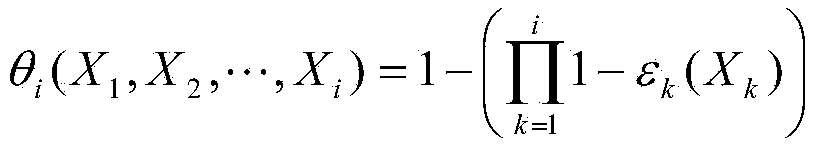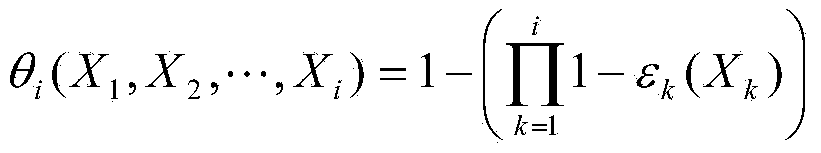Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
158results about How to "Not easy to attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
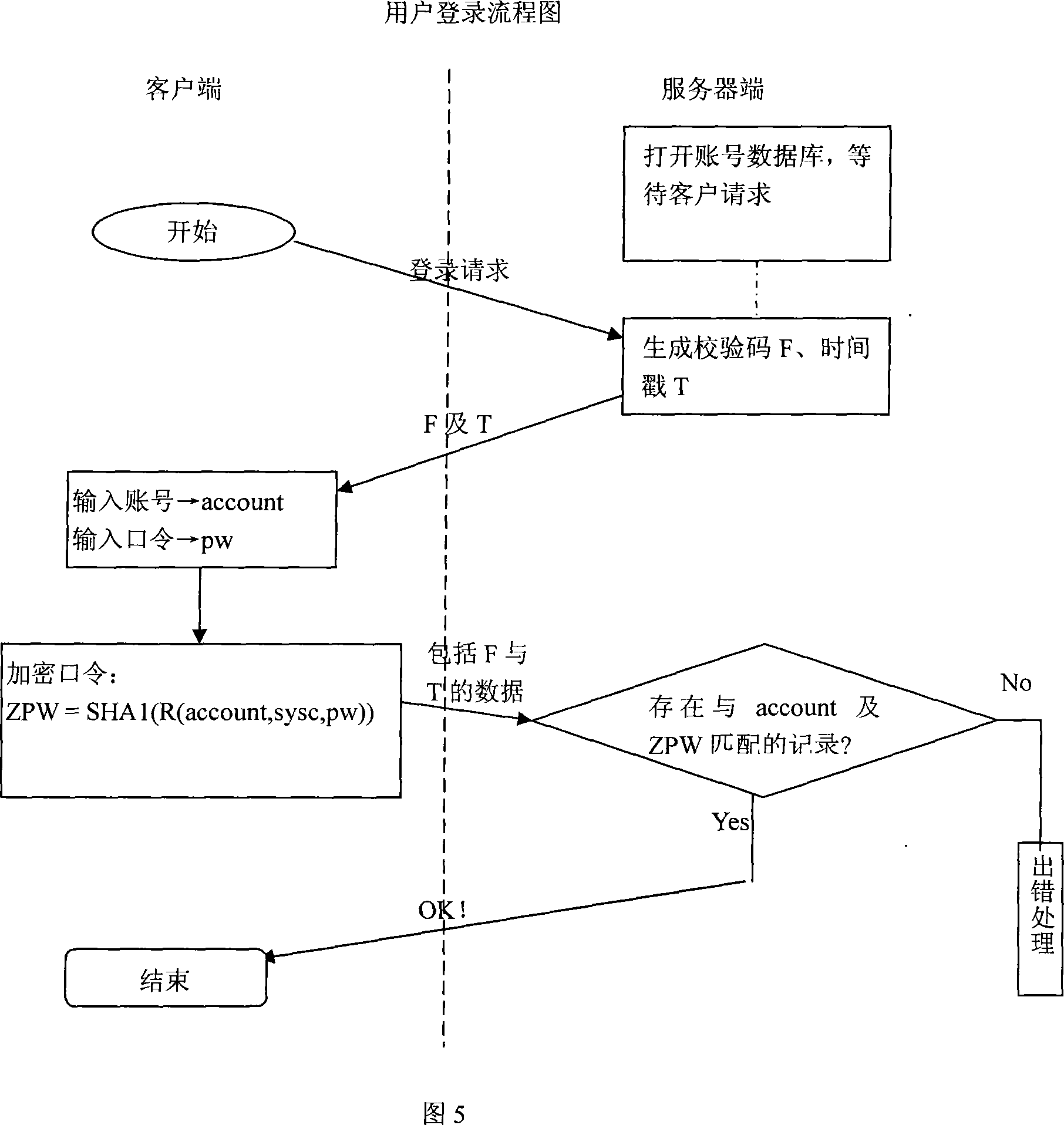
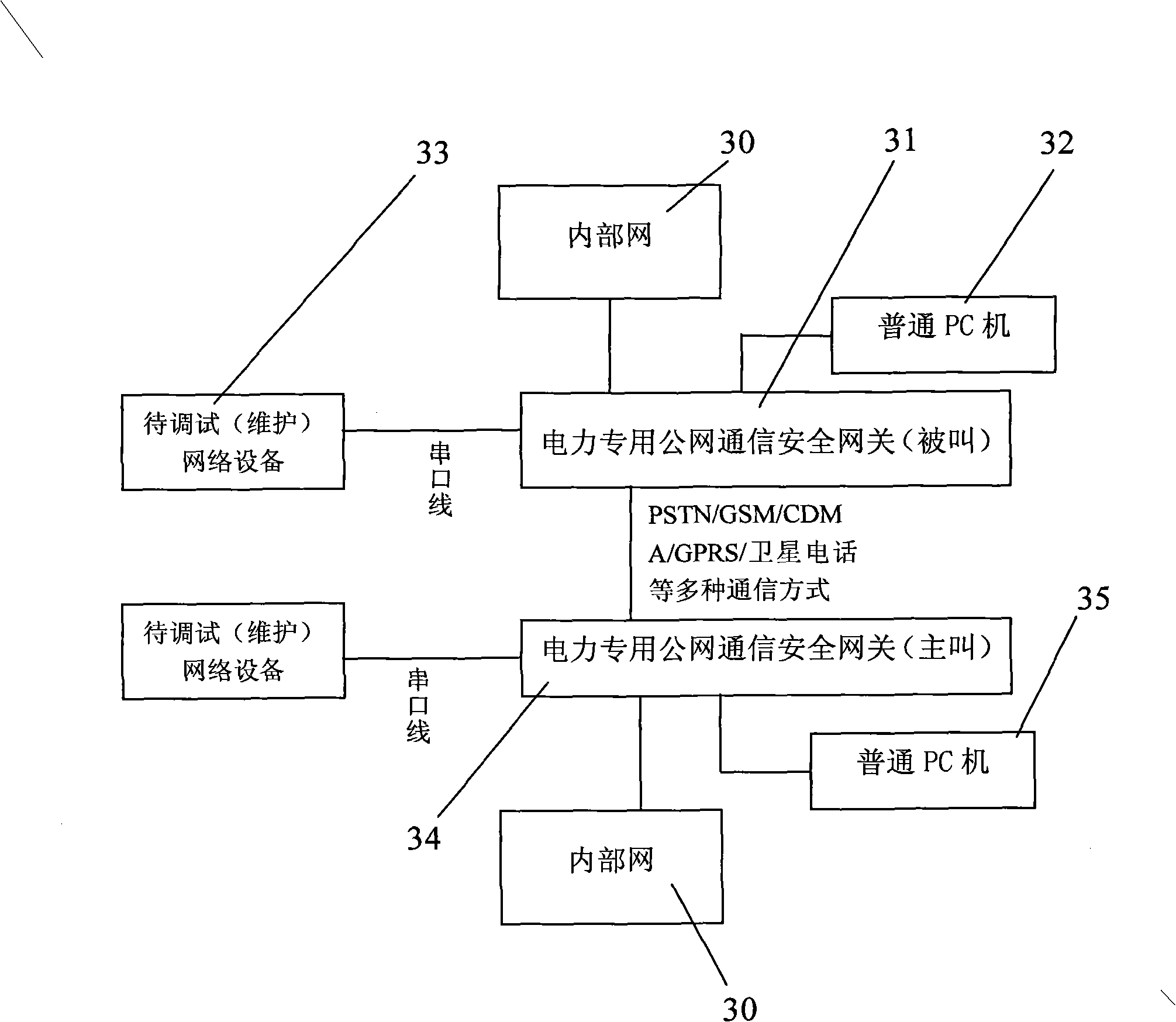
Security protection method of communication data of special electricity public network
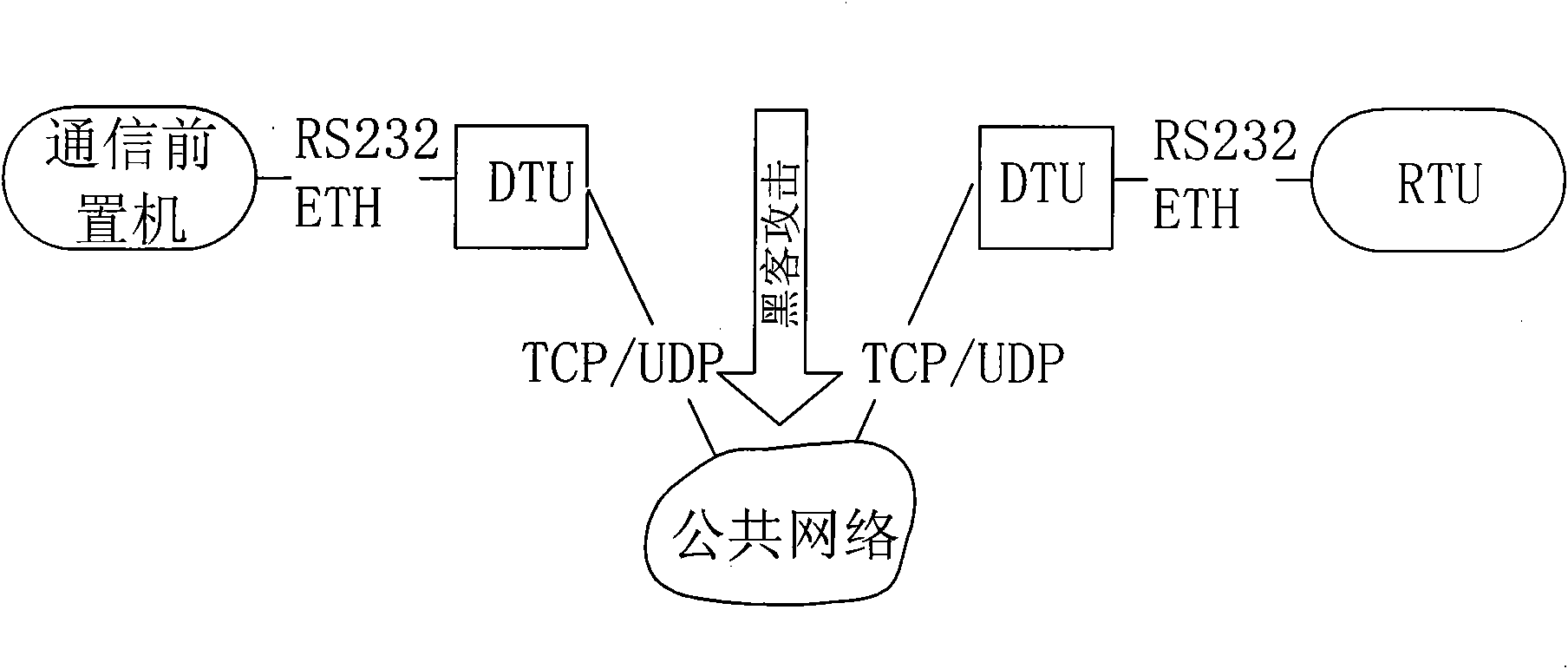
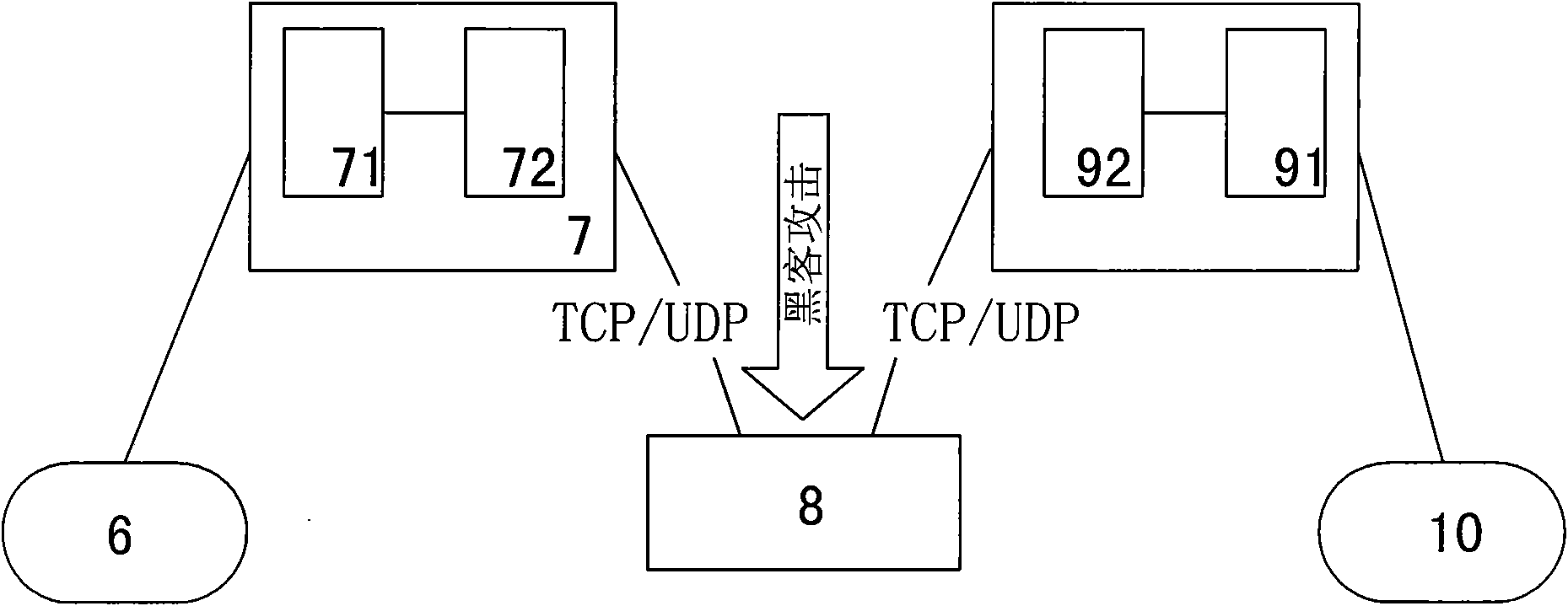
ActiveCN101662359AReal-time uninterruptible productionControl securityNetwork connectionsSecuring communicationCommunications securityElectricity
The invention discloses a security protection method of communication data of a special electricity public network, which provides secure and reliable data communication for the data communication ofthe special electricity public network by adopting the technical means of network isolation, right control, identity authentication and transmission encryption, realizes the purpose of securely usingthe public network for communication at any time and in any places without making any change to the application environment or software. In the process of application, a calling telecontrol communication security gateway (7) and a called telecontrol communication security gateway (9) are connected to a public network (8) by dialing; an encrypted public network communication channel is establishedfor the communication between a communication front-end processor (6) and a remote RTU (10); and the data is connected with the telecontrol communication security gateway (7) from the communication front-end processor (6) through a serial port or network, connected with the public network (8) through the calling telecontrol communication security gateway (7), connected with the called telecontrolcommunication security gateway (9) from the public network (8), and then connected with the remote RTU (10) through the serial port or the network. The invention can be widely applied to the field ofsecurity protection of the communication data of the public network.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
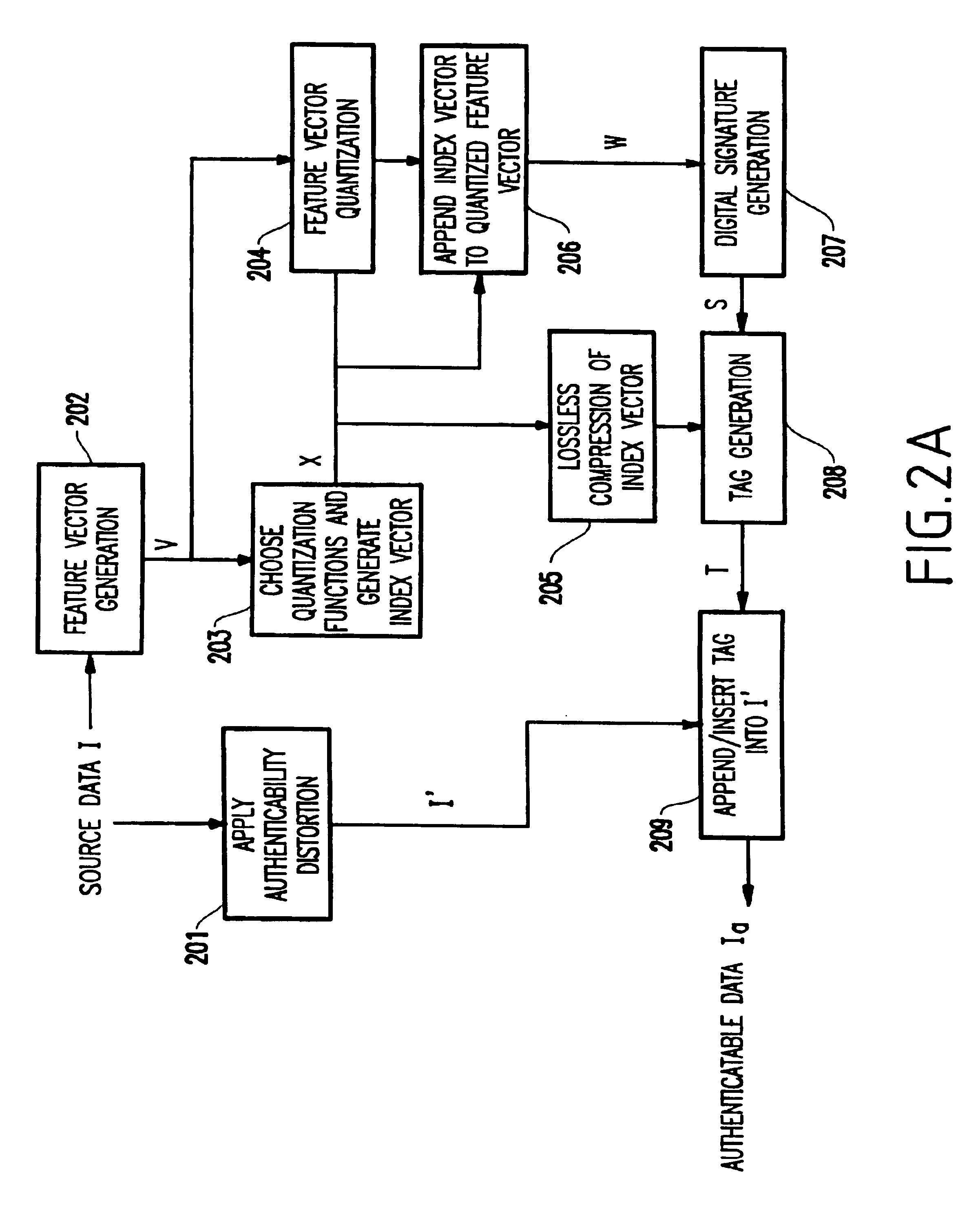
Cryptography-based low distortion robust data authentication system and method therefor
InactiveUS6907527B1Hard to findMinimizing and reducing distortionData processing applicationsUser identity/authority verificationLow distortionAuthentication system
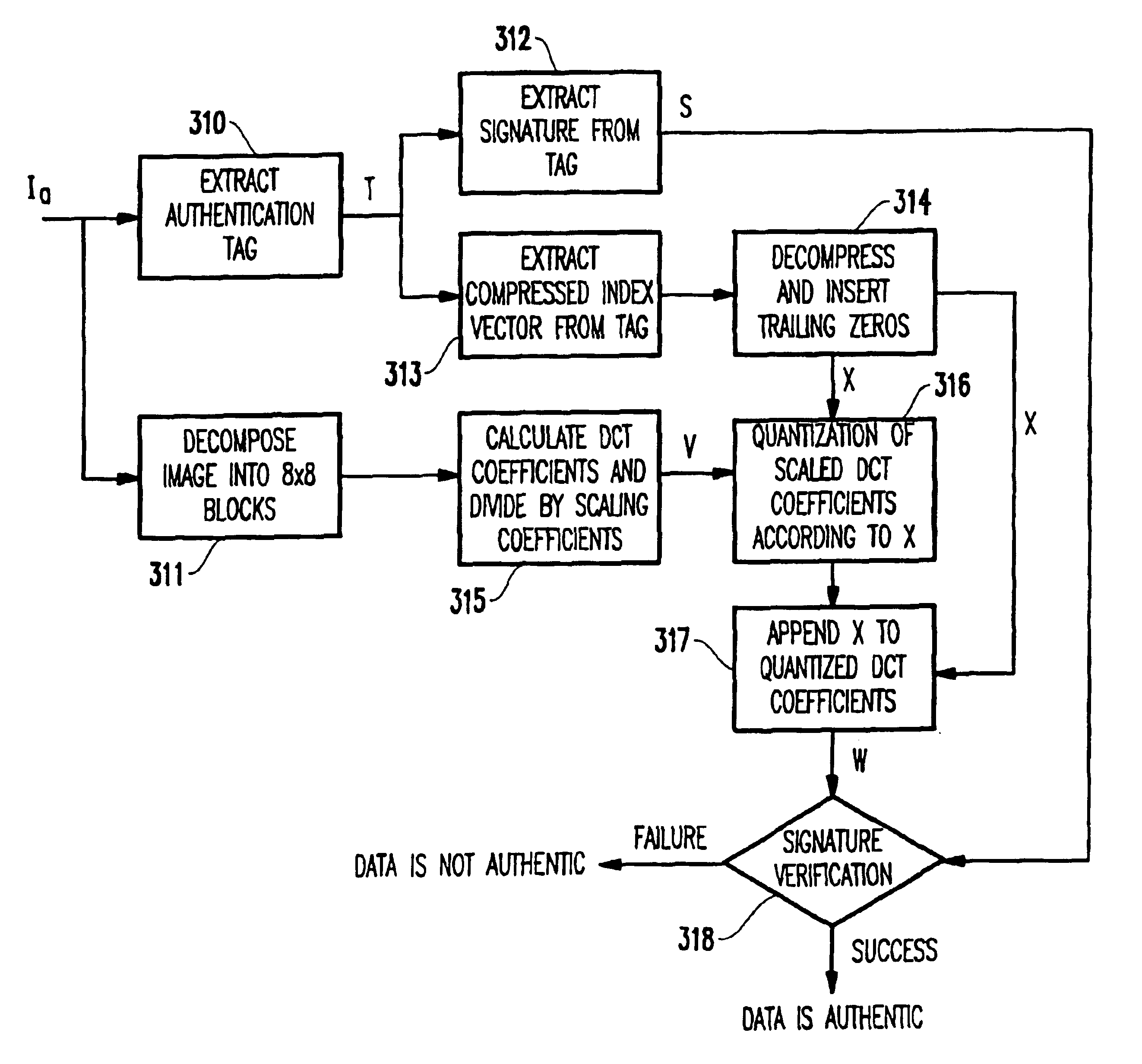
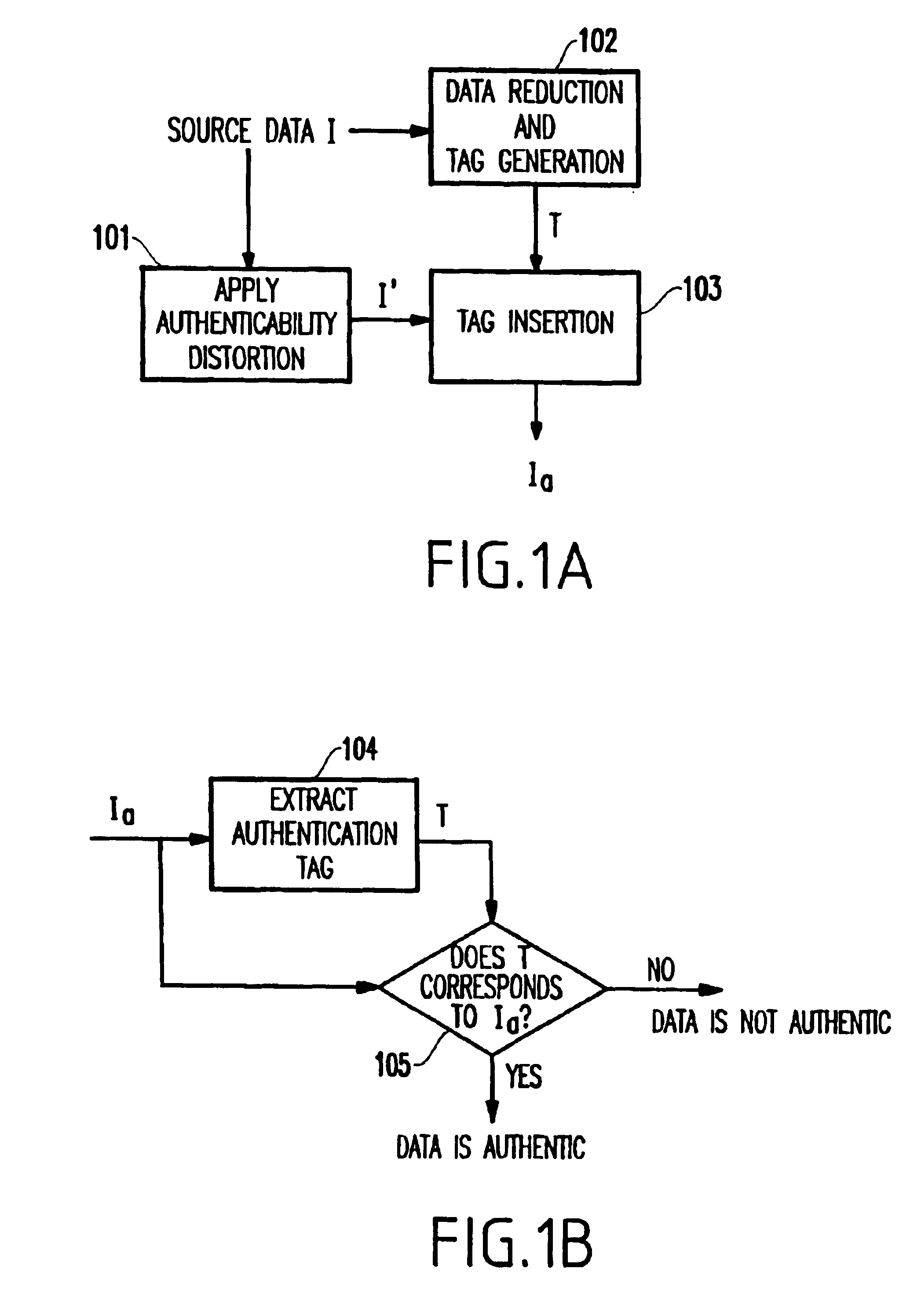
A method (and system) for generating an output file from a source file where benign modifications to a content of the output file still render the output file authentic, includes constructing an index vector from the source file, quantizing the source file, generating an authentication mark from the quantized source file and the index vector, generating an authentication tag by appending the index vector to the authentication mark, and generating the output file by appending the authentication tag to the source file.
