Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
135 results about "Critical event" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
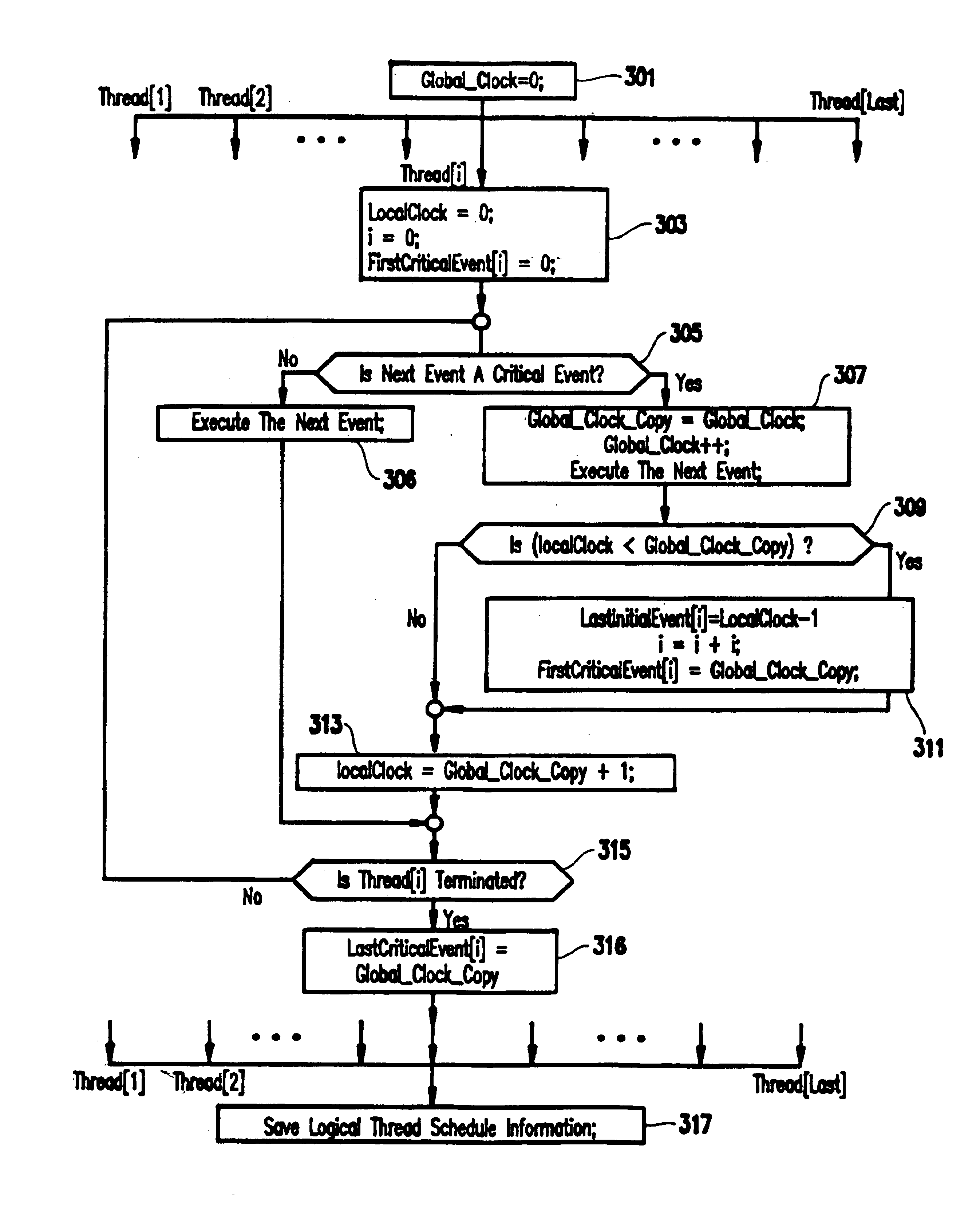
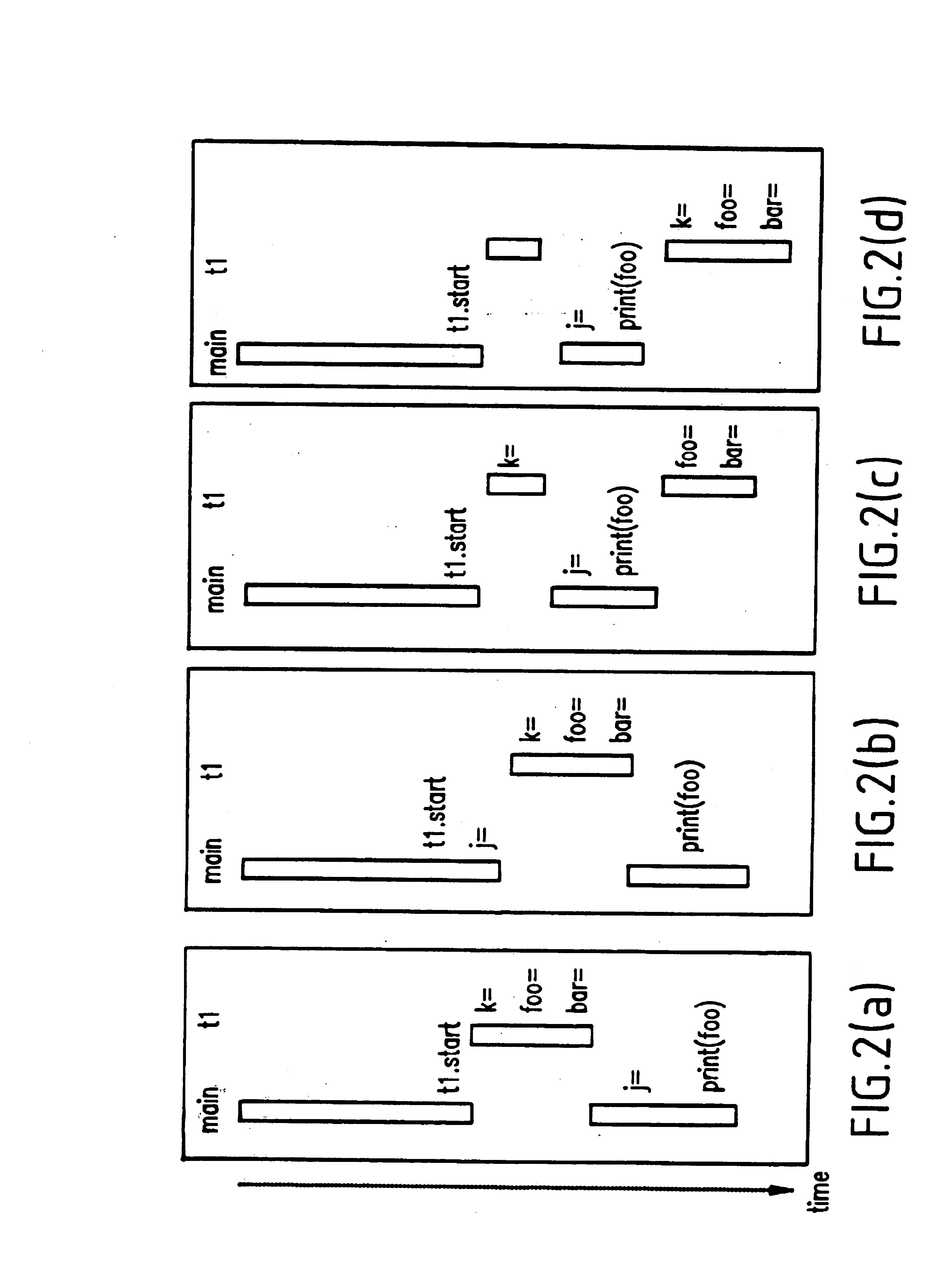
Method and system for recording and replaying the execution of distributed java programs
InactiveUS6832367B1Easy to copyGuaranteed orderError detection/correctionSpecific program execution arrangementsStream socketThread scheduling
A method for recording and replaying execution of distributed programs on a computer system in a distributed environment, includes identifying an execution order of critical events of a program, generating groups of critical events of the program, wherein for each group, critical events belonging to the group belong to a common execution thread, and generating for each execution thread a logical thread schedule that identifies a sequence of the groups so as to allow deterministically replaying a non-deterministic arrival of stream socket connection requests, a non-deterministic number of bytes received during message reads, and a non-deterministic binding of stream sockets to local ports.
Owner:IBM CORP
Security Monitoring and Control
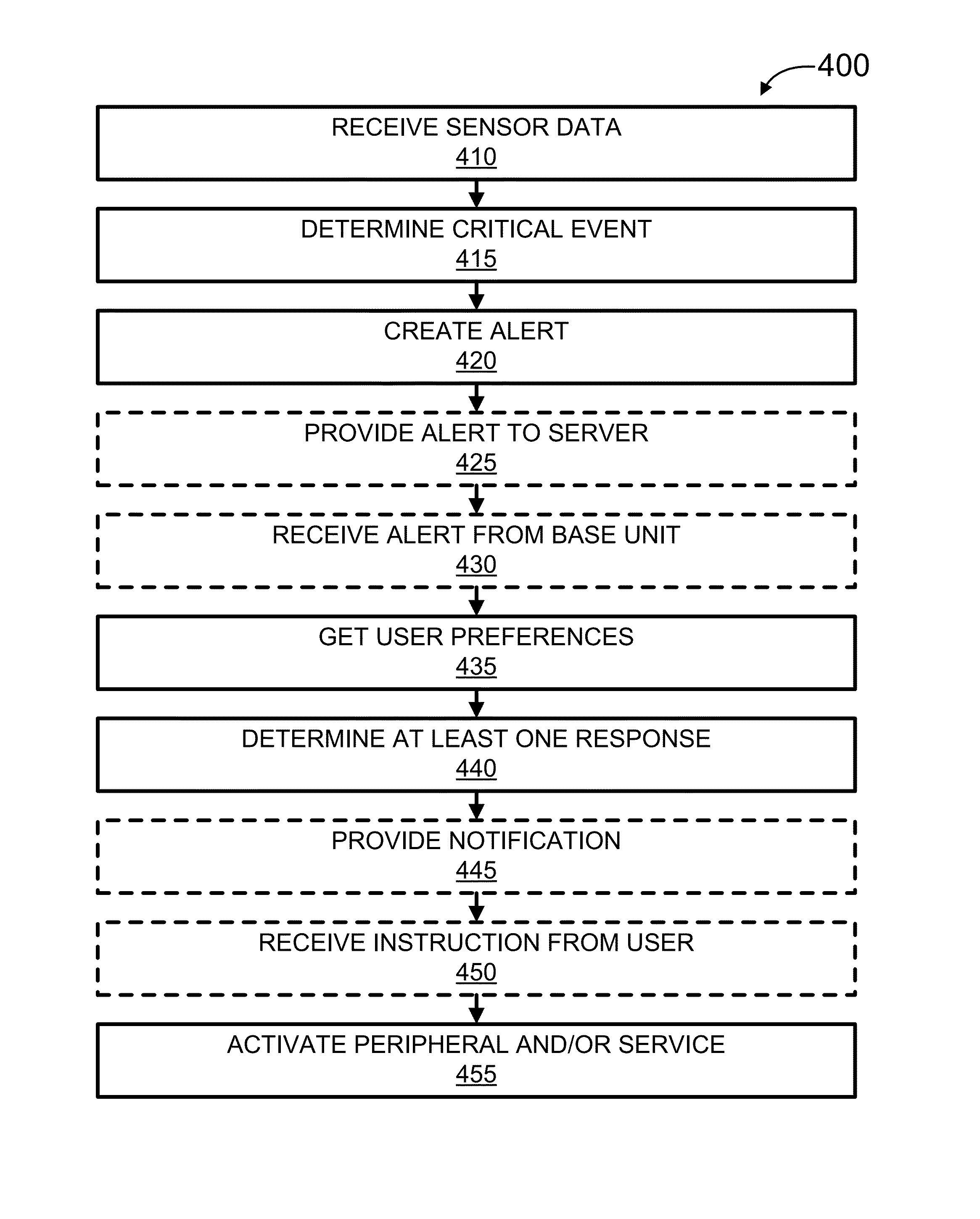
ActiveUS20150339912A1Burglar alarm mechanical actuationControl systemStructure of Management Information
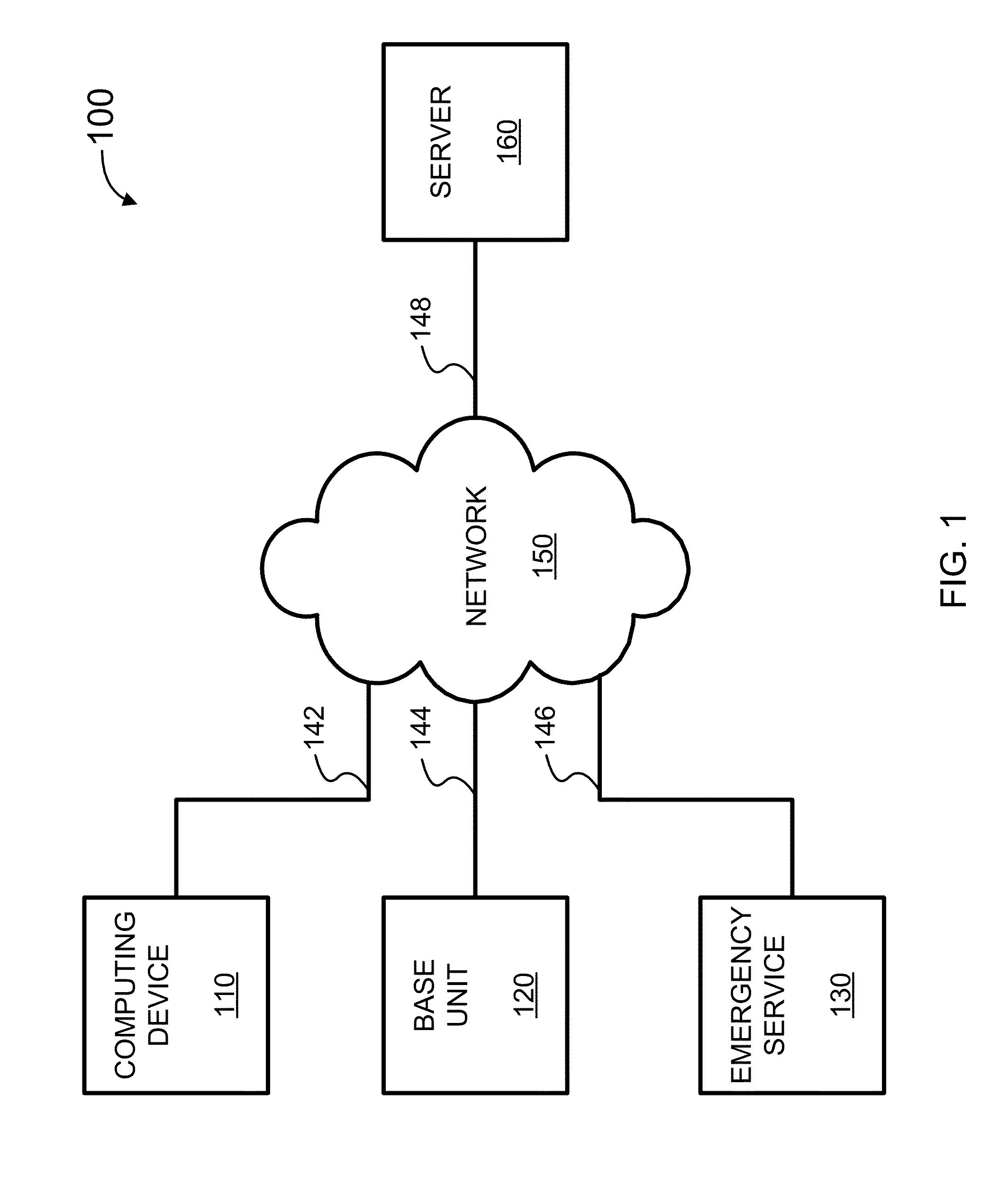
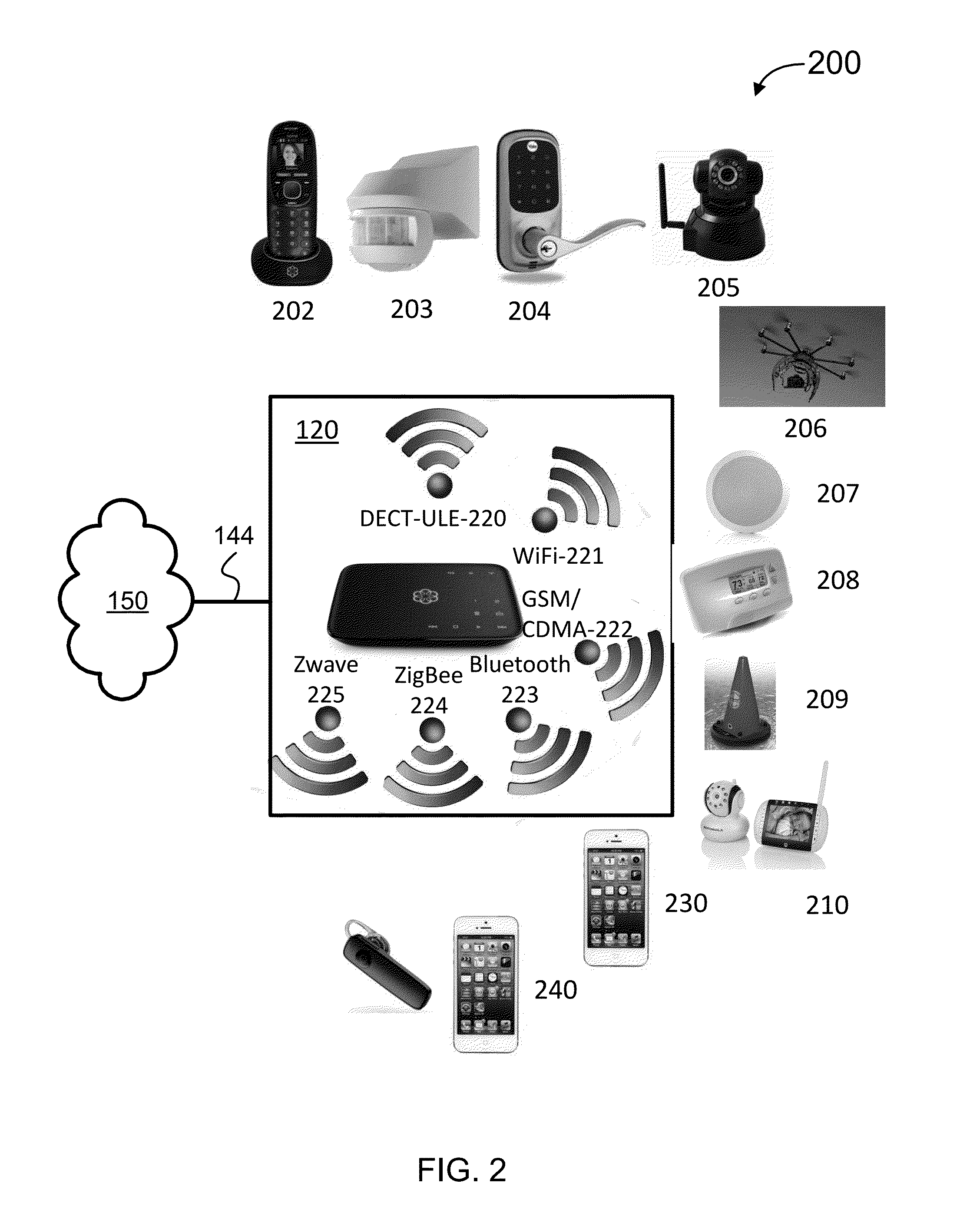
Systems, methods, and software for monitoring and controlling a security system for a structure are provided herein. An exemplary method may include receiving sensor data from at least one first peripheral, the sensor data associated with at least one of activity inside and activity outside of a structure; determining a critical event based in part on the sensor data; creating an alert based in part on the critical event; getting user preferences associated with at least one of a user and a base unit; determining a response based in part on the alert and user preferences; and activating at least one of a second peripheral and a service based in part on the response.
Owner:OOMA
Method for managing resource assets for emergency situations
InactiveUS20030125998A1Easy accessInformation quickly and efficientlyResourcesSpecial data processing applicationsDatabase interfaceDaily operation
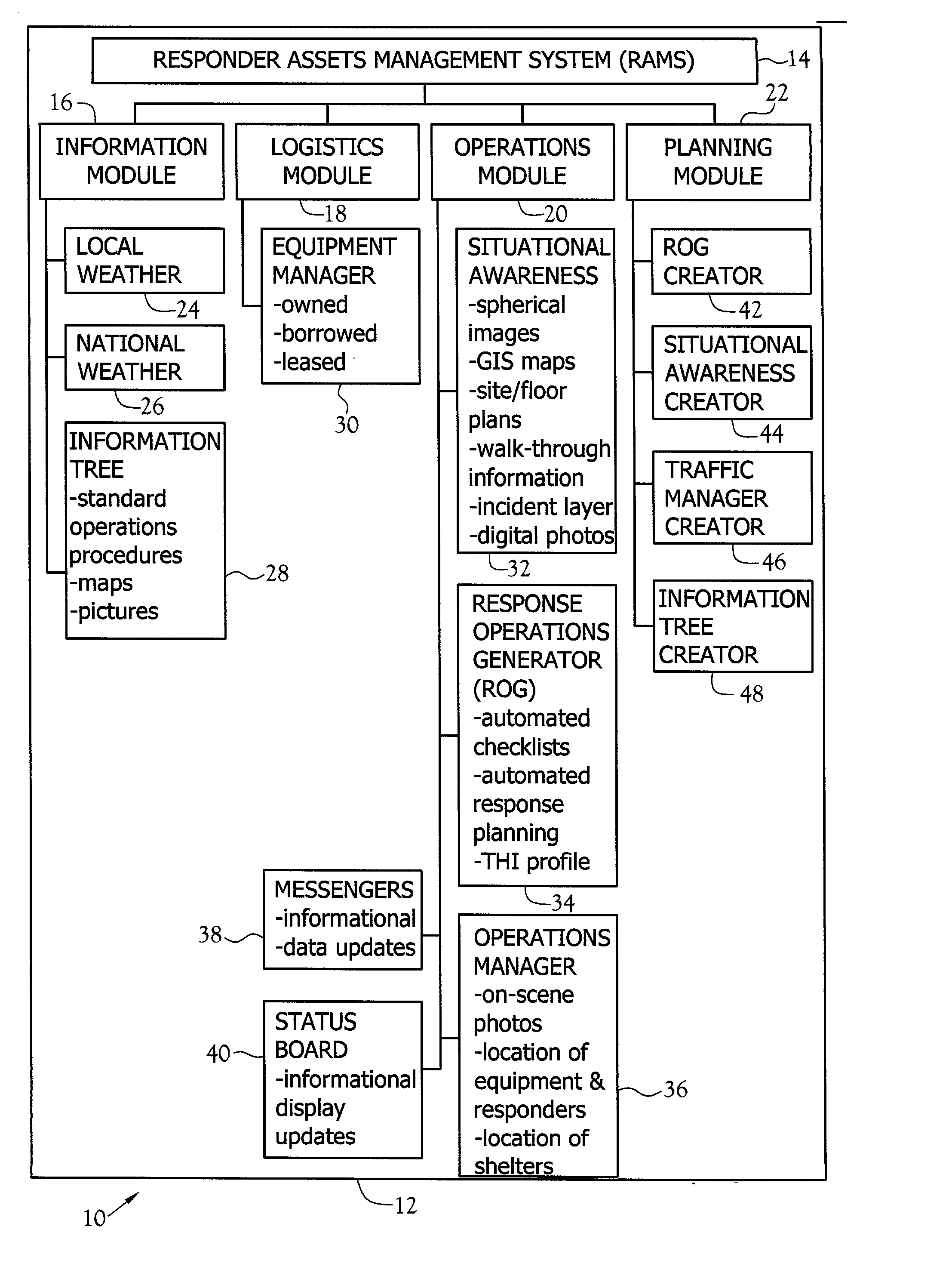
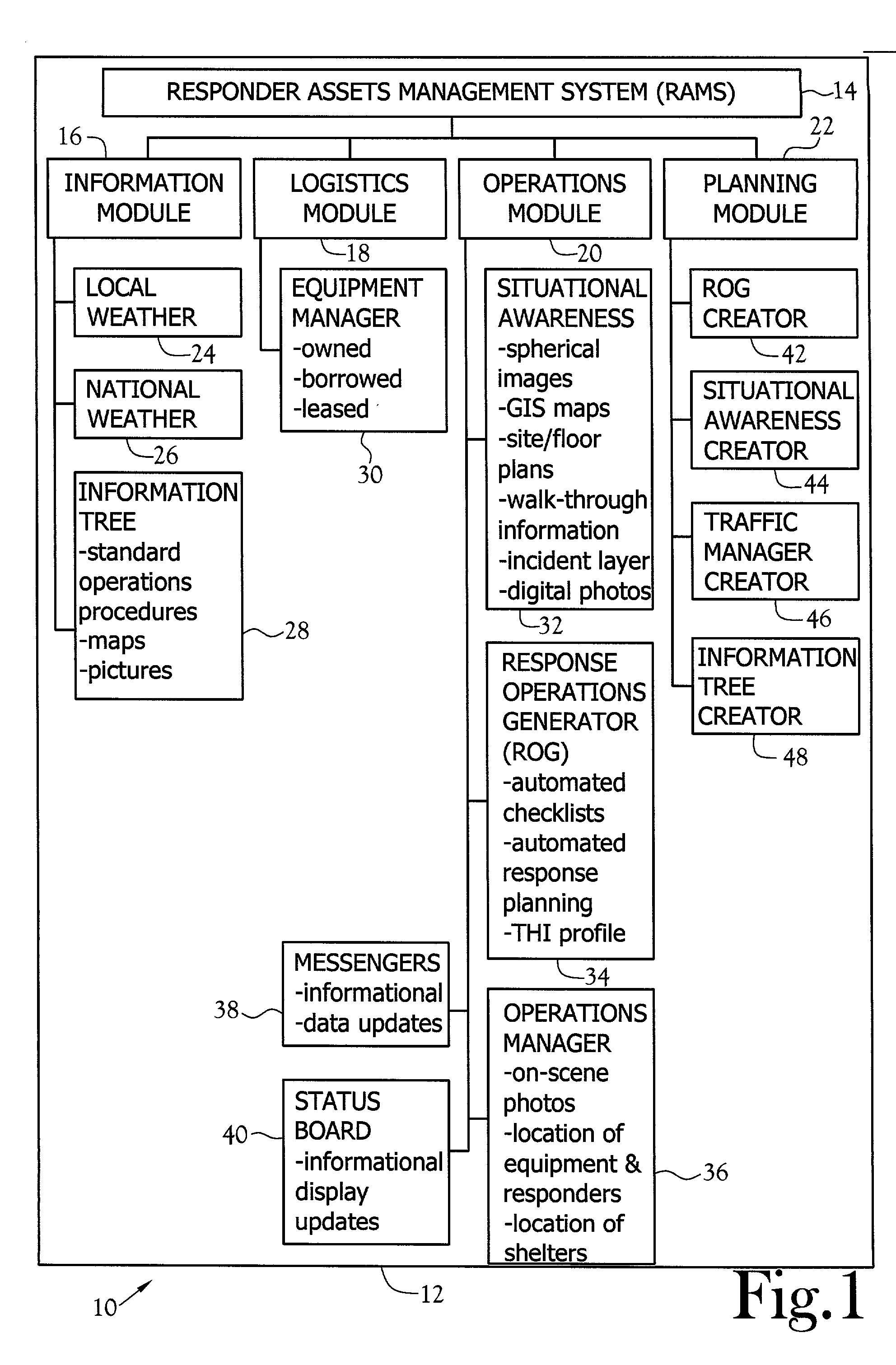
A method for collecting, organizing, presenting, and using data relative to the scene of an emergency situation is disclosed. The method uses a Responder Assets Management System (RAMS) composed of four modules including information, logistics, operations, and planning. The information module makes general information immediately available to responders. The logistics module assists in managing equipment resources during a contingency and includes an equipment manager interface for managing equipment used to respond to an emergency situation. The operations module supports daily operations responsibilities and scales to handle significant emergencies and includes at least one of a situational awareness interface, a response options generator (ROG) interface, an operations manager interface, a messenger interface and a status board interface. The situational awareness interface is designed for emergency and crisis response managers to provide enhanced, community-wide situational awareness using full immersion, spherical images, Geographic Information System (GIS) maps, site and floor plans, and a database interface to provide virtual walk-through, pre-incident plans, for contingency planning, training visualization, and operational support. The ROG interface provides automated response and resource estimates to decision-makers in command posts and on-site in developing a response to significant, unplanned events. The operations manager interface is used by a remote headquarters to monitor an on-going operation. The messenger interface is a pre-formatted, topic oriented messaging system that supports both informational messages and messages that automatically update system data and displays. The status board interface is a situation display of key situational awareness data. The planning module assists users in planning for critical events.
