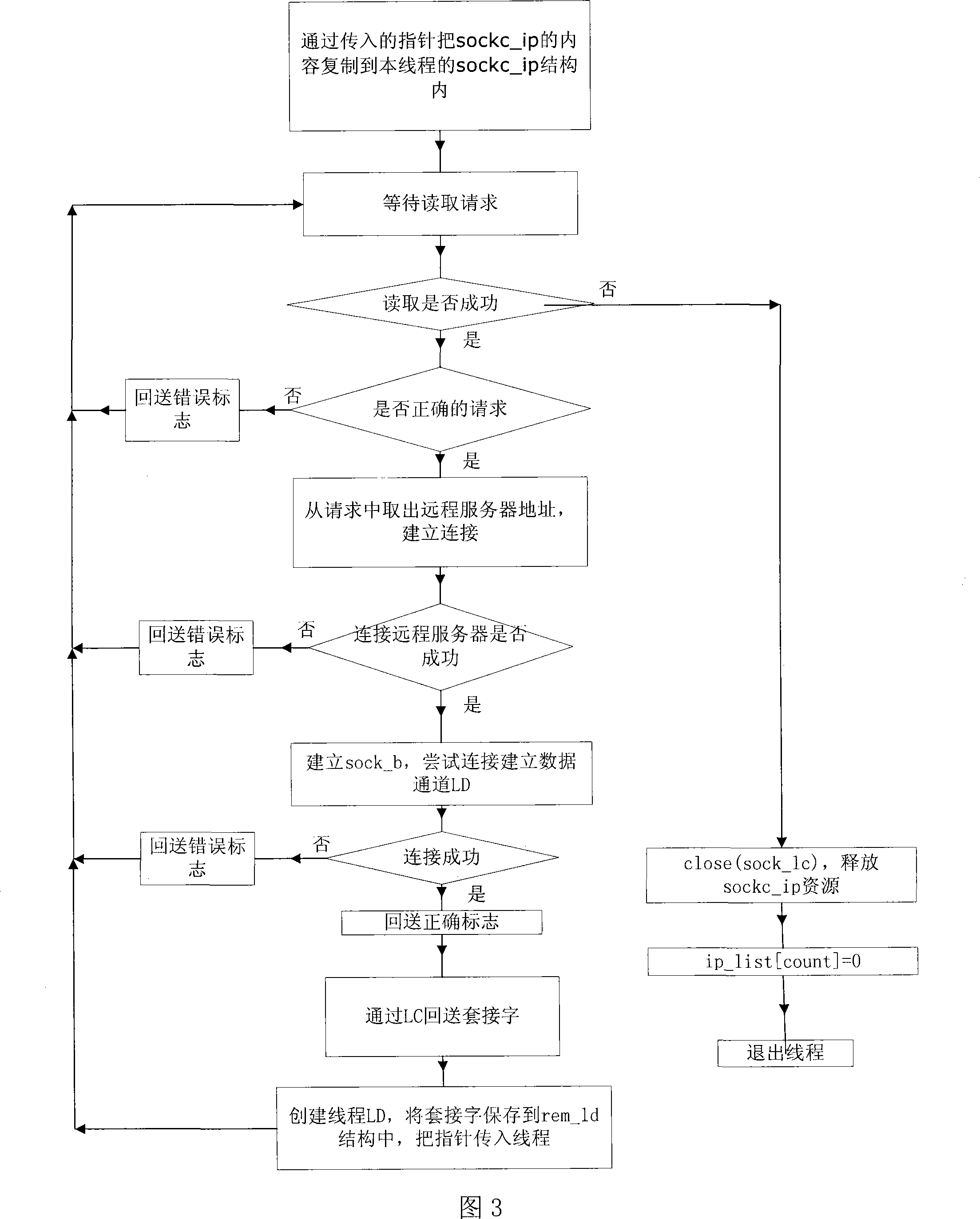
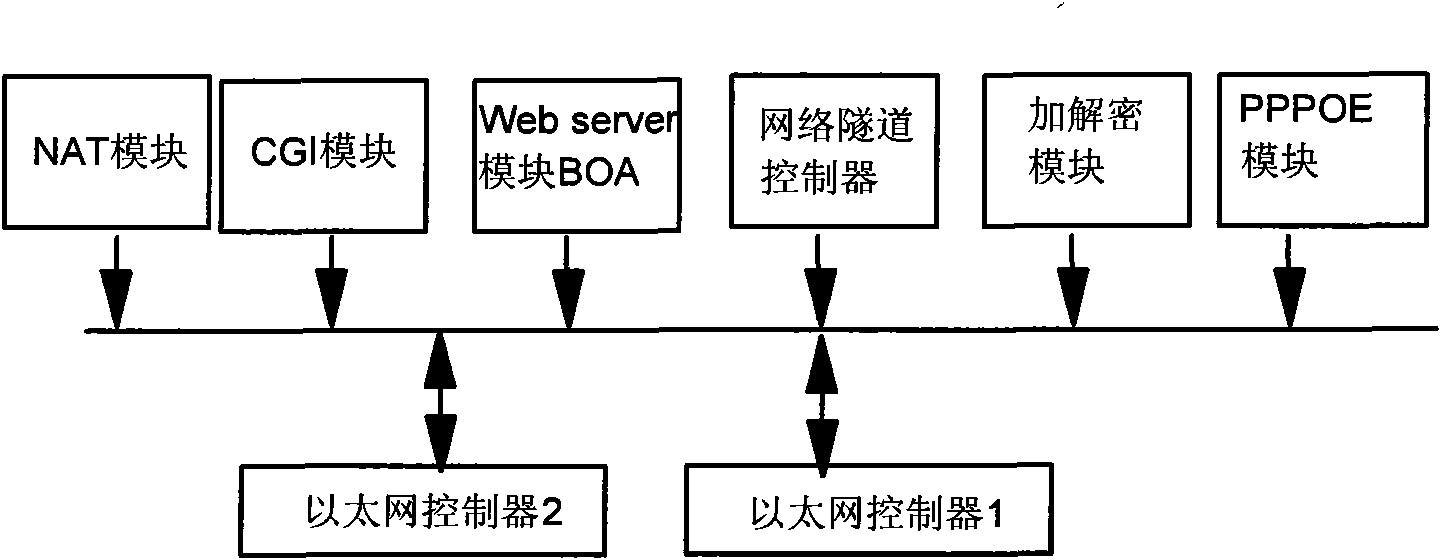
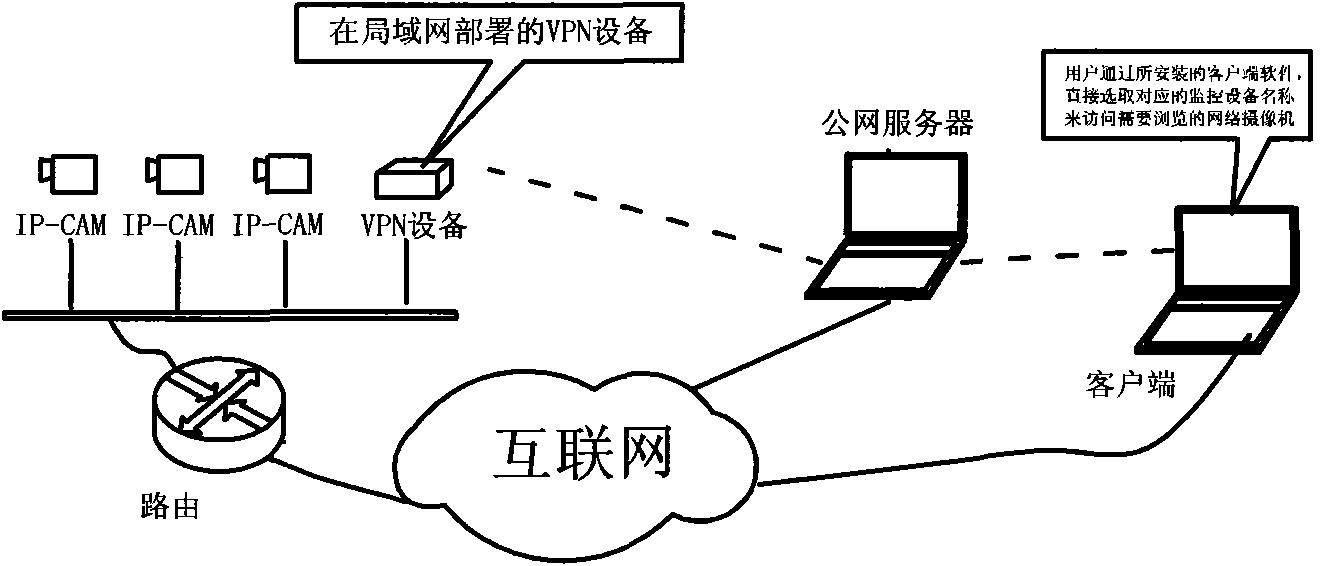
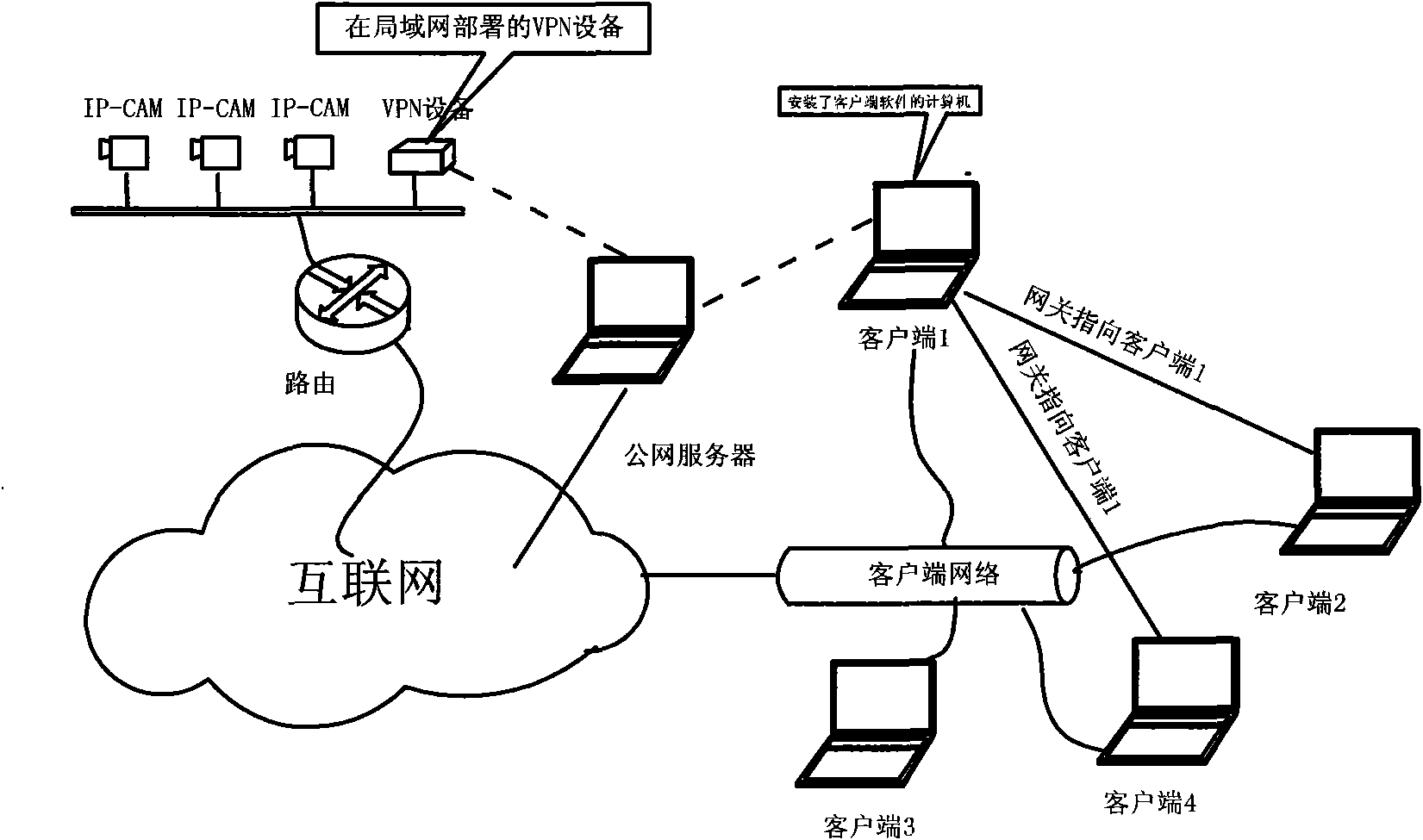
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
249results about How to "Data transmission security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
System and method for remote monitoring elevator base on wireless network
ActiveCN101374357ARealize managementEasy to useTelemetry/telecontrol selection arrangementsTransmission systemsThe InternetData field
The invention discloses an elevator remote monitor system and method based on wireless network. The system includes: an elevator data field collection device independent with an elevator control system, a monitor platform and a monitor terminal, the elevator data field collection device is composed of a carriage top data collection device and a control board data collector which are communicated with each other. The method includes: the monitor terminal sends a request to the monitor platform for acquiring the elevator data; the monitor platform sends the request to the elevator data field collection device through the wireless communication network; the elevator data field collection device sends the elevator field data to the monitor platform through the wireless communication network; the monitor platform sends data to the monitor terminal through internet; when the elevator breaks down, the monitor platform sends data to the monitor terminal and the hand-held or vehicle-mounted interface device. The field data of the elevator can be directly acquired on internet according to the invention, thereby the remote monitor and management of the elevator are realized, without the limitation of the field wiring and elevator space position.
Owner:建研机械检验检测(北京)有限公司 +2
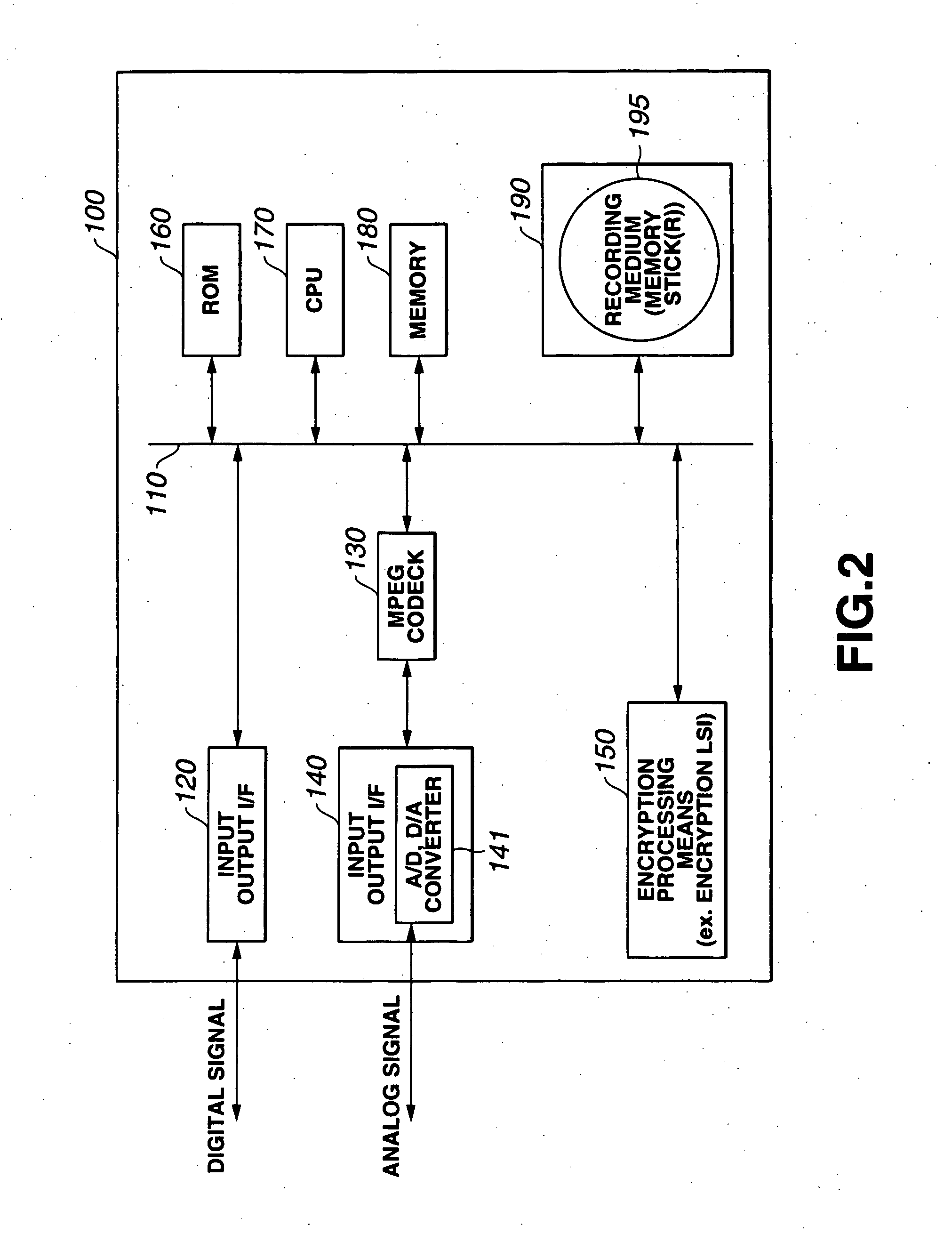
Method and System for Access Control and Data Protection in Digital Memories, Related Digital Memory and Computer Program Product Therefor
ActiveUS20080089517A1Prevent tamperingData transmission securityAcutation objectsDigital data processing detailsInternal memoryData memory
A digital memory such as a memory card for mobile communication equipment, is adapted to be accessed by a plurality of users and have protected data stored therein. The memory is dynamically partitionable in private memory areas for storing data therein and has associated therewith a secrecy tool for securely allocating to the users respective private areas and permitting the users to access the respective private areas via a secure session channel to perform read / write commands in the respective private areas. Typically, the memory / card includes: a card interface controller for managing a physical communication layer between the digital memory and external host equipment, an internal memory having associated therewith a hardware lock to control access to the internal memory, a set of cryptographic modules to manage the secure session channel between the users and the digital memory, and a memory certificate for certifying a public key associated with the digital memory.
Owner:TELECOM ITALIA SPA
Security protection method of communication data of special electricity public network
ActiveCN101662359AReal-time uninterruptible productionControl securityNetwork connectionsSecuring communicationCommunications securityElectricity
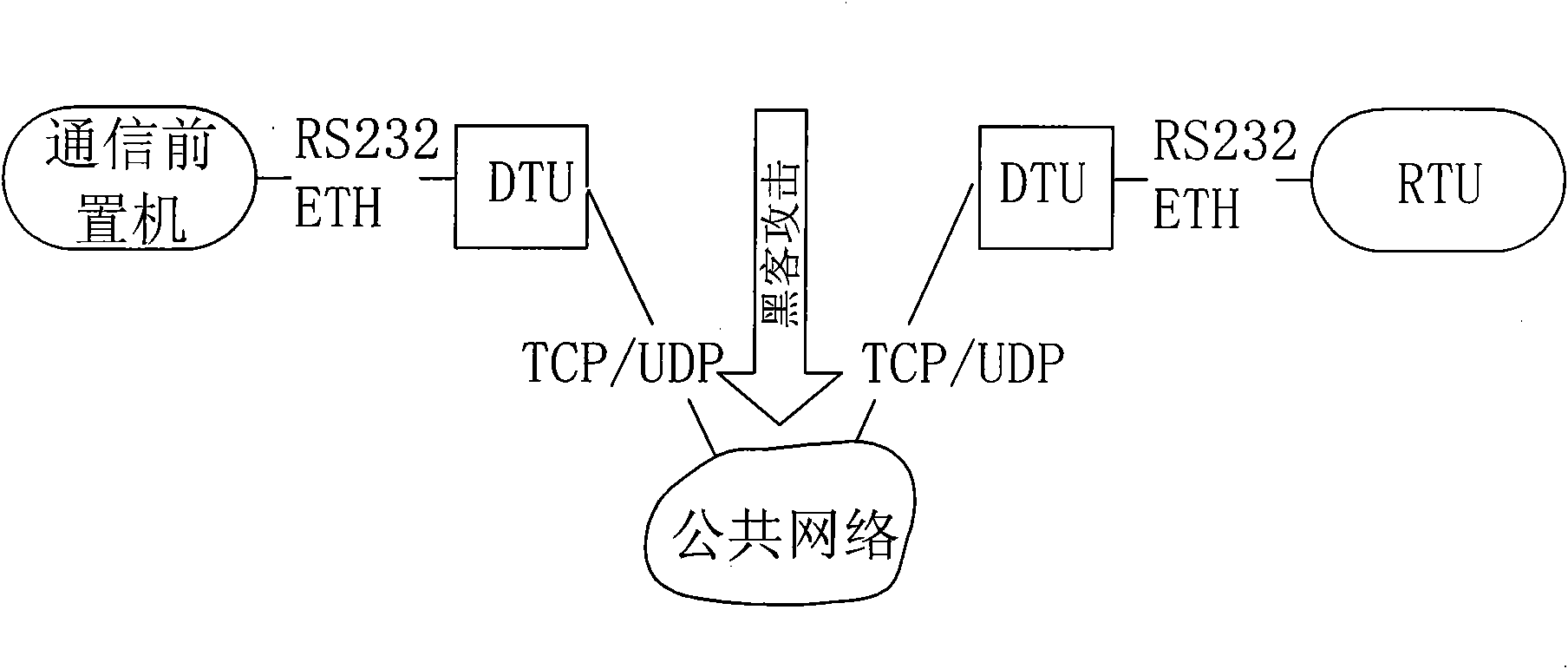
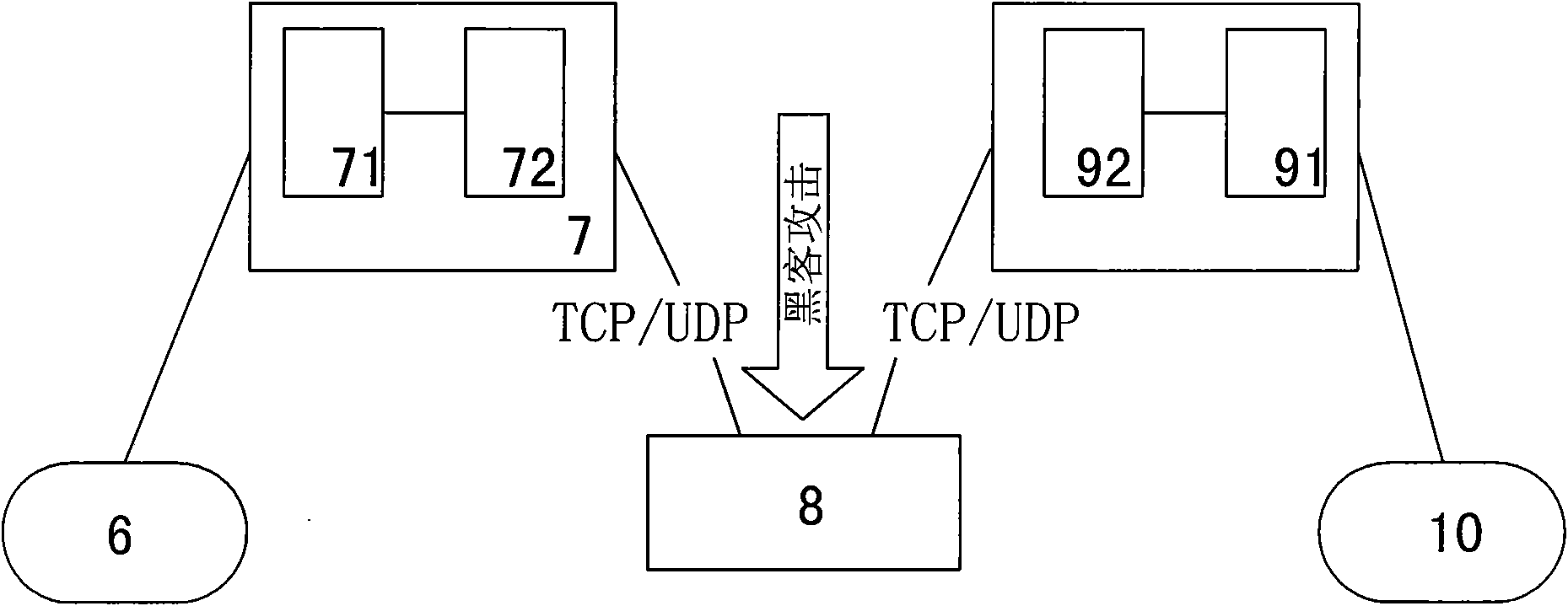
The invention discloses a security protection method of communication data of a special electricity public network, which provides secure and reliable data communication for the data communication ofthe special electricity public network by adopting the technical means of network isolation, right control, identity authentication and transmission encryption, realizes the purpose of securely usingthe public network for communication at any time and in any places without making any change to the application environment or software. In the process of application, a calling telecontrol communication security gateway (7) and a called telecontrol communication security gateway (9) are connected to a public network (8) by dialing; an encrypted public network communication channel is establishedfor the communication between a communication front-end processor (6) and a remote RTU (10); and the data is connected with the telecontrol communication security gateway (7) from the communication front-end processor (6) through a serial port or network, connected with the public network (8) through the calling telecontrol communication security gateway (7), connected with the called telecontrolcommunication security gateway (9) from the public network (8), and then connected with the remote RTU (10) through the serial port or the network. The invention can be widely applied to the field ofsecurity protection of the communication data of the public network.
