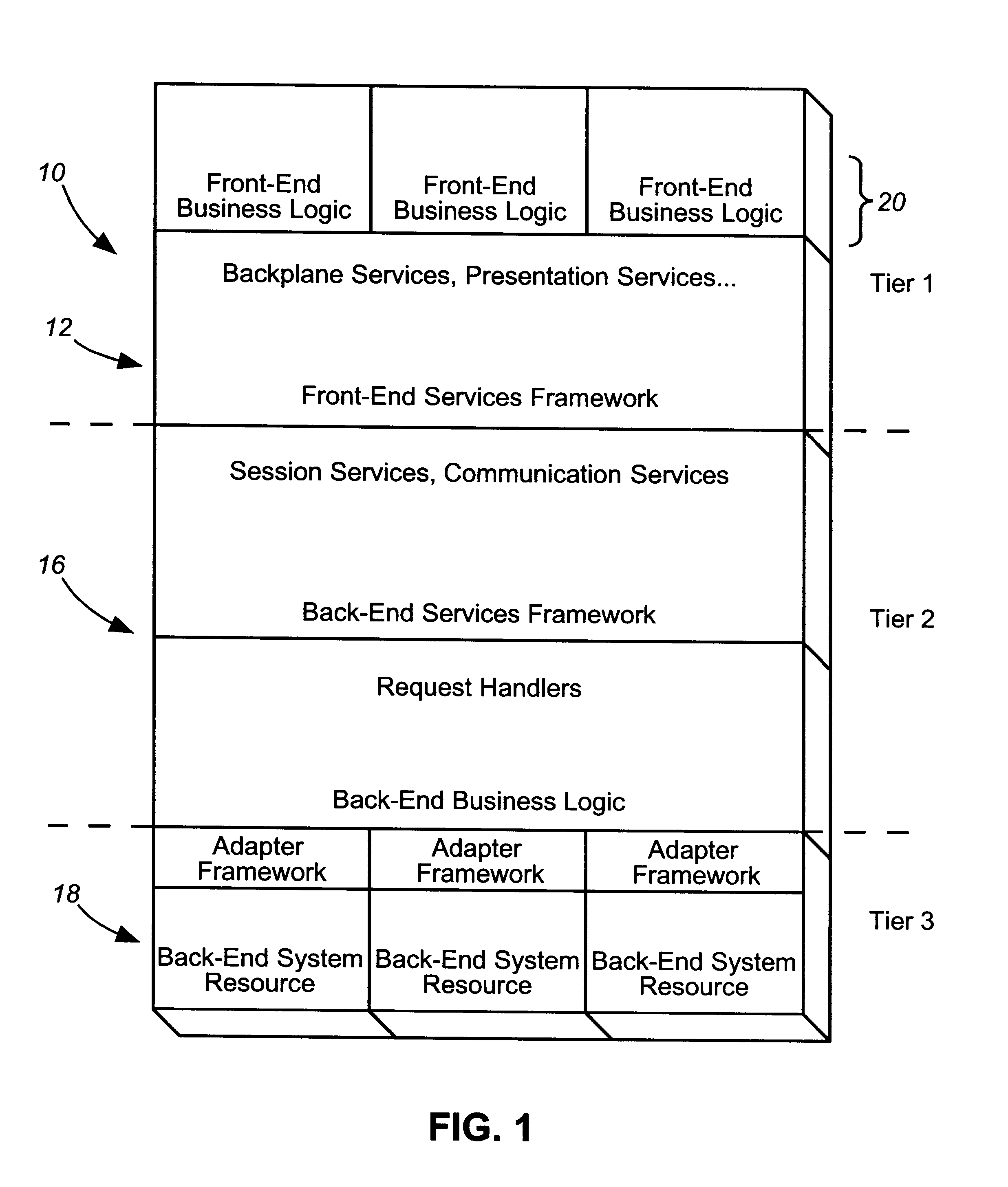
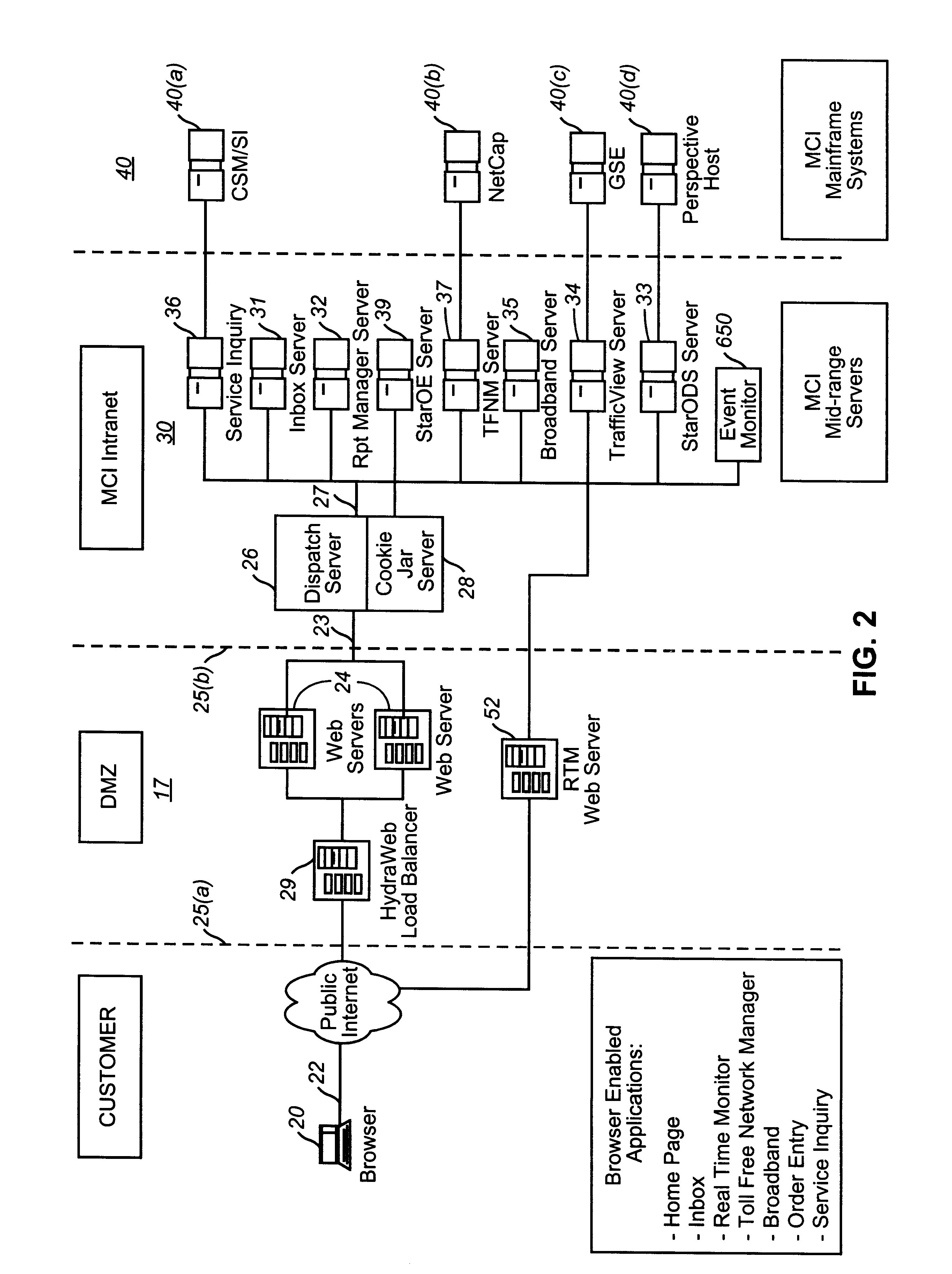
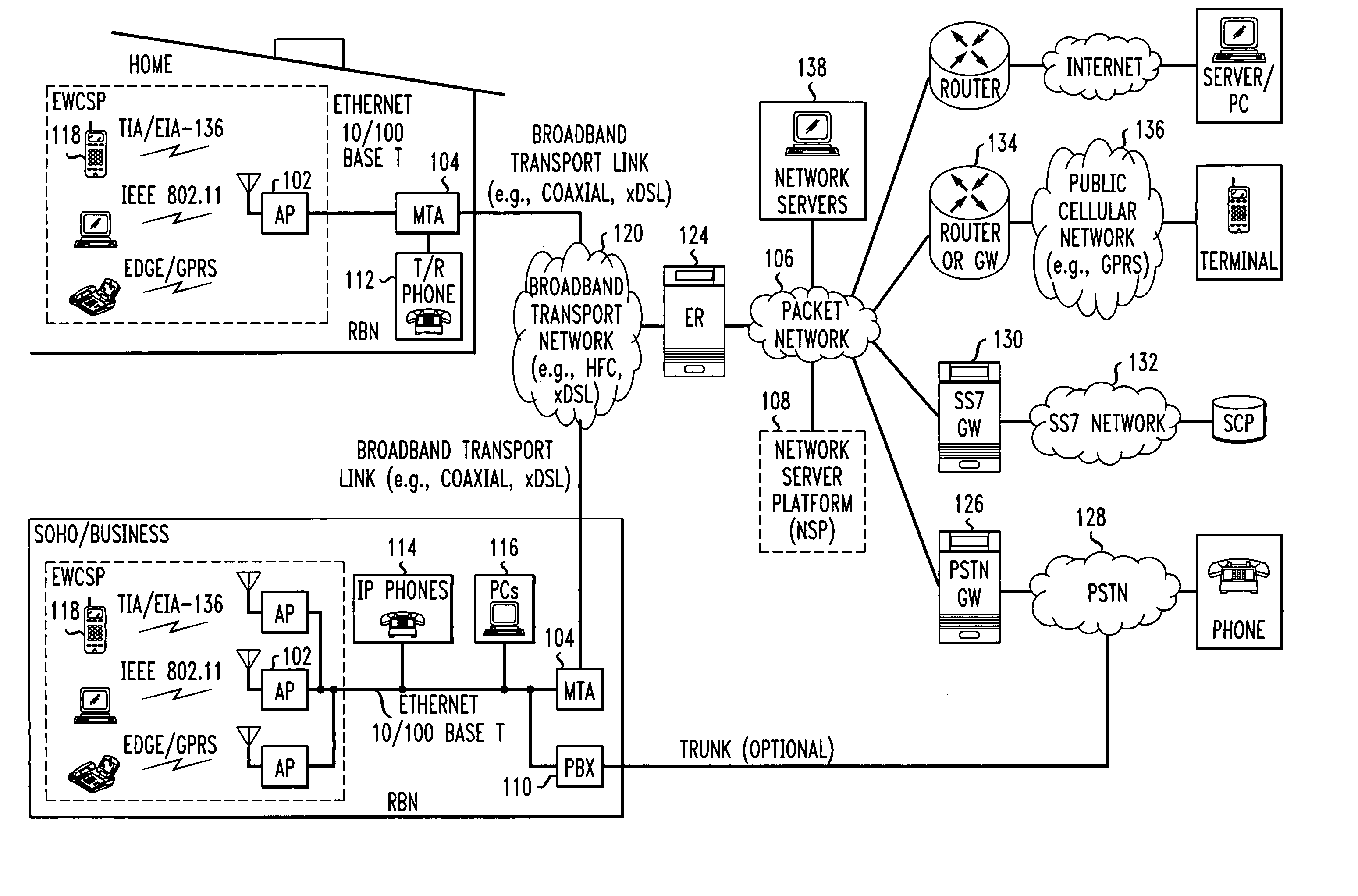
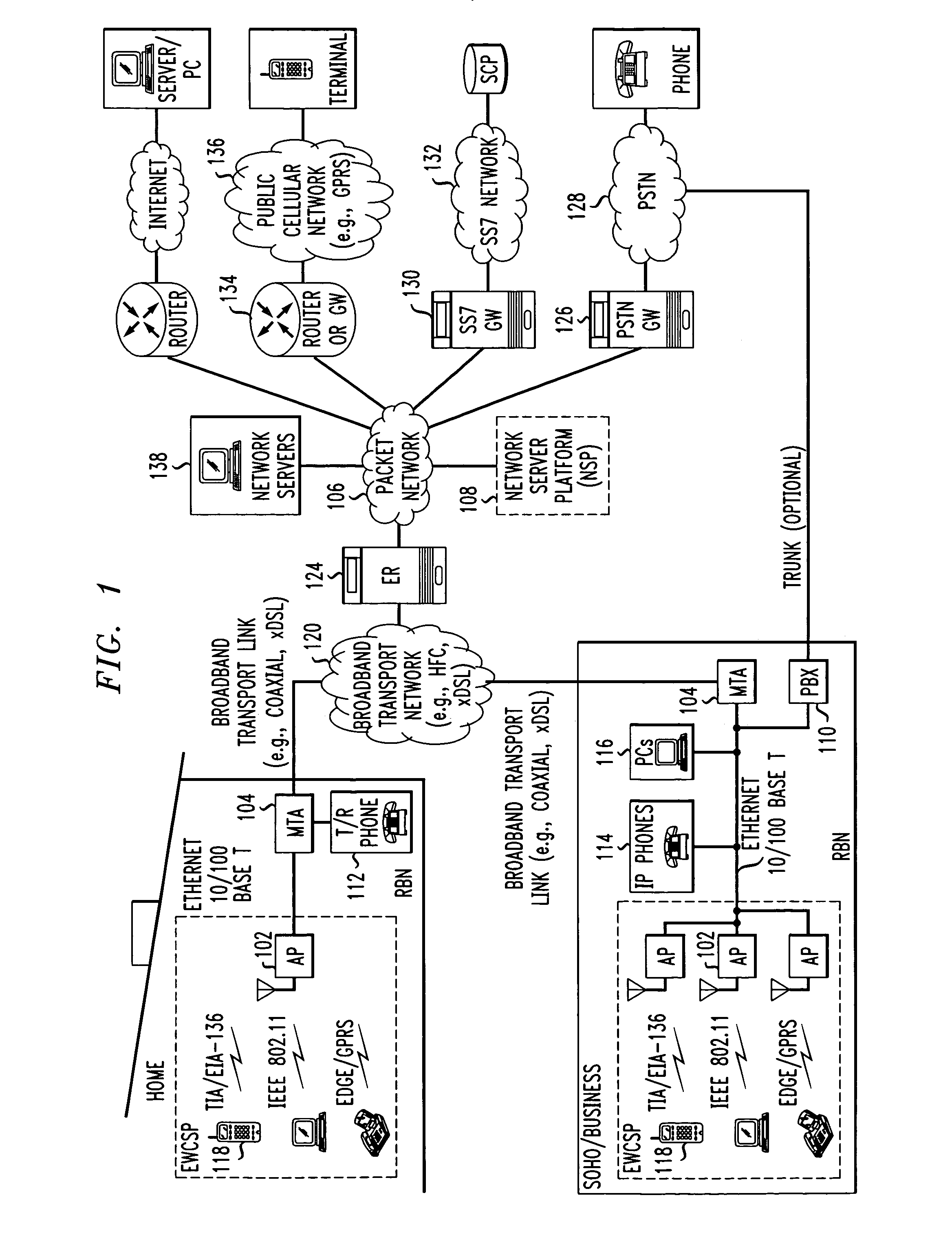
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3723 results about "Intranet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
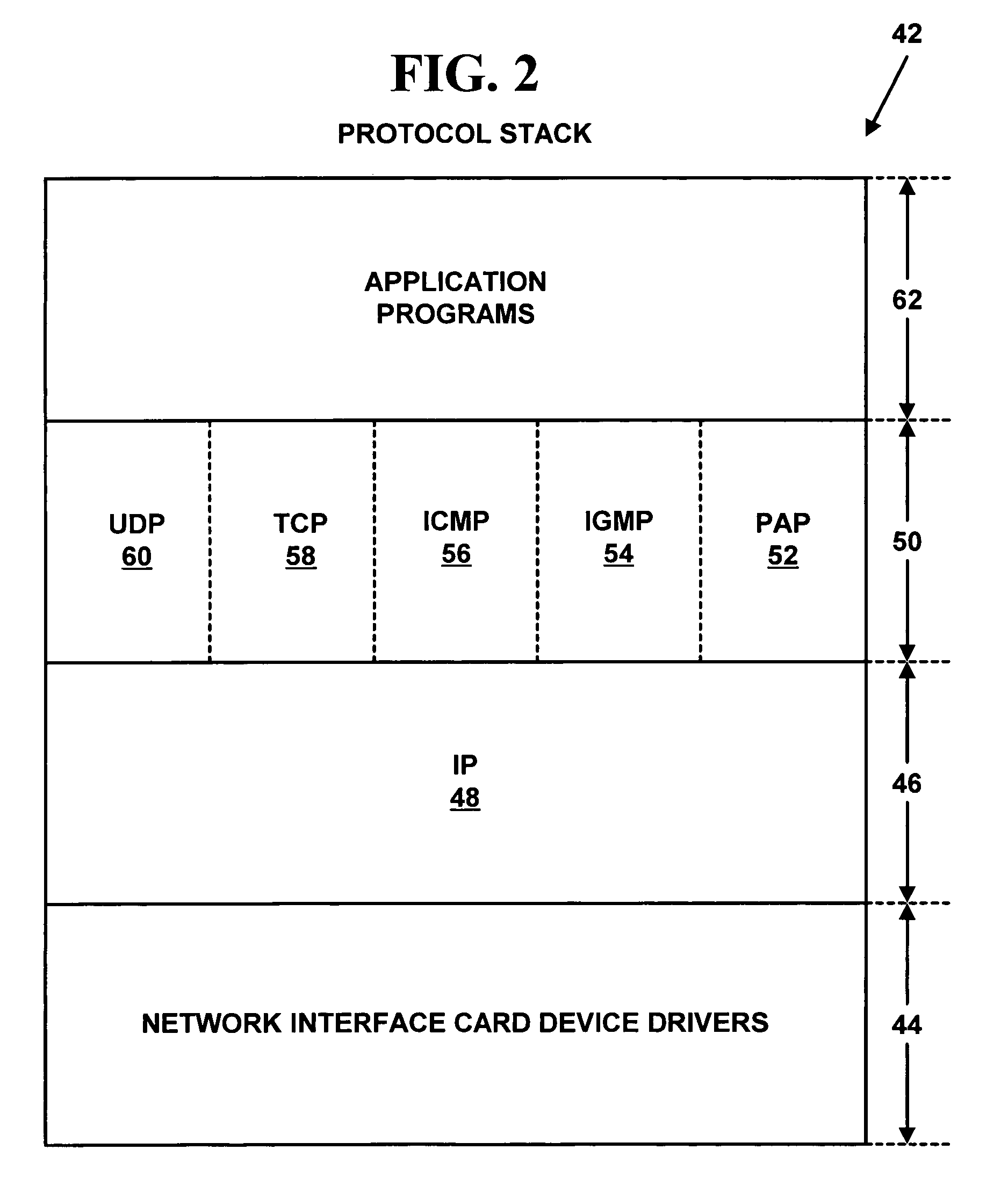
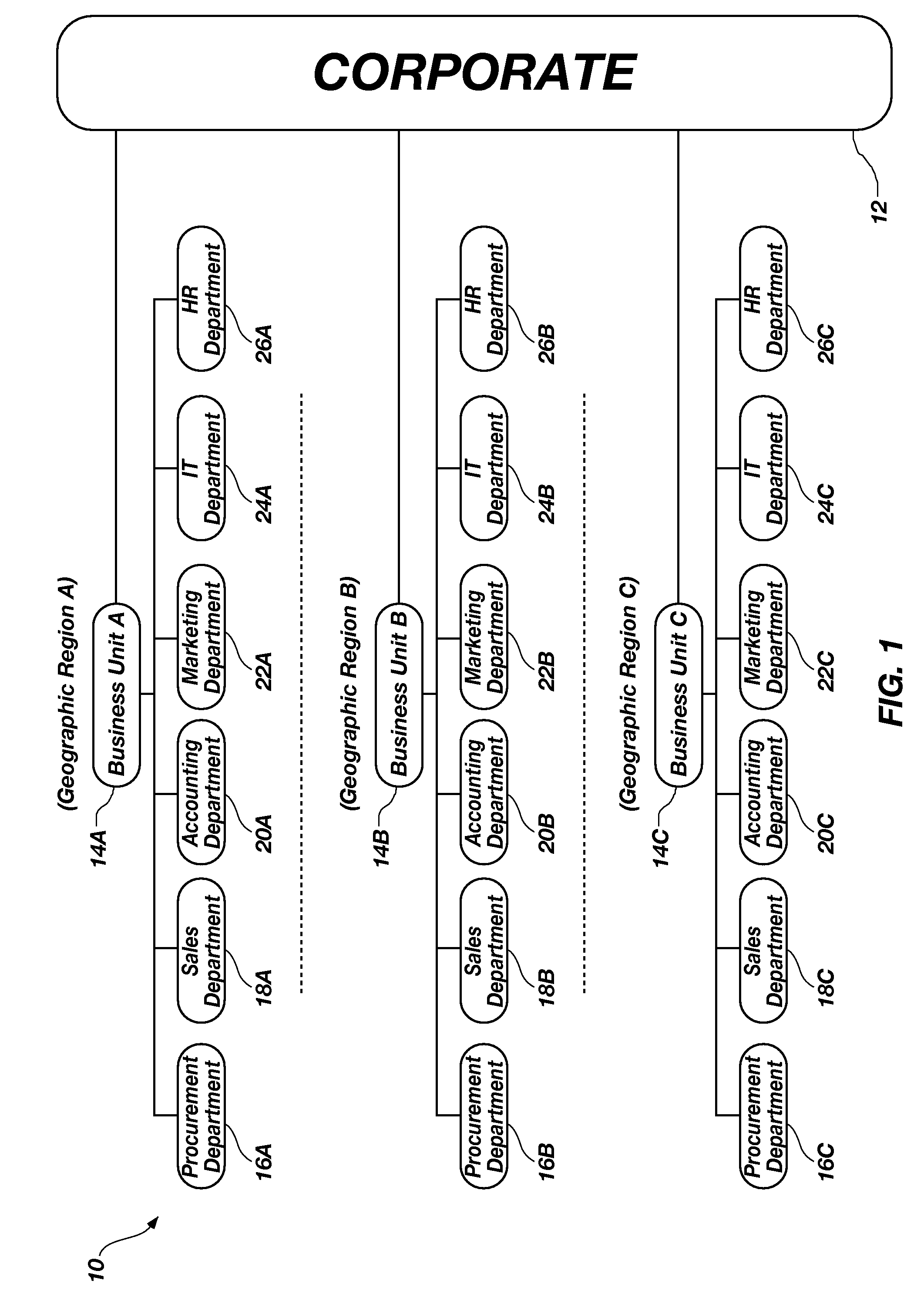
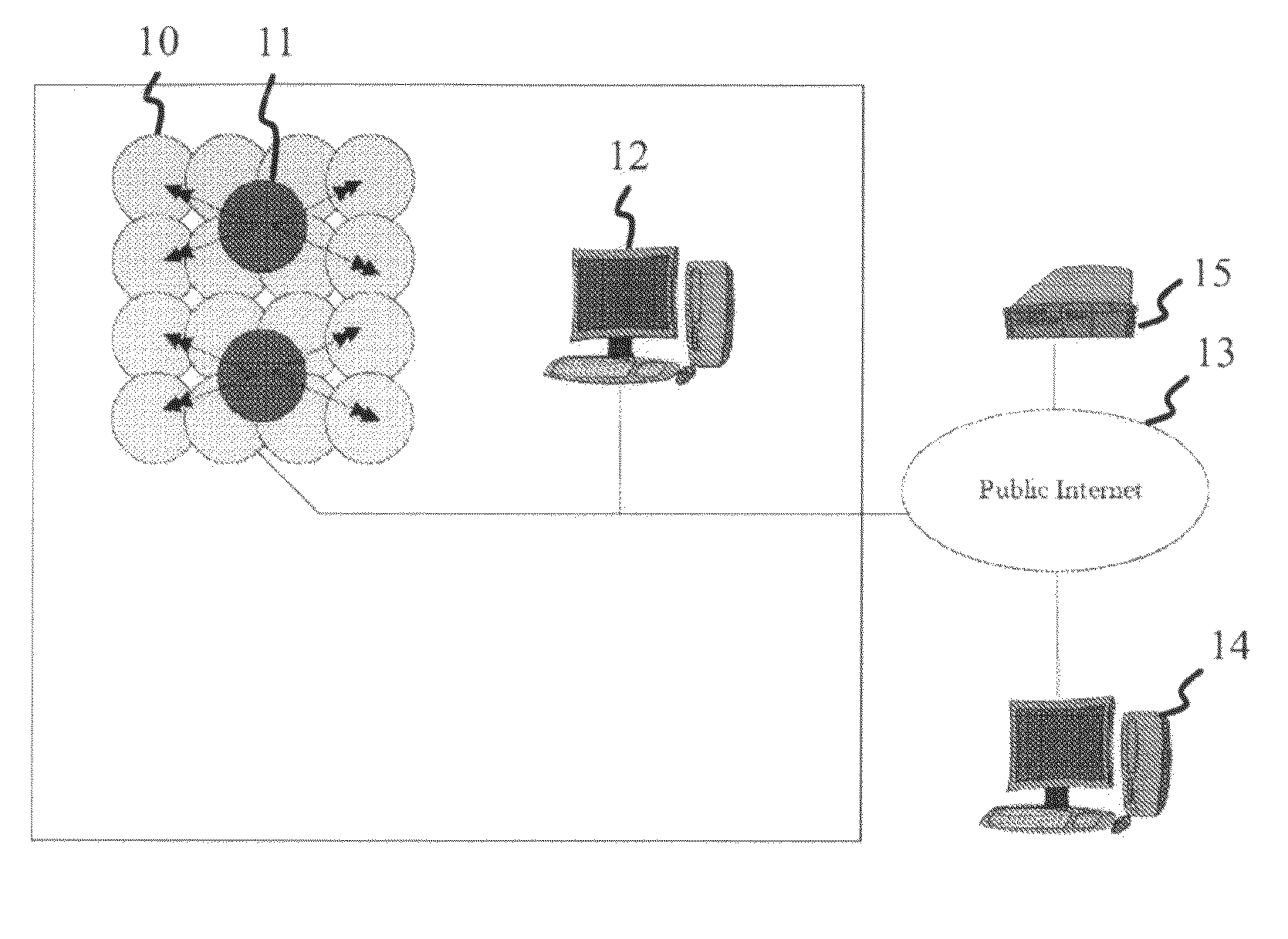
An intranet is a computer network for sharing corporate information, collaboration tools, operational systems, and other computing services only within an organization, and to the exclusion of access by outsiders to the organization. The term is used in contrast to public networks, such as the Internet, but uses most of the same technology based on the Internet Protocol Suite.
Multimedia surveillance and monitoring system including network configuration
InactiveUS6970183B1High bandwidthSignalling system detailsColor television detailsVideo monitoringStructure of Management Information
A comprehensive, wireless multimedia surveillance and monitoring system provides a combination of megapixel digital camera capability with full motion video surveillance with a network, including network components and appliances such as wiring, workstations, and servers with the option of geographical distribution with various wide area carriers. The full service, multi-media surveillance system is capable of a wide range of monitoring techniques utilizing digital network architecture and is adapted for transmitting event data, video and / or image monitoring information, audio signals and other sensor and detector data over significant distances using digital data transmission over a LAN, wireless LAN, Intranet or Internet for automatic assessment and response including dispatch of response personnel. Both wired and wireless appliance and sensor systems may be employed. GPS dispatching is used to locate and alert personnel as well as to indicate the location of an event. Automatic mapping and dispatch permits rapid response. The wireless LAN connectivity permits local distribution of audio, video and image data over a relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area Network) or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Centralized monitoring stations have access to all of the surveillance data from various remote locations via the Internet or the WAN. A server provides a centralized location for data collection, alarm detection and processing, access control, dispatch processing, logging functions and other specialized functions. The server may be inserted virtually anywhere in the Intranet / Internet network. The topology of the network will be established by the geographic situation of the installation. Appropriate firewalls may be set up as desired. The server based system permits a security provider to have access to the appliance and sensor and surveillance data or to configure or reconfigure the system for any station on the network.