Owner:RAMSAFE TECH
Method and apparatus for deterministic replay of java multithreaded programs on multiprocessors
InactiveUS6854108B1Reduce in quantityGood runtime performanceSoftware testing/debuggingSpecific program execution arrangementsMulti processorThread scheduling
A method (and apparatus) of determinstically replaying an observable run-time behavior of distributed multi-threaded programs on multiprocessors in a shared-memory multiprocessor environment, wherein a run-time behavior of the programs includes sequences of events, each sequence being associated with one of a plurality of execution threads, includes identifying an execution order of critical events of the program, wherein the program includes critical events and non-critical events, generating groups of critical events of the program, generating, for each given execution thread, a logical thread schedule that identifies a sequence of the groups associated with the given execution thread, and storing the logical thread schedule for subsequent reuse.
Owner:IBM CORP
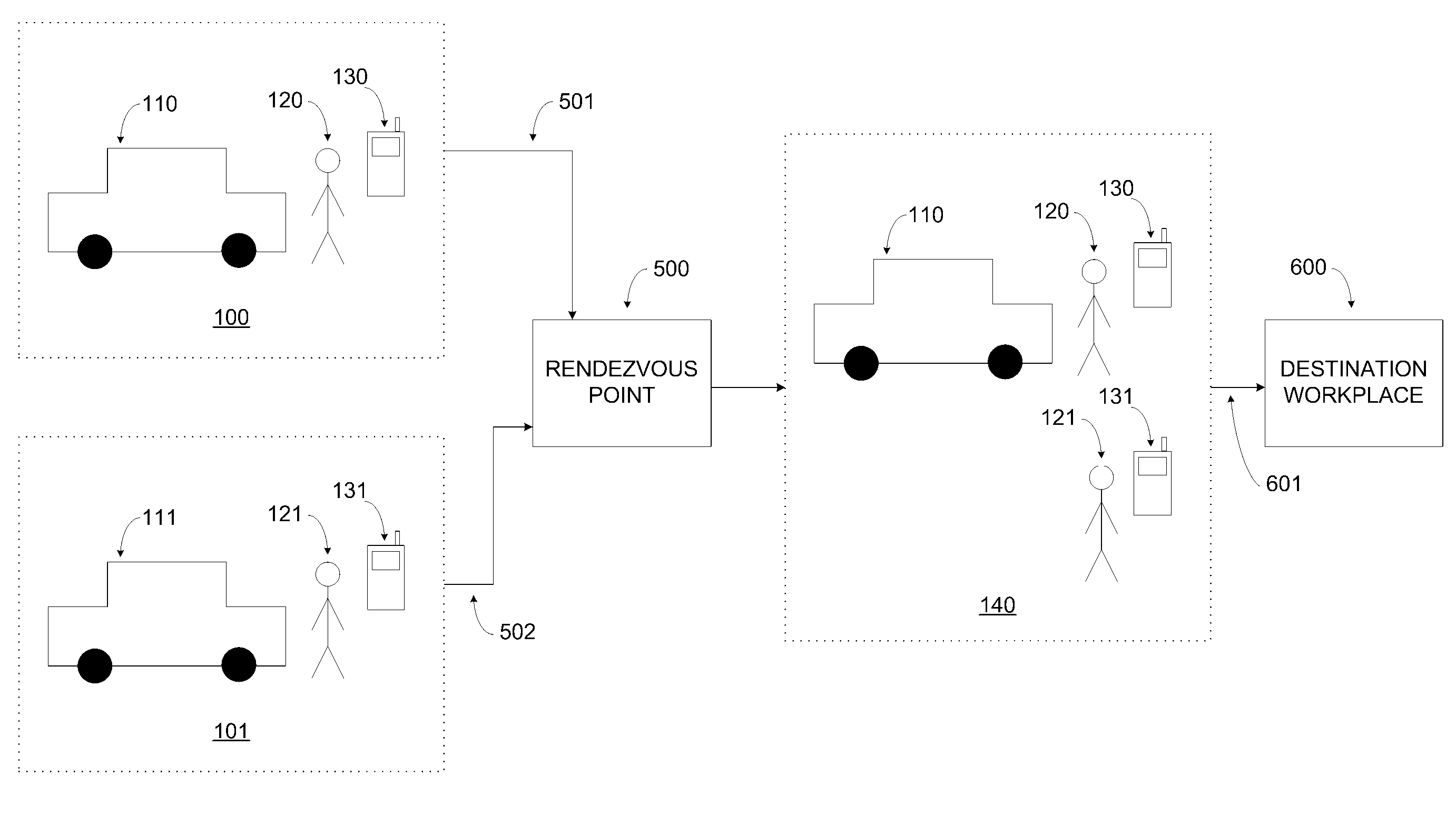
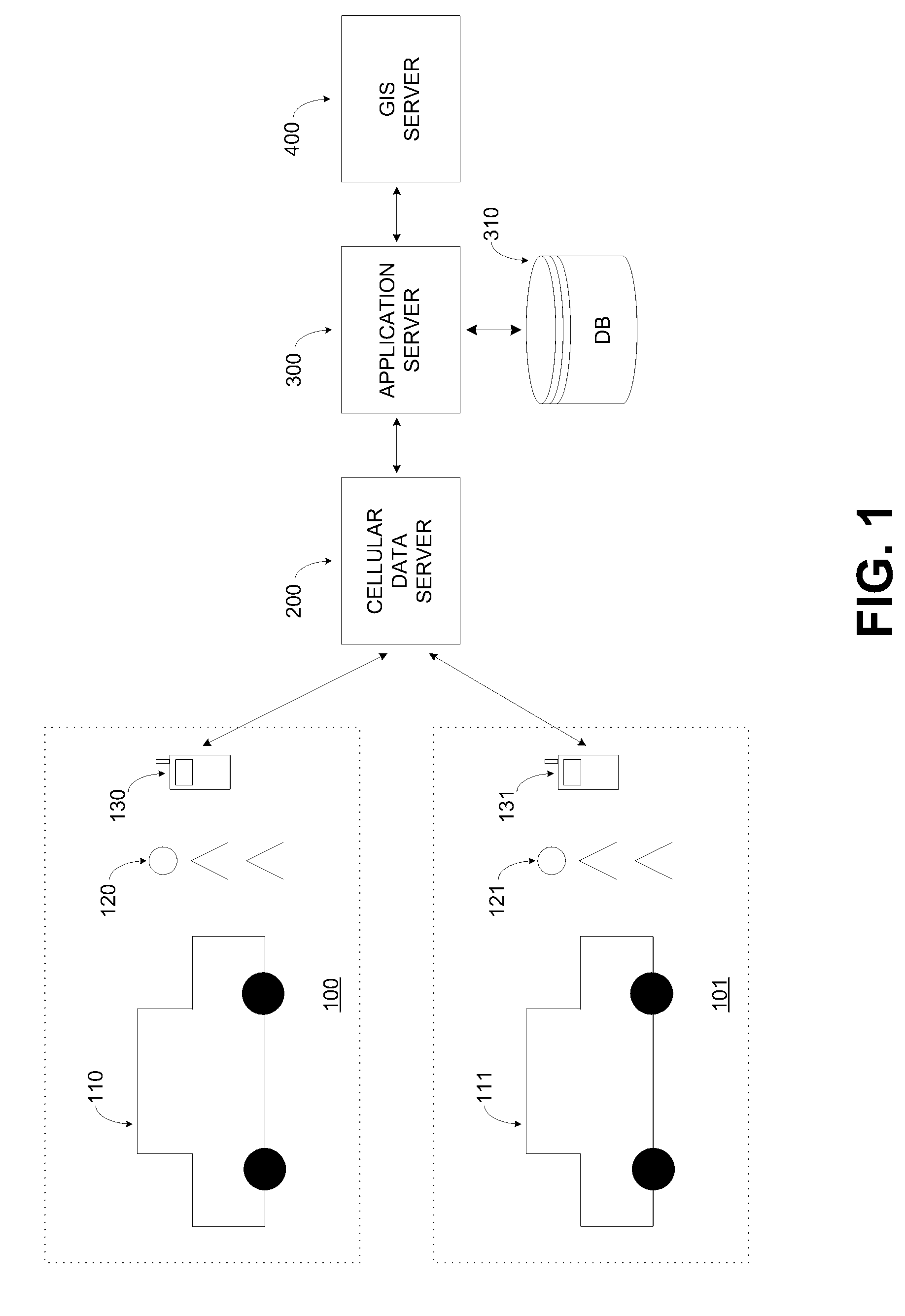
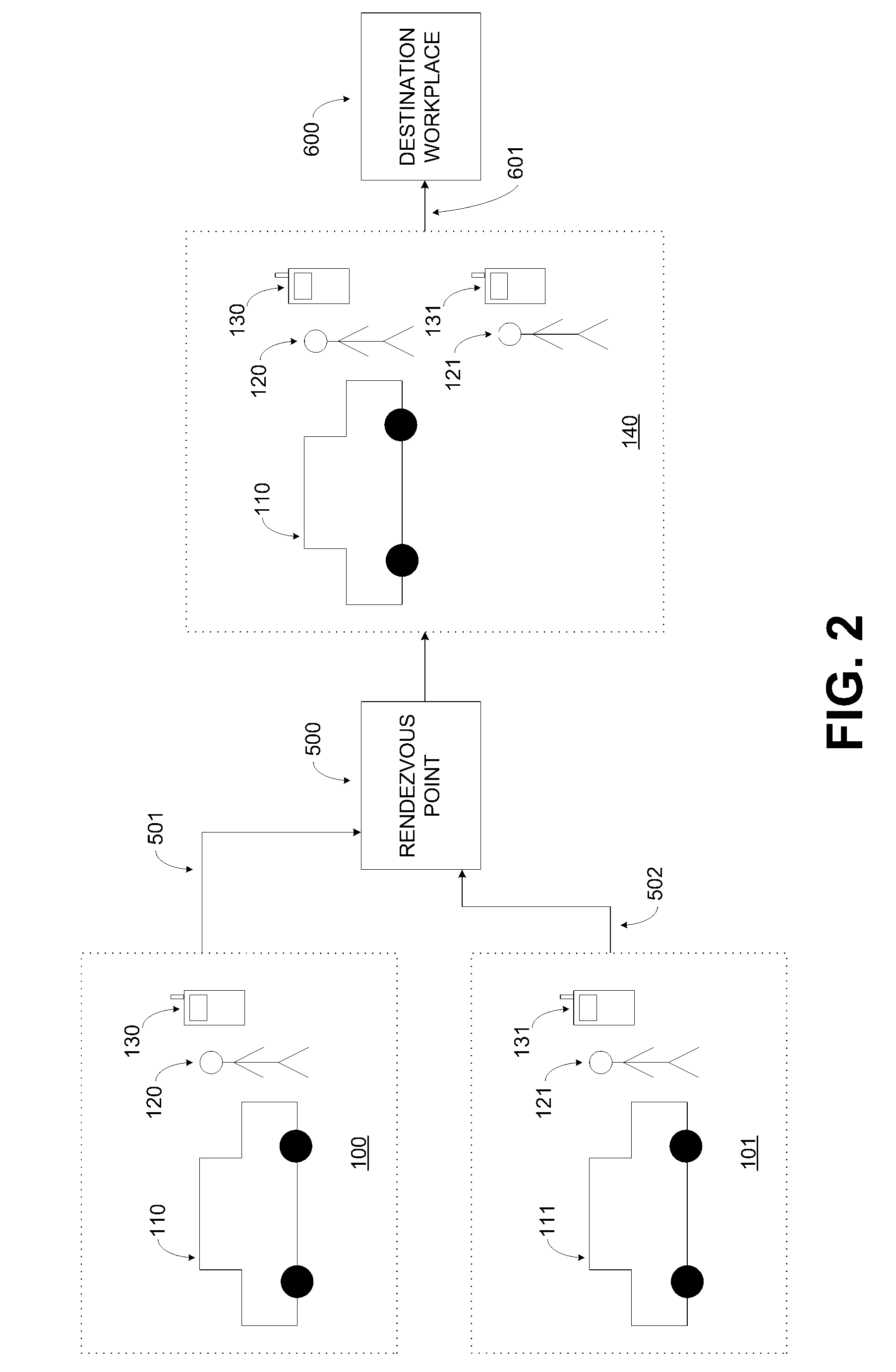
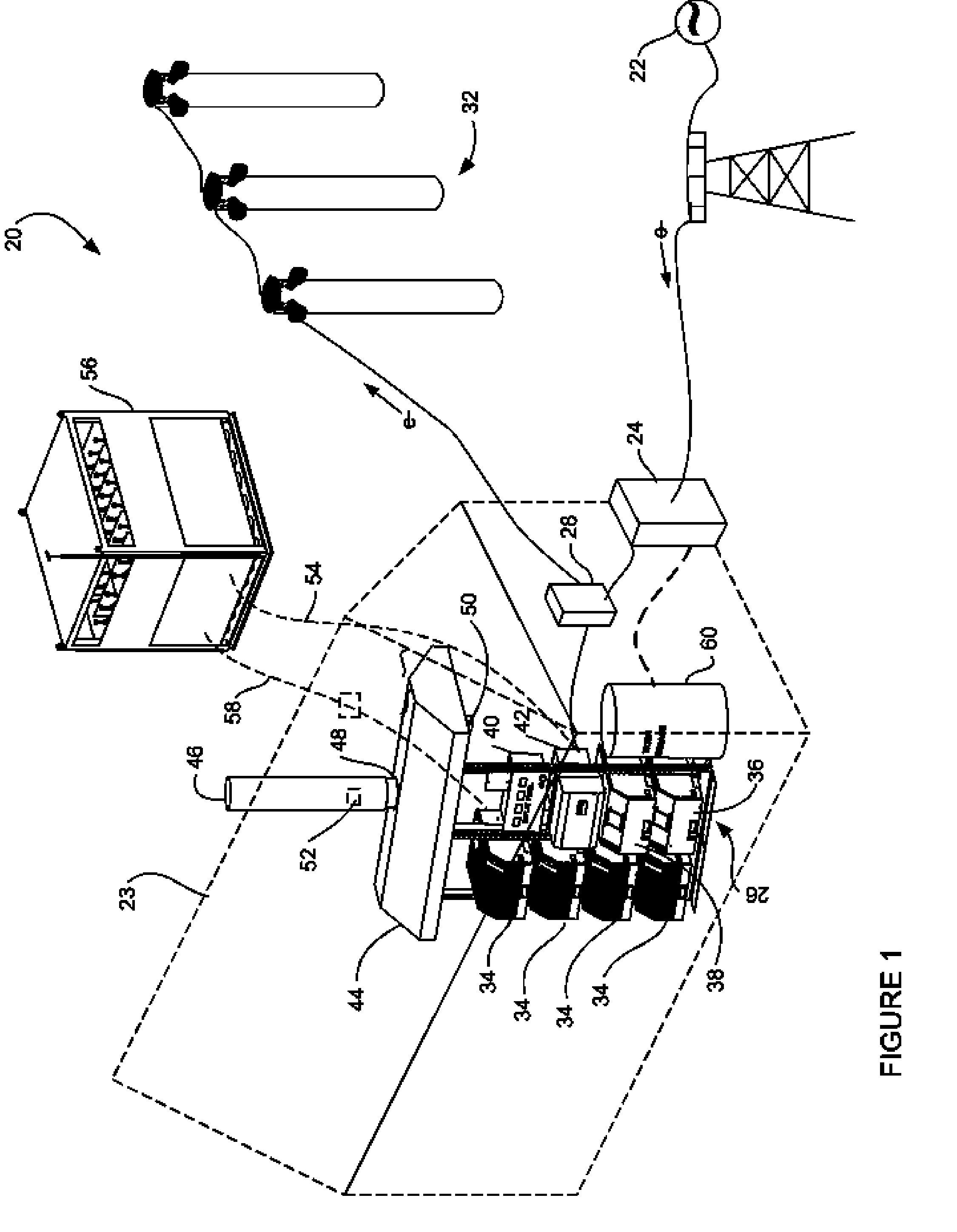
Method for GPS carpool rendezvous tracking and personal safety verification
InactiveUS7136747B2Safe operation is assuredStable and reliableAnalogue computers for vehiclesAnalogue computers for trafficApplication serverComputer science
Rendezvous tracking subsystem uses GPS-enabled cell phones communicating with an application server for tracking the whereabouts of carpool participants and for providing on-time status of participants en-route to designated rendezvous points. Safety subsystem can be used to verify safe arrival of participants at carpool destinations. Participants can configure safety subsystem by defining escalation rules and procedures to follow when safety critical events occur.
Owner:HAILO TECH LLC
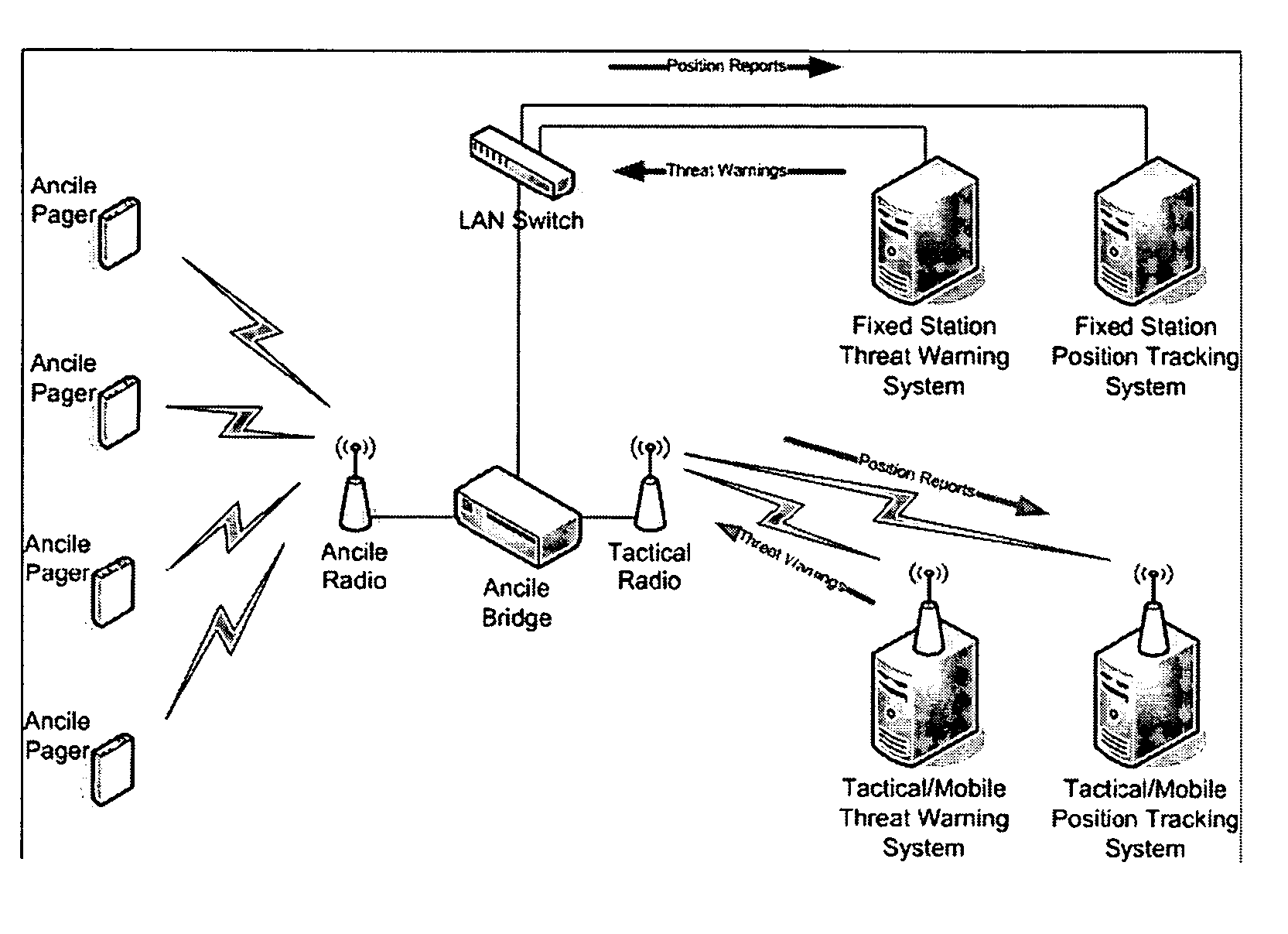
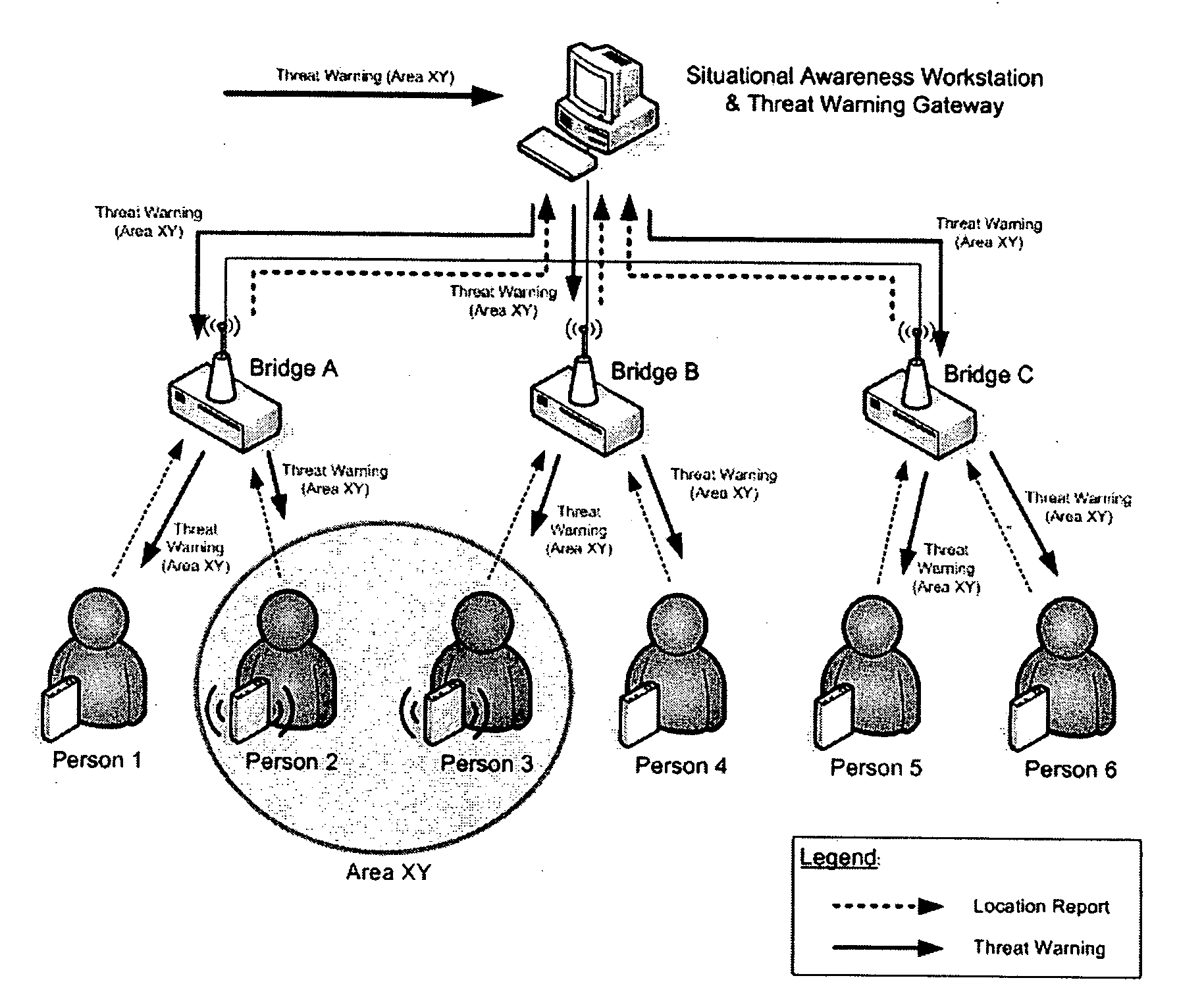
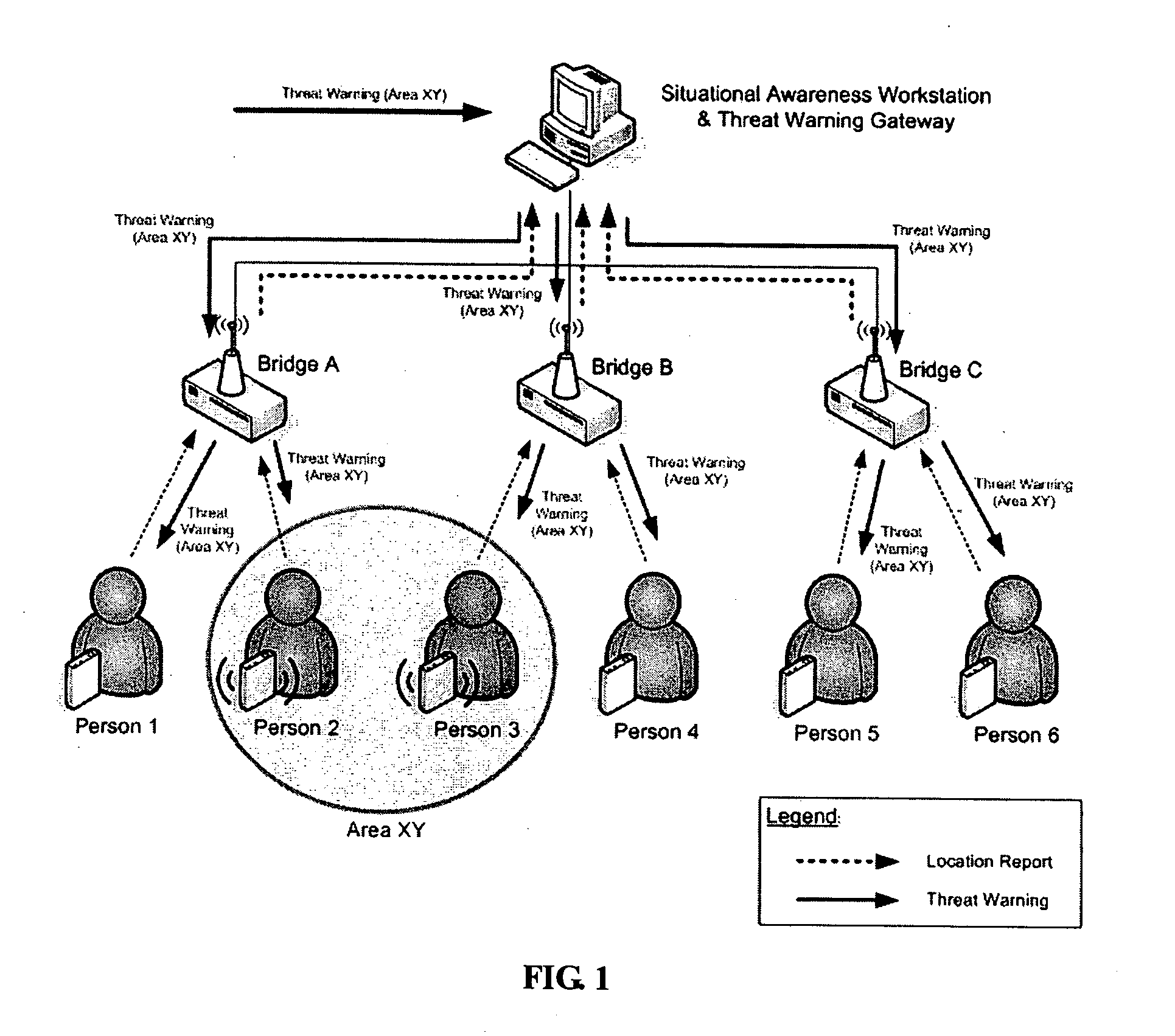
System, user warning and positioning device for use therein, and computer program product therefor, for tactical distributed event warning notification for individual entities
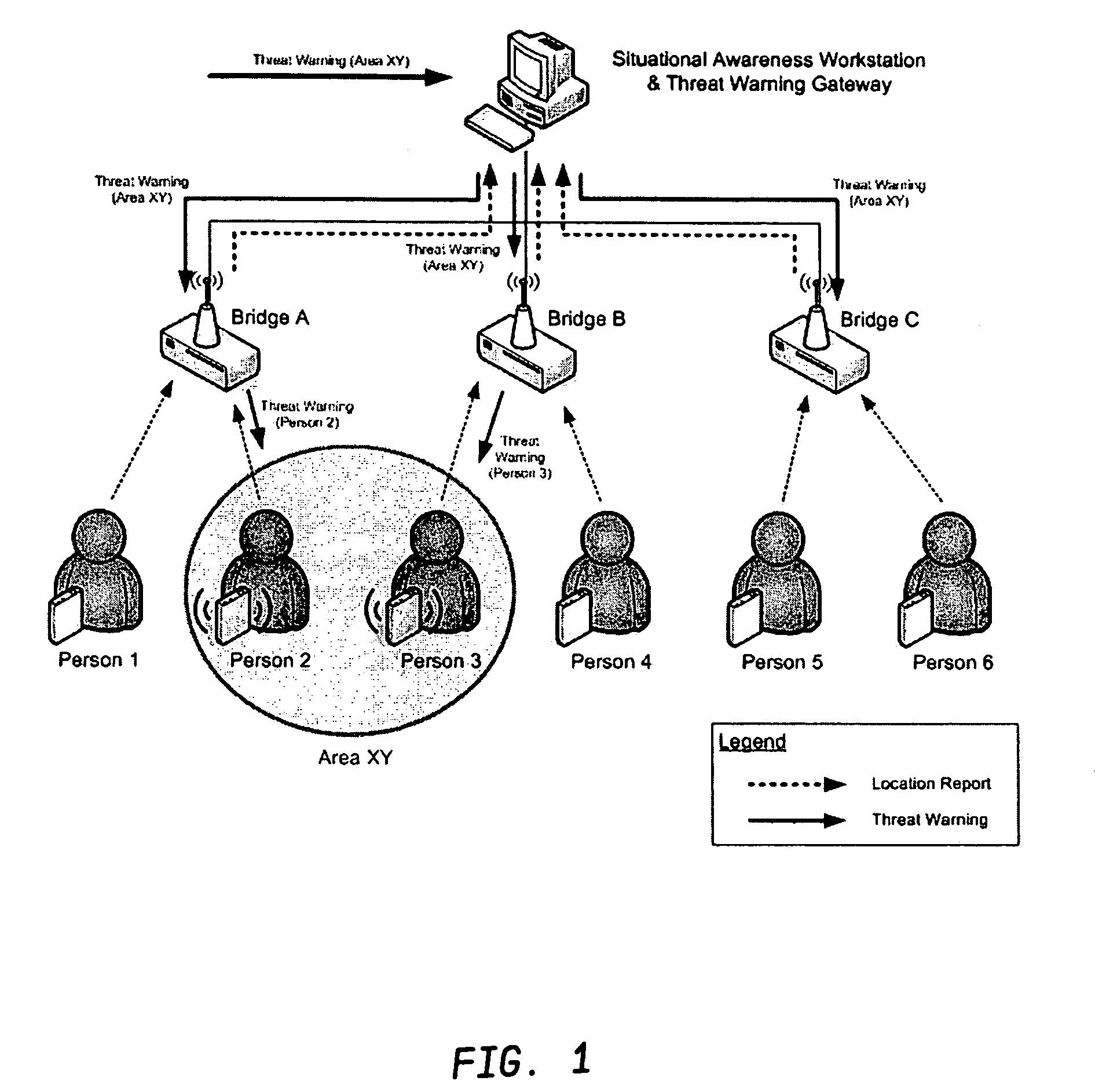
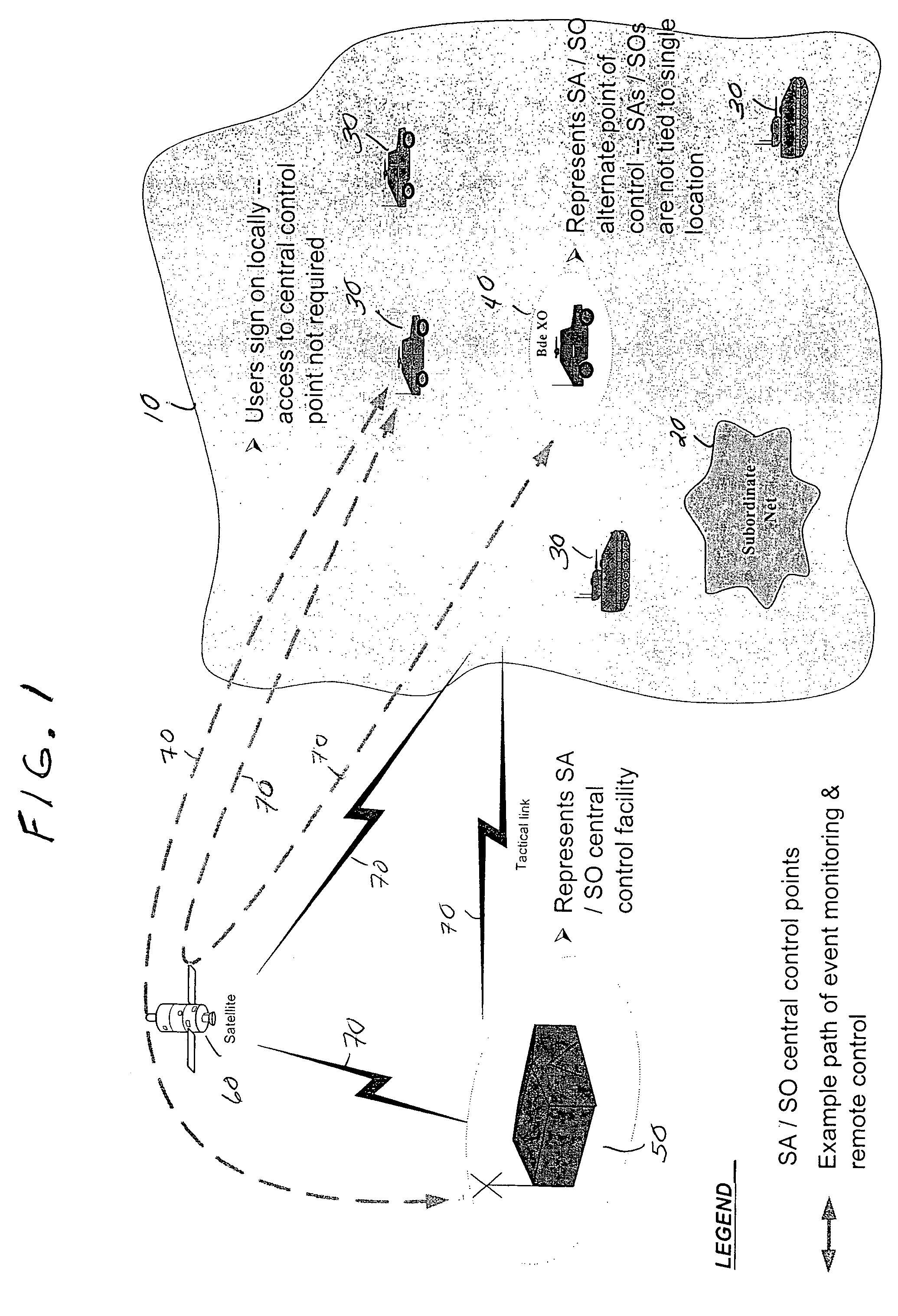
ActiveUS7764185B1Prevent basic triangulation effortEmergency connection handlingElectric testing/monitoringCommand and controlControl system
A system, device, and computer program product is provided for the centralized or distributed warning of existing or developing significant events and / or threats to users of the device within their locale, while reporting the location of all users of the system to existing command and control systems. A pager-like user warning and positioning device, worn by or carried by the individual user, or mounted in a vehicle or vessel, having a geographical positioning means therein, periodically transmits the geographical location of the individual user, vehicle or vessel, and listens for warning / notification event messages transmitted by a network bridge or central station. When an event / threat warning is received by the device, the device alerts the user via indicia relative to the event / situation, including audible spoken warnings and instructions on how to react, and may retransmit the event / threat warning to other nodes in the network.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE UNITED STATE OF AMERICA +1
