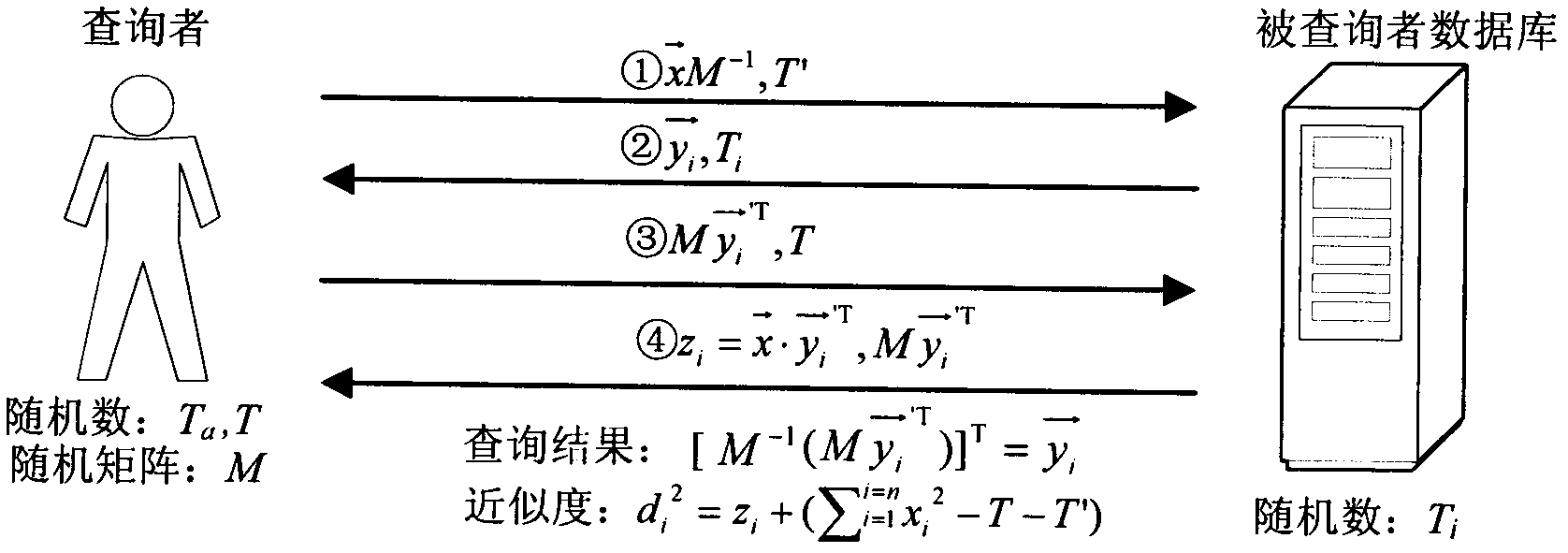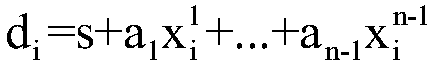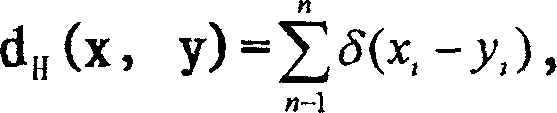Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
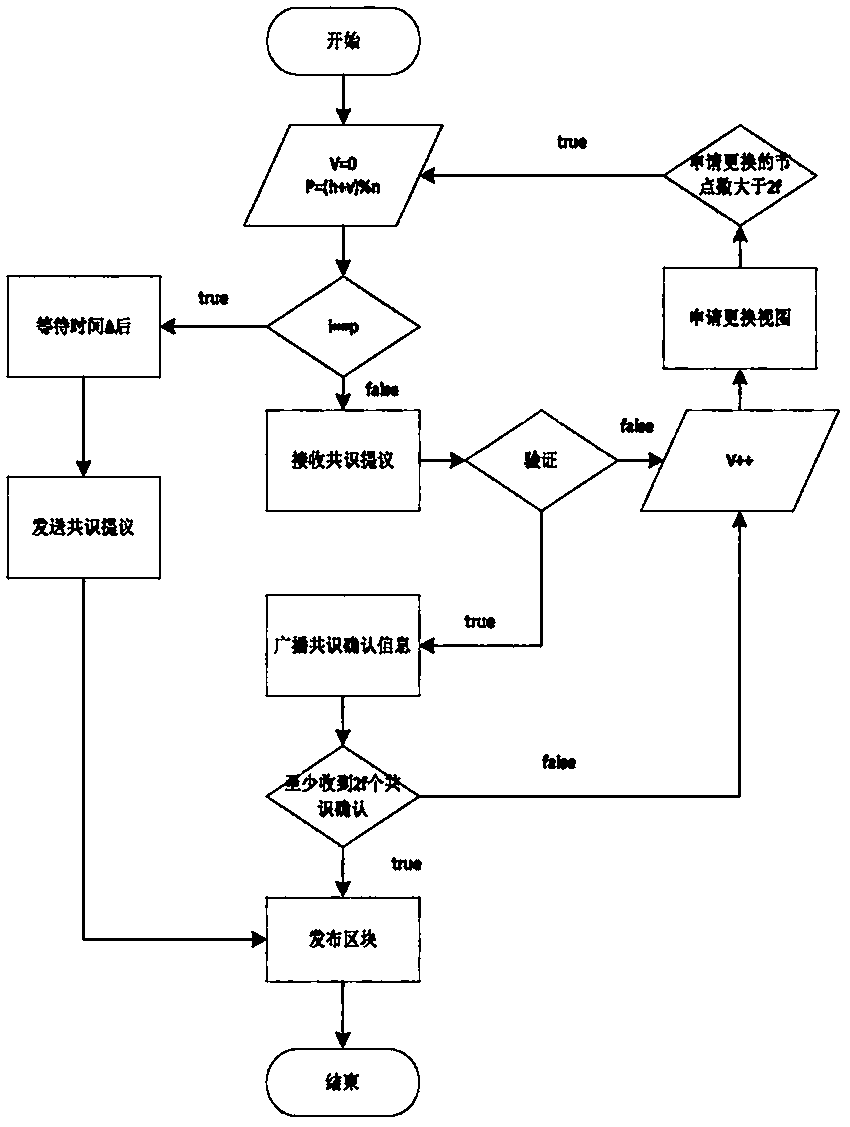
290 results about "Secure multi-party computation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Secure multi-party computation (also known as secure computation, multi-party computation (MPC), or privacy-preserving computation) is a subfield of cryptography with the goal of creating methods for parties to jointly compute a function over their inputs while keeping those inputs private. Unlike traditional cryptographic tasks, where cryptography assures security and integrity of communication or storage and the adversary is outside the system of participants (an eavesdropper on the sender and receiver), the cryptography in this model protects participants' privacy from each other.
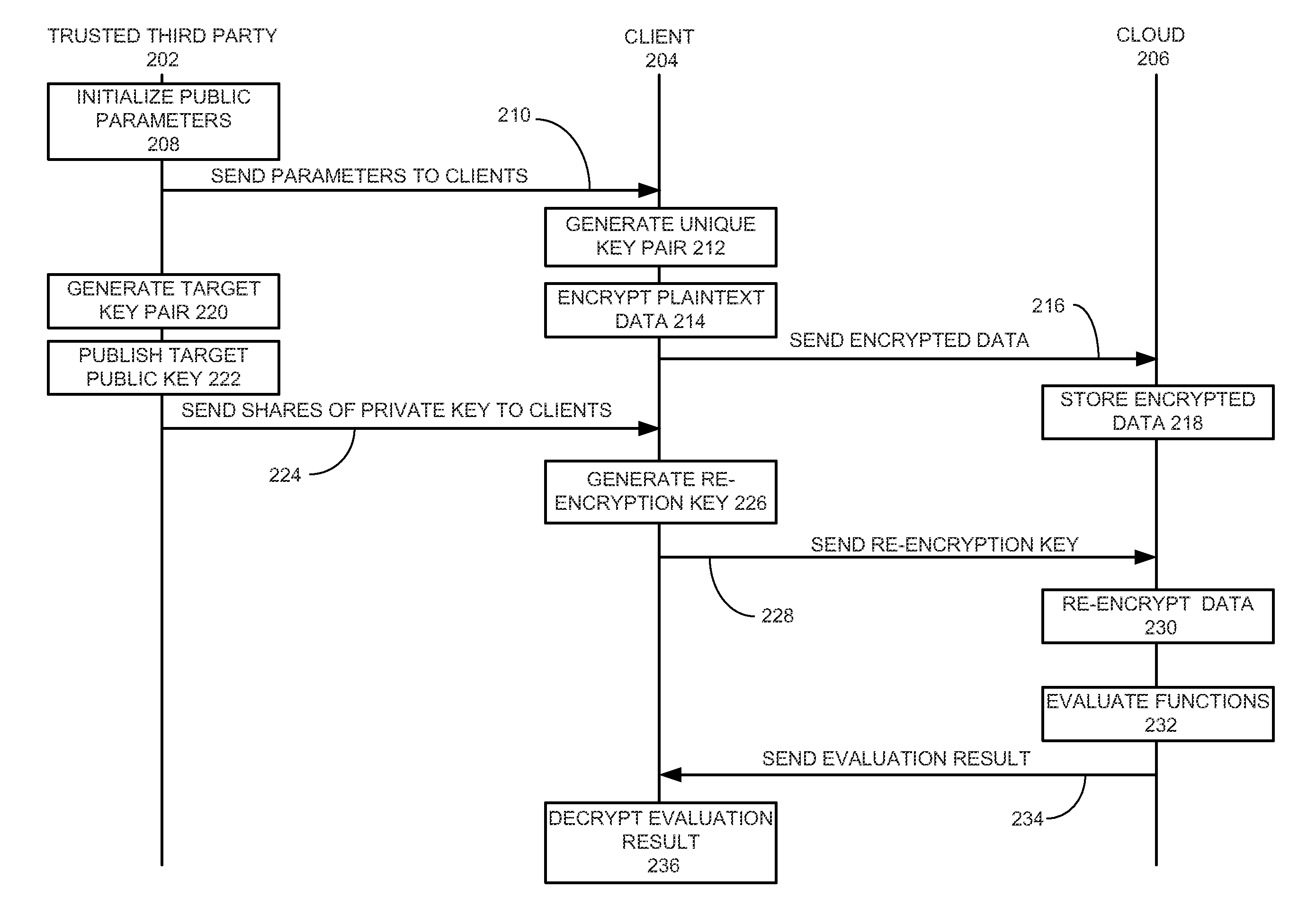
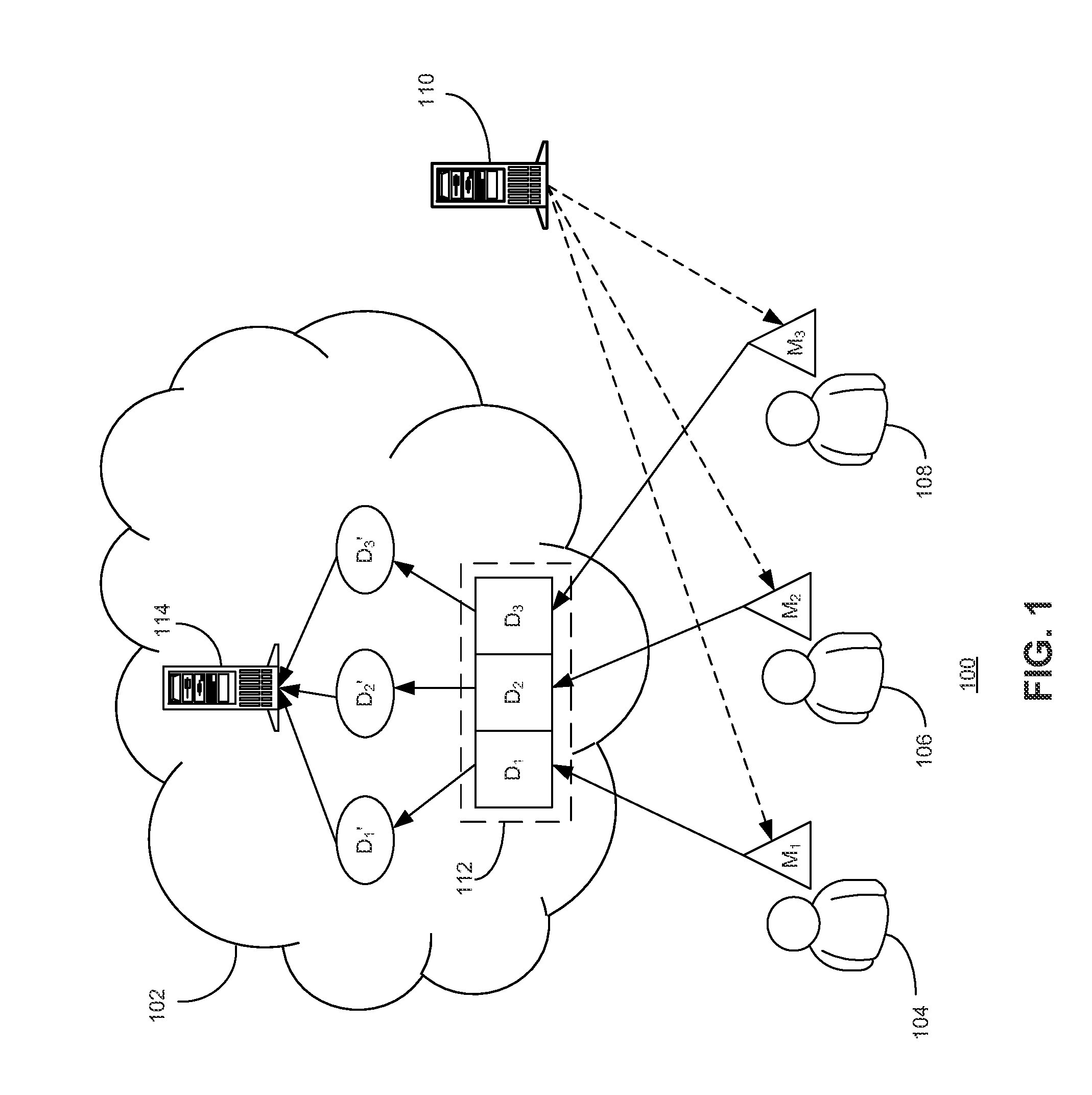
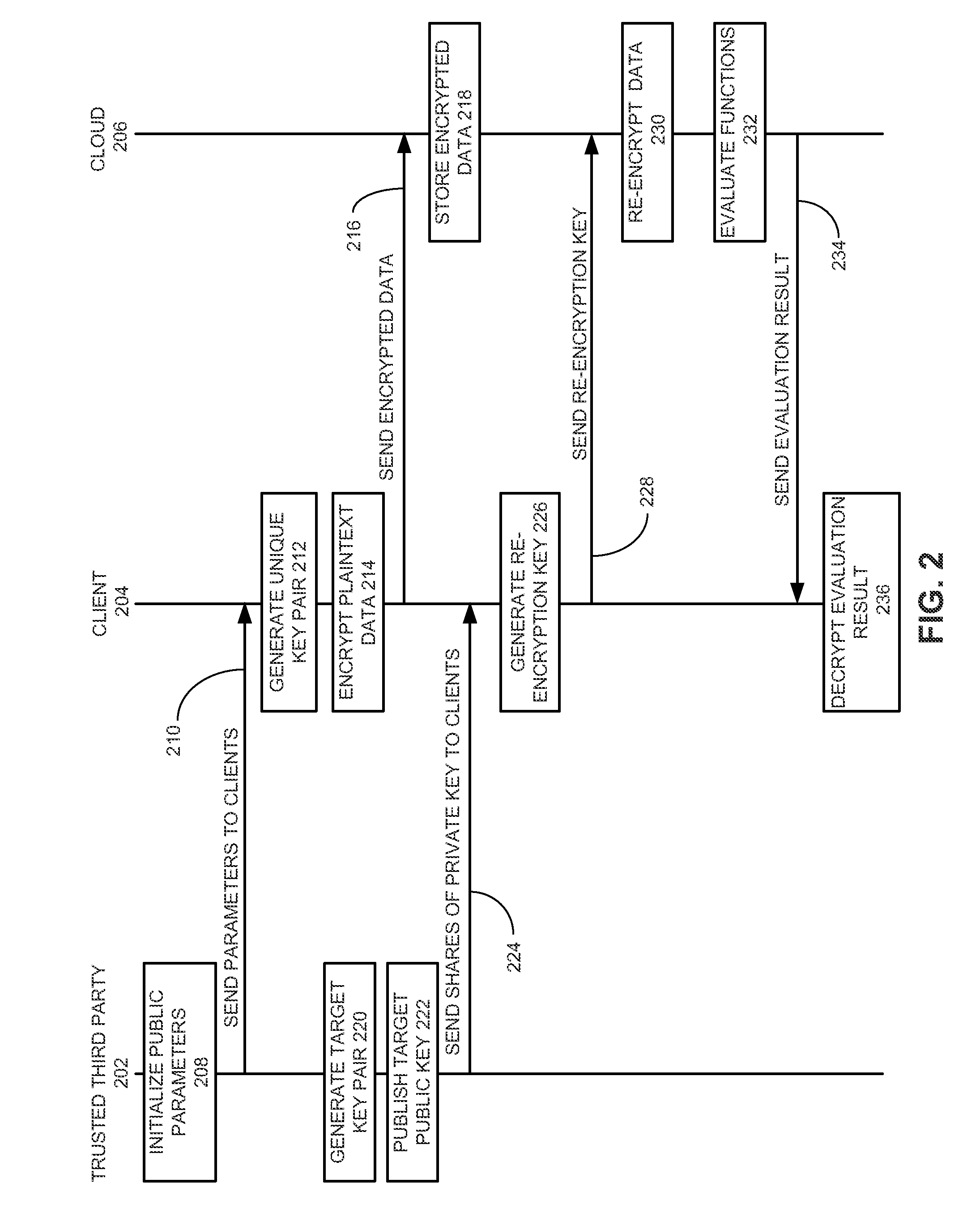
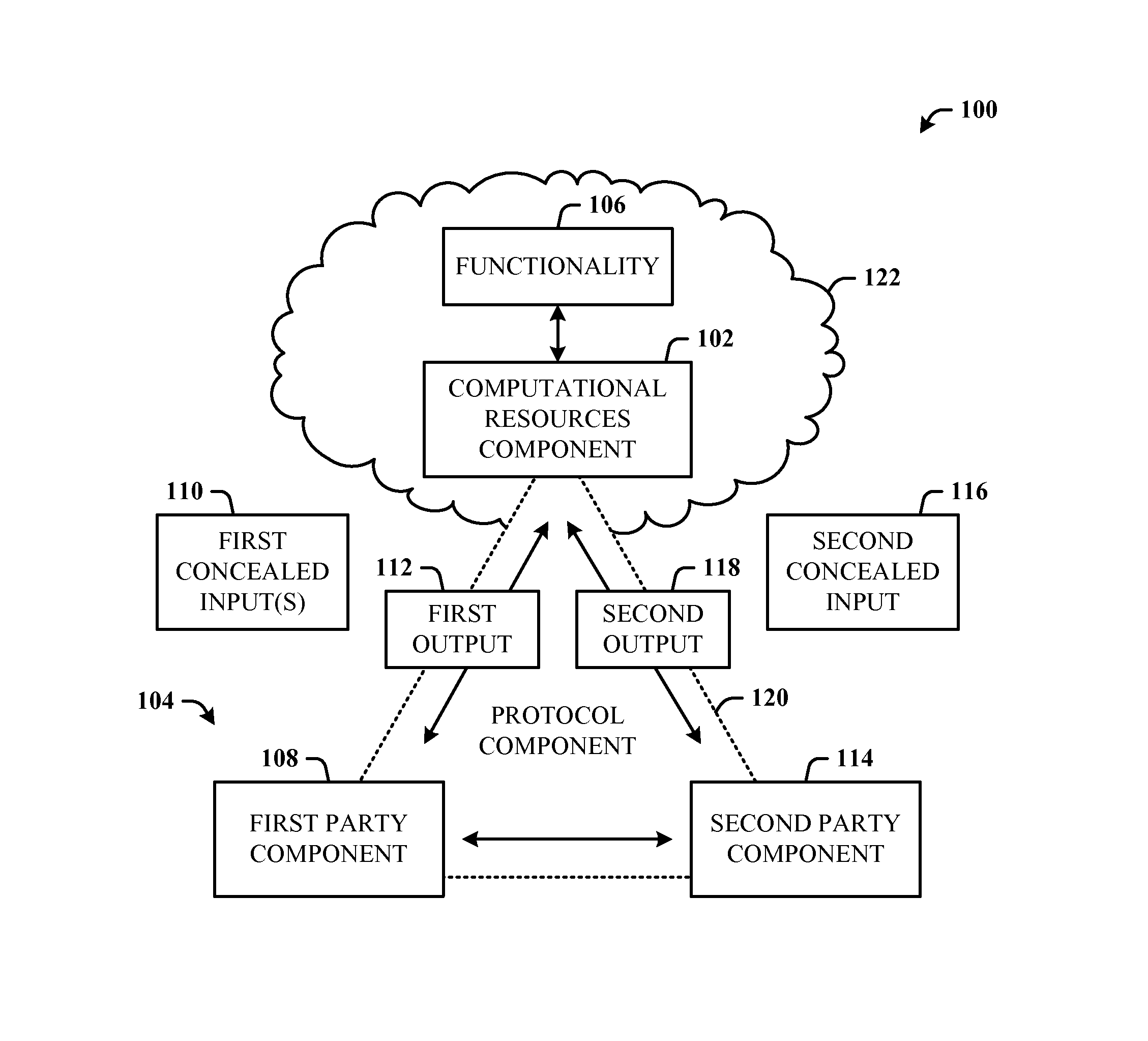
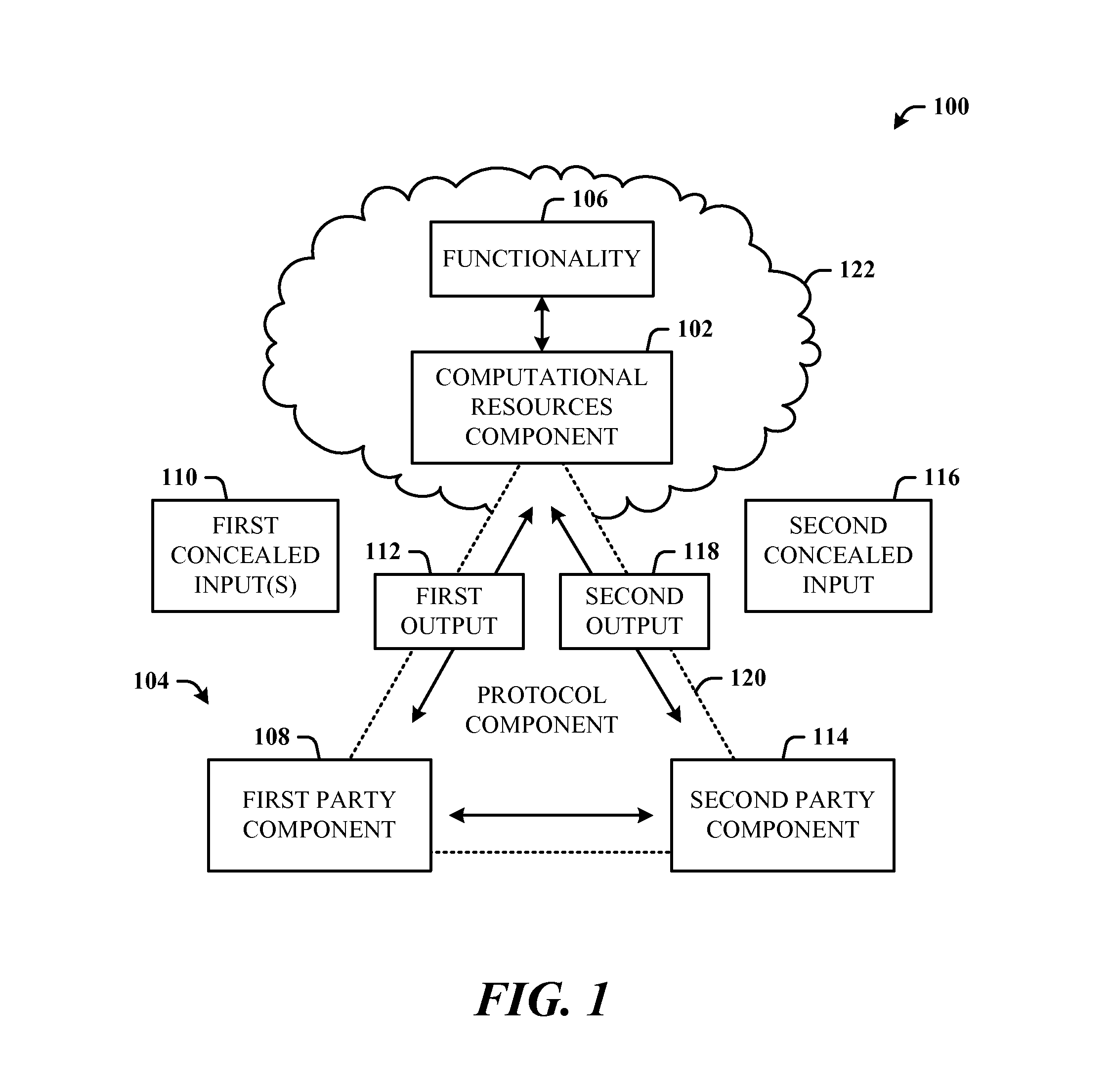
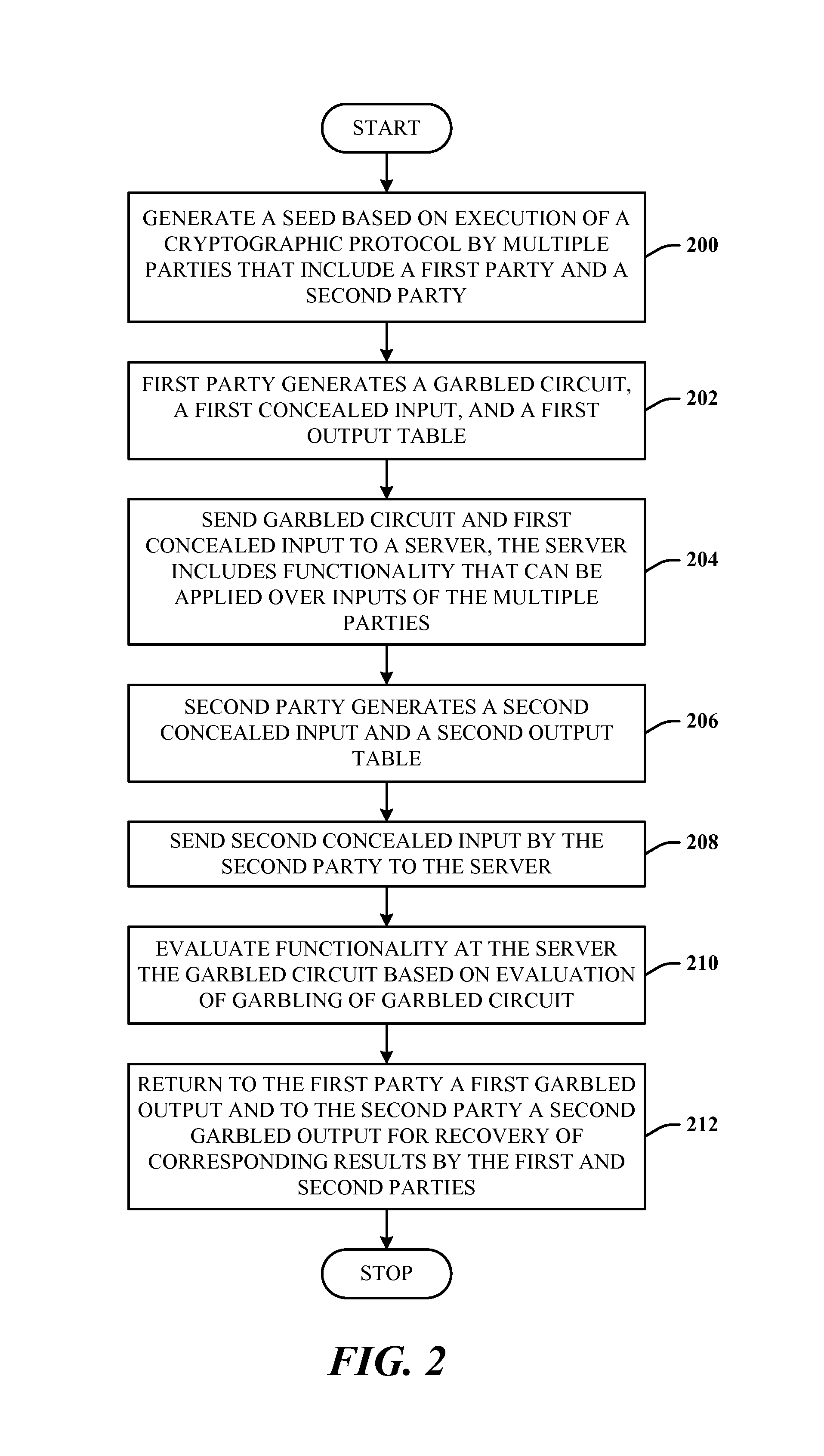
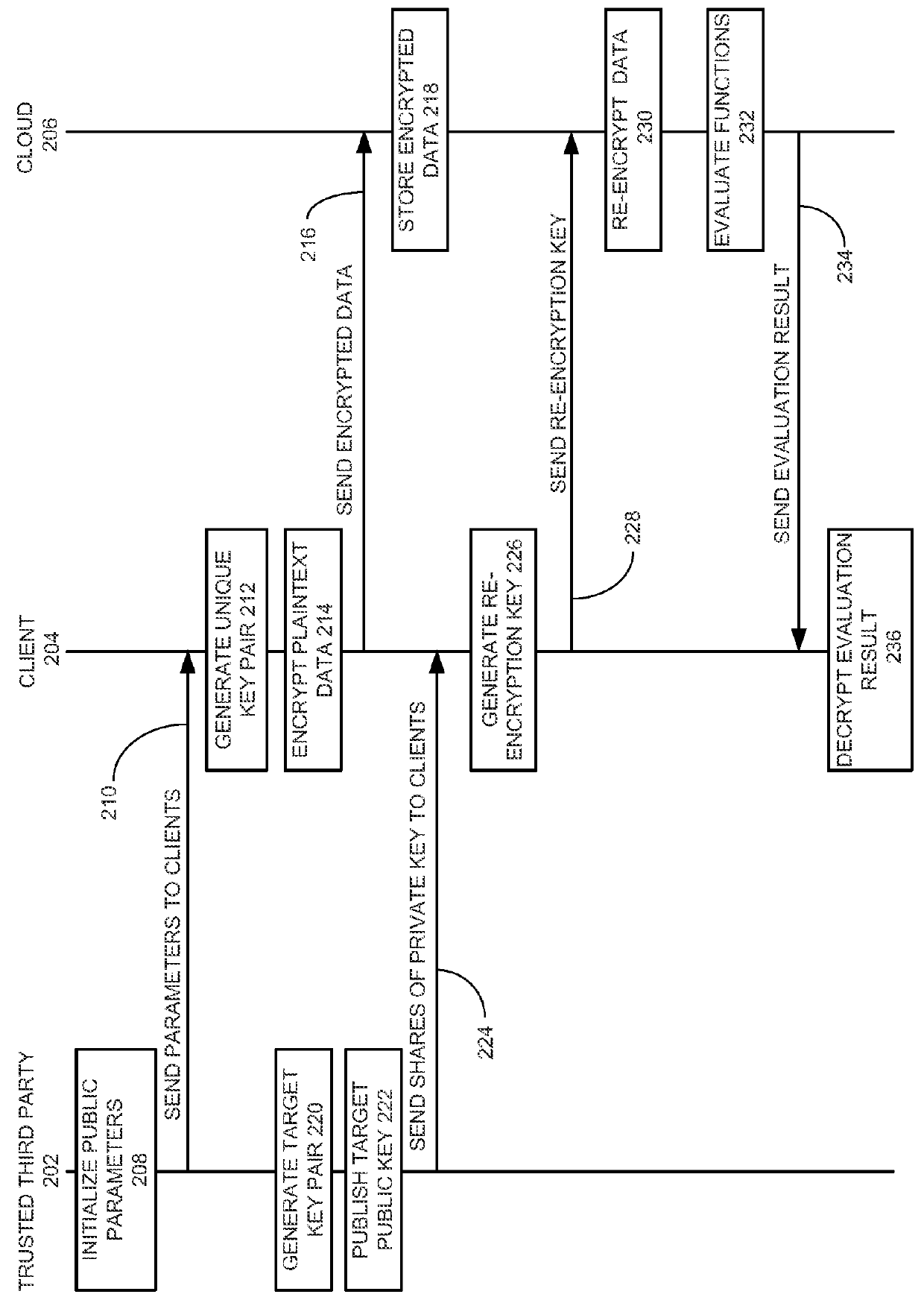
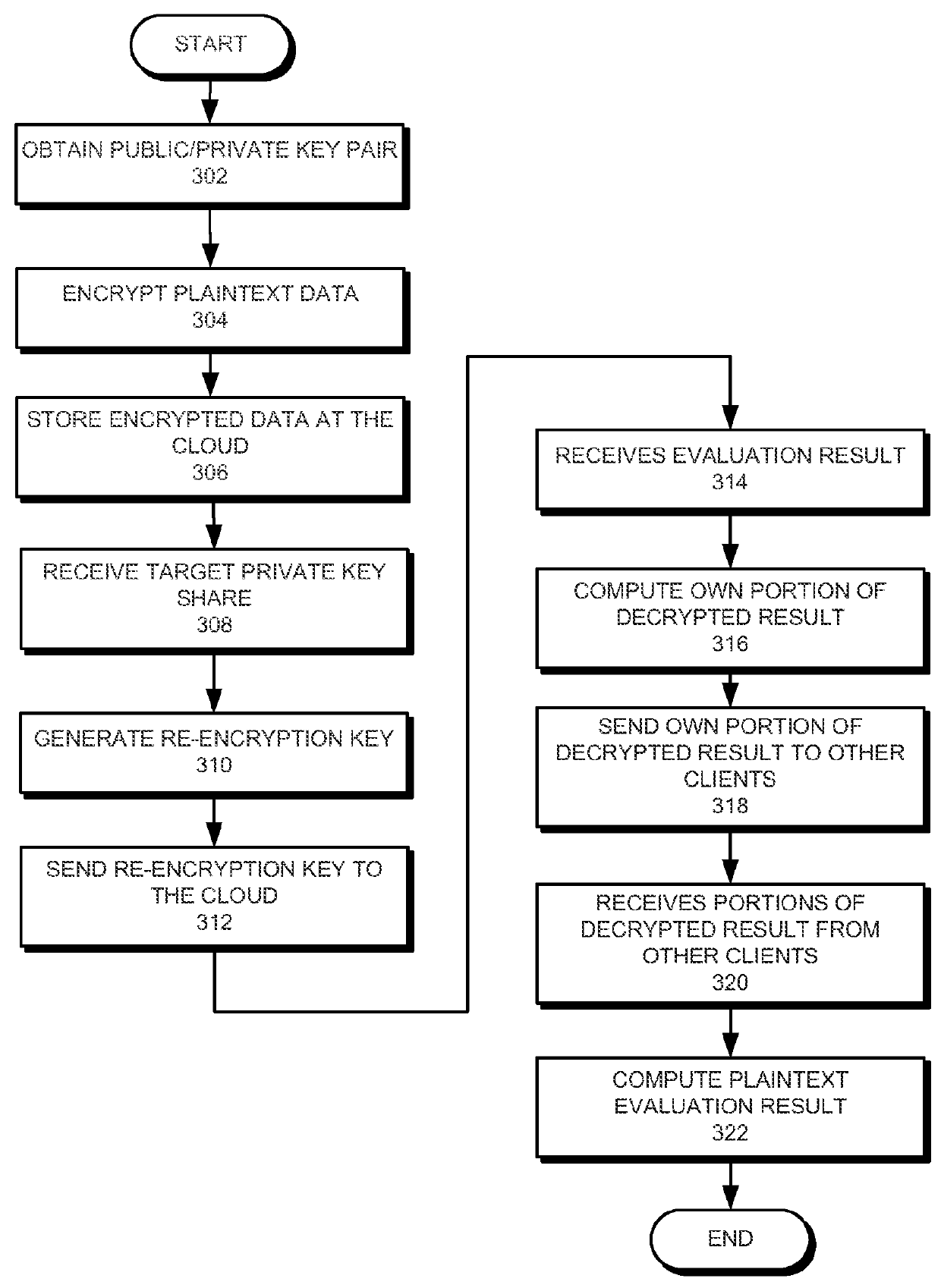
Method and system for secure multiparty cloud computation
One embodiment of the present invention provides a system for performing secure multiparty cloud computation. During operation, the system receives multiple encrypted datasets from multiple clients. An encrypted dataset associated with a client is encrypted from a corresponding plaintext dataset using a unique, client-specific encryption key. The system re-encrypts the multiple encrypted datasets to a target format, evaluates a function based on the re-encrypted multiple datasets to produce an evaluation outcome, and sends the evaluation outcome to the multiple clients, which are configured to cooperatively decrypt the evaluation outcome to obtain a plaintext evaluation outcome.
Owner:FUTUREWEI TECH INC
Information sharing and secure multi-party computing model based on block chain
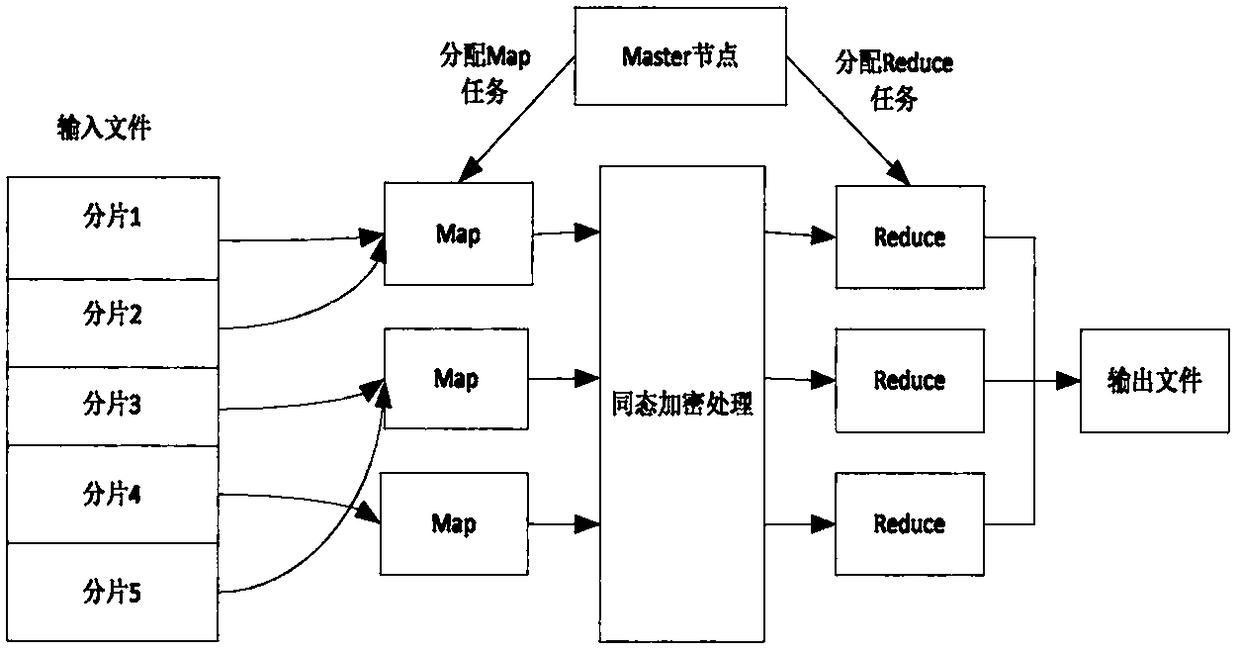
The invention discloses an information sharing and safe multi-party computing protocol based on a block chain, mainly solves the problem that the existing secure multi-party computation is easy to cause the user to be unable to control the data independently that is easy to get the data by the third party. The technical solutions are as follows: 1) constructing the storage model, and storing the index table information on the chain and the database under the chain in the way. 2) constructing a data sharing model,wherein users can access their data by authorizing a third party or revoke their privileges at any time. 3) using the consensus mechanism of the block chain to ensure the consistency among nodes; 4) Based on the correctness of nodes, using MapReduce programming model, the model isdivided into two phases: Map and Reduce, and the master node assigns the tasks of Map and Reduce to the nodes; 5) Map node uses the improved homomorphic encryption algorithm for encryption calculation; 6) Reduce node integrates the encrypted data to output data files.
Owner:全链通有限公司
System and method for recognizing speech securely using a secure multi-party computation protocol
InactiveUS7937270B2Secret communicationSpeech recognitionHide markov modelSecure multi-party computation