Owner:PR NEWSWIRE
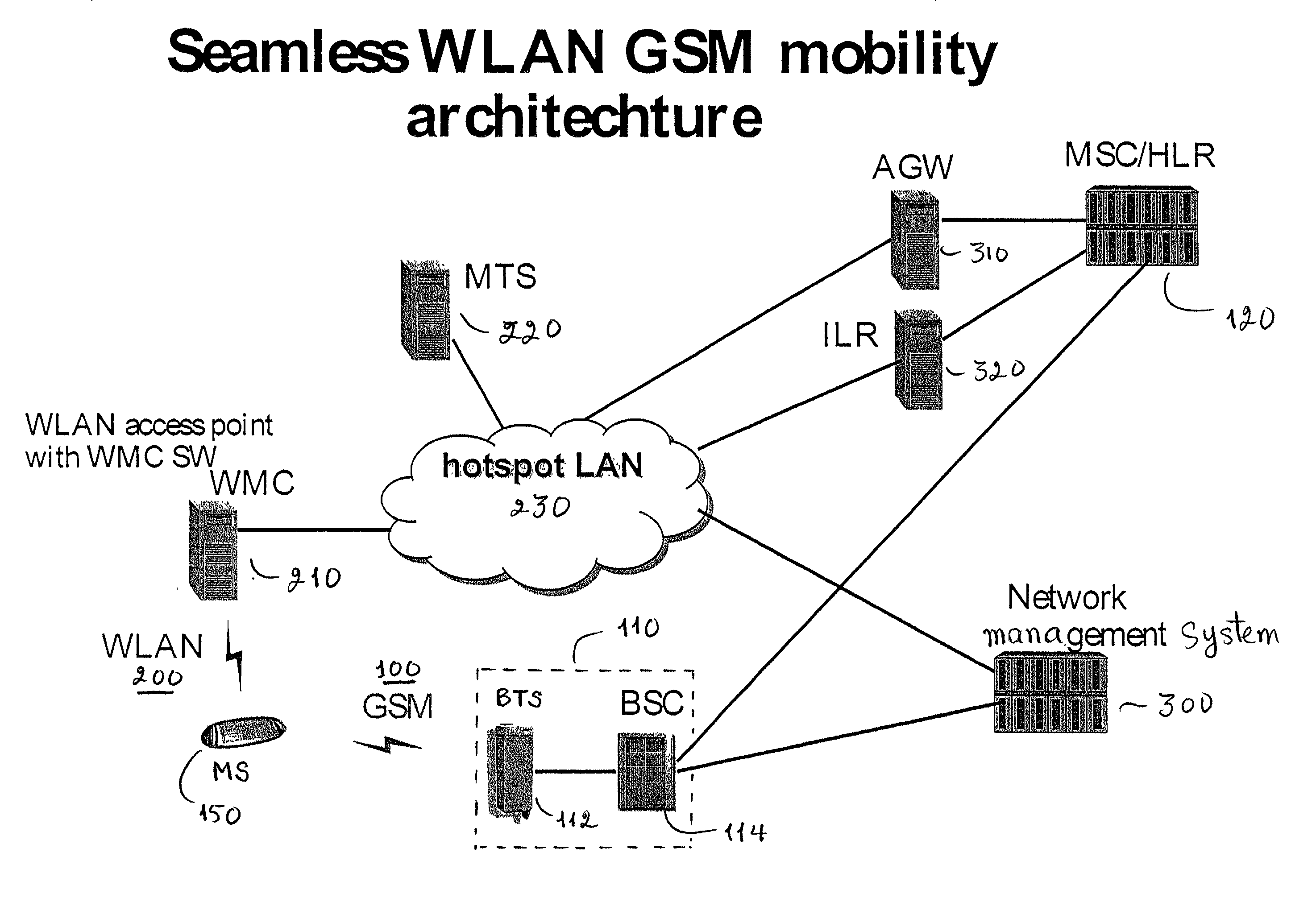
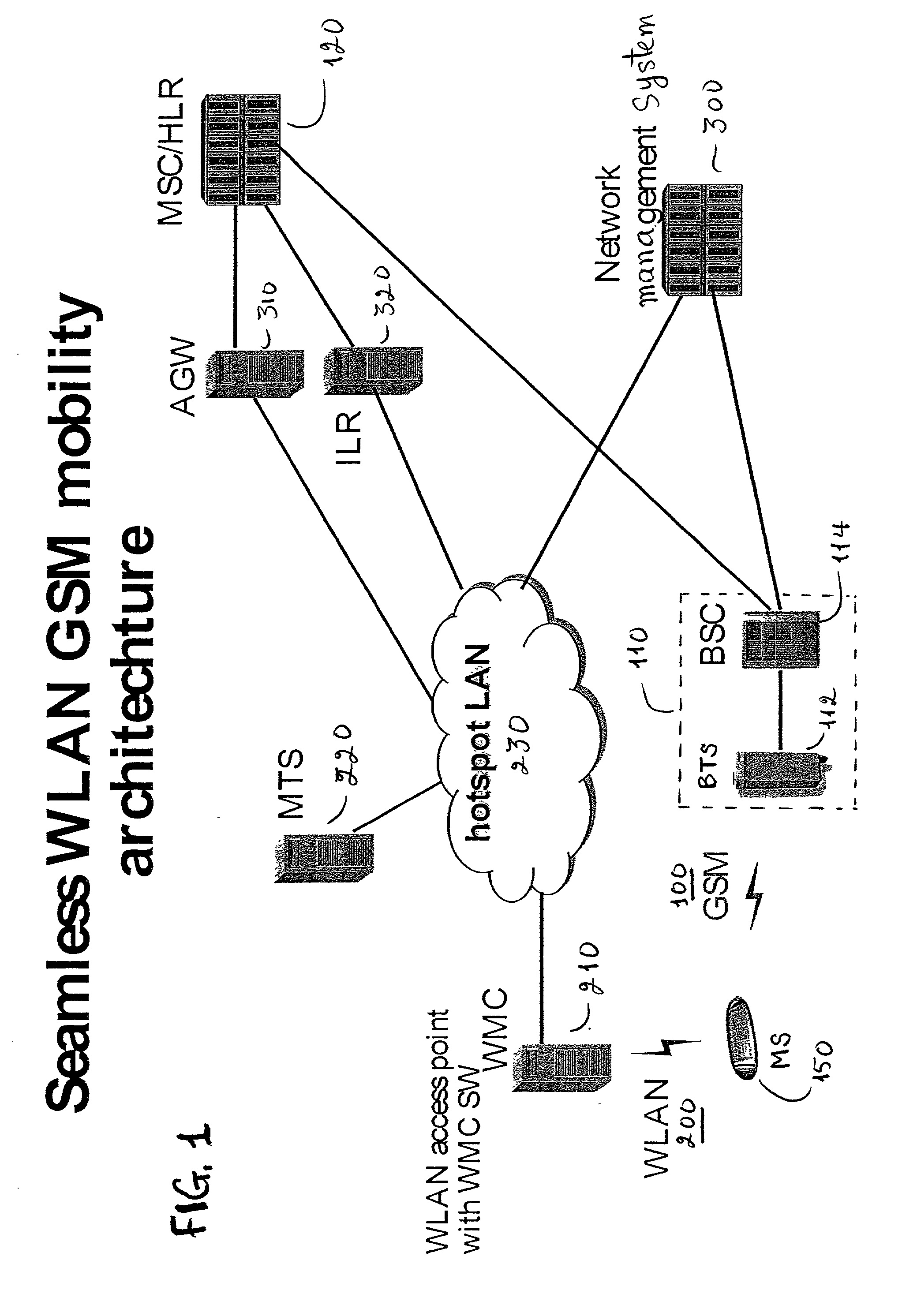
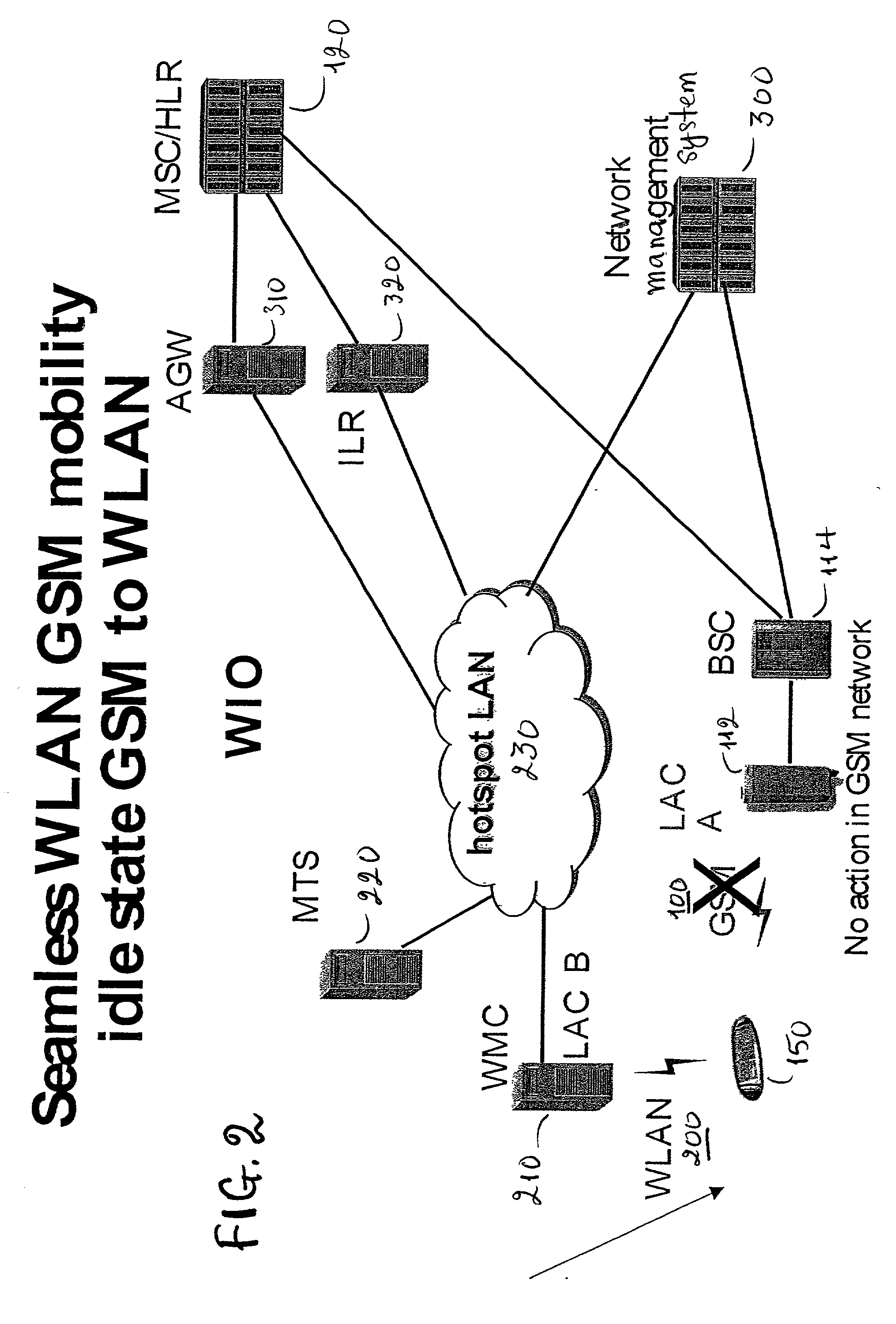
GSM Networks and solutions for providing seamless mobility between GSM Networks and different radio networks
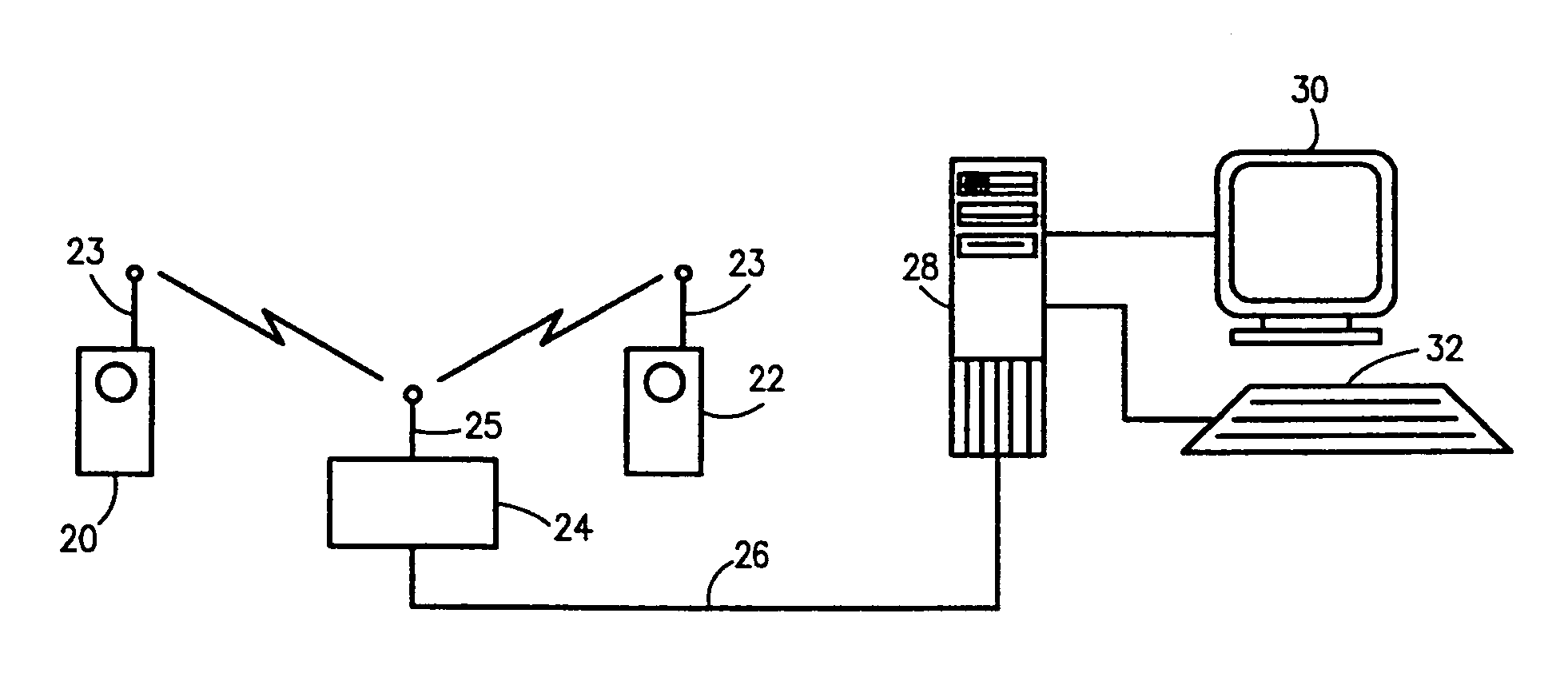
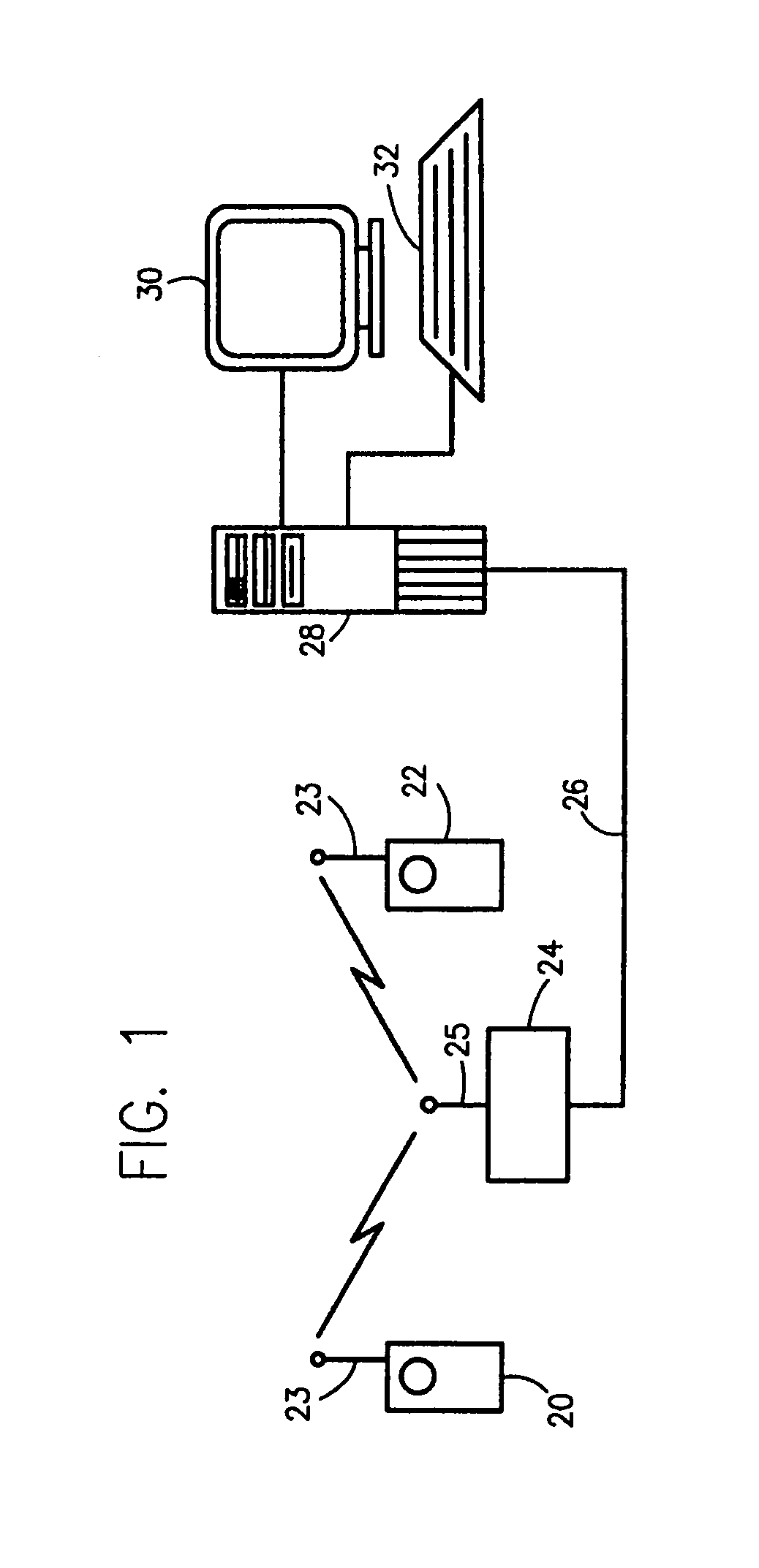
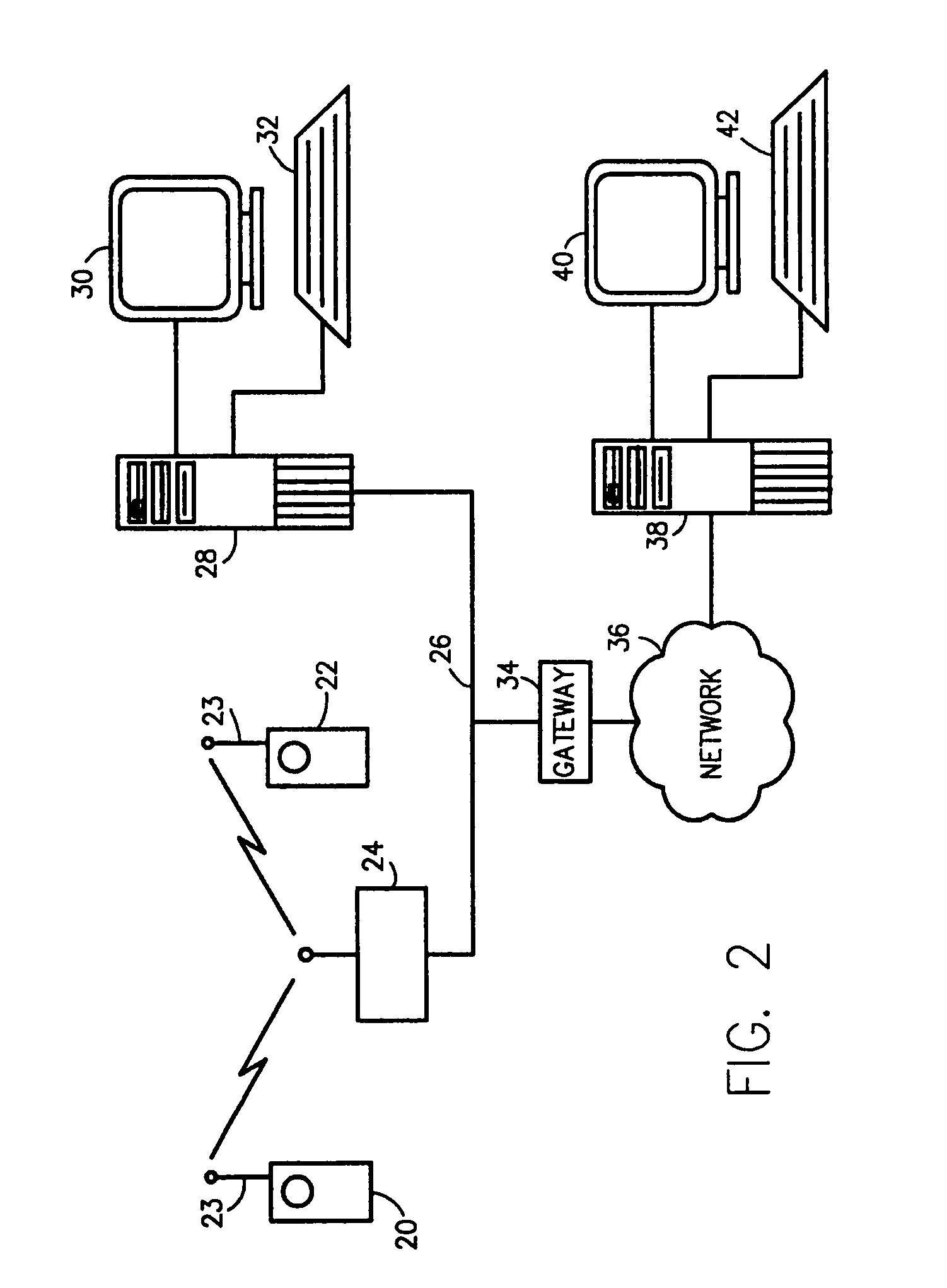
InactiveUS20020147008A1Data switching by path configurationSubstation equipmentRadio networksDual mode
A network architecture for Wireless Intranet Office (WIO) applications including a local radio network such as a wireless local area network (WLAN) which comprises a Wireless Mobile Center (WMC) arranged to serve as a WLAN access point; a GSM network which comprises a Mobile Station (MS) in a form of a dual-mode cellular phone to access both WLAN and GSM radio technologies, a Base Station (BS) arranged to convert a radio signal from the Mobile Station (MS) for communication, a Mobile Switching Center (MSC) arranged to establish call connection; and a Handover Module implemented in either the Mobile Station (MS) or the Wireless Mobile Center (WMC) for providing seamless mobility between the GSM network and the wireless LAN, when the Mobile Station (MS) roams between the GSM network and the wireless LAN.
Owner:RPX CORP
Secure virtual community network system
ActiveUS20040249911A1Convenient introductionMultiple digital computer combinationsOffice automationPrivate networkPublic network
A private virtual dynamic network is provided for computing devices coupled to public networks or private networks. This enables computing devices anywhere in the world to join into private enterprise intranets and communicate with each other. In one embodiment, the present invention provides a separate private virtual address realm, seen to each user as a private network, while seamlessly crossing public and private network boundaries. One implementation of the present invention uses an agent to enable an entity to participate in the network without requiring the member to add new hardware or software.
Owner:F POSZAT HU
System, apparatus and method for automatic address updating of outgoing and incoming user messages in a communications network
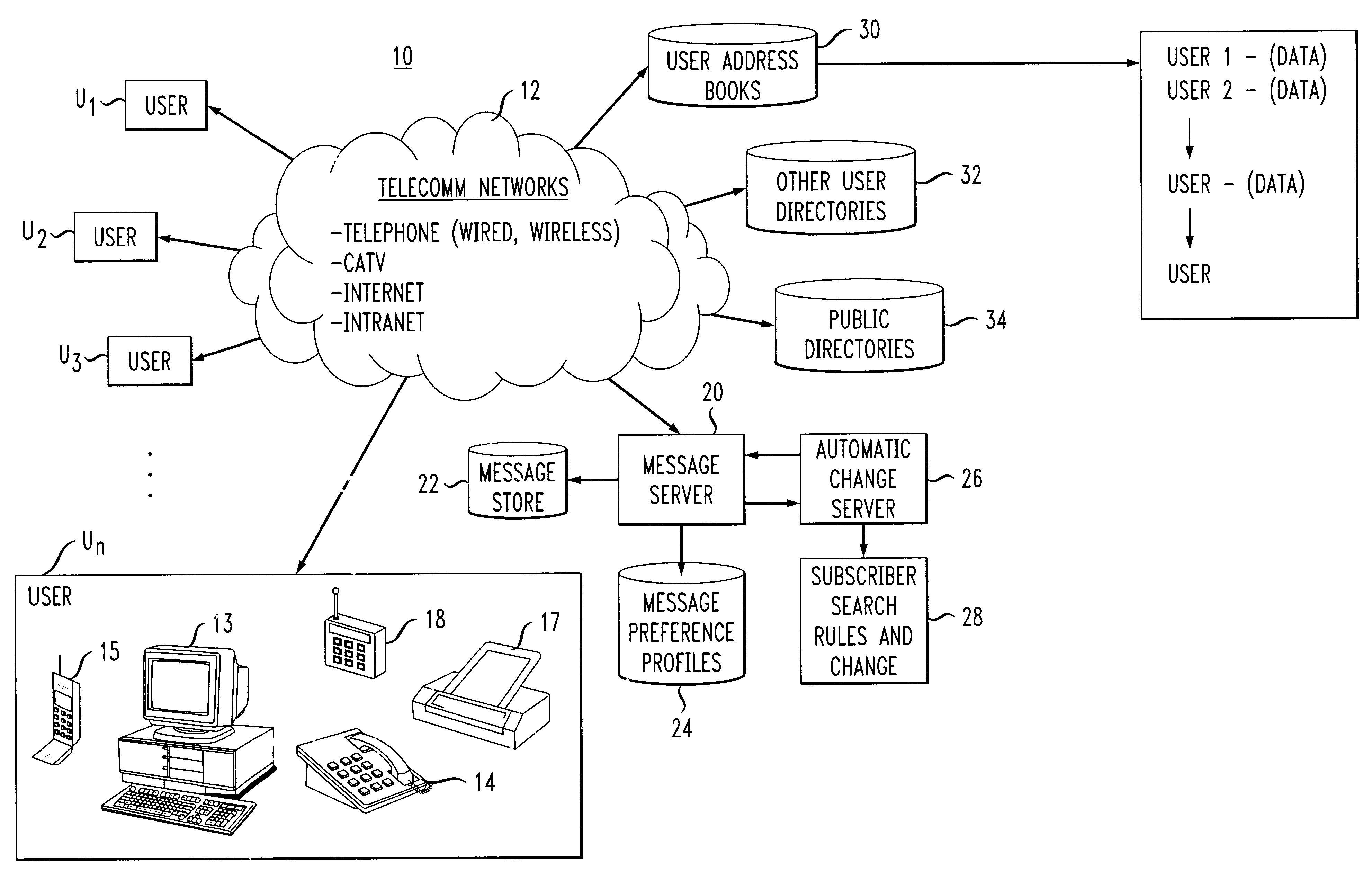
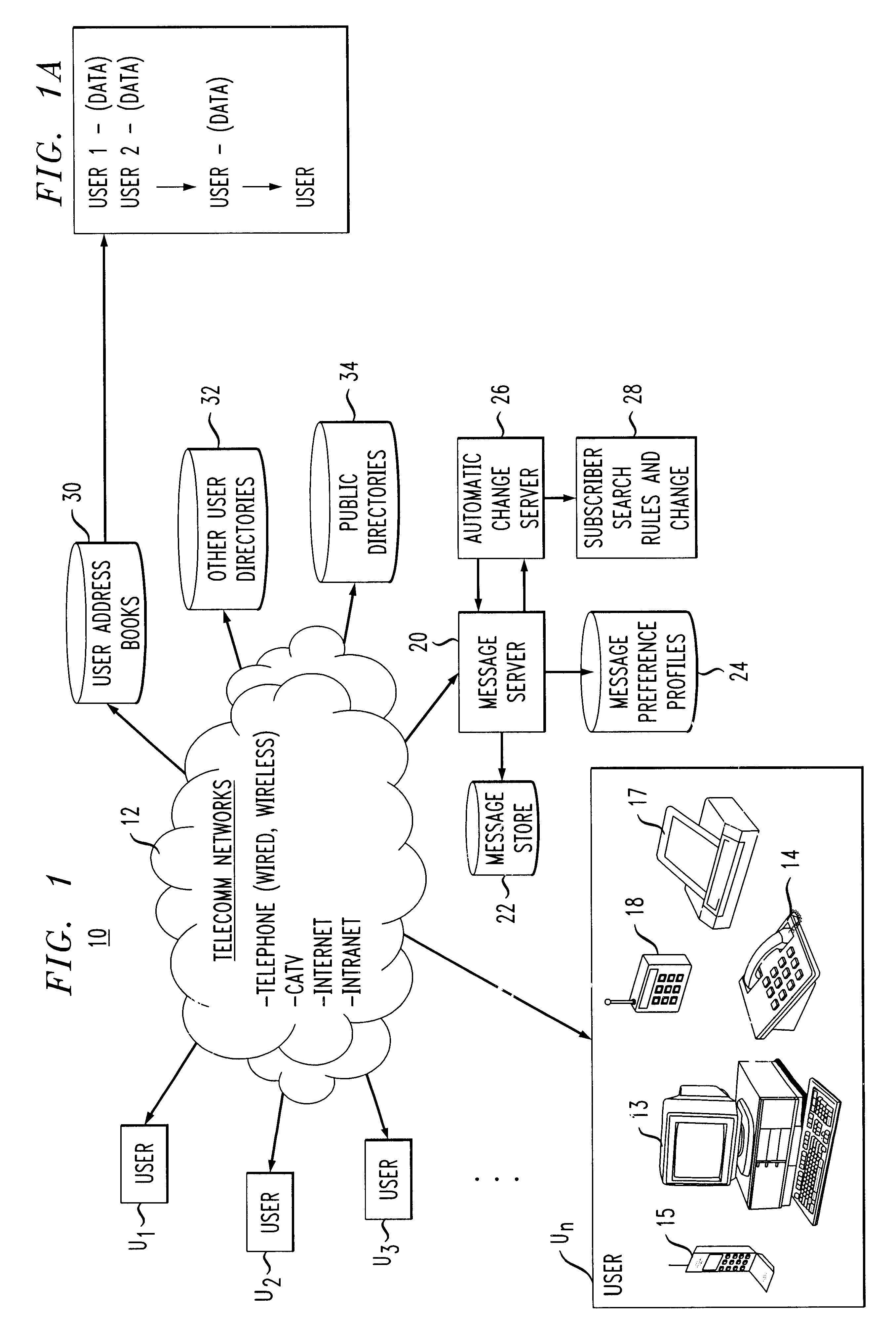
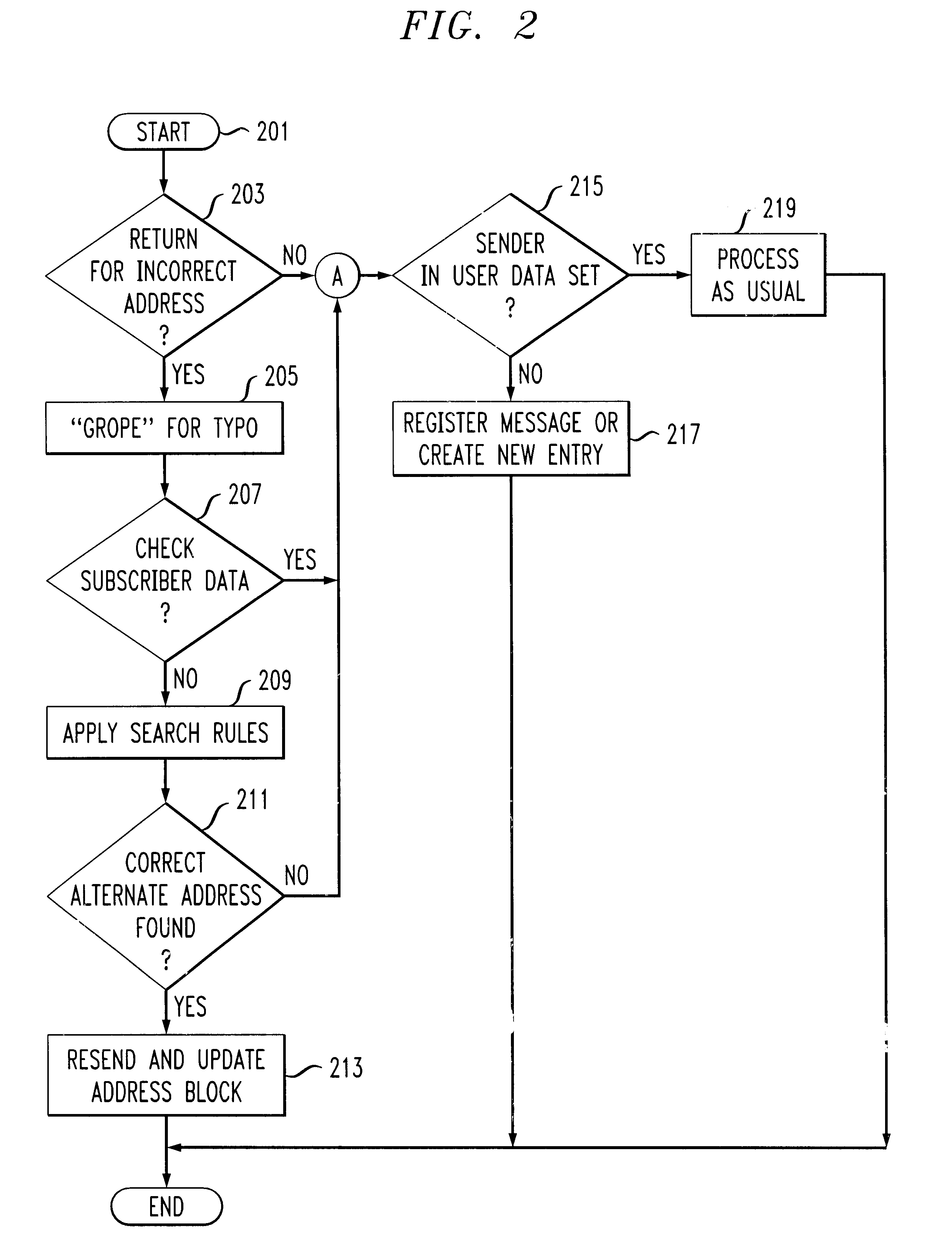
A system, apparatus and method automatically update address information of a user's outgoing and incoming messages to / from a communication network thereby relieving the user of the burden of manually entering address changes into a user address book. A plurality of users are coupled through terminals to a server in the communication network for exchanging telephone, CATV, Internet, intranet for messaging, facsimile, etc purposes. The server includes a message store; stored message profile; and is coupled to a change server linked to a network. The change server includes search rules and change options provided by the users in directing the change server in finding correct and alternative address information when erroneous or unknown information is detected in the outgoing and incoming messages. Each user address book includes a series of contacts for each user. Each contact is identified by an identification number, ID, including a name and address. The server detects message headers where a "Send To Address" is not in the address book. The change server is activated and accesses external databases for correct or alternative addresses in accordance with search rules provided by the user. The alternative or correct address books address information is installed in the users address book and the "Send To Message" process is executed. For returned messages incorporating erroneous information, the search server is again activated to access the databases for correct address information, after which the user's address book is updated thereby eliminating the time-consuming, irritating manual process of updating the user address book for outgoing and incoming messages.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
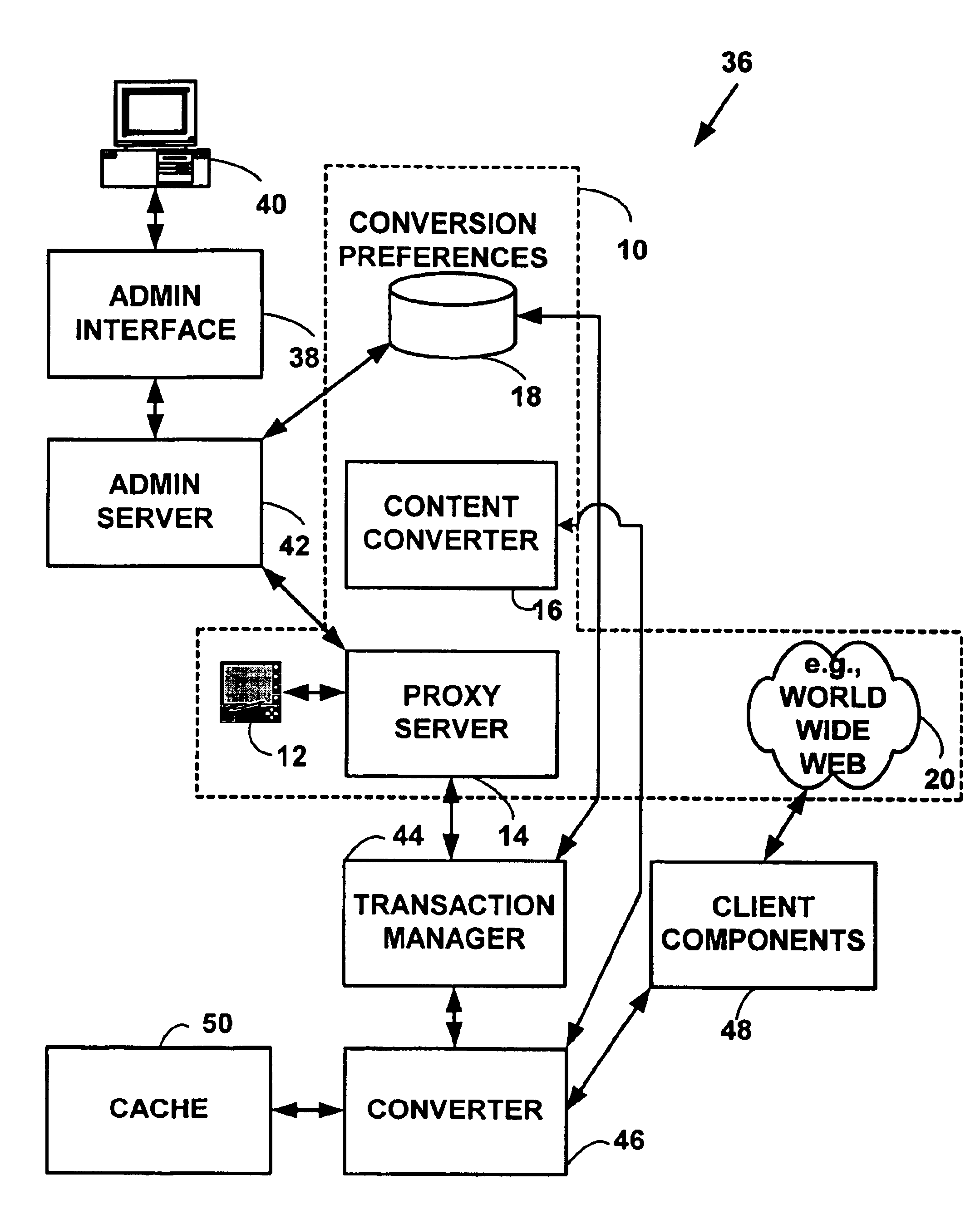
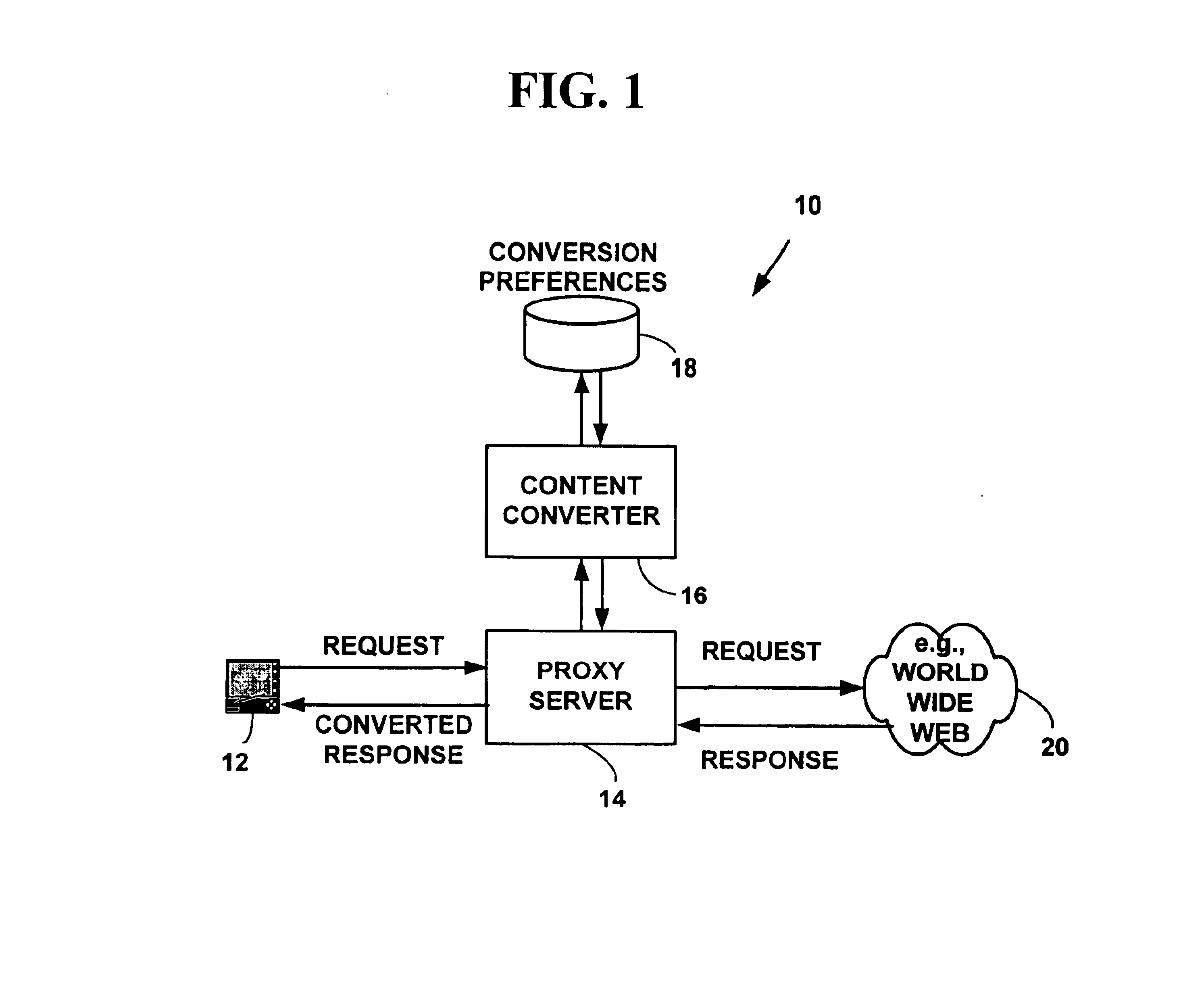
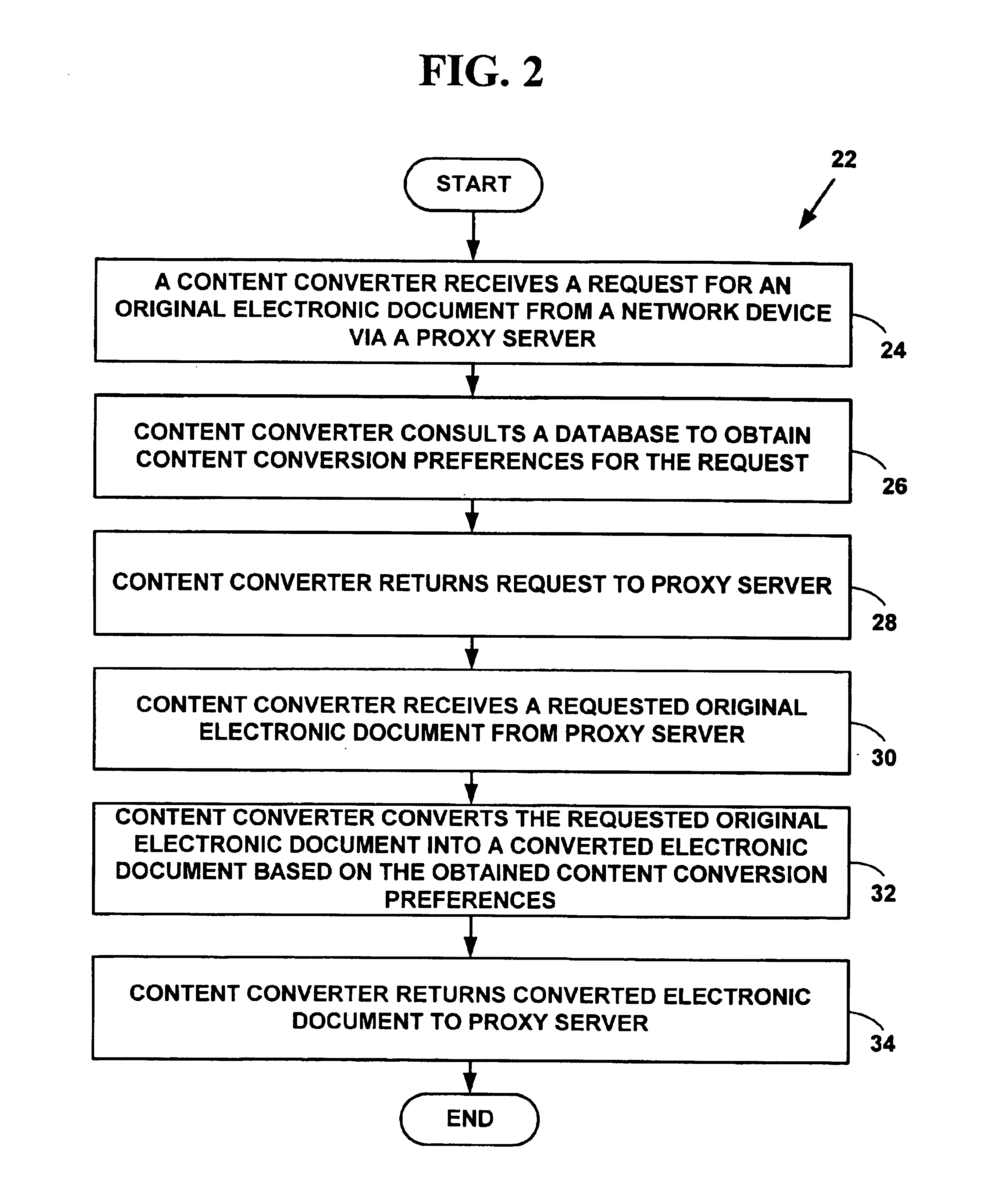
Method and system for content conversion of hypertext data using data mining
InactiveUS6925595B1Digital data information retrievalData processing applicationsElectronic documentUser device
Method and system for content conversion of electronic data using data mining. A user is able select one or more hypertext elements from one or more hypertext electronic document for conversion based on user conversion preferences. For example, a user selects one or more display elements from one or more “web-pages” from the World-Wide-Web on the Internet or an intranet. The hypertext elements are extracted from one or more hypertext electronic documents and converted into a format suitable for display on a user device based on user conversion preferences. Selected hypertext elements are extracted and converted using data mining conversion operations. The data mining conversion operations allow a user to extract only desired display information displayed from a hypertext element and convert the display information into a format different than that defined for the original electronic document. The converted display information is appropriate for a user device such as hand-held, wireless phone, personal digital assistant, or other device.
