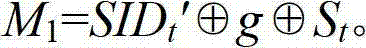Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
117 results about "Security privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Privacy and security are related. Privacy relates to any rights you have to control your personal information and how it’s used. Think about those privacy policies you’re asked to read and agree to when you download new smartphone apps. Security, on the other hand, refers to how your personal information is protected.
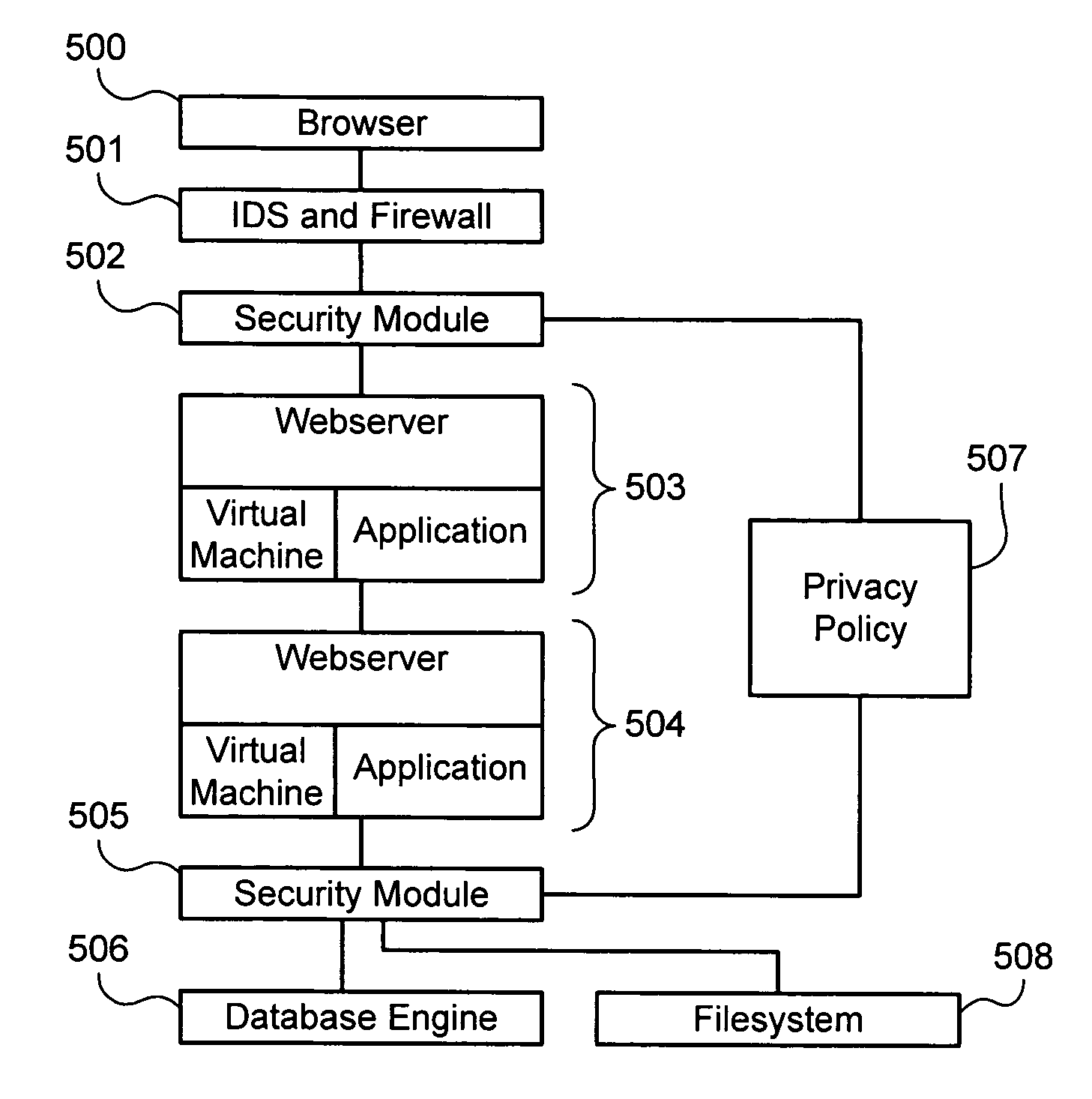
Establishing and enforcing security and privacy policies in web-based applications
ActiveUS20060143688A1Enhances security and privacyIncrease flexibilityMemory loss protectionUnauthorized memory use protectionObject handlingWeb application
Method, system, and computer code for implementing security and privacy policy in a web application having an execution environment in which a representation of each object handled by the execution environment accommodates data and an associated tag. An inbound tagging rule is established for tagging inbound objects according to a respective source of each of the inbound objects. A tag is assigned to an object being operated on by the execution environment based on the inbound tagging rule. A security / privacy rule is established for performing security / privacy actions on outbound objects according to a respective tag of each of the outbound objects. A security / privacy action is performed on the object being operated on by the execution environment based on the security / privacy rule.
Owner:FORTRA LLC
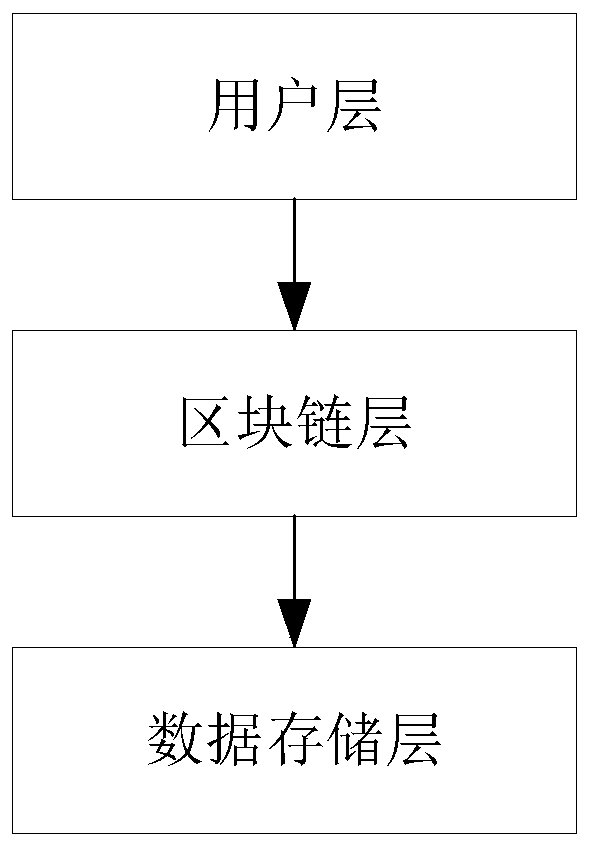
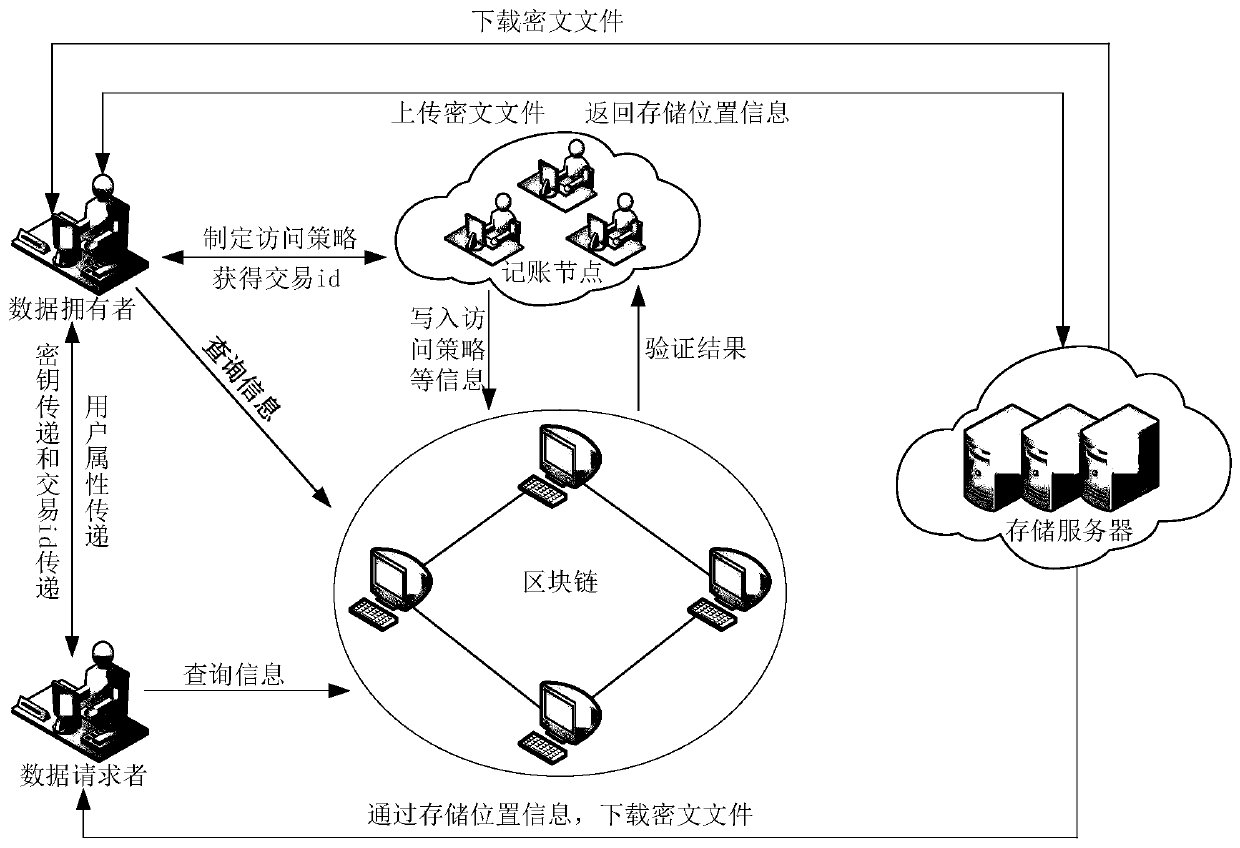
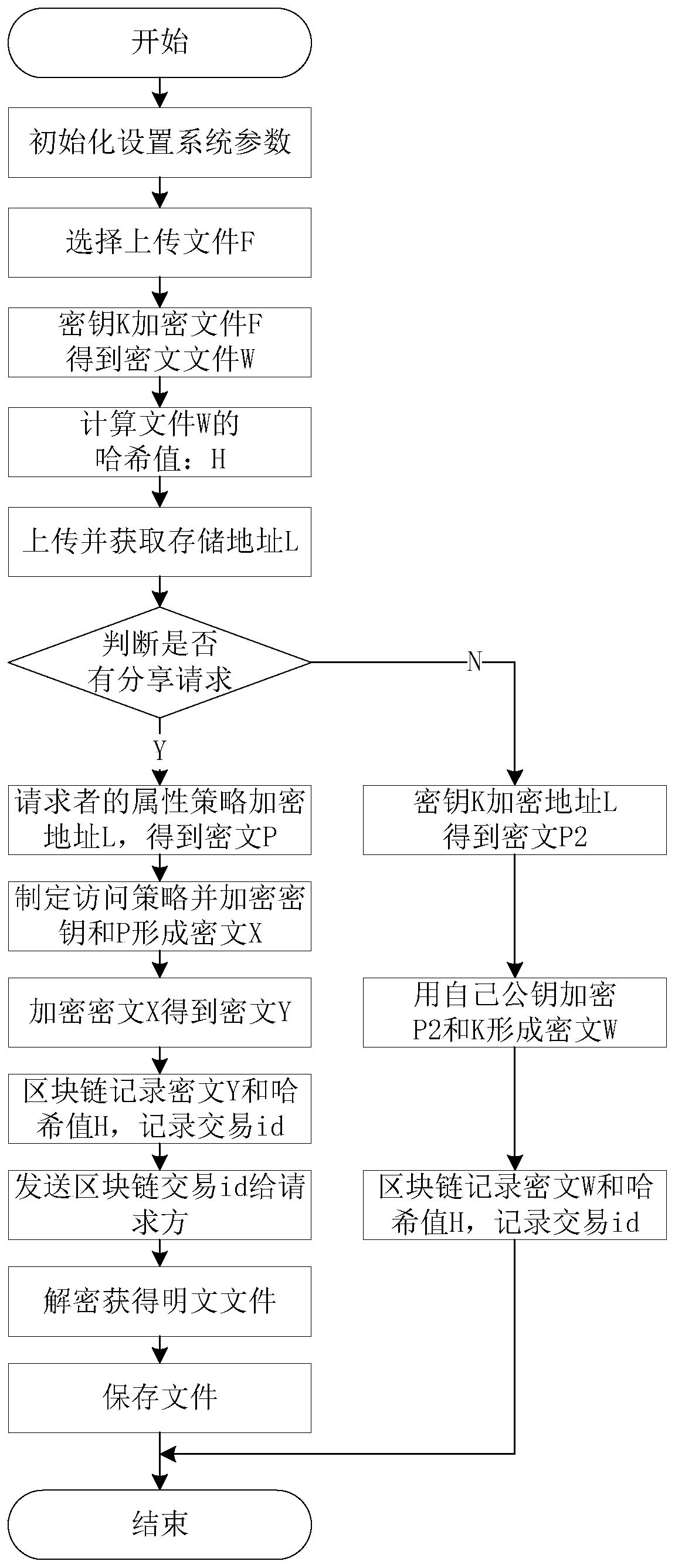
Data file security privacy storage and sharing method based on a block chain
ActiveCN109768987AImplement security managementRealize ciphertext sharingUser identity/authority verificationCiphertextData file
The invention relates to the field of computers and data storage, in particular to a data file security privacy storage and sharing method based on a block chain, which comprises a user layer, a blockchain layer and a data storage layer, and is characterized in that the user layer is used by a user to encrypt and upload data, encrypt and share data and receive data shared by other users; the blockchain layer is used for public storage of hash check codes of double encrypted ciphertext data and cloud storage data, and files are shared among users through transaction id; the data storage layeris used for storing and downloading ciphertext data; according to the invention, the availability and integrity of cloud storage data are effectively ensured; the user can conveniently verify the access permission, multi-user sharing of the data is achieved, the storage overhead and management overhead of the user on the secret key are reduced, the control force of the data owner on the data is improved, ciphertext sharing of the data is achieved, and the safety and privacy of the storage system are improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
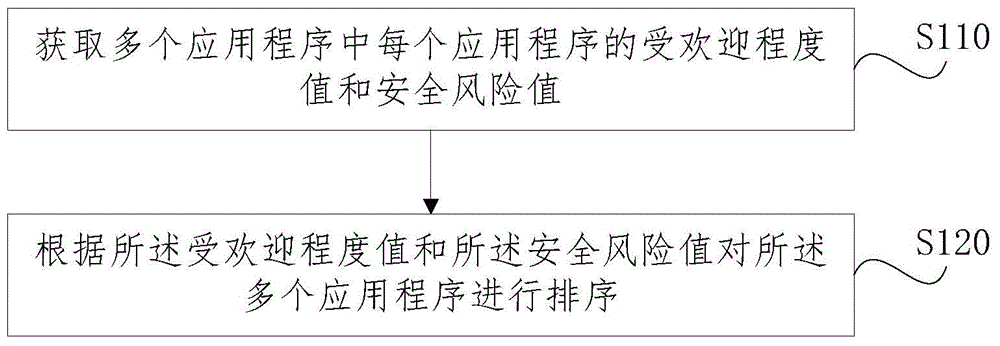
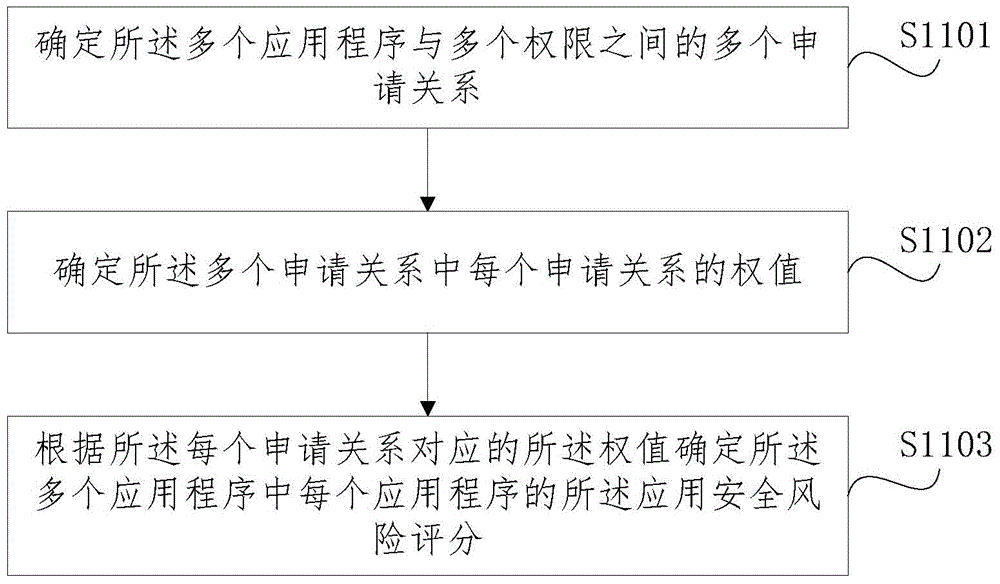
Application program recommending method and device
ActiveCN104090967AMeet popSatisfy securityPlatform integrity maintainanceCommerceSecurity privacyMultiple applications
The embodiment of the invention discloses an application program recommending method and device. The method comprises the steps that the popularity degree value and the safety risk value of each application program in a plurality of application programs are obtained; the application programs are sorted according to the popularity degree values and the safety risk values. According to the technical scheme, the application programs are sorted according to the popularity degree values and the safety risk values of the application programs, therefore, the application program which can better meet the popularity preference and the safety preference of a user can be recommended to the user preferentially, and safety privacy can be guaranteed while the user enjoys the application program with abundant functions.