Owner:IBM CORP
Implicit user verification and privacy protection method based on multi-dimensional behavior characteristics
ActiveCN103533546AEffective defenseEasy to useSecurity arrangementHigh level techniquesFeature vectorUser verification
The invention relates to an implicit user verification and privacy protection method based on multi-dimensional behavior characteristics. The method comprises the steps as follows: a, data of mobile equipment operation behaviors of a legitimate user is collected; b, a legitimate user operation characteristic model is established; c, a support vector machine is utilized for comparing current behavior characteristic vector with the legitimate user operation characteristic model, so that an operation comparing conclusion about whether a current user is legitimate is obtained, and the confidence level of the operation comparing conclusion is obtained; and d, probability that the current user is legitimate is calculated by a confidence level algorithm according to the current behavior characteristic vector and the confidence level, when the probability of the legitimate user is higher than a set threshold value, the current user is confirmed to be legitimate, otherwise, mobile equipment starts a privacy protection protocol which is set in advance. According to the implicit user verification and privacy protection method based on the multi-dimensional behavior characteristics, the power consumption is low, the probability of simulation and attack is low, accurate user identity recognition can be performed under the condition that the user cannot perceive, and a corresponding privacy protective measure is taken.
Owner:苏州美信互联信息技术有限公司
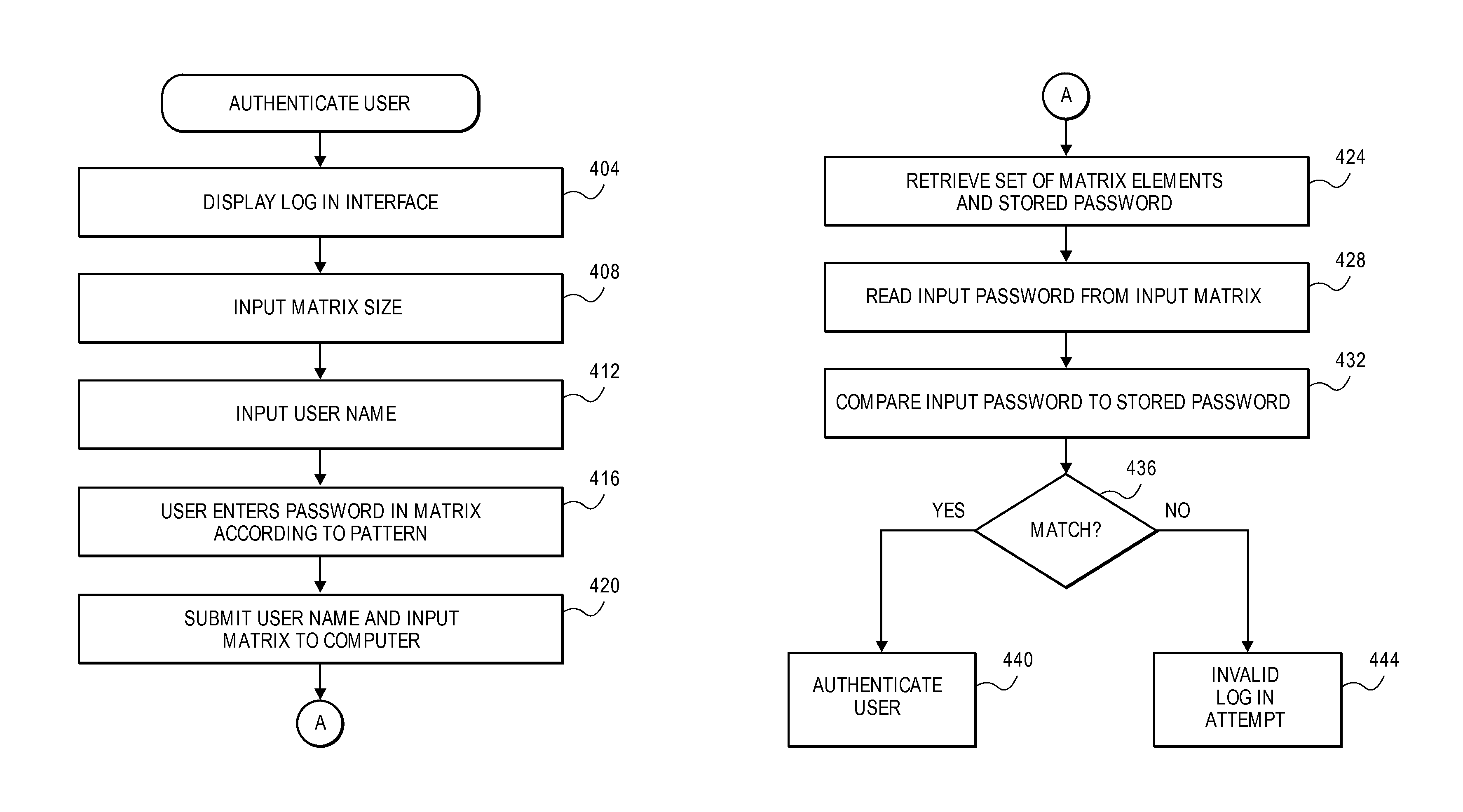
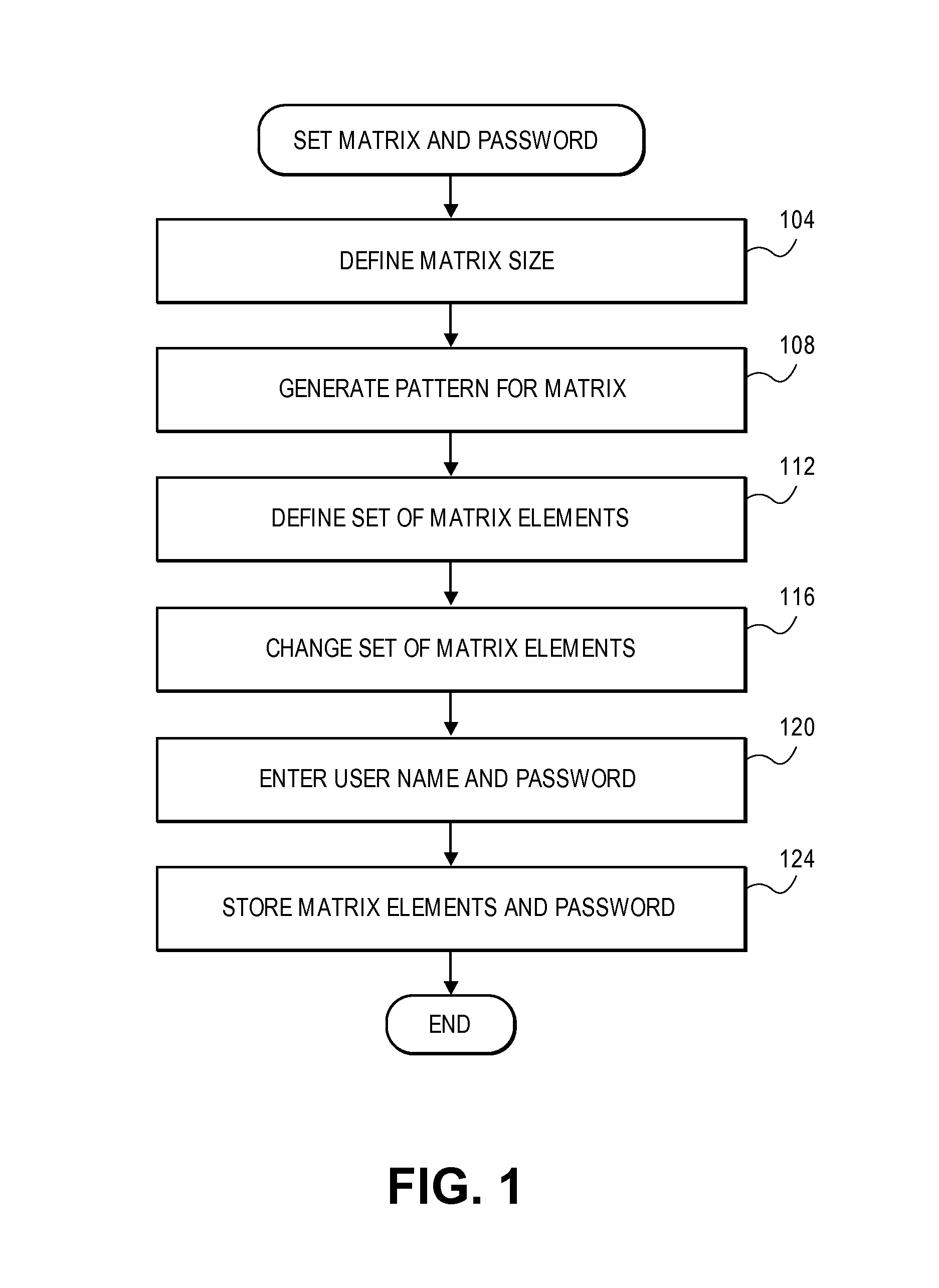
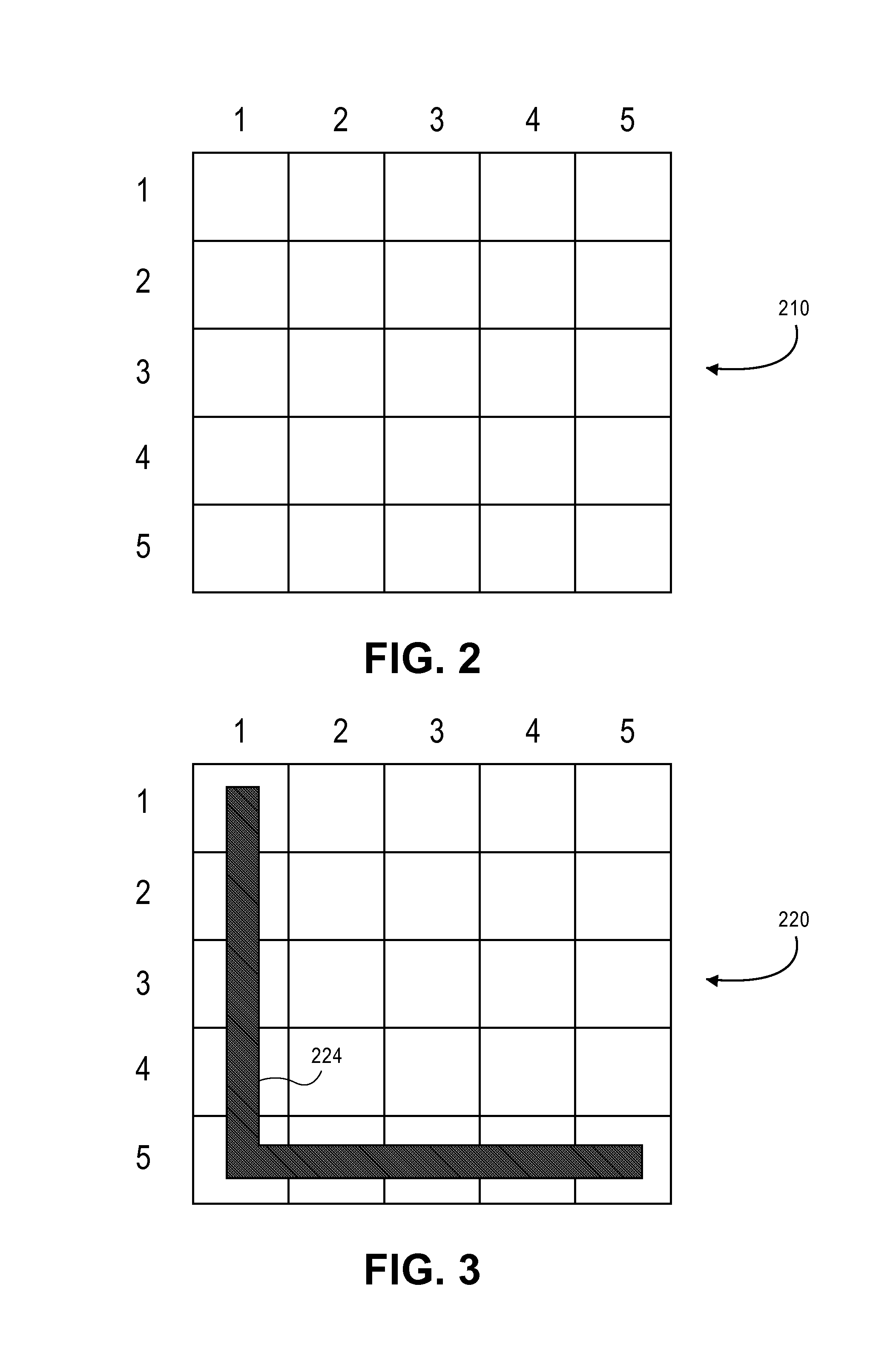
Password protection using pattern
A user generates a pattern in a matrix (or two-dimensional grid) and enters a user name and an associated password. This username, password and pattern are stored locally on a computing device or are transmitted to a remote computer server for later authentication. Upon authentication, an input matrix is displayed. The user enters the password into the matrix in the form of the pattern, and also enters the username. The computer retrieves the previously stored pattern and password with the username. The previously stored pattern is used to read the input password from the input matrix. A match with the stored password indicates authentication. Alternatively, the input matrix only includes the pattern and password is entered separately. The input matrix may also be filled with random characters to improve security. The stored pattern is compared to the input pattern using image analysis or by comparing a set of coordinates.