Owner:OPEN TV INC
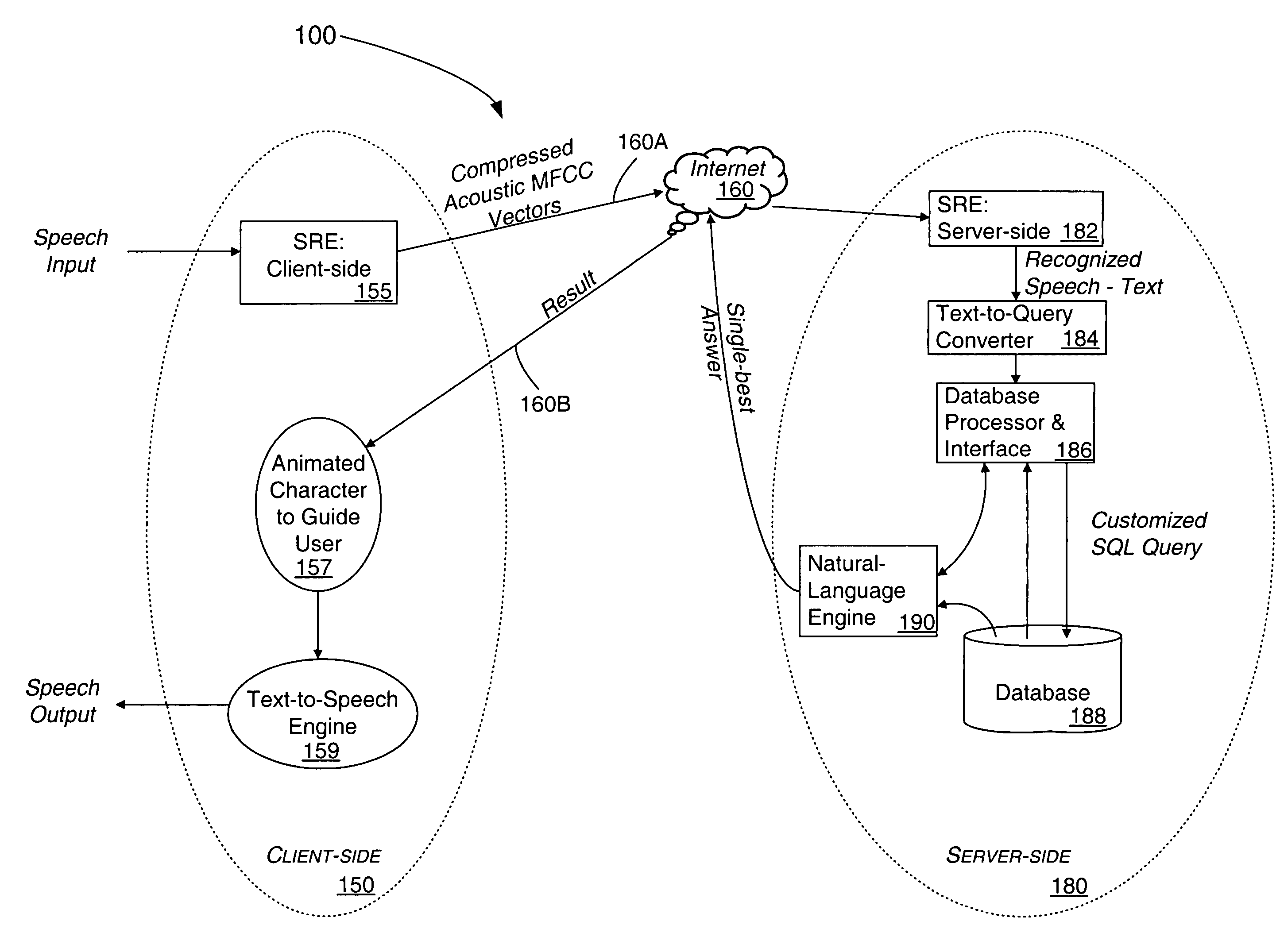
Method for processing speech signal features for streaming transport
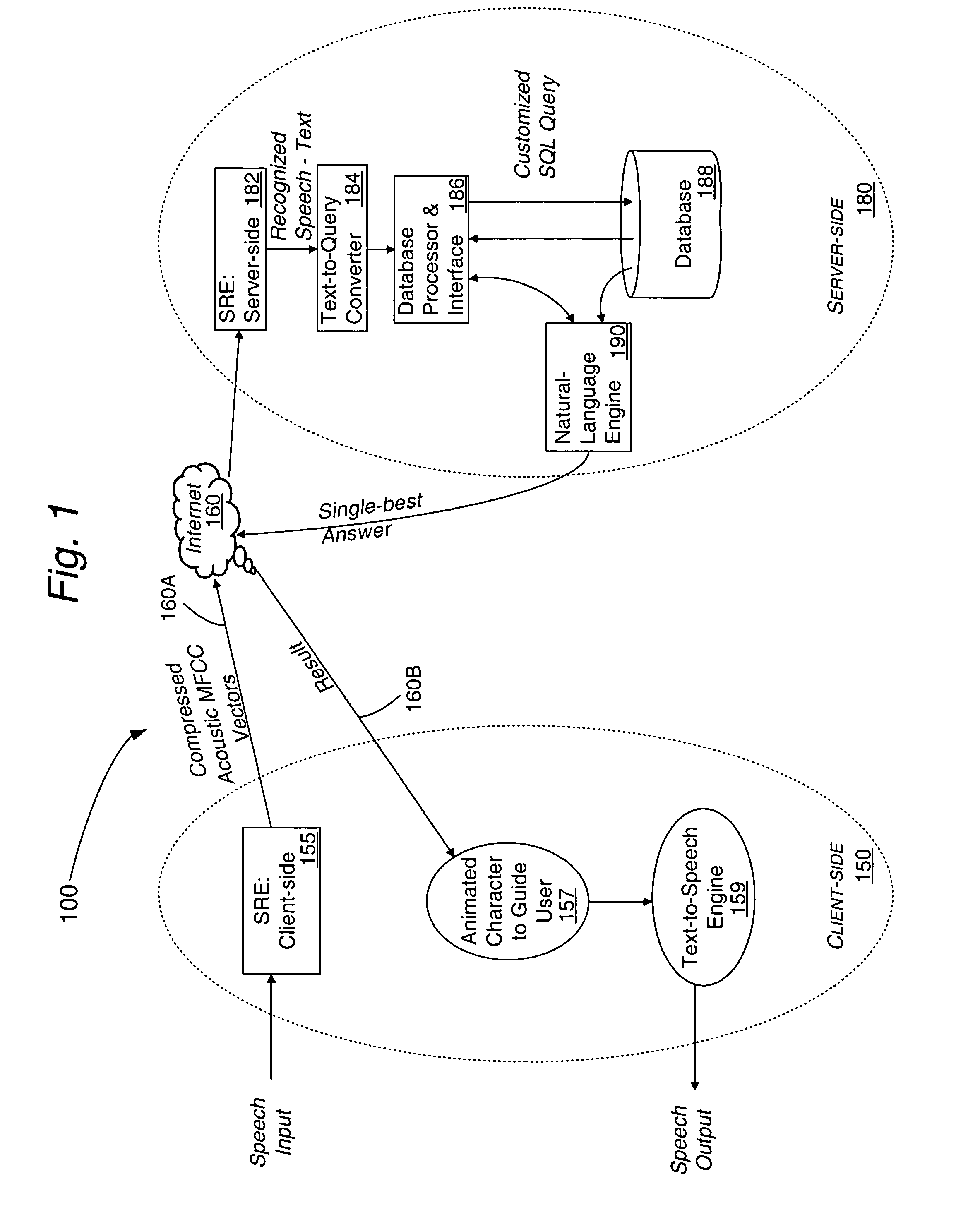
InactiveUS7376556B2Flexibly and optimally distributedImprove accuracyNatural language translationData processing applicationsNetwork onClient server systems
Speech signal information is formatted, processed and transported in accordance with a format adapted for TCP / IP protocols used on the Internet and other communications networks. NULL characters are used for indicating the end of a voice segment. The method is useful for distributed speech recognition systems such as a client-server system, typically implemented on an intranet or over the Internet based on user queries at his / her computer, a PDA, or a workstation using a speech input interface.
Owner:NUANCE COMM INC
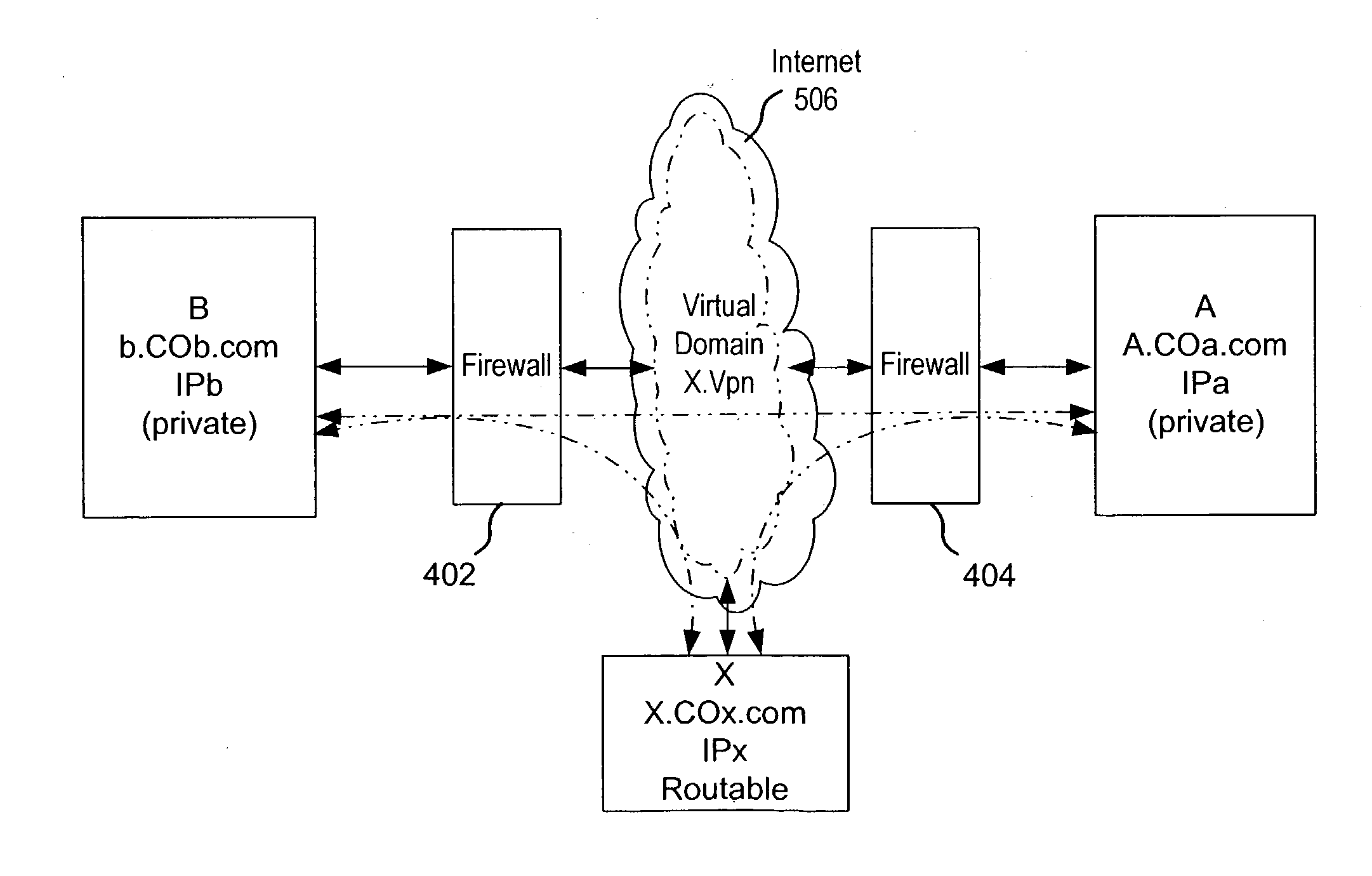
Private Allocated Networks Over Shared Communications Infrastructure
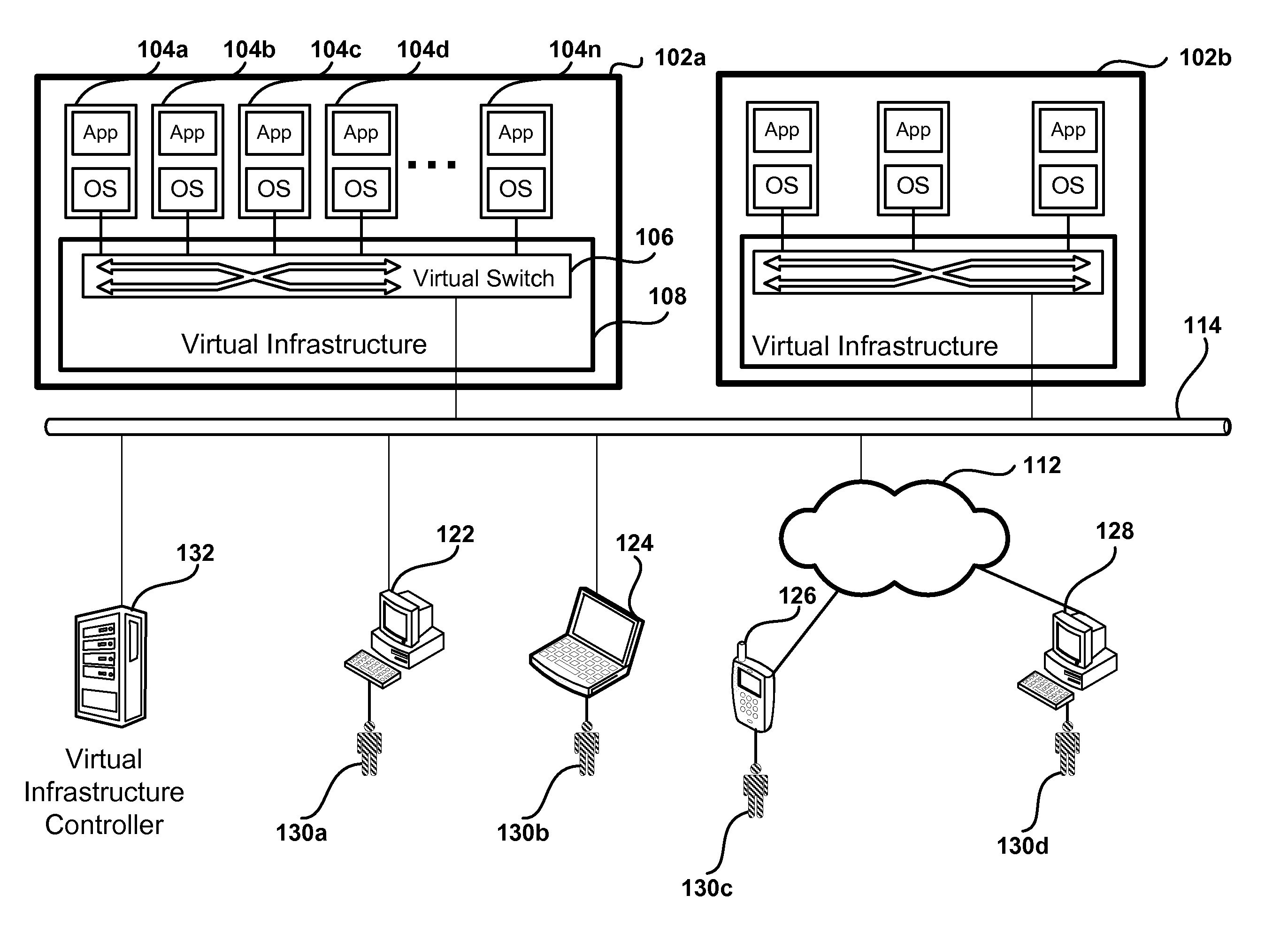
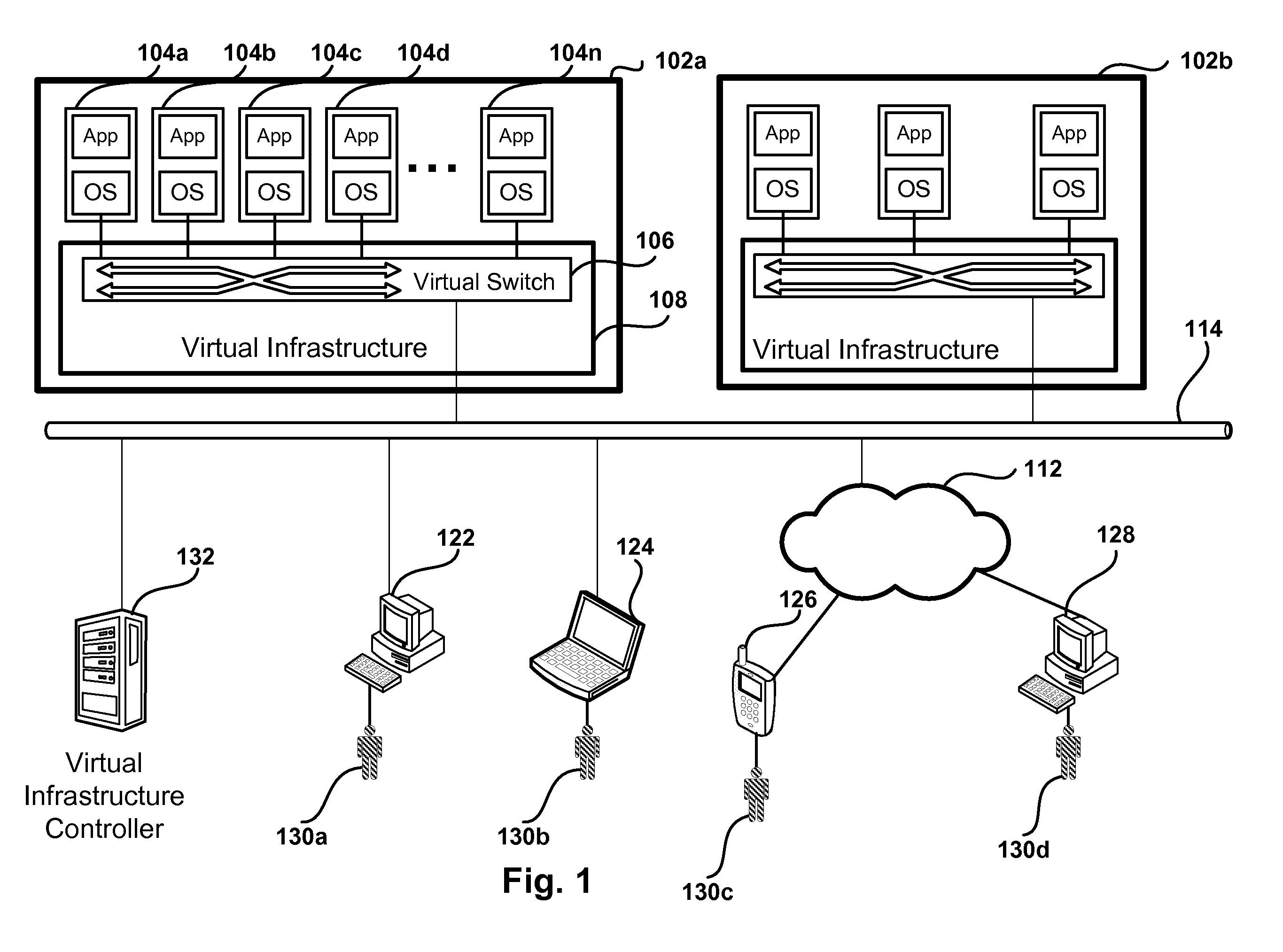
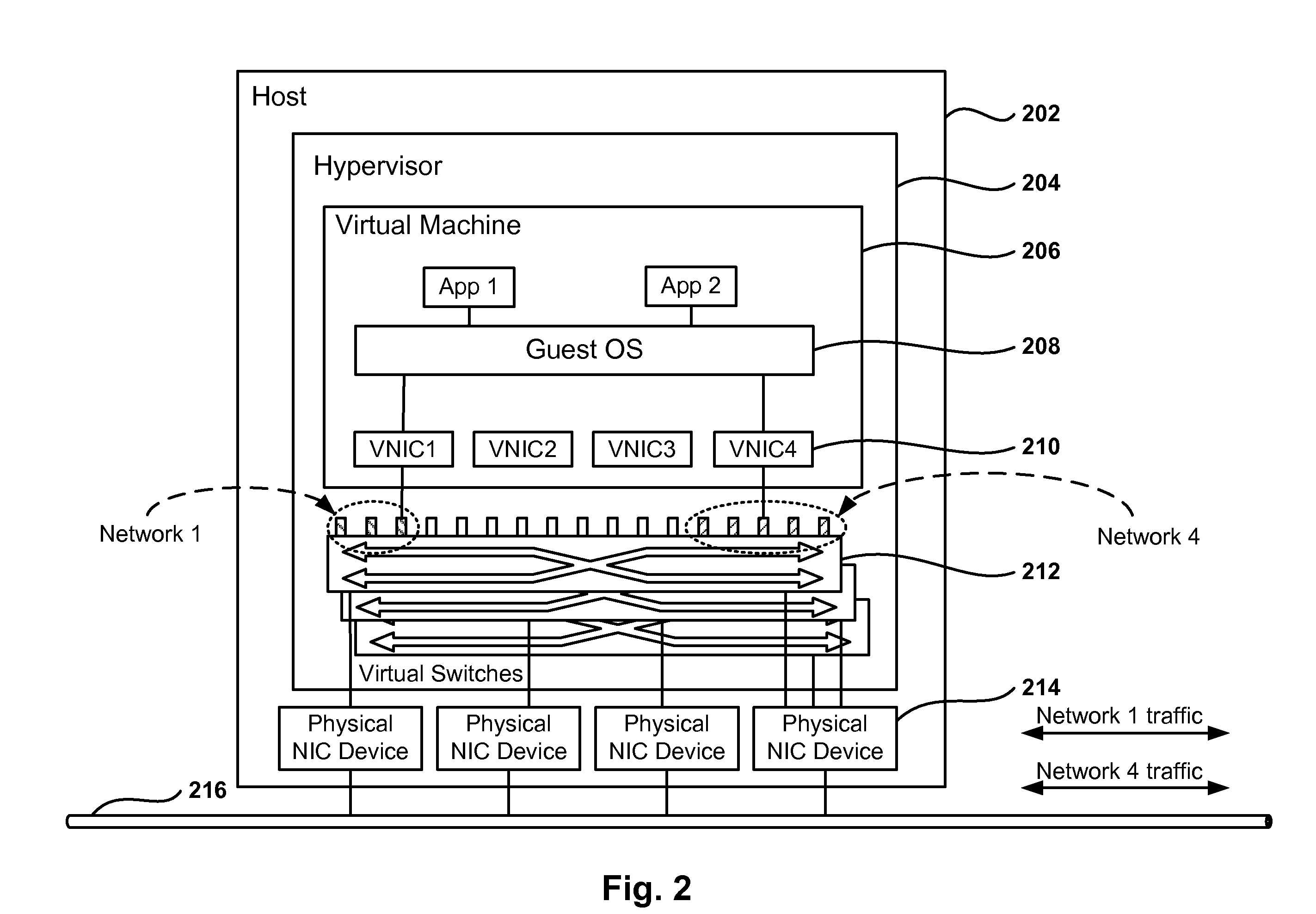
Methods and systems for implementing private allocated networks in a virtual infrastructure are presented. One method operation creates virtual switches in one or more hosts in the virtual infrastructure. Each port in the virtual switches is associated with a private allocated network (PAN) from a group of possible PANs. In one embodiment, one or more PANs share the same physical media for data transmission. The intranet traffic within each PAN is not visible to nodes that are not connected to the each PAN. In another operation, the method defines addressing mode tables for the intranet traffic within each PAN. The entries in the addressing mode tables define addressing functions for routing the intranet traffic between the virtual switches, and different types of addressing functions are supported by the virtual switches.
Owner:NICIRA
Method and apparatus for establishing dynamic tunnel access sessions in a communication network
InactiveUS7117526B1Key distribution for secure communicationPublic key for secure communicationTelecommunications linkCommunication link
A method and apparatus for implementing dynamic tunnel access sessions at a network device within a communications network. The tunnel access sessions are created between a network device, typically a gateway device and a network service, such as the Internet or a corporate intranet. The dynamic tunnel access sessions provide for subscriber-transparent tunneling. The present invention does not require special client-side software to be loaded on the remote host of the subscriber, and does not require any manual configuration of the remote host. A subscriber is capable of establishing more than one tunnel access session to more than one network service during a network session. Additionally, more than one subscriber who accesses the communication network via the network device is able to establish a communication link with a pre-existing tunnel.