Owner:CHINA SOUTHERN POWER GRID COMPANY +1
Internet-of-Things platform system and cloud platform thereof, and local terminal
ActiveCN109587242AIncrease opennessOpen implementationInterprogram communicationDigital data protectionClosed platformIot gateway
The invention discloses an Internet-of-Things platform system and a cloud platform thereof, and a local terminal. The cloud platform includes an IoT gateway, a streaming media service module, a rulesengine module, a general service module, a management center, a visualization module and an open gateway. The local terminal includes an edge gateway and a sensing device, and the edge gateway includes an acquisition module, a video server and a display module. The edge gateway is configured to connect an IoT-related hardware facility and the sensing device in the weak current system to obtain data of the sensing device and upload the data to the cloud platform; and the cloud platform is configured to connect downwards with the sensing device and the local terminal to obtain data and connect upwards with service and application. According to the technical scheme, the Internet-of-Things platform system and the cloud platform thereof, and the local terminal have good openness and good safety, and high-reliability and cross-system message channel capability.
Owner:华润置地控股有限公司
Secure data transfer
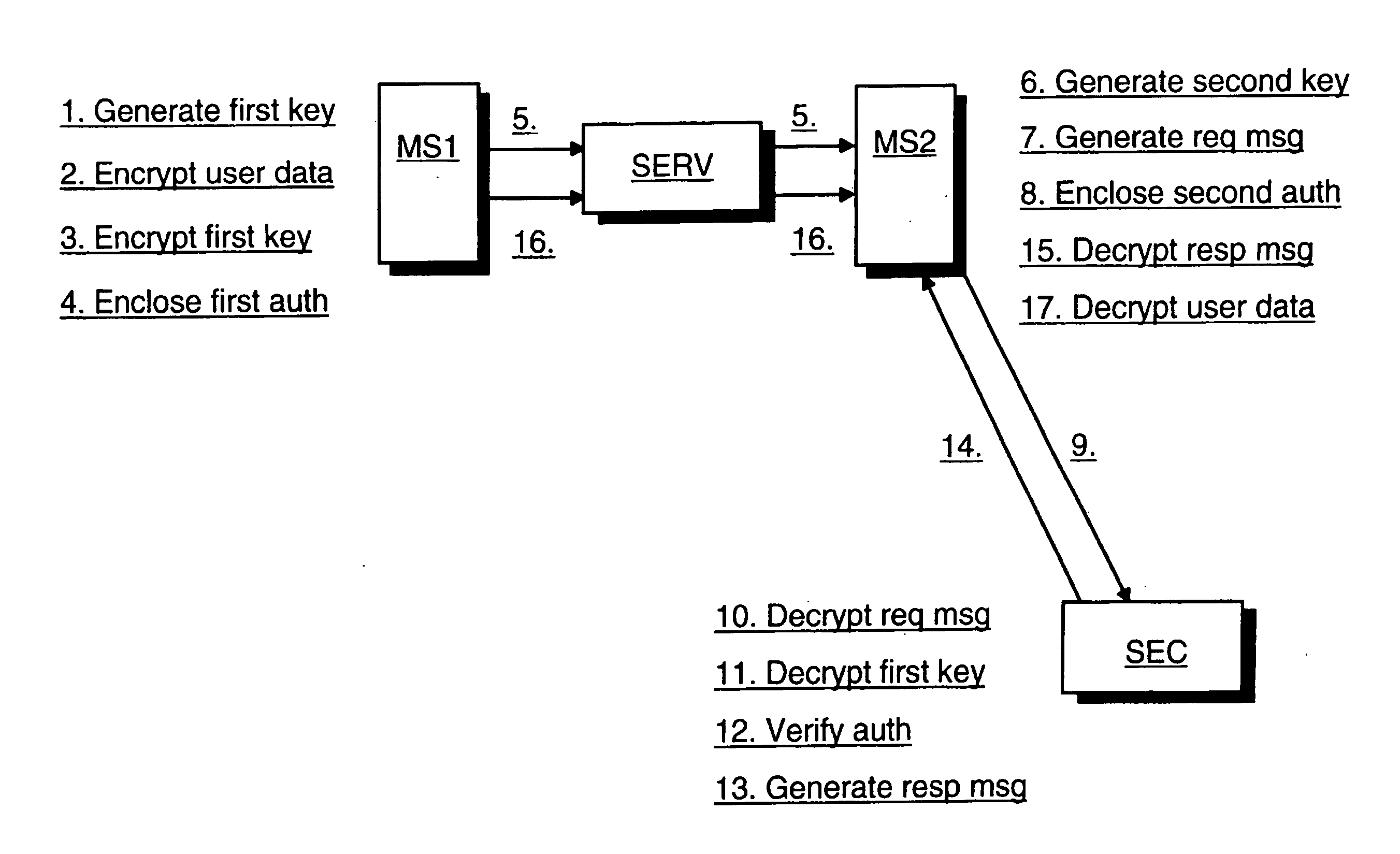
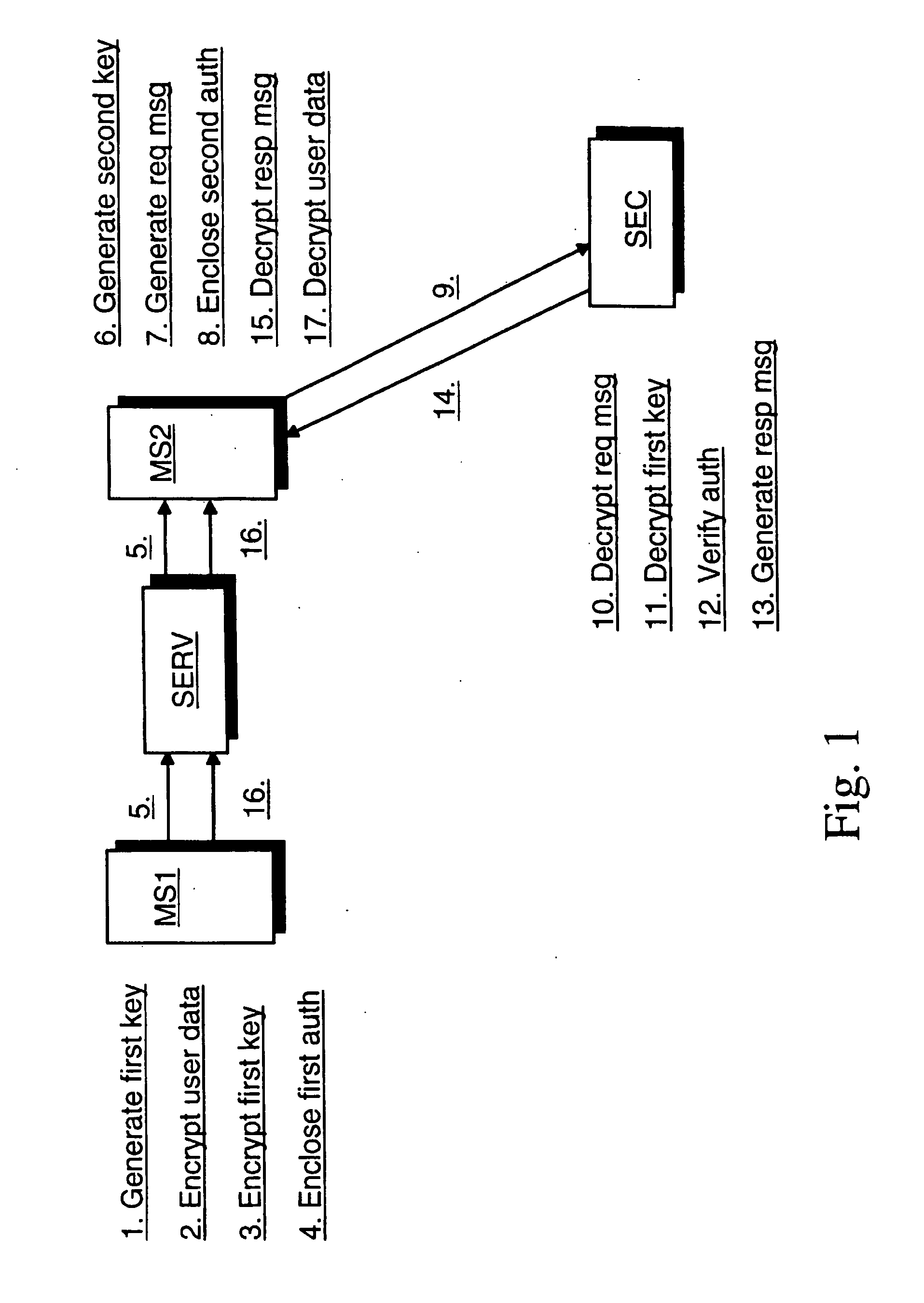
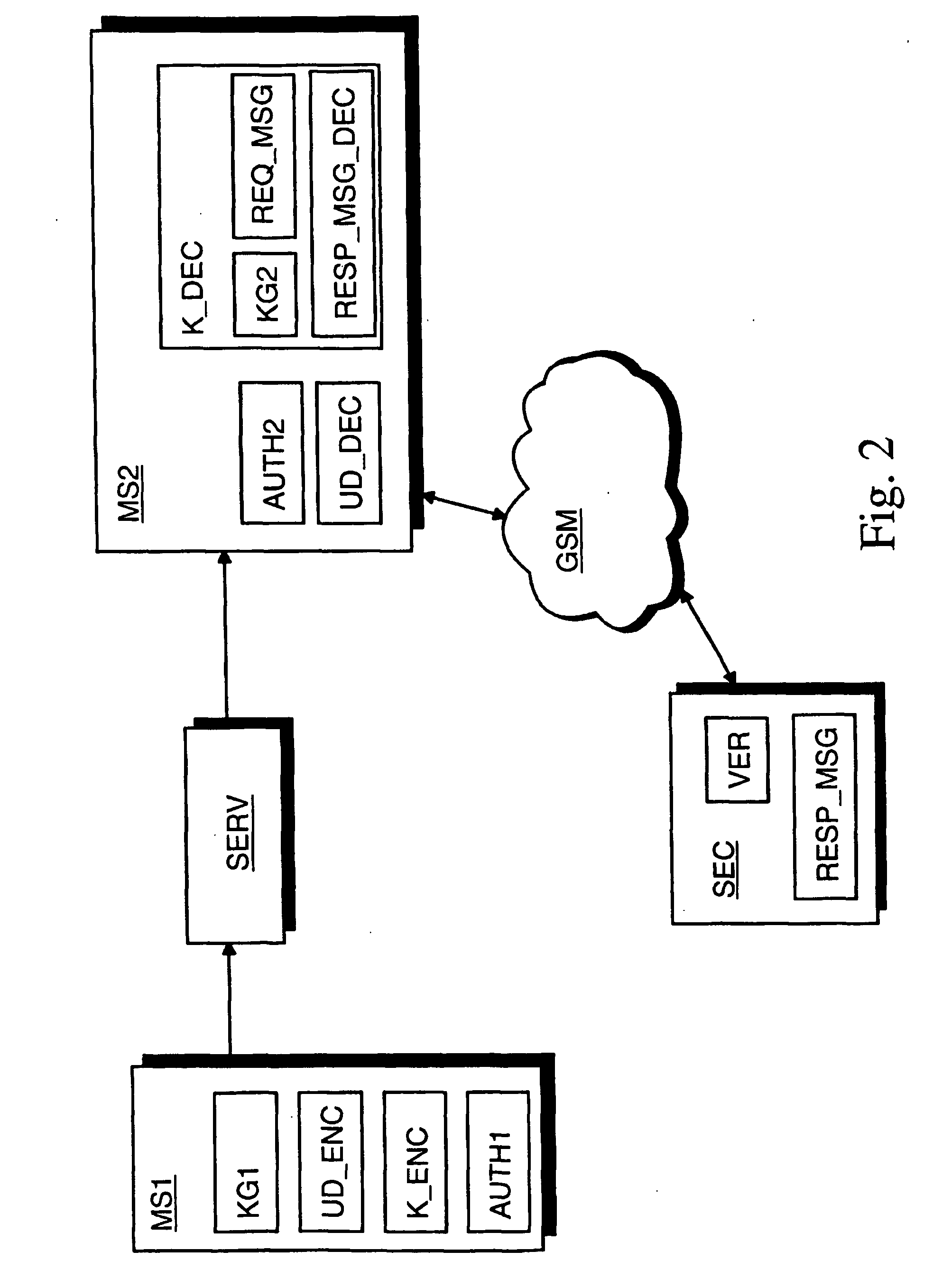
ActiveUS20070016781A1Secure transmissionData transmission securityKey distribution for secure communicationUser identity/authority verificationThird partyTerminal equipment
The invention concerns secure data transfer from a first radio communication device of a first party to a second radio communication device. A random first symmetric key is generated at the first terminal device. User data of the first terminal device is encrypted with the first symmetric key. The first symmetric key is encrypted with a public key of a third party. The encrypted first symmetric key is sent from the first terminal device to the second terminal device via a transfer device. The encrypted first symmetric key is decrypted at the second terminal device by utilizing a secret key associated with the public key and comprised in a security device of the third party. The encrypted user data is sent from the first terminal device to the second terminal device via the transfer device. The encrypted user data is decrypted at the second terminal device with the first symmetric key.
Owner:NOKIA TECHNOLOGLES OY
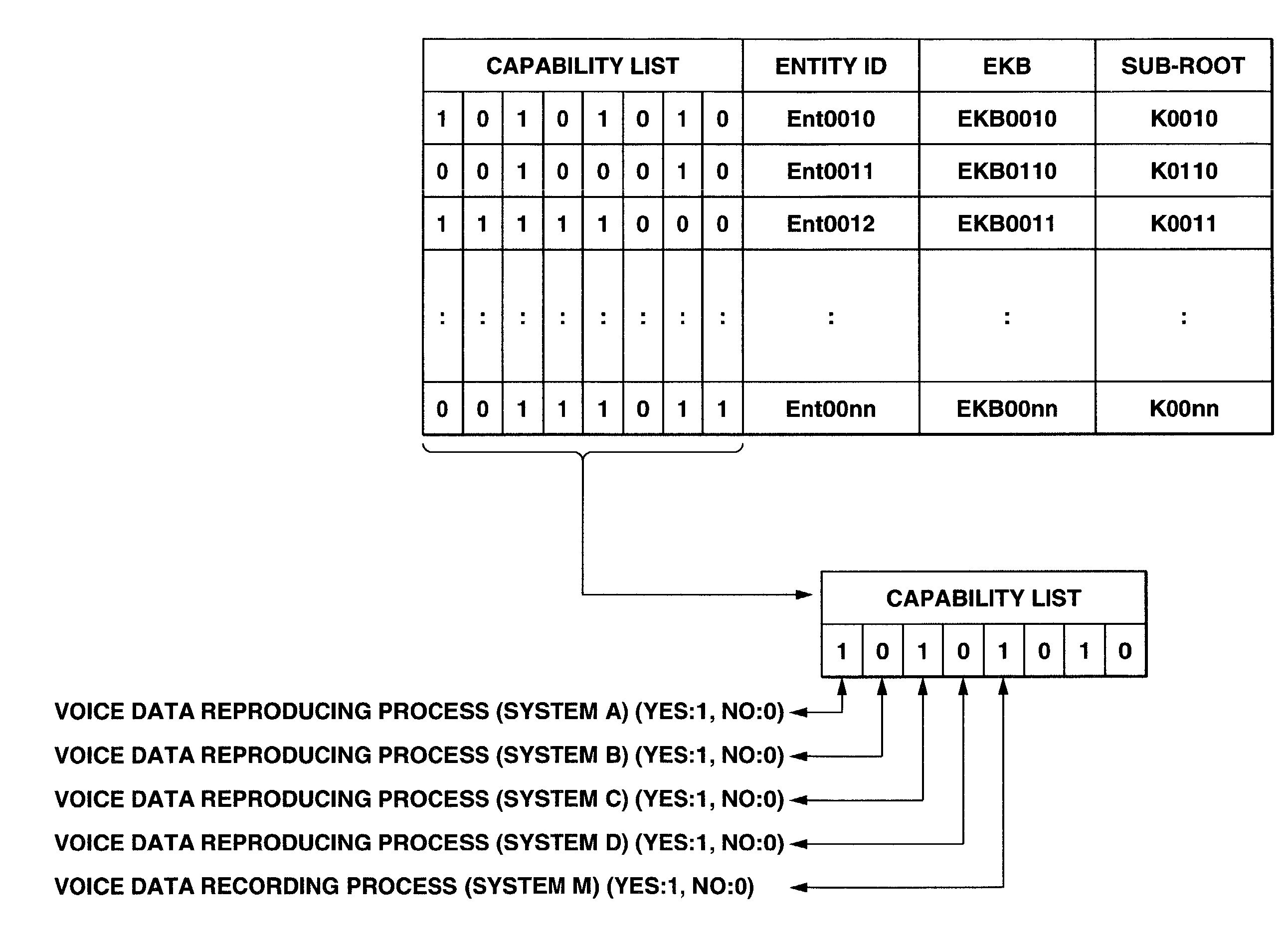
Information processing system and method using encryption key block
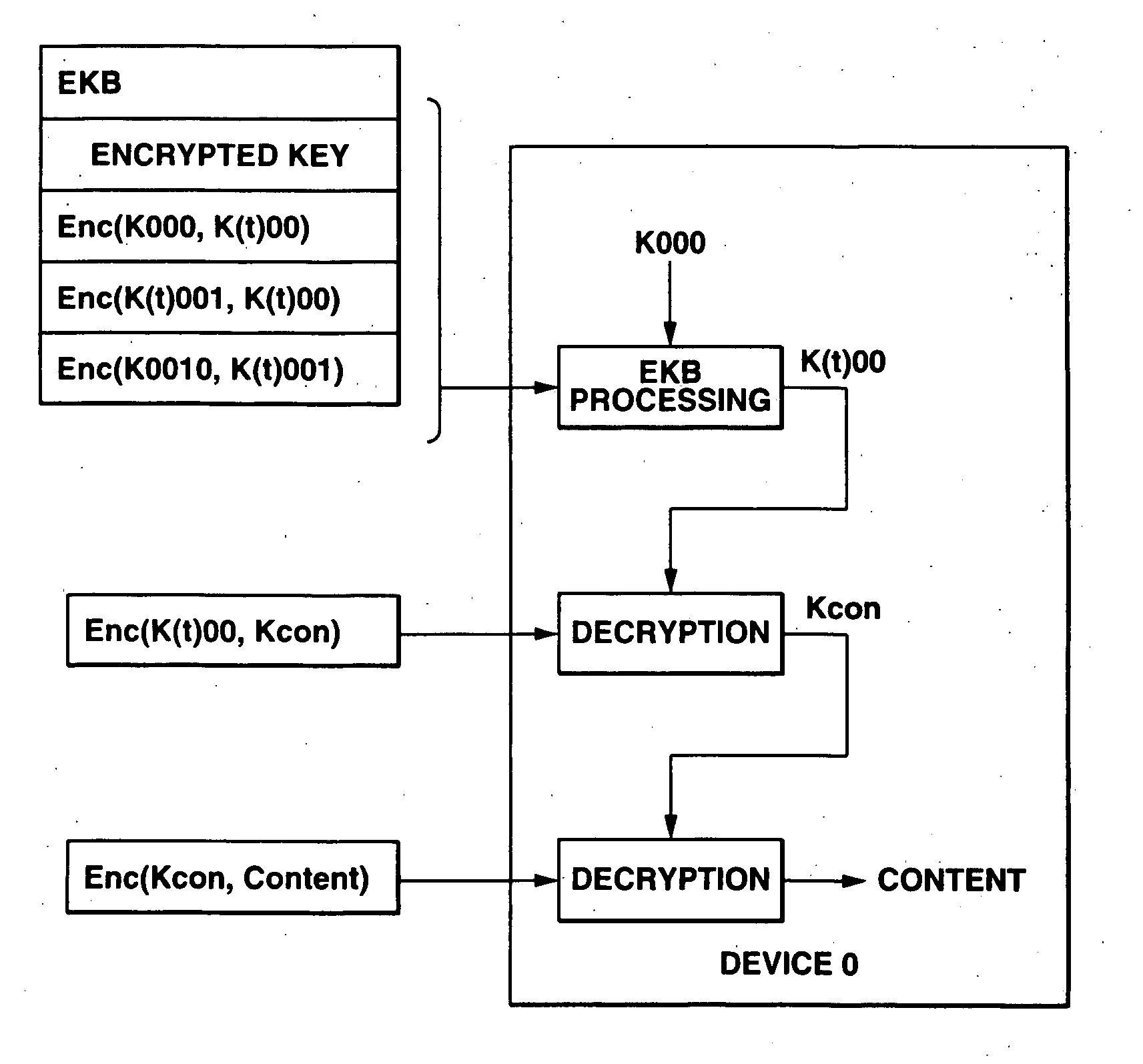
InactiveUS20070263875A1Data transmission securitySecure transmissionKey distribution for secure communicationRecord information storageInformation handling systemData processing
An information processing system and method using an encryption key block sets sub-trees classified based on data processing ability of the devices (capability) in a key tree in which respective keys are corresponded to a root, nodes and leaves of a tree in which a plurality of devices are constituted as the leaves, generates a sub-enabling key block which is effective for an entity in a managing subject of each sub-tree (entity), and generates an enabling key block decodable only by the entities having common capability. Also, an information processing system and method using an encryption key block manages a partial tree of a key tree (sub-tree), generates a sub-enabling key block based only on a key set corresponding to nodes or leaves included in the sub-tree, and generates an enabling key block decodable only by selected entities by using the sub-enabling key block. Thus, it is possible to generate and distribute an enabling key block corresponding to data processing ability of a device and to manage devices by dividing a hierarchical key tree structure.
Owner:SONY CORP
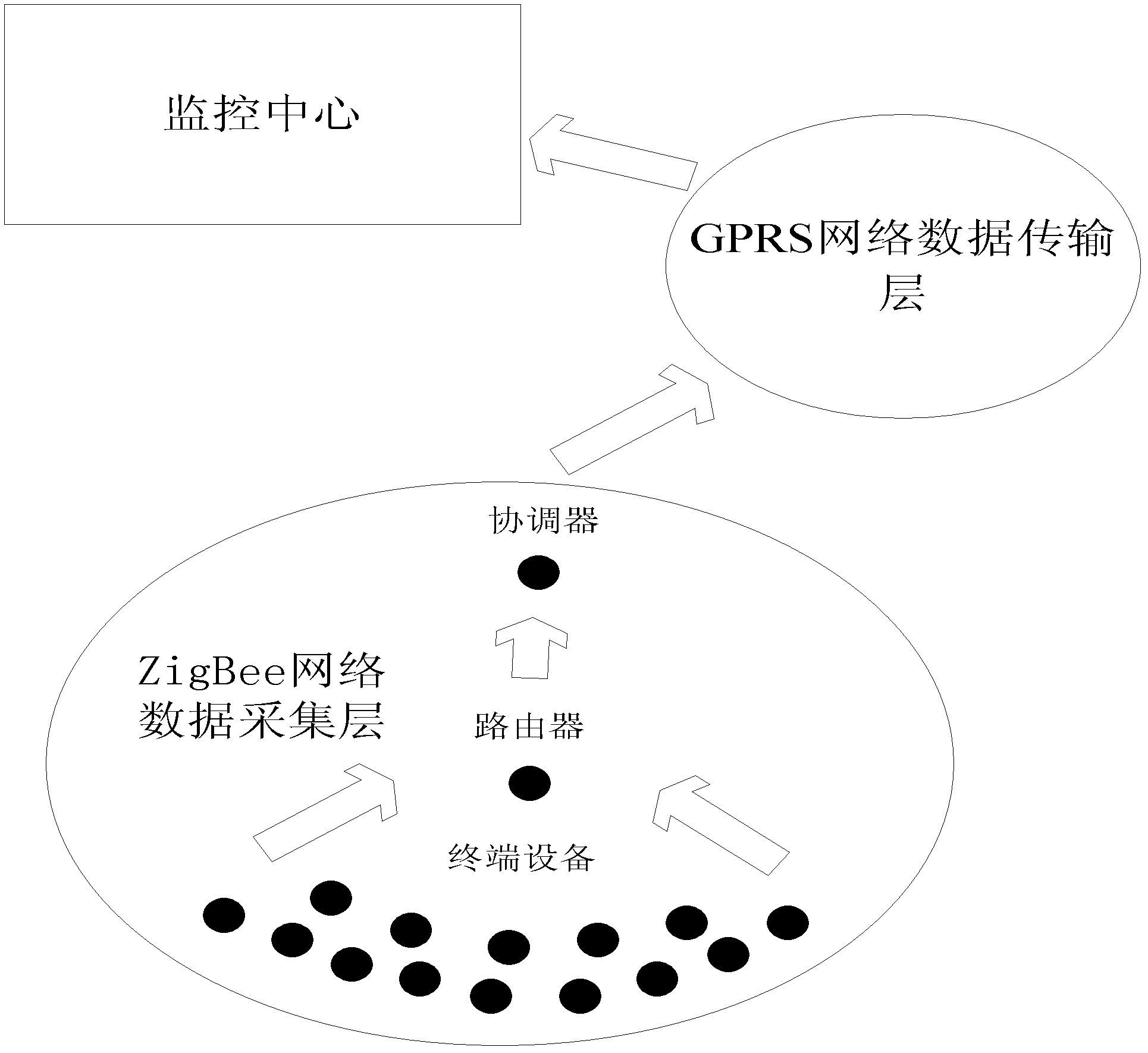
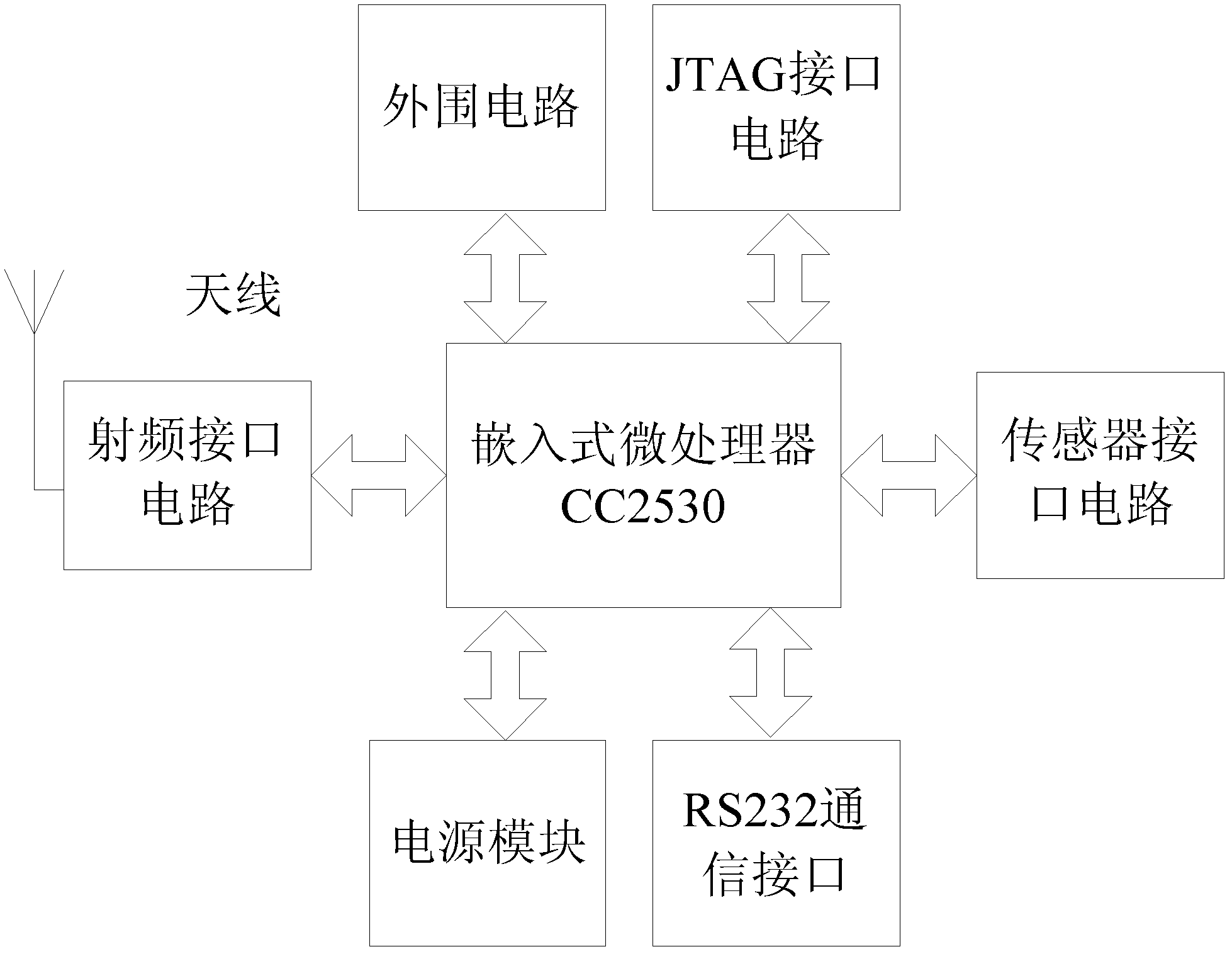
ZigBee network monitoring system combined with general packet radio service (GPRS)
InactiveCN103200704AReduce buildLow maintenanceTransmission systemsNetwork topologiesGeneral Packet Radio ServiceCommunication quality
The invention belongs to the field of wireless sensor network communication, in particular to a ZigBee network wireless monitoring system combined with the general packet radio service (GPRS). In order to overcome the defects existing in wired monitoring system data transmission and to satisfy urgent demands for wireless monitoring systems by certain special environment, a wireless monitoring system combined with GPRS networks and ZigBeenetworks is provided. The ZigBee network monitoring system combined with the GPRS specifically comprises a ZigBee network data collecting layer, a GPRS network data transmission layer and a monitor center, wherein a personal computer (PC) serves as a management layer in the monitor center. The ZigBee network monitoring system combined with the GPRS is capable of guaranteeing reliable and real-time transmission of data and reducing investing and maintaining cost, good in communication quality, low in power dissipation and capable of reducing shortcomings existing in long distance communication.