Owner:TREND MICRO INC
Cryptographic method for a white-box implementation
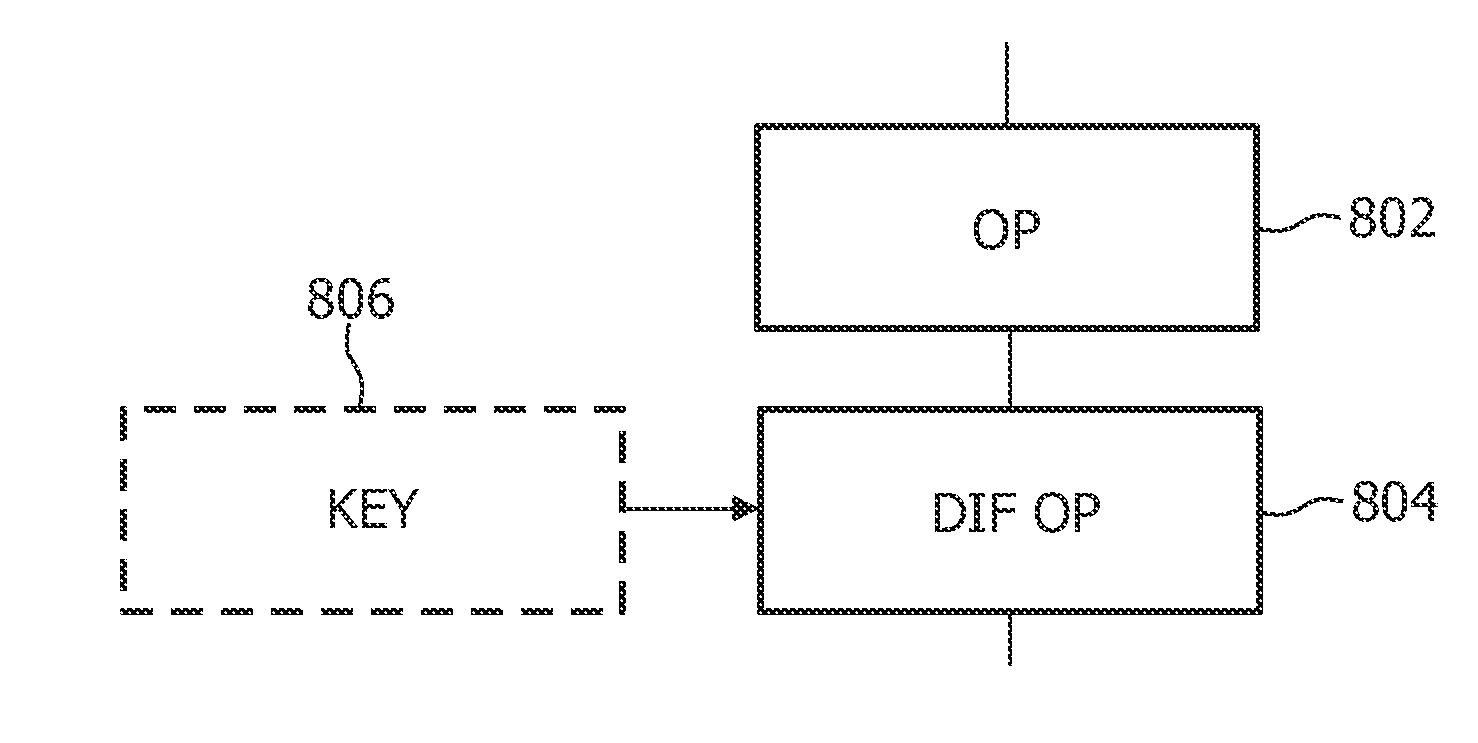
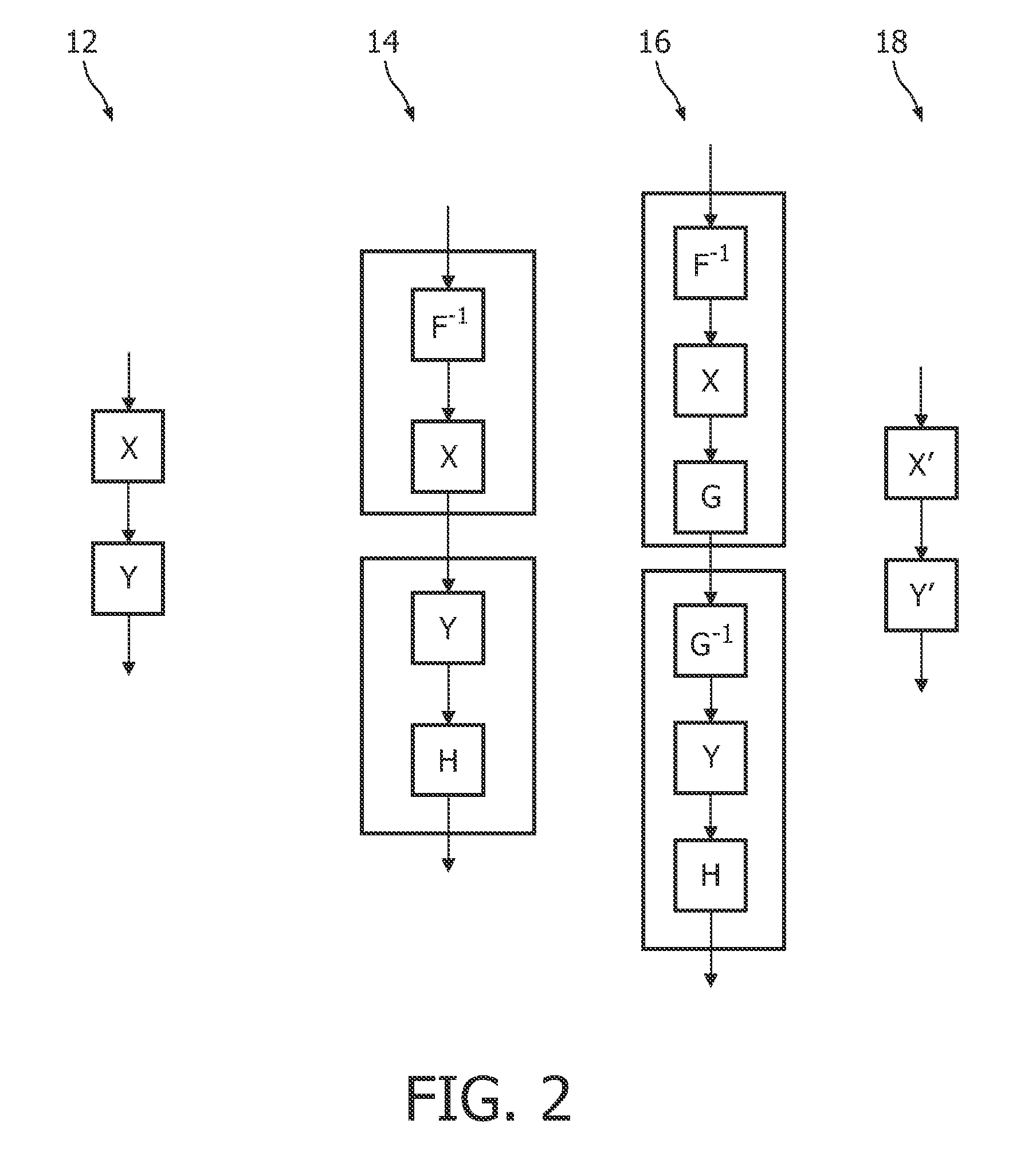
InactiveUS20100080395A1Not easy to attackSimple methodKey distribution for secure communicationSecret communicationDiffusion operatorTheoretical computer science
A cryptographic method is implemented in a white-box implementation thereof. The method comprises applying a plurality of transformations (802) each replacing an input word by an output word, and applying a diffusion operator (804) to a concatenation of a plurality of the output words for diffusing information represented by the output words among the output words. A key (806) to the cryptographic method comprises information representing the diffusion operator. The diffusion operator satisfies a property that a change of one bit in an input to the diffusion operator corresponds to a change of more than one bit in an output of the diffusion operator.
Owner:IRDETO ACCESS
Protection of a portable object against denial of service type attacks
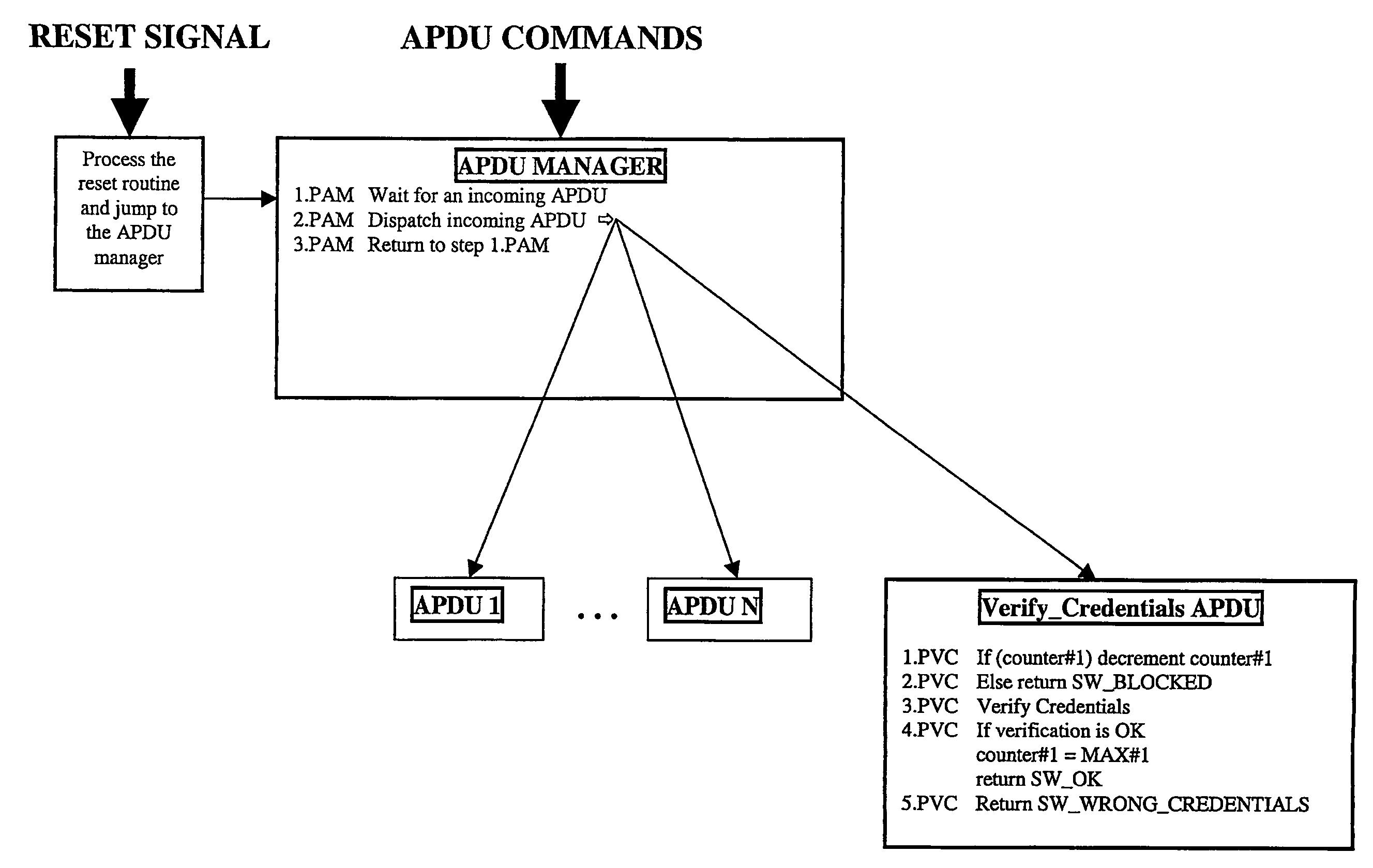
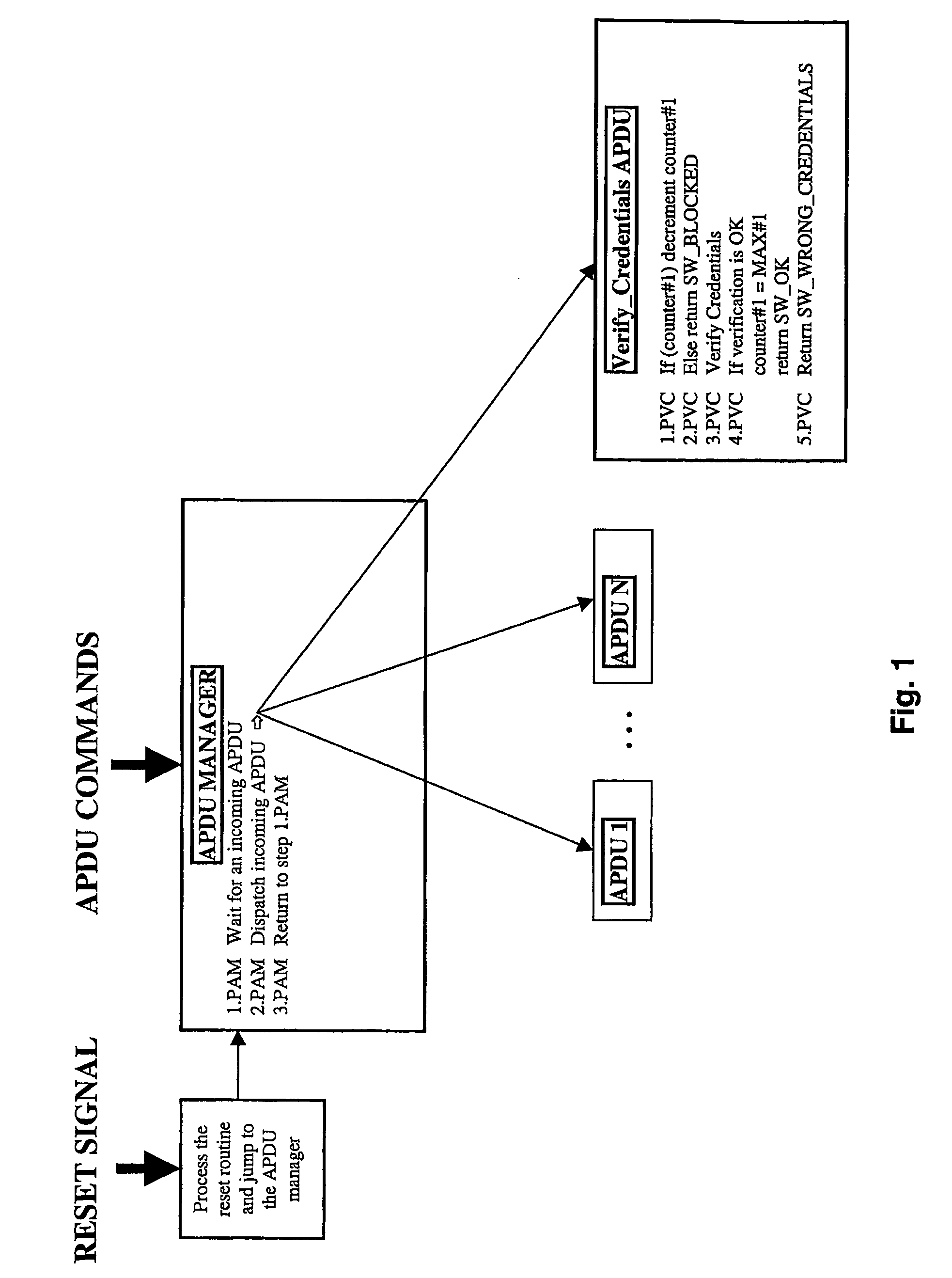
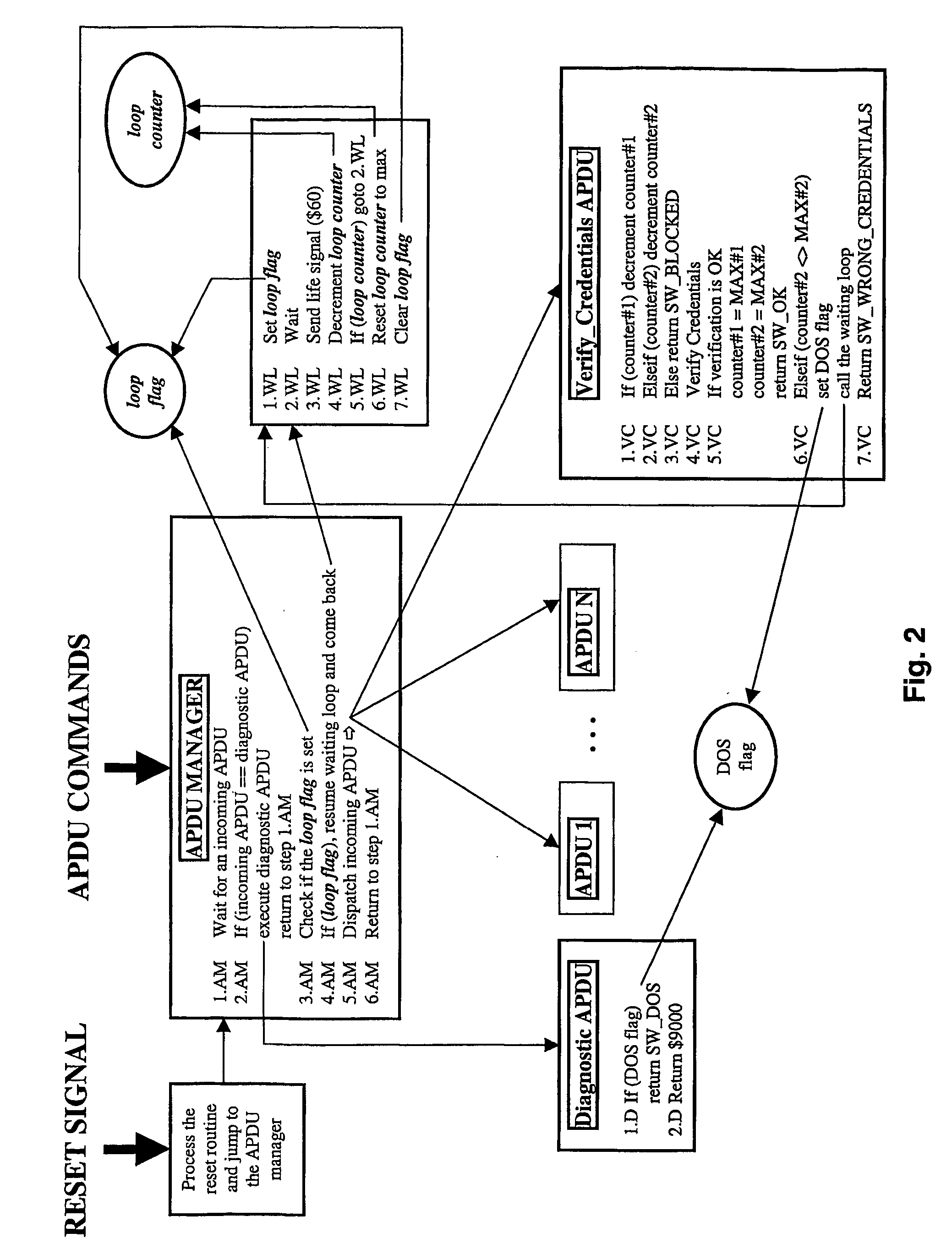
InactiveUS20060015938A1Reduce decreaseNot easy to attackMemory loss protectionDetecting faulty computer hardwareComputer securityInternet privacy
A portable object comprises a memory where at least one credential is stored. The credential is associated with a service and used to verify that the entity requesting a service is an authorized entity for accessing the service. The method for protecting a portable object against denial of service type attacks comprises the steps of: verifying that the entity requesting a service is an authorized entity for accessing the service, based on an algorithm involving the credential, delivering the requested service only when the verification step succeeded, blocking the credential associated with the service after a certain number of verification step failed. When the verification step failed, the method further comprises the steps of waiting during a duration before allowing a new verification step.