System and method for semi-distributed event warning notification for individual entities, and computer program product therefor
An information system, method, and computer program product is provided for the semi-distributed warning of existing or developing significant events and / or threats to all network bridges in the system, and then to affected users carrying a user warning and positioning device, while reporting the location of all user's carrying the user warning and positioning devices of the system to existing command and control systems. The present invention's future event warning capabilities permit those same users to be warned of impending events in enough time for the users to take positive actions in response to these events and / or address those events. The system of the present invention includes a pager-like user warning and positioning device, worn by or carried by the individual user, or mounted in a vehicle or vessel, having a geographical positioning means therein, which periodically transmits the geographical location of the individual user, vehicle or vessel to local network bridges, and listens for warning / notification event messages transmitted by the local network bridge. When an event / threat warning is received by an affected user warning and positioning device, the pager-like user warning and positioning alerts the user via indicia relative to the event / situation, including audible spoken warnings and instructions on how to react, and may retransmit the event / threat warning to other user warning and positioning devices in the network, provided the threat has not occurred and the event / threat warning has not been previously relayed.
Owner:UNITED STATES OF AMERICAS AS REPRESENTED BY THE UNITED STATES OF AMERICA THE +1
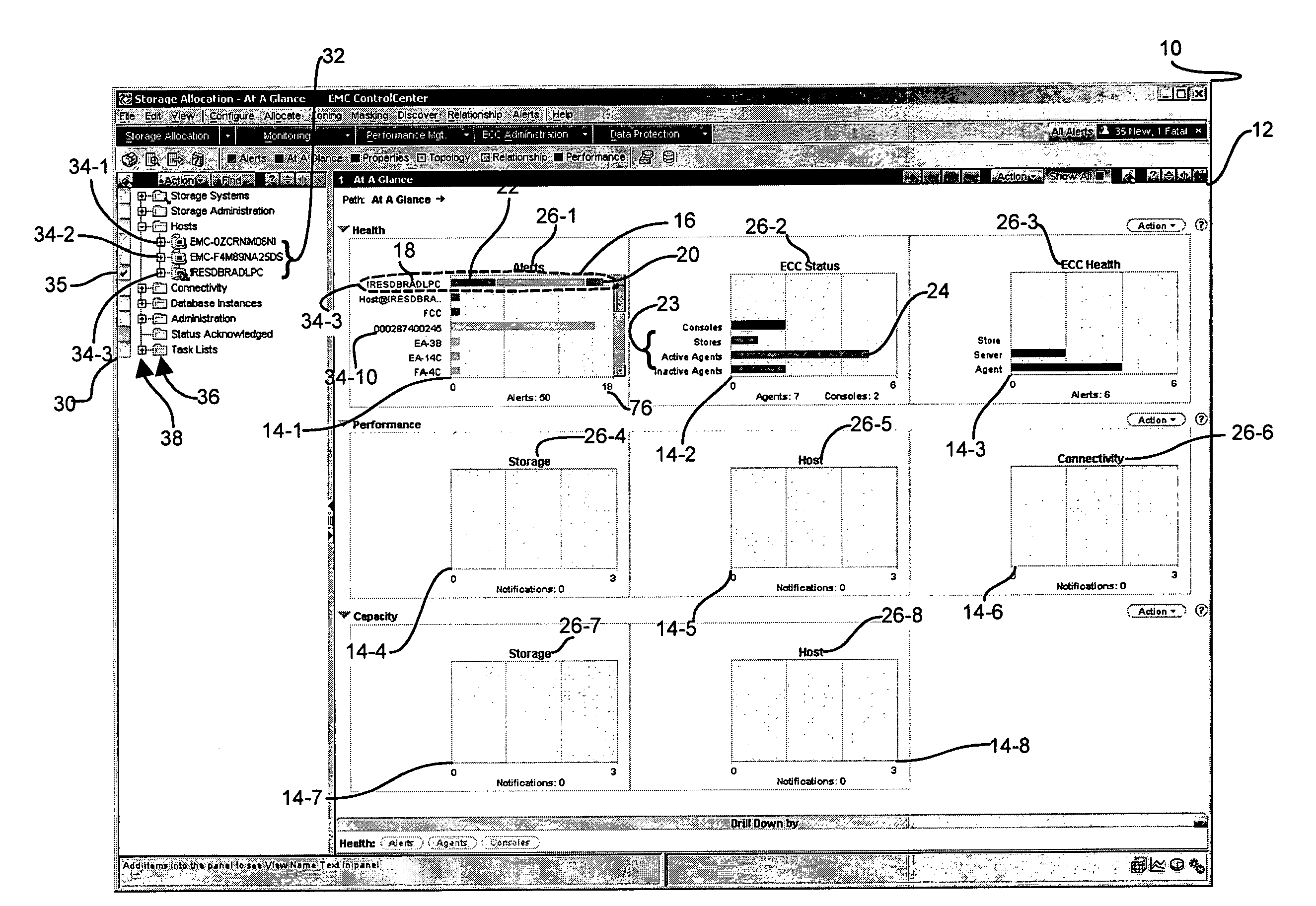
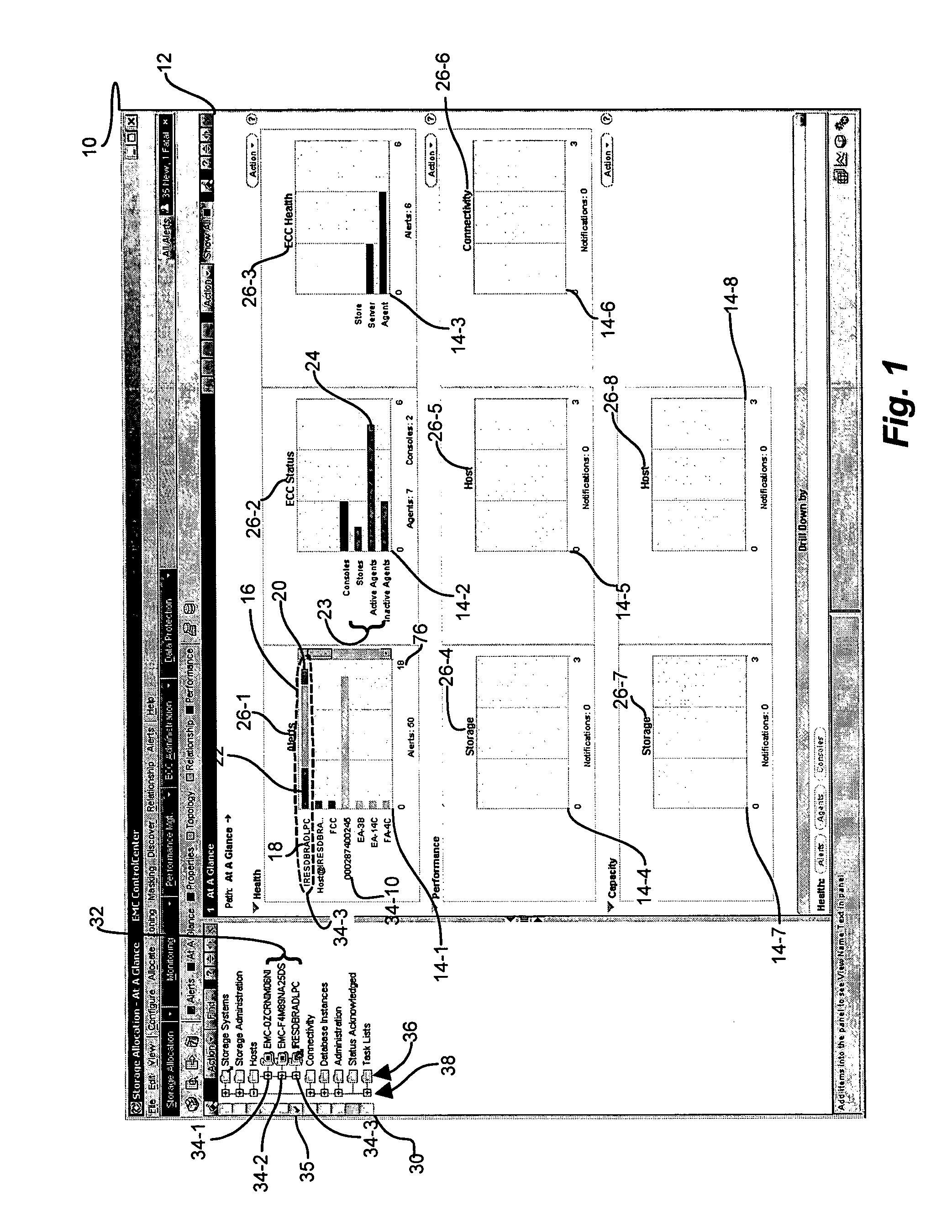
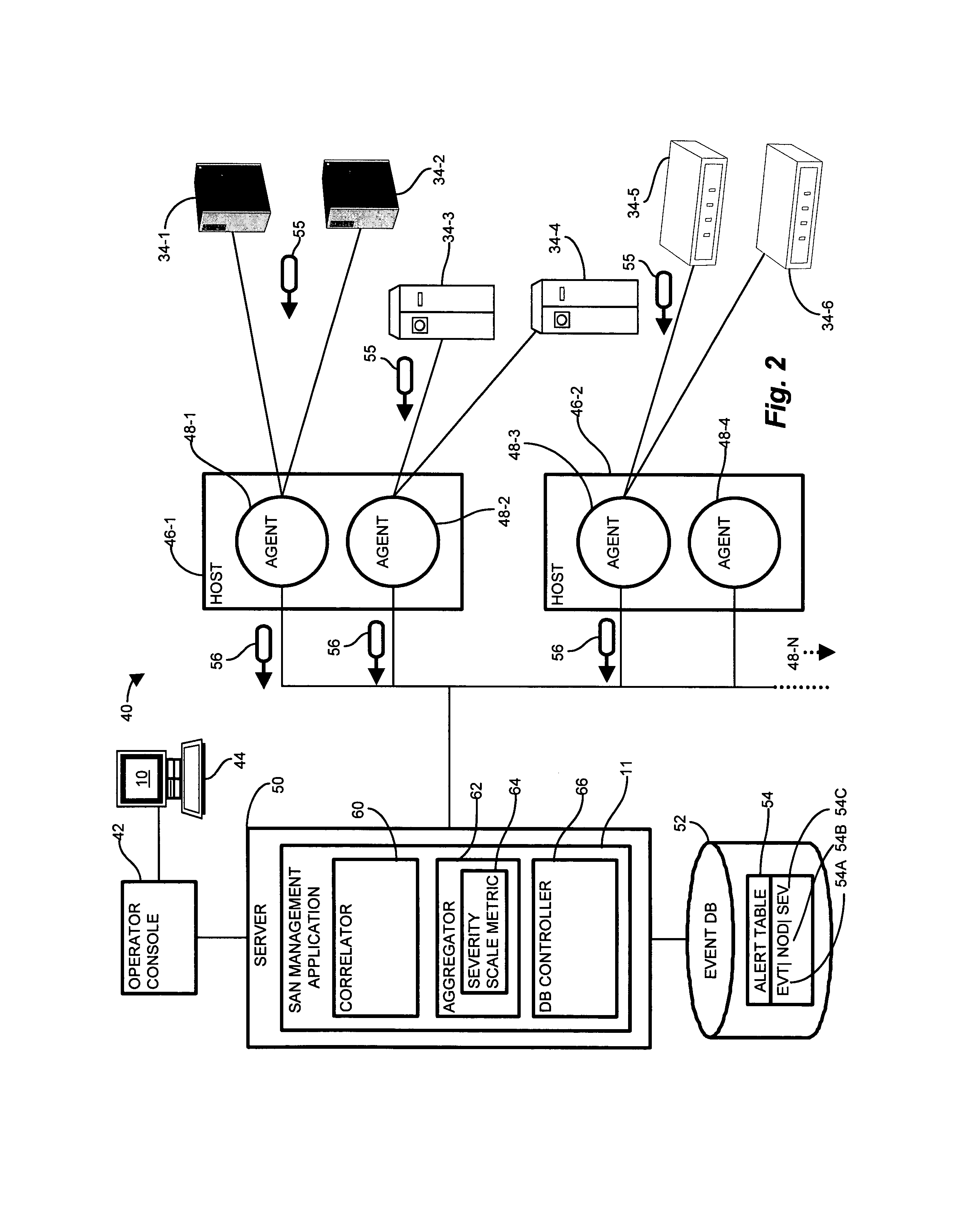
System and methods for processing and displaying aggregate status events for remote nodes
ActiveUS7603458B1Rapid diagnosisLess efficientDigital computer detailsTransmissionArray data structureStorage area network
A status monitoring and reporting mechanism which distinguishes more significant events and prominently displays events pertaining to nodes, interconnections, and other network entities which may present problems, and to suppresses benign messages which may not require immediate attention, provides an “at a glance” view of overall system health. By processing and displaying aggregate status events from a plurality of agent components to highlight the most severe and critical events from among a large volume of general status events allows an operator to quickly diagnose potential problems before detrimental results occur, and helps maintain a general efficient system health by isolating less efficient areas to allow for timely remedial action prior to failure. Various agents disseminated in a storage area network determine and report status events back to a central server. The server receives, aggregates, and processes the status events to display a status array indicative of overall system health.
