Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
11766 results about "Structure of Management Information" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, the Structure of Management Information (SMI), an adapted subset of ASN.1, operates in Simple Network Management Protocol (SNMP) to define sets ("modules") of related managed objects in a Management Information Base (MIB).
Multimedia surveillance and monitoring system including network configuration
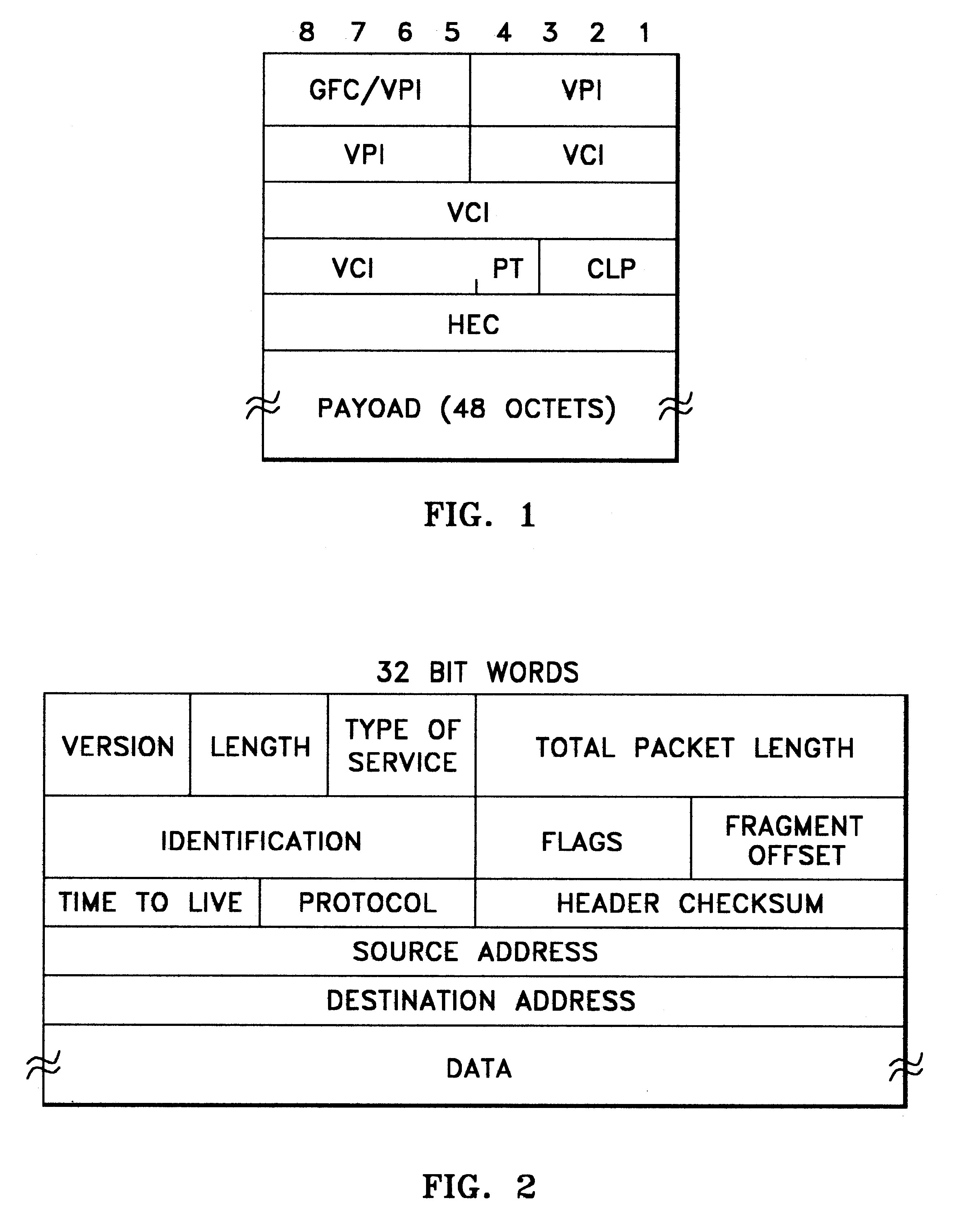
InactiveUS6970183B1High bandwidthSignalling system detailsColor television detailsVideo monitoringStructure of Management Information
A comprehensive, wireless multimedia surveillance and monitoring system provides a combination of megapixel digital camera capability with full motion video surveillance with a network, including network components and appliances such as wiring, workstations, and servers with the option of geographical distribution with various wide area carriers. The full service, multi-media surveillance system is capable of a wide range of monitoring techniques utilizing digital network architecture and is adapted for transmitting event data, video and / or image monitoring information, audio signals and other sensor and detector data over significant distances using digital data transmission over a LAN, wireless LAN, Intranet or Internet for automatic assessment and response including dispatch of response personnel. Both wired and wireless appliance and sensor systems may be employed. GPS dispatching is used to locate and alert personnel as well as to indicate the location of an event. Automatic mapping and dispatch permits rapid response. The wireless LAN connectivity permits local distribution of audio, video and image data over a relatively high bandwidth without requirement of a license and without relying on a common carrier and the fees associated therewith. The surveillance system may be interfaced with a WAN (wide area Network) or the Internet for providing a worldwide, low cost surveillance system with virtually unlimited geographic application. Centralized monitoring stations have access to all of the surveillance data from various remote locations via the Internet or the WAN. A server provides a centralized location for data collection, alarm detection and processing, access control, dispatch processing, logging functions and other specialized functions. The server may be inserted virtually anywhere in the Intranet / Internet network. The topology of the network will be established by the geographic situation of the installation. Appropriate firewalls may be set up as desired. The server based system permits a security provider to have access to the appliance and sensor and surveillance data or to configure or reconfigure the system for any station on the network.
Owner:PR NEWSWIRE
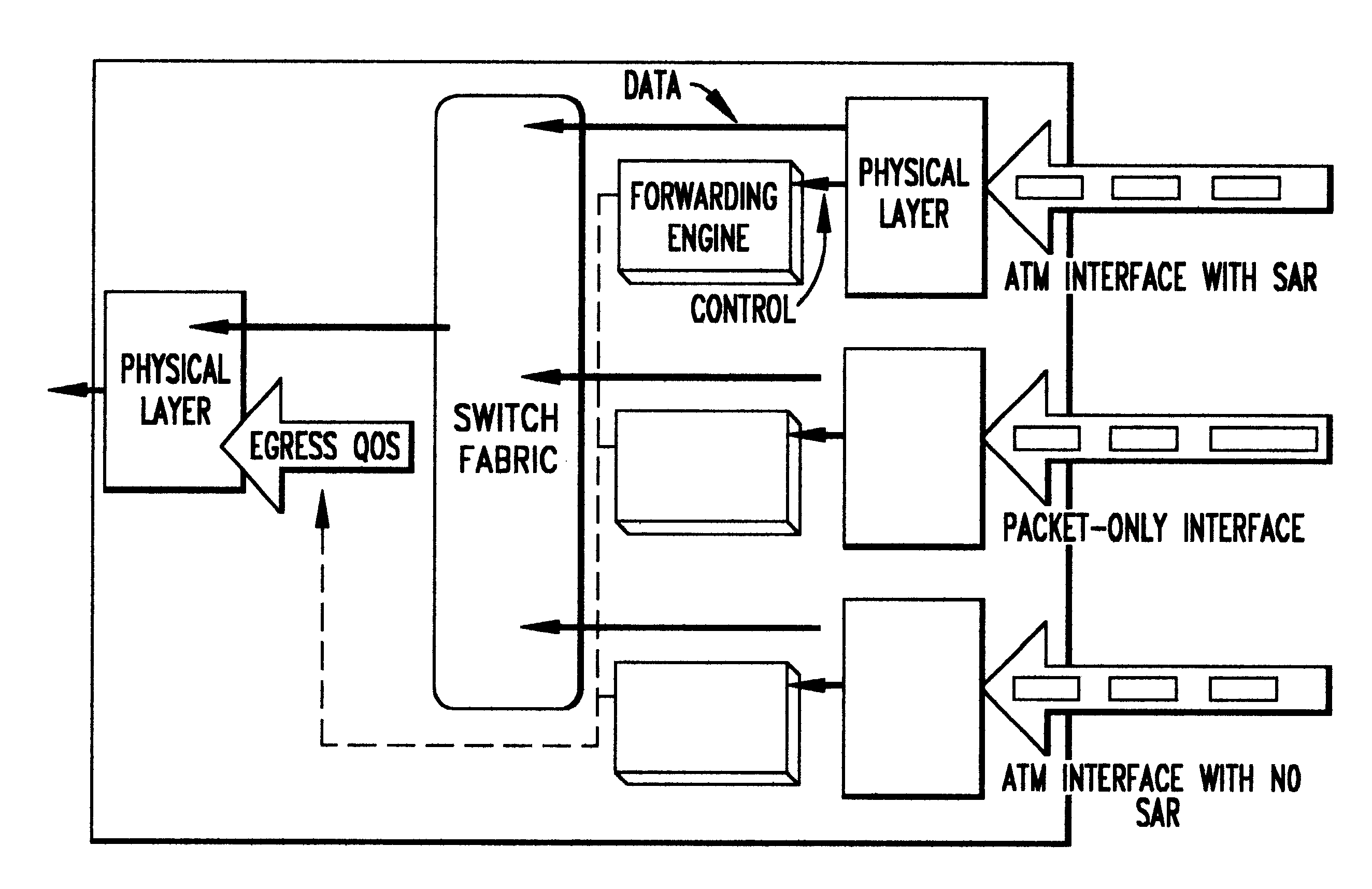
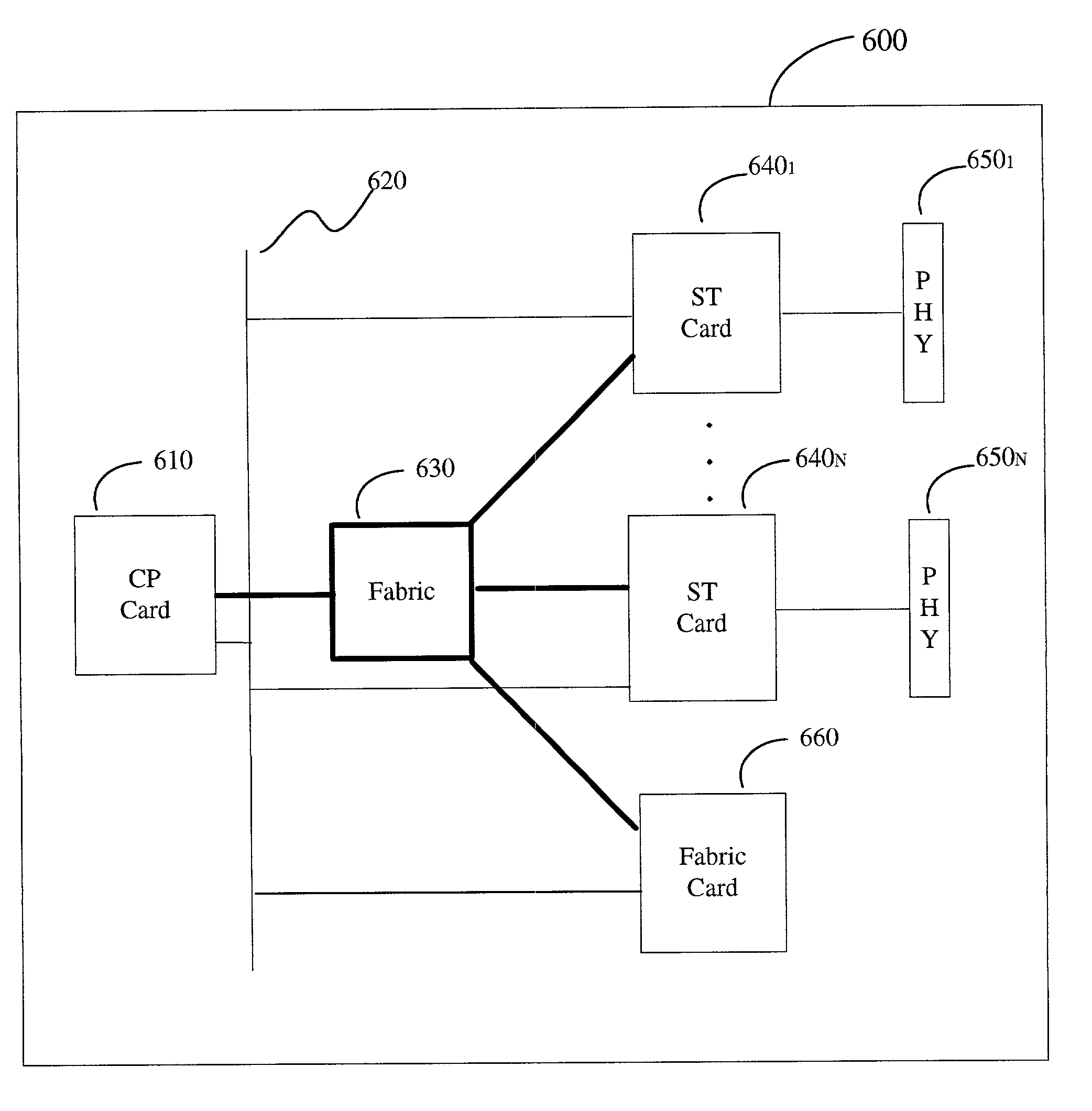
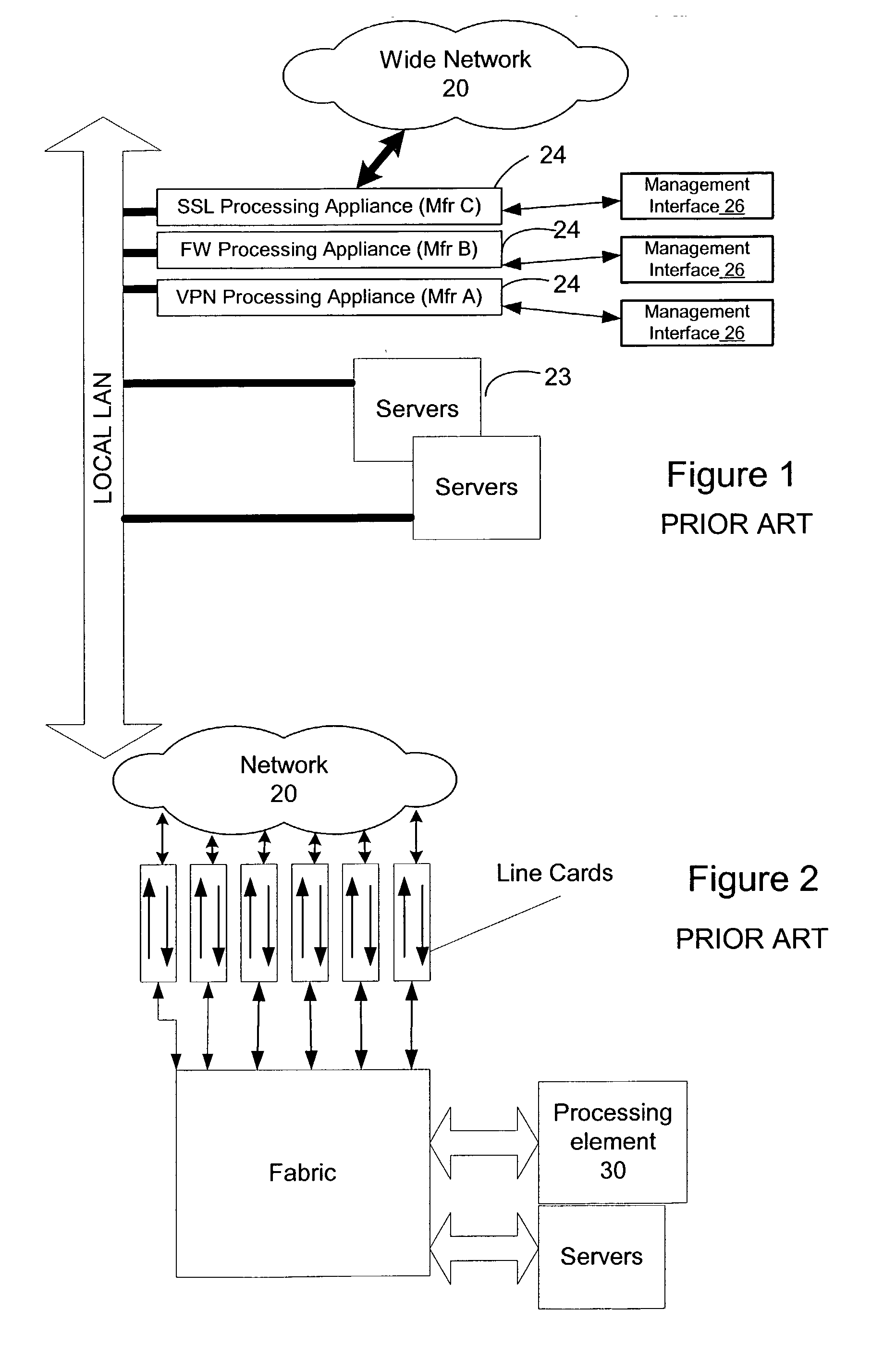
System architecture for and method of processing packets and/or cells in a common switch
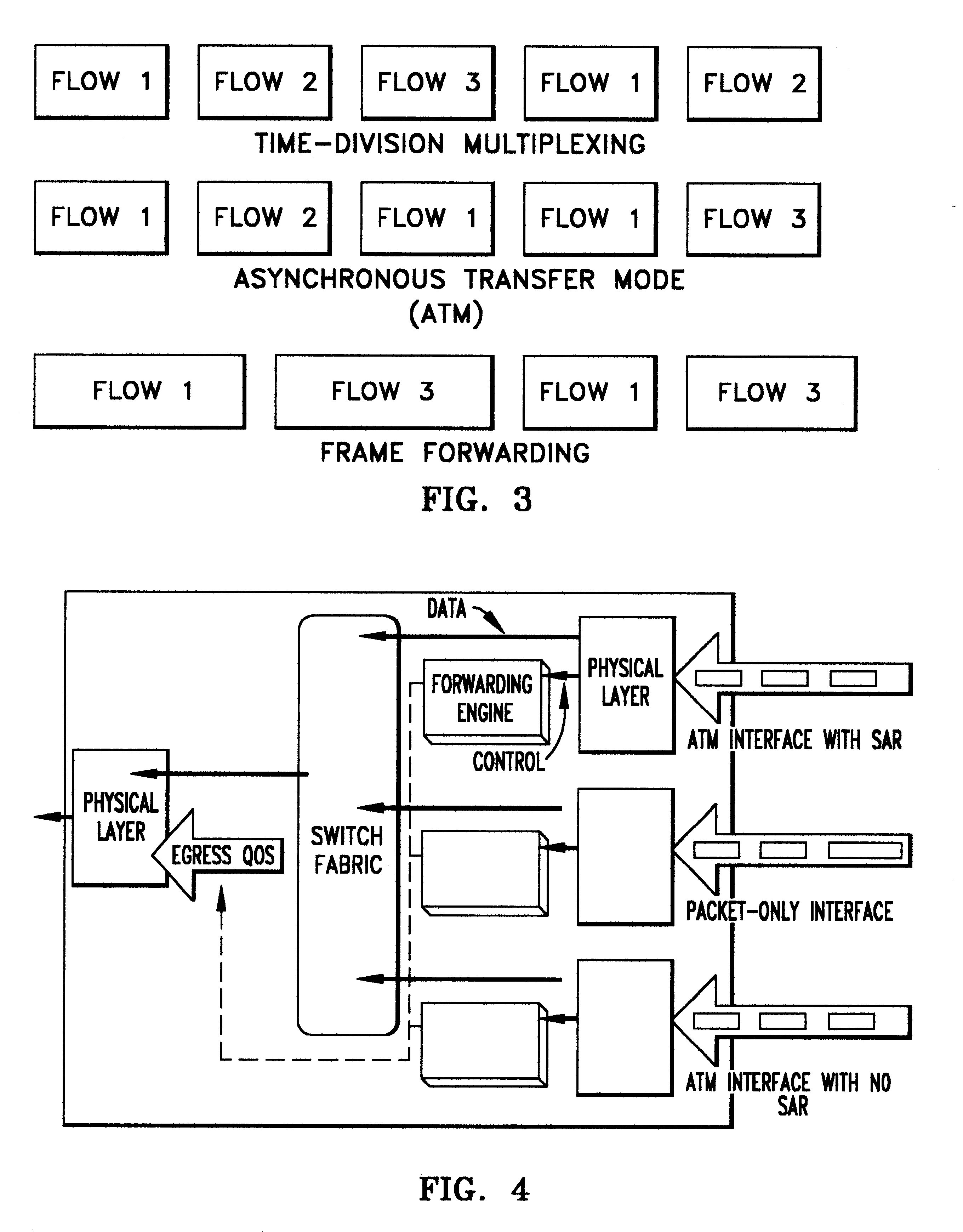
InactiveUS6259699B1Without impacting performance aspectPromote resultsData switching by path configurationStore-and-forward switching systemsAtm switchingQos management
A novel networking architecture and technique for transmitting both cells and packets or frames across a common switch fabric, effected, at least in part, by utilizing a common set of algorithms for the forwarding engine (the ingress side) and a common set of algorithms for the QoS management (the egress part) that are provided for each I / O module to process packet / cell information without impacting the correct operation of ATM switching and without transforming packets into cells for transfer across the switch fabric.
Owner:WSOU INVESTMENTS LLC +1
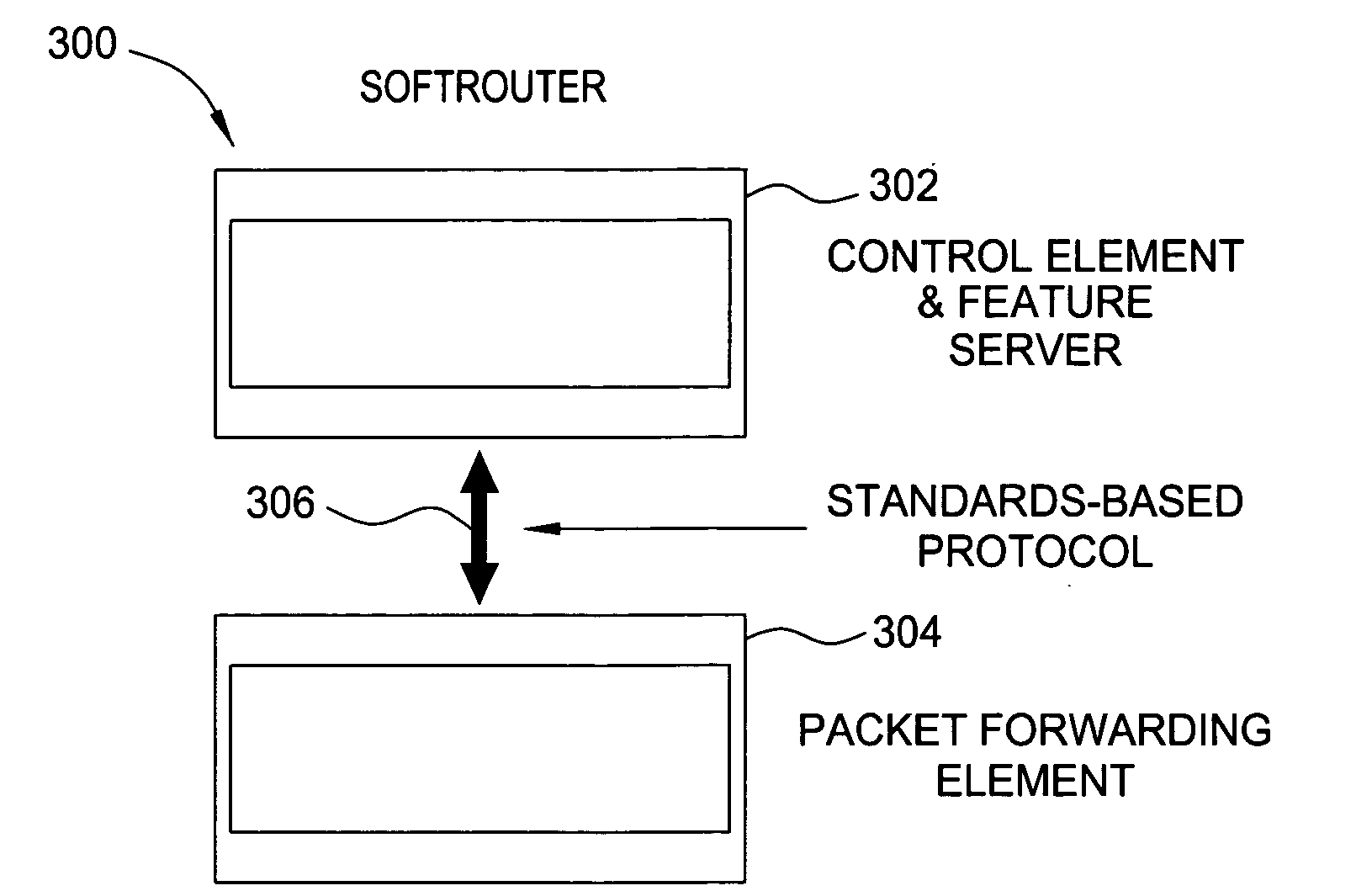
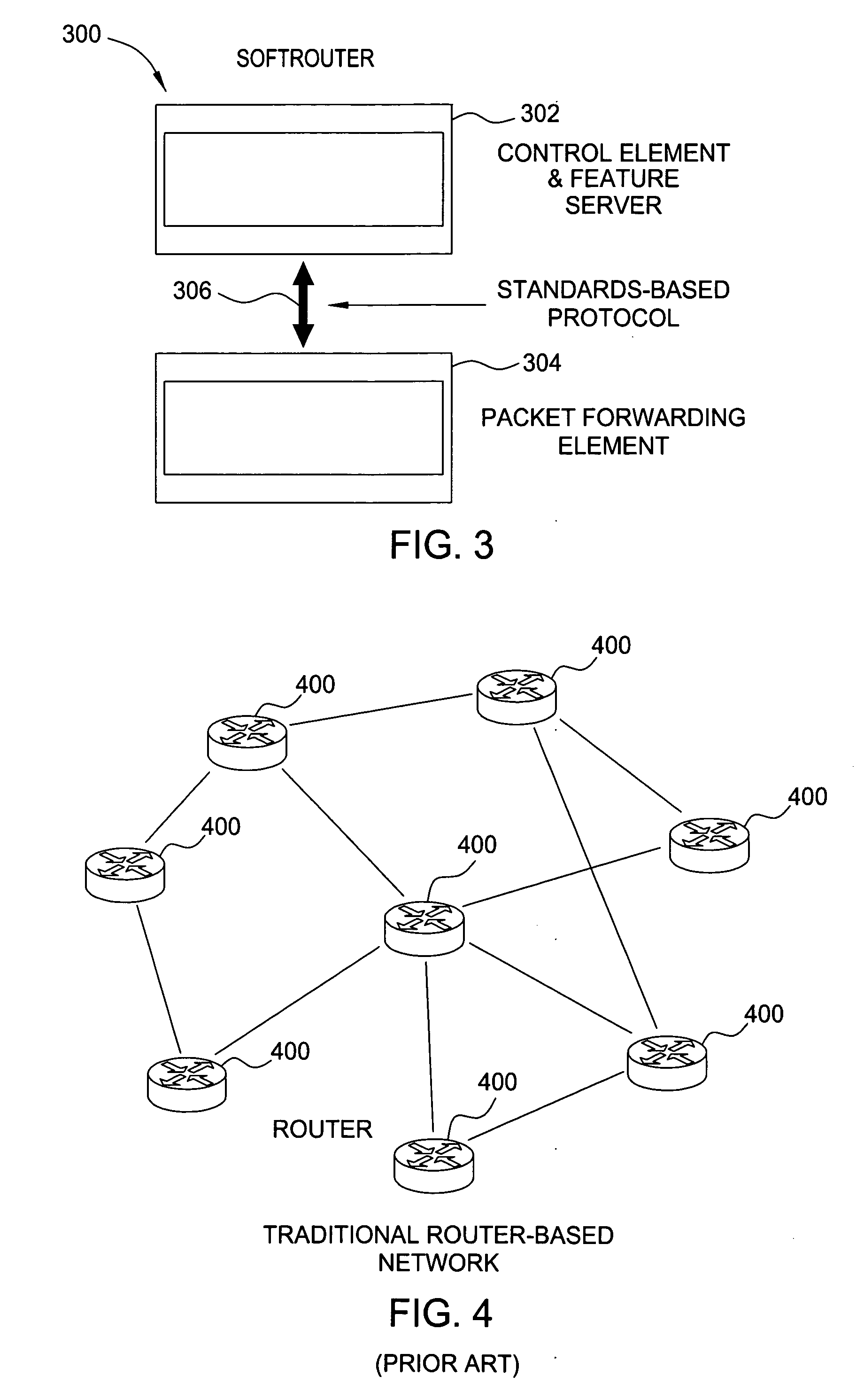
Softrouter separate control network
ActiveUS20060092976A1Time-division multiplexData switching by path configurationTraffic capacityExtensibility
An embodiment of the exemplary SoftRouter architecture includes two physically separate networks, a control plane network and a data plane network. The data plane network is one physical network for the data traffic, while the control plane network is another physical network for the control traffic. The topology of the data plane network is made up of interconnected forwarding elements (FEs). The topology of the control plane network is made up interconnected control elements (CEs). This physical independence of the control plane network from the data plane network provides for a secure mechanism to communicate among the CEs in the control plane network. In addition, this physical independence provides improved reliability and improved scalability, when compared to the traditional router architecture, where control plane message are in-band with the data plane.
Owner:NOKIA TECHNOLOGLES OY
System and method for configuring computer applications and devices using inheritance
InactiveUS20020091819A1Multiple digital computer combinationsData switching networksStructure of Management InformationNetwork topology
A system and method using inheritance for the configuration, management, and / or monitoring of computer applications and devices via a computer network are disclosed. The method generally comprises determining a hierarchical tree structure based upon locations of devices in a network topology, each device being a node in the hierarchical tree structure, determining policies for each node in the hierarchical tree structure to be enforced by an agent corresponding to each node, the agent being in communication with the device and the resources corresponding to the device, and communicating the policy to the corresponding agent, wherein the policies corresponding to the resources of each device are selectively inherited along the hierarchical tree structure of the network directory.
