDigital computer detailsMultiprogramming arrangementsData domainBasic service
A system and method is described for effective management of a User Interface (UI) of a wireless device by implementing direct mapping between the application data domain and UI screens and controls. The device has an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application, including a series of linked screen and data component definitions, and their interactions can simplify the development effort and reduce resource allocation. The data domain for this category of applications is defined using the atomic data component definitions. The communication between a device user interface and data components is defined using atomic screen component definitions. Both screen and data component definitions are described in metadata using a structured definition language such as XML. The relationships between the screen and data component definitions are embedded in the XML definitions in the form of screen / data mappings. Typically, rendered screens for display are derived from some underlying data component and screens controls affected by user events impact the current state (or data representation) of the application Changes to the application domain data are automatically synchronized with the user interface, and user-entered data is automatically reflected in the application domain data. The primary mechanism behind this synchronization is the mapping of screens and data. This mechanism enables creation of dynamic and interactive screens. All changes to the data component can be immediately reflected on the screen and vice versa. This model allows building effective wireless applications based on server-to-device notifications. The data updates asynchronously pushed from the server are instantaneously reflected at the UI screen.
Owner:GOOGLE TECH HLDG LLC
Computer-implemented control of access to atomic data items
InactiveUS6052688AEasy accessData processing applicationsDigital data information retrievalData processing systemAccess structure
A method and a system for accessing data in a computer-based data processing system is described. The method comprises the steps of initiating and maintaining data access nodes in a variable access structure. Each access node is provided with references to other access nodes and / or to data items representing an object, each data item carrying only the amount of information which is relevant for its purpose. The data items or the references are provided with a time parameter thus enabling version control and the possibility to handle static or slowly changing data and frequently changed and updated data in a corresponding manner. The access nodes comprise access control parameters for access control from a safety point of view as well as for enabling different views of the access structure and underlying data and objects.
Owner:RPX CORP
System and method for building component applications using metadata defined mapping between message and data domains
ActiveUS20050198100A1Reduce complexitySimplify development workMultiple digital computer combinationsProgram loading/initiatingData domainBasic service
It is desirable to drive down the complexity involved in developing the wireless application by reducing the need to do any explicit coding, as well as reducing device resources utilized by the application when provisioned. Having an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application as a series if application components, and their interactions, can simplify the development effort and reduce resource allocation. The wireless application is described as a set of components. The data domain for this category of applications is defined using atomic data components. The communication between the device and a server is defined using atomic message components. Both message and data components are described in metadata using a structured definition language such as XML. The relationships between the message and data components are embedded in the XML definitions in the form of message / data mappings. Typically, outgoing messages are derived from some underlying data component and incoming messages affect the current state (or data representation) of the application. It is therefore apparent that the metadata defined mapping relationship is preferable between the expression of data and message components.
Owner:MALIKIE INNOVATIONS LTD
System and method for building component applications using metadata defined mapping between message and data domains
ActiveUS7698383B2Drive down the complexity involvedReduce resource utilizationDigital data processing detailsMultiprogramming arrangementsData domainBasic service
It is desirable to drive down the complexity involved in developing the wireless application by reducing the need to do any explicit coding, as well as reducing device resources utilized by the application when provisioned. Having an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application as a series if application components, and their interactions, can simplify the development effort and reduce resource allocation. The wireless application is described as a set of components. The data domain for this category of applications is defined using atomic data components. The communication between the device and a server is defined using atomic message components. Both message and data components are described in metadata using a structured definition language such as XML. The relationships between the message and data components are embedded in the XML definitions in the form of message / data mappings. Typically, outgoing messages are derived from some underlying data component and incoming messages affect the current state (or data representation) of the application. It is therefore apparent that the metadata defined mapping relationship is preferable between the expression of data and message components.
Owner:MALIKIE INNOVATIONS LTD
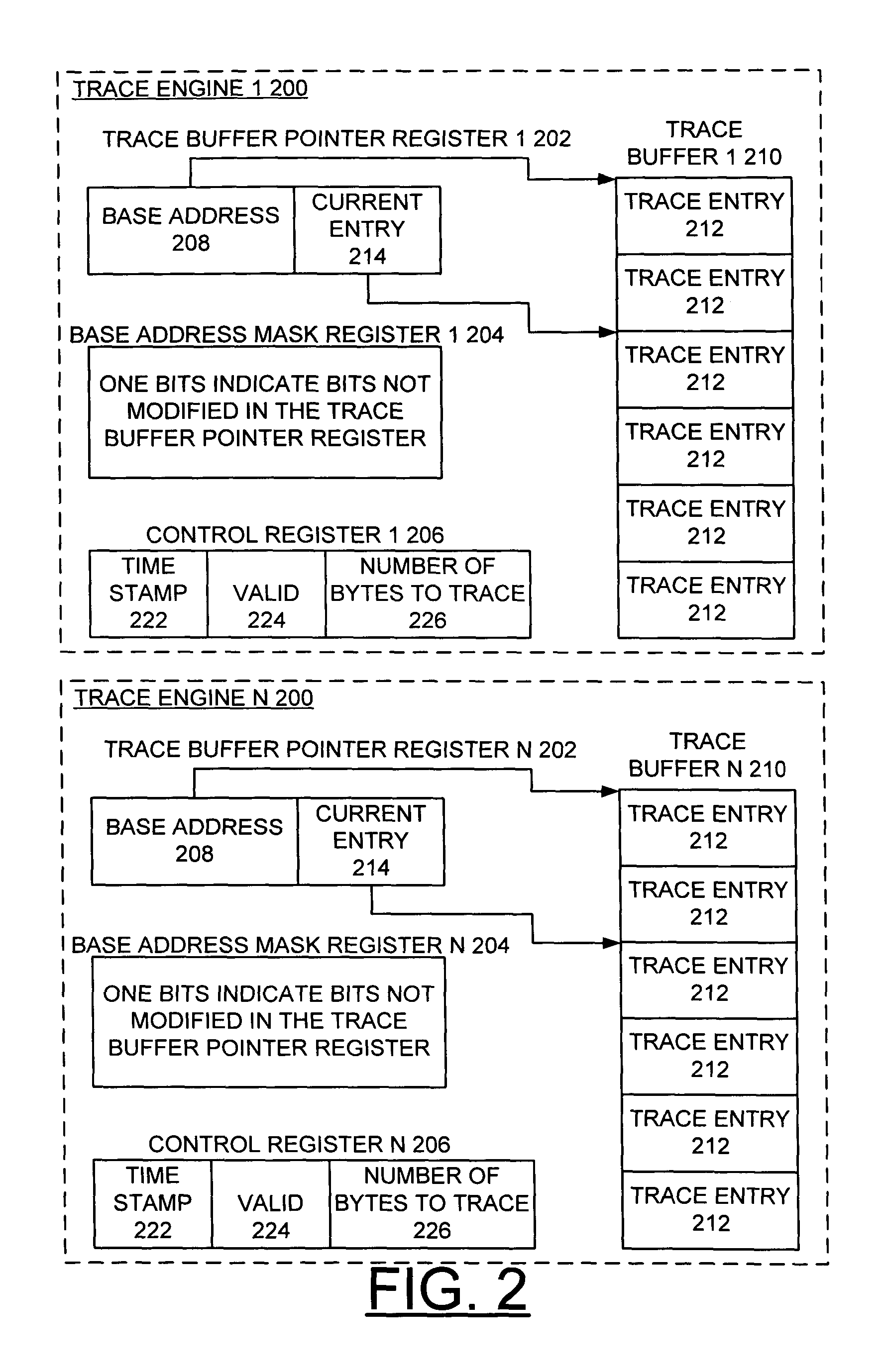
Method, apparatus and computer program product for implementing atomic data tracing
ActiveUS20050060516A1Negative effectError detection/correctionGeneral purpose stored program computerParallel computingTrace buffer
A method, apparatus and computer program product are provided for implementing atomic data tracing in a processor system including an auxiliary processor unit (APU) coupled to a central processor unit (CPU). The auxiliary processor unit (APU) processes a trace instruction. When a trace instruction is identified by the APU, the APU signals the CPU with a pipeline stall signal for stalling the CPU and checks for an enabled trace engine as specified by the trace instruction. When the trace engine for the trace instruction is enabled, then the trace data is written into a trace buffer. The APU signals the CPU with an op done signal for allowing the CPU to continue with instruction processing.
Owner:META PLATFORMS INC
Method, apparatus and computer program product for implementing atomic data tracing
ActiveUS7383428B2Negative effectError detection/correctionGeneral purpose stored program computerCoprocessorTrace buffer
A method, apparatus and computer program product are provided for implementing atomic data tracing in a processor system including an auxiliary processor unit (APU) coupled to a central processor unit (CPU). The auxiliary processor unit (APU) processes a trace instruction. When a trace instruction is identified by the APU, the APU signals the CPU with a pipeline stall signal for stalling the CPU and checks for an enabled trace engine as specified by the trace instruction. When the trace engine for the trace instruction is enabled, then the trace data is written into a trace buffer. The APU signals the CPU with an op done signal for allowing the CPU to continue with instruction processing.