A system and method recognizes speech securely using a secure multi-party computation protocol. The system includes a client and a server. The client is configured to provide securely speech in a form of an observation sequence of symbols, and the server is configured to provide securely a multiple trained hidden Markov models (HMMs), each trained HMM including a multiple states, a state transition probability distribution and an initial state distribution, and each state including a subset of the observation symbols and an observation symbol probability distribution. The observation symbol probability distributions are modeled by mixtures of Gaussian distributions. Also included are means for determining securely, for each HMM, a likelihood the observation sequence is produced by the states of the HMM, and means for determining a particular symbol with a maximum likelihood of a particular subset of the symbols corresponding to the speech.
Owner:MITSUBISHI ELECTRIC RES LAB INC
Internet of things application scene-based protection method of privacy query and private identity verification
InactiveCN102196431APrivacy protectionPrivacy Flexible and ComprehensiveSecurity arrangementPersonalizationCiphertext
The invention discloses an Internet of things application scene-based protection method of privacy query and private identity verification. The protection method comprises scene-based flexible privacy protection, protection in privacy query and privacy protection in identity verification. In the scene-based flexible privacy protection, privacy protection strategies under different scenes are set by grading privacy data according to different scenes frequency reached by a user so as to effectively realize personalized flexible privacy protection; in the protection method of the privacy query, results of approximate query are acquired by decomposing the privacy data, adding random number and matrixes and calculating the difference value between the privacy data and the query value so as to realize the privacy protection of the query input and the query result in intelligent query; and in the protection method of the private identity verification, the cipher text of a verified person identity certificate is directly used for verification by a secure multi-party calculation method under the condition that the privacy data are not exposed so as to protect the privacy of the verified person.
Owner:苏州普康智慧养老产业科技有限公司
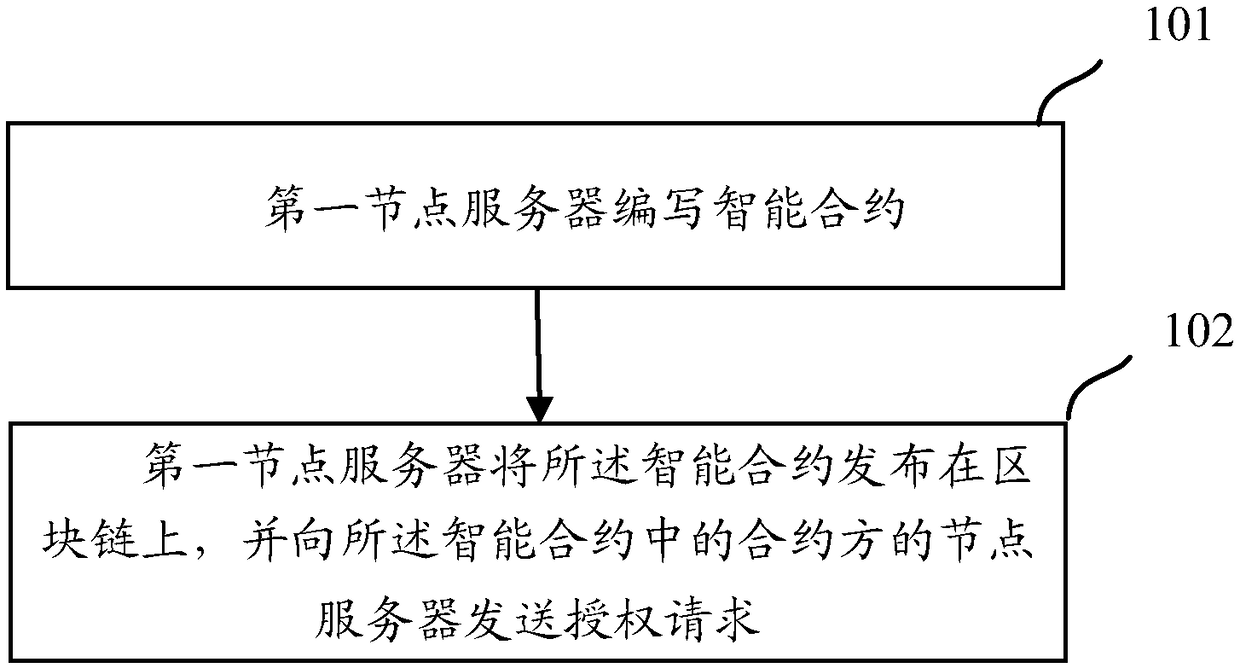
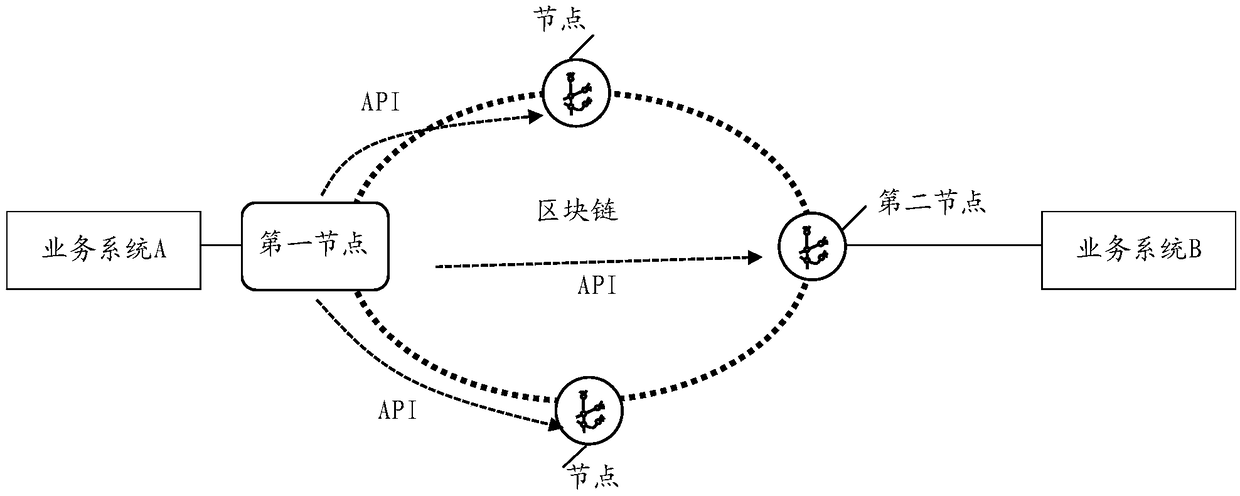
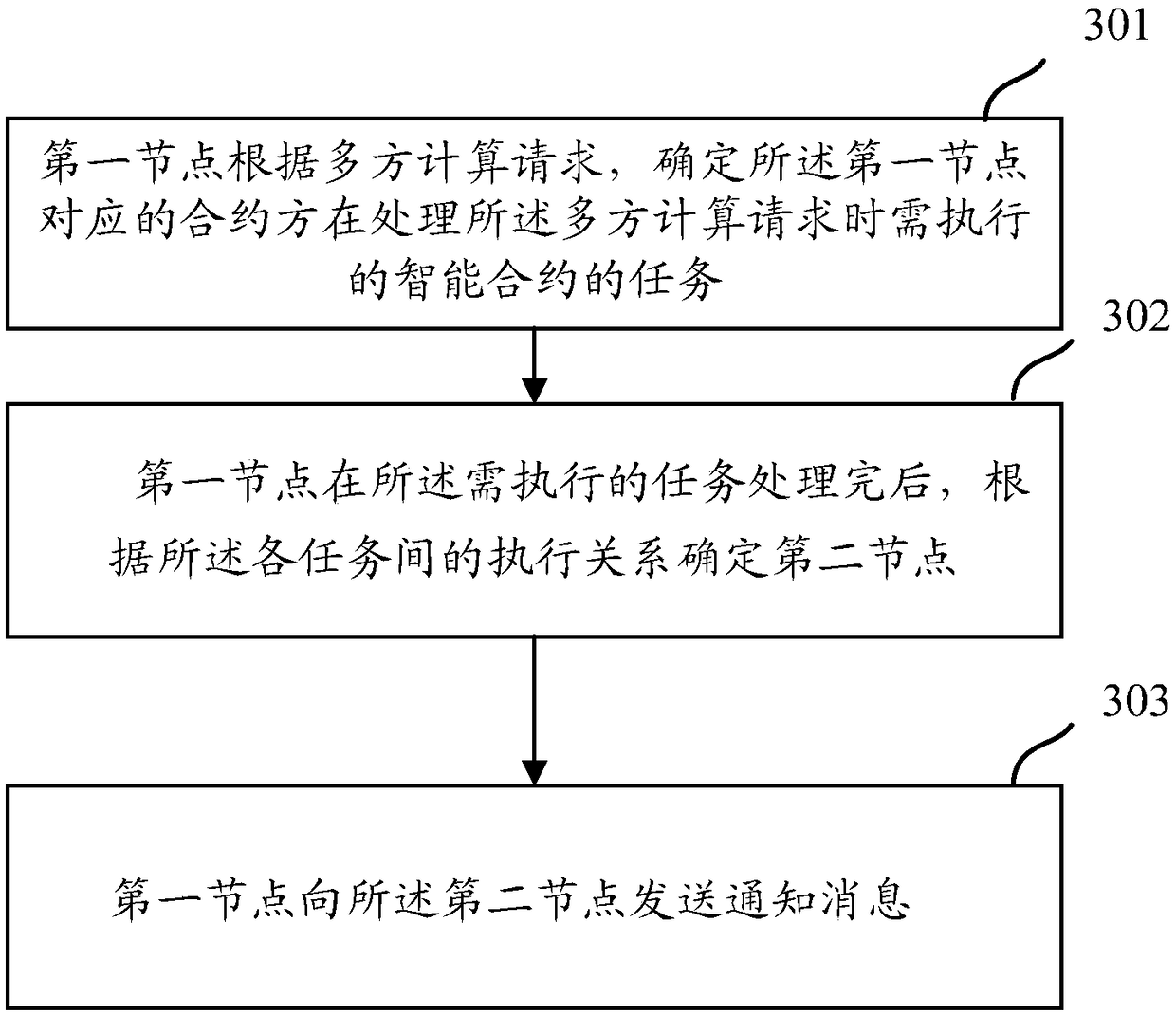
A safe multi-party calculation method and a related device
The invention discloses a safe multi-party computing method and a related device. The method comprises the following steps: a first node determines a task of an intelligent contract to be executed bya contract party corresponding to the first node when processing the multi-party computing request according to the multi-party computing request; The intelligent contract includes tasks of each contractor executing the multi-party computing request and execution relationships among the tasks; The first node is any one of the contracting parties; The first node determines a second node according to the execution relationship among the tasks after the tasks to be executed are processed. The second node is a node corresponding to the next task among the contractors executing the multi-party computing request; The first node sends a notification message to the second node; The notification message is used to instruct the second node to process the multi-party computing request.