Owner:MCAFEE INC
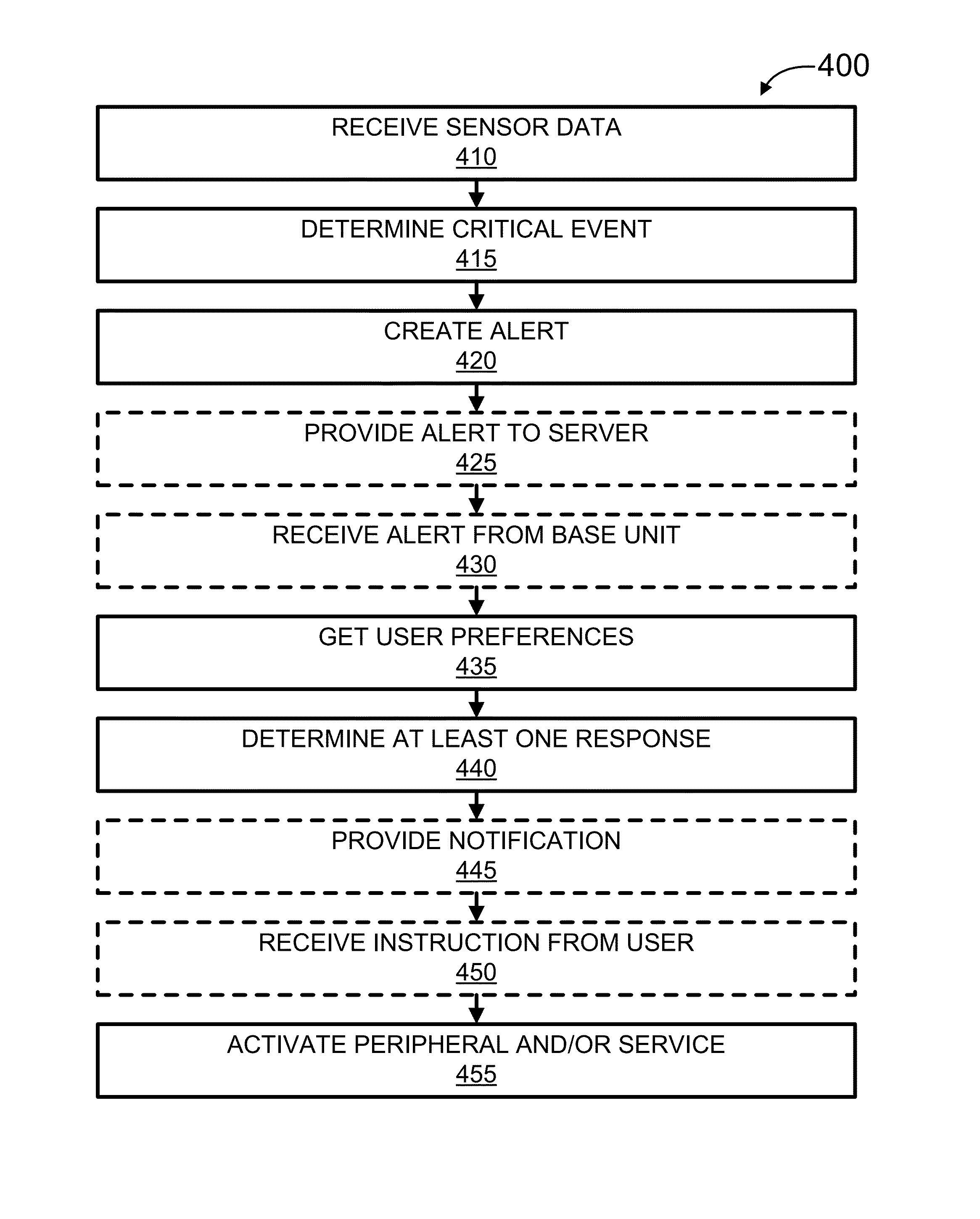
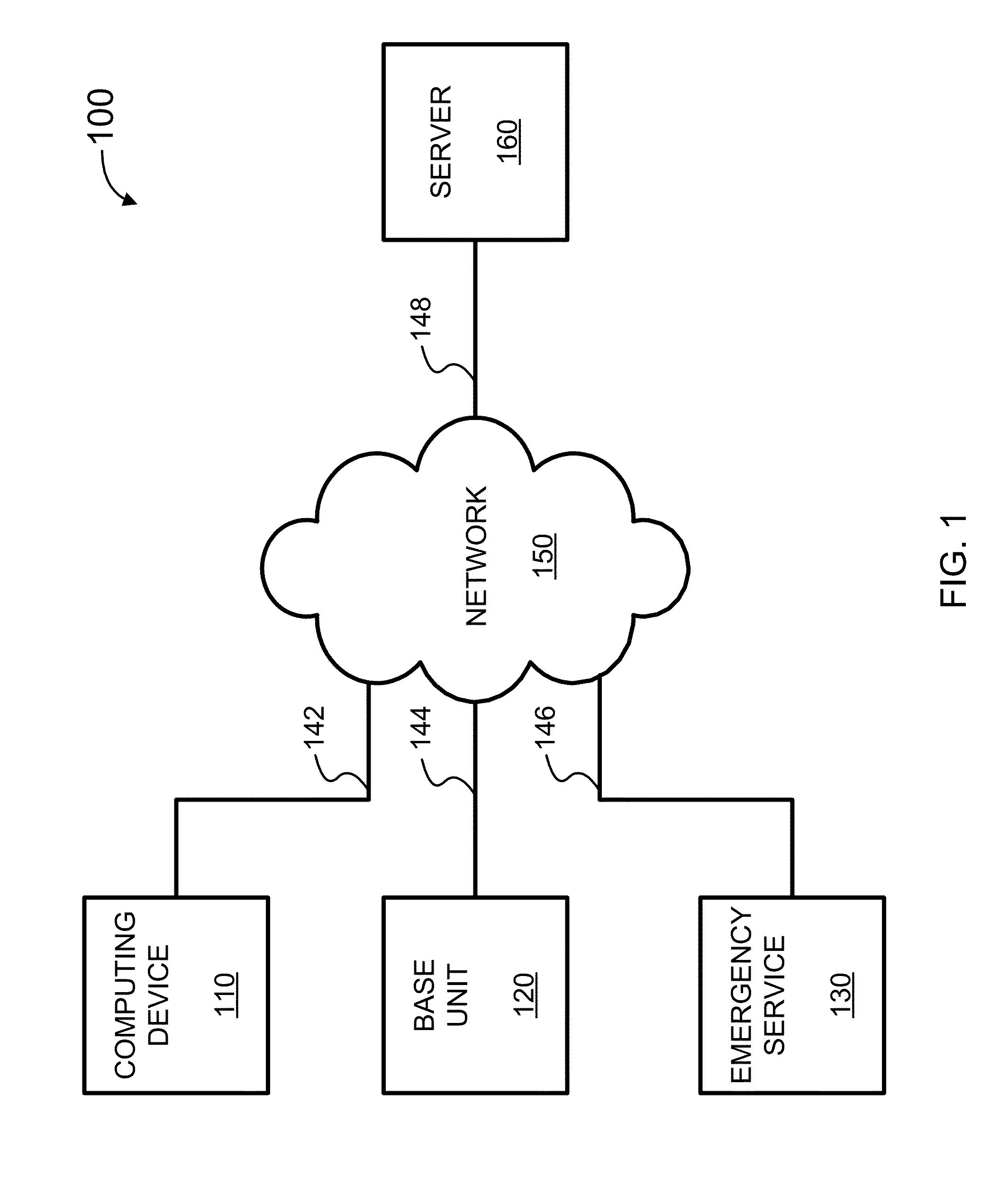
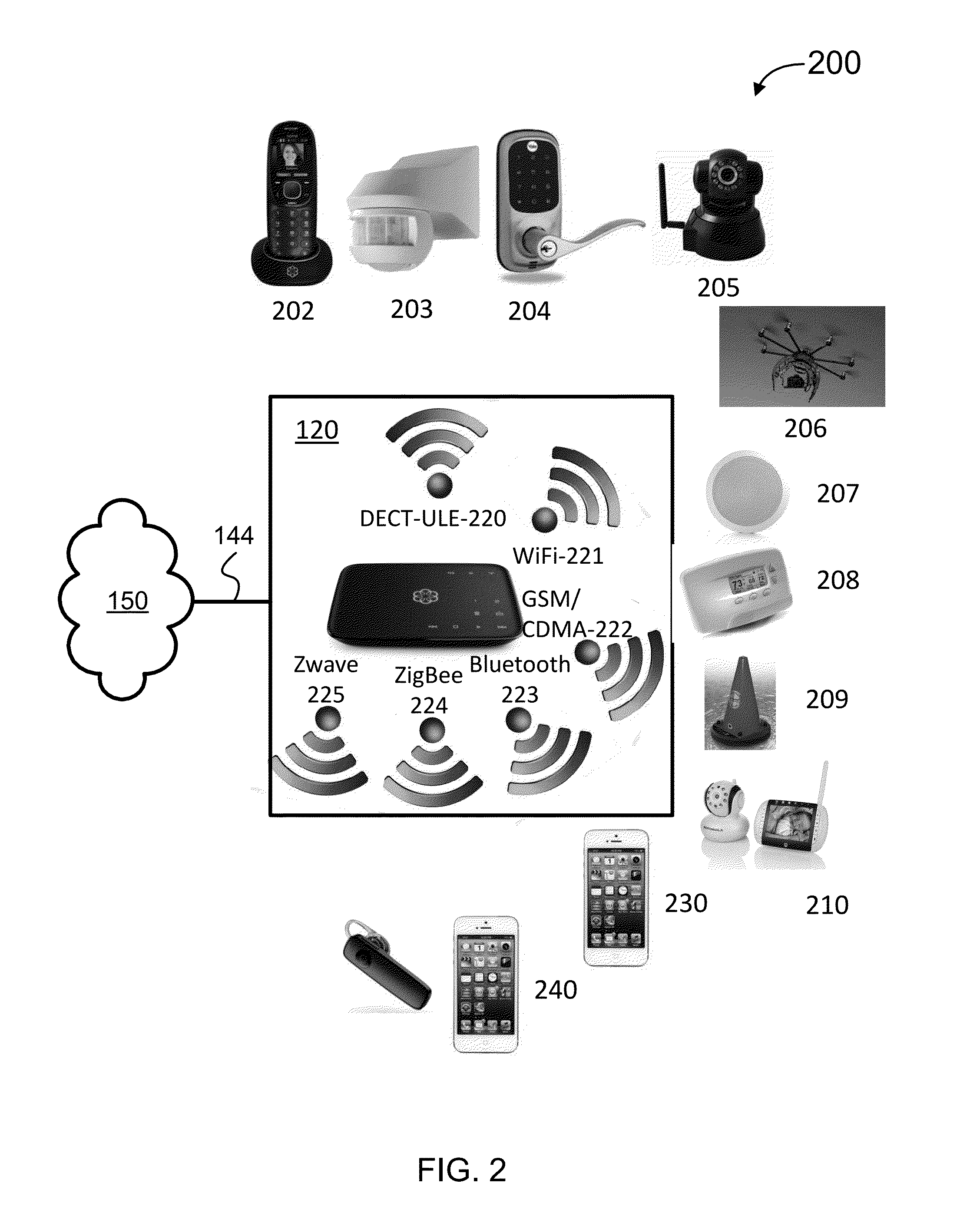
Security Monitoring and Control
ActiveUS20150339912A1Burglar alarm mechanical actuationControl systemStructure of Management Information
Systems, methods, and software for monitoring and controlling a security system for a structure are provided herein. An exemplary method may include receiving sensor data from at least one first peripheral, the sensor data associated with at least one of activity inside and activity outside of a structure; determining a critical event based in part on the sensor data; creating an alert based in part on the critical event; getting user preferences associated with at least one of a user and a base unit; determining a response based in part on the alert and user preferences; and activating at least one of a second peripheral and a service based in part on the response.
Owner:OOMA
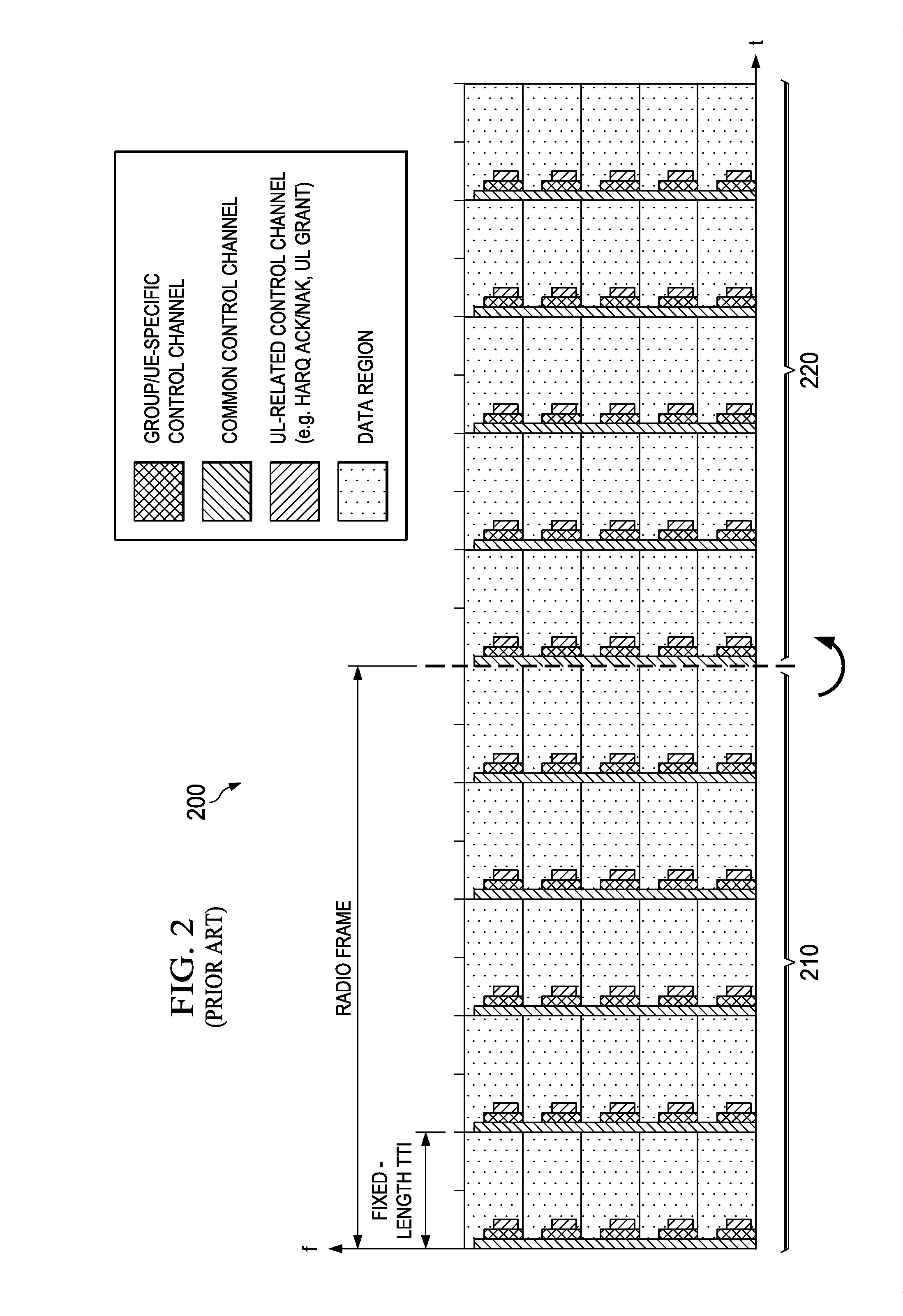
System and Method for Adaptive Transmission Time Interval (TTI) Structure
ActiveUS20140071954A1Length be adaptNetwork traffic/resource managementTime-division multiplexQuality of serviceStructure of Management Information
Methods and devices are provided for communicating data in a wireless channel. In one example, a method includes adapting the transmission time interval (TTI) length of transport container for transmitting data in accordance with a criteria. The criteria may include (but is not limited to) a latency requirement of the data, a buffer size associated with the data, a mobility characteristic of a device that will receive the data. The TTI lengths may be manipulated for a variety of reasons, such as for reducing overhead, satisfy quality of service (QoS) requirements, maximize network throughput, etc. In some embodiments, TTIs having different TTI lengths may be carried in a common radio frame. In other embodiments, the wireless channel may partitioned into multiple bands each of which carrying (exclusively or otherwise) TTIs having a certain TTI length.
Owner:HUAWEI TECH CO LTD
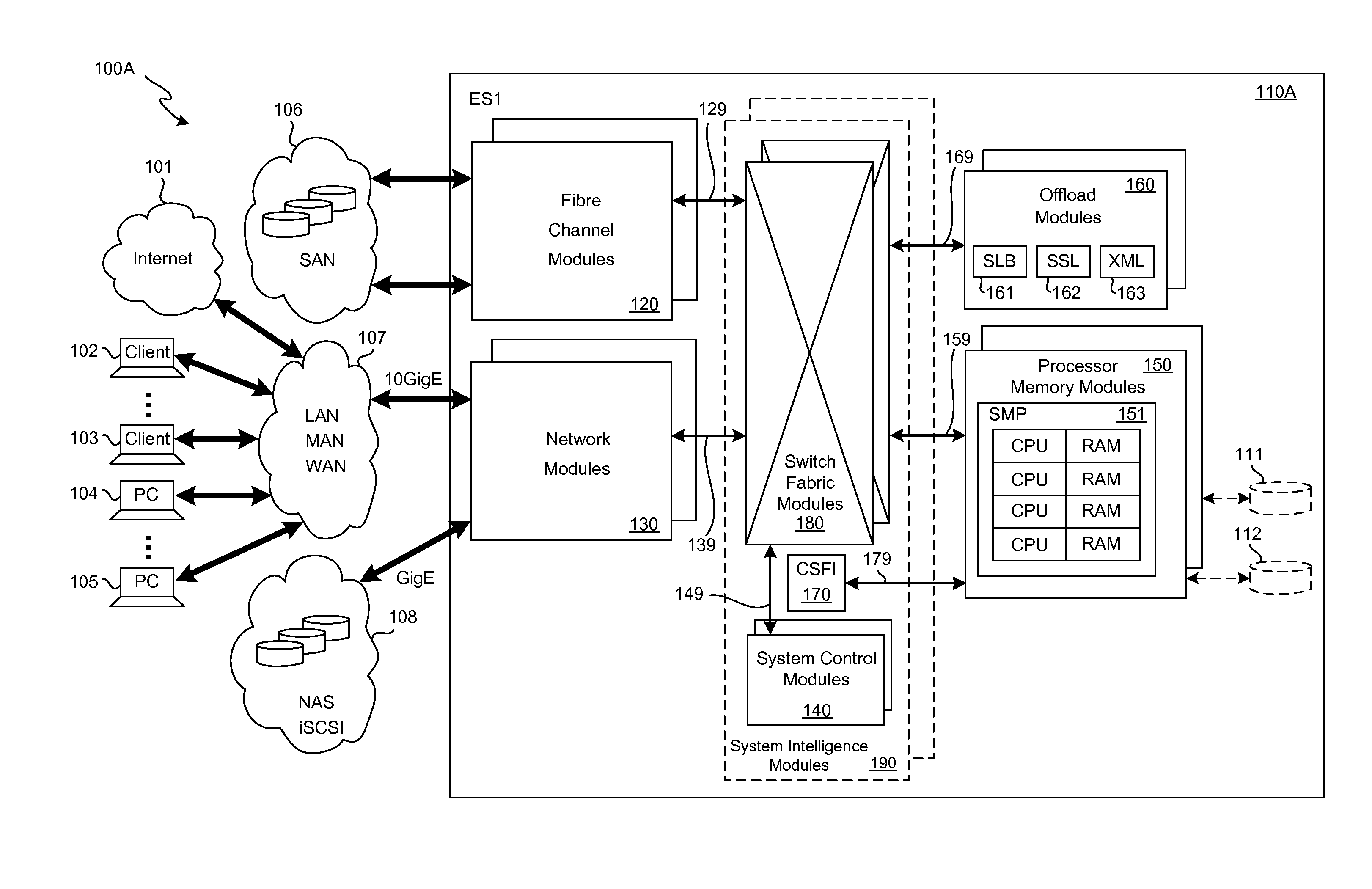
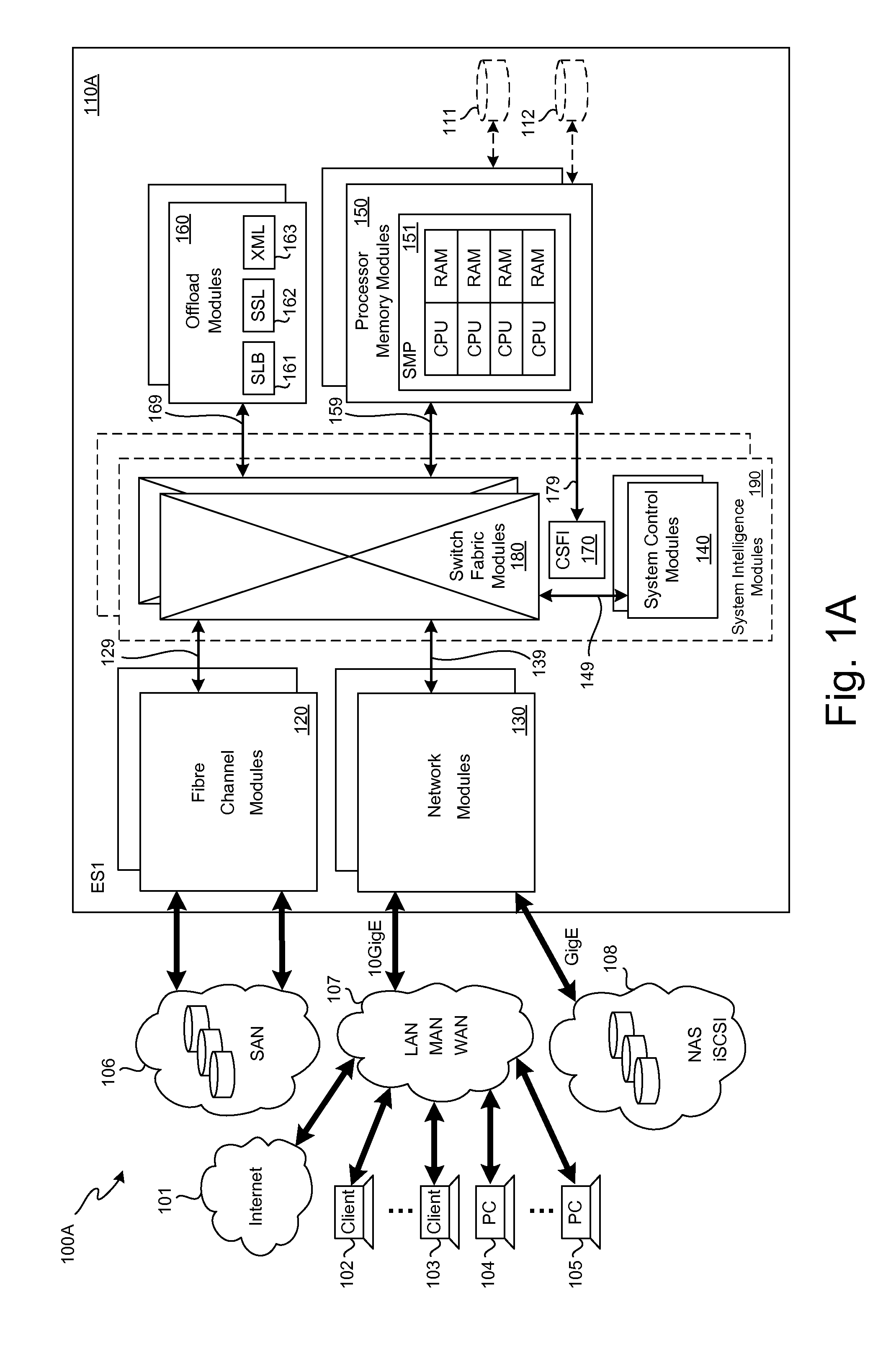
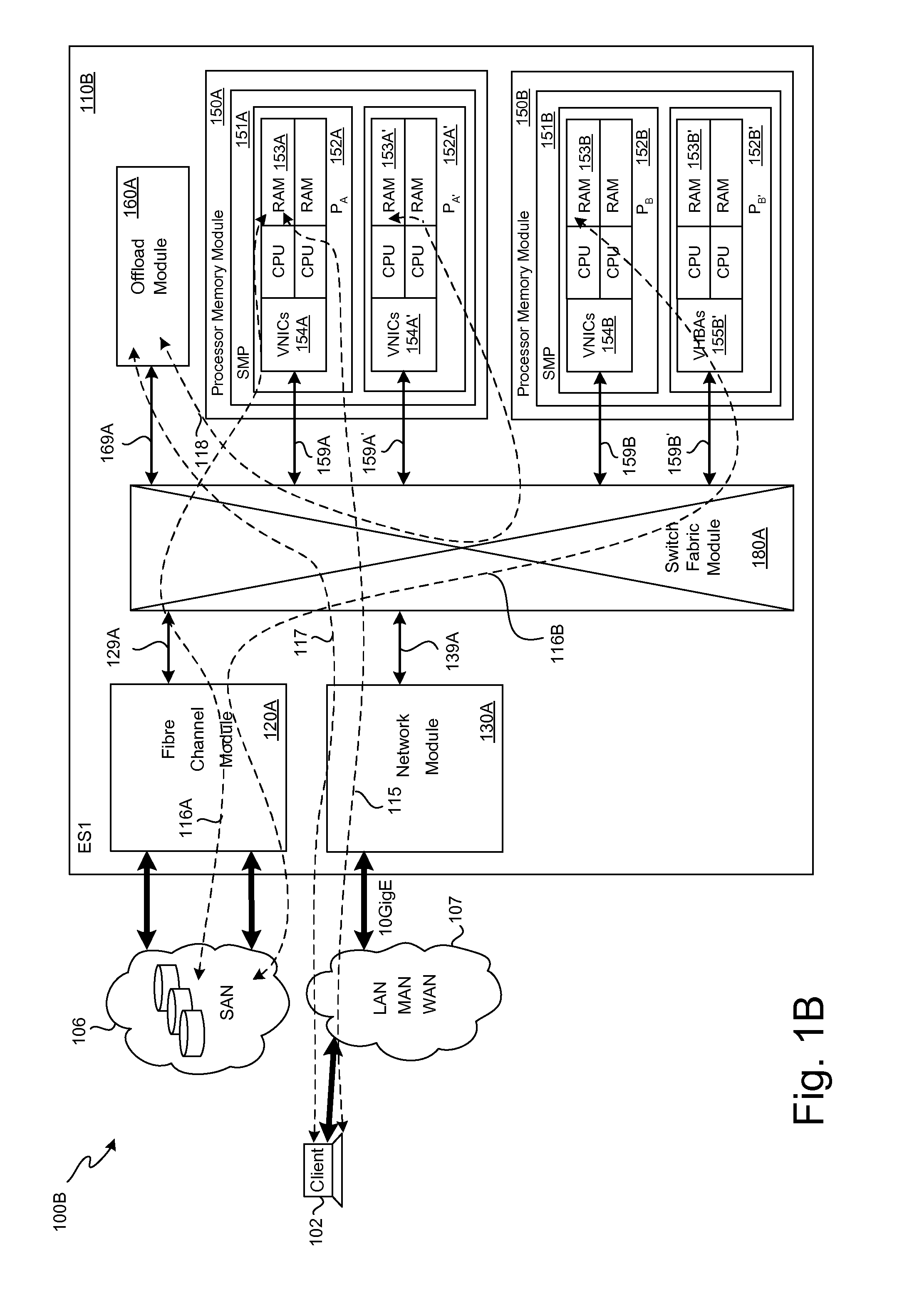
Storage traffic communication via a switch fabric in accordance with a VLAN
ActiveUS20130151646A1Improve performanceImprove efficiencyDigital computer detailsTransmissionTraffic capacityControl store
A plurality of SMP modules and an IOP module communicate storage traffic via respective corresponding I / O controllers coupled to respective physical ports of a switch fabric by addressing cells to physical port addresses corresponding to the physical ports. One of the SMPs executes initiator software to partially manage the storage traffic and the IOP executes target software to partially manage the storage traffic. Storage controllers are coupled to the IOP, enabling communication with storage devices, such as disk drives, tape drives, and / or networks of same. Respective network identification registers are included in each of the I / O controller corresponding to the SMP executing the initiator software and the I / O controller corresponding to the IOP. Transport of the storage traffic in accordance with a particular VLAN is enabled by writing a same particular value into each of the network identification registers.
Owner:ORACLE INT CORP
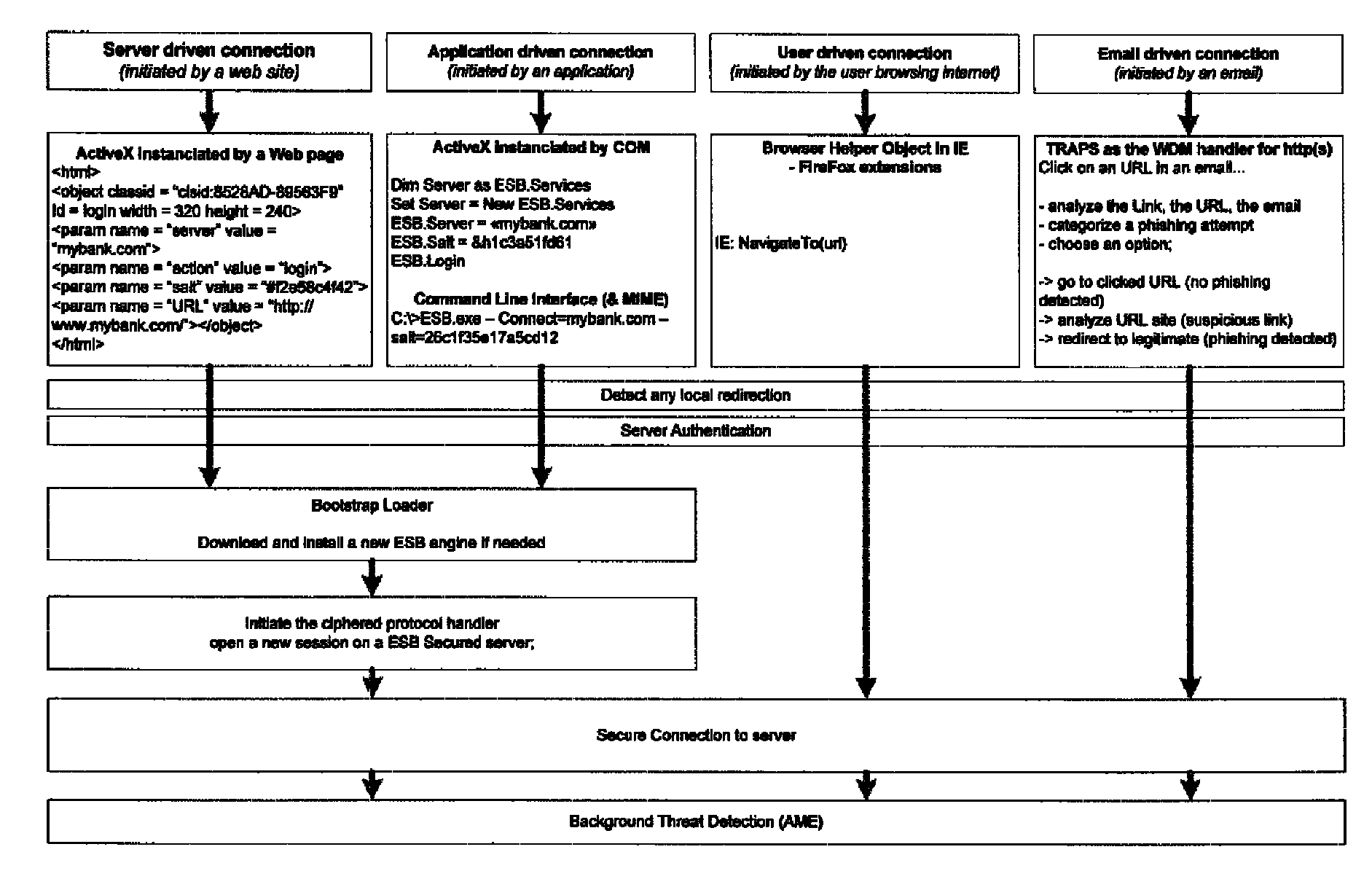
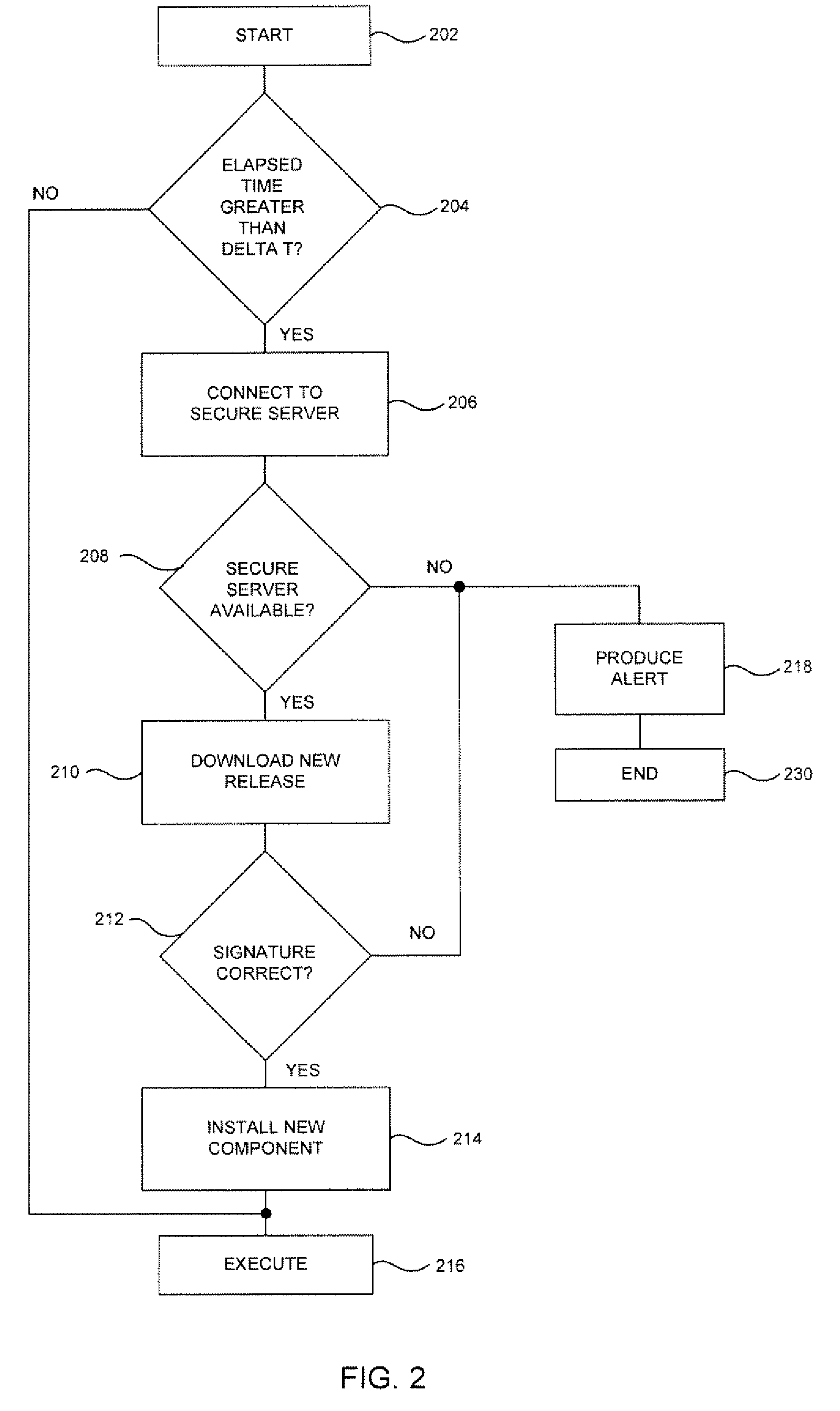
System and method for authentication, data transfer, and protection against phishing
ActiveUS8578166B2Key distribution for secure communicationDigital data processing detailsElectronic communicationStructure of Management Information
Methods and systems for secure electronic data communication over public communication networks. A secure data communication component may be utilized to implement a communication protocol. New versions of the data communication component may be generated, with each version containing a different communication protocol. Source code of the data communication component may be modified using a polymorph engine to create a functionally-equivalent component having a different code structure. An anti-phishing component may intercept a link in an electronic communication activated by a user, analyze the link and the electronic communication, determine a phishing risk to the user posed by the link, and direct the user to a location indicated by the link or redirect the user to a valid location. A server authentication component may detect and prevent DNS attacks, injections, and defacing activities.