Owner:BEIJING ZHIGU RUI TUO TECH
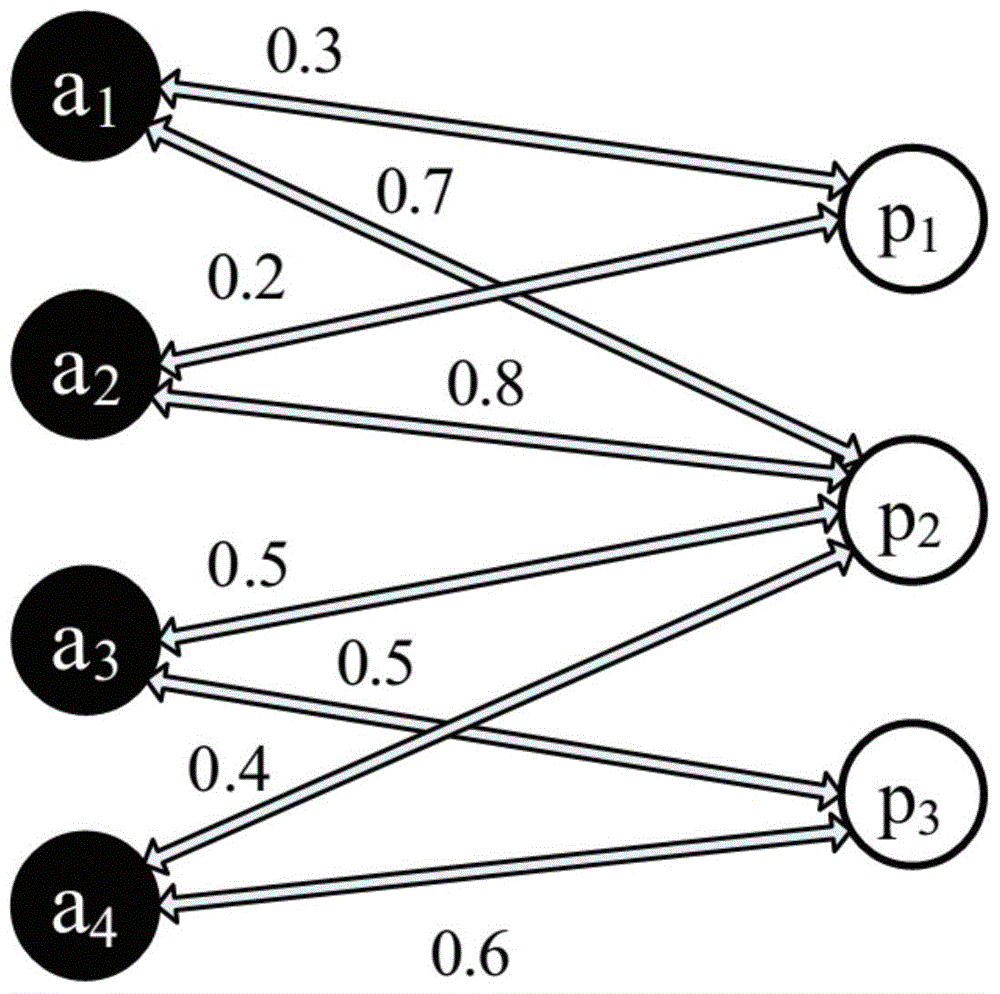
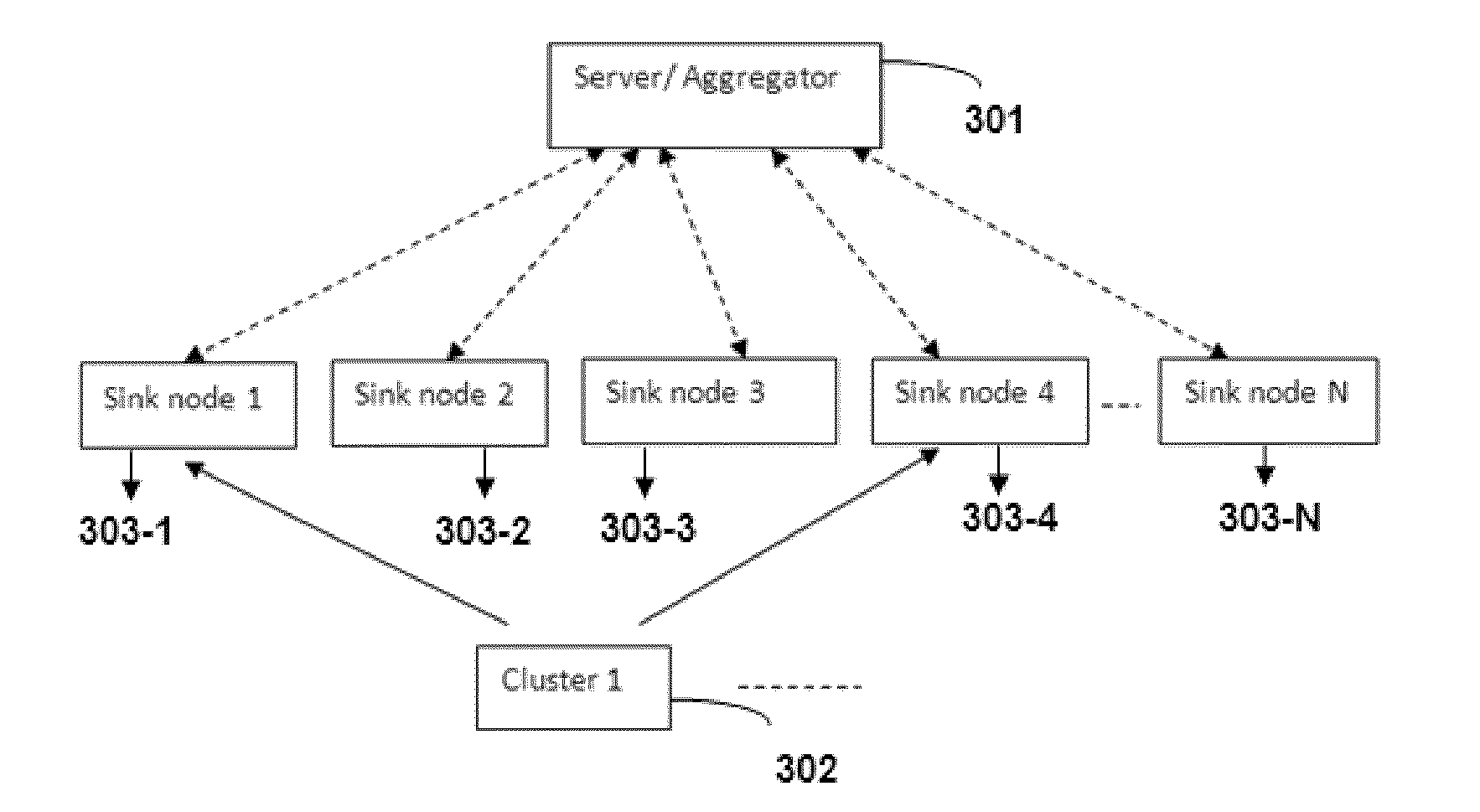
Method and system for preserving privacy during data aggregation in a wireless sensor network
ActiveUS20140047242A1Efficient and secure aggregation schemePrivacy protectionUser identity/authority verificationNetwork topologiesWireless mesh networkData aggregator
A computer-based system and method for secured privacy preservation scheme while data aggregation in a non-hierarchical wireless sensor network that lacks peer-to-peer communication between the communicating sensor nodes is disclosed. The method and system adopts formation of self-adaptive efficient cluster formation for robust privacy preservation in the network by grouping the multiple sensor nodes in the network to form multiple clusters that enables low computation overhead and high scalability in the network. The method and system of the invention discloses an effective twin-key management scheme that provides establishment of secure communication among the sensor nodes and the secure communication between at least one sensor node with the sever node performing the function data aggregation of the data collected by the sensor nodes.
Owner:TATA CONSULTANCY SERVICES LTD
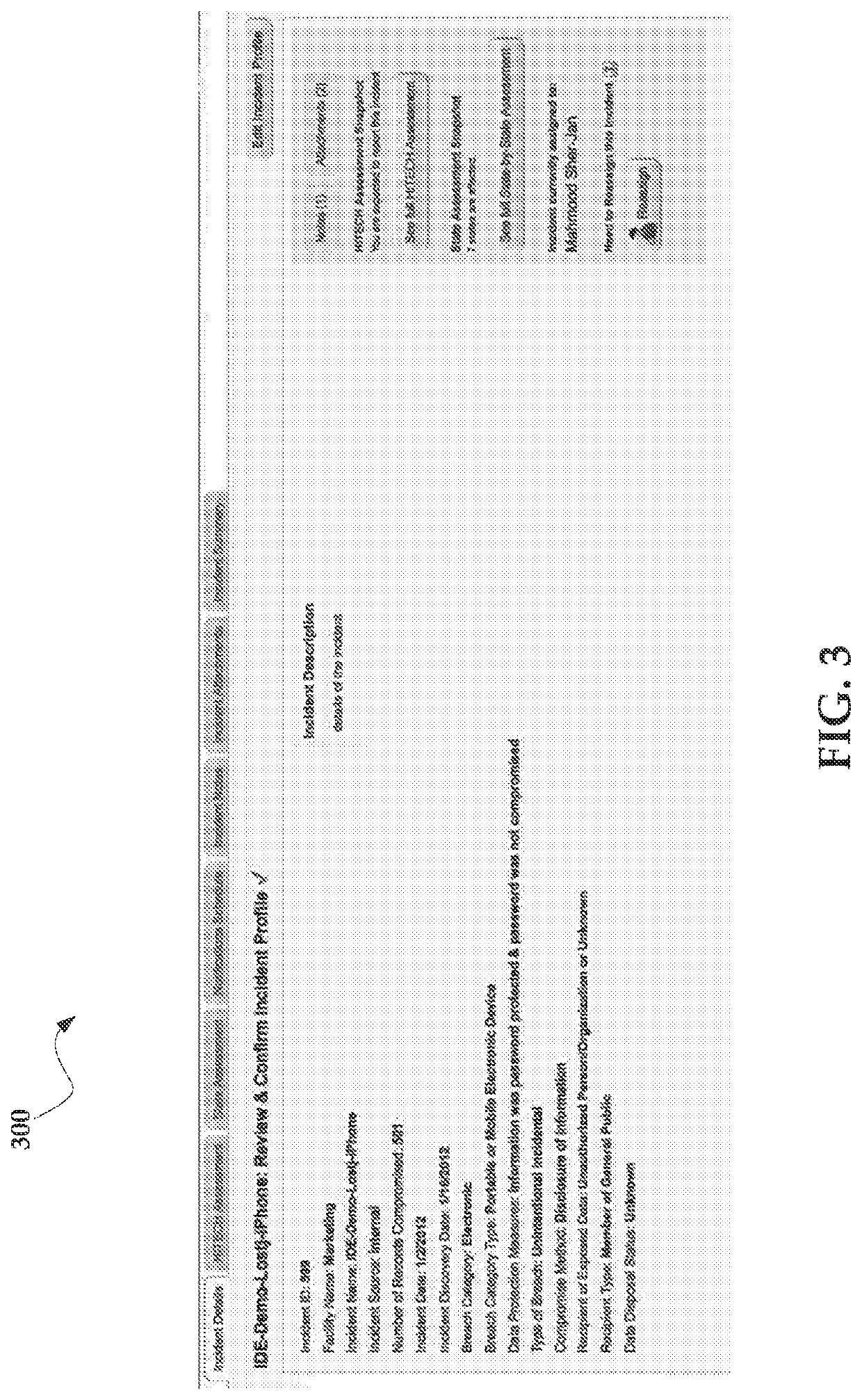
Systems and methods for managing data incidents having dimensions
Provided herein are exemplary systems, methods and / or media for managing a data incident including receiving, via an incident server, in response to an occurrence of the data incident, data incident data that comprises information corresponding to the data incident, the data incident further including information from a plurality of departments or functions in an organization to result in comprehensive management and a comprehensive resolution of the data incident including a dimension. The dimension may include security, privacy, record management, compliance, fraud, health, safety, and / or a policy violation.
Owner:RADAR LLC
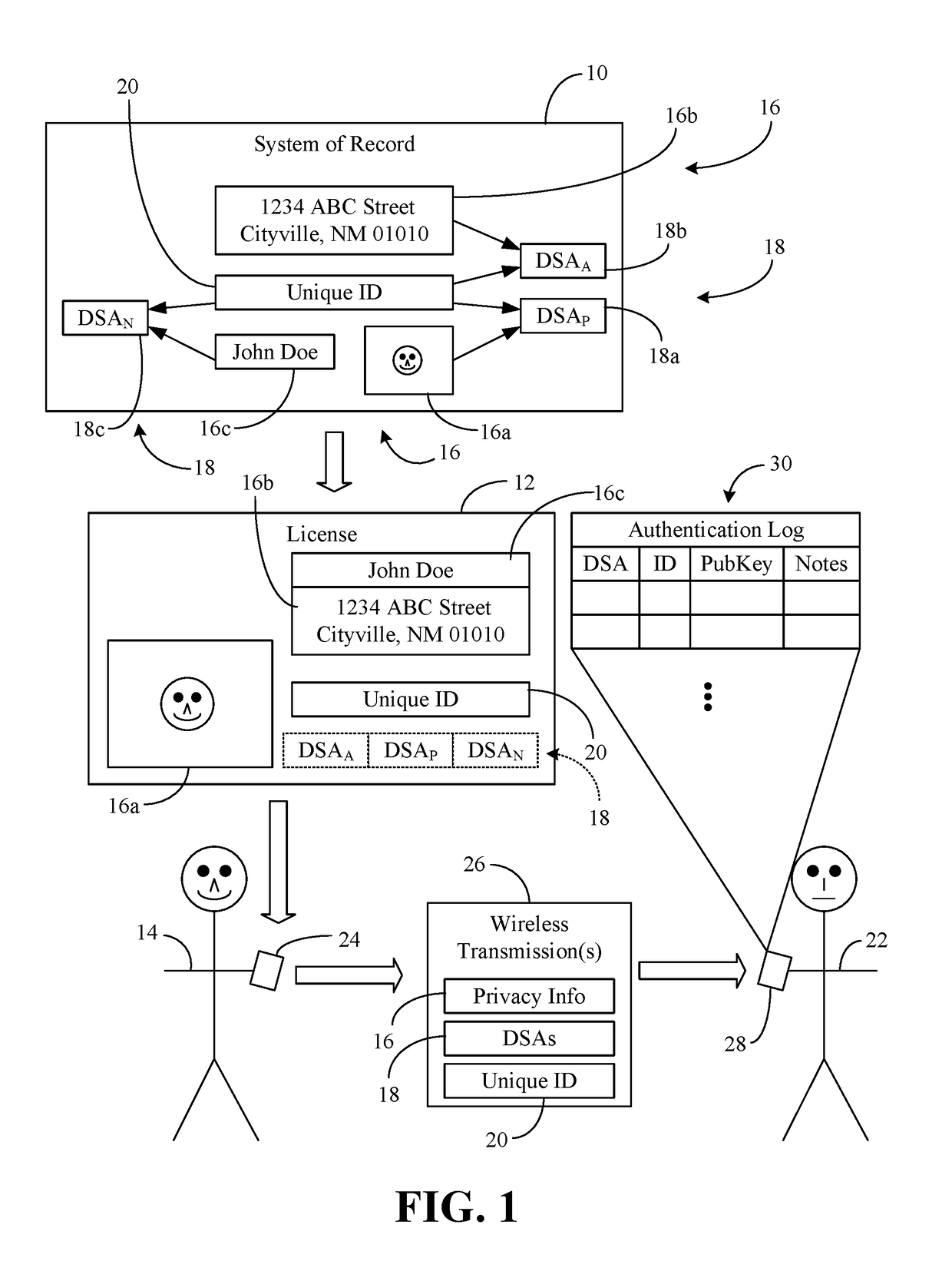
Digital license authentication with secure privacy logging
InactiveUS20180341775A1Public key for secure communicationUser identity/authority verificationPublic key authenticationDigital signature
Methods and systems may provide for technology to receive, by a computing device, privacy information, a unique identifier (ID) and one or more digital signatures associated with the privacy information and the unique ID. Additionally, the technology may store the unique ID and the digital signature(s) to a record of an authentication log on the computing device and delete the privacy information from the computing device. In one example, the technology conducts a public key authentication of the digital signature(s).
Owner:IBM CORP
Radio frequency identification (RFID) safety communication method established according to ultra-lightweight RFID bidirectional authentication protocol
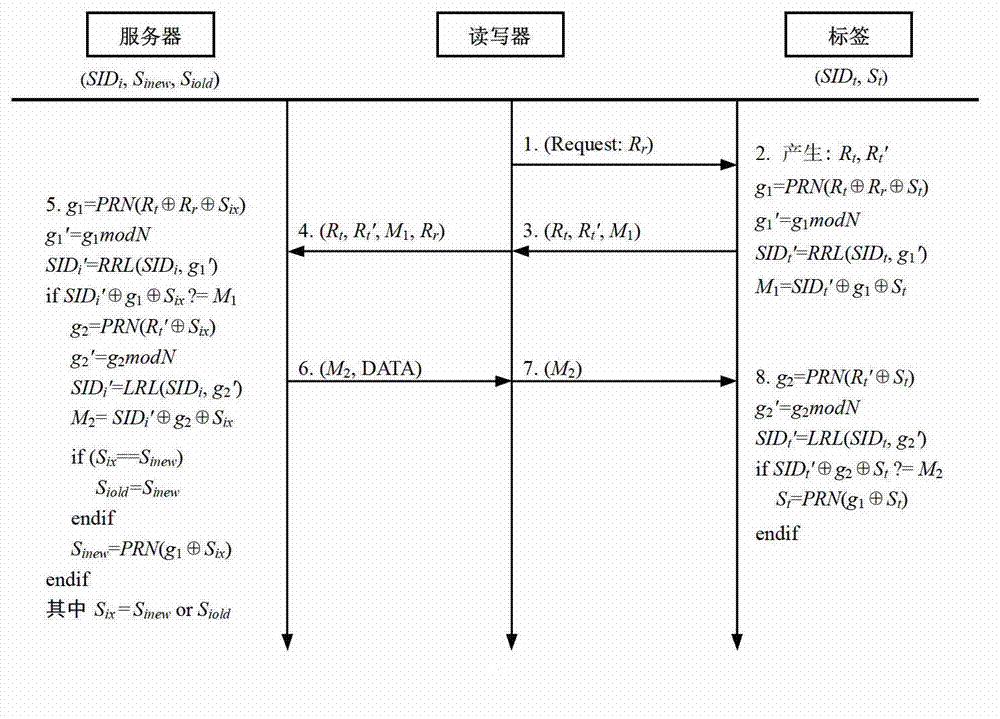
InactiveCN102880891ATroubleshoot key synchronization issuesSolve the forward security problemCo-operative working arrangementsExclusive orNumber generator
The invention discloses a radio frequency identification (RFID) safety communication method established according to an ultra-lightweight RFID bidirectional authentication protocol. By adoption of the method, the security problems of a low-grade tag RFID system can be effectively solved. The method has the main characteristics of security, high efficiency, simplicity and practicability. A tag is only required to provide simple operation such as random number generator operation, exclusive-OR operation, modular operation (MOD) and displacement. Resources required by the simple operation are extremely limited, so the scheme is in complete accordance with an EPCglobal C1G2 tag specification, has the characteristics of low storage cost, low operation cost, low communication cost, novel and simple algorithm and the like, and is easy to implement. The method has the advantages that the problems about synchronization of the tag and a rear-end database key, forward security and security privacy (privacy leak, flow analysis and positioning tracking) can be effectively solved, and the common security problems of an RFID system about imitation attack, cloning attack, monitoring attack, replay attack and denial-of-service attack are solved. The method is quite applicable to solving the security problems of an EPCglobal C1G2 RFID tag.