Owner:NOMADIX INC
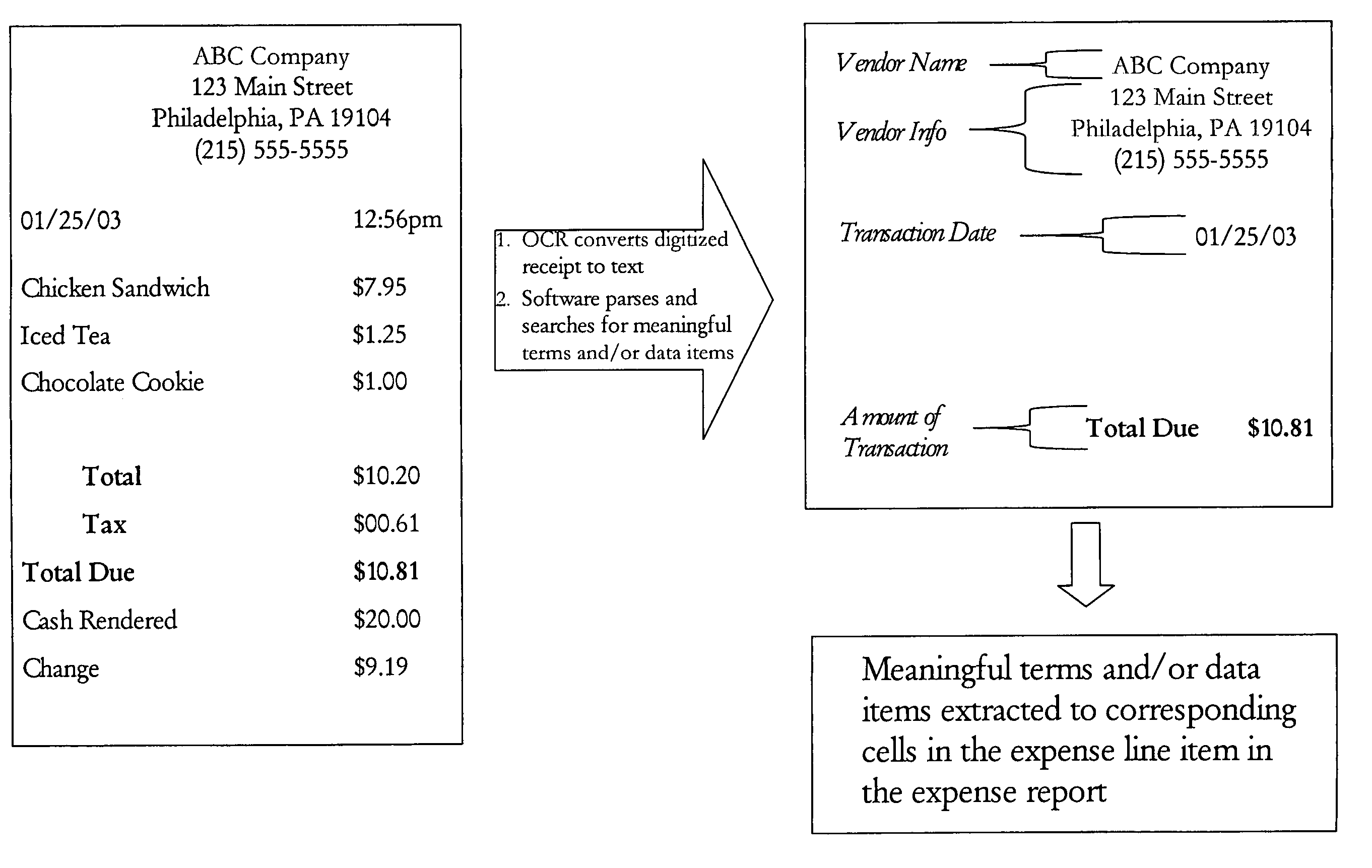
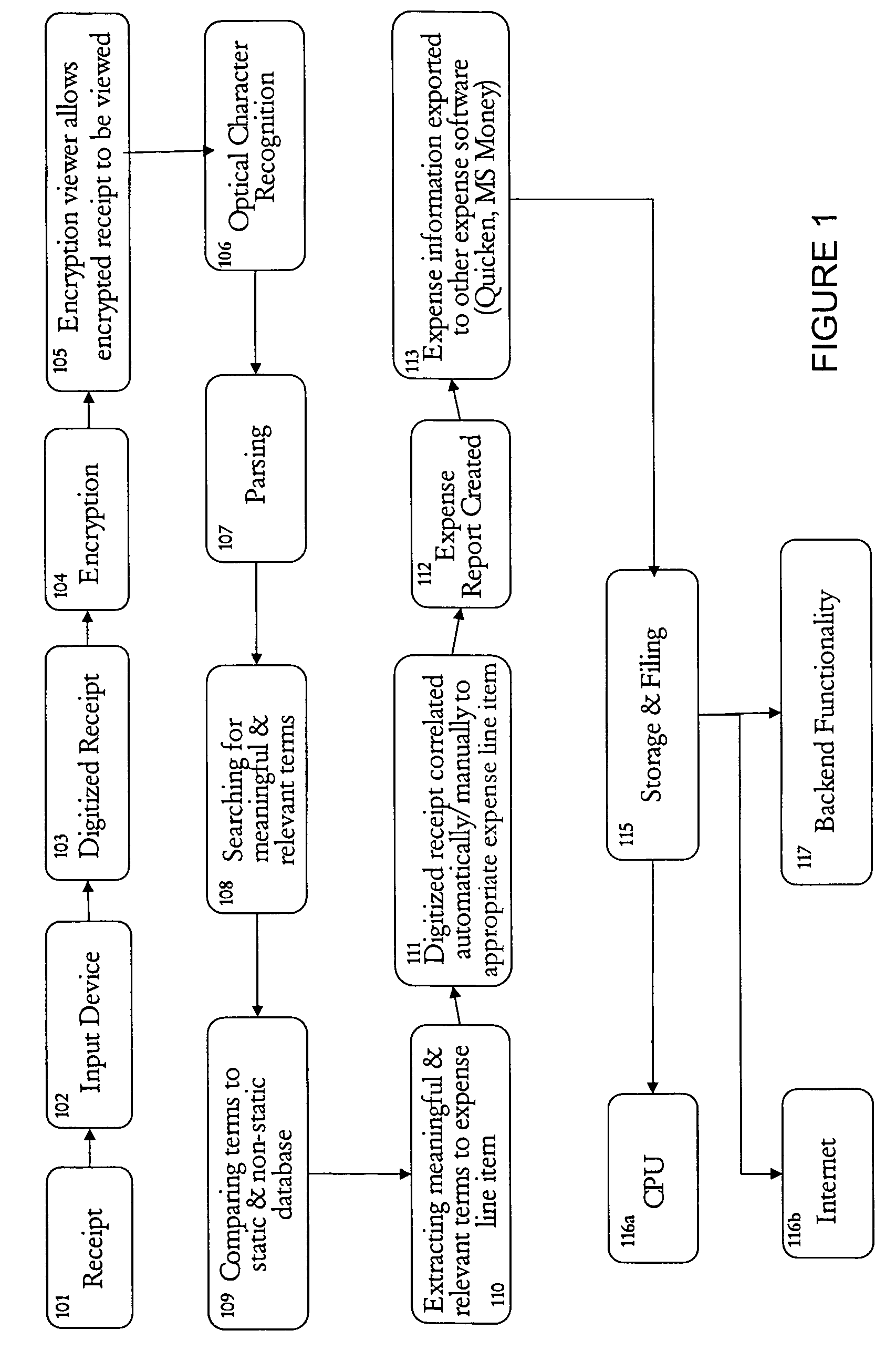
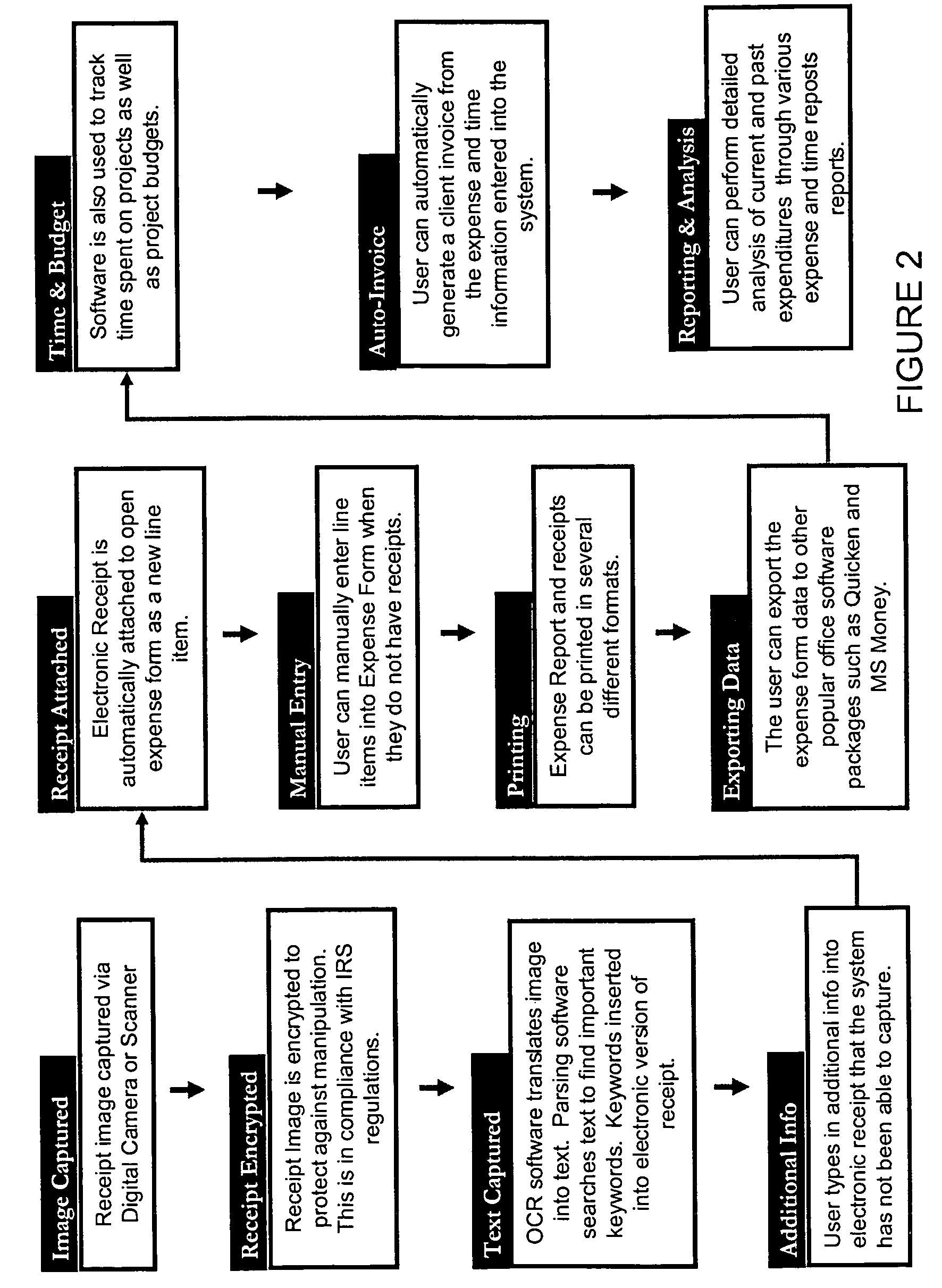
System and method for capture, storage and processing of receipts and related data
ActiveUS7069240B2Easy to editConvenient reviewComplete banking machinesFinanceThird partyComputer graphics (images)
The present invention is a system comprising image capture device, such as a scanner or digital camera connected to a computer processor that is able to capture and store images, and method of using the same for storing and processing expense receipts. The computer processor analyzes the images of the receipts, converts the images to text, analyzes the data, extracts expense data, and puts the data into an expense report. The end user can review the captured expense data, correct it or add to it. Preferably, the system displays the image of the receipt side-by-side with the captured expense data to make review and editing easier. In a preferred embodiment the image capture device is portable, such as a handheld scanner or digital camera, so that a user can scan receipts while traveling and discard the receipt. Also, in a preferred embodiment, the images are encrypted to prevent tampering by the user or a third party, and thereby preserve the integrity of the receipt image. In one preferred embodiment, receipt images or uploaded via the Internet an intranet, or other network to a remote data storage facility to further protect the images, both from tampering and from loss.
Owner:THE NEAT COMPANY INC DOING BUSINESS AS NEATRECEIPTS
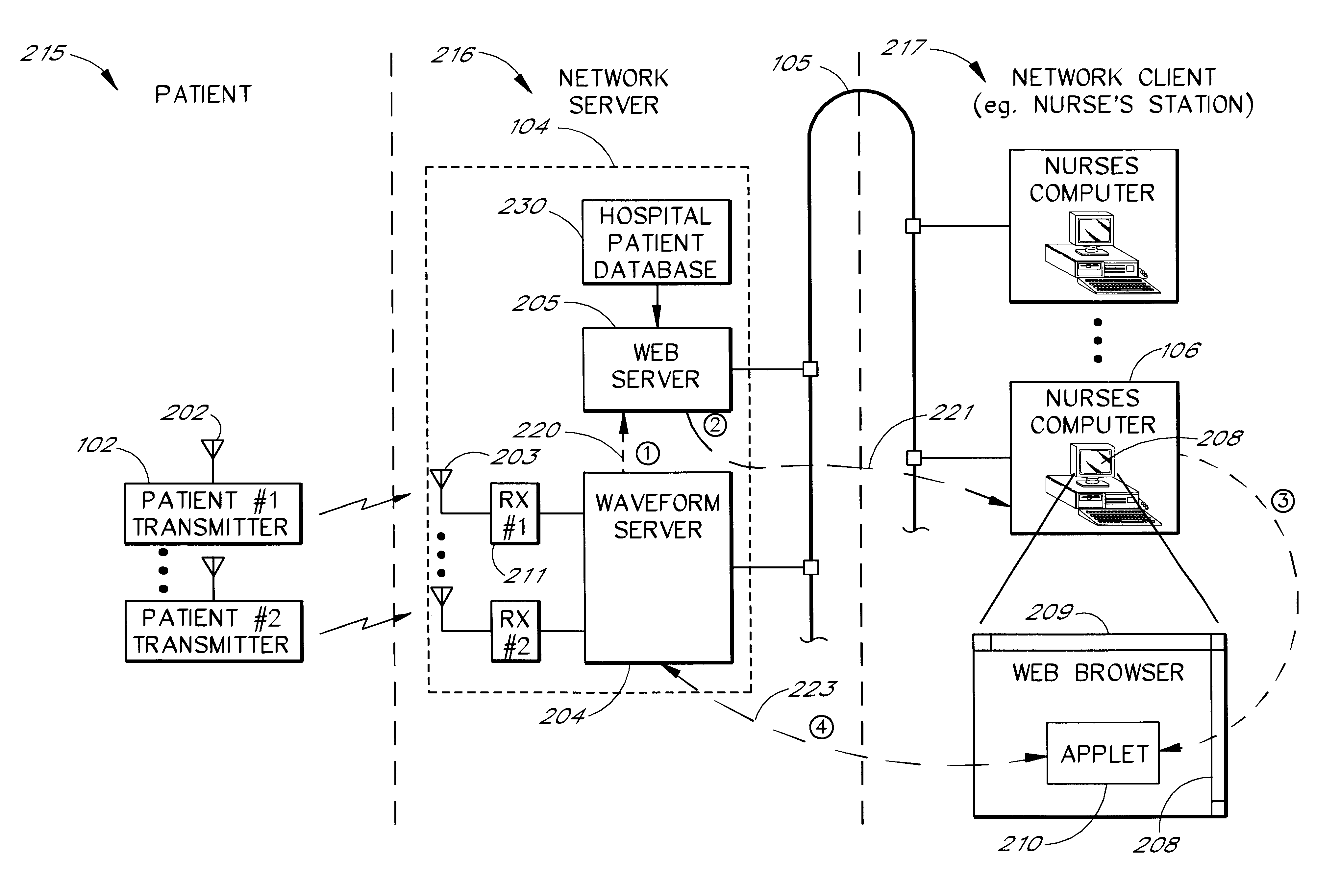
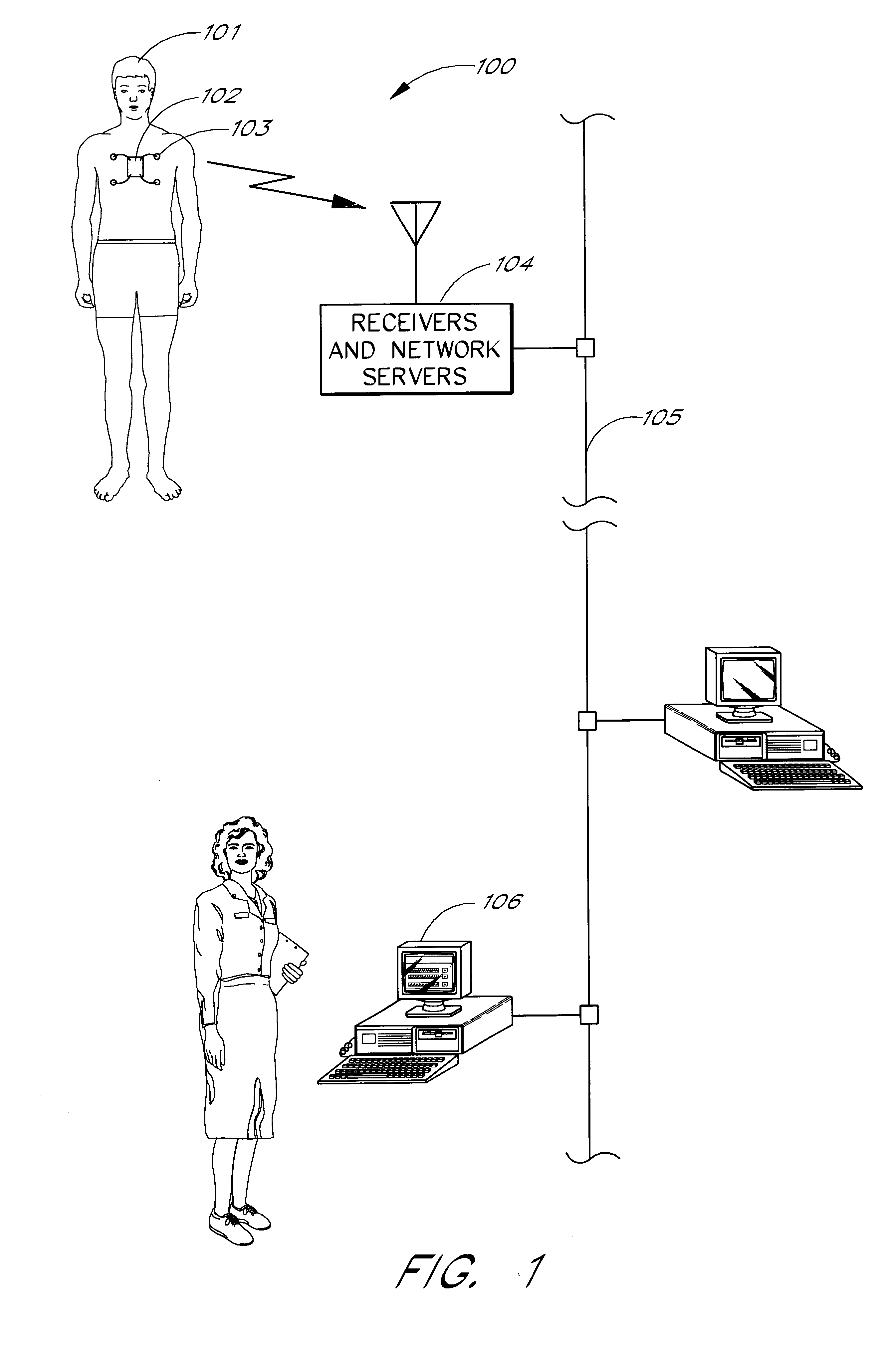
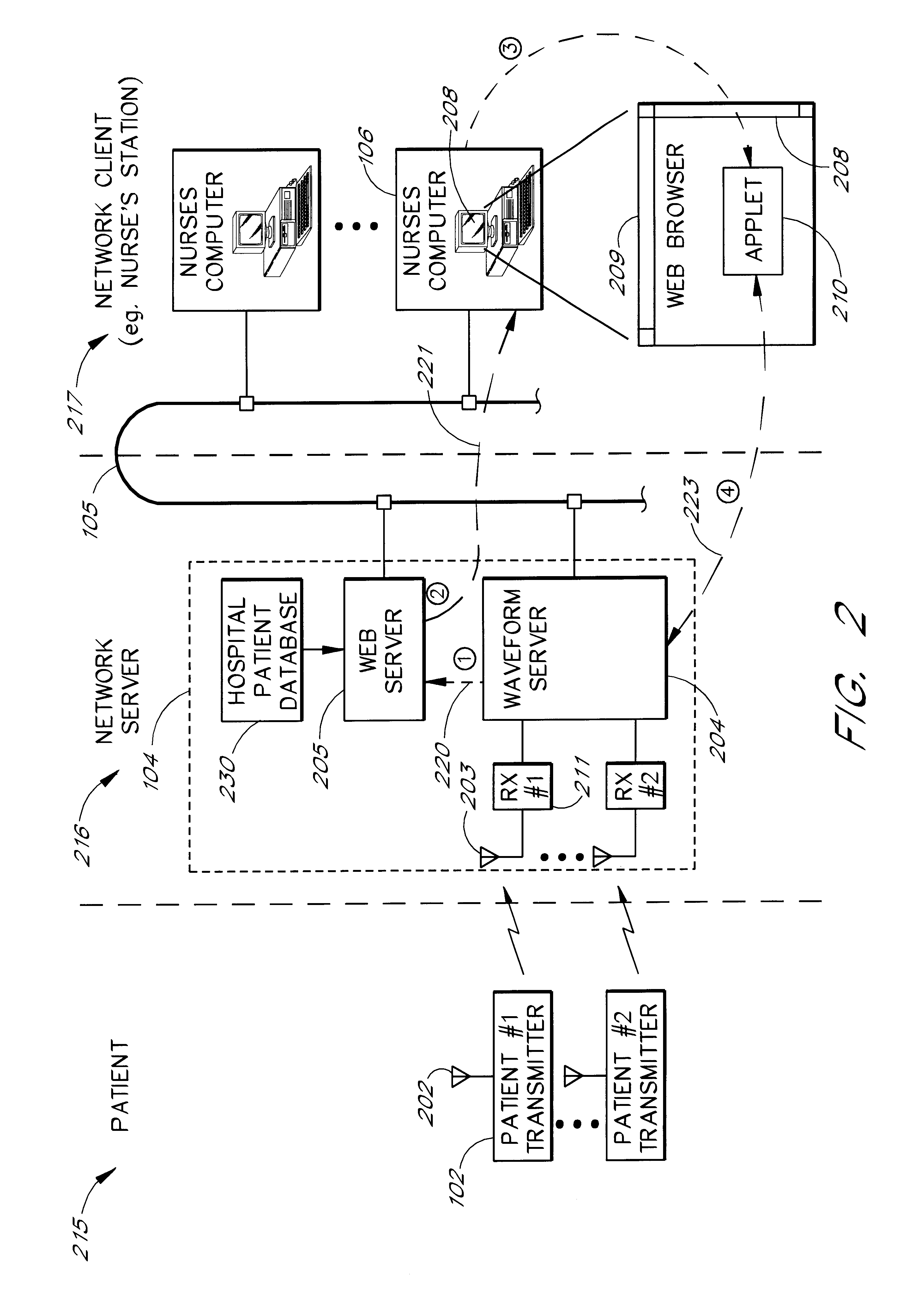
Intranet-based medical data distribution system
InactiveUS6871211B2Low costRapid designMultiple digital computer combinationsAngiographyWeb servicePatient data
A network based medical telemetry system that uses, to the greatest extent possible, standard hardware and software components. The system allows clinicians using computers anywhere in a large hospital to view physiologic data from patients of the hospital. Each patient is fitted with a set of sensors that measure physiologic properties of the patient (e.g., EKG sensors). The sensors are connected to a transmitter that relays the physiologic data to a central server. The central server comprises a WEB server that supplies basic patient data such as the patient's name and medical history. The central server also comprises a waveform server which supplies the physiologic data, in real-time or near real-time. Workstation, used by a clinician receives the basic patient data from the Web server and the physiologic data from the waveform server, and produces a combined display. The combined display is continuously updated, showing, for example, the patient's EKG.
Owner:GE MEDICAL SYST INFORMATION TECH
Method and system for distributed network address translation with network security features
InactiveUS7032242B1Digital data processing detailsUser identity/authority verificationSecurity associationIp address
A method and system for distributed network address translation with security features. The method and system allow Internet Protocol security protocol (“IPsec”) to be used with distributed network address translation. The distributed network address translation is accomplished with IPsec by mapping a local Internet Protocol (“IP”) address of a given local network device and a IPsec Security Parameter Index (“SPI”) associated with an inbound IPsec Security Association (“SA”) that terminates at the local network device. A router allocates locally unique security values that are used as the IPsec SPIs. A router used for distributed network address translation is used as a local certificate authority that may vouch for identities of local network devices, allowing local network devices to bind a public key to a security name space that combines a global IP address for the router with a set of locally unique port numbers used for distributed network address translation. The router issues security certificates and may itself be authenticated by a higher certificate authority. Using a security certificate, a local network device may initiate and be a termination point of an IPsec security association to virtually any other network device on an IP network like the Internet or an intranet. The method and system may also allow distributed network address translation with security features to be used with Mobile IP or other protocols in the Internet Protocol suite.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
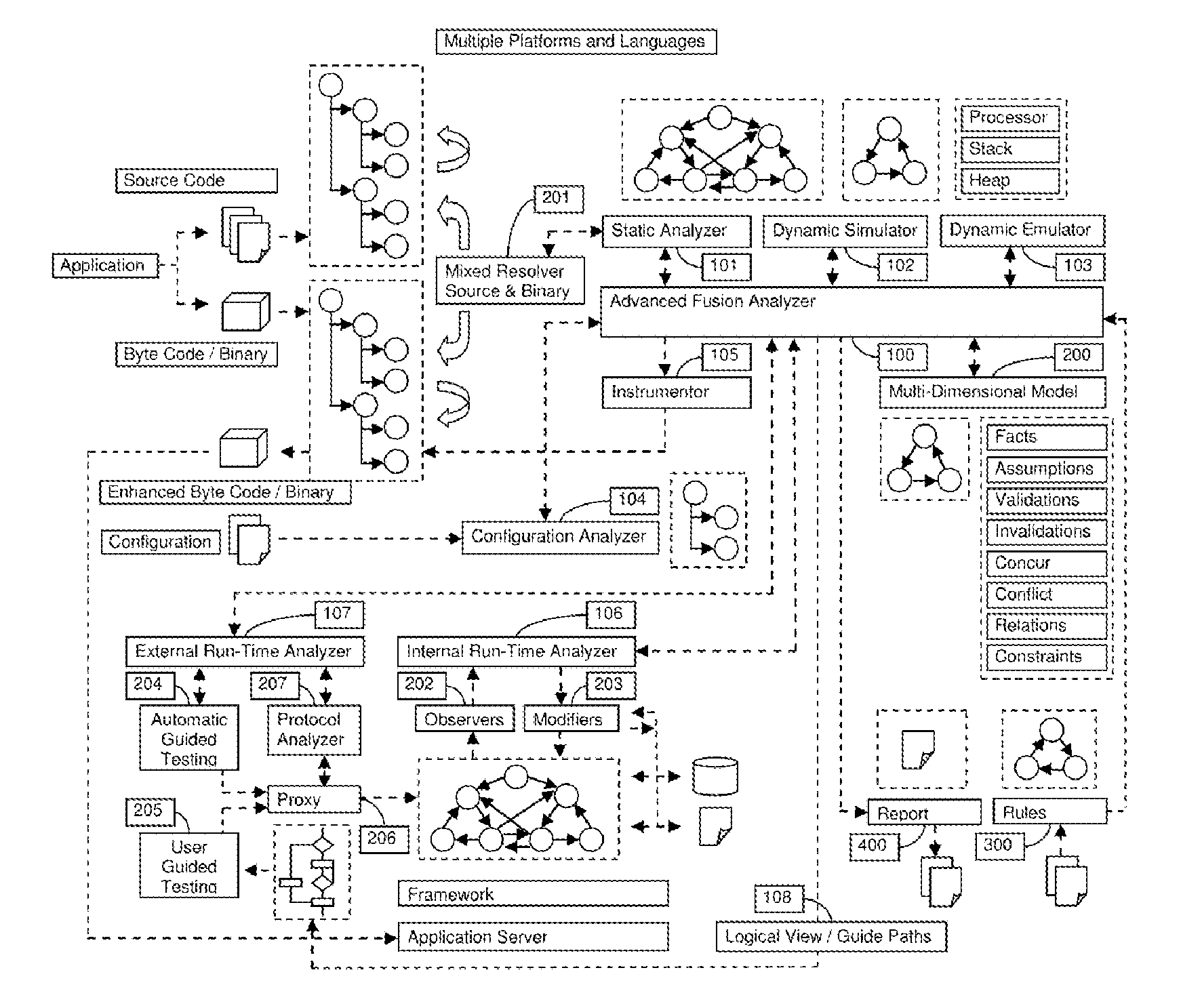
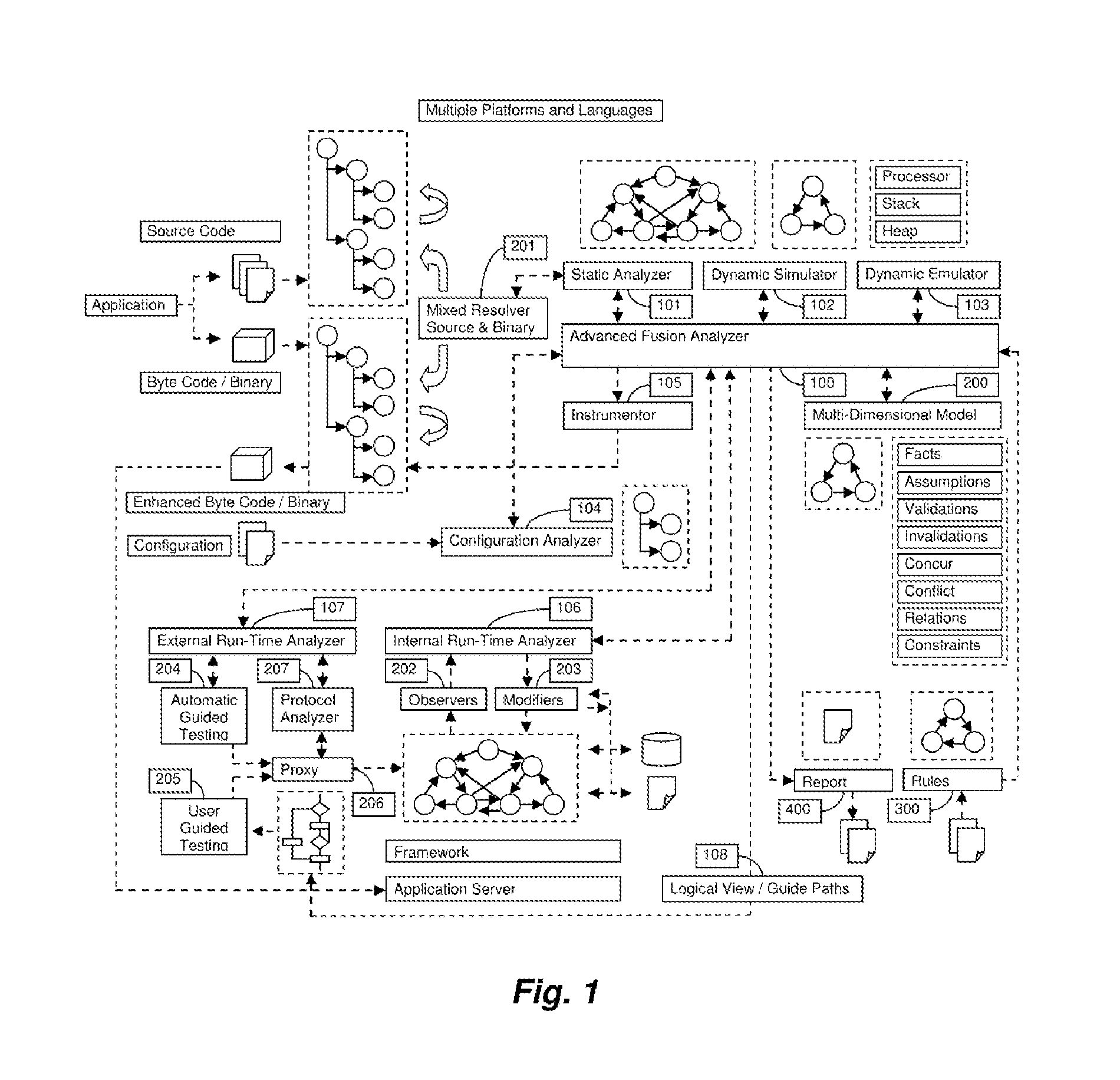
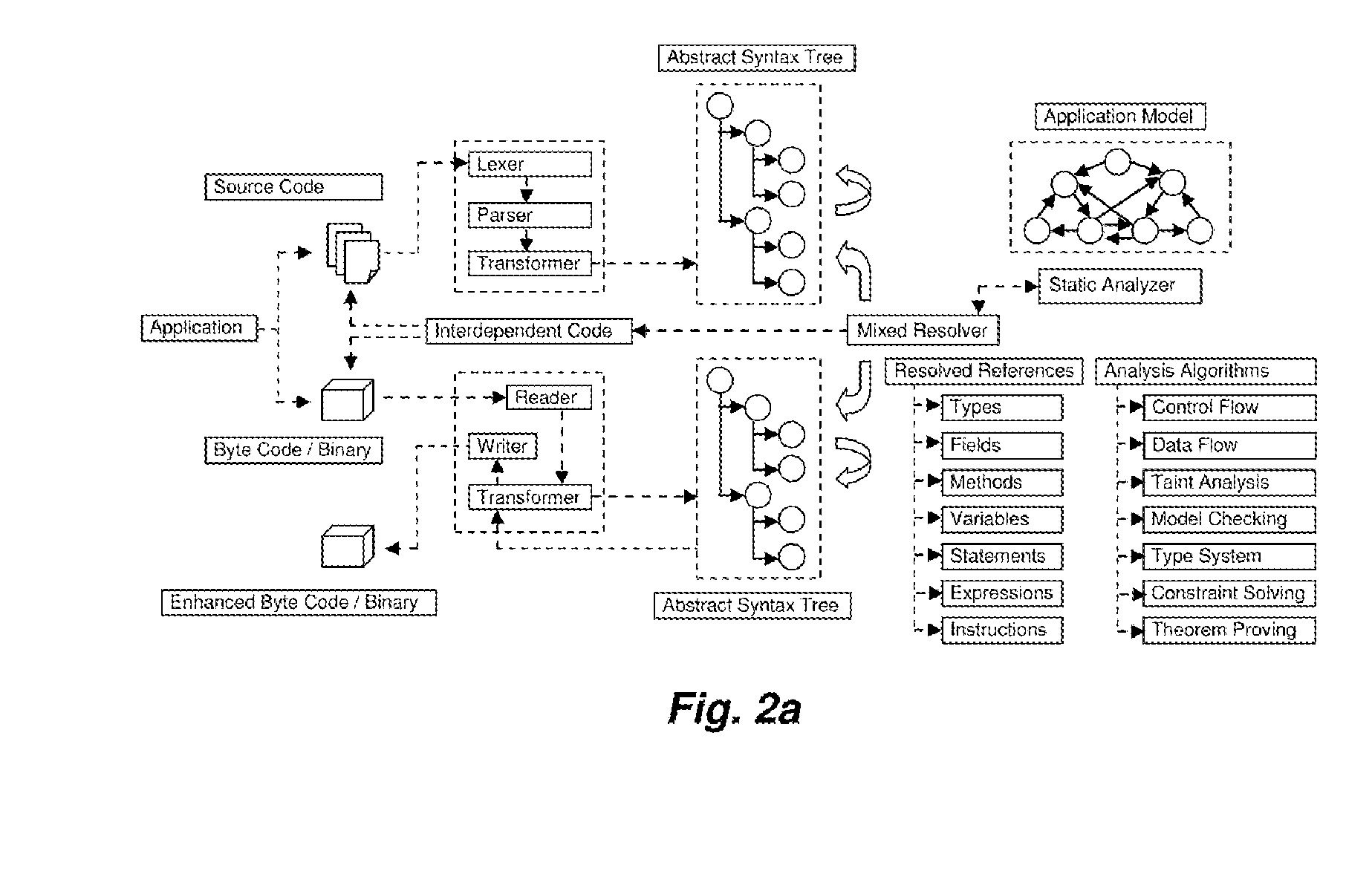
A System for analyzing applications in order to find security and quality issues
InactiveUS20150309813A1Accurate analysisError detection/correctionComputer security arrangementsMachine controlWeb application
The present invention relates to field of application and more specifically to analysis of applications for determining security and quality issues. The present invention describes an application analysis system providing a platform for analyzing applications which is useful in finding security and quality issues in an application. In particular, the present invention is composed of an advanced fusion analyzer which gains an understanding of the application behavior by using a multi-way coordination and orchestration across components used in the present invention to build an continuously refine a model representing knowledge and behavior of the application as a large network of objects across different dimensions and using reasoning and learning logic on this model along with information and events received from the components to both refine and model further as well as drive the components further by sending information and events to them and again using the information and events received as a result to further trigger the entire process until the system stabilizes. The present invention is useful in analysis of internet / intranet based web applications, desktop applications, mobile applications and also embedded systems as well as for hardware, equipment and machines controlled by software.