Owner:EMC IP HLDG CO LLC
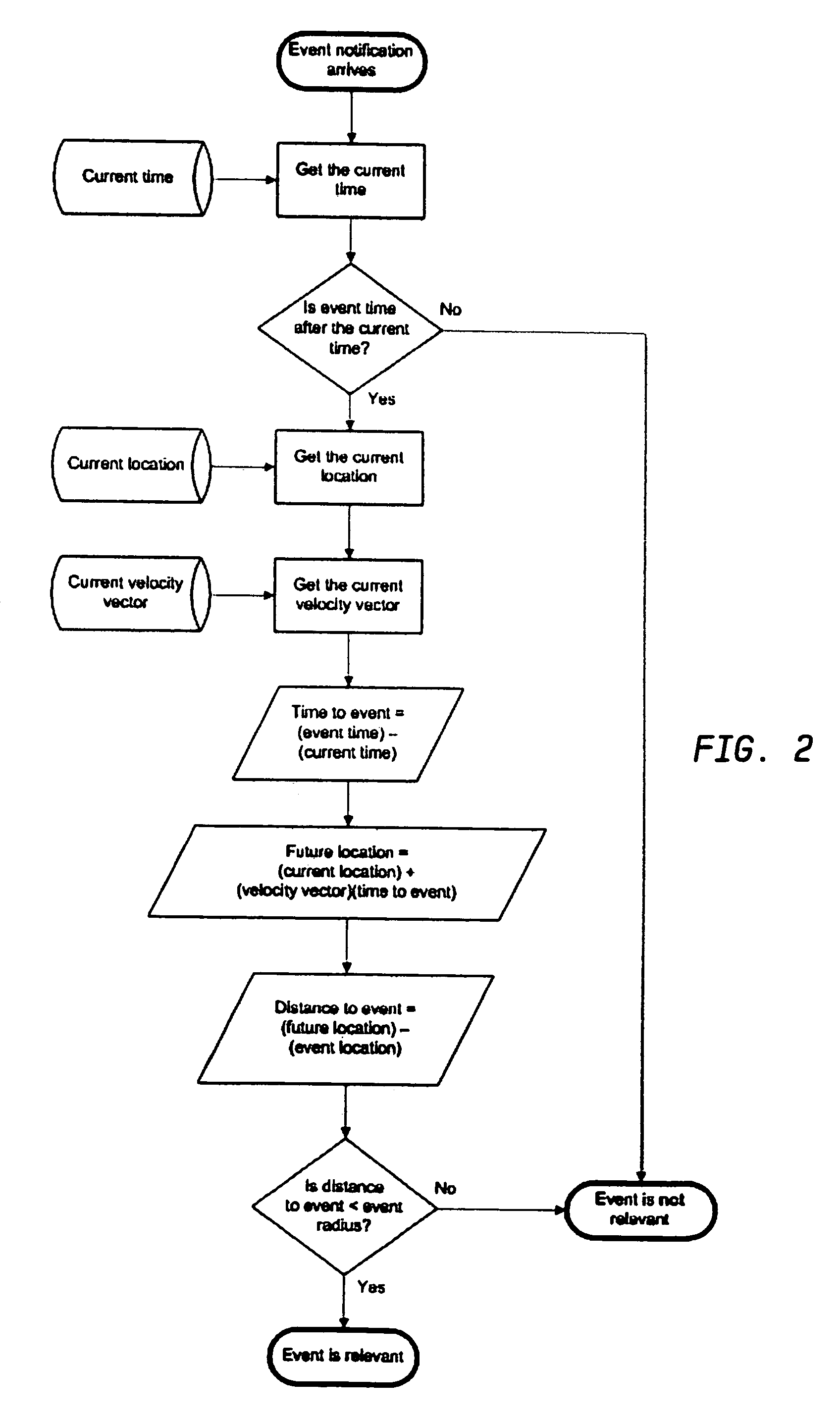
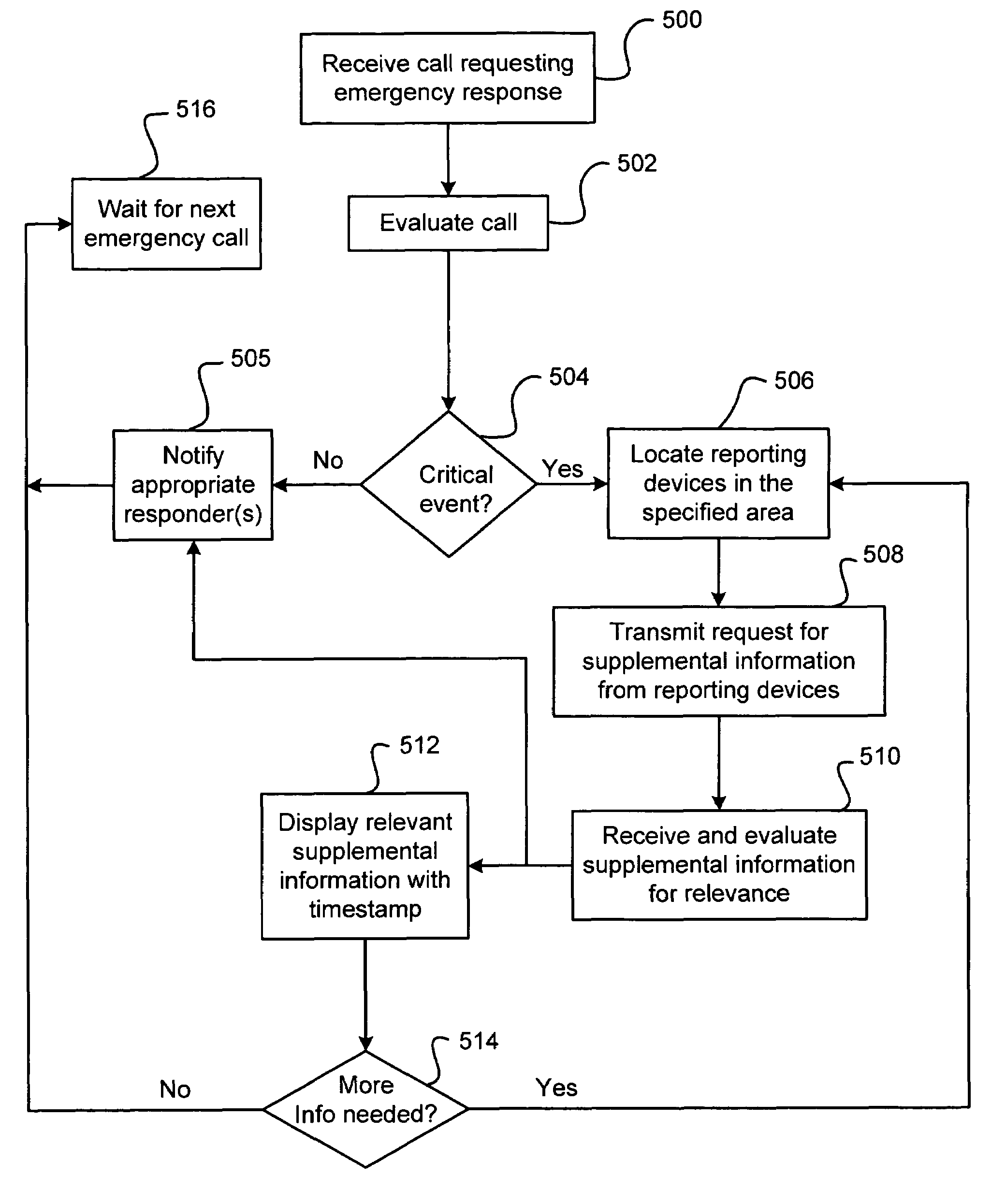
Method and system for collecting contemporaneous information relating to a critical event
InactiveUS7646854B2Emergency connection handlingTelephonic communicationEmergency responseReal-time computing
The present invention is directed to a method and system for collecting contemporaneous information relating to a critical event. The method includes receiving a call requesting an emergency response to a critical event and in response to the call, using at least one communication network to transmit a request for supplemental information from reporting devices located in a specified area related to the critical event. The supplemental information is received over the at least one communication network.
Owner:SCENERA TECH
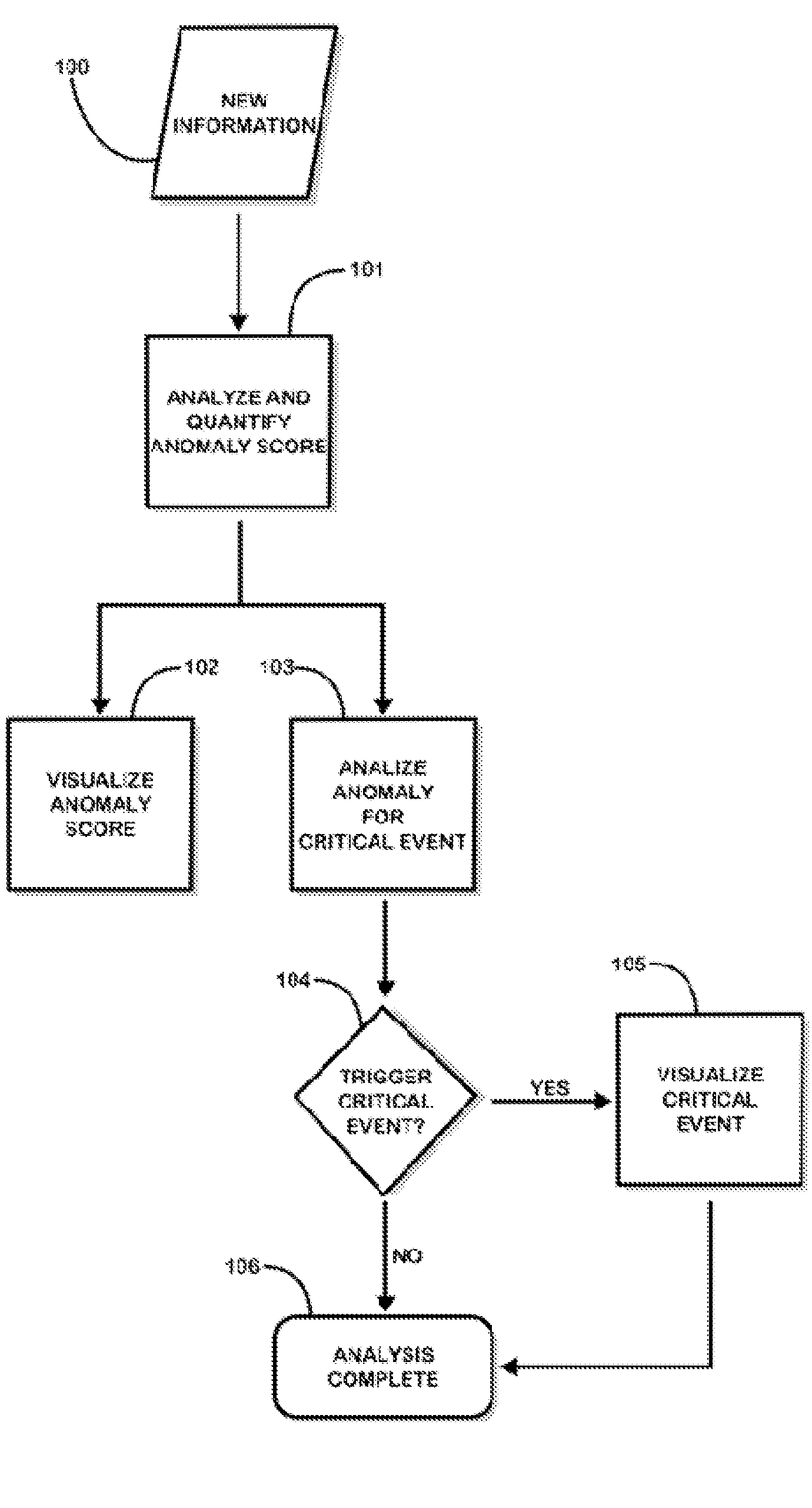
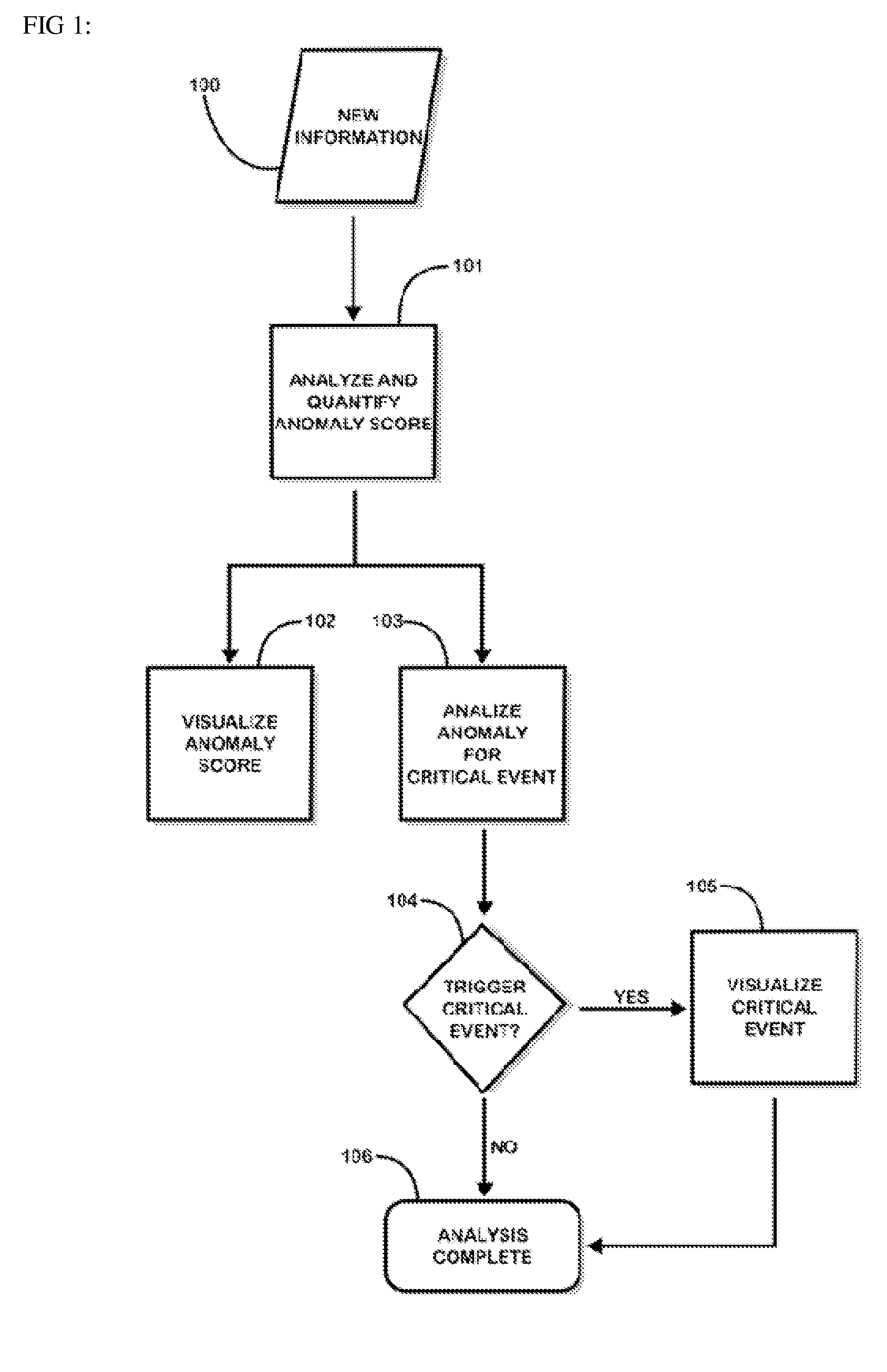
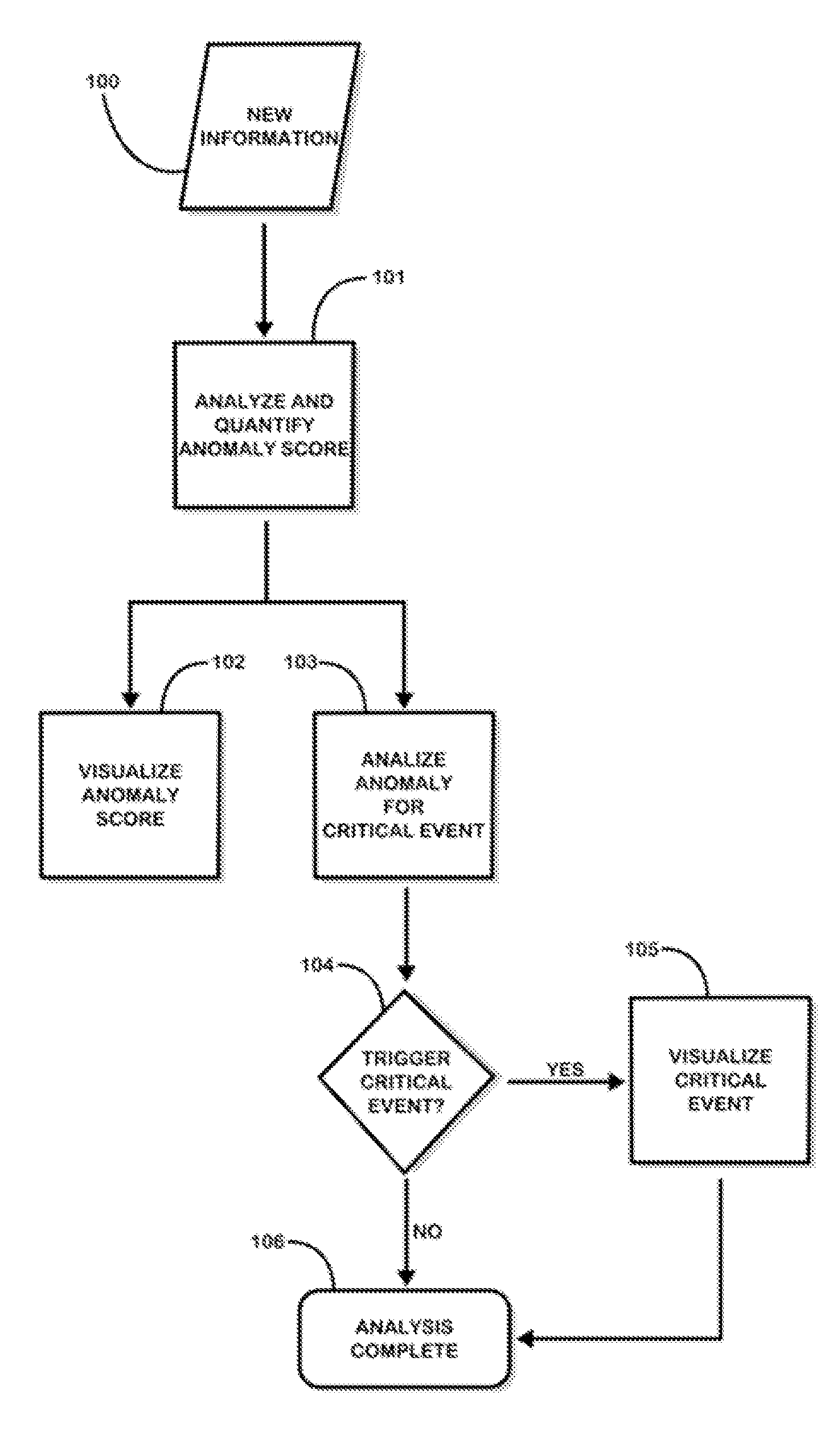
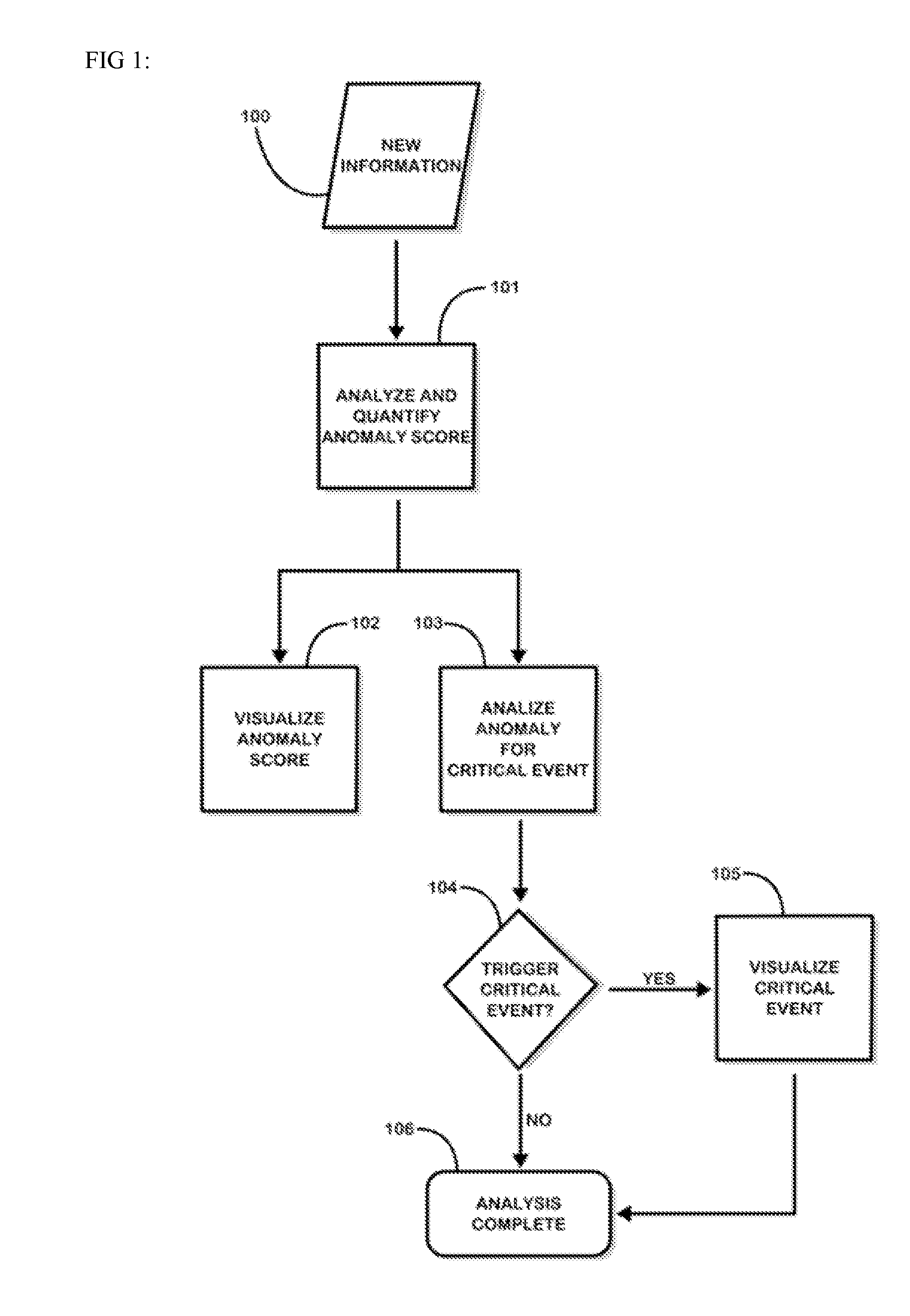
Fusion and visualization for multiple anomaly detection systems
InactiveUS20080215576A1Quickly comprehendDigital data information retrievalSpecial data processing applicationsAnomaly detectionData source
The present invention is a method for detecting anomalies against normal profiles and for fusing and visualizing the results from multiple anomaly detection systems in a quantifying and unifying user interface. The knowledge patterns discovered from historical data serve as the normal profiles, or baselines or references (hereinafter, called “normal profiles”). The method assesses a piece of information against a collection of the normal profiles and decides how anomalous it is. The normal profiles are calculated from historical data sources, and stored in a collection of mining models. Multiple anomaly detection systems generate a collection of mining models using multiple data sources. When a piece of information is newly observed, the method measures the degree of correlation between the observed information and the normal profiles. The analysis is expressed and visualized through anomaly scores and critical event notifications that are triggered by fusion rules, thus allowing a user to see multiple levels of complexity and detail in a single view.