Owner:MORGAMON
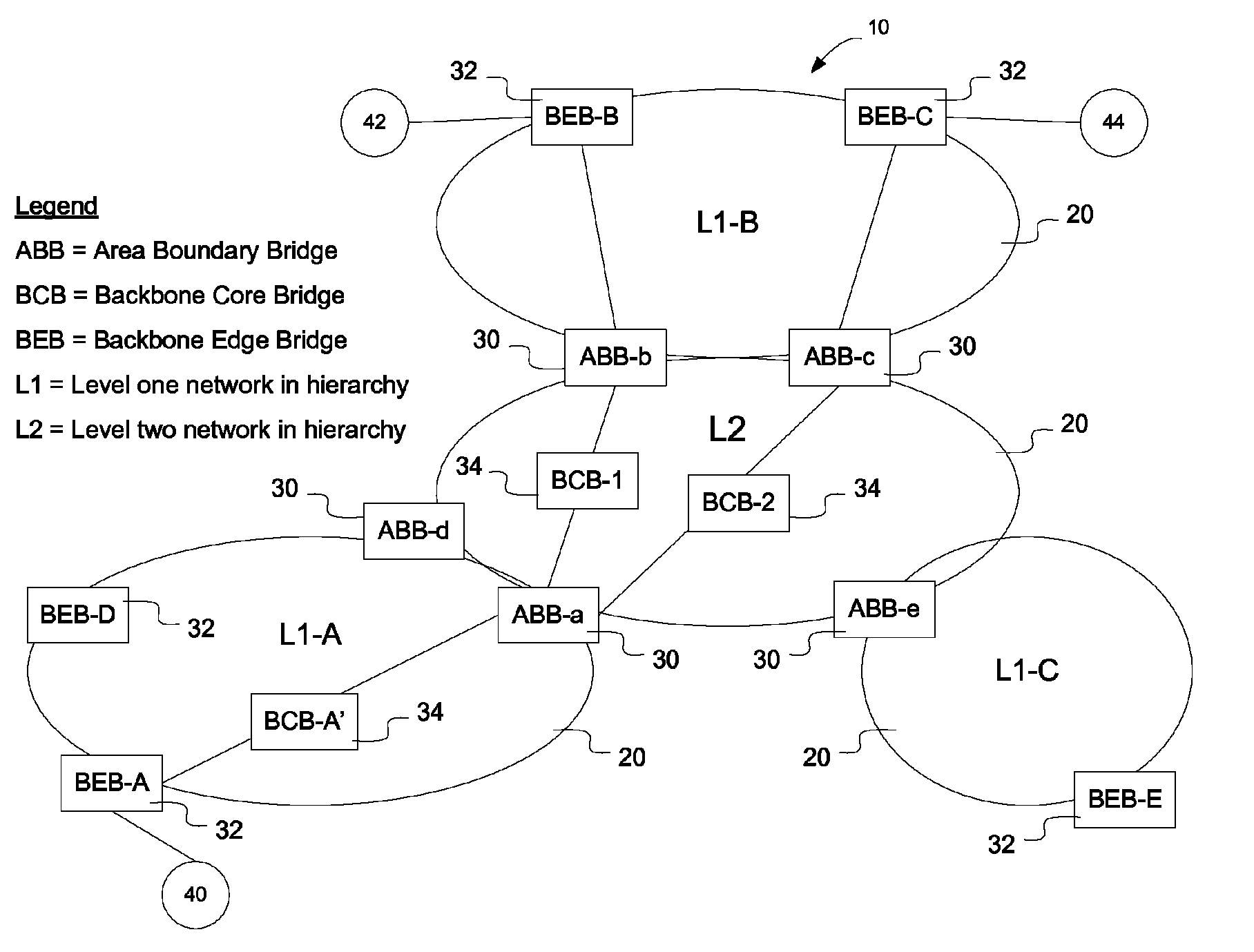
Method and apparatus for exchanging routing information and the establishment of connectivity across multiple network areas
InactiveUS8223668B2Easy to operateMultiple digital computer combinationsNetworks interconnectionStructure of Management InformationNetwork structure
Owner:RPX CLEARINGHOUSE
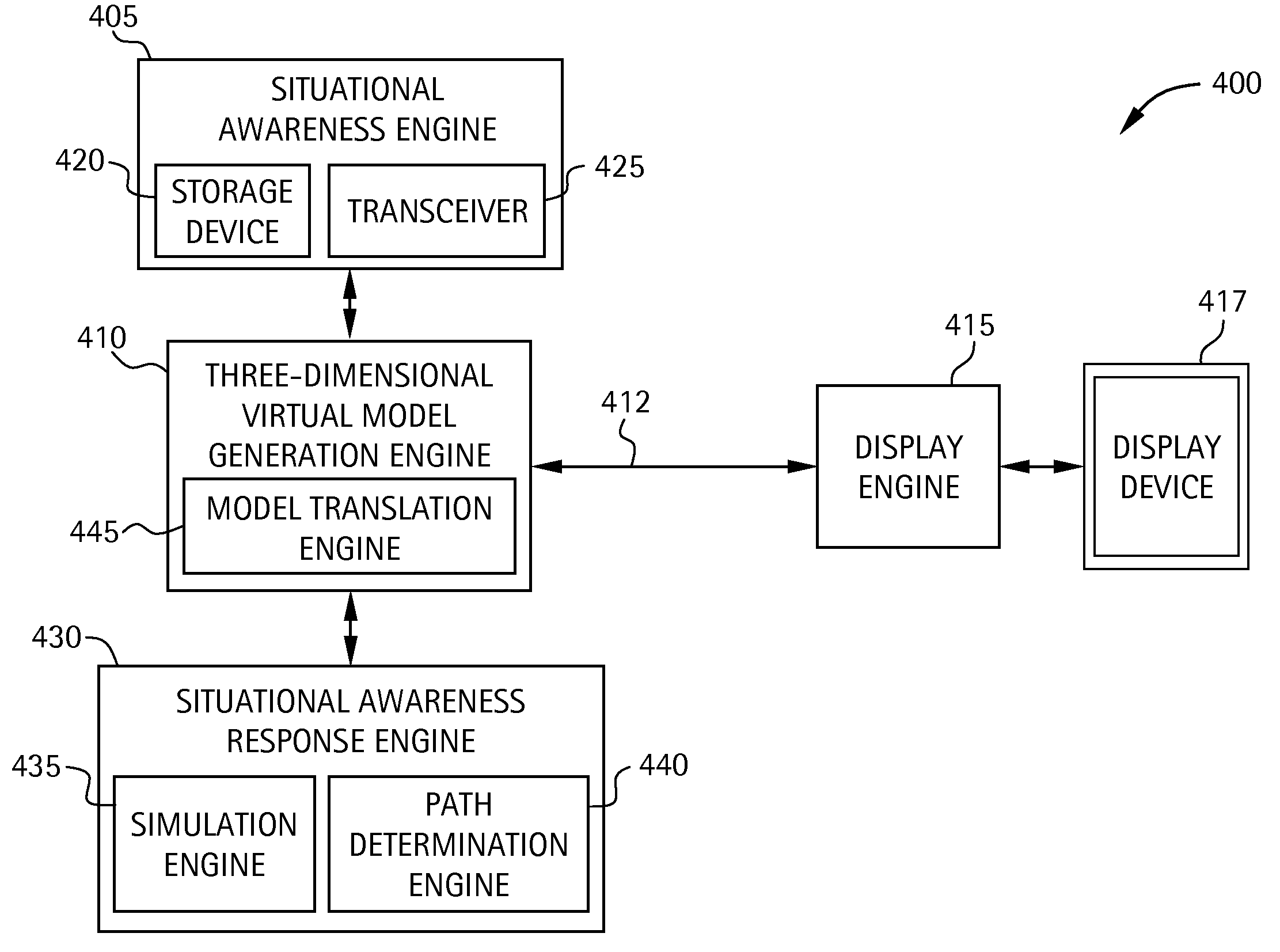
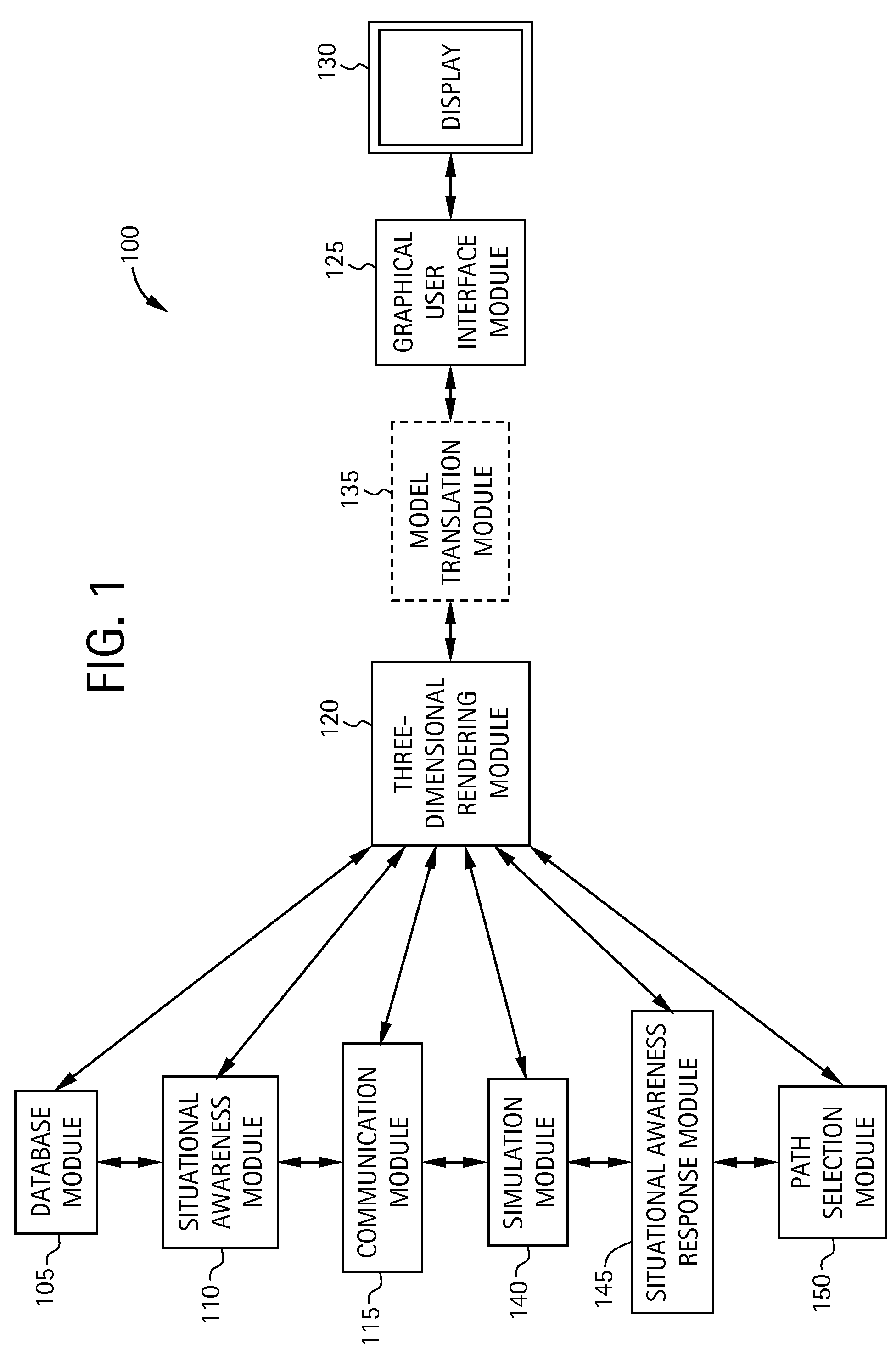
Computer-based system and method for providing situational awareness for a structure using three-dimensional modeling
InactiveUS20080062167A1Geometric CADSpecial data processing applicationsGraphicsGraphical user interface
A system for providing real-time or near real-time situational awareness for a structure includes a database module for storing structural information associated with the structure. The system includes a situational awareness module for gathering situational awareness information associated with the structure. The system includes a three-dimensional (3-D) rendering module in communication with the database module and the situational awareness module for rendering a 3-D virtual model of the structure utilizing the structural information associated with the structure, and for integrating into the 3-D virtual model the situational awareness information associated with the structure. The system includes a graphical user interface module in communication with the 3-D rendering module for displaying to a user the 3-D virtual model of the structure integrating the situational awareness information associated with the structure.
Owner:ERIS TECH CORP
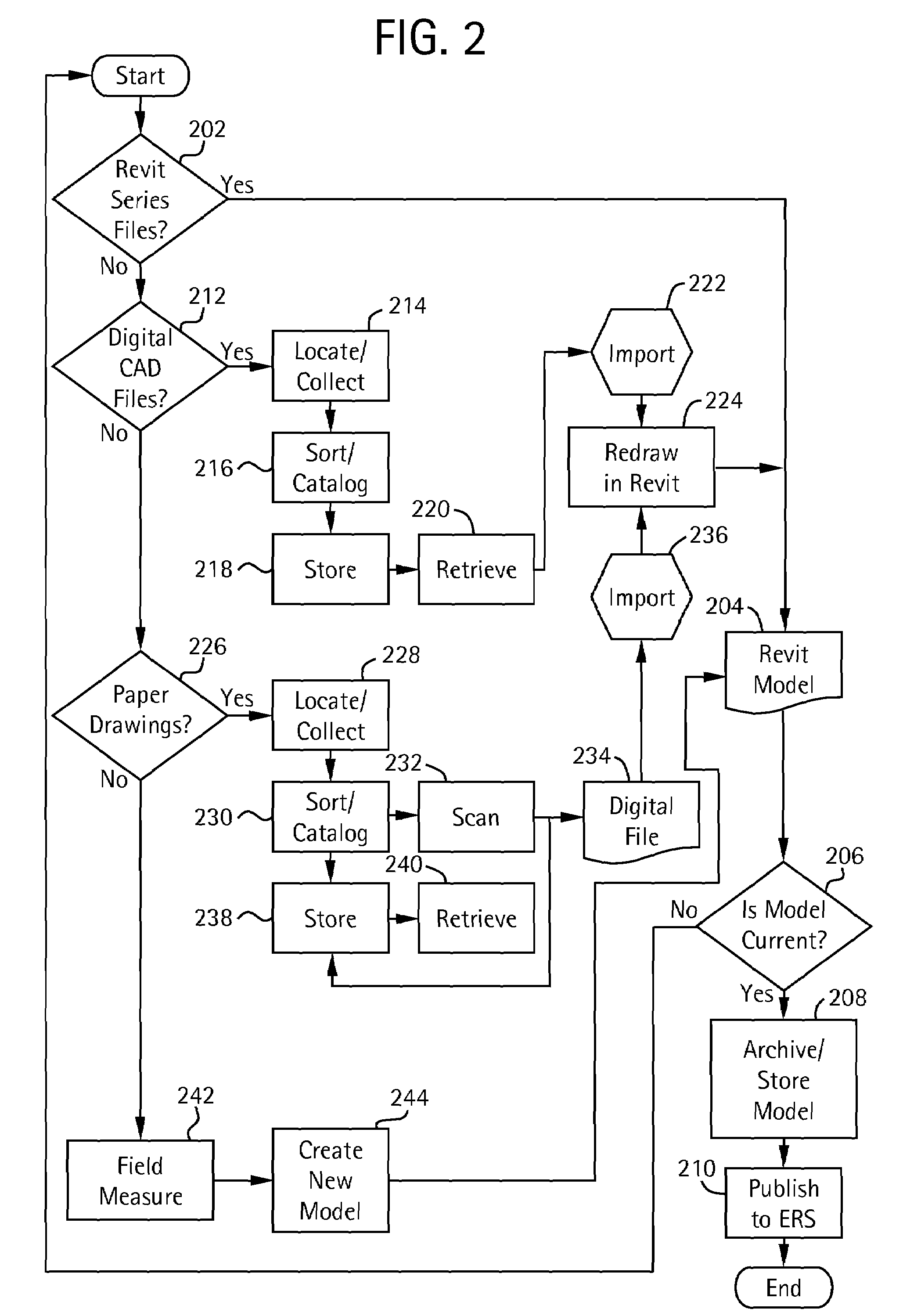
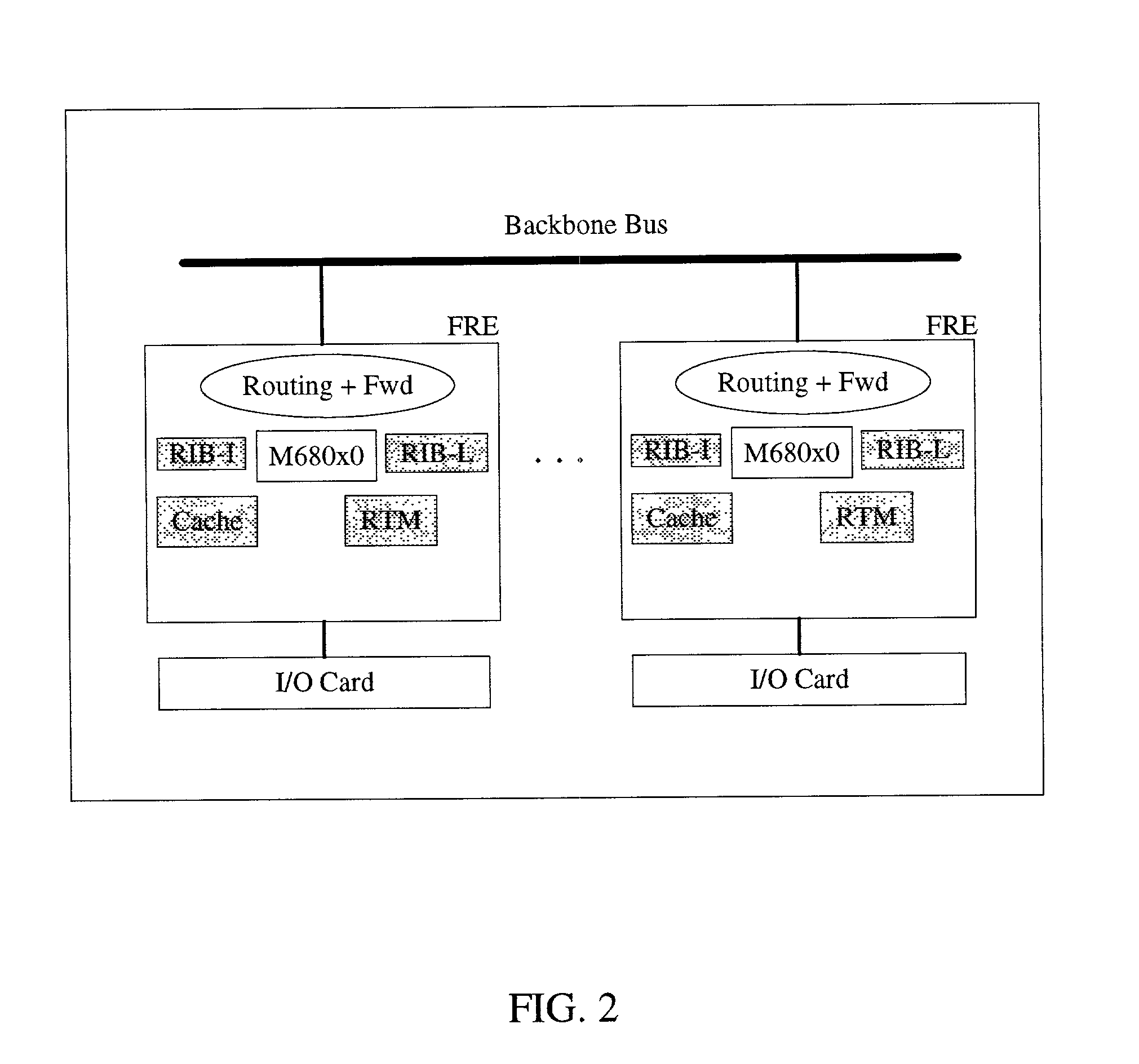
Information routing system and apparatus
ActiveUS6999454B1Time-division multiplexGeneral purpose stored program computerTraffic capacityRouting table
An information routing system and apparatus includes separate control and forwarding planes. The control plane is split into box management control functions and routing control functions. The box management control functions are isolated to a single processing card, while the routing control functions are distributed across multiple processing cards. The routing table is also distributed across multiple processing cards. The multiple processing cards are interconnected via a high-speed backplane bus for control plane traffic and by a fabric for forwarding plane traffic.
Owner:RPX CLEARINGHOUSE
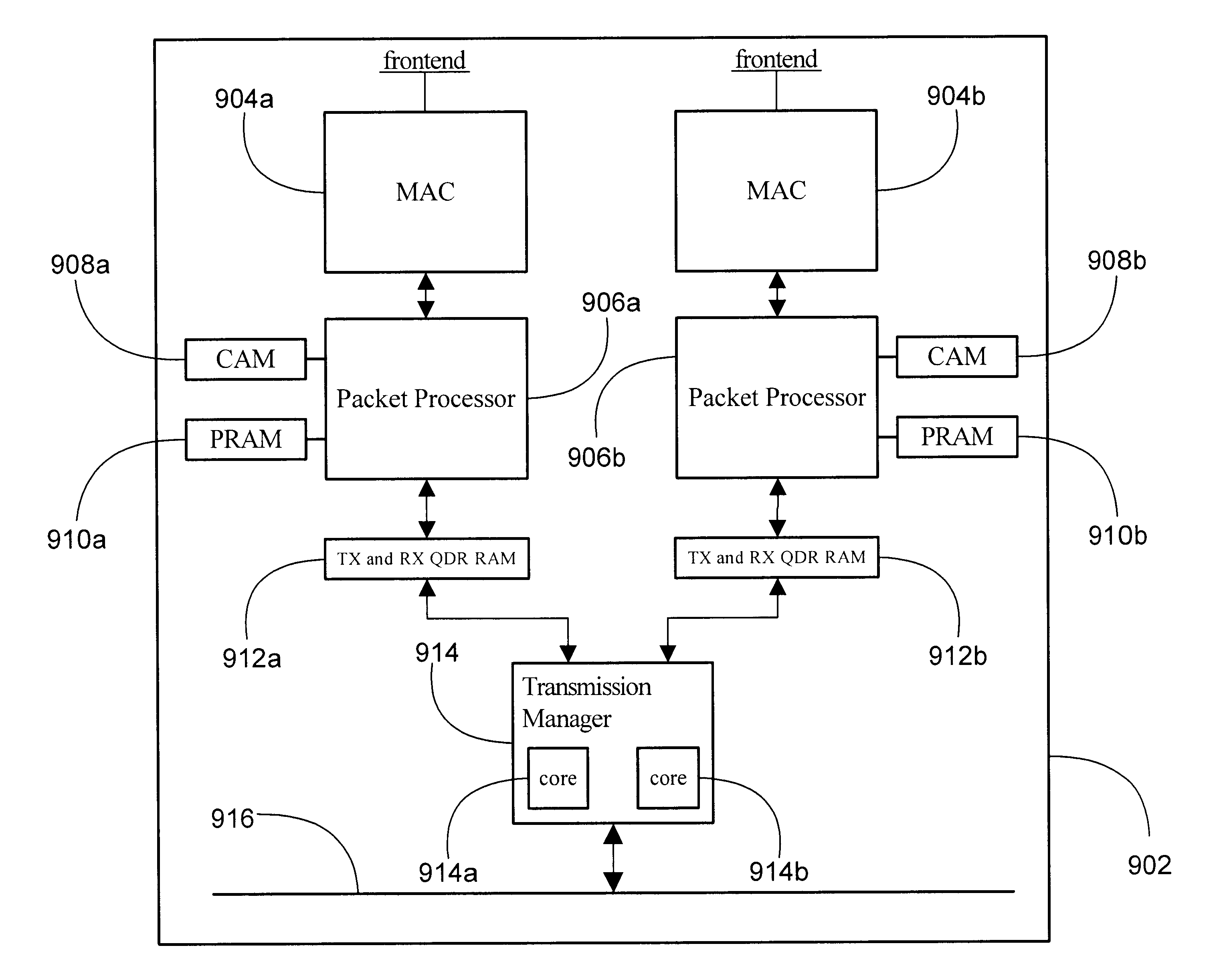
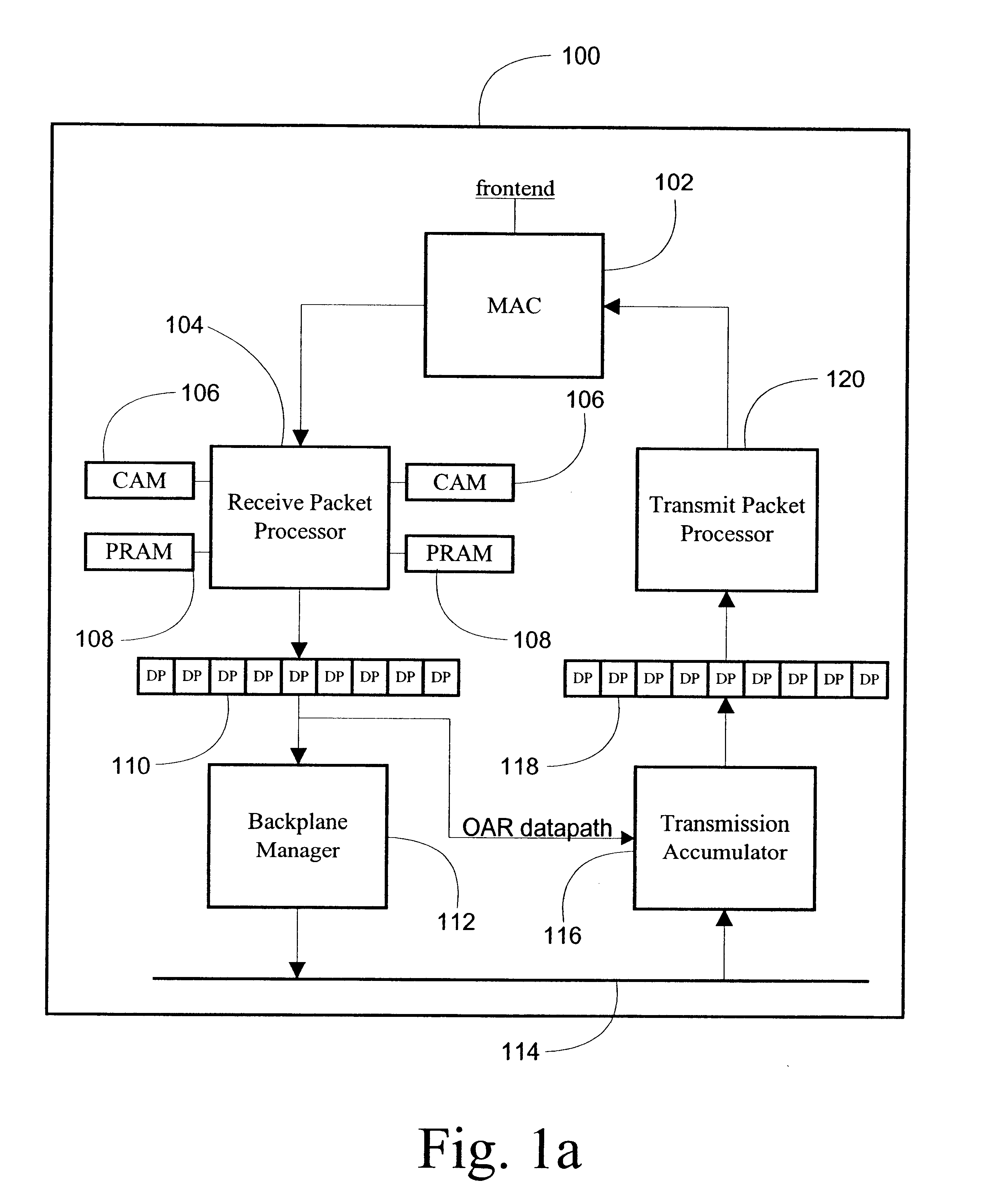
System and method for high speed packet transmission implementing dual transmit and receive pipelines
InactiveUS6901072B1Multiplex system selection arrangementsCircuit switching systemsGigabitStructure of Management Information
The present invention provides systems and methods for providing data transmission speeds at or in excess of 10 gigabits per second between one or more source devices and one or more destination devices. According to one embodiment, the system of the present invention comprises a first and second media access control (MAC) interfaces to facilitate receipt and transmission of packets over an associated set of physical interfaces. The system also contemplates a first and second field programmable gate arrays (FPGA) coupled to the MAC interfaces and an associated first and second memory structures, the first and second FPGAs are configured to perform initial processing of packets received from the first and second MAC interfaces and to schedule the transmission of packets to the first and second MAC interface for transmission to one or more destination devices. The first and second FPGAs are further operative to dispatch and retrieve packets to and from the first and second memory structures. A third FPGA, coupled to the first and second memory structures and a backplane, is operative to retrieve and dispatch packets to and from the first and second memory structures, compute appropriate destinations for packets and organize packets for transmission. The third FPGA is further operative to receive and dispatch packets to and from the backplane.