Owner:IAPPSECURE SOLUTIONS PVT
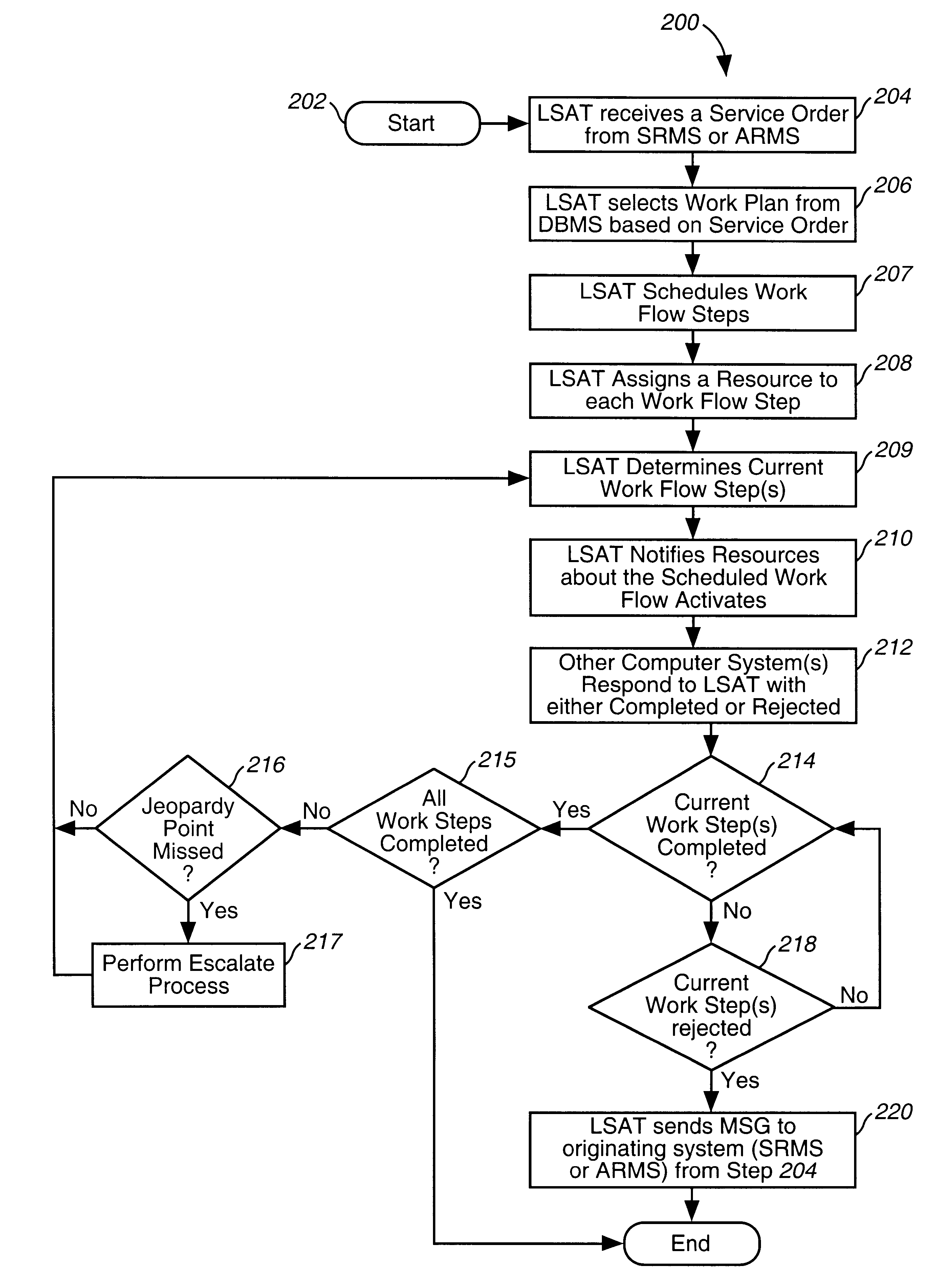
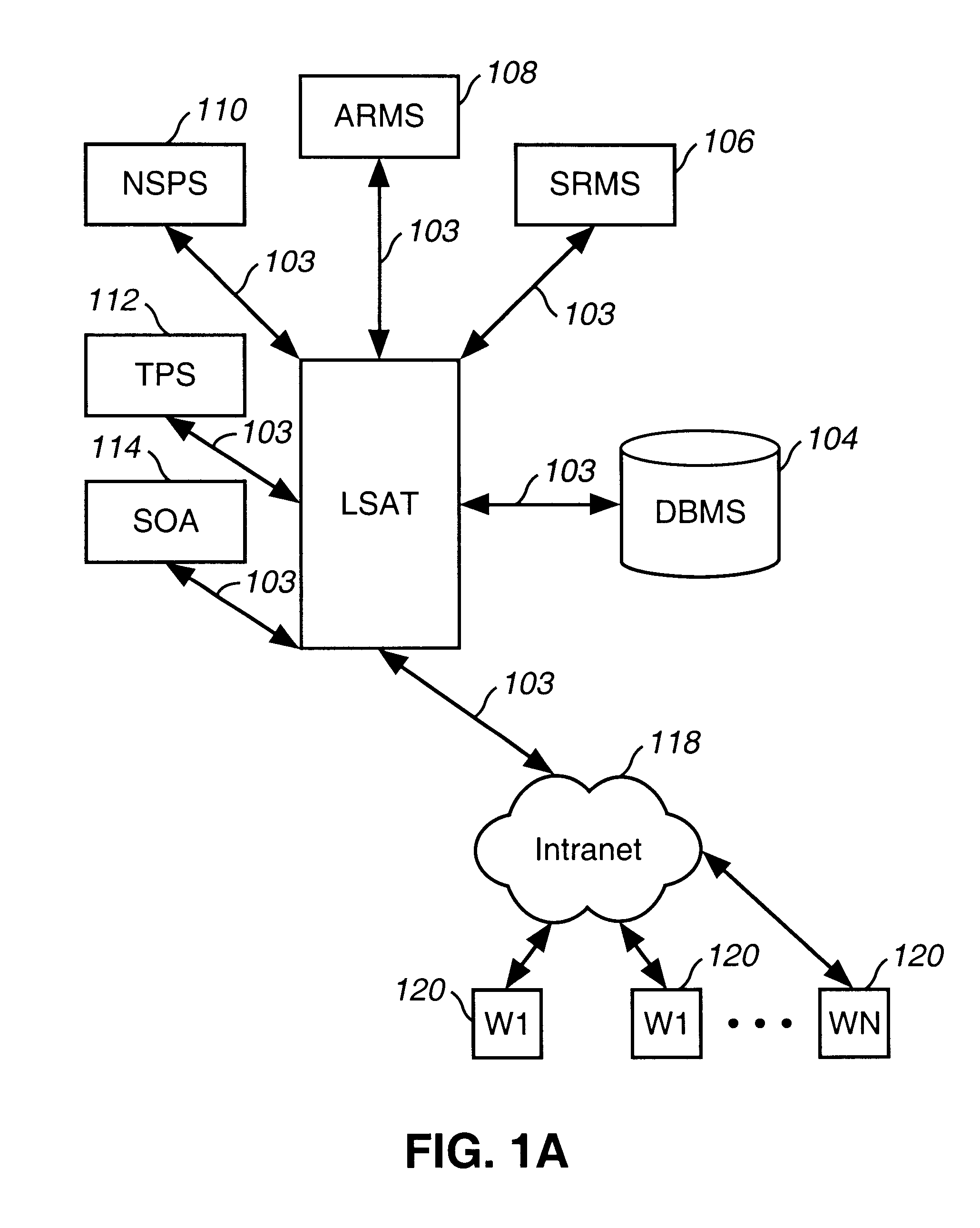
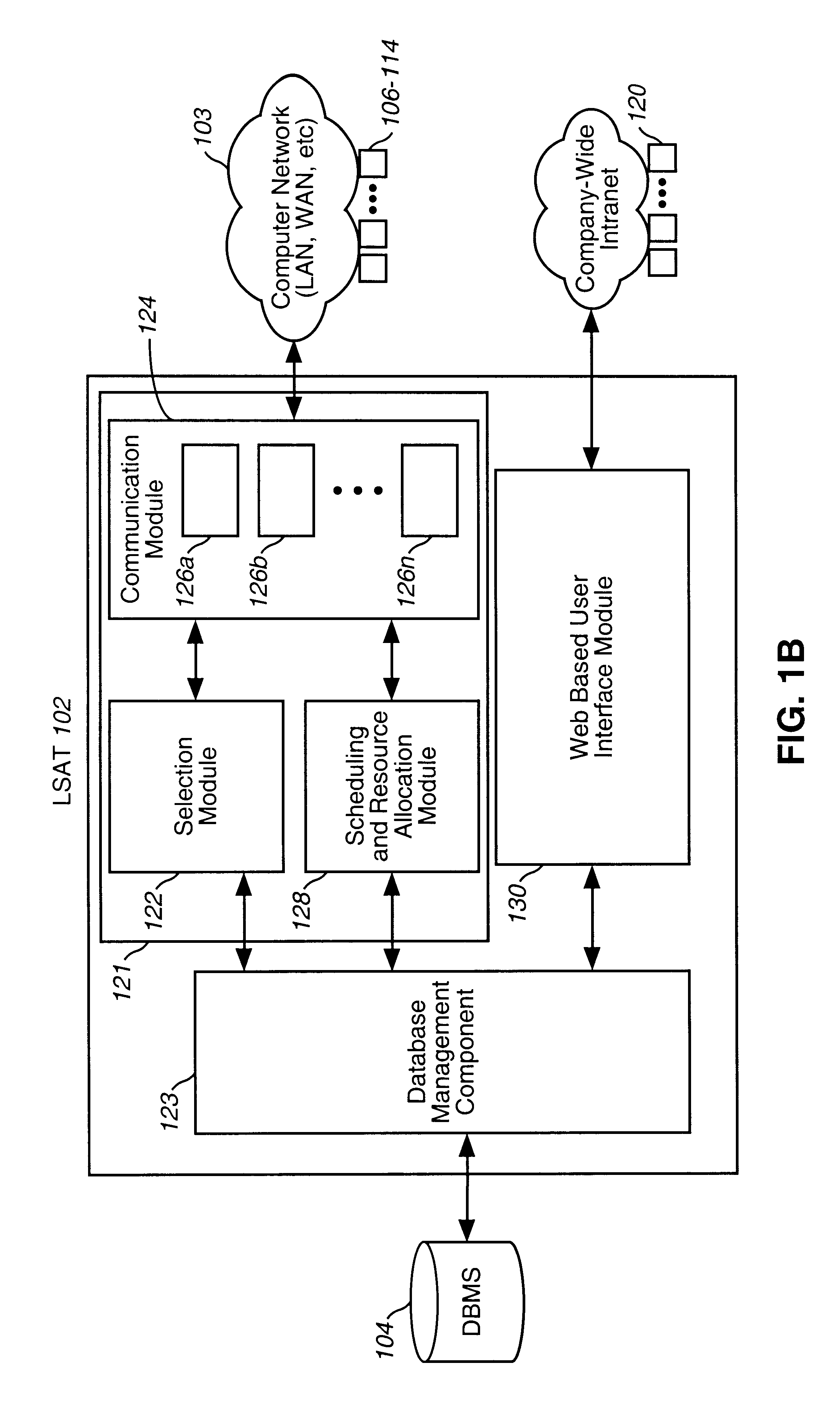
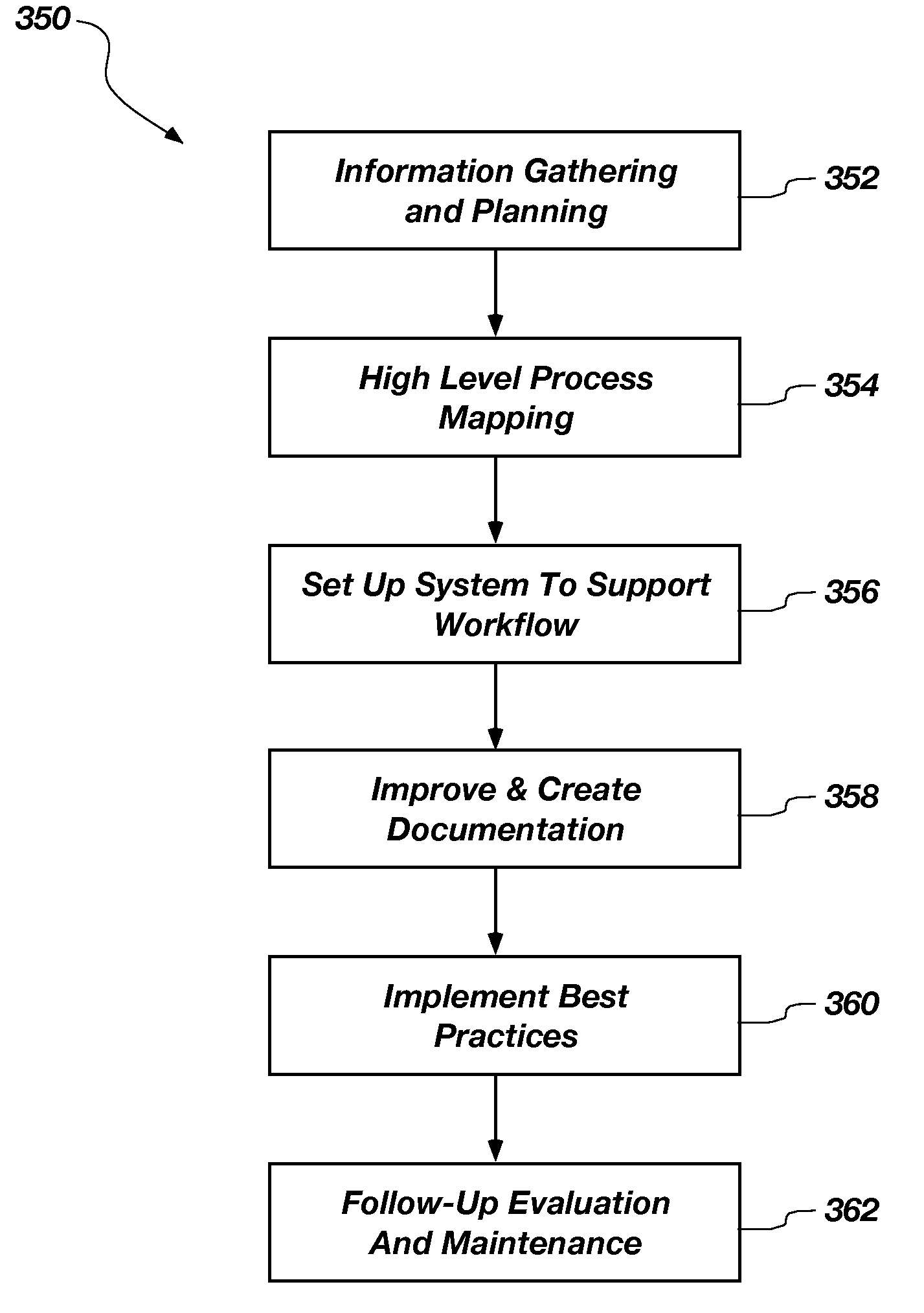
System and method for managing the workflow for processing service orders among a variety of organizations within a telecommunications company
A system and method for managing the workflow for processing Service Orders among a variety of organizations within a telecommunications company. The system and method coordinates all of the tasks and activities related to order processing among the various entities within the telecommunications company. Workflows are used to model business procedures used for processing Service Orders. Each workflow comprises a plurality of workflow steps. Business process models are depicted as workflow diagrams. Upon receipt of a Service Order, an appropriate Work Plan is selected based on information within the Service Order. Each workflow step is assigned a Resource and is scheduled for completion. The Workflow steps are then placed in In-boxes associated with the selected Resource. Once the processing steps have been scheduled, a current work step is calculated. Notification messages are sent to the appropriate systems to notify them to begin activity associated with the current work step. The system is automatically notified when the current work step is complete, so that the next work step can be processed in a similar fashion. Detailed statistical information is maintained for audit and reporting purposes. Users log-on to remote workstations coupled with a company-wide Intranet or the like. From the remote workstations, users from various organizations view their In-boxes and other detailed information about Service Orders according to selectable requests. Workflow steps can be transferred and re-assigned using the remote workstations. Detailed statistical information is maintained for audit and reporting purposes. Reports reflecting the effectiveness of workforce management and work administration is obtained.
Owner:VERIZON PATENT & LICENSING INC
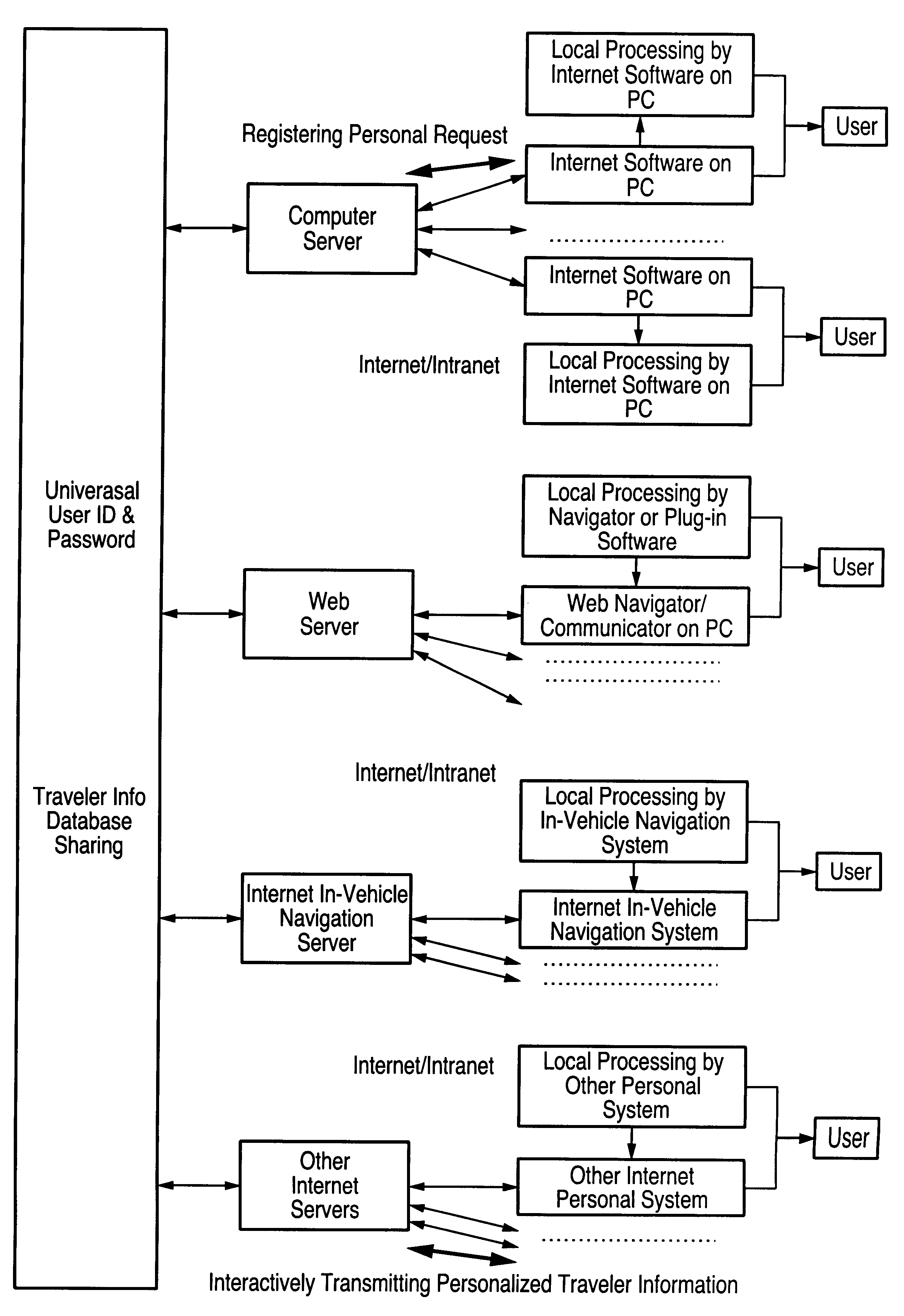
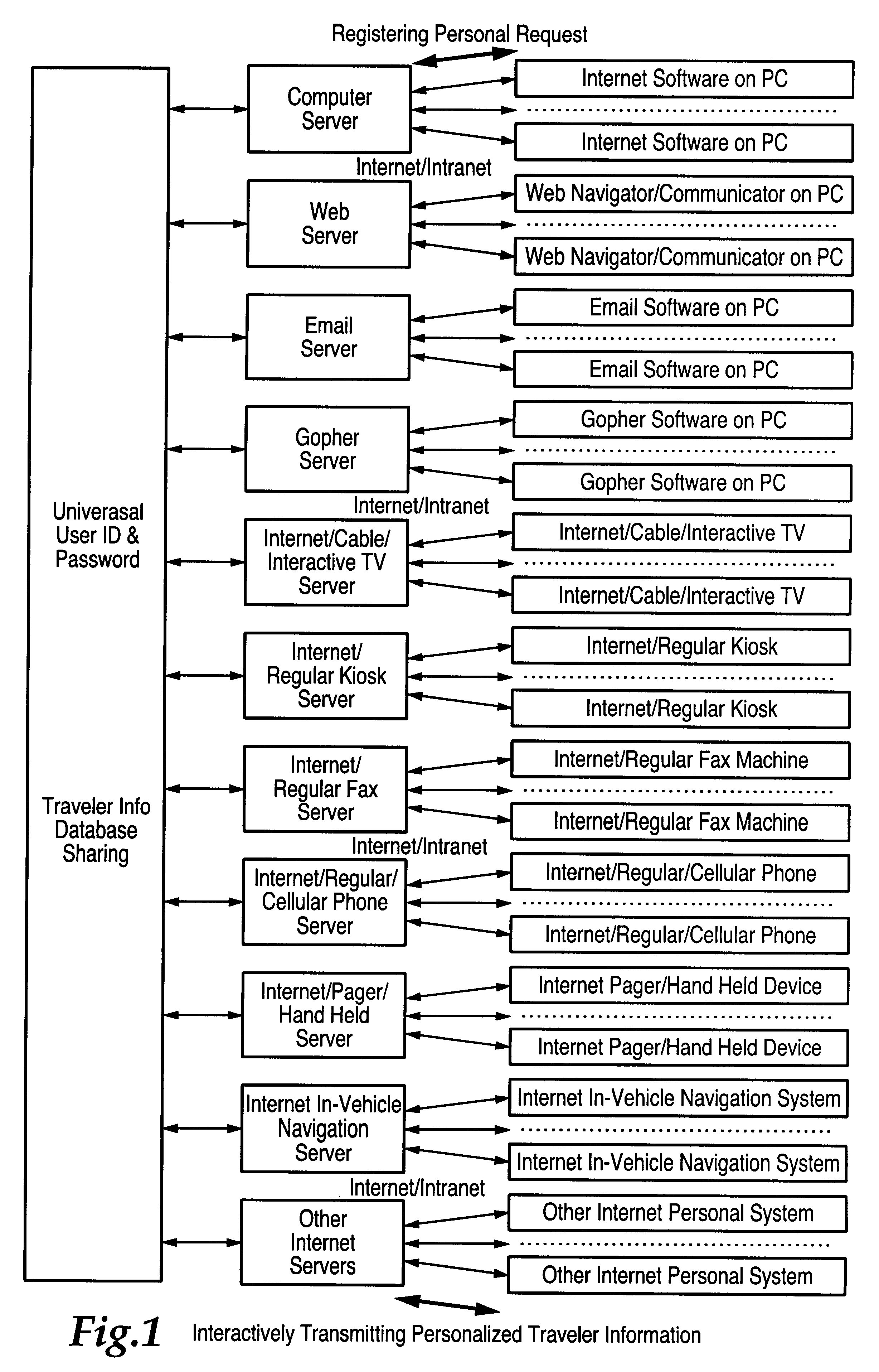
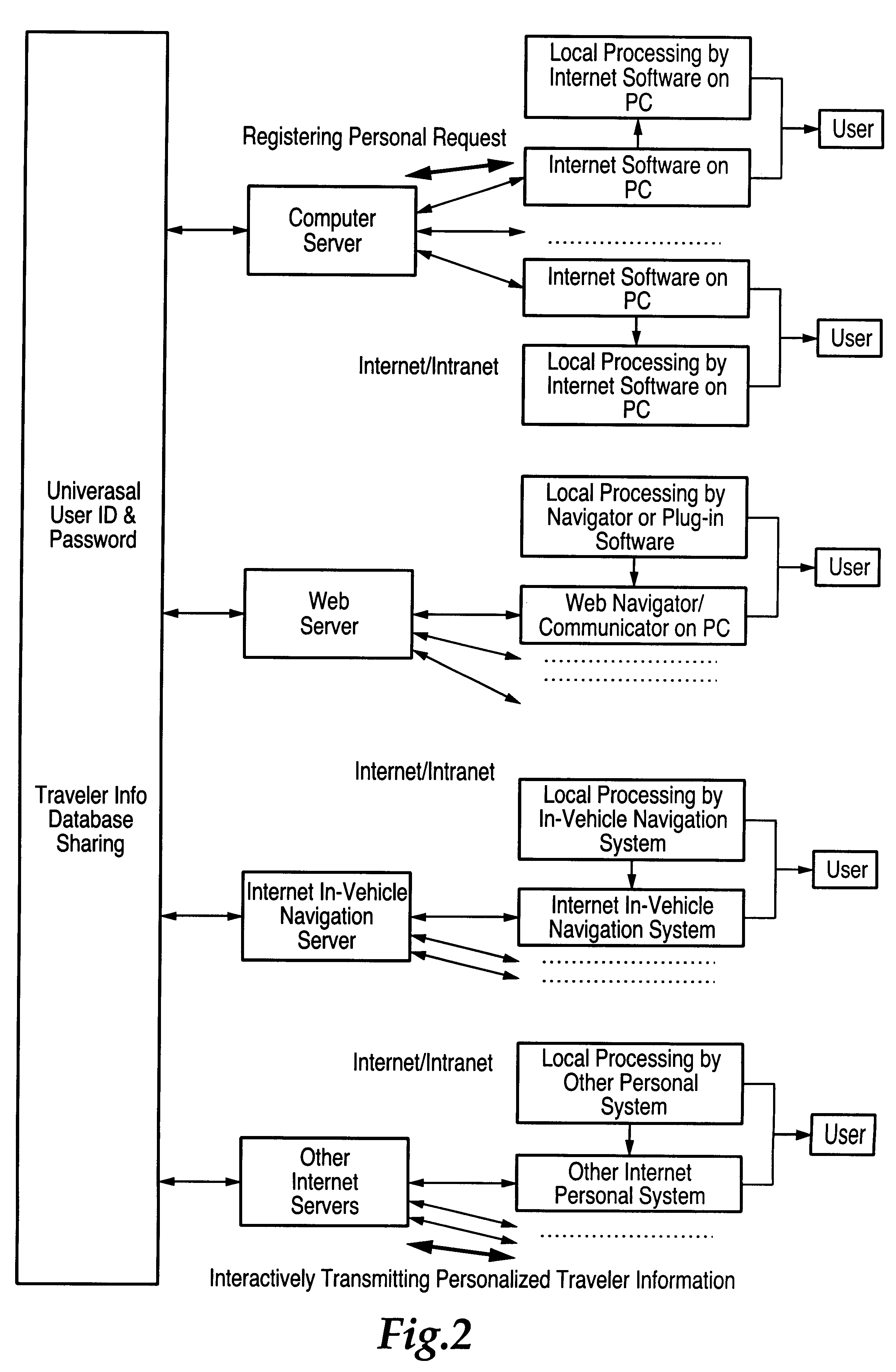
Central processing and combined central and local processing of personalized real-time traveler information over internet/intranet
InactiveUS6209026B1ForecastingMultiple digital computer combinationsUtility computingPersonalization
An Internet utility which receives information about a proposed trip, including trip origin, destination and time. The web based utility calculates at least one route and provides periodic automatic updates of information related to the route such as traffic and weather conditions. Other information which may be automatically periodically transmitted includes information about other transportation systems which may interface with a trip such as airline departure or arrival times. Specific information related to a trip or destination such as availability of parking at the destination also constitute the automatically transmitted information.
Owner:ITERIS INC
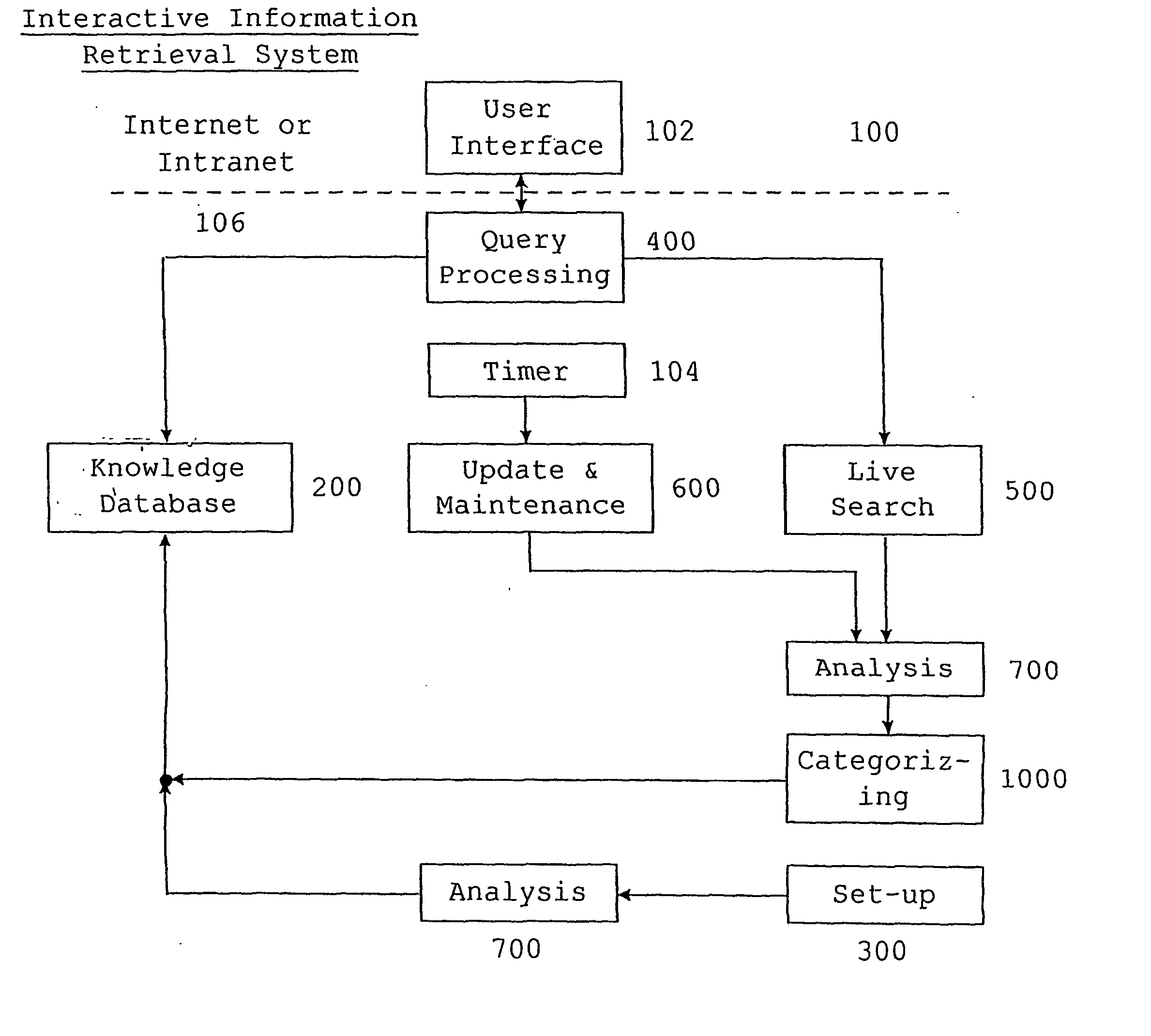
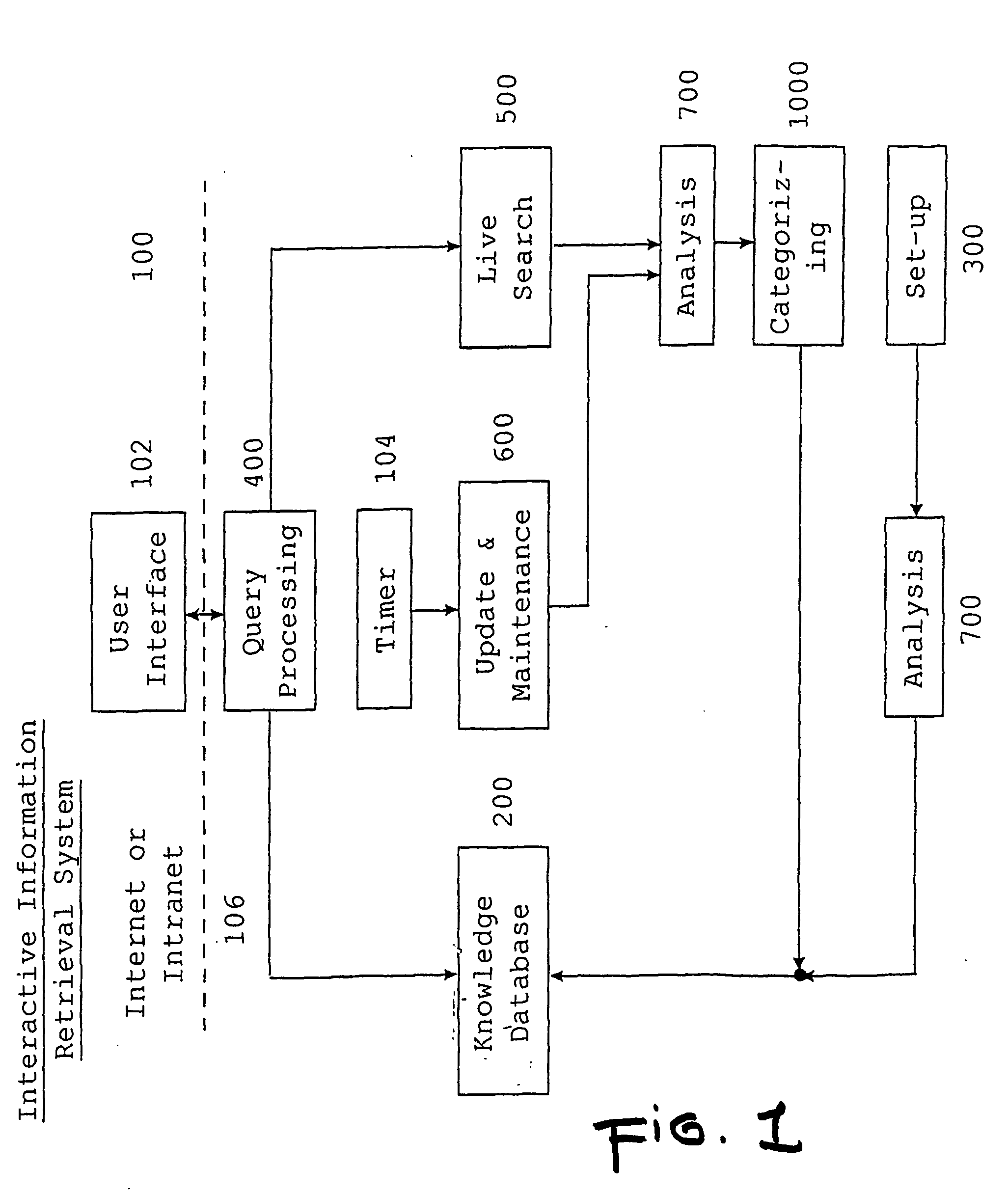
Category based, extensible and interactive system for document retrieval
InactiveUS20050108200A1High precisionReduction in relevant document recall rateWireless commuication servicesData switching networksDocument analysisPaper document
In information retrieval (IR) systems with high-speed access, especially to search engines applied to the Internet and / or corporate intranet domains for retrieving accessible documents automatic text categorization techniques are used to support the presentation of search query results within high-speed network environments. An integrated, automatic and open information retrieval system (100) comprises an hybrid method based on linguistic and mathematical approaches for an automatic text categorization. It solves the problems of conventional systems by combining an automatic content recognition technique with a self-learning hierarchical scheme of indexed categories. In response to a word submitted by a requester, said system (100) retrieves documents containing that word, analyzes the documents to determine their word-pair patterns, matches the document patterns to database patterns that are related to topics, and thereby assigns topics to each document. If the retrieved documents are assigned to more than one topic, a list of the document topics is presented to the requester, and the requester designates the relevant topics. The requester is then granted access only to documents assigned to relevant topics. A knowledge database (1408) linking search terms to documents and documents to topics is established and maintained to speed future searches. Additionally, new strategies are presented to deal with different update frequencies of changed Web sites.