Owner:AXALTO SA
Secure distributed storage system and method
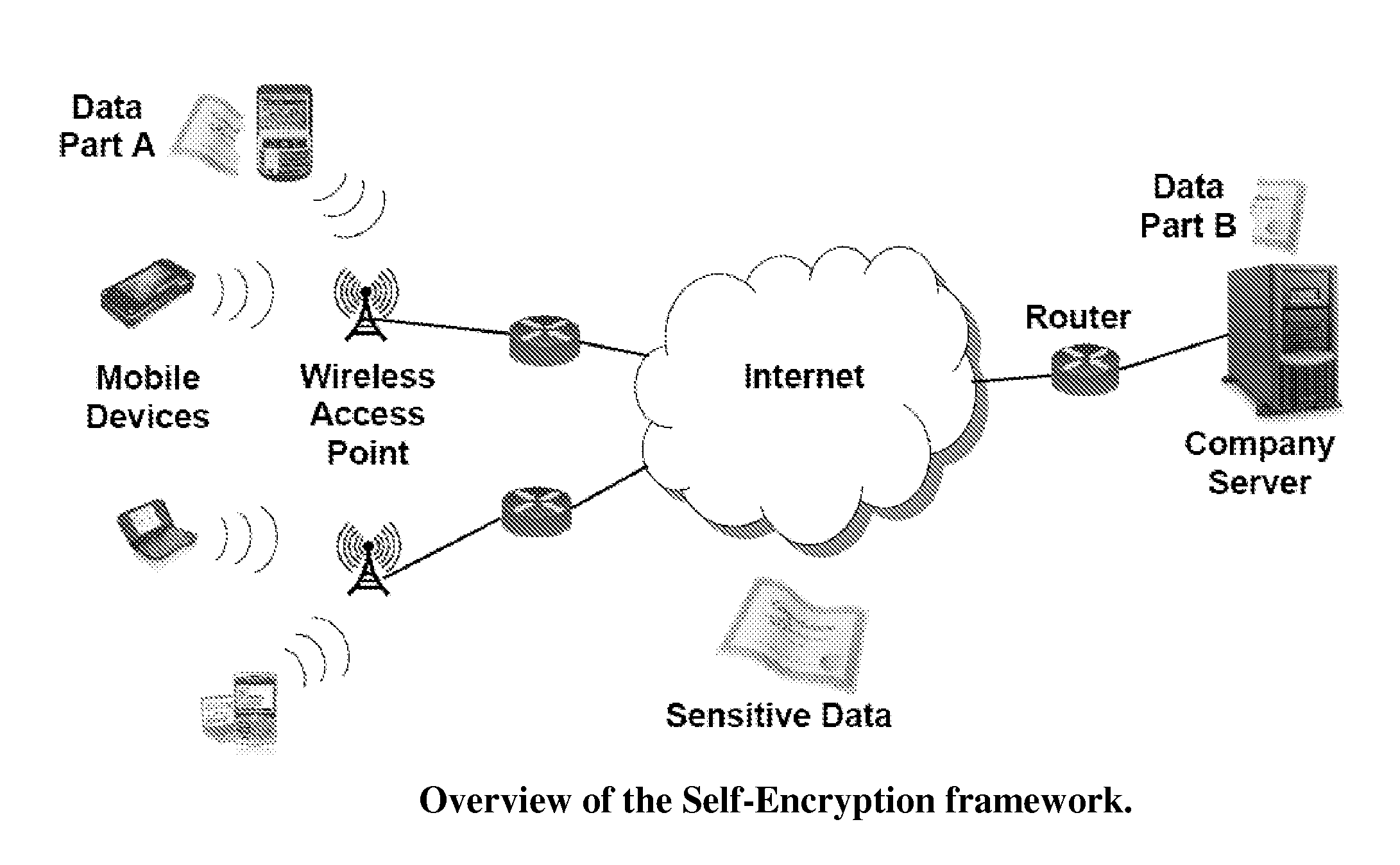
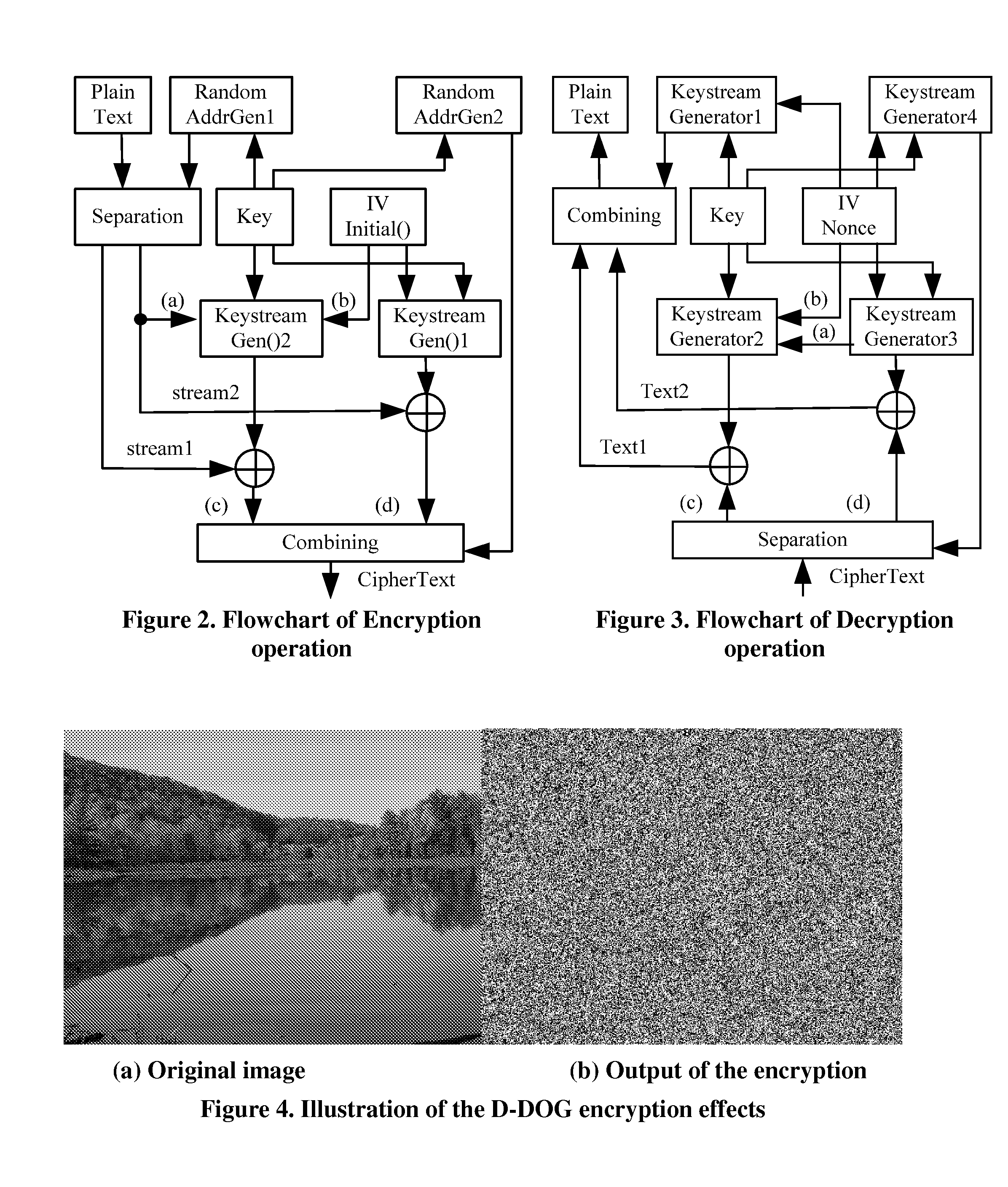
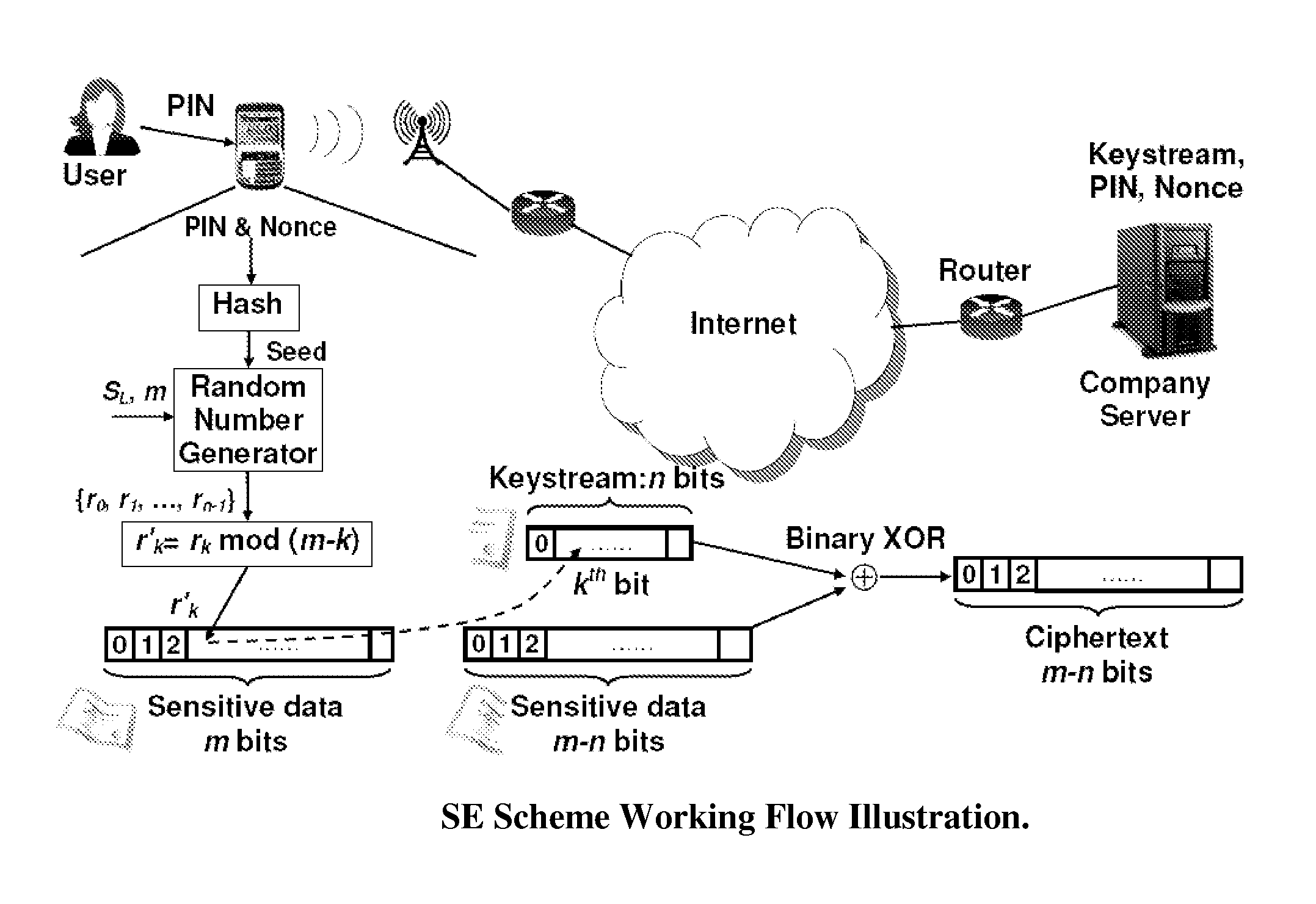
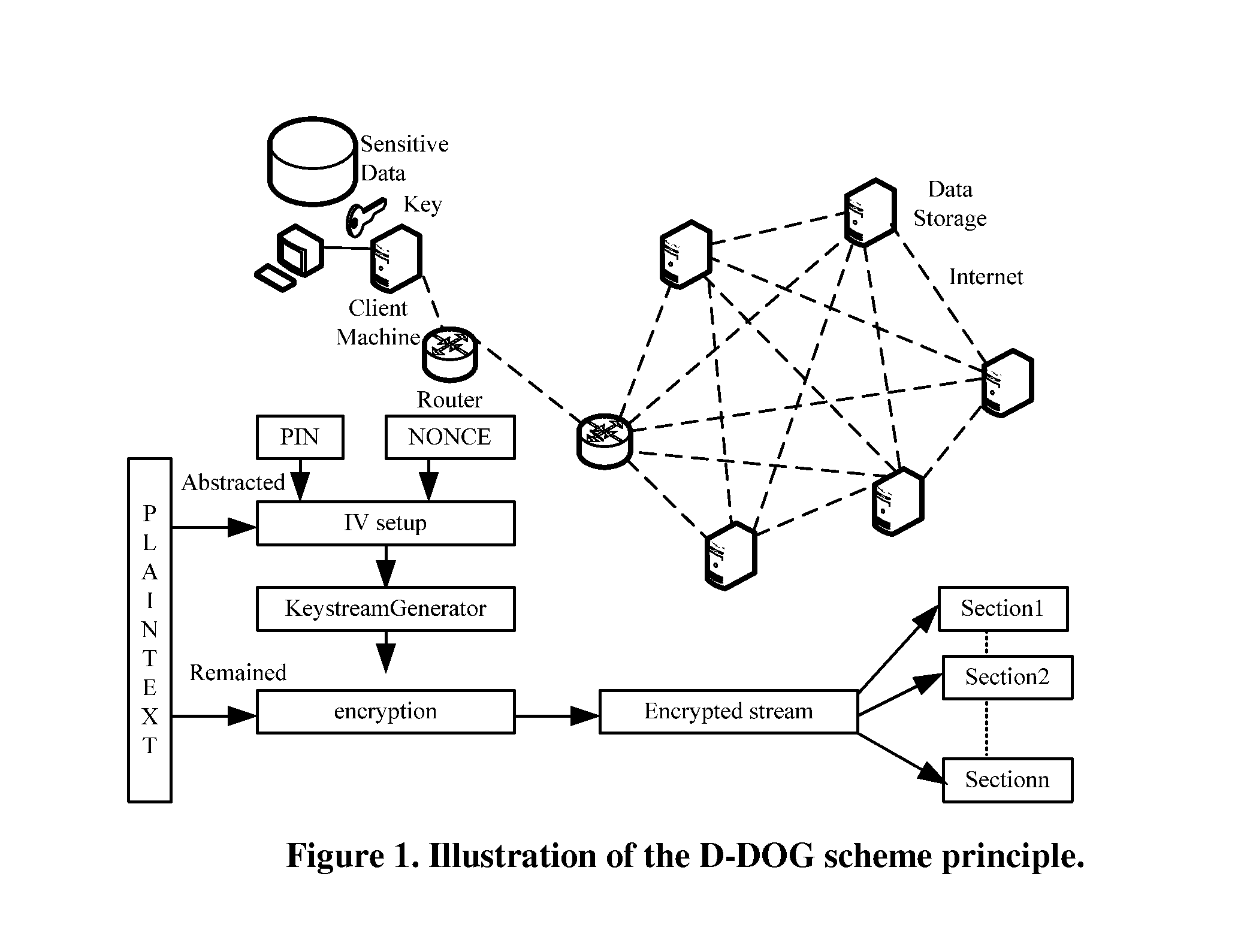
ActiveUS20110197056A1Less and less-robustProtect informationSecuring communicationOriginal dataKeystream
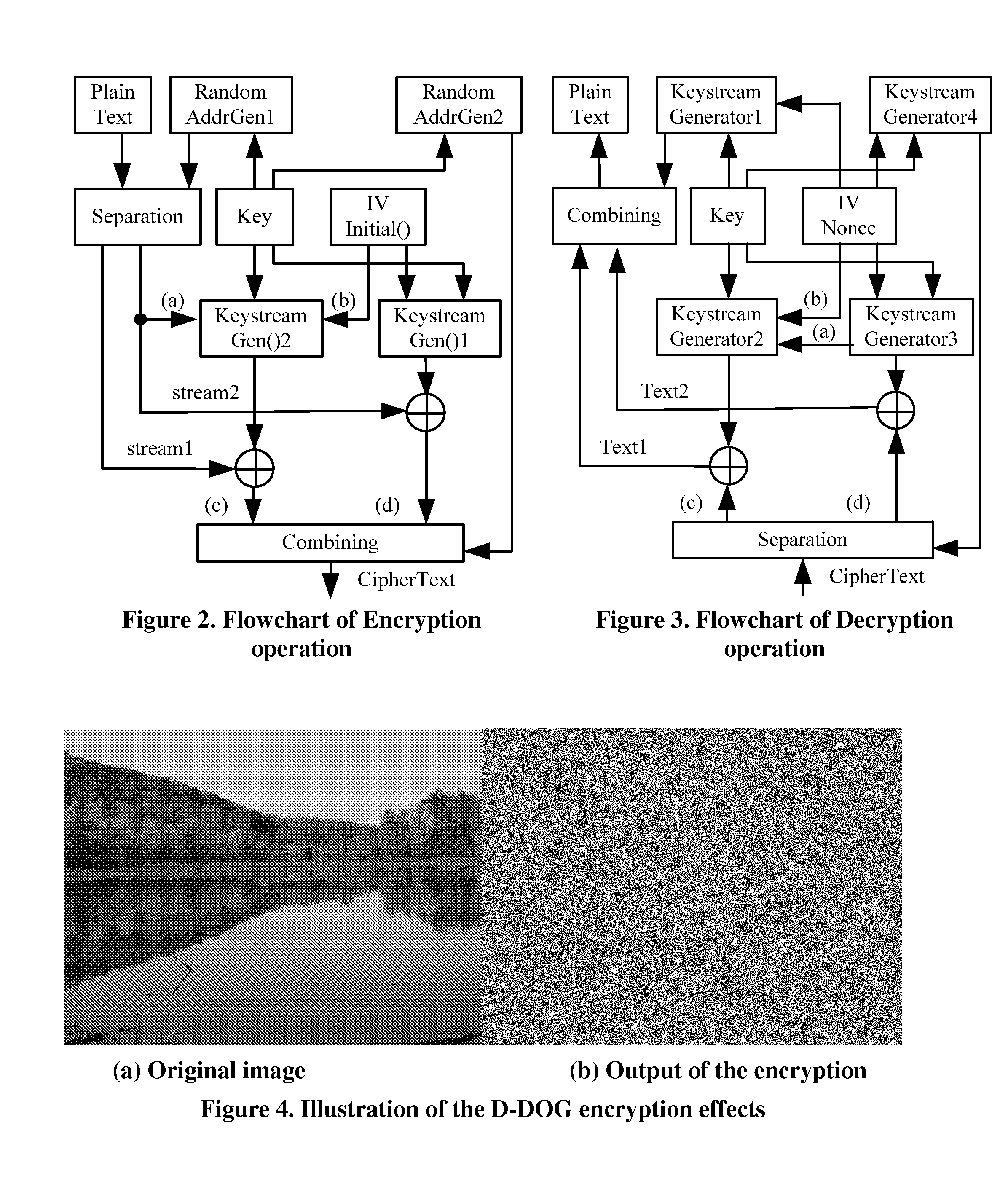
Moving from server-attached storage to distributed storage brings new vulnerabilities in creating a secure data storage and access facility. The Data Division and Out-of-order keystream Generation technique provides a cryptographic method to protect data in the distributed storage environments. In the technique, the Treating the data as a binary bit stream, our self-encryption (SE) scheme generates a keystream by randomly extracting bits from the stream. The length of the keystream depends on the user's security requirements. The bit stream is encrypted and the ciphertext is stored on the mobile device, whereas the keystream is stored separately. This makes it computationally not feasible to recover the original data stream from the ciphertext alone.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Identity authentication method with privacy protection and password retrieval function
InactiveCN101145911AImprove securityAvoid lostUser identity/authority verificationHash functionOriginal data
The invention discloses an identity authentication method with privacy protection and password recovery. When a user registers on line and / or logins, the original data input by the user are processed by data fusion and are hidden; next, the data obtained by data fusion is encrypted using one-way hash function, only the transformed results are then transmitted to a server end, the server program stores the transformed results when the user registers, and when the user logins or recovers the password, the identity authentication is accomplished by comparing the transformed results with the stored results during registration. By using the data fusion and the one-way hash function, the method encrypts the original 'question' and 'answer' data input by the user, which greatly enhances the privacy of the user's data, avoids a network manager from being attacked, greatly increases network security, avoids loss to the user caused by the user's data being stolen, and is applied for various network users to register on line and / or login.
Owner:JIANGHAN UNIVERSITY
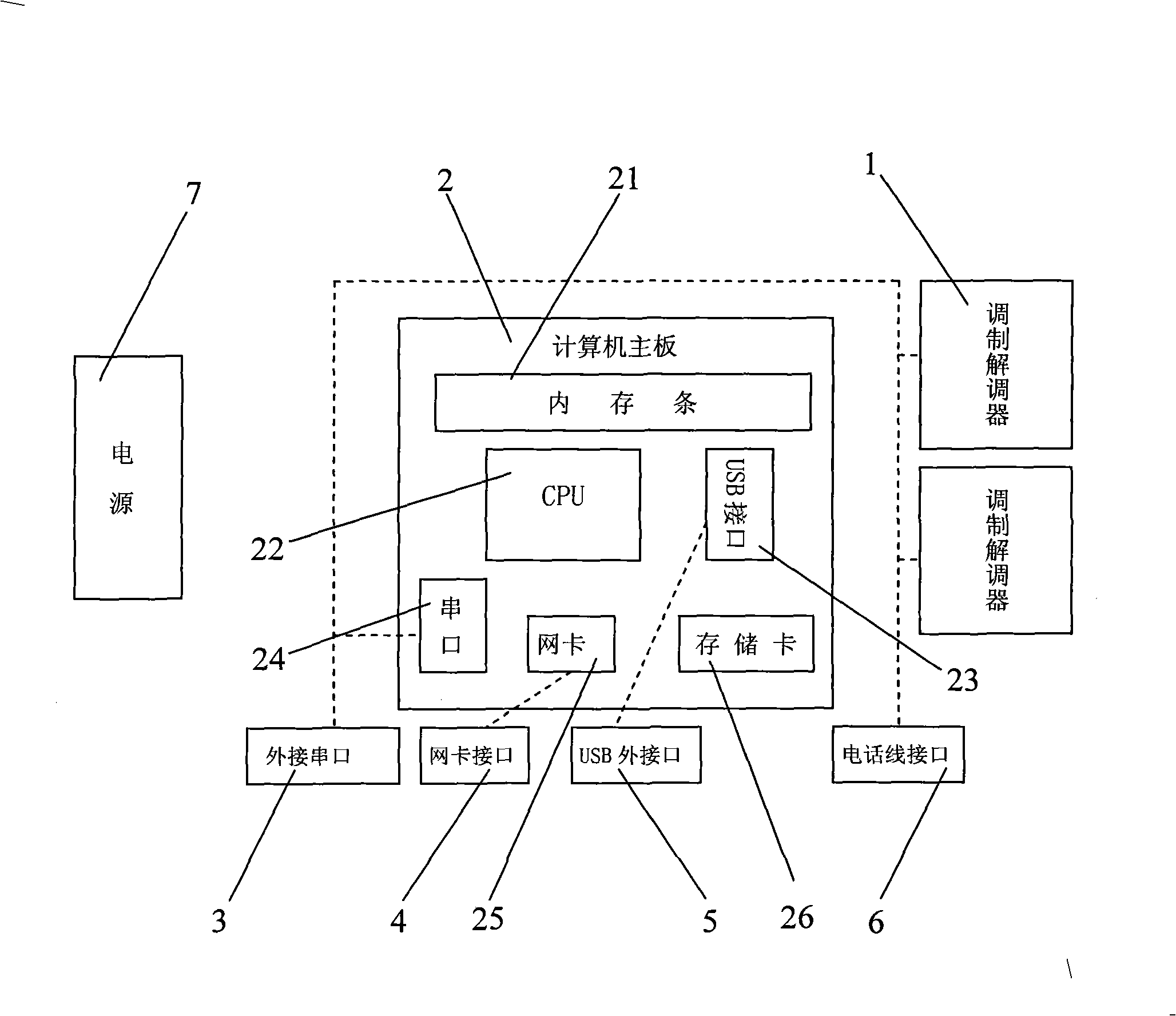
Electric force special public network communication secure gateway
ActiveCN101494624AFacilitate communicationEasy to useNetwork connectionsCommunications securityLow speed
The invention discloses a public network communicating security gateway dedicated for electric power, aims at providing a public network communicating security gateway dedicated for electric power which has convenient communication, safe use, dedicated equipments with multiple emergent data transmission channels, and is not easy to be attacked, and comprises at least a modem (1), a computer mainboard (2), a network card interface (4), a USB external interface (5), a telephone line interface (6), a power source (7), a managing and configuring modular device, a PPP network access module device, an authenticating module device, a VPN module device, a communicating protocol rules auditing module device dedicated for electric power and a network serial port converting module device, and all the module devices are arranged on the computer mainboard (2). The public network communicating security gateway dedicated for electric power can be widely applied in the field of network communication with high security and low speed requirements.