Owner:CHANGZHOU INST OF ADVANCED MFG TECH
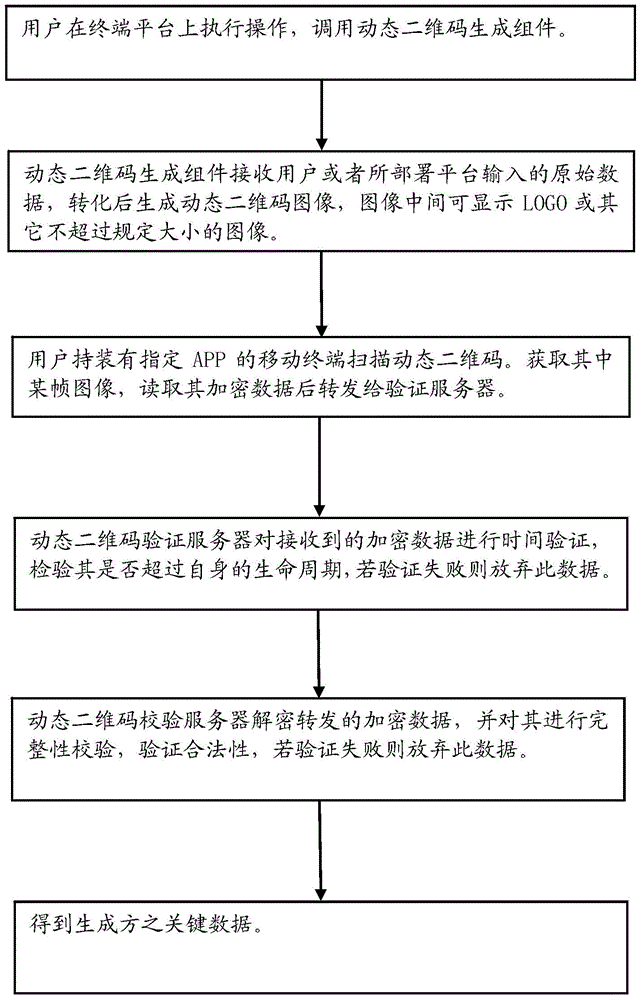
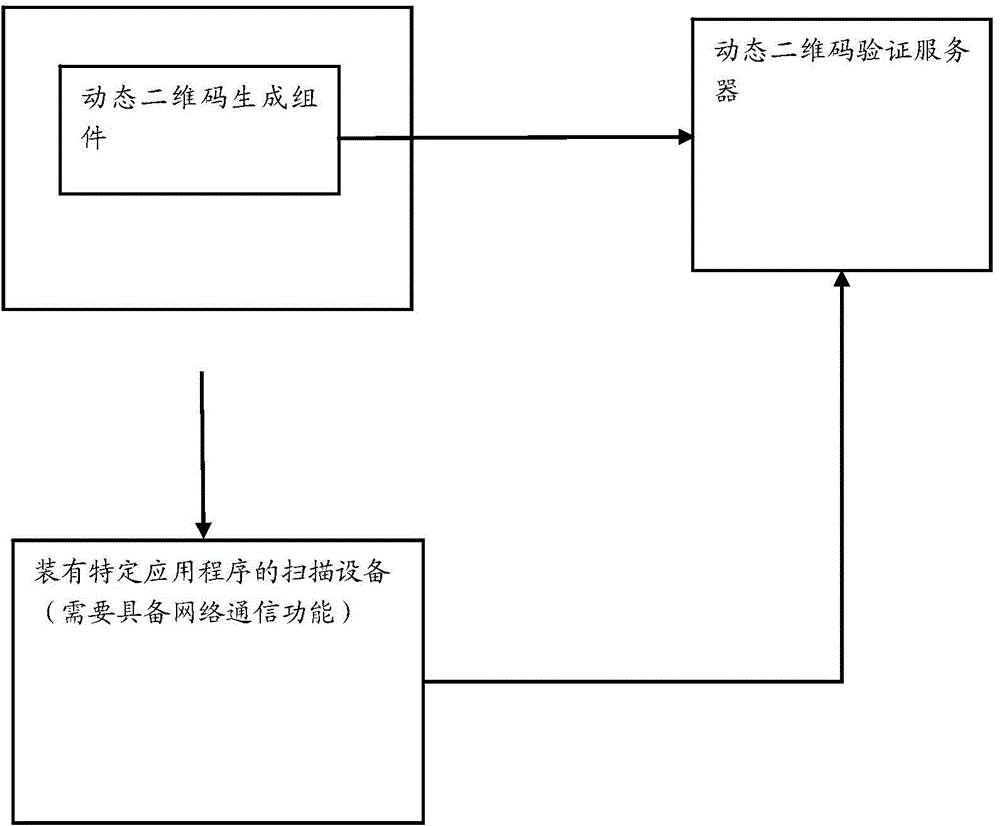
Method and system for generating and verifying dynamic two-dimensional code
InactiveCN104618334AData transmission securityEnsure information securityEncryption apparatus with shift registers/memoriesRecord carriers used with machinesData transmissionData content
The invention refers to the technical field of coding and decoding of a two-dimensional code, and particularly relates to a method for generating and verifying a dynamic two-dimensional code. The method for generating and verifying the dynamic two-dimensional code includes the following steps: generating the dynamic two-dimensional code according to original data input by a user and encrypting the data content of the dynamic two-dimensional code; applying a mobile terminal to scan the dynamic two-dimensional code and performing time verification, data decryption, inspection of data integrity and hardware information matching on one frame of obtained dynamic two-dimensional code data; if the whole inspections are passed, performing subsequent normal flows; otherwise, giving up the data. The dynamic two-dimensional code makes that every two-dimensional code image is dynamically encrypted and generated by using different secrete keys respectively within a period of time on the basis of an original QR Code; its content is encrypted through a security algorithm according with the national password standard and then mixed, so that the data transmission is safer.
Owner:ATMU CHINA TECH
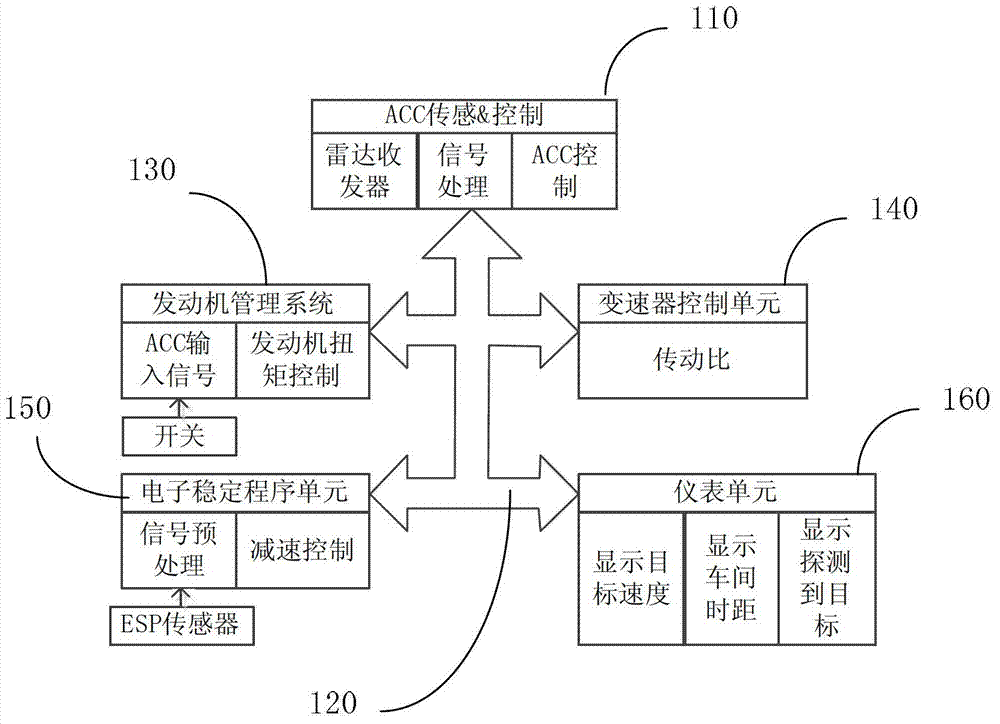
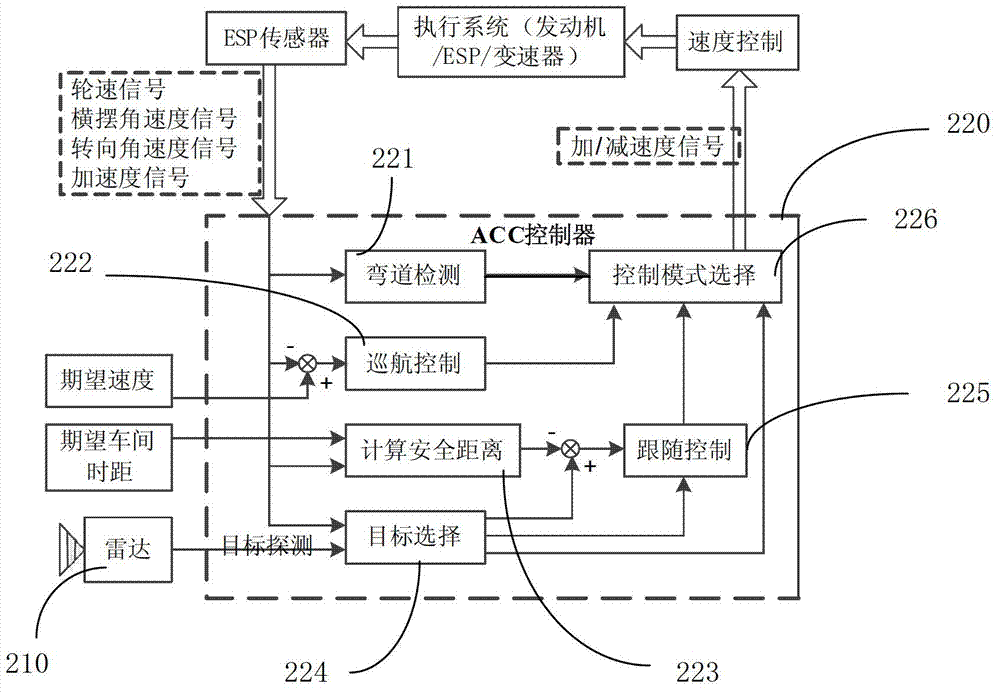
Self-adaptive cruise control system of vehicle
The invention discloses a self-adaptive cruise control system of a vehicle. The self-adaptive cruise control system comprises a self-adaptive cruise sensing and controlling device, and a FlexRay bus which is connected with the self-adaptive cruise sensing and controlling device, an engine management system, a transmission control unit, an electronic stability program unit and an instrument unit. The self-adaptive cruise control system disclosed by the invention can be used for enhancing the response speed of an ACC (adaptive cruise control) system, and improving the sensitivity and safety of cruise driving.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
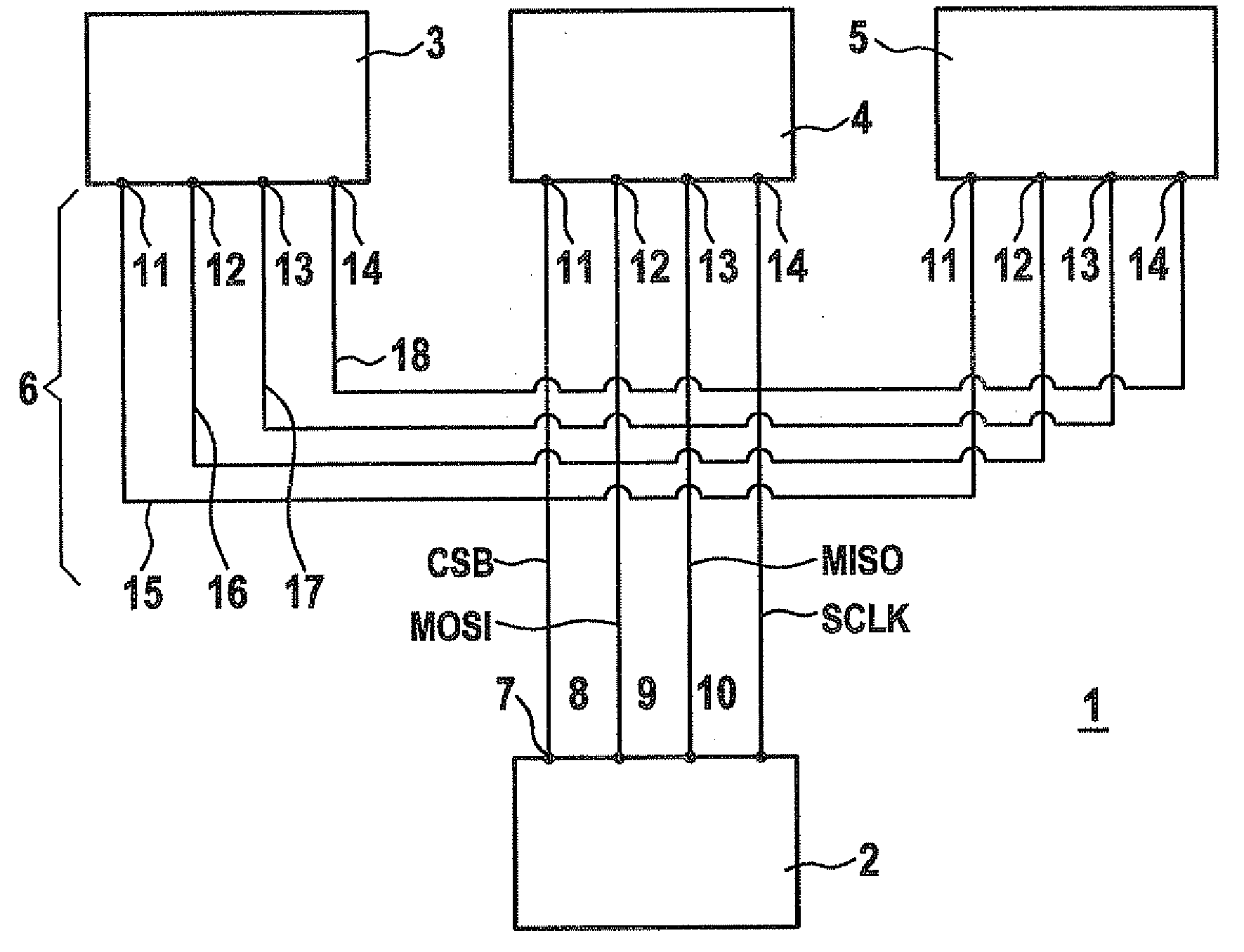
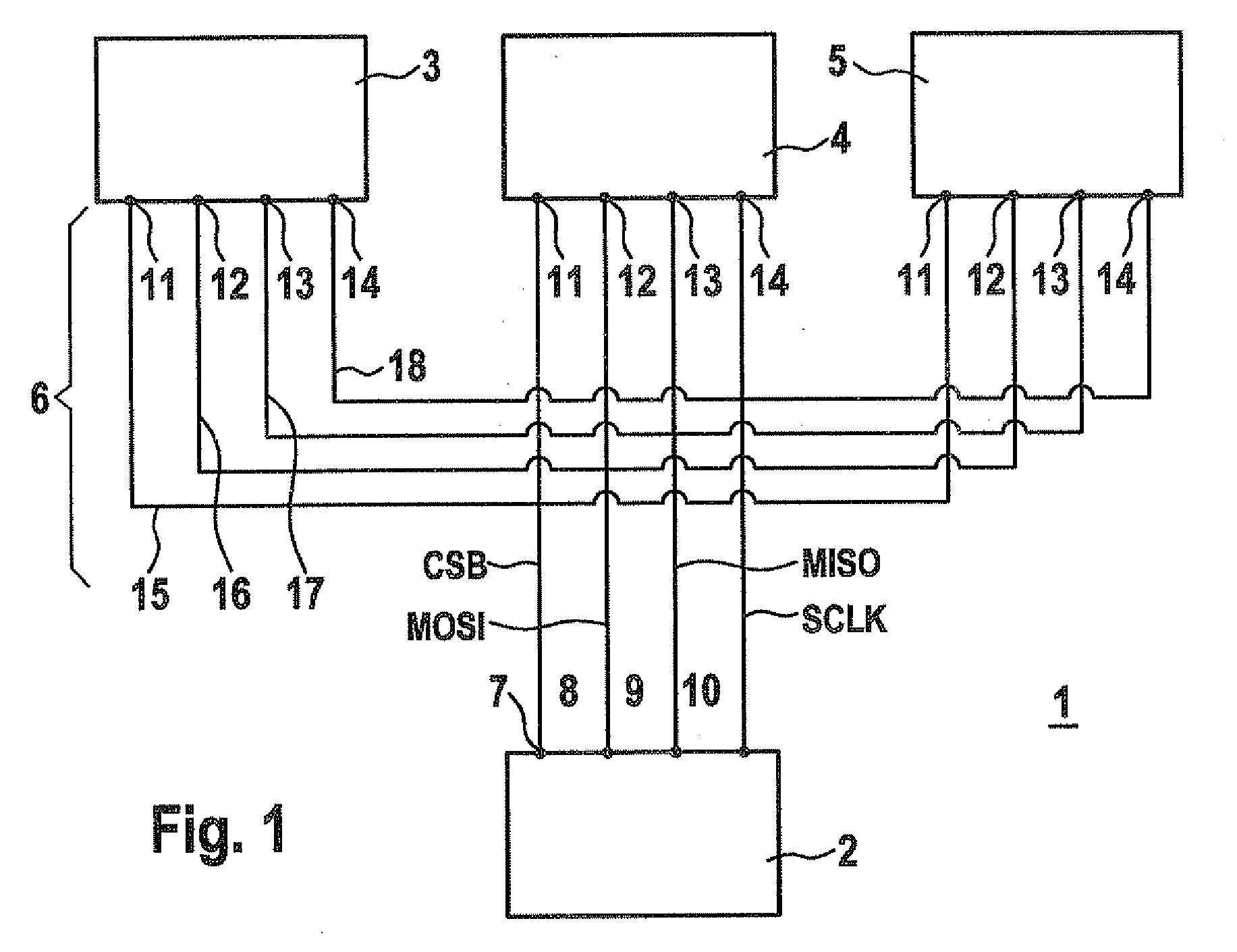
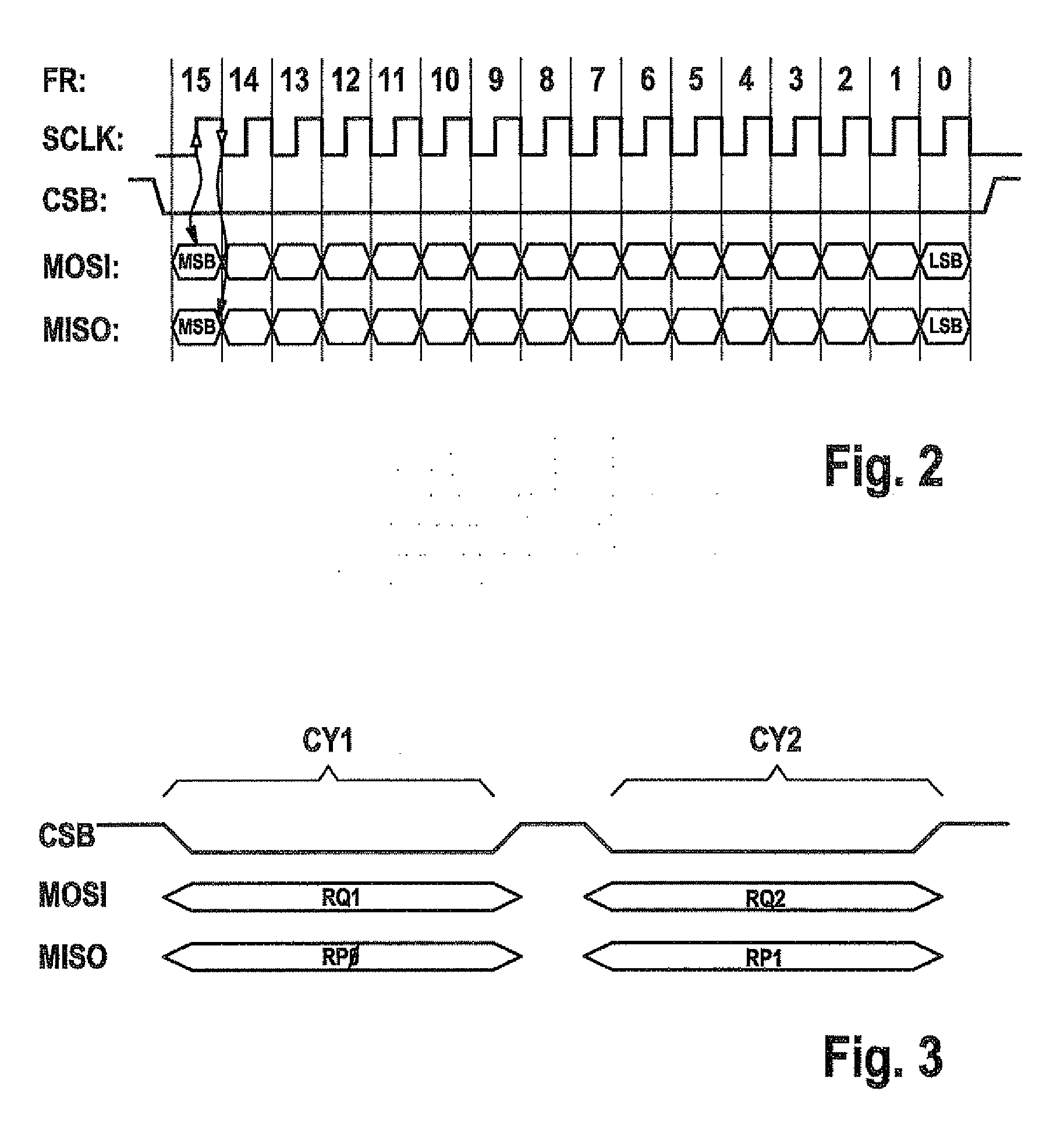
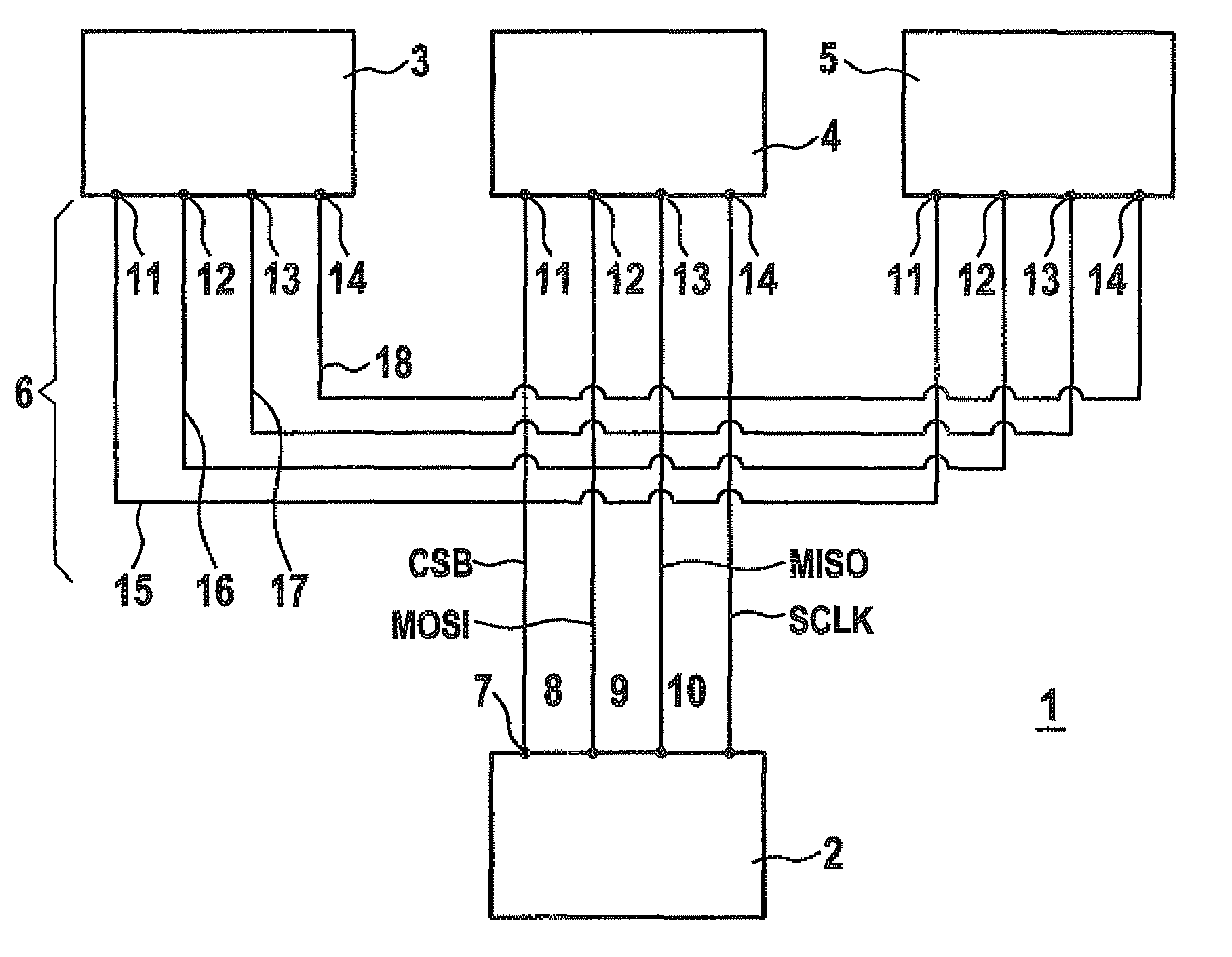
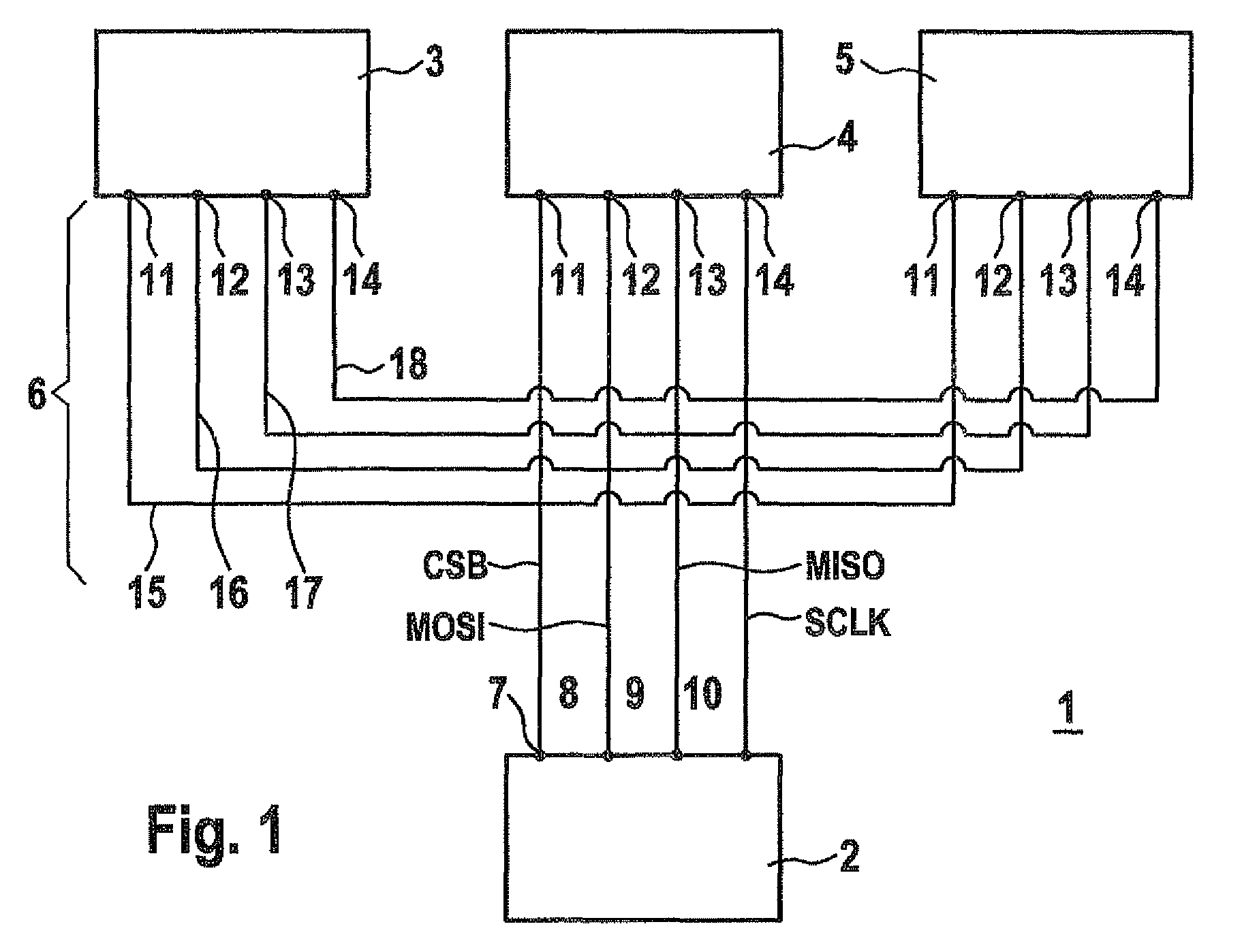
Data transmission method between master and slave devices
ActiveUS20100138576A1Quick identificationFacilitate transmissionInput/output processes for data processingData conversionData transmissionEmbedded system
A method for transmitting data frames between a master device and one or more slave devices via a bus system having at least one request line for transmitting request data frames from the master device to the slave devices, a response line for transmitting response data frames from the slave devices to the master device and at least one selection line for activating the slave devices, the request data frames and the response data frames being transmitted together with at least one address bit for addressing one of the slave devices, the useful data bits and at least one length-indicating bit for indicating the data frame length.
Owner:ROBERT BOSCH GMBH
Information processing system and method using encryption key block
InactiveUS7269257B2Data transmission securitySecure transmissionKey distribution for secure communicationUnauthorized memory use protectionInformation processingComputer hardware
An information processing system and method using an encryption key block sets sub-trees classified based on data processing ability of the devices (capability) in a key tree in which respective keys are corresponded to a root, nodes and leaves of a tree in which a plurality of devices are constituted as the leaves, generates a sub-enabling key block which is effective for an entity in a managing subject of each sub-tree (entity), and generates an enabling key block decodable only by the entities having common capability. Also, an information processing system and method using an encryption key block manages a partial tree of a key tree (sub-tree), generates a sub-enabling key block based only on a key set corresponding to nodes or leaves included in the sub-tree, and generates an enabling key block decodable only by selected entities by using the sub-enabling key block. Thus, it is possible to generate and distribute an enabling key block corresponding to data processing ability of a device and to manage devices by dividing a hierarchical key tree structure.