Owner:QUANTUM INTELLIGENCE
Road safety warning system and method
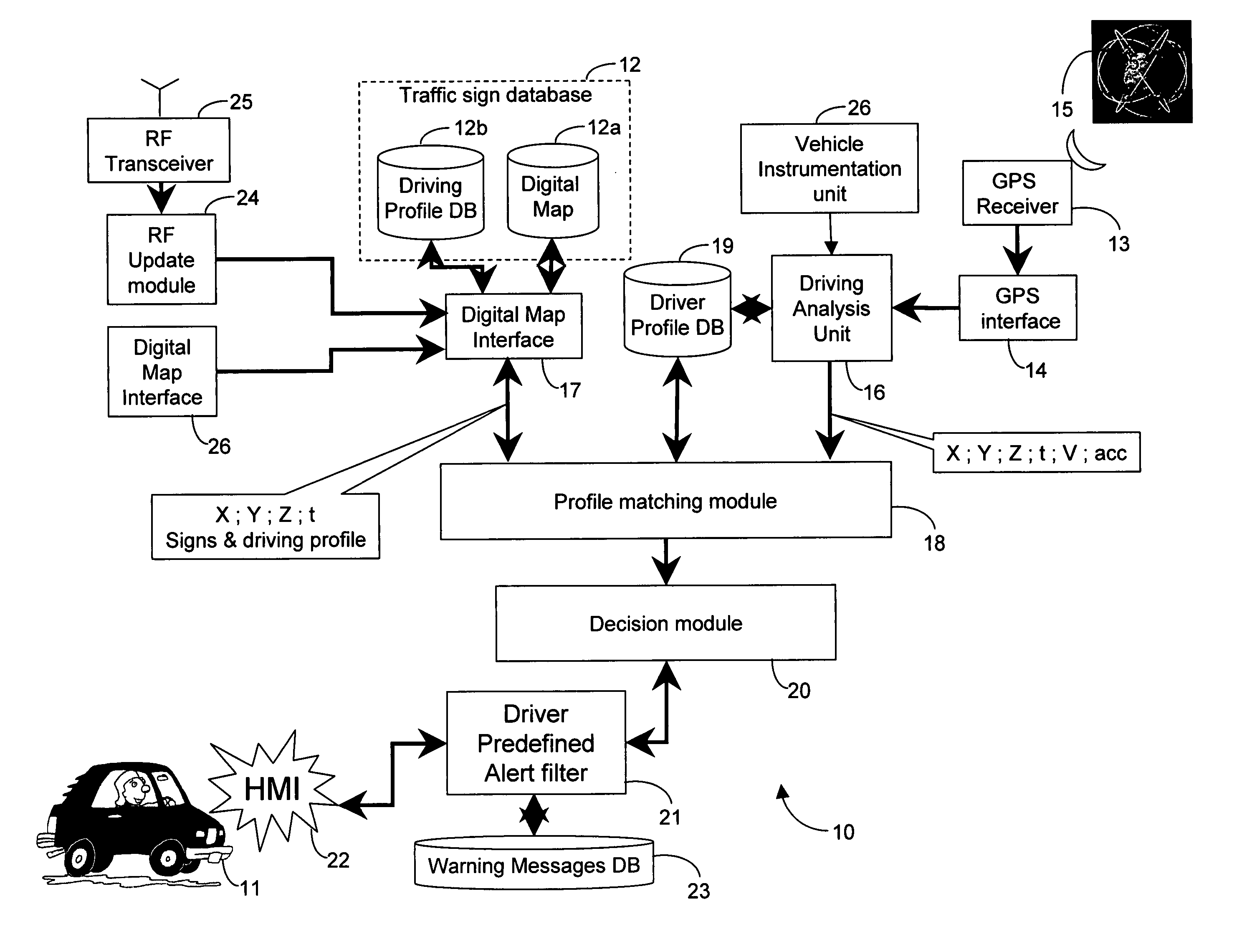
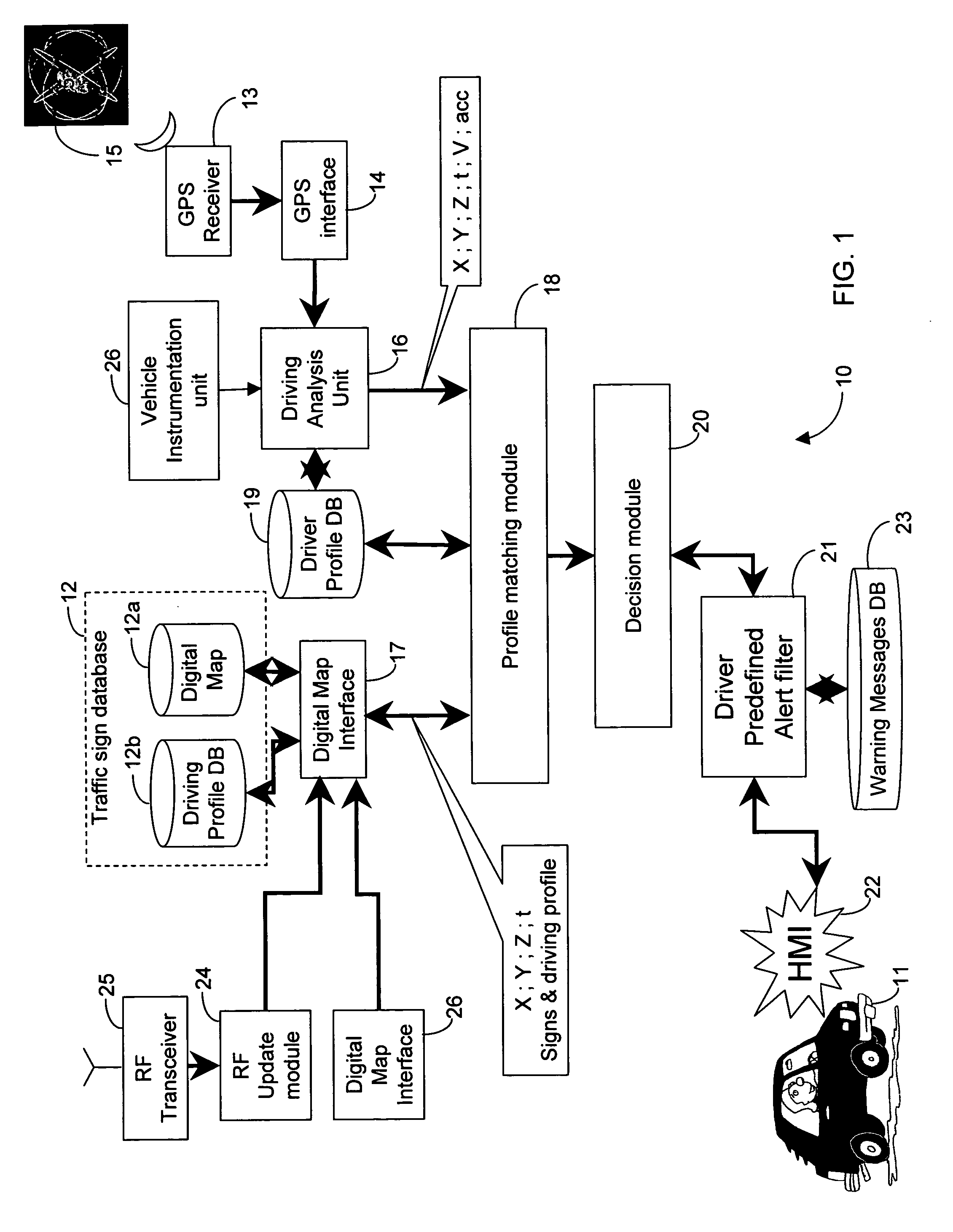
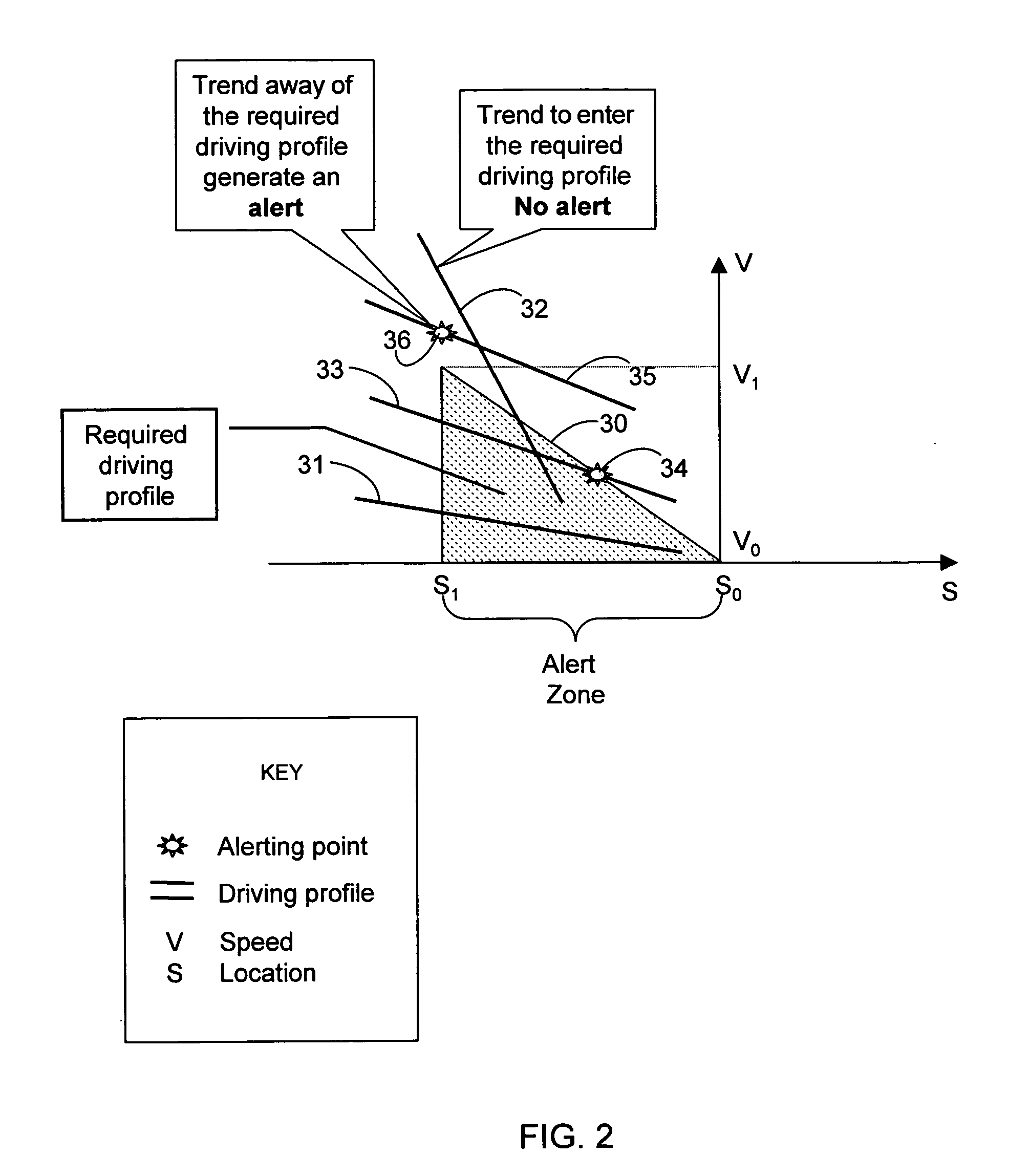
InactiveUS20050083211A1Instruments for road network navigationArrangements for variable traffic instructionsDriver/operatorIn vehicle
An in-vehicle system for tracking events that occur at specific locations of a transportation route and alerting a driver of an impending significant event includes a location determination unit for determining an instantaneous location of the vehicle, and an event determination unit coupled to the location determination unit and responsive to the instantaneous location of the vehicle for communicating with an events database for obtaining an impending traffic sign that the vehicle is about to confront based on the vehicle's instantaneous location. A decision module coupled to the event determination unit is responsive to current parameters of the vehicle for determining whether the current parameters of the vehicle are conducive to safe driving based on the impending event, and a warning unit coupled to the decision module is responsive to at least one current parameter of the vehicle not being conducive to safe driving for alerting the driver of the impending event.
Owner:SHIRI YOSSEF
Hybrid method for event prediction and system control
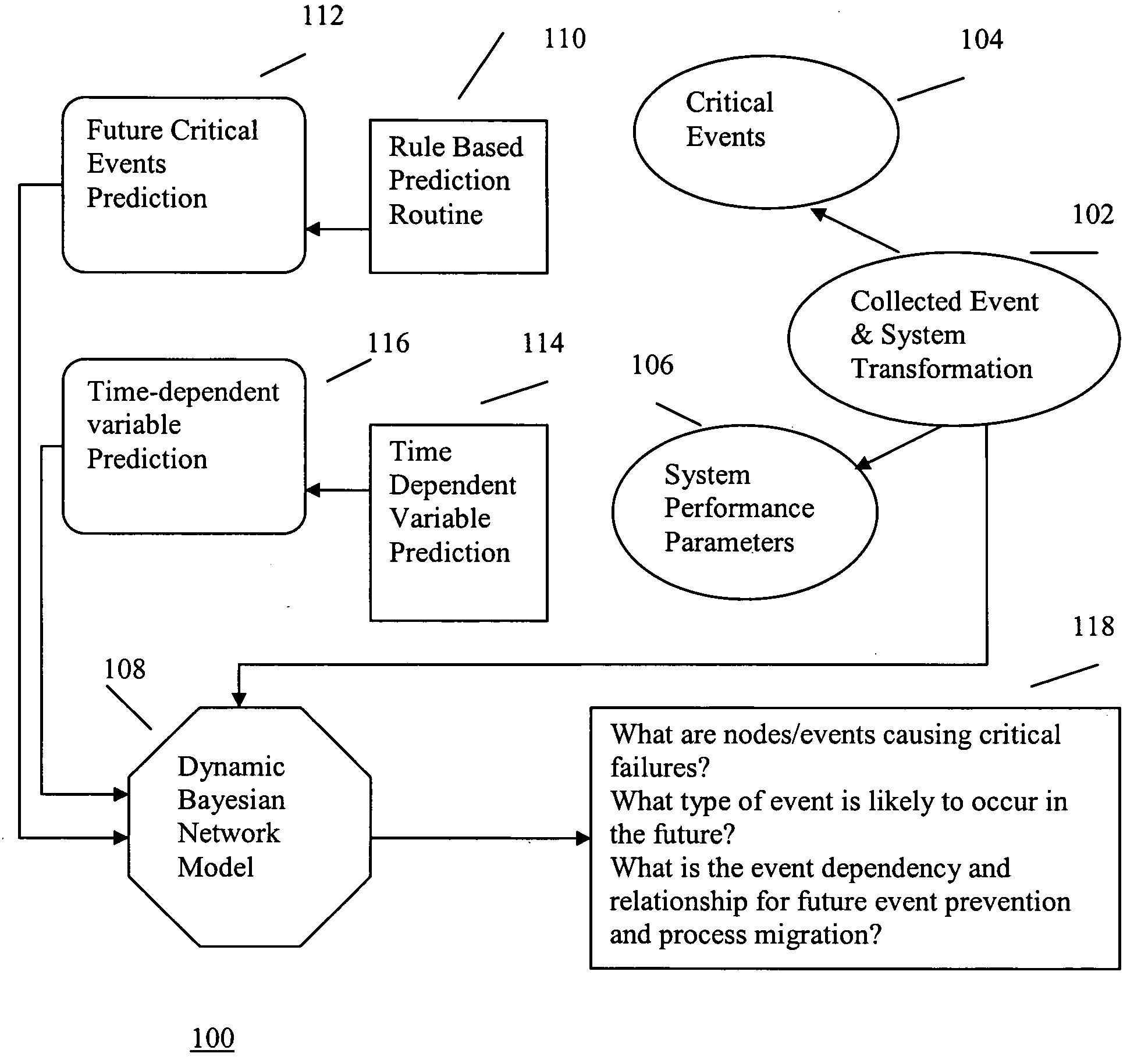
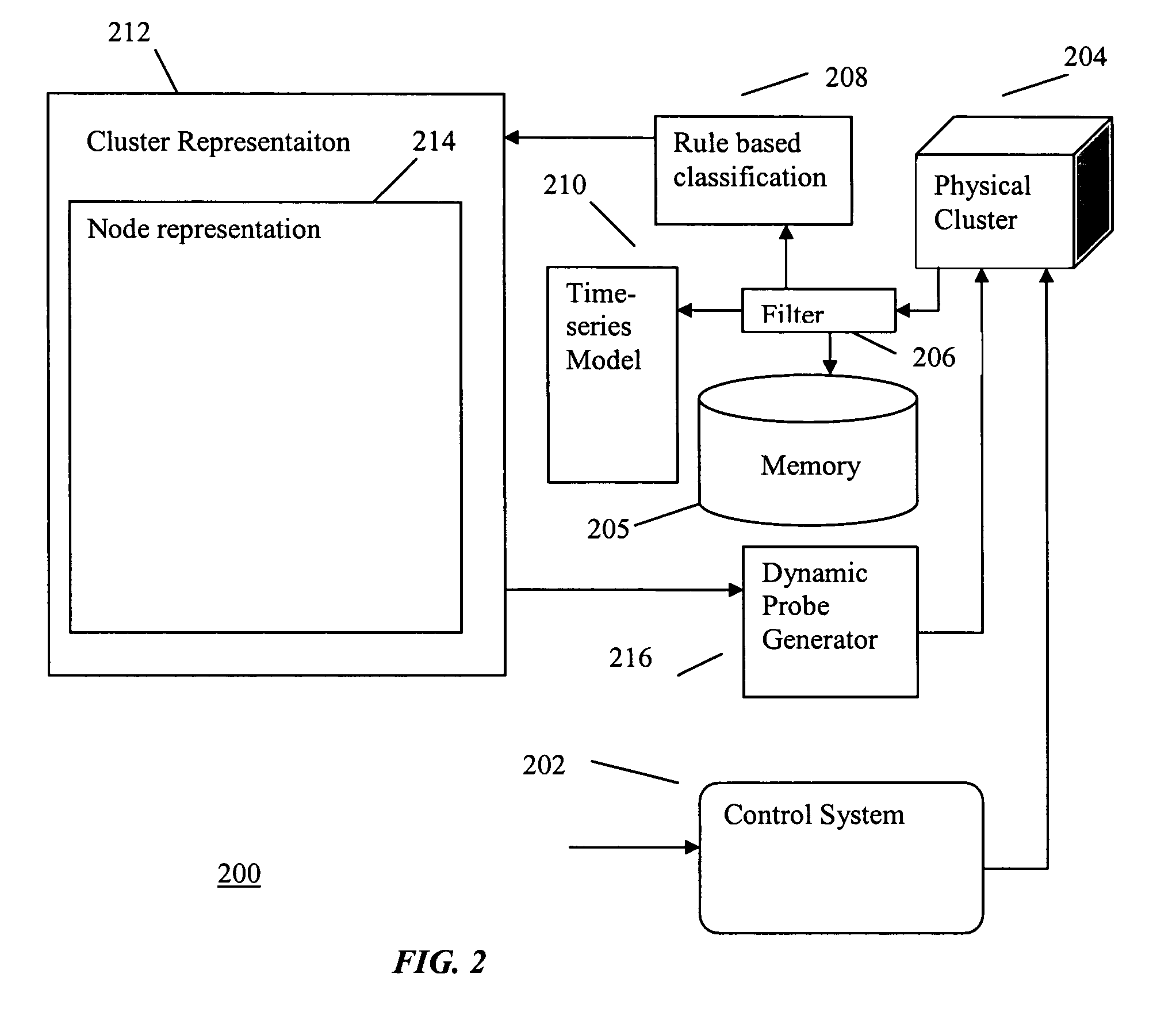
InactiveUS20050114739A1Data processing applicationsDigital computer detailsComputer clusterHybrid approach
A hybrid method of predicting the occurrence of future critical events in a computer cluster having a series of nodes records system performance parameters and the occurrence of past critical events. A data filter filters the logged to data to eliminate redundancies and decrease the data storage requirements of the system. Time-series models and rule based classification schemes are used to associate various system parameters with the past occurrence of critical events and predict the occurrence of future critical events. Ongoing processing jobs are migrated to nodes for which no critical events are predicted and future jobs are routed to more robust nodes.
Owner:GLOBALFOUNDRIES INC
Fault tree map generation
InactiveUS20090083576A1Reduce time expenditureMore time economyError detection/correctionDesign optimisation/simulationGraphicsTree topping
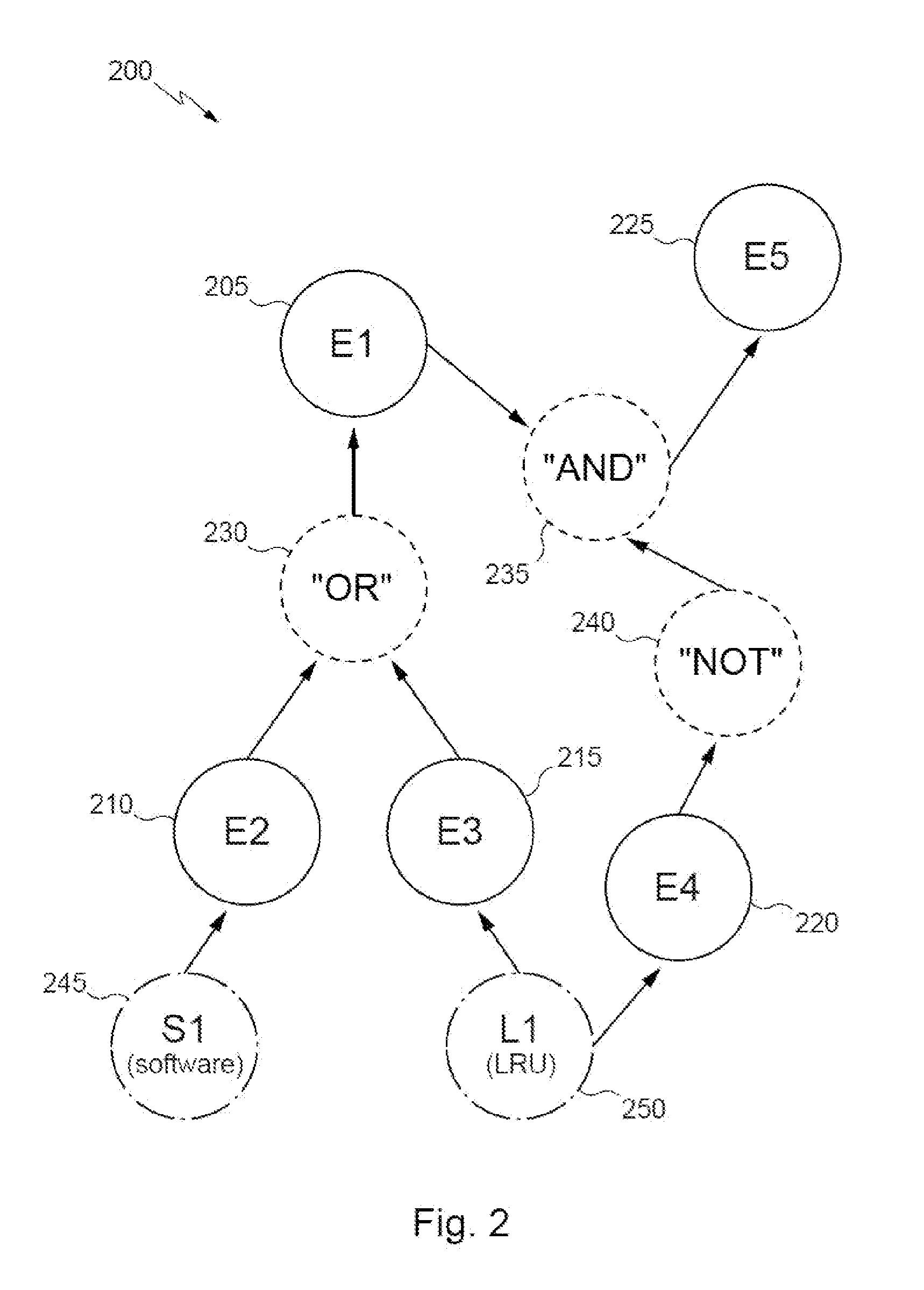
A method for Fault Tree Map generation employs to transformation of Fault Trees of production installation, specific installation, technical system (Hardware and integrated Hardware / Software) to new Fault Tree diagram (Fault Tree Map), which permits drastically compact the Fault Tree depiction and facilitates performing of the Fault Tree qualitative analysis, including evaluation of combination of latent failures and evident failures, repeated events and critical events position influence, and failure propagation potentiality, besides facility of localization of each Fault Tree logical Gate and relevant failures in the fault tree printed report. Generation takes place using special symbols, which permit to reflect the Fault Tree logic, present all Fault Tree failures with graphically identification of the failure type, and show the failure repetition and also the failure critically (importance) to Fault Tree Top Event probability. The method presents exceptional advantages to analysis of large-scale, extended Fault Trees, allowing vastly decrease the time of analysis and elevate the analysis quality and Fault Tree perception, including for specialists, who are not the Fault Tree authors.