Owner:META PLATFORMS INC
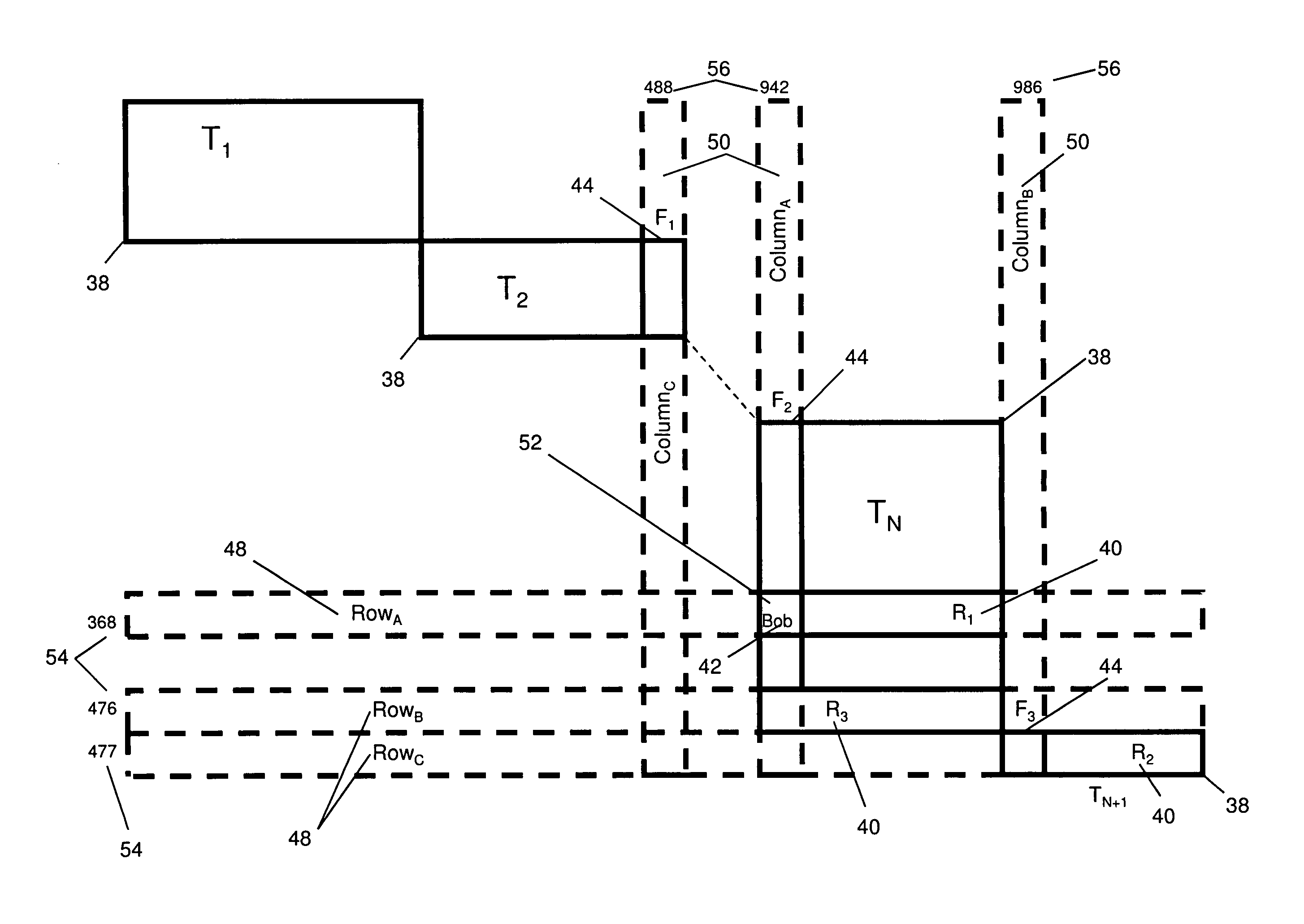
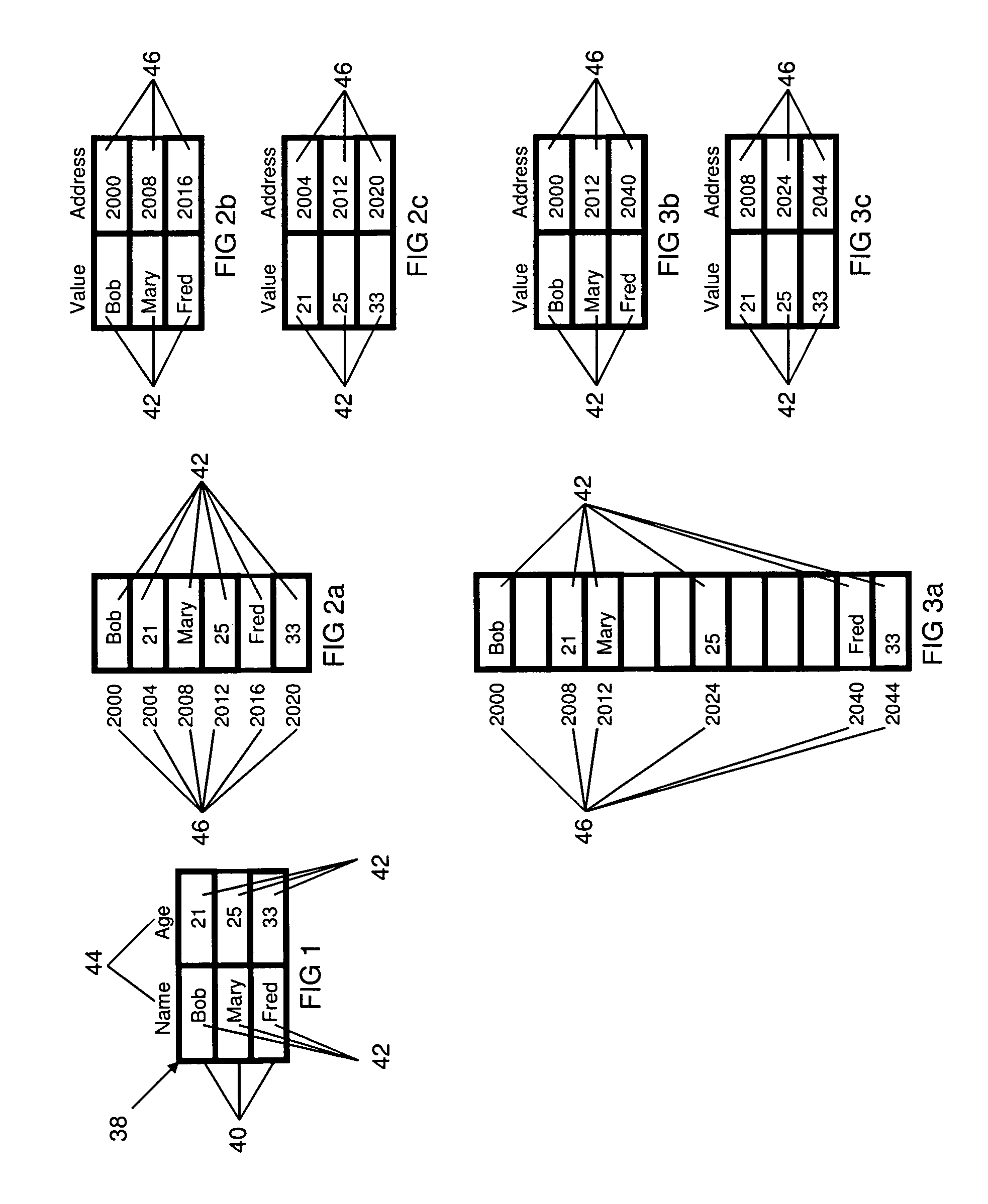
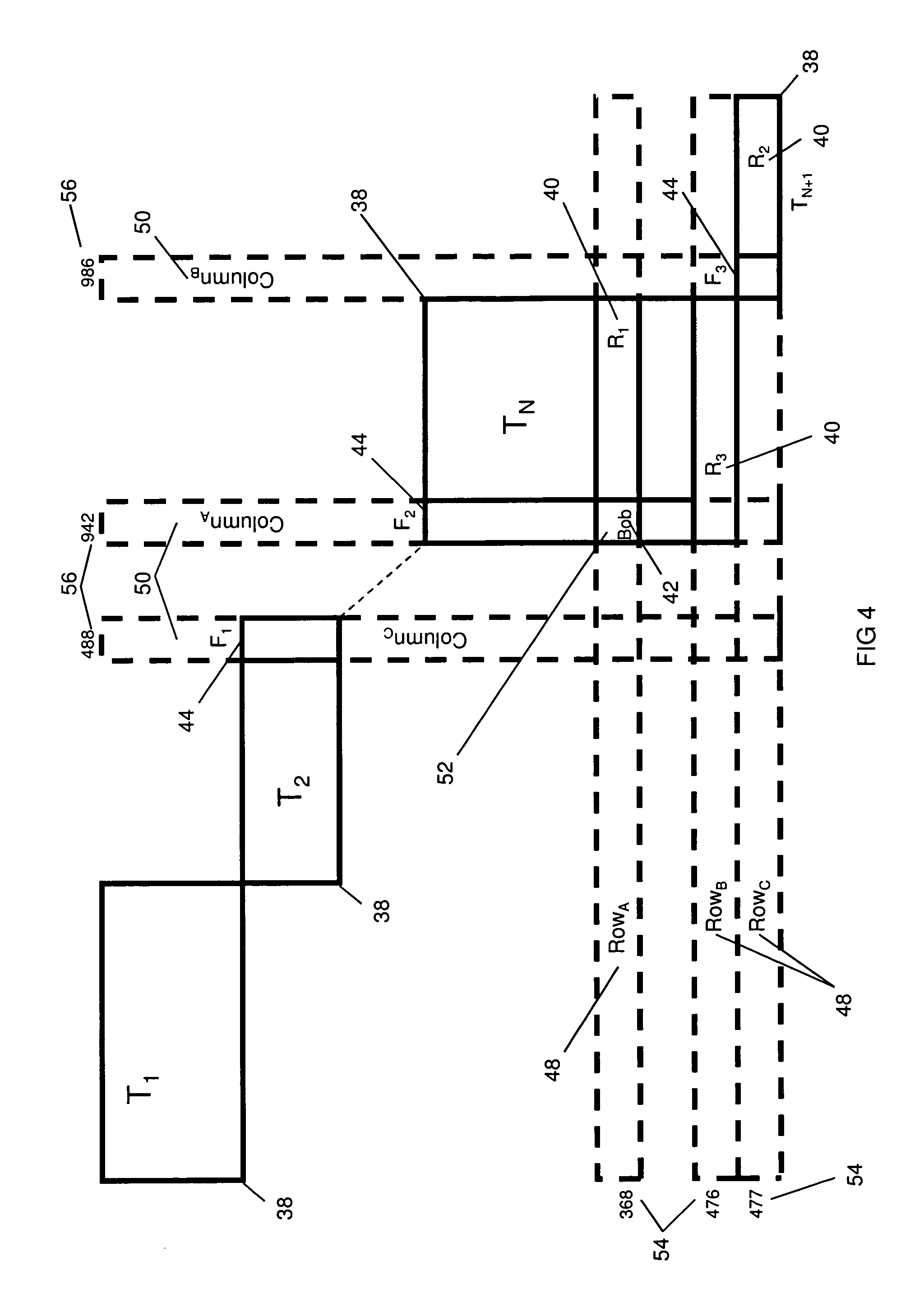
Two-dimensional data storage system
InactiveUS8108431B1Facilitates field-level lockingSimplify access operationsDigital data information retrievalDigital data processing detailsArray data structureData access
A method providing a level of indirection that abstracts the details of physical data storage, requiring neither indexing nor contiguity of data elements in physical storage for efficient data access. Tables are organized in a diagonal pattern (with a natural implementation in electronic spreadsheets), where the region occupied by each table is expandable and shrinkable. A novel query processing mechanism applies successive expressions in a query to progressively smaller arrays of references to a table's records. A novel method for implementing join operations avoids data replication, where the table derived from the join contains a matrix of references to values in the original tables. The derived table can subsequently be used to update the original tables via references, where this capability can be utilized in a user interface supporting atomic data entry transactions, where users may edit the derived table, and the corresponding original tables are atomically updated.