Owner:SONY CORP
Robot cloud platform based on big data cloud computing support and working method
ActiveCN110430260ARelieve stressPrevent Malicious ConnectionsDatabase distribution/replicationCharacter and pattern recognitionCloud processingData access
The invention provides a robot cloud platform based on big data cloud computing support and a working method, and the platform comprises a resource layer used for collecting robot data and uploading the robot data to a platform layer through an edge computing layer; a platform layer which is used for processing and storing the data, comprises a big data storage service module, a big data analysis service module, an algorithm engine module and a basic management service module, and is used for providing big data storage service, big data analysis service, an algorithm engine and basic management service; and an application layer comprising a cloud service platform and a mobile application side, and a user provides various analysis application functions and remote monitoring based on the robot for the user by calling various services of the platform layer. The invention has the advantages that an equipment layer supports data access of various robots at home and abroad, the edge computing layer can perform equipment authentication to prevent malicious connection, data preprocessing reduces cloud processing pressure, and data encryption and breakpoint resume guarantee data transmission safety and transmission stability.
Owner:安徽领云物联科技有限公司
Vehicle mounted video monitoring system and monitoring method thereof
InactiveCN101335880ANo mutual interferenceData transmission securityClosed circuit television systemsVideo monitoringBlind zone
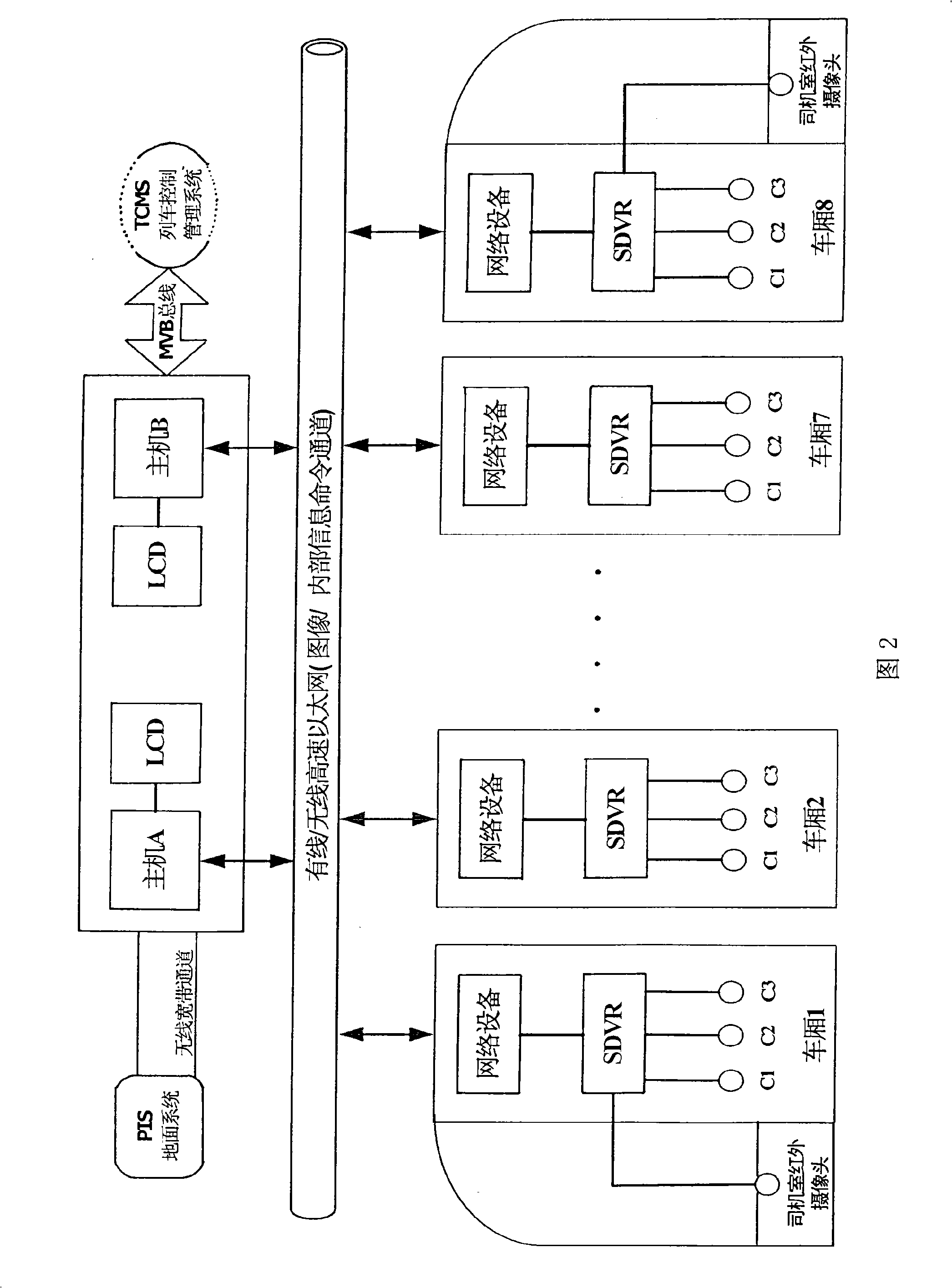
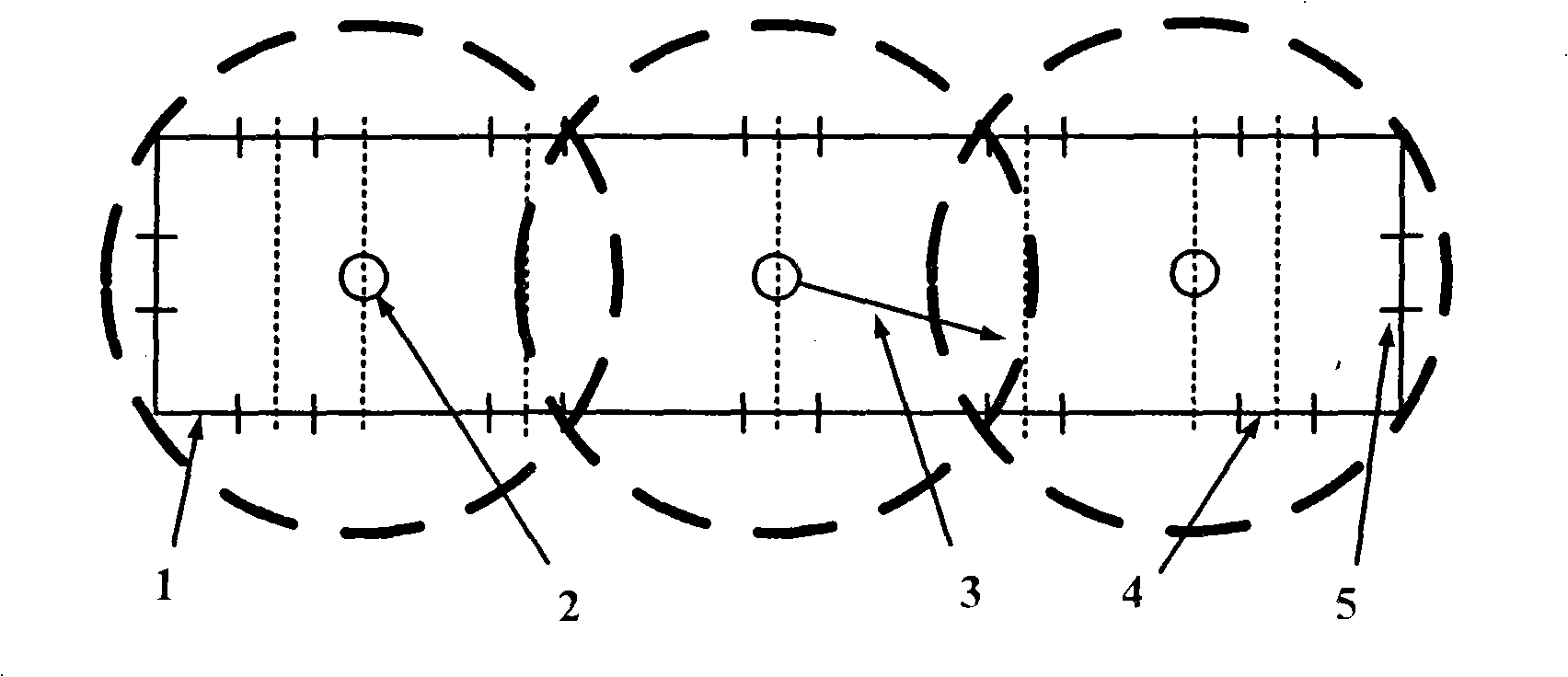
The present invention relates to a vehicle mounted video monitoring system and monitoring method thereof. The invention adopts a symmetric structure, one set of system host computer, a liquid crystal touch screen display and an infrared video camera are respectively provided in the beginning and the end driver rooms of the train. The two system host computers are identical, three 360-degree static wide angle cameras are respectively mounted in equidistance at the top of each compartment, a set of video processing apparatus and network device is mounted in the wire distributing groove, data transmission between compartments adopts the wired connecting passage apparatus or wireless connecting passage apparatus, each host computer can perform data transmission between every video camera, and the video camera is connected with video processing and storage apparatus (SDVR). The invention has advantages of no blind zone of compartment monitoring, seamless connection between the automobile door and the platform, safe and reliable data transmission; friendly man-machine interface, facilitating operation, easy operation and maintenance; and system reserved interface to TCMS and PIS.
Owner:SHANGHAI RAILWAY COMM
Storage service middleware based on mobile caching
ActiveCN101335765AIncrease speedData transmission securityTransmissionMetadata managementNetwork data
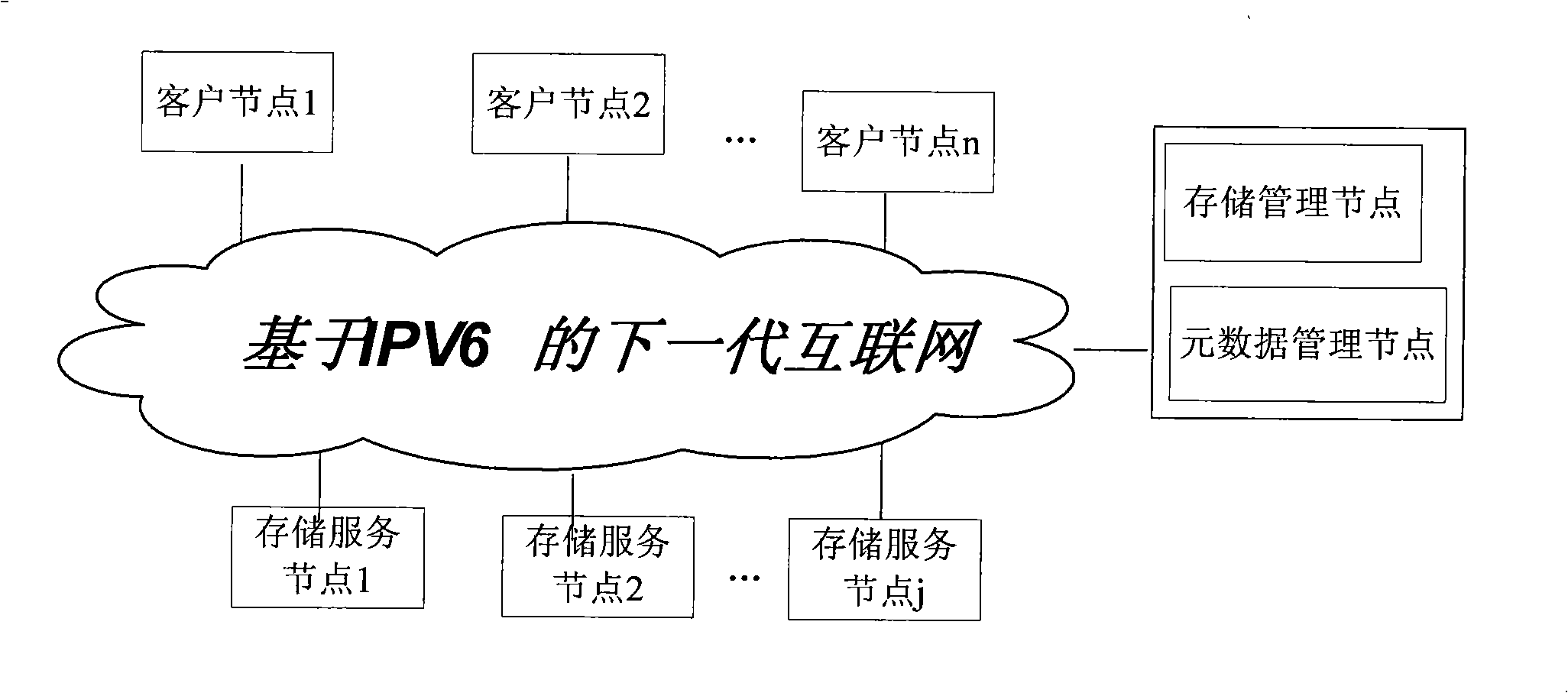
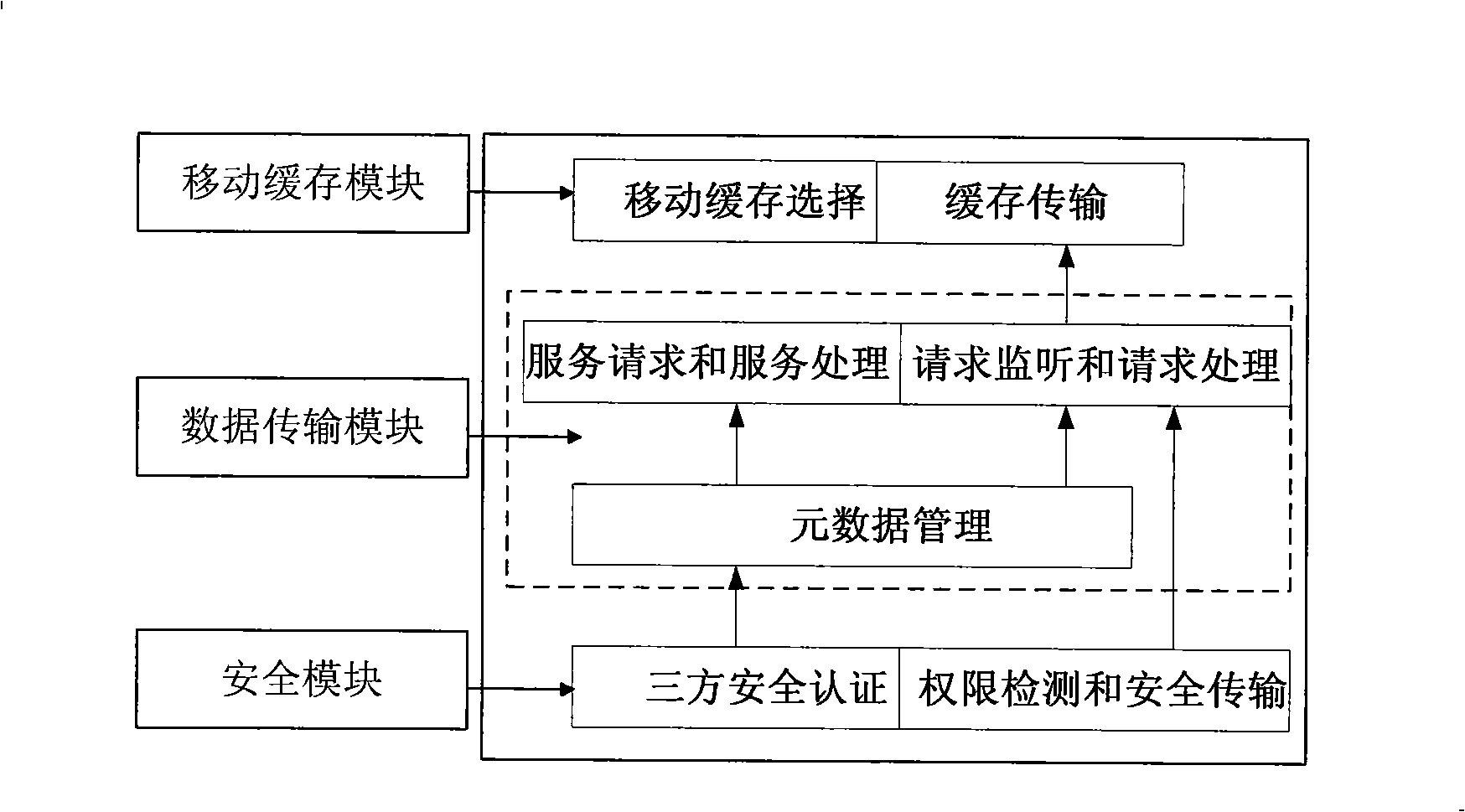
Wide area networks (WAN) storing service intermediate parts based on the mobile caching technique, pertains to data accessing management intermediate parts in the computer network memory technique field, which resolve problems of slow data transmission and bad safety of IPv6 WAN distributed storage system. The present invention includes data transmission, mobile caching and security modules, wherein, the data transmission module includes metadata management, service request, and service processing sub-modules, as well as request monitoring and request handling sub-modules; the mobile caching module includes a mobile caching selection sub-module and a mobile caching transmission sub-module; the security module includes a tripartite safety authentication sub-module and a authority detection sub-module. The invention realizes a compact and quick response from customer nodes to storage systems; makes full use of high performance and high-speed network band-width between storing service nodes; during data transmission, dynamically selects optimal storing service nodes for data as mobile caching; has a comprehensive and practical storage service function, and fast and secure data transmission performance; and ensures high-speed and security of network data moving.