Owner:AVAGO TECH INT SALES PTE LTD
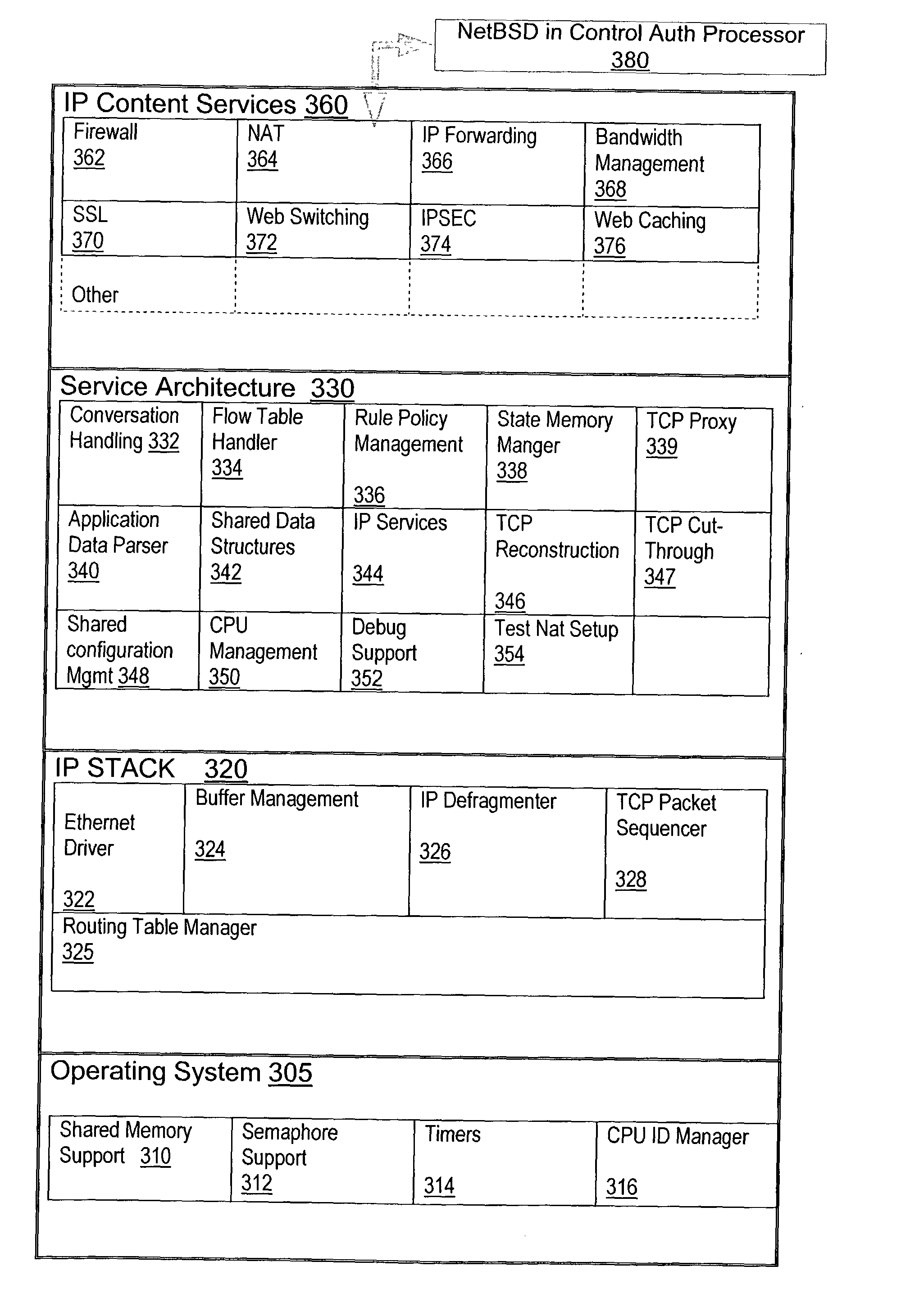
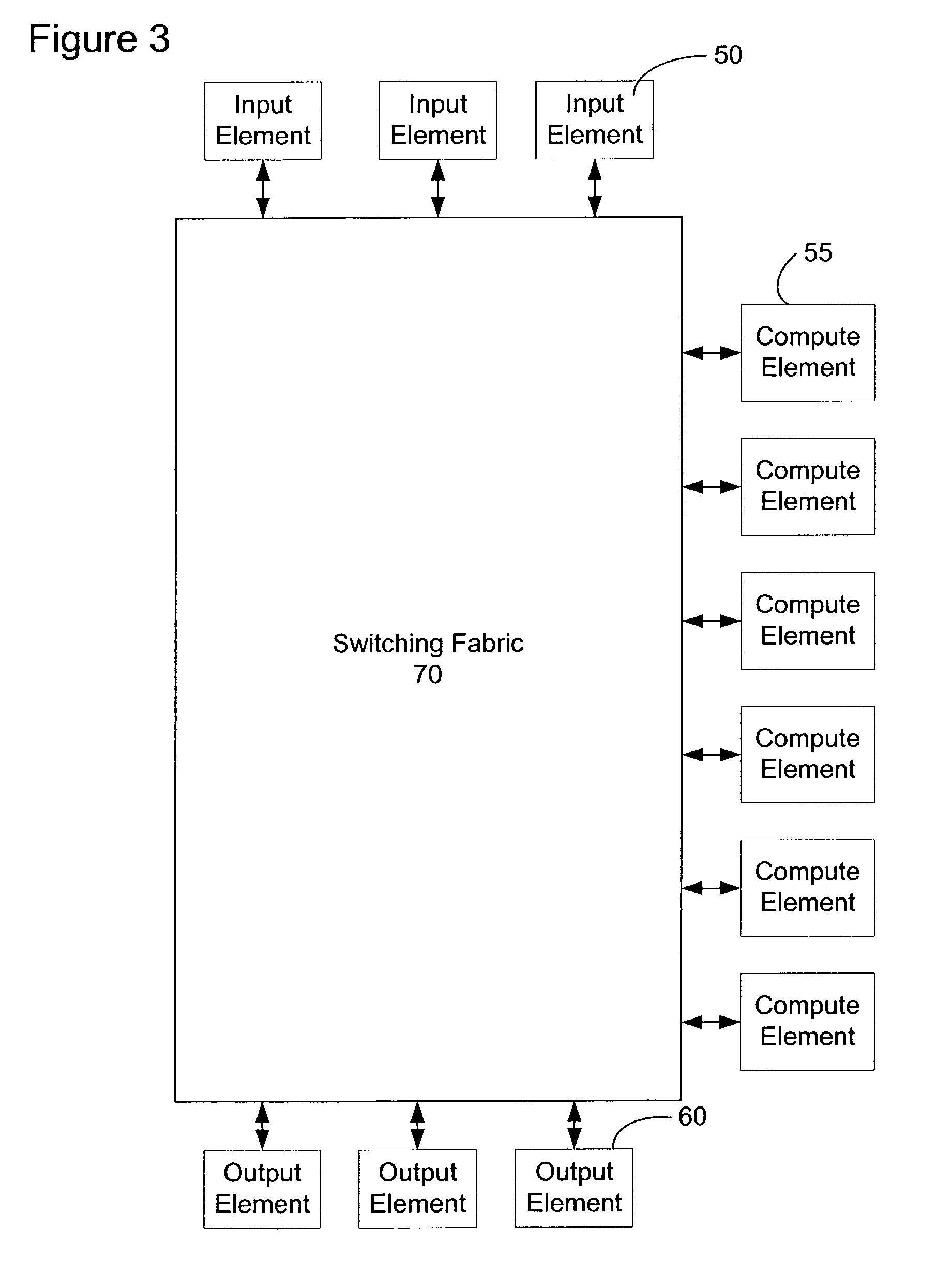
Content service aggregation system
ActiveUS20030126233A1Easy to processMultiple digital computer combinationsElectric digital data processingPrivate networkStructure of Management Information
A network content service apparatus includes a set of compute elements adapted to perform a set of network services; and a switching fabric coupling compute elements in said set of compute elements. The set of network services includes firewall protection, Network Address Translation, Internet Protocol forwarding, bandwidth management, Secure Sockets Layer operations, Web caching, Web switching, and virtual private networking. Code operable on the compute elements enables the network services, and the compute elements are provided on blades which further include at least one input / output port.
Owner:NEXSI SYST +1
Integrated forensics platform for analyzing it resources consumed to derive operational and architectural recommendations
ActiveUS20110145657A1Easy to analyzeHardware monitoringResourcesStructure of Management InformationPhysical system
A method for facilitating forensic analysis of operational data for an IT infrastructure includes deriving performance data from a plurality of physical systems, network elements and storage devices in an IT infrastructure via a toolset comprising a plurality of IT monitoring and metrics tools, importing the performance data into an integrated forensics platform, aggregating the imported data, and analyzing the aggregated data to determine resources consumed. Each tool is communicatively interfaced with one or more of the physical systems, network elements and storage devices.
Owner:EMC IP HLDG CO LLC
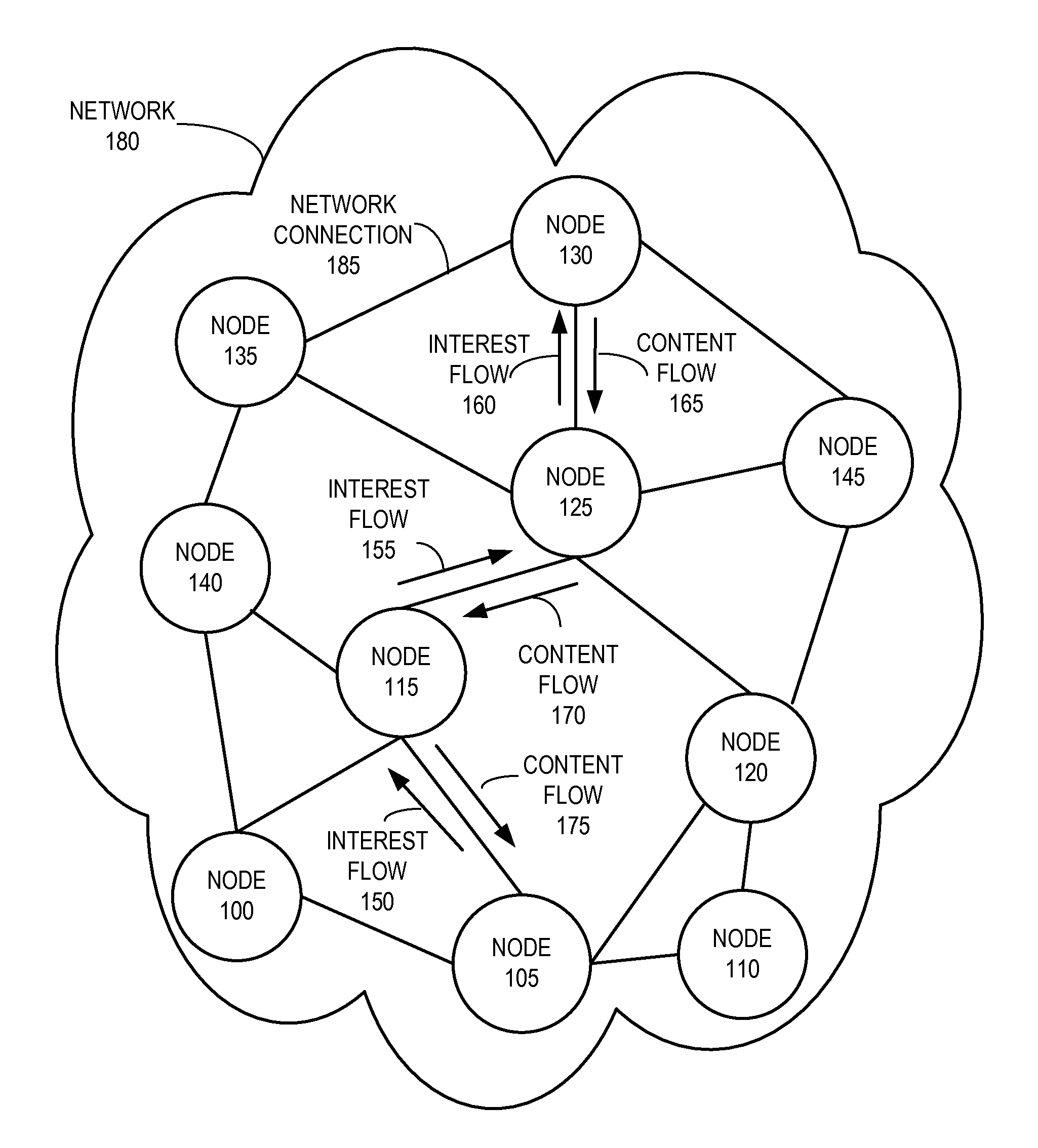
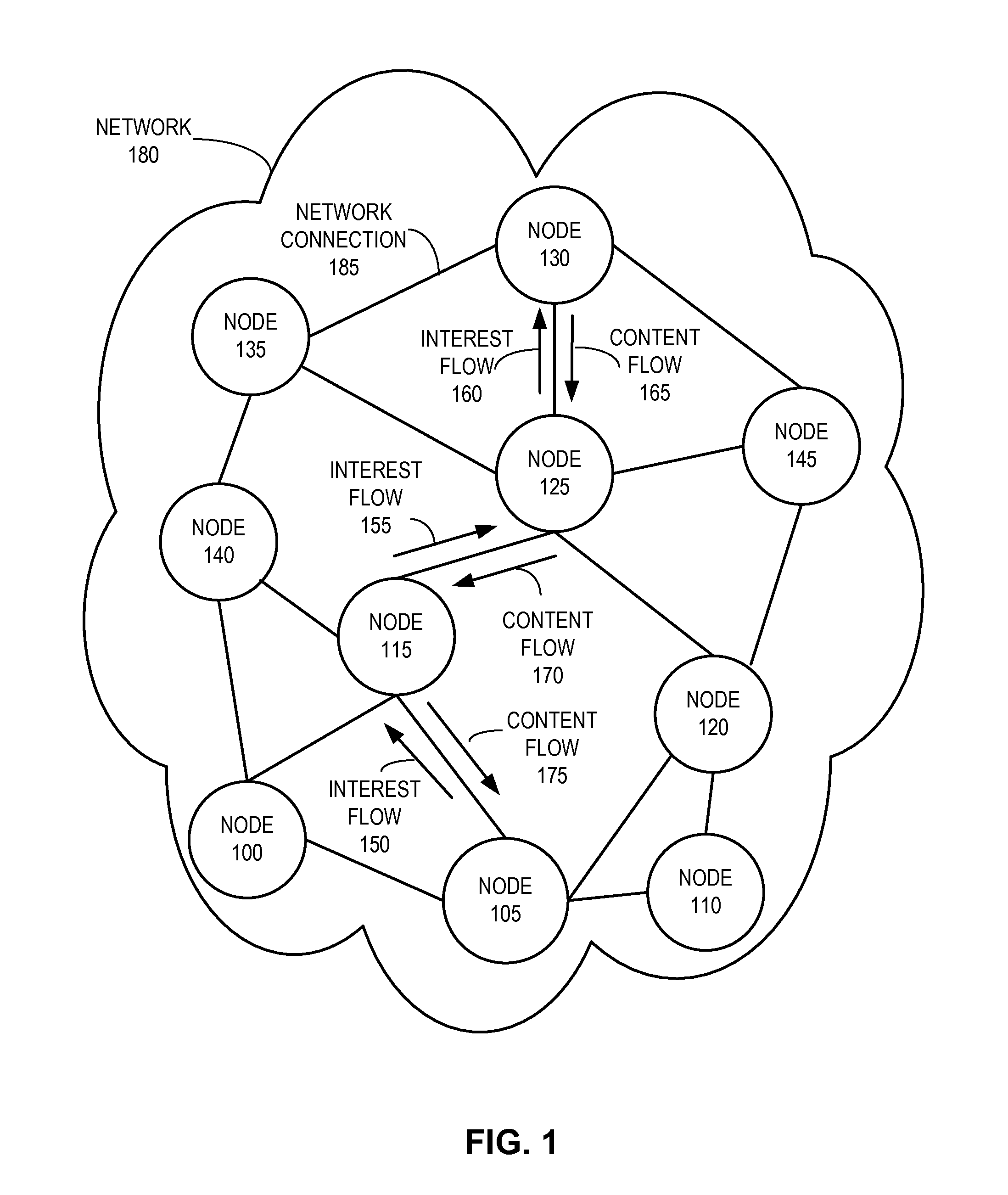
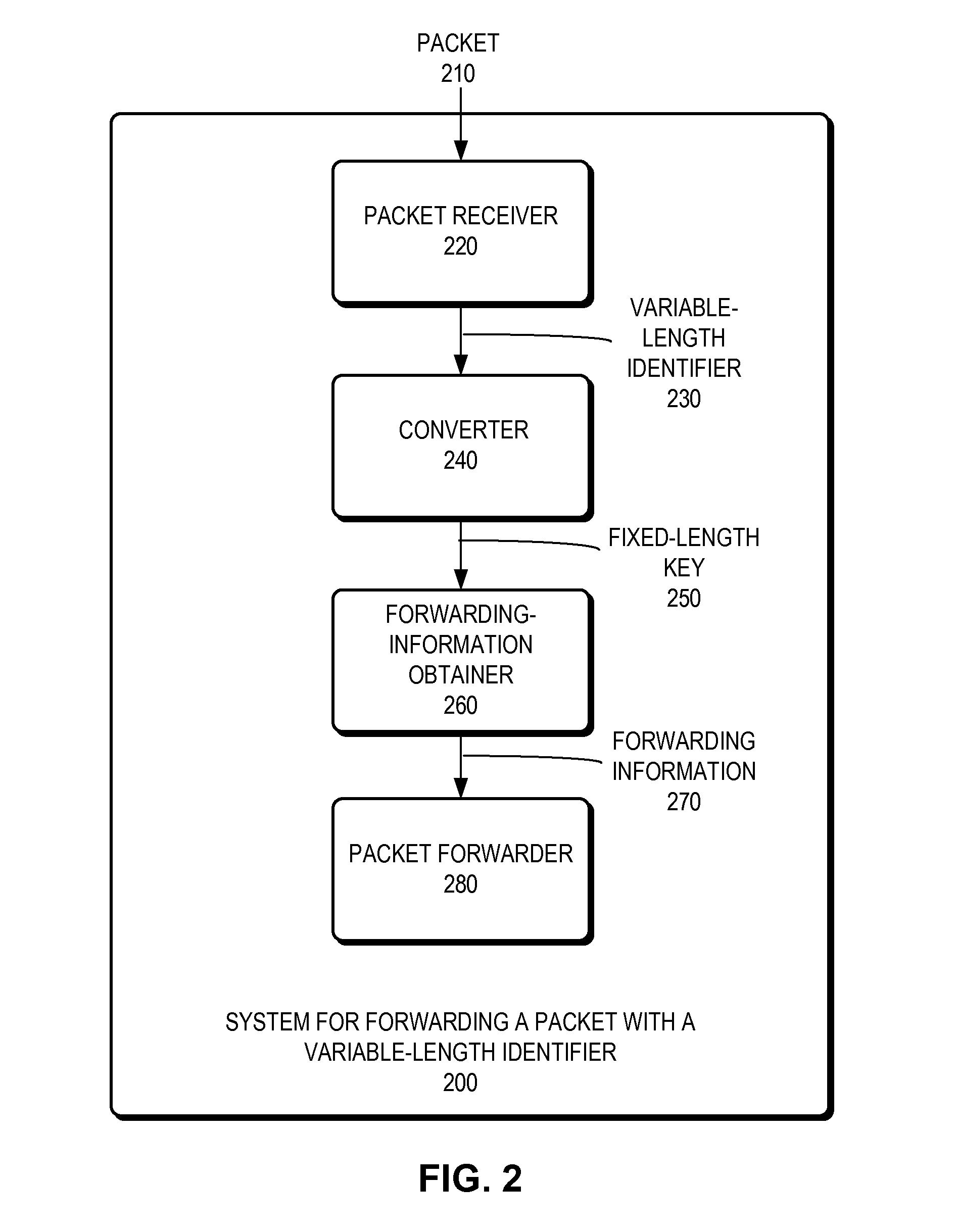
System for forwarding a packet with a hierarchically structured variable-length identifier
ActiveUS8160069B2Data switching by path configurationStructure of Management InformationLongest prefix match
One embodiment provides a system that receives a packet with a hierarchically structured variable-length identifier (HSVLI). An HSVLI indicates a piece or collection of content and may be hierarchically structured, comprising contiguous components ordered from a most general level to a most specific level. The length of a respective identifier is not fixed. During operation, the system converts the HSVLI into a fixed-length key. Subsequently, the system obtains forwarding information based on one or more longest-prefix matches with a longest-prefix-match lookup engine using the fixed-length key. Next, the system forwards the packet to an output port based on the forwarding information.
Owner:CISCO TECH INC
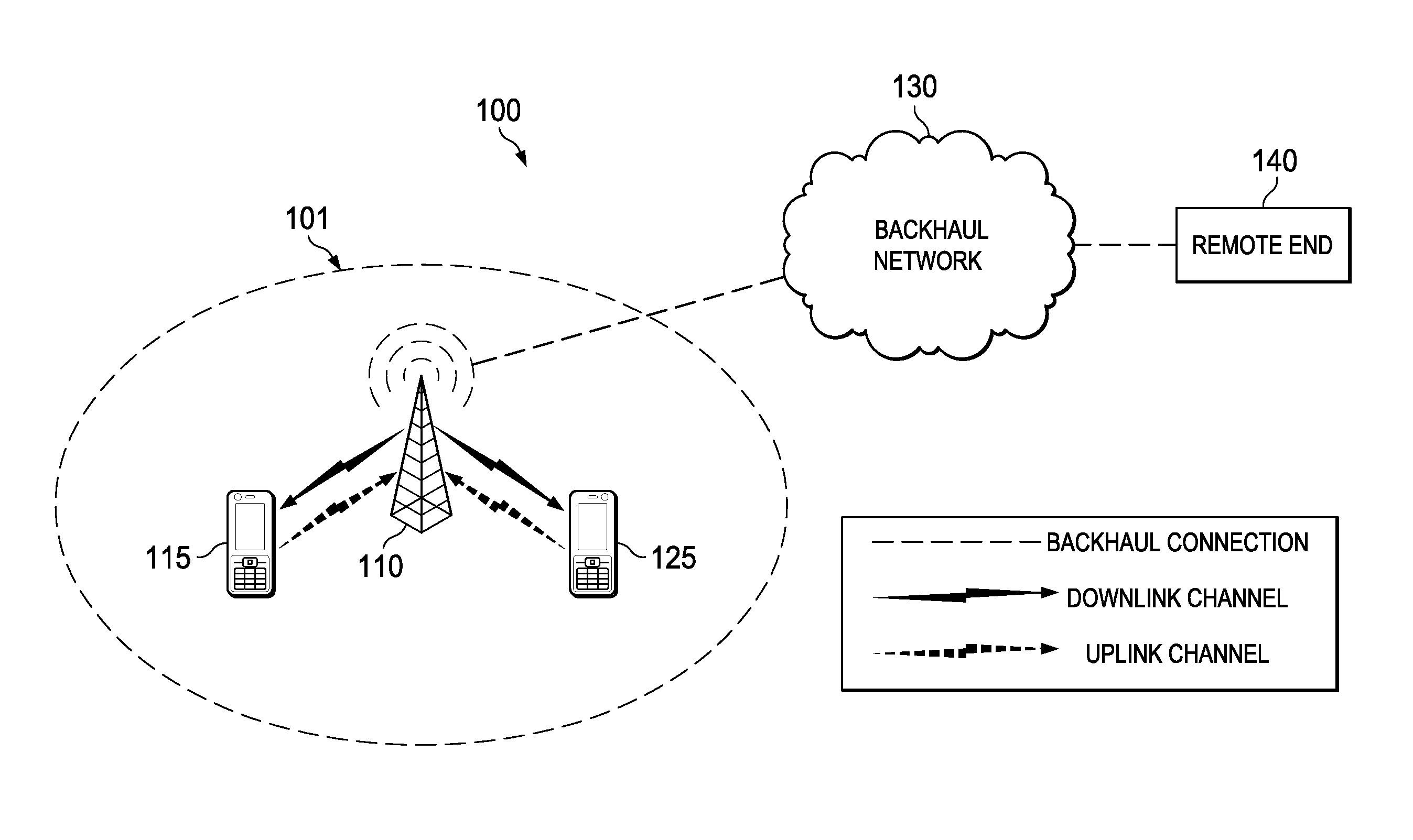
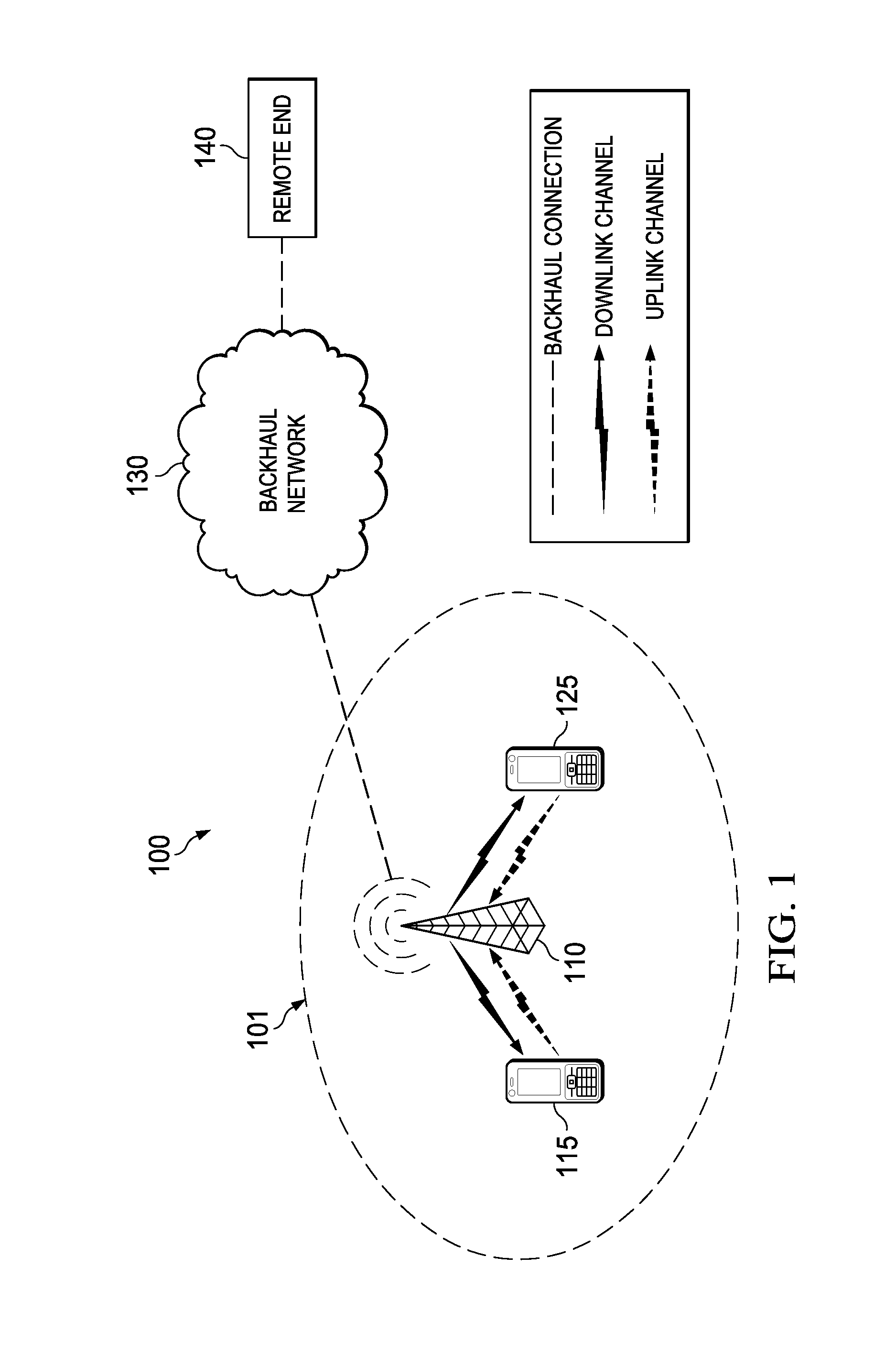
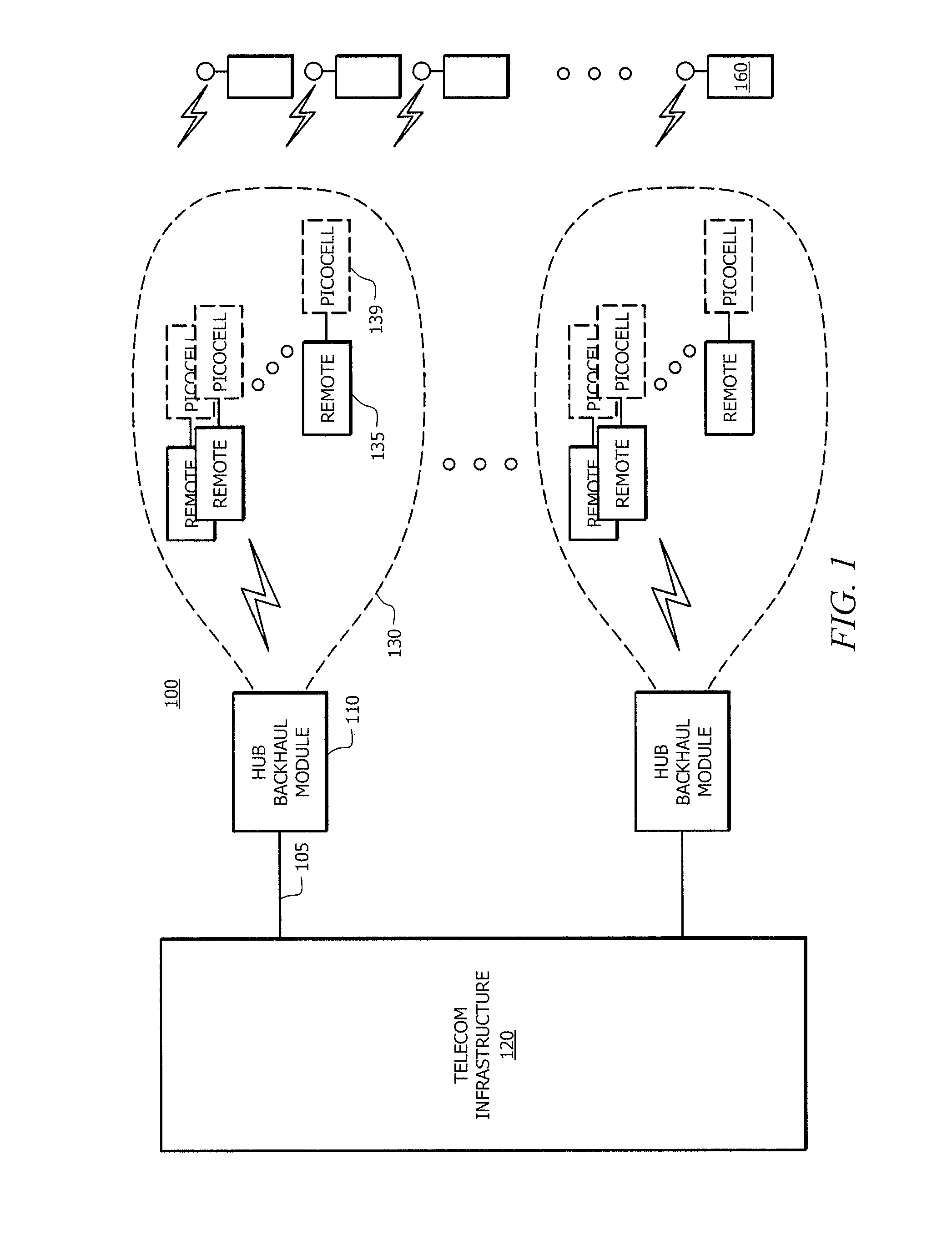
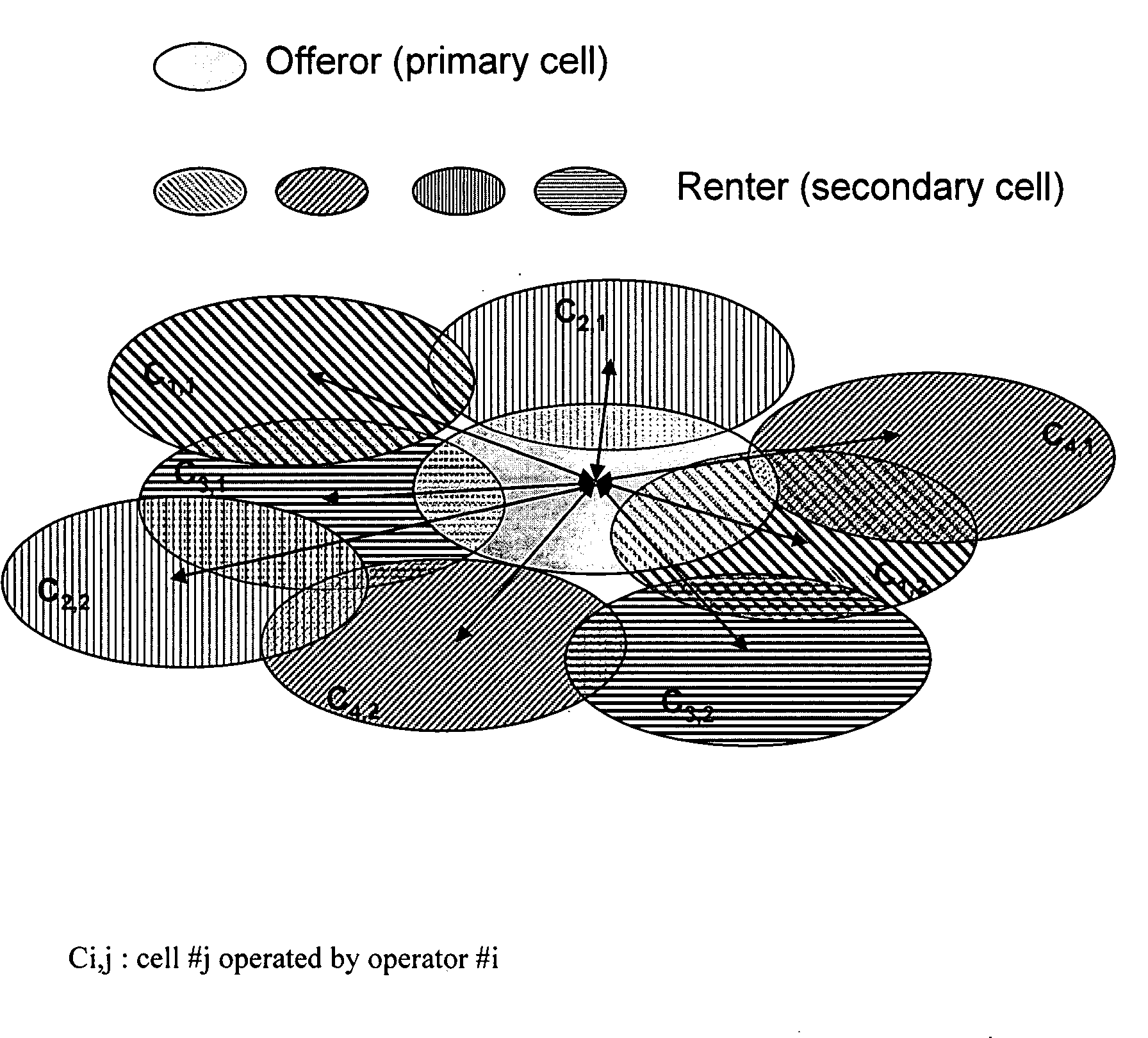
Methods and systems for frequency reuse in multi-cell deployment model of a wireless backhaul network
Systems and methods for frequency reuse in a multi-cell deployment model of a wireless backhaul network are shown. According to embodiments, a wireless backhaul network includes a plurality of cells, each of which includes one or more hubs supporting wireless backhaul communication utilizing a cell deployment geometry and wireless communication frequency assignments adapted to facilitate heterogeneous cell configurations within the wireless backhaul network. In particular, embodiments provide frequency planning for initial deployment, build out, and expansion of a plurality of cells providing wireless backhaul communication so as to implement a predetermined wireless frequency reuse pattern providing alternating utilization of a plurality of wireless communication frequencies by the cells of the backhaul network.
