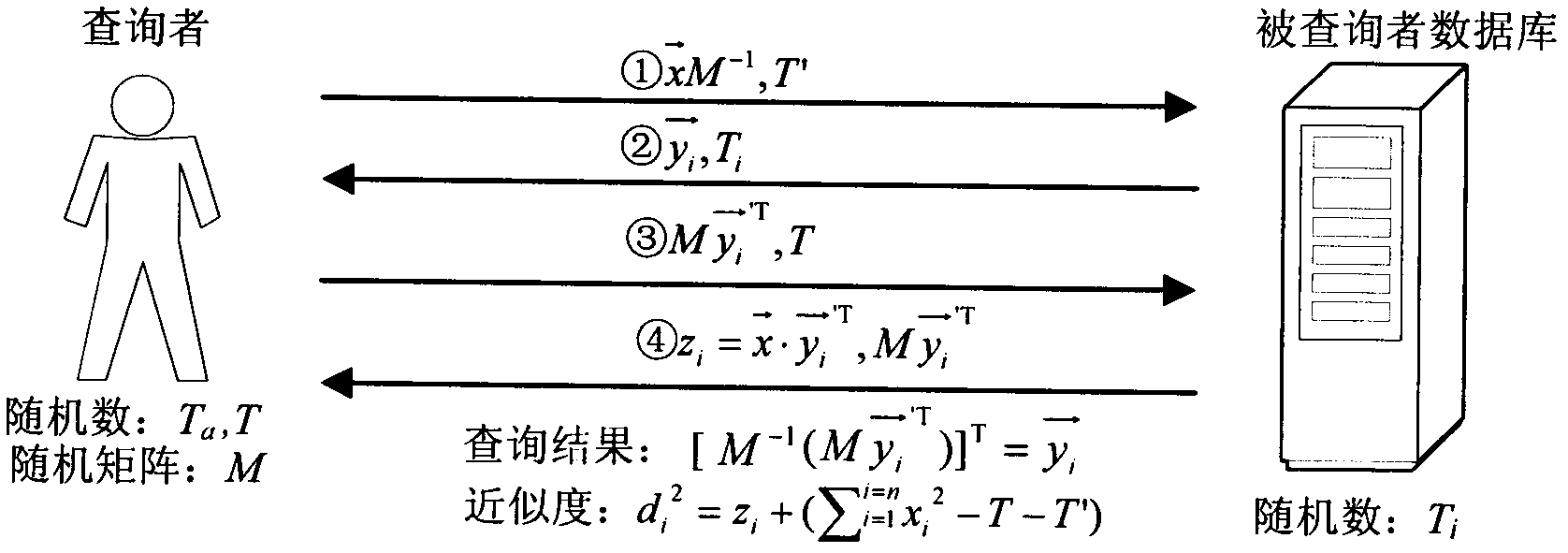Internet of things application scene-based protection method of privacy query and private identity verification
A technology of identity verification and application scenarios, applied in the fields of secure data query and identity verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
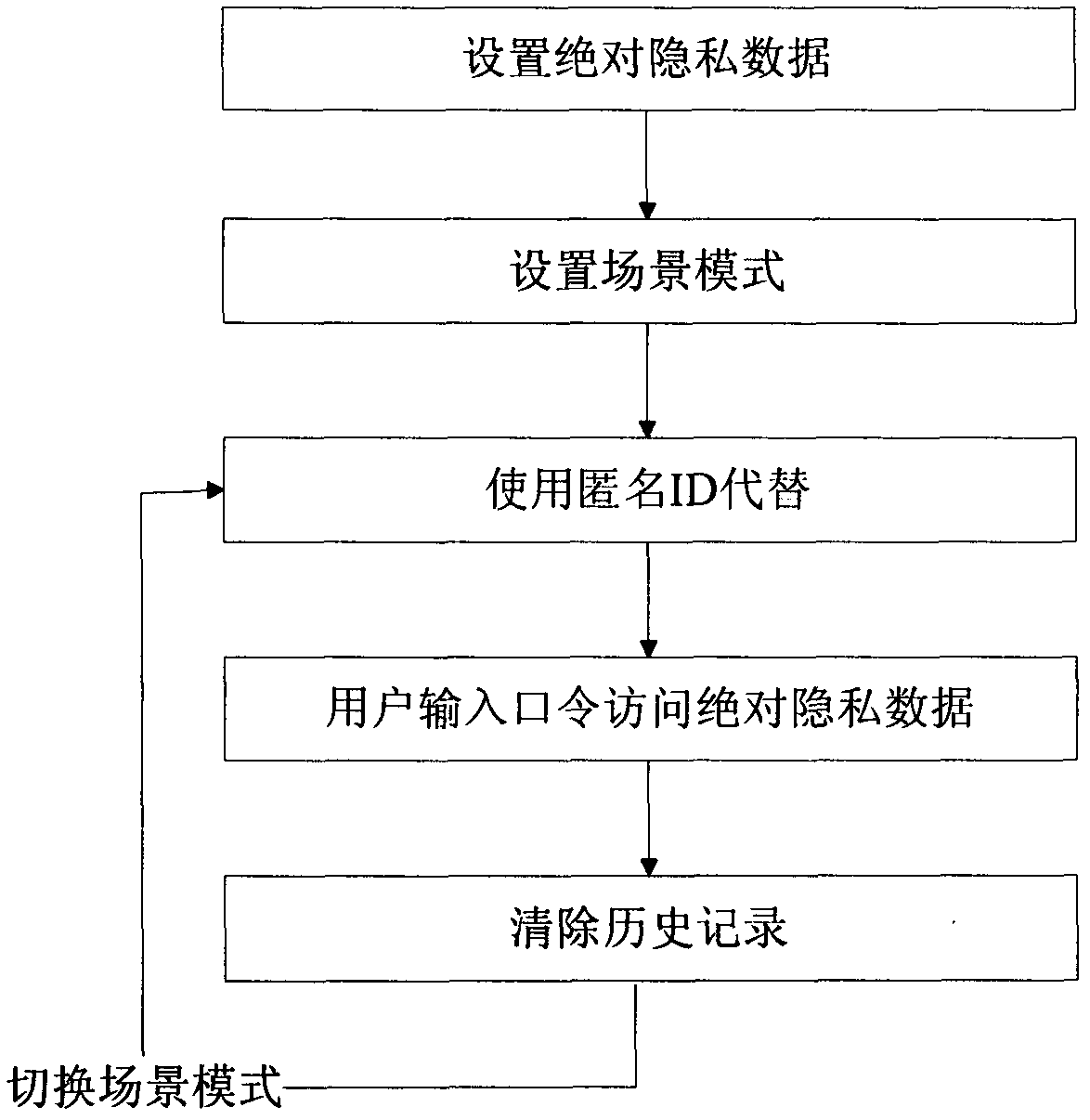
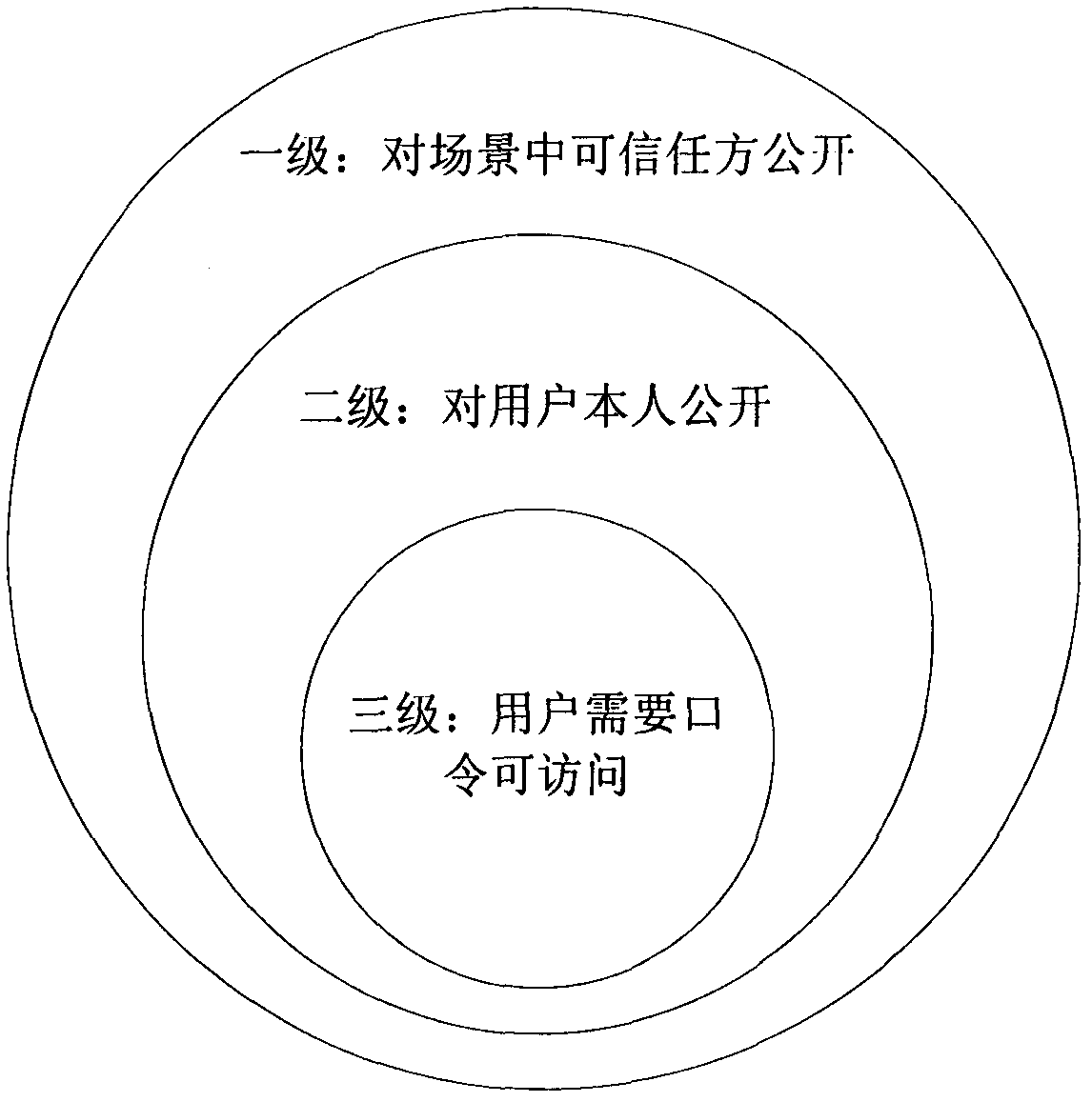
[0060] Through a series of activities of user Xiao Wang in the application scenario of the Internet of Things, the protection method of privacy query and privacy authentication based on the application scenario of the Internet of Things is further explained in detail. In this example, Xiao Wang went to a company on a business trip to handle official business, and then entered the company's parking lot to park. After finishing his work, Xiao Wang drove to Xinjiekou for shopping, and found the nearest parking lot with berths through his mobile phone for parking. (like Figure 5 As shown), after shopping, Xiao Wang continued to go to the Security Bureau to perform a secret task. During this series of activities, Xiao Wang hoped that his private information would be protected. First of all, in the parking lot of a certain company, Xiao Wang does not want the management center of the parking lot to obtain information such as his vehicle’s violation record and his own driving recor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com