Owner:HUAZHONG UNIV OF SCI & TECH
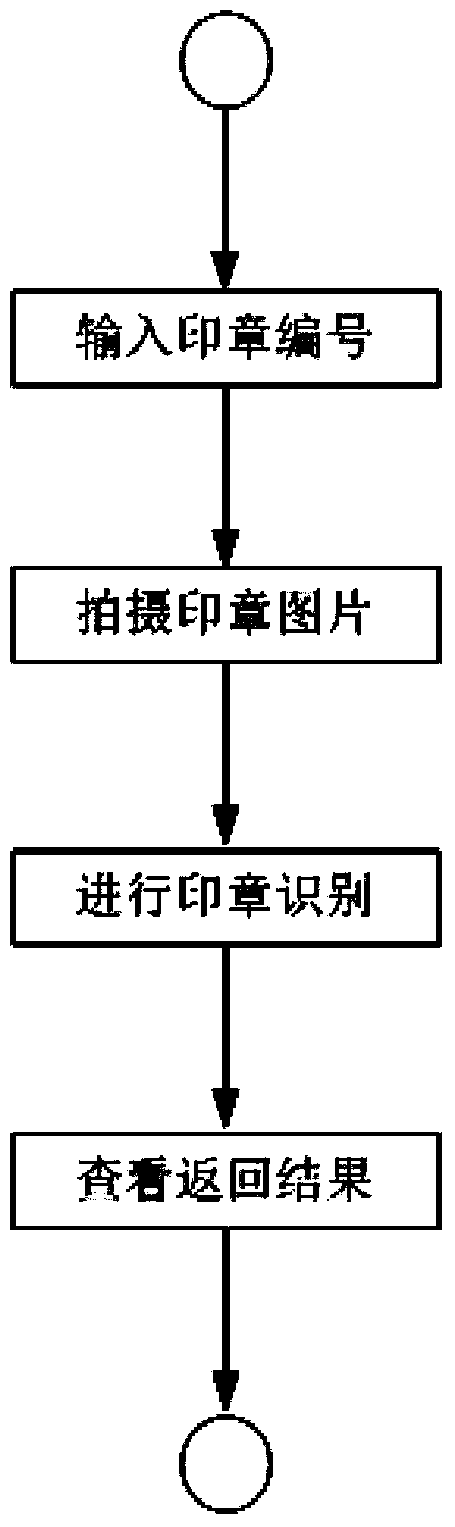
Method and device for recognizing authenticity of seal
InactiveCN104008369ABroad marketConvenient transactionCharacter and pattern recognitionClient-sideComputer science
The invention provides a method and device for recognizing the authenticity of a seal, and relates to the technical field of seal recognizing. The invention aims at providing the method and device fore remotely recognizing the authenticity of the seal. A client-side collects the pattern of the seal and the serial number of the seal, and uploads the pattern and the serial number to a server. The server finds out the copy image of the seal according to the serial number of the seal, and a system enters recognizing stages, wherein the recognizing stages include seal impression extraction, seal impression registration and authenticity recognizing. In the process of seal impression extraction, the seal impression is extracted through a PCNN burning technology, and the extracted seal impression is then repaired through a rapid advancing restoration algorithm. In the process of seal impression registration, the extracted seal impression is rotated and deformed, and the spatial location relationship of the extracted seal impression is adjusted to be matched with the copy seal impression. In the process of authenticity recognizing, authenticity recognizing is conducted by comparing the registered seal impression with the copy seal impression, the difference degree of the two images is calculated through a partitioning technology, and authenticity recognizing is conducted on the seal according to a set threshold.
Owner:SICHUAN UNIV
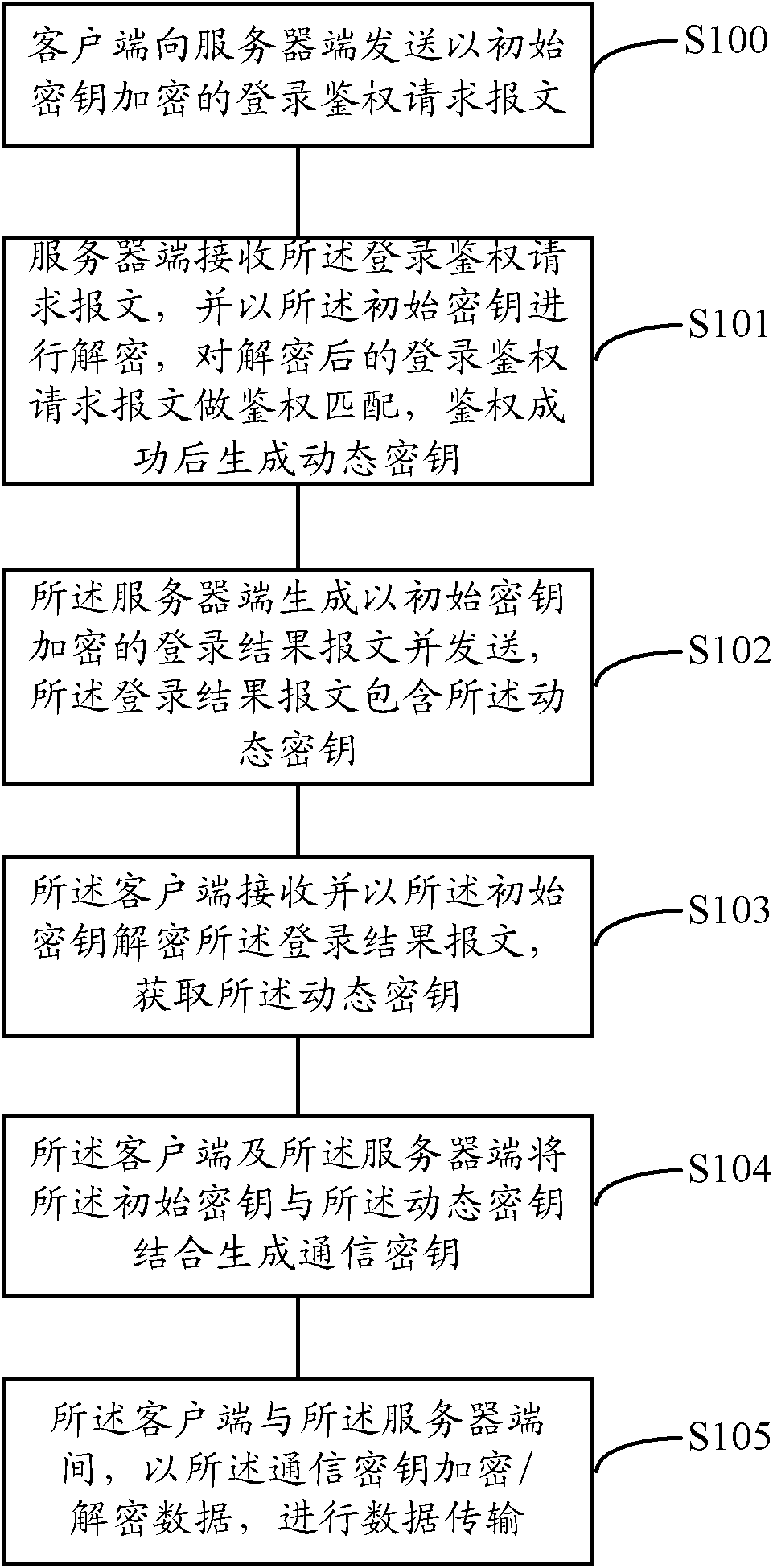
Encryption/decryption method and system for data transmission
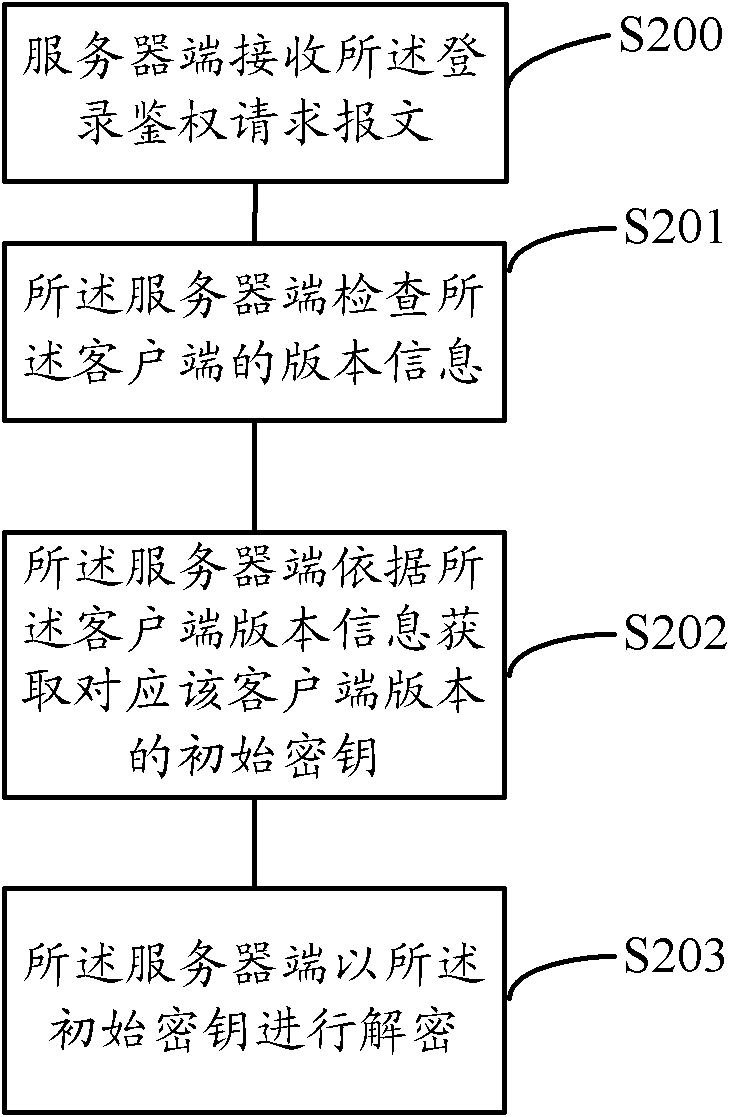
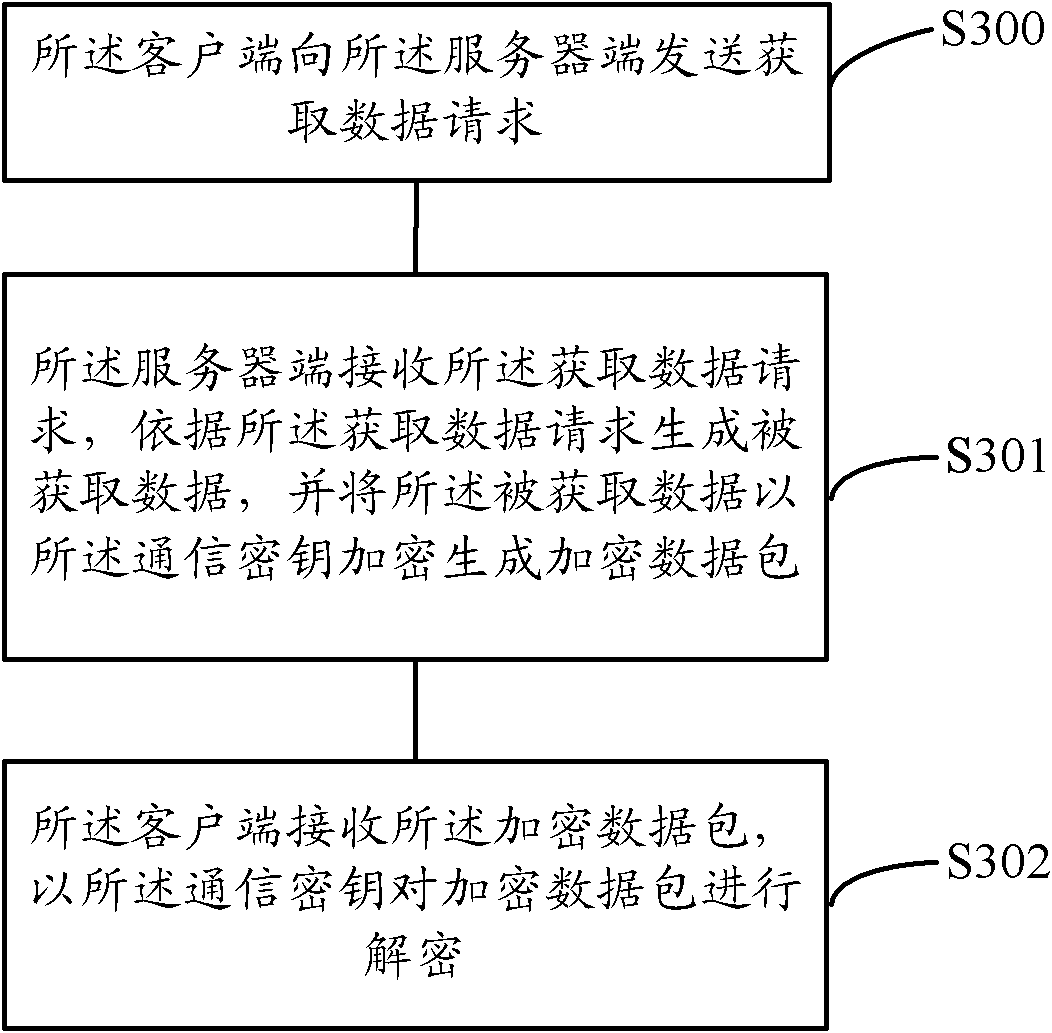
InactiveCN102118392AData transmission securityAvoid the risk of being easily caughtUser identity/authority verificationData switching networksClient-sideData transmission
The invention discloses an encryption / decryption method and a system for data transmission. The method comprises the steps as follows: a client side sends a login authentication request message that is encrypted through an initial key to a server side; the server side receives the login authentication request message, performs the authentication matching after decryption, and generates a dynamic key; the server side generates and sends a login result message; the client side receives the login result message and acquires the dynamic key; the client side and the server side combine the initial key with the dynamic key so as to generate a communication key; and the communication key is utilized to encrypt / decrypt data between the client side and the server side. The system comprises: a login authentication unit, a first communication unit and a communication key generating unit all positioned on the client side; and a second communication unit, an authentication matching unit, a dynamic key generating unit, a login result unit and the communication key generating unit all positioned on the server side. Therefore, the problem that an interact protocol between the client side and the server side is easy to be decoded can be solved.
Owner:南京朗睿软件科技有限公司
Air control system for micro civil unmanned plane
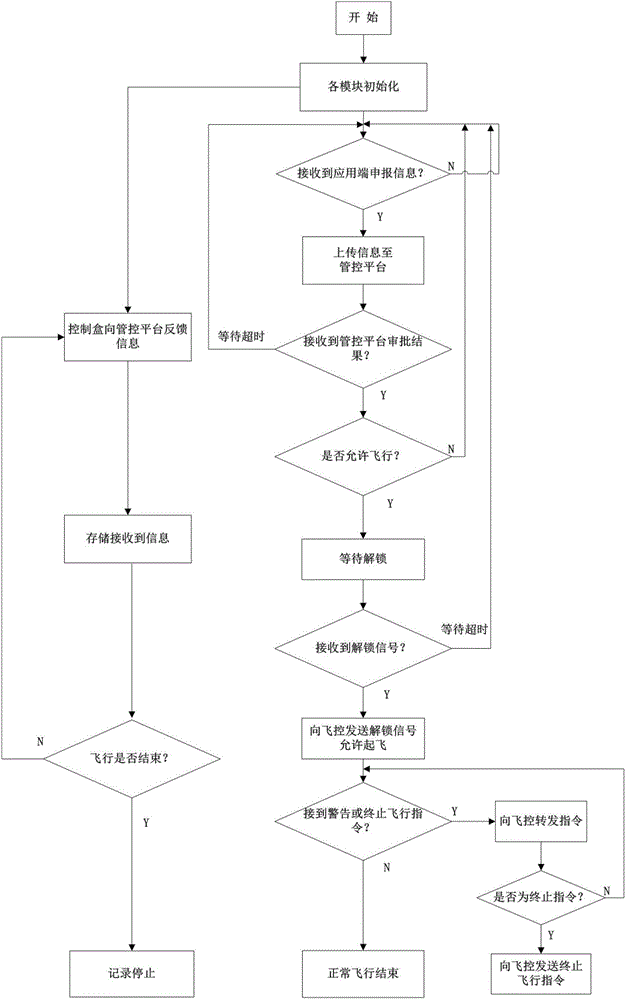
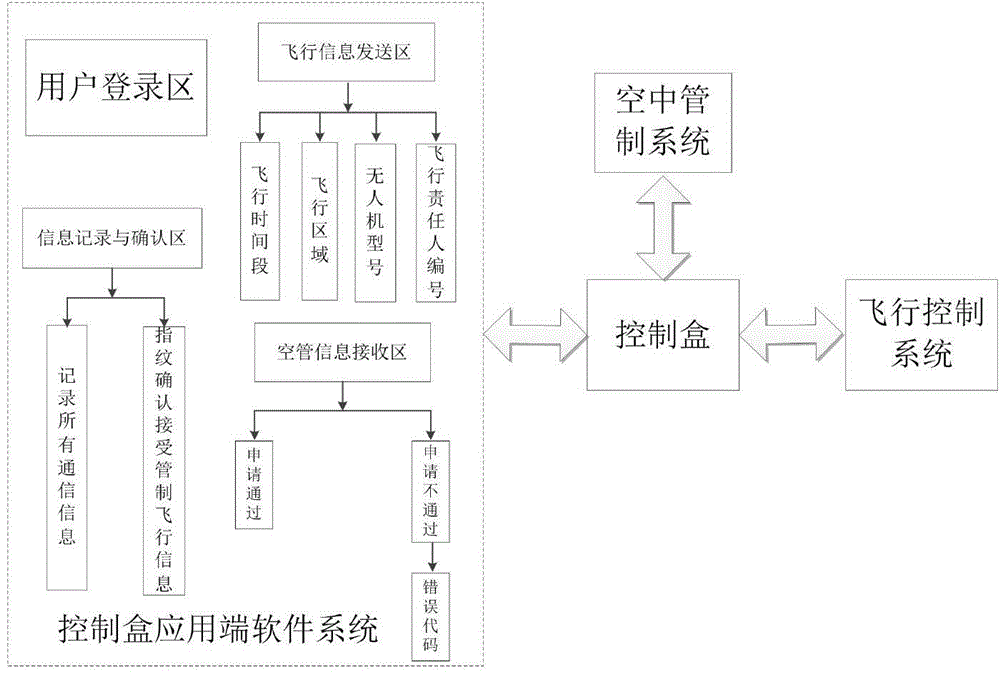
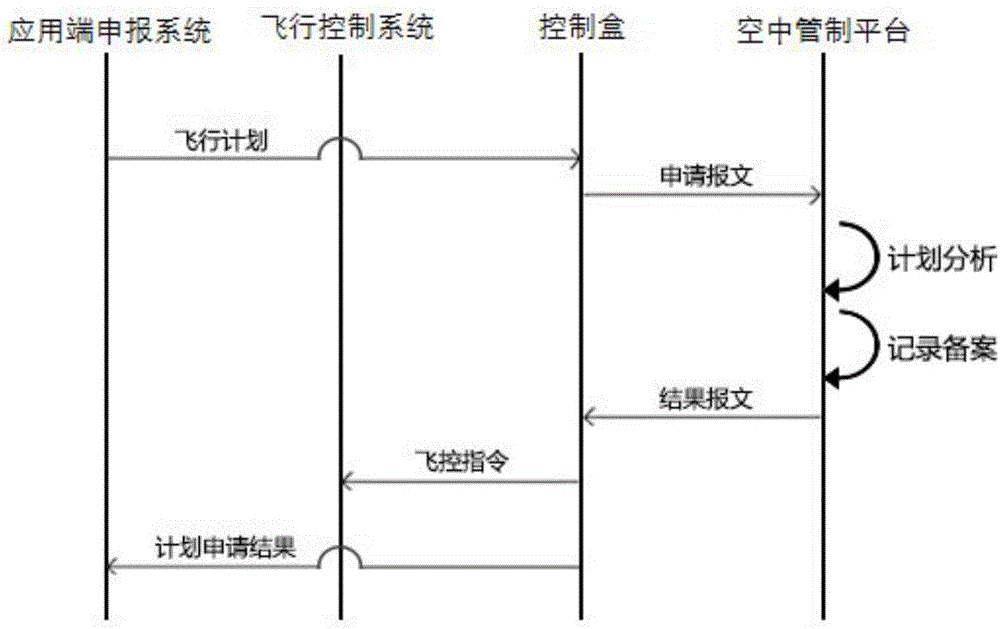
InactiveCN105654782ARealize air-ground integration functionSecure transmissionUser identity/authority verificationAircraft traffic controlHandsetLaptop
The invention discloses an air control system for a micro civil unmanned plane. The air control system comprises an air control platform, a control box and an application end report system. A multi-frequency multi-stage communication connection mode is employed for communication between the air control platform and the control box, the application end report system takes a notebook computer, a flat computer or an intelligent handset as an operation carrier, connection with the control box can be realized through USB, WiFi and Bluetooth modes, the report information is transmitted by the application end report system through a communication module of the control box to the air control platform, report approval is carried out by the air control platform through integrating the report information of a database, the third party and other users, the approval result information is fed back, the feedback information is received by the control box and is stored, and the feedback information is fed back and is sent to the application end report system. According to the air control system, plenty of micro unmanned planes flooding into the market are taken as objects, the civil unmanned plane control system having properties of low cost and high performance is developed, and the purpose of air control on the micro unmanned planes in good or bad states is realized.
Owner:安徽翼讯飞行安全技术有限公司
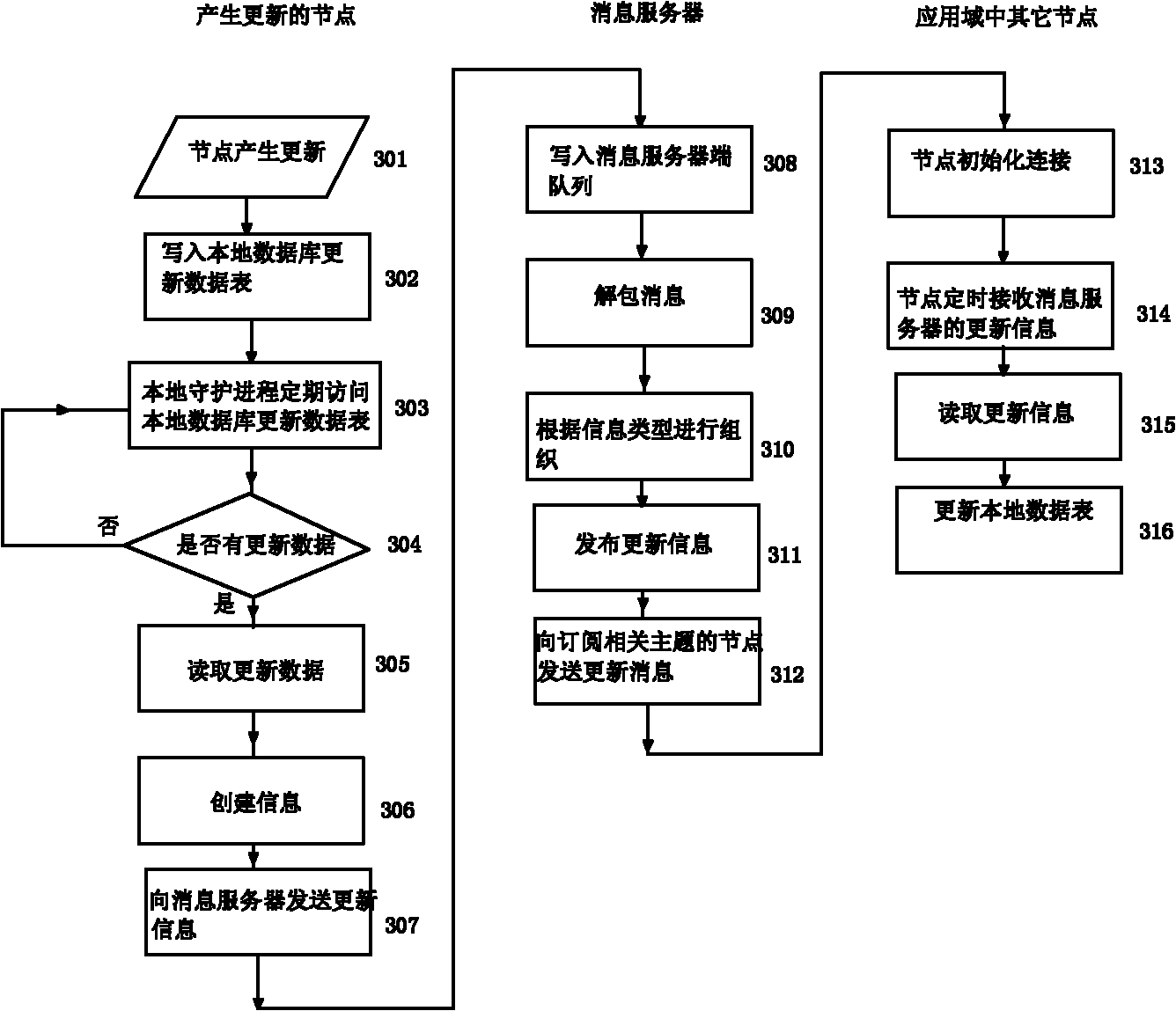
Method for synchronously updating data based on grid GIS (Geographic Information System)
The invention relates to the field of grid GIS (Geographic Information System), in particular to a method for synchronously updating data based on grid GIS. The method comprises the following steps of: (1) updating the spatial data of a node, and writing into an update data table in a node database; (2) regularly accessing the update data table in a node database by a local daemon process, and reading and sending the update data to a message server in the existence of update content; (3) receiving the update data by the message server, reorganizing the sent update data table, writing into a data table of the message server, releasing an update message, and sending the message to nodes subscribing relative subjects; and (4) regularly accessing the message server to receive the message by are ceiving end, and updating the local data table according to the acquired data table of the message server. The method for synchronously updating data based on grid GIS provides a method for universally, rapidly and synchronously updating the node data in a distributed heterogeneous system.