Owner:SUN YAT SEN UNIV
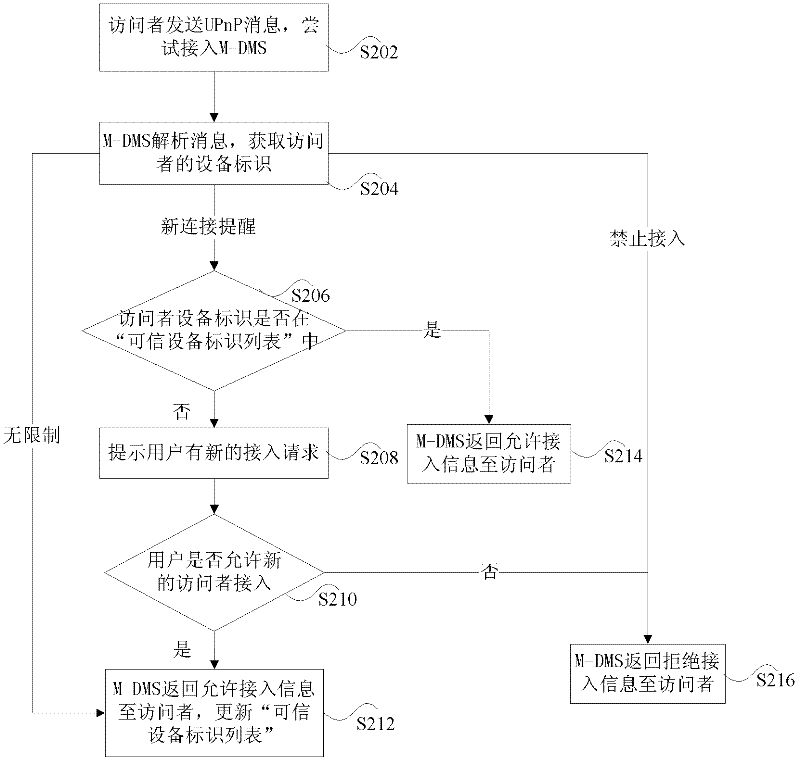
Access control method and access control device of digital living network alliance (DLNA) equipment
InactiveCN102571776AImprove securityMeet needsHome automation networksSecurity privacyMedia access control
The invention discloses an access control method and an access control device of digital living network alliance (DLNA) equipment. The access control method provided by the invention comprises the following steps that: a M-DMS (Mobile Digital Media Server) in the DLNA receives an access message of other DLNA equipment from the DLNA equipment; and M-DMS obtains equipment identifications of other DLNA equipment; and the M-DMS determines to allow other DLNA equipment to access for control according to the equipment identifications. According to the invention, the safe access control conforming to norms of DLNA can be realized in the DLNA network without adding of additional equipment, so that the safety of the M-DMS is enhanced, the requirements of users for security privacy are met, and the user experience is improved.
Owner:ZTE CORP
Secure multi-party computing method based on trusted hardware and block chain
PendingCN112380565AImplement secure multi-party computationImprove execution efficiencyDigital data protectionPlatform integrity maintainanceComputer hardwareTrusted hardware
The invention discloses a secure multi-party computing method based on trusted hardware and a block chain, which comprises the following steps that: a user encrypts input parameters and inputs the encrypted input parameters into a trusted execution environment, the trusted execution environment exchanges data with other participants through the block chain, executes a computing function in the trusted execution environment after collecting all the inputs, and outputs a result; based on the scheme, a plurality of participants can complete data sharing of security privacy under the condition ofprotecting respective data privacy, and finally, a distributed arbitrary multi-party joint computing task is realized. A fair data exchange process of multi-party participants is realized by utilizinga block chain, meanwhile, privacy protection is carried out on data exchange by utilizing an encryption algorithm, and the obtained encrypted data is decrypted and calculated in a trusted computing environment, so that an efficient and safe multi-party computing process is realized.
Owner:TIANYI ELECTRONICS COMMERCE
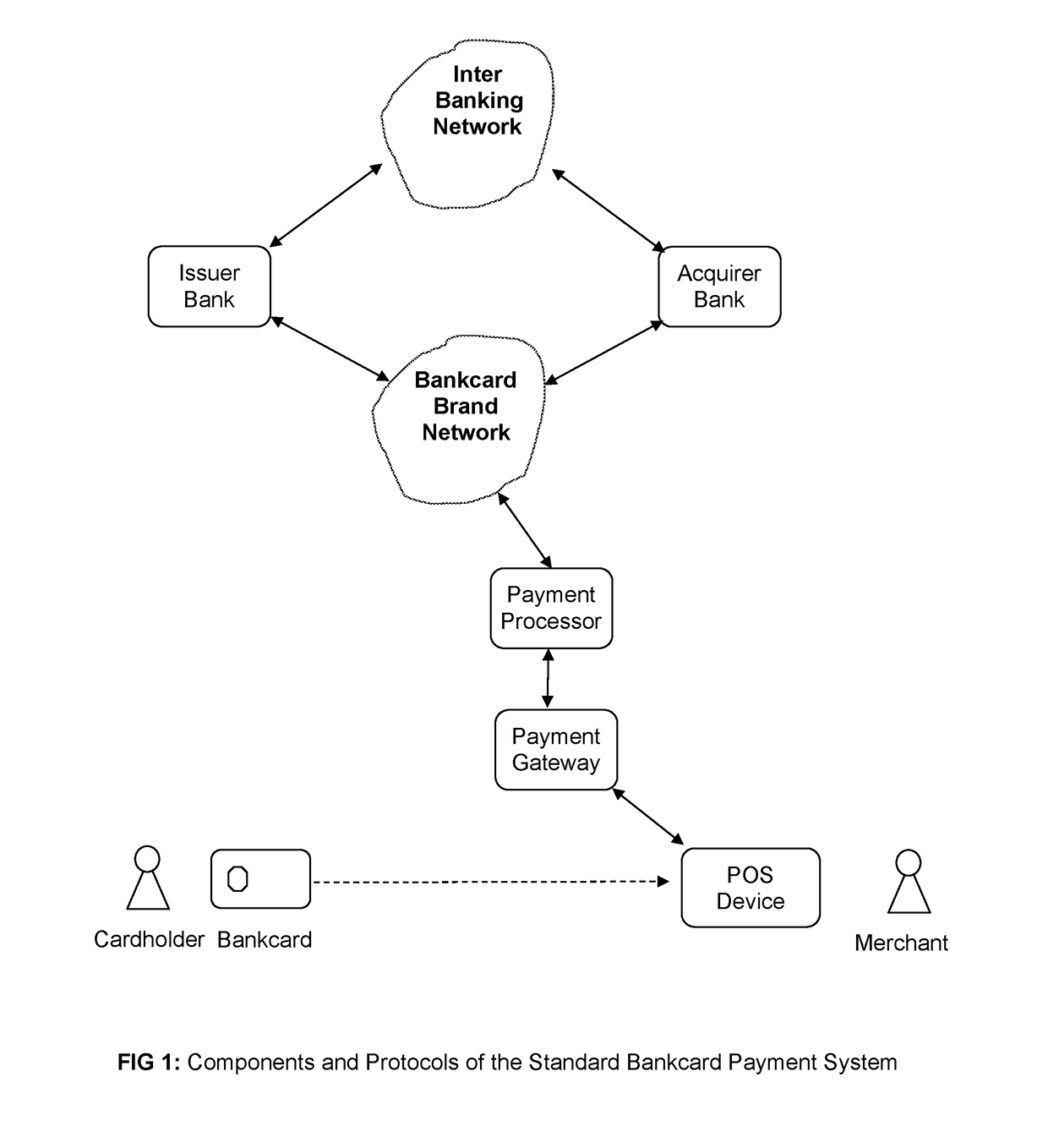
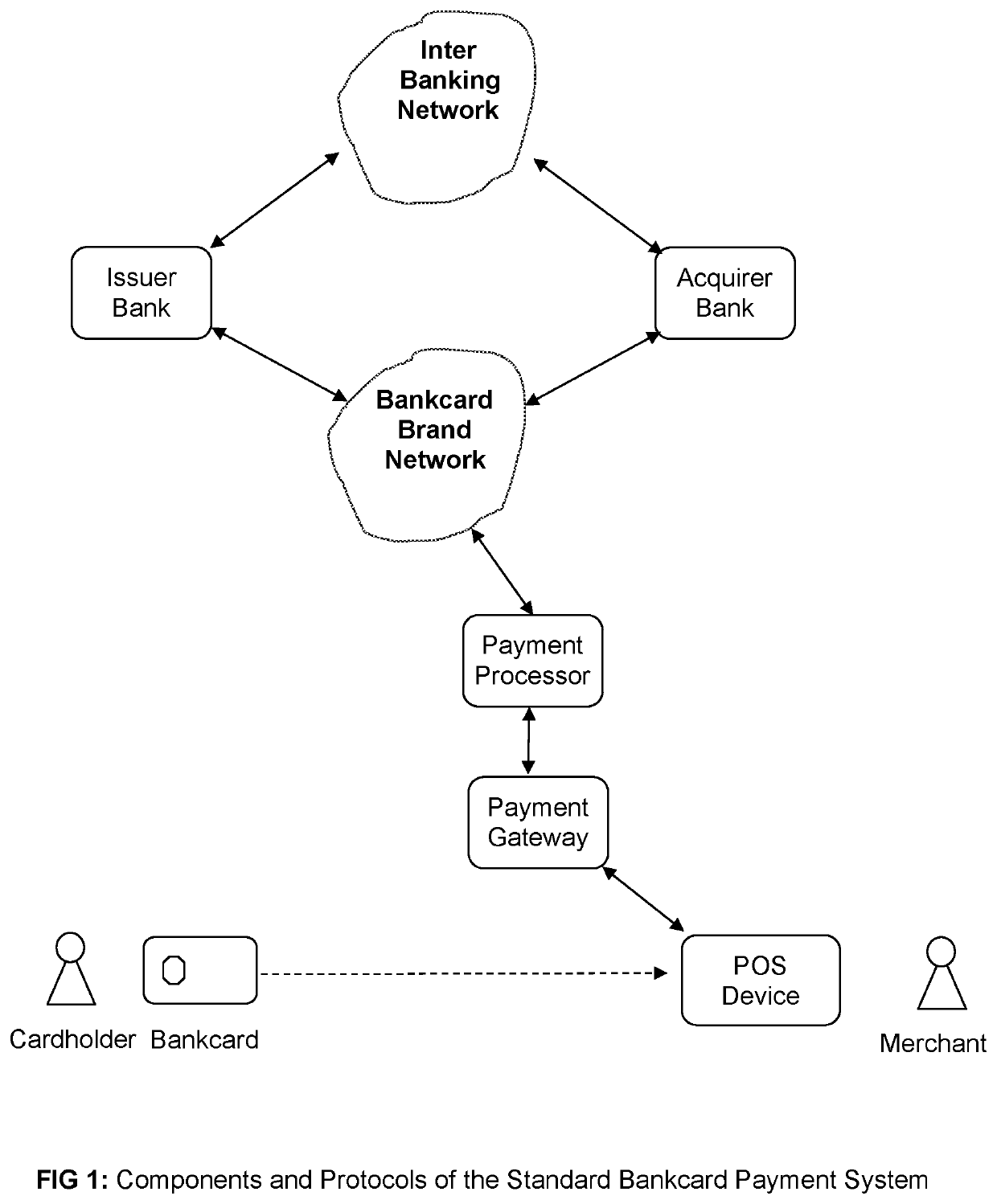
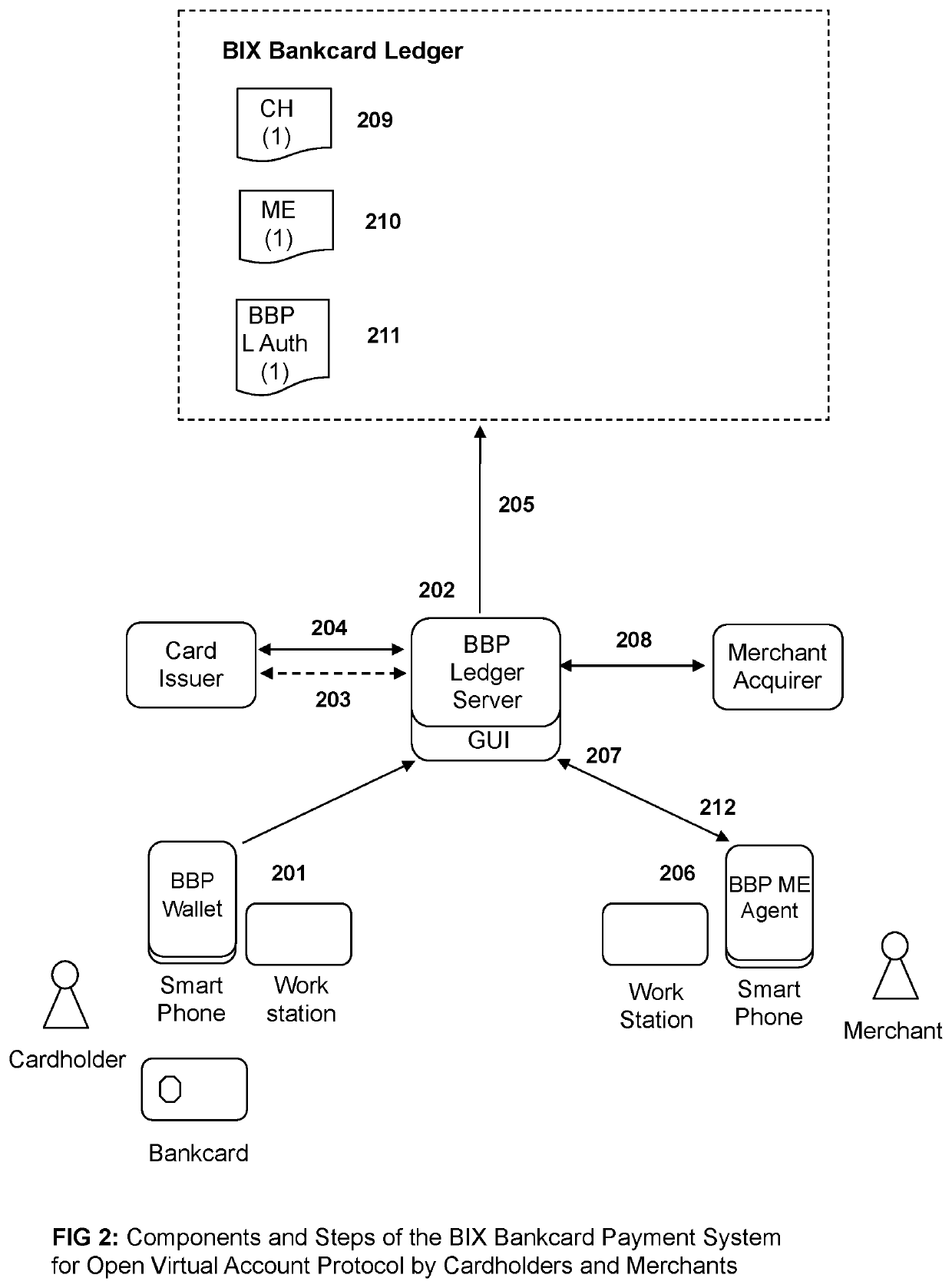
Secure Payment Transactions based on the Public Bankcard Ledger
ActiveUS20170357970A1Improve efficiencyImprove securityCryptography processingCredit schemesThird partyPayment transaction
A system for bankcard payments, wherein payments are peer-to-peer transactions between the cardholder and merchant without participation from any third party. The system uses standard bankcards and supports both debit and credit card payments. For authorization of payments the system uses a special, global, distributed, append-only, and secure public bankcard ledger. The entries in the ledger are virtual accounts used for bankcard payments, organized into account chains. The system provides security, privacy, anonymity, and untraceability for cardholders and their transactions. The system allows for various users of the system to participate in transactions using preexisting payment systems. In one embodiment, specially designed mobile software modules and an innovative payment protocol all for transactions to be made between users.