Owner:AUTOTELIKA
Data asset management and monitoring method based on artificial intelligence technology
The invention relates to the technical field of computer application, in particular to a data asset management and monitoring method based on an artificial intelligence technology. The method comprises the steps of connecting an external data source, atomic data, a data discovery engine and the like. Multiple technologies such as artificial intelligence, big data and a knowledge graph are fused, traditional enterprise data asset quality management and monitoring work is replaced by 100%, the accuracy of data asset combing and business process combing is greatly improved, the workload of personnel is reduced, and resources are saved.
Owner:徐峰 +1
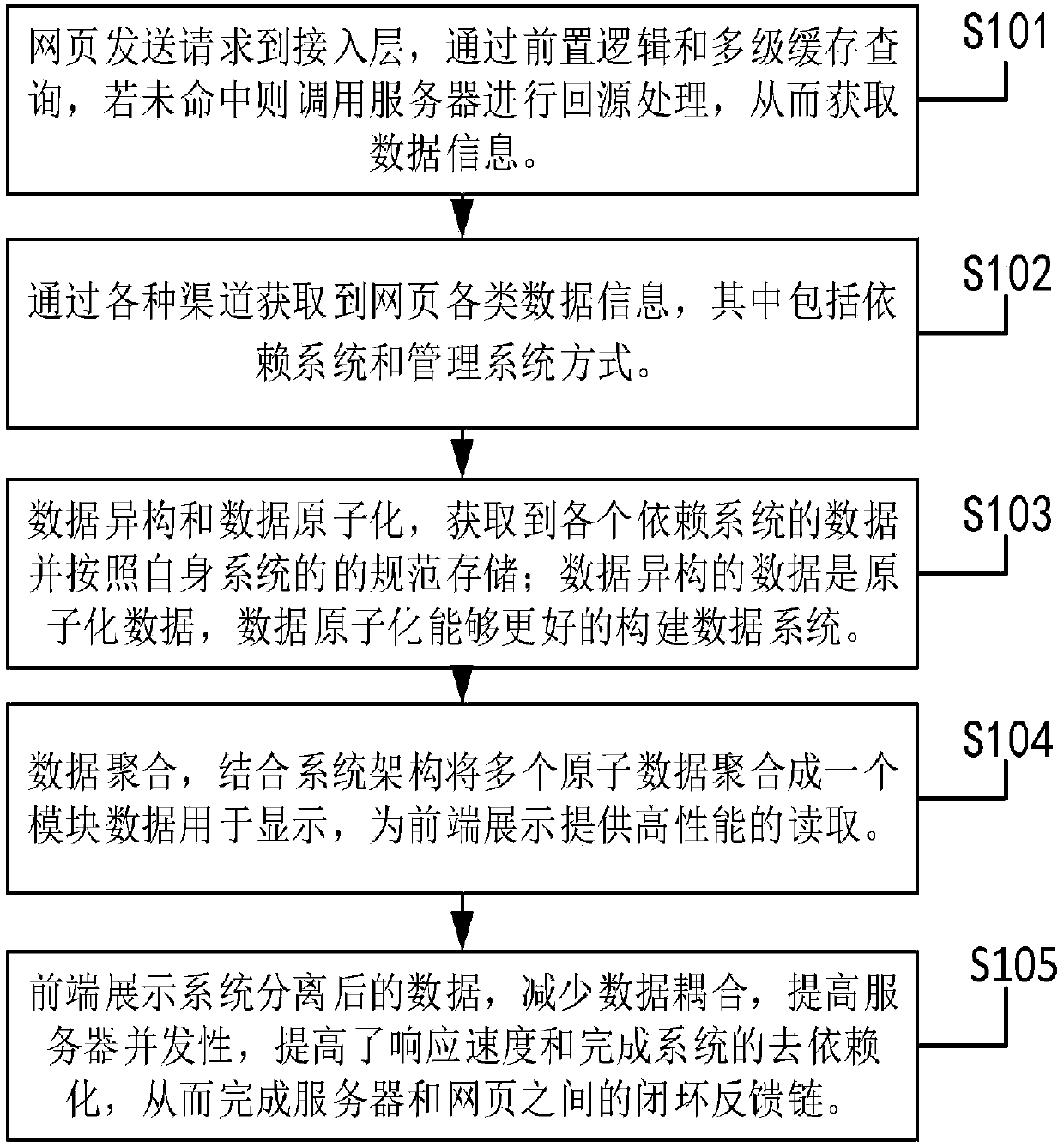
Closed-loop ecological feedback chain system based on server and webpage
InactiveCN107704582AEasy constructionImprove performanceWebsite content managementTransmissionData informationClosed loop feedback
The invention discloses a closed-loop ecological feedback chain system based on a server and a webpage and relates to the field of webpage and server technology. According to the system, first, the webpage sends request data to an access layer, data query is performed through front logic and a multi-level cache, the server is called to perform source return processing, and data information is acquired; data isomerization and data atomization are performed, wherein data of all dependent systems is acquired, stored and atomized; through data atomization, a data closed-loop system can be better constructed; data aggregation is performed, wherein multiple pieces of atomic data are aggregated into one piece of module data for transmission in combination with a system architecture, and high-performance reading is provided for front-end page display; and for the data separated by a front-end display system, data coupling is reduced, and a closed-loop feedback chain between the server and thewebpage is completed. Through the system, a response can be quickly made to a user request when a large amount of access is received, so that user experience is improved; the problem that data acquisition is limited by a third-party interface is solved, redundancy brought by data dependence is avoided, and the ecological closed-loop chain is formed to lower maintenance cost.
Owner:ANHUI KONKA ELECTRONICS
Two-party security privacy comparison method based on block chain
The invention discloses a two-party security privacy comparison method based on a block chain. The two-party security privacy comparison method based on the block chain is used for comparing a certainresource in a data sharing platform under the condition that two participating parties do not leak own information and do not know the opposite parties. The two participating parties firstly agree resources to be compared; communication connection is established between participating parties, then, one party decomposes resources to be compared into a plurality of atomic data; the atomic data areencrypted, a ciphertext is transmitted to the other party by using an unintentional transmission protocol, and the other party participating in the encryption also decomposes the own data into a plurality of atomic data, encrypts the atomic data, compares the encrypted atomic data with the received data according to the circuit table, and returns a final comparison result to the other party. According to the comparison method, data privacy protection is achieved to a certain extent.