Owner:CHINA UNIONPAY
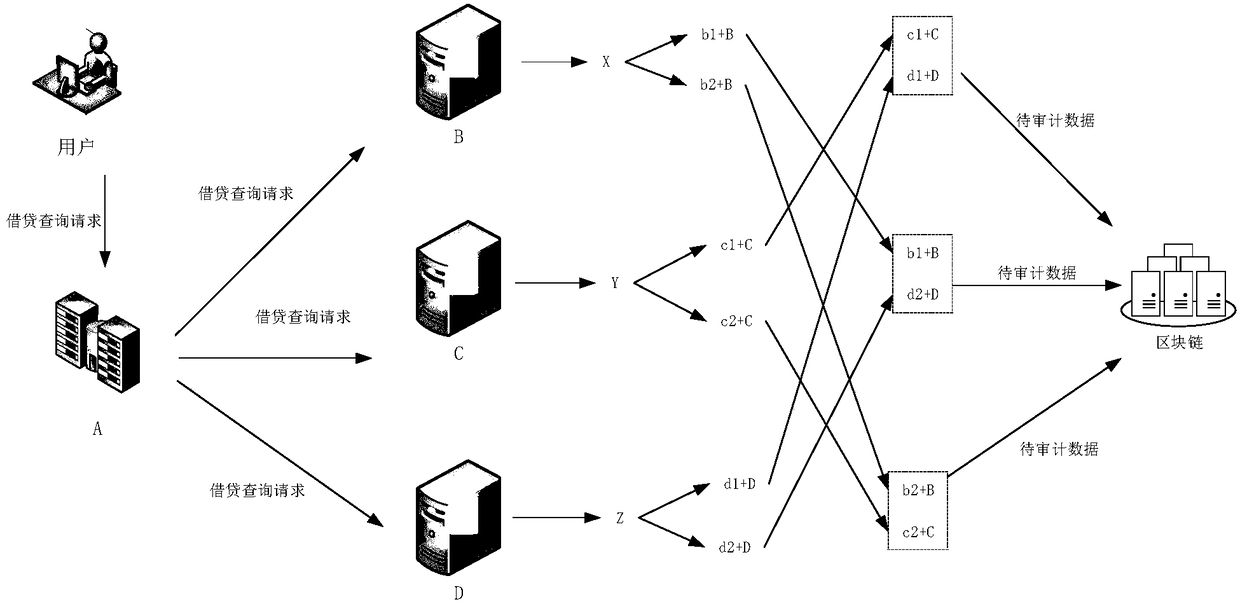
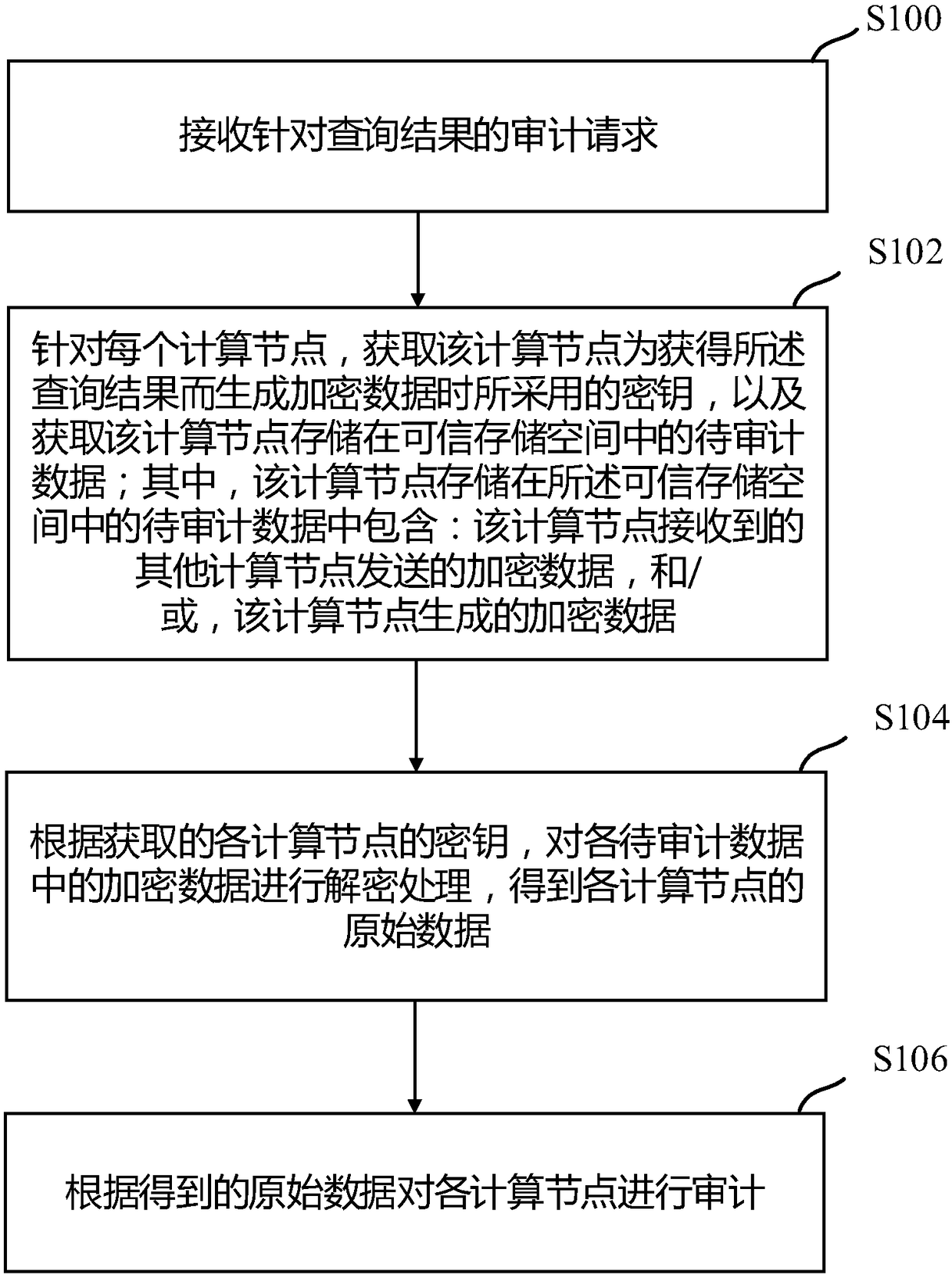
Method and device for data auditing
ActiveCN108364223AReduce the possibility of tamperingPrevent leakageFinanceMultiple keys/algorithms usageOriginal dataSecure multi-party computation
The invention discloses a method and a device for data auditing. For each computing node, received encrypted data sent from other computing nodes and / or encrypted data generated by the computing nodecan be stored in a trusted storage space as data to be audited when secure multi-party computation is carries out according to a query request. Thus, if an agent receives an auditing request for a query result corresponding to the query request later, the agent can acquire the encrypted data contained in the data to be audited from the trusted storage space for decryption processing according to secret keys acquired from the computing nodes, so as to obtain original data of the computing nodes, and conduct auditing on the computing nodes according to the original data.
Owner:ADVANCED NEW TECH CO LTD
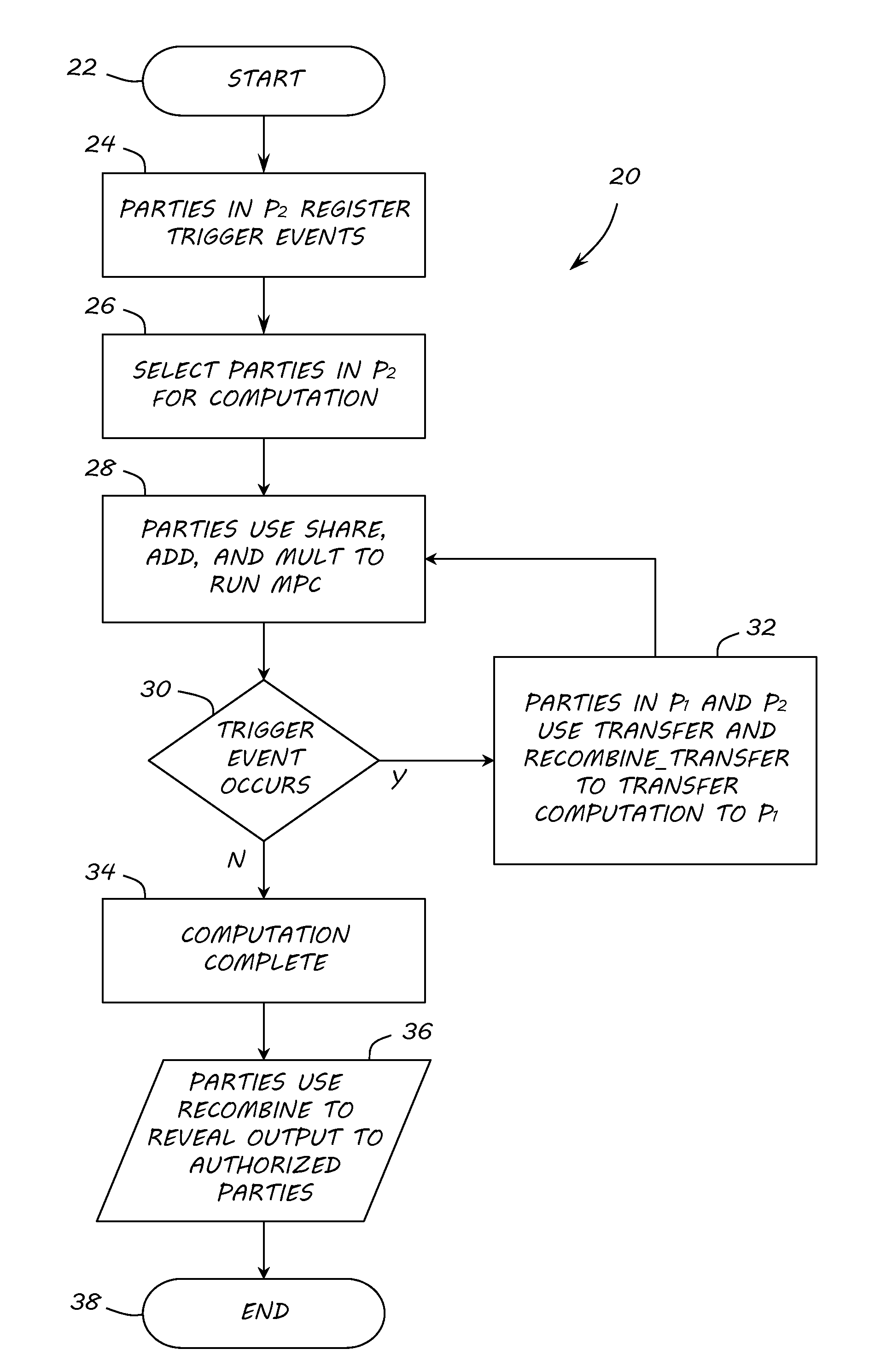
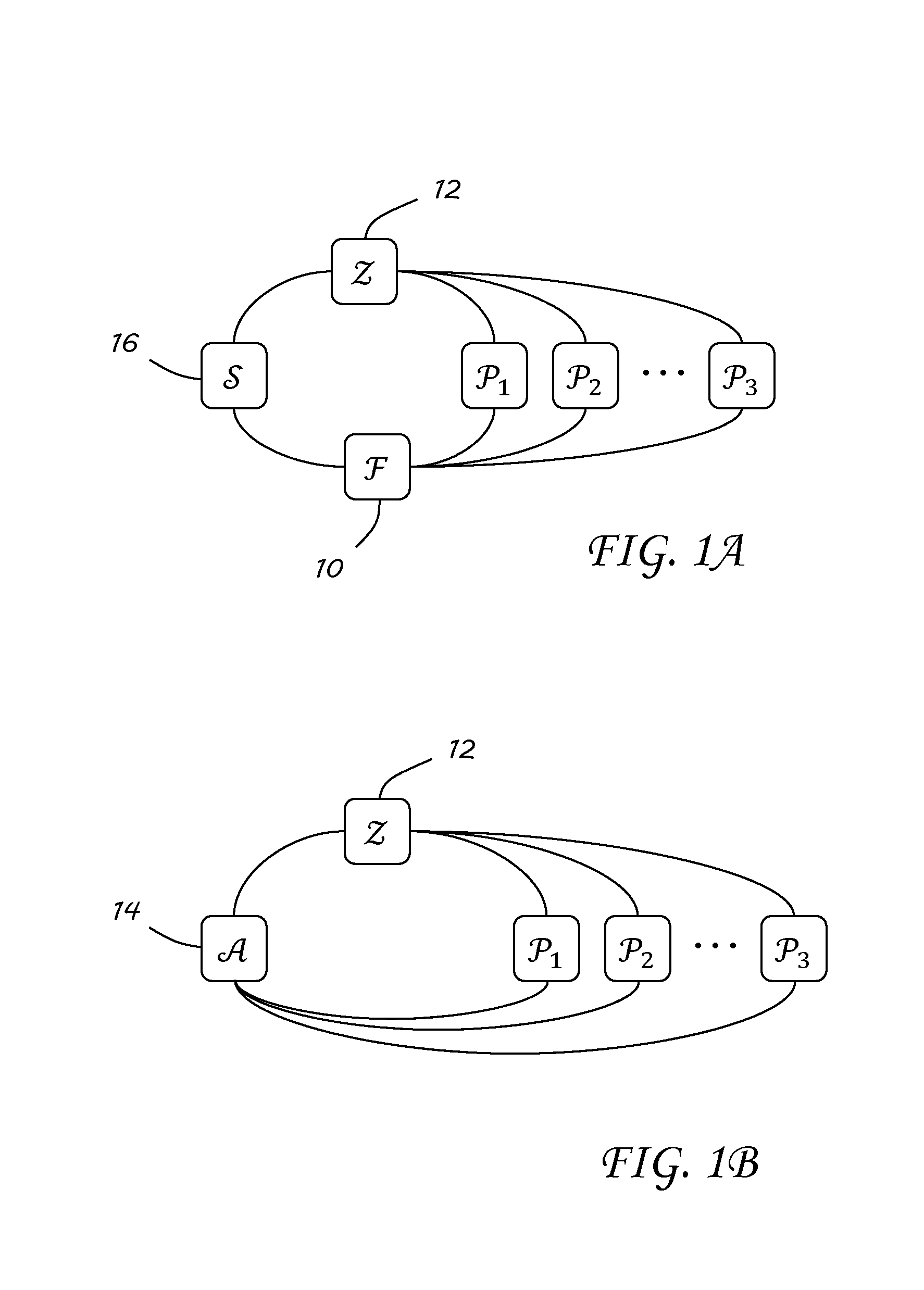
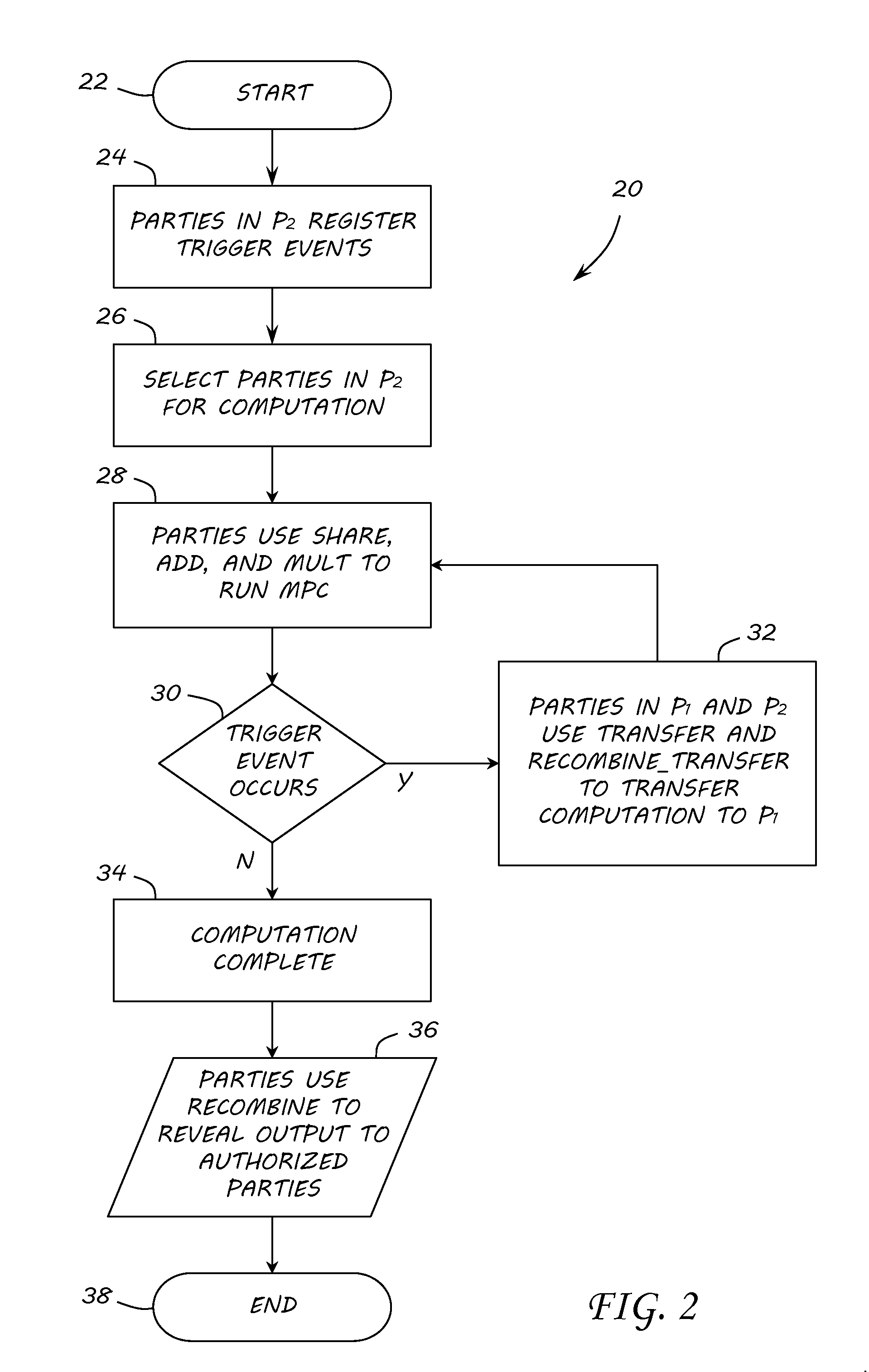
Transferable Multiparty Computation
ActiveUS20160335440A1Digital data protectionCommunication with homomorphic encryptionSecure multi-party computationComputer security
Owner:GOVERNMENT OF THE UNITED STATES AS REPRESENTED BY THE SEC OF THE AIR FORCE
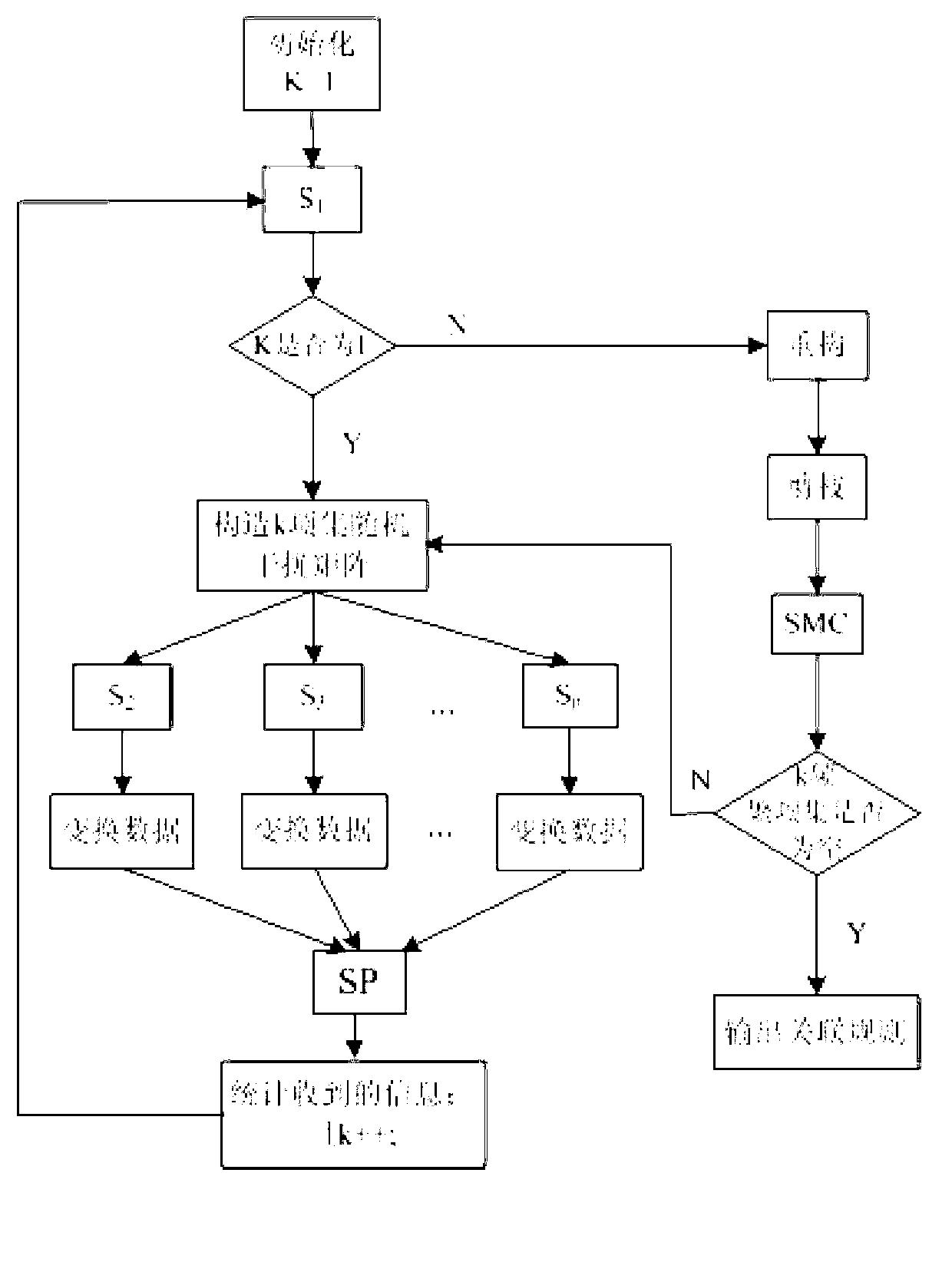
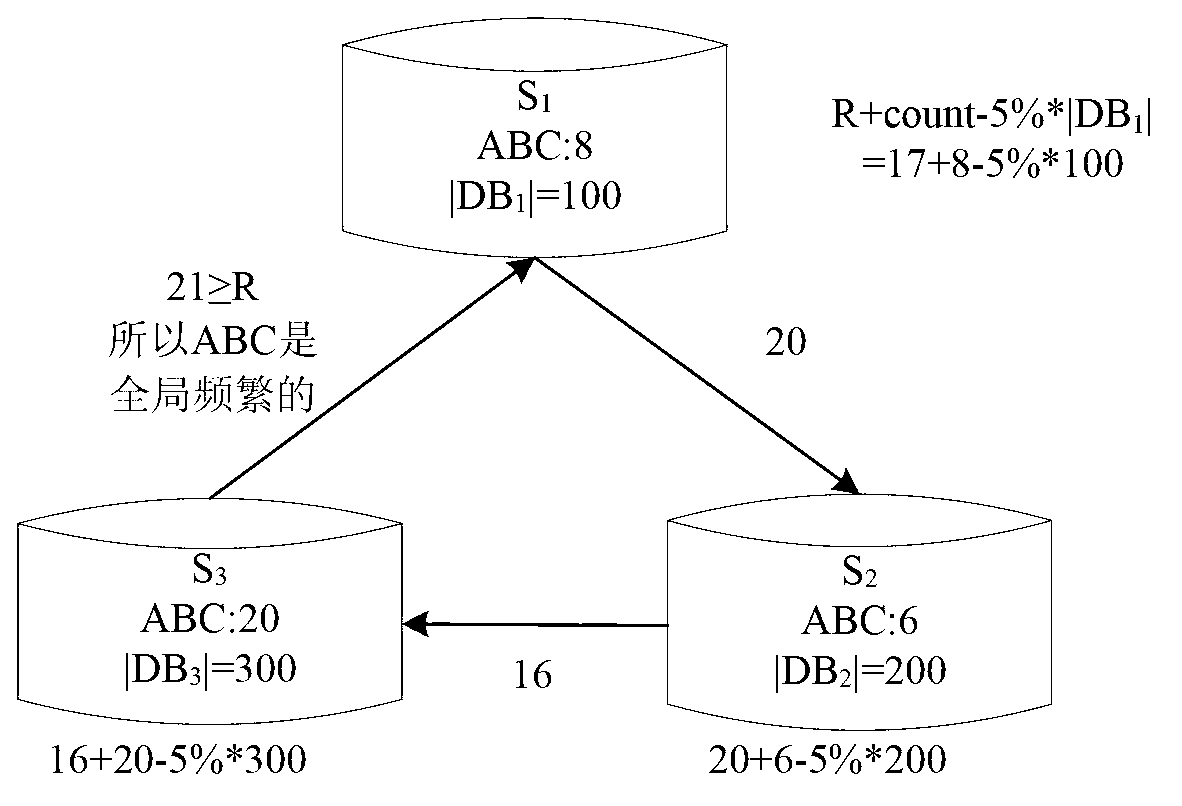
Association rule mining method for privacy protection under distributed environment
InactiveCN103150515AProtect Association RulesImprove digging accuracyDigital data protectionSpecial data processing applicationsTheoretical computer sciencePrivacy protection
The invention provides an association rule mining method for privacy protection under a distributed environment. The association rule mining method is used to carry out global mining on multiple data and comprises the steps of: structuring a random disturbance matrix of item sets, carrying out disturbance transformation on data, making statistics on the summation of supporting number matrixes after disturbance, restructuring data distribution, precisely calculating the global support degree of the item sets in a space after pruning, and the like. According to the method disclosed by the invention, by means of structuring the random disturbance matrix to disturb a plurality of attributes at the same time and taking the correlation among the attributes into consideration in a disturbance process, the recover precision is effectively improved; after the supporting number of the item sets is evaluated by using a disturbance method, the final global frequent item set is determined by secure multi-party computation after pruning is carried out based on minimum support degree, thus, the communication traffic is effectively reduced, the mining efficiency is improved, a better compromise between the mining efficiency and the mining precision can be acquired, and the association rule mining method has a wider application range.
Owner:JIANGSU UNIV
Server-aided multi-party protocols
ActiveUS9077539B2Much of communication burdenMuch of computationKey distribution for secure communicationDigital data processing detailsThird partyInternet privacy
Owner:MICROSOFT TECH LICENSING LLC
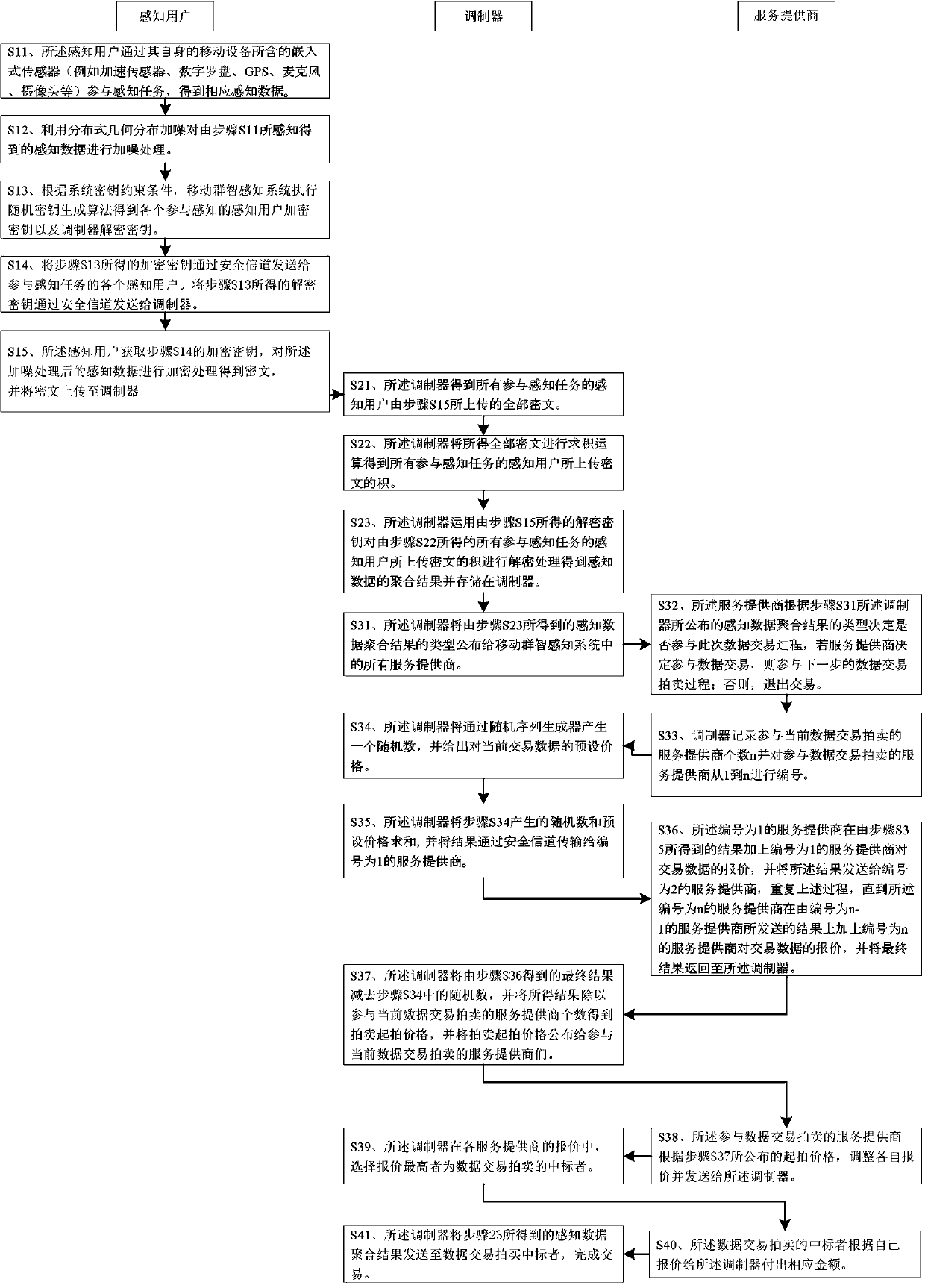
Privacy protection method and system in mobile crowd sensing
ActiveCN107707530APrevent leakageReduce computational overheadKey distribution for secure communicationBuying/selling/leasing transactionsSensing dataPrivacy protection
The invention provides a privacy protection method and system in mobile crowd sensing. The method comprises sensing data uploading, sensing data aggregation and sensing data transaction stages, and the system comprises a mixed excitation sensing module, a sensing data noise adding module, a user key generation module, a sensing data encryption module, an encrypted data uploading module, a sensingdata aggregation module, a sensing data decryption module, a secure multi-party computation module and a sensing data transaction auction module. By adoption of the privacy protection method and system, an effective mechanism is established to improve the degree of participation of the sensing user and the authenticity of the sensing data; and moreover, the leakage of the personal privacy data ofthe sensing user is effectively protected, the false data of malicious users is prevented, the computational overhead of the involved algorithm is low, a secure and efficient design target is achieved, the privacy protection method and system is suitable for large-scale promotion and use and can be applied to actual production and life processes.