Owner:COGISUM INTERMEDIA
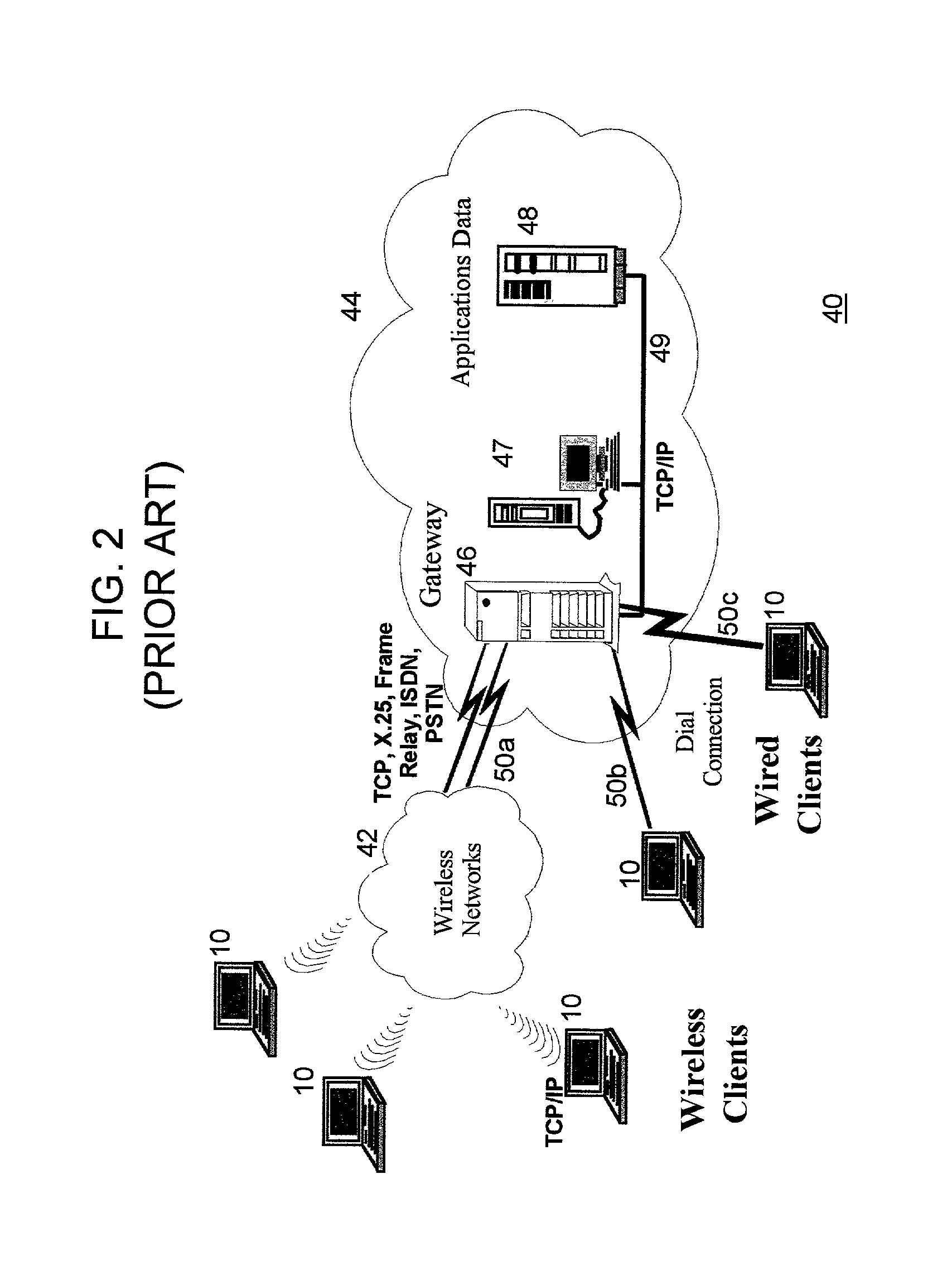
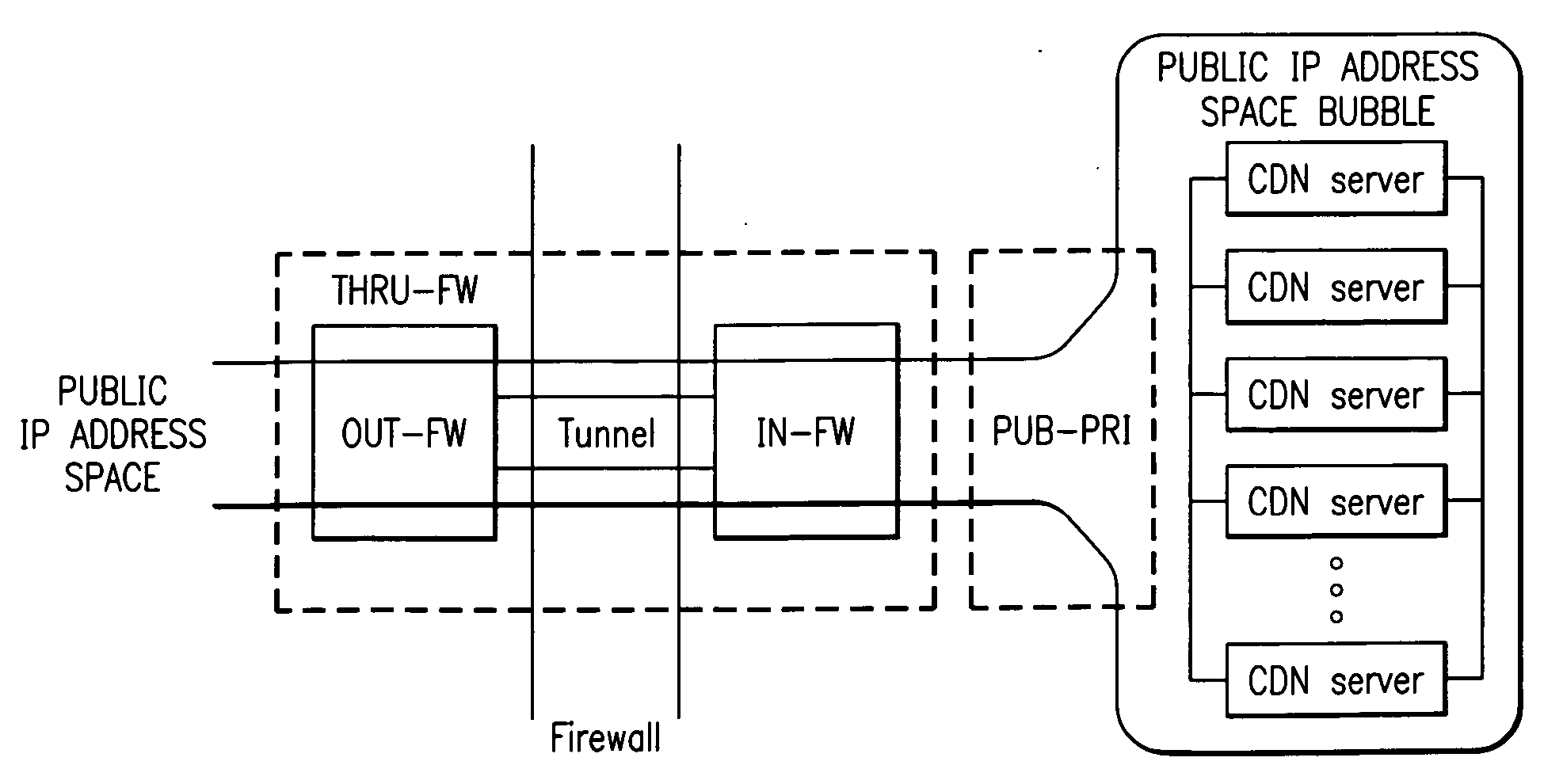
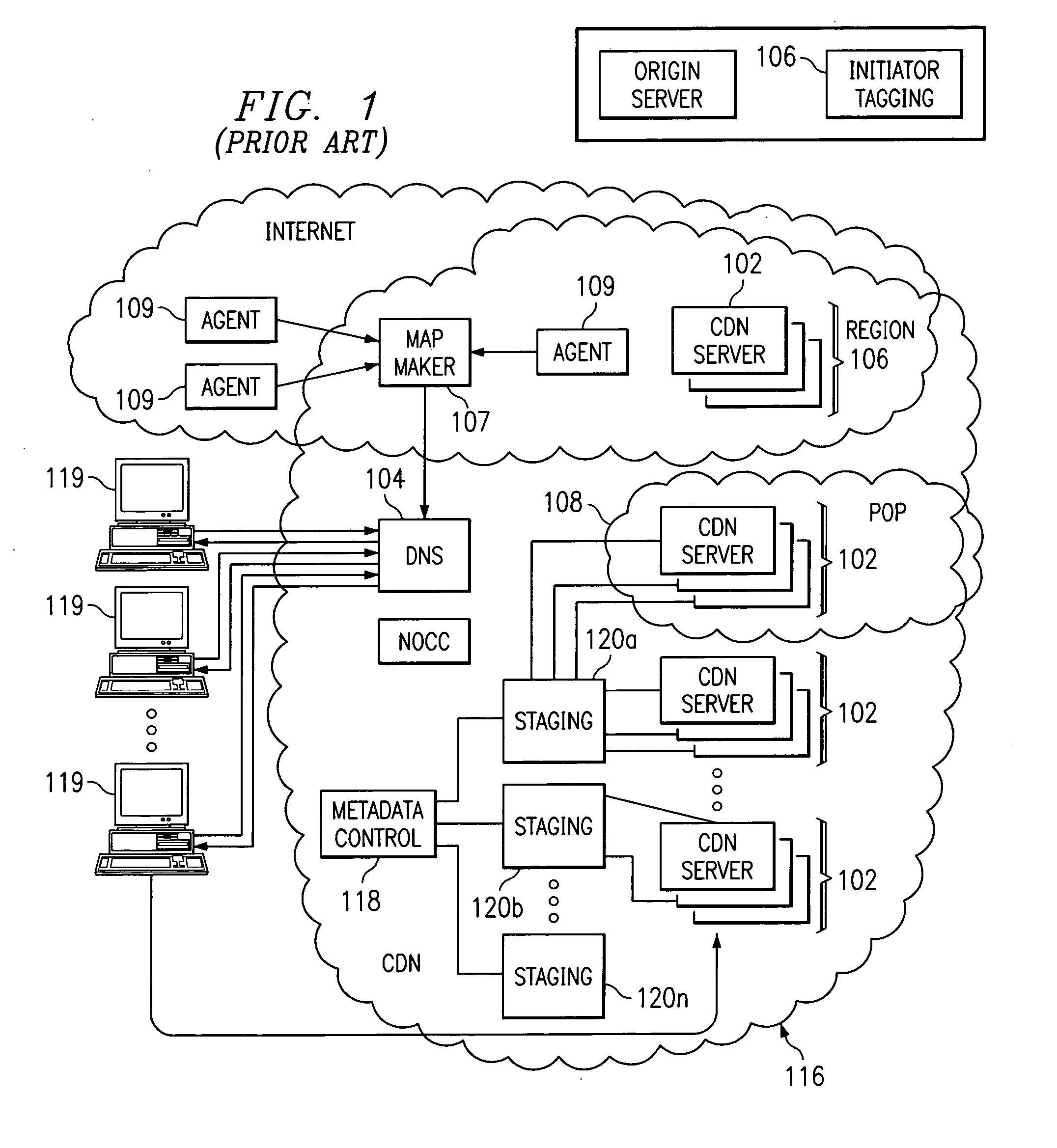
Extending an Internet content delivery network into an enterprise
ActiveUS7096266B2Efficient and cost-effectiveEfficient managementMultiple digital computer combinationsSecuring communicationInternet contentPrivate network
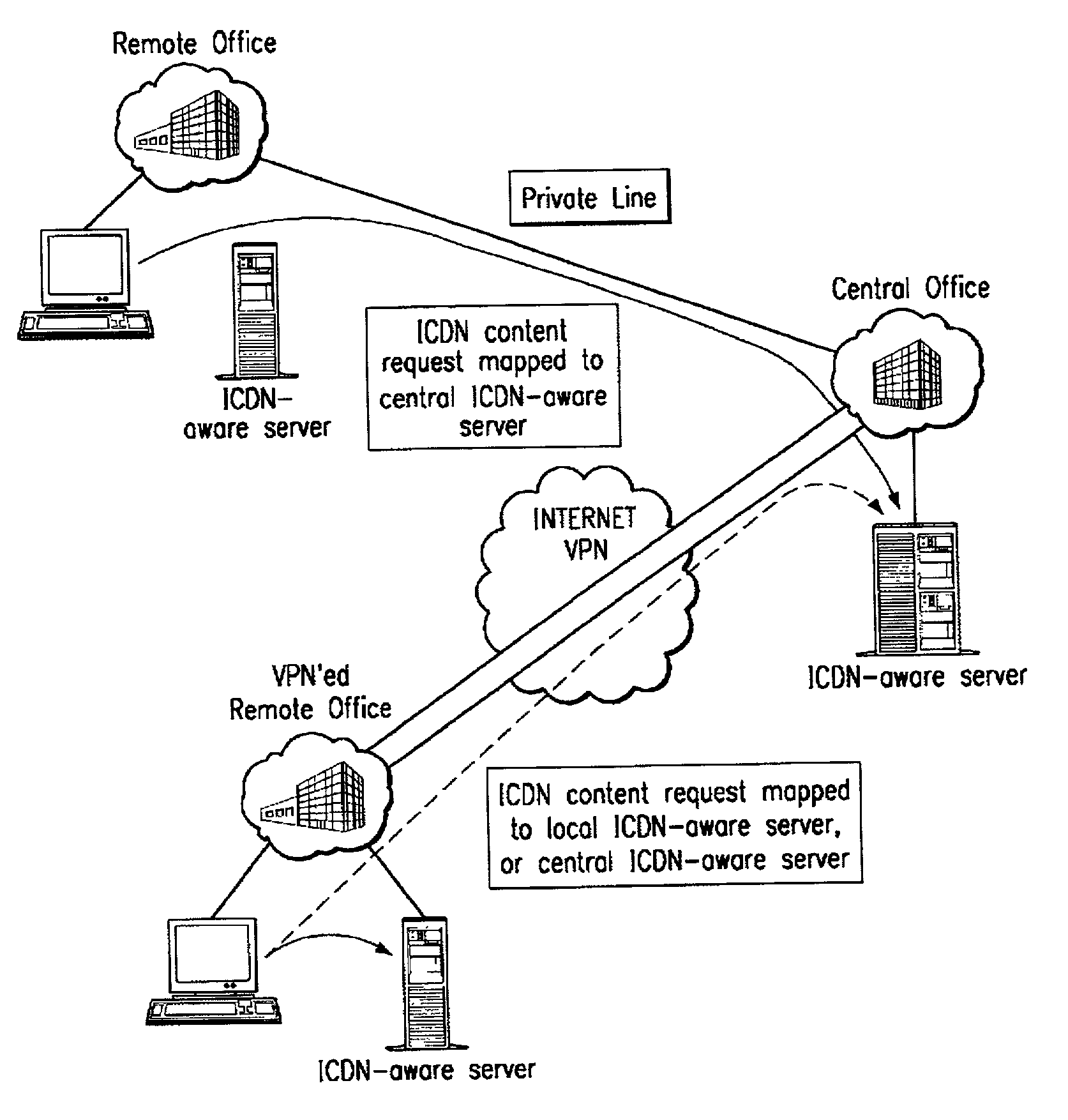
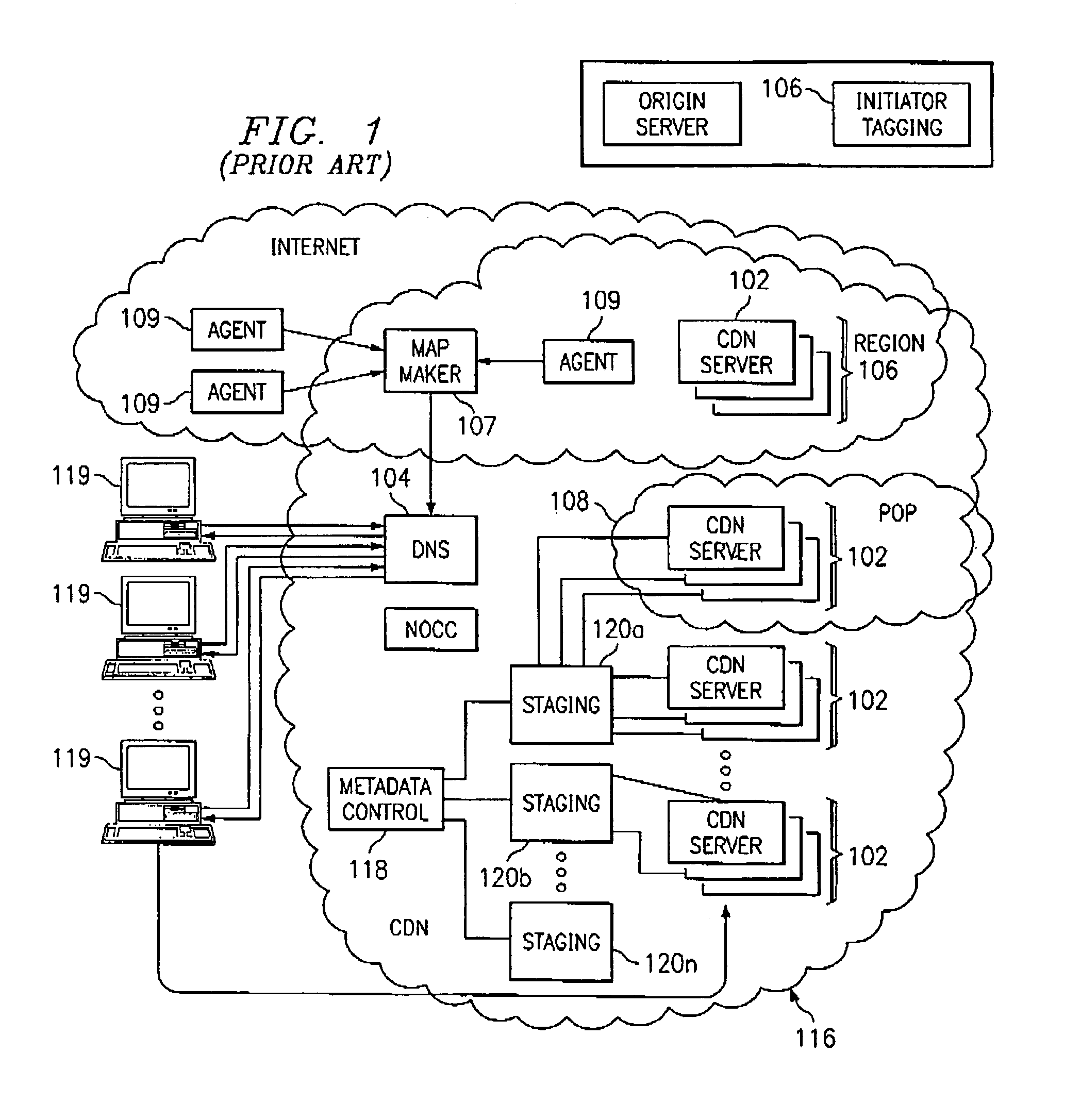
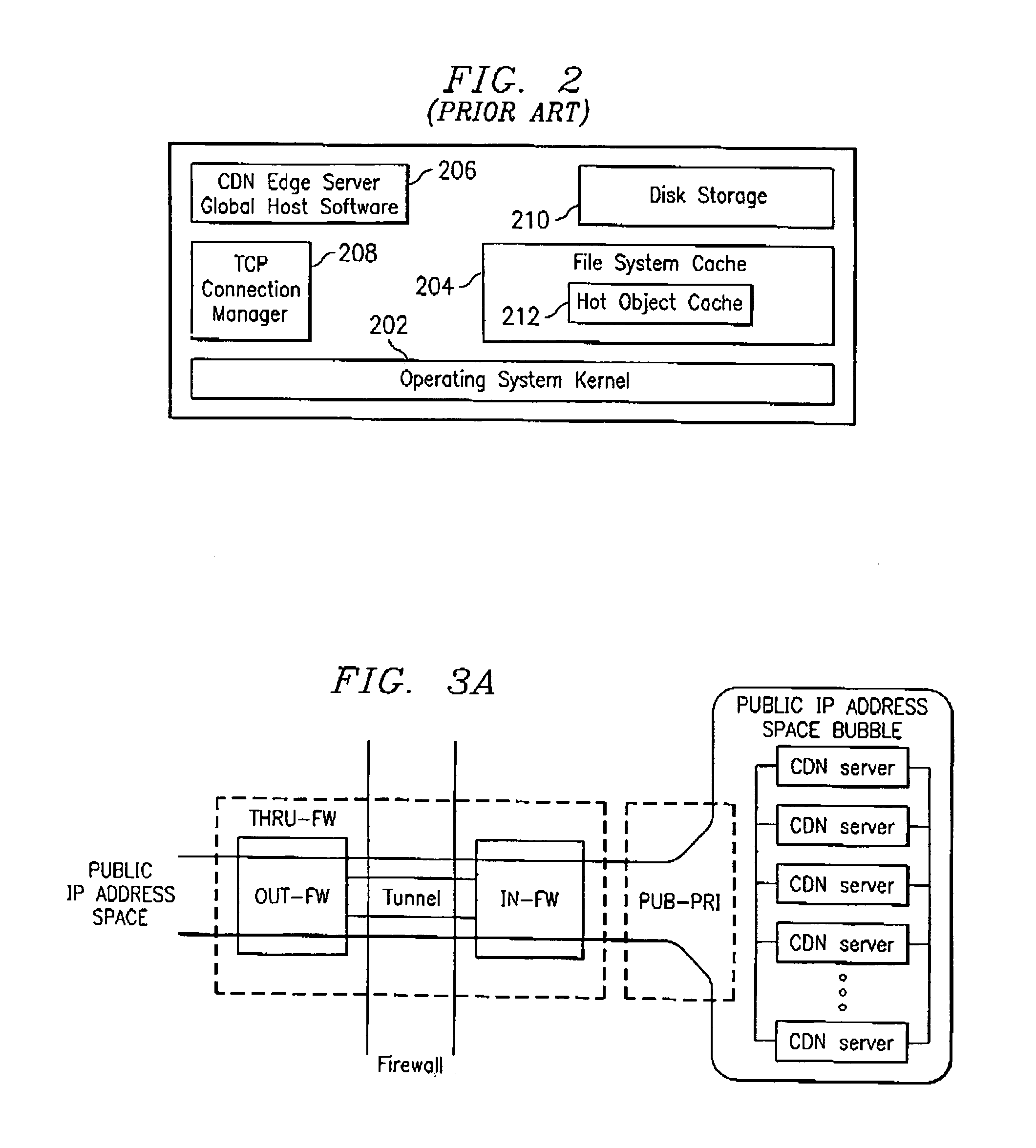
An Internet content delivery network deploys one or more CDN server regions in an enterprise and manages those regions as part of the Internet CDN. In one aspect of the invention, a CDN service provider (CDNSP) deploys one or more CDN regions behind an enterprise's corporate firewall(s). The regions are used to deliver Internet content—content that has been tagged or otherwise made available for delivery over the Internet from the CDN's content servers. This content includes, for example, content that given content providers have identified is to be delivered by the CDN. In addition, the enterprise may tag intranet content, which is then also served from the CDN regions behind the firewall. Intranet content remains secure by virtue of using the enterprise's existing security infrastructure. In accordance with another aspect of the invention, the CDNSP implements access controls and deploys one or more CDN regions outside an enterprise's firewall(s) such that intranet content can be served from regions located outside the firewall(s). In this embodiment, the CDNSP can provide granular control, such as permissions per groups of users. In this way, the CDNSP, in effect, extends a conventional virtual private network (VPN) to all or a portion of the ICDN, thereby enabling the CDNSP to use multiple regions and potentially thousands of content servers available to serve the enterprise's internal content. In addition to making internal content available from the edge of the network, the CDNSP provides a mechanism by which an enterprise may share secure data with its business partner(s) without setting up any special infrastructure.
Owner:AKAMAI TECH INC
Systems and methods for cloud bridging between intranet resources and cloud resources
Embodiments of the present solution provide a cloud bridge to bring network transparency between the otherwise disparate networks of the datacenter and cloud service provider. For example, appliances may be deployed in the datacenter and on the edge of the cloud. These appliances may be configured or designed and constructed to communicate with each other and recognize and understand the local IP and / or public IP network information of the on-premise datacenter of the enterprise and the cloud datacenter. These appliances may manage the flow of network traffic between the on-premise and cloud datacenters in a manner to appear and act seamlessly and transparently as a single network spanning both the on-premise and cloud data centers.
Owner:CITRIX SYST INC
Integrated system for network layer security and fine-grained identity-based access control
ActiveUS6986061B1Simple technologyUser identity/authority verificationDigital computer detailsKey exchangeMedia access control
Owner:TREND MICRO INC
Extending an internet content delivery network into an enterprise
InactiveUS20060282522A1Efficient and cost-effectiveEfficient managementMultiple digital computer combinationsElectric digital data processingInternet contentPrivate network
An Internet content delivery network deploys one or more CDN server regions in an enterprise and manages those regions as part of the Internet CDN. In one aspect of the invention, a CDN service provider (CDNSP) deploys one or more CDN regions behind an enterprise's corporate firewall(s). The regions are used to deliver Internet content—content that has been tagged or otherwise made available for delivery over the Internet from the CDN's content servers. This content includes, for example, content that given content providers have identified is to be delivered by the CDN. In addition, the enterprise may tag intranet content, which is then also served from the CDN regions behind the firewall. Intranet content remains secure by virtue of using the enterprise's existing security infrastructure. In accordance with another aspect of the invention, the CDNSP implements access controls and deploys one or more CDN regions outside an enterprise's firewall(s) such that intranet content can be served from regions located outside the firewall(s). In this embodiment, the CDNSP can provide granular control, such as permissions per groups of users. In this way, the CDNSP, in effect, extends a conventional virtual private network (VPN) to all or a portion of the ICDN, thereby enabling the CDNSP to use multiple regions and potentially thousands of content servers available to serve the enterprise's internal content. In addition to making internal content available from the edge of the network, the CDNSP provides a mechanism by which an enterprise may share secure data with its business partner(s) without setting up any special infrastructure.