Owner:HANGZHOU QULIAN TECH CO LTD
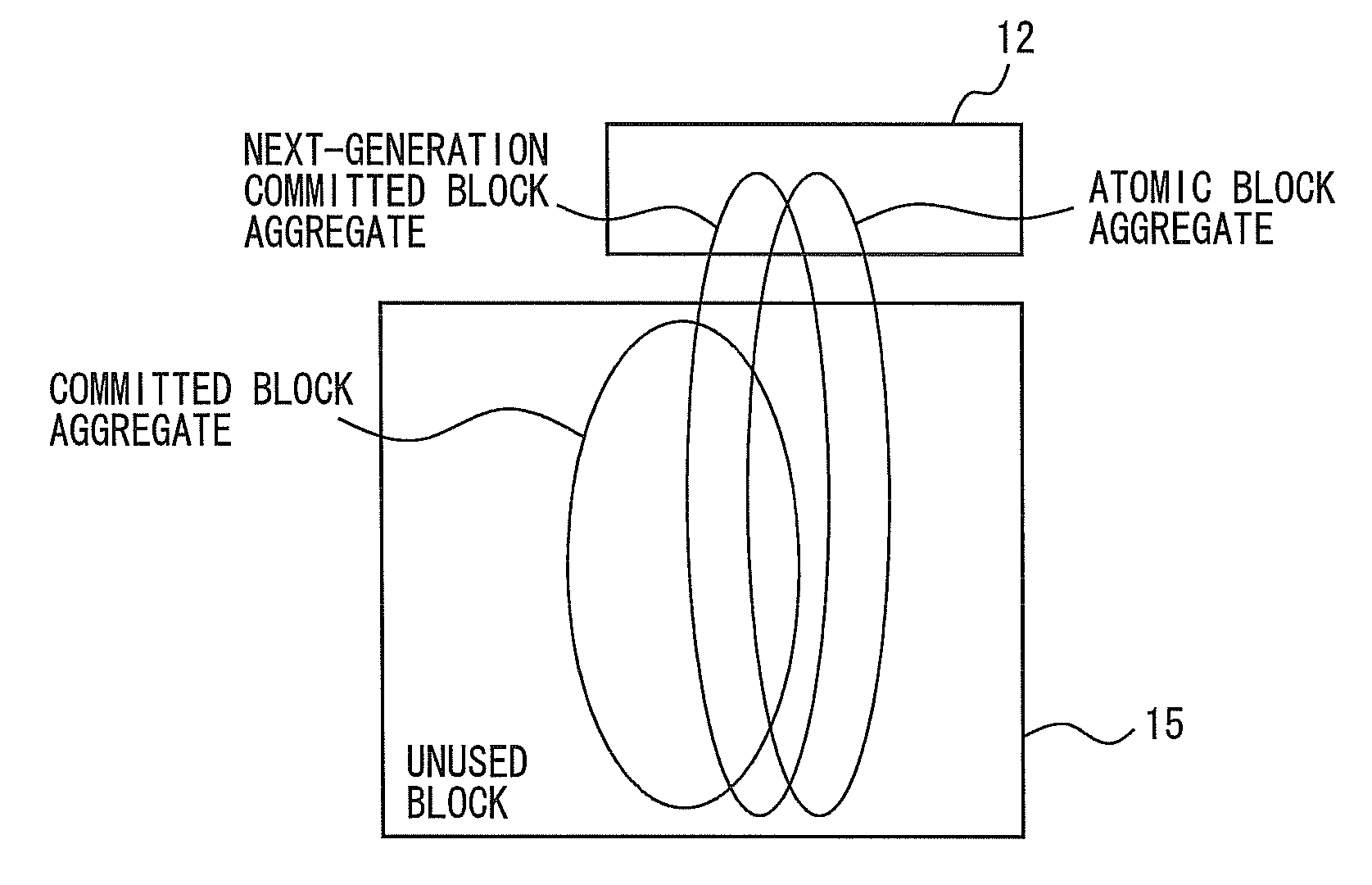
Data storage system and data storage program
ActiveUS20110022813A1Avoid influenceDigital data information retrievalError detection/correctionParallel computingData store
Atomic data are stored in blocks on a hard disk. The blocks are grouped into a committed block aggregate P1, which exists only on the hard disk, a next-generation committed block aggregate C1, which is converted into a committed block aggregate at predetermined times, and an atomic block aggregate S3, which is created for every user based on the committed block aggregate C1. User A makes desired data changes to S3. When user A terminates the data processing, the block aggregate storing the data is merged, like from the atomic block aggregate S4 to committed block aggregate C2, and stored on the hard disk as a committed block aggregate P3.
Owner:KYOTO SOFTWARE RES
Hardware fault detection method based on reducing program
InactiveCN101751334AEffective detection of permanent faultsIncrease differentiationSoftware testing/debuggingControl flowFault tolerance
The invention discloses a hardware fault detection method based on a reducing program, and aims at increasing space-time difference when a source program and a redundant program run, overcoming the problems, such as data overflow and the like, and improving the fault detection rate of transient faults and permanent faults. The technical scheme comprises: traversing the source program, pre-processing the source program, finding out the atomic data in the source program, and constructing an atomic data list and a data command association list; then dividing the source program into a plurality of reducible program blocks, constructing a reducible program block list and a control flow chart, and constructing an operation relation chart for each reducible program block; then finding out an optimal reducing path for each reducible program block; and finally inserting a fault-tolerance command into each reducible program block, and encoding the source program into which the fault-tolerance command is inserted as a target code. The invention can be used for detecting the transient faults and the permanent faults, improve the fault detection rate, overcome the problem of data overflow, and save storage resource.
Owner:NAT UNIV OF DEFENSE TECH
Data service dependency graph-based automatic generation method for data combination view for university
ActiveCN106909696AHigh degree of automationMulti-dimensional databasesSpecial data processing applicationsData setData needs
The invention discloses a data service dependency graph-based automatic generation method for a data combination view for a university. The method comprises the steps of firstly packaging a data set of various departments of the university into atomic data service, packaging and registering the atomic data service on the basis of an REST technology and carrying out unified management; secondly, building a data service dependency graph of various departments of the university according to an internal dependency relationship in the atomic data service; thirdly, automatically combining the atomic data service to generate composite data service according to data requirements of a user on the basis of the service dependency graph; and finally executing the composite data service to generate the data combination view, and returning the data combination view to the user in a form of a table. An effective automatic generation method for the data combination view is provided for data integration of various departments of the university, so that the automatic degree is improved.
Owner:ZHEJIANG UNIV OF TECH
System and method for building component applications using metadata defined mapping between message and data domains
ActiveCN1662011AProgram control using stored programsMultiprogramming arrangementsData domainBasic service
It is desirable to drive down the complexity involved in developing the wireless application by reducing the need to do any explicit coding, as well as reducing device resources utilized by the application when provisioned. Having an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application as a series of application components, and their interactions, can simplify the development effort and reduce resource allocation. The wireless application is described as a set of components. The data domain for this category of applications is defined using atomic data components. The communication between the device and a server is defined using atomic message components. Both message and data components are described in metadata using a structured definition language such as XML. The relationships between the message and data components are embedded in the XML definitions in the form of message / data mappings. Typically, outgoing messages are derived from some underlying data component and incoming messages affect the current state (or data representation) of the application. It is therefore apparent that the metadata defined mapping relationship is preferable between the expression of data and message components.
Owner:RES IN MOTION LTD
Atomic command retry in a data storage system
ActiveUS7752340B1Error prevention/detection by using return channelTransmission systemsData transmissionData store
A data transfer retry method includes:A. receiving a particular atomic data transfer command from a director;B. processing identification information associated with the particular atomic data transfer command;C. comparing the identification information associated with the particular atomic data transfer command to identification information of a previous atomic data transfer command received from the director;D. determining that the particular atomic data transfer command is a retry command of the previous atomic data transfer command received from the director;E. determining a status of the execution of the previous atomic data transfer command received from the director; andF. processing the particular atomic data transfer command based on the status of the execution of the previous atomic data transfer command determined in Step E.