Owner:RIBBON COMM OPERATING CO INC
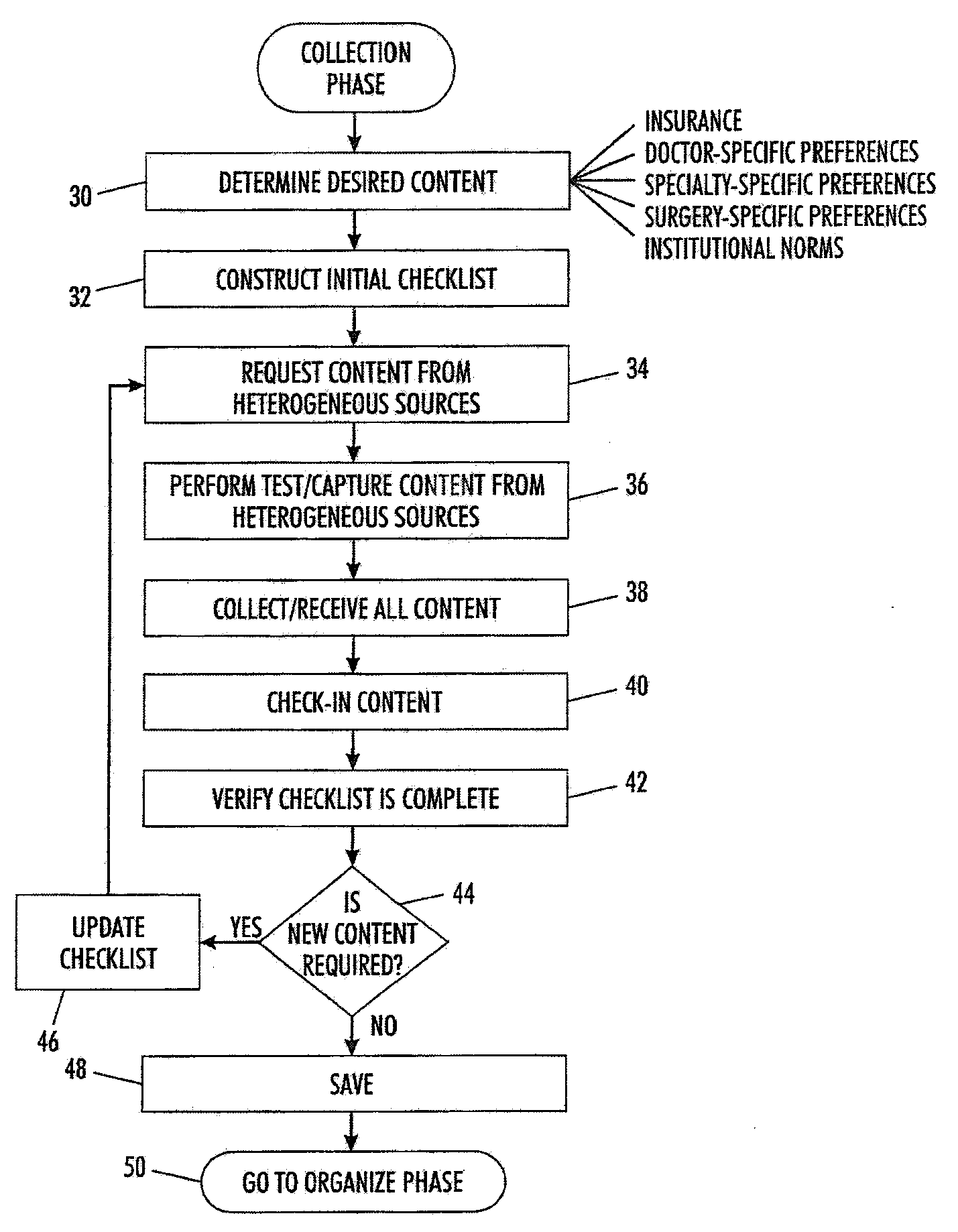
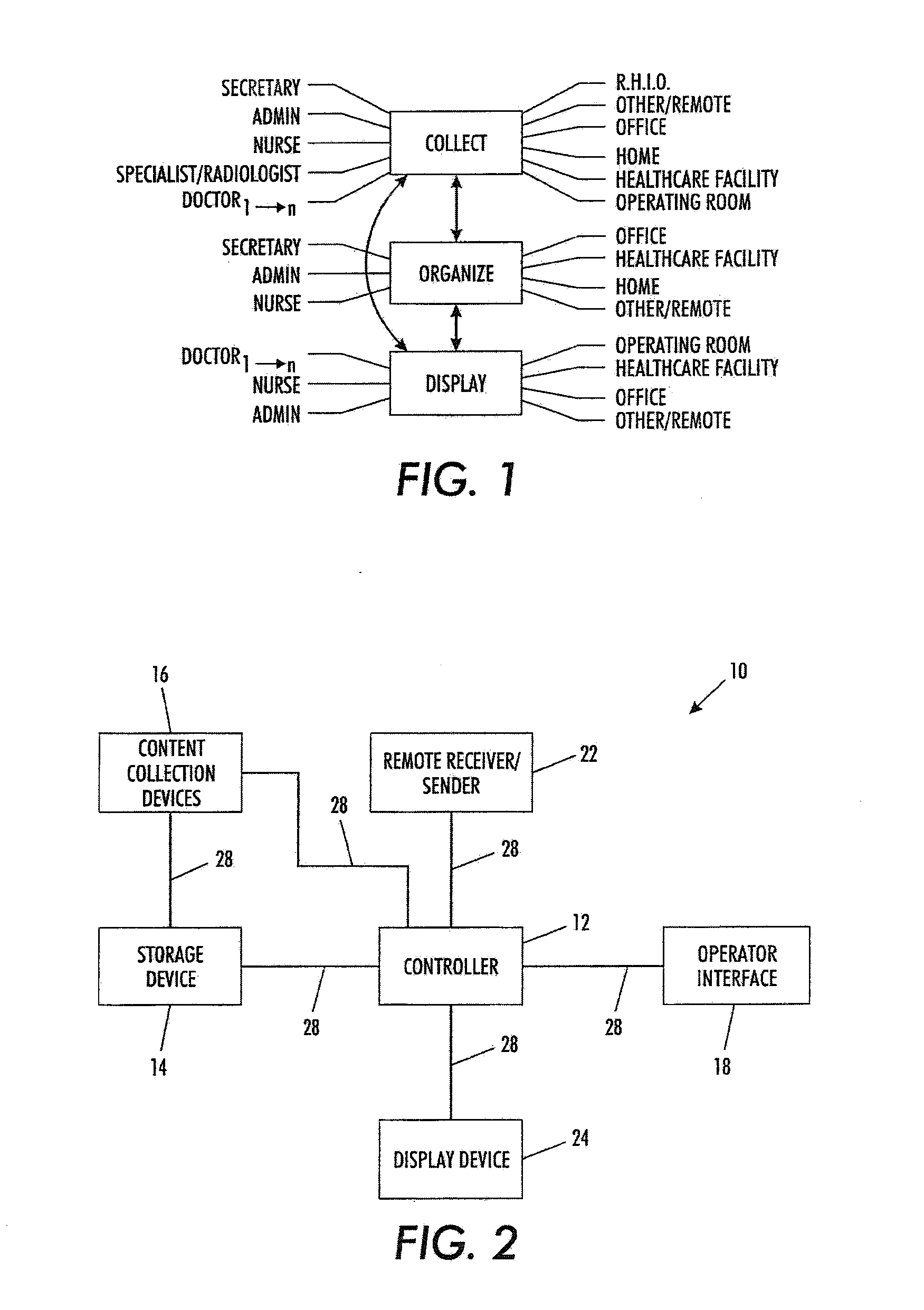
Automated information management process
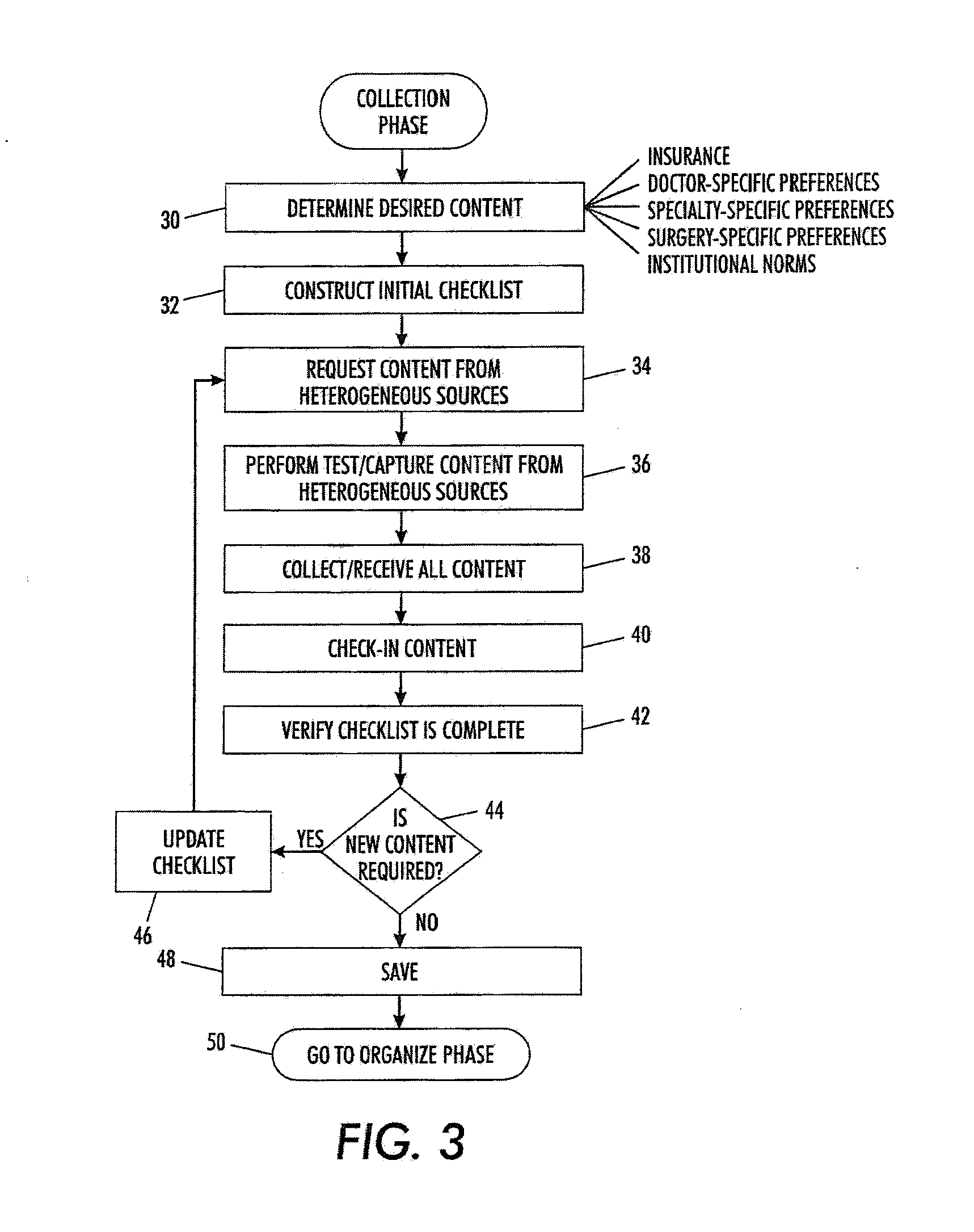
InactiveUS20090182577A1Medical automated diagnosisResourcesManagement processStructure of Management Information
A method of automating a healthcare facility workflow process includes creating a rule set governing at least one of a collection phase, an organize phase, and a display phase of the healthcare facility workflow process. The rule set is based on at least one of a plurality of decision factors. The method also includes automatically processing a plurality of content based on the rule set. Automatically processing the plurality of content includes one of collecting the plurality of content from a plurality of heterogeneous content sources, organizing the plurality of content based on a desired content hierarchy, and displaying at least one content of the plurality of content based on the desired content hierarchy.
Owner:CARESTREAM HEALTH INC
Content usage control system, content usage apparatus, computer readable recording medium with program recorded for computer to execute usage method
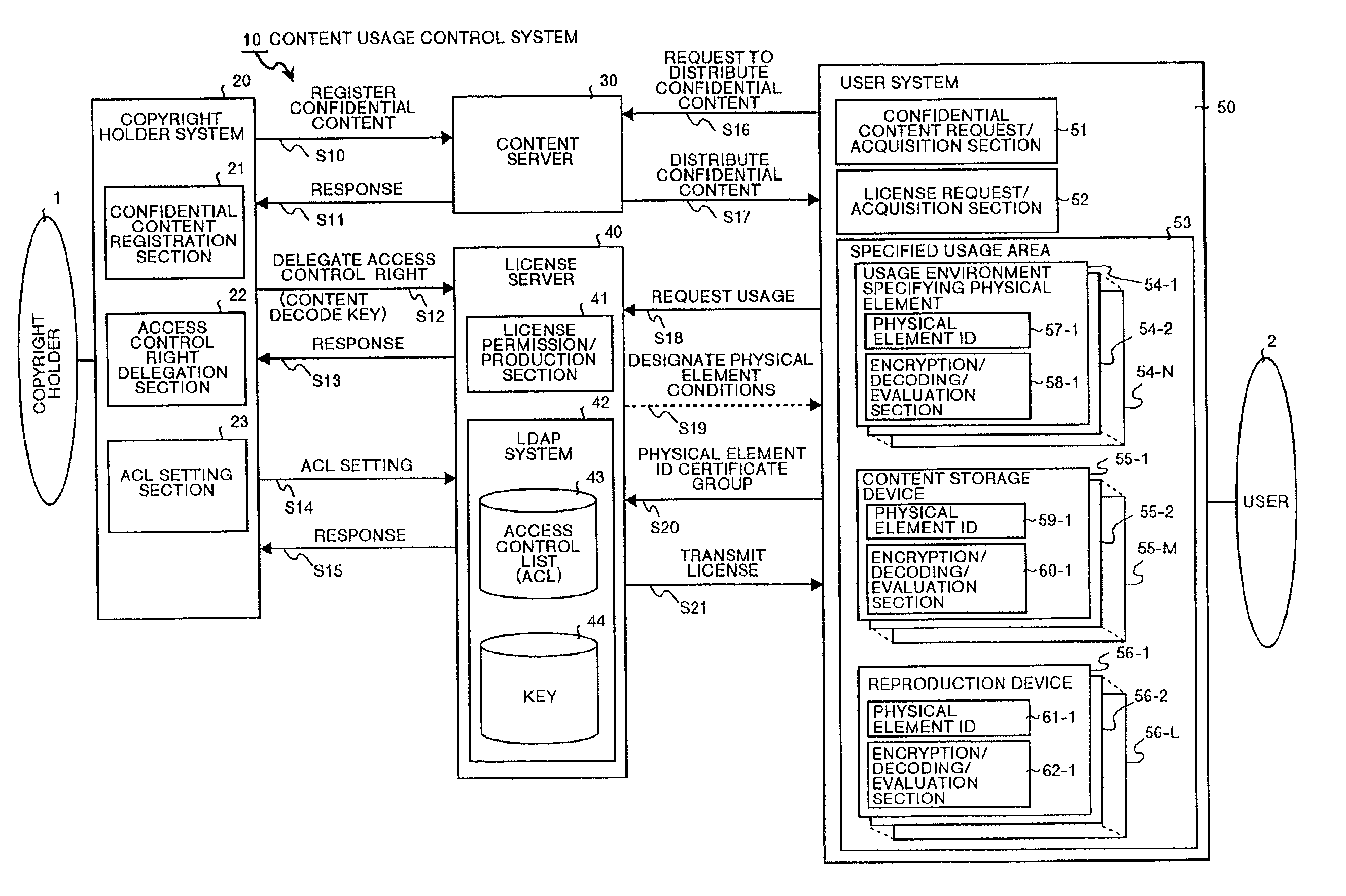
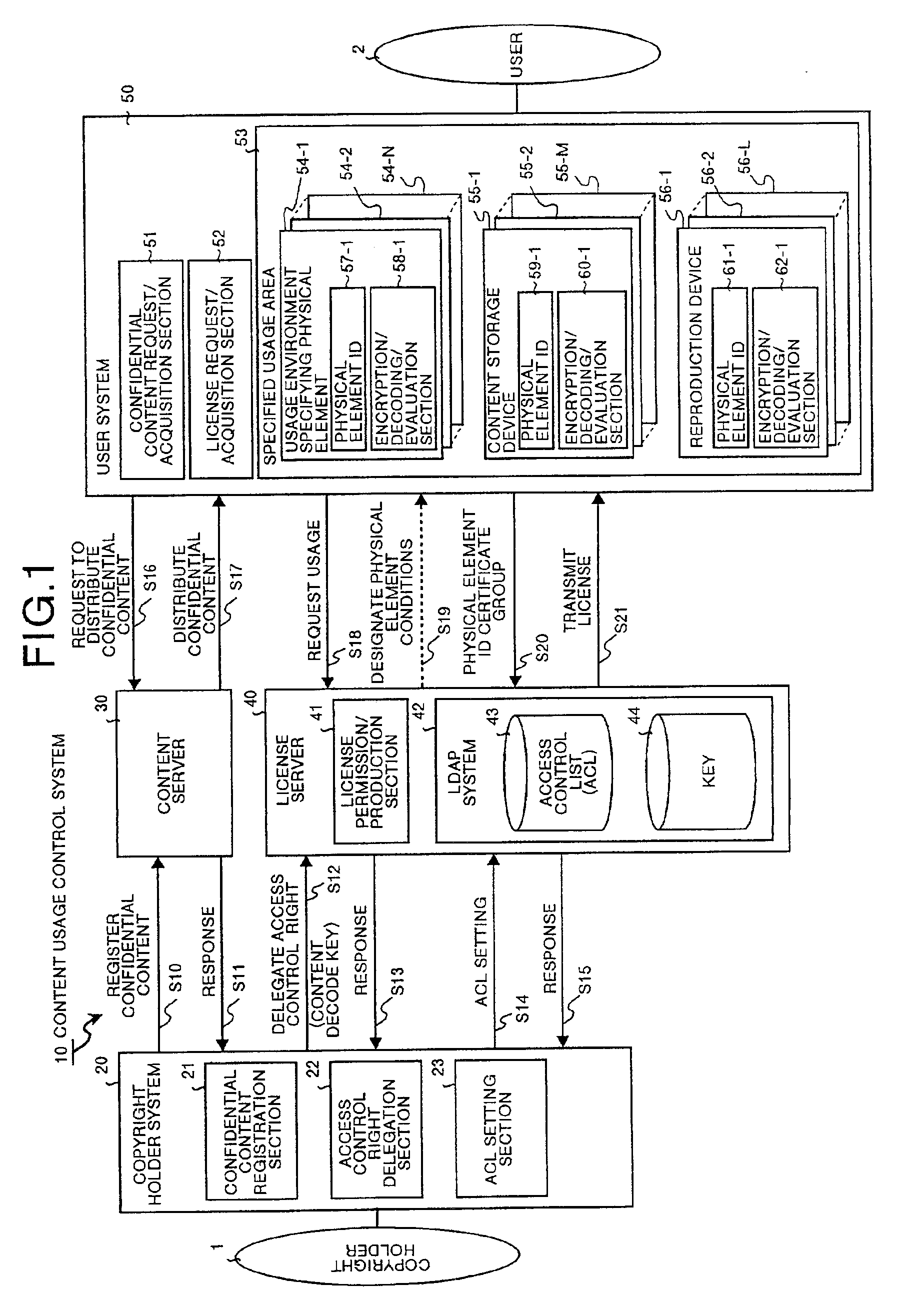
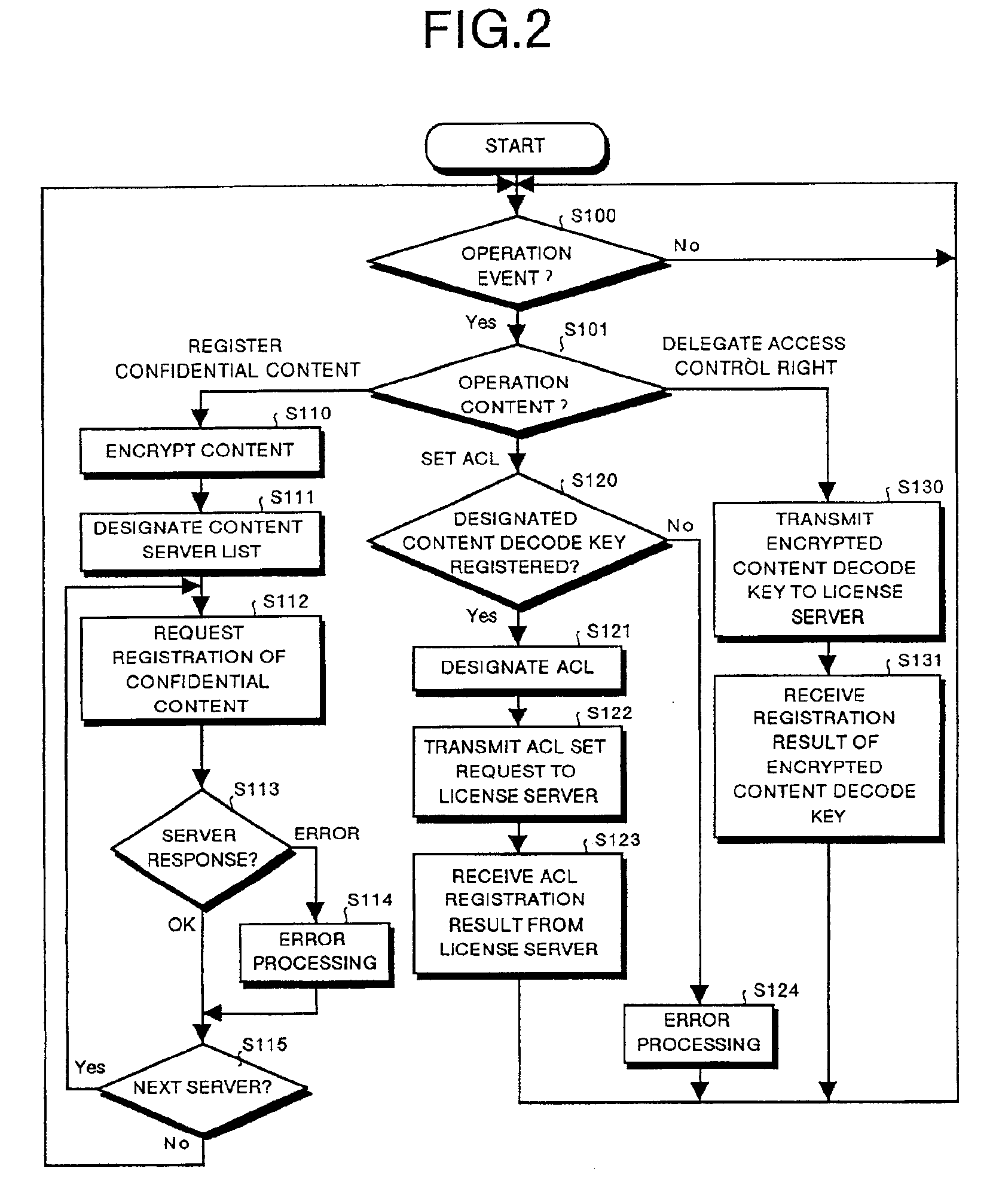
InactiveUS6873975B1Prevent illegal useImprove accuracyDigital data processing detailsAnalogue secracy/subscription systemsControl systemStructure of Management Information
A content usage control system comprises a copyright holder system, content server, license server and user system. The ACL setting section of the copyright holder system sets a license ACL expressed as a structure by a combination of logic sums and logic products of a plurality of partial licenses for the content, based on the user ID and a plurality of physical element IDs including media used in the user system, and stores the license ACL in an access control list. The license server controls the usage of the content by the user utilizing the access control list.
Owner:FUJITSU LTD
Method and apparatus for distributing content
InactiveUS8412707B1Metadata text retrievalDigital data processing detailsPrivate networkThe Internet
Owner:USTRINGER
Secure cloud fabric to connect subnets in different network domains
ActiveUS20140337500A1Digital computer detailsData switching networksStructure of Management InformationNetwork topology
A secure virtual network platform connects two or more subnets in different or separate network domains. The secure virtual network can use the under layer physical networks in various domains as an IP forwarding fabric without changing any existing firewalls, security settings, or network topology. A first type of connection across the virtual network involves connecting server groups. A second type of connection across the virtual network involves connecting a server group to a physical network. A third type of connection across the virtual network involves connecting a physical network to another physical network.