Owner:AKAMAI TECH INC
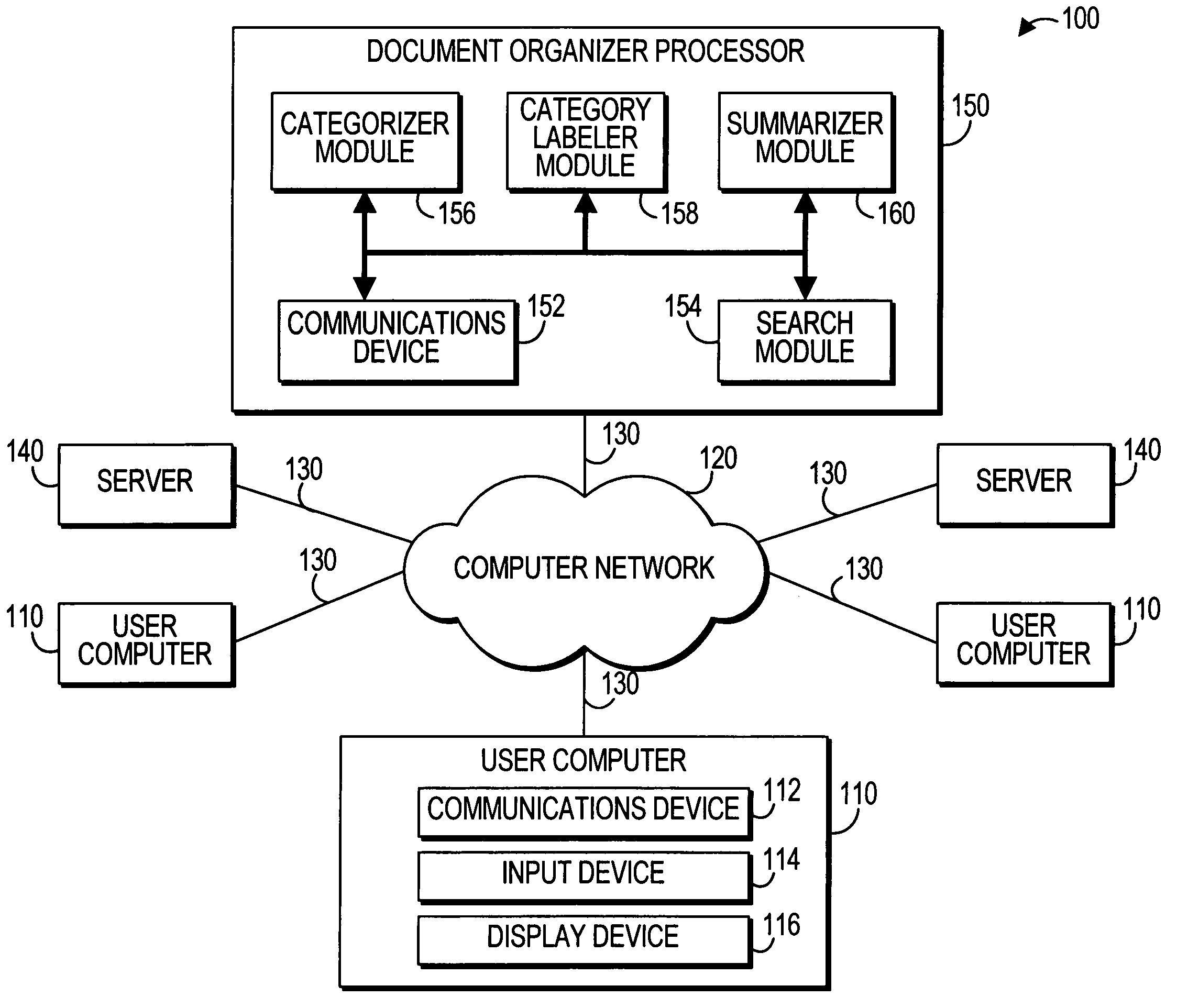
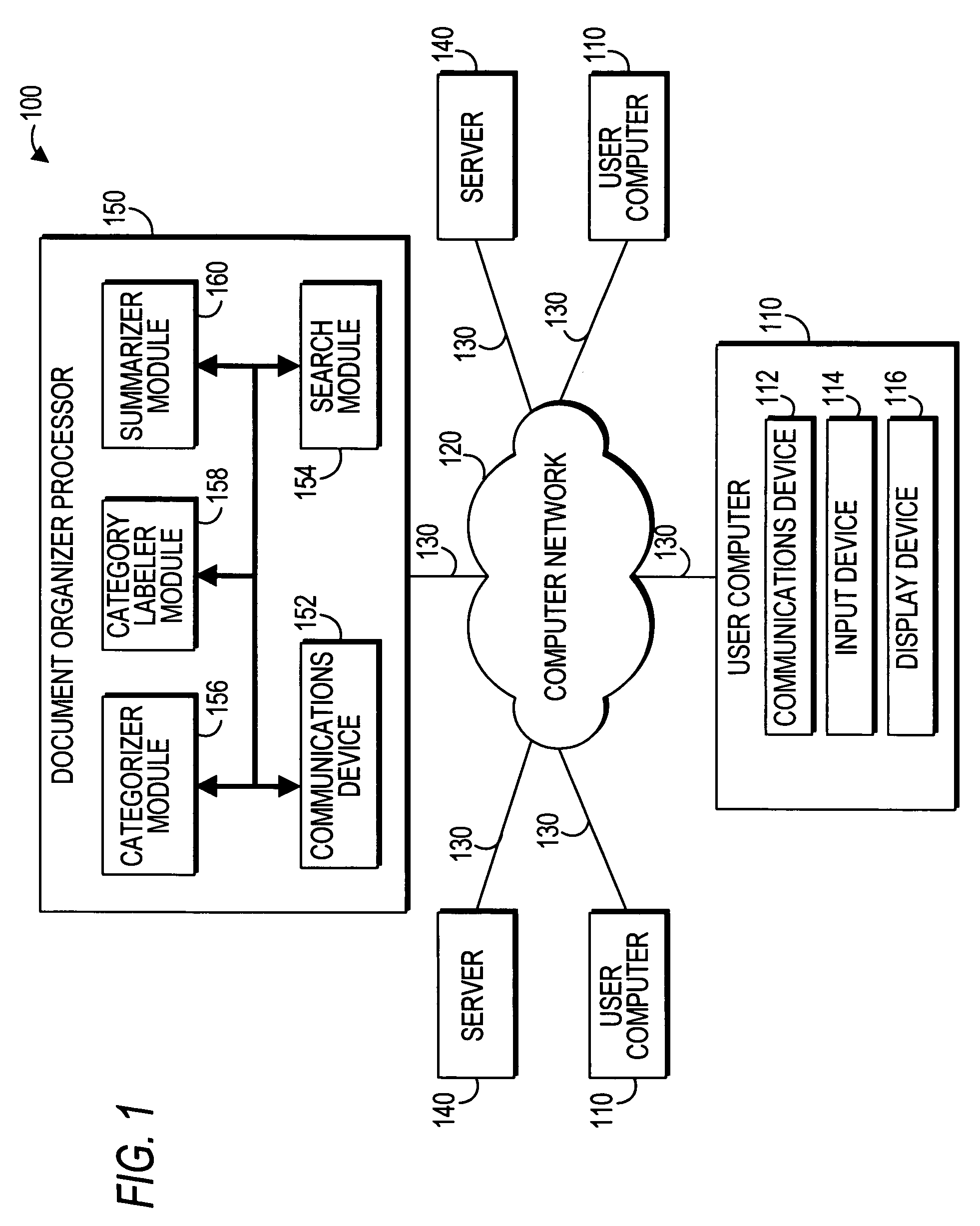
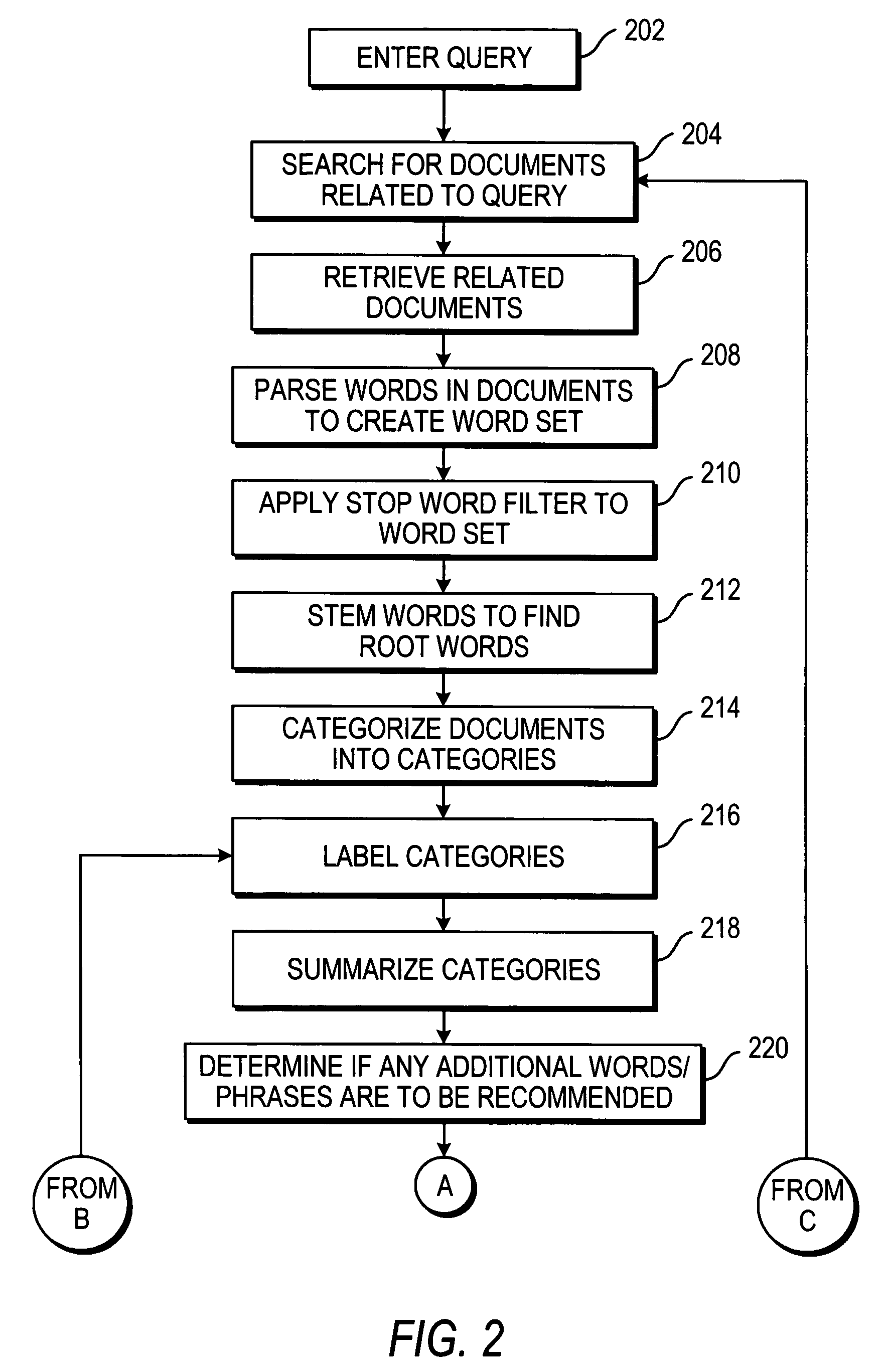
Systems and methods for document searching and organizing
InactiveUS7185001B1High resolutionSpeed up searchData processing applicationsWeb data indexingDocument preparationDocumentation
Systems and methods interactive document search, retrieval, categorization, and summarization are provided. A document organizer processor may analyze the content of documents, such as web pages and text documents, downloaded from a computer network, such as the Internet or an intranet, in response to a user's search query. After receiving a search query from a user, the processor may locate documents related to the query, parse words in the documents into a word set, filter out unnecessary words, group the documents into categories, provide labels for the categories, construct summaries of the documents in each category, determine if any additional words or phases are to be recommended, present the labels and summaries to the user, and enable the user to iteratively refine the search.
Owner:FLASHLIGHT CONCEPTS
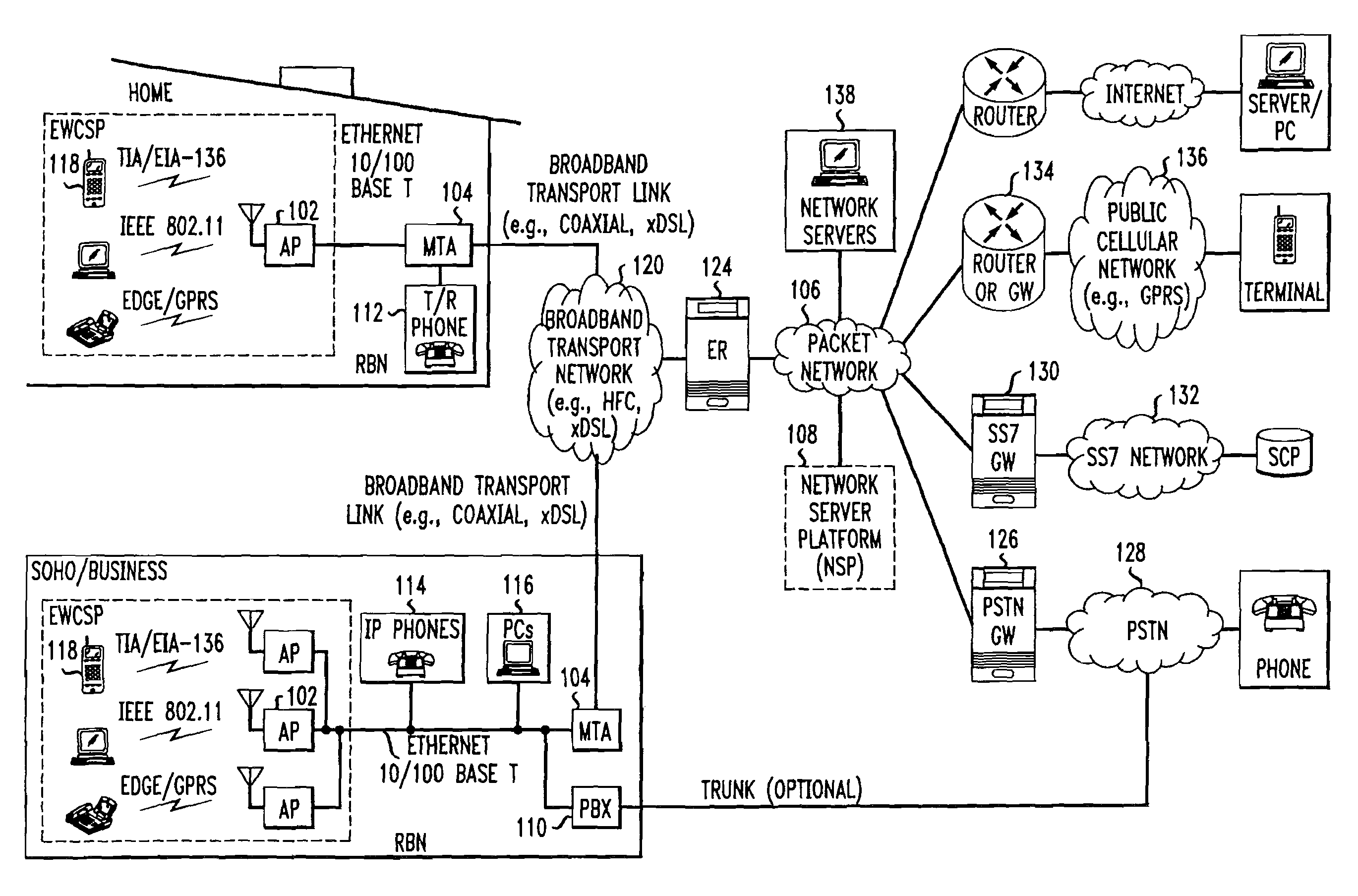
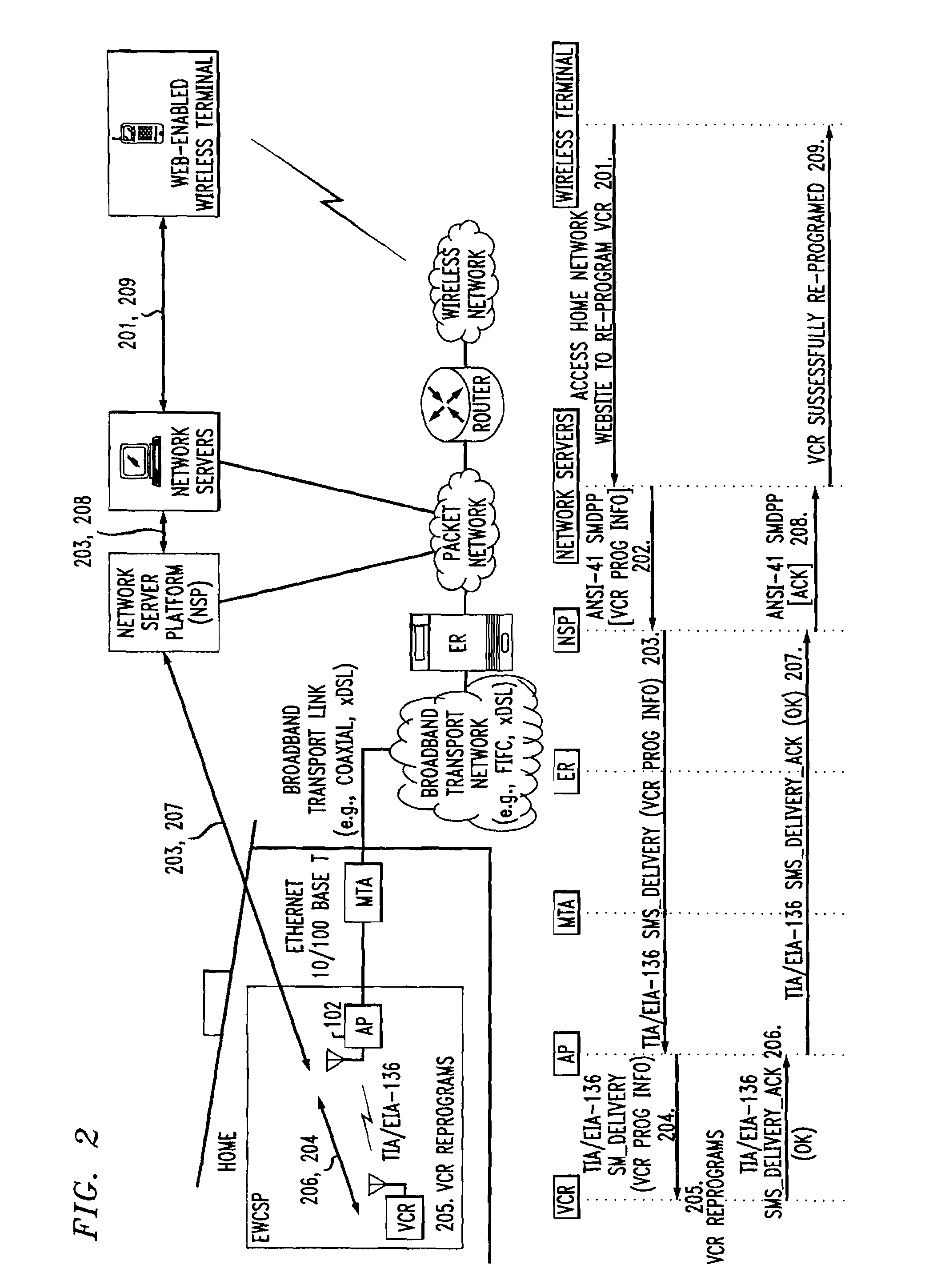
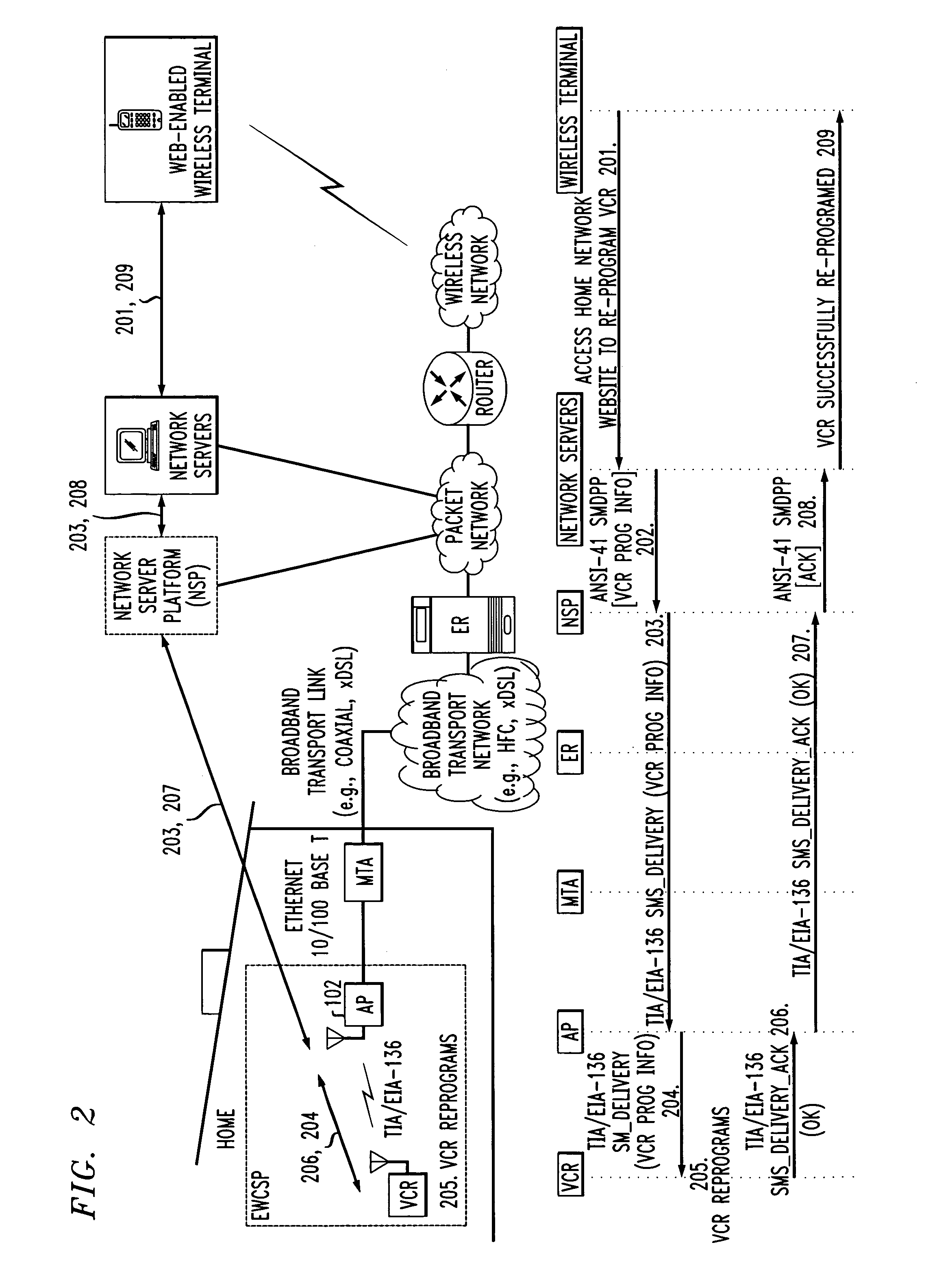
Computer readable medium with embedded instructions for providing communication services between a broadband network and an enterprise wireless communication platform within a residential or business environment
InactiveUS8155155B1Easy maintenanceCost-effectivelyError preventionFrequency-division multiplex detailsModem deviceBroadband transmission
The present invention sets forth computer-readable non-transitory medium having computer-executable instructions for providing network-centric service distribution method that integrates a wireless access system / service with conventional telecommunications services in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN). The RBN communicates with the service provider's broadband transport network and broadband packet network to facilitate end-to-end packet telecommunication services. Signals from a plurality of wireless devices are accepted and forwarded to an IEEE 802.11b interface for a wireless modem and / or to an Ethernet interface for a Voice over Internet Protocol (VOIP) / Ethernet Processor, where the forwarded signals comprise intranet telephony and data.
Owner:AT & T INTPROP II LP
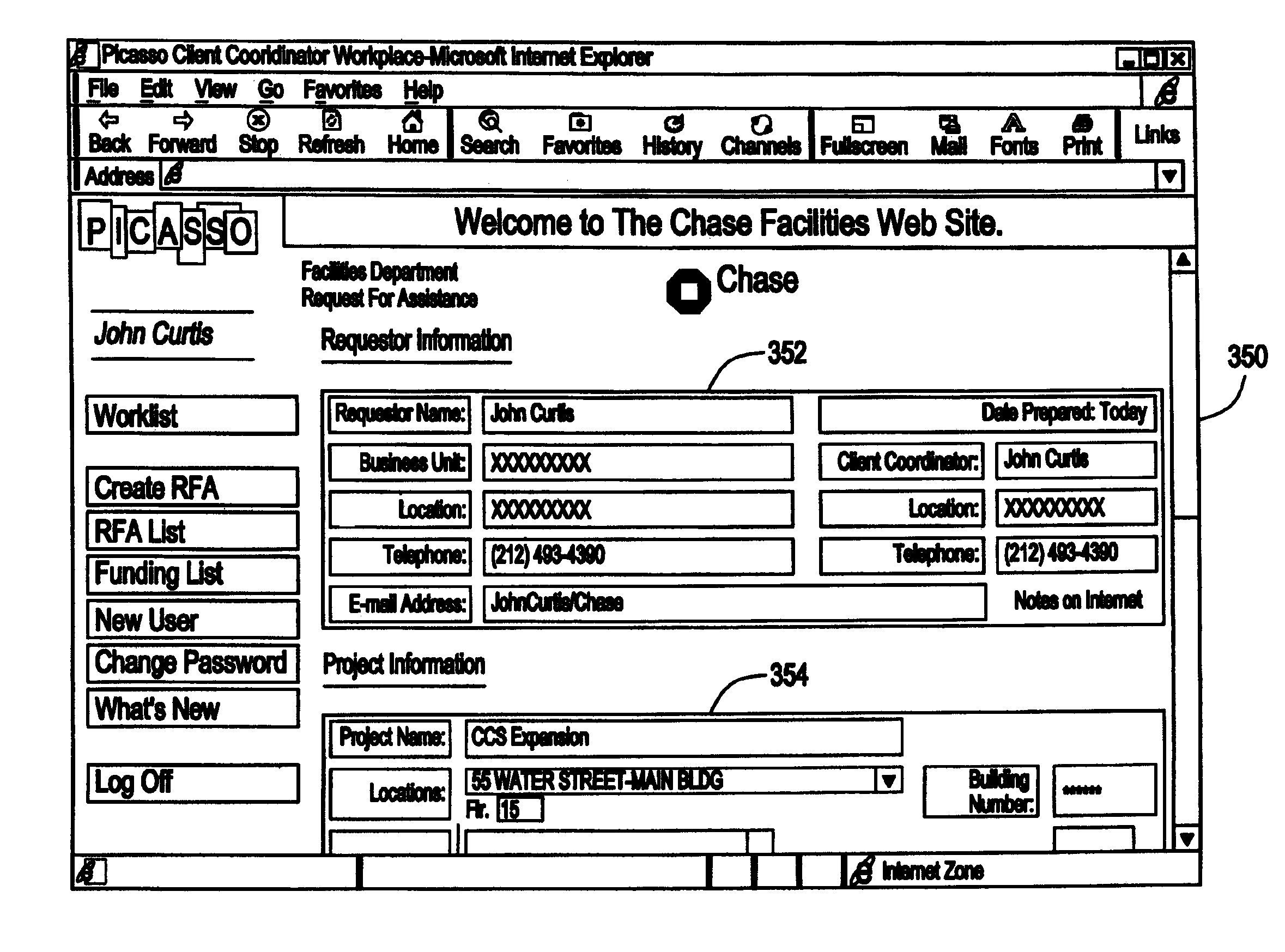
System and method for providing funding approval associated with a project based on a document collection
InactiveUS7321864B1Maximal functionalityReduced functionalityPayment architectureOffice automationDocumentation procedureAutomatic control
A system and method for providing project management tools to support construction, renovations, maintenance and other projects. The system automates the creation, processing and approval cycles of the numerous documents involved with each project. The system provides standardized work processes through processing templates. The system provides automated control and management of the process. The system allows project initiation and funding approval by clients throughout the corporation via a desktop browser coupled to a corporate Intranet. A software application embodying the present invention and its underlying technology are appropriate for a paper intensive area. It reduces the approval cycle of projects. It automates the creation, processing and approval cycle of documents by routing documents electronically for on-line approval.
Owner:JPMORGAN CHASE BANK NA
Network based classified information systems
A system for automatically creating databases containing industry, service, product and subject classification data, contact data, geographic location data (CCG-data) and links to web pages from HTML, XML or SGML encoded web pages posted on computer networks such as the Internet or Intranets. The web pages containing HTML, XML or SGML encoded CCG-data, database update controls and web browser display controls are created and modified by using simple text editors, HTML, XML or SGML editors or purpose built editors. The CCG databases may be searched for references (URLs) to web pages by use of enquiries which reference one or more of the items of the CCG-data. Alternatively, enquiries referencing the CCG-data in the databases may supply contact data without web page references. Data duplication and coordination is reduced by including in the web page CCG-data display controls which are used by web browsers to format for display the same data that is used to automatically update the databases.
Owner:HANGER SOLUTIONS LLC +1
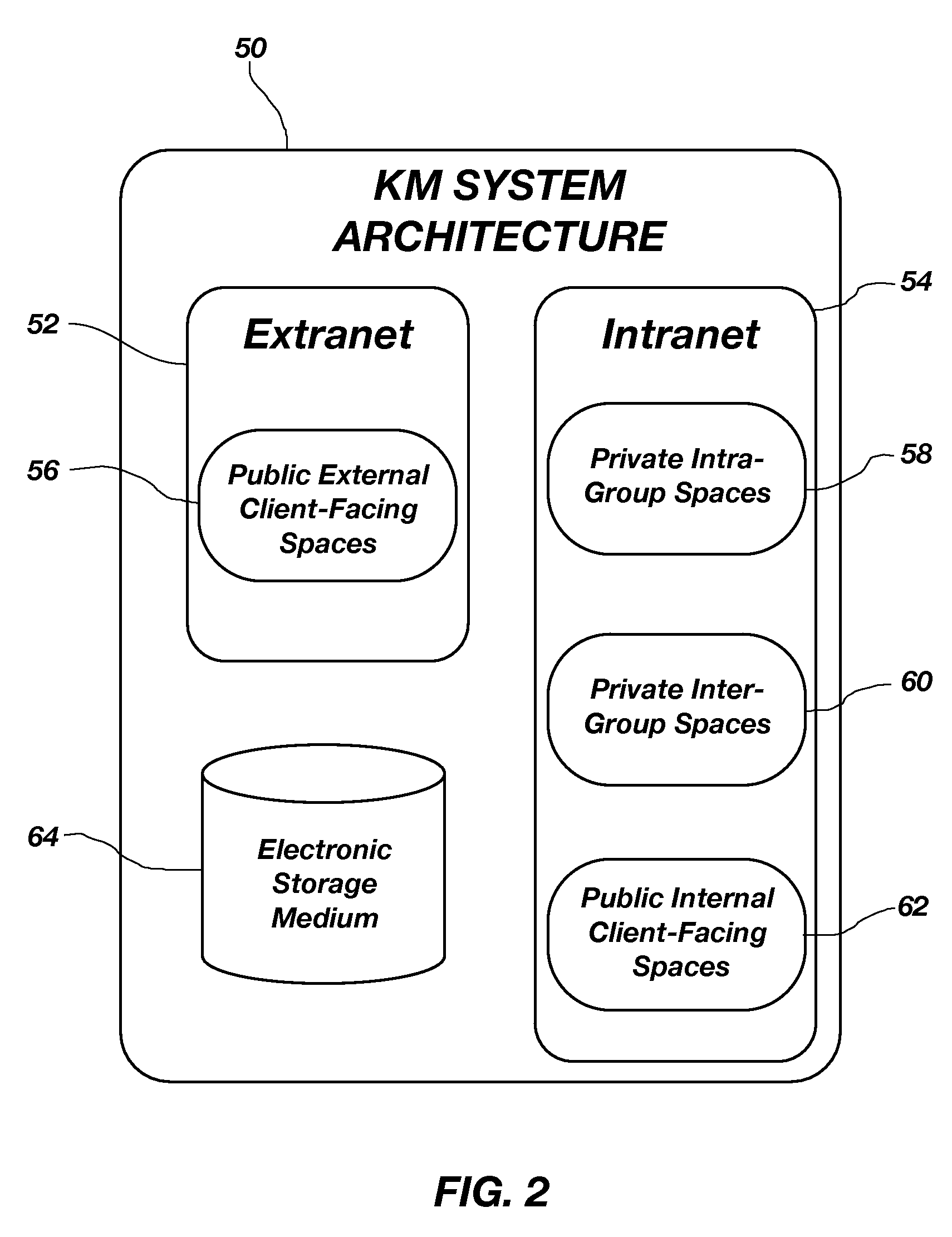
System and method for knowledge management
A system and method for knowledge management in an organization. The system and method employs an intranet site whereby members of the organization can easily and efficiently access explicit knowledge and tacit knowledge relevant to complete processes in an organization. As members of an organization communicate and collaborate with each other using the present disclosure, new knowledge or ideas or best practices may form as a result of the collaboration which then should also be captured and codified as explicit knowledge.
Owner:INGRAM MICRO INC
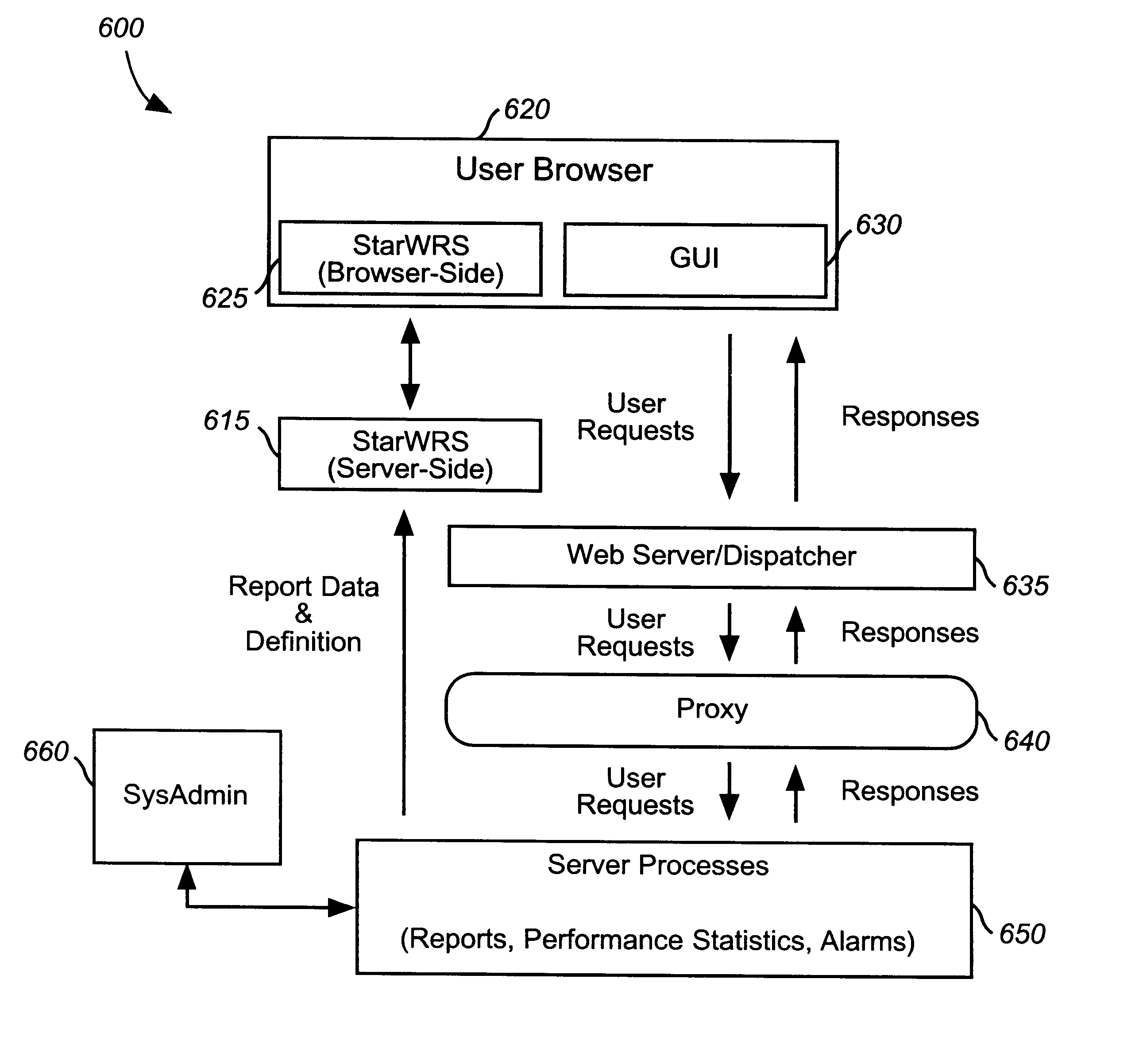
Integrated proxy interface for web based alarm management tools
InactiveUS6473407B1Error preventionFrequency-division multiplex detailsGraphicsGraphical user interface
A Web-based fault and alarm management tool that enables customers to monitor and analyze the performance of their voice and data network via a graphical user interface is provided. The tool provides customers an Internet / Intranet access to near real-time alarms, events, and performance statistics and configuration reports corresponding to their switched network, including voice network, broadband, dedicated point-to-point circuits, and signaling services, for enabling customers to make informed network management decisions. A Web-based fault and alarm management infrastructure which enables the secure initiation, acquisition, and presentation of customer reports relating to network management via a Web browser on any computer is also provided.