Owner:MUFTIC SEAD
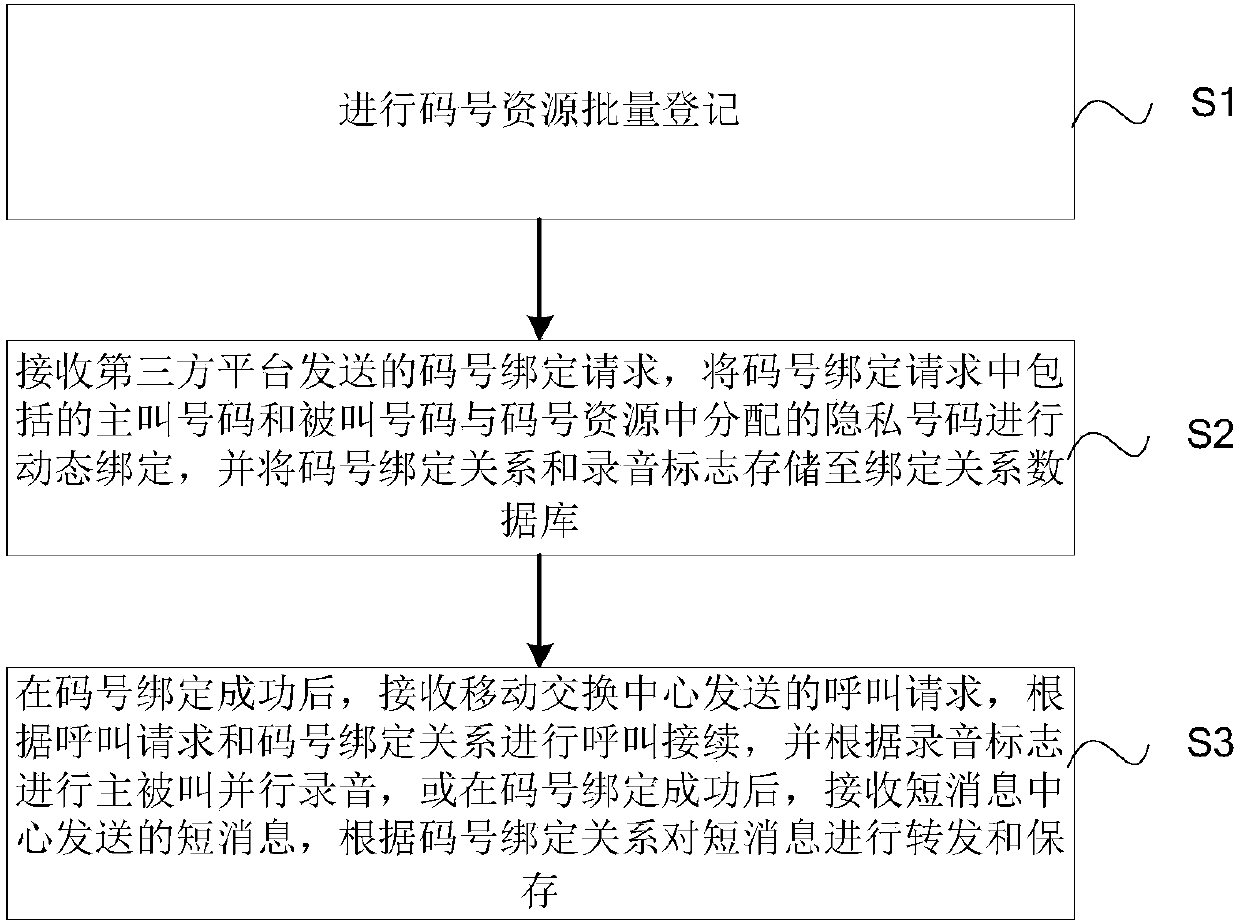
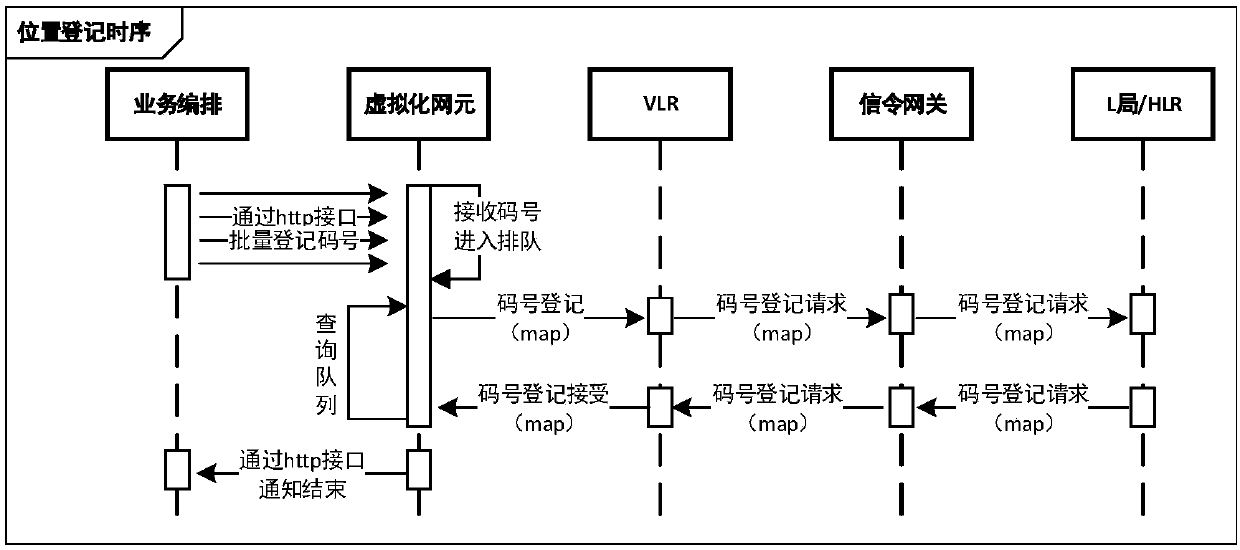
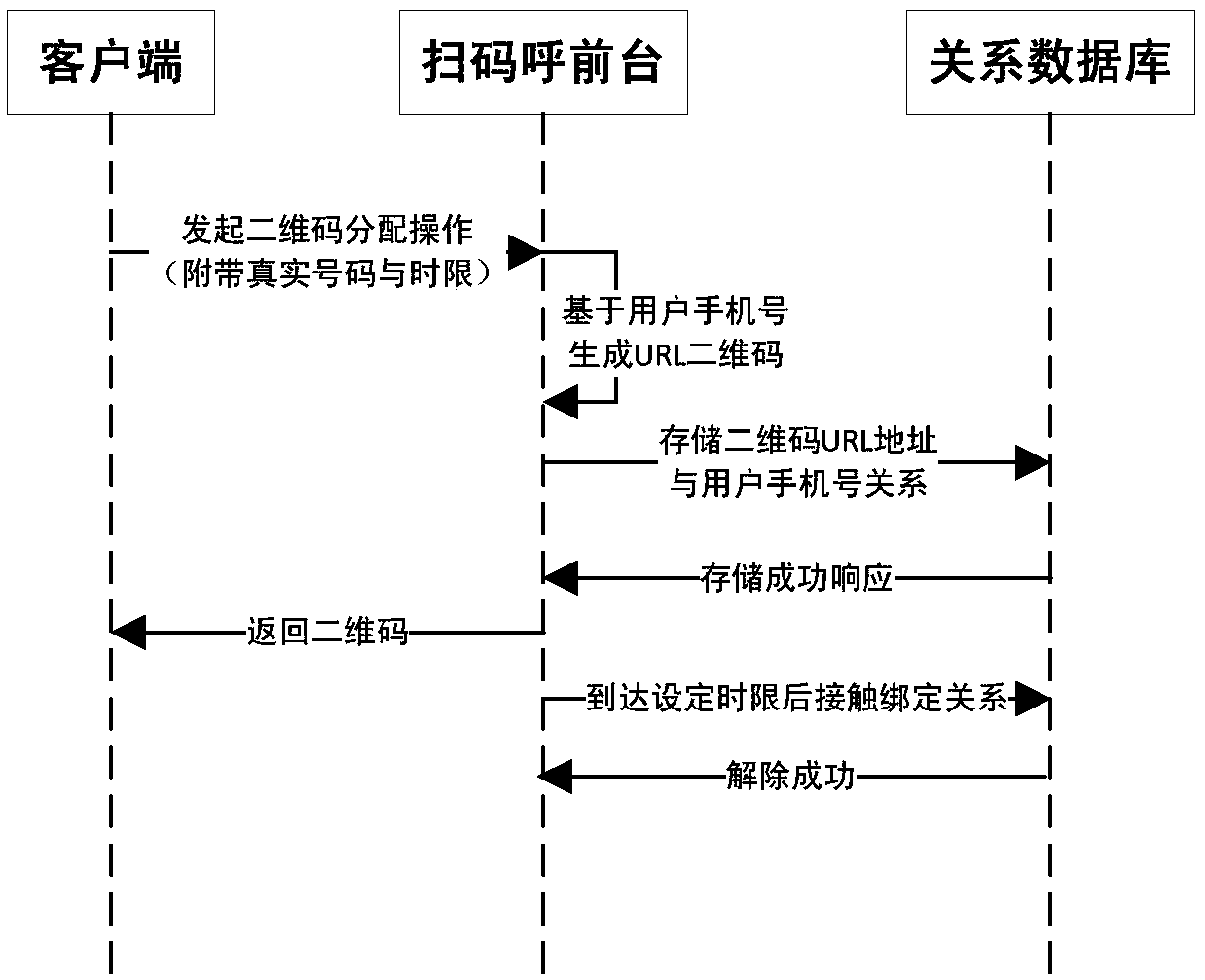
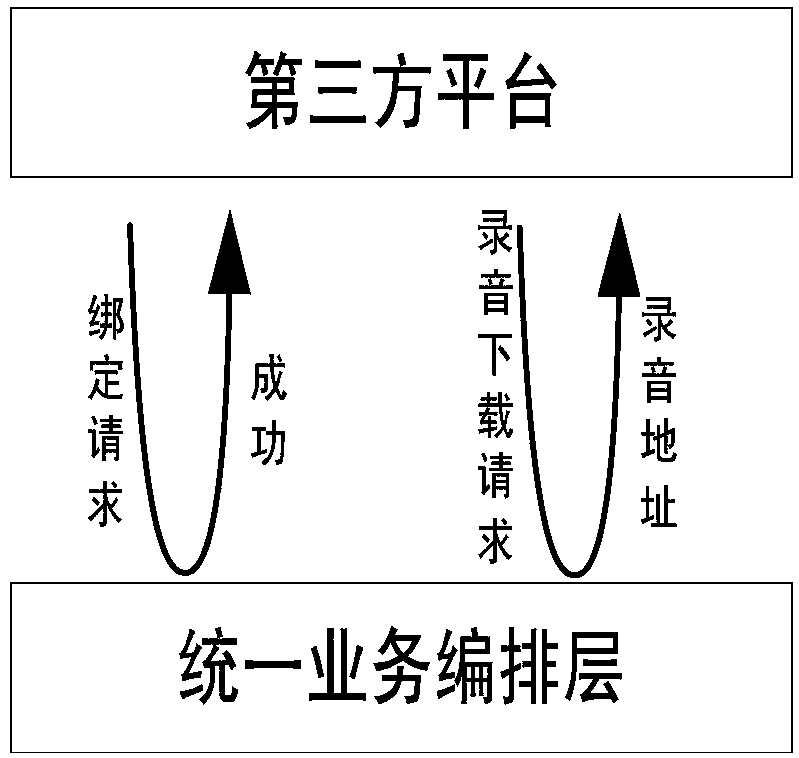
Mobile phone number security privacy protection method and platform based on mobile Internet
ActiveCN107809749AGuaranteed privacy and securityRelational databasesCommmunication supplementary servicesThird partyThird platform
The invention discloses a mobile phone number security privacy protection method and platform based on the mobile Internet. The method comprises the steps of S1, carrying out code number resource batch registration; S2, receiving a code number binding request sent by a third platform, carrying out code number binding according to the code number binding request, and storing a code number binding relationship and a recording mark to a binding relationship database; and S3, after the code number binding is successful, receiving a call request sent by a mobile switching center, carrying out callconnection according to the call request, and carrying out calling and called parallel recording, or receiving a short message sent by a short message center, and forwarding and storing the short message. The method and the platform have the beneficial effects that private numbers and true numbers of two parties are bound, the binding relationship is stored, and a called true number is queried indirectly according to the private numbers and the binding relationship, so the privacy security of a mobile phone number of the a user is ensured.
Owner:中国东盟信息港股份有限公司
Power grid data sharing method and system based on block chain and data resource directory
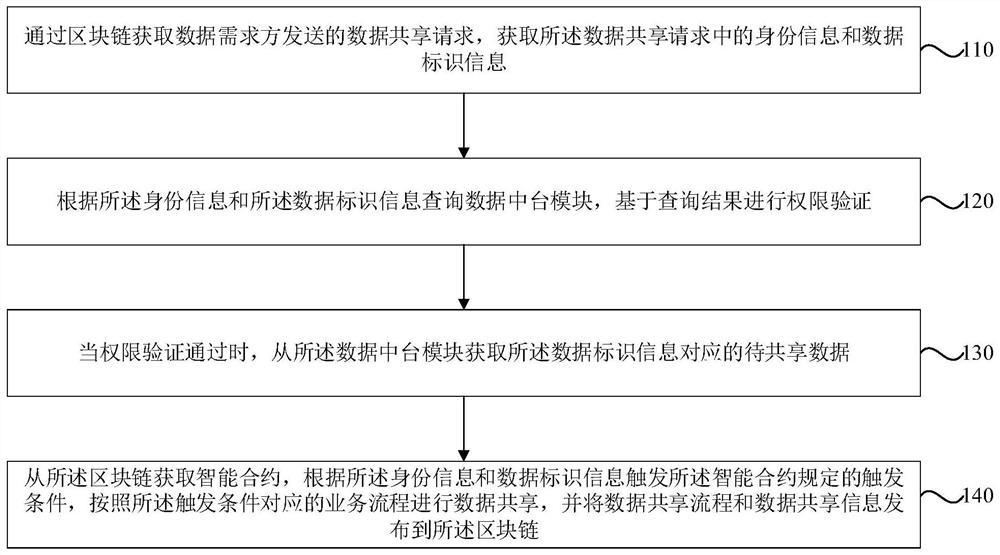
PendingCN112463843AGuaranteed full recordGuaranteed traceabilityData processing applicationsDatabase management systemsData centerPower grid
The invention discloses a power grid data sharing method and system based on a block chain and a data resource directory. The method comprises the steps of obtaining a data sharing request sent by a data demander through a block chain, and obtaining identity information and data identification information in the data sharing request; querying a data middle station module according to the identityinformation and the data identification information, and performing authority verification based on a query result; when the authority verification is passed, obtaining to-be-shared data correspondingto the data identification information from the data center station module; and obtaining the smart contract from the block chain, triggering a triggering condition specified by the smart contract according to the identity information and the data identification information, performing data sharing according to a service process corresponding to the triggering condition, and publishing the data sharing process and the data sharing information to the block chain, so that whole-course recording and traceability of power grid data in the aspects of access convergence, business processes, use circulation and the like are ensured, and the problems of power grid data in the aspects of right confirmation authentication, security privacy and credible sharing are solved.
Owner:国家电网有限公司大数据中心
Blockchain data transaction system and method based on proxy re-encryption and smart contract
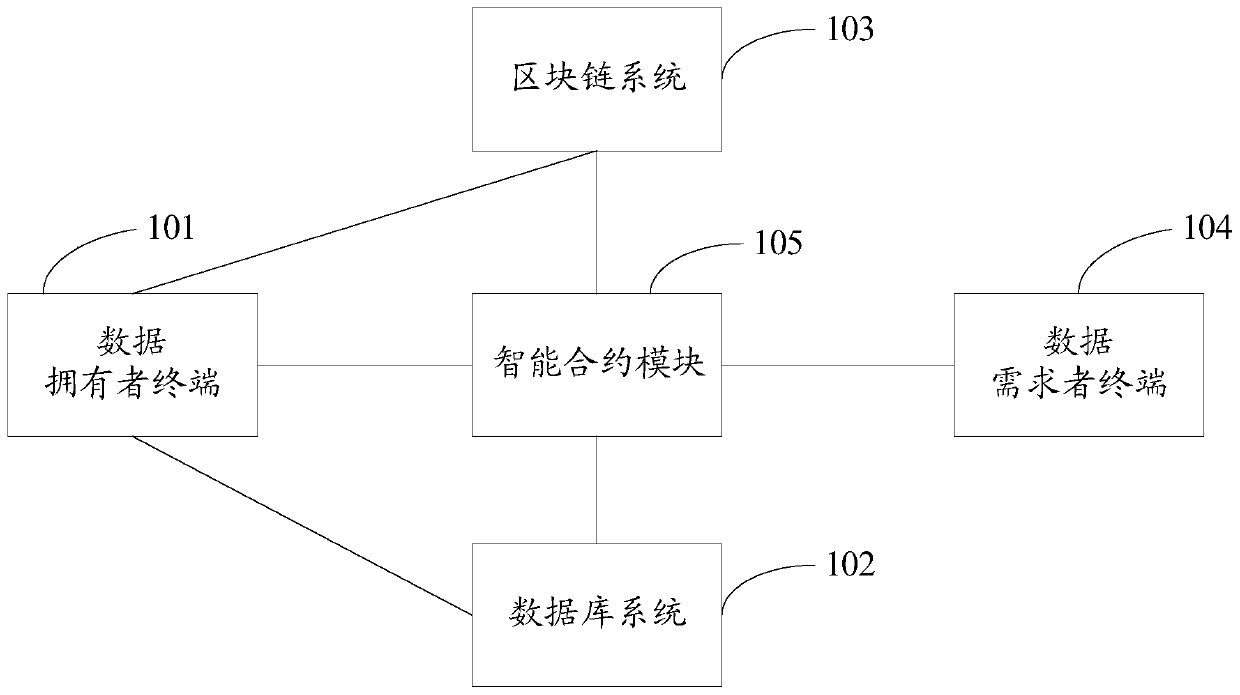
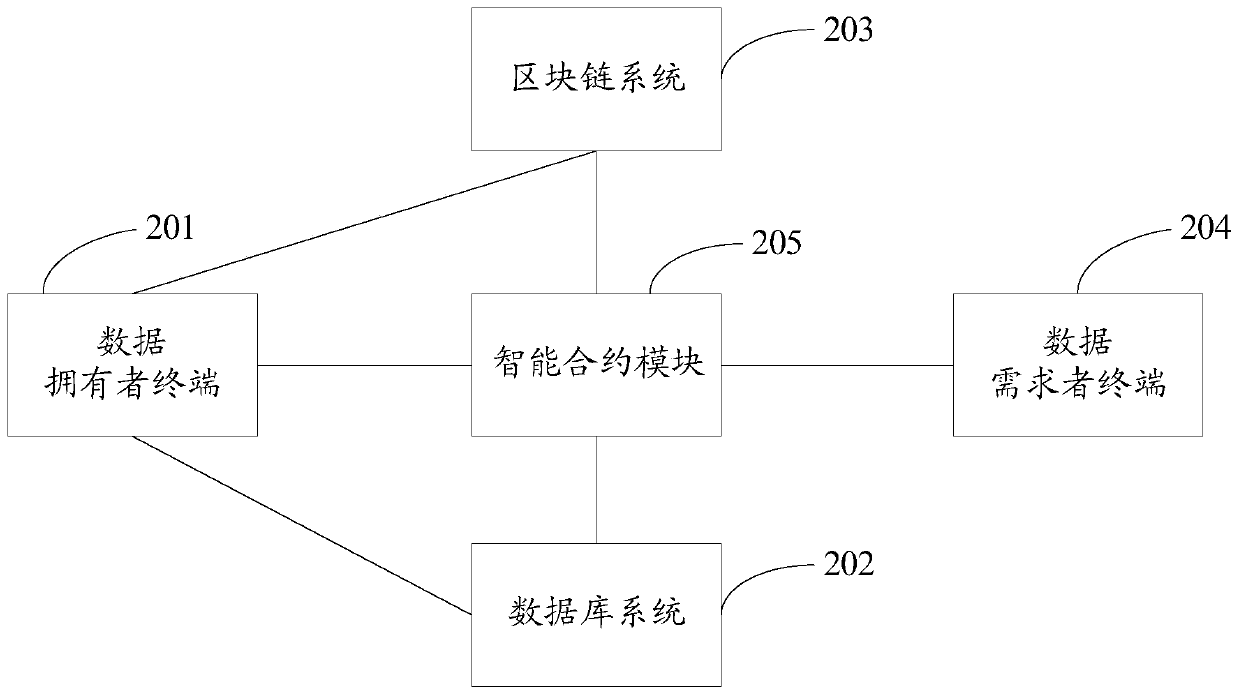
ActiveCN110430186AGuaranteed privacy and securityRealize economic valueKey distribution for secure communicationFinanceTransaction dataData needs
The invention discloses a blockchain data transaction system and a blockchain data transaction method based on proxy re-encryption and an intelligent contract. The system comprises a data owner terminal, a database system, a blockchain system, a data demander terminal and an intelligent contract module. According to the method, the security privacy of the transaction data can be ensured by using the proxy re-encryption technology, and the efficient and automatic execution of the data transaction can be realized by using the smart contract, so that the security privacy and efficiency problems of the blockchain data transaction are solved. The economic value of the data is realized, and the application value of the data is brought into full play.