Owner:ZENTERA SYST
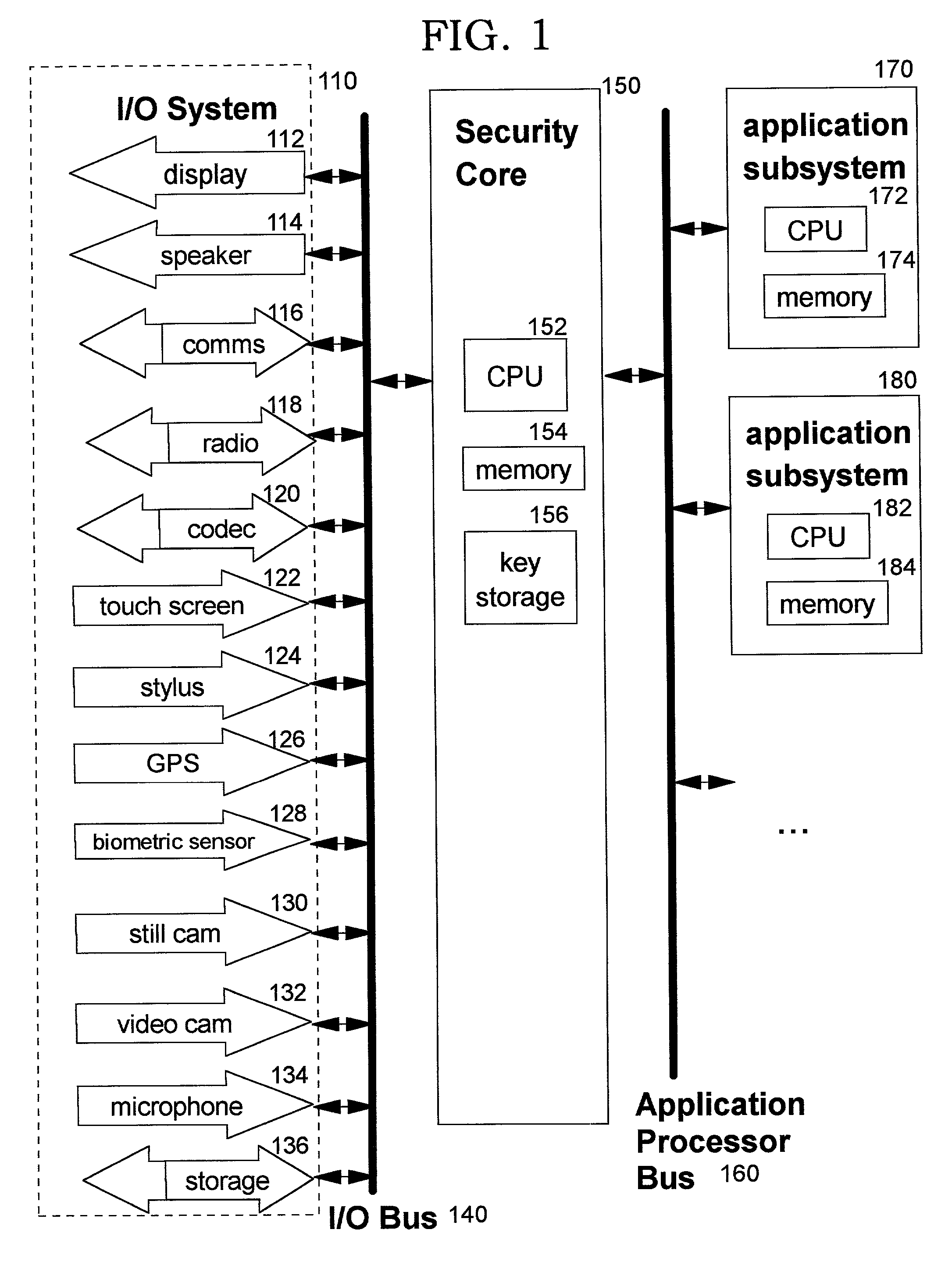
Secure integrated device with secure, dynamically-selectable capabilities
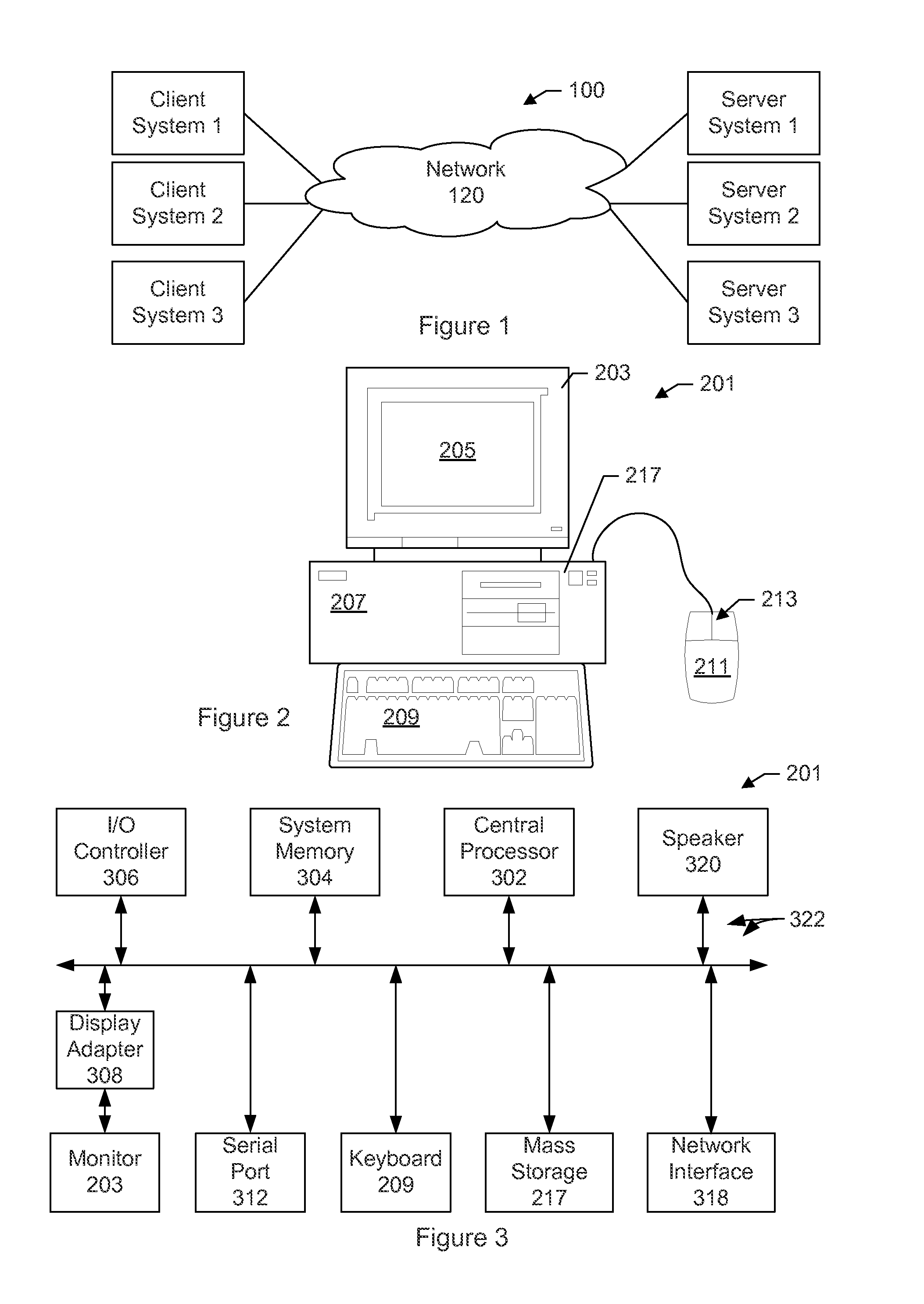
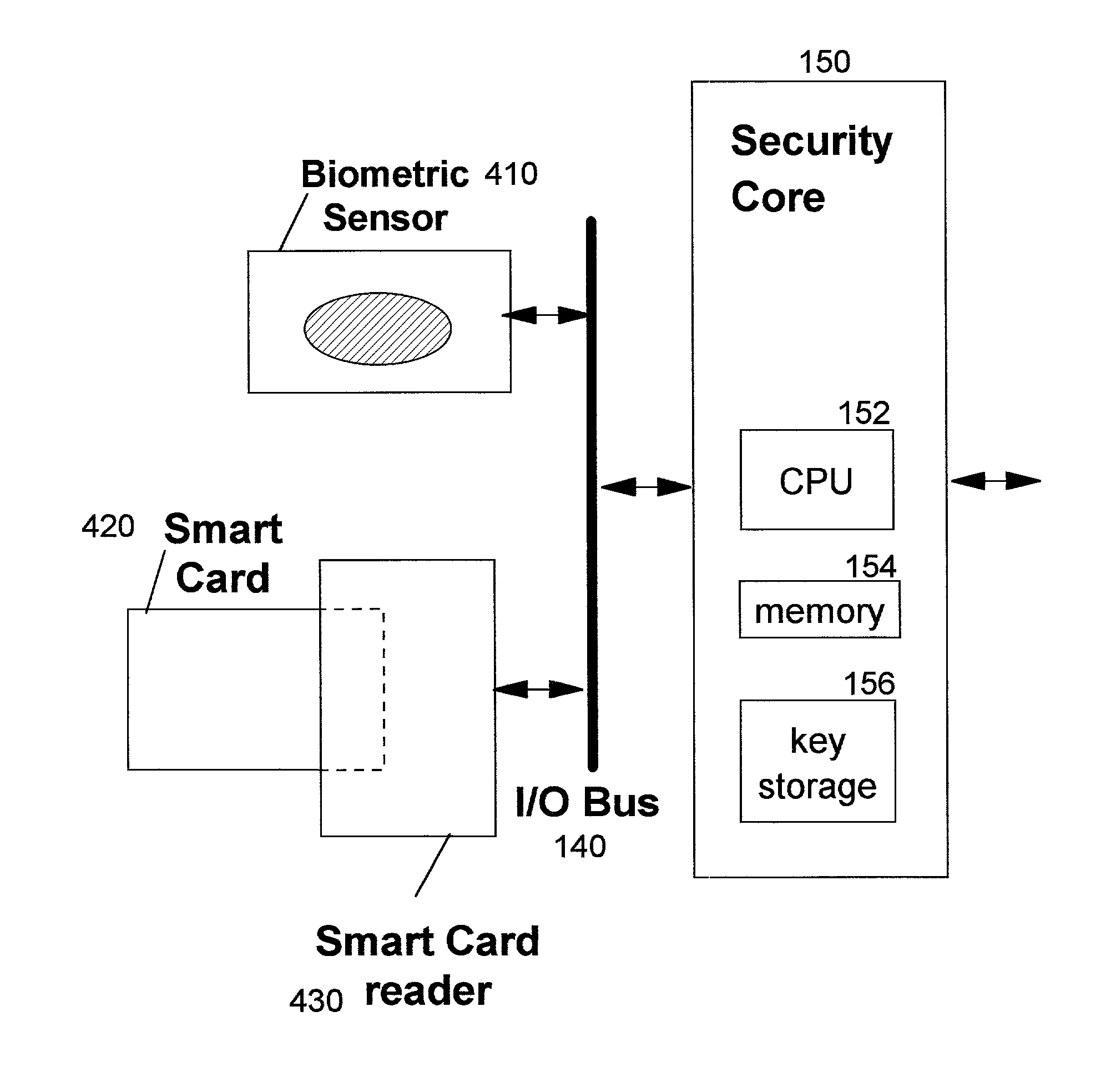
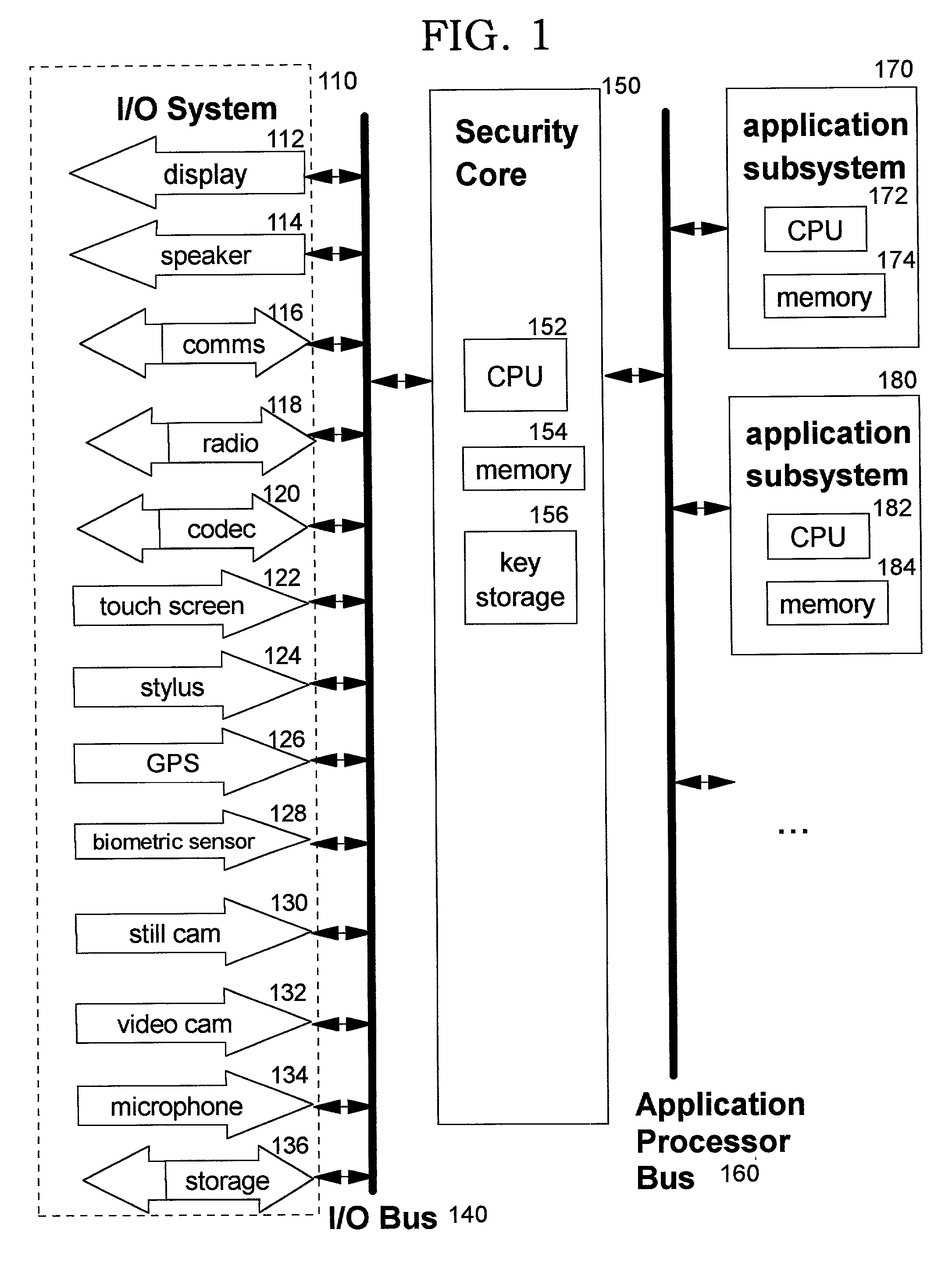
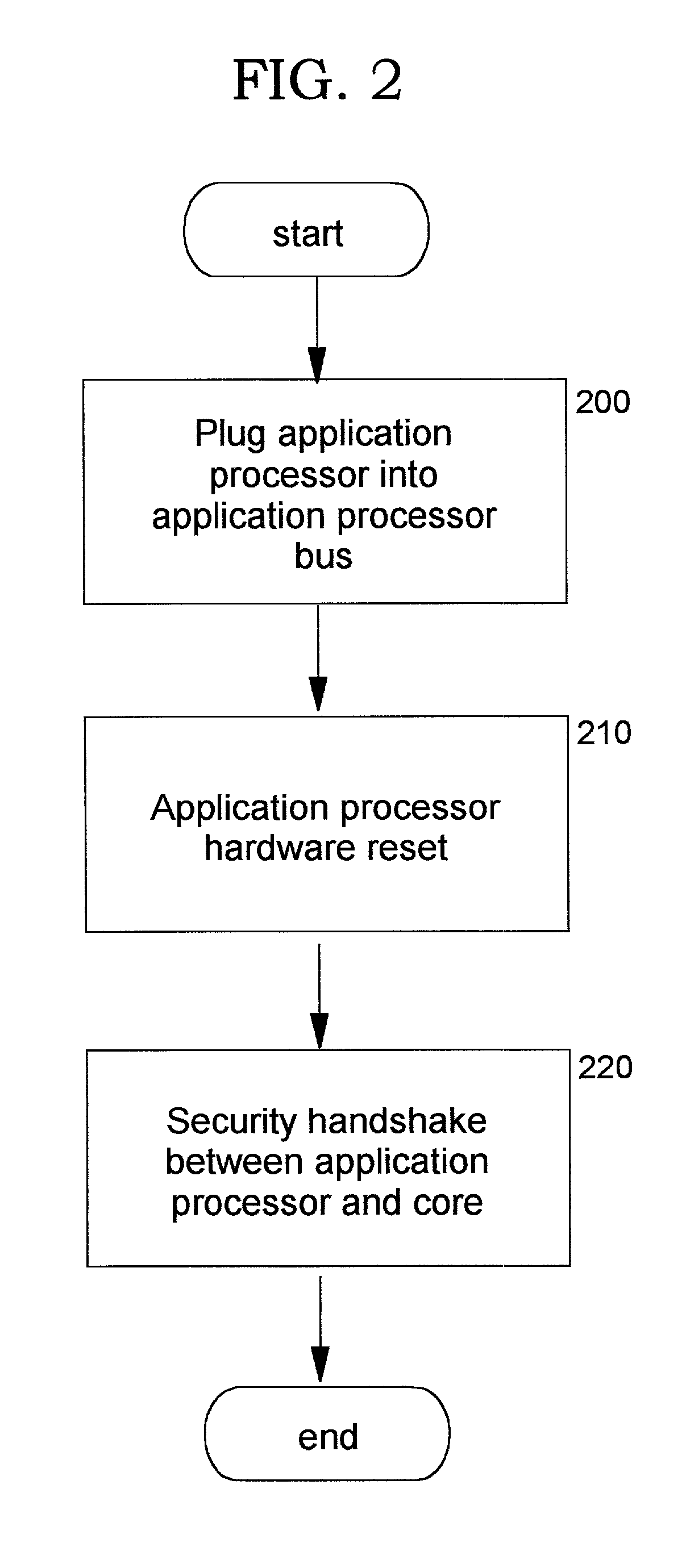
InactiveUS20030159044A1Improve securityUser identity/authority verificationDigital data protectionStructure of Management InformationOutput device
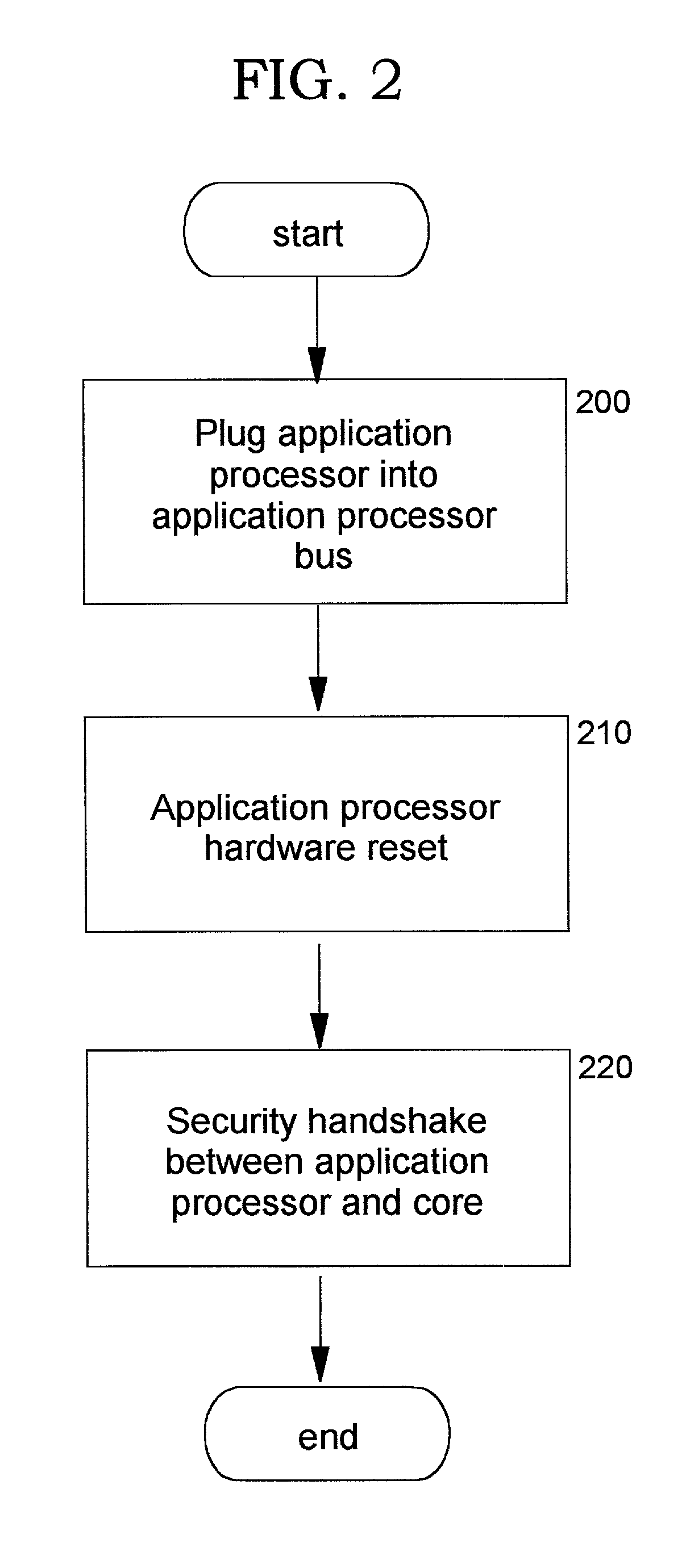
A method, system, computer program product, and method of doing business by providing a secure integrated device (such as a pervasive computing device) for which operating capabilities can be dynamically yet securely selected (including, but not limited to, pluggable connection of input / output devices and / or application processors that provide selected functions). Each input / output (I / O) device and application processor to be used is plugged in to a bus of a security core, and authenticates itself to the security core using public key infrastructure techniques, thereby creating a secure multi-function device. All of the multi-function device's input and output interactions with its environment necessarily traverse an I / O bus under the sole control of the security core. The only communication path between an application processor and the external environment (such as an I / O device) is through an application processor bus, which is likewise under control of the security core. Thus a user may dynamically yet securely select the capabilities of a multi-function device, and because each I / O device and application processor in use by that multi-function device is authenticated, the security of transactions or network services performed when using such devices is improved.
Owner:IBM CORP
Method and system for handling program, project and asset scheduling management
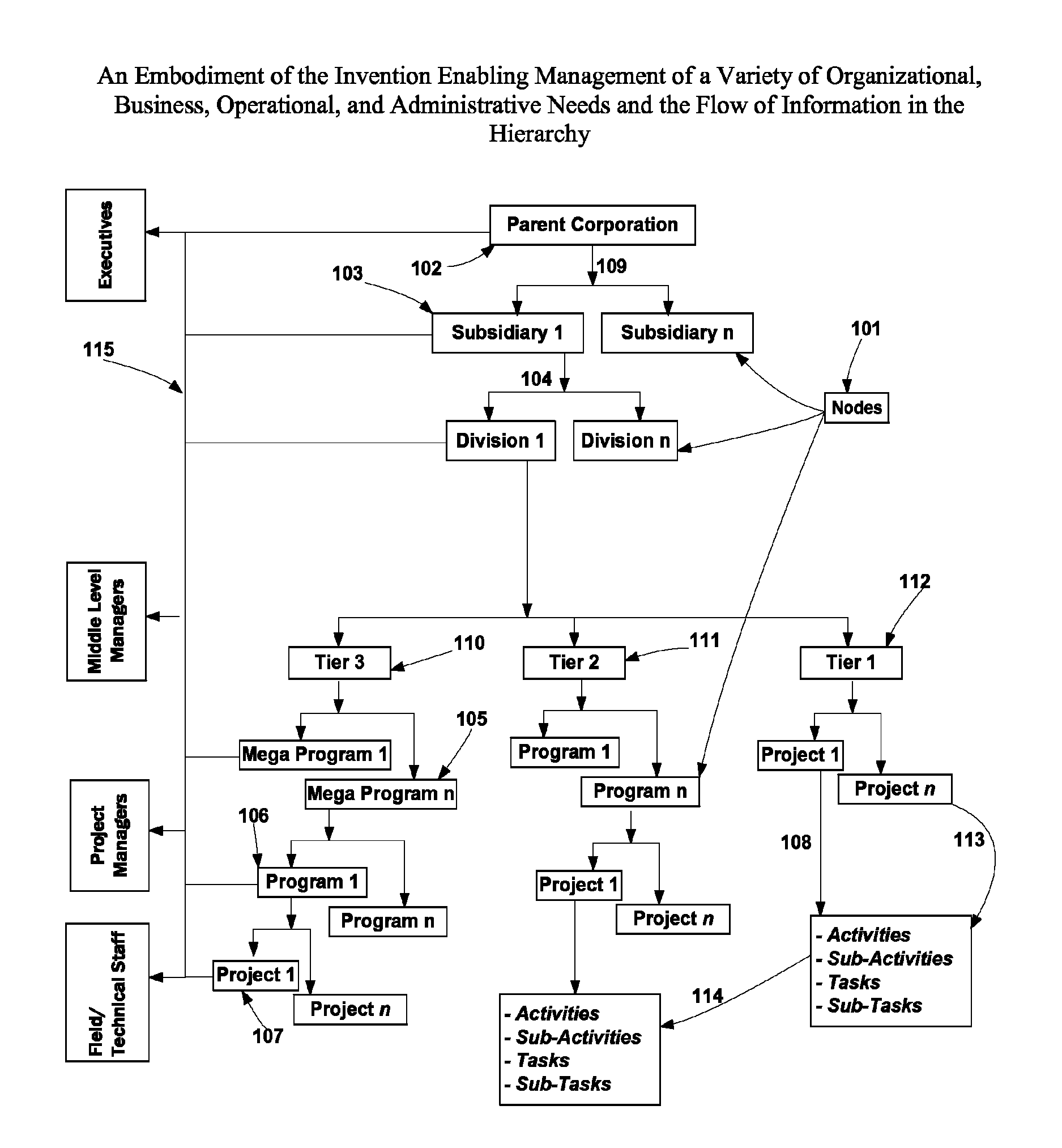
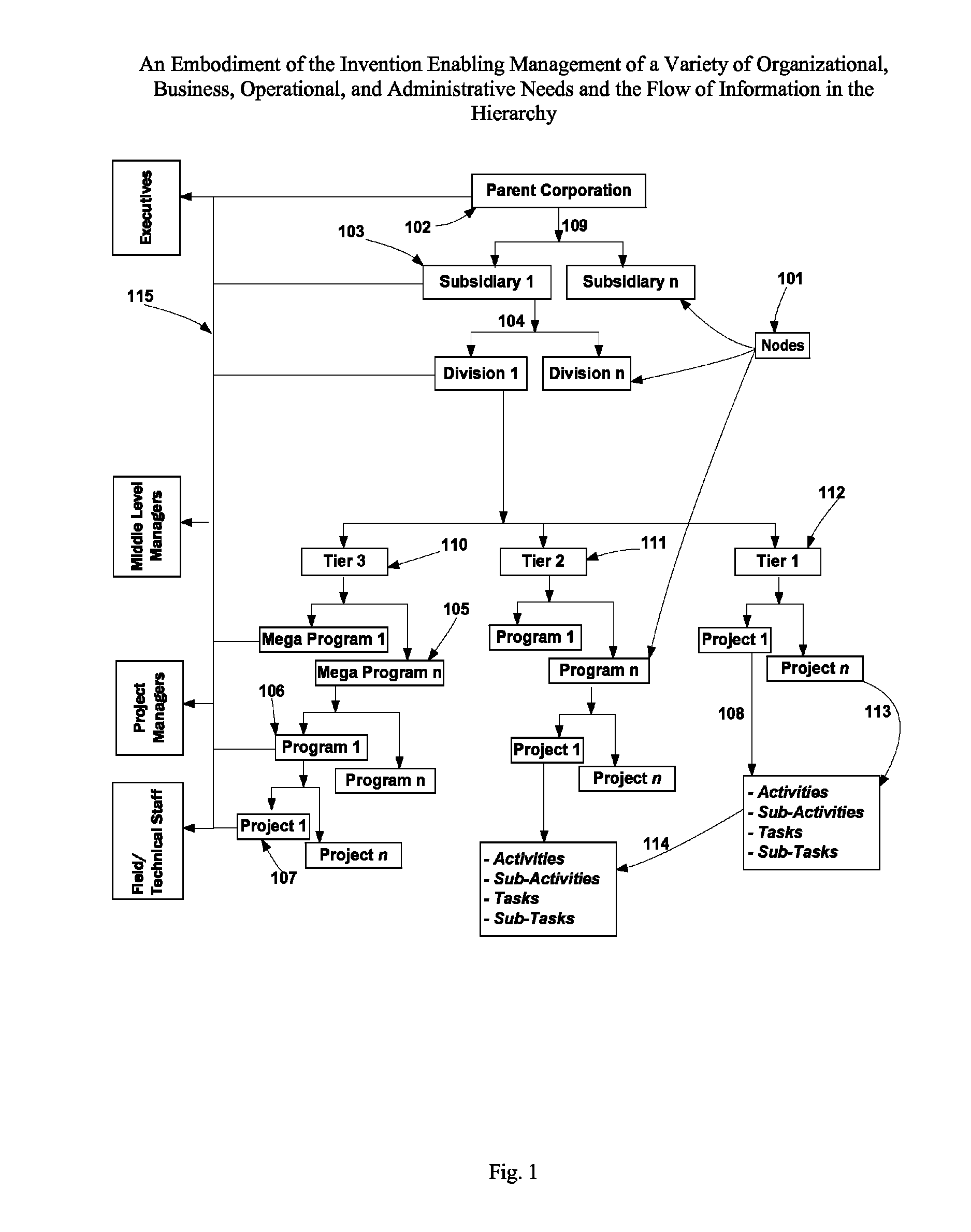
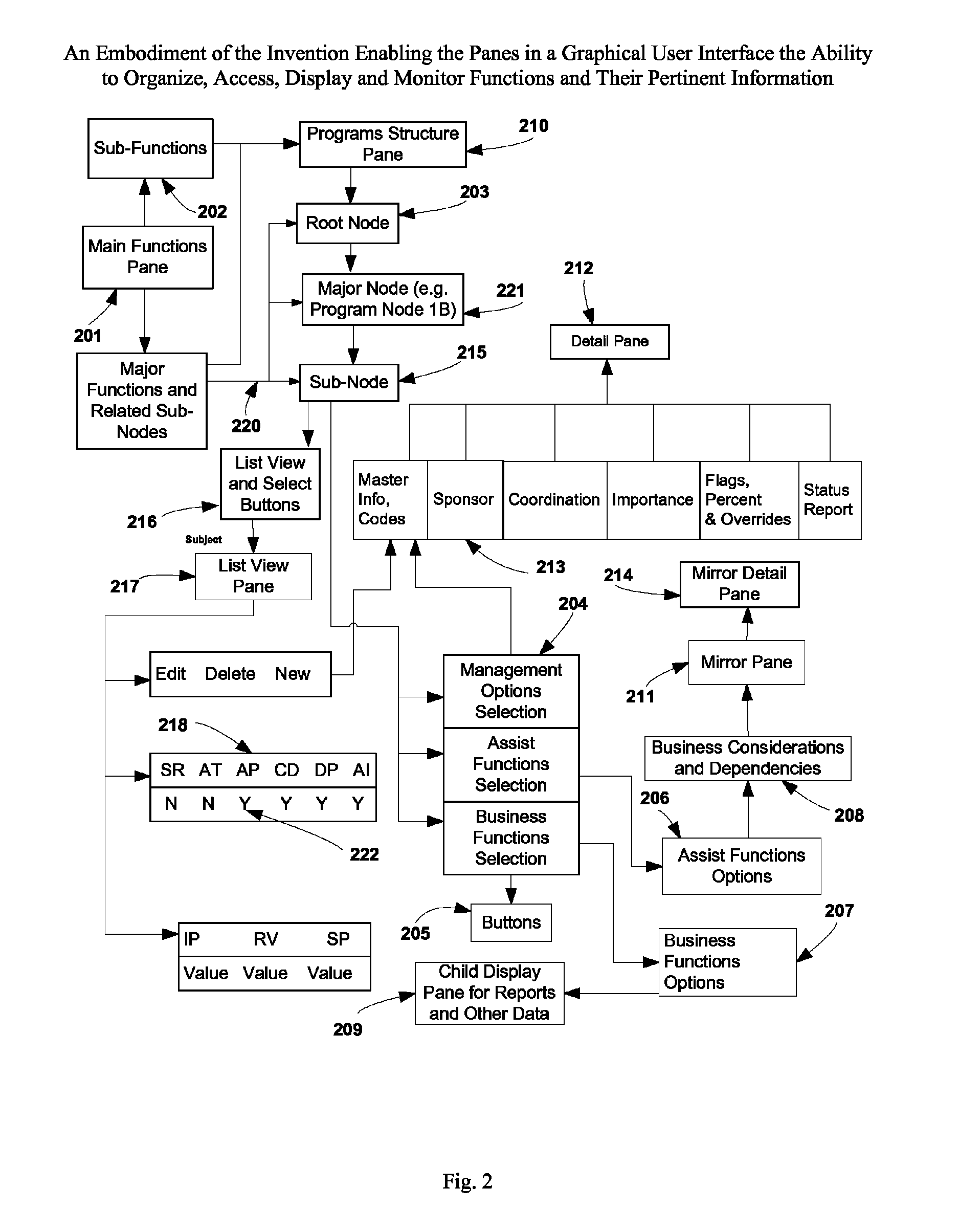
The invention comprises management of programs and mega-programs with emphasis on project level and above in a hierarchy that enables aggregation of information navigating up, and breakdown of details navigating down the hierarchy. It provides the flexibility of combining real-time management of budget with multiple editions, on call, asset tracking and capacity management of people and non-people resources within the same structure, vendor management, and real-time cross-program interlinking of dependencies and business considerations. The invention enables invocation of each function at every node in the hierarchy and localizes the related information at the invoking source. The functions encompass management of action items, status reports, approvals, meetings / decision making, issues, risks, change management and attachments with built in workflows that enable interactive collaboration and action triggering within the system and across external systems through condition and threshold setting. The universal structure enables management of organization layers and project initiatives.