Owner:EMBRAER SA
Hybrid method for event prediction and system control
InactiveUS7451210B2Data processing applicationsDigital computer detailsHybrid approachComputer cluster
Owner:GLOBALFOUNDRIES INC
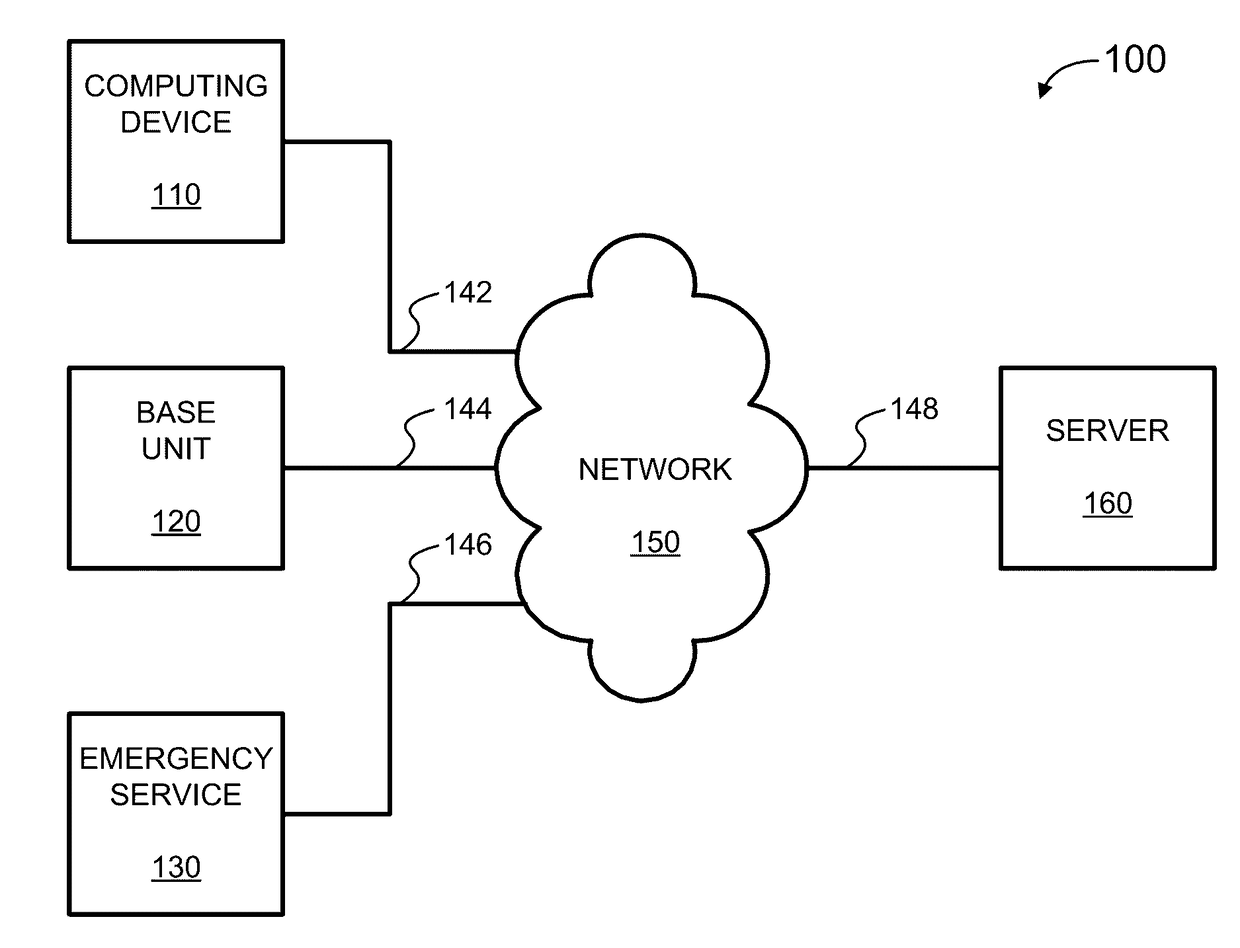
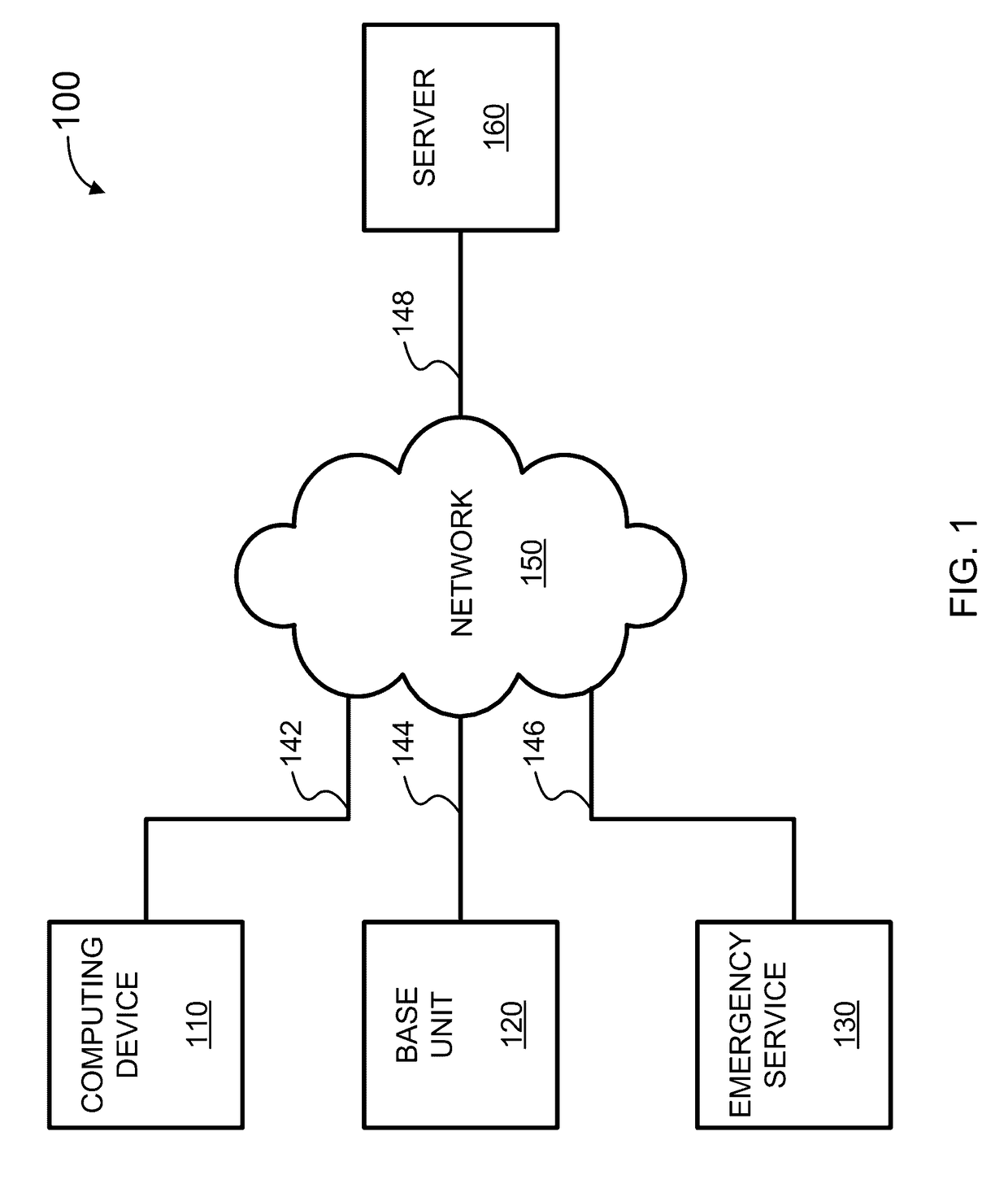
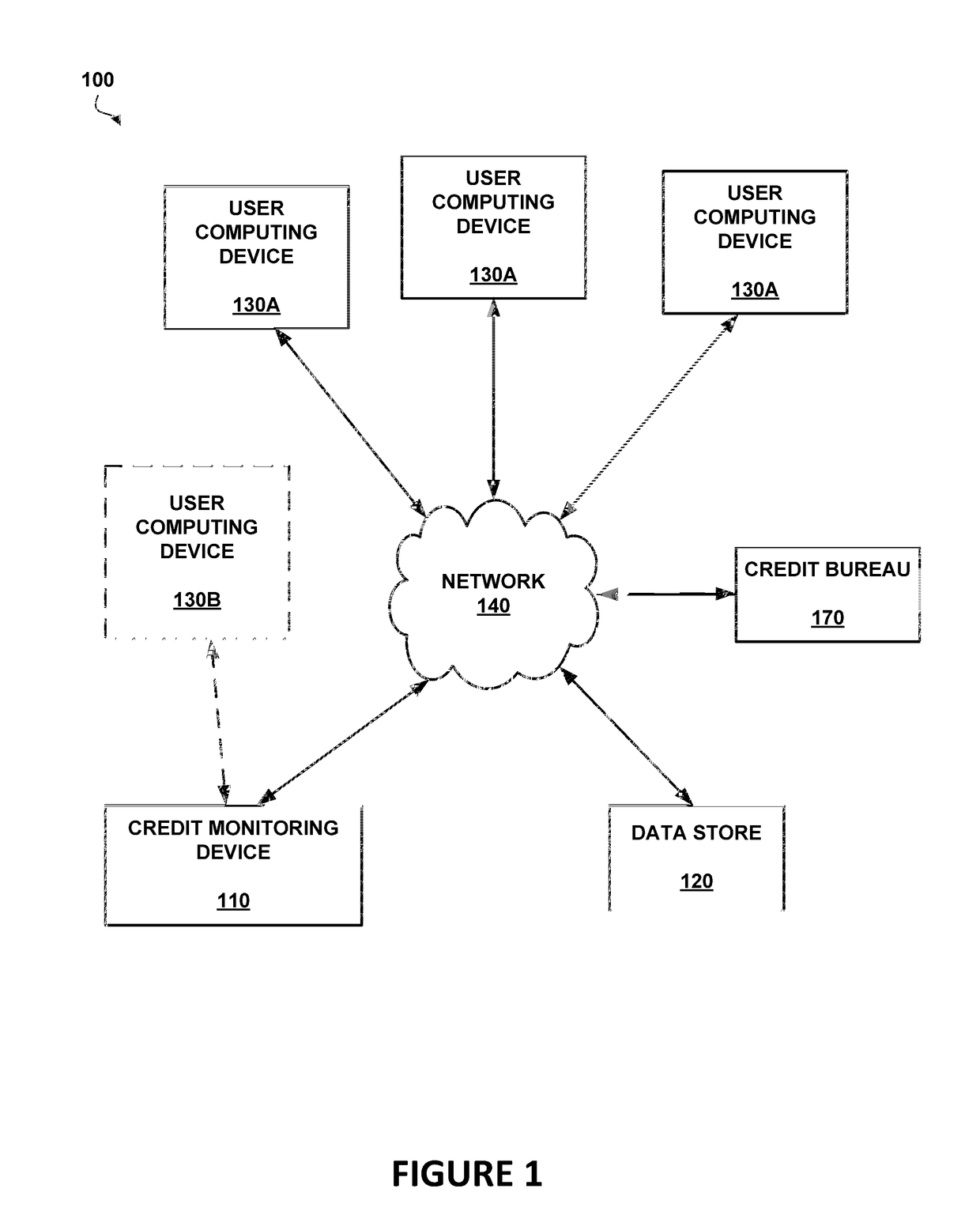
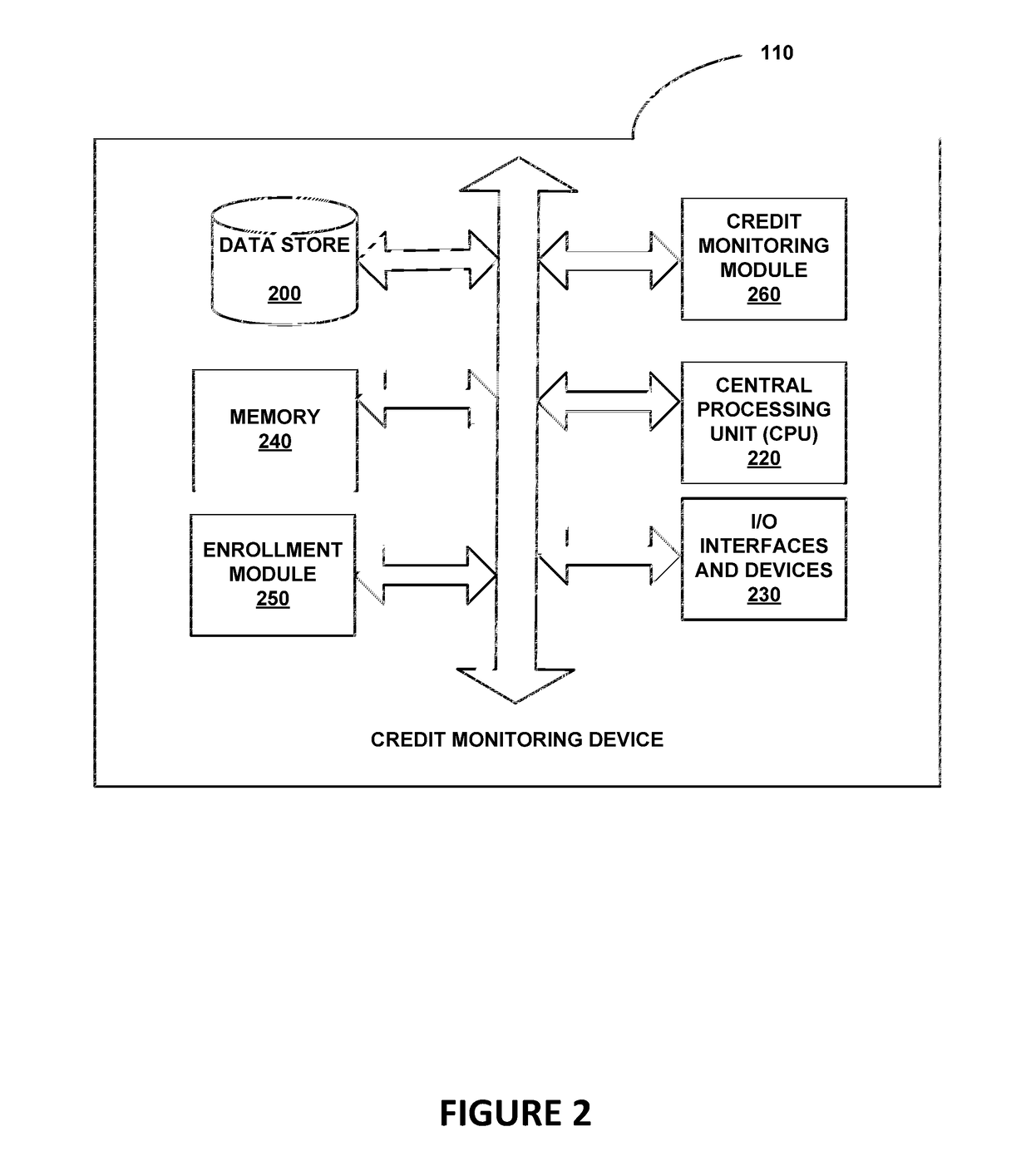
Indirect monitoring and reporting of a user's credit data
Methods and systems of monitoring and reporting of changes to a user's credit data are provided. One embodiment includes providing a service, hosted by a data server, that allows the user to access the service via a communication terminal. The service may also request enrollment data, including identity verification data, from the user. Further, the service may periodically access and monitor the user's credit data for a change in the user's credit data via a connection between the data server and a credit bureau even if the data server has not received sufficient identity verification data from the user. Additionally, the service may determine whether a change detected in the user's credit data is a significant event. When an event or a significant event in the user's credit data is detected, the service may alert the user of the fact that an event has occurred even if the data server has not received sufficient identity verification data from the user.
Owner:CONSUMERINFO COM
Dynamically drilling-down through a health monitoring map to determine the health status and cause of health problems associated with network objects of a managed network environment
InactiveUS7146568B2Quick responseAccurately respondData processing applicationsDigital computer detailsDrill downHealth problems
User-configurable group views allow an administrator of a managed network, upon noticing that an icon is indicative of a critical event having occurred, as reflected in the color, shape, or other such indicator of the icon, to “drill down” to the network device or service that is the subject of the critical event and to then view an event or trap message associated with the critical event that is stored as a field of the network device or service effected by the critical event.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
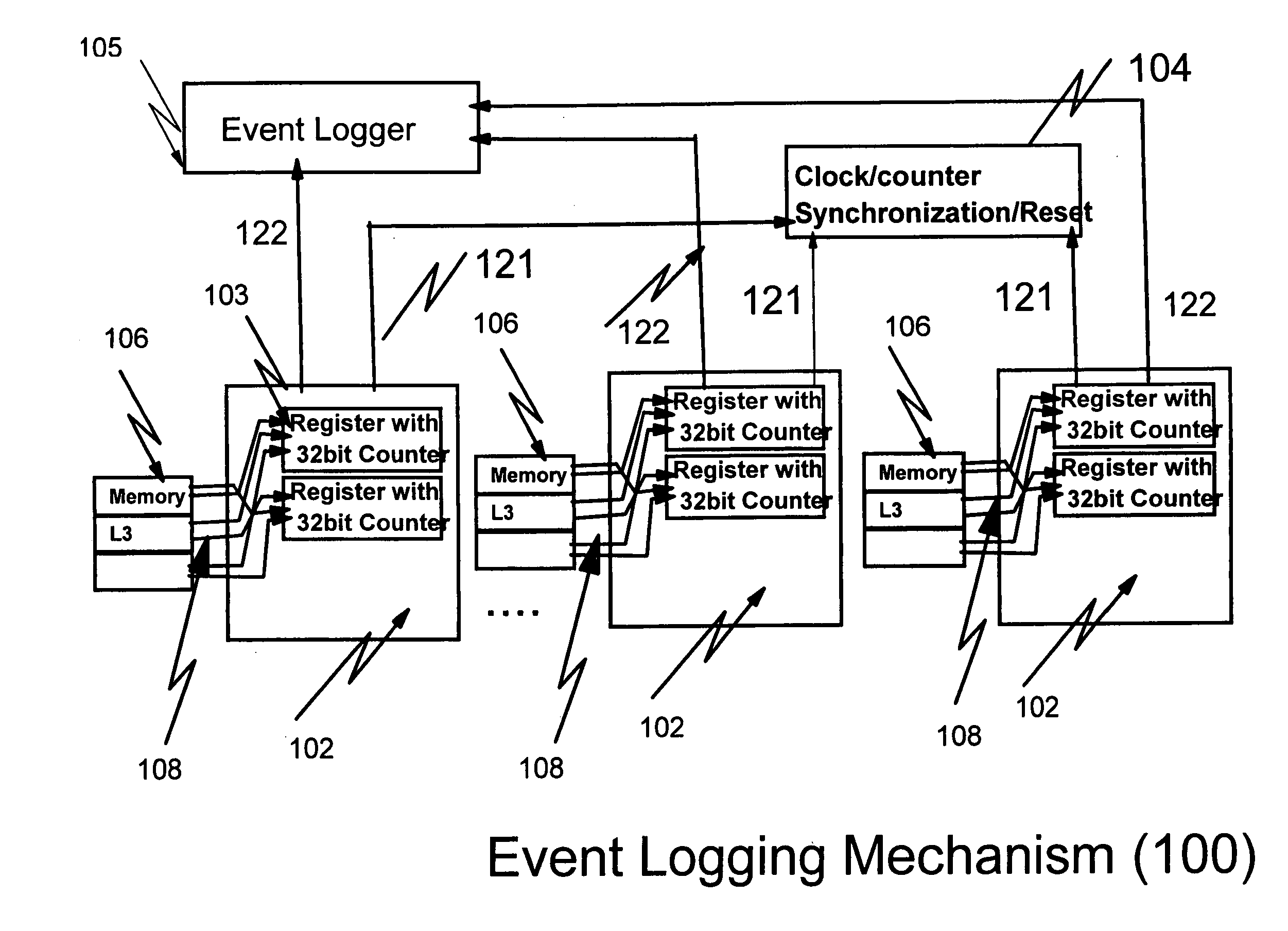
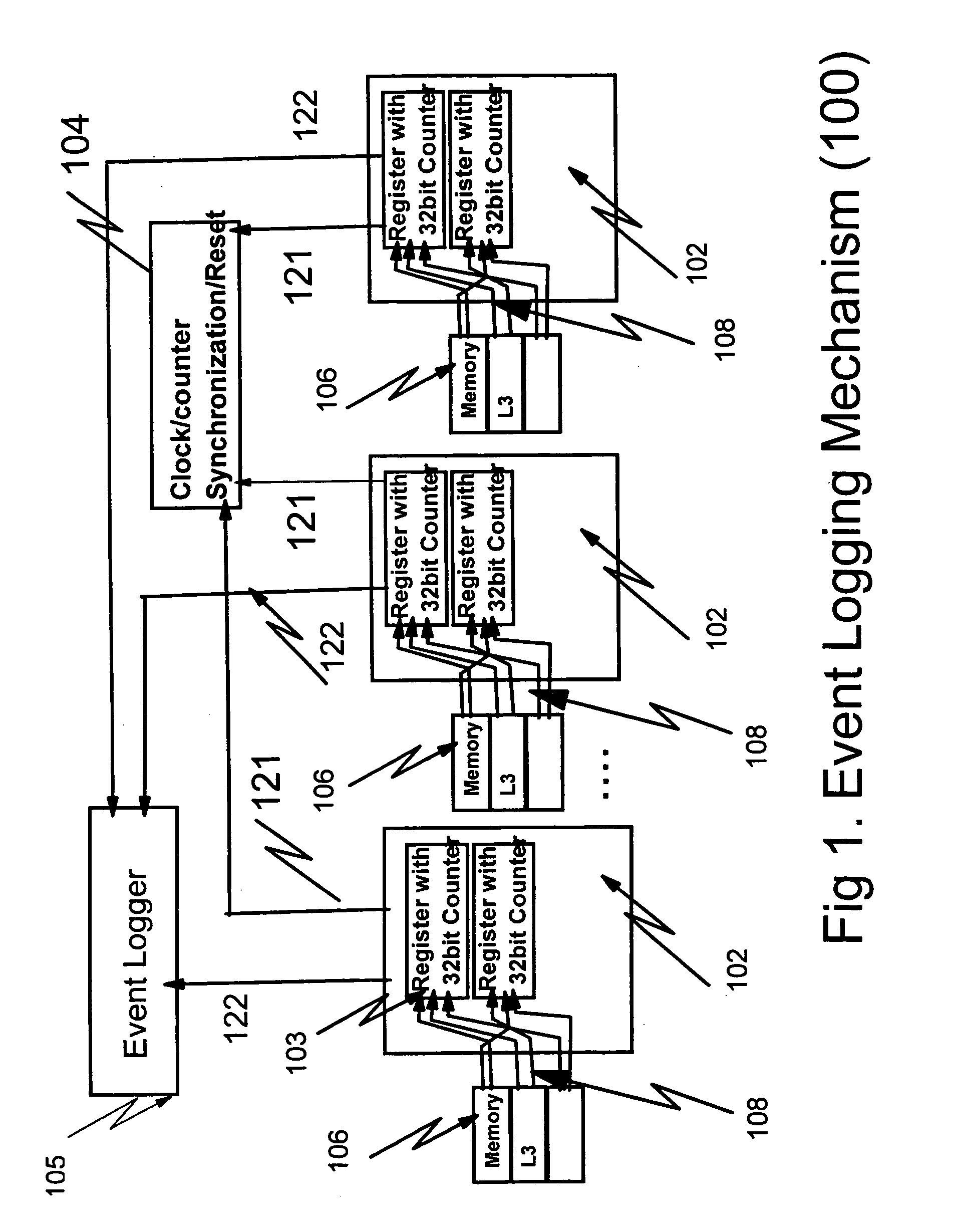
Hardware/software based indirect time stamping methodology for proactive hardware/software event detection and control
InactiveUS20050144532A1Error detection/correctionDigital computer detailsEvent triggerRemedial action
An improved method and apparatus for time stamping events occurring on a large scale distributed network uses a local counter associated with each processor of the distributed network. Each counter resets at the same time globally so that all events are recorded with respect to a particular time. The counter is stopped when a critical event is detected. The events are masked or filtered in an online or offline fashion to eliminate non-critical events from triggering a collection by the system monitor or service / host processor. The masking can be done dynamically through the use of an event history logger. The central system may poll the remote processor periodically to receive the accurate counter value from the local counter and device control register. Remedial action can be taken when conditional probability calculations performed on the historical information indicate that a critical event is about to occur.
Owner:IBM CORP
Information fusion for multiple anomaly detection systems
InactiveUS20110213788A1Quickly comprehendDigital data information retrievalDigital data processing detailsAnomaly detectionData source
The present invention is a method for detecting anomalies against normal profiles and for fusing and visualizing the results from multiple anomaly detection systems in a quantifying and unifying user interface. The knowledge patterns discovered from historical data serve as the normal profiles, or baselines or references (hereinafter, called “normal profiles”). The method assesses a piece of information against a collection of the normal profiles and decides how anomalous it is. The normal profiles are calculated from historical data sources, and stored in a collection of mining models. Multiple anomaly detection systems generate a collection of mining models using multiple data sources. When a piece of information is newly observed, the method measures the degree of correlation between the observed information and the normal profiles. The analysis is expressed and visualized through anomaly scores and critical event notifications that are triggered by fusion rules, thus allowing a user to see multiple levels of complexity and detail in a single view.
Owner:QUANTUM INTELLIGENCE
Security monitoring and control
Systems, methods, and software for monitoring and controlling a security system for a structure are provided herein. An exemplary method may include receiving sensor data from at least one first peripheral, the sensor data associated with at least one of activity inside and activity outside of a structure; determining a critical event based in part on the sensor data; creating an alert based in part on the critical event; getting user preferences associated with at least one of a user and a base unit; determining a response based in part on the alert and user preferences; and activating at least one of a second peripheral and a service based in part on the response.
Owner:OOMA
Indirect monitoring and reporting of a user's credit data
Methods and systems of monitoring and reporting of changes to a user's credit data are provided. One embodiment includes providing a service, hosted by a data server, that allows the user to access the service via a communication terminal. The service may also request enrollment data, including identity verification data, from the user. Further, the service may periodically access and monitor the user's credit data for a change in the user's credit data via a connection between the data server and a credit bureau even if the data server has not received sufficient identity verification data from the user. Additionally, the service may determine whether a change detected in the user's credit data is a significant event. When an event or a significant event in the user's credit data is detected, the service may alert the user of the fact that an event has occurred even if the data server has not received sufficient identity verification data from the user.
Owner:CONSUMERINFO COM
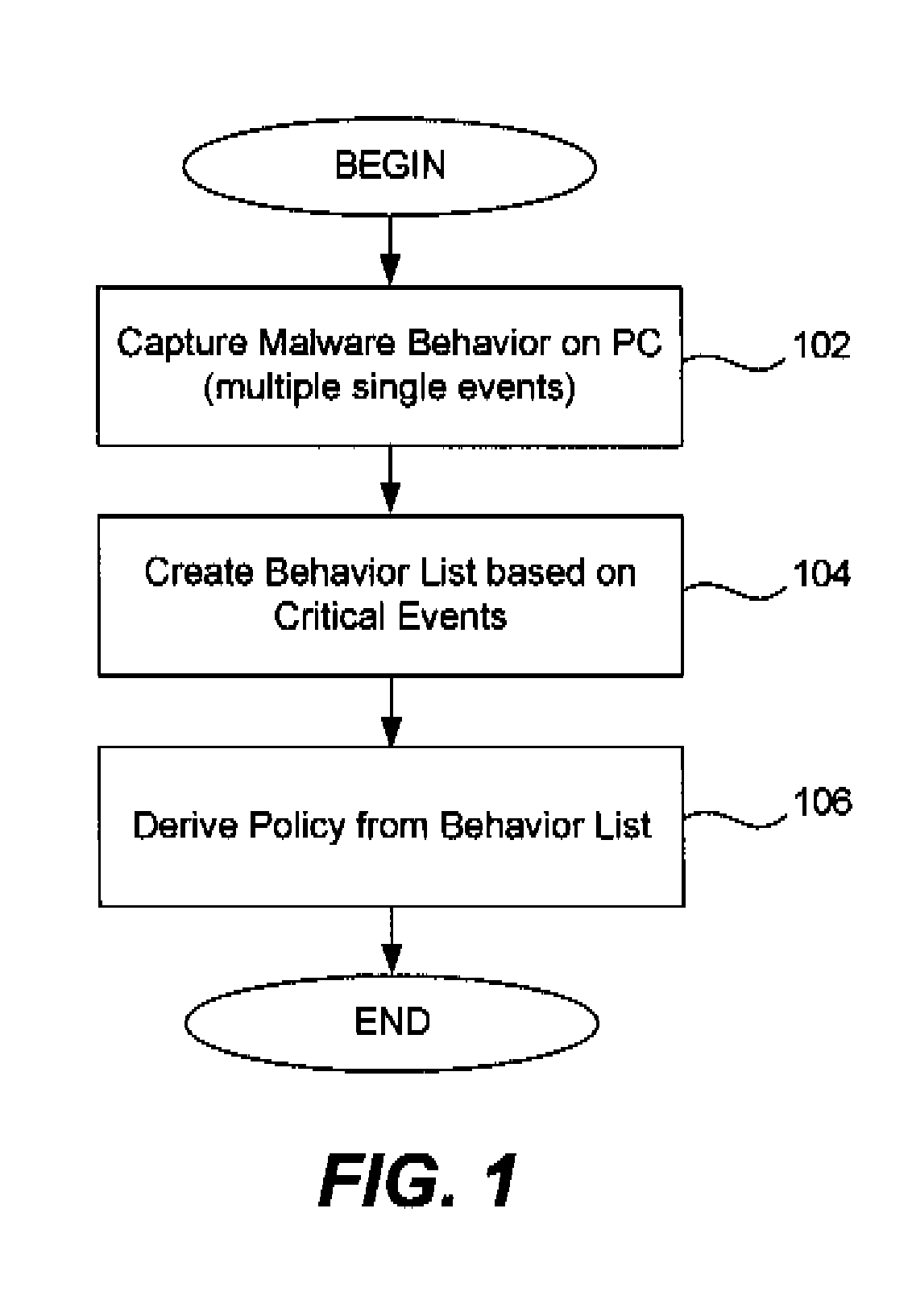
Malware behavior analysis and policy creation
ActiveUS9117078B1Facilitates malware behavior analysisEasy to analyzePlatform integrity maintainanceEvent triggerComputerized system
Creating a policy to be used by a malware prevention system uses multiple events triggered by malware. A sample of malicious computer code or malware is executed in a computer system having a kernel space and a user space. Event data relating to multiple events caused by the malicious code executing on the computer system are captured and stored. The event data is configured using a specific property that facilitates malware behavior analysis. A behavior list is then created utilizing the multiple events and associated event data. The behavior list, together with data in a malware behavior database, is used to derive a policy for use in a malware prevention system. The computer system is free of any malicious code, including viruses, Trojan horses, or any other unwanted software code. The malicious computer code executes without any constraints so that the execution behavior of the malicious code may be observed and captured. Critical events are selected based on the user's expertise and experience in dealing with malware and a sequential stream including the event as the events occur is created.
Owner:TREND MICRO INC
System and method for tactical distributed event warning notification for individual entities, and computer program product therefor
ActiveUS20080316021A1Effective distributionTelemedicineElectric testing/monitoringPagerCommand and control
An information system, method, and computer program product is provided for the distributed warning of existing or developing significant events and / or threats to users carrying a user warning and positioning device, while reporting the location of all user's carrying the user warning and positioning devices of the system to existing command and control systems. The present invention's future event warning capabilities permit those same users to be warned of impending events in enough time for the users to take positive actions in response to these events and / or address those events. The system of the present invention includes a pager-like user warning and positioning device, worn by or carried by the individual user, or mounted in a vehicle or vessel, having a geographical positioning means therein, which periodically transmits the geographical location of the individual user, vehicle or vessel, and listens for warning / notification event messages transmitted by a network bridge or situational awareness workstation (central processing means). When an event / threat warning is received by the user warning and positioning device, the pager-like user warning and positioning alerts the user via indicia relative to the event / situation, including audible spoken warnings and instructions on how to react, and may retransmit the event / threat warning to other user warning and positioning devices in the network, provided the threat has not occurred and the event / threat warning has not been previously relayed.