Owner:EMC IP HLDG CO LLC
Network device and traffic control method and device thereof
ActiveCN104601490AAvoid affecting teleportationAchieve loose couplingData switching networksQuality of serviceNetwork packet
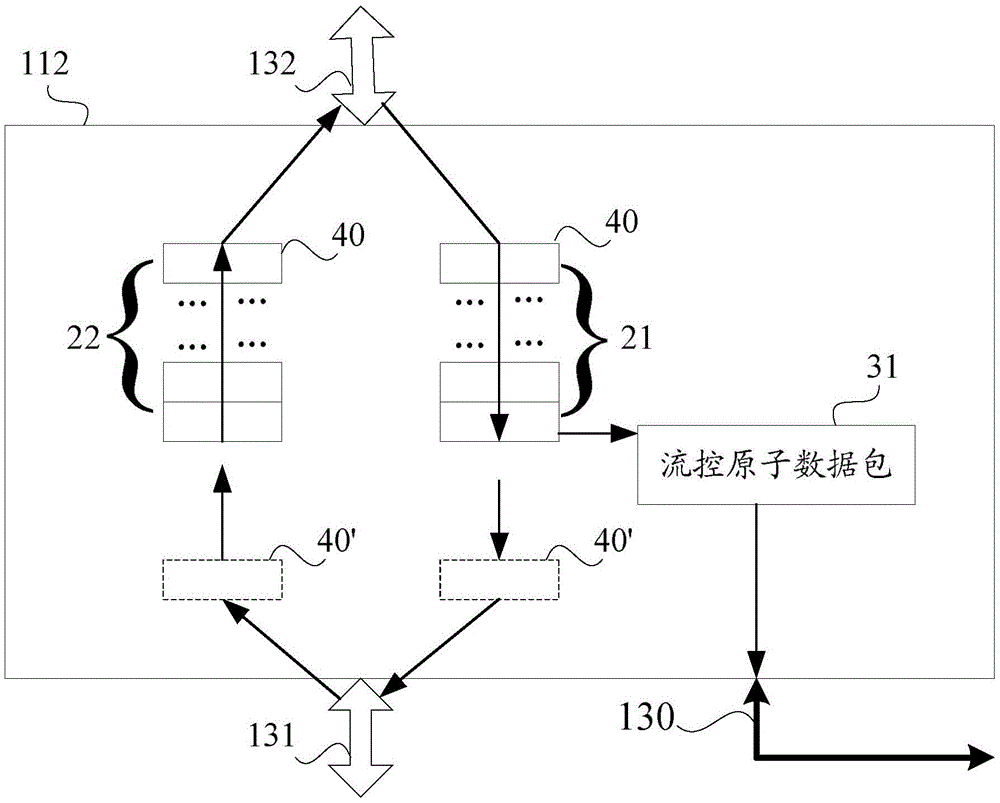
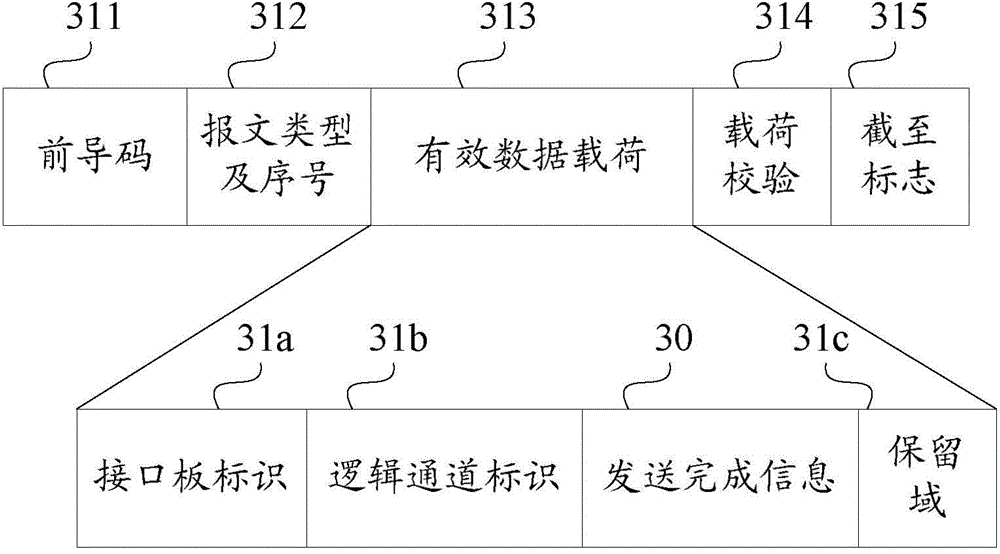
The invention discloses a network device and a traffic control method and device thereof. A logical device of an interface board is capable of packaging transmitting completion information of data Ethernet messages in the outgoing direction into a traffic control atomic data packet for reporting; the traffic control atomic data packet is capable of forwarding the transmitting completion information to a logical device of a main board through a management bus; the logical device of the main board analyzes the traffic control atomic data packet to obtain the transmitting completion information, packaging the transmitting completion information into a traffic control message, writing the transmitting completion information into a memory of the main board for a CPU (central processing unit) of the main board to read; thus, the CPU of the main board is capable of sensing whether or not the data Ethernet messages in the outgoing direction are jammed in time, and outgoing-directional QOS (quality of service) of the network device can be accurately achieved. Meanwhile, transmission of reporting effect data Ethernet messages of the transmitting completion information can be avoided, and loose coupling between transmitting and receiving of the data Ethernet messages is achieved for the CPU.
Owner:NEW H3C TECH CO LTD
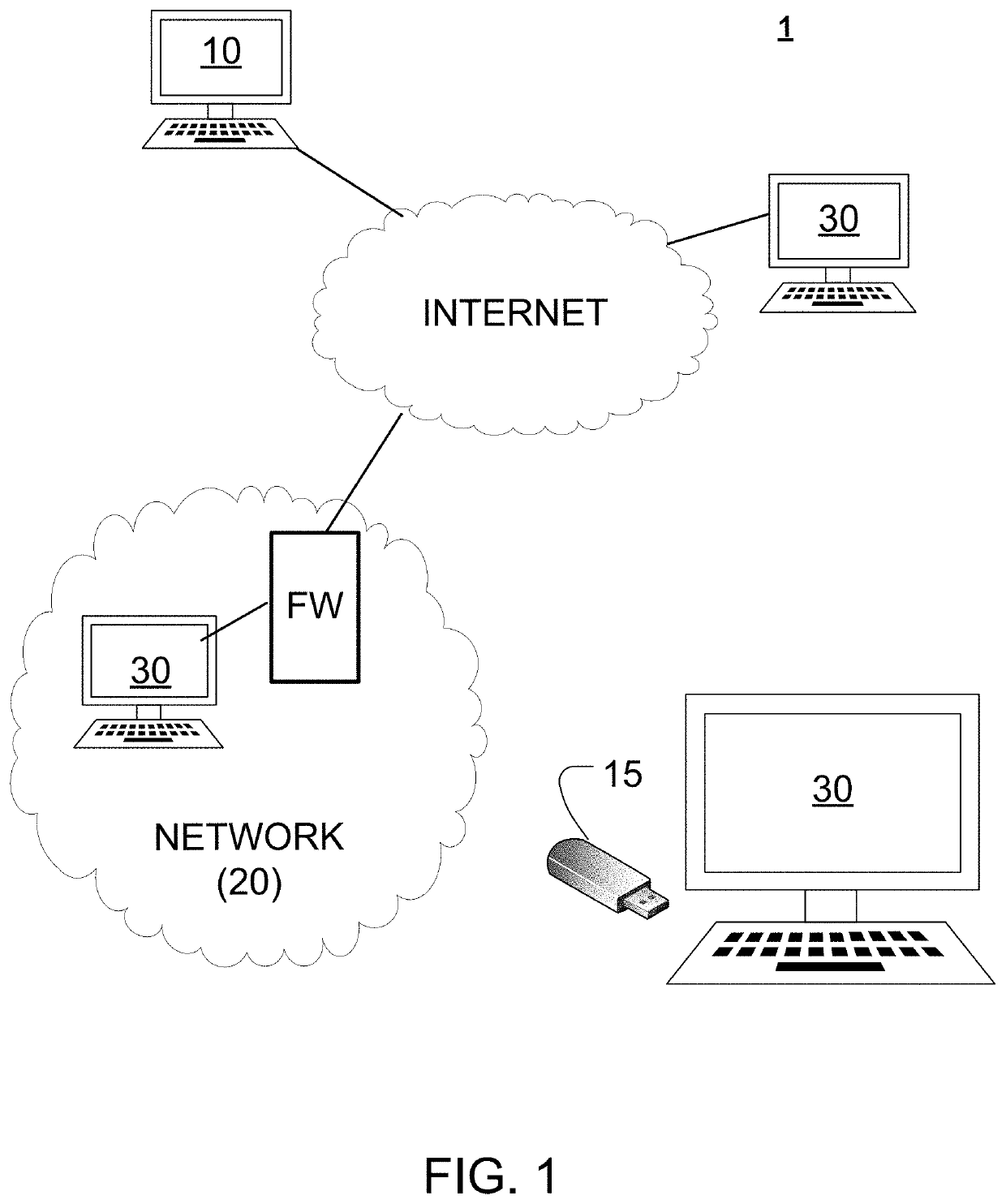
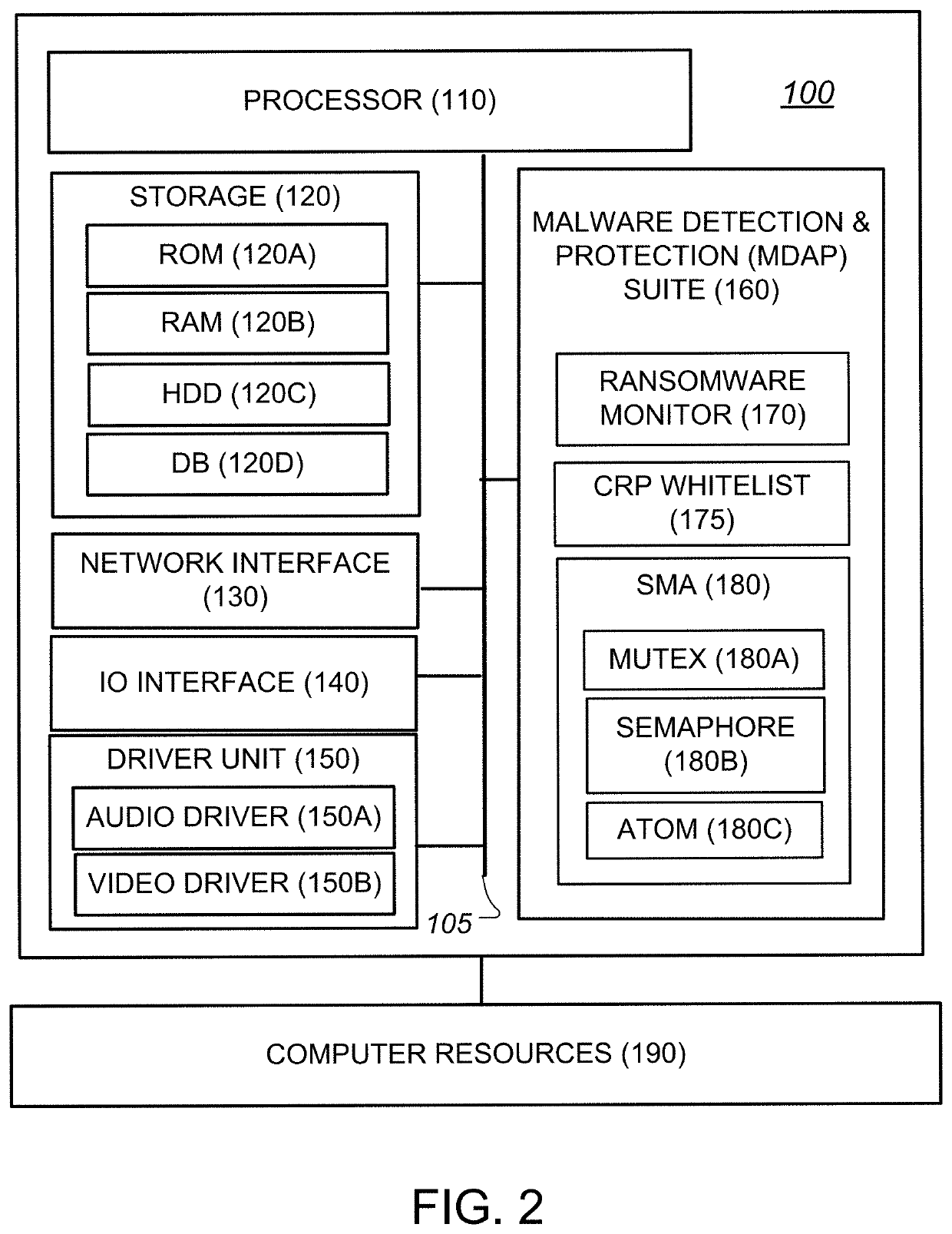
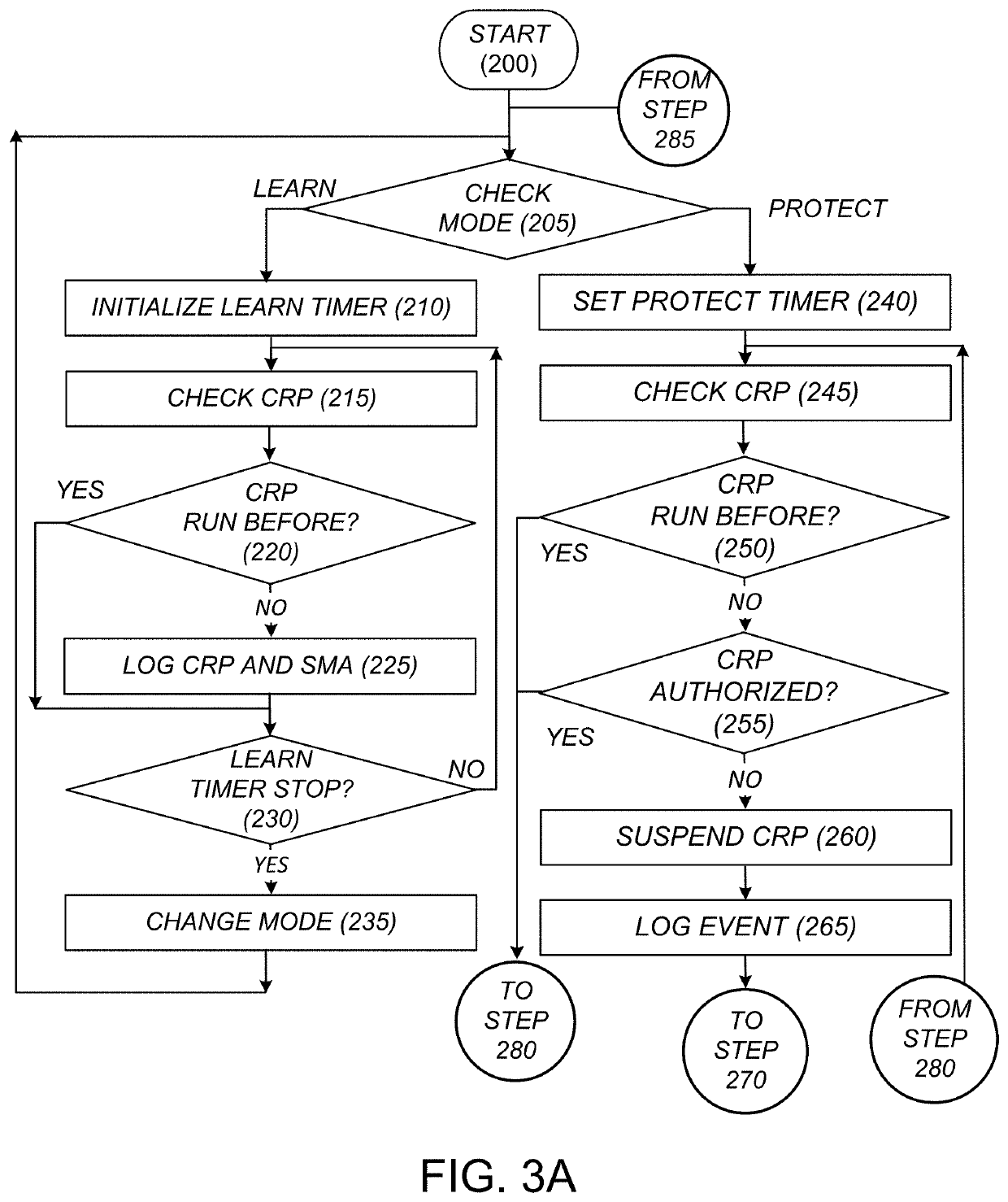
System and method for protecting against ransomware without the use of signatures or updates
ActiveUS20220050896A1Internal/peripheral component protectionPlatform integrity maintainanceComputer resourcesOperational system
A cybersecurity solution for preventing malware from infecting a computing device or a computer resource on the computing device. The solution can include detecting a computer resource process running or attempting to run on an operating system and comparing details of the computer resource process against an authorized processes database containing details of previously run computer resources processes to determine if the computer resource process is running or attempting to run for a first time on the operating system. The solution can include adding, during a learning mode, the details of the computer resource process to the authorized processes database when it is determined that the computer resource process is running or attempting to run for the first time on the operating system, and suspending, during a protect mode, the computer resource process from running on the operating system when it is determined that the computer resource process is running or attempting to run for the first time on the operating system. The details of the computer resource process can include at least one of semaphore data, mutex data or atom data for the computer resource process.
Owner:SAUDI ARABIAN OIL CO
Insight engine
ActiveUS20150378987A1Unstructured textual data retrievalNatural language data processingGraphicsUnstructured data