Owner:武汉中地数码科技有限公司 +2
Quantum seal stamping and verifying system, and configuration, stamping process and verifying method thereof
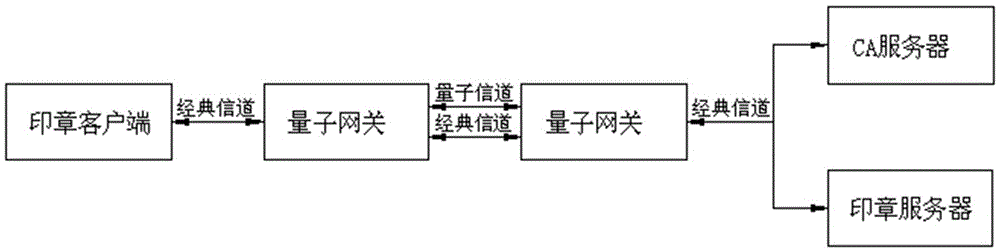
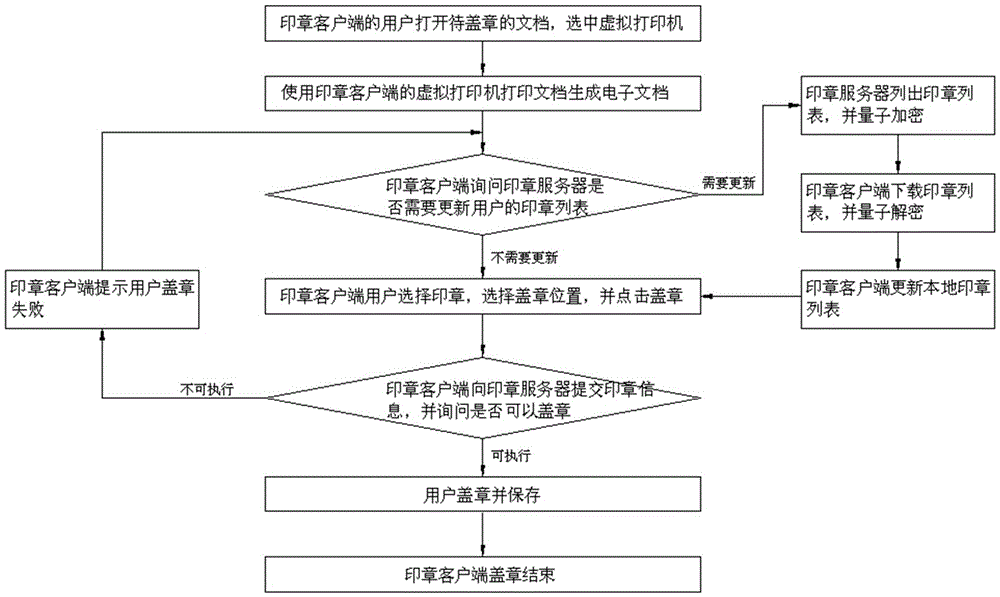
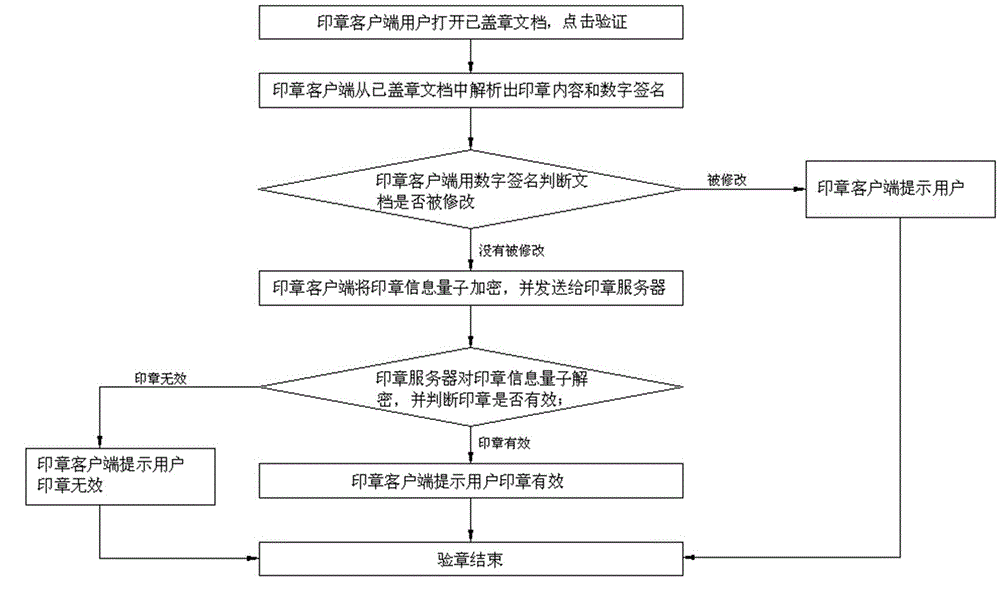
ActiveCN105119941AGuaranteed absolute security transmissionImprove reliabilityKey distribution for secure communicationValidation methodsQuantum channel
A quantum seal stamping and verifying system provided by this invention comprises a seal client, a quantum gateway of the seal client, a server quantum gateway, a CA (Certification Authority) server and a seal server; the seal client is connected with the quantum gateway of the seal client through a classical channel; the seal server and the CA server are connected with the quantum gateway of the seal server through the classical channel; the quantum gateway of the seal client and the quantum gateway of the seal server are connected with a quantum channel through the classical channel. The invention provides a quantum seal stamping and verifying system, and a configuration, a stamping process and a verifying method thereof, wherein the system is difficult to be cracked and is capable of greatly improving the validity and the authority of the seal.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
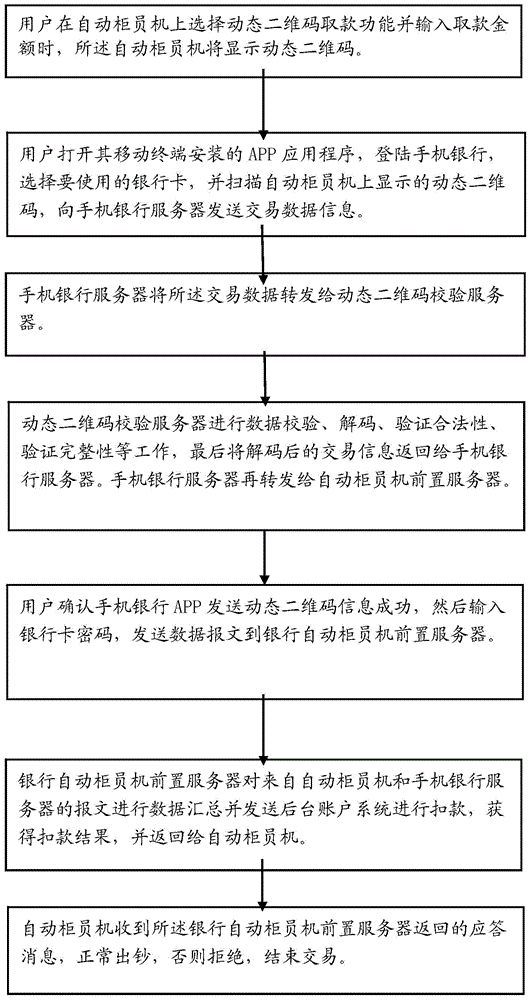
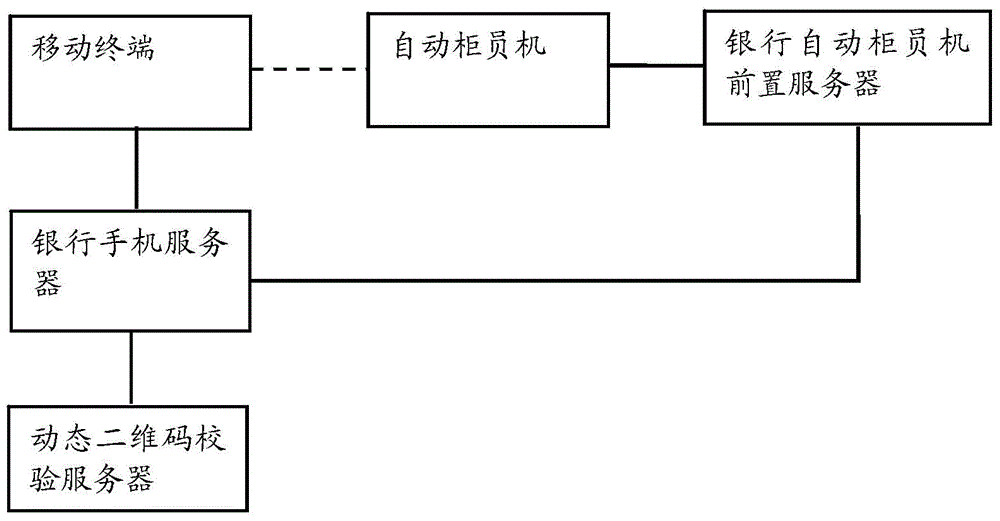
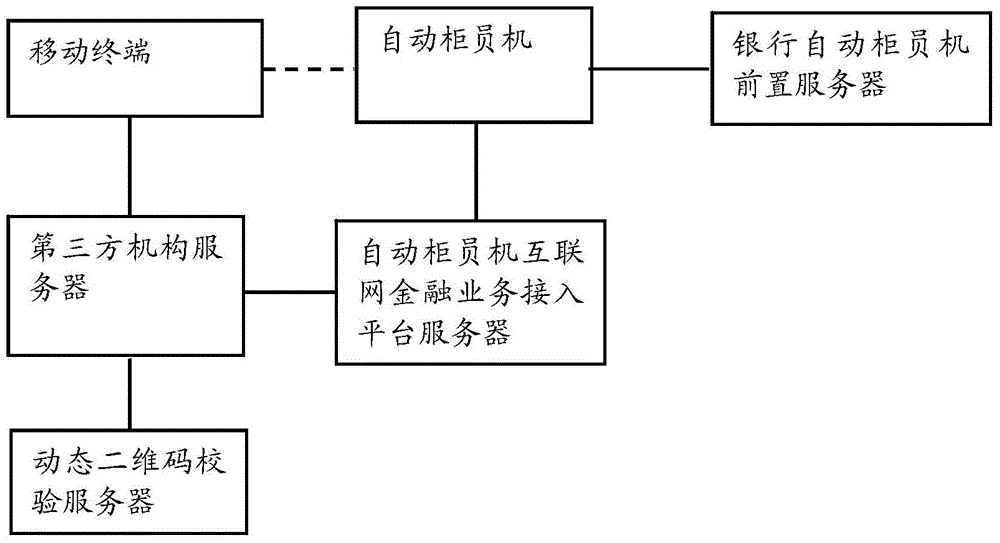
Automatic tell machine money withdrawing method and system based on dynamic two-dimensional code
InactiveCN104464117AEnsure safetyEnsure financial securityComplete banking machinesKey distribution for secure communicationComing outComputer hardware
The invention relates to the technical field of coding and decoding of two-dimensional codes, in particular to an automatic tell machine money withdrawing method based on a dynamic two-dimensional code. The method comprises the steps that 1, a dynamic two-dimensional code image is displayed on an automatic tell machine; 2, the dynamic two-dimensional code image displayed on the automatic tell machine is scanned through a mobile phone bank app on a mobile phone, and transaction data information is sent to a mobile phone bank server; 3, the mobile phone bank server transmits the transaction data to a dynamic two-dimensional code verification server; 4, the dynamic two-dimensional code verification server conducts data verification, decoding and time confirmation; 5, sending a data message to a prepositive server of the automatic tell machine in a packaged mode after a user inputs a corresponding bank card password into the automatic tell machine; 6, the prepositive server of the automatic tell machine feeds a responding message back, money comes out if the feedback process is normal, and a prompt message comes out to end the transaction otherwise. Compared with existing static two-dimensional money withdrawing processes, the dynamic two-dimensional code verification technology has the advantage that a more complicated safety mechanism is adopted, and therefore the financial safety of the user is better guaranteed.
Owner:ATMU INFORMATION TECH
Method and device for serially transferring data, having switchable data encoding
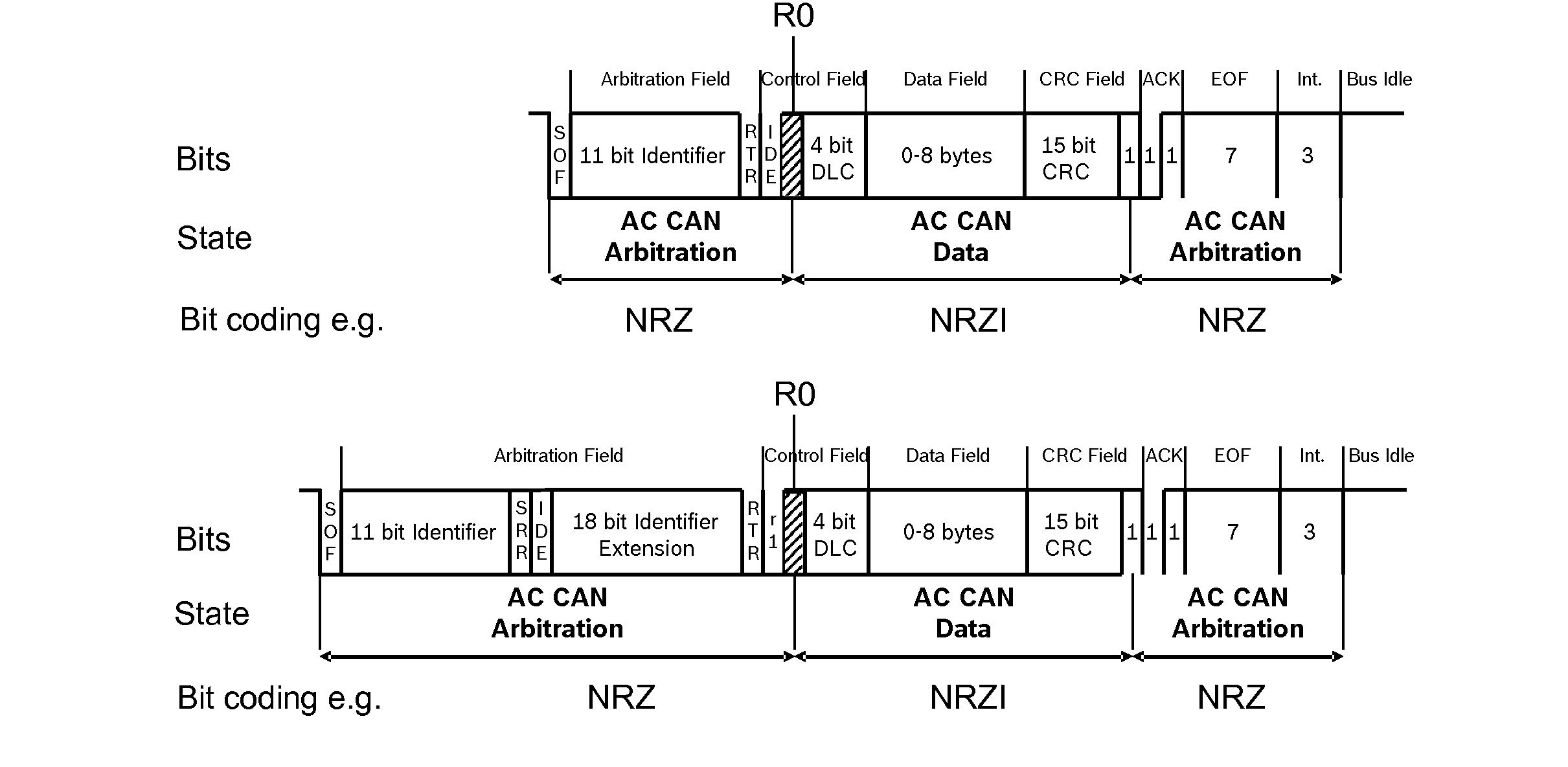
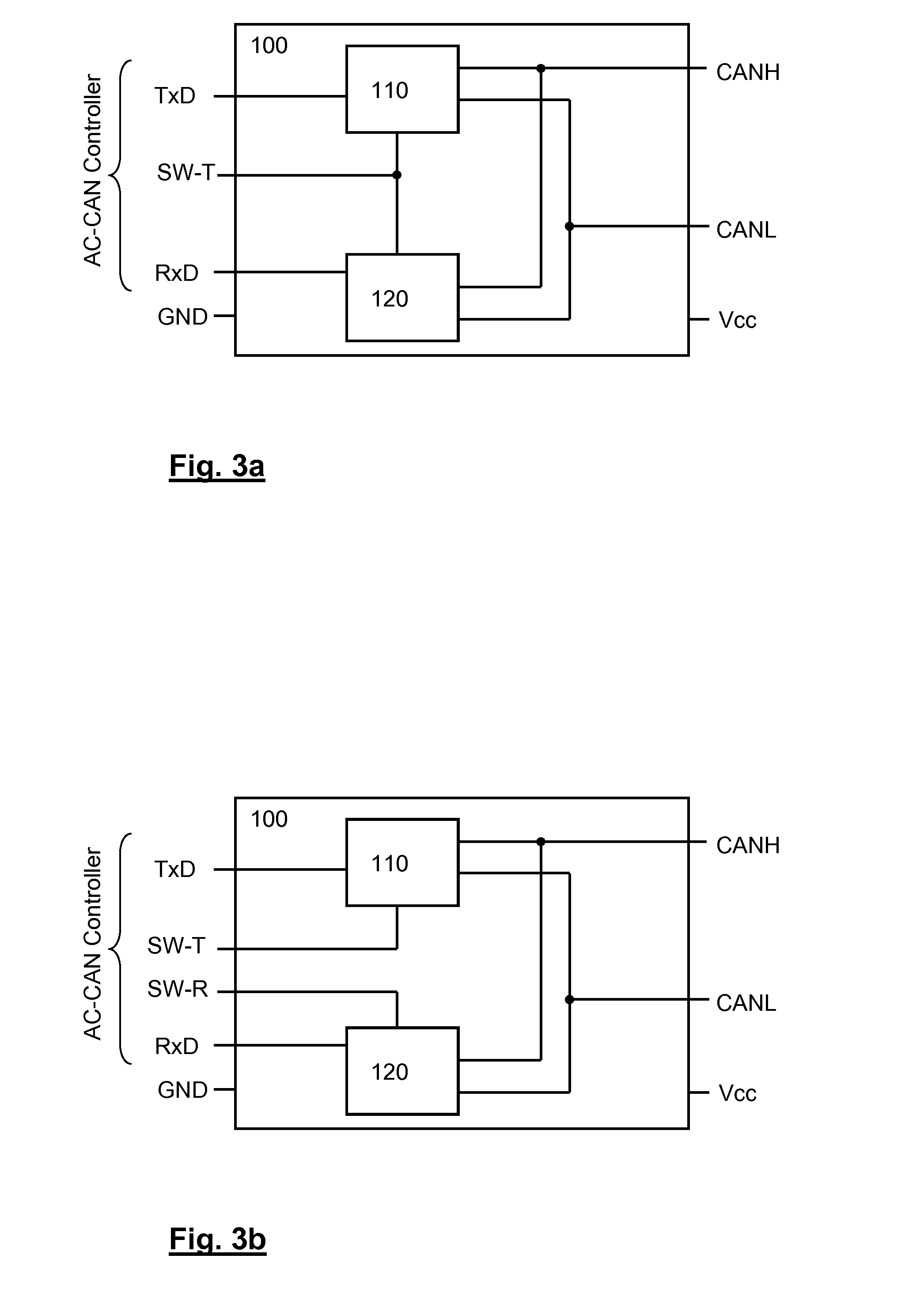
ActiveUS20140298133A1Short timeEmission reductionCode conversionError detection onlyProcessing elementData encoding
A method and an apparatus for data transfer in a network having at least two data processing units that exchange messages via the network are described, the exchanged messages having a logical structure in accordance with the CAN specification ISO 11898-1, coding of the bits for at least one first predefinable region within the exchanged messages being accomplished according to the method in accordance with the CAN standard ISO-11898-1, and such that when a switchover condition exists, coding of the bits for at least one second predefinable region within the exchanged messages is accomplished according to a method departing from the CAN standard ISO 11898-1.
Owner:ROBERT BOSCH GMBH
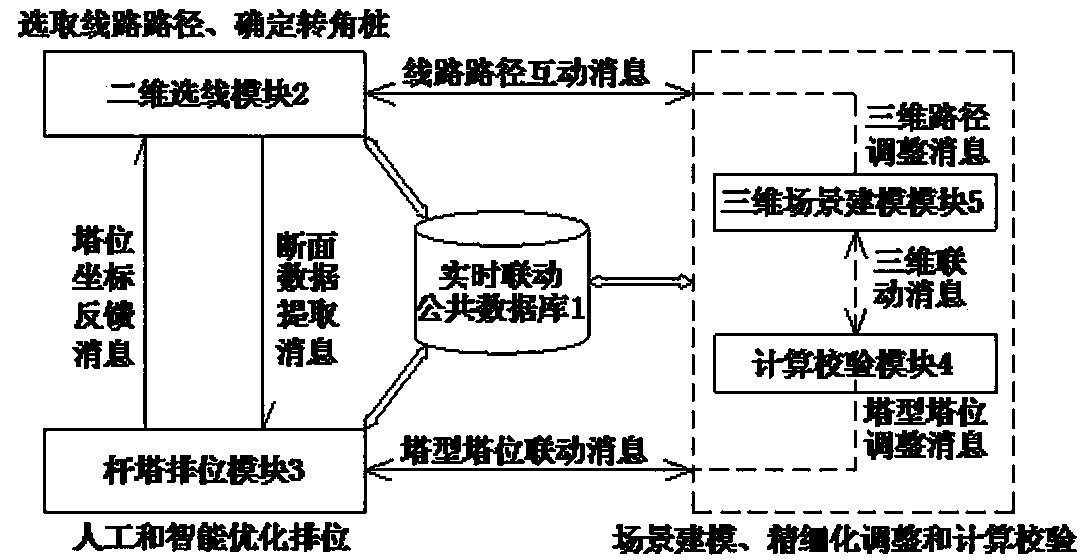
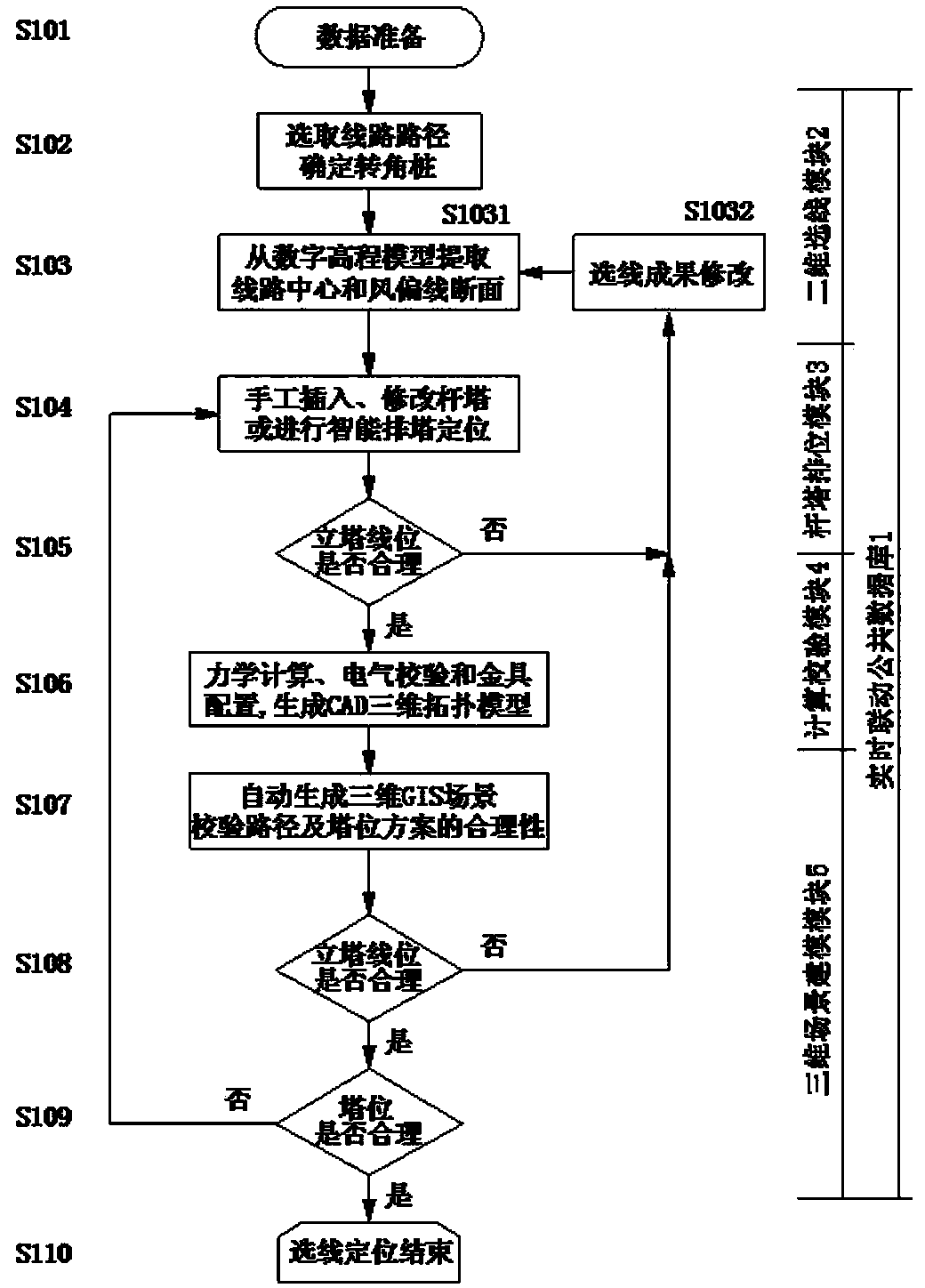
System and method for multi-window linked line selection and tower arrangement positioning of power transmission lines
ActiveCN104008241AEnsure consistencyAvoid direct transferSystems intergating technologiesSpecial data processing applicationsSimulationDiscretization
The invention discloses a system and a method for multi-window linked line selection and tower arrangement positioning of power transmission lines. The system and the method are used for realizing real-time linkage of multi-window line selection, tower arrangement positioning and scene modeling. The method comprises the steps of selecting line routes by use of a two-dimensional line selection module and by virtue of message communication and a real-time linkage common database, and determining corner poles, performing discretization on a digital elevation model along the center of lines and a windage yaw line to extract section data, realizing manual and intelligent optimized arrangement of poles and towers by use of a pole and tower arrangement module, carrying out linked feedback of tower coordinates after arrangement to a GIS (Geographic Information System) line selection module, and carrying out scene modeling, fine adjustment and calculation verification in real time in a three-dimensional scene modeling module and a calculation verification module. The system and the method is characterized in that the advantages of two dimensions and three dimensions are combined, multi-dimensional information such as geographical distribution, topography and landforms, crisscross spanning objects and power transmission equipment, and multi-window linkage of line selection, tower arrangement positioning, calculation verification and three-dimensional scene modeling module is realized, and therefore, the traditional operation manner can be effectively improved and the working efficiency can be raised.