Owner:NAGAR AJAY R +1
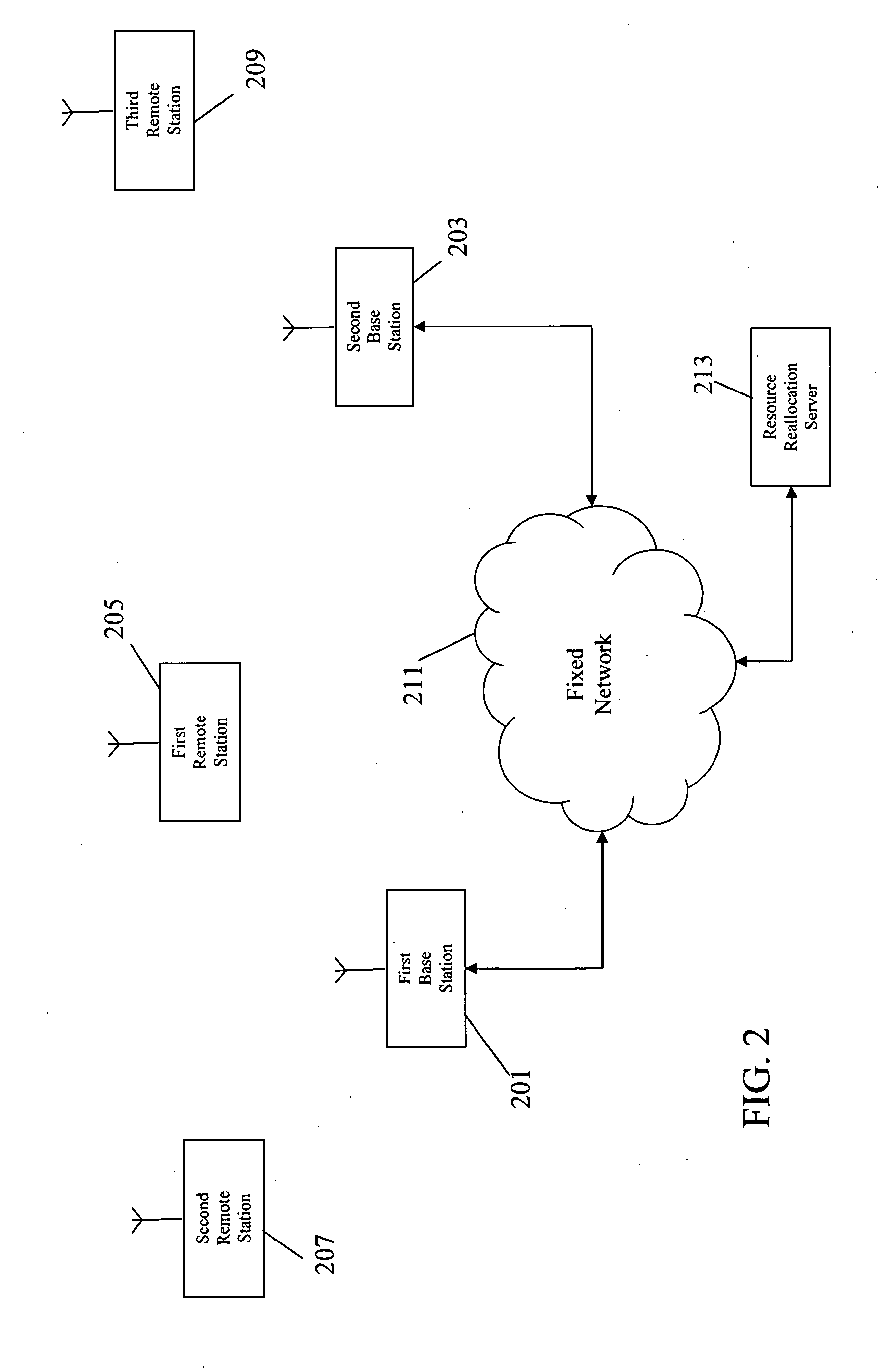
Resource exchange discovery in a cellular communication system
ActiveUS20090161614A1Efficient disseminationEasy to useConnection managementWireless commuication servicesAir interfaceStructure of Management Information
A cellular communication system comprises a set of base stations (201,203) which transmit downlink resource exchange discovery messages to remote terminals in resource allocations of a Media Access Control, MAC, frame structure. The discovery messages may indicate that a base station has resource available for reallocation to another base station or that a base station is seeking resource to be allocated from another base station. A remote terminal (205) comprises a receiver (401, 403) which receives a first message of the downlink resource exchange discovery messages from at least a first base station (201). A discovery message transmit processor (407) generates a second message, which is an uplink resource exchange message comprising resource exchange data determined from the first message, and transmits this to a second base station (203). The second base station (203) then initiates a temporary air interface resource reallocation with the first base station in response to receiving the second message.
Owner:MOTOROLA SOLUTIONS INC
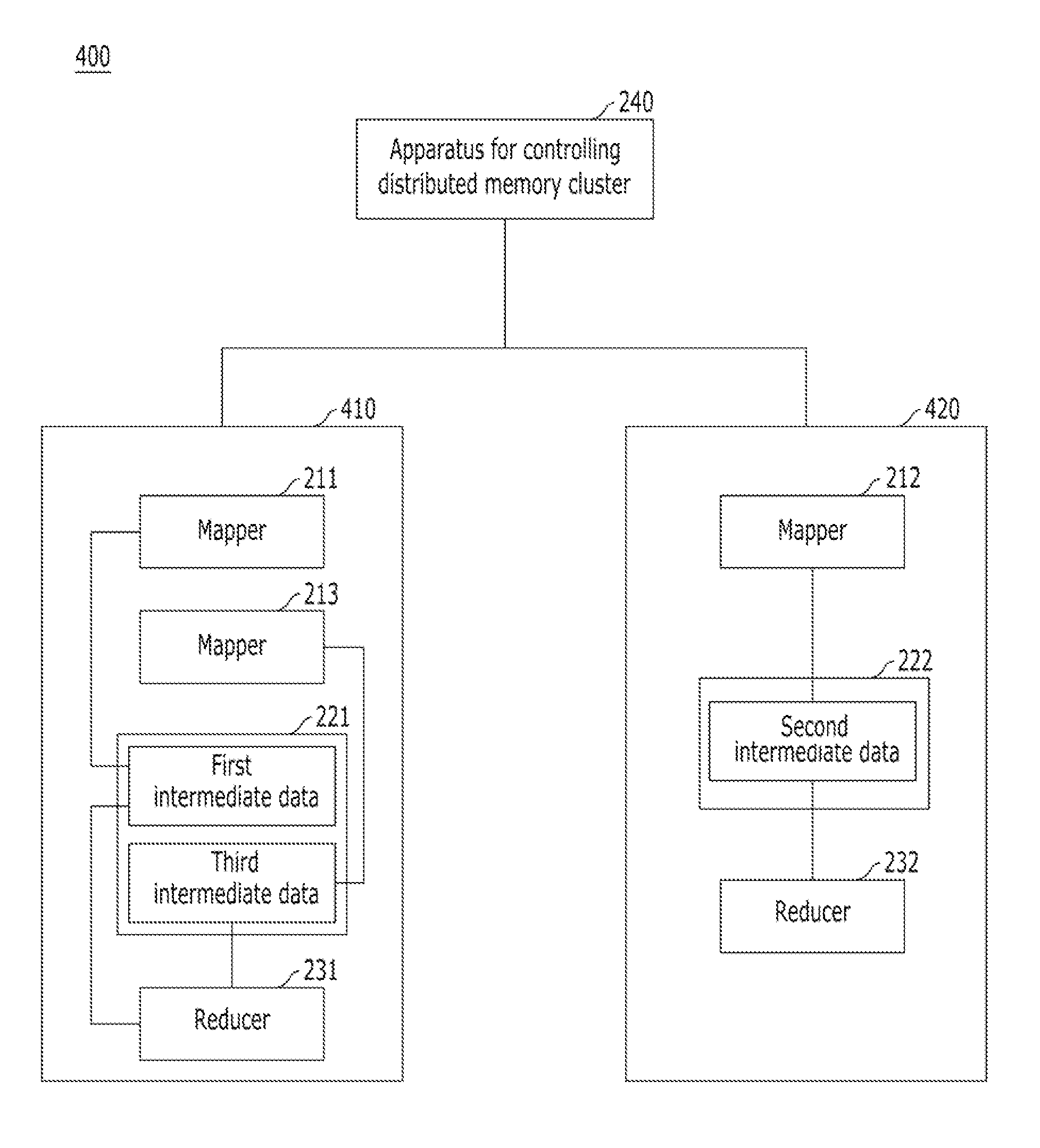
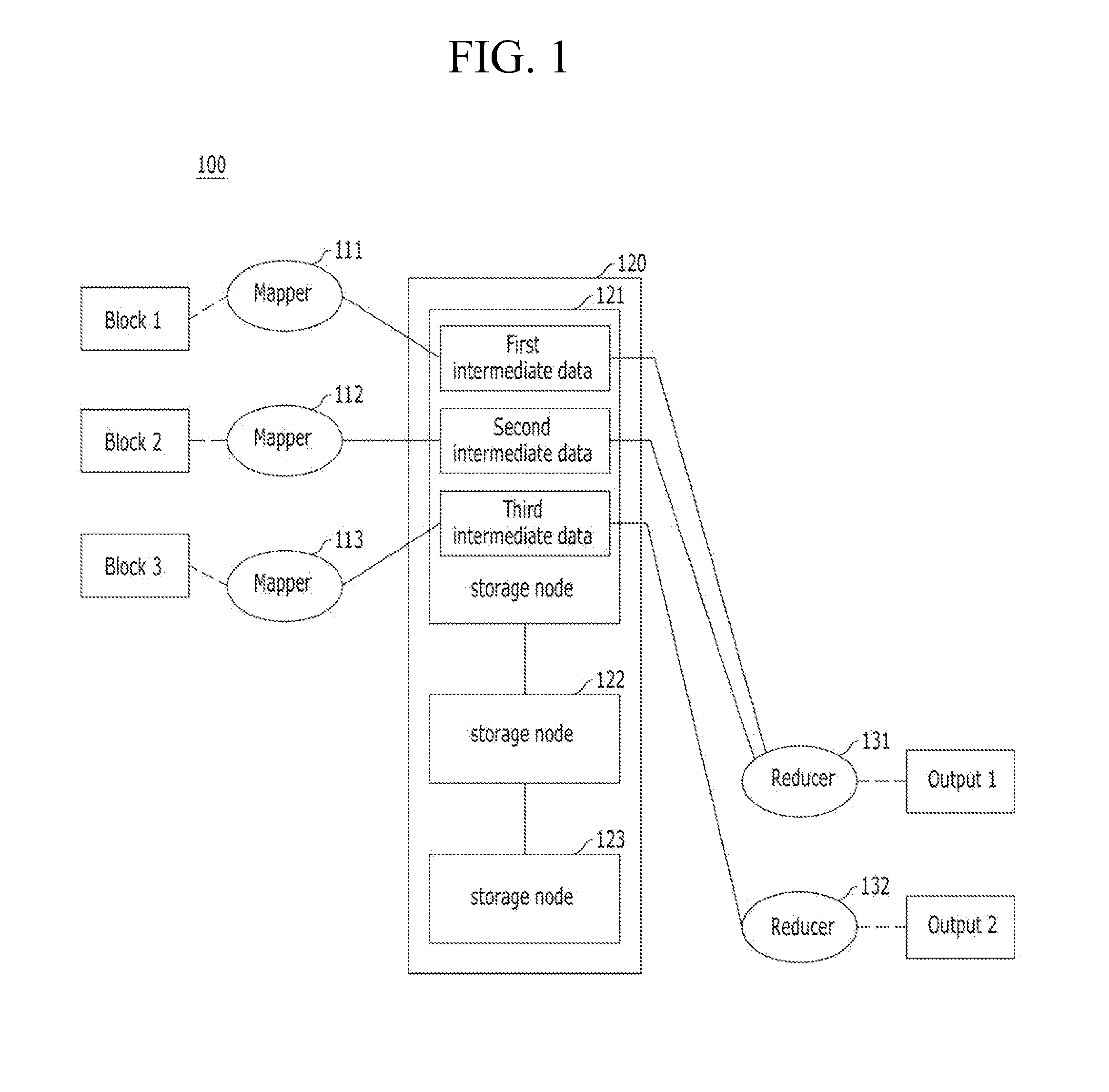
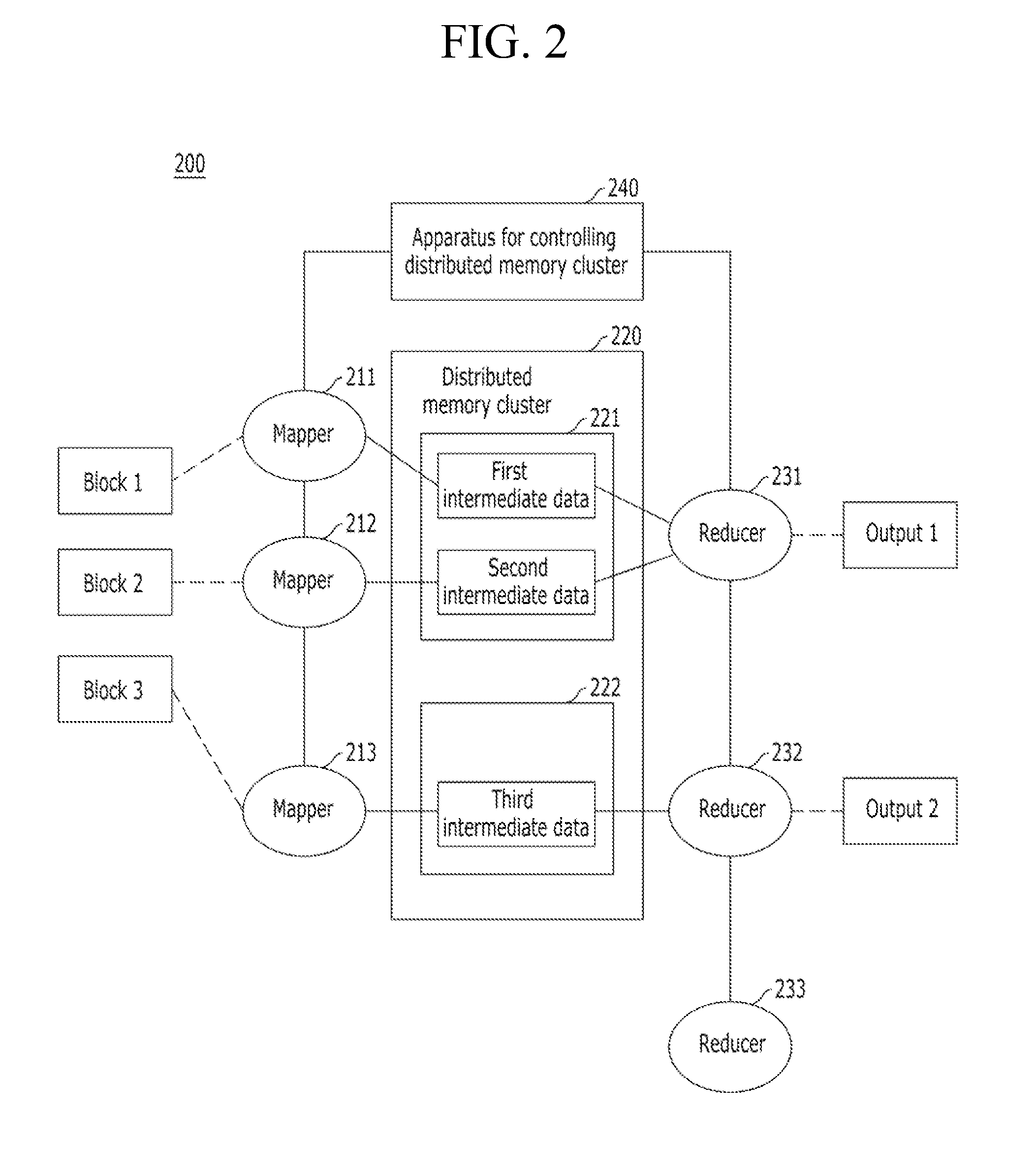
Apparatus and method for controlling distributed memory cluster
ActiveUS20120209943A1Valid choiceMemory adressing/allocation/relocationDigital computer detailsNode clusteringDistributed memory
Provided are an apparatus and method for controlling a distributed memory cluster. A distributed computing system may include a computing node cluster, a distributed memory cluster, and a controlling node. The computing node cluster may include a plurality of computing nodes including first computing nodes that each generates associated data. The distributed memory cluster may be configured to store the associated data of the first computing nodes. The controlling node may be configured to select memory blocks of the associated data for distribution on the distributed memory cluster based on a node selection rule and memory cluster structure information, and to select second computing nodes from the computing node cluster based on a location selection rule and the memory cluster structure information.
Owner:KT CORP
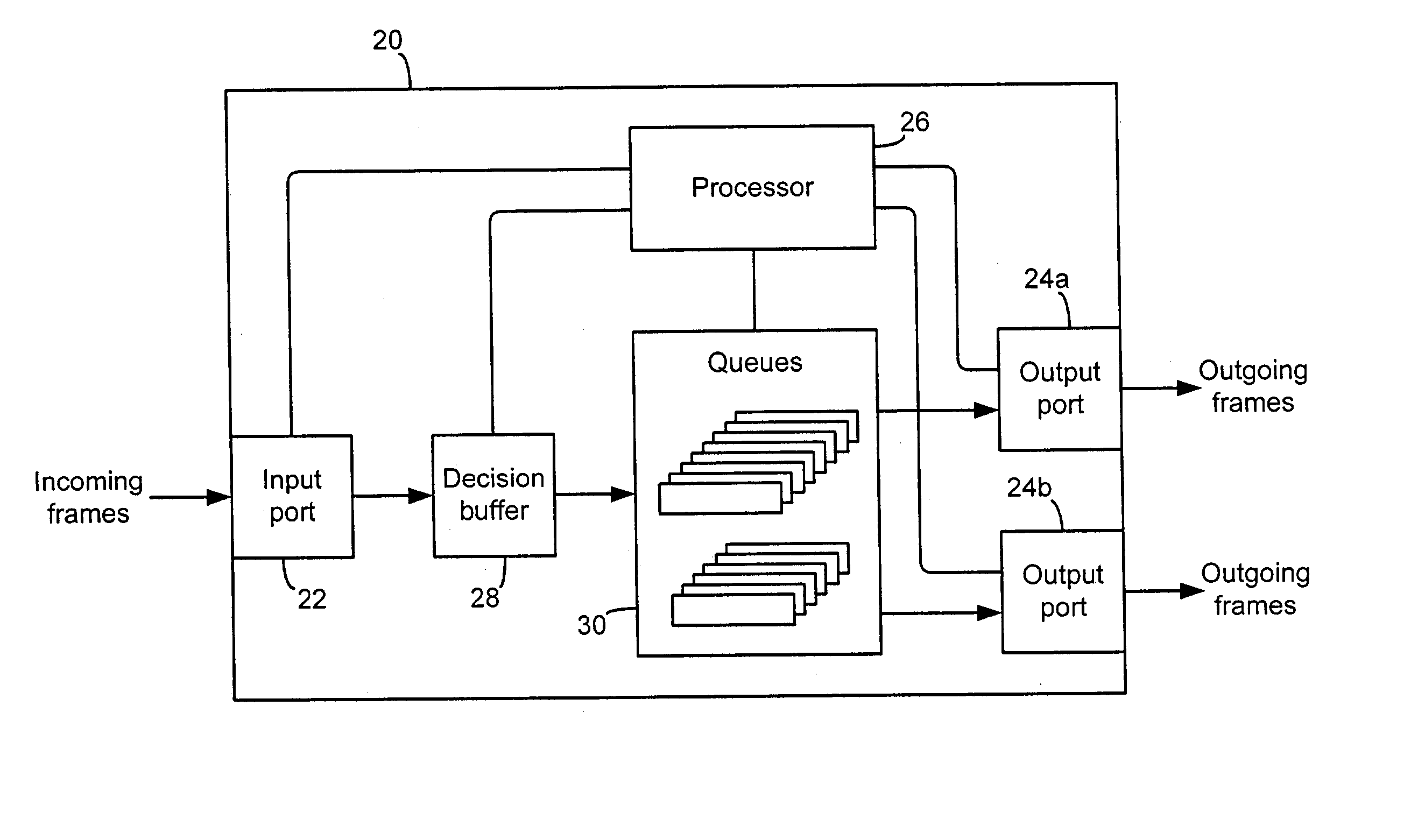
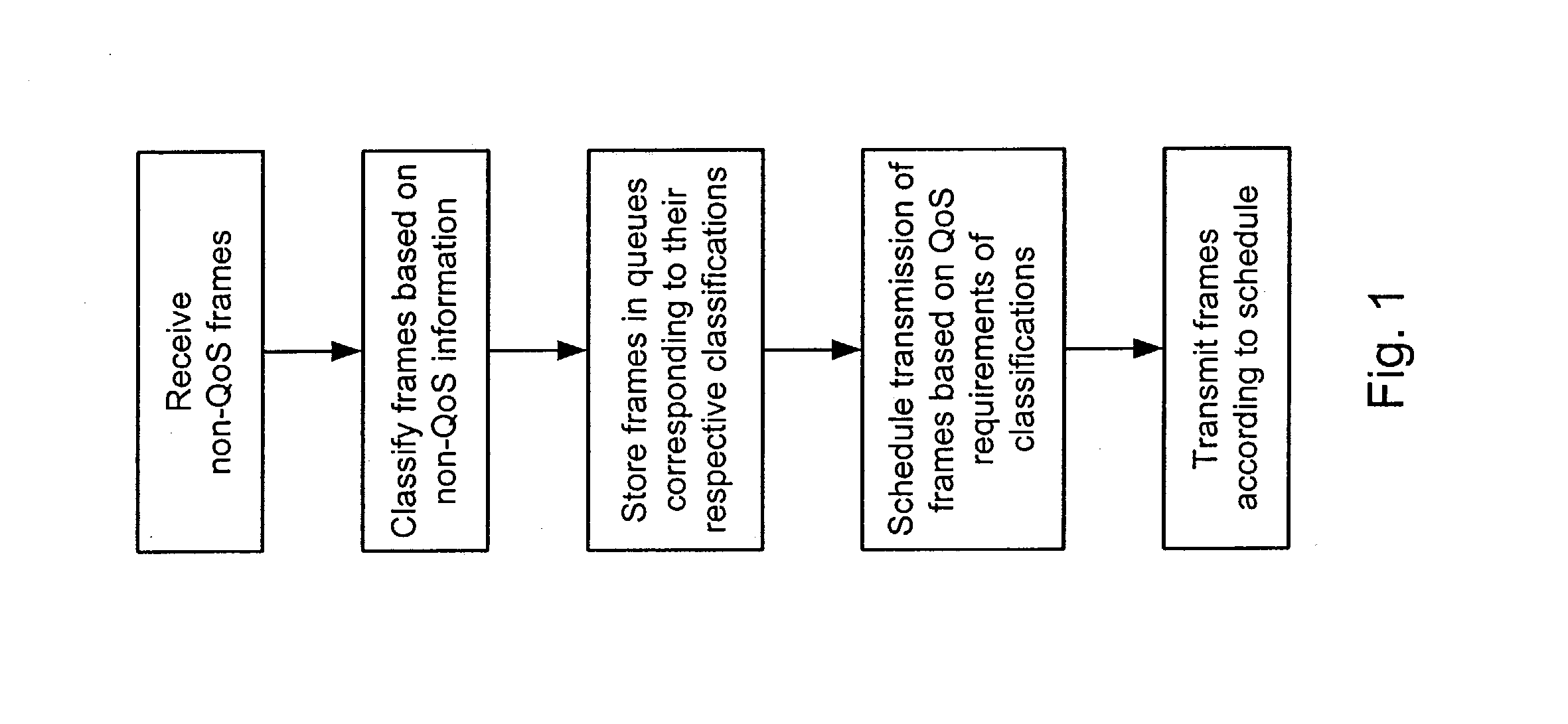
Systems and methods for providing quality of service (QoS) in an environment that does not normally support QoS features
Systems and methods for providing fractional bandwidth communication channels in classes of service that do not normally support these types of channels. In one embodiment, a method comprises receiving one or more frames, wherein each frame contains non-QoS header information, classifying the one or more frames based on the corresponding non-QoS header information and scheduling delivery of the one or more frames based upon corresponding frame classifications, wherein frames in classifications corresponding to QoS circuits are scheduled in a manner that meets QoS requirements associated with the QoS circuits. When the frames are classified, they are forwarded to dynamically allocated queues corresponding to the respective classifications. Frames are scheduled for delivery from the queues according to a modified bin-filling algorithm that is designed to meet the QoS requirements of the respective circuits. This method may be implemented, for example, in a Fibre Channel Class 2 or Class 3 fabric.
Owner:QOS IP
Location-based addressing lighting and environmental control system, device and method
ActiveUS7889051B1Less bandwidthAttenuation bandwidthElectric signal transmission systemsMultiple keys/algorithms usageLight equipmentControl system
Location-Based Addressing (LBA) is a method of controlling and commissioning networked lighting devices. The lighting devices communicate over a wireless network using radio frequency communication protocols. The lighting devices are commissioned or grouped based on their respective locations in a building floor plan or a building architecture. The lighting devices are commissioned to respond to radio frequency communications that correspond to their respective locations. This imposed location-based architecture reduces the amount of transmitted data required to control the lighting devices and, thus, reduces the radio bandwidth required to control the lighting devices. In other words, controlling devices “multicast” instructions and controlled devices “listen” for instructions and act only upon instructions that correspond to their respective location. Hand shaking or two-way communication between the controlling devices and the controlled devices is not required.