Embodiments of the invention provide systems and methods for generating natural language insights about a set of data. More specifically, embodiments of the present invention are directed to methods and systems that transform data into insights or actionable information. The output generated by embodiments of the present invention would be equivalent to that of an observation made or insights gathered by a qualified data scientist presented with the same data. Embodiments as described herein can include an insight engine that can analyze both structured and unstructured data and generate information in a natural language of the user's choice. Insights provided by embodiments described herein can be supported by an ability to drilldown to graphs / tables and atomic data and provide a good starting point for further analysis.
Owner:ORACLE INT CORP
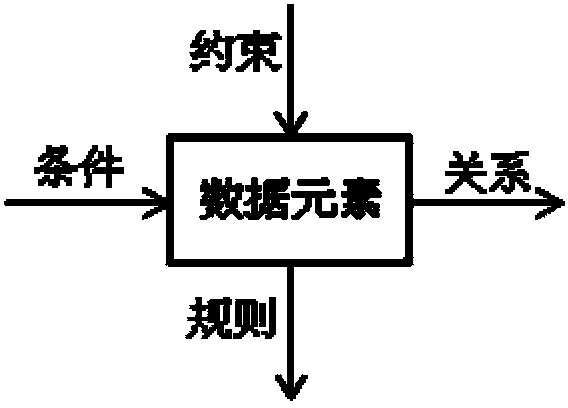
Building method of atomic data element models
ActiveCN104346393AThe modeling process is clear and simpleRich in designSemantic analysisSpecial data processing applicationsElement modelObject Relationship
The invention provides a building method of atomic data element models. The method includes: dividing and classifying various concepts related in an operating process according to 6W (where, when, who, which, what and why) rules to obtain a concept catalogue composed of multiple items arranged in order, each item comprising an identifier field, a data element name field, a data element class field and a data element type field. The items include a time data element item, a location data element item, an object data element item, a participant data element item, a business activity data element item, a material data element item, a characteristic data element item and a reference data element item. The method further includes defining storage structures of the data element models and storing the data element models according to the storage structures. The method has such advantages that the building process is clear and simple, the concept hierarchy is clear, the concept relationship is clear, and a transaction flow diagram, an object relation diagram and system function structures are easily derived.
Owner:KARAMAY HONGYOU SOFTWARE +1
Systems and methods for generating natural language insights about sets of data
ActiveUS9378270B2Unstructured textual data retrievalNatural language data processingGraphicsData set
Embodiments of the invention provide systems and methods for generating natural language insights about a set of data. More specifically, embodiments of the present invention are directed to methods and systems that transform data into insights or actionable information. The output generated by embodiments of the present invention would be equivalent to that of an observation made or insights gathered by a qualified data scientist presented with the same data. Embodiments as described herein can include an insight engine that can analyze both structured and unstructured data and generate information in a natural language of the user's choice. Insights provided by embodiments described herein can be supported by an ability to drilldown to graphs / tables and atomic data and provide a good starting point for further analysis.