Owner:CEEC JIANGSU ELECTRIC POWER DESIGN INST
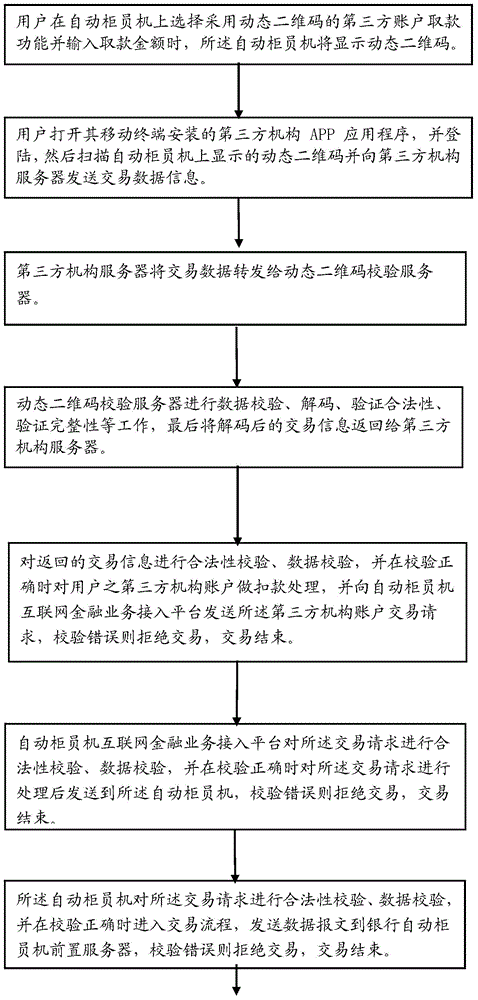
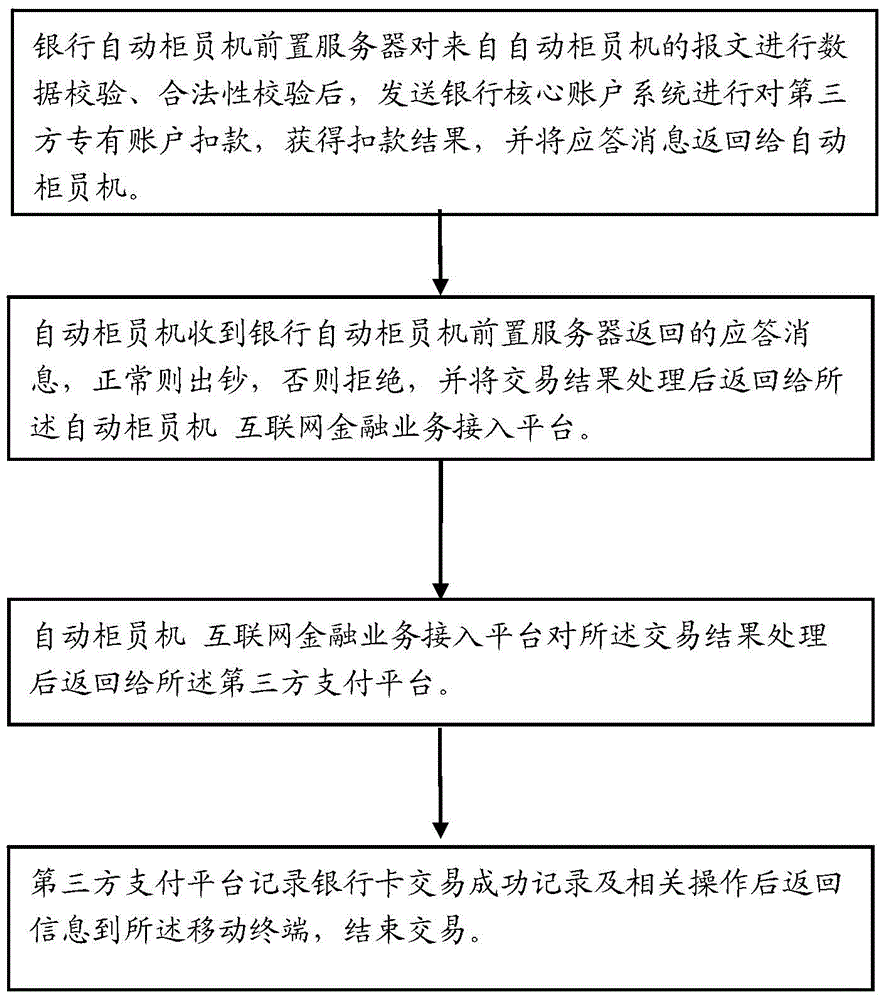
Third-party account ATM (automatic teller machine) withdrawing method and system based on dynamic two-dimension codes
InactiveCN104599408AEnsure safetyEnsure financial securityComplete banking machinesPayment protocolsThird partyData information
The invention relates to the technical field of encoding and decoding two-dimension codes, in particular to a third-party account ATM (automatic teller machine) withdrawing method based on dynamic two-dimension codes. The method comprises the following steps that a user can choose a third-party organization no-card withdrawing function of the dynamic two-dimension codes on an ATM, the ATM can display dynamic two-dimension code images, the user can log in third-party organization APP application programs to scan the dynamic two-dimension codes and send transaction data information to a third-party organization server, the third-party organization server can transmit the transaction data to a dynamic two-dimension code checking server, the dynamic two-dimension data checking server can check data and finally returns the transaction information to the third-party organization server, and the third-party organization server can check the legality of the transaction information and then checks the transaction information again. When the transaction information is not legal, transaction is refused and finishes. Compared with an existing static two-dimension code withdrawing program, a dynamic two-dimension code checking technique utilizes a more complex security mechanism to guarantee financial security of the user.
Owner:ATMU INFORMATION TECH
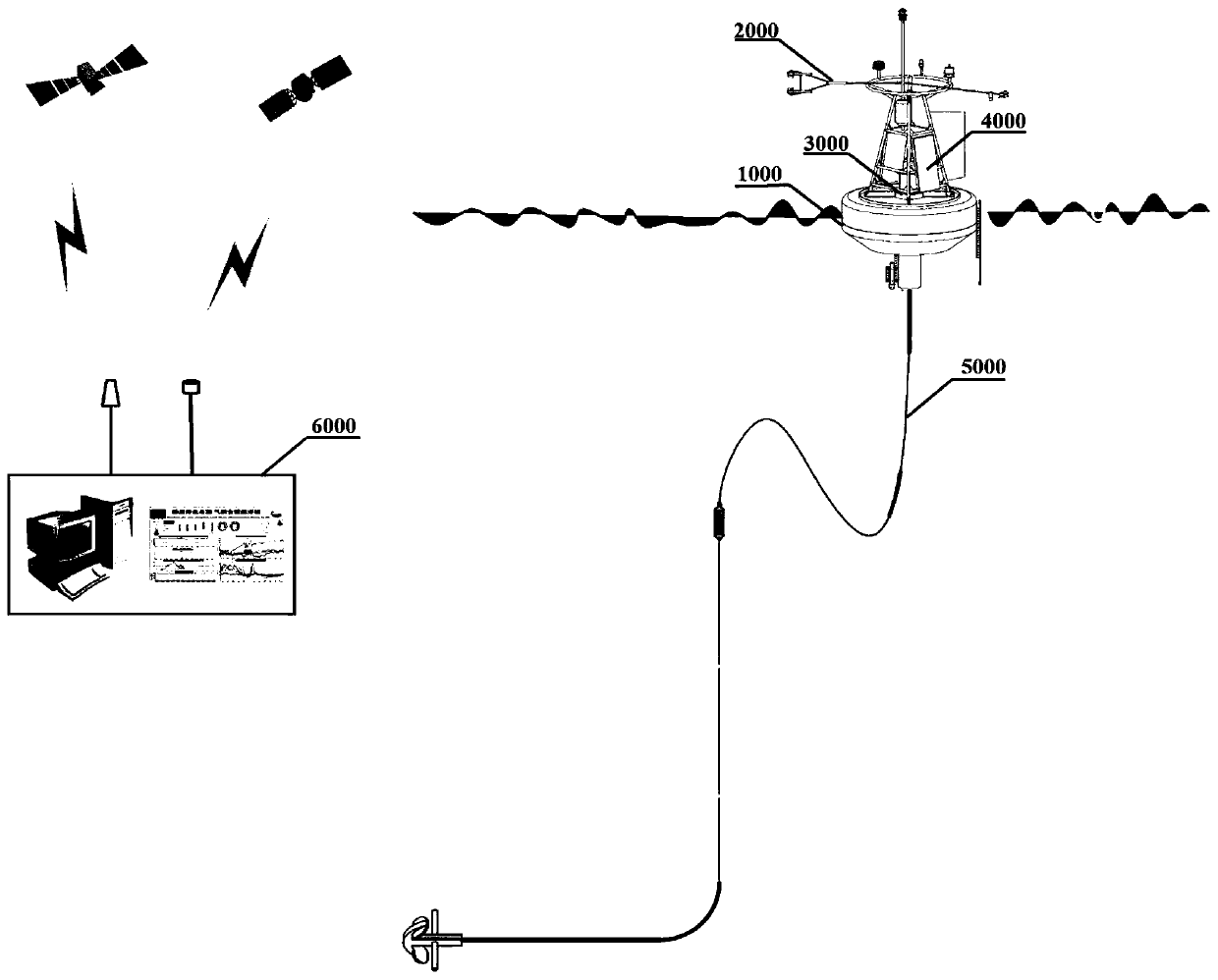
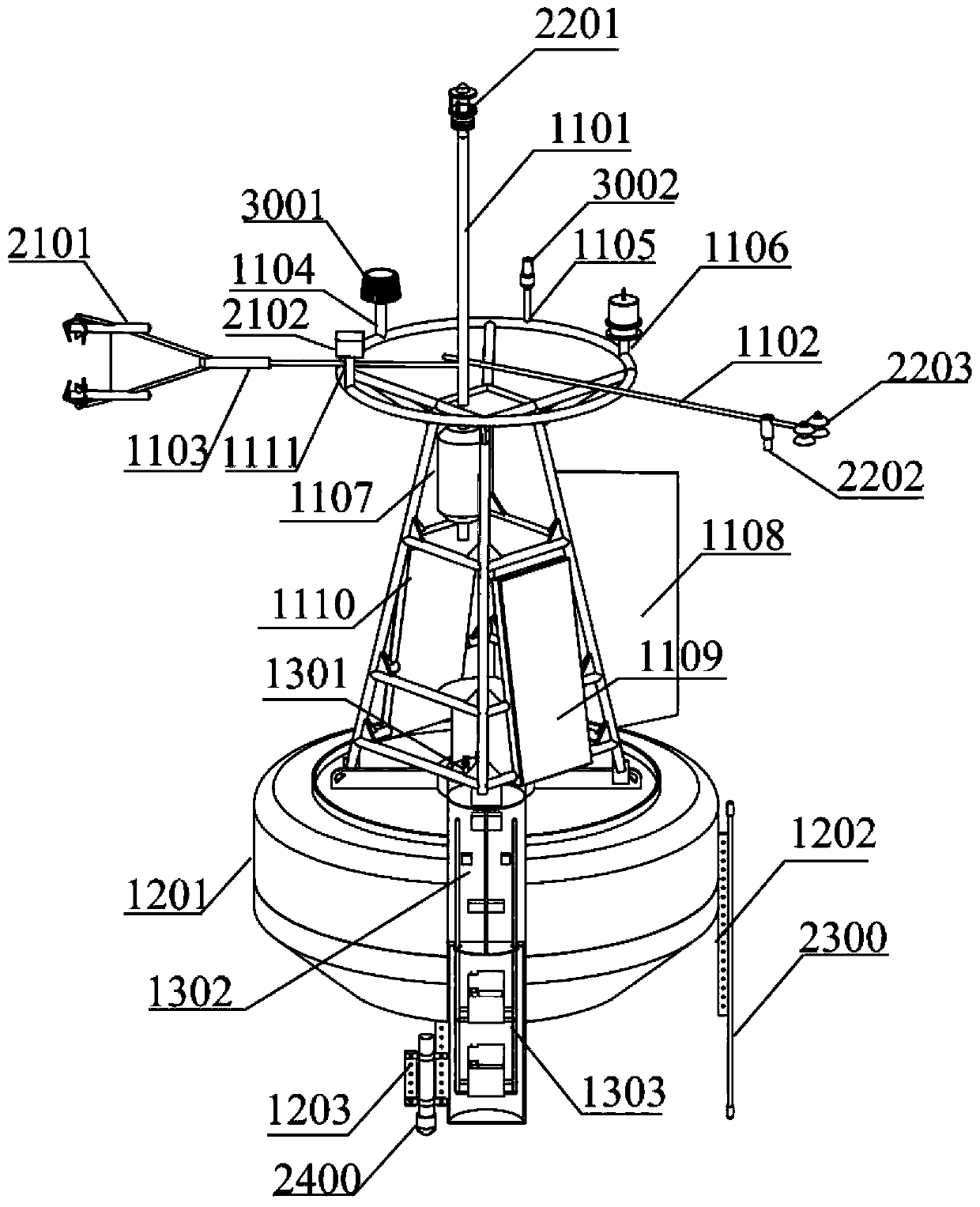
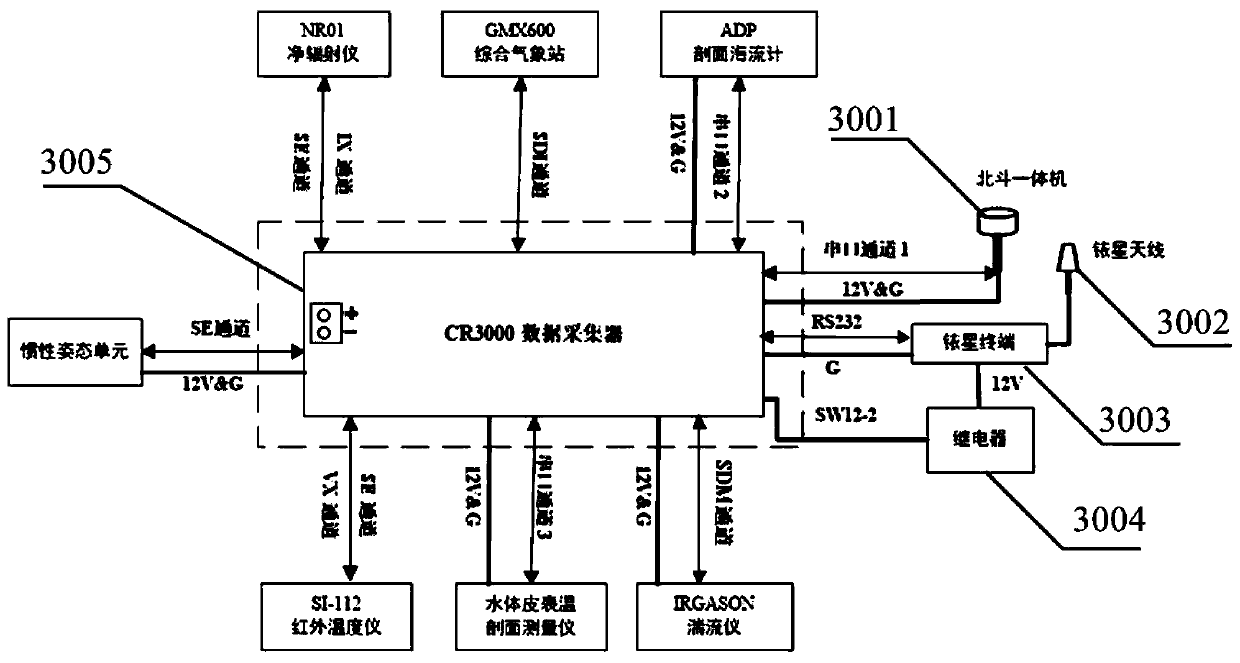
Sea-gas coupled real-time observation buoy system based on Beidou satellite and Iridium satellite double-satellite communication
ActiveCN110203333AHigh security requirementsReduced security requirementsBatteries circuit arrangementsWaterborne vesselsIridiumOpen sea
The invention discloses a sea-gas coupled real-time observation buoy system based on Beidou satellite and Iridium satellite double-satellite communication. The sea-gas coupled real-time observation buoy system comprises a sea-gas coupled observation sensor unit, a data collecting communication control unit, an anchoring unit, a buoy body platform, a power supplying unit and a data processing center. The buoy data collecting communication control unit adopts a Beidou satellite system to transmit conventional block method sea-gas flux, upper-layer sea current profile and buoy operation state parameters which have high requirements on data safety and low requirements on the communication quantity, and adopts an Iridium satellite system to transmit high frequency eddy related and high-resolution seawater skin surface temperature profile data which have high requirements on the communication quantity. A buoy can synchronously observe turbulence flux parameters of an eddy-related method of amovable platform, flux parameter of a block method, the seawater 0-1.0 m high-resolution skin surface temperature profile and the 0-70 m upper-layer sea current profile in real time in real time. Thesea-gas coupled real-time observation buoy system is suitable for being released in deep and open sea, and has the characteristics of diverse sea-gas interface observation parameter, safe data transmission and the like.
Owner:SOUTH CHINA SEA INST OF OCEANOLOGY - CHINESE ACAD OF SCI
Data transmission method between master and slave devices
ActiveUS8516174B2Data transmission securityInput/output processes for data processingData conversionData transmissionEmbedded system
A method for transmitting data frames between a master device and one or more slave devices via a bus system having at least one request line for transmitting request data frames from the master device to the slave devices, a response line for transmitting response data frames from the slave devices to the master device and at least one selection line for activating the slave devices, the request data frames and the response data frames being transmitted together with at least one address bit for addressing one of the slave devices, the useful data bits and at least one length-indicating bit for indicating the data frame length.