Owner:THE WATT STOPPER
Cloud platform supporting fusion network service and operating method thereof
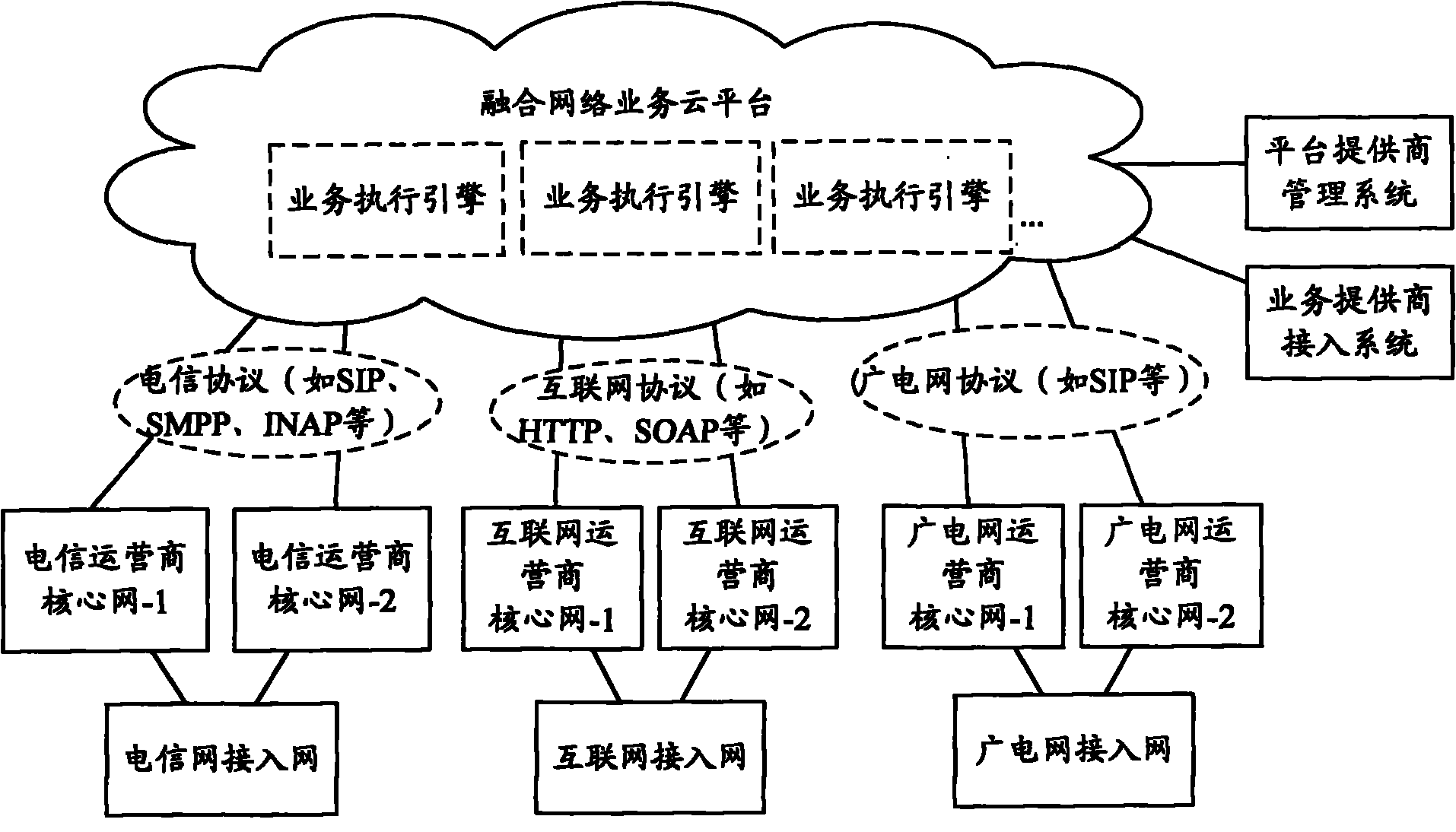
InactiveCN101969391APromote innovationGood varietyData switching by path configurationGPRS core networkClosed platform
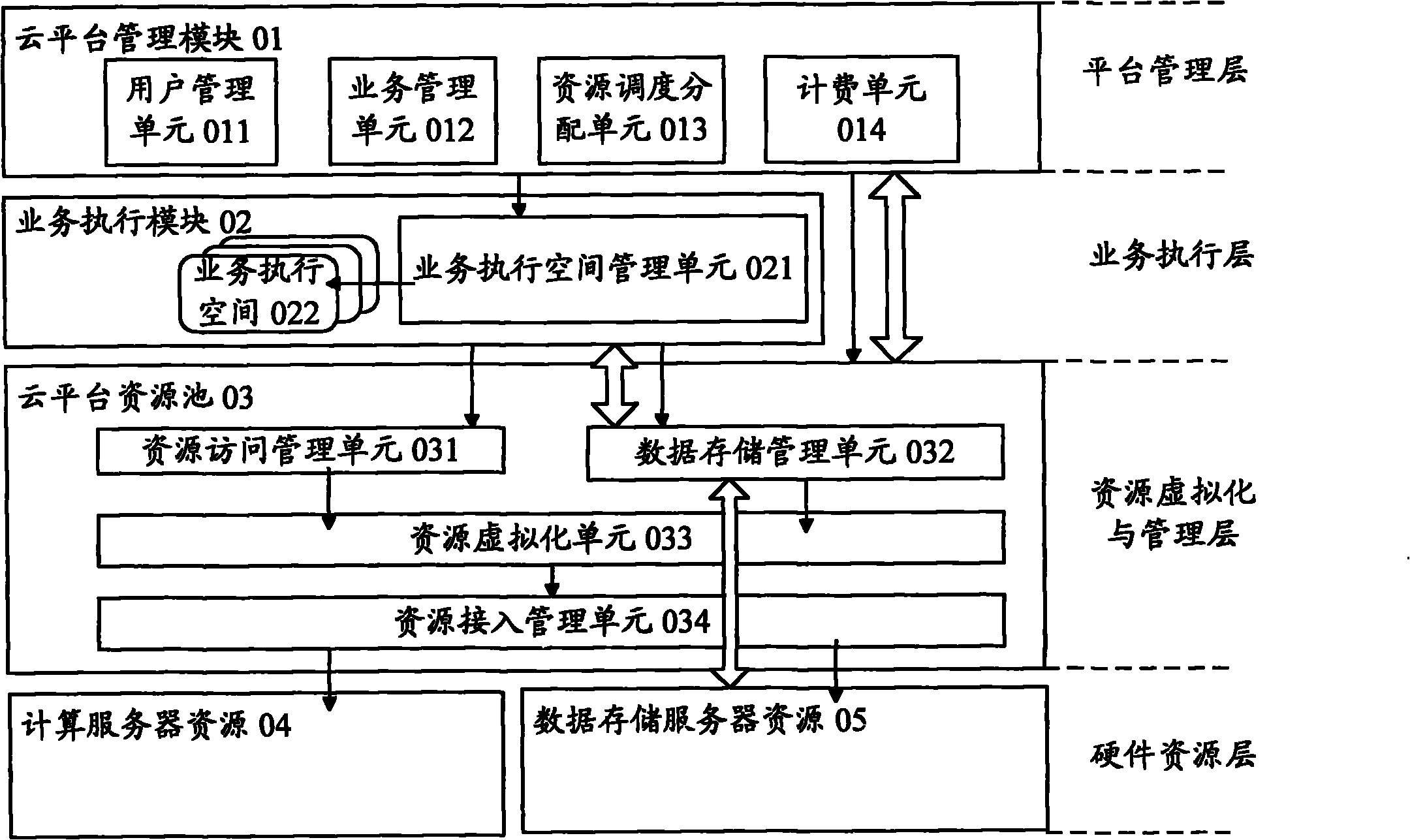
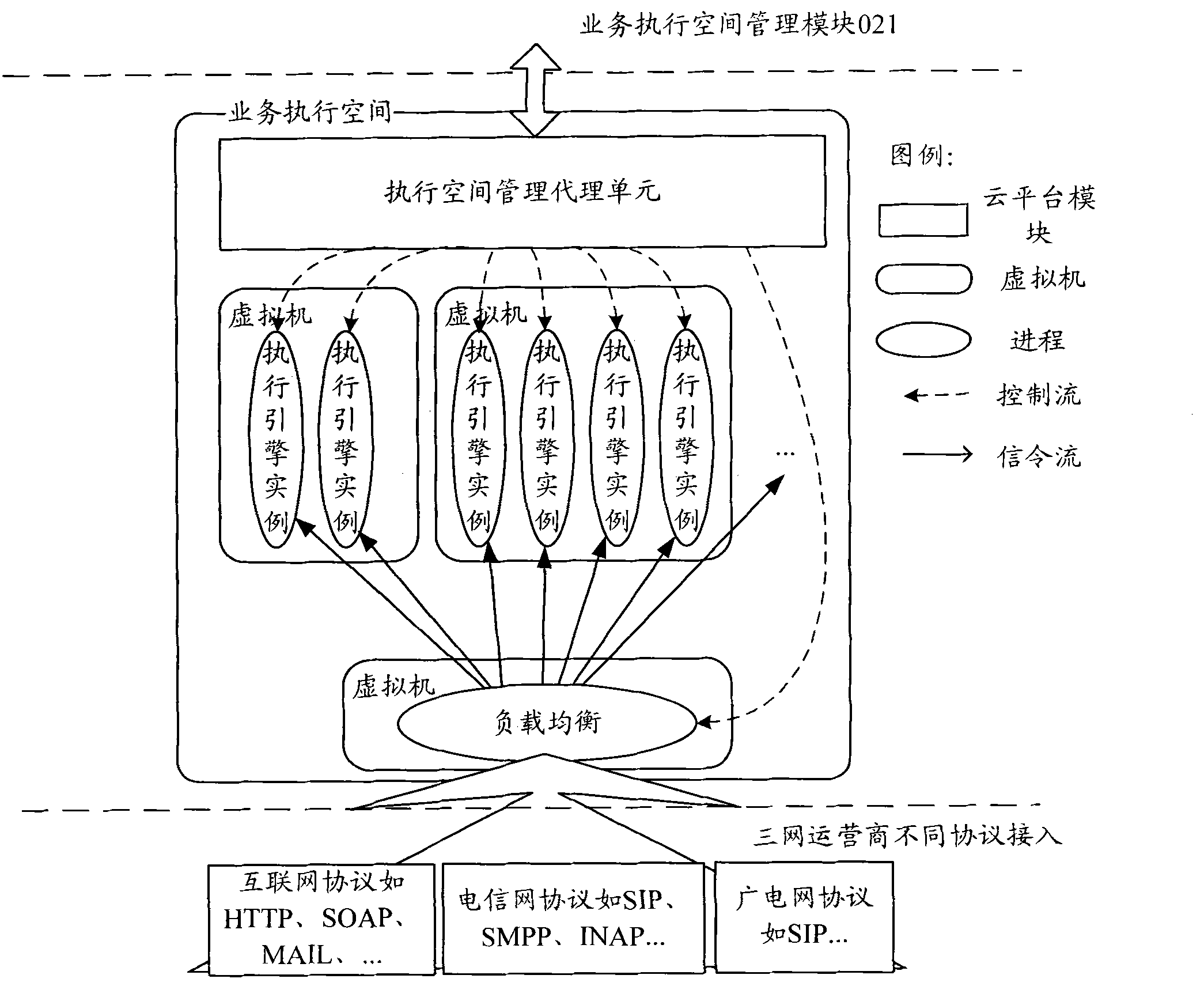
The invention relates to a cloud platform supporting fusion network service and an operating method thereof. The cloud platform is provided with a plurality of hardware and software resources, and is connected with three access networks of a telecommunication network, an interconnection network and a broadcasting and television network respectively through three core networks of operators of the three networks and the corresponding communication protocol to allow platform users (including the operators of the three networks or service providers and the like) to rent platform resources according to respective requirements to deploy respective services and operational capabilities. The cloud platform has a layered structure, and is provided with a platform management layer, a service execution layer, a resource virtualization and management layer and a hardware resource layer respectively from top to bottom, and in an interactive mode among the layers, an upper-layer module uses the function provided a lower-layer module in a mode of interface call. The cloud platform supports the platform users to adjust the rent resources dynamically and conveniently according to actual requirements, and simultaneously, provides the access capability on the resources of the three networks and convenience for the development and operation of the fusion network service by the platform users.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Secure integrated device with secure, dynamically-selectable capabilities
InactiveUS6968453B2Conveniently and economically providedEnsure safetyUser identity/authority verificationDigital data protectionStructure of Management InformationOutput device
A method, system, computer program product, and method of doing business by providing a secure integrated device (such as a pervasive computing device) for which operating capabilities can be dynamically yet securely selected (including, but not limited to, pluggable connection of input / output devices and / or application processors that provide selected functions). Each input / output (I / O) device and application processor to be used is plugged in to a bus of a security core, and authenticates itself to the security core using public key infrastructure techniques, thereby creating a secure multi-function device. All of the multi-function device's input and output interactions with its environment necessarily traverse an I / O bus under the sole control of the security core. The only communication path between an application processor and the external environment (such as an I / O device) is through an application processor bus, which is likewise under control of the security core. Thus a user may dynamically yet securely select the capabilities of a multi-function device, and because each I / O device and application processor in use by that multi-function device is authenticated, the security of transactions or network services performed when using such devices is improved.
Owner:INT BUSINESS MASCH CORP
Method and system for distribution of wireless signals for increased wireless coverage using power lines
InactiveUS6243571B1Minimize signalingGuaranteed uptimeCordless telephonesInterconnection arrangementsTelecommunicationsWireless transmission
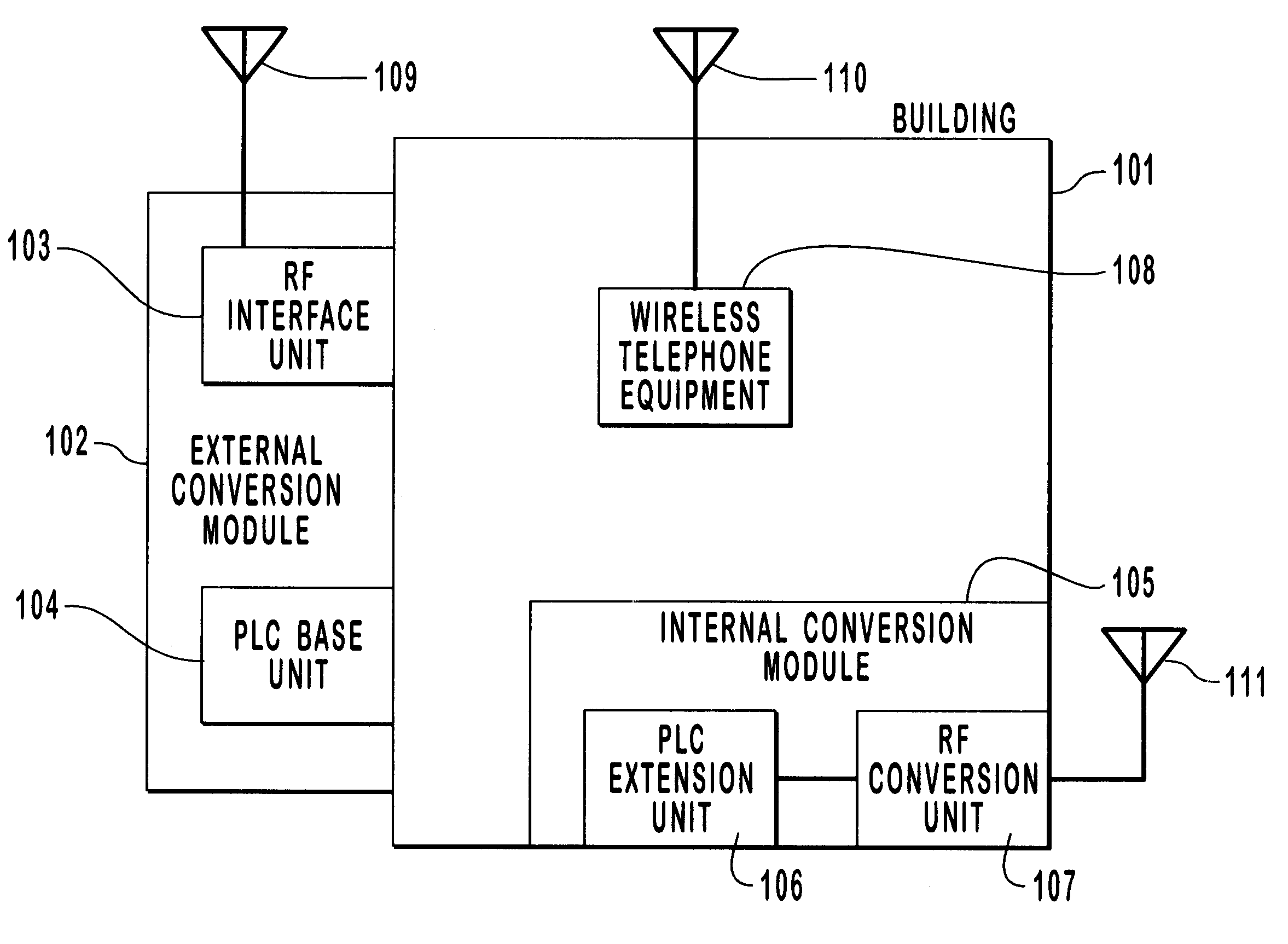
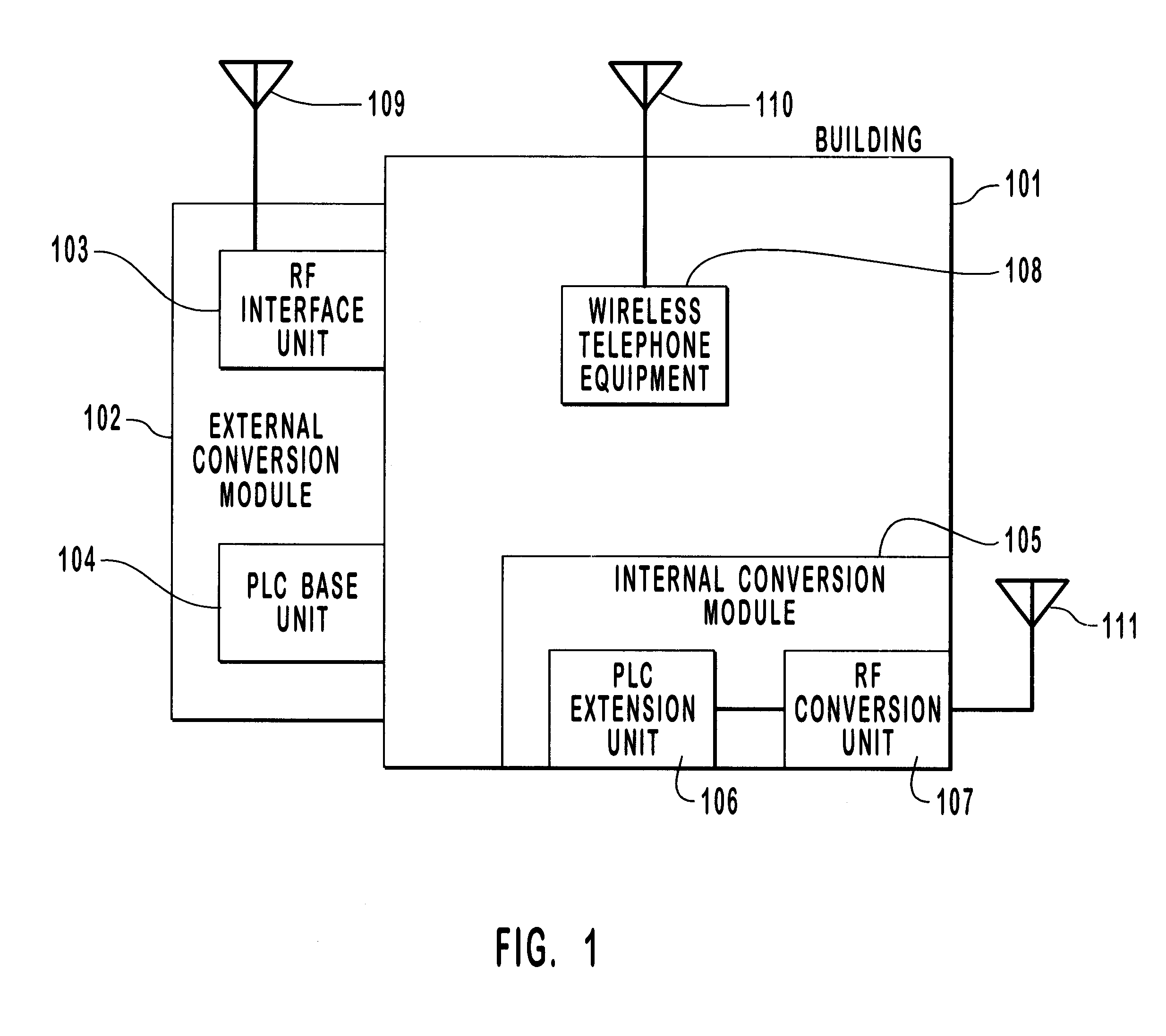
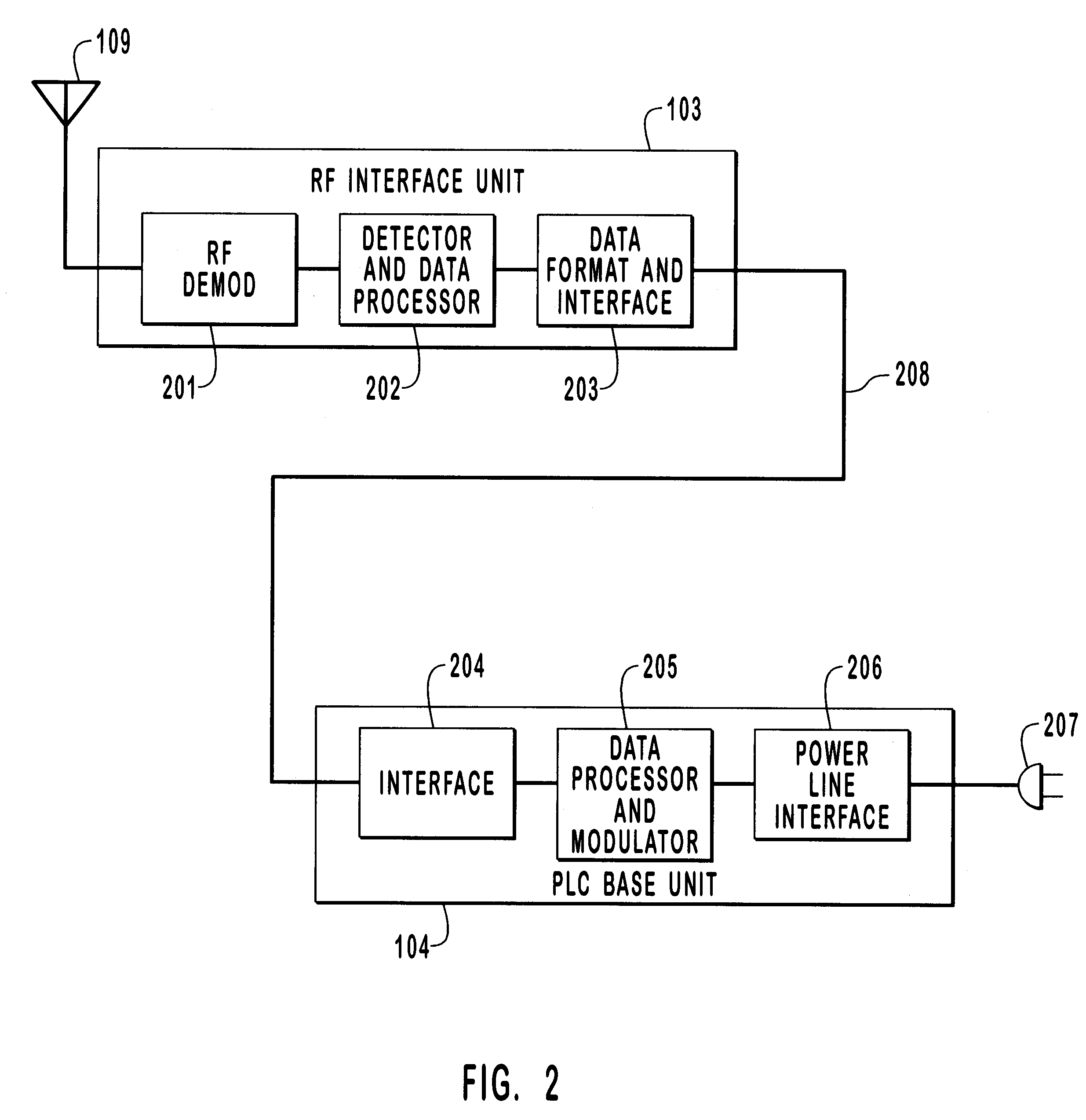
A method and system for the reception, conversion and distribution of wireless communication signals received from such communication devices as PCS, Cellular, and Satellite over AC power lines commonly found within a building, office, home or other structure is disclosed. This invention specifically provides for the distribution of wireless signals in structures where otherwise signal degradation and / or blockage are common. Moreover, this invention takes advantage of the existing AC power lines to create a communication channel avoiding the necessity of rewiring the building or other structure. This invention provides important improvements to the signal coverage and reception of wireless transmitted signals within buildings and other structures and does so in an efficient and cost effective manner.
Owner:GULA CONSULTING LLC
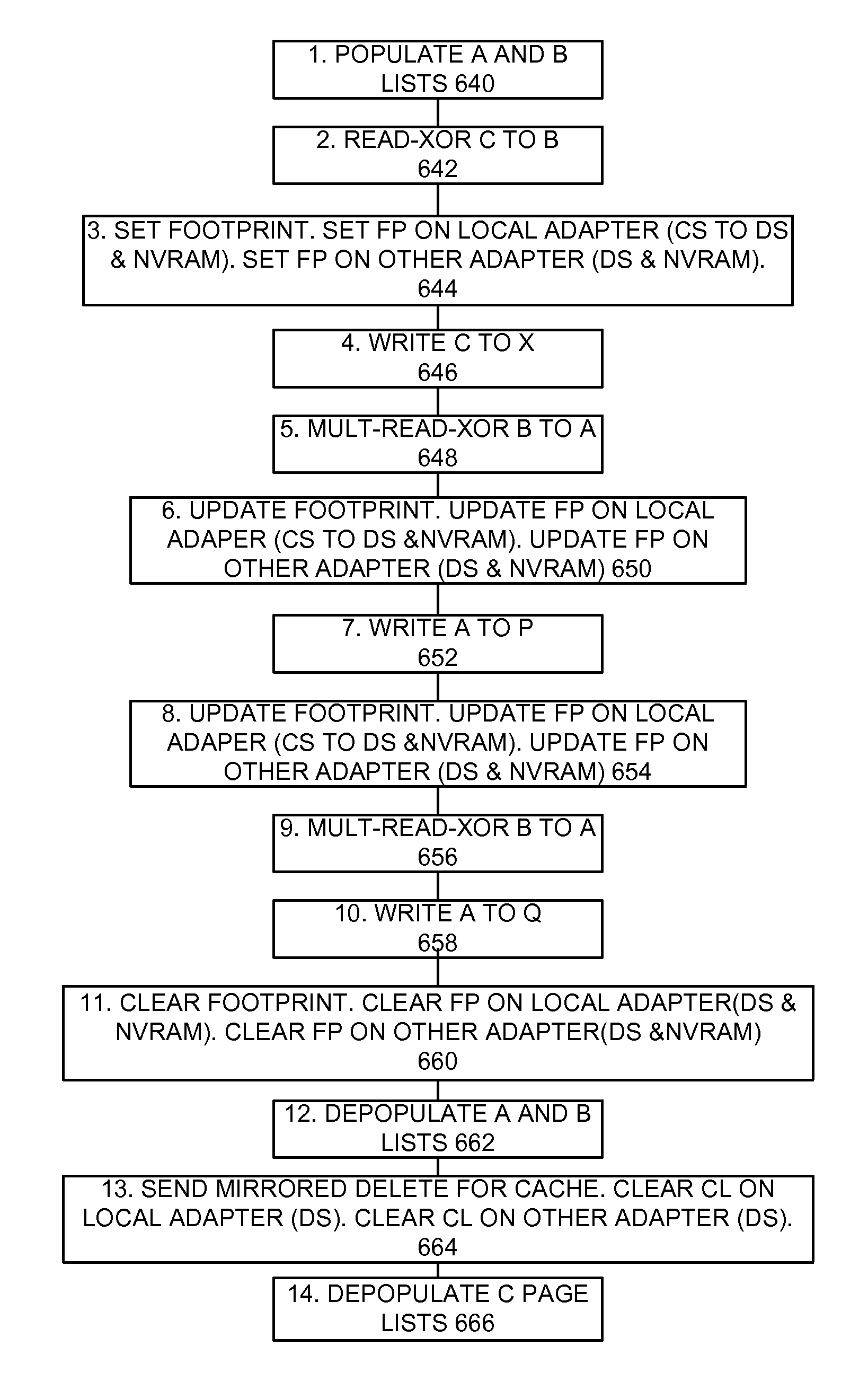
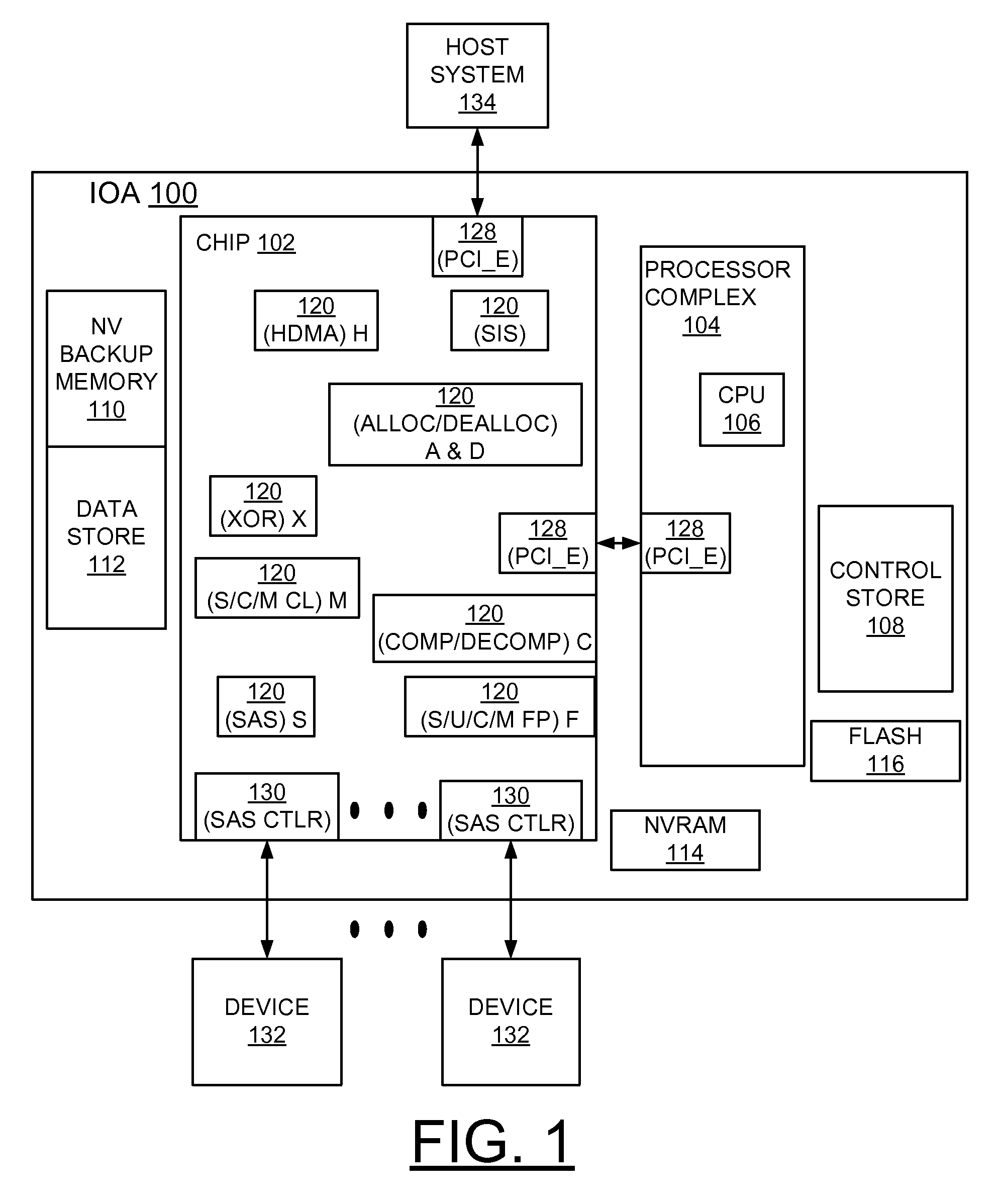
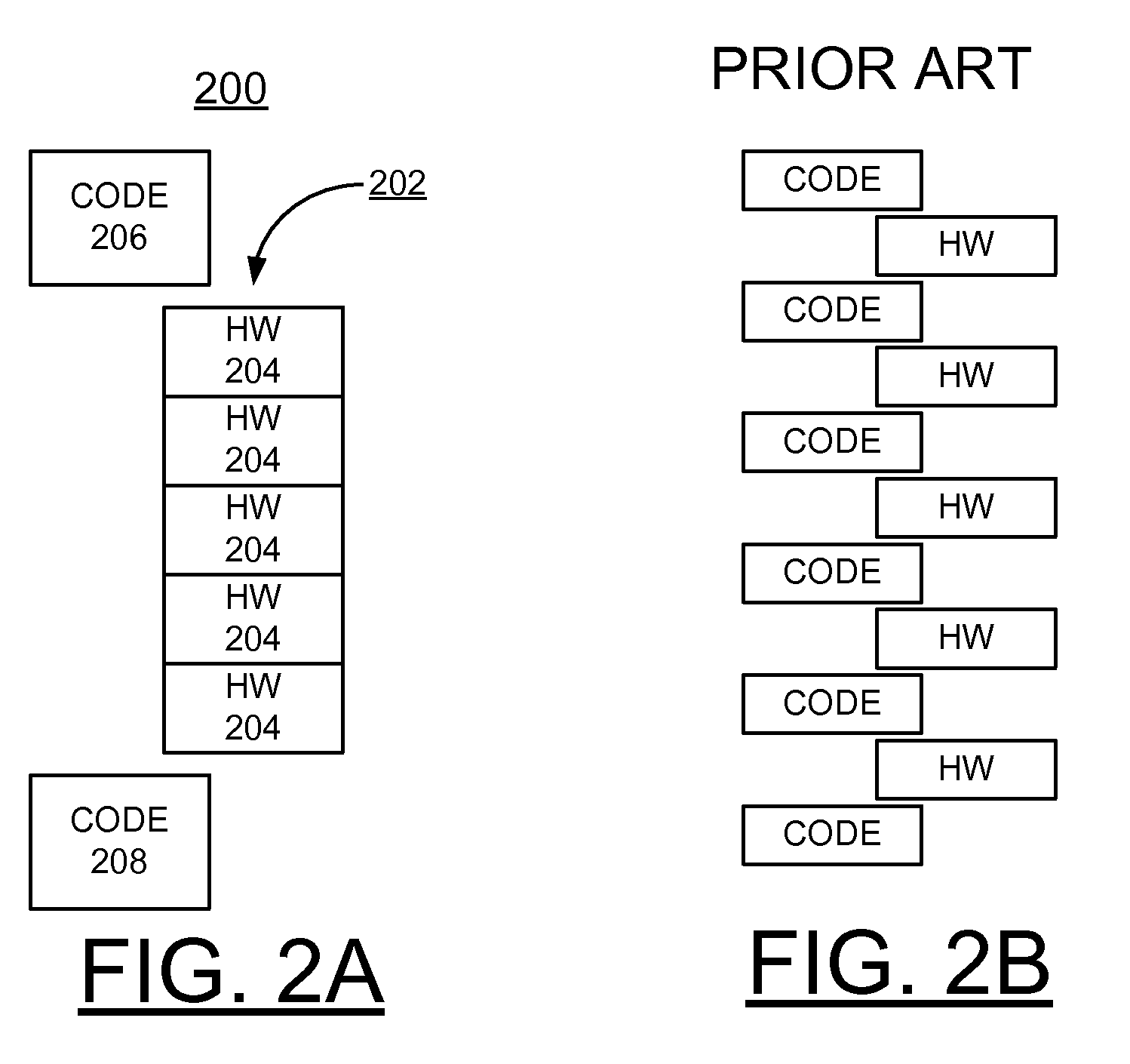
Implementing storage adapter performance optimization with chained hardware operations minimizing hardware/firmware interactions
InactiveUS8544029B2Overcome disadvantagesMinimize writing event queue entryInput/output to record carriersSpecific program execution arrangementsStructure of Management InformationEvent queue
A method and controller for implementing storage adapter performance optimization with chained hardware operations minimizing hardware and firmware interactions, and a design structure on which the subject controller circuit resides are provided. The controller includes a plurality of hardware engines; and one or more processors. An event queue is coupled to at least one processor notifying the processor of a plurality of predefined events. A control block is designed to control an operation in one of the plurality of hardware engines including the hardware engine writing an event queue entry. A plurality of the control blocks are selectively arranged in a predefined chain to minimize the hardware engine writing event queue entries to the processor.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com