Owner:FUJIAN NORMAL UNIV
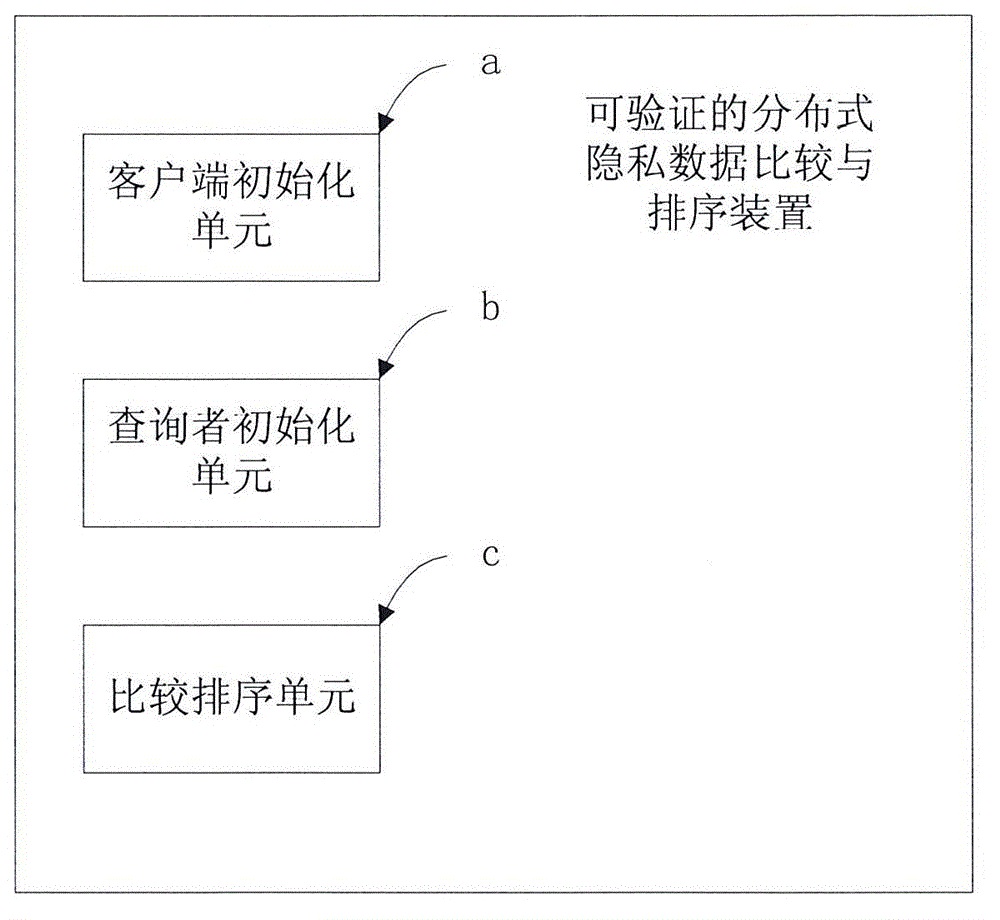
Verifiable distributed privacy data comparing and sorting method and device
The invention relates to the field of secure multi-party computation, in particular to a verifiable distributed privacy data comparing and sorting method and a device. The method and the device have the beneficial effects that through the steps of sorting the privacy data of n client sides by using a distributed client side initialization, inquirer initialization and inquirer Pa use merge sorting algorithm and the like; aiming at the situation that the data is stored on a large quantity of distributed nodes, a ceterless mode is completely adopted in the whole inquiry process by utilizing a digital signature and a semi-homomorphic encryption system; all the client side data is encrypted by using a client side public key and is only decrypted by a client side private key to ensure data privacy; and through a verification mechanism, all client sides can not input false data and can also not affectedly behave the comparing and sorting results.
Owner:无锡绿野千传科技有限公司
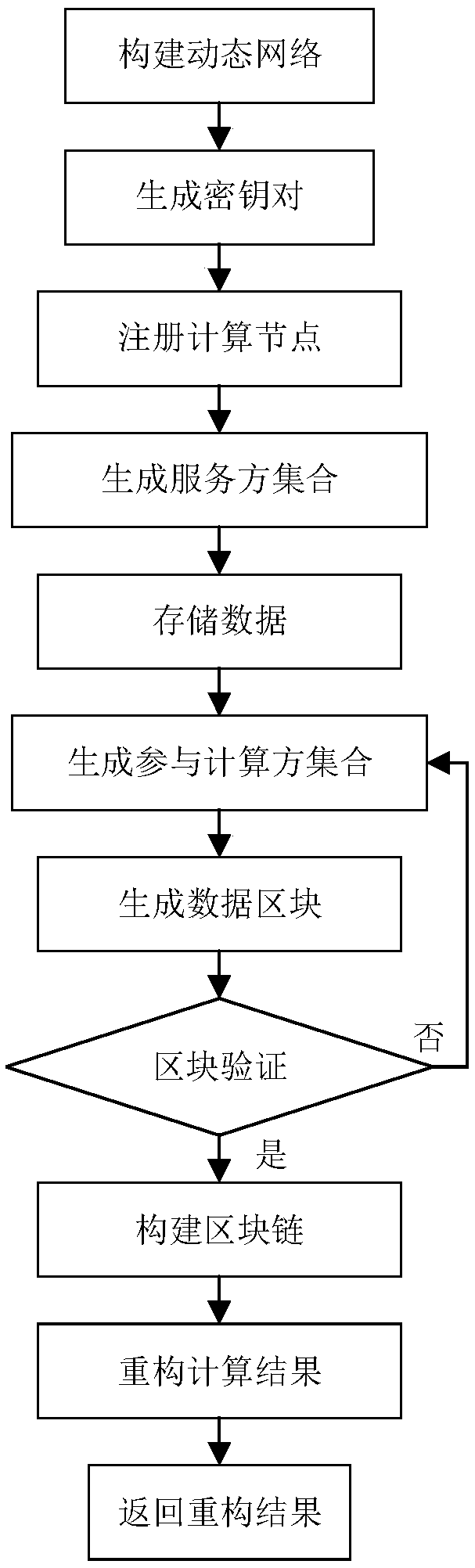
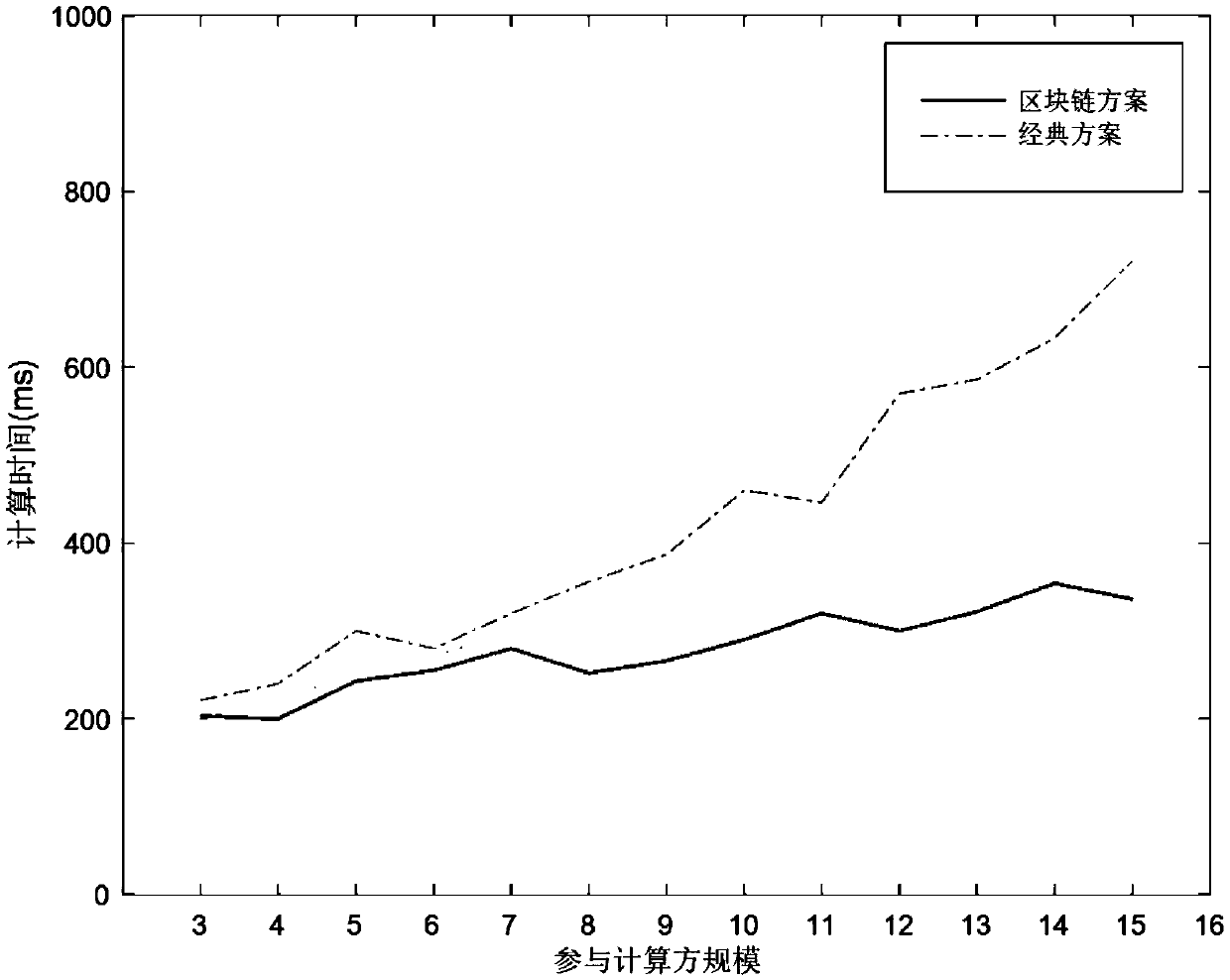
Privacy protection method based on blockchain cloud outsourcing computing data
ActiveCN108712429AOvercoming scalabilityOvercome securityPublic key for secure communicationExtensibilityData privacy protection
The invention discloses a privacy protection method based on blockchain cloud outsourcing computing data, and mainly solves the problem of high time complexity and scalability of the data privacy protection technology in the current cloud outsourcing computing process. The technical scheme is of using log information of a computing node to construct a blockchain, and using the blockchain technology to perform secure storage verification of the computing data; using the quorum technology to select a suitable computing node set for each round of computing to complete the computing task; and adopting a secure multi-party computing method based on threshold secret sharing to segment and reconstruct secret information. The privacy protection method based on blockchain cloud outsourcing computing data in the invention overcomes the problem that in the prior art, the computing network lacks the scalability and security and the complexity of the data verification process is high; and the scalability of the computing network and the efficiency of the computing process are greatly improved while the data privacy can be effectively ensured.
Owner:XIDIAN UNIV
General protocol for proactively secure computation
ActiveUS9449177B1Key distribution for secure communicationDigital data protectionSecret shareSecure multi-party computation
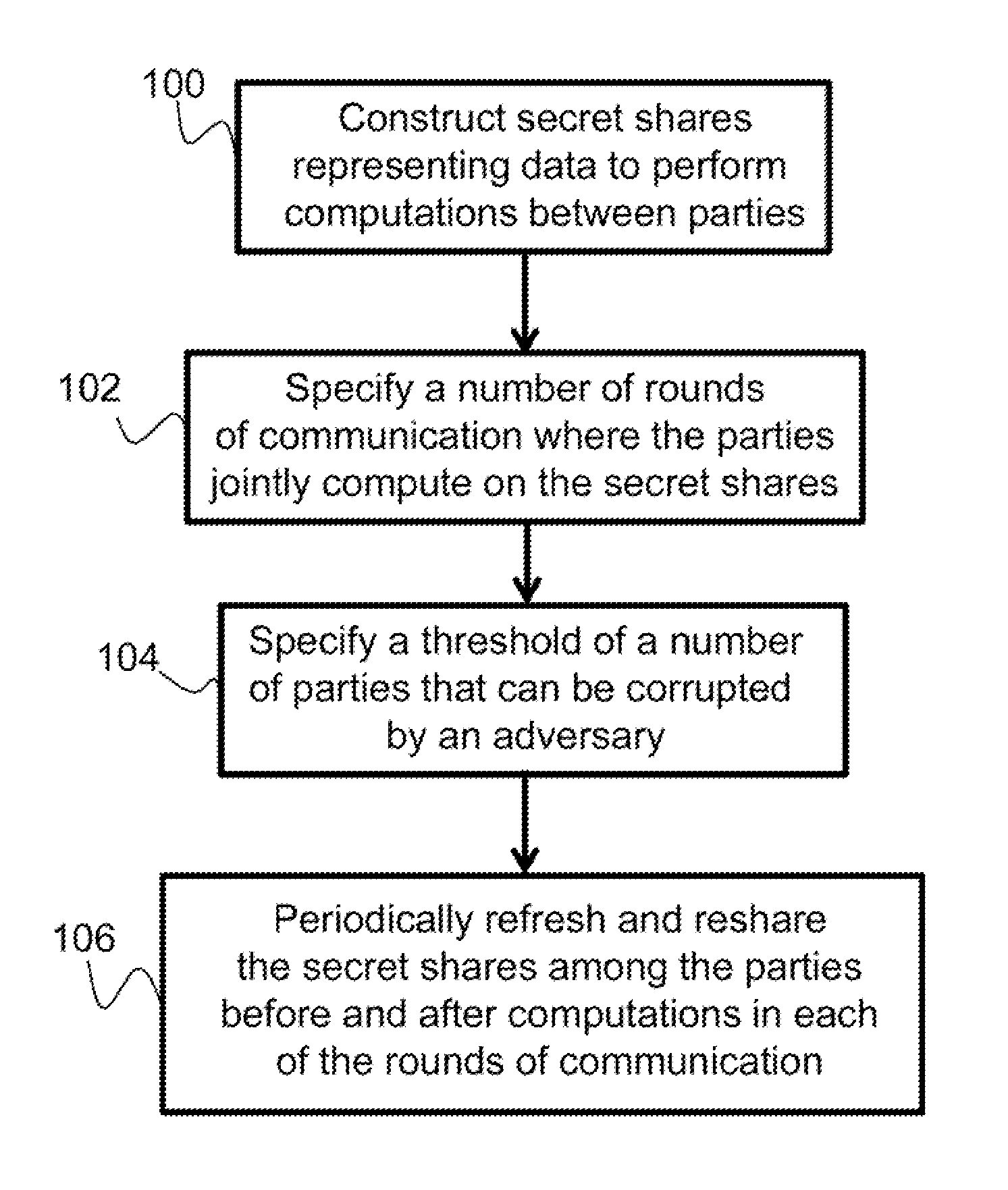
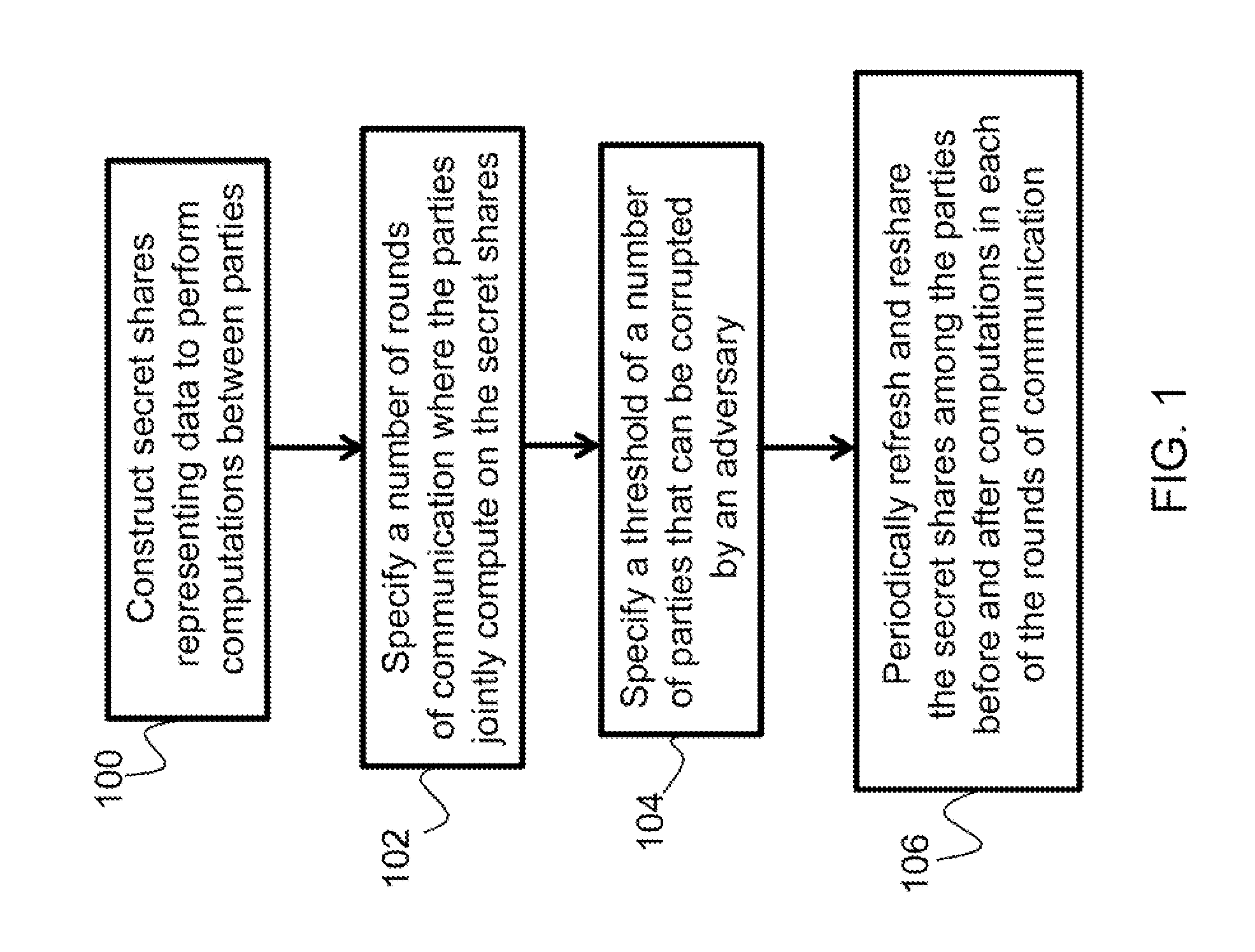
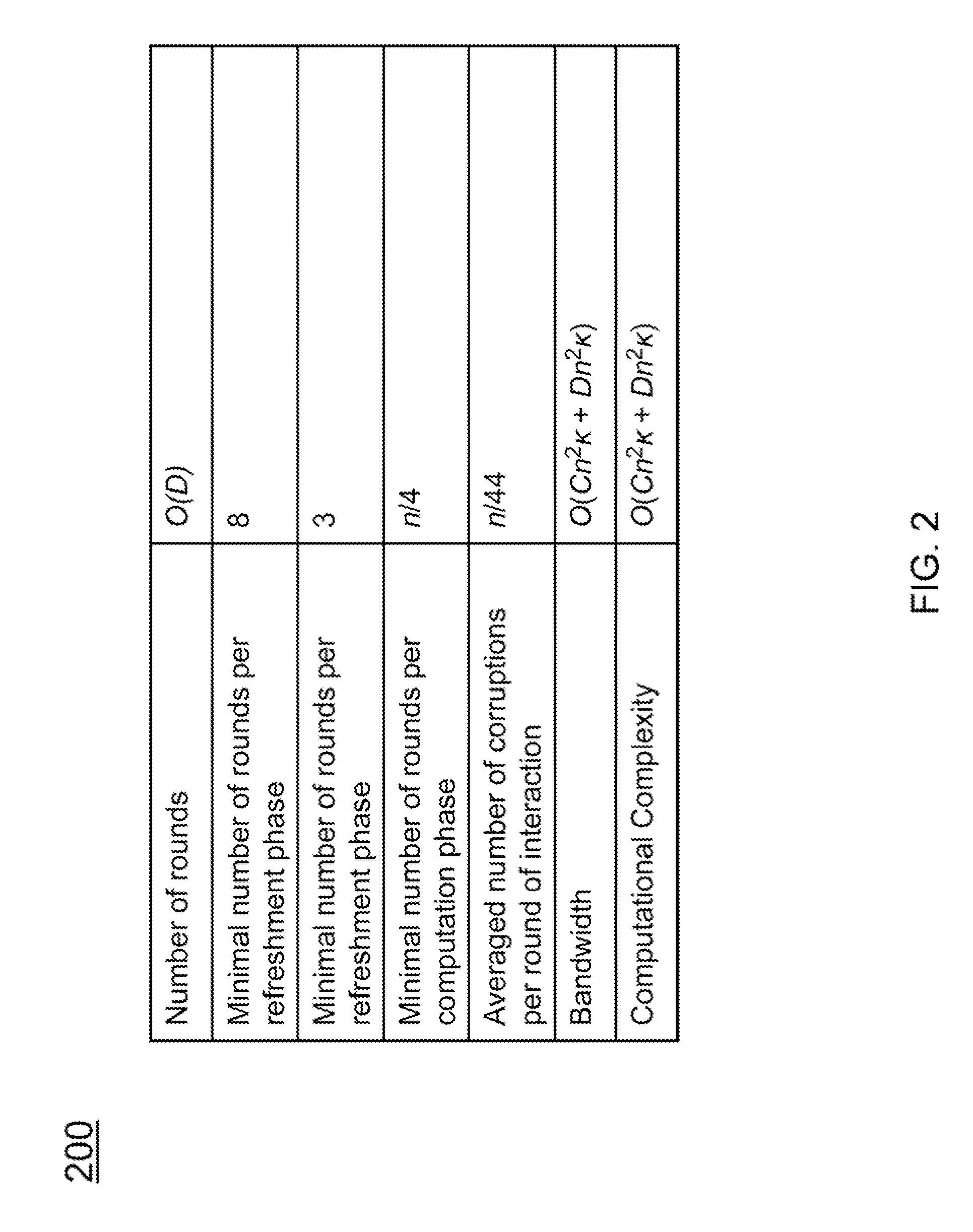
Described is a system for proactively secure multi-party computation (MPC). Secret shares representing data are constructed to perform computations between a plurality of parties modeled as probabilistic polynomial-time interactive turing machines. A number of rounds of communication where the plurality of parties jointly compute on the secret shares is specified. Additionally, a threshold of a number of the plurality of parties that can be corrupted by an adversary is specified. The secret shares are periodicially refreshed and reshared among the plurality of parties before and after computations in each of the rounds of communication. The data the secret shares represent is proactively secured.