Owner:STATE GRID E COMMERCE CO LTD +2
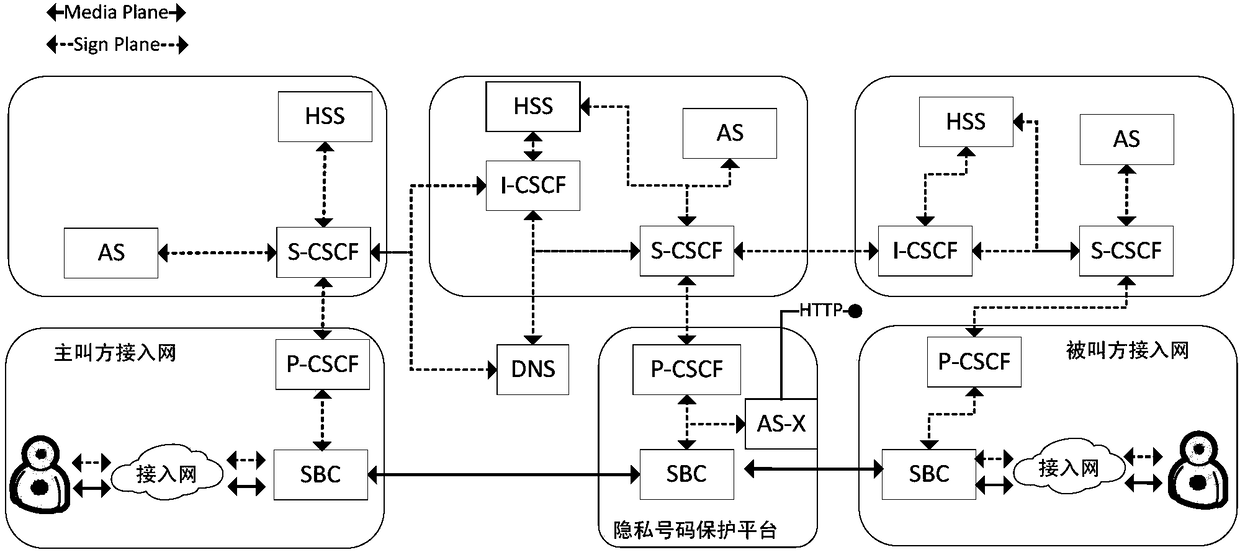
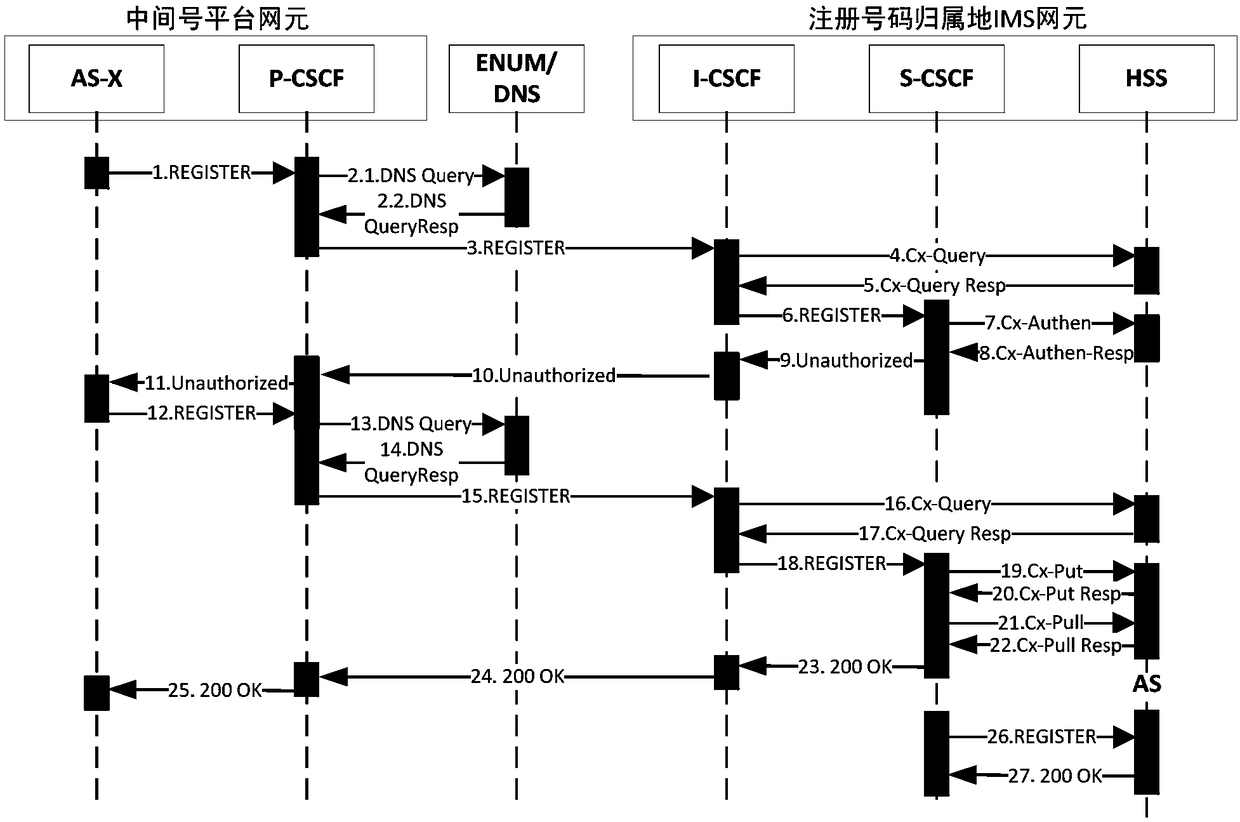
Mobile phone security privacy number protection platform based on IMS networking
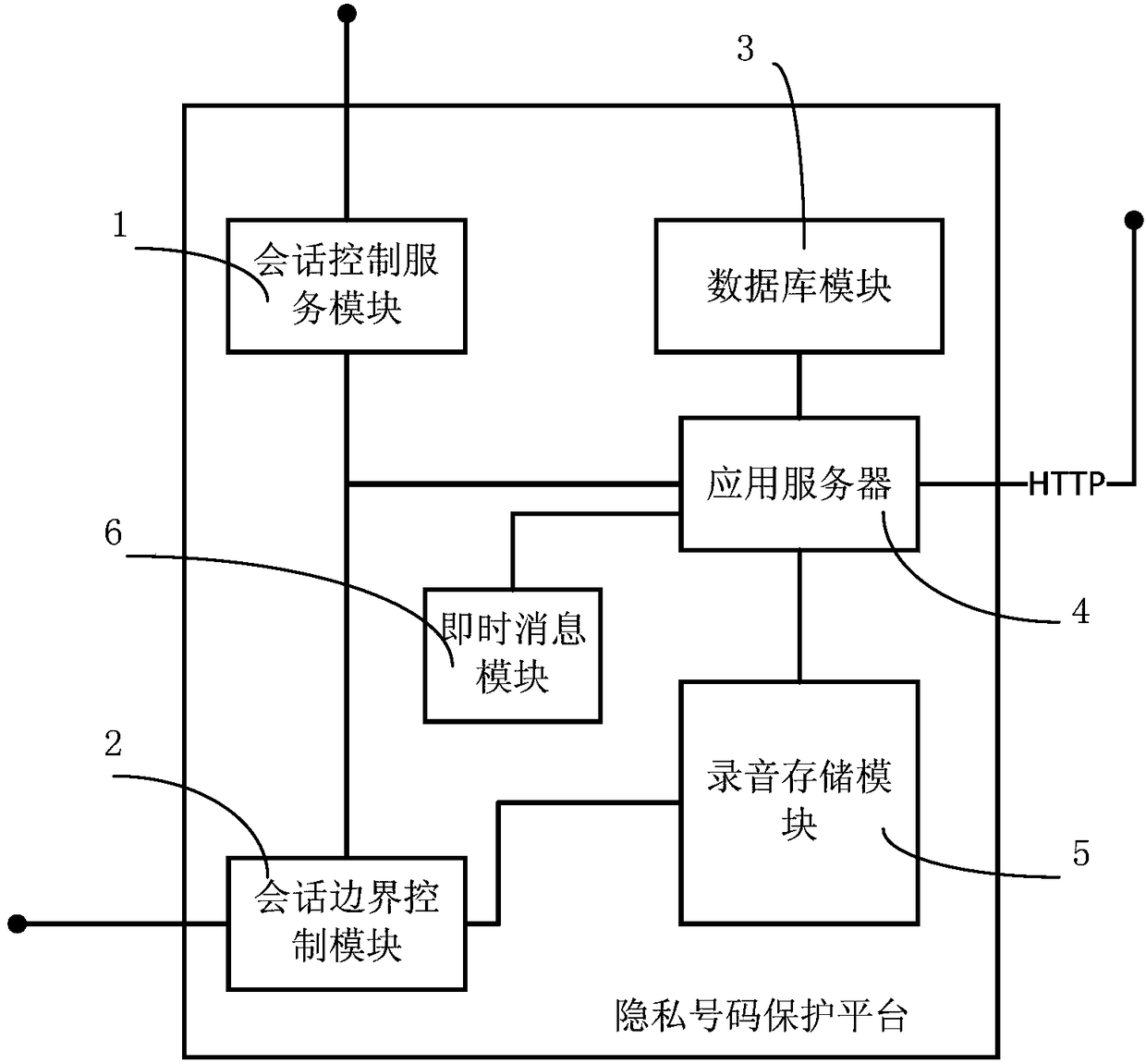
ActiveCN108521404AAchieve protectionEasy to useSpecial service for subscribersMessaging/mailboxes/announcementsThird partyContinuation
The invention discloses a mobile phone security privacy number protection platform based on IMS networking and belongs to the field of the operator service platforms. The platform comprises a sessioncontrol service module, a session boundary control module, a database module, and an application server; the session control service module is connected with the session boundary control module, and the session control service module, the session boundary control module, and the database module are all connected with the application server. By establishing a platform to serve a third-party platform, when an ordinary user uses a call or short message service on the third-party platform, the call or short message service is transferred to the mobile phone security privacy number protection platform, and the communication continuation between a calling user and a called user is realized through an intermediate number. The ordinary user adopts temporary registration in the mobile phone security privacy number protection platform, and the intermediate number is bound when in communication, and binding of the intermediate number is unlocked after the third-party platform is quit.
Owner:中国东盟信息港股份有限公司
Anonymous making-friends method, system and network server
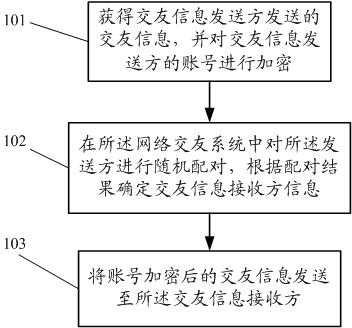
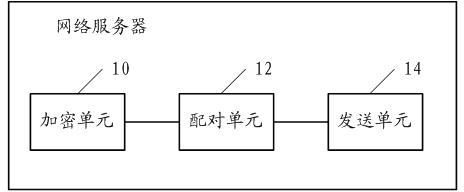
ActiveCN102594721AEnsure safetyComputer security arrangementsData switching networksNetwork serviceSecurity privacy
The embodiment of the invention discloses an anonymous making-friends method, a system and a network server. The method is used in the anonymous network making-friends system and comprises the following steps of: obtaining making-friends information sent by a making-friends information sender, and encrypting the account number of the making-friends information sender; randomly mating senders in the network making-friends system, and determining the information of a making-friends information receiver according to a mating result; and sending the making-friends information with the encrypted account number to the making-friends information receiver. As the method is adopted, anonymous making-friends can be realized, and the security privacy of users is ensured.
Owner:TENCENT TECH (SHENZHEN) CO LTD
User mobile phone safety privacy protection method based on two-dimensional codes
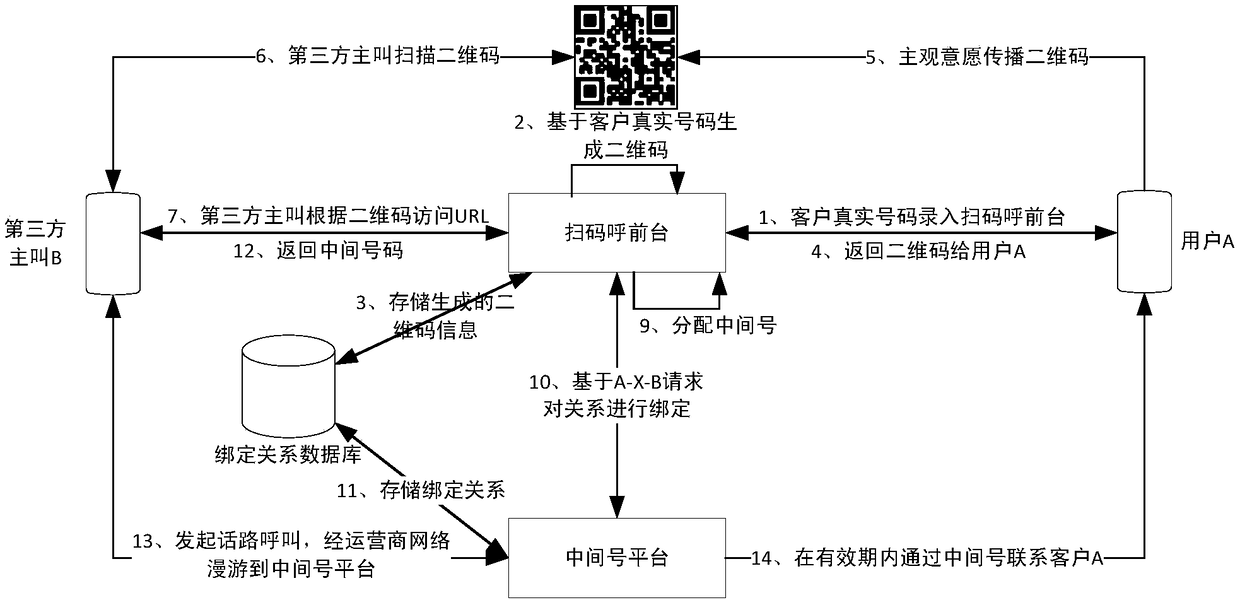
InactiveCN108777750AConserve communication service resourcesReduce operating costsSpecial service for subscribersSensing by electromagnetic radiationMobile Telephone NumberRelational database
The present invention discloses a user mobile phone safety privacy protection method based on two-dimensional codes, belonging to the technical field of privacy conversation. The method comprises thesteps of: obtaining two-dimensional codes and registration by a user through a mobile phone client; allowing a code-scanning call reception to respond to a client request, generating two-dimensional codes, identifying two-dimensional code information and completing dynamic distribution of the middle codes; generating a mapping relation of the two-dimensional codes and user mobile phone numbers bythe code-scanning call reception and storing the mapping relation to a relation database; allowing a middle number platform to be connected with the code-scanning call reception and a telecom core network to respond to a binding service request from the code-scanning call reception; generating a code number binding relation and performing storage; allowing the middle number platform to perform binding of calling party numbers, middle code numbers and called party numbers to generate a code number binding relation and perform storage; and finally, performing relay connection of the calling party numbers, the middle code numbers and the called party numbers in the conversation through the telecom core network. The user mobile phone safety privacy protection method can meet the demands of mobile phone number privacy protection in different conditions so as to save the communication service resources and reduce the operation cost.