Owner:UNITED STATES OF AMERICA AS REPRESENTED BY THE UNITED STATES OF AMERICA THE +1
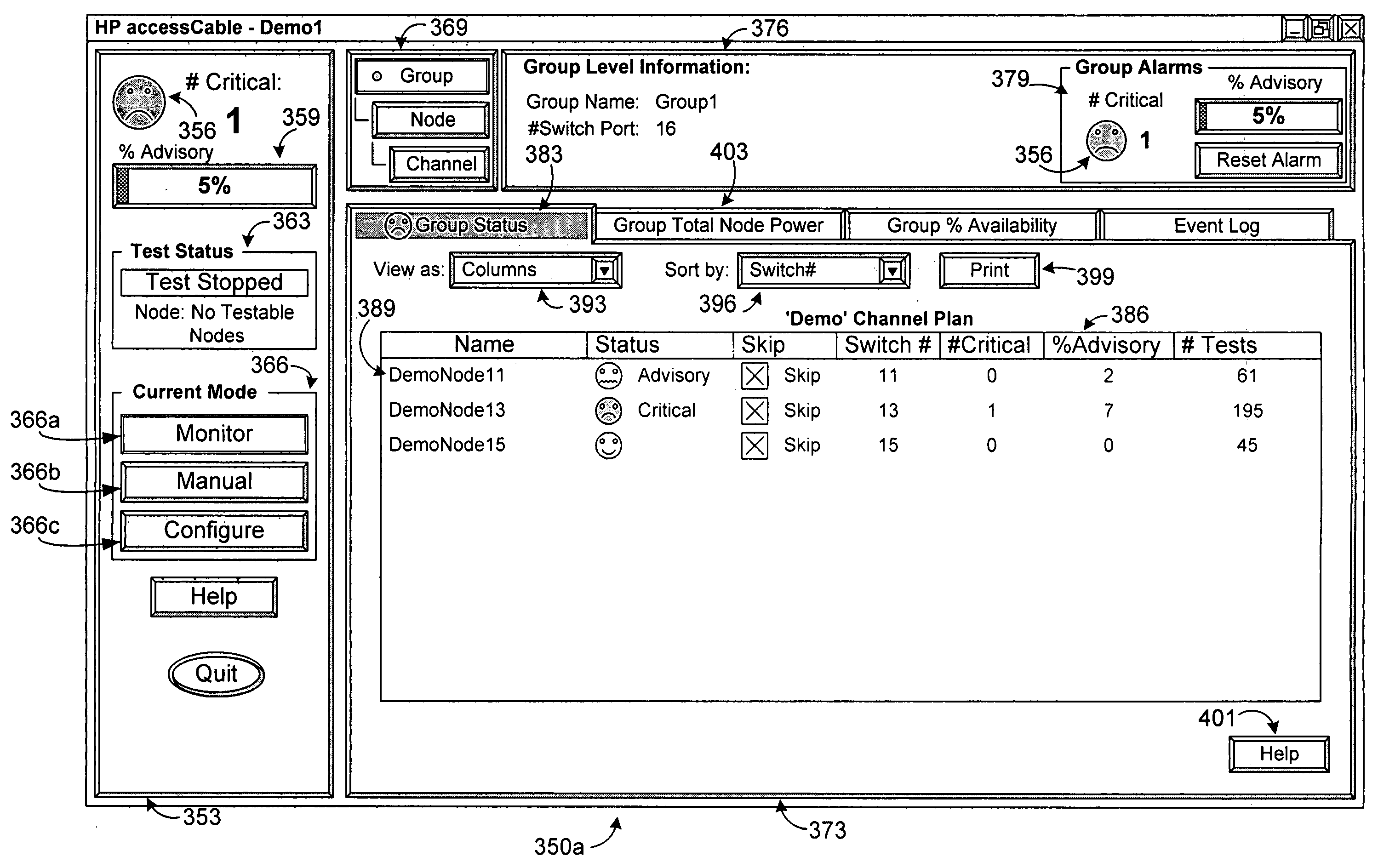
Monitoring system and method implementing warning interface logic
InactiveUS7080398B1Effective monitoringQuick and efficientTwo-way working systemsSelective content distributionSpectrum analyzerDisplay device
Channel and test plans are implemented in connection with a plurality of nodes that communicate signals. The channel plan enables a monitoring system to, among other things, conduct automatic periodic test plans, comprising tests, on the nodes, based upon the predefined data specified in the channel plan. The monitoring system includes a controller controlling a spectrum analyzer and a node interface switch. Notably, the controller also enables user friendly plan set-up and warning interface logic implementation. The warning interface logic generates a channel percent advisory indicator on the display device within a channel level interface component upon an occurrence of an advisory event in a channel associated therewith and generates a channel critical alarm indicator on the display device within a channel level interface component upon an occurrence of a critical event in a channel associated therewith.
Owner:VIAVI SOLUTIONS INC
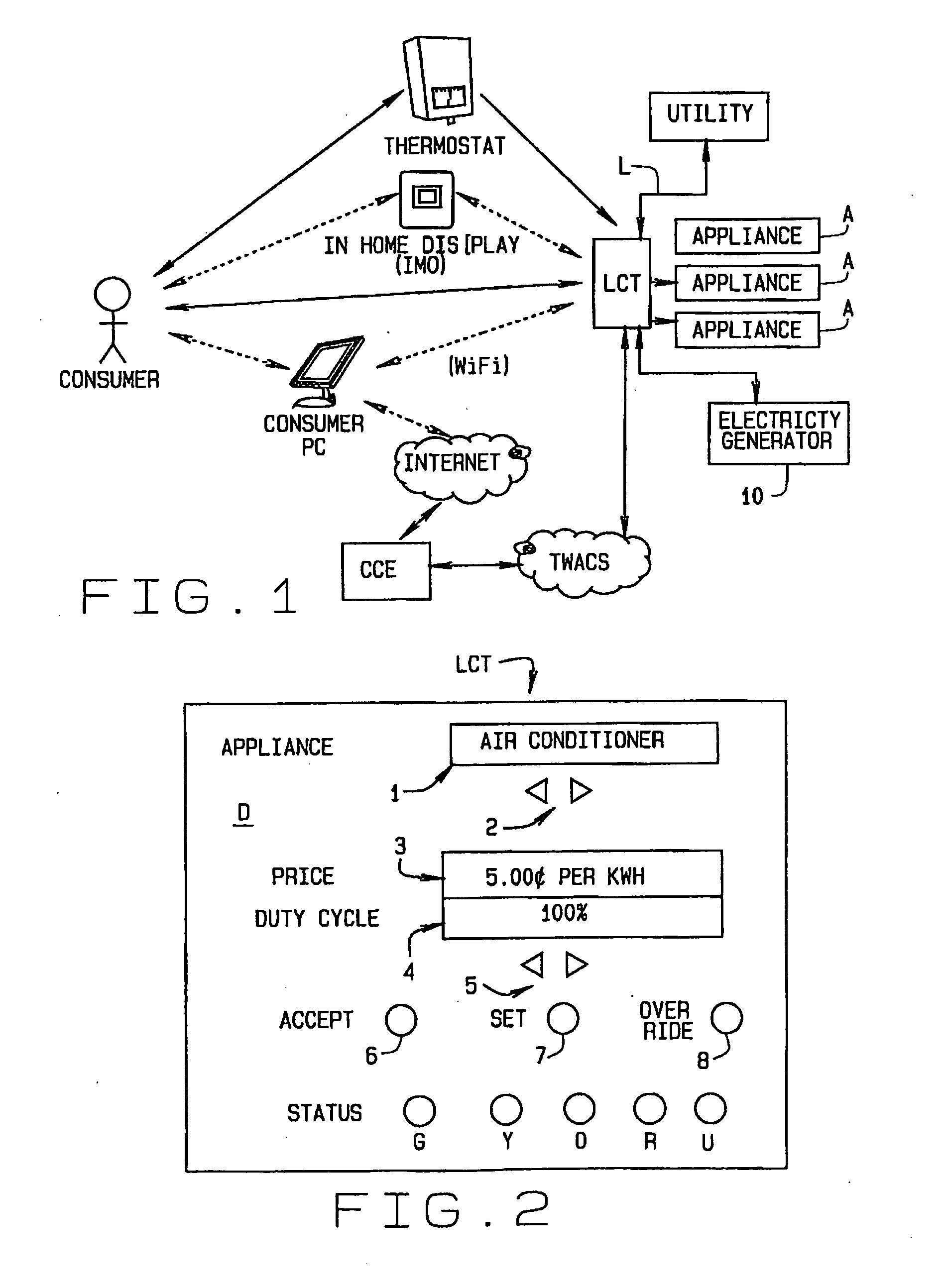
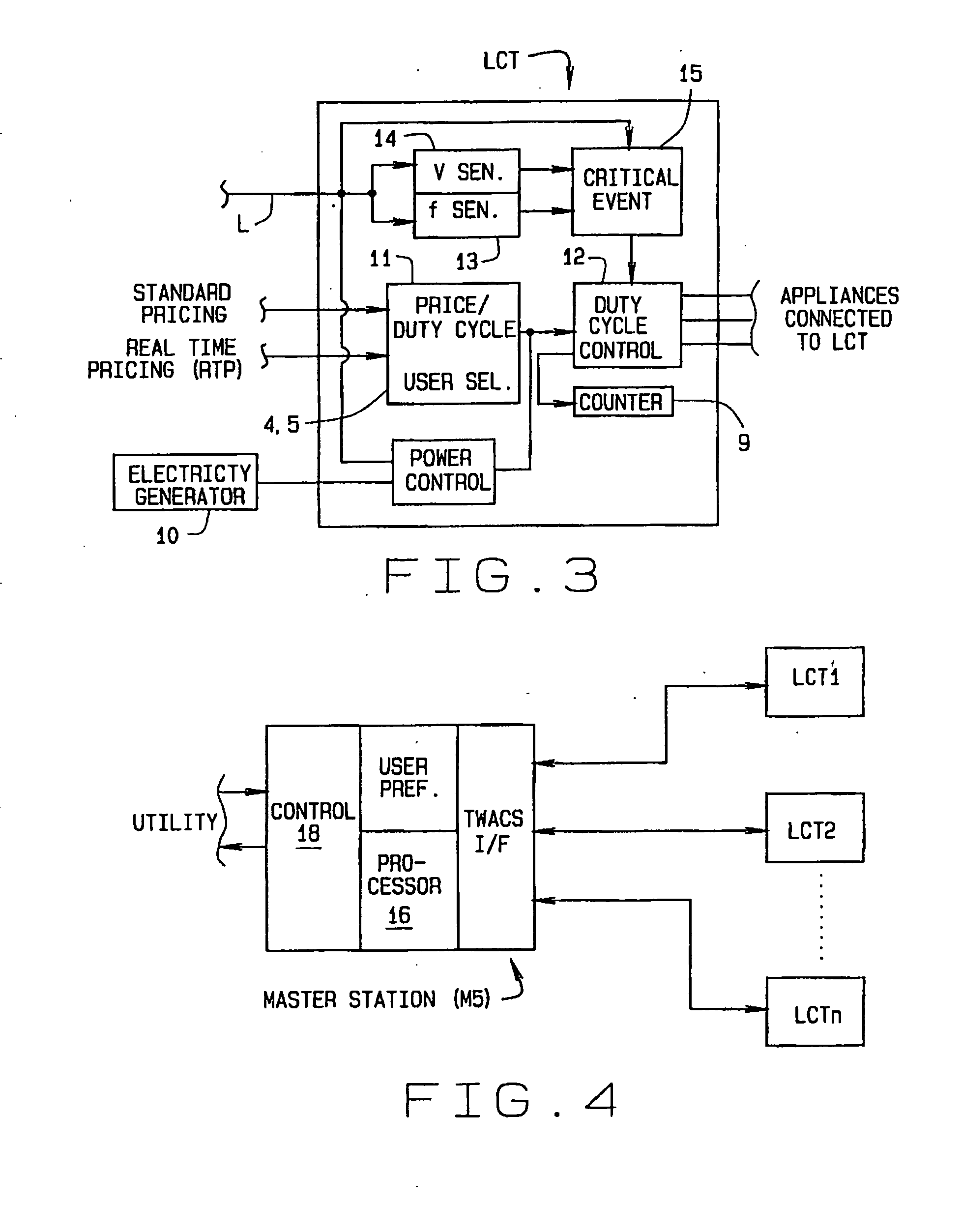
Achieving energy demand response using price signals and a load control transponder
ActiveUS20120101651A1Lower Level RequirementsReduce and shutoff deviceMechanical power/torque controlLevel controlProgram planningEngineering
A method of Demand Response (DR) utilizing a Load Control Transponder (LCT) installed at the location of an electricity consumer. A DR program, in conjunction with the LCT, allows a consumer to determine, in advance, when they will reduce their demand on an electricity supply system. The consumer is informed of price points at which the cost of energy increases due to overall demand. The consumer then determines if, and when, they will reduce their demand on the system when a price point is reached. In addition, when an unplanned, critical event occurs, the method enables the utility to bypass any intermediate consumer established settings and immediately and directly drop the level of energy consumption to the consumer's lowest selected level for continuing service thereby to shed sufficient load on the system to maintain an adequate level of electricity supply. Once the event has been resolved, the method enables the utility to restore the consumer's previous level of usage.
Owner:ACLARA TECH LLC
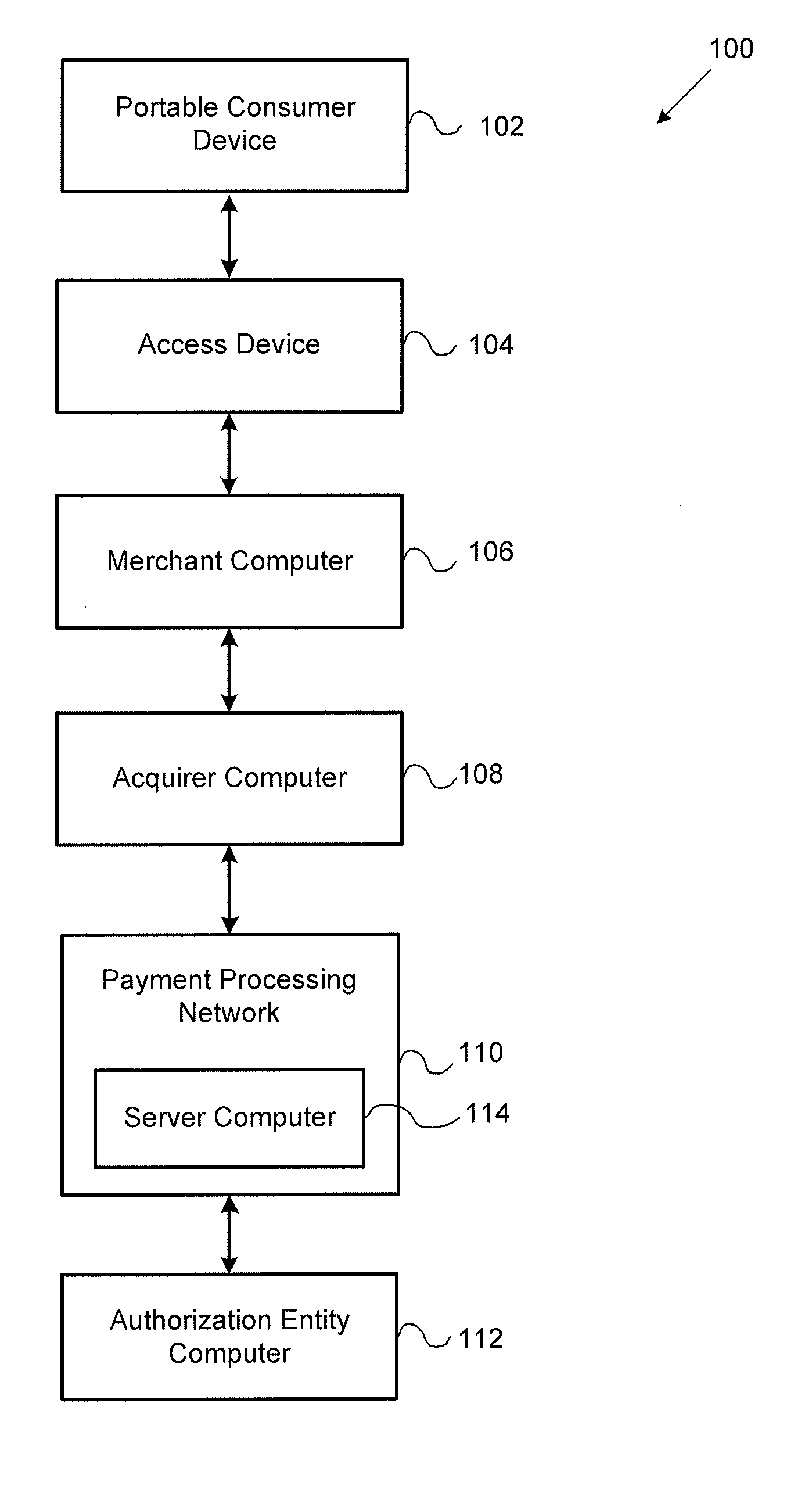
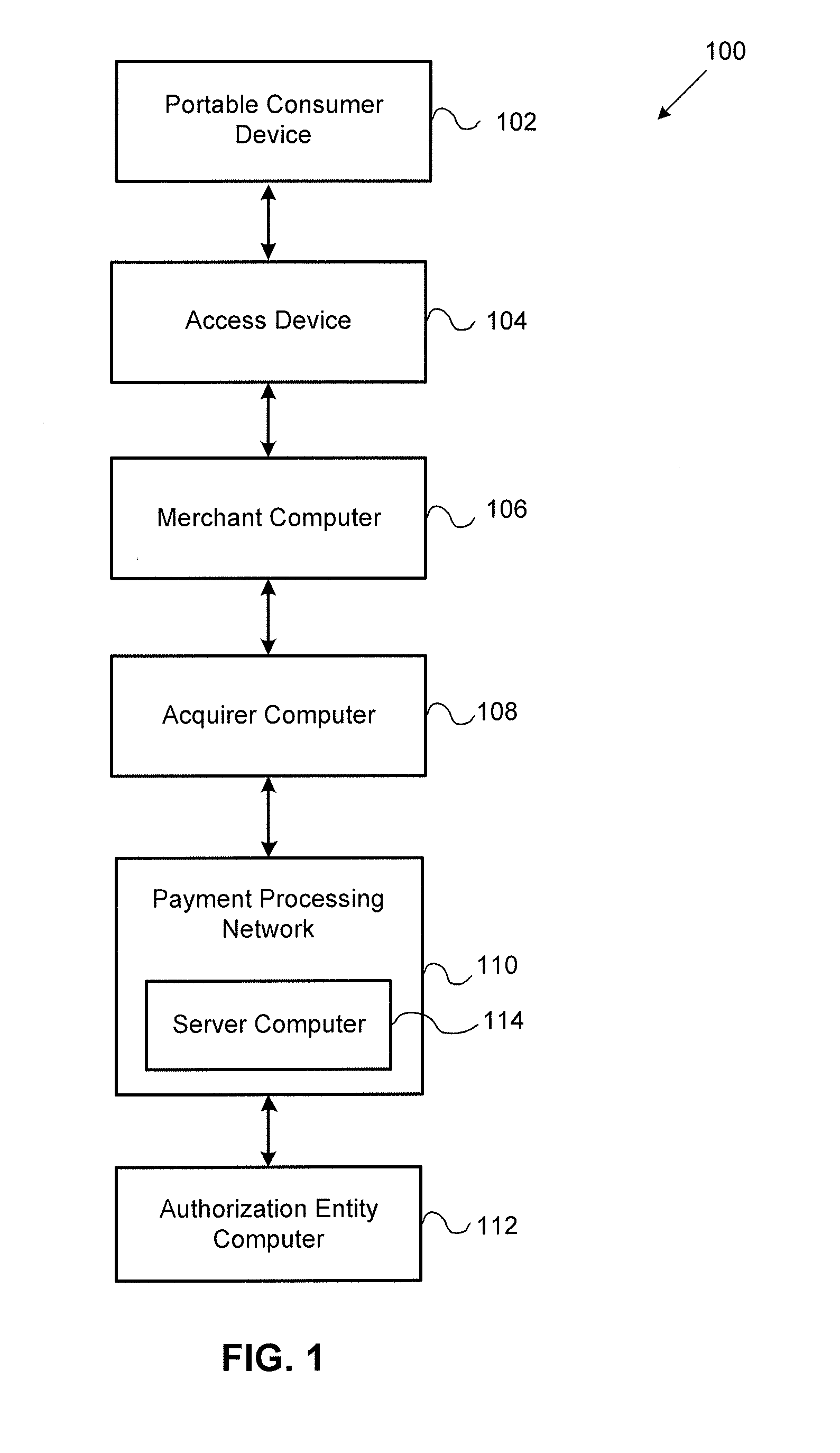
Processor Issuer Detection and User Level Stand-In Authorization
ActiveUS20140304158A1Improved authorization outcomePromote resultsFinanceProtocol authorisationPaymentParallel computing
Embodiments of the invention are directed to systems and methods for stand-in processing using data driven capabilities. Transaction activity of an issuer may be monitored to detect a major incident and to automatically invoke stand-in processing. By modeling each individual account holder's behavior, improved authorization outcomes may be provided by a payment processing network during stand-in processing.
Owner:VISA INT SERVICE ASSOC
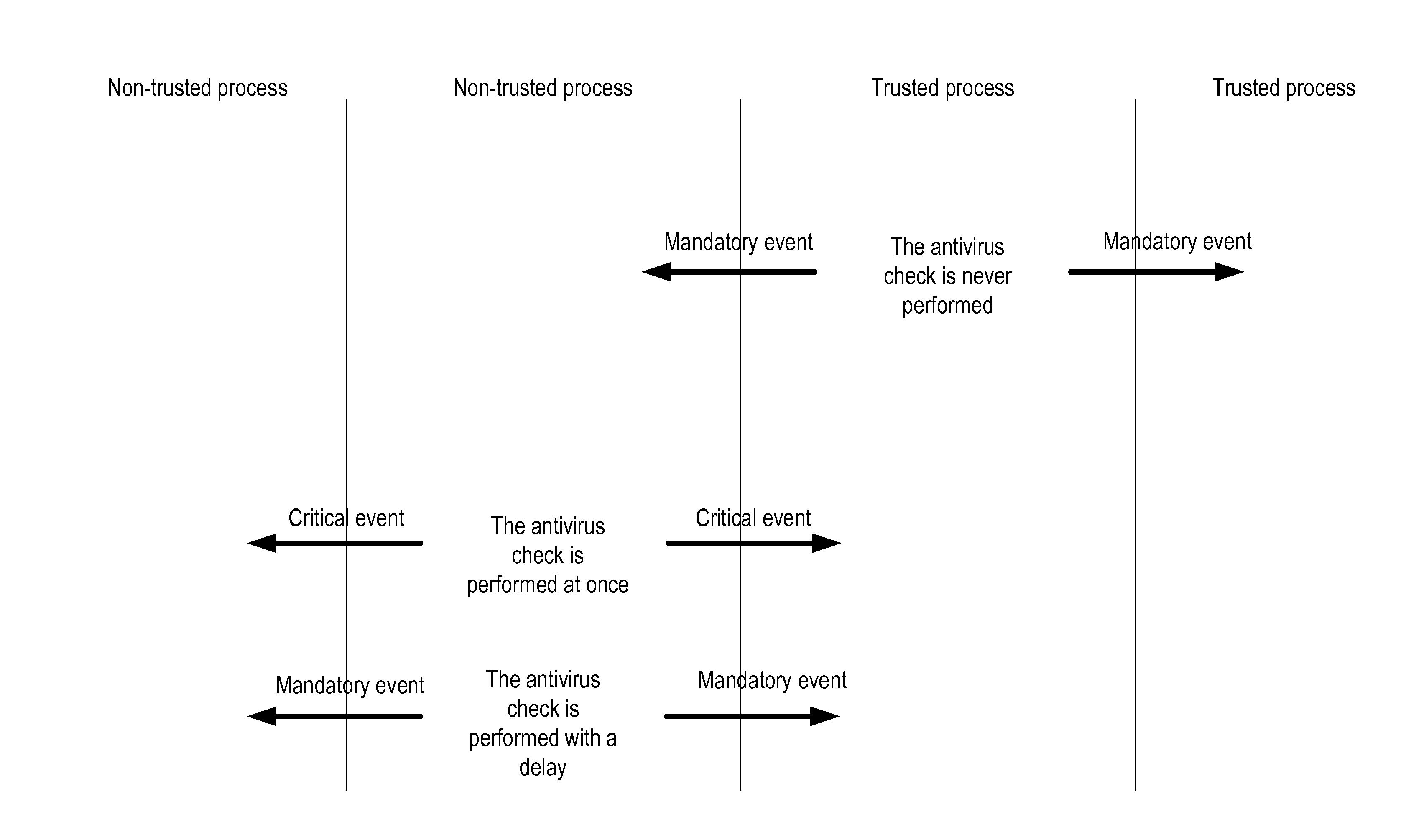
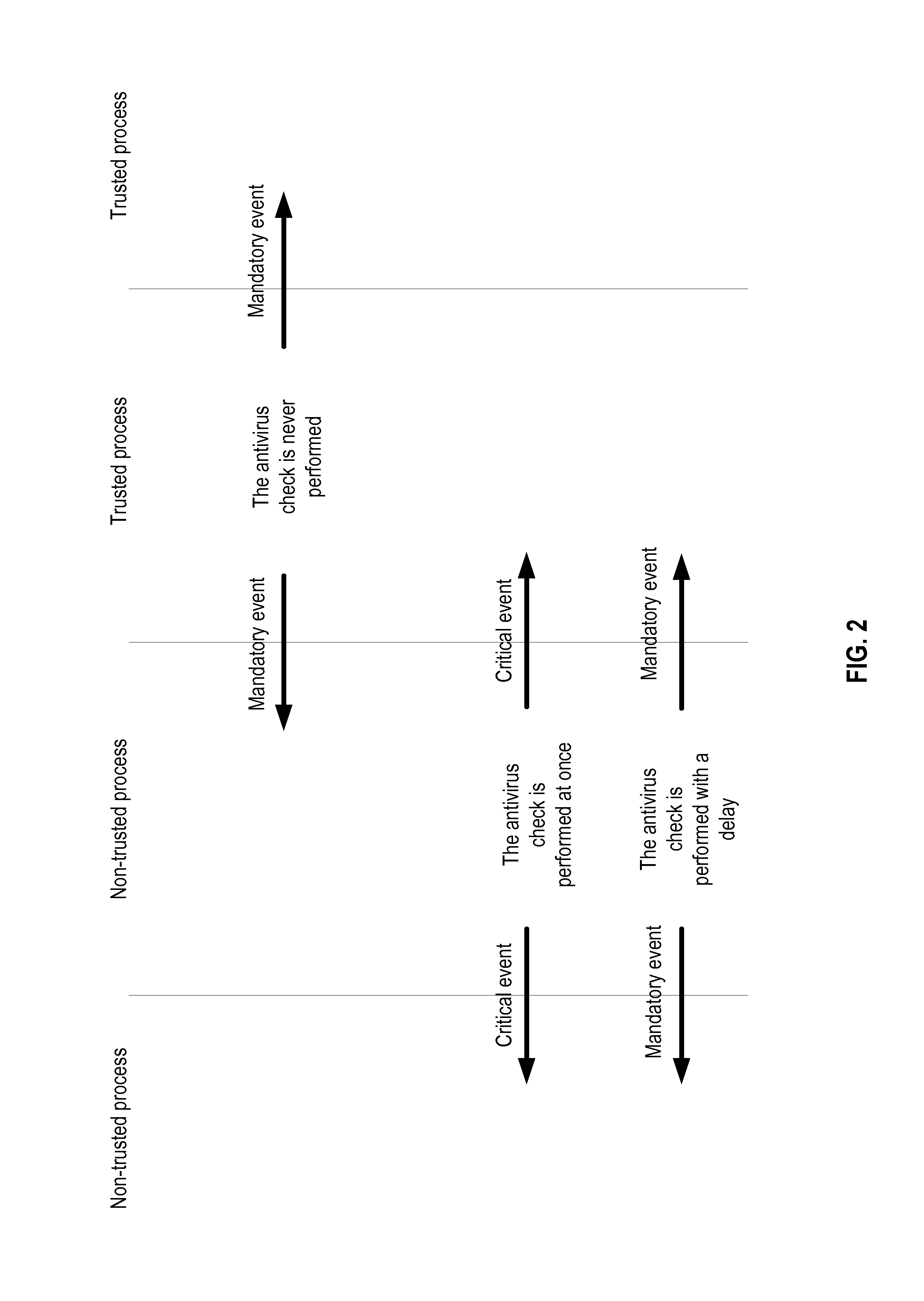
System and method for reducing load on an operating system when executing antivirus operations
ActiveUS20150163231A1Memory loss protectionError detection/correctionMalware analysisOperational system
An initial trust status is assigned to a first object, the trust status representing one of either a relatively higher trust level or a relatively lower trust level. Based on the trust status, the first object is associated with an event type to be monitored, where the event type is selected from among: essential events, occurrence of which is informative as to trust status evaluating for an object, and critical events, including the essential events, and additional events, occurrence of which is informative as to execution of suspicious code. Occurrences of events relating to the first object are monitored. In response to the first object being assigned the relatively higher trust level, only the essential events are monitored. In response to the first object being assigned the relatively lower trust level, the critical events are monitored. A need for performing malware analysis is determined based on the trust status of the first object and the event type. In response to determination of the need for performing the malware analysis, the malware analysis for the first object is either performed, or not.