Owner:HRL LAB
Secure multiparty computing method, device and system
ActiveCN108809623AReduce occupancyImprove computing efficiencySecuring communicationTheoretical computer scienceSecure multi-party computation
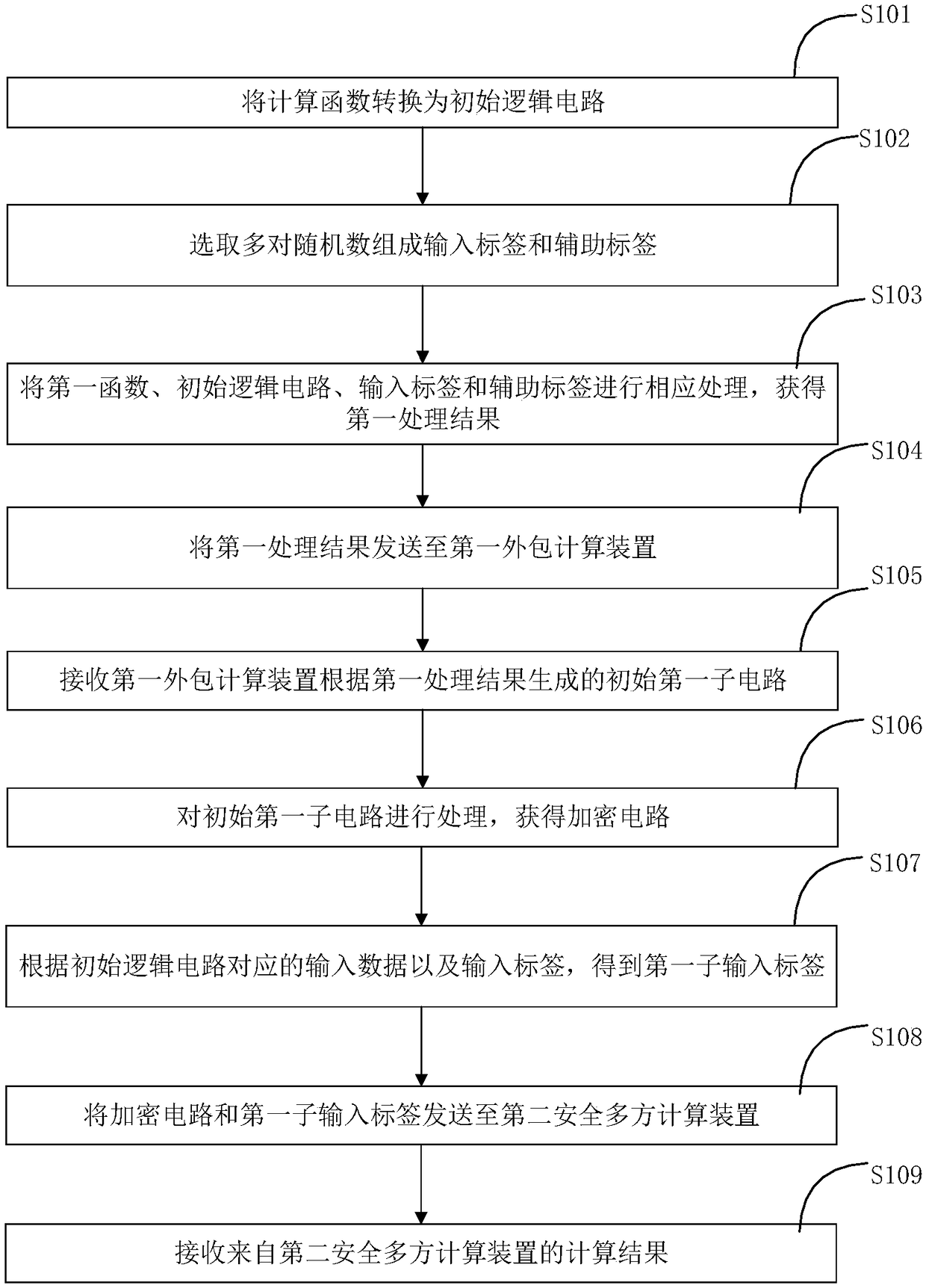
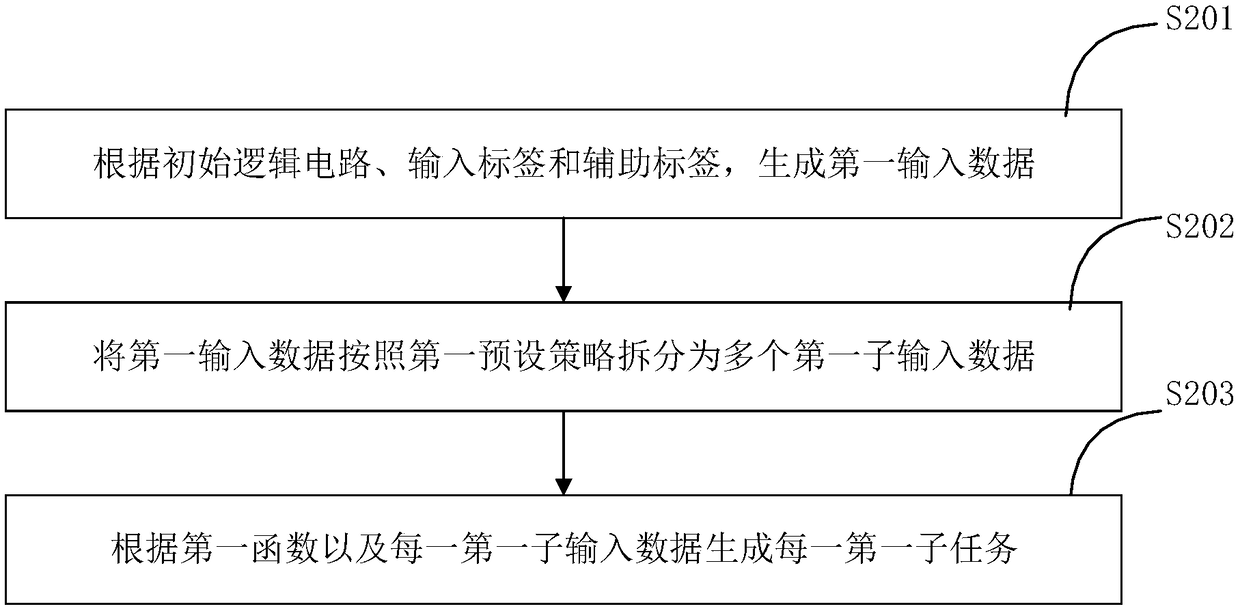
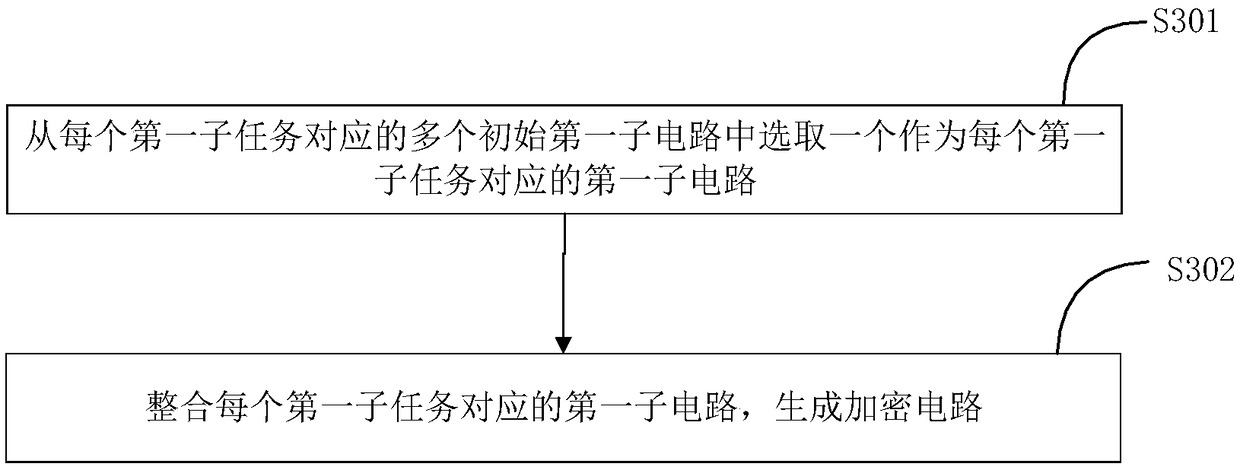
The invention provides a secure multiparty computing method, device and system. The secure multiparty computing method comprises the steps of converting a computing function into an initial logic circuit; selecting multiple pairs of random number so as to form an input label and an auxiliary label; processing a first function, the initial logic circuit, the input label and the auxiliary label correspondingly, so as to obtain a first processing result; sending the first processing result to a first outsourced computing device; receiving an initial first sub-circuit generated by the first outsourced computing device according to the first processing result; processing the initial first sub-circuit so as to acquire an encrypted circuit; obtaining a first sub-input label according to input data corresponding to the initial logic circuit and the input label; sending the encrypted circuit and the first sub-input label to a second secure multiparty computing device; and receiving a computingresult from the second secure multiparty computing device. Fewer local resources are used, computing efficiency is improved, and the performance of the secure multiparty computing technology is improved.
Owner:JUZIX TECH SHENZHEN CO LTD
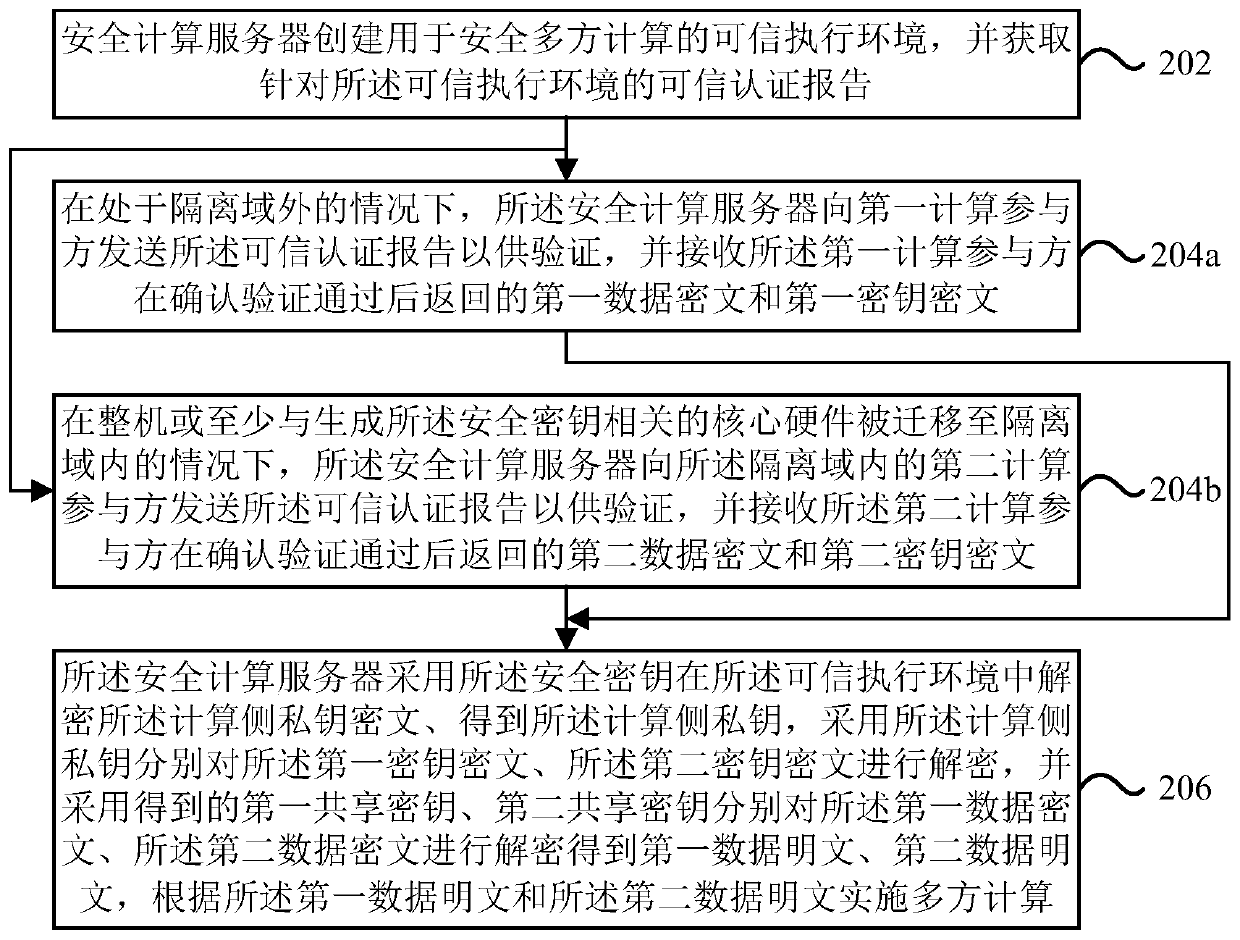
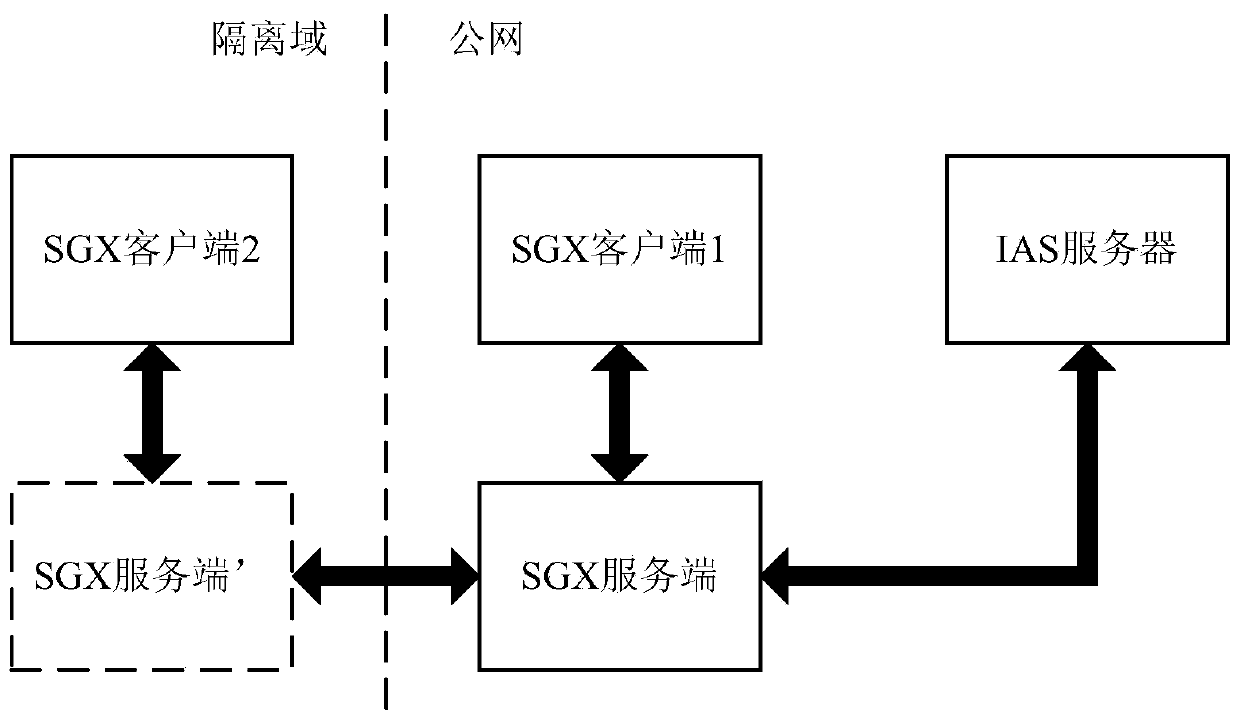
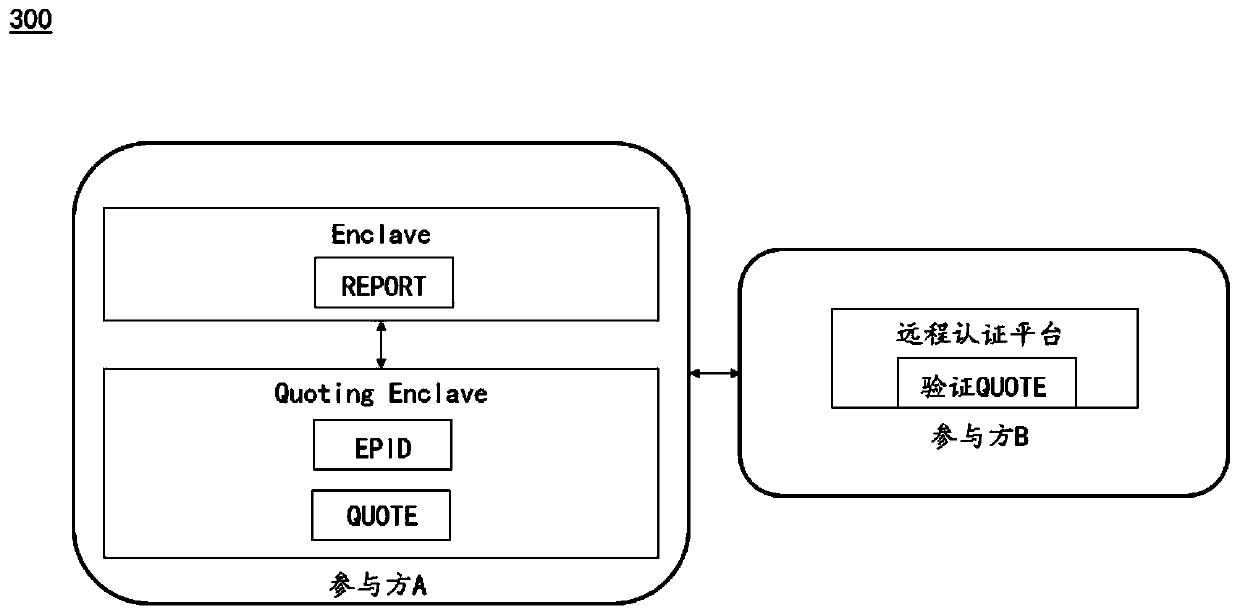
Cross-domain secure multi-party computing method and device based on trusted execution environment
One or more embodiments of the invention provide a cross-domain secure multi-party computing method and device based on a trusted execution environment. The method comprises the following steps: a secure computing server creates a trusted execution environment for secure multi-party computing; encrypting and storing a computing side private key generated in the trusted execution environment by using a security key maintained by the security computing server; as the security computing server at least migrates the core hardware related to the security key to the isolation domain, therefore, thesecurity key can be normally generated inside or outside the isolation domain, the data ciphertext and the key ciphertext provided by each computing participant inside and outside the isolation domainare smoothly decrypted, and secure multi-party computing processing is carried out in a trusted execution environment. The technical scheme of the invention can be applied to service processing processes in various scenes, such as an artificial intelligence scene, a block chain scene and the like.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Method and system for secure multiparty cloud computation
One embodiment of the present invention provides a system for performing secure multiparty cloud computation. During operation, the system receives multiple encrypted datasets from multiple clients. An encrypted dataset associated with a client is encrypted from a corresponding plaintext dataset using a unique, client-specific encryption key. The system re-encrypts the multiple encrypted datasets to a target format, evaluates a function based on the re-encrypted multiple datasets to produce an evaluation outcome, and sends the evaluation outcome to the multiple clients, which are configured to cooperatively decrypt the evaluation outcome to obtain a plaintext evaluation outcome.
Owner:FUTUREWEI TECH INC
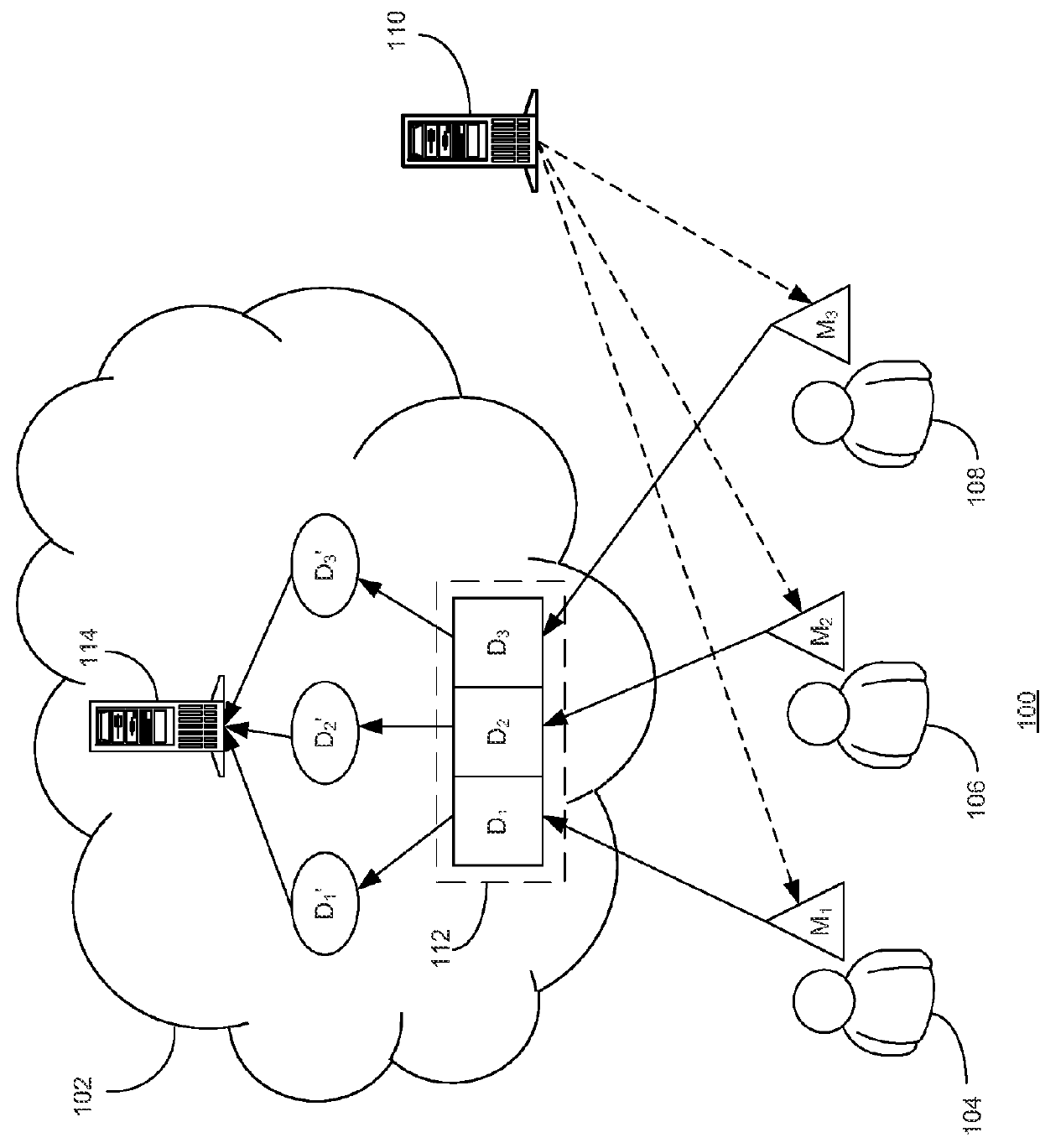
Systems and methods for secure data aggregation and computation
ActiveUS20200226284A1Digital data information retrievalFinanceInformation controlTheoretical computer science
Systems and methods for data aggregation and processing are provided in manner that is decentralized and preserves privacy. A data aggregation and computation system may include an interface, a controller, and one or more clusters of computation nodes. The interface may receive an inquiry from a requesting entity for computing information regarding an individual based on pieces of information held by a plurality of entities. The controller may communicate an identifier for the individual to a processor system associated with each of the entities based on the inquiry. The clusters of computation nodes may each receive encrypted data fragments from each of the processor systems, the data fragments comprising unrecognizable fragments that no individual processor system can re-assemble to recover the information, perform secure, multi-party computations based on the data fragments, and generate a result based on the secure, multi-party computations for the individual.
Owner:EXPERIAN INFORMATION SOLUTIONS
Data processing method, device and system
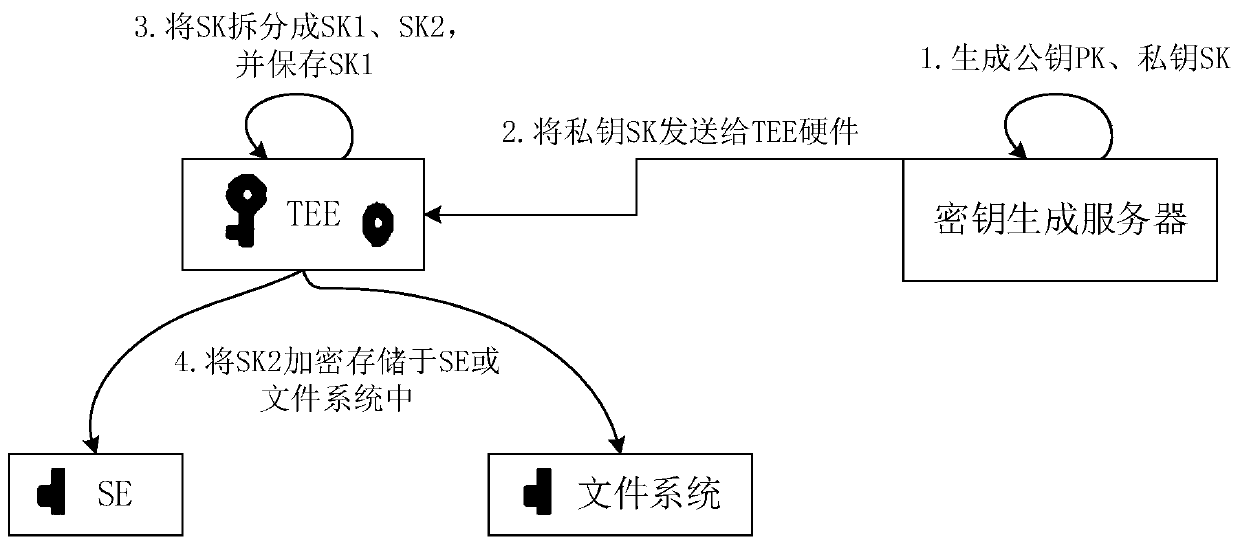
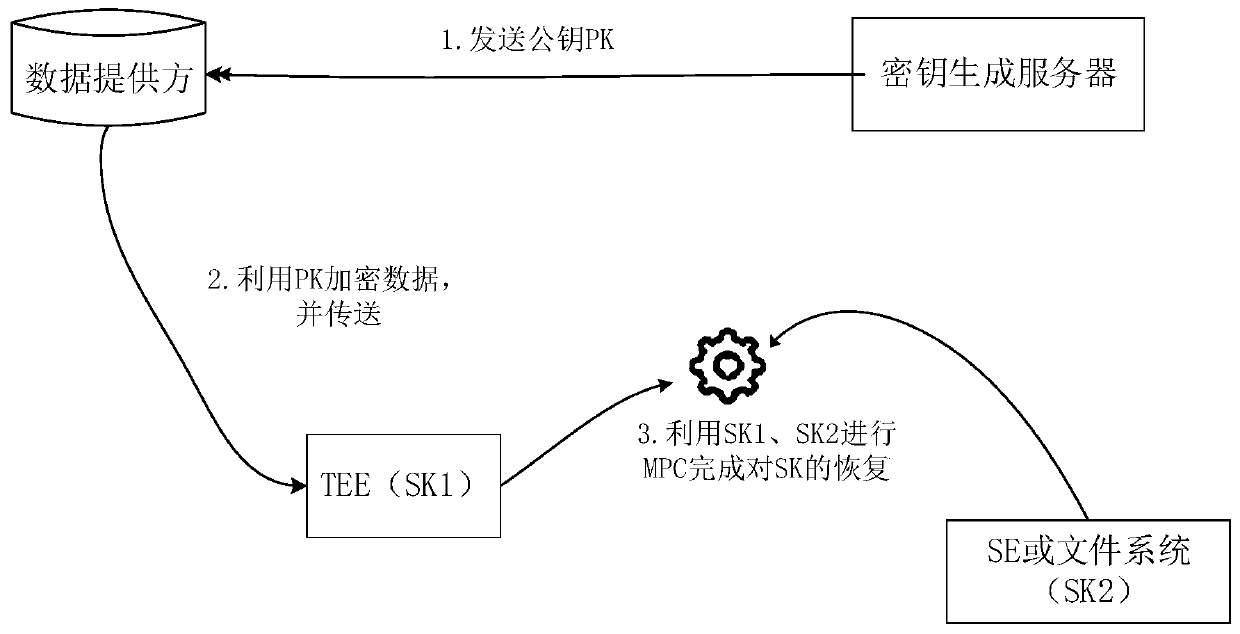
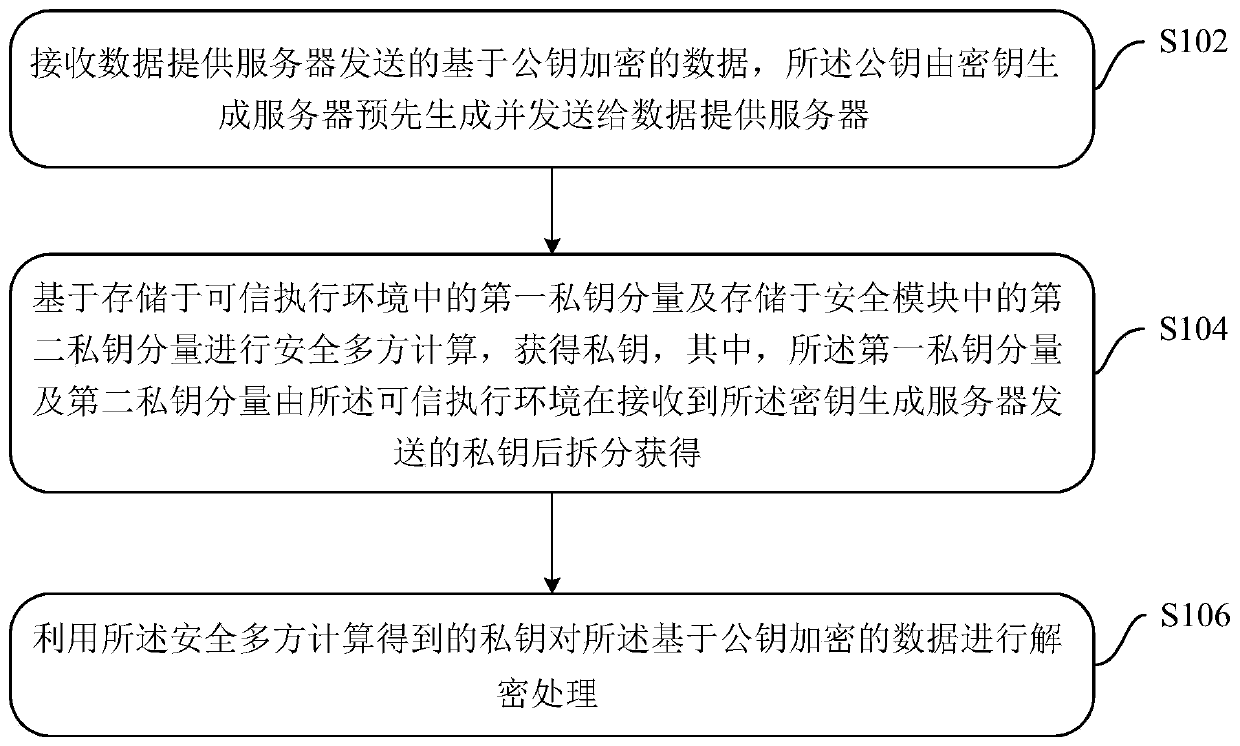
ActiveCN110278078AAchieve recoveryReduce theftKey distribution for secure communicationTerminal equipmentComputer module
The embodiment of the invention discloses a data processing method, device and system. The system comprises a key generation server, a terminal device and a data providing server, and a TEE and a security module are arranged in the terminal device. The data providing server encrypts the data based on a public key, and the public key is pre-generated by a key generation server. The TEE receives the data encrypted based on the public key and initiates secure multi-party calculation. The TEE and security module performs secure multi-party calculation by using a first private key component stored in the TEE and a second private key component stored in the security module in a joint manner to obtain a private key, and the first private key component and the second private key component are obtained by splitting the TEE after the TEE receives the private key sent by the key generation server. The TEE decrypts the encrypted data by using a private key obtained by secure multi-party calculation. By means of the embodiments of the present specification, the security of TEE hardware data processing can be enhanced.