Owner:珠海市鸿瑞信息技术股份有限公司 +1
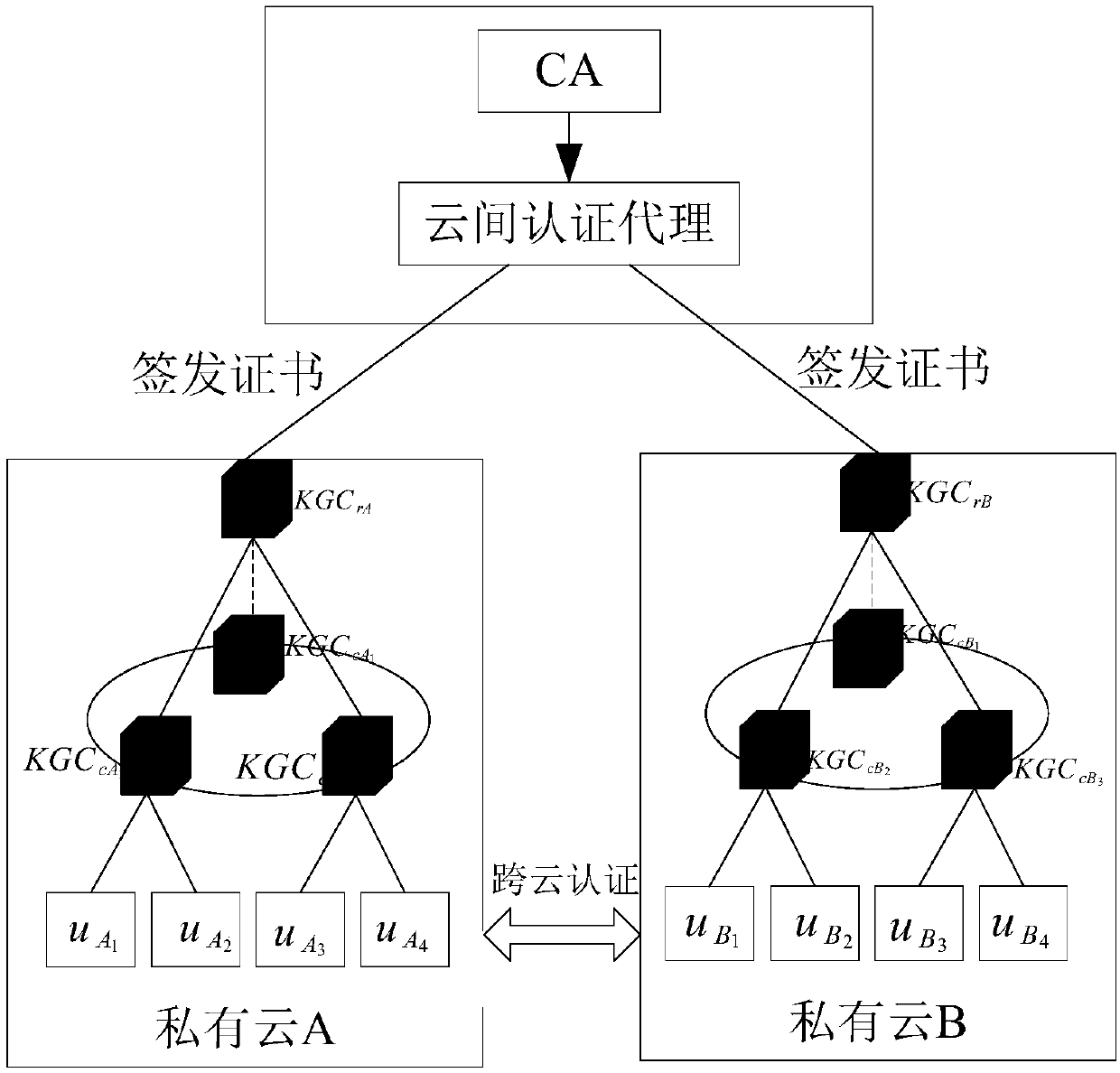
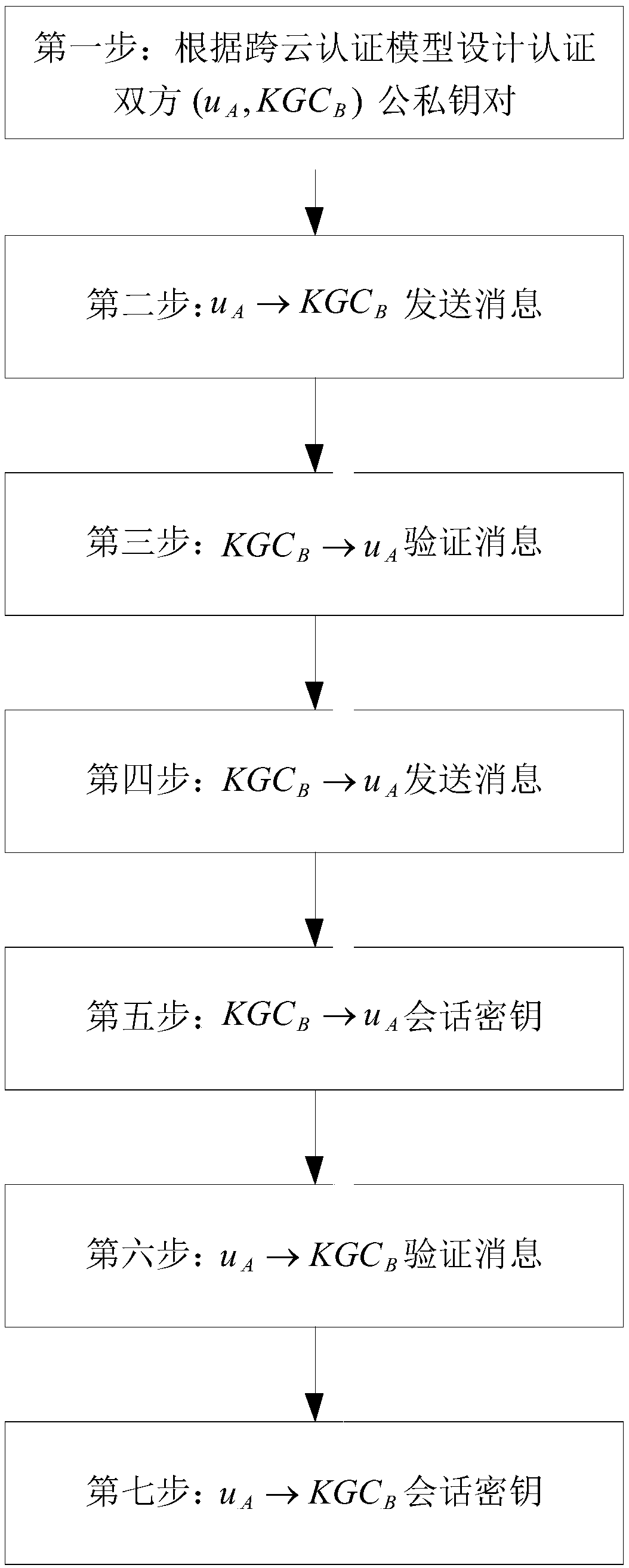
Cross-cloud security certification system and method based on identifier
ActiveCN108667616ANot easy to attackAvoid safety hazardsKey distribution for secure communicationPublic key for secure communicationRound complexityComputation complexity
The invention discloses a cross-cloud security certification system and a cross-cloud security certification method based on an identifier, in order to mainly solve the problem that cloud service providers within cloud domains securely manage privacy data of users. The cross-cloud security certification system introduces a layered identifier model and adopts a shared key ring structure, so that identity identifier of the user is unique; the user can get rid of a series of complicated certificate operations, thereby expanding a large-scale cloud network environment. The cross-cloud security certification method comprises the steps of: designing public and private key pairs for the users and the cloud service providers respectively by using the cross-cloud security certification system; sending and verifying messages; and performing key agreement to achieve identifier certification of both certification sides. The cross-cloud security certification system and the cross-cloud security certification method of the invention have the beneficial effects that: a cross-cloud certification model is built and a certificateless key agreement protocol is adopted, each link has safety protection, thus security and reliability of the whole system can be ensured; in addition, a computation complexity is low, thus certification and secure access requirements on the condition that the users in acloud environment respectively belong to different cloud domains can be met, and a practical application requirement that only one-time certification is needed for different cloud domains also can bemet.
Owner:XIDIAN UNIV
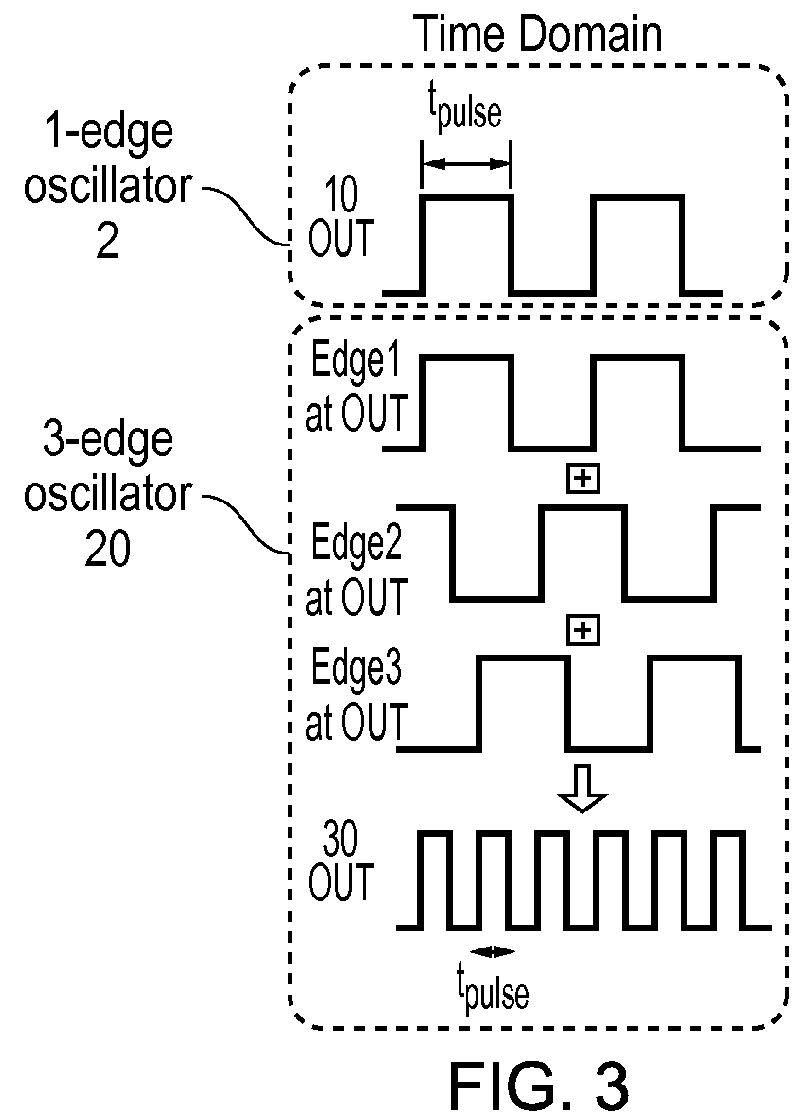
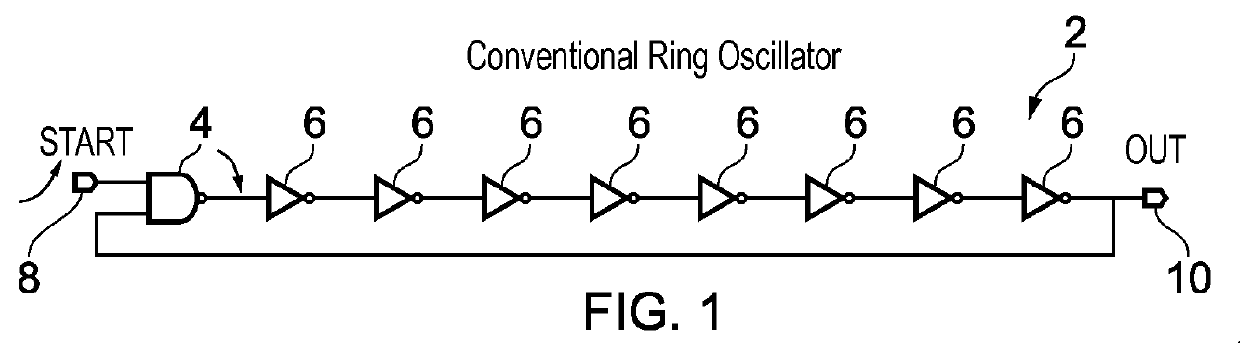
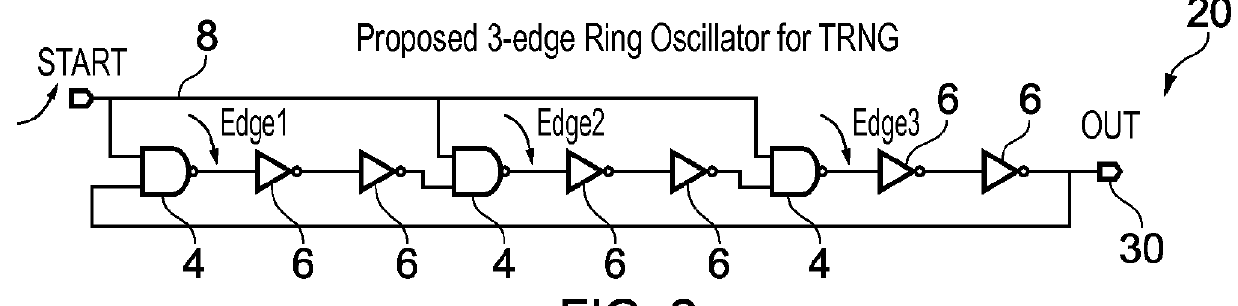
True random number generator
ActiveUS9335972B2Simpler and cheap constructionIncrease randomnessRandom number generatorsPulse generation by logic circuitsStart timeNumber generator
A true random number generator comprises a ring oscillator which is triggered to start oscillating in a first mode of oscillation at an oscillation start time. The first mode of oscillation will eventually collapse to a second mode of oscillation dependent on thermal noise. A collapse time from the oscillation start time to the time at which the oscillator collapses to the second mode is measured, and this can be used to determine a random number. The TRNG can be synthesized entirely using standard digital techniques and is able to provide high randomness, good throughput and energy efficiency.
Owner:RGT UNIV OF MICHIGAN
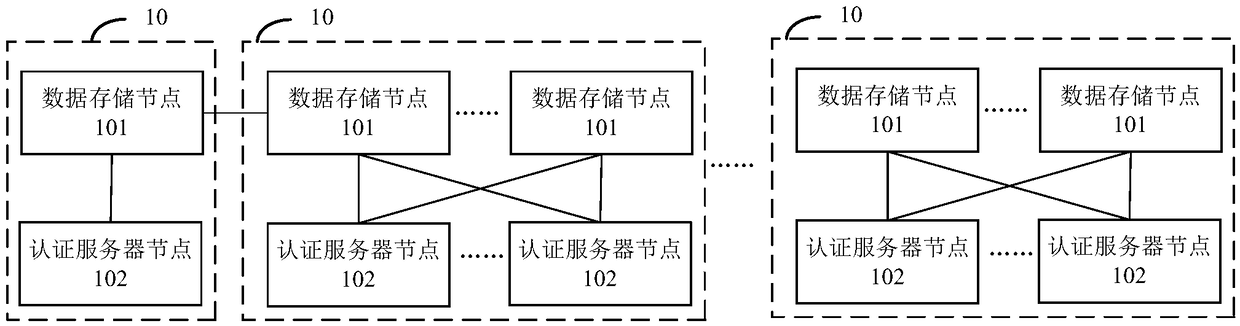
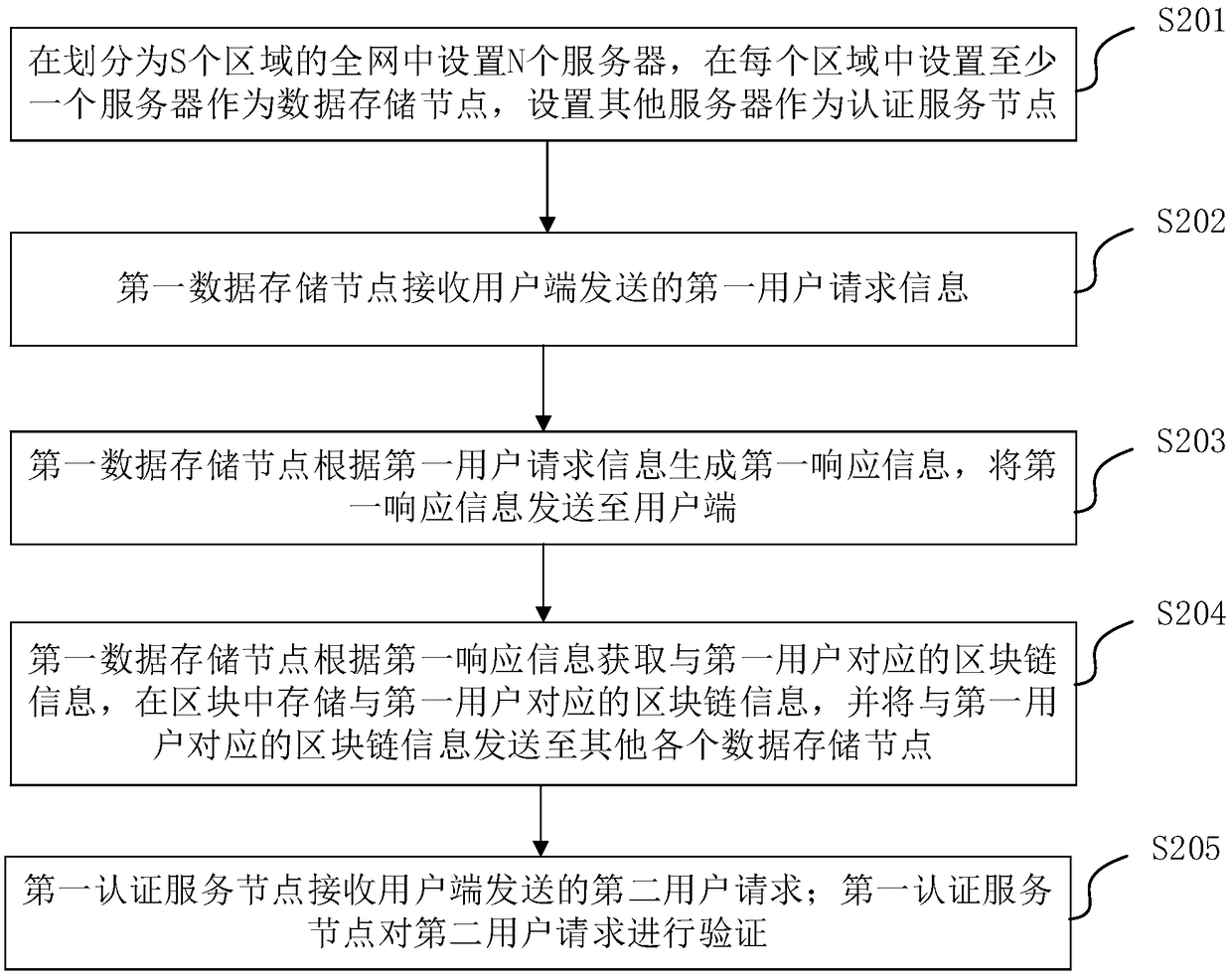
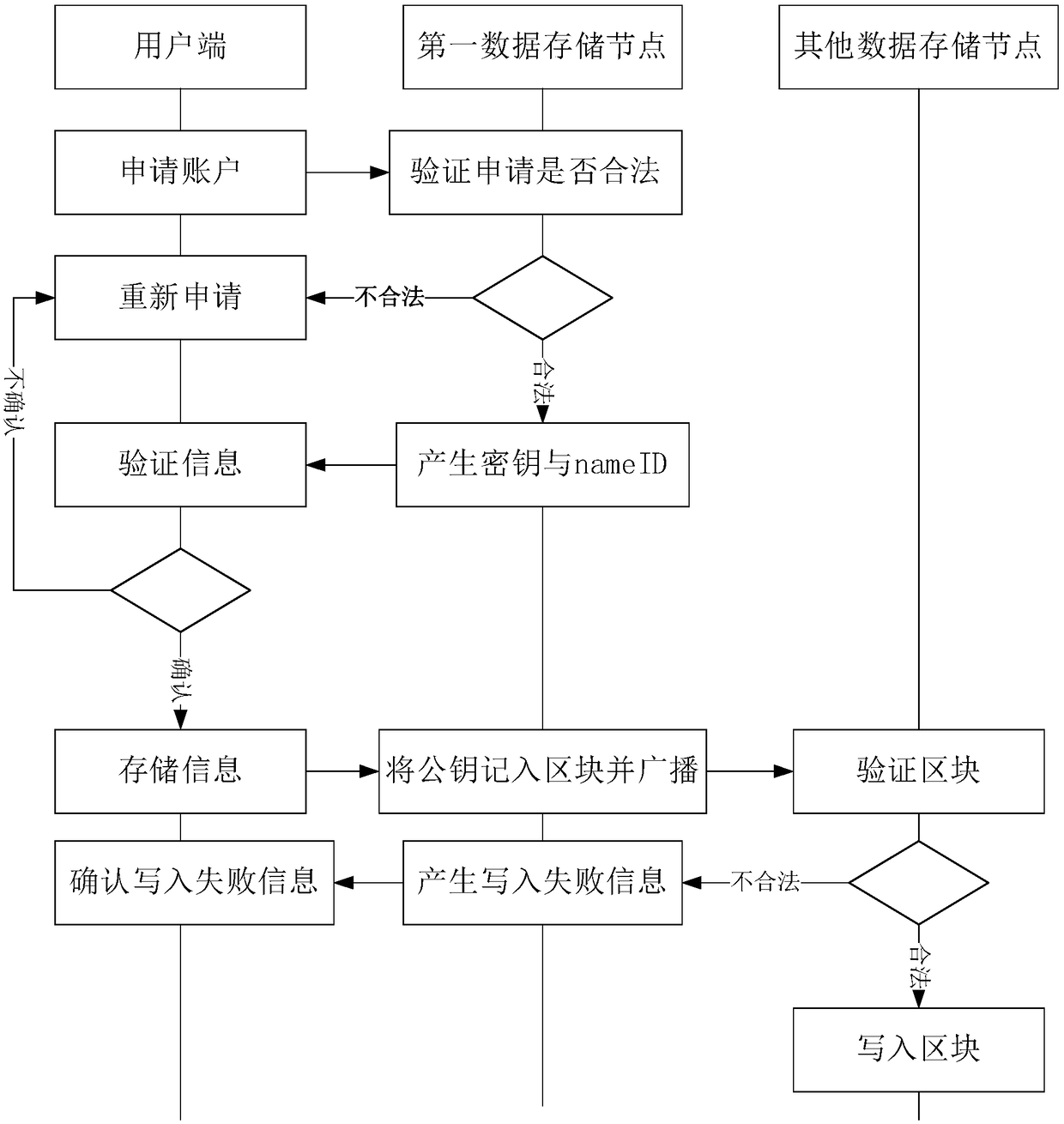
Whole-network unified online authentication method and system based on block chain
The invention provides a whole-network unified online authentication method and system based on a block chain. The method comprises the following steps that N servers are arranged in the whole networkdivided into S areas, and at least one server is arranged in each area to serve as a data storage node, wherein other servers are set as authentication service nodes; a first data storage node receives first user request information sent by a user side; the first data storage node generates first response information according to the first user request information, and sends the first response information to the user side; the first data storage node acquires block chain information corresponding to a first user according to the first response information, stores the block chain information corresponding to the first user in a block, and sends the block chain information corresponding to the first user to other data storage nodes; and the first authentication service node receives a second user request sent by the user side, and verifies the second user request.
Owner:BEIJING INFORMATION SCI & TECH UNIV
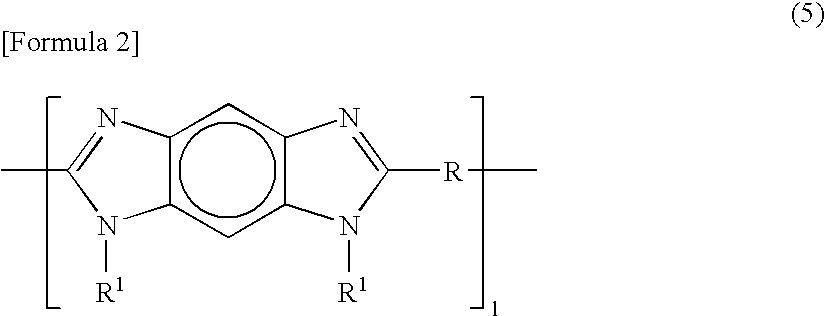
Highly Durable Electrode Catalyst Layer
ActiveUS20080096078A1Good chemical stabilityEmission reductionOrganic-compounds/hydrides/coordination-complexes catalystsActive material electrodesElectrically conductivePolymer chemistry
An electrode catalyst layer characterized by comprising composite particles comprising electrode catalyst particles supported on electrically conductive particles, a perfluorocarbonsulfonic acid resin (component A) and a polyazole compound (component B), the content of the composite particles being 20 to 95% by weight, the total weight of component A and component B being 5 to 80% by weight, the weight ratio between component A and component B (A / B) being 1 to 999.
Owner:ASAHI KASEI KK
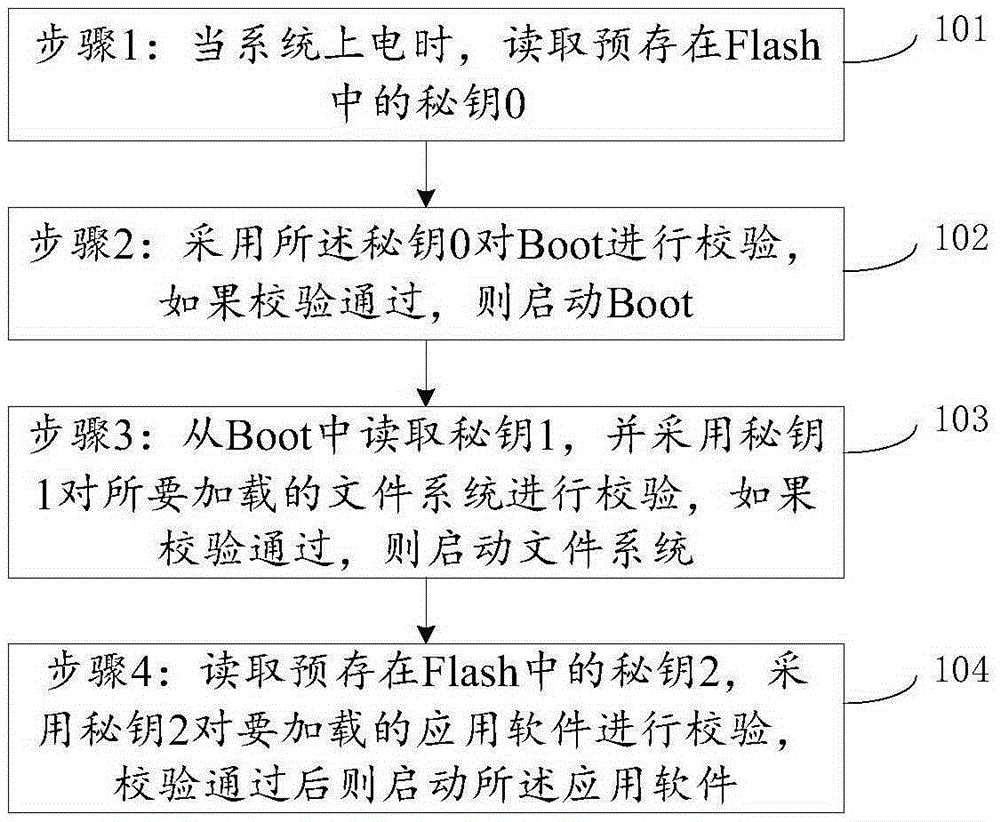
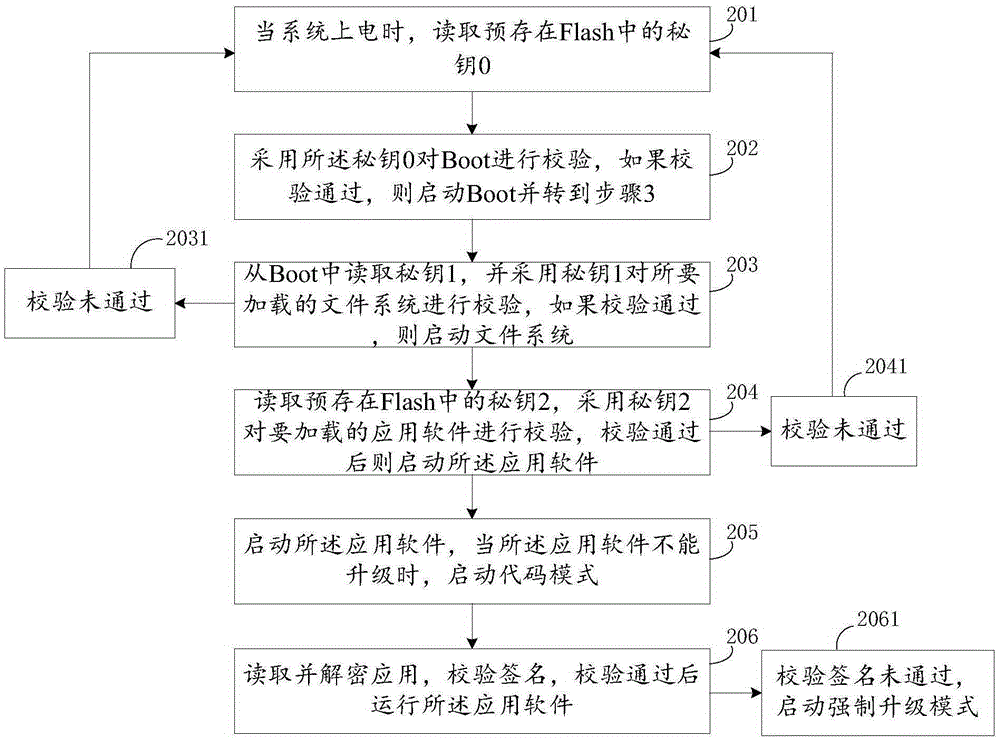
Application software calling method for intelligent terminal
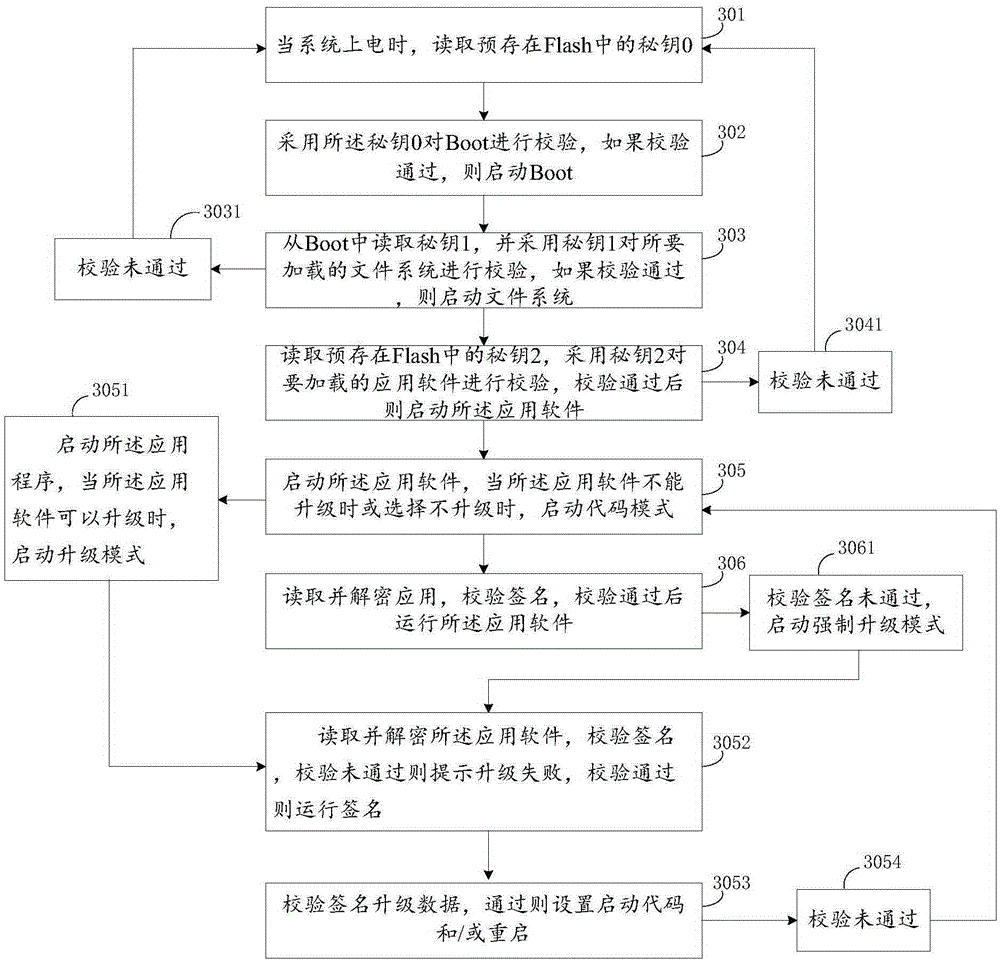
ActiveCN105354050ARun accuratelyNot easy to attackDigital data protectionProgram loading/initiatingFile systemSoftware engineering
The present invention relates to the field of safety of intelligent terminals and particularly relates to an application software calling method for an intelligent terminal. The application software calling method comprises the following steps: powering up a system, and reading a key 0 in a Flash; verifying a Boot by adopting the key 0, and after verification is passed, starting the Boot; reading a key 1 in the Boot, verifying a loaded file system, and after verification is passed, starting the file system; and reading a key 2 in the Flash, verifying loaded application software, and after verification is passed, starting the application software. According to the application software calling method for the intelligent terminal, which is provided by the present invention, in the starting and / or upgrading process of the intelligent terminal, authorized legal software can be correctly operated or an authorized program can be reloaded, and the intelligent terminal is difficult to be attacked by Hackers.
Owner:SHENZHEN JIUZHOU ELECTRIC
Drug for treating bronchitis and bronchial asthma of 7-15 year old children
ActiveCN102552773AImprove immunityAchieve recoveryOrganic active ingredientsPeptide/protein ingredientsDiseaseBelamcanda chinensis
The invention relates to a drug for treating bronchitis and bronchial asthma of 7-15 year old children, which consists of oral Chinese medicinal decoction and acupuncture point injection. The active ingredients of Chinese medicinal decoction consists of a variety of Chinese herbal medicines, comprising Herba Ephedrae Praeparata, Schisandra chinensis, Astragalus mongholicus, American ginseng, Radix Pseudostellariae, a pair of gecko, Zaocys dhumnades, Morinda officinalis, Lumbricus, Herba Epimedii, Sinapis alba, Semen Descurainiae (Lepidium apetalum and / or Descurainia sophia), Ginkgo biloba seed, Ramulus Cinnamomi, Radix Paeoniae Alba, Radix Rehmanniae Praeparata, Fructus Psoralea, Achyranthes bidentata, Fructus Lycii, black ant, Poria cocos, Largehead Atractylodes Rhizome, Rhizoma Dioscoreae, Radix Glycyrrhizae, Scorpion, Divaricate saposhnikovia root, Belamcanda chinensis, Prunus mume, white mulberry root-bark, processed Tussilago farfara flower, Stemona Root, Lily Bulb, Semen Armeniacae Amarum, Ganoderma, Manchurian wildginger, Angelica sinensis, Cornus officinalis and Bombyx Batryticatus (Bombyx mori and / or Beauveria bassiana). The acupuncture point injection is one of nucleotide and casein, placenta tissue fluid and Astragalus mongholicus injection. The drug of the invention can treat both principal and secondary aspects of disease, determine the treatment based on differentiation of symptoms and signs, enhance body immunity, and recover the function of impaired lung, spleen, kidney and heart, and has the advantages of high cure rate and no recurrence.
Owner:孟庆云 +1
Method, device and system for preventing video fingerprint attacks
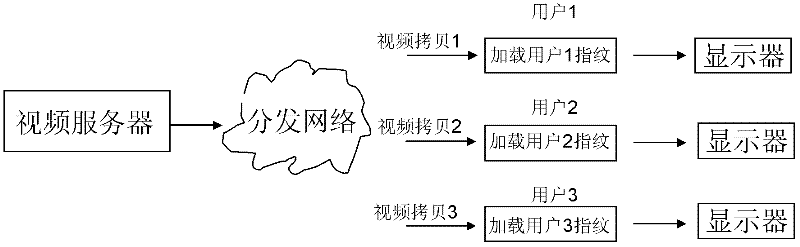
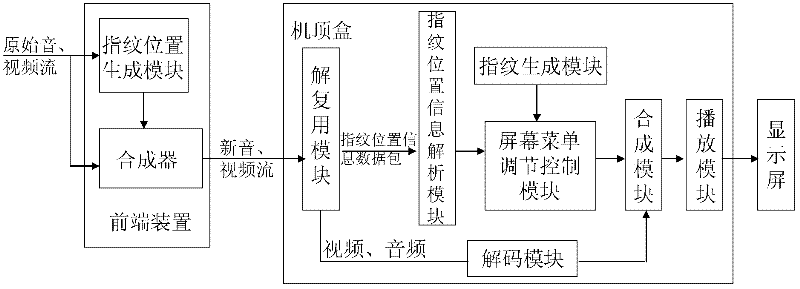
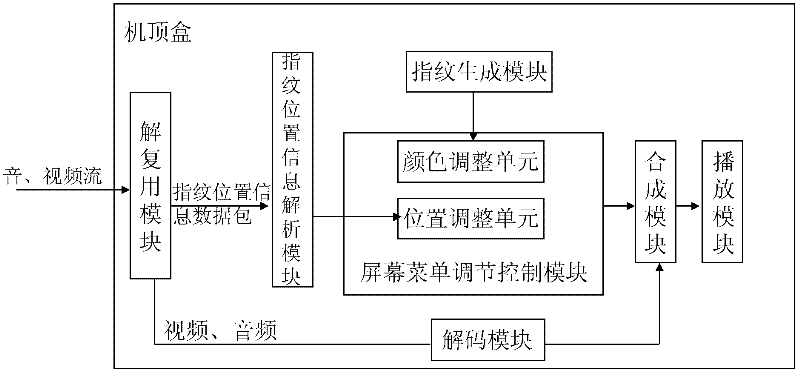
ActiveCN102647635ANot easy to attackAvoid attackSelective content distributionNetwork packetVideo quality
The invention discloses a method, a device and a system for preventing video fingerprint attacks. The method includes that a terminal generates user fingerprint information which can identify video sources and obtains fingerprint position information of a current frame period from a data packet storing the fingerprint position information of the current frame period; OSD (on screen display) invisible fingerprints are obtained by modifying parameters of a screen menu adjusting controller through a universal screen menu adjusting interface according to the user fingerprint information generated by the terminal and the fingerprint position information in the current frame period and are overlaid on original videos decoded to obtain videos with invisible fingerprints. By inserting the invisible fingerprints in the videos by modifying the parameters of the OSD controller and on the condition without affecting video quality, the video fingerprints are not easy to be attacked, robustness of the video fingerprints is improved, and the purpose of preventing the video fingerprints is achieved. Meanwhile, trouble in customizing a terminal decoding module of a set-top box is eliminated through the OSD universal interface.
Owner:北京视博数字电视科技有限公司
Double-ship telescopic airbag type floating deck
ActiveCN105775052ASmall targetNot easy to attackWaterborne vesselsFloating bridgesAirbag deploymentAirplane
A double-ship telescopic airbag type floating deck comprises a left ship, a right ship and a plurality of same telescopic airbag type floating bridges, wherein the left ship and the right ship are symmetrically distributed; the telescopic airbag type floating bridges are arranged between the left ship and the right ship; each telescopic airbag type floating bridge comprises a push rod mechanism, an upper rope mechanism, a lower rope mechanism, a swinging plate, a caterpillar band, a left airbag and a right airbag; the telescopic airbag type floating bridges are parallel to each other; the two ends of the telescopic airbag type floating bridges are connected with support plates of the left ship and the right ship; the push rod mechanisms comprise cylinder bodies, push rods and guide wheels; the swinging plates are rotationally connected with one side, close to the ship body, of the upper part of the support plate of the right ship; the upper rope mechanisms comprise upper ropes, electric motors and winding drums; the caterpillar bands comprise T-shaped frames and plate groups; the two ends of the upper parts of the T-shaped frames are rotationally connected with the left plate groups and the right plate groups, respectively; the two sides of the lower parts of the T-shaped frames are connected with one ends of the left airbags and the right airbags in a sealed way; and the other ends of the left airbags and the right airbags are connected with the support plates of the left ship and the right ship in a sealed way. The invention can be used as the water plane floating runway decks and floating bridges for carrying people and vehicles.
Owner:YANSHAN UNIV
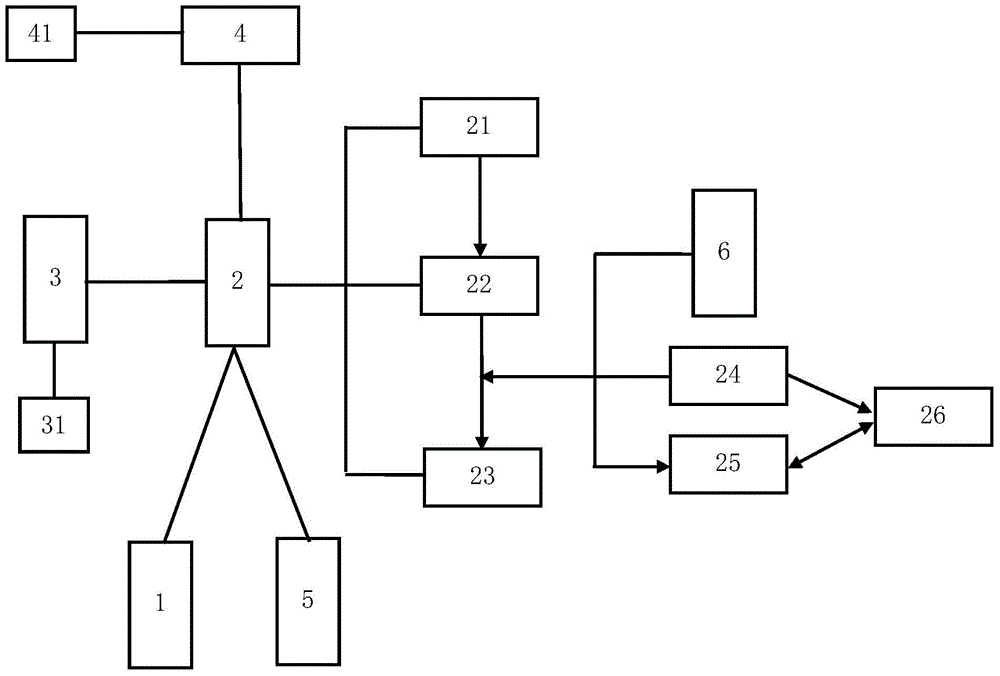
Web page evidence preservation method and device
The invention relates to a web page evidence preservation method and device. The device comprises a client side, a cloud access server and a cloud storage server. The client side is connected with the cloud access server through the Internet, and the cloud access server is connected with the cloud storage server. The cloud access server comprises an address mark receiving and analyzing module, a data access and obtaining module and a data transmitting module. Through the improvement on the preservation step, equipment connection, preservation content, the preservation means and the verification mode, preserved web page evidences meet the requirement for electronic evidences regulated by laws, and can be directly used for the notarization or litigation phase.
Owner:HANGZHOU ANCUN NETWORK TECH
High-pressure gas preservation method
InactiveCN103423583AStrong construction adaptabilityImprove securityMining devicesContainer filling methodsWater contentRebar
The invention belongs to the technical field of gas storage, and relates to a preservation method of high-pressure gas deeply embedded underground. According to the invention, an area with hard geological structure is selected as a gas preservation site; a base is dug on the selected gas preservation site; a construction channel or a working chamber is preserved in the base; a cylindrical steel liner is welded in the inner cavity of the base through the construction tunnel and the working chamber; network steel bar concrete or network steel bar asphalt mixture is filled in the space between the steel liner and the base, and an anti-corrosion treatment is carried out on the periphery of the steel liner; compressed gas to be stored is filled into the steel liner through a gas inlet pipe and a valve on the top of the steel liner under the control of a compression pump, and the state in the steel liner is controlled through a monitoring device; high-pressure gas stored in the steel liner is monitored regularly, such that gas pressure, temperature, water content, and density parameters of high-pressure gas stored in the steel liner are controlled in real time. The process principle is reliable, storage safety is good, control is flexible, operation cost is low, and the method is environment-friendly.
Owner:COOEC ENPAL ENG
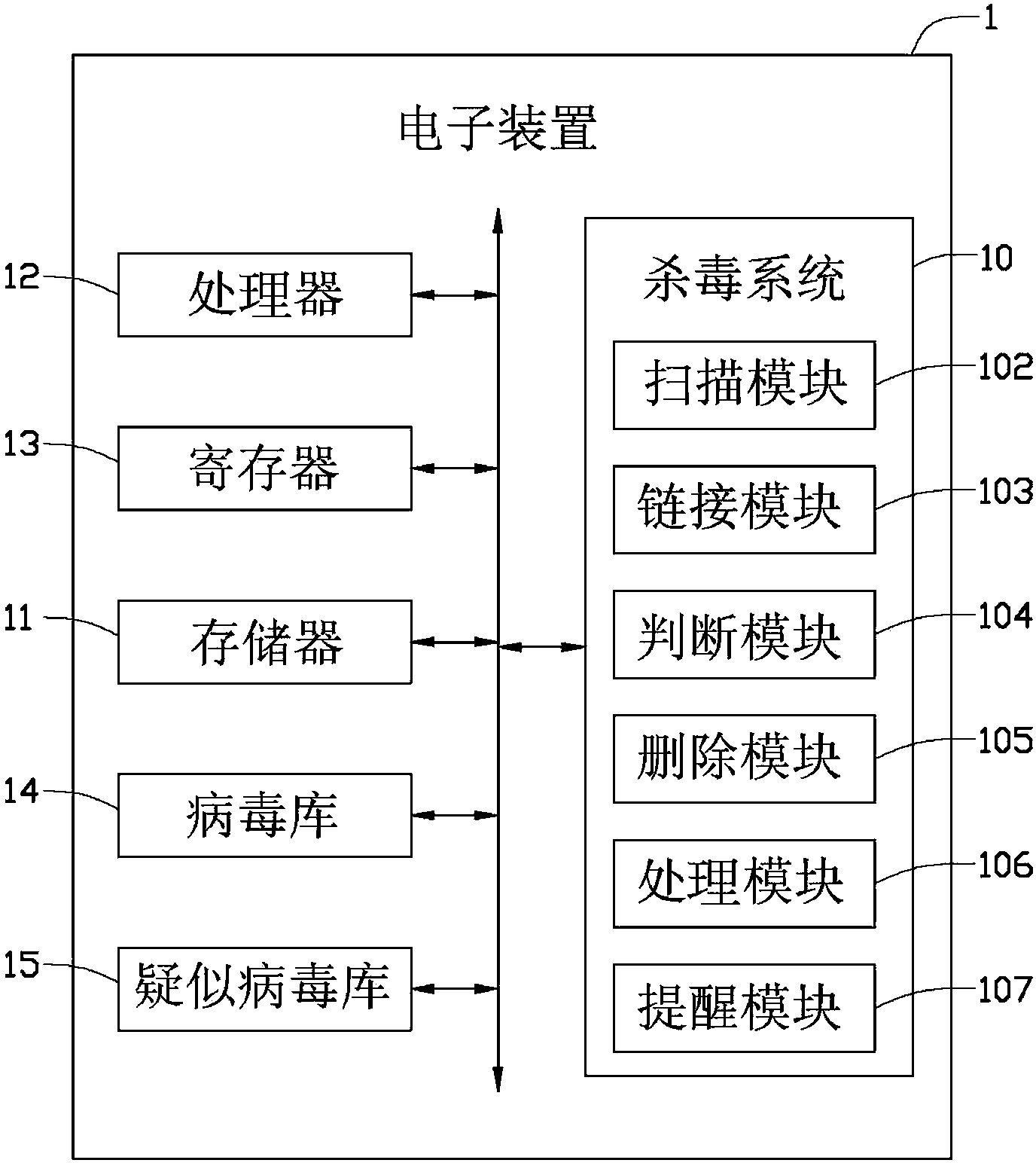
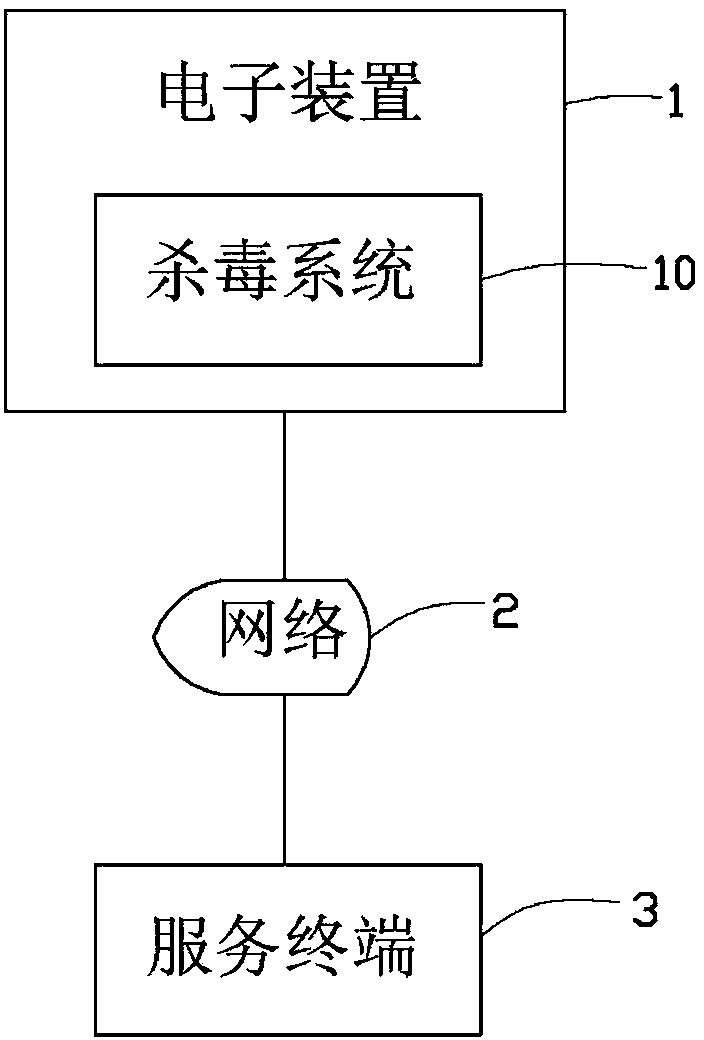
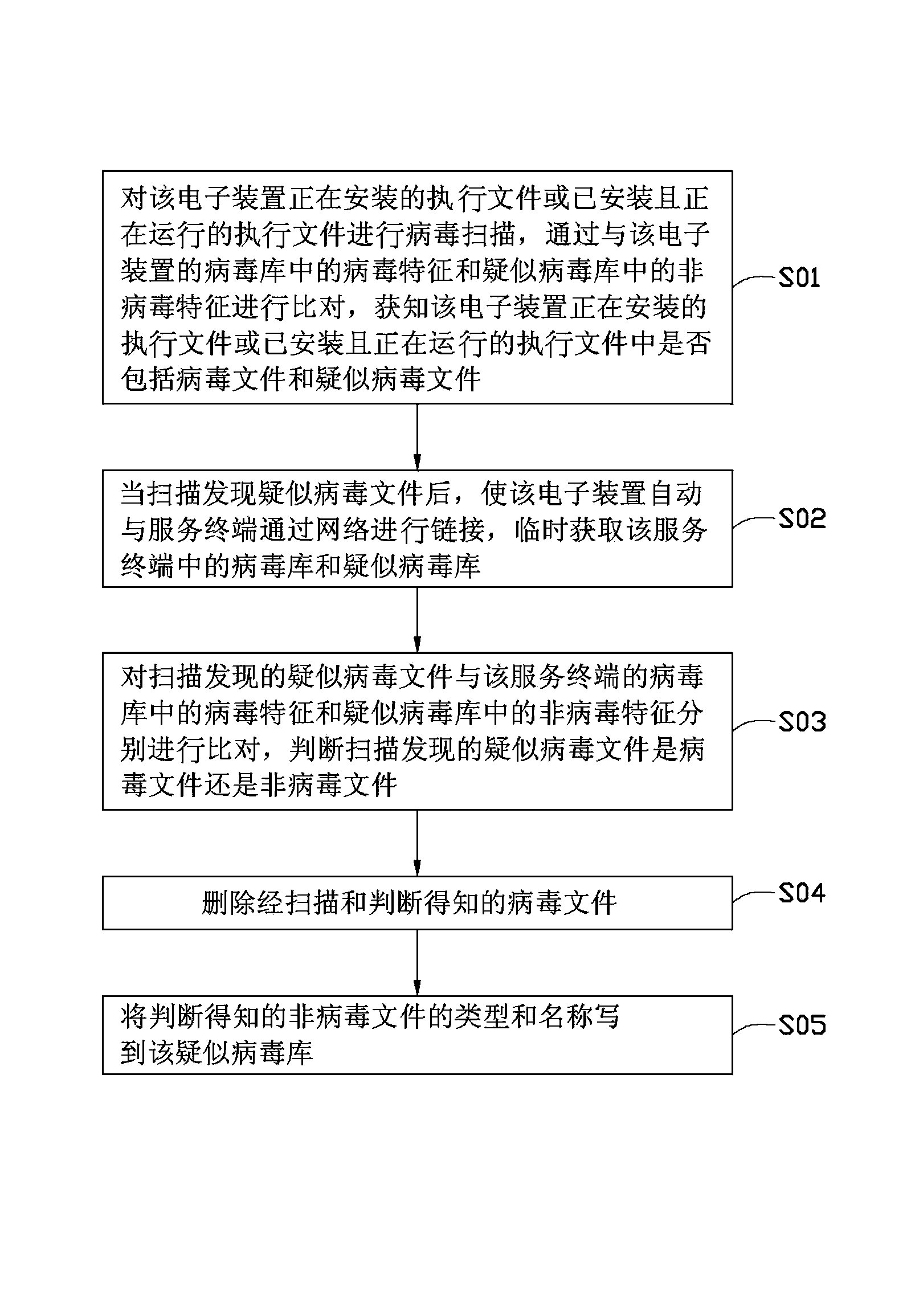
Virus killing system and method for electronic device
InactiveCN103425928ANot easy to attackEasy to usePlatform integrity maintainanceComputer scienceVirus
In a virus prevention method of an electronic device, executable files that are being installed in the electronic device are compared with the virus characteristics in virus database of the electronic device. The electronic device communicates with a server through a network, and a virus database and a suspected virus database of the server are accessed when one or more suspected files are determined. The one or more suspected files are compared with virus characteristics of virus samples in the virus database and non-viral characteristic of non-virus samples in the suspected virus database of the server, so as to determine whether the one or more suspected files are virus files. The determined one or more virus files intruded in the executed files are deleted.
Owner:FU TAI HUA IND SHENZHEN +1
Secure distributed storage system and method
ActiveUS8862900B2LengthNot easy to attackEncryption apparatus with shift registers/memoriesUser identity/authority verificationCiphertextKeystream
Moving from server-attached storage to distributed storage brings new vulnerabilities in creating a secure data storage and access facility. The Data Division and Out-of-order keystream Generation technique provides a cryptographic method to protect data in the distributed storage environments. In the technique, the Treating the data as a binary bit stream, our self-encryption (SE) scheme generates a keystream by randomly extracting bits from the stream. The length of the keystream depends on the user's security requirements. The bit stream is encrypted and the ciphertext is stored on the mobile device, whereas the keystream is stored separately. This makes it computationally not feasible to recover the original data stream from the ciphertext alone.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Method and transmitting device for securely creating and sending an electronic message and method and receiving device for securely receiving and processing an electronic message
ActiveUS20100325414A1Standardize the interfaceSimple methodDigital data protectionMultiple digital computer combinationsVirtualizationInternal memory
The subject matter relates to a method for securely creating and sending an electronic message, whereby the message is created using a first application running in a secure operating system, the created message is stored in a storage that can only be accessed by the secure operating system and a virtualizing unit. In a second application executed by the virtualizing unit, the internal storage is analyzed for the presence of a message and, if the message is present, the message is transmitted to a receiver. The subject matter also relates to a method for securely receiving and processing an electronic message, whereby an external storage is analyzed for the presence of a message using a second application and, if the message is present, the message is transmitted to the internal storage. The presence of the message is polled using the first application and, if the message is present, the message is transmitted from the internal storage to the first application for processing. The subject matter further relates to a transmitting device for carrying out the method for securely creating and sending the electronic message and a receiving device for carrying out the method for securely receiving and processing the electronic message.
Owner:SIEMENS AG
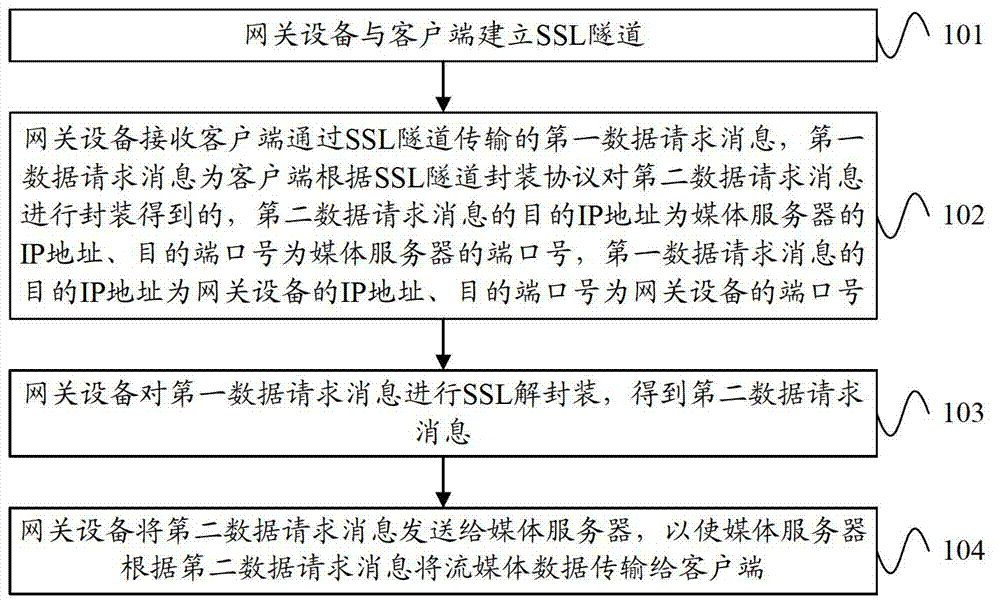
Audio Watermark Embedding and Extraction Based on Chaos and Wavelet Transform
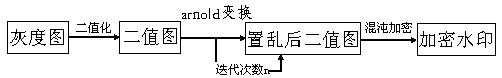
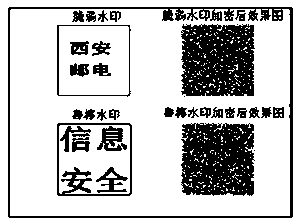
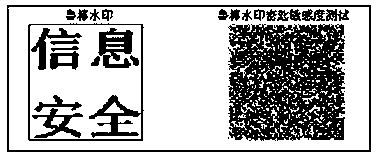
ActiveCN109344578AImprove securityNot easy to attackSpeech analysisImage watermarkingAudio watermarkWavelet decomposition
The audio watermark embedding method based on chaos and wavelet transform comprises the following steps: step 1, preprocessing the watermark, 1) scrambling the binary watermark; 2) encrypting that binary watermark; 2, embeding that robust watermark and the fragile watermark into the low frequency and the high frequency of the wavelet domain respectively; The audio watermark extraction method basedon chaos and wavelet transform comprises the following steps: firstly, wavelet decomposition is carried out on the audio signal containing watermark to find out the position corresponding to the audio element whose low frequency or high frequency component is smaller than the original set threshold value, and then one-dimensional noise-like extraction operation is carried out; Secondly, the extracted noise-like image is transformed into two-dimensional image format and encrypted image. At last, that encrypt image is decrypted by chaos and inverse Arnold transform, and the embed watermark is obtained. It has the characteristics of strong concealment, high robustness and easy to detect attacks.
Owner:XIAN UNIV OF POSTS & TELECOMM
Polyparaphenylene benzo dioxazole fiber containing fluorine on surface and preparation method thereof
ActiveCN104911895AHigh activityImprove mechanical propertiesFibre typesHydrogen fluorideAir atmosphere
The invention discloses a polyparaphenylene benzo dioxazole fiber containing fluorine on surface, which is prepared through the following steps: the body of the polyparaphenylene benzo dioxazole fiber is treated by using a hydrogen fluoride gas, then is mixed by using fluorine / oxygen / inert gas, is subjected to fluoridation for 10 seconds to 2 hours at 5-150 DEG C, and finally is stored in air atmosphere for at least one hour. A contact angle between the surface of the obtained fiber and water is 60-90 degrees, the interlaminar shear strength of a composite material prepared from the fiber and epoxy resin is 30-45MPa, the tensile strength of an impregnated filament is 5.0-5.3GPa, and the tensile modulus is 264-280GPa. The polyparaphenylene benzo dioxazole fiber containing fluorine on surface is high in surface activity, interfacial interaction between the fiber and matrix resin is strong, the interlaminar shear strength of the composite material prepared by using the fiber can be improved by 50-125%, the tensile strength of the impregnated filament is improved by 4-10%, and the modulus is improved by 10-16%. According to the invention, the fluorination rate is high, the treatment time is short, the process is simple and controllable, the cost is relatively low, and the fiber has relatively strong application prospect.
Owner:SICHUAN UNIV
Proxy realizing device
The invention provides a proxy realizing device which comprises a proxy server and an intranet terminal. After registration of a user, the intranet terminal logs in the proxy server, an access request is sent to the proxy server actively to obtain request information of the user, according to the request information of the user, a corresponding content result is searched from an information application system or file of the intranet and returned to the proxy server, and the proxy server returns the content result of the request to the user. The proxy realizing device has the advantages that an extranet user needs only to access the proxy server, an intranet server needs not to implement port mapping, operation is simple, an intranet system tends not to be attacked by virus of the extranet, and the security of the intranet is improved; and the user needs not to do complex configuration operations, the learning cost of the user is reduced, and the working efficiency and quality of the user are improved.
Owner:SUZHOU JINGYIHUI INFORMATION TECH
Cryptographic system arranged for key sharing
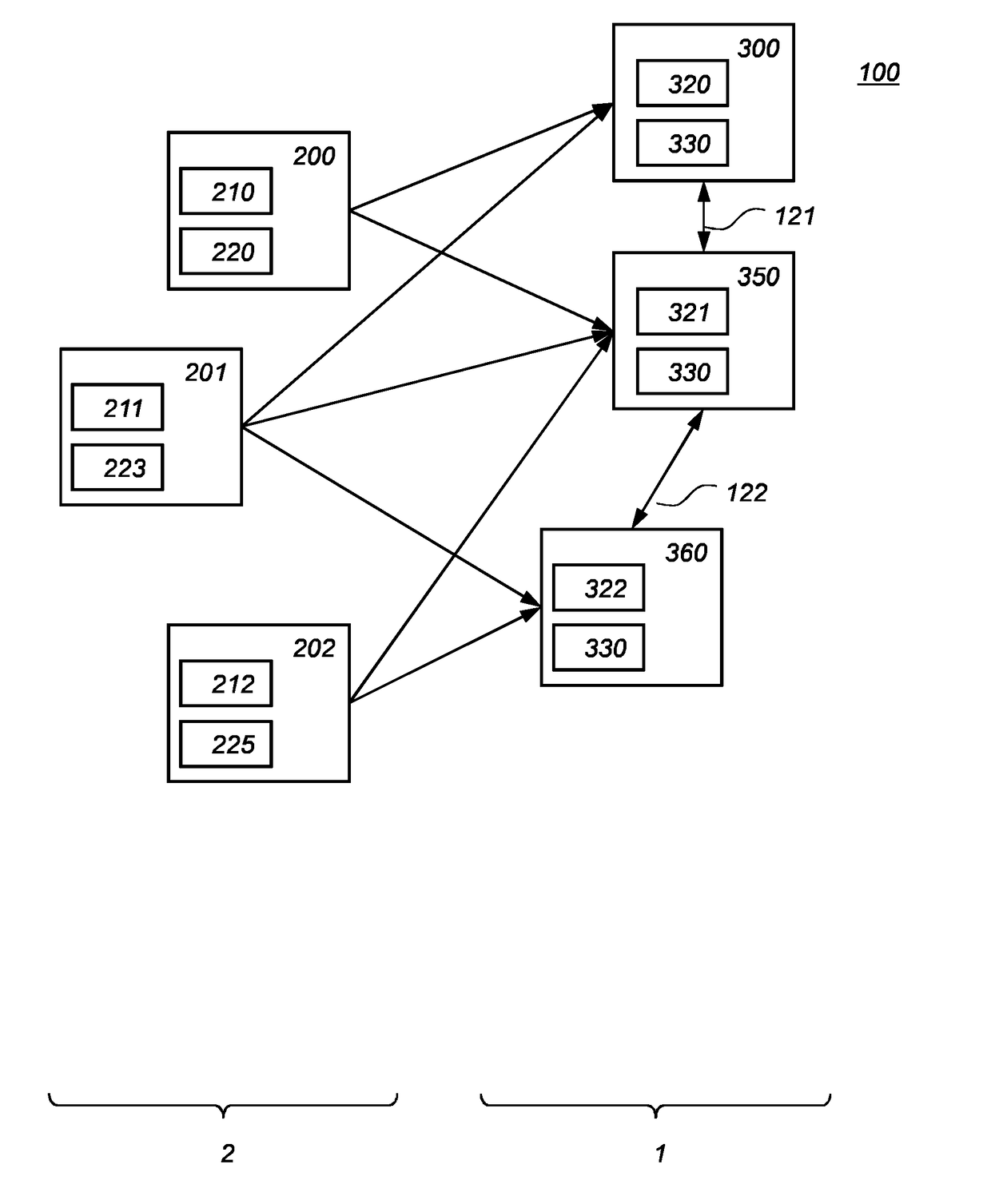
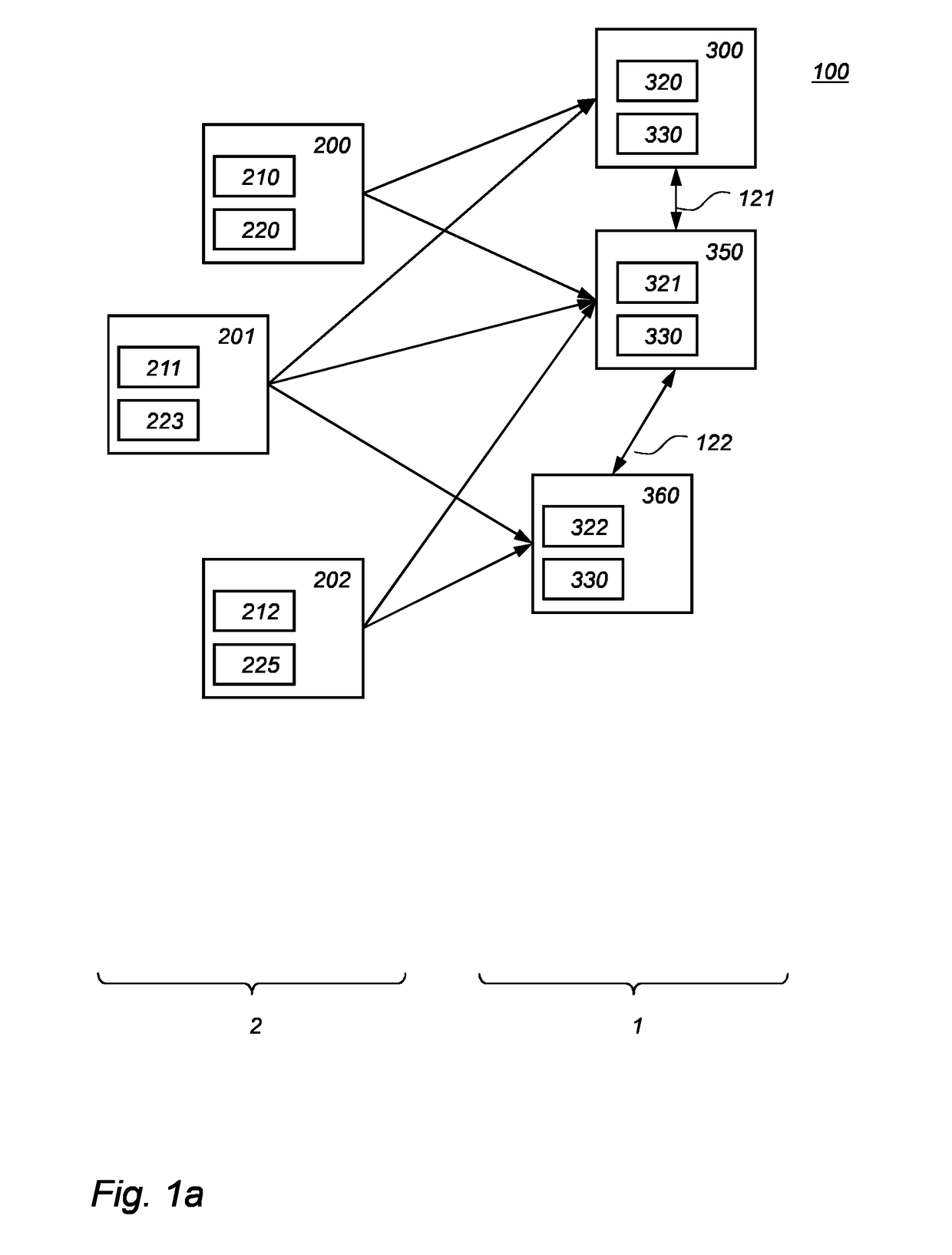
ActiveUS20170310472A1Lower requirementNot easy to attackKey distribution for secure communicationPublic key for secure communicationComputer hardwareKey sharing
A cryptographic system is provided comprising multiple configuration servers (200, 201, 202) arranged to configure multiple network devices (300, 350, 360) for key sharing. Each configuration server comprising a computation unit (220) arranged to compute local key material for the network device from root key material specific to the configuration server and the network device identity number of the network device that is being configured. At least two configuration servers of the multiple configuration servers provide computed local key material to said network device. The network devices are configured to determine a shared key with any one of multiple network devices. A network device comprises a shared key unit (330) arranged to derive a shared key from another network device's identity number and at least two of the multiple local key materials of the network device.
Owner:KONINKLJIJKE PHILIPS NV
Random number generating device, true random number generator and system-level chip
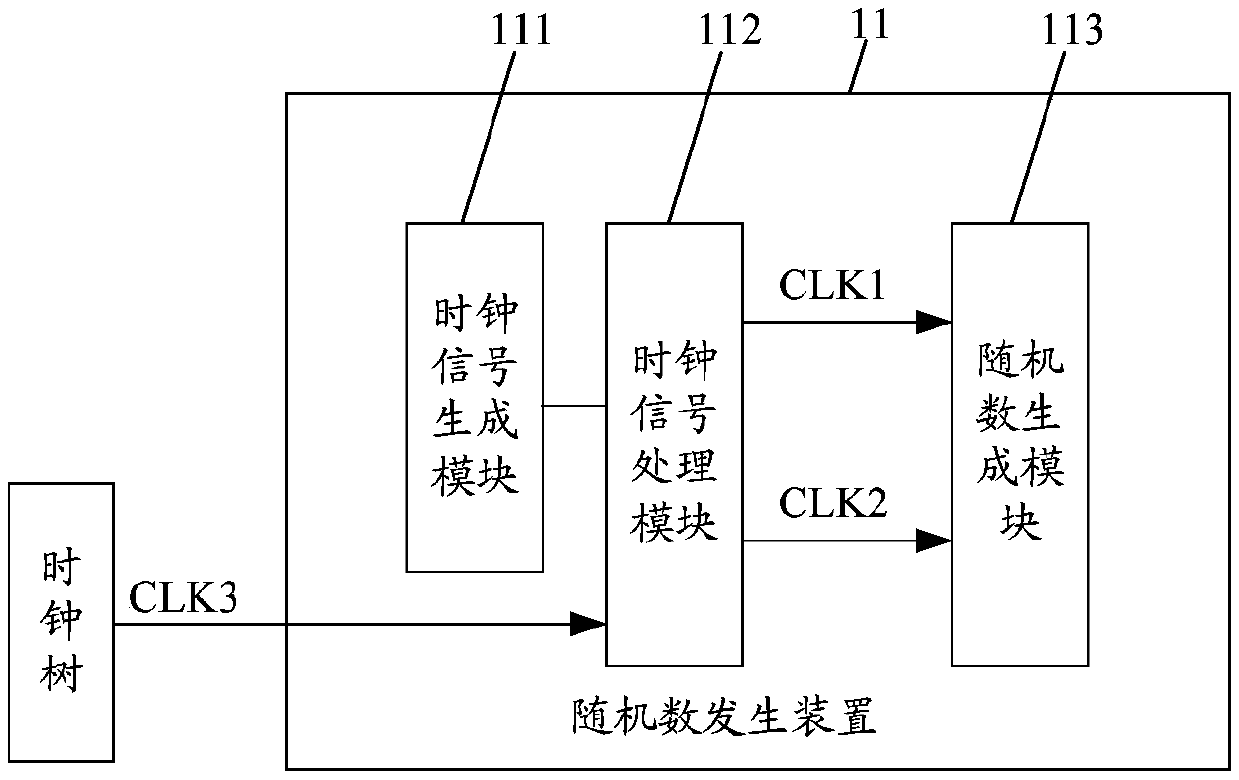
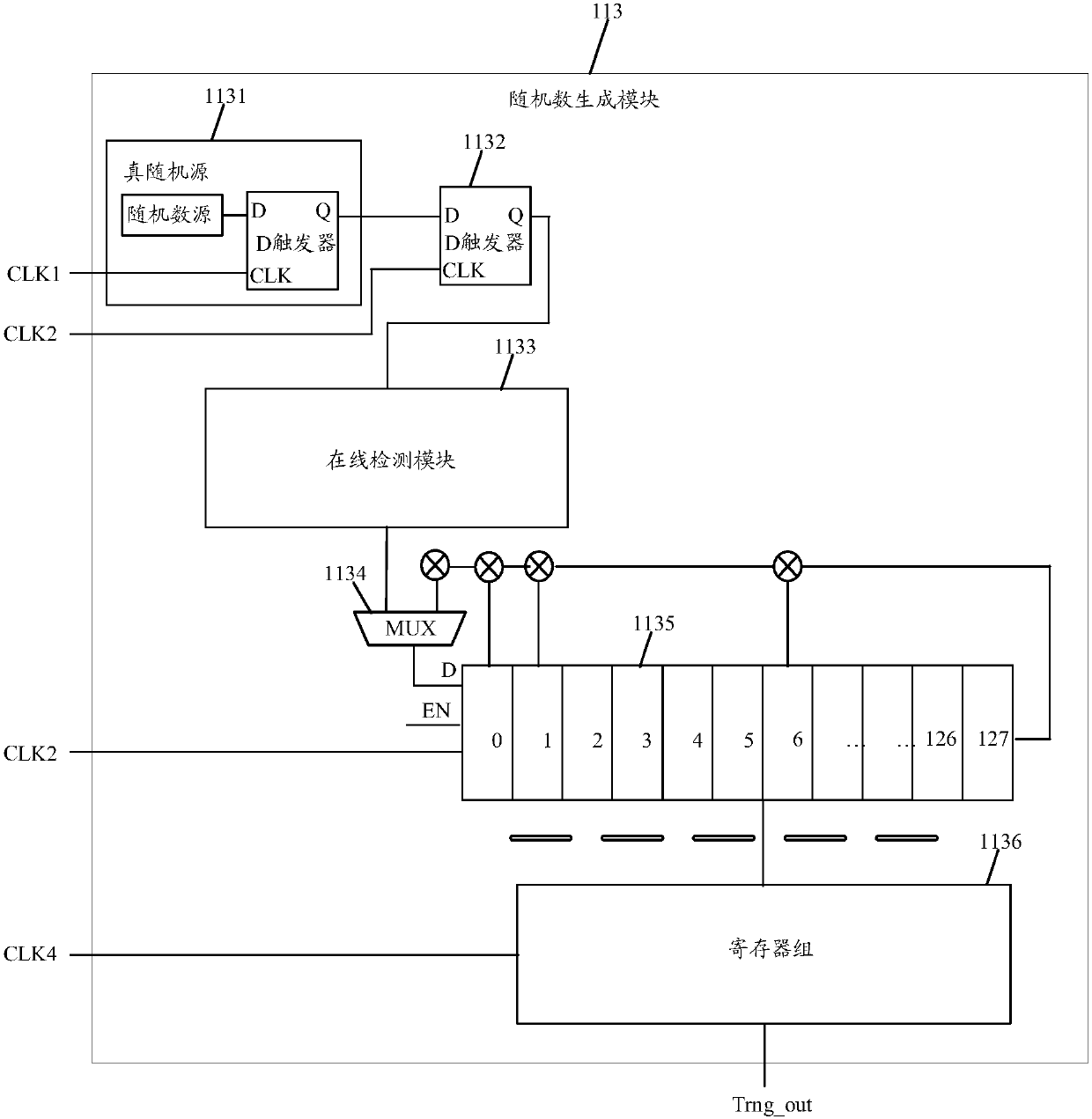
ActiveCN107797788ANot easy to attackReduced probability of predictabilityRandom number generatorsComputer moduleClock tree
The invention discloses a random number generating device, a true random number generator and a system-level chip. The random number generating device comprises a clock signal generating module used for generating two low-frequency clock signals with the same frequency and opposite phases, and a clock signal processing module comprising a detection module, a frequency division module and an outputmodule, wherein the detection module is used for detecting whether or not the two generated clock signals are abnormal, the frequency division module is used for dividing the frequency of a clock signal from a clock tree to obtain two clock signals with the same frequency and opposite phases, and the output module is used for outputting the two generated clock signals if it is detected that two generated clock signals are normal, and outputting the two clock signals acquired in the frequency dividing process if it is detected that the two generated signals are abnormal. The random number generating device further comprises a random number generating module used for generating random numbers according to the two clock signals outputted by the output module. According to the embodiment of the invention, the probability that the generated random numbers are predictable is reduced.
Owner:DATANG MICROELECTRONICS TECH CO LTD
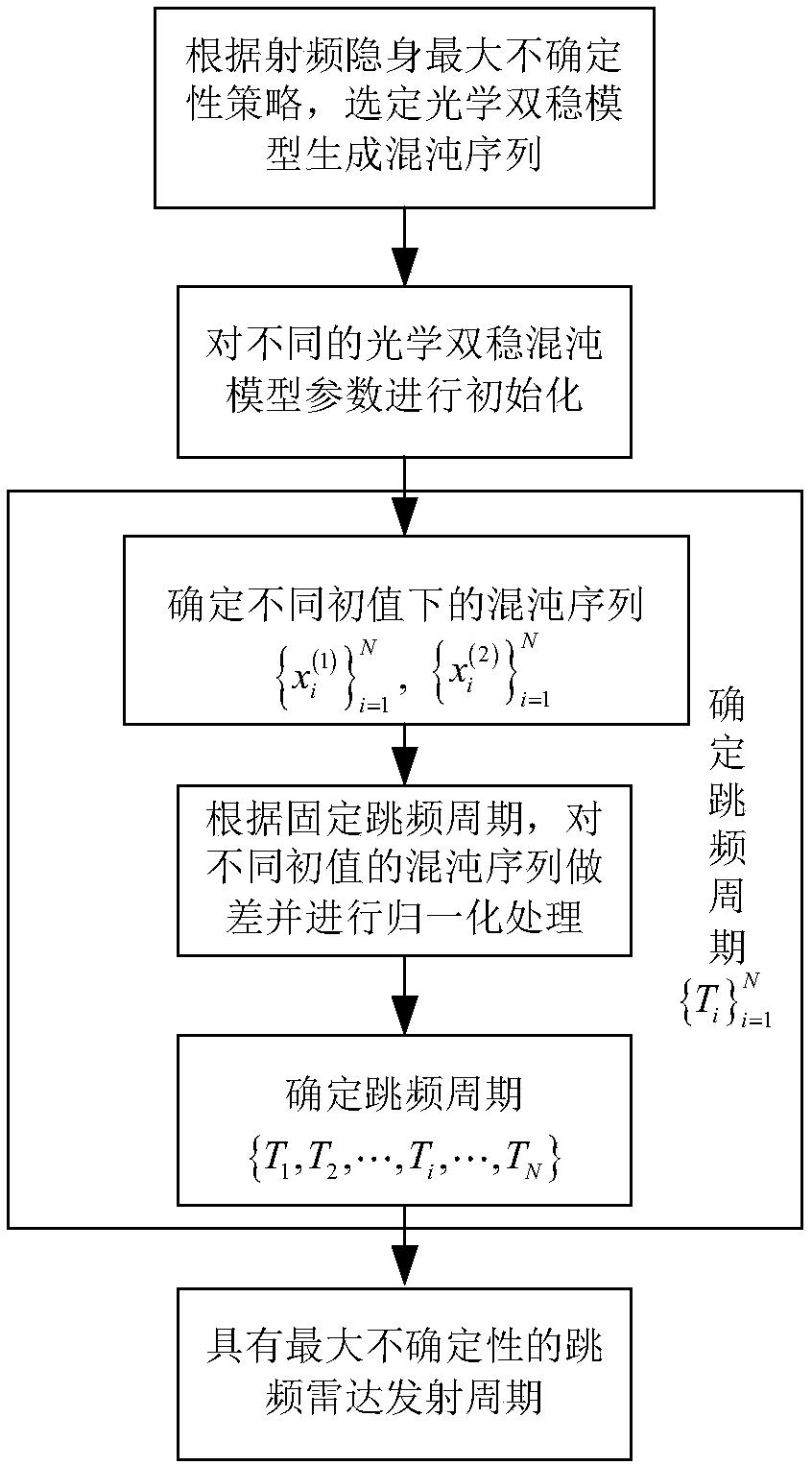
Frequency hopping radar transmission period design method based on optical bistable chaotic model
InactiveCN108089163AGuaranteed Maximum UncertaintyMaximum Uncertainty SatisfactionWave based measurement systemsRadar systemsAdaptive optimization
The invention discloses a frequency hopping radar transmission period design method based on an optical bistable chaotic model. The method is characterized in that taking the maximization of the uncertainty of the frequency hopping period of a radar system as an optimization objective, the optical bistable model in the chaotic theory is utilized to generate a chaotic sequence with the pseudo-random, quasi-noise and non-periodic characteristic changes, and the mapping and normalization processing on the sequence in a radar frequency hopping period space is carried out, so that the self-adaptionoptimization design is carried out on the radar frequency hopping transmission period. The beneficial effects of the invention are that an optical bistable chaotic model is used for carrying out theoptimization design on the radar frequency hopping transmission period, and the frequency hopping period with the pseudo-random, quasi-noise and non-periodic characteristic changes, the maximum uncertainty of the signal parameters of the frequency hopping radar is maximized, and therefore the radio frequency stealth performance of the radar system is improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method, device and system for streaming media service request
ActiveCN102932359ANot easy to attackAvoid risks such as data lossTransmissionIp addressData transport
The invention discloses a method, a device and a system for a streaming media service request. The method comprises that a Security Socket Layer (SSL) tunnel is set up between a gateway device and a client; first data request information which is transmitted by the client through the SSL tunnel is received, second data request information is encapsulated by the client in accordance with an SSL tunnel encapsulating protocol, then the first data request information is obtained, a target internet protocol (IP) address and a port number of the second data request information are an IP address and a port number of a media server, and a target IP address and a port number of the first data request information are an IP address and a port number of the gateway device; and the first data request information is subjected to SSL decapsulation, the second data request information is obtained, the second data request information is sent to the media server, and the media server is used for transmitting steaming media data to the client. Therefore, the port number of the media server cannot be exposed to the client directly, the media server is not attacked easily, and the hazards that the media server crashes and data are lost are avoided.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
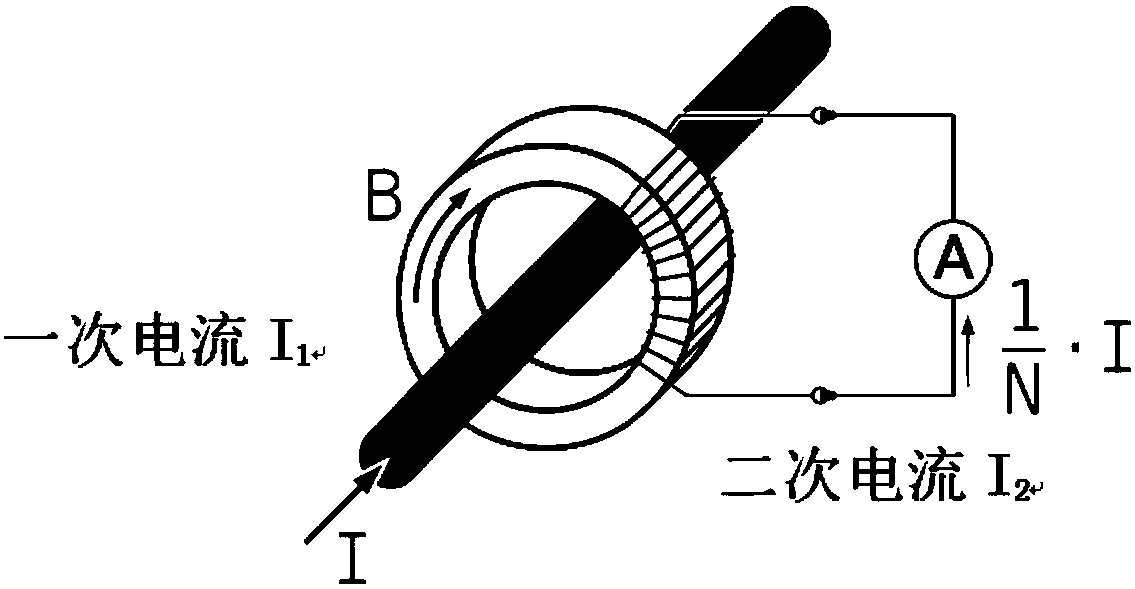
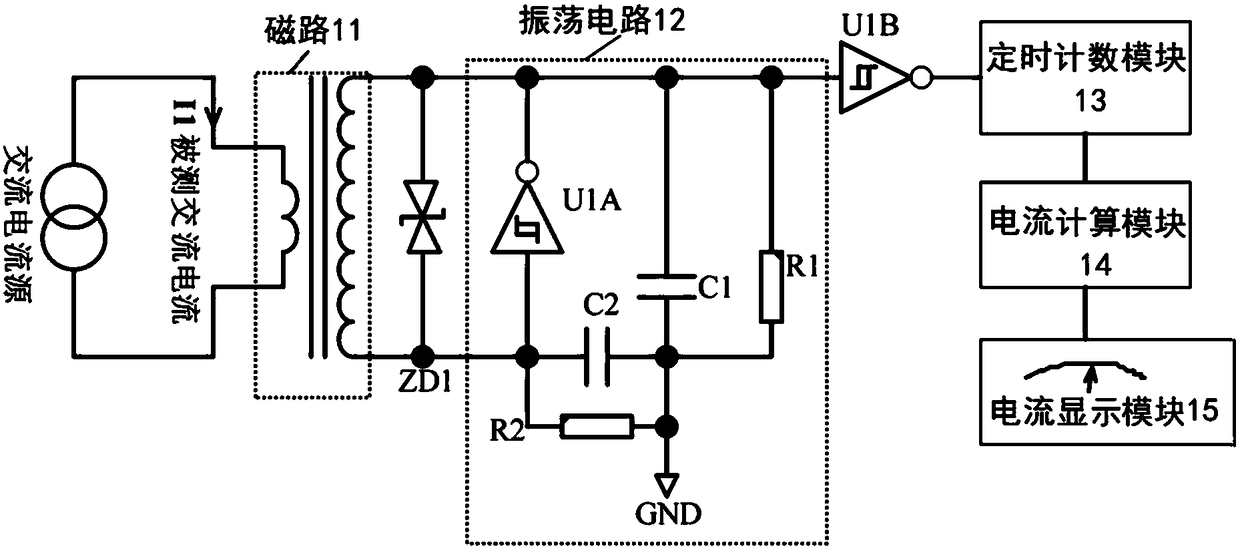
Alternating current measuring device
ActiveCN108459193ANot easy to attackImprove securityCurrent measurements onlyAlternating currentConductor Coil
The invention discloses an alternating current measuring device. The alternating current measuring device comprises a magnetic circuit, an oscillating circuit, a timing counting circuit, a current calculating module and a current display module, wherein the magnetic circuit comprises a magnetic core, a primary winding and a secondary winding, the magnetic circuit is used for realizing impedance transformation, the oscillating circuit is connected with the secondary winding and is used for generating the oscillation frequency, the timing counting circuit is connected with the oscillating circuit and is used for acquiring the periodic frequency mean of measured current fundamental waves, the current calculating module is connected with the timing counting circuit and is used for calculatinga detected current value according to the periodic frequency mean of the measured current fundamental waves, and the current display module is connected with the current calculating module and is usedfor displaying the detected current value acquired by the current calculating module through calculation. The alternating current measuring device is advantaged in that the principle is relatively complex and is not obvious, so the alternating current measuring device is not easily attacked by humans, and safety is improved.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com