Owner:VERIZON PATENT & LICENSING INC
Broadband network with enterprise wireless communication method for residential and business environment
InactiveUS7010002B2Easy to optimizeCost-effective deploymentMultiplex system selection arrangementsTelephone data network interconnectionsModem deviceBroadband transmission
The present invention sets forth a network-centric service distribution architecture and method that integrates a wireless access system / service in the residence, SOHO, business or public environment through the use of a local broadband network, such as a Residential-Business Broadband Network (RBN), to the service provider's broadband transport network and to a service provider's broadband packet network that facilitates end-to-end packet telecommunication services. Access functions for connecting said service provider's broadband packet network to the RBN via said service provider's broadband transport network are provided. Call and service termination functions to a plurality of local RBN devices are also provided. Signals from a plurality of wireless devices are accepted and forwarded to an IEEE 802.11b interface for a wireless modem and / or to an Ethernet interface for a Voice over Internet Protocol (VOIP) / Ethernet Processor, where the forwarded signals comprise intranet telephony and data. Voice signals are also accepted from a plurality of tip / ring interfaces and forwarded to a broadband transport interface for back haul of data and voice packets. A service provider can deploy services in an integrated voice, data and multimedia environment cost-effectively based on one broadband packet network.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
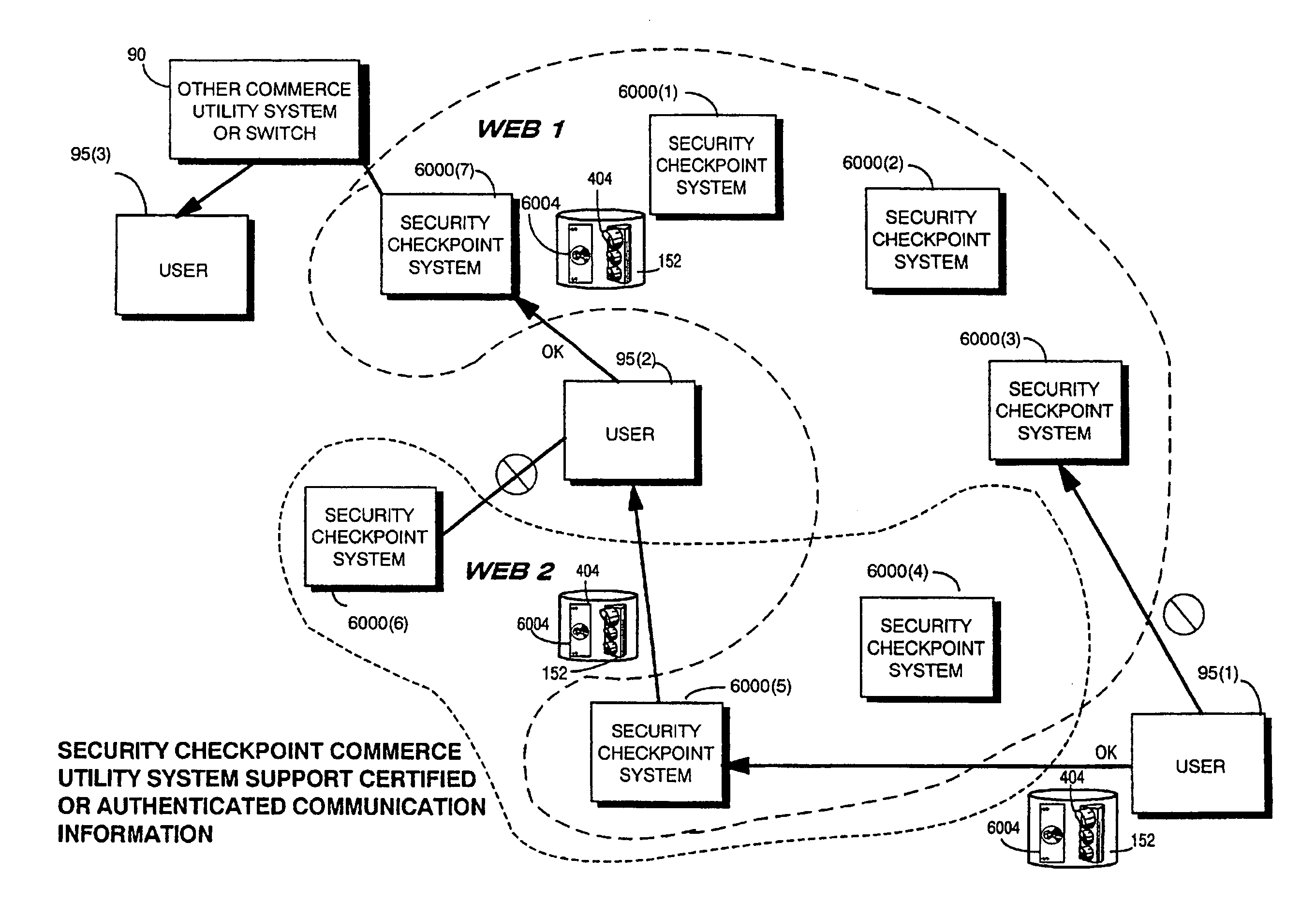
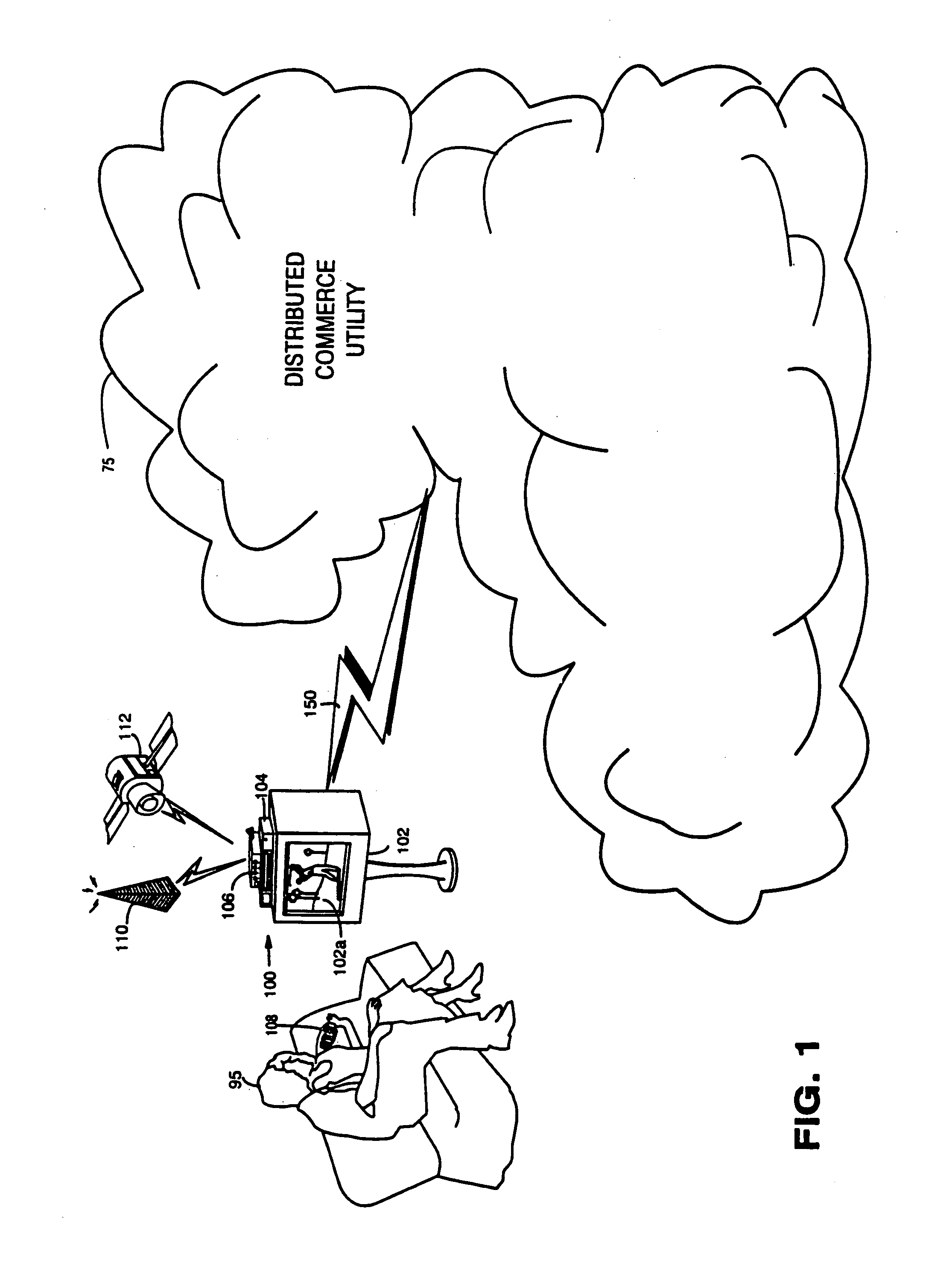
Trusted infrastructure support systems, methods and techniques for secure electronic commerce transaction and rights management
InactiveUS7165174B1Improve efficiencyIncrease flexibilityPublic key for secure communicationDigital data processing detailsTransaction managementBusiness management
The present inventions provide an integrated, modular array of administrative and support services for electronic commerce and electronic rights and transaction management. These administrative and support services supply a secure foundation for conducting financial management, rights management, certificate authority, rules clearing, usage clearing, secure directory services, and other transaction related capabilities functioning over a vast electronic network such as the Internet and / or over organization internal Intranets.These administrative and support services can be adapted to the specific needs of electronic commerce value chains. Electronic commerce participants can use these administrative and support services to support their interests, and can shape and reuse these services in response to competitive business realities.A Distributed Commerce Utility having a secure, programmable, distributed architecture provides administrative and support services. The Distributed Commerce Utility makes optimally efficient use of commerce administration resources, and can scale in a practical fashion to accommodate the demands of electronic commerce growth.The Distributed Commerce Utility may comprise a number of Commerce Utility Systems. These Commerce Utility Systems provide a web of infrastructure support available to, and reusable by, the entire electronic community and / or many or all of its participants.Different support functions can be collected together in hierarchical and / or in networked relationships to suit various business models and / or other objectives. Modular support functions can combined in different arrays to form different Commerce Utility Systems for different design implementations and purposes. These Commerce Utility Systems can be distributed across a large number of electronic appliances with varying degrees of distribution.
Owner:INTERTRUST TECH CORP
End-to-end service quality monitoring method and system in a radio network
ActiveUS20110096678A1Prevent data security threatGuaranteed continuous availabilityError preventionTransmission systemsQuality of serviceRadio networks
The present invention discloses a method and a system for service quality monitoring in a network comprising radio interfaces. The measurements are end-to-end measurements between the end user and chosen network element. The measurements are implemented using monitoring stations which can monitor the traffic passively or actively by transmitting test signals. The antenna beam directions of the monitoring stations can be controlled. The performance server works as a counterpart of the active tests. A reporting suite may define the performed measurements and it also collects the measurement data from different monitoring stations. Monitoring data from several corporate intranets can also be collected to an external server through internet connection.
Owner:7SIGNAL OY
Efficient large-scale access control for internet/intranet information systems
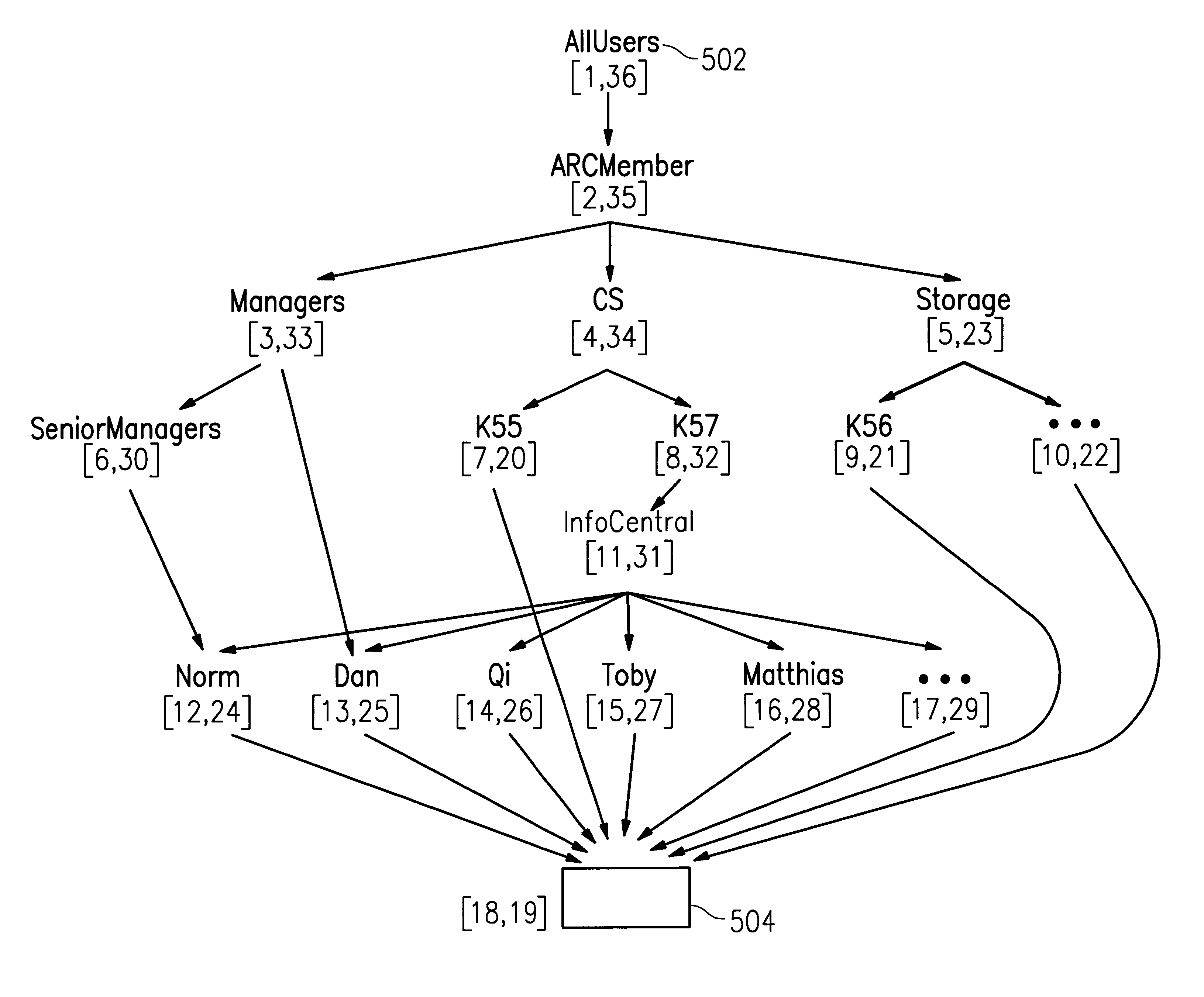
InactiveUS6219667B1Data processing applicationsDigital data processing detailsDecompositionInformation object
An efficient method and apparatus for regulating access to information objects stored in a database in which there are a large number of users and access groups. The invention uses a representation of a hierarchical access group structure in terms of intervals over a set of integers and a decomposition scheme that reduces any group structure to ones that have interval representation. This representation allows the problem for checking access rights to be reduced to an interval containment problem. An interval tree, a popular data structure in computational geometry, may be implemented to efficiently execute the access-right checking method.
Owner:IBM CORP
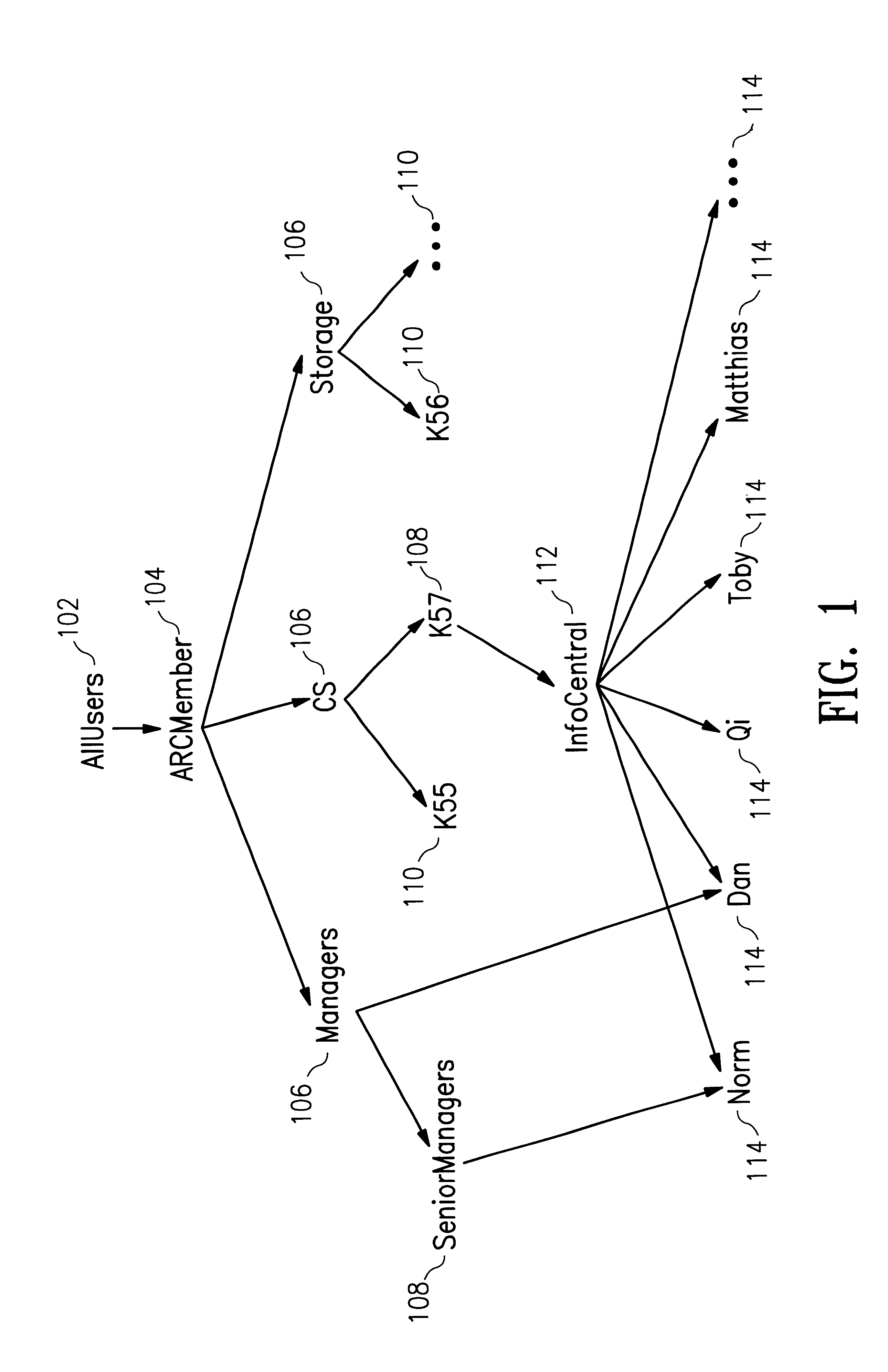
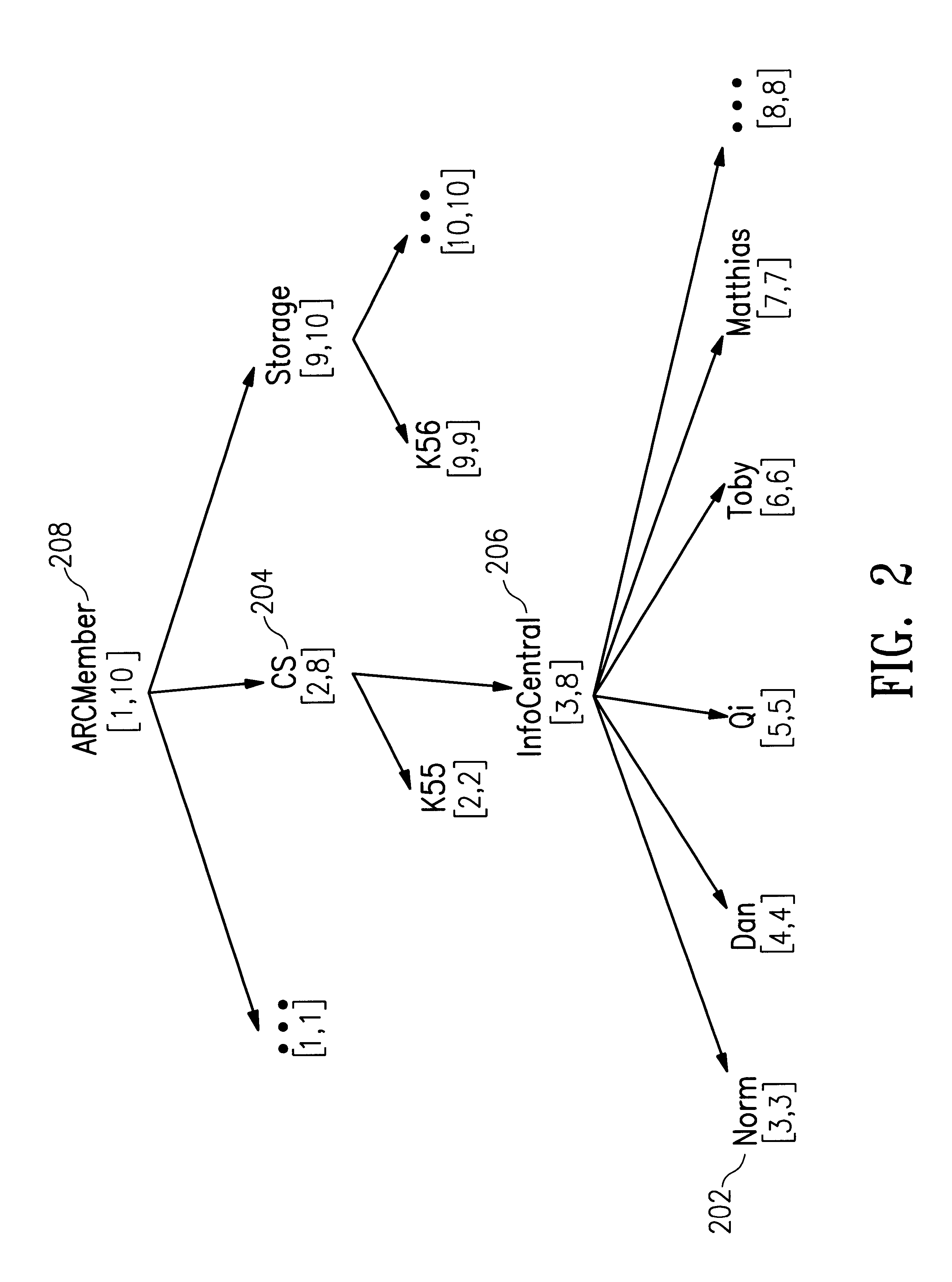
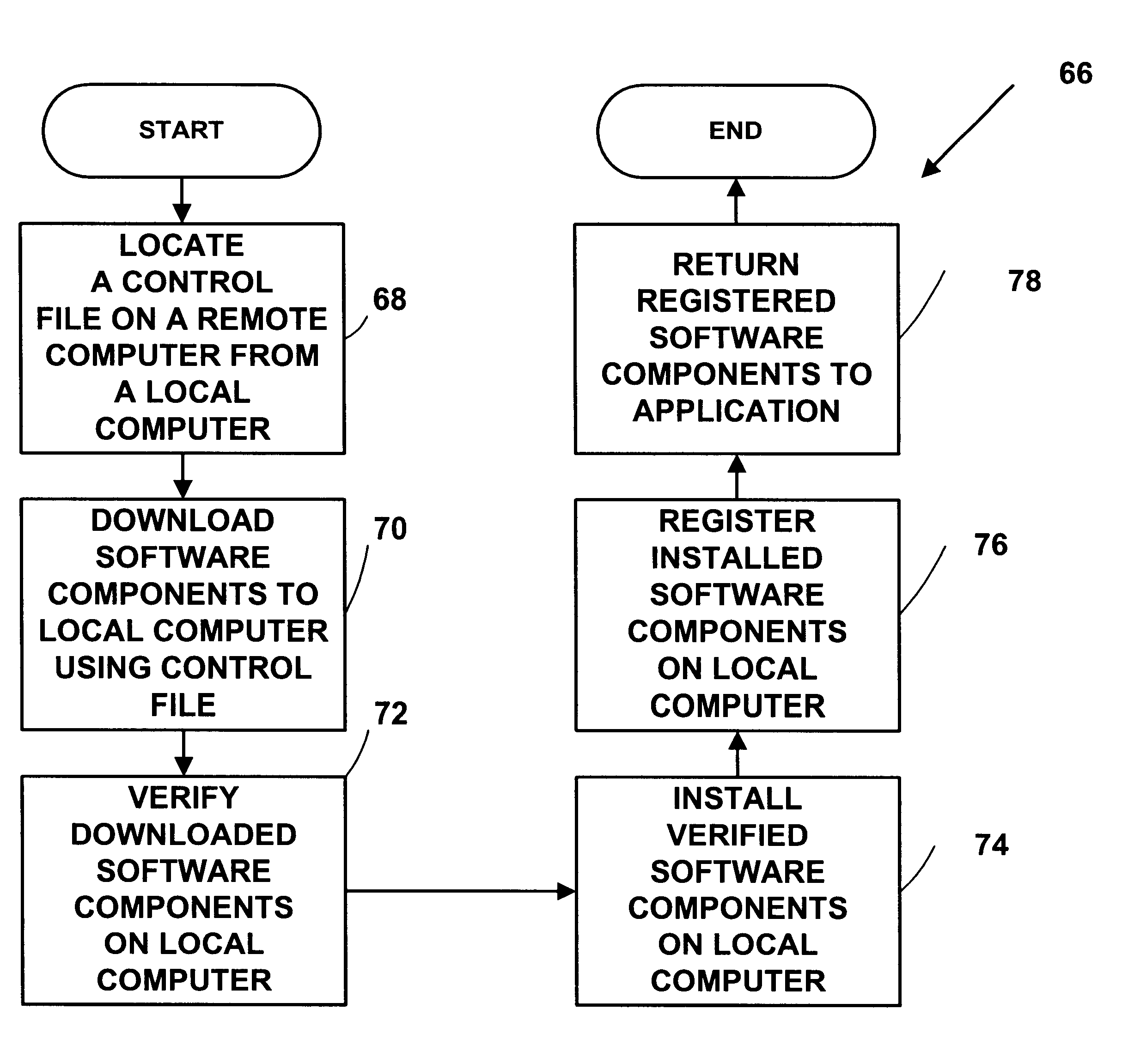
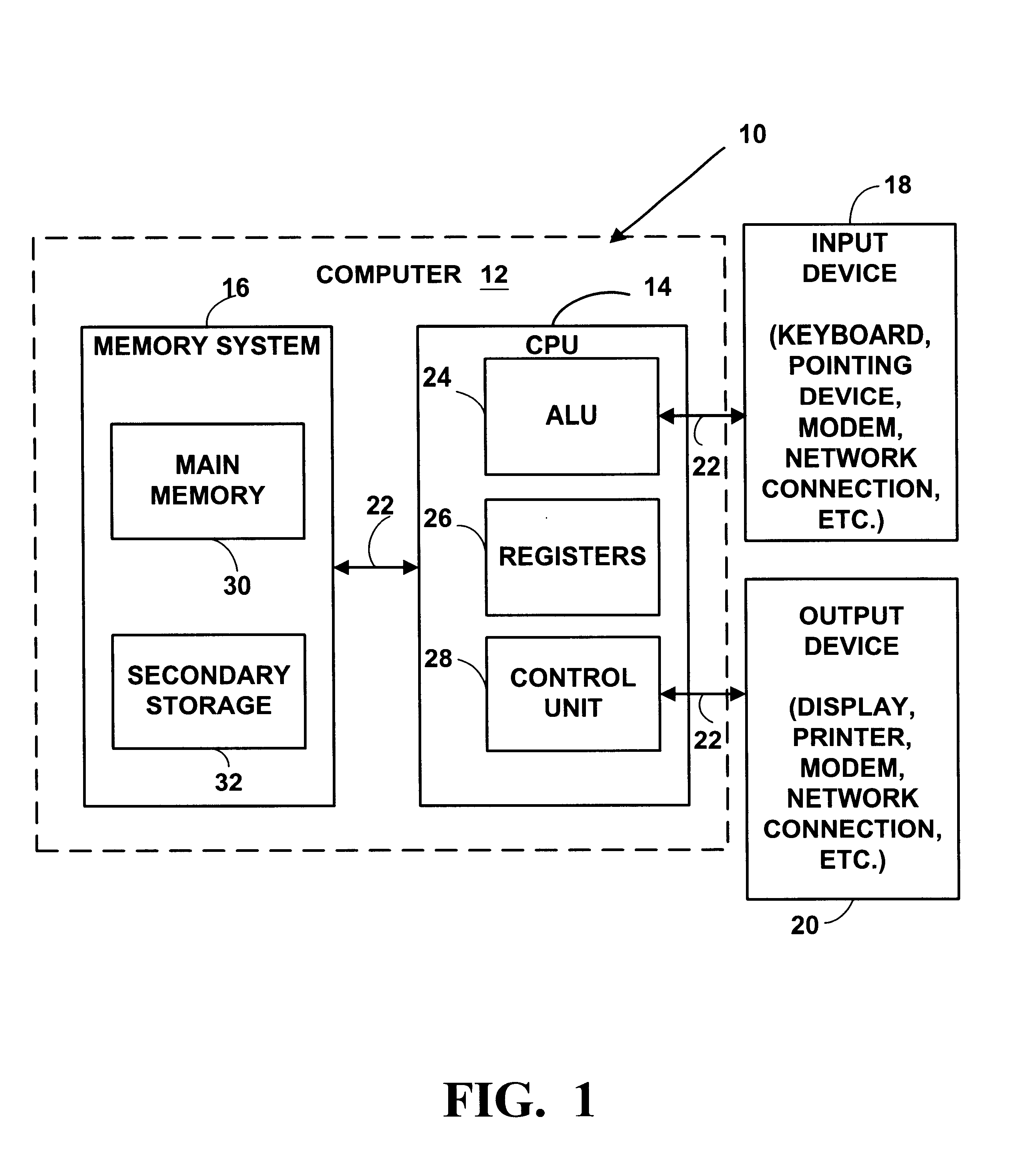
Automatic software downloading from a computer network
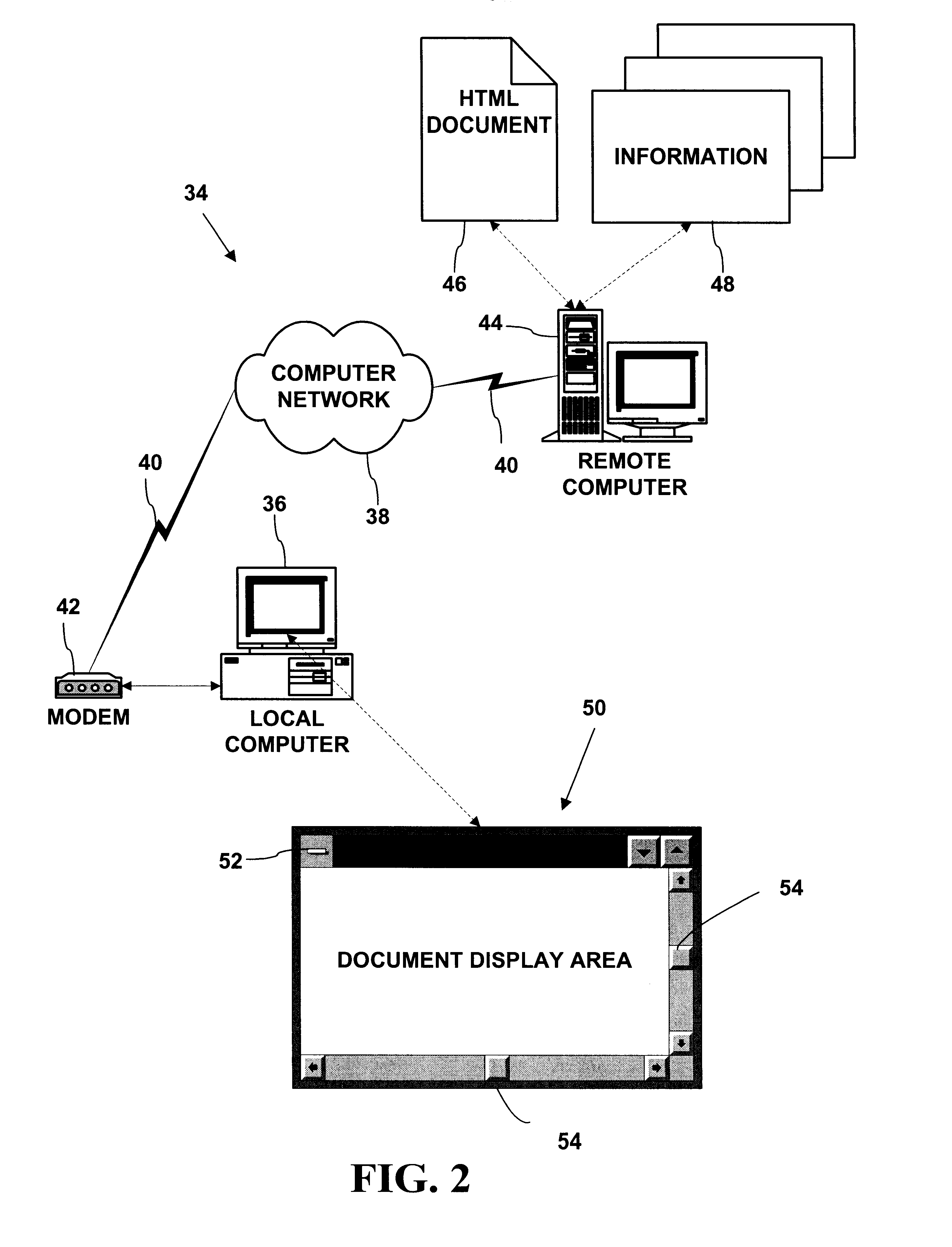
Methods and systems automatically download computer software components from a computer network like the Internet or an intranet. The methods and systems can be used to provide dynamic or interactive multimedia components in HTML documents with HTML <OBJECT> tags. The HTML <OBJECT> tags can contain parameters including uniform resource locators (URLs) which reference dynamic or interactive multimedia components on remote computers. Network browsers and other applications can obtain computer software components from a computer network like the Internet or an intranet in a uniform, portable, architecture-neutral, robust manner. The computer software components obtained can be used to provide a variety of new multimedia functionality to an application program.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com