Owner:ORACLE INT CORP
Quantitative analysis method for analyzing the elemental composition of materials by means of libs technique
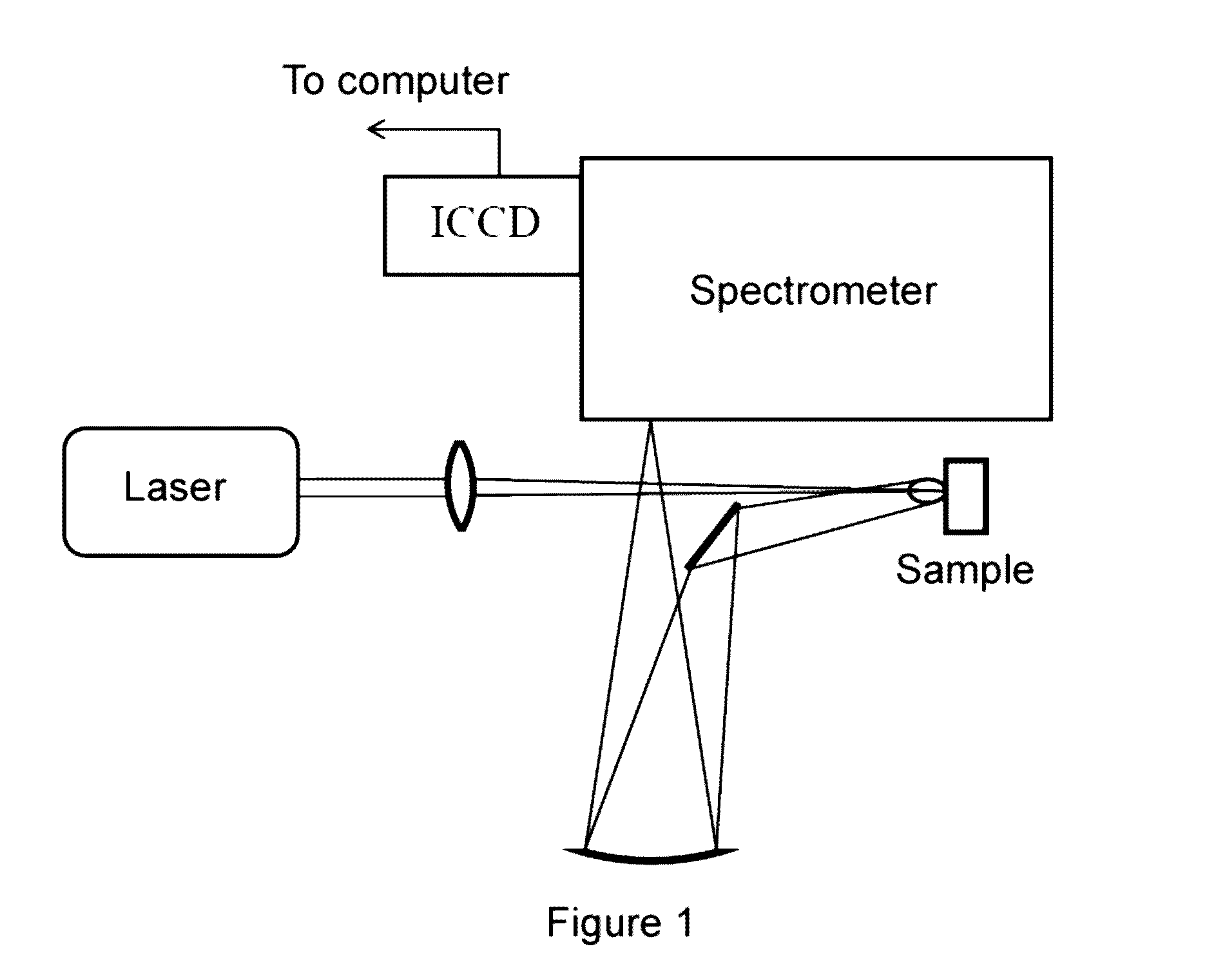
ActiveUS20160334336A1Solve problemsEmission spectroscopyAnalysis by thermal excitationElemental compositionPartition of unity
The quantitative analysis method for analyzing the composition of materials of the invention is based on a functional relationship (curve Cσ) between line intensity and the concentration of the element in the material. The method comprises: obtaining characteristic parameters, selecting the spectral lines of neutral atoms and ions of the elements of interest, obtaining their atomic data; calculating, for the selected lines, a line crosssection; measuring line intensities; determining the concentrations of the elements of interest by means of fitting two graphs Cσ, one for neutral atoms and another for ions with a unit charge, the fitting being performed by means of an iterative algorithm which compares the experimental graphs with the curves Cσ calculated with a plasma model; calculating, for the data of the graphs Cσ, the product of line optical depth by Lorentzian width; evaluating, for the data of the graphs Cσ, a condition on the validity limit of the model, the datum for which the mentioned product is greater being eliminated if the condition is not complied with; repeating the three preceding steps until all data comply with the mentioned condition. The invention has the advantage of not requiring prior calibrations.
Owner:UNIV PUBLICA DE NAVARRA PAMPLONA
System and method for building wireless applications
ActiveCN1661554AProgram control using stored programsSoftware engineeringData domainApplication software
A system and method is described for effective management of a User Interface (UI) of a wireless device by implementing direct mapping between the application data domain and UI screens and controls. The device has an intelligent wireless device runtime environment (Device Runtime) that provides a set of basic services to manage the wireless application, including a series of linked screen and data component definitions, and their interactions can simplify the development effort and reduce resource allocation. The data domain for this category of applications is defined using the atomic data component definitions. The communication between a device user interface and data components is defined using atomic screen component definitions. Both screen and data component definitions are described in metadata using a structured definition language such as XML. The relationships between the screen and data component definitions are embedded in the XML definitions in the form of screen / data mappings. Typically, rendered screens for display are derived from some underlying data component and screens controls affected by user events impact the current state (or data representation) of the application Changes to the application domain data are automatically synchronized with the user interface, and user-entered data is automatically reflected in the application domain data. The primary mechanism behind this synchronization is the mapping of screens and data. This mechanism enables creation of dynamic and interactive screens. All changes to the data component can be immediately reflected on the screen and vice versa. This model allows building effective wireless applications based on server-to-device notifications. The data updates asynchronously pushed from the server are instantaneously reflected at the UI screen.
Owner:GOOGLE TECH HLDG LLC
Acquisition agent deployment method and device
ActiveCN110430158AImprove collection effectReduce consumptionTransmissionData acquisitionNetwork data
The invention provides an acquisition agent deployment method and an acquisition agent deployment device. The method comprises the steps of constructing a threat-acquisition tree of a network according to a target network-data service library, a data service-potential threat event attribute library, a threat event-feature beacon library and an acquisition agent-threat detection atomic data item library; for any potential threat event, obtaining a risk value of the potential threat event according to the confidence degree of the potential threat event monitored by the acquisition agent and theinfluence of the potential threat event; determining whether each equipment node is a risk point or not according to the risk value of each potential threat event and the threat-acquisition tree; anddeploying the acquisition agent on the risk point according to the risk point in the network, the acquisition capability of the acquisition agent and a preset constraint condition. According to the invention, the data acquisition capability is improved, and resources consumed by data acquisition and analysis are reduced.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Logless atomic data movement
ActiveCN103425722ADatabase distribution/replicationSpecial data processing applicationsComputer architectureAtomic data
A system and method of logless atomic data movement. An internal transaction is started within a multi-level storage architecture, the internal transaction to merge data from the first level storage structure to the second level storage structure. Committed data is read from a first level storage structure of the multi-level storage architecture as specified by the internal transaction. The committed data from the first level storage structure is inserted into a second level storage structure in a bulk insertion process, and the committed data is marked as being deleted from the first level storage. The internal transaction is then committed to the multi-level storage architecture when the committed data has been inserted into the second level storage structure.
Owner:SAP AG
Data processing method and device, storage medium and electronic equipment
PendingCN114817389AHighly configurableEasy maintenanceDatabase management systemsMulti-dimensional databasesTheoretical computer scienceLogisim
The invention discloses a data processing method and device, a storage medium and electronic equipment. The method comprises the following steps: configuring atomic data indexes; wherein the atomic data indexes comprise fields of multiple service types and values of the fields, and the atomic data indexes are located in a real-time or offline calculation layer; configuring a data processing logic rule base in a service interface layer, wherein the data processing logic rule base comprises a plurality of calculation rule expressions; wherein the real-time or offline computing layer and the service interface layer are two different levels in the data service system; analyzing each data processing logic in the data processing logic rule base to obtain a plurality of task script sets; and obtaining a value of a corresponding field from the atomic data index according to each task script set. According to the invention, the technical problems of poor configurability of data service and inconvenience in system updating and maintenance in the prior art are solved.
Owner:PING AN TECH (SHENZHEN) CO LTD
Test case generation method and device
PendingCN113704077AKeep the relationshipBusiness relationshipSoftware testing/debuggingAlgorithmData preparation
The invention discloses a test case generation method and device. The method comprises the following steps: receiving a test case generation request; obtaining a test scene and corresponding test atomic data, and determining the test atomic data and the test scene according to business log data stored in the offline log library; and based on a preset case template, performing case assembly processing on the test scene and the test atomic data to generate a test case. According to the scheme provided by the invention, the test scene and the test atomic data are generated based on the service log data formed by the real service request stored in the offline log, the association relationship between services is reserved, the problem that data required by a traditional performance test is difficult to prepare is solved, the generated test scene is comprehensive, namely, the full-scene performance test is supported, the universality is improved, and the test case coverage rate is also ensured. And moreover, no influence is generated on a production system, and the safety is improved.