Owner:中国东盟信息港股份有限公司
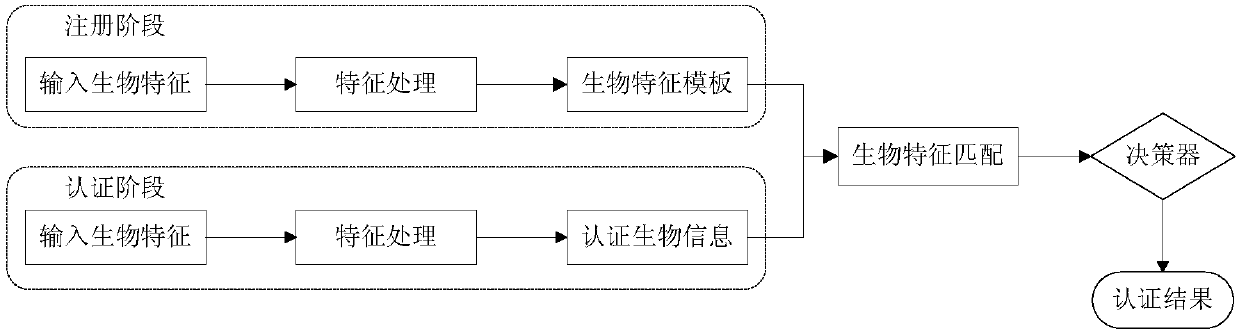
Biological characteristic sensitive information outsourcing identity authentication method based on homomorphic encryption
ActiveCN107919965AImprove securityImprove efficiencyKey distribution for secure communicationUser identity/authority verificationData privacy protectionData transmission
The invention relates to a biological characteristic sensitive information outsourcing identity authentication method based on homomorphic encryption, to provide users with a more secure identity authentication method based on biological characteristics. Compared with a traditional biological characteristic authentication method, the method includes a Somewhat homomorphic encryption method based on RLWE construction and a message coding method, which can conduct fast computation processing on the biological characteristic information after user encryption, and effectively solve the secure privacy problem brought by data outsourcing. The transmission, storage and computation of user biological characteristic information are under an encrypted state in a register stage and an authenticationstage, and the replay attack can be effectively resisted by the random number bought in a data transmission process. As a result, the method can realize secure identity authentication based on biological characteristic sensitive information outsourcing in the case of user data privacy protection.
Owner:HANGZHOU DIANZI UNIV
A privacy protection data publishing method based on conditional probability distribution
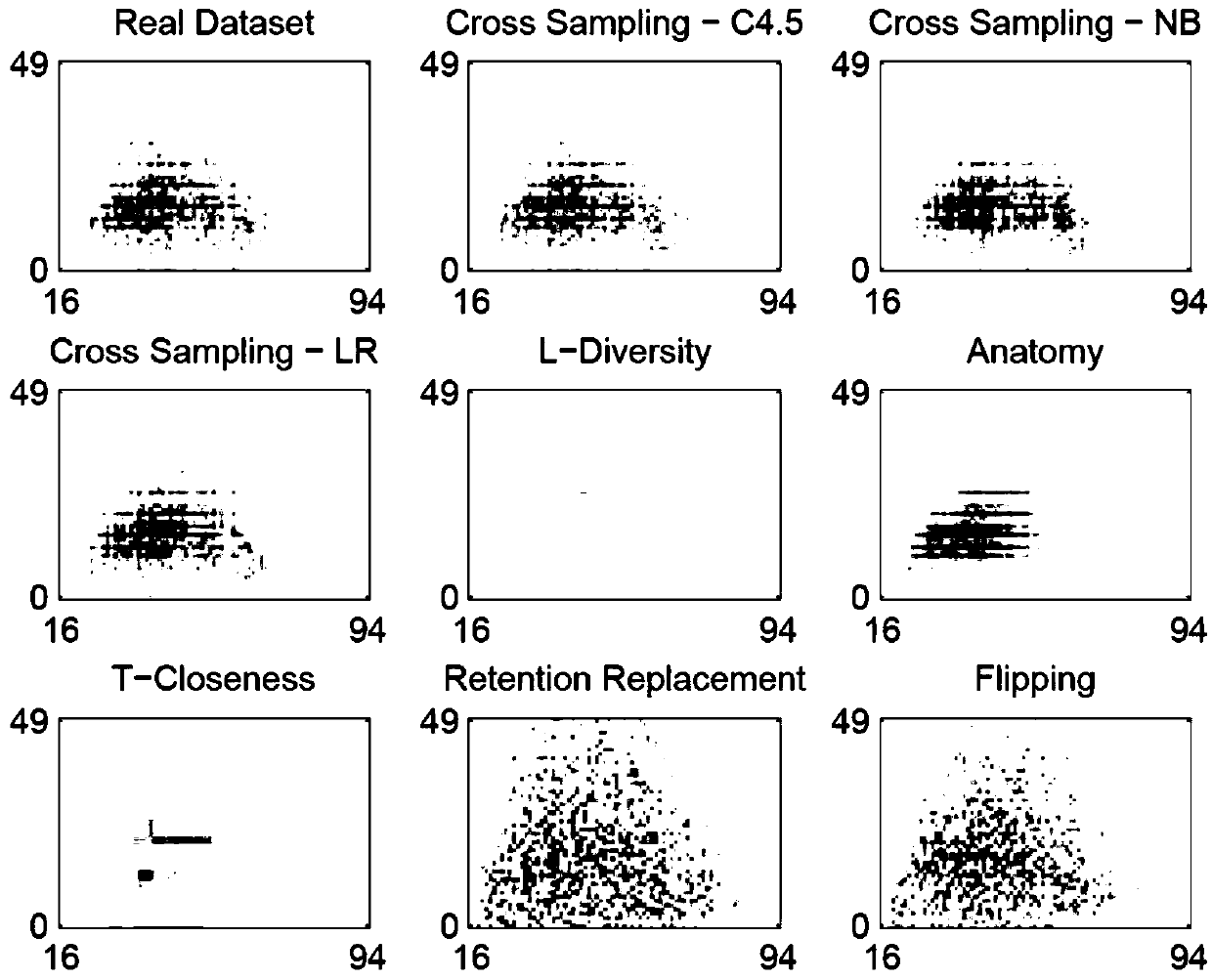
ActiveCN109543445AAvoiding the choice problemProtect data privacyDigital data protectionData setPrivacy protection
The invention belongs to the technical field of information security and privacy protection, and is a privacy protection data publishing method based on conditional probability distribution. Accordingto the conditional probability distribution, an attacker's prior knowledge is modeled so that the attacker has different prior knowledge in different transactions. Then using the constructed model and quasi-identifier attribute value, the sensitive attribute value of each record is predicted, and the original value is replaced with the predicted value, and then published. There is no direct correlation between the predicted values of the published sensitive attributes and the original values, which effectively protects the privacy of user data. The predicted distribution of sensitive attribute values is similar to the real distribution, which effectively controls the distribution error and ensures the availability of the published dataset better than that of the generalized and stochasticresponse method. The invention can provide privacy protection mechanism for data release in various social fields such as medical treatment, finance, credit generation, transportation and the like, and provides support for application of data in scientific research and social service while protecting user data privacy.
Owner:FUDAN UNIV
Privacy matching method based on exchange encryption in social network
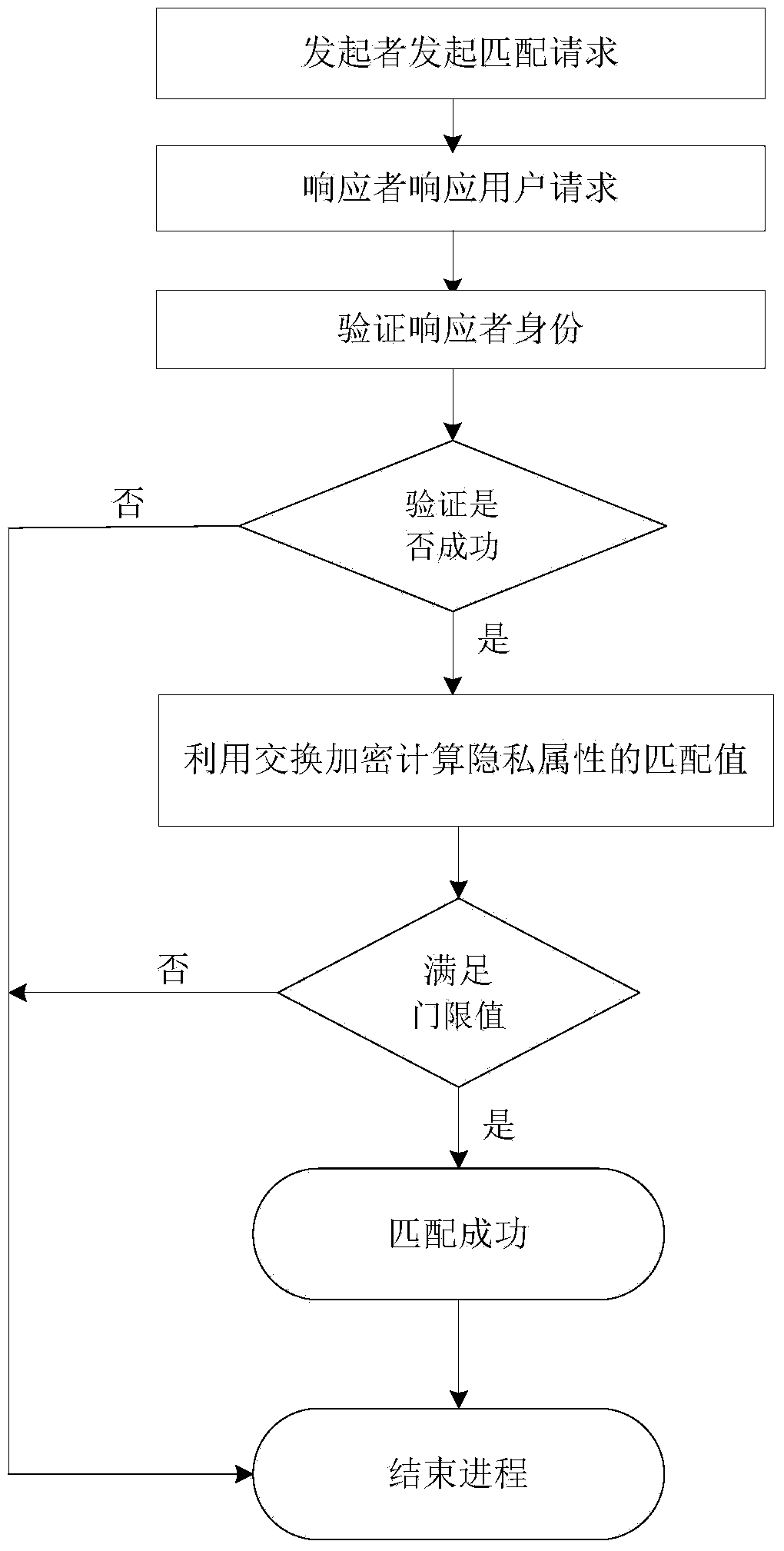
InactiveCN103795737AAccurate calculationSmall amount of calculationUser identity/authority verificationSecurity privacySocial web
The invention discloses a privacy matching method based on exchange encryption in a social network. The problem that both parties and multiple parties in an existing mobile social network cannot effectively carry out safe privacy matching is mainly solved. The implementation process comprises the steps that (1) a communication system framework of a user and a dynamic IDA is built to distribute a dynamic ID to the user at regular intervals; (2) an initiator user verifies the dynamic identity of a responder user; (3) the exchange encryption and comparison are carried out on the personal attribute of the initiator user and the personal attribute of the responder user; (4) the initiator user calculates the matching similarity of the initiator user and the responder user, and whether matching is allowed to be carried out or not is determined through comparison between the matching similarity and a threshold value. According to the method, the number of the common attributes of the users and the priority of the corresponding attributes are considered at the same time, the privacy of the users is protected, meanwhile, the matching efficiency of the users is improved, the users can find a friend matched with the users best accurately, efficiently and safely, and the method can be used in the mobile social network.
Owner:XIDIAN UNIV
Mobile phone number security privacy protection method and platform based on mobile internet
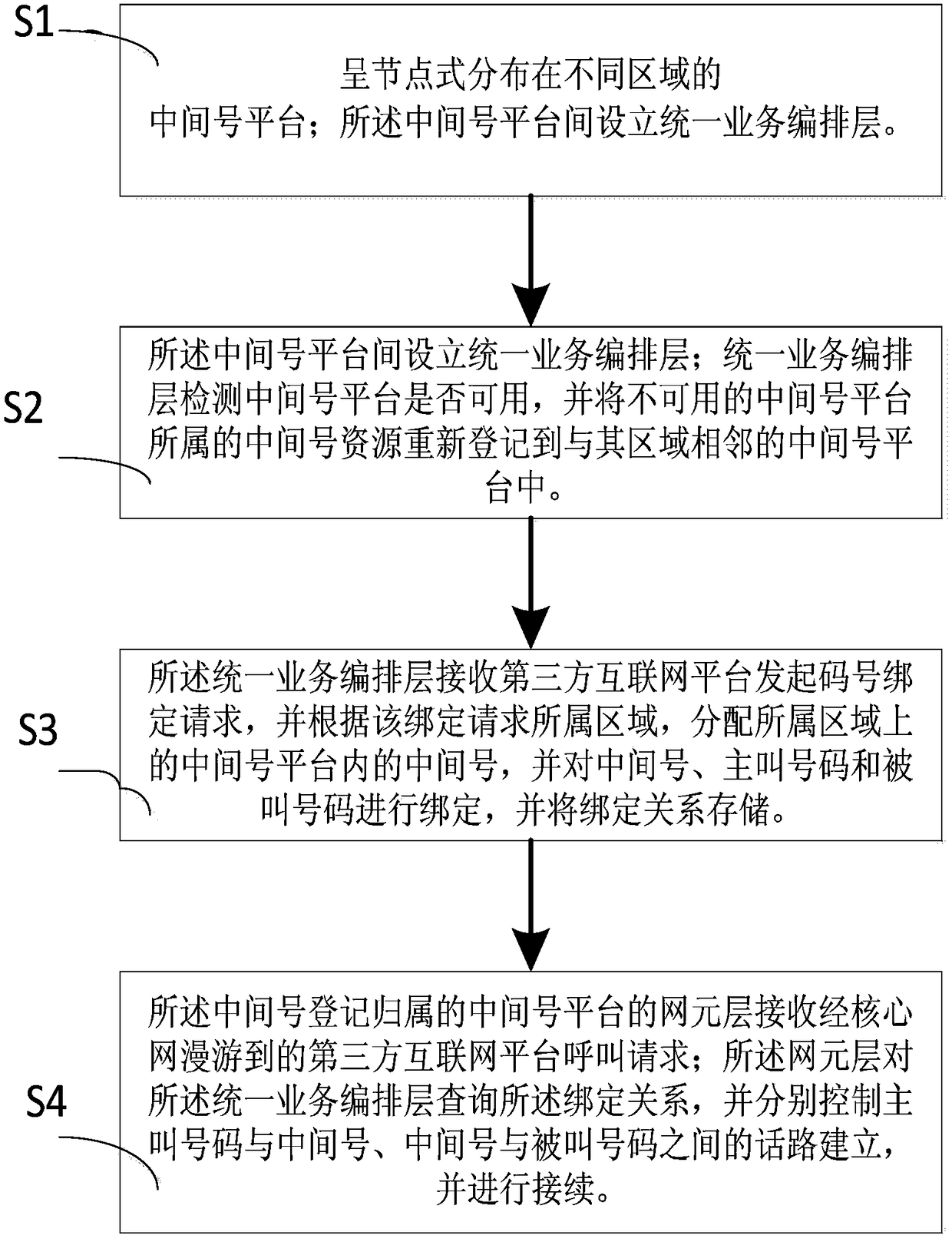
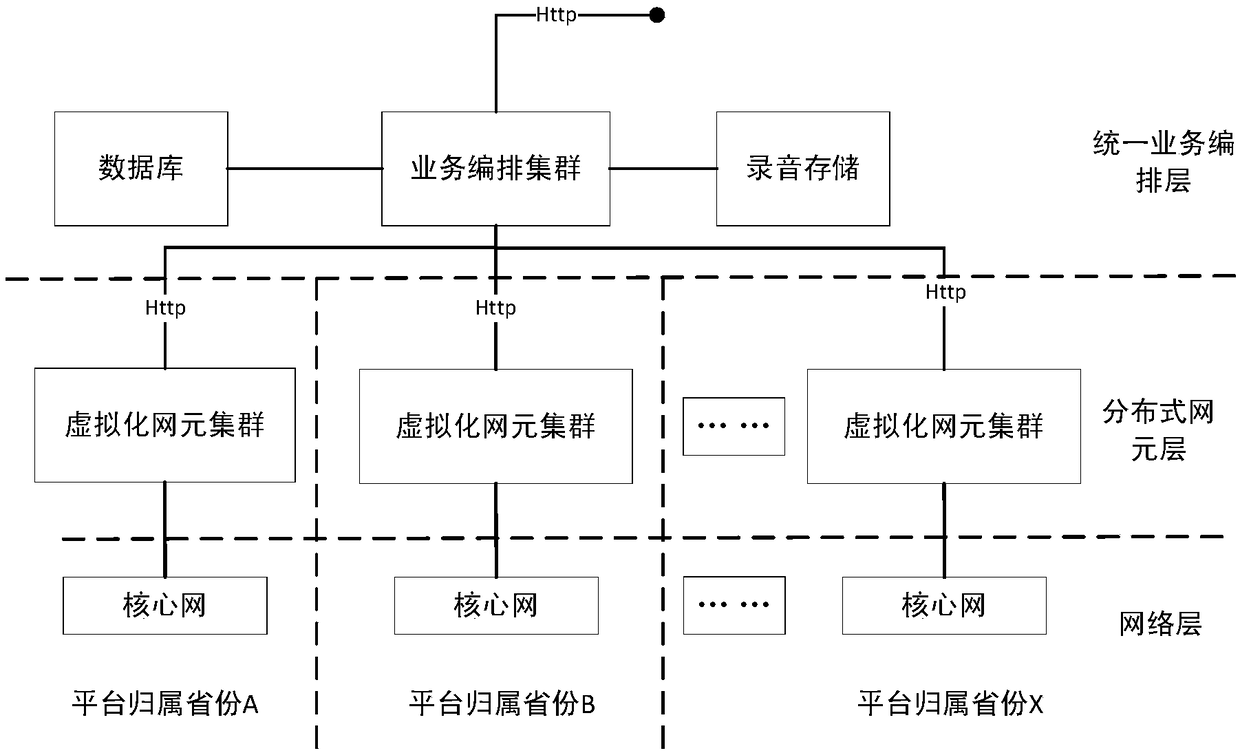
ActiveCN108566498AEliminate protection capability suspension issuesImprove latencySpecial service for subscribersMessaging/mailboxes/announcementsCommunications securityMobile Telephone Number
The invention discloses a mobile phone number security privacy protection method based on mobile internet and belongs to the field of communication security protection. A plurality of intermediate number platforms arranged in different areas for providing intermediate number services are included; an uniform service arrangement layer is set up between the intermediate number platforms; the uniformservice arrangement layer receives a code number binding request initiated by a third-party internet platform, allocates, according to an area belonging to the binding request, the intermediate number in the intermediate number platform on the area belonging to the request and performs binding, and stores the binding relationship; a network element layer of the intermediate number platform belonging to the intermediate number registering receives a call request roaming to the third-party internet platform through a core network; and the network element layer queries a binding relationship forthe uniform service arrangement layer, respectively controls the session establishment between a calling number and the intermediate number, and between the intermediate number and a called number, and performs continuity. According to the method and the platform in the invention, the problem of stopping the security privacy number protection capability caused by problems such as single node downtime is solved by establishing the multi-node and unified scheduling strategy nationwide.