Owner:JUZIX TECH SHENZHEN CO LTD
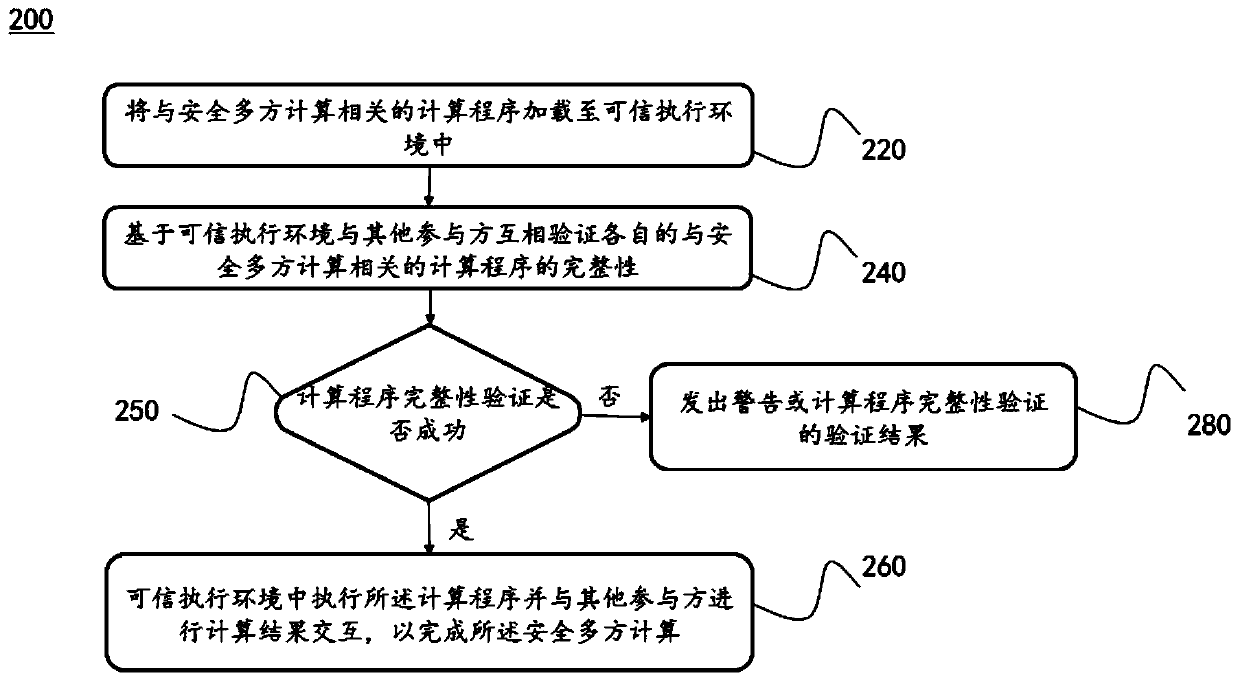
Secure multi-party calculation method and system based on trusted execution environment
The embodiment of the invention discloses a secure multi-party calculation method and system based on a trusted execution environment. The method comprises the following steps: loading a calculation program related to secure multi-party calculation into a trusted execution environment; based on the trusted execution environment and other participants, verifying the integrity of respective calculation programs related to secure multi-party calculation; If the integrity verification of the calculation program succeeds, executing the calculation program in a trusted execution environment and performing calculation result interaction with other participants to complete the secure multi-party calculation. According to the specification, a calculation program related to secure multi-party calculation is loaded to a trusted execution environment for running; malicious tampering of a calculation program is avoided, safe multi-party calculation suitable for a semi-honest attack model is improved into safe multi-party calculation suitable for a malicious attack model, and the purposes that private data is protected against leakage, and meanwhile the calculation speed is not reduced are achieved.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
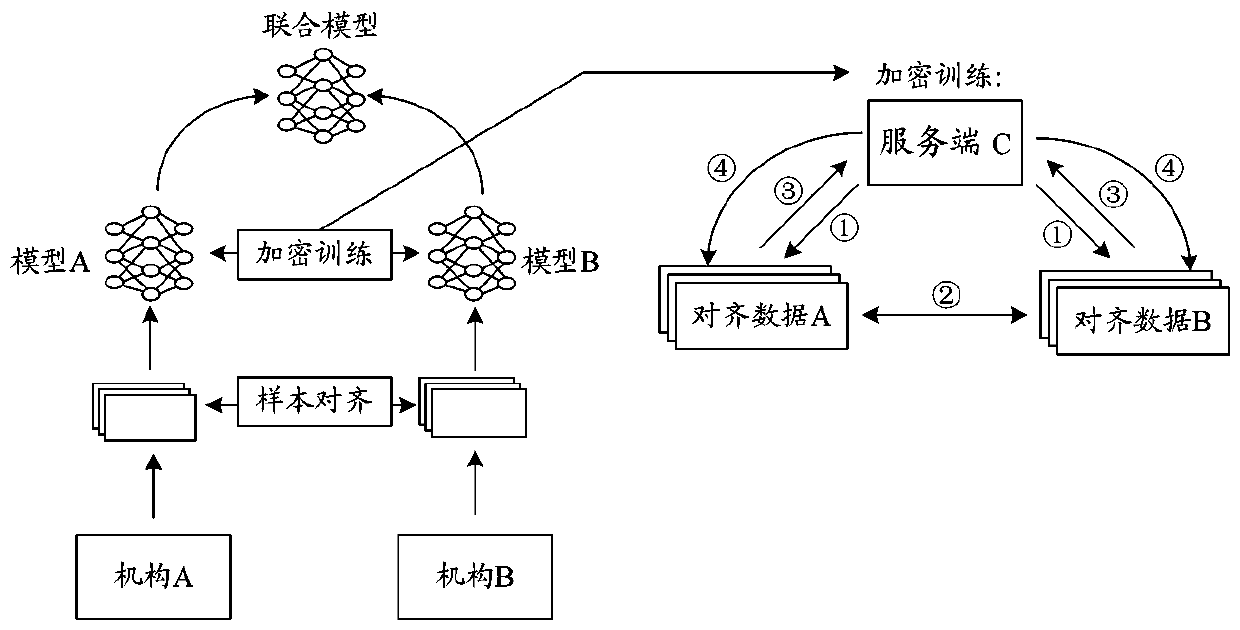
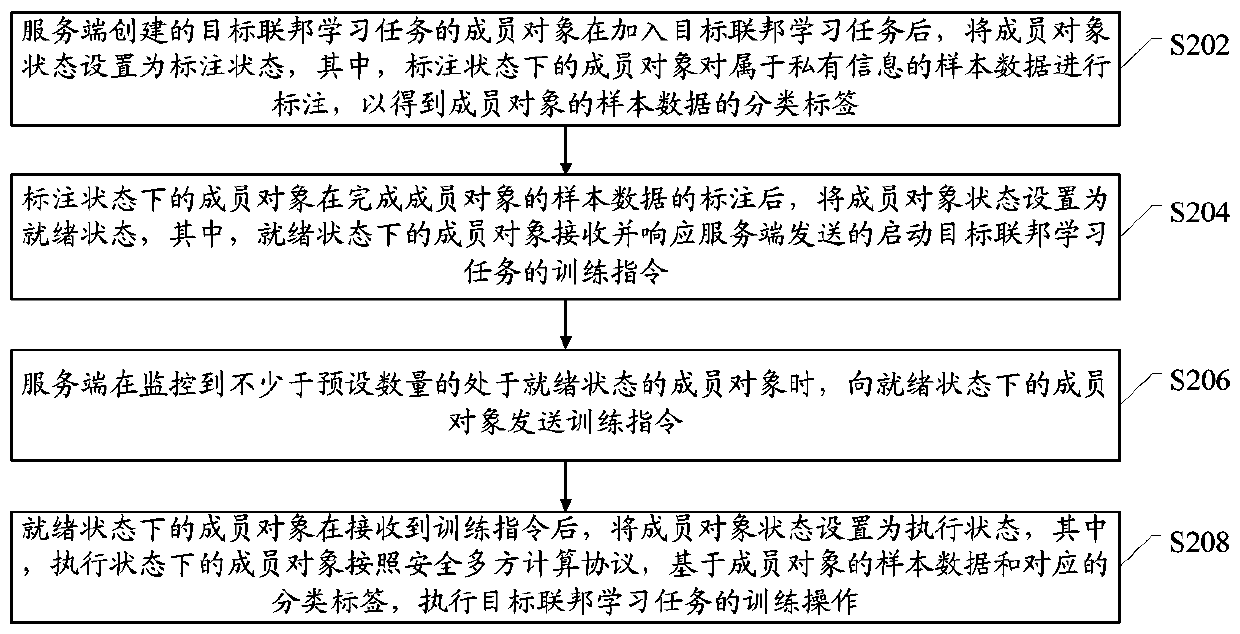
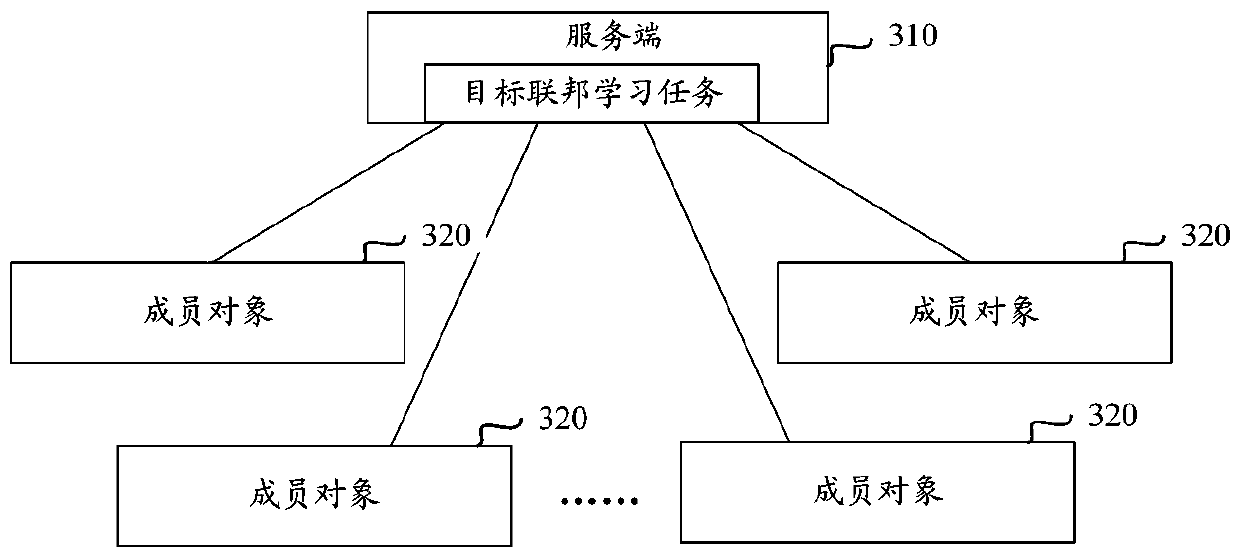
Federated learning method and system based on state machine, client and electronic equipment
The embodiment of the invention provides a federated learning method and system based on a state machine, a client and electronic equipment. After member objects of a target federation learning task created by the server are added into the target federation learning task, the states of the member objects are set as annotation states so as to annotate sample data belonging to private information, and classification labels of the sample data are obtained. And after the member objects in the labeling state are labeled, the states of the member objects are set to be ready states so as to receive and respond to a training instruction which is sent by the server and is used for starting the target federated learning task. And when the server monitors not less than a preset number of member objects in the ready state, a training instruction is sent to the member objects in the ready state. And after receiving the training instruction, the member object in the ready state sets the member object state as an execution state, so as to execute the training operation of the target federated learning task based on the sample data and the corresponding classification label according to a secure multi-party computing protocol.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
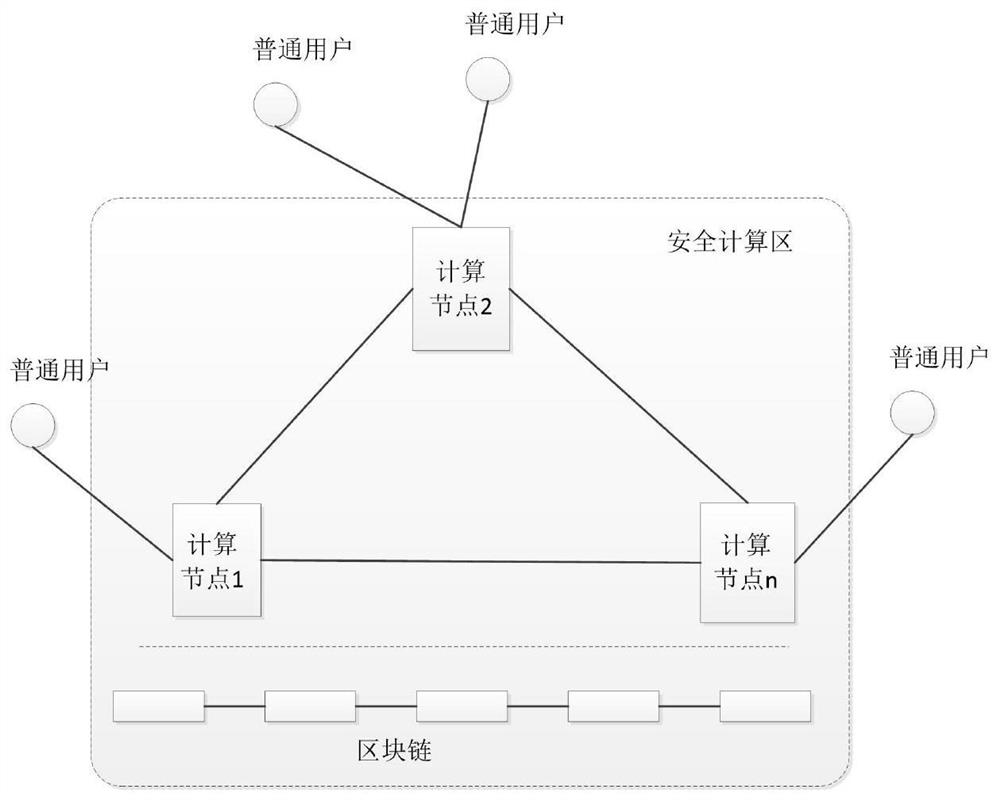
Secure multi-party computing method based on trusted hardware and block chain
PendingCN112380565AImplement secure multi-party computationImprove execution efficiencyDigital data protectionPlatform integrity maintainanceComputer hardwareTrusted hardware
The invention discloses a secure multi-party computing method based on trusted hardware and a block chain, which comprises the following steps that: a user encrypts input parameters and inputs the encrypted input parameters into a trusted execution environment, the trusted execution environment exchanges data with other participants through the block chain, executes a computing function in the trusted execution environment after collecting all the inputs, and outputs a result; based on the scheme, a plurality of participants can complete data sharing of security privacy under the condition ofprotecting respective data privacy, and finally, a distributed arbitrary multi-party joint computing task is realized. A fair data exchange process of multi-party participants is realized by utilizinga block chain, meanwhile, privacy protection is carried out on data exchange by utilizing an encryption algorithm, and the obtained encrypted data is decrypted and calculated in a trusted computing environment, so that an efficient and safe multi-party computing process is realized.
Owner:TIANYI ELECTRONICS COMMERCE
Method and device for efficient multiparty multiplication
InactiveCN1875569APromote generationReduce processingKey distribution for secure communicationComputations using contact-making devicesTheoretical computer scienceElGamal encryption
The invention introduces, in the framework of secure multiparty computation based on homomorphic threshold cryptosystems, a protocol and a special type of multiplication gate that can be realized in a surprisingly simple and efficient way using just standard homomorphic threshold ElGamal encryption. As addition gates are essentially for free, the conditional gate not only allows for building a circuit for any function, but actually yields efficient circuits for a wide range of tasks.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Data link method based on privacy protection and secure multi-party computing
ActiveCN110609831AEnsure safetyGuaranteed privacyDigital data information retrievalCharacter and pattern recognitionClassification methodsPrivacy protection
The invention discloses a data link method based on privacy protection and secure multi-party computing. According to the method, local data is partitioned by adopting an improved k-means classification method, so that the comparison frequency among data records is reduced, the method has relatively good expandability for a large database, and the execution efficiency of privacy protection recordlinks is also improved; according to the method, by utilizing the property of the reversible matrix and a Shamir threshold secret sharing scheme, good safety is ensured when two or more recording-level Bloom filters are relatively similar, and user sensitive information is prevented from being acquired by an enemy. The method provided by the invention has good expansibility and small calculation overhead, and is suitable for a real environment with a large real data volume.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
A secure multi-party calculation implementation method and device, a computer device and a storage medium
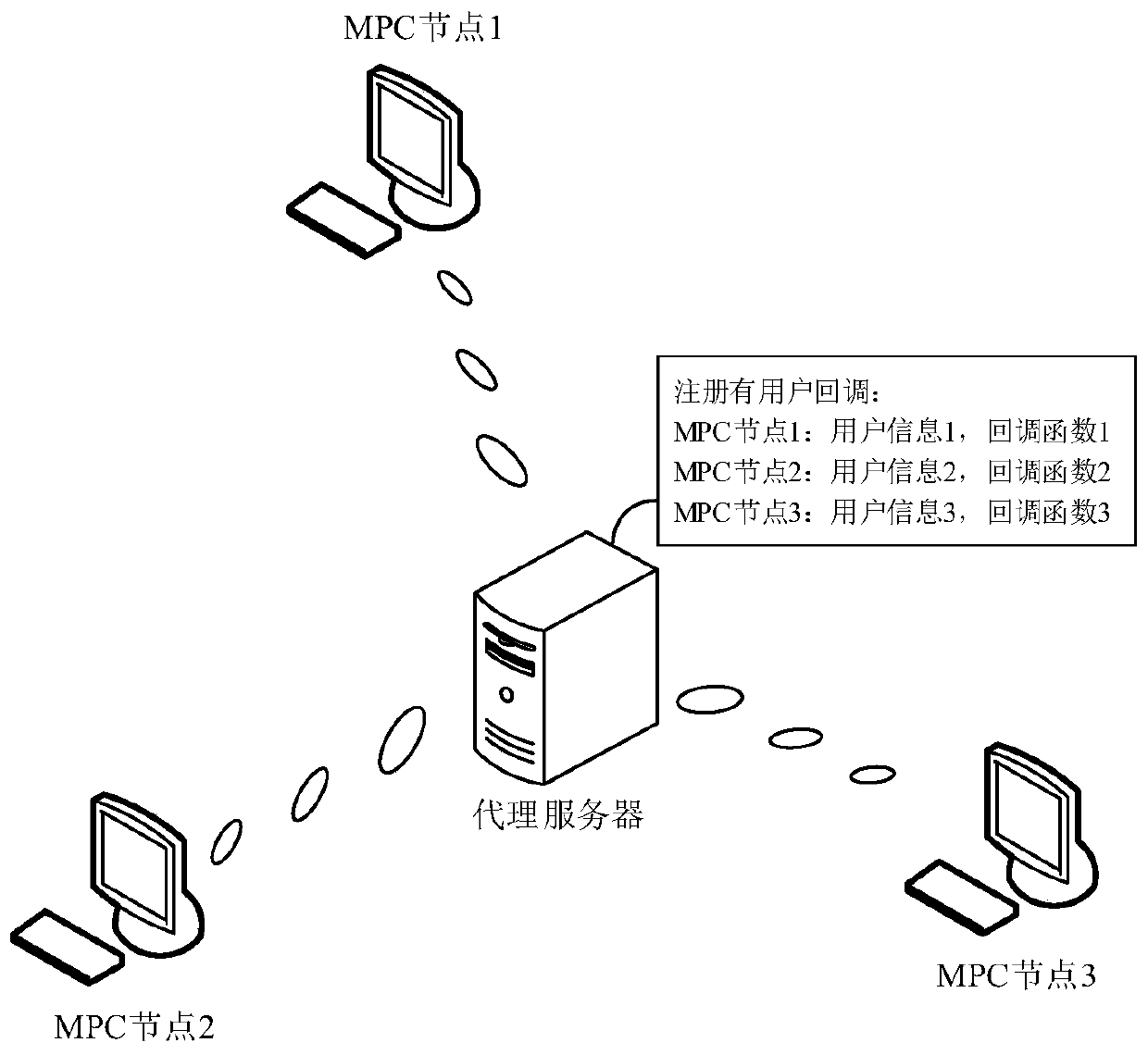
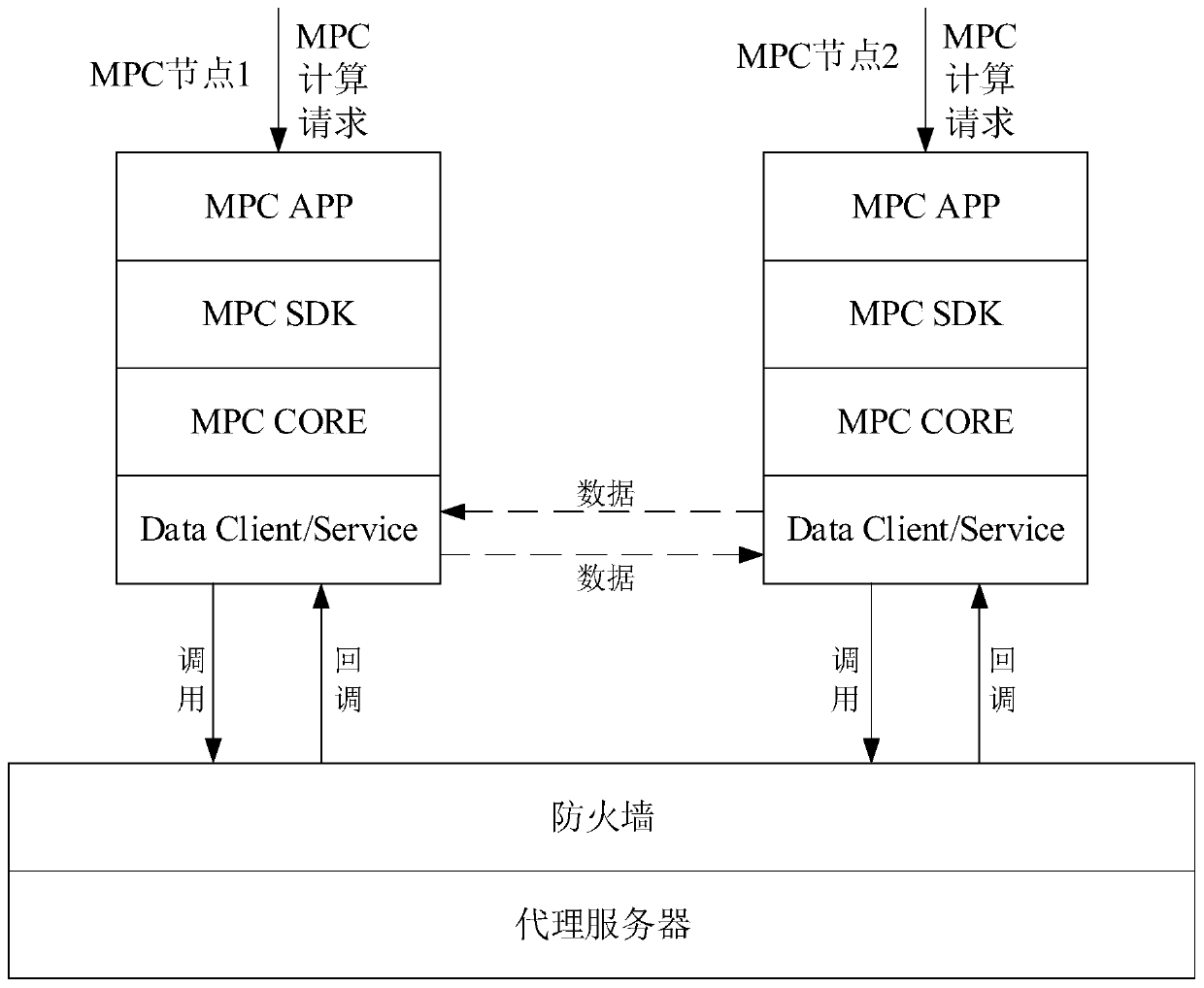
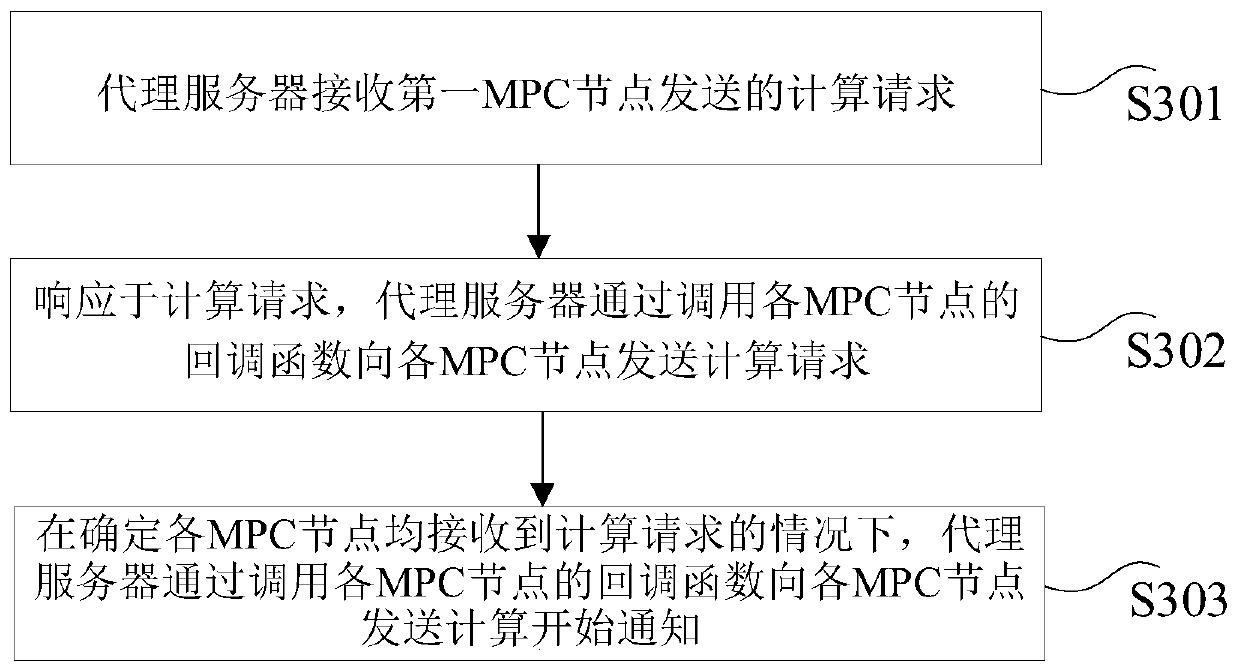
InactiveCN110175461AImprove computing efficiencyImprove efficiencyDigital data protectionProxy serverSecure multi-party computation
The invention provides a secure multi-party calculation implementation method and device, a computer device and a storage medium. The method comprises the steps that a proxy server receives a calculation request sent by a first MPC node, wherein the first MPC node is one MPC node in a plurality of MPC nodes, and a callback function of each MPC node in the plurality of MPC nodes is registered in the proxy server; in response to the calculation request, the proxy server sends the calculation request to each MPC node by calling the callback function of each MPC node; and under the condition thatit is determined that each MPC node receives a calculation request, the proxy server sends a calculation start notification to each MPC node by calling the callback function of each MPC node, whereinthe calculation start notification is used for indicating each MPC node to execute the safe multi-party calculation. According to the above method, the secure multi-party calculation cooperation service can be constructed in a more flexible and configurable manner, and the task cooperation efficiency and the calculation efficiency are effectively improved.
