Secure multi-party computing method based on trusted hardware and block chain
A secure multi-party computing and blockchain technology, applied in the field of secure multi-party computing based on trusted hardware and blockchain, can solve the problems of not supporting complex or flexible computing tasks and low efficiency, and achieve high protocol execution efficiency , Computationally efficient and efficient effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
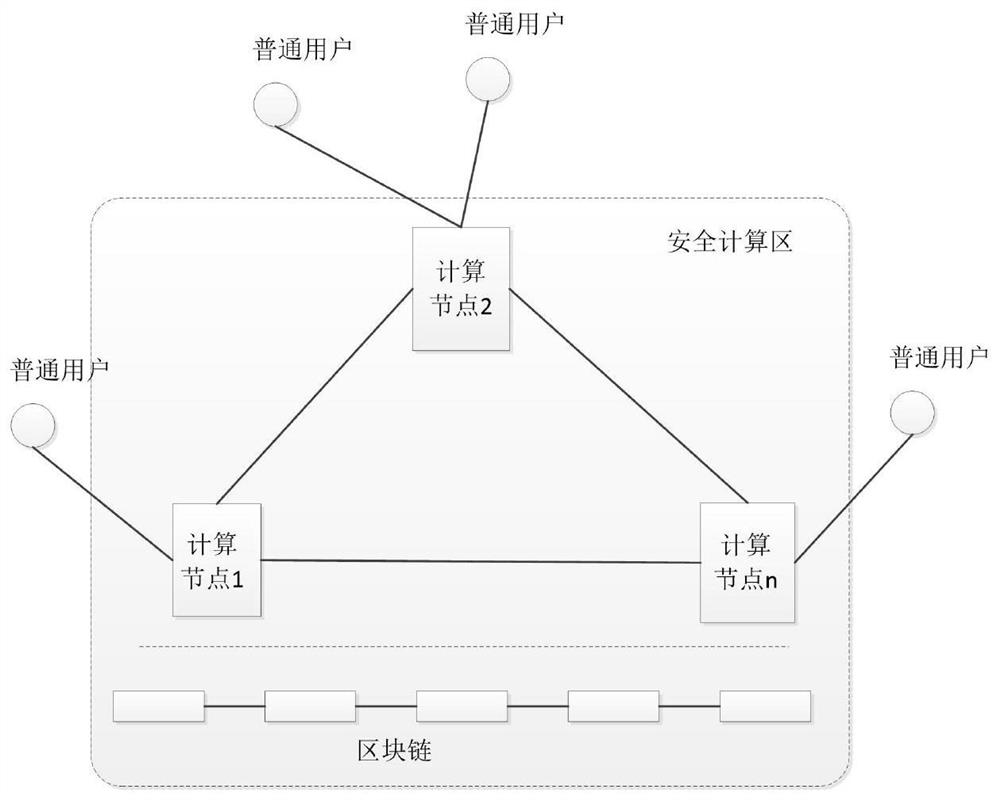
[0028] like Figure 1-4 As shown, the present invention provides a secure multi-party computing method based on trusted hardware and blockchain. The user encrypts the input parameters and inputs them into the trusted execution environment, and the trusted execution environment exchanges data with other participants through the blockchain. After all the inputs are collected, the calculation function is executed in the trusted execution environment and the results are output. The scheme includes four main links: 1. Data input; 2. Data uplink; 3. Data exchange; 4. Calculation output; Taking the ground calculation process as an example, the main process steps are as follows:
[0029] S1. Data input
[0030] like figure 1 As shown in step ①, all participants use the public key of the local trusted execution environment for their input plaintext (for example, the plaintext data required by node P1 is DataPlain) (for example, the public key of the local trusted execution environmen...
comparative approach 1
[0047] A multi-party data sharing method and device ----- CN202010410004.2
[0048] The comparative invention solution provides a multi-party data sharing method and device for sharing data between a rights management platform, a trusted computing unit under a trusted execution environment, a data user, a data provider and a data center.
[0049] In the present invention, block chain is used as trusted data intermediary storage medium, and smart contracts are used to realize trusted data processing. This comparison scheme stores encrypted data in the data center, which is a centralized scheme and cannot handle data securely. The other party's solution adopts a unified authority management platform, which has centralization problems such as single point of failure. The present invention is adapted to the requirements of multi-party secure computing scenarios, and the comparison scheme is not aimed at secure multi-party computing scenarios.
comparative approach 2
[0051] A multi-party privacy computing system based on trusted execution environment ----- CN202010012463.5
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com