Owner:中国东盟信息港股份有限公司
Method and system of silent biometric security privacy protection for smart devices
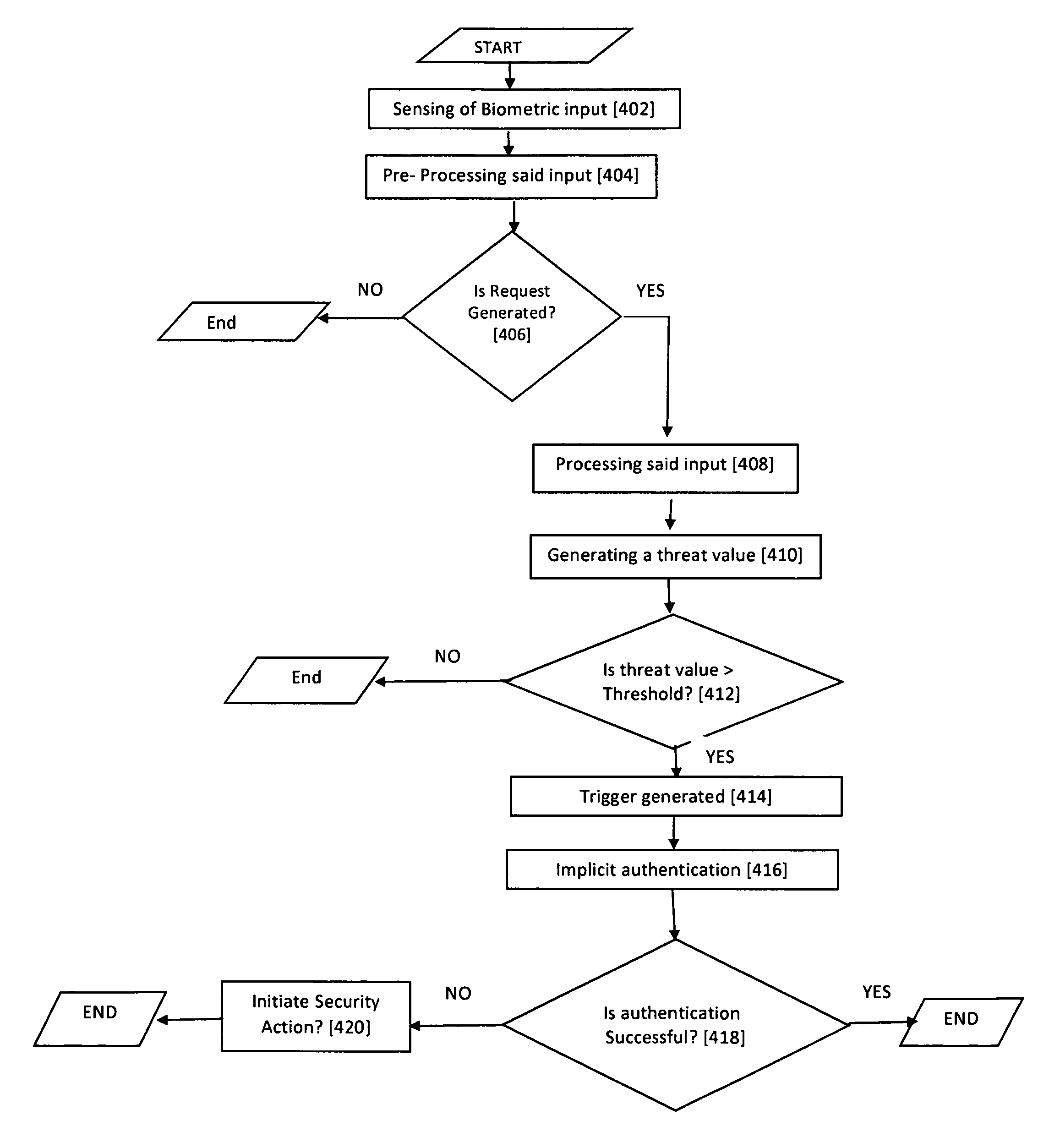
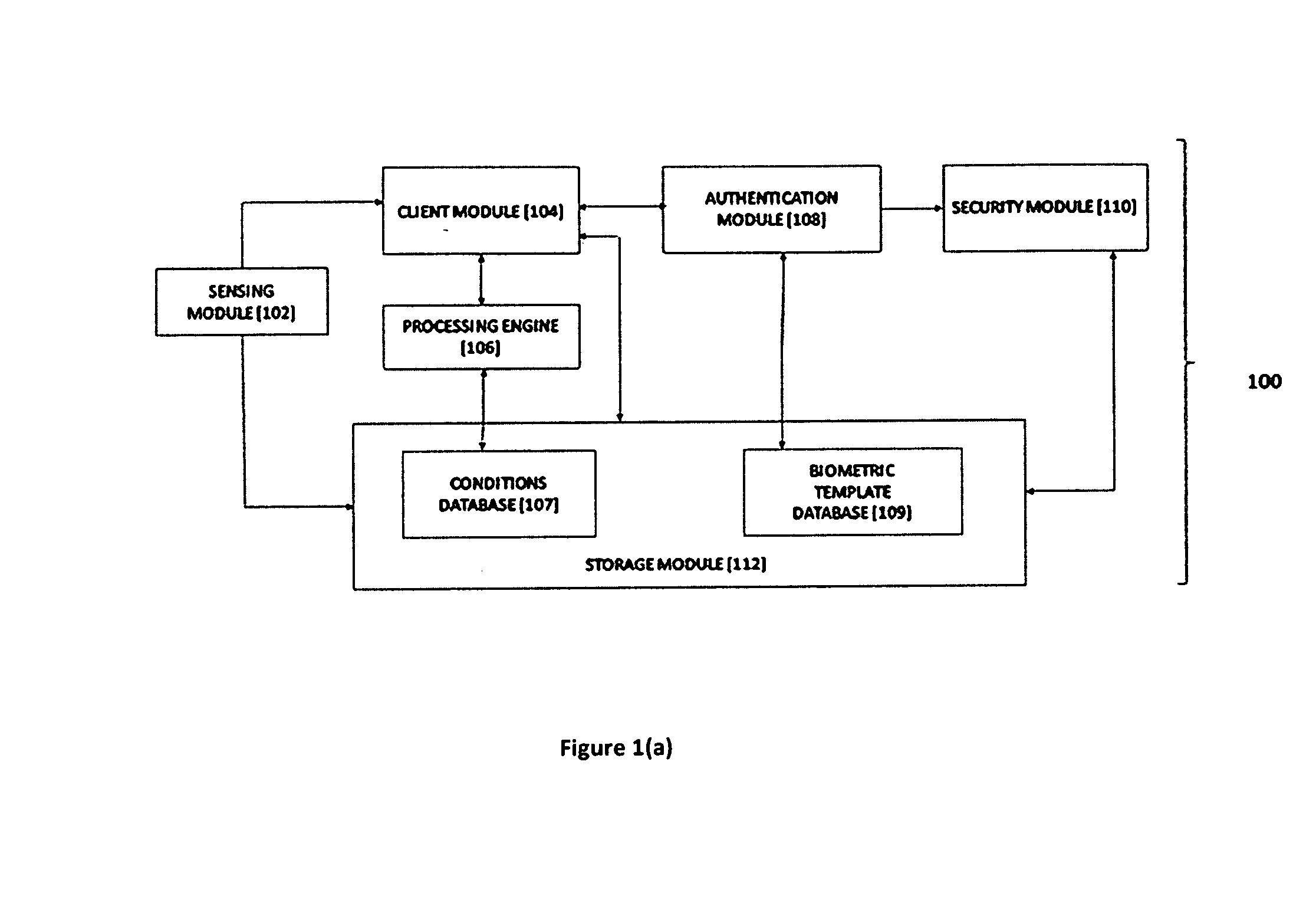
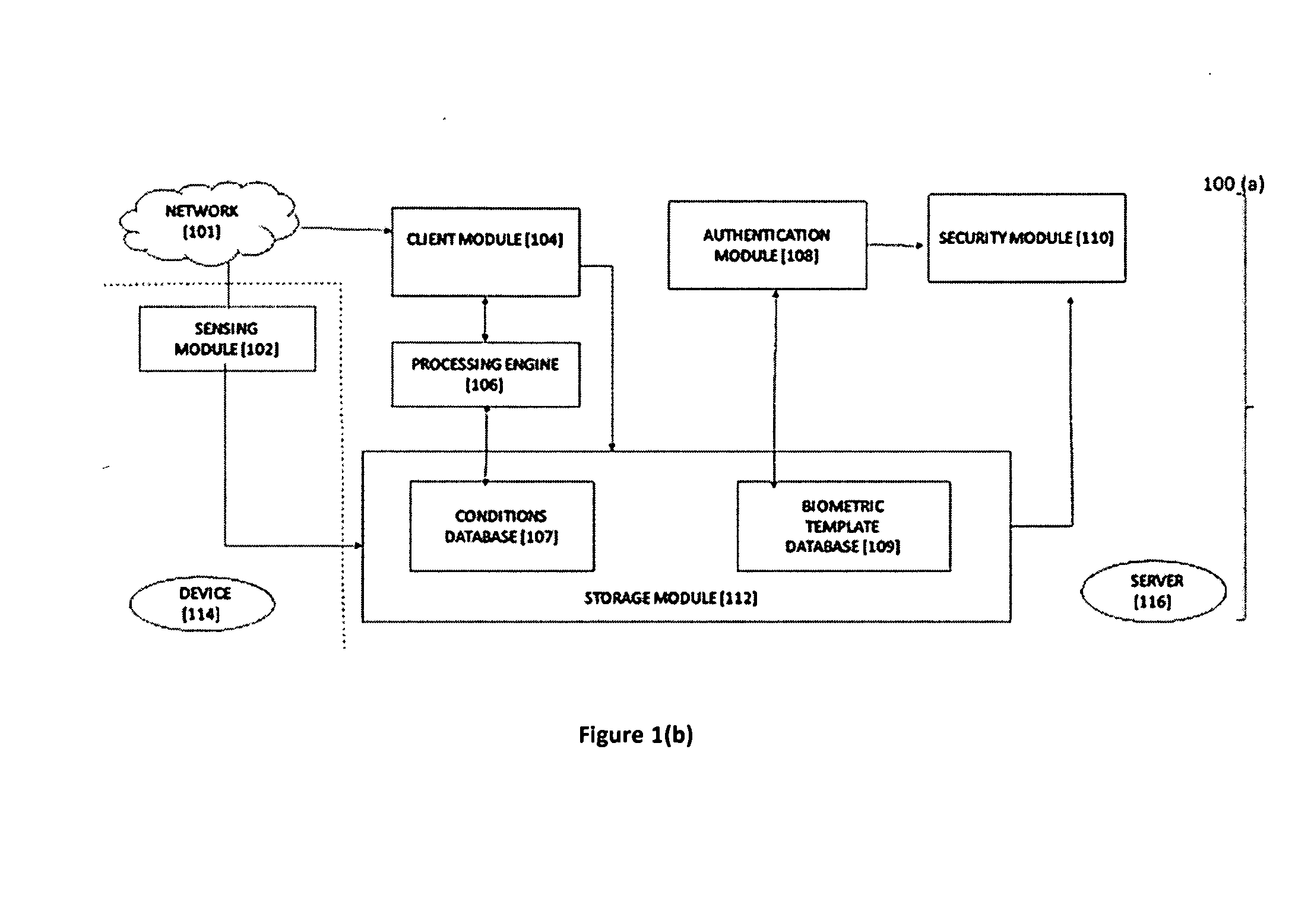
ActiveUS20160188862A1Digital data processing detailsMultiple digital computer combinationsPrivacy protectionInformation security
An efficient, secured and robust system and method for information security and privacy protection of smart devices, by silent biometric authentication mechanism, is disclosed. The system includes a sensing module associated with biometric sensors, a client module associated with processing engine and an authentication module for silently identifying unauthorized users and managing device security without compromising users' device-experience. The system is also configured with a security action module for tackling an intruder, detecting the source of attack and notifying the authorized user of such an attack.
Owner:JIO PLATFORMS LTD
Blockchain-based store fixed asset management system
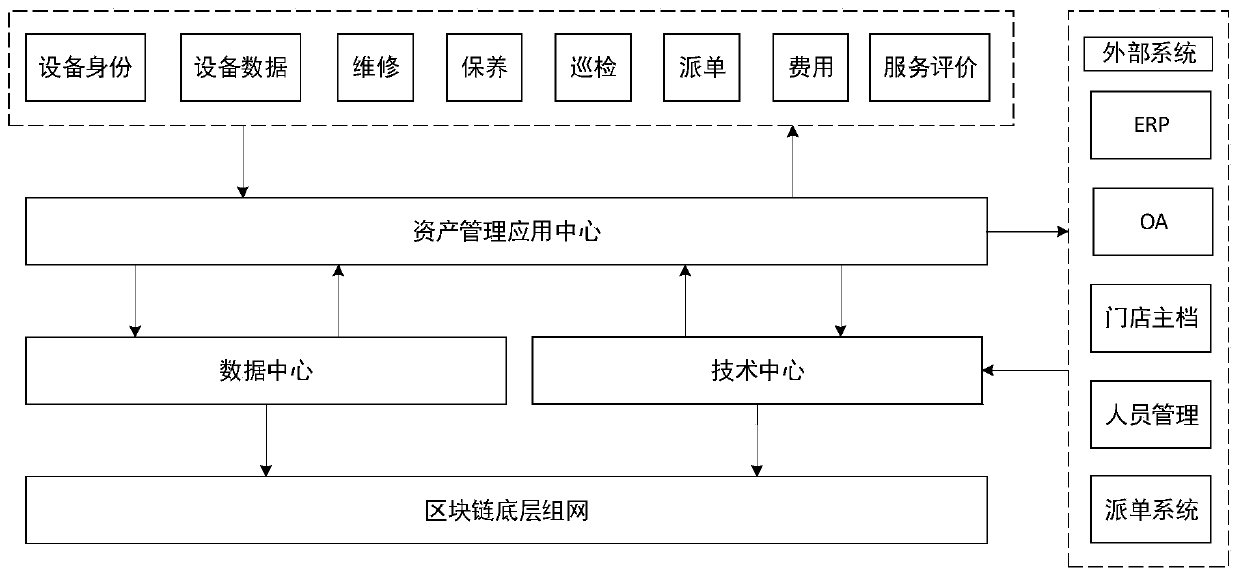
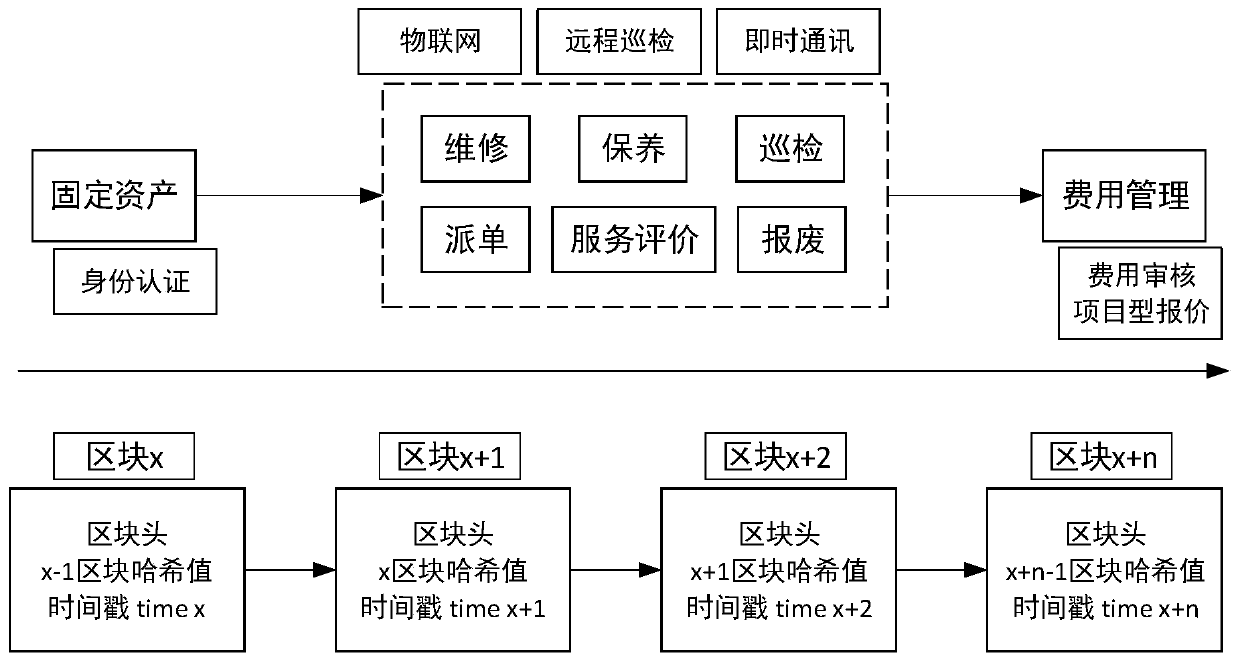
ActiveCN110942224AReliable dataLow costDigital data protectionPayment protocolsData centerManagement process
The invention provides a blockchain-based store fixed asset management system, which comprises an asset management application center, a data center and a technical center which are established on thebasis of blockchain underlying networking, and is in butt joint with an external system through links of the asset management application center, the data center and the technical center. The asset management application center, the data center and the technical center carry out identity authentication on fixed assets of a store and carry out adaptation and networking according to a standard protocol. The identity information is stored into a blockchain; the real-time latest state of the fixed assets is collected, asset data generated in the asset management process are collected and uploadedin real time, calculation rules are made for all the uploaded data in advance through an intelligent contract, rapid screening of the data and equipment data processing are conducted, and full-life-cycle automatic management of the fixed assets of the store is completed. The system has the advantages of being good in safety privacy, high in opening degree, convenient for merchant manufacturer entering and docking, and more intelligent in state change settlement.