Owner:JUZIX TECH SHENZHEN CO LTD
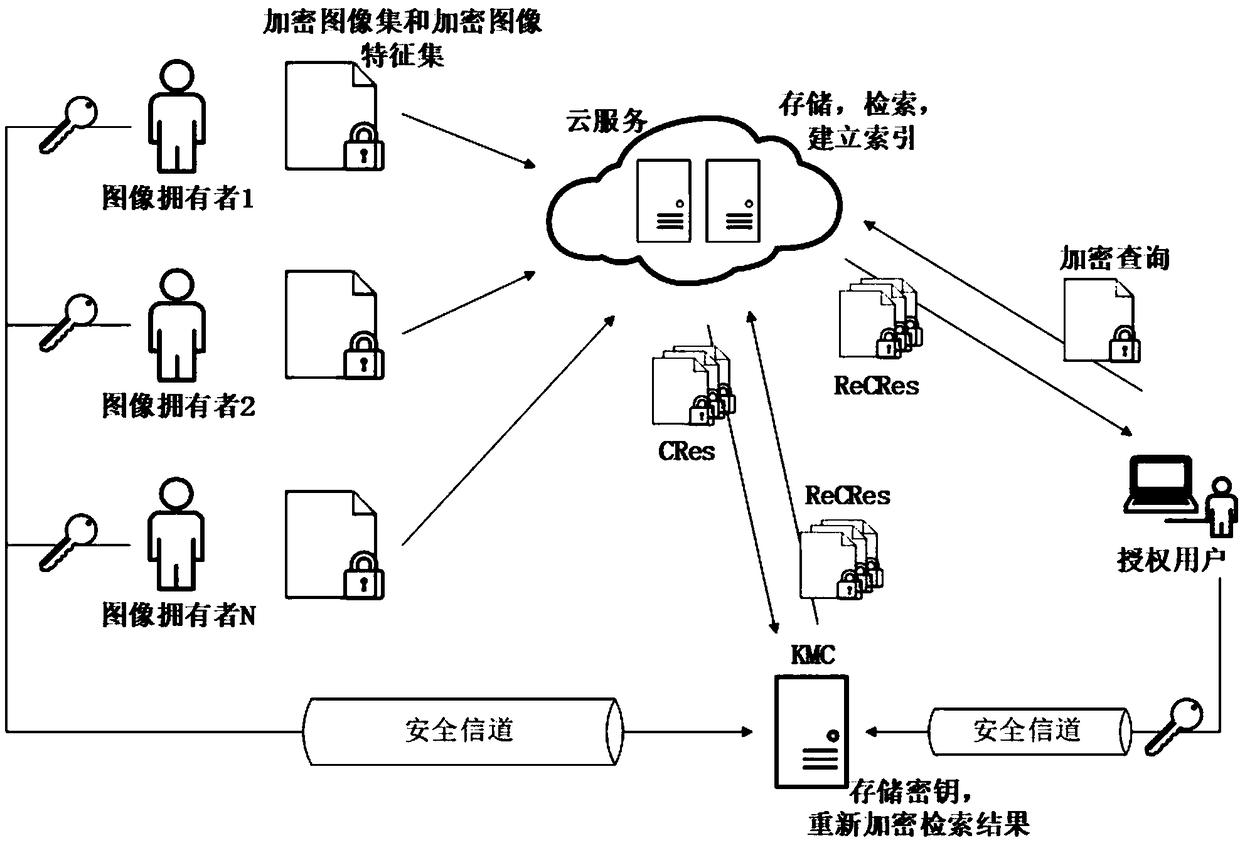
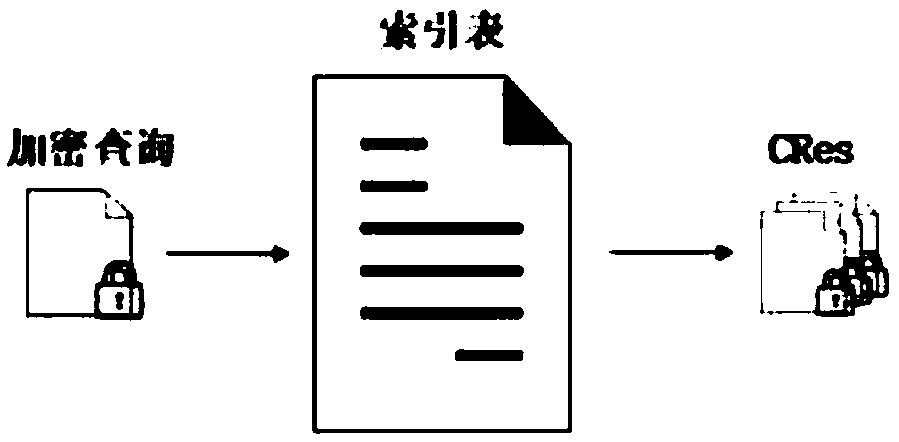
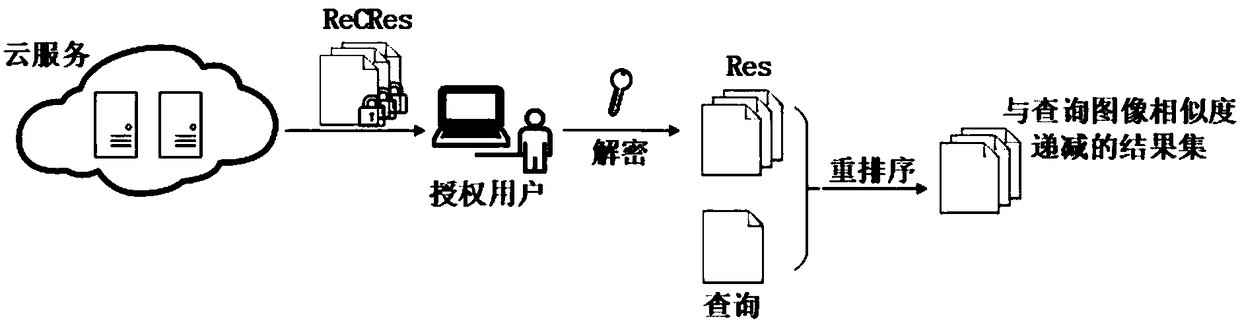
Multi-source encrypted image retrieval method supporting privacy protection
ActiveCN108256031AReduce overheadSolve the problem of image privacy protectionTransmissionSpecial data processing applicationsPrivacy protectionImaging Feature
The invention provides a multi-source encrypted image retrieval method supporting privacy protection, and belongs to the technical field of encrypted image retrieval. The method comprises the steps that thought encryption image features of secure multiparty computation is used, an image owner makes images, encrypted with a private key, of the owner and the image features outsourced to a cloud server, and the cloud server performs retrieval in an encrypted image library submitted by a user and returns the encrypted retrieval result to a query user. Accordingly, the image privacy protection problem occurring when multiple image owners outsource the images to a cloud for retrieval can be solved, the image owner and the user do not need a communication secret key, the communication cost is reduced, and the actual application prospect is better met; meanwhile, a new image similarity measurement method is provided, by means of the measurement method, the phenomenon that in the retrieval process, similarity information between the images stored in the cloud server is revealed to the cloud server can be prevented, and the private information of the images on the cloud server is further protected.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
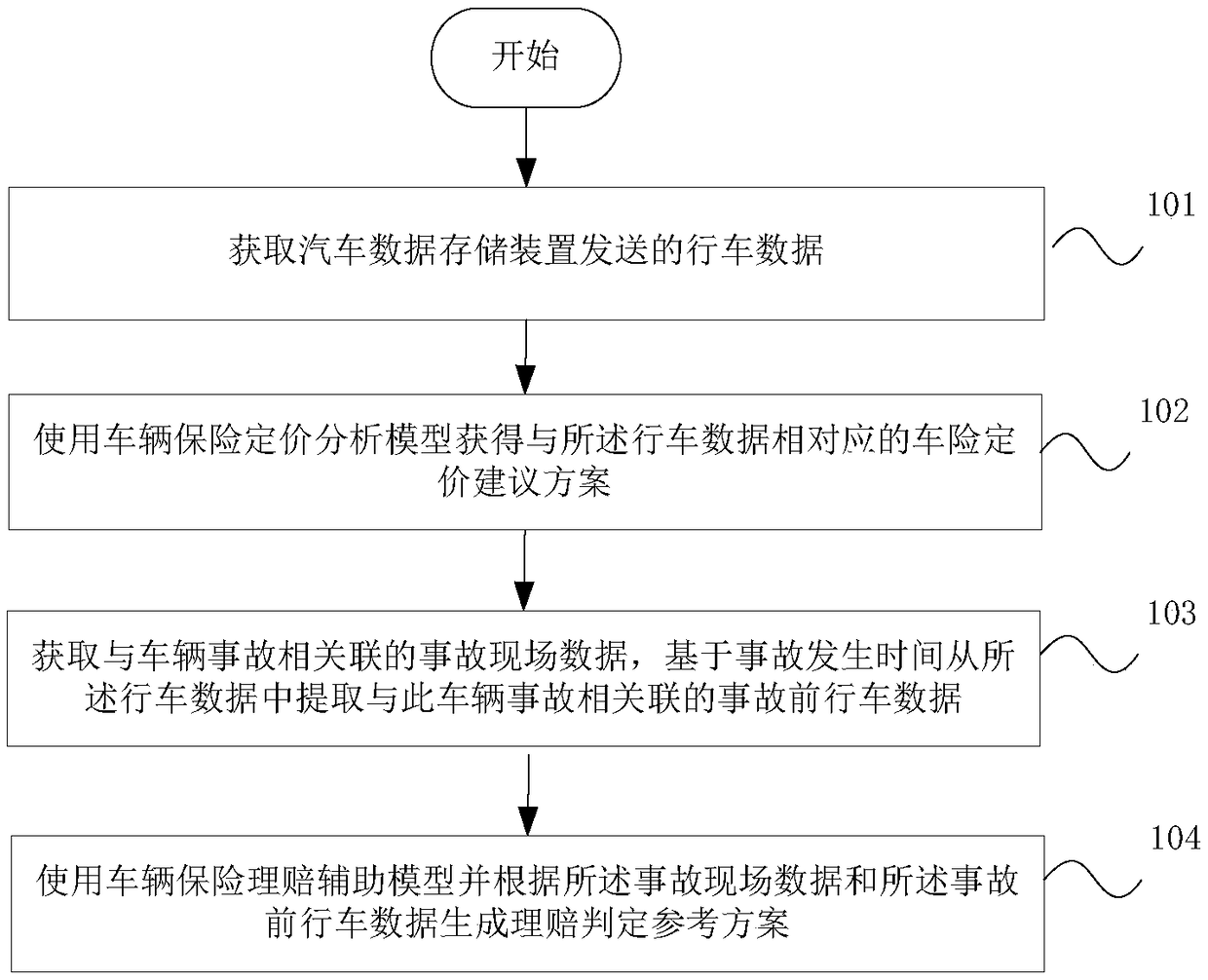
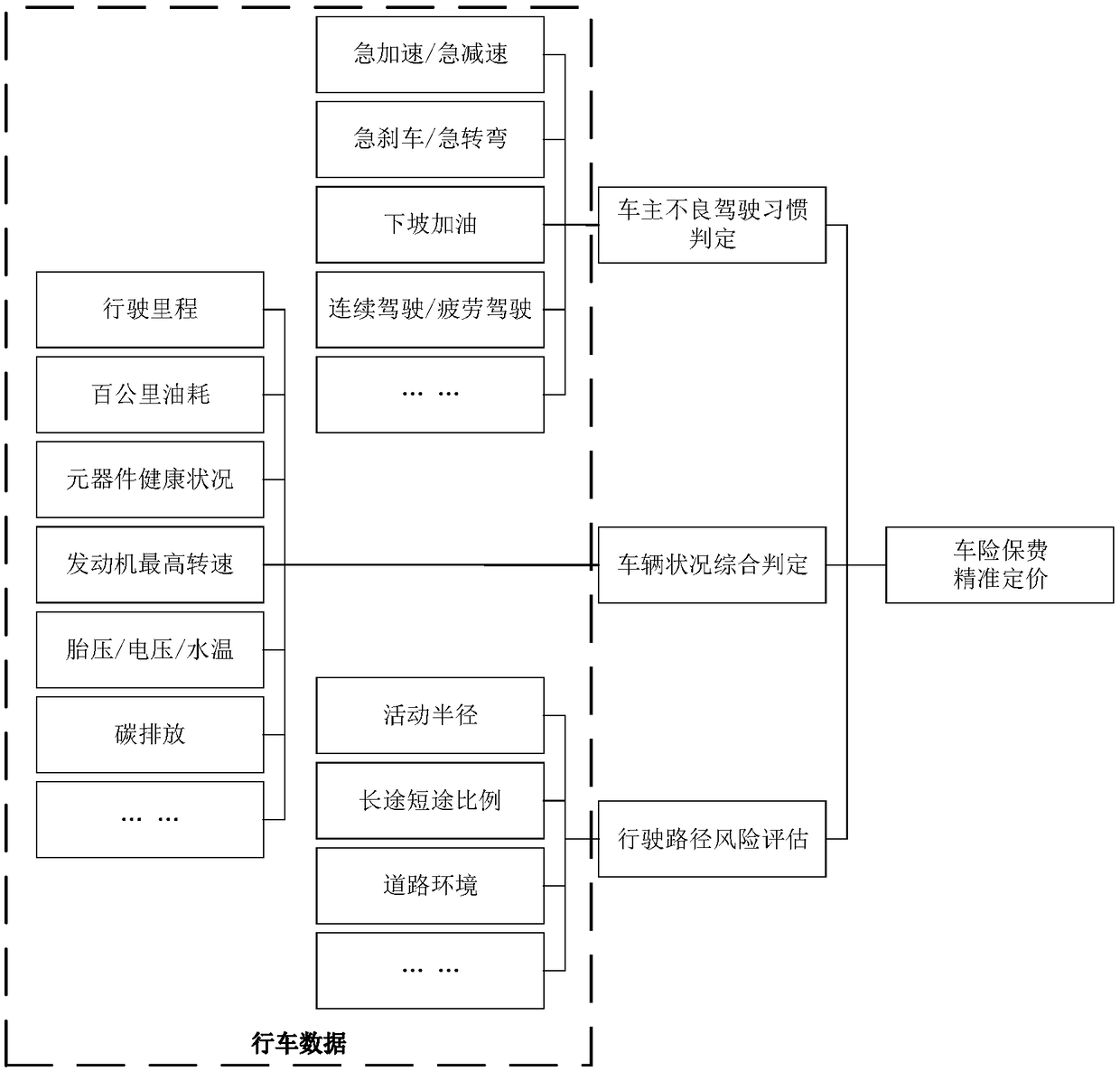
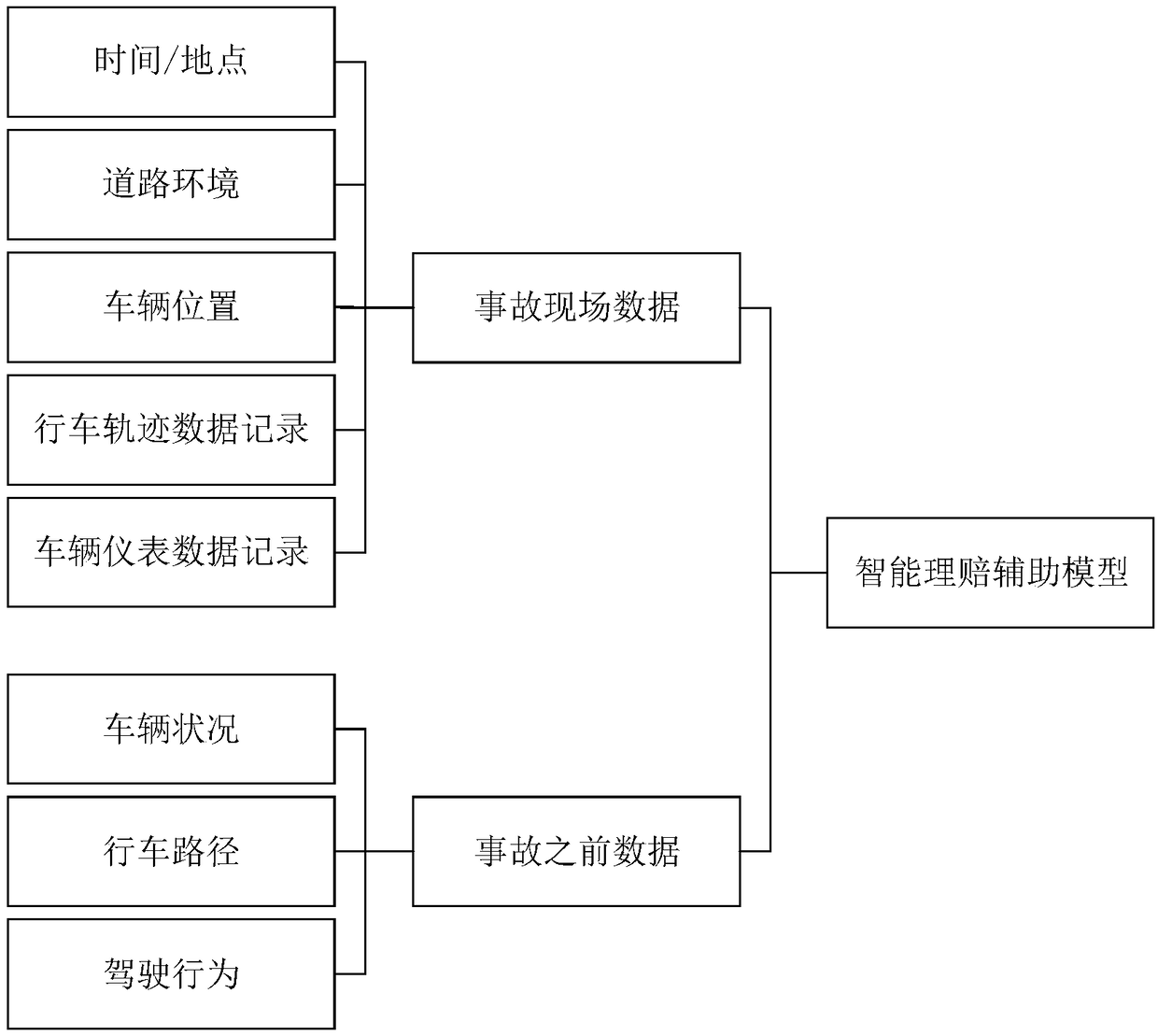
Vehicle insurance service data analysis method and system
InactiveCN108734592AGuaranteed reliabilityAvoid dishonest nodesFinanceInterconnectionAnalysis method
The embodiment of the invention discloses a vehicle insurance service data analysis method and system. The method comprises the steps of obtaining a vehicle pricing suggestion scheme corresponding todriving data through utilization of a vehicle insurance pricing analysis module; obtaining accident site data associated with a vehicle accident, and extracting before-accident driving data associatedwith the vehicle accident from the driving data based on accident occurring time; and generating a claim settlement decision reference scheme according to the accident site data and the before-accident driving data through utilization of a vehicle insurance claims settlement auxiliary model. According to the method and the system provided by the invention, the smart car information interconnection industry-oriented vehicle insurance data analysis method based on a safety multiparty computing system is provided; the reference for vehicle insurance precise pricing can be provided; a vehicle before-event risk threshold is computed; an accident process and an after-event site are analyzed; the reference for precise claim settlement decision can be provided; and the data is stored and verifiedthrough adoption of a blockchain technology, so the data is prevented from being tampered or disturbed.
Owner:深圳市图灵奇点智能科技有限公司 +1
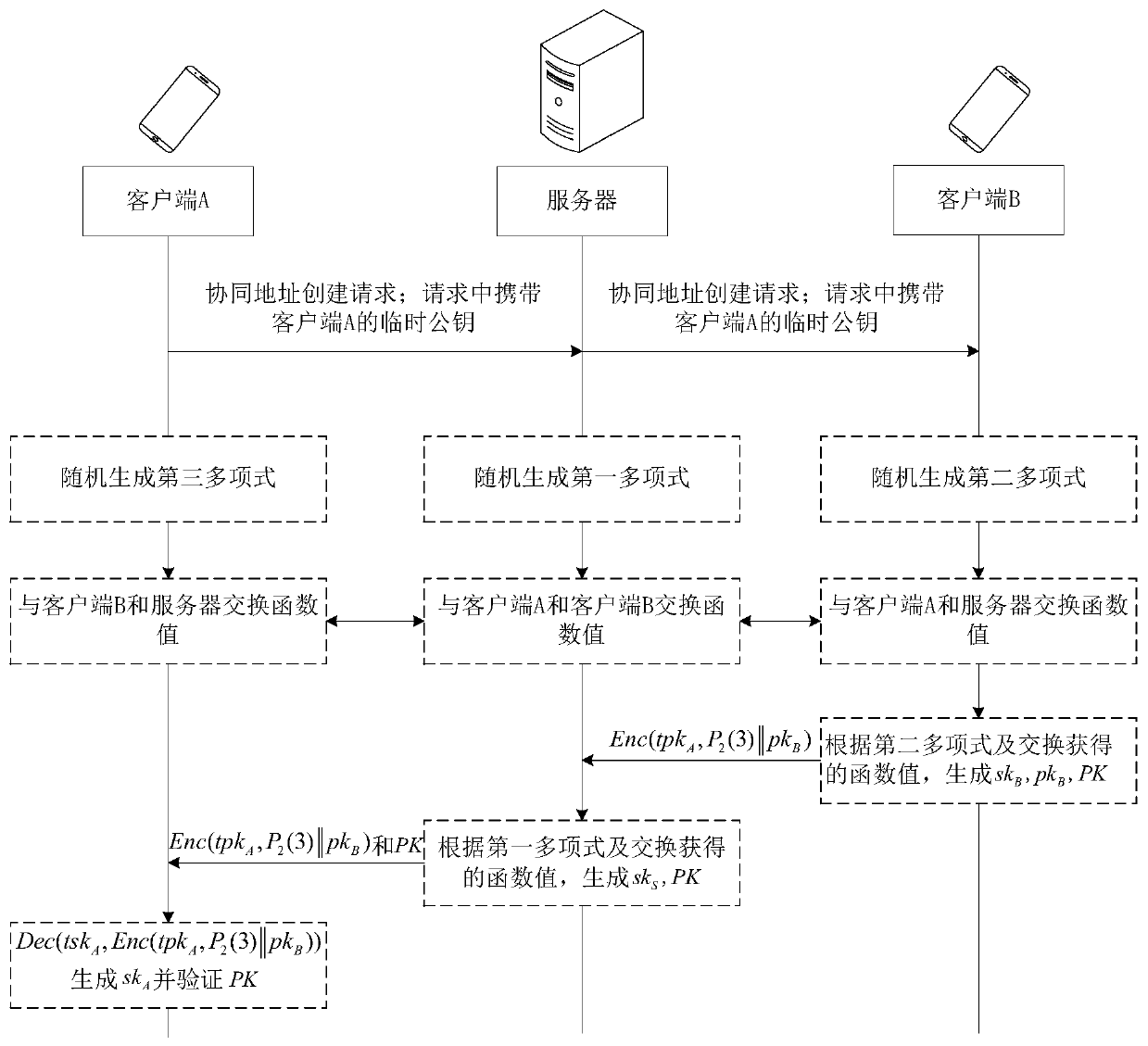
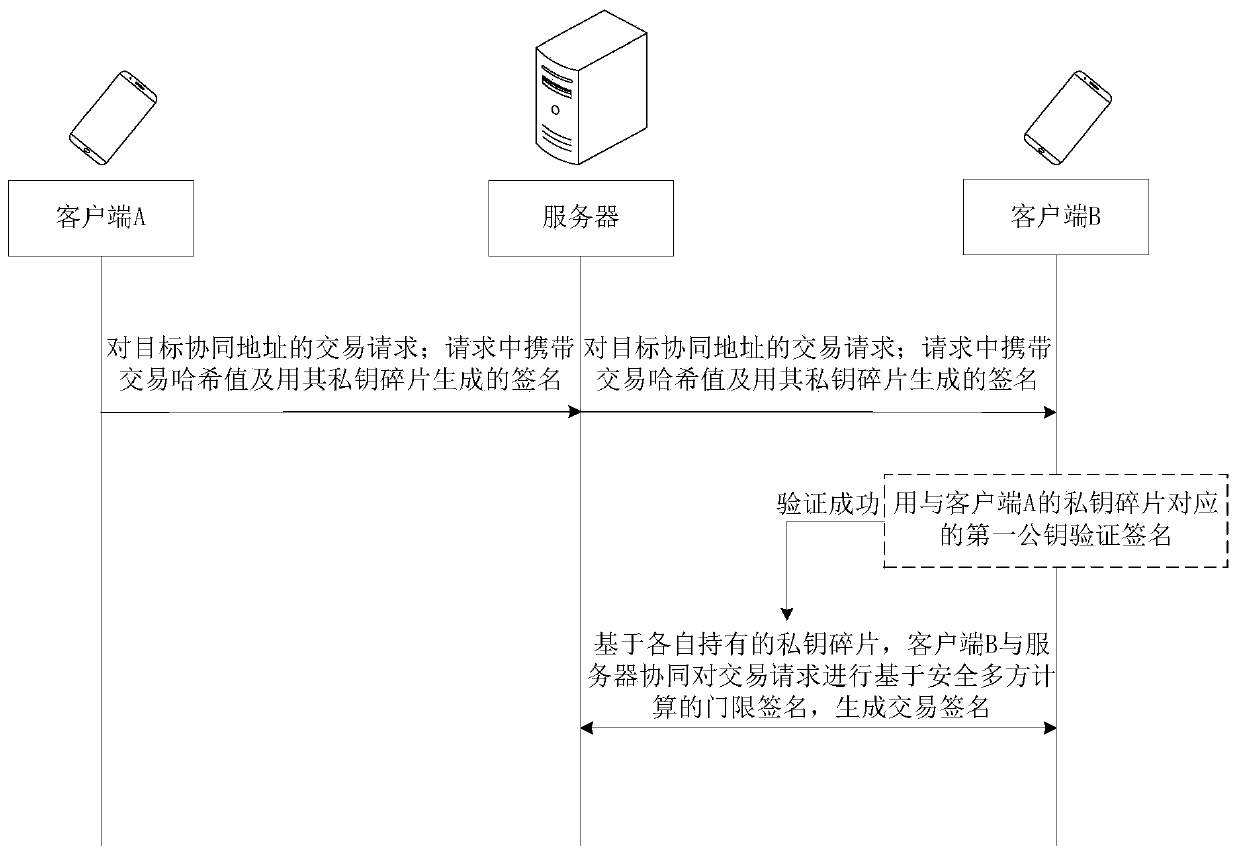
Private key recovery method and device, collaborative address creation method and device, collaborative address signing method and device and storage medium
ActiveCN110289968AImprove securityImprove convenienceKey distribution for secure communicationFinancePasswordSecure multi-party computation
The embodiment of the invention provides a private key recovery method and device, a collaborative address creating method and device, a collaborative address signing method and device and a storage medium. The collaborative address signing method comprises the following steps: receiving a transaction request initiated by a first client for a target cooperative address, wherein the transaction request comprises a transaction hash value and a signature generated by the first client by using a private key fragment of the first client; verifying the signature by using a first public key corresponding to the private key fragment; and when the signature passes the verification, based on private key fragments held by the user, cooperating with a server to carry out threshold signature based on secure multi-party calculation on the transaction request so as to generate a transaction signature. According to the embodiment of the invention, the security and convenience of the password currency wallet can be improved.