Owner:AO KASPERSKY LAB
Hydrogen Storage System and Method of Operation Thereof
A regenerative fuel cell system is provided having at least one hydrogen storage container fluidly coupled to at least one hydrogen generator and at least one power generator. Each power generator further includes a fuel cell fluidly coupled to the hydrogen storage container, an electric energy storage device, and an unregulated dc bus electrically connected to said fuel cell and said electric storage device. The system further provides for a health monitoring system for determining the occurrence of critical events which may necessitate the disabling of the system.
Owner:PROTON ENERGY SYST
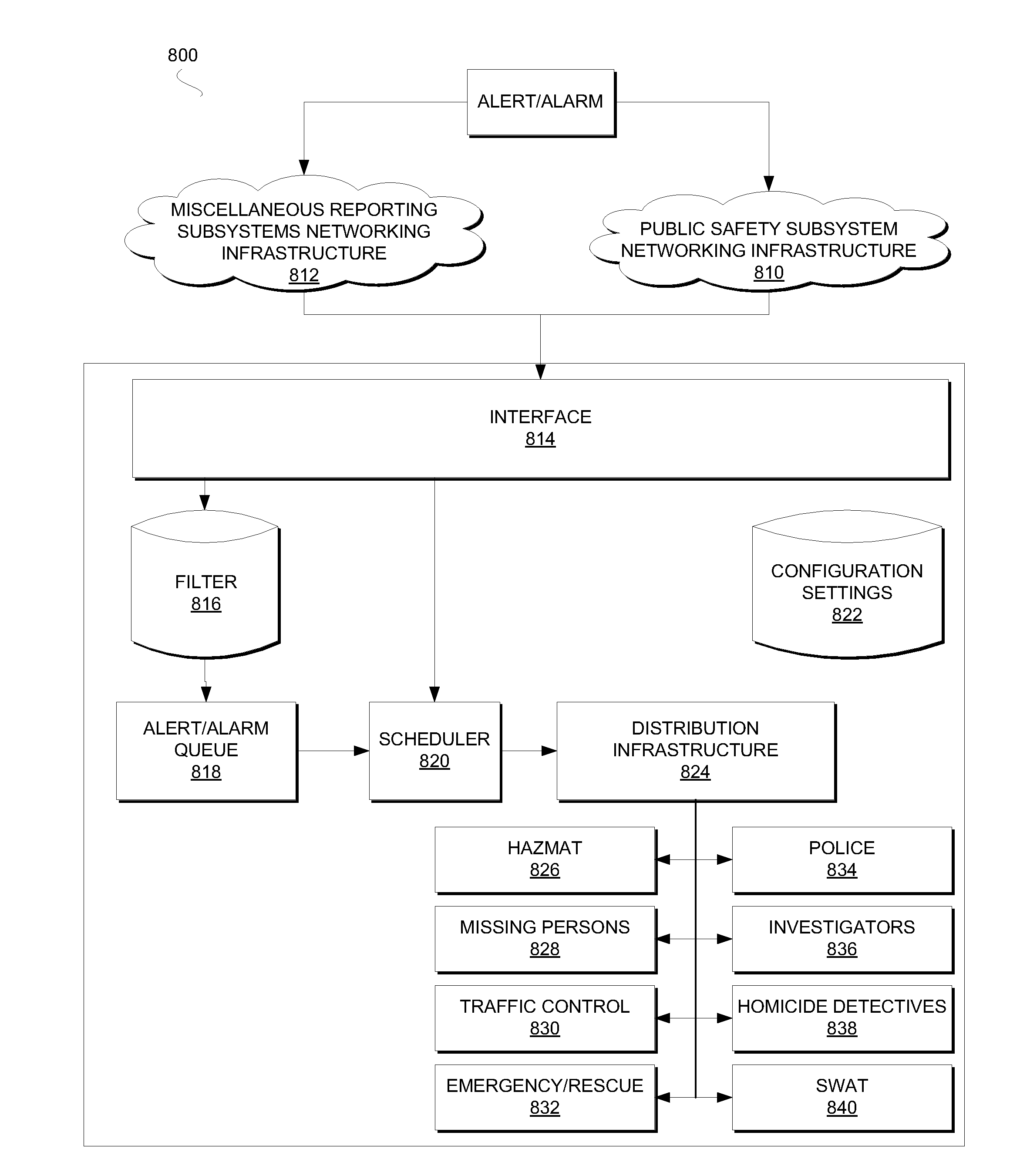
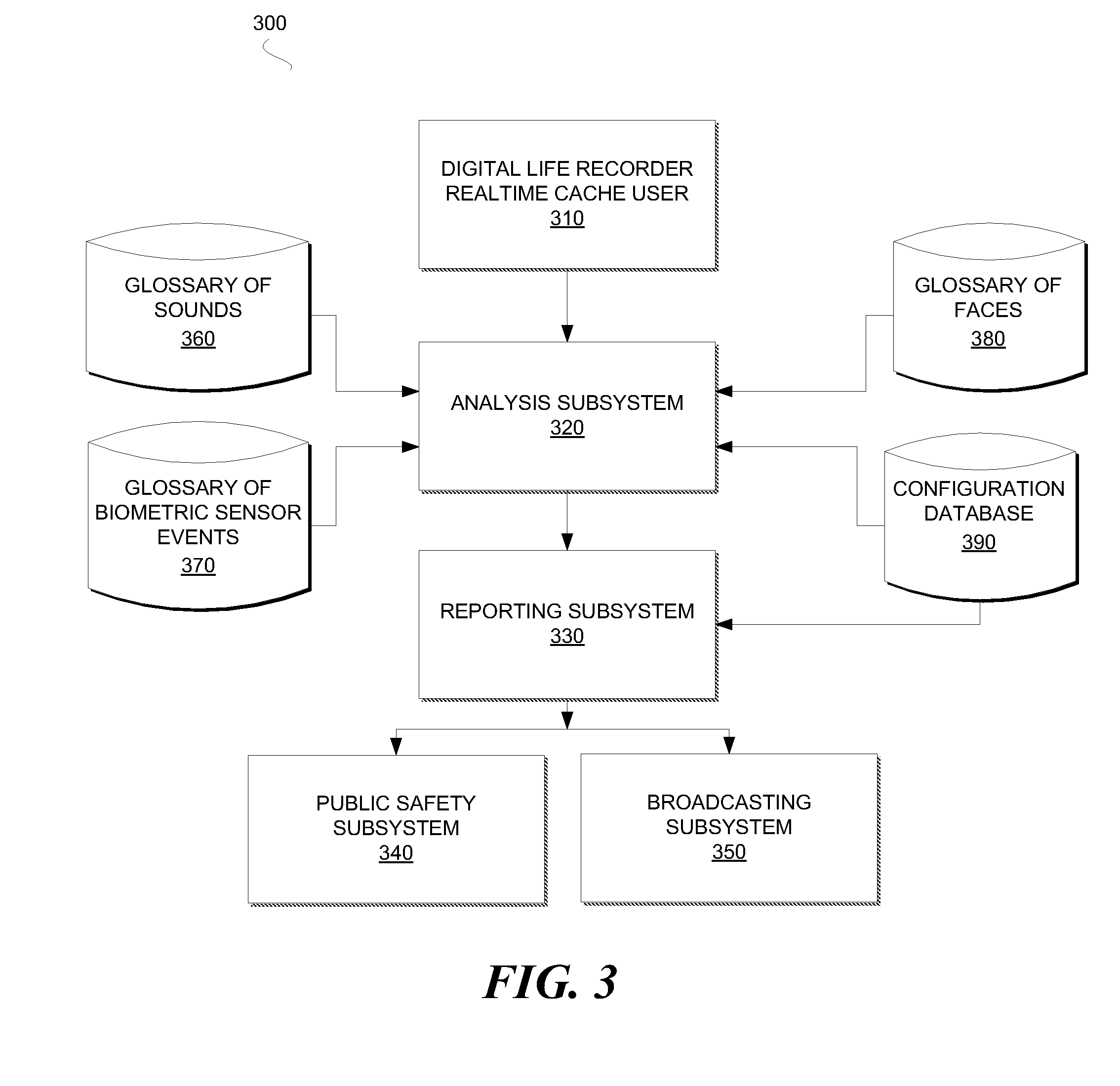
System and Method for Detecting and Broadcasting a Critical Event
ActiveUS20090295572A1Minimize response timeAutomatically determineFrequency-division multiplex detailsTime-division multiplexData treatmentBroadcasting
A system and method for detecting and reporting a critical event. Events may be continually detected by sensors and processed as digitized data. The digitized data may be compared to signature data stored in glossaries. If a match exists between the digitized data and the signature data, the event may be reported. An analysis of the event may be performed and based on a result of the analysis, an alarm notice may be sent.
Owner:UNILOC 2017 LLC
System and method for distributed network acess and control enabling high availability, security and survivability
InactiveUS7278023B1Public key for secure communicationUser identity/authority verificationSurvivabilityWide area network
Owner:NORTHROP GRUMMAN SYST CORP
Method, devices and program for computer-aided preventive diagnostics of an aircraft system, using critical event charts
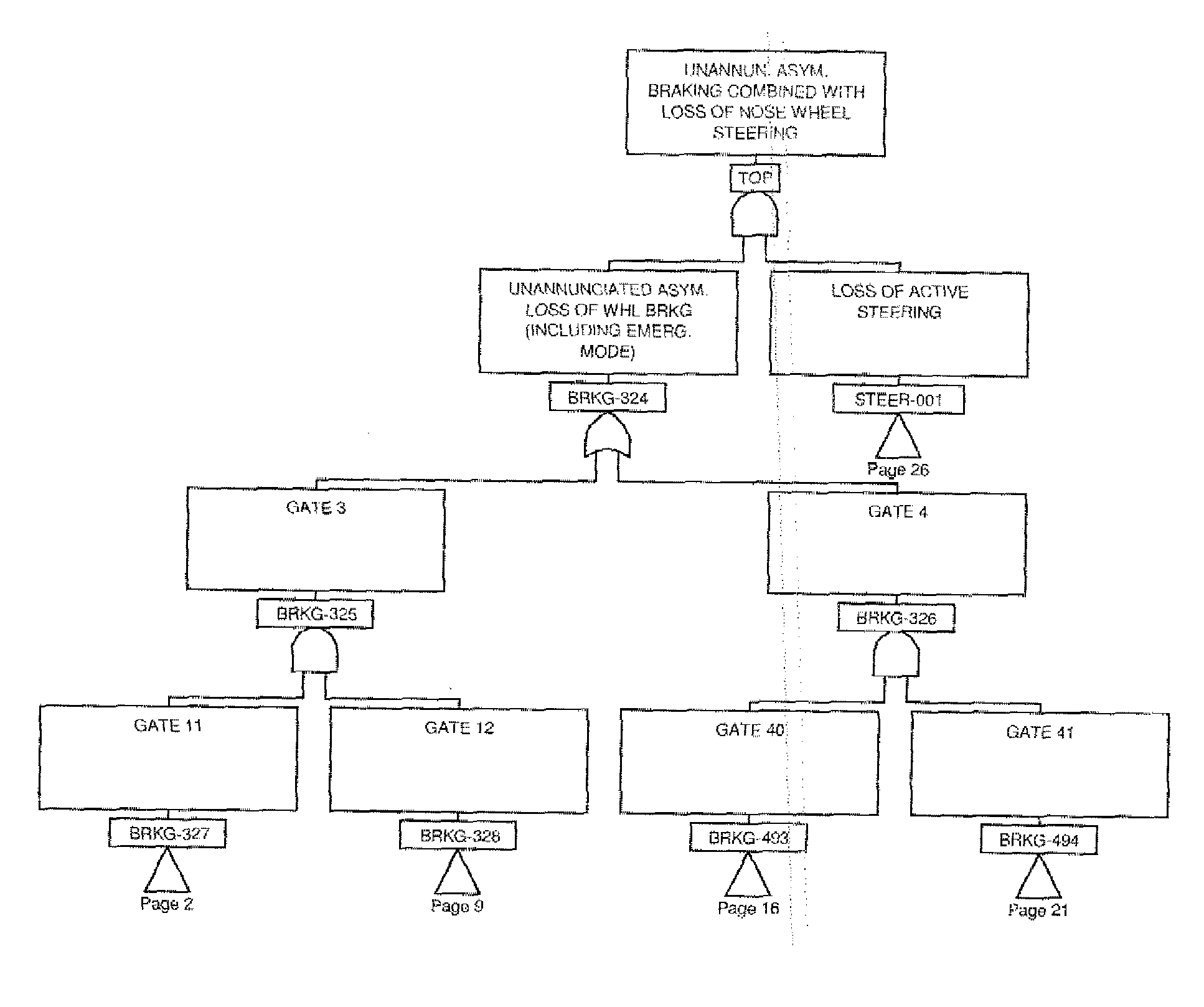
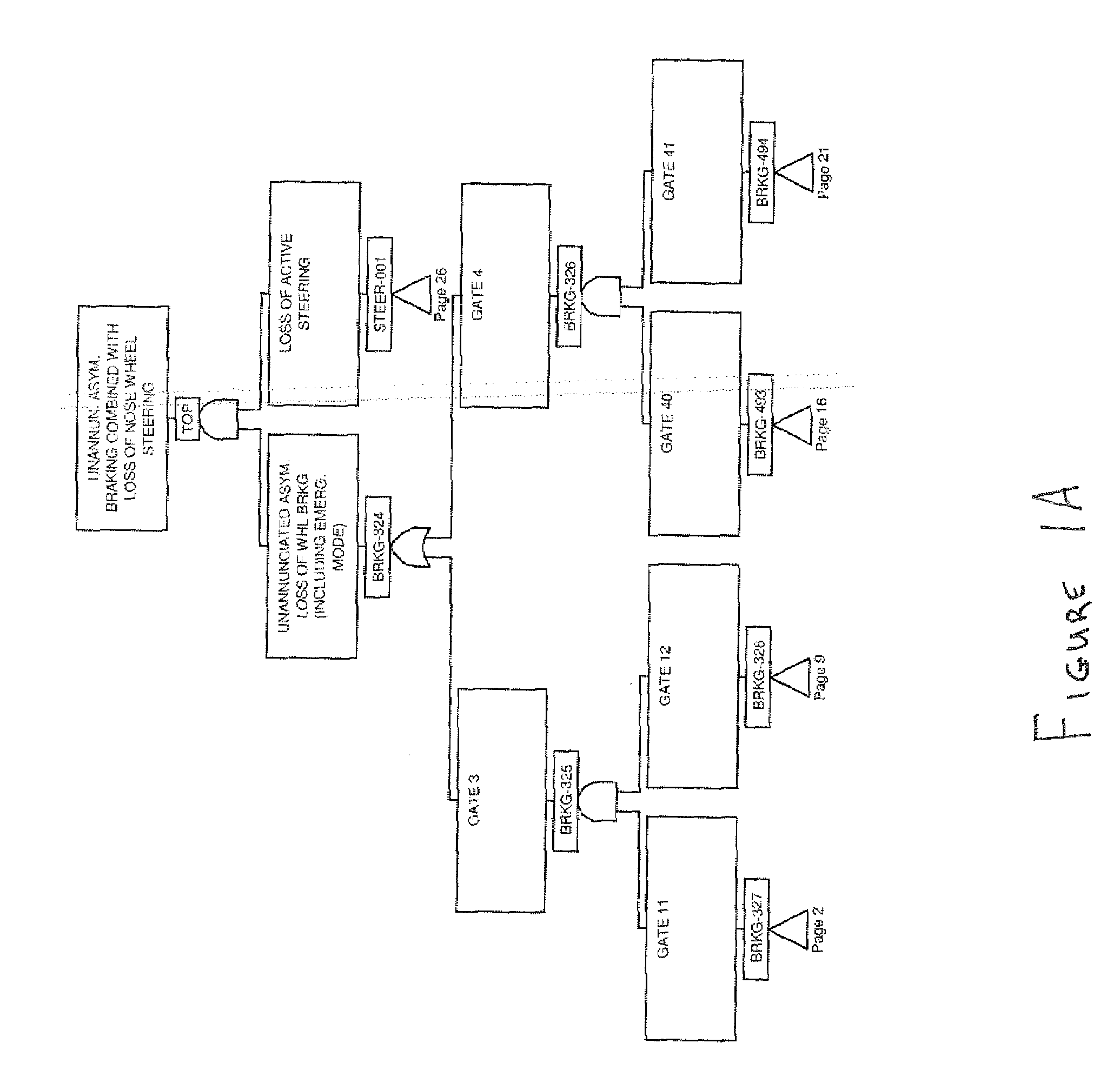
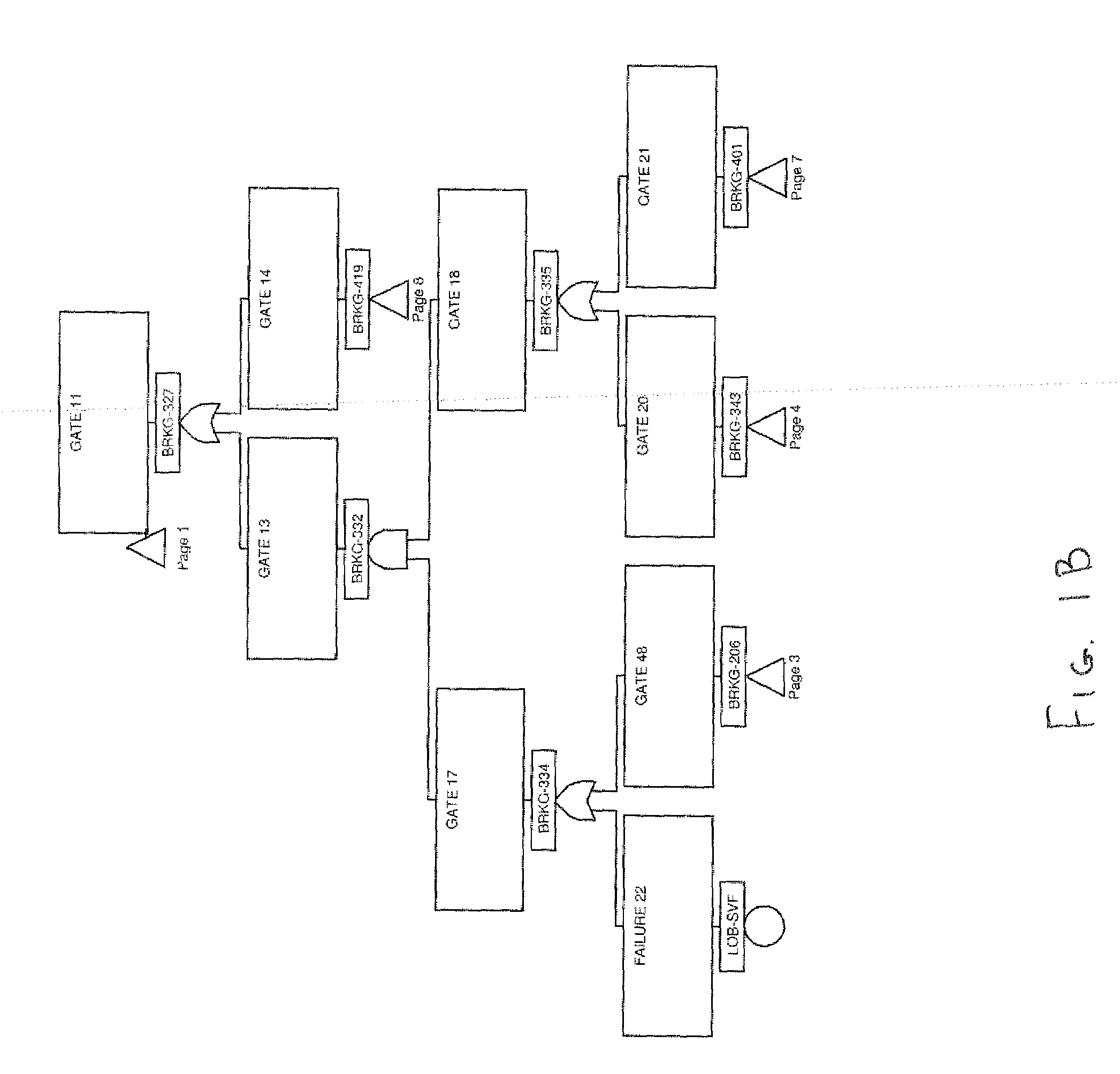
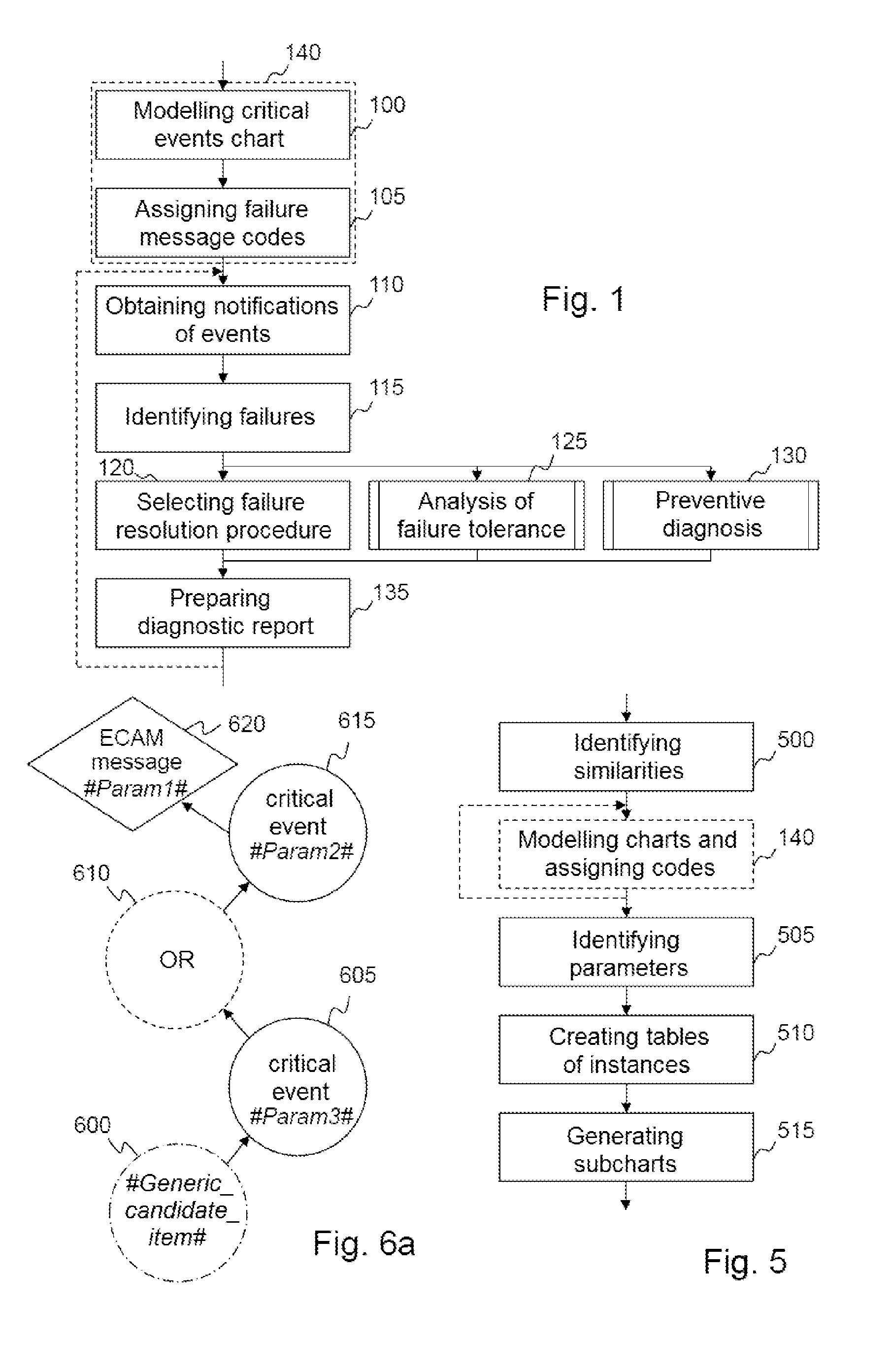
ActiveUS20130274992A1Facilitate decision-makingEasy maintenanceVehicle testingRegistering/indicating working of vehiclesFlight vehicleComputer-aided
Aided preventive diagnostics of an aircraft system, comprising a plurality of subsystems at least one of which comprises a subsystem configured for monitoring and notifying a detected event, using critical event charts. After receiving a message notifying the occurrence of said detected event, a minimal diagnostic set relative to said at least one detected event, comprising a plurality of elements each represented by a node of said critical event chart is created, each element of said minimal diagnostic set being determined according to at least one logical implication relation of said critical event chart with a node representing said at least one received notification message. At least some of the elements of said minimal diagnostic set are then ranked, said ranked elements forming part of said diagnostic report.
Owner:AIRBUS OPERATIONS (SAS)
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com