Owner:CHINA MOBILE GROUP ZHEJIANG +1
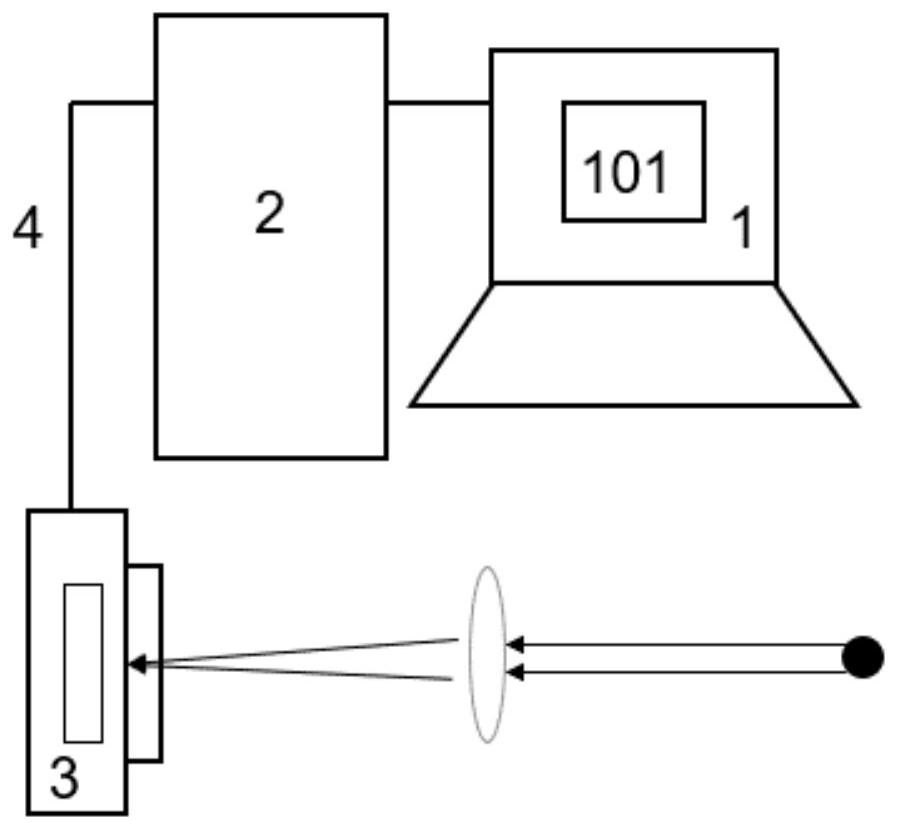
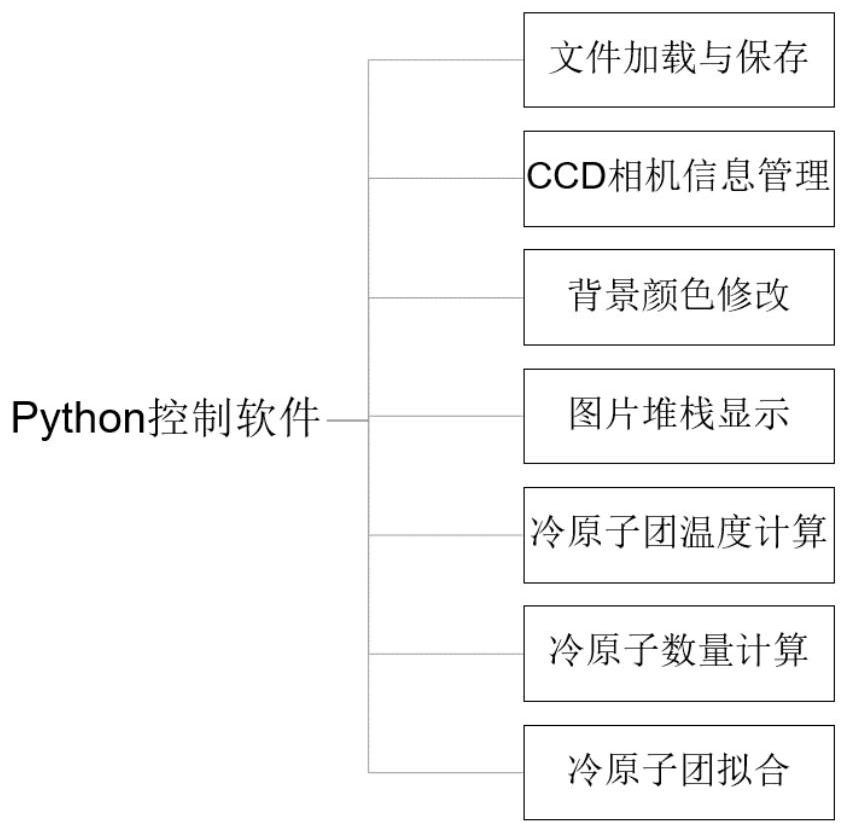
Python-based cold atom data acquisition and analysis system
PendingCN111880867AFlexible modificationSimplify data processing operationsMaterial analysis by optical meansExecution for user interfacesReal time analysisData acquisition
The invention discloses a python-based cold atom data acquisition and analysis system. The system comprises a computer, a USB interface and a CCD camera, wherein the computer is used for operating Python control software and processing data acquired by the CCD camera; the USB interface is used for connecting the computer and the CCD camera; and the CCD camera is used for shooting a cold atomic group to obtain data and transmitting the data to the computer through the USB interface. Hardware control and real-time analysis of cold atom data acquisition are integrated under a unified software framework, and flexible increase and decrease of hardware models and increase and decrease of new analysis methods are supported. Extra data access and various conversion processes are avoided, the processing speed is higher, the data processing and analysis time is remarkably saved, experimental data is easy to record, and the efficiency of cold atom experimental research is improved.
Owner:SOUTH CHINA NORMAL UNIVERSITY
Method for predicting whether solid solution is formed or not based on atom combination data
InactiveCN113643767AConvenient summaryNo chemical pollutionChemical property predictionMacroscopic scaleComputational physics
Prediction of macroscopic properties of substances is fundamentally a quantum mechanics and statistical mechanics solving problem. However, the problem is too complex, and the thermodynamic method cannot forecast whether an unknown solid solution is formed. According to the method, atomic data is tried to be combined, and then a data mining technology is utilized to establish whether a phase diagram forms a solid solution or not based on atomic combination data, especially whether an oxysalt binary phase diagram forms a solid solution or not. According to the atom combination data-data mining method, the tedious intermediate step of solving a thermodynamic function through atom parameters is omitted, an atom parameter set is directly mapped to a certain phase diagram feature, a simple and clear semi-empirical function is obtained, and a series of phase diagram laws are well summarized.
Owner:上海帆阳信息科技有限公司
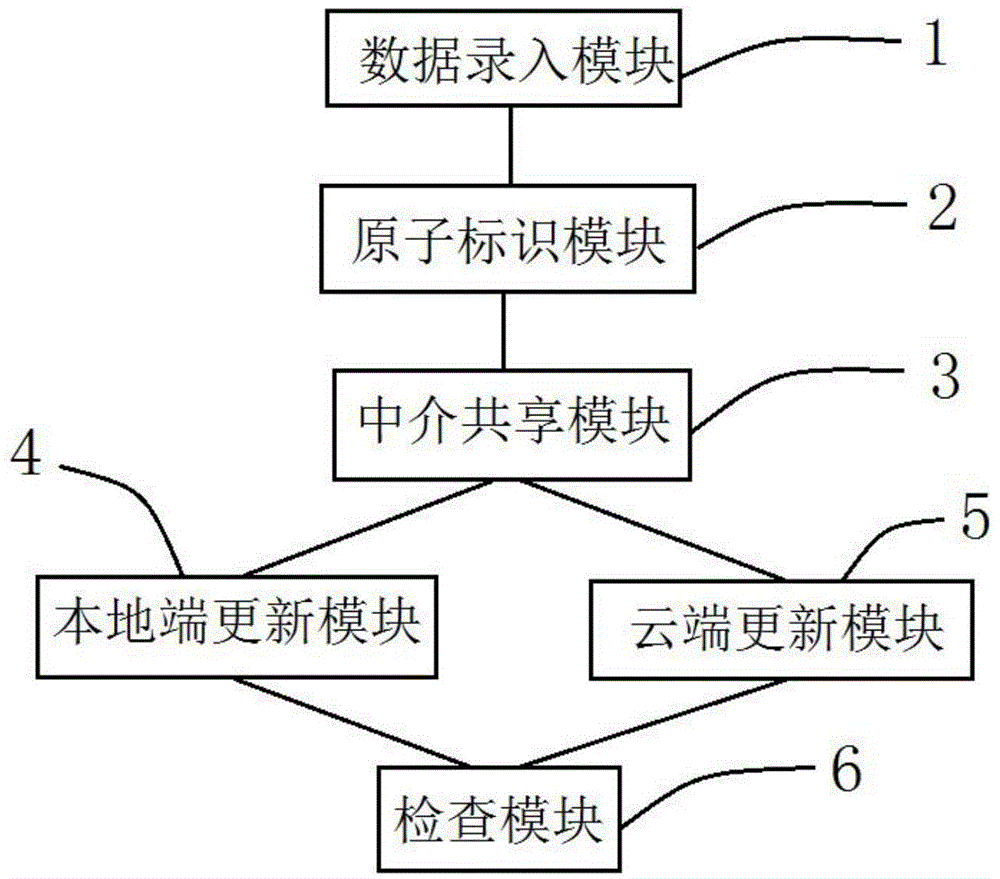
Method and system for synchronizing local end and cloud end data
The invention discloses a method and system for synchronizing local end and cloud end data. The method comprises the steps that the basic data of a product and / or service is recorded at a local end and a cloud end; the atomic data identification of the basic data of the recorded product and / or service is defined; the local end and cloud end share the basic data with the atomic data identification to an intermediary server; the local end obtains the basic data of the product and / or service with the atomic data identification from the intermediary server to update the data to be used by a user; and the cloud obtains the basic data of the product and / or service with the atomic data identification from the intermediary server to update the data to be used by the user. The invention provides the method and system for synchronizing local end and cloud end data, the real-time synchronization of the product and / or service of the local end and the cloud end can be realized, and the safety is high.
Owner:上海物易网络科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com