Owner:JUZIX TECH SHENZHEN CO LTD
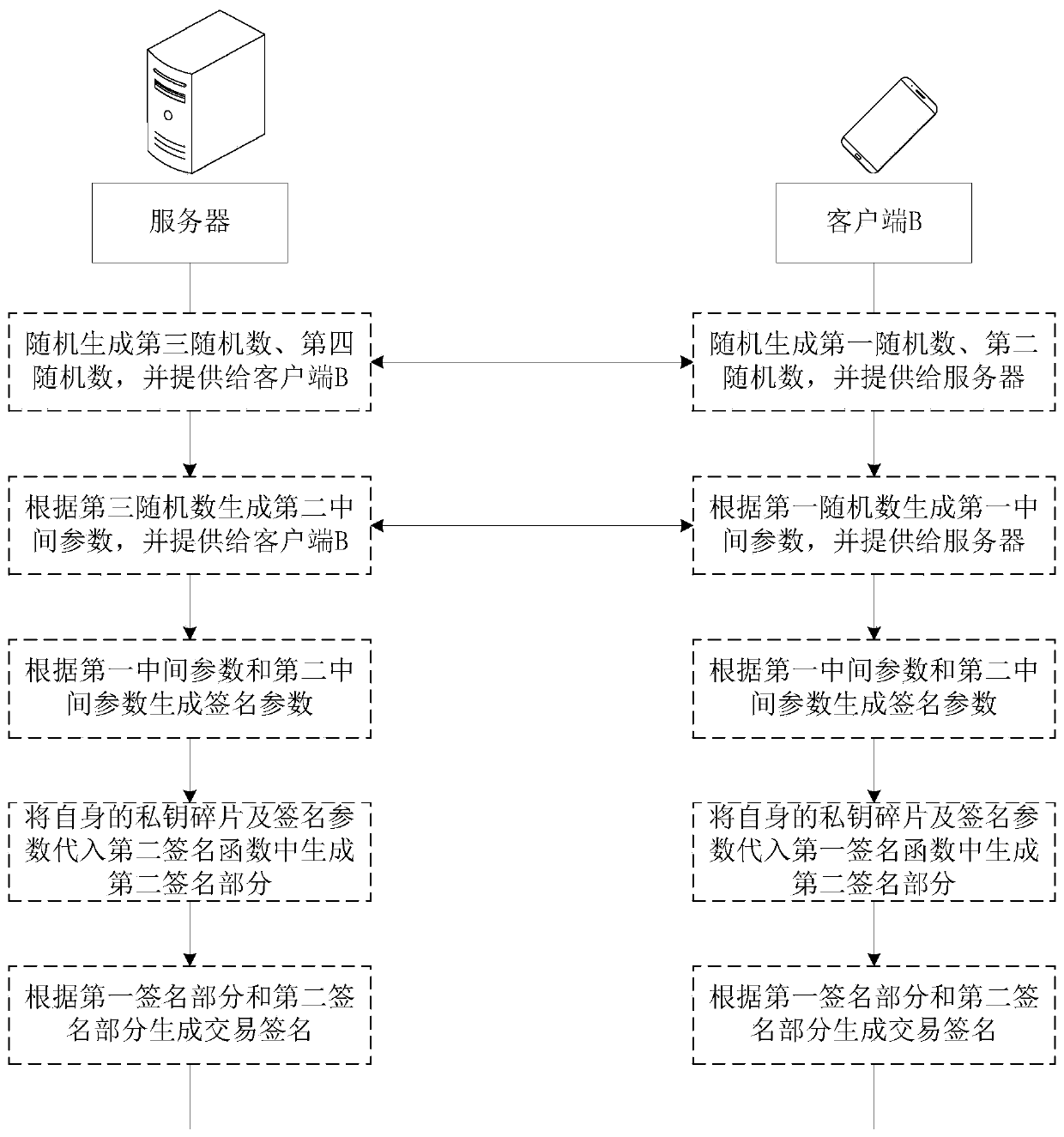
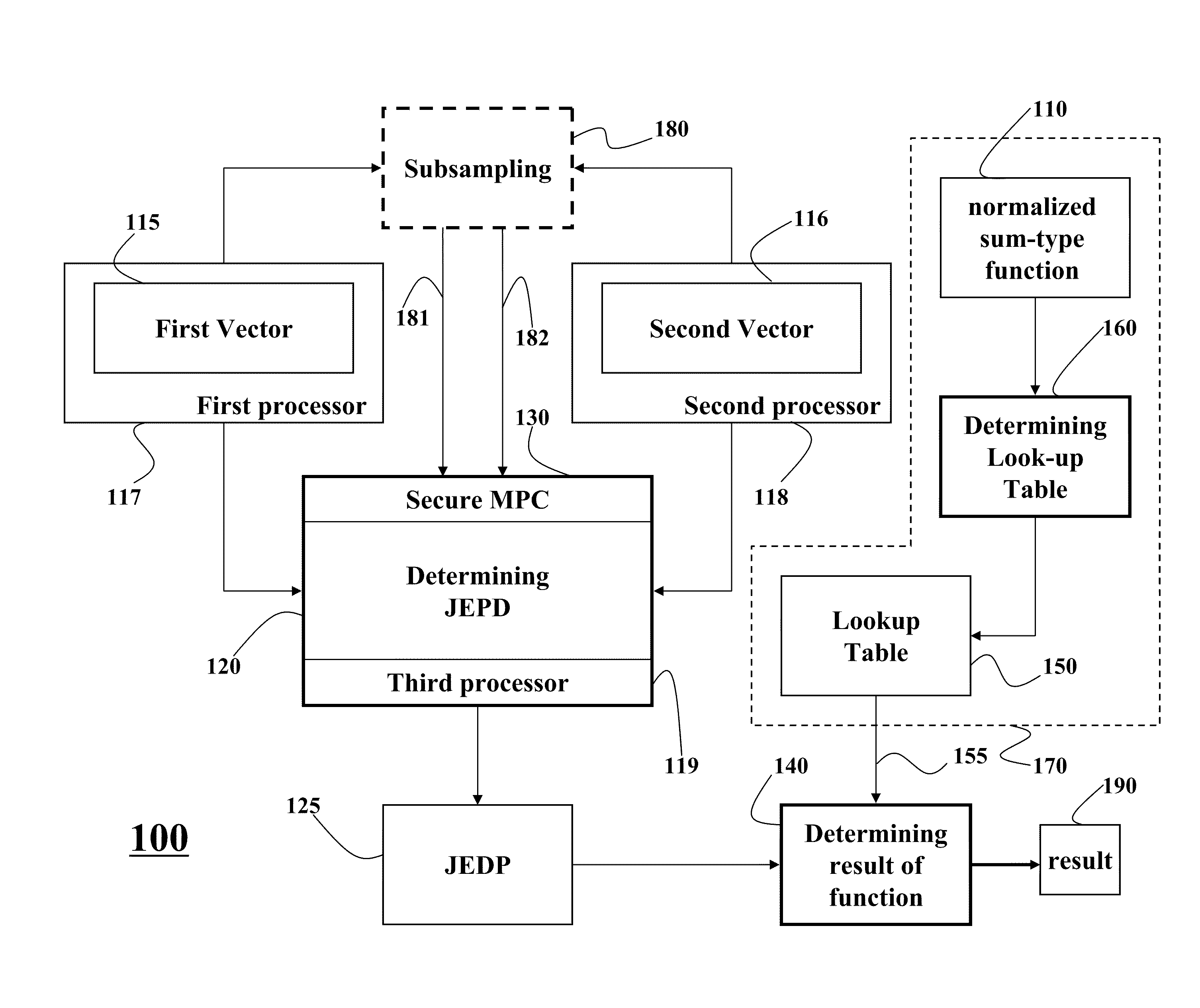
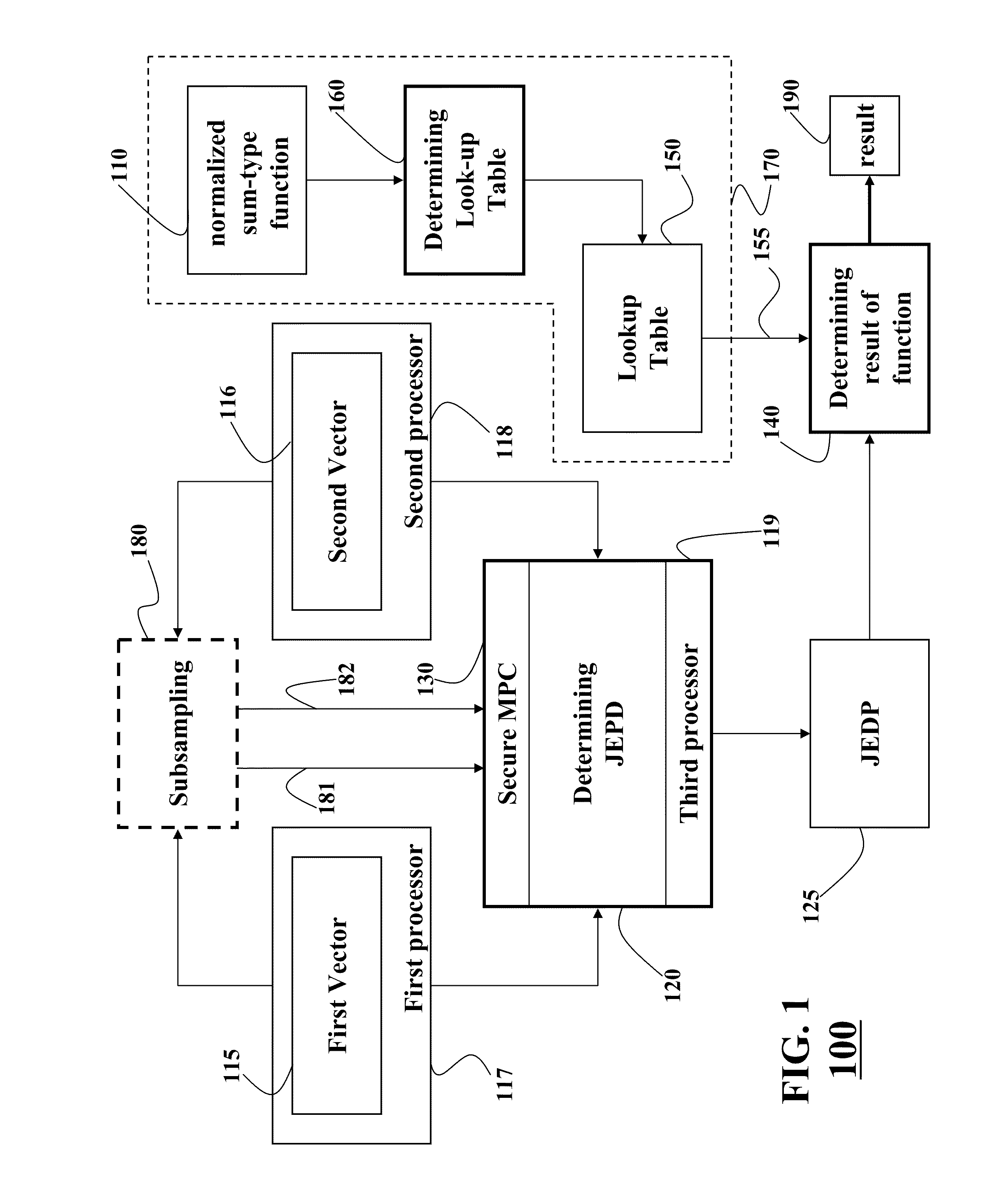
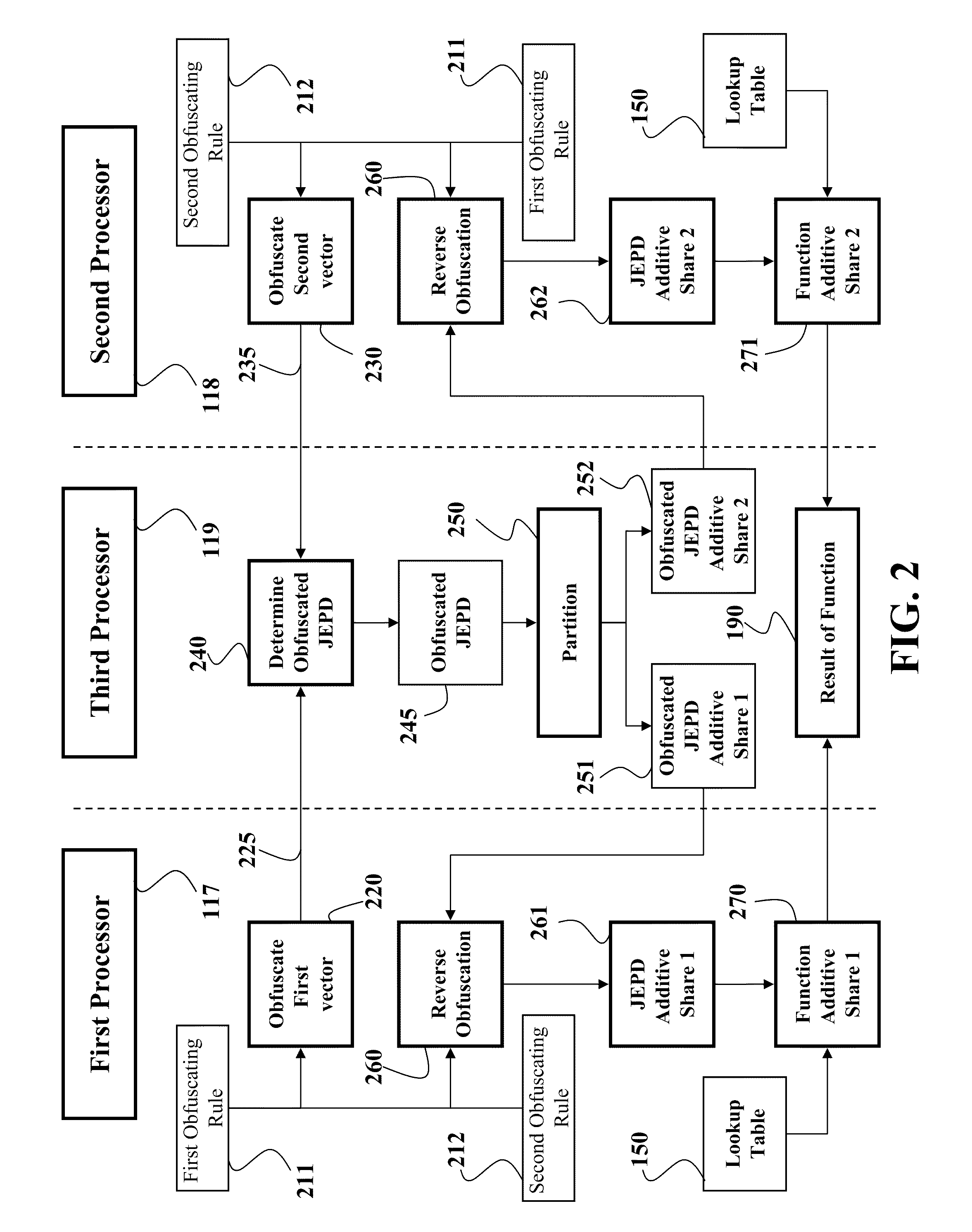
Secure Multi-Party Computation of Normalized Sum-Type Functions
ActiveUS20110040820A1Reduce complexityReduce transmissionCode conversionCoding detailsSecure multi-party computationEmpirical probability
Embodiments of present invention disclose a system and a method for determining a result of a function applied to a first vector and a second vector, wherein the function is a normalized sum-type function. The first vector is stored at a first processor, and the second vector is stored at a second processor. The system and the method determine a joint empirical probability distribution (JEPD) of the first vector and the second vector using a secure multi-party computation. The function is determined as a normalized summation of products of values of the JEPD with corresponding values of the function.
Owner:MITSUBISHI ELECTRIC RES LAB INC
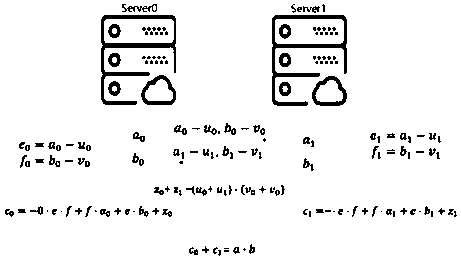
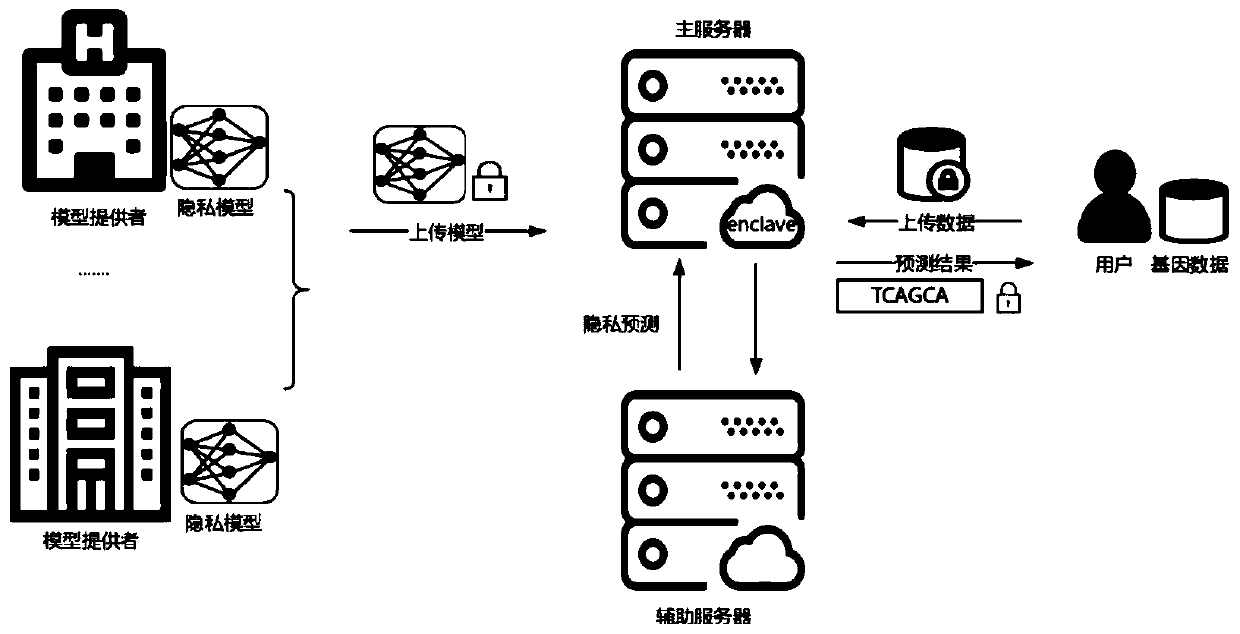
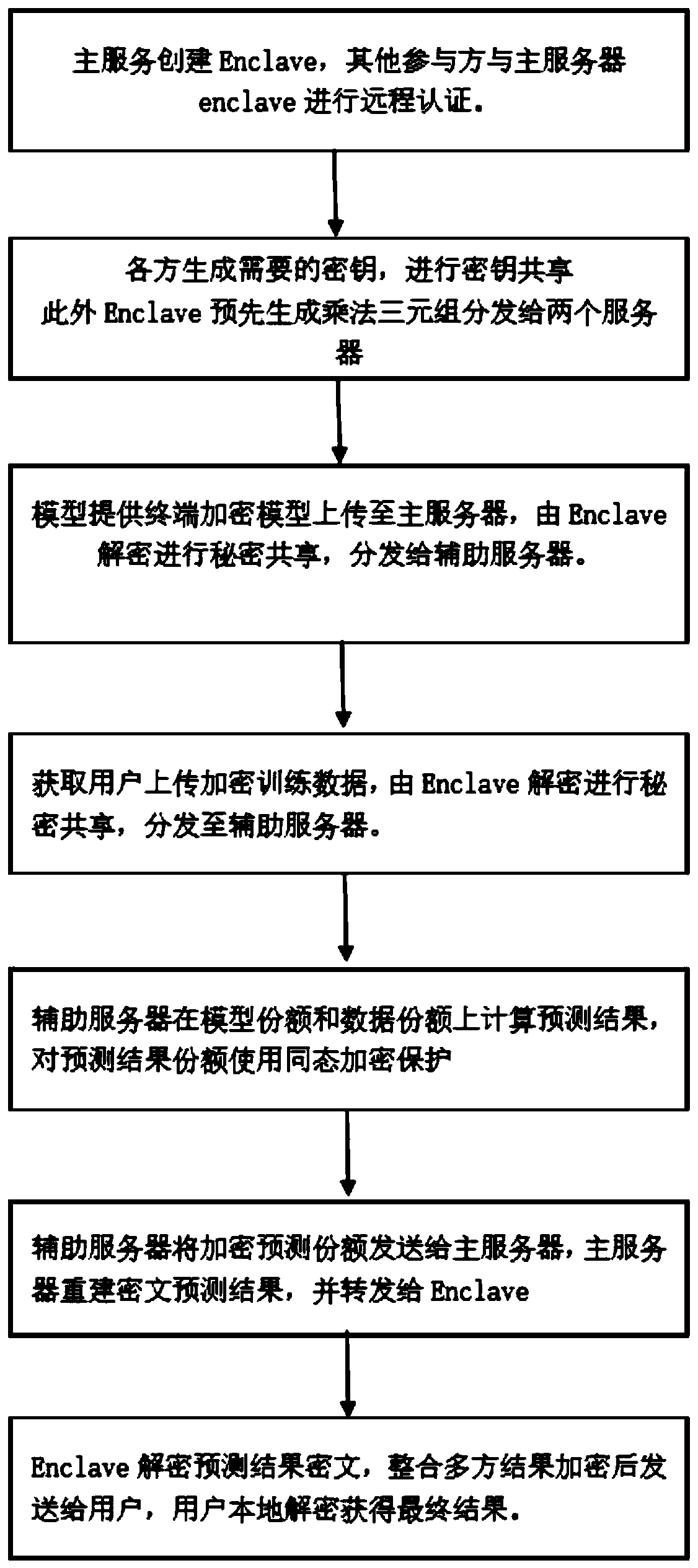
Data privacy protection-oriented machine learning prediction method and system
ActiveCN111275202APrevent theftReliable two-way securityDigital data protectionMachine learningData privacy protectionEngineering
The invention provides a data privacy protection-oriented machine learning prediction method and system. The method comprises the following steps of obtaining encrypted data; the main server creates acredible area, and decrypts the obtained to-be-predicted data and the prediction model in the credible area; the main server carries out secret sharing on the decrypted to-be-predicted data and the prediction model to obtain a data secret share and a model share respectively, and distributes the data secret share and the model share to an unconspired auxiliary server and the main server; the auxiliary server and the main server respectively perform prediction calculation to obtain a prediction result share; and the main server carries out secret reconstruction on all the prediction result shares, forwards the reconstructed prediction result shares to the trusted area for integration and encryption, and sends the reconstructed prediction result shares to the to-be-predicted data providingterminal, and the data providing terminal decrypts the reconstructed prediction result shares to obtain a prediction result predicted according to the model. Privacy security of the two parties is protected by combining secure multi-party computing and an SGX technology, and the security problem in the prediction service providing process is solved.
Owner:UNIV OF JINAN
KNN classification service system and method supporting privacy protection
ActiveCN110011784AEnsure privacy is not leakedRealize Analysis and PredictionCharacter and pattern recognitionCommunication with homomorphic encryptionCryptographic protocolPrivacy protection
The invention belongs to the field of machine learning and privacy protection, and particularly relates to a KNN classification service system and method supporting privacy protection. The architecture of the system comprises a model owner and a client; the method of the KNN classification service system supporting privacy protection comprises the following steps: 1) a preparation stage: generating a public key and a private key, and encrypting training data according to the public key; 2) a classification stage: two parties interact with keys; and the client encrypts to-be-tested data throughthe public key, the model owner completes encrypted data classification by cooperating with the client through a security protocol based on the encrypted training data, and finally obtains a classification result and sends the classification result to the client. According to the method, training data and to-be-tested data are encrypted by using homomorphic encryption calculation, a secure basicprotocol is constructed by combining a secure multi-party calculation technology and homomorphic encryption, and a secure KNN classifier is constructed based on the secure basic protocol, so that thetwo parties realize analysis and prediction of personal data on the premise of ensuring that the privacy of the personal data is not leaked.
Owner:NORTHEASTERN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com