Owner:JIANGSU RONGZE INFORMATION TECH CO LTD
Identity authentication method and system based on touch screen equipment and security and privacy encryption method
InactiveCN104200147AUniquely identifiableImprove securityDigital data authenticationTransmissionUser inputPassword
The invention discloses an identity authentication method and system based on touch screen equipment. The method comprises the steps that a user operates the touch screen equipment to generate touch behavior data; the touch behavior data are stored and uploaded; the touch behavior data are analyzed and processed so as to identify whether the touch screen equipment is operated by the user in person or not, and if yes, identify authentication succeeds; if not, the steps are executed again until the user passes identity authentication. The invention further discloses a security and privacy encryption method. The identity authentication method and system based on the touch screen equipment and the security and privacy encryption method have the advantages that unique identifiability is provided, only operations of binding personnel are recognized, and even if other users input correct content, it is judged that the operation is not carried out by the user in person; information security is improved, the other users cannot carry out operation even though inputting the same passwords as the user, and the user does not need to worry about the technical problem of password leakage.
Owner:王洋 +1
Privacy protection batch authentication method without pairing operation in vehicular ad hoc network
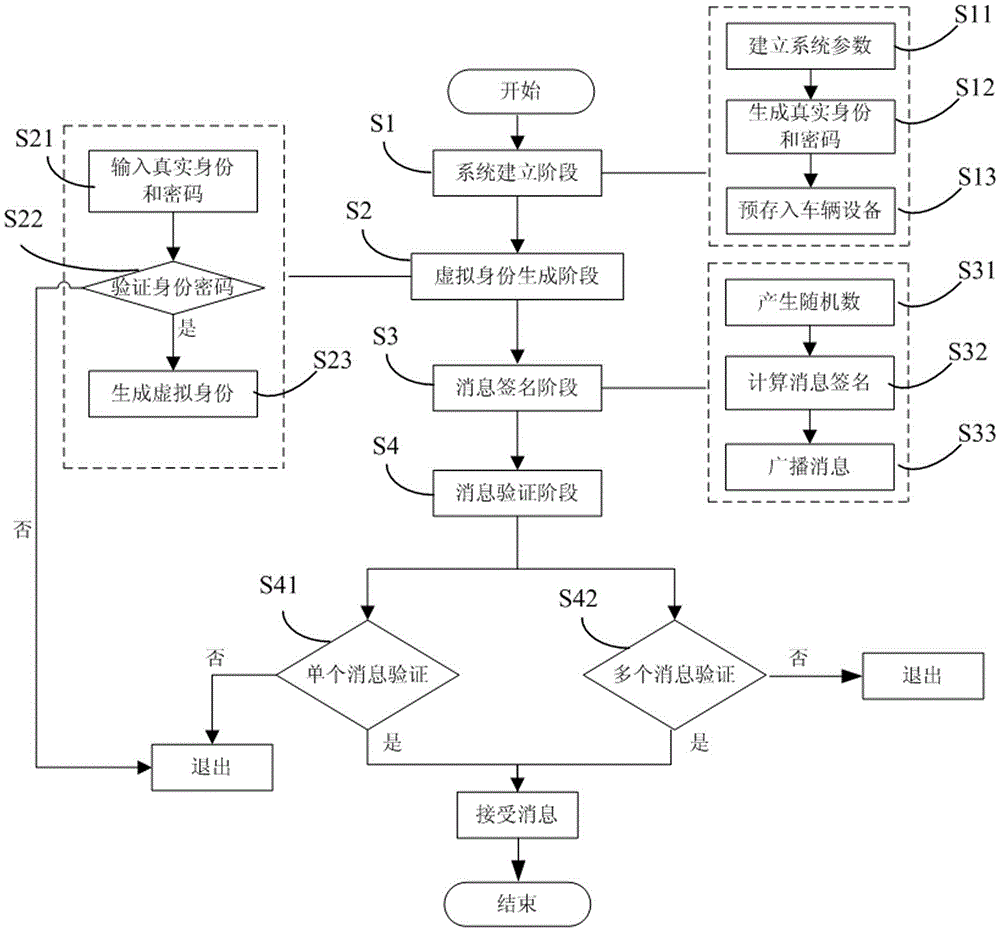
InactiveCN105656634AReduce overheadShorten the timeKey distribution for secure communicationUser identity/authority verificationPasswordPrivacy protection
The invention provides a privacy protection batch authentication method without a pairing operation in a vehicular ad hoc network. The privacy protection batch authentication method comprises the following steps: S1, establishing a system parameter by a credible mechanism in the vehicular ad hoc network, generating a system master key, and broadcasting the system master key to a roadside unit and all vehicles, and generating a real identity and a corresponding password for each vehicle by the credible mechanism, and storing the real identity and the corresponding password in each vehicle together with the system parameter; S2, verifying the real identity and the password of the vehicle which is about to broadcast a message, and establishing a corresponding virtual identity after passing the verification; S3, signing the message to be broadcasted by the vehicle through the established virtual identity, and broadcasting the signed message to the roadside unit and other vehicles; and S4, verifying the broadcasted message in one or more modes by the roadside unit and other vehicles, and accepting the broadcasted message after the verification is passed. According to the privacy protection batch authentication method provided by the invention, no pairing operation is needed in the message signature or verification, and the three problems of security, privacy protection and authentication efficiency in the vehicular ad hoc network can be solved at the same time.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
Two-party security privacy comparison method based on block chain
The invention discloses a two-party security privacy comparison method based on a block chain. The two-party security privacy comparison method based on the block chain is used for comparing a certainresource in a data sharing platform under the condition that two participating parties do not leak own information and do not know the opposite parties. The two participating parties firstly agree resources to be compared; communication connection is established between participating parties, then, one party decomposes resources to be compared into a plurality of atomic data; the atomic data areencrypted, a ciphertext is transmitted to the other party by using an unintentional transmission protocol, and the other party participating in the encryption also decomposes the own data into a plurality of atomic data, encrypts the atomic data, compares the encrypted atomic data with the received data according to the circuit table, and returns a final comparison result to the other party. According to the comparison method, data privacy protection is achieved to a certain extent.
Owner:HANGZHOU QULIAN TECH CO LTD
Context-aware-based security access control method for RFID system
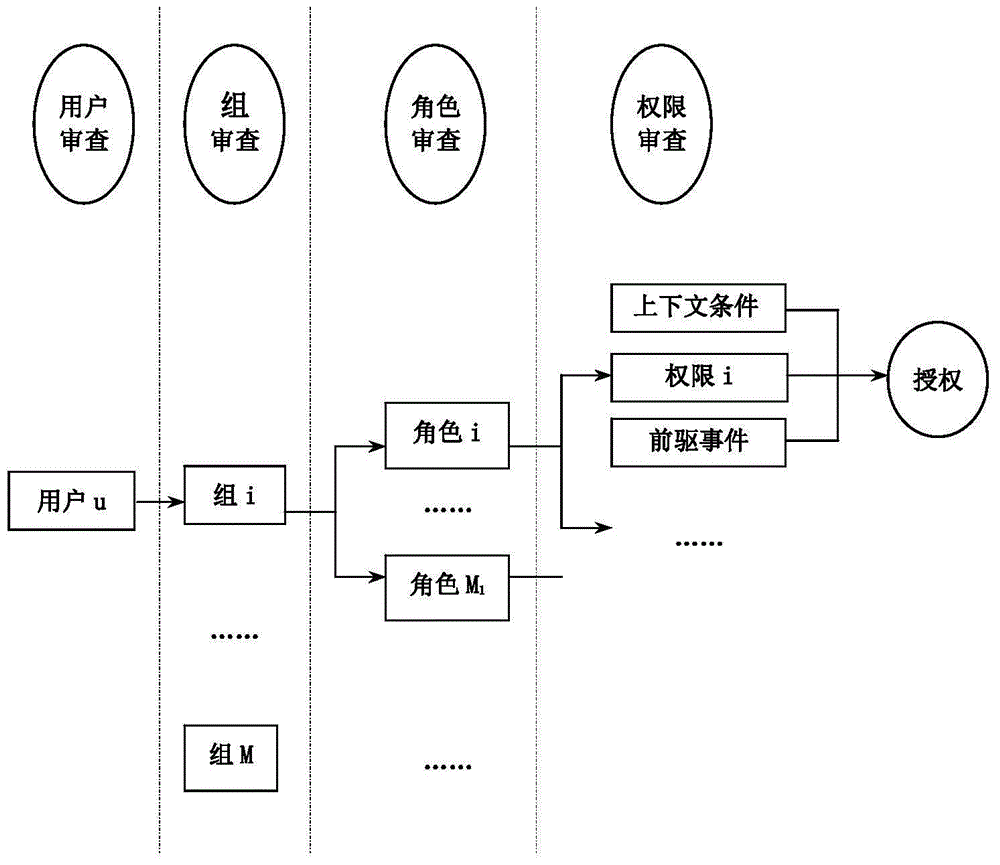
InactiveCN103560994ASolve security and privacy issuesMeet the needs of flexible, changeable and complex application environmentsDigital data authenticationTransmissionThe InternetContext based
The invention discloses a context-aware-based security access control method for an RFID system. The method is implemented based on a data base comprising a user set, a user group set, a role set, a permission set and an operation set. The method comprises an initialization step, a dynamic permission authorization review step and a user access control step composed of context condition review, precursor operation review and permission review. The method of the invention has context-aware computing power, and can be used to perceive user context information so as to adjust the action of the RFID system in an intelligent manner, satisfy flexible and complex application environment demands, effectively solve the RFID system security privacy problem in the Internet of things environment, and support the minimum authorization rule, the functional separation strategy and the dynamic veto authorization strategy.
Owner:SUN YAT SEN UNIV
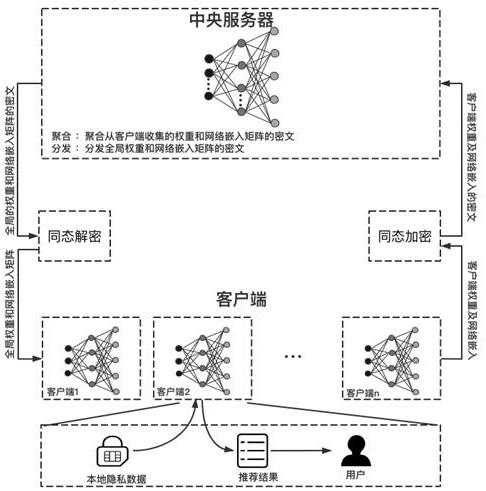
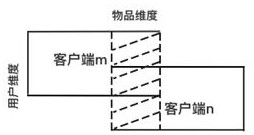
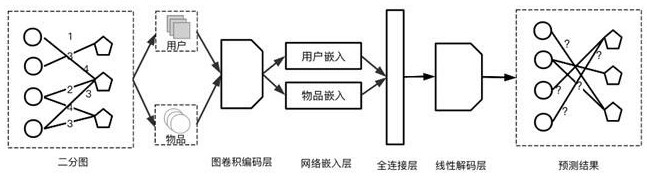
Graph neural network federal recommendation method for privacy protection
ActiveCN113420232ASolve the island problemLocal raw data is not leakedDigital data information retrievalDigital data protectionPrivacy protectionEngineering
The invention discloses a graph neural network federal recommendation method for privacy protection. At present, many academic strategies provide recommendation methods such as matrix decomposition, collaborative filtering and the like to improve the recommendation accuracy, but in the proposed methods, the recommendation accuracy, the problem of data islands, the problem of how to jointly train a plurality of clients, and the security and privacy of data cannot be taken into account at the same time. The method comprises three parts of contents: performing graph neural network recommendation based on each client of a bipartite graph, performing joint training of a graph neural network recommendation method based on federated learning, and performing homomorphic encryption of server and client transmission data facing privacy protection. According to the graph neural network federal recommendation method for privacy protection, a plurality of clients can be combined in a data island environment to carry out graph neural recommendation modeling training for ensuring privacy and data security, so that the recommendation accuracy of all the clients is remarkably improved, and the data security is protected.
Owner:HANGZHOU DIANZI UNIV
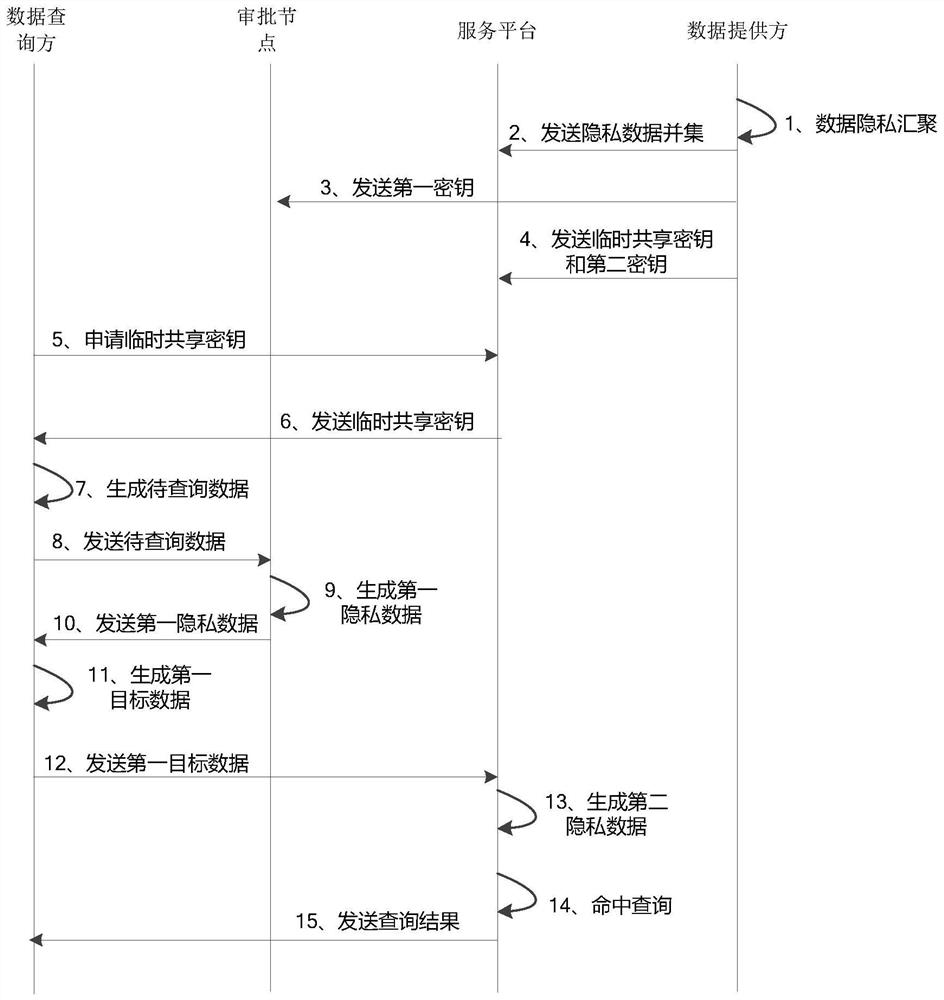
Private data query method and device and electronic equipment
ActiveCN113536379AReduce the number of communication roundsAvoid time costDatabase queryingDigital data protectionData providerEngineering
The invention provides a private data query method and device and electronic equipment, and relates to the technical field of data security. The method comprises the following steps: receiving a private data query request, wherein the private data query request comprises to-be-queried data; conducting privacy processing on the to-be-queried data through a first secret key, generating first privacy data, wherein the first secret key is provided by a data provider; and sending the first privacy data, so that the first privacy data becomes second privacy data after being processed, and the service platform performs hit query on the privacy data in the privacy database based on the second privacy data. According to the private data query method and apparatus, and the electronic device provided by the invention, real-time online service or support is not provided depending on all data providers any more, and the number of communication rounds and time cost can be reduced on the premise of ensuring security privacy.
Owner:CCB FINTECH CO LTD
Secure payment transactions based on the public bankcard ledger
ActiveUS10535065B2Improve efficiencyImprove privacyFinanceCryptography processingThird partyPayment transaction
A system for bankcard payments, wherein payments are peer-to-peer transactions between the cardholder and merchant without participation from any third party. The system uses standard bankcards and supports both debit and credit card payments. For authorization of payments the system uses a special, global, distributed, append-only, and secure public bankcard ledger. The entries in the ledger are virtual accounts used for bankcard payments, organized into account chains. The system provides security, privacy, anonymity, and untraceability for cardholders and their transactions. The system allows for various users of the system to participate in transactions using preexisting payment systems. In one embodiment, specially designed mobile software modules and an innovative payment protocol all for transactions to be made between users.
Owner:MUFTIC SEAD
Data privacy protection method and device, electronic equipment and storage medium
PendingCN112182643AProtect data privacyPrevent leakageDigital data protectionData privacy protectionUser privacy
The invention relates to the technical field of data privacy protection, and particularly provides a data privacy protection method and device, electronic equipment and a storage medium. The data privacy protection method comprises the following steps: acquiring maintenance request information, and determining maintenance personnel, wherein the maintenance request information comprises fault information of a to-be-maintained product and user privacy information; performing desensitization processing on the user privacy information, and sending maintenance order information to the maintenance personnel, wherein the maintenance order information comprises fault information of a to-be-maintained product and user privacy information after desensitization processing. According to the invention,the maintenance efficiency can be ensured, and the security privacy protection of the data is ensured.
Owner:GREE ELECTRIC APPLIANCES INC +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com