Owner:ROBERT BOSCH GMBH
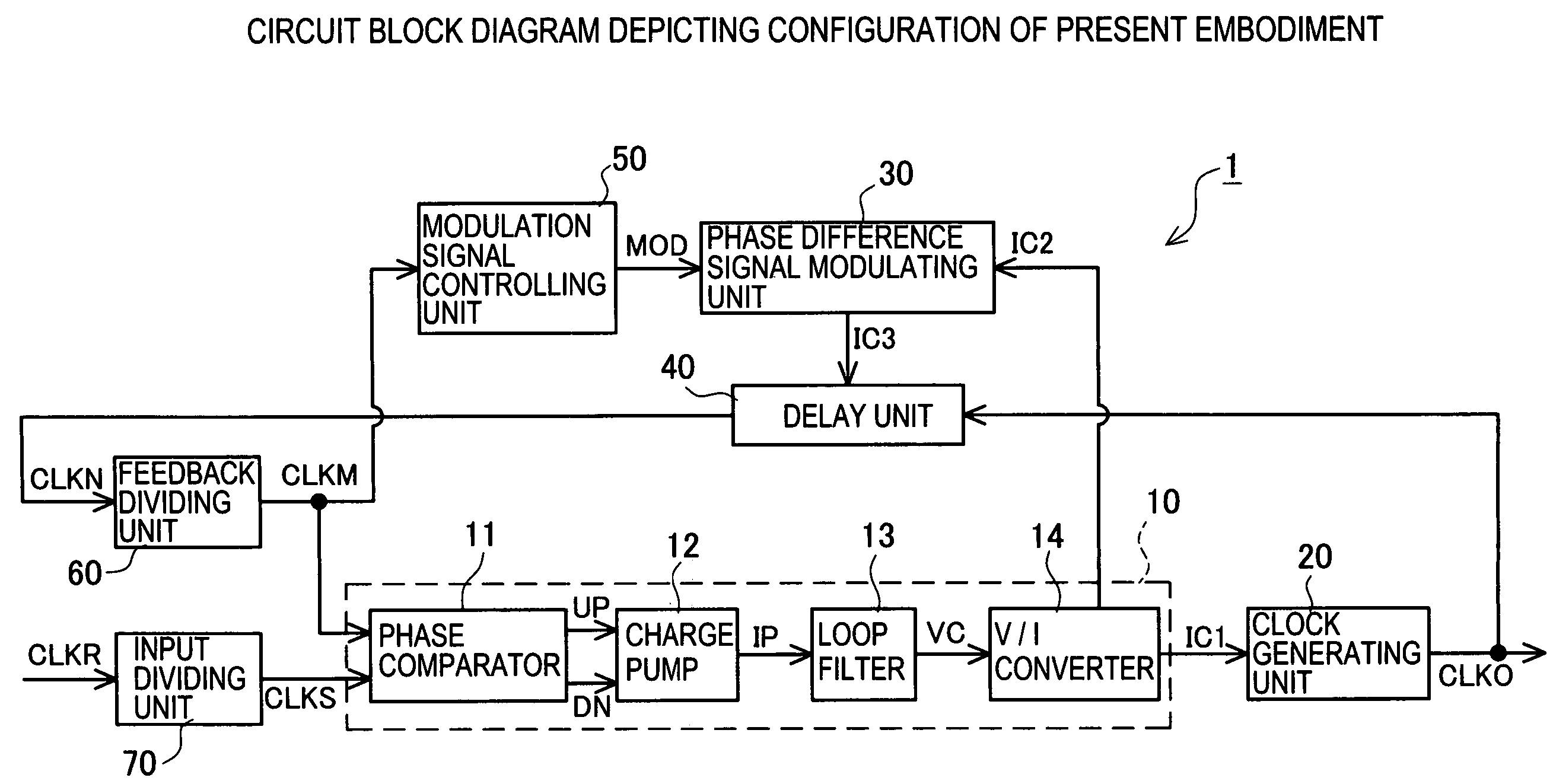
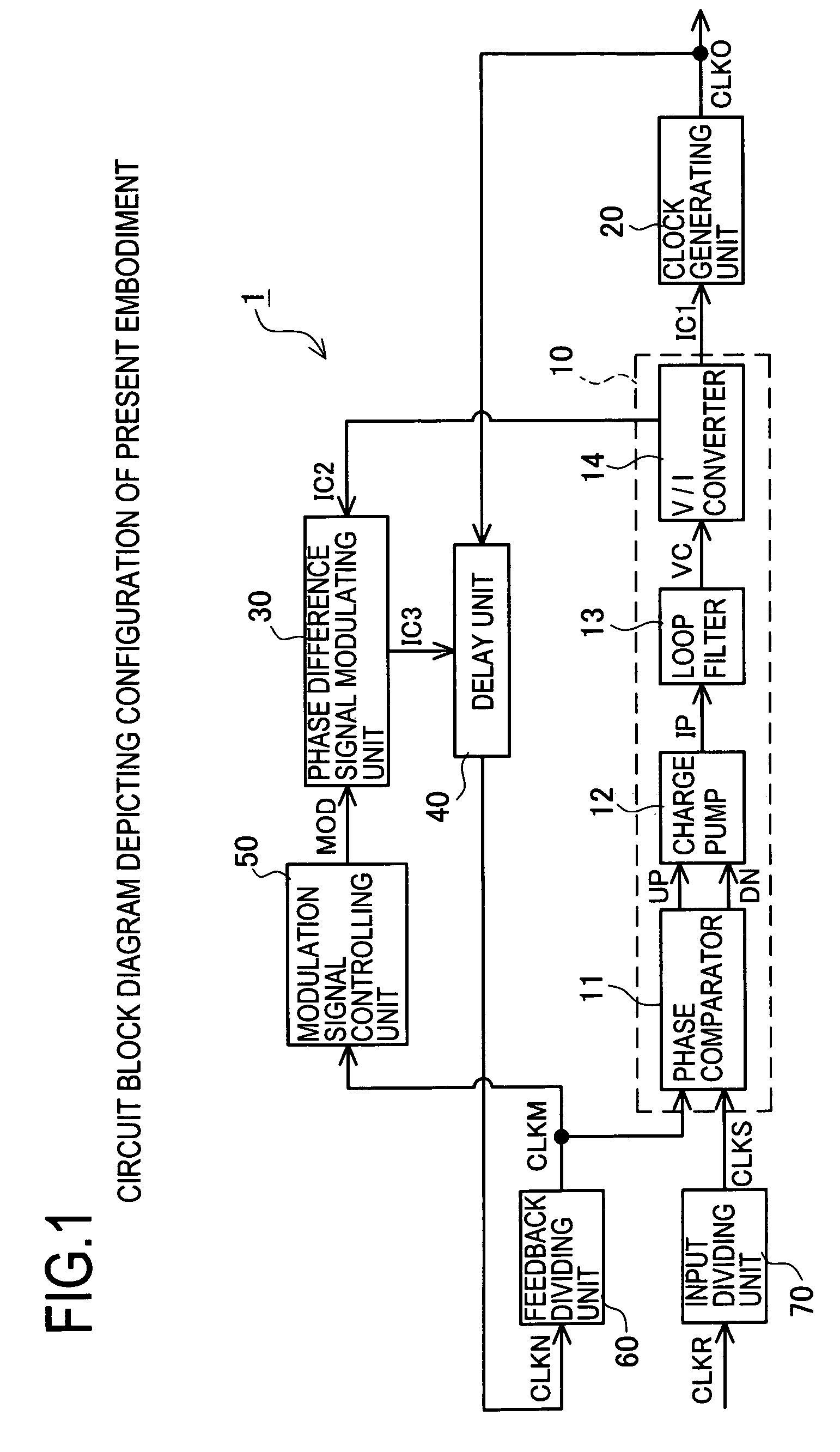
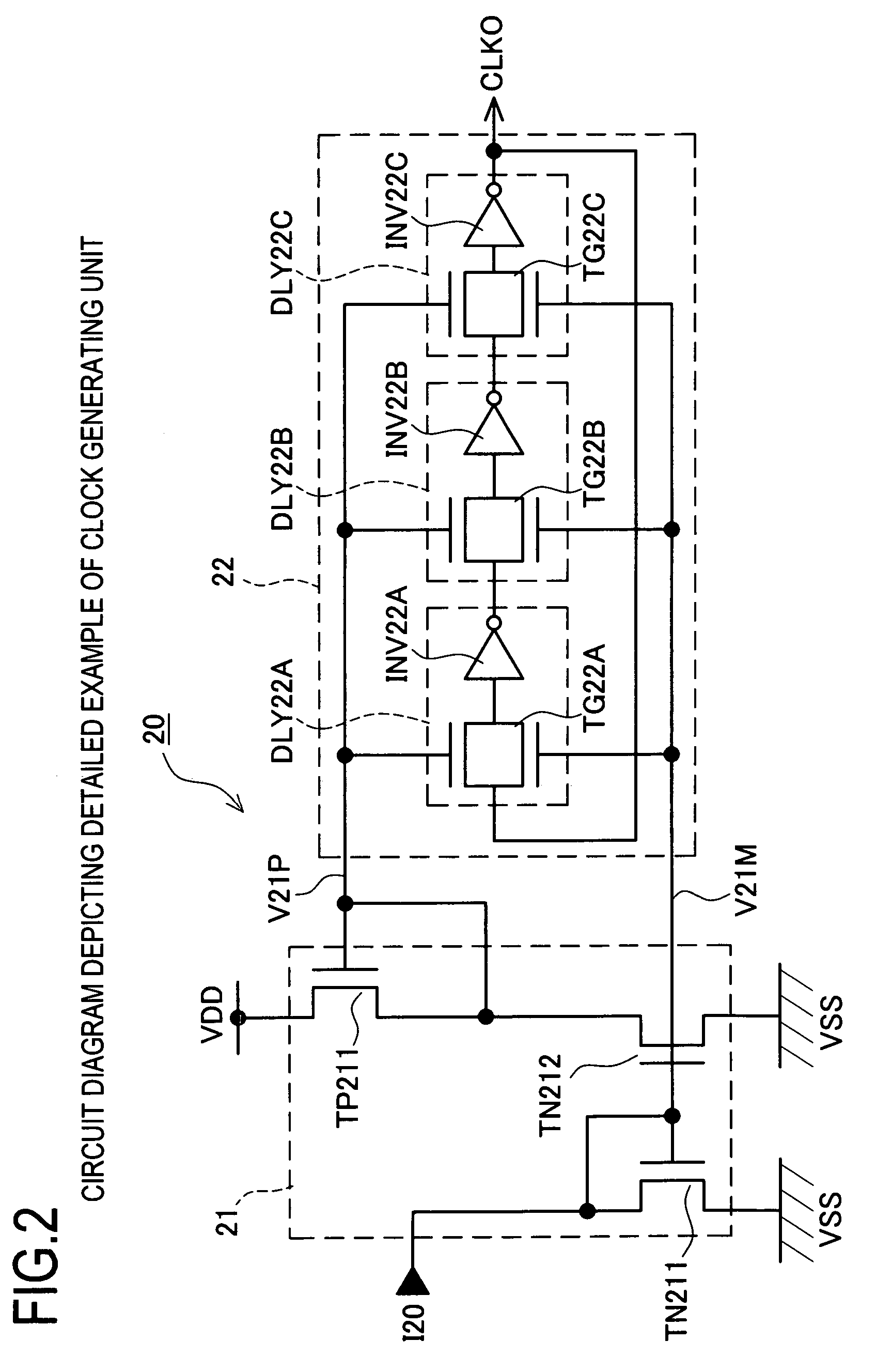
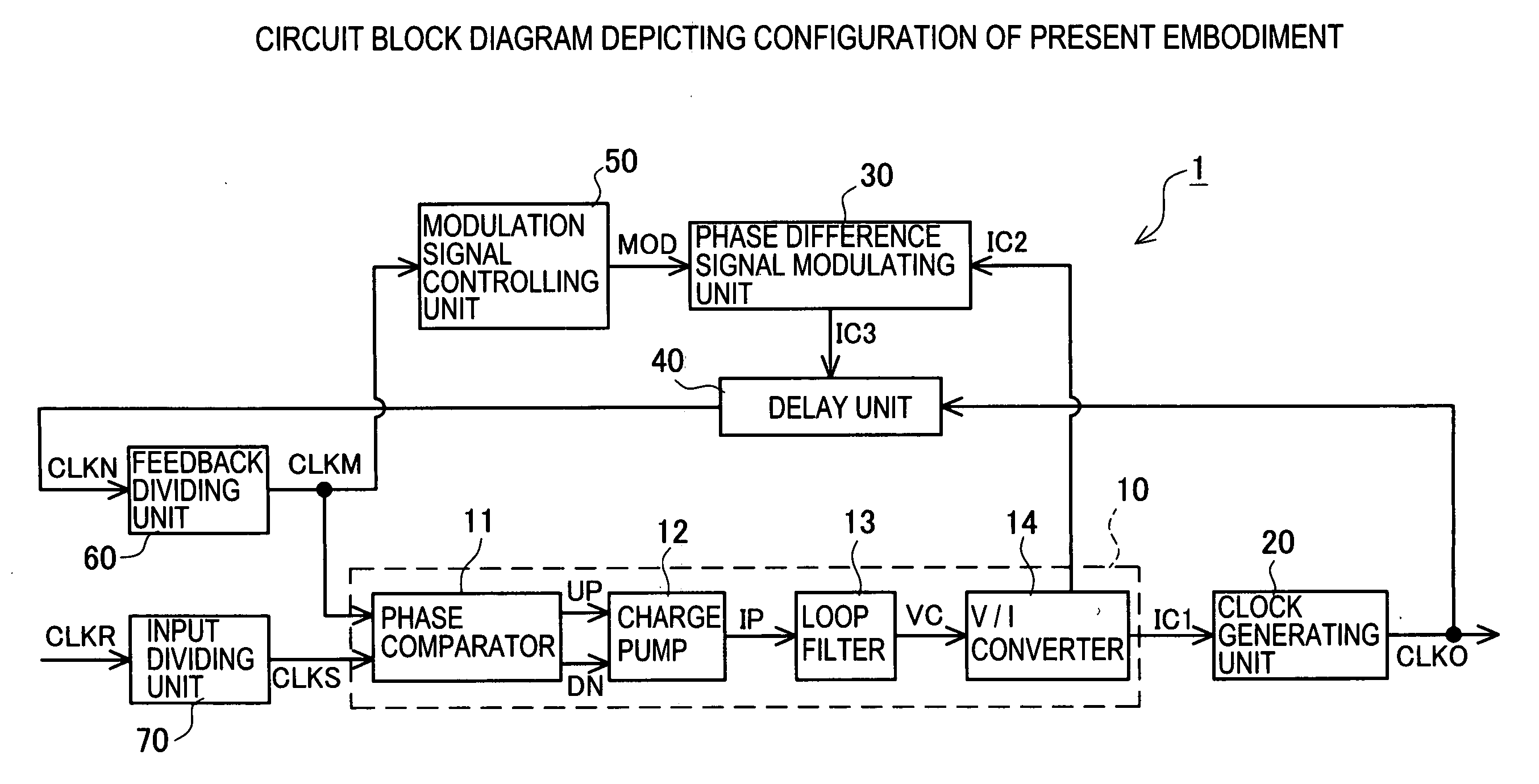
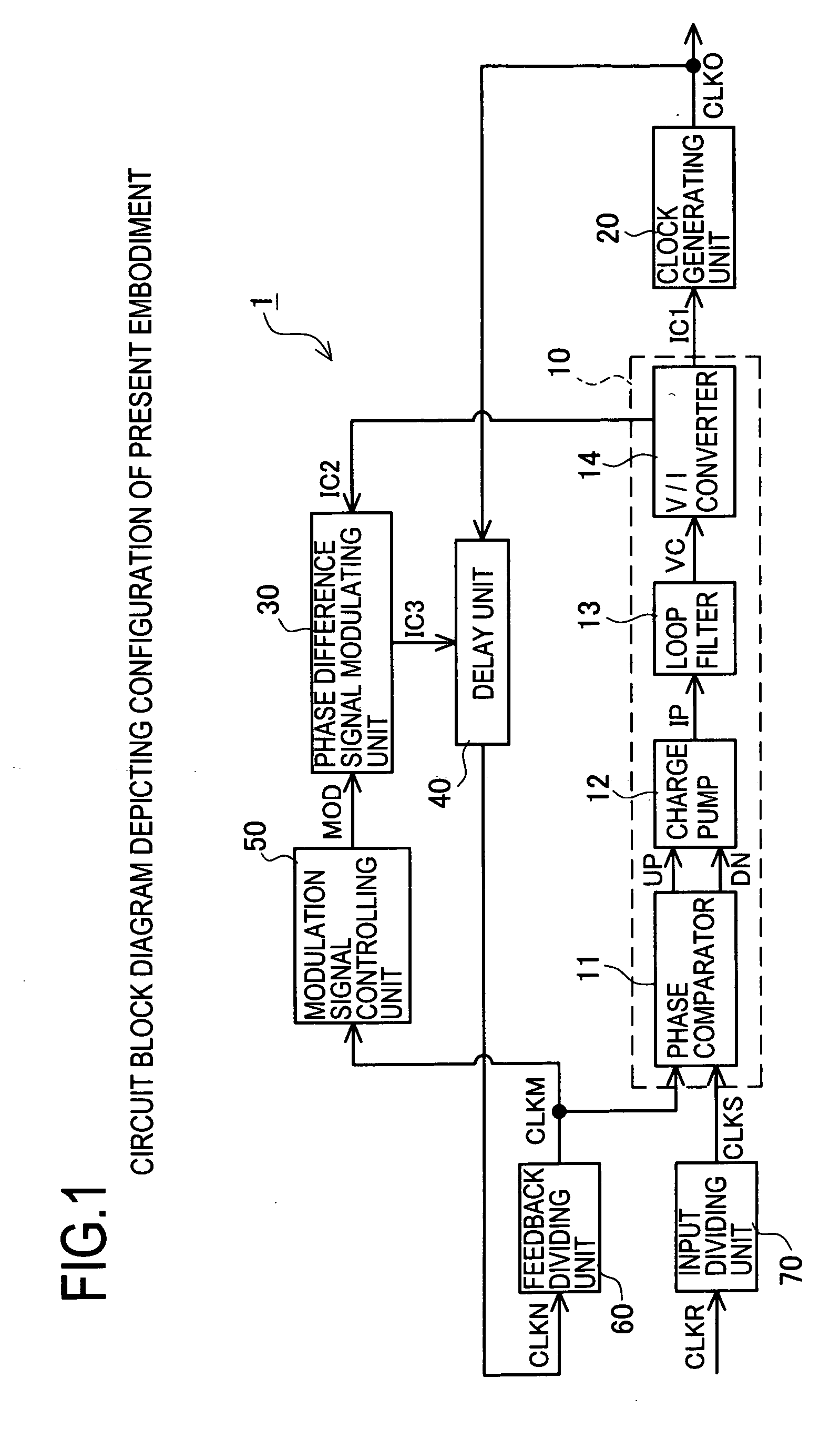
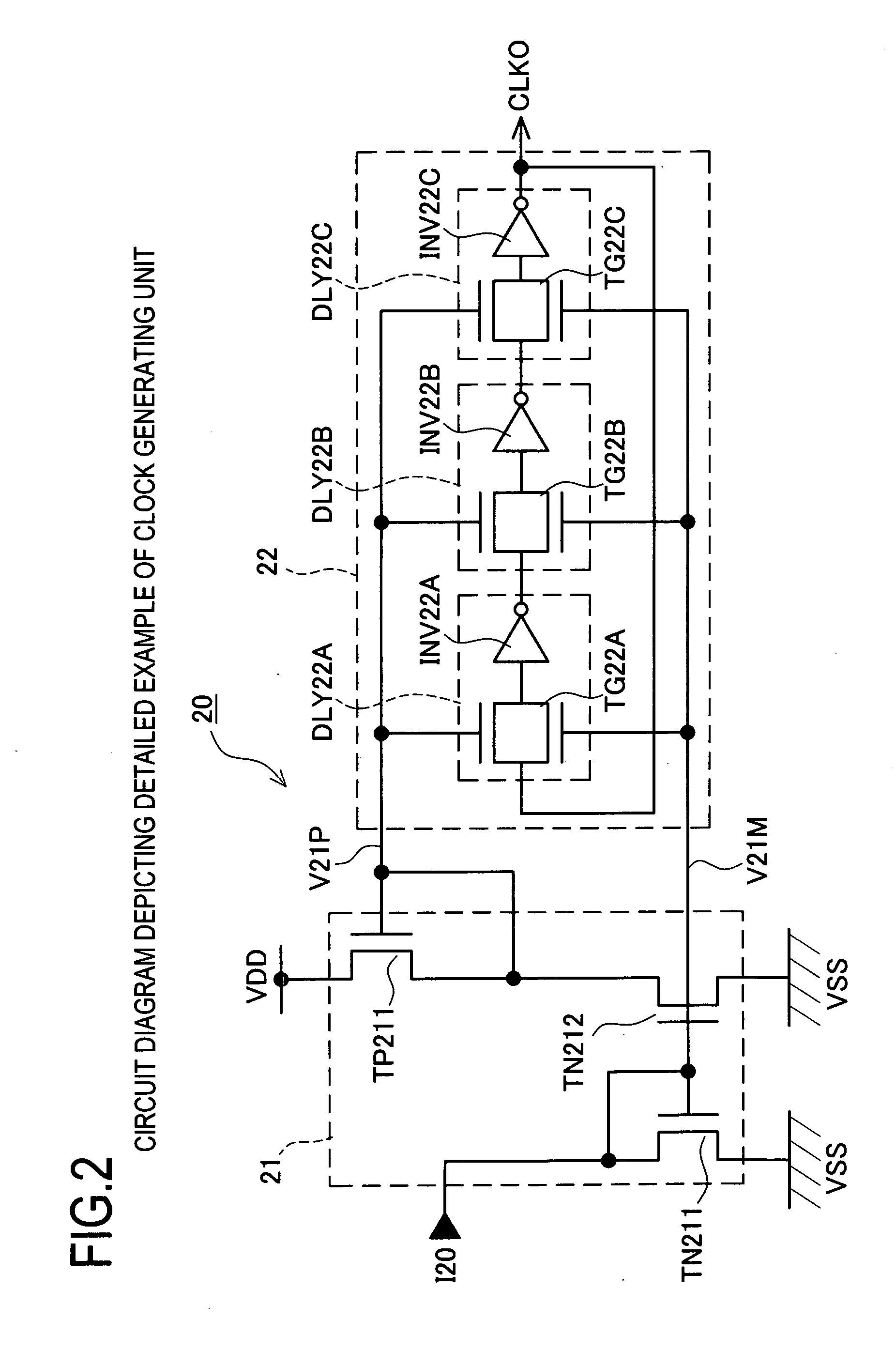
Clock generating circuit and clock generating method
ActiveUS7215165B2Reduce impactEarly detectionPulse automatic controlSingle output arrangementsFrequency spectrumPhase difference
The invention provides a clock generating circuit for generating a spectrum spread clock and carrying out high-speed and accurate phase control of a reference clock signal and an output clock signal, which is composed of compact circuits, and a method for generating the clock. The spectrum spread clock generating circuit 1 is provided with a phase comparator unit 10 that compares the reference clock signal CLKS with the internal clock signal in terms of a phase difference, and outputs a control current IC1 in compliance with the result of comparison; a clock generating unit 20 for generating an output clock signal CLKO; a phase difference signal modulating unit 30 for outputting a control current IC3; and a delay unit 40 for delaying the output clock in compliance with the control current IC3 and outputting the internal clock signal CLKN.
Owner:MONTEREY RES LLC
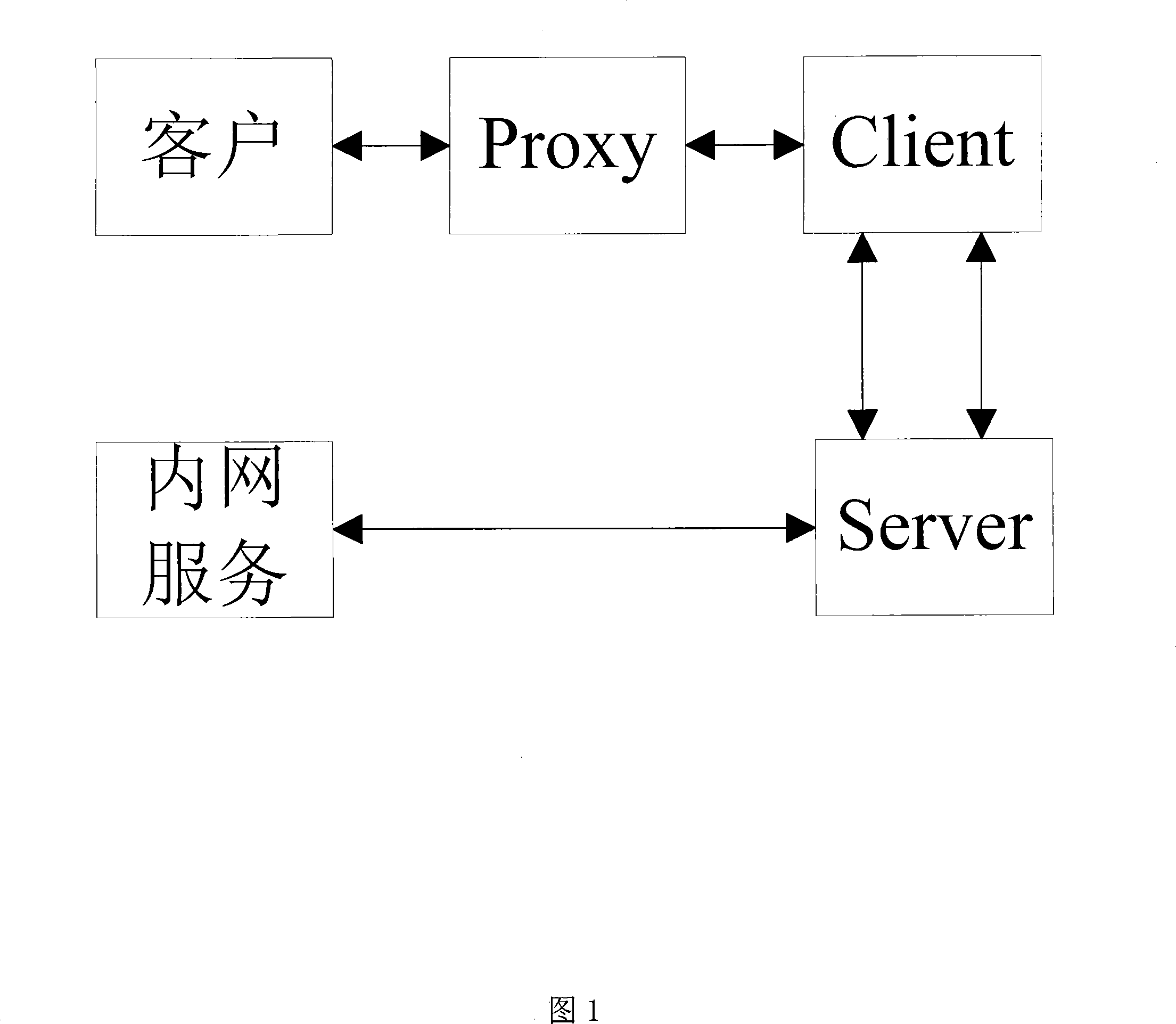
Fire wall/subnet penetration method based on intranet node forwarding technology
InactiveCN101175036ALow costSecurity Services and Data TransmissionData switching networksData transmissionIntranet
The invention discloses a firewall / subnet penetration method based on intranet node forwarding technology, which includes three modules: Proxy (agent) module, Client (user) module, and Server (server) module. The Proxy module is mainly responsible for collecting user requests and forwarding them to the Client module; the Client module is mainly responsible for establishing a connection with the Server module and forwarding requests from the Proxy module; the Server module is mainly responsible for actively establishing a connection with the Client module, and the processing is performed by The request forwarded by the Client module obtains the corresponding resource and forwards it. The present invention utilizes existing protocols and platforms to effectively reduce the cost of firewall / subnet penetration and can achieve relatively safe service and data transmission.
Owner:NANJING UNIV
Remote access gateway surpassing NAT based on P2P-VPN technology
InactiveCN101854313ASolve the problem of accessing the internal network from the external networkLow costNetworks interconnectionNetwork connectionsIp addressClient-side
The invention relates to a remote access gateway surpassing NAT based on a P2P-VPN technology. The gate is based on the internet technology, combines embedded system application, and establishes point-to-point tunnel connection with client software which works on a terminal under the assistance of a server on a public network through a virtual VPN network technology; once the connection is established, the server on the public network does not participate in the communication between the P2P-VPN gateway and the client software, and the client software and the P2P-VPN gateway are in real P2P connection, thereby realizing the surpassing of NAT in the network and providing a bridge between remote access and control for a user, so that the user realizes the remote access of information like media and data; and compared with the prior art, the gateway has the advantages of stable performance, wide scope of adaptable networks and strong NAT surpassing capability, can realize non-computer on-duty service and can construct cross-regional internal network with low cost without the address of the public network.
Owner:济南维优科技开发有限公司
Clock generating circuit and clock generating method
ActiveUS20060290393A1Reduce impactEarly detectionPulse automatic controlSingle output arrangementsFrequency spectrumPhase difference
The invention provides a clock generating circuit for generating a spectrum spread clock and carrying out high-speed and accurate phase control of a reference clock signal and an output clock signal, which is composed of compact circuits, and a method for generating the clock. The spectrum spread clock generating circuit 1 is provided with a phase comparator unit 10 that compares the reference clock signal CLKS with the internal clock signal in terms of a phase difference, and outputs a control current IC1 in compliance with the result of comparison; a clock generating unit 20 for generating an output clock signal CLKO; a phase difference signal modulating unit 30 for outputting a control current IC3; and a delay unit 40 for delaying the output clock in compliance with the control current IC3 and outputting the internal clock signal CLKN.
Owner:MONTEREY RES LLC
Electronic evidence storage method based on block chain smart contract
ActiveCN110223068ARealize the core logic functionTransparent deposit processElectronic credentialsTransmissionTamper resistanceEvidence analysis
The invention requests to protect an electronic evidence storage method based on a block chain smart contract, and the method comprises the steps: carrying out the evidence storage through the smart contract by a evidence storage person, carrying out the query of evidence information through the smart contract by a verification person, carrying out the evidence downloading through the smart contract by a researcher, and carrying out the uploading of an evidence analysis result through the smart contract. The smart contract is a key logic module for realizing the method and exchanges data withthe block chain, so that the integrity, the verifiability and the tamper resistance of the electronic evidence are ensured. And meanwhile, all data operations are recorded on the block chain, so thatthe traceability of the electronic evidence is realized.
Owner:广东灏